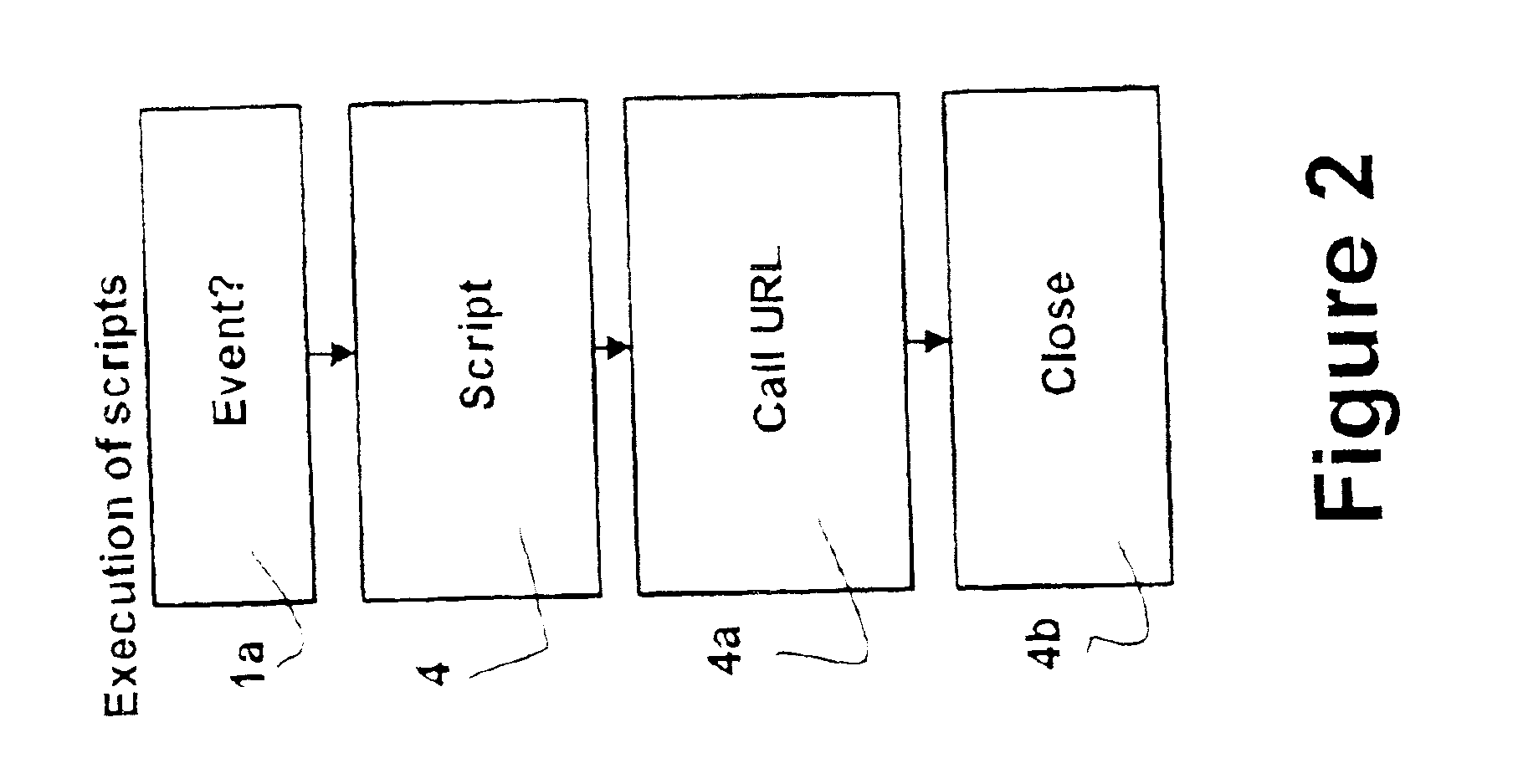
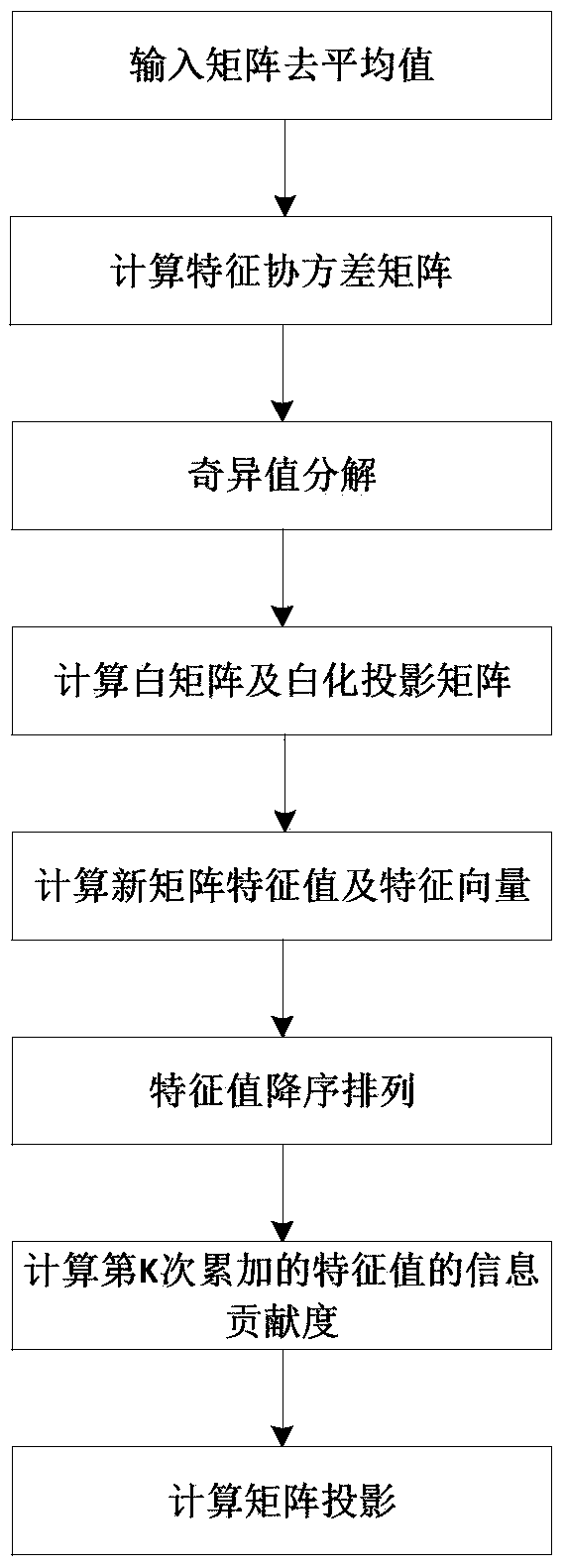
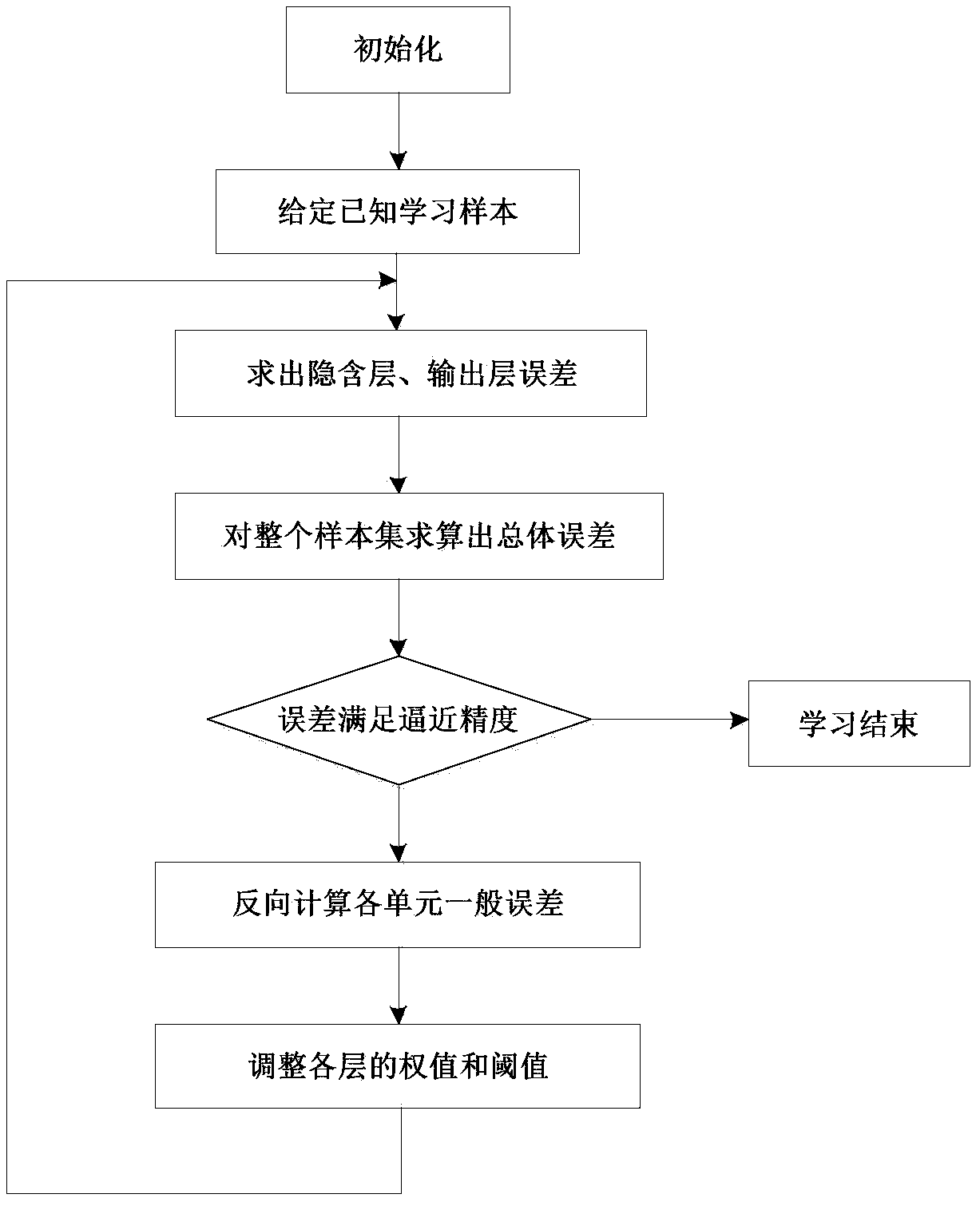
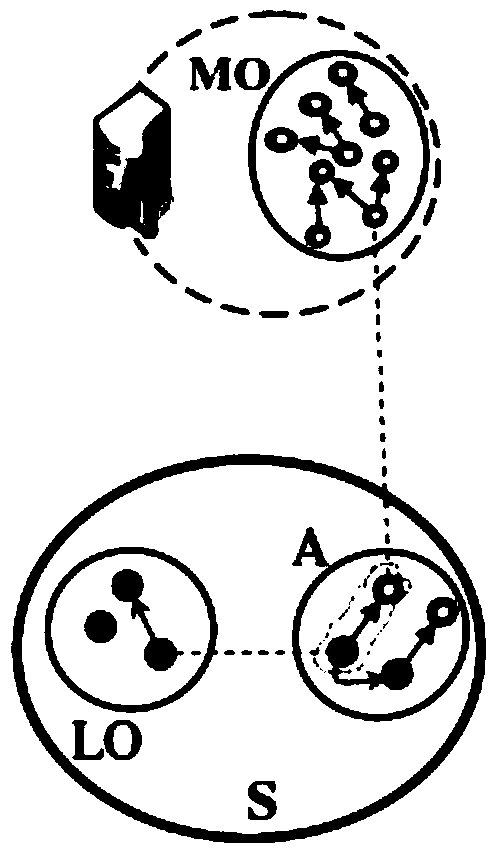
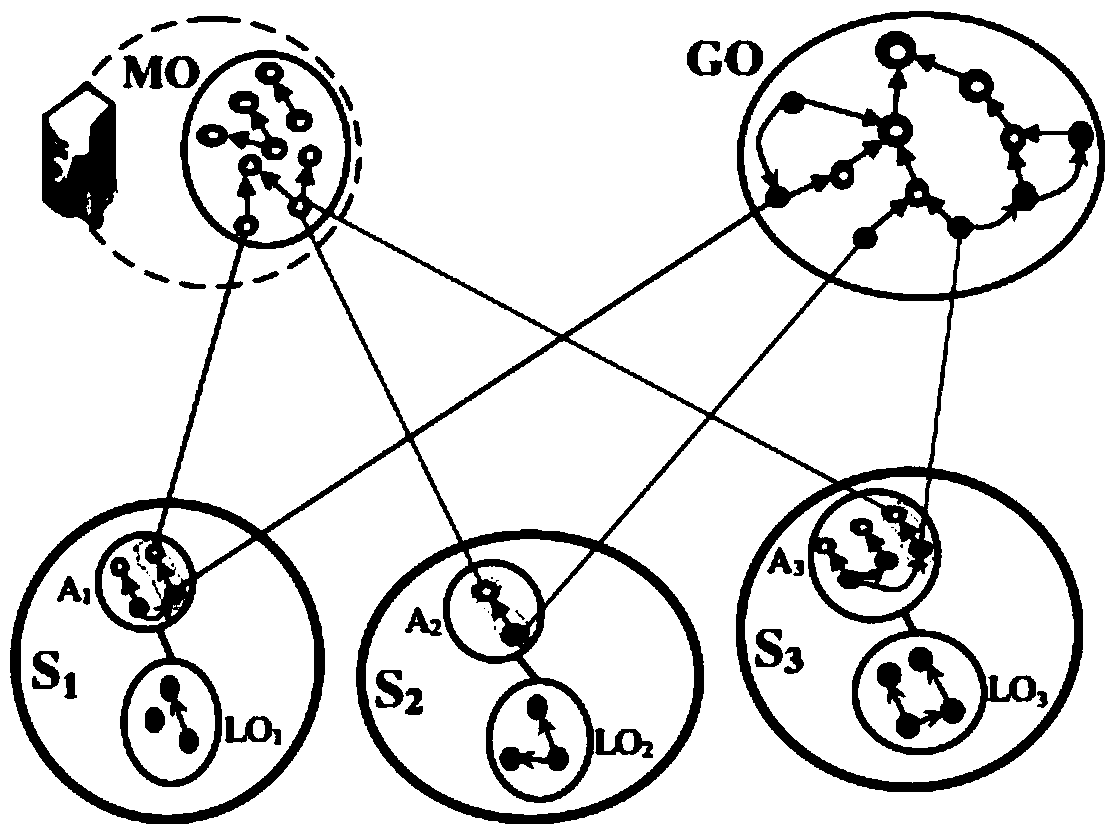
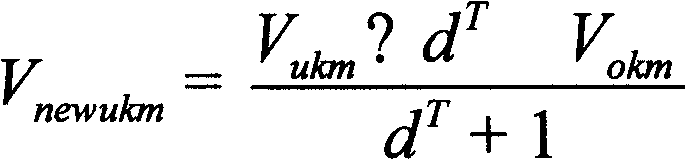Patents
Literature
182 results about "Rule of inference" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
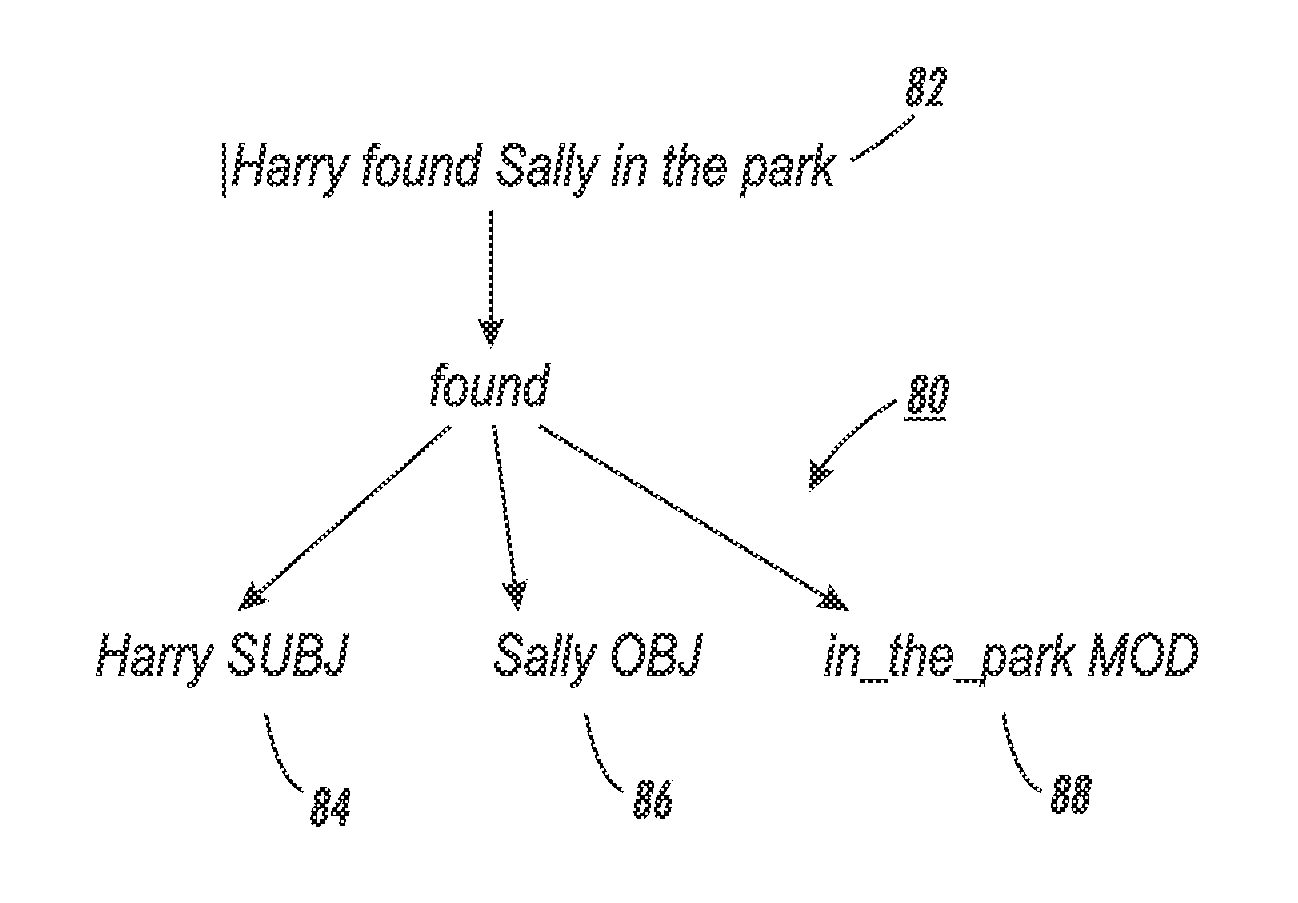
In logic, a rule of inference, inference rule or transformation rule is a logical form consisting of a function which takes premises, analyzes their syntax, and returns a conclusion (or conclusions). For example, the rule of inference called modus ponens takes two premises, one in the form "If p then q" and another in the form "p", and returns the conclusion "q". The rule is valid with respect to the semantics of classical logic (as well as the semantics of many other non-classical logics), in the sense that if the premises are true (under an interpretation), then so is the conclusion.
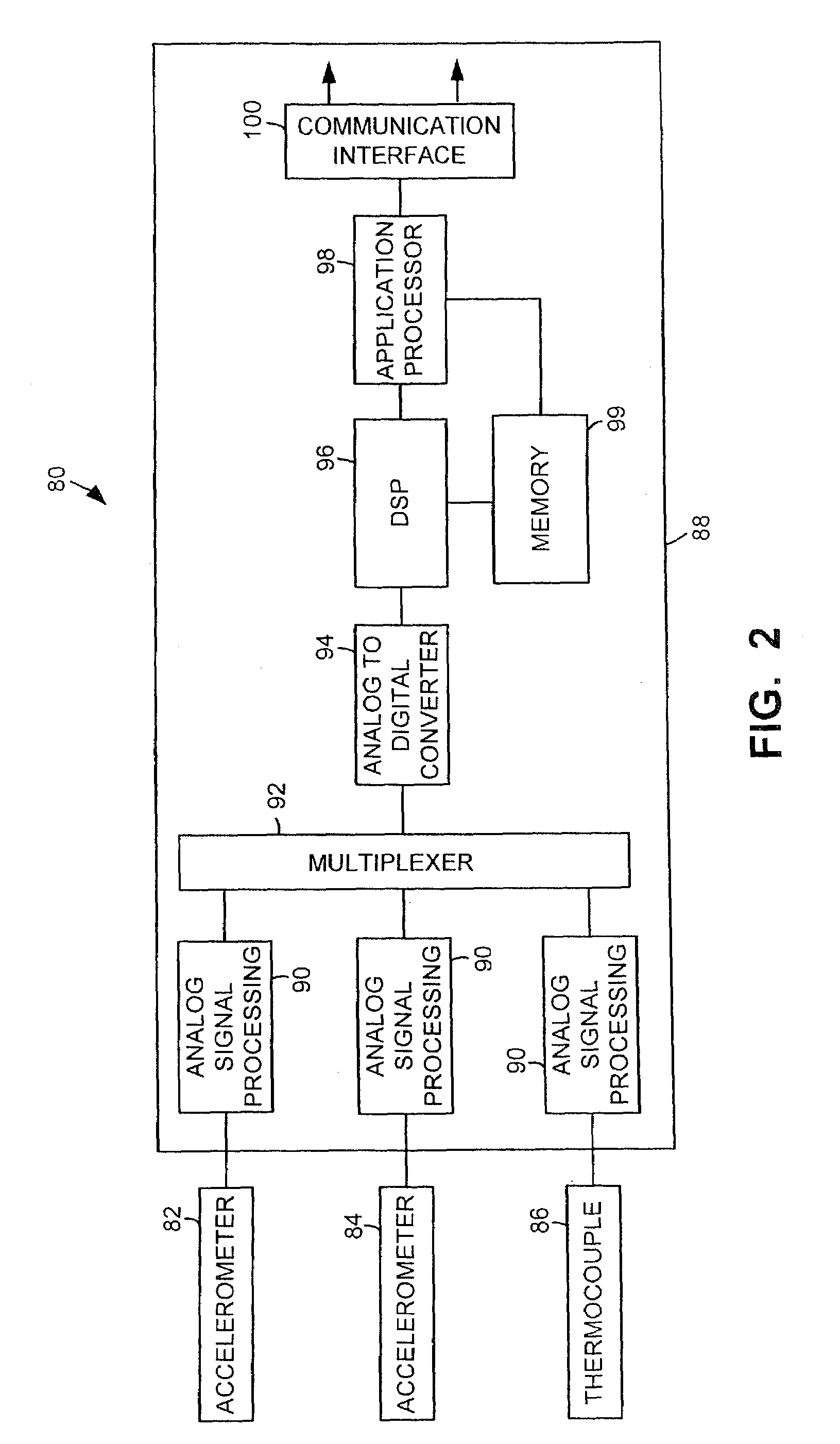
Machine fault information detection and reporting
InactiveUS7142990B2Quick identificationEasy to installAmplifier modifications to reduce noise influenceComputer controlCavitationLogical operations
Sensors detect machine parameters such as vibration, turning speed, and temperature, and a local processor performs logic operations based on the parameters and inference rules to produce fault information that is reported to a system processor, which selectively uses the fault information to control the plant machines. The inference rules include rules for determining faults as to balance, alignment, bearing condition, electrical condition, and cavitation. The inference rules are contained in rules code that is separate from the analysis code that performs the logical operations. Thus, the inference rules may be easily changed without changing other code, such as the analysis code.
Owner:COMPUTATIONAL SYST
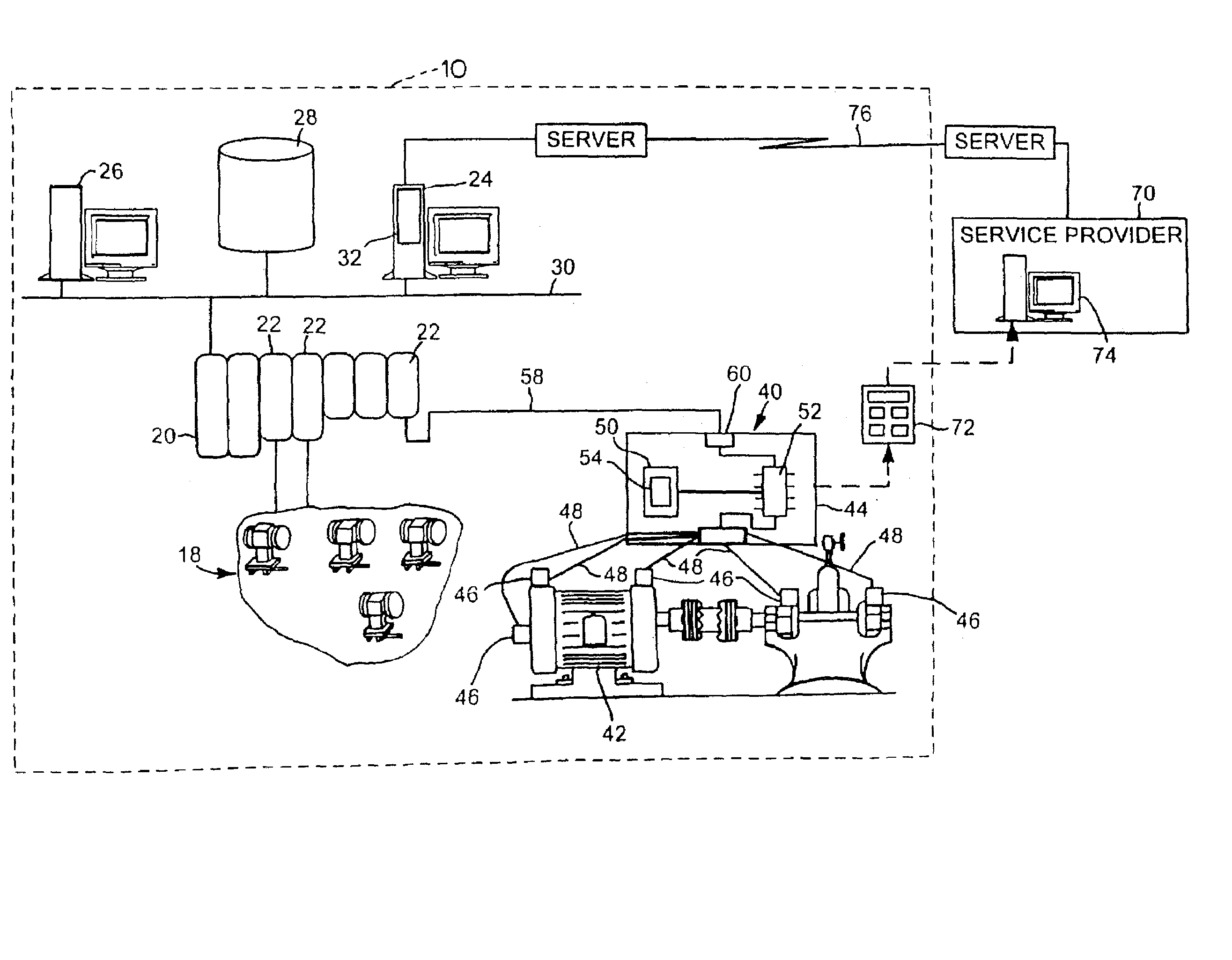
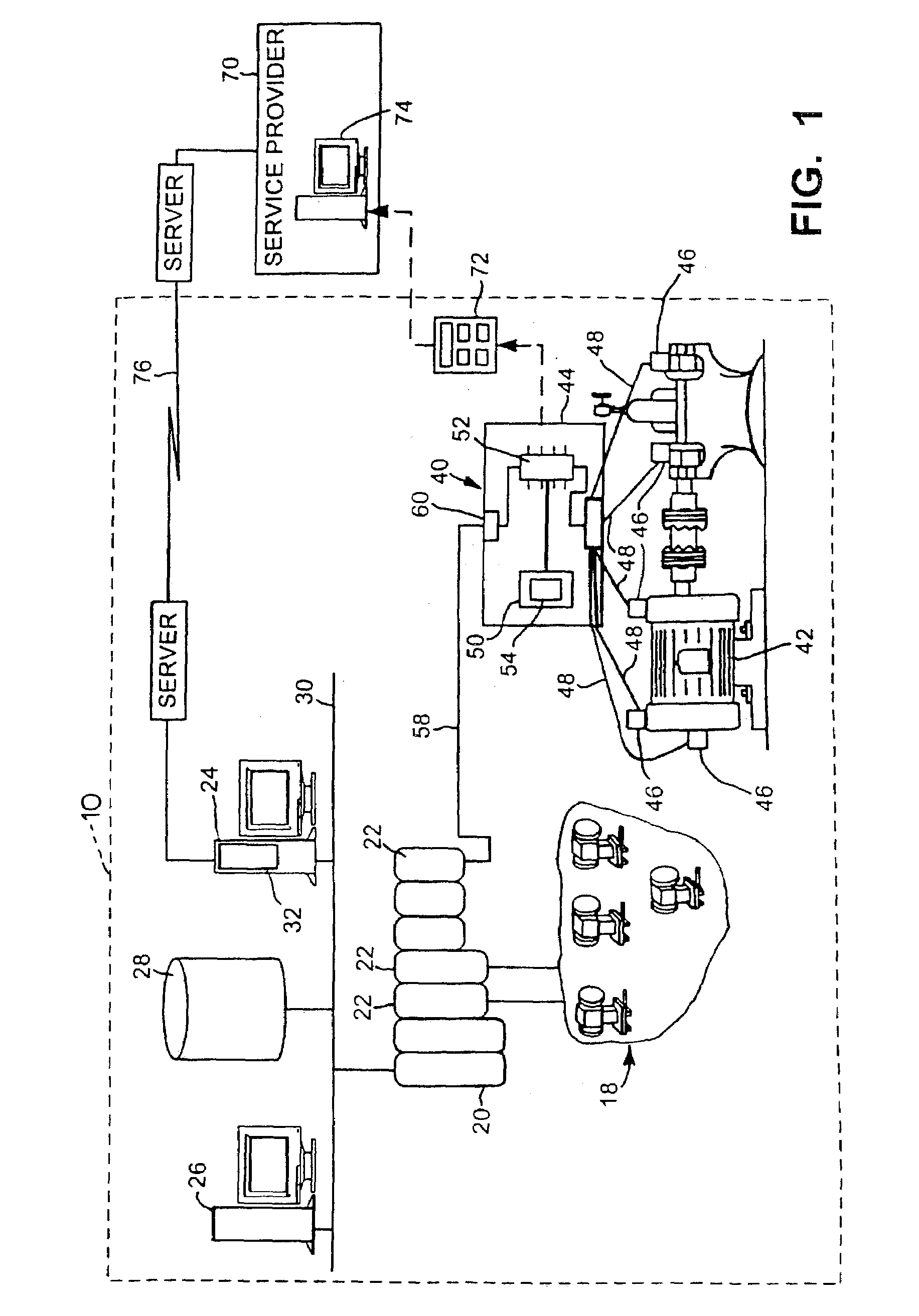
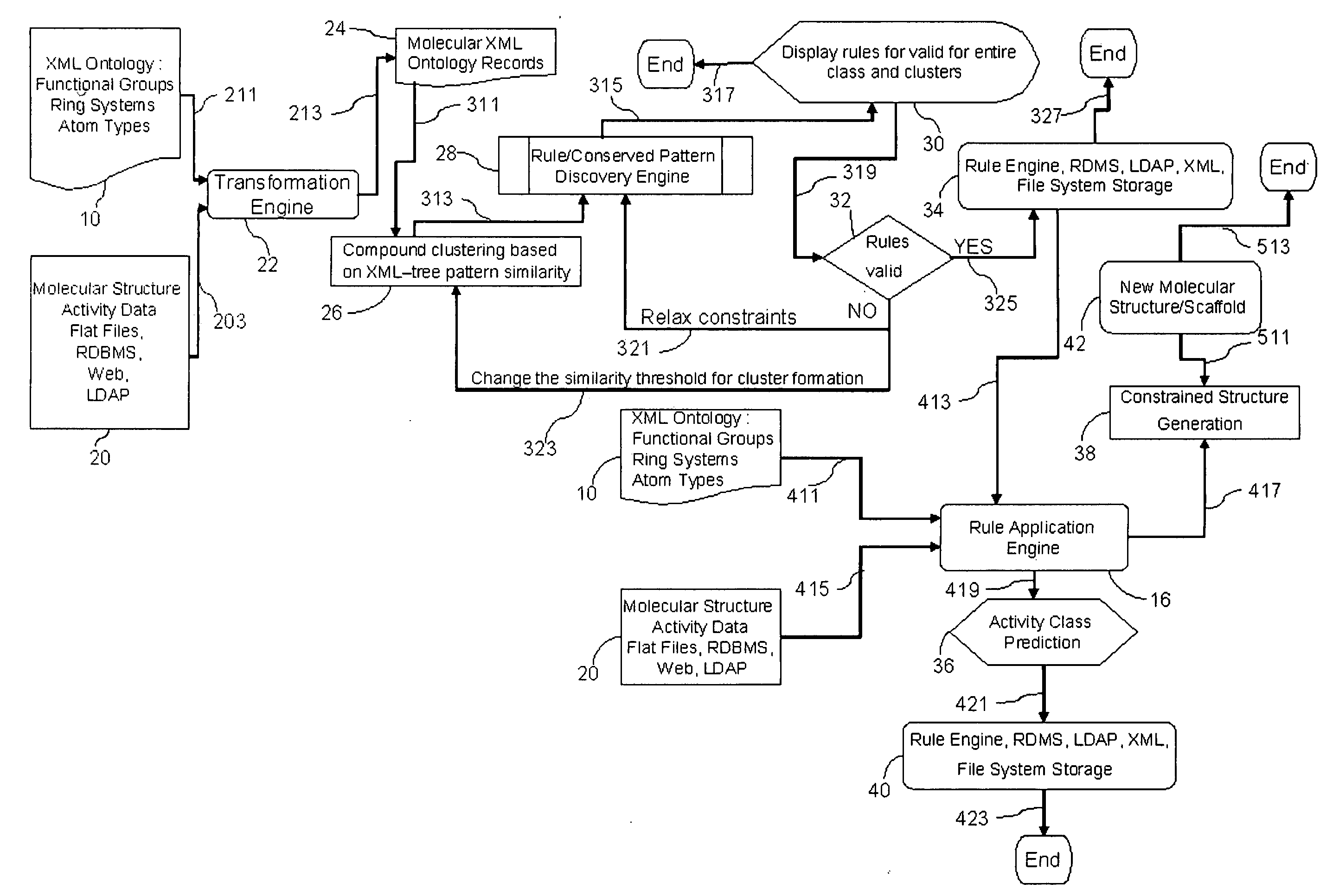
Automated molecular mining and activity prediction using XML schema, XML queries, rule inference and rule engines
InactiveUS20090228445A1Efficient and accessibleDigital data processing detailsRelational databasesXML schemaCausal inference
Method and system for analyzing relationship between molecular structure and biological activity in one or more molecules by transforming molecular structure data into a hierarchical representation of chemical concepts and descriptors and detecting common tree-like patterns in the data.
