Patents
Literature
59 results about "Business protocols" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
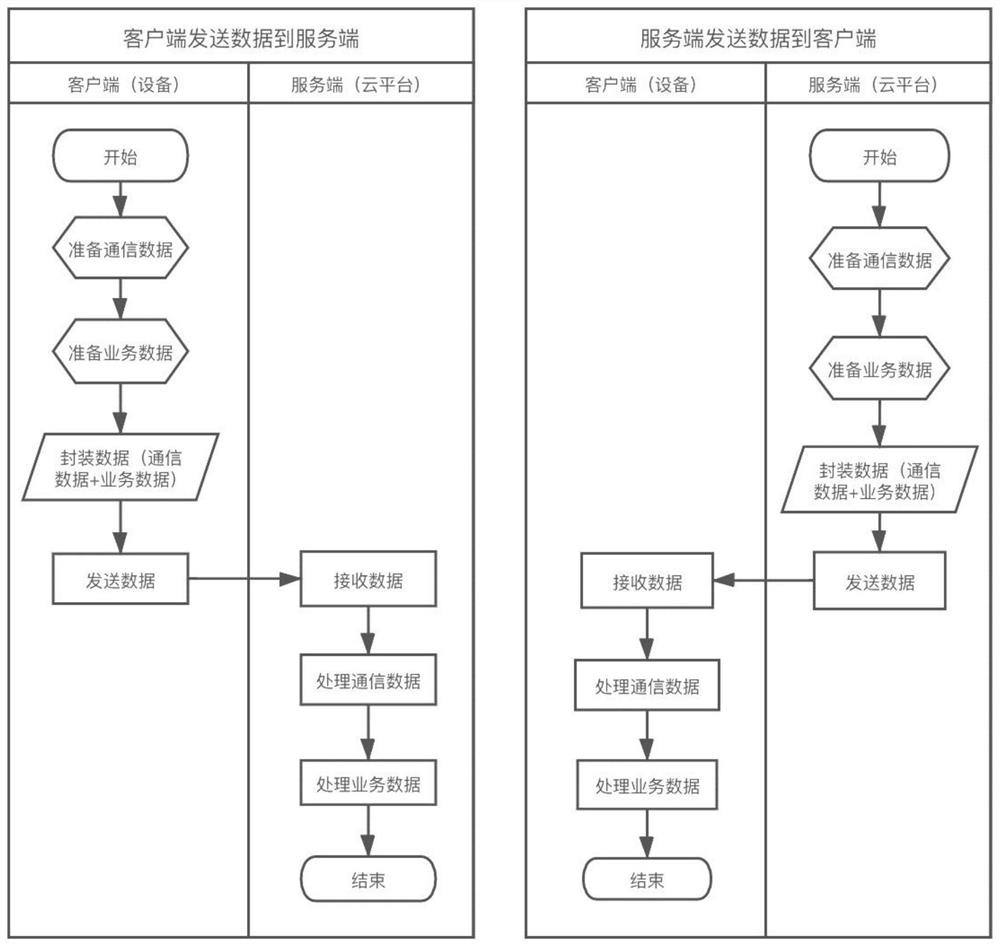
The business protocol is comprised of three protocols: document, exchange, and process (of which business actions and collaborations are a part).
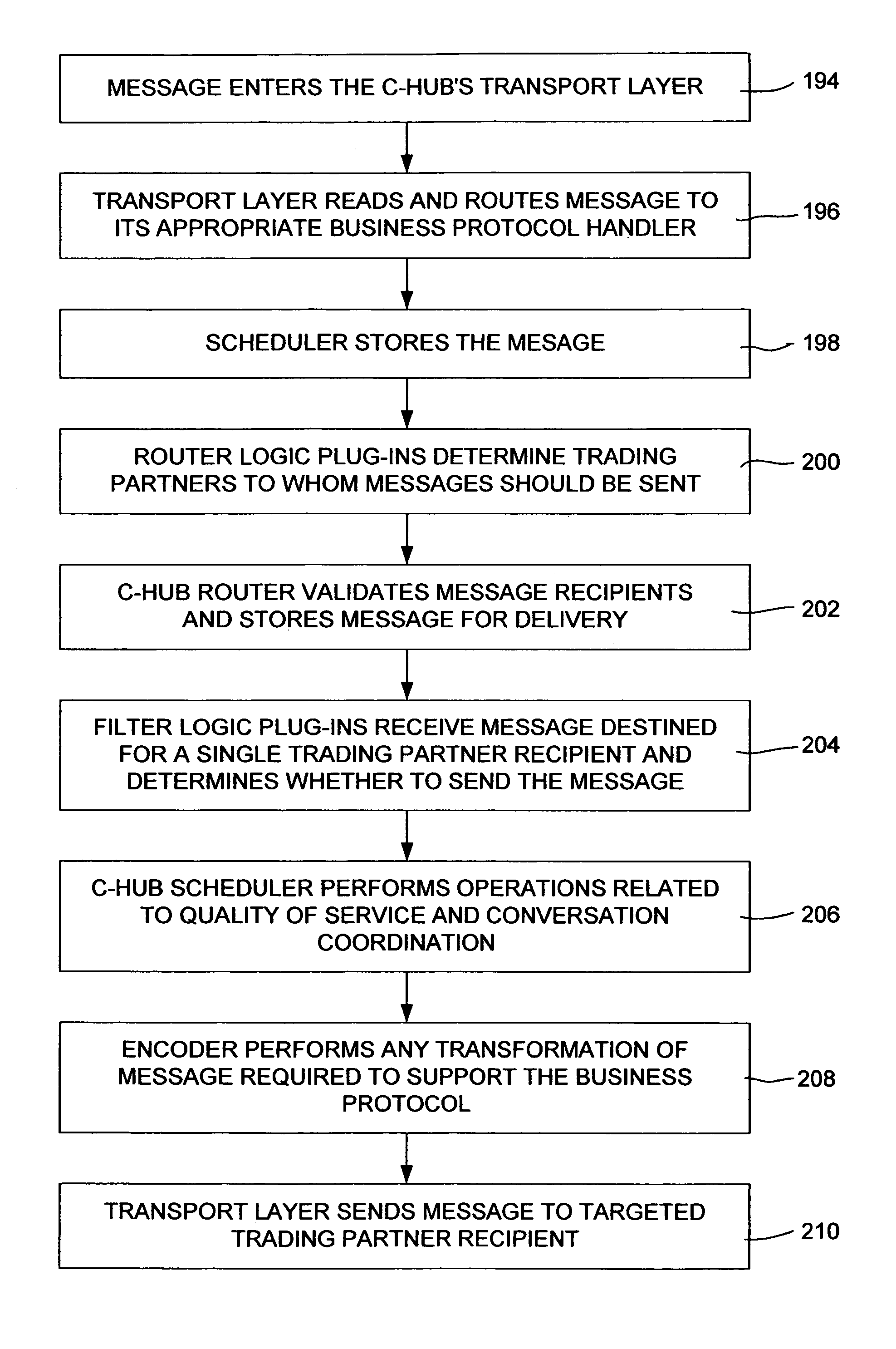
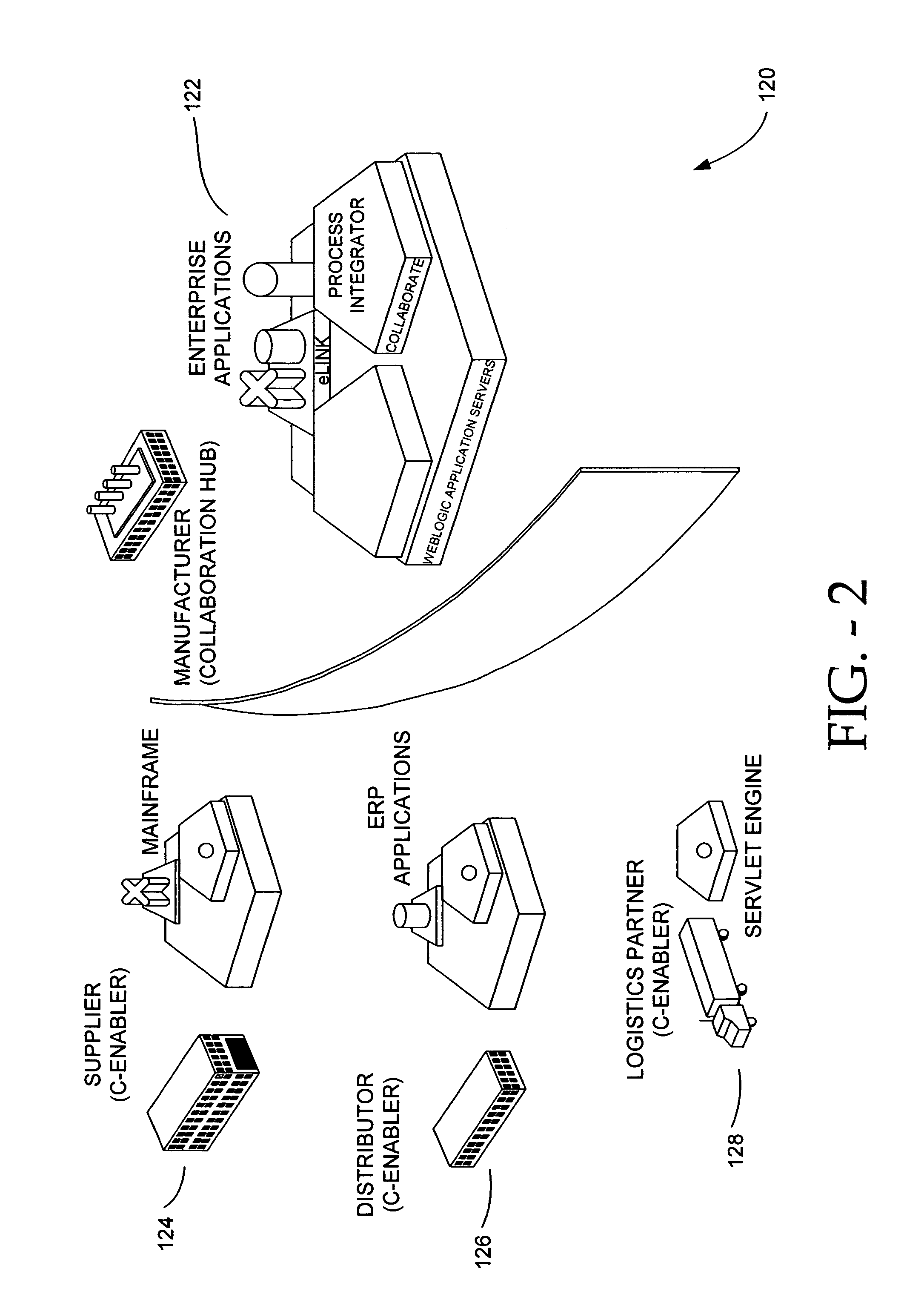
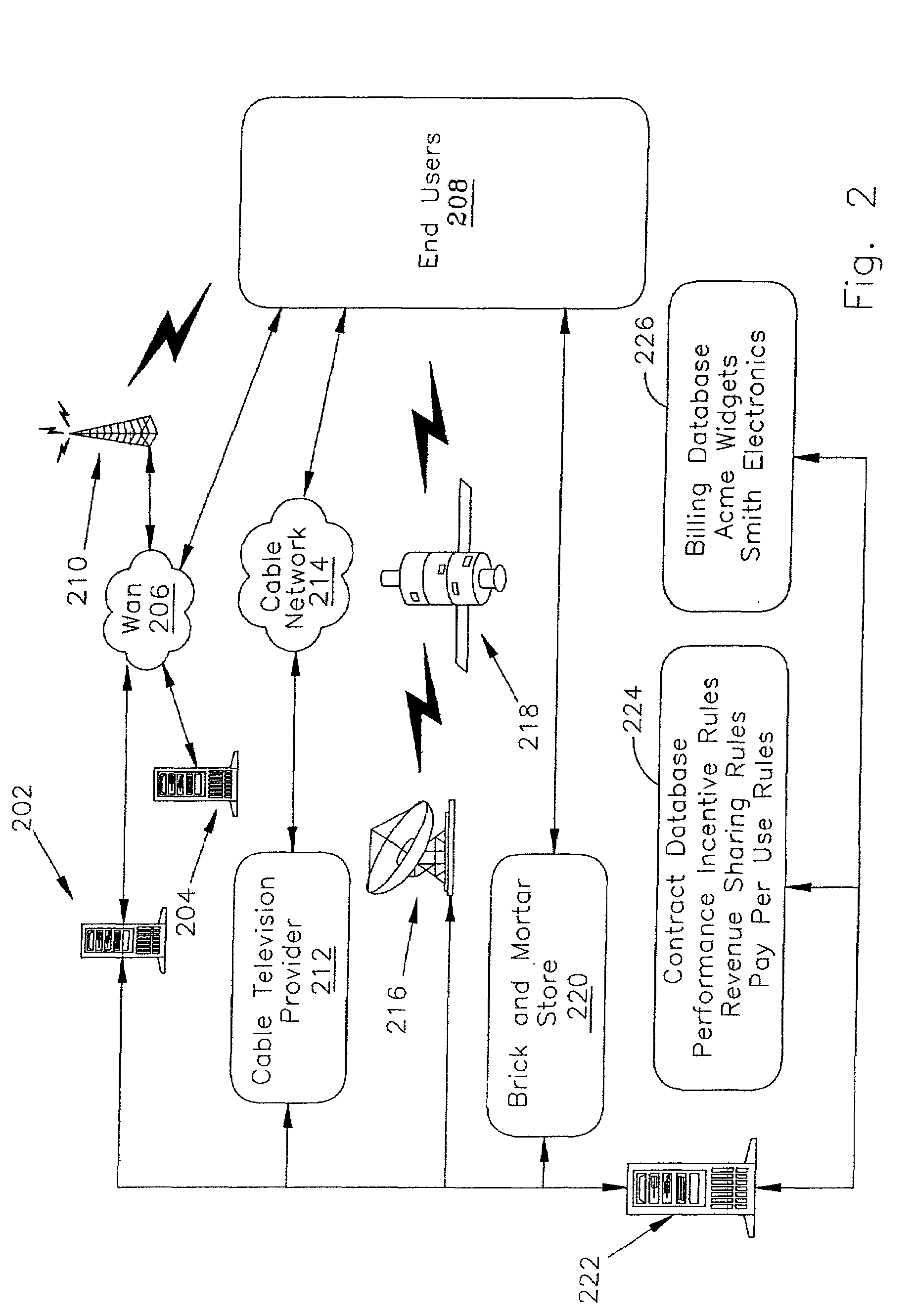
Collaboration system for exchanging of data between electronic participants via collaboration space by using a URL to identify a combination of both collaboration space and business protocol
InactiveUS7249157B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsE-commerceUniform resource locator
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides an open market collaboration system for enterprise wide electronic commerce. An embodiment of the invention includes a collaboration system that allows the exchange of data between participants in an electronic commerce environment, comprising a collaboration hub for the transfer of data between participants, a collaboration space defining the rules governing said transfer of data and the role of said participants, and a hub transport that allows a participant to send and receive data from the collaboration hub in accordance with the definitions of the collaboration space.
Owner:ORACLE INT CORP
Secure Internet E-Commerce
InactiveUS20080306877A1Improved consumer convenience managingImprove filtering effectDigital data authenticationBilling/invoicingPaymentInvoice
A secure Internet based website electronically facilitating Internet entry of an account-owner to a pre-registered account on the secure Internet based website; escorting the owner to a merchant Internet site and therewith transmitting to the merchant site a one-time password, wherein said one-time password is thereafter identifiable by the secure Internet based website; receiving an invoice from the merchant Internet site wherein said invoice includes the one-time password; validating the one-time password; and presenting the invoice to the account owner. Now, if the secure Internet site receives an invoice approval from the owner, then the secure Internet site electronically providing the merchant Internet site with payment and delivery details necessary to complete a commercial agreement between the owner and the merchant wherein said agreement corresponds to specification, terms, and conditions associated with the invoice.
