Patents
Literature
35 results about "CryptoLocker" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running Microsoft Windows, and was believed to have first been posted to the Internet on 5 September 2013. It propagated via infected email attachments, and via an existing Gameover ZeuS botnet. When activated, the malware encrypted certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displayed a message which offered to decrypt the data if a payment (through either bitcoin or a pre-paid cash voucher) was made by a stated deadline, and it threatened to delete the private key if the deadline passes. If the deadline was not met, the malware offered to decrypt data via an online service provided by the malware's operators, for a significantly higher price in bitcoin. There was no guarantee that payment would release the encrypted content.
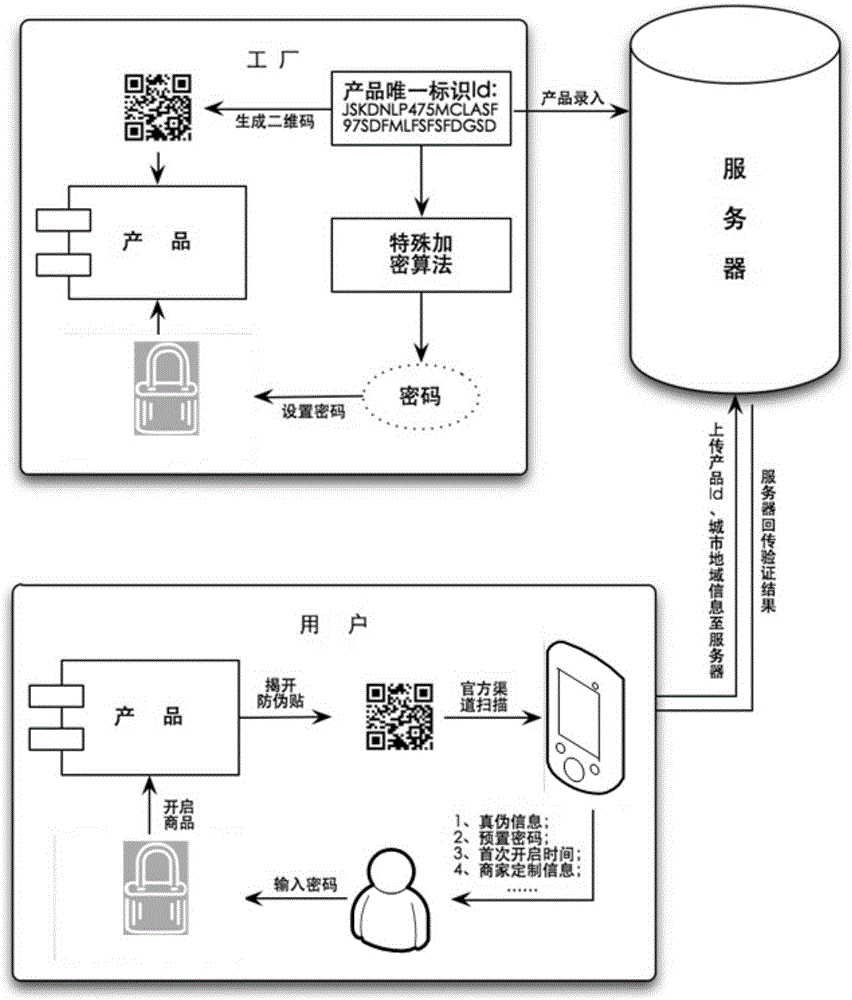
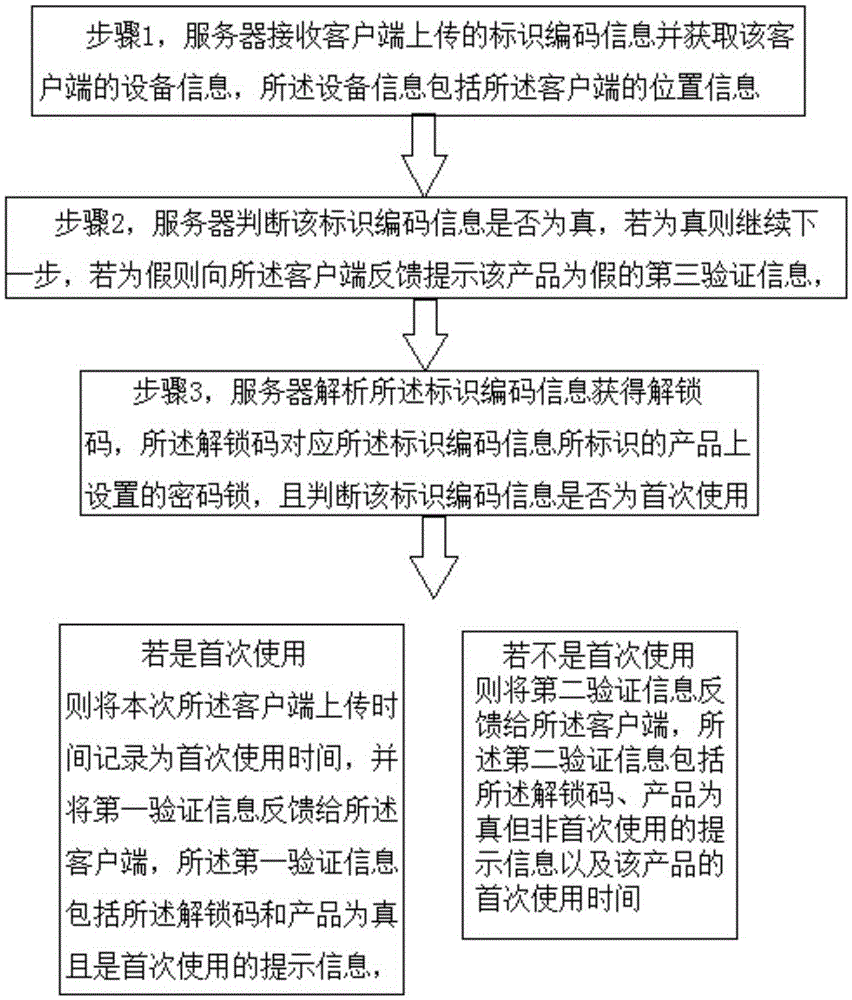
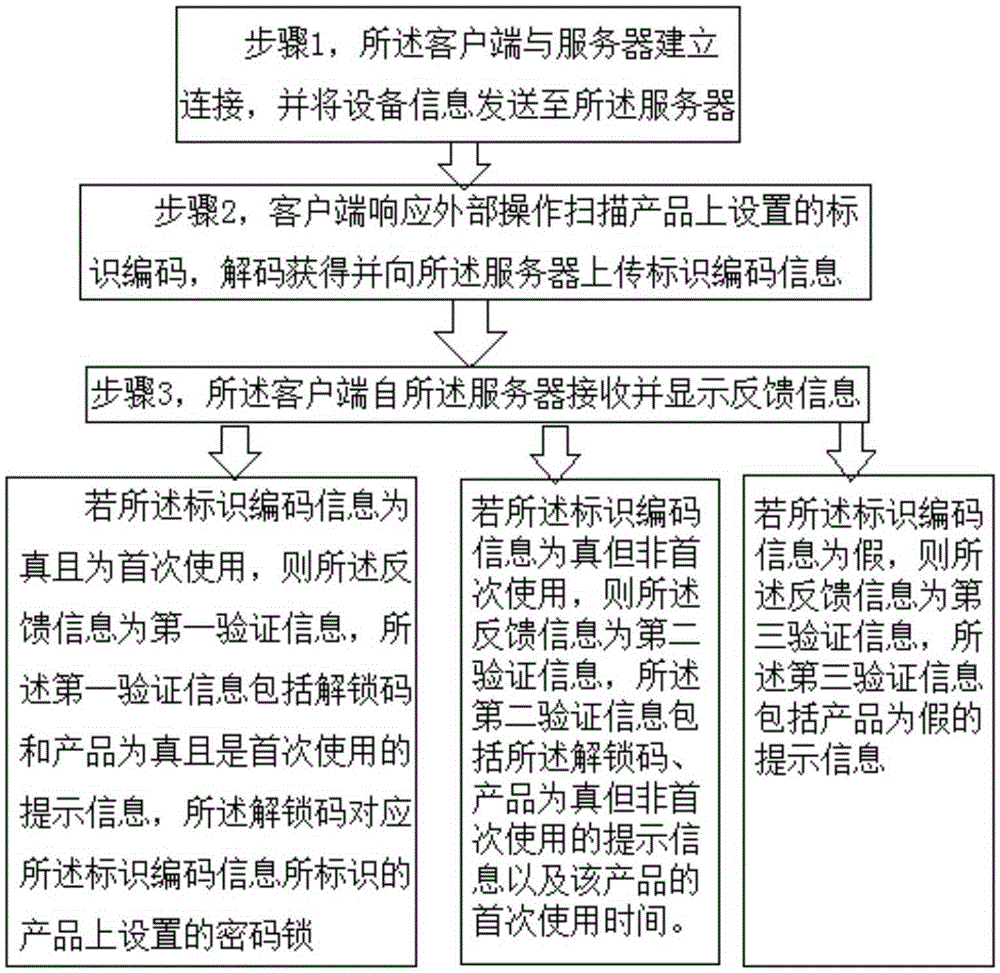
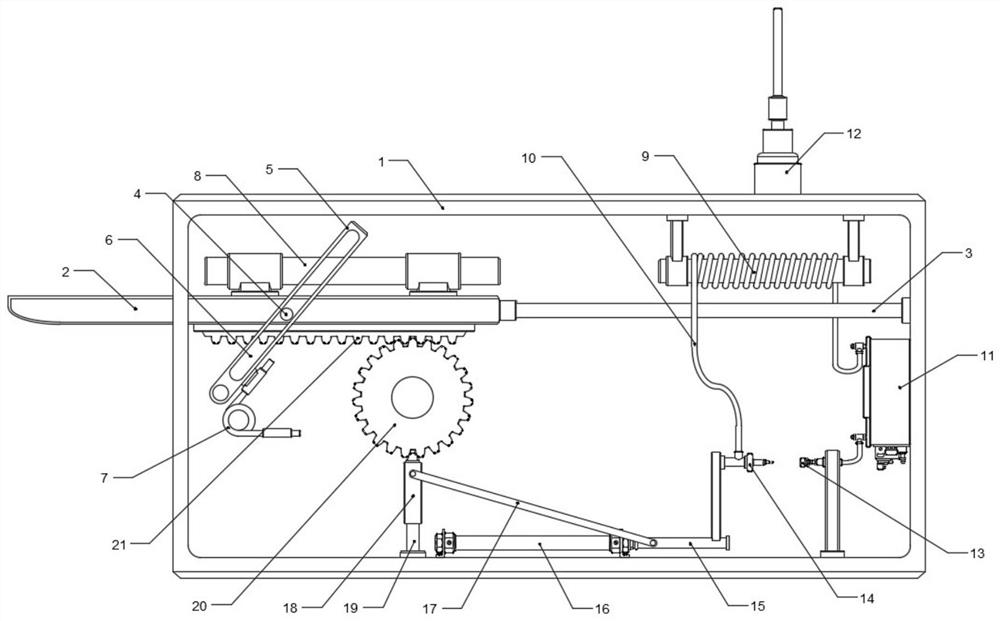
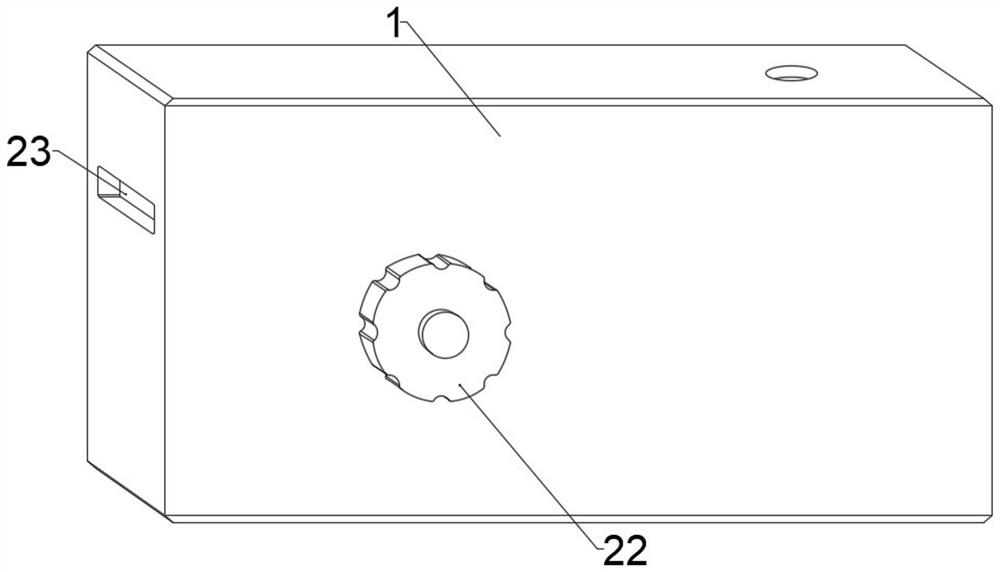
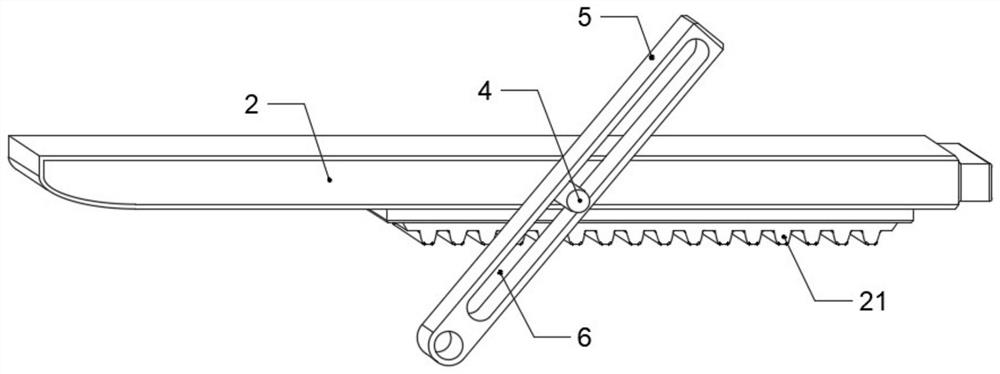
Anti-counterfeiting verification and sales information obtaining method and anti-counterfeiting verification and sales information obtaining system
InactiveCN105260892AReduce complexityRealize accurate statisticsCommerceTime distributionClient-side
Owner:SHANGHAI QIAOMA ELECTRONICS TECH
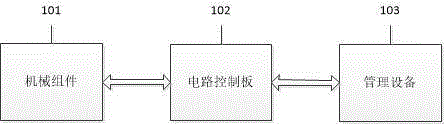
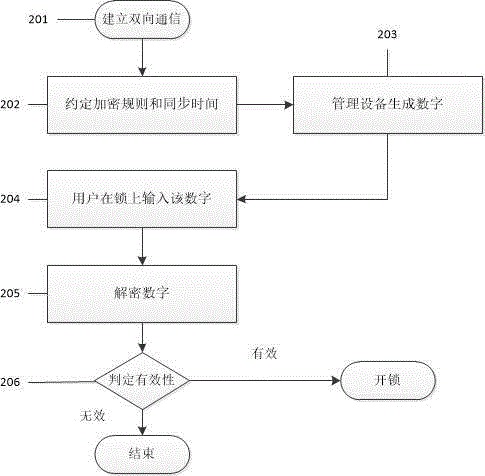
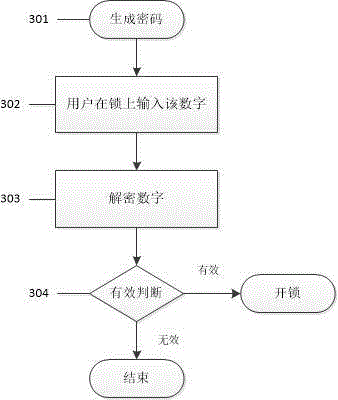
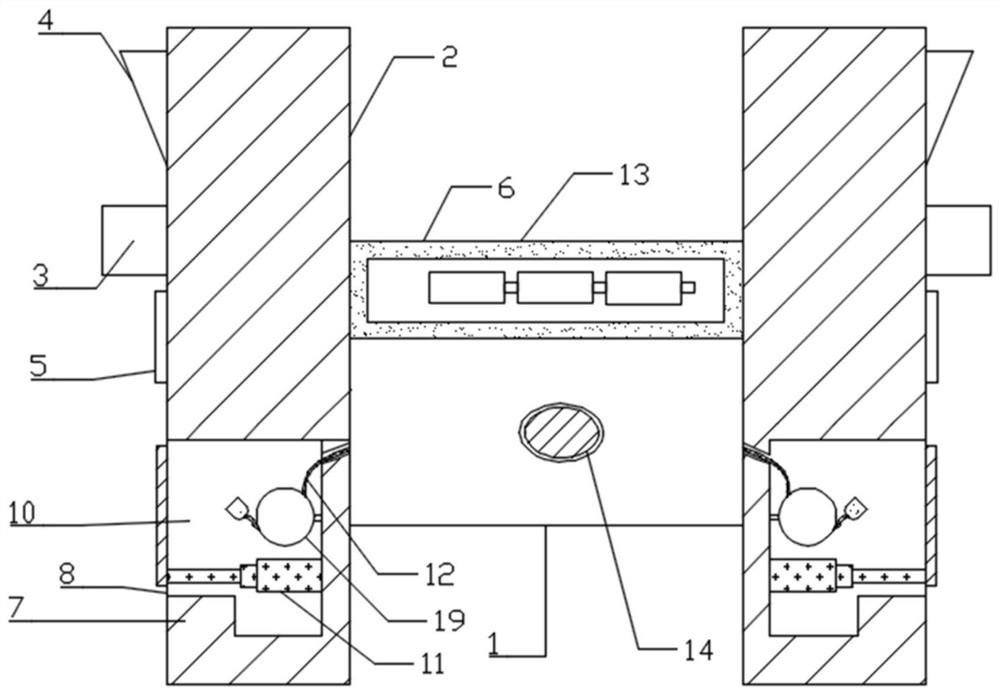
Timeliness coded lock and implementation method
InactiveCN105261092ALow costEasy and convenientElectric permutation locksIndividual entry/exit registersCommunication interfaceCurrent time
The invention discloses a timeliness coded lock and an implementation method. Card swiping locks, networking locks and the like on the present market can be widely replaced. The timeliness coded lock comprises a control circuit board, a mechanical part and a management device. The control circuit board comprises one or more processors, a storage device and one or more modules. The one or more modules run in cooperation with the processors and the storage device and are used for being communicated with assigned devices through various communication interfaces, storing assigned calculation rules, carrying out operation according to the assigned calculation rules, calculating current time, providing input interfaces through which users input passwords, decrypting the passwords, judging valid periods of the passwords, storing the passwords, judging the validity and the functions of the passwords and executing corresponding actions according to the validity and the functions of the passwords. The mechanical part comprises assemblies such as a lock body, a lock cylinder, a key, a handle and a shell and is used for controlling locking and unlocking of the door lock. The management device comprises one or more processors, a storage device and one or more modules. The one or more modules run in cooperation with the processors and the storage device and are used for being communicated with the door lock, generating the assigned calculation rules, carrying out operation according to the assigned calculation rules and generating the corresponding passwords according to the operation results.