Owner:SYST BIOLOGY 1 PVT
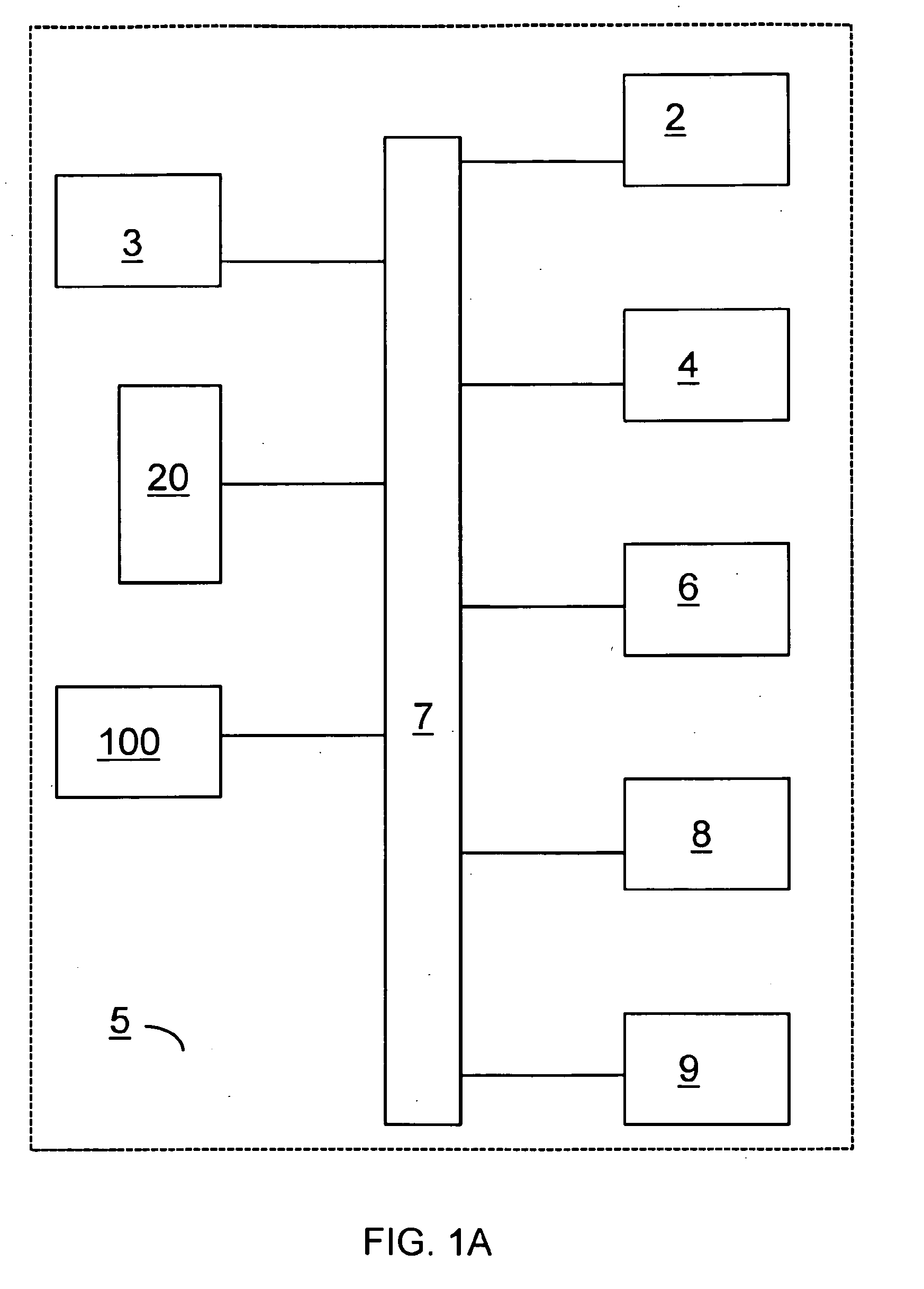
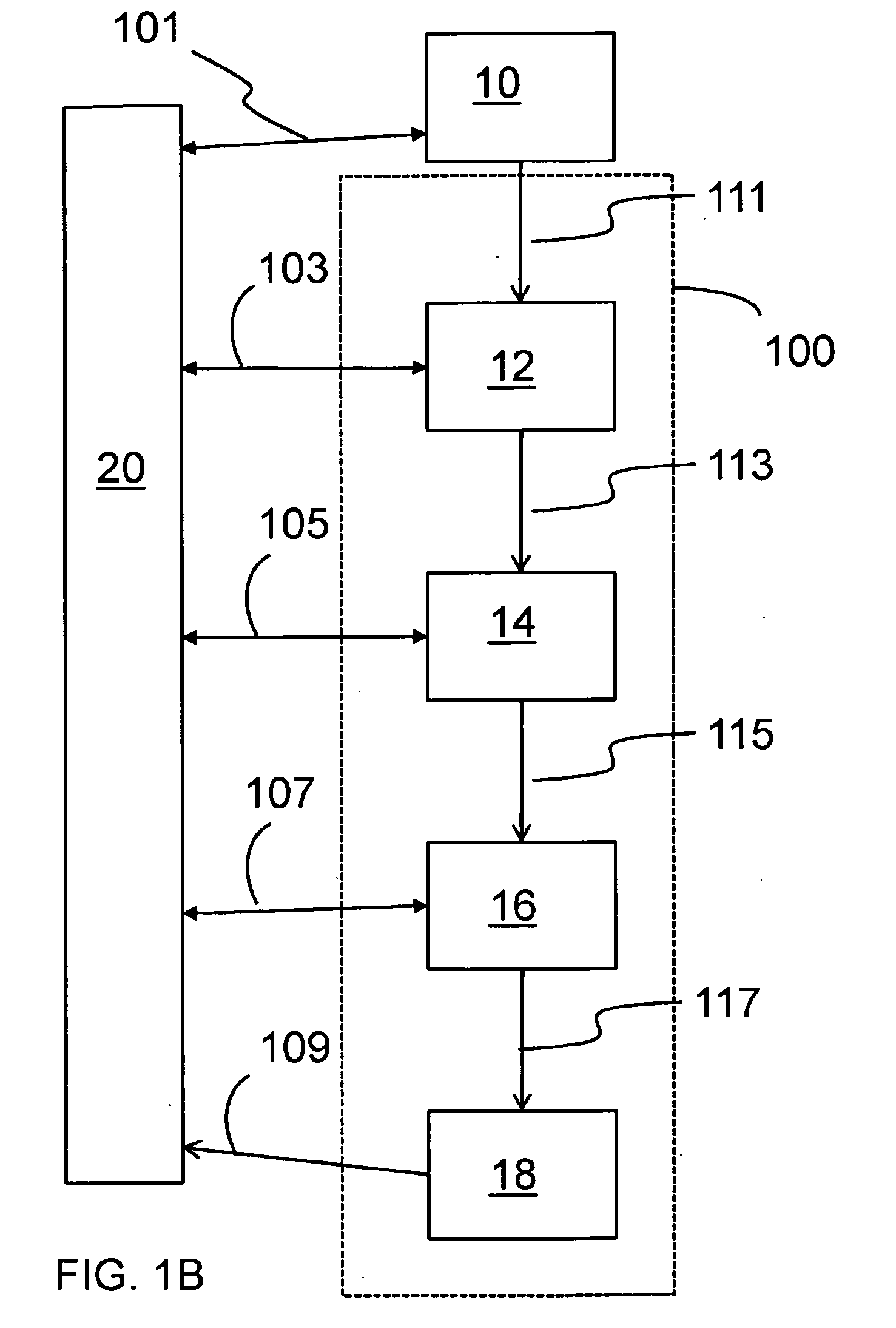
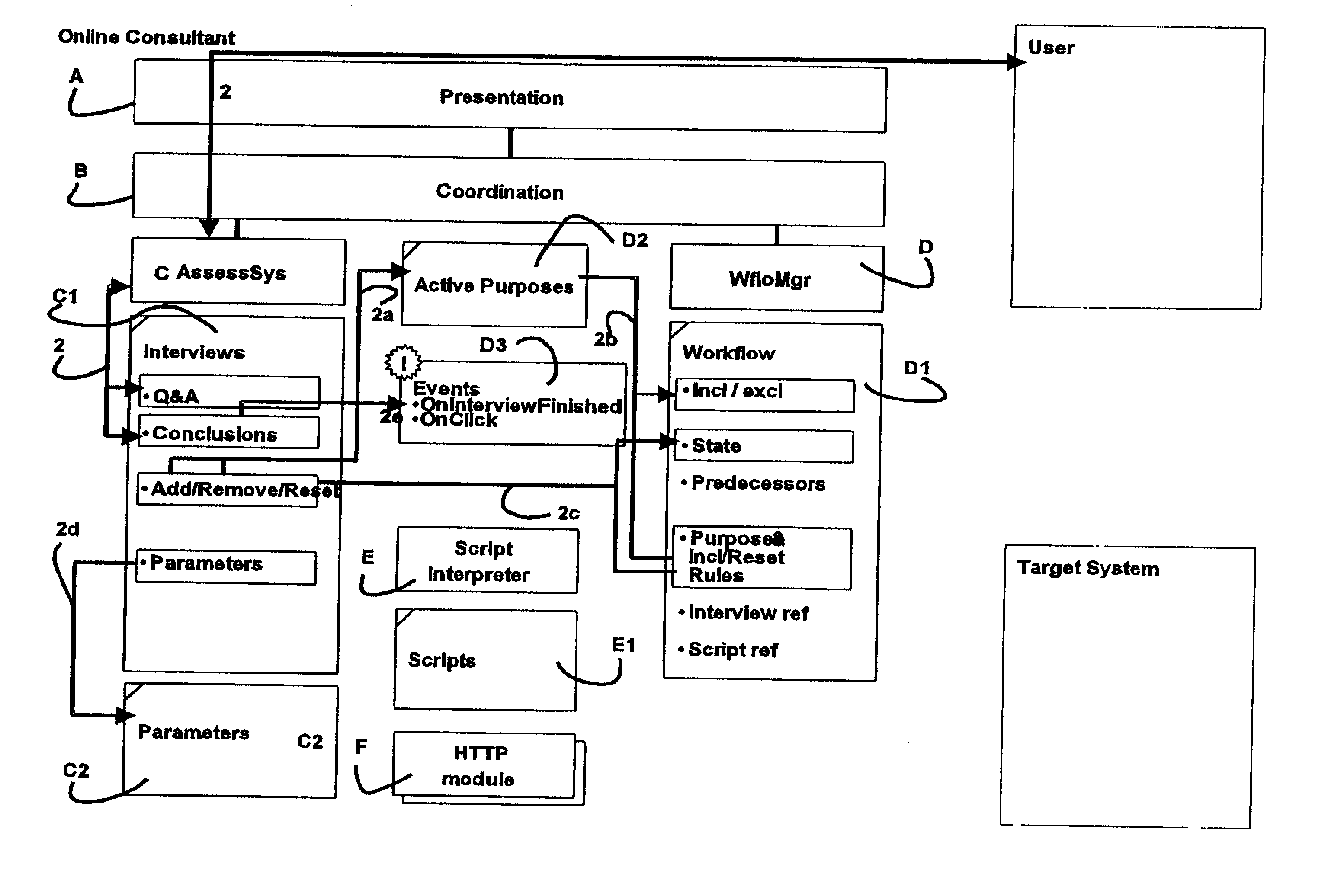
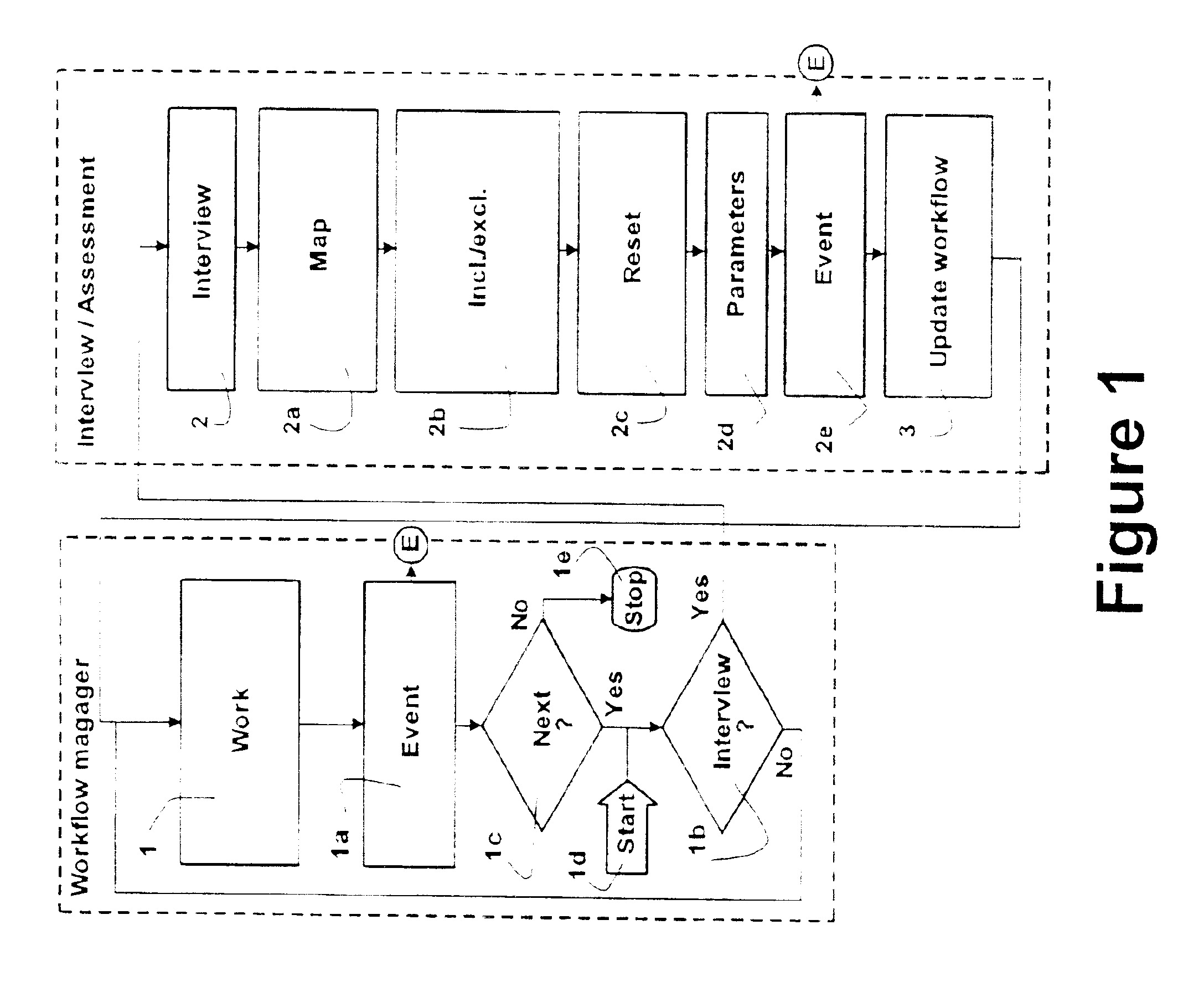
Method for generating a workflow on a computer, and a computer system adapted for performing the method
InactiveUS6895573B2Easy to useMinimum waste of effortMultiprogramming arrangementsChaos modelsSoftware engineeringComputerized system
A method for generating a workflow on a computer. Assessment data, e.g. defining a need, is obtained from a user. Based thereon, a workflow including a logical sequence of interdependent steps to be made is created using an assessment system. A number of workflow steps are presented to the user in a logical order, and results from the progress of one or more steps may be gathered. The workflow may be modified thereon, if needed, using sub-solutions, logic rules, inference rules and said results by adding and / or removing steps to / from said workflow based on a list of purposes and knowledge of the order in which some or all steps must be made. After modifying the workflow, the presentation thereof is started by the next or more unfinished steps which are not dependent on an unfinished step, thereby forming an adaptive procedure.
Owner:RESULTMAKER
Database-based inference engine for RDFS/OWL constructs
ActiveUS20100036788A1Improve efficiencyAvoid overheadDigital data processing detailsKnowledge representationIncremental maintenanceRelational database
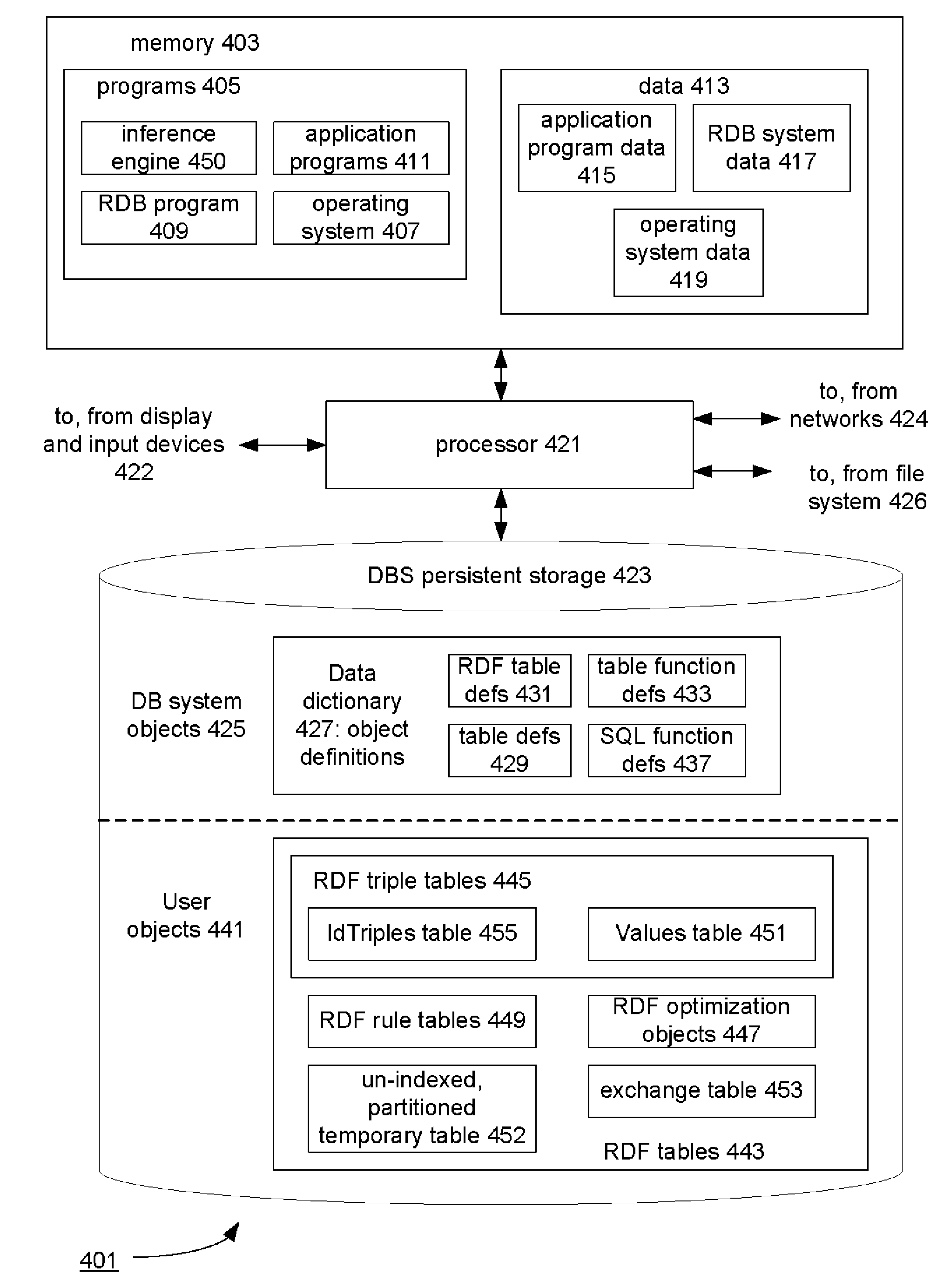
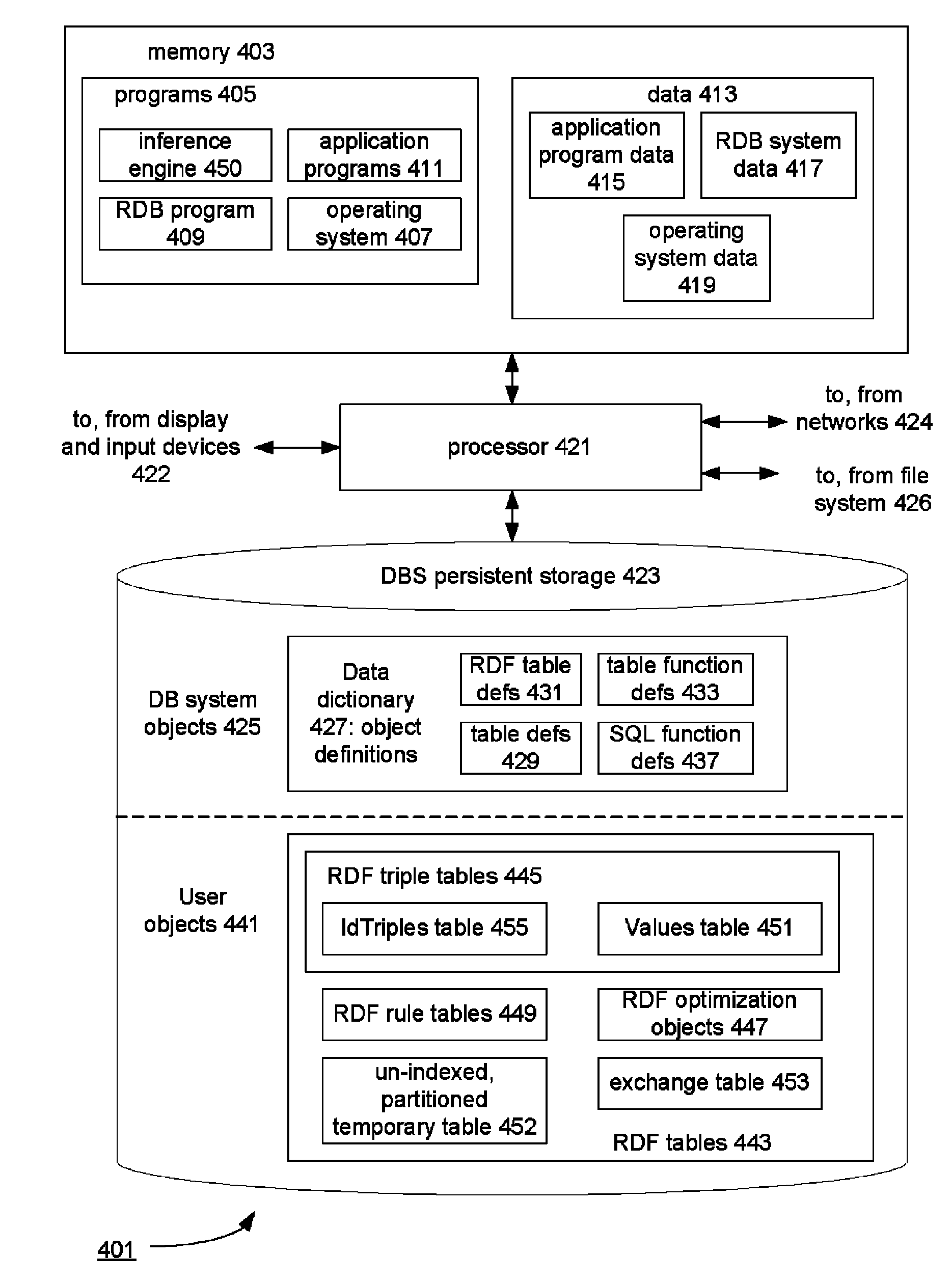
An un-indexed, partitioned temporary table and an exchange table are used in the inferencing of semantic data in a relational database system. The exchange table has the same structure as a semantic data table storing the semantic data. In the inferencing process, a new partition is created in the semantic data table. Inference rules are executed on the semantic data table, and any newly inferred semantic data generated is added to the temporary table. Once no new data is generated, the inferred semantic data is copied from the temporary table into the exchange table. Indexes that are the same as indexes for the semantic data table are built for the exchange table. The indexed data in the exchange table is then exchanged into the new partition in the semantic data table. By use of the un-indexed, partitioned temporary table, incremental maintenance of indexes is avoided, thus allowing for greater efficiency.
Owner:ORACLE INT CORP
Database-based inference engine for RDFS/OWL constructs
ActiveUS8401991B2Improve efficiencyAvoid overheadDigital data processing detailsKnowledge representationIncremental maintenanceRelational database
An un-indexed, partitioned temporary table and an exchange table are used in the inferencing of semantic data in a relational database system. The exchange table has the same structure as a semantic data table storing the semantic data. In the inferencing process, a new partition is created in the semantic data table. Inference rules are executed on the semantic data table, and any newly inferred semantic data generated is added to the temporary table. Once no new data is generated, the inferred semantic data is copied from the temporary table into the exchange table. Indexes that are the same as indexes for the semantic data table are built for the exchange table. The indexed data in the exchange table is then exchanged into the new partition in the semantic data table. By use of the un-indexed, partitioned temporary table, incremental maintenance of indexes is avoided, thus allowing for greater efficiency.
Owner:ORACLE INT CORP
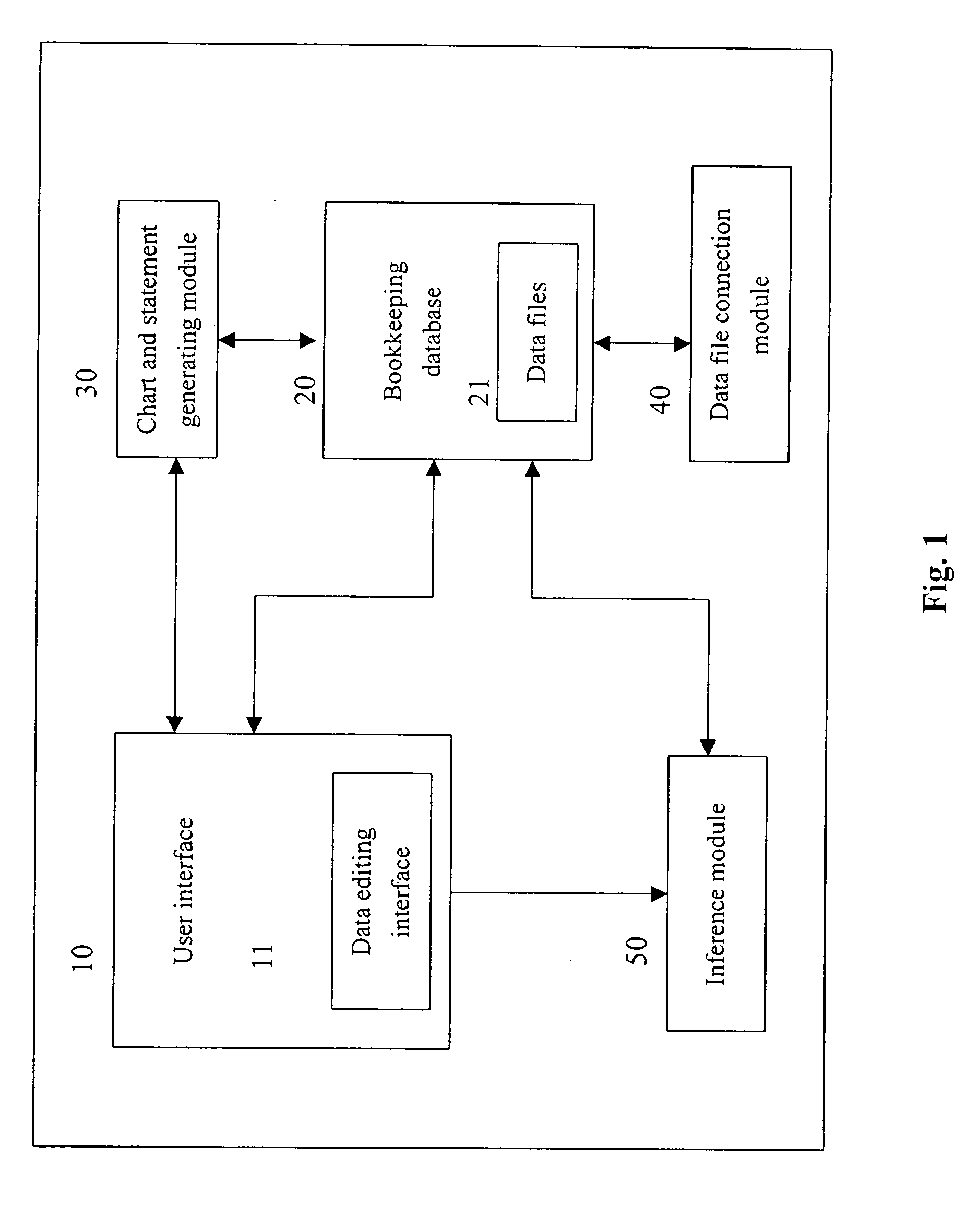
Automatic bookkeeping system
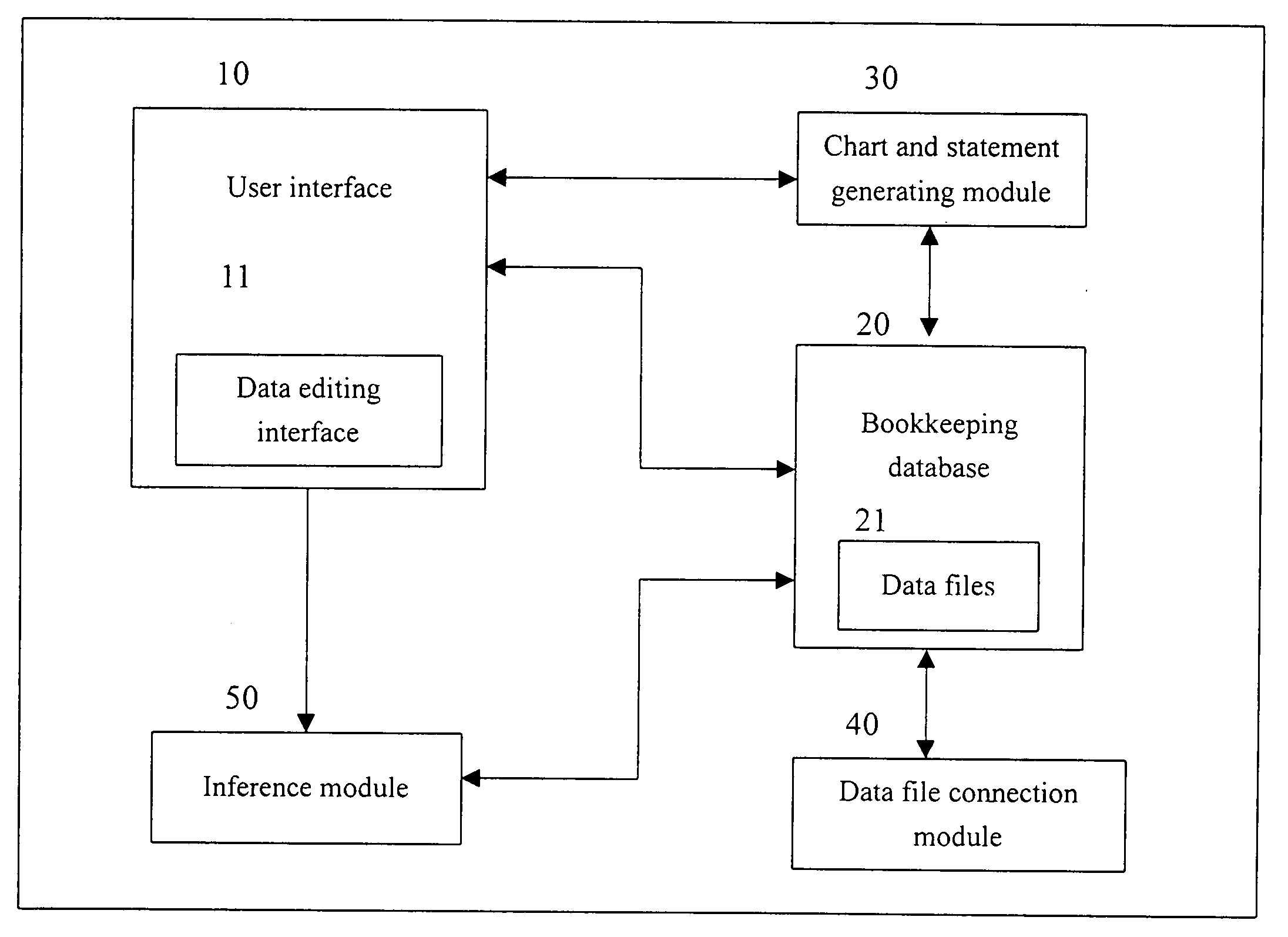
An automatic bookkeeping system comprises: a user interface, comprising a plurality of bookkeeping data editing interface allowing user to input, revise and delete useful bookkeeping data; a bookkeeping database, comprising a plurality of bookkeeping data files to record bookkeeping data; a chart and statement generating module provided with formats and definitions of a plurality of bookkeeping related chart and statement to automatically obtain needed data from said bookkeeping database and to generate bookkeeping related charts and statements using the obtained data according to format and definitions of particular chart or statement; a data file connection module to automatically connect a unit of input data to related bookkeeping data files according to features of said unit of input data to generate one or more unit of bookkeeping data; and an inference module, provided with a plurality of financial inference rules, to obtain data from said bookkeeping database and to operate according to particular inference rules using the obtained data. Charts and statements generated by the automatic bookkeeping system include: journal, ledger, income statement, balance sheet and other financial statements.