Owner:P C S M
Distributed transaction event matching
InactiveUS7552205B2Multiple digital computer combinationsPayment protocolsMultiple platformDistributed computing
Owner:ACCENTURE GLOBAL SERVICES LTD
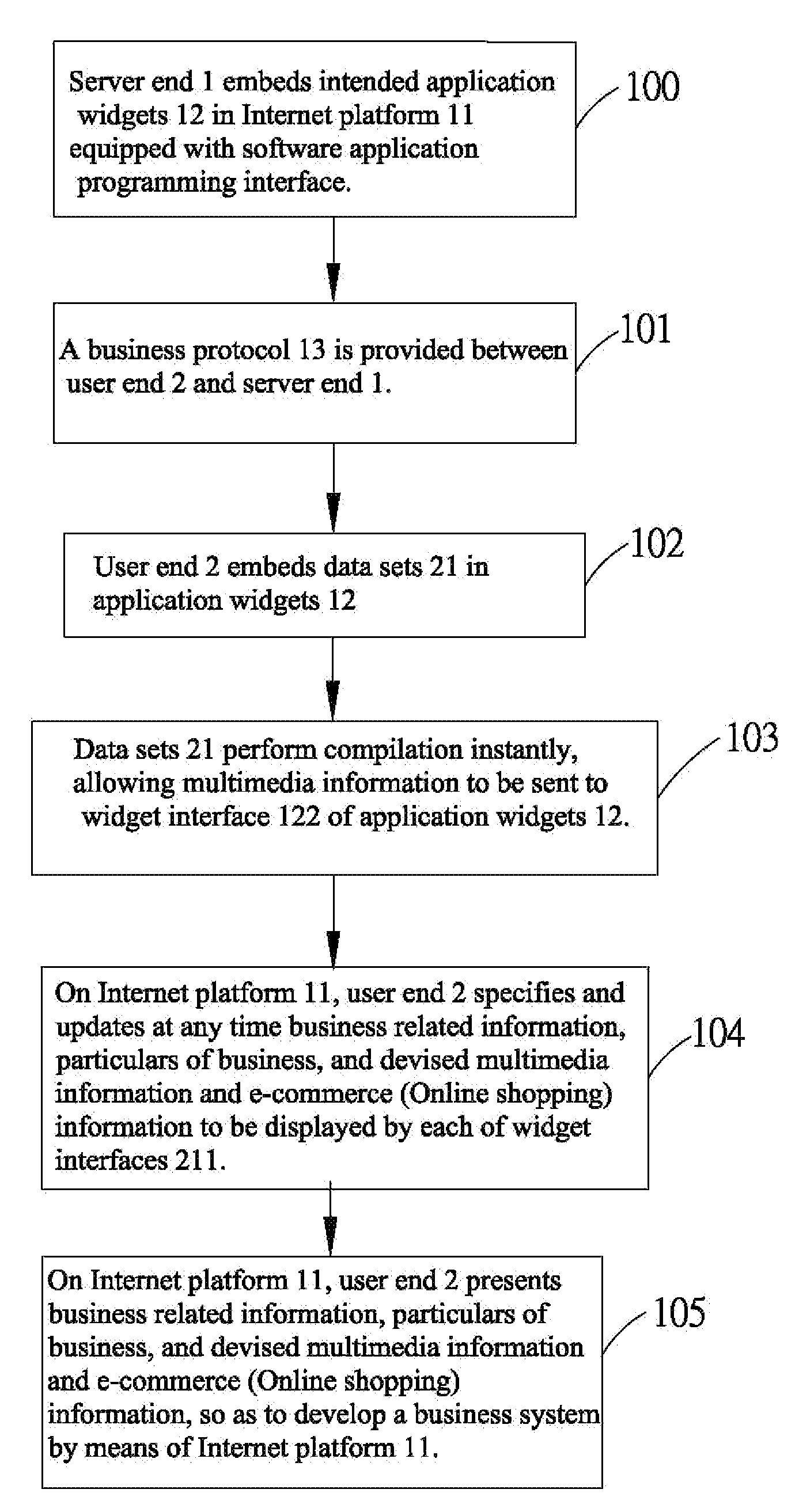
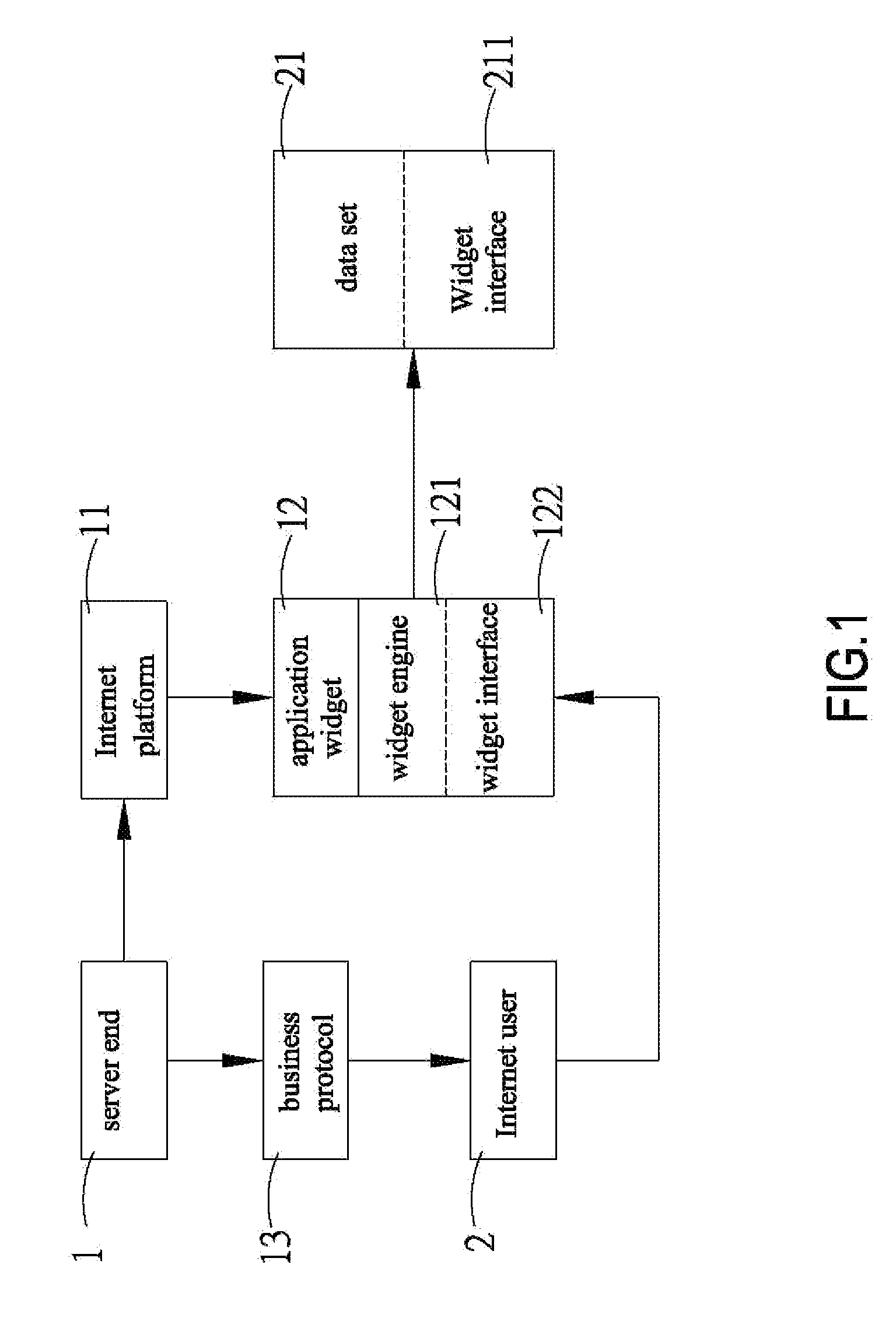
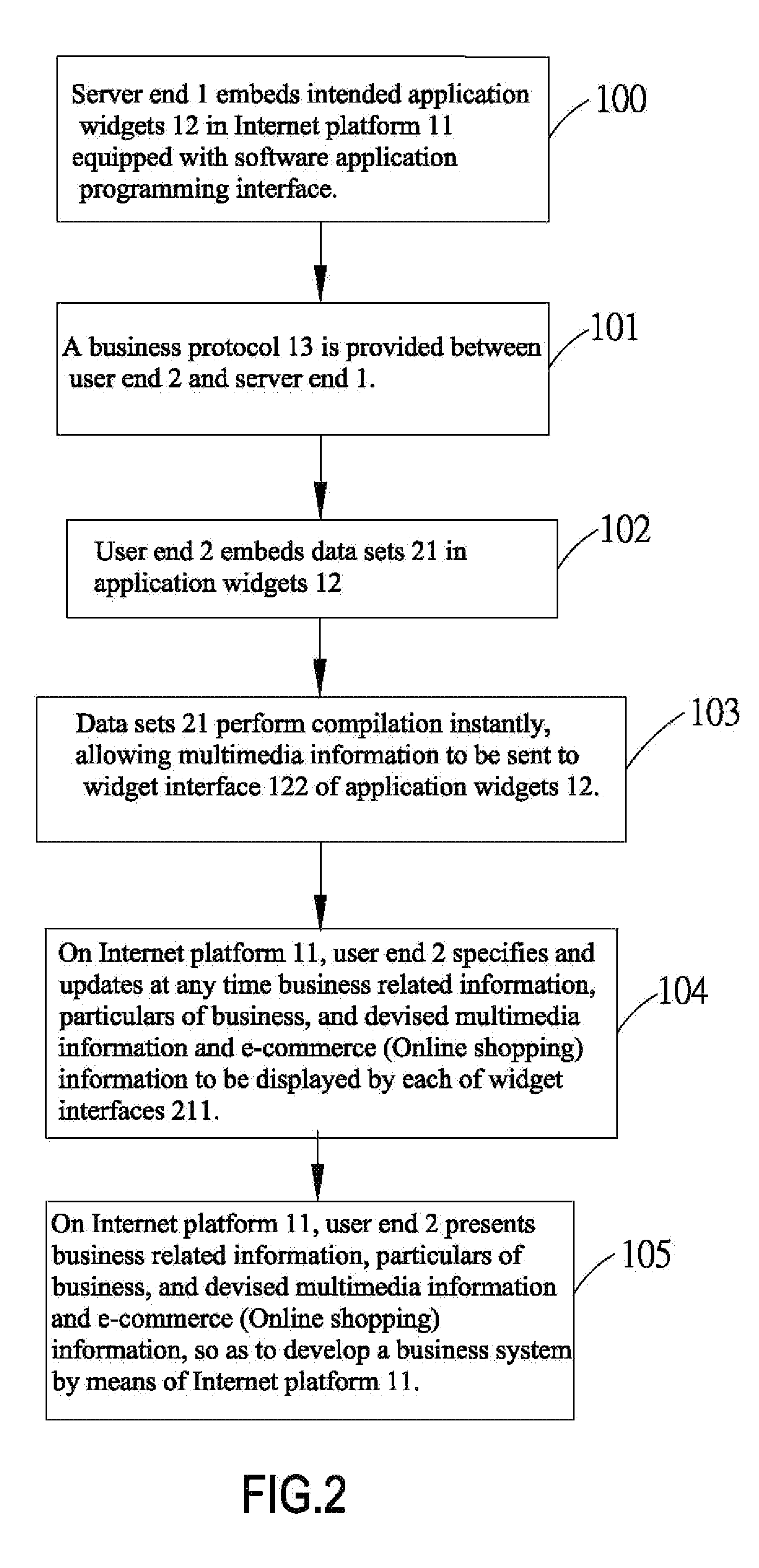
Business model based on multi-level application widgets and system thereof
ActiveUS20100114729A1Addressing slow performanceReal-time interactionBuying/selling/leasing transactionsData setApplication programming interface
Provided is a business model based on multi-level application widgets and a system thereof, including: embedding, by a server end, intended application widgets in an Internet platform equipped with a software application programming interface; providing a business protocol between a user end and the server end, thus giving the user end authority to embed data sets in the application widgets and to conduct display, operation, sales, and real-time interaction within the same window; determining, by the user ends, whether at least an application widget or a data set is to be embedded in each of the data sets again, so as to finalize the multi-level application widgets. Accordingly, the user end enhances promotion and thereby expands business on the Internet platform at the server end.
Owner:CHU YU HUA
Method and system for detecting white list of data stream based on regular expression
ActiveCN110661680APrecise detection and protectionOther databases queryingData switching networksData packService protocol
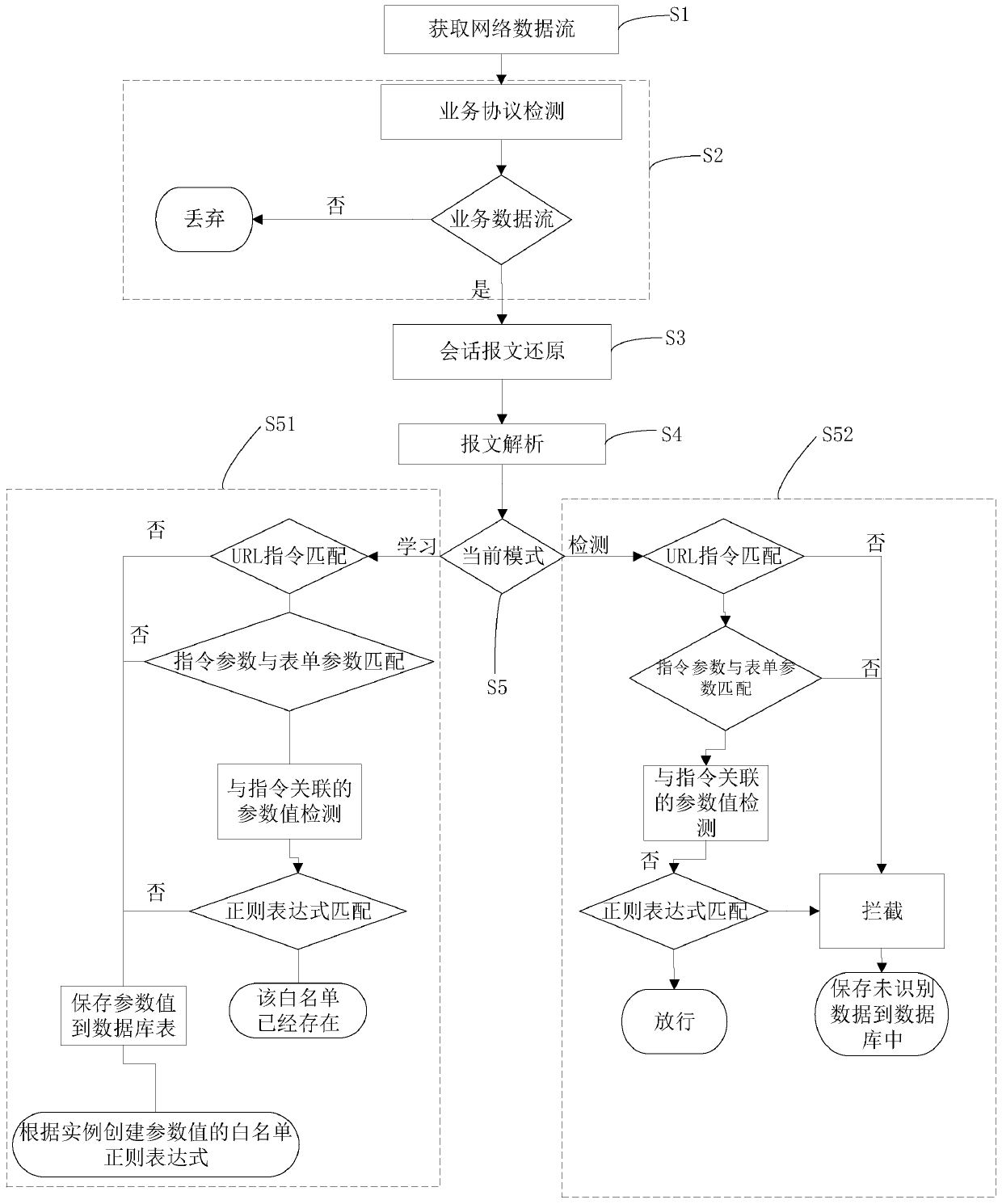
The invention discloses a method for detecting a white list of a data stream based on a regular expression. The method comprises the following steps: S1, acquiring a network data stream; S2, detectinga service protocol: carrying out service protocol detection on the network data flow, and judging whether the network data flow conforms to a service protocol or not; if the judgment result of the service protocol is no, discarding the service protocol; if the service protocol judgment result is yes, identifying the network data flow as a service data flow, and executing the next step; S3, restoring the session message to obtain a complete message; S4, making message analysis on the complete message to obtain message data, wherein the message data comprises a parameter value, an instruction and an instruction parameter; and S5, executing white list learning processing or white list detection processing on the message data according to the current mode. The invention further discloses thesystem for detecting white list of the data stream based on a regular expression. The recognizable effective service data stream is released, and data of various new and old attack behaviors is marked as abnormal service stream data to be intercepted so as to carry out accurate detection and protection on the system.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Business protocol index data collecting method and system
ActiveCN107026767AImplement auto-discoveryRapid positioningData switching networksTraffic capacityLinux kernel
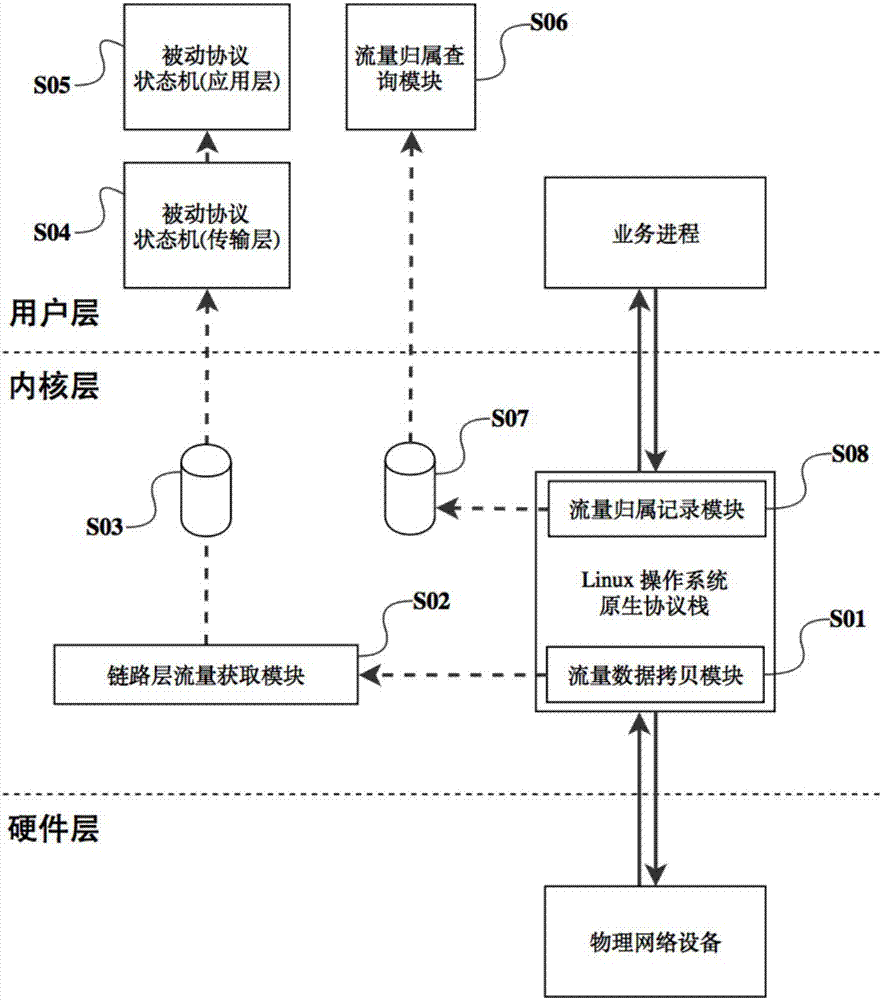
The invention provides a business protocol index data collecting method and system. The method comprises the following steps: using acquired business traffic to drive state transition of a protocol stack by use of a passive protocol stack analysis technology; correctly subjecting the traffic data to a source procedure and a target procedure, and automatically bringing the service of the target procedure into a monitoring object so as to realize the automatic discovery of the monitoring object; automatically deducing the business association information between the services after correctly subjecting the traffic data to the source and target procedures; correctly recognizing an abnormal source service object according to the association between the services of the procedures when a linkage abnormality is produced, thereby helping an operation and maintenance staff to fast position the abnormality; acquiring the traffic data by use of a pure bypass way, wherein the monitoring way has no any invasive requirement on the business party; and inserting a traffic data copying module in an Linux kernel module so as to acquire the complete physical traffic at the two-layer packet level, wherein the acquired data is more complete.
Owner:SHANGHAI QINIU INFORMATION TECH
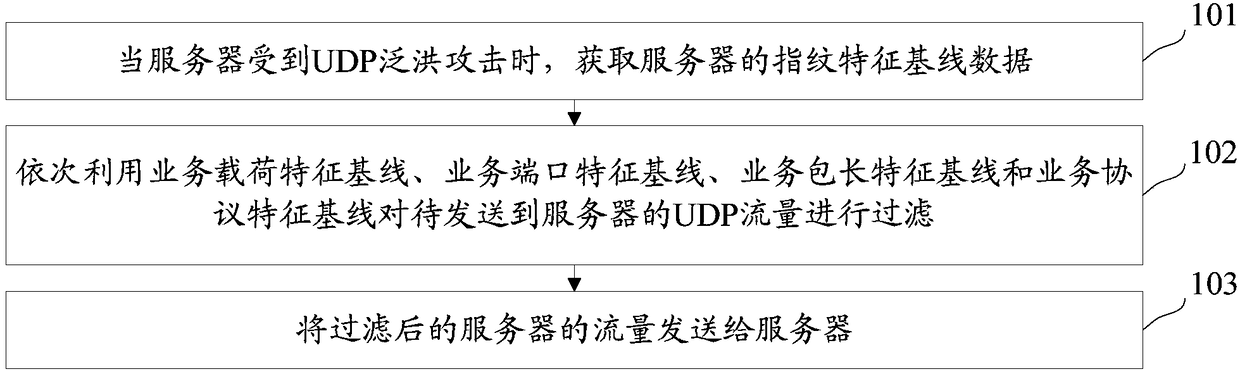
User datagram protocol traffic filtering method and device, server and memory medium
ActiveCN108737447ANo out of serviceImprove the protective effectTransmissionBaseline dataTraffic capacity
The invention discloses a user datagram protocol traffic filtering method and device, a server and a memory medium and belongs to the field of network security. The method comprises the steps of obtaining fingerprint feature baseline data of the server when the server bears a user datagram protocol flooding attack, wherein the fingerprint feature baseline data comprises a business load feature baseline, a business port feature baseline, a business packet length feature baseline and a business protocol feature baseline; and filtering user datagram protocol traffic which is about to be sent to the server, through sequential utilization of the business load feature baseline, the business port feature baseline, the business packet length feature baseline and the business protocol feature baseline, until the user datagram protocol traffic which is about to be sent to the server in the unit time is smaller than a security threshold; and sending the filtered traffic to the server.
