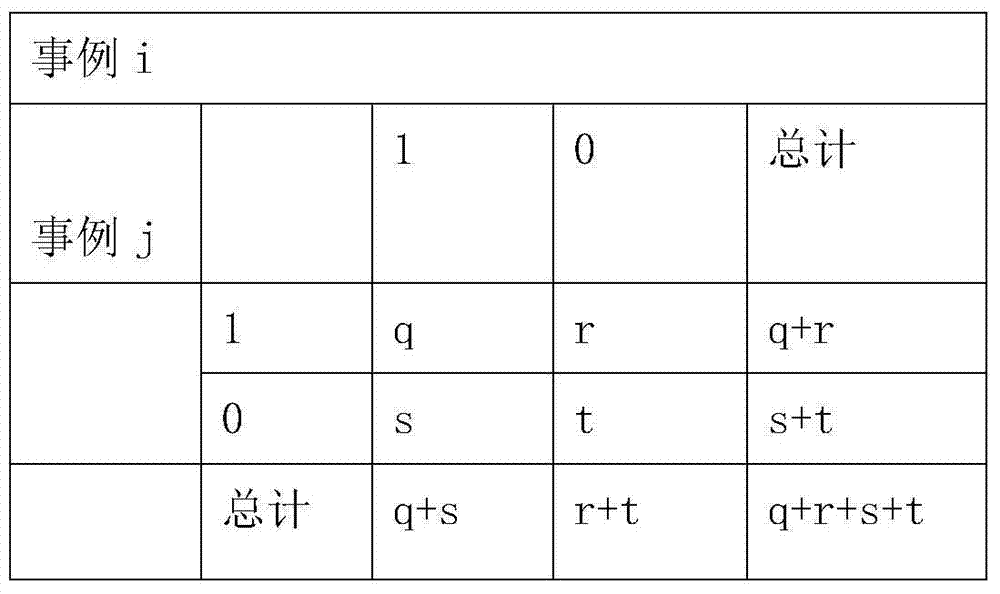
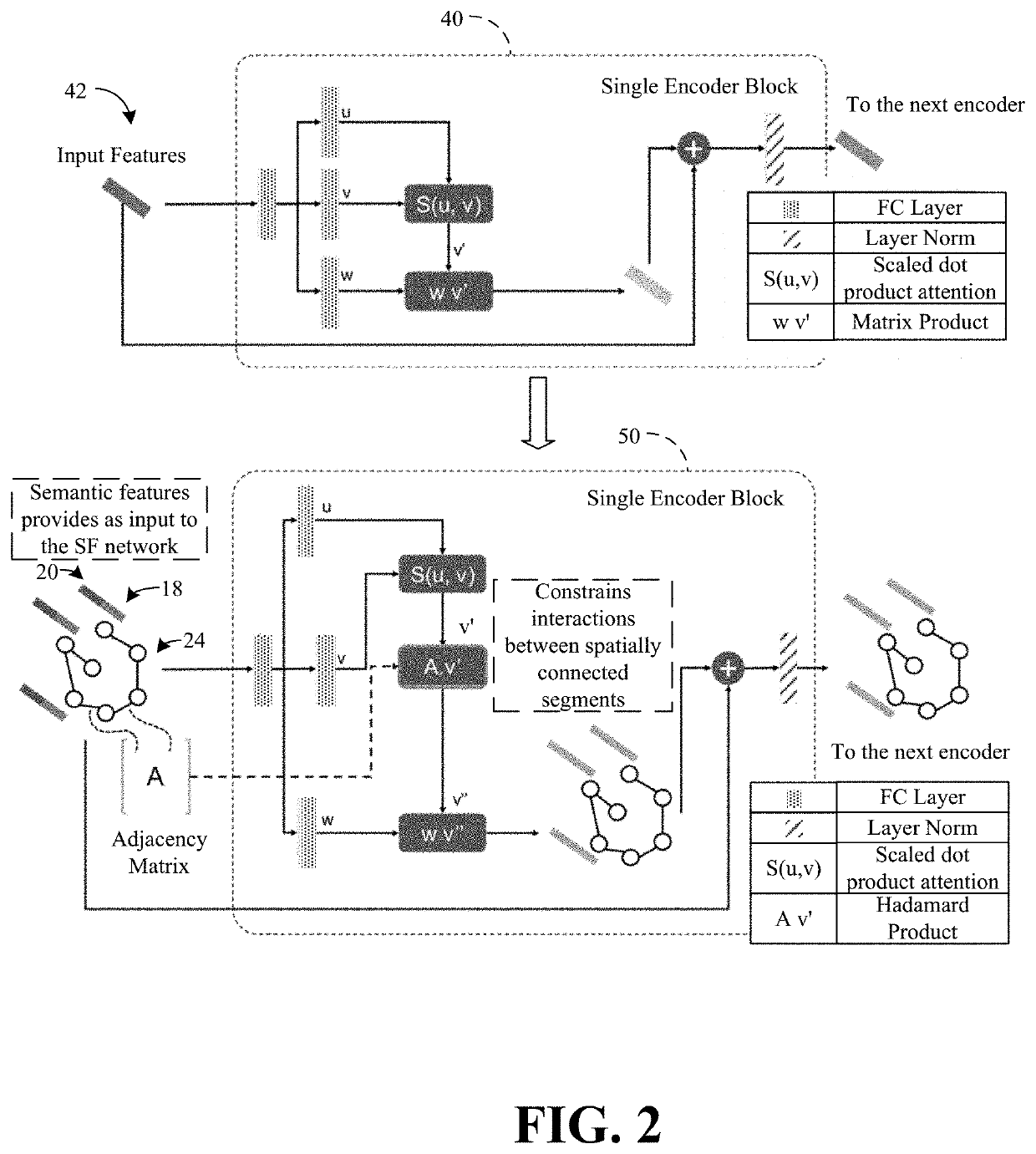
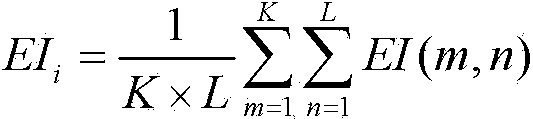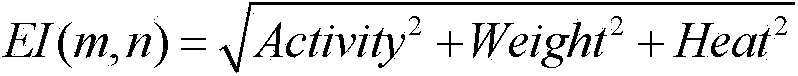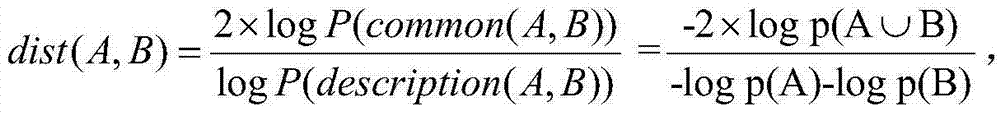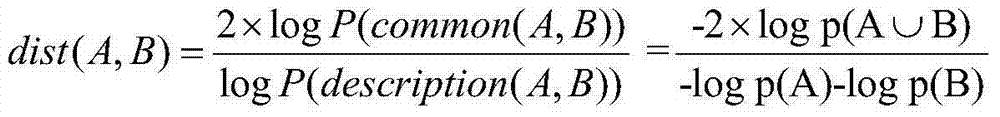Patents
Literature
49 results about "Instance selection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Instance selection (or dataset reduction, or dataset condensation) is an important data pre-processing step that can be applied in many machine learning (or data mining) tasks. Approaches for instance selection can be applied for reducing the original dataset to a manageable volume, leading to a reduction of the computational resources that are necessary for performing the learning process. Algorithms of instance selection can also be applied for removing noisy instances, before applying learning algorithms. This step can improve the accuracy in classification problems.
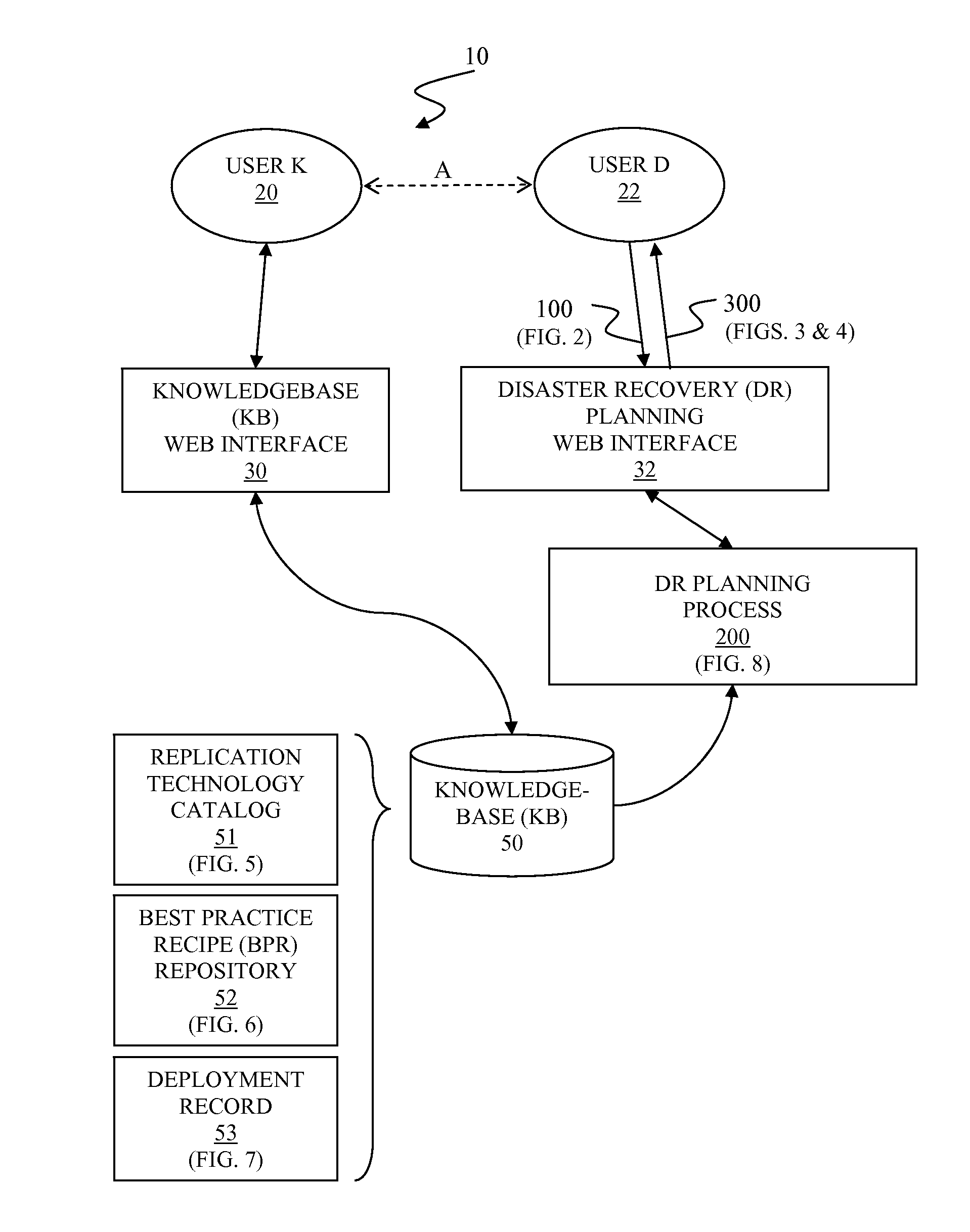
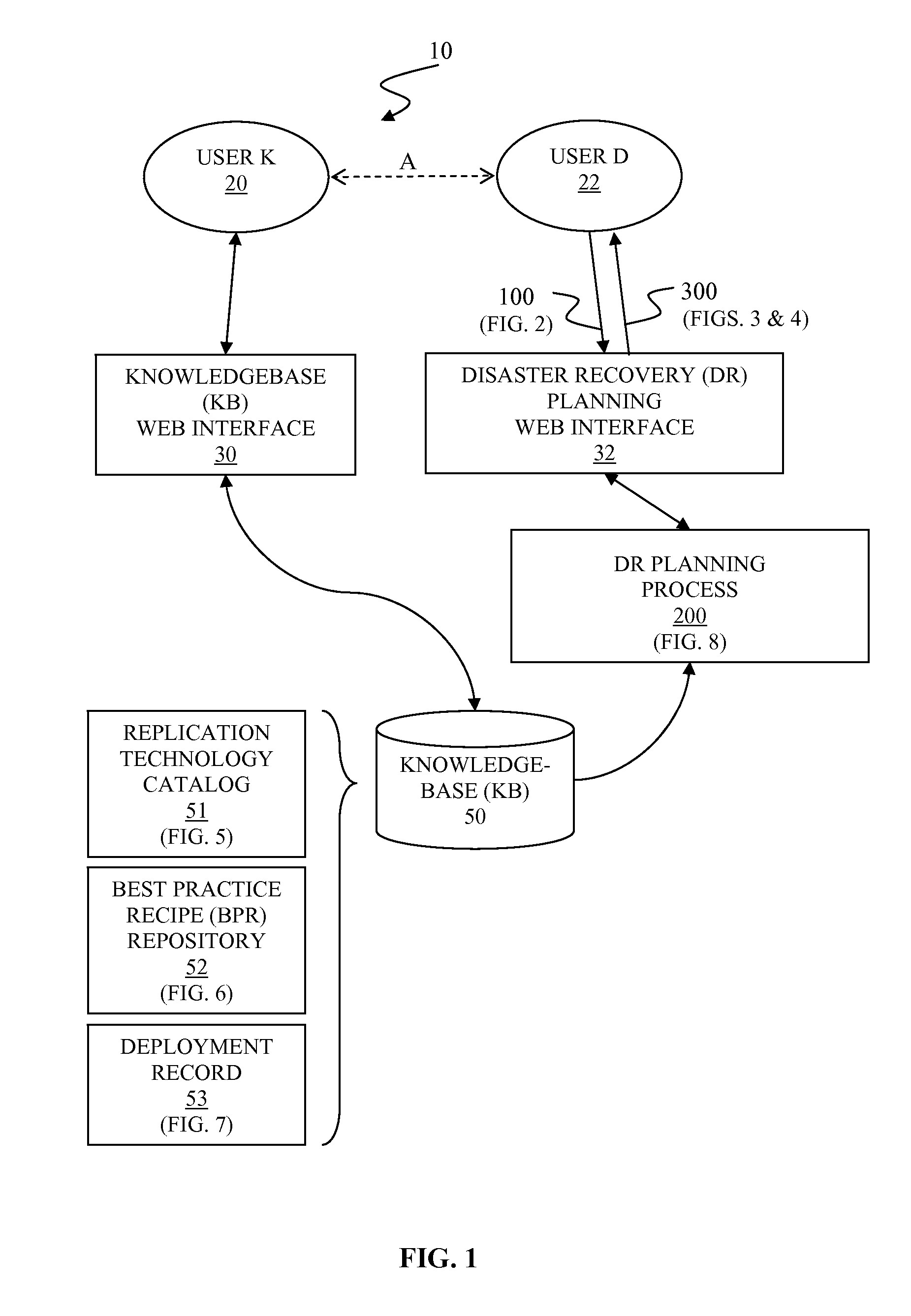
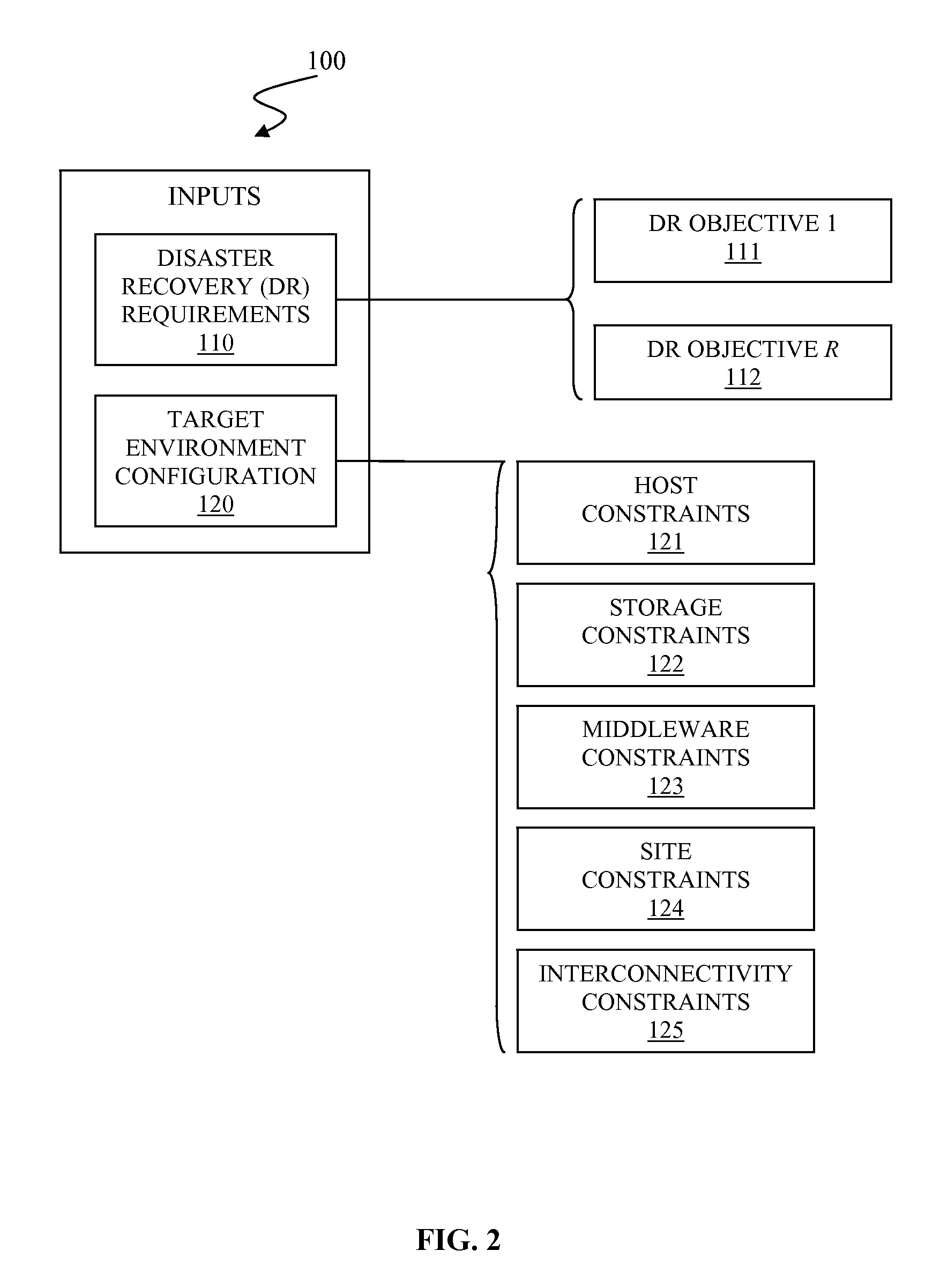
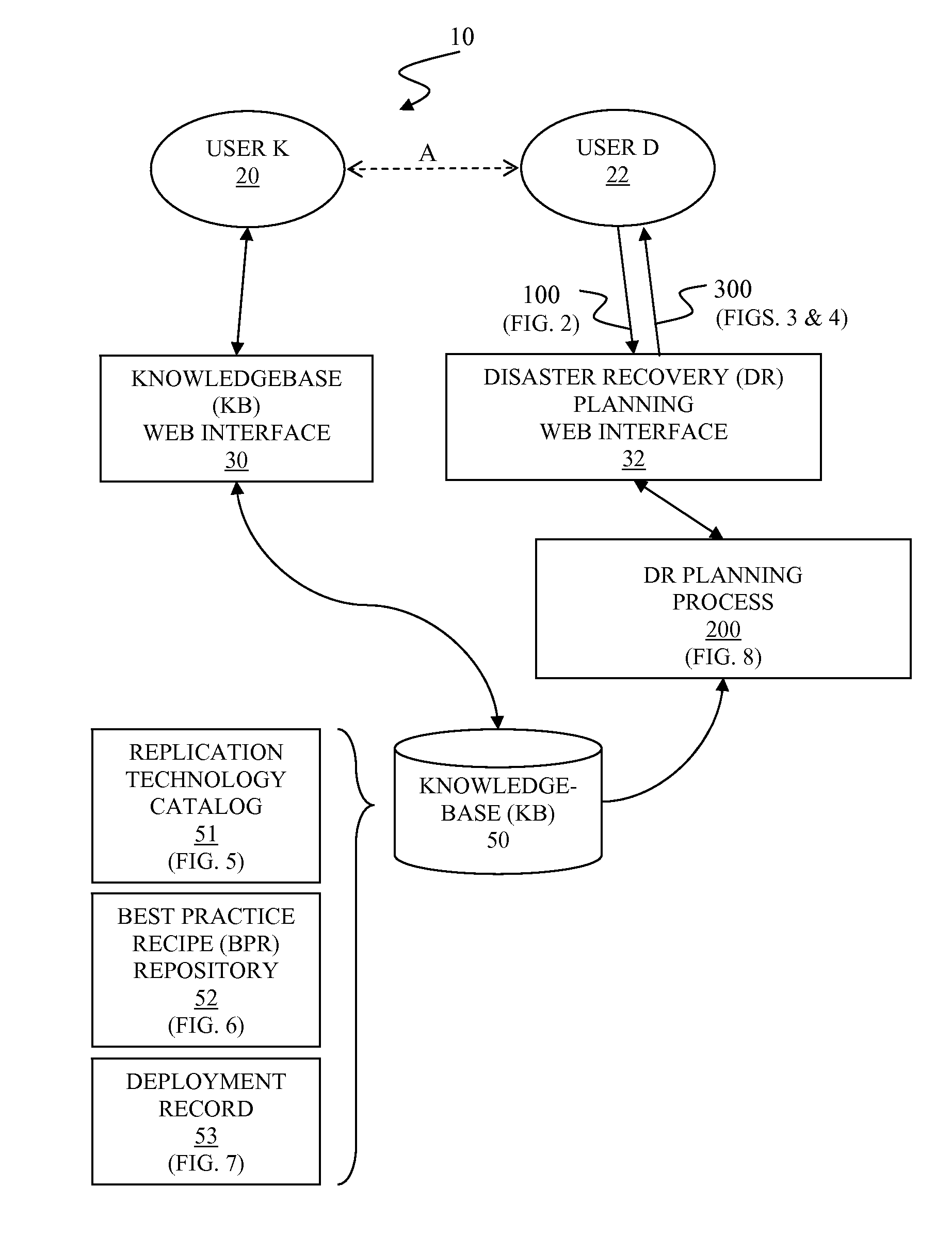
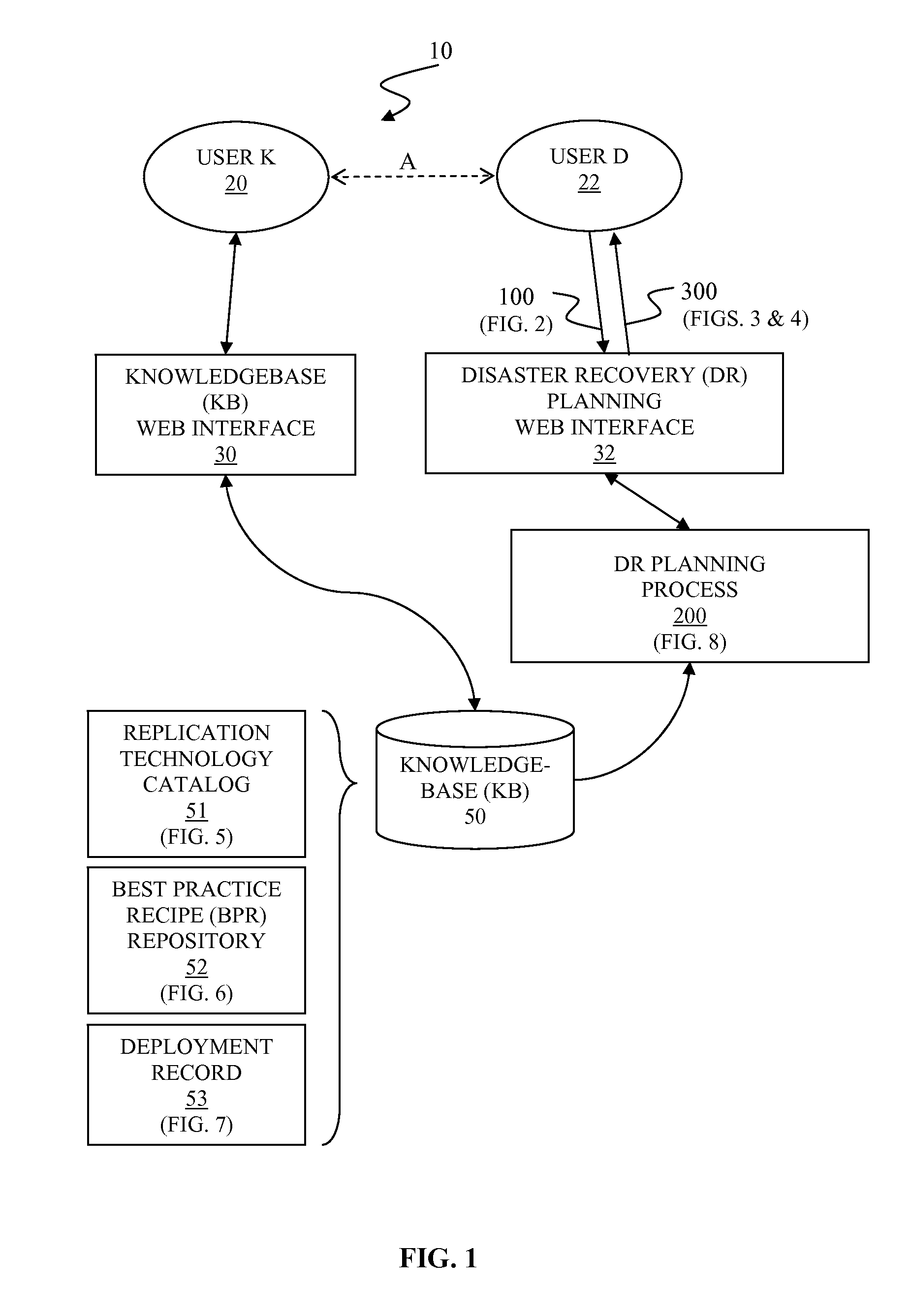
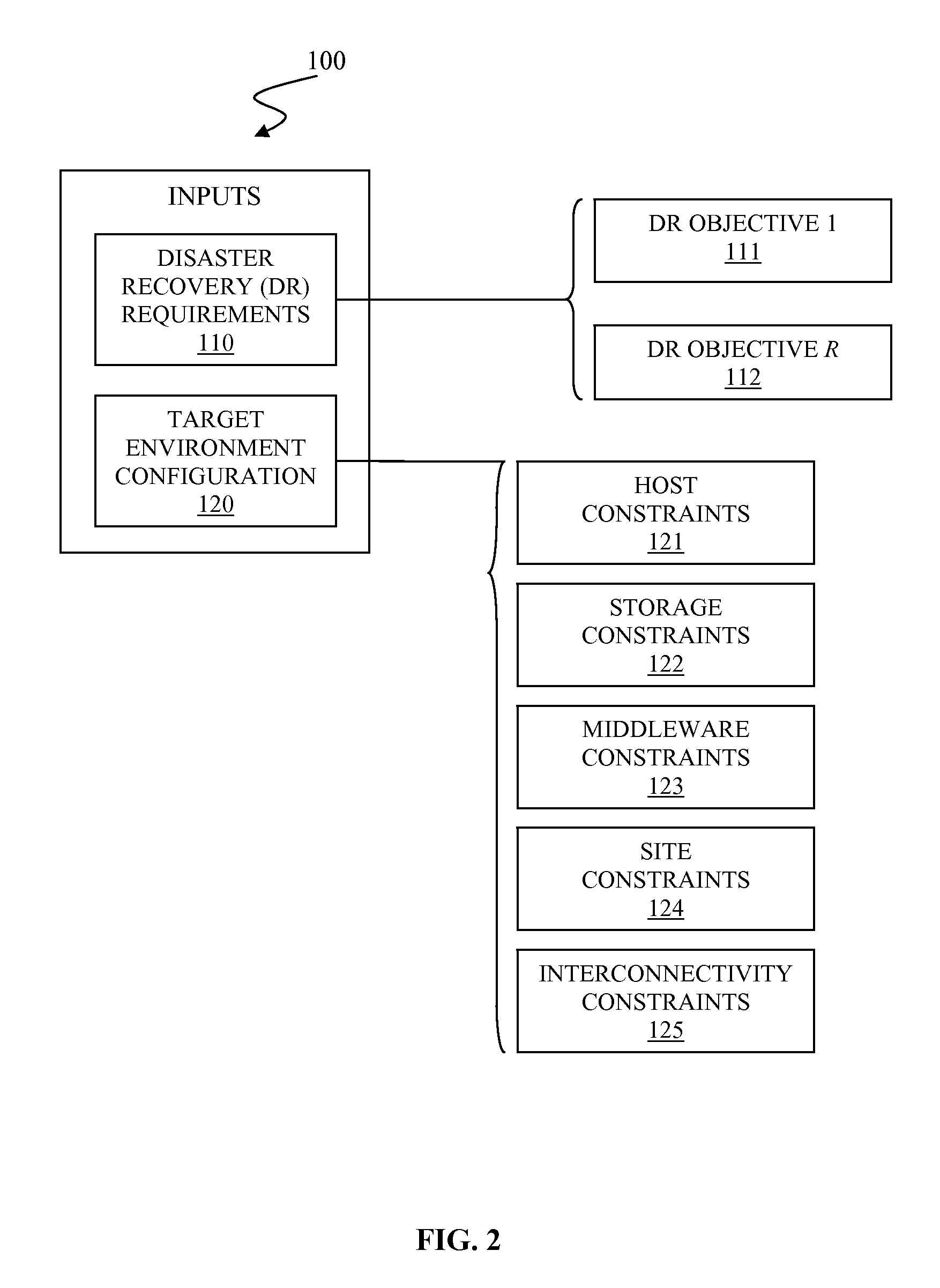
Automated disaster recovery planning
InactiveUS20110022879A1Non-redundant fault processingKnowledge representationProgram planningGood practice
A system and associated method for automated disaster recovery (DR) planning. A DR planning process receives disaster recovery requirements and a target environment configuration from a user to design DR plans for the target environment configuration that meets disaster recovery requirements. The DR planning process accesses a knowledgebase containing information on replication technologies, best practice recipes, and past deployment instances. The DR planning process creates the DR plans by analyzing the disaster recovery requirements into element risks, associating replication technologies to protect each element risks, combining associated replication technologies based on the best practice recipes, and selecting highly evaluated combination based on the past deployment instances. The DR planning process presents the DR plans as classified by replication strategy-architecture combination for each DR plans and marks how strongly each DR plans are recommended.
