Patents
Literature
72 results about "End-user computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
End-user computing (EUC) refers to systems in which non-programmers can create working applications. EUC is a group of approaches to computing that aim to better integrate end users into the computing environment. These approaches attempt to realize the potential for high-end computing to perform problem-solving in a trustworthy manner.
System and Method for Management of End User Computing Devices
InactiveUS20080120350A1Special data processing applicationsFile systemsOperational systemFile system
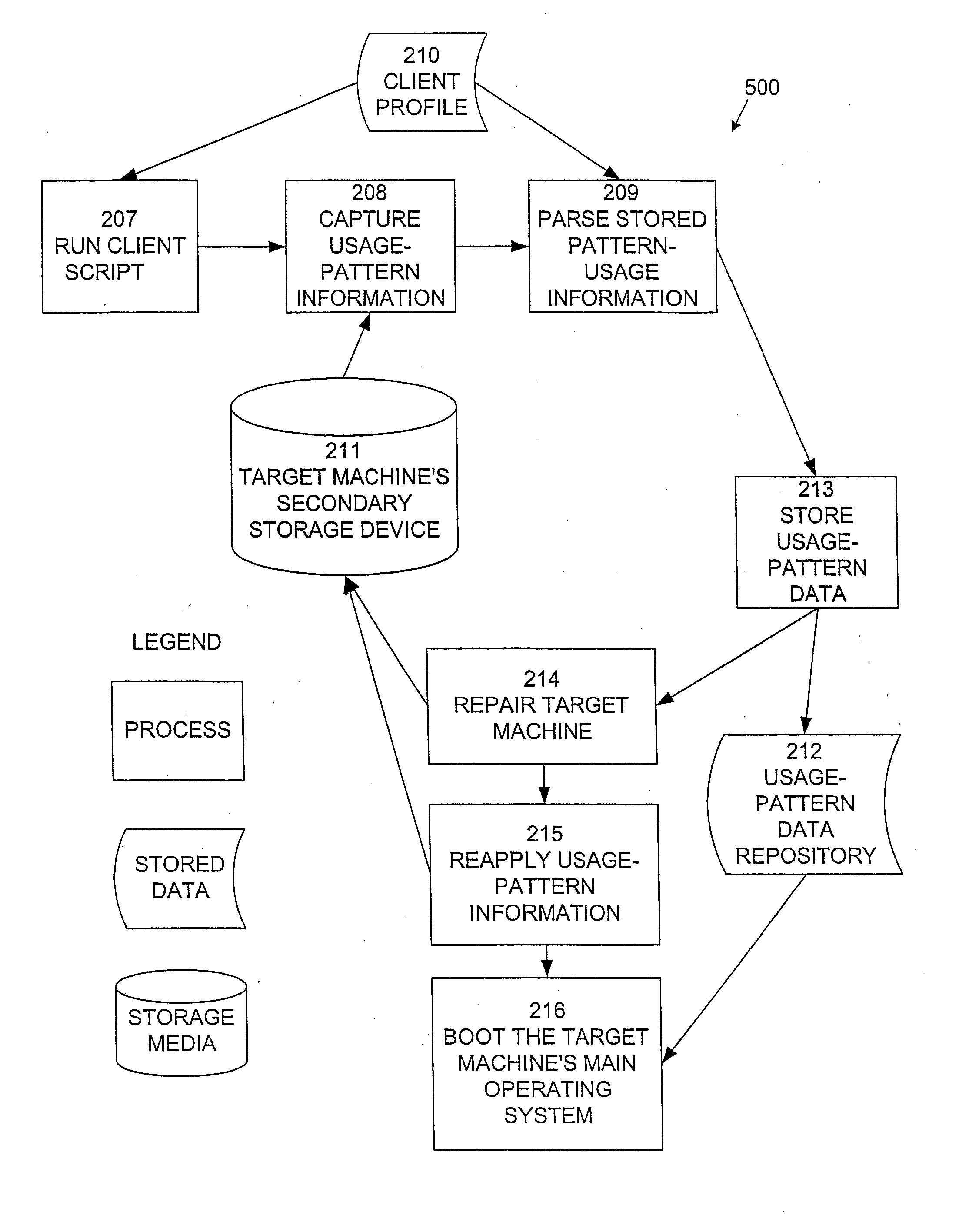
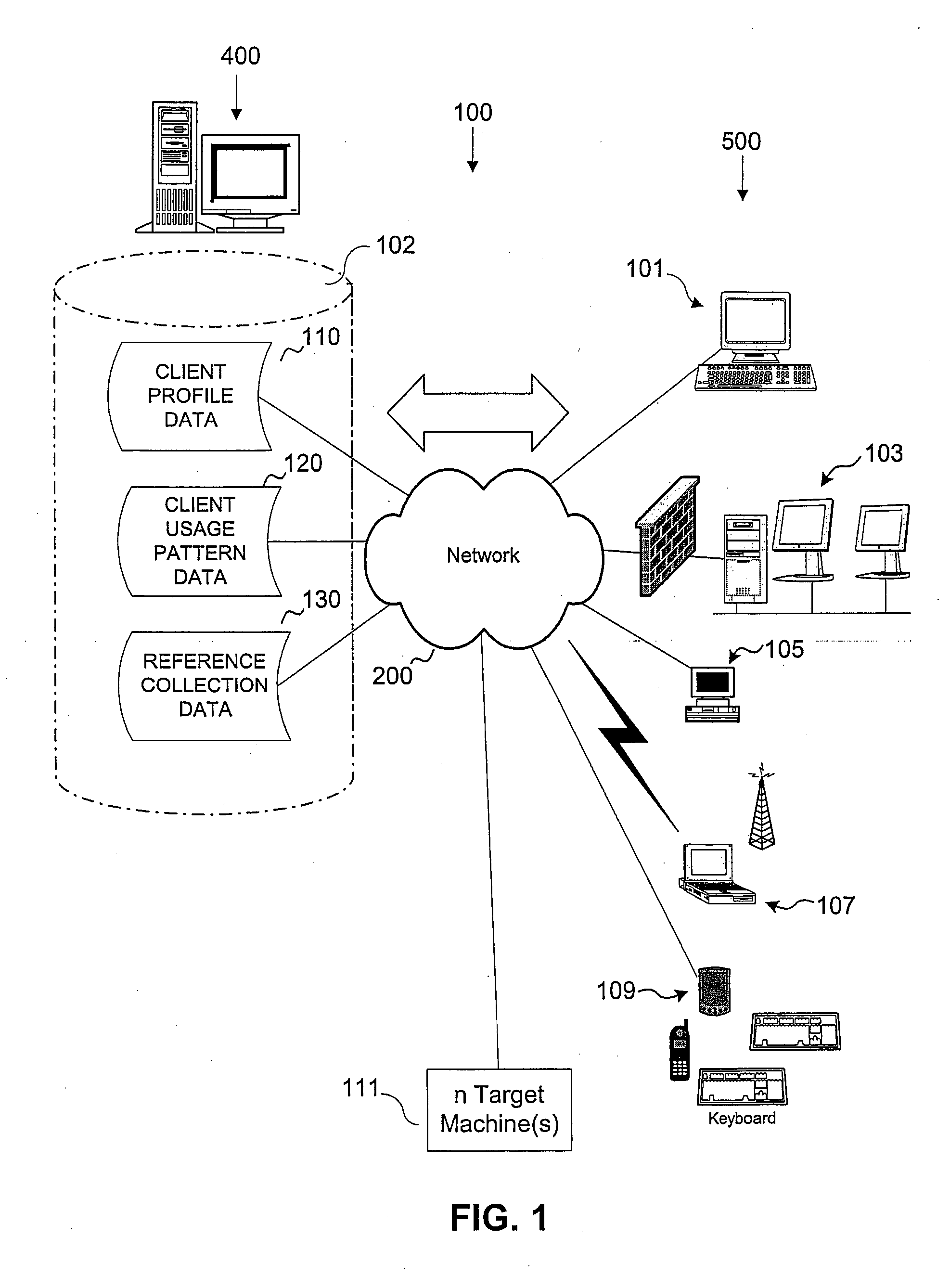
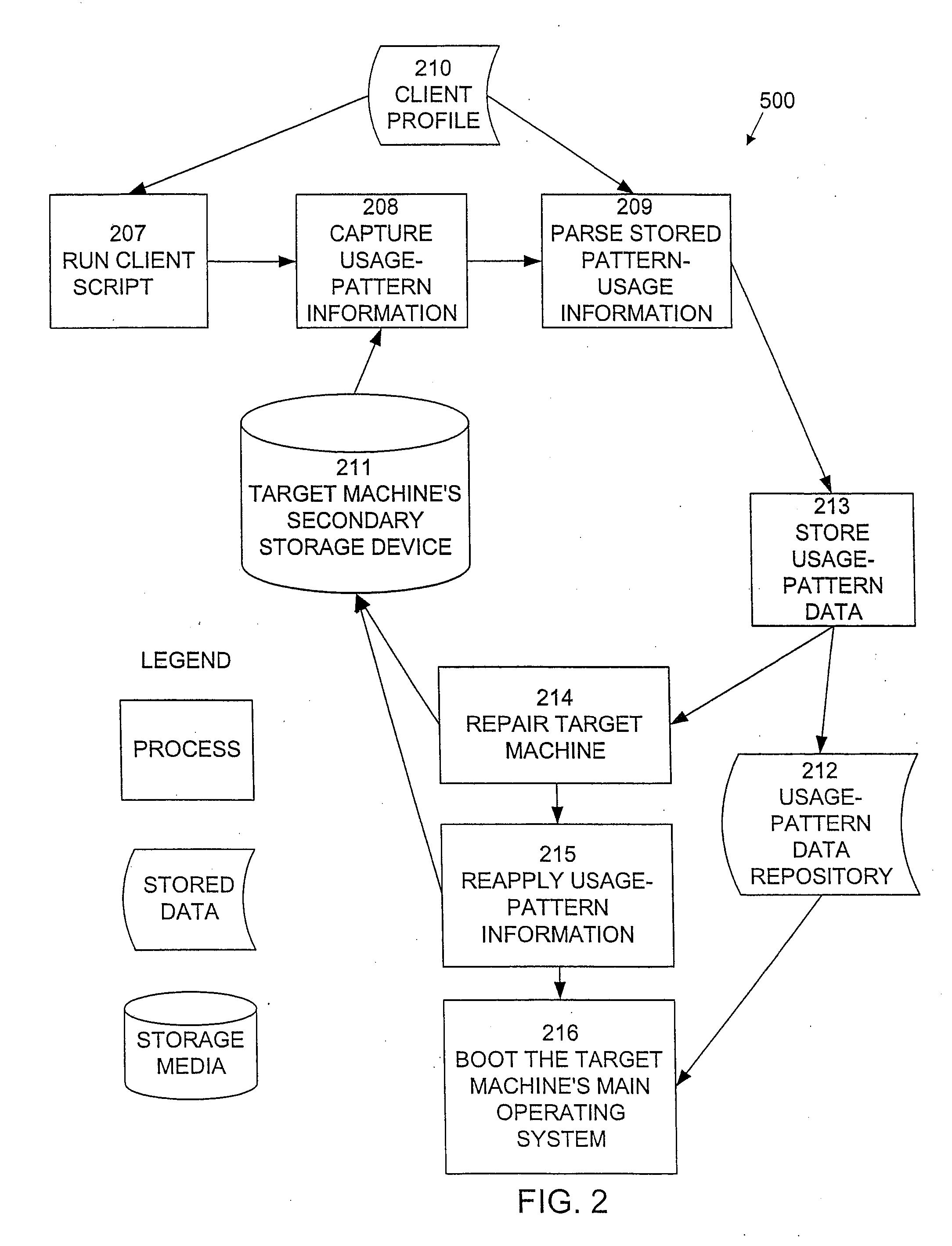
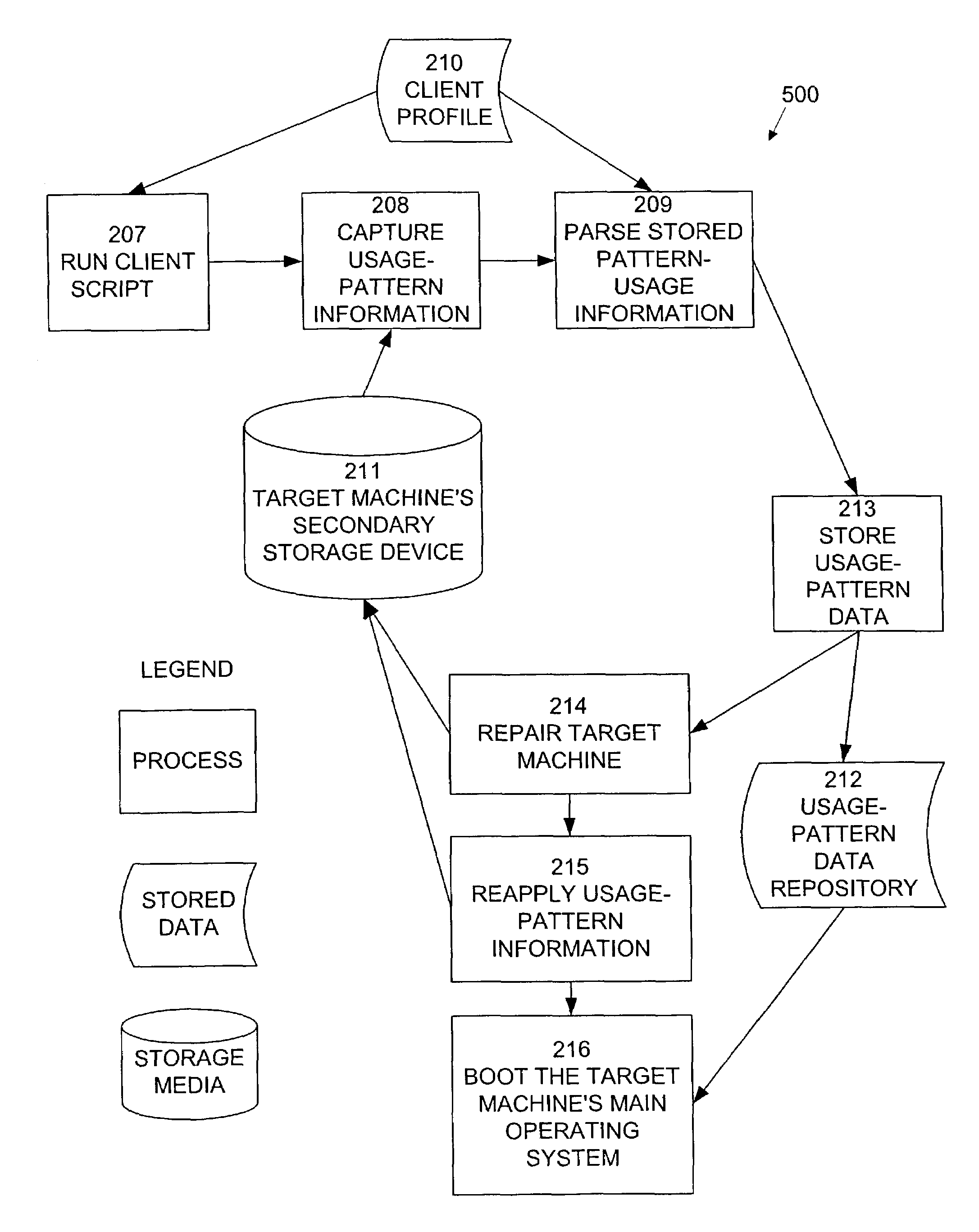
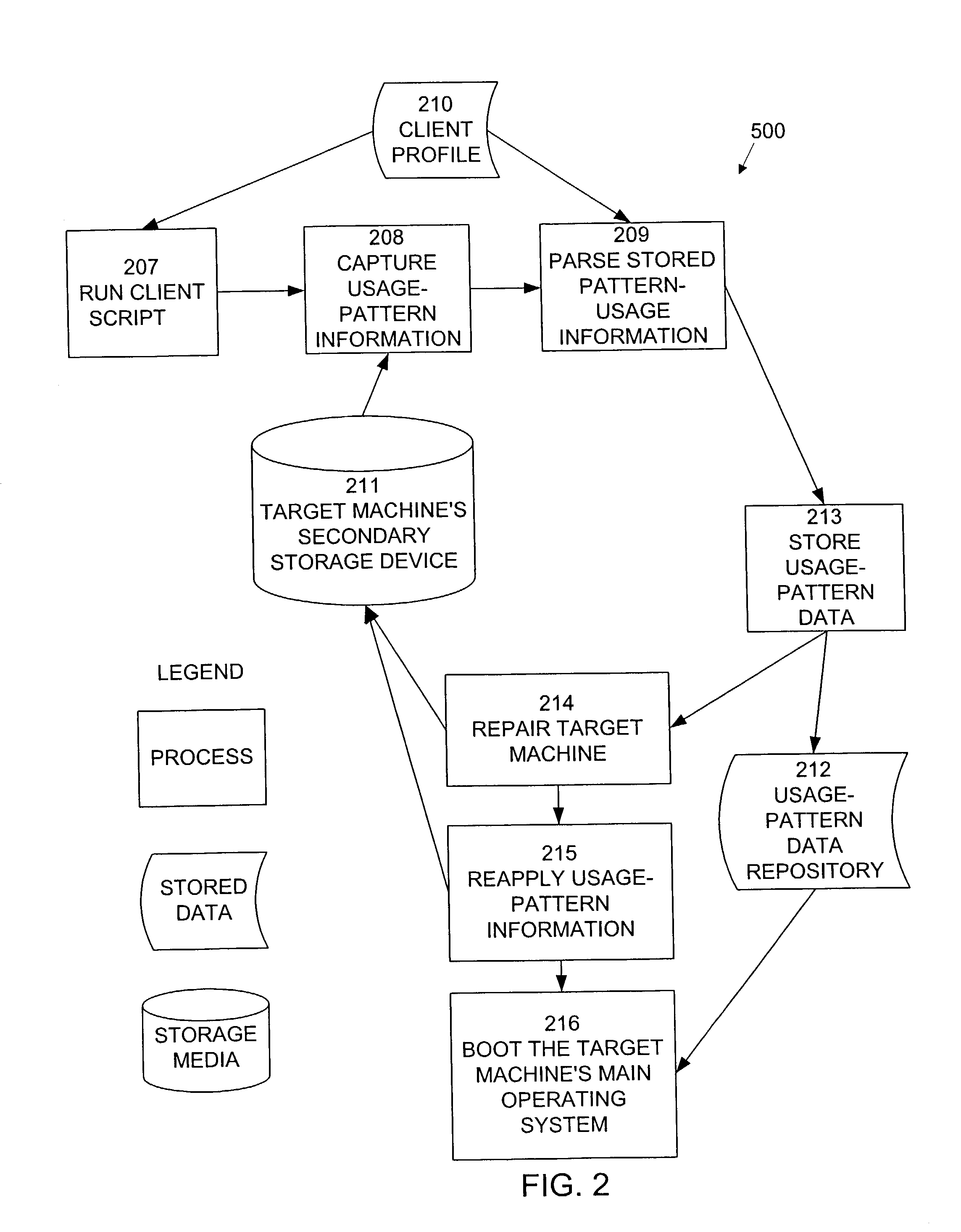
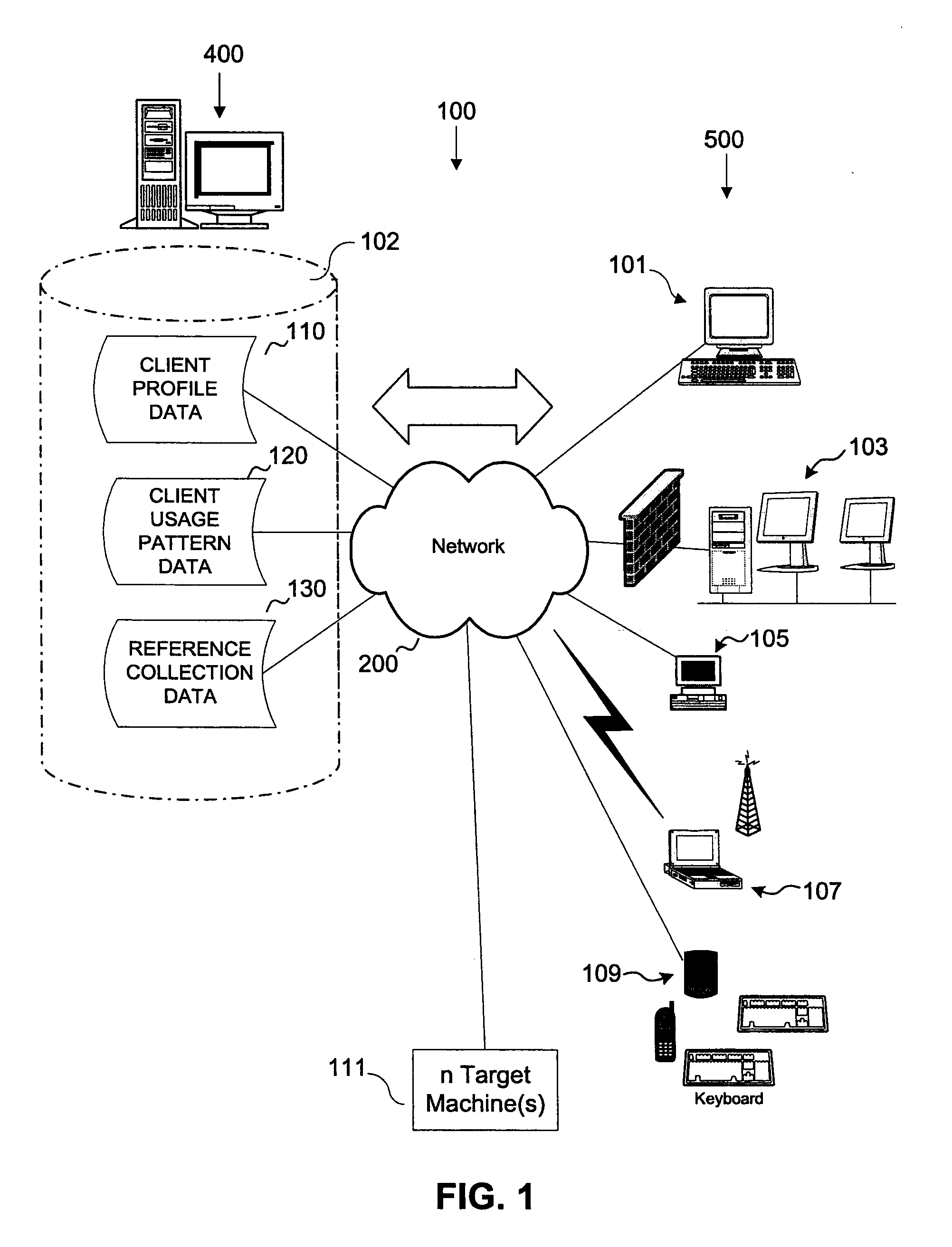
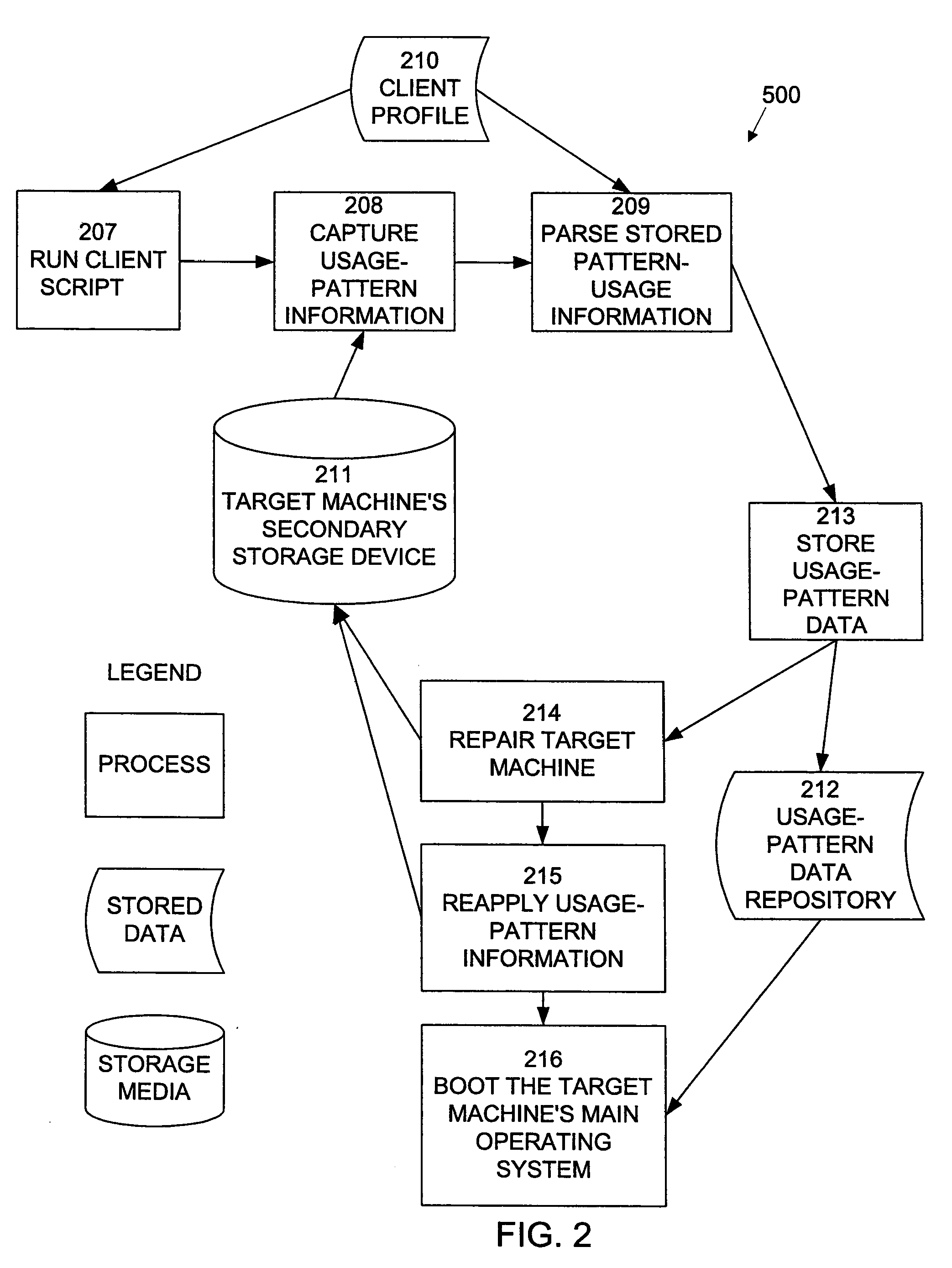
A system and method is provided for the repair of operating system and application binary files and configuration data files at pre-operating system boot stage by comparing attributes of the files against a reference collection of such files stored on a server during each reboot or restart cycle while creating and restoring a collection of dynamic operating system binary files, configuration data files, file system structures and hardware system attributes unique to the configuration and use of the system on a server for subsequent pre-operating system repair operations.
Owner:PERSYSTENT TECH CORP
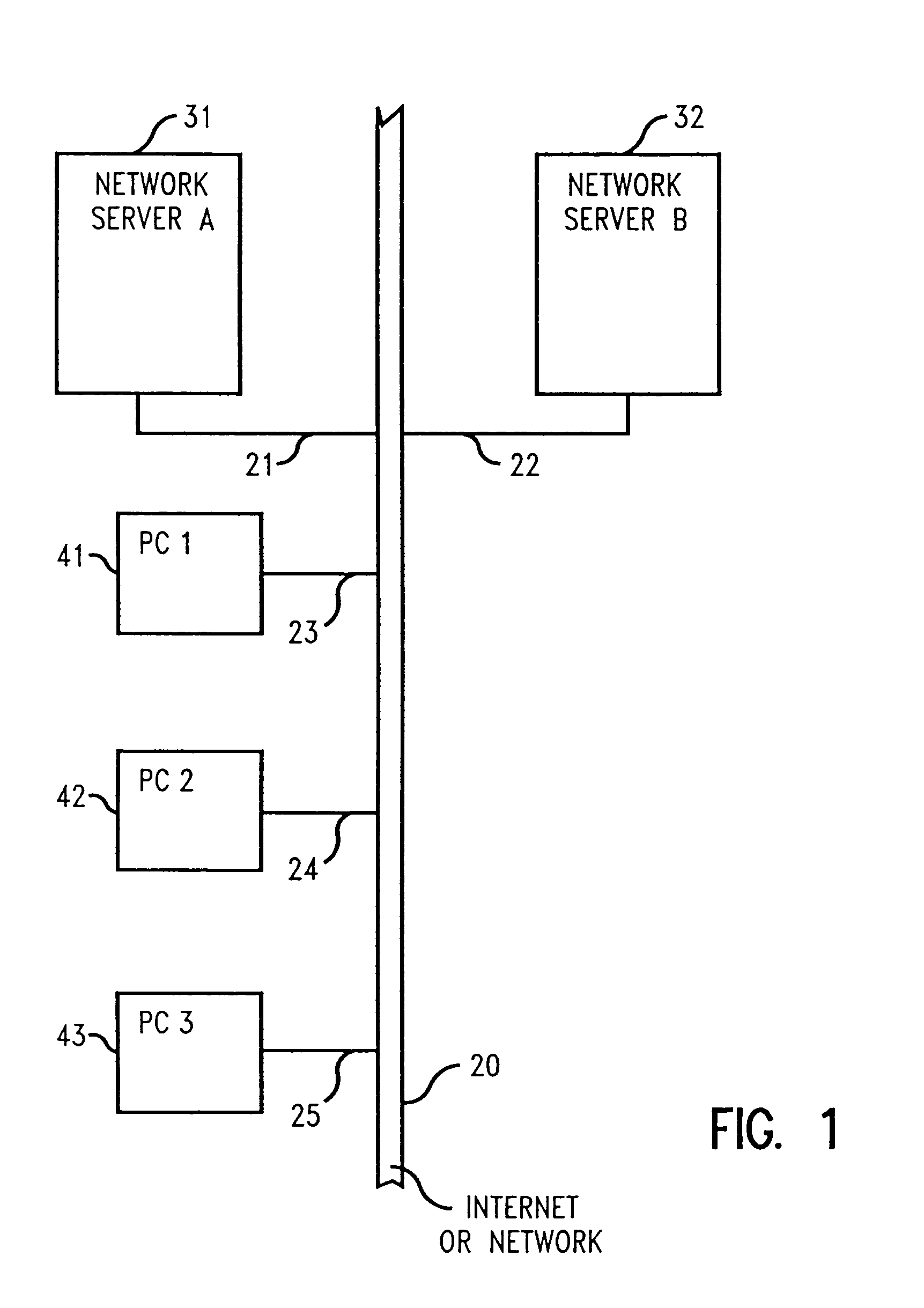
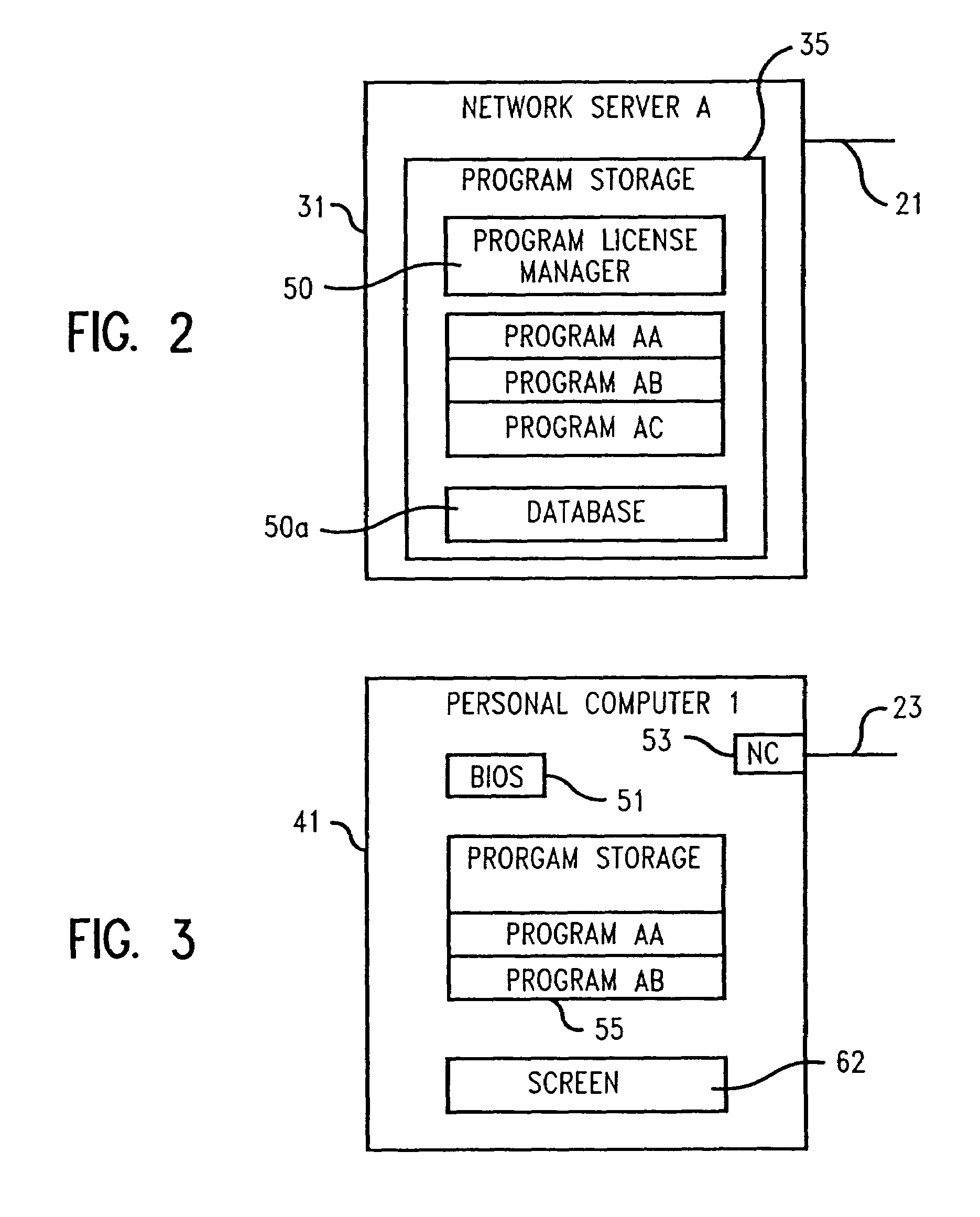
Licensed application installer
InactiveUS6948168B1Data processing applicationsSoftware engineeringComputer terminalApplication software
A method and system of installing licensed software on an end user's computer comprising having a program storage device and a unique computer identifier distinguishing the end user computer from other computers, e.g., a BIOS serial number or a network adapter address. The network computer contains a plurality of different software for license to end users and a database listing computer identifiers licensed to run the software. The end user computer sends to the network computer a command to run a program identifying to the end user computer the software listed as licensed by the computer identifier of the end user computer. The network computer contacts the end user computer and determine its end user computer identifier, verifies listing of the end user computer identifier in the network computer database, and identifies to the end user computer all of the software on the network computer program storage device listed as licensed by the computer identifier of the end user computer using an executable program on the network computer. The end user computer sends to the network computer a selection of the software to be downloaded. The network computer downloads the selected software and installs it on the end user computer program storage device.
