Patents
Literature
52results about How to "Problems be reduced eliminated" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
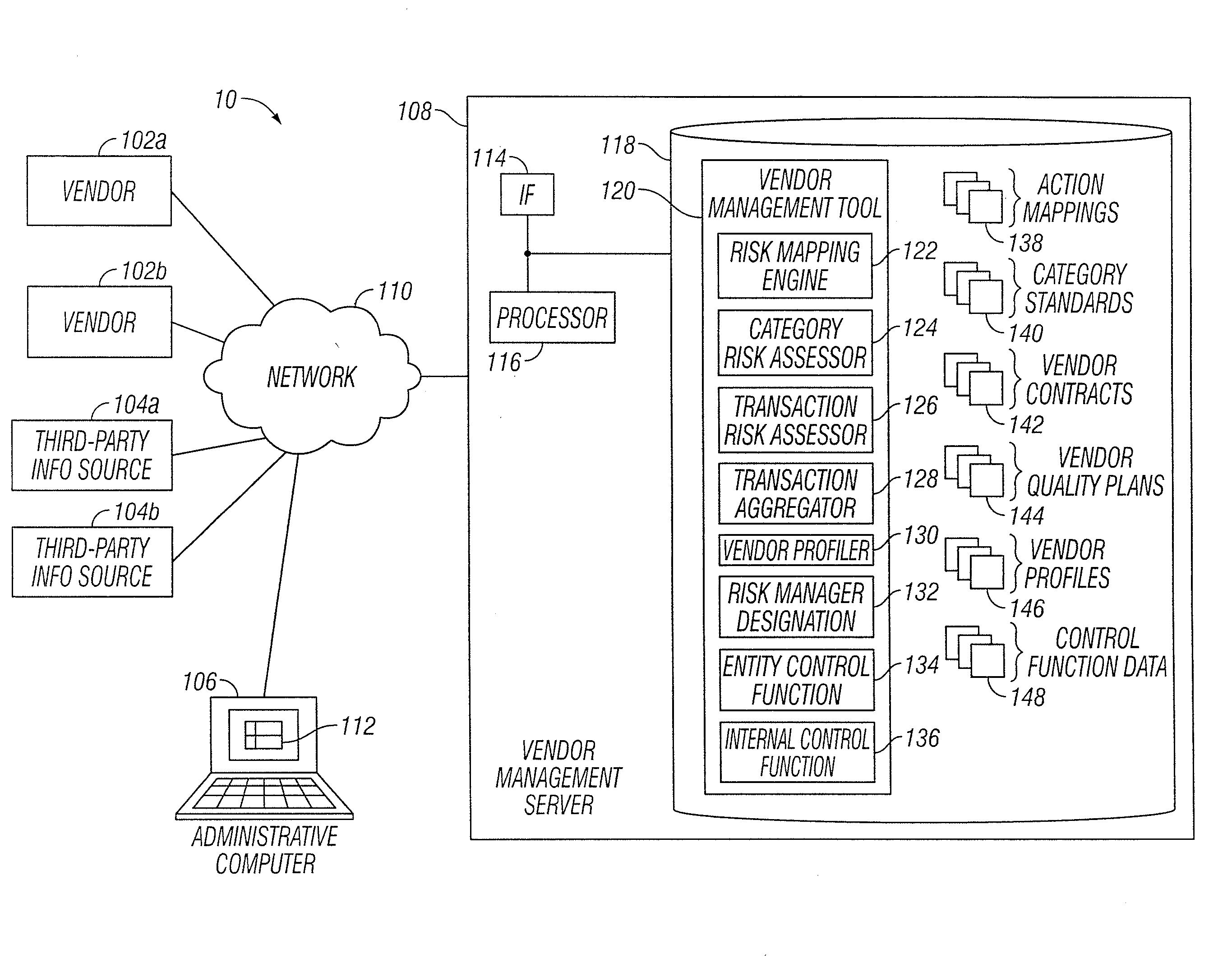
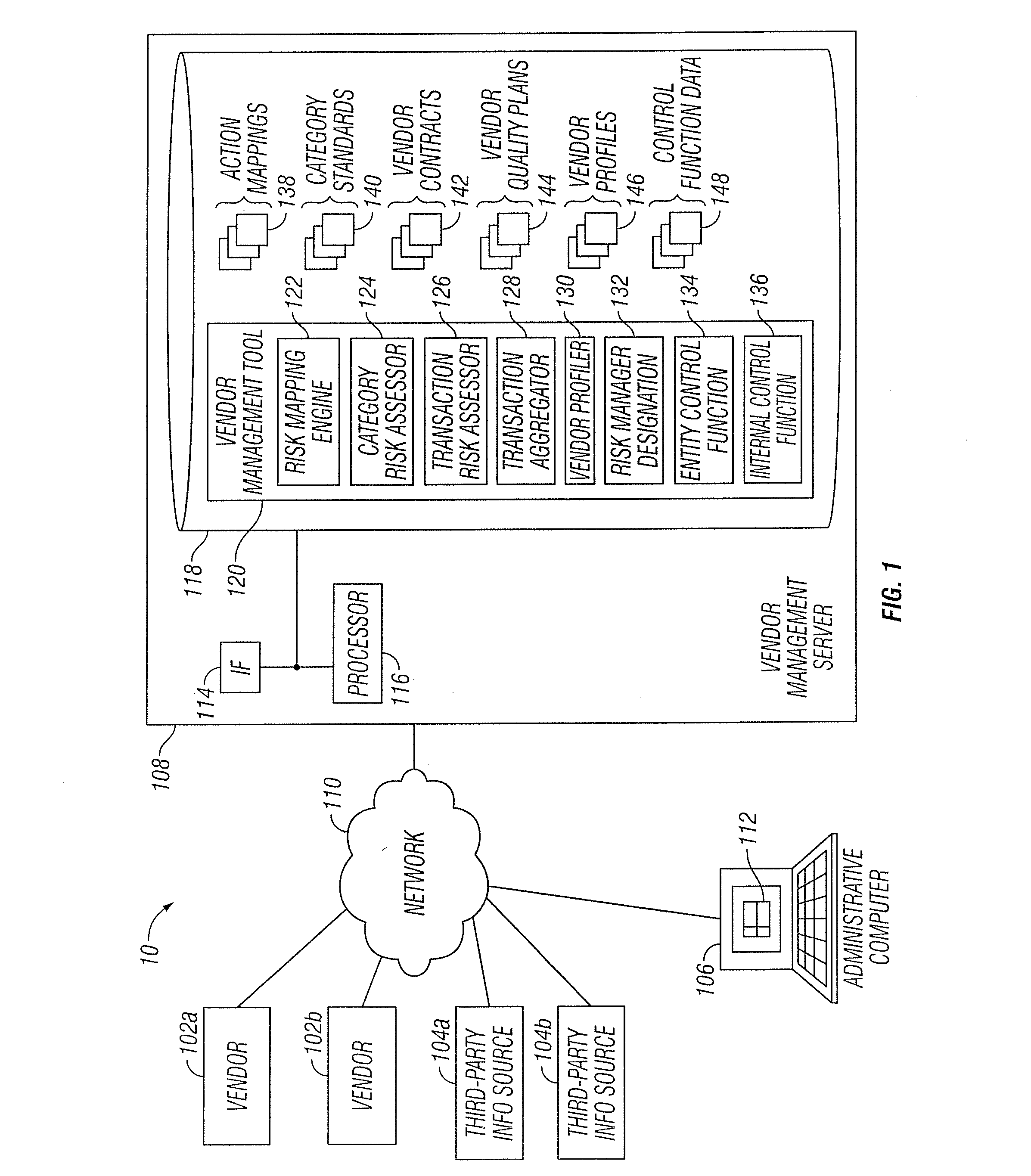
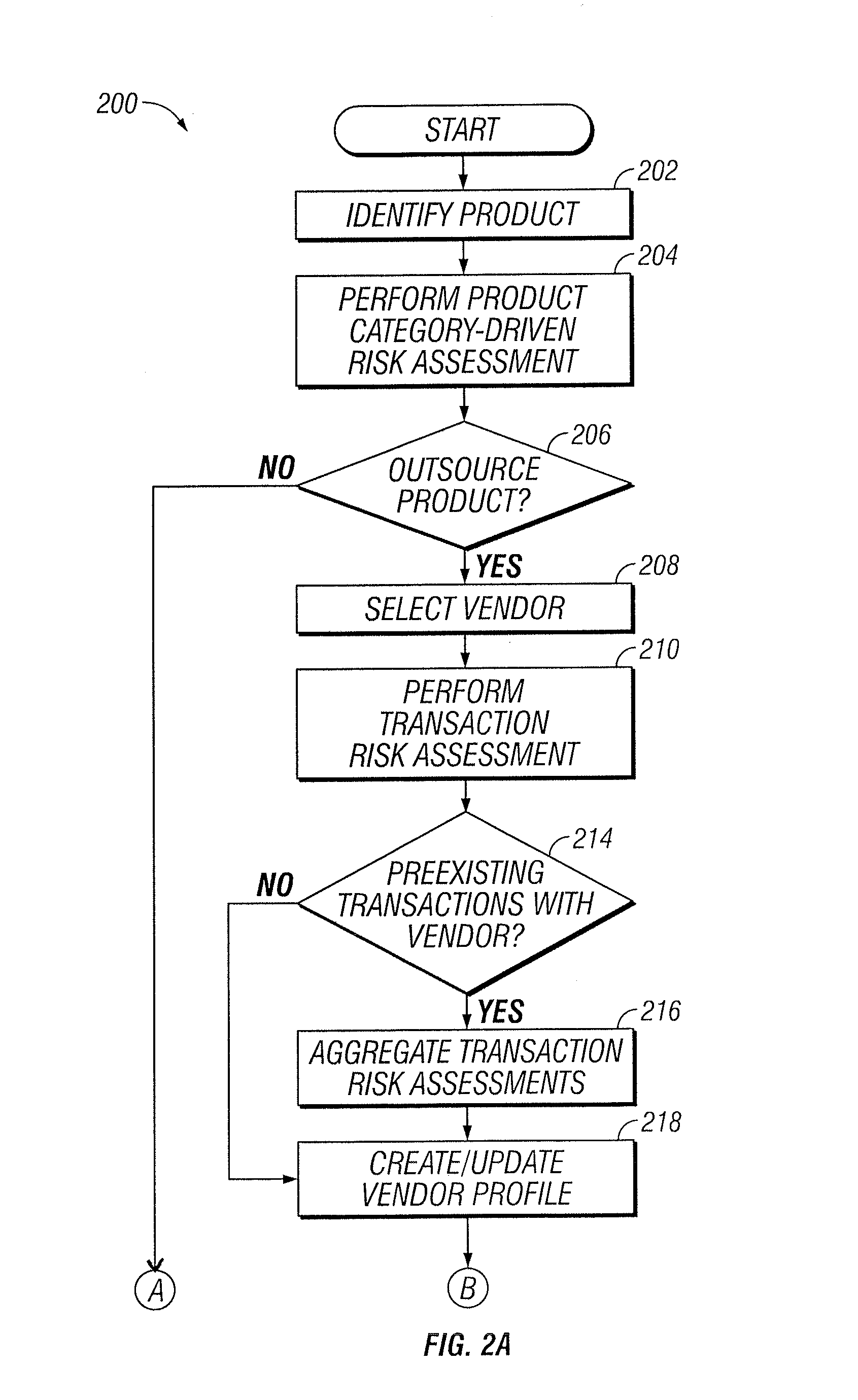
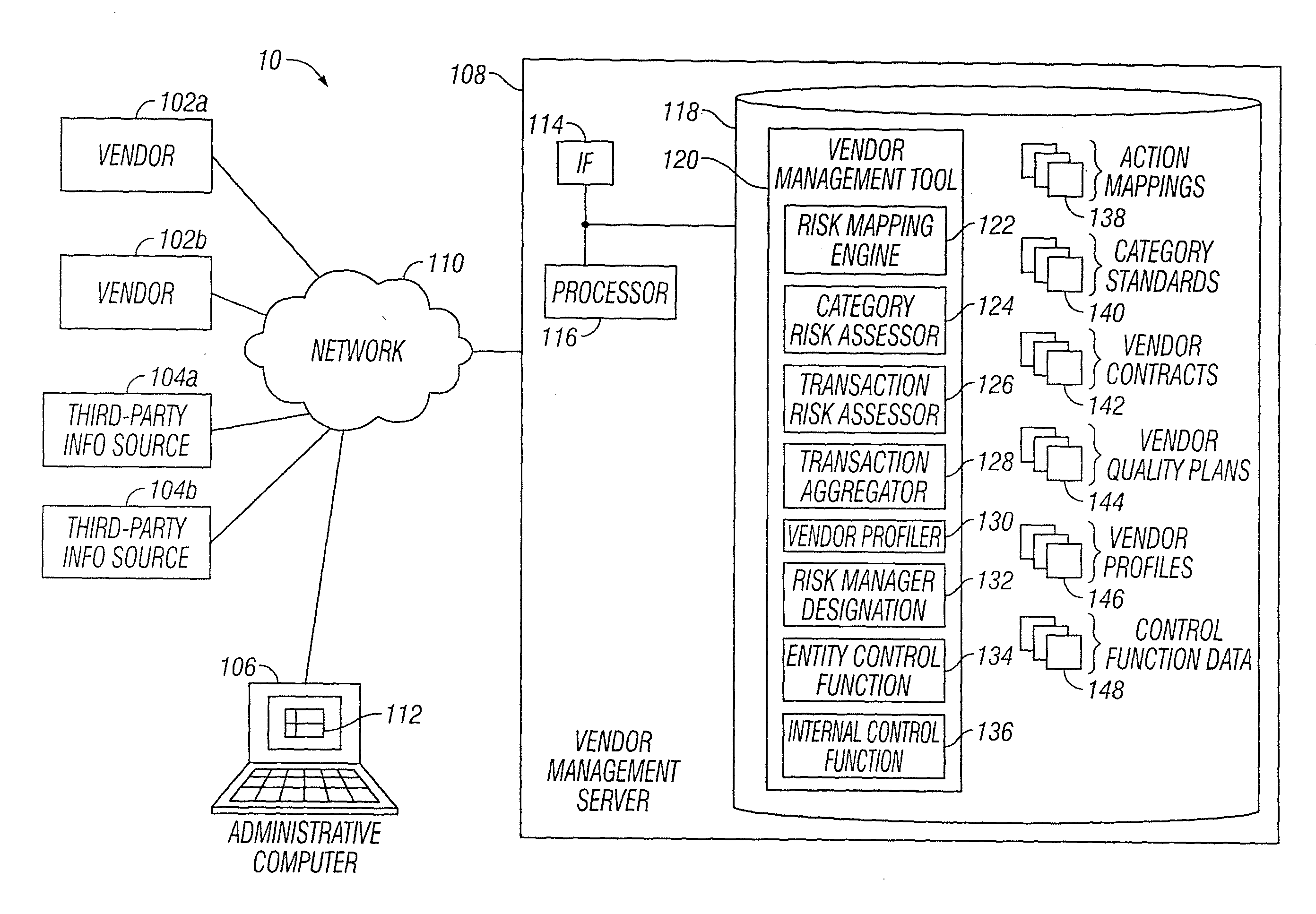
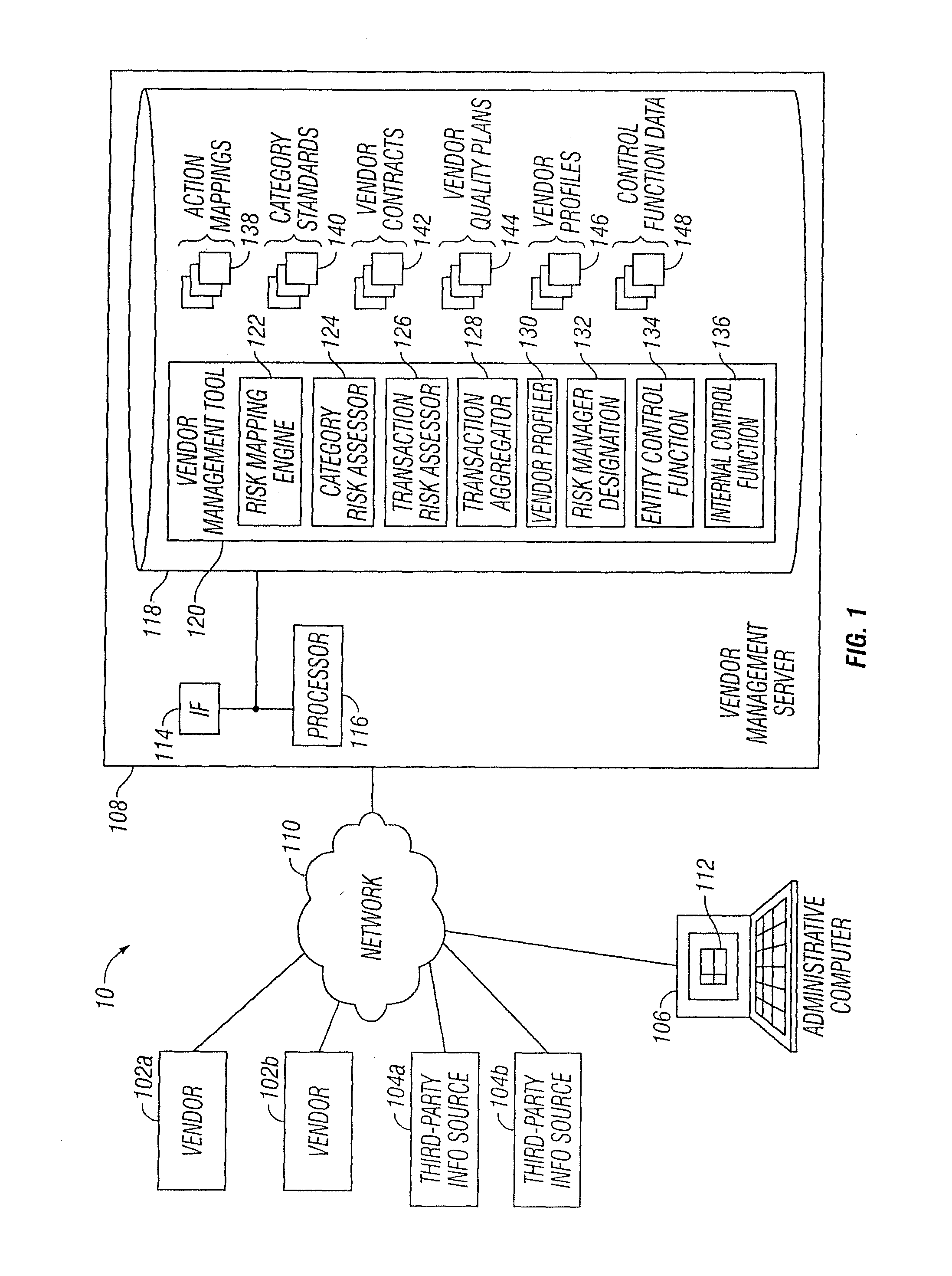
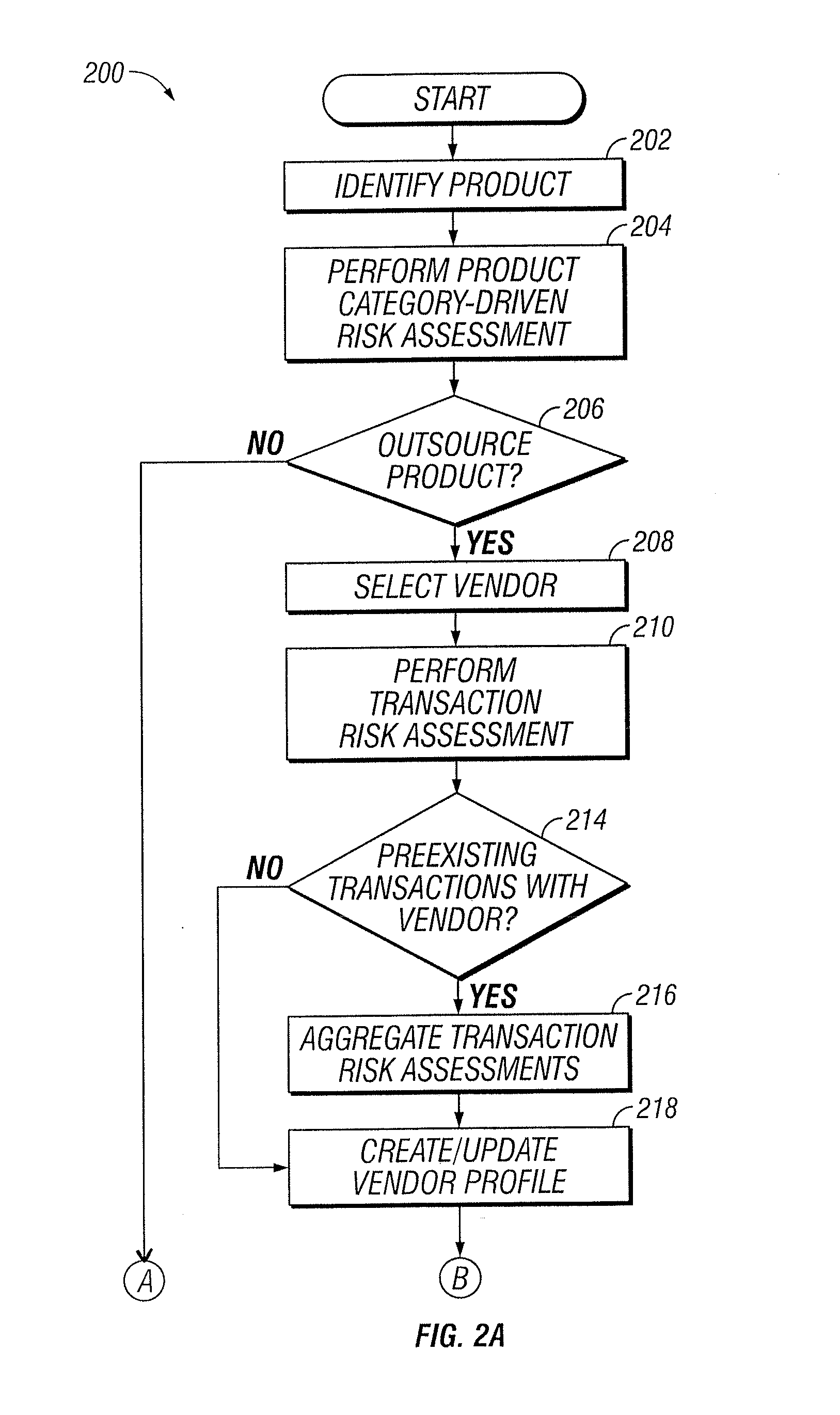
Vendor Management System
InactiveUS20150242778A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedFinanceResourcesDriving riskEngineering
Managing a vendor may comprise identifying a product to be supplied to an entity. Risk elements associated with the product may be determined by performing a product category-driven risk assessment. A transaction level risk assessment is performed for one or more vendors proposed to supply the product to the entity. At least one management action is determined for reducing risk for a risk element of the plurality of risk elements associated with supplying the product to the entity by a selected vendor from a group comprising the one or more vendors proposed to the supply the product to the entity, wherein the at least one management action is determined according to results of the product category-driven risk assessment and the transaction level risk assessment for the selected entity. A vendor level quality plan for the selected vendor is created that comprises the at least one management action.
Owner:BANK OF AMERICA CORP
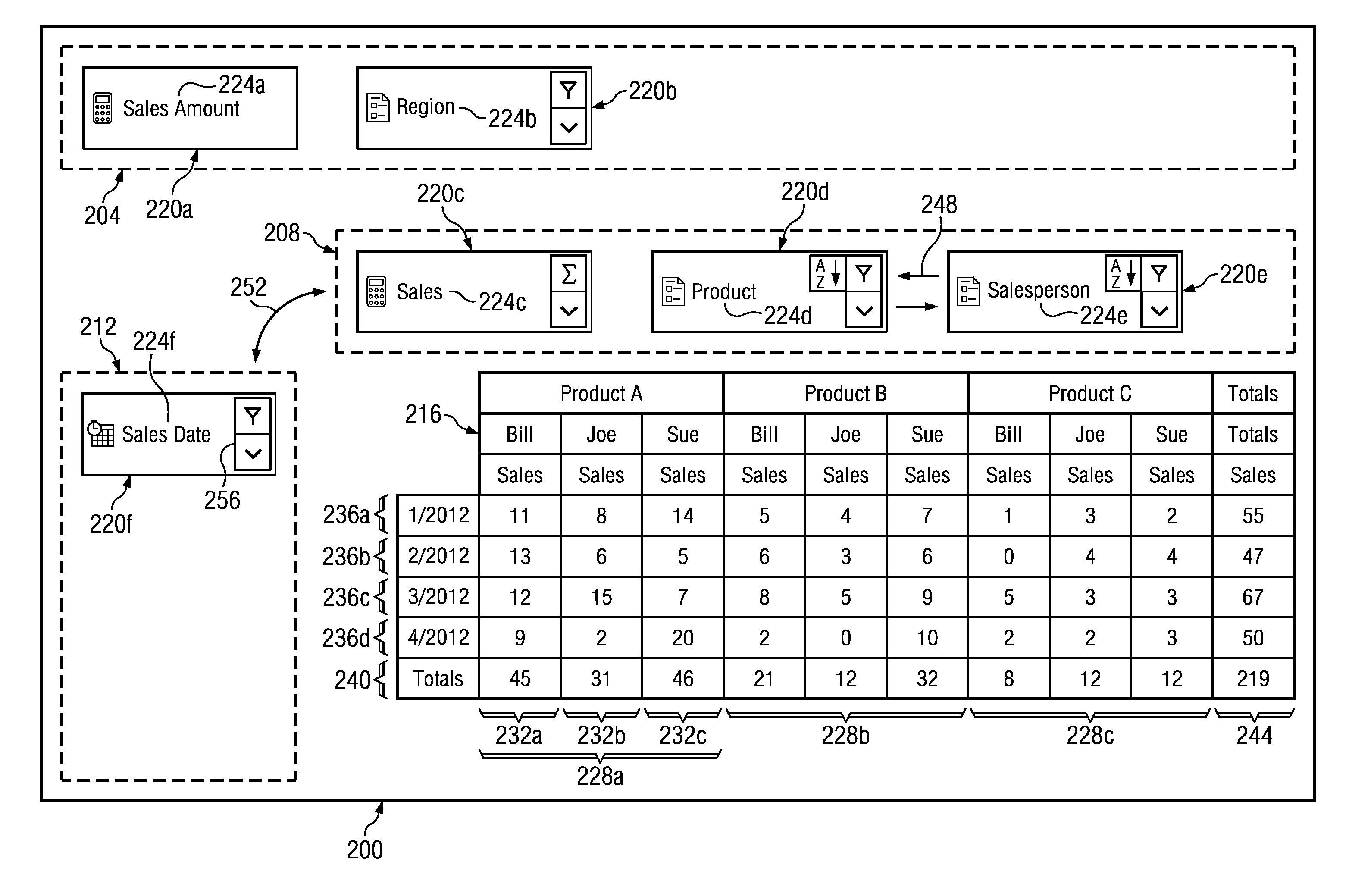
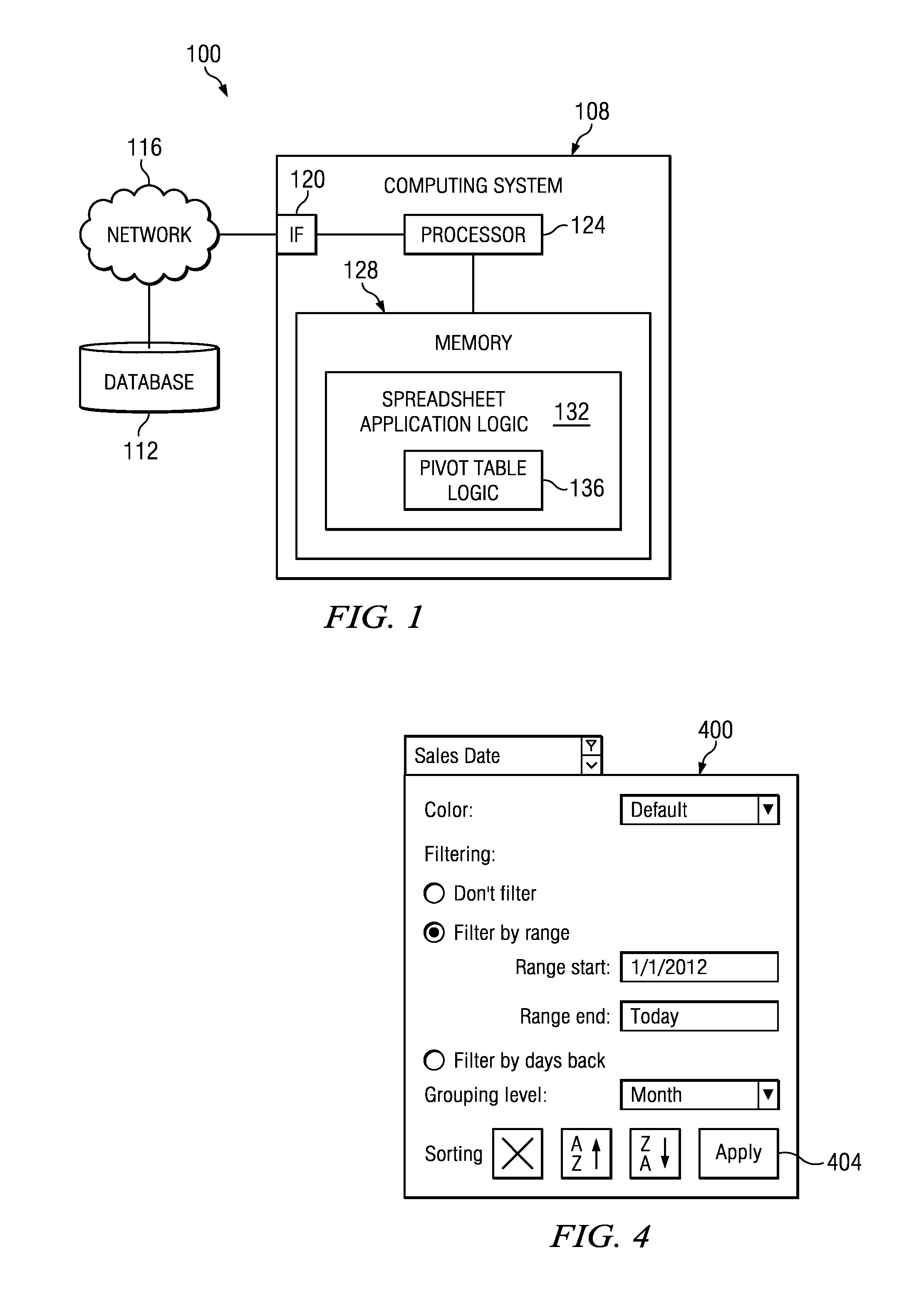
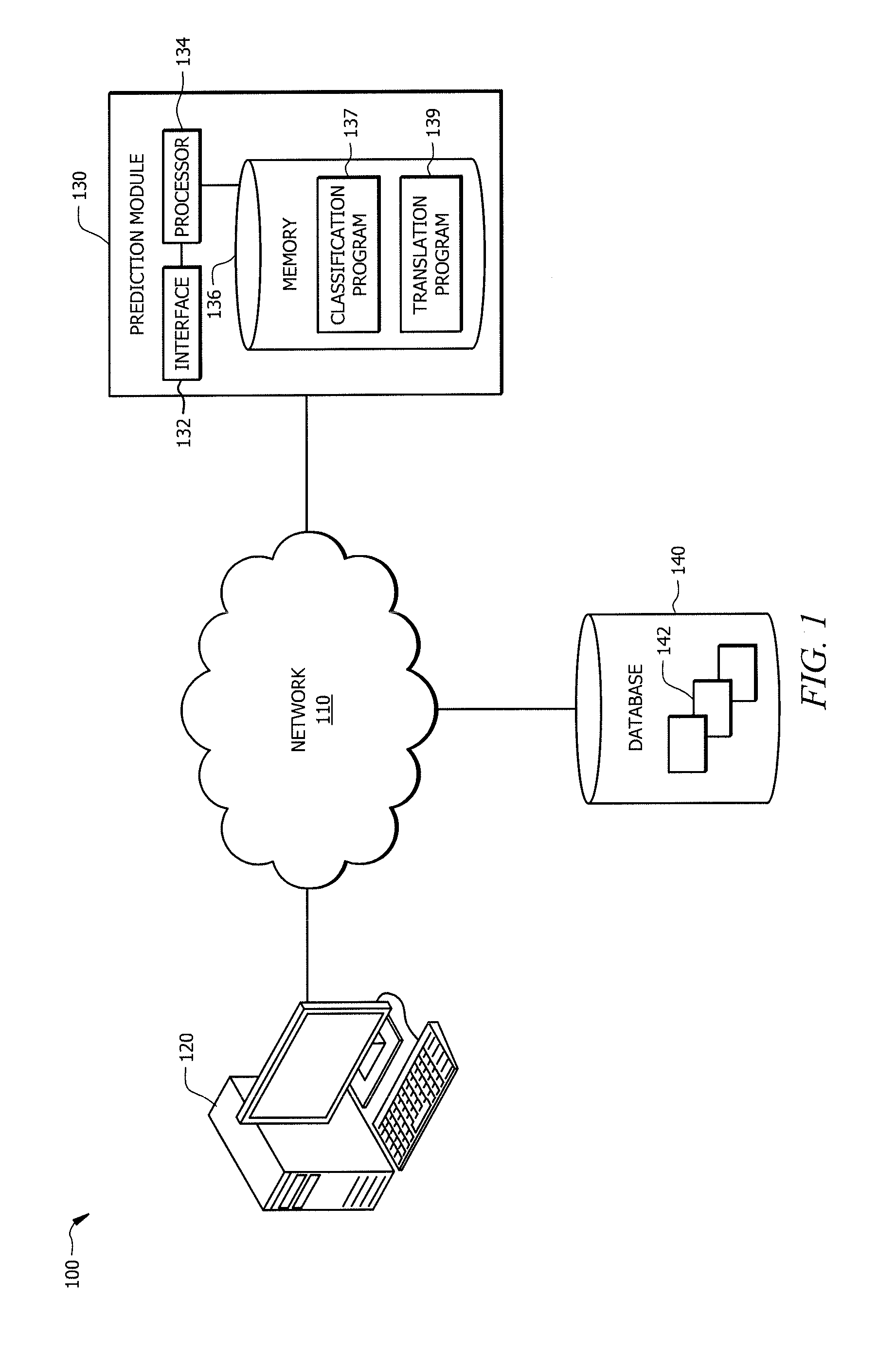
Dynamic Pivot Table Creation and Modification
InactiveUS20140019842A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedText processingSpecial data processing applicationsData setComputer science
In an exemplary embodiment, a method includes determining a plurality of field identifiers of a data set. A plurality of field cells that each correspond to a field identifier of the plurality of field identifiers are generated and displayed within an available fields region. A column field region and a row field region are displayed. A first field cell of the plurality of field cells is moved from the available fields region to the column field region or the row field region in response to a first input from a user. The pivot table is updated to include one or more rows or columns corresponding to the first field cell upon detection of the movement of the first field cell to the column field region or the row field region.