Owner:GLOBALFOUNDRIES INC
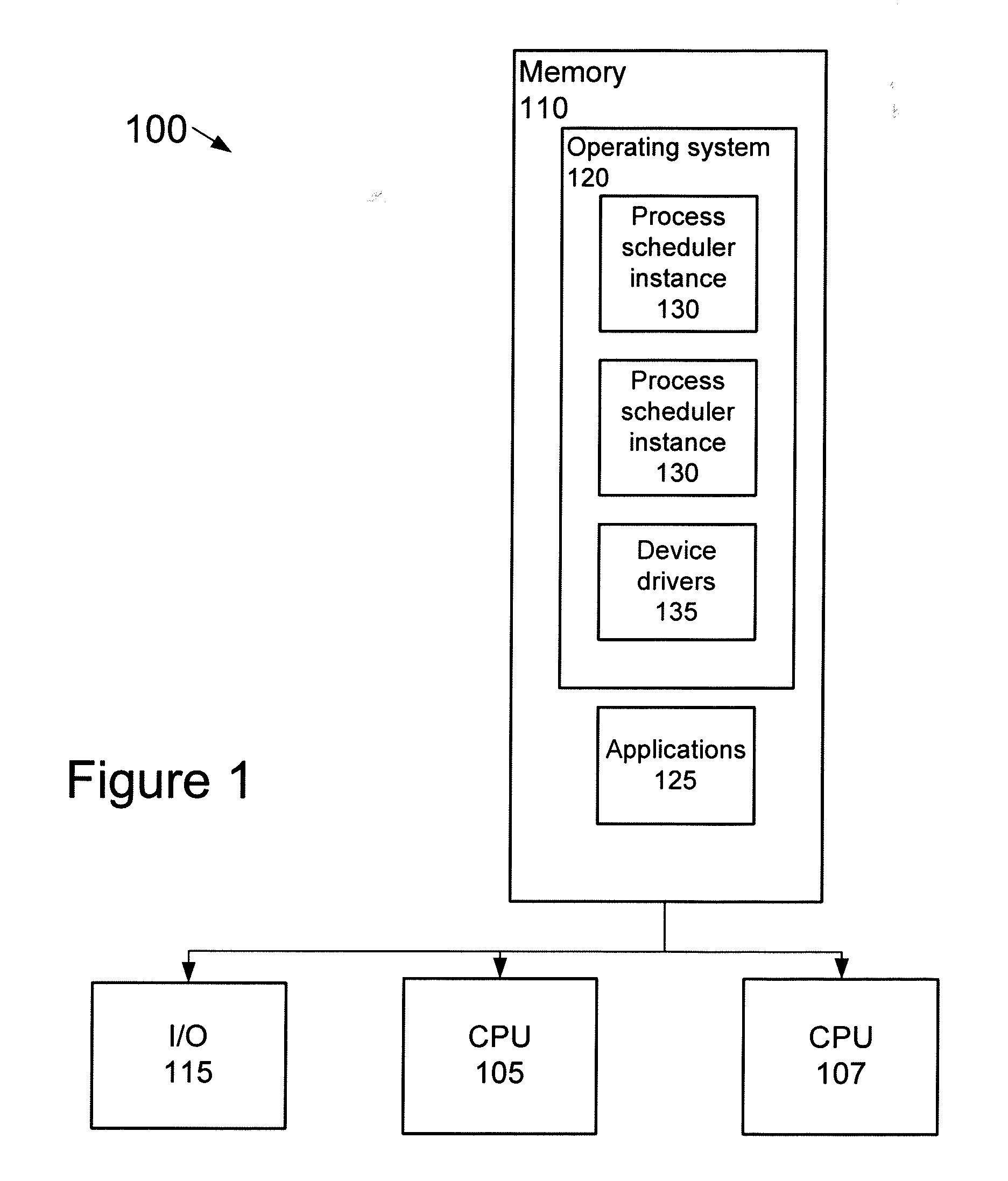
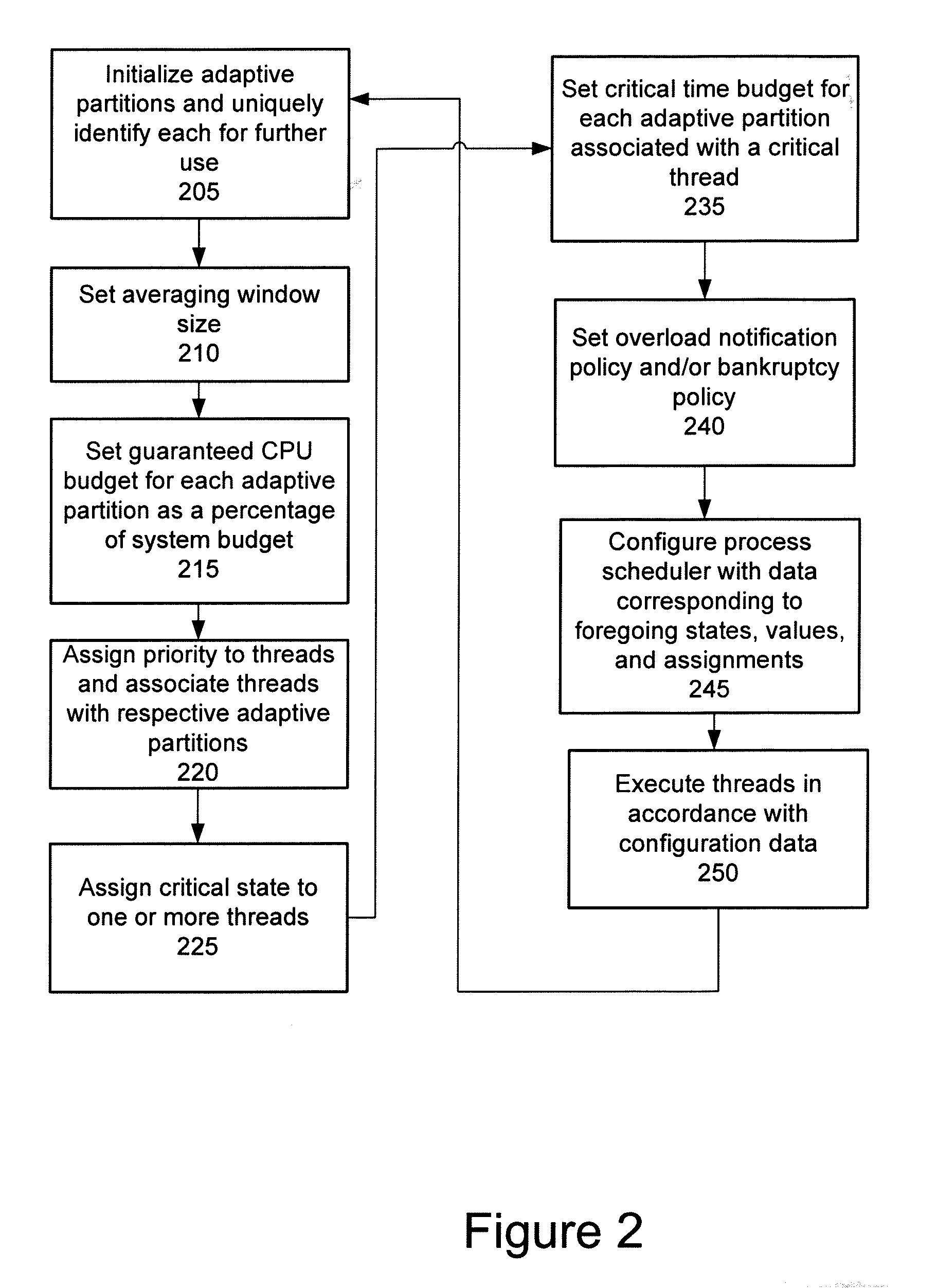
Adaptive partitioning scheduler for multiprocessing system
A symmetric multiprocessing system includes multiple processing units and corresponding instances of an adaptive partition processing scheduler. Each instance of the adaptive partition processing scheduler selectively allocates the respective processing unit to run process threads of one or more adaptive partitions based on a comparison between merit function values of the one or more adaptive partitions. The merit function for a particular partition of the one or more adaptive partitions may be based on whether the adaptive partition has available budget on the respective processing unit. The merit function for a particular partition associated with an instance of the adaptive partition scheduler also, or in the alternative, may be based on whether the adaptive partition has available global budget on the symmetric multiprocessing system.
Owner:MALIKIE INNOVATIONS LTD
Automated disaster recovery planning
InactiveUS7992031B2Non-redundant fault processingKnowledge representationInstance selectionGood practice
Owner:GLOBALFOUNDRIES INC
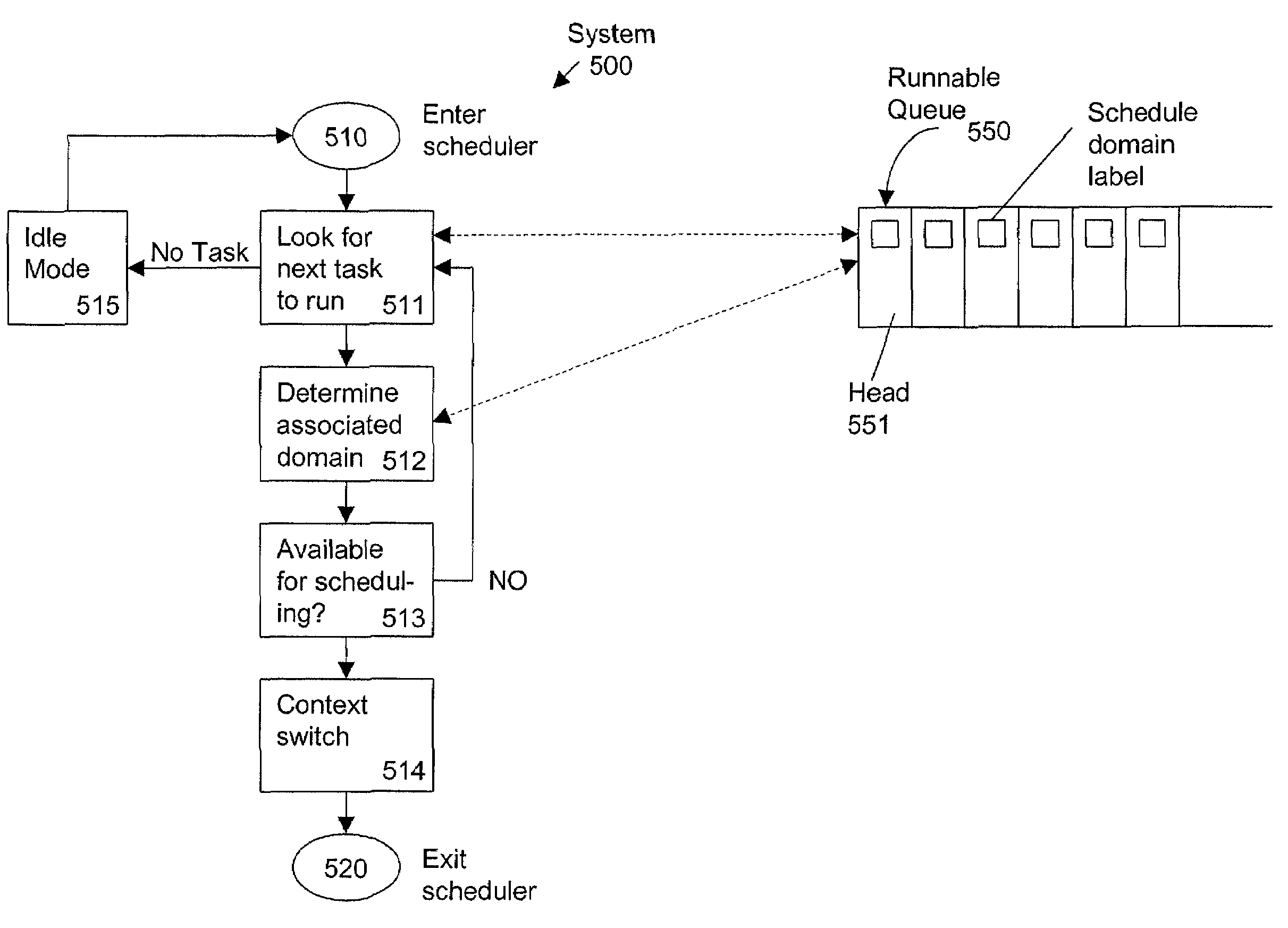
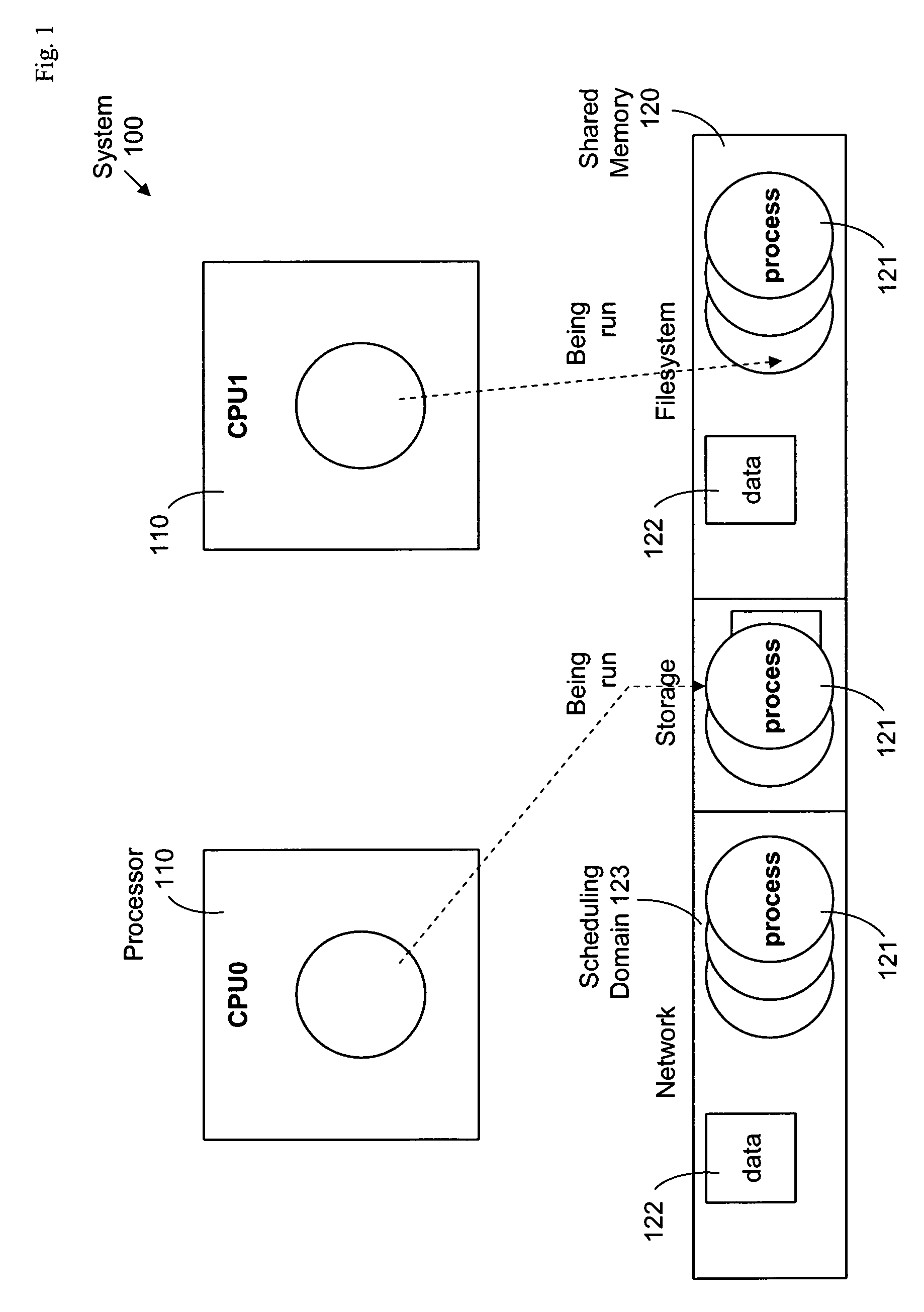
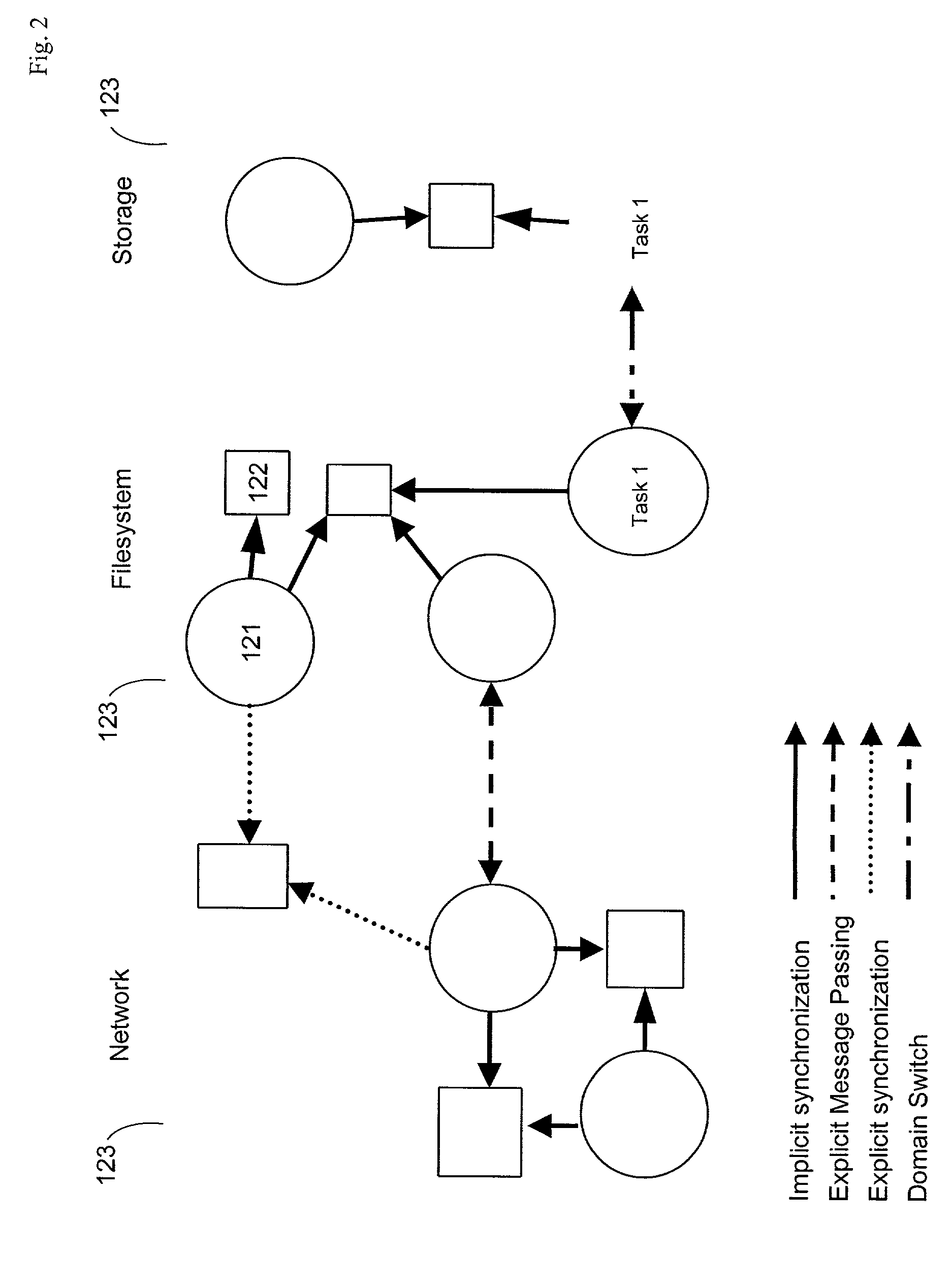
Symmetric multiprocessor synchronization using migrating scheduling domains
ActiveUS7694302B1Good for load balancingEasy to useResource allocationProgram synchronisationInstance selectionSystem usage
The invention provides a method and system for scheduling tasks in an MP system, and provides parallel execution of those tasks while implicitly synchronizing access to resources used by that system. Tasks in the system are each assigned to a scheduling domain, thus associating those tasks with a set of resources controlled by that domain. A scheduler operating at each processor implicitly synchronizes those resources controlled by each domain, by scheduling only one task for each domain to execute concurrently in the system. Because each instance of the scheduler selects which task is next run independently of its processor, each domain can migrate from one processor to another; thus, each domain can have a task executing on any processor, so long as no domain has two tasks executing concurrently in the system. Thus, domains are not bound to any particular processor. Hence the method and system are symmetric.