Owner:TENCENT TECH (SHENZHEN) CO LTD
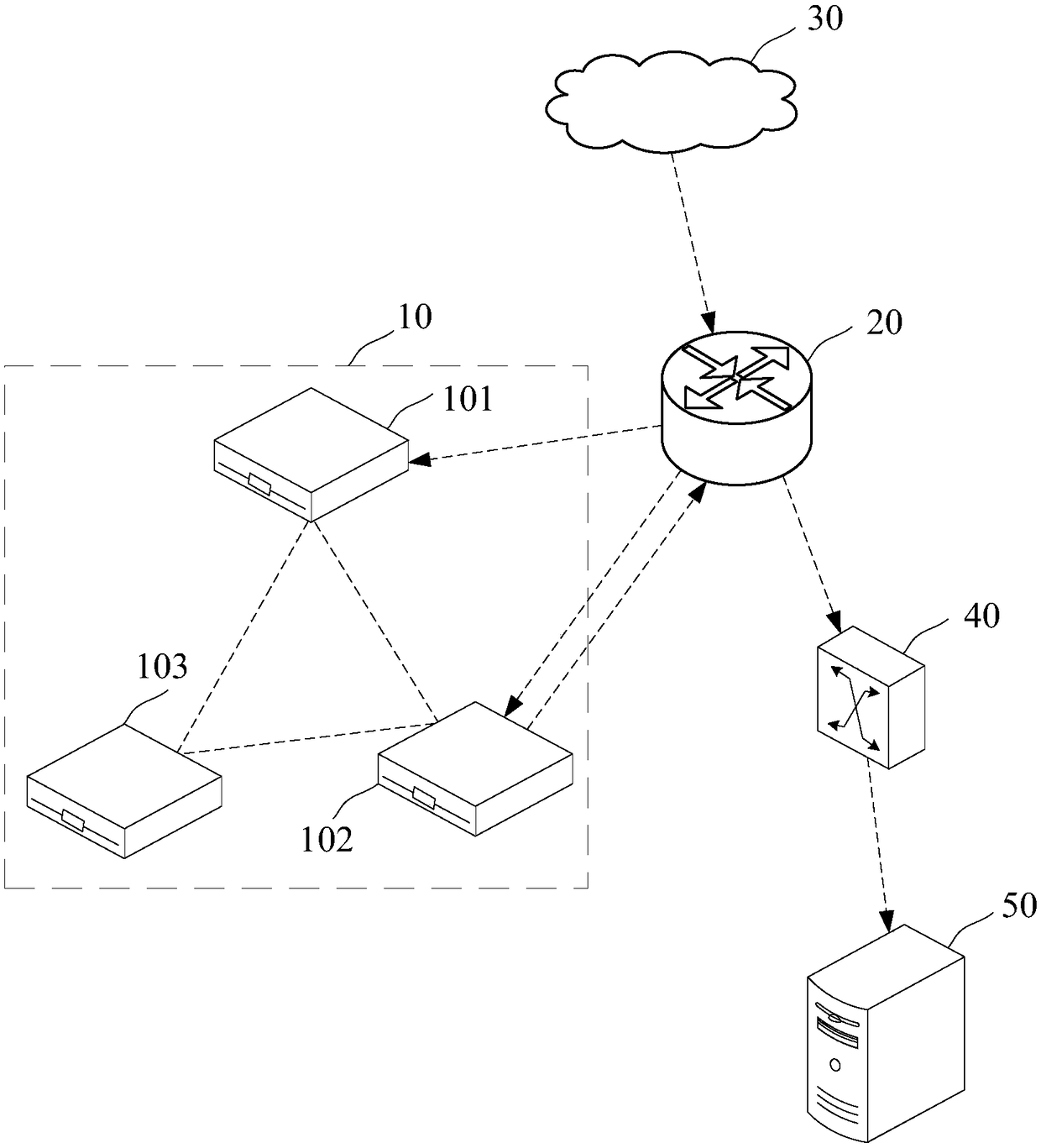
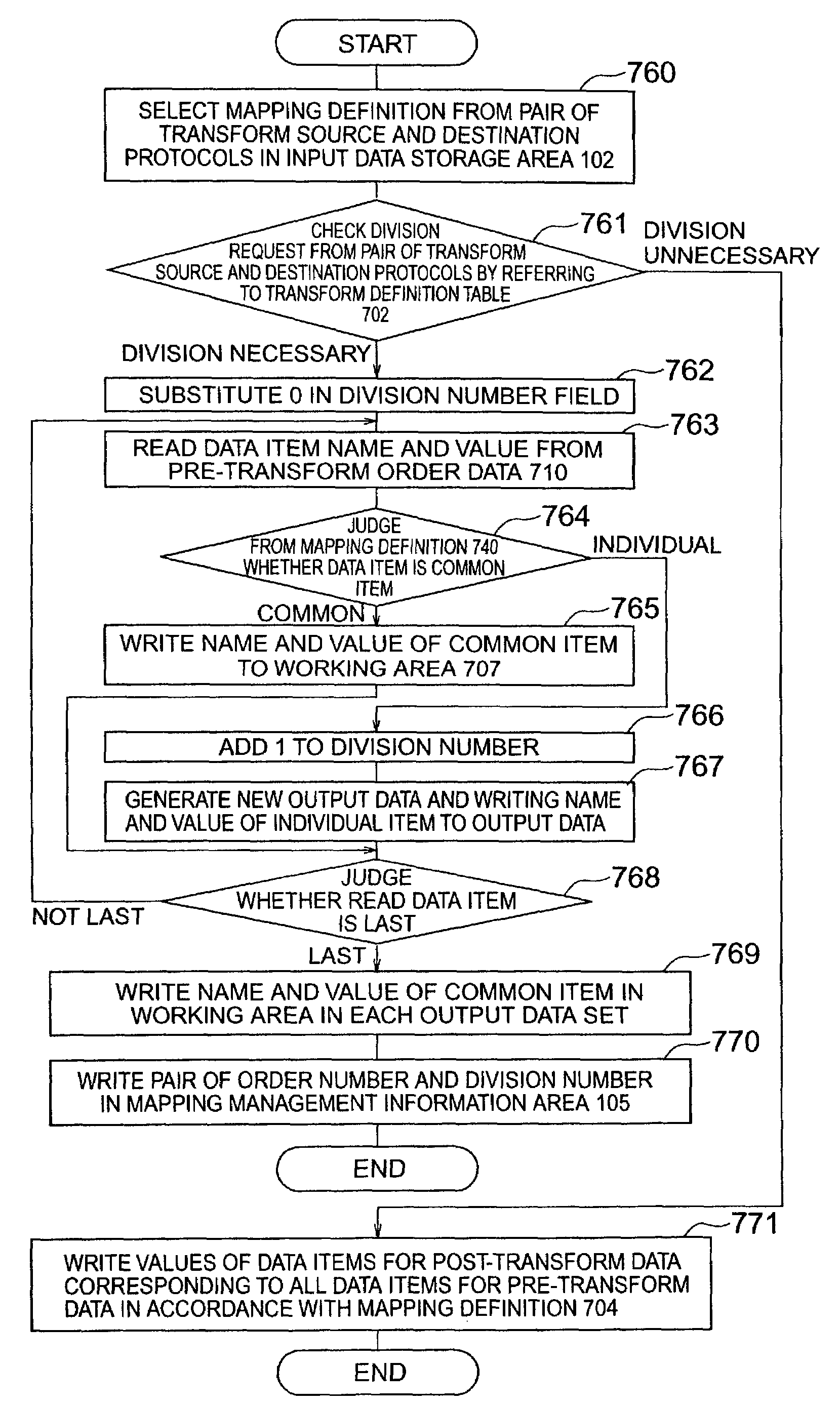
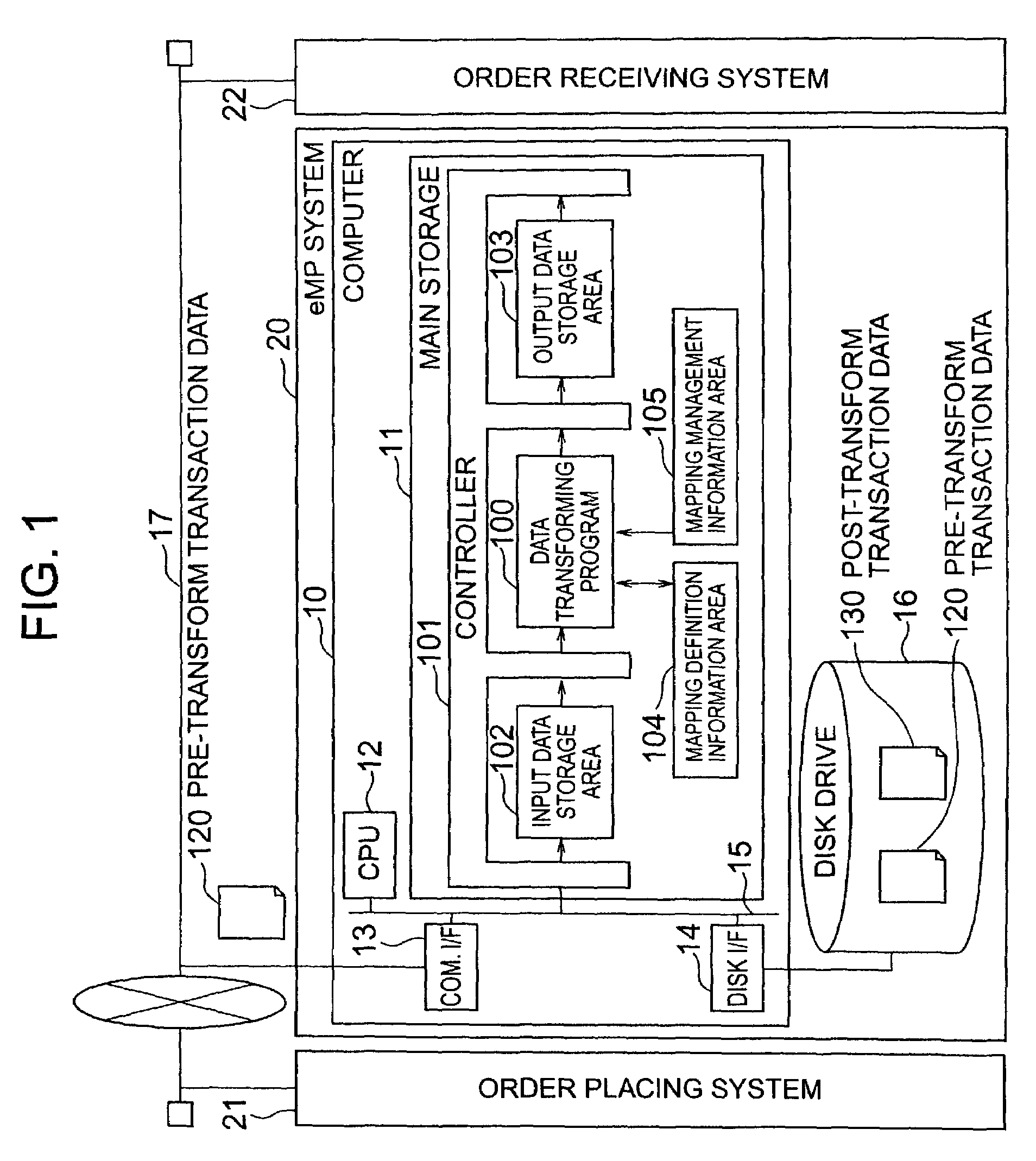
Method for transforming data between business protocols
InactiveUS7257637B2Multiple digital computer combinationsBuying/selling/leasing transactionsTransaction dataDatabase
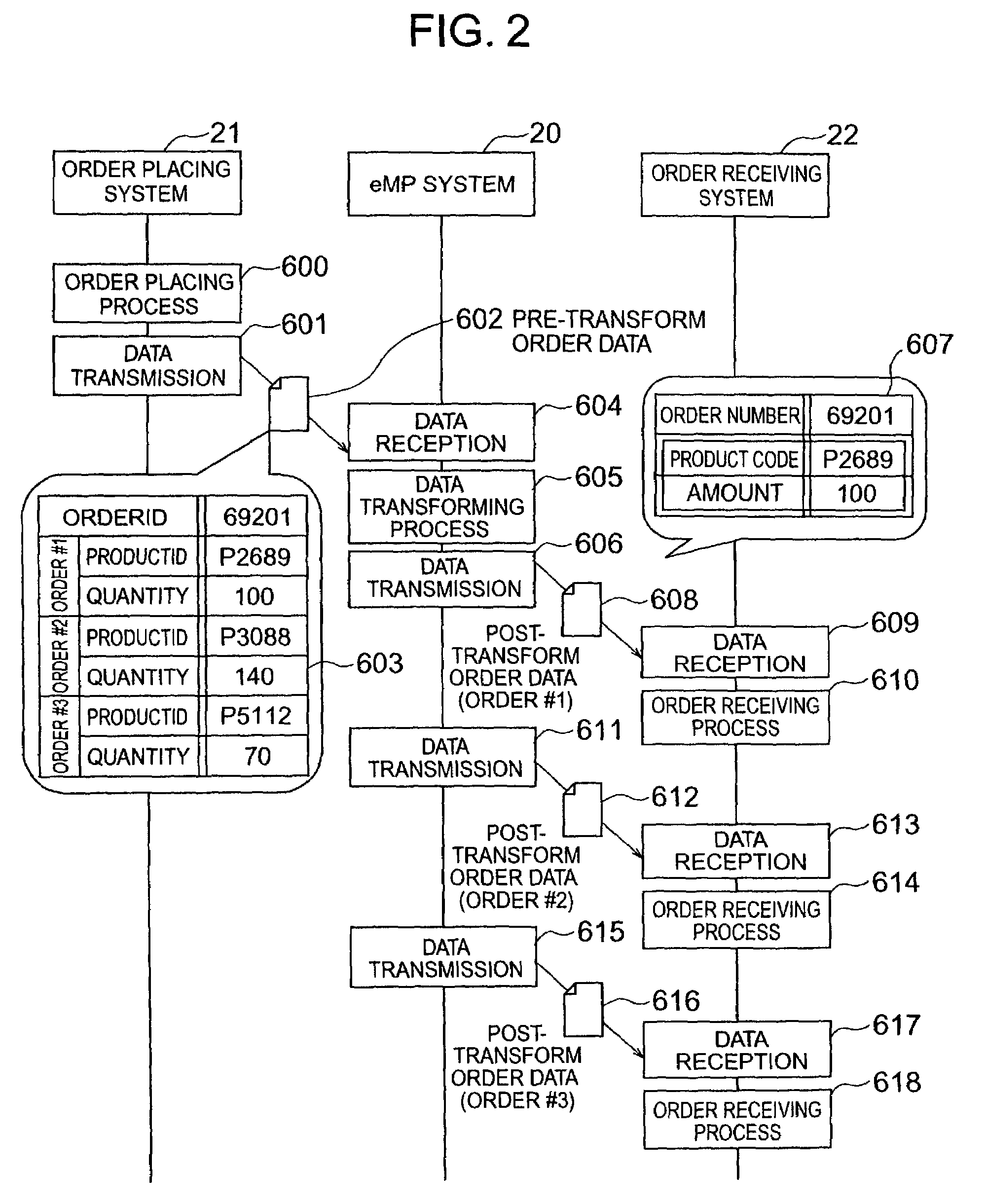
A data transforming method is provided which can perform a transforming process of transforming collective order data for a plurality of products into individual order data for each individual product and a transforming process in which order data is inherited to a response data transforming process. For each combination of transform source and destination protocols, various designation information is stored beforehand in a mapping definition information area and transaction data is transferred in accordance with the designation information. Designation information includes information of a request for an individual order data division process and a collective response data collection process and information of a correspondence between data items of transaction data.
Owner:HITACHI LTD
Business protocol policy injection
InactiveUS20050261918A1CommerceSpecial data processing applicationsBusiness activitiesBiological activation
The present invention is a method, system and apparatus for for dynamic business protocol based policy injection in a cross-enterprise business process management system. In accordance with the present invention, a defined business process can be re-factored to permit the handling of business process transformation events. Moreover, one or more mappings to the event handlers can be registered as can one or more business transformation operatives configured to specify the activation of specific business activities at particular places within the business process. Once re-factored, the business process can be “seeded” with a business process transformation policy. Subsequently, upon receipt of a business process transformation event, the instance of the business transformation operative can be located and the specific business activities can be activated and the business process can be suitably configured according to the mapped business transformation operatives and through the operation of the event handlers.
Owner:IBM CORP
Data transmission method and device between 5G core network and power service platform
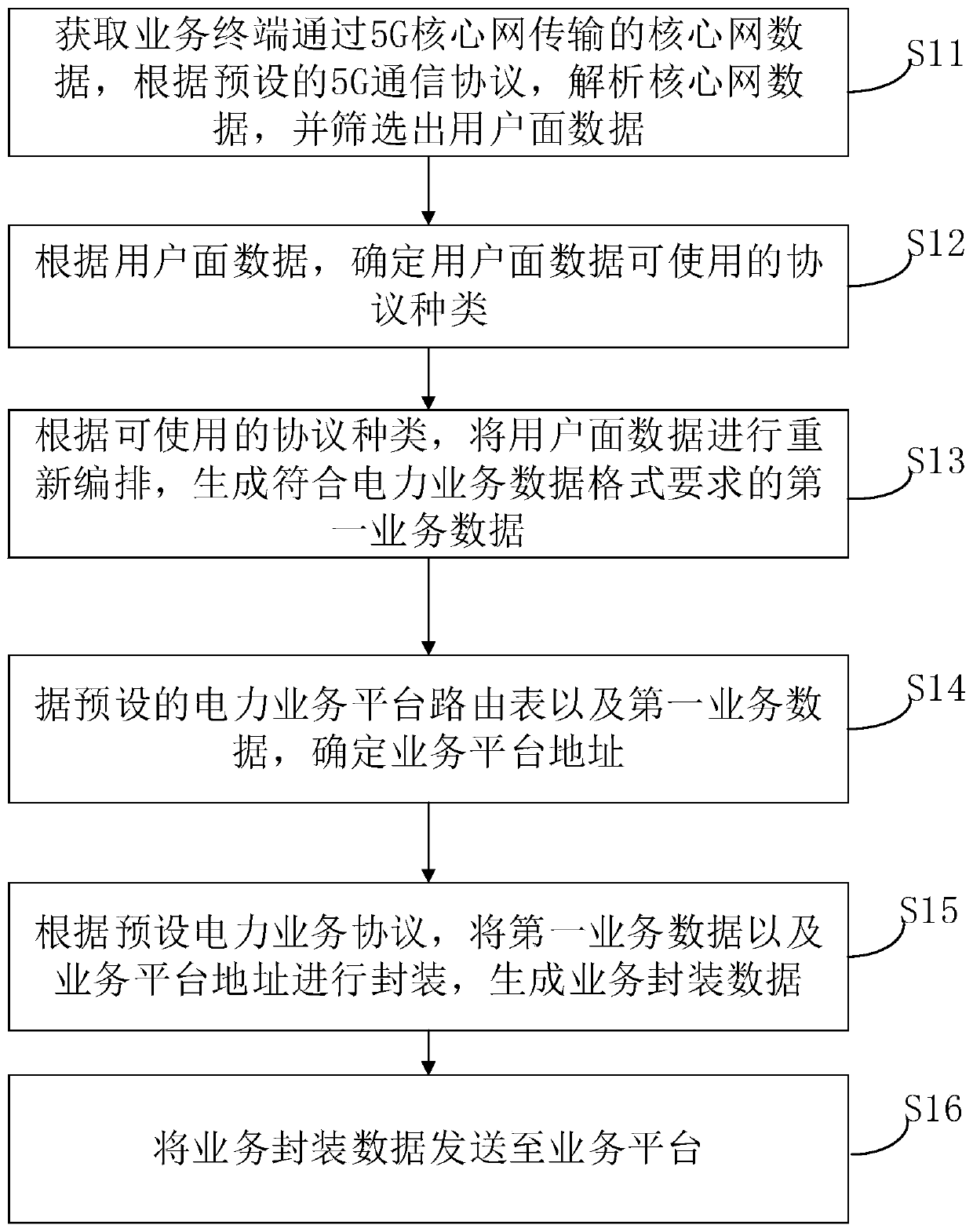
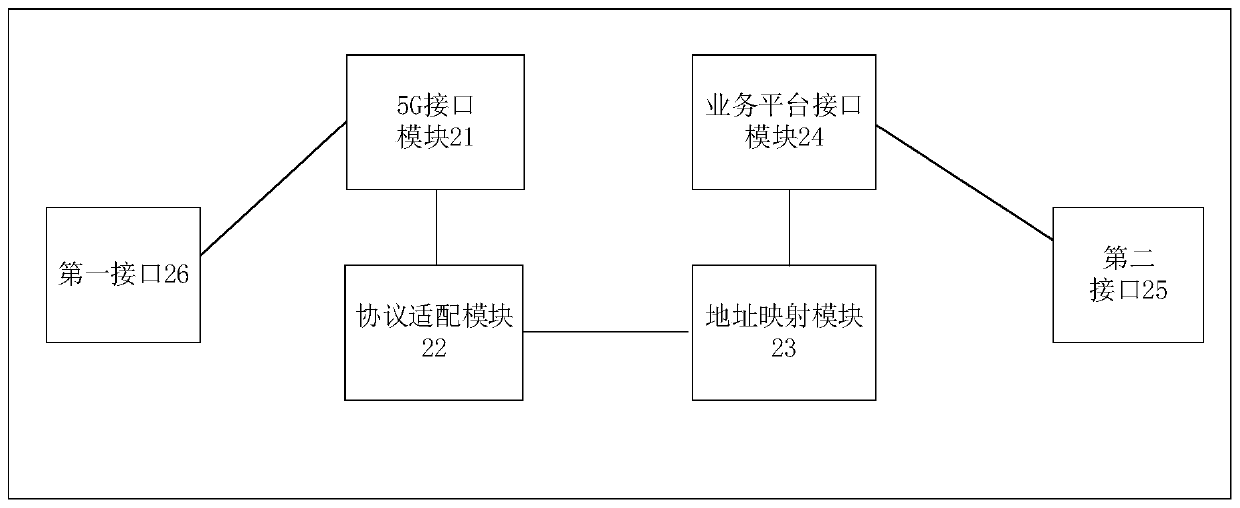
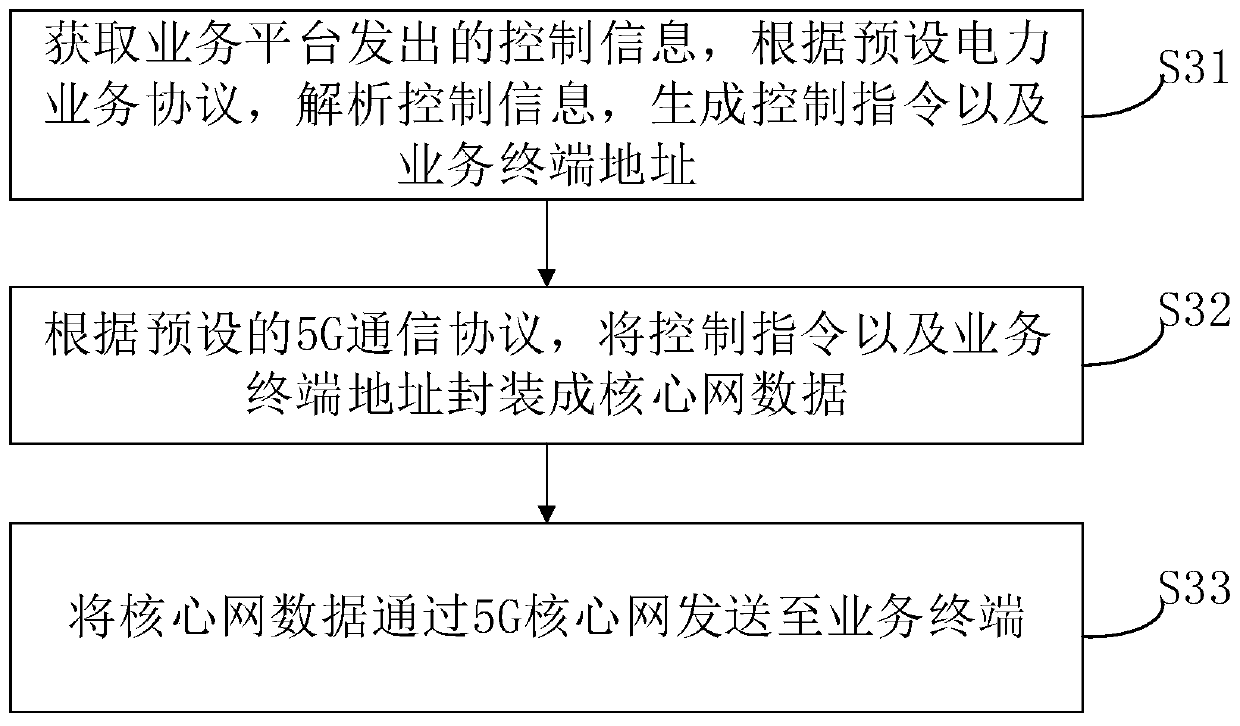
PendingCN111491032AStable supportRealize intelligent upgradeTransmissionInstrumentsComplete dataEncapsulated data
The embodiment of the invention provides a data transmission method and device between a 5G core network and a power service platform. The method comprises the following steps: receiving core networkdata transmitted by a power service terminal through a 5G core network, analyzing the core network data according to a preset 5G communication protocol, screening out power business data generated bythe power business terminal; and determining an adaptive power business protocol according to the user plane data, rearranging the user plane data to generate data meeting the format requirement of the power business data, determining a corresponding destination address, generating business encapsulation data, and sending the business encapsulation data to a corresponding power business platform to complete data transmission. By implementing the invention, the problem that the power service data and the 5G mobile communication technology cannot be compatible and adapted in the prior art is solved, the bidirectional data interaction between the power service platform and the power service terminal through the 5G is realized, and the application advantages of the 5G in the power grid are fully exerted.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +1
Online payment system, online payment method and device, medium and server
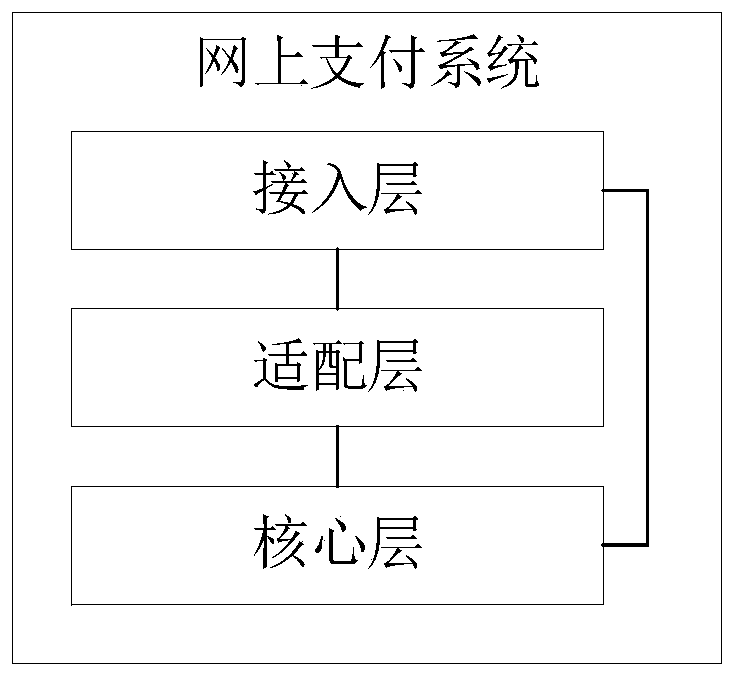
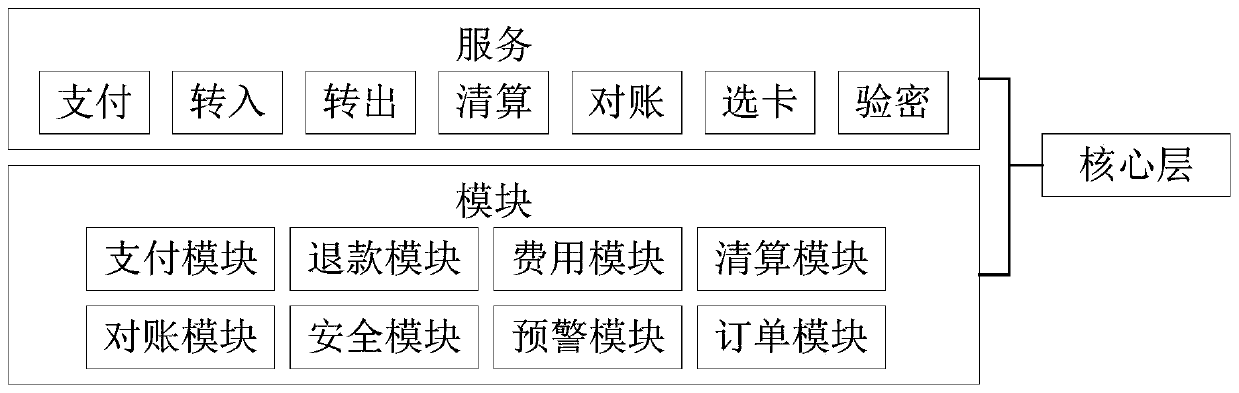
PendingCN110874728AReduce couplingQuick responsePayment protocolsPoint-of-sale network systemsComputer architectureEmbedded system
The embodiment of the invention is suitable for the technical field of payment and provides an online payment system, an online payment method and device, a medium and a server. The system comprises an access layer, an adaptation layer and a core layer, wherein the access layer is used for detecting a payment instruction transmitted through any payment channel, identifying a payment carrier for generating the payment instruction, calling an interface corresponding to the payment carrier, and transmitting the payment instruction to the adaptation layer and the core layer through the interface;the adaptation layer is used for determining the payment channel for transmitting the payment instruction and providing a target business protocol adapted to the payment channel for the core layer; and the core layer is used for calling a target function module corresponding to the payment channel based on the target business protocol, and executing the payment instruction by adopting the target function module. According to the embodiment of the invention, the system architecture is designed in a layered manner, so that the coupling degree between modules of each layer is reduced, the serviceexpansion is facilitated, and the quick response to service requirements is realized.