Owner:BANK OF AMERICA CORP
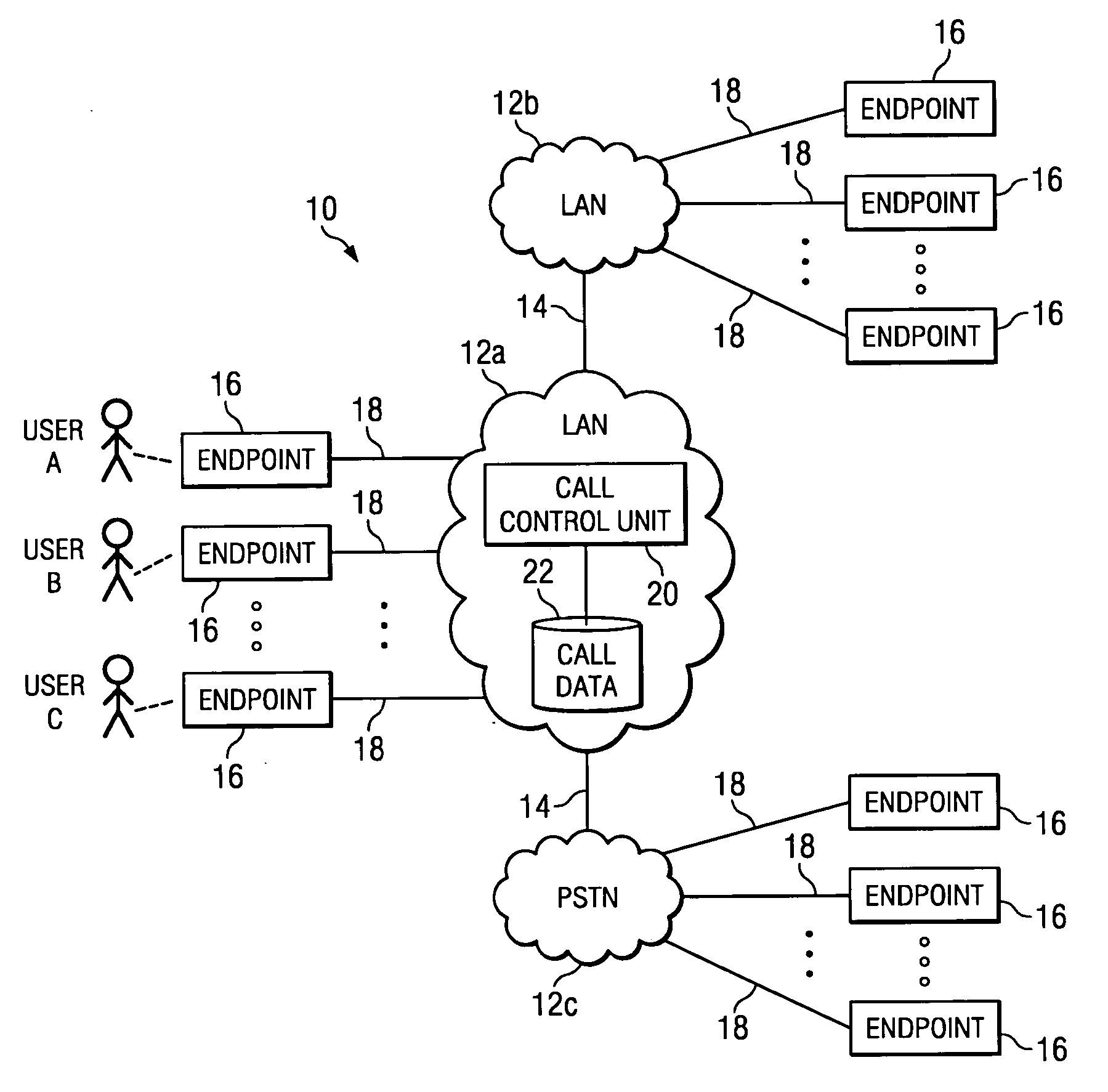
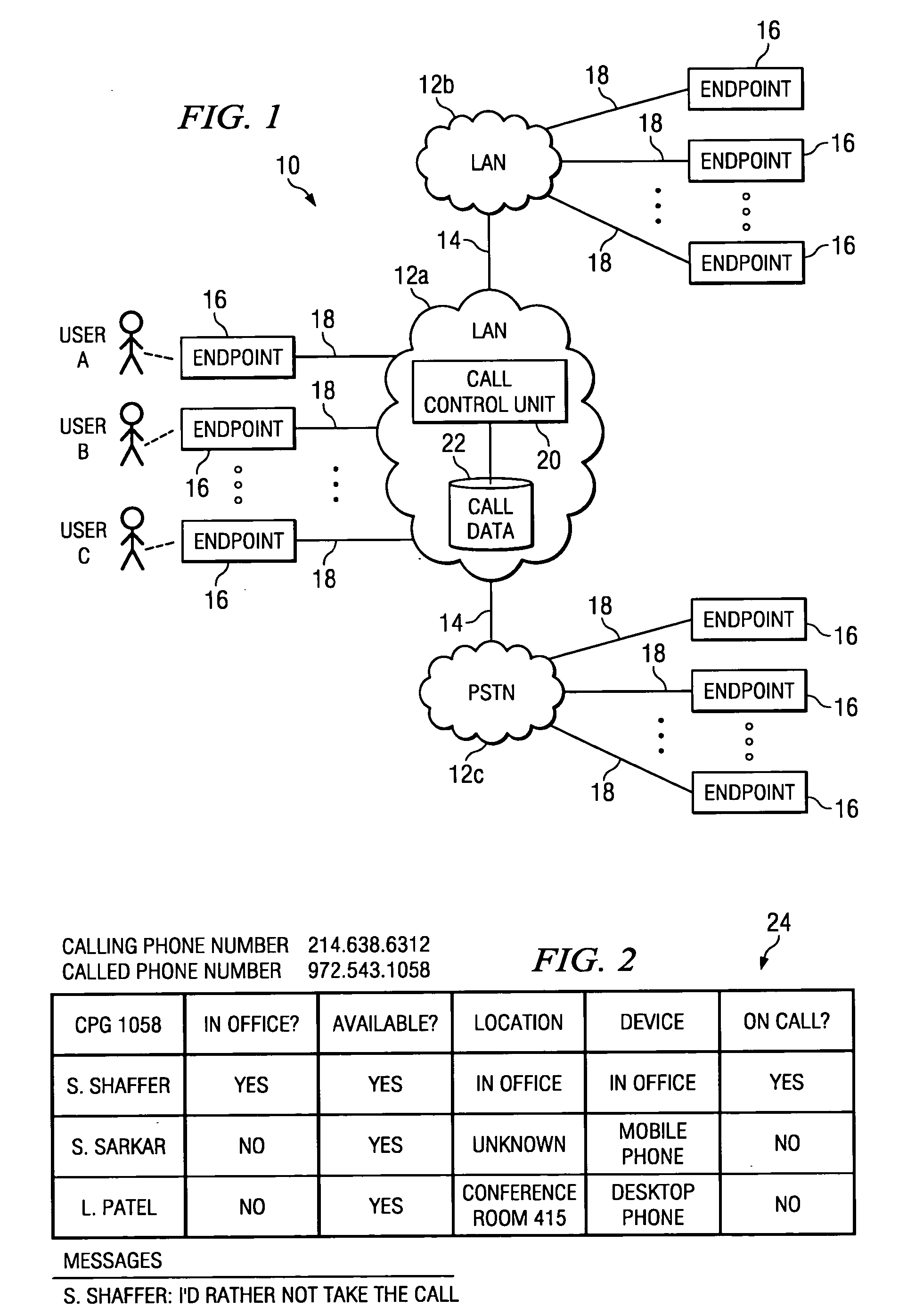
Enhanced call pickup
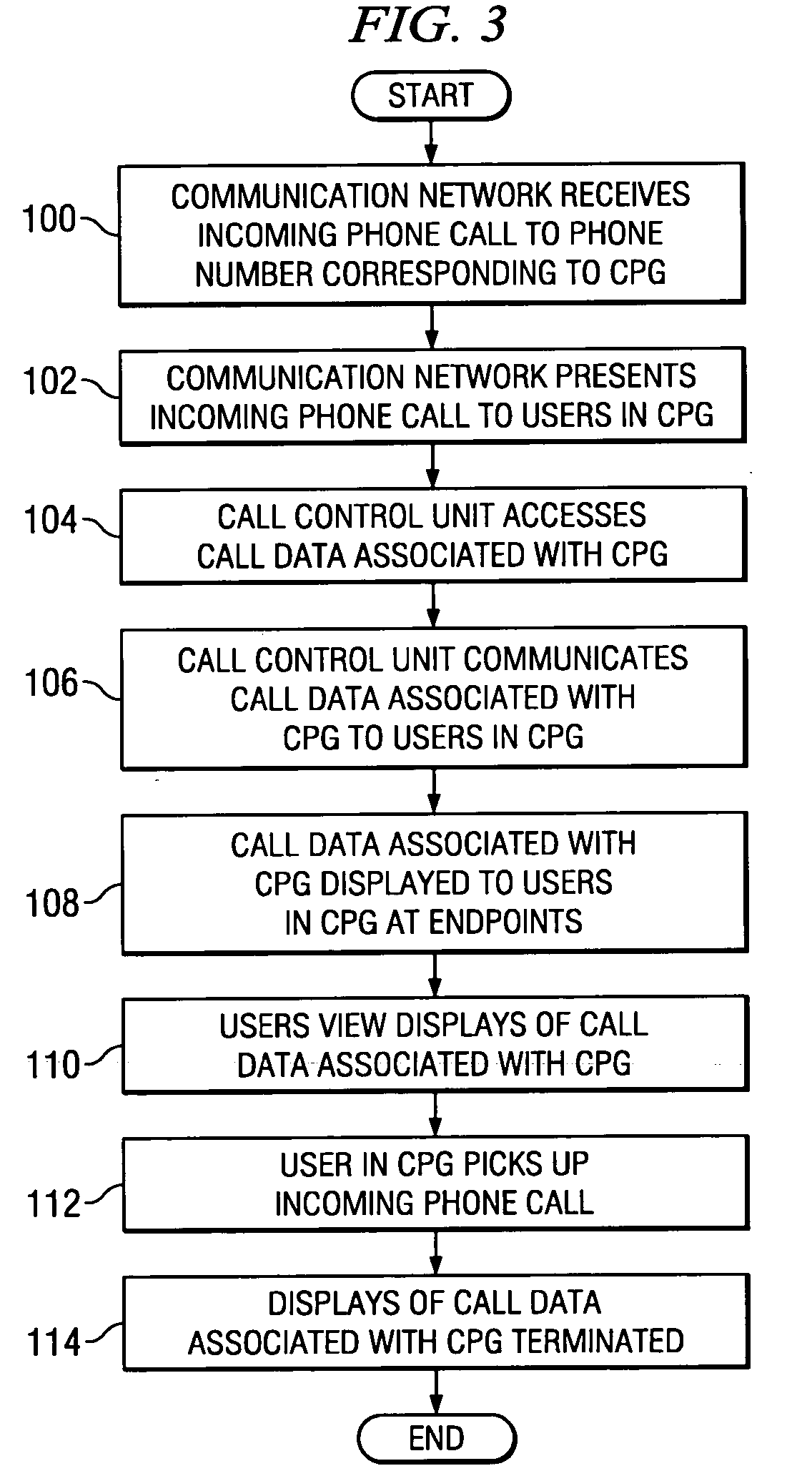
InactiveUS20050238157A1Enhanced call pickupFacilitate decision-makingInterconnection arrangementsSpecial service for subscribersWorld Wide WebTelephony
In one embodiment, a method for enhanced call pickup includes accessing data indicating a current status of each of one or more users in a call pickup group (CPG) with respect to an incoming phone call to a phone number corresponding to the CPG and communicating the data to one or more endpoints of one or more users in the CPG for display to one or more users in the CPG. A display of the data to a first user in the CPG facilitates the first user determining a current status of each of one or more second users in the CPG to facilitate a decision by the first user regarding whether to pick up the incoming phone call.
Owner:CISCO TECH INC
Adjustable Breathing Device
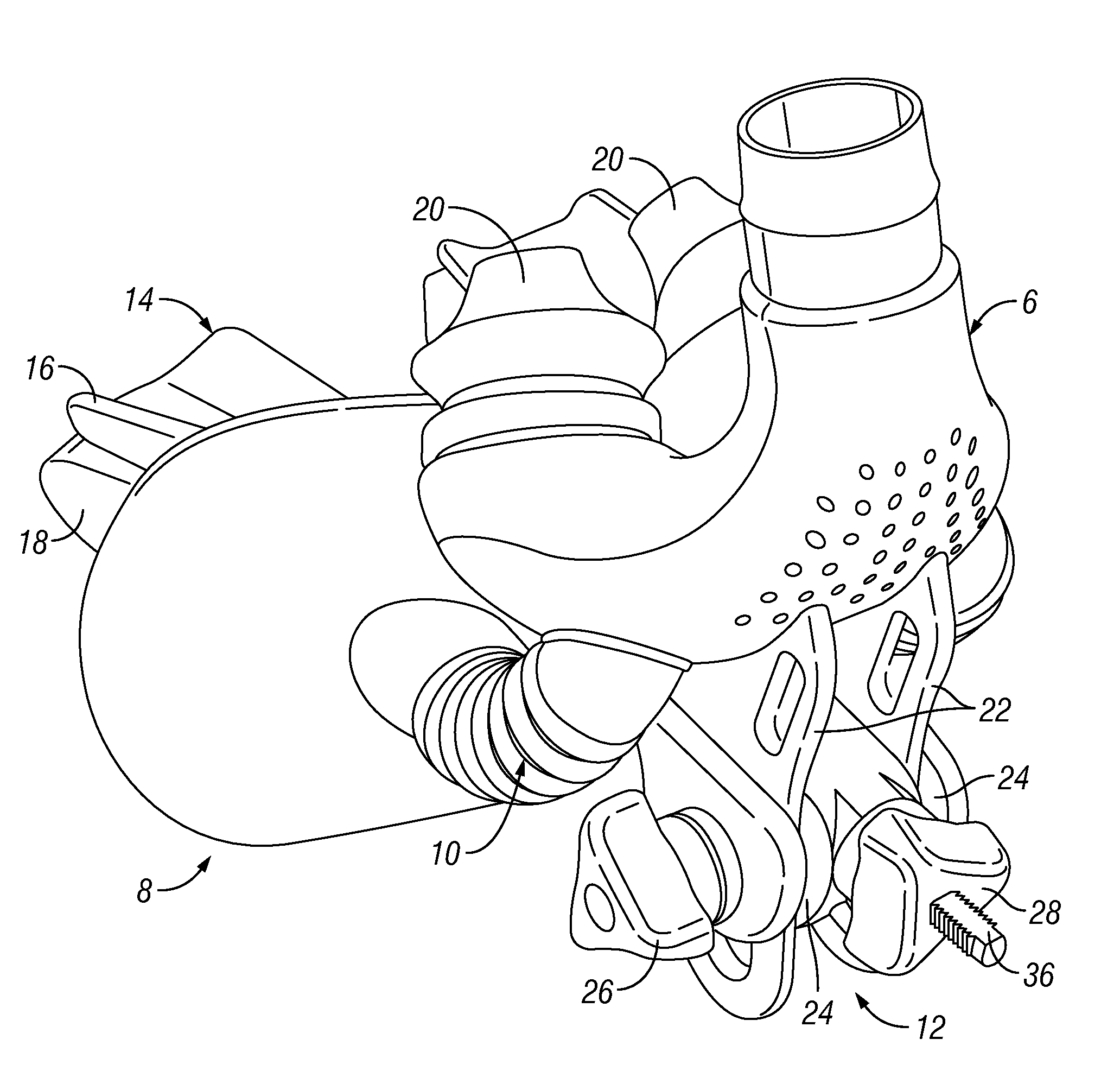
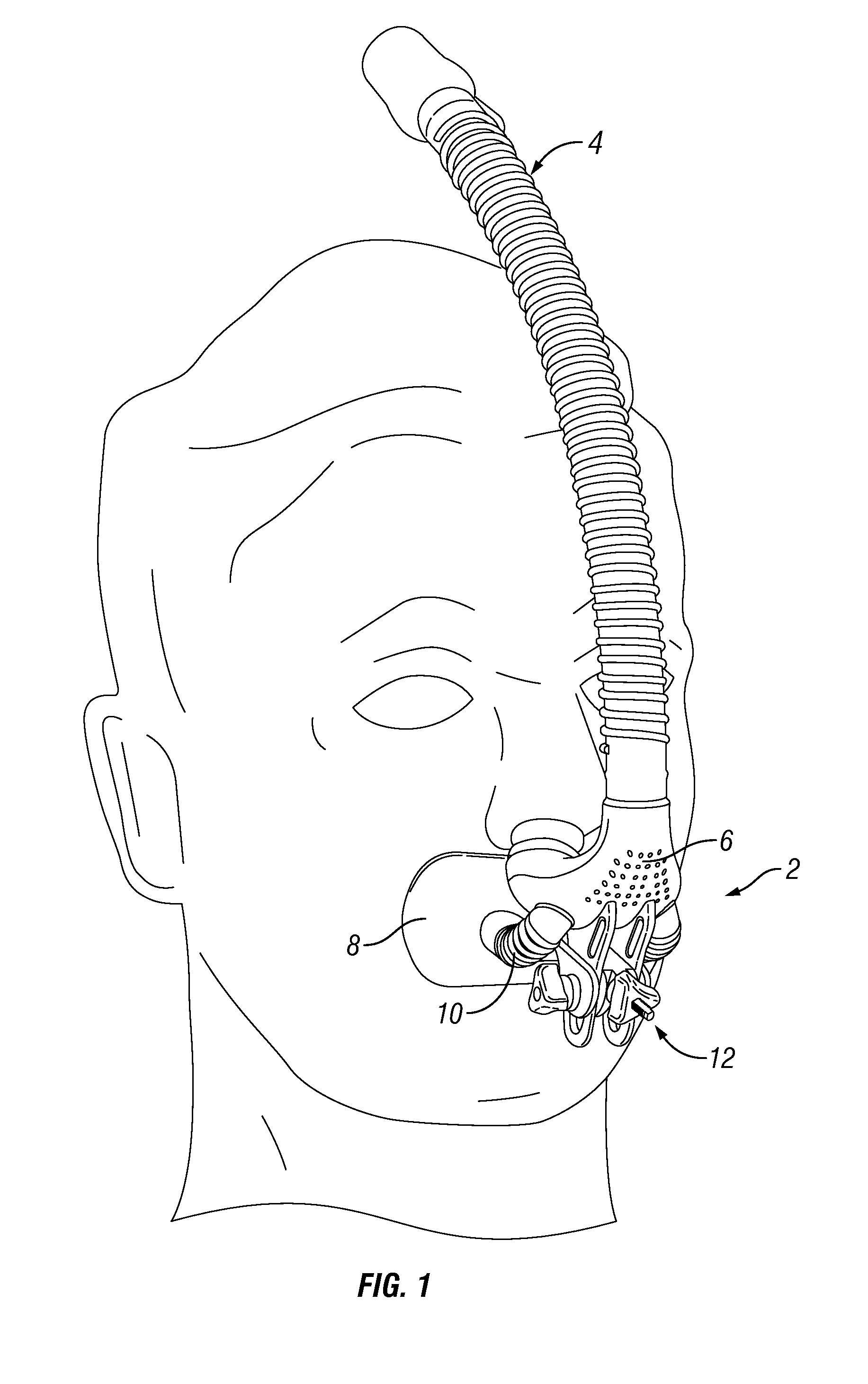
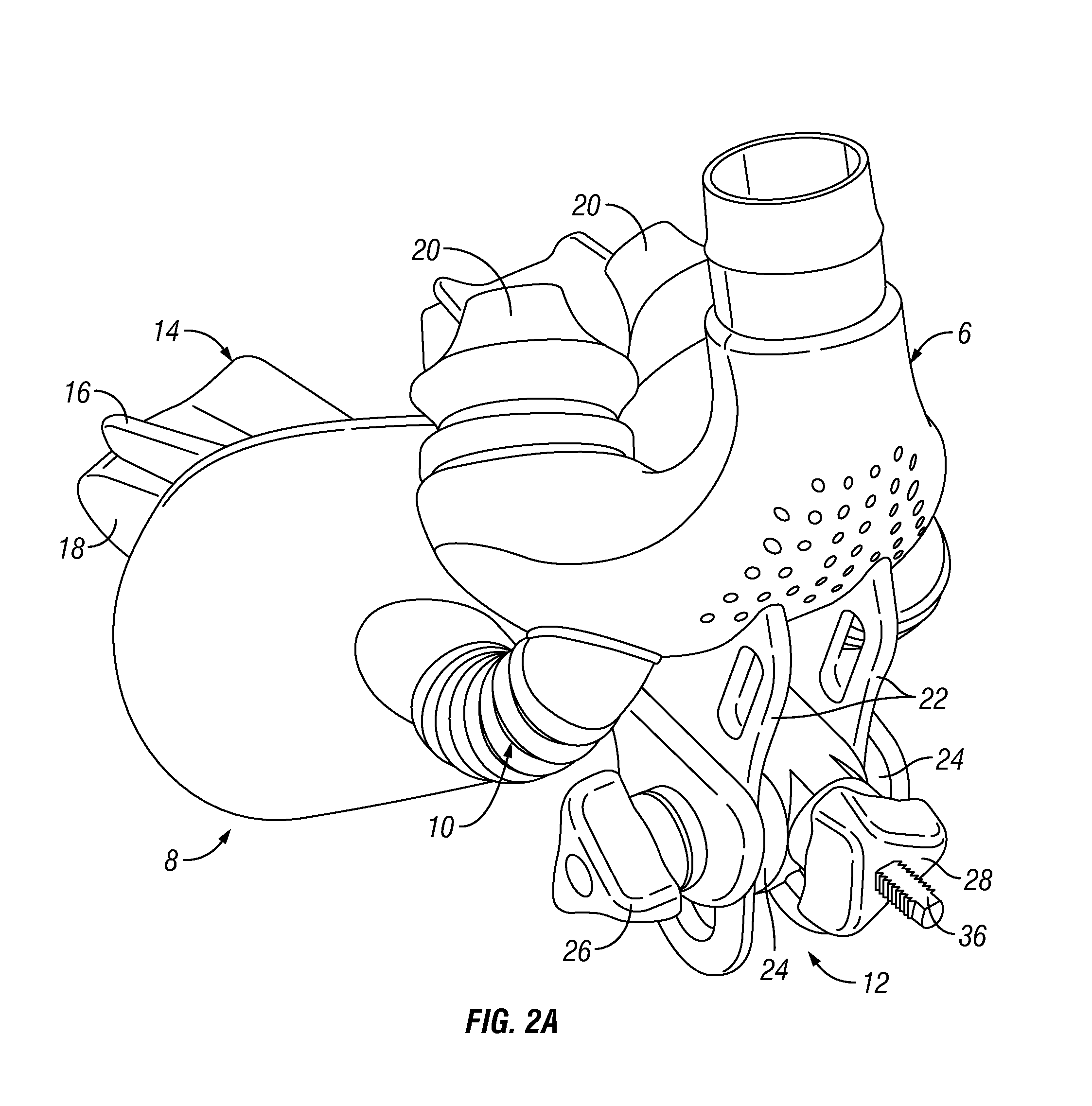
PendingUS20140290668A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedRespiratory masksBreathing masksInterior spaceNose
According to one embodiment, a breathing device includes an oral appliance arch, a post, and first and second masks that are separately adjustable relative to the oral appliance arch. The first mask defines a first interior space and is configured to deliver gas to a user's nose when the first mask is connected to a gas delivery device. The second mask defines a second interior space and is configured to be adjustably secured to the post and to form a substantial seal around the user's oral cavity when pressed against a portion of the user's mouth. The post is coupled to the oral appliance arch and is configured to adjustably secure the first mask relative to the oral appliance arch.
Owner:AIRWAY TECH
System and method for dynamic pricing in an unbalanced market
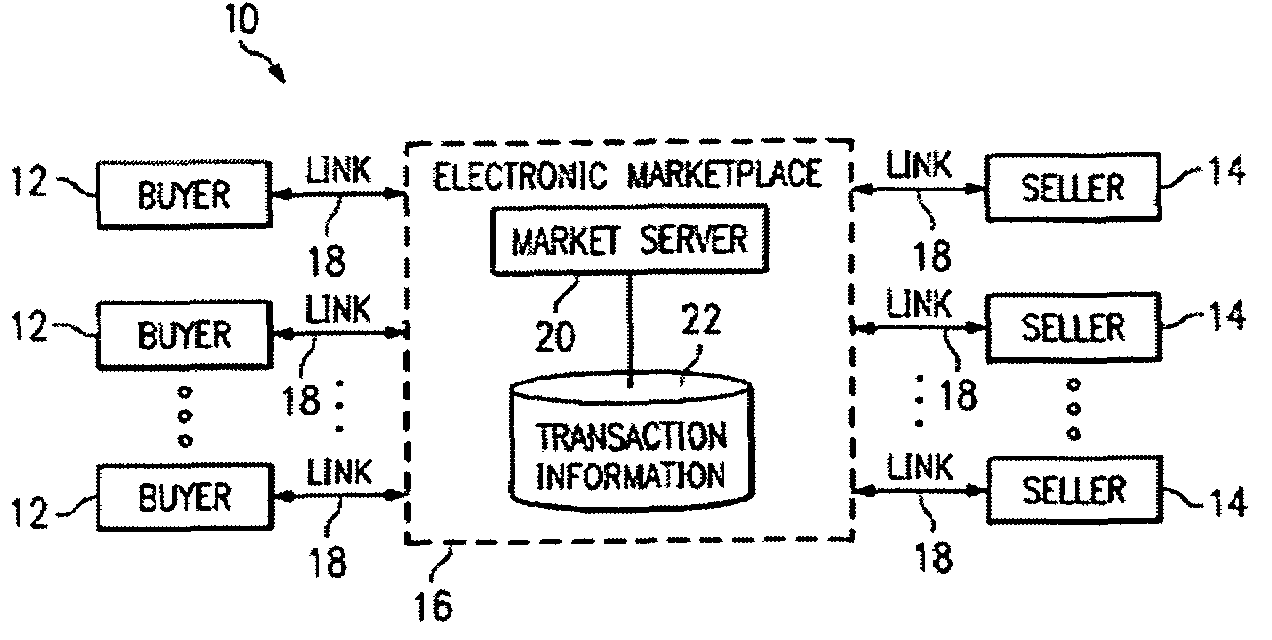
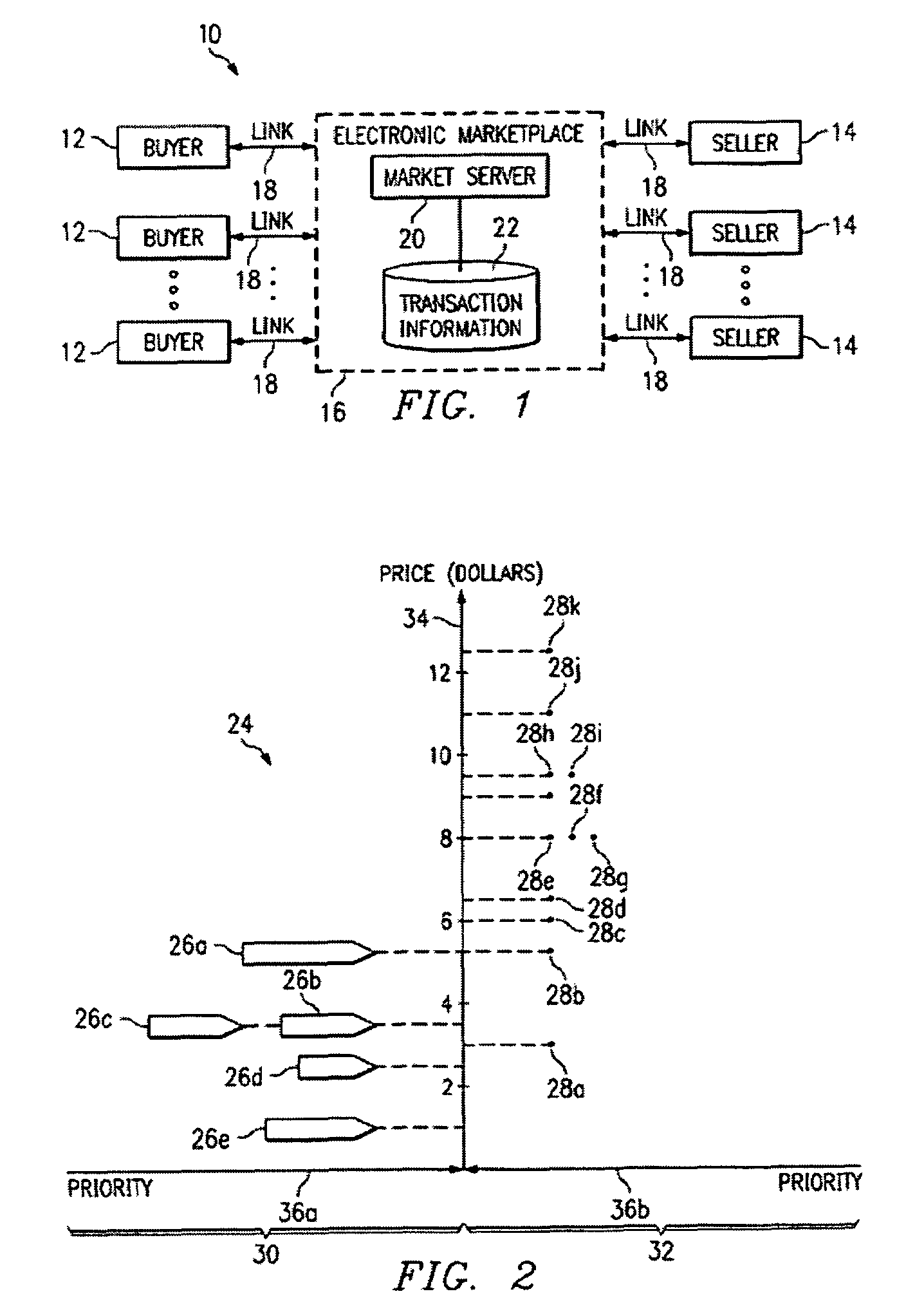
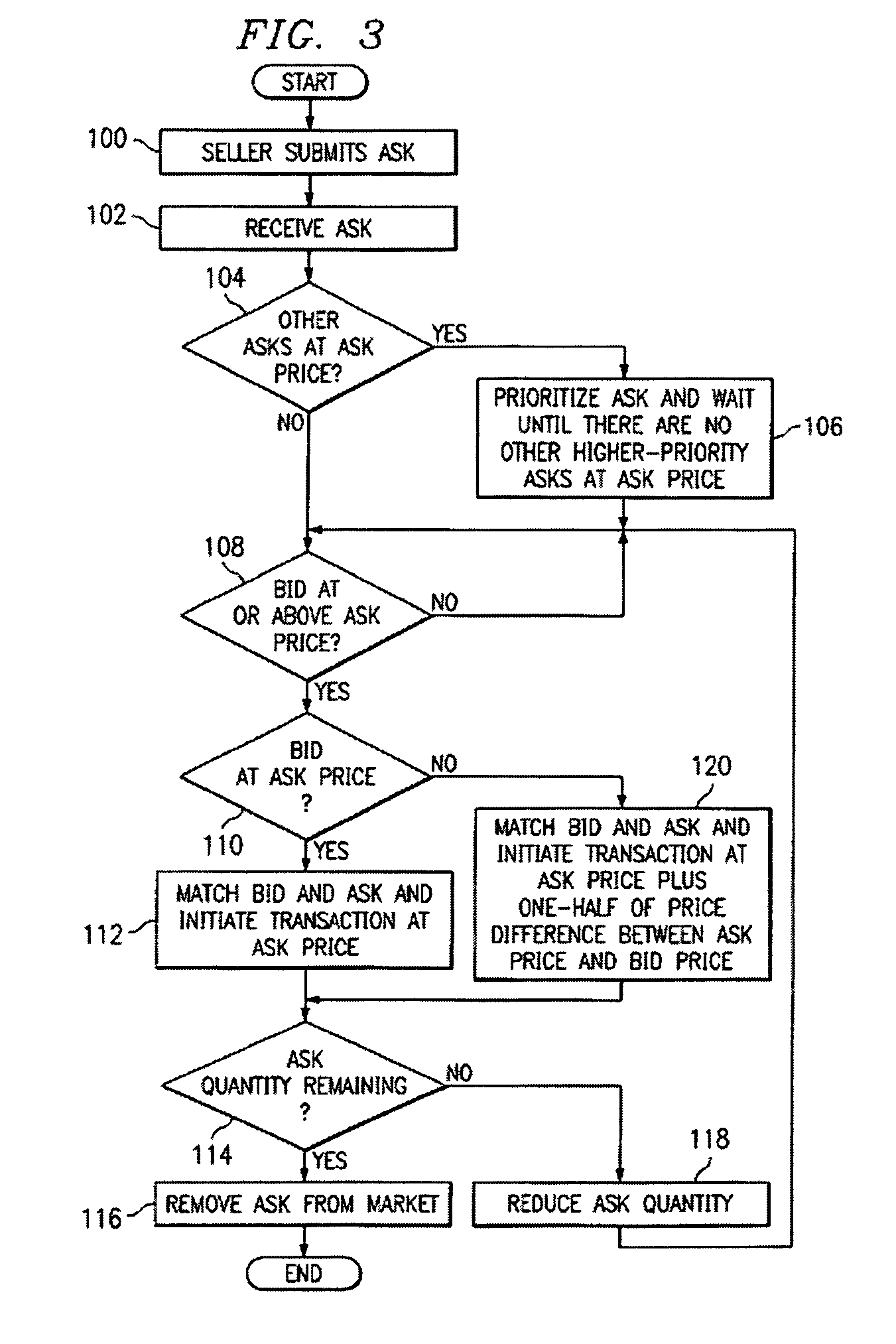
InactiveUS7562044B1Disadvantages can be reduced eliminatedProblems be reduced eliminatedFinanceBuying/selling/leasing transactionsBalancing marketComputer science
Owner:BLUE YONDER GRP INC
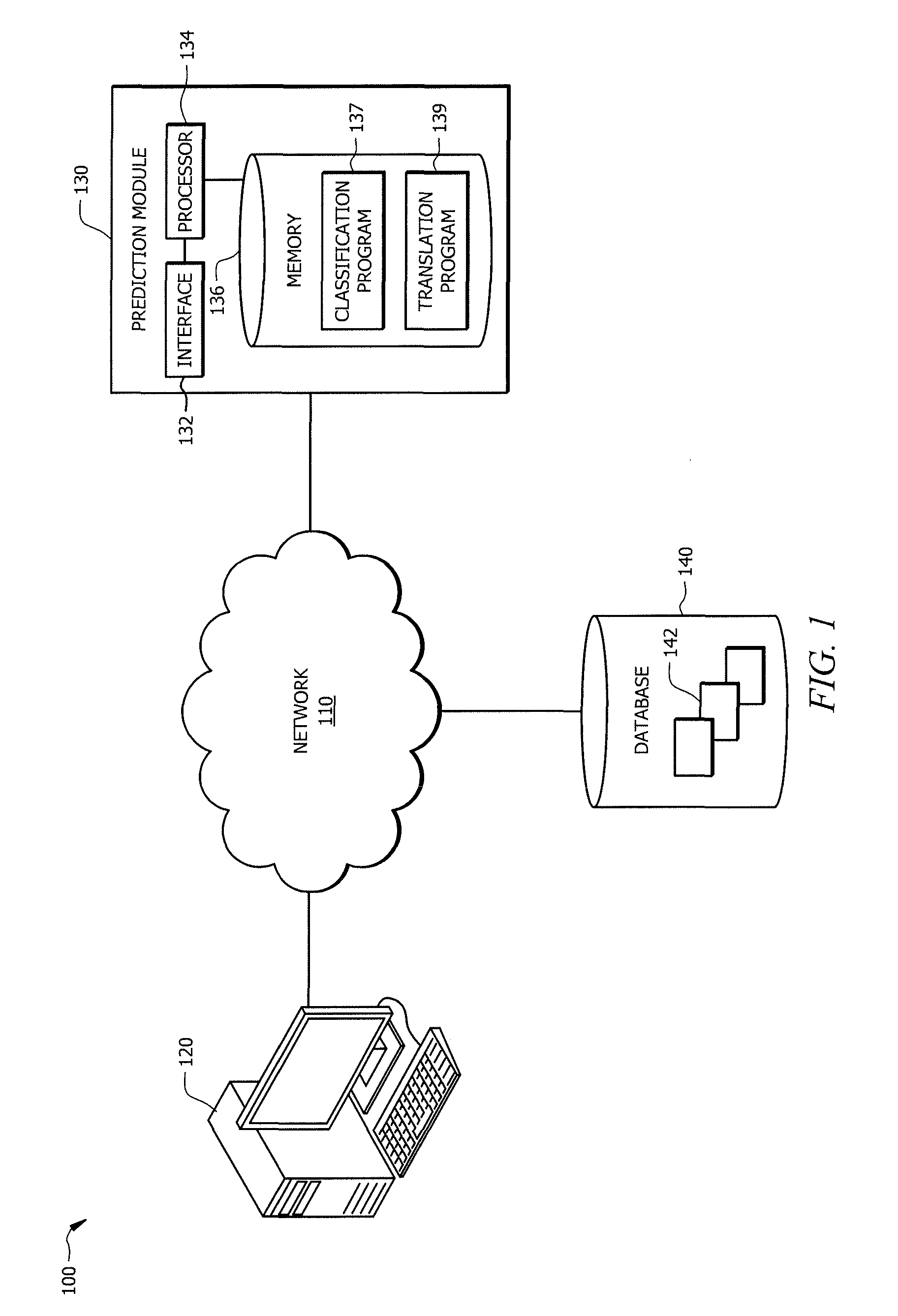
Enhancing classification and prediction using predictive modeling
ActiveUS9171259B1Increasing running timeIncreasing computational resourceEnsemble learningDigital computer detailsData setPredictive modelling
In one embodiment, a system for enhancing predictive modeling includes an interface operable to receive a first dataset. The system may also include a processor communicatively coupled to the interface that is operable to generate a holdout dataset based on the first dataset. The processor may also train each of a plurality of boosting models in parallel using the first dataset, wherein for each of a number of iterations, training comprises: building a one-level binary decision tree to train a split-node variable; calculating an impurity of the split-node variable; and calculating an optimal split node, wherein the optimal split node is the split-node variable with a lowest impurity between the plurality of boosting models. The system may then determine a final model based on one of the plurality of boosting models that provides the lowest error rate when applied to the holdout dataset.
