Patents
Literature
306 results about "OPC Data Access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
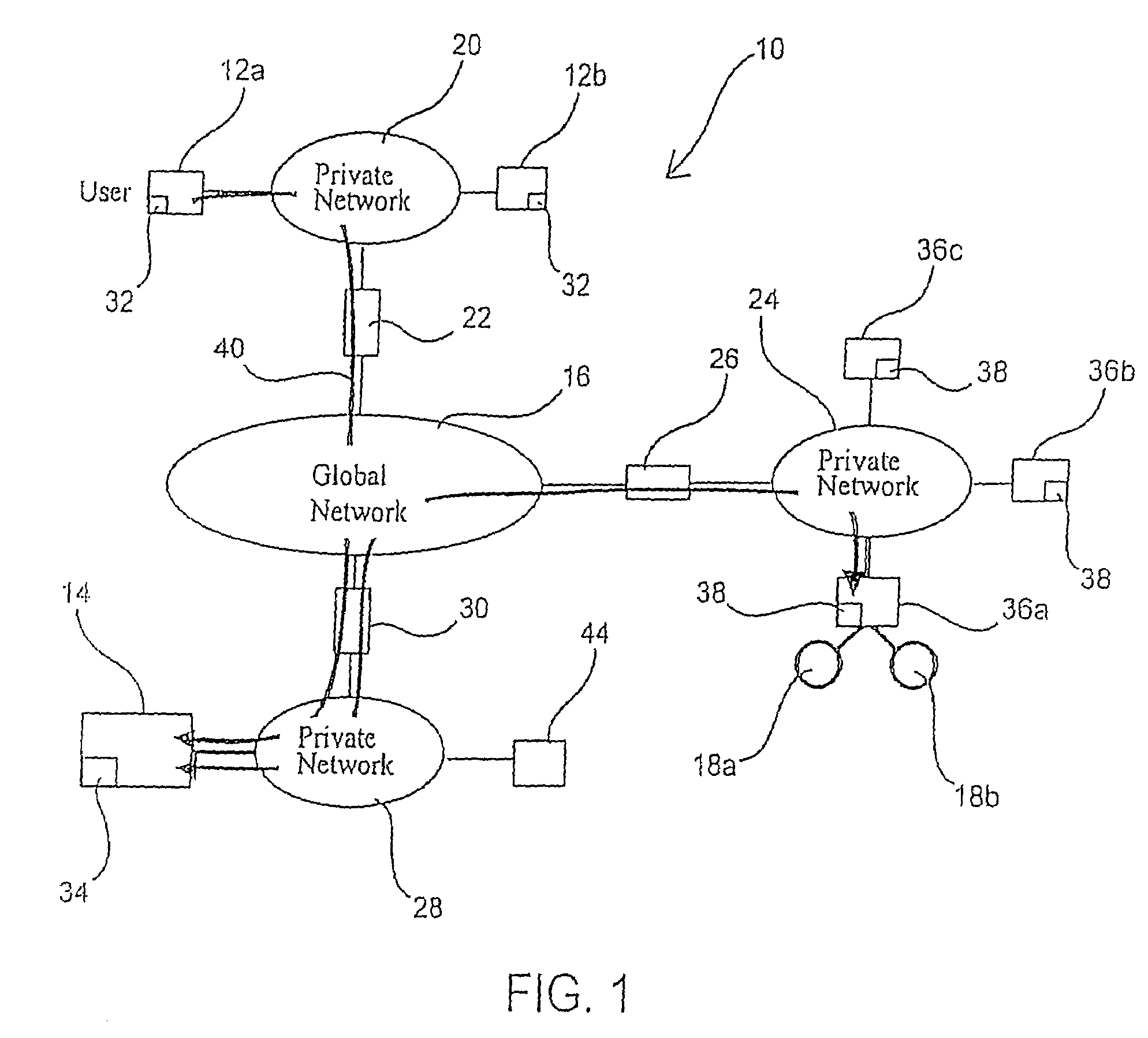
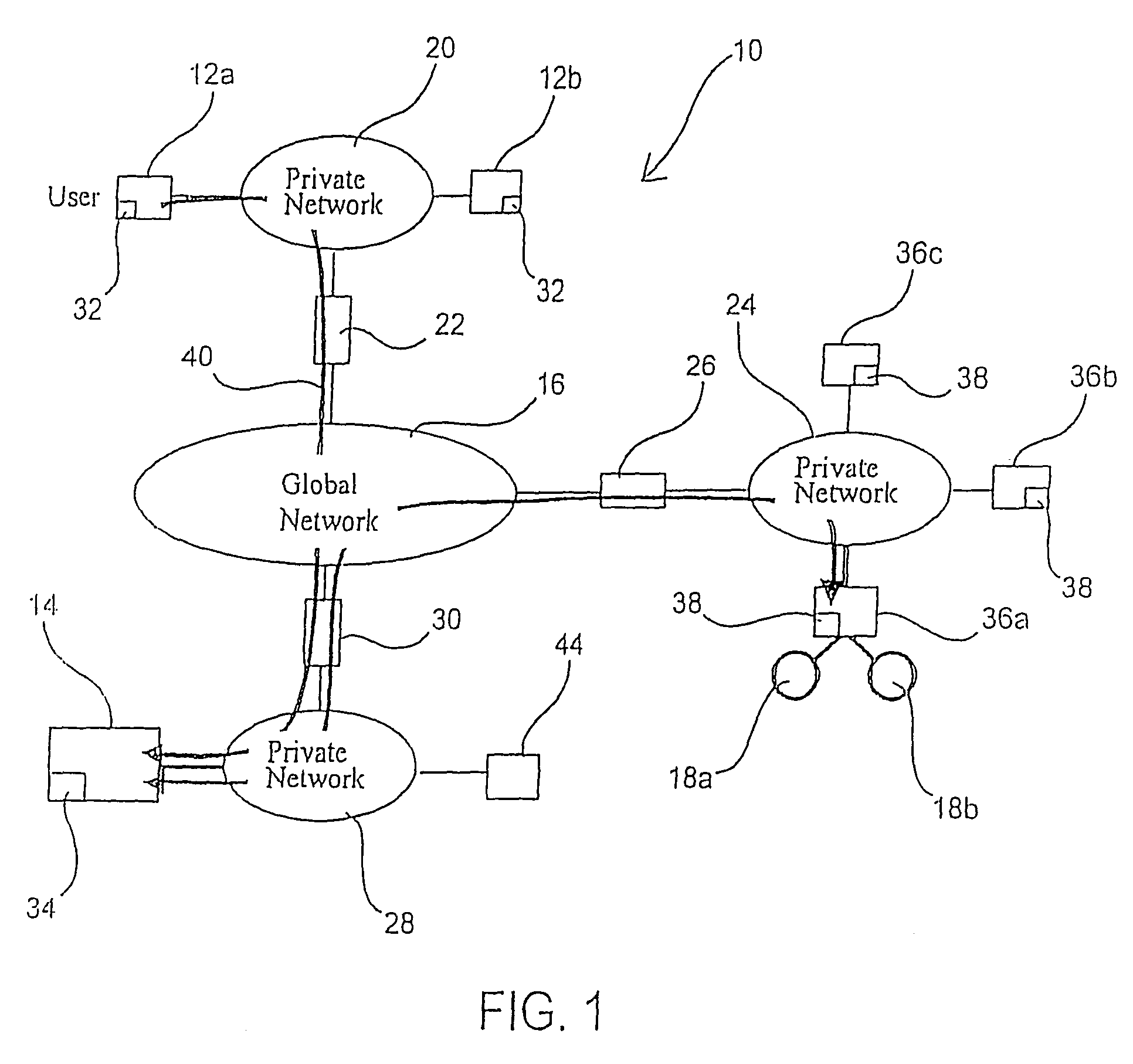
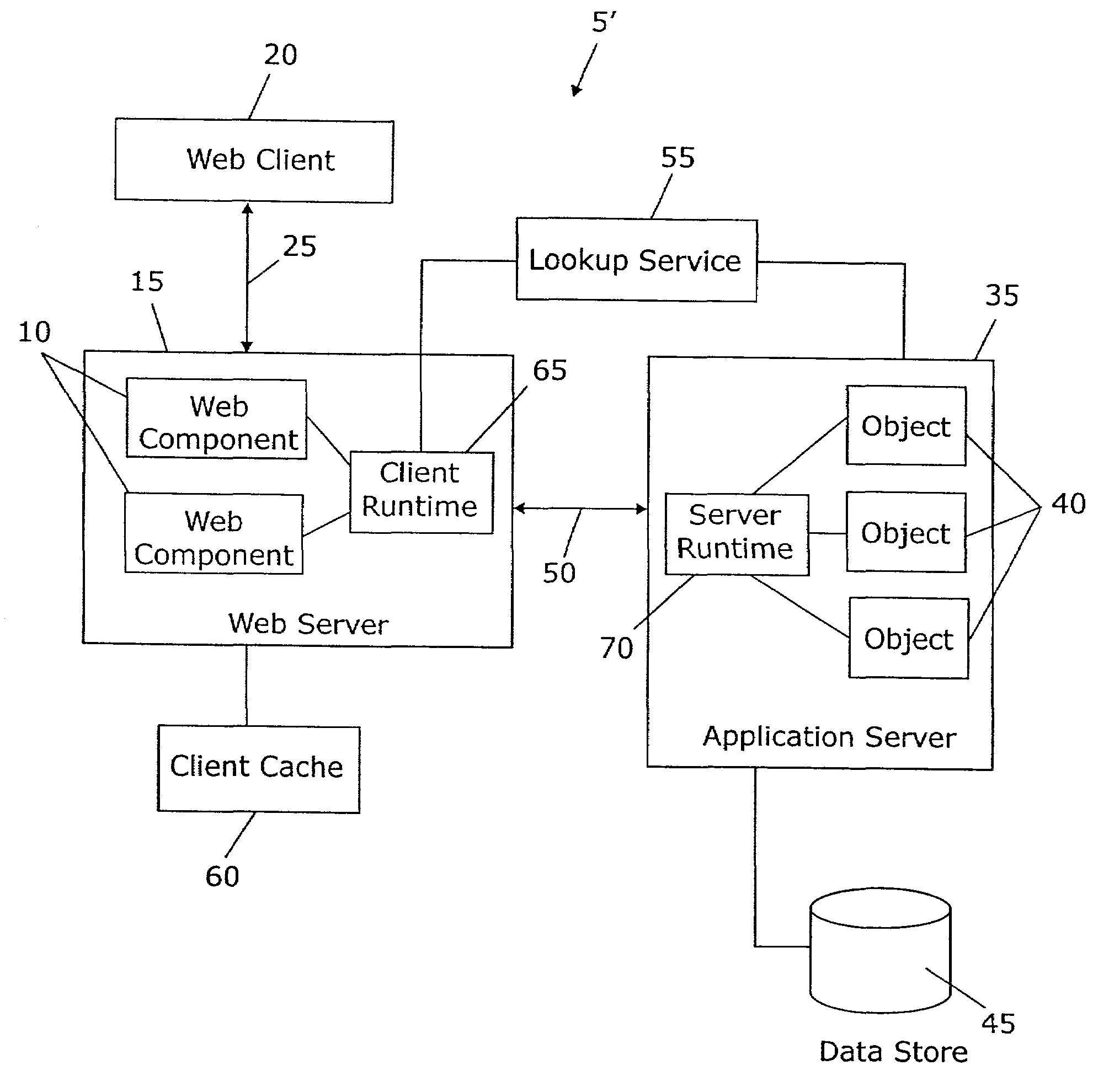
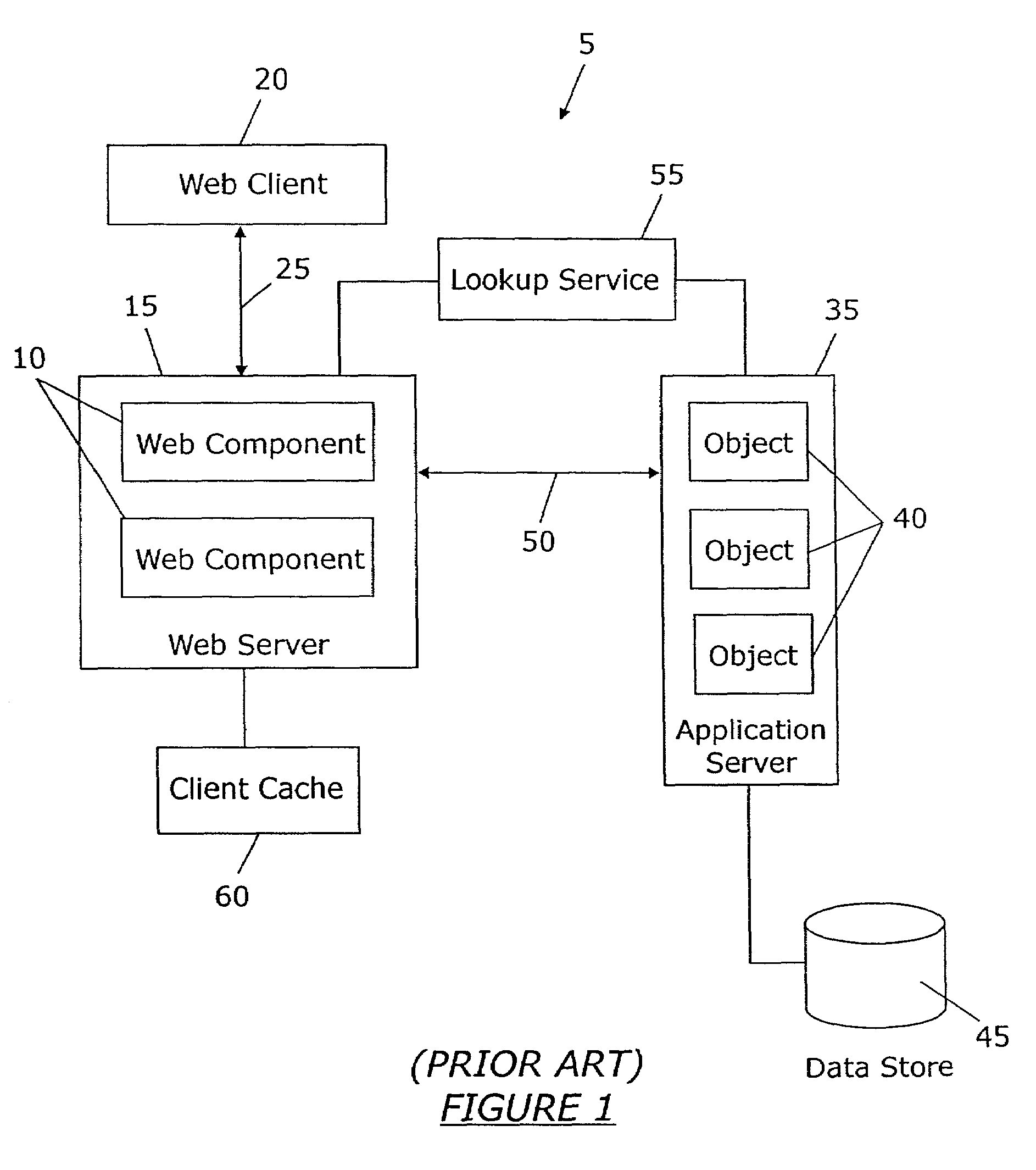
The OPC Data Access Specification is the first of a group of specifications known as the OPC Classic Specifications. OPC Data Access is a group of client-server standards that provides specifications for communicating real-time data from data acquisition devices such as PLCs to display and interface devices like Human-Machine Interfaces (HMI), SCADA systems and also ERP/MES systems. The specifications focus on the continuous communication of data.
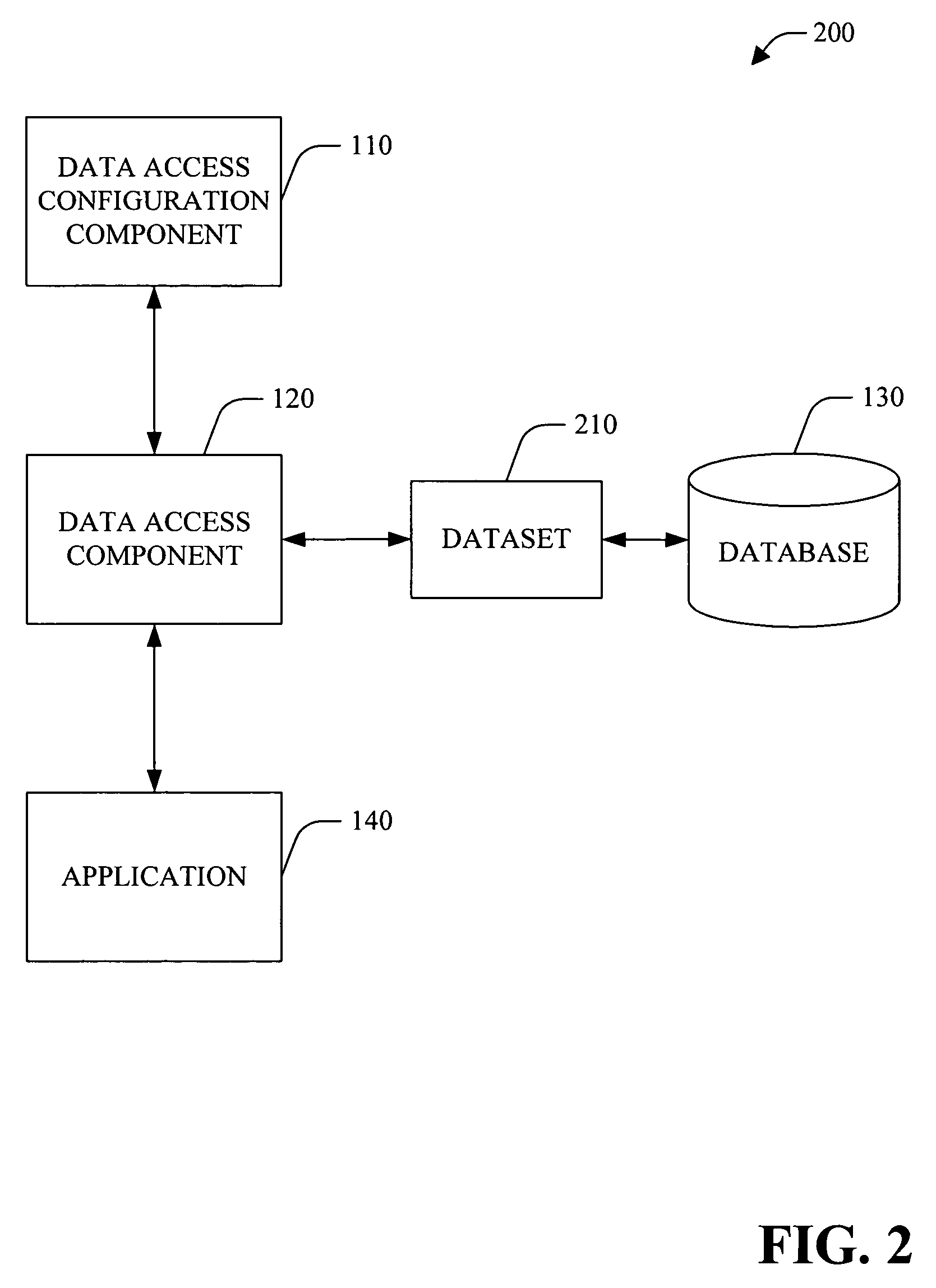
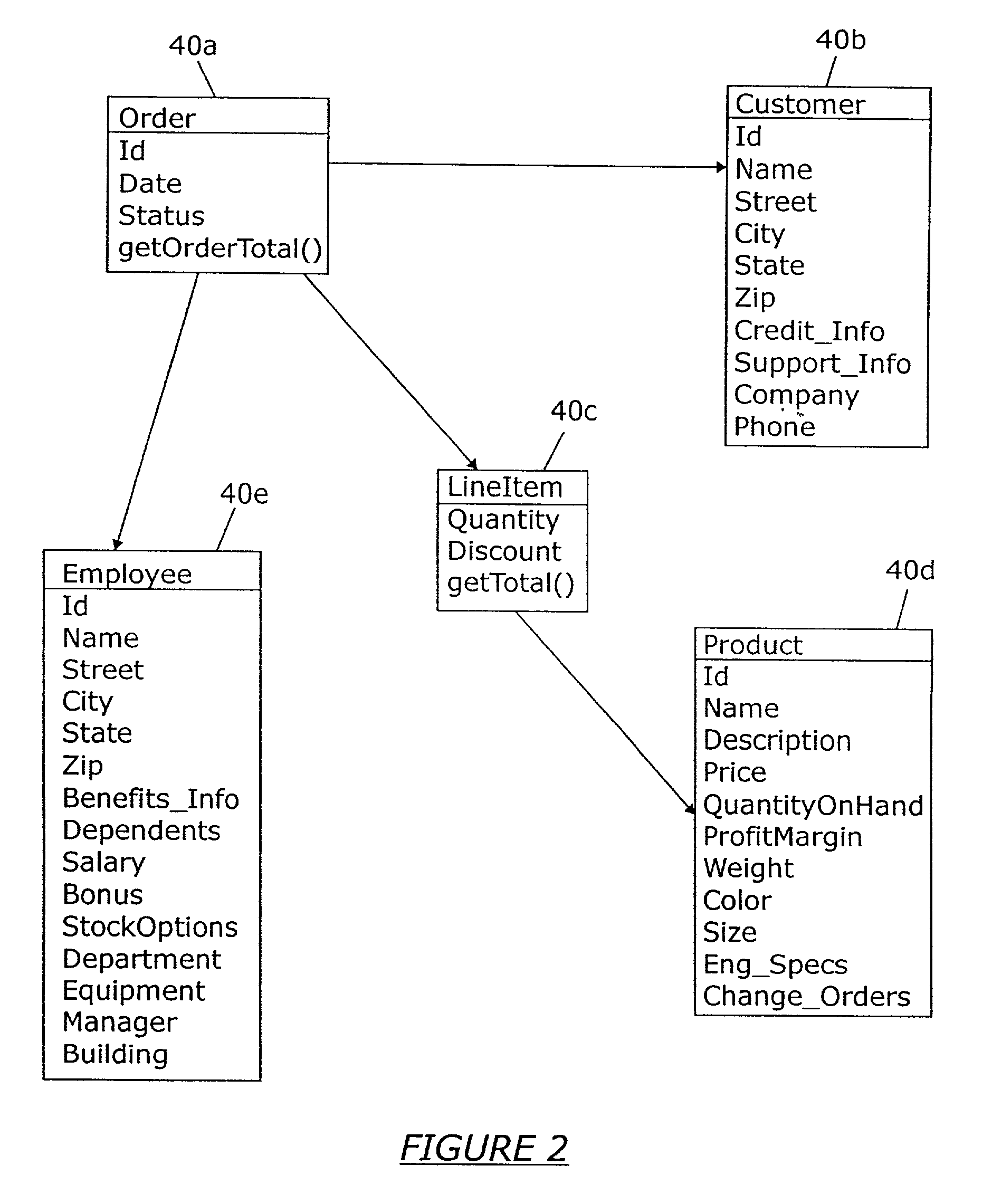
Data access system
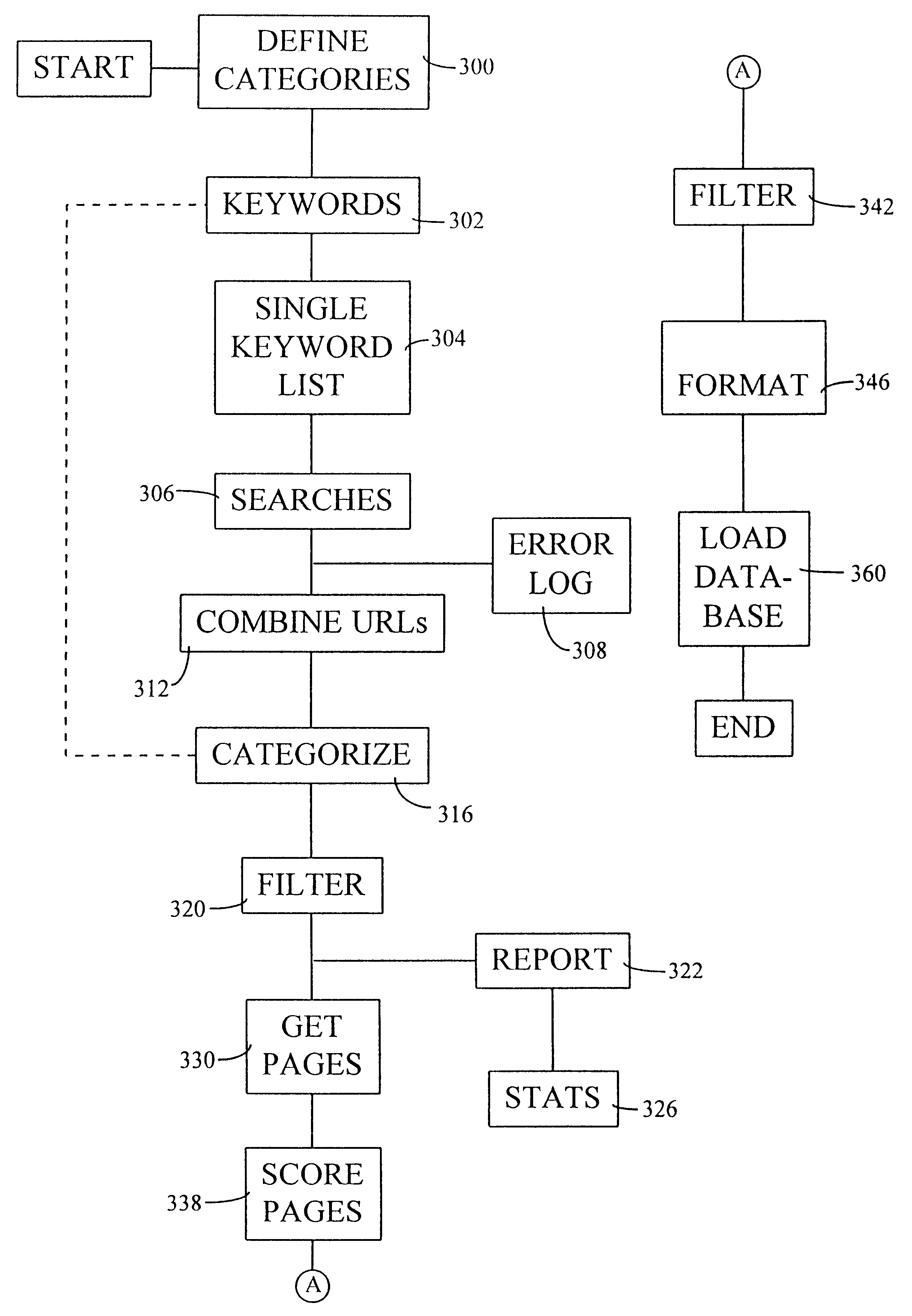
A method of automatically creating a database on the basis of a set of category headings uses a set of keywords provided for each category heading. The keywords are used by a processing platform to define searches to be carried out on a plurality of search engines connected to the processing platform via the Internet. The search results are processed by the processing platform to identify the URLs embedded in the search results. The URLs are then used to retrieve the pages to which they refer from remote data sources in the Internet. The processing platform then filters and scores the pages to determine which pages are the most relevant to the original categories. Internet location information for the most relevant pages is stored in the database.
Owner:SUFFOLK TECH
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7546353B2Reduce bandwidth requirementsLimited dataDigital data processing detailsUser identity/authority verificationNetwork connectionData access
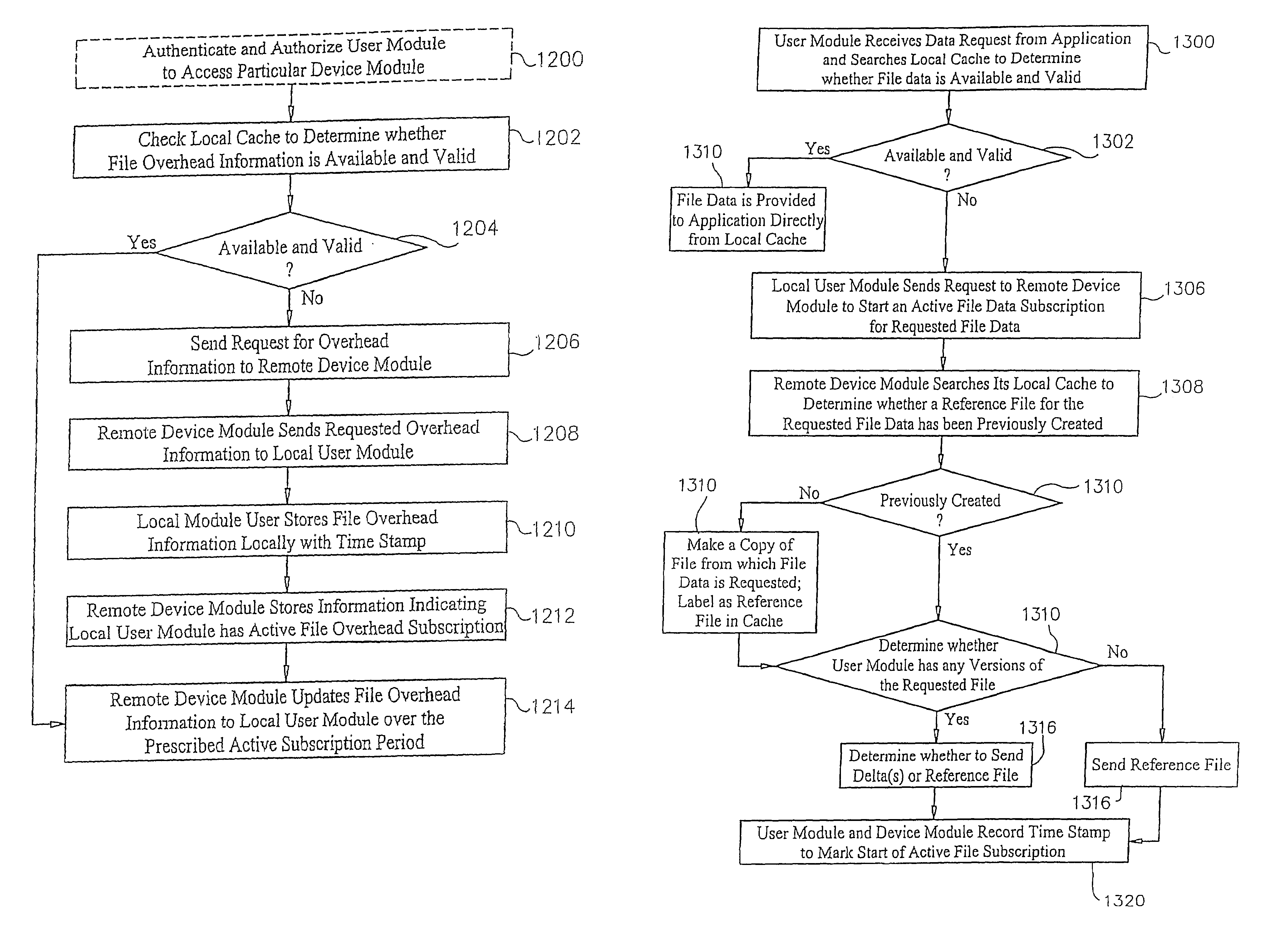
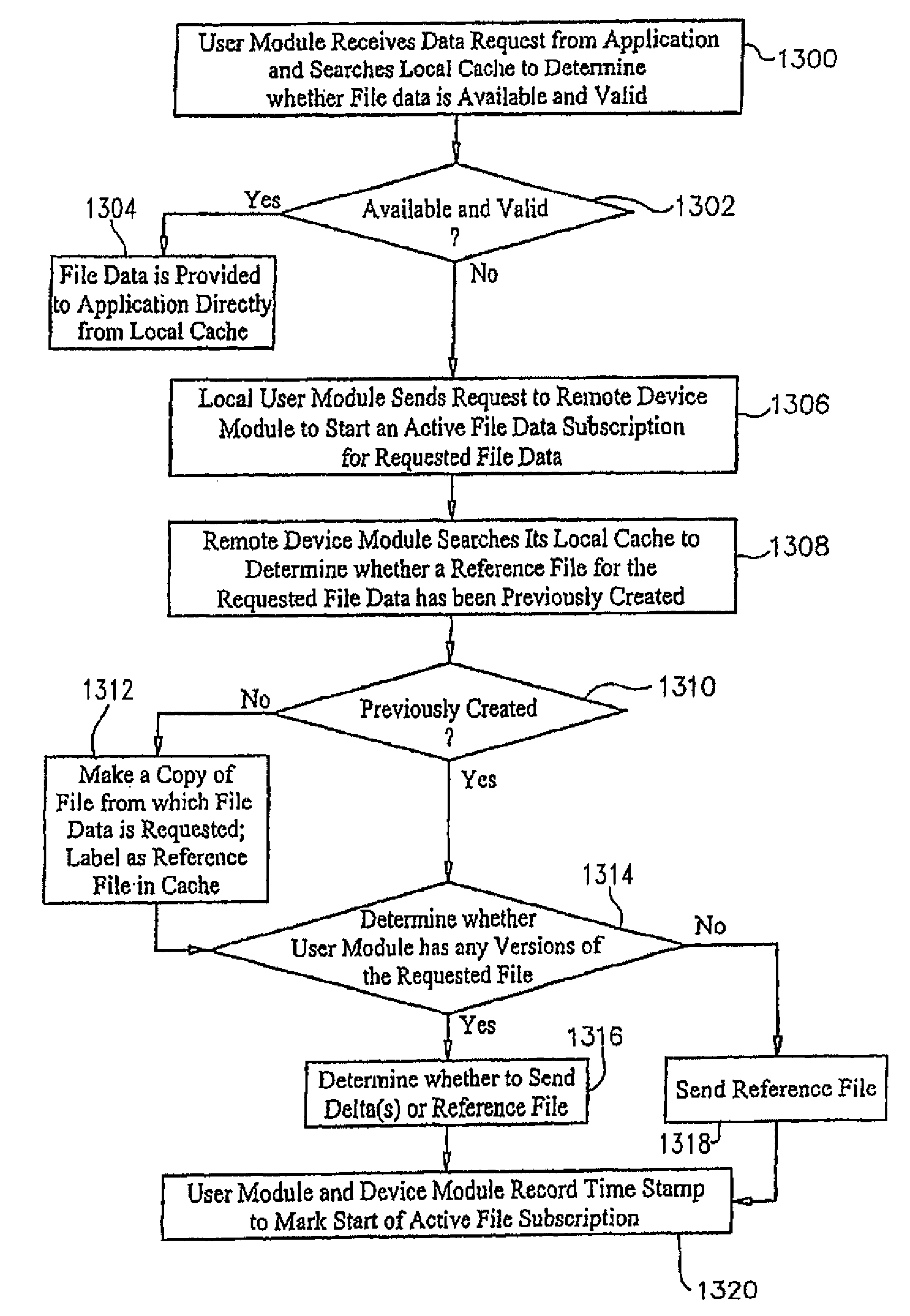
Applications, systems and methods for efficiently accessing data and controlling storage devices among multiple computers connected by a network. Upon receiving a request for access to data originally stored in a remote storage device, determining whether the data is already available and valid in a local storage device. Accessing the data from the local storage device if the data is available and valid. Authenticating a request for a secure connection between a local computer associated with the local storage device and a remote computer associated with the remote storage device. Securely connecting the local computer with the remote computer. Requesting the data from the remote storage device, over the network, if the data is not locally available and valid. Receiving data over the network from the remote storage device, and storing the data in the local storage device for direct local access thereto.
Owner:WESTERN DIGITAL TECH INC
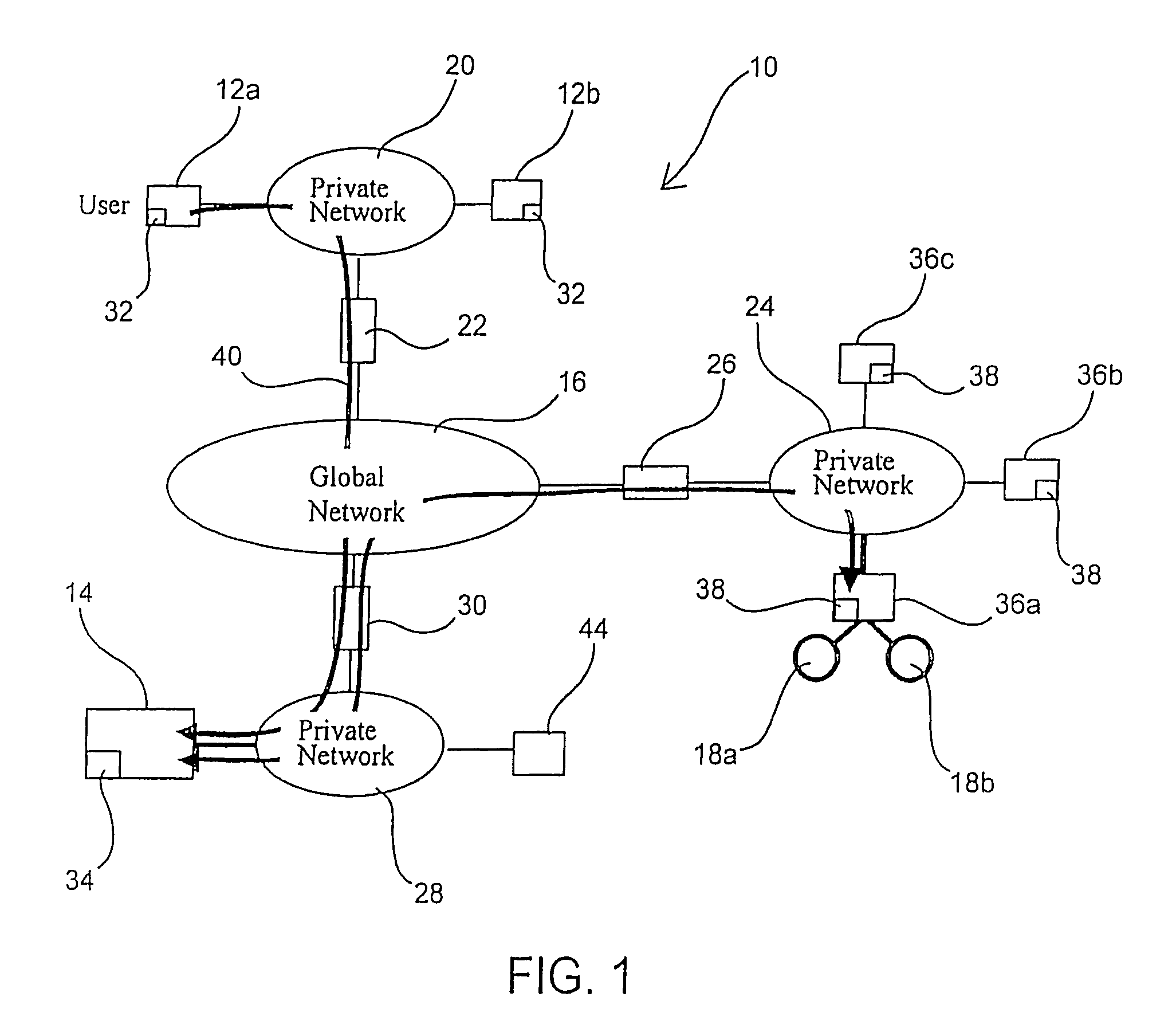
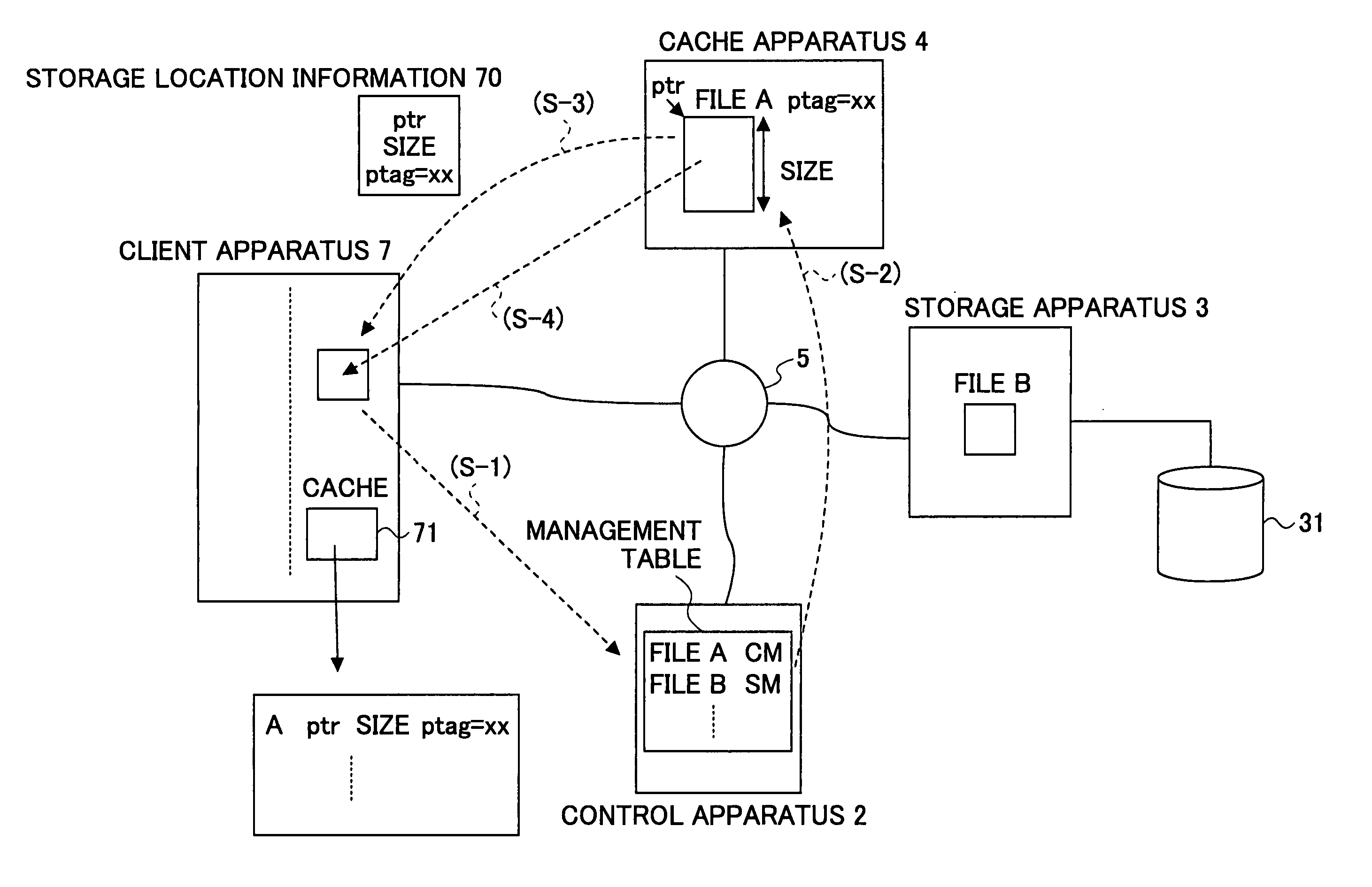
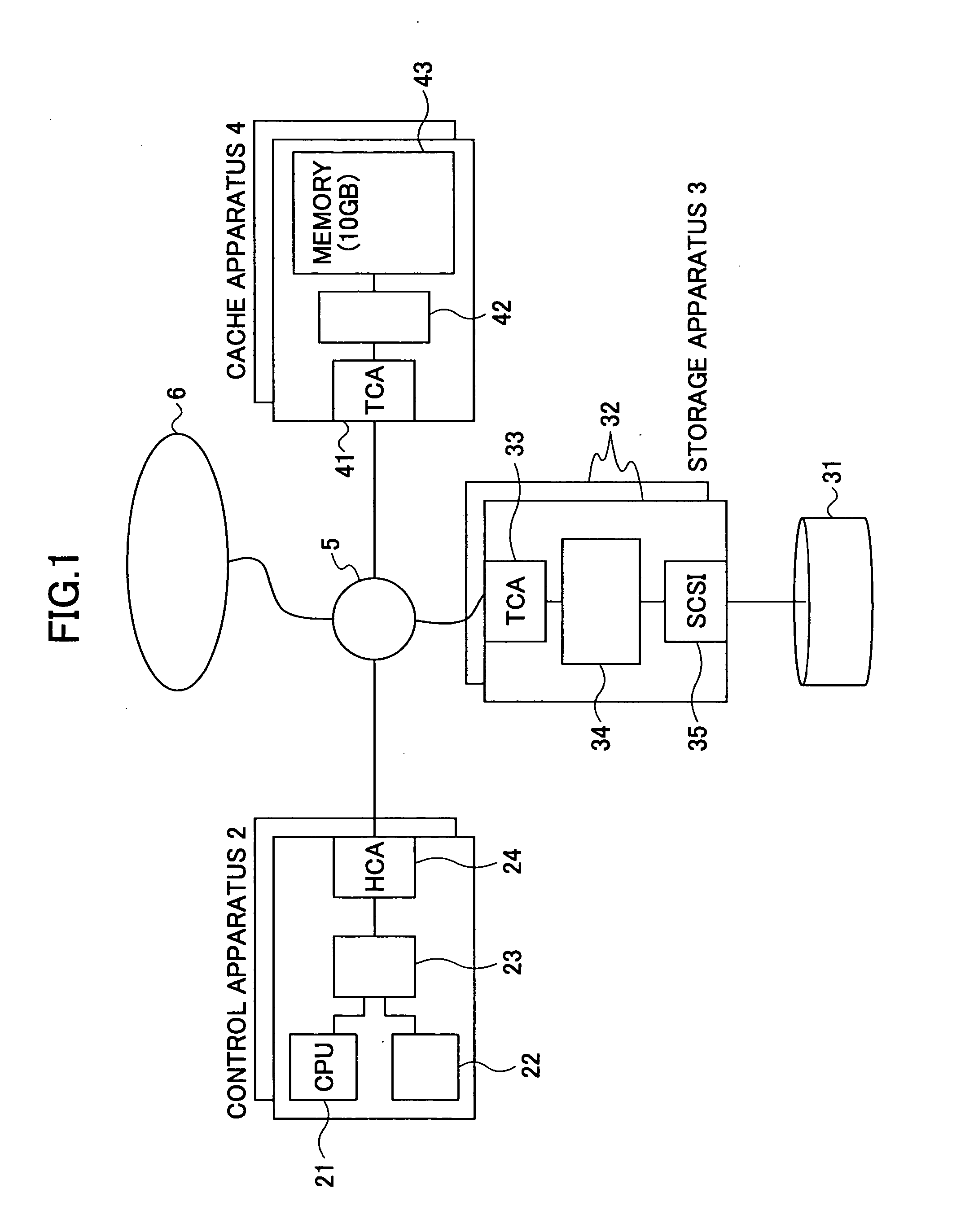
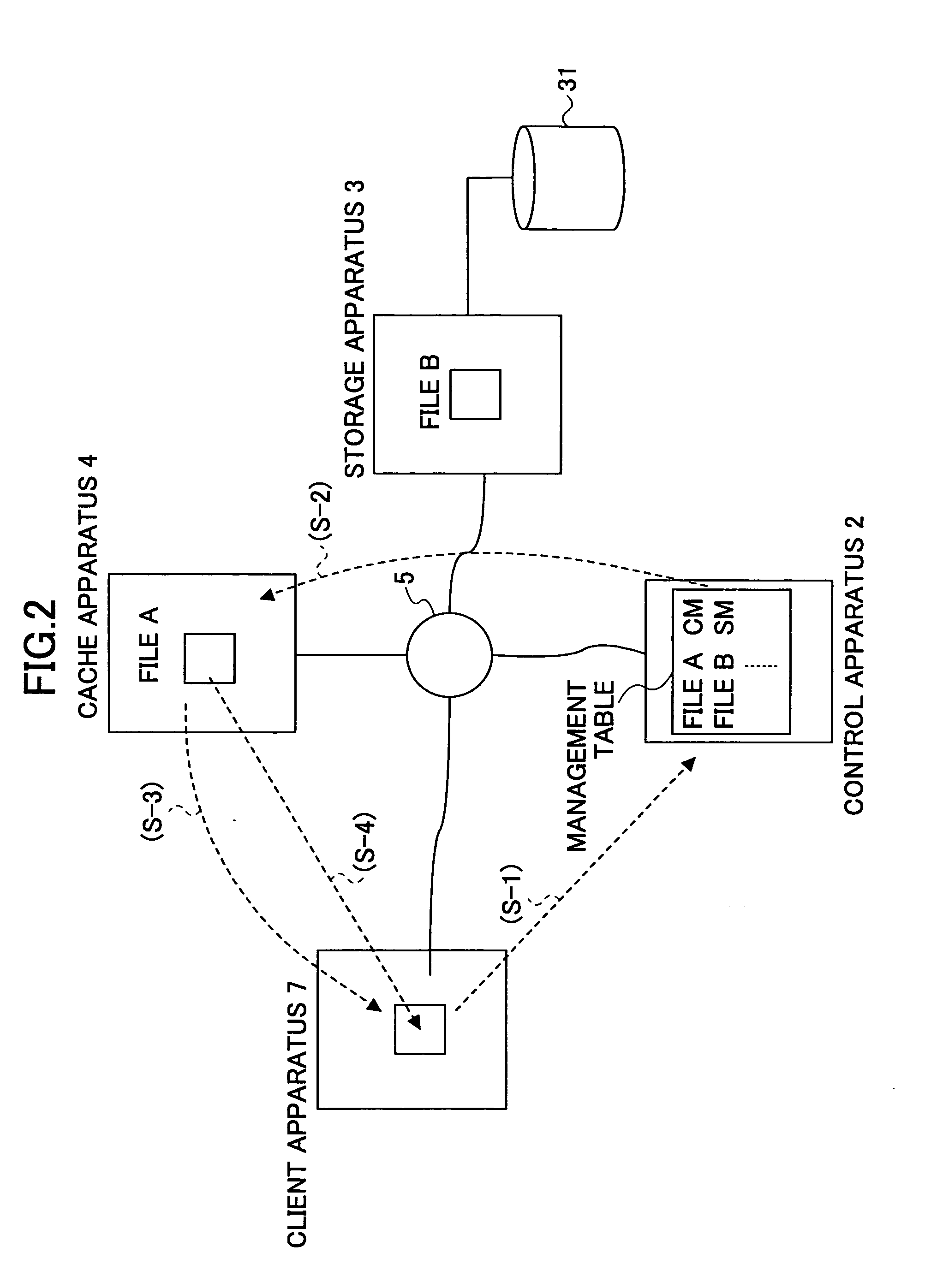
Data access responding system, storage system, client apparatus, cache apparatus, and method for accessing data access responding system
InactiveUS20060041614A1Lower latencyHigh access frequencyMemory architecture accessing/allocationInput/output to record carriersData accessClient-side
A control apparatus provides a transfer instruction to one of storage apparatus and a cache apparatus, in which relevant data is stored, when receiving an access request from a client apparatus for the data for which the storage location is managed; and the one of the storage apparatus and the cache apparatus receiving the transfer instruction directly returns a reply message, to the client apparatus, having information of the storage location of the data added thereto, which data the access request requests.
Owner:FUJITSU LTD
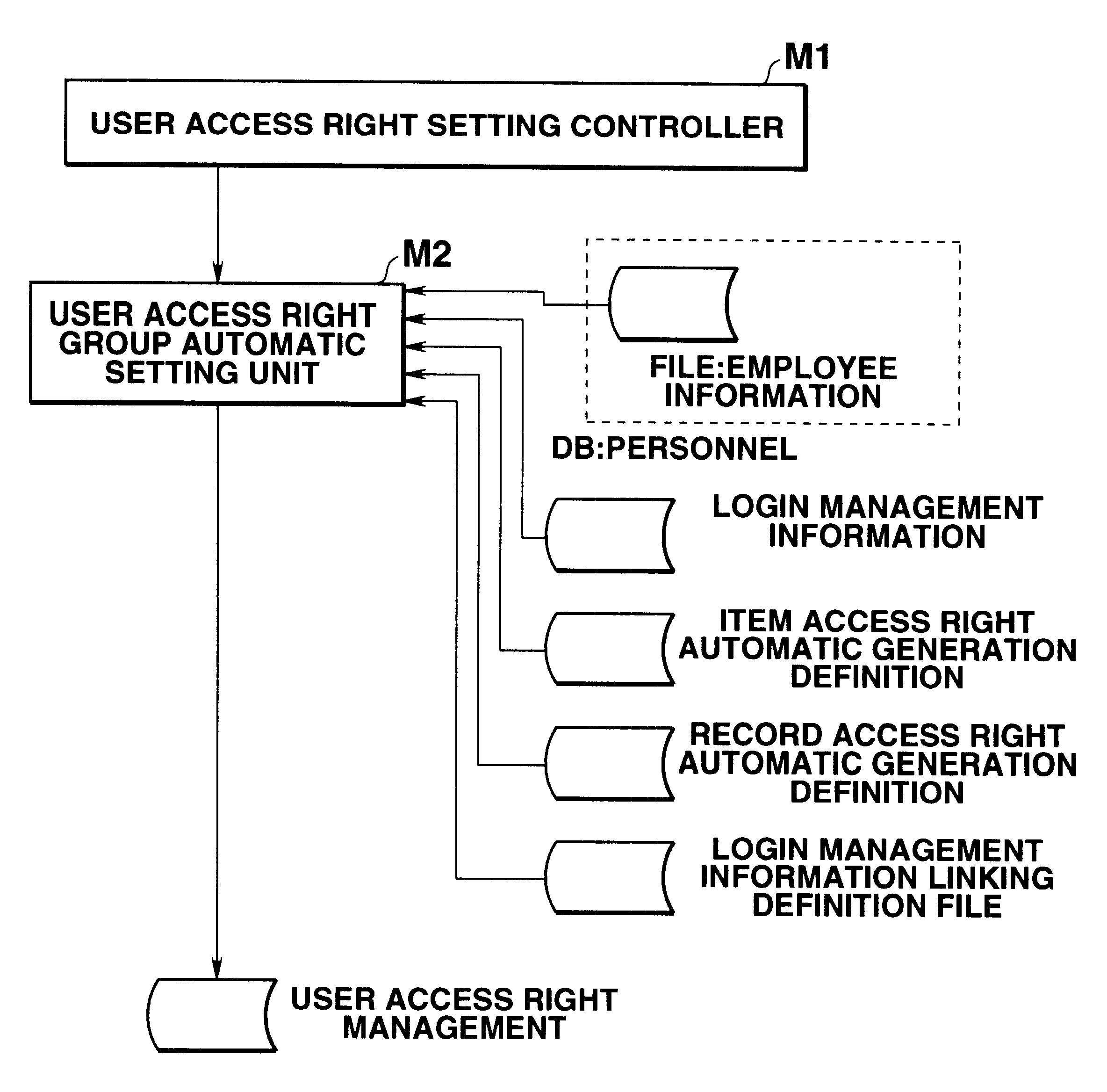
Data access control apparatus for limiting data access in accordance with user attribute
InactiveUS6275825B1Reduce loadPrevent setting errorsData processing applicationsDigital data processing detailsData access controlRights management
This invention provides a data access control apparatus arranged to automatically set access right information limiting data access, in accordance with a user attribute when a user accesses a database. In setting, for a plurality of users, access right information corresponding to each user, the load on an operator can be reduced, and access right information setting errors can be prevented. An automatic setting unit reads out information from a login management information file and an employee information file on the basis of definition information of a definition files to automatically generate a user access right management file which stores a login ID, an item access right, and a record access right group code for each user. When a login ID is input in accessing the employee information file, a setting controller refers to the management file to determine a user group to which the user belongs and an access enabled / disabled state of the data on the basis of the access right made to correspond to this user group.
Owner:CASIO COMPUTER CO LTD
Proximity-based system for automatic application or data access and item tracking
ActiveUS20110221568A1Electric signal transmission systemsDigital data processing detailsInternet privacyData access
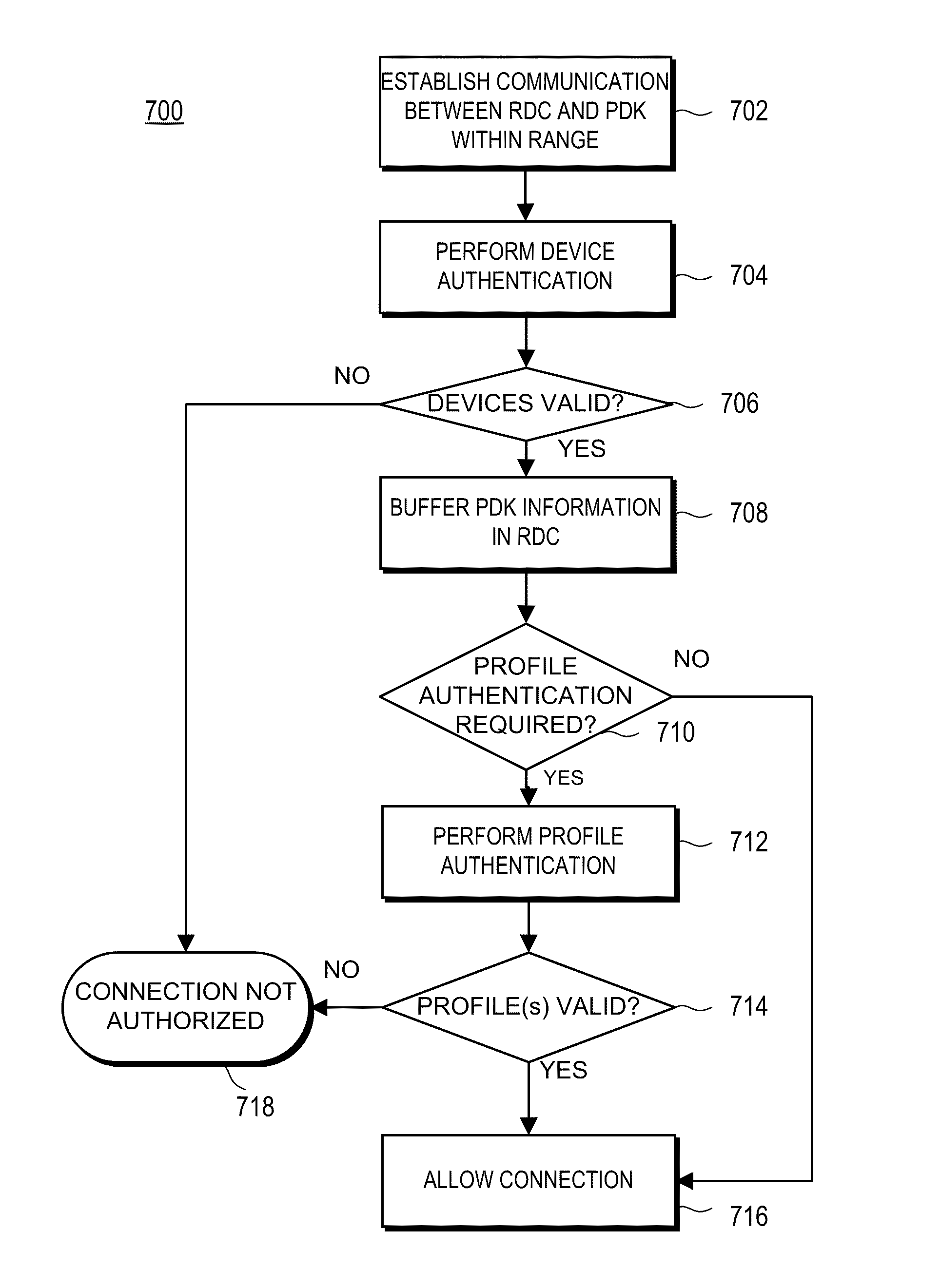
A system and method provide automatic access to applications or data. A portable physical device, referred to herein as a Personal Digital Key or “PDK”, stores one or more profiles in memory, including a biometric profile acquired in a secure trusted process and uniquely associated with a user that is authorized to use and associated with the PDK. The PDK wirelessly transmits identification information including a unique PDK identification number, the biometric profile and a profile over a secure wireless channel to a reader. A computing device is coupled to the reader. An auto login server is coupled to the reader and the computing device and launches one or more applications associated with a user name identified by the received profile.
Owner:PROXENSE
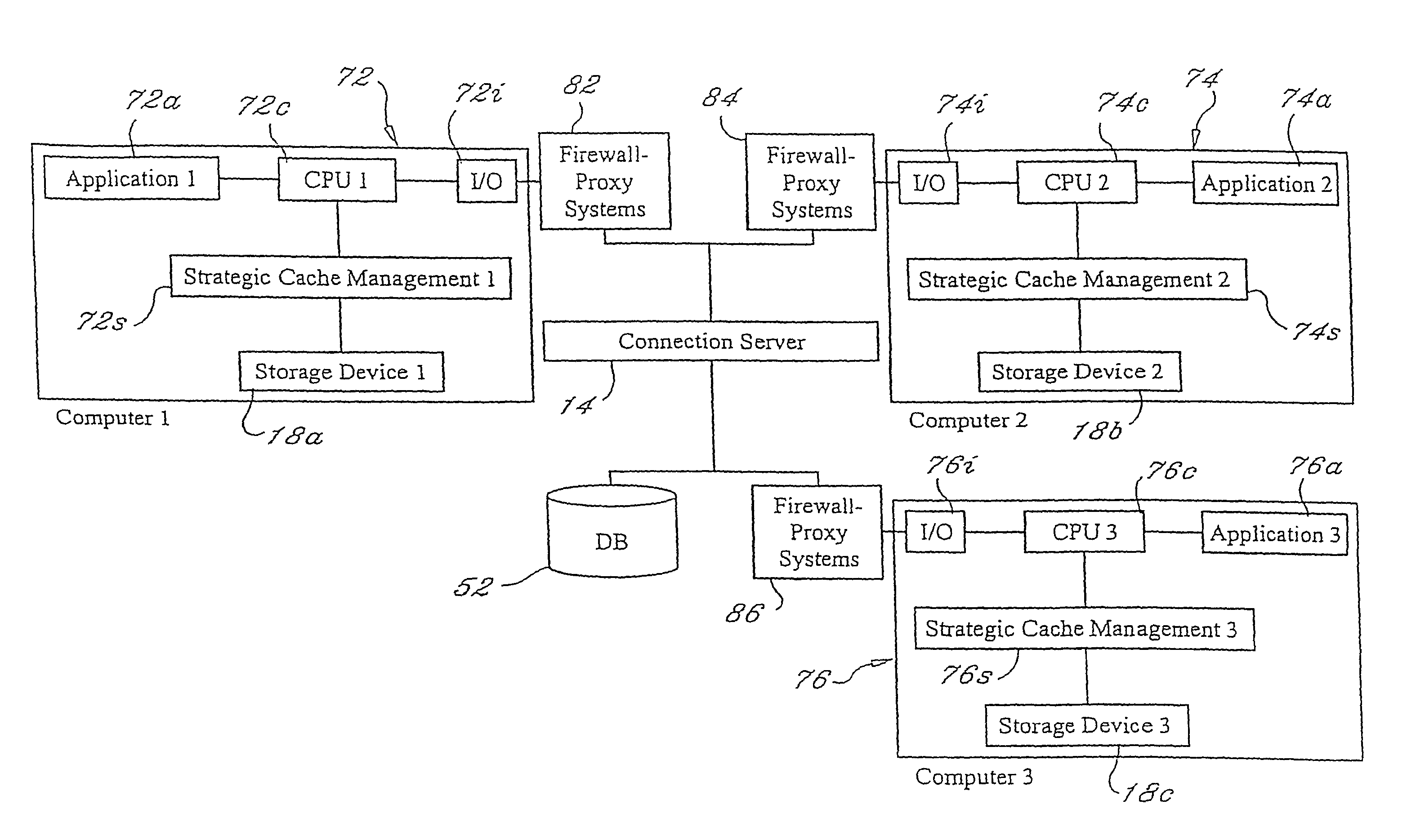
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7587467B2Efficiently accessing and controllingMinimizes bandwidth requirementDigital data processing detailsMultiple digital computer combinationsData accessApplication software
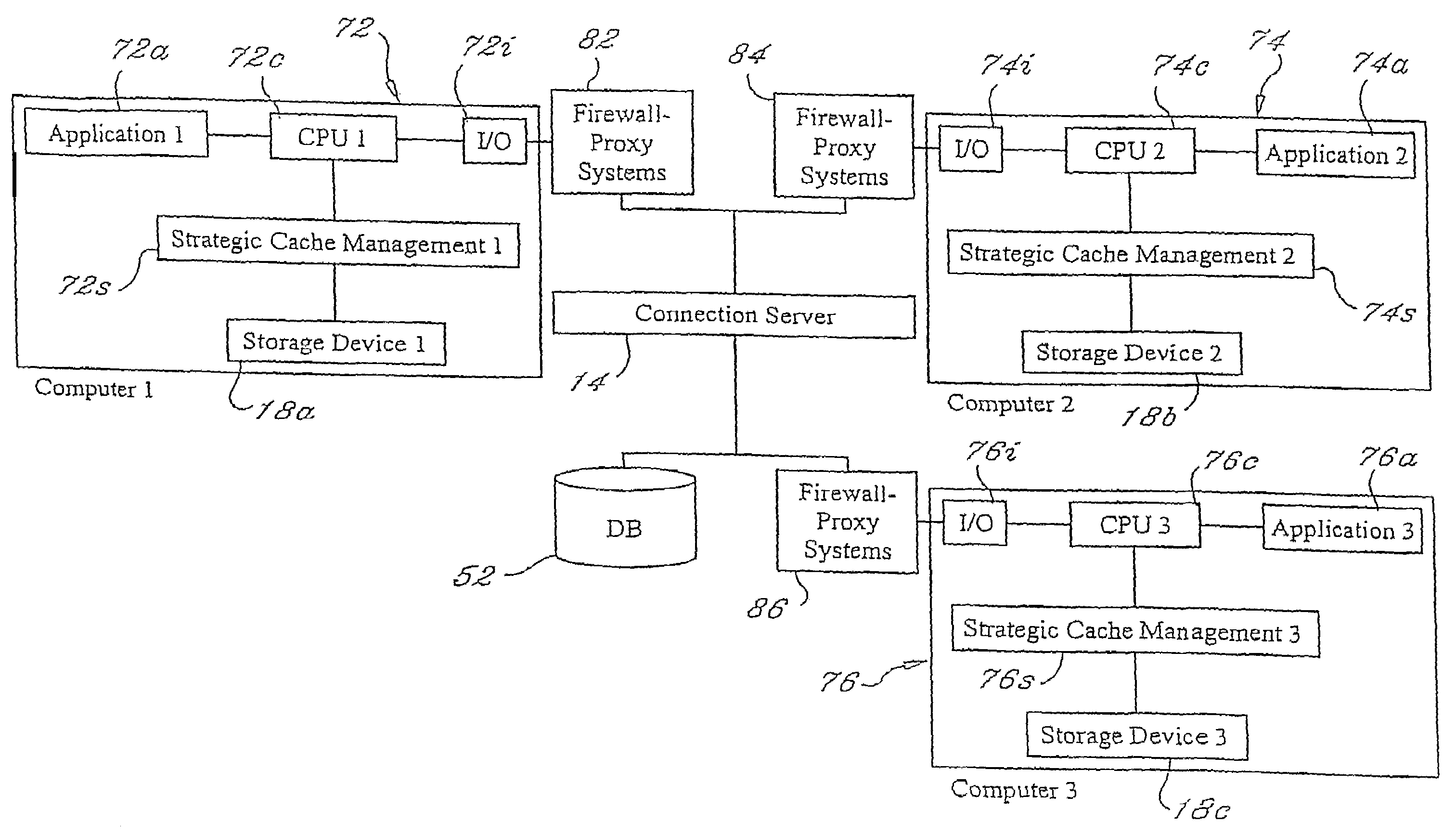
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Strategic cache management processes are provided to manage the data in cache memory of the storage devices involved. Communication of data over the network may be managed by means of one or more connection servers which may also manage any or all of authentication, authorization, security, encryption and point-to-multipoint communications functionalities. Alternatively, computers may be connected over a wide area network without a connection server, and with or without a VPN. Data transmissions may be managed to minimize bandwidth and may be temporally and / or spatially compressed.
Owner:WESTERN DIGITAL TECH INC
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7917628B2Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
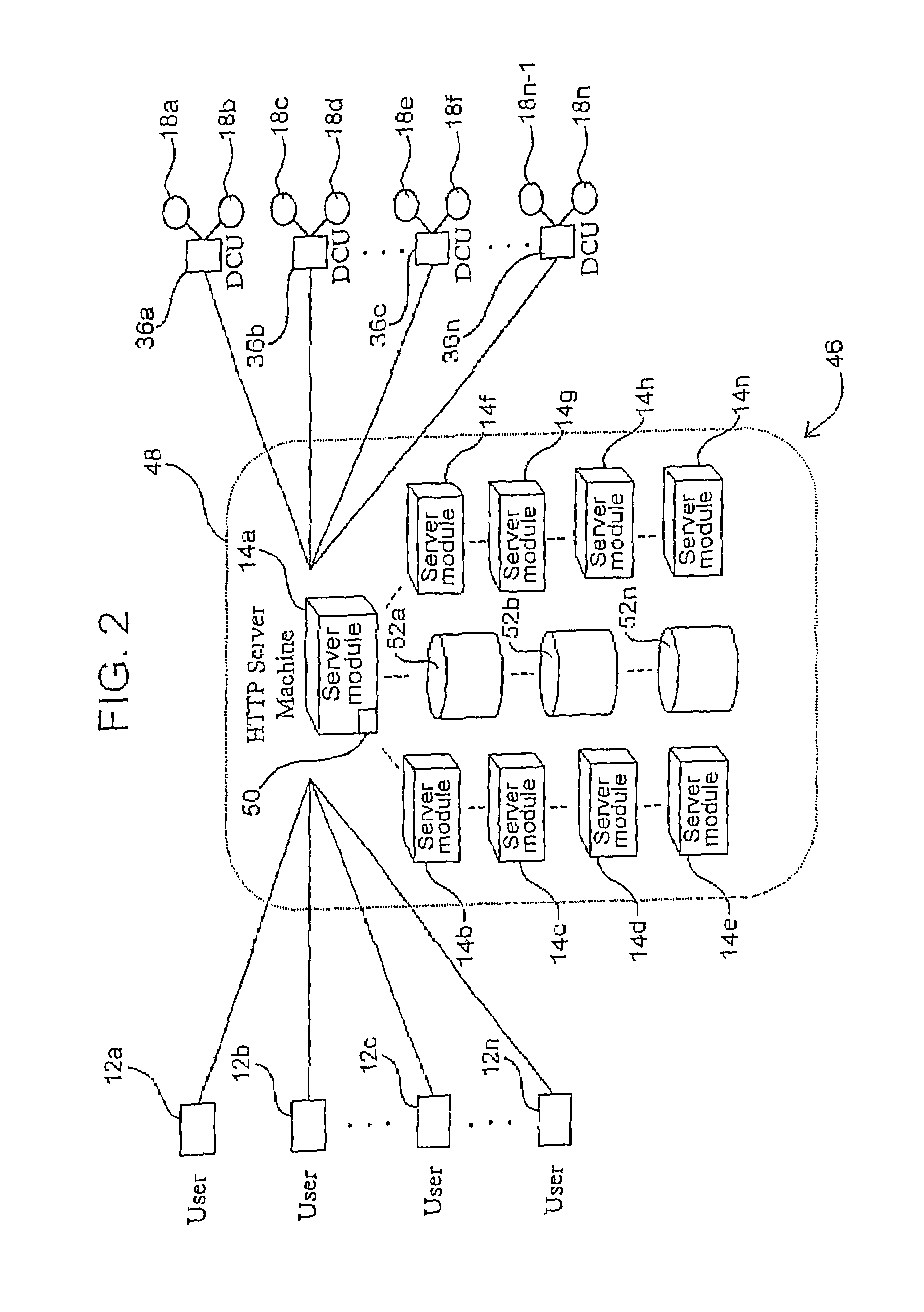
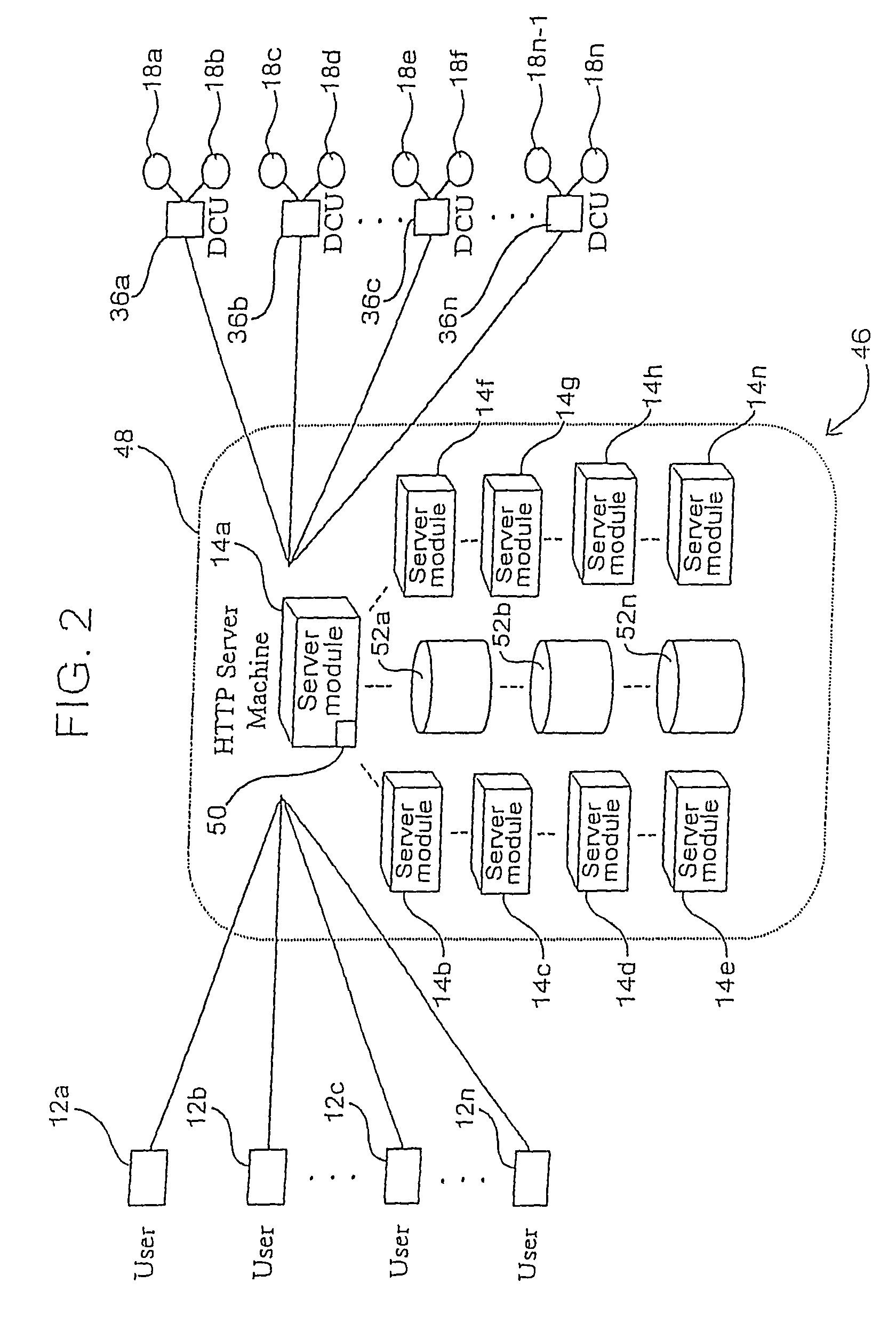
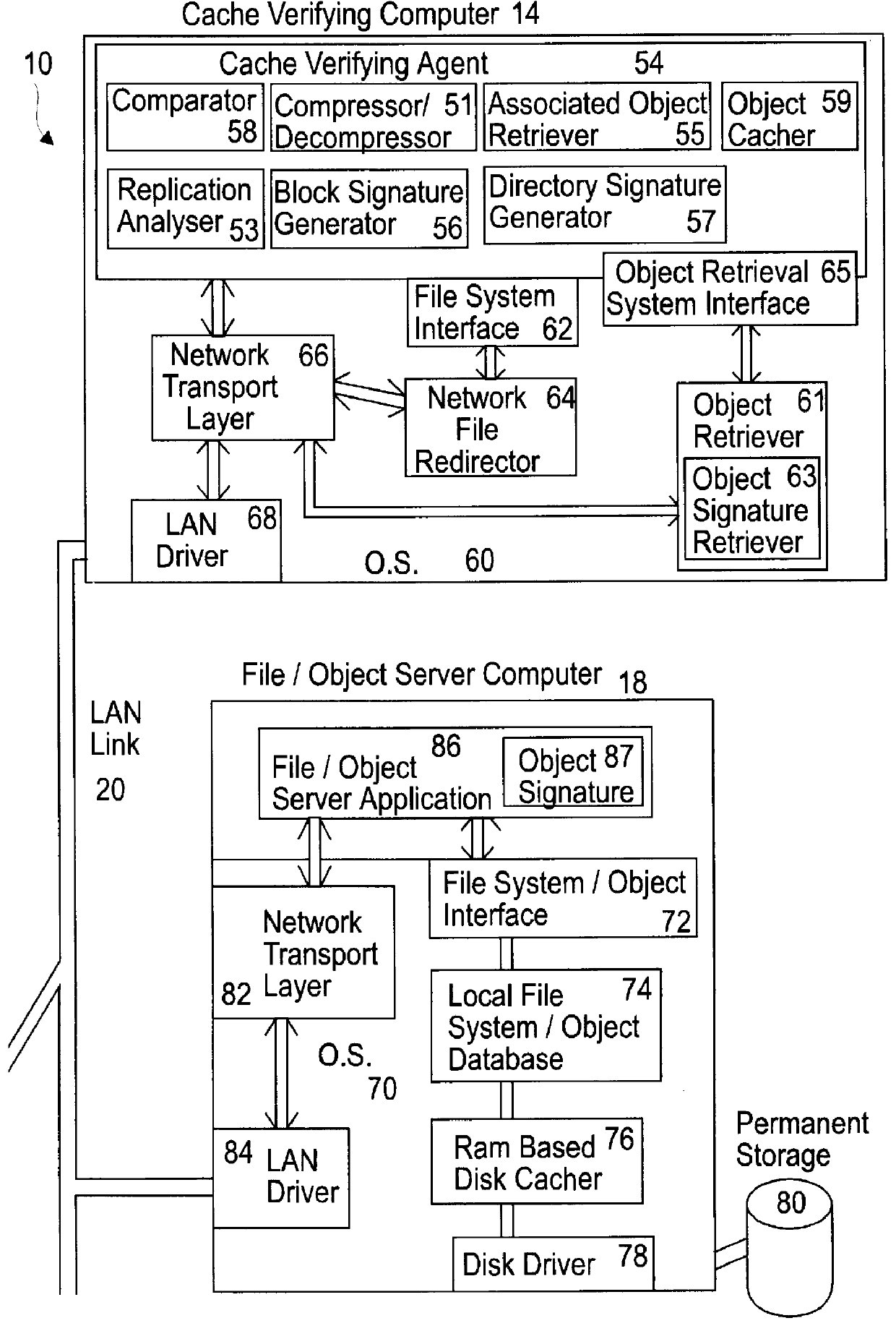
Apparatus and method for increased data access in a network file object oriented caching system
An apparatus for increased data access in a network includes a file / object server computer having a permanent storage memory, a cache verifying computer operably connected to the file / object server computer in a manner to form a network for rapidly transferring data, the cache verifying computer having an operating system, a first memory and a processor capable of performing an operation on data stored in the permanent storage memory of the file / object server computer to produce a signature of the data characteristic of one of a file, an object and a directory, a remote client computer having an operating system, a first memory, a cache memory and a processor capable of performing an operation on data stored in the cache memory to produce a signature of the data, a communication server operably connected to the remote client computer to the cache verifying computer and the file / object server computer and comparators operably associated with the cache verifying computer and remote client computer for comparing the signatures of data with one another to determine whether the signature of data of the remote client is valid.
Owner:COMTECH EF DATA
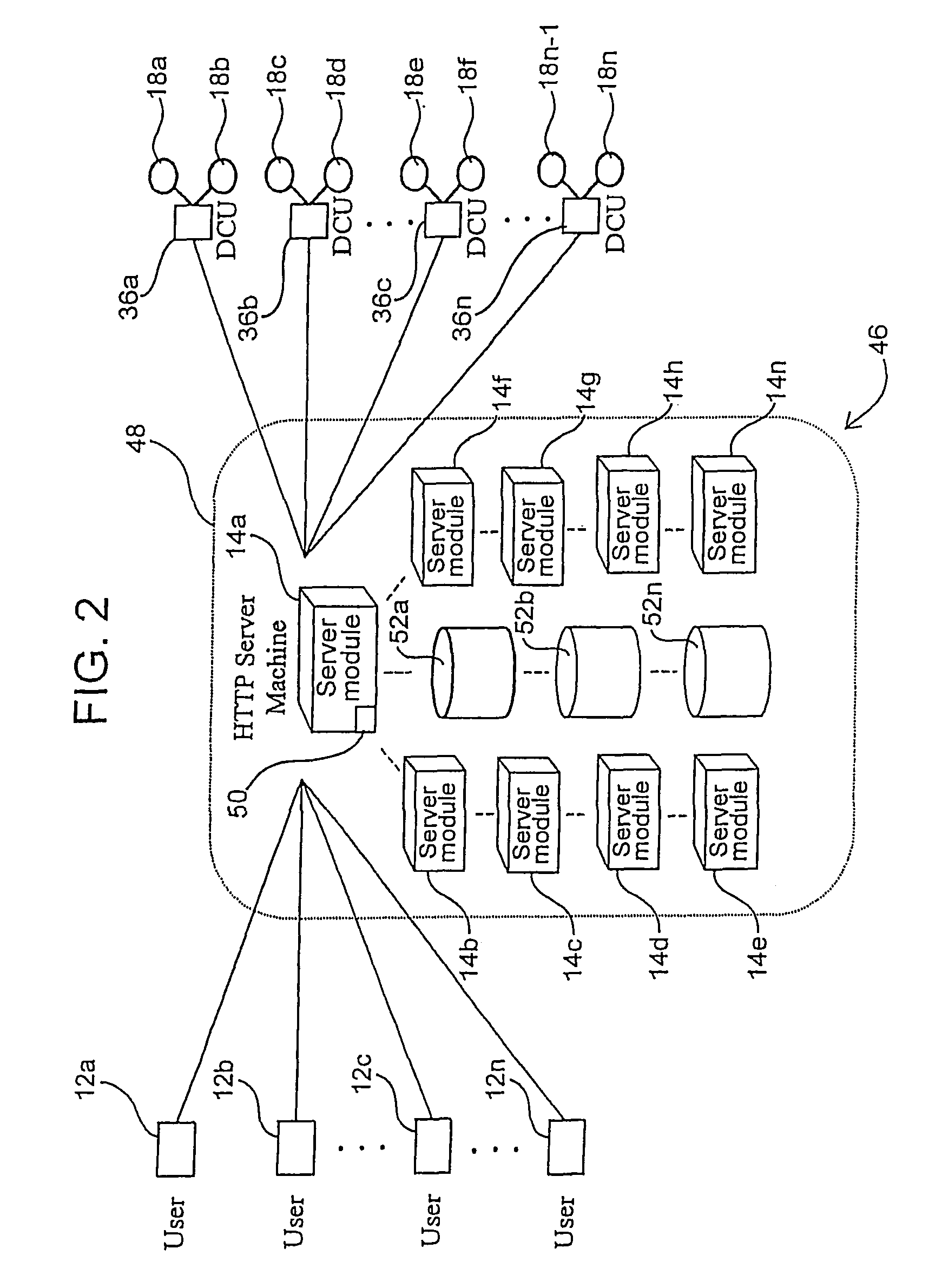
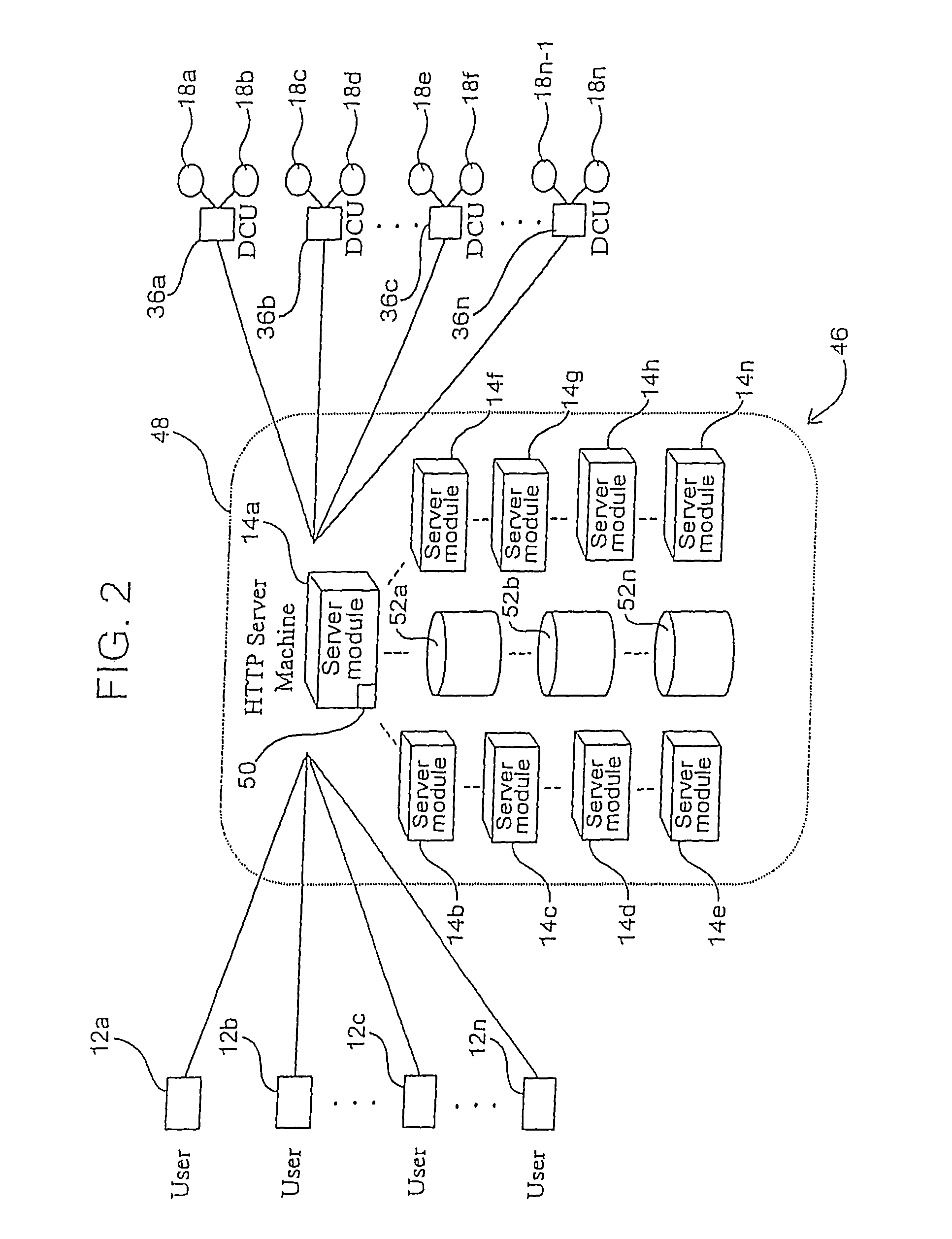
Method and system for managing performance of data transfers for a data access system
InactiveUS7277938B2Avoid prohibitive raw data storageData processing applicationsDigital computer detailsThe InternetData access
A method and system of managing performance of data transfers for a data access system providing data transfers from content servers to remote users in response to user requests, includes calculating performance data summaries at least at a subset of the user sites and transmitting the data for receipt for remote summarization and storage. The data include information indicative of transfer size, throughput, transfer time, source, time and date. The method and system include selecting a quantity of the performance data received, preferably over a time interval, and summarizing and storing the data. Further summarizes can also be calculated. The data may be used to ascertain conditions and manage the performance of the data access system. In the preferred embodiment, the method and system measure performance of Internet HTTP server applications. The method and system can monitor the performance of a plurality of data access systems, selecting performance data depending on the source of the data transfer for separate summarization and storage thus enabling a high volume of data transfer monitoring.
Owner:MICROSOFT TECH LICENSING LLC
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7934251B2Digital data processing detailsUser identity/authority verificationNetwork connectionDisplay device
Applications, systems and methods for securely and remotely operating a remote computer from a local computer over a network while providing seamless, firewall-compliant connectivity. Secure and remote operation includes authenticating at least one remote computer for connection to at least one computer over the network and / or at least one local computer for connection to at least one remote computer over the network; establishing a secure connection between the at least one local computer and the at least one remote computer over the network; and integrating a desktop of at least one remote computer on a display of at least one local computer. The connections may be made over a public network, as well as through multiple firewalls without loss of functionality.
Owner:WESTERN DIGITAL TECH INC
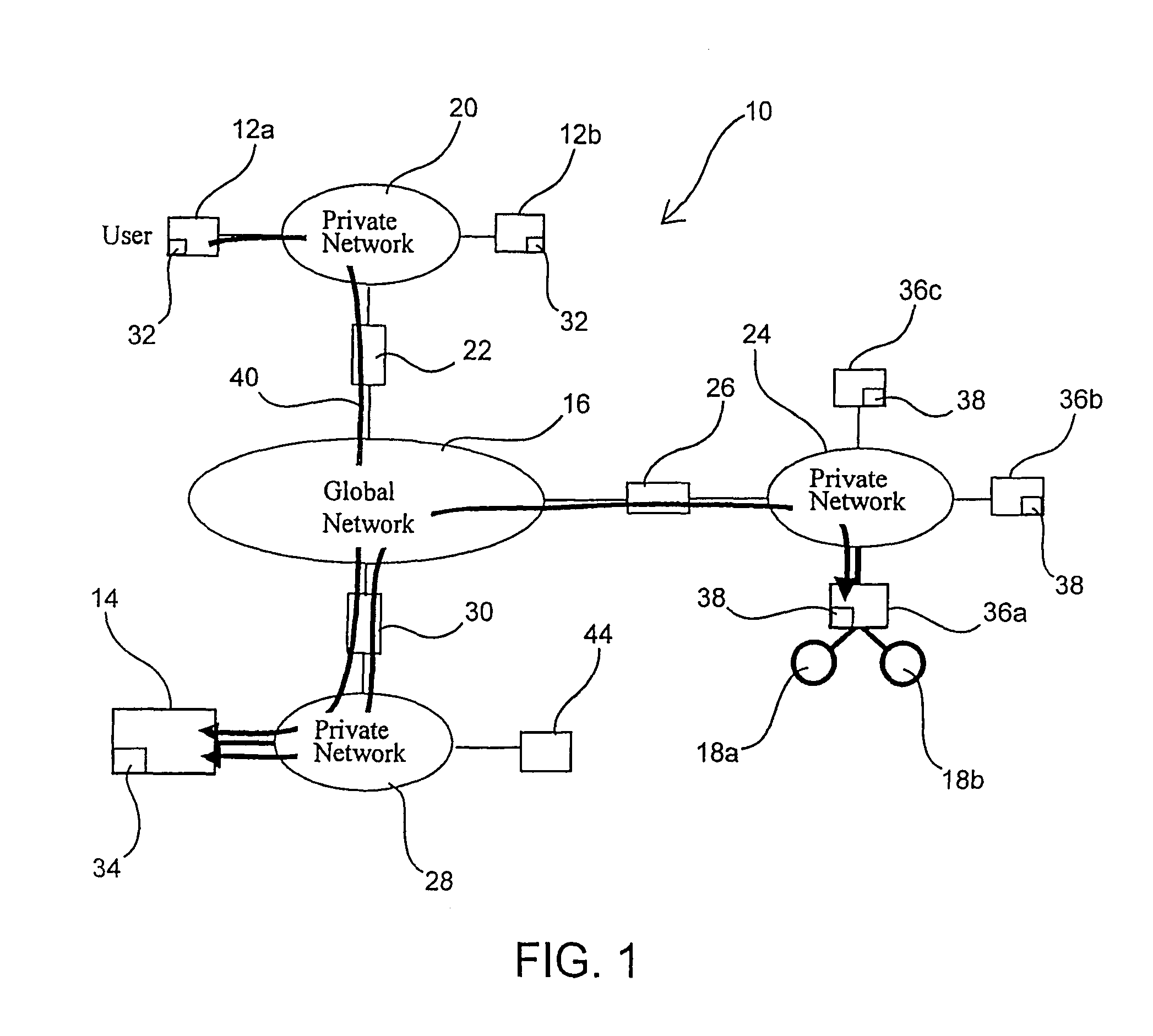
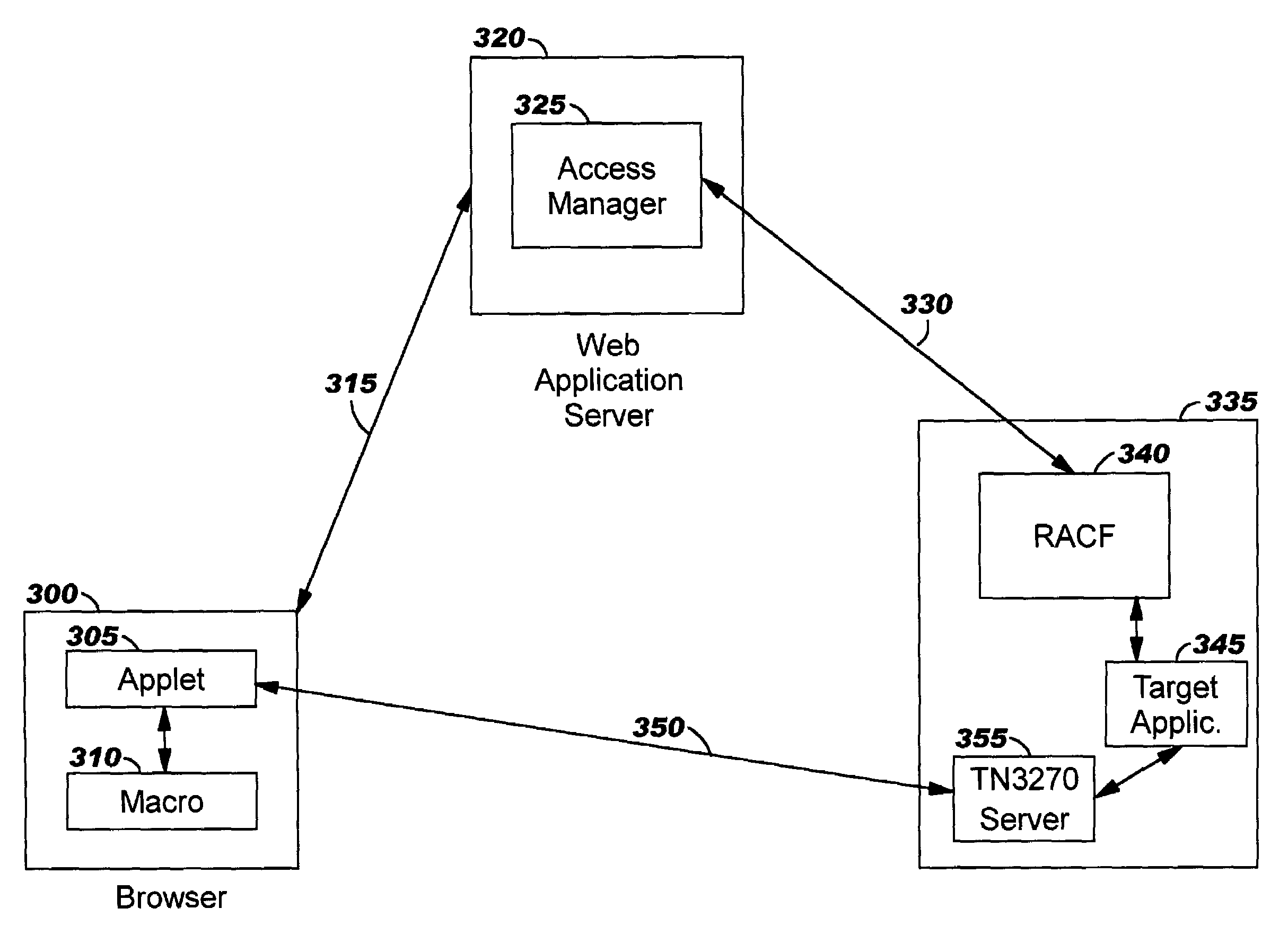
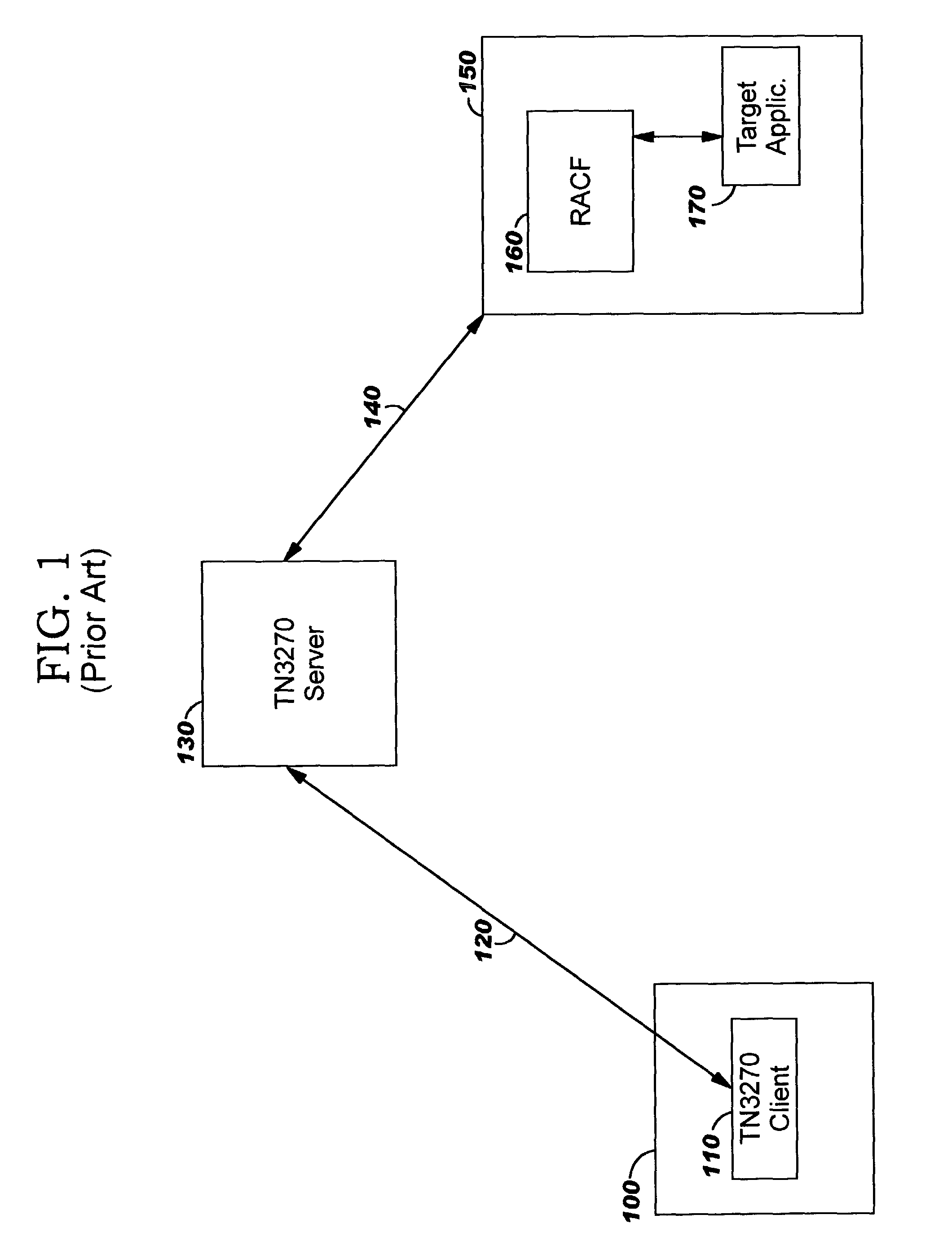
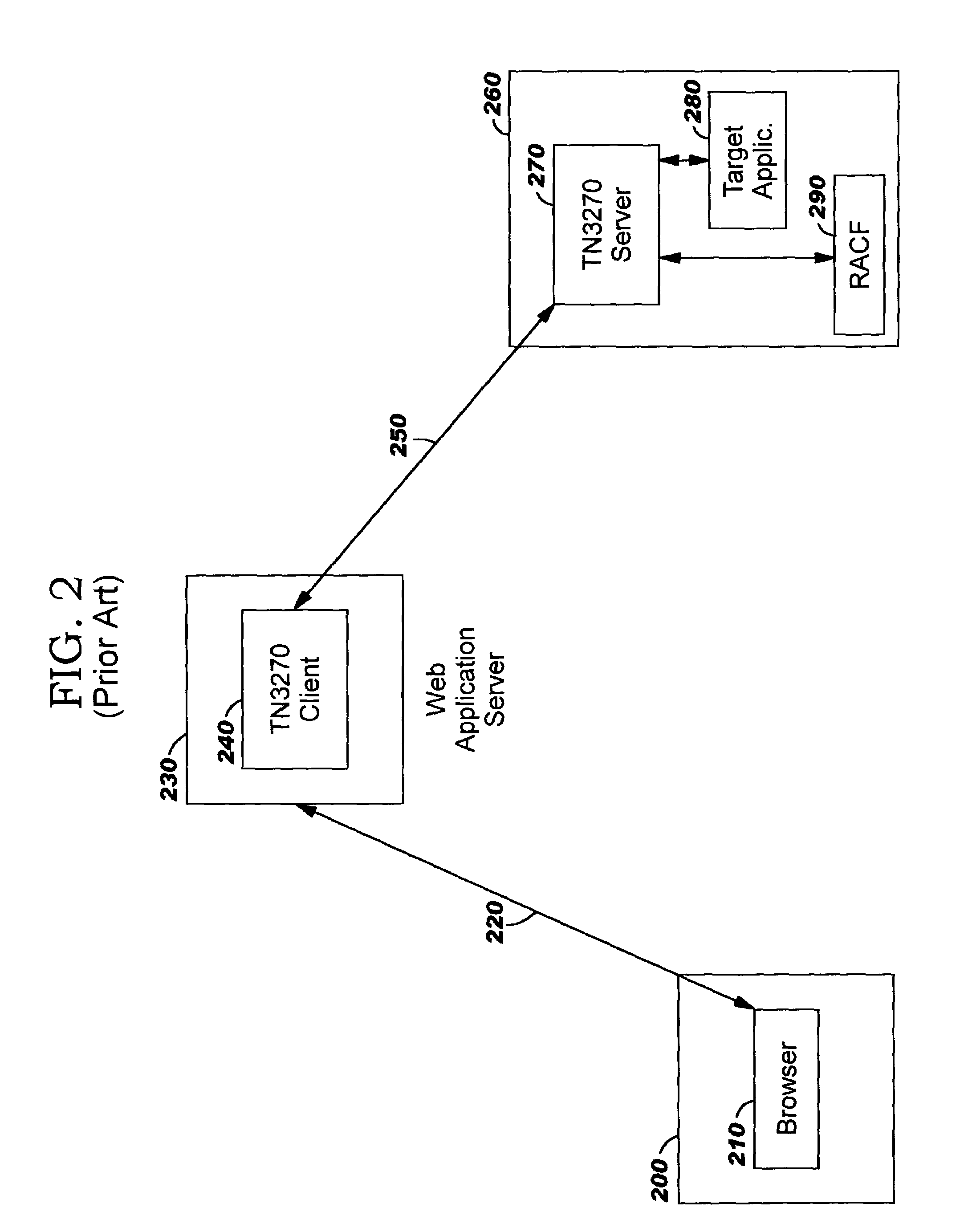
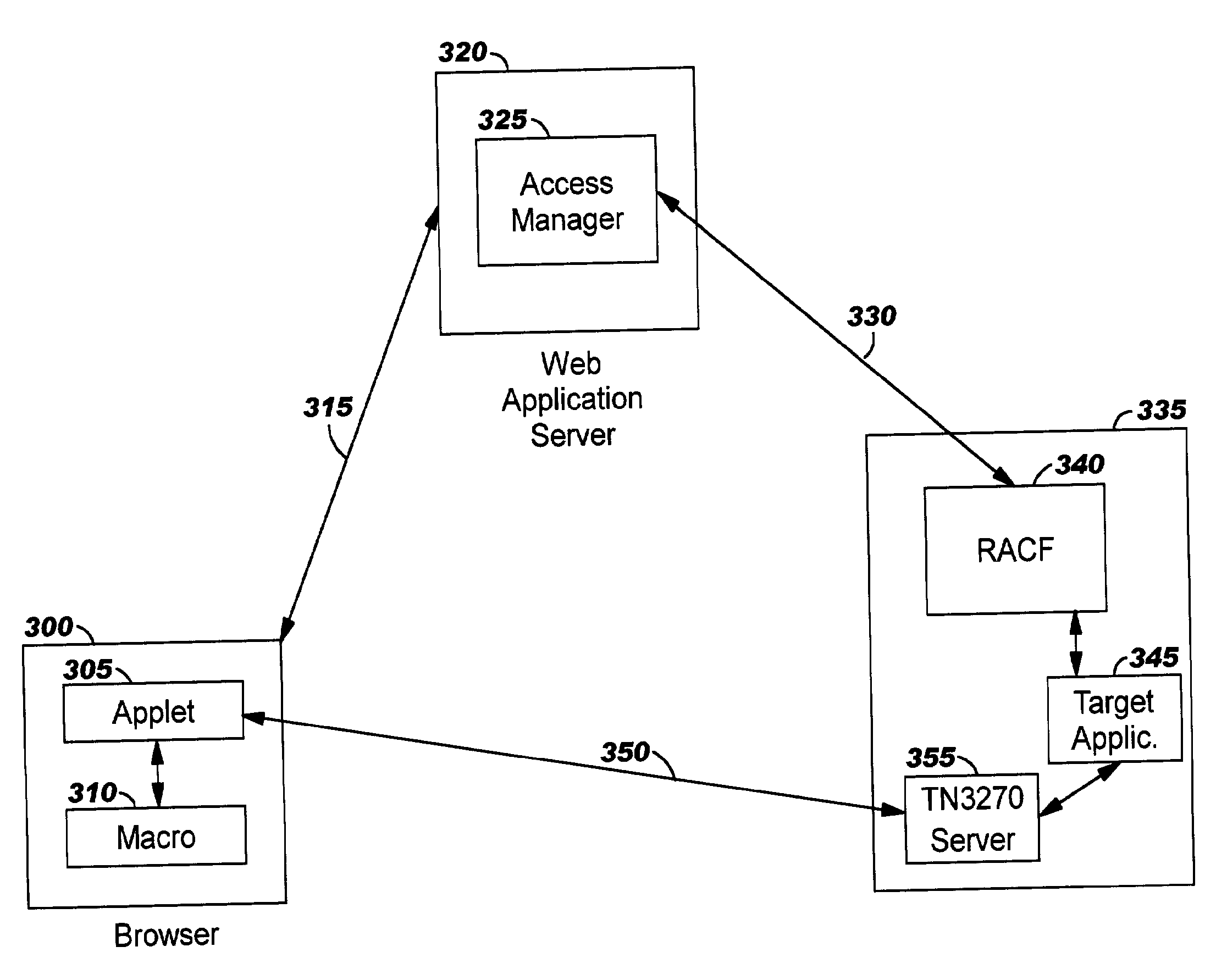
Integrating legacy application/data access with single sign-on in a distributed computing environment
ActiveUS7426642B2Conveniently and securely accessDigital data processing detailsComputer security arrangementsModem deviceData stream
The present invention provides methods, systems, computer program products, and methods of doing business whereby legacy host application / system access is integrated with single sign-on in a modem distributed computing environment. A security token used for signing on to the modem computing environment is leveraged, and is mapped to user credentials for the legacy host environment. These user credentials are programmatically inserted into a legacy host data stream, thereby giving the end user the look and feel of seamless access to all applications / systems, including not only modem computing applications / systems but also those residing on (or accessible through) legacy hosts. In addition to providing users with the advantages of single sign-on, the disclosed techniques enable limiting the number of user identifiers and passwords an enterprise has to manage.
Owner:HULU
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS8688797B2Digital data processing detailsMultiple digital computer combinationsData accessApplication software
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Communication of data over one or more networks may be managed by means of one or more connection servers which may also manage any or all of authentication, authorization, security, encryption and point-to-multipoint communications functionalities. Alternatively, computers may be connected over a wide area network without a connection server, and with or without a VPN. In any case, file structure integrating means are configured to integrate a file structure of accessible files accessed at a second or first computer, into a file structure contained at the first or second computer, respectively.
Owner:WESTERN DIGITAL TECH INC
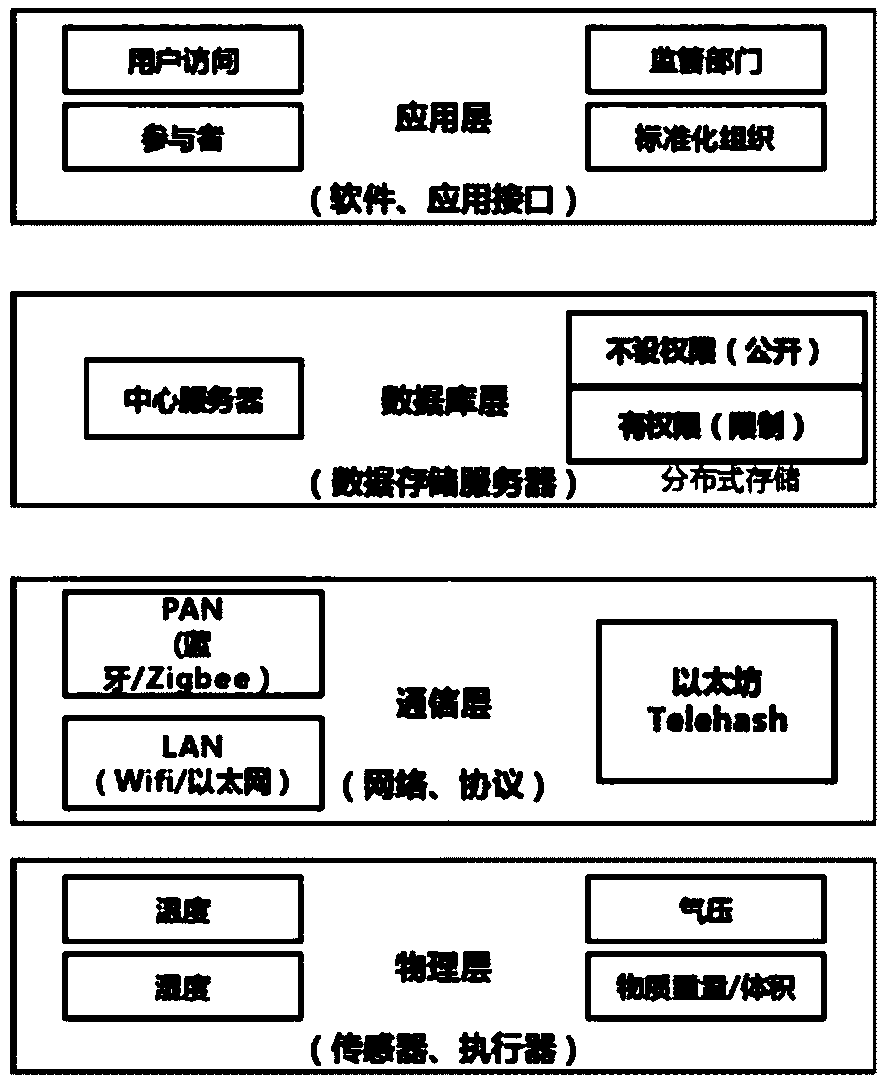
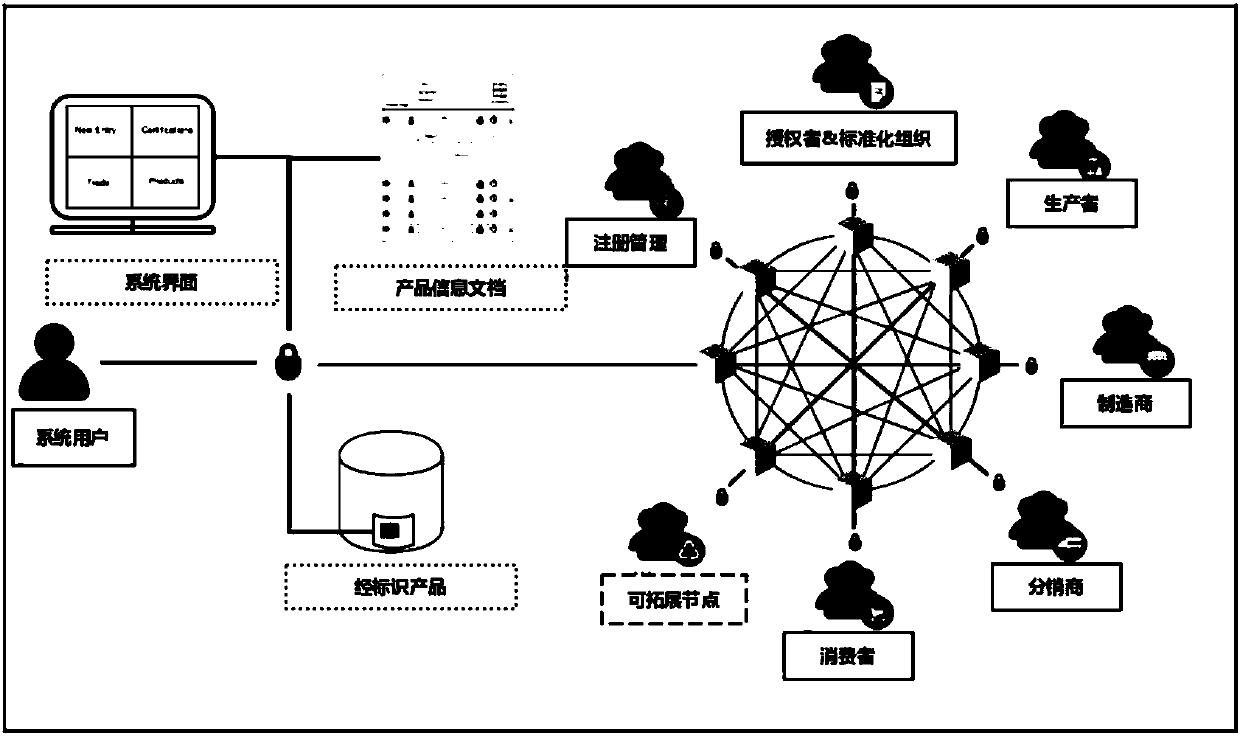
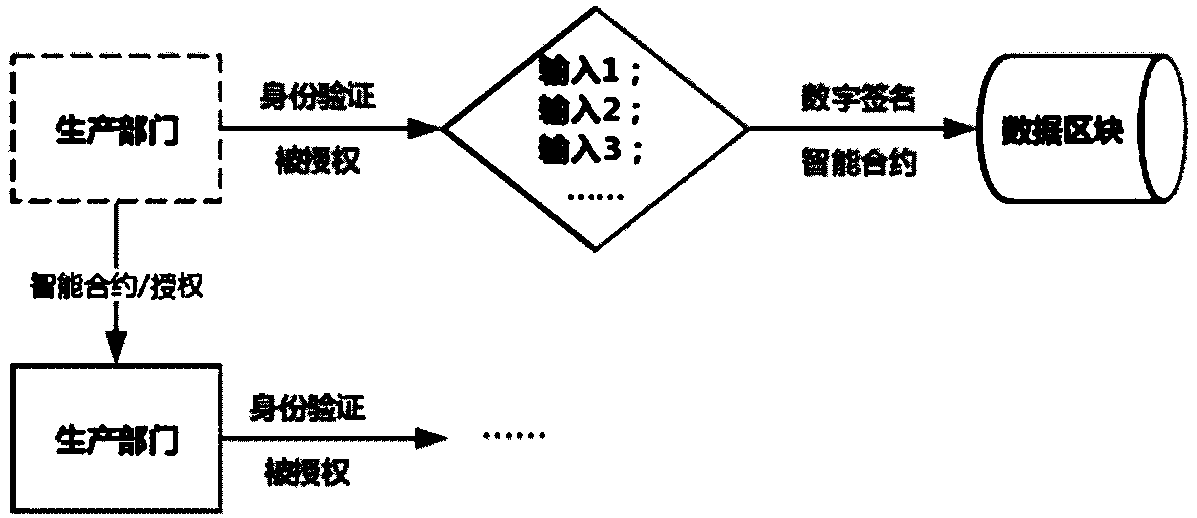
Blockchain technology-base agricultural product traceability method
InactiveCN107909372ASolve non-standard collectionFix security issuesCommerceDigital signatureData access
The invention relates to a blockchain technology-base agricultural product traceability method. According to the method, a block chain technology is applied to the database layer and communication layer of a system; agricultural products are coded through a global unified identification system; a data entry process uses digital signatures and smart contracts, so that it can be ensured that data are not tampered; all the data are stored in a blockchain and can be accessed by authorized nodes; and the right of data access depends on the roles and functions of participants in a supply chain. Withthe method adopted, problems such as non-standard information collection, insecure data storage, the vulnerability of a central system to attacks and failure to ensuring privacies in the process of information exchange between enterprises of a traditional agricultural product traceability system can be solved.
Owner:FUDAN UNIV
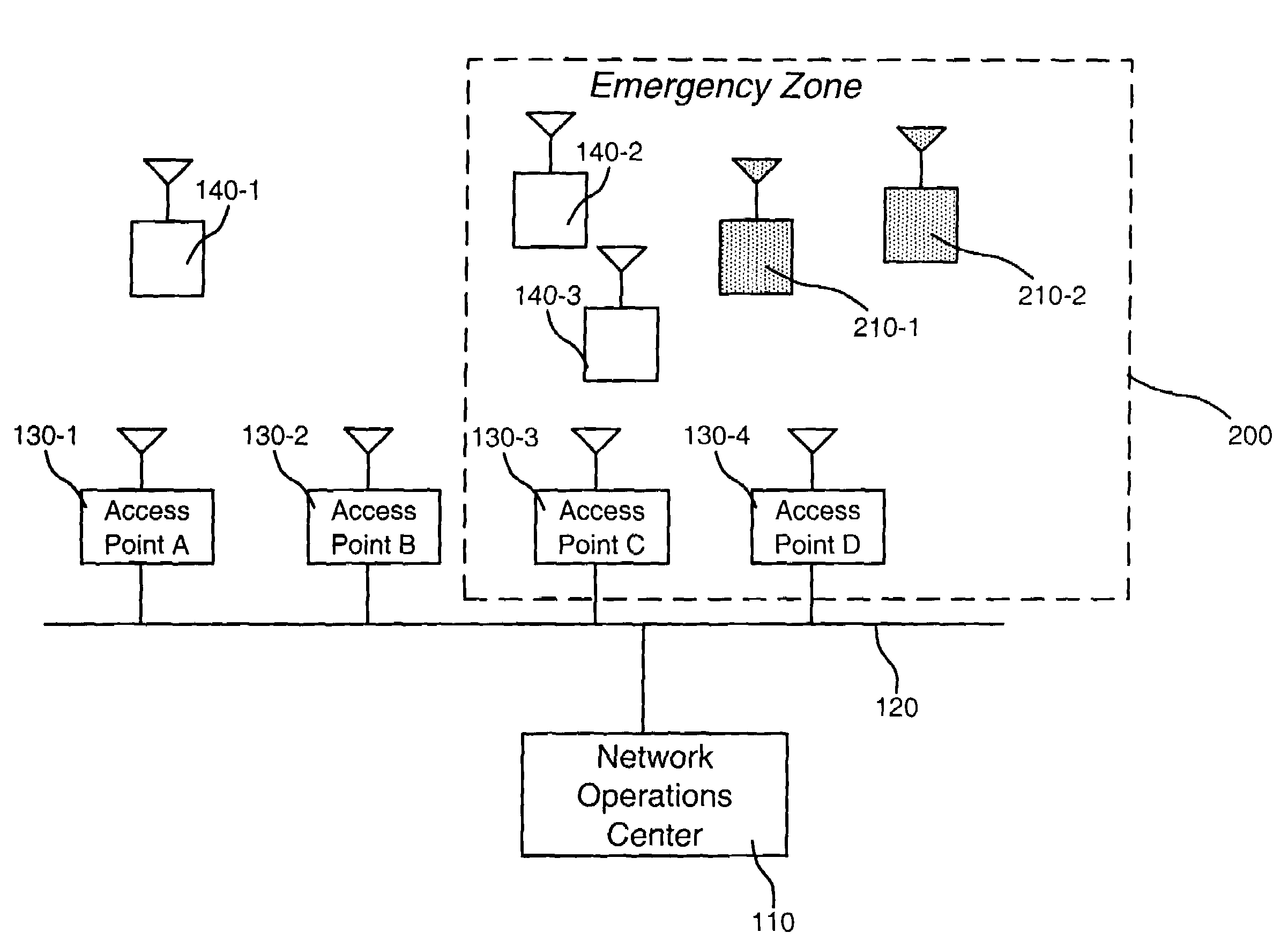
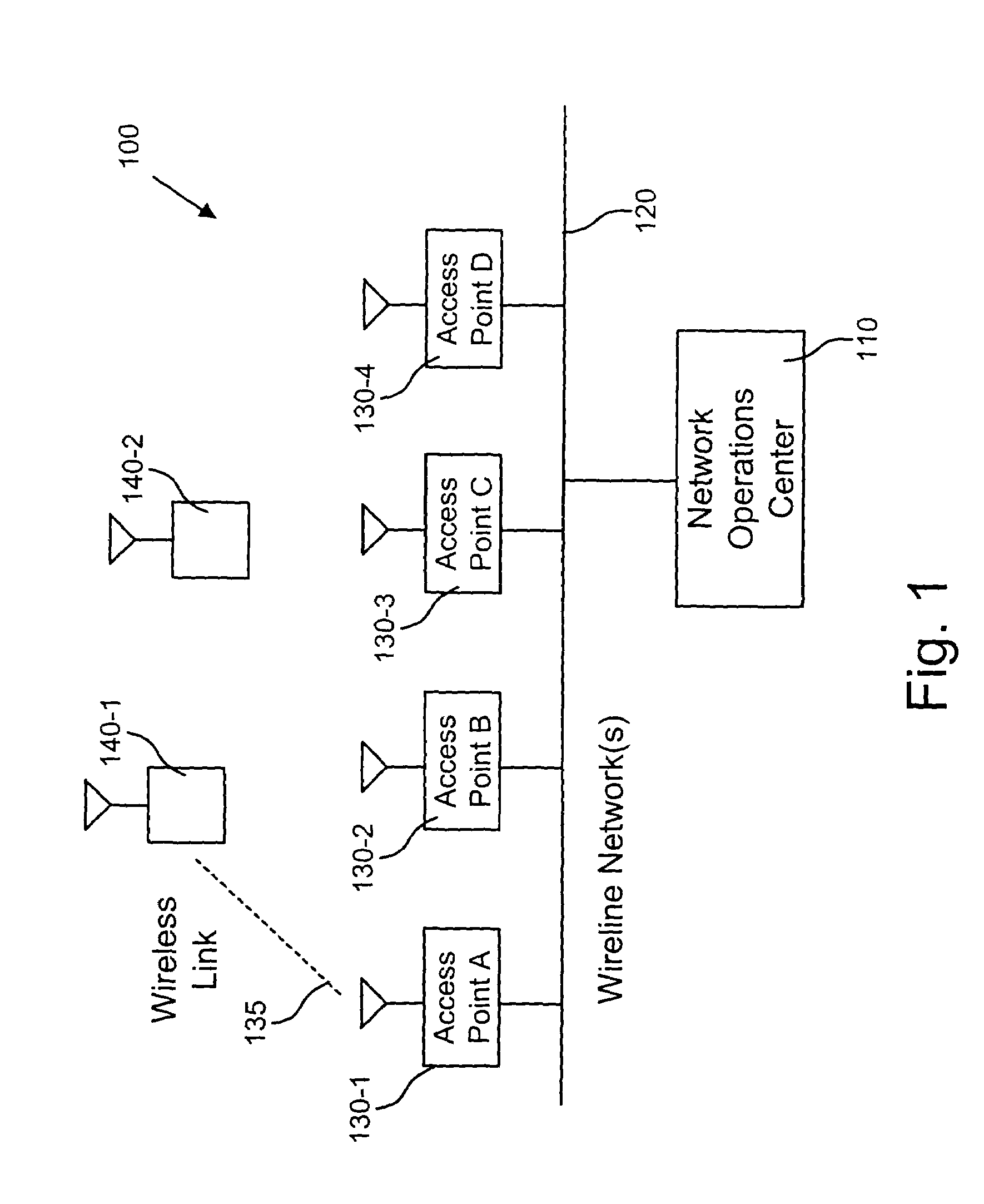
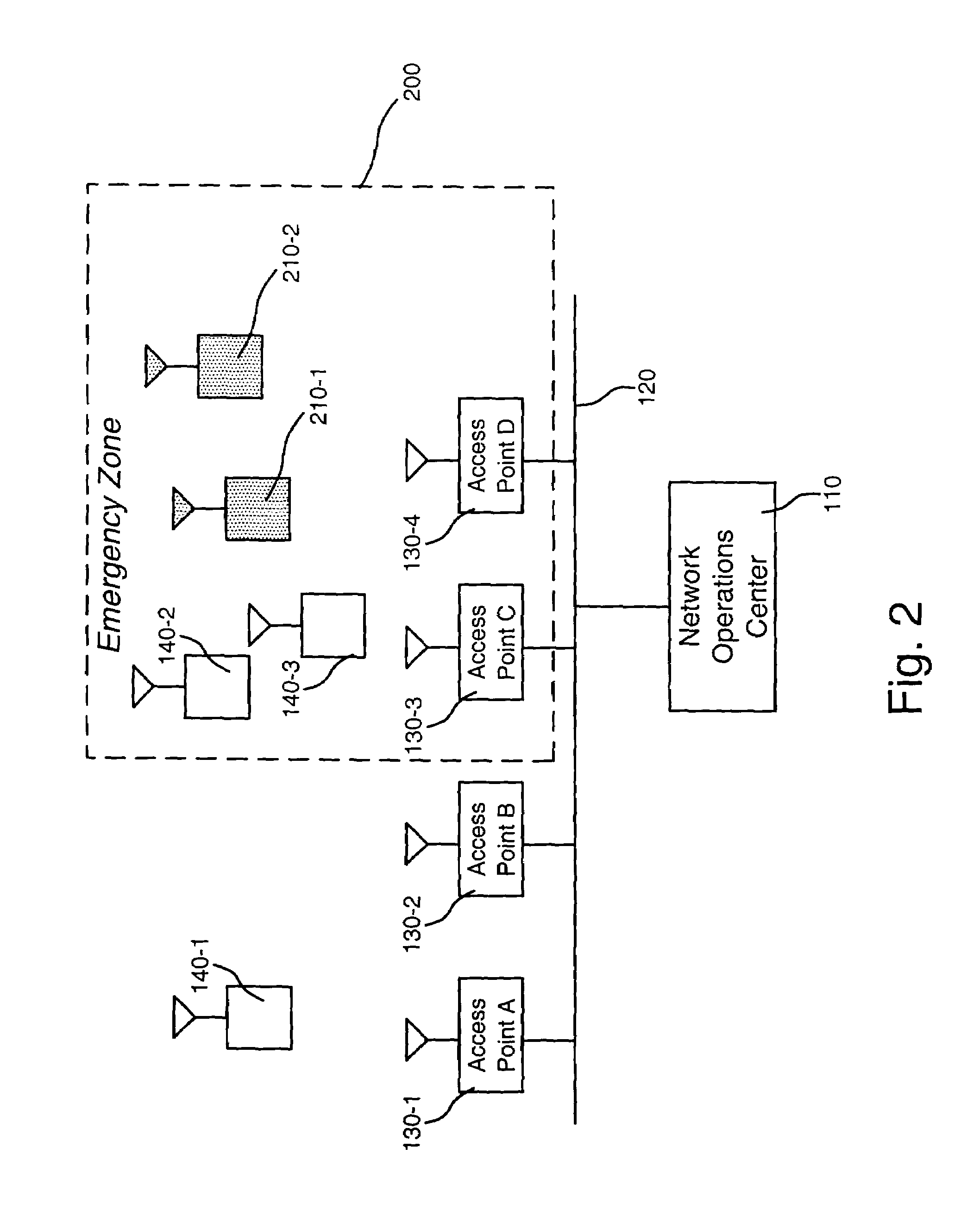
Emergency services for wireless data access networks
InactiveUS7158803B1Facilitate data communicationLimiting data accessEmergency connection handlingTelephonic communicationAccess networkUser device
A system [100] for facilitating wireless data communication may include an operations center [110] configured to implement access control rules [305] within an emergency zone [200] and an access device [130 / 310] configured to provide data access to a network [320] for user devices [140] and emergency devices [210]. The access device [130 / 310] may include a memory [340] configured to store the access control rules [305] that provide preferential access to the network for the emergency devices [210] within the emergency zone [200].
Owner:RAYTHEON BBN TECH CORP +1
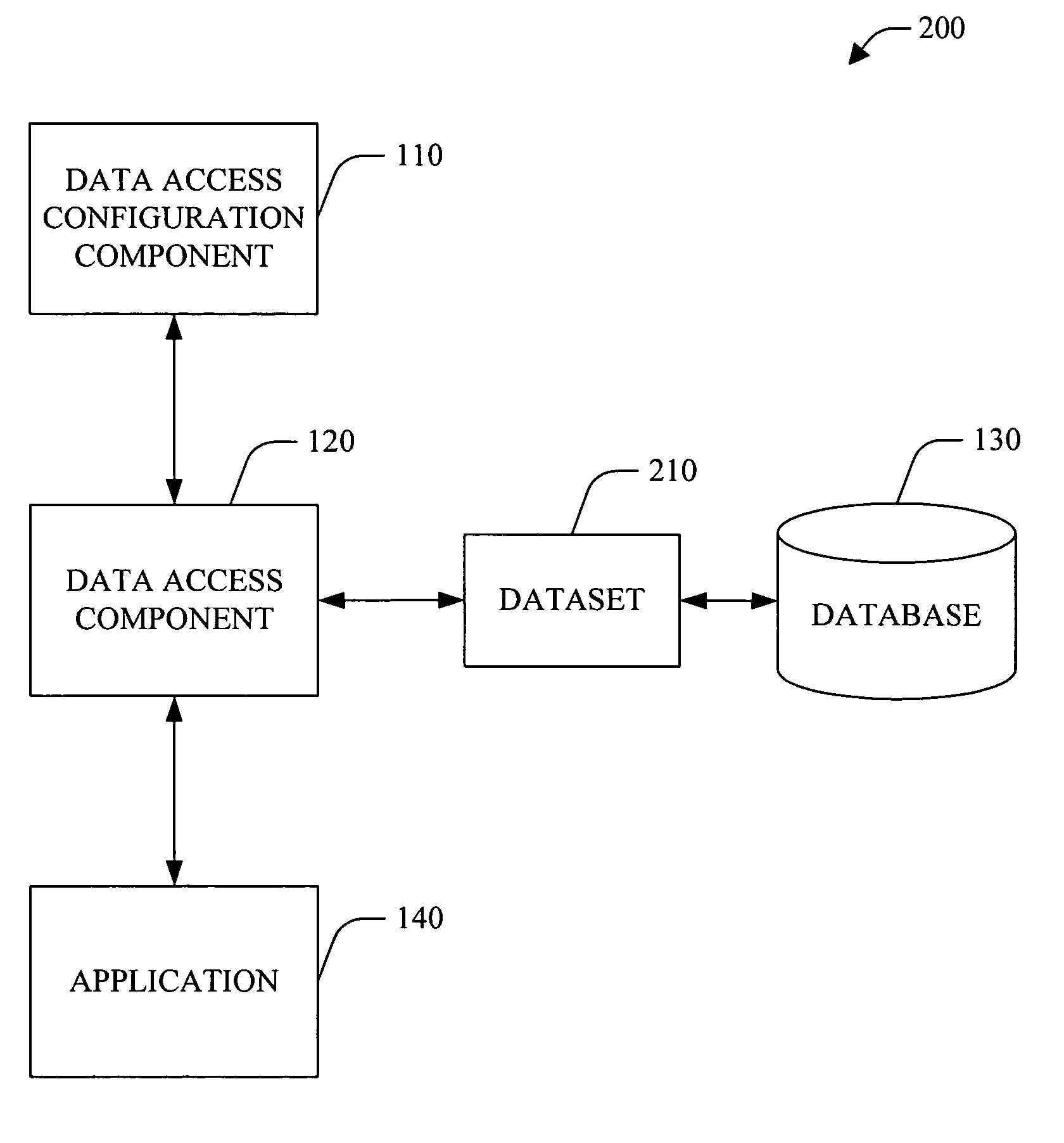
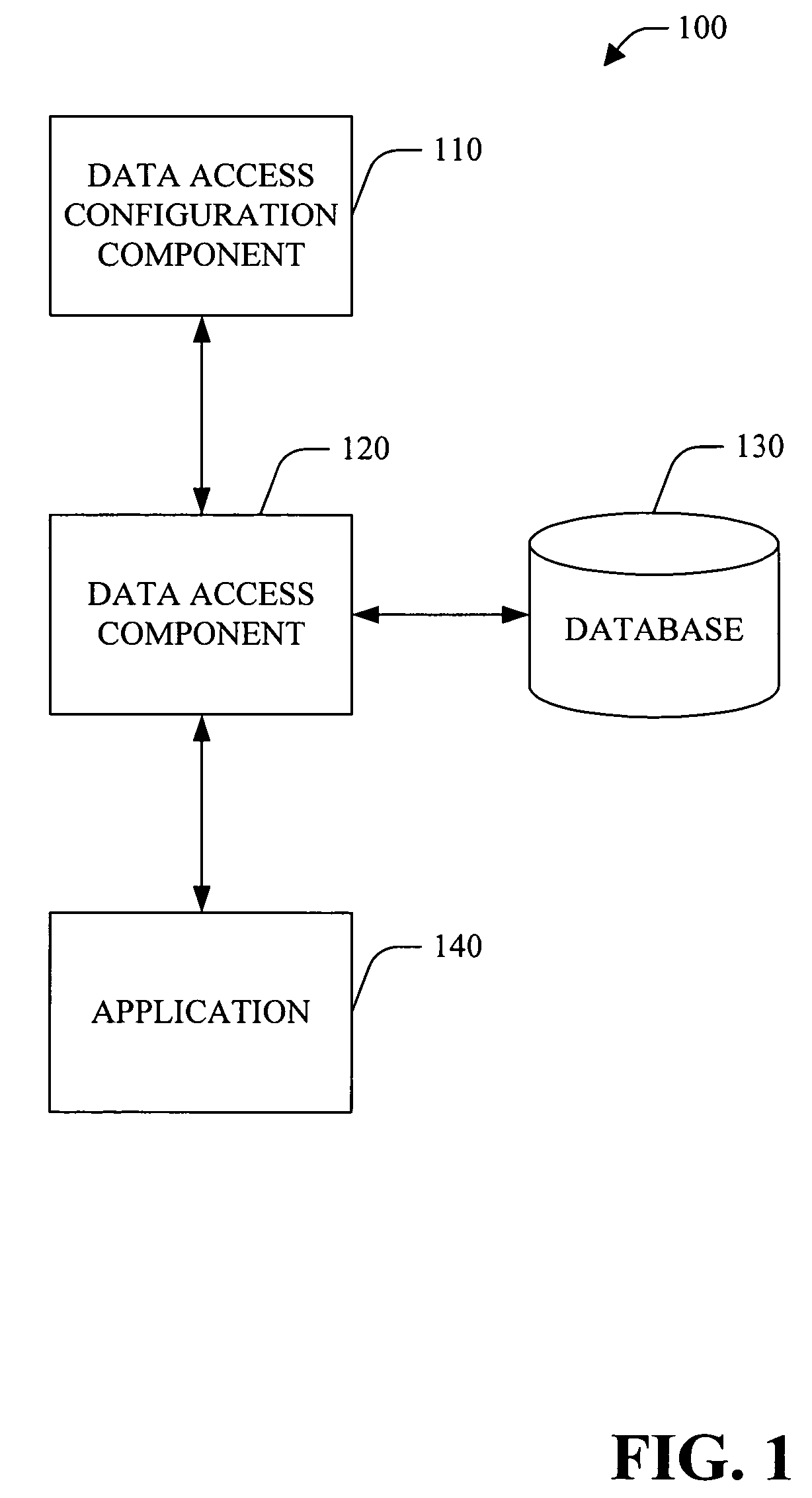
Data access layer design and code generation
InactiveUS7711740B2Easy data accessEasy accessDigital data processing detailsSoftware designCommon Language RuntimeData access
A system and method that facilitate data access in a software development environment is provided. The system generates strongly typed objects that encapsulate raw, untyped data access logic and groups together like database commands in a common data access component. The system provides a mapping between database types and common language runtime data types including the impedance mismatch of null representations. The system configures data access component(s) that are employed at design-time to facilitate access to data object(s) by application(s) and allows a user of the configured data access component(s) to improve developer productivity and / or reduce the quantity of runtime errors introduced into code. The data access component can be instanced on multiple forms components and / or with the developer's own class(es). Thus, change(s) to a query and / or interface are accomplished within the data access component and be available to the forms components and / or object(s) that utilize the data access component.
Owner:MICROSOFT TECH LICENSING LLC
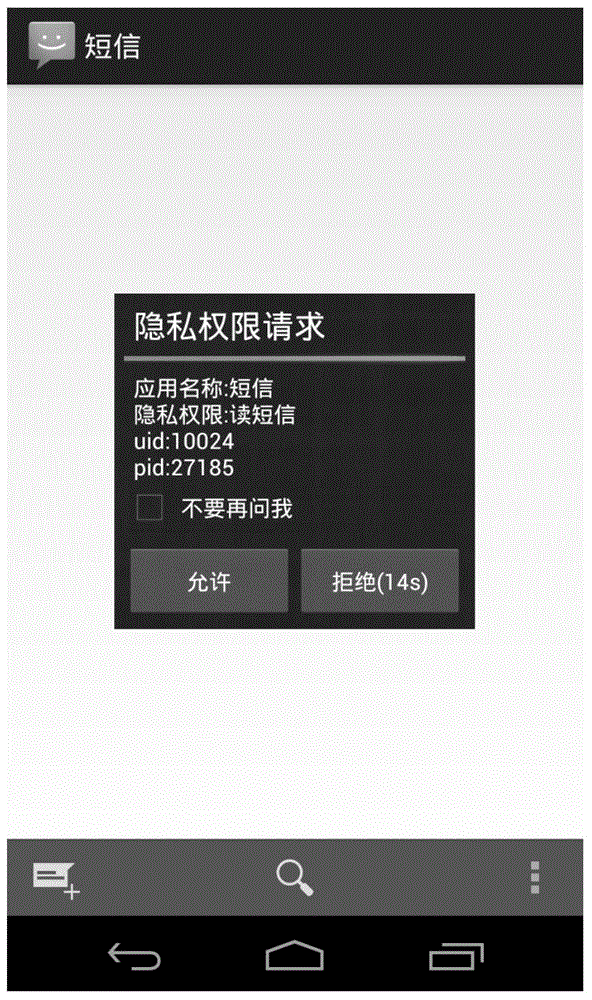
Mobile equipment privacy authority control method, mobile equipment privacy authority control device and corresponding mobile phone equipment
InactiveCN105072255ARealize managementEasy to manageDigital data protectionSubstation equipmentInternet privacyData access
The invention provides a mobile equipment privacy authority control method. The method comprises the steps: receiving a preset event notification, sent by a background service, of privacy data access, wherein the event notification of the privacy data access is generated based on a behavior that the background service intercepts an application program calling a privacy data access interface; in response to the event notification, providing a visual interface to receive a user's authorization instruction for the access privacy data; and, according to the corresponding authorization instruction, notifying the background service to release or prohibit the privacy data access. At the same time, the invention further provides a mobile equipment privacy authority control device and mobile phone equipment. On the condition that an obtaining system root is prevented from causing a system risk, the method and the device can effectively control an access authority of the application program for user privacy data, prevent a leakage of the user privacy data and improve the experience degree.
Owner:BEIJING QIHOO TECH CO LTD +1
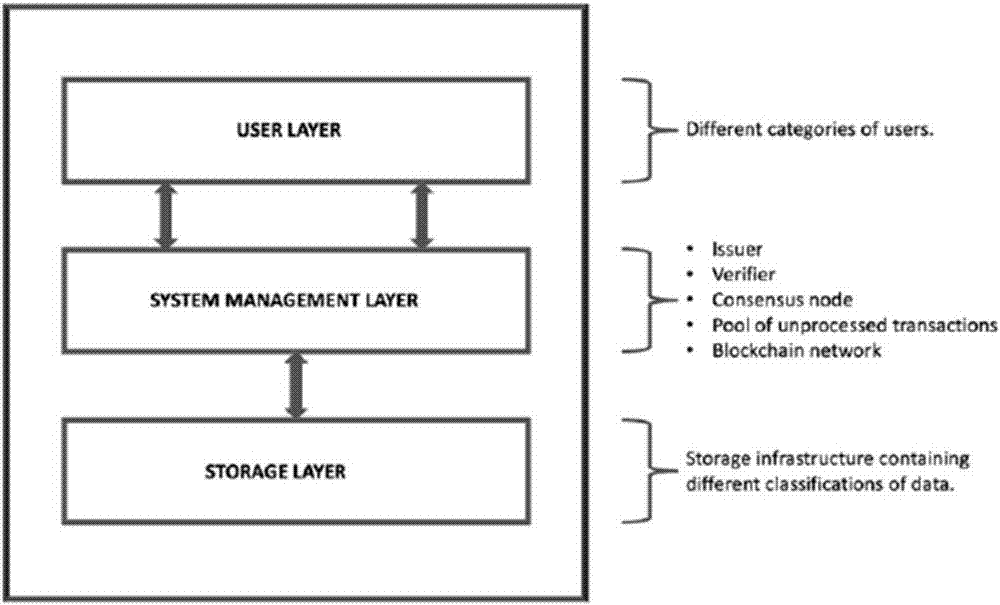
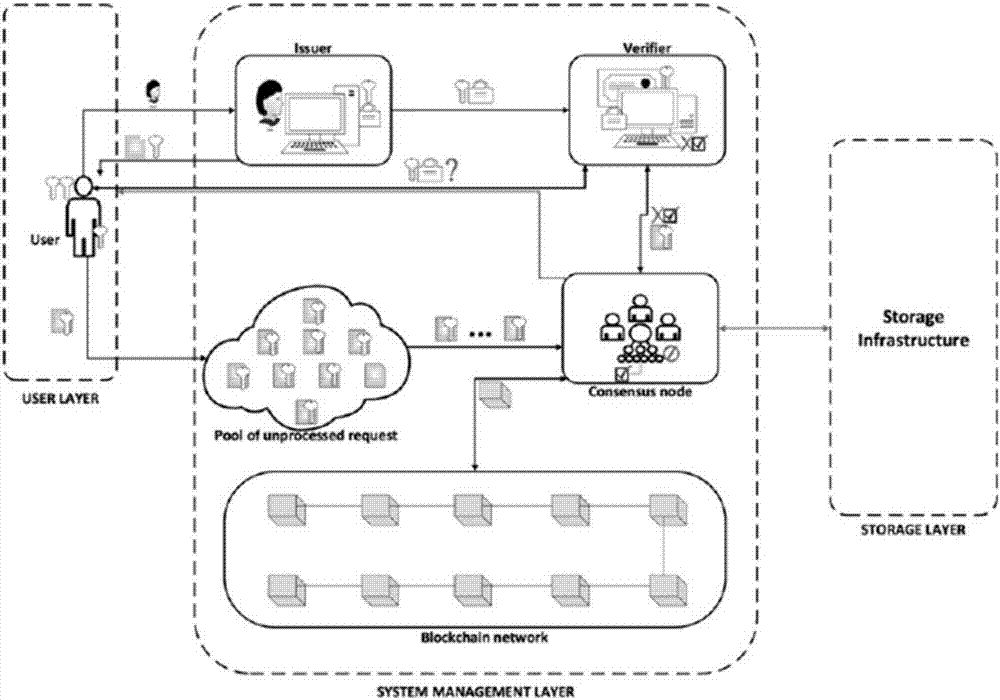
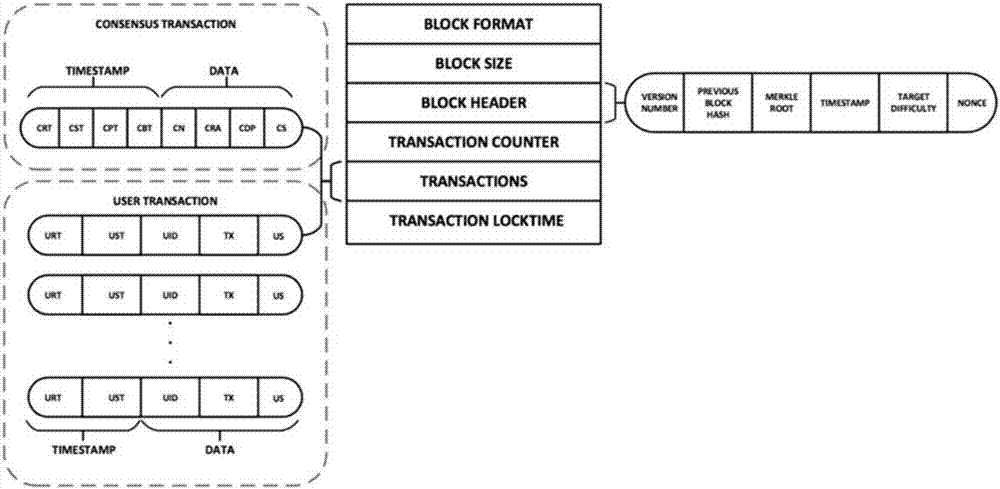
Block chain based data access control system
InactiveCN107070938AAchieve sharingSolve technical problems that are vulnerable to theftKey distribution for secure communicationUser identity/authority verificationSystems managementControl system
The invention discloses a block chain based data access control system. The block chain based data access control system comprises a user layer used for a user to send a registration application or a data access request to subordinates; a system management layer used for receiving the registration request or the data access request; and a storage layer used for the user layer to perform data access after the registration application and the data access request pass verification. When sending the registration application, password checking and verification between the system management layer and the user layer is carried out for three times, the system management layer generates a transaction public key and a transaction private key based on the last password and hands in the transaction public key to the system management layer for keeping; and when sending the data access request, the system management layer takes out and verifies a block of the data access request which is encrypted by the last password and signed by the transaction private key, and the user obtains the access permission of data stored in the storage layer after the successful verification. The block chain based data access control system solves the technical problem that user data are stolen easily due to adoption of a centralized deployment mode in the prior art.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS8793374B2Digital data processing detailsMultiple digital computer combinationsData accessRemote computer
Owner:WESTERN DIGITAL TECH INC
Method and system for managing performance of data transfers for a data access system
A method and system of managing performance of data transfers for a data access system providing data transfers from content servers to remote users in response to user requests, includes calculating performance data summaries at least at a subset of the user sites and transmitting the data for receipt for remote summarization and storage. The data include information indicative of transfer size, throughput, transfer time, source, time and date. The method and system include selecting a quantity of the performance data received, preferably over a time interval, and summarizing and storing the data. Further summarizes can also be calculated. The data may be used to ascertain conditions and manage the performance of the data access system. In the preferred embodiment, the method and system measure performance of Internet HTTP server applications. The method and system can monitor the performance of a plurality of data access systems, selecting performance data depending on the source of the data transfer for separate summarization and storage thus enabling a high volume of data transfer monitoring.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic object usage pattern learning and efficient caching
InactiveUS7062756B2Digital data information retrievalDigital computer detailsData accessPattern learning
A method for transparently optimizing data access. The method includes gathering information related to data usage when a system is processing and determining a usage pattern of the system using gathered information.
Owner:ORACLE INT CORP
Processing method and system of data access
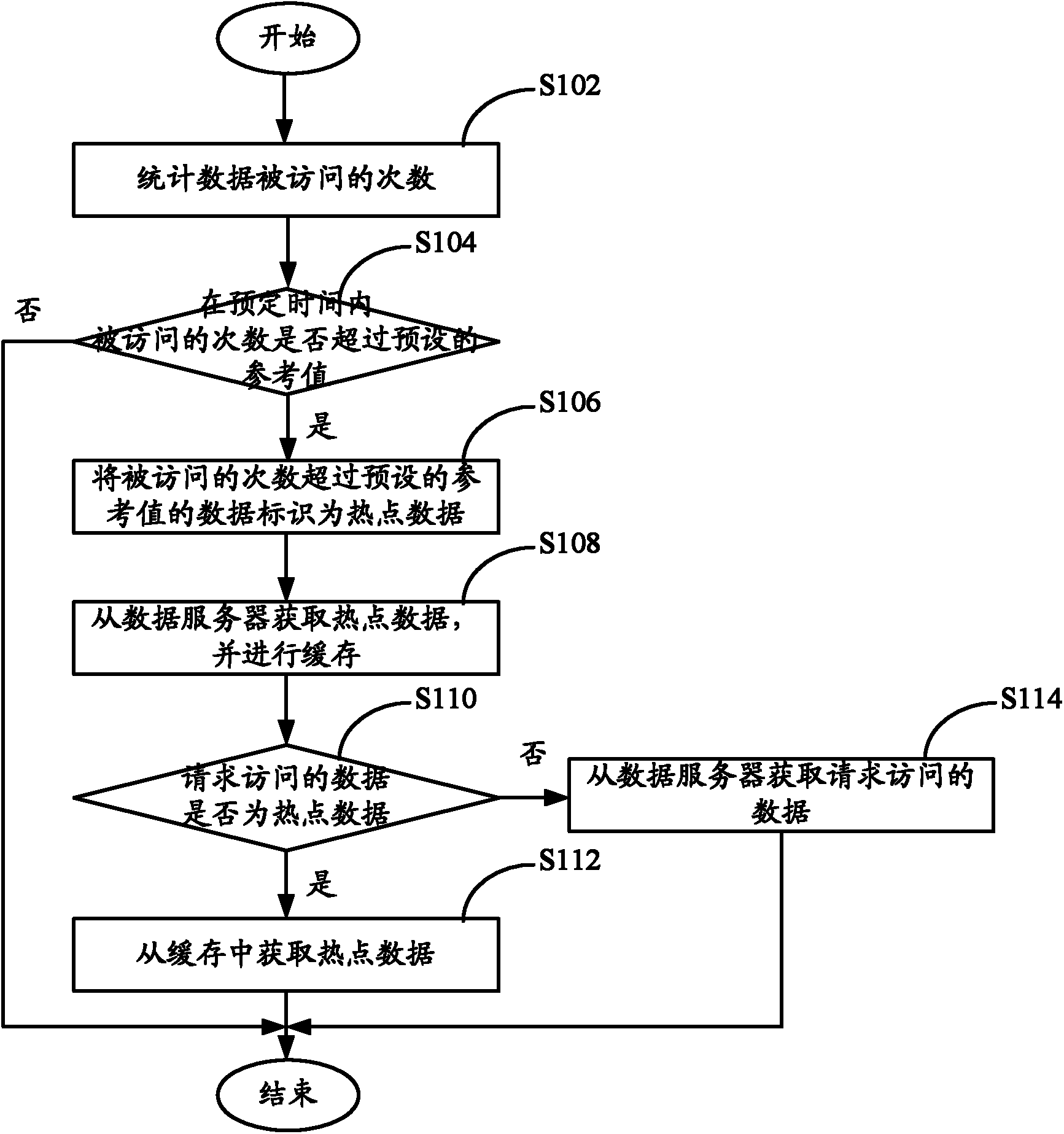
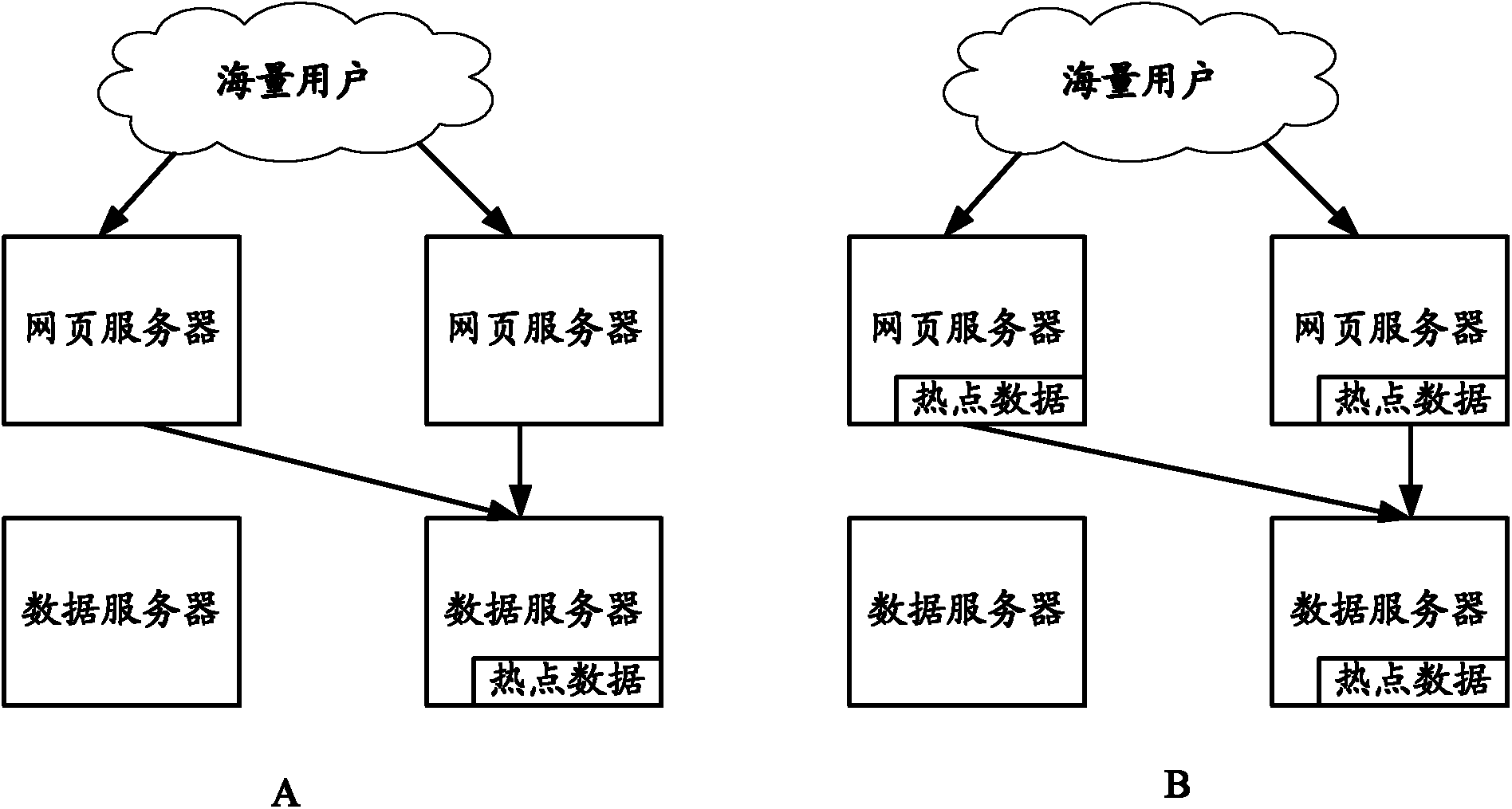
ActiveCN103177005AAvoid resource exhaustionRelieve pressureSpecial data processing applicationsAccess timeData access
The invention provides a processing method and a system of data access. The method comprises the following steps: accessed times of data are counted; whether the accessed times in scheduled time exceed the preset reference value or not is judged, if the times exceed the preset value, the data are identified to hot spot data; the hot spot data are obtained from a data server and cached; whether the data requiring to access are the hot spot data or not is judged, if the data are the hot spot data, the hot spot data are obtained from the caching, and if the data are not the hot spot data, the data requiring to access in the data server are obtained. The processing method and the system of the data access can reduce the pressure of the data server, and therefore capacity of data access is improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Trustworthiness decision making for access authentication
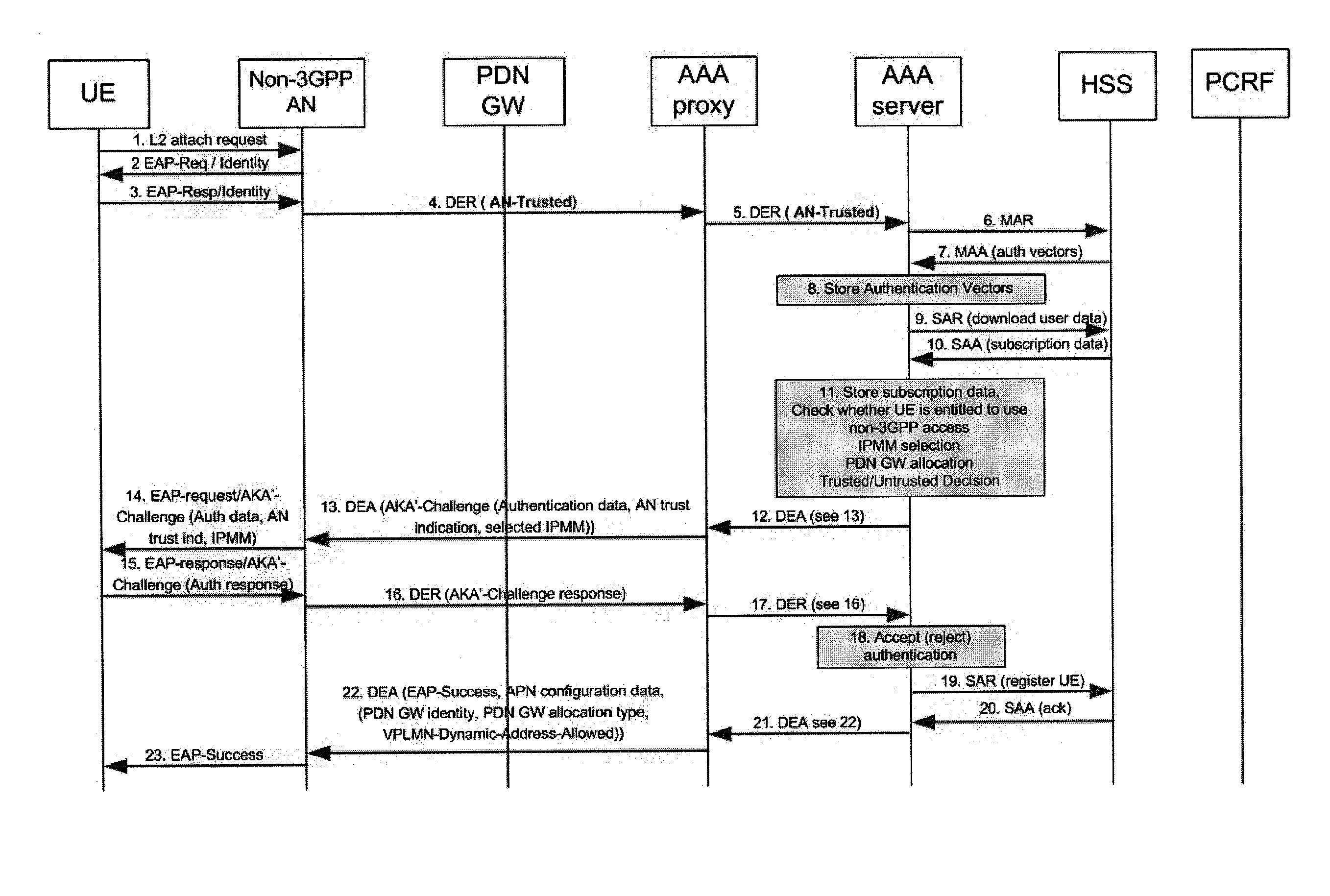
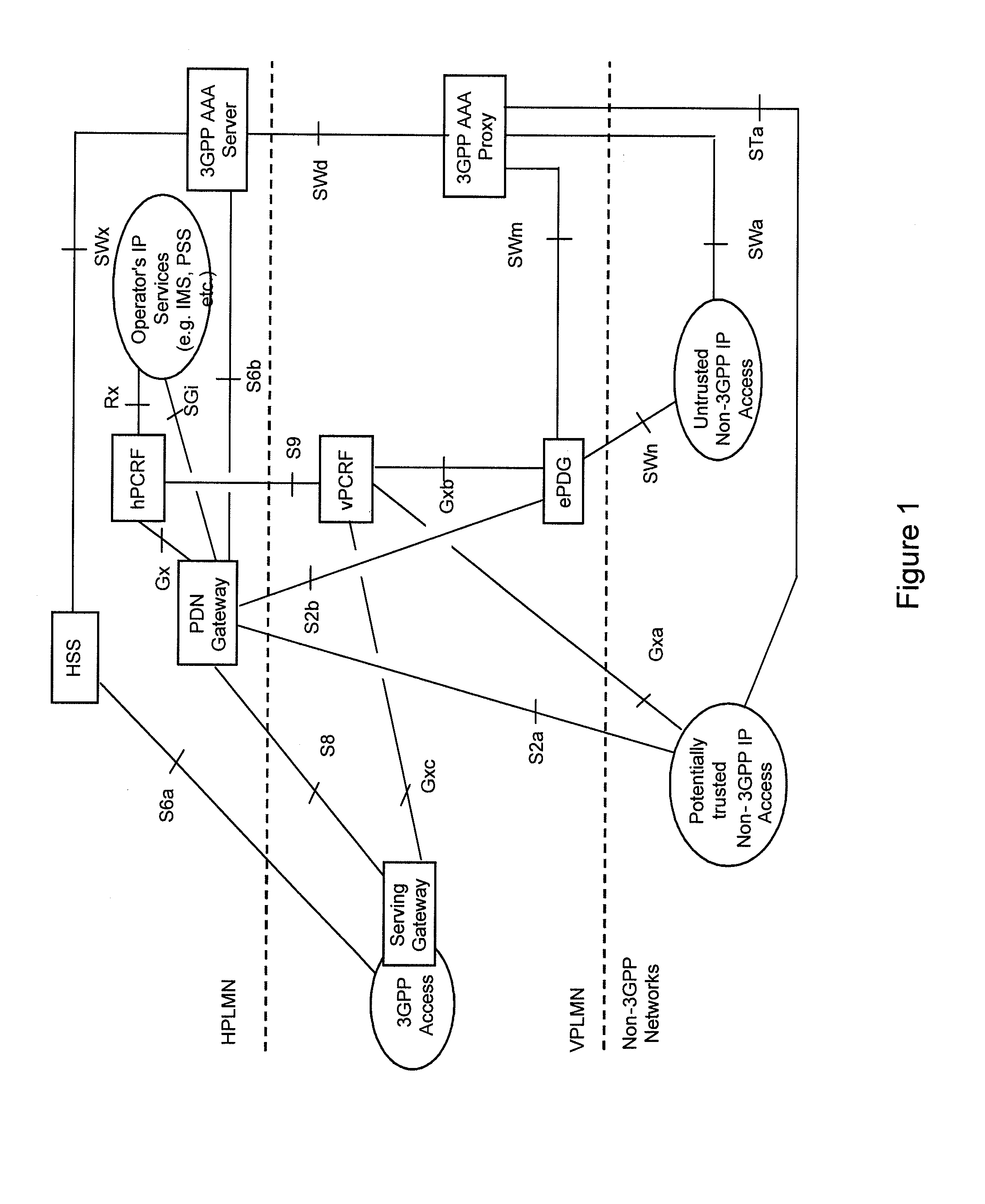
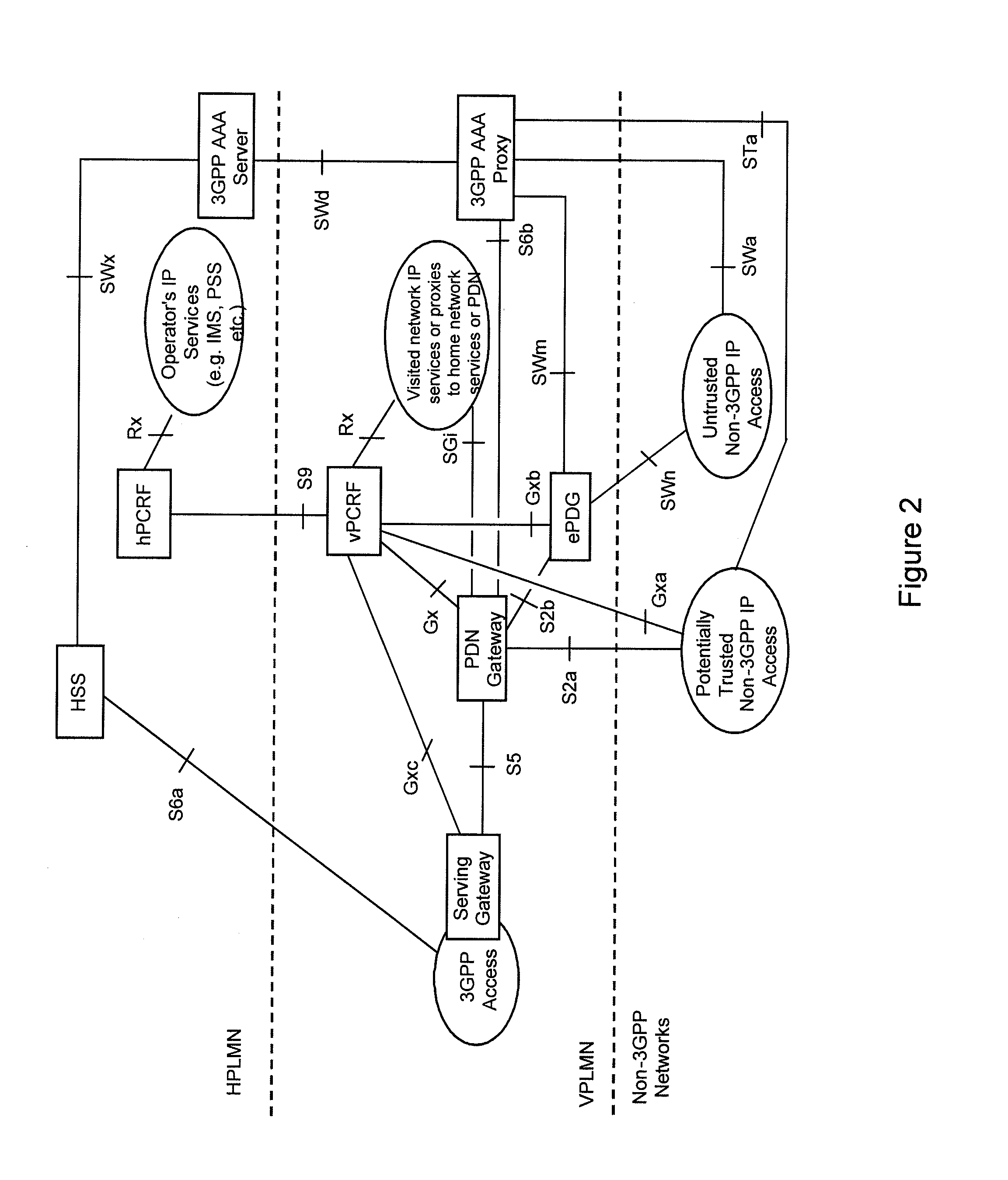
ActiveUS20110225632A1Improve resource utilizationEfficient measurementDigital data processing detailsAssess restrictionAccess networkRadio access network
There are provided measures for trustworthiness decision making for access authentication, for example relating to the trustworthiness of non-3GPP access networks within a 3GPP-compliant packet data system, exemplary comprising receiving an indication about a provisional trustworthiness of an access network, which provides packet data access for a roaming user, with respect to a visited network of said user from a network element of said visited network, determining the applicability of local breakout or home routing for each subscribed access point name of said user, and deciding about a final trustworthiness of said access network based upon the received provisional trustworthiness indication and the determined routing applicability for each subscribed access point name of said user.
Owner:NOKIA TECHNOLOGLES OY
Integrating legacy application/data access with single sign-on in a distributed computing environment
ActiveUS20080263365A1Digital data processing detailsUnauthorized memory use protectionData streamDistributed Computing Environment
The present invention provides methods, systems, computer program products, and methods of doing business whereby legacy host application / system access is integrated with single sign-on in a modern distributed computing environment. A security token used for signing on to the modern computing environment is leveraged, and is mapped to user credentials for the legacy host environment. These user credentials are programmatically inserted into a legacy host data stream, thereby giving the end user the look and feel of seamless access to all applications / systems, including not only modern computing applications / systems but also those residing on (or accessible through) legacy hosts. In addition to providing users with the advantages of single sign-on, the disclosed techniques enable limiting the number of user identifiers and passwords an enterprise has to manage.
Owner:HULU
Data access in a distributed environment
ActiveUS7149806B2Computer security arrangementsMultiple digital computer combinationsLimited accessTime segment
A method and system for providing a first network resource limited access to a second network resource. A method embodying the invention includes receiving profile data. Using the profile data, temporary credentials are then generated for accessing the second network resource. The temporary credentials are then made available to the first network resource. In a preferred embodiment, the temporary credentials are invalidated following a termination event such as the lapse of a set time period or after the second resource has been accessed.
Owner:HEWLETT PACKARD DEV CO LP
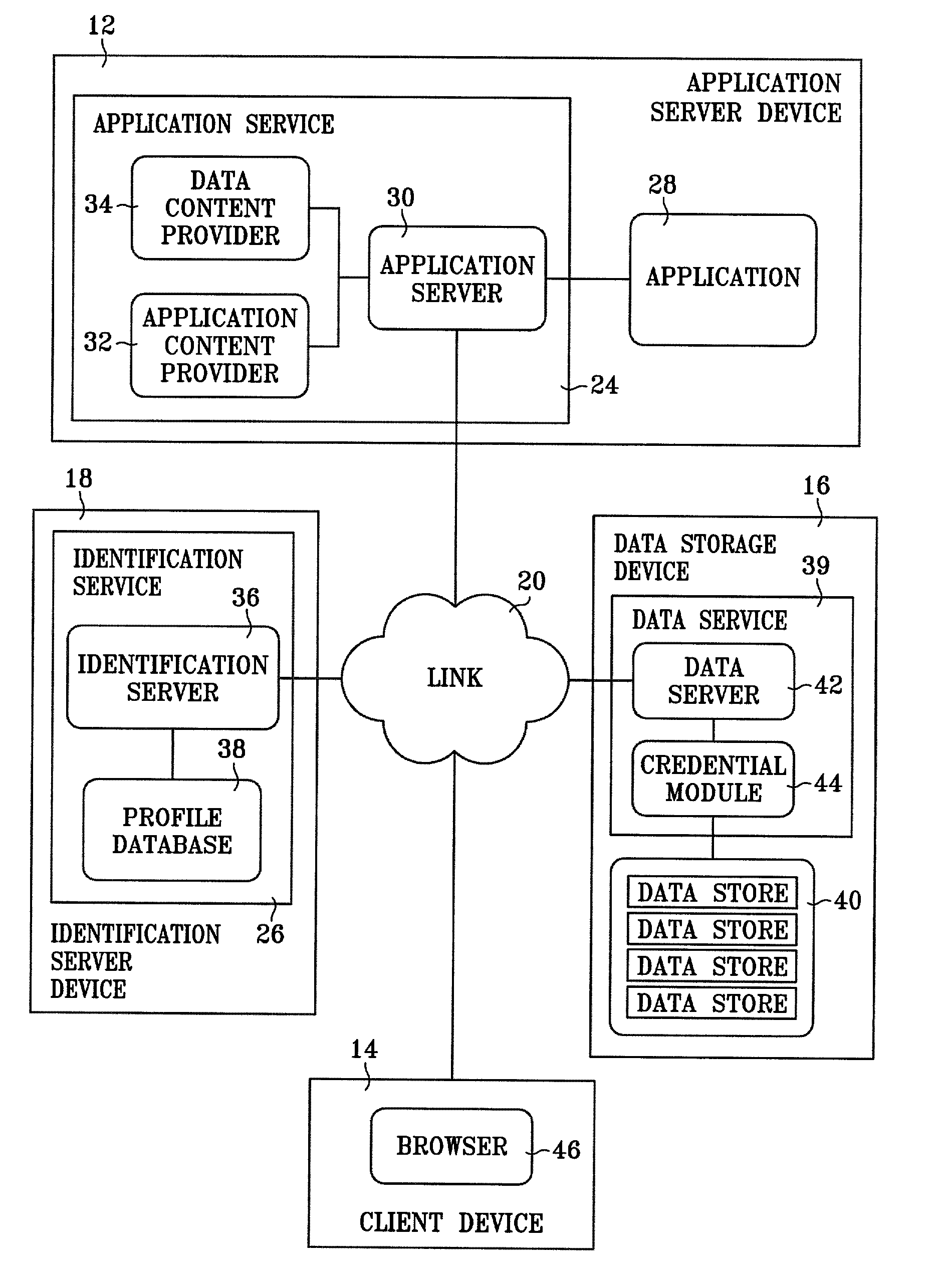
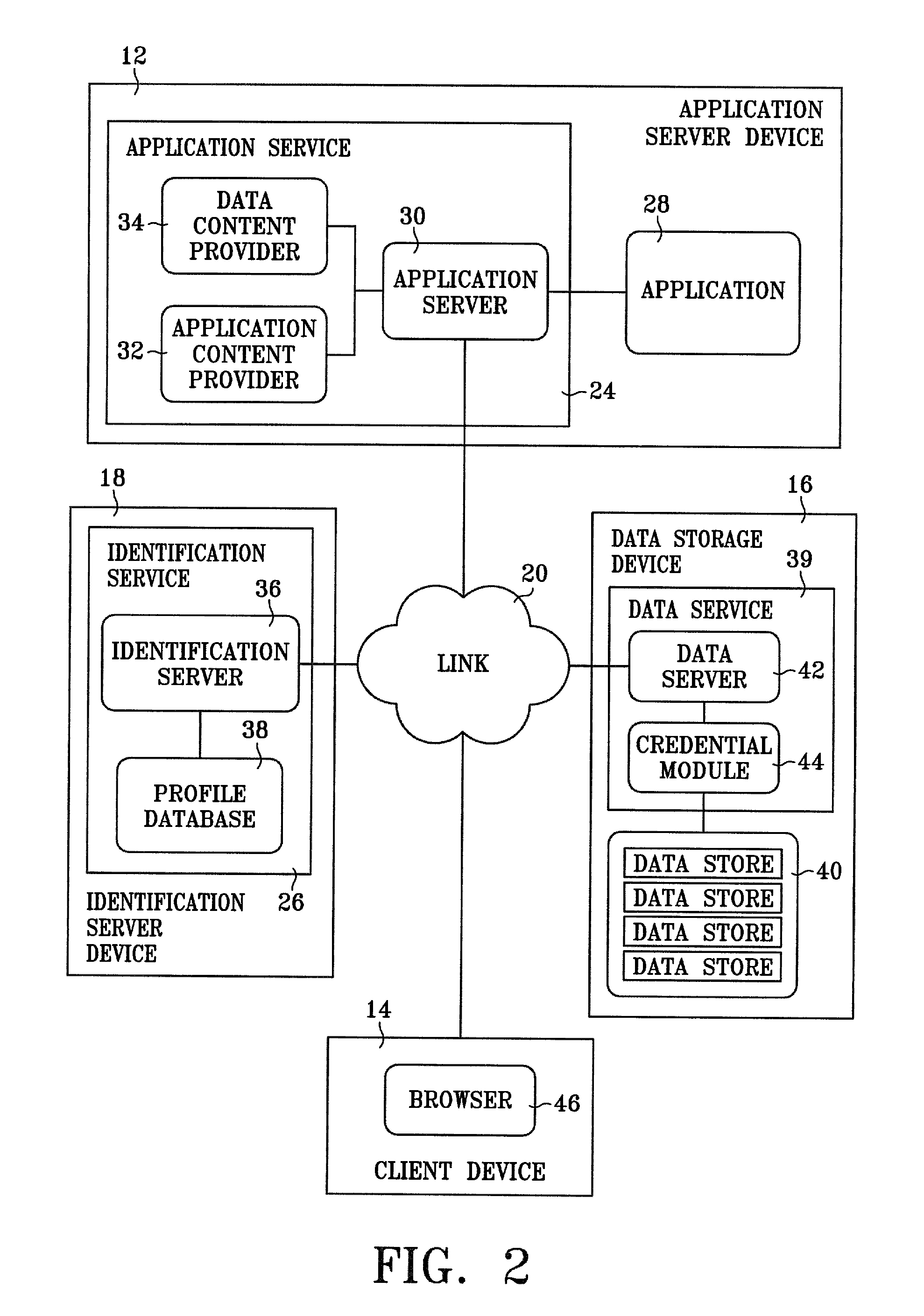
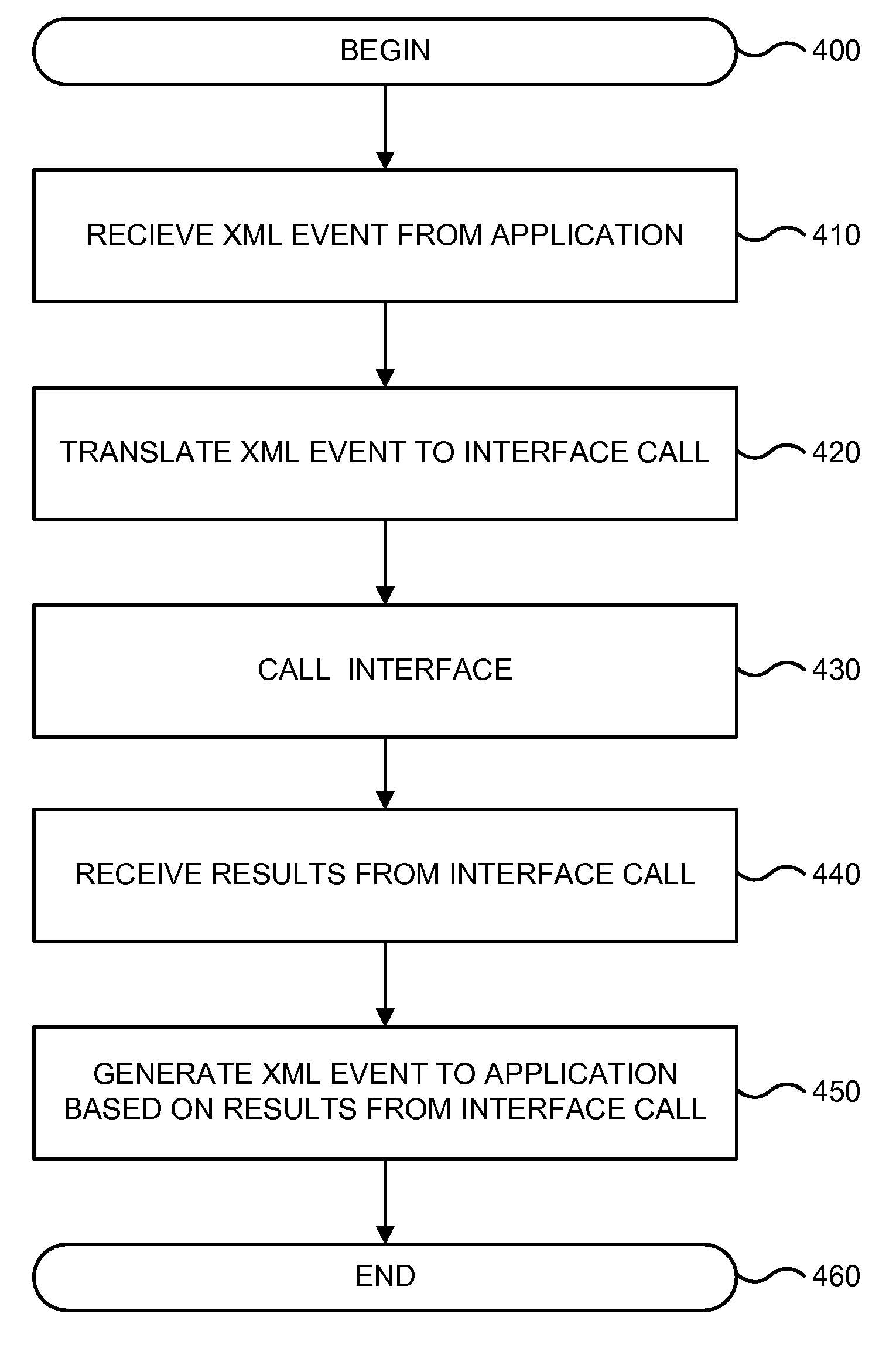
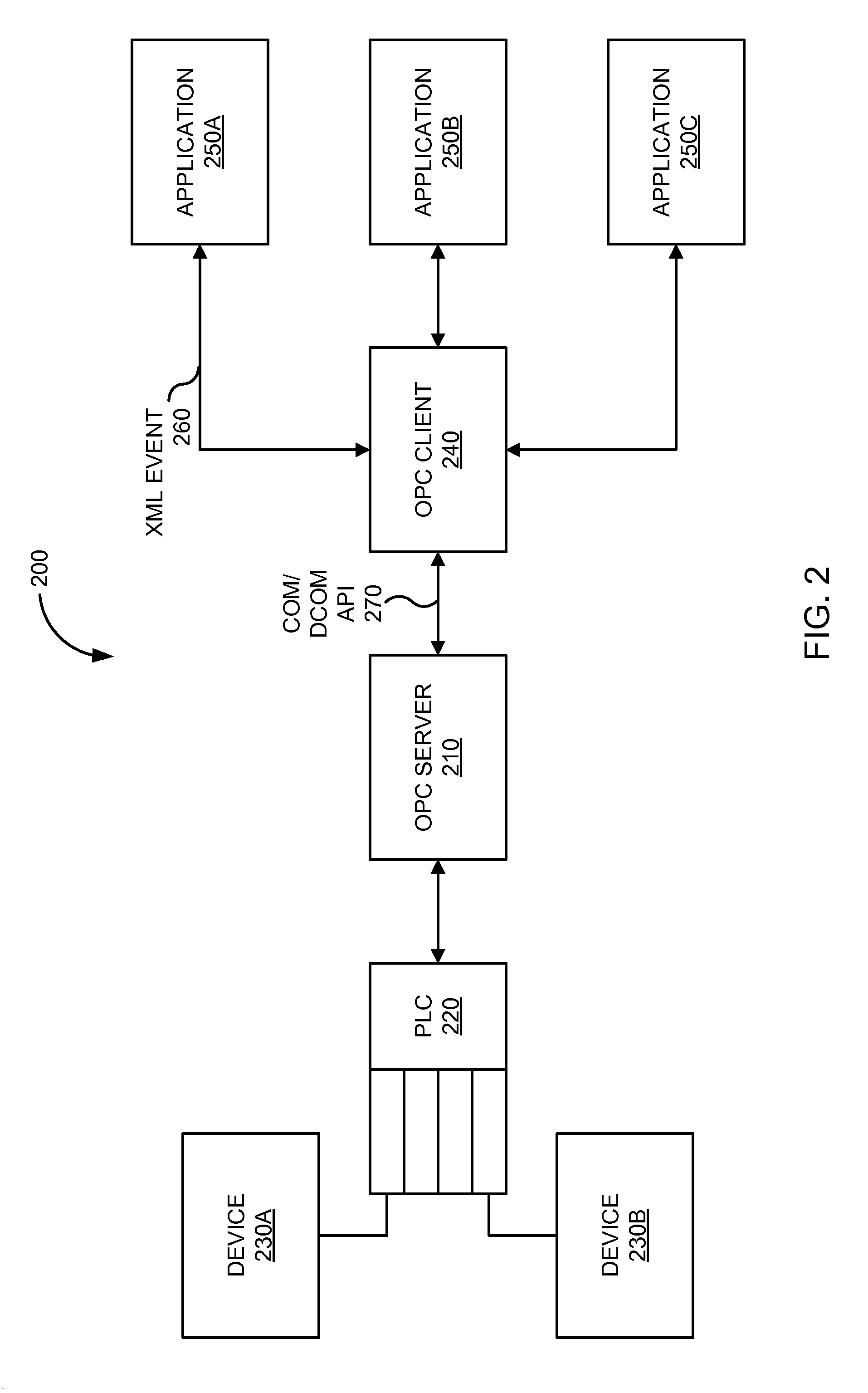
Xml-based event driven interface for opc data access
ActiveUS20100114994A1Digital data processing detailsNatural language data processingWeb serviceData access
Communication from applications may be carried in XML-based events through sockets, Web services, JMS, HTTP, telnet channels, and the like to an OPC client. The OPC client may include an event engine configured to process the XML-based events, and convert them to appropriate COM / DCOM API invocations. In some embodiments, the OPC client buffers collected data from the COM / DCOM API, and transmits the buffered data in an XML event to an application based on a subscription time schedule and / or value condition. The OPC client allows service oriented event-driven applications to interact with industry devices remotely via the open architecture provided by the OPC specification using a business level language syntax.
Owner:ORACLE INT CORP
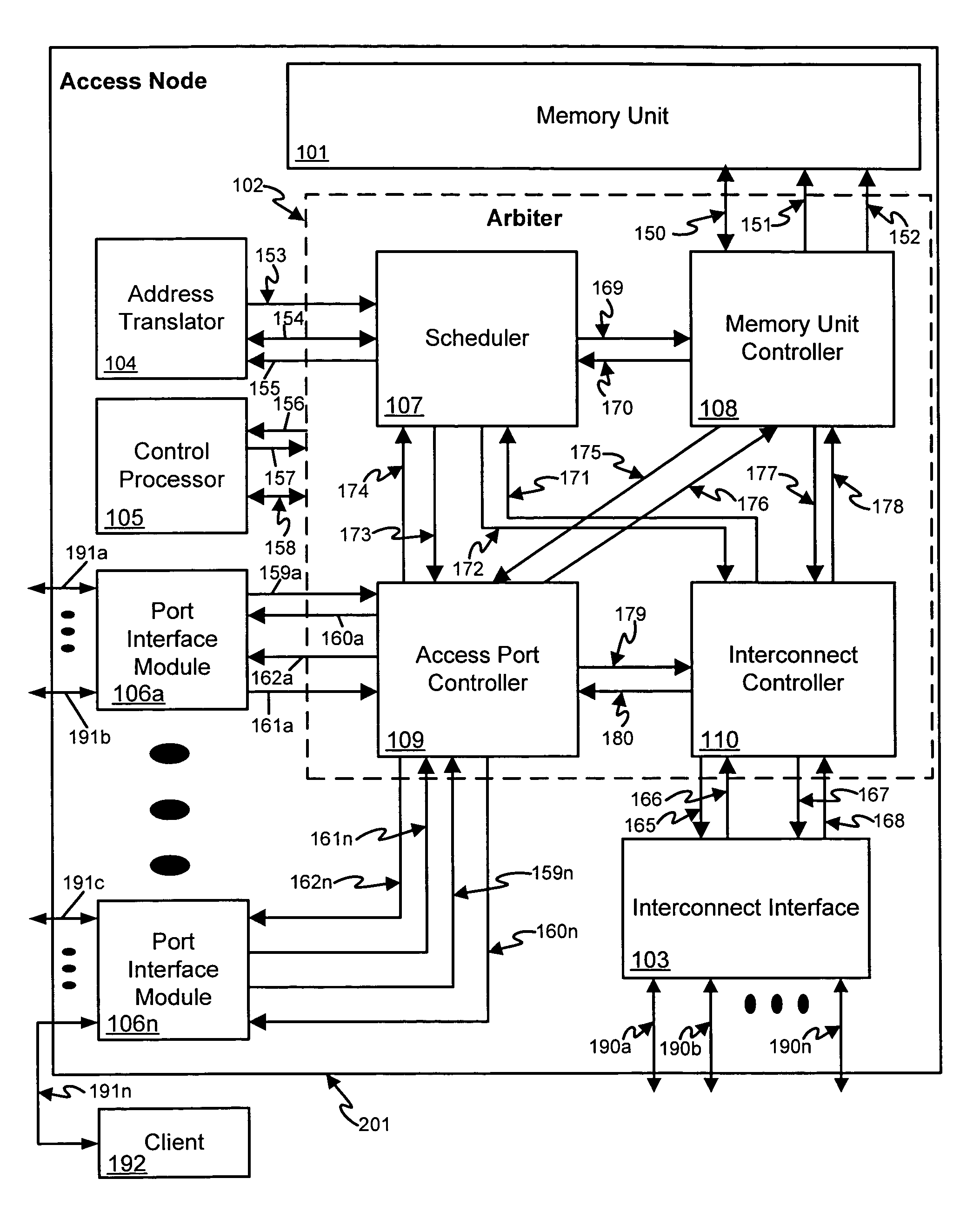
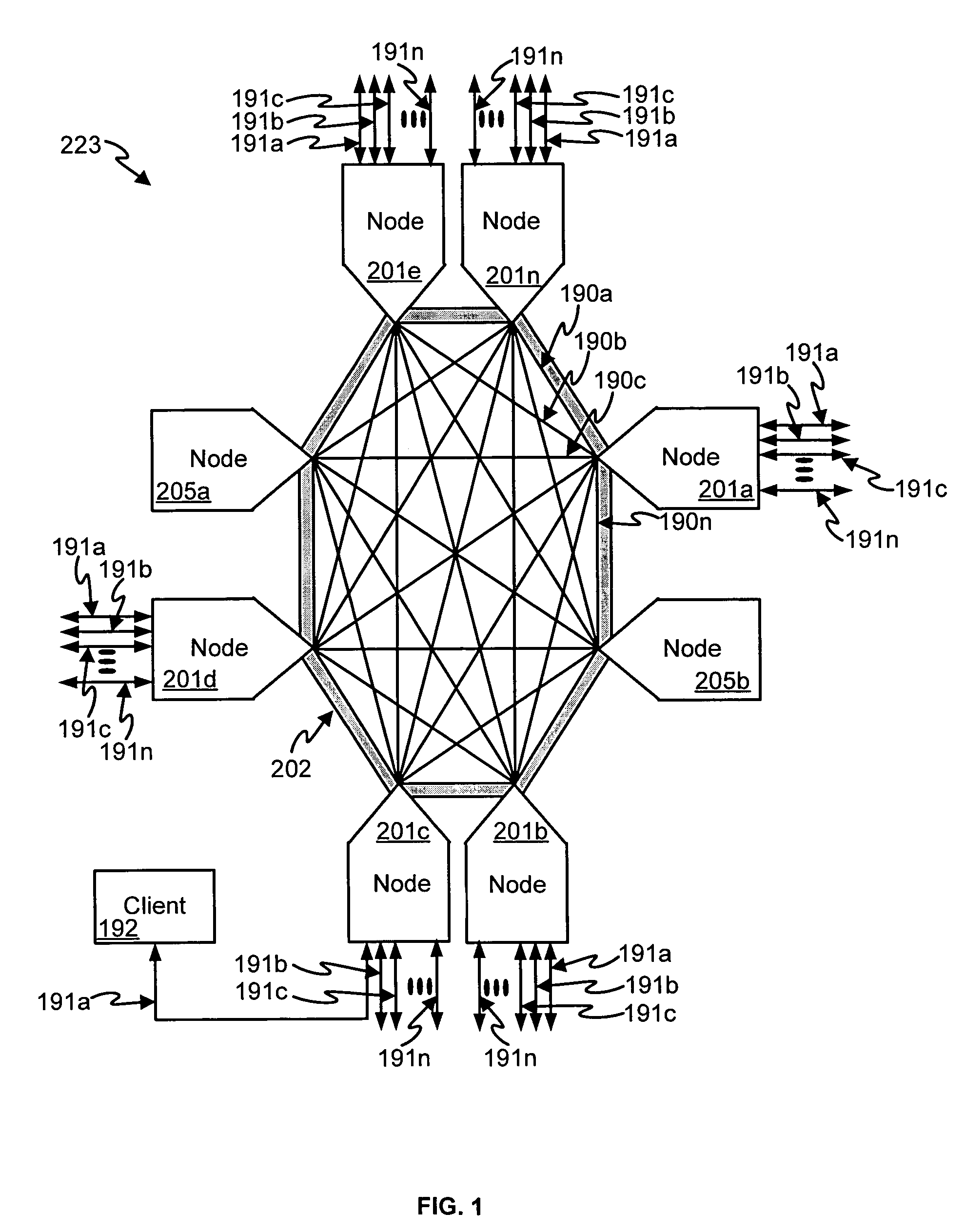
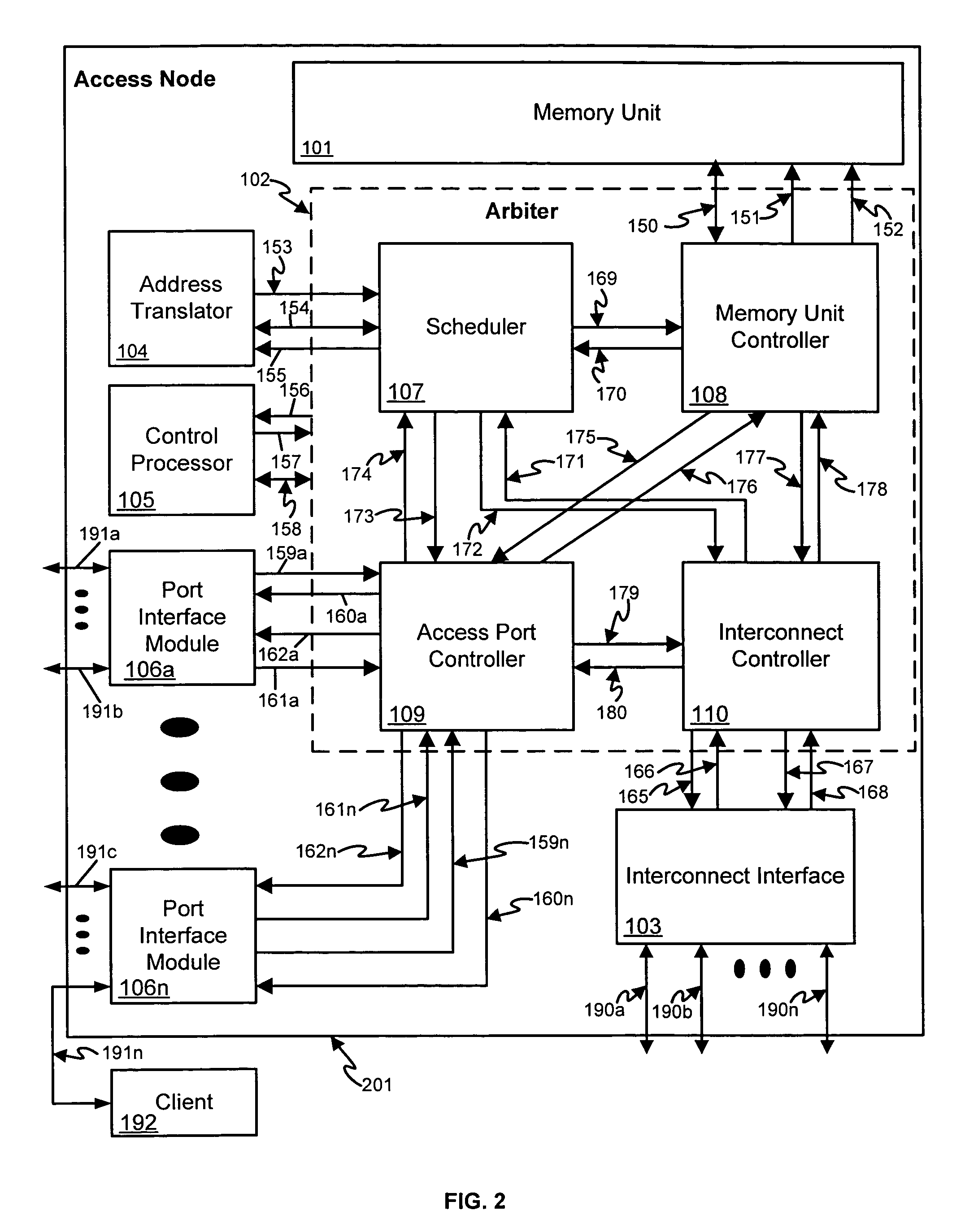
Data access and address translation for retrieval of data amongst multiple interconnected access nodes
ActiveUS7240143B1Large storage capacityStorage capacity expansionMemory adressing/allocation/relocationMicro-instruction address formationMemory addressVirtualization
A low-latency storage memory system is built from multiple memory units such as high-density random access memory. Multiple access ports provide access to memory units and send the resultant data out interface ports. The memory units communicate with the access ports through an interconnected mesh to allow any access port to access any memory unit. An address virtualization mechanism using address translators allows any access port of the memory storage system to access requested data as abstract objects without regard for the physical memory unit that the data is located in, or the absolute memory addresses within that memory unit.
Owner:GOOGLE TECH HLDG LLC
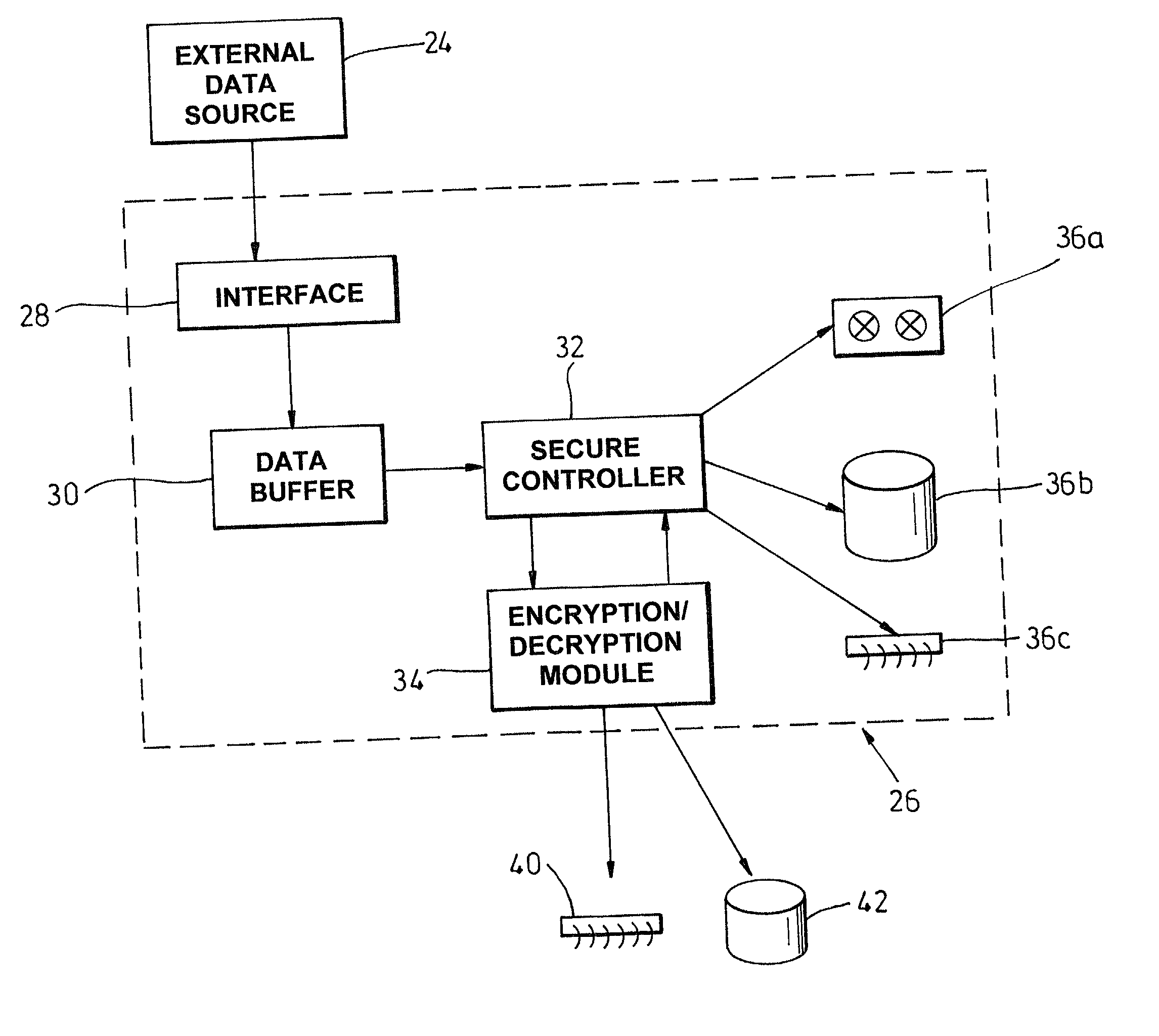
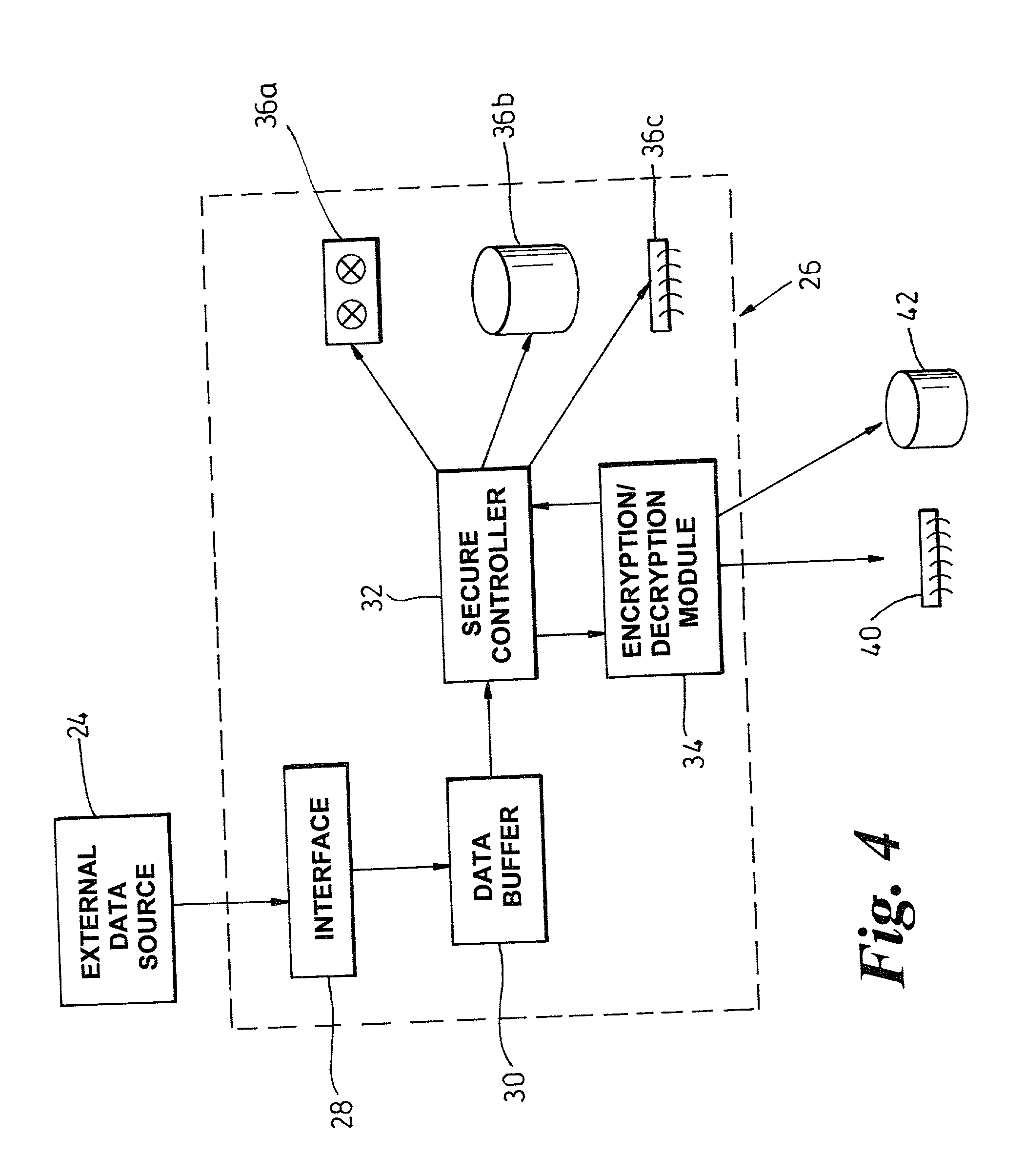
Restricted data access
InactiveUS20020138747A1Digital data processing detailsUser identity/authority verificationComputer hardwareData access
A data storage medium 10 adapted to restrict access to data 20 stored thereupon by encrypting control login 18, 22 which directs storage devices 62, 64 where to look for the data 20 on the storage medium 10 and a method for providing such a storage medium 10.
Owner:HEWLETT PACKARD DEV CO LP
Reader/writer apparatus, data access system, data access control method, and computer product
InactiveUS20080136599A1Solve problemsMemory record carrier reading problemsCo-operative working arrangementsComputer hardwareData access control
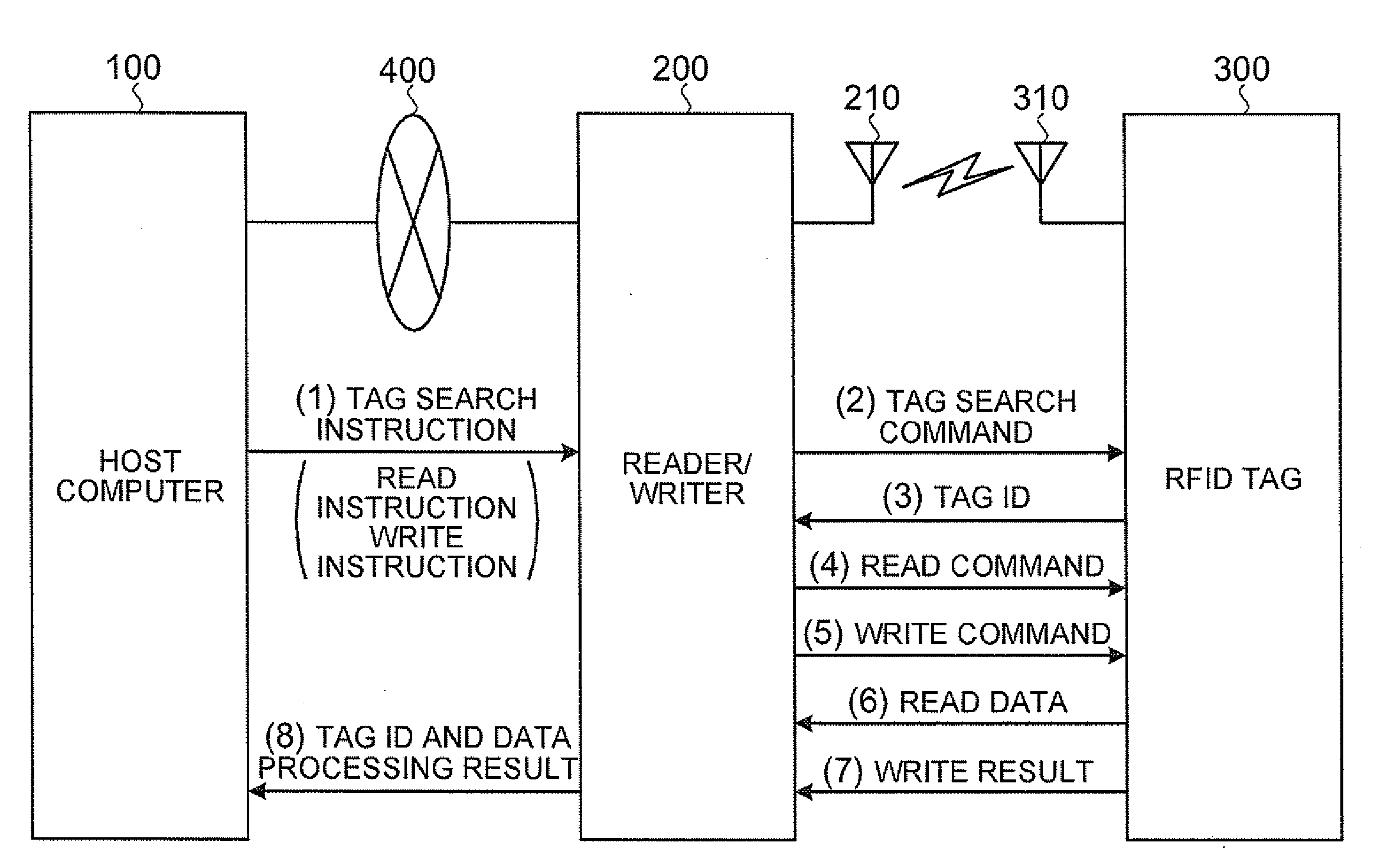
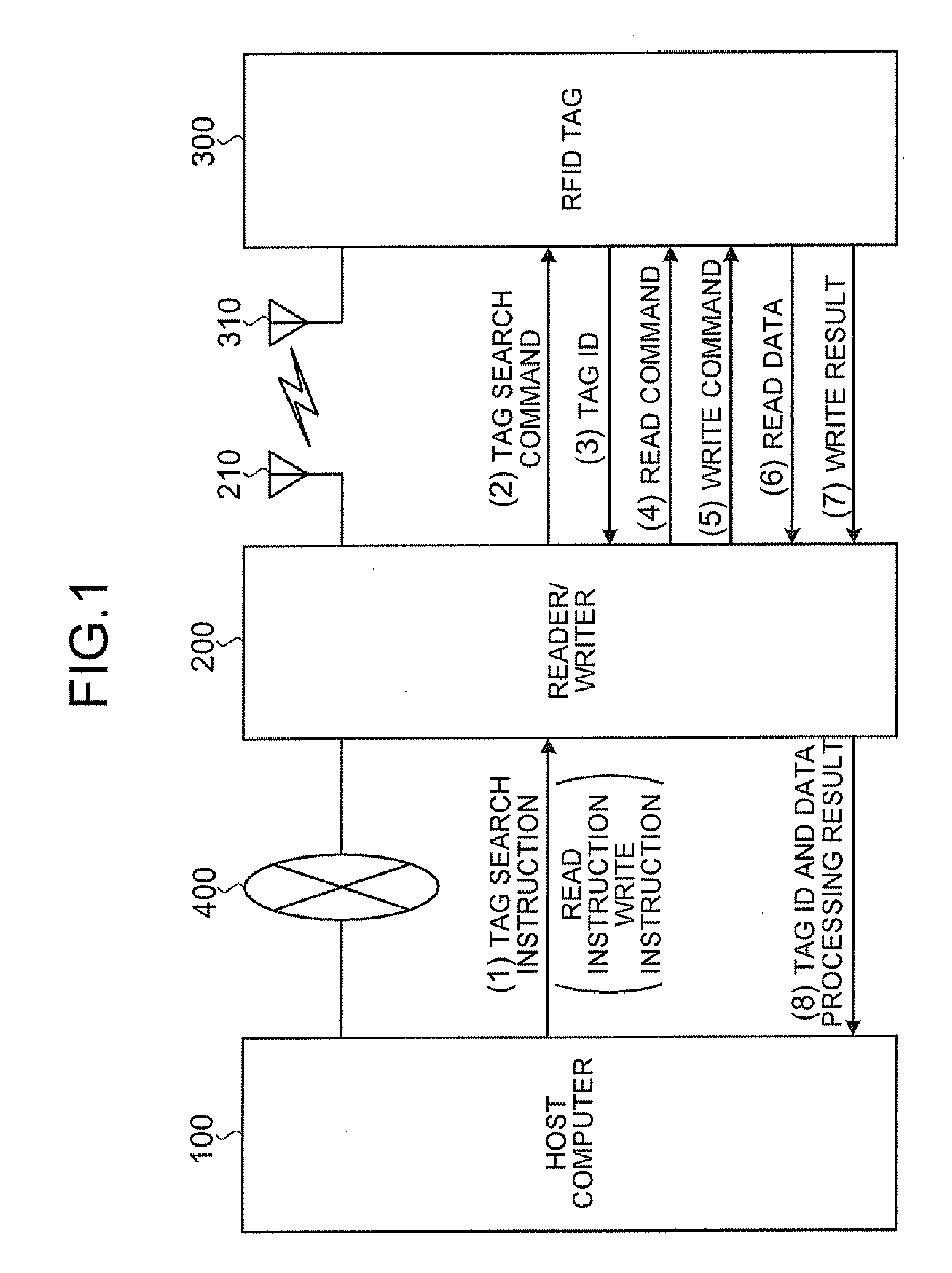
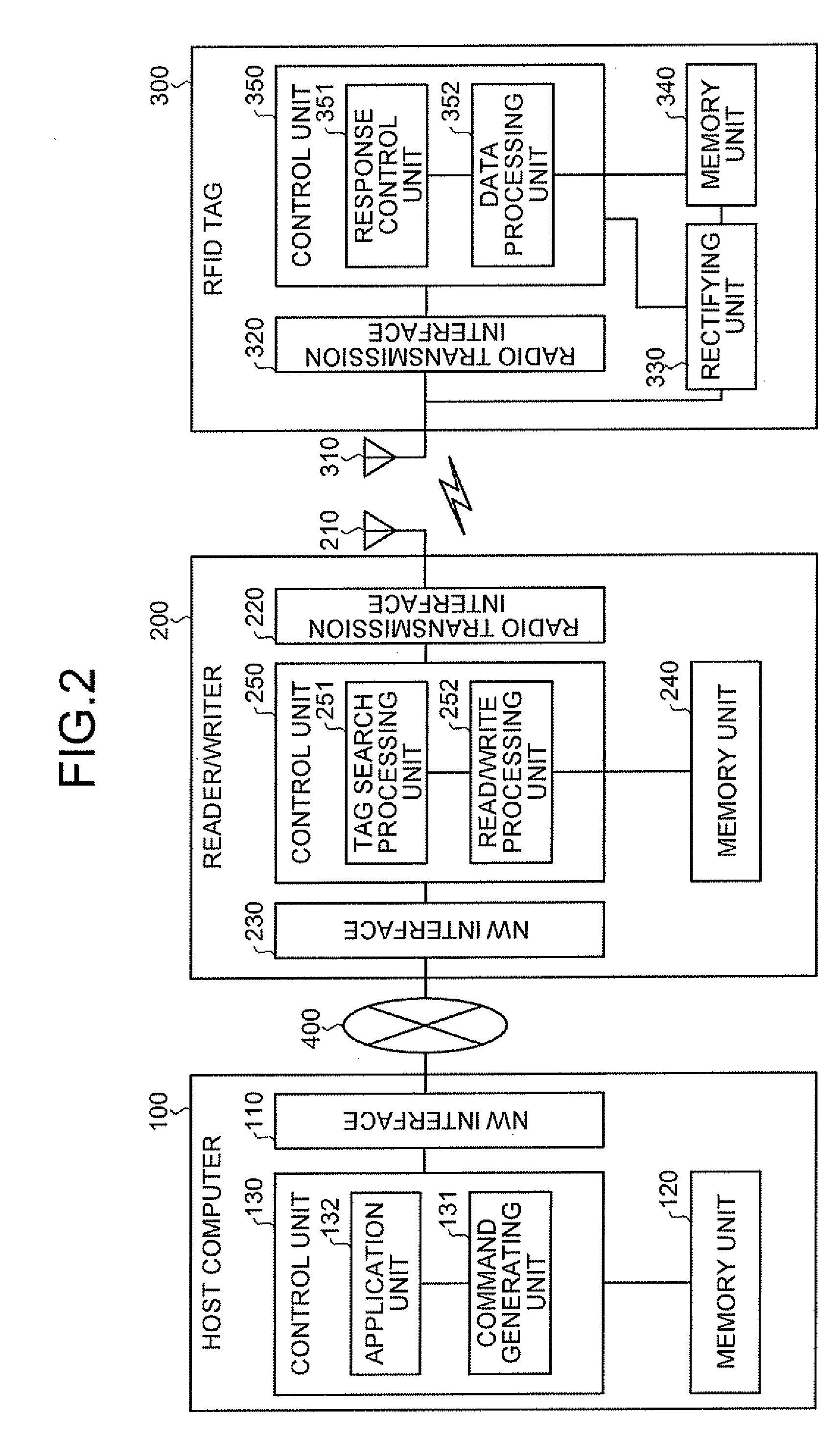
A reader / writer apparatus includes a tag search instruction receiving unit that receives a tag search instruction from a host apparatus. The tag search instruction includes a data read instruction and / or a data write instruction on the RFID tag. The reader / writer apparatus also includes a tag identification information requesting unit that transmits to the RFID tag a request for transmission of tag identification information uniquely identifying the RFID tag when the tag search instruction receiving unit receives the tag search instruction; and a data processing requesting unit that transmits a data read request and / or a data write request to the RFID tag identified by the tag identification information based on the read instruction and / or the write instruction when receiving the tag identification information transmitted from the RFID tag in response to the request for transmission transmitted from the tag identification information requesting unit.
Owner:FUJITSU LTD
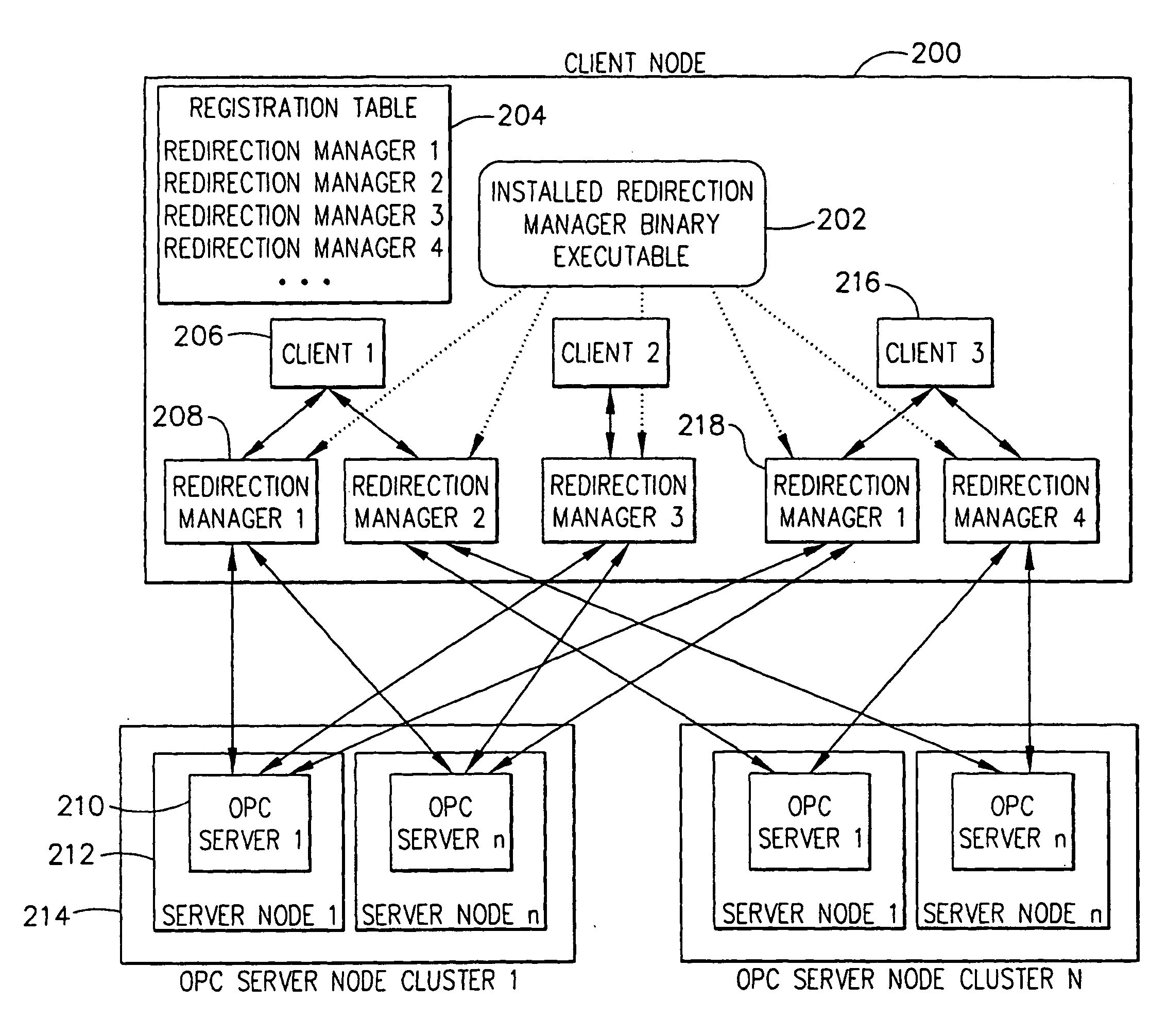
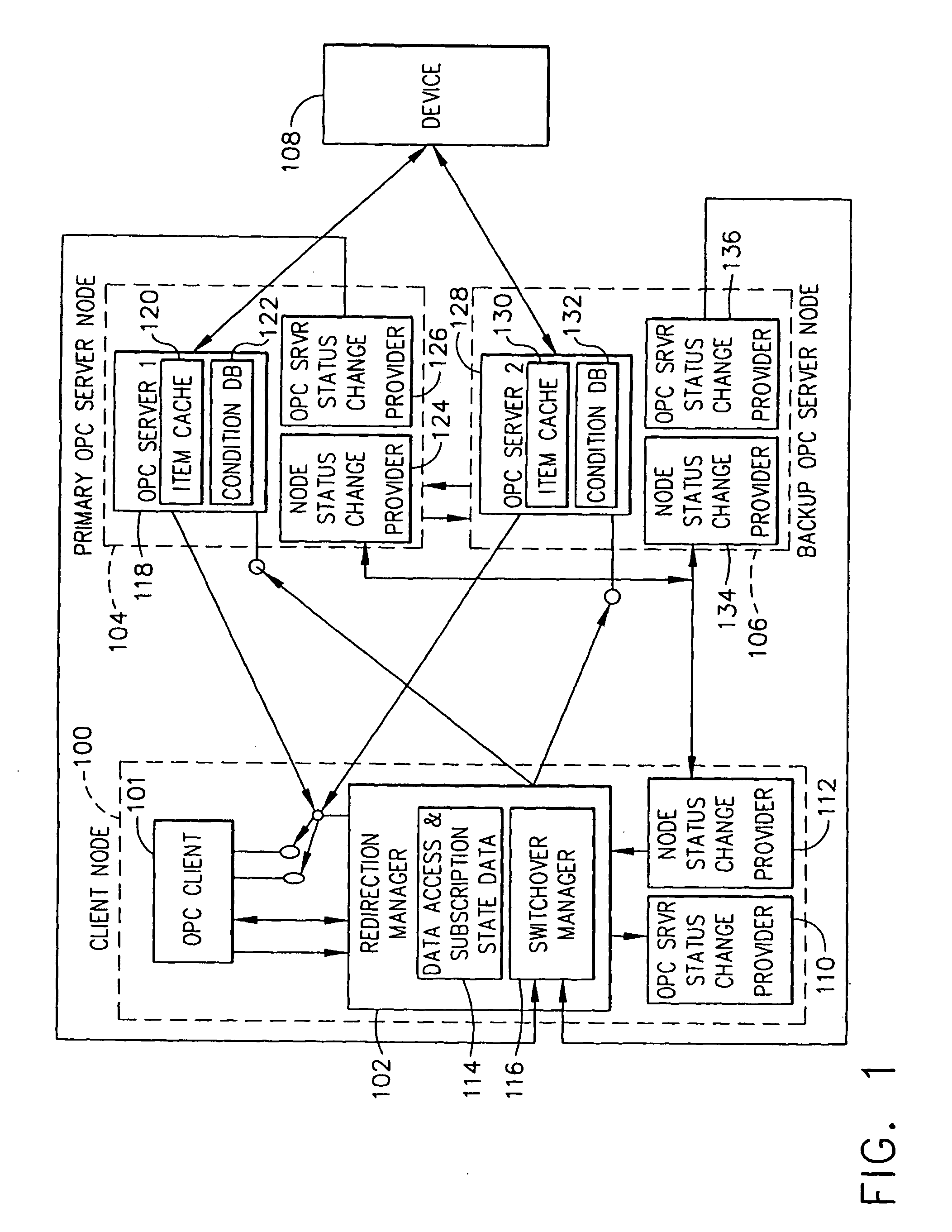
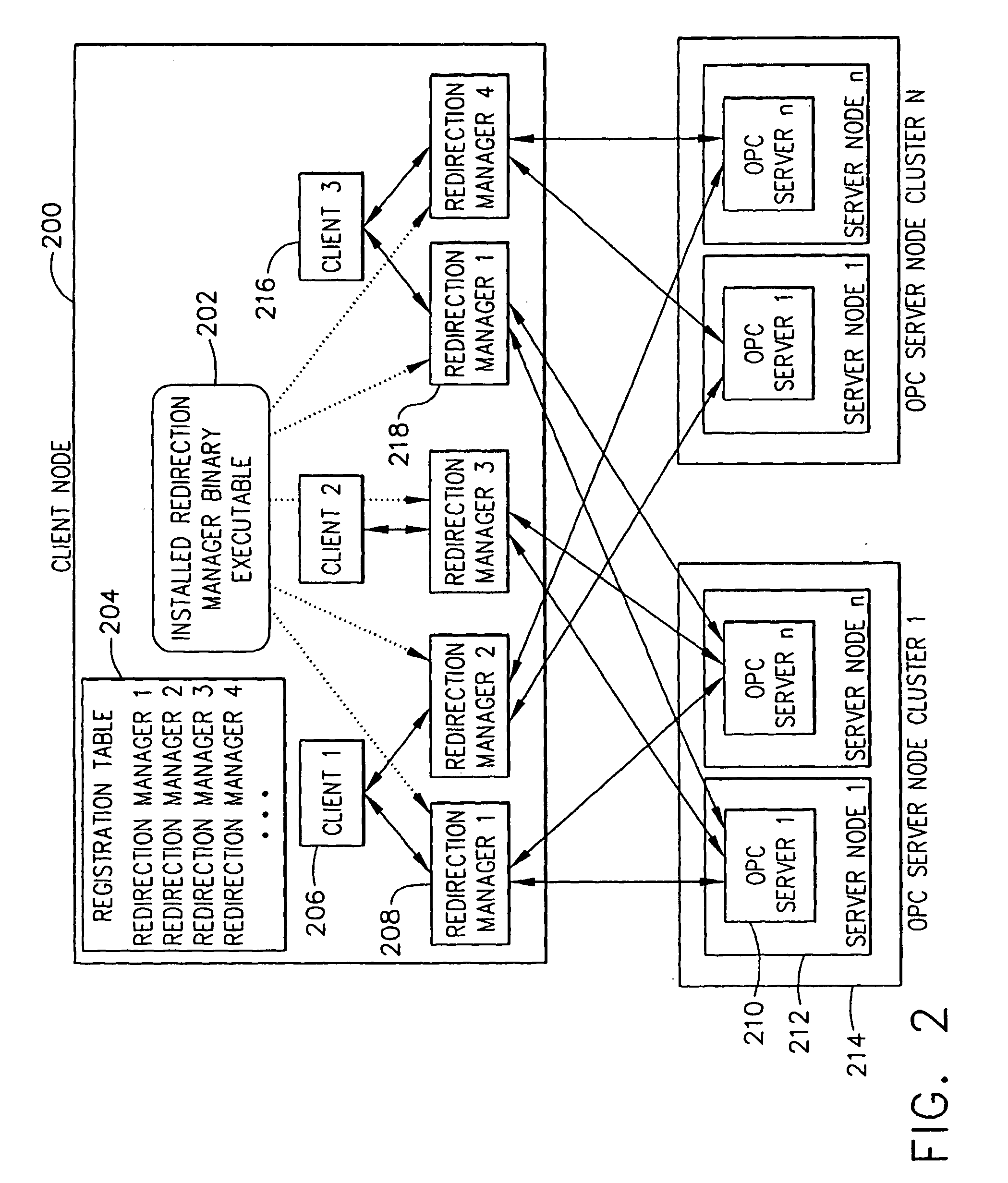
OPC server redirection manager
An OPC redirection manager maintains the information necessary for taking appropriate action when the target OPC server fails and for ensuring that no bad status is returned to the client. Any existing OPC client needing seamless failover between target OPC data access and / or alarm and event servers will connect to a uniquely configured instance of the redirection manager instead of connecting to the primary server. The client application continues to perform OPC related tasks as usual. Because each client connection is unique, the redirection manager itself is not a single point of failure. Each configured redirection manager instance monitors the health of the target server mode and the target server itself by subscribing to failure events.
Owner:HONEYWELL INT INC
Method of managing data access of a storage medium and storage controller
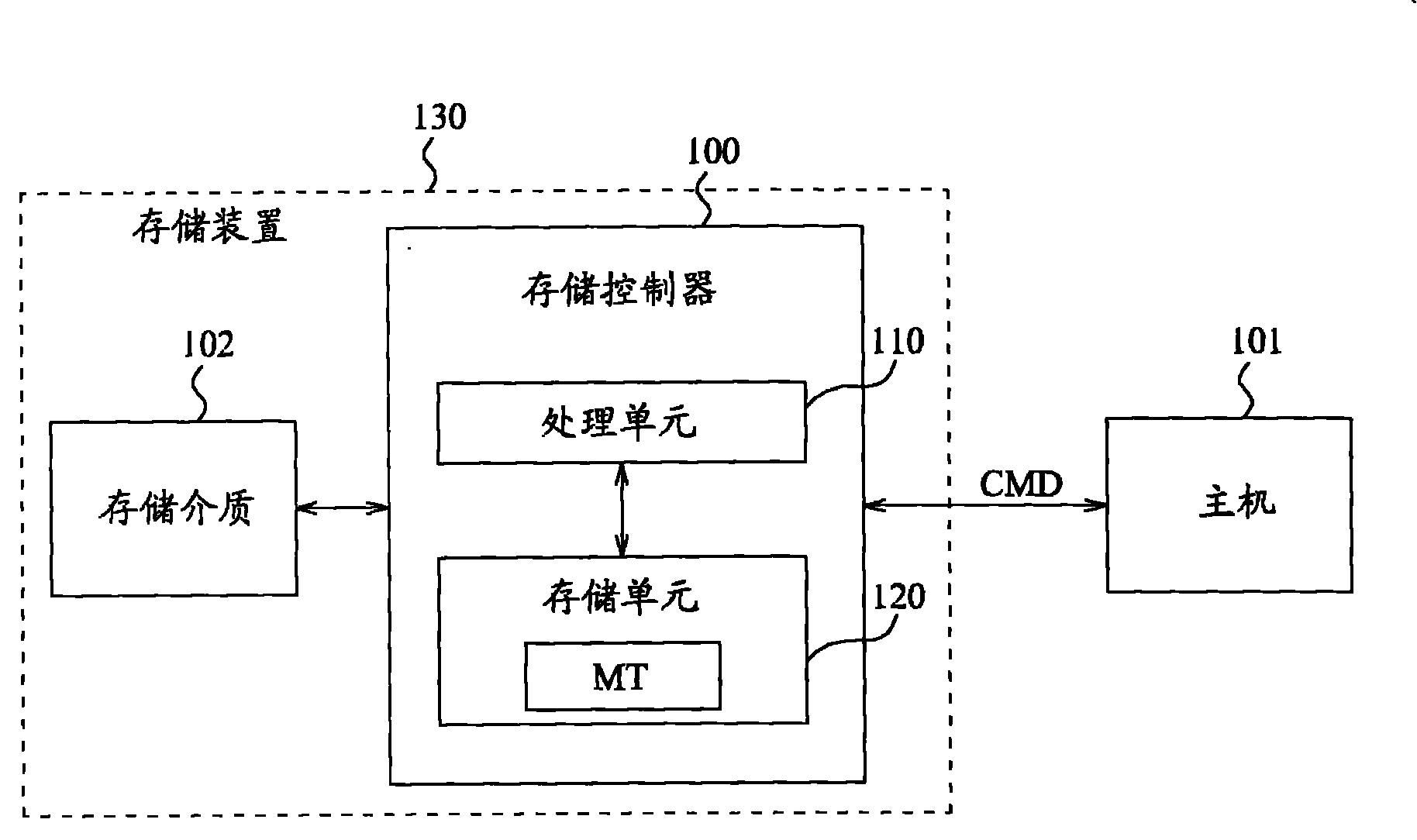
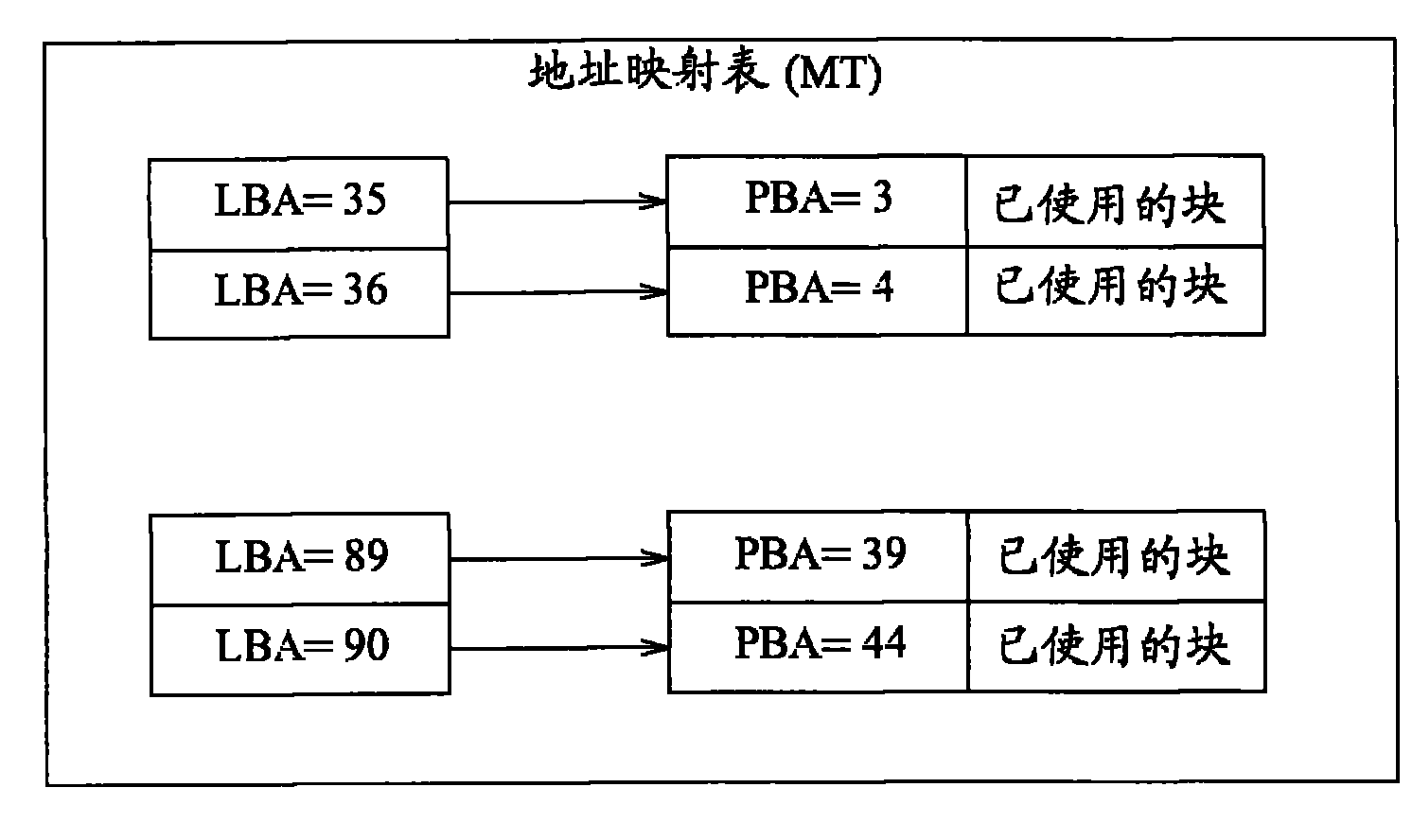
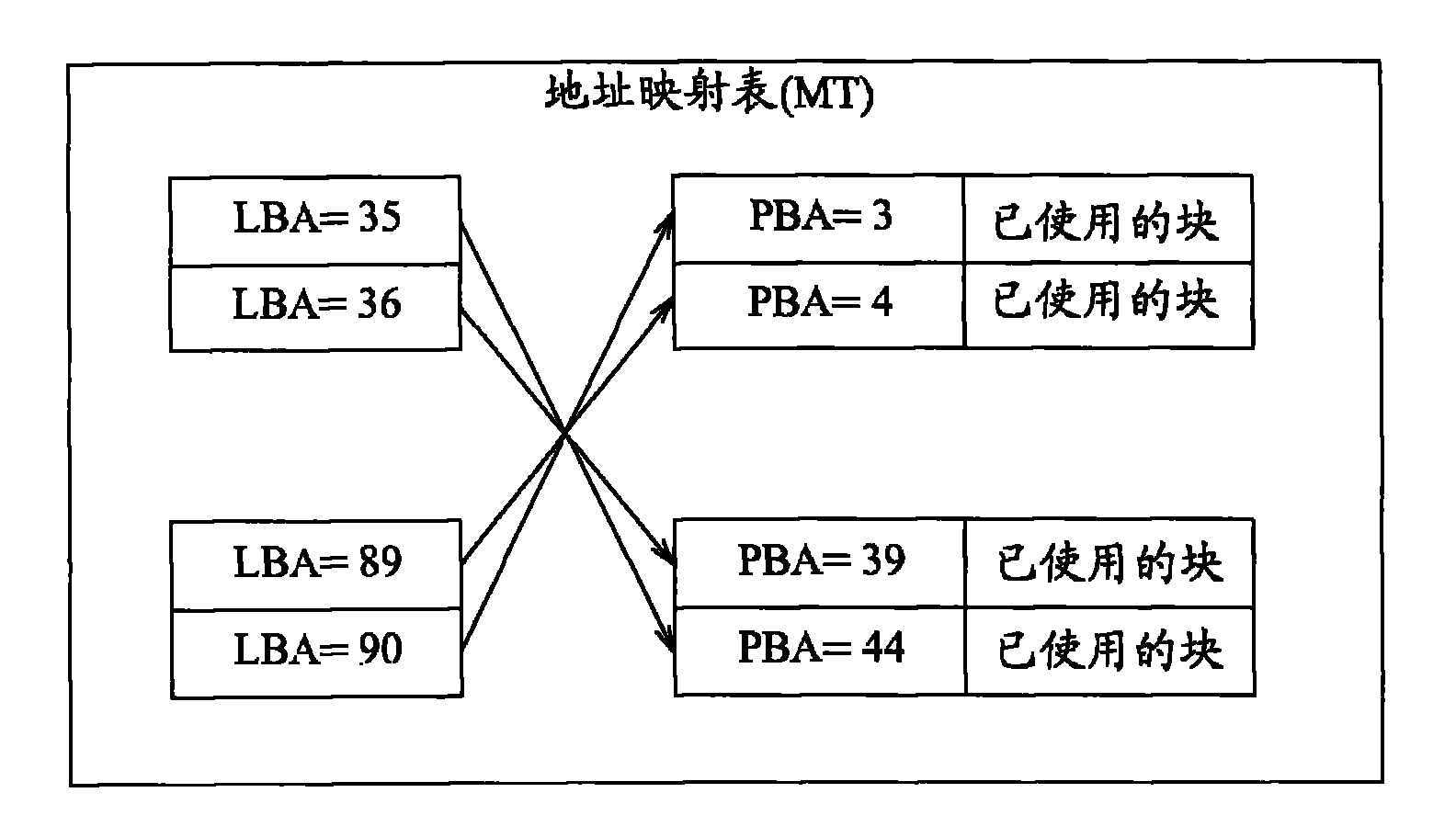
ActiveCN102063377AImprove finishing effectMemory architecture accessing/allocationInput/output to record carriersControl storeData access
The invention relates to a method of managing data access of a storage medium and a storage controller. The storage controller for managing data access of the storage medium comprises: a storage unit, storing an address mapping table to record at least a physical address of a first data stored in the storage medium, where the physical address of the first data is mapped to a logical address of the first data; and a processing unit, coupled to the storage unit, wherein when receiving a command for handling at least the first data in the storage medium internally, the processing unit processes the address mapping table to serve the command without controlling the storage medium to physically accessing at least the first data stored therein; a plurality of command sets are sent through effective load data of the single command; and the processing unit searches the plurality of command sets sent by the single command for subsequently updating the address mapping table so as to respond the single command. One advantage of the invention is to improve the performance for collating the paper fragmentation.
Owner:MEDIATEK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com