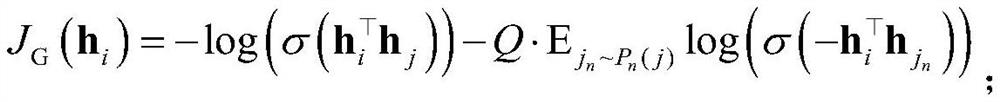Patents
Literature
34results about How to "Purify the network environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
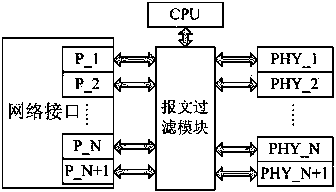
Method for filtering network messages of process level of intelligent substation
InactiveCN103378654AEffective smooth transmissionSmooth transmissionCircuit arrangementsData switching networksSmart substationPhysical layer
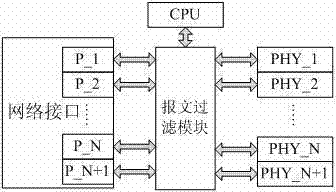
Provided is a method for filtering network messages of a process level of an intelligent substation. A network of the process level of the intelligent substation is connected with various devices which comprise a merging unit, an intelligent terminal, a switchboard, a protection device and a measuring and control device, wherein the devices are used for sending and receiving SV messages and GOOSE messages, message filtering modules are additionally arranged between network interfaces and physical layers of the devices, the received messages are filtered additionally in a message filtering mode, traffic limitation is performed on the messages with MAC addresses assigned by the devices, key fields of the messages with the MAC addresses assigned by the devices are recognized, repeated messages are filtered, the messages without the MAC addresses assigned by the devices are discarded or forwarded, and broadcasting messages are discarded or forwarded. According to the method, the accurate management of the GOOSE messages and the SV messages can be achieved through the merging unit, the intelligent terminal, the switchboard, the protection device and the measuring and control device in the intelligent substation.
Owner:NR ELECTRIC CO LTD +1
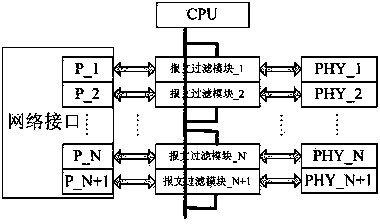
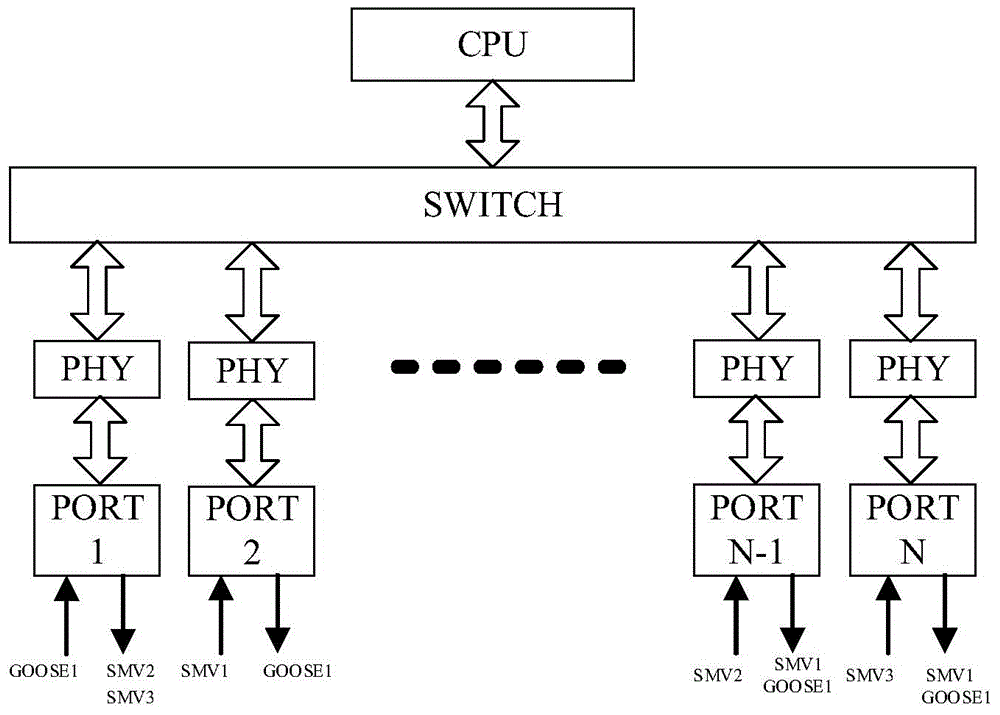
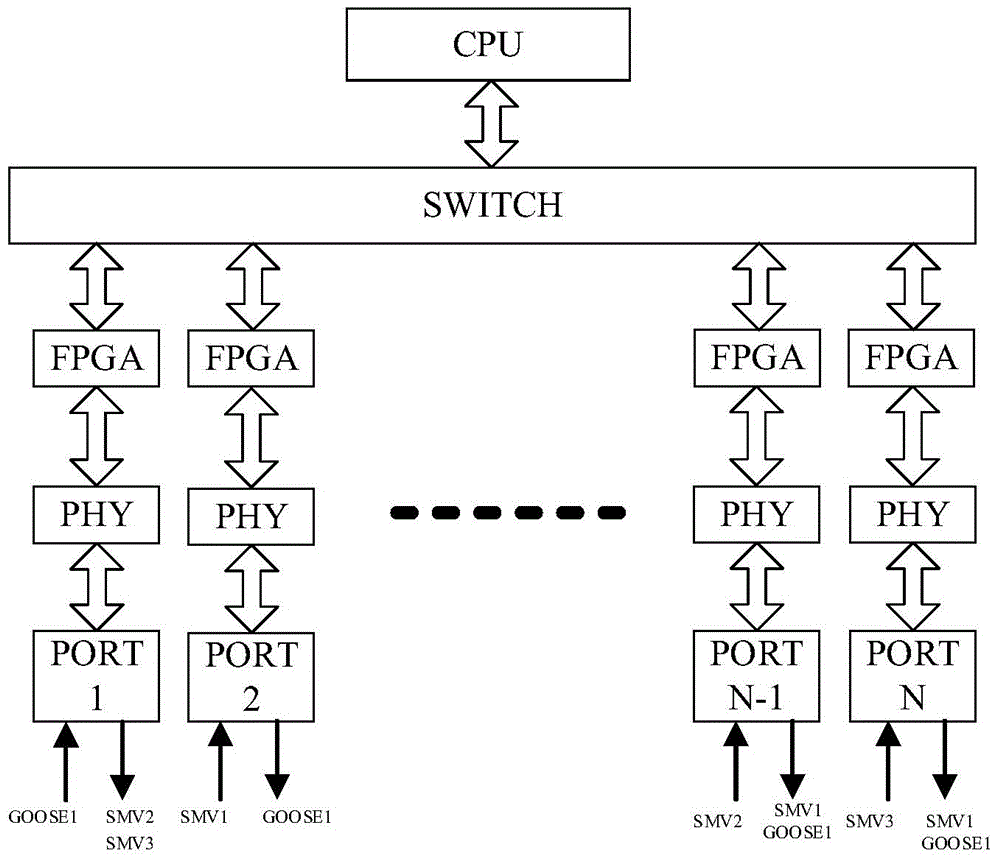
Network message management method of intelligent substation process layer switch
InactiveCN104917705APrecise managementSolve problems that cannot be precisely suppressedData switching networksTraffic capacitySmart substation
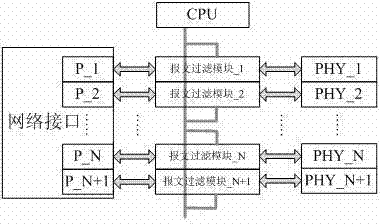
The invention discloses a network message management method of an intelligent substation process layer switch. The method comprises the following steps: adding FPGA between the switch and PHY, a switch CPU sending a message management strategy to the FPGA, and realizing the network message management of the switch through the FPGA; the FPGA checking legality of network messages through network message key words, and processing the illegal messages according to the message management strategy; the FPGA counting traffics of different network messages according to the network message key words, and processing the message with overrun traffic according to the message management strategy; the FPGA checking correctness of the legal network message, precisely positioning the error message according to the network message key word, and processing the abnormal message according to the message management strategy. The problem that the network message at the intelligent substation cannot be precisely inhibited is solved, the hidden danger that a network storm is capable of forming on a communication network of the intelligent substation is eliminated.
Owner:STATE GRID CORP OF CHINA +2
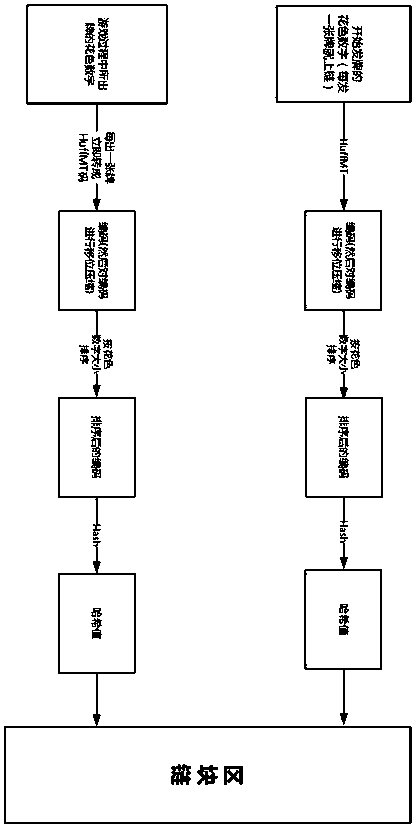
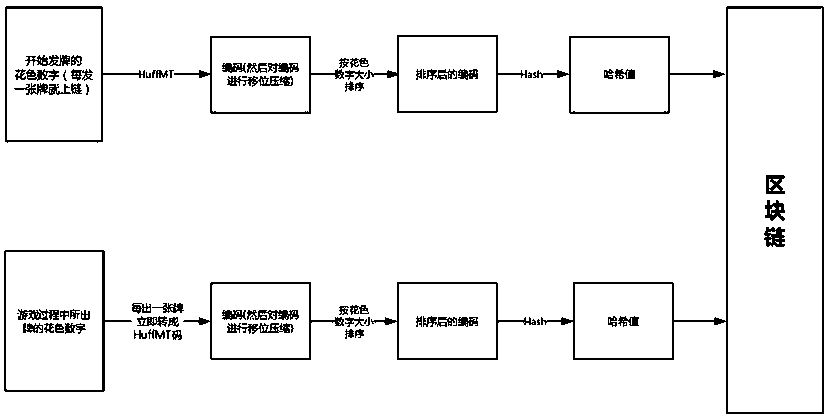
Card game anti-cheating method and system based on block chain intelligent contract
ActiveCN109985389AGuaranteed verifiabilityGuaranteed to be tamper-proofUser identity/authority verificationVideo gamesComputer hardwareEncryption
The invention provides a card game anti-cheating method and system based on a block chain intelligent contract. The method comprises the following steps of: storing card drawing information and card issuing information of a player on the block chain by using a coding method and an encryption method; comparing a Hash value A and a Hash value B of a winner in the block chain; if the two values are the same, that cheating behavior occurs is determined, if the two values are not the same, that cheating behavior does not occur is determined. According to the invention, the defect of the existing combination of the block chain and the game is considered, the application scene is changed, and the cheating behavior is effectively found out by utilizing a unique mechanism of the block chain for de-trust and de-centralization. Meanwhile, the chess and card game data is not complex, too much burden is not caused during operation, the cost is low, the effect is obvious, and the serious situation of cheating of the current card game can be effectively improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
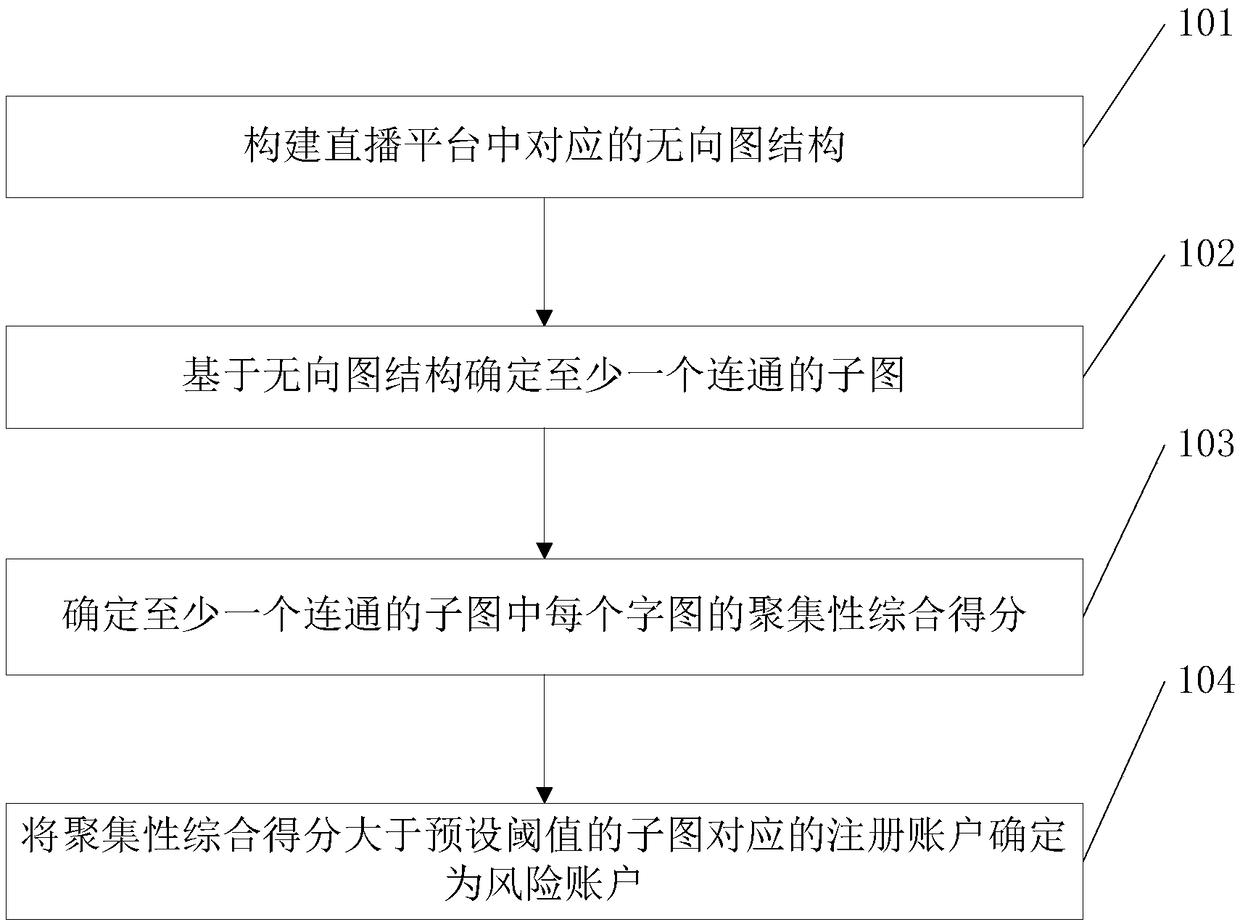
A method of determining a risk account and associated equipment
ActiveCN109460930AAccurate identificationPurify the network environmentDigital data authenticationResourcesUndirected graphTheoretical computer science