Owner:ACTIVISION PUBLISHING
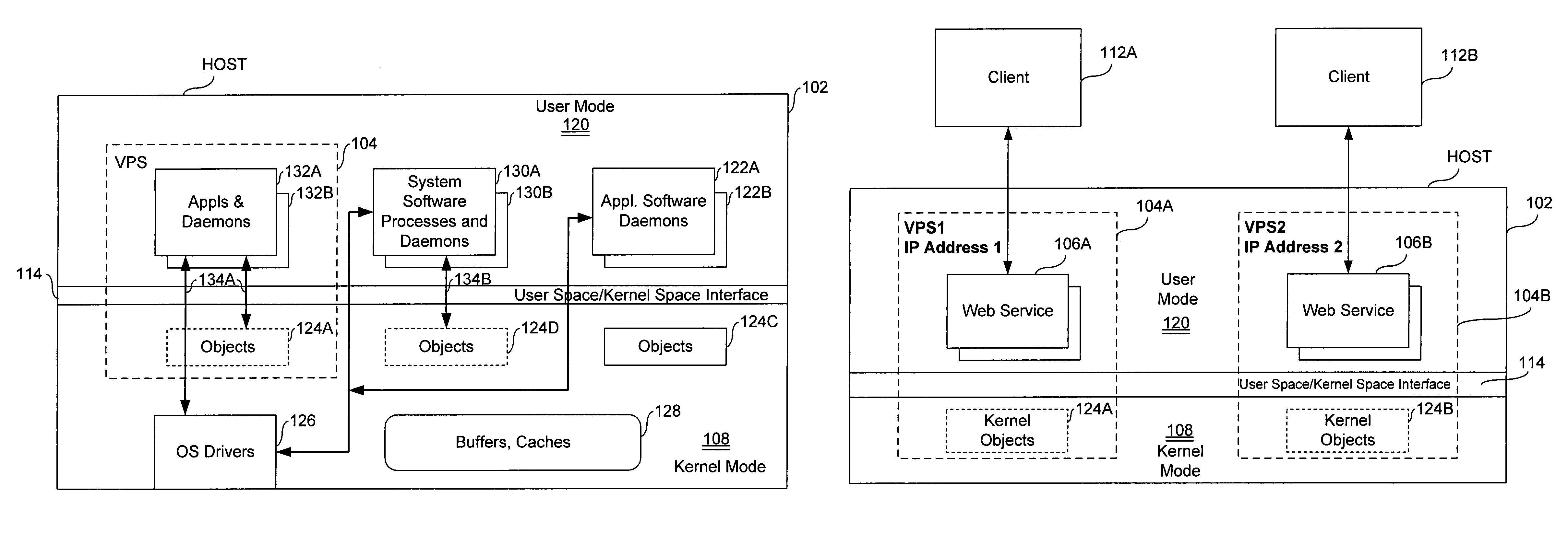
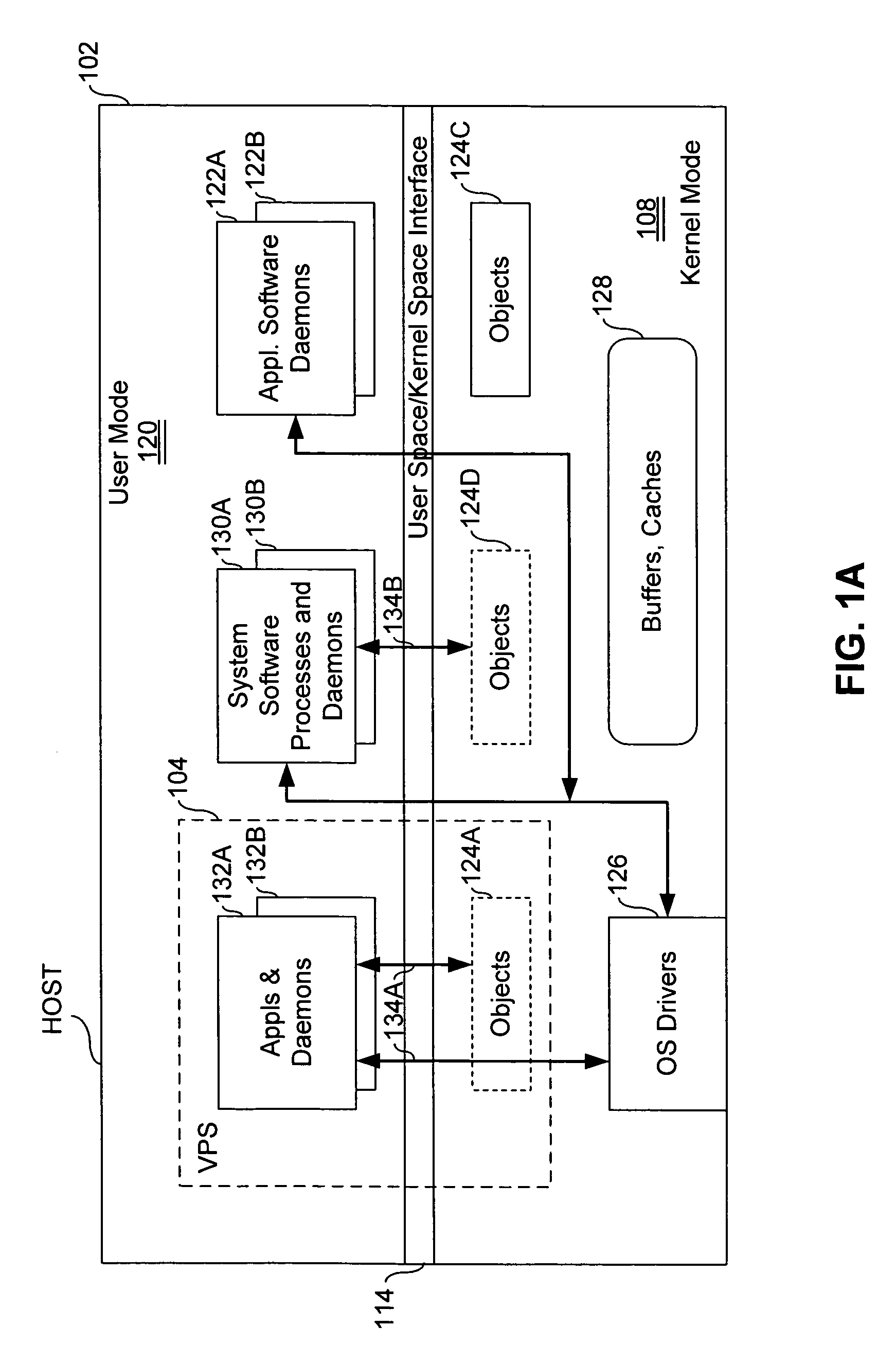
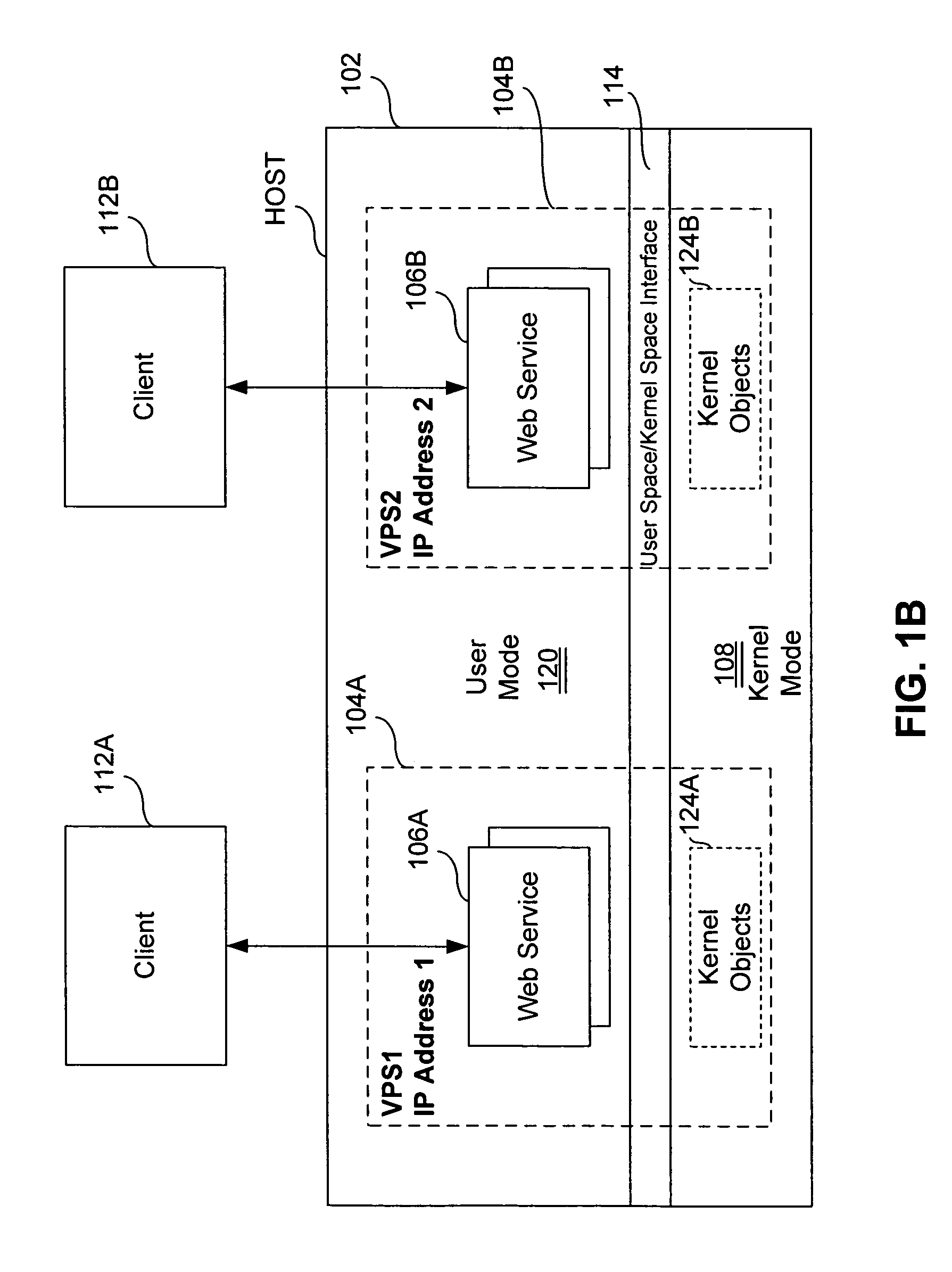
Virtual private server with enhanced security
ActiveUS7461144B1Improve securityData processing applicationsDigital computer detailsComputer resourcesOperational system
An end user computer includes a processor running an operating system. A plurality of virtual private servers (VPSs) are supported within the operating system. A plurality of applications are available to a user of the end user computer. The applications are launched within different VPSs. At least one of the VPSs has multiple applications launched within it. At least two of the applications are launched within different VPSs, and communicate with each other using secure communications means, such as firewalls, proxies, dedicated clipboards, named pipes, shared memory, dedicated inter-process communications, Local Procedure Calls / Remote Procedure Calls, API, network sockets, TCP / IP communications, network protocol communications and memory mapped files. The VPSs can be dynamically created and terminated. VPS control means are available to the user and include means for creation / termination of VPSs, a file system and registry backup, control information for backup / restore of data on a VPS level, placement of applications / processes rules for creation / support of corresponding VPSs, granulation of isolation for VPS / applications / processes, computer resource control, definition of permissible operations for inter-VPS communication, means for definition of permissible operations for inter-process communications.
Owner:VIRTUOZZO INT GMBH
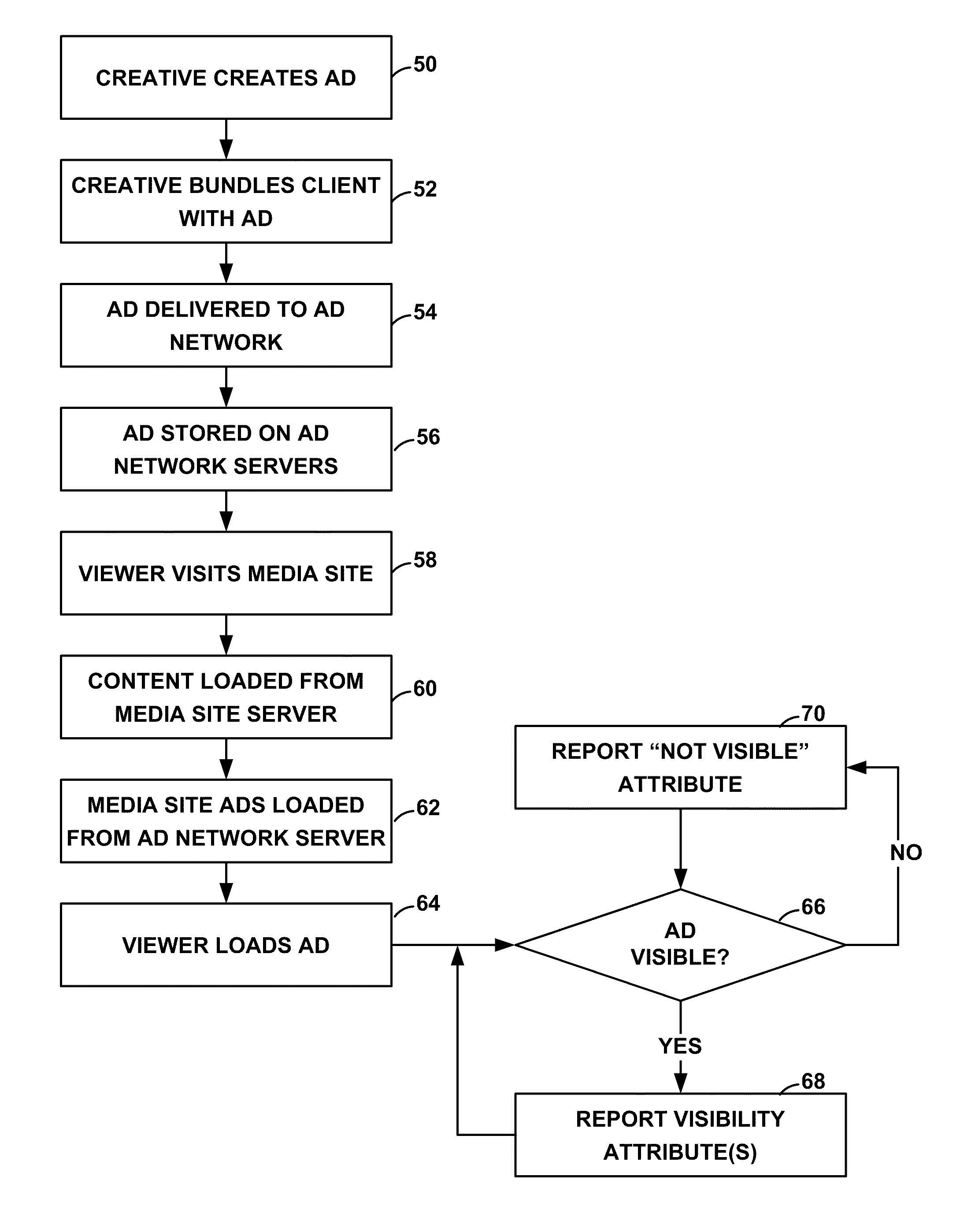
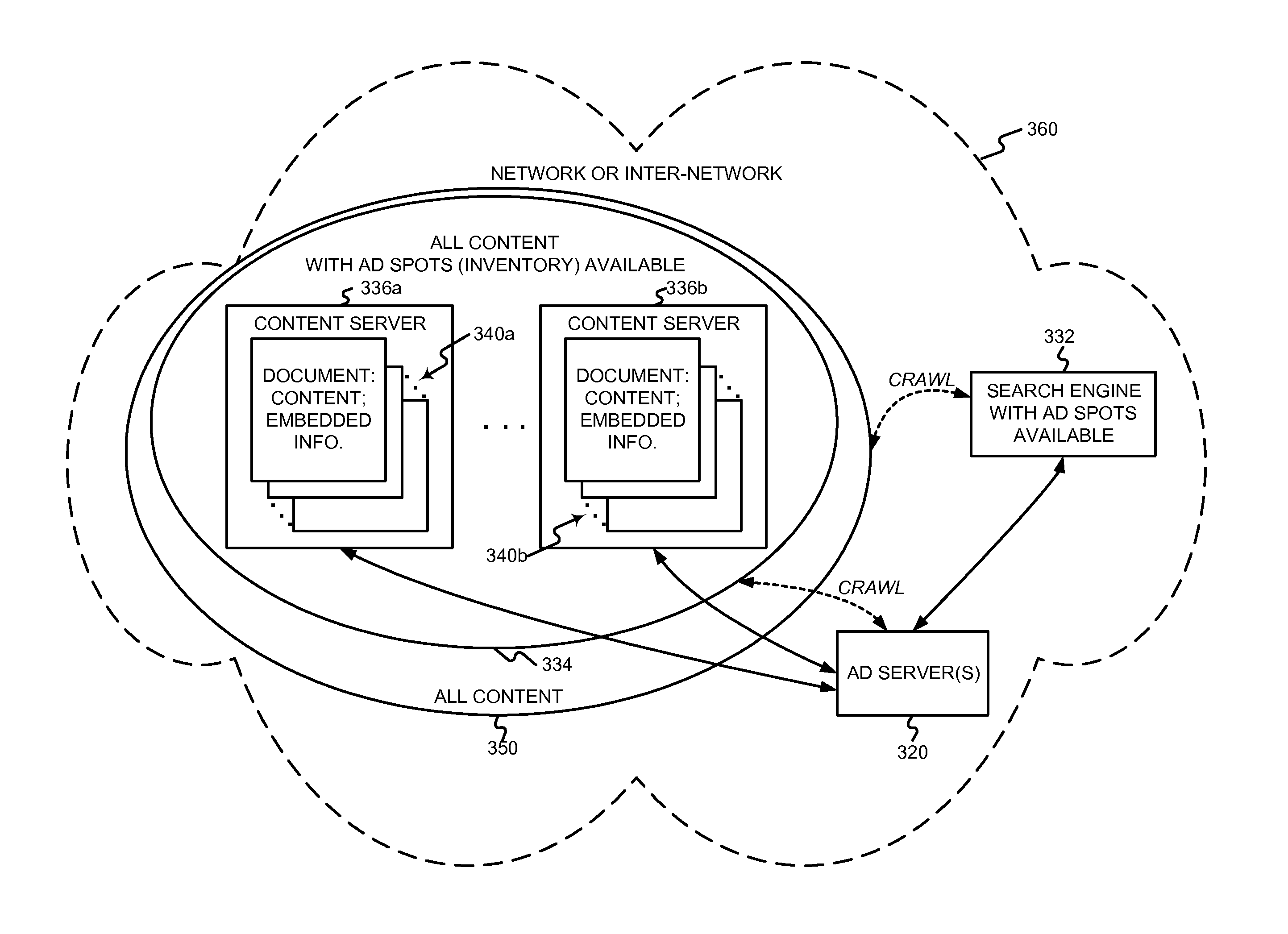
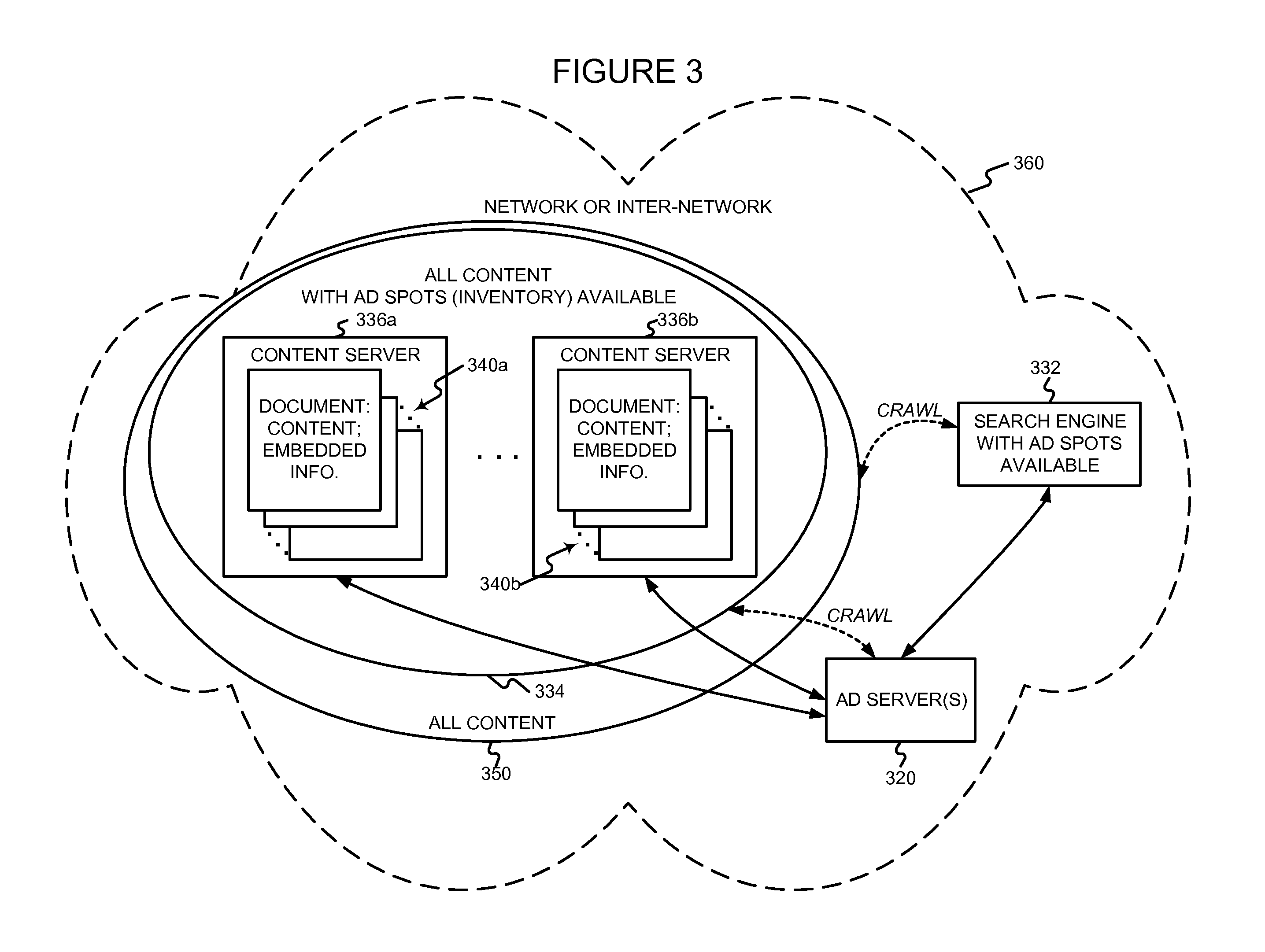
System and method for measuring effectiveness of electronically presented advertizing
InactiveUS20110196735A1Efficient developmentQuick understandingDigital data processing detailsAnalogue secracy/subscription systemsDisplay deviceComputer terminal
Disclosed in one general aspect is a method of evaluating the presentation of advertising content on end-user computer displays that includes sending an integrated advertisement program that includes advertising content through a computer network to end-user computers in response to requests from browsers running on the end-user computers. The integrated advertisement program is accessed on each of the end-user computers after it is received from a server on that computer. The integrated advertisement program determines a display attribute of the advertising content in the integrated advertisement program on each of the end-user computers, and reports the detected display attribute from each of the end-user computers through the computer network to a monitoring application.
Owner:BURT AB
Method of and apparatus for delivery of proprietary audio and visual works to purchaser electronic devices
InactiveUS20010037304A1Computer security arrangementsBuying/selling/leasing transactionsSupercomputerData warehouse
A method of delivering audio and audio visual works to users of computer terminals includes the steps of: providing a data warehouse of digitized works; providing program means for end user computers to access, select and play at least one of the works; providing means for controlling end user access to the works and for collecting payment for playing at least one of the works; and diverting a portion of the payment for playing the at least one work to the holder of a copyright to the at least one work. The method preferably includes the additional steps of encrypting the works; and providing the end user with program means for deciphering the works. The method still further preferably includes additional the steps of delivering advertising matter to the end user with each work the end user selects and plays; keeping a record of the particular works each end user selects and plays; customizing advertising delivered to the end user to fit within any pattern of work selection by the particular end user. An apparatus for performing the method is also provided, including a computer hive made up of several inter-linked computers having specialized functions, the computers operating in unison to build a supercomputer that has shared disk space and memory, in which each node belongs to the collective and possesses its own business rules and membership to an organization managerial hierarchy.
Owner:PAIZ RICHARD S
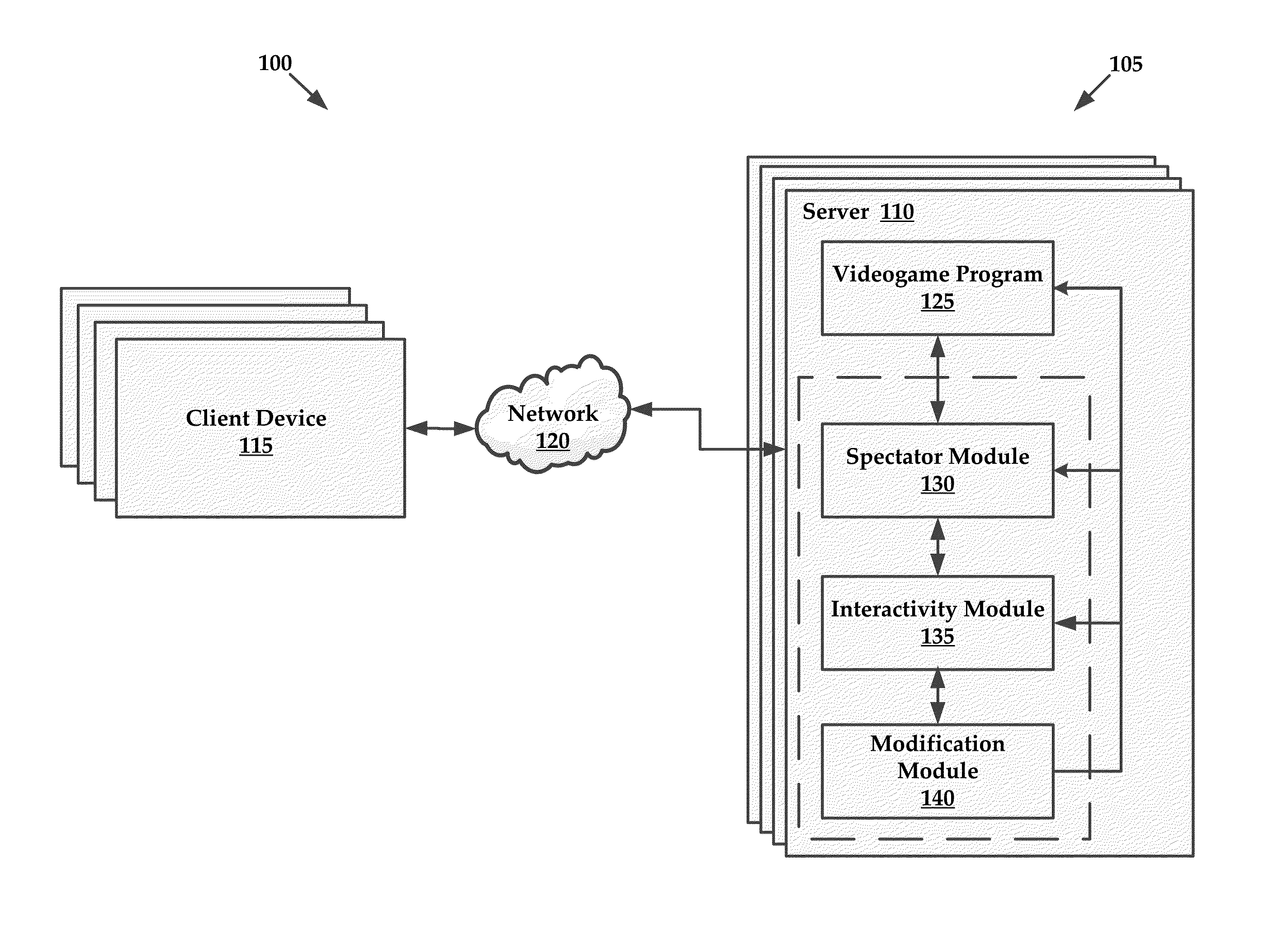
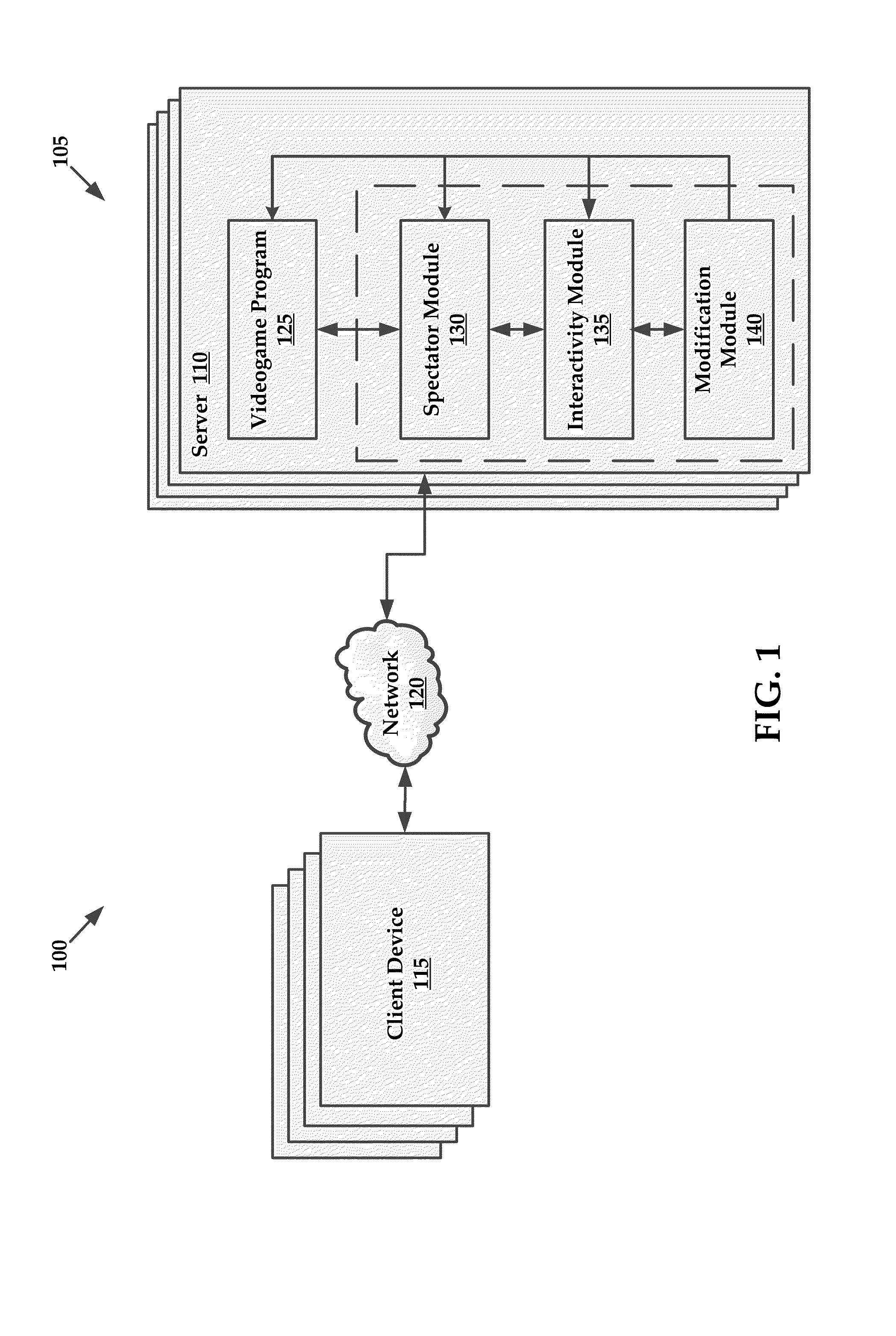
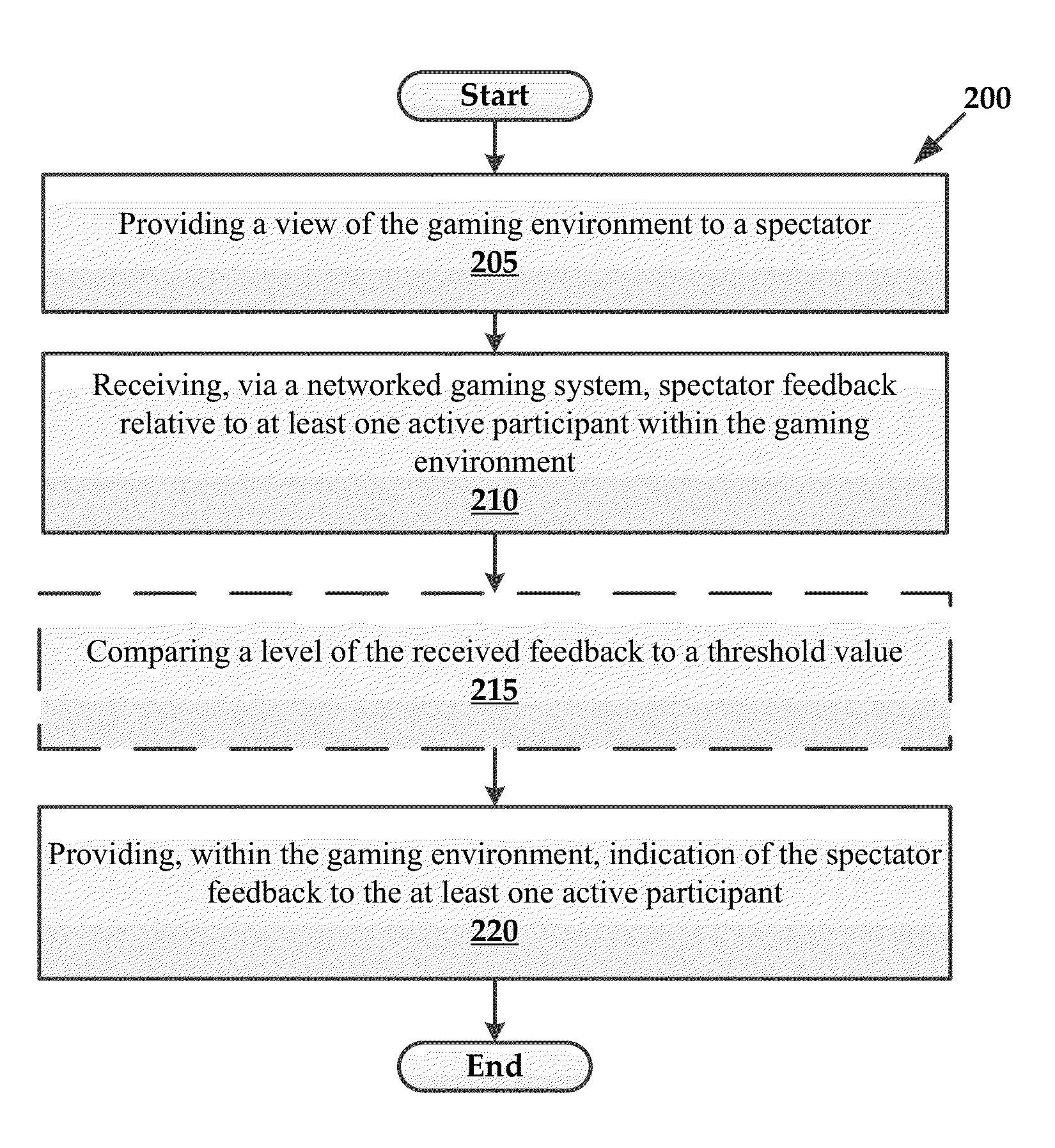
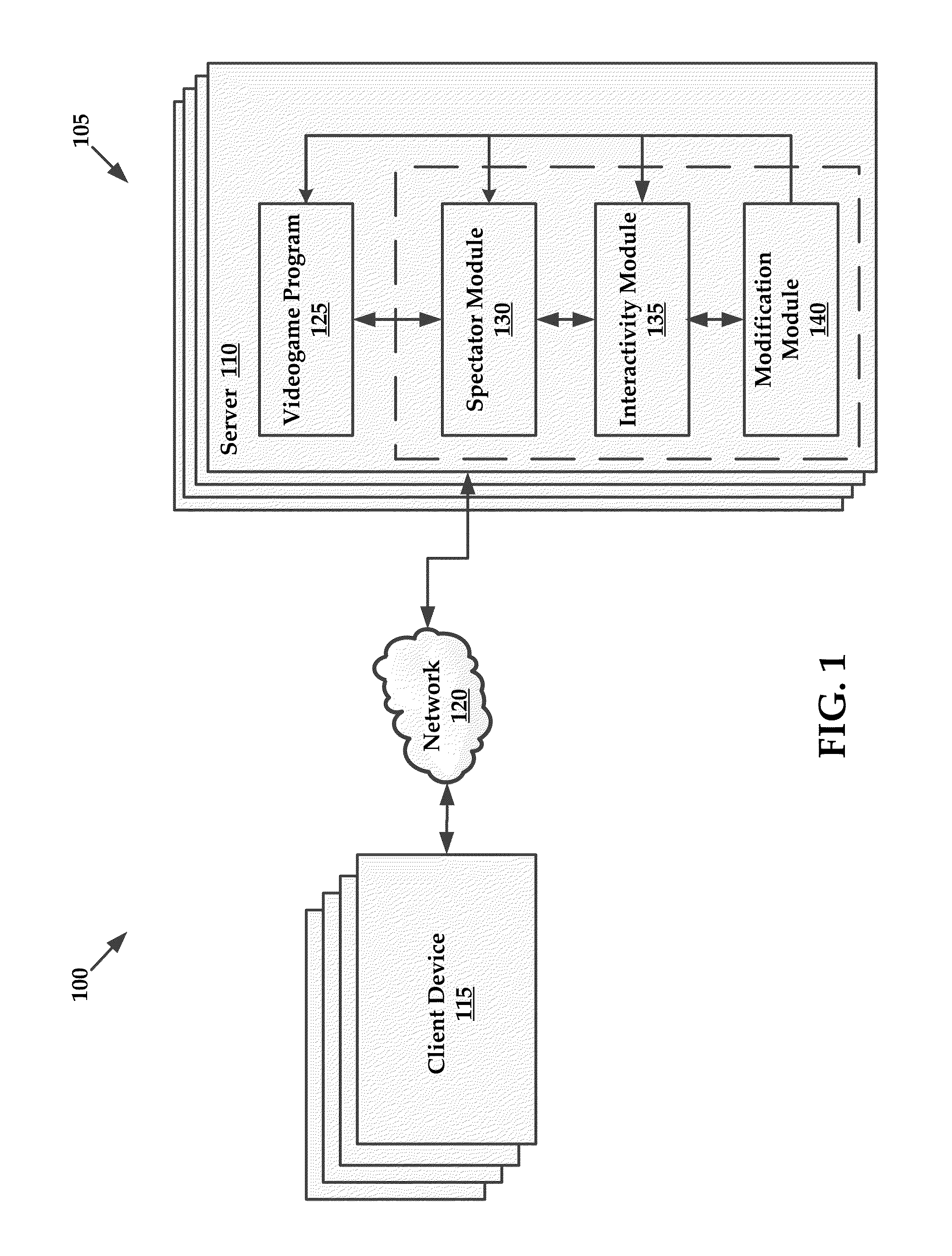
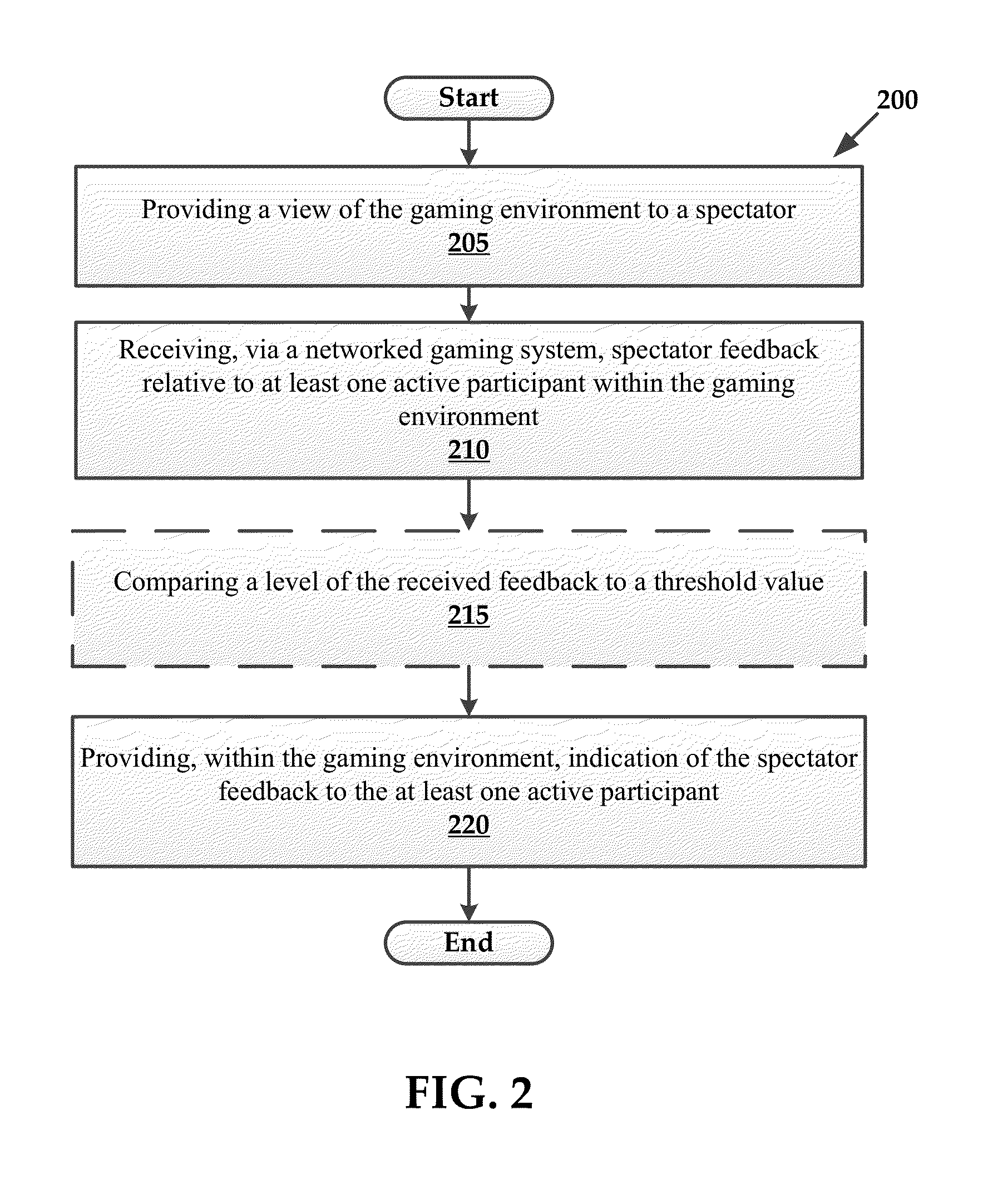
Interactive spectator features for gaming environments
InactiveUS20140004951A1Enhanced interactionEnvironmental promotionVideo gamesSpecial data processing applicationsComputer terminalEnd-user computing
Systems and methods for exchanging virtual rewards for computing resources are provided herein. Exemplary methods may include receiving access to a portion of computing resources of an end user computing system and providing a virtual reward within a gaming environment to an end user in exchange for utilizing an amount of the portion of the computing resources of the end user computing system.