Owner:LU LI CHIN
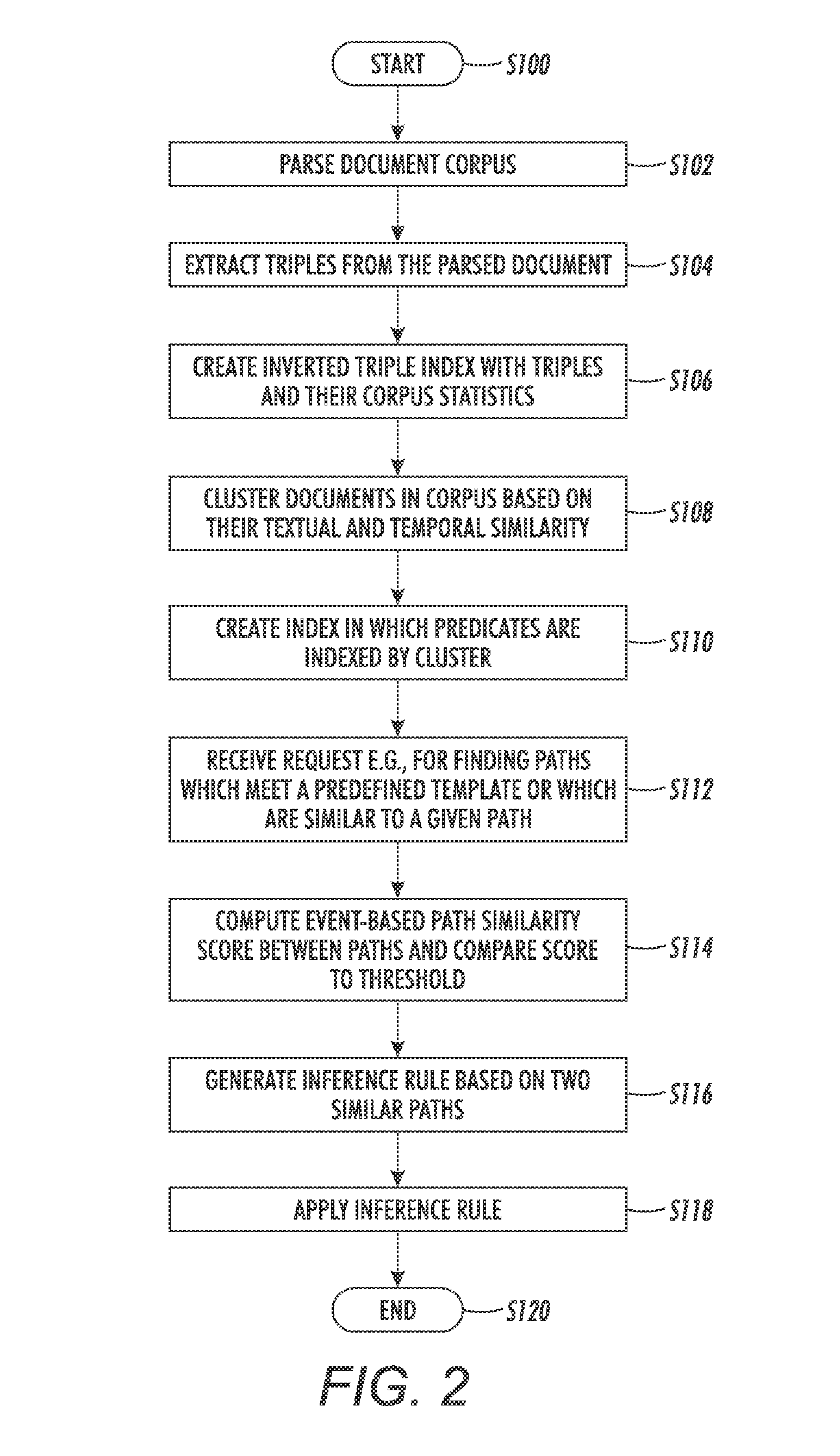
Refining inference rules with temporal event clustering
InactiveUS20150127323A1Semantic analysisSpecial data processing applicationsTemporal similarityCluster based
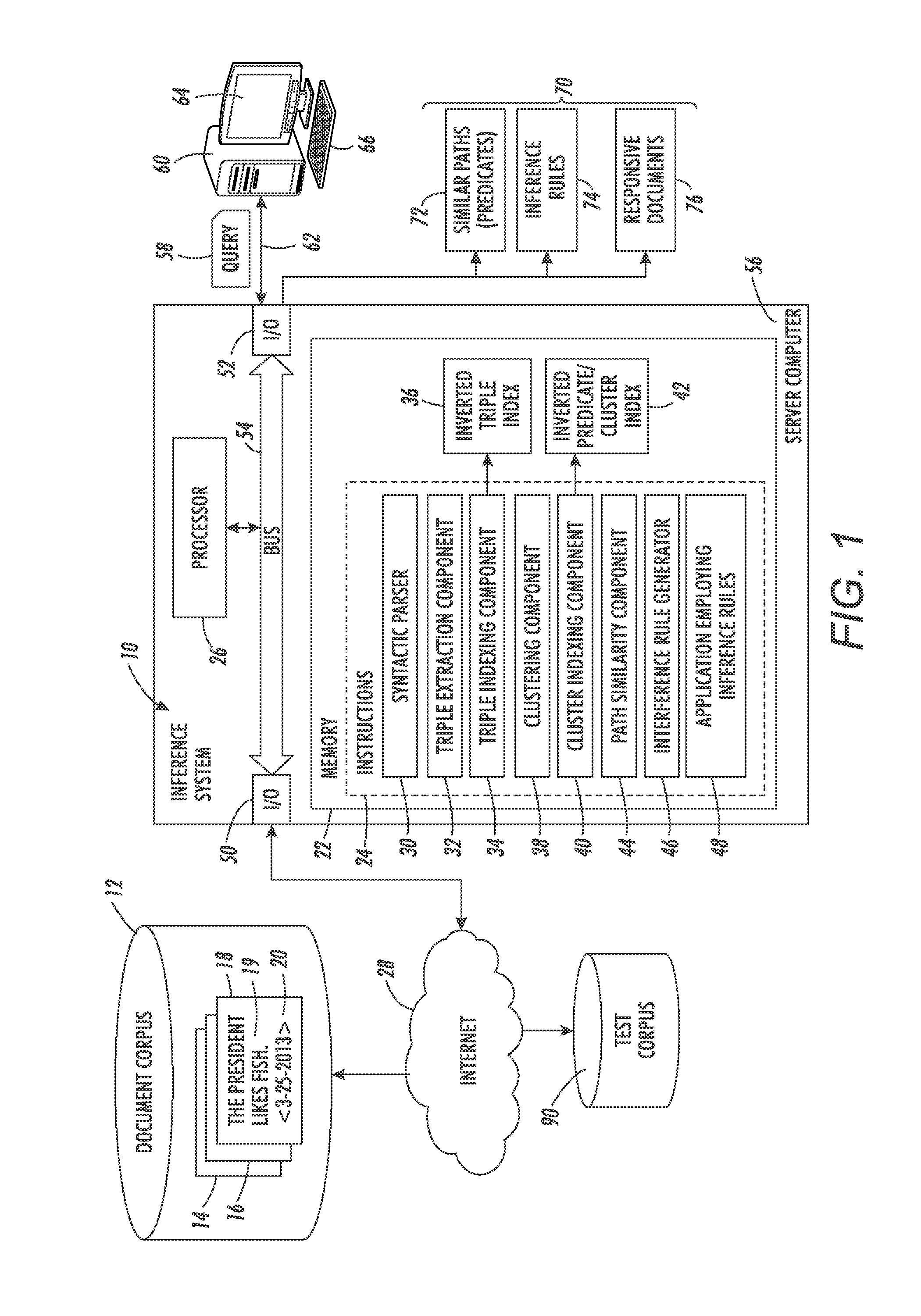
A method for computing similarity between paths includes extracting corpus statistics for triples from a corpus of text documents, each triple comprising a predicate and respective first and second arguments of the predicate. Documents in the corpus are clustered to form a set of clusters based on textual similarity and temporal similarity. An event-based path similarity is computed between first and second paths, the first path comprising a first predicate and first and second argument slots, the second path comprising a second predicate and first and second argument slots, the event-based path similarity being computed as a function of a corpus statistics-based similarity score which is a function of the corpus statistics for the extracted triples which are instances of the first and second paths, and a cluster-based similarity score which is a function of occurrences of the first and second predicates in the clusters.
Owner:XEROX CORP
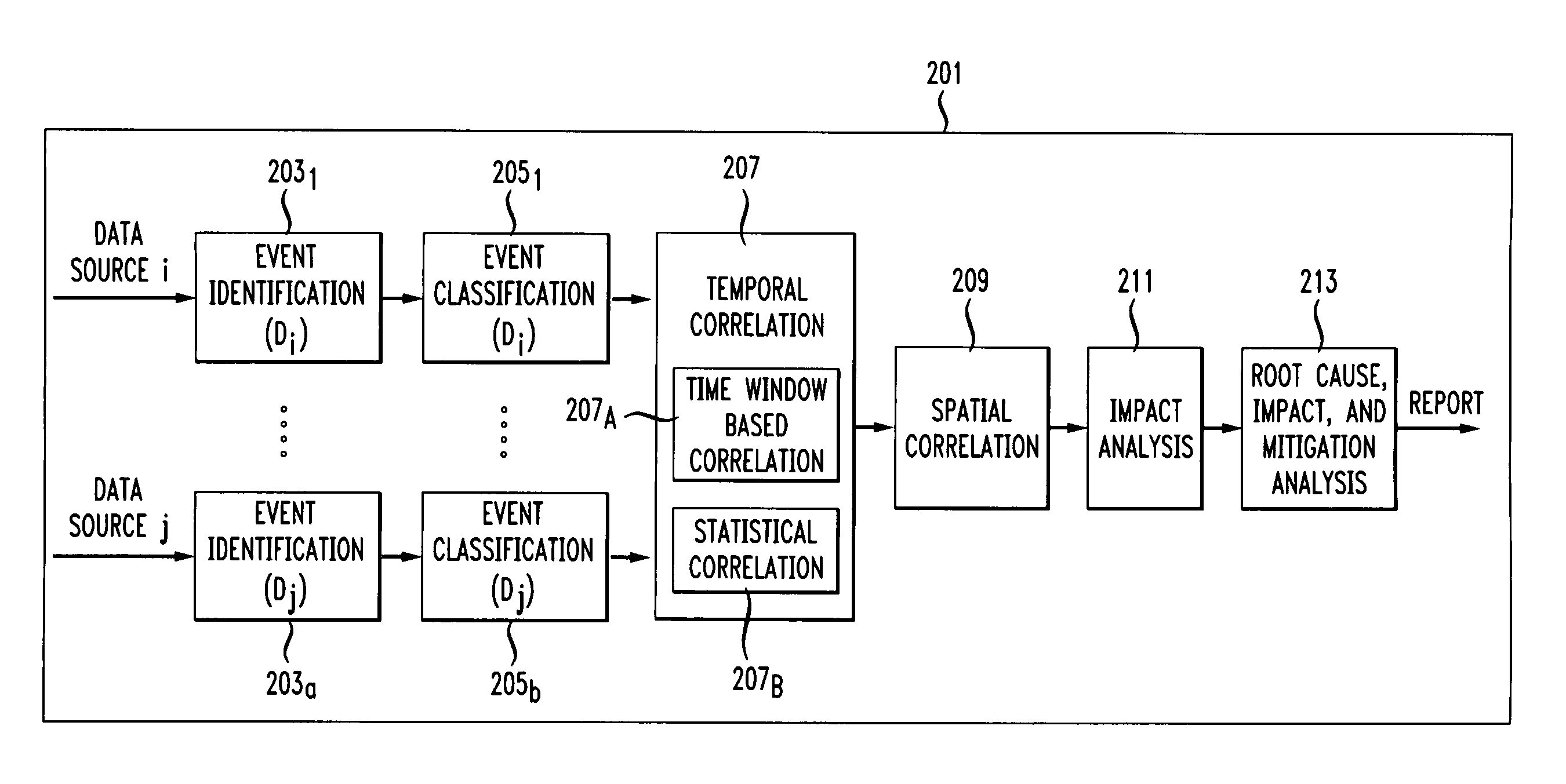
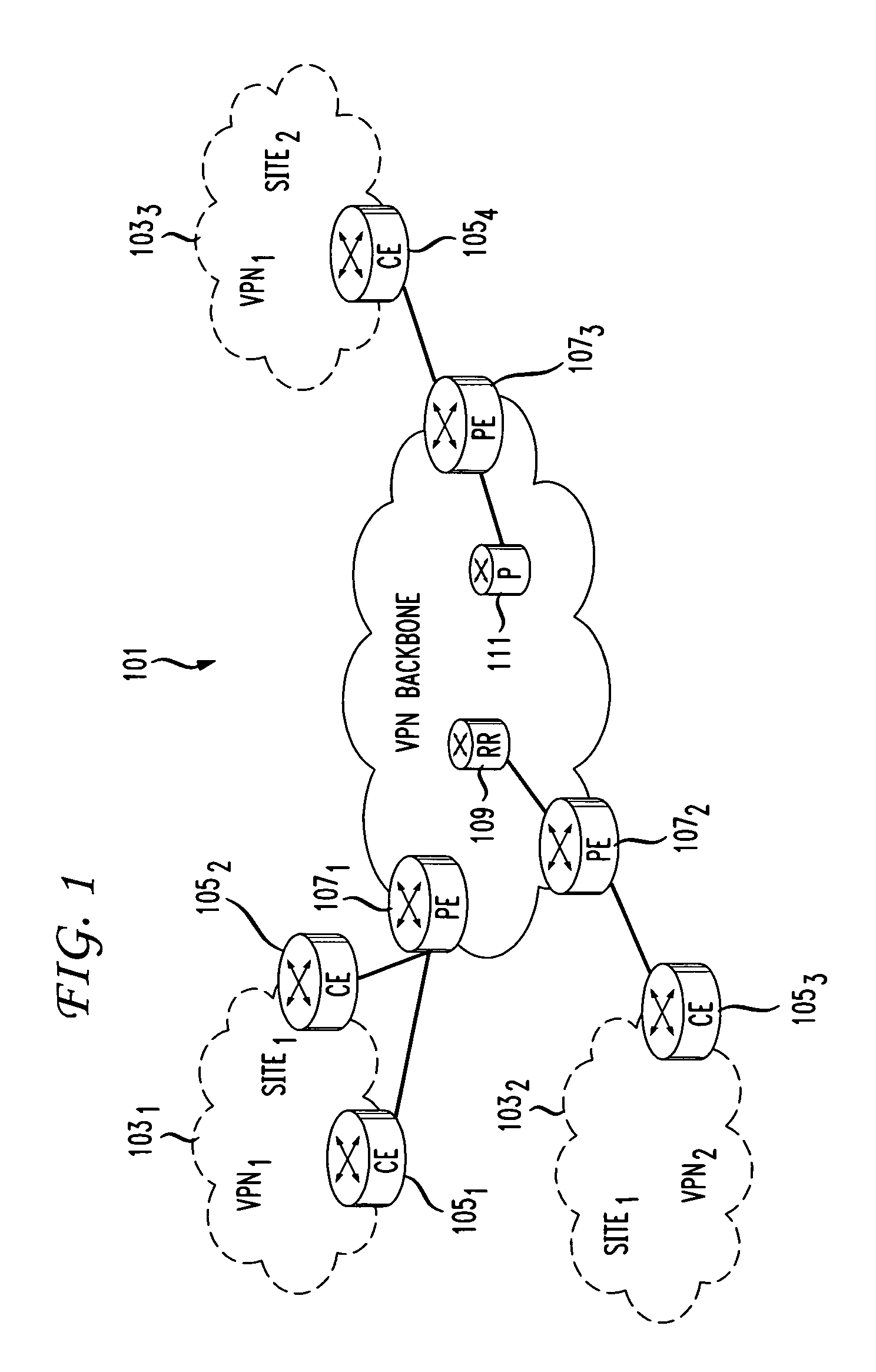
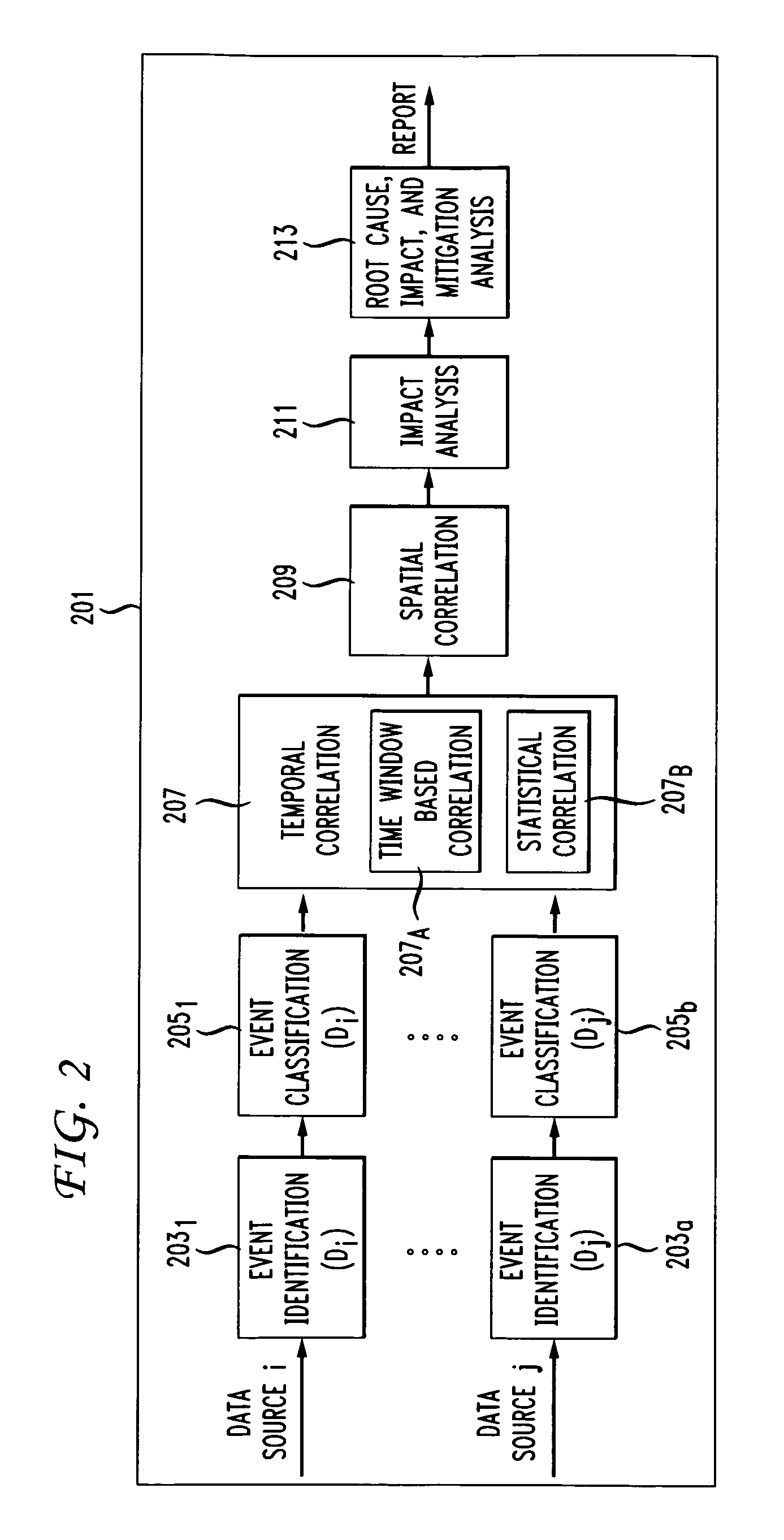
Scalable and robust troubleshooting framework for VPN backbones
InactiveUS7889666B1Network delayRobust to data imperfectionError preventionTransmission systemsExtensibilityData source
A system and method is disclosed for a scalable and robust network troubleshooting framework for VPN backbones addressing scalability and data imperfection. The framework takes advantage of lattice data structures to identify multi-dimensional hierarchical events that occur frequently across multiple data sources. Correlation schemes and inference rules are created for diagnosing network events and generating actionable reports for important events.
Owner:AT&T INTPROP II L P
Prediction method and system of litigation outcome
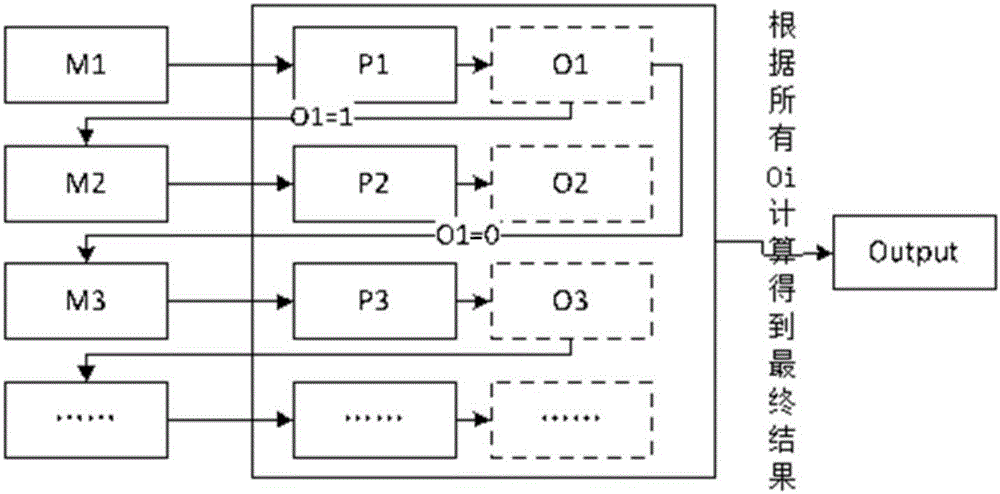
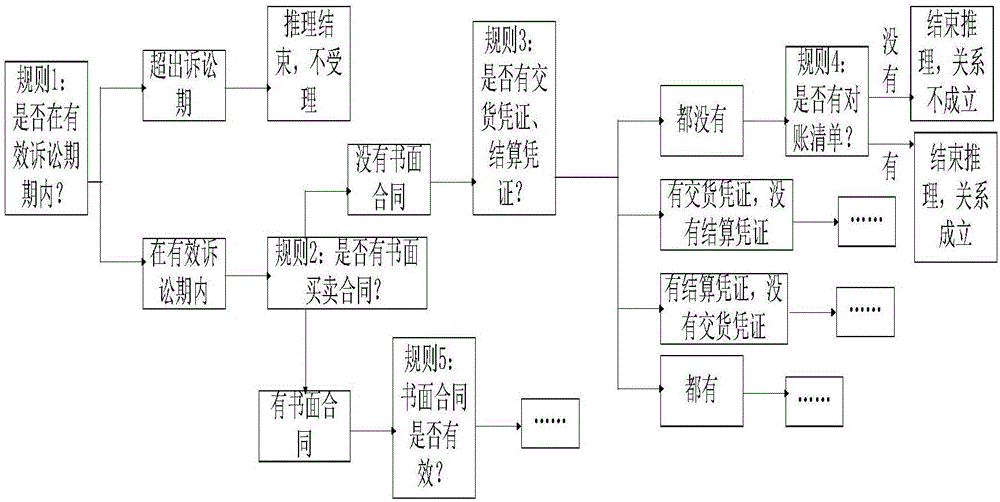
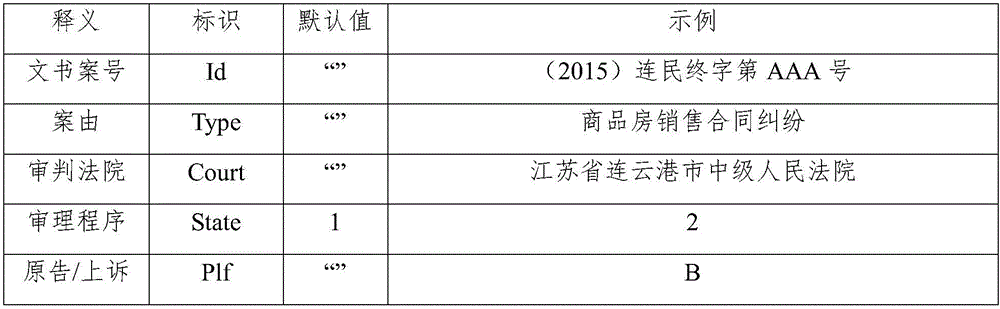
The invention provides a prediction method and system of a litigation outcome. The method comprises the following steps: establishing a knowledge inference library of a predetermined subject, wherein the knowledge inference library is used for storing inference rules, and a plurality of inference steps of the inference rules; constructing a prediction model based on the knowledge inference library of the predetermined subject, wherein a neural network block of each prediction model is corresponding to one inference step, the inference data needed by each inference step is corresponding to one data type, and each data type is corresponding to an input type of the neural network block; processing a judgment document corresponding to the predetermined subject to obtain a training sample data set, training and modifying the prediction model; acquiring to-be-detected data, extracting a data pair with attribute and attribute value based on the predefined feature word library to form a to-be-detected data feature information set; judging a suitable subject of the to-be-detected data based on the to-be-detected data feature information set, and inputting into the prediction model to predict. The method and system provided by the invention can guide the people to predict the outcome of a law case and are strong in practicability.
Owner:点击律(上海)网络科技有限公司
System and method for presenting electronic medical records
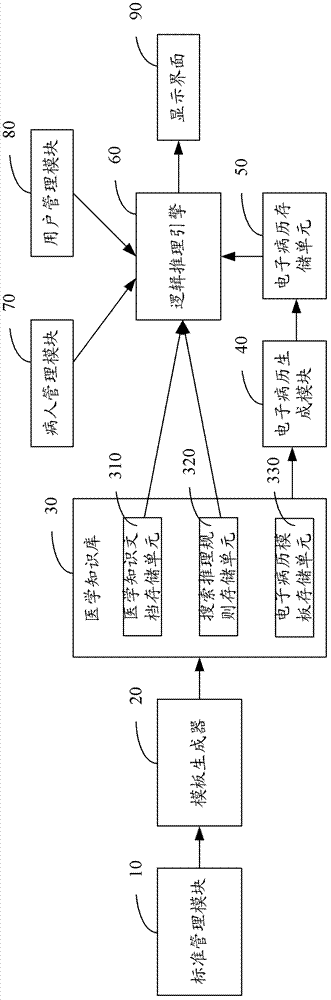
The invention provides a system and a method for presenting electronic medical records. The system comprises a standard management module, a template generator, an electronic medical record generating module, a logical inference engine and a display interface. The standard management module generates data element documents; the template generator generates electronic medical record templates, medical knowledge documents and search and inference rules according to the data element documents; the electronic medical record generating module loads the electronic medical record templates to generate electronic medical records; the logical inference engine obtains the electronic medical records according to patient information, calls the medical knowledge documents according to patients diseases and / or chief complaints, calls the search and inference rules according to the patient diseases and / or the chief complaints and specialized categories and / or service types of medical staff, and performs search and formalized inference on information in the electronic medical records by using the search and inference rules and the medical knowledge documents to obtain electronic medical record data subsets; and the display interface displays the electronic medical record data subsets. By means of the system and the method for presenting electronic medical records, the implicit inference and query can be performed on the electronic medical records, so that the interesting electronic medical record information can be presented on account of specific diseases and / or chief complaints and various specialized medical staff.