Owner:PING AN BANK CO LTD
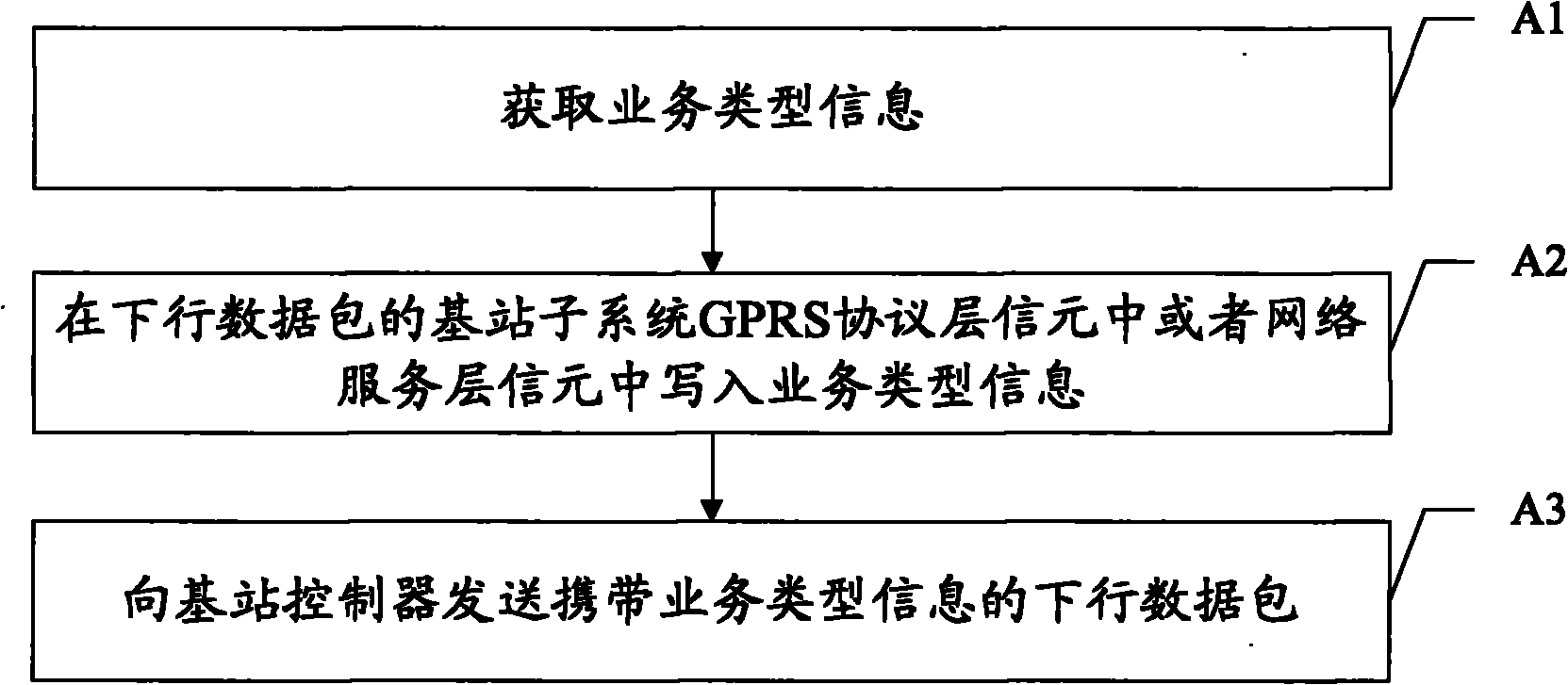
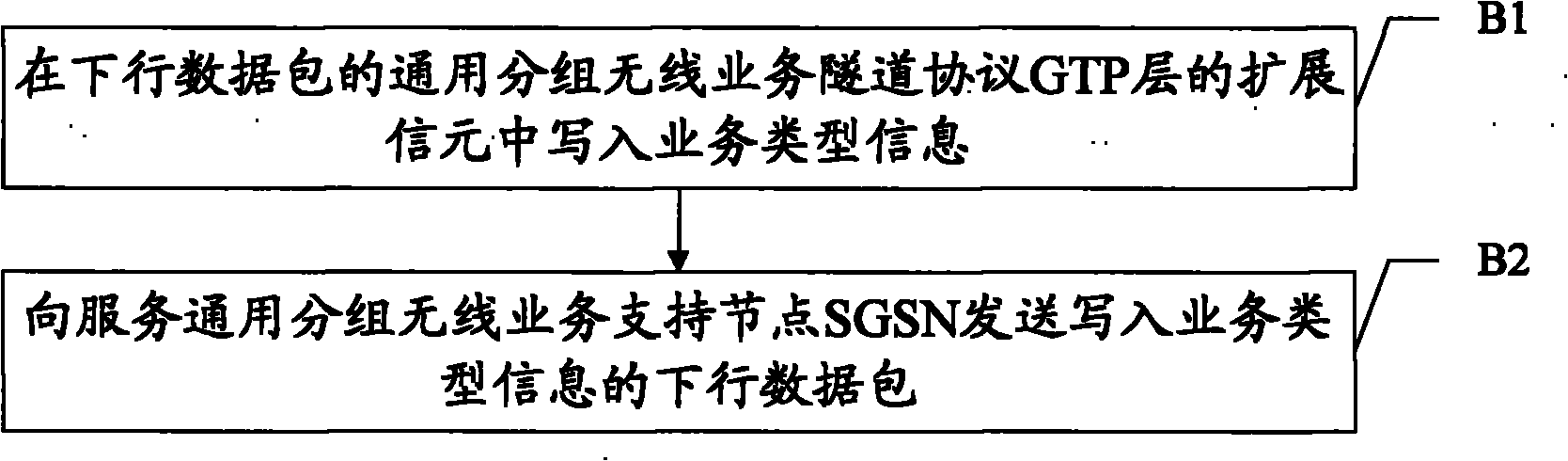
Business type information transferring method, system and associated equipment
ActiveCN102137343AReduce processing loadReduce processingAssess restrictionConnection managementNetwork packetNetwork service
The invention discloses a business type information transferring method, a system and associated equipment. The method comprises the steps of obtaining business type information, writing the business type information in a cell of a general packet wireless business protocol BSSGP (Base Station System GPRS protocol) layer or a cell of a network service layer of a base station subsystem of a downlink packet, and sending the downlink packet carrying the business type information to a base station controller. The embodiment of the invention can reduce the times of processing a protocol stack when the base station controller obtains the business type information, thus lightening the processing load of the base station controller.
Owner:HUAWEI TECH CO LTD
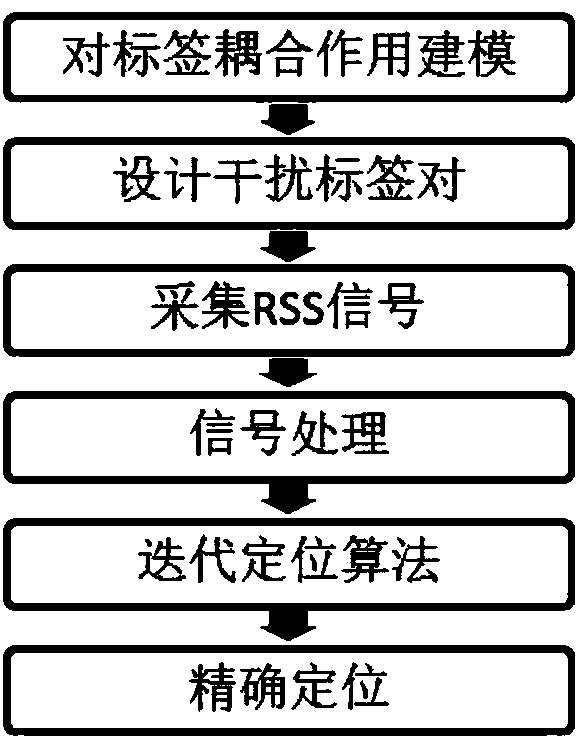
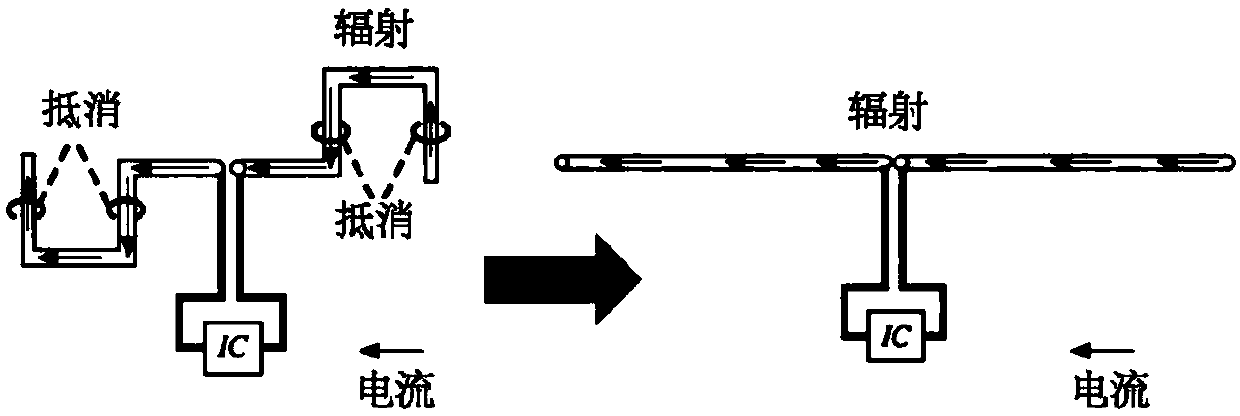
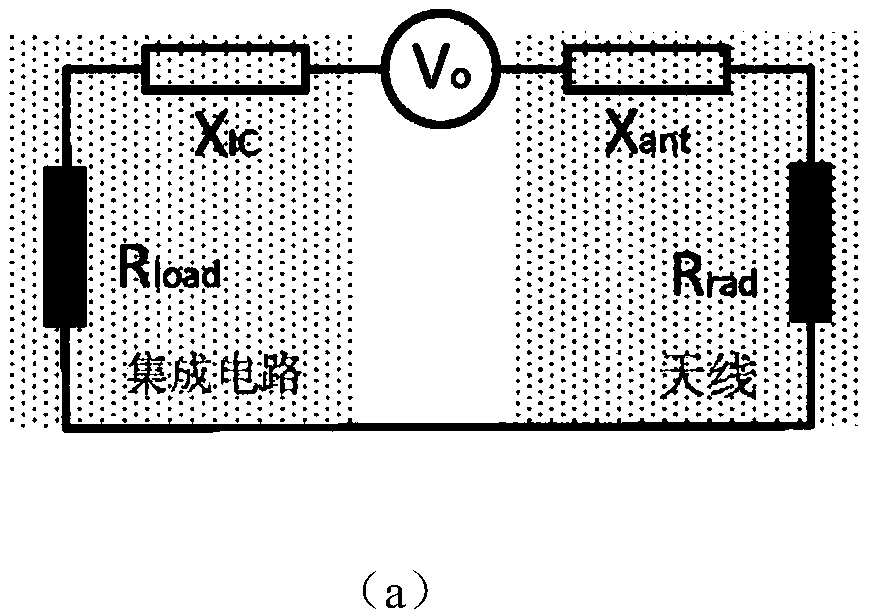
Ultrahigh frequency RFID label accurate positioning method based on label coupling effect
ActiveCN108549922AAchieve precise positioningLow costRecord carriers used with machinesSensing by electromagnetic radiationAntenna designRSS
The invention discloses an ultrahigh frequency RFID label accurate positioning method based on a label coupling effect; based on existing business protocols, the method can use a business RFID deviceand a single antenna to accurately position a target label without pre-training a database. The method comprises the following steps: studying an antenna design mode of RFID labels, building an equivalent circuit and modeling a label coupling effect, and designing to obtain a reasonable interference label pair under theory support; enabling a RFID reader to work under a fixed frequency mode, moving the interference label pair, tracking influences on the target label RSS by the interference label pair, and accurately positioning the target label via signal processing and iteration positioning.The positioning method only needs one RFID antenna and a RFID label group to finish accurate positioning, includes absolute positioning and relative positioning, and is low in cost and high in precision.