Owner:李凯
Computer software encryption protection device
ActiveCN113158268AImprove securityReduce usageInternal/peripheral component protectionPasswordSecret code
The invention discloses a computer software encryption protection device, and the device structurally comprises a main machine body, an encryption storage disc, a storage disc interface protection cover and a machine body side cover. The invention has the following beneficial effects that a positioning chip is arranged in the storage disc and matched with a built-in hidden transmission line needing a secret key core board for turning transmission, and when the device is not used and carried, the transmission line of the equipment can be only connected with the positioning chip by pulling out the key core board, and the equipment can be normally read, transmitted and used only after the corresponding key core board is inserted and the transmission line is changed, so the safety after the equipment is lost is improved; a non-prompt hidden instruction detection and setting module is arranged on the basis of equipment software password frequency locking, and a secondary password module is matched, so that software locking of the equipment can perform advanced password input after a hidden instruction is input after a secondary password is locked, and secondary frequency locking is unlocked through the advanced password; therefore, the situation that the disk cannot be used due to malicious disk locking and wrong password input is better prevented.
Owner:福建金成信息科技有限公司
Novel security and secrecy intelligent information acquisition device and method
InactiveCN111159674AUniqueness guaranteedTo achieve the effect of security and confidentialityDigital data protectionDigital data authenticationData transformationEngineering
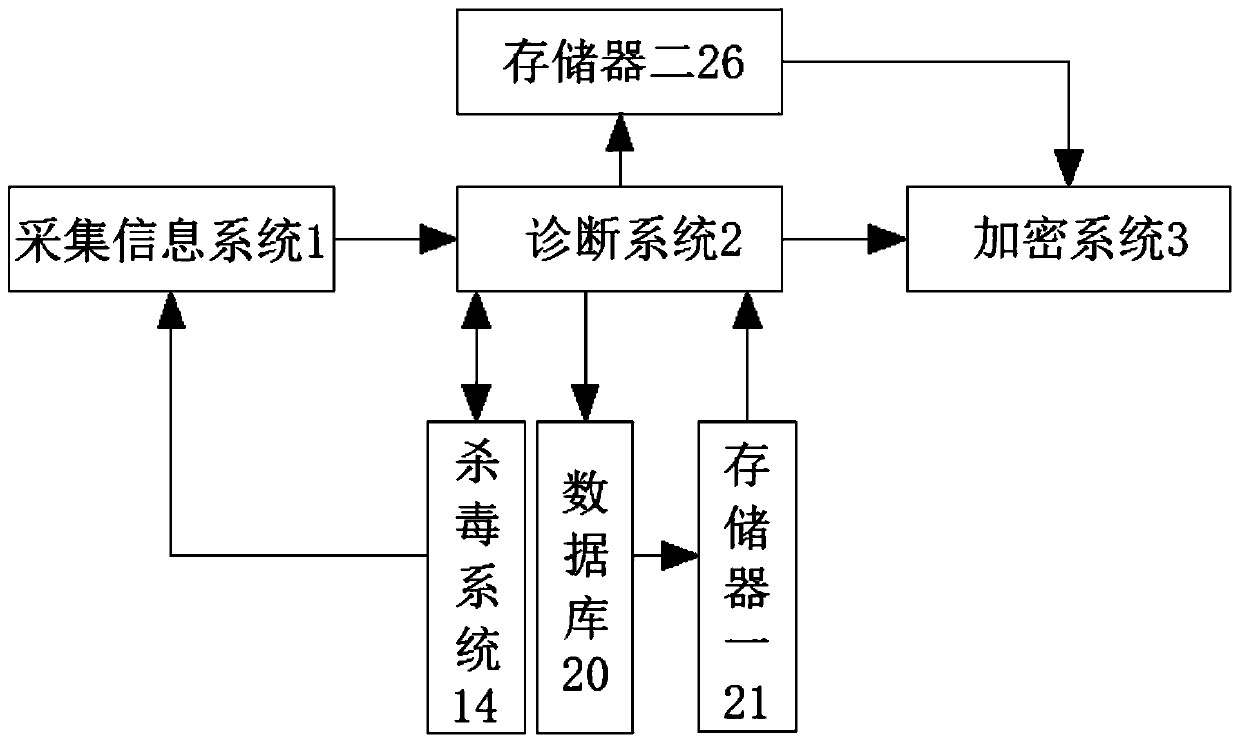
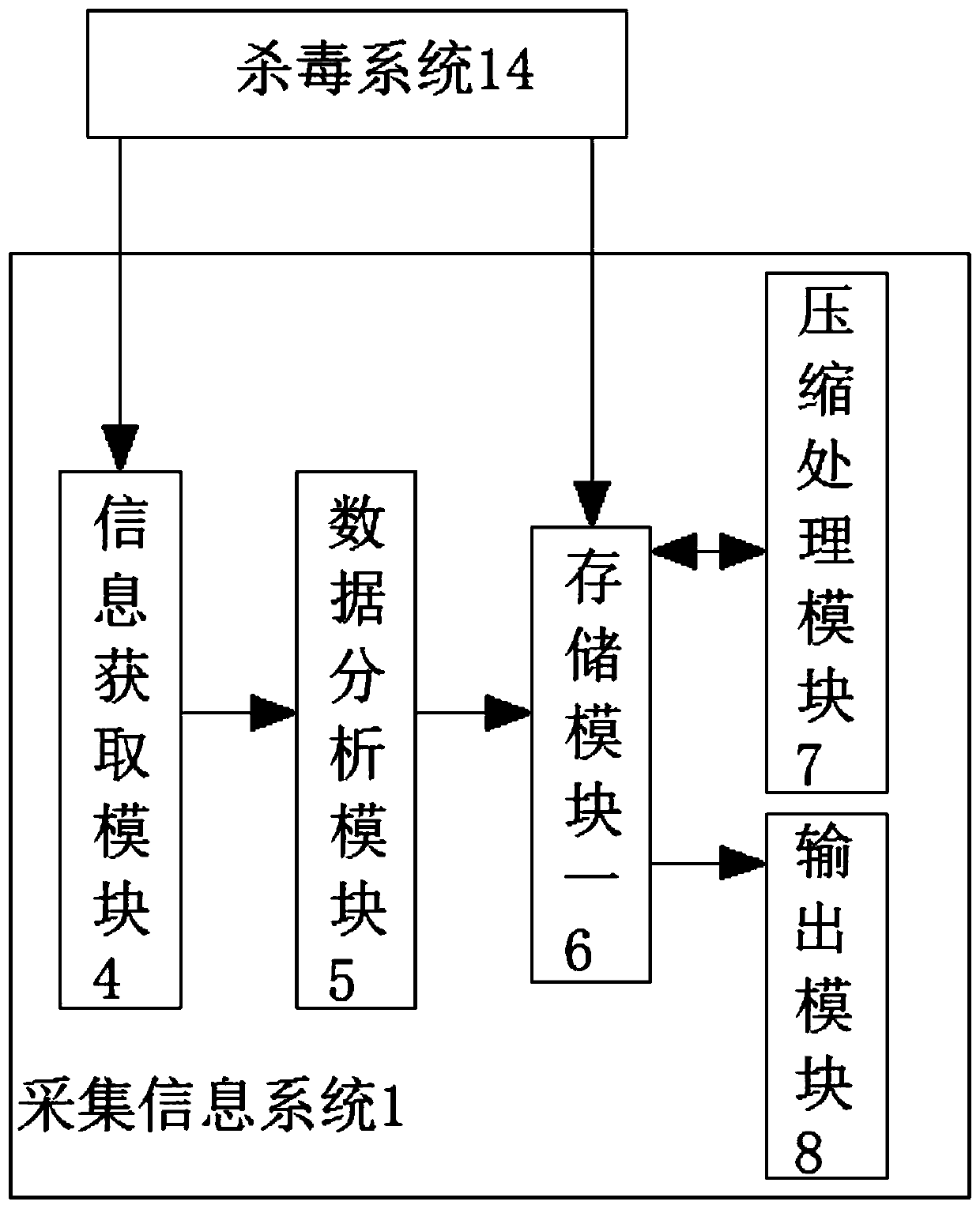
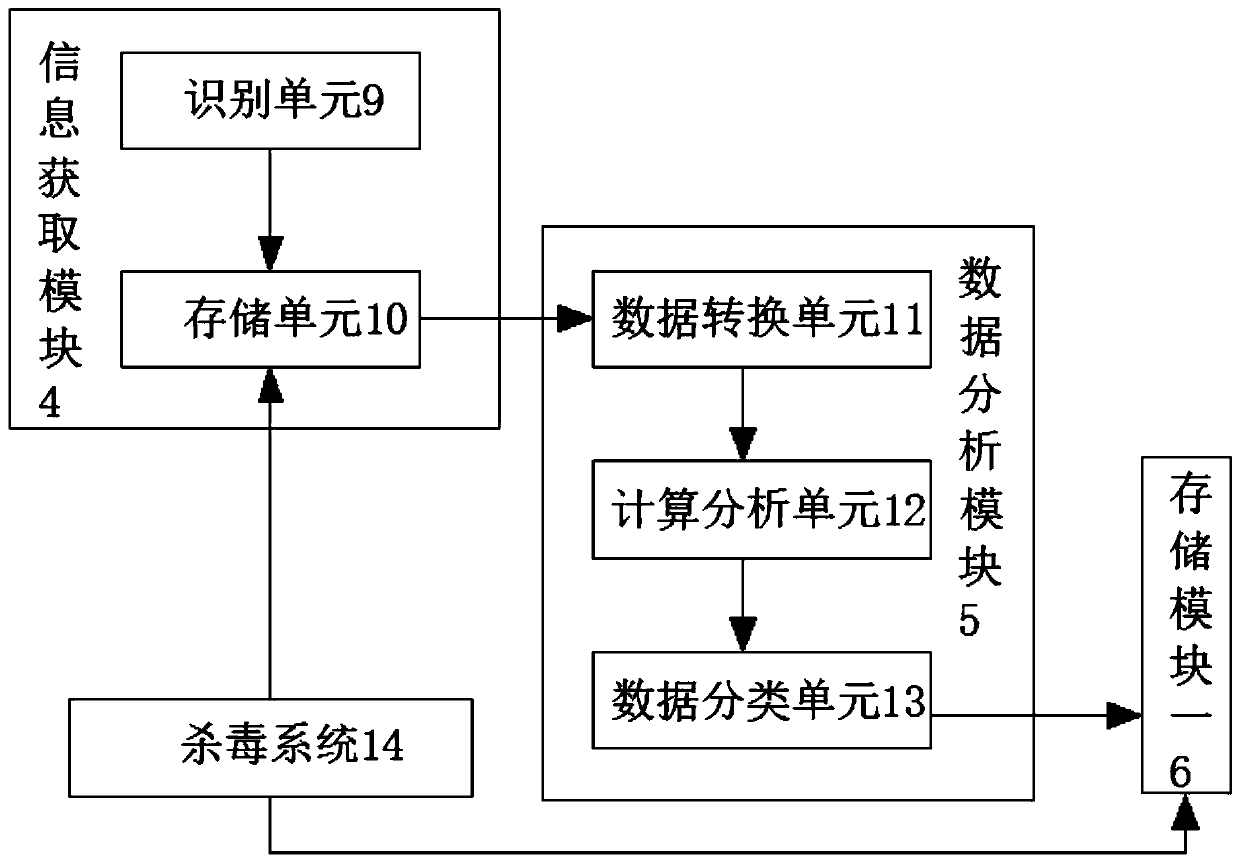
The invention discloses a novel security and secrecy intelligent information acquisition device and method and relates to the field of information acquisition devices. The system comprises an information acquisition system, a diagnosis system and an encryption system, the information acquisition system comprises an information acquisition module, a data analysis module, a storage module I, a compression processing module and an output module, the information acquisition module comprises an identification unit and a storage unit, and the data analysis module comprises a data conversion unit, acalculation analysis unit and a data classification unit. According to the invention, the information acquisition system, the diagnosis system, the encryption system, the data analysis module and a central processor are arranged, the problem that most of password locks for existing intelligent information collection devices cannot store the visiting information of authorized starting password users and unauthorized starting password users through collection, and only the authorized starting password users can check the visiting information of the visiting users is solved.