Owner:NANTONG KANGSHENG MEDICAL EQUIP
Method and device for preventing from computer virus
InactiveCN101158999AAvoid destructionCut off the transmission routePlatform integrity maintainanceData contentRisk evaluation
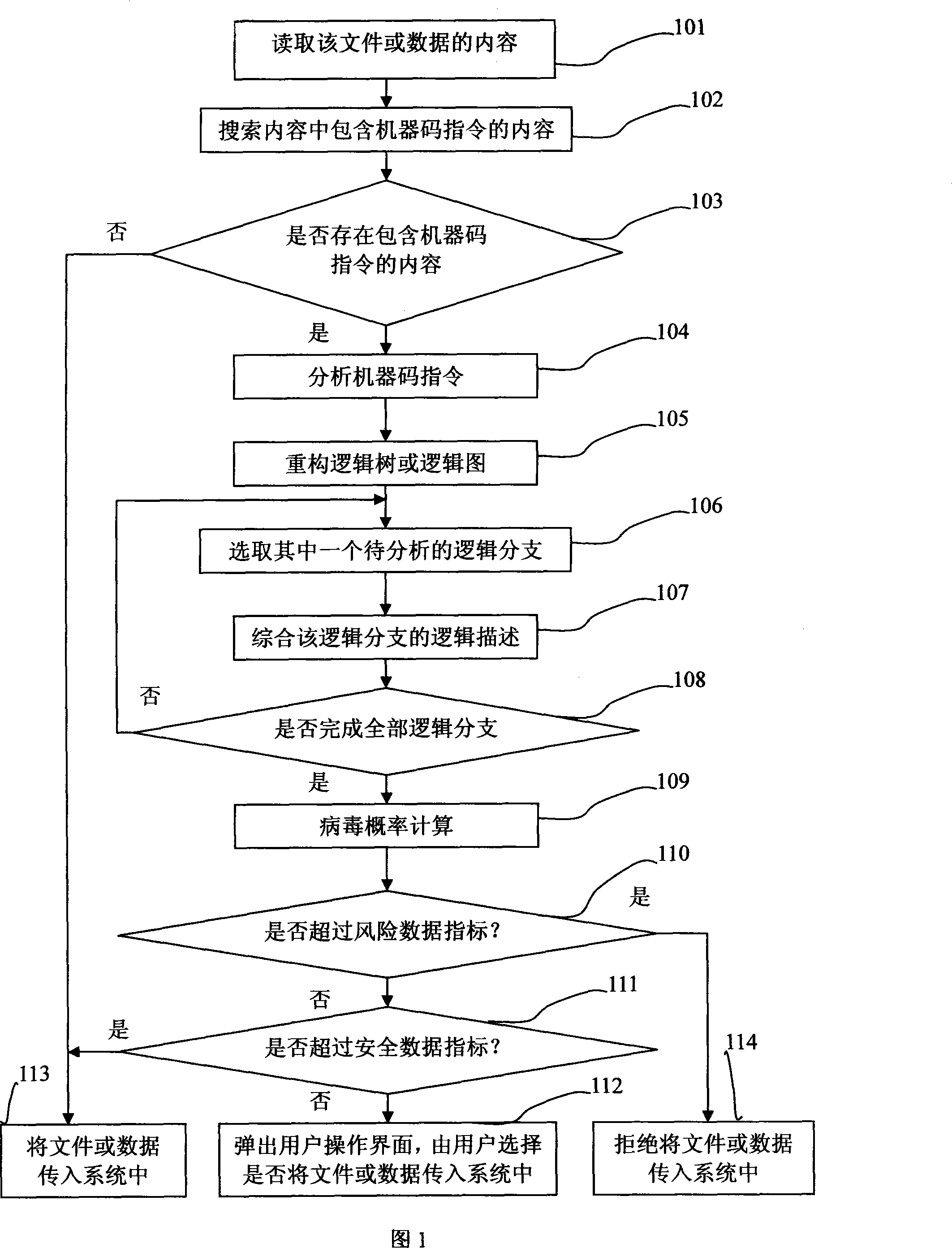
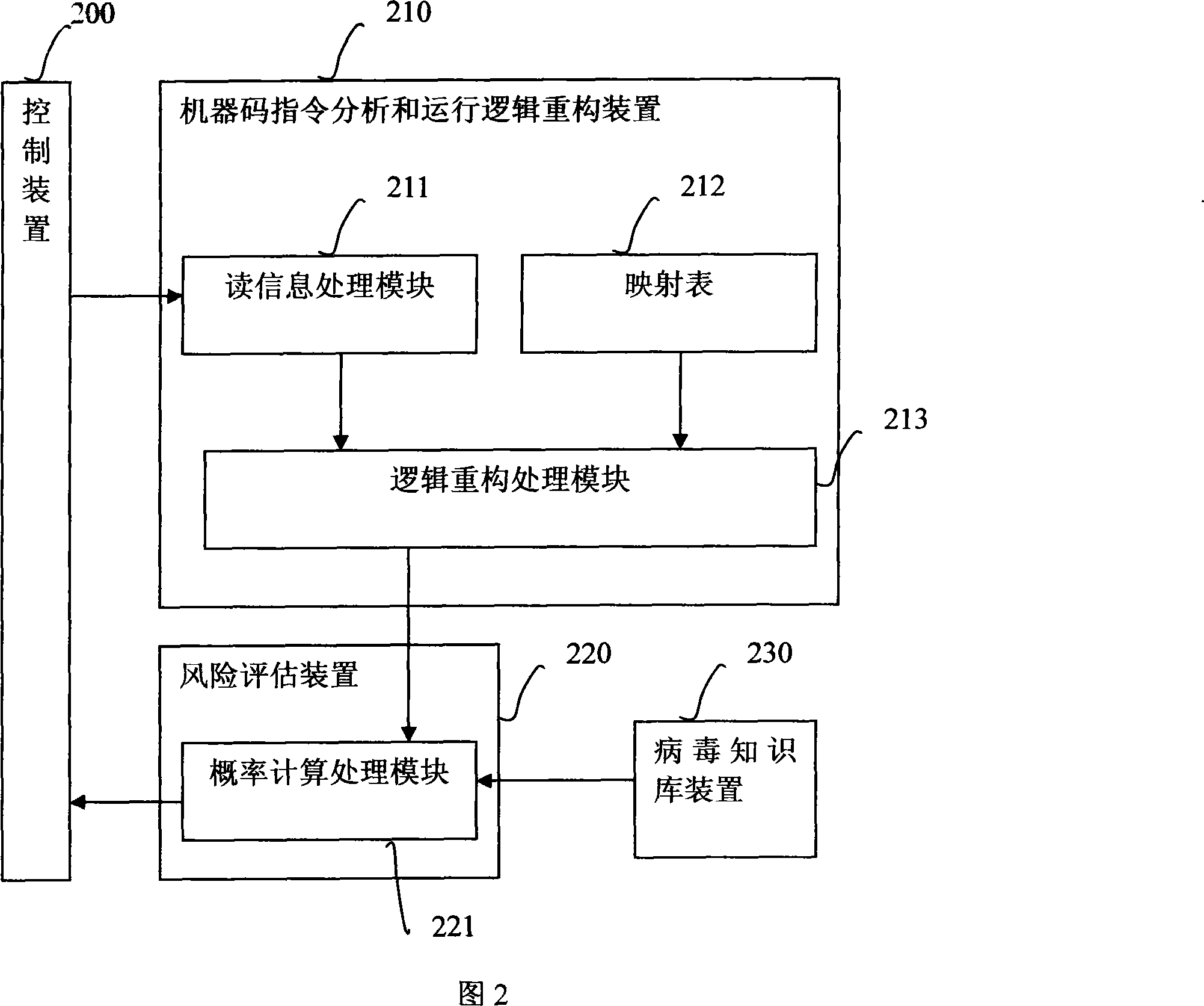
The invention provides a method for preventing computer virus. The method includes the steps that: before an external file or data are needed to be transferred into an information system, reading the whole content of the file or data first; executing a machine code instruction analysis on the content of the file or data and reorganize the operation logic; executing a simulation run on the result of the machine code instruction analysis and the result of reorganization, and giving a result report generated by the simulation run; inferring and determining the result report generated by the simulation run using the knowledge of the virus knowledge base and the inference rule, and obtaining the result of whether the file has the probability of virus existence or not; according to the result of the probability of virus existence, automatically or manually control whether the external file or data are able to be transferred into the information system or not. The invention also provides a device for realizing the method, and the device comprises a machine code instruction analysis and operation logic reorganization device, a control device, a risk assessment device, and a virus knowledge base device. The invention can effectively prevent the broadcast of computer virus.
Owner:BEIJING PAIRUIGEN SCI & TECH DEV
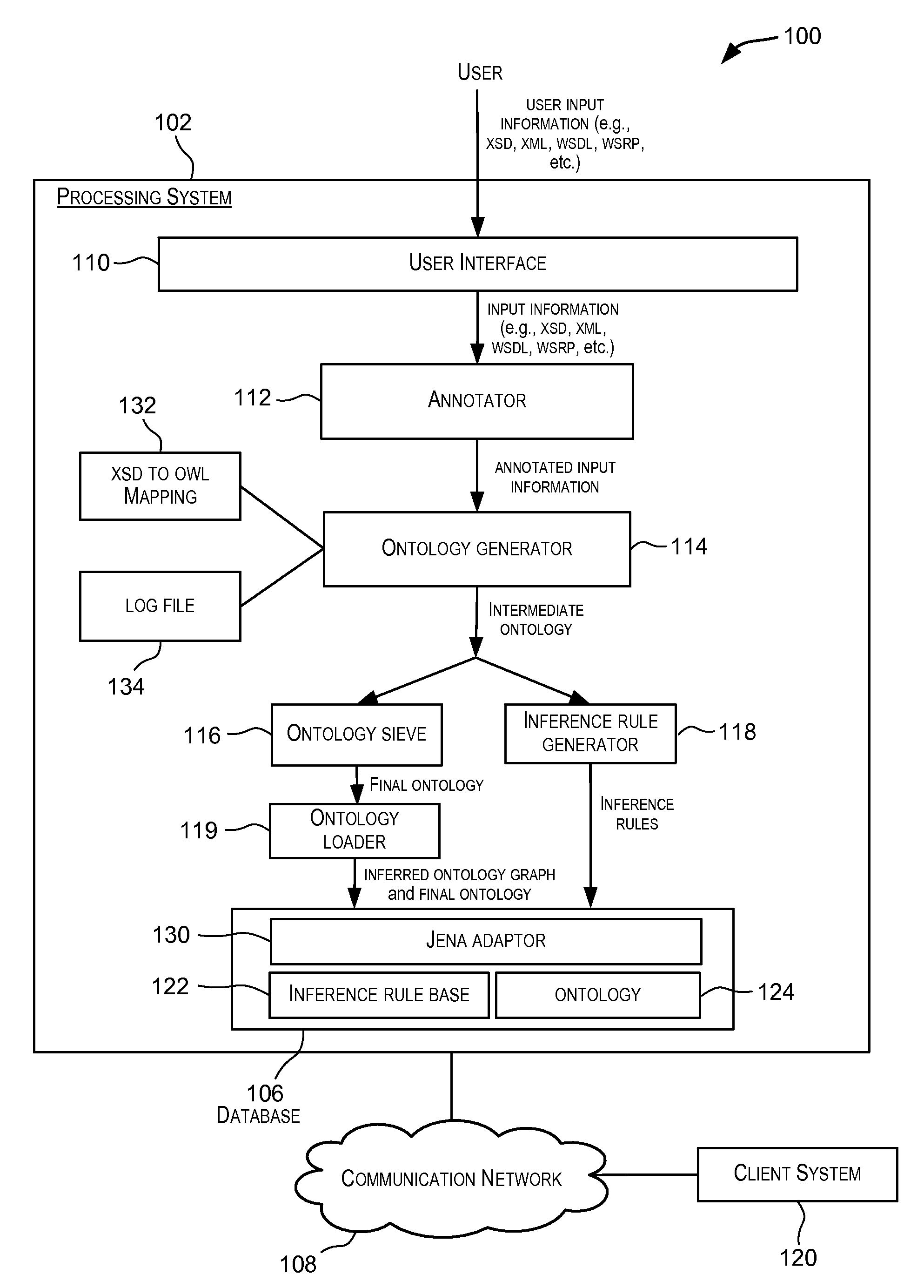
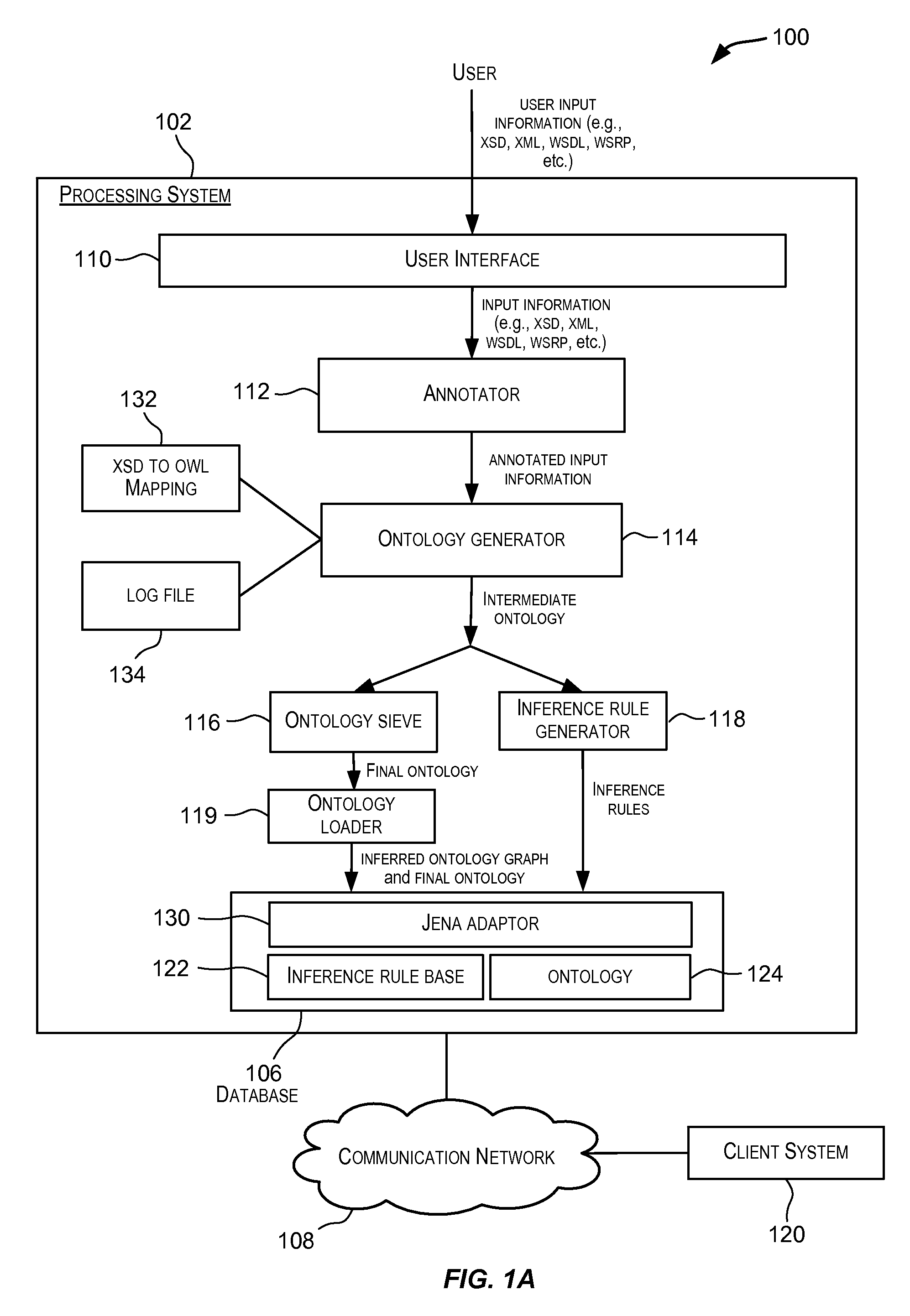
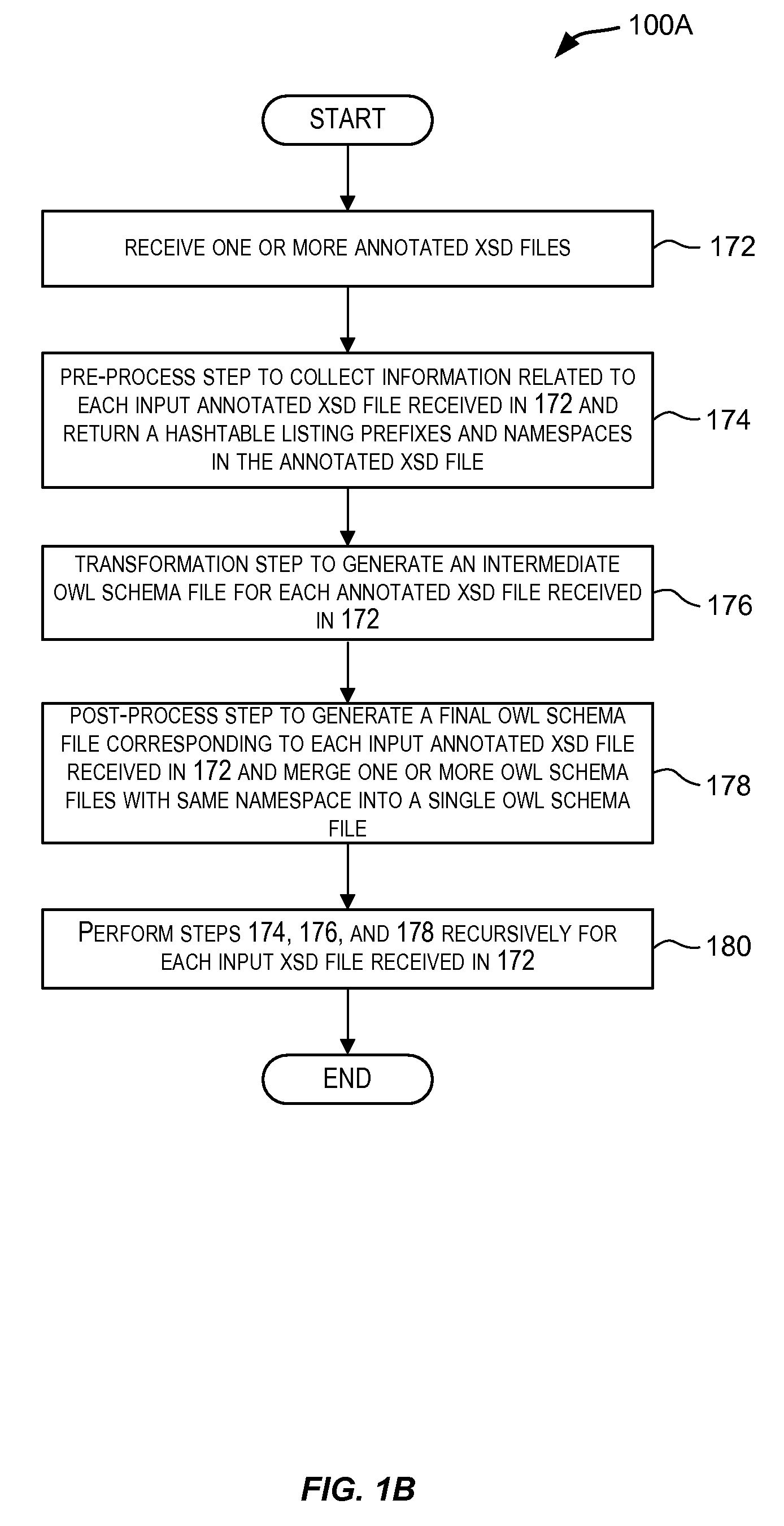
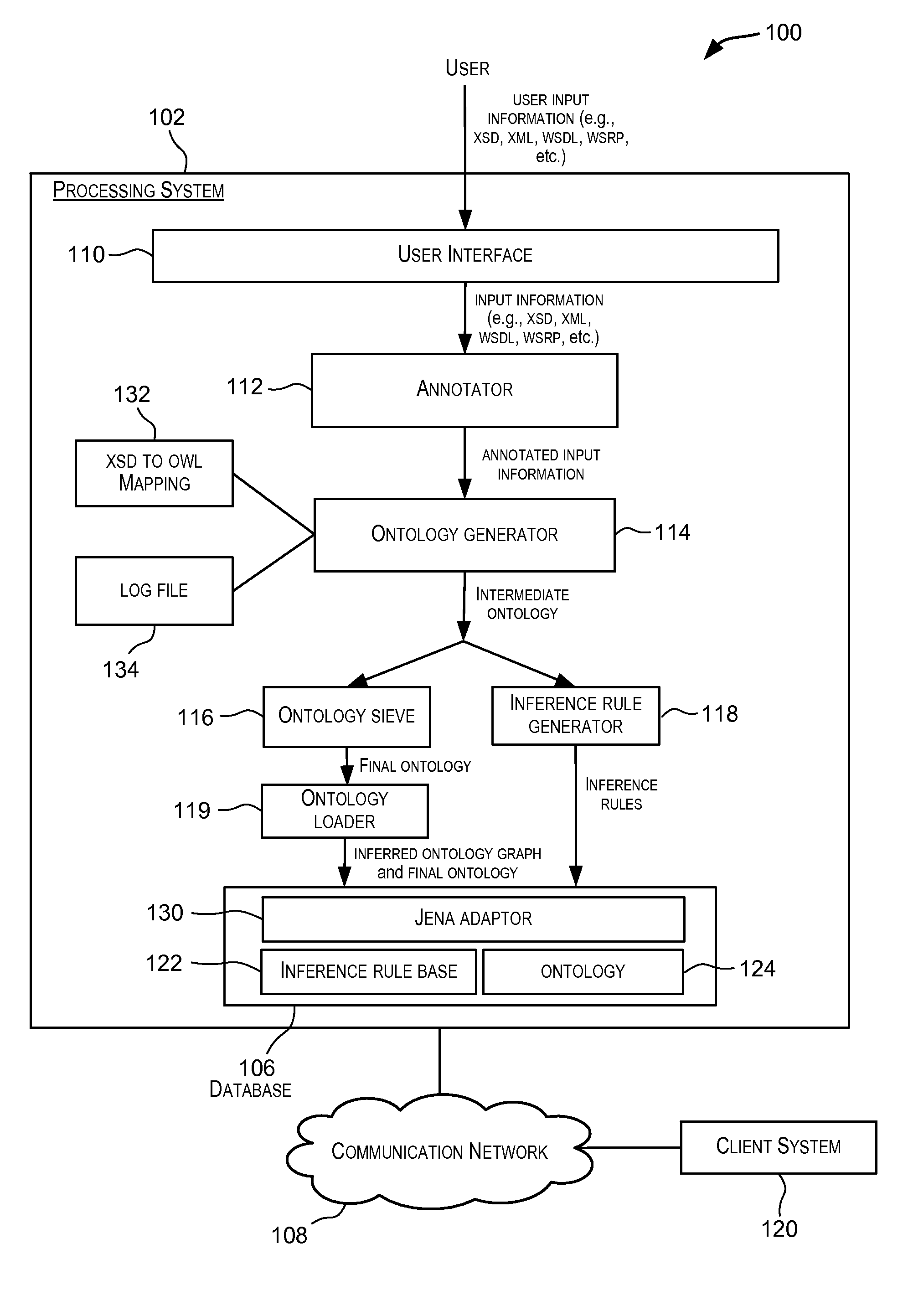
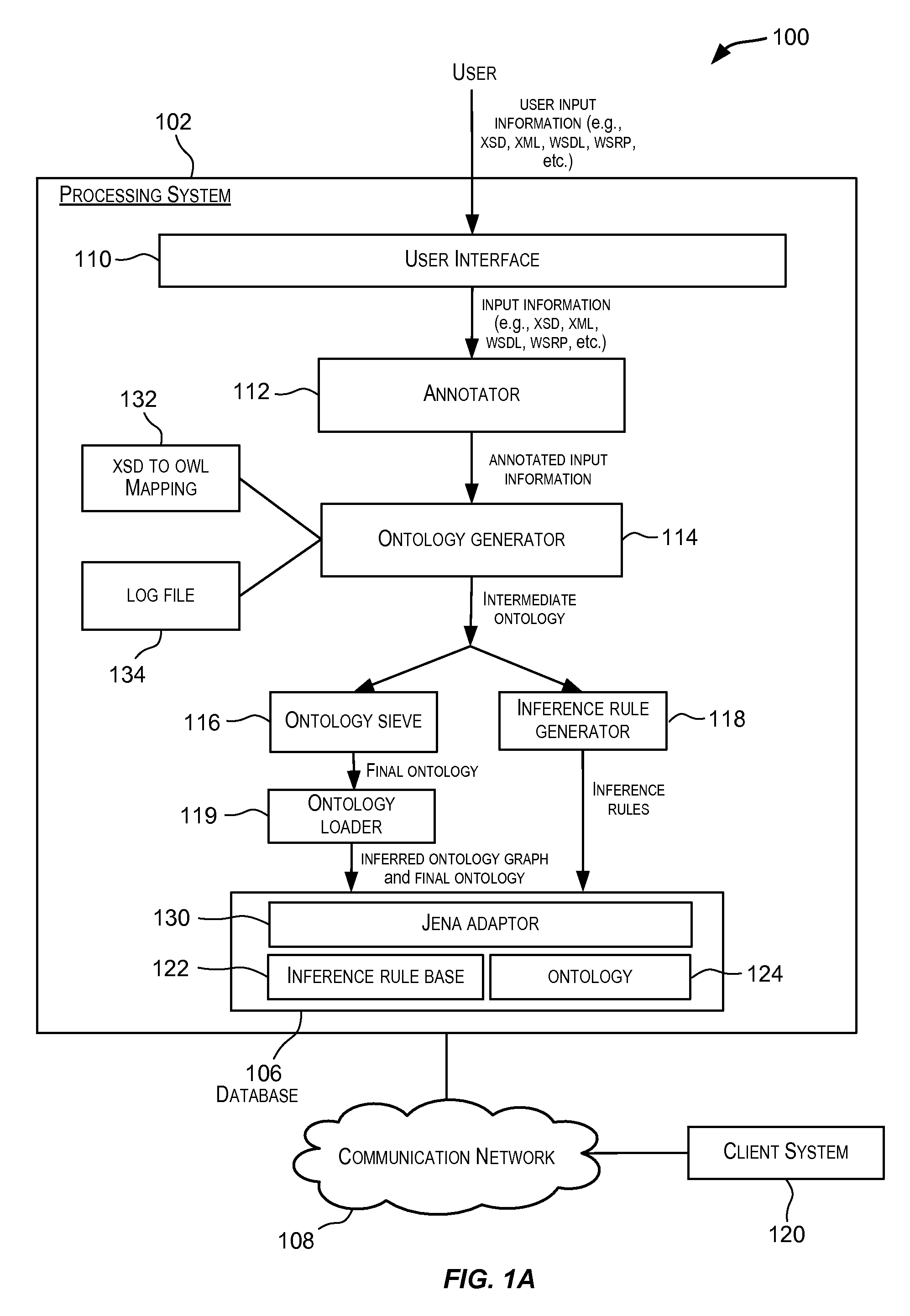
Techniques for automated generation of ontologies for enterprise applications
ActiveUS20100228782A1Digital data information retrievalDigital data processing detailsApplication softwareXML
Embodiments of the present invention provide techniques for generating ontologies. In one embodiment, techniques are provided for automatically generating an ontology based upon input information. The input information may, for example, be in the form of XSD, XML, WSDL, or WSRP, etc. The automatically generated ontology may be encoded in OWL or other RDF-compliant language. A set of inference rules may also be automatically generated using the input information. The automatically generated ontology and the set of inference rules may be stored in a database for further processing.
Owner:ORACLE INT CORP
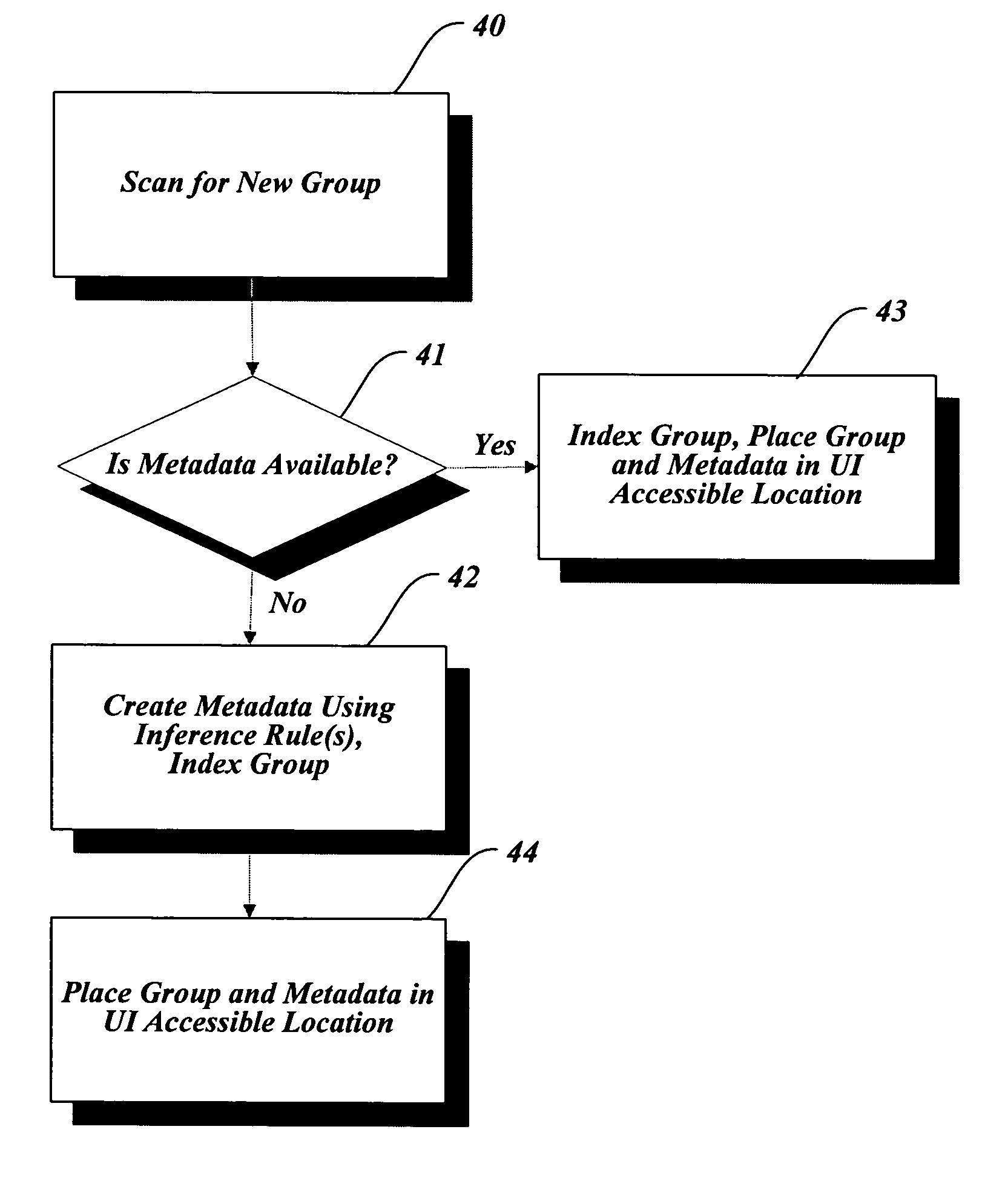
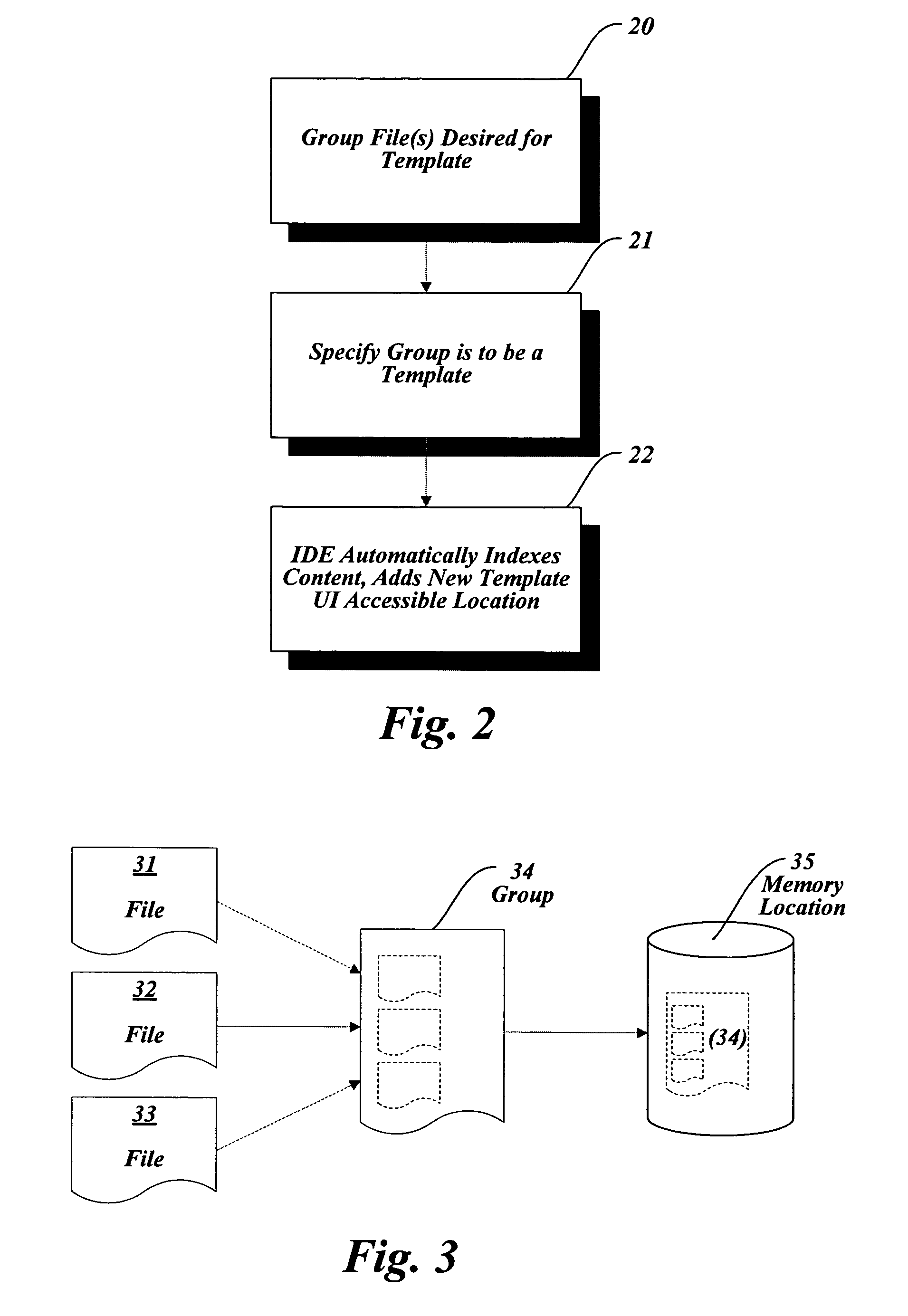
Systems and methods for creating a template from an existing file
InactiveUS20060080329A1Digital data processing detailsUser identity/authority verificationFile systemDatabase
Systems and methods for creating a template from an existing file are provided. The user can package one or more file(s) into a group and specify that the group is to be converted into a template. An IDE process can automatically index the content of the group and create a metadata file to represent the indexed content. The IDE process may employ a set of standard inference rules to index the content. The indexed file group and metadata can serve as a template for creating new files with properties of the original file(s). Additionally, templates can be provided with a set of default properties when no specific template properties are specified by a user. Completed templates can be added to a User Interface (UI) accessible location, such as a collection of templates accessible to UI dialog processes for opening new files.