Owner:BANK OF AMERICA CORP
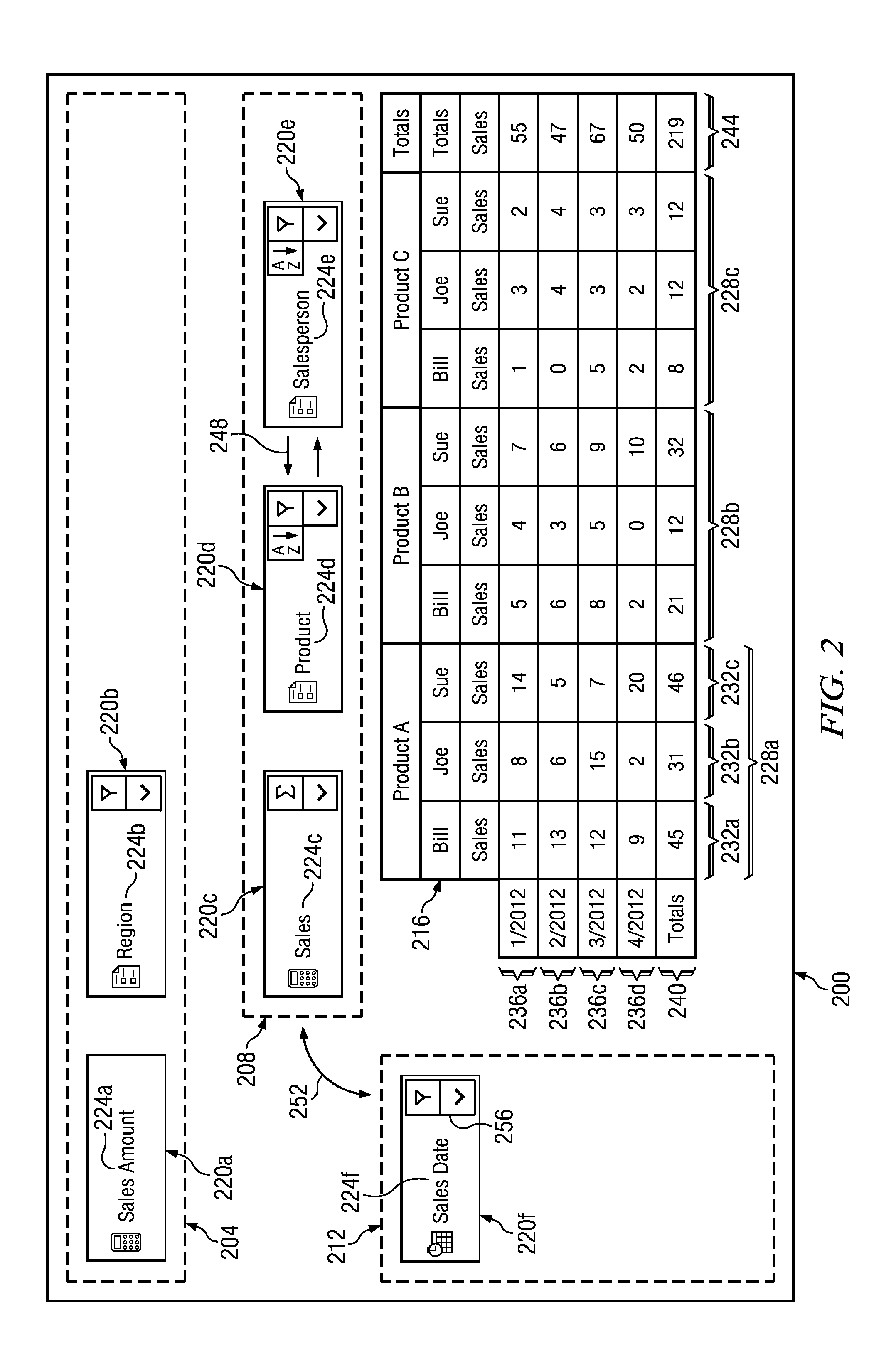
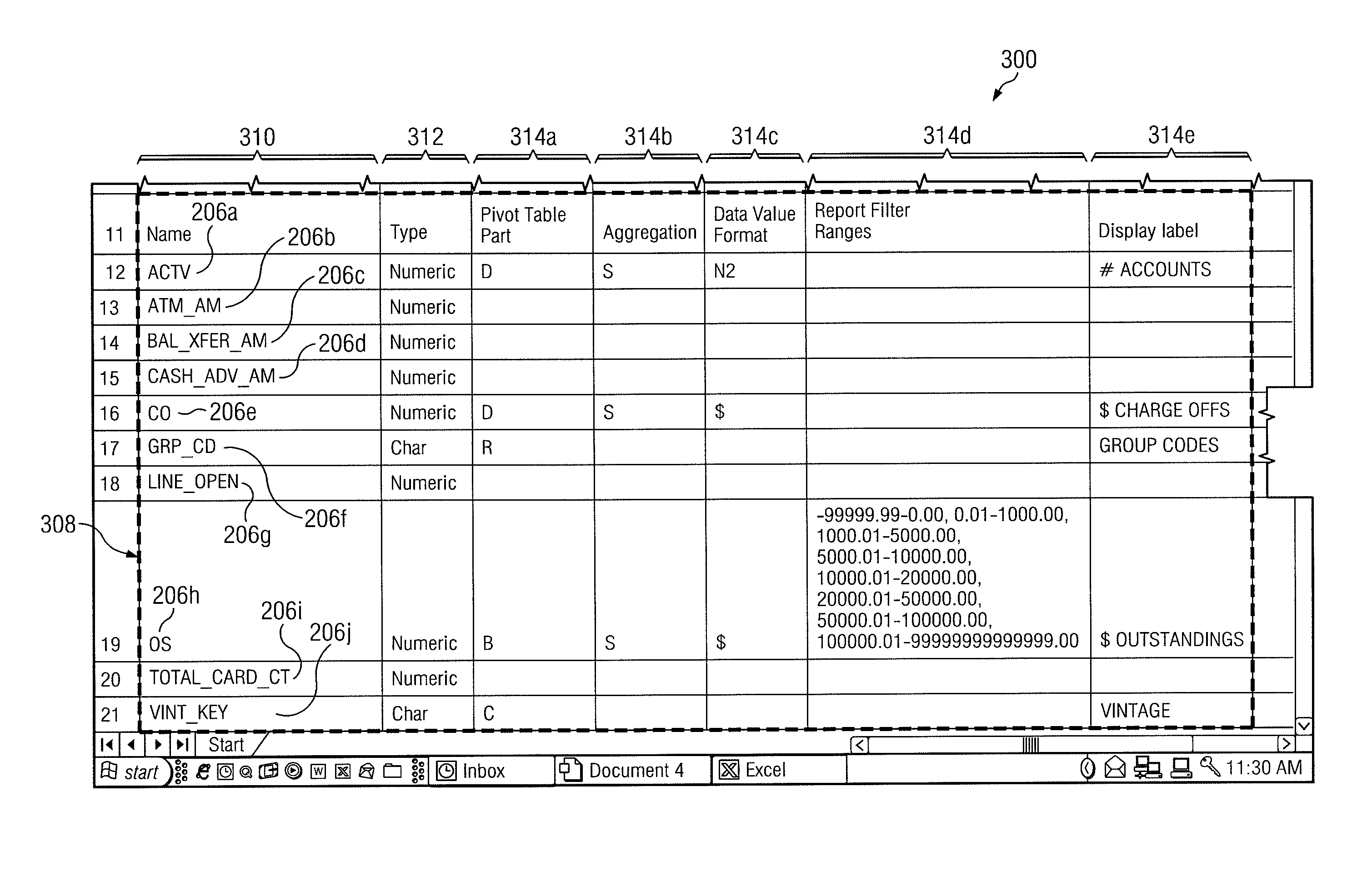
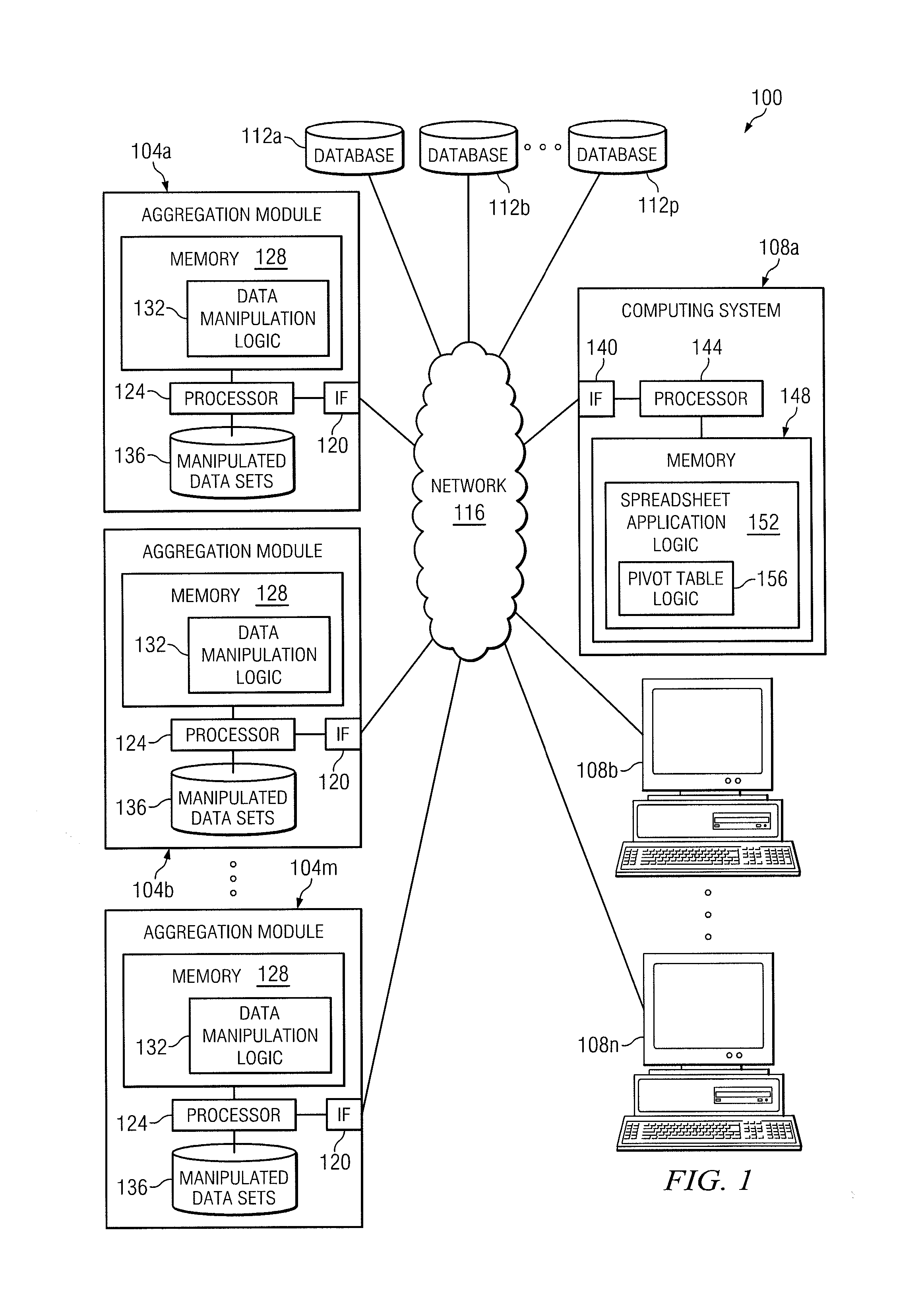
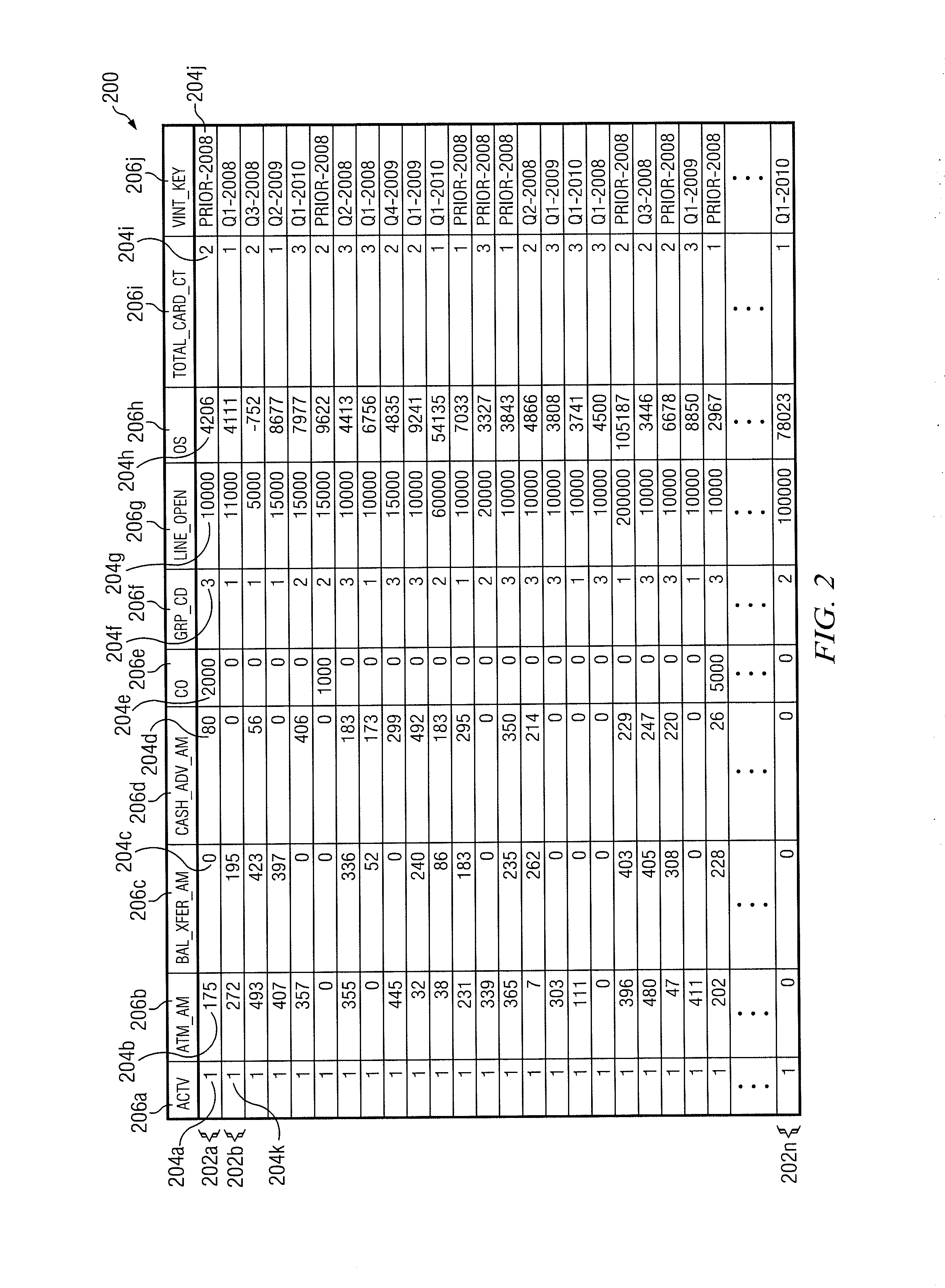
Generating A Pivot Table From An Aggregated Data Set
InactiveUS20130179443A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedDigital data information retrievalDigital data processing detailsData setData value
In an exemplary embodiment, a method includes receiving a request to access a data set comprising a plurality of data entries. A data entry comprises one or more data values that are each associated with a field identifier of a plurality of field identifiers. The method may further include, determining the plurality of field identifiers of the data set. A plurality of formatting preferences associated with the plurality of field identifiers may be received. A request to generate a first aggregated data set comprising an aggregation of two or more data entries of the plurality of data entries may be communicated. The aggregation may be based on the plurality of formatting preferences. A pivot table may be generated according to the formatting preferences and the aggregated data set. The first pivot table may comprise at least one column field, a plurality of row fields, and a plurality of table entries.
Owner:BANK OF AMERICA CORP
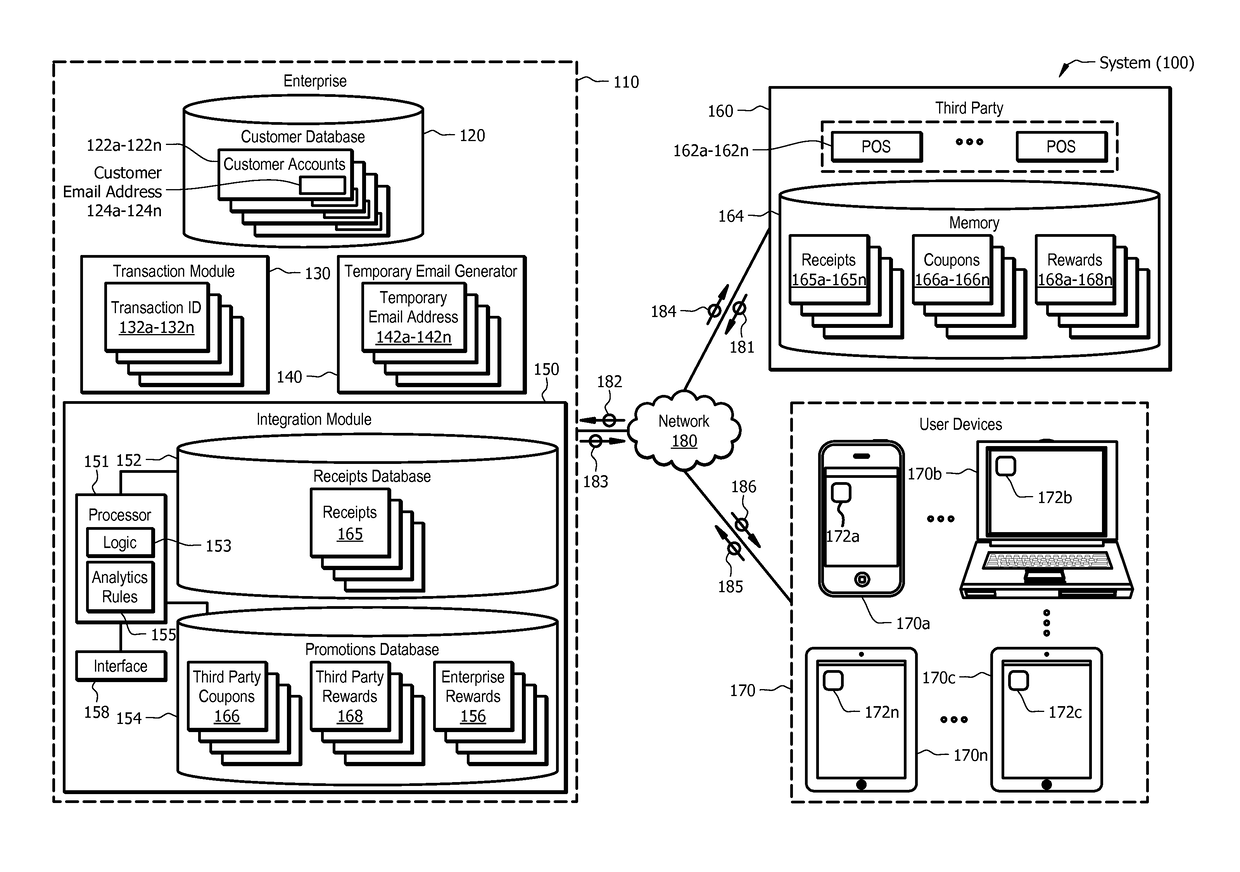
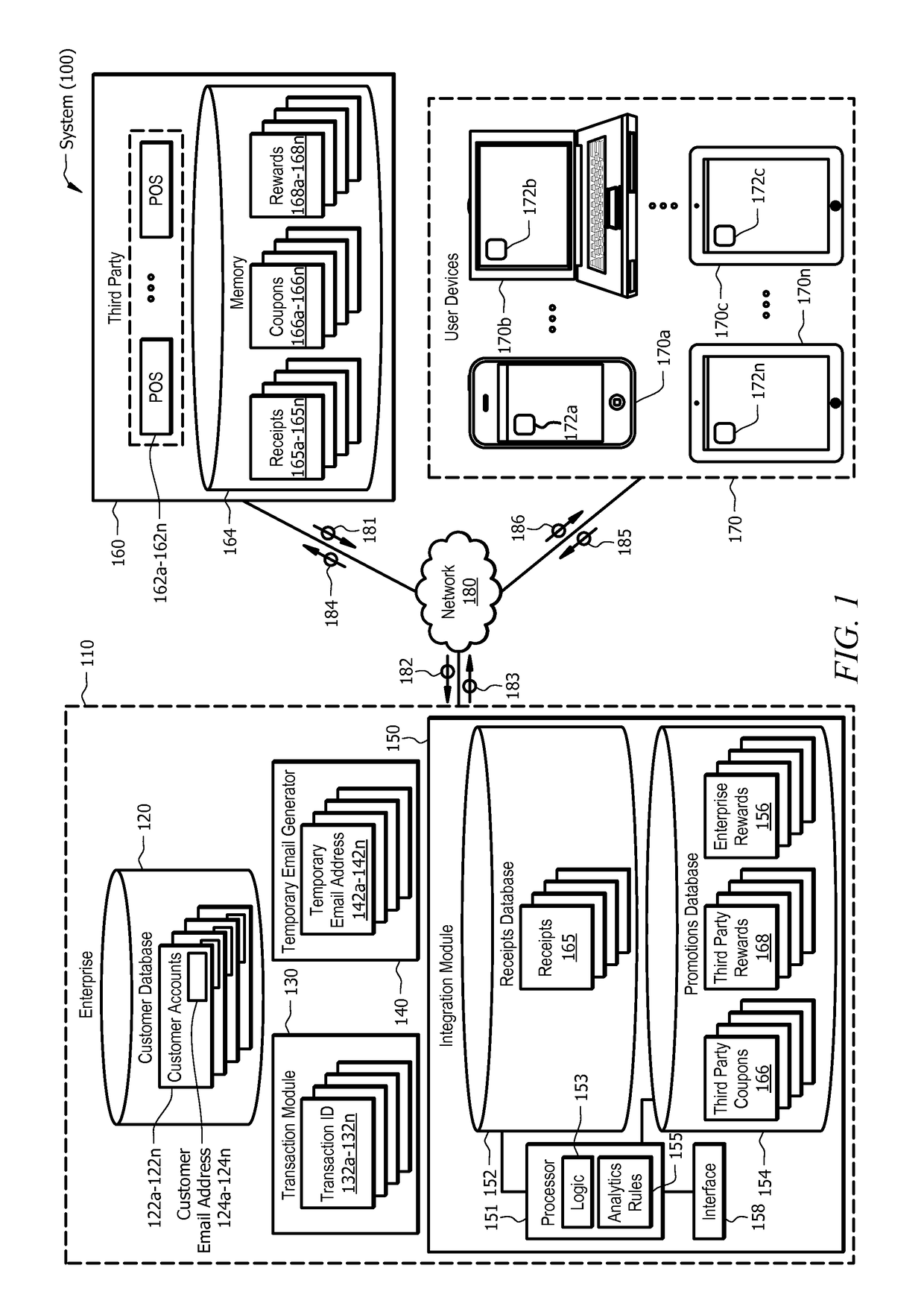
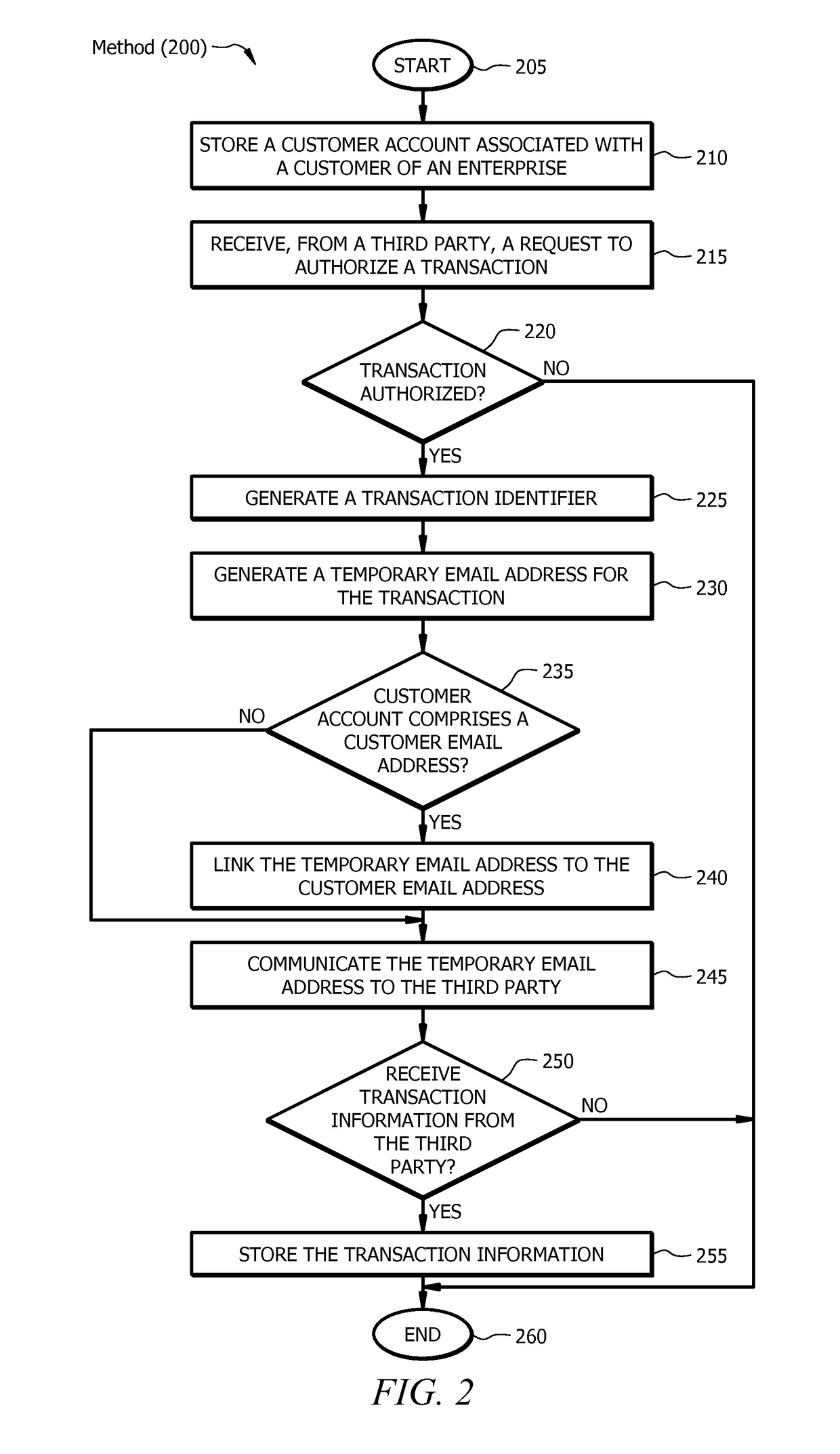
System and method for transaction-based temporary email
ActiveUS20170103392A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedTransmissionMarketingThird partyEmail address
According to one embodiment, a system comprises a customer database operable to store a customer account associated with a customer of an enterprise. The system also comprises a transaction module operable to receive, from a third party, a request to authorize a transaction. The transaction module is further operable to authorize the transaction and generate, in response to the authorized transaction, a transaction identifier to identify the transaction. The system further comprises a temporary email generator operable to generate a temporary email address for the transaction in response to the generated transaction identifier, link the temporary email address to a customer email address, and communicate the temporary email address to the third party. Additionally, the system comprises an integration module operable to receive transaction information from the third party and store the transaction information, wherein the transaction information is associated with the temporary email address.
Owner:JPMORGAN CHASE BANK NA
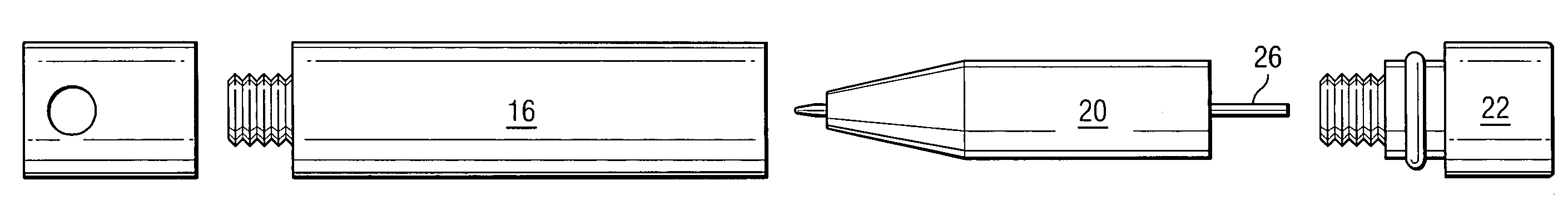
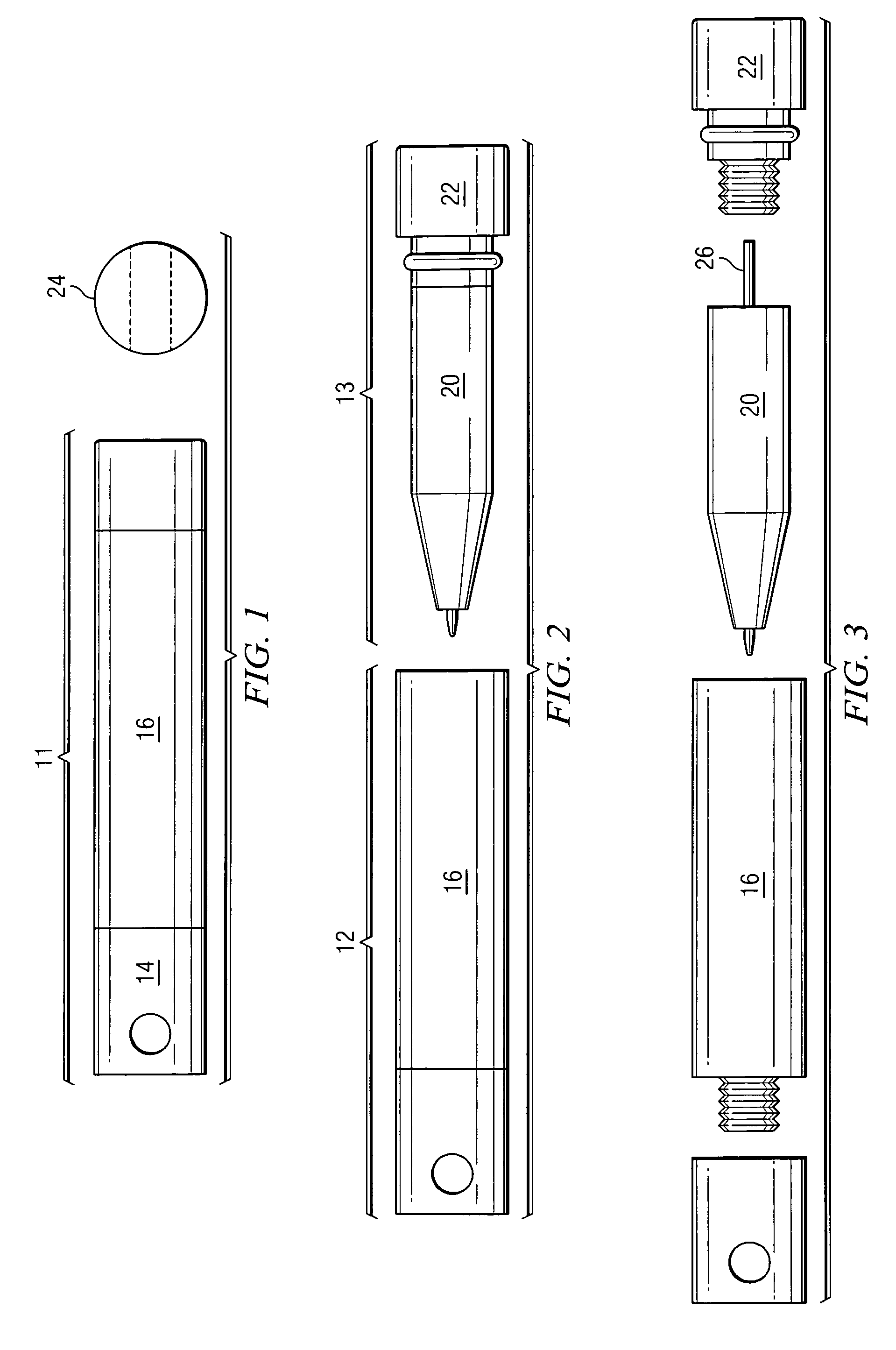
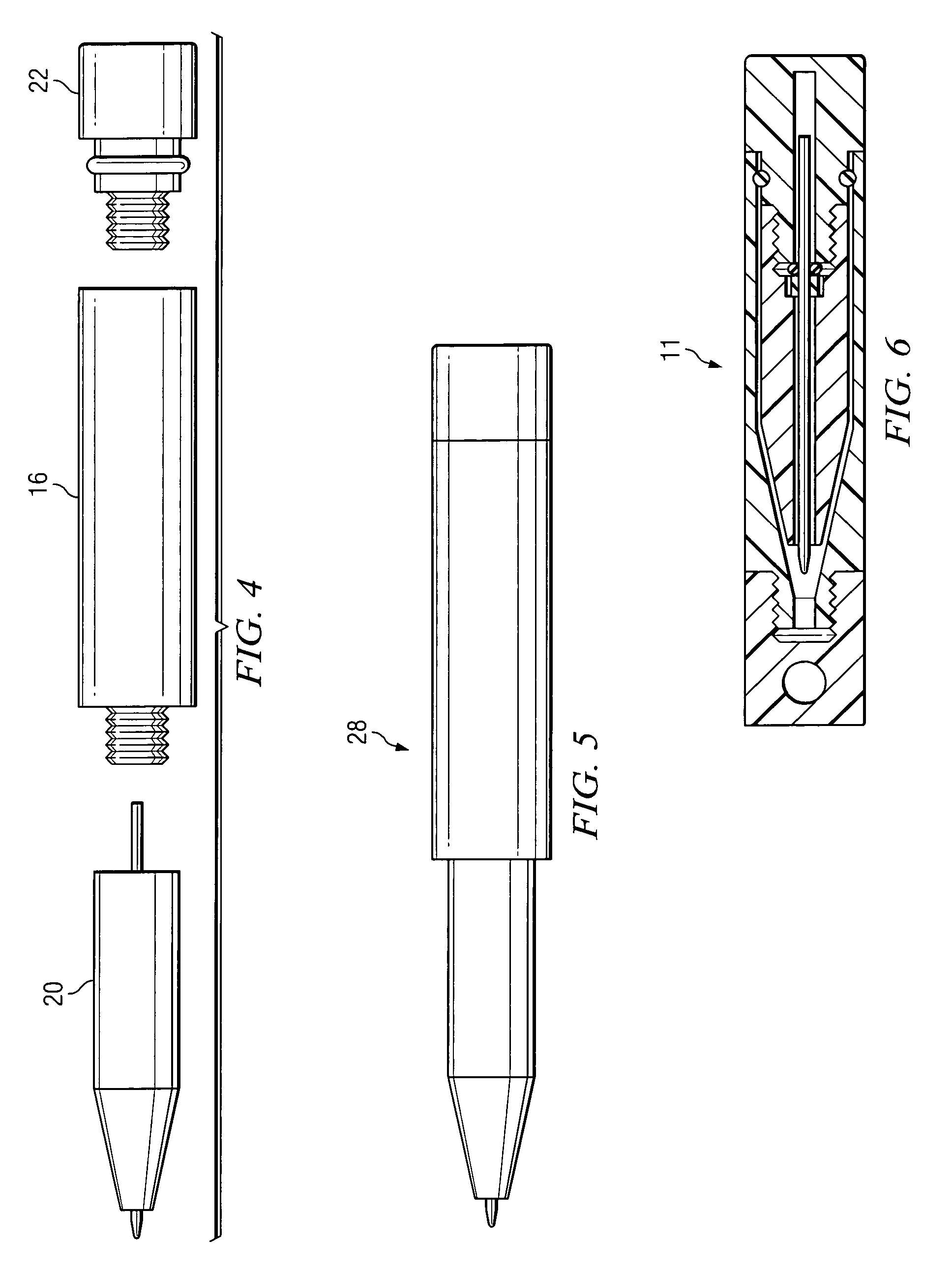
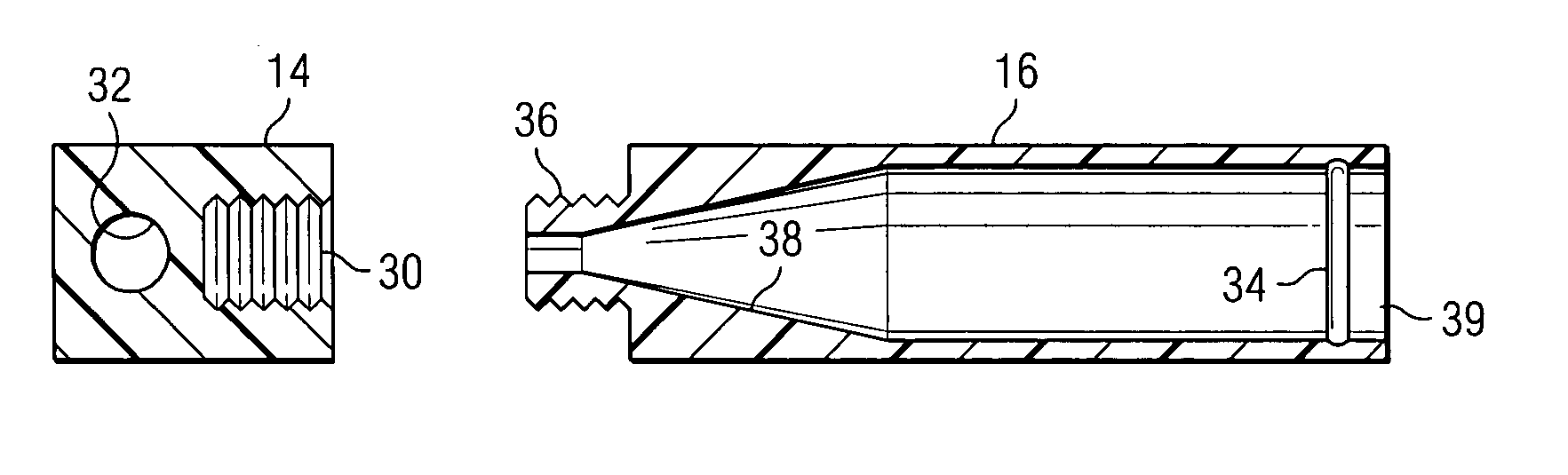
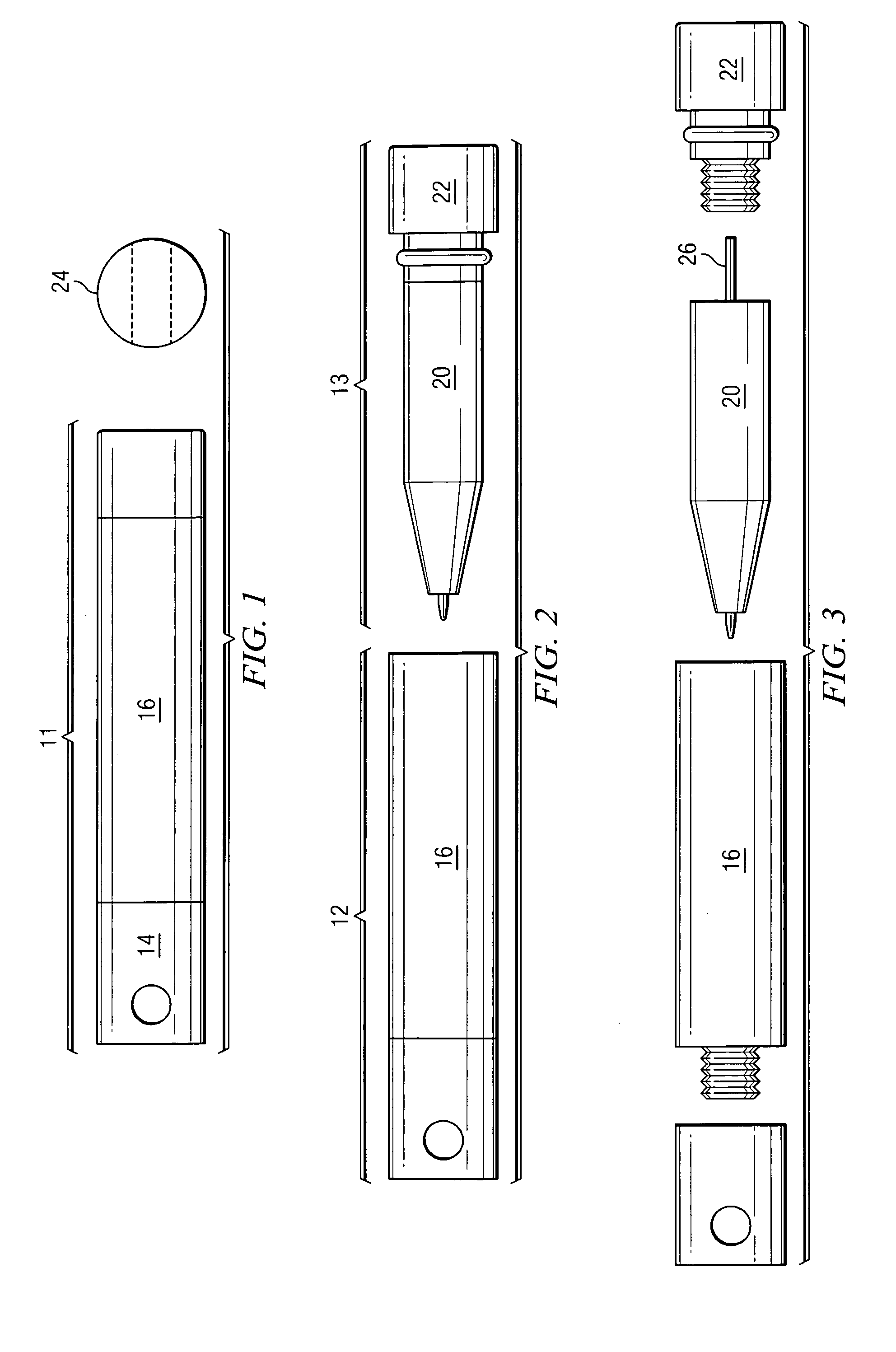
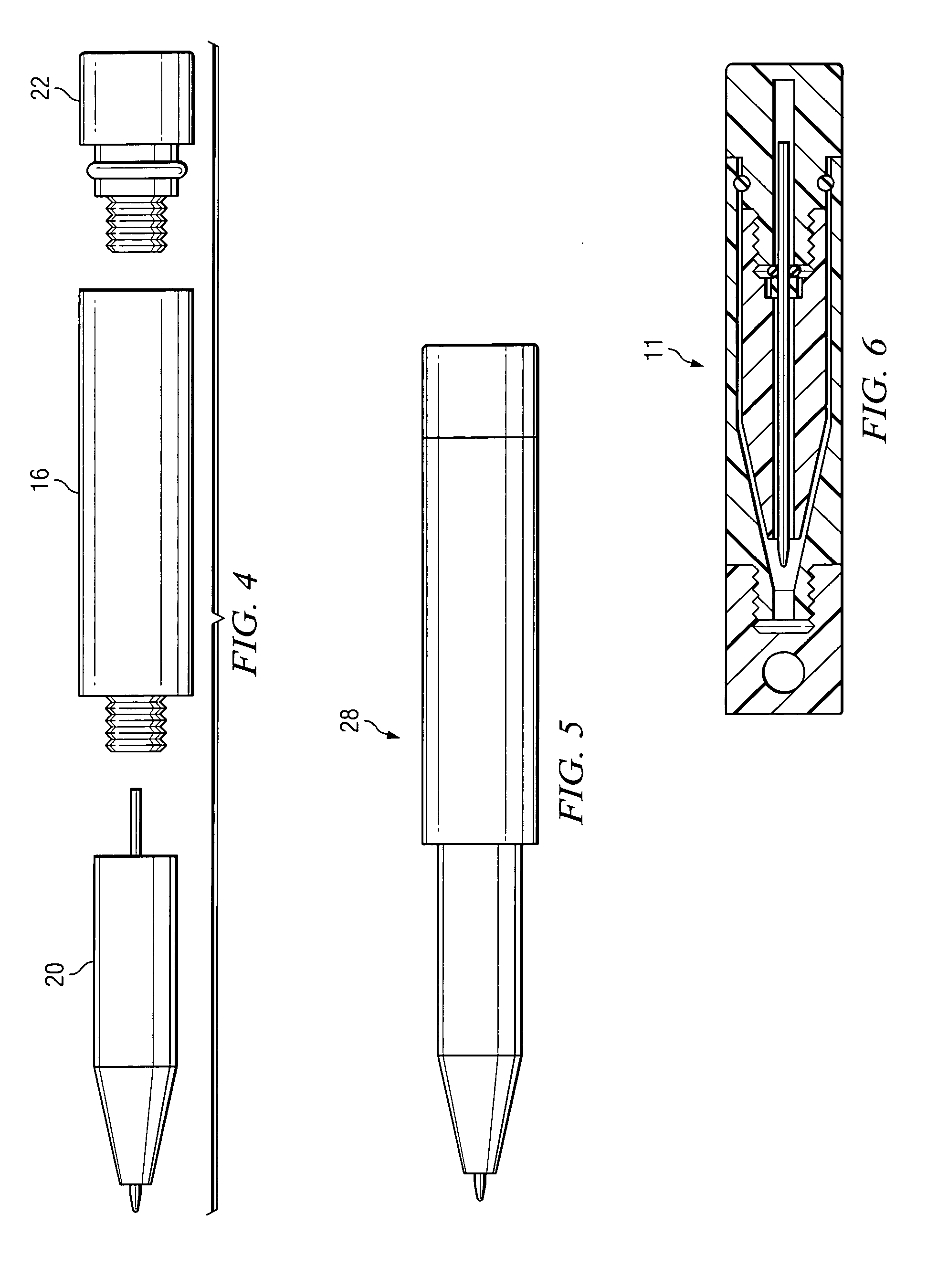
Convertible multi-use writing instrument
ActiveUS7168105B2Disadvantages can be reduced eliminatedProblems be reduced eliminatedWriting connectorsPropelling pencilsEngineering
In one embodiment, a convertible multi-use writing instrument includes a quick-use arrangement including a quick-use writing instrument and a quick-use cap for encapsulating the quick-use writing instrument. The quick-use arrangement is convertible to a full-size arrangement. The convertible multi-use writing instrument also includes the full-size arrangement. The full-size arrangement includes a full-size writing instrument that is convertible to the quick-use arrangement.