Owner:HUIZHOU UNIV
Talent evaluation method based on block chain and federal learning technology
PendingCN113901497AEnsure fairness and justiceProtect private dataDigital data protectionMachine learningKey (cryptography)Image manipulation
According to the invention, a 1+X certificate alliance chain, a cryptographic operation module, a federal learning module, an applet, a storage module, an image processing input module, an image processing output module, a sound processing input module, a sound processing output module, a fingerprint identification module, a employment demand and talent matching degree algorithm and an intelligent contract code are established based on WeBank FISCO-BCOS. An asymmetric key pair is generated through the cryptography operation module, a public key, a coded lock number, learning and practical training record types, purposes, ranges and owner information are registered in a block chain, assets are bound with identity information, dual authentication is performed through CA, a block chain technology and a federated learning technology are used, the occupational levels of talents are fairly evaluated through a machine learning algorithm, a federated machine learning model is stored on a federated learning block chain, and the whole process of data and the machine learning model is recorded and traced. The invention has the beneficial effects that the evaluation is accurate, and cheating is avoided.
Owner:深圳市云程科创智能技术有限公司
Binding tape with disposable password protection function
InactiveCN103086069AMeet anti-counterfeiting protection issuesEliminate counterfeitingFlexible elementsPuzzle locksLocking mechanismSecret code
The invention discloses a binding tape with a disposable password protection function and relates to the binding tape. The binding tape with the disposable password protection function comprises at least one binding tape and a password binding tape body for using a disposable password to unidirectionally lock the binding tape, wherein the password binding tape body comprises a box body, a password disk group arranged in the box body and at least one elastic part. The elastic part is used for unidirectionally locking or releasing the password lock sheet corresponding to the binding tape and continuously exerting acting force toward one direction to push the password lock sheet under control of the password disk group. Each password disk of the password disk group is provided with a locking mechanism corresponding to the password lock sheet, and the password lock sheet is locked with each password disk under the pushing of the elastic part when each password disk is rotated to a password position, and meanwhile, the password lock sheet is unlocked with the binding tape. The binding tape with the disposable password protection function is disposable after password protection locking.
Owner:四川讯卫通科技有限责任公司
Authentication method, system and device based on improved cryptographic algorithm
PendingCN114297612AImprove securityCharacter and pattern recognitionDigital data protectionAlgorithmPassword
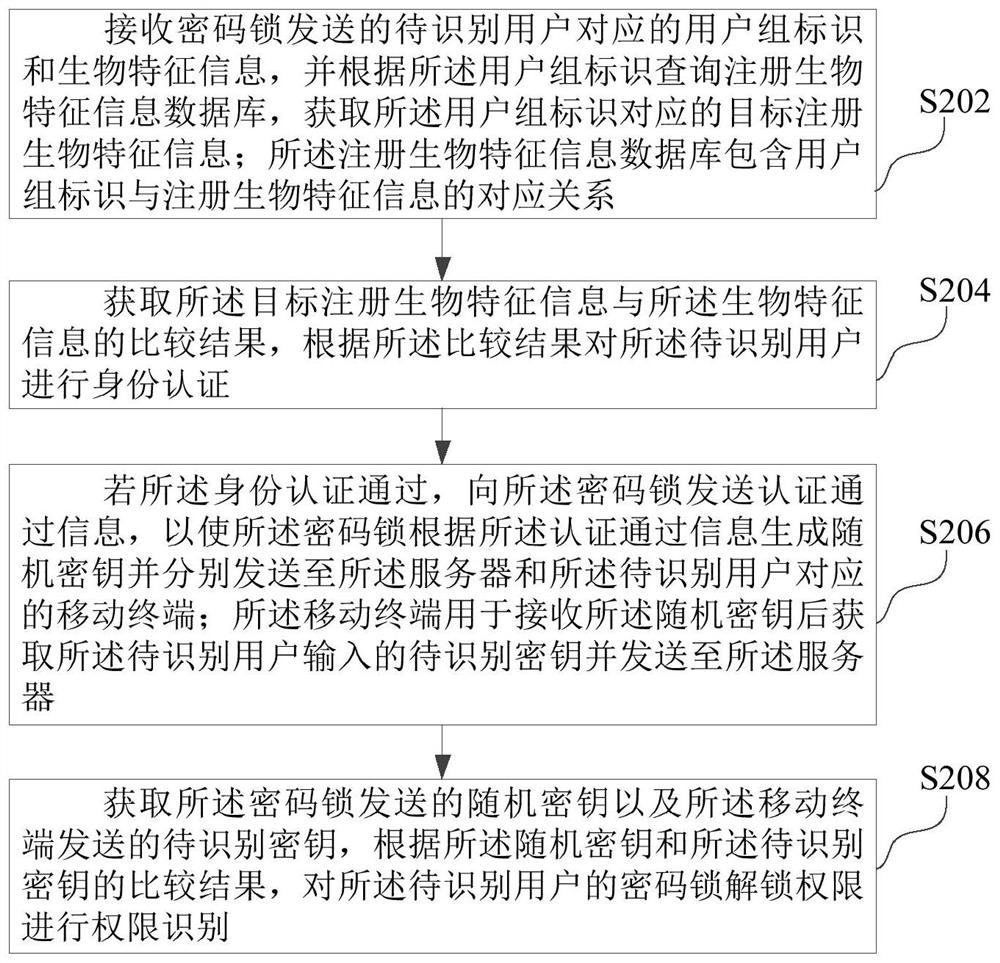
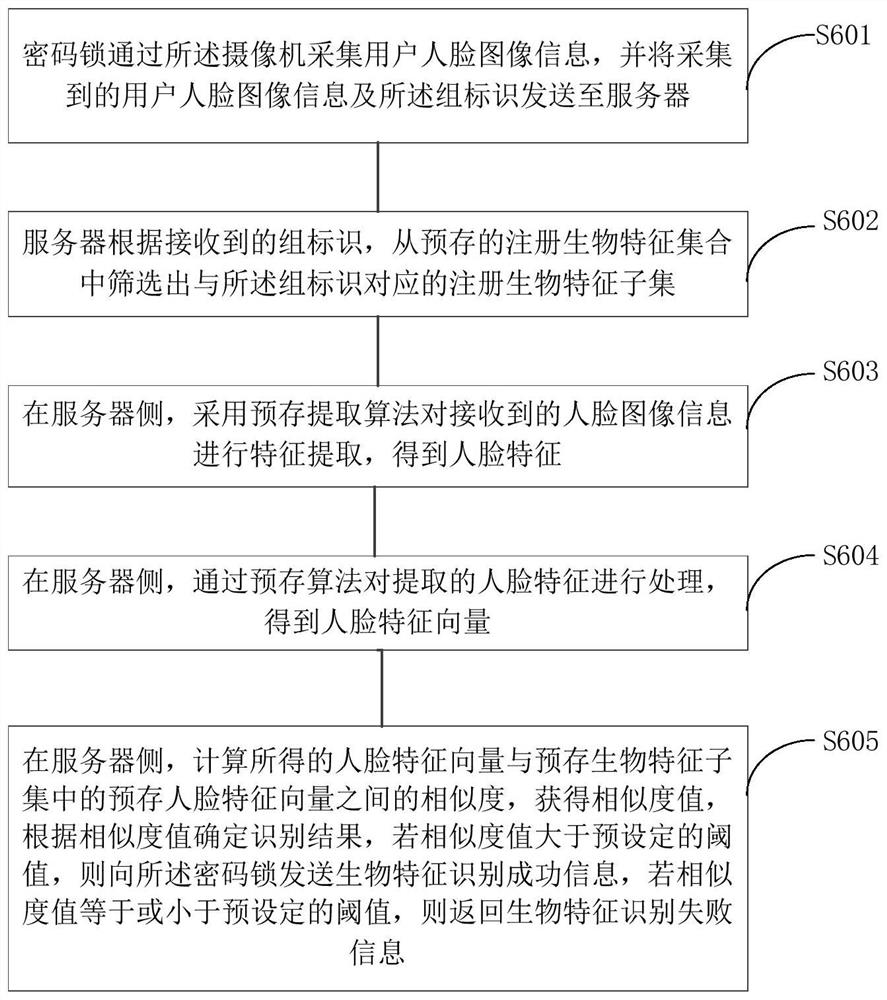
The invention relates to an authentication method, system and device based on an improved cryptographic algorithm, computer equipment and a storage medium. The method comprises the following steps: acquiring target registration biological characteristic information corresponding to a user group identifier by utilizing the user group identifier of a to-be-identified user through a server, identifying the identity of the to-be-identified user according to a comparison result of the target registration biological characteristic information and the biological characteristic information of the to-be-identified user sent by a coded lock, and sending the to-be-identified user to the coded lock after the identity authentication is passed. The authentication passing information is sent to the coded lock, the coded lock receives the information, generates a random key and sends the random key to the server and the mobile terminal of the user to be recognized, and therefore the server can compare the key input by the user and sent by the mobile terminal with the random key, and authority authentication is conducted on the coded lock unlocking authority of the user to be recognized. Compared with a traditional verification mode through a password, the password lock unlocking authority of the user is authenticated by verifying the biological characteristics and the random key of the user, and the authority identification safety is improved.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Combined fingerprint password system and operation method
InactiveCN112419550AReduce the shortcomings of easily forgotten passwordsImprove securityIndividual entry/exit registersKey pressingPassword
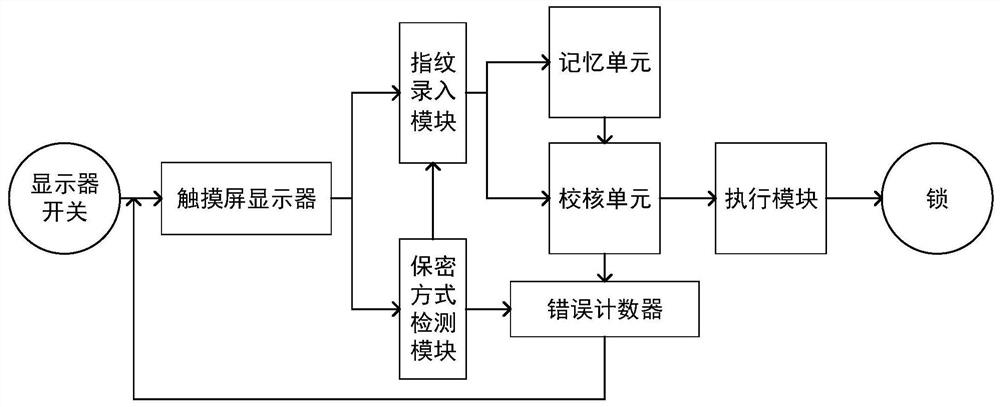
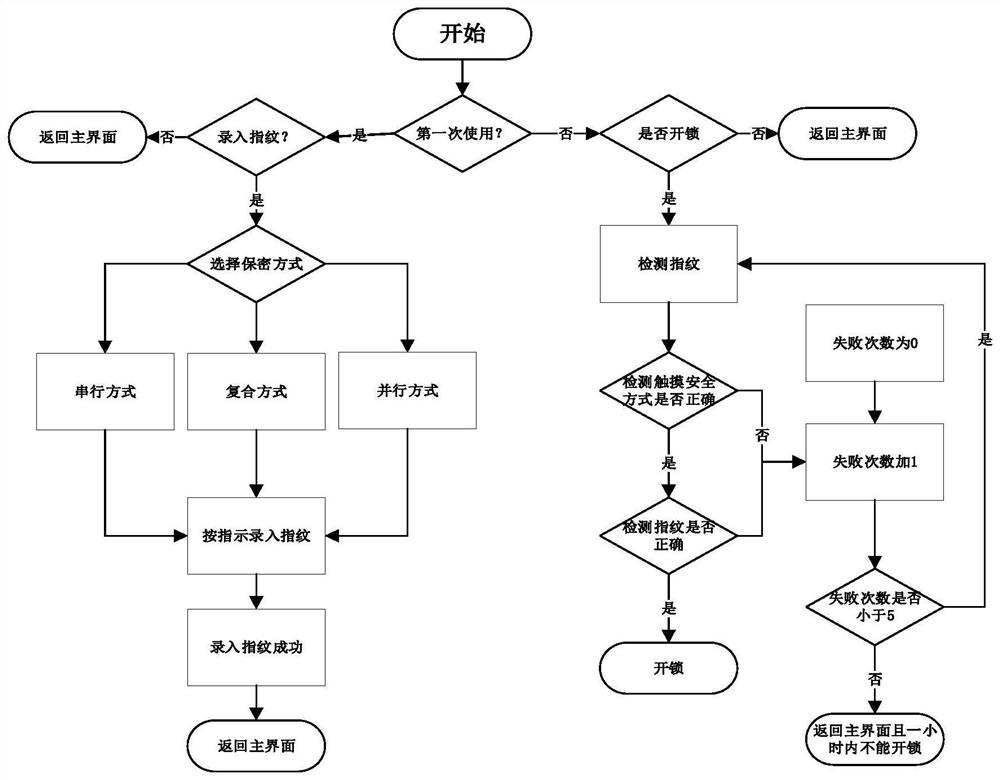
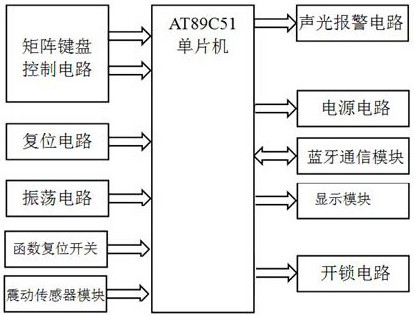
The invention discloses a combined fingerprint password system and an operation method. The combined fingerprint password system comprises a display switch, a touch screen display, a fingerprint inputmodule, an encryption mode detection module, a memory module, a check module, an execution module, a lock and an error counter; when the system is used for the first time, a fingerprint input function is selected on the touch screen display, an encryption mode is selected to be a serial mode, a parallel mode or a composite mode, and fingerprints are input according to system prompts; during unlocking, an unlocking function is selected on the touch display screen, a fingerprint password is input according to the encryption mode, the check module checks the fingerprint password, if the fingerprint password is wrong, inputting the fingerprint password again and feeding back error information to the error counter at the same time, and if the input fingerprint password is correct, the execution module drives the lock to be unlocked; according to the invention, the safety performance is improved by combining the diversity and complexity of the key password and the uniqueness of the fingerprint password, and meanwhile, the defect that the password is easy to forget by a key password lock is reduced to a certain extent, so that the risk that the password is cracked by a person by adoptinga single fingerprint is reduced.