Owner:MICROSOFT TECH LICENSING LLC
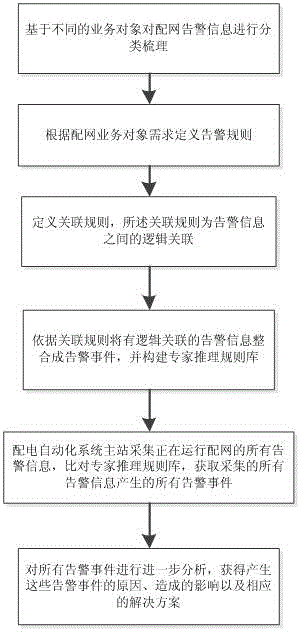
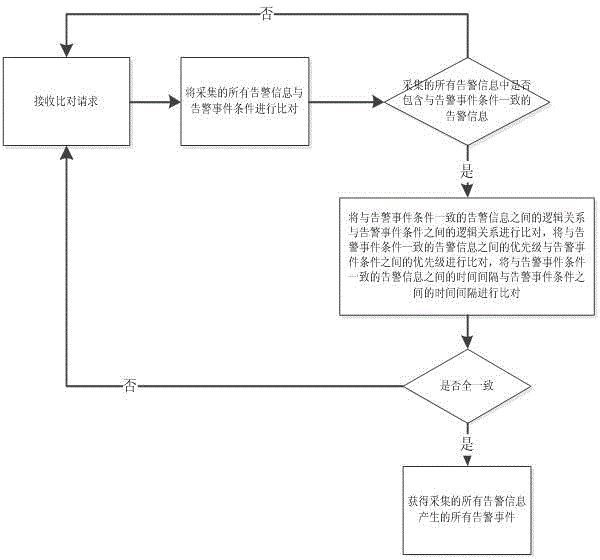
Multi-business-object-oriented distribution network warning information integrated rational analysis method
ActiveCN104133986ARealize classification integrationMake up for security risksSpecial data processing applicationsPrimary stationSimulation
The invention discloses a multi-business-object-oriented distribution network warning information integrated rational analysis method, which comprises the following steps that: 1, distribution network warning information is classified and sorted on the basis of different business objects; 2, a warning rule is defined according to distribution network business object requirements; 3, an association rule is defined, and the association rule is the logic association among a plurality of pieces of warning information; 4, the warning information with the logic association is integrated into warning events according to the association rule, and an expert rational rule base is built; 5, a power distribution automation system main station collects all warning information of an operating distribution network, compares the expert rational rule base and obtains all warning events generated by all collected warning information; and 6, the warning events are further analyzed, and the reasons, the caused influence and the corresponding solutions of the generated warning events are obtained. The multi-business-object-oriented distribution network warning information integrated rational analysis method provided by the invention realizes the classification and the sorting on the distribution network information, and also realizes the auxiliary fault judgment and handling.
Owner:STATE GRID CORP OF CHINA +1
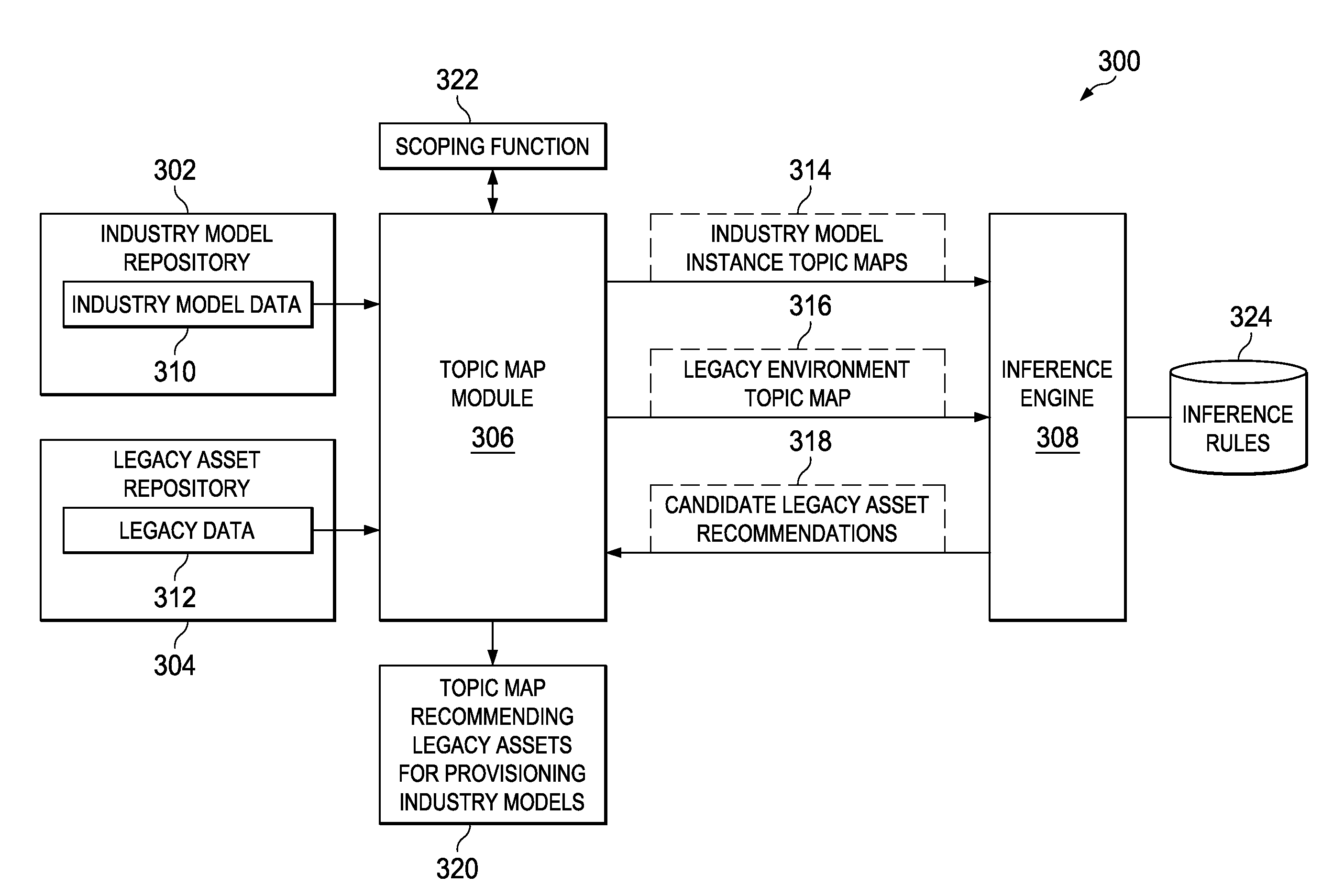
Standard Based Mapping of Industry Vertical Model to Legacy Environments
ActiveUS20110099139A1Facilitates great machine interpretabilityReduce in quantityOffice automationFuzzy logic based systemsEnterprise application integrationTechnical standard
A standard based mapping of industry vertical models to legacy environments to suggest points of enterprise application integration. A representation of a first domain comprising industry model instance data is generated in a standard-based format from an enterprise industry model. A representation in the standard-based format of a second domain comprising legacy data is generated from the legacy environment. A set of inference rules is applied against the representation of enterprise industry model instance data and the representation of legacy data. One or more candidate legacy assets in the representation of legacy data capable of implementing an aspect of the enterprise industry model are identified. The identified one or candidate legacy assets for implementing the aspect of the enterprise industry model are then recommended to a user.
Owner:IBM CORP
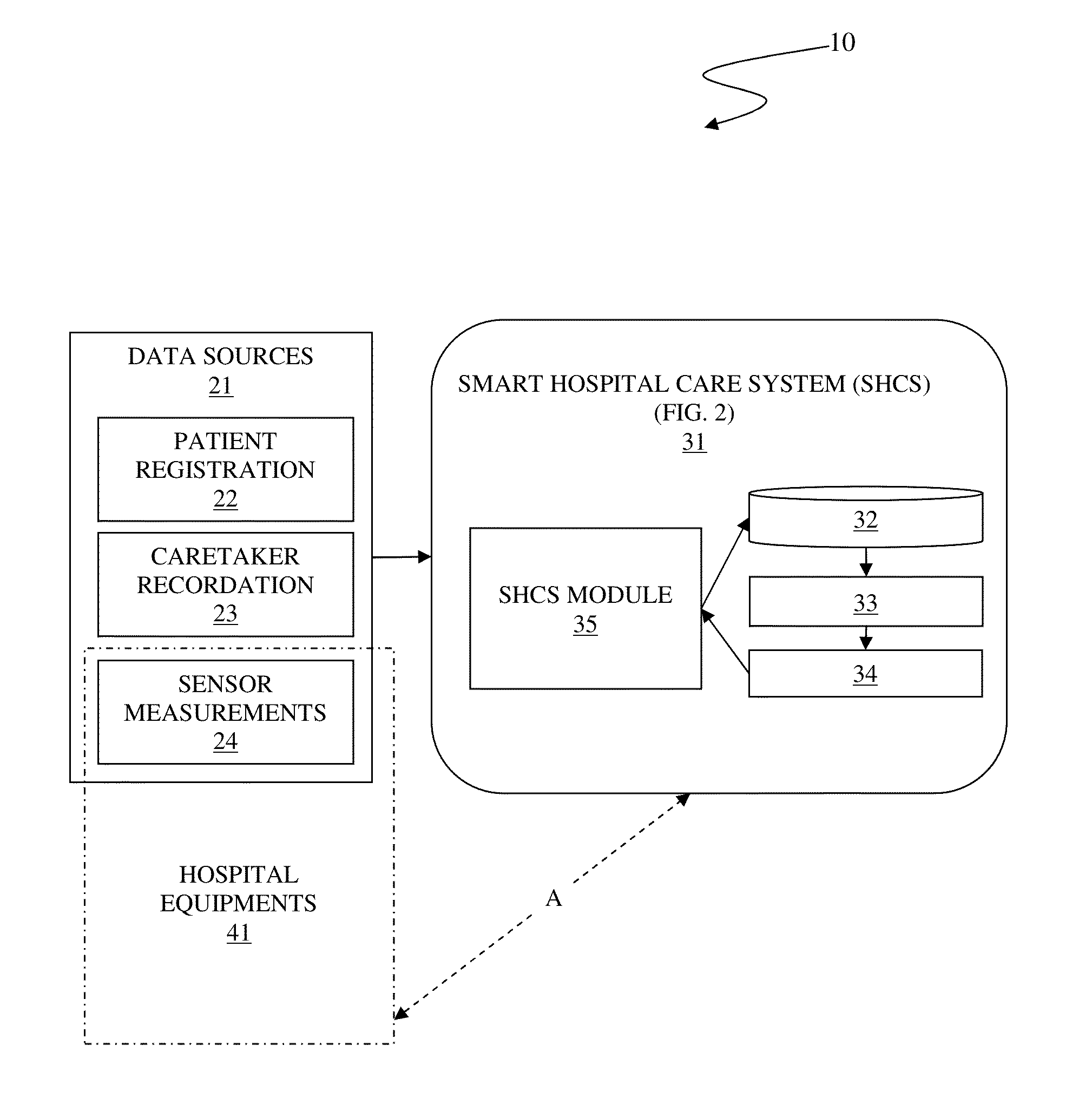
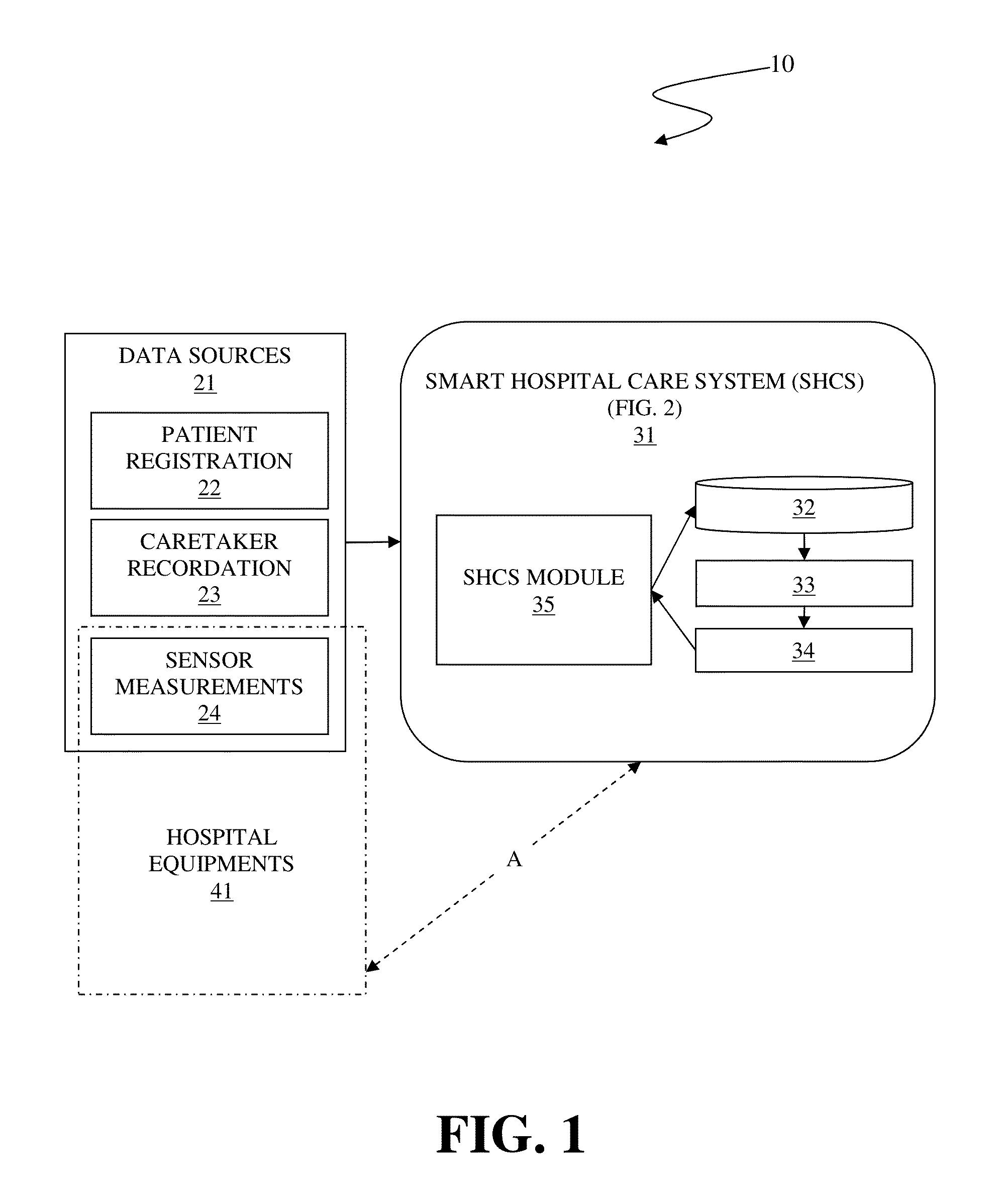
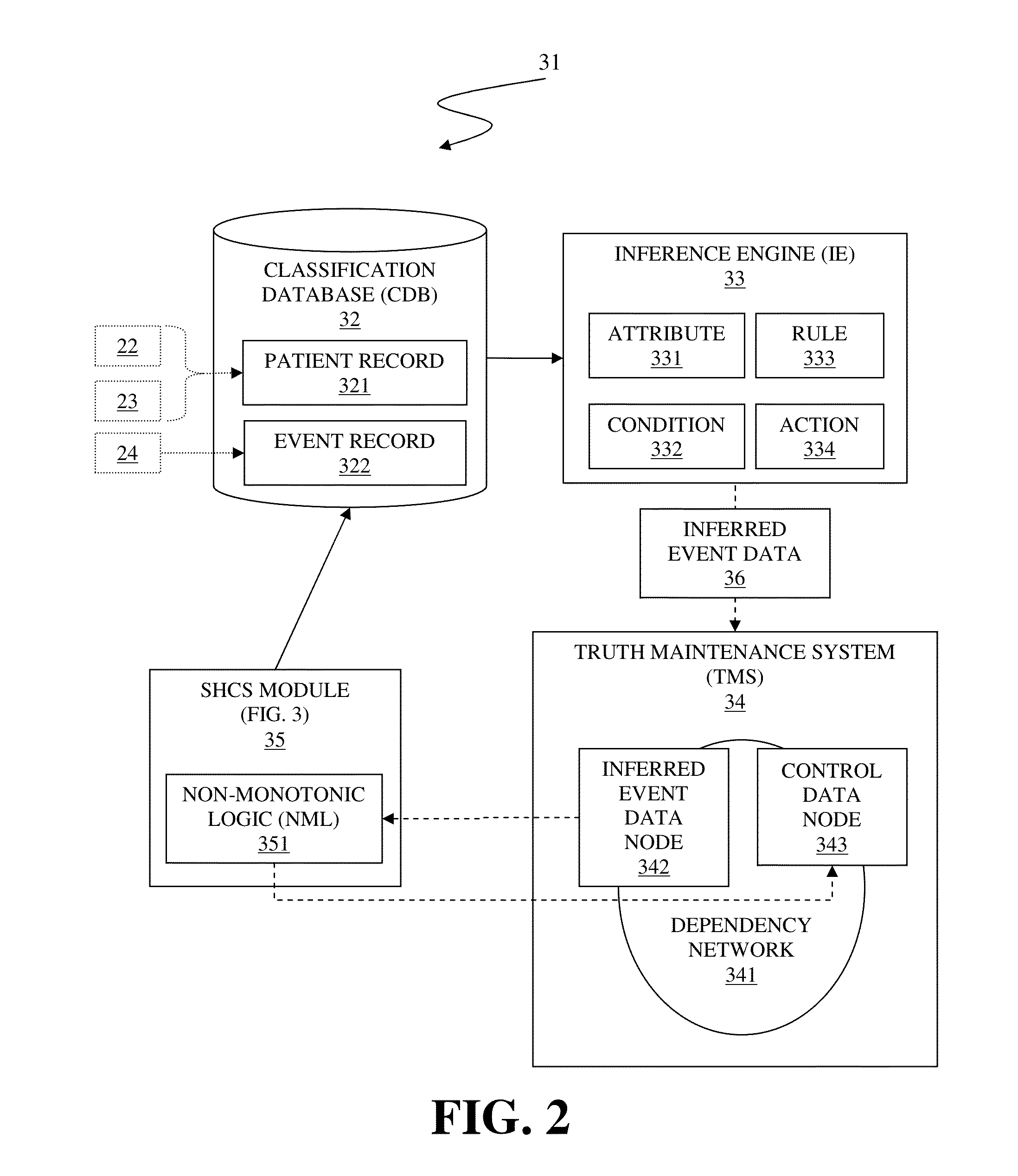
Smart hospital care system
A system and associated method for automatically controlling a hospital equipment of in-patient care environment is performed by a module coupled to a classification database, an Inference Engine (IE), a Truth Maintenance System (TMS), and the hospital equipment. Upon admitting a patient, a patient record related to the patient is created and events for the patient are recorded. Based on inference rules of the IE, inferred event data is generated and subsequently control data to manipulate the hospital equipment is generated. Pursuant to new event affecting truth of the inferred event data, the inferred event data may be renewed and new control data based on the renewed inferred event data is created to ensure that the control data is based on the latest event related to the patient.
Owner:IBM CORP
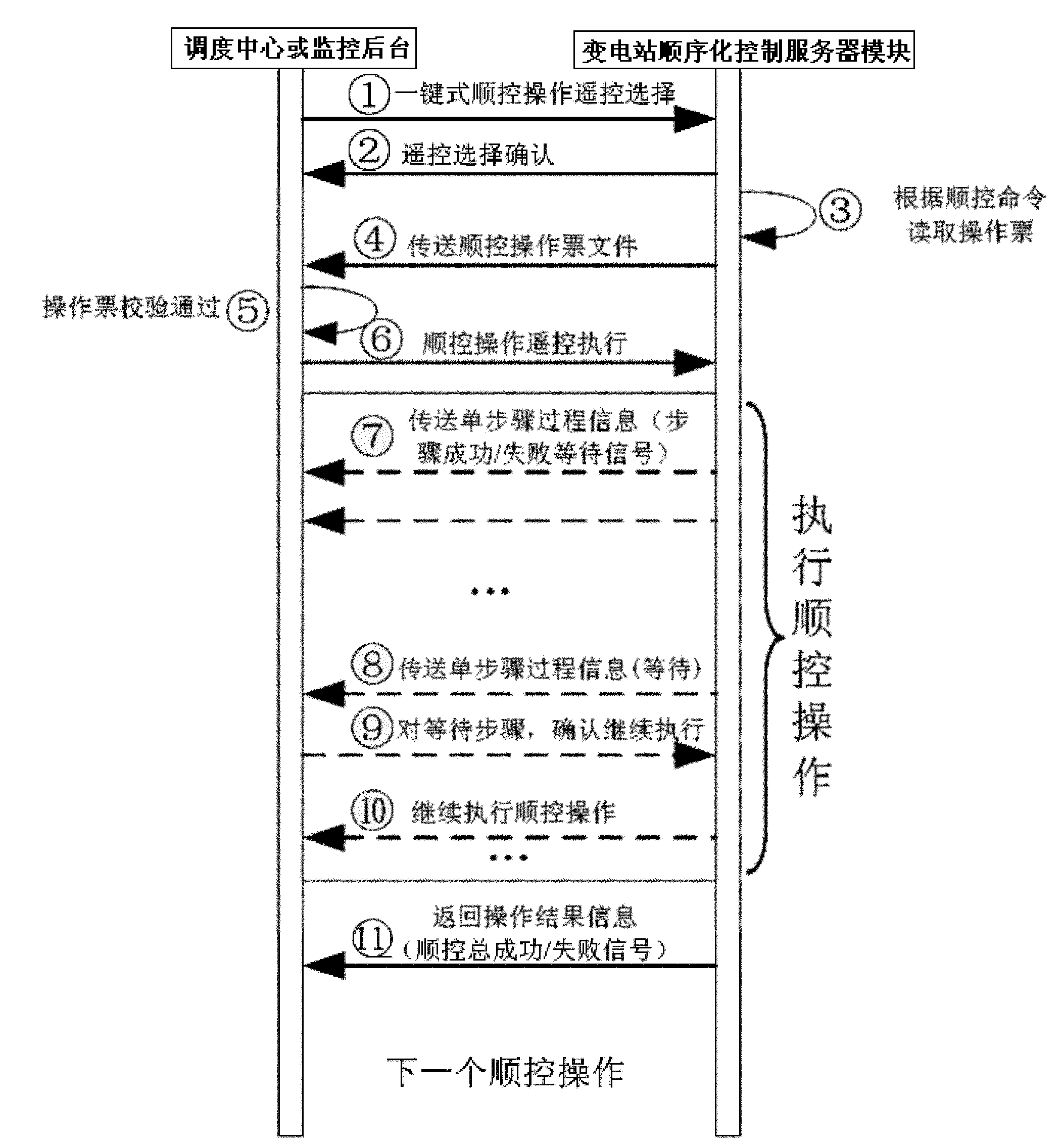
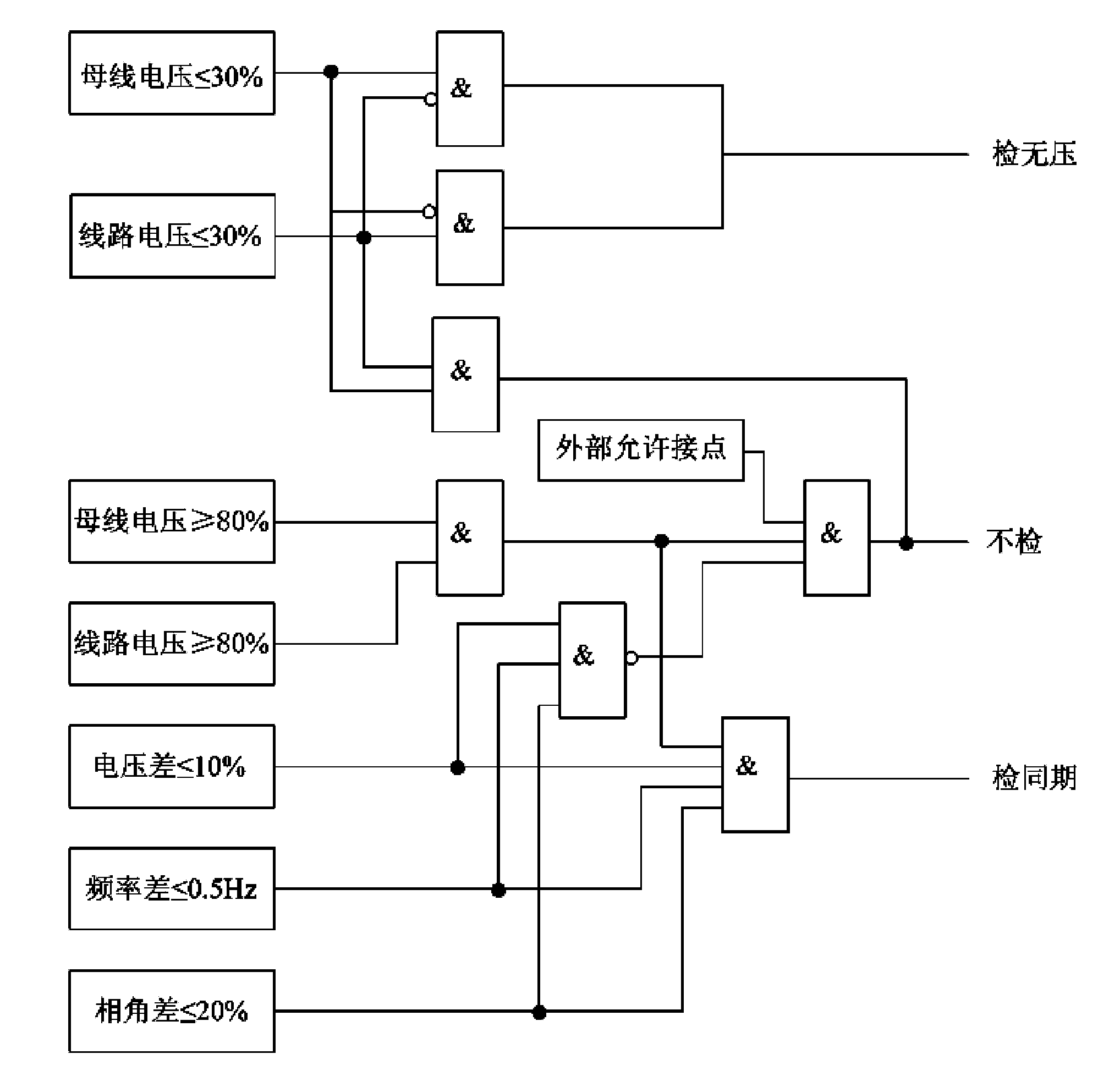
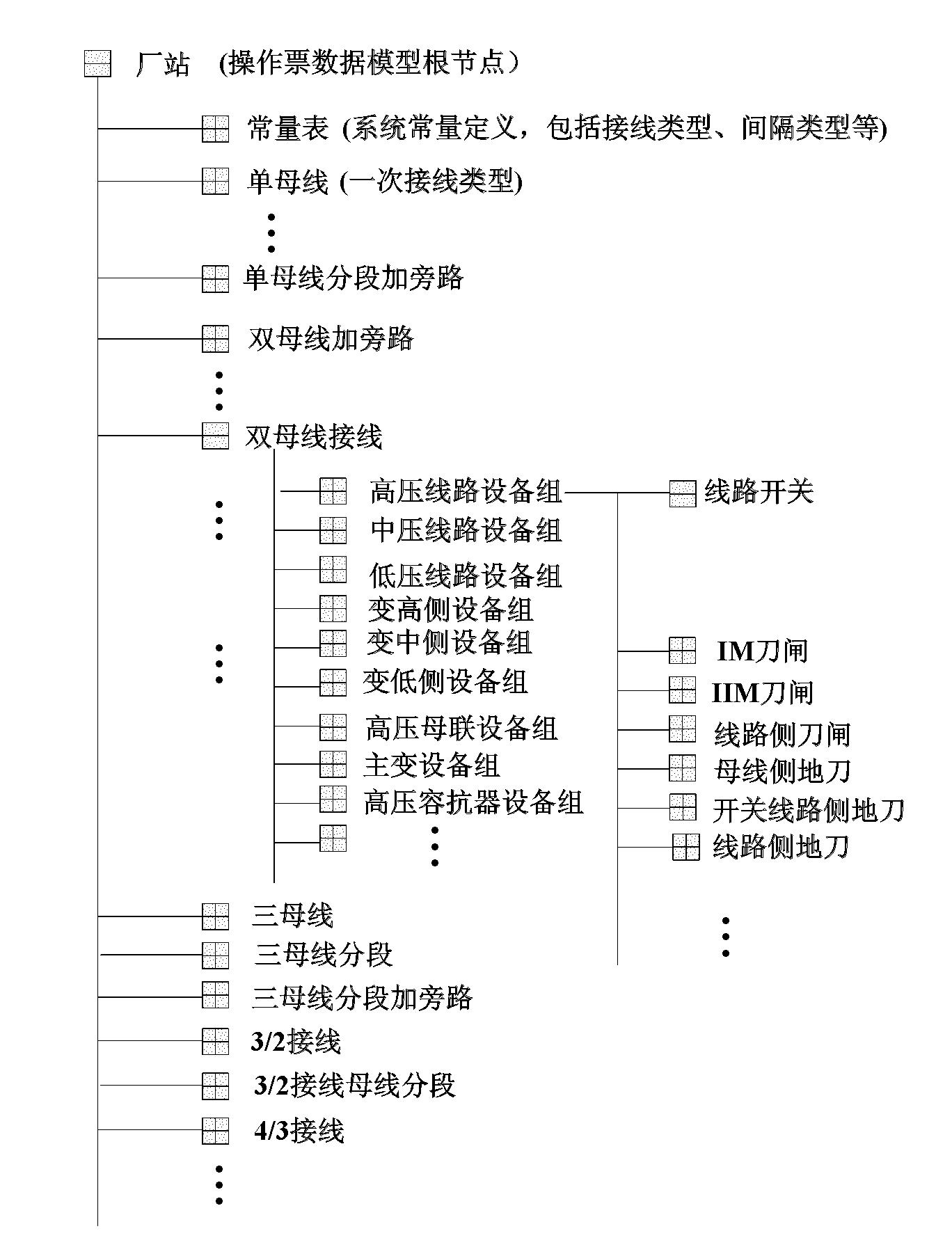
Transformer substation sequentialization control system with visualization and interactivity
ActiveCN102064611AWith visualizationImprove interactivityEmergency protective circuit arrangementsInformation technology support systemTransformerControl system
The invention discloses a transformer substation sequentialization control system with visualization and interactivity. The invention proposes that a ticket printing system which is easier to use is provided for sequential control in a way of establishing concrete operation tickets and template operation tickets, a general template ticket data model irrelevant to concrete equipment of a transformer substation is established according to the generality of a primary electric wiring model of the transformer substation, a mapping method from the template operation tickets to common operation tickets is provided, an inference rule in an intelligent ticket printing process is proposed, original manual confirmation is substituted by an intelligent video system access sequentialization control system and an intelligent video system can be in service and out of service, a synchronous switch-on mode is automatically calculated according to multiple factors, i.e. line side voltages, bus side voltages, frequencies, phase angles, and the like, the interactivity of the sequential control system by establishing the communication process of the sequentialization control system and scheduling interaction and proposing the processing mode during a fault and the content of the sequential control is improved by introducing secondary equipment and control operation relevant to protection to the sequentialization control system.