Owner:NETWORK APPLIANCE INC
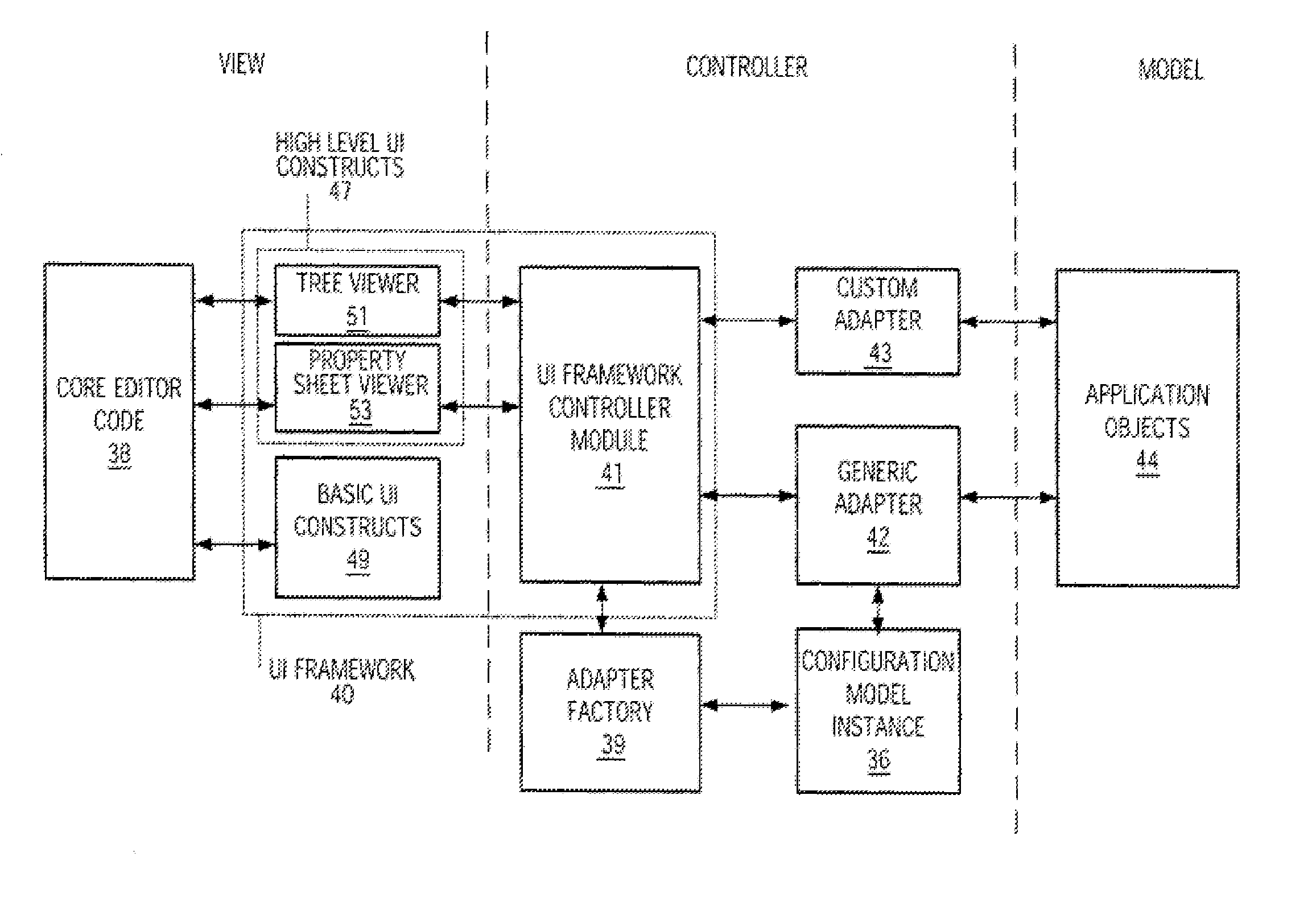
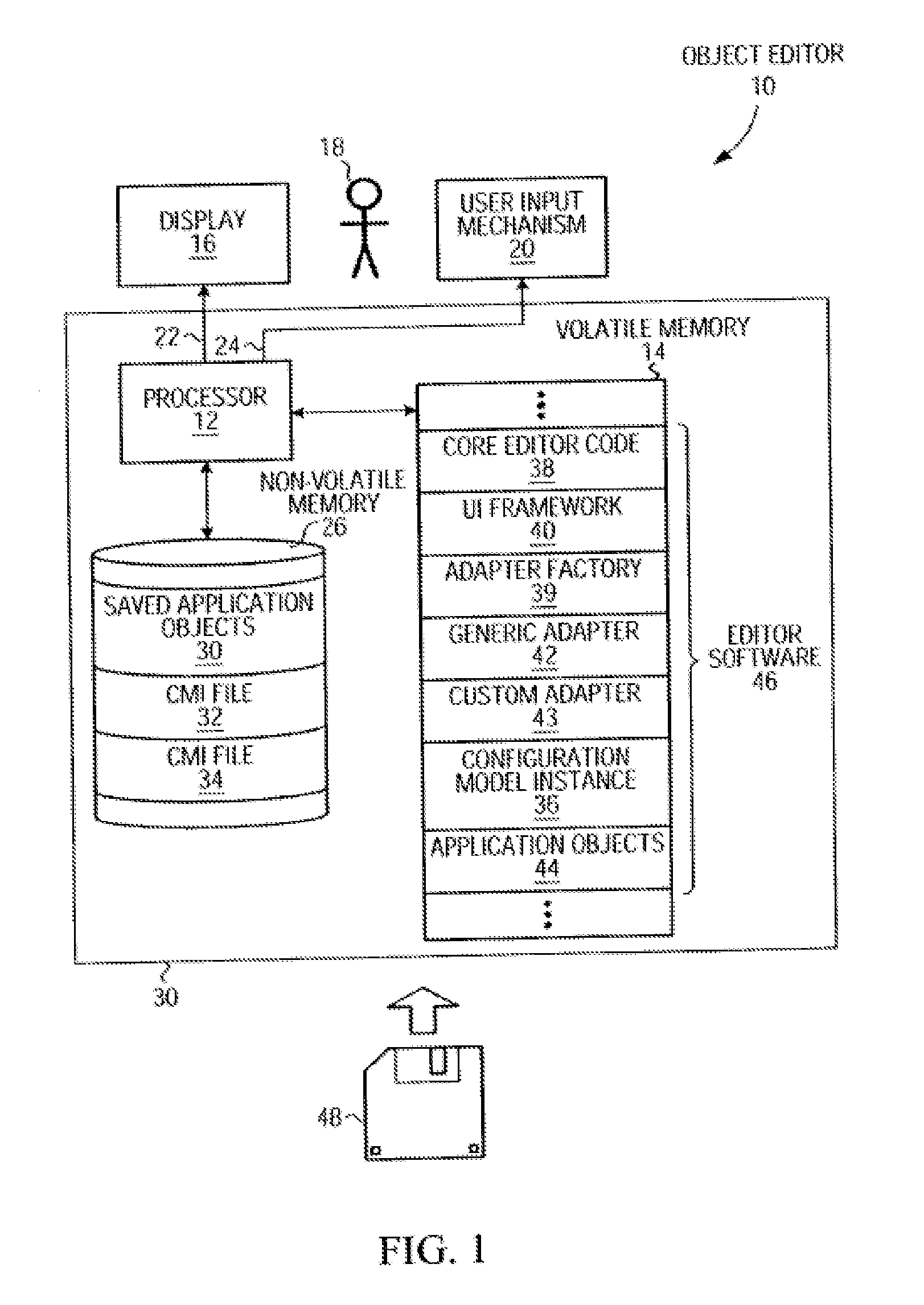
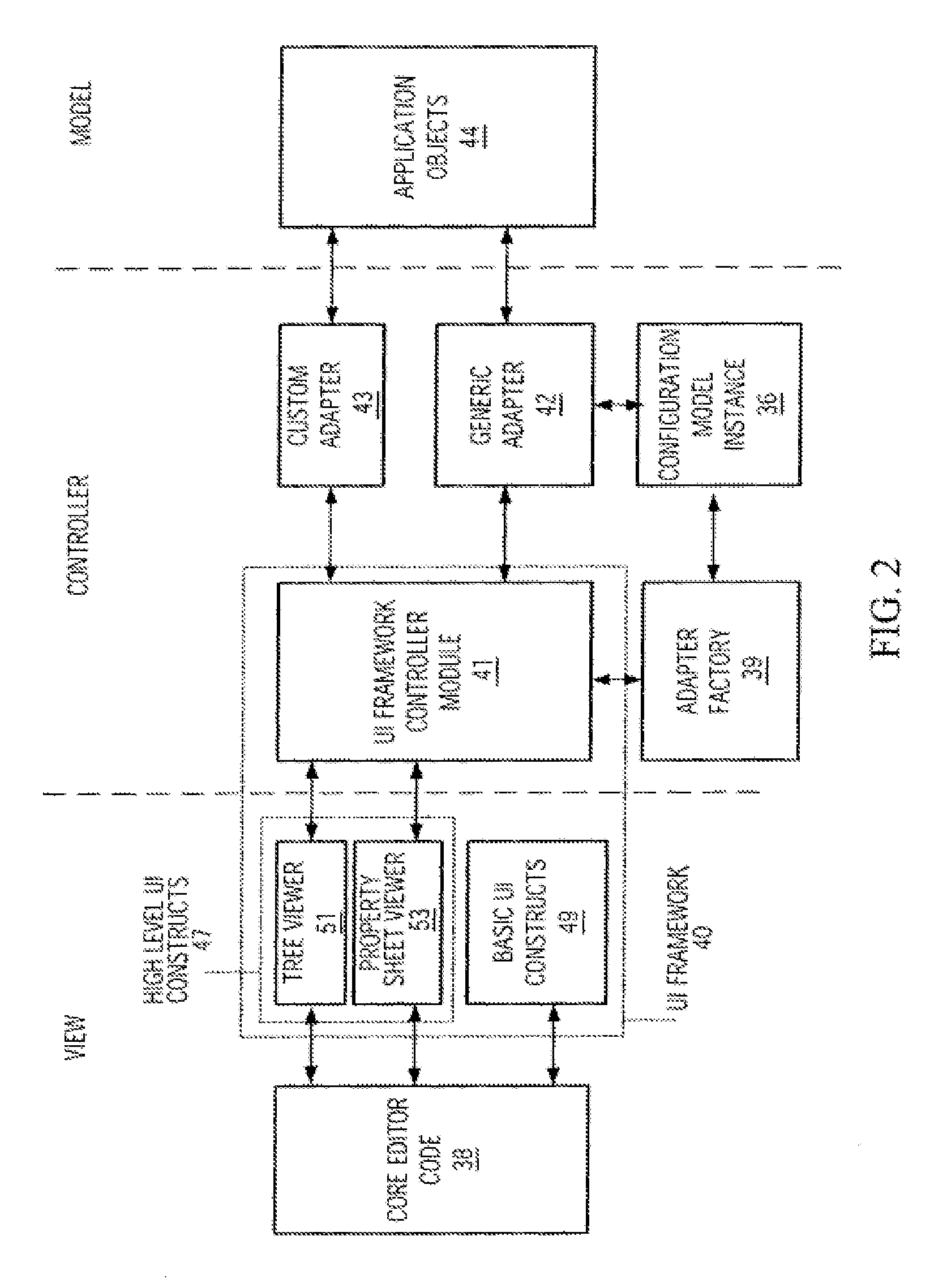
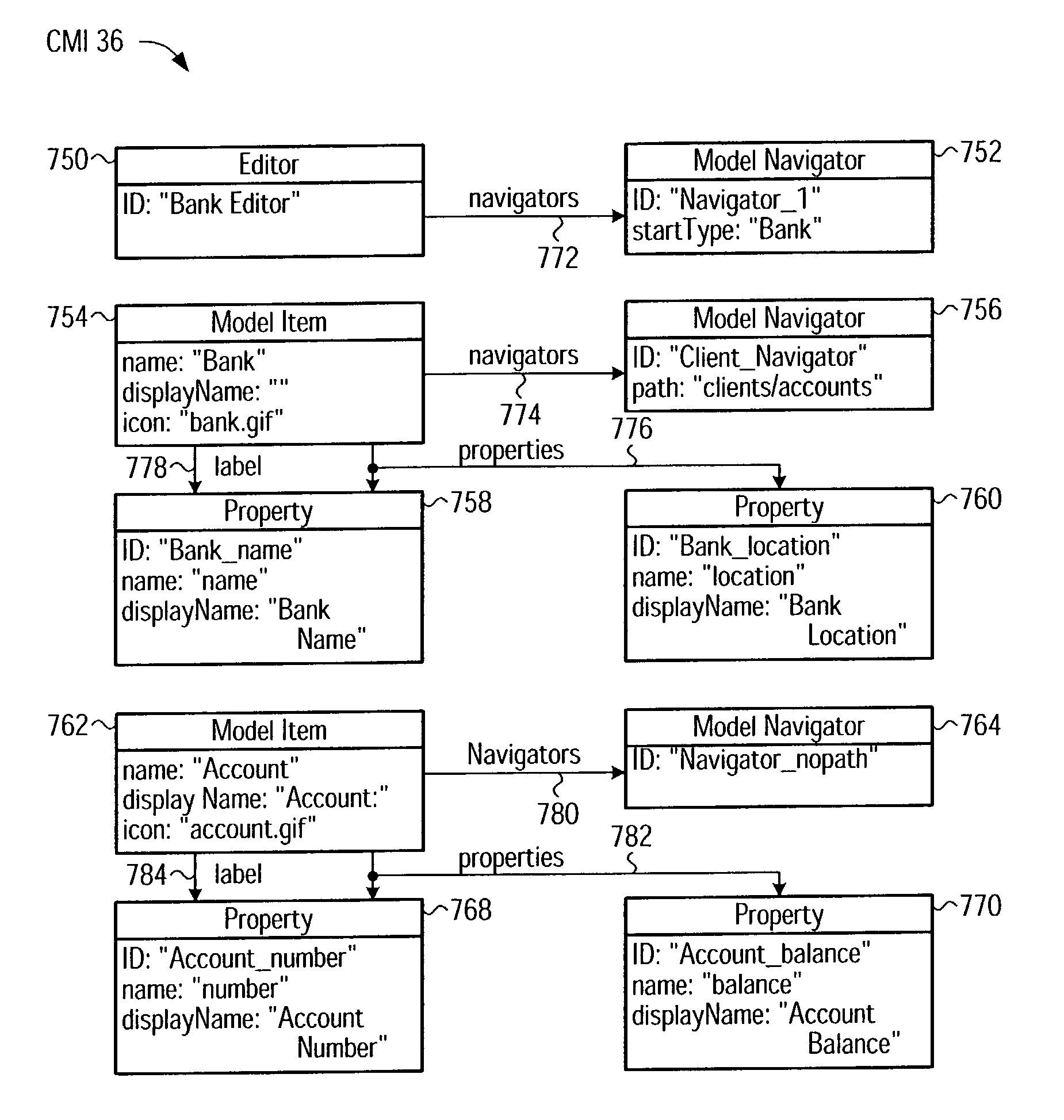
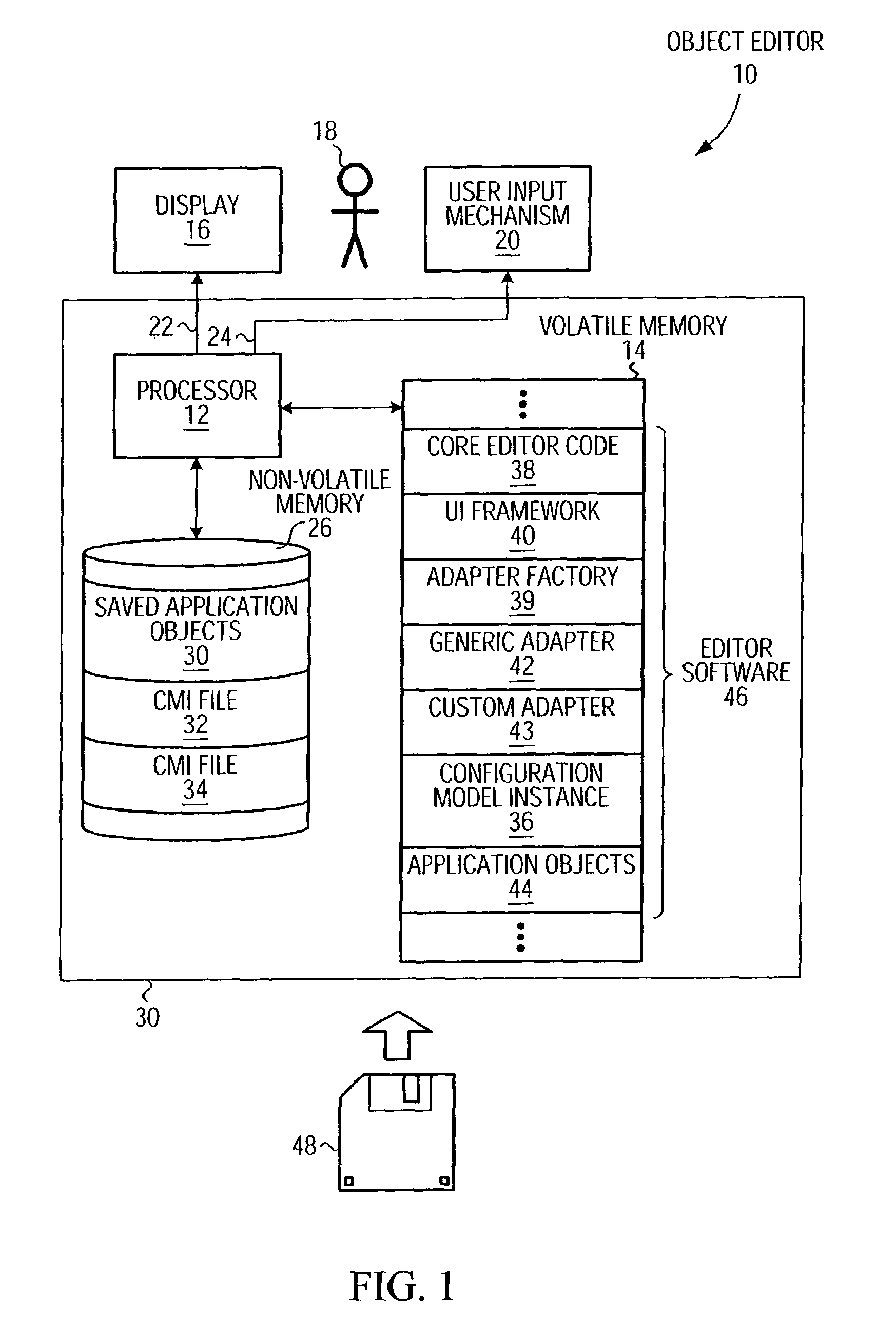
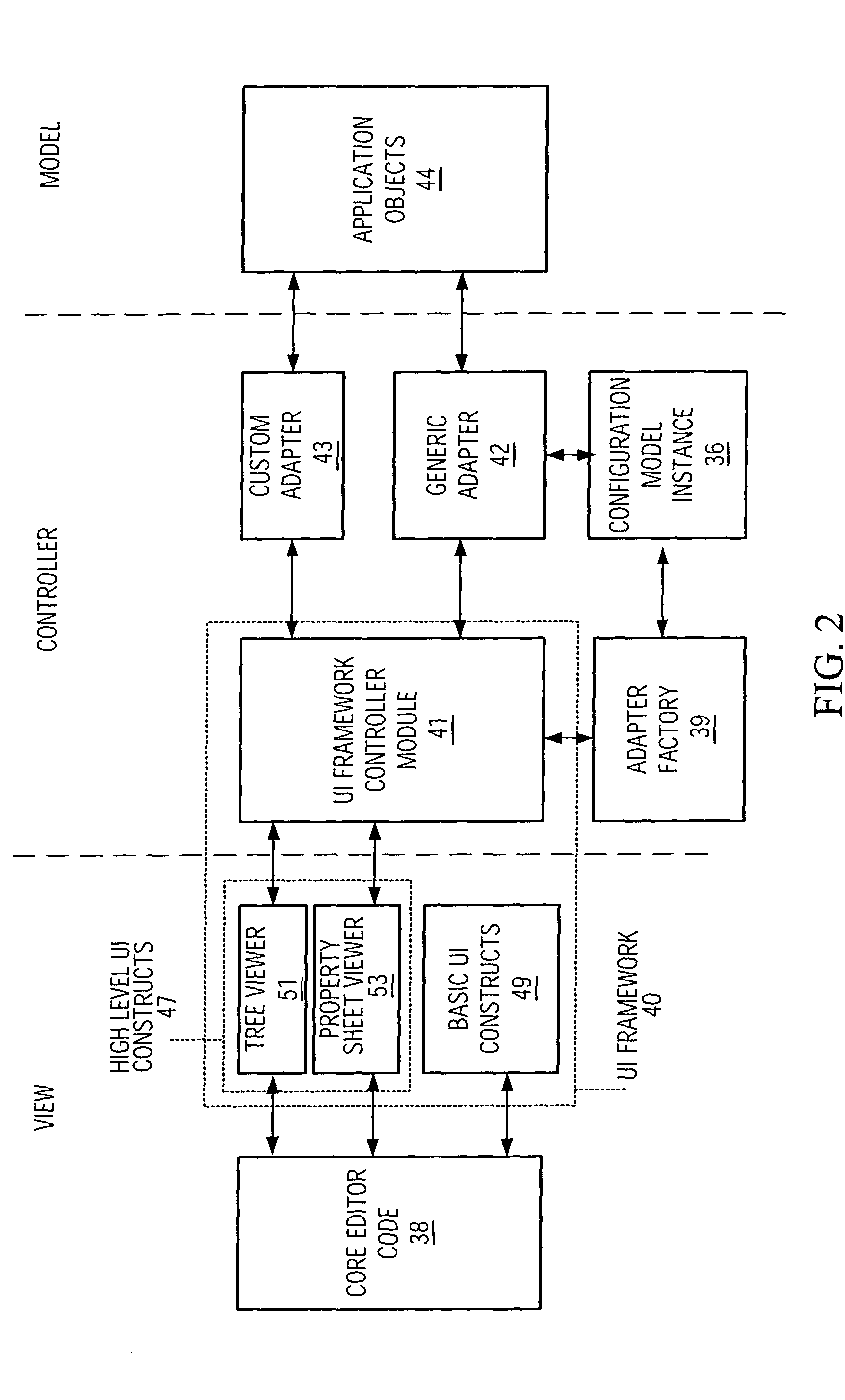
Configuration Model for Configuring an Adapter Software Component to Selectively Access Software Objects and Object Editor Using Instance of Same
An object editor capable of displaying a set of application software objects, which may include objects with a dynamic reflection capability (“reflective objects”), includes an object oriented configuration model instance (CMI), a generic adapter, and a UI framework. The CMI is particular to the set of application objects to be edited and defines a particular view of these objects to be provided by the editor. The CMI is external to the generic adapter and includes settings that control which application objects will be accessed and the manner of access, and in particular, which application objects will be visible, which of the visible objects' attributes will be displayed, the arrangement of displayed application objects and attributes, and the appearance of the displayed objects and attributes. The CMI is stored as a serialized XML file. The generic adapter reads the de-serialized CMI's current settings, selectively accesses the set of application objects to be edited and their attributes as dictated by the CMI settings, and passes the accessed information to the UI framework for display. The adapter uses reflection to access the attributes and associations of reflective objects. The CMI settings may be changed between editor invocations to cause objects or their attributes to be accessed and displayed differently, or not at all. The editor may be configured to edit a new set of software objects by substituting a new CMI corresponding to that set of objects. A CMI and generic adapter may be used in conjunction with applications other than an object editor, in which case the CMI settings define a manner of selectively accessing the application objects and may affect the operation of the application.
Owner:IBM CORP
Configuration model for configuring an adapter software component to selectively access software objects and object editor using instance of same
An object editor capable of displaying a set of application software objects, which may include objects with a dynamic reflection capability (“reflective objects”), includes an object oriented configuration model instance (CMI), a generic adapter, and a UI framework. The CMI is particular to the set of application objects to be edited and defines a particular view of these objects to be provided by the editor. The CMI is external to the generic adapter and includes settings that control which application objects will be accessed and the manner of access. The generic adapter reads the de-serialized CMI's current settings, selectively accesses the set of application objects to be edited and their attributes as dictated by the CMI settings, and passes the accessed information to the UI framework for display.
Owner:IBM CORP
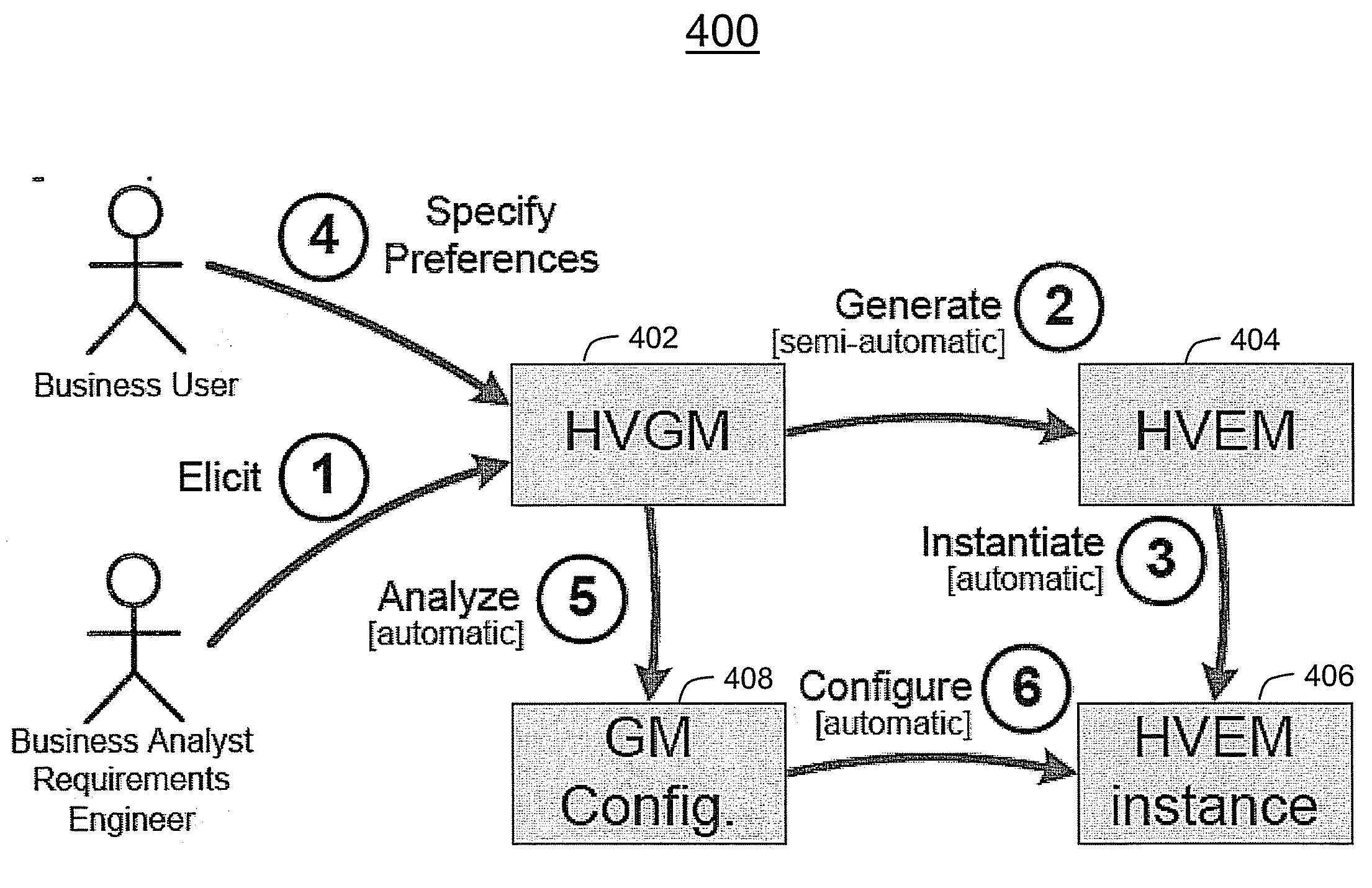
Method and tool for business process adaptation using goal modeling and analysis
A business process (BP) adaptation system (400) includes a High-Variability enriched Goal Model (HVGM) (402) that captures and refines goals of a business process (BP) while modeling alternative options where the model captures non-functional or quality attributes used in an evaluation of a performance of the BP and an estimation of how various BP alternatives affect the quality attributes. The system further includes a High-Variability workflow-level / directly Executable Model (HVEM) (404), where the system is based on goal modeling and analysis for eliciting intentions behind a BP to achieve a desired goal and the HVGM explicitly models non-functional or quality concerns. The system can further include a semi-automatic generator (604) of BP metrics based on the quality attributes specified in the HVGM and a runtime infrastructure (610) where each deployed BP instance reflects a configuration selected for that instance in a corresponding portion of the HVGM.