Owner:RED 5 STUDIOS
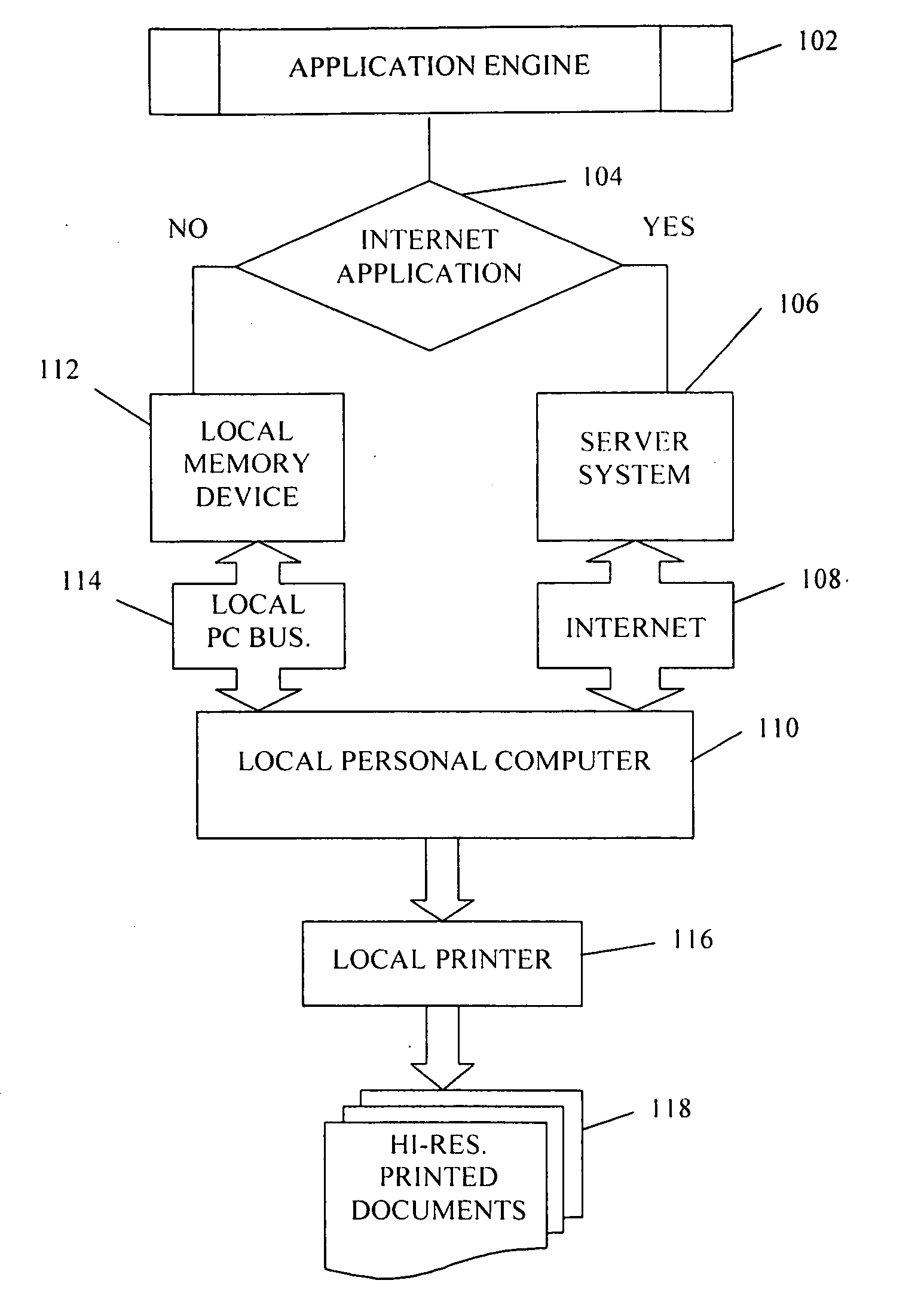
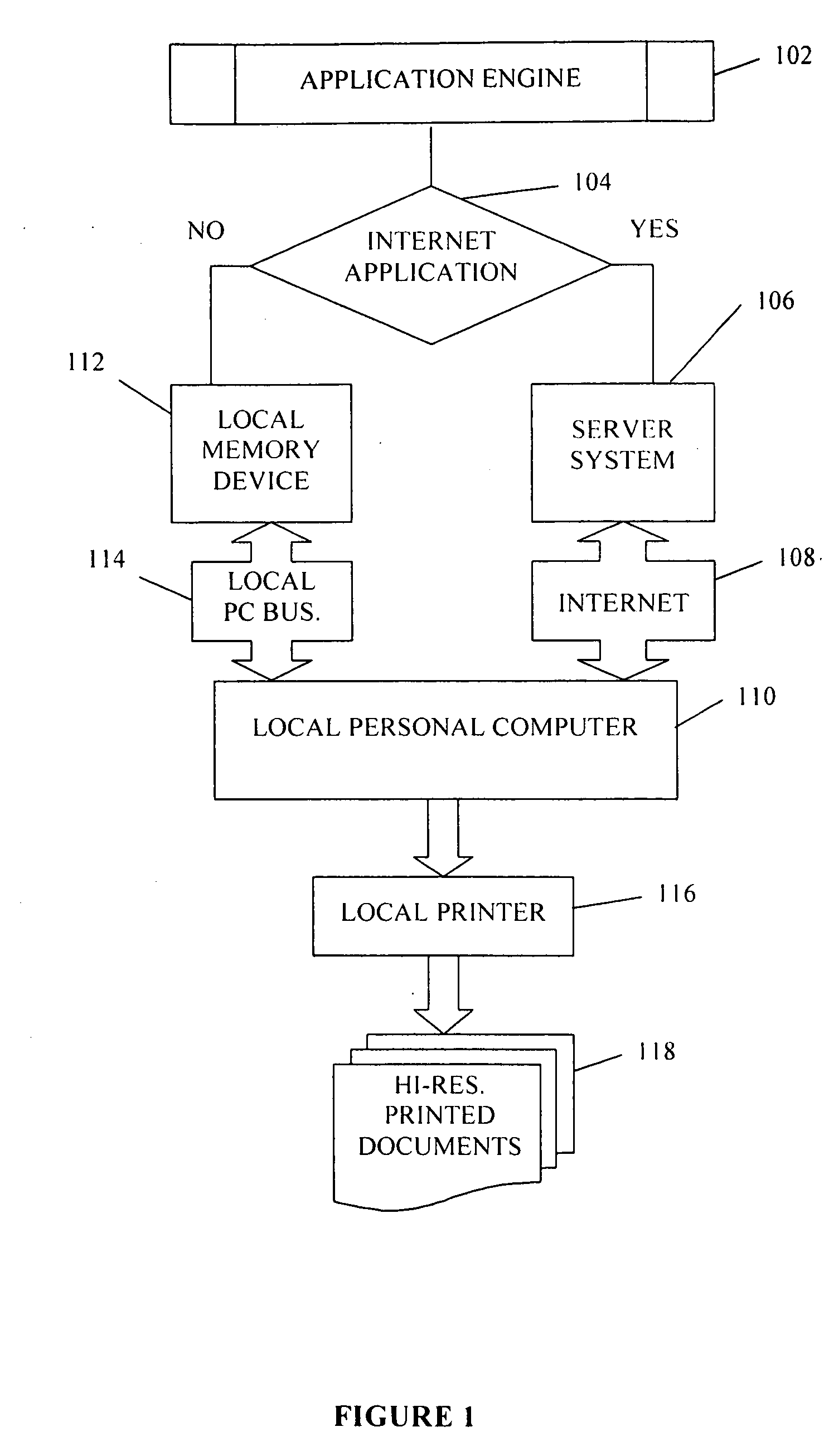
Process for creating and printing customized document at end user computer and printer
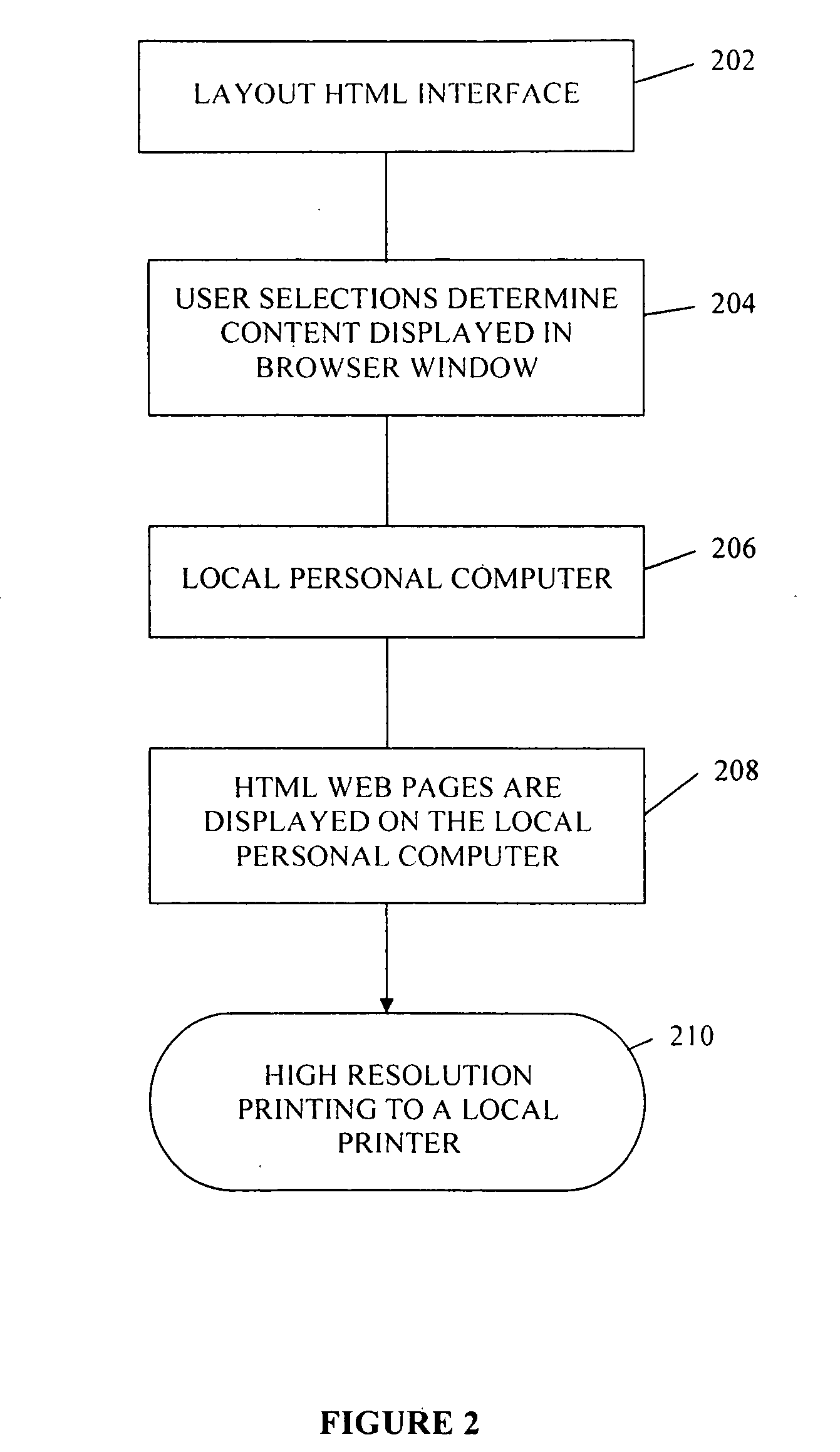
InactiveUS20050262437A1High resolutionNatural language data processingTransmissionGraphicsWeb browser
A customized document is created at an end user local computer by utilizing a plug-in program installed within a web-browser of the local computer to access and request from a memory device, such as an Internet server, a pre-prepared and unalterable document layout and desired pre-prepared document content, including a graphics image, text, and image and text orientation. The end user in some instances is able to specify the text, select its font type and size, and import end user provided digital image. The graphic image may be edited at the local computer. The document request is fulfilled using the plug-in to interface with the memory device and retrieve the necessary document layout and content, and the user is provided the option of saving the document at the local computer-e-mailing the document, or printing the document using a printer connected to the local computer.
Owner:PATTERSON DENNIS M +1
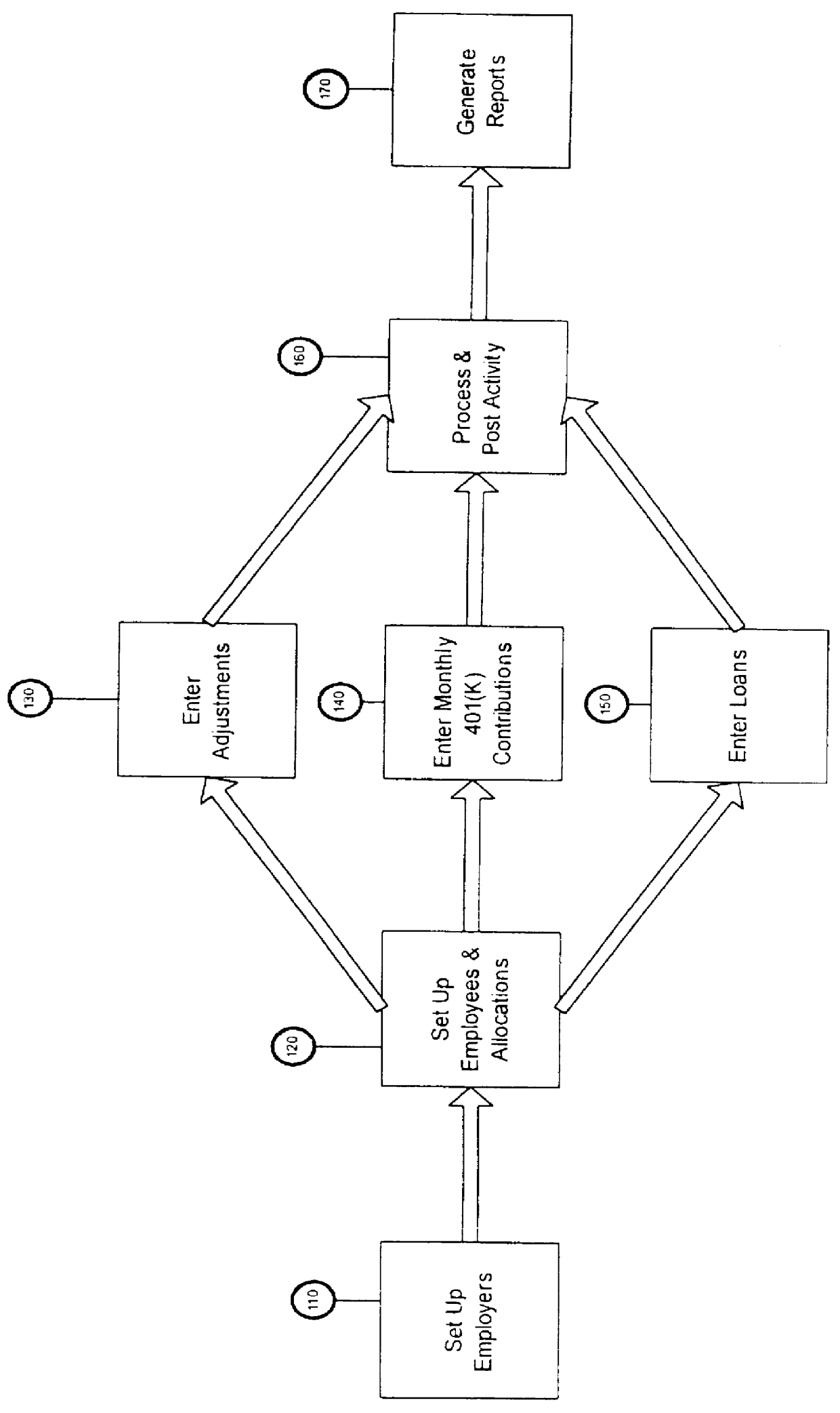
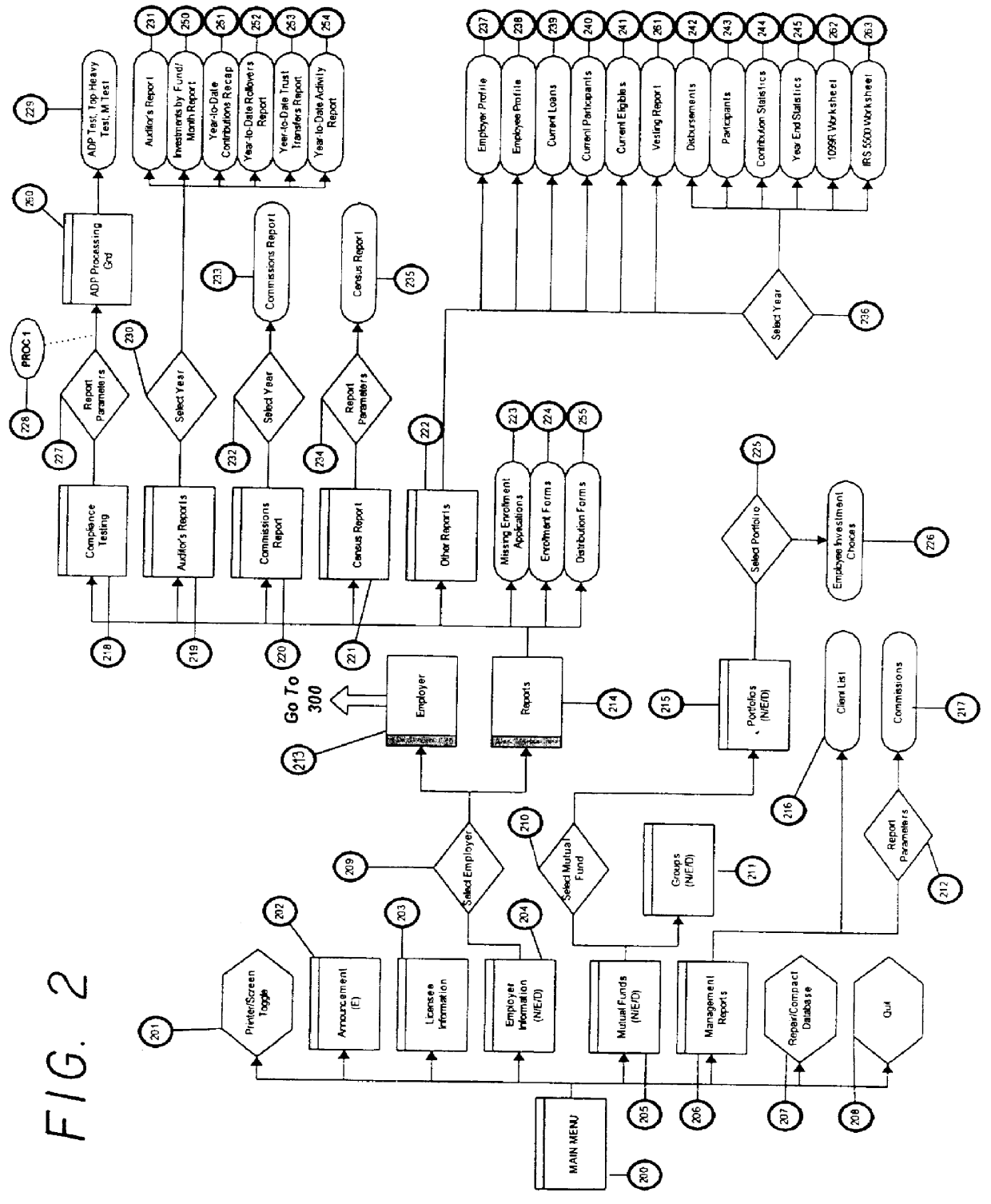
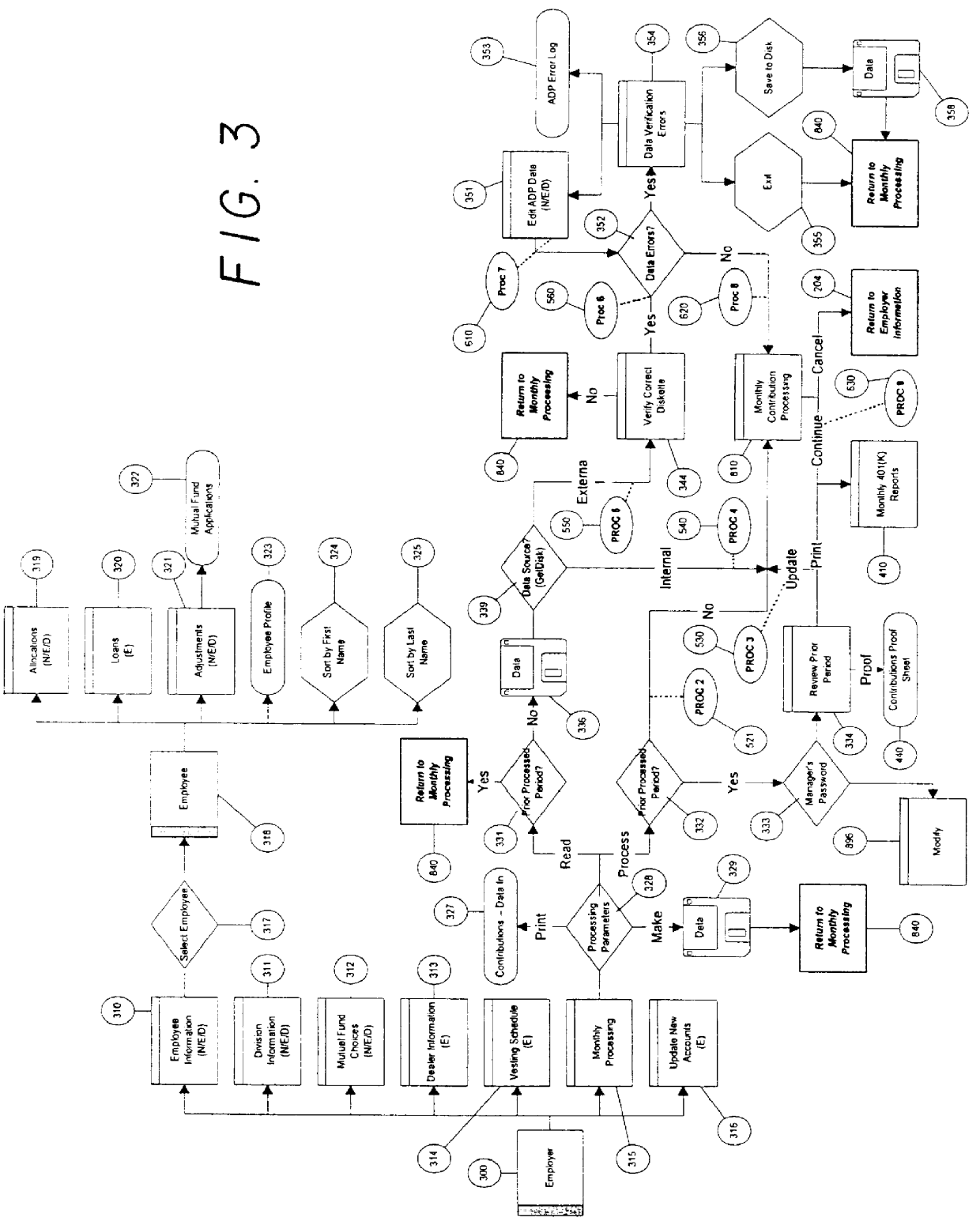
401K user software
A computer-based 401(k) plan offers unlimited access to virtually all SEC-regulated investment options-with no restrictions on the number of mutual fund families or their investments that a company can choose for its plan. The system and method provide an end-user computer-based system with individualized accountability as opposed to prior art pooled systems.
Owner:401K PRO INC
System and method for management of end user computing devices
ActiveUS7603440B1Digital computer detailsSpecial data processing applicationsOperational systemFile system
A system and method is provided for the repair of operating system and application binary files and configuration data files at pre-operating system boot stage by comparing attributes of the files against a reference collection of such files stored on a server during each reboot or restart cycle while creating and restoring a collection of dynamic operating system binary files, configuration data files, file system structures and hardware system attributes unique to the configuration and use of the system on a server for subsequent pre-operating system repair operations.