Owner:ADELMAN GREGORY M
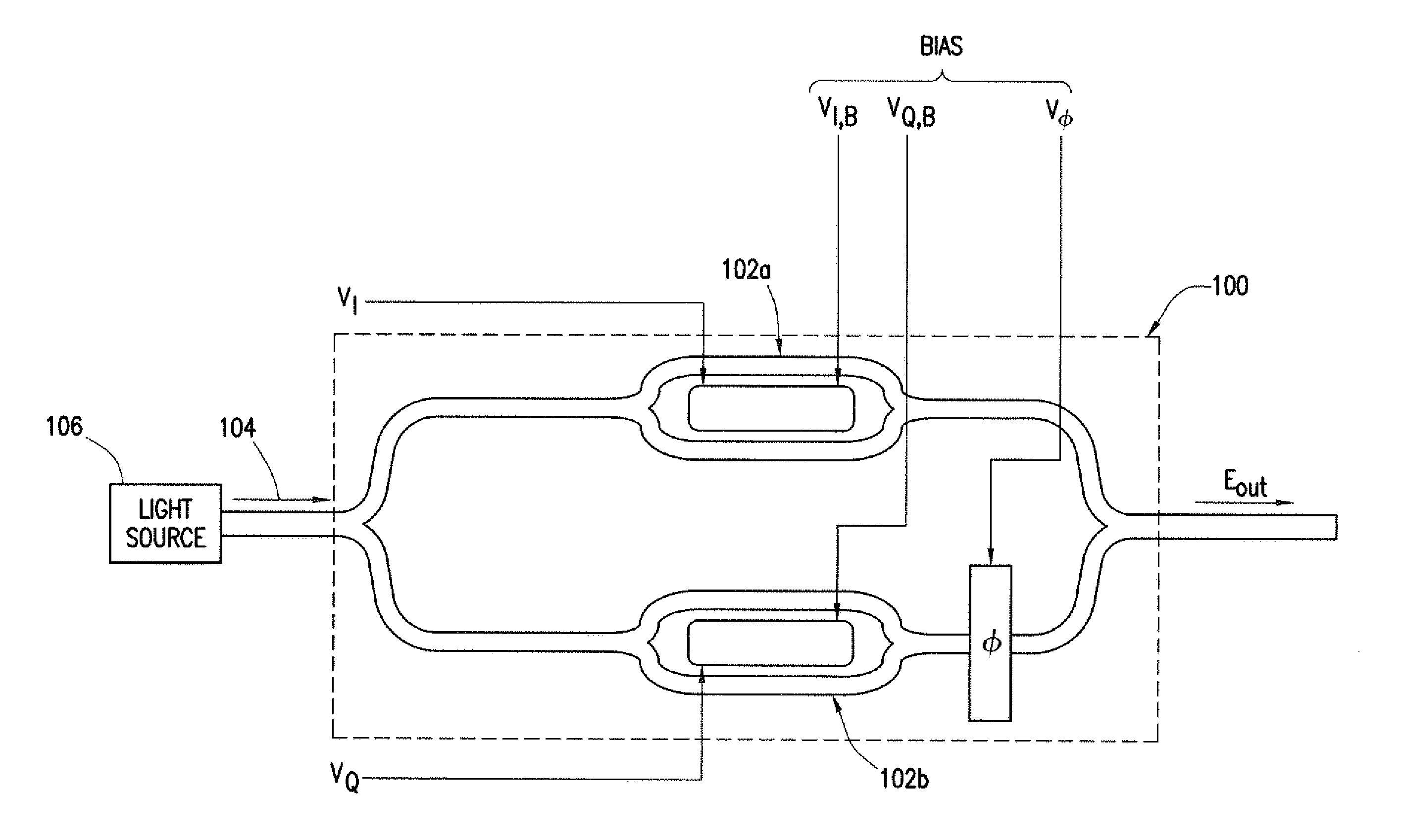
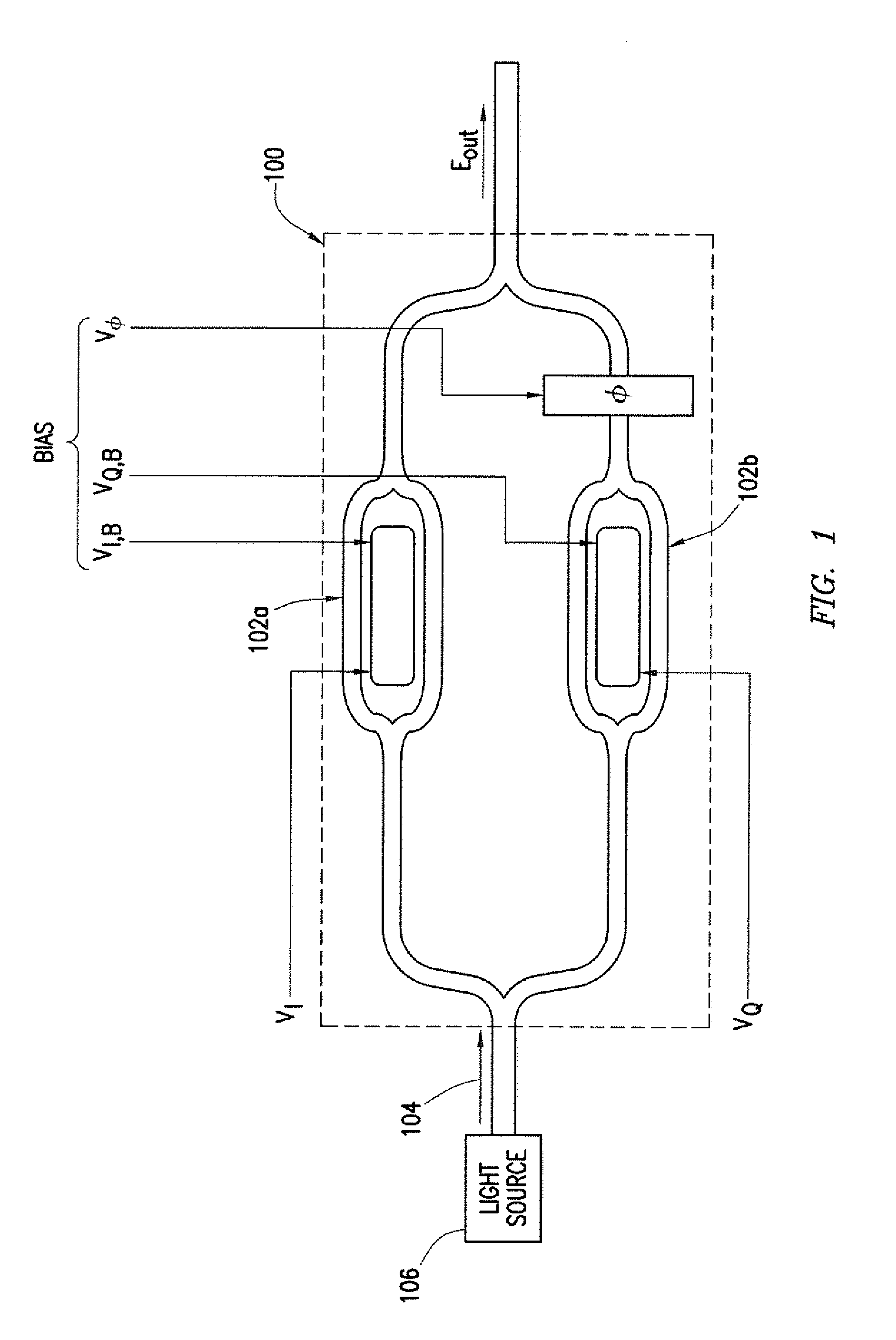
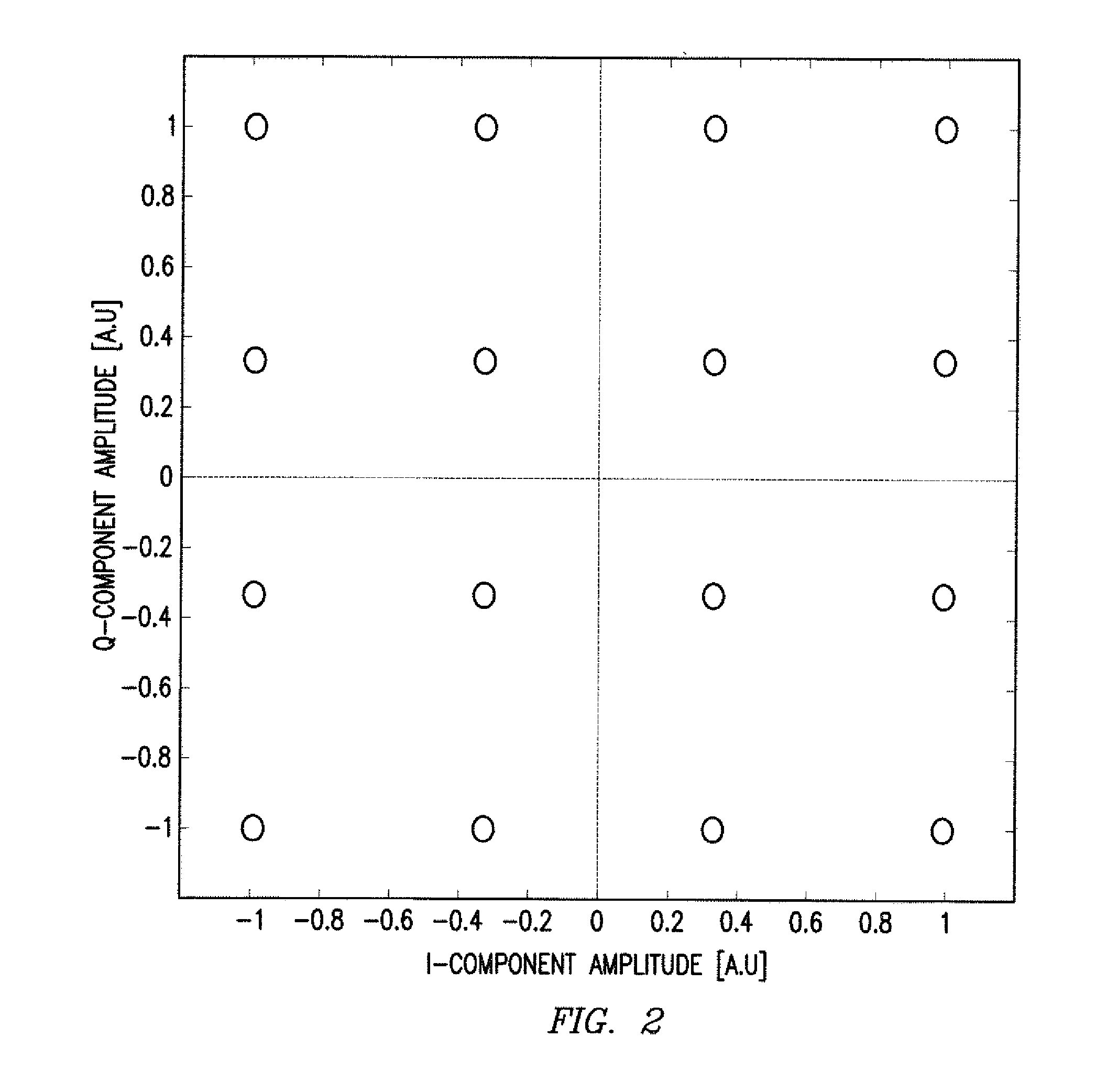
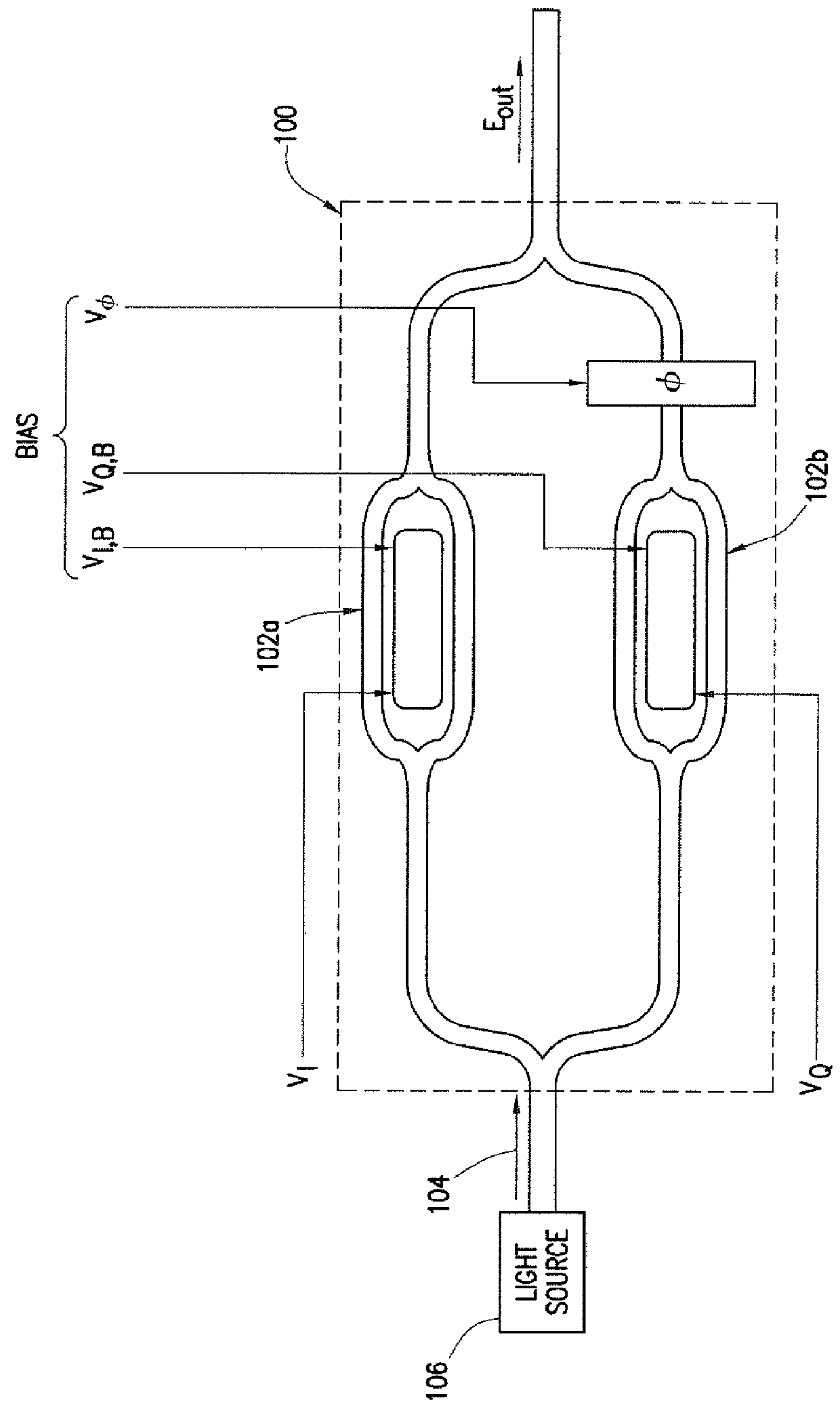
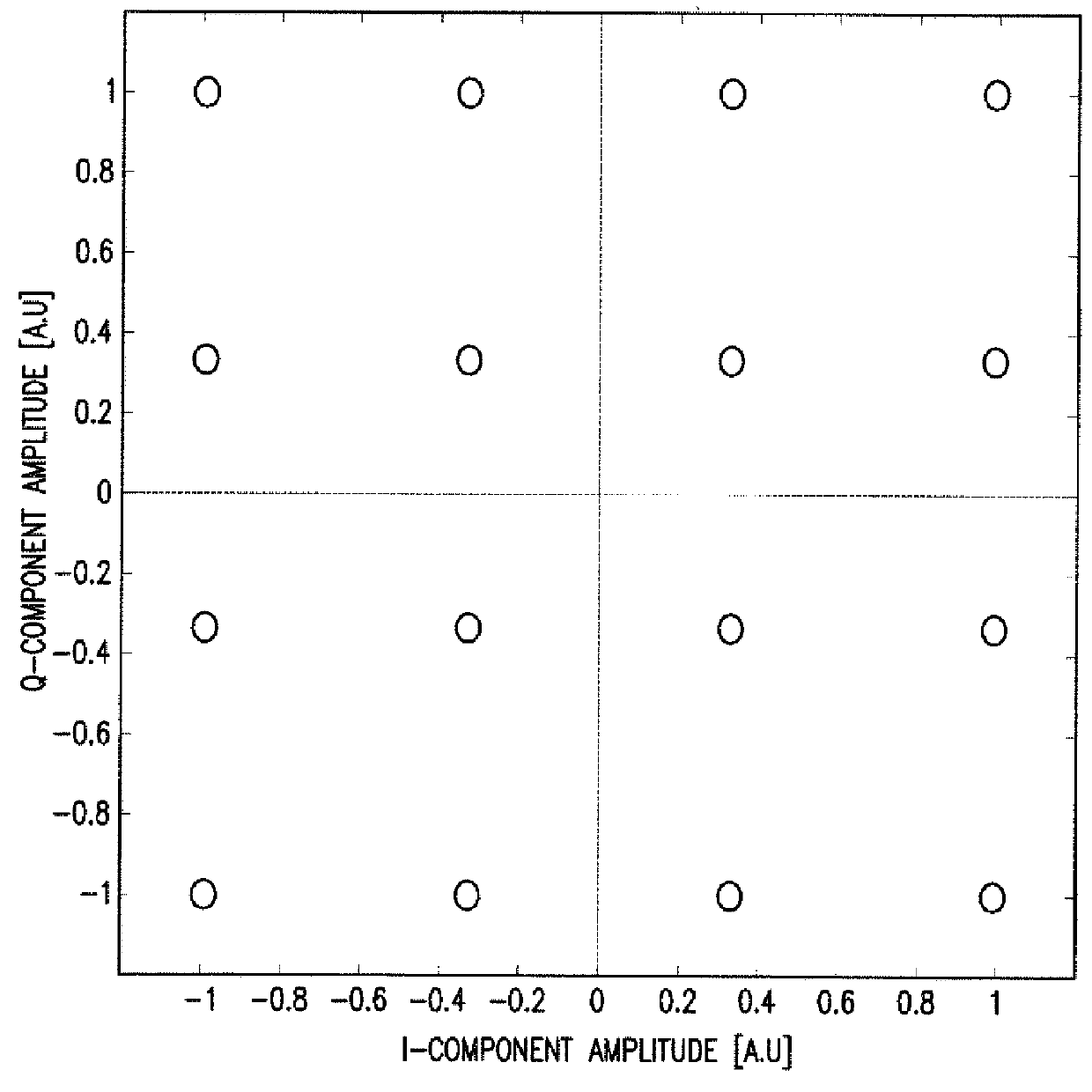
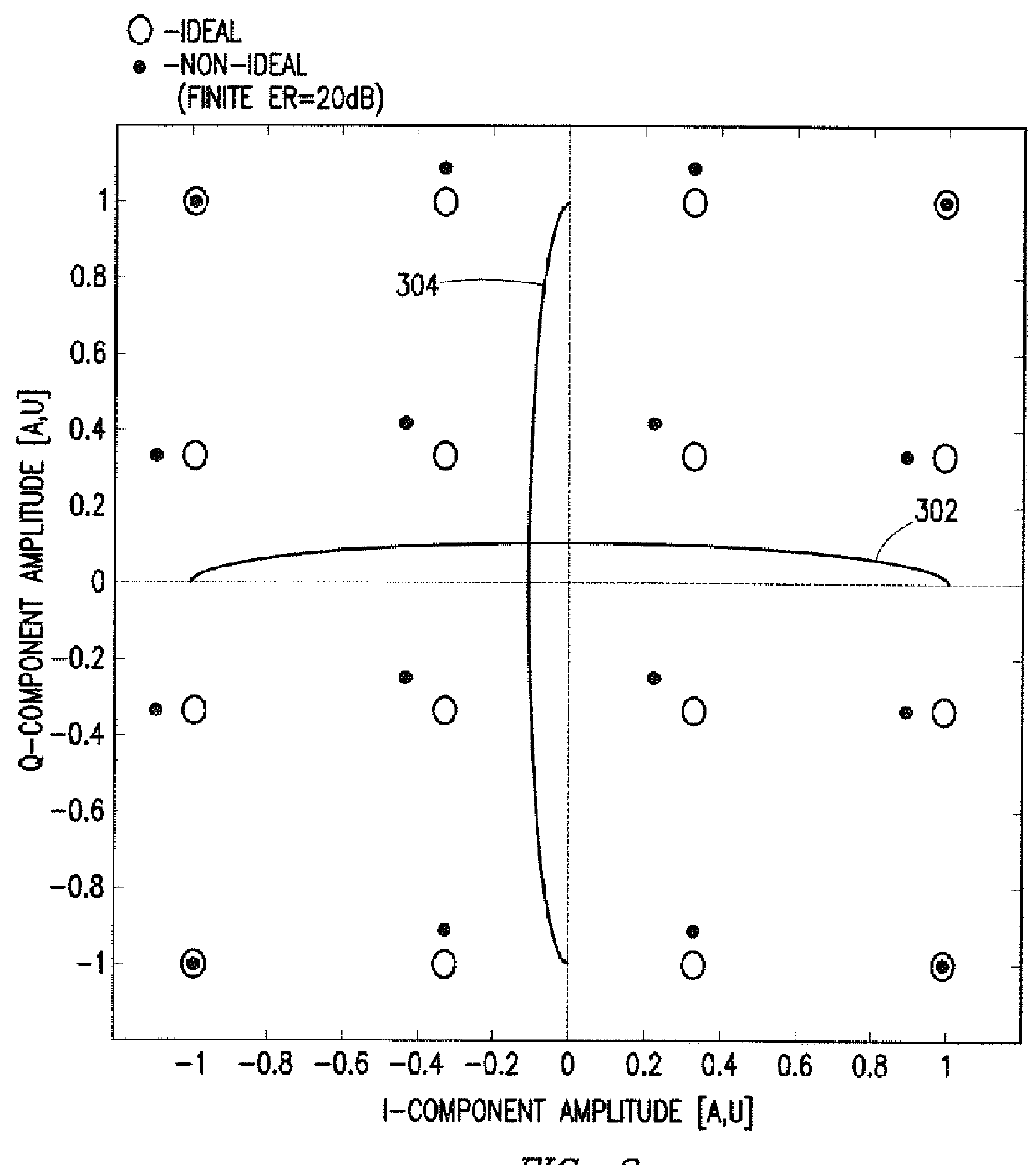
System and Method for Monitoring and Control of an Optical Modulator for an M-QAM Transmitter
ActiveUS20140233965A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedElectromagnetic transmittersOptical power meterPhase shifted
A system includes an optical power meter operable to generate an optical power signal corresponding to the optical power of a received output signal generated by an optical IQ-modulator. The system further includes a processor operable to receive the optical power signal and determine, based on a minimization algorithm and the received optical power signal, a first bias voltage to be applied to a first sub-modulator of the optical IQ-modulator and a second bias voltage to be applied to a second sub-modulator of the optical IQ-modulator. The system may also include a peak power meter operable to generate a peak power signal corresponding to the peak power of the received output signal generated by the optical IQ-modulator, wherein the processor is further operable to determine, based on a minimization algorithm and the received peak power signal, a third bias voltage to be applied to a phase shift component of the optical IQ-modulator.
Owner:FUJITSU LTD
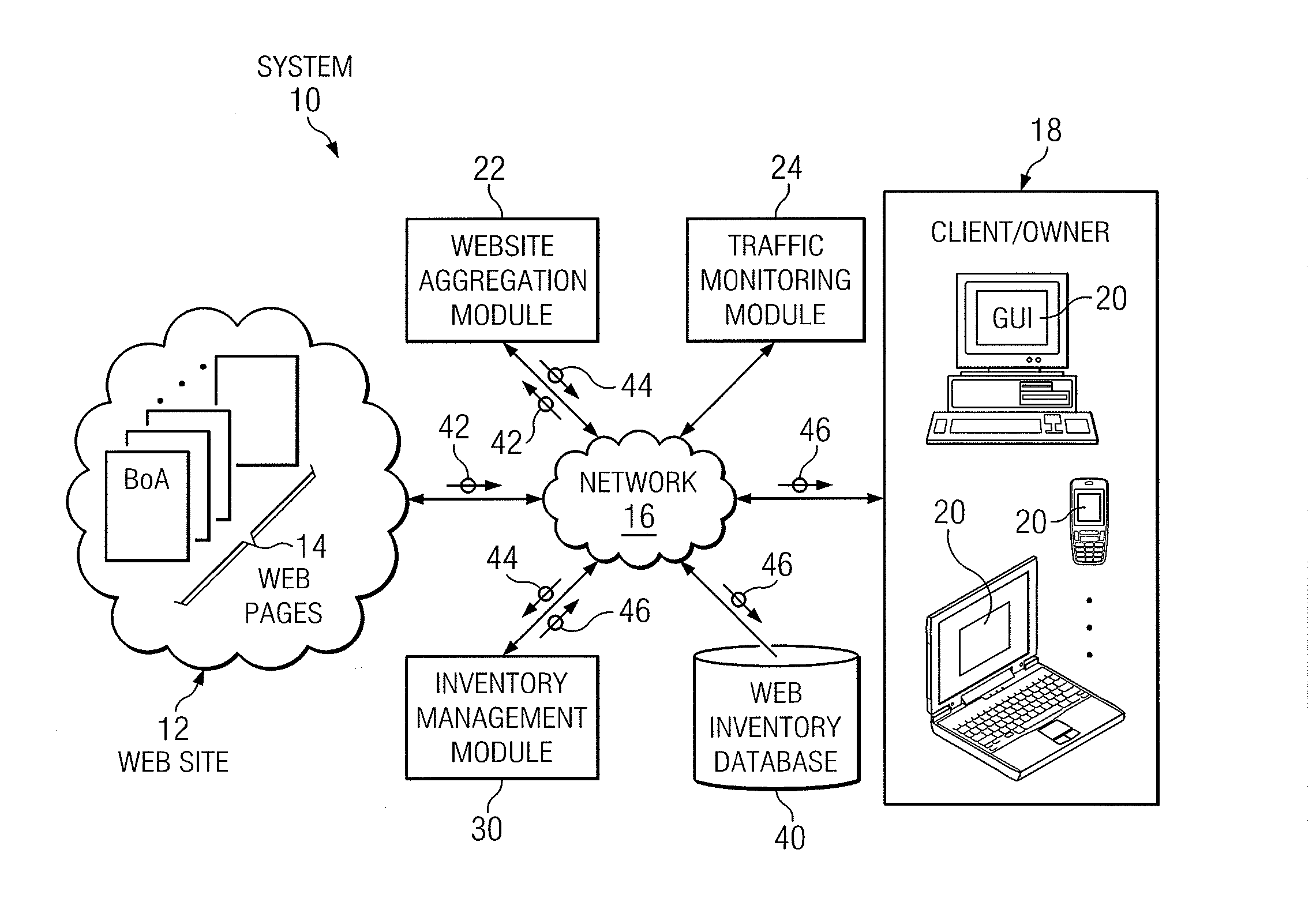
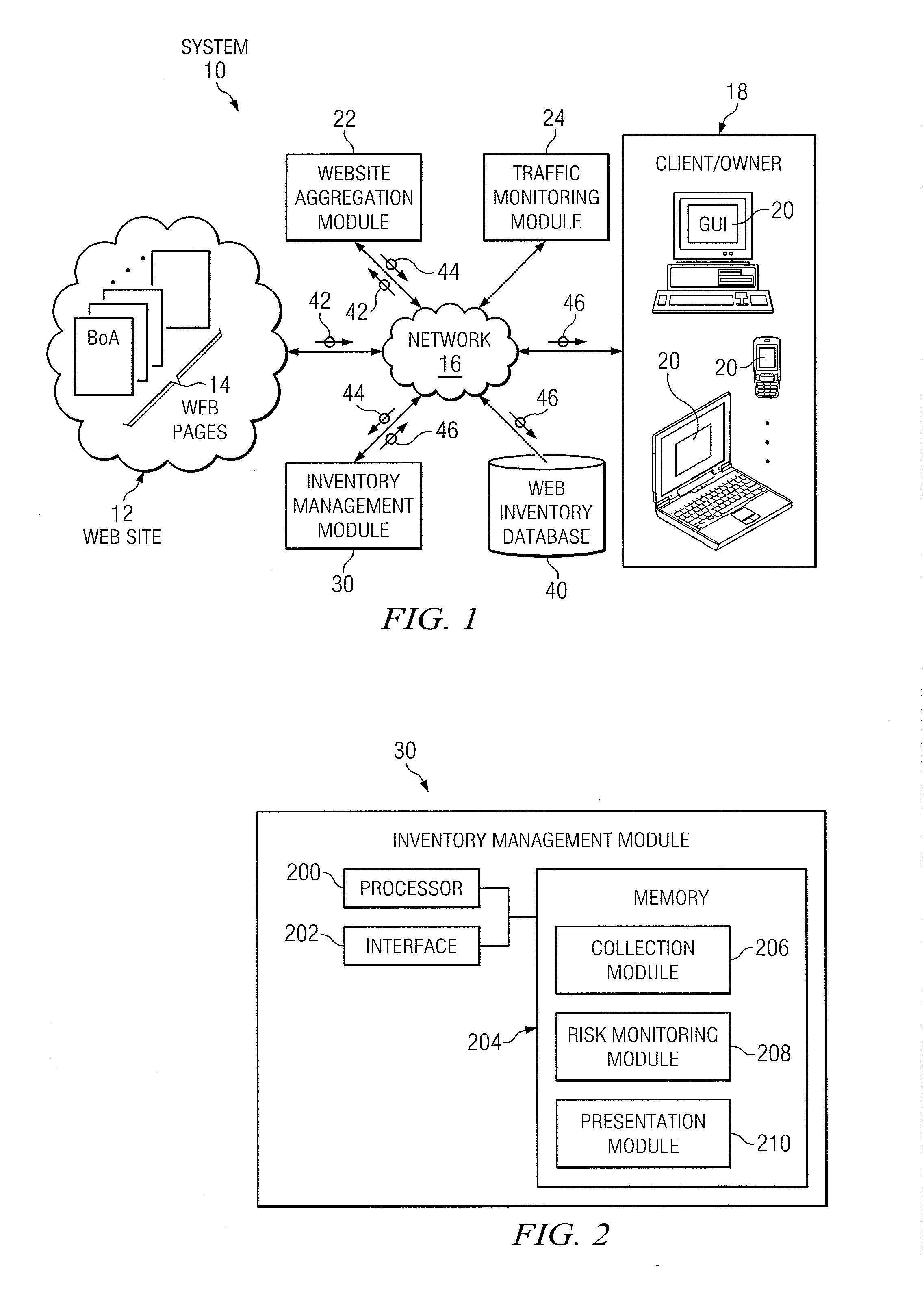
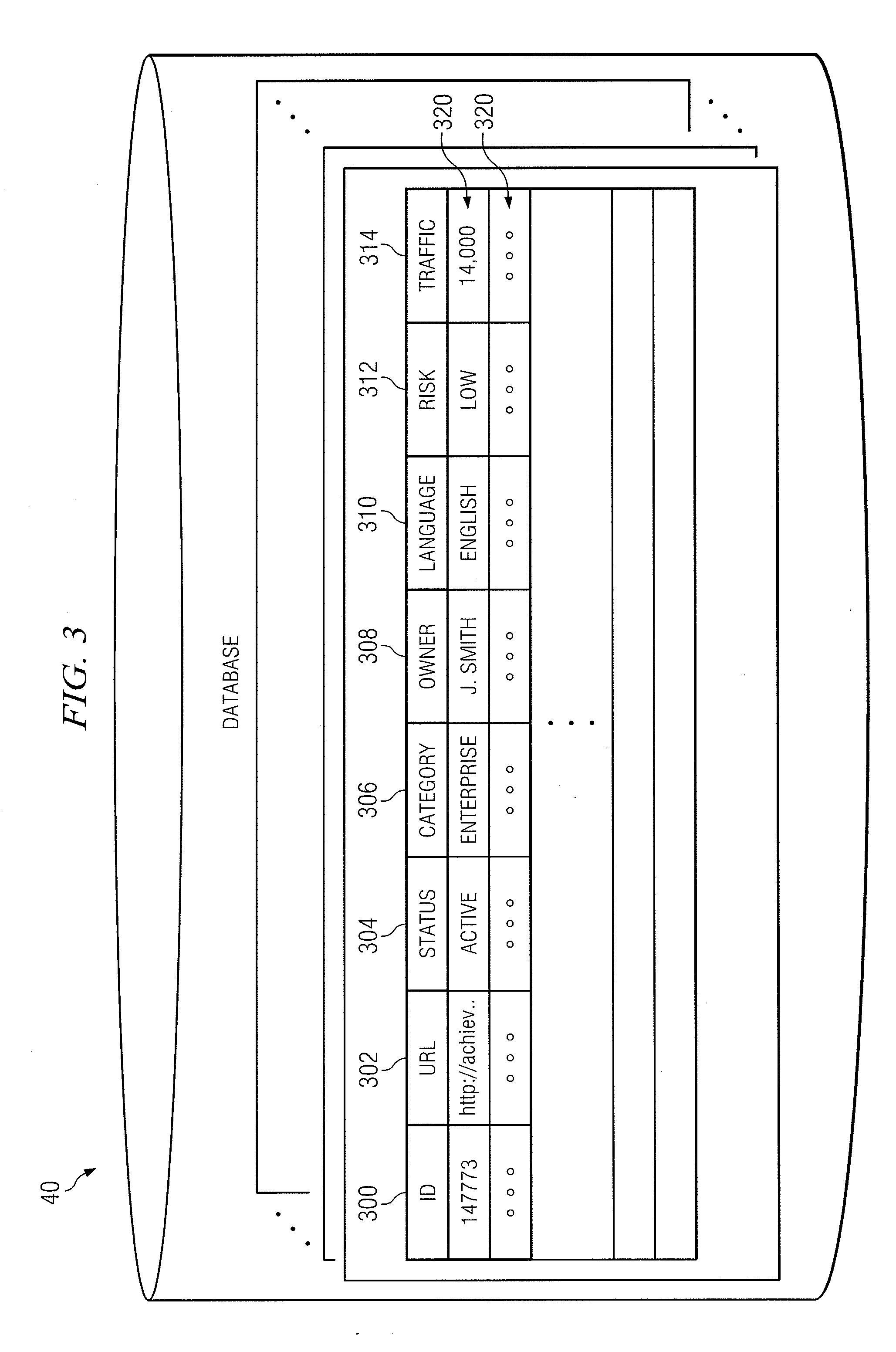
Management of an inventory of websites
ActiveUS20120047161A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedDigital data processing detailsWebsite content managementRisk factorWeb page
A method includes receiving web page identifiers associated with a website and determining whether the web page identifiers identify redundant web pages of the website. One or more web page identifiers are removed from the web page identifiers that identify redundant web pages to create a group of web page identifiers. A user responsible for at least one of the web pages identified in the group of web page identifiers is determined. A risk level is determined for each of the web pages identified in the group based on a plurality of risk factors, the user is associated with the risk level, and the association between the user and the risk level is stored in a database.