Owner:IBM CORP
5G network slice instance dynamic switching method and function
InactiveCN109951440AImprove reliabilityGuaranteed to be normalTransmissionSecurity arrangementCommunications securityPattern perception
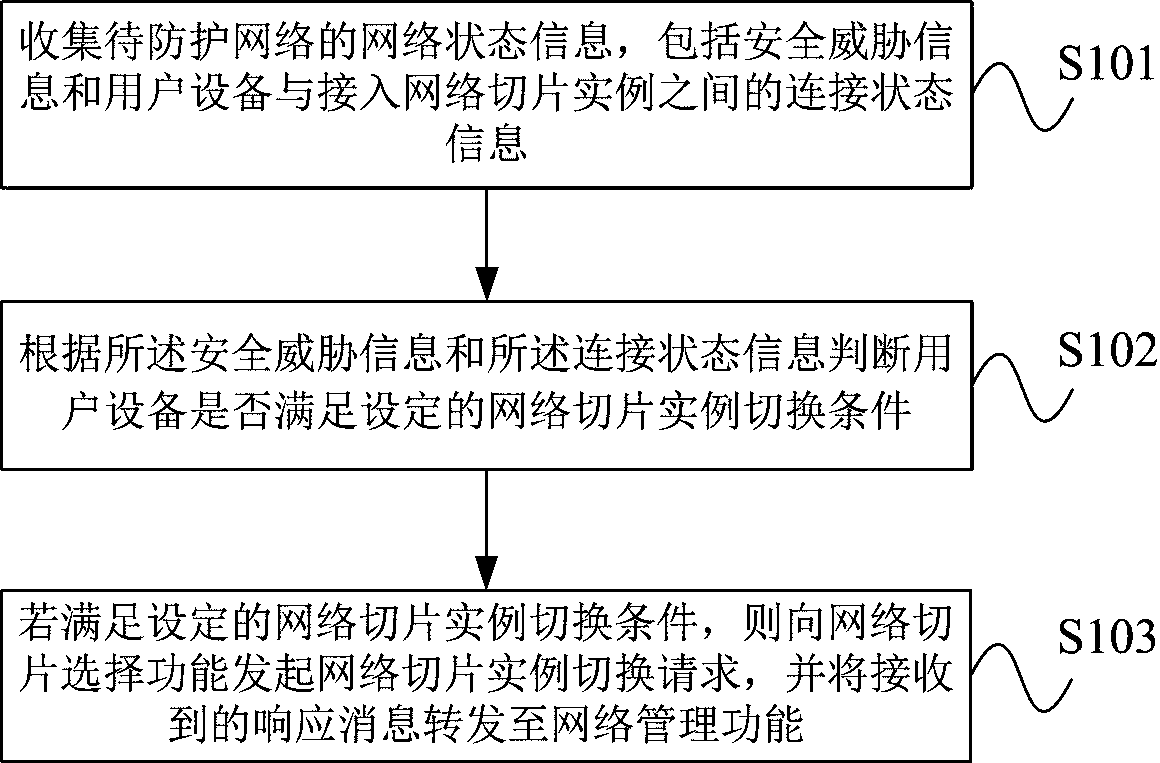
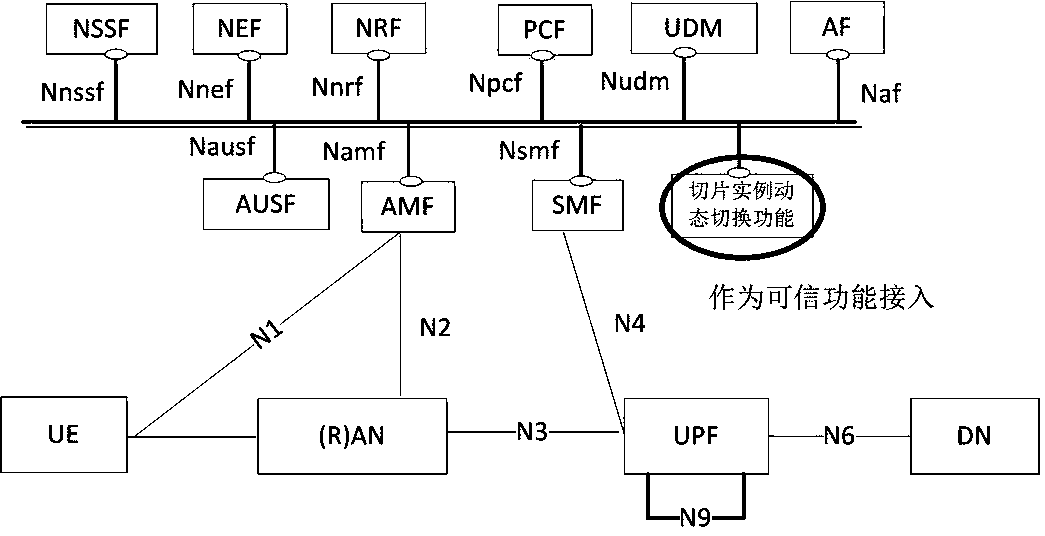
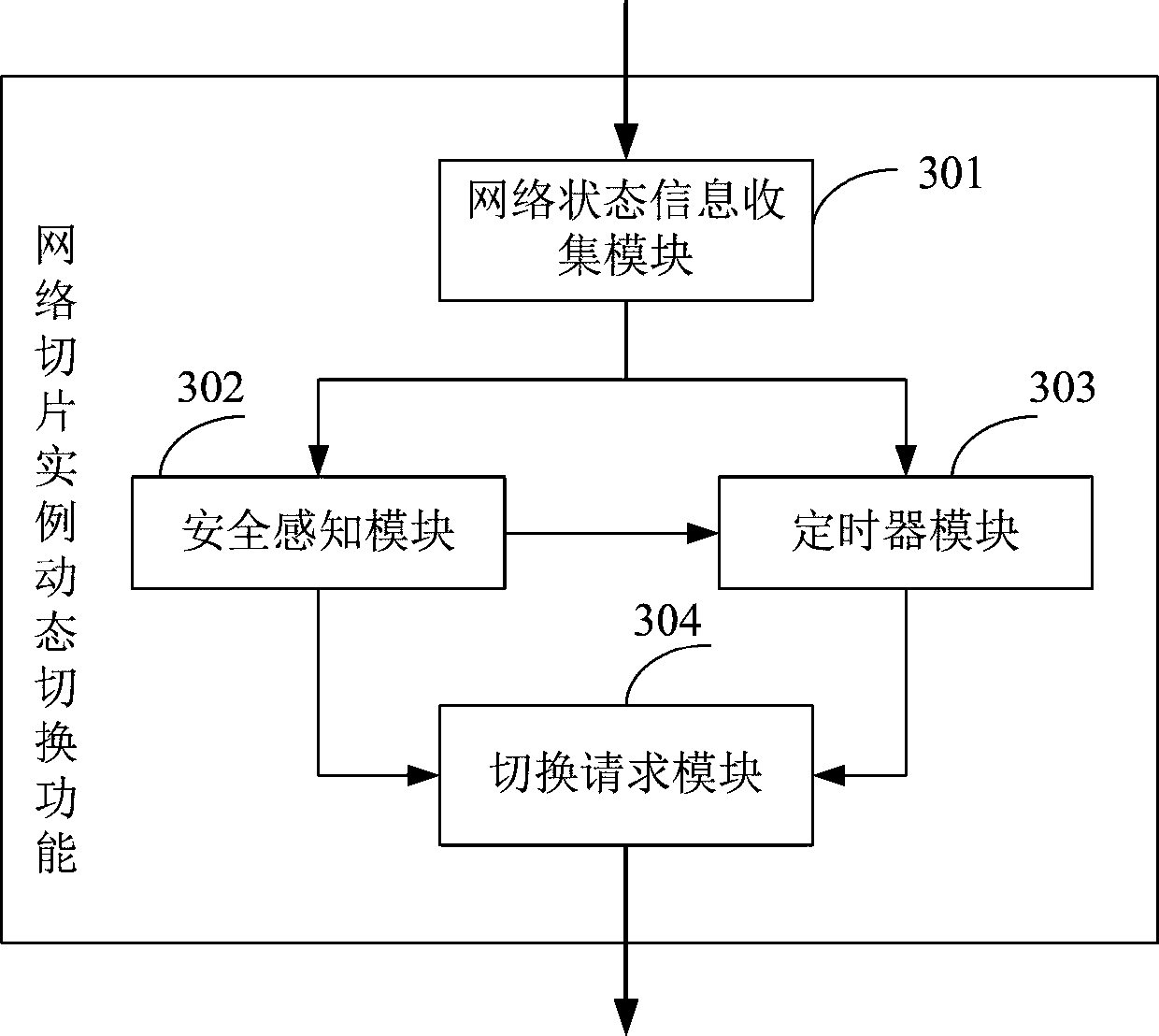
The invention provides a 5G network slice instance dynamic switching method and function. The method comprises the following steps: collecting network state information of a to-be-protected network, wherein the network state information comprises security threat information and connection state information between user equipment and an access network slice instance; judging whether the user equipment meets a set network slice instance switching condition or not according to the security threat information and the connection state information; if yes, initiating a network slice instance switching request to a network slice selection function, wherein the request comprises user equipment information, original network slice instance information and a new network slice instance selection standard; and forwarding the received response message to the network management function, so that the network management function notifies the original network slice instance and the new network slice instance to switch the network slice instance. The dynamic switching function comprises a network state information collection module, a security perception module, a timer module and a switching requestmodule. According to the invention, active defense can be realized, and the communication security of the UE is ensured.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
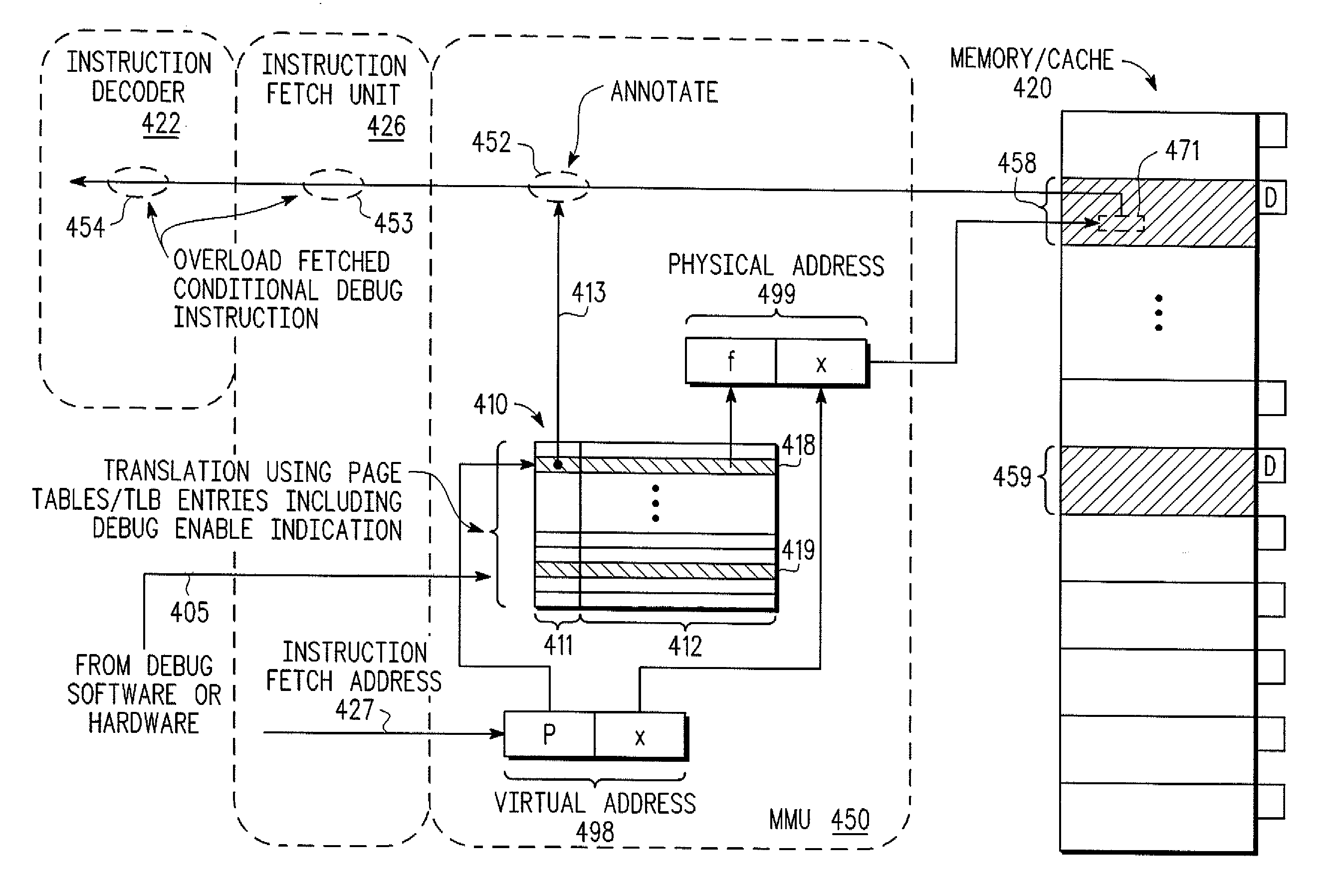
Qualification of conditional debug instructions based on address
ActiveUS20090235059A1Digital computer detailsSpecific program execution arrangementsParallel computingSemantics
A processor implementation supports selection of an execution mode for debug instruction instances based on respective addresses thereof in addressable memory can provide an attractive mechanism for executing debug instructions in a way that allows some instances of the instructions to operate with debug semantics while suppressing other instances by executing them with no-operation (NOP) semantics. In some embodiments, selection of operative execution semantics may be based on attributes of a memory page in which a particular debug instruction instance resides. In some embodiments, portions of an address space may be delimited (e.g., using values stored in bounding registers and addresses of particular debug instruction instances compared against the delimited portions to select appropriate execution semantics. In some embodiments, both types of evaluations may be used in selecting appropriate execution semantics for a particular debug instruction instance.
Owner:SONY CORP +2
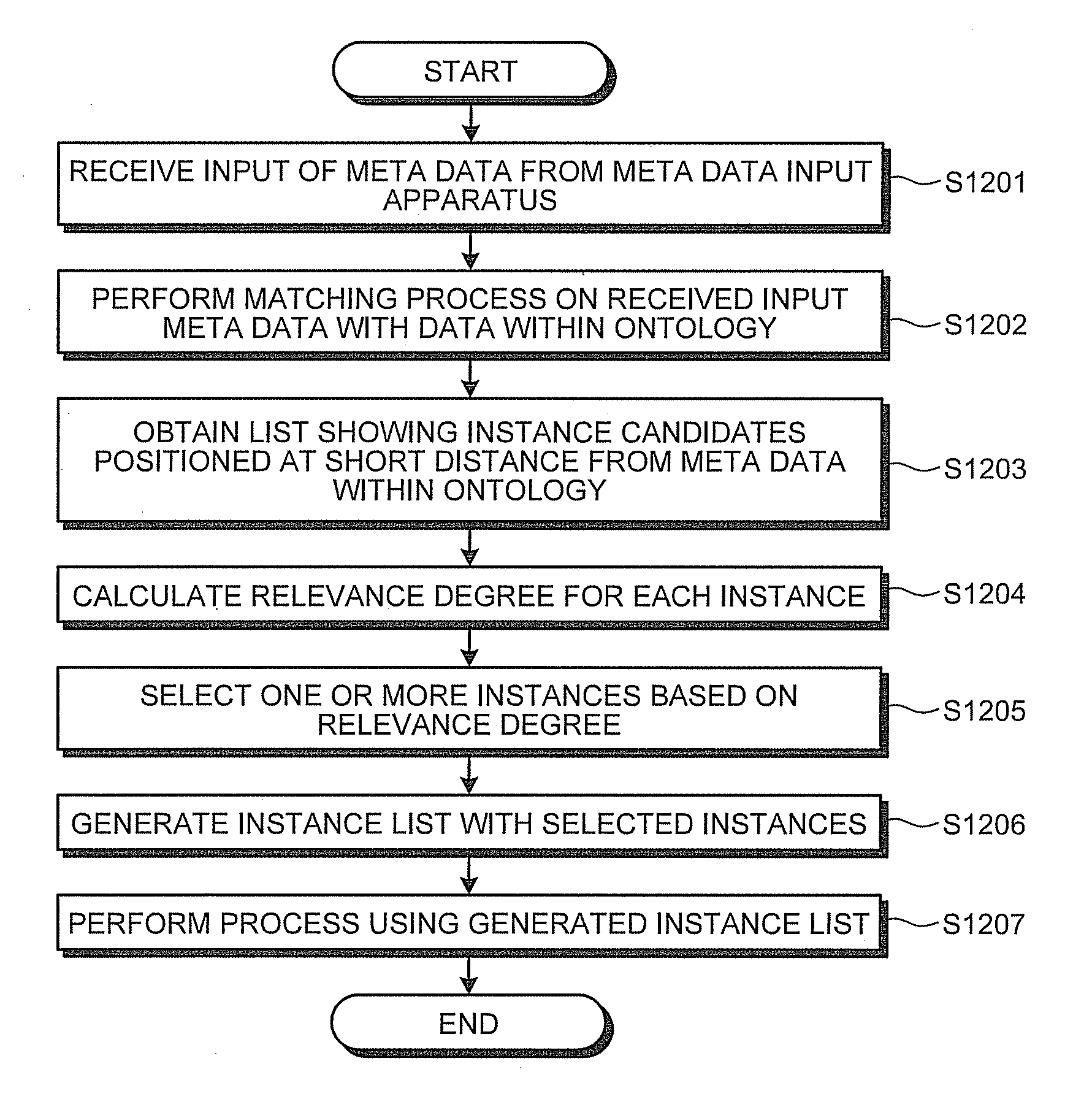
Apparatus, method and computer program product for selecting instances
InactiveUS20080082524A1Improve the level ofDigital data information retrievalSpecial data processing applicationsInstance selectionComputer program
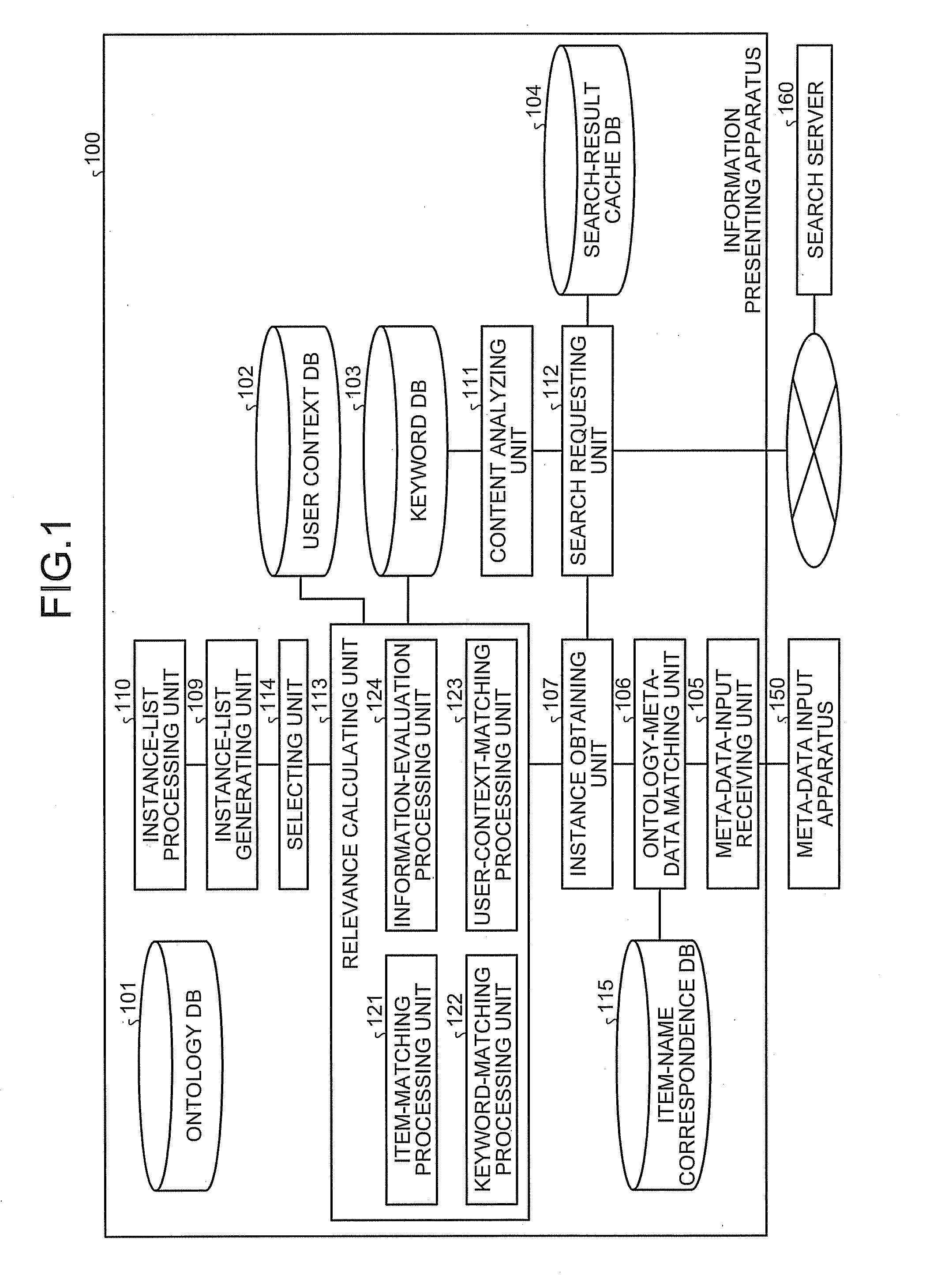
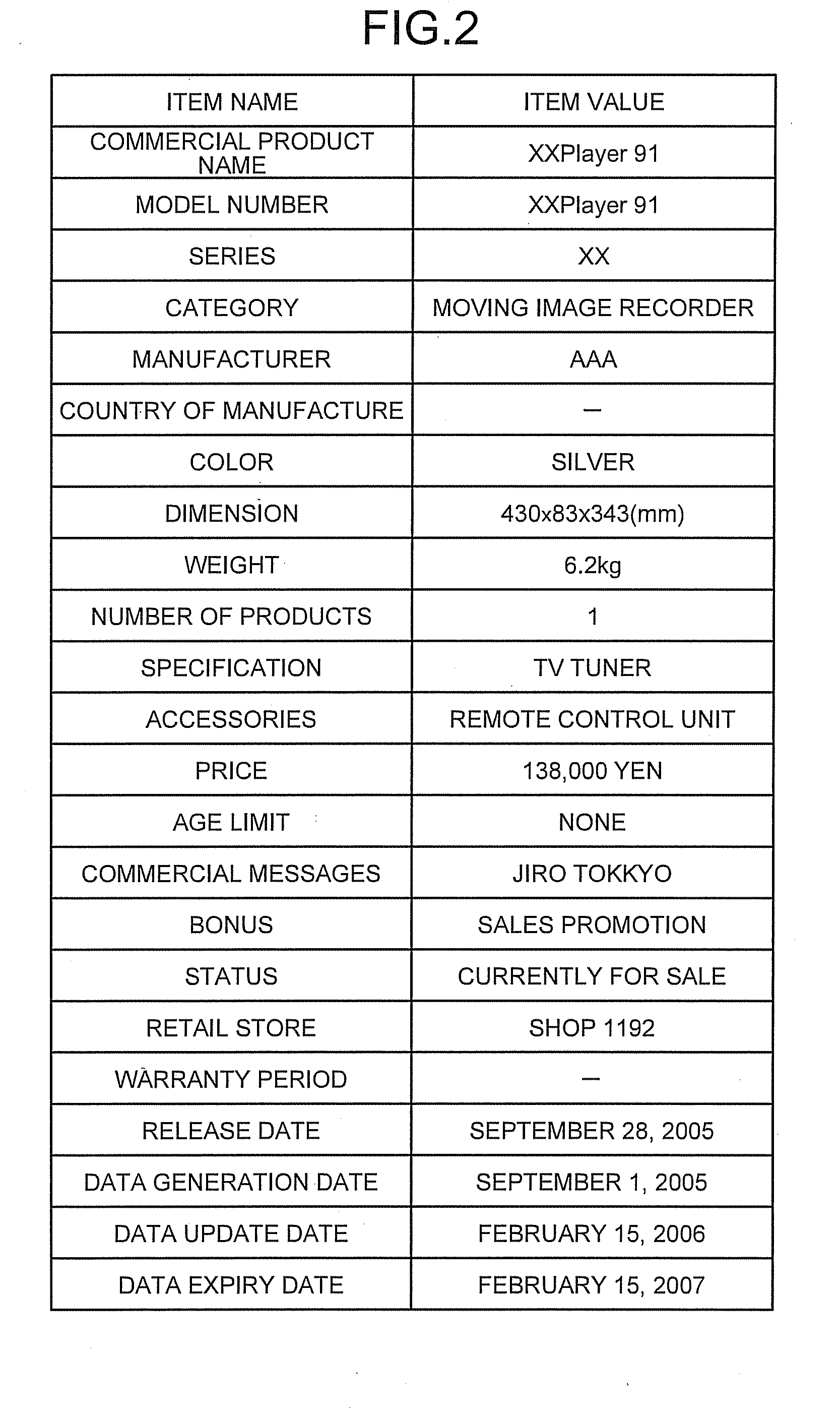
An instance selecting apparatus stores a plurality of instances each of which includes an item name and an item value. The item name denotes the name of an item, whereas the item value denotes the value of the item. When having received a meta information that includes an item name and an item value, the instance selecting apparatus calculates, for each of the instances, a relevance degree showing a relationship between the instance and the meta information, by applying a weighting coefficient to a level of similarity between the meta information and at least one of the item name and the item value of the instance. The instance selecting apparatus then selects one or more of the instances having a higher level of relevance with the meta information, based on the relevance degrees.