Owner:XI AN JIAOTONG UNIV
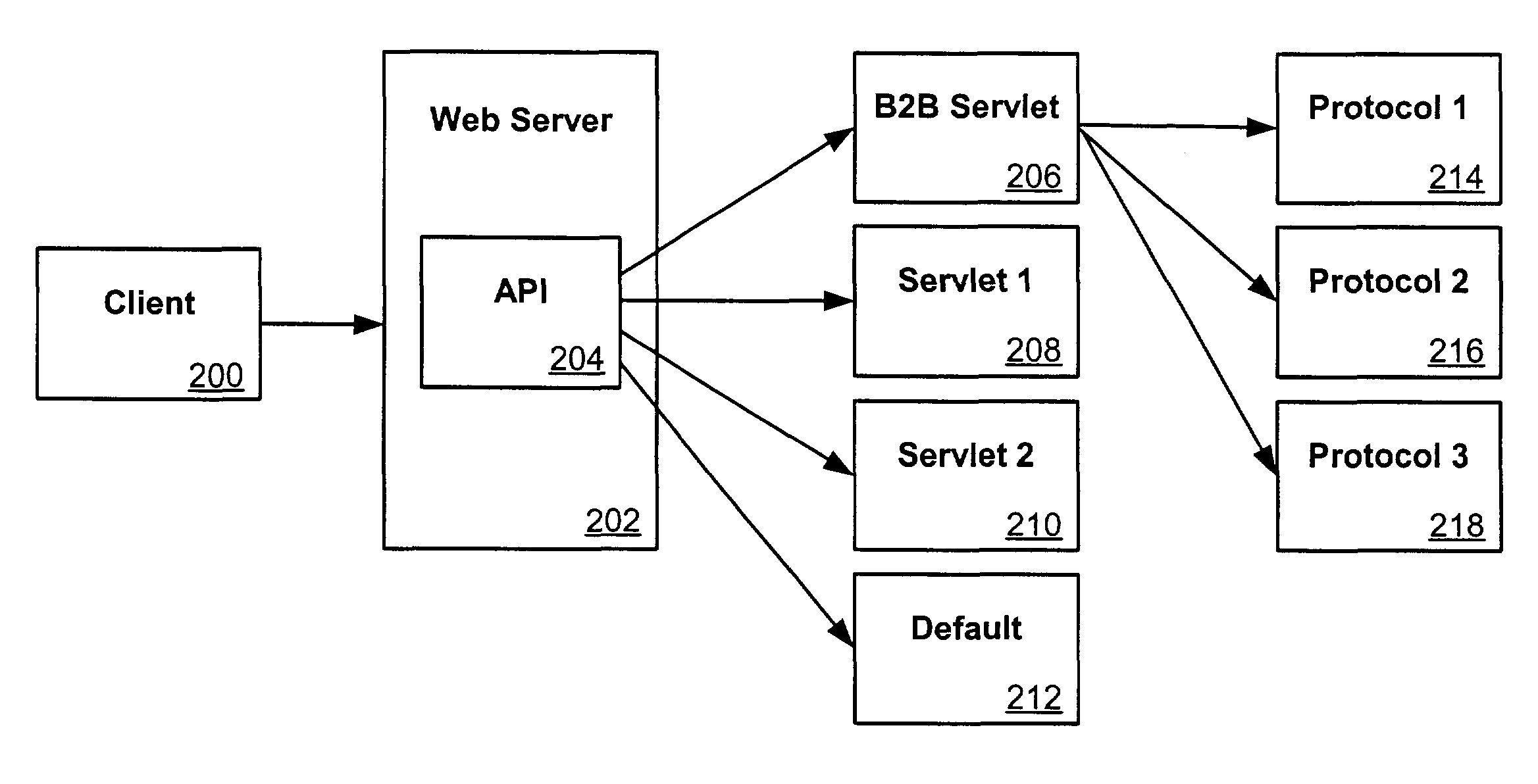
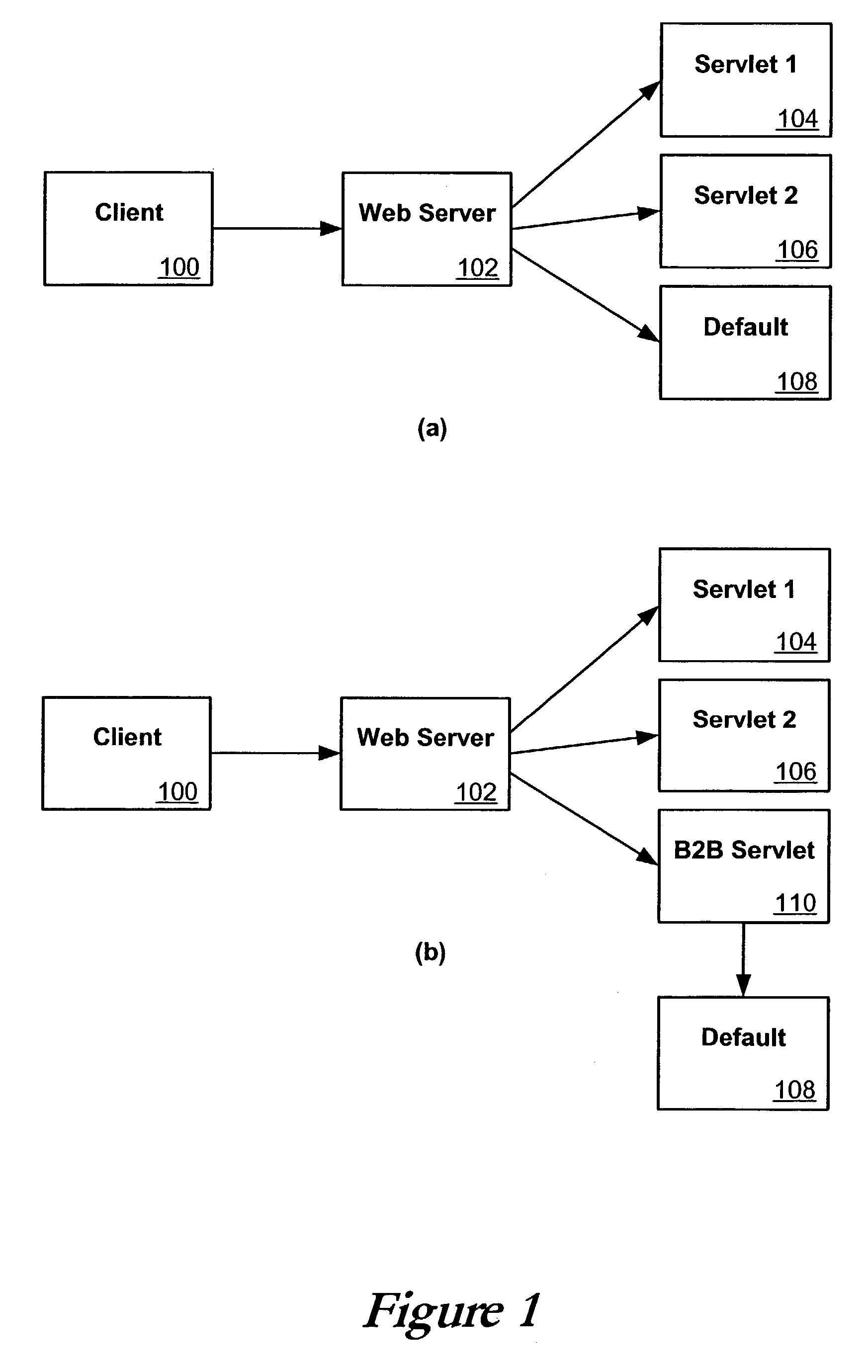
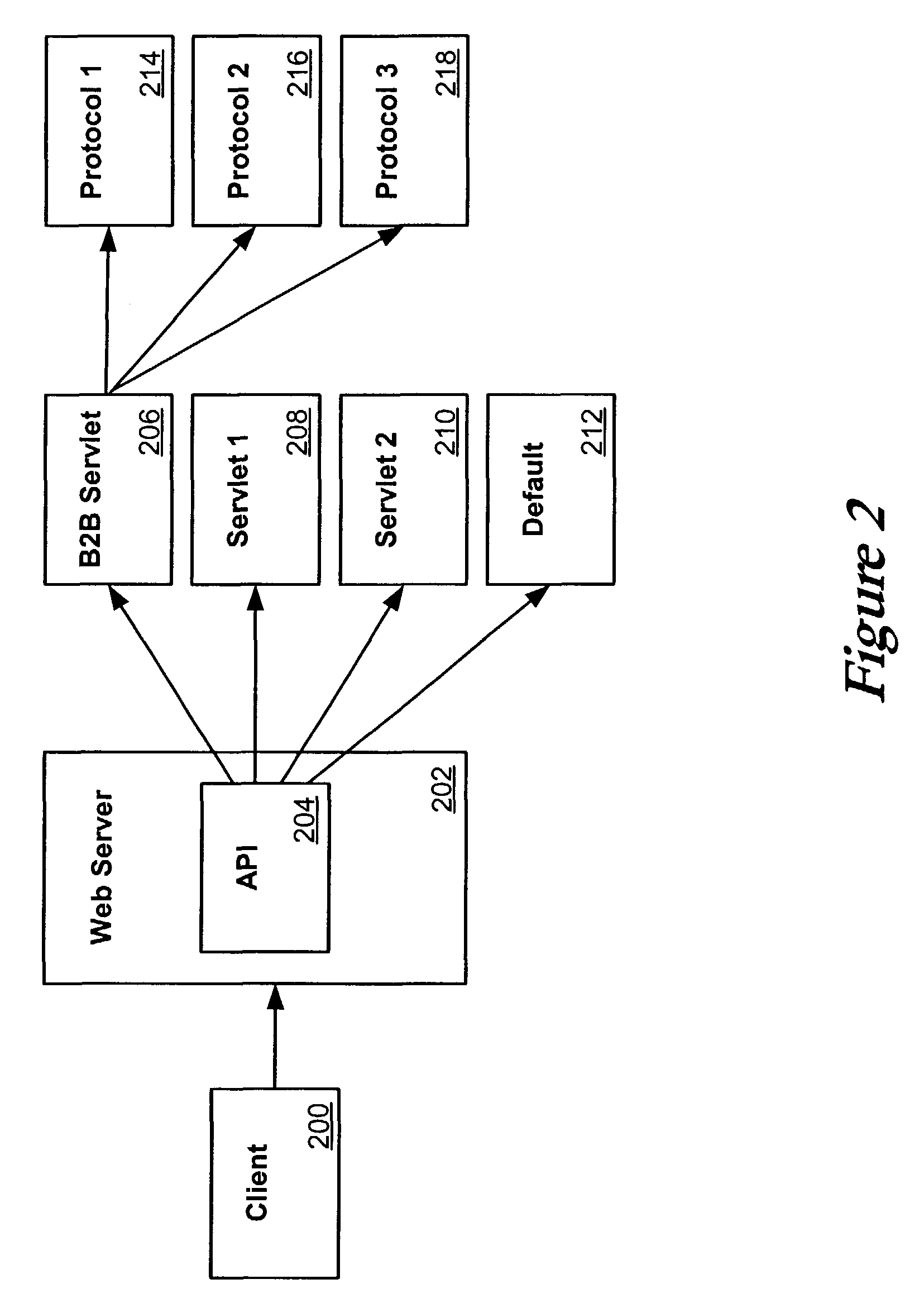
Single servlets for B2B message routing
ActiveUS8135772B2Multiple digital computer combinationsBuying/selling/leasing transactionsMessage routingLookup table
A number of approaches can be taken to improve the routing of client requests to business protocol destinations. In one such approach, a business servlet registers itself as a default servlet such that it receives any request not recognized by the system. In another embodiment, internal APIs can be used to route all messages to a business servlet, which can use internal APIs to redirect the request if the business servlet does not recognize the request. In another embodiment, filters can be used in conjunction with a lookup table containing address information to route requests to the proper destination.This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
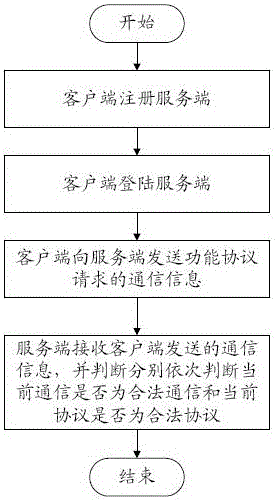
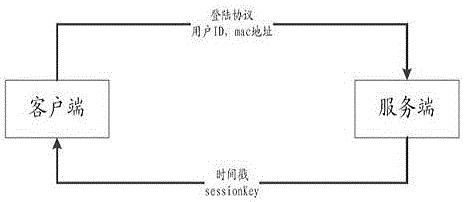
Method for verifying authority of network communication user
The invention belongs to the technical field of computer network communication, and discloses a method for verifying the authority of a network communication user. A client sends communication information of a functional protocol request to a server, and the functional protocol comprises user ID, sessionkey, current time stamp of the server and other business protocols. The step of obtaining the current time stamp of the server includes the client obtains the time stamp before the current functional protocol is sent, adding the user login time obtaining the client time stamp and subtracting the time stamp of the serve to obtain the time stamp difference. The server receives the communication information sent by the client, and determines whether the current communication is legal and whether the current protocol is legal. The validity of a service request sponsor and the requested protocol is completed, and the current communication is strictly protected against leakage.
Owner:MEIBEIKE TECH CO LTD
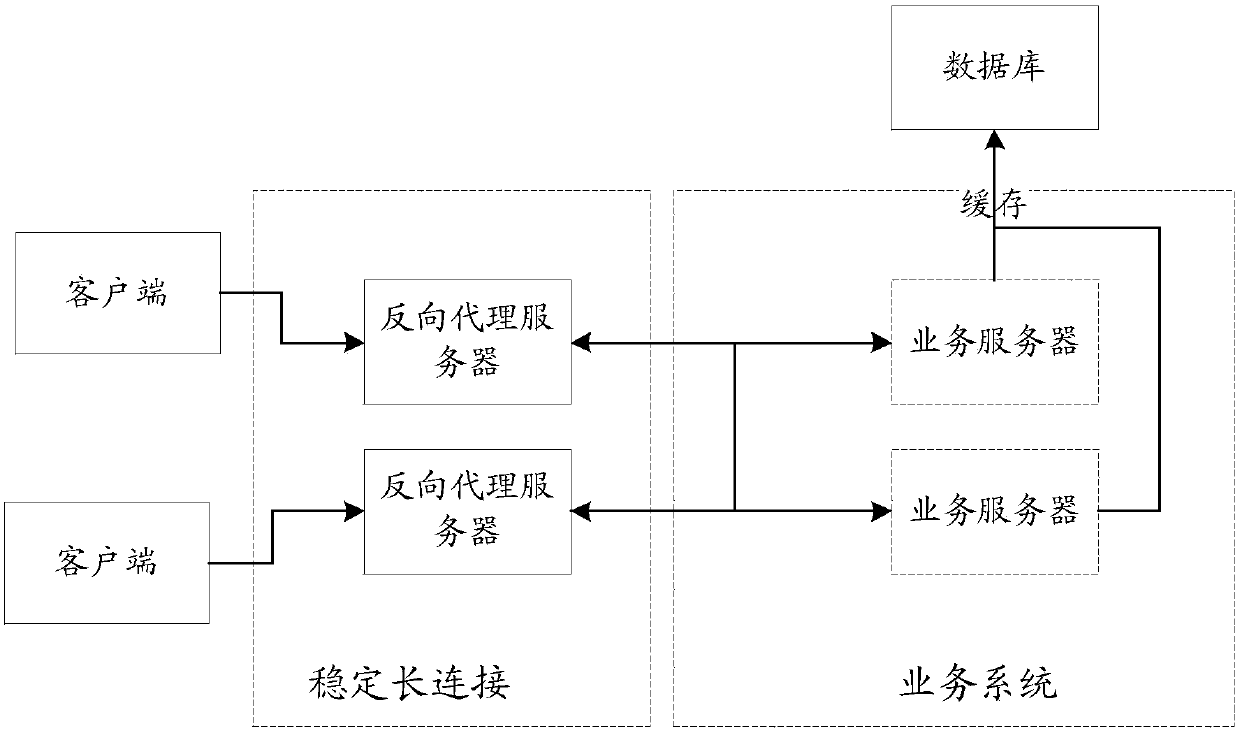
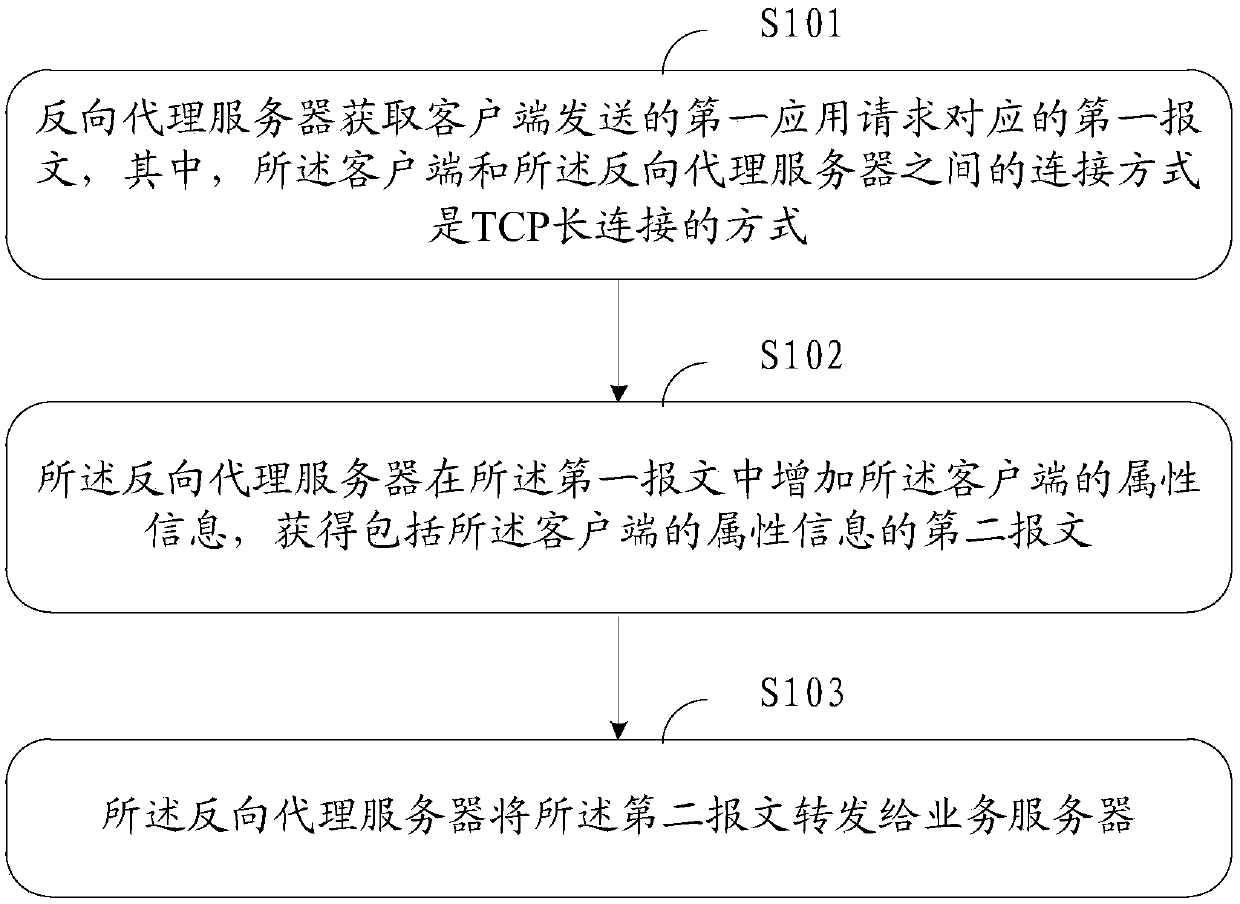
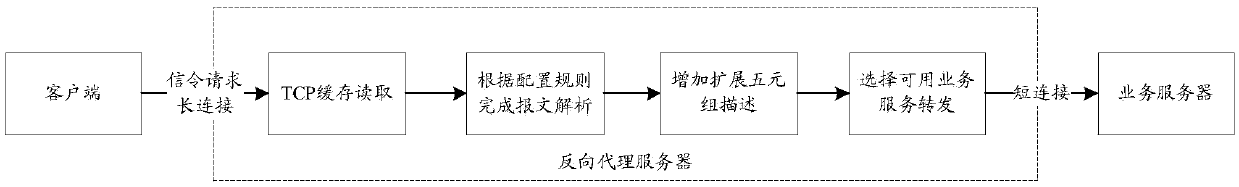
Business processing method to decouple TCP (transmission control protocol) persistent connections, reverse proxy server and business server
ActiveCN107872538AAchieve decouplingEasy to upgradeTransmissionReverse proxyHTTP persistent connection
The invention discloses a business processing method to decouple TCP (transmission control protocol) persistent connections, a reverse proxy server and a business server. In whole architecture, a client is connected to the reverse proxy server and interacts with a business server through the reverse proxy server, the client is connected with the reverse proxy server in a TCP persistent connectionmanner, and the TCP persistent connection is a stable persistent connection; the reverse proxy server acquires a first message corresponding to a first application request sent by the client, adds attribute information of the client to the first message, and acquires a second message including the attribute information of the client; the business server receives and processes businesses for the second message. Therefore, the attribute information, such as custom quintet information, of the client can be extended to a business protocol so as to arrive at business and link decoupling, and overall business service updating and expanding are facilitated.
Owner:ZHEJIANG DAHUA TECH CO LTD
Decoupling transmission method and system with communication layer and service layer separated
ActiveCN112261037AImprove scalabilityConvenient and fast iterative expansionTransmissionService protocolCommunication layer
The invention provides a decoupling transmission method and system with a communication layer and a service layer separated, the communication layer is responsible for transmission and analysis of a communication protocol, and the service layer is responsible for transmission and analysis of a service protocol; the sending end distinguishes a communication instruction and a service instruction according to the communication layer and the service layer and transmits the communication instruction and the service instruction to the communication layer and the service layer of the receiving end through a communication protocol and a service protocol respectively, and the communication layer and the service layer of the receiving end receive, analyze and execute corresponding instructions respectively. According to the invention, communication and service layers are decoupled and layered, so that expansion of different protocols is facilitated.