Owner:SOUTHWEST JIAOTONG UNIV
Encryption and decryption authentication method for fingerprint electronic lock and fingerprint electronic lock
ActiveCN111739200AImprove securityIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordEngineering
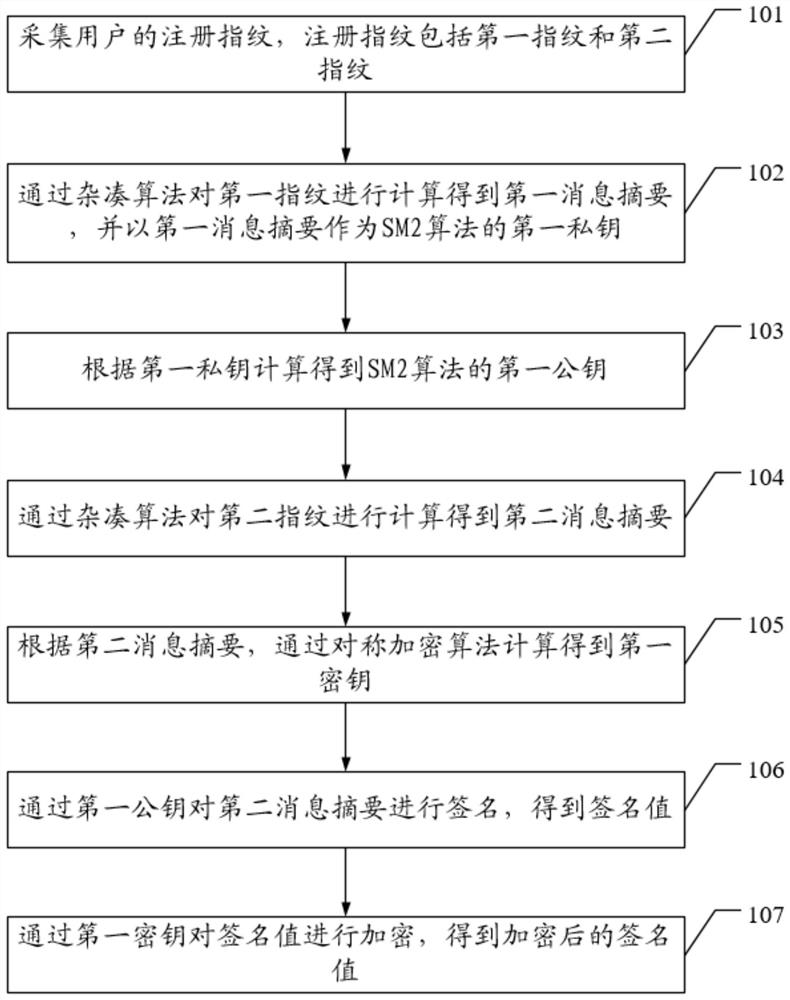
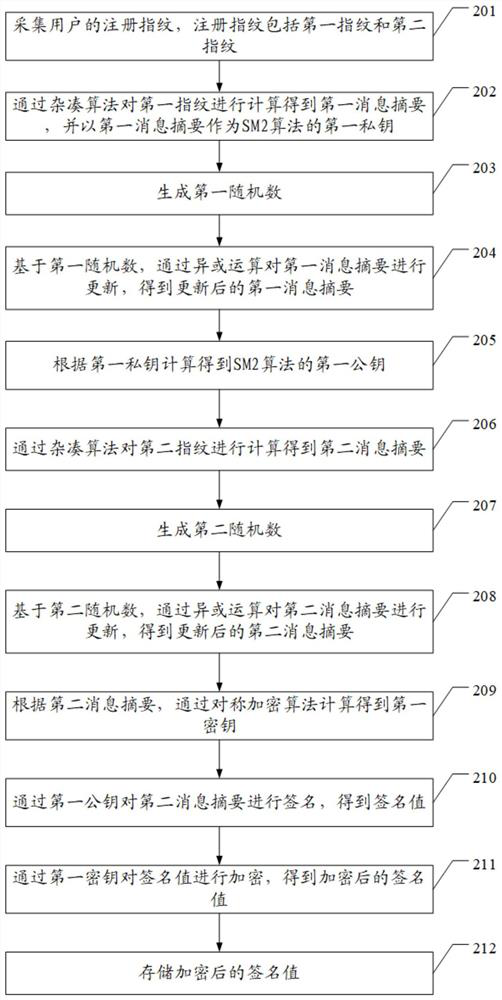
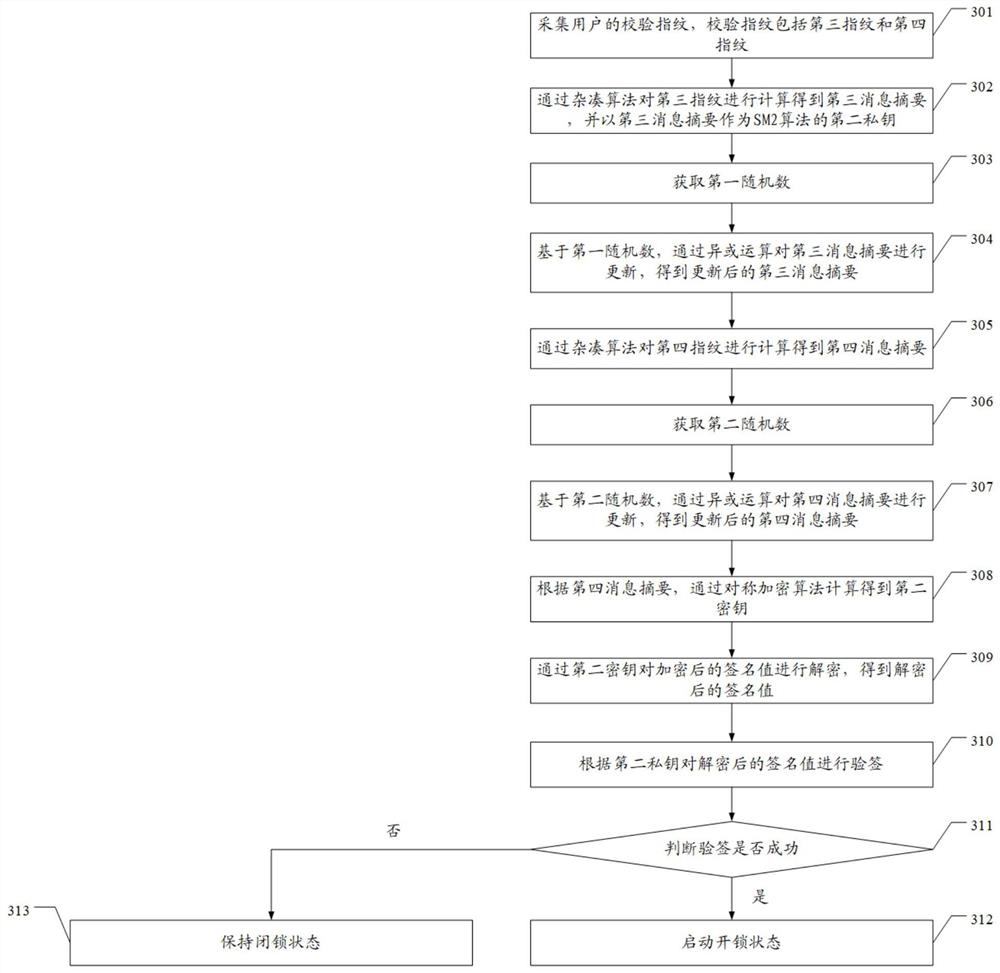
The invention discloses an encryption and decryption authentication method for a fingerprint electronic lock and the fingerprint electronic lock, and the encryption method comprises the steps: collecting a registration fingerprint of a user, wherein the registration fingerprint comprises a first fingerprint and a second fingerprint; calculating the first fingerprint through a hash algorithm to obtain a first message digest, and taking the first message digest as a first private key of an SM2 algorithm; calculating to obtain a first public key of the SM2 algorithm according to the first privatekey; calculating the second fingerprint through a hash algorithm to obtain a second message digest; according to the second message digest, calculating a first secret key through a symmetric encryption algorithm; signing the second message digest through the first public key to obtain a signature value; encrypting the signature value through the first secret key, obtaining the encrypted signaturevalue, and therefore the technical problem that due to the fact that an existing electronic coded lock stores a set fingerprint password into a nonvolatile memory, due to the fact that the fingerprint password is not encrypted, great potential safety hazards exist is solved.
Owner:GUANGDONG UNIV OF TECH
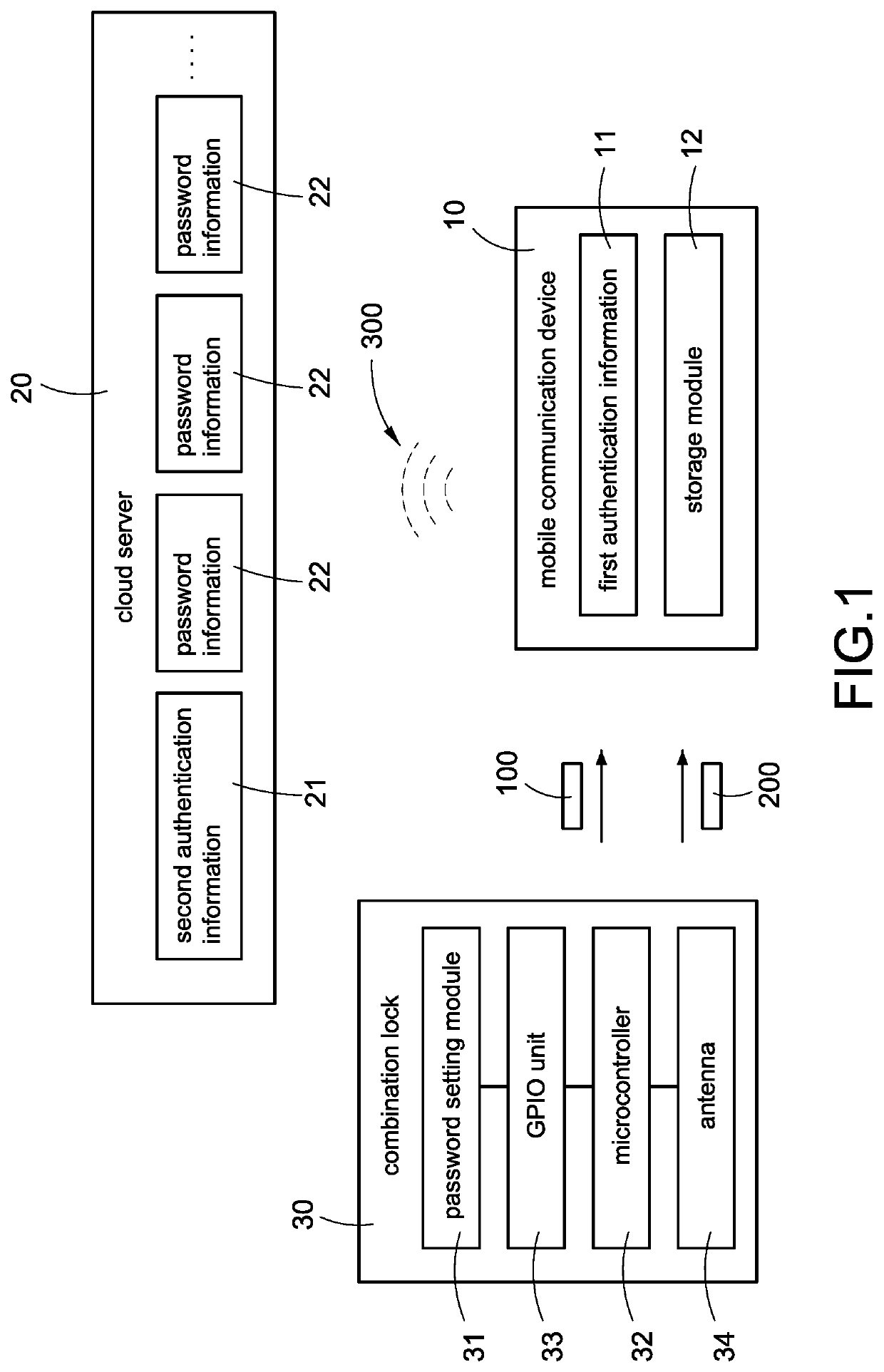
Combination lock system and method of operating the same
ActiveUS20210303671A1Improve securityDigital data authenticationIndividual entry/exit registersPasswordEngineering
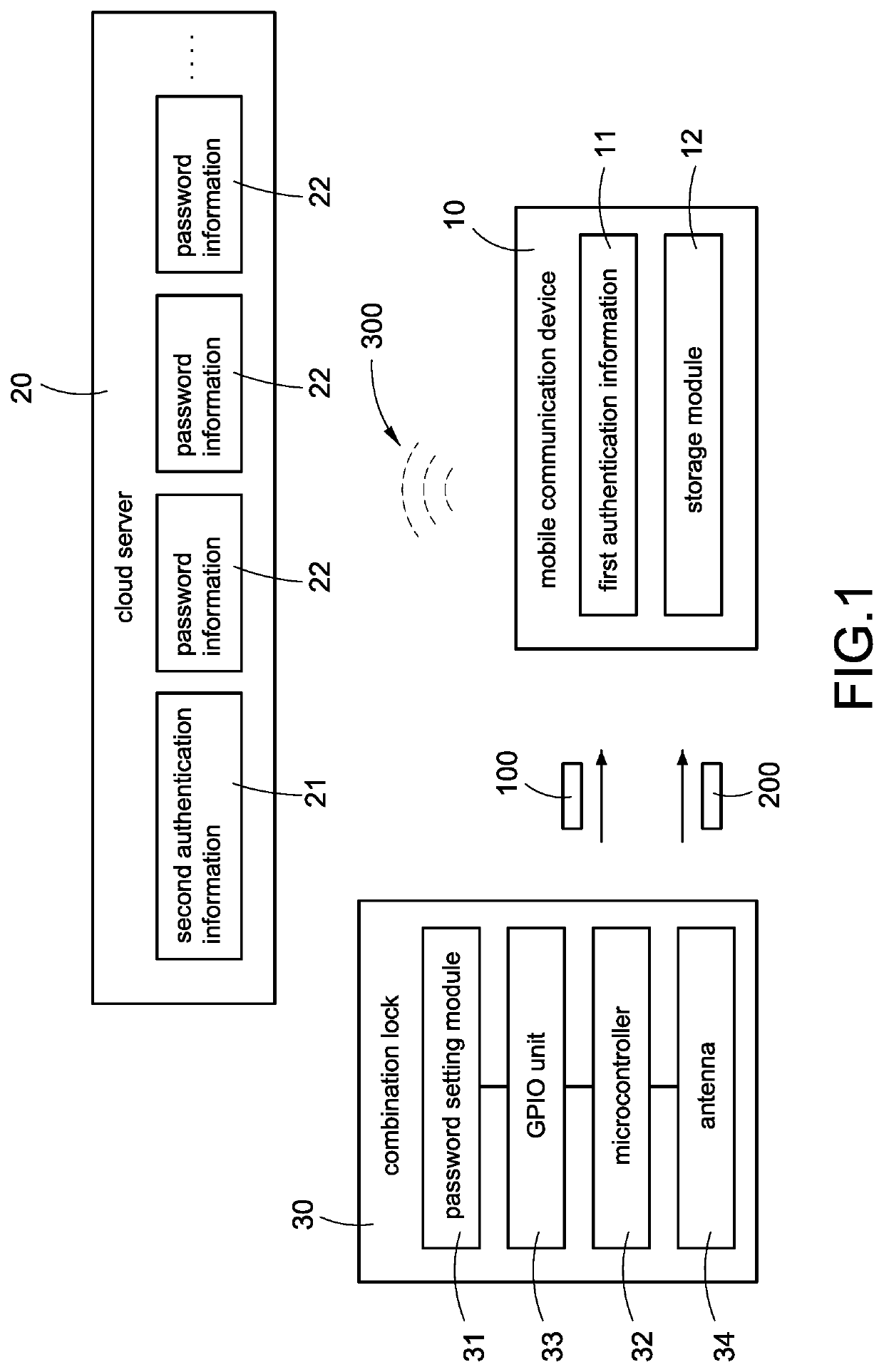
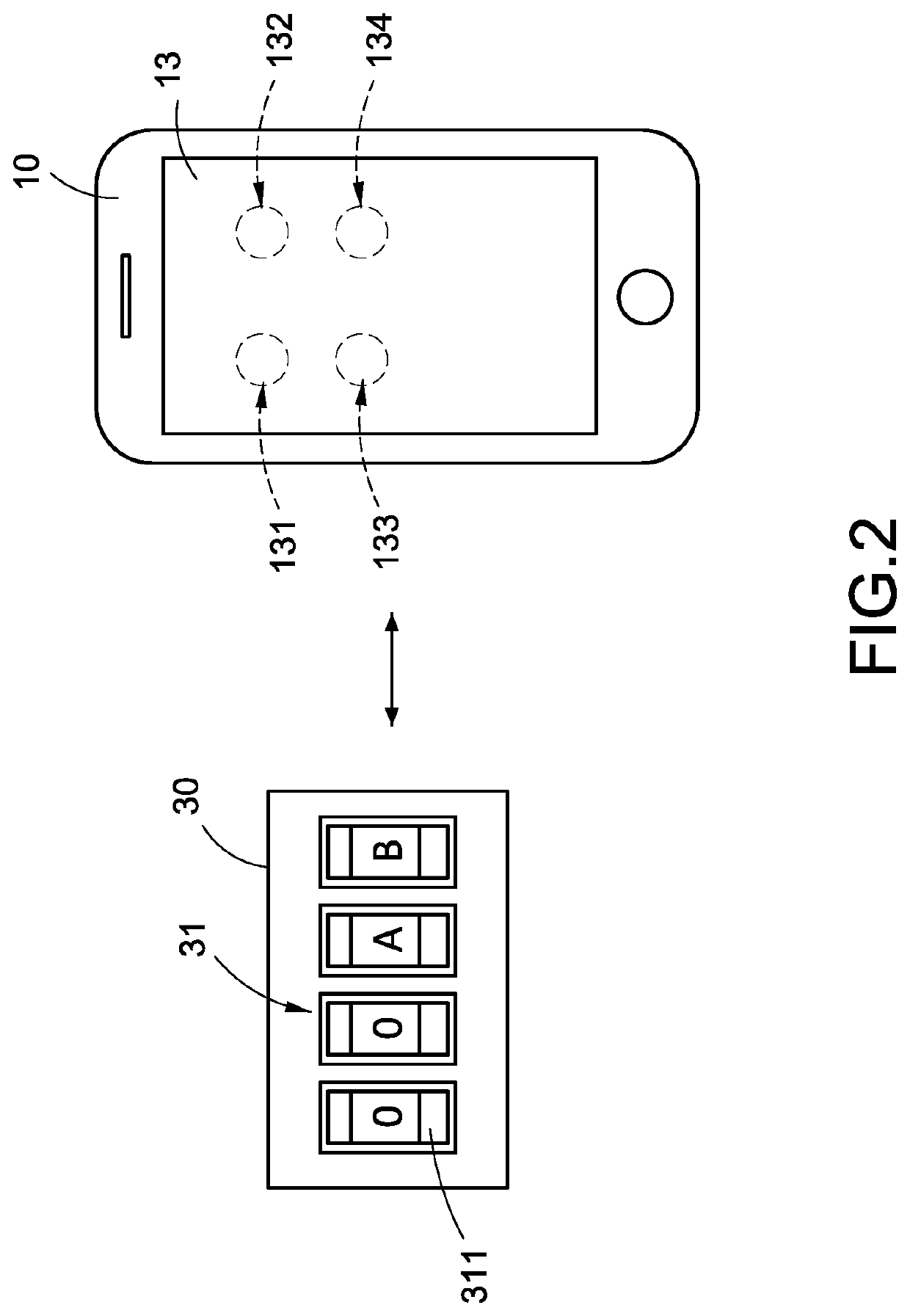
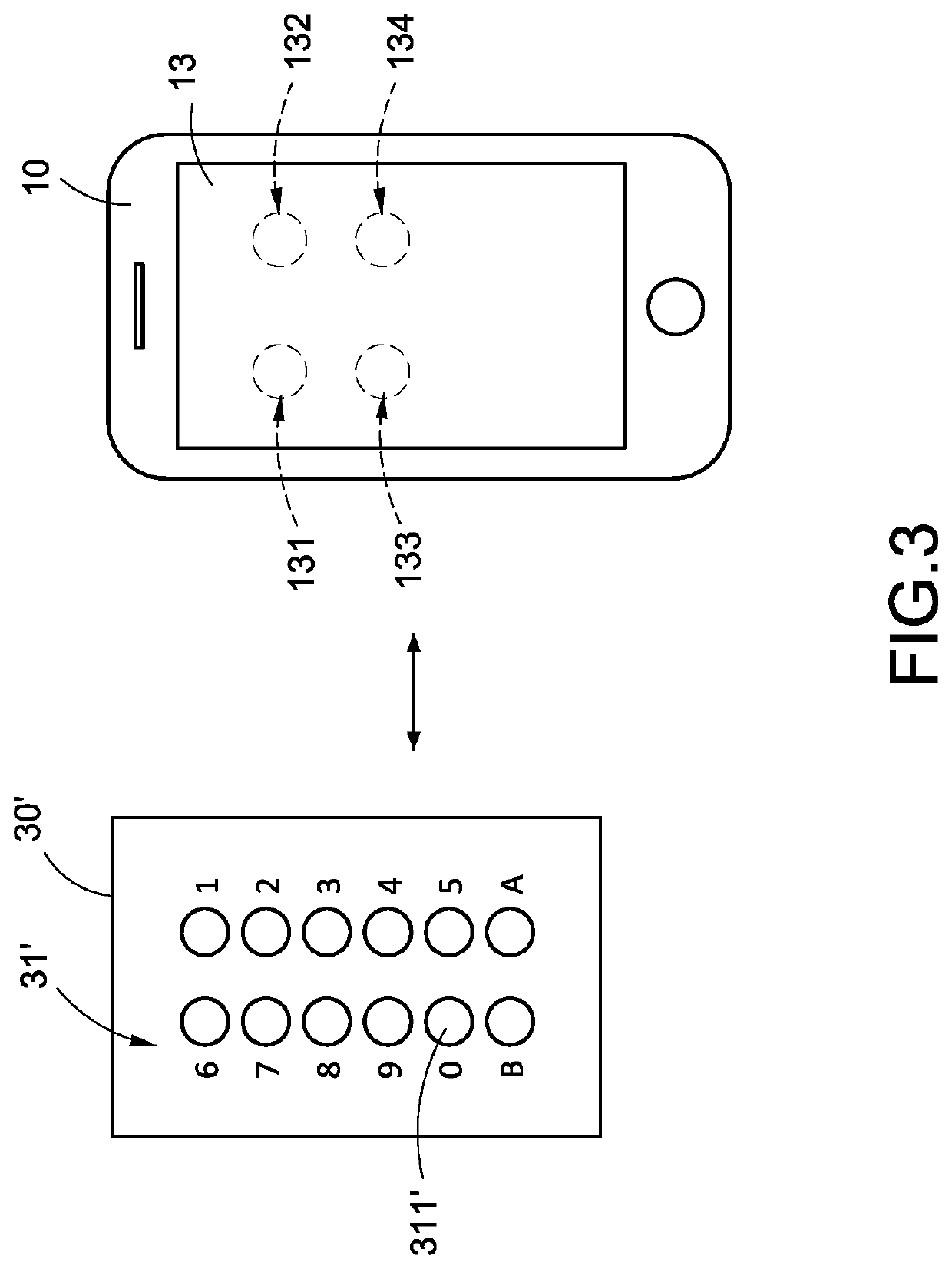
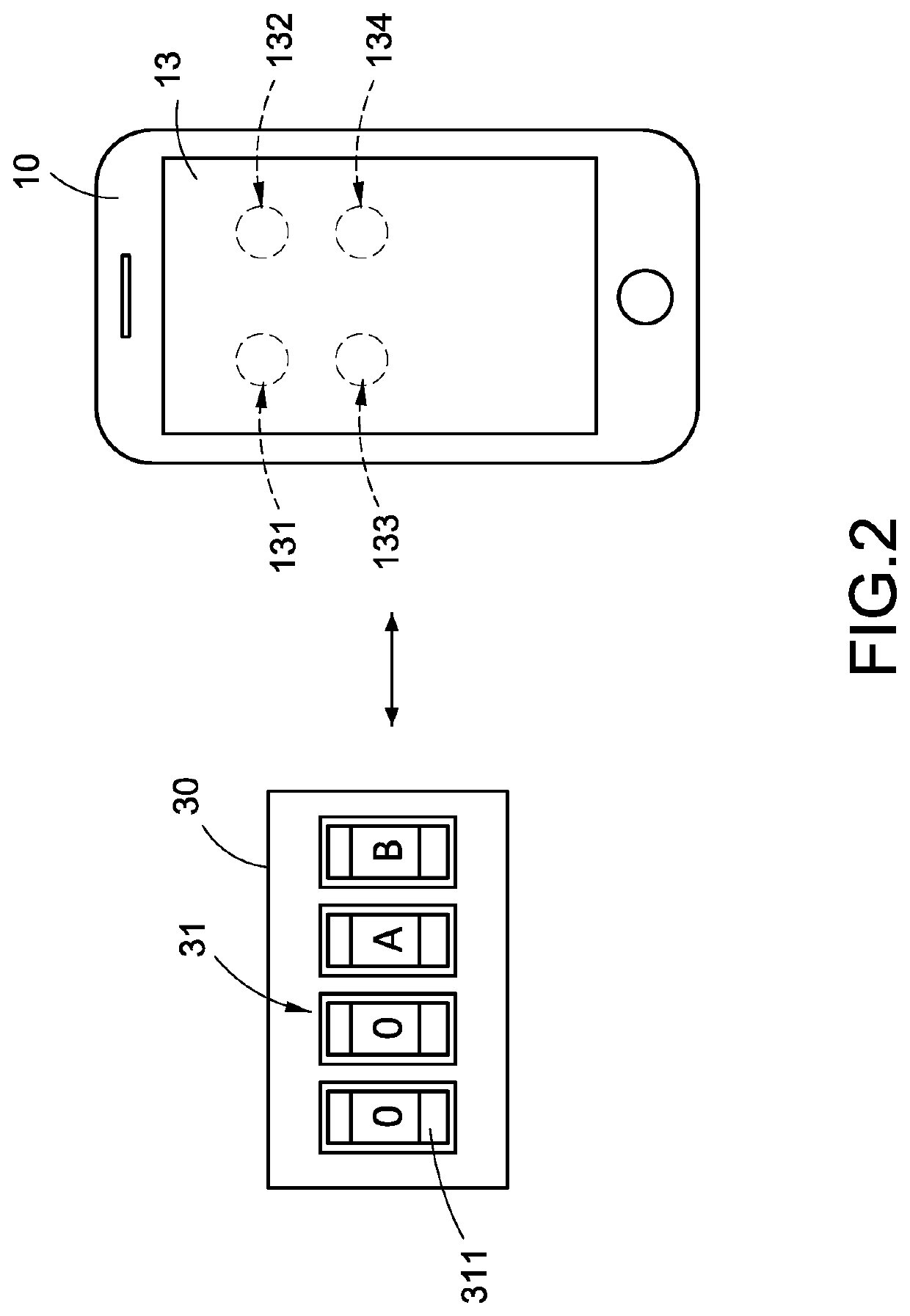
A combination lock system includes a mobile communication device (10, 10′), a cloud server (20) and a combination lock (30, 30′). When the cloud server (20) determines that the mobile communication device (10, 10′) matches authentication information, the cloud server (20) outputs password information (22) corresponding to the authentication information to the mobile communication device (10, 10′), and the combination lock (30, 30′) obtains an electric energy and the password information (22) from the mobile communication device (10, 10′). When the combination lock (30, 30′) determines that one of the characters of the password setting module (31, 31′) matches one of the characters of the password information (22) corresponding to a corresponding arrangement order, the mobile communication device (10, 10′) displays display information.
Owner:REAL LOCKS & SECURITY
A bicycle locking device and its control method
ActiveCN107364514BImprove securityImprove human-computer interactionAnti-theft cycle devicesIndividual entry/exit registersClient-sideTwo-way communication
The invention discloses a bicycle locking device which comprises a lock shell. A first relocking unit, a screw lock unit, a meshing-lock unit, an alarm and a voice prompt are arranged on the lock shell, a first steel wire rope and a second steel wire rope used for extending out of or retracting into the lock shell are located in the lock shell and arranged on two sides of a cryptography lock unit, the screw lock unit comprises a first screw, a second screw and two sliding rails, the first screw and the second screw slide oppositely along the sliding rail, one ends of the first screw and the second screw, facing to each other are connected to be locked through a screw, and the meshing-lock unit comprises a first meshing lock and a second meshing lock which move oppositely in a meshed manner. The bicycle locking device and a control method thereof have the advantages that high security is achieved through triple anti-theft protection of the first relocking unit, the screw lock unit and the meshing-lock unit, two-way communication with a client side can be achieved with alarm and voice prompt functions, remote locking and unlocking operations of a bicycle are performed, man-machine interaction and intelligent level are high, and broad application prospect is achieved.
Owner:HOHAI UNIV CHANGZHOU
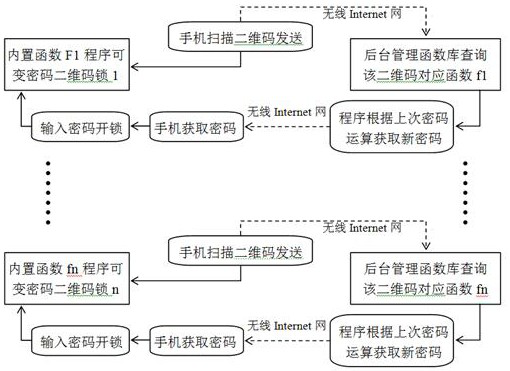
A lock, a two-dimensional code identification, and a password lock power supply module that uses a mobile phone to scan a two-dimensional code corresponding function to obtain a variable password
ActiveCN107316367BImplement variable password functionWith automatic adjustment functionIndividual entry/exit registersComputer hardwarePassword
The invention relates to a lock that uses a mobile phone to scan the corresponding function of a two-dimensional code to obtain a variable code, a two-dimensional code mark, and a combination lock power supply module, and belongs to the technical field of electronic information and shared locks. The present invention consists of 4 cipher disks, 4 cipher knobs, two-dimensional code signs, two-dimensional code built-in holes, elastic pressing keys, keyboard conductive rubber, etc.; each two-dimensional code corresponds to an independent function Fn, and this function exists As long as there is the same initial value in the memory of the variable password lock (8) and in the function library of the background management server, the same calculation result will be obtained. Scan and send the QR code with the mobile phone to obtain the input password for unlocking. The variable password function is realized; when the wrong password is entered more than three times in a row, a warning is issued; self-charging can be completed. Scan the QR code of the lock with the mobile phone to realize the function of the logistics network, which greatly reduces the cost of the lock and the development of the lock management program in the early stage, and only needs to develop the background management program.
Owner:山东创工信息科技有限公司
An Encrypted File Extraction Device for Electronic Commerce Based on Photoresistor
The present invention relates to the technical field of e-commerce, and discloses an encrypted file extracting device for e-commerce based on a photoresistor, which includes a casing and a rotating shaft, and a motor is movably connected to the outside of the casing, and a gear is movably connected to the outside of the motor. , gear two is meshed with the outside of gear one, the outside of gear two is fixedly connected with a rotating rod, and the outside of the rotating rod is movably connected with a rotating cylinder; through the shell, motor, gear one, gear two, rotating rod, rotating cylinder, inclined plate, Under the interaction between the slide bar, the push rod and the movable bar, the user can only start the operation of the device through the external fingerprint code lock, which ensures the protection of the device and strengthens the security of the file hard disk , and the transmission between the structures can make the push rod reciprocate, which provides a basis for the user to extract the corresponding files later, ensures the convenience of file extraction, and saves time and effort.
Owner:聊城八月瓜大数据服务有限公司
Dynamic coded lock based on Internet of Things
InactiveCN112288916AAvoid situations where the door cannot be openedEasy to useIndividual entry/exit registersThe InternetStructural engineering
The invention relates to the technical field of coded locks, and in particular relates to a dynamic coded lock based on the Internet of Things. The dynamic coded lock comprises a lock body and covering plates, the two ends of the lock body are connected with the covering plates, one side of each covering plate is provided with a handle, a storage groove is formed above each handle, a password input disc is arranged below each handle, the lower end of each covering plate is provided with a wire storage groove, a through hole is formed in one side of each wire storage groove, one end of each through hole is connected with a wire duct cover, one end of each wire duct cover is provided with a rebounding device, a charging wire is arranged in each wire storage groove, a power supply device is arranged on the upper end face of the lock body, the charging wires are electrically connected with the power supply device, a spring bolt is arranged on one side of the lock body, a groove is formed in one end of the spring bolt, a rubber layer is connected into the groove through a connecting column, and a spring is arranged on the outer side of the connecting column in a sleeving mode. The charging wires electrically connected with the power supply device are arranged on the covering plates on the two sides of the lock body, equipment is charged on the outer side when the electric quantity of the power supply device is used up, and use is more convenient.
Owner:江苏燕鸥研学云数据科技有限责任公司
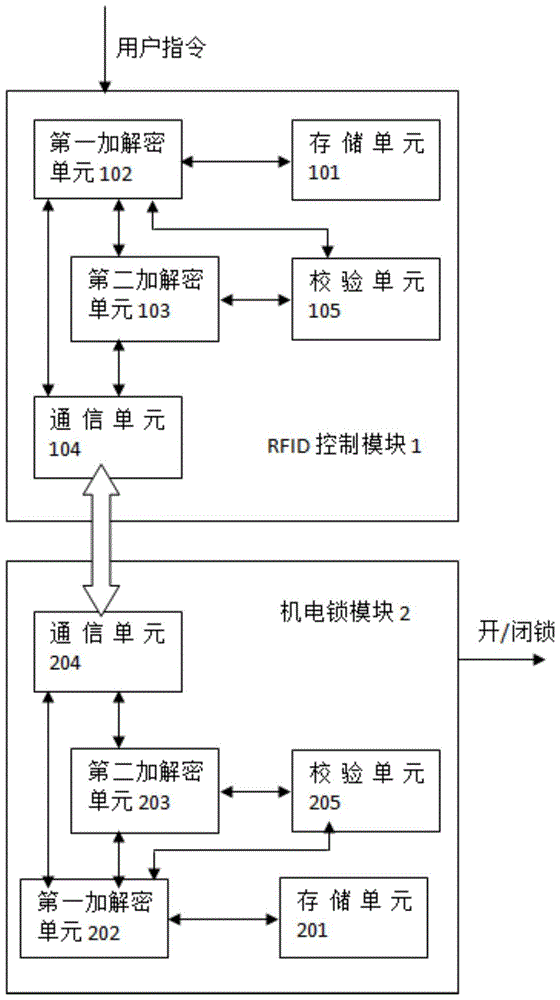
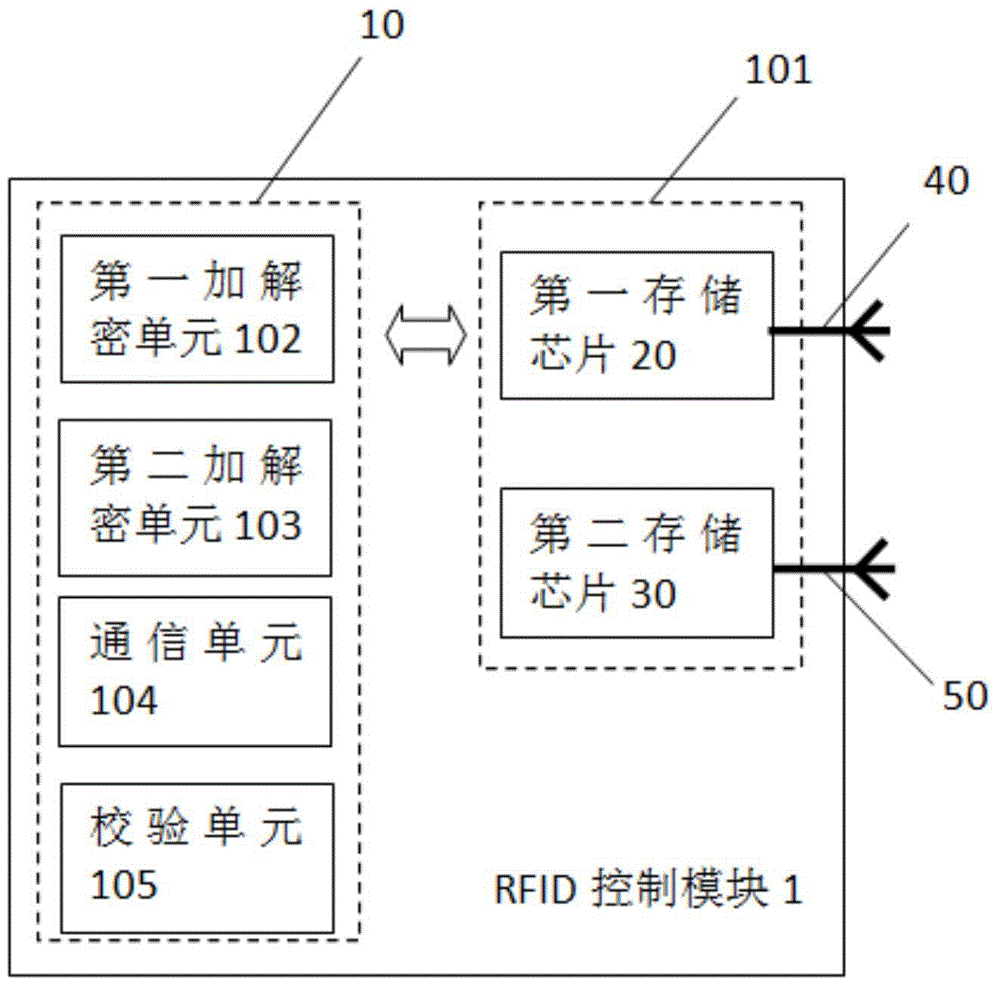
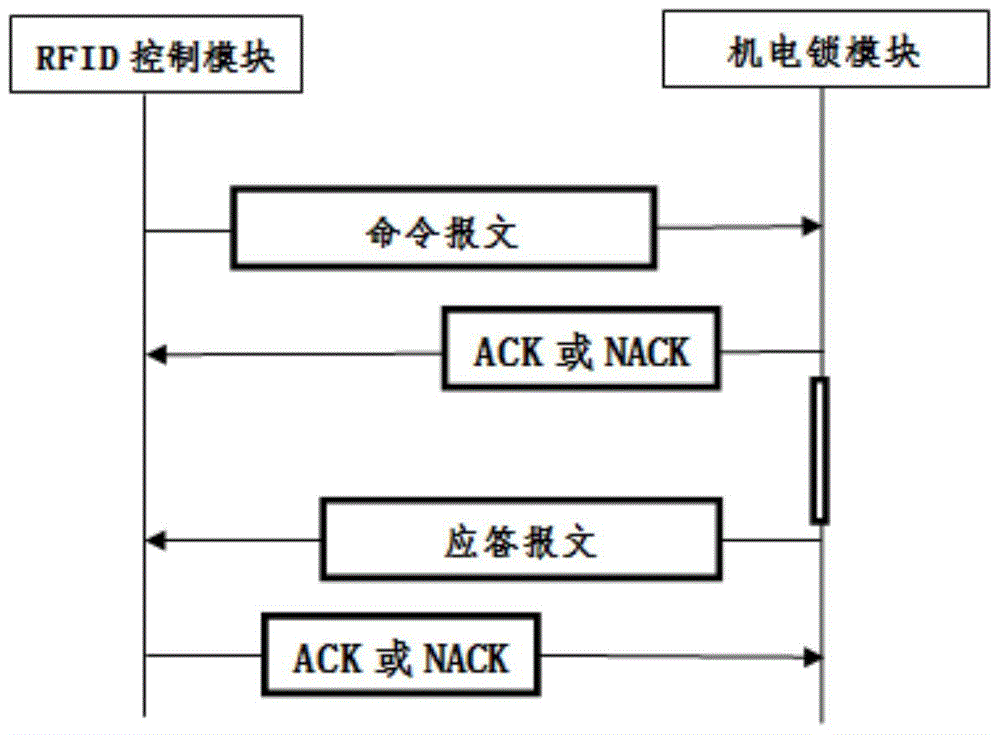
Data transmission method, electronic combination lock device and control method thereof
ActiveCN104104499BSimple structureSolve the security problem of data transmissionError preventionEncryption apparatus with shift registers/memoriesPlaintextCommunication unit
The invention discloses an electronic coded lock device which comprises a RFID (Radio Frequency Identification) control module and an electromechanical lock module. The RFID control module and the electromechanical lock module respectively comprise a storage unit, a communication unit, a checking unit, a first encryption and decryption unit and a second encryption and decryption unit, wherein each storage unit is arranged to store an initial secret key and a communication secret key plaintext; each communication unit is arranged to realize mutual communication between the RFID control module and the electromechanical lock module; each first encryption and decryption unit is arranged to perform a CRC8 (Cyclic Redundancy Check 8) checking algorithm and perform DES (Data Encryption Standard) encryption algorithm for one time; each second encryption and decryption unit is arranged to perform the DES encryption algorithm for multiple times; each checking unit is arranged to check data transmitted between the RFID control module and the electromechanical lock module. The invention further discloses a data transmission method in the electronic coded lock device and a control method of the electronic coded lock device.
Owner:SHENZHEN POKA ELECTRONICS EQUIP
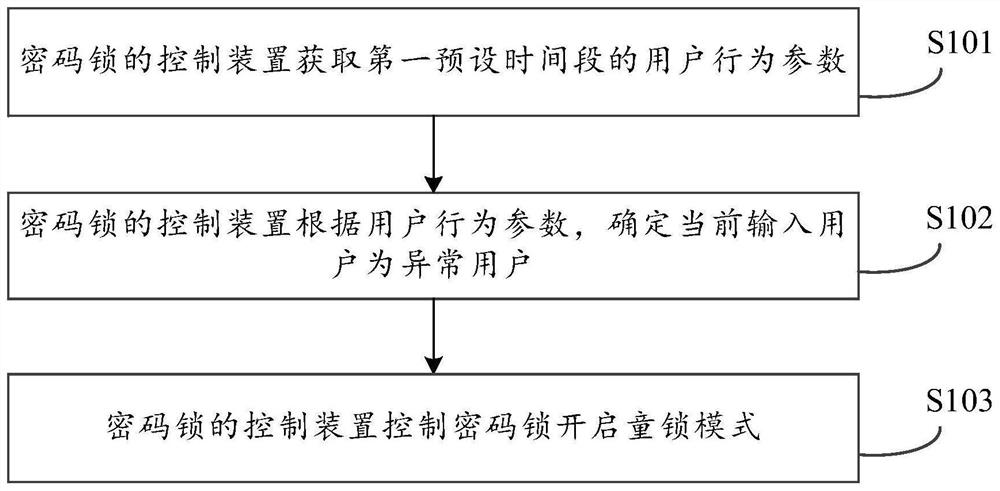
Combination lock control method, device and computer-readable storage medium
The present application provides a control method, device and computer-readable storage medium of a password lock, which relate to the technical field of control. The control method of the coded lock can weaken the attractiveness of the coded lock to children and prevent children from using the coded lock as a toy, thereby improving the battery life of the coded lock. The method includes: the control device of the combination lock obtains user behavior parameters in a first preset time period; then, the control device of the combination lock determines that the current input user is an abnormal user according to the user behavior parameters, and then controls the combination lock to enable the child lock mode. Wherein, the child lock mode includes: turning off the input prompt sound of the key of the combination lock, and controlling the opening of the combination lock when the trigger operation of the key of the combination lock satisfies a preset trigger condition.
Owner:宁波公牛智能科技有限公司
Combination lock system and method of operating the same
ActiveUS11341226B2Improve securityDigital data authenticationIndividual entry/exit registersPasswordEngineering
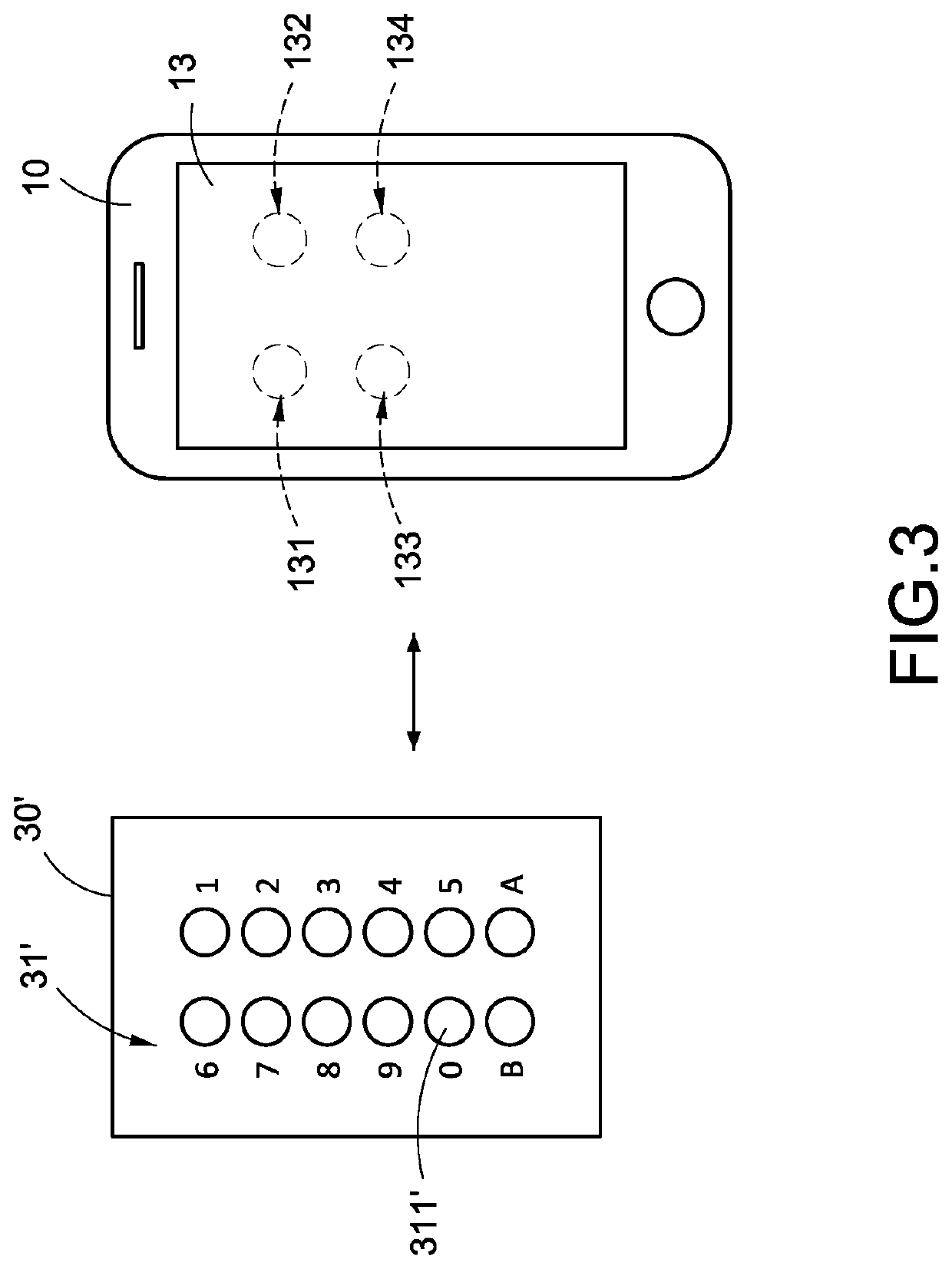
A combination lock system includes a mobile communication device (10, 10′), a cloud server (20) and a combination lock (30, 30′). When the cloud server (20) determines that the mobile communication device (10, 10′) matches authentication information, the cloud server (20) outputs password information (22) corresponding to the authentication information to the mobile communication device (10, 10′), and the combination lock (30, 30′) obtains an electric energy and the password information (22) from the mobile communication device (10, 10′). When the combination lock (30, 30′) determines that one of the characters of the password setting module (31, 31′) matches one of the characters of the password information (22) corresponding to a corresponding arrangement order, the mobile communication device (10, 10′) displays display information.
Owner:REAL LOCKS & SECURITY
A project supervision monitoring system based on bim
ActiveCN111885287BEasy to disassembleEasy to installTelevision system detailsColor television detailsSoftware engineeringMonitoring system
Owner:惠州建安工程项目管理有限公司
A combination lock system based on geographic location and its unlocking method
ActiveCN112252853BReduce security risksIncrease the difficultyElectric permutation locksIndividual entry/exit registersTransceiverPassword
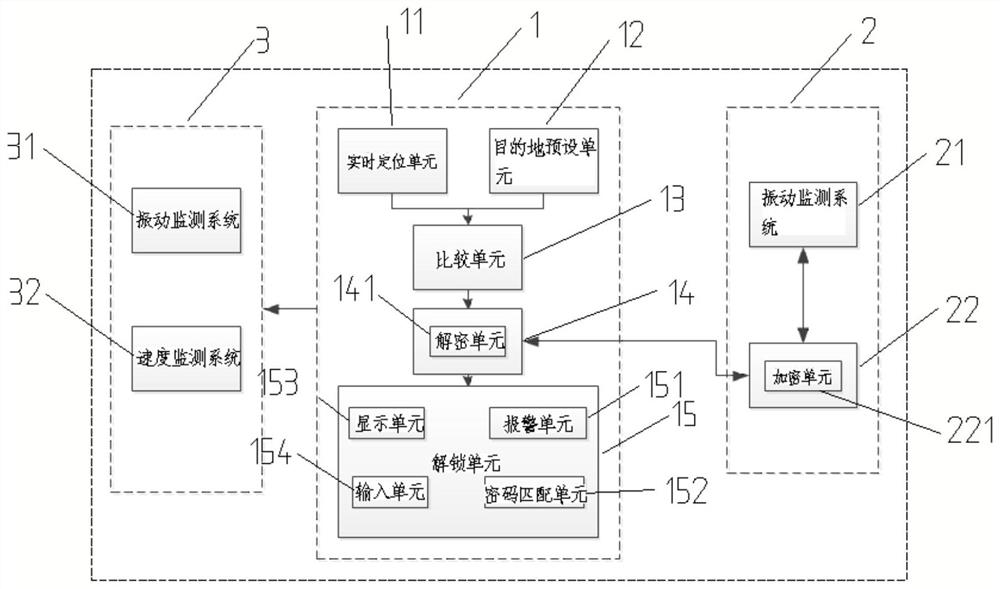
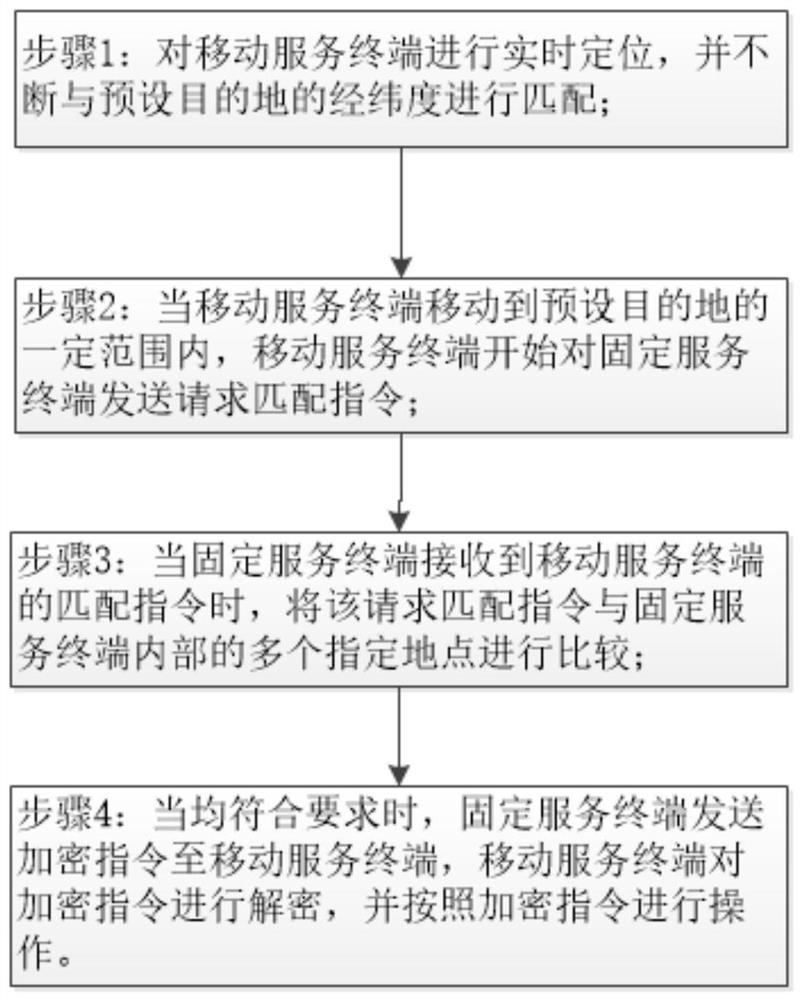
The invention provides a combination lock system based on geographic location and its opening method, wherein the combination lock system includes two service terminals, the two service terminals are respectively a mobile service terminal and a fixed service terminal, and the mobile service terminal It includes a real-time positioning unit, a destination preset unit, a comparison unit and a first instruction transceiving unit, the real-time positioning unit and the destination preset unit are connected to the comparison unit, the comparison unit is connected to the first instruction transceiver unit, and the The fixed service terminal includes a second command transceiving unit and a verification unit, the second command transceiving unit is connected to the first command transceiving unit, and the verification unit is connected to the second command transceiving unit, and the corresponding invention also provides the password The opening method of the lock system, the present invention can open the combination lock based on the geographic location, and is provided with multiple guarantees at the same time, which is suitable for fields with high guarantee requirements.
Owner:相克军 +1
A WeChat lock unlocking method
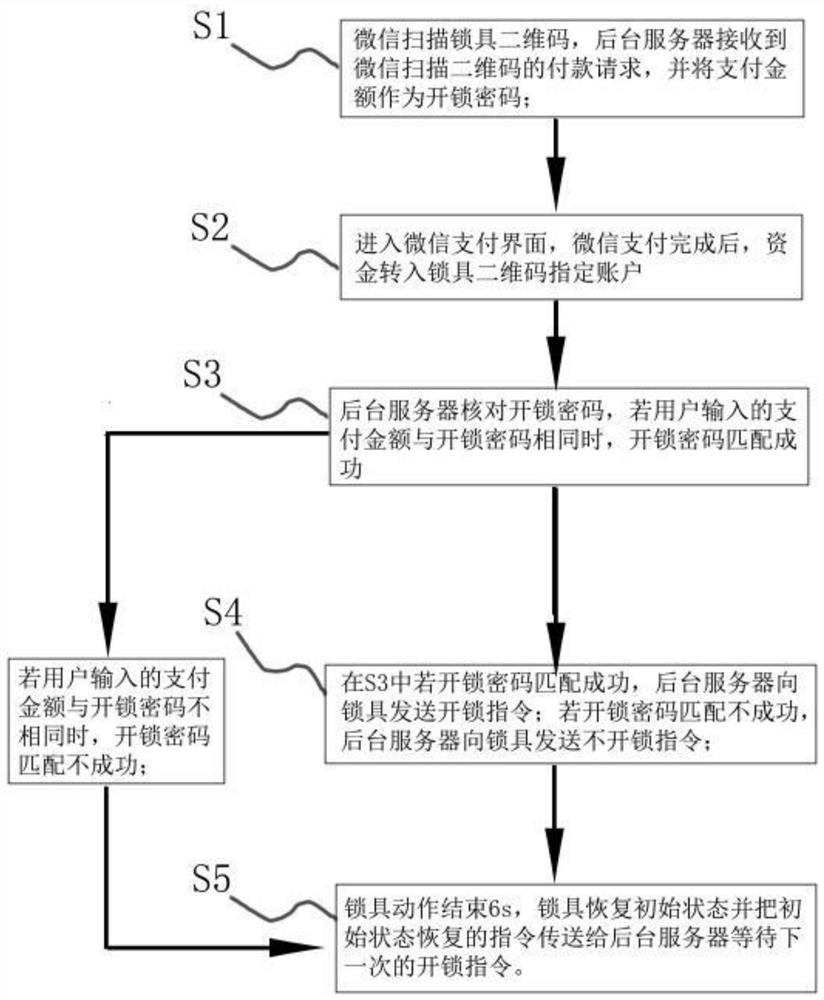
ActiveCN108460873BFast scan code paymentImprove confidentialityIndividual entry/exit registersPaymentPassword
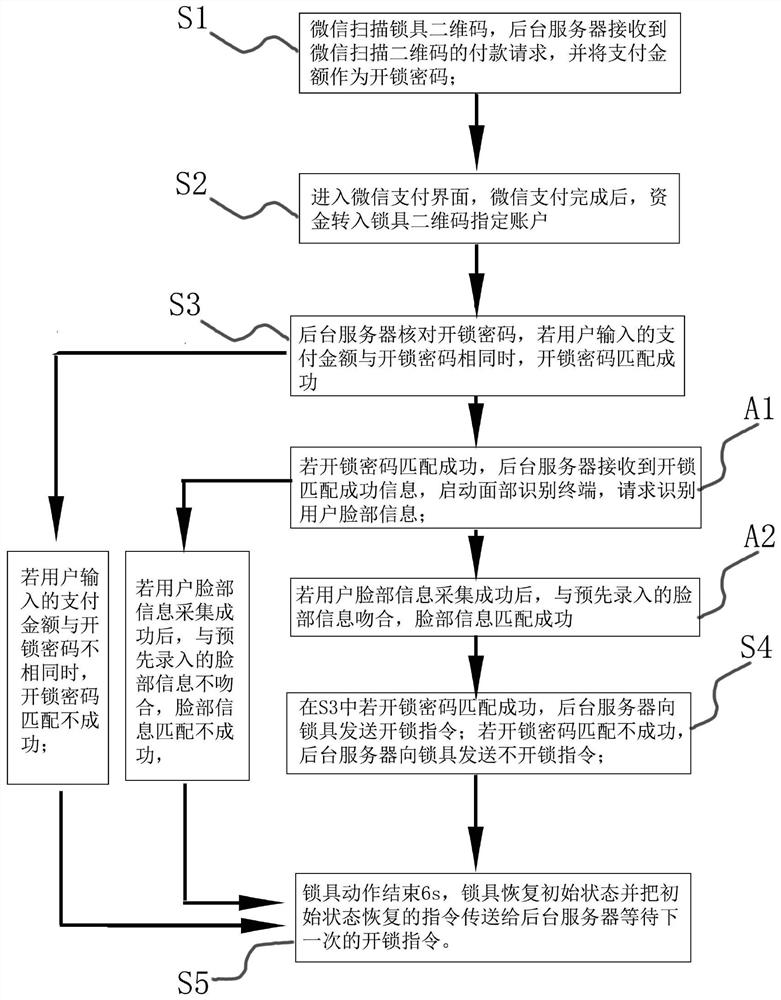
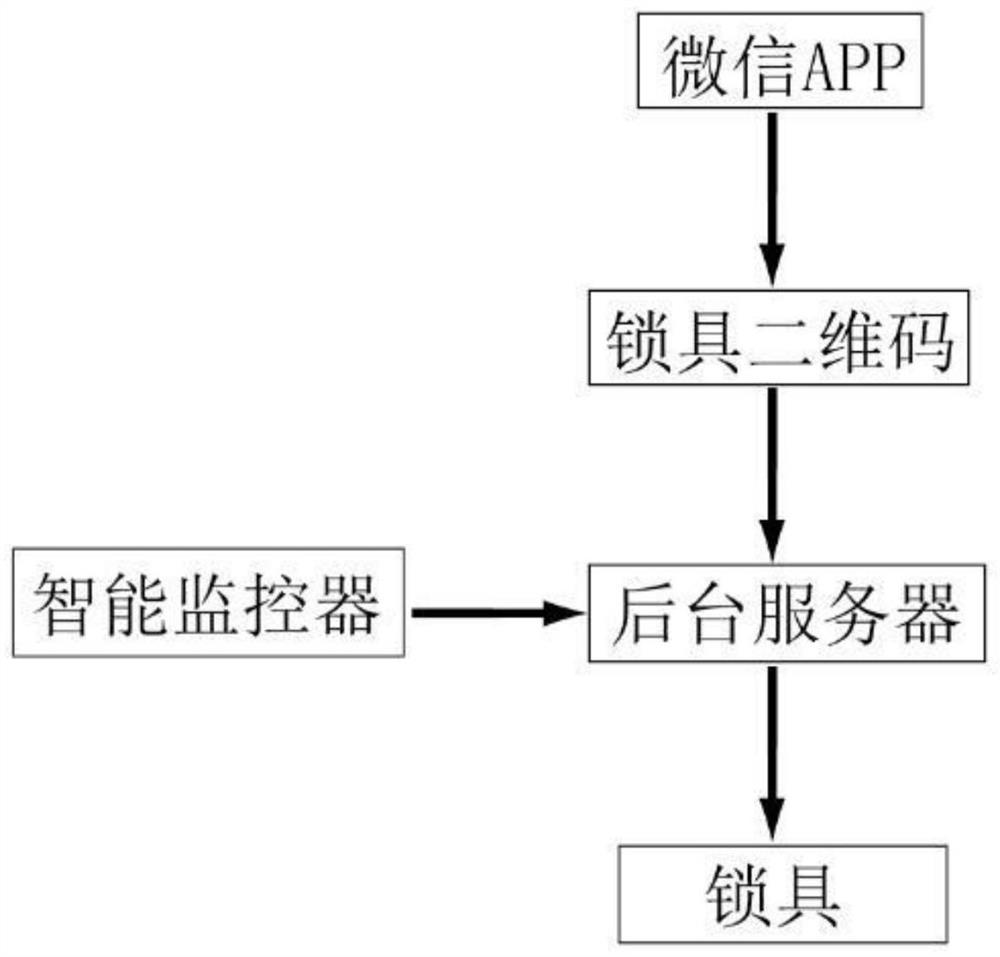
The invention discloses a WeChat lock unlocking method comprising: scanning the QR code of a lock with WeChat, the background server receives the payment request for scanning the QR code on WeChat, and uses the payment amount as the unlock password to request the user to input; enters the WeChat payment interface, and after the WeChat payment is completed , the funds are transferred to the account designated by the QR code of the lock; if the payment amount input by the user is the same as the unlock password, the unlock password matching is successful; if the payment amount input by the user is not the same as the unlock password, the unlock password matching is unsuccessful; in S2 If the unlock password matches successfully, the background server sends an unlock command to the lock; if the unlock password fails to match, the background server sends a no-unlock command to the lock; 6 seconds after the lock action ends, the lock returns to the initial state and sends the command to restore the initial state to the background The server waits for the next unlock command. The invention is a brand-new unlocking method of an electronic combination lock, which not only realizes the development of the "Internet +" lock industry, but also realizes double safety protection.
Owner:BEIHAI JICI MOTOR DEV
Detachable mechanical combination lock
ActiveCN111764753BAnti-theft opening performance unchangedStrong anti-destructive opening performancePuzzle locksPermutation locksComputer hardwarePassword
A detachable mechanical combination lock, which relates to the field of turntable-type mechanical combination locks, in which the operation of checking numbers is completed by directly rotating six knobs; the cam mechanism is driven by the handle to rotate to realize unlocking and locking; After the linkage shaft movably connected with the shaft passes through the lock body, it first drives the overload protection device and the code changing device to rotate, and then returns to the lock body along the coaxial axis, and drives the saw gear and the thumb wheel to rotate, and finally makes the 6 follower wheels with gaps Follow the rotation. When unlocking, the cam first pushes the locking plate to insert into the tooth groove of the saw gear, and the knob plate can no longer rotate, and then the push-pull plate pushes the oblique long hole on the horizontal slide plate to make the follower wheel move laterally and separate from the thimble on the dial wheel Contact, finally make the flashboard insert in the gap of each follower wheel, the cam continues to rotate and unlock, so it is impossible to technically open the lockset. When the handle or the knob is twisted forcefully, both can rotate idly; password change operation and garbled code operation are simple and easy.
Owner:北京德昱嘉诚科技有限公司
Remote opening and closing control structure of mechanical combination lock for important warehouse doors
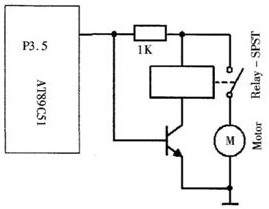
ActiveCN111706183BAchieve lockingRealize remote intelligent controlNon-mechanical controlsElectric permutation locksPasswordControl engineering
The invention discloses a remote opening and closing control structure of a mechanical combination lock for an important warehouse door, which includes a combination lock fixing frame, the combination lock is fixedly installed in the combination lock fixing frame, and the outside of the combination lock body has a scale fixed plate and a scale turntable integrated with it , there is a zero-calibration dial outside the scale dial, and a corresponding groove is opened in the center of the zero-calibration dial and the scale dial. into the groove, the stepper motor is controlled by an external controller. The present invention can realize remote intelligent control, saves manual rotation password, realizes the requirement of unattended opening and closing, reduces labor cost, and has convenient operation and high safety performance.
Owner:JINAN RONGXIAO TECH CO LTD
Software encryption device based on data acquisition
PendingCN112989366AReduce harmSimple structureCarrier indicating/warning arrangementsApparatus modification to store record carriersComputer hardwarePassword
Owner:陕西紫光宏祥智能科技有限公司
A special safe for confidential documents used in financial engineering
ActiveCN112610110BAvoid crackingImprove protectionBurglar alarm by openingBuilding locksInternet privacyPassword
The invention discloses a special safe for confidential documents used in financial engineering, which comprises an electronic lockbox, an alarm device is provided on the electronic lockbox, and a plurality of U-shaped placement plates arranged in parallel in the electronic lockbox, a placement box, a lifting assembly, Two sets of destruction components, identification components, multiple card boards, induction unit, wireless communication module and controller. The invention has a double insurance structure, which can prevent the electronic combination lock on the electronic combination box from being cracked. If you want to take out the confidential file, you need to pass the password verification of the electronic combination lock. After the verification is successful, you need to identify the identity of the person who opened the box Identification, correct identification can finally take out the confidential documents, which can effectively prevent the password on the electronic combination lock from being cracked, and the protection is strong, and when the electronic combination box and the U-shaped placement board for placing the confidential documents are violently damaged, the confidential documents will be automatically deleted Destruction, to prevent leakage of confidential documents.
Owner:JIANGXI UNIVERSITY OF FINANCE AND ECONOMICS
Steel ball password lock core of plug-in inner overlapping digital disk
InactiveCN101769096AIncrease the number ofImprove securityPuzzle locksPermutation locksLogistics managementConfidentiality
The invention relates to a steel ball password lock core of a plug-in inner overlapping digital disk, which is characterized by comprising a rotating core, a mounting frame, at least two digital disks and a connecting press plate, wherein the mounting frame, the digital disks and the connecting press plate are sequentially overlapped and penetrated through the rotating core; a lever plate is installed between the mounting frame and the connecting press plate, and a spring which is fixed on the mounting frame pulls a limiting rod of the lever plate; a code relay roller is clamped between the digital disks and the lever plate which are overlapped, a roller shaft is embedded in a U-shaped notch of isolating plates of the digital disks, and a roller is embedded among the isolating plates and rolled on rotating disks of the digital disks; each rotating disk is provided with a coding hole, and a coding pin is plugged into one of the coding holes. The digital disks are built-in and indestructible; the 10-30 system can be selected, and the digit can be arbitrarily selected between 2 and 12. The invention has sufficient password digit, good confidentiality, simple structure, strong adaptability and high reliability and is widely used for a vault, national defense, public security and a safety box and particularly applied to logistics equipment, such as railway wagons, containers, and the like.
Owner:何西荣
Modular integrated network security data encryption protection device
PendingCN112865963AImprove securityEnsure safetyKey distribution for secure communicationCasings/cabinets/drawers detailsStructural engineeringEmbedded system
The invention discloses a modular integrated network security data encryption protection device which comprises an outer box body, sliding grooves are formed in the upper end and the lower end in the outer box body, a host is movably connected in the sliding grooves and the other sliding groove, a hinge is fixedly connected to the front side of the left end of the outer box body, and a front cover is rotationally connected to the front end of the outer box body through the hinge. A through groove is formed in the front cover, a coded lock is fixedly connected to the front end of the front cover, vibration sensors which are distributed at equal intervals are fixedly connected to the inner walls of the left end and the right end of the outer box body, heat dissipation grooves are formed in the left end and the right end of the outer box body, dustproof nets are fixedly connected into the heat dissipation grooves, and positioning grooves which are symmetrical left and right are formed in the lower end of the outer box body. An infrared distance measuring sensor is mounted in the positioning groove. According to the modular integrated network security data encryption protection device, the encryption mode is more reliable, cracking is not prone to occurring, the data security is higher, encryption protection is also set for the host, and the data security is further guaranteed.
Owner:天目数据(福建)科技有限公司
A multifunctional security combination lock
Owner:安徽先启电子科技有限公司
A portable password toolbox for power operation
ActiveCN112454309BSave energyFast transferNon-mechanical controlsElectric permutation locksComputer hardwarePassword
The invention discloses a portable cipher toolbox for power operation, which includes a carrying unit, an adjusting unit and a cipher lock unit, wherein the carrying unit includes a box body, a top cover hinged to the box body, and the box body and the top The same side of the cover is provided with an electronic lock; and, the adjustment unit includes an adjustment assembly, and the adjustment assembly is arranged on both sides of the box body; the code lock unit includes an identification assembly, and the code lock unit is located in the box On one side of the body, the identification component is connected to the electronic lock through a circuit; the present invention is provided with a carrying unit, an adjusting unit and a combination lock unit, and the present invention enables the staff to carry out the transfer without carrying a toolbox to save money. The physical strength of the staff can also speed up the transfer speed of the staff, thereby improving the work efficiency of the staff. The password lock unit requires the staff to perform fingerprint verification every time the tool box is opened, thereby greatly reducing the probability of the maintenance tool being stolen .
Owner:GUIZHOU POWER GRID CO LTD
An intelligent thing-linked anti-theft door password lock structure
ActiveCN112343433BAvoid Forced UnlockRealize multi-way unlockingNon-mechanical controlsAutomatic controlRemote control
Owner:湖南星香源科技有限责任公司
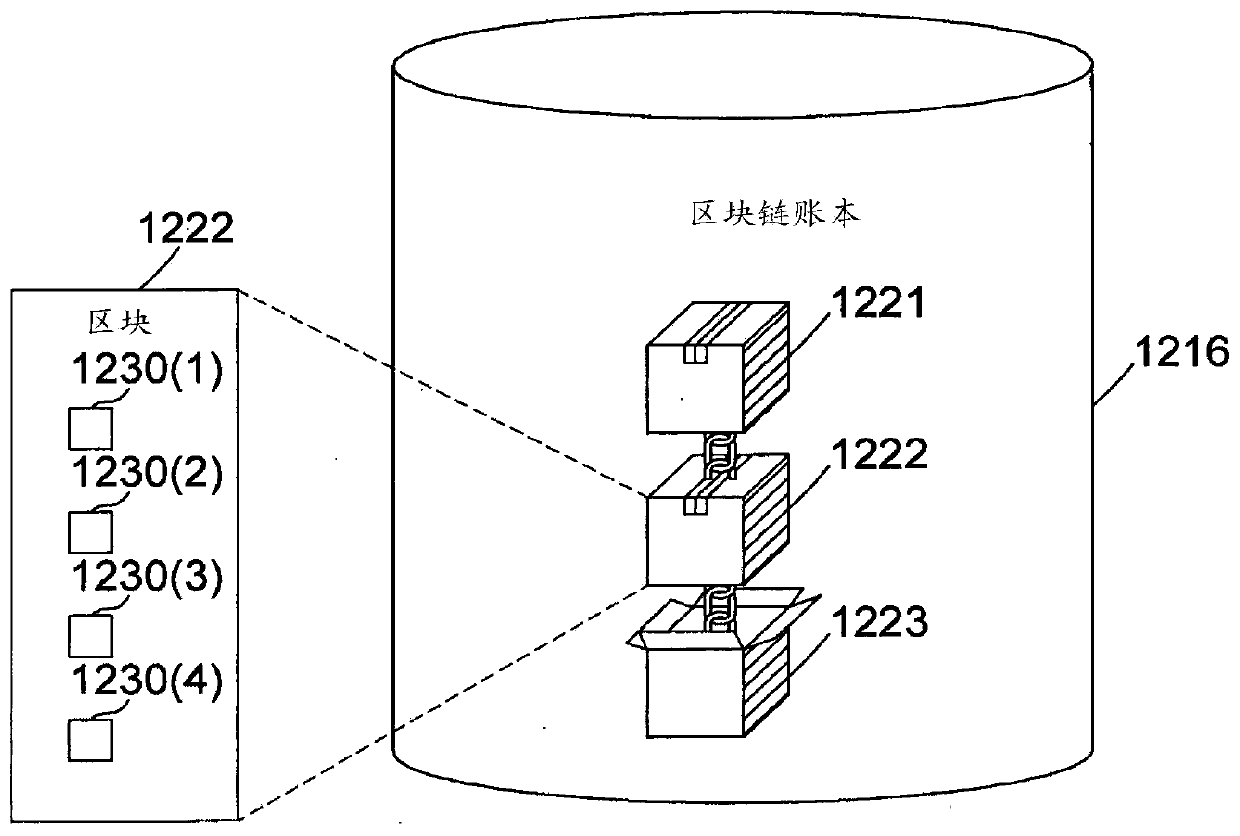
Blockchain-implemented security systems and methods for blinded outcome selection
PendingCN111466098APublic key for secure communicationUser identity/authority verificationComputer networkInternet privacy
There may be provided a blockchain-implemented security method. It may be implemented using a blockchain network. Embodiments of the blockchain-implemented security method involve a first party and asecond party. The blockchain-implemented security method generates a plurality of n cryptographic locks based on combinations of encrypted versions of a first plurality of n secrets generated by the first party and encrypted versions of a second plurality of n secrets generated by the second party. One secret belonging to the first plurality of n secrets generated by the first party is randomly selected. And a cryptographic key that unlocks a particular cryptographic lock of the plurality of n cryptographic locks is generated, wherein the particular cryptographic lock corresponds to the randomly selected one secret belonging to the first plurality of n secrets generated by the first party.
Owner:NCHAIN HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com