Owner:BANK OF AMERICA CORP
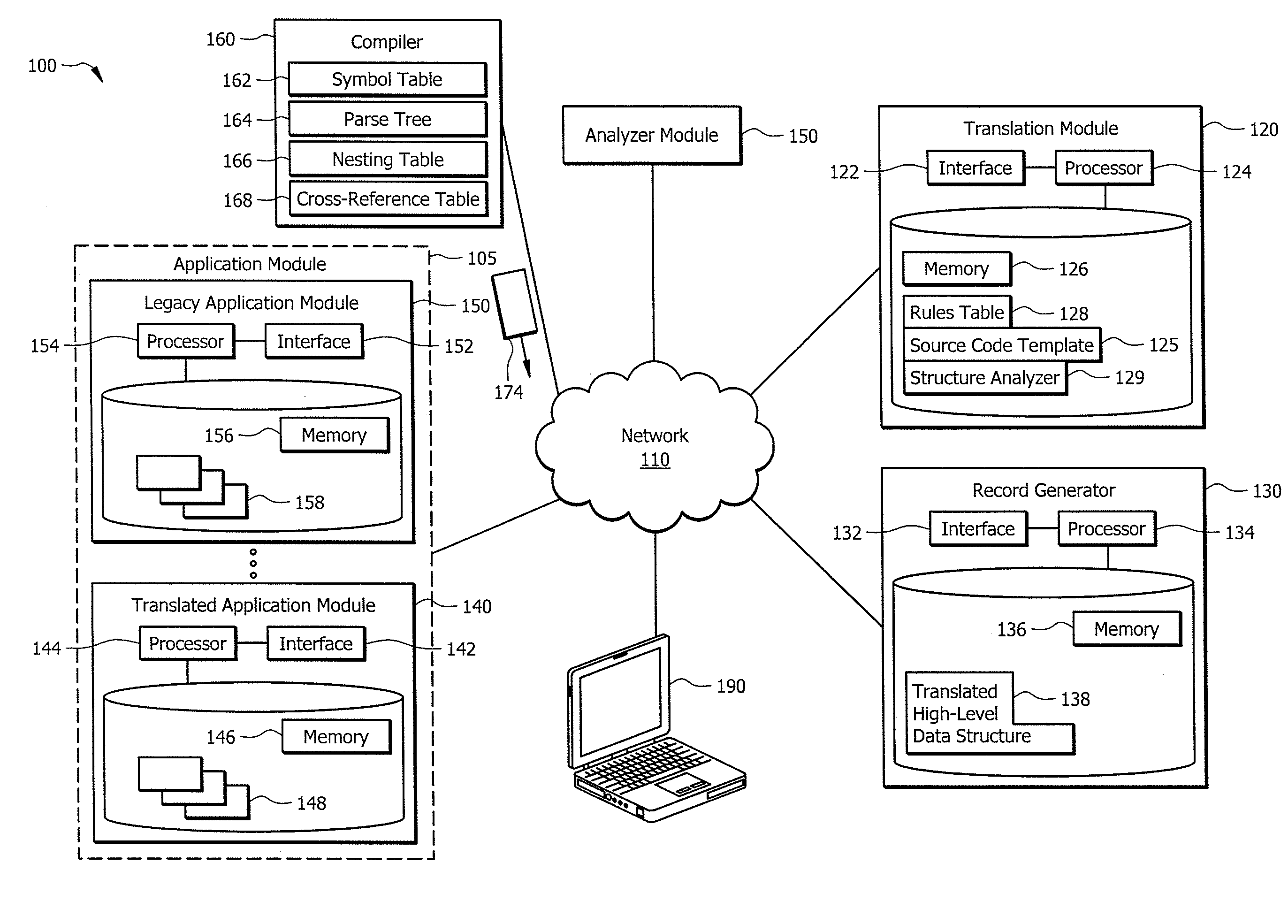
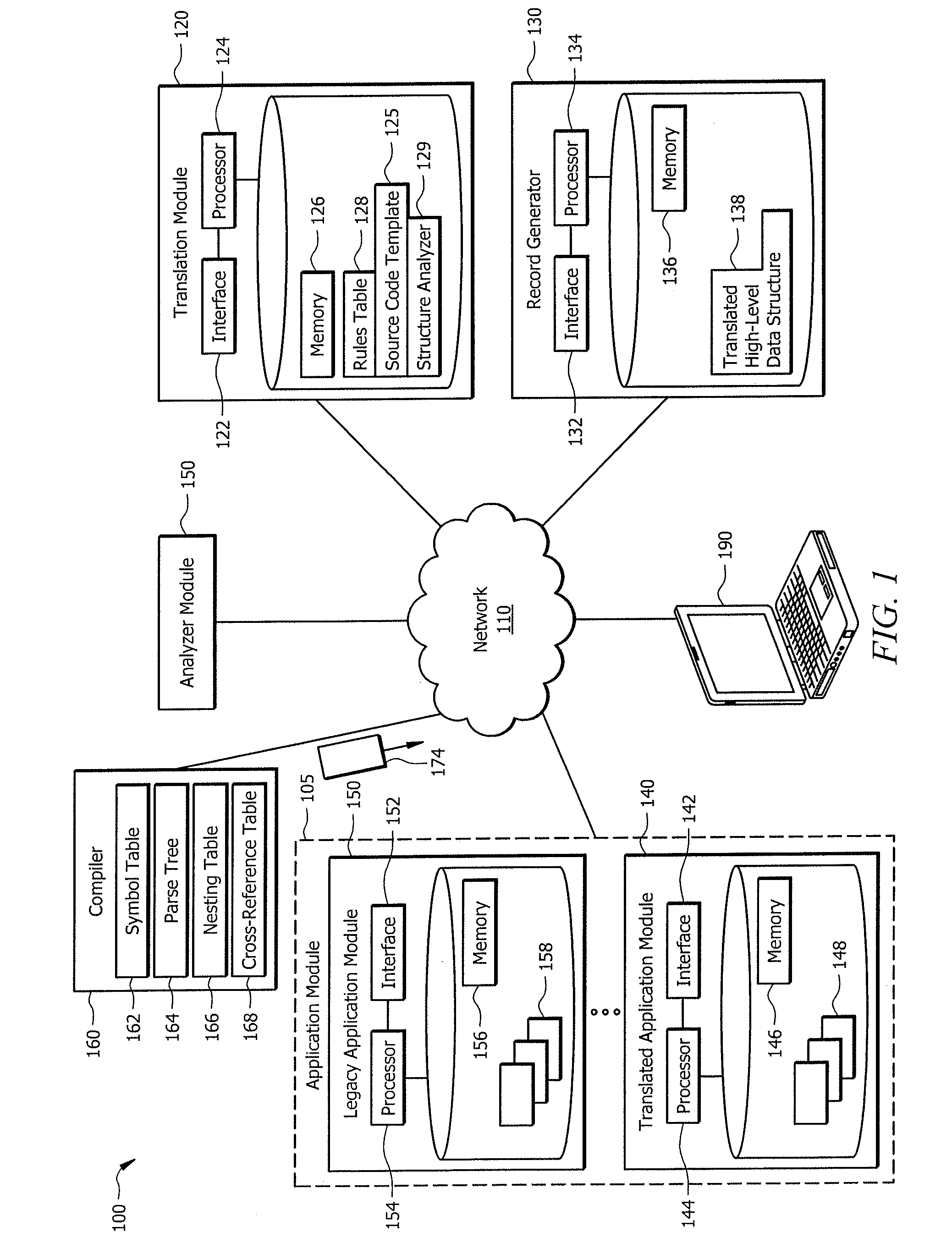
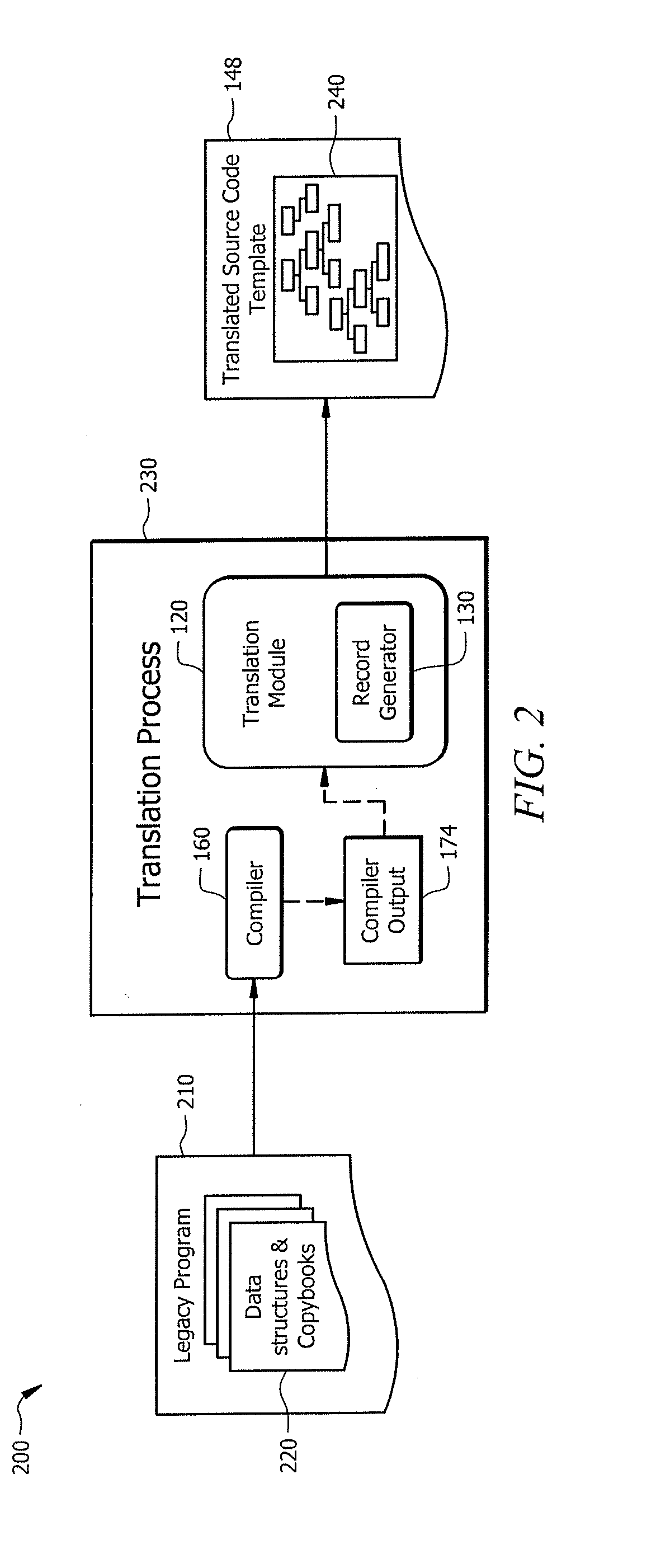
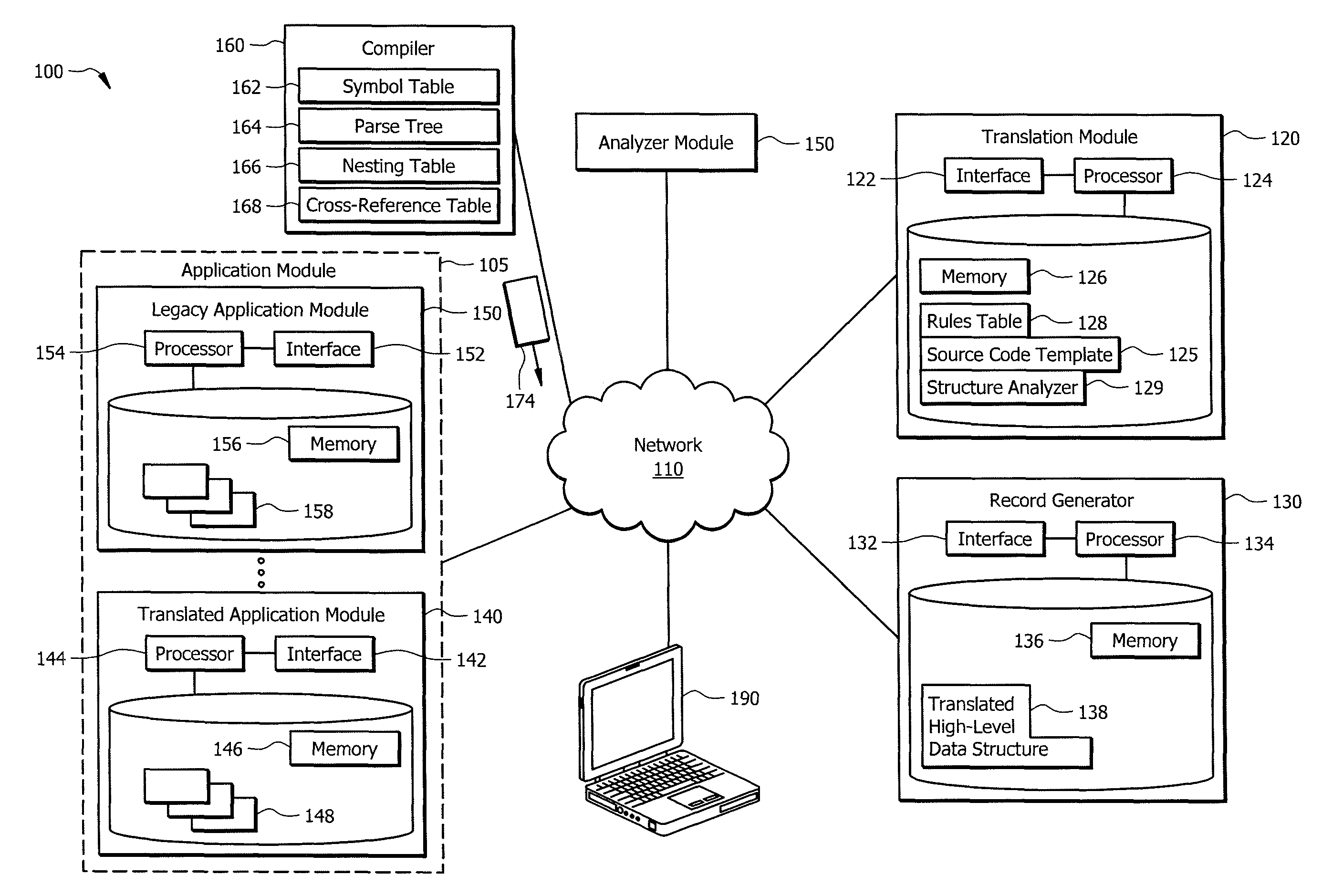
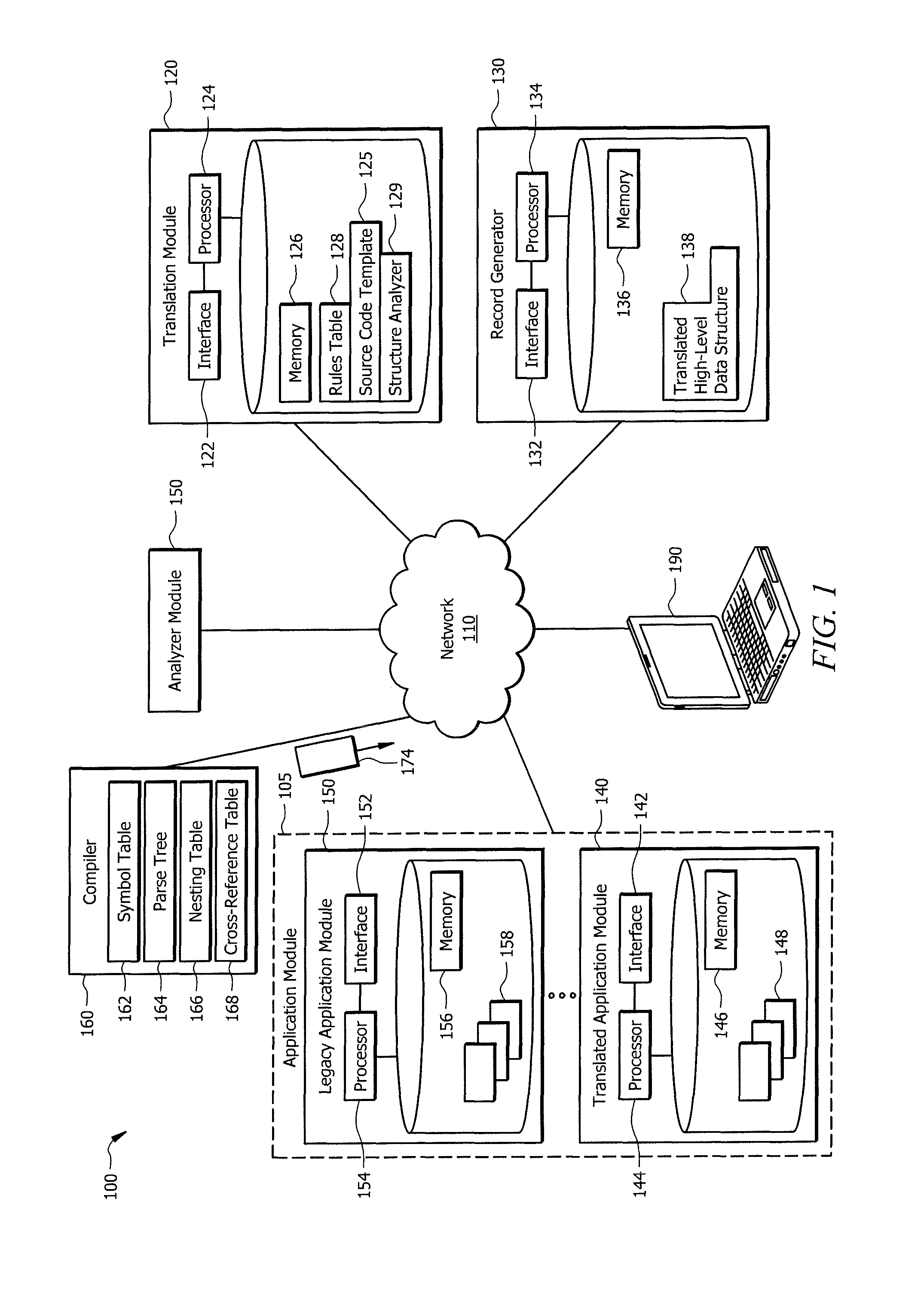
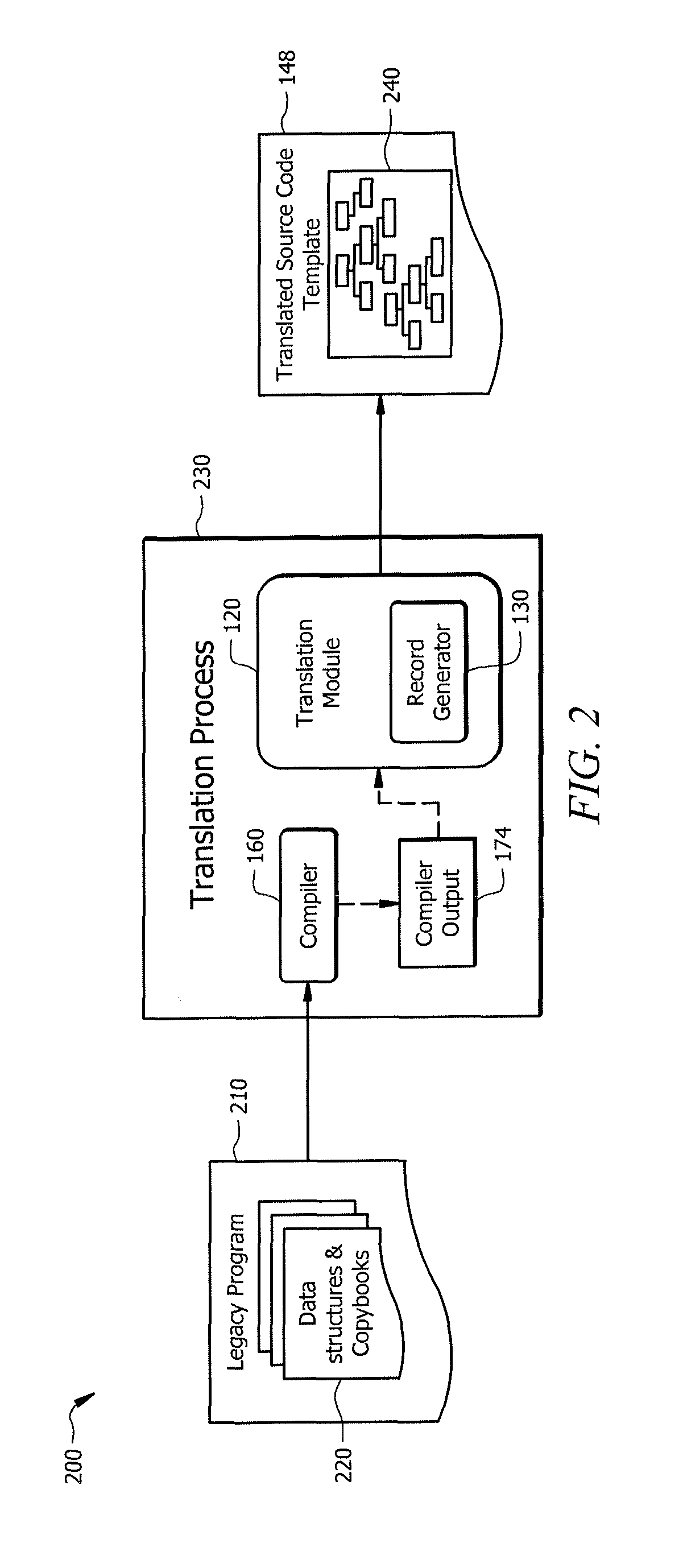
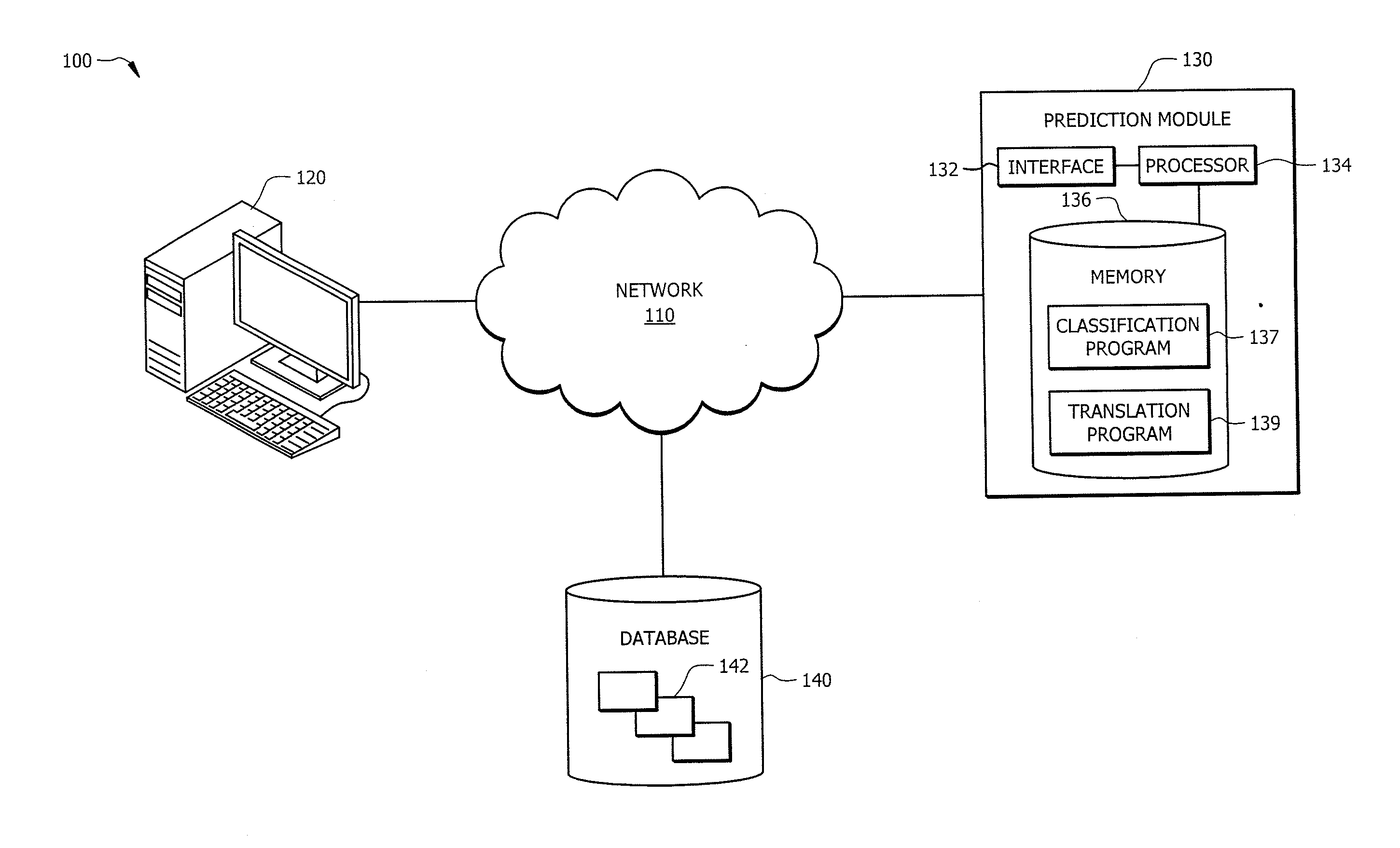
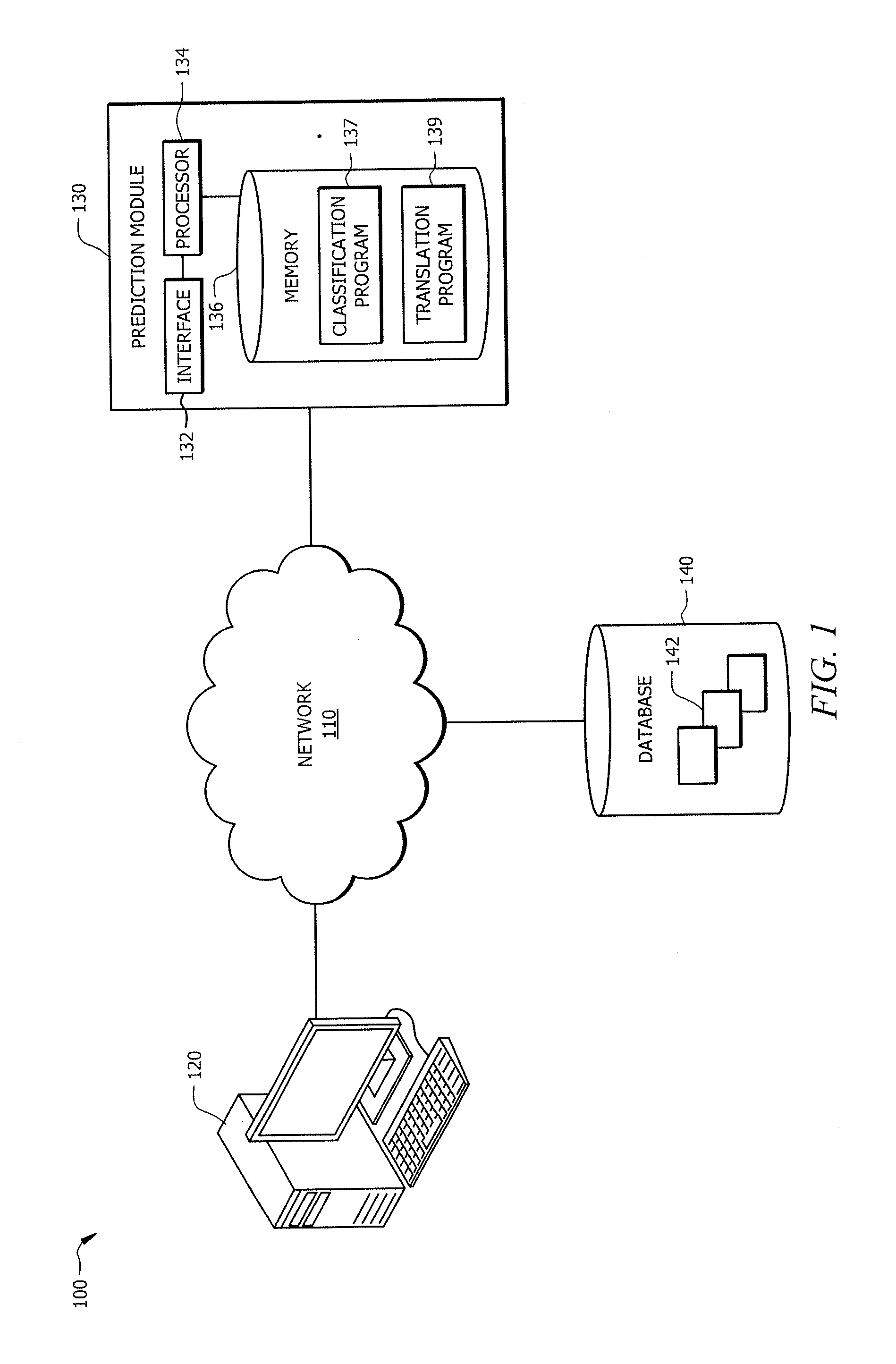
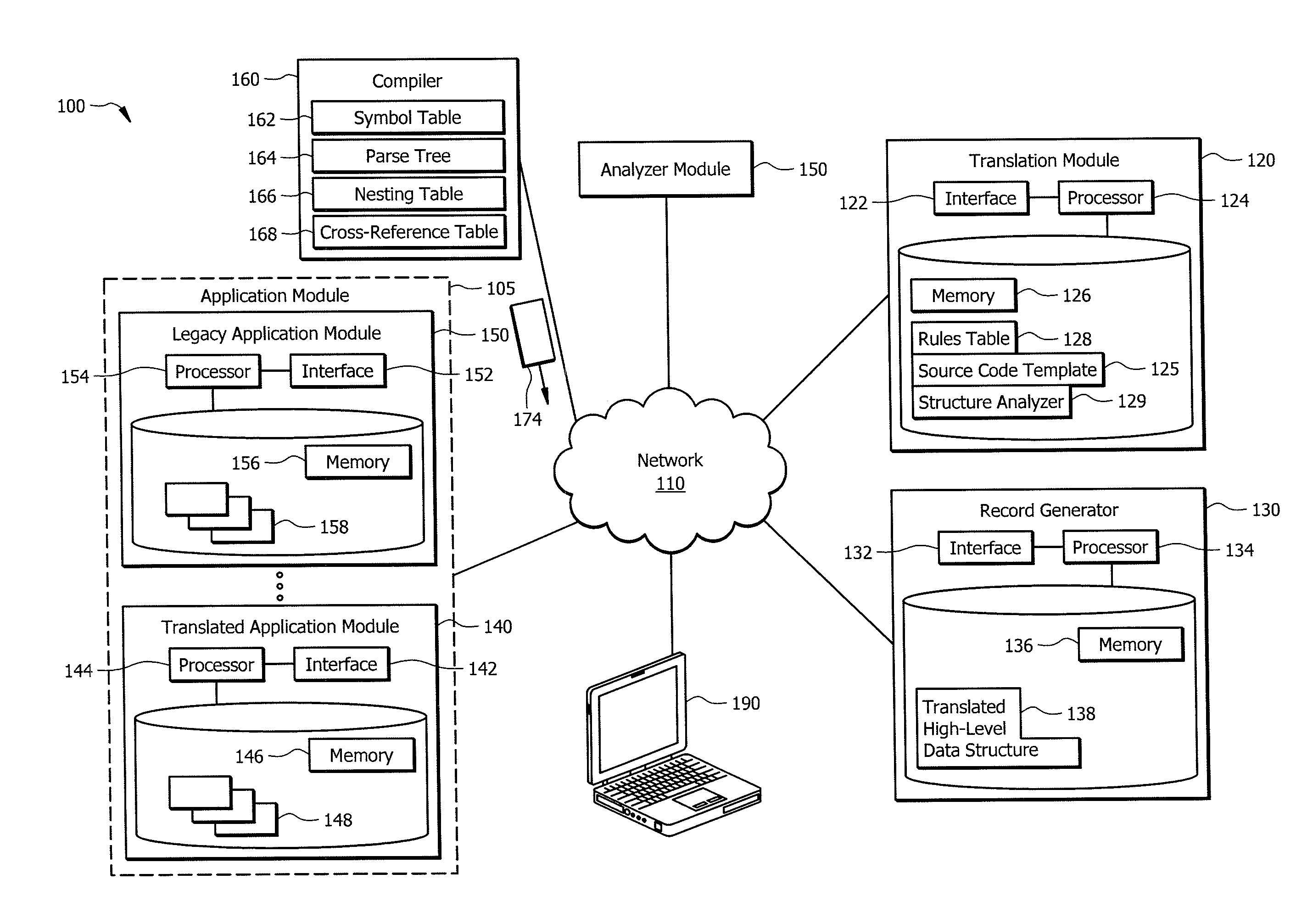
Leveraging legacy applications for use with modern applications
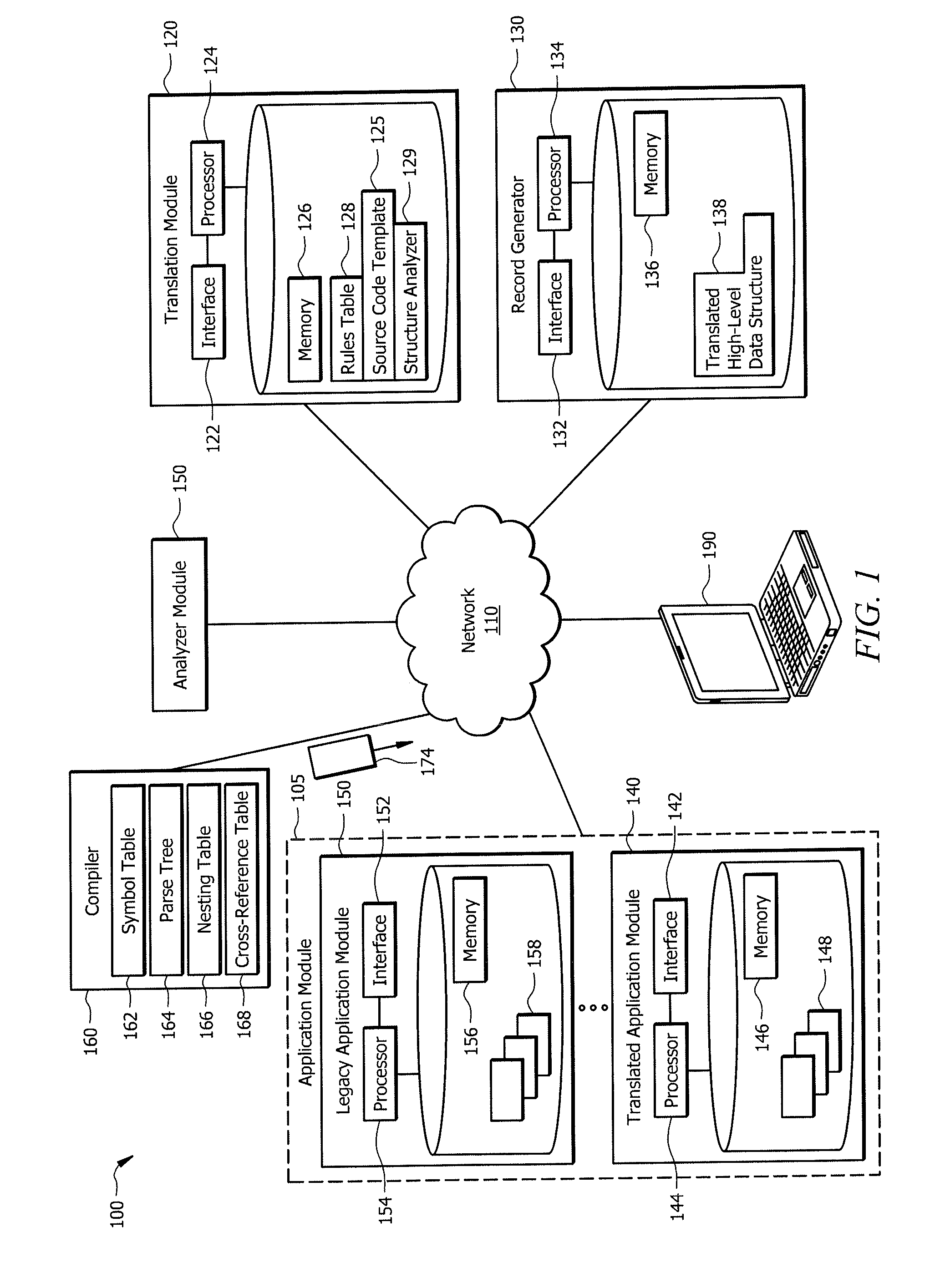
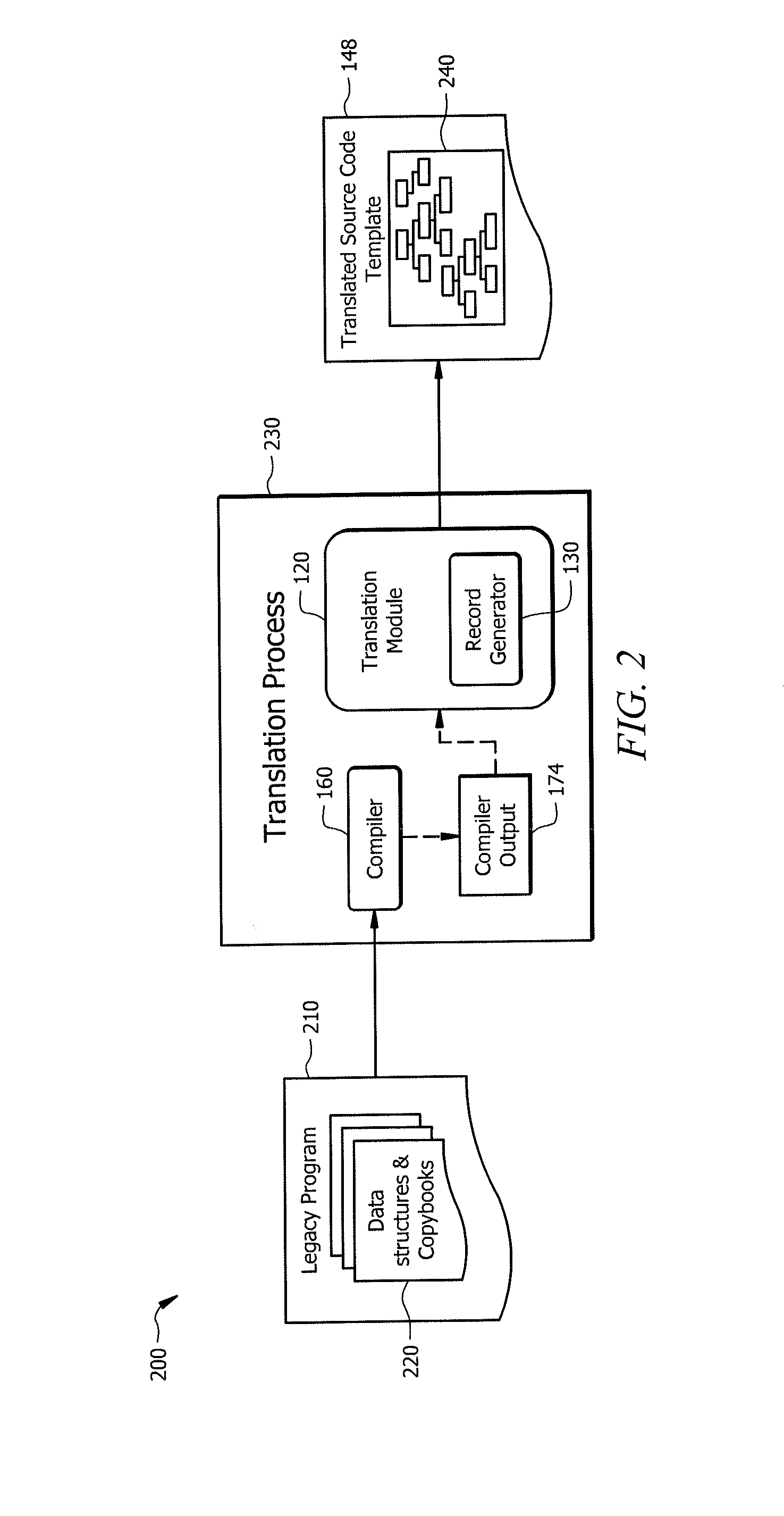
ActiveUS20160132308A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedProgram controlMemory systemsSource codeHuman language
An apparatus of one embodiment translates computer code from a first programming language to a second programming language. The apparatus includes an interface, a memory, and a processor. The interface is operable to receive a compiler output that is associated with source code written in a first programming language. The memory is operable to store the compiler output. The processor is communicatively coupled to the interface and the memory and is operable to analyze the data structures within the compiler output, build an internal representation of the source code based on the compiler output, and create a source code template associated with a second programming language.
