Patents
Literature
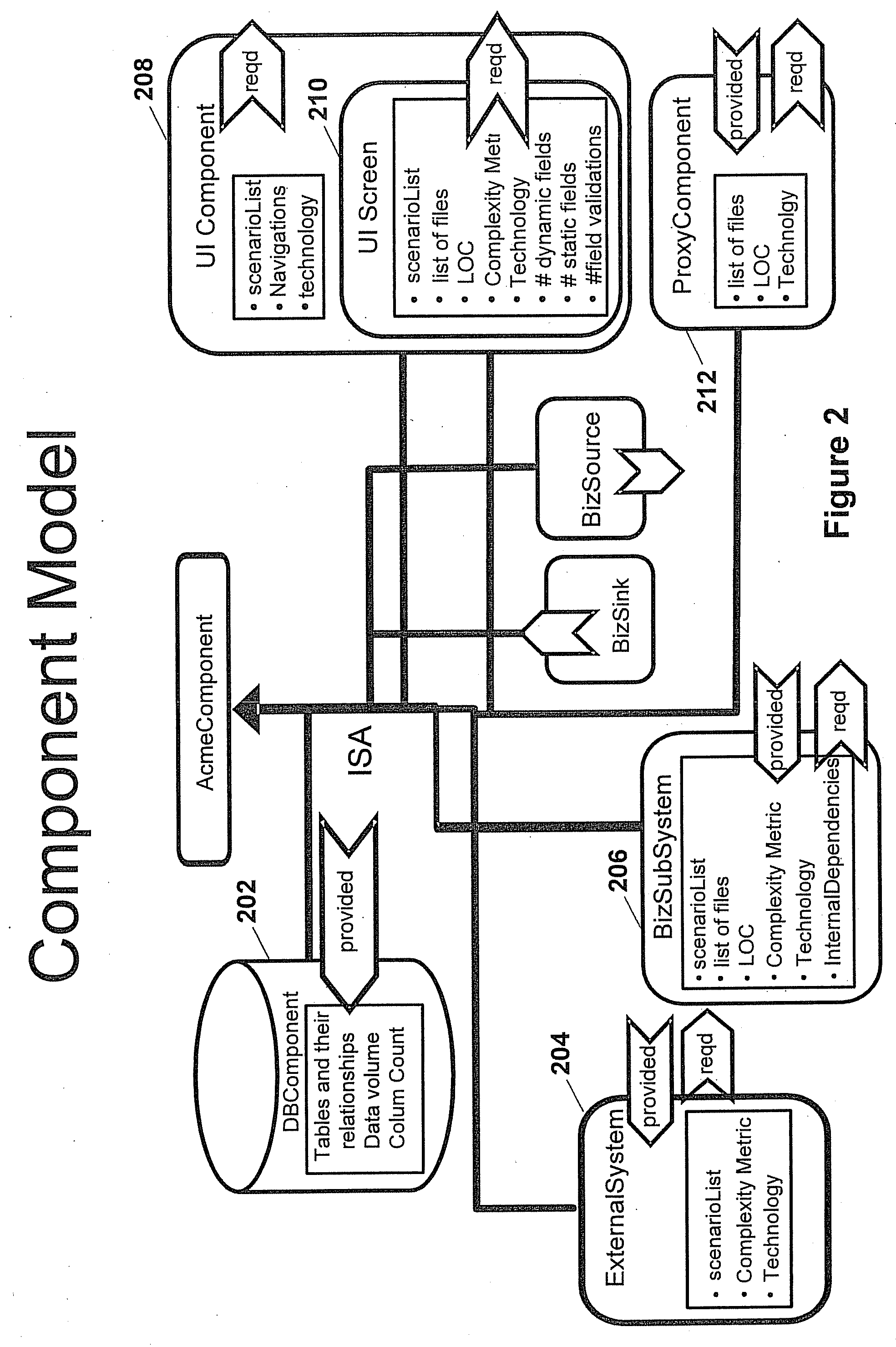
124 results about "Software changes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software changes are one type of IT service change. Many domain-specific change processes can exist to change IT services in various ways. IT service change management can be seen as the high-level process and software change management can be seen as the domain-specific implementation.
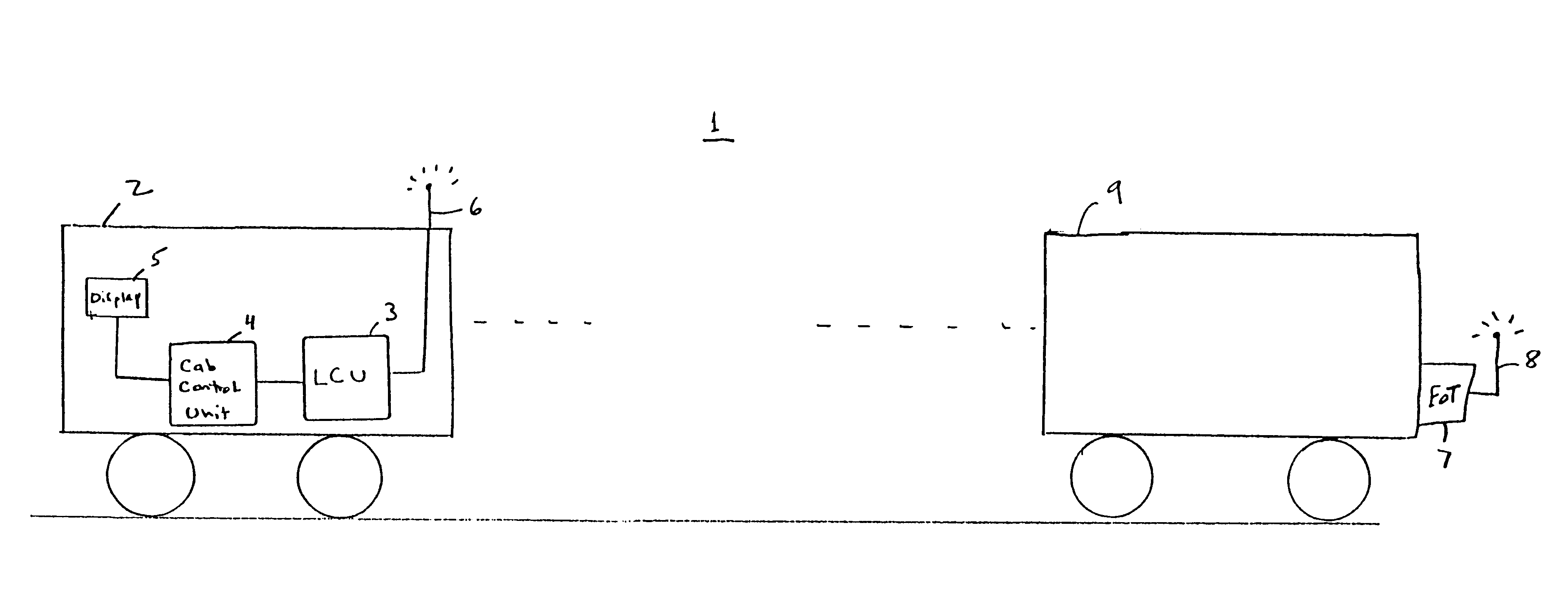
Dual-protocol locomotive control system and method
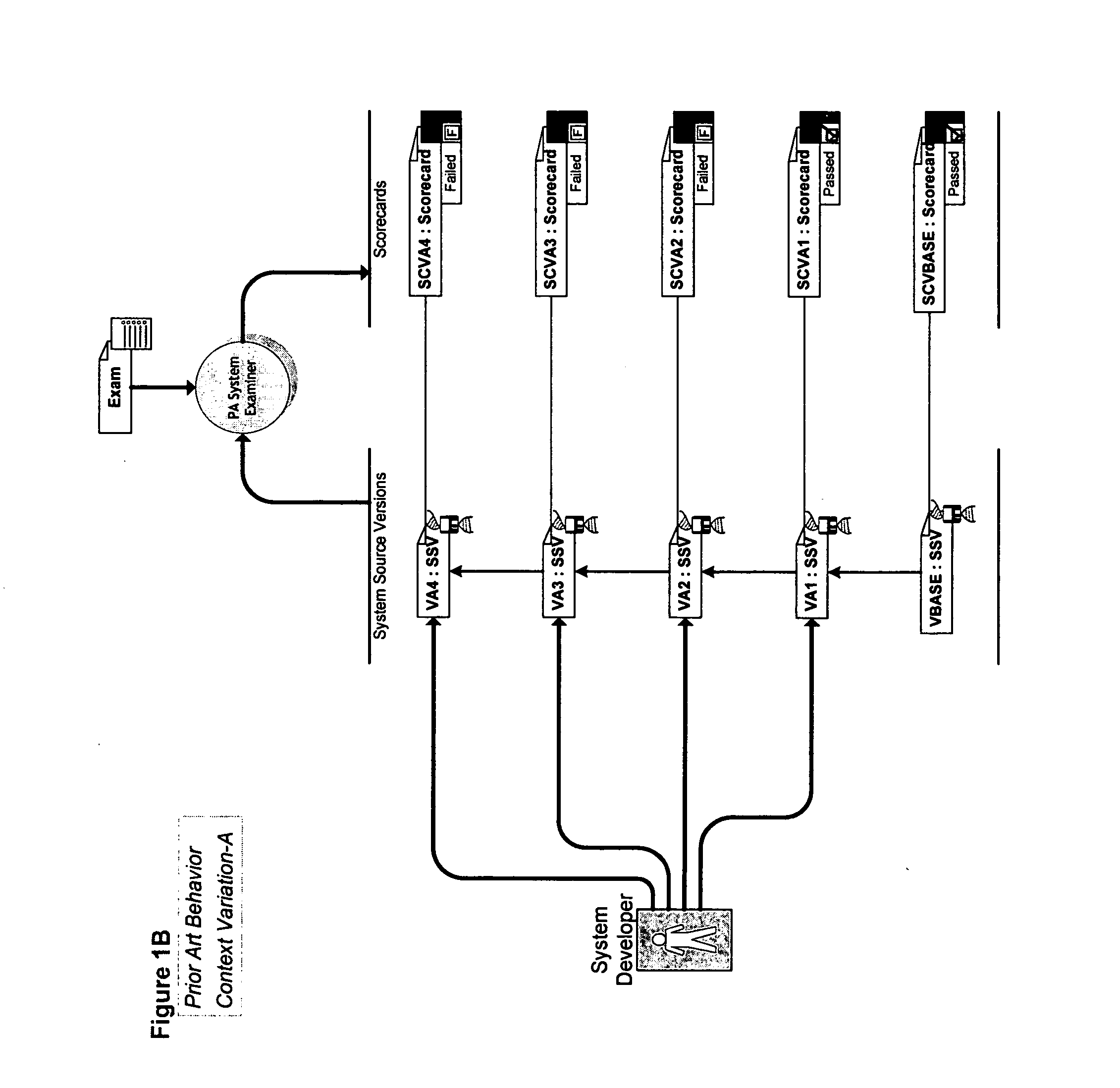
InactiveUS6322025B1Easy to operateImprove securityCircuit arrangementsSignalling indicators on vehicleCommunications systemTelecommunications link
An intra-train communication system includes a locomotive control unit (LCU) establishes a communications link between a lead unit and a remote unit which operate using different protocols and / or in different frequency bands. To accomplish this objective, the LCU automatically detects the type of lead unit and remote unit installed on the train. If the types are not the same, the LCU resolves any serial link protocol and arming differences that might exist in a manner virtually transparent to train operators. As a result, data is communicated between the lead and remote units in a way which requires less operator intervention and no software changes to the control computer of the head unit.
Owner:WESTINGHOUSE AIR BRAKE TECH CORP
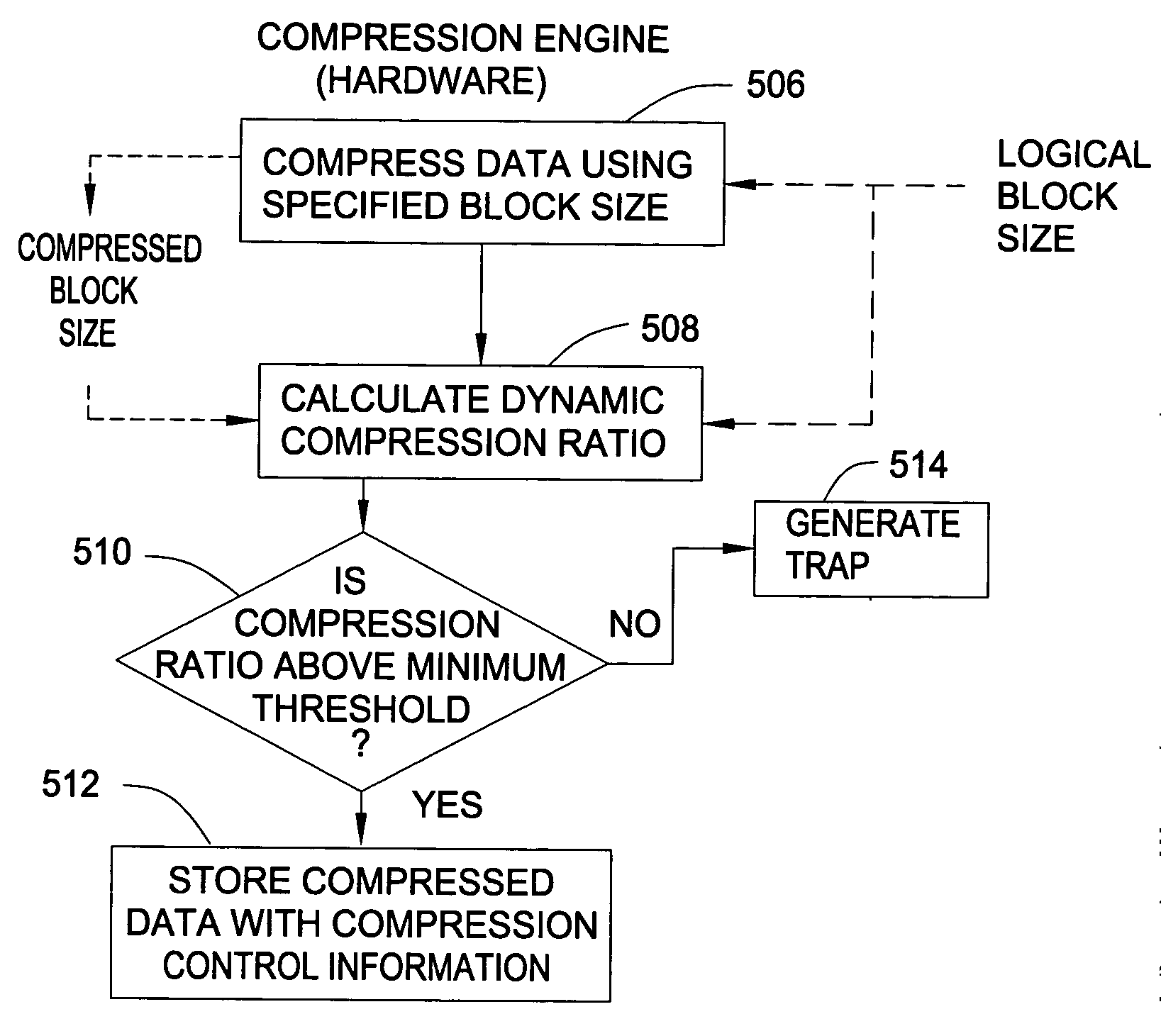
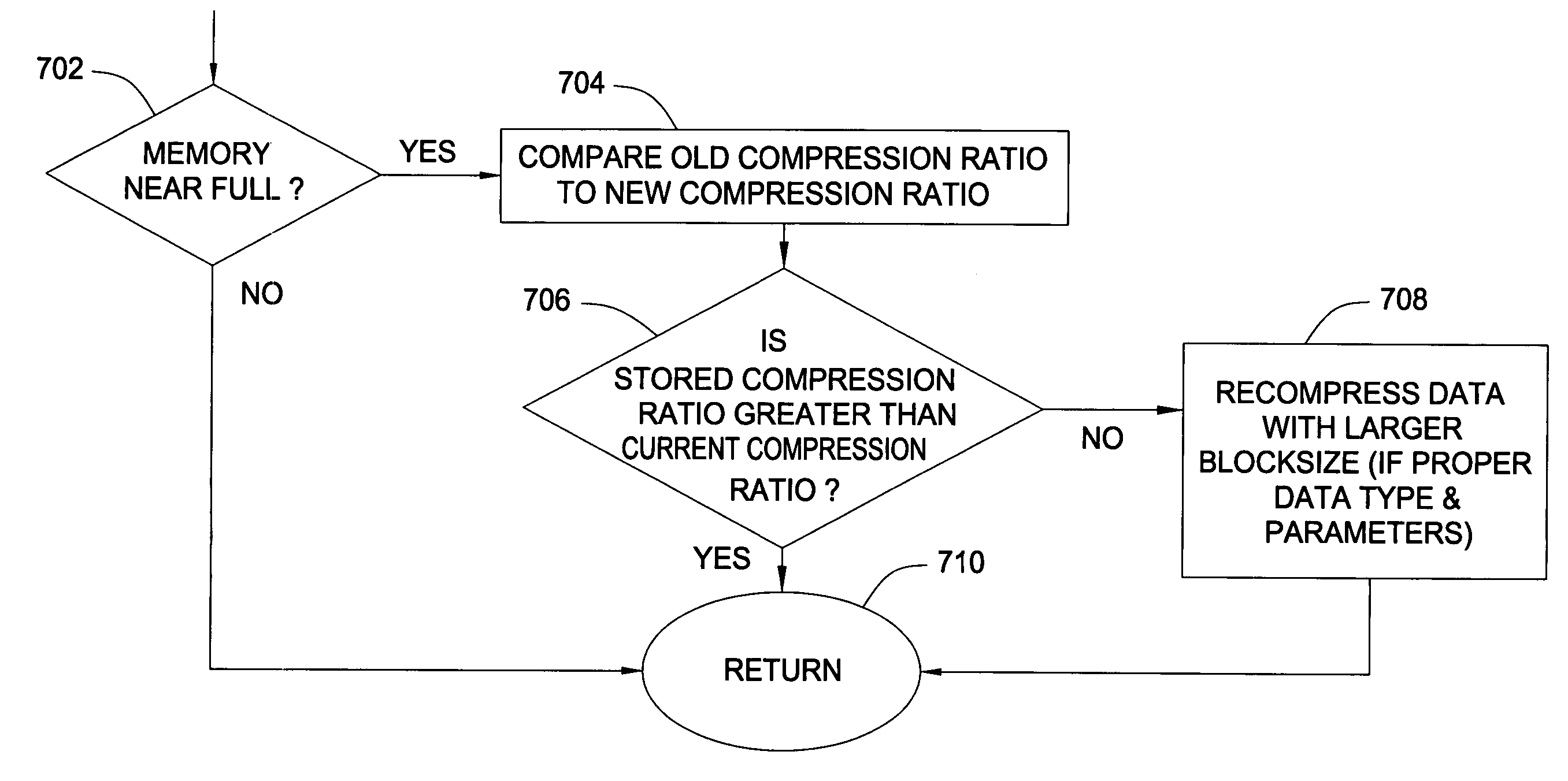
Adaptive memory compression
InactiveUS20050071579A1Increasing data blockMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingTerm memory
Compressed memory systems and methods that reduce problems of memory overflow and data loss. A compression engine compresses blocks of data for storage in a compressed memory. A compression monitor monitors the achieved compression ratio and provides a software trap when the achieved compression ratio falls below a minimum. After the trap is provided software monitors the fill state of the compressed memory. If the compressed memory is approaching full, the software changes the block size to improve the compression ratio.
Owner:IBM CORP
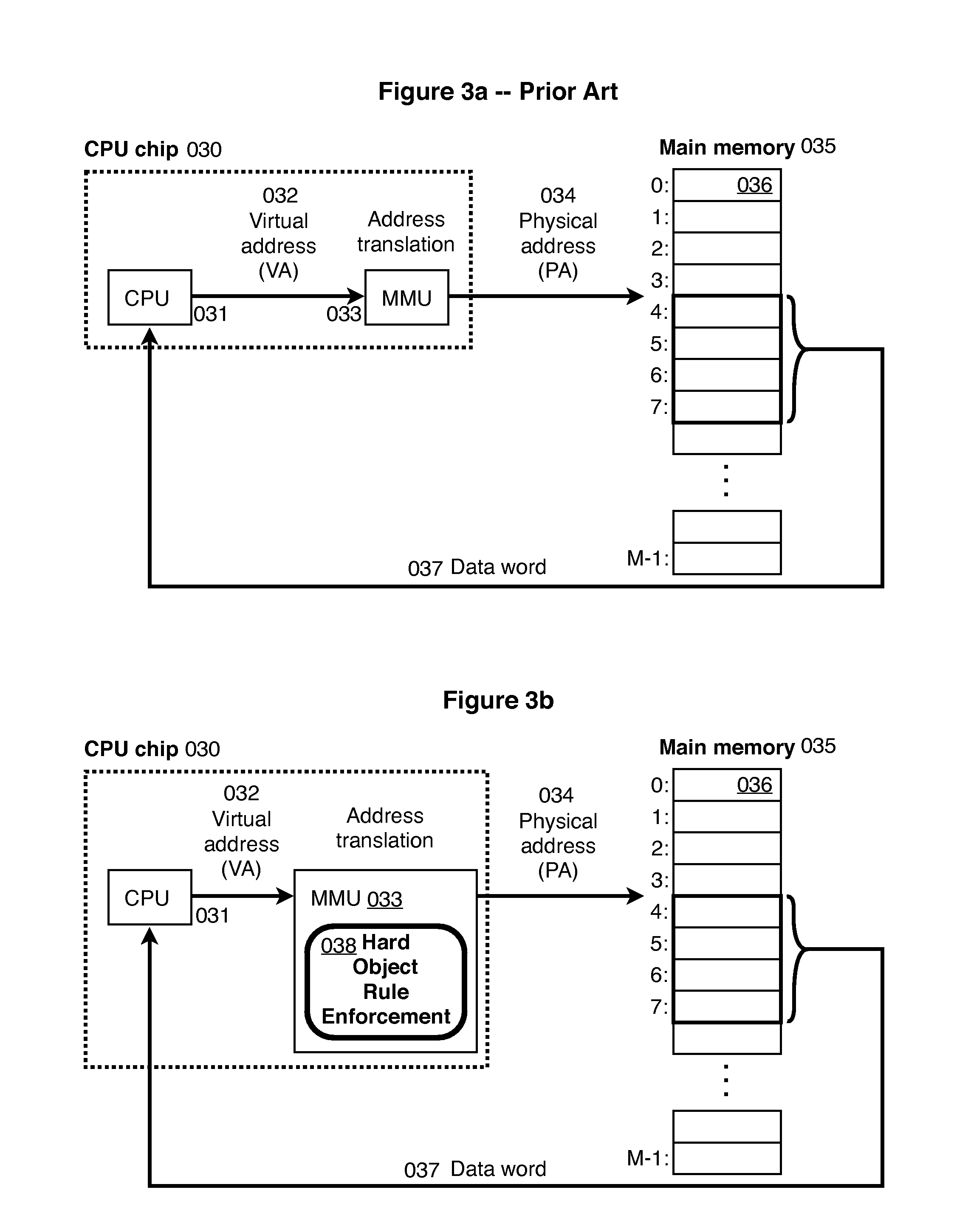
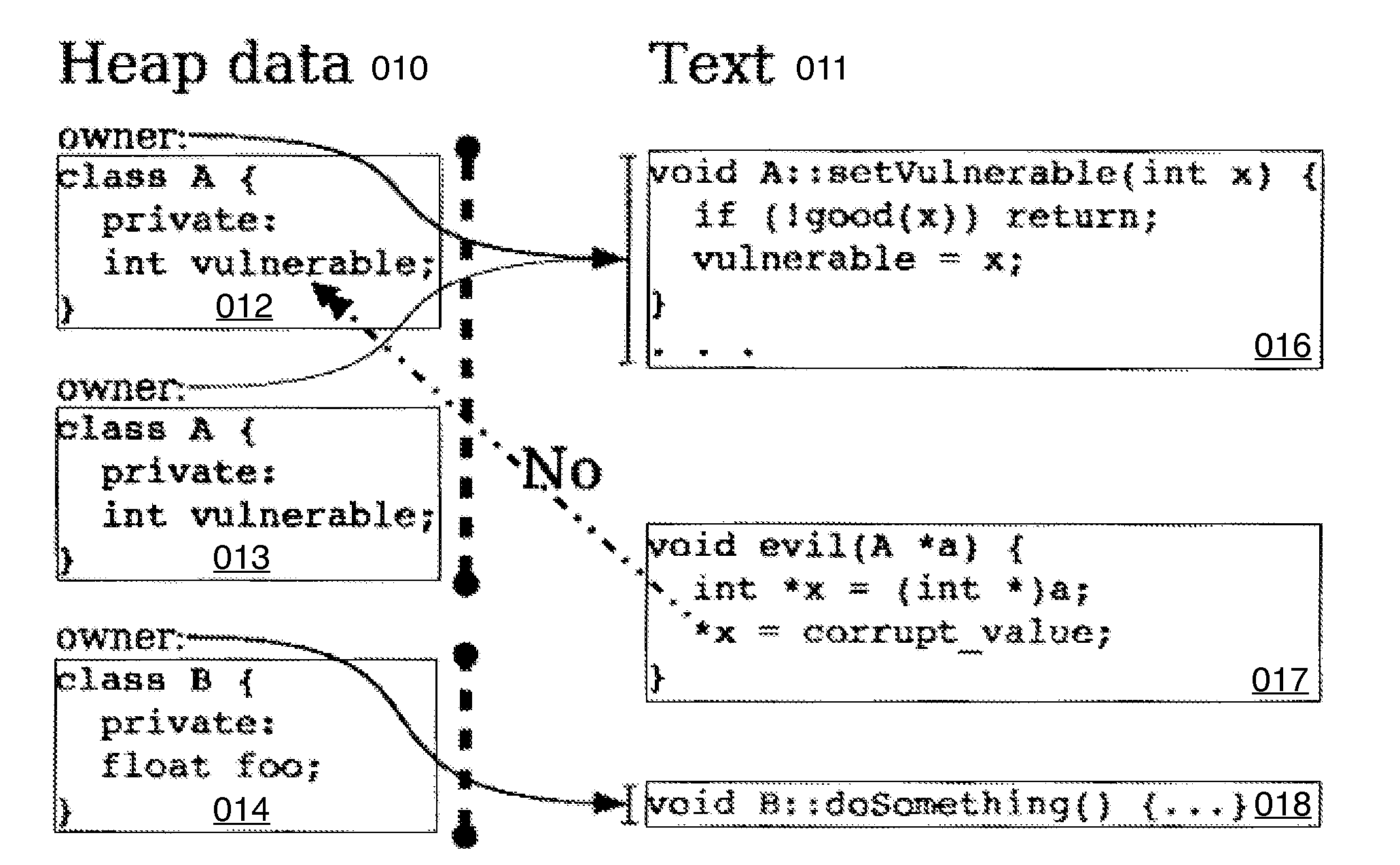
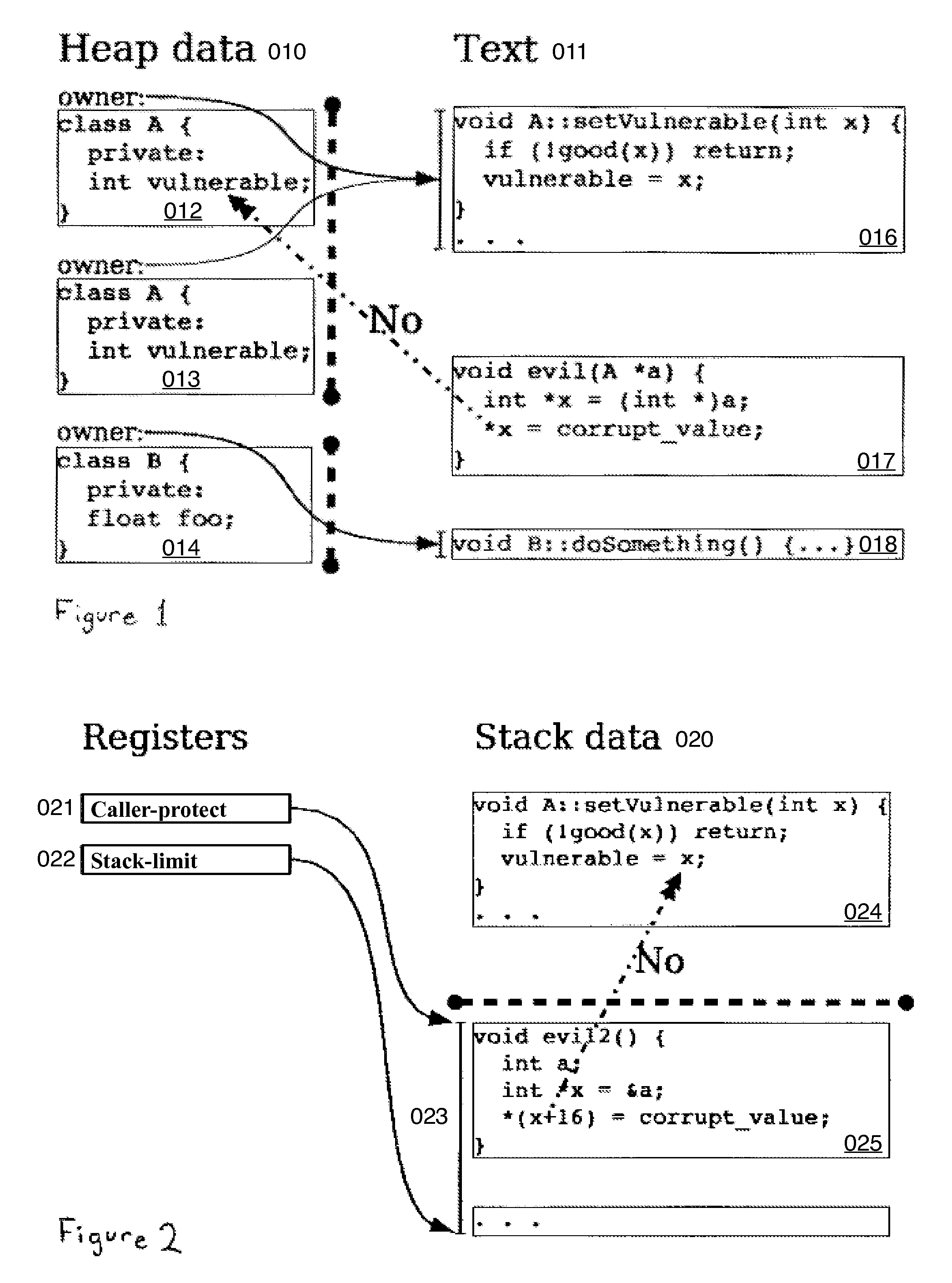
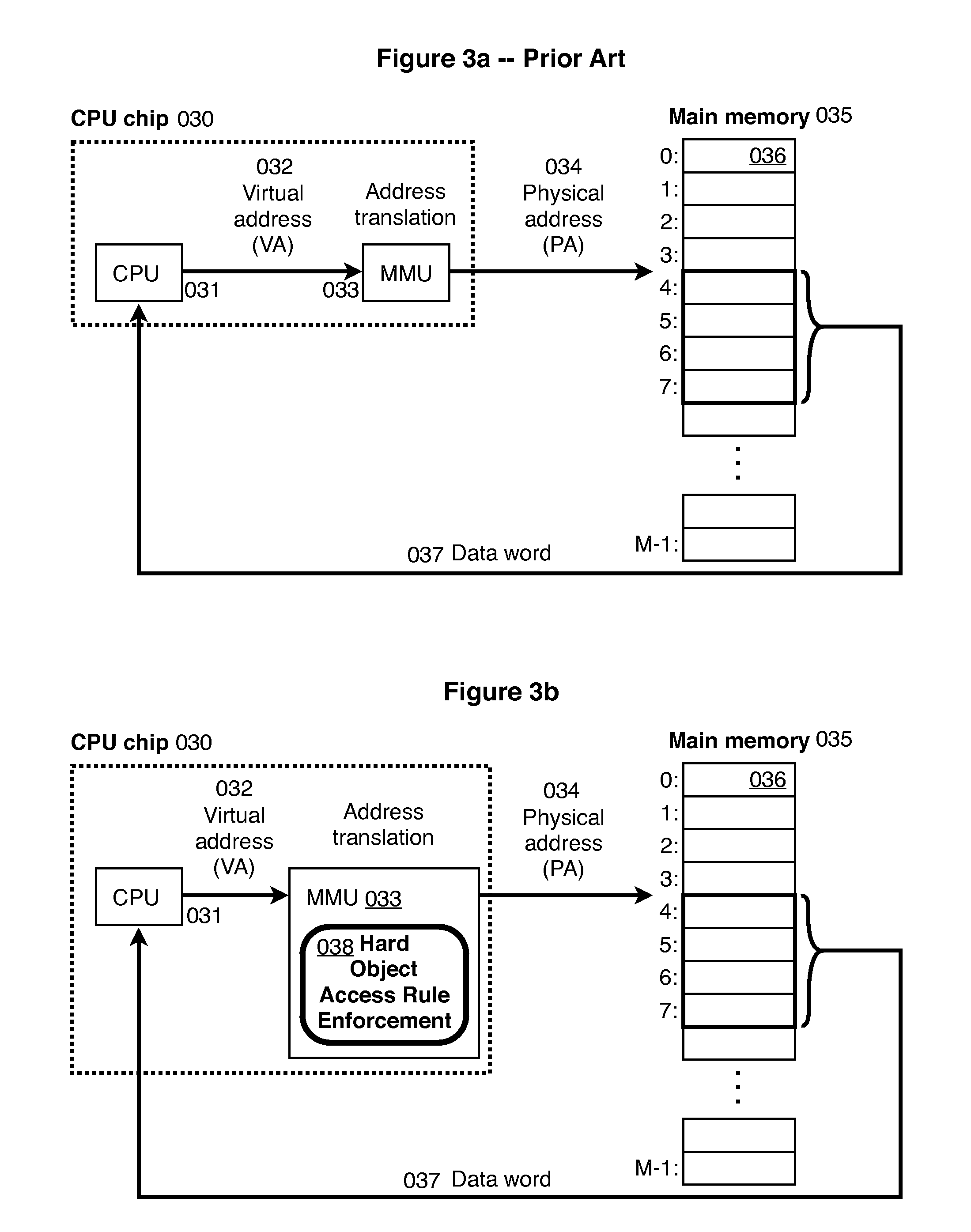
Hard Object: Hardware Protection for Software Objects
ActiveUS20080222397A1Efficiently implement enforceable separation of programDigital computer detailsAnalogue secracy/subscription systemsProcessor registerPhysical address
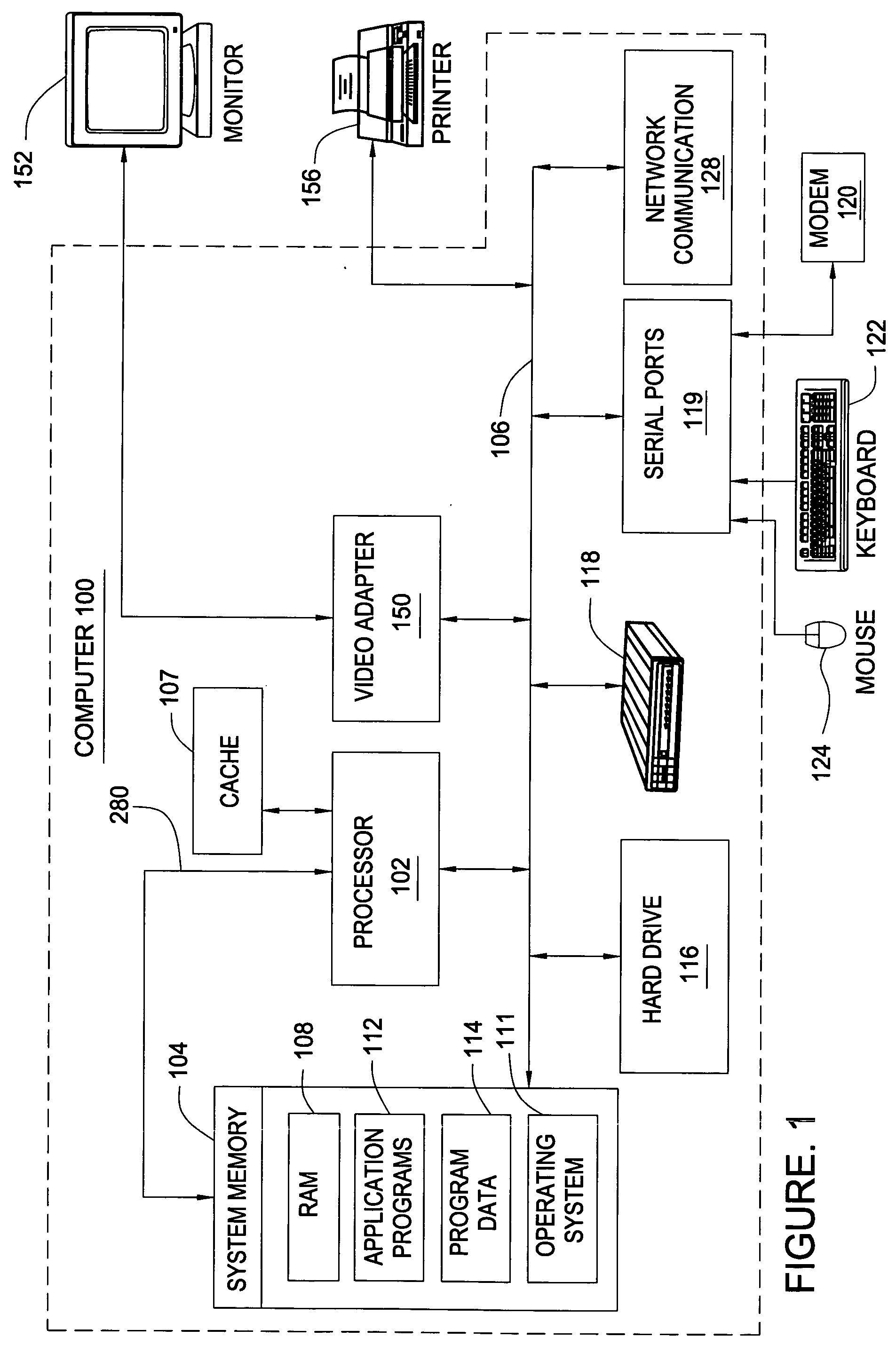
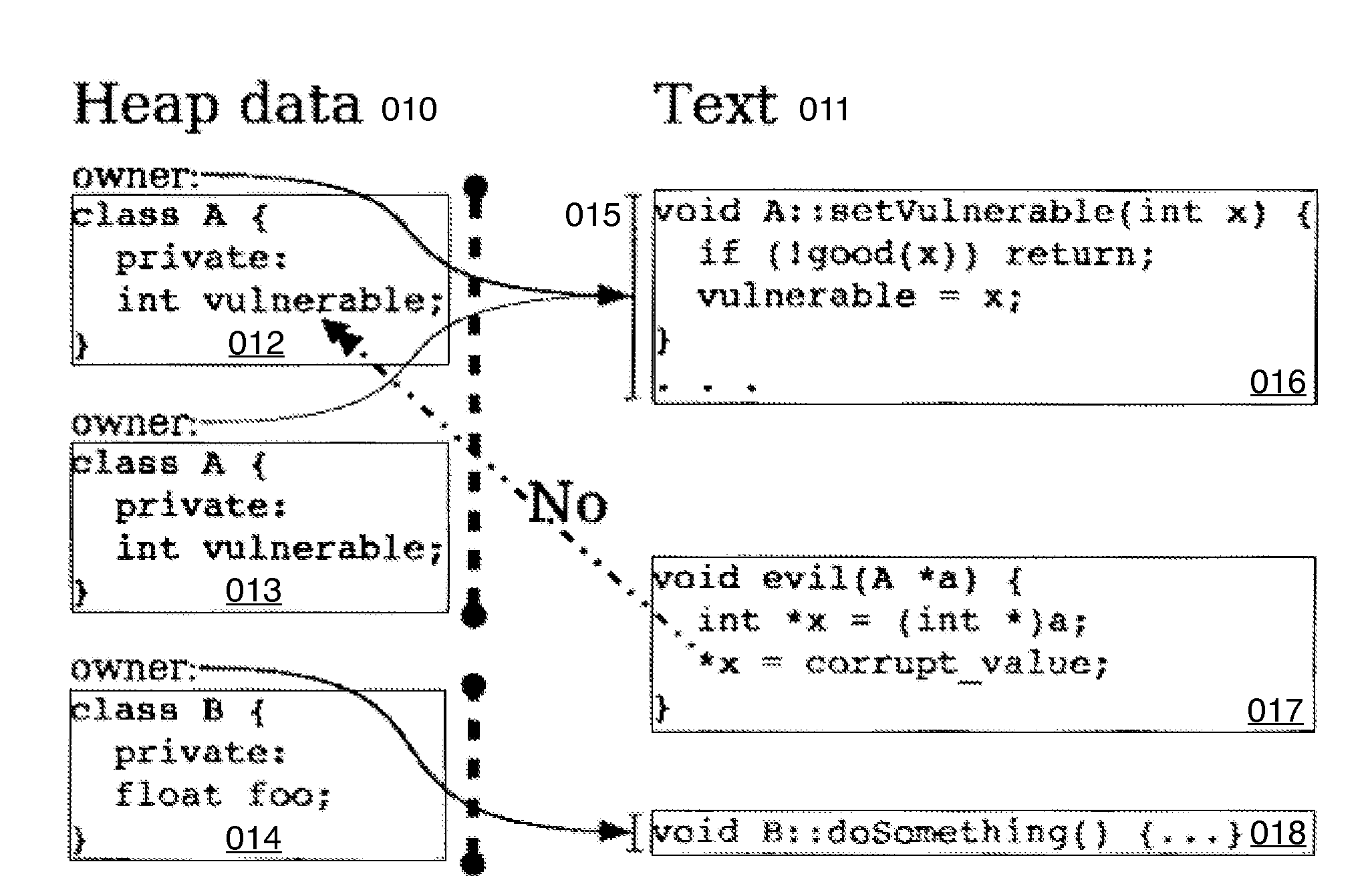
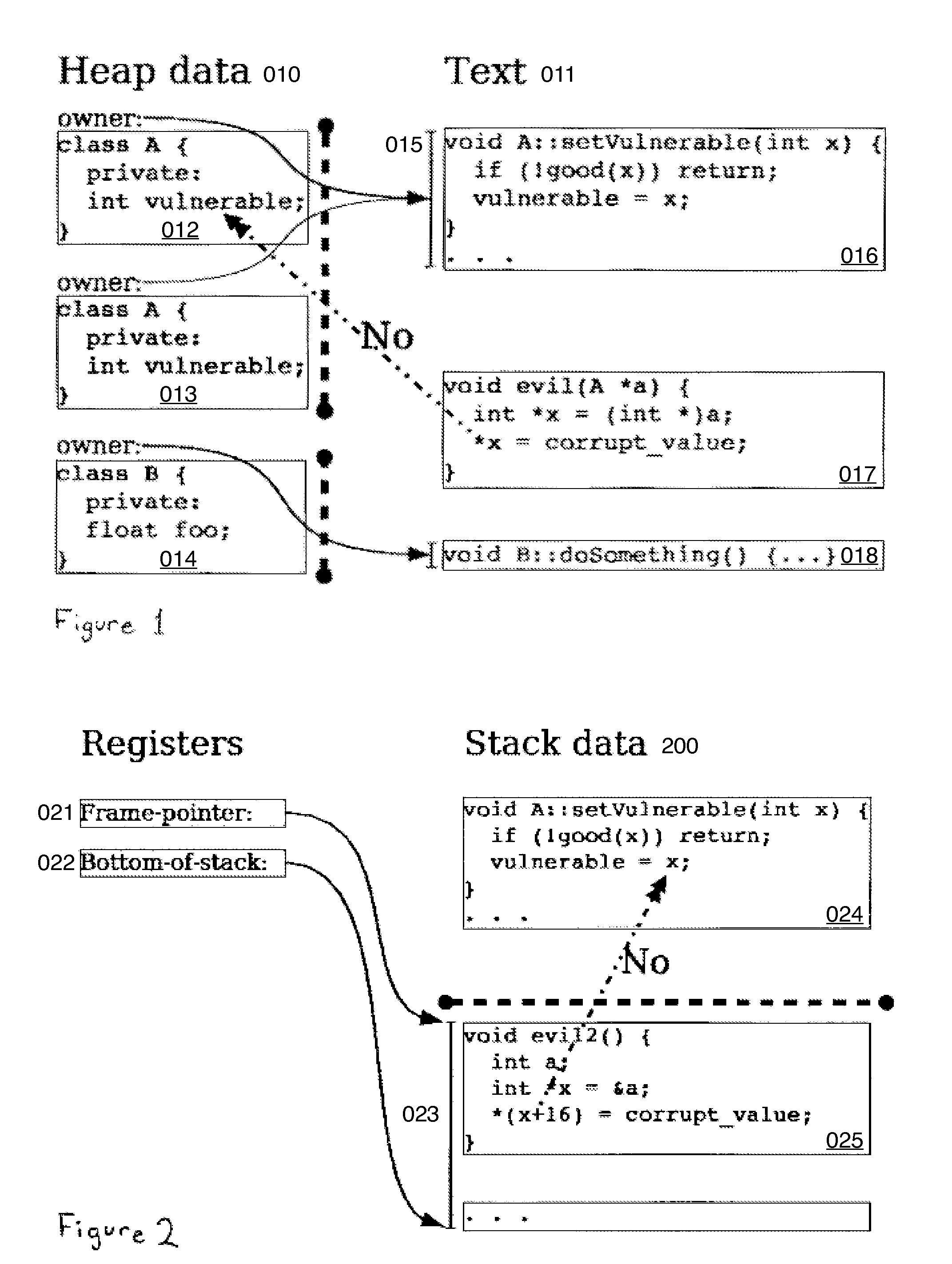
In accordance with one embodiment, additions to the standard computer microprocessor architecture hardware are disclosed comprising novel page table entry fields 015 062, special registers 021 022, instructions for modifying these fields 120 122 and registers 124 126, and hardware-implemented 038 runtime checks and operations involving these fields and registers. More specifically, in the above embodiment of a Hard Object system, there is additional meta-data 061 in each page table entry beyond what it commonly holds, and each time a data load or store is issued from the CPU, and the virtual address 032 translated to the physical address 034, the Hard Object system uses its additional PTE meta-data 061 to perform memory access checks additional to those done in current systems. Together with changes to software, these access checks can be arranged carefully to provide more fine-grain access control for data than do current systems.
Owner:WILKERSON DANIEL SHAWCROSS +1
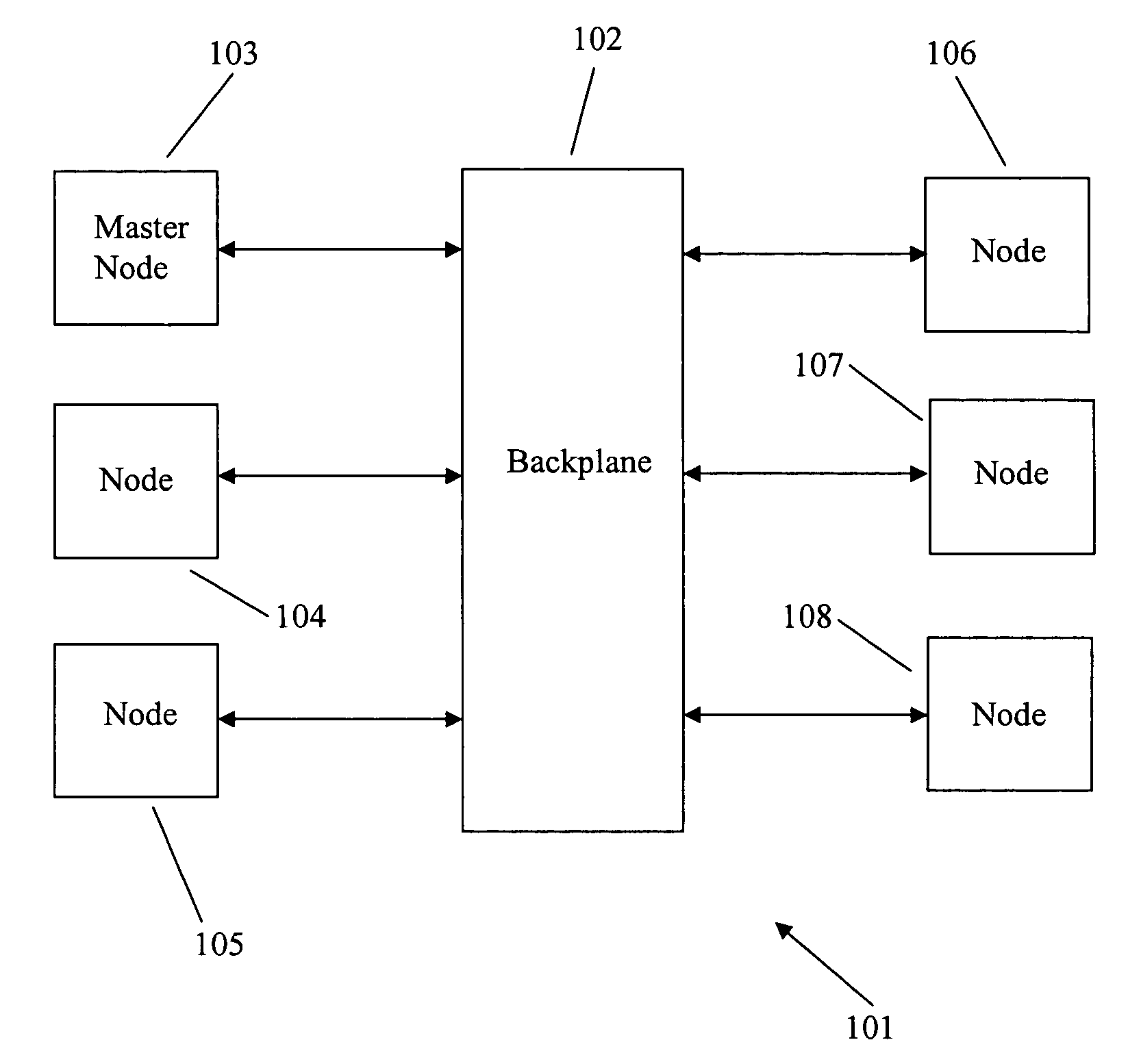
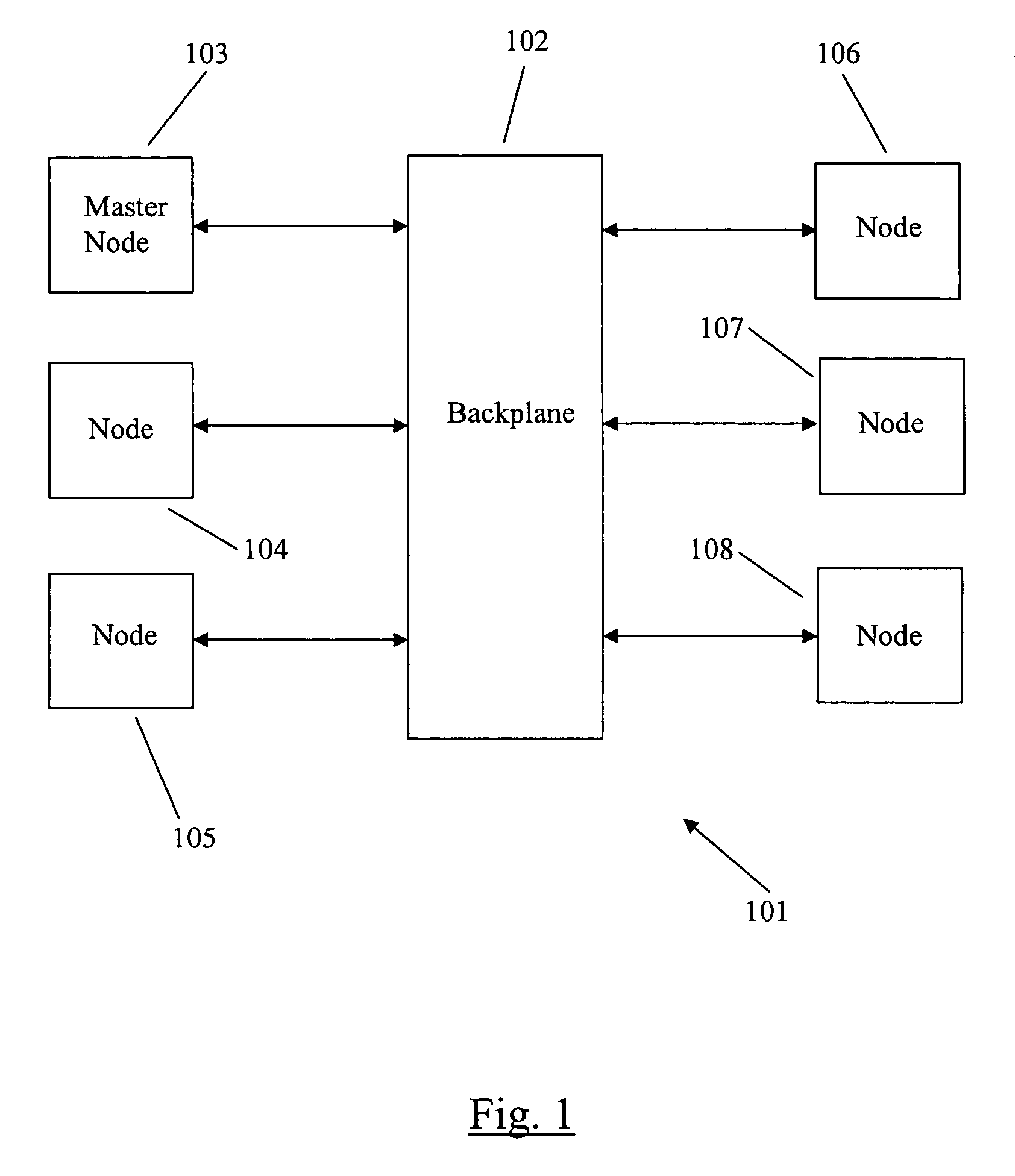
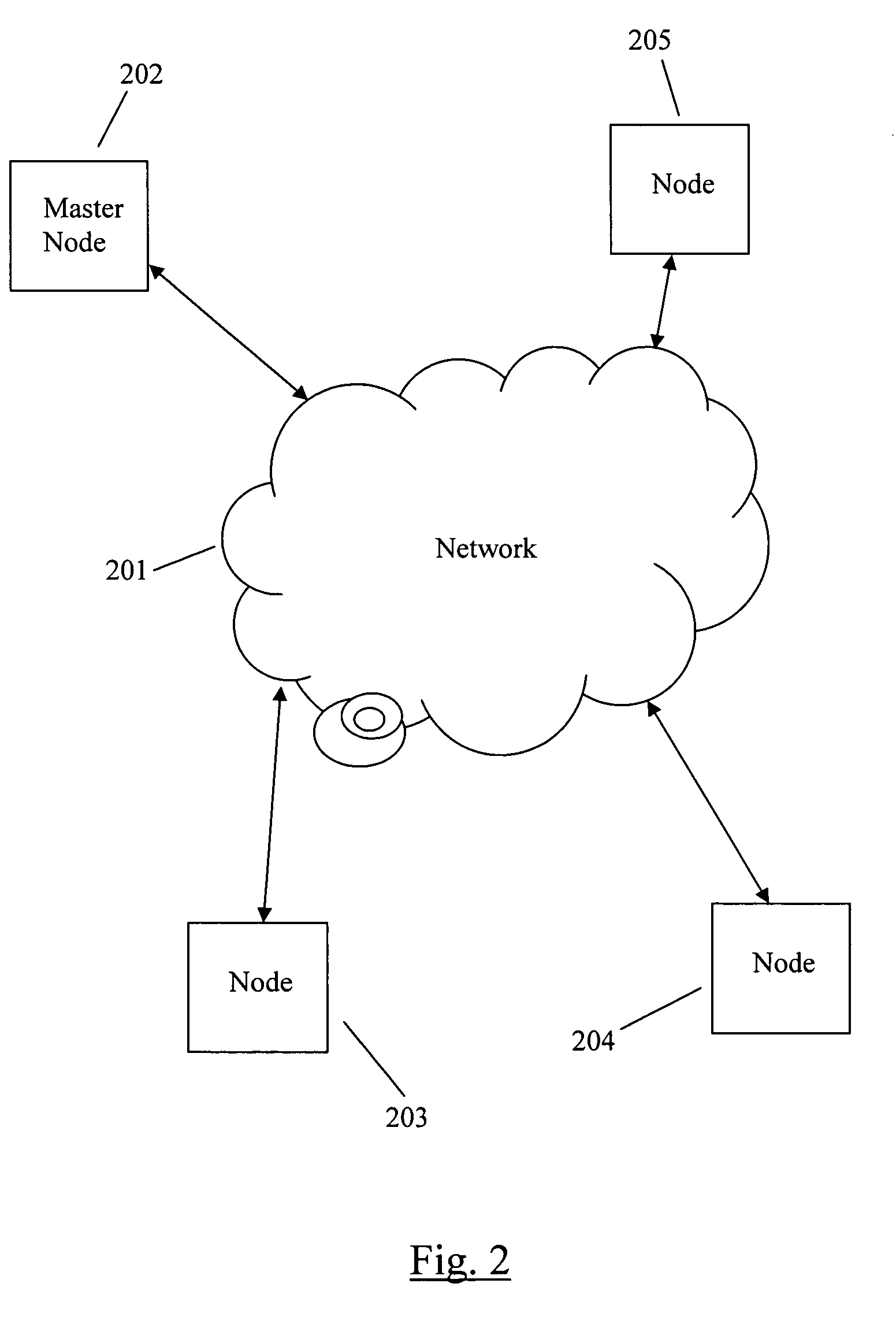
Software change modeling for network devices
InactiveUS7376945B1Software engineeringSpecific program execution arrangementsApplication softwareSource code
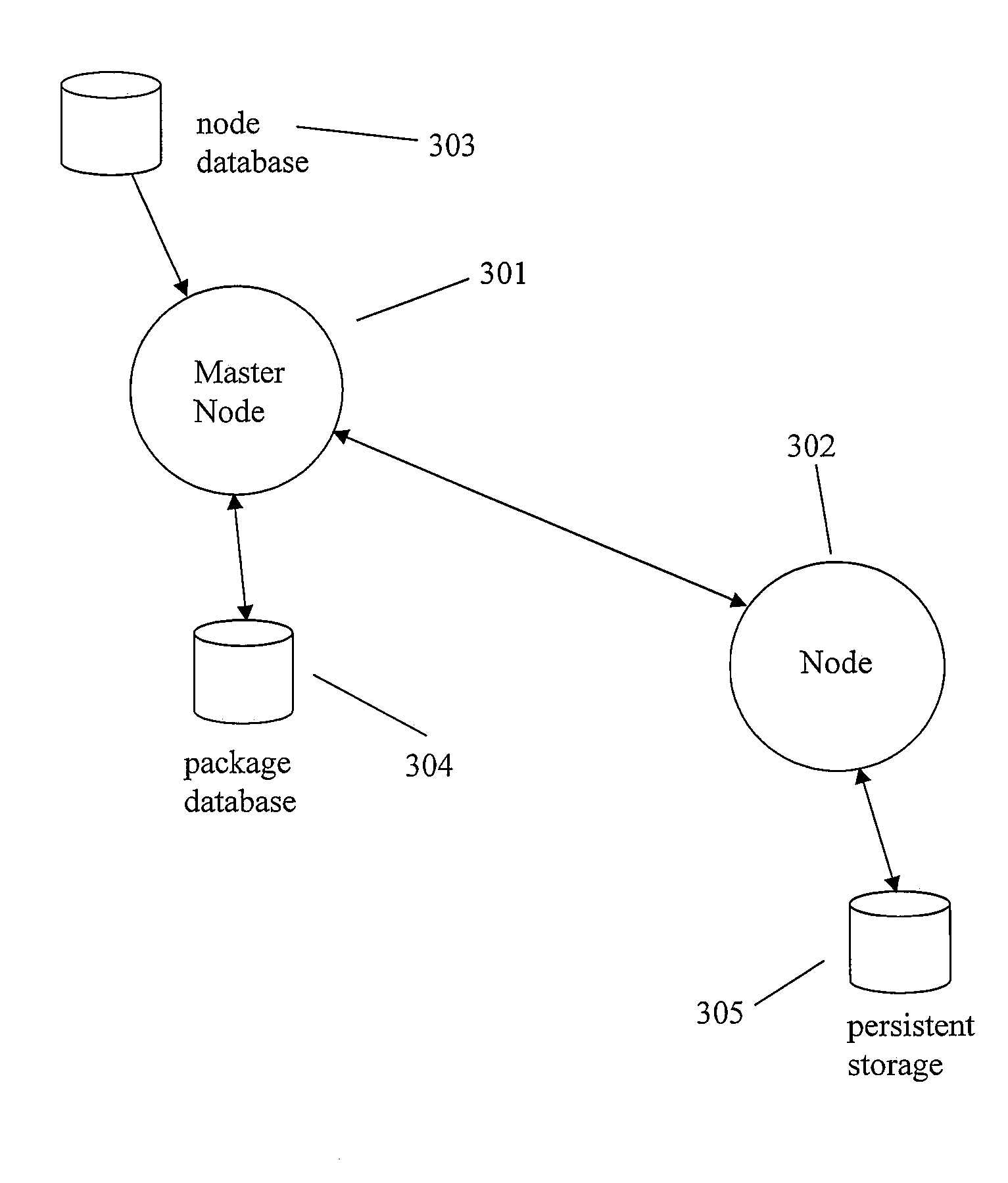
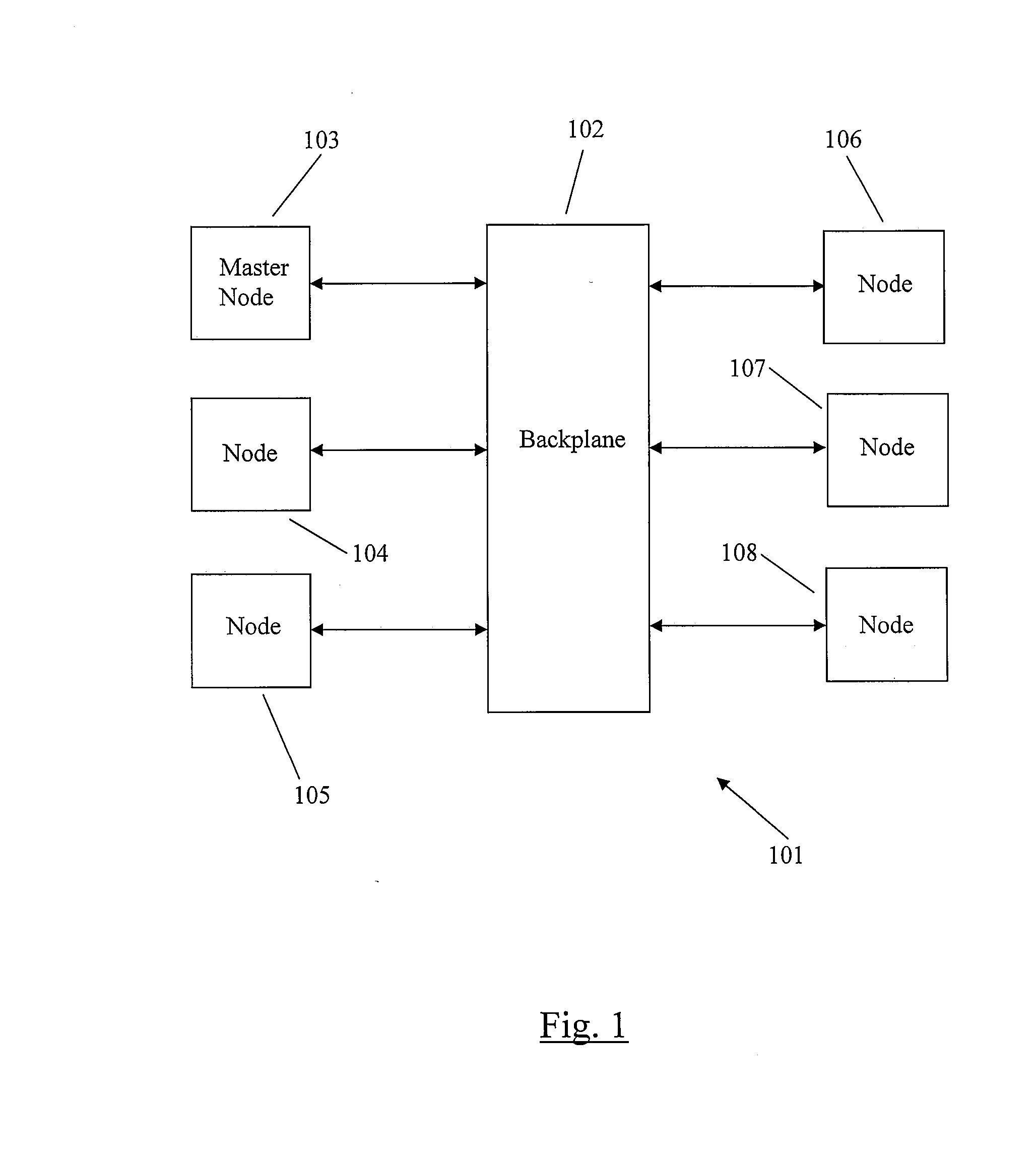
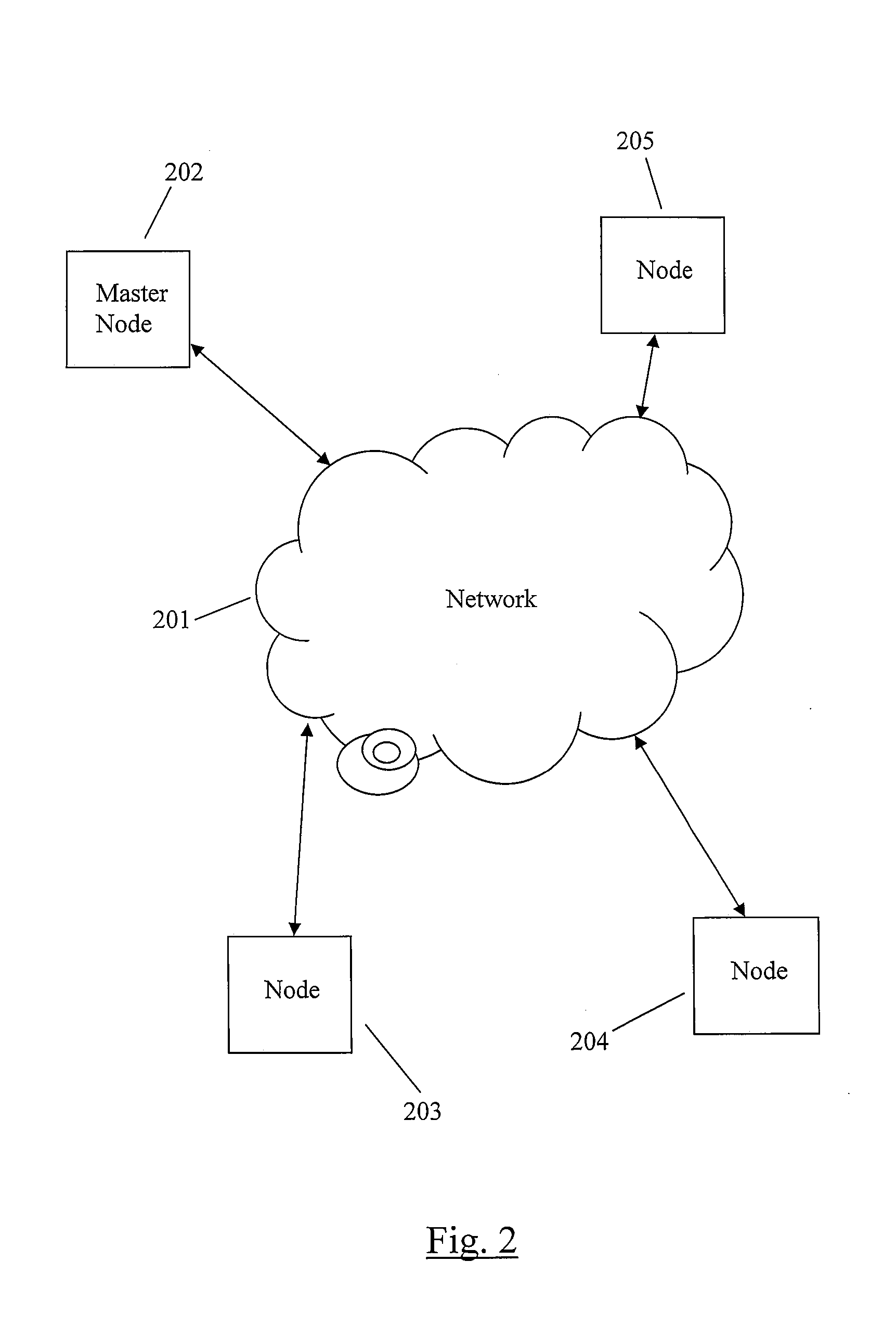
A method for software change modeling for network devices provides dynamic (on the device) and static (computer) change modeling. The same source code and libraries are used for both modeling applications, allowing a user to see the impact of activating or deactivating specific software modules without affecting the actual node. A master node passes a node the identity of the software package(s) to be updated and the dependencies. The node notifies its running processes about the update. If any of the processes determine that the update will degrade or have a negative impact on the operation of the node, it returns a veto to the node which sends a list of the processes that are impacted along with the reasons why to the master node.
Owner:CISCO TECH INC
Method and apparatus for packet data service discovery
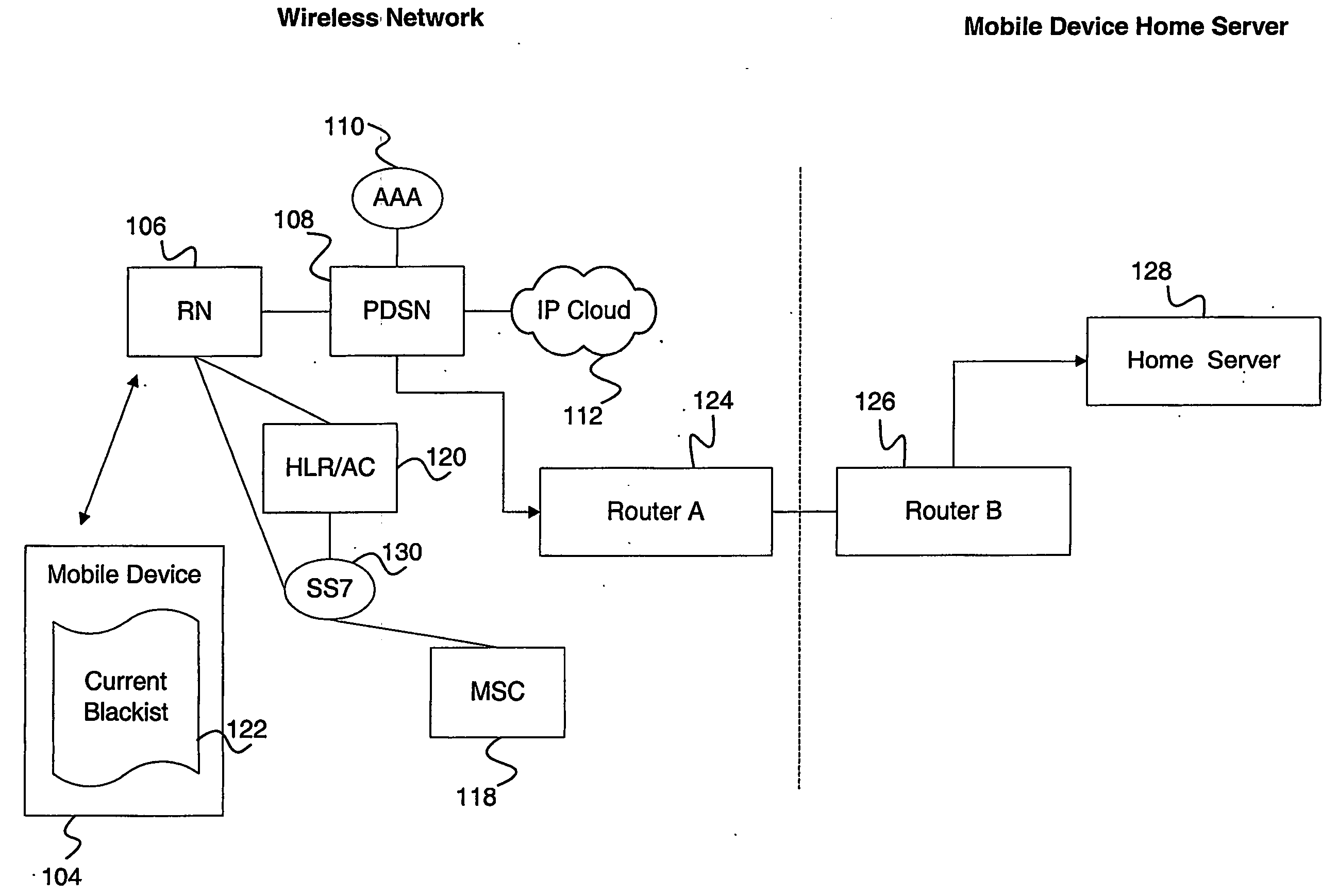
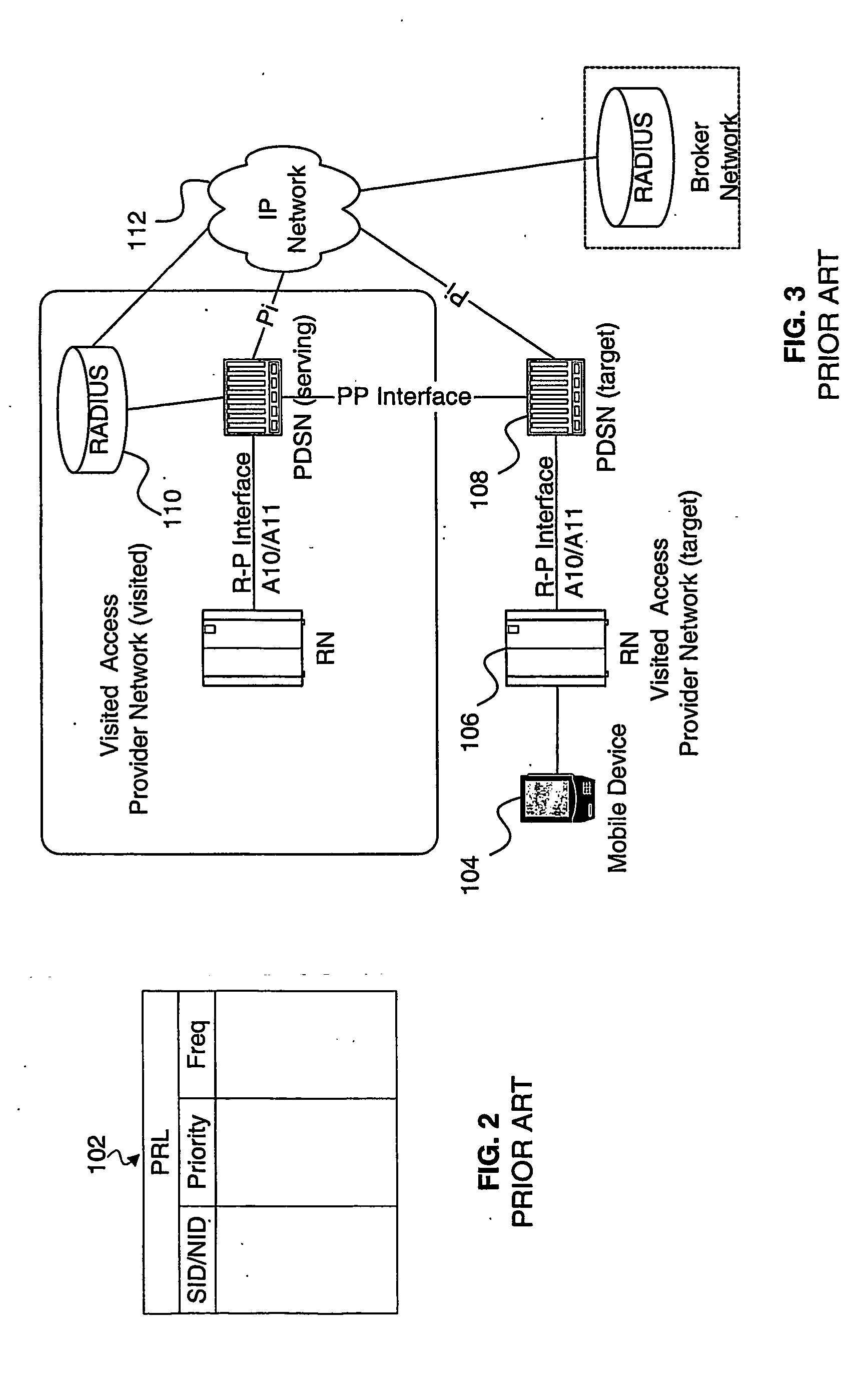
A method and apparatus for packet data service discovery are described. A current blacklist comprising entries for wireless networks not providing packet data services (i.e. either not supporting the services or not having a packet data services roaming agreement) is kept in memory of the mobile device based on previous attempts to connect to such networks. Current preferred roaming lists identify whether a given wireless network can be acquired, but do not identify whether a data services roaming agreement exists. At least one of the following advantages is provided: no advance knowledge of data services roaming agreements is required; no mobile device software change is required when the data services roaming agreement changes; mobile device can notify a server of a wireless network status change; significant power savings at the mobile device; and avoid unnecessary network access, which in turn saves network resources and capacity.
Owner:MALIKIE INNOVATIONS LTD
Enforcing alignment of approved changes and deployed changes in the software change life-cycle
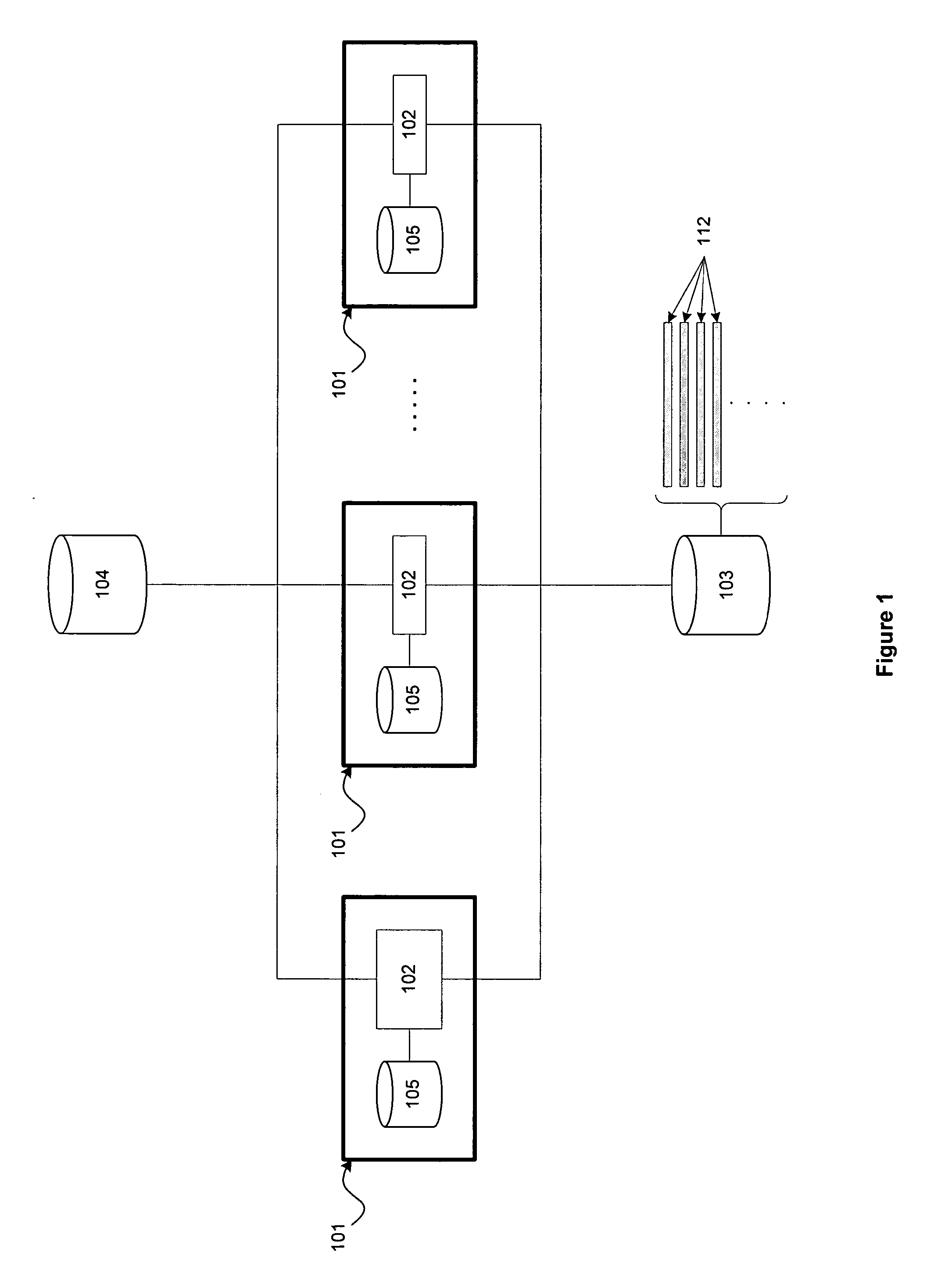
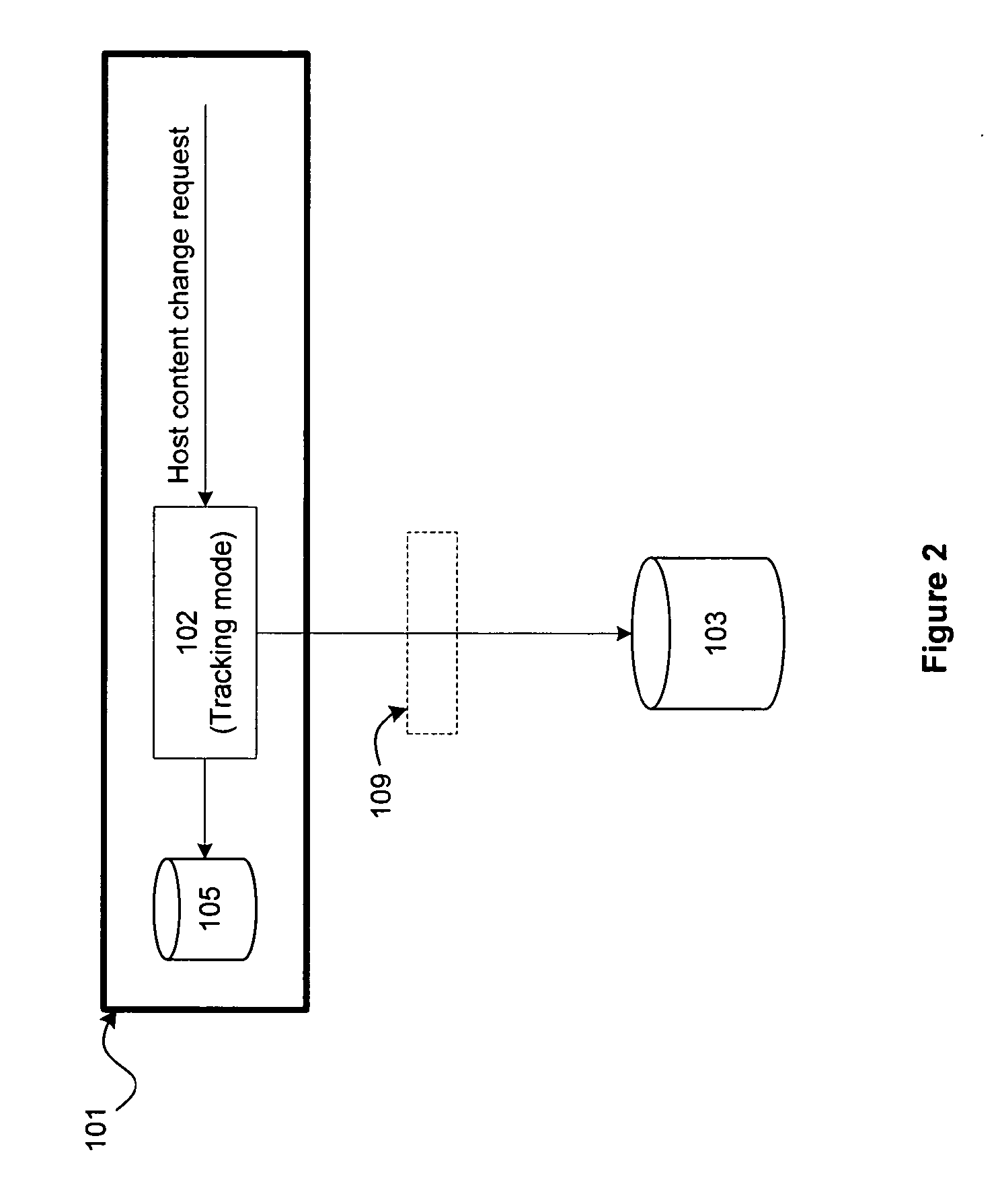
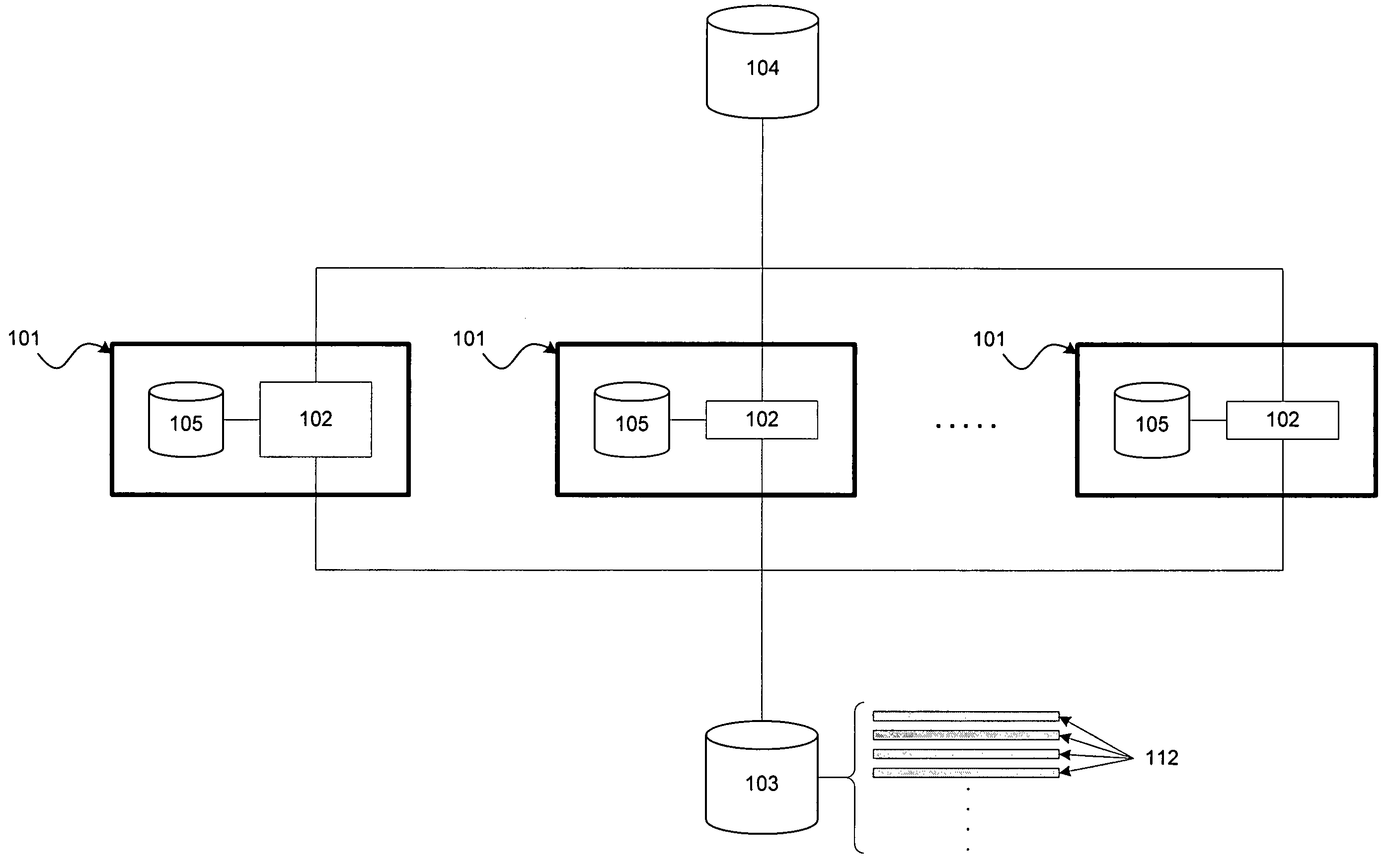
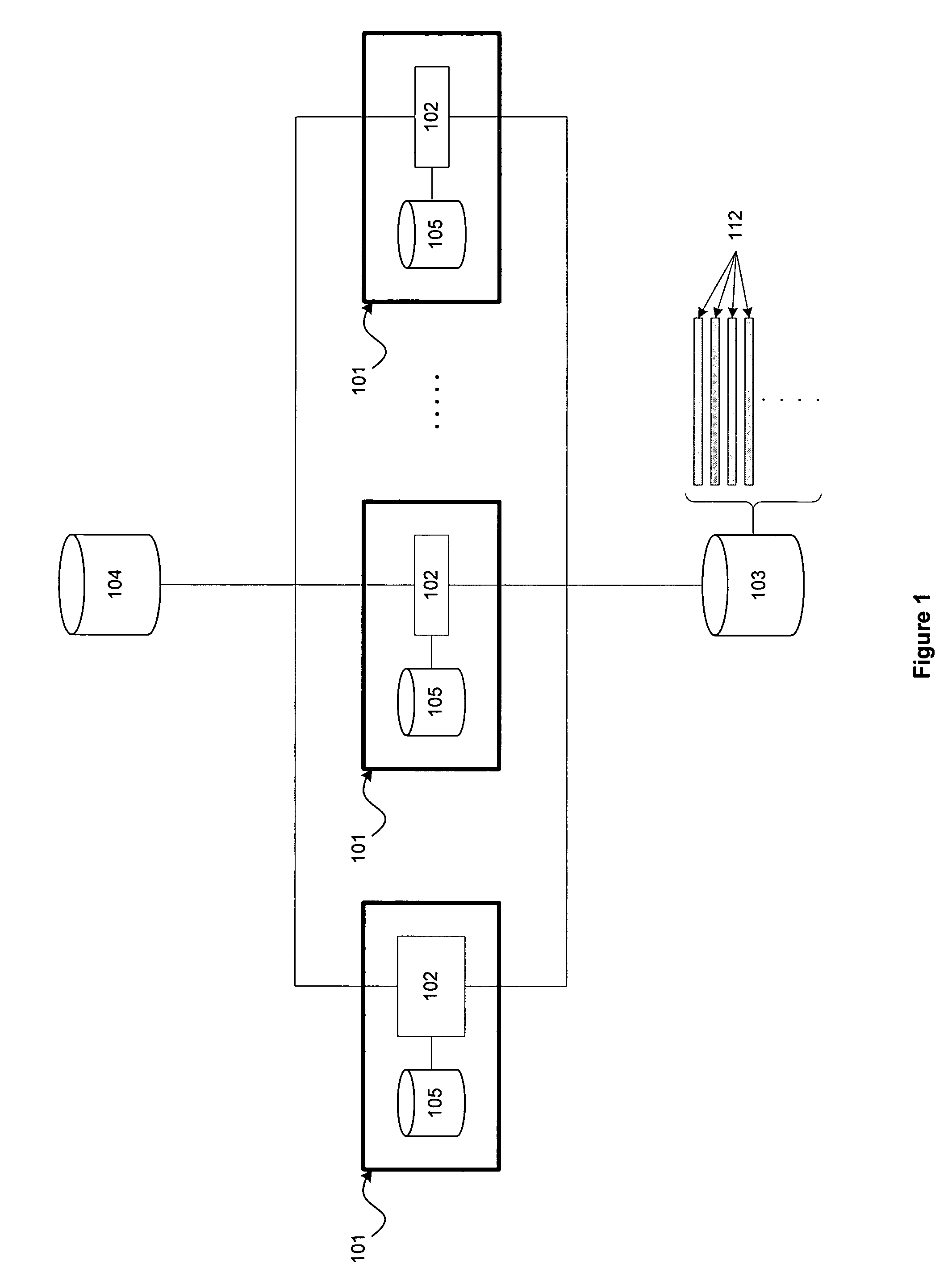
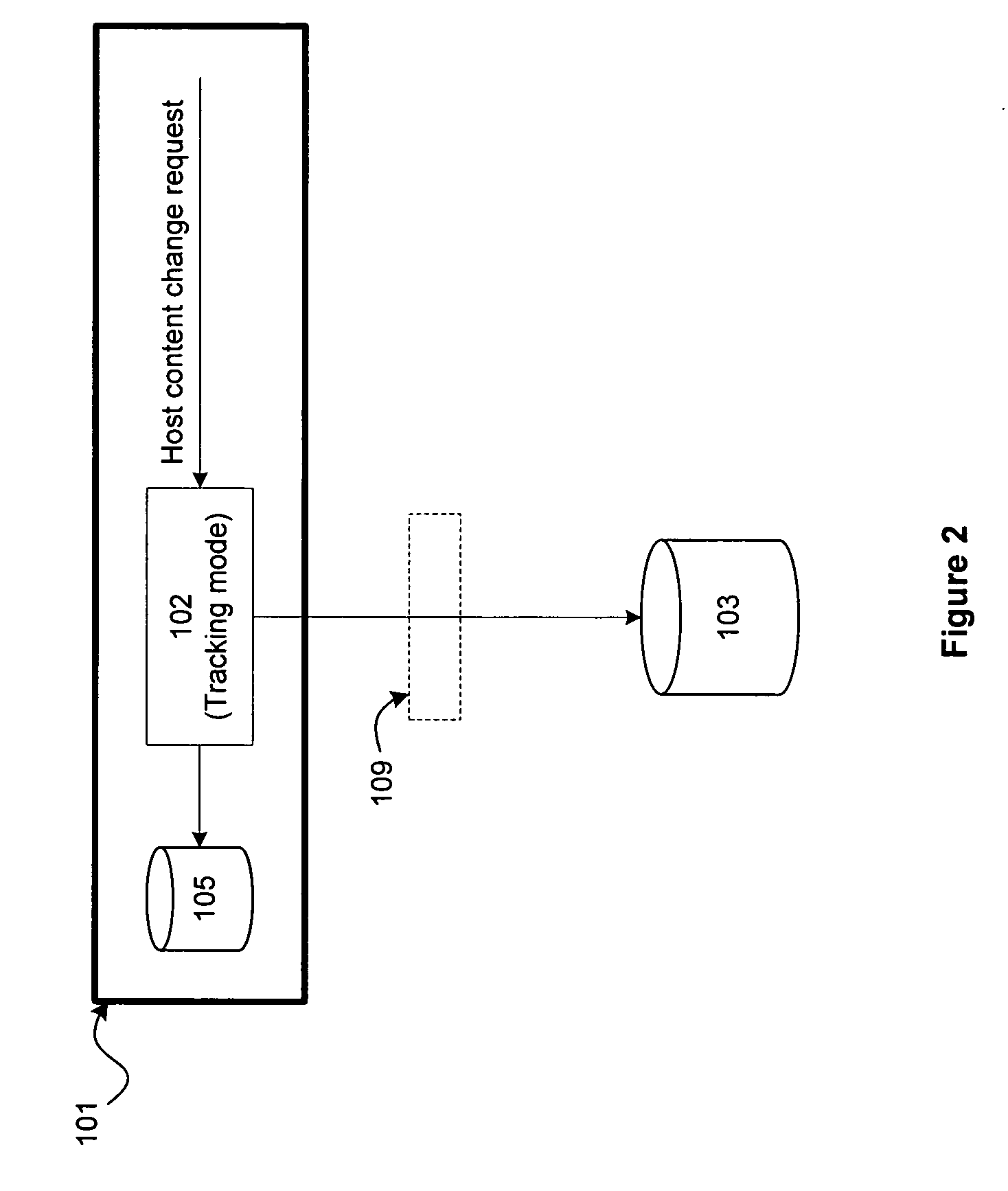
On a host, host content change requests are intercepted in real-time. In a tracking mode, the change requests are logged and allowed to take effect on the host. In an enforcement mode, the change requests are logged and additionally compared against authorized change policies and a determination is made whether to allow the change to take effect or to block the changes, thereby enforcing the authorized change policies on the host. Tracking and enforcement can be done in real-time. In either mode and at any time, the logged changes can be reconciled against a set of approved change orders in order to identify classes of changes, including changes that were deployed but not approved and changes that were approved but not deployed.
Owner:MCAFEE LLC
Enforcing alignment of approved changes and deployed changes in the software change life-cycle
InactiveUS7757269B1Digital data processing detailsUser identity/authority verificationComputer scienceChange request
On a host, host content change requests are intercepted in real-time. In a tracking mode, the change requests are logged and allowed to take effect on the host. In an enforcement mode, the change requests are logged and additionally compared against authorized change policies and a determination is made whether to allow the change to take effect or to block the changes, thereby enforcing the authorized change policies on the host. Tracking and enforcement can be done in real-time. In either mode and at any time, the logged changes can be reconciled against a set of approved change orders in order to identify classes of changes, including changes that were deployed but not approved and changes that were approved but not deployed.
Owner:MCAFEE LLC
Software change modeling for network devices
A method for software change modeling for network devices provides dynamic (on the device) and static (computer) change modeling. The same source code and libraries are used for both modeling applications, allowing a user to see the impact of activating or deactivating specific software modules without affecting the actual node. A master node passes a node the identity of the software package(s) to be updated and the dependencies. The node notifies its running processes about the update. If any of the processes determine that the update will degrade or have a negative impact on the operation of the node, it returns a veto to the node which sends a list of the processes that are impacted along with the reasons why to the master node.
Owner:CISCO TECH INC
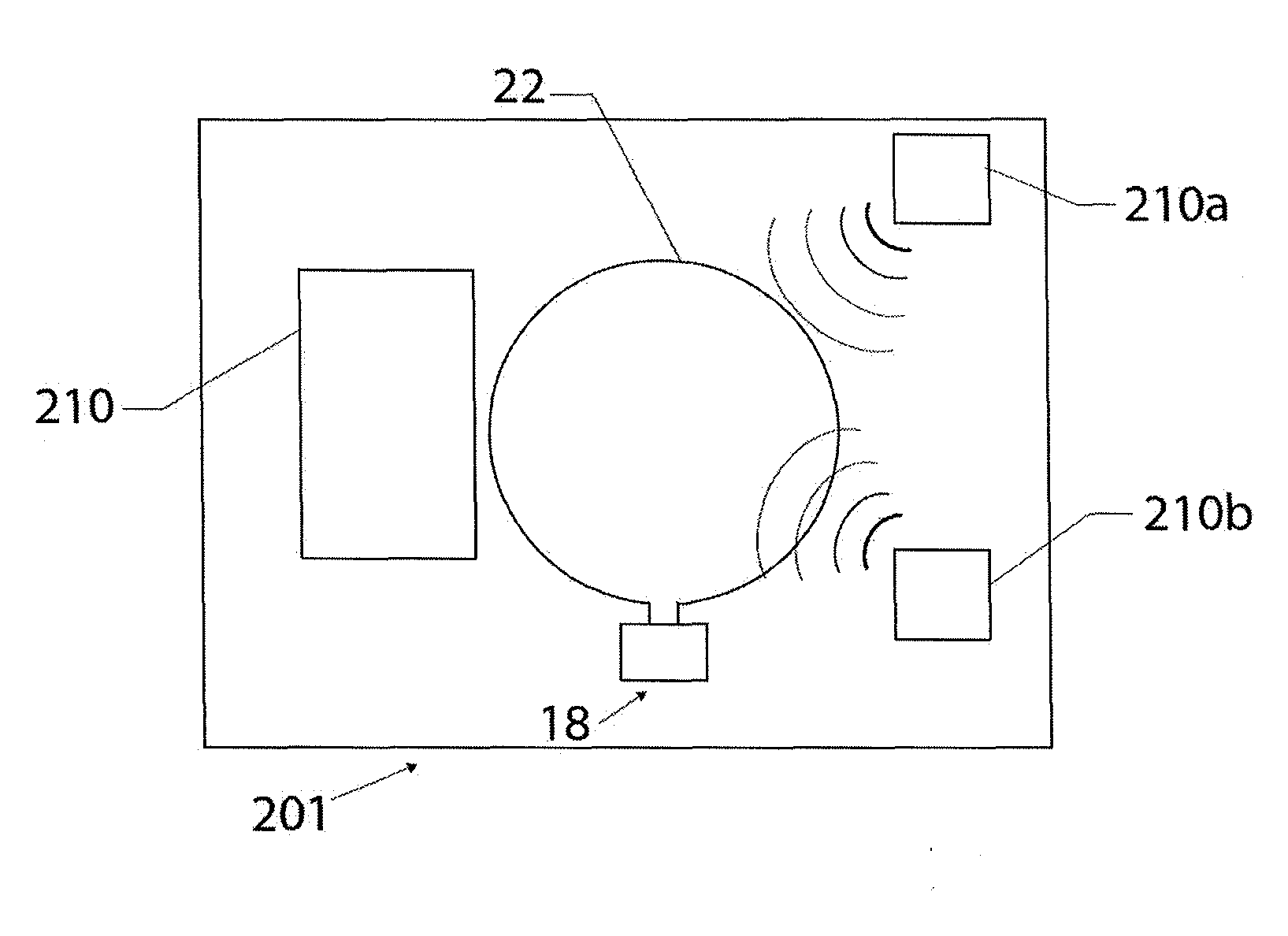
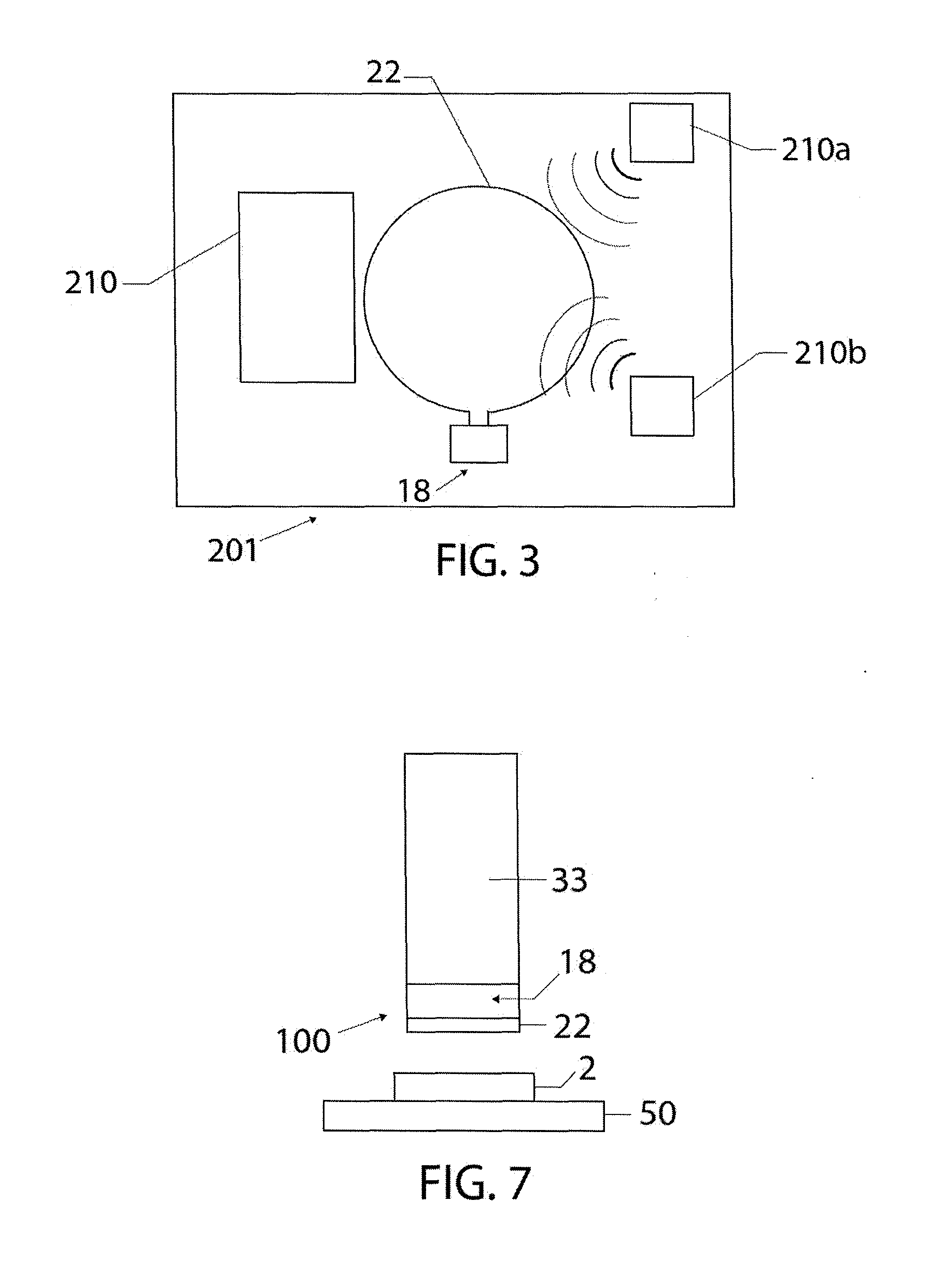
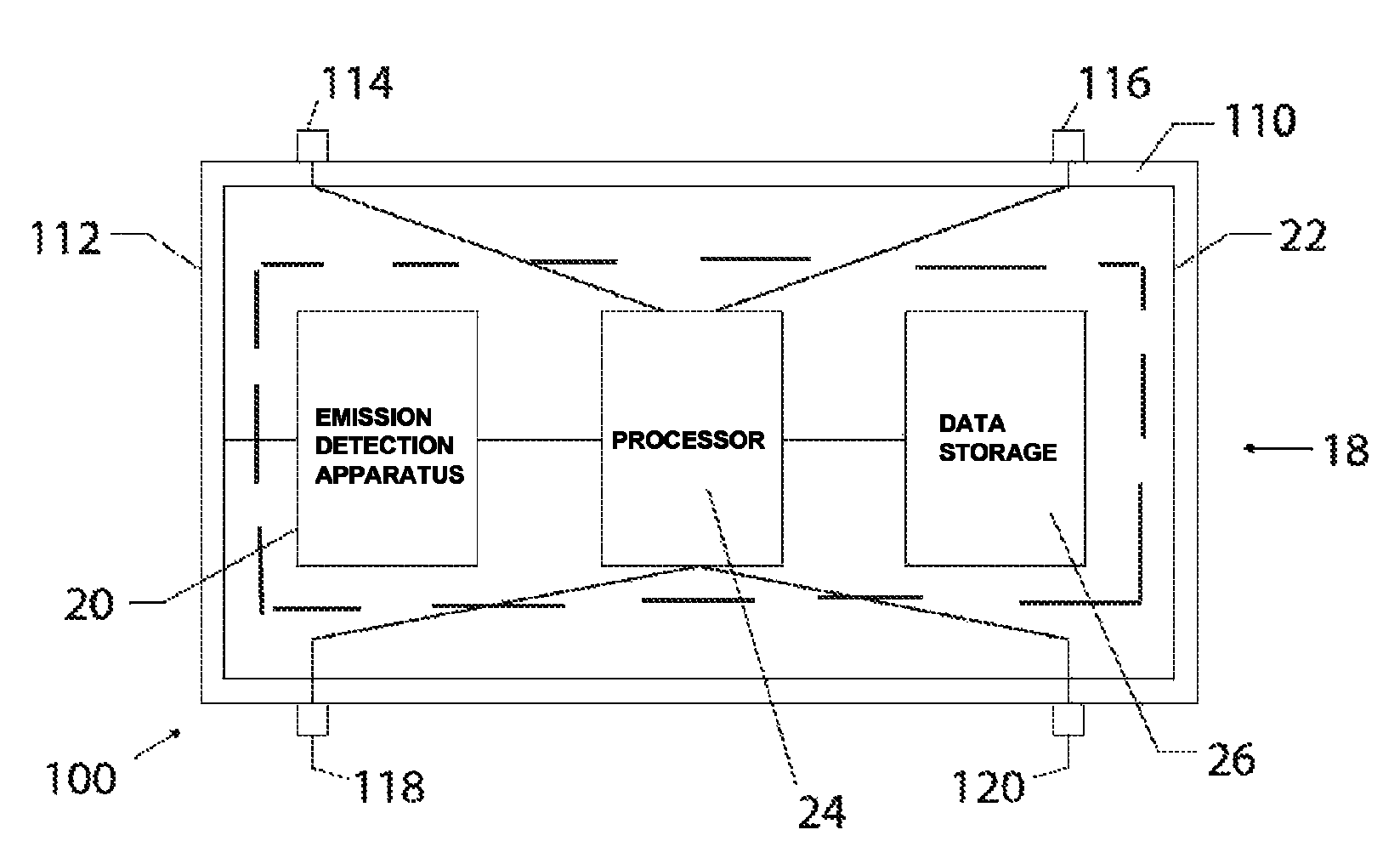
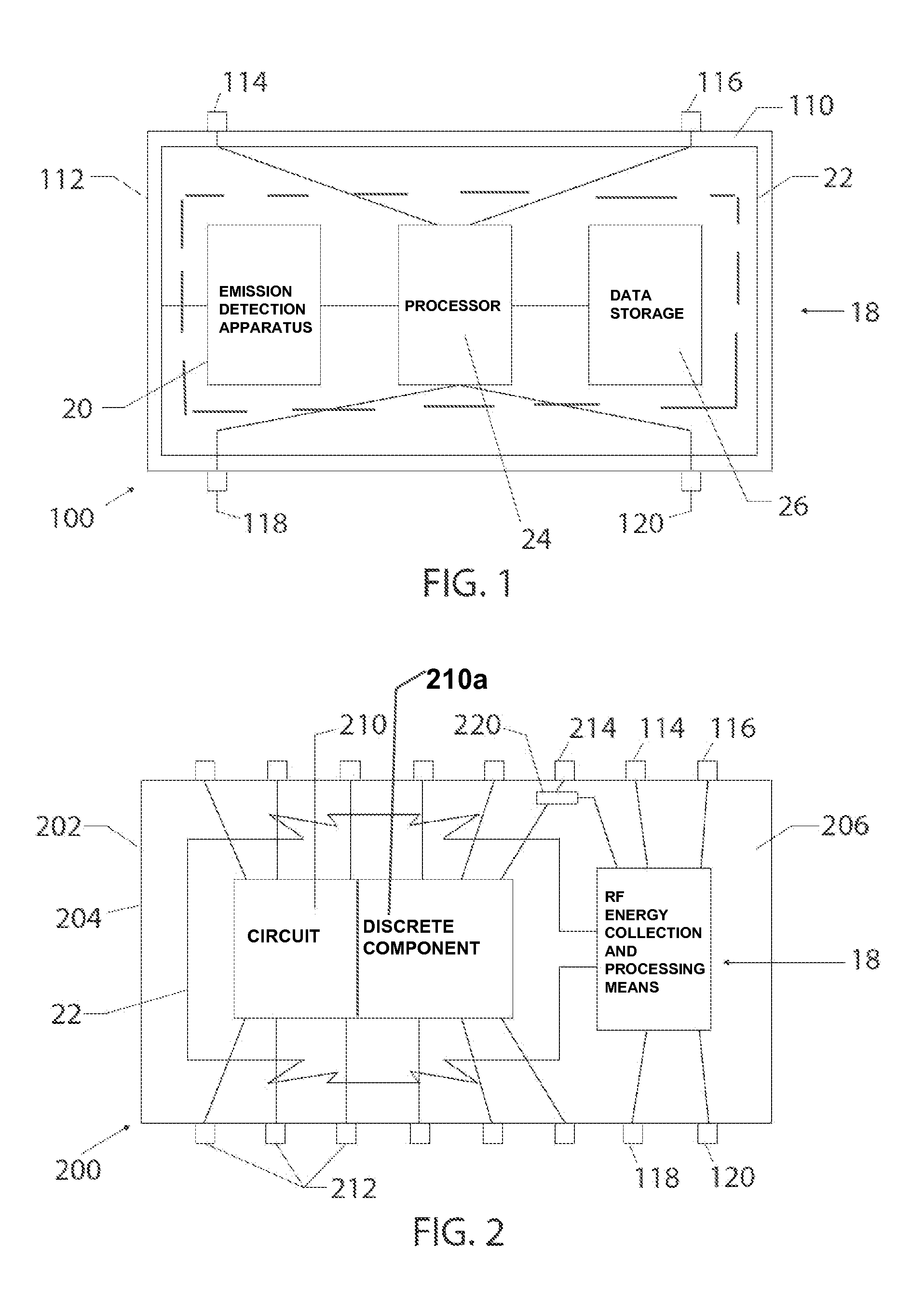
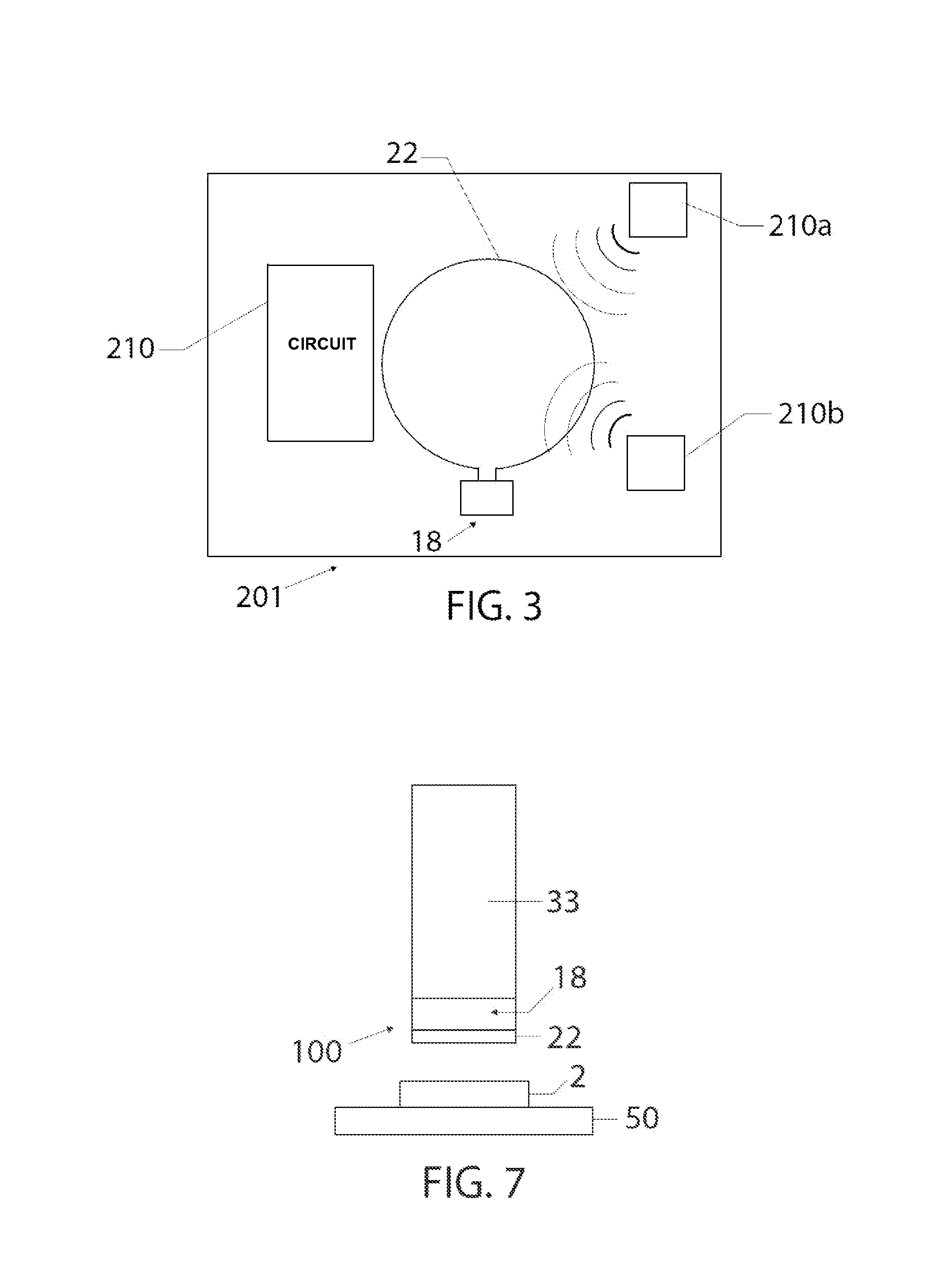
Integrated circuit with electromagnetic energy anomaly detection and processing
ActiveUS20120223403A1Constant monitoringSemiconductor/solid-state device detailsSolid-state devicesIntegrated circuitSoftware changes
An integrated circuit includes an antenna, a die manufactured from a semiconducting material, an RF energy collection and processing means disposed on or within said die and including at least a receiver and a processing means, an input configured to supply power to said RF energy collection and processing means and an output for operative communication by said RF energy collection and processing means. The integrated circuit is configurable and operable to provide at least one of electromagnetic emission anomaly detection, tamper detection, anti-tamper monitoring, degradation monitoring, health monitoring, counterfeit detection, software changes monitoring, firmware changes monitoring and monitoring of other RF energy anomalies.
Owner:NOKOMIS
Hard object: constraining control flow and providing lightweight kernel crossings
InactiveUS20120151184A1Specific access rightsGeneral purpose stored program computerSemanticsSystem call
A method providing simple fine-grain hardware primitives with which software engineers can efficiently implement enforceable separation of programs into modules and constraints on control flow, thereby providing fine-grain locality of causality to the world of software. Additionally, a mechanism is provided to mark some modules, or parts thereof, as having kernel privileges and thereby allows the provision of kernel services through normal function calls, obviating the expensive prior art mechanism of system calls. Together with software changes, Object Oriented encapsulation semantics and control flow integrity in hardware are enforced.
Owner:WILKERSON DANIEL SHAWCROSS +1
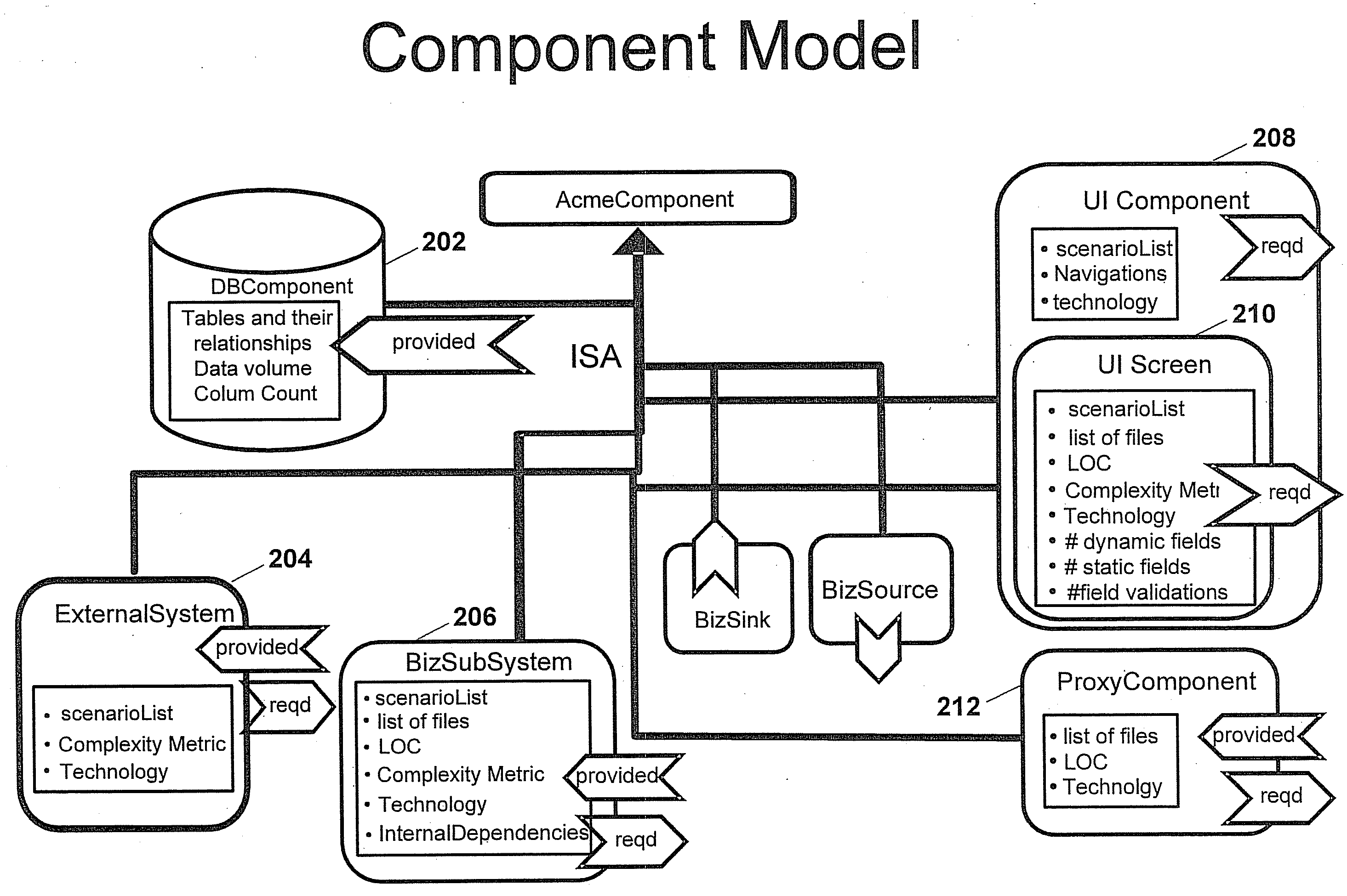
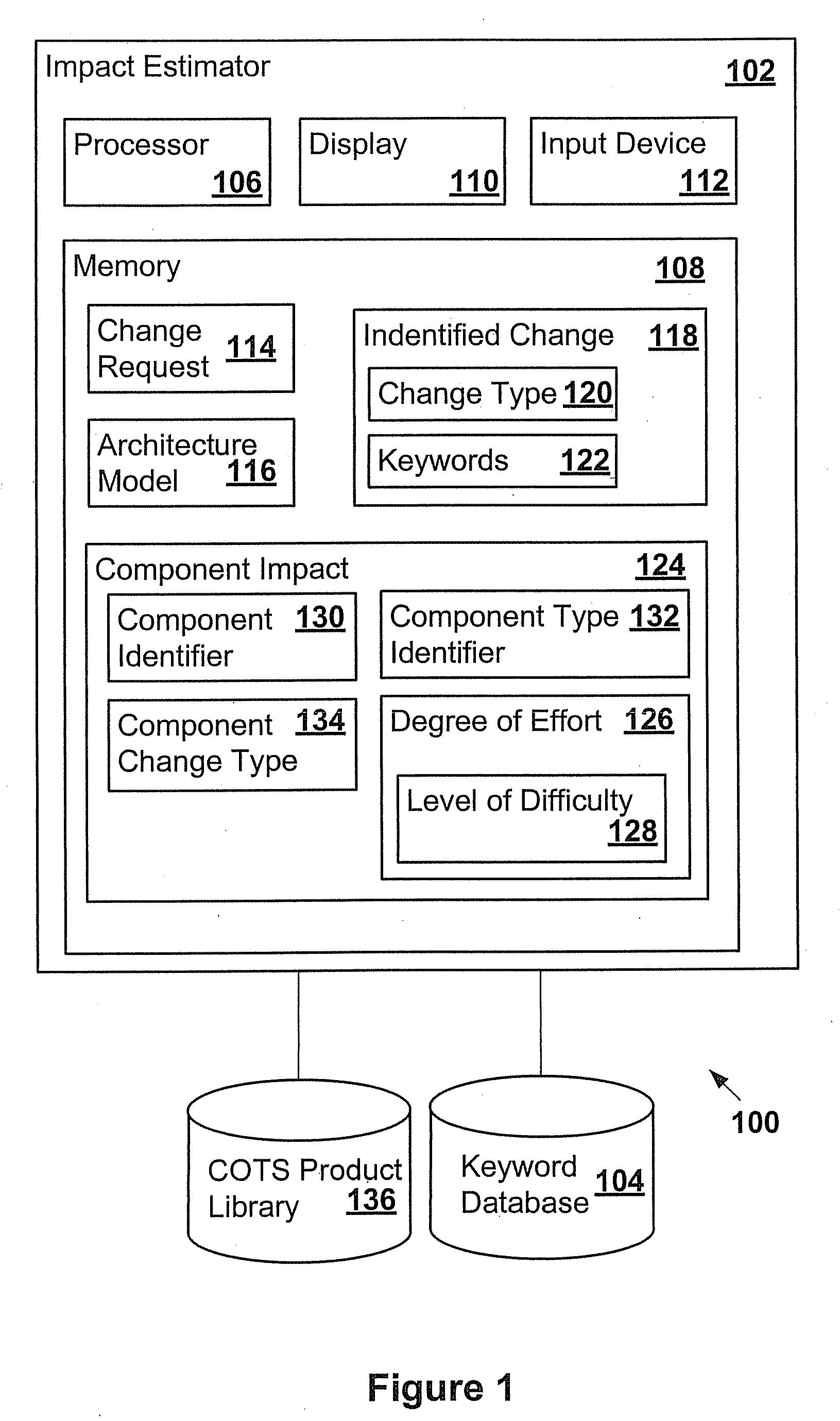
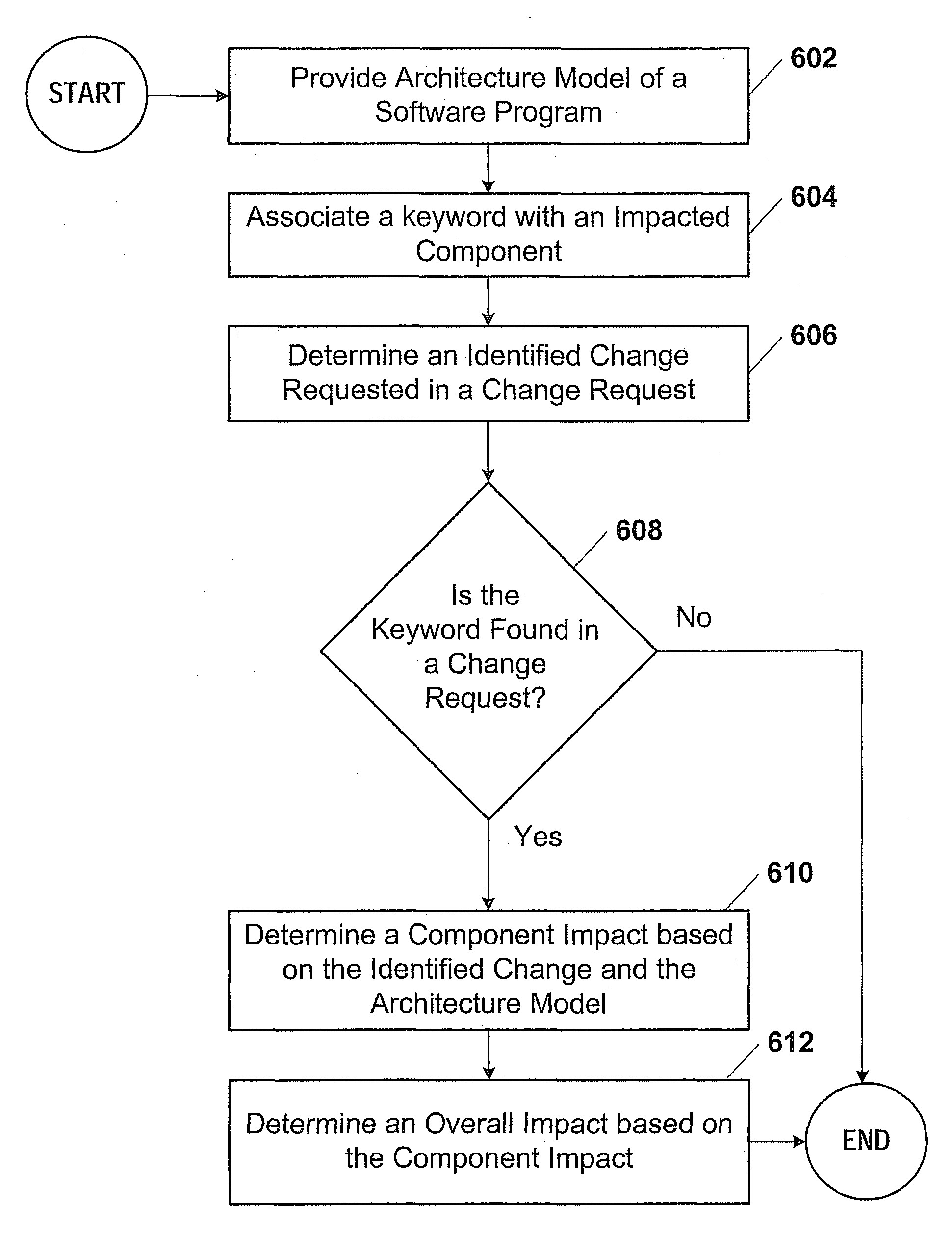
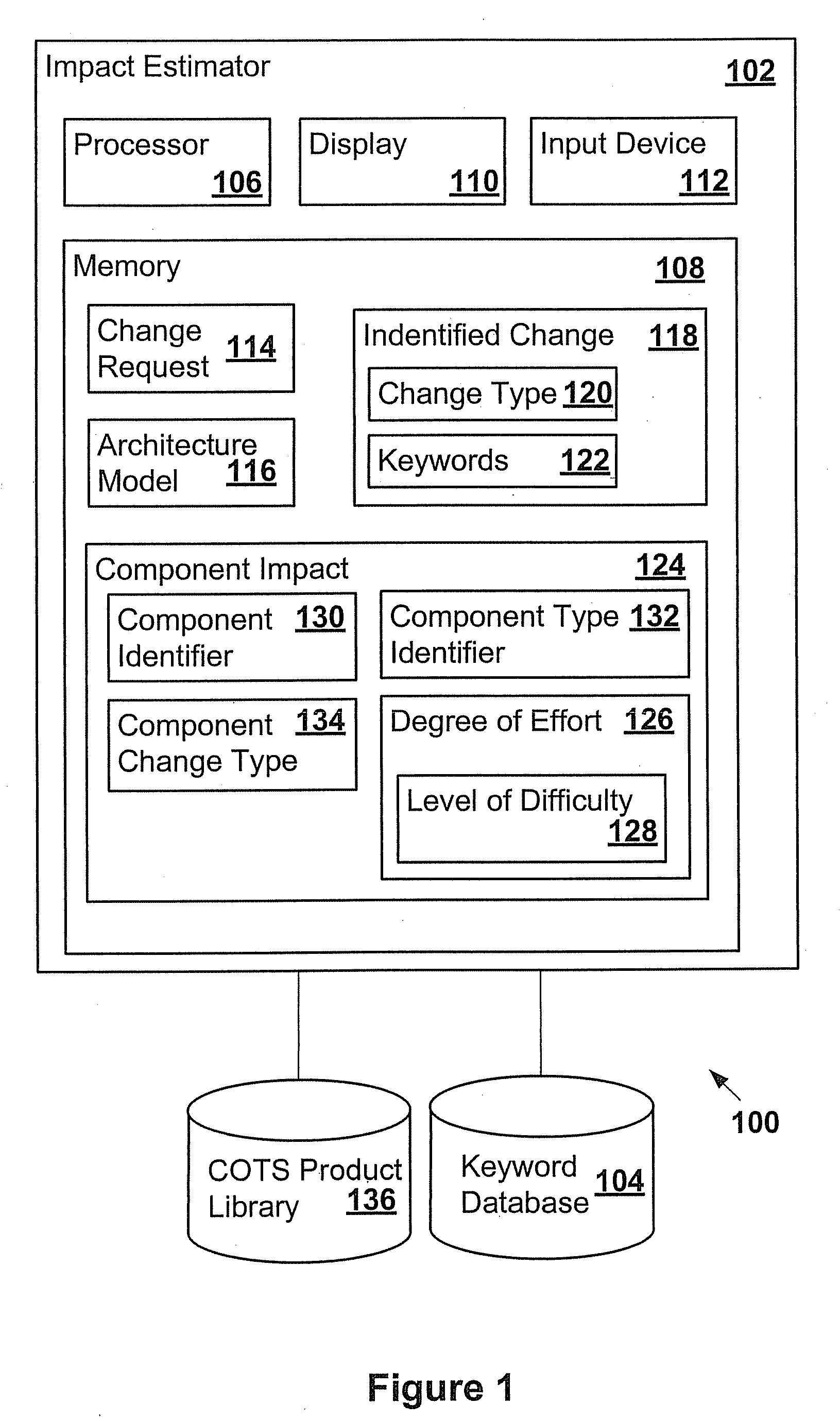
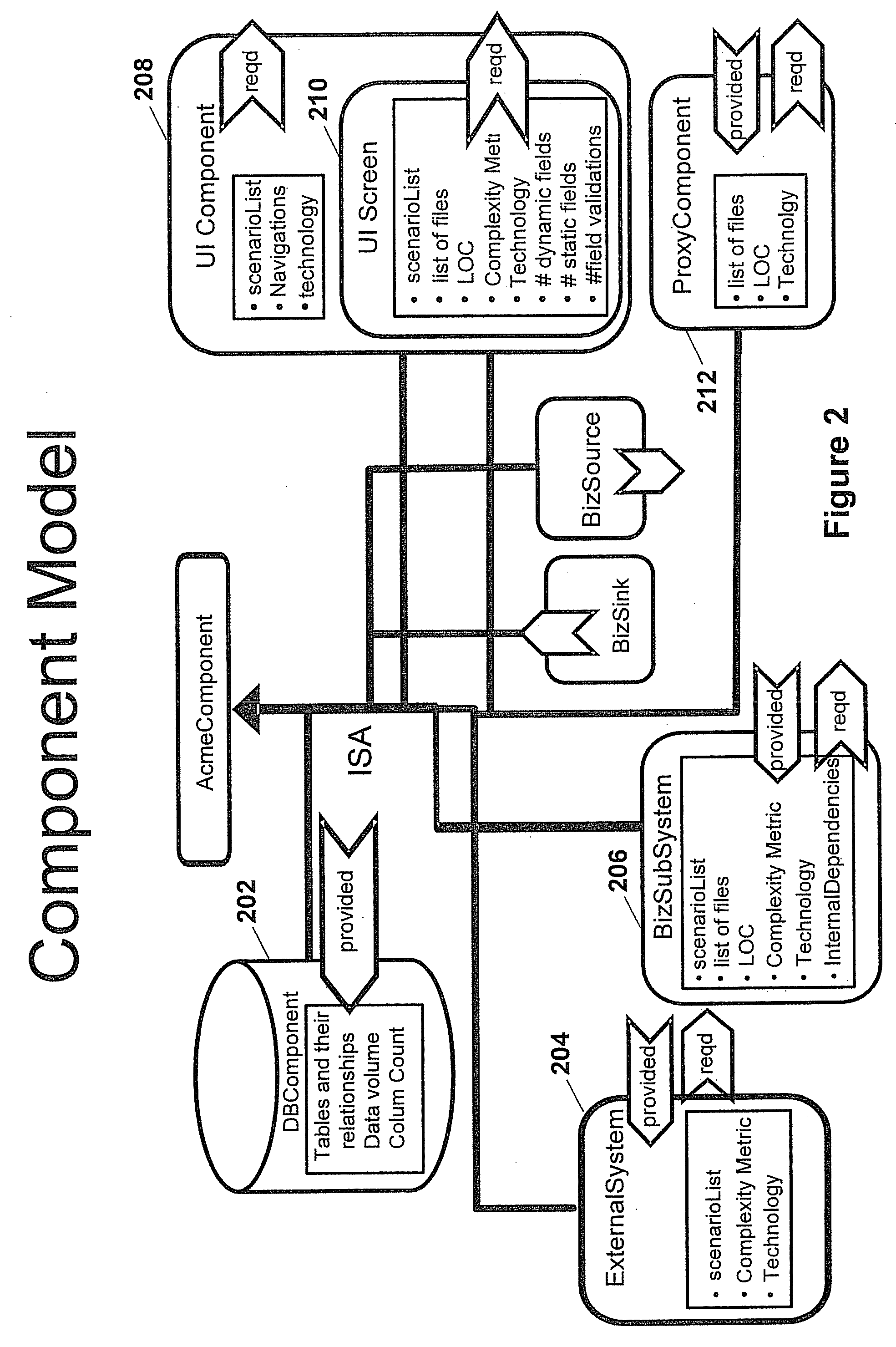
Impact analysis of software change requests
In one example, a system is provided to determine the impact of implementing a change request on a software program. The system may include an architecture model of the software program that includes components. Each of the components may have attributes that may be used by the system to determine a degree of effort to modify each respective one of the components. Components may be associated with keywords. The system may search the change request for the keywords to identify components that may be impacted by the change request. The system may determine the degree of effort to modify any impacted component based on the architecture model. The system may determine the overall impact on the software program based on the degree of effort determined for the impacted components.
Owner:ACCENTURE GLOBAL SERVICES LTD
Function-variable portable computer mainboard
The invention provides a wearable computer main board with variable functions, which is designed in view of variable application requirements of a wearable computer and the defects of single function, performance upgrade and function extension of the existing technical realization methods. Chips such as FPGA / CPLD / FPAA, and the like with overprogram characteristics are connected to a plurality of interfaces and a bus line of the wearable computer main board, and the FPGA / CPLD has a restructural function on the board by the overprogram characteristics according to the customization of multiple function requirements. Original hardware change such as chip replacement, device replacement, and the like is converted into software change with rewritten content reset by an IP core. The wearable computer main board can be upgraded easily so as to shorten development period, improve applicability and reduce development cost.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
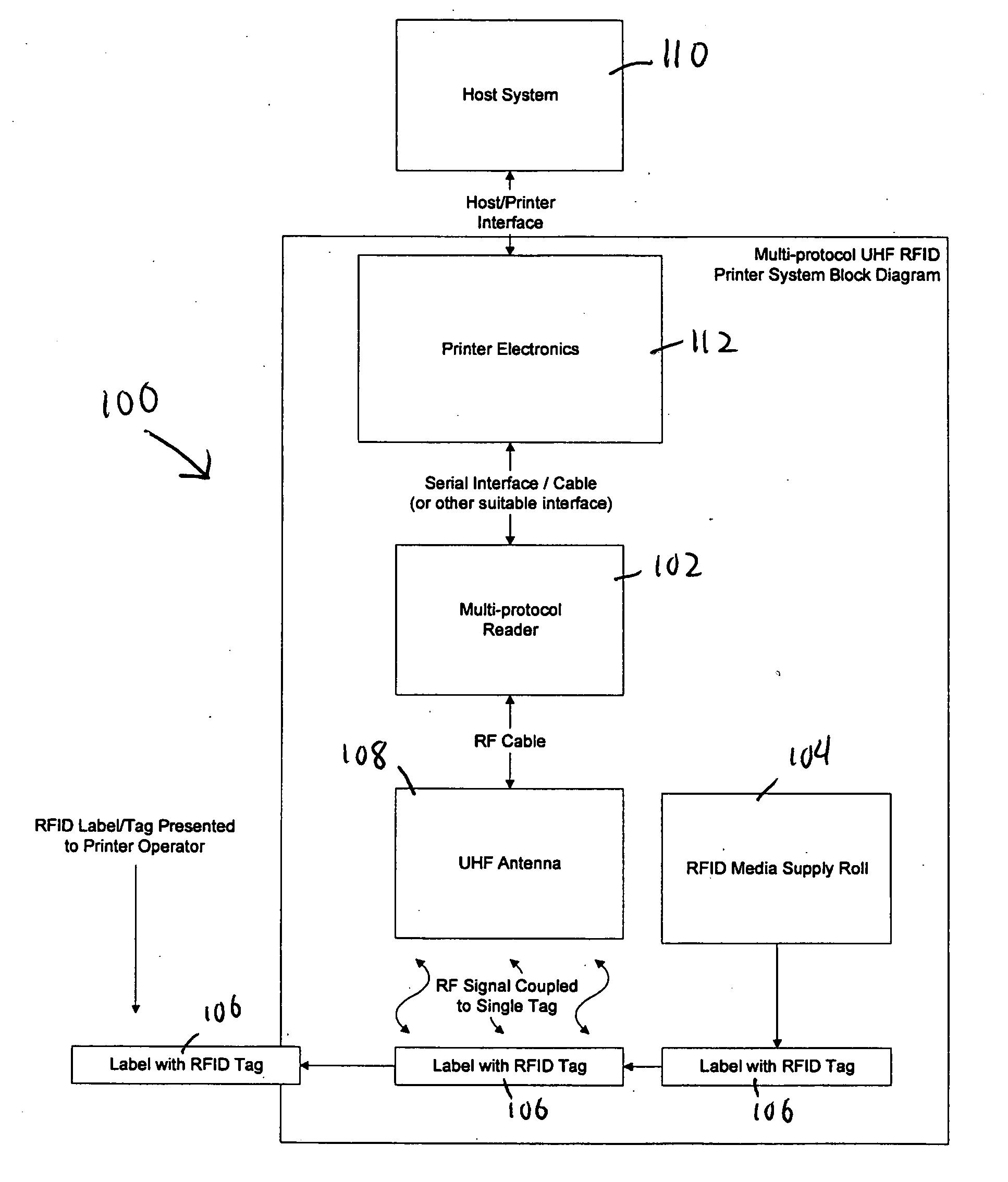
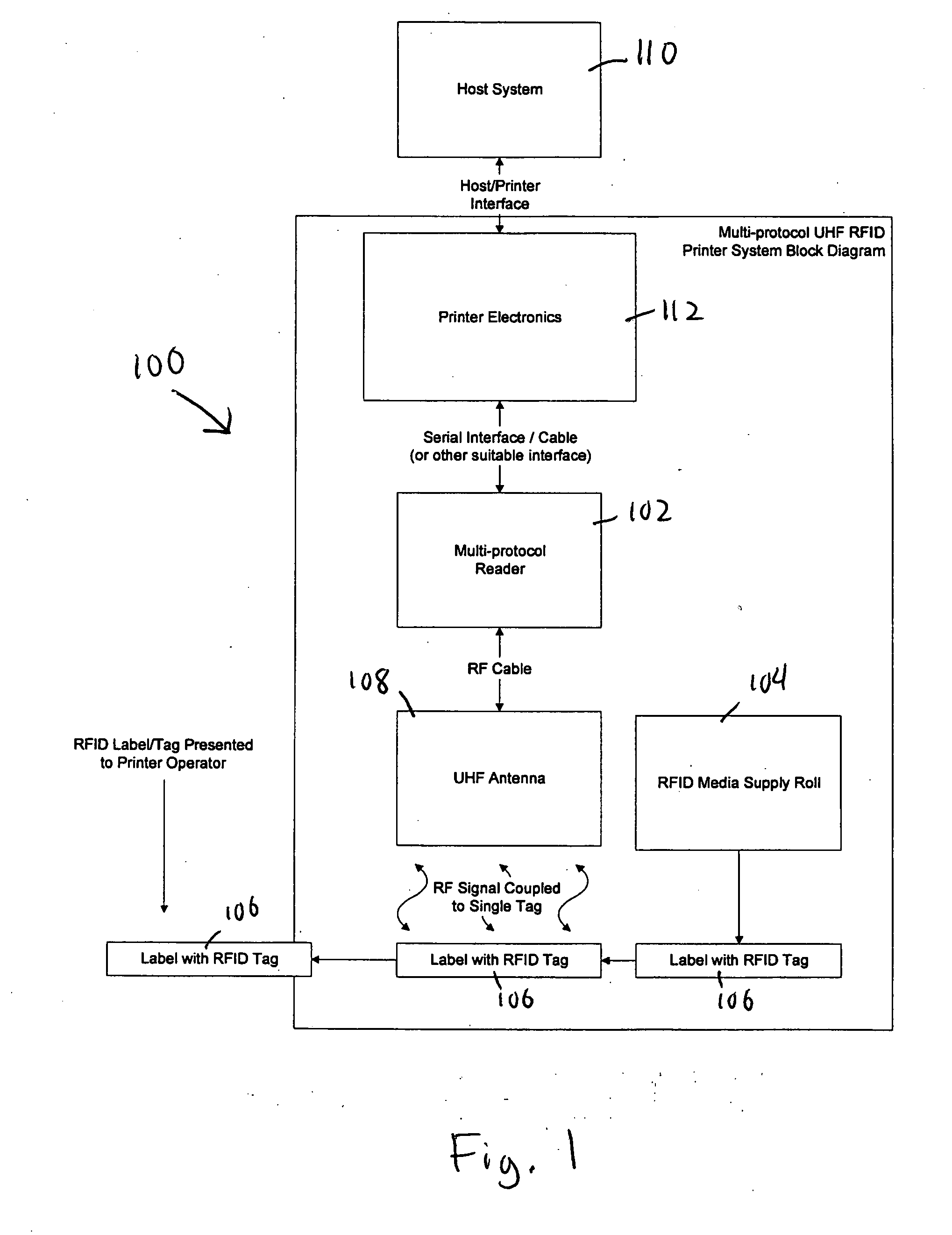
Auto sense and encode printer system for multiple classes of RFID tags
An RFID printer system and method interrogates or accesses RFID tags automatically using a user-defined sequence of settings for different RFID tags or classes. Once a successful interrogation is completed, the settings are saved and the saved settings are used for interrogation on the next tag. Each new roll of tags / labels starts interrogation with the first of the settings. Consequently, the printer system can read from and write to tags of more than one class without hardware or software changes in the printer.
Owner:PRINTRONIX INCORPORATED
Protecting computers from malware using a hardware solution that is not alterable by any software
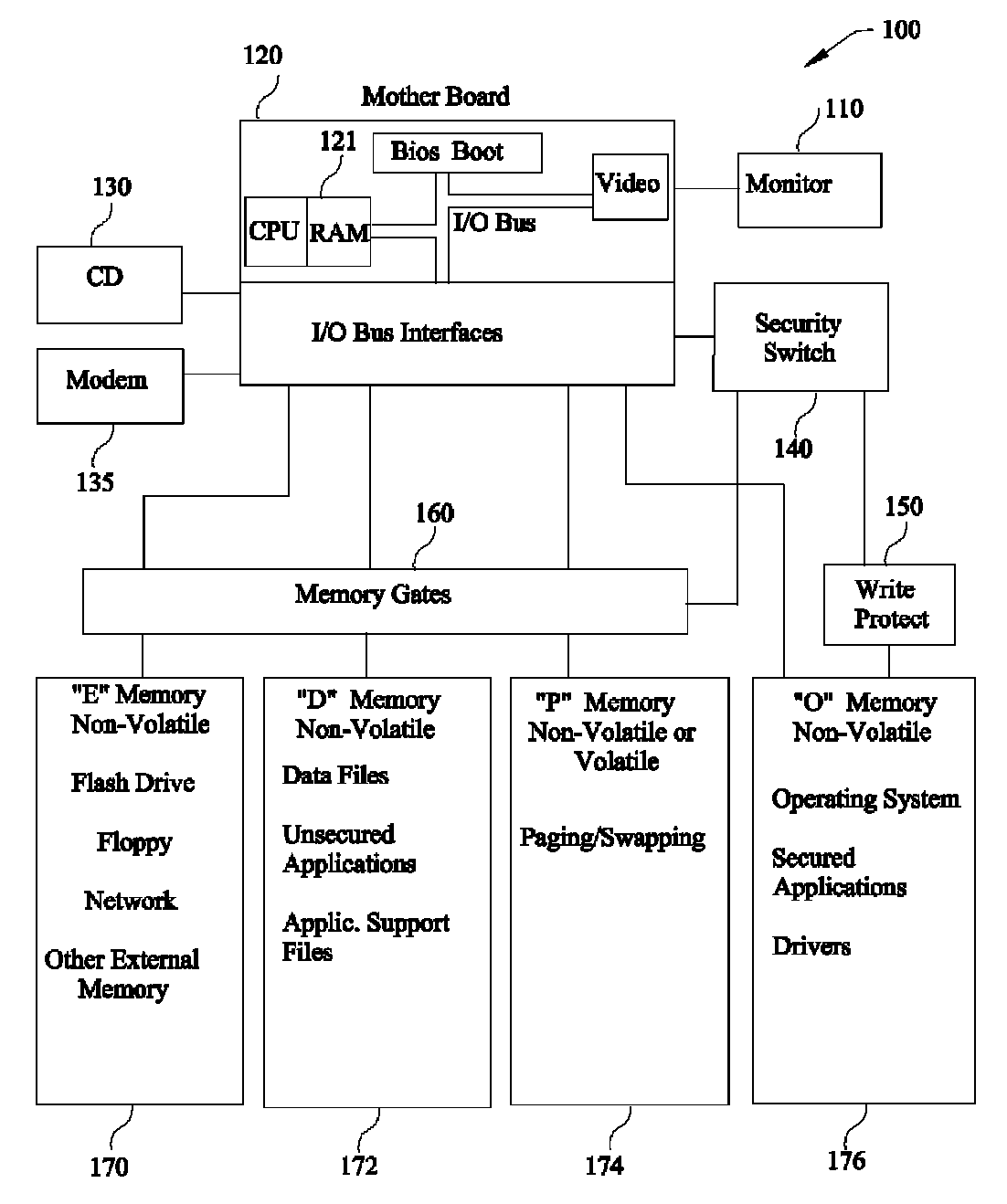
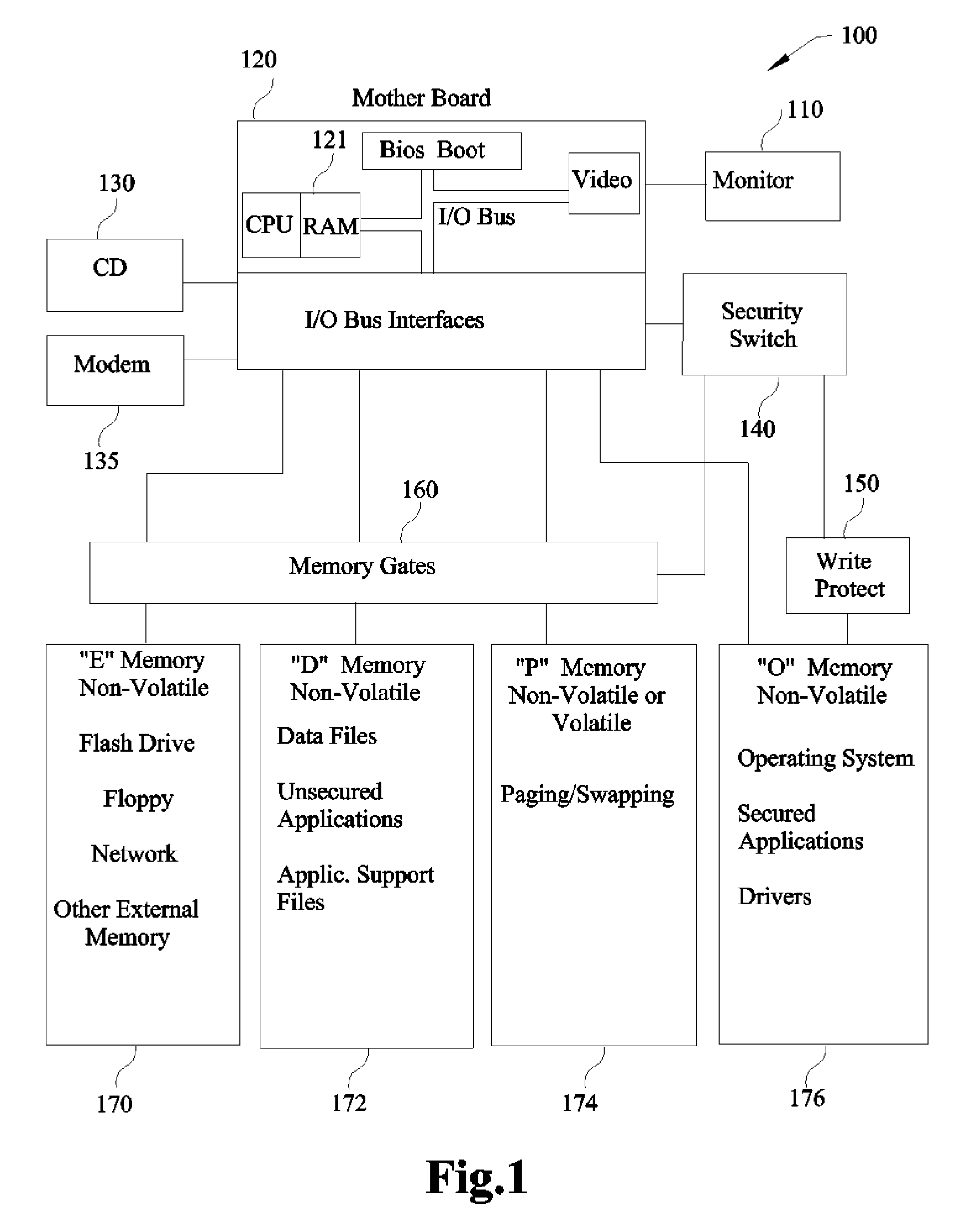
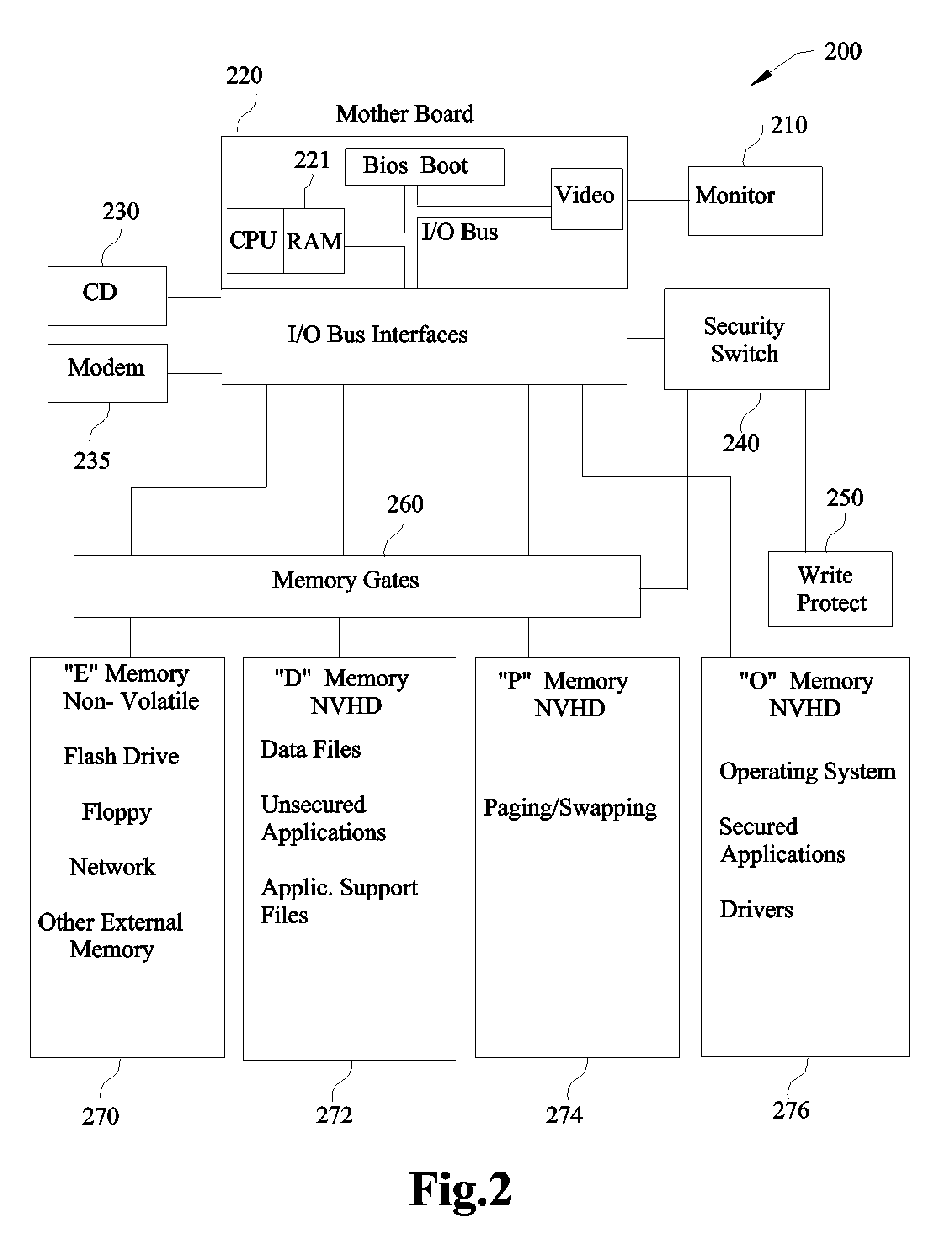
InactiveUS8082585B1Memory loss protectionDigital data processing detailsComputer hardwareOperational system
A Computer System that protects itself from Malware by assuring the security of critical software elements including but not limited to Operating Systems, Applications and I / O Drivers. These critical software elements cannot be altered by Malware during normal operation of the Computer especially when connected to the Internet, the primary vehicle for malware. When deviating from normal computer operation such as downloading updated Operating Systems or secured Applications, this invention erases or blocks all memory that could possibly be contaminated with Malware from affecting the critical software elements. This invention is unique because the Malware protection is invoked and implemented by hardware not alterable by any software, or dependent on understanding existing or new Malware.
Owner:GIVONETTI RAYMOND R
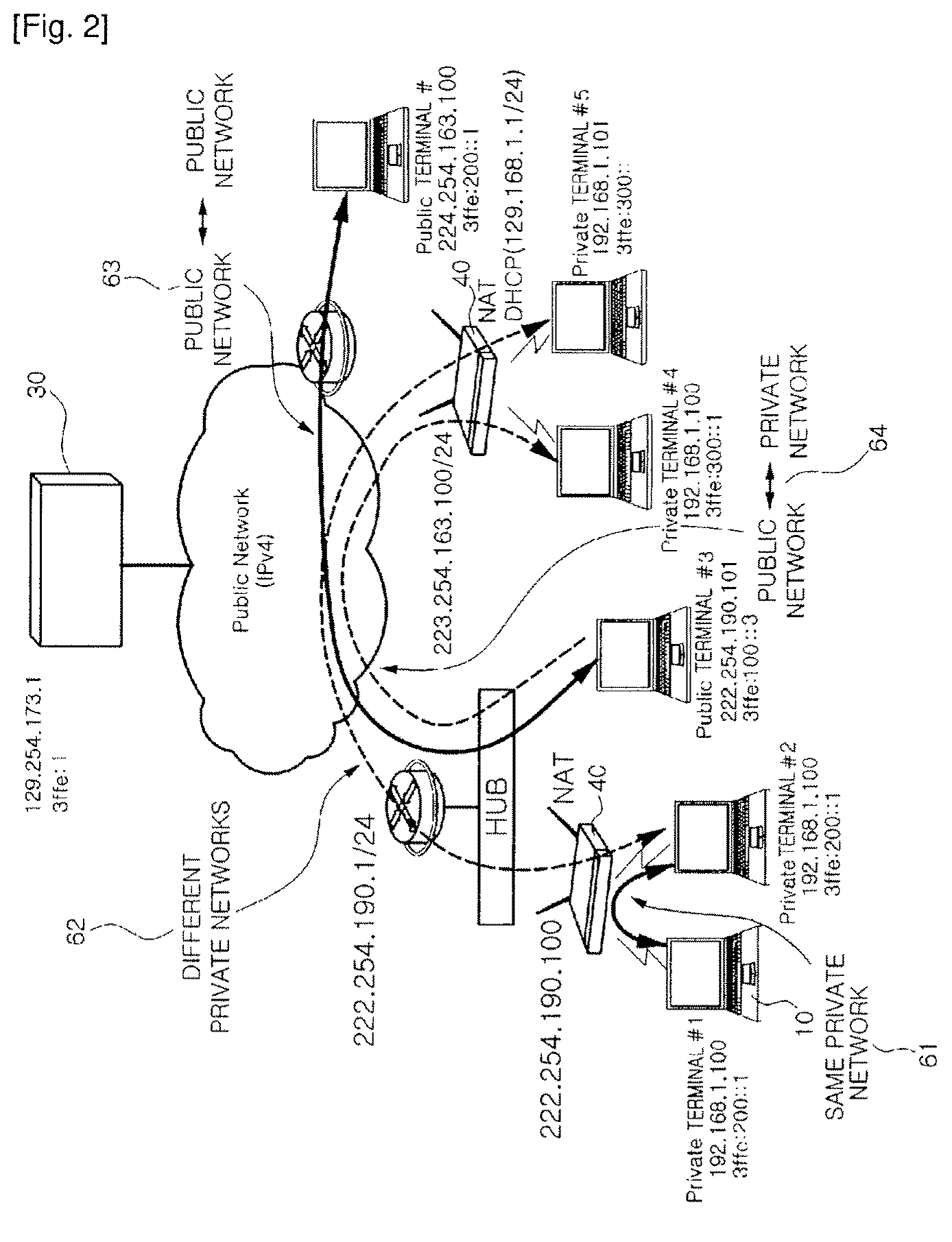
Method for configuring control tunnel and direct tunnel in ipv4 network-based ipv6 service providing system
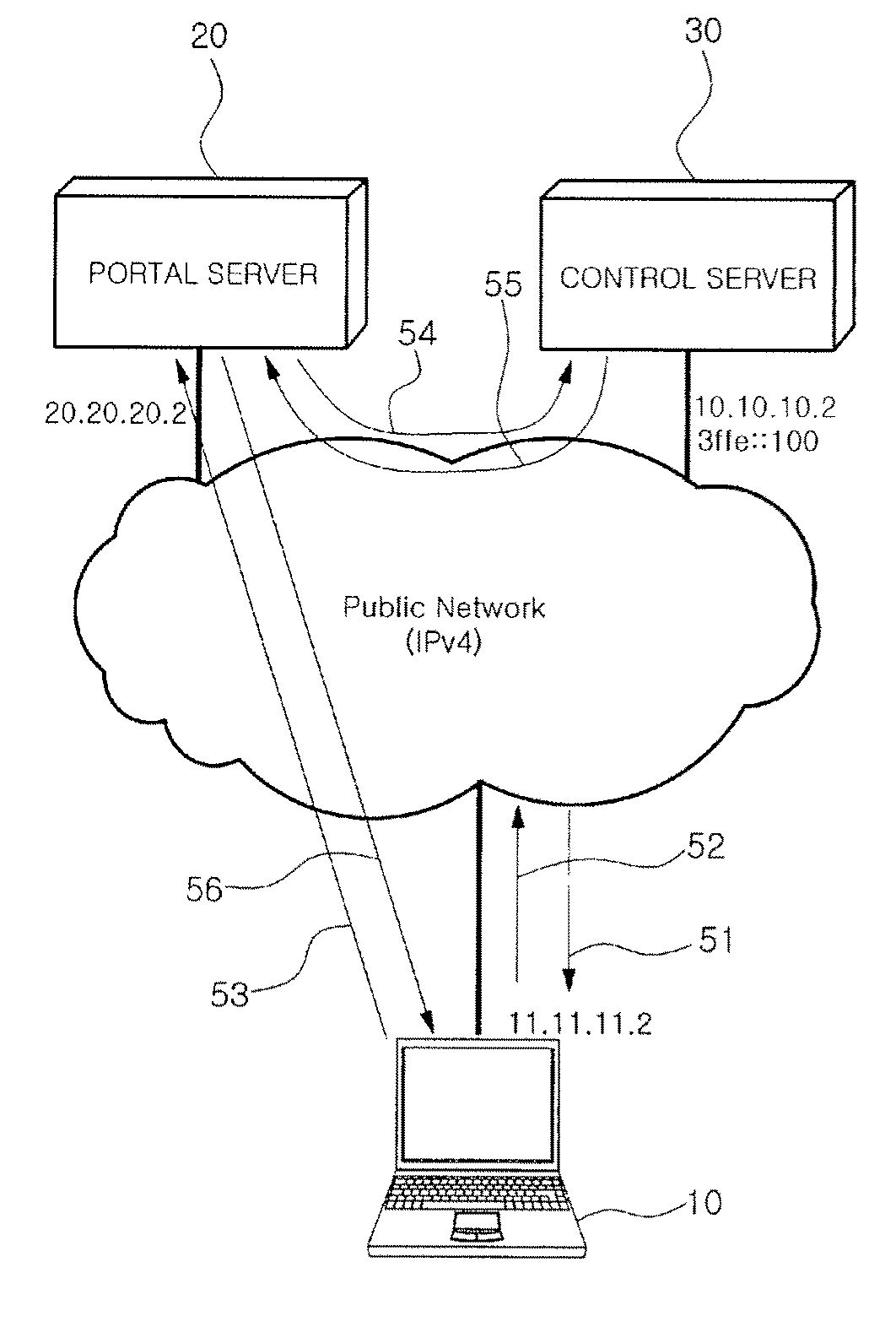
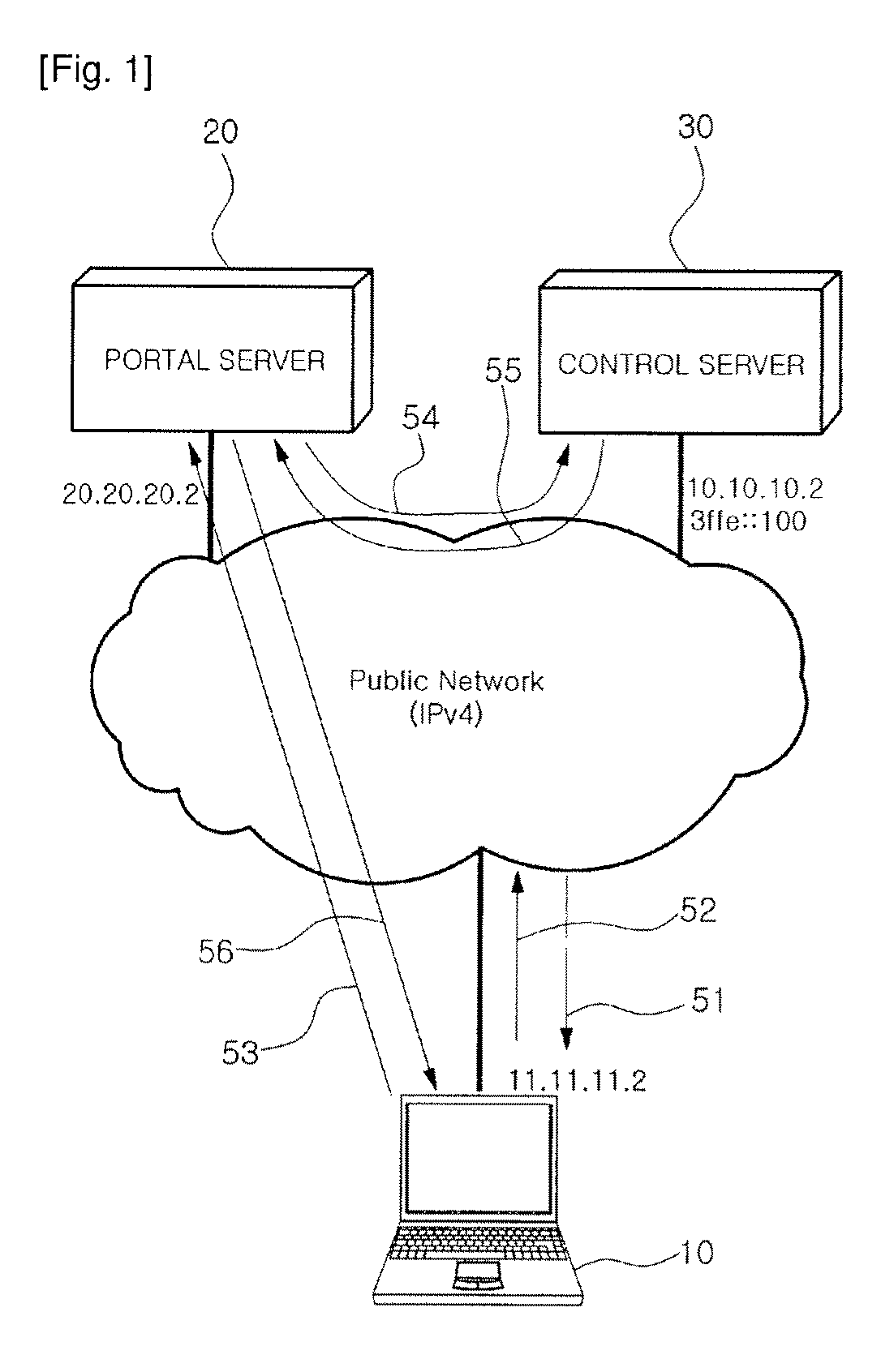
ActiveUS20100008260A1Low costMinimizing cost burdenNetworks interconnectionNetwork connectionsCost burdenService information
Provided is a method for configuring a control tunnel and a direct tunnel in an IPv4 network-based IPv6 service providing system. To provide IPv6 service, when a random request terminal receives a tunnel response message from a control server by using service information downloaded from a portal server at the time of initialization, the request terminal configures a control tunnel with the control server, and is registered to the control server. The request terminal transmits and receives a direct tunnel request message and a direct tunnel response message with a counterpart terminal by using its terminal information learned during the control tunnel configuration, i.e., network position information and status information, thereby configuring a direct tunnel. Thus, IPv6 communication is made through IPv4 based IPv6 tunneling, so that IPv6 application services that are not yet widely used can easily come into wide use. Also, only software change of each terminal and a control server is required without changing existing network equipment, so that a cost burden of a service provider can be minimized.
Owner:ELECTRONICS & TELECOMM RES INST +1
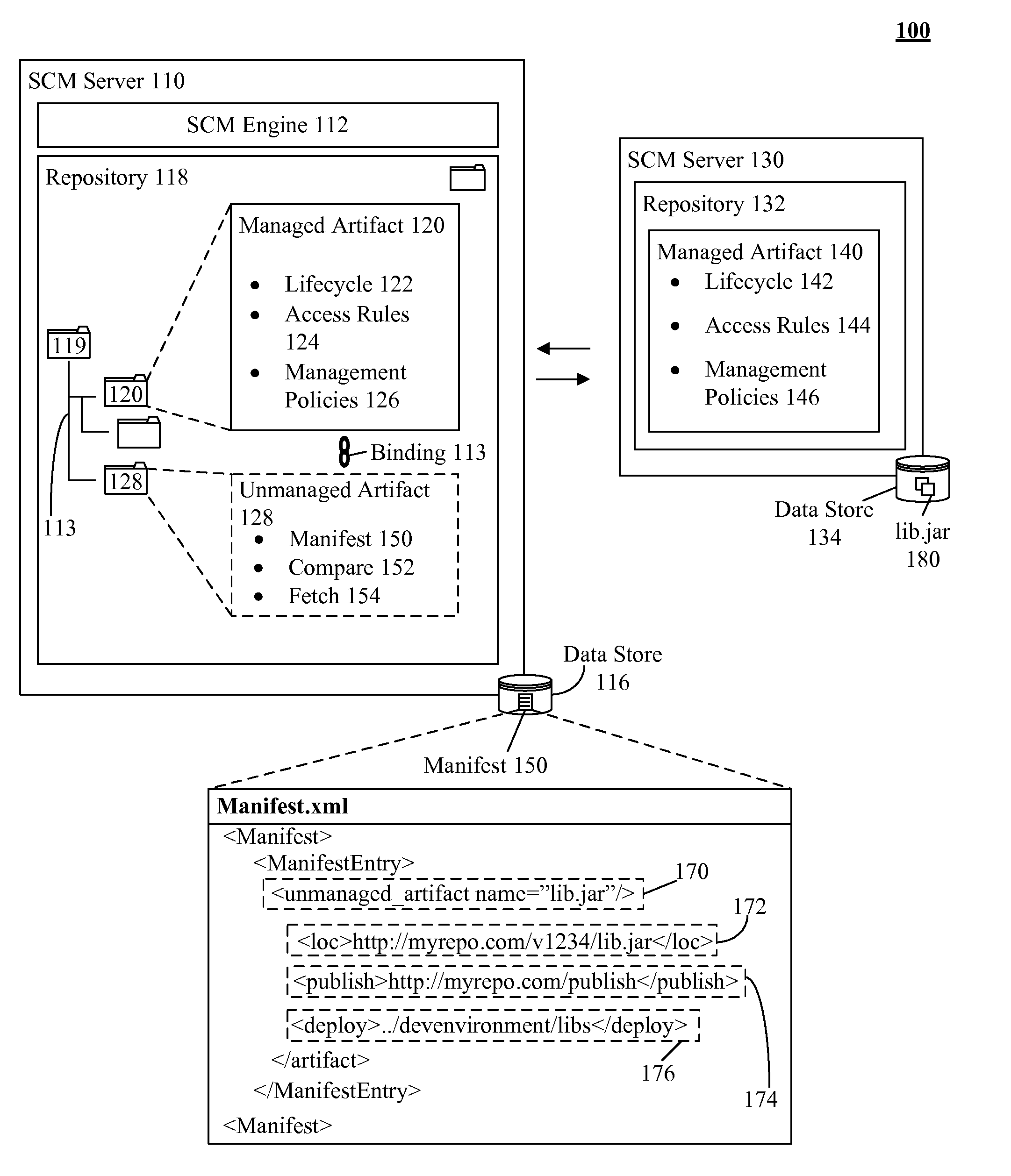
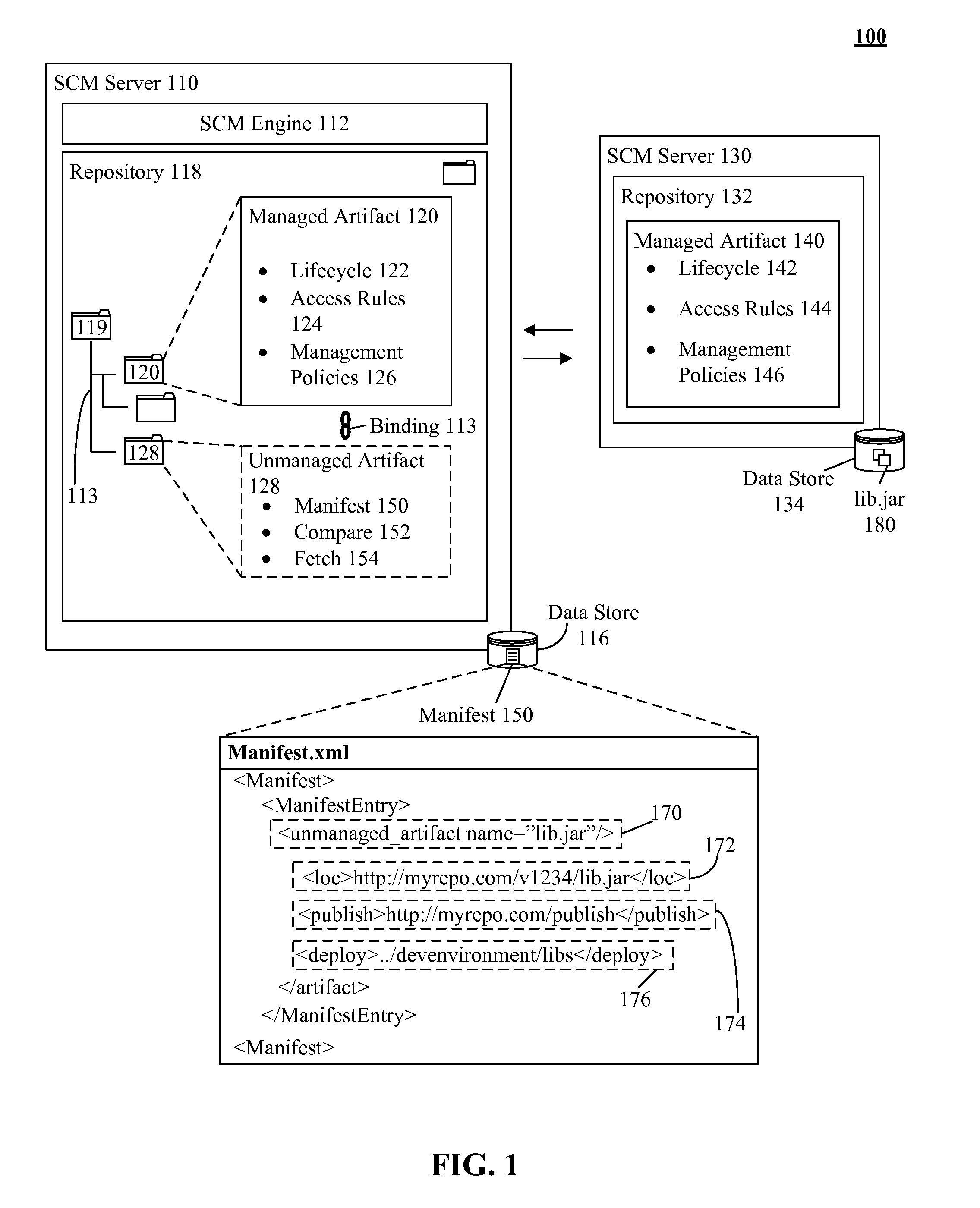
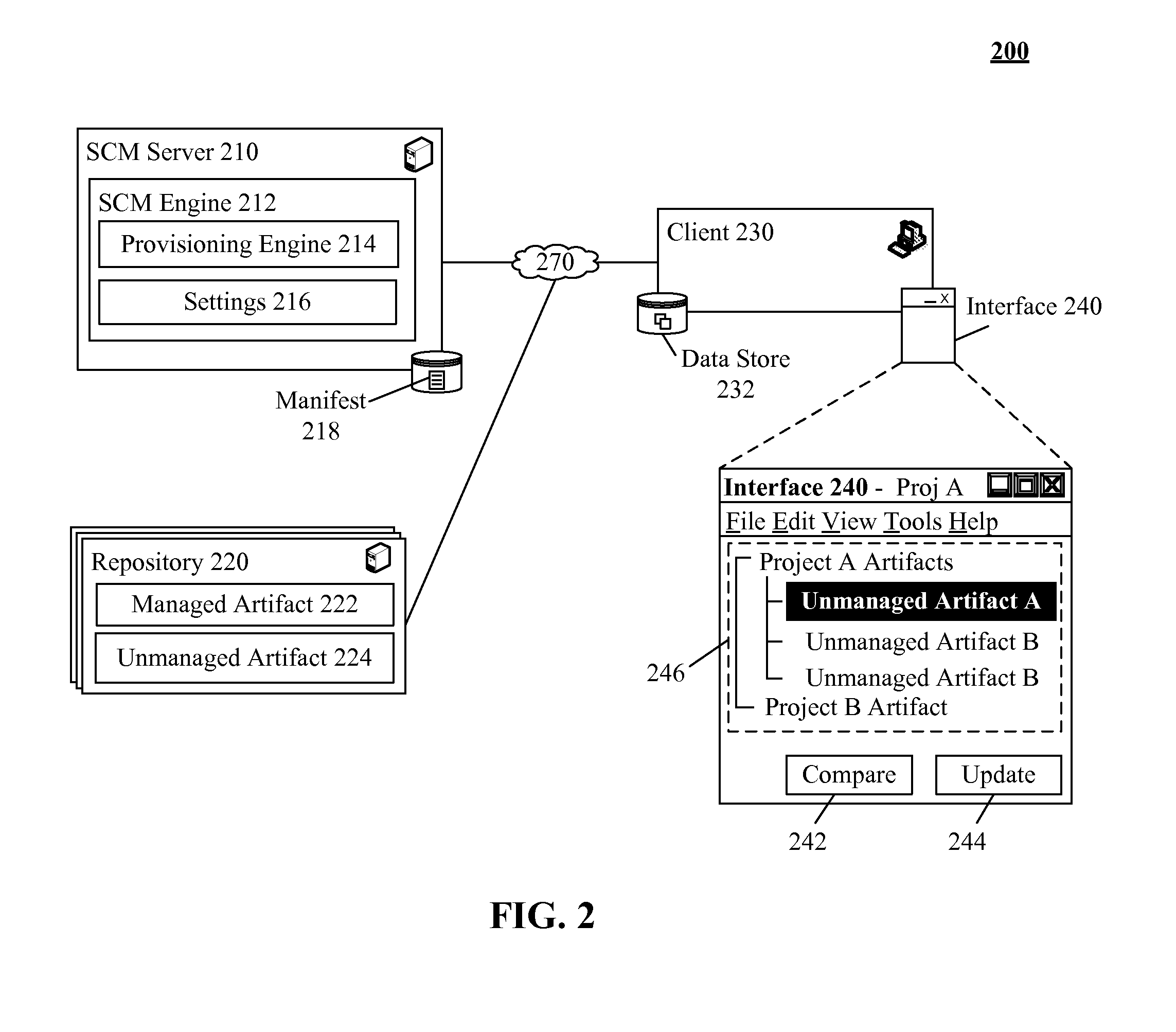
Software change management extension for uniformly handling artifacts with relaxed contraints
InactiveUS20110307862A1Version controlSpecific program execution arrangementsChange managementData type
Software change management (SCM) systems can be extended to uniformly handle artifacts which lack constraints typically imposed on managed items. In the solution, a data type associated with a SCM system can enable management of unmanaged artifacts. Unmanaged artifacts can include, but is not limited to, artifacts which lack can traditional change management constraints, managed artifacts not directly associated with the SCM, artifacts with different constraints than the SCM imposed constraints, and the like. In one embodiment, an unmanaged artifact can have different lifecycles, policies, and the like which can make it unsuitable for traditional management approaches by the SCM. The SCM can utilize the data type to manage unmanaged artifacts without requiring significant change in functionality of the SCM by permitting change management processes to be applied to the unmanaged artifacts.
Owner:IBM CORP
Integrated circuit with electromagnetic energy anomaly detection and processing
ActiveUS9059189B2Constant monitoringSemiconductor/solid-state device detailsSolid-state devicesSemiconductor materialsAnomaly detection
An integrated circuit includes an antenna, a die manufactured from a semiconducting material, an RF energy collection and processing device disposed on or within the die and including at least a receiver and a processing device, an input configured to supply power to said RF energy collection and processing device and an output for operative communication by said RF energy collection and processing device. The integrated circuit is configurable and operable to provide at least one of electromagnetic emission anomaly detection, tamper detection, anti-tamper monitoring, degradation monitoring, health monitoring, counterfeit detection, software changes monitoring, firmware changes monitoring and monitoring of other RF energy anomalies.
Owner:NOKOMIS
Adaptive memory compression
InactiveUS7188227B2Memory architecture accessing/allocationMemory adressing/allocation/relocationComputer hardwareParallel computing
Compressed memory systems and methods that reduce problems of memory overflow and data loss. A compression engine compresses blocks of data for storage in a compressed memory. A compression monitor monitors the achieved compression ratio and provides a software trap when the achieved compression ratio falls below a minimum. After the trap is provided software monitors the fill state of the compressed memory. If the compressed memory is approaching full, the software changes the block size to improve the compression ratio.
Owner:INT BUSINESS MASCH CORP
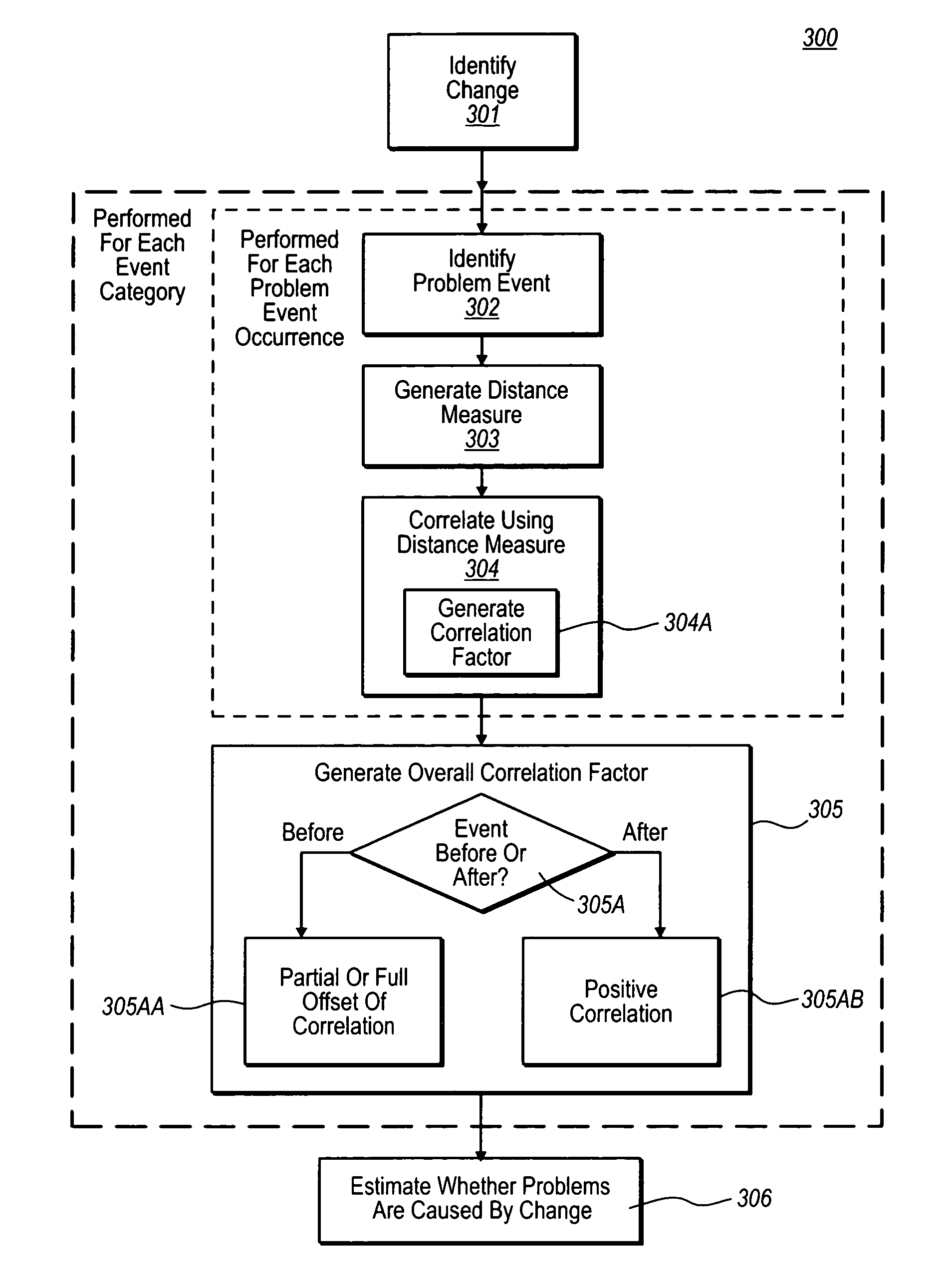
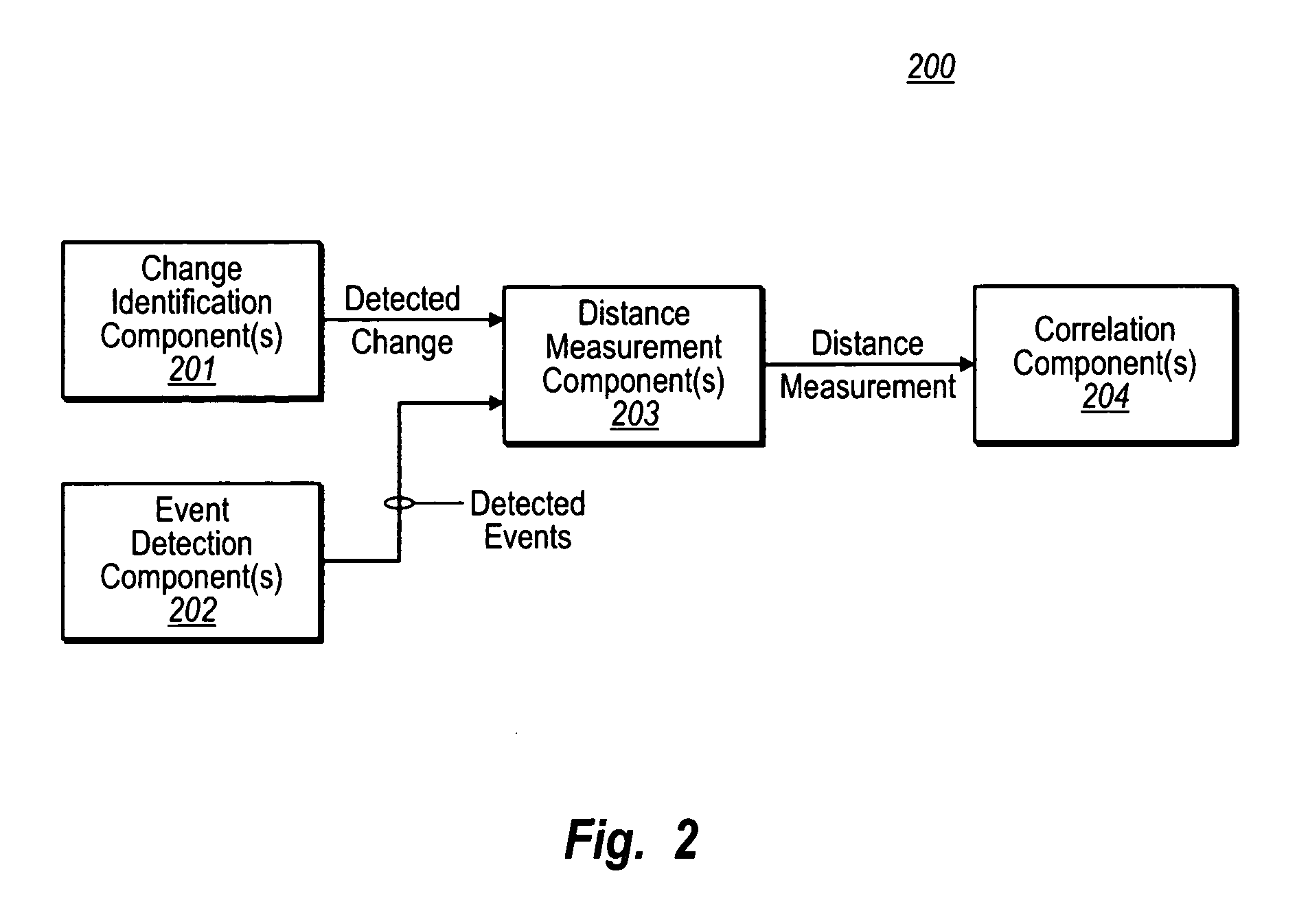
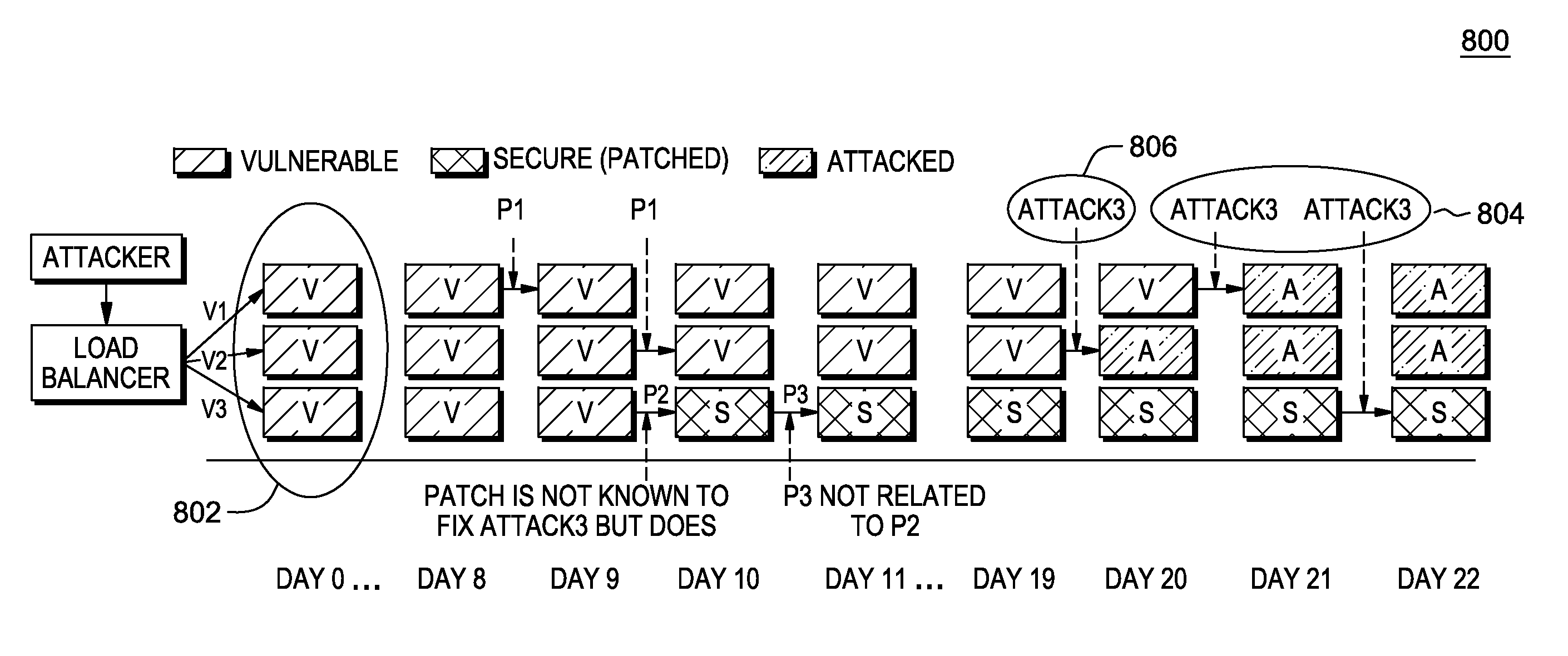
Automatically estimating correlation between hardware or software changes and problem events
InactiveUS7774657B1Overcome problemsError detection/correctionProgram loading/initiatingComputer hardwareReliability engineering
Automated estimation that a hardware or software change is correlated with one or more problem events. In addition to identifying that a change has occurred, one or more problem events are identified that have occurred after the change. Problem events are then correlated with the change using a distance measure between the change and the at least one correlated problem event. For most, if not all, of the distance measure, the greater the distance measure, the less the change is correlated with each correlated problem event. The distance measure may be a time interval, an activity-weighted interval, or any other type of distance measure.
Owner:CA TECH INC
Impact analysis of software change requests
Owner:ACCENTURE GLOBAL SERVICES LTD
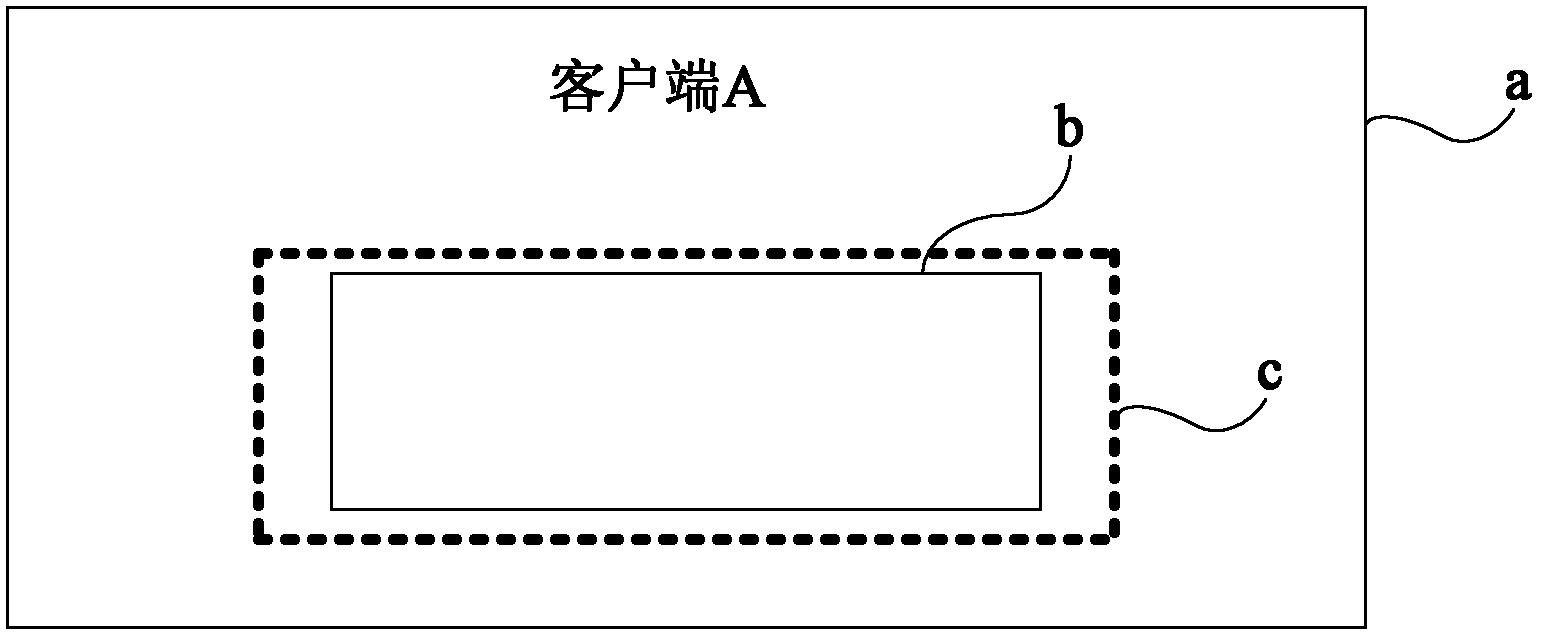
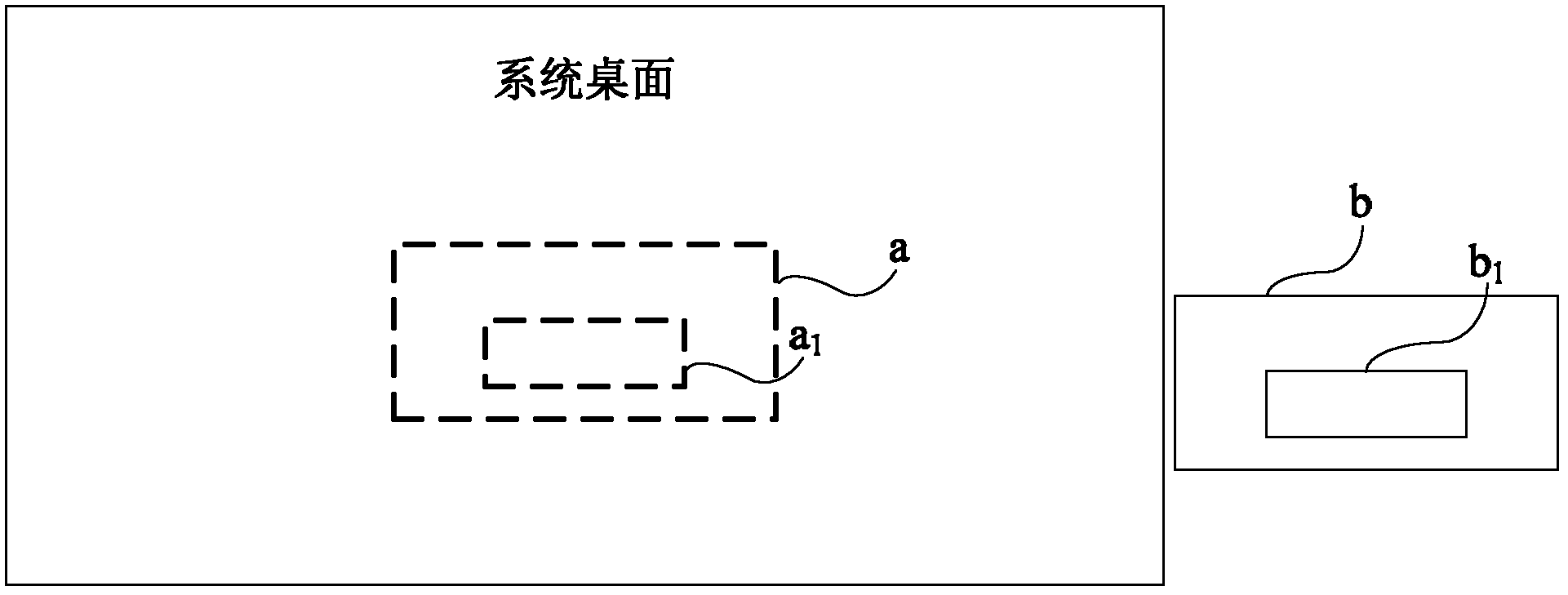
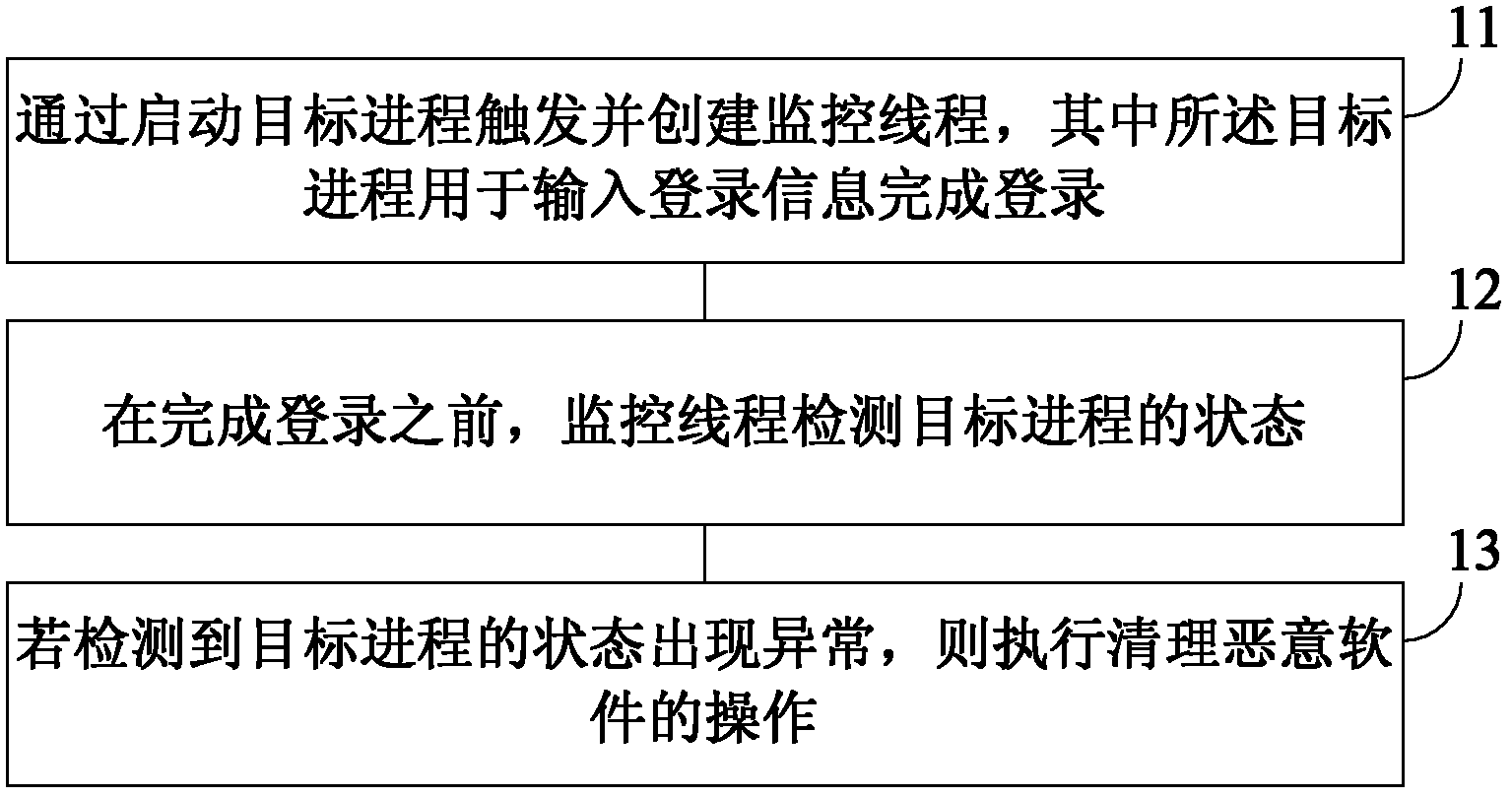
Method and device for preventing login information from being stealed
Owner:BEIJING QIHOO TECH CO LTD
System and method for tracking software changes
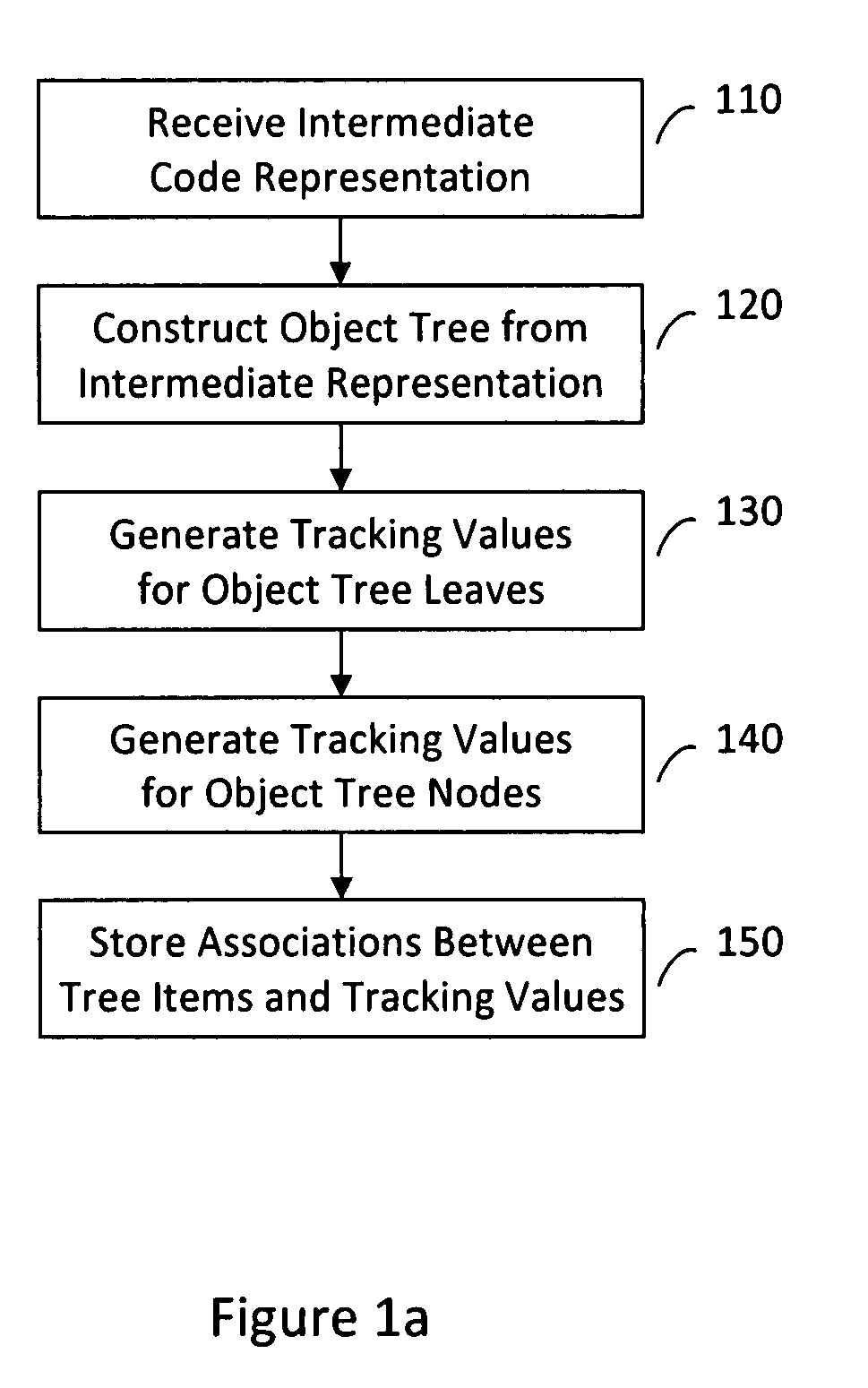
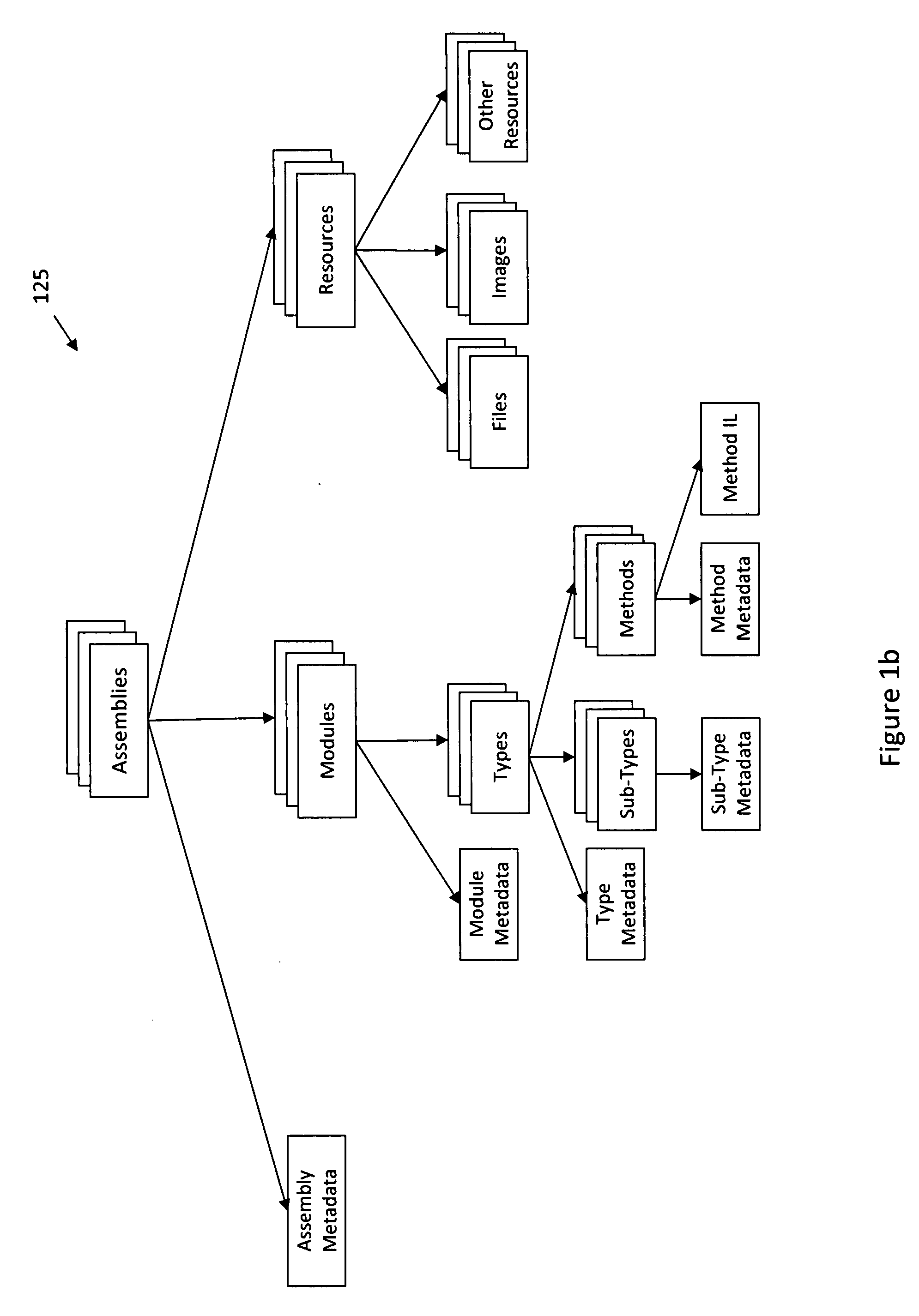
InactiveUS20090100410A1Effective trackingEffectively recognize similarityVersion controlReverse engineeringData miningIntermediate language
A system and method may be used to track software changes by analyzing intermediate language level representations of the software. For example, software changes may be tracked by analyzing object-oriented program code that includes one or more non-native binary executables based on an intermediate language. The program code may be associated with metadata describing content of the non-native binary executables. An object tree, which includes a plurality of nodes, may be constructed to represent the non-native binary executables and the metadata describing the content of the non-native binary executables. One or more of the plurality of nodes may be hashed to associate respective digest values with the hashed nodes, such that changes in the received program code can be tracked using the digest values associated with the hashed nodes.
Owner:RPX CORP
Software manufacturing factory
InactiveUS20070083859A1Simple processImproved system configurationVersion controlSpecific program execution arrangementsAutomatic controlSoftware system
This invention discloses an automated software development system that includes an automated version control and evaluation processing platform for automatically evaluating a quality and value of a plurality of software changes and corresponding versions of a software system for automatically controlling an automated software development and change process of the software system. The automated version control and evaluation processing platform further includes a database for storing statistic and relevant data including the quality and value of the plurality of software changes and versions of the software system. The automated version control and evaluation-processing platform further applies the statistic and relevant data for automatically controlling an automated software development and change process of the software system.
Owner:VELIDOM
Method and system for switching between video modes in consumer electronics
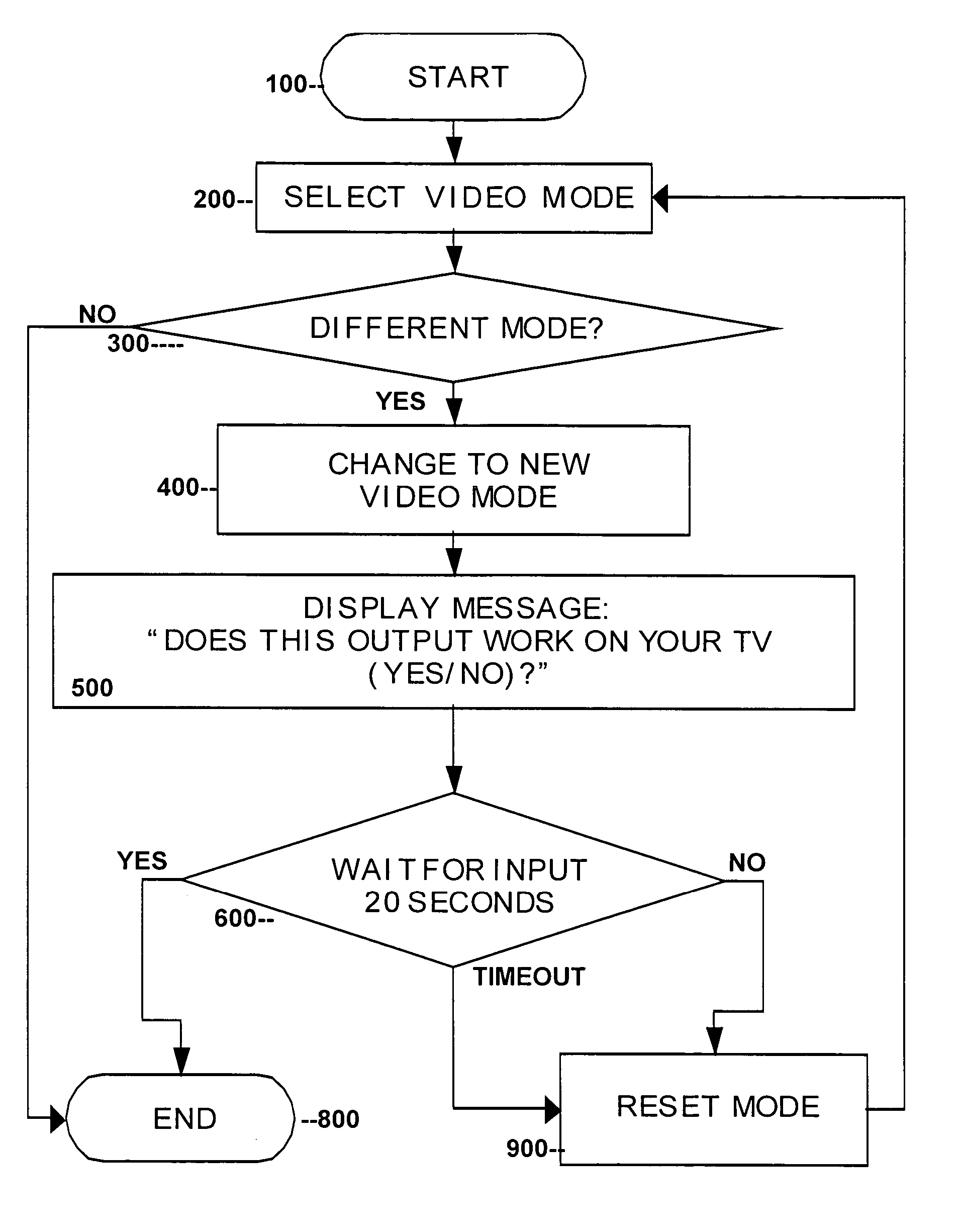
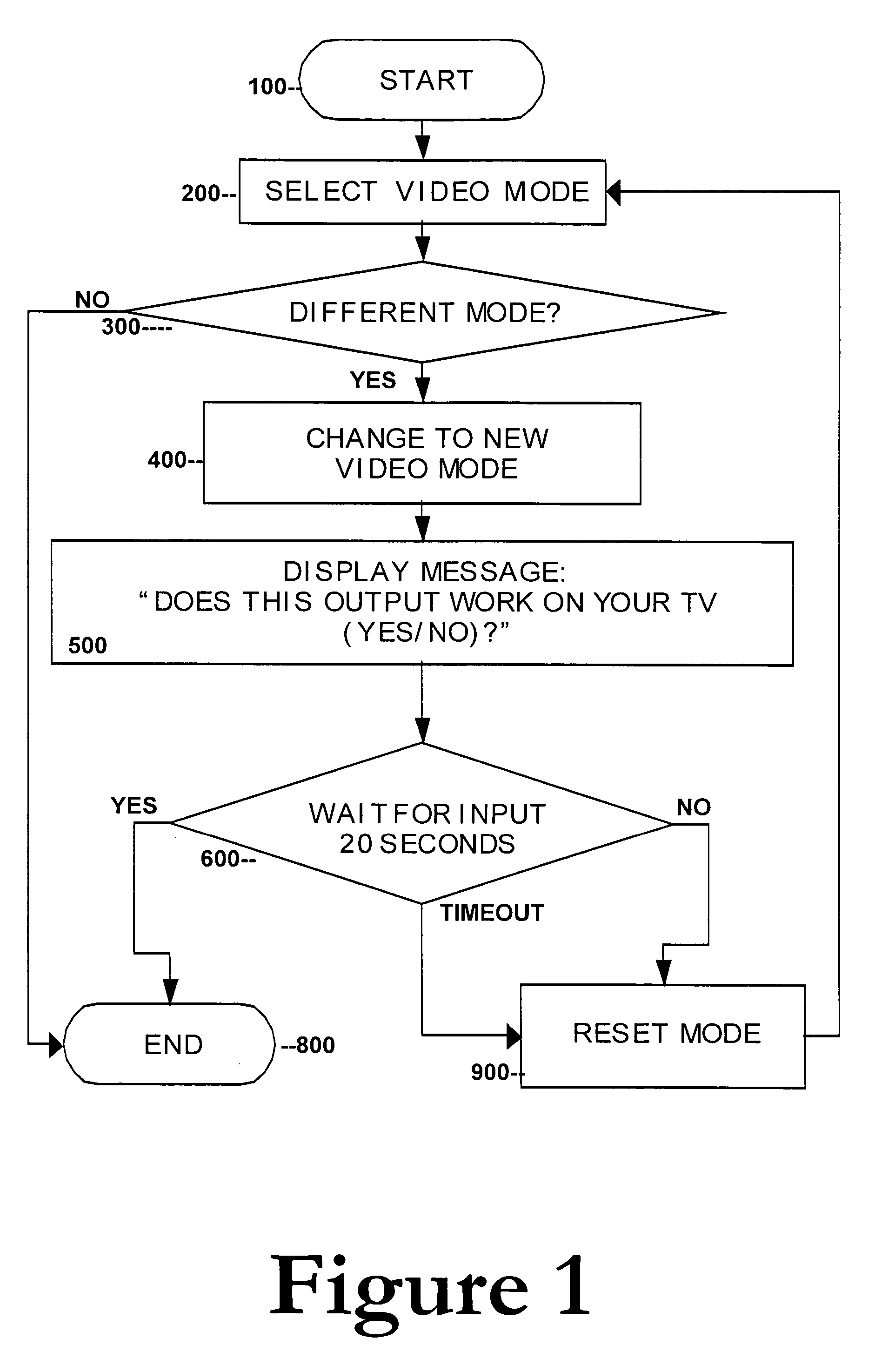
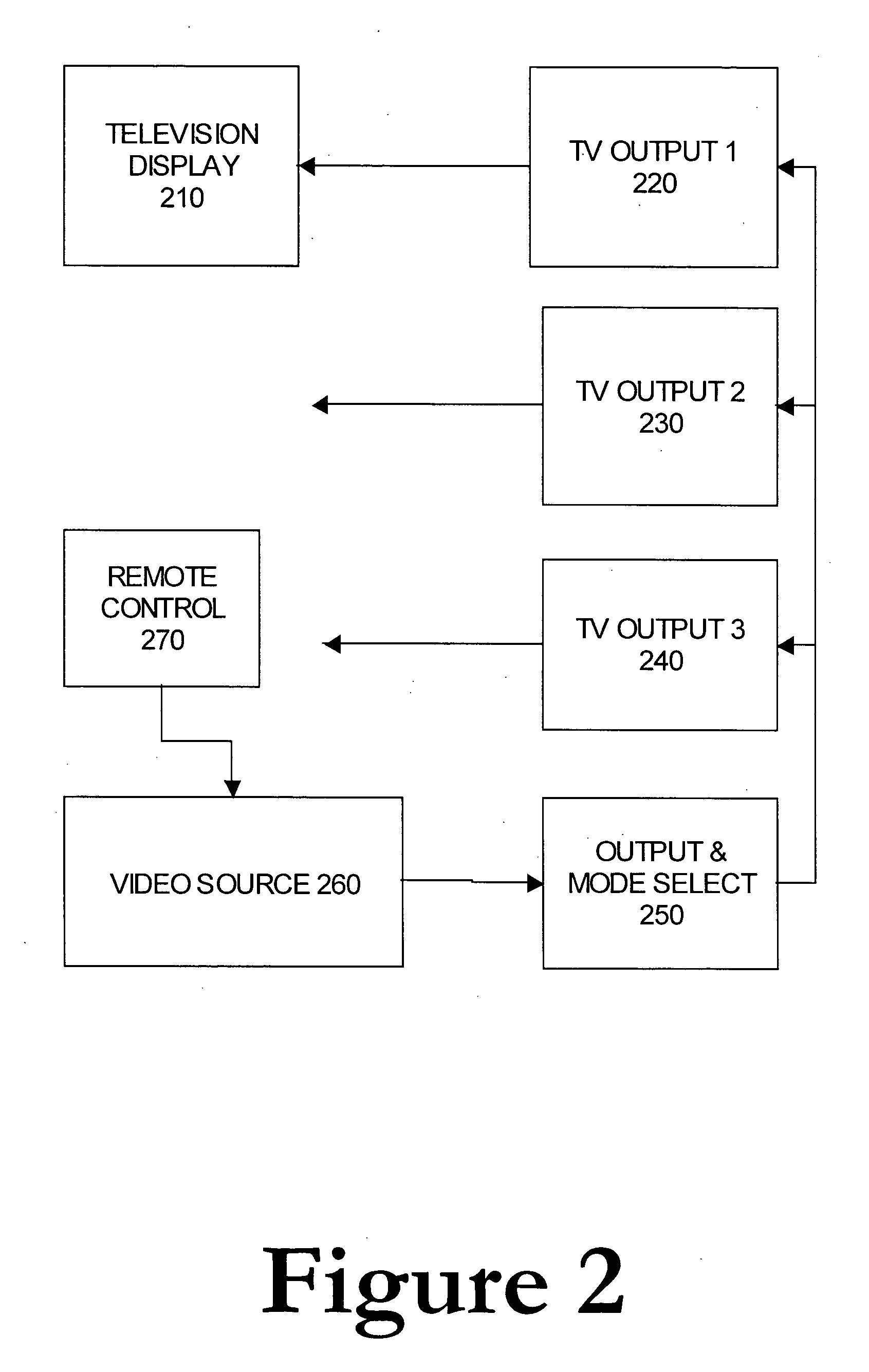
InactiveUS20060007359A1Better customer satisfactionEliminate needTelevision system detailsTelevision system scanning detailsOperational systemDisplay device
DVD players and the like may support multiple video formats, including interlaced and progressive scan video. If a user selects a mode (e.g., progressive scan) not supported by their monitor or television, then the user may lose the video image output, and can no longer see the GUI (Graphical User Interface) which would allow the user to switch back to the previous mode. The present invention solves this problem by providing a method and system whereby a new display mode or resolution is generated and a message displayed requesting the user to confirm whether the resultant display is acceptable. If the user does not respond to the message after a predetermined period of time (e.g., 20 seconds), then the system reverts back to the previous resolution or mode. The system thus prevents and corrects for the cases where a user selects an inappropriate video output. In addition, a user-friendly interface, which results in better customer satisfaction, is provided. Moreover, while minor software changes to the operating system of the consumer electronic video device (e.g., DVD player) may be required, the need for new hardware is eliminated.
Owner:MAGNUM SEMICONDUCTOR
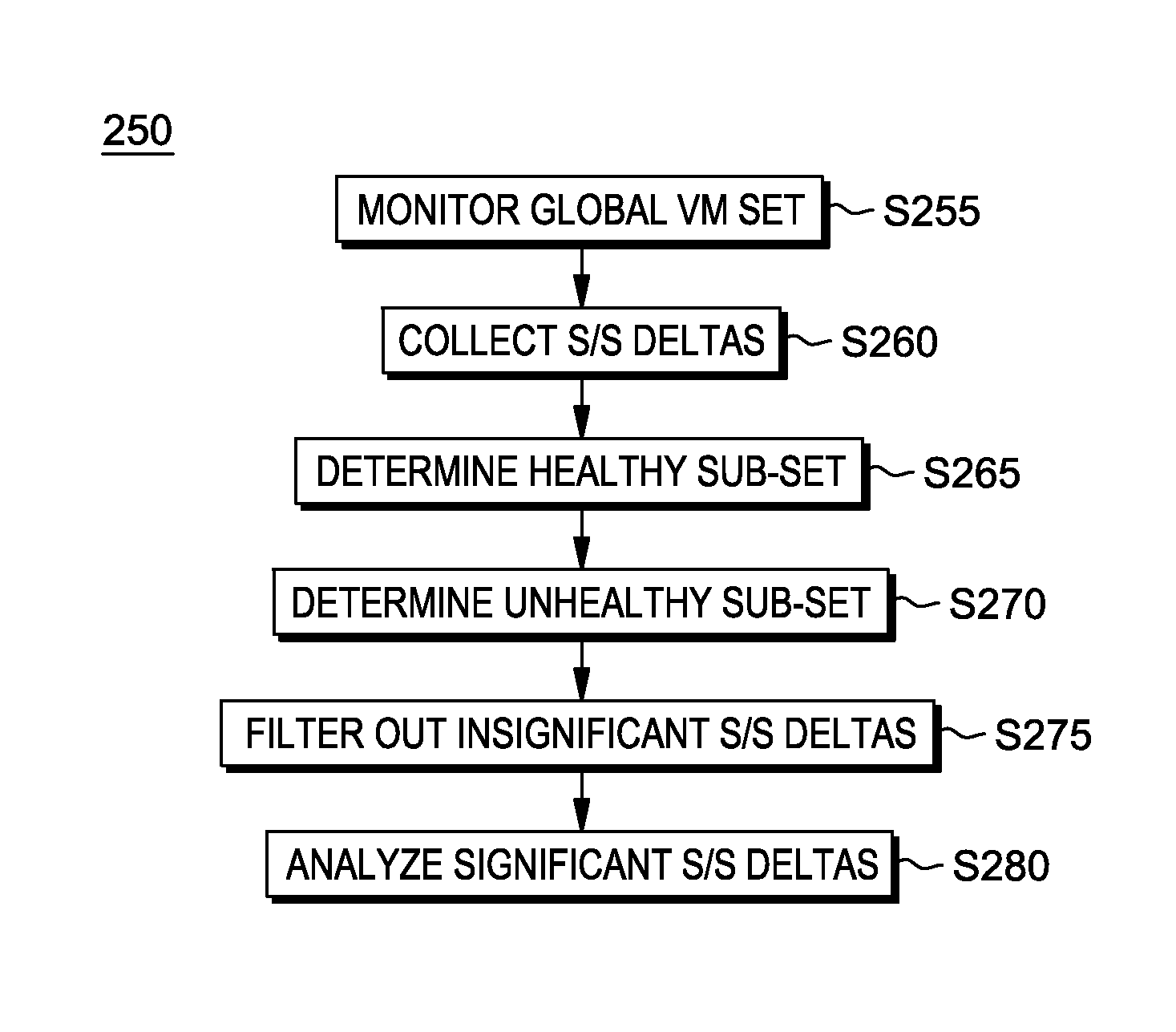
Security policy generation based on snapshots of similar virtual machines
InactiveUS20160321455A1Platform integrity maintainanceSoftware simulation/interpretation/emulationSecurity policyVirtual machine
Determining which snapshot deltas tend to occur in: (i) healthy virtual machines (VMs) that have been subject to an attack yet remained healthy, and / or (ii) unhealthy VMs that have apparently been adversely affected by an attack. Snapshot deltas that occur in at least some (or more preferably all) of the healthy VM subset provide information about software changes (for example, updates, configuration changes) that may be helpful. Snapshot deltas that occur in at least some (or more preferably all) of the unhealthy VM subsets provide information about software changes (for example, updates, configuration changes) that may be unhelpful.
Owner:IBM CORP
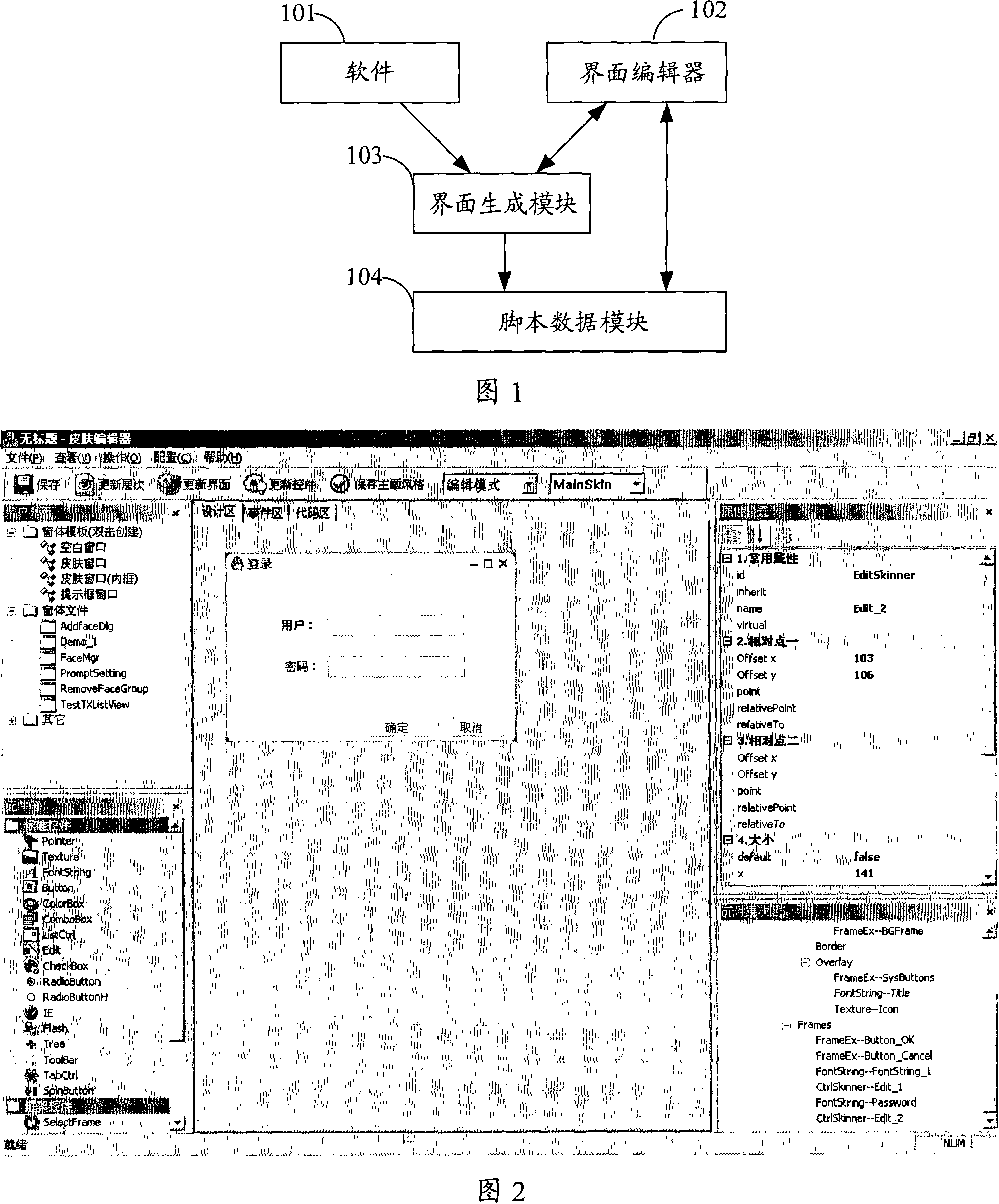
Window system and its interface editing method
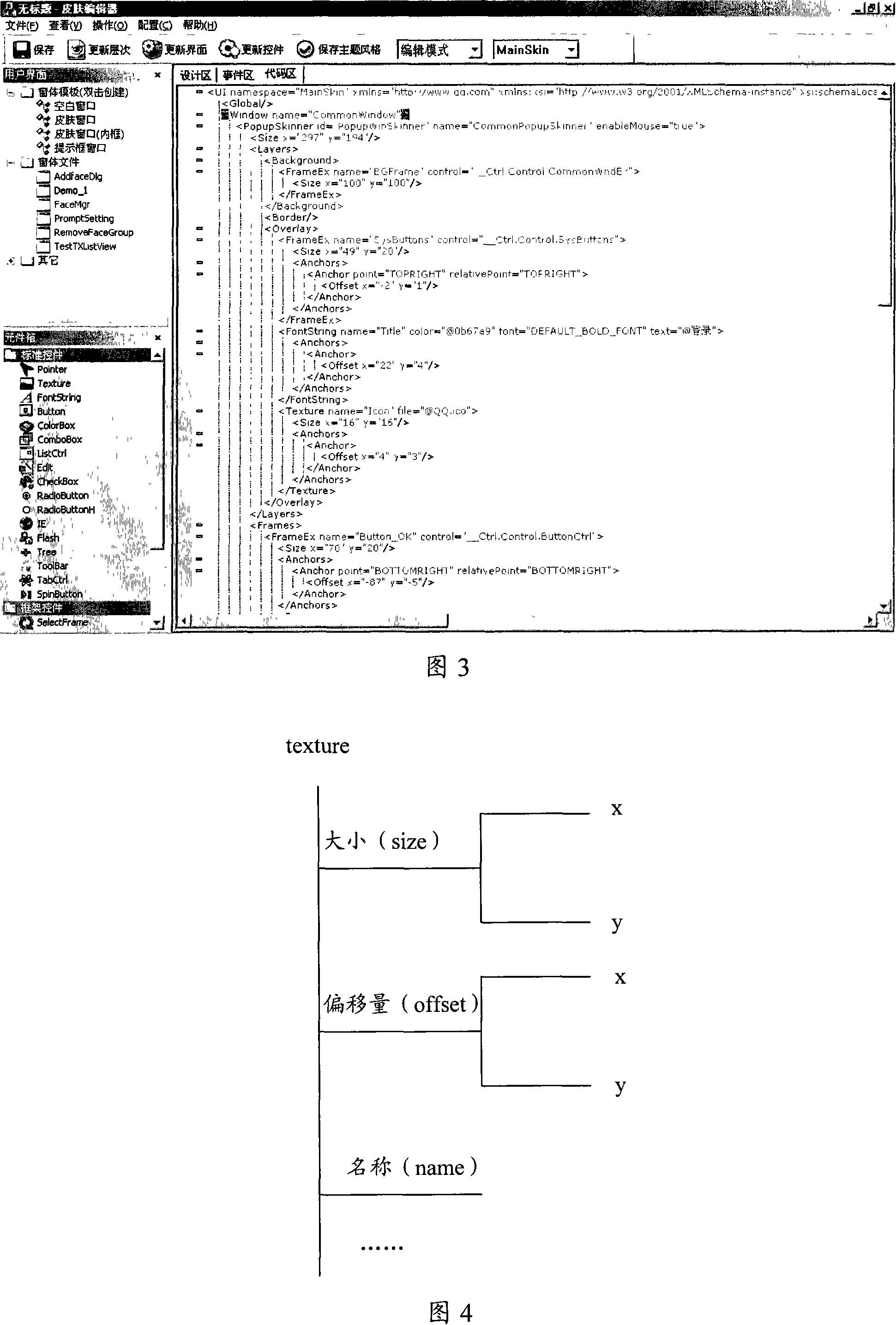
ActiveCN101071374APromote rapid developmentSpecific program execution arrangementsSoftware engineeringDEVS
The invention applied to the field of computer programming provides Windows interface and editing methods. The systems include: software; the software interface to edit handling interface editor; a number of storage software interface scripts script Data Module, and accept software or interface editor of the call, read the script interface to generate corresponding data interface module interface generation. The invention will be implemented through software in the case of the interface formation of the independent, thus reducing the need for changes in the interface and software changes the risk. At the same time, the editor interface module generated by the timely generation interface is the editing interface provides developers with software interface development environment that allows developers to rapidly develop interface.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for automatically adapting to mobile terminal
InactiveCN102314364AImprove R&D efficiencyShorten the development cycleProgram loading/initiatingUser needsOperational system
The invention discloses a method for automatically adapting to a mobile terminal. The method comprises the following steps of: setting software change caused by user requirement change or hardware configuration change according to a microprocessor chip and an embedded operating system selected for the mobile terminal; forming a series of parameters and various parameter files, wherein the parameter files are independent of image files of the embedded operating system in the mobile terminal; and matching the image files with different parameter files to automatically adapt to software change caused by specific user requirement change or specific hardware configuration change, wherein the parameter files are independent of the publishing and / or updating of the image files, and the image files are not required to be updated when the software change occurs. The method contributes to further increasing the product research and development efficiencies, shortening the product research and development periods and better publishing products more quickly.
Owner:北京登合科技有限公司
Automatic checking method for change influence degree of model
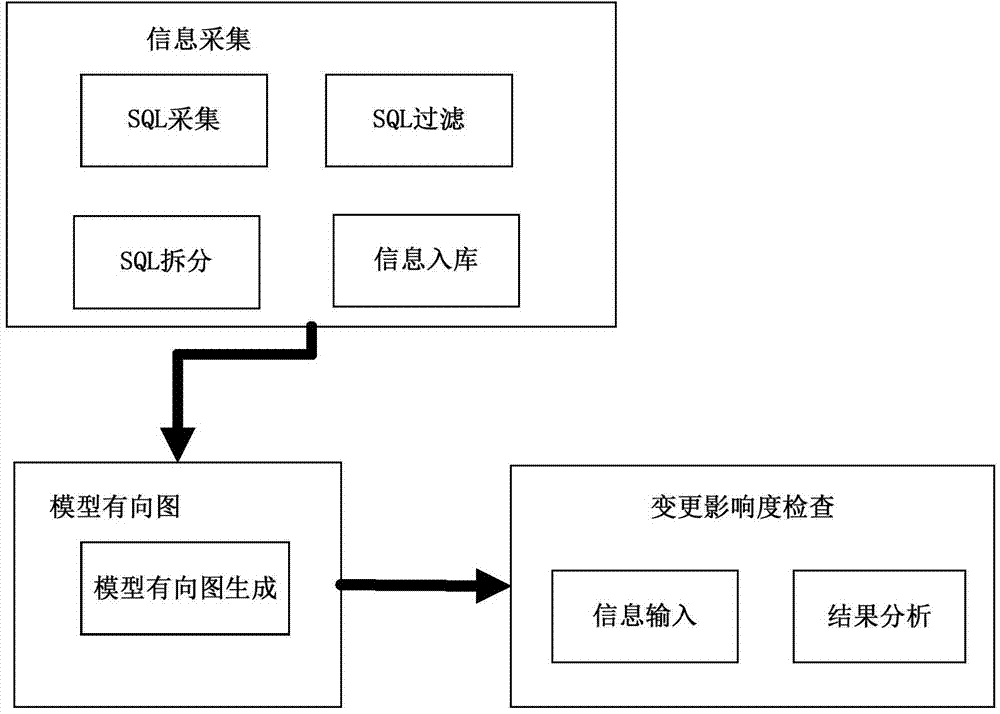
ActiveCN104750496AComprehensive riskImprove intuitivenessSpecific program execution arrangementsSoftware systemPhysical modelling
The invention discloses an automatic checking method for change influence degree of a model. The automatic checking method comprises the following steps: a), collecting and analyzing SQL (structured query language) sentences performed by a database, and recording correlation between tables in the database; b) generating a correlation base line of a system data model to obtain a constrained graph of a system physical model, generating a physical model digraph according to the system service flow, and constructing a data model-service functional diagraph; c) when the software system has model changes, inputting the corresponding change information, and distinguishing the change influence range and the service functions according to the digraph and the functional digraph. According to the automatic checking method for change influence degree of the model disclosed by the invention, the SQL information of the database is collected, the model digraph is generated, the software change influence degree is analyzed from the software system physical model, the change influence range and the service function pots of the model are intelligently judged, and the risk and design defects are distinguished in advance, so that the intuition, the sufficiency and the efficiency of the change influence degree analysis are improved.
Owner:SHANGHAI SNC NET INFORMATION TECH CO LTD
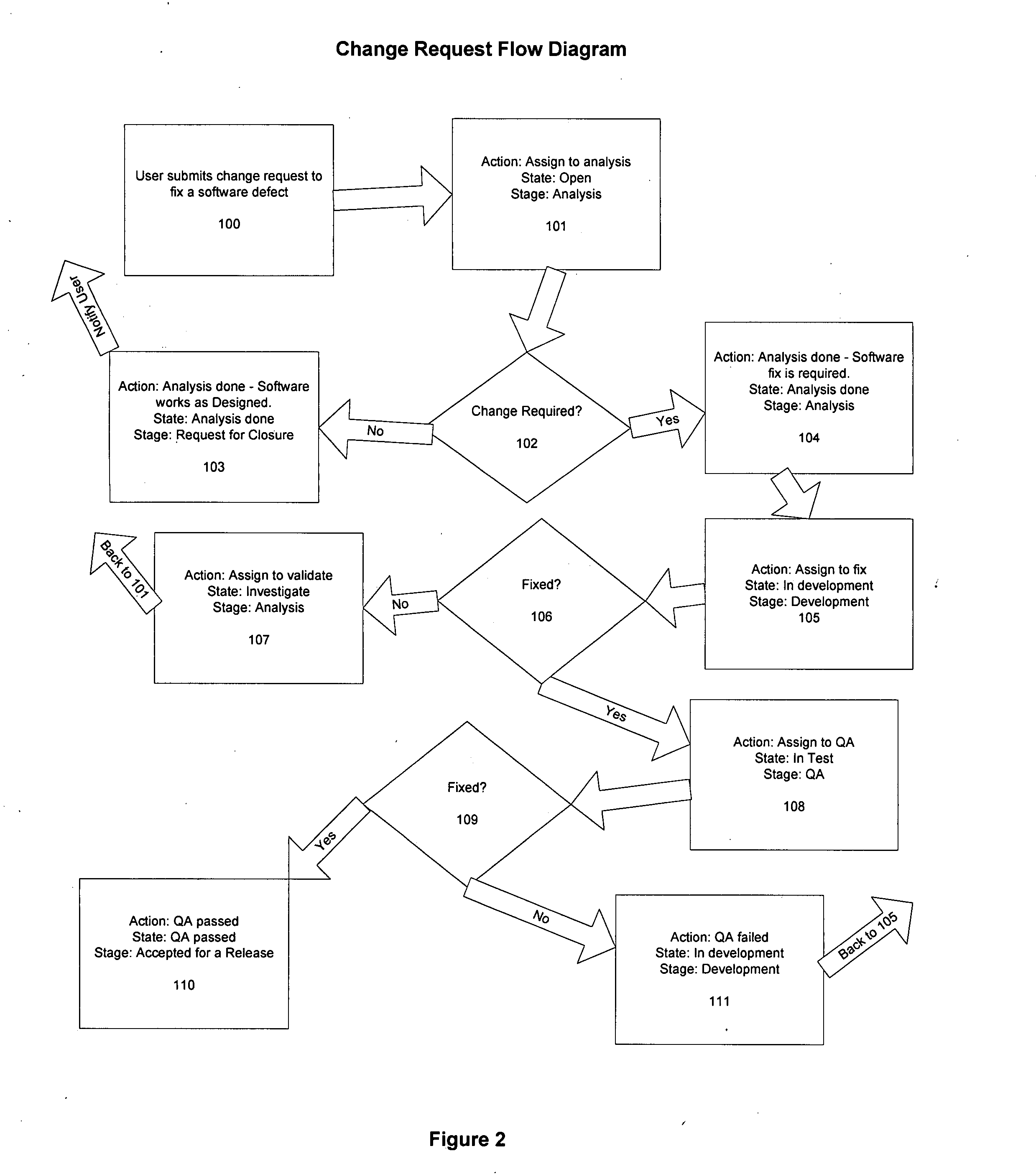
Fully integrated software change request system which includes but not limited to the following modules: change request, migration request, work flow engine project, collaboration, code movement, document tracking, code execution, status notification and database schema snapshot as well as various reporting capabilities.
InactiveUS20080216056A1Version controlSpecific program execution arrangementsDocumentation procedureSoftware development
A fully integrated Information Technology Software Development Life Cycle (SDLC) request management system comprising of a centralized database and a web interface which includes but not limited to the following modules: Change Request, Migration Request, Work Flow Engine, Project, Collaboration, Code Movement, Document Tracking, Code Execution, Status Notification and Database Schema Snapshot as well as various reporting capabilities are disclosed.The SDLC request management system is installed on a server and accessed by a plurality of users over a communication network. A request to work on a piece of software is entered by a user in the change request module. Based on the predefined setting of a default workflow, the workflow engine will route the request to the appropriate personnel. Whether or not it is determined that the request requires a change in a piece of software, a notification will be made on the system and, the collaboration module will send out emails to all involved in this request. If it is determined that work needs to be done on a piece of software then, a project will be opened for the request and the workflow engine controls the life cycle. The developed code is moved to the various environments by the code movement module and the code execution, executes the code in any environment. Project documents, databases schema and execution return status are also captured in the system.
Owner:BATE STEPHEN +1
Security policy generation based on snapshots of similar virtual machines
InactiveUS9563777B2Error detection/correctionPlatform integrity maintainanceSecurity policyVirtual machine
Determining which snapshot deltas tend to occur in: (i) healthy virtual machines (VMs) that have been subject to an attack yet remained healthy, and / or (ii) unhealthy VMs that have apparently been adversely affected by an attack. Snapshot deltas that occur in at least some (or more preferably all) of the healthy VM subset provide information about software changes (for example, updates, configuration changes) that may be helpful. Snapshot deltas that occur in at least some (or more preferably all) of the unhealthy VM subsets provide information about software changes (for example, updates, configuration changes) that may be unhelpful.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com