Owner:NARI TECH CO LTD +1
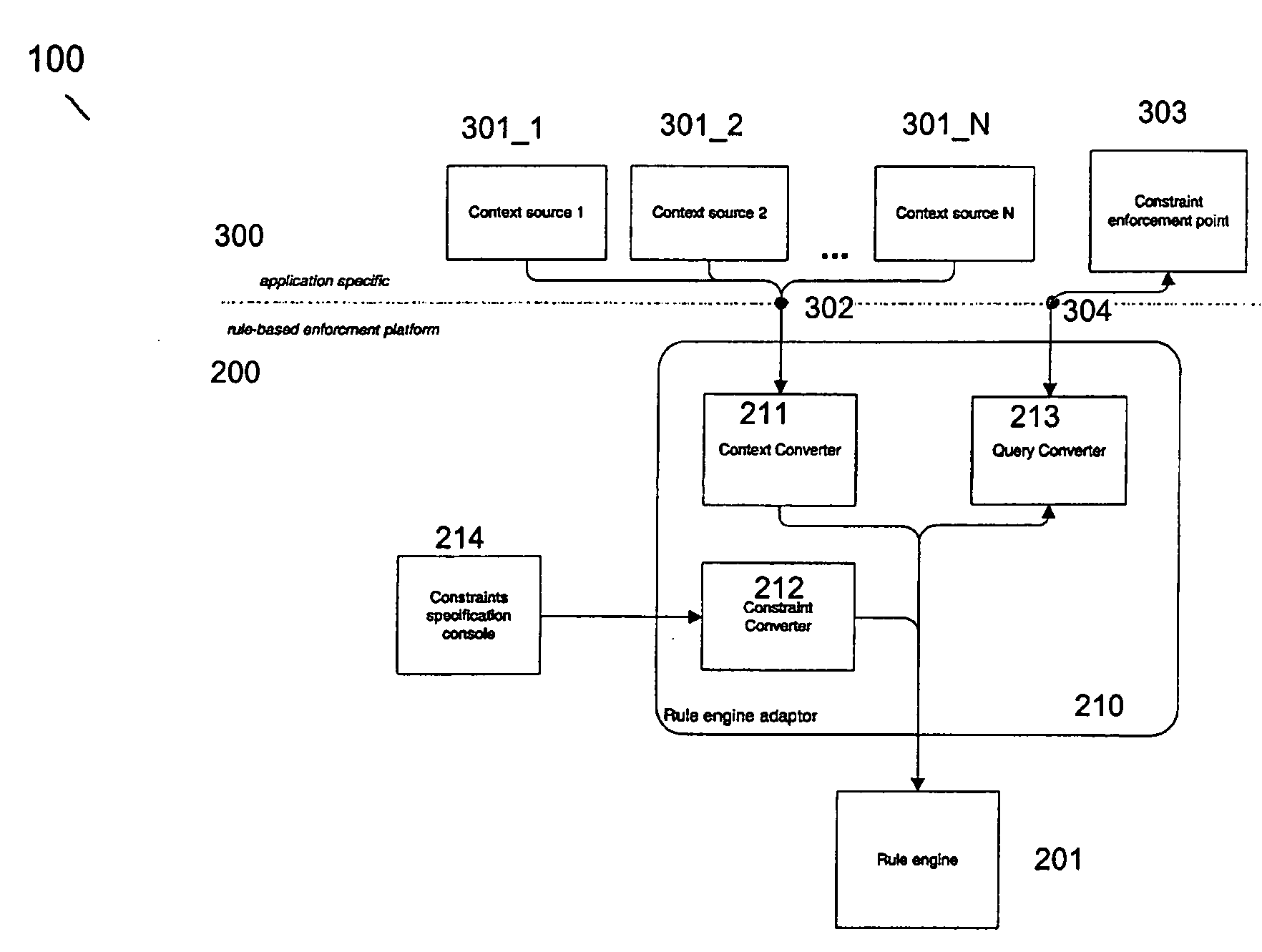
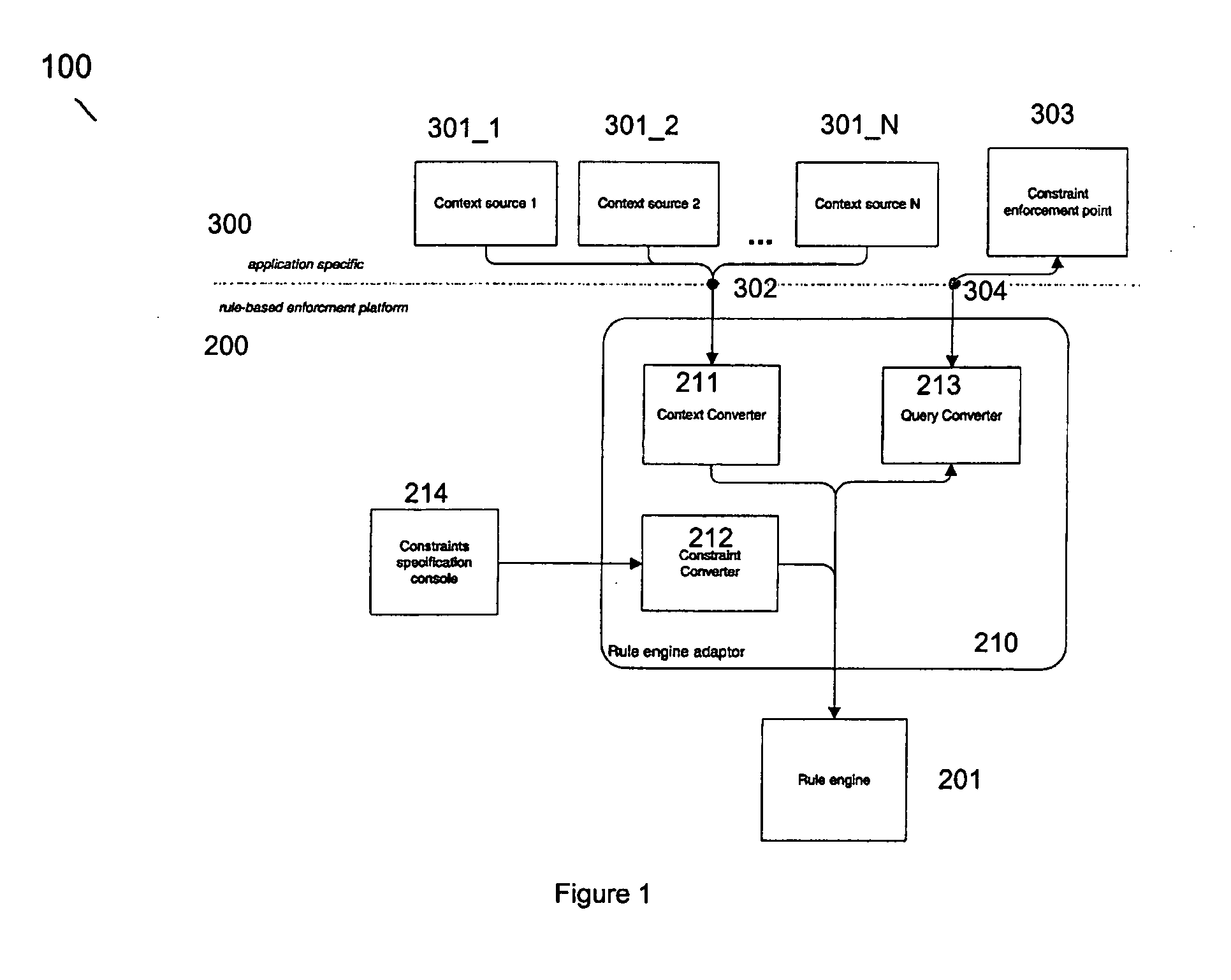
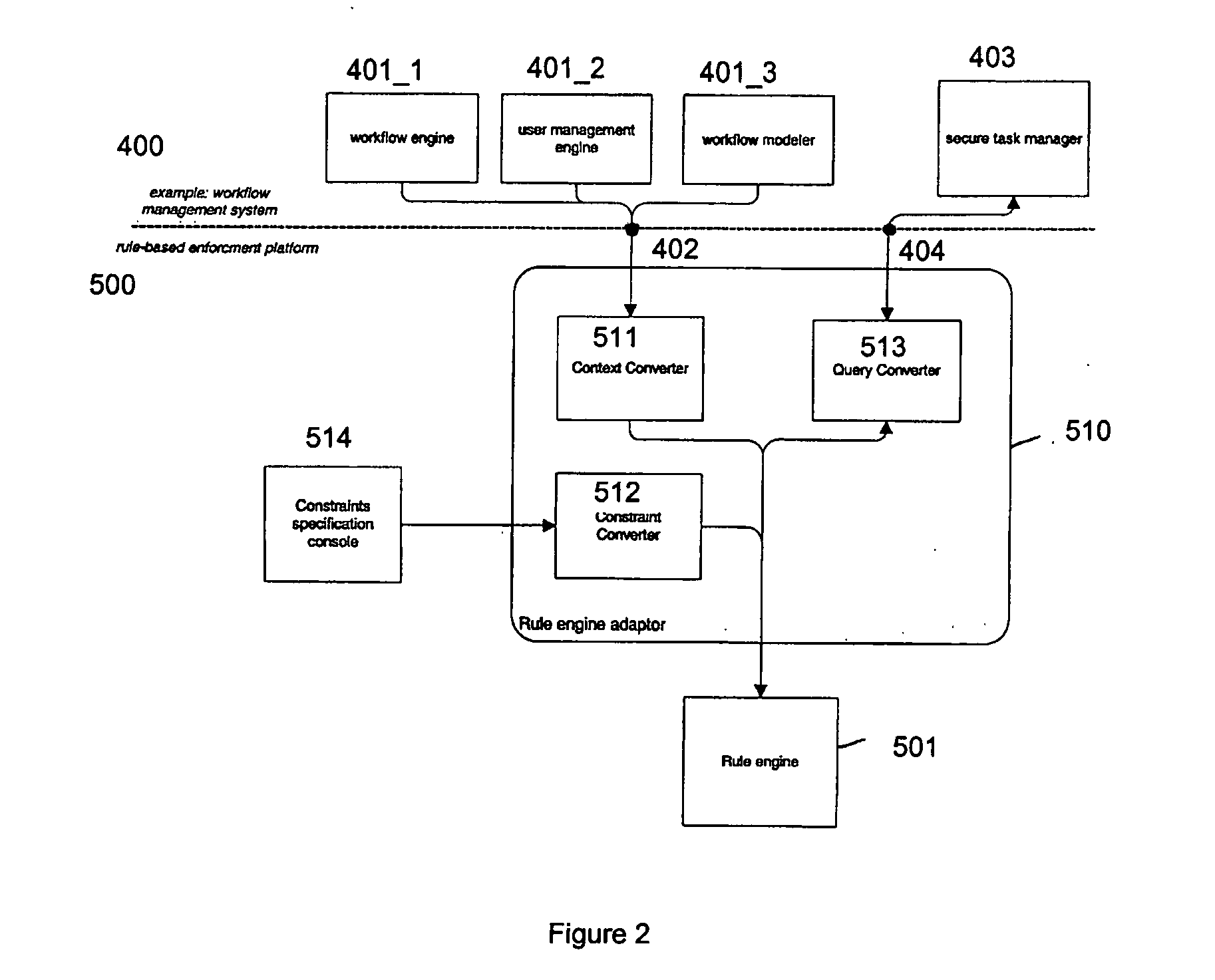
Access control system, a rule engine adaptor, a rule-based enforcement platform and a method for performing access control
ActiveUS20070203881A1Digital data protectionSpecial data processing applicationsInformation resourceApplication software
An access control system provides access control to at least one information resource associated with at least one application within a computer network. The system comprises a plurality of context sources being relevant for the at least one application and providing context information, a constraint specification console providing an interface to specify application specific constraints based on the context sources, a rule engine capable of handling facts and applying inference rules on those facts, an application specific constraint enforcement point configured for receiving access requests, hence querying facts and further being responsible for making access decisions regarding the information resource based on those facts and on application specific constraints and a rule engine adaptor acting as intermediary in communication of the rule engine with the context sources, the constraint specification console and the enforcement point, respectively, so as to allow access control to the at least one information resource based on specified application specific constraints with regard to context information originating from the context sources.
Owner:SAP AG
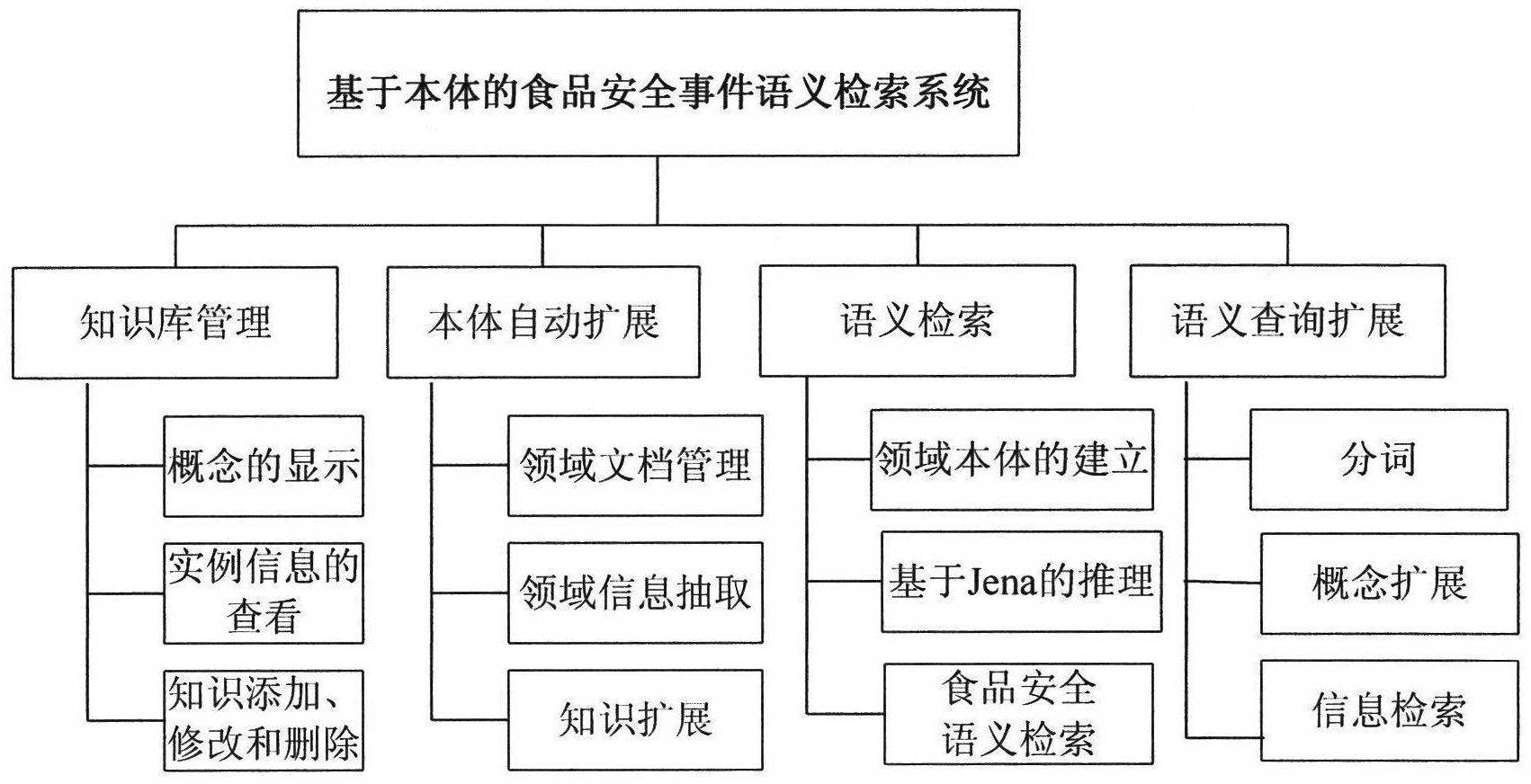
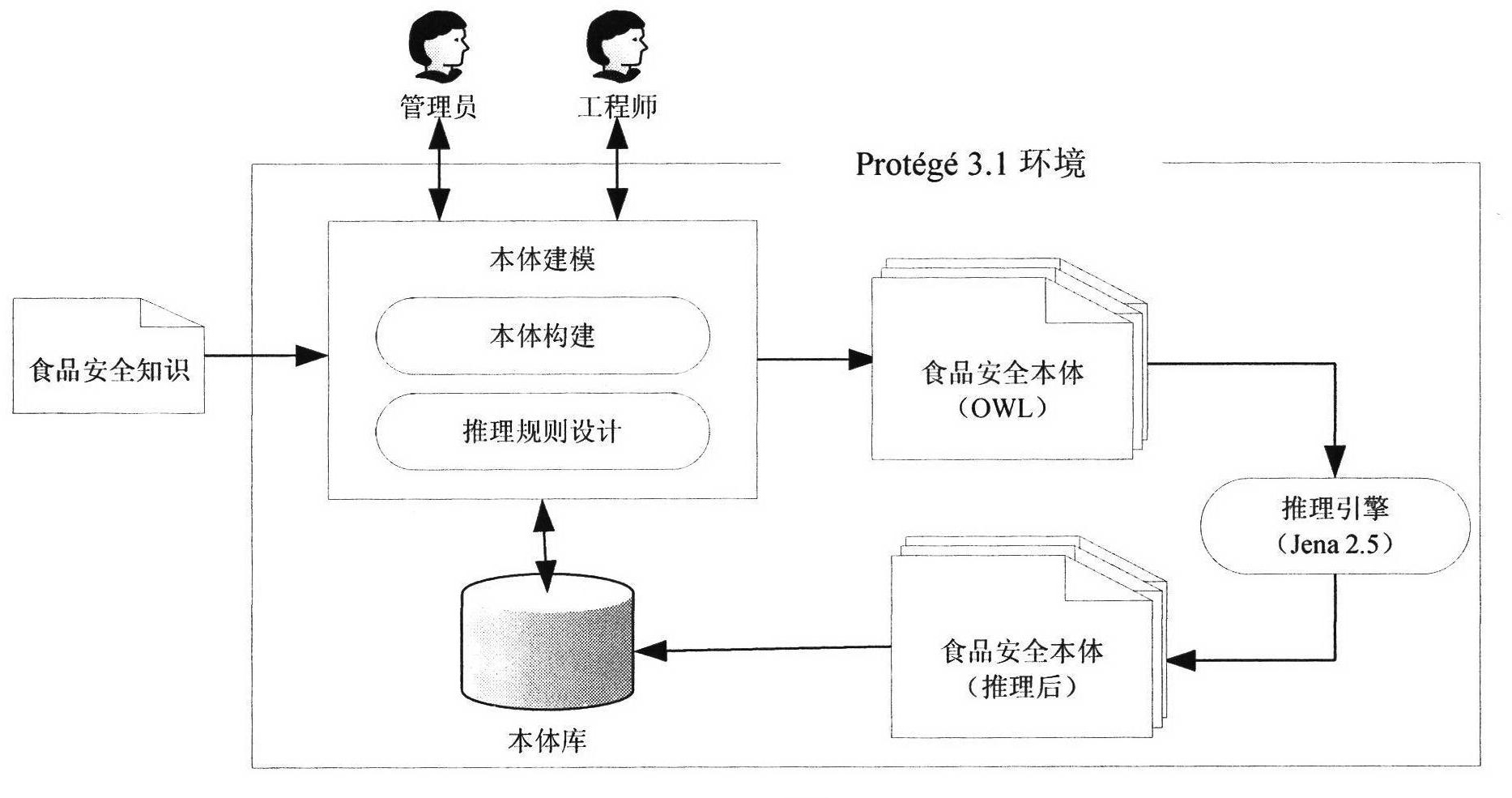
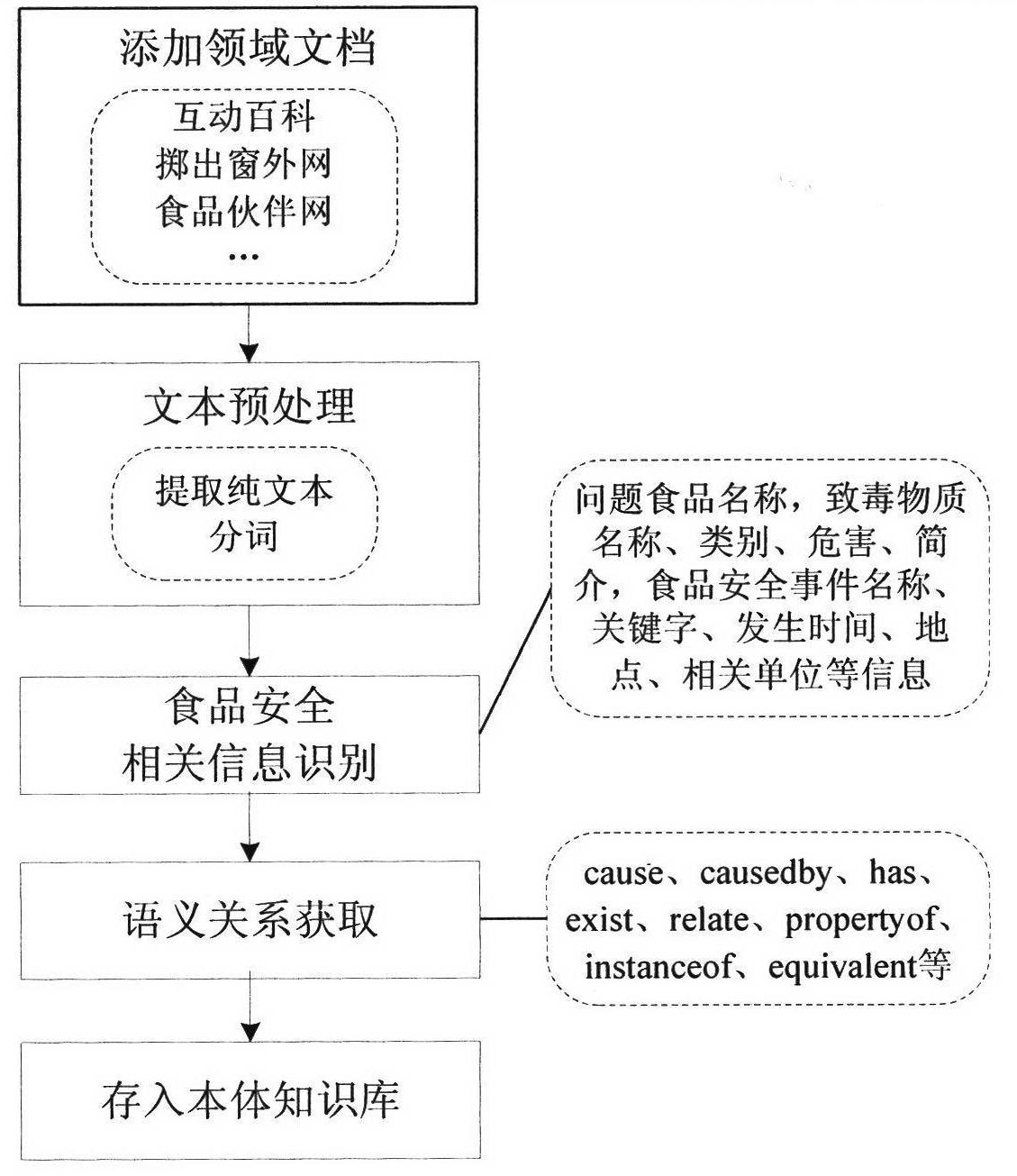
Body-based food security event semantic retrieval system
InactiveCN102622453AImplement auto-scalingImplement Semantic RetrievalSpecial data processing applicationsFood safetyUser input
The invention provides a body-based food security event semantic retrieval system. Firstly, a food security field body which mainly relates to knowledge of food security event, problem food and intoxicating substances is established; automatic expansion of the food security body is realized based on an information extraction technology; inference rules are designed according to a semantic relationship among concepts of the food security bodies, so that the knowledge in the field of food security is reasoned; the semantic retrieval of the food security knowledge in a body base can be realized, concept information which has a semantic relationship with food security event keywords can be retrieved according to the food security event keywords input by users, detailed information of the food security event and the intoxicating substances can be checked, and if the users input problem food, the food security event information related with the problem food can be retrieved; and a body-based semantic inquiring expanding method is provided, so that the concepts which have a specific semantic relationship with user inquiry words can be expanded, and the recall ratio and precision ratio of the retrieval system can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
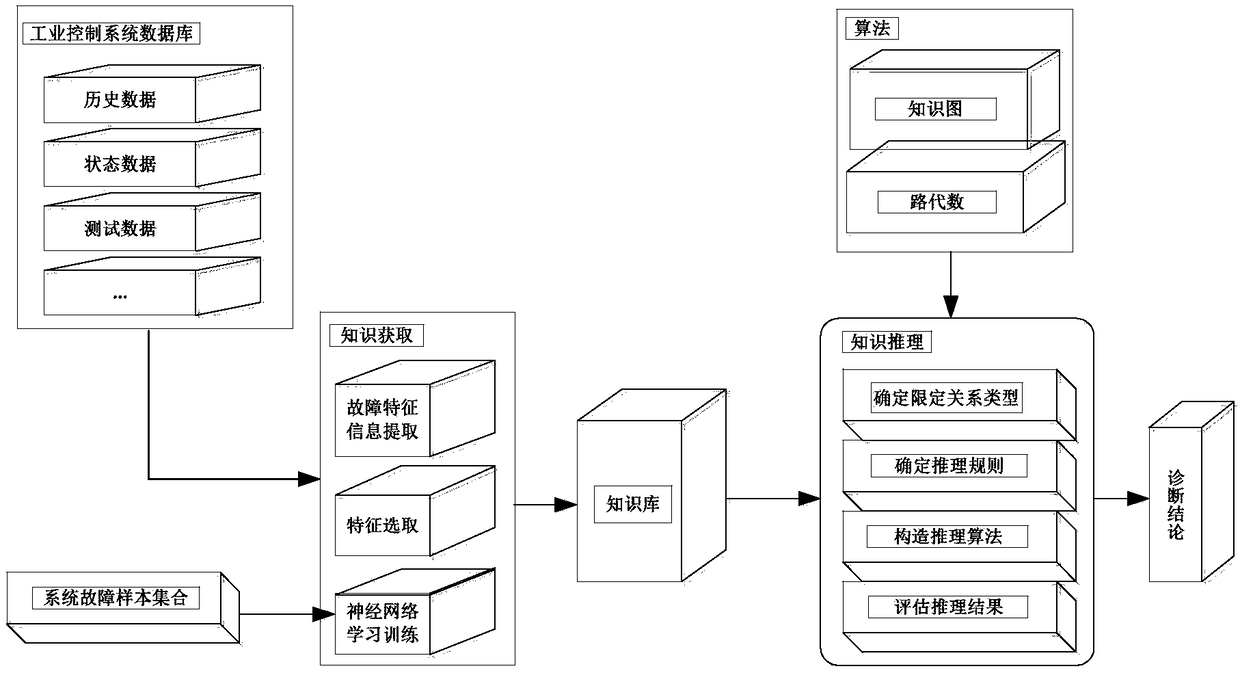
Knowledge-based fault diagnosis method
ActiveCN109491816AOvercoming the \"Combination Explosion\"Overcome \"infinite recursion\" and other problemsFault responseInference methodsMachine learningInference
The invention discloses a knowledge-based fault diagnosis method. The method comprises the following steps: establishing a typical fault case database; extracting fault feature information and selecting main data variables by adopting a signal processing technology and a main component analysis method; Learning the fault sample by using an improved neural network algorithm; the comprehensive representation of the diagnosis knowledge is realized by adopting a mode of combining a generation type rule and a framework; constructing a system fault propagation model through data analysis and the relationship among the devices in the system, and defining a system fault propagation path; and based on the obtained fault knowledge, constructing a knowledge graph, and giving an inference rule by utilizing a road algebra theory to realize fault positioning based on knowledge inference. Through an improved neural network algorithm and a knowledge reasoning theory, automatic acquisition of knowledgeand accurate positioning of faults are realized, the diagnosis precision is improved, and a basis is provided for fault diagnosis of an industrial control system.