Owner:BANK OF AMERICA CORP
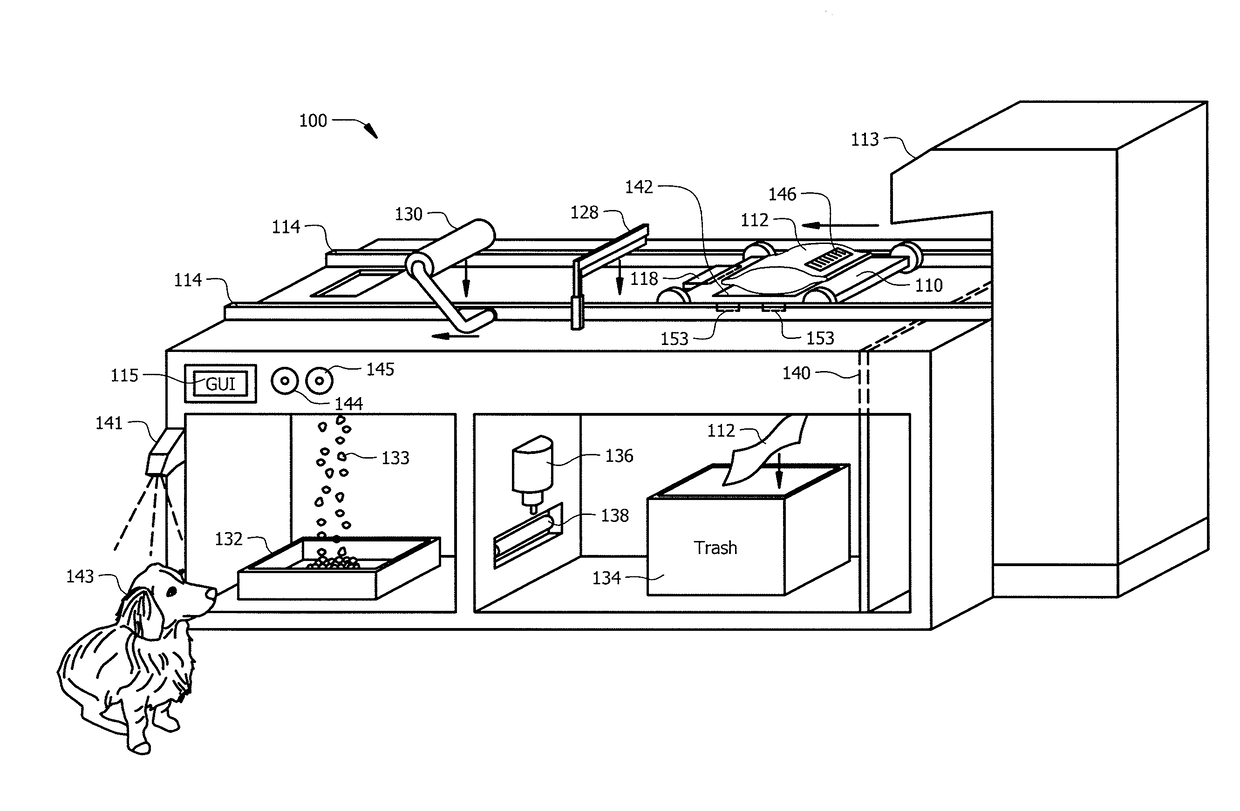
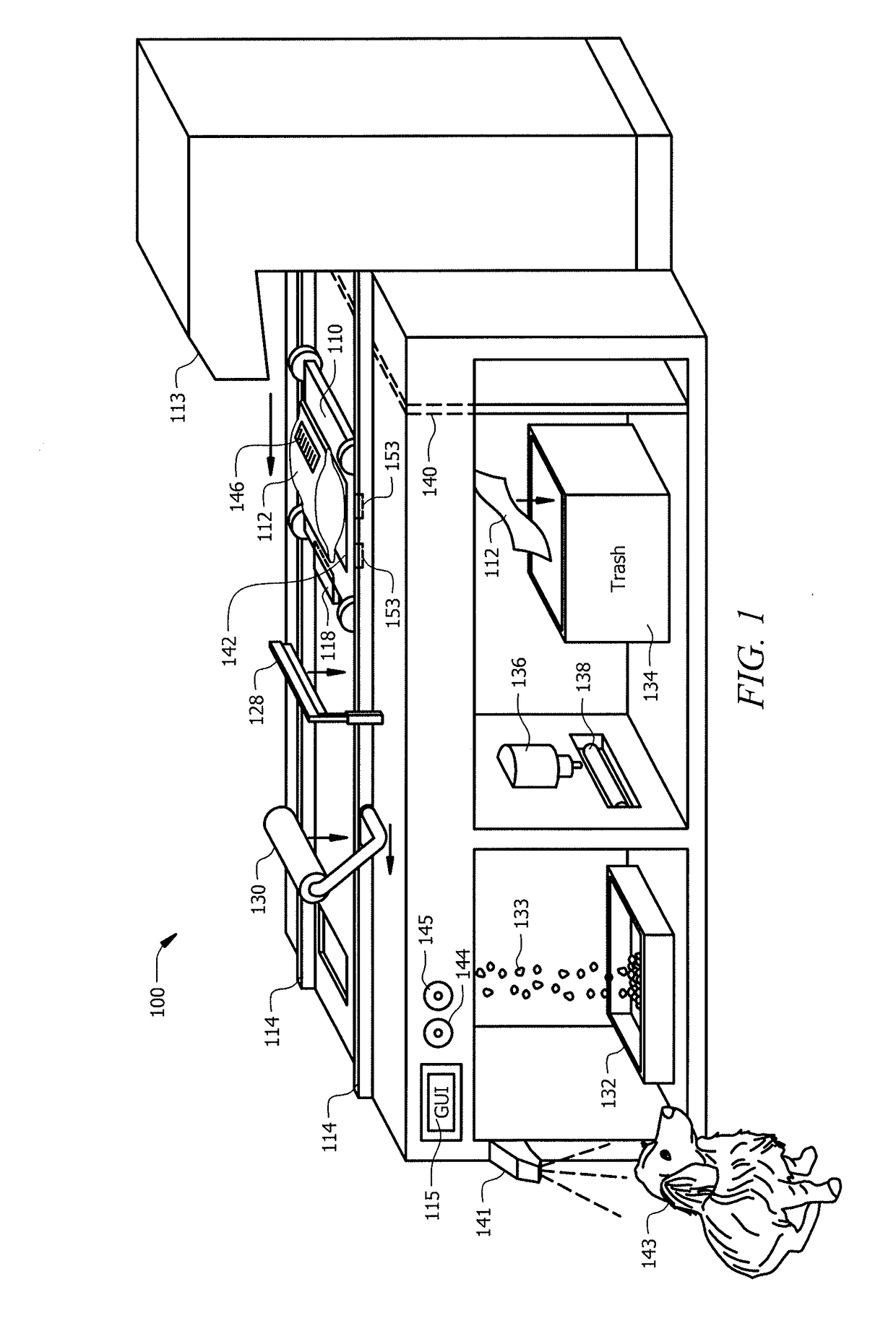
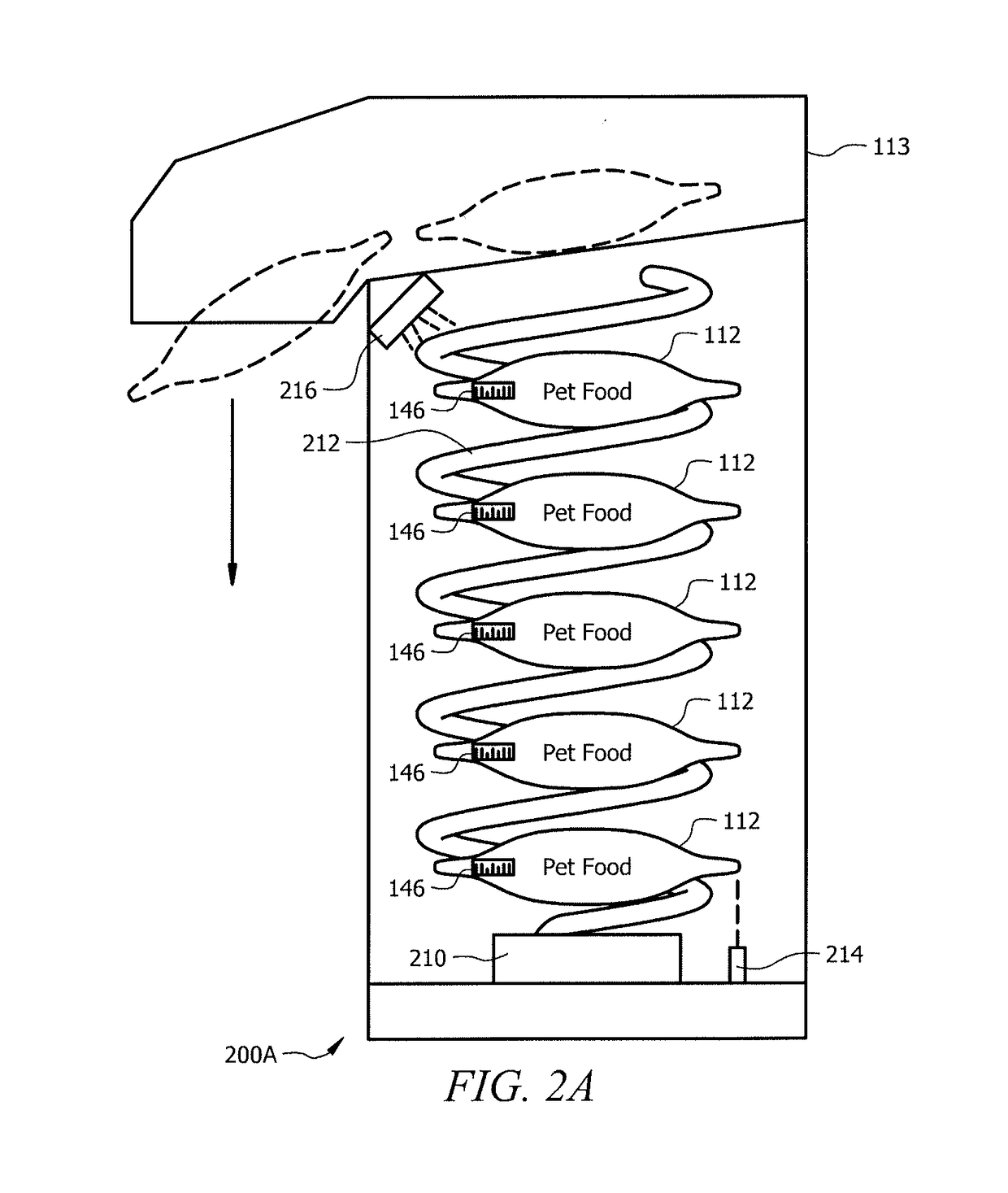
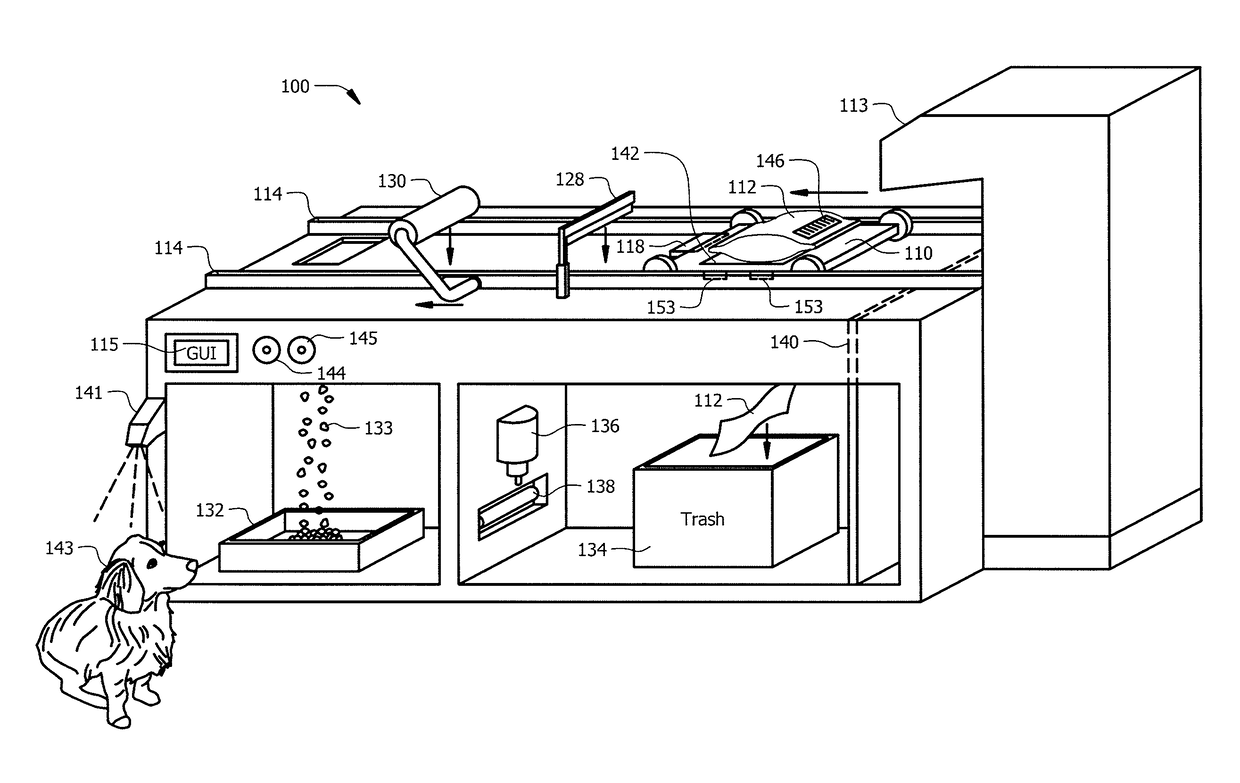
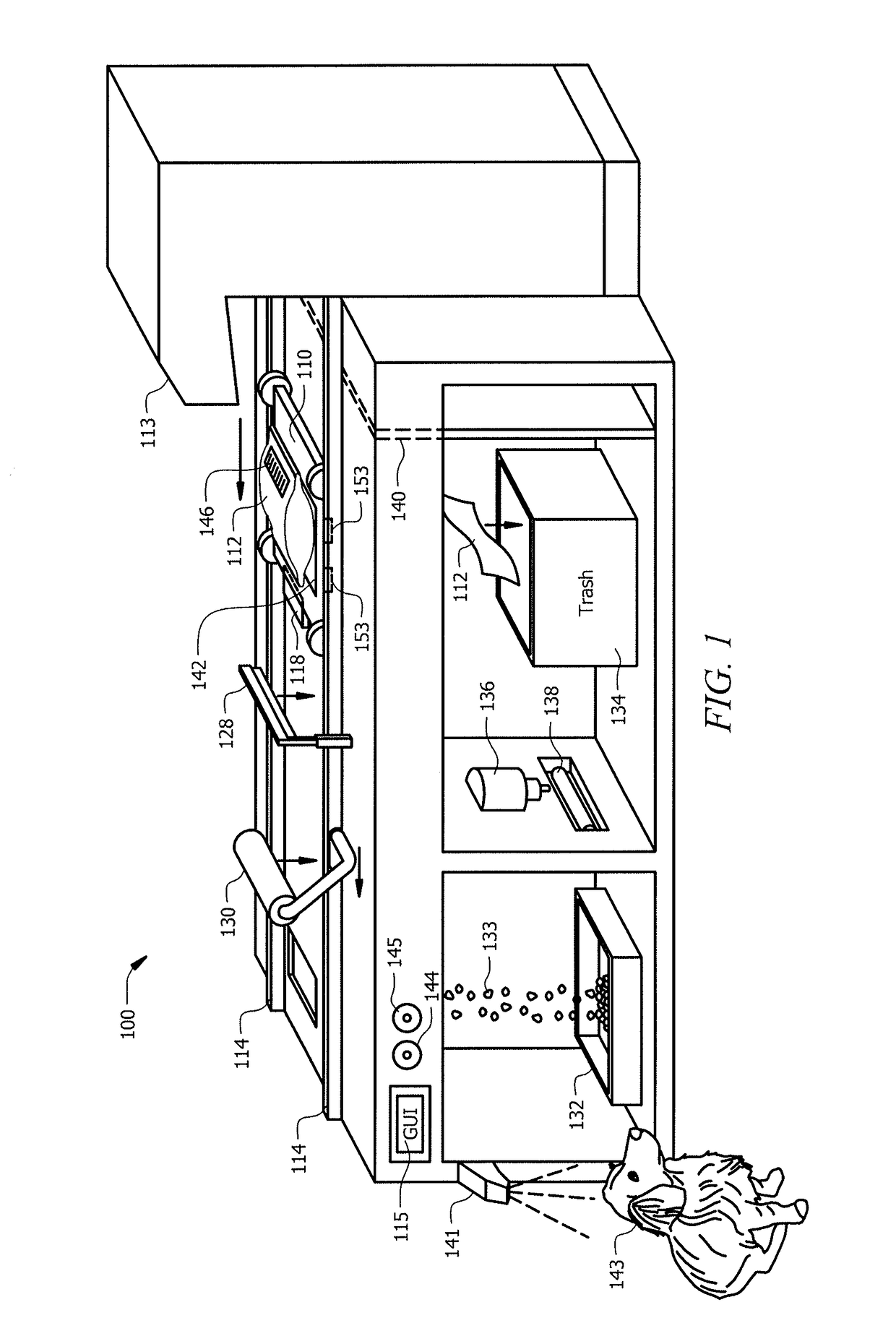
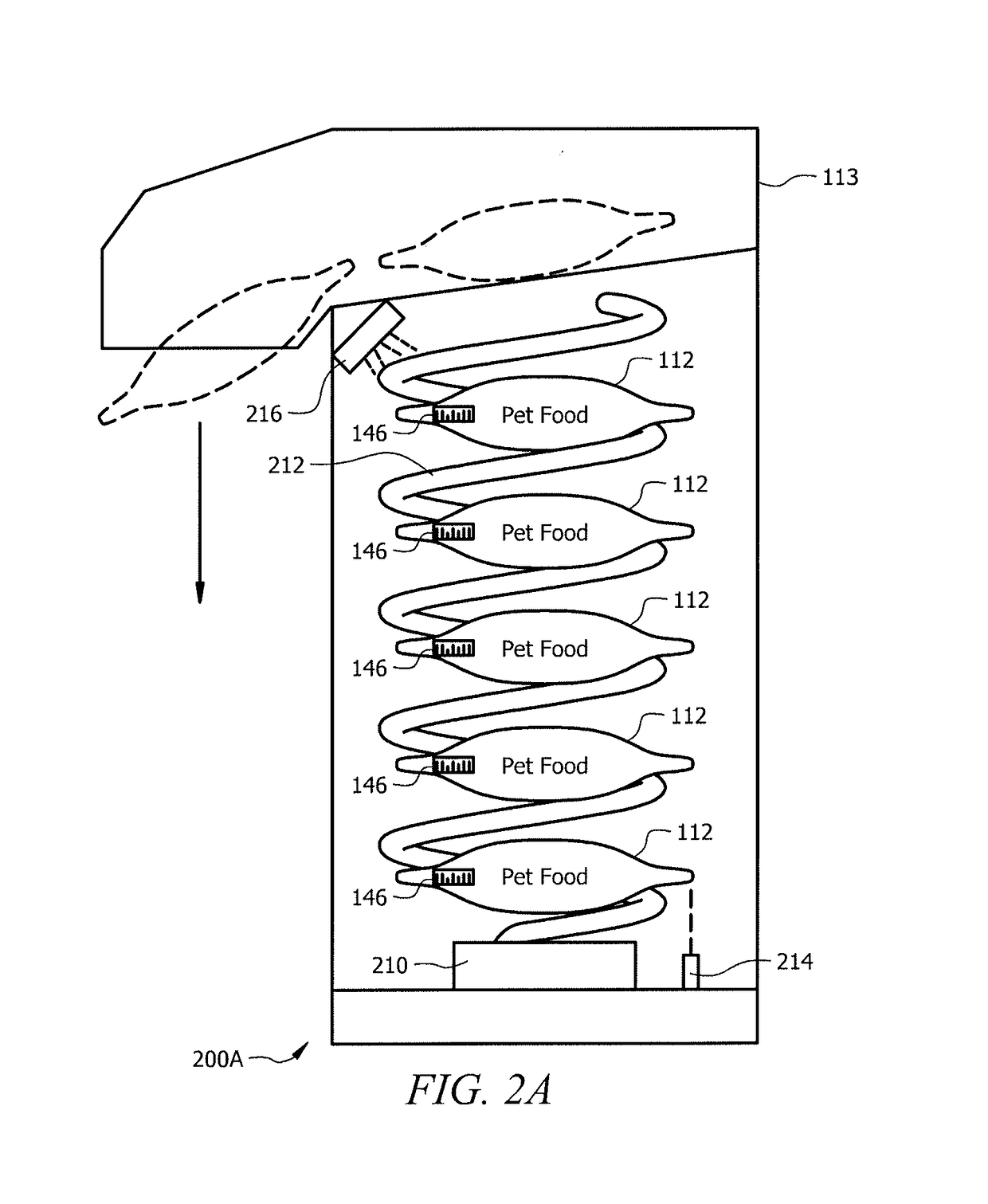
Intelligent pet food dispenser
InactiveUS20170099803A1Improves pet healthDisadvantages can be reduced eliminatedAnimal feeding devicesCleaning using toolsLitterEngineering
In one embodiment, a system for dispensing pet food includes a chamber, a transport conveyor, a blade, and an extractor. The chamber may dispense a pet found pouch to the transport conveyer. The transport conveyor may receive the pet food pouch and transport the pet food pouch to the blade wherein the blade may cut open the pet food pouch. The transport conveyor may then move the opened pet food pouch to the extractor. The transport conveyor may activate the extractor causing the extractor to lower onto the transport conveyor and extract pet food from the pet food pouch into a food tray. The transport conveyor may dispose the pet food pouch into a trash tray by releasing a trapdoor.
Owner:NEIGHBORS CONNOR
Convertible multi-use writing instrument
ActiveUS20050175396A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedWriting connectorsPropelling pencilsEngineering
In one embodiment, a convertible multi-use writing instrument includes a quick-use arrangement including a quick-use writing instrument and a quick-use cap for encapsulating the quick-use writing instrument. The quick-use arrangement is convertible to a full-size arrangement. The convertible multi-use writing instrument also includes the full-size arrangement. The full-size arrangement includes a full-size writing instrument that is convertible to the quick-use arrangement.
Owner:ADELMAN GREGORY M
Intelligent pet food dispenser
InactiveUS10034453B2Disadvantages can be reduced eliminatedProblems be reduced eliminatedAnimal feeding devicesBags openingLitterEngineering
In one embodiment, a system for dispensing pet food includes a chamber, a transport conveyor, a blade, and an extractor. The chamber may dispense a pet found pouch to the transport conveyer. The transport conveyor may receive the pet food pouch and transport the pet food pouch to the blade wherein the blade may cut open the pet food pouch. The transport conveyor may then move the opened pet food pouch to the extractor. The transport conveyor may activate the extractor causing the extractor to lower onto the transport conveyor and extract pet food from the pet food pouch into a food tray. The transport conveyor may dispose the pet food pouch into a trash tray by releasing a trapdoor.
Owner:NEIGHBORS CONNOR
Leveraging legacy applications for use with modern applications
ActiveUS9317266B1Improve productivityEasy maintenanceProgram controlMemory systemsSource codeHuman language
An apparatus of one embodiment translates computer code from a first programming language to a second programming language. The apparatus includes an interface, a memory, and a processor. The interface is operable to receive a compiler output that is associated with source code written in a first programming language. The memory is operable to store the compiler output. The processor is communicatively coupled to the interface and the memory and is operable to analyze the data structures within the compiler output, build an internal representation of the source code based on the compiler output, and create a source code template associated with a second programming language.
Owner:BANK OF AMERICA CORP
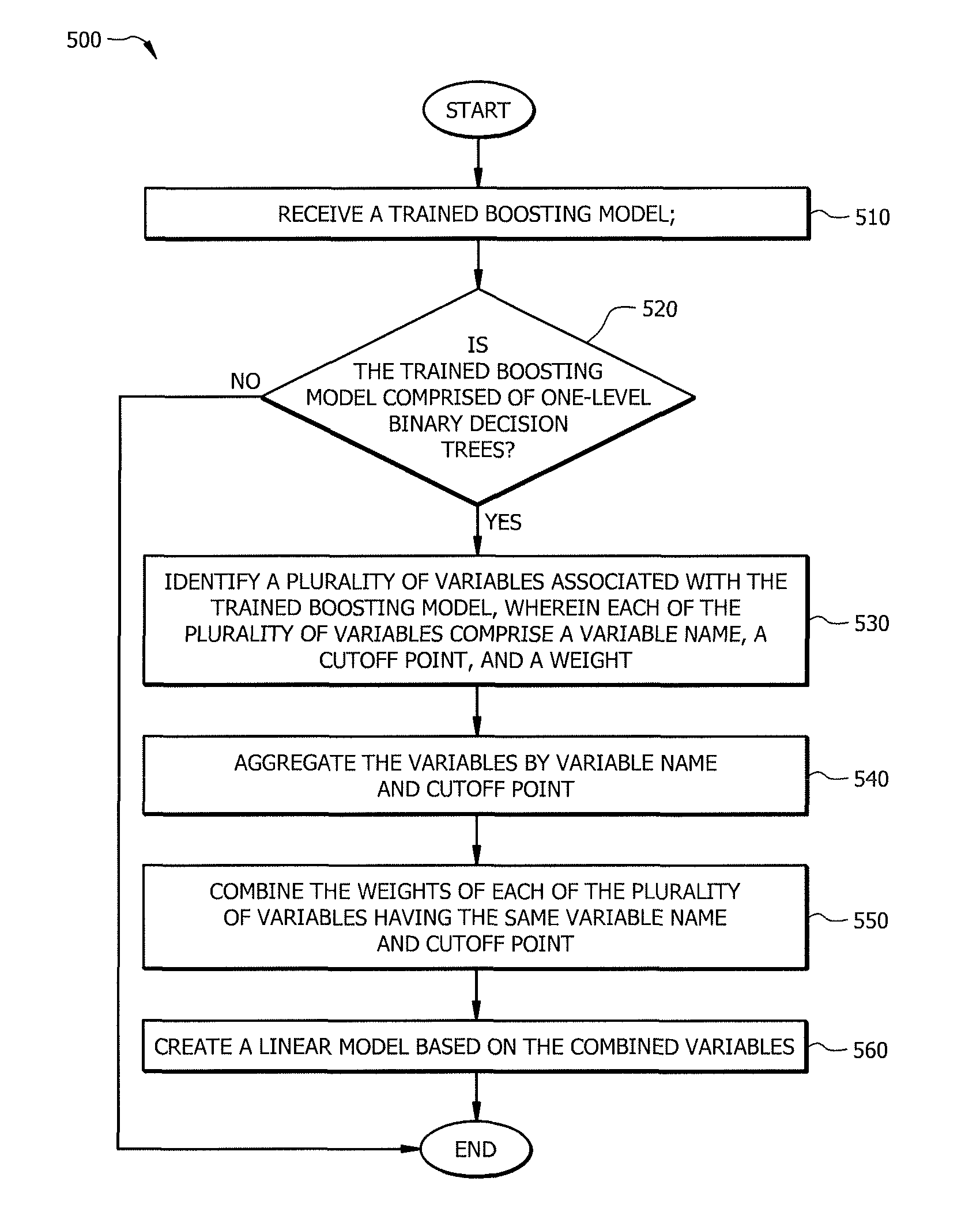
Transforming predictive models
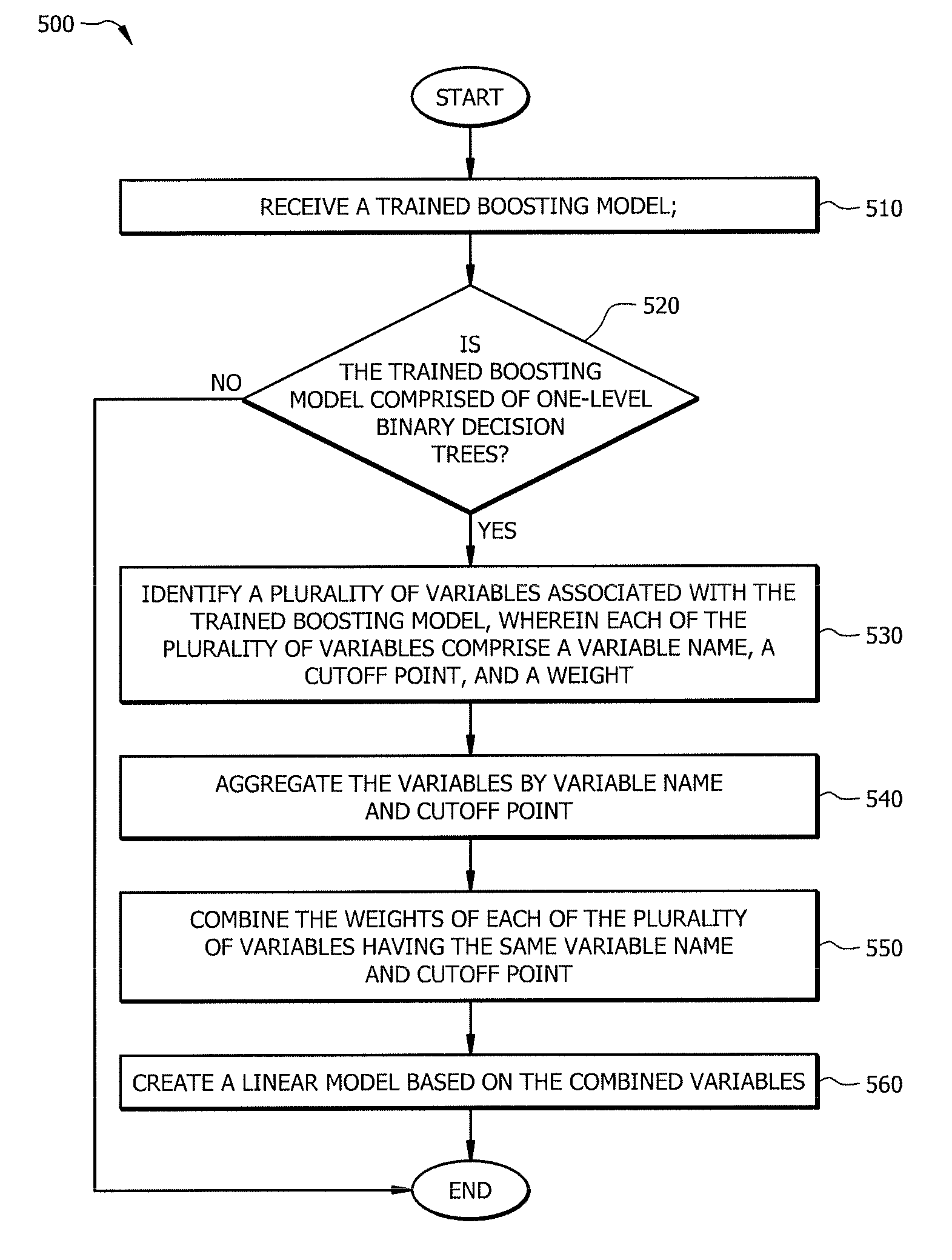
ActiveUS9280740B1Reduce Algorithmic ComplexityOvercome problemsEnsemble learningDigital computer detailsTheoretical computer scienceLinear model
According to one embodiment of the present disclosure, a system for translating a boosting algorithm includes an interface communicatively coupled to a processor. The interface is operable to receive a trained boosting model. The processor is operable to identify a plurality of split-node variables associated with the trained boosting model. Each of the plurality of split-node variables comprises a variable name, a cutoff point, and a weight. The processor may aggregate the split-node variables by variable name and cutoff point and then combine the weights of each of the plurality of split-node variables having the same variable name and cutoff point. The processor may then create a linear model based on the combined variables.
Owner:BANK OF AMERICA CORP
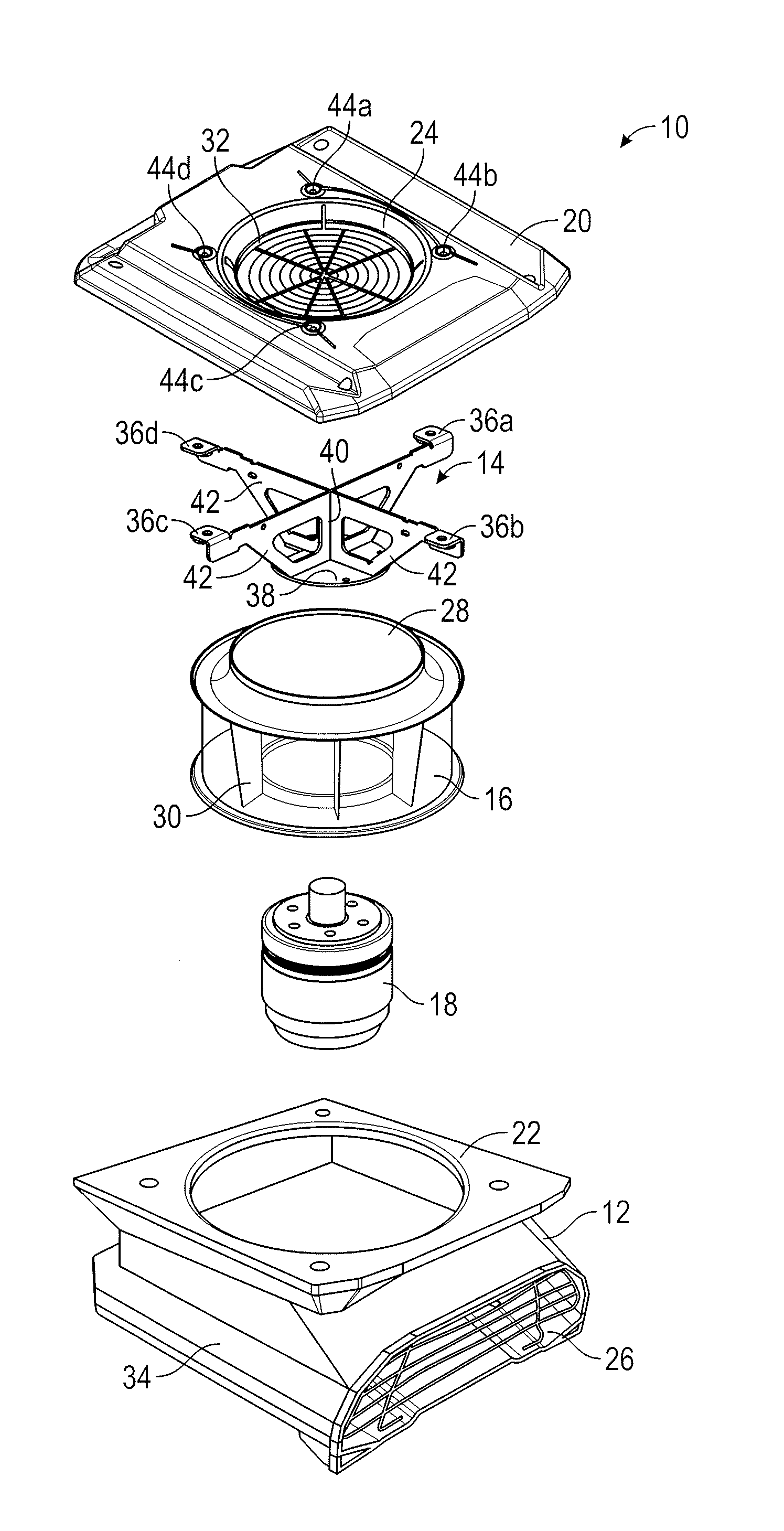
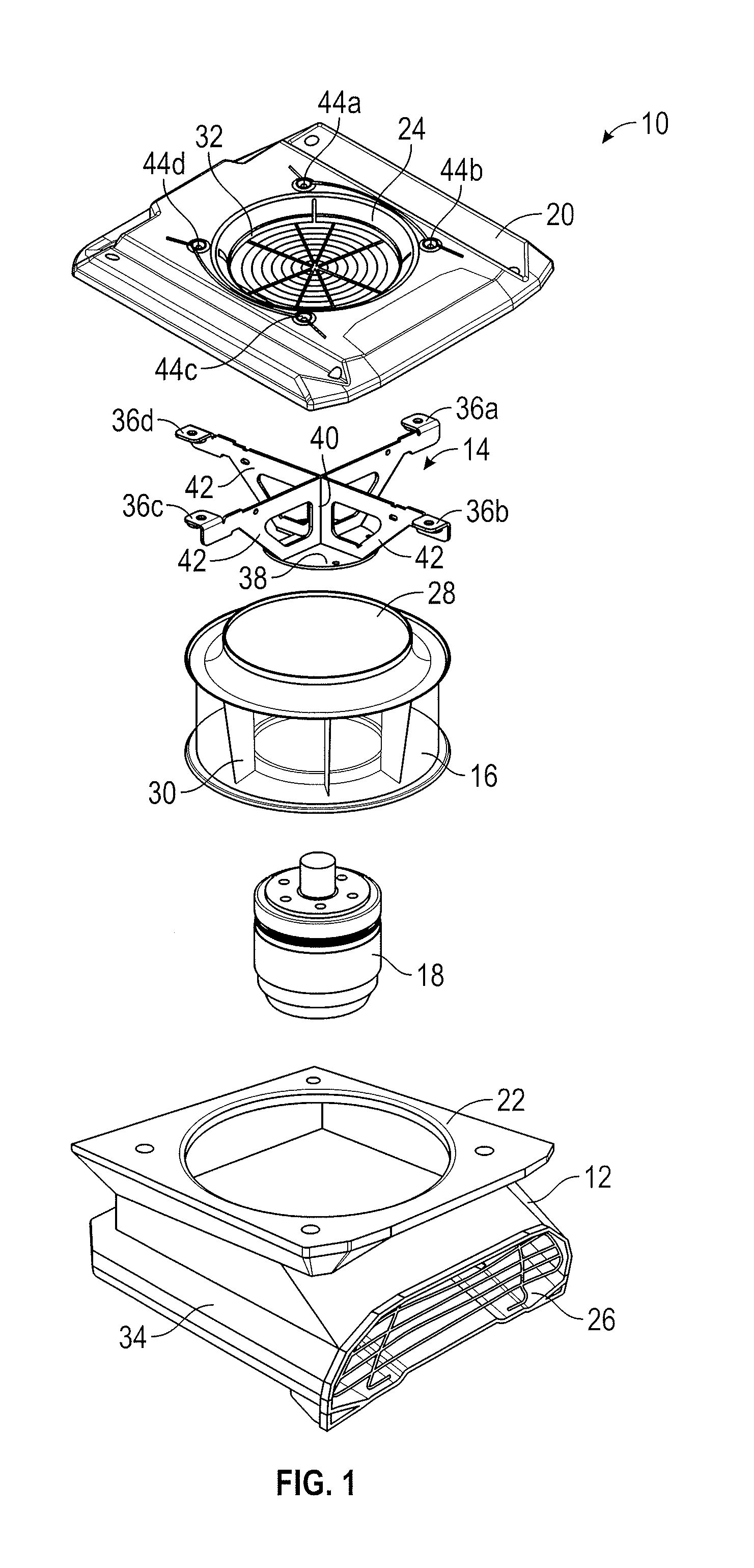
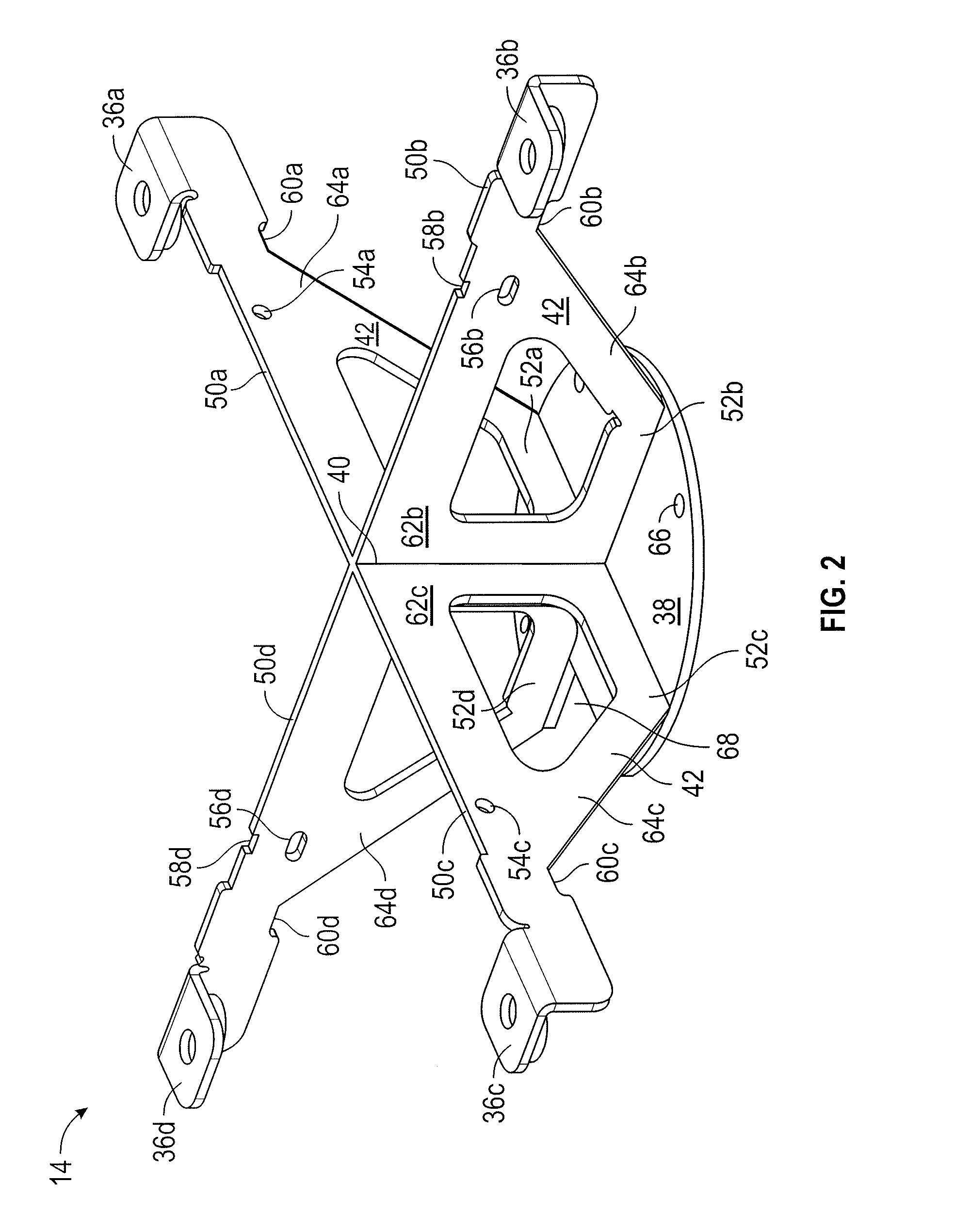
Fan and mounting bracket for an air mover
ActiveUS20160327063A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedPump componentsPump installationsImpellerEngineering
An air mover comprising a housing with a top portion is disclosed. A mounting bracket is recessed into the housing through the top portion of the housing. The mounting bracket comprises a plurality of top chords intersecting at a first portion of an inner web and a plurality of bottom chords intersecting at a second portion of the inner web. The mounting bracket also has a base plate coupled to the plurality of bottom chords. A motor is coupled to the base plate of the mounting bracket. An impeller is coupled to the motor. The air mover further comprises a housing cover that has an inlet ring positioned on the top portion of the housing. The housing cover is coupled to the mounting bracket via the mounting flanges and a portion of the inlet ring protrudes into the impeller inlet inside the housing.
Owner:THERMA STOR LLC
Transforming predictive models
ActiveUS20160203405A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedEnsemble learningDigital computer detailsTheoretical computer scienceLinear model
A system for translating a boosting algorithm includes an interface communicatively coupled to a processor. The interface is operable to receive a trained boosting model. The processor is operable to identify a plurality of split-node variables associated with the trained boosting model. Each of the plurality of split-node variables comprises a variable name, a cutoff point, and a weight. The processor may aggregate the split-node variables by variable name and cutoff point and then combine the weights of each of the plurality of split-node variables having the same variable name and cutoff point. The processor may then create a linear model based on the combined variables. The processor may further create a performance scorecard based on the combined weight, and create a model evaluation based on the error rate of the trained boosting model.