Owner:上海挚想科技有限公司
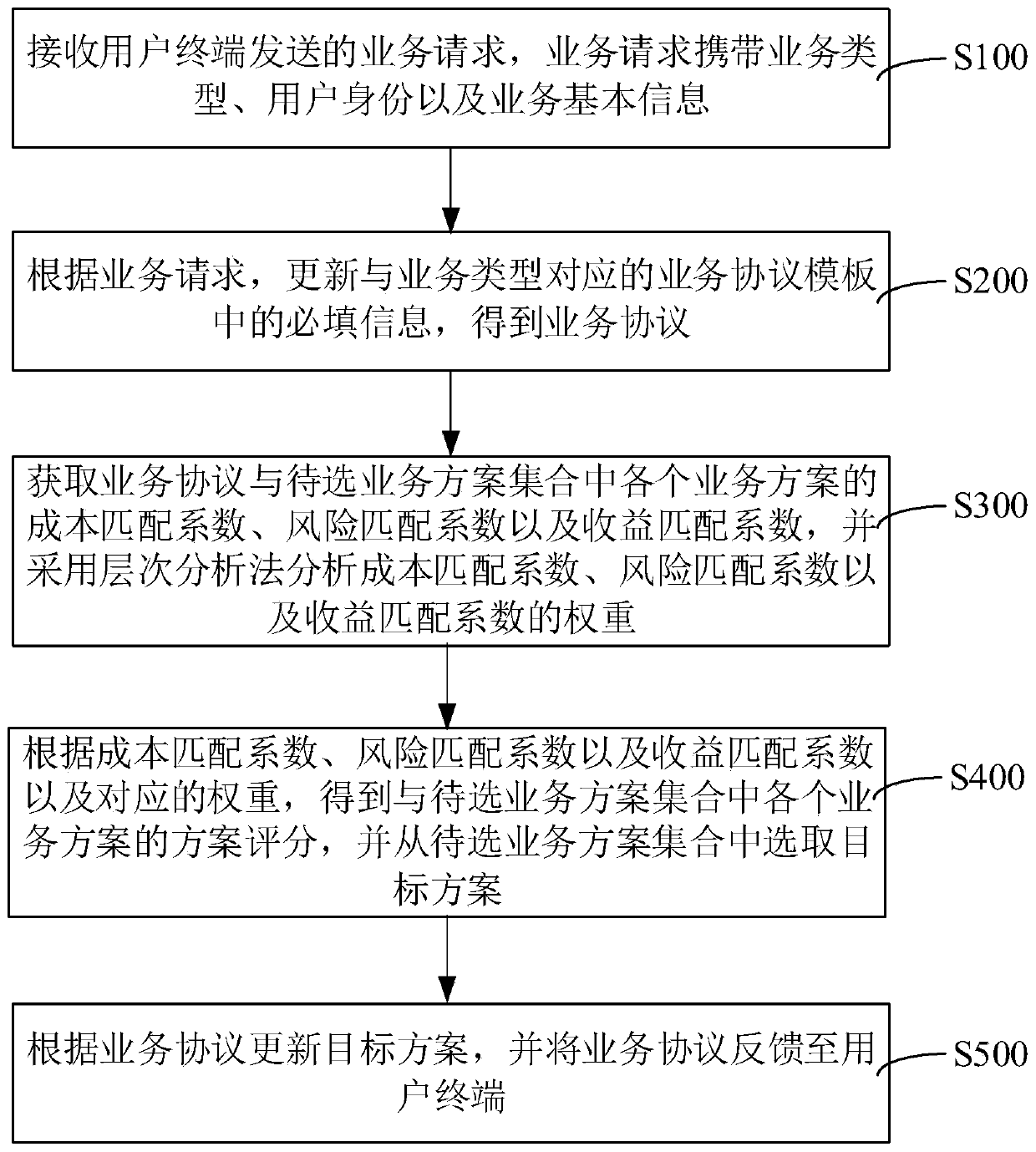
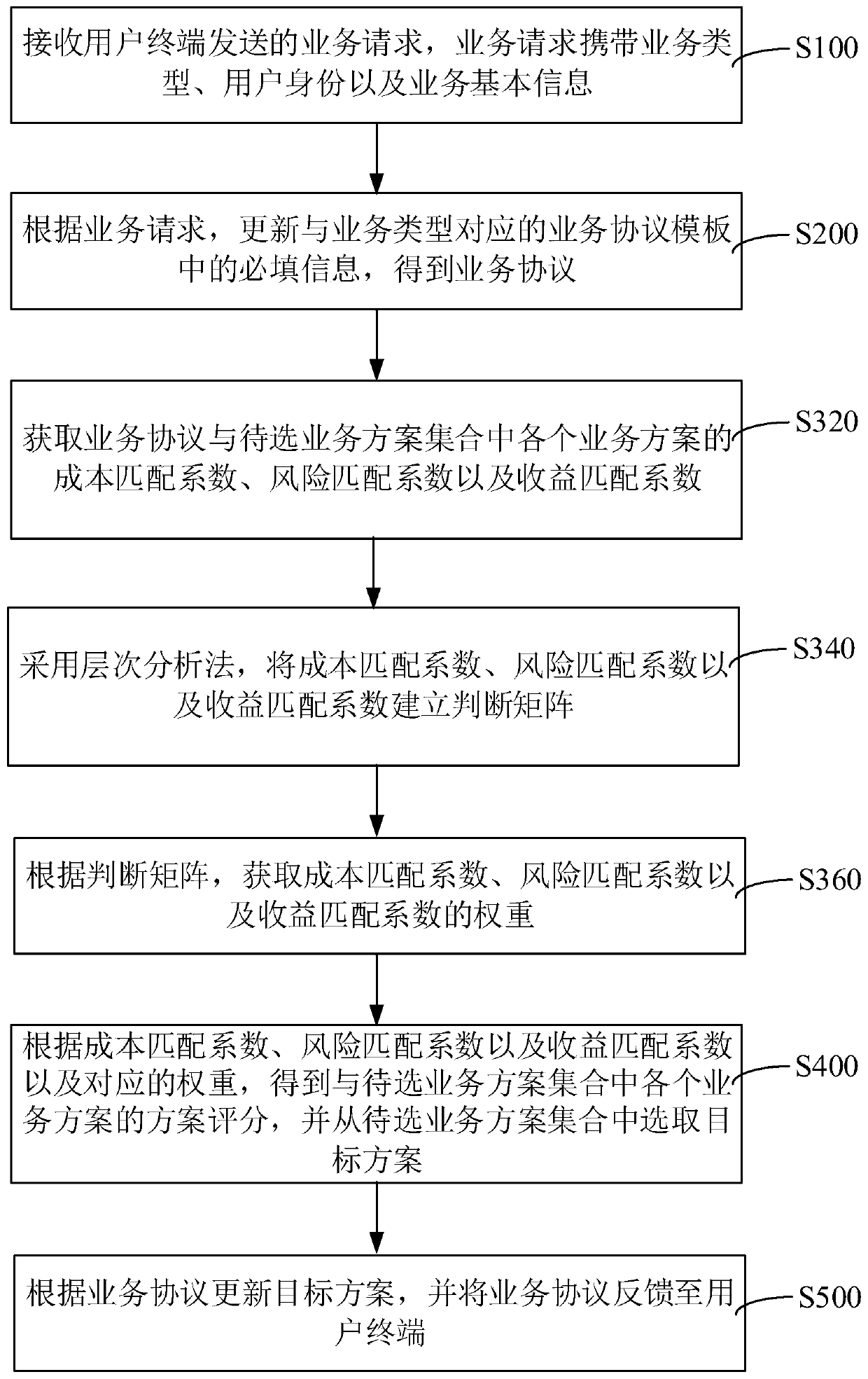
Service processing method and system, computer equipment and storage medium
The invention relates to the technical field of big data, is applied to the service processing industry, and provides a service processing method and system, computer equipment and a storage medium. The bank server receives a service request sent by a user terminal, necessary information in a service protocol template corresponding to the service type is updated, service protocols are obtained, ato-be-selected service scheme set is obtained, the cost, the risk and the income are considered from three aspects, and the cost, the risk and the income are weighted by adopting an analytic hierarchyprocess; and a target scheme most matched with the current service protocol is selected from a to-be-selected service scheme set, the target scheme is updated according to the service protocol, and the service protocol is fed back to the user terminal. In the whole process, the most suitable service scheme (target scheme) is matched from service scheme combination, resetting is not needed, and the whole service processing process is simple and convenient.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
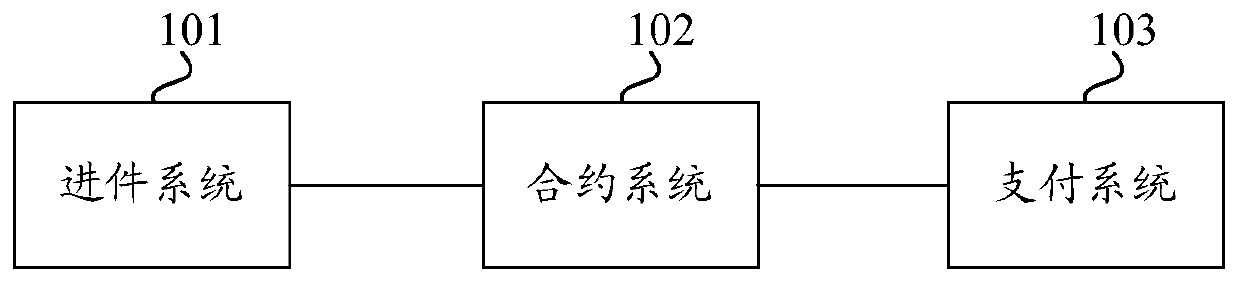
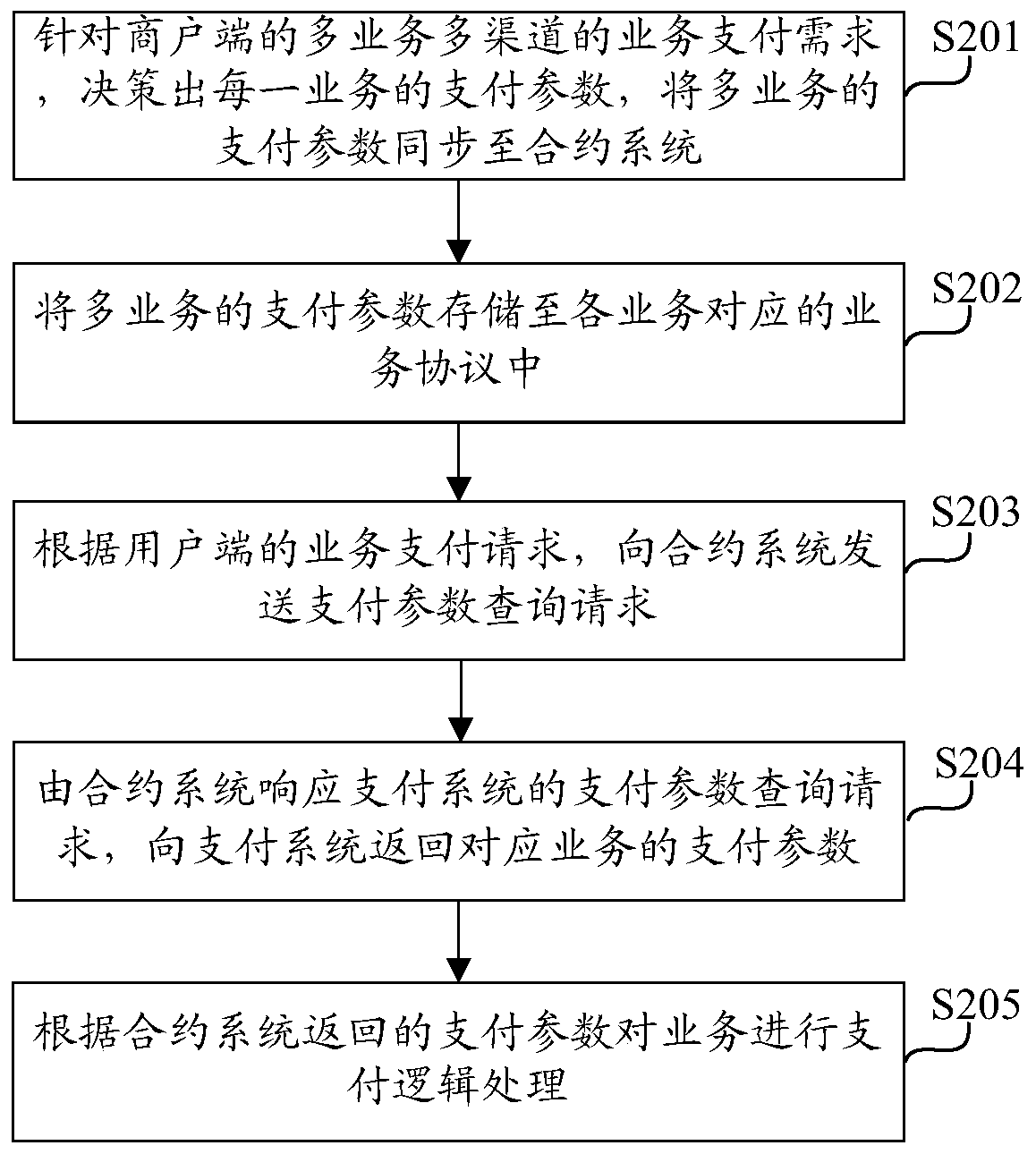
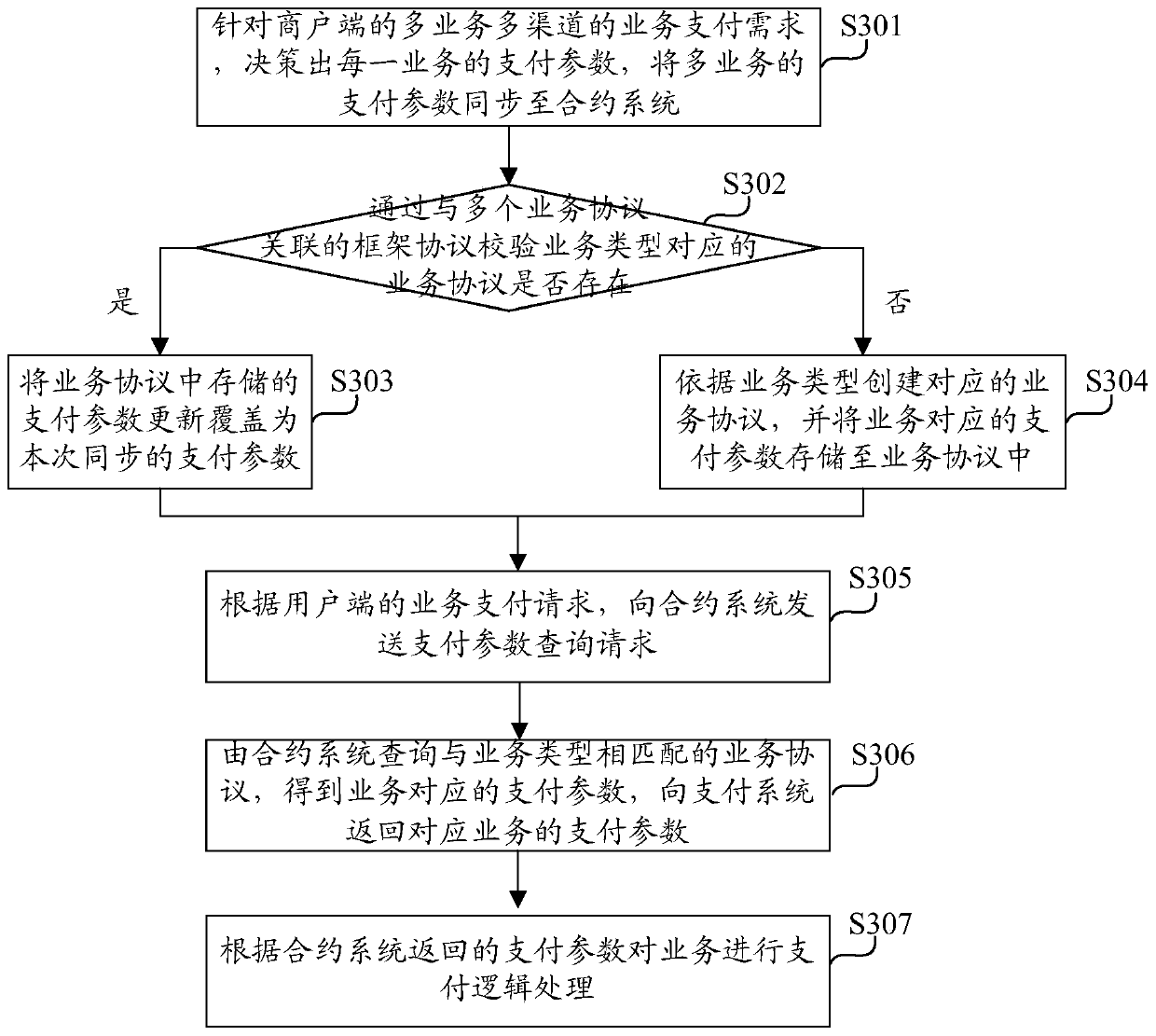
Contract-based payment data processing device and method
ActiveCN110717756AReduce maintenance costsReduce complexityPayment protocolsComputer networkPayment system
The invention discloses a contract-based payment data processing device and method. The device comprises an admission system which is suitable for deciding payment parameters of each service accordingto multi-service and multi-channel service payment requirements of a merchant side and synchronizing the payment parameters of the multiple services to a contract system; a contract system suitablefor respectively managing a plurality of business protocols, wherein payment parameters of corresponding businesses are stored in each business protocol; responding to a payment parameter query request of the payment system, and returning payment parameters of the corresponding service to the payment system; a payment system suitable for sending a payment parameter query request to the contractsystem according to the service payment request of the user side; and performing payment logic processing on the business according to the payment parameters returned by the contract system. Based onthe scheme, a software architecture scheme with high cohesion and low coupling is realized, the maintenance cost of the platform is reduced, the reliability of a payment link is improved, the complexity of an e-commerce platform is effectively reduced, and expansion capability of the e-commerce platform is improved.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
Templated protocol generation and management method
PendingCN113312033ASave human resourcesImprove work efficiencySoftware designCreation/generation of source codeService protocolSoftware engineering
The invention discloses a templated protocol generation and management method, which comprises the steps of constructing a configuration tool program file, and pre-defining an interface variable name; generating a target protocol template; judging common text content and variable value fields of the protocol by using a regular expression; replacing the variable value with a + variable coding value, and recording the value as a special variable; splicing the replaced character strings into html tags, and storing the html tags in a database; querying the replaced character string, generating a protocol file in a pdf format, and performing protocol signature; and when the service protocol needs to be changed, querying the template, editing the variable to be modified, and generating the latest protocol template. According to the method, template management can be carried out, interfaces and variables corresponding to services can be configured, protocol templates can be added, corresponding service variables can be configured, protocol templates which can be filled with corresponding data according to actual service scenes can be generated, protocol management of the supply chain financial platform can be carried out, manpower resources for research and development are saved, and working efficiency is improved.