Owner:KK TOSHIBA
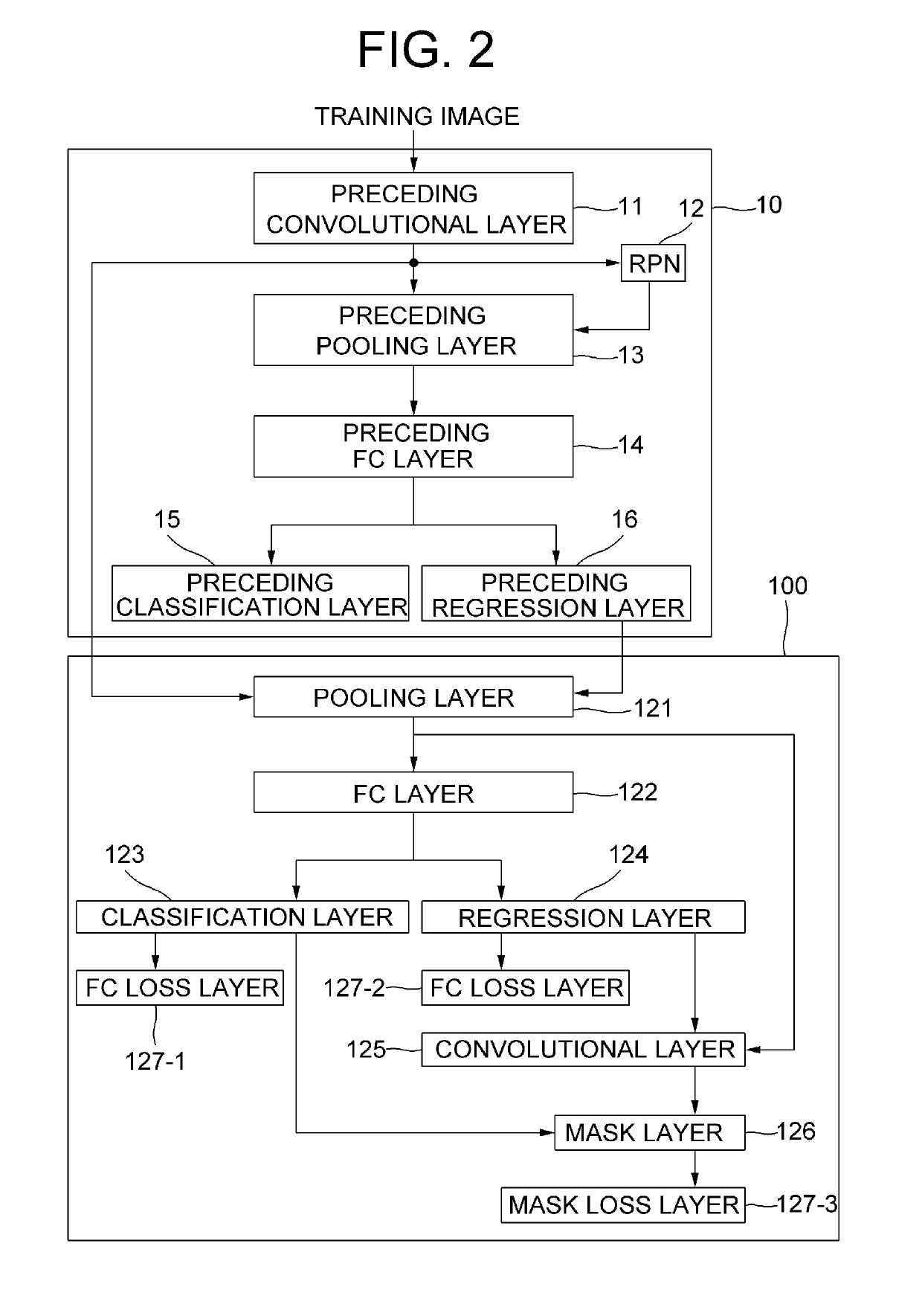
Method for detecting pseudo-3D bounding box based on CNN capable of converting modes according to poses of objects using instance segmentation and device using the same
A method for detecting a pseudo-3D bounding box based on a CNN capable of converting modes according to poses of detected objects using an instance segmentation is provided to be used for realistic rendering in virtual driving. Shade information of each of surfaces of the pseudo-3D bounding box can be reflected on the learning according to this method. The pseudo-3D bounding box may be obtained through a lidar or a rader, and the surface may be segmented by using a camera. The method includes steps of: a learning device instructing a pooling layer to apply pooling operations to a 2D bounding box region, thereby generating a pooled feature map, and instructing an FC layer to apply neural network operations thereto; instructing a convolutional layer to apply convolution operations to surface regions; and instructing a FC loss layer to generate class losses and regression losses.
Owner:STRADVISION
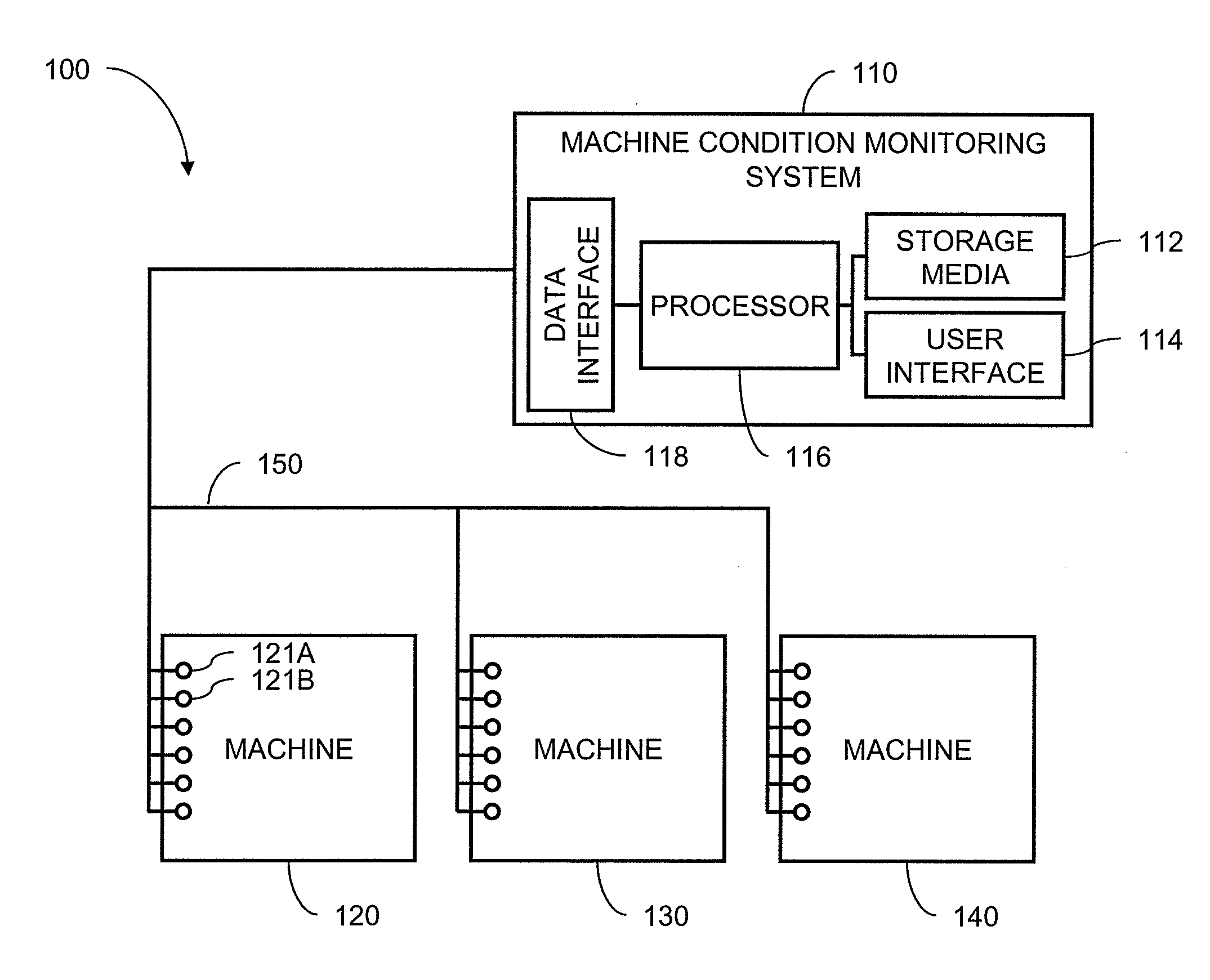
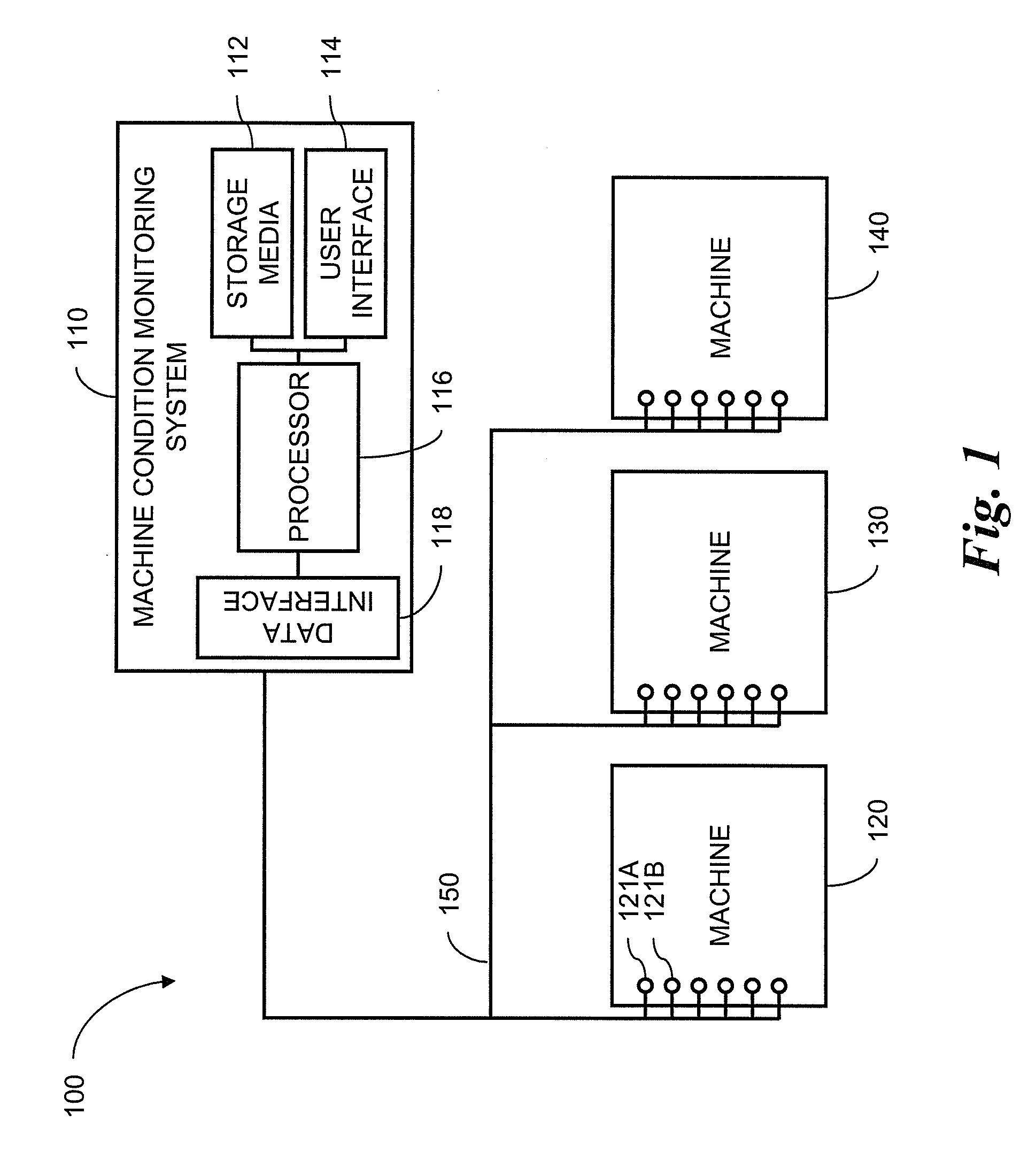
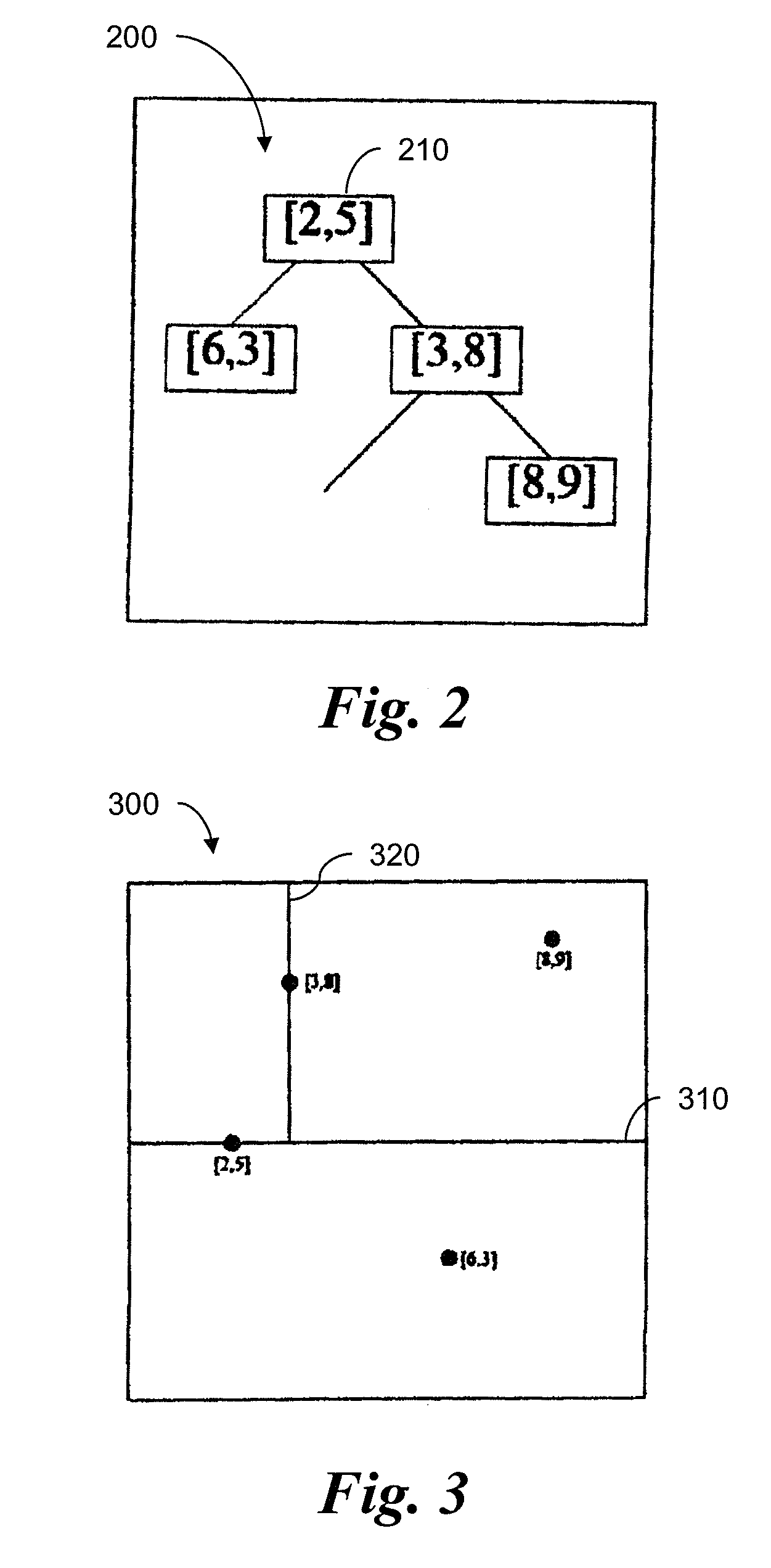
Use of Sequential Clustering for Instance Selection in Machine Condition Monitoring
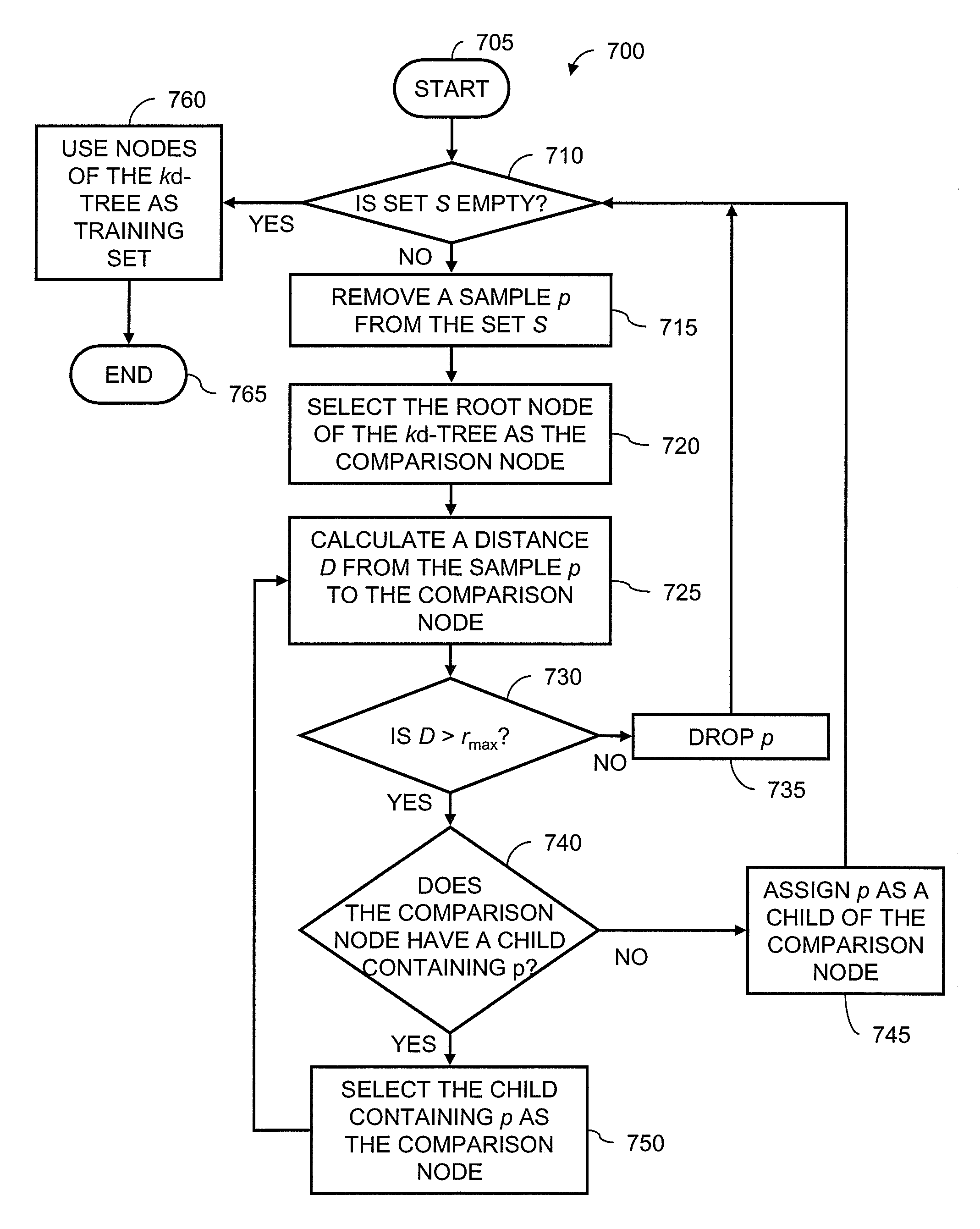
A method is provided for selecting a representative set of training data for training a statistical model in a machine condition monitoring system. The method reduces the time required to choose representative samples from a large data set by using a nearest-neighbor sequential clustering technique in combination with a kd-tree. A distance threshold is used to limit the geometric size the clusters. Each node of the kd-tree is assigned a representative sample from the training data, and similar samples are subsequently discarded.