Owner:BANK OF AMERICA CORP
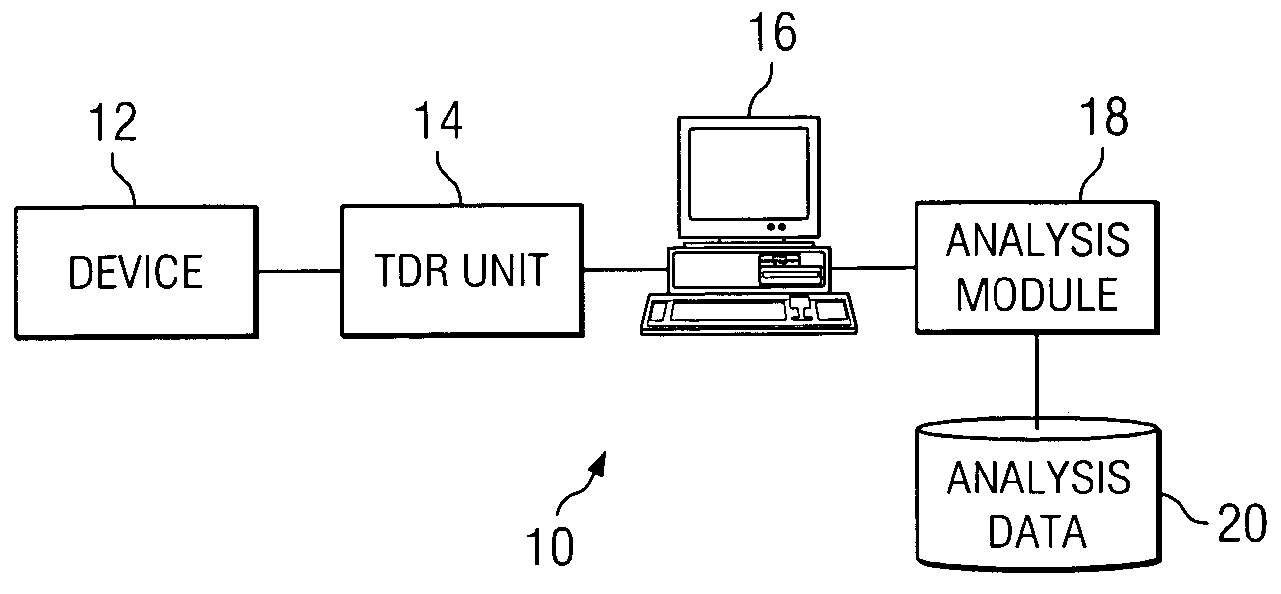
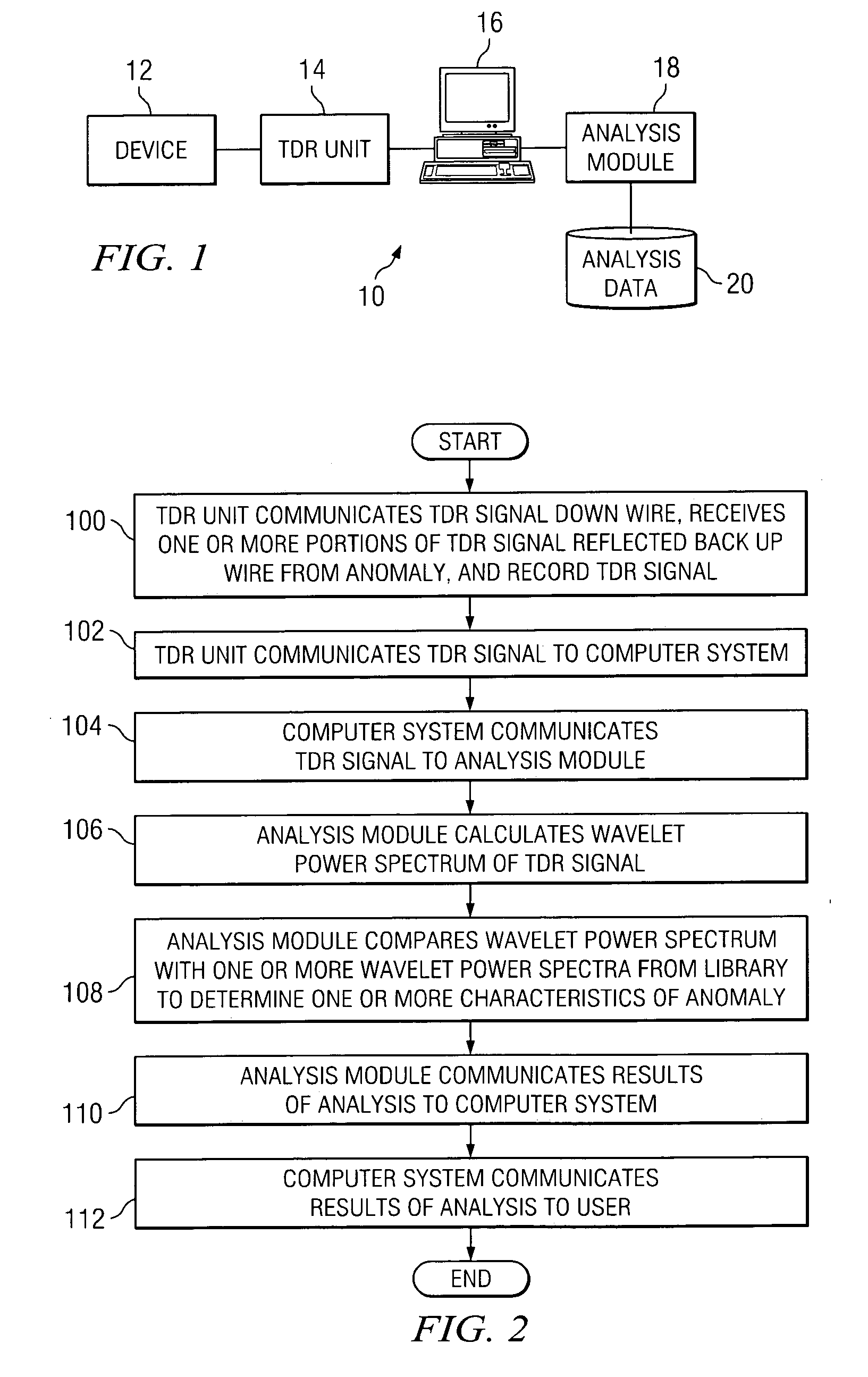
Wavelet analysis of one or more time domain reflectometry (TDR) signals to determine one or more characteristics of one or more anomalies in a wire
ActiveUS20050021256A1Easy to analyzeDisadvantages can be reduced eliminatedSpectral/fourier analysisResistance/reactance/impedenceTime domainComputer science
In one embodiment, a method for wavelet analysis of one or more time domain reflectometry (TDR) signals to determine one or more characteristics of one or more anomalies in a wire includes receiving a TDR signal that has reflected back up a wire from an anomaly in the wire, calculating a wavelet analysis result from a wavelet analysis of the TDR signal, accessing a library of one or more reference wavelet analysis results that each correspond to one or more known anomalies having one or more known characteristics, and comparing the wavelet analysis result with one or more reference wavelet analysis results. If the wavelet analysis result corresponds to one or more particular reference wavelet analysis results, it is indicated that the anomaly in the wire has one or more particular known characteristics of one or more particular known anomalies corresponding to the one or more particular reference wavelet analysis results. If the wavelet analysis result of the TDR signal does not correspond to one or more reference wavelet analysis results, it is indicated that the anomaly in the wire lacks one or more known characteristics of one or more known anomalies corresponding to one or more reference wavelet analysis results in the library.
Owner:TEXAS INSTR INC
System and method for monitoring and control of an optical modulator for an M-QAM transmitter
ActiveUS9344194B2Disadvantages can be reduced eliminatedProblems be reduced eliminatedElectromagnetic transmittersOptical power meterPhase shifted
Owner:FUJITSU LTD
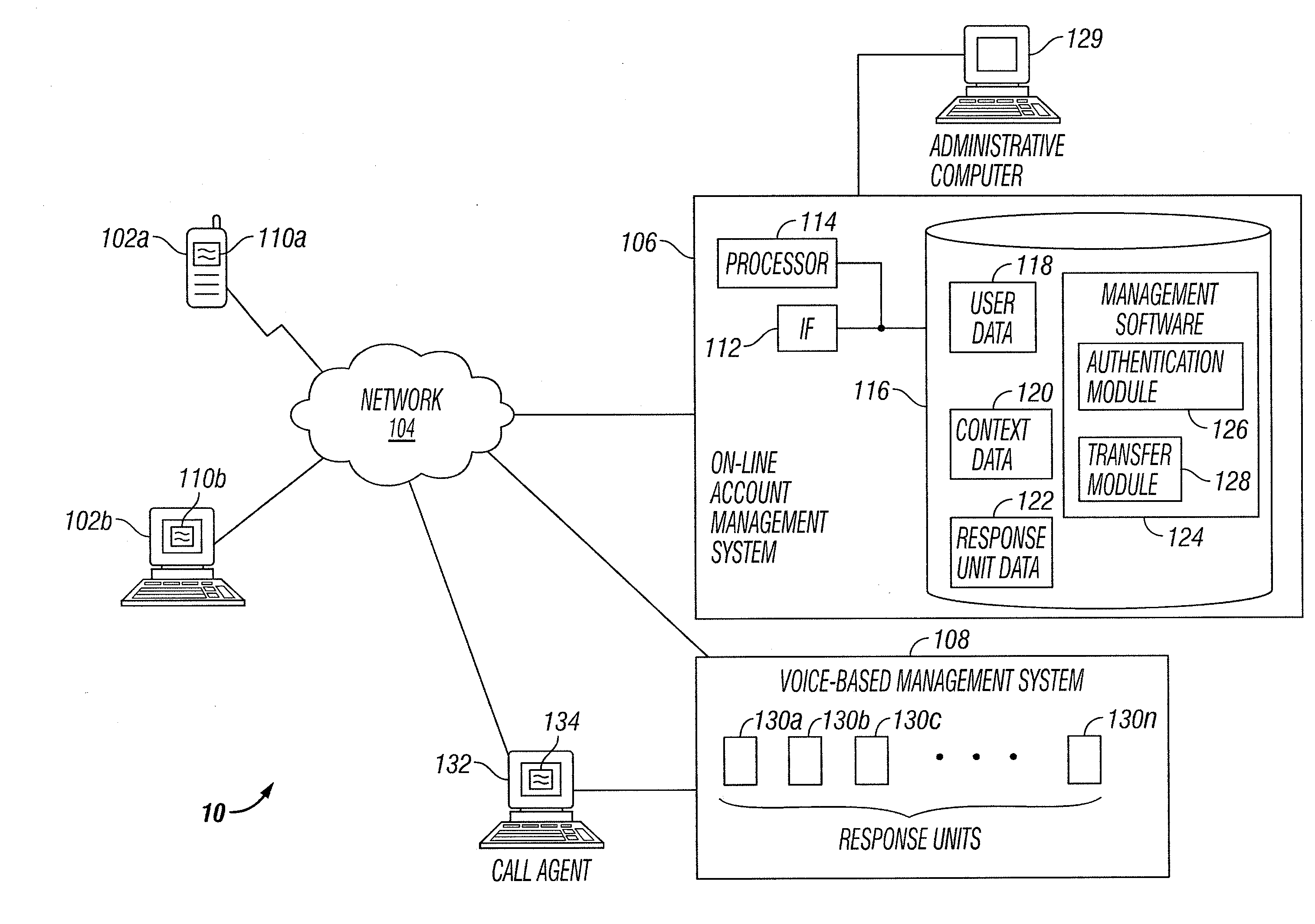
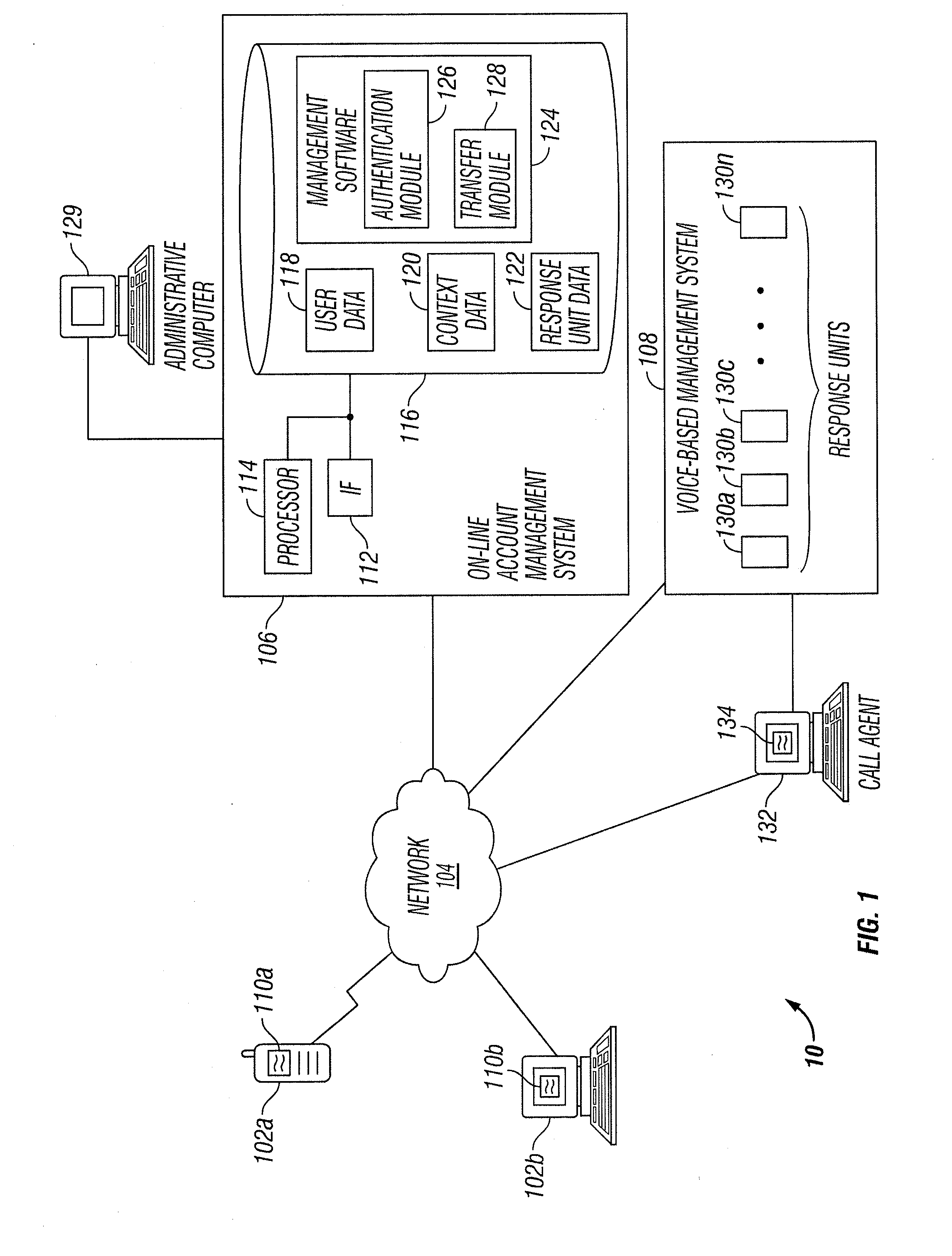
Communication with a Voice-Based Account Management System
InactiveUS20140101732A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedDigital data processing detailsMultiple digital computer combinationsLine managementComputer science
According to an embodiment, a method facilitates communication with a voice-based management system. An authentication credential is received. Based on the authentication credential, a user is allowed to access an on-line management system operable to facilitate management of an account. The on-line management system receives a request to connect the user to a voice-based management system operable to facilitate providing a response to a question included in the request. A user type associated with the user is determined. A context associated with the question included in the request is determined. A response unit in the voice-based management system is determined according to the user type and the context. The user is connected to the response unit in the voice-based management system without requiring the user to provide the authentication credential to the response unit.
Owner:BANK OF AMERICA CORP
Vendor Risk And Performance Profile
InactiveUS20150242776A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedFinanceResourcesEngineeringRisk element
Establishing a vendor profile may comprise identifying a plurality of risk elements associated with a vendor that supplies one or more products to an entity. Any completed management actions for the vendor that mitigate risk associated with any of the identified risk elements are identified. A performance requirement for the vendor associated with at least one of the products supplied by the vendor to the entity is identified. A performance measurement for the identified performance requirement for the vendor is identified. A residual risk for at least one of the identified risk elements is determined according to a completed management action that reduces risk associated with the at least one of the identified risk elements. A performance level is determined according to the performance requirement and the performance measurement. A vendor profile is created according to the identified risk elements, completed management actions, identified performance requirements, and performance measurement.
Owner:BANK OF AMERICA CORP
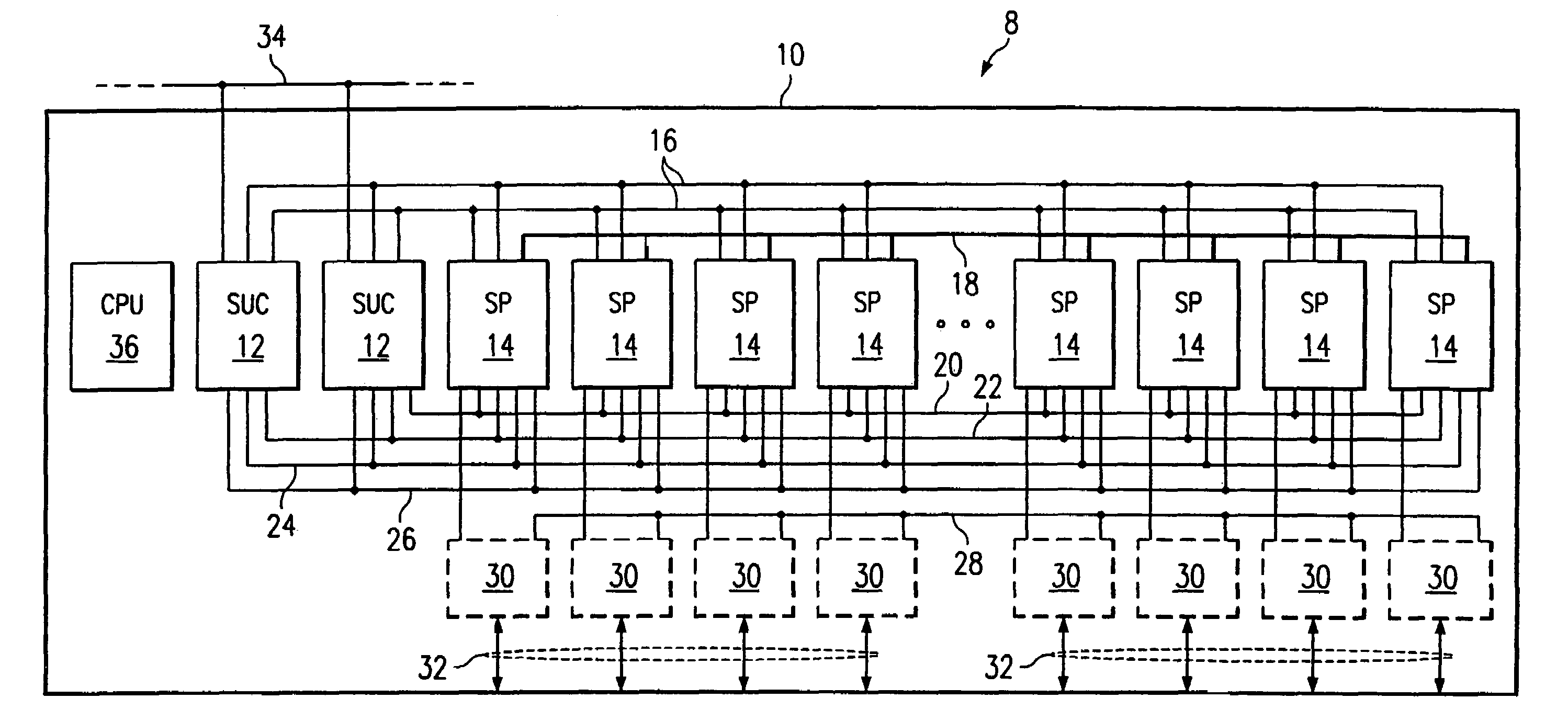
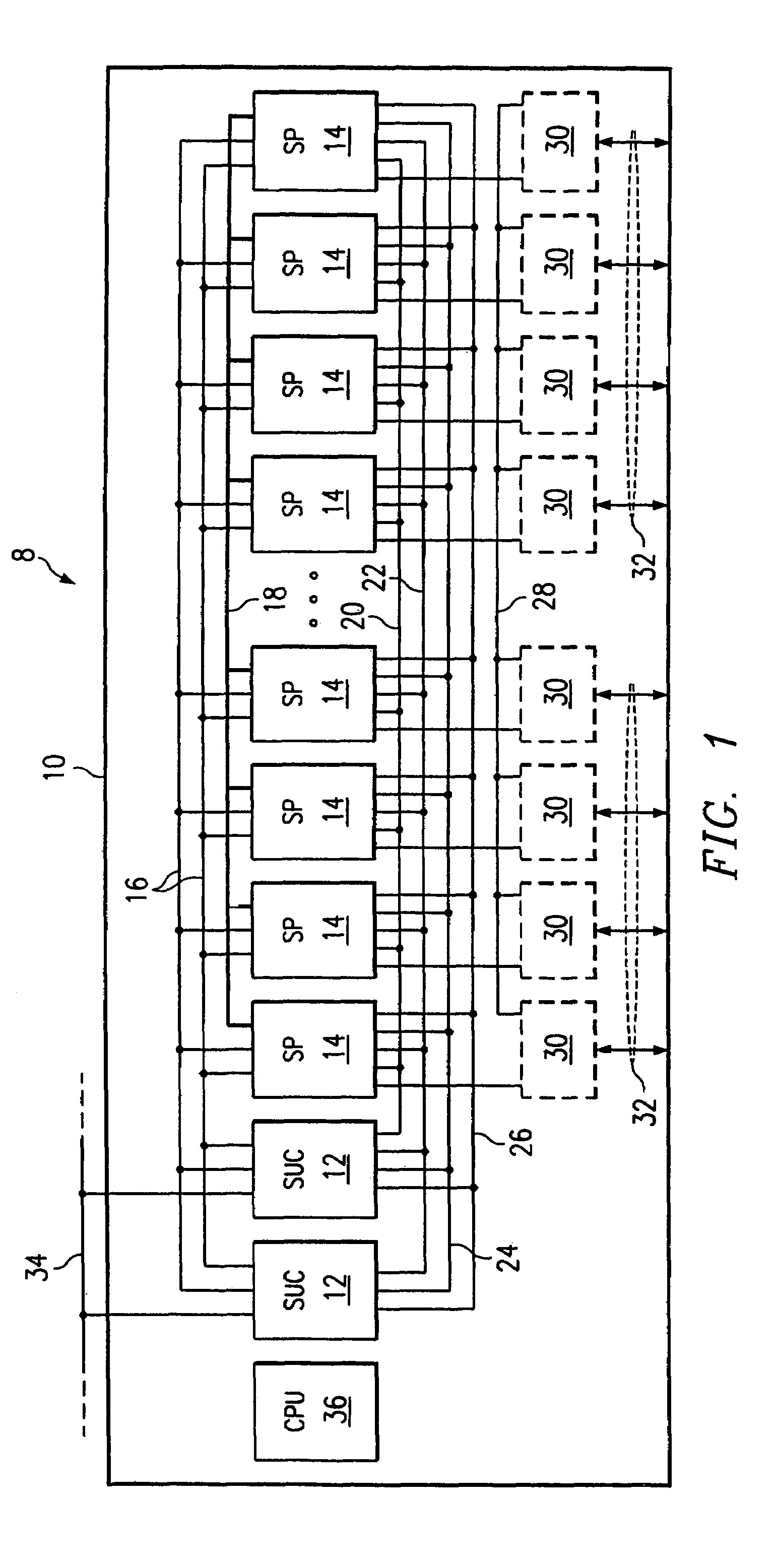
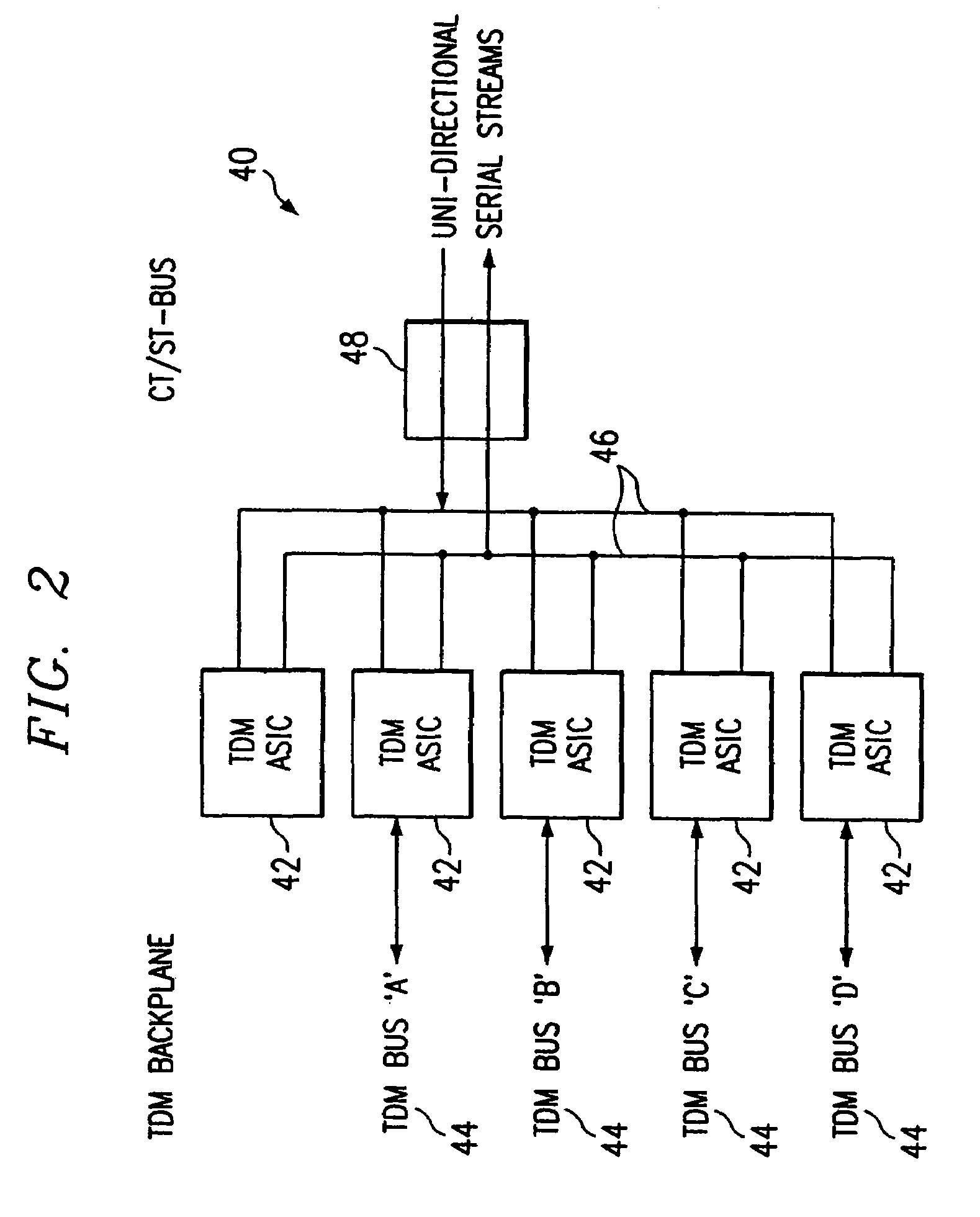
TDM switching system and ASIC device
InactiveUS7457285B1Increase port densityImprove scalabilityTime-division multiplexCircuit switching systemsEmbedded systemNetwork interface
In one embodiment, a switching system includes a backplane and multiple cards that each support multiple ASIC devices. Each ASIC device is associated with a subset of the network interfaces associated with the switching system. At least one ASIC device on a card may communicate switched data to an outgoing network interface associated with the card. Remaining ASIC devices on the card may communicate switched data to one or more other cards, using the backplane, for communication to one or more outgoing network interfaces associated with the other cards. In another embodiment, a device for switching data from a first bus to a second bus in a TDM switching system is provided. In another embodiment, a method for switching data between a plurality of network interfaces in a switching system is disclosed.
Owner:CISCO TECH INC
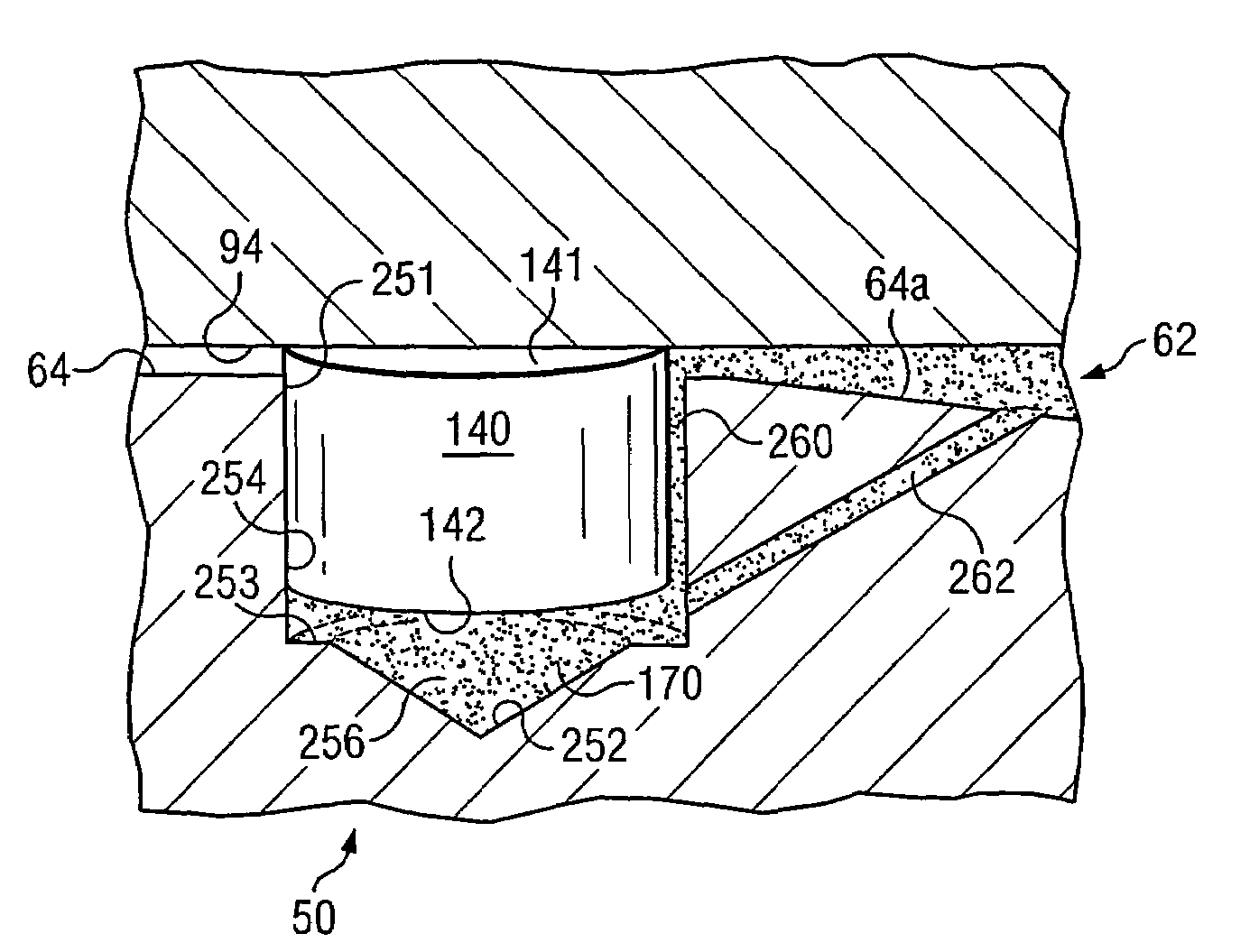
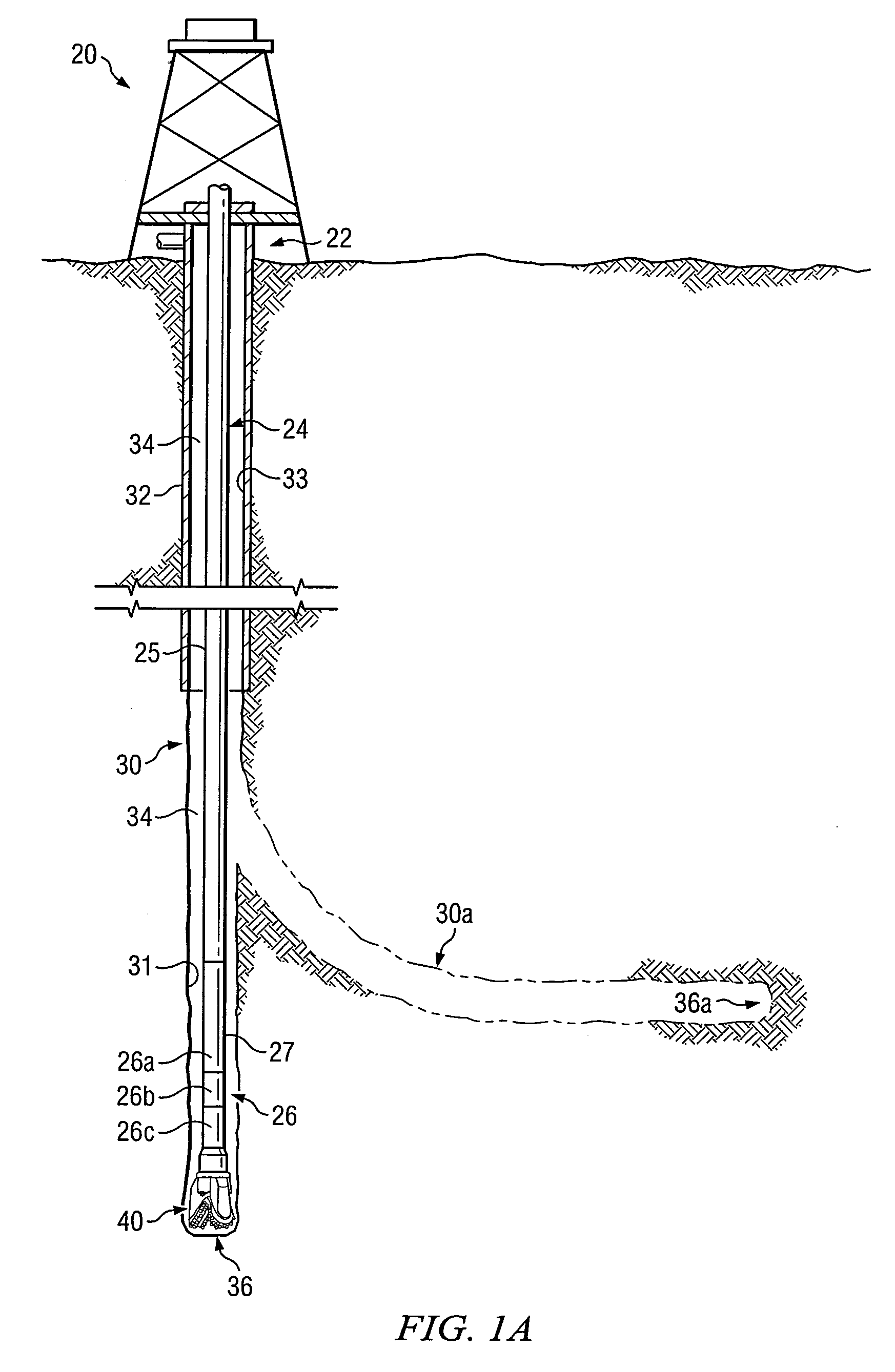
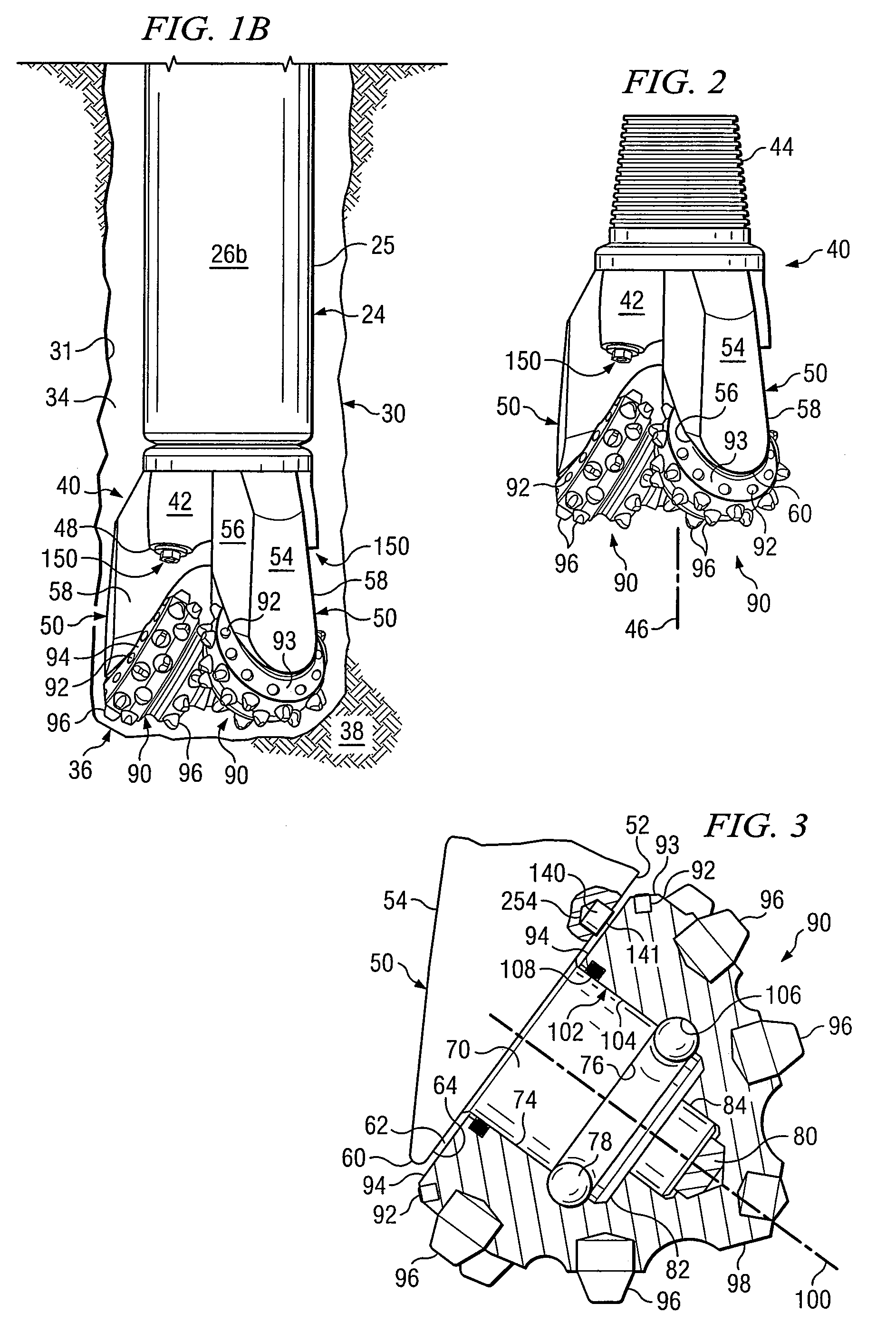
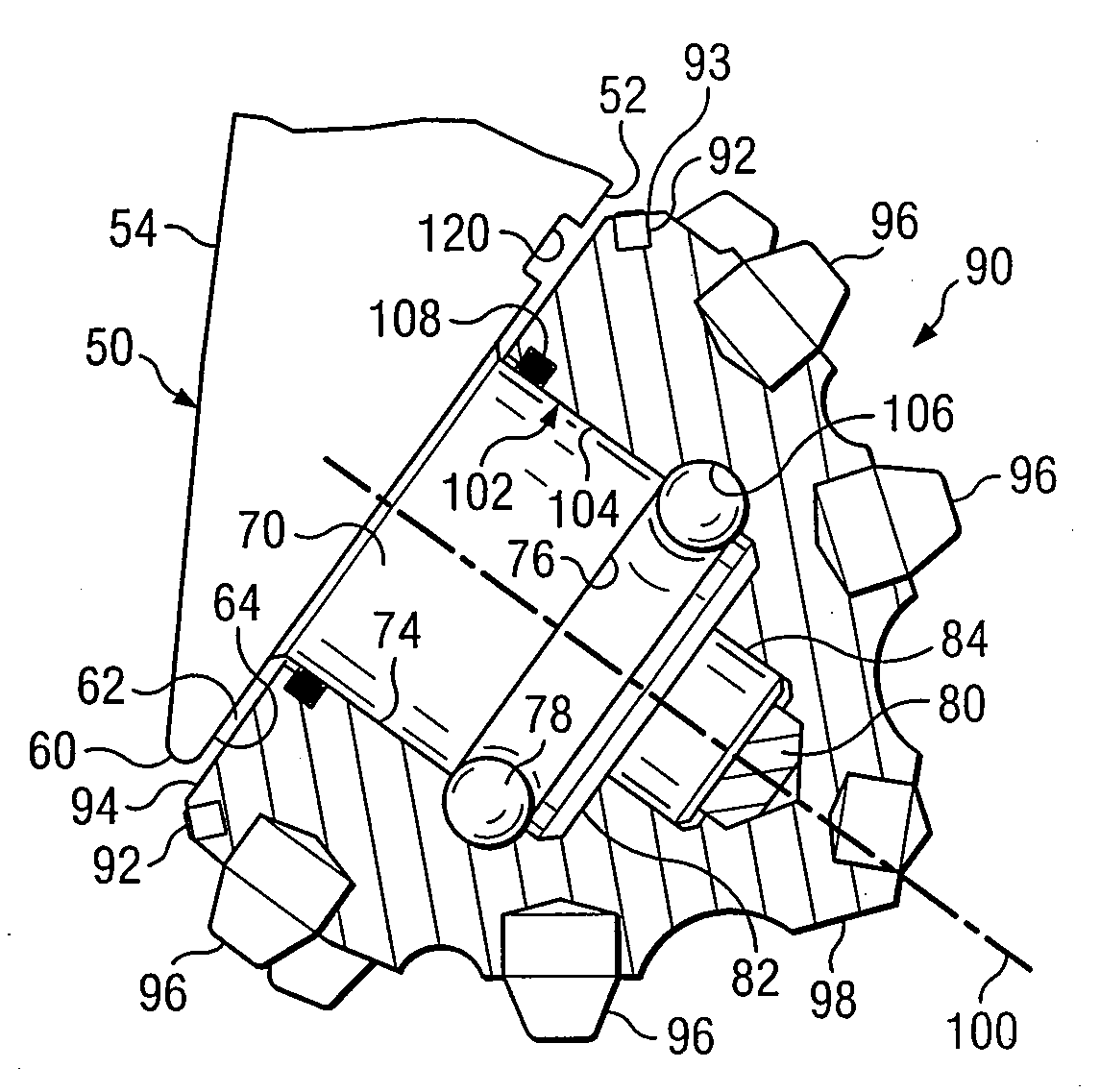
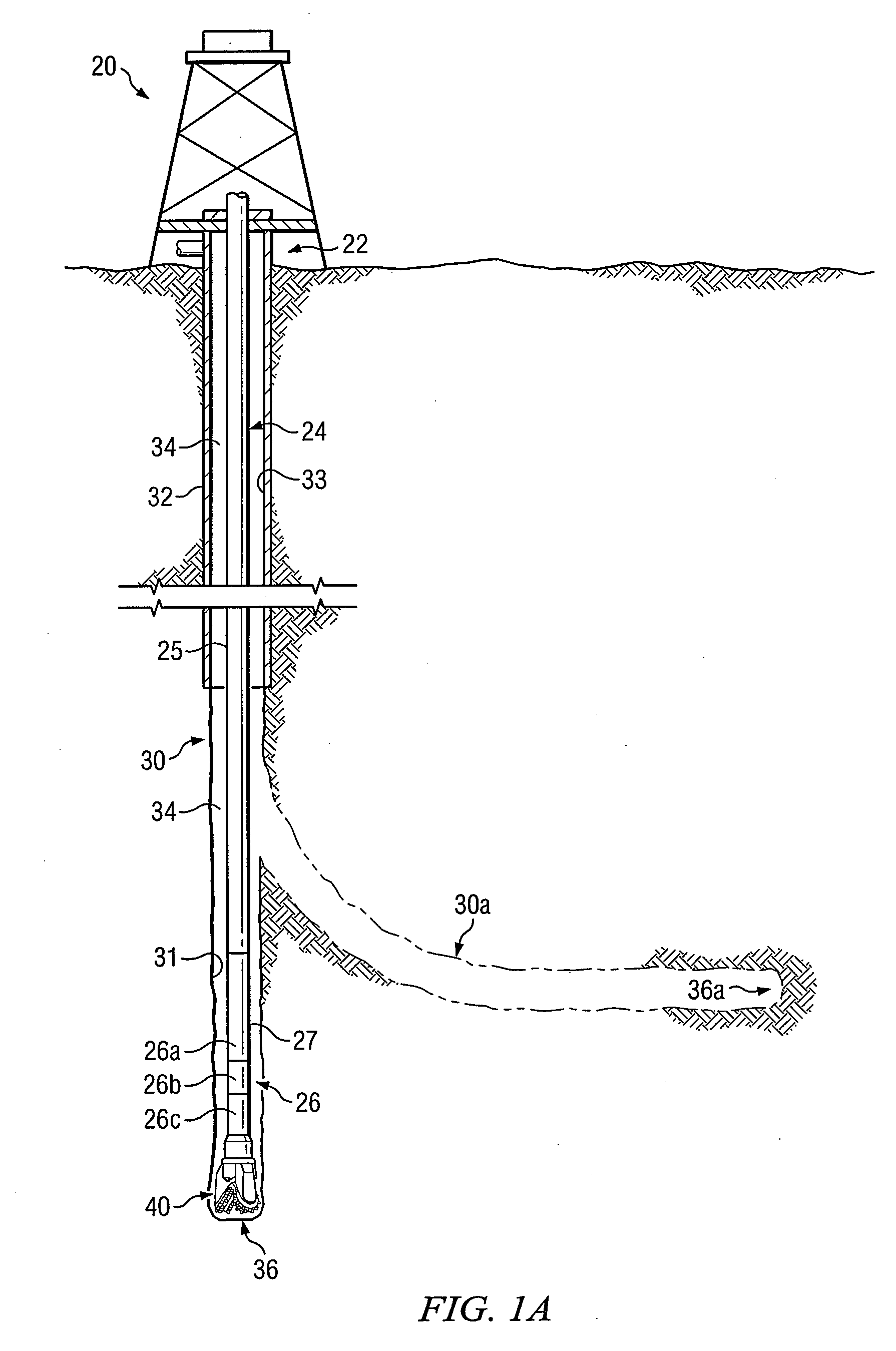
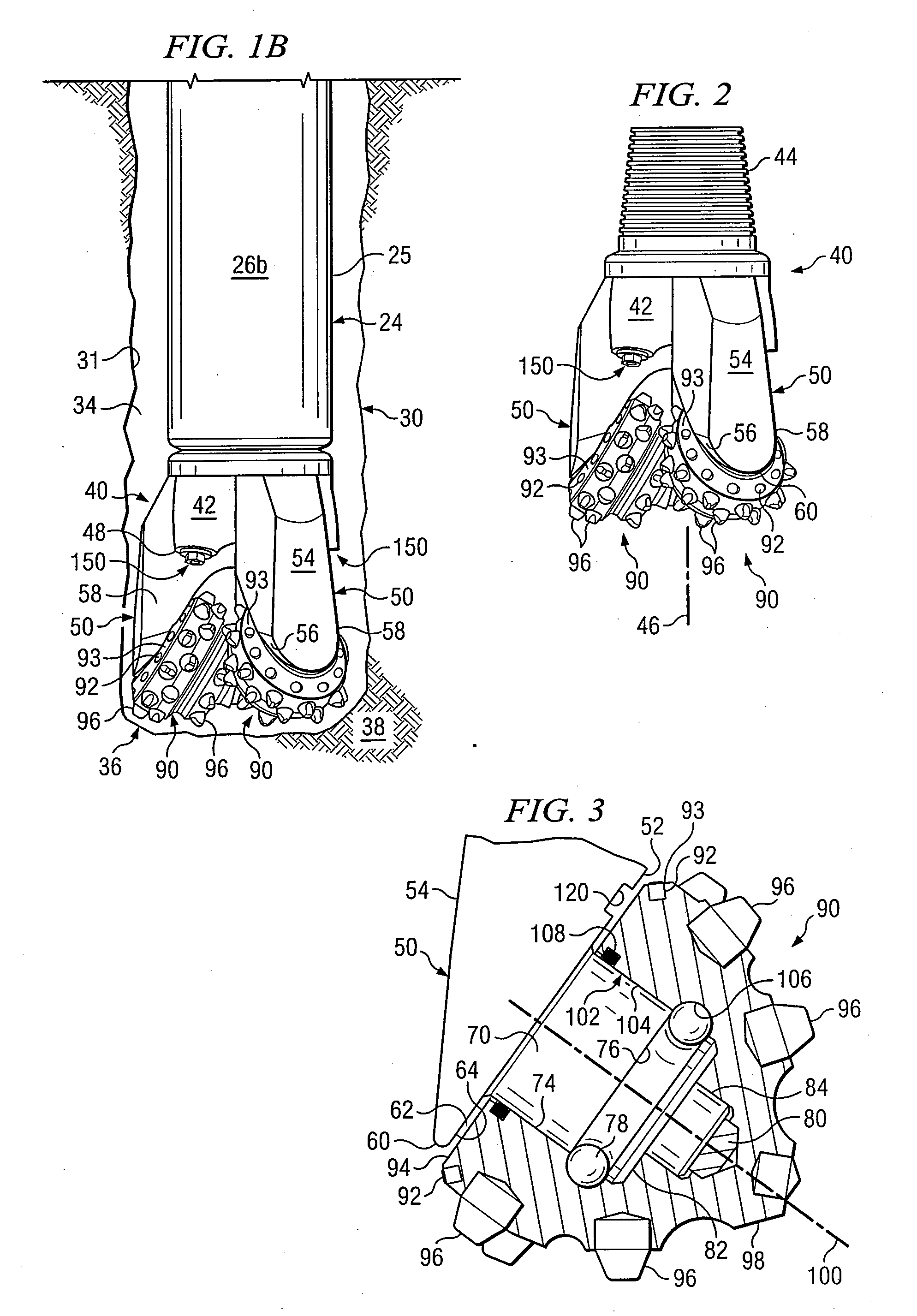
Roller cone drill bit with debris diverter plugs
InactiveUS7543660B2Prolong lifeDisadvantages can be reduced eliminatedDrill bitsConstructionsEngineeringMechanical engineering
A roller cone drill bit having a bit body with at least one support arm extending from the bit body. Each support arm may have an associated spindle extending inwardly. A respective cone assembly may be rotatably disposed on each spindle. At least one diverter plug may be disposed in a hole formed in each support arm. A void space may be formed between one end of each diverter plug and the bottom of the associated hole. At least one fluid flow passageway may extend from the surface of the associated support arm to the void space to allow communication of fluid containing debris with the void space. Rotating action of the roller cone drill bit and associated cone assemblies may force packing of debris into the void space which results in biasing the diverter plug outwardly from the associated hole to contact adjacent portions of the associated cone assembly.
Owner:HALLIBURTON ENERGY SERVICES INC
Roller Cone Drill Bit With Enhanced Debris Diverter Grooves
InactiveUS20070261891A1Extending downhole drilling lifeHigh trafficDrill bitsConstructionsEngineeringFlow diverter
A roller cone drill bit having a bit body with at least one support arm extending from the bit body. Each support arm may have an interior surface and exterior surface with an associated spindle extending from the interior surface. A respective cone assembly may be rotatably disposed on each spindle. A gap formed between interior portions of each cone assembly and exterior portions of the associated spindle with a fluid seal disposed in the gap to block fluid flow therethrough. Each cone assembly includes a generally circular back surface disposed adjacent to the interior surface of the associated support arm. A flow diverter groove formed in the interior surface of each support arm spaced from the associated spindle. Each diverter groove having a variable geometry to enhance the flow of fluid containing downhole debris away from the associated real assembly, and each diverter groove having a variable geometry.
Owner:HALLIBURTON ENERGY SERVICES INC
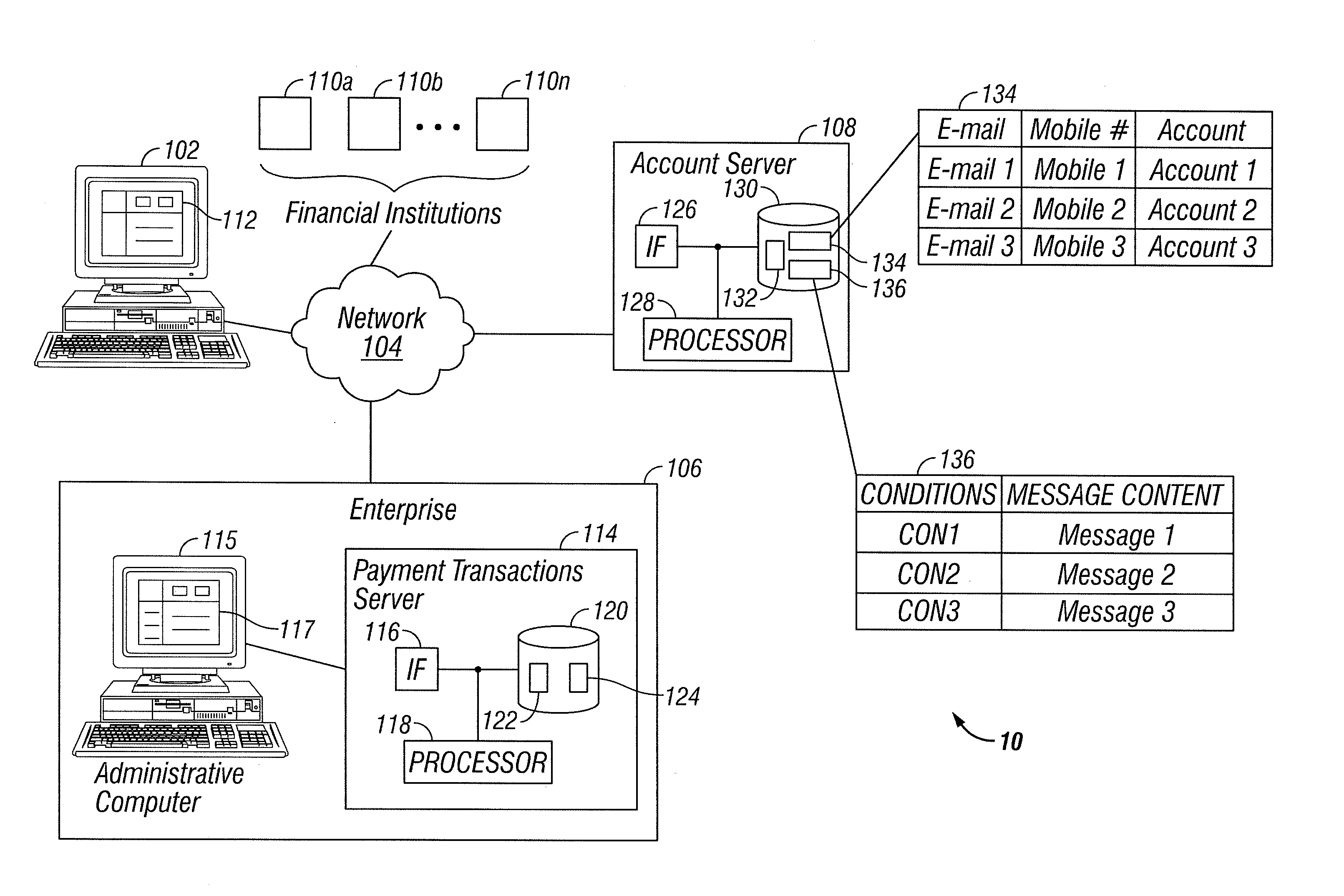
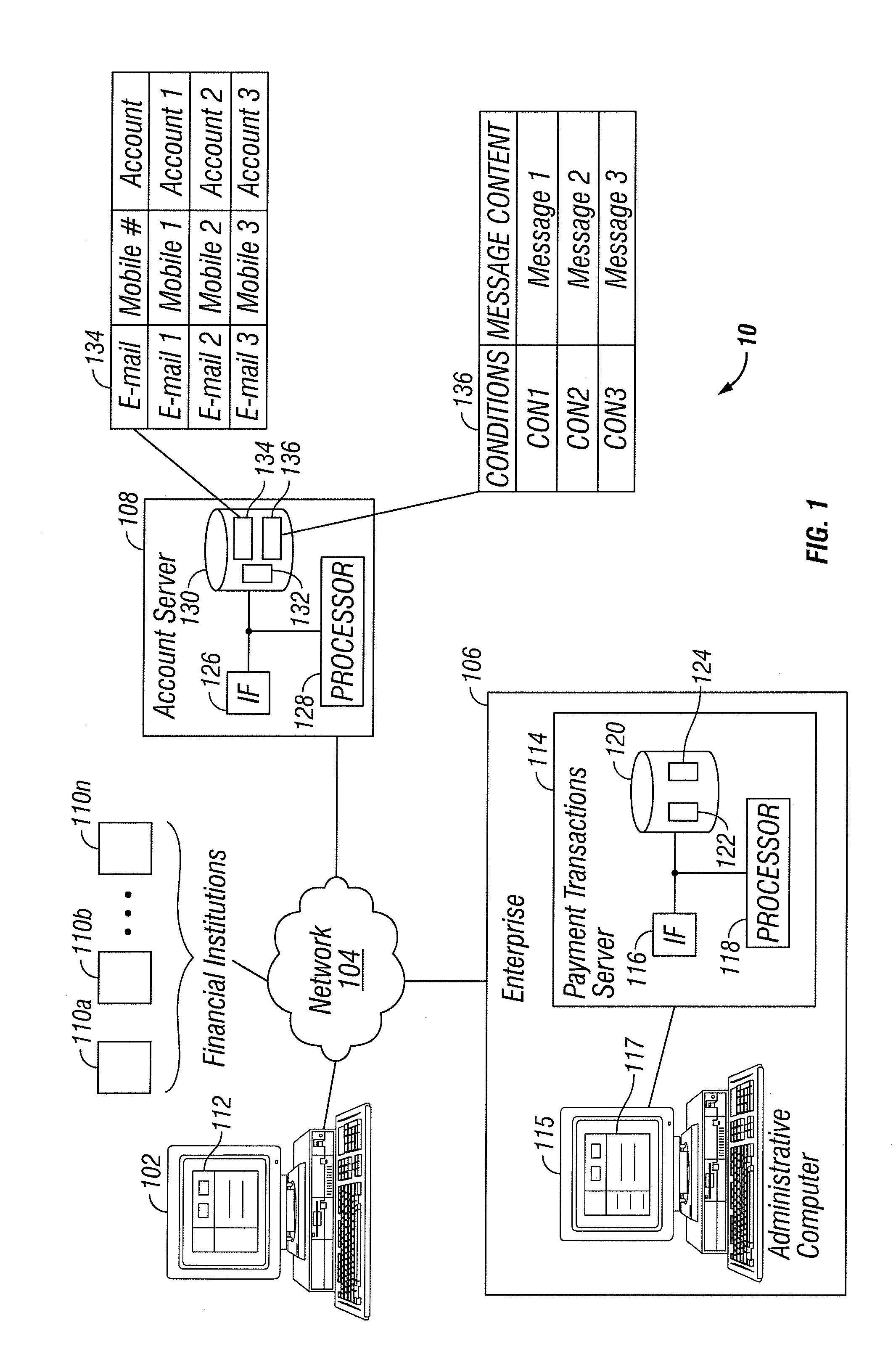
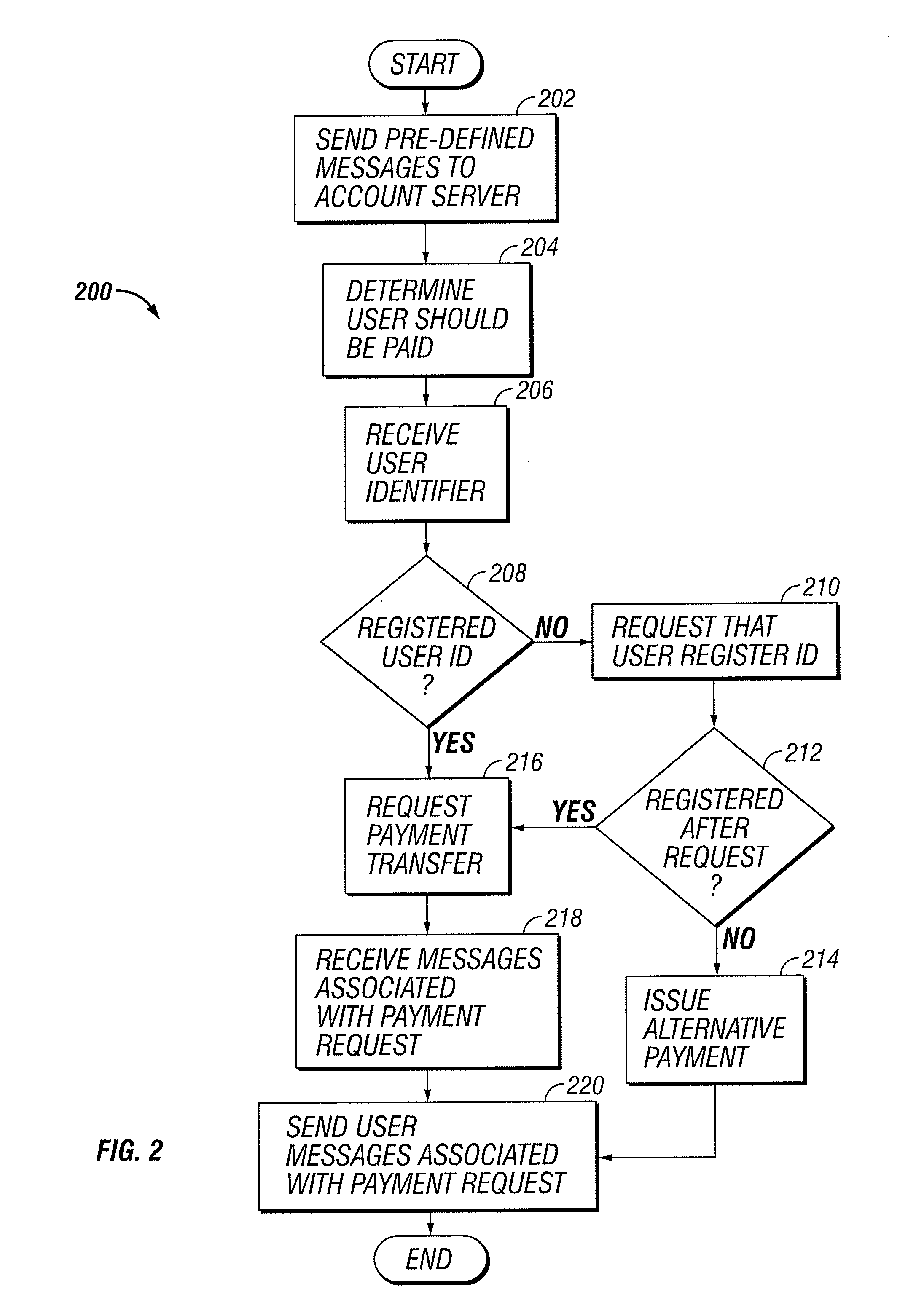
Payment Processing with a User Identifier
InactiveUS20140122334A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedFinanceProtocol authorisationInternet privacyUser identifier
According to an embodiment, a payment is processed. It is determined that a user should receive a payment. A user identifier associated with the user is received. The user identifier allows the user to receive communications. The user identifier does not comprise information regarding any financial account of the user. Whether the user identifier is registered with an account server operable to maintain associations between user identifers and financial accounts is determined. The user is requested to register the user identifier with the account server if the user identifier is not registered with the account server. Transfer of the payment is facilitated by a selected one of a transfer to a financial account associated with the user identifier and issuance of the payment by an alternative mechanism according to whether the user identifier is registered with the account server.
Owner:BANK OF AMERICA CORP
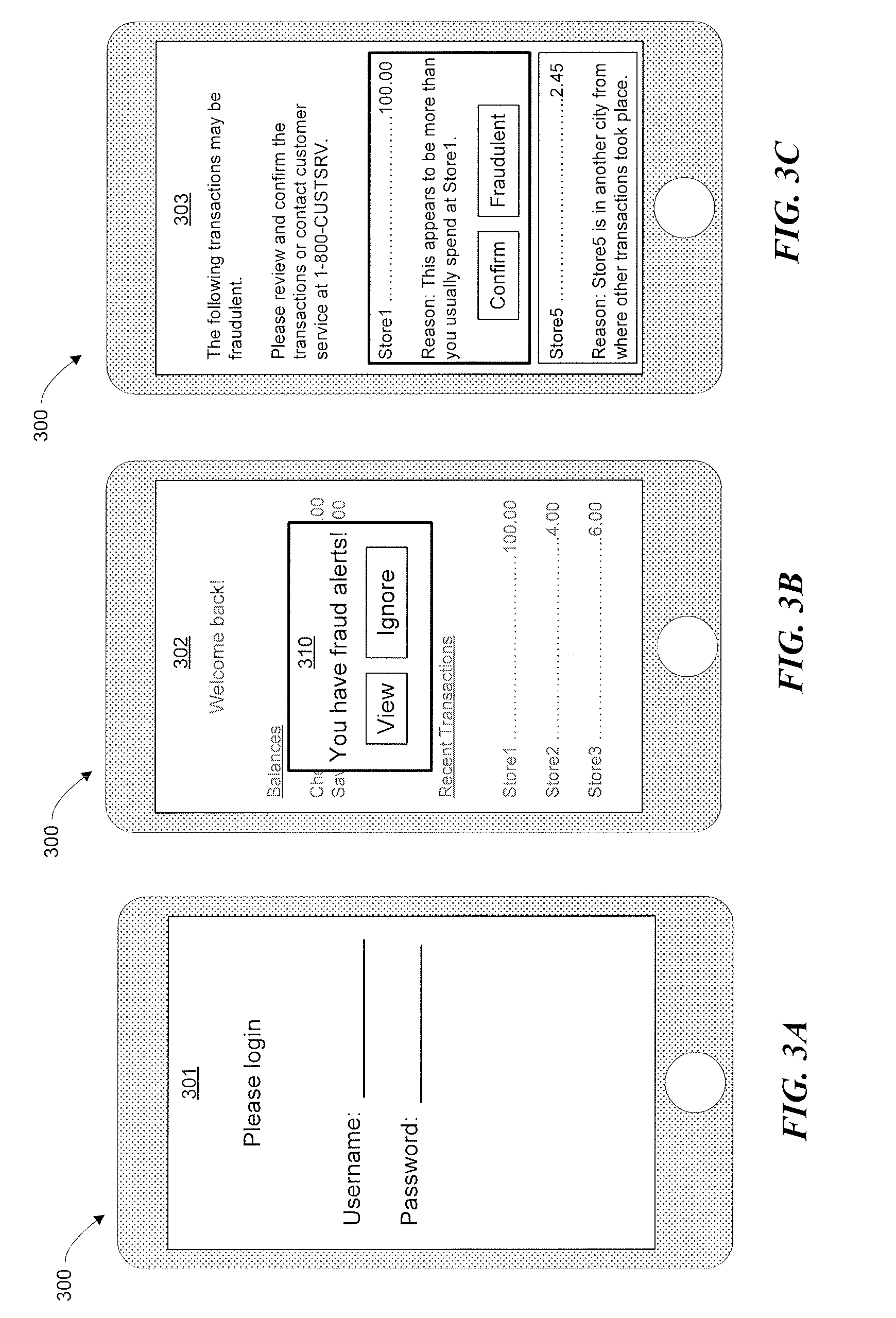
Periodic Fraud Checks
InactiveUS20170061440A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedPayment circuitsProtocol authorisationOperating system
According to one embodiment, a system includes a memory comprising instructions; an interface; and a processor communicatively coupled to the memory and the interface. The interface is configured to receive an indication of a trigger event associated with a user account. The processor is configured, when executing the instructions, to select one or more transactions of a plurality of transactions associated with the user account, determine, for each of the selected transactions using one or more rules, whether the transaction is potentially fraudulent, and generate, for each transaction identified as potentially fraudulent, a notification comprising an identification of the transaction.
Owner:BANK OF AMERICA CORP
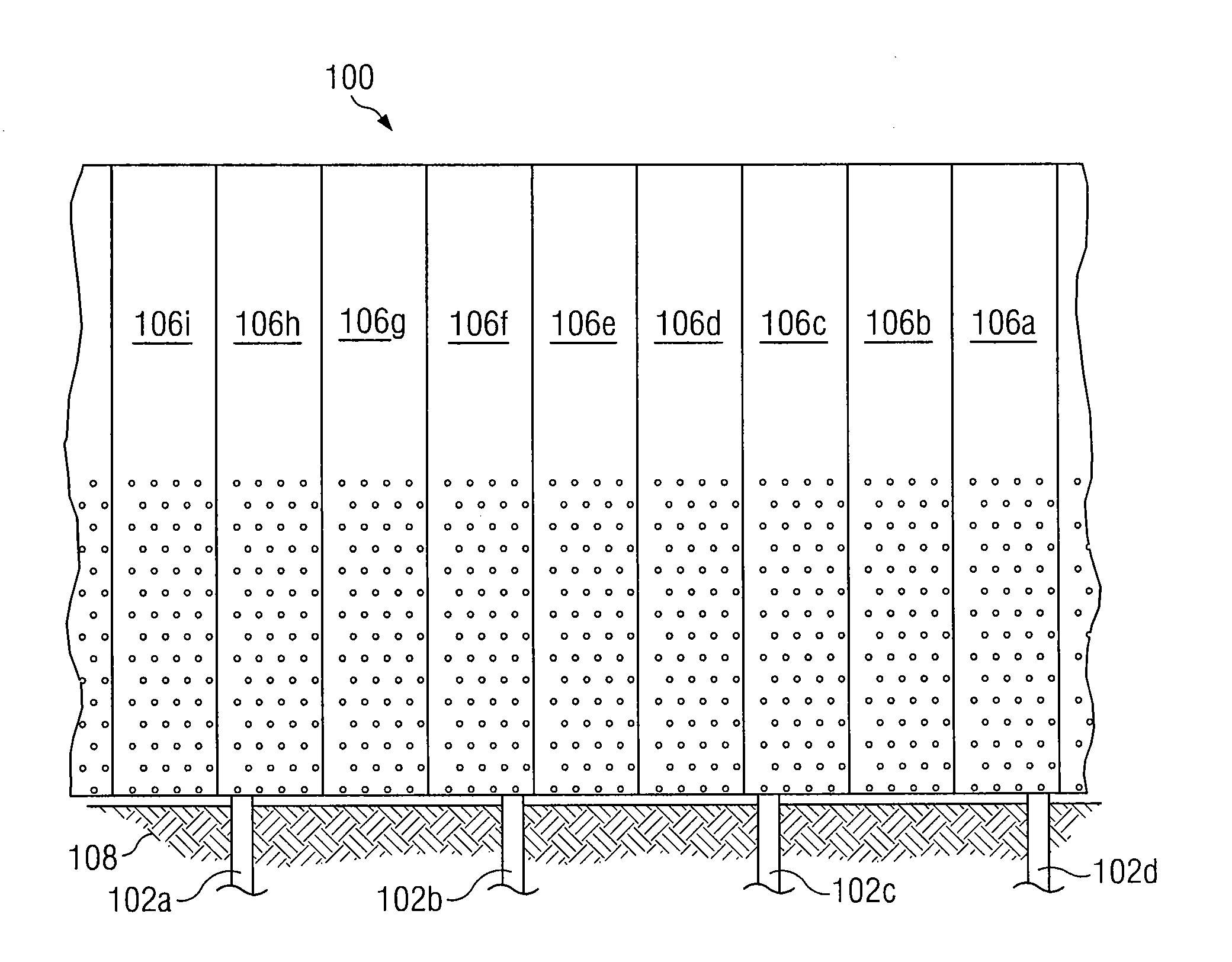
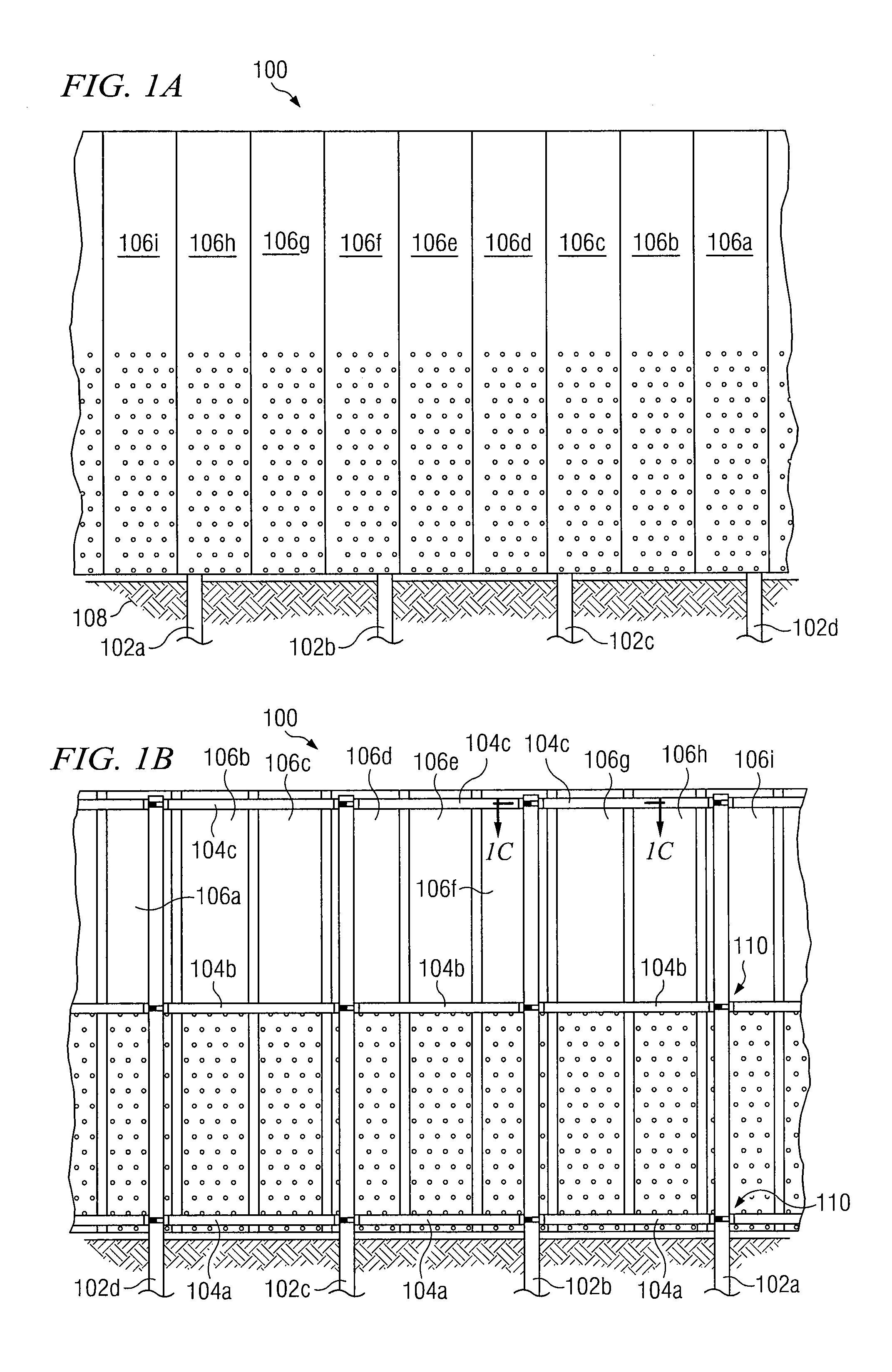
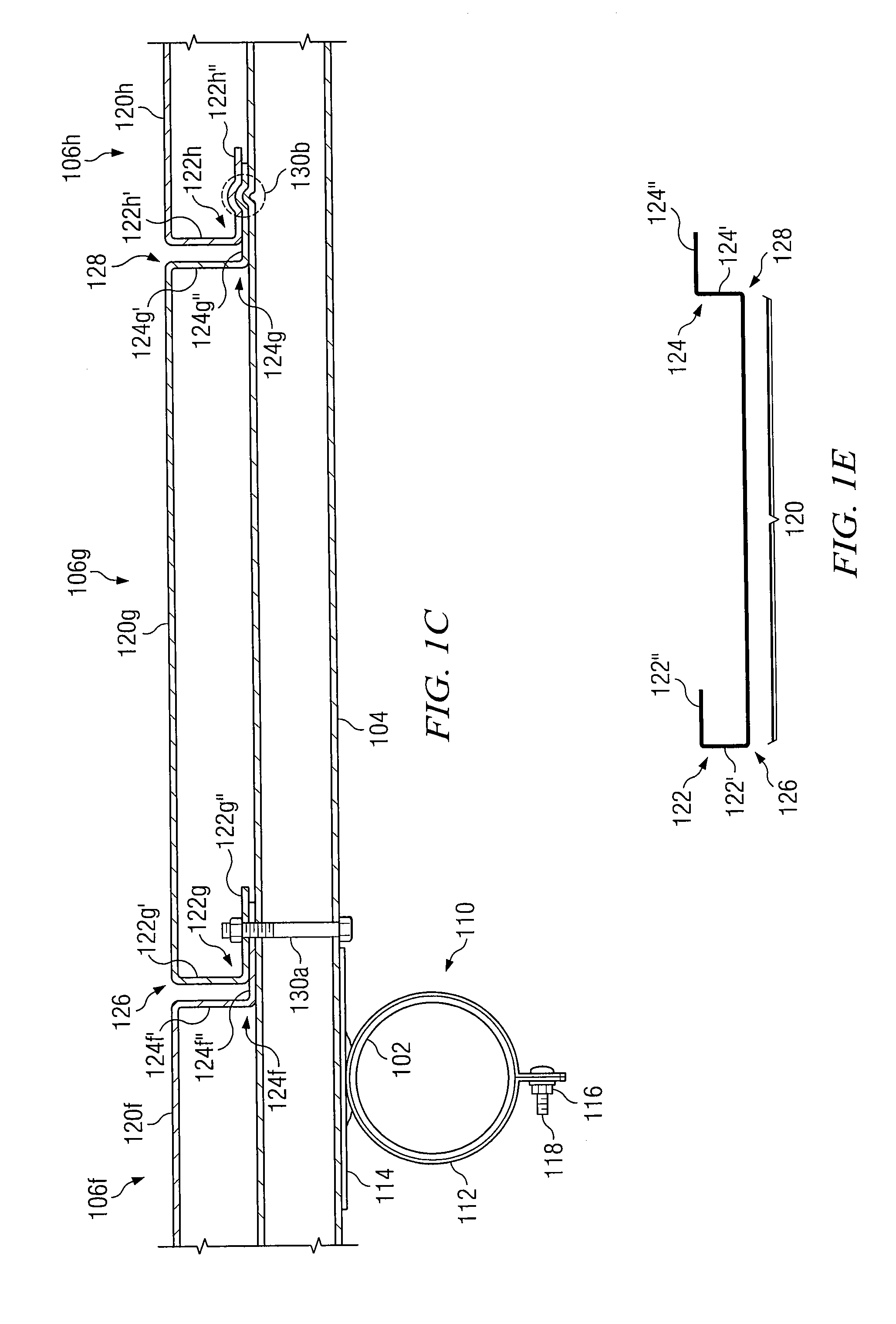
Panel Fence System and Method
InactiveUS20090321698A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedStrutsFencingEngineeringFlange
In certain embodiments, a fence system includes a support member and a rail attached to the support member such that the rail extends across the support member. The fence system further includes a first panel and a second panel each comprising a primary panel portion having a first edge and a second edge. A first flange is located along at least a portion of the first edge of the primary panel portion, and a second flange is located along at least a portion of the second edge of the primary panel portion. The first and second panels are secured to the rail such that the second edge of the primary panel portion of the first panel is adjacent to the first edge of the primary panel portion of the second panel. The second flange of the first panel is matingly coupled to the first flange of the second panel.
Owner:PAYNE FENCE PRODS
Leveraging Legacy Applications for Use with Modern Applications
ActiveUS20160132307A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedProgram controlMemory systemsApplication softwareSource code
An apparatus of one embodiment translates computer code from a first programming language to a second programming language. The apparatus includes an interface, a memory, and a processor. The interface is operable to receive a compiler output that is associated with source code written in a first programming language. The memory is operable to store the compiler output. The processor is communicatively coupled to the interface and the memory and is operable to analyze the data structures within the compiler output, build an internal representation of the source code based on the compiler output, and create a source code template associated with a second programming language.
Owner:BANK OF AMERICA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com