Owner:716TH RES INST OF CHINA SHIPBUILDING INDAL CORP
System and method for constructing level knowledge base based on inference
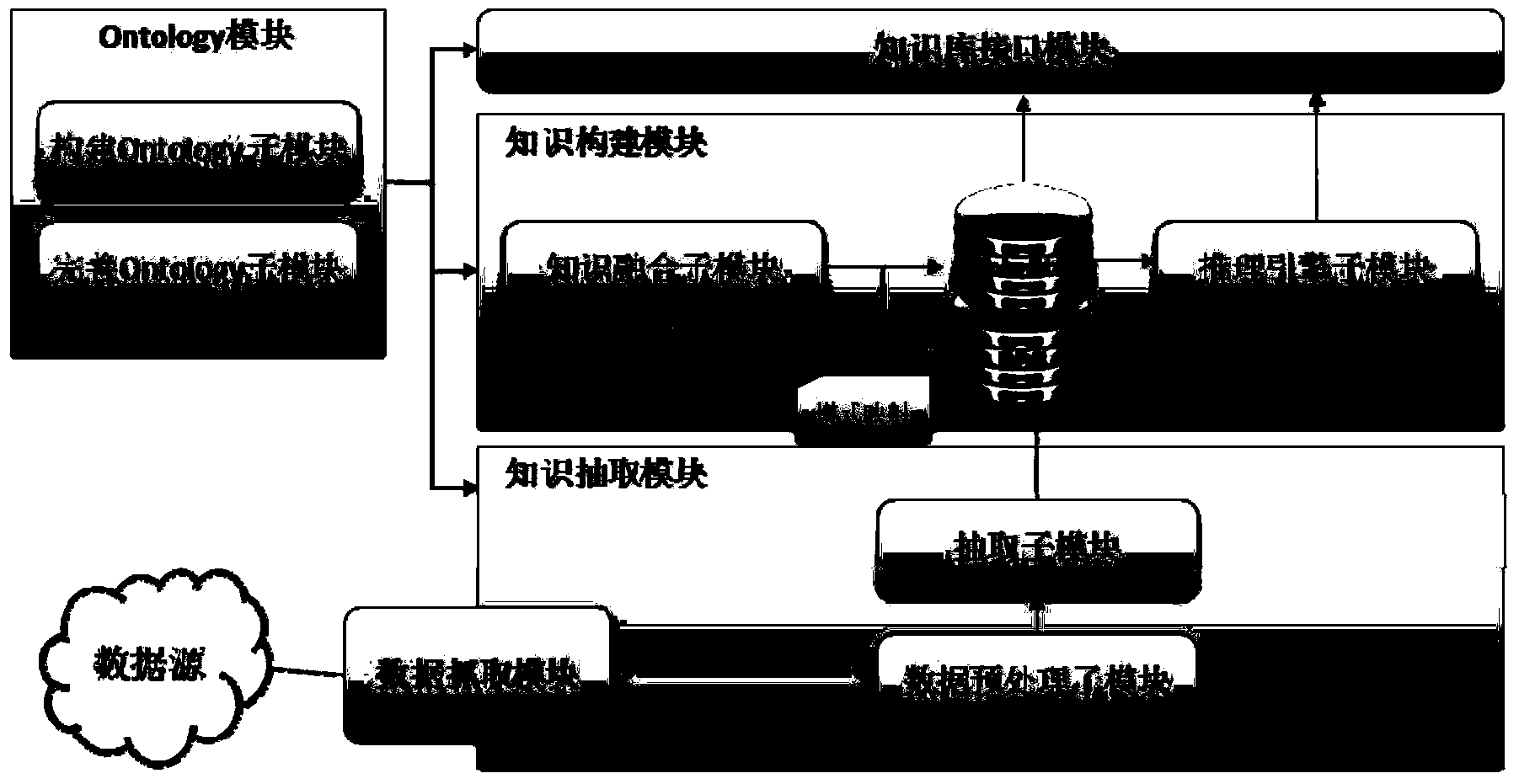
ActiveCN103646025AImprove update efficiencyWeb data navigationSpecial data processing applicationsBasic knowledgeData scraping
The invention provides a system and method for constructing a level knowledge base based on inference. The system comprises a data capturing module, an Ontology module, a knowledge extraction module and a knowledge construction module, the Ontology module is used for constructing and updating field Ontology, classification Ontology and overall Ontology, the knowledge extraction module is used for extracting attribute content in each data source to obtain needed field knowledge, the attribute content can be mapped into the field Ontology, the knowledge construction module comprises a knowledge fusion sub-module and an inference engine sub-module, the knowledge fusion sub-module is used for fusing and storing the field knowledge from all the data sources in the same field to obtain a basic knowledge base, the inference engine sub-module is used for calling the Ontology module and defining the classification Ontology, related inference rules are made, the inference rules are applied to the basic knowledge base, and potential knowledge is obtained and stored in classification knowledge bases corresponding to all classifications. The system and method can facilitate the maintenance and update of the knowledge base.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
Admission control method and system in heterogeneous wireless network environment
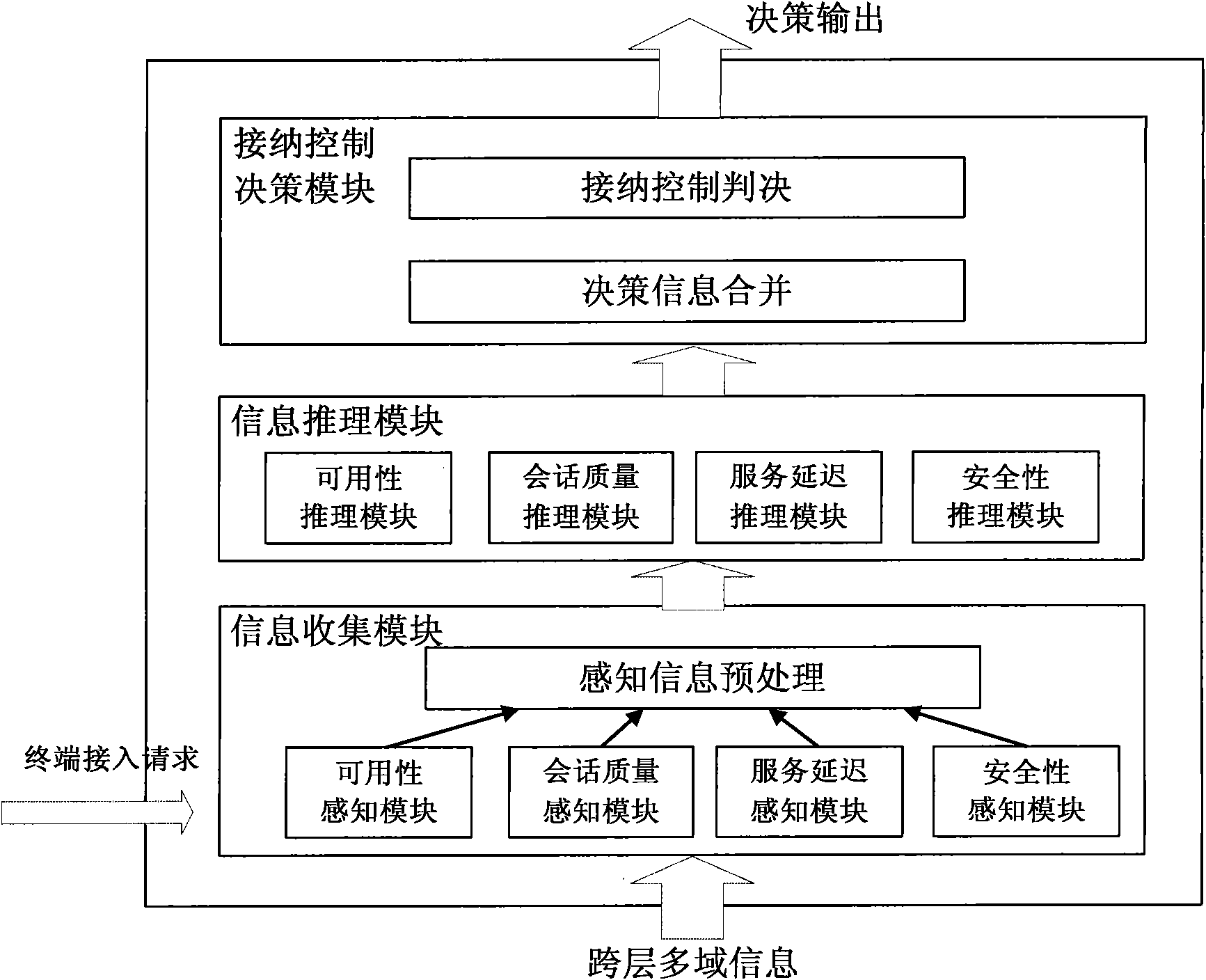
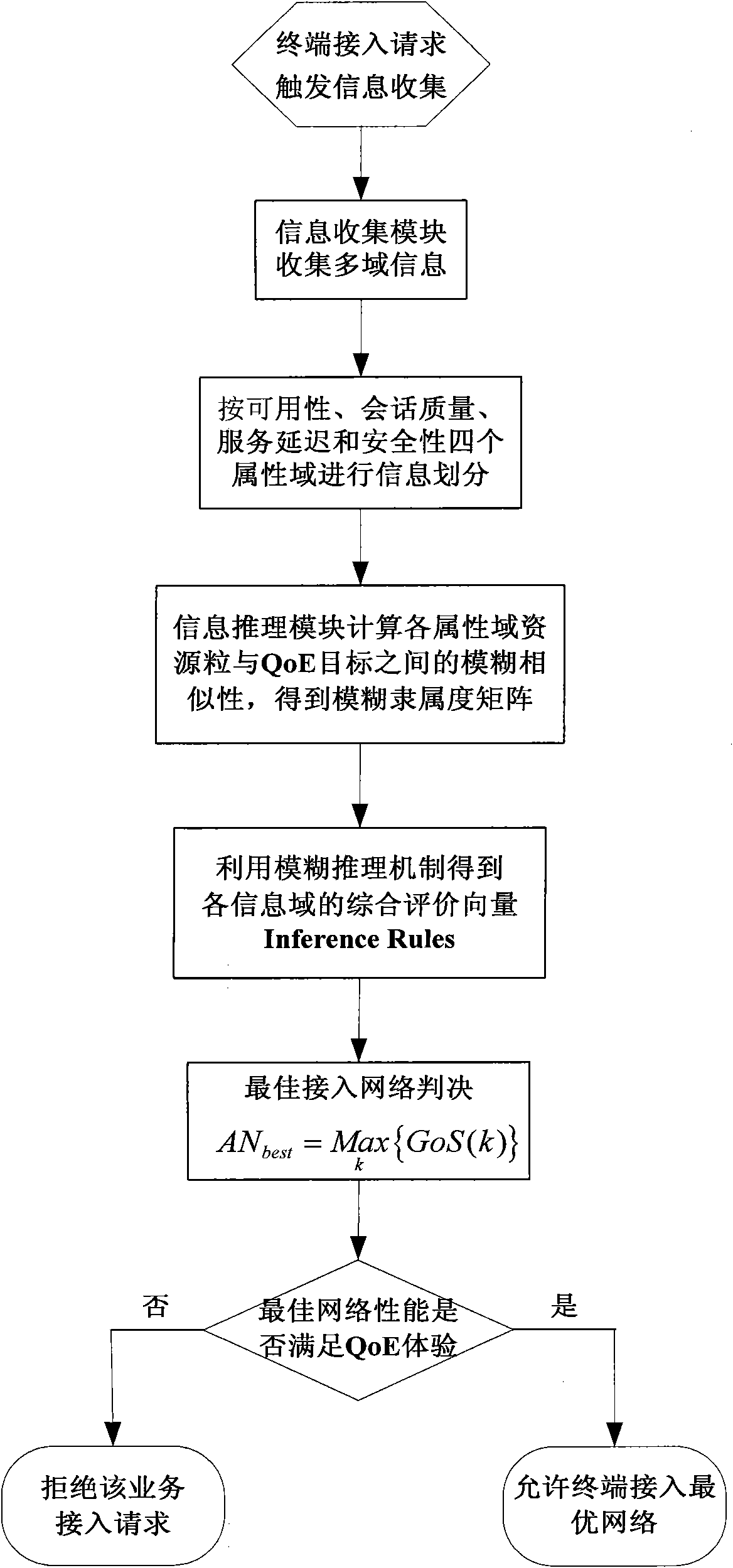
InactiveCN101820665AModeling Abstract RealizationAchieve the purpose of abstractionAssess restrictionGrade of servicePerformance index
The invention discloses an admission control method and an admission control system in a heterogeneous wireless network environment. The method comprises the following steps of: when an access request is received, collecting the multi-domain information of each network and acquiring a target quality of experience (QoE) vector of a user in the access request by using an admission control entity; performing granularity partition on the information of each attribute domain in the multi-domain information according to a predefined performance index to form information granularity vectors of each attribute domain; according to the target QoE vector of a user terminal and a predefined fuzzy membership function, establishing fuzzy membership grade vectors of resource grains in each attribute domain; based on fuzzy evaluation vectors and inference rules of the resource grains in each attribute domain, establishing mapping relationships between the fuzzy evaluation vectors of the resource grains in each attribute domain and a network comprehensive evaluation index so as to acquire a comprehensive evaluation vector; and according to comprehensive evaluation, selecting the network having the highest network grade of service as an access network. Through the method and the system, an effective admission control strategy is designed for the heterogeneous wireless network and the overall performance of the heterogeneous wireless network is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Network user behaviors personalization expression method based on semantic matrix
InactiveCN101334783AEasy to masterEasy to understand and handleSpecial data processing applicationsPersonalizationNetwork behavior
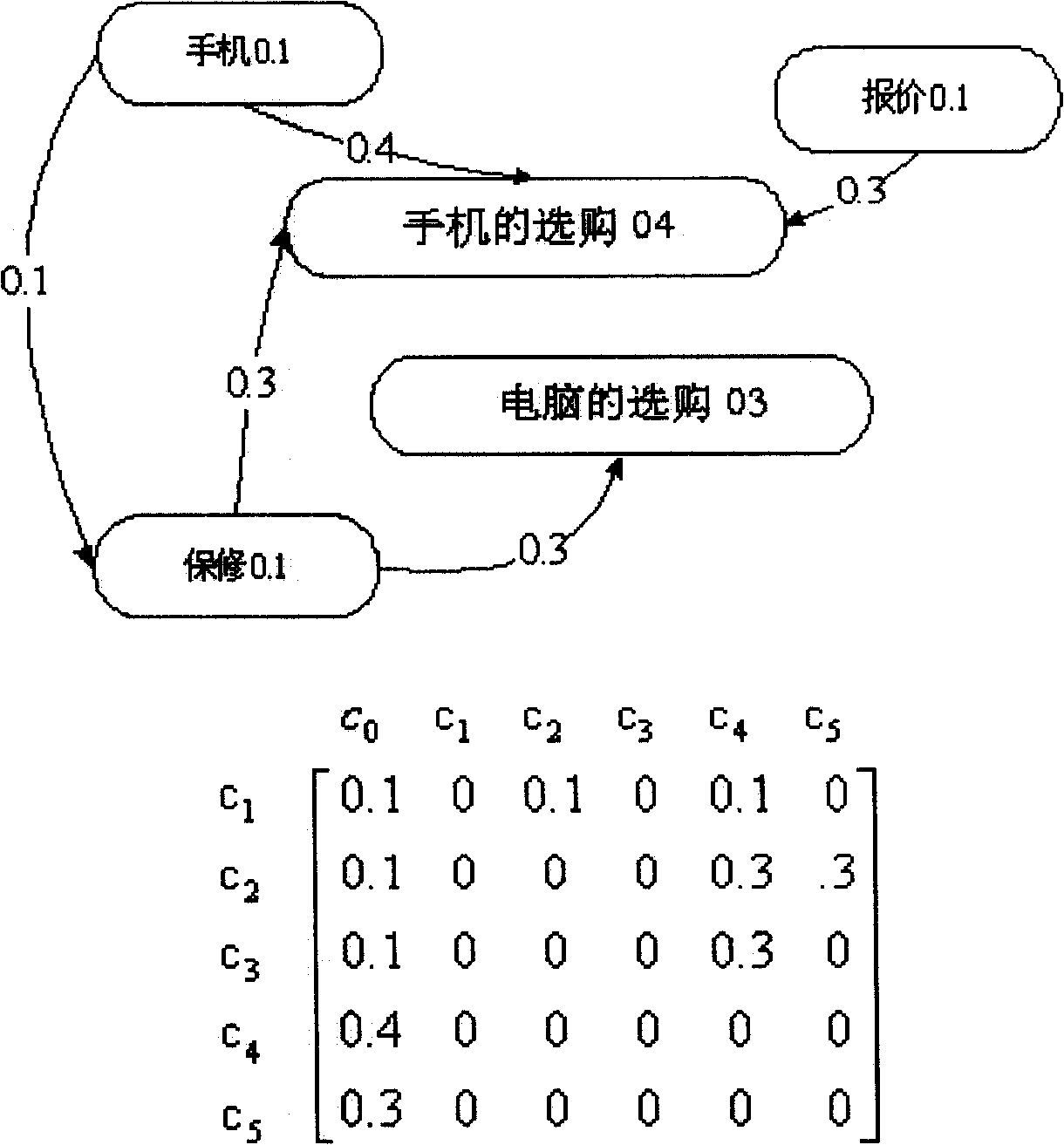
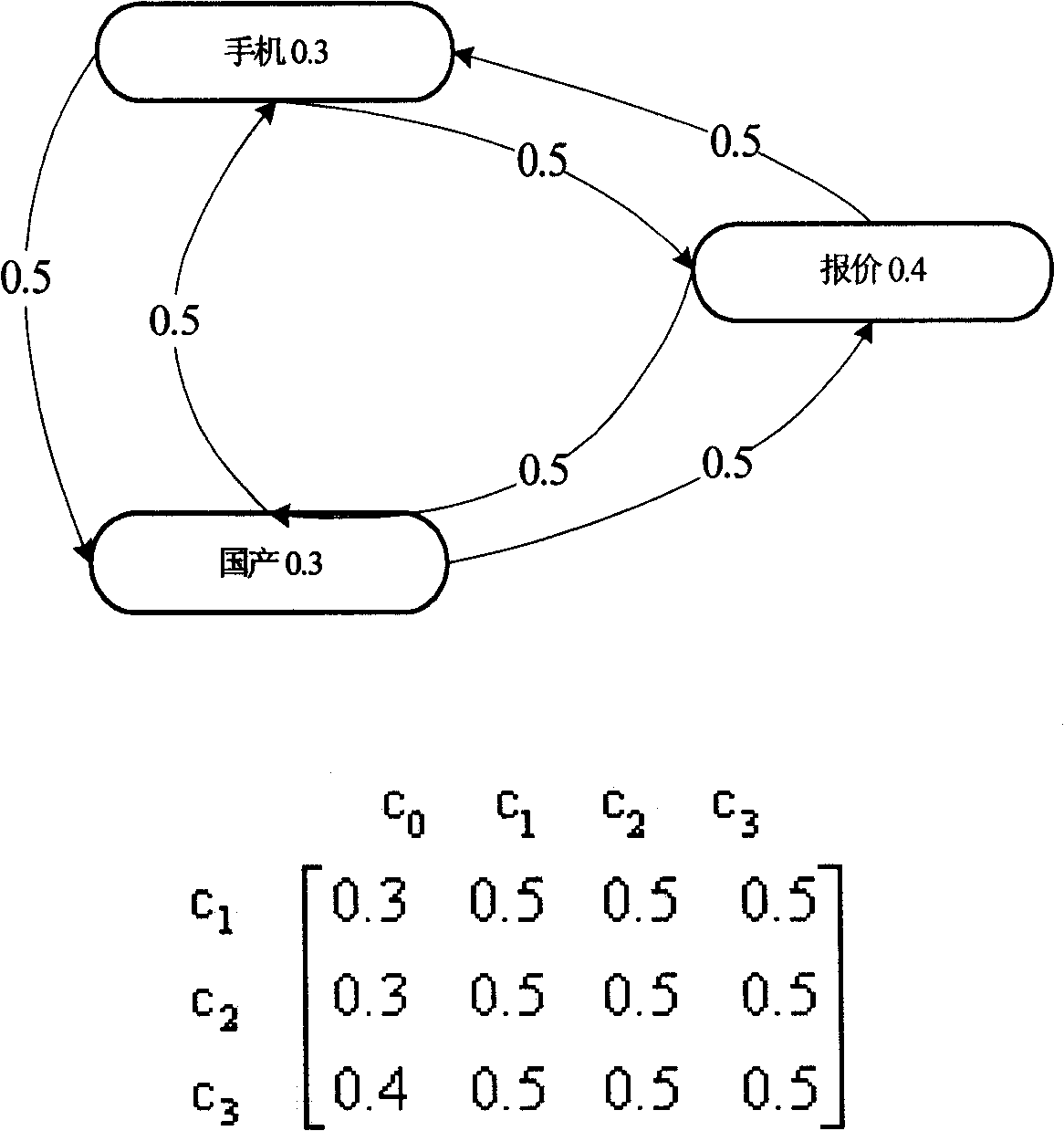
The invention relates to a network user behavior individualization expression method defining influence factors of network user behavior into: operation content, operation type and operation weight. A semantic matrix is formed according to the types of user behavior and items in the semantic matrix represent the interested concepts of users and values in the semantic matrix represent the interested concepts of users and the relevance between concepts and the relevance degree; the user behavior semantic matrix can be updated and evolved according to the changing of user preference. The core of the invention is to form the semantic matrix from the point of user browse behavior and content analysis and to describe individualized characteristics of network user behavior on the basis of inference rules of matrix operation. The method can promptly and effectively express the individualized behavior of network users so as to lead a computer to master and carry out understanding process. The invention can provide technical solutions for realizing individualized searching and active push.
Owner:SHANGHAI UNIV
Rule-Based Selection of Content
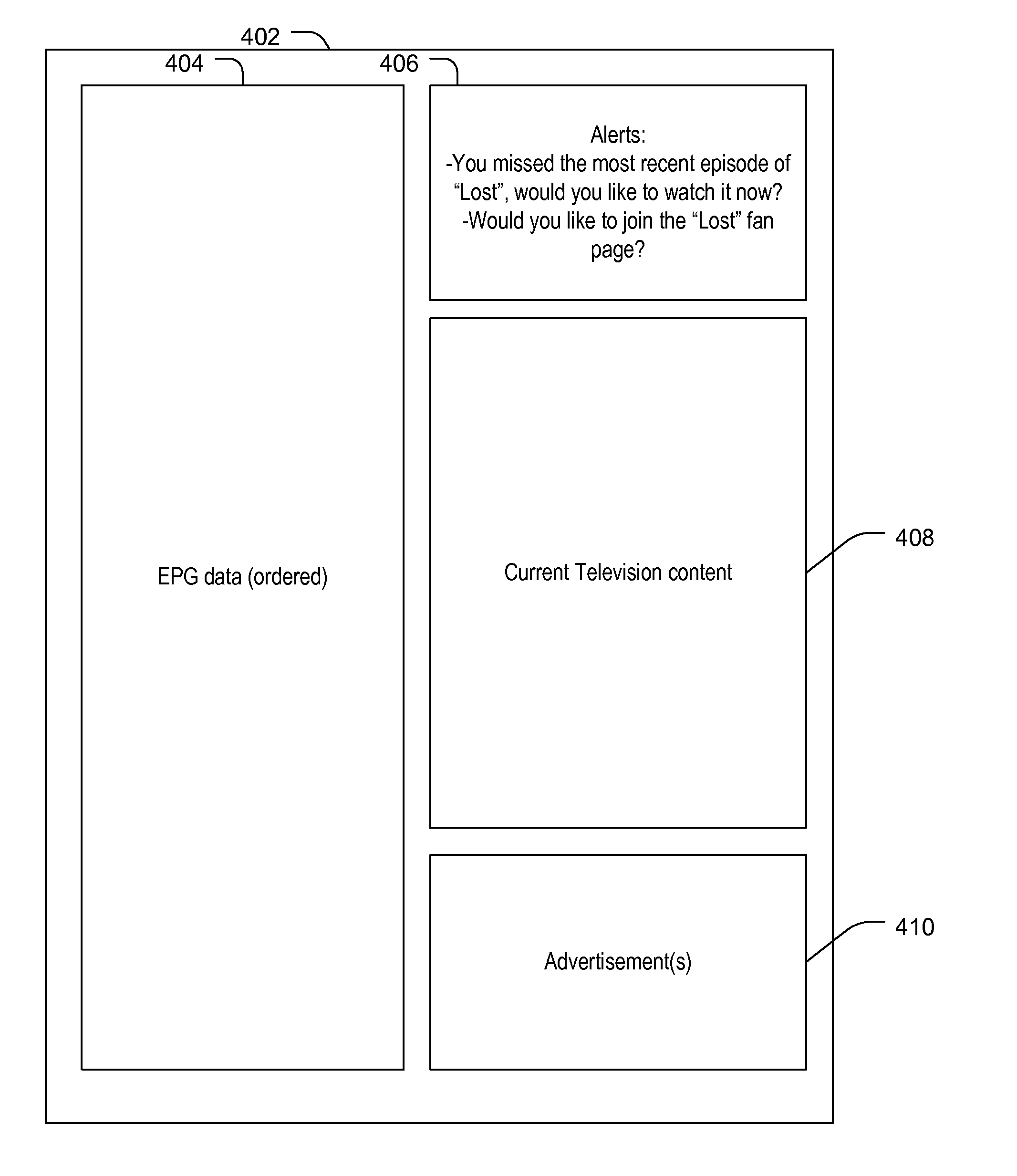
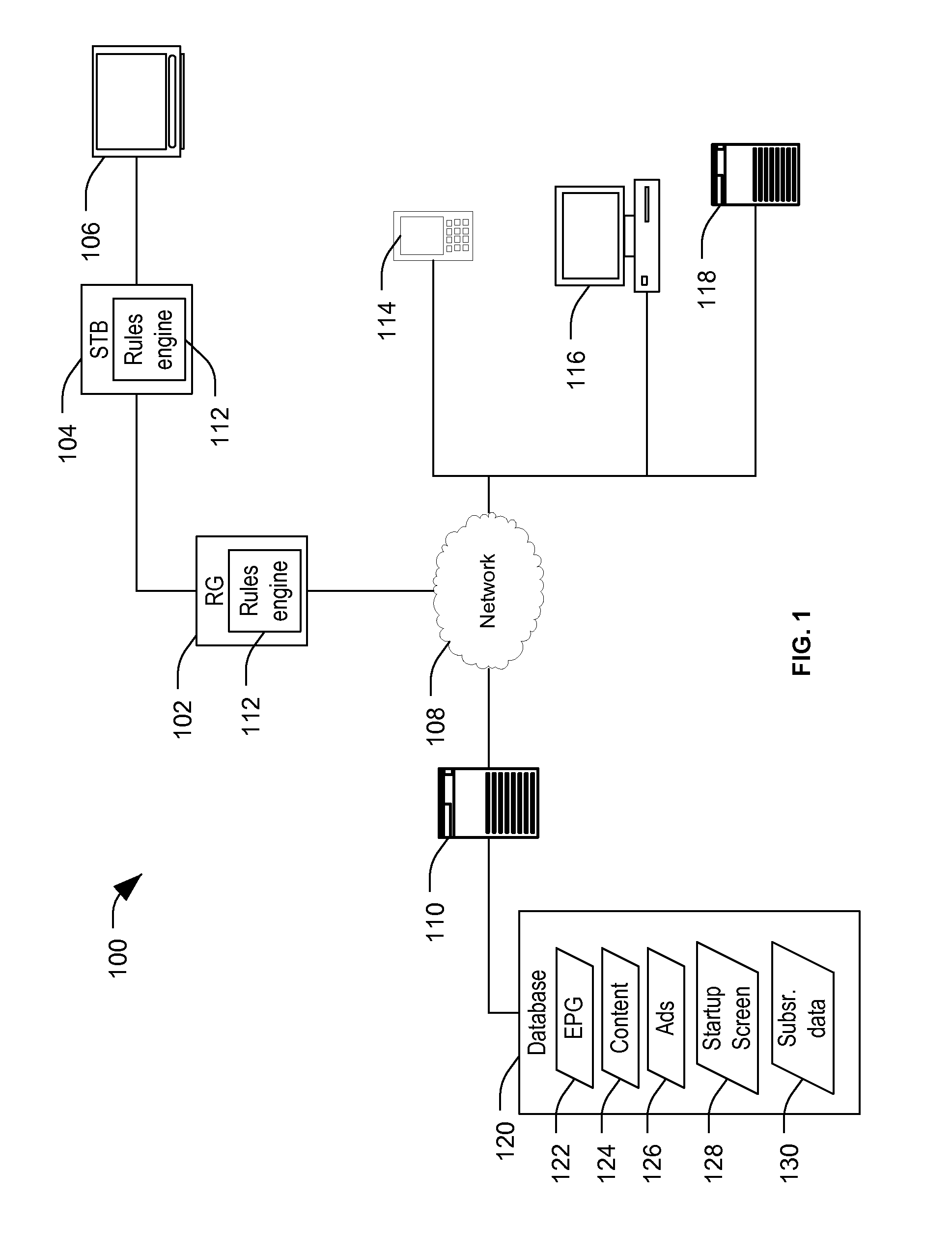
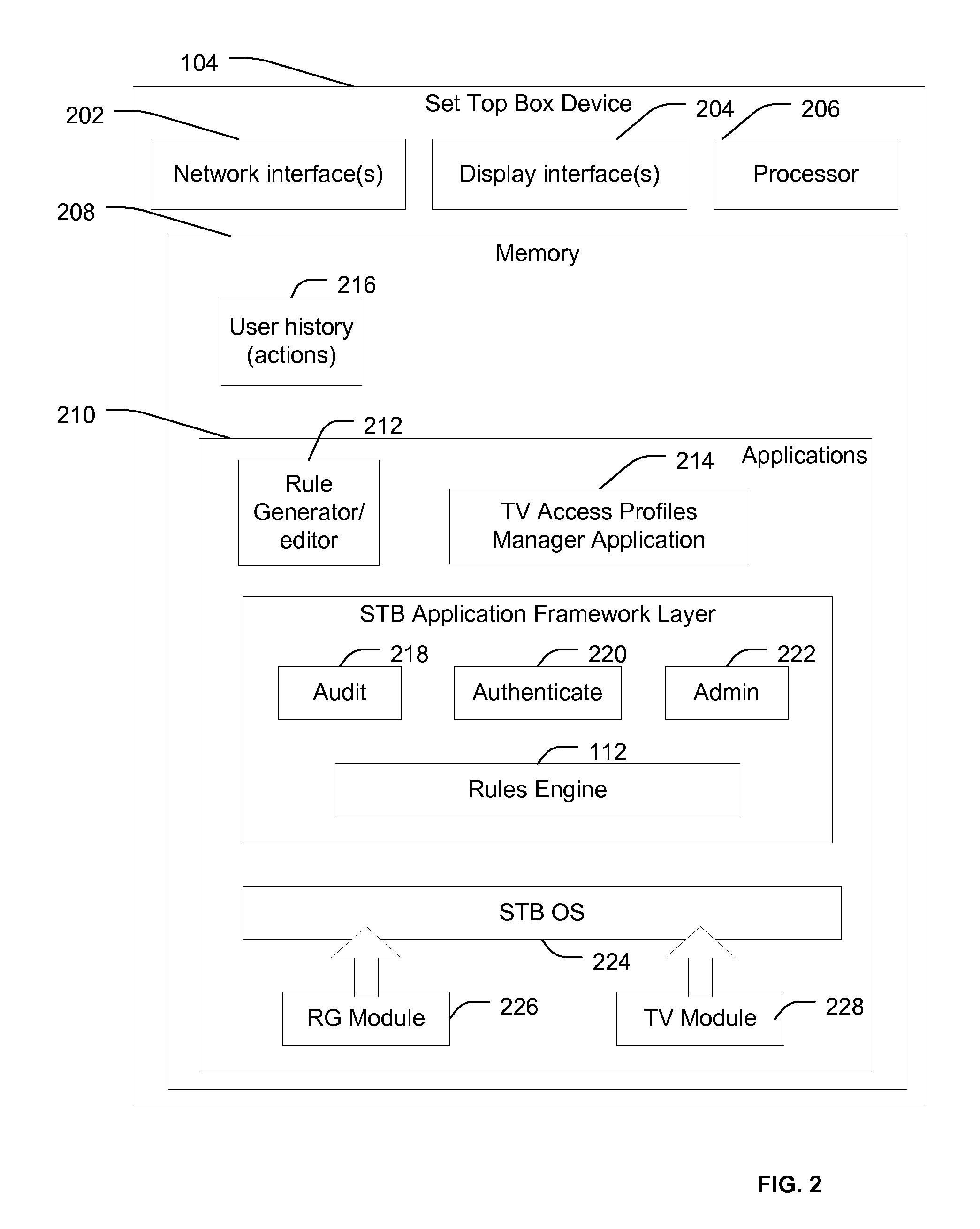
ActiveUS20120151527A1Television system detailsColor television detailsDisplay deviceCustomer-premises equipment
A method includes, at a customer premise equipment (CPE) device, accessing data descriptive of content available via a network coupled to a network interface of the CPE device. A plurality of rules are analyzed using a forward-inferencing rules engine to determine whether one or more of the rules are satisfied based on the data. The rules include at least one user defined rule and at least one automatically generated rule, where the at least one automatically generated rule is automatically generated based on user history information. The method includes selecting particular content of the content available via the network for presentation via a display device.
Owner:AT&T INTPROP I L P
Techniques for automated generation of ontologies for enterprise applications
ActiveUS8214401B2Digital data information retrievalDigital data processing detailsApplication softwareXML
Embodiments of the present invention provide techniques for generating ontologies. In one embodiment, techniques are provided for automatically generating an ontology based upon input information. The input information may, for example, be in the form of XSD, XML, WSDL, or WSRP, etc. The automatically generated ontology may be encoded in OWL or other RDF-compliant language. A set of inference rules may also be automatically generated using the input information. The automatically generated ontology and the set of inference rules may be stored in a database for further processing.
Owner:ORACLE INT CORP
Ontology-based intelligent retrieval system for information security event
InactiveCN105550189AImplement Semantic RetrievalWeb data indexingSemantic analysisSemantic searchData mining
The invention designs and realizes an ontology-based intelligent retrieval system for an information security event, which is a system for performing information retrieval of the information security event based on an ontology, and contains knowledge from the field of information security. The goal of designing the system is to provide knowledge accumulation in the field of information security for a user, and the system has a certain intelligent semantic retrieval function, so that the user can obtain required information security event related knowledge and information. A design concept is that firstly, an initial information security event domain ontology is established based on OWL, then information security event domain related information is acquired, and a relationship between information security event domain concepts is extracted, thereby realizing automatic expansion of the information security event domain ontology; secondly, an inference rule is designed according to a semantic relationship of the information security event ontology, and the information security event ontology is inferred based on Jena; and finally, the query expansion and sorting are carried out based on the information security event ontology and semantic similarity calculation, thereby realizing semantic retrieval of the information security event.