Owner:UTOPIC SOFTWARE LLC
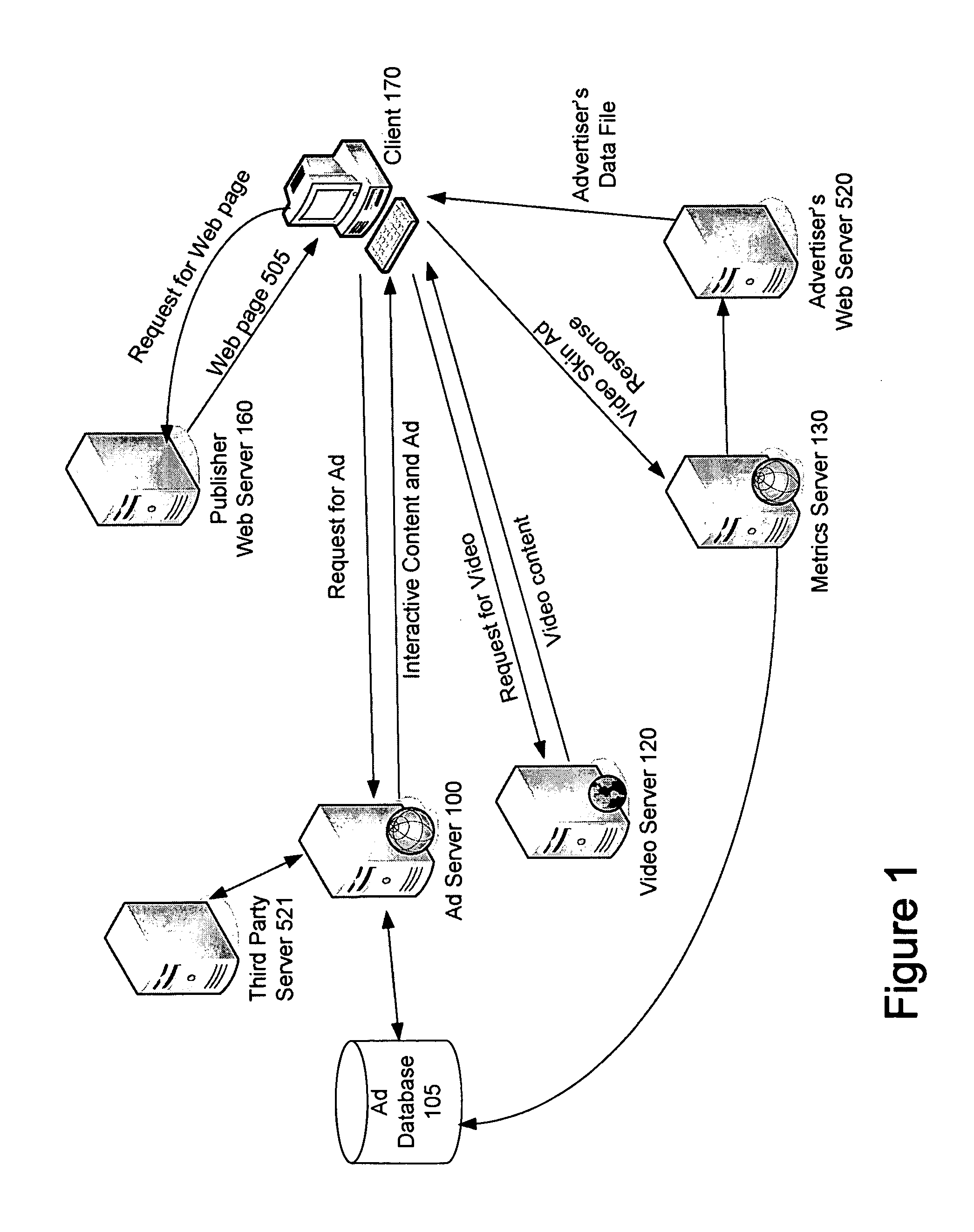
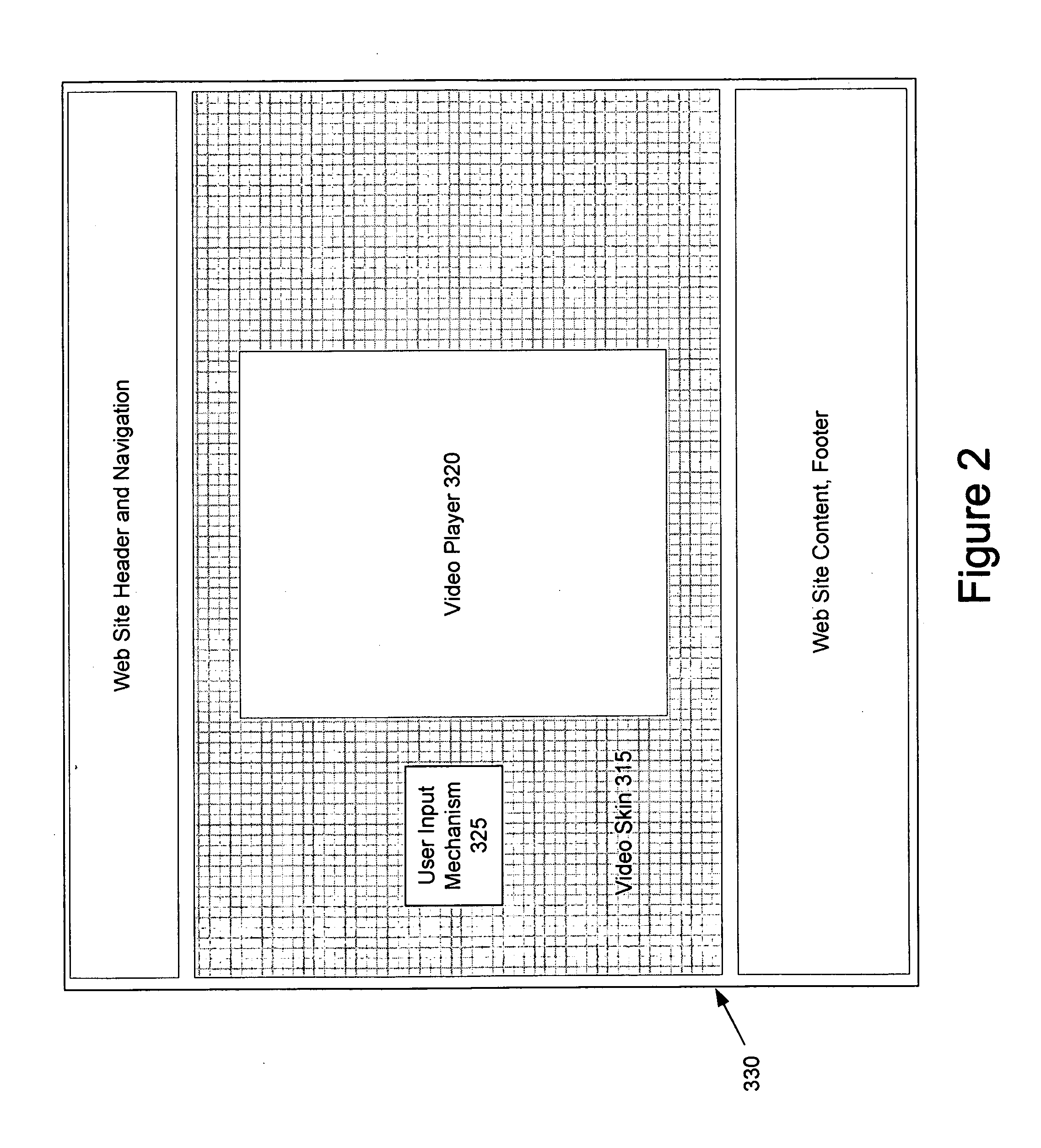
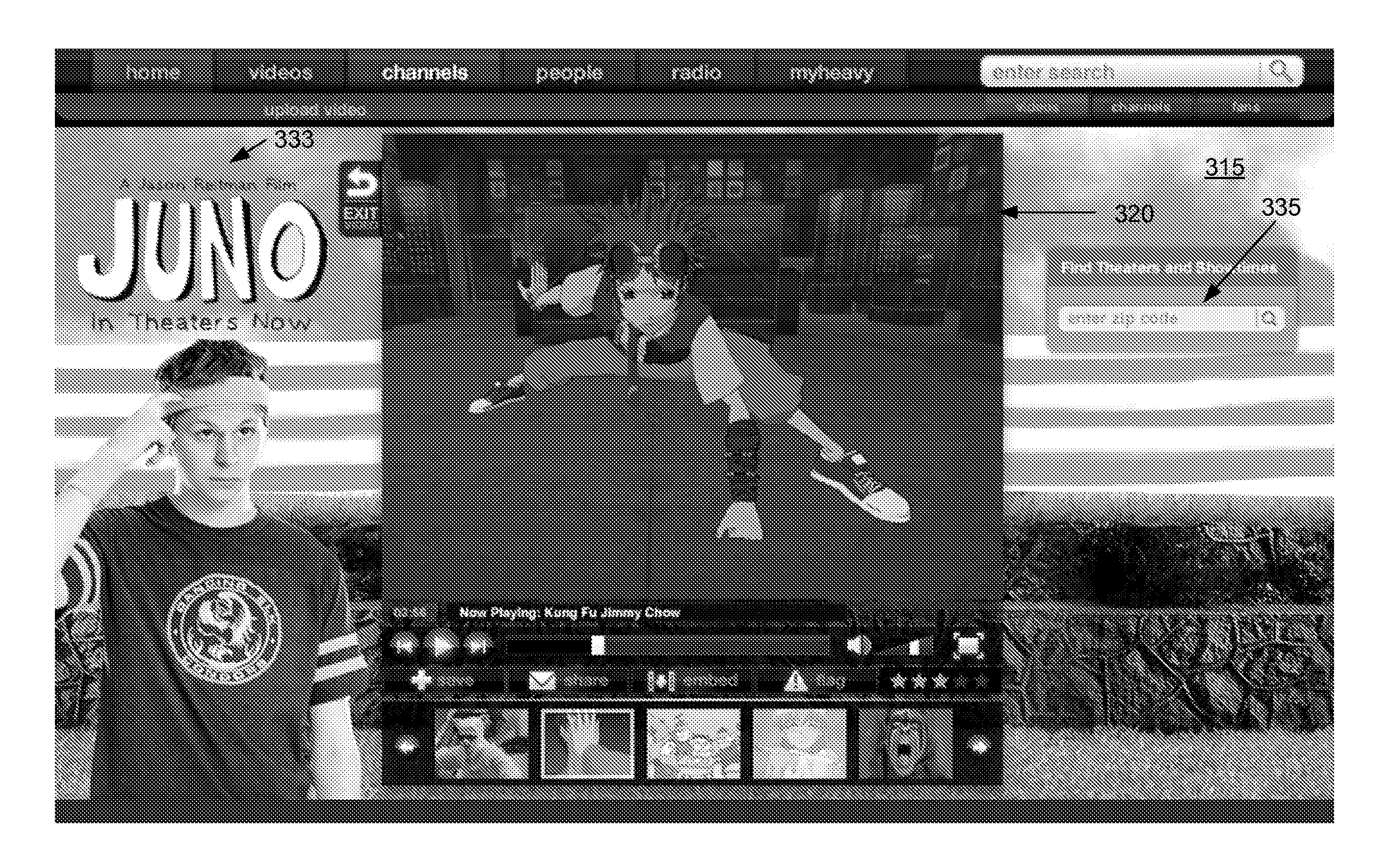
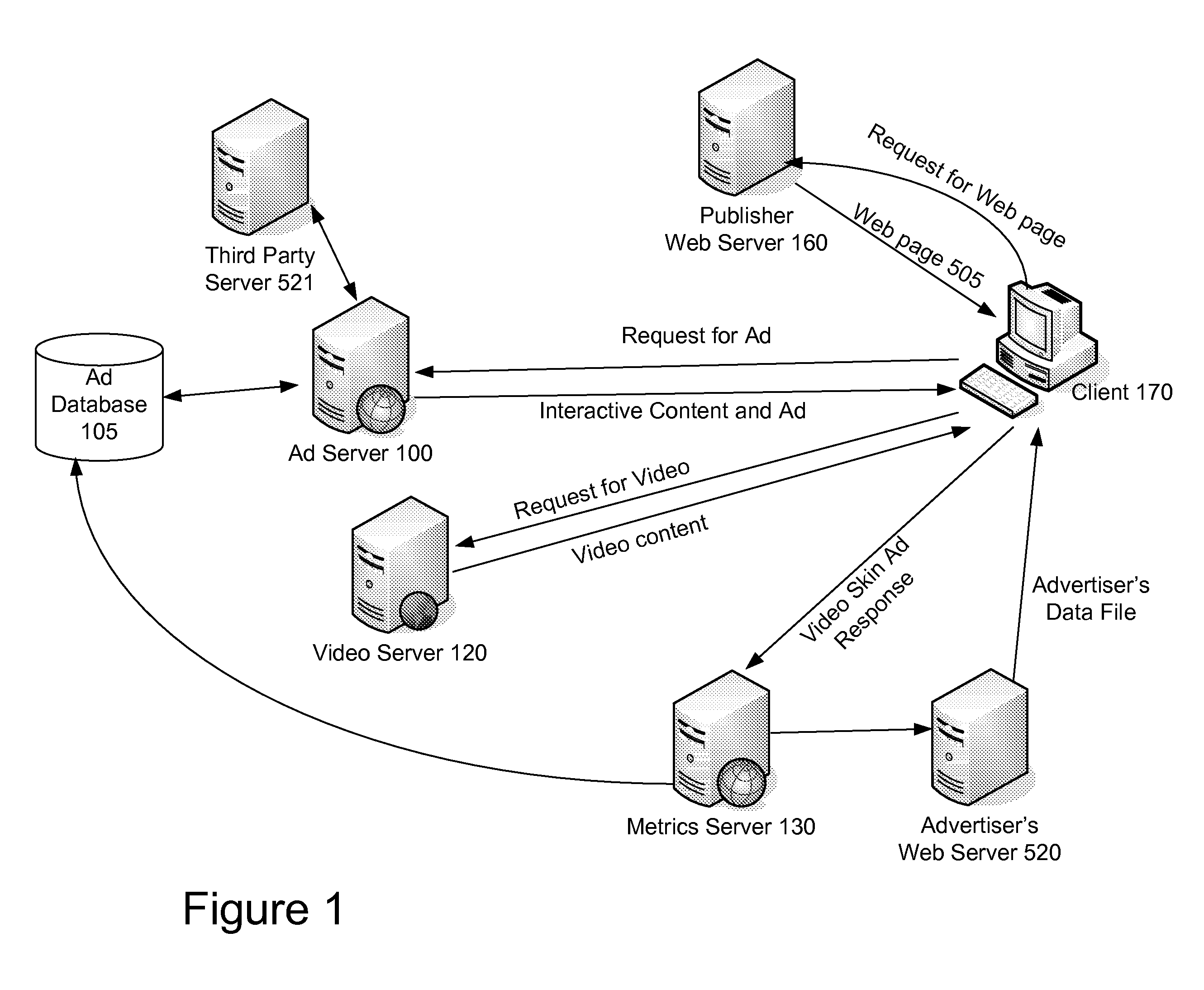
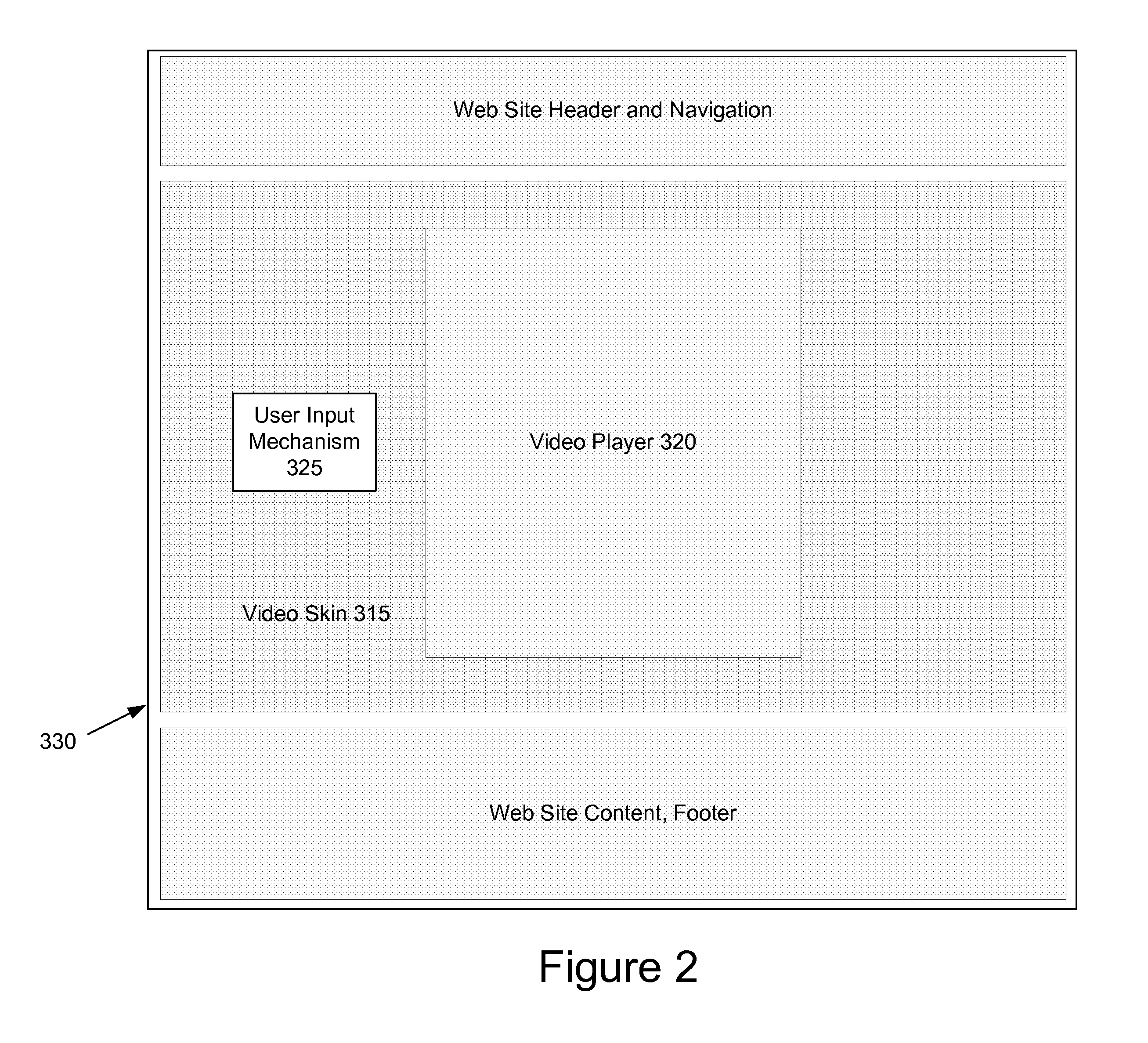
System and Method for Providing Sequential Video and Interactive Content
InactiveUS20080288983A1Input/output for user-computer interactionTelevision system detailsWeb siteVideo storage
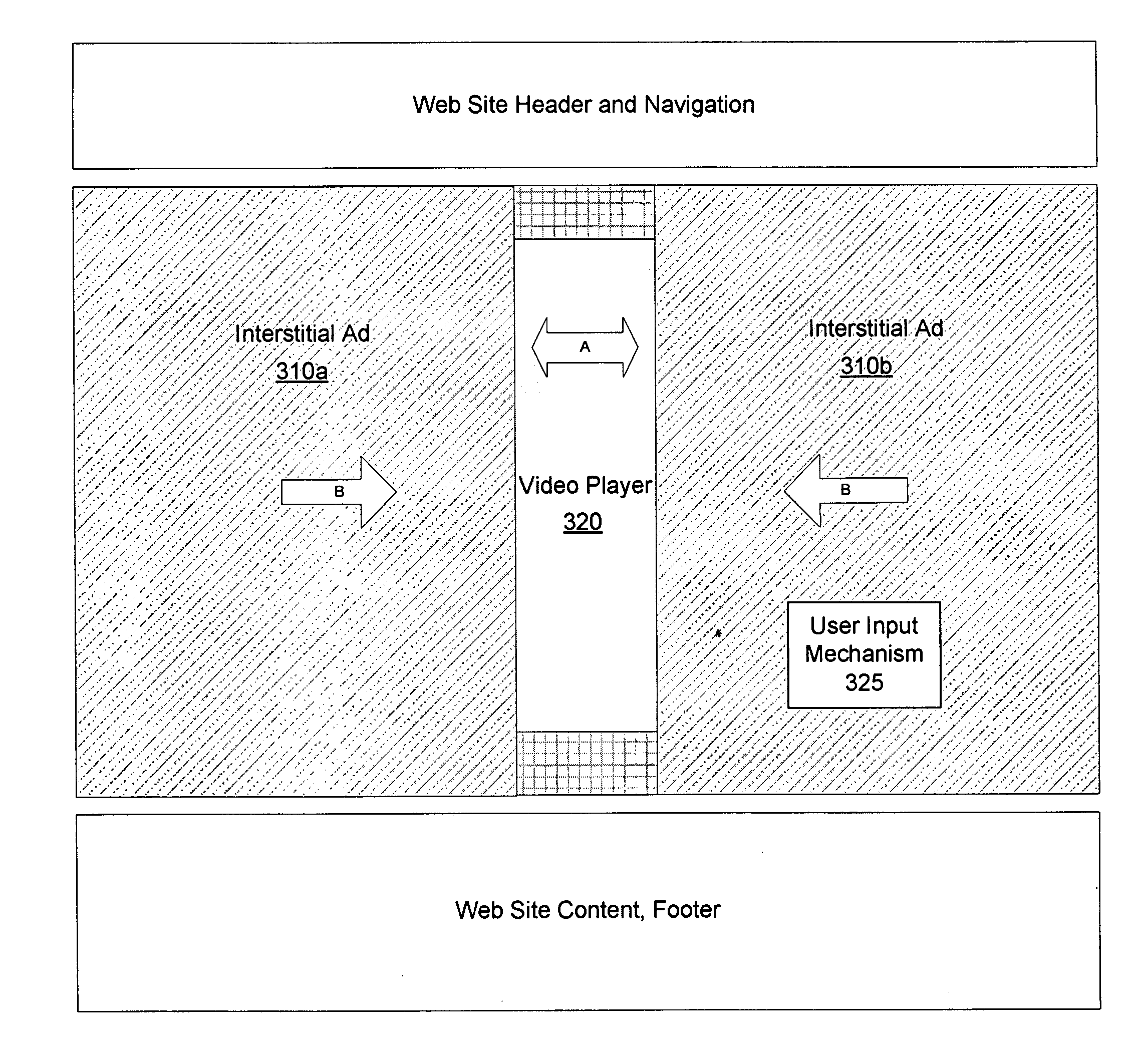
A system and method of providing sequential video and contextual based content to an end user viewing video content in a video player on an end user computing device is provided. In one embodiment, the method comprises storing a plurality of videos in a memory, storing a plurality of advertisements in a memory, receiving a plurality of requests from a plurality of different clients and wherein each request includes information identifying a first video and each of the plurality of clients initiates its request from one of a plurality of web pages and wherein the plurality of web pages form part of a plurality of different web sites. In addition, the plurality of web pages may include program code configured to cause a video to be presented in the video player. The method further comprises for each received request, selecting a plurality of videos based on information of the first video; and selecting a plurality of advertisements, wherein at least one of the plurality of advertisements is selected based on information of the first video and at least one of the plurality of advertisements is selected based on information of a selected video. In addition, the method may comprise for each received request, transmitting the plurality of videos to the requesting client for sequential presentation by the client; and transmitting the plurality of advertisements to the requesting client and wherein at least some of the plurality of advertisements are configured to be presented concurrently with a received video.
Owner:UTROM PROCESSING
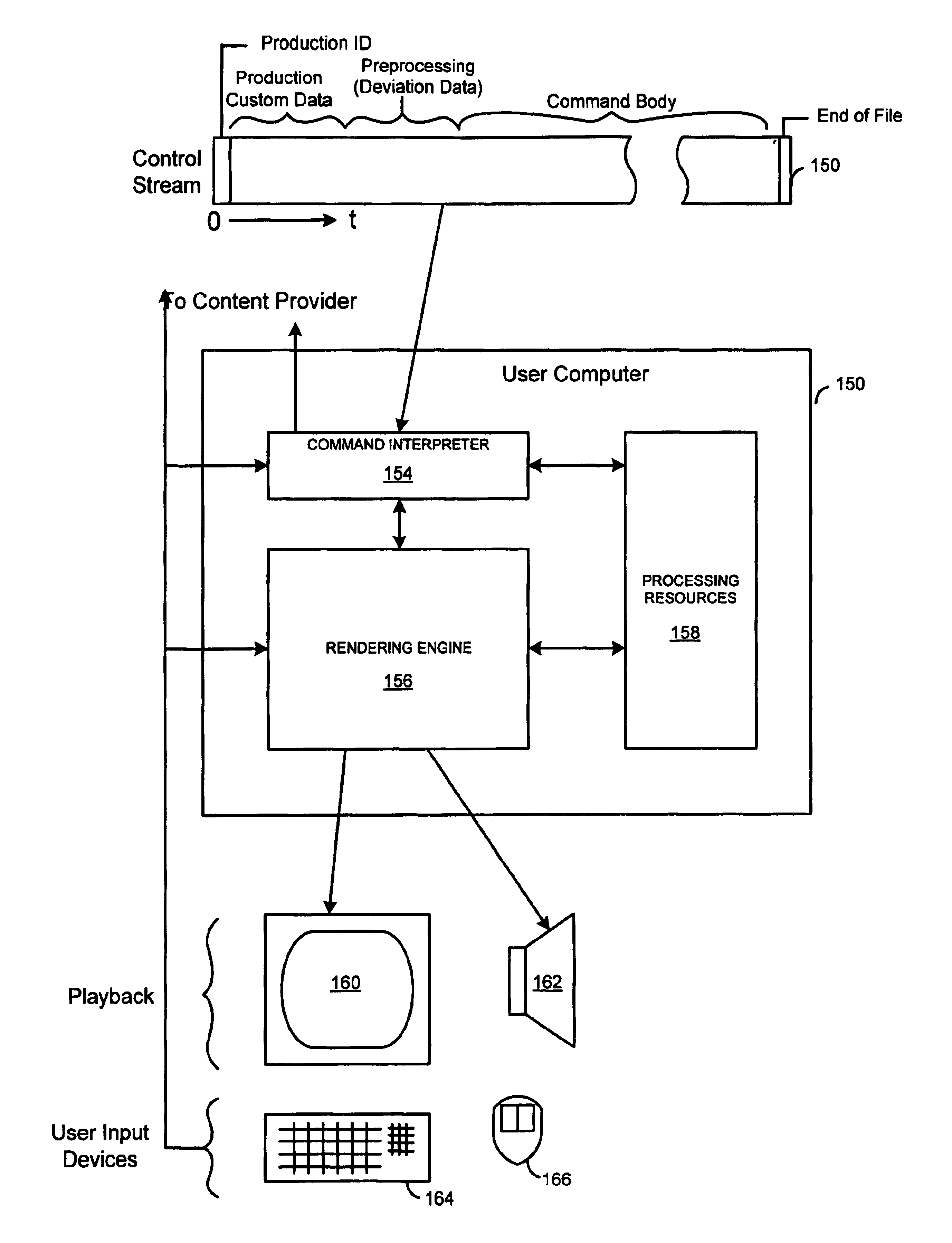
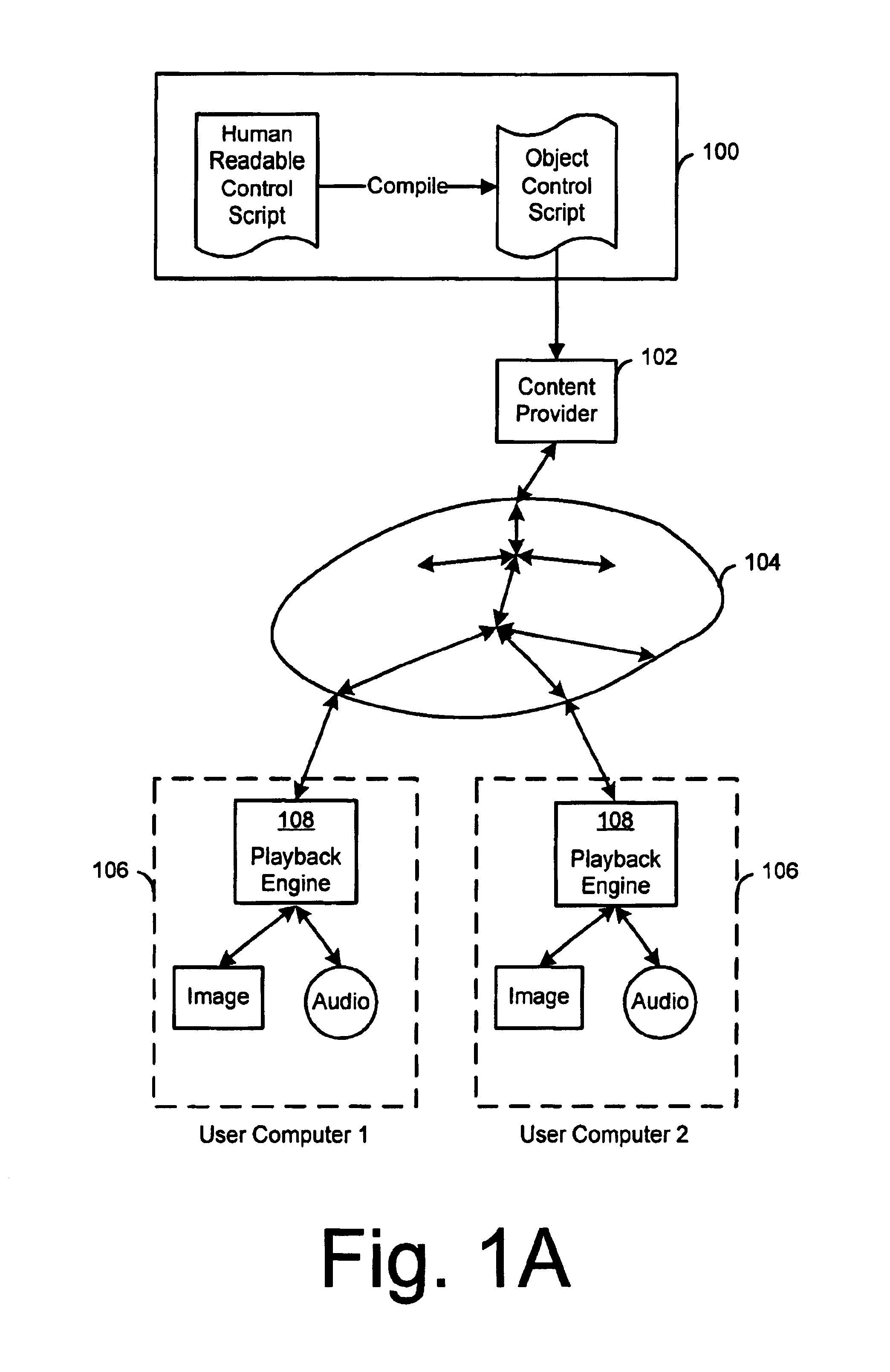
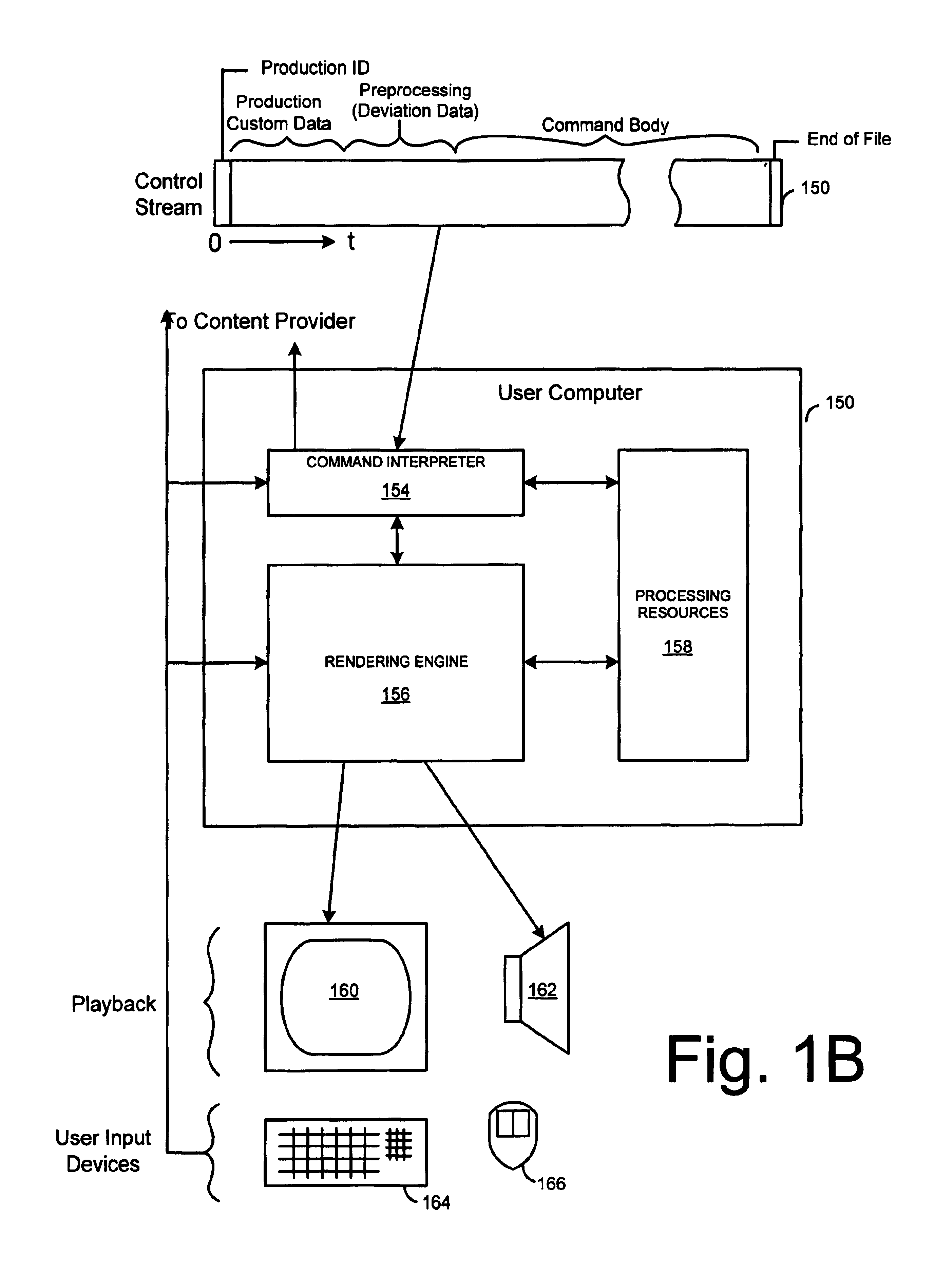
Creation and playback of computer-generated productions using script-controlled rendering engines
InactiveUS6947044B1Simple to useUnderstand intuitiveDigital data processing detailsPicture reproducers using cathode ray tubesViewpointsCommand language
A system for controlling a rendering engine by using specialized commands. The commands are used to generate a production, such as a television show, at an end-user's computer that executes the rendering engine. In one embodiment, the commands are sent over a network, such as the Internet, to achieve broadcasts of video programs at very high compression and efficiency. Commands for setting and moving camera viewpoints, animating characters, and defining or controlling scenes and sounds are described. At a fine level of control math models and coordinate systems can be used make specifications. At a coarse level of control the command language approaches the text format traditionally used in television or movie scripts. Simple names for objects within a scene are used to identify items, directions and paths. Commands are further simplified by having the rendering engine use defaults when specifications are left out. For example, when a camera direction is not specified, the system assumes that the viewpoint is to be the current action area. The system provides a hierarchy of detail levels. Movement commands can be defaulted or specified. Synchronized speech can be specified as digital audio or as text which is used to synthesize the speech.
Owner:DIGIMEDIA TECH LLC
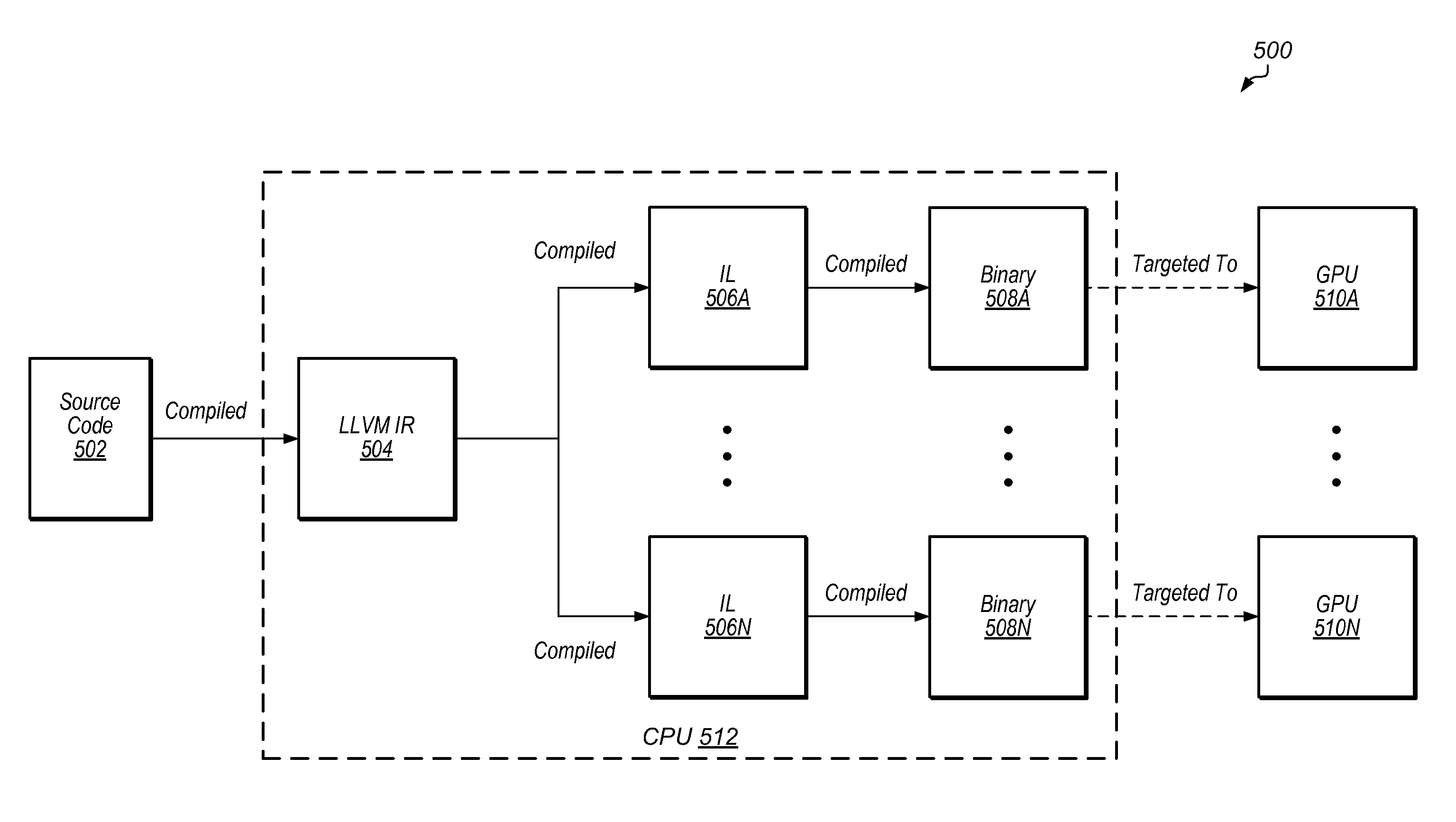
Software libraries for heterogeneous parallel processing platforms
InactiveUS20130141443A1Architecture with multiple processing unitsCode compilationParallel processingSource code
Systems, methods, and media for providing libraries within an OpenCL framework. Library source code is compiled into an intermediate representation and distributed to an end-user computing system. The computing system typically includes a CPU and one or more GPUs. The CPU compiles the intermediate representation of the library into an executable binary targeted to run on the GPUs. The CPU executes a host application, which invokes a kernel from the binary. The CPU retrieves the kernel from the binary and conveys the kernel to a GPU for execution.
Owner:ADVANCED MICRO DEVICES INC
Systems and methods for recording and recreating interactive user-sessions involving an on-line server
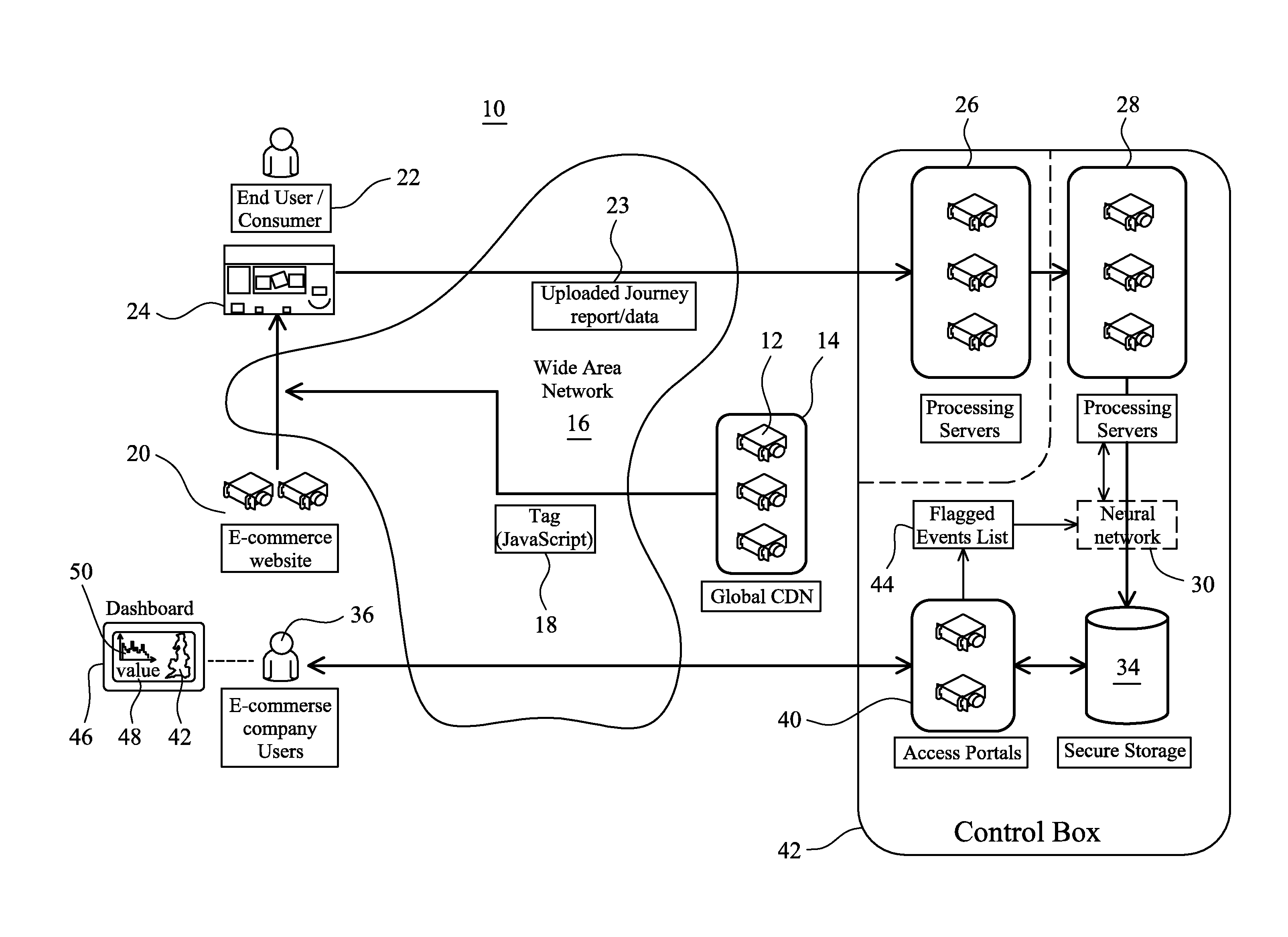
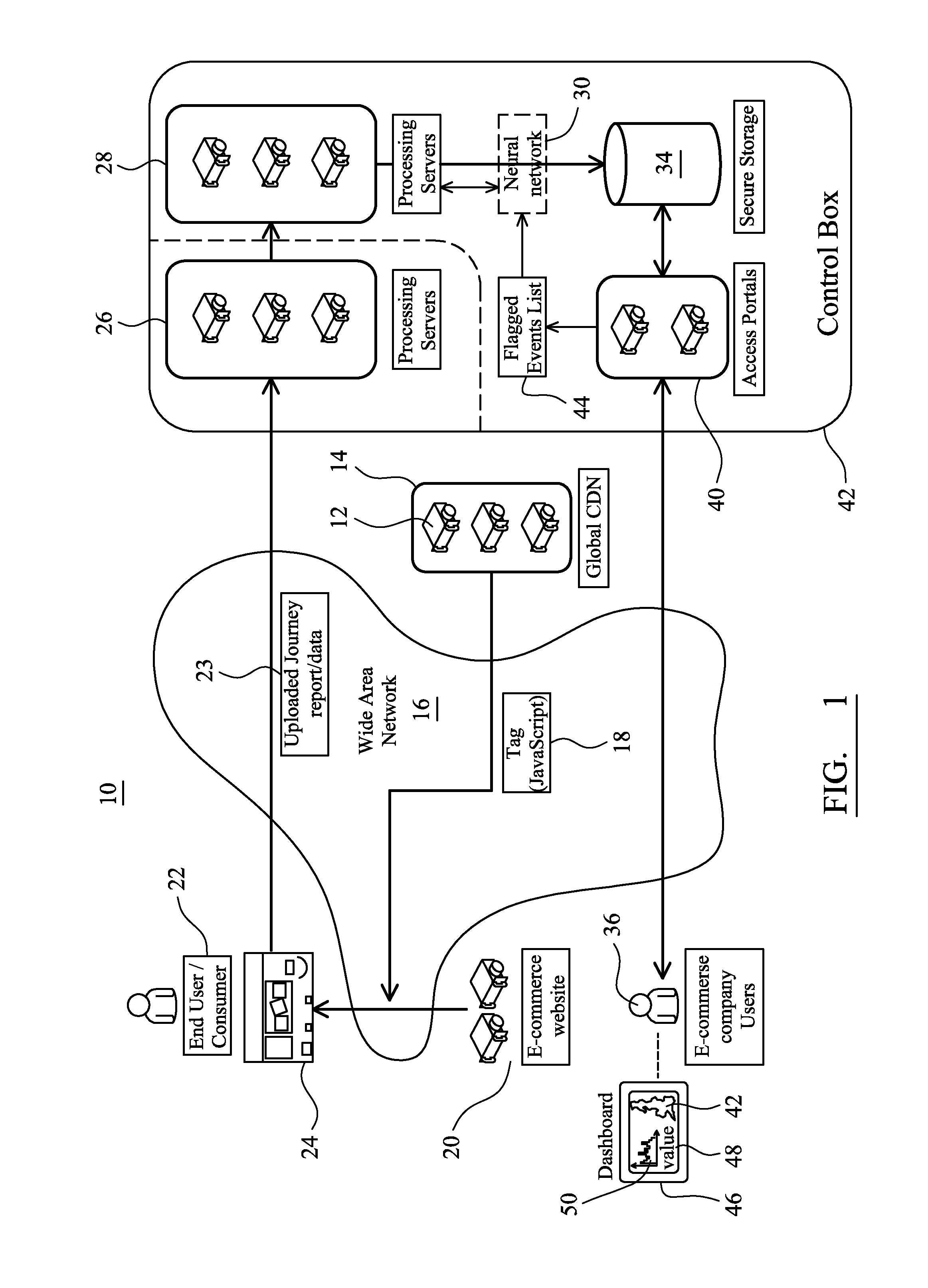
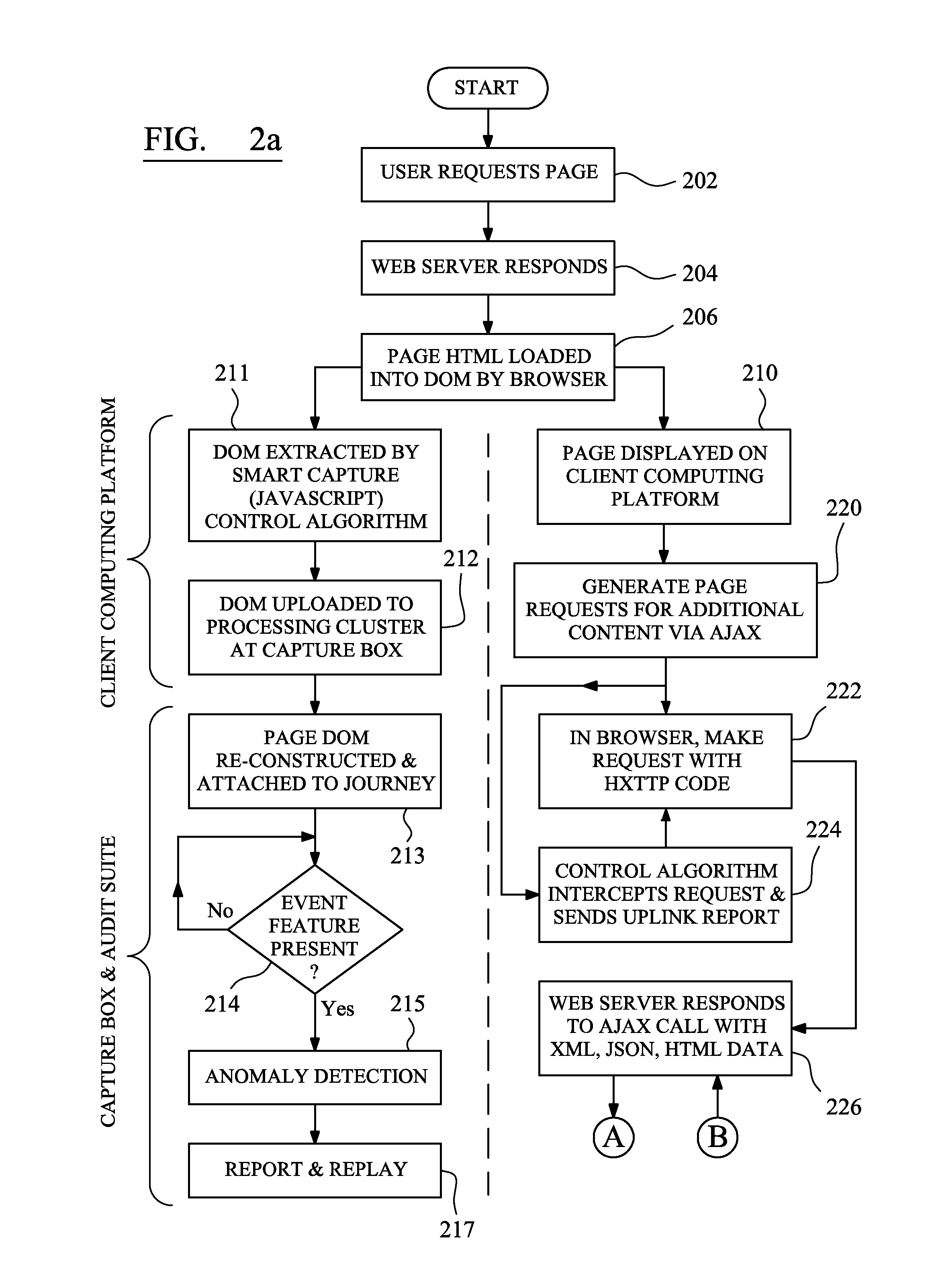
ActiveUS20160191351A1Function increaseFast and inexpensiveError detection/correctionMultiple digital computer combinationsContent distributionWeb browser
An auditing system and method are used to capture and report an interactive client journey between a web-browser and a website. Instantiation of control code at an end-user computing device, typically initiated in response to a tag embedded in a website, initiates capture of server and request headers from the perspective of the locally-executing web-browser. The control code causes the sending of an uplink journey report to a cloud-based processing server that uses the report to interpret the server and request headers to imply real-time interactions between the end-user, the web-browser executing on the computing device and the web-server. Client-side capture provides for easy installation of control code that can be delivered directly from a content distribution network. The processing server correlates the server and request headers with predefined flagged events related to at least one of operation of the web-server and data processing at the web-server.
Owner:LOGROCKET INC
System and Method for Management of End User Computing Devices
InactiveUS20100030878A1Digital computer detailsSpecial data processing applicationsOperational systemFile system
A system and method is provided for the repair of operating system and application binary files and configuration data files at pre-operating system boot stage by comparing attributes of the files against a reference collection of such files stored on a server during each reboot or restart cycle while creating and restoring a collection of dynamic operating system binary files, configuration data files, file system structures and hardware system attributes unique to the configuration and use of the system on a server for subsequent pre-operating system repair operations.
Owner:PERSYSTENT TECH CORP
System and method for on-site electronic software distribution
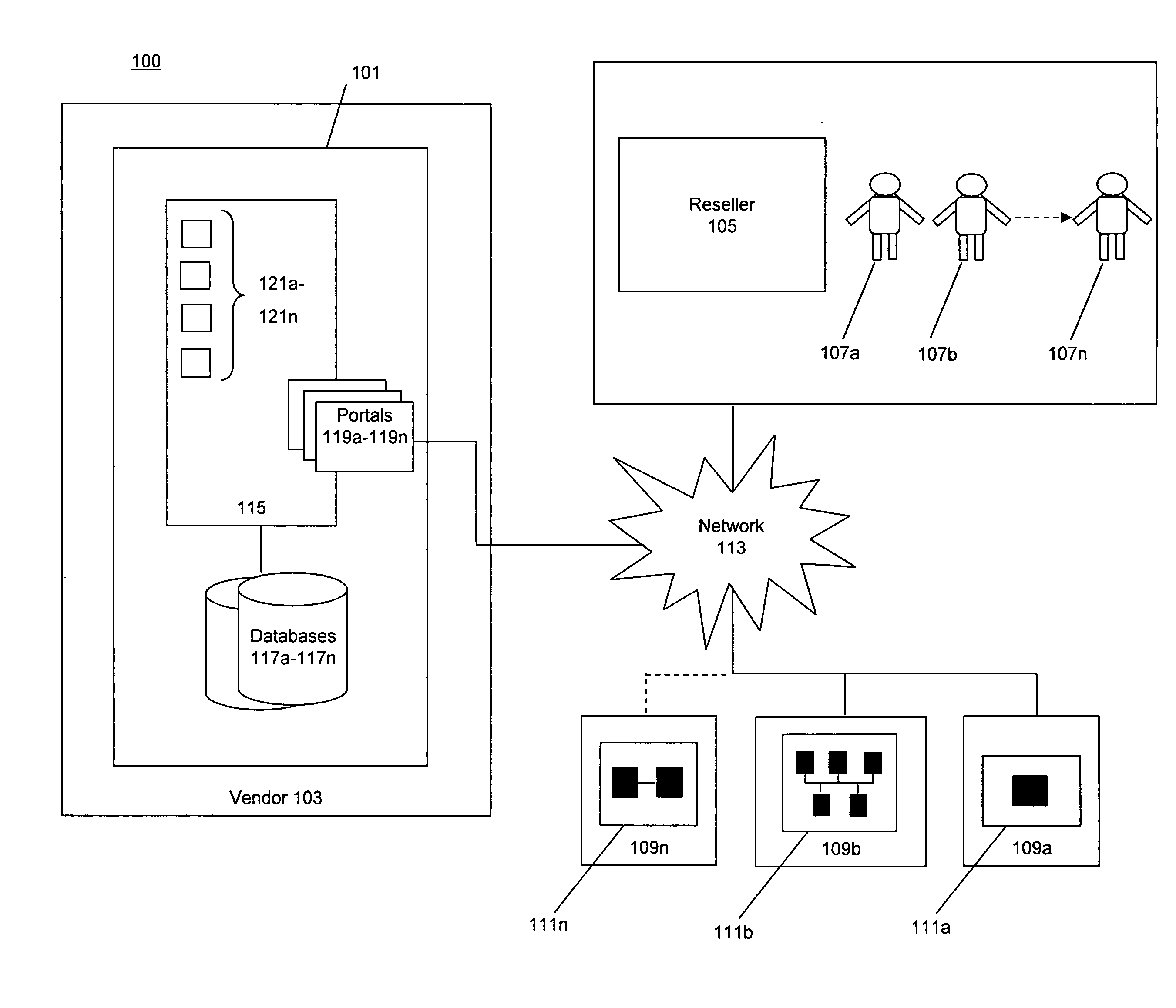
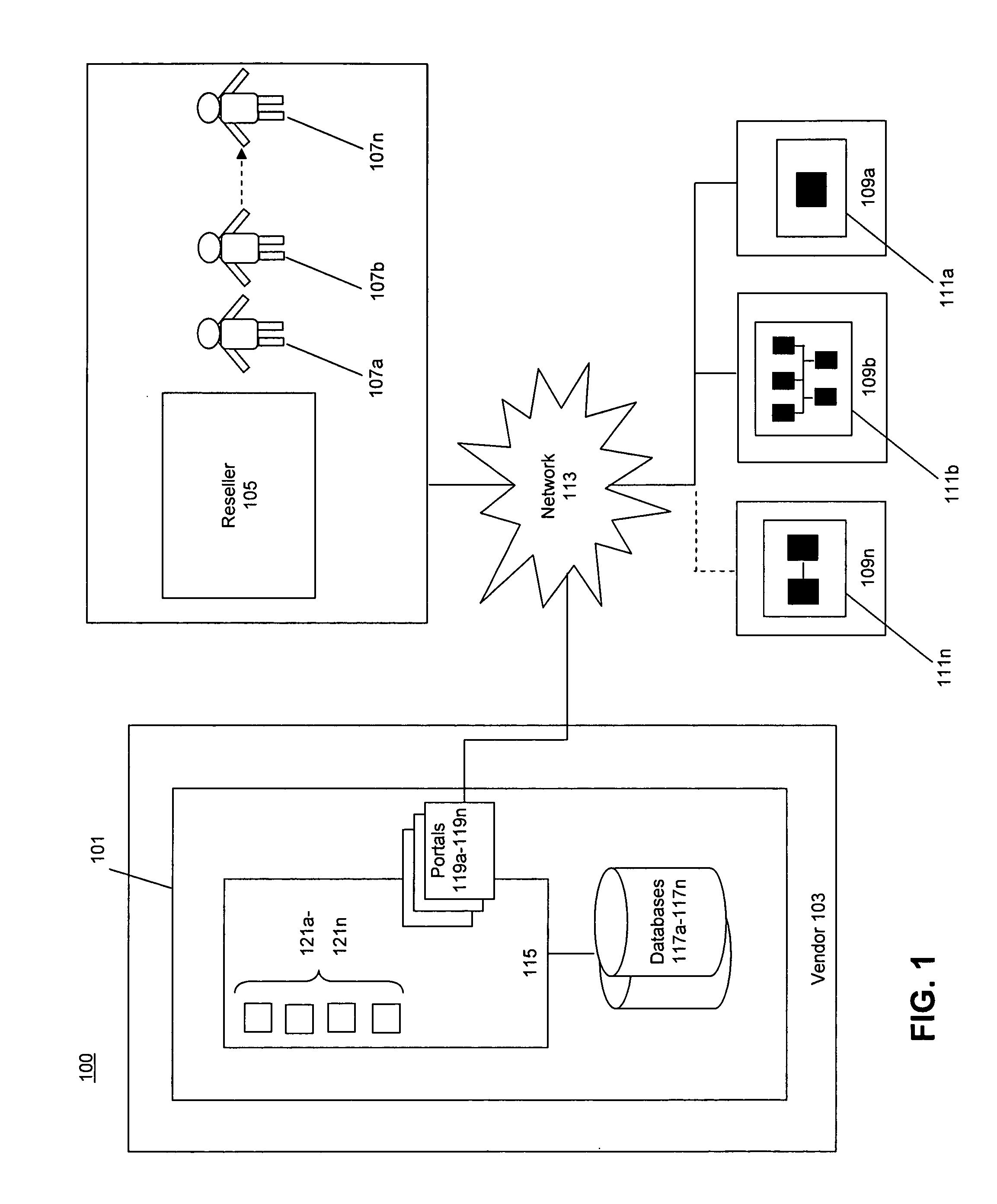
InactiveUS20080033882A1Increase salesImprove efficiencyData processing applicationsComputer security arrangementsSoftware distributionDistribution system
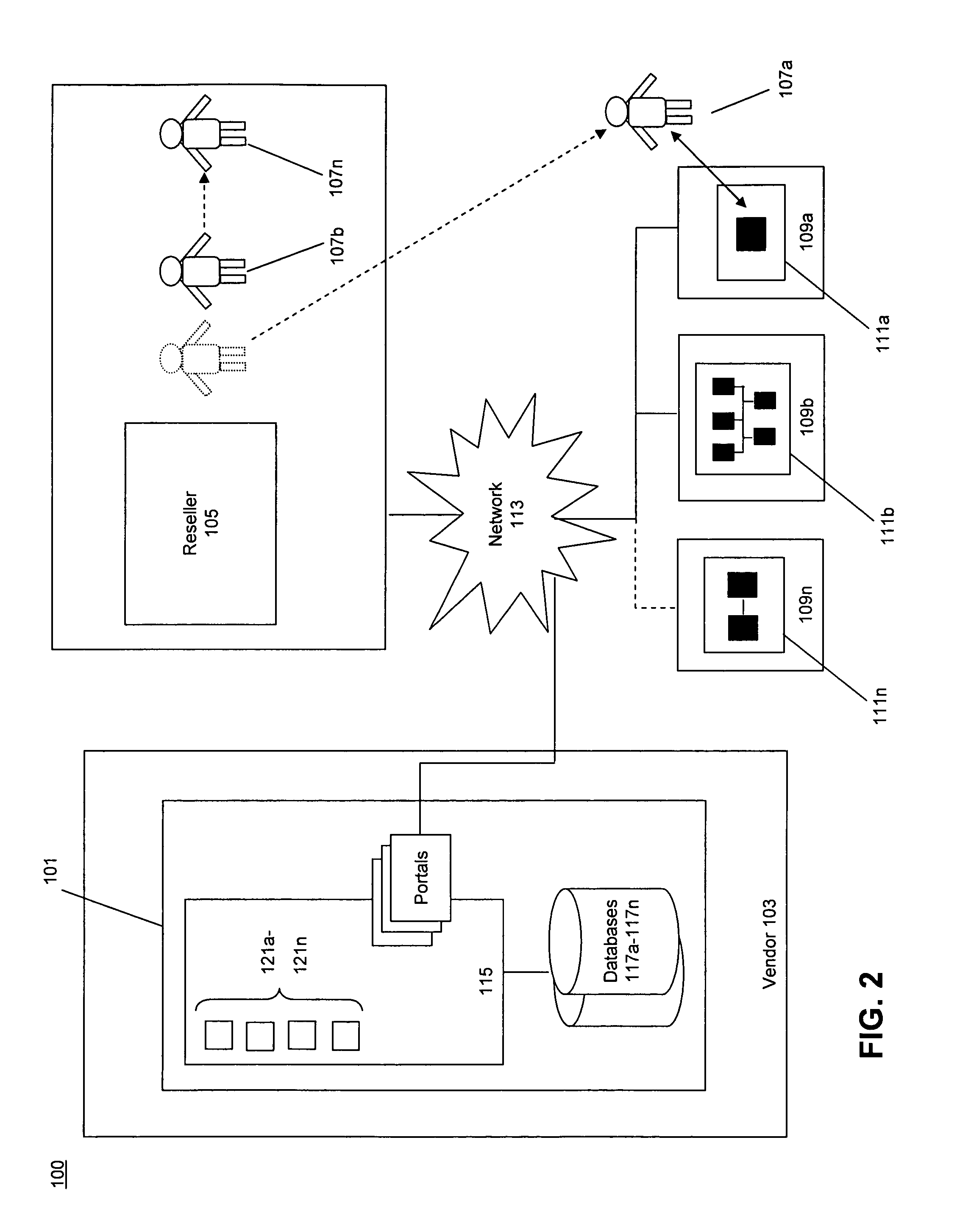
The invention provides a system and method for electronic distribution of software products via a technician-enabled on-site electronic distribution model that includes a vendor, an electronic distribution system operated by the vendor, one or more resellers, one or more technicians, and one or more end-users. A reseller and a technician associated with the reseller are registered to the electronic distribution system. During an onsite visit to with an end-user, the technician uses the end-user's computer system to access the electronic distribution system and download one or more software products to the end-users computer system. The reseller / technician and the end-user handle the financial transactions involving delivery of the downloaded products to the end-user, while the vendor charges the reseller for the software products downloaded from the electronic distribution system.
Owner:CA TECH INC
Method and system for detecting captive portals
ActiveUS8479263B1Minimal numberFast and efficient and reliable and secureDigital data processing detailsMultiple digital computer combinationsWeb serviceCaptive portal
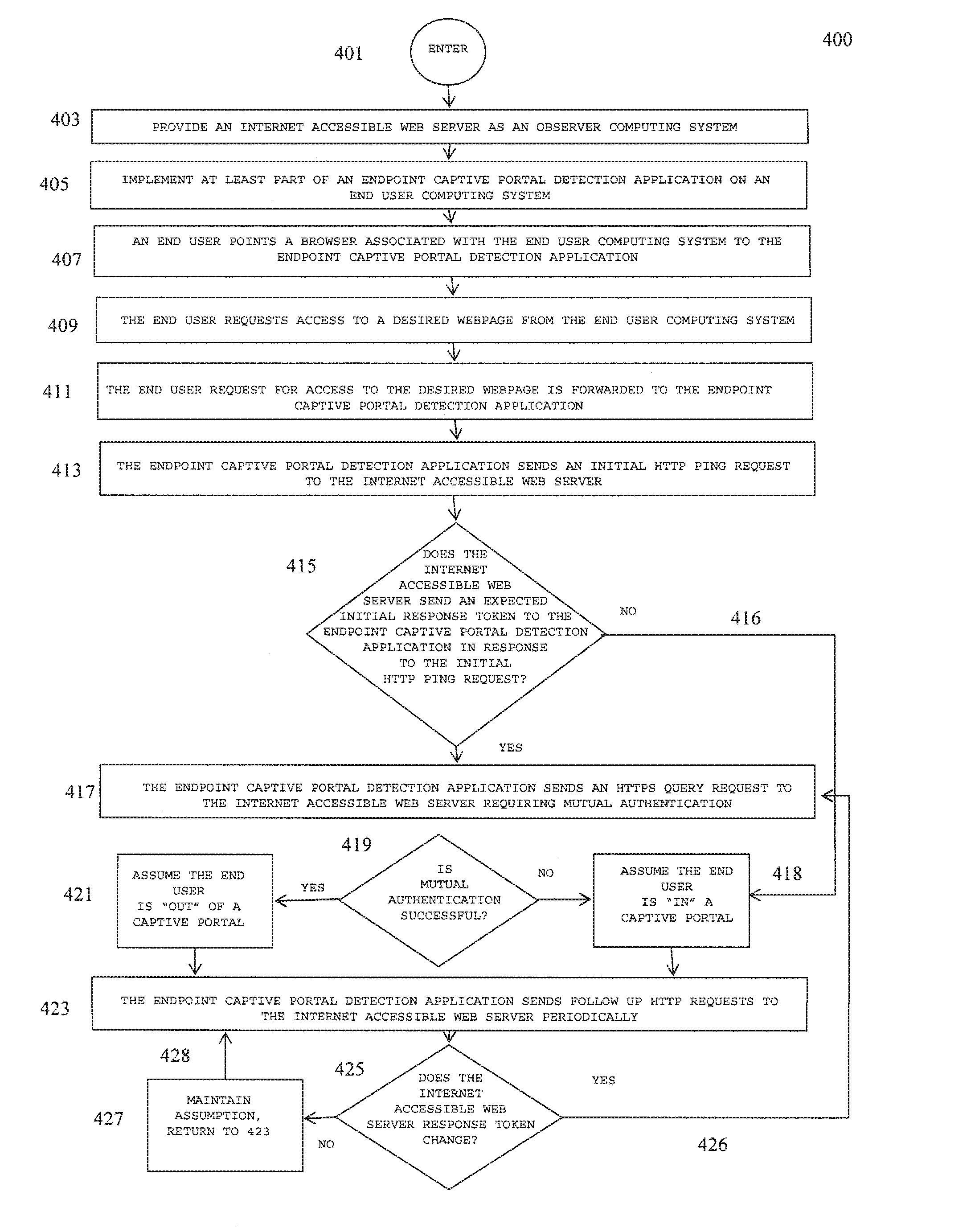
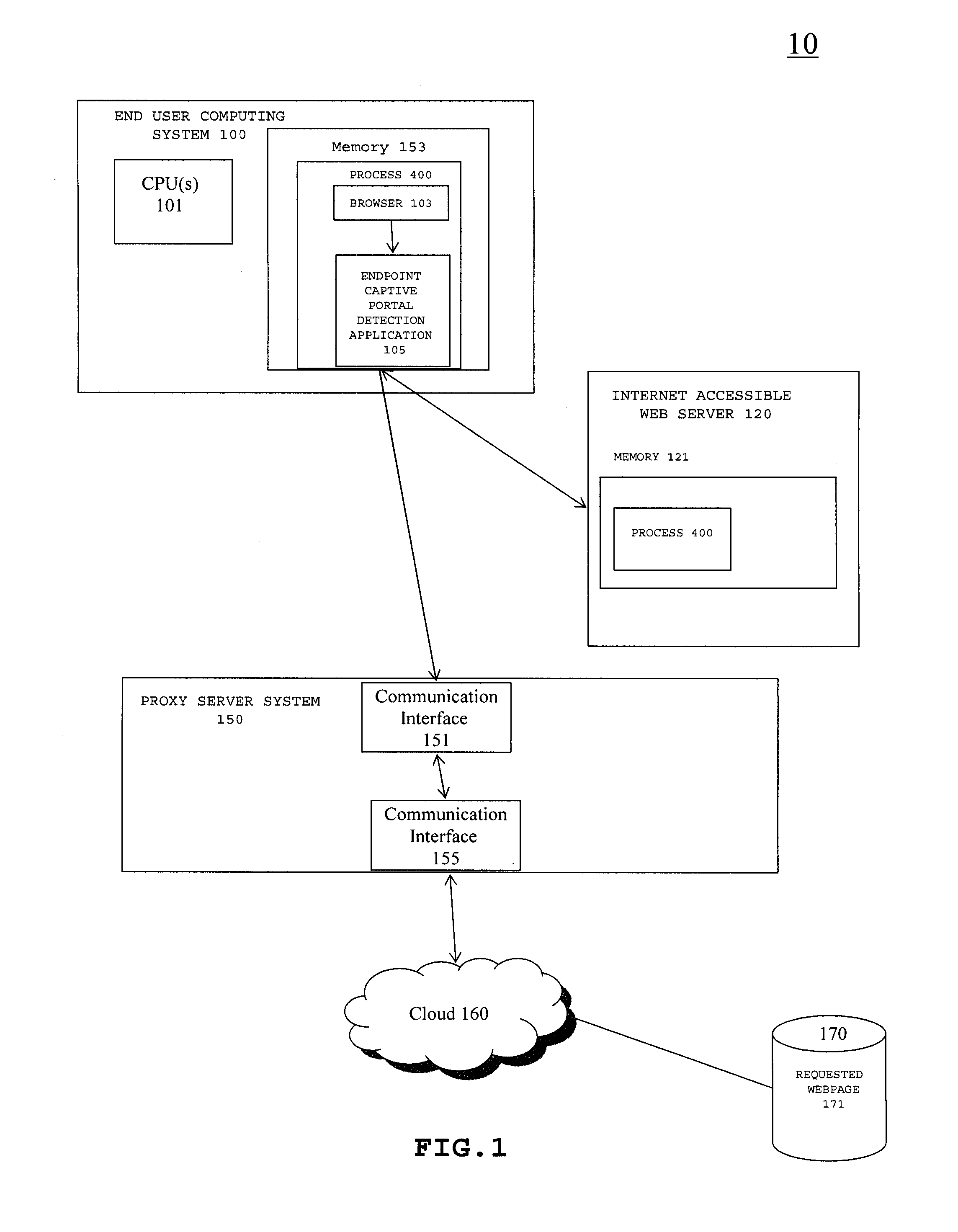
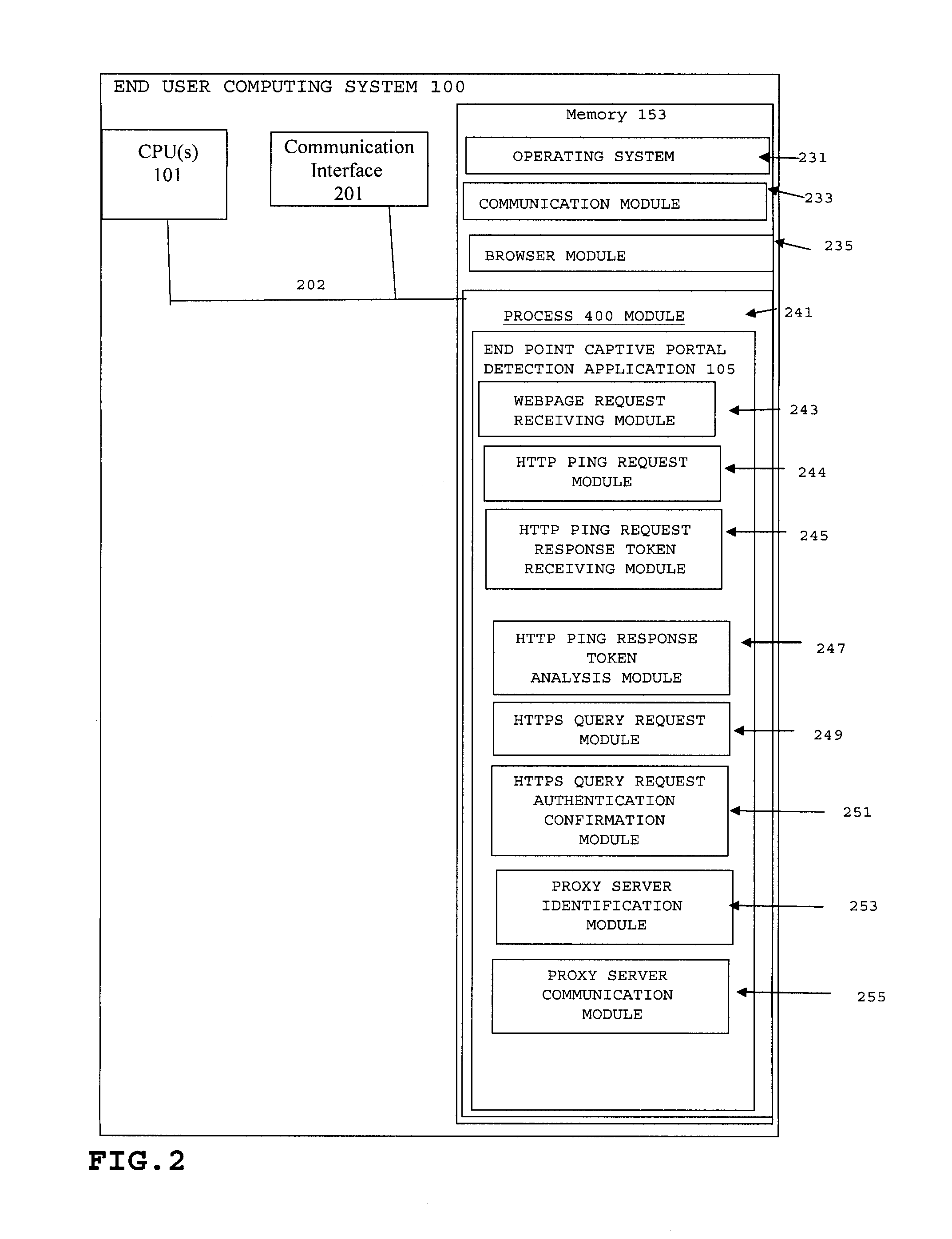
A method and system for detecting captive portals includes a two phase captive portal detection process whereby an initial HTTP ping request is sent from the endpoint captive portal detection application on an end user computing system to an Internet accessible web server. The Internet accessible web server is expected to return an initial response token to the endpoint captive portal detection application in response to the initial HTTP ping request and if the expected initial response token is received, an initial HTTPS query request is then sent together with the returned initial response token that requires server / client mutual authentication. If mutual authentication is accomplished, then it is determined that the user is not in a captive portal. Follow up HTTP ping requests are then periodically generated by the endpoint captive portal detection application and if the responses to the follow up HTTP ping requests do not change, i.e., the token does not change, no new HTTPS query request is sent.
Owner:GEN DIGITAL INC
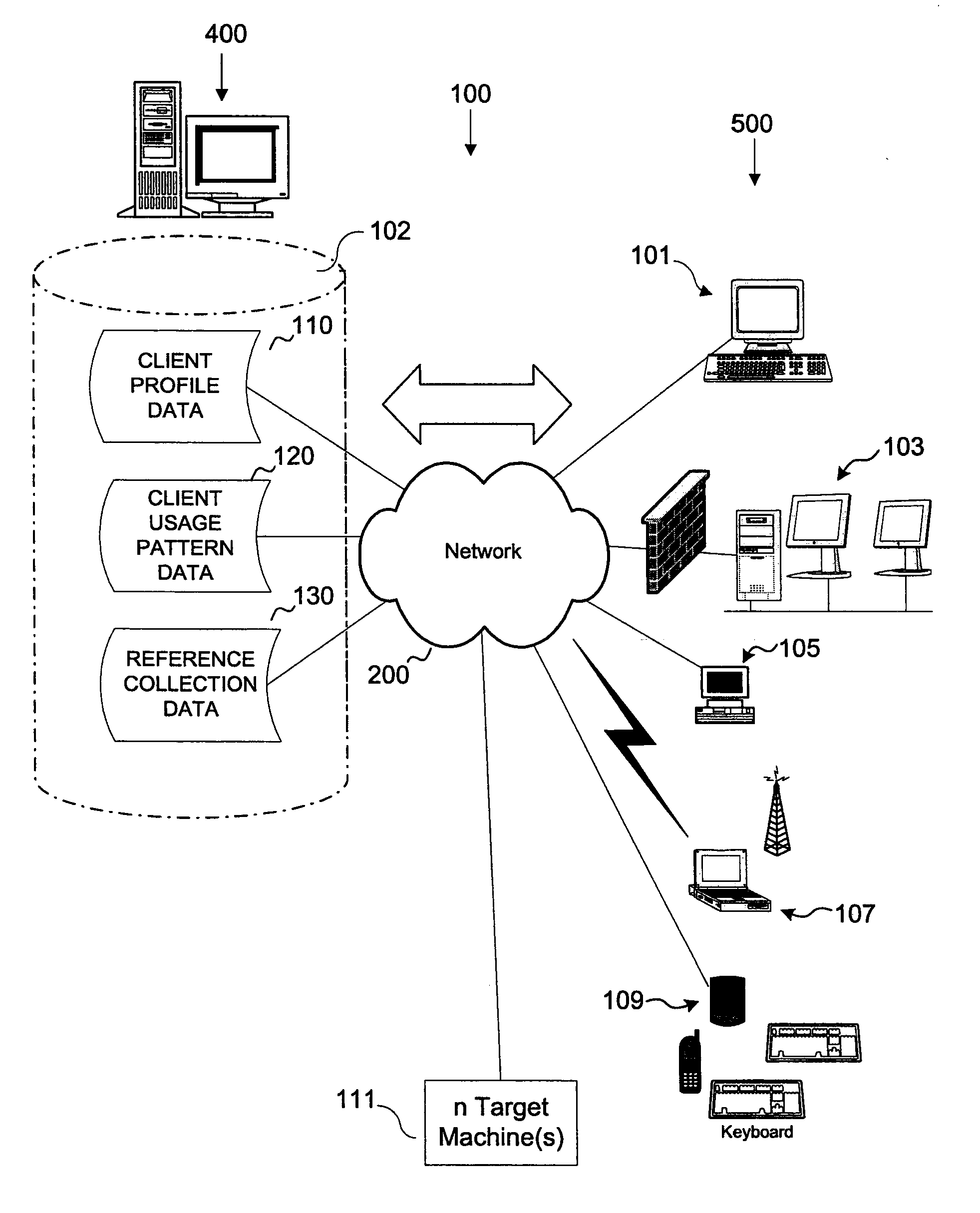
Methods of selectively distributing data in a computer network and systems using the same
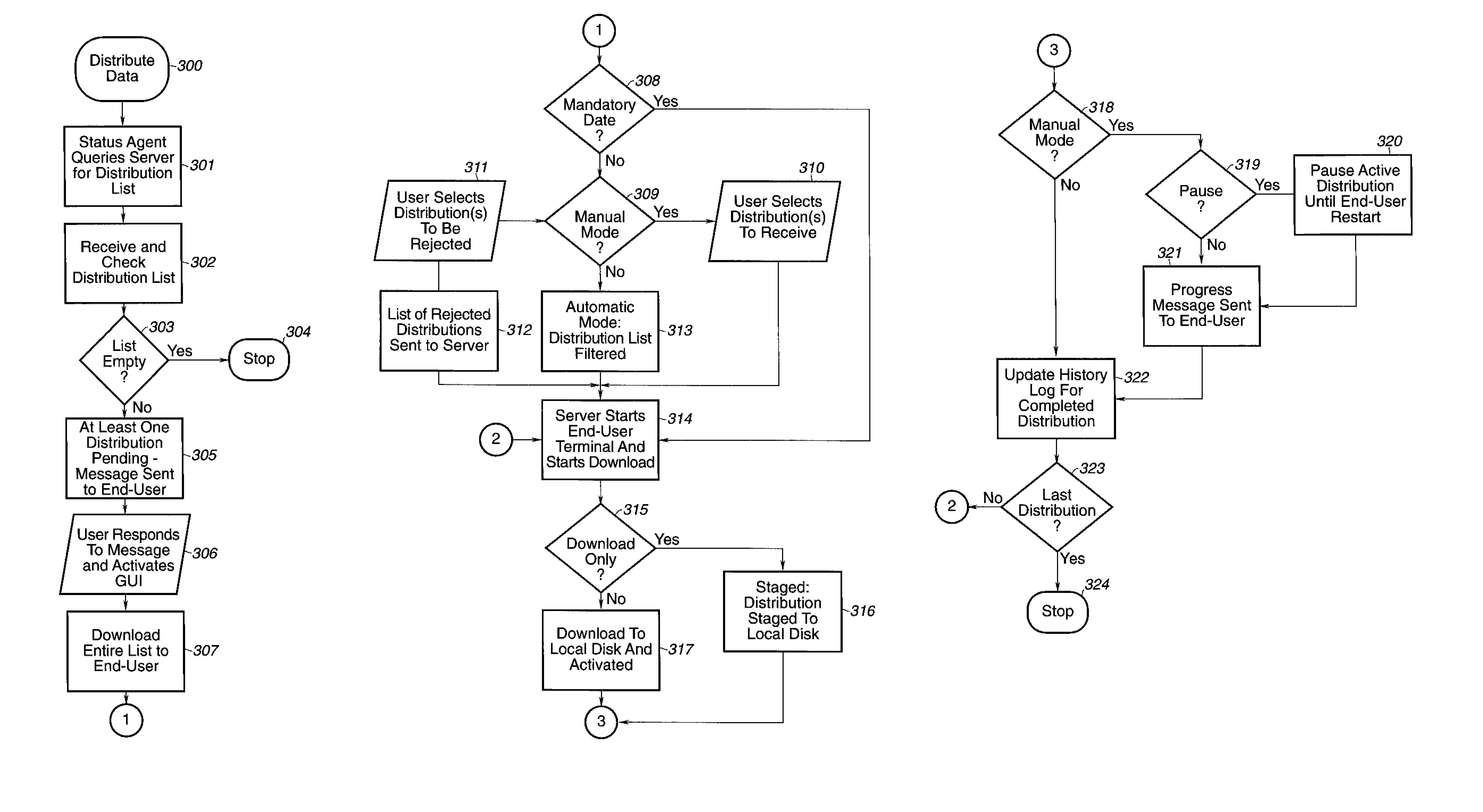
InactiveUS7191208B1Conveniently updateConveniently and patchMultiple digital computer combinationsProgram loading/initiatingEnd-user computingEnd user
A method of distributing data in a network including a server and an end-user computer. The end-user computer queries the server for a distribution list and then receives that list from the server. The end-user computer then determines if the distribution list is non-empty, and if it is non-empty, selects a distribution from the distribution list using a selected one of manual and automatic modes. The selected distribution is then downloaded from the server to the end-user computer.
Owner:WORKDAY INC
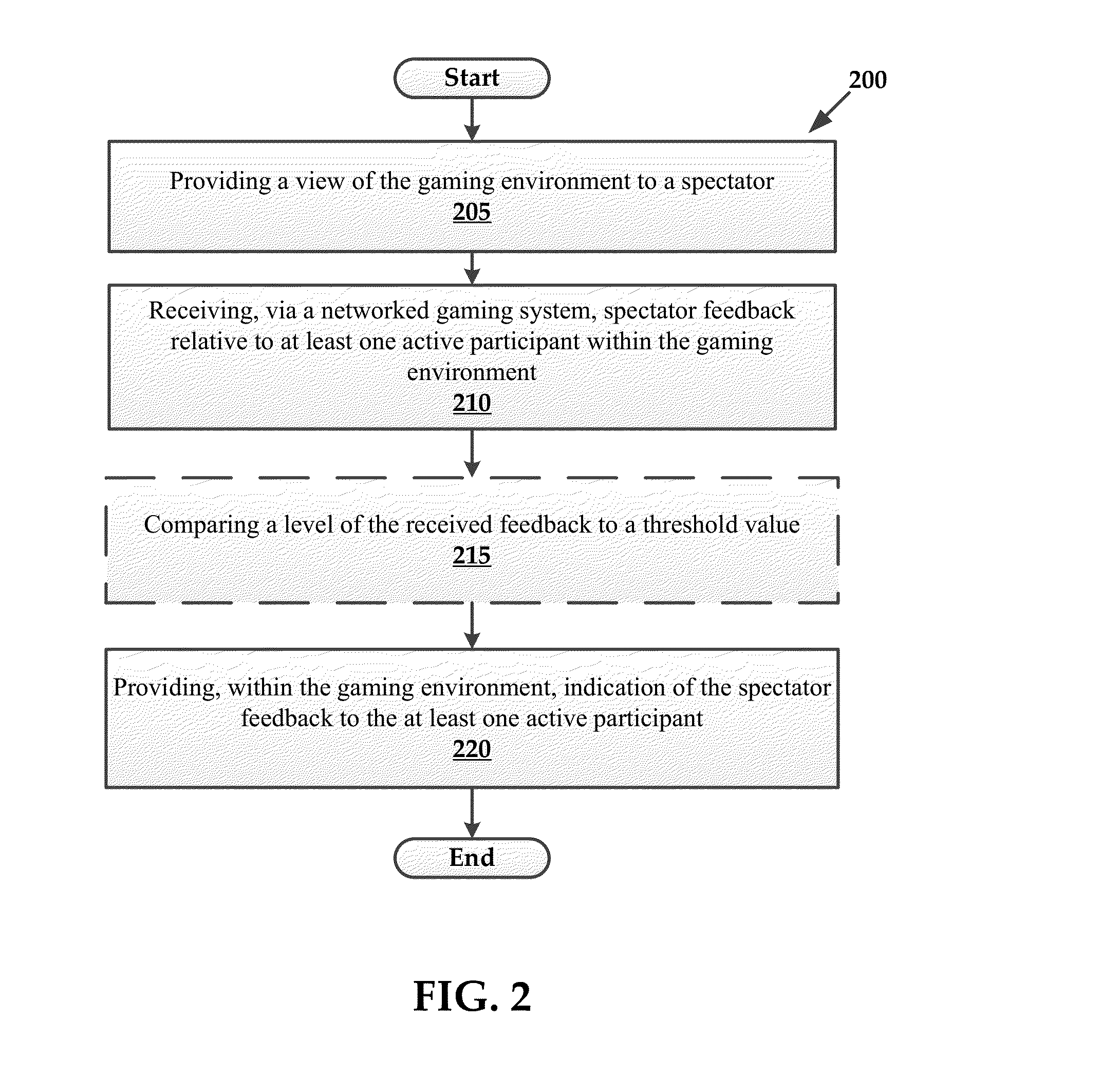
Interactive spectator features for gaming environments
InactiveUS8628424B1Video gamesSpecial data processing applicationsHuman–computer interactionEnd-user computing
Systems and methods for exchanging virtual rewards for computing resources are provided herein. Exemplary methods may include receiving access to a portion of computing resources of an end user computing system and providing a virtual reward within a gaming environment to an end user in exchange for utilizing an amount of the portion of the computing resources of the end user computing system.
Owner:RED 5 STUDIOS
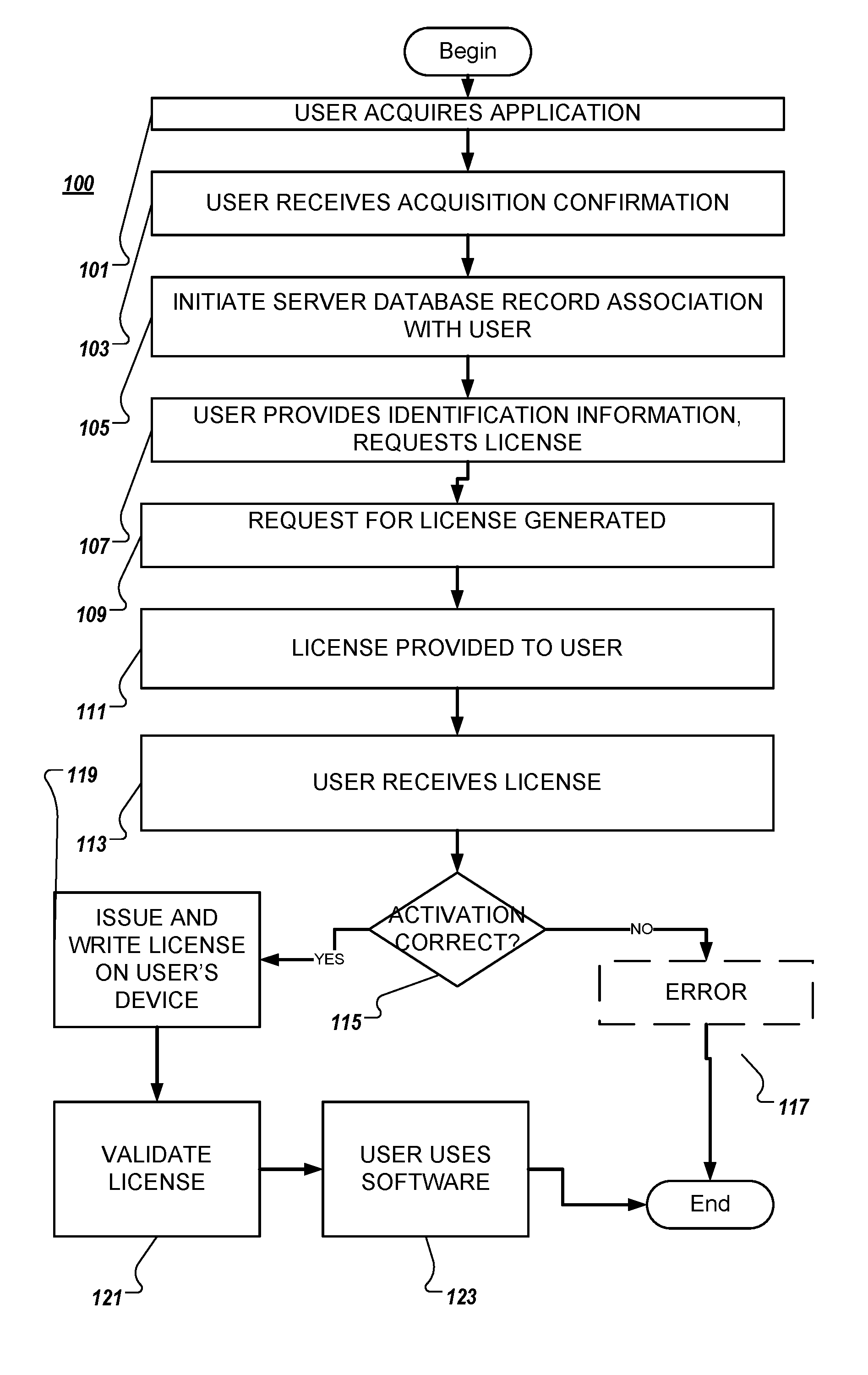
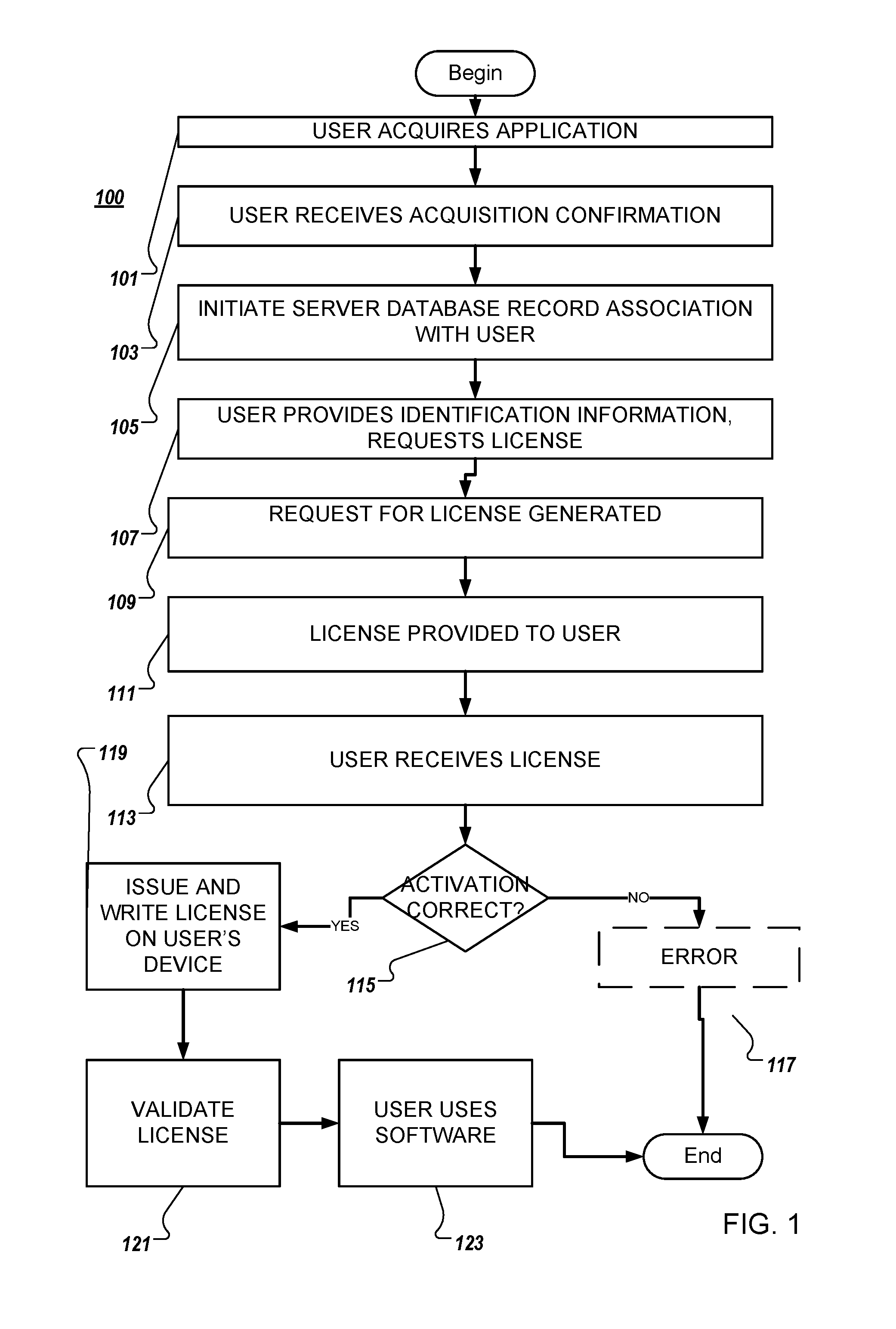
System and method for software activation and license tracking
ActiveUS20160232334A1Simplify the activation processPrevent unauthorizedUser identity/authority verificationProgram/content distribution protectionSoftware distributionSoftware development
System and method for software activation and further tracking of its states on an end-user computing device (computer) was developed to provide software developers a flexible and secure tool for software distribution and gathering statistics of usage of software activation. The method consists of the following logical steps: (a) obtaining an acquisition confirmation; (b) requesting for a license; (c) issuing and delivering the license to End User; (d) verification of license on the User's computer; (e) storing the license on the User's computer; (f) periodic tracking of activation state, (g) another action with the User's license.
Owner:MACPAW WAY LTD
Securing executable content using a trusted computing platform
InactiveUS7694139B2Reduce riskIncrease probabilityUser identity/authority verificationComputer security arrangementsComputerized systemTrusted Computing
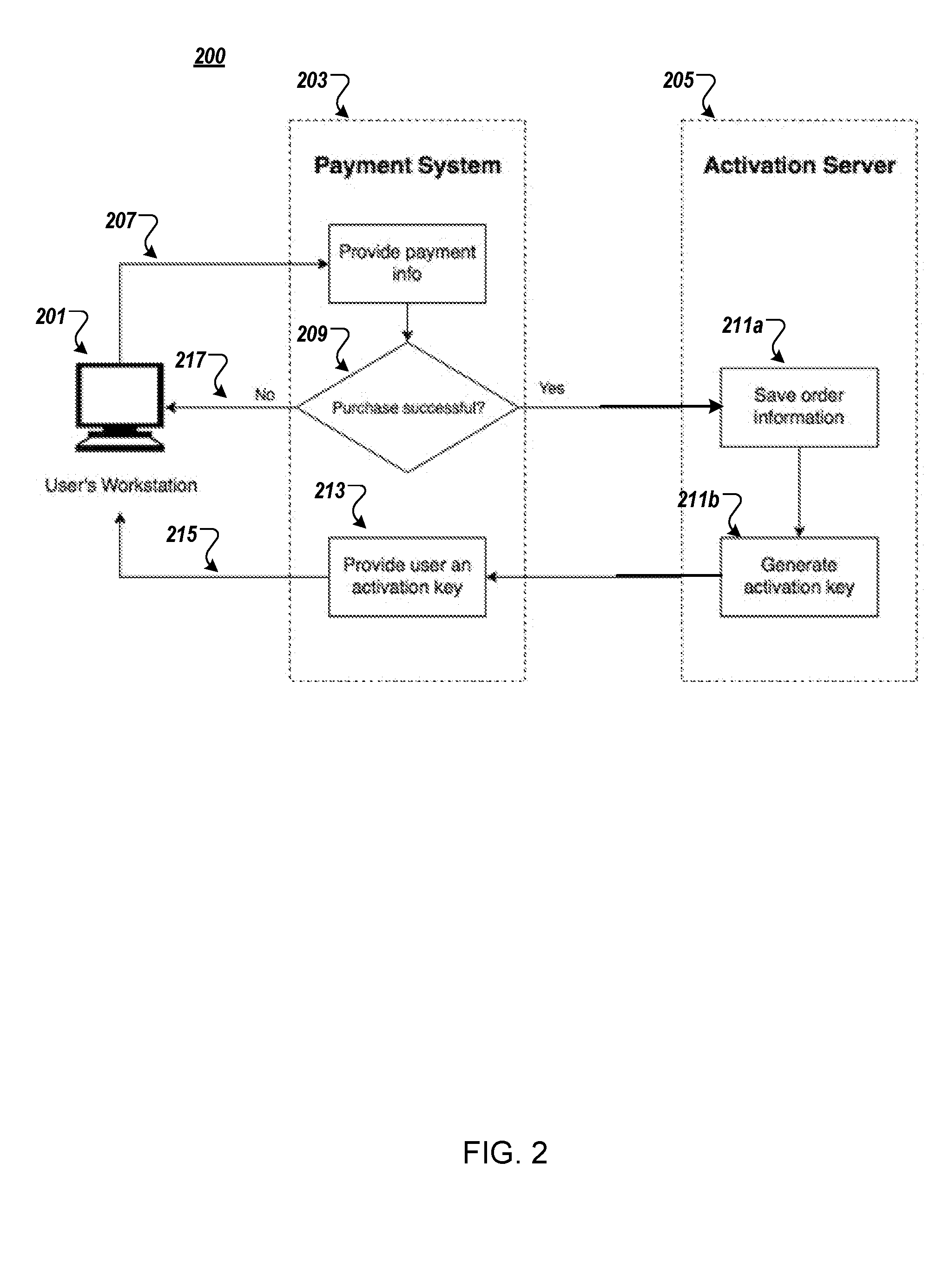
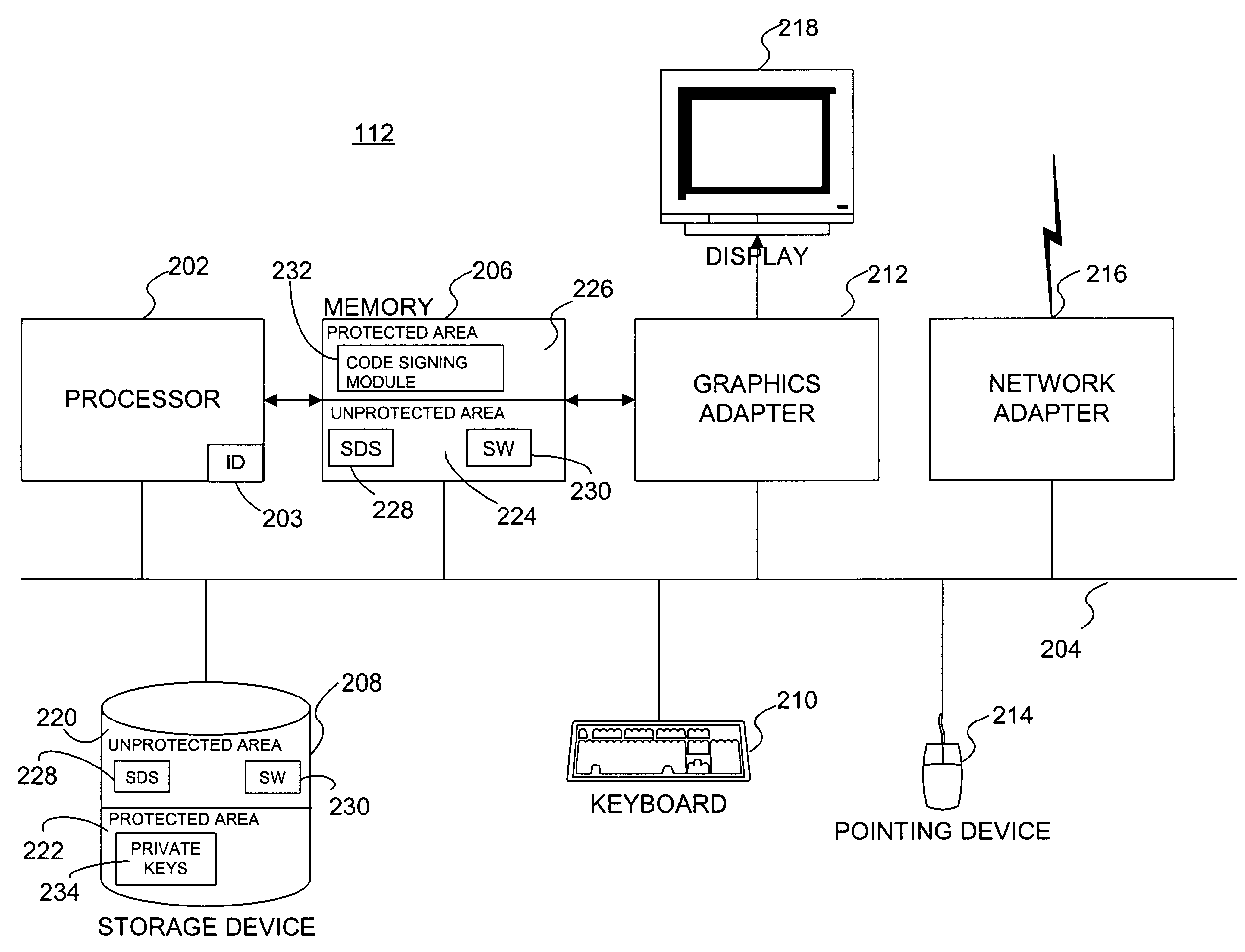
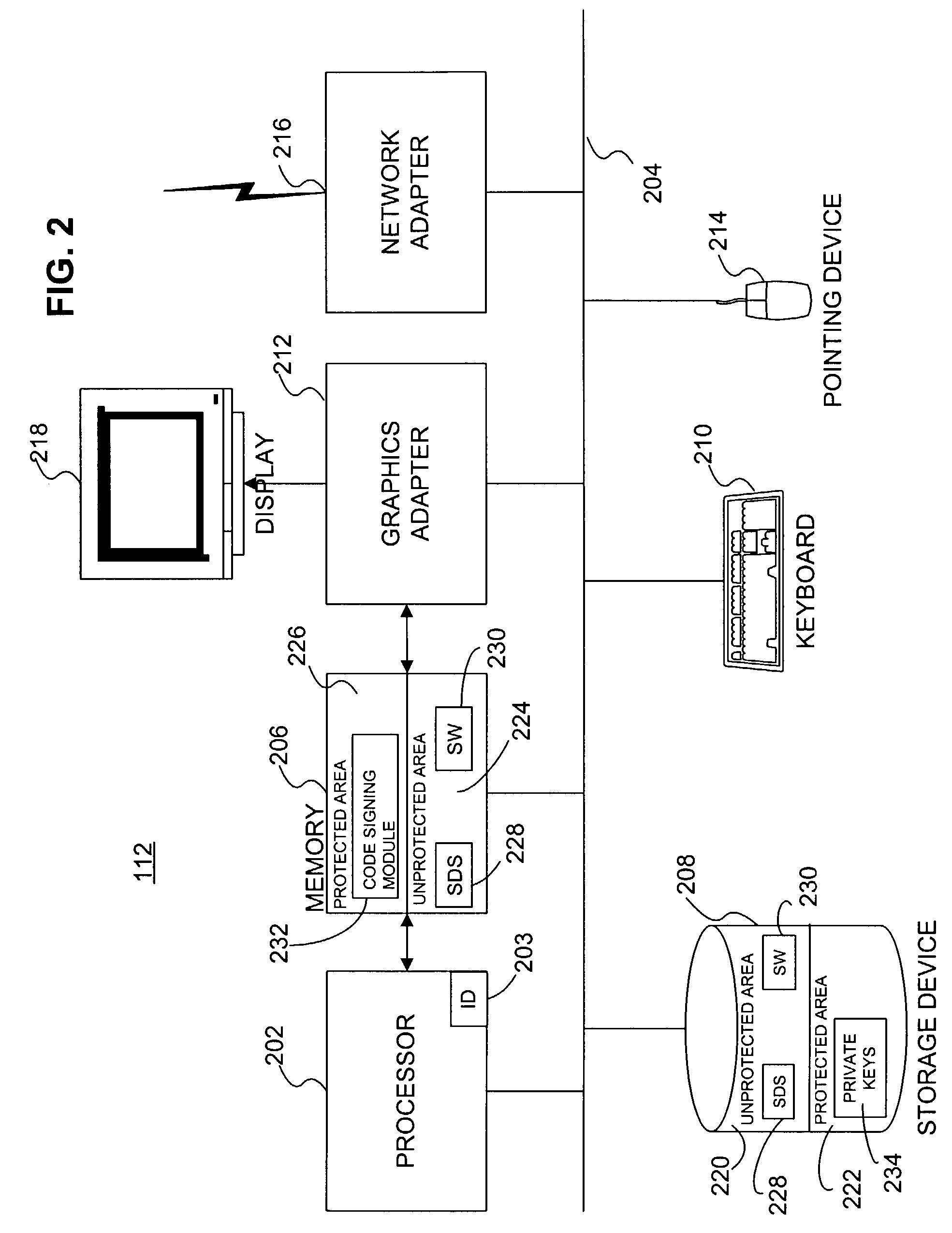
A software development system (SDS) (228) digitally signs software (230) developed on the system. The SDS (228) executes on a computer system (112) having a trusted computing platform. The platform includes protected areas (220, 226) that store data and cannot be accessed by unauthorized modules. A code signing module (232) executing in a protected area (226) obtains a private / public key pair and a corresponding digital certificate. The SDS (228) is configured to automatically and transparently utilize the code signing module (232) to sign software (230) produced by the system. End-user systems (114) receive the certificate with the software and can use it to verify the signature. This verification will fail if a parasitic virus or other malicious code has altered the software (230). Accordingly, the SDS (228) greatly reduces the risk of malicious code executing on the end-user computer system (114).
Owner:CA TECH INC
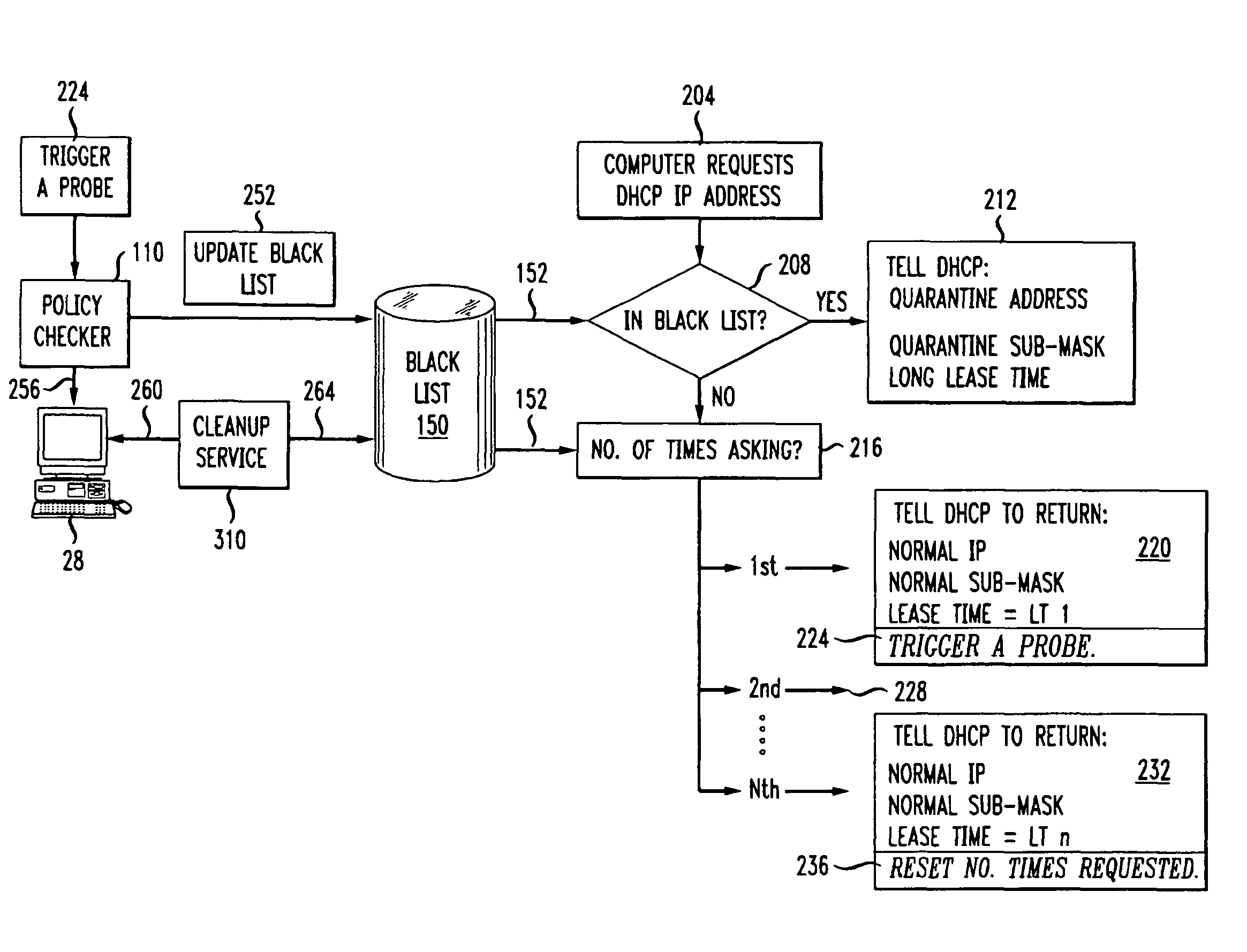
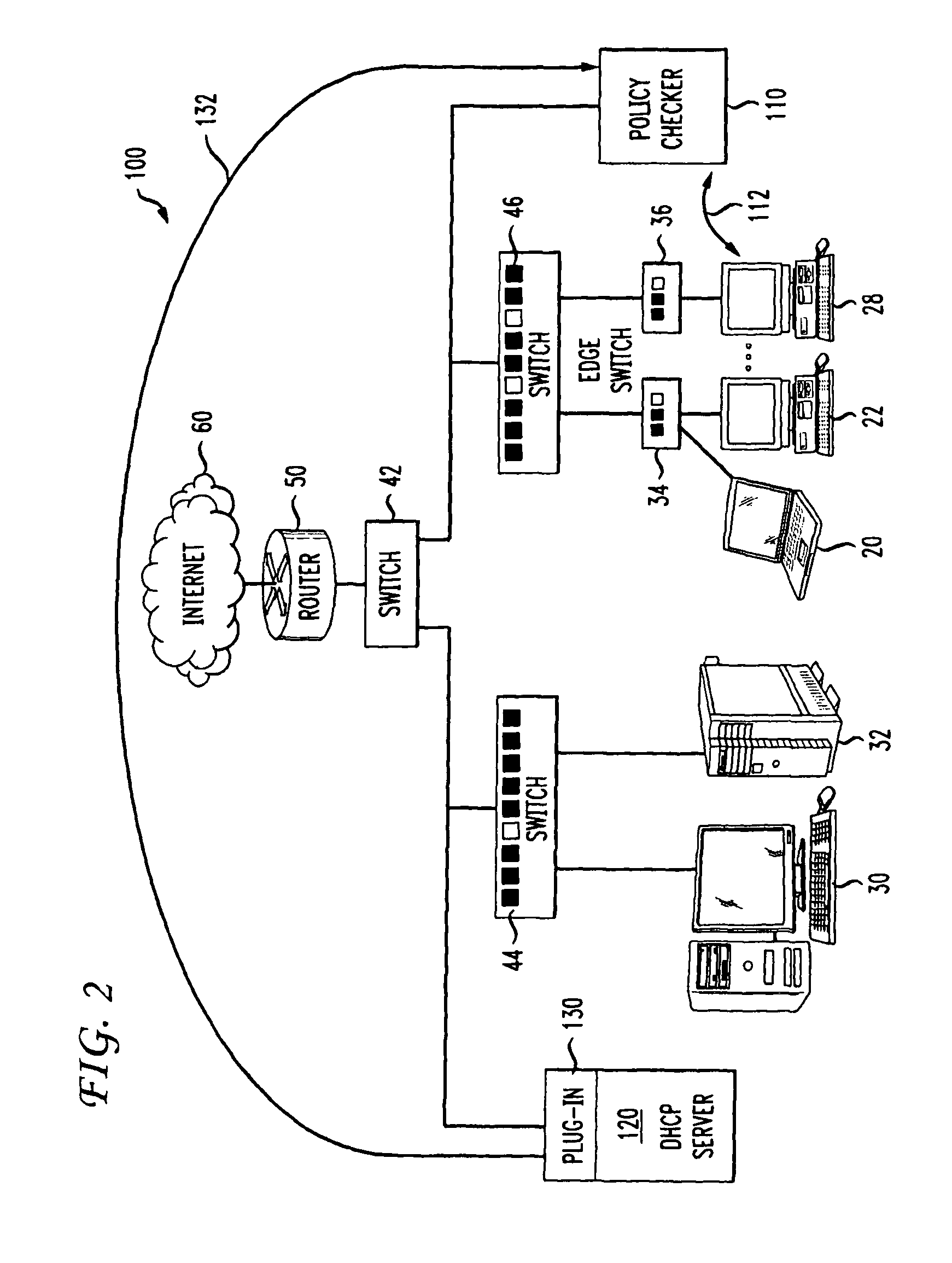
DHCP-based security policy enforcement system
ActiveUS8312270B1User identity/authority verificationMultiple digital computer combinationsIp addressNetwork packet
A plug-in module of a DHCP server enforces a security policy of a computer network. The module receives a request to provide an IP address for an end-user computer. A blacklist database is consulted to determine if the computer is not in compliance with the policy. If not compliant, the module returns to the computer a special IP address, a special default gateway and a lease time; the special IP address places the computer in a restricted network segment of the network where it cannot send network packets to other computers. If compliant, the computer receives an IP address and a lease time. The first time an IP address is requested a probe is triggered to determine if the computer is compliant using software not present on the computer. A cleanup service located in the restricted segment remove malware and updates software. Lease times increase after each successful request of an IP address.
Owner:TREND MICRO INC
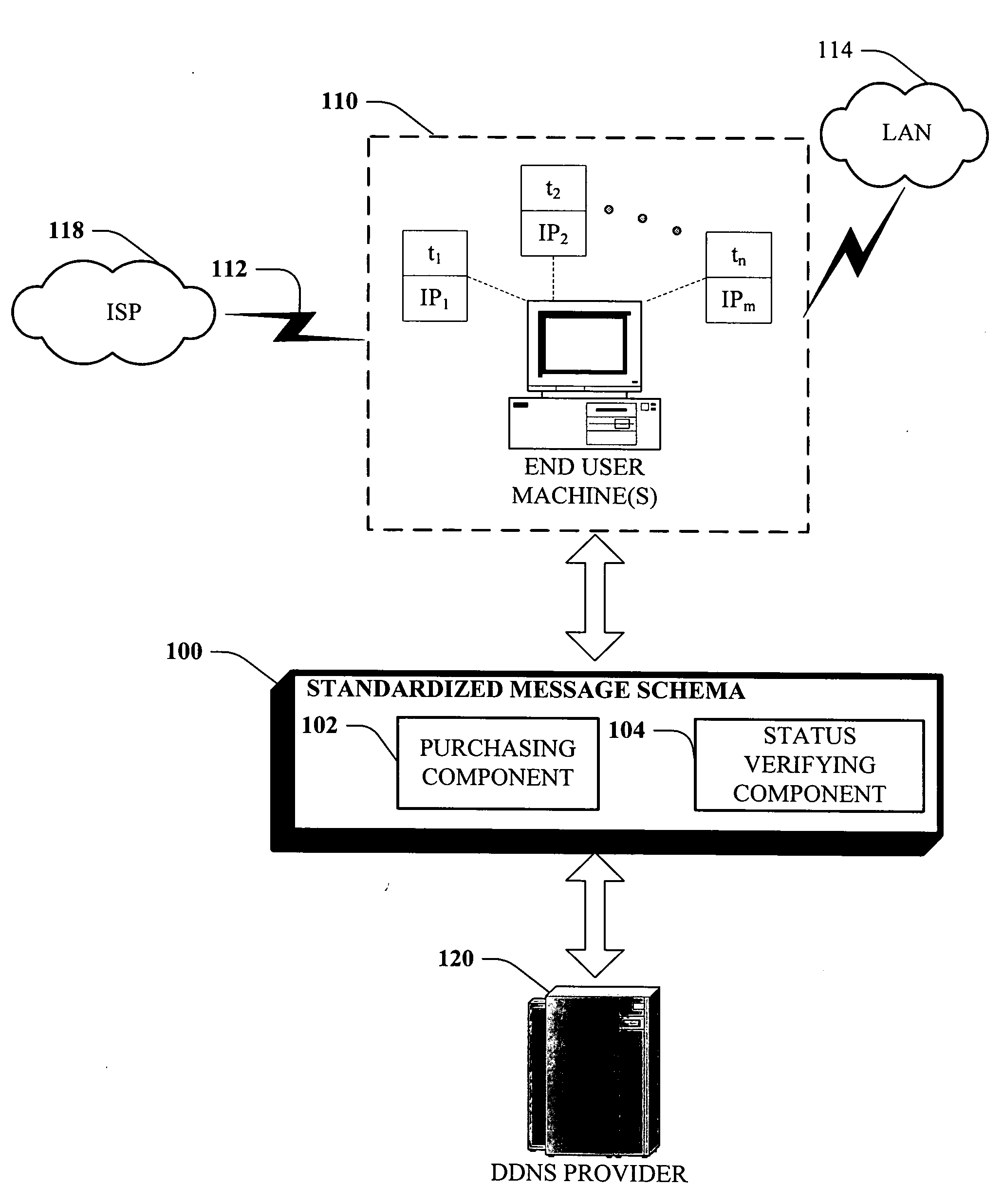
Message based network configuration of dynamic domain name services
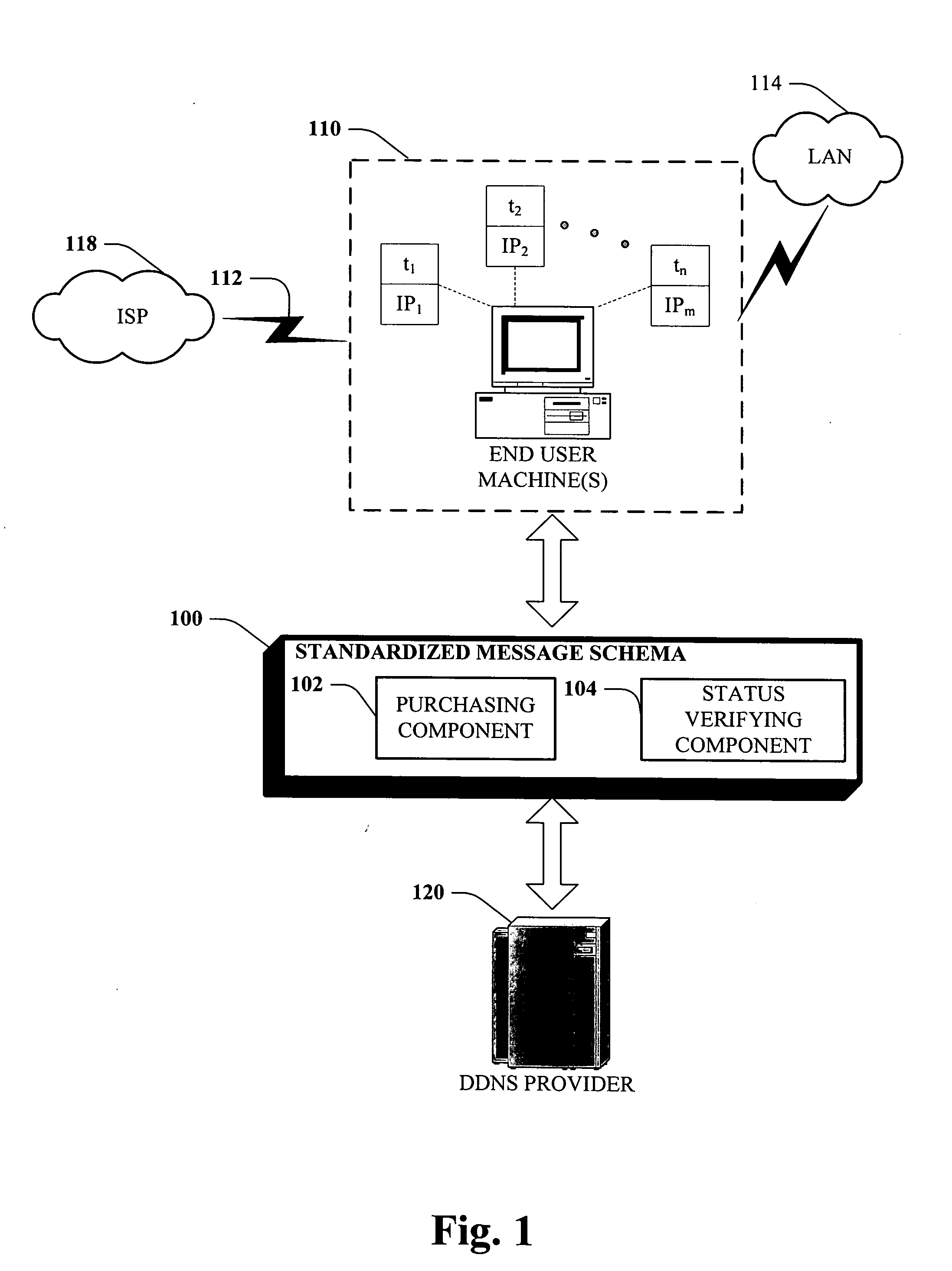
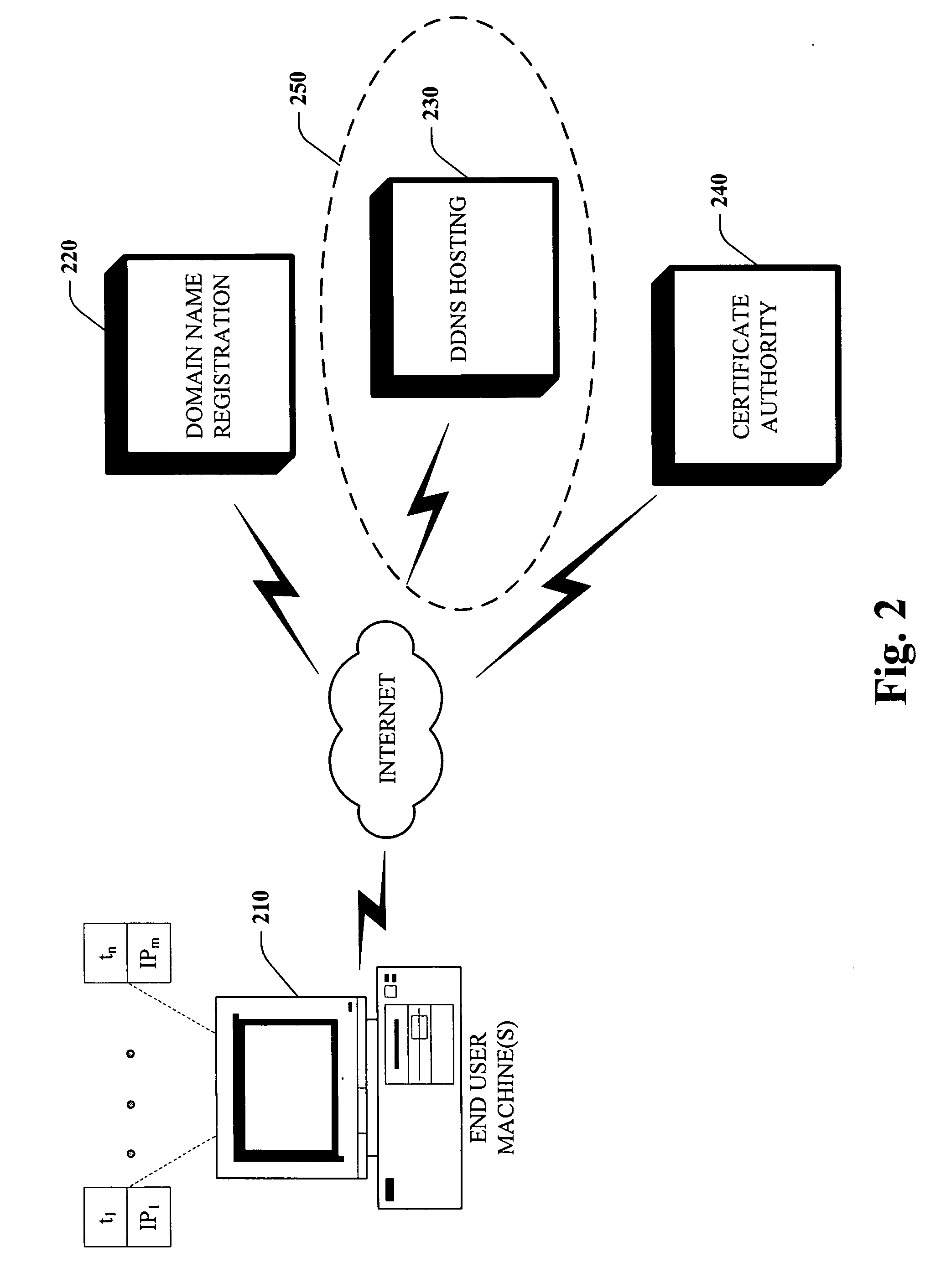
InactiveUS20060129503A1Facilitates initial server configurationSimple configurationMultiple digital computer combinationsPayment architectureDomain nameTraffic capacity
Systems and methodologies that facilitate hosting of a domain name and access of users to the Internet, by using a well defined protocol to interact with a plurality of Dynamic Domain Name Service (DDNS) providers, via employing; a purchasing component and a status verifying component. Once a user has selected a domain name, the purchasing component can automatically query the provider(s) for terms of the service plan to host such domain name associated with dynamic IP addresses. The status verifying component can verify the IP address of the end user machine and supply it to the DDNS, to manage in-bound traffic to the user's domain name.
Owner:MICROSOFT TECH LICENSING LLC
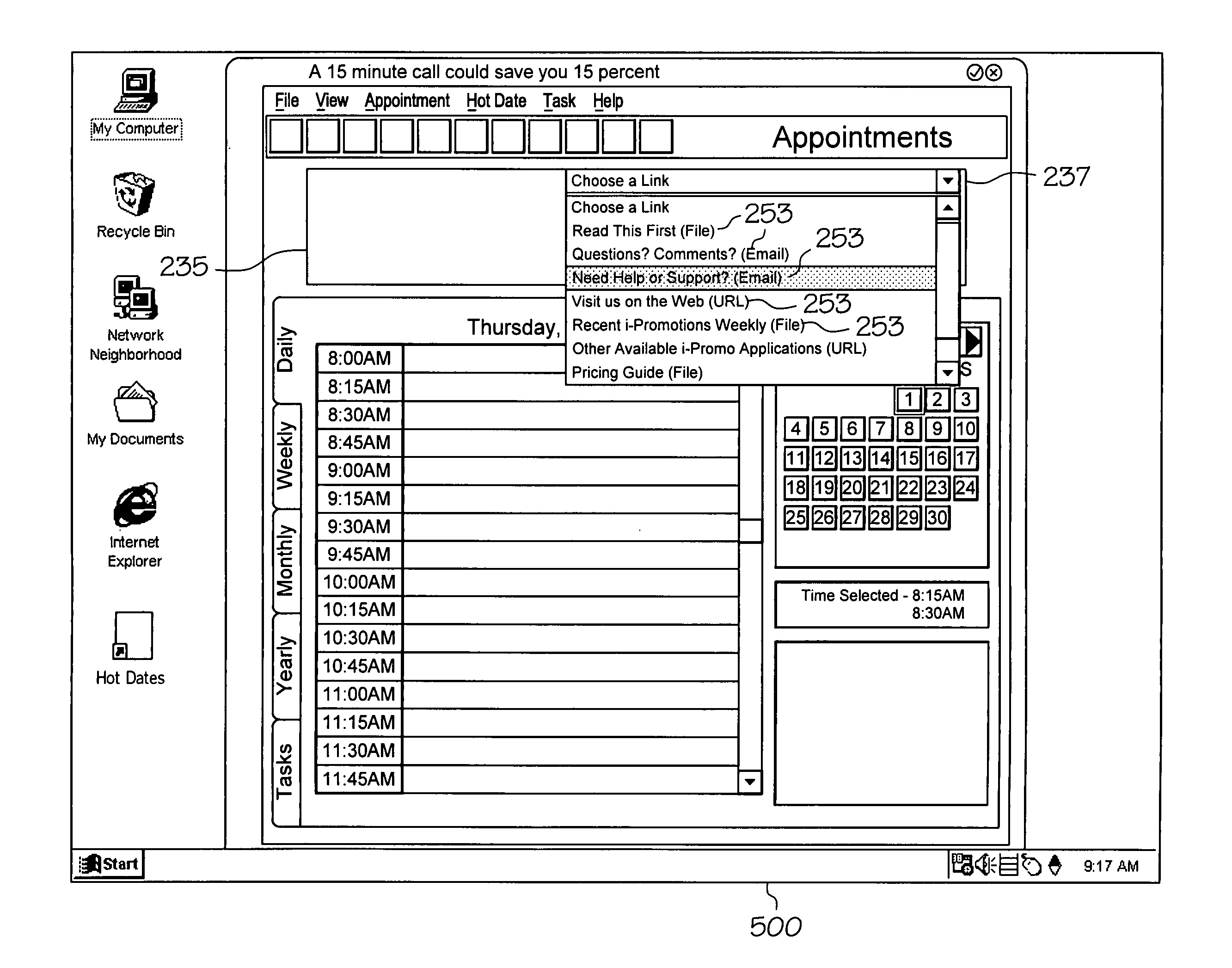
Multiple destination banners
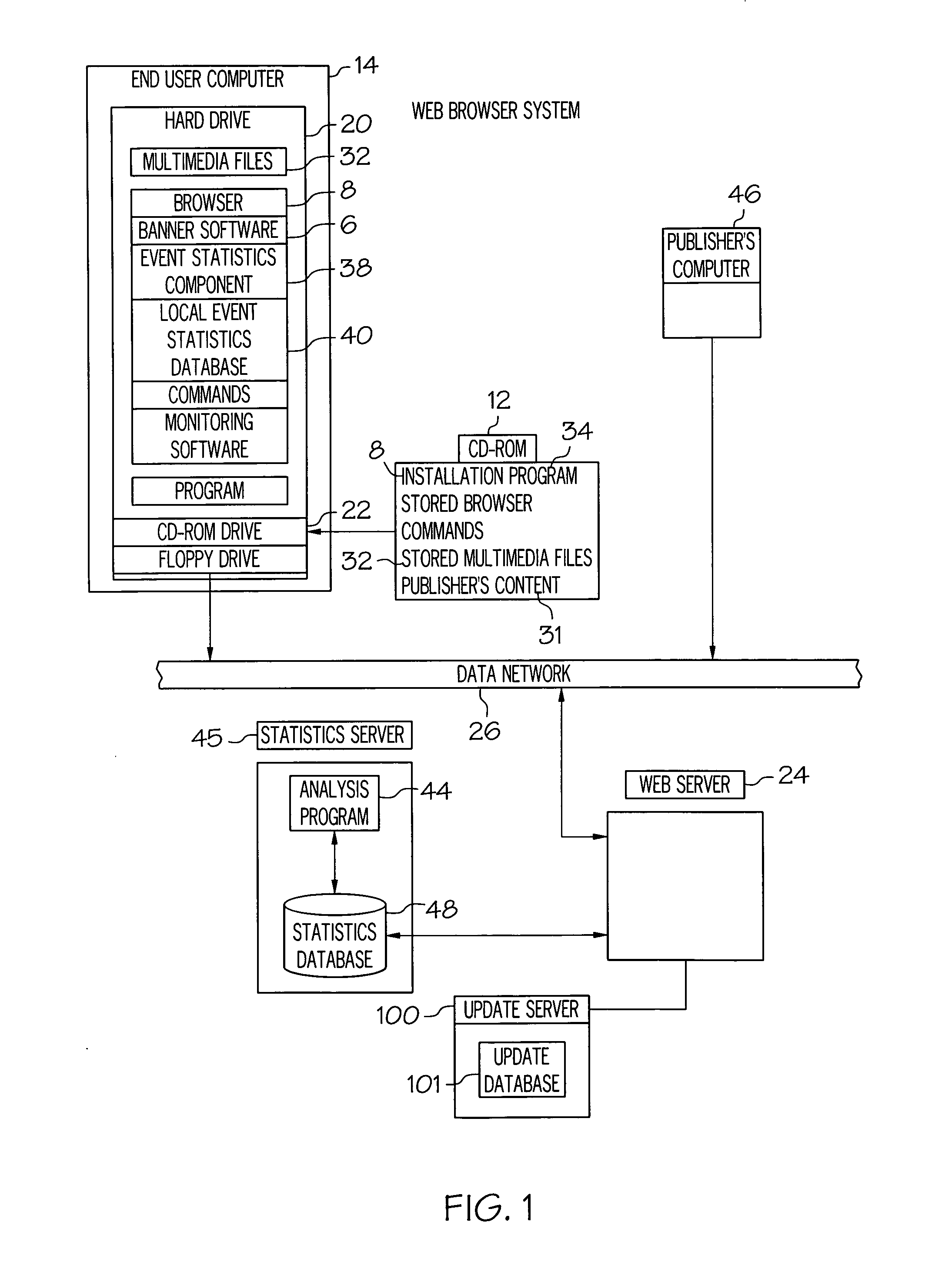
The present invention provides software, methods, and computer systems for displaying banner ads with a set of navigation options presented to an end-user, such as a customer or consumer, who selects or clicks on the displayed banner ad. The navigation options include URLs on a network to which the end-user computer is connectable. The invention includes software, systems, and methods for allowing the publisher to define and update the set of options. The invention includes software, systems, and methods for recording display event statistics for the banner ad whether the end-user is viewing the banner ad either off-line or on-line. The invention also includes a means for targeting and sending messages across the network to end-users.
Owner:DIRECT BUSINESS TECH
System and Method for Providing Sequential Video and Interactive Content
ActiveUS20110202953A1Selective content distributionElectrical cable transmission adaptationVideo storageWeb site
A system and method of providing sequential video and contextual based content to an end user viewing video content in a video player on an end user computing device is provided. In one embodiment, the method comprises storing a plurality of videos in a memory, storing a plurality of advertisements in a memory, receiving a plurality of requests from a plurality of different clients and wherein each request includes information identifying a first video and each of the plurality of clients initiates its request from one of a plurality of web pages and wherein the plurality of web pages form part of a plurality of different web sites. In addition, the plurality of web pages may include program code configured to cause a video to be presented in the video player. The method further comprises for each received request, selecting a plurality of videos based on information of the first video; and selecting a plurality of advertisements, wherein at least one of the plurality of advertisements is selected based on information of the first video and at least one of the plurality of advertisements is selected based on information of a selected video. In addition, the method may comprise for each received request, transmitting the plurality of videos to the requesting client for sequential presentation by the client; and transmitting the plurality of advertisements to the requesting client and wherein at least some of the plurality of advertisements are configured to be presented concurrently with a received video.
Owner:NYTELL SOFTWARE LLC
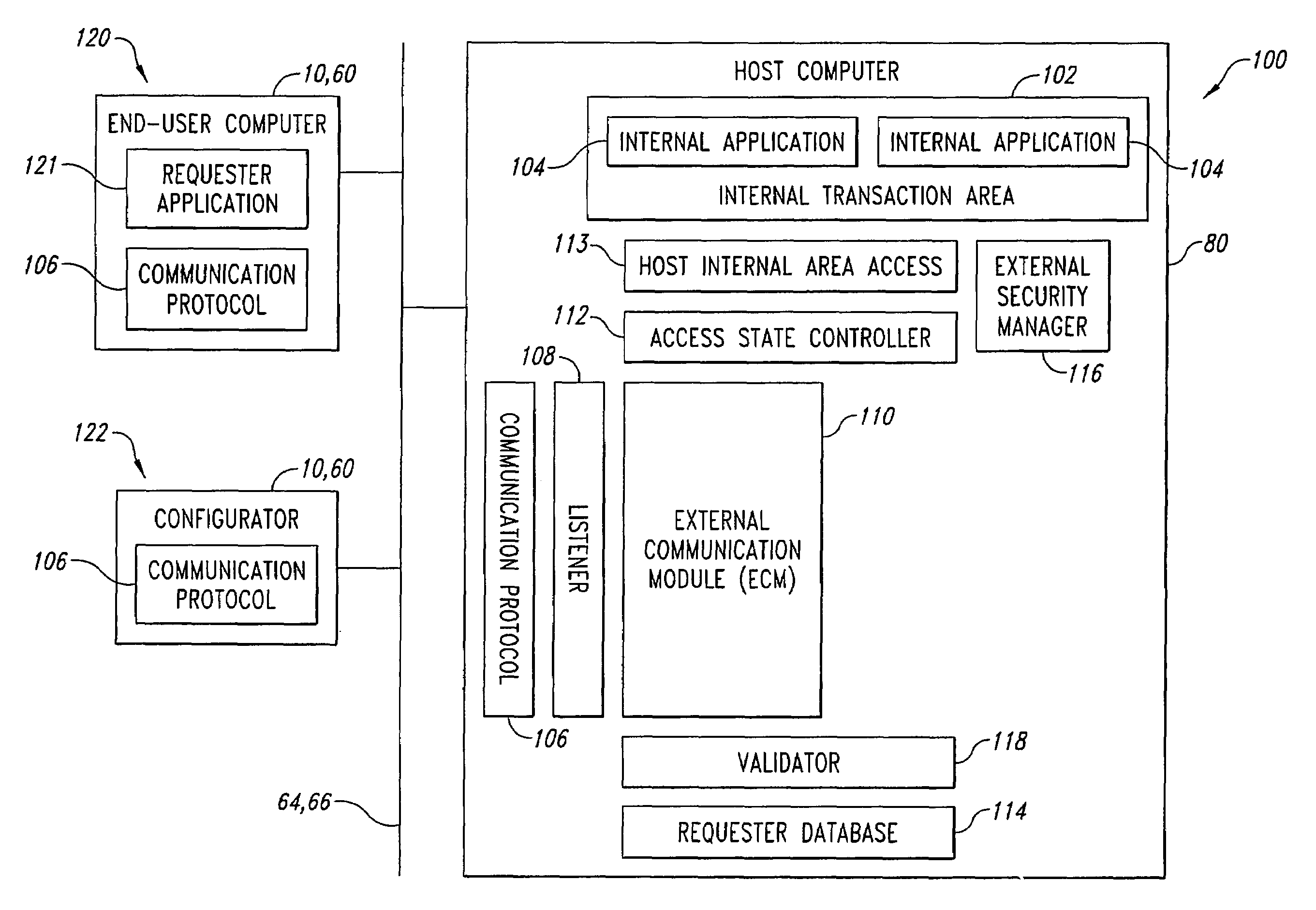
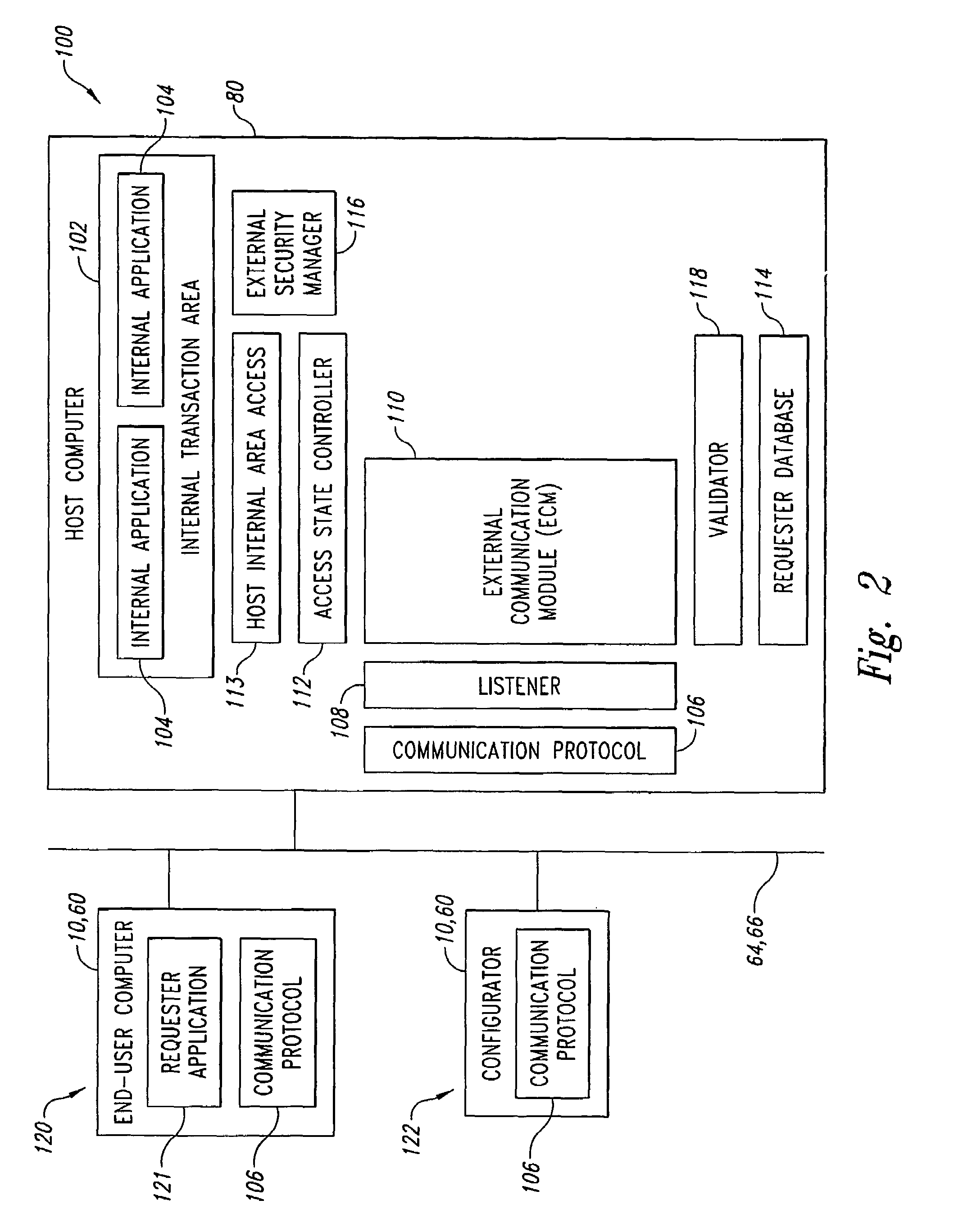
System and method for transaction access control
InactiveUS6980989B2Data processing applicationsDigital data processing detailsApplication softwareValidator
A computer implemented system controls transaction access of requester applications running on end-user computers having network protocol addresses, to internal applications and their associated transactions running in internal transaction areas of host computer systems. Related to each network protocol address, a requester database contains information related to each network protocol address including end-user identification, possible username and password and instructions, possible priority levels of select transactions, and authorized transactions. A listener listens for a connect request from one of the end-user computers. A validator, using the requester database, determines whether the end-user computer has a valid network protocol address. An external communication module receives subsequent transaction requests from validated end-user computers and a validator in conjunction with a requester database determines among other things whether the transactions requested are authorized for particular end-user computers. Usernames and passwords are sent to an external security manager for authorized transactions.
Owner:ATTACHMATE
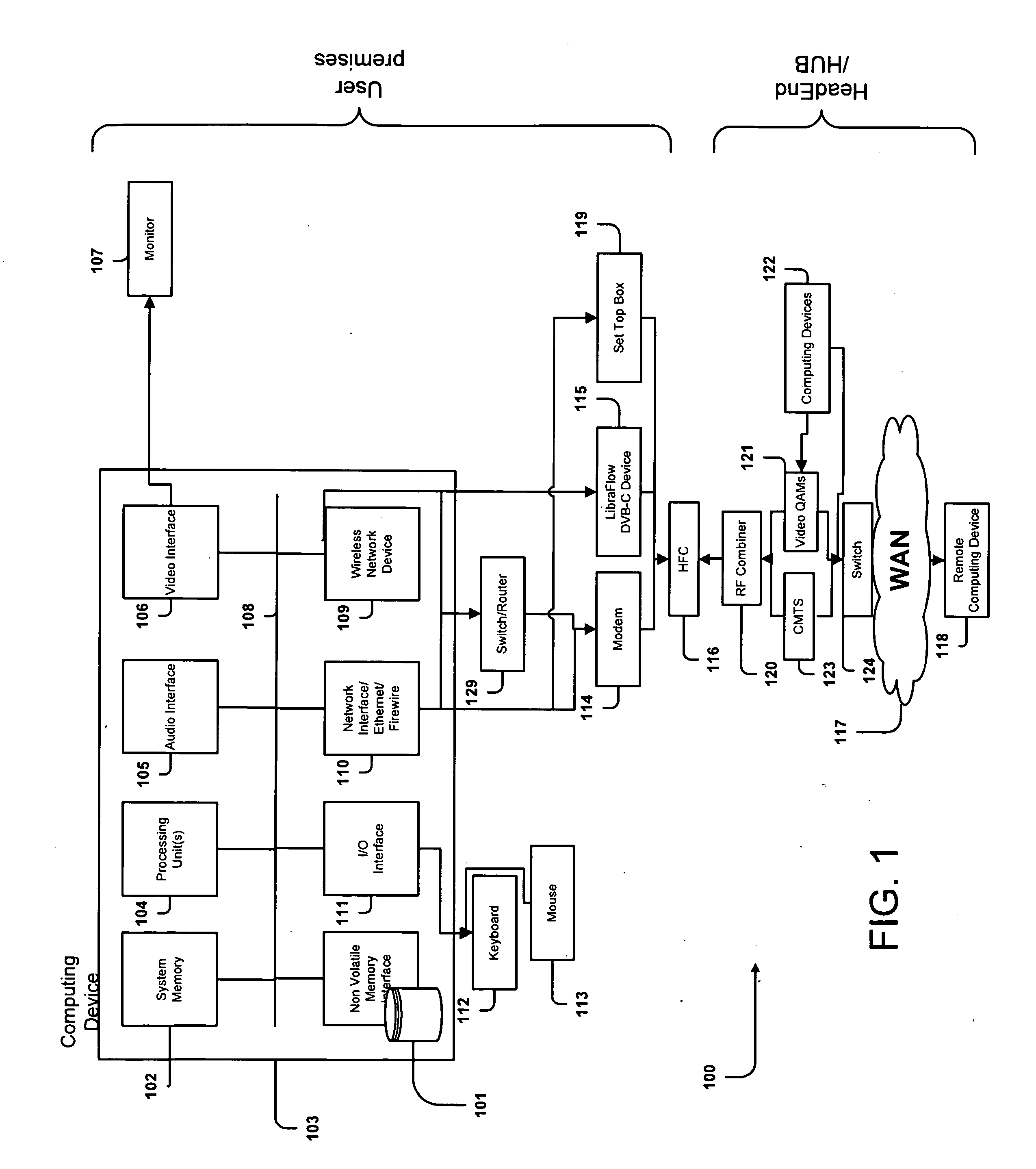
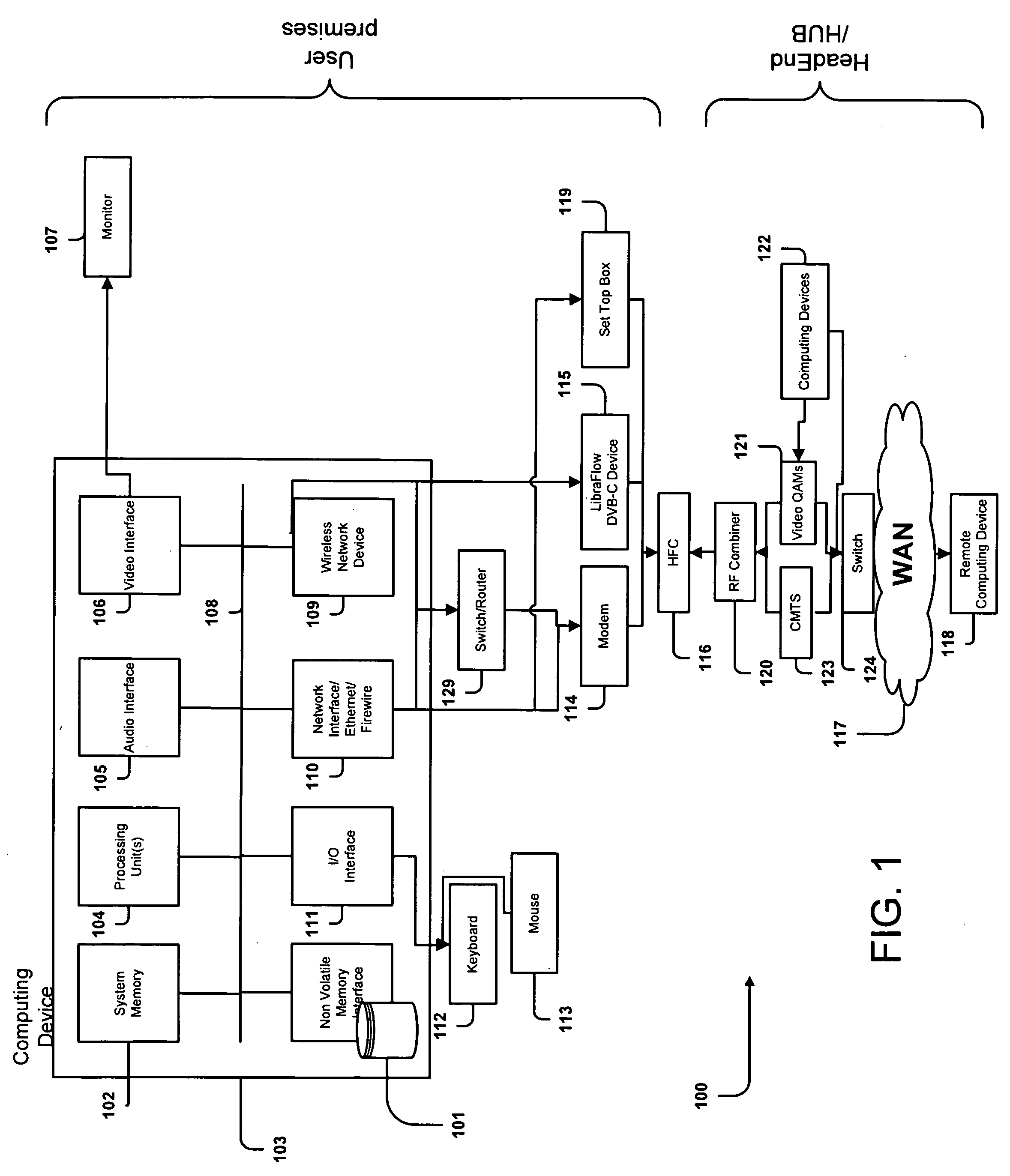
Methods and System for Efficient Data Transfer Over Hybrid Fiber Coax Infrastructure
InactiveUS20120271922A1Improve transmission efficiencyImprove reliabilityBroadband local area networksMultiple digital computer combinationsFiberDOCSIS
The invention is directed to a method for providing client-server data transfer over a Hybrid Fiber Coax network, comprising interfacing, at a client, a channel, wherein the channel is one of a video channel and a DOCSIS channel, intercepting a content request made from an end-user computing device, notifying a server of a relevant intercepted message via one of using an interactive channel and tagging the request, selecting content sent by the server over the channel, processing the content selected so as to return it to its IP traffic format, and forwarding the content in its IP traffic format to the end-user computing device.
Owner:HARMONIC INC
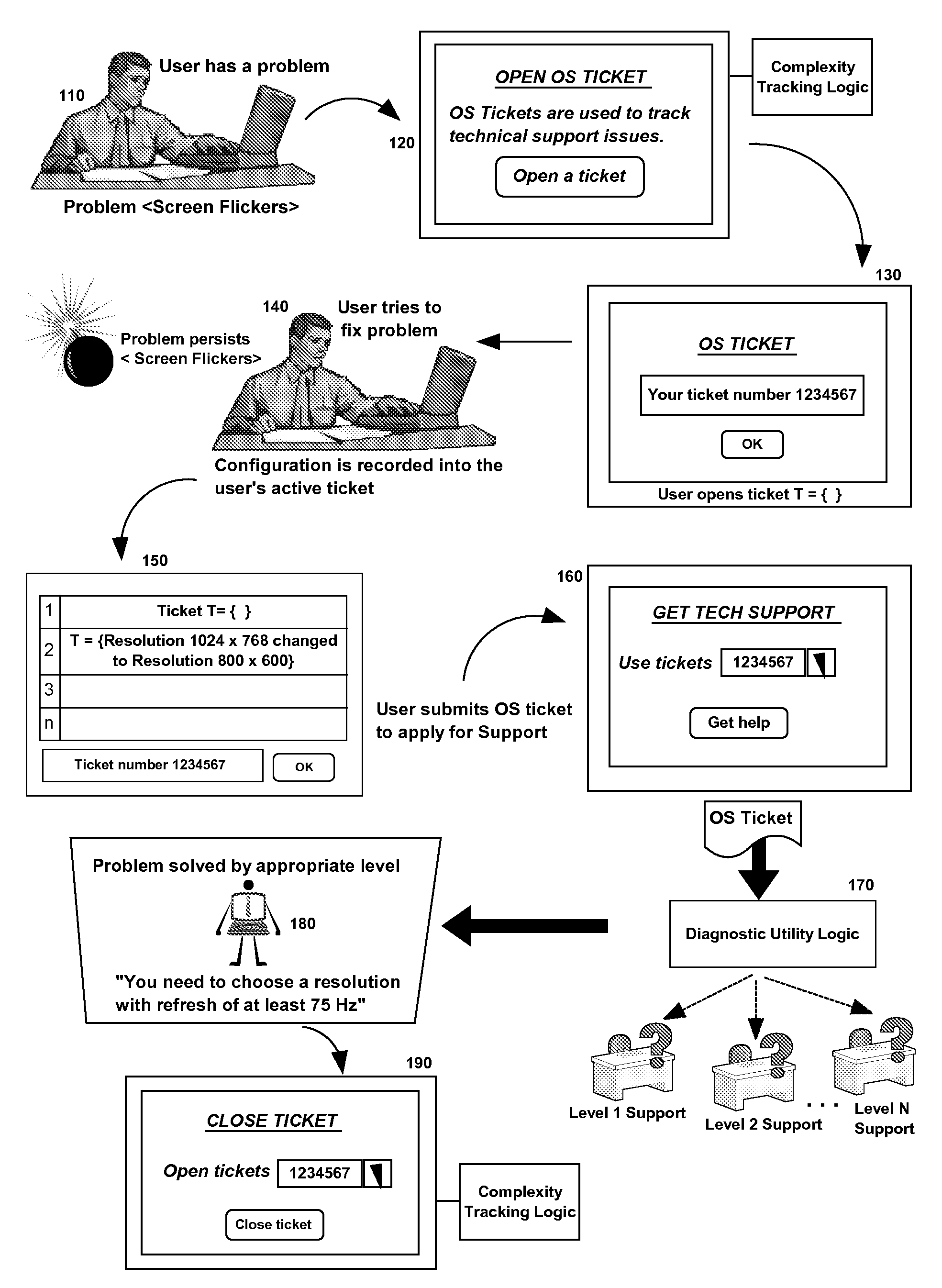
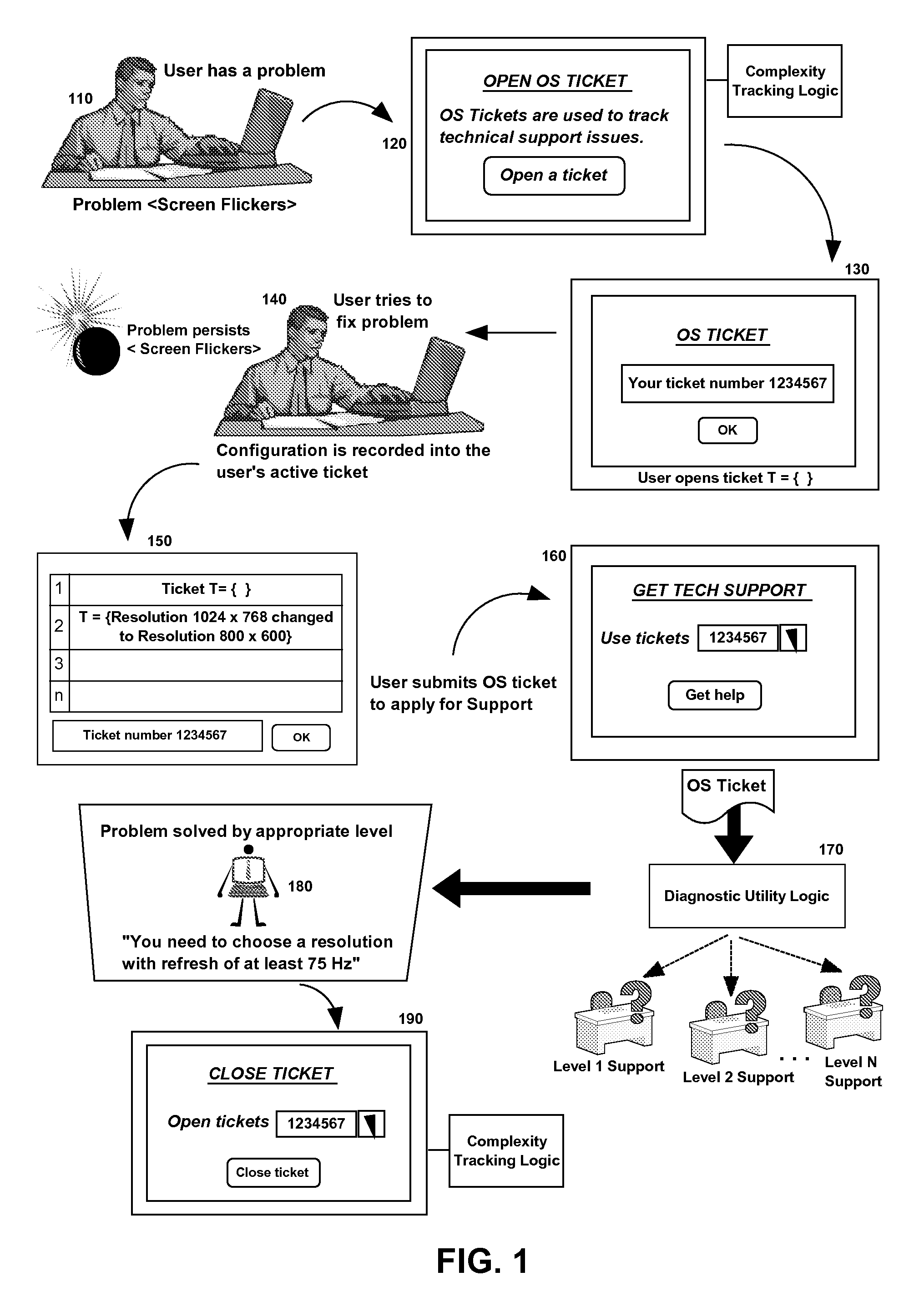
Intelligent problem tracking electronic system for optimizing technical support
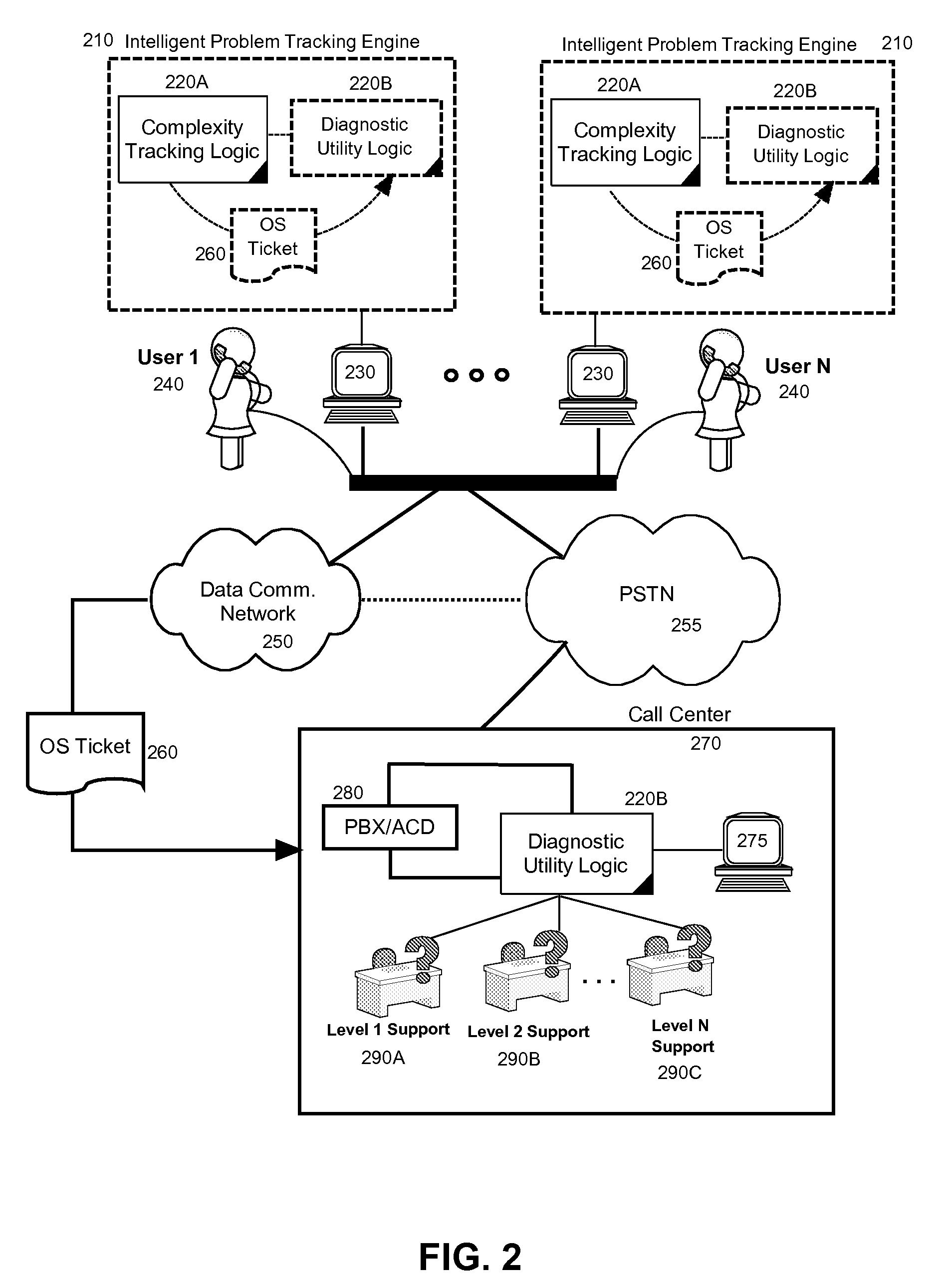
ActiveUS20100057657A1Non-redundant fault processingKnowledge representationElectronic systemsSystem optimization
Embodiments of the present invention address deficiencies of the art in respect to technical support management and provide a novel and non-obvious method, system and computer program product for intelligent problem tracking to optimize technical support. In an embodiment of the invention, a method for intelligent problem tracking can include receiving recorded information of tracked end user behavior collected in an end user computing system while the end user addresses a problem in the end user computing system, determining a level of technical sophistication of the user based upon the recorded information, selecting a technical support level corresponding to the determined level of technical sophistication of the user, and transmitting a resolution to the problem in a message to the end user computing system commensurate with the selected technical support level.
Owner:IBM CORP
Data retrieval in a hybrid cloud
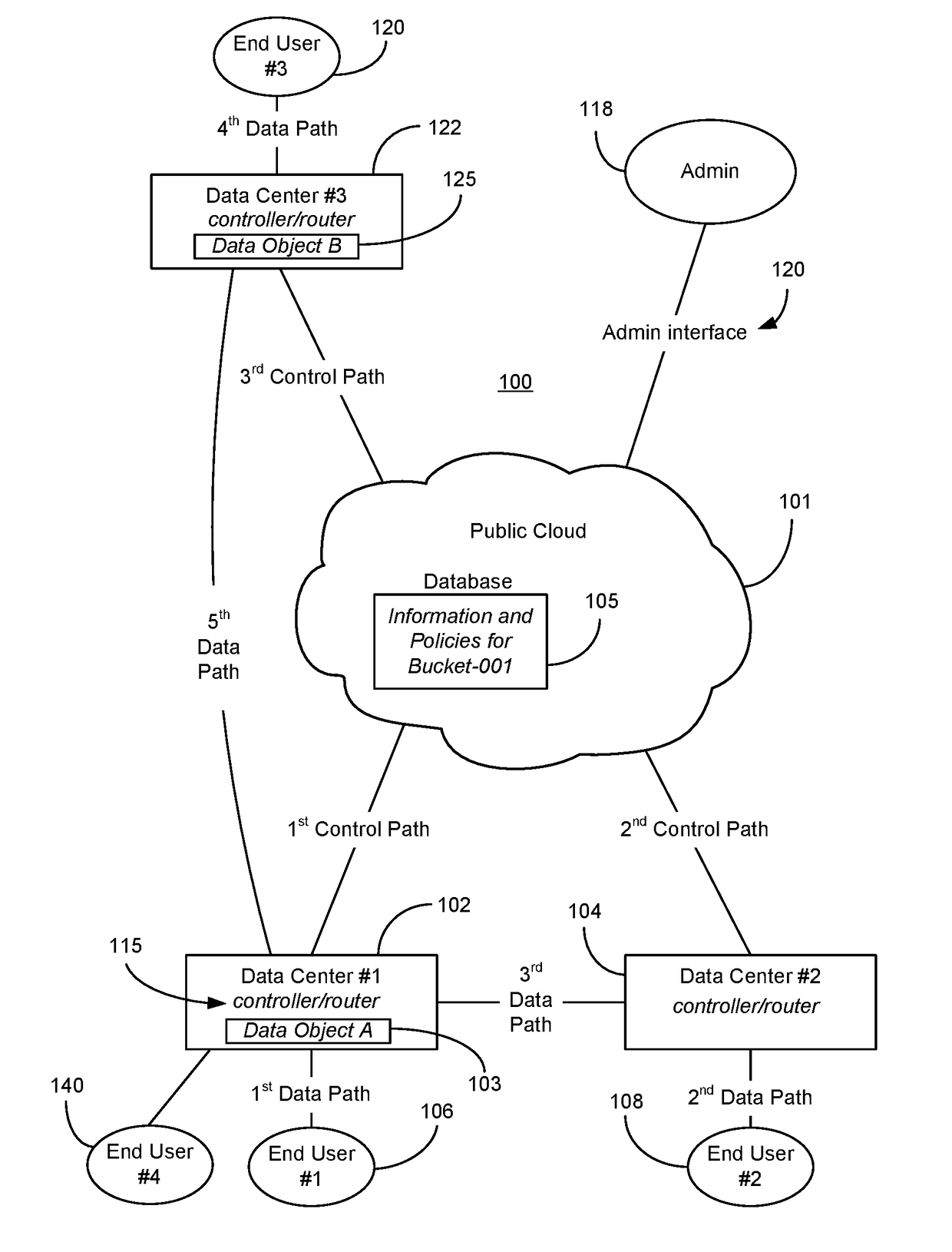
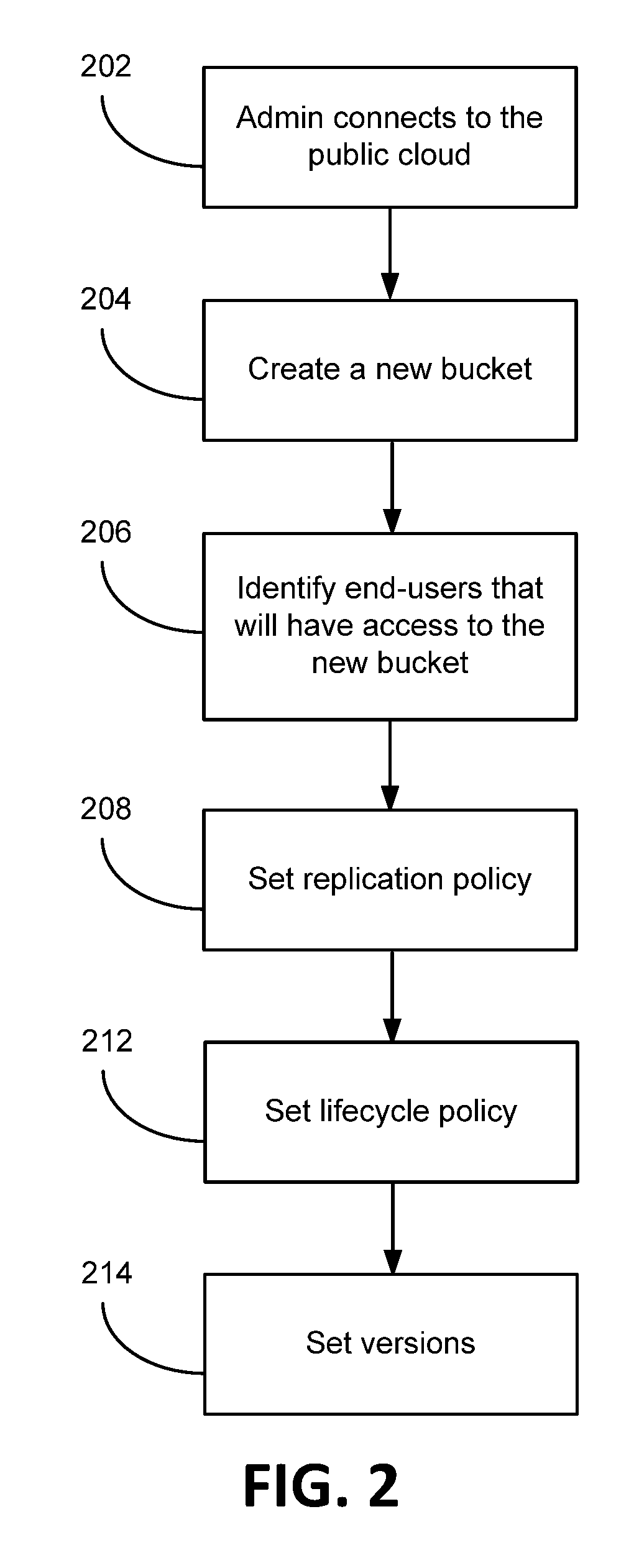
InactiveUS20180084052A1CostPerformanceWeb data indexingError detection/correctionMass storageData center
A cloud environment is provided generally having at least one private data center possessing a controller / routing system and nonvolatile mass storage, a plurality of data objects retained in the nonvolatile mass storage, and a public cloud storage service provider linked to the controller / routing system. The public cloud storage service provider possessing a database containing policy decisions and metadata of the plurality of data objects. When data objects are uploaded to the cloud environment, the private data center is in possession of the data objects, the public cloud is not in possession of the data objects. The private data center is not in possession of the policy decisions and the metadata for the plurality of data objects, rather the public cloud storage service provider is. The public cloud storage service provider adapted to be communicatively linked to an end-user computing system by way of the controller / routing system. The end-user able to retrieve data objects from the cloud environment via the private data center that ascertains location information of one or more target data objects from one or more private data centers. The data objects retrieved do not pass through the public cloud service provider, but rather over data pathways independent of the public cloud service. The data center is independent of the public cloud storage provider.
Owner:SPECTRA LOGIC
Serving content-relevant advertisements with client-side device support
InactiveUS20110145731A1Input/output for user-computer interactionSpecial service provision for substationDocumentation procedureDocument Identifier
A client-side application (such as a browser, a browser plug-in, a browser toolbar plug-in, etc. on an end user's computer) is used to support the serving of content-relevant ads to the client device. The client-side application may provide such support by sending document information (such as a document identifier, document content, content relevance information, etc.) to a content ad server. The client-side application may also be used to combine content of the document and the content-relevant ads. For example, the client-side application may combine content of the document and the ads in a window (e.g., in a browser window), may provide the ads in a window above, below, adjacent to a document window, may provide the ads in “chrome” of the browser, etc.
Owner:ANDERSON DARRELL +6
Methods and System for Efficient Data Transfer Over Hybrid Fiber Coax Infrastructure
ActiveUS20090168649A1Improve reliabilityAccelerates data deliveryError preventionTransmission systemsFiberDOCSIS
The invention is directed to a method for providing client-server data transfer over a Hybrid Fiber Coax network, comprising interfacing, at a client, a channel, wherein the channel is one of a video channel and a DOCSIS channel, intercepting a content request made from an end-user computing device, notifying a server of a relevant intercepted message via one of using an interactive channel and tagging the request, selecting content sent by the server over the channel, processing the content selected so as to return it to its IP traffic format, and forwarding the content in its IP traffic format to the end-user computing device.
Owner:HARMONIC INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com