Owner:SIEMENS CORP +1
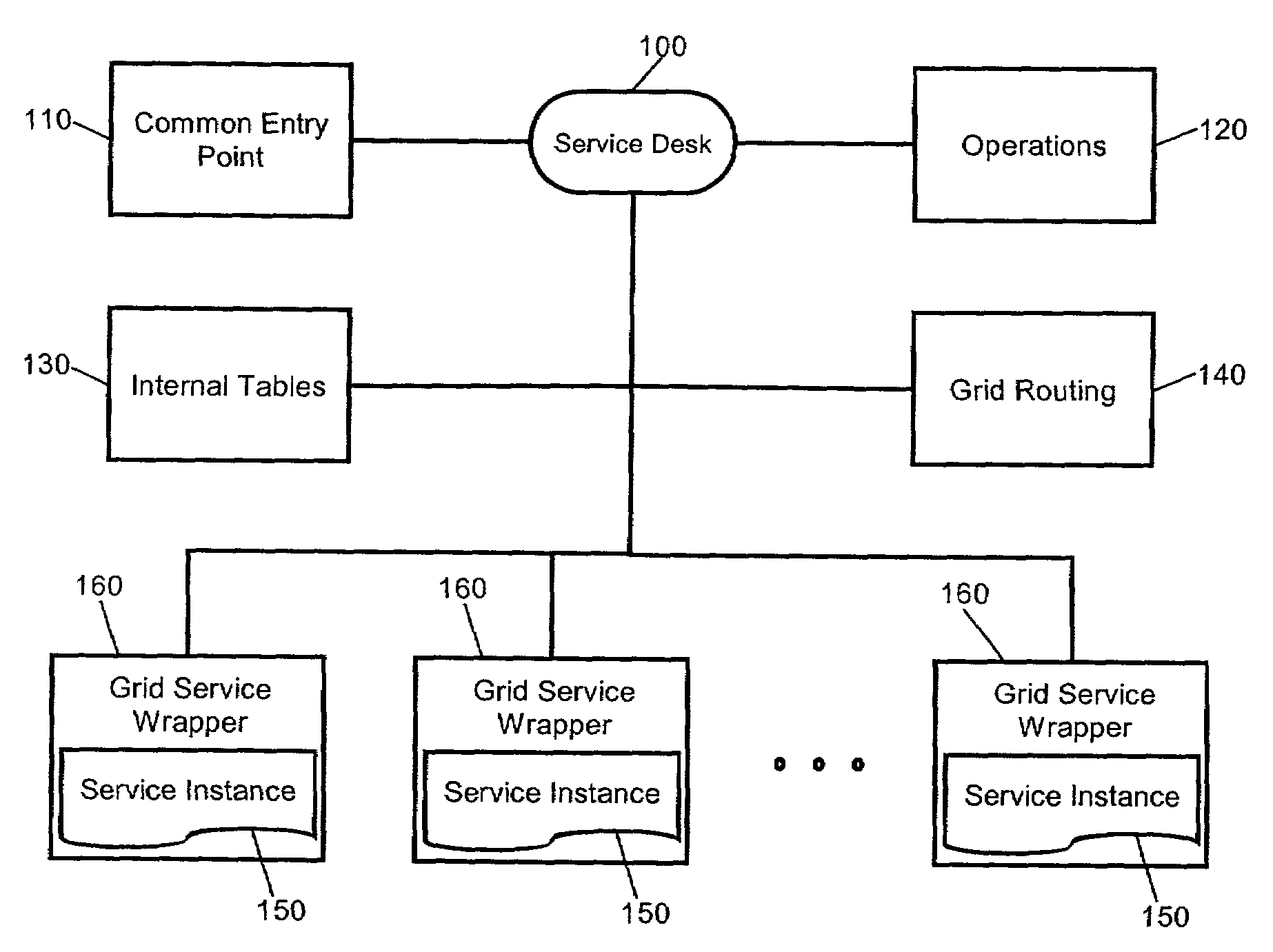
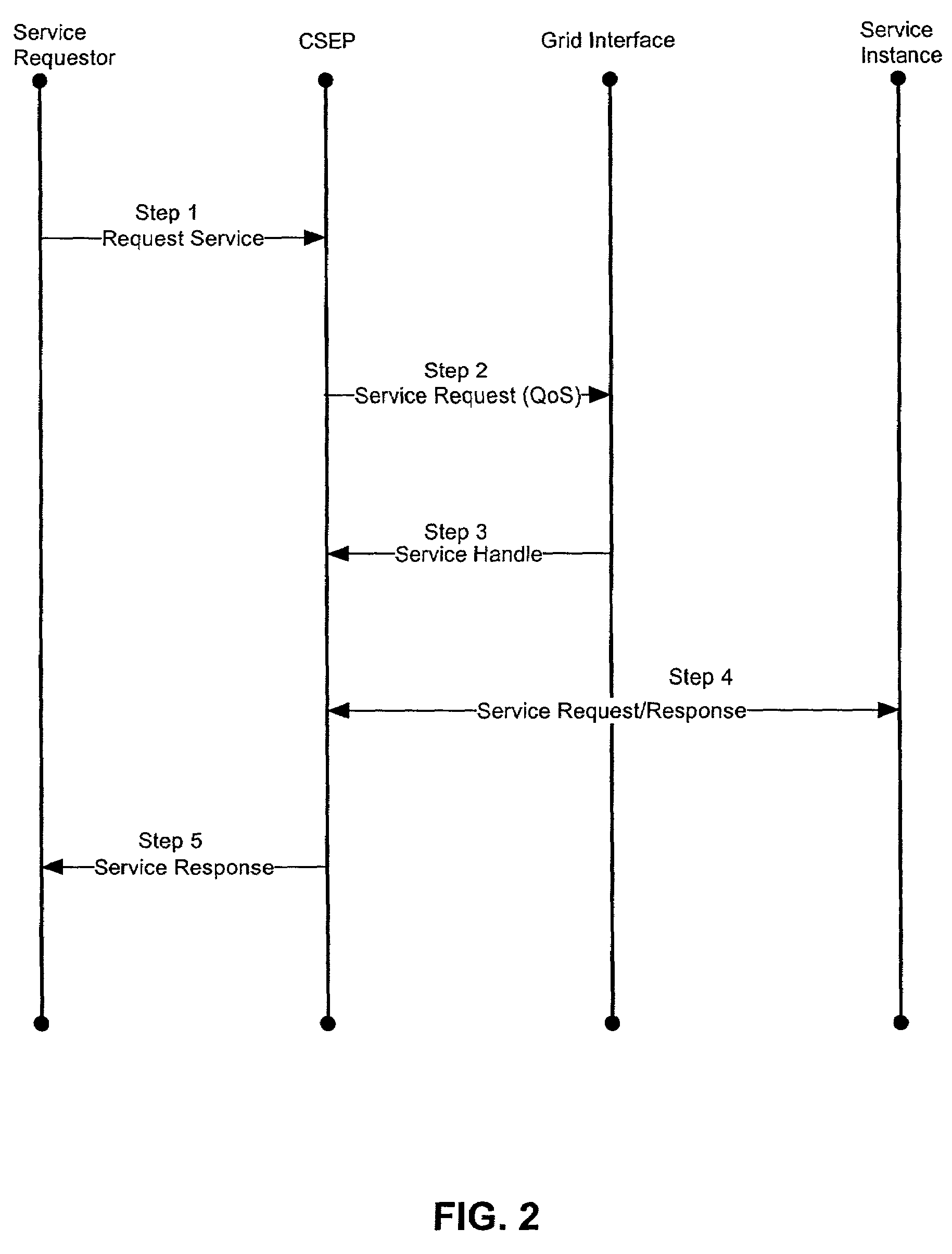
Dynamic binding and fail-over of comparable web service instances in a services grid
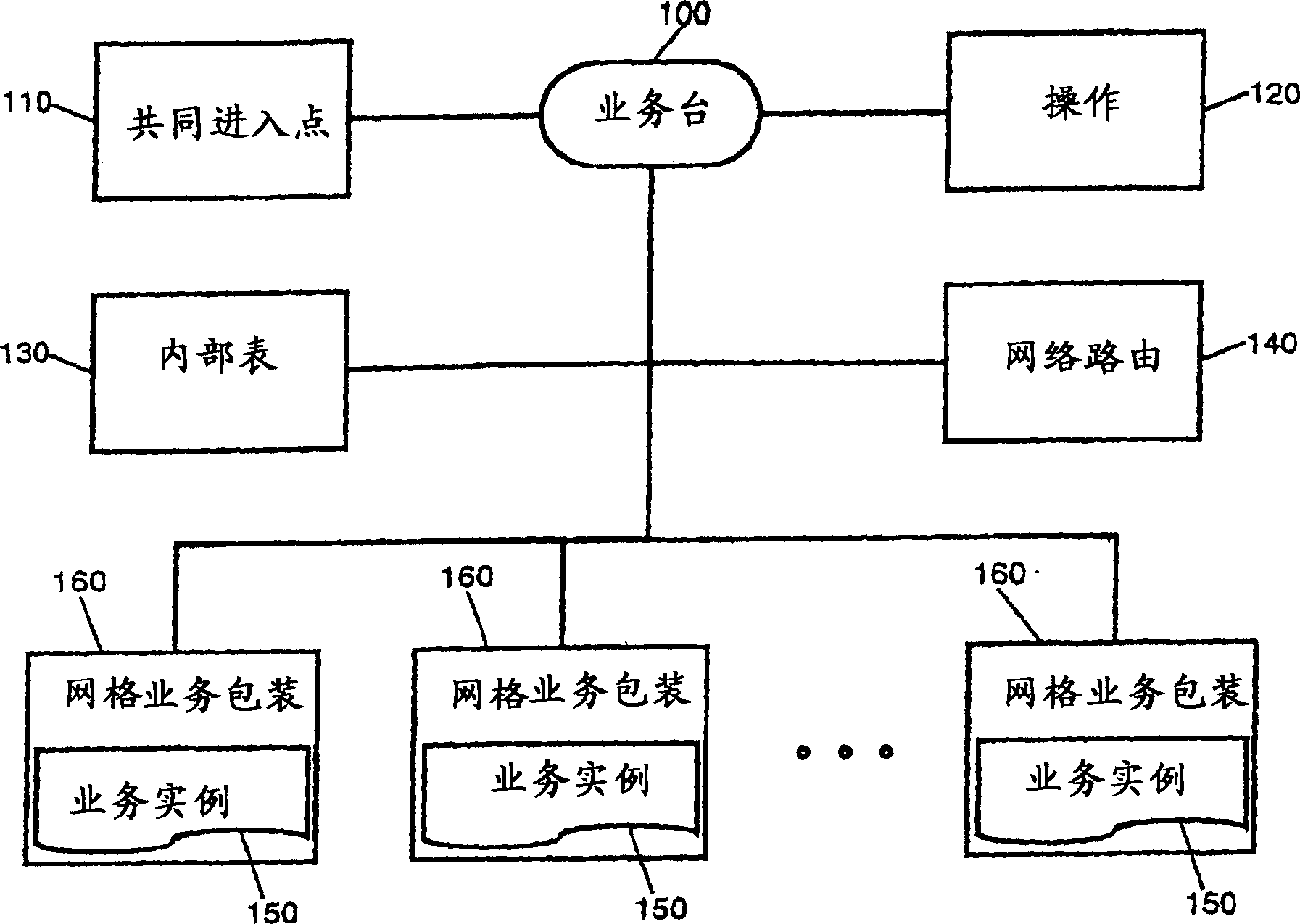
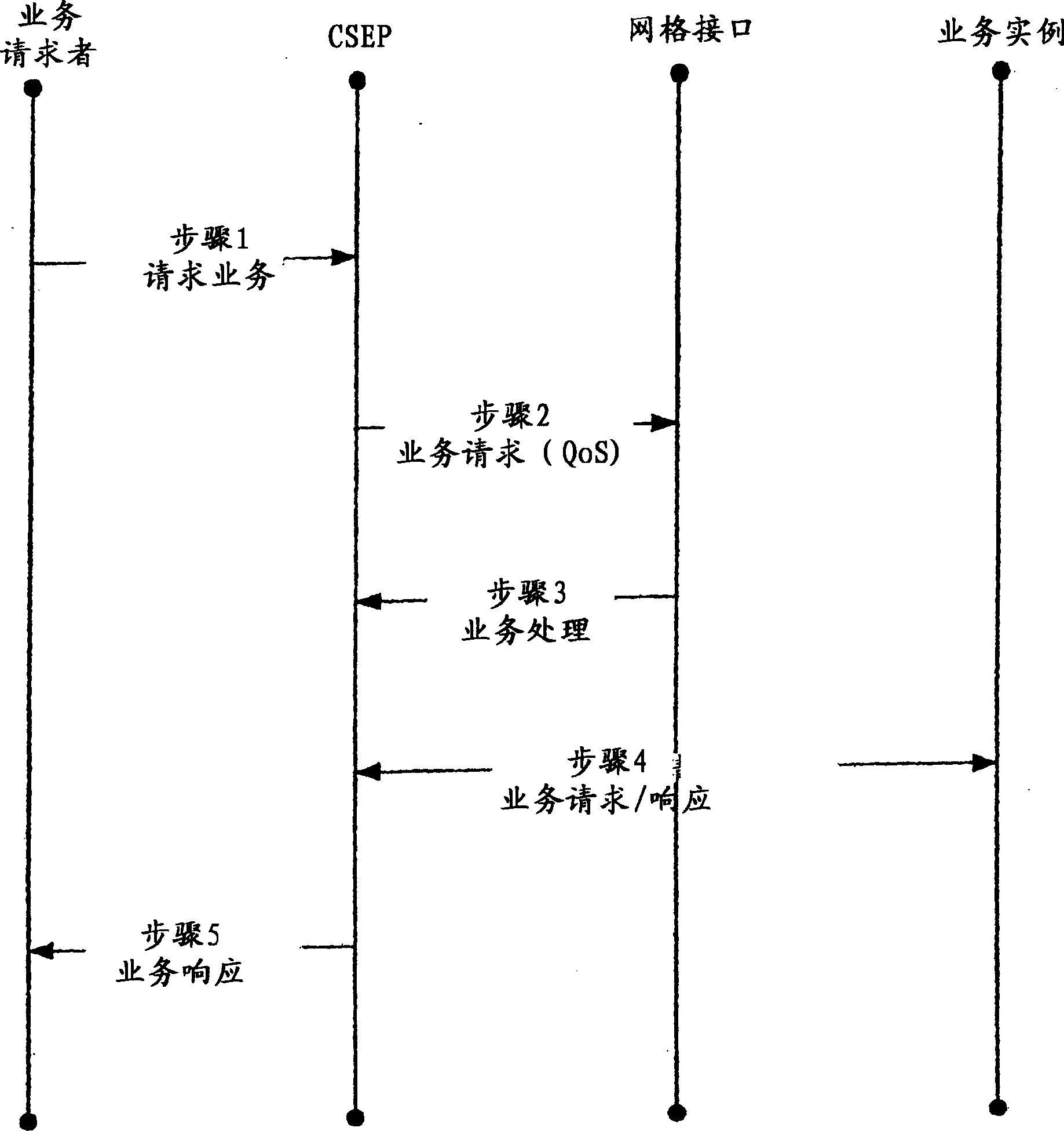
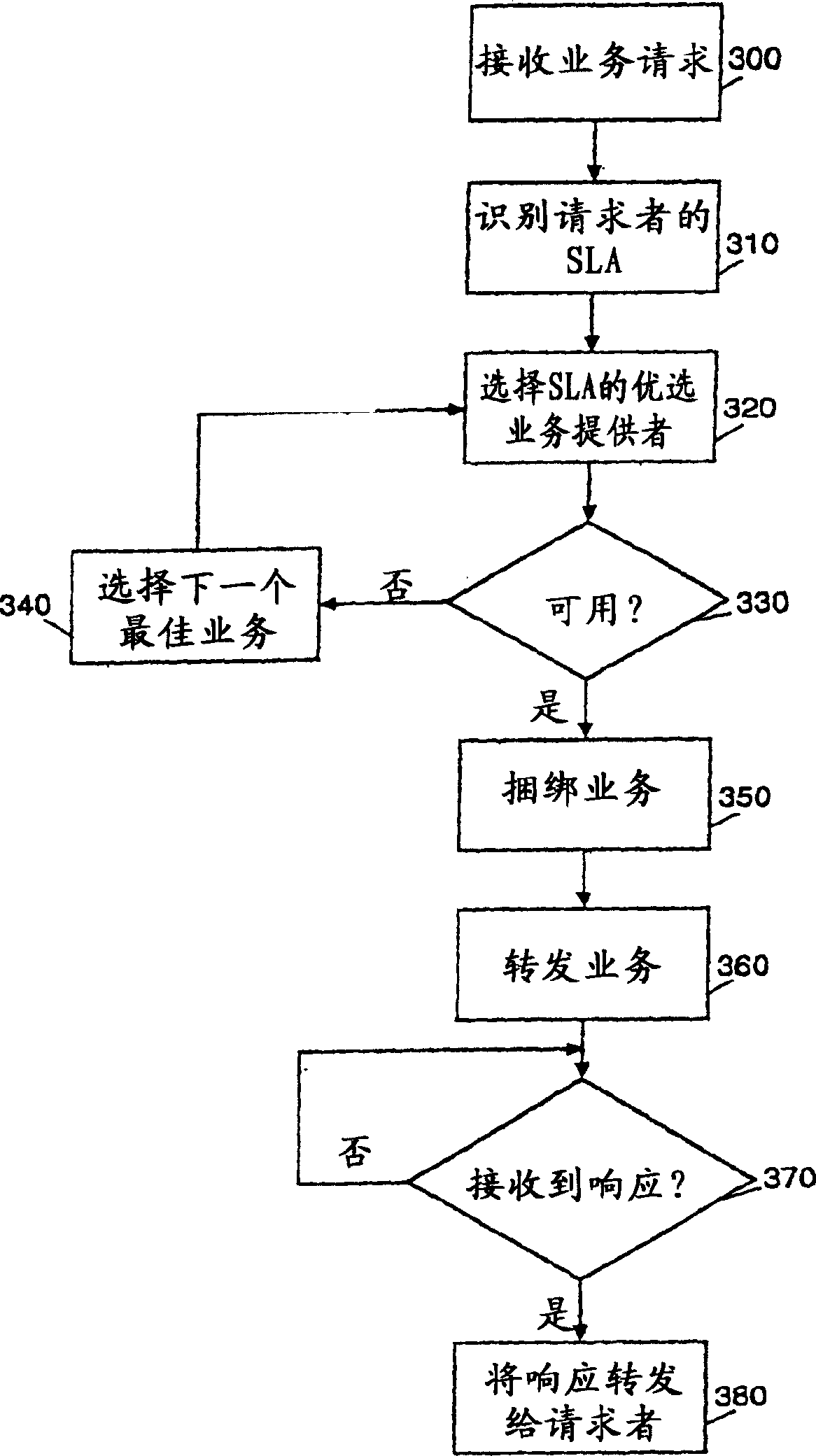
ActiveUS7647523B2Monitor performanceResource allocationError detection/correctionFailoverWeb service
A computing services grid. The grid can include a service desk coupled to one or more computing service instances. Each service instance can conform to an interface which is common to all service instances in the grid. A routing component can be disposed in the grid. Specifically, the routing component can route individual service requests to individual ones of the service instances. An instance selection service is used to satisfy QoS characteristics associated with the requester of the service. The grid further can include a service instance monitoring component. The monitoring component can monitor the performance of individual service instances charged with processing individual service requests. Fail-over logic can be configured to re-route service requests from selected service instances to others of the service instances where the monitoring component detects a fail-over condition in the selected service instances. In that regard, fail-over conditions can include error conditions and a performance deficiency conditions in which the performance of a selected service instance lags behind guaranteed levels of performance.
Owner:SERVICENOW INC
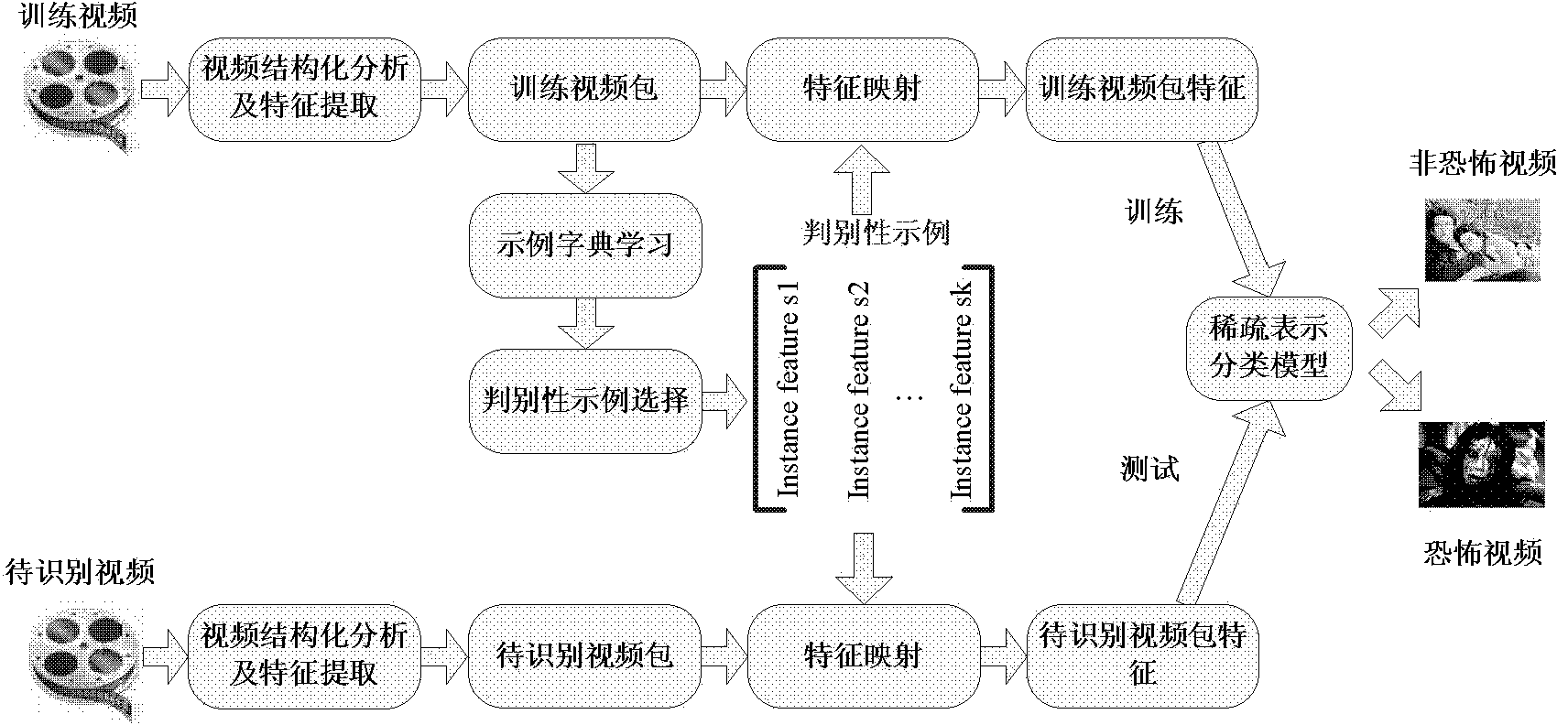
Horror video identification method based on discriminant instance selection and multi-instance learning
ActiveCN103413125AImprove classification recognition rateImprove discrimination abilityCharacter and pattern recognitionFeature vectorInstance selection
The invention discloses a horror video identification method based on discriminant instance selection and multi-instance learning. The method comprises the steps of extracting the video shot of each video in a training video set and selecting an emotional representative frame and an emotional mutation frame for each video shot to show the shot, extracting the audio and video characteristics of the shots as video instances to form a video instance set, selecting a discriminant video instance from the video instance set, calculating the similarity distances between the video instances and the discriminant video instance in the training video set to obtain a characteristic vector set, carrying out sparse reconstruction on the characteristic vector of the video to be identified and the characteristic vector set corresponding to the training video set, and identifying the class of the video according to reconstruction errors. The novel horror video identification method based on the discriminant instance selection and the multi-instance learning is applied to horror film scene identification, is of great academic significance and social significance and has wide application prospects.
Owner:人民中科(北京)智能技术有限公司
Nearest neighbor filling method of non-fixed k values
InactiveCN103544218AImprove rationalityImprove filling qualityNeural learning methodsSpecial data processing applicationsRound complexityMissing data
The invention provides a nearest neighbor filling method of non-fixed k values. The method mainly aims at overcoming the defects of an existing nearest neighbor filling method. The method comprises the steps that firstly, reasonable definitions are performed on various attribute distance computational formulas; then, an appropriate k value is selected with regard to each missing instance by using the mode of sparse coding, and meanwhile the attributes which most conform to the missing instances are selected; finally, k non-missing instances closest to the missing instances are selected for missing value filling according to the obtained k values. According to the method, the instance problem of missing data filling can be solved, furthermore, the reasonability of missing value filling can be enhanced, and filling quality can be improved without increasing filling complexity. The method is easy to implement and only refers to some simple mathematical models when codes are edited.
Owner:GUANGXI NORMAL UNIV
Fine-grained resource response system based on load balancing algorithm of container cluster
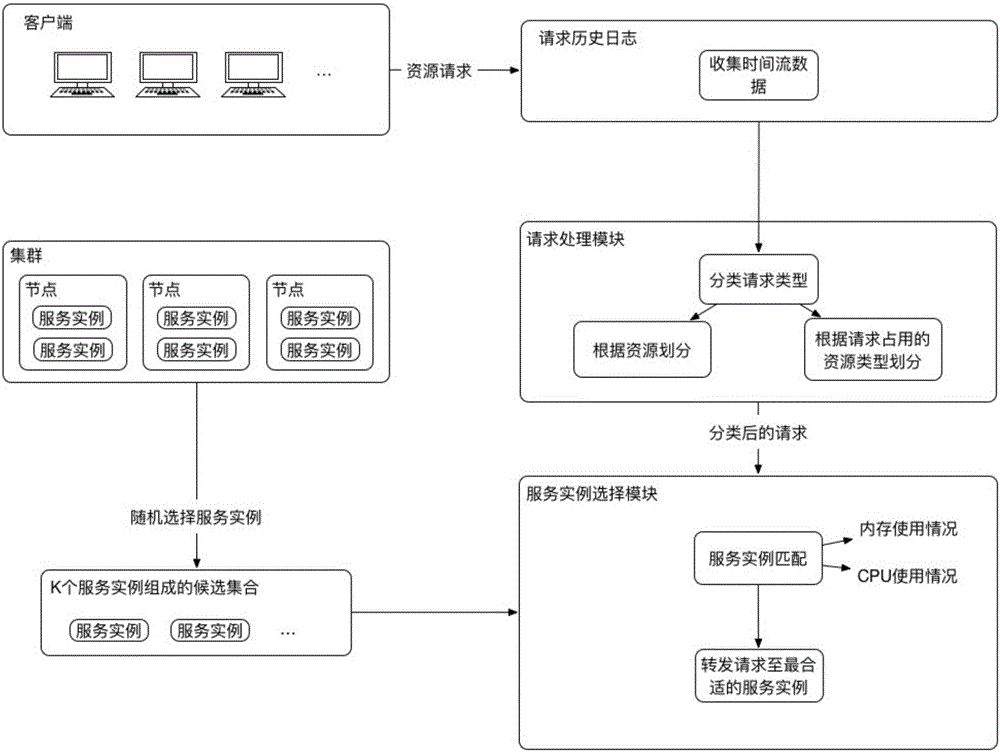
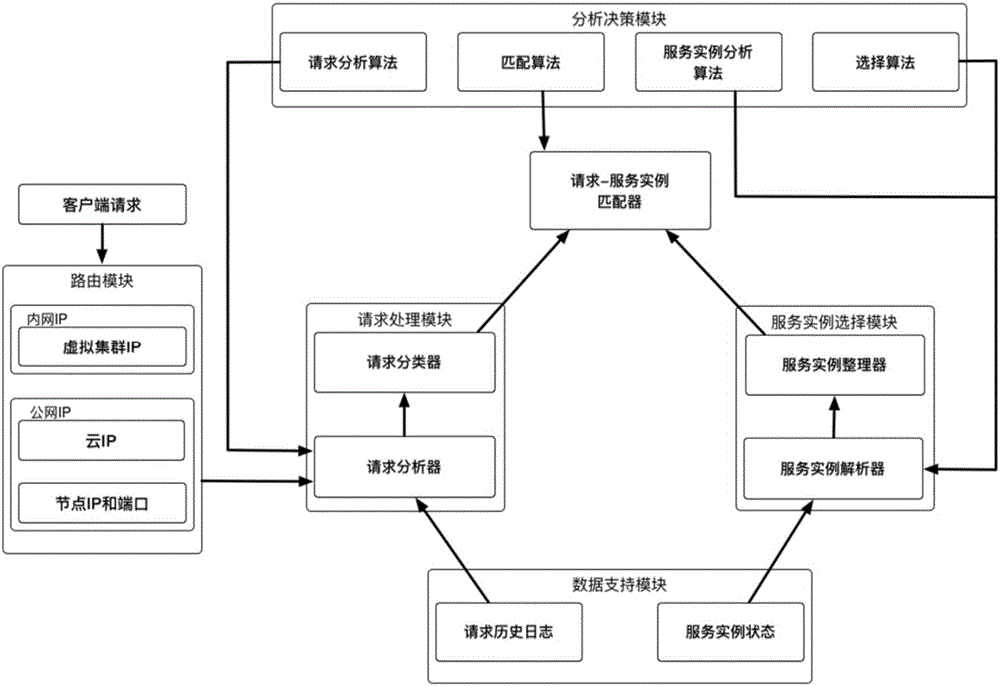
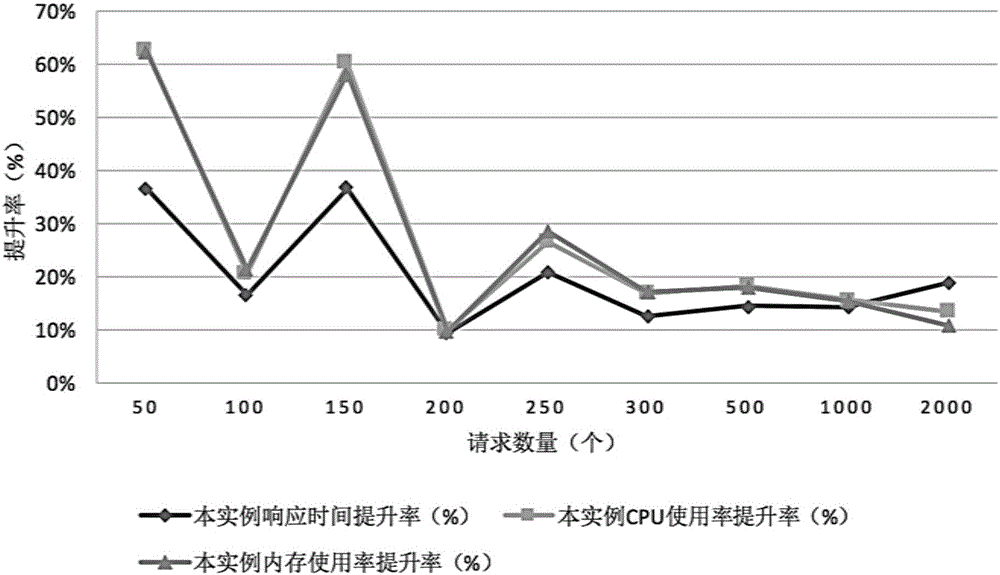
ActiveCN105872082AAvoid strandedImprove resource usageTransmissionResource utilizationInstance selection
A fine-grained resource response system based on a load balancing algorithm of a container cluster comprises a request processing module, a data support module, an analysis and decision module, a service instance selection module and a request-service instance matcher, wherein the request processing module calls the data support module and the analysis and decision module to analyze and classify requests and sends a request classification result to the request-service instance matcher; the request-service instance matcher initiates a selection request to the service instance selection module, and the service instance selection module calls the data support module and the analysis and decision module for analyzing and selecting service instances and sends a service instance selection result to the request-service instance matcher; the request-service instance matcher calls the analysis and decision module to perform group matching and individual matching sequentially according to the request classification result and the service instance selection result, and issues the requests to the corresponding service instances according to a matching result, and resource response is realized. The system has a better resource utilization rate.