Owner:中企云链(北京)金融信息服务有限公司
Telephone port allocation method
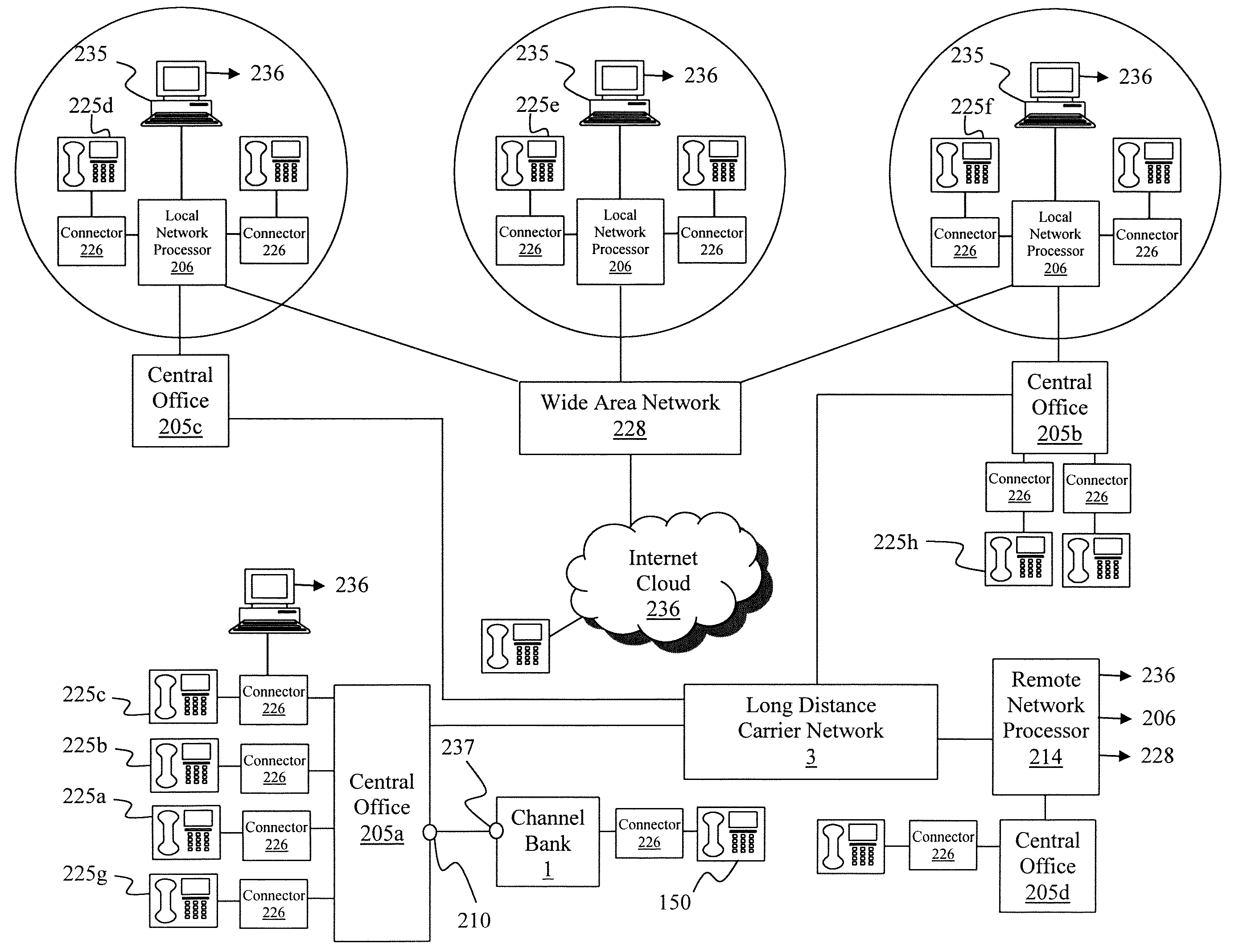
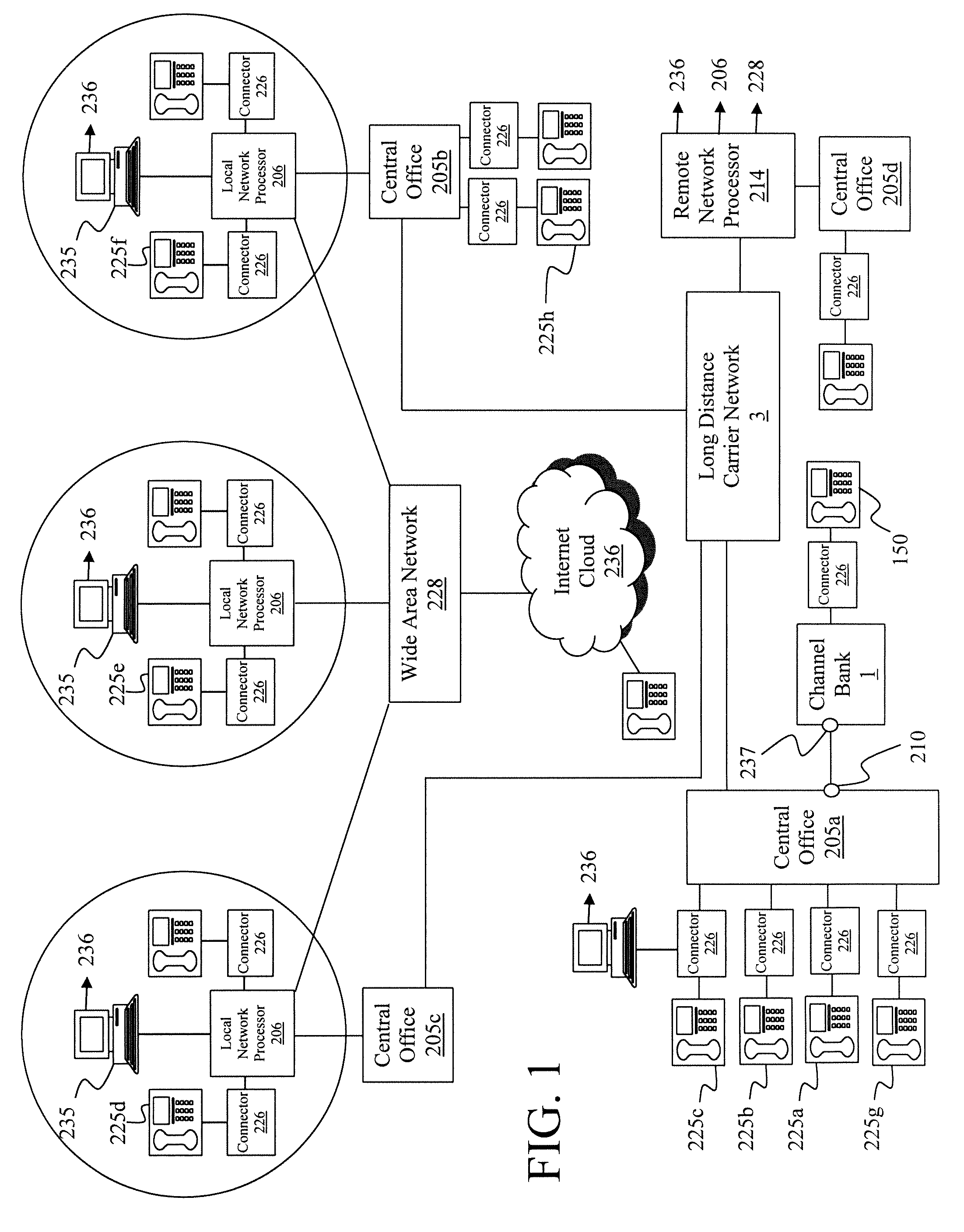
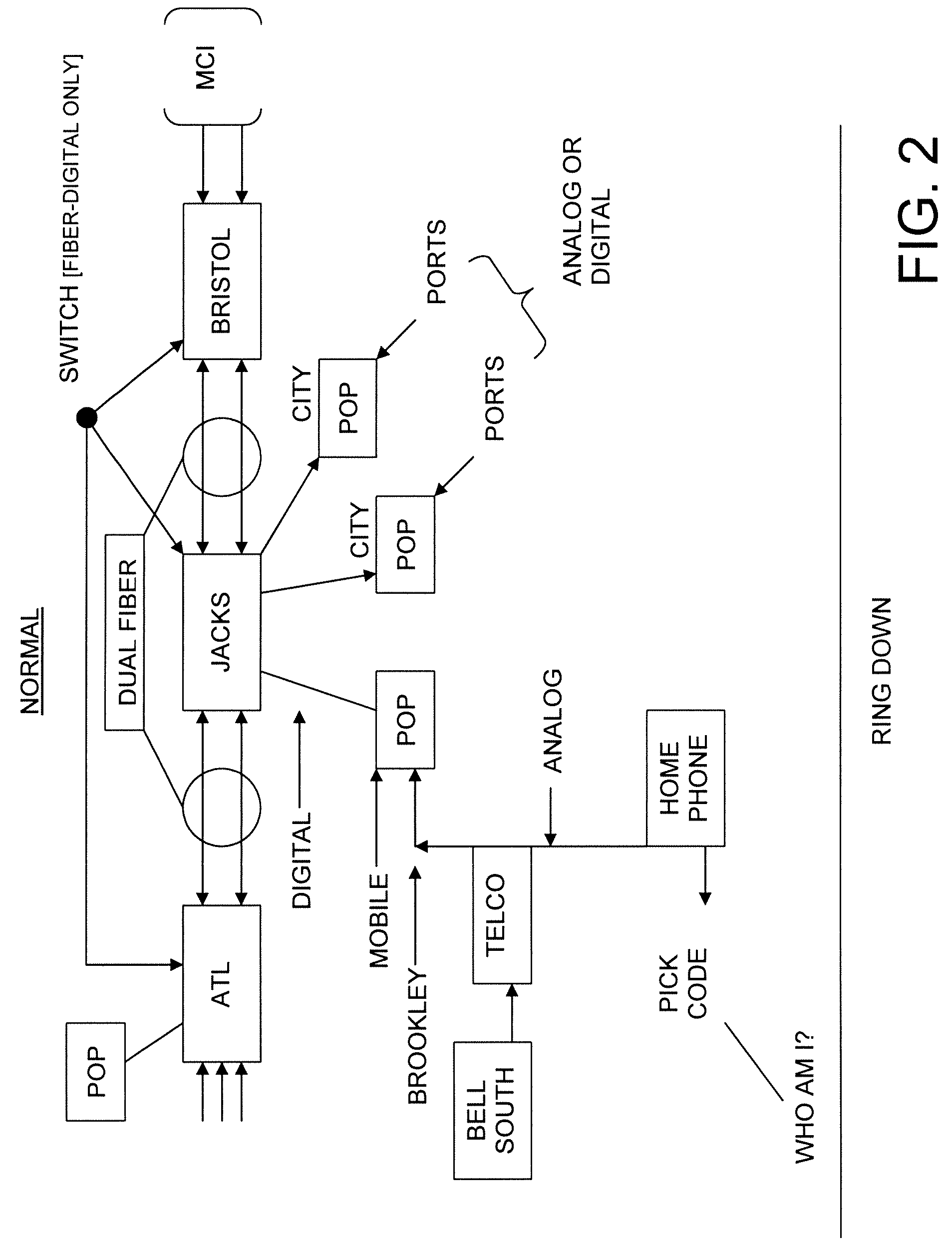
ActiveUS20030179874A1Simple processImprove efficiencyInterconnection arrangementsTransmissionNetwork connectionNetwork processor
A method is described for handling multiple telephone and data calls having different data type or business protocols an originating phone, phone being broadly defined as the originating device whether phone or computer, wherein there is an originating phone and a destination phone with or without monitoring phones connected through a network, whether a telephone or data network by establishing a remote network processor having incoming and outgoing ports controlled by the remote network processor which has the steps of generating a plurality of protocols applicable to the incoming and outgoing ports; storing the protocols in a database; selecting a protocol for the incoming and outgoing ports; accepting a call from the originating phone on the incoming port; determining if the call is to be completed; setting parameters for completing the call based on the protocols; and completing the call.
Owner:GLOBAL TELLINK
UDP traffic filtering method, device, server and storage medium
ActiveCN108737447BNo out of serviceImprove the protective effectTransmissionBaseline dataUser Datagram Protocol
The invention discloses a user datagram protocol traffic filtering method and device, a server and a memory medium and belongs to the field of network security. The method comprises the steps of obtaining fingerprint feature baseline data of the server when the server bears a user datagram protocol flooding attack, wherein the fingerprint feature baseline data comprises a business load feature baseline, a business port feature baseline, a business packet length feature baseline and a business protocol feature baseline; and filtering user datagram protocol traffic which is about to be sent to the server, through sequential utilization of the business load feature baseline, the business port feature baseline, the business packet length feature baseline and the business protocol feature baseline, until the user datagram protocol traffic which is about to be sent to the server in the unit time is smaller than a security threshold; and sending the filtered traffic to the server.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and equipment for implementing multi-protocol stack cluster service application
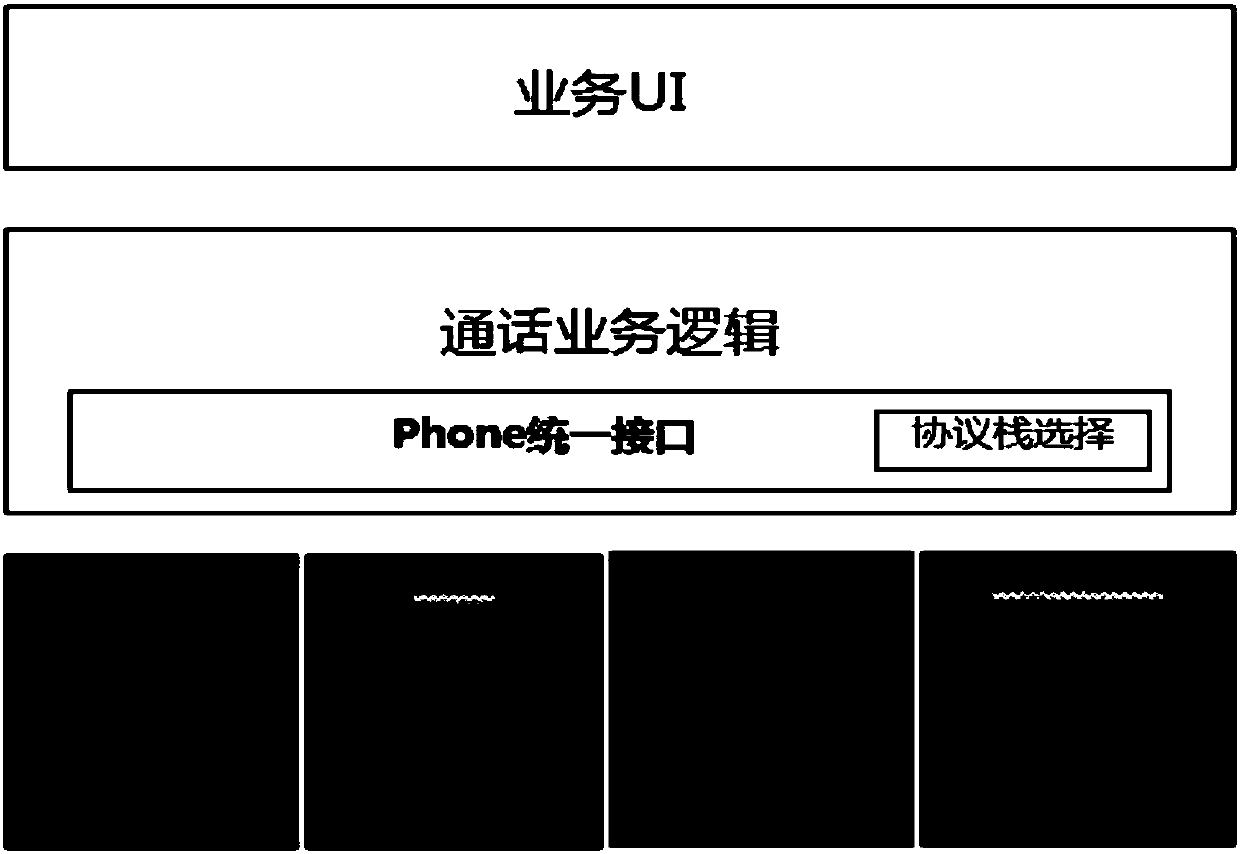
InactiveCN111131129ASolve the problem of reasonable coexistenceImprove experienceNetwork topologiesBroadcast service distributionService protocolMulti protocol
The invention discloses a method for implementing a multi-protocol stack cluster service application, which comprises the steps of normalizing a service user interface (UI) and a service, and shielding perception of an upper-layer service to a bottom-layer multi-protocol stack; abstracting a flow shared by the multiple protocol stacks, and shielding function differences of the protocol stacks forthe upper-layer service; and selecting an appropriate protocol stack from the multiple protocol stacks to work according to the type of the terminal on which the current application is installed andthe current network mode. The invention further discloses corresponding equipment for implementing the multi-protocol stack cluster service application. By applying the technical scheme disclosed by the invention, a plurality of existing cluster service protocol stacks can work cooperatively at the same time.
Owner:CHENGDU TD TECH LTD
Information display method and device
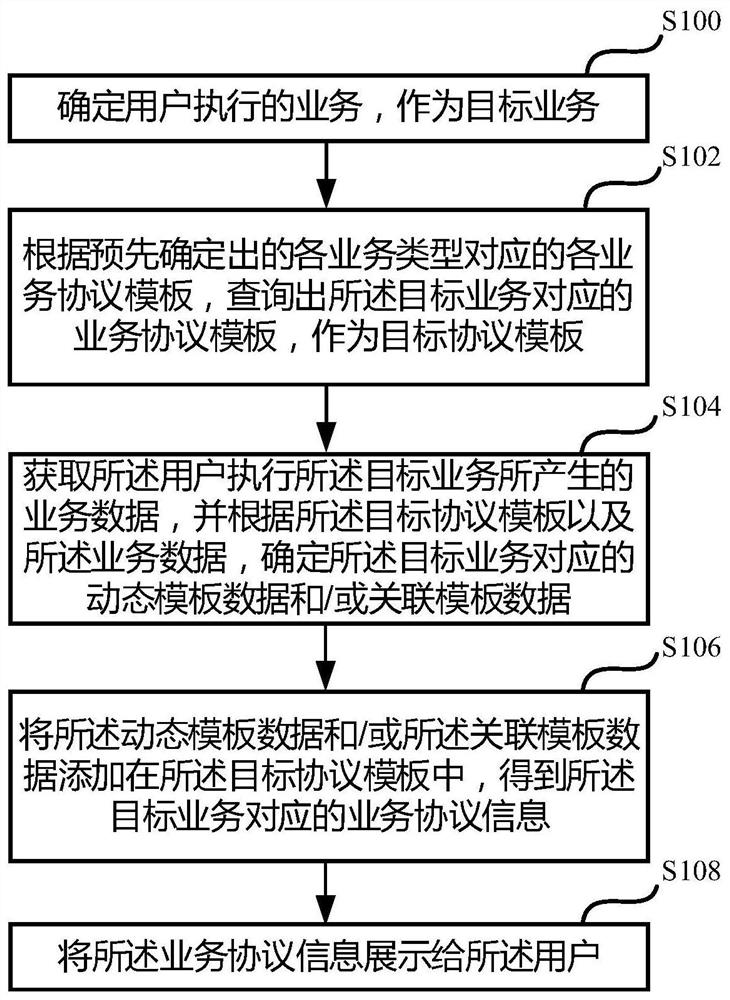
PendingCN112419073AAvoid modificationAvoid Redundant ContentFinanceNatural language data processingService protocolEngineering
The invention discloses an information display method and device, and the method comprises the steps: determining a business executed by a user as a target business; querying a service protocol template corresponding to the target service as a target protocol template according to each predetermined service protocol template corresponding to each service type; acquiring service data generated whenthe user executes the target service, and determining dynamic template data and / or associated template data corresponding to the target service according to the target protocol template and the service data; adding the dynamic template data and / or the associated template data into the target protocol template to obtain service protocol information corresponding to the target service. and displaying the service protocol information to the user. According to the method, the service data is added to the target protocol template corresponding to the target service, so that a large amount of redundant content is avoided, the configuration efficiency is improved, and the labor cost is reduced.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Application protocol screening and matching method based on content filtering
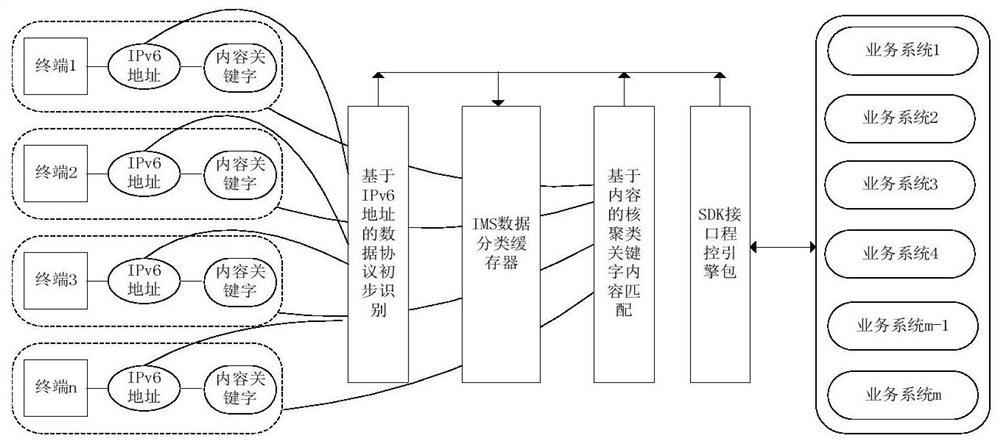
InactiveCN112825518AReduce development difficultyImprove integration efficiencyTransmissionPower exchangeTransmission technology
The invention relates to application protocol screening and matching method research based on content filtering, and belongs to the field of power data exchange transmission technology innovation. The traditional power exchange network introduces the IMS technology to change the interaction mode of the B2B due to the limitation of the interface and system processing capability, thereby solving the development bottleneck of the business multimedia expansion of the power exchange network. In order to better meet the special requirements of a power grid on the aspects of safety, high efficiency and future service bearing, the invention provides an IMS capability-based open service access architecture, deployment authentication, firewall and other means to enhance the access safety of internal and external network services, and, through the processes of service protocol type matching, protocol recombination, kernel clustering protocol filtering and the like, the exchange service handling capacity is reduced. According to the invention, innovative technical contents are provided from the aspects of IMS power grid service development architecture, protocol processing, interface conversion and the like, and a basis with technical practice value is provided for power grid construction.
Owner:HUBEI ELECTRIC ENG CORP +1
Telephone port allocation method
ActiveUS7564961B2Minimize duplicationIncrease flexibilityInterconnection arrangementsTransmissionNetwork connectionNetwork processor
A method is described for handling multiple telephone and data calls having different data type or business protocols an originating phone, phone being broadly defined as the originating device whether phone or computer, wherein there is an originating phone and a destination phone with or without monitoring phones connected through a network, whether a telephone or data network by establishing a remote network processor having incoming and outgoing ports controlled by the remote network processor which has the steps of generating a plurality of protocols applicable to the incoming and outgoing ports; storing the protocols in a database; selecting a protocol for the incoming and outgoing ports; accepting a call from the originating phone on the incoming port; determining if the call is to be completed; setting parameters for completing the call based on the protocols; and completing the call.