Owner:XUCHANG UNIV
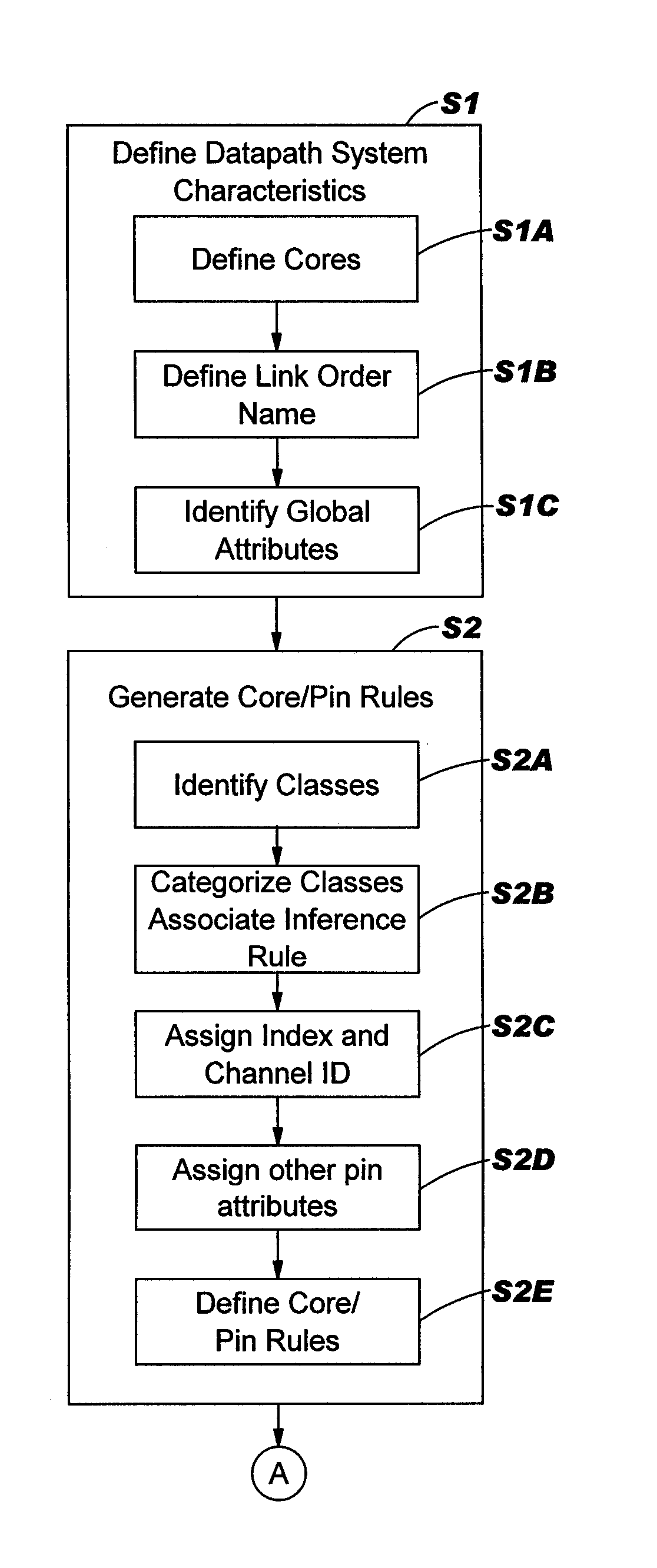
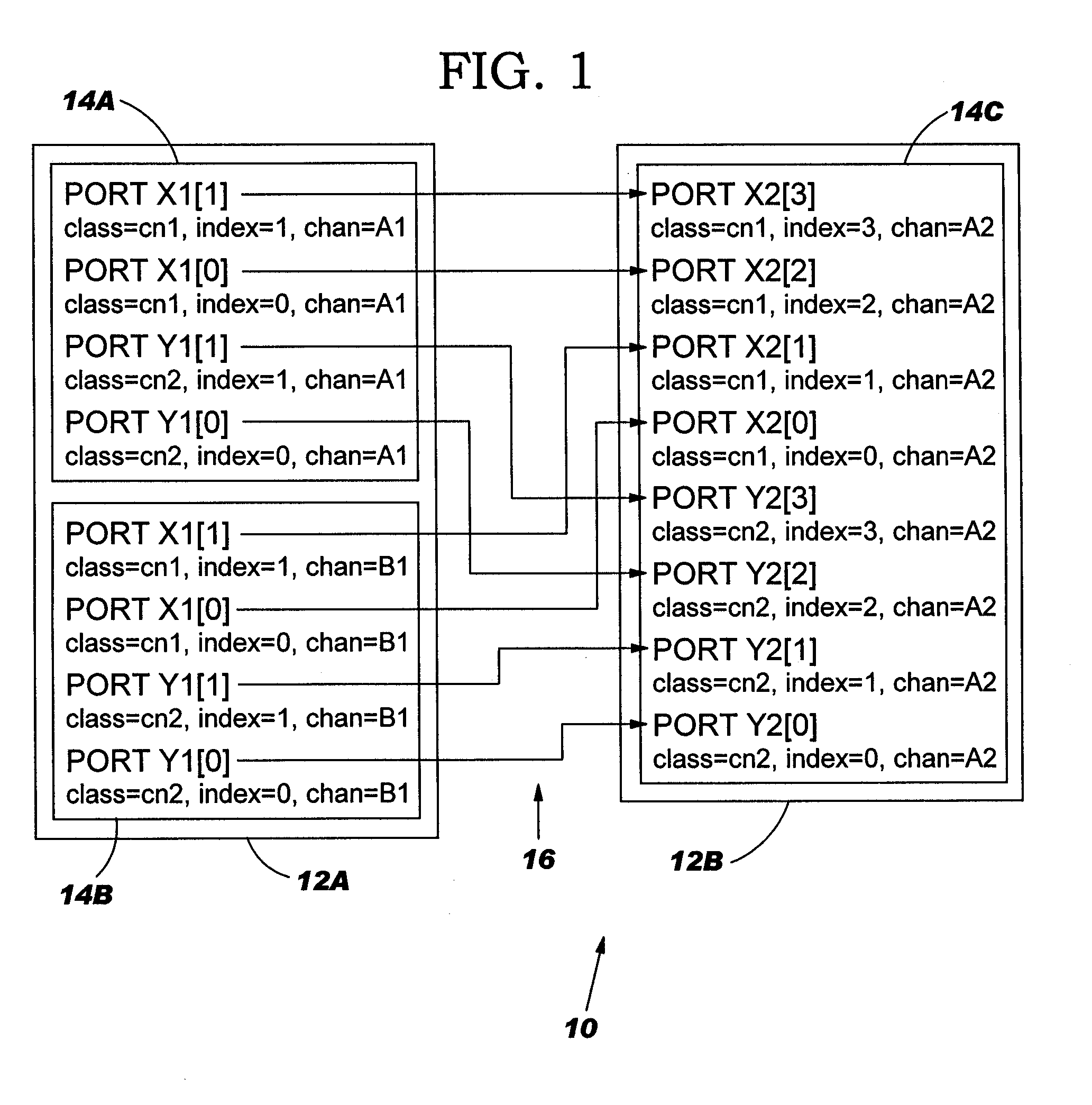
Method, system and program product for building an automated datapath system generating tool
InactiveUS20050257179A1Computer aided designSpecial data processing applicationsType inferenceDatapath
A method, system and program product for building an automated bit-sliced datapath system generating tool so design can be performed at a higher level, and automated generation of the synthesizable HDL representation can be accomplished are disclosed. A method defines datapath system characteristics, defines core / pin rules, and then constructs class-type inference rules that can be used for automatically generating the datapath system. An “orthogonal bundling” technique is used that groups pin by a class, and also by a channel identifier. The class-type inference rule corresponding to each class uses of the following factors to infer appropriate wiring: 1) number and type of pins in the class created by the instantiation of cores by the user; 2) attribute definitions on pins set by library core / pin rules; 3) user selection of “global attributes”; 4) user definition of channel bit order (“link orders”) to imply the order of connection between stages; and 5) user-defined attributes set on pin classes.
Owner:GOOGLE LLC
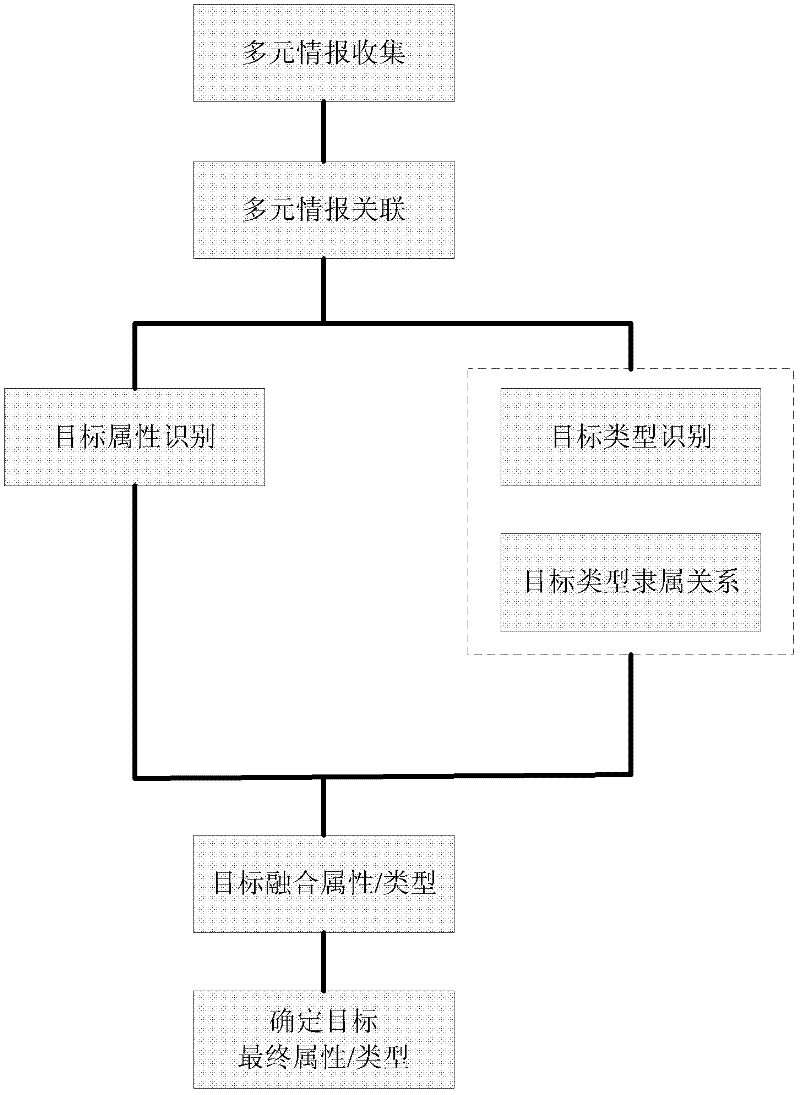
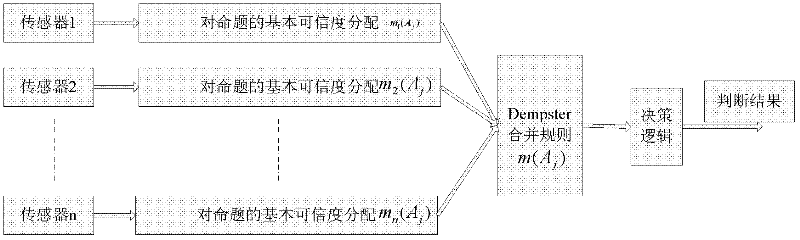
Comprehensive target identification method based on uncertain reasoning
ActiveCN102393912AImprove accuracyImprove reliabilityCharacter and pattern recognitionData setGoal recognition
The invention discloses a comprehensive target identification method based on uncertain reasoning. Various reconnaissance equipment and methods are adopted for scouting a same target so as to obtain target information and accomplish multielement information association, and the information on properties and types sent by each information source is fused and calculated by DS (data set) evidences based on the uncertain reasoning principle, thereby obtaining the final property and type information of the target. With the method, firstly, the information utilization rate on the plurality of information sources is enhanced, and the advantages of different information reconnaissance methods are utilized sufficiently; secondly, by a type knowledge base, the relationships of administrative subordination among different level types are established so as to obtain a more specific target type; thirdly, by adopting a DS evidence theory fusing method, prior probability and conditional probability intensity are not needed, and the requirements on preconditions are looser; and fourthly, the comprehensive target identification method can run under different working modes, thereby enhancing the reliability on target identification.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
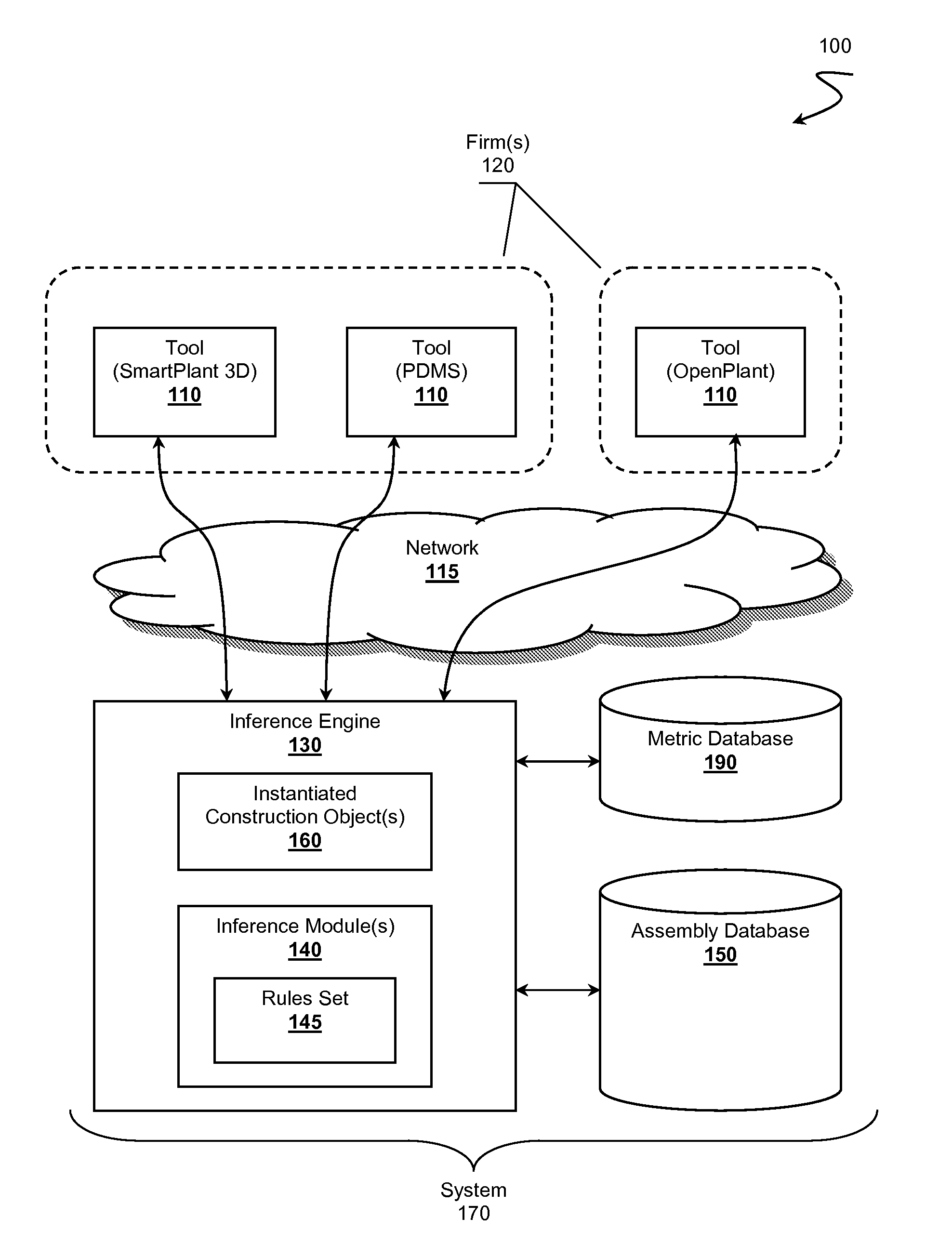
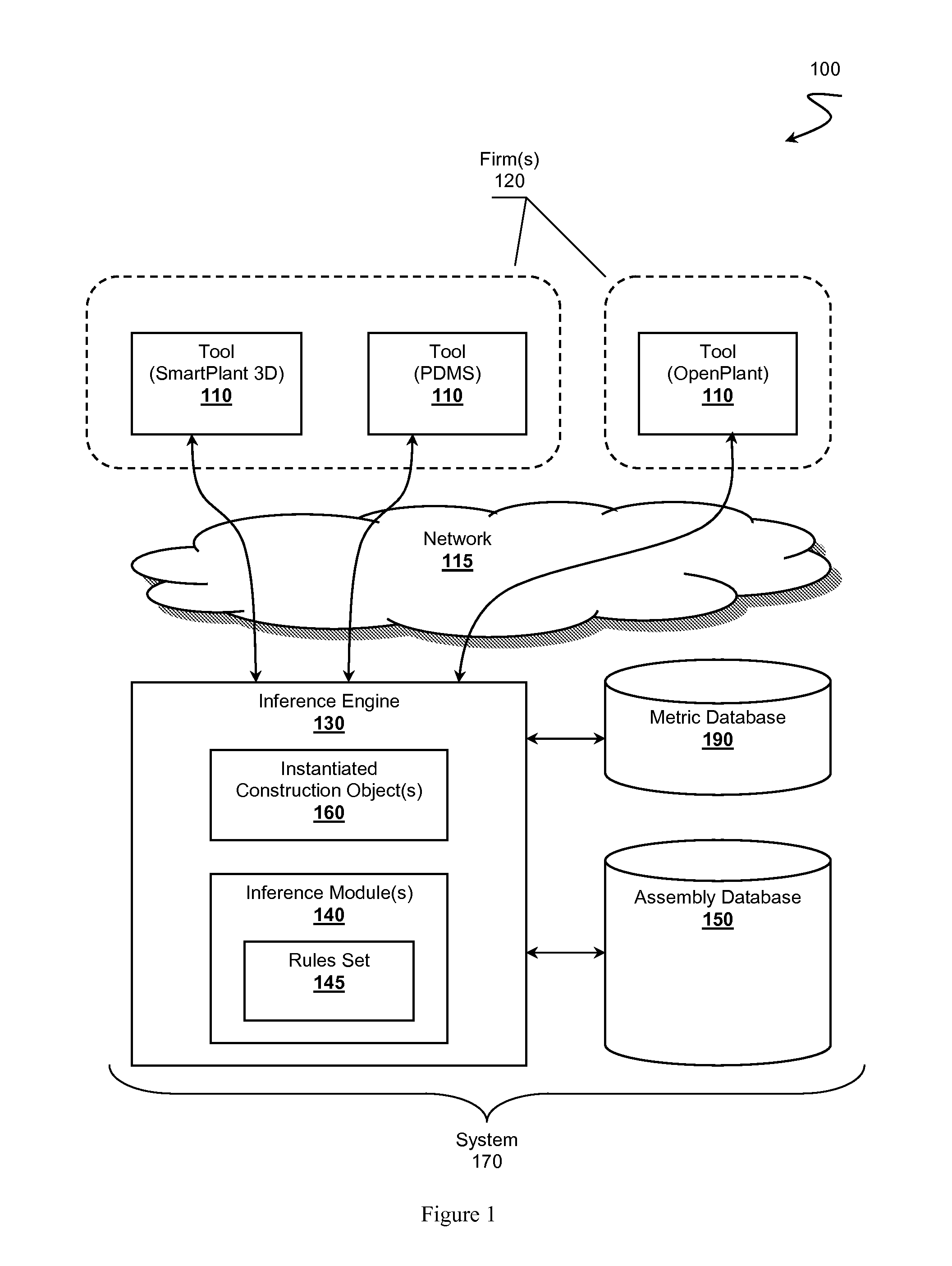
Intelligent Plant Development Library Environment
InactiveUS20120072386A1OptimizationGeometric CADKnowledge representationAbductive reasoningCable tray
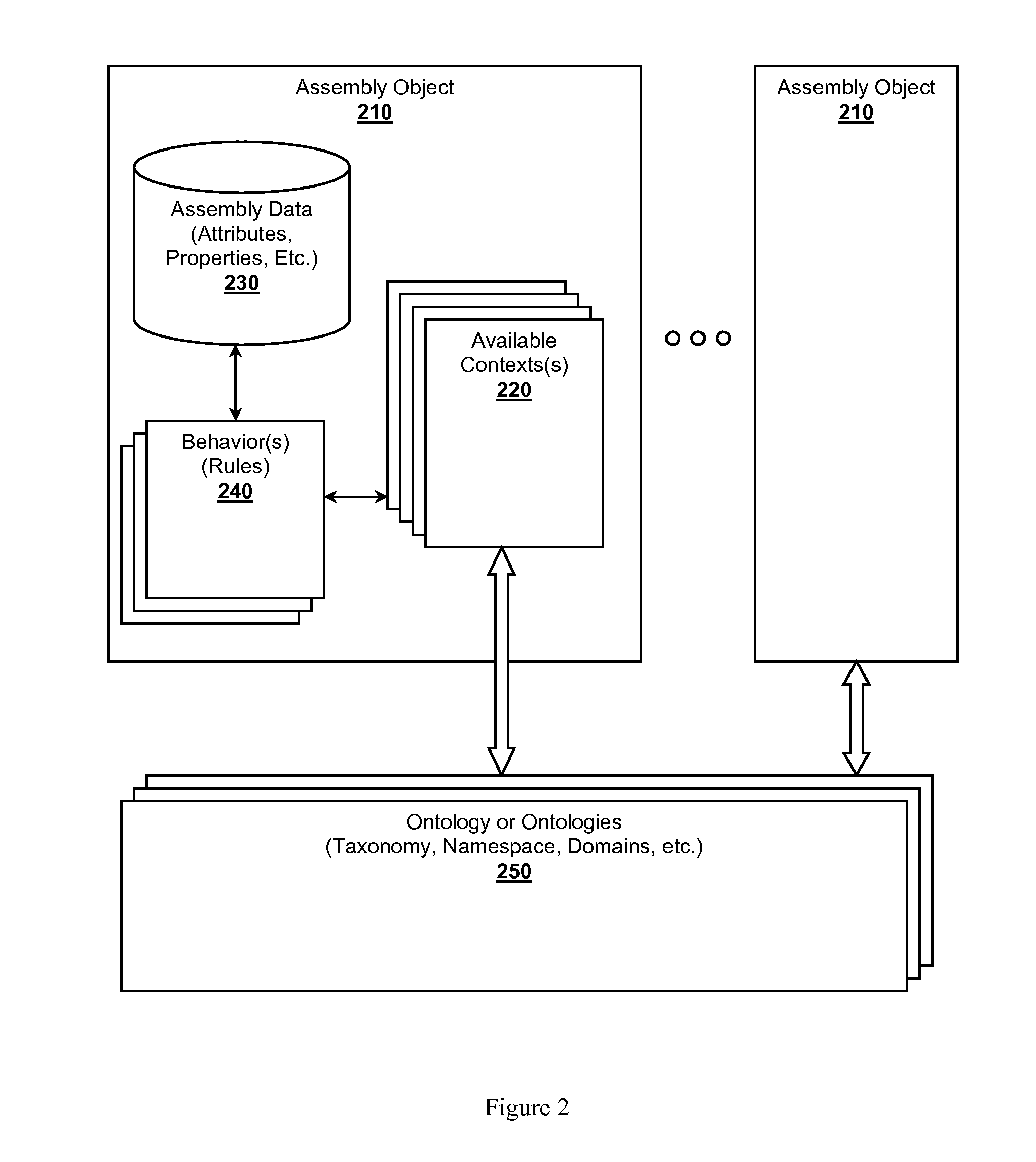
An intelligent plant development library environment is presented. Contemplated environments comprise an EPC knowledge system capable of incorporating know-how of one or more construction firms in the form of assembly objects. Assembly objects represent construction components (e.g., bolts, cable trays, pipes, processing units, deliverables, etc.) that can be incorporated into a plant design. Assembly objects are stored in an assembly database and include available contexts considered relevant to the assembly objects. An inference engine is utilized to derive a specified context related to a plant design from one or more design tools. The inference engine applies rule sets to infer which assembly objects to instantiate as construction objects. The inference engine can further configure the design tools to incorporate the instantiated construction objects into a plant construction project model. Example rule sets include forward chaining rules, backward chaining rules, case-based reasoning rules, inductive reasoning rules, or abductive reasoning rules.
Owner:FLUOR TECH CORP
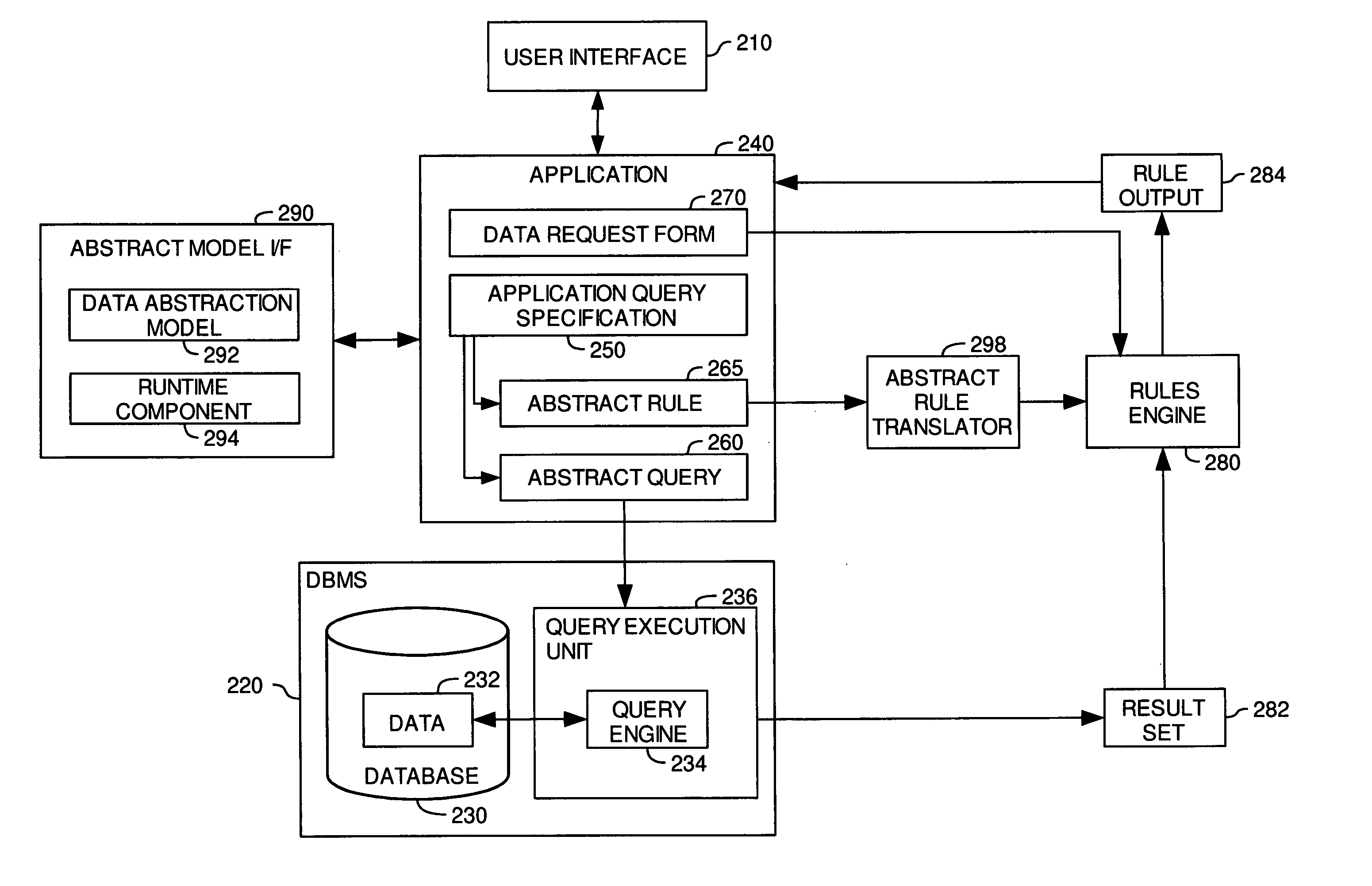
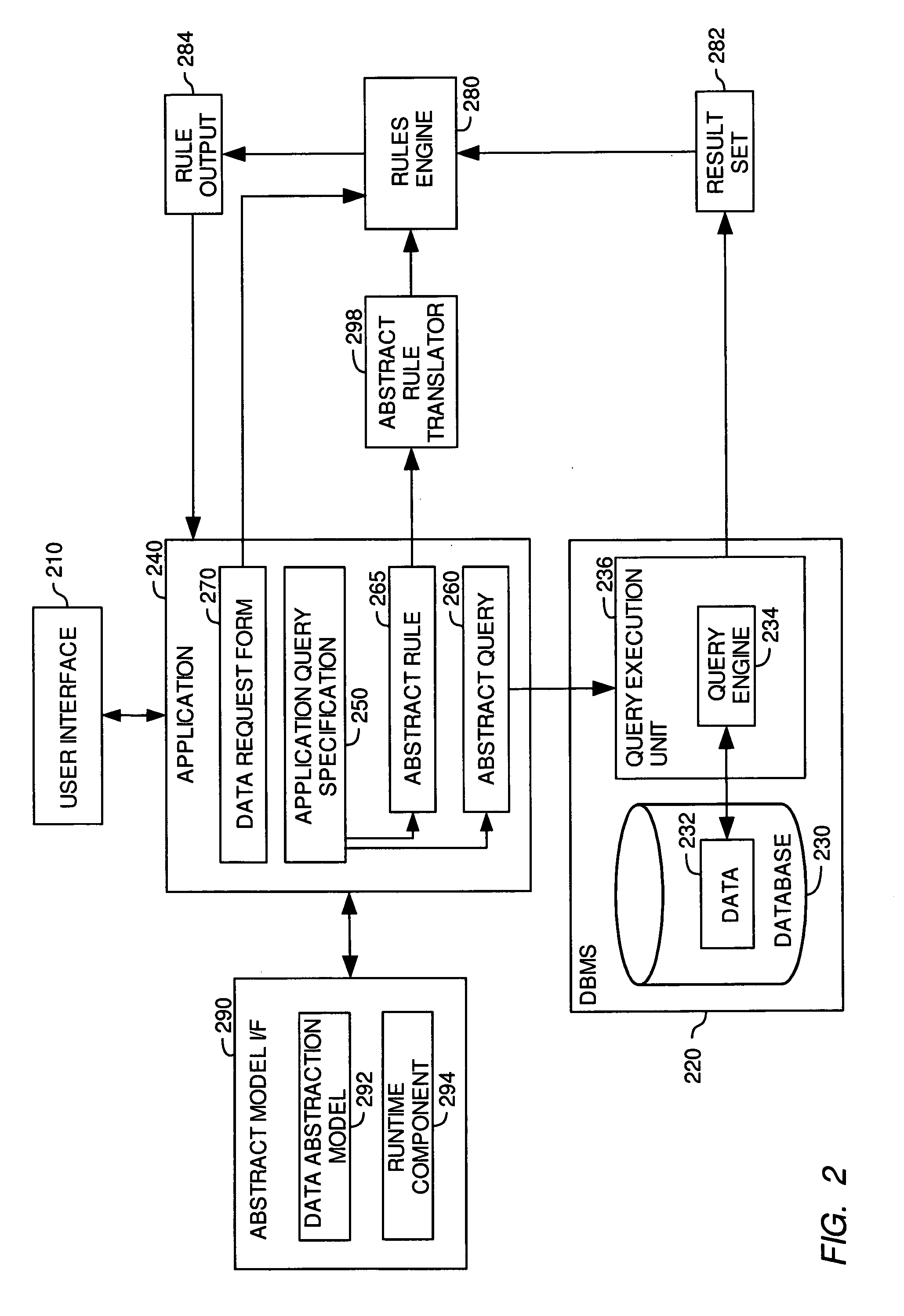
Strict validation of inference rule based on abstraction environment
InactiveUS20070112853A1Data processing applicationsKnowledge representationProgramming languageData value
A method, system and article of manufacture for processing rule sets and, more particularly, for processing abstract rule sets. One embodiment provides a computer-implemented method of managing execution of an analysis routine configured to process one or more inputs. The analysis routine is defined by at least one abstract rule set having one or more abstract rules each having a conditional statement and a consequential statement. The method comprises determining, from the retrieved analysis routine, a predefined validating condition that needs to be satisfied by at least one of the inputs, and validating a particular data value defining the at least one of the inputs on the basis of the predefined validating condition. If the particular data value is not validated, a predefined action configured to avoid execution of the analysis routine on invalid inputs is performed.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com