Owner:SHANGHAI LANDFUN INFORMATION TECH CO LTD
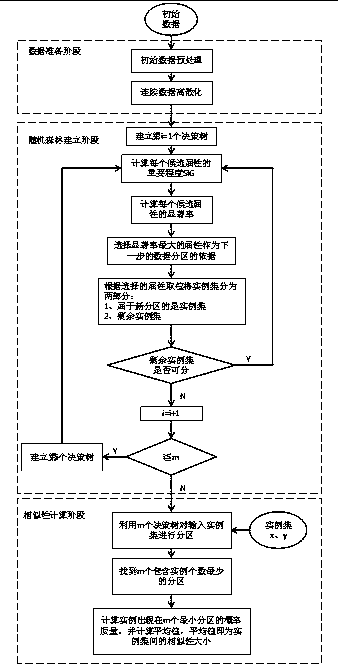
Similarity measurement method based on attribute selection
InactiveCN108804635ASignificantly highImprove performanceCharacter and pattern recognitionSpecial data processing applicationsInformation processingData set
The invention relates to the technical field of information processing, and in particular relates to a similarity measurement method based on attribute selection. The method comprises the steps of a data preparation stage: preprocessing initial data and performing discretization on continuous data sets; a random forest building stage comprising attribute selection and instance division, selectingan attribute with the maximum conspicuousness in the attribute set to partition instances of data sets, and then iteratively building a partition forest comprising m decision making trees; and a similarity computing stage: computing the size of similarity between any x and y instance sets according to the M decision making trees of the partition forest. Significance of the attribute is consideredwhen the partition forest is built, the problem that the algorithm is relatively high in complexity and complex in computing process when high-dimensional data is processed is overcome, and compared with the other algorithms, the method has better performance when in outlier detection, and the high-dimensional data can be effectively processed.
Owner:GUANGDONG POWER GRID CO LTD +1
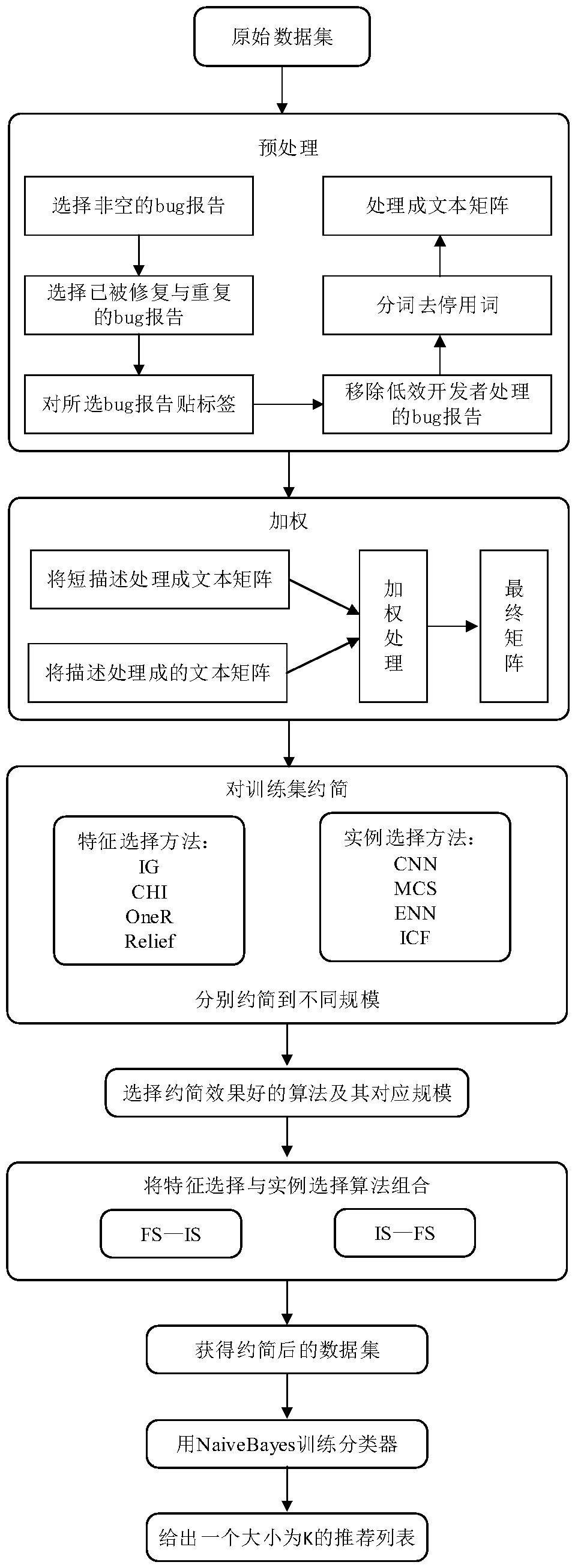
A method for enhancing automatic bug report distribution by adopting a weighted optimization training set
InactiveCN109255029ASmall scaleQuality improvementSpecial data processing applicationsText database clustering/classificationData setInstance selection
The invention discloses a method for enhancing automatic bug report distribution by adopting a weighted optimization training set. By weighting the bug report dataset, the information frequency in theshort description is improved. Combined with feature selection algorithm and instance selection algorithm, a smaller and higher quality training set is obtained by reducing noise words and redundantinstances, which improves the accuracy of bug classification, saves the time cost and labor cost of bug assignment, and improves the work efficiency.
Owner:DALIAN MARITIME UNIVERSITY
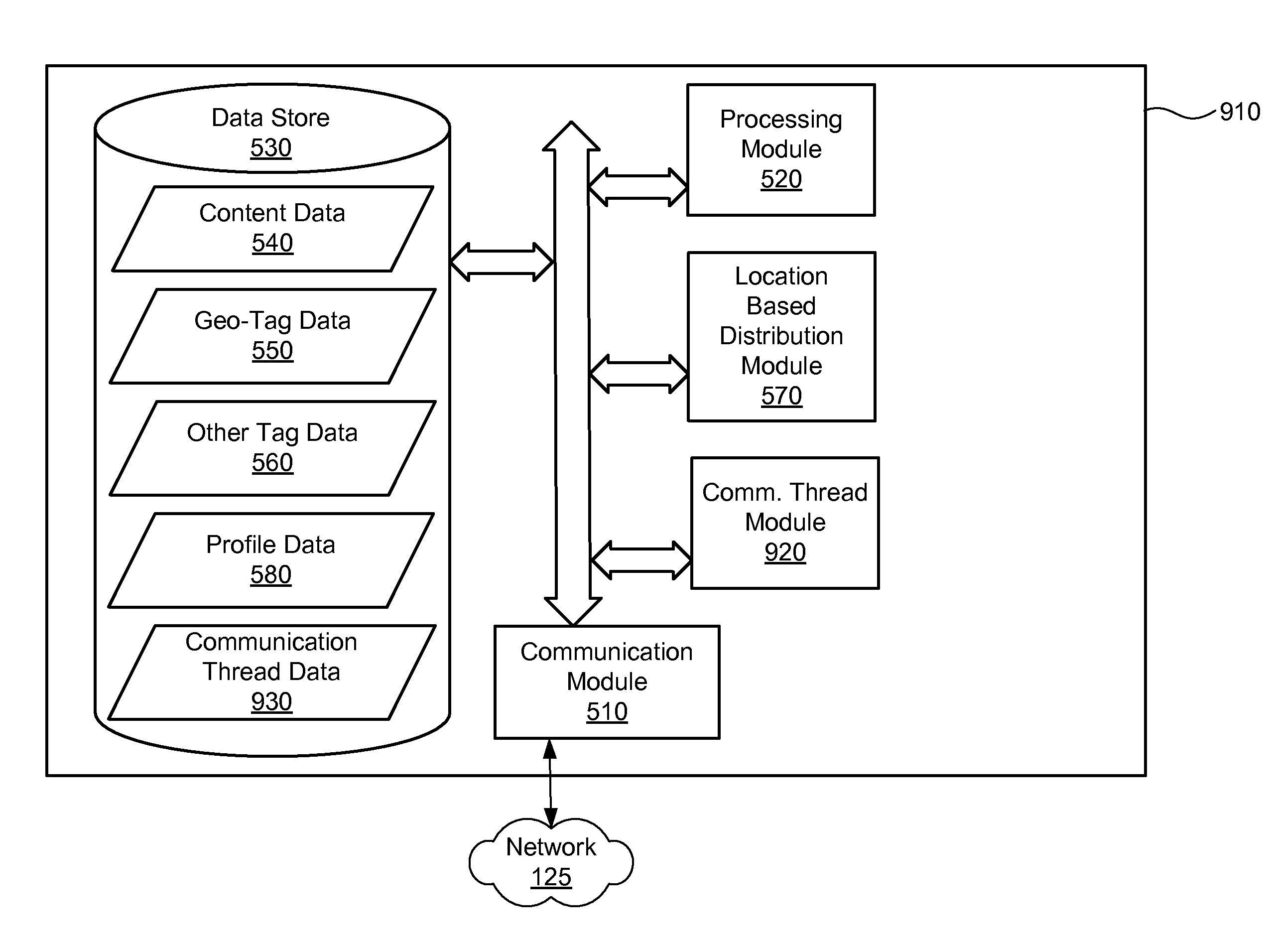
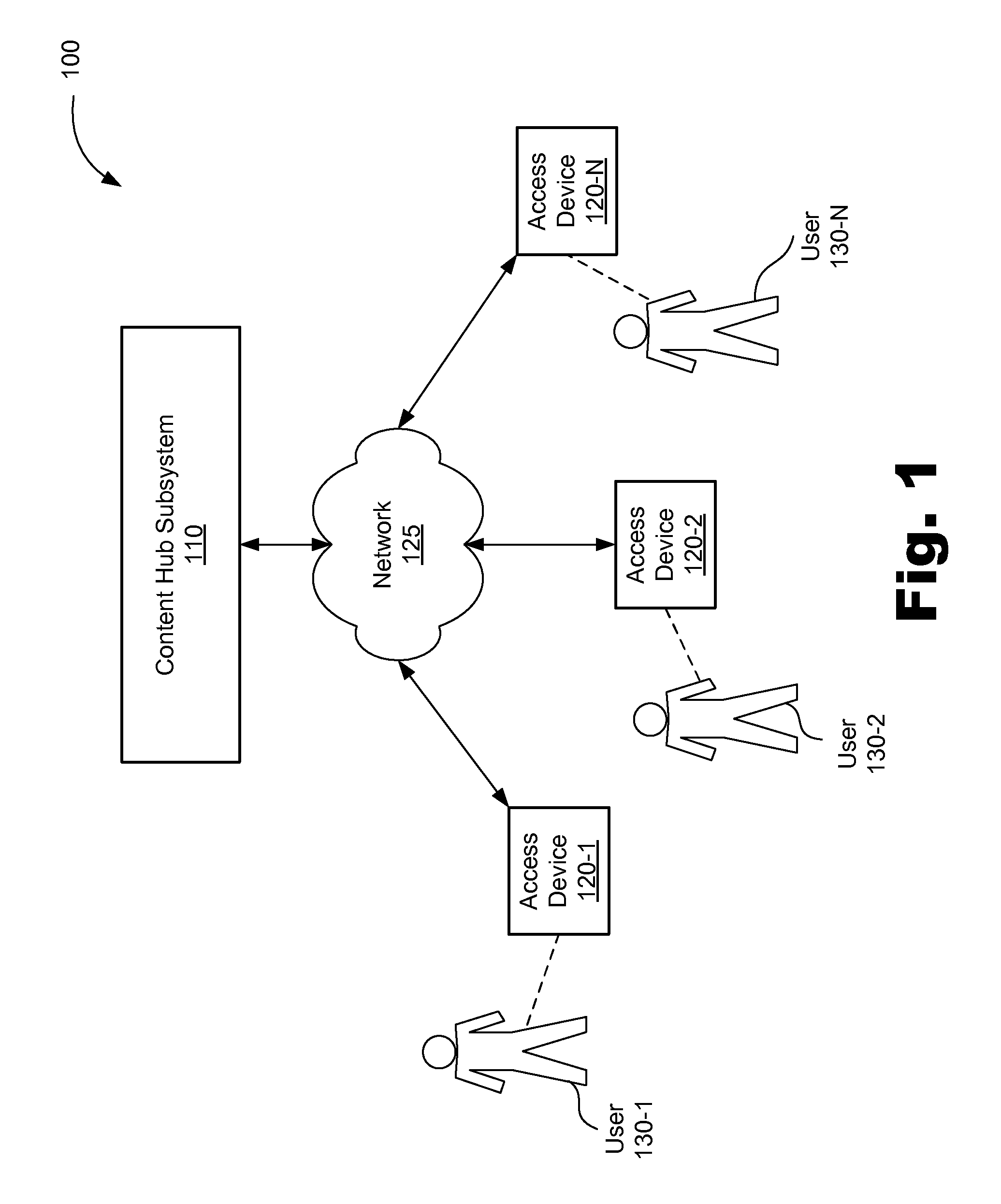
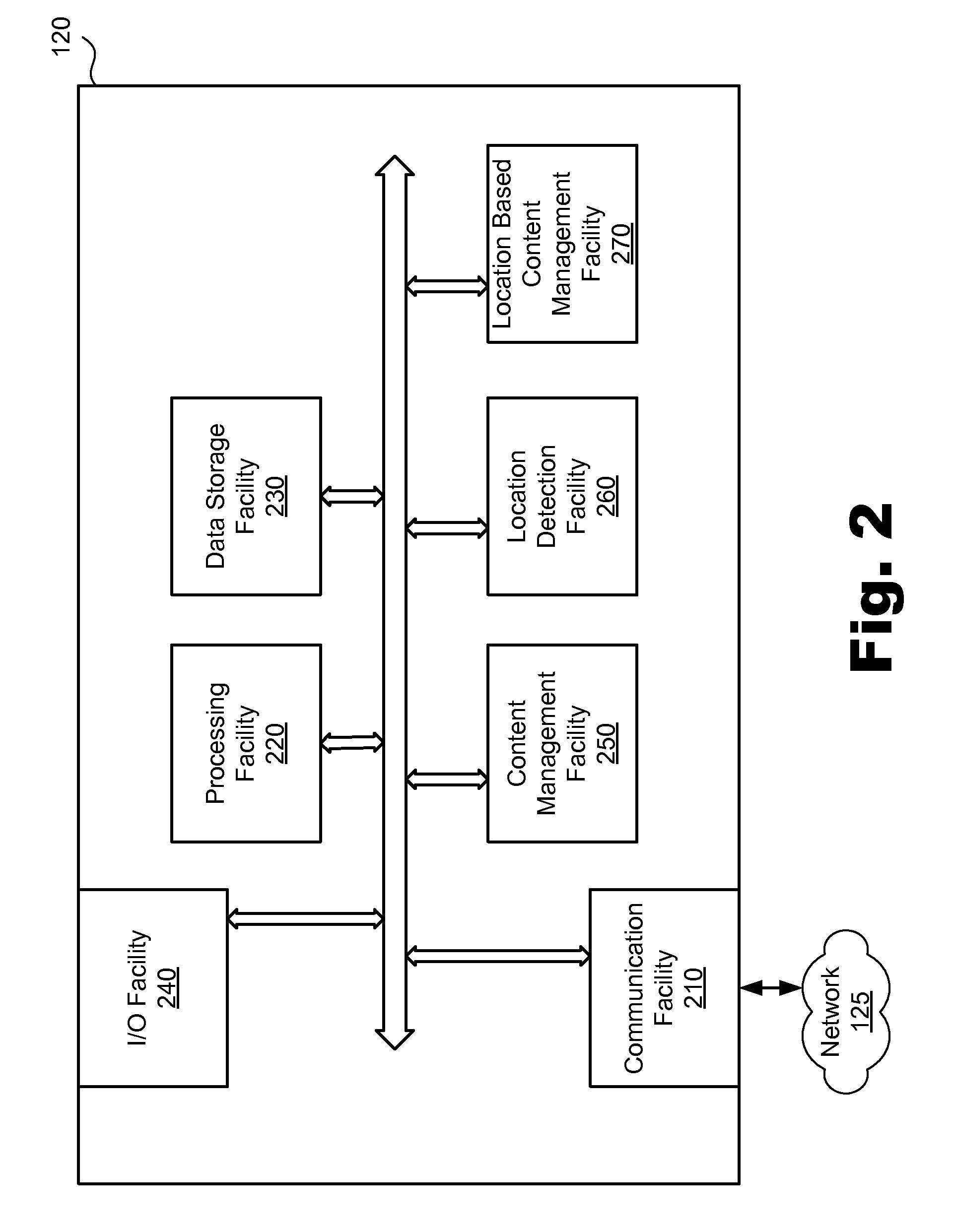
Location based content aggregation and distribution systems and methods
ActiveUS7882201B2Instruments for road network navigationAdvertisementsGeolocationDistribution system
In an exemplary method, a content posting is received from an access device connected to a network. The content posting includes data representative of a content instance and a geographic location associated with the content instance. The content posting is stored. The content instance is selectively distributed to at least one other access device connected to the network based on the geographic location. In certain embodiments, the selective distribution includes determining that the other access device is located physically proximate to the geographic location and making the content instance accessible to the other access device in response to the determination. In certain embodiments, the method further comprises the access device creating the content instance, detecting the geographic location as a physical location of the access device, and associating the geographic location with the content instance.
Owner:META PLATFORMS INC
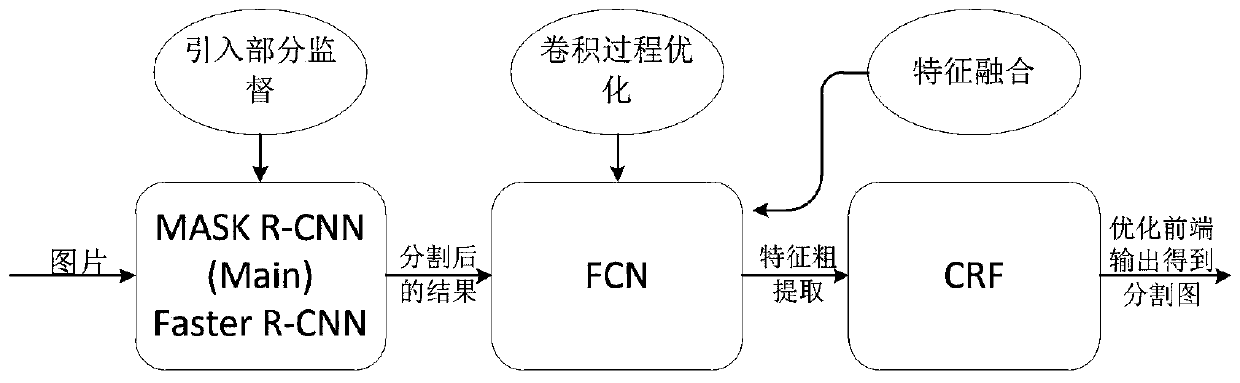
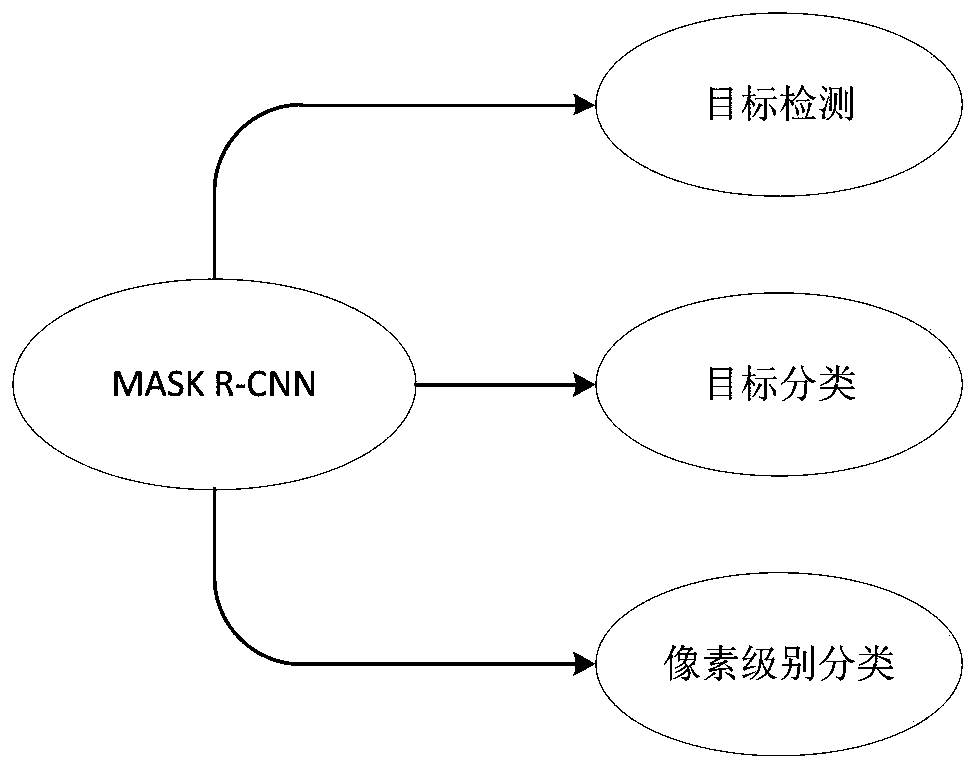
Method for improving instance segmentation based on unmanned driving technology
InactiveCN110276378ALow costOptimize detection resultsCharacter and pattern recognitionNeural architecturesInstance selectionComputer vision
The invention discloses a method for improving instance segmentation based on an unmanned driving technology. According to the method, targets are detected and classified on the basis of the Faster R-CNN based on the MASK R-CNN, and then instance segmentation is achieved through FCN feature coarse extraction and CRF optimization output. The method comprises the following specific implementation steps: step 1, classifying targets by using a partial supervision method; step 2, adopting depth separable convolution in the semantic segmentation convolution process to obtain features; and step 3, performing feature fusion optimization on the features obtained by the convolutional layer, introducing semantic information in a low layer, and introducing spatial information in a high layer. According to the method, relatively good target detection and classification results are established at relatively low cost. The method adopts depth separable convolution, thus improving the precision of a segmentation result and the efficiency of a computer, and reducing time loss.
Owner:HANGZHOU DIANZI UNIV
A software bug report classification system and classification method
InactiveCN109213865ASmall scaleQuality improvementCharacter and pattern recognitionText database clustering/classificationData setSoftware bug
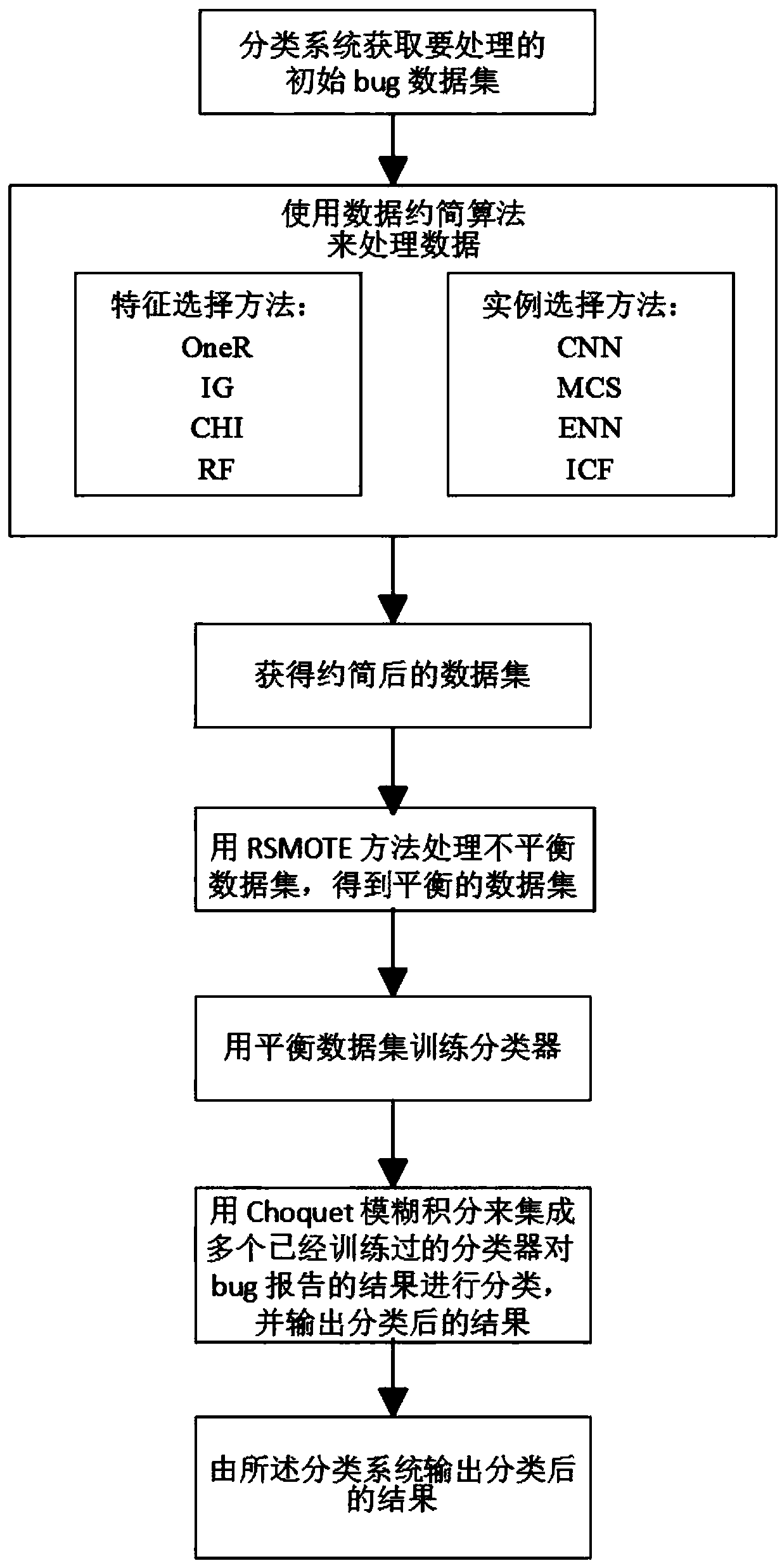
The invention discloses a software bug report classification system and a classification method. The system comprises a training part and a test part. The training part comprises a data set acquisition module, a data reduction module and an unbalanced data set processing module. The test part comprises a bug report input module and a result classification output module. The main steps of the classification method include using a data reduction algorithm to process data, using an RSMOTE method to process an unbalanced data set, training a classifier with the obtained balanced data set, and integrating a plurality of trained classifiers with Choquet fuzzy integrals to classify the results of a bug report. The invention reduces the data scale on the sample dimension and the word dimension through the method of combining the feature selection and the instance selection, improves the recognition degree of the severity of the bug report by using the integrated training method based on Choquet fuzzy integrals, and avoids the uncertainty of random sampling at the same time.
Owner:DALIAN MARITIME UNIVERSITY
Multi-view masters for graphical designs
ActiveUS20200065355A1Software engineeringNatural language data processingGraphicsSoftware engineering
Owner:AXURE SOFTWARE SOLUTIONS
A computing services grid
InactiveCN1656776AResource allocationMultiple digital computer combinationsFailoverInstance selection
A computing services grid. The grid can include a service desk coupled to one or more computing service instances. Each service instance can conform to an interface which is common to all service instances in the grid. A routing component can be disposed in the grid. Specifically, the routing component can route individual service requests to individual ones of the service instances. An instance selection service is used to satisfy QoS characteristics associated with the requester of the service. The grid further can include a service instance monitoring component. The monitoring component can monitor the performance of individual service instances charged with processing individual service requests. Fail-over logic can be configured to re-route service requests from selected service instances to others of the service instances where the monitoring component detects a fail-over condition in the selected service instances. In that regard, fail-over conditions can include error conditions and a performance deficiency conditions in which the performance of a selected service instance lags behind guaranteed levels of performance.
Owner:IBM CORP
Multi-view masters for graphical designs
Owner:AXURE SOFTWARE SOLUTIONS INC
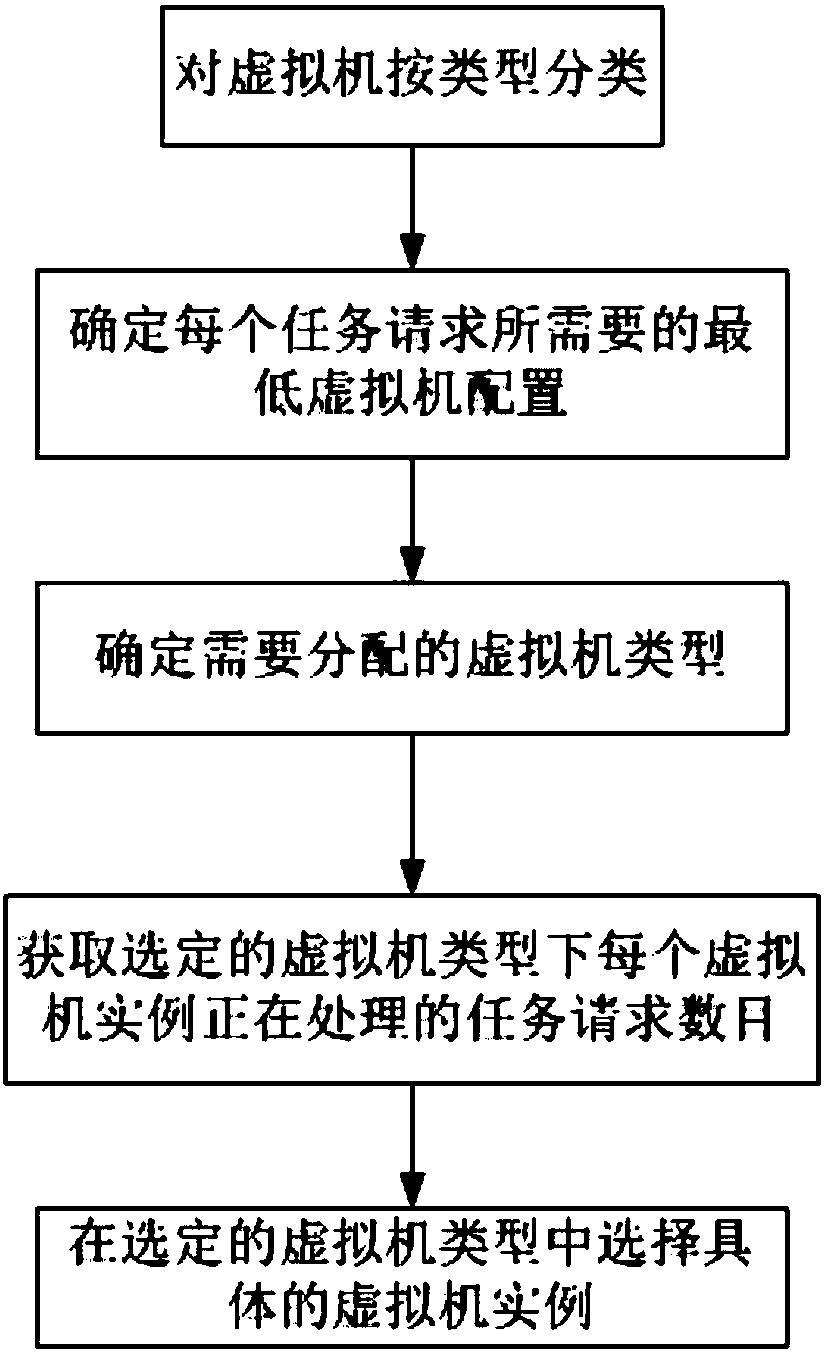
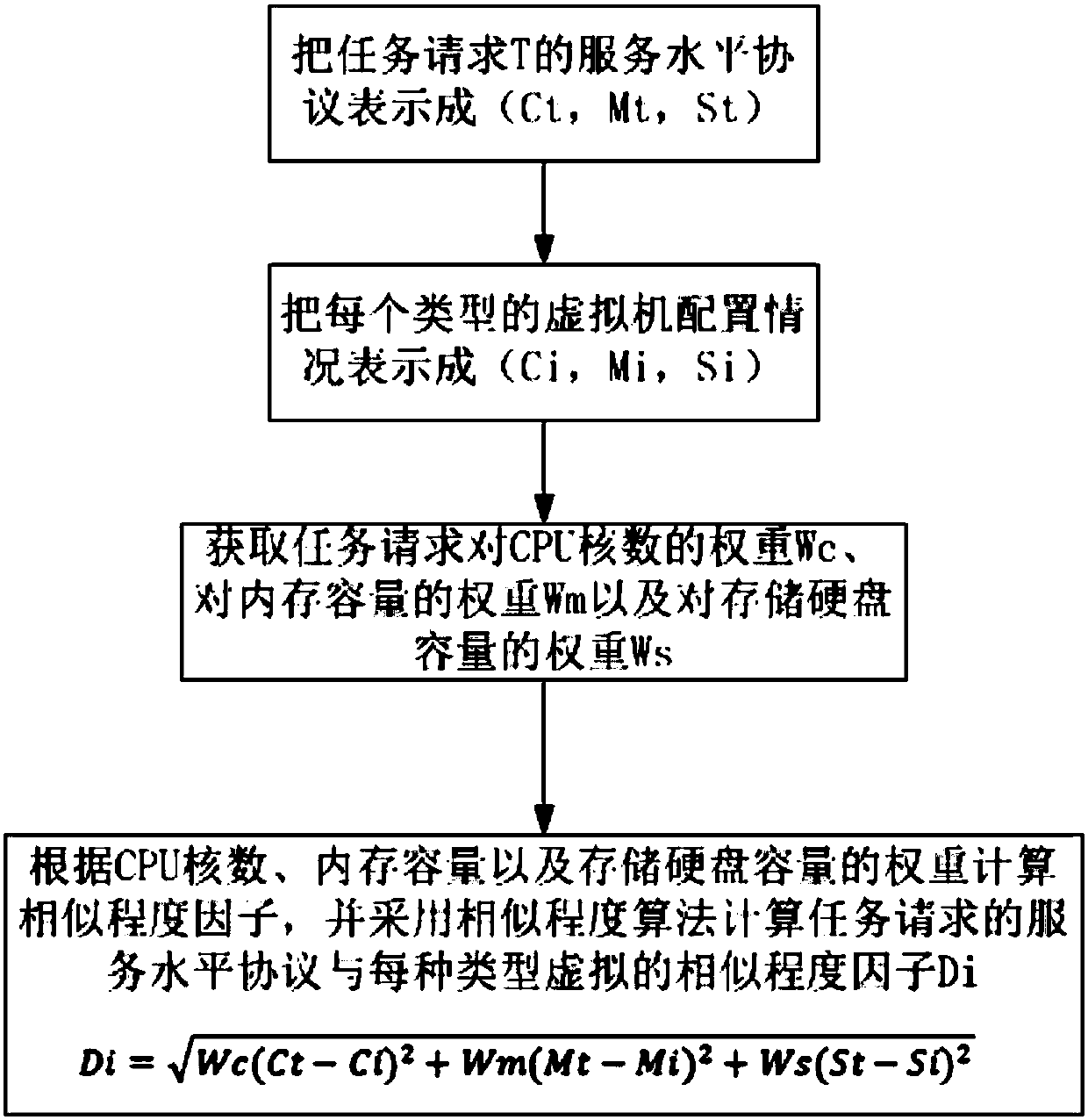
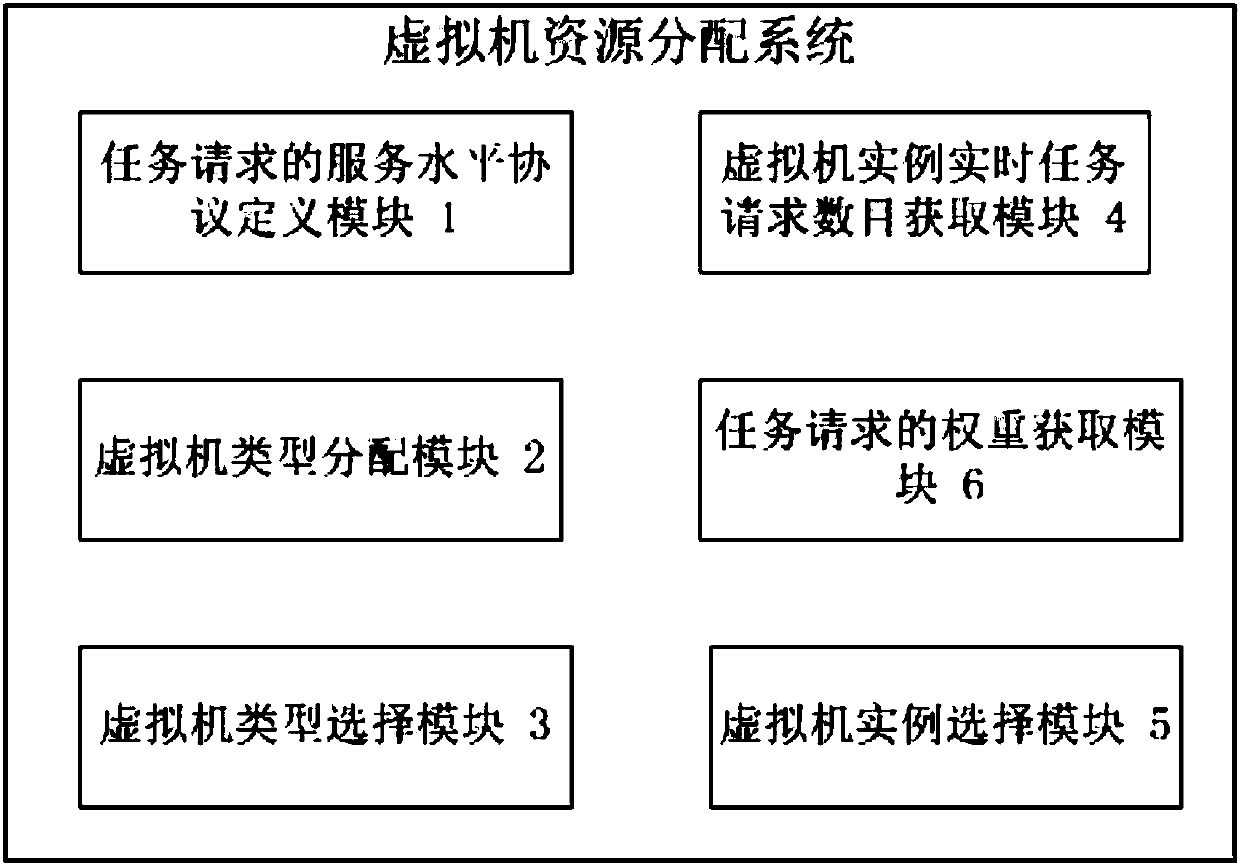
Method and system for allocating virtual machine resources
InactiveCN107861820AMeet Service Level AgreementsIncrease profitResource allocationSoftware simulation/interpretation/emulationService-level agreementInstance selection
The invention provides a method and system for allocating virtual machine resources. The method includes the steps of firstly, classifying virtual machines according to types; secondly, determining the minimum virtual machine configuration needed by each task request; thirdly, determining the virtual machine types which need to be allocated; fourthly, acquiring the processing task request number of each virtual machine instance under the selected virtual machine type; selecting a specific virtual machine instance in the selected virtual machine type. The system comprises a task-request servicelevel agreement definition module, a virtual machine type allocation module, a virtual machine type selection module, a virtual machine instance real-time taste request number acquiring module and avirtual machine instance selection module. The method and the system have the advantages that the adjustable virtual machine resource allocation method is used according to specific business, the service level agreements of the business are satisfied, the utilization rate of the single virtual machine is increased, and accordingly the overall processing ability of a bottom-layer physical machine is increased.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
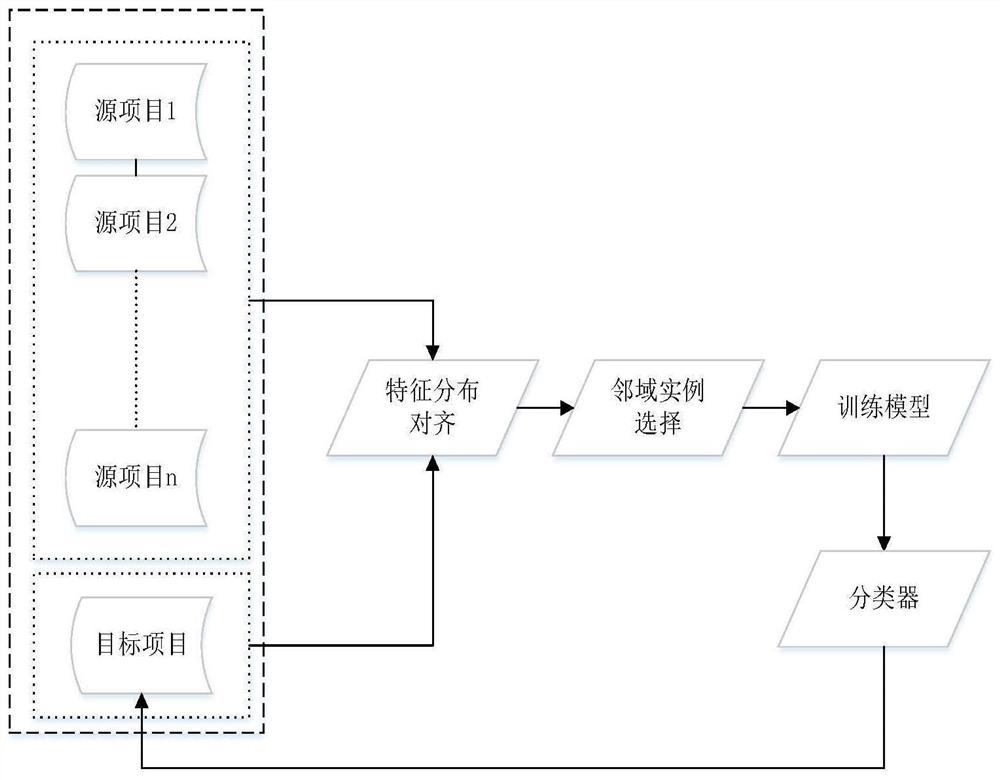
Cross-project defect prediction method based on feature distribution alignment and neighborhood instance selection
PendingCN113157564AReduce distribution varianceImproving Defect Prediction PerformanceCharacter and pattern recognitionSoftware testing/debuggingData setEngineering
A cross-project defect prediction method based on feature distribution alignment and neighborhood instance selection specifically comprises the following steps: selecting source projects from a software defect data set, combining all the source projects to form a source project set, and selecting a target project; calculating a covariance matrix of the source item set and a covariance matrix of the target item; eliminating the correlation between the features of the source item set, filling the feature correlation of the target item into the source item set, and selecting instances with high similarity with instances in the target item from the source item set data after feature alignment to form a training instance set TS; and training a Logistic model by using the training instance set TS, and performing defect prediction classification on each instance in the target project by using the Logistic model. According to the cross-project software defect prediction method, the selection of the training data required by the model is achieved by adopting the feature distribution alignment method and the neighborhood instance selection method, the difference between projects and instances in the cross-project software defect prediction method is effectively solved, and the defect prediction performance is improved.
Owner:XUZHOU NORMAL UNIVERSITY
Multi-view masters for graphical designs
ActiveUS20200167521A1Natural language data processingVisual/graphical programmingGraphicsSoftware engineering
Owner:AXURE SOFTWARE SOLUTIONS INC
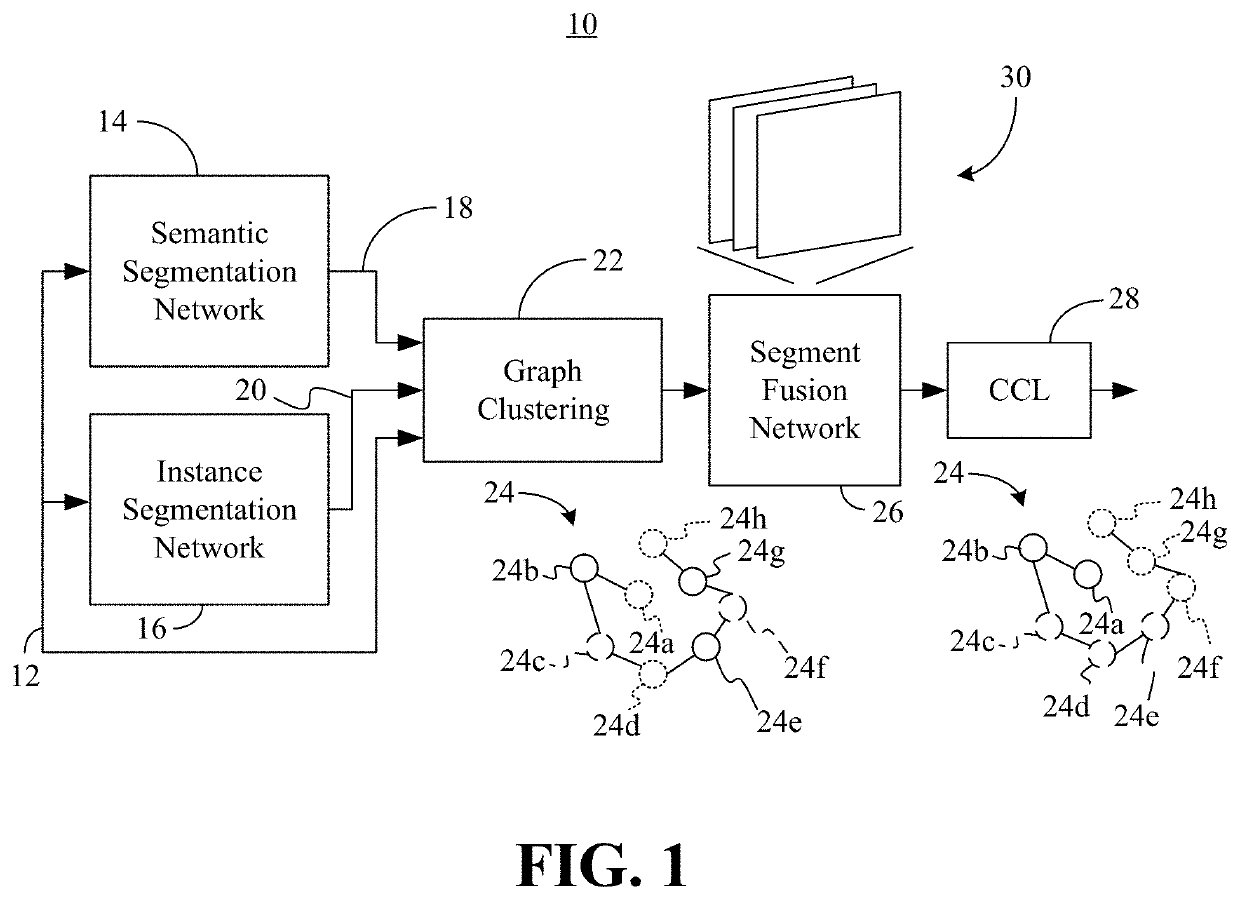
Segment fusion based robust semantic segmentation of scenes
Owner:INTEL CORP
Object extraction method and device
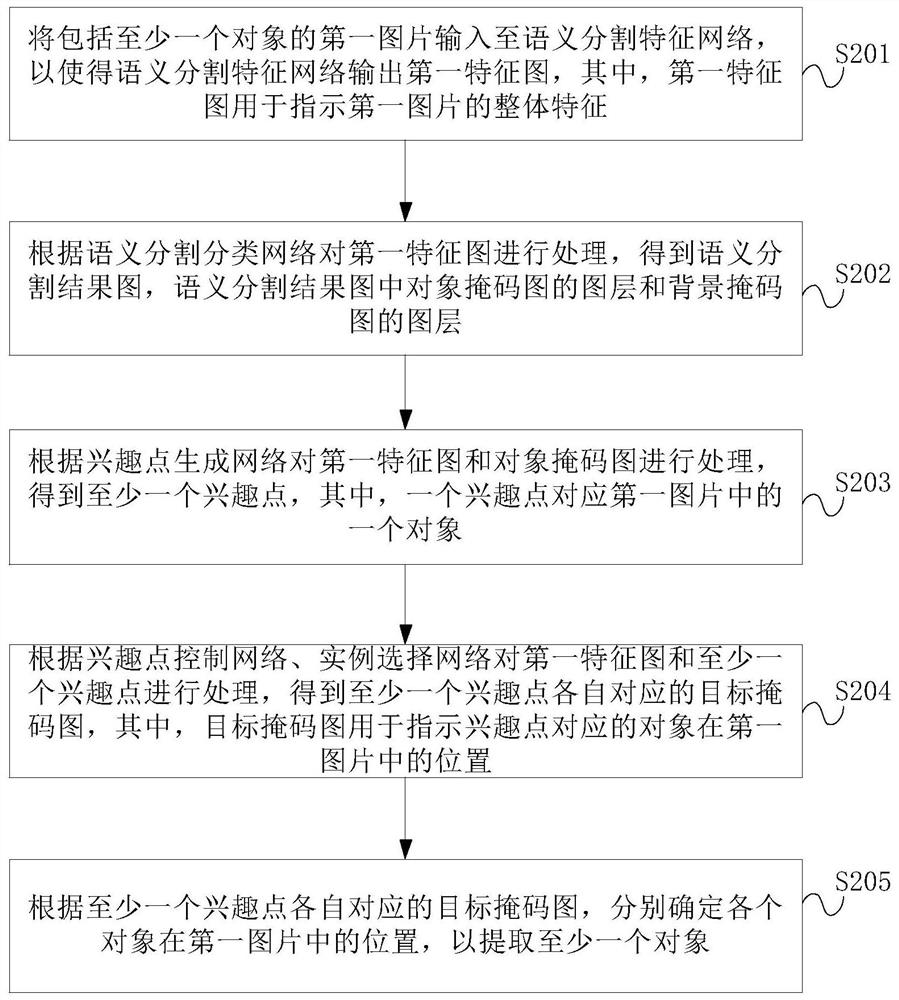
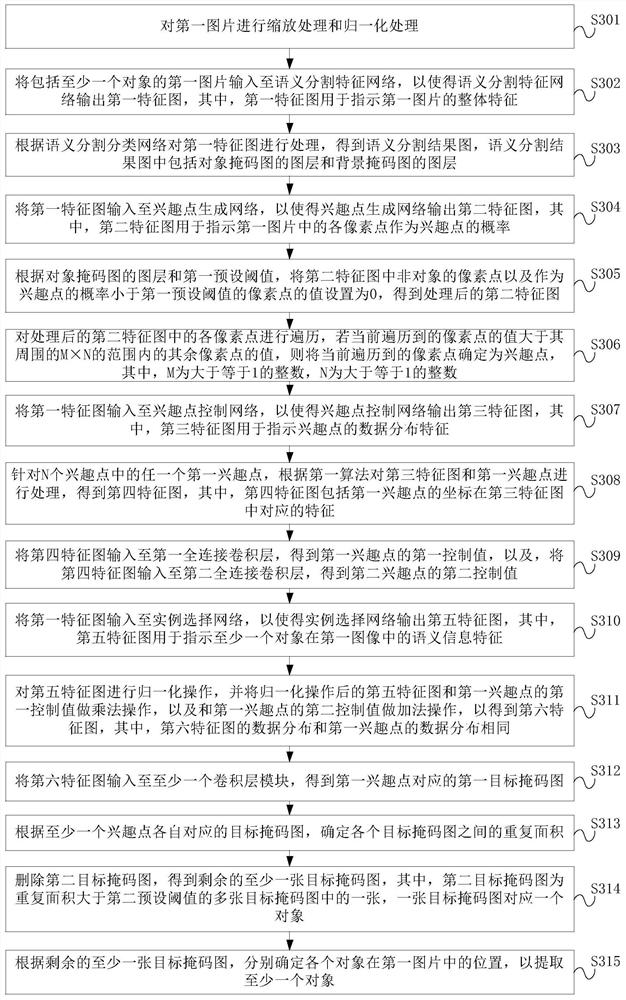
PendingCN114494712AAvoid poor extractionCharacter and pattern recognitionNeural architecturesPattern recognitionNetwork output
The embodiment of the invention provides an object extraction method and device, and the method comprises the steps: inputting a first picture comprising at least one object into a semantic segmentation feature network, so as to enable the semantic segmentation feature network to output a first feature map. The first feature graph is processed according to the semantic segmentation classification network, a semantic segmentation result graph is obtained, and the semantic segmentation result graph comprises a graph layer of the object mask graph and a graph layer of the background mask graph. And processing the layers of the first feature graph and the object mask graph according to the interest point generation network to obtain at least one interest point. And processing the first feature map and the at least one interest point according to the interest point control network and the instance selection network to obtain a target mask map corresponding to the at least one interest point. And respectively determining the position of each object in the first picture according to the target mask graph corresponding to the at least one interest point so as to extract at least one object. According to the embodiment of the invention, the effect and accuracy of extracting the rod-shaped object are effectively ensured.
Owner:NAVINFO
Use of sequential nearest neighbor clustering for instance selection in machine condition monitoring
A method is provided for selecting a representative set of training data for training a statistical model in a machine condition monitoring system. The method reduces the time required to choose representative samples from a large data set by using a nearest-neighbor sequential clustering technique in combination with a kd-tree. A distance threshold is used to limit the geometric size the clusters. Each node of the kd-tree is assigned a representative sample from the training data, and similar samples are subsequently discarded.
Owner:SIEMENS CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com