Owner:GLOBAL TELLINK
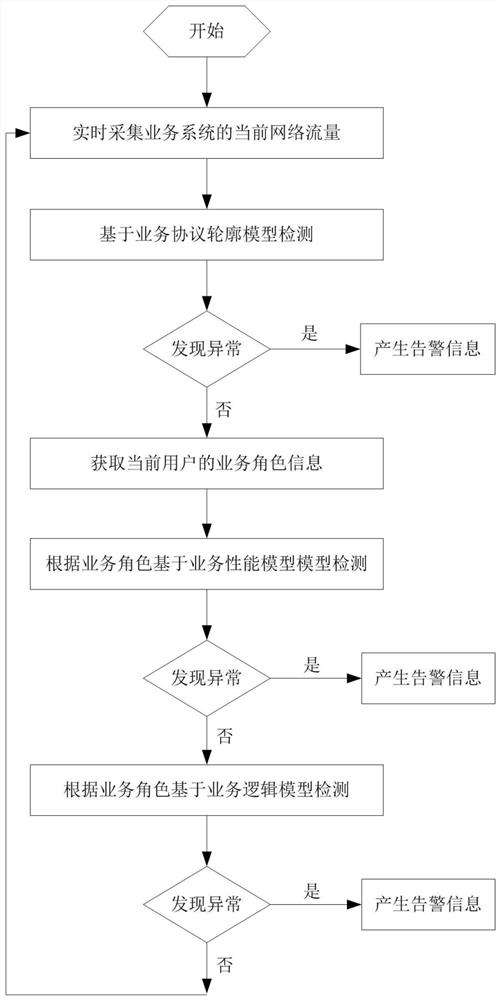
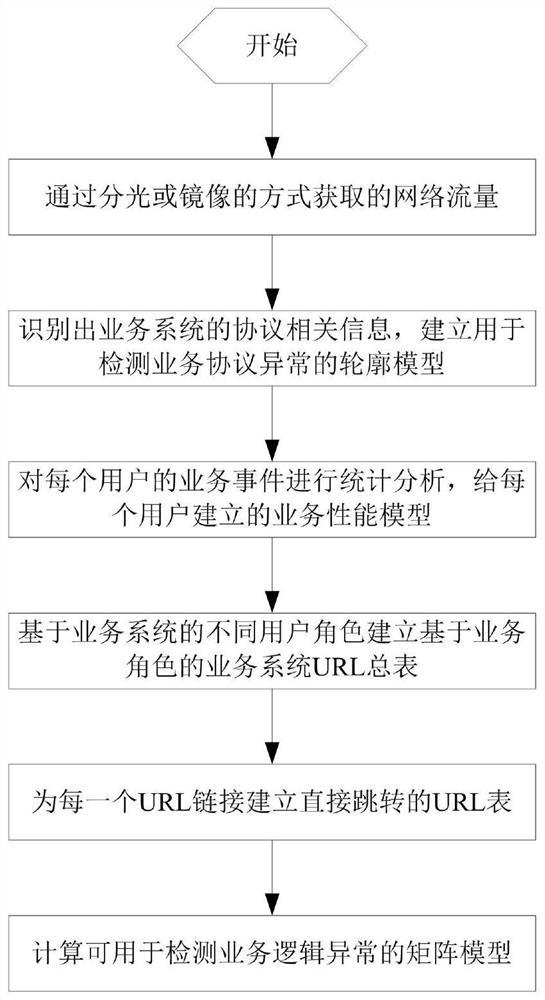
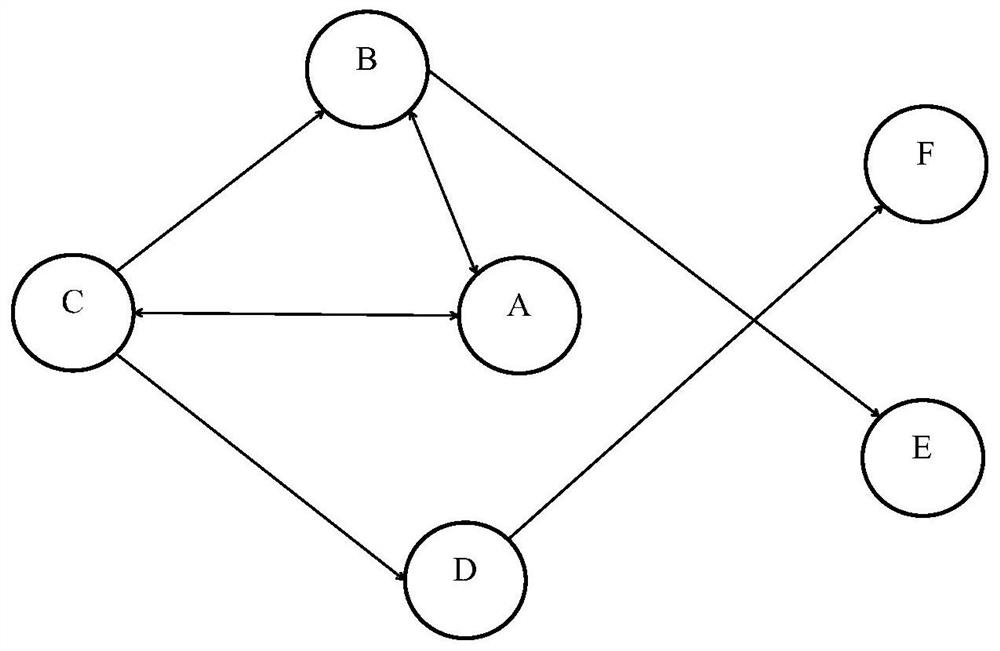
Anomaly detection method and system based on business flow
ActiveCN108616529BAvoid violationsStrengthen internal controlTransmissionService flowBusiness process
Owner:CHENGDU UNIV OF INFORMATION TECH
Live broadcast service system, live broadcast method and server
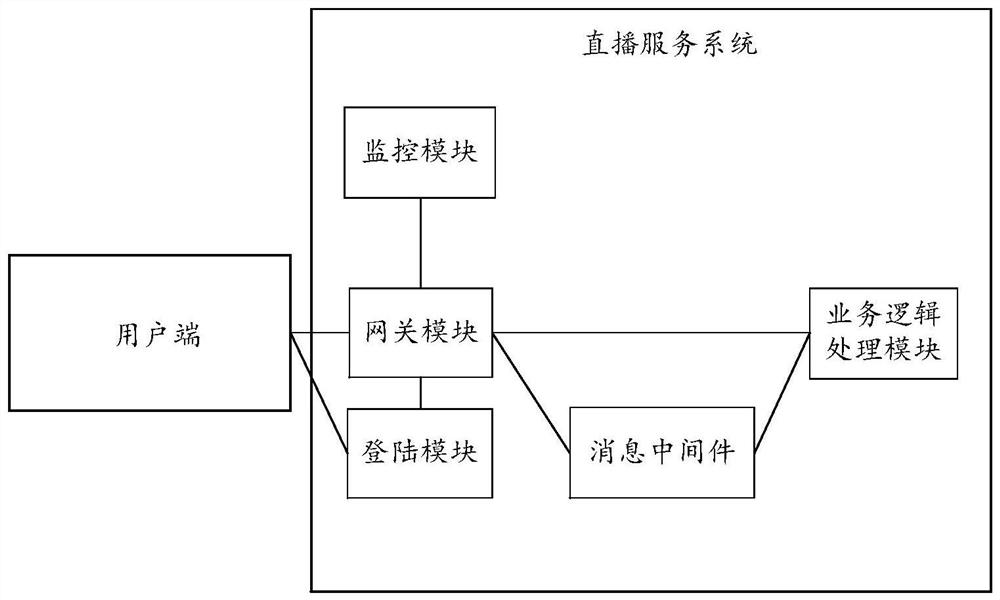
ActiveCN113132745AImprove usabilityImprove construction efficiencyTransmissionSelective content distributionService protocolData storing
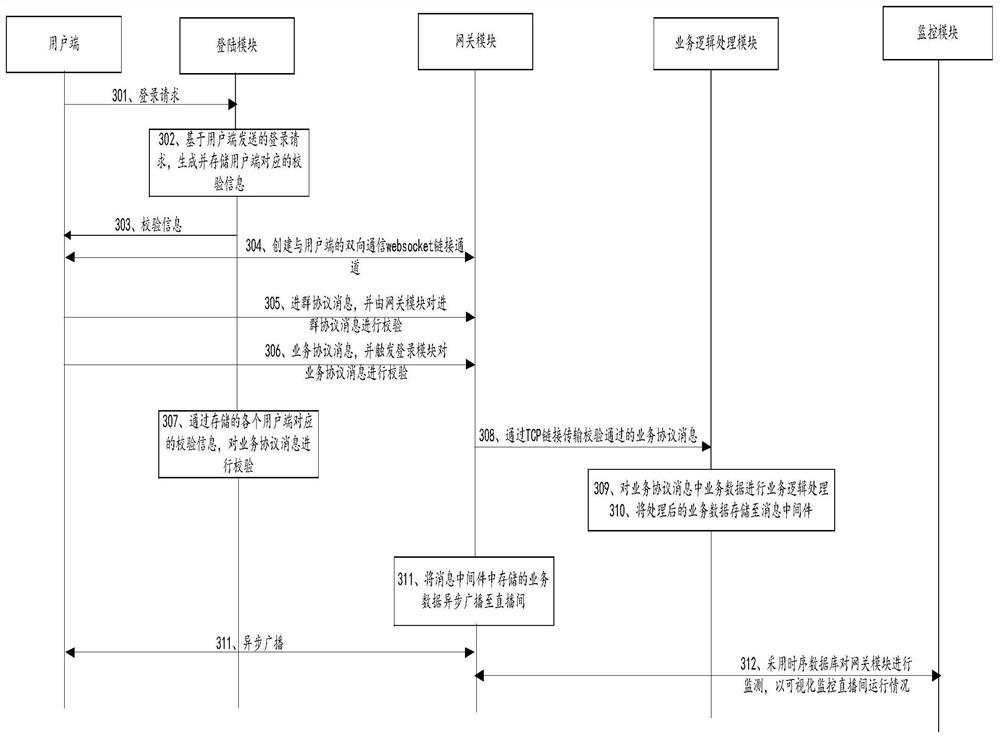
The invention provides a live broadcast service system, a live broadcast method and a server. In the system, a login module receives a login request sent by each user side, generates and stores verification information corresponding to each user side based on the login request, and feeds back the verification information to each user side; a gateway module creates a link channel with a user side meeting a live broadcast room login condition, verifies a group entering protocol message received through the link channel, and receives a service protocol message through the link channel; the login module verifies the service protocol message through the verification information; the gateway module transmits the verified service protocol message to a service logic processing module through a TCP link; the service logic processing module performs service logic processing on service data in the service protocol message and stores the service data in the message middleware; the gateway module asynchronously broadcasts the service data stored in the message middleware to the live broadcast room; and a monitoring module visually monitors the operation condition of the live broadcasting room through a time sequence database.
Owner:PERFECT WORLD HLDG GRP CO LTD
Block chain cross-chain method, device, equipment and product
PendingCN114356606AReduce wasteMeet the needs of cross-chain businessInterprogram communicationDatabase distribution/replicationComputer networkBusiness enterprise
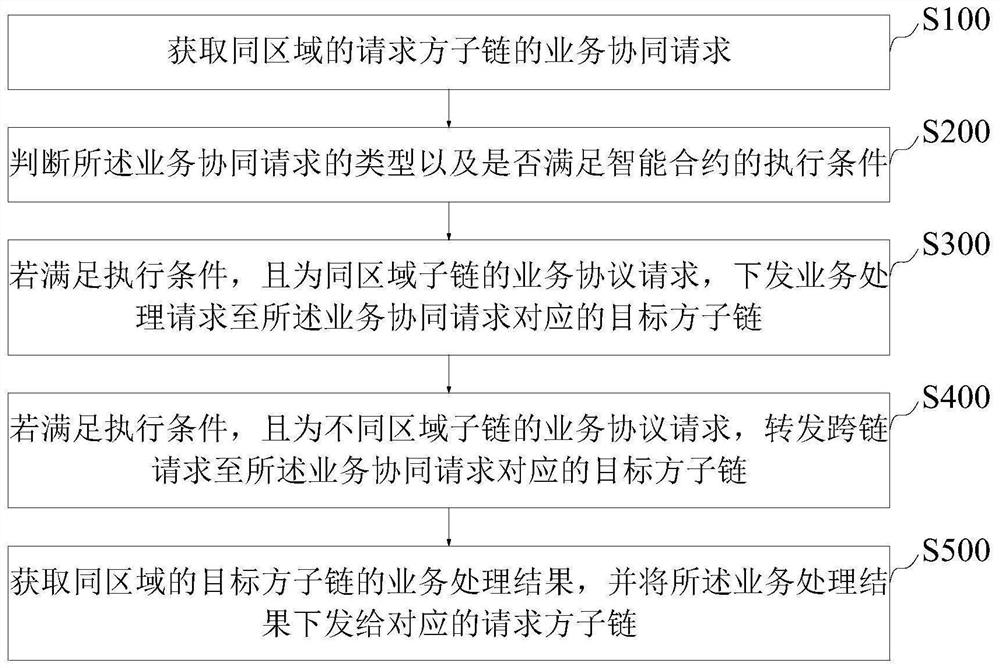
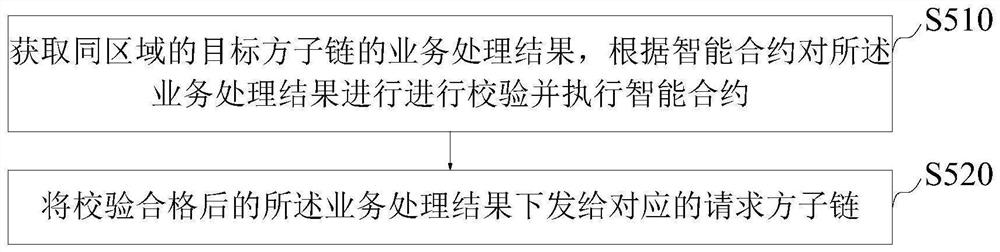
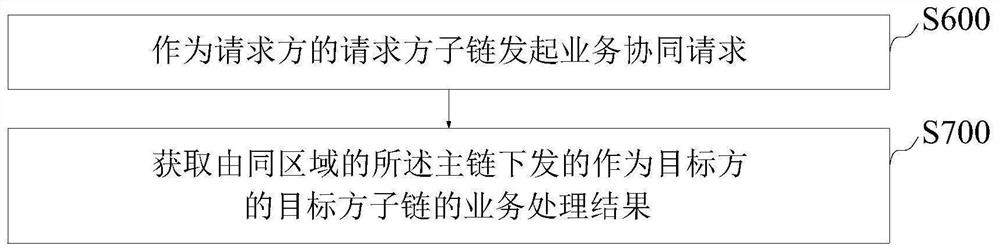
The invention provides a cross-chain method, device, equipment and product of a block chain, and relates to the field of block chains, the method comprises the following steps: obtaining a business cooperation request of requester sub-chains in the same region; judging the type of the business cooperation request and whether an execution condition of the smart contract is satisfied; if the execution condition is met and the request is a service protocol request of the same-region sub-chain, issuing a service processing request to a target sub-chain corresponding to the service collaboration request; if the execution condition is met and the service protocol requests are different regional sub-chains, forwarding the cross-chain request to a target sub-chain corresponding to the service collaboration request; and obtaining a service processing result of the target party sub-chain in the same area, and issuing the service processing result to the corresponding requester sub-chain. According to the invention, cross-chain owner intelligent contract management is realized, data of all business parties can be intercommunicated under the condition of keeping privacy, and the problem of insufficient data sharing between provinces and cities, between places, between enterprises and governments and between departments is solved.
Owner:熵链科技福建有限公司
Intelligent control system, method and device
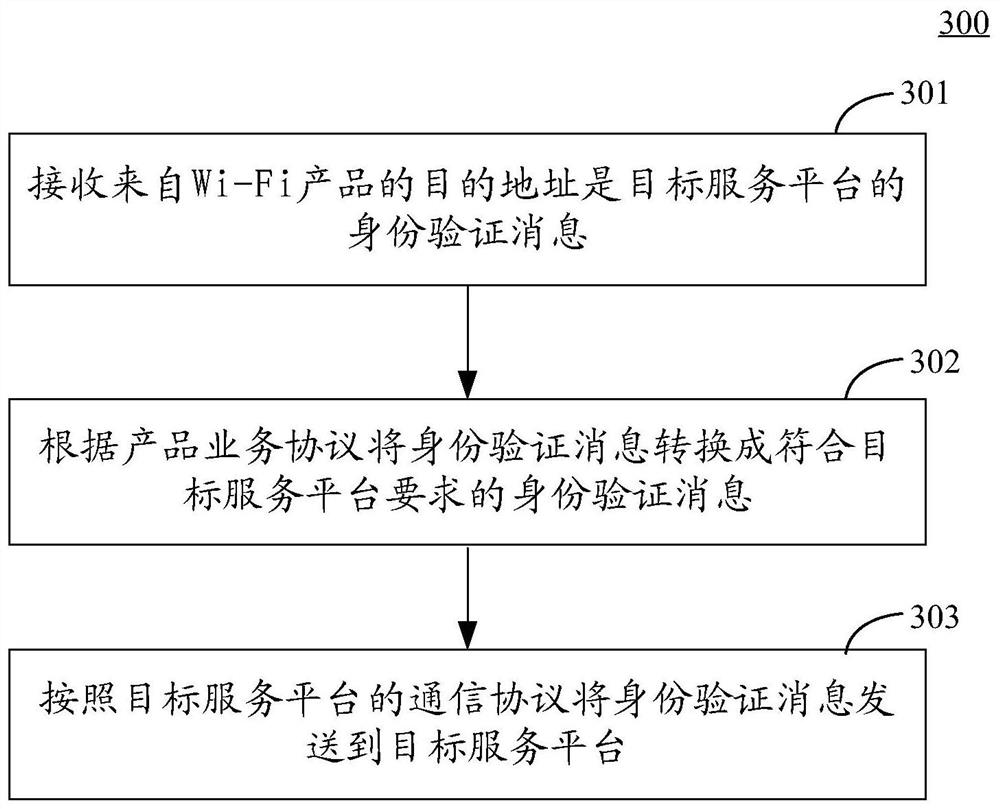
PendingCN113630298ASave hardware resourcesImprove developmentProgramme controlNetwork topologiesService protocolEmbedded system
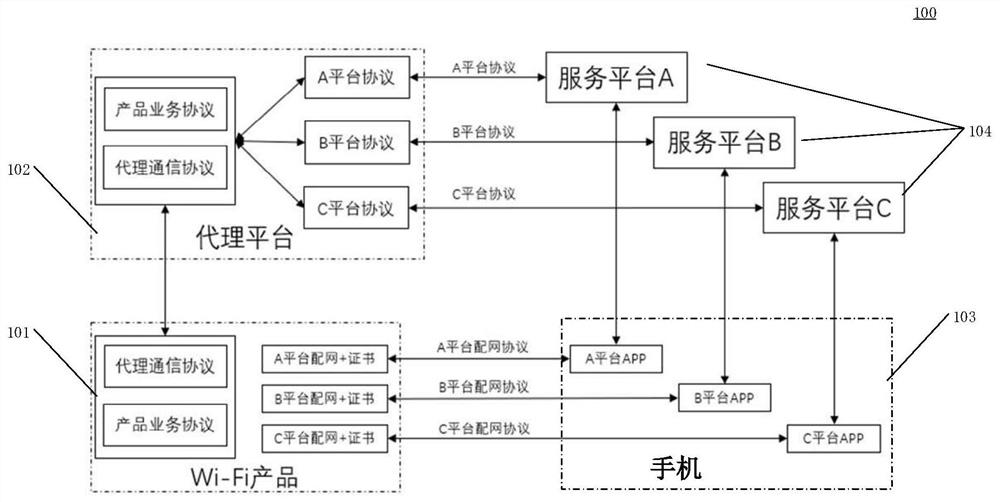
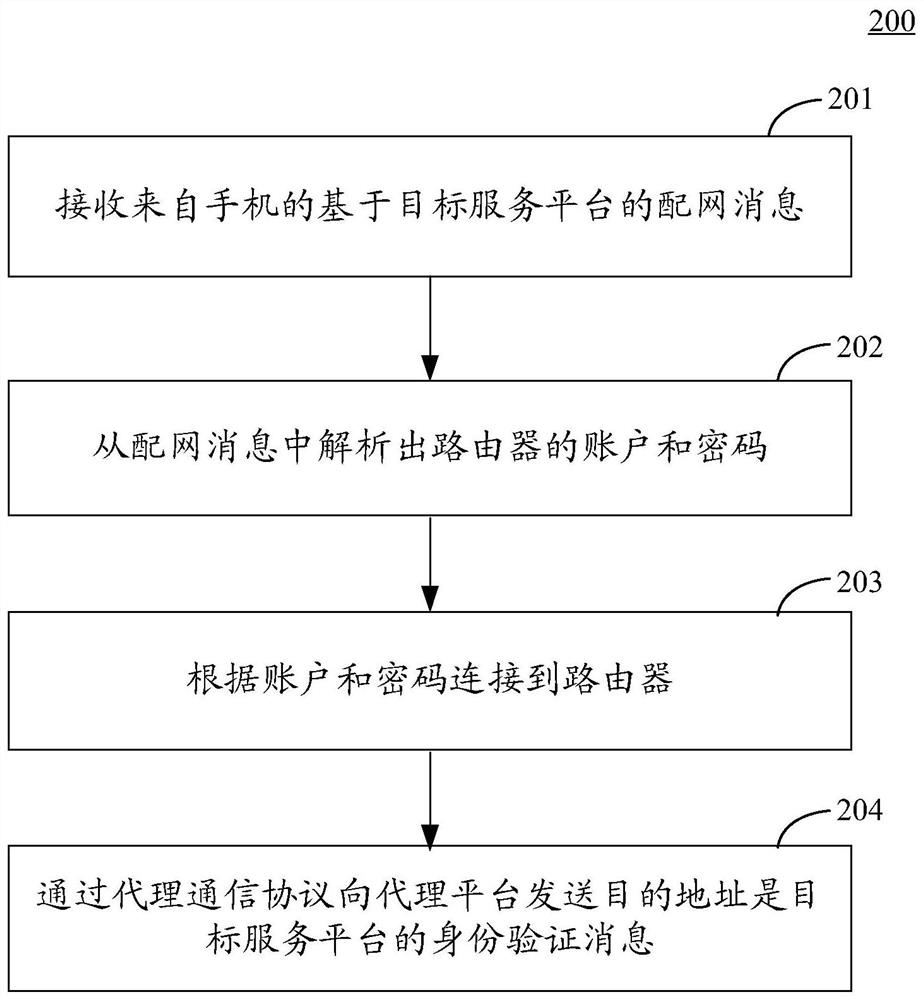
The embodiment of the invention discloses an intelligent control system, method and device. The specific implementation mode of the system comprises a Wi-Fi product which carries out message interaction with an agent platform through an agent communication protocol and a product service protocol and carries out message interaction with APPs of platforms on a mobile phone through distribution network information and certificate information of the platforms; a proxy platform which converts instructions from different service platforms into instructions in a uniform format through a proxy communication protocol and a product service protocol, then forwards the instructions to the Wi-Fi product, converts messages from the Wi-Fi product into a target format according to a protocol of a target service platform, and then sends the messages to the target service platform through a communication protocol of the target service platform; a mobile phone which is provided with an APP of at least one platform and is used for carrying out network distribution on the Wi-Fi product; and at least one service platform which receives the control instruction sent by the mobile phone, sends the control instruction to the proxy platform through a platform protocol, and forwards the control instruction to the Wi-Fi product through the proxy platform. According to the system, the Wi-Fi product can be compatible with more platform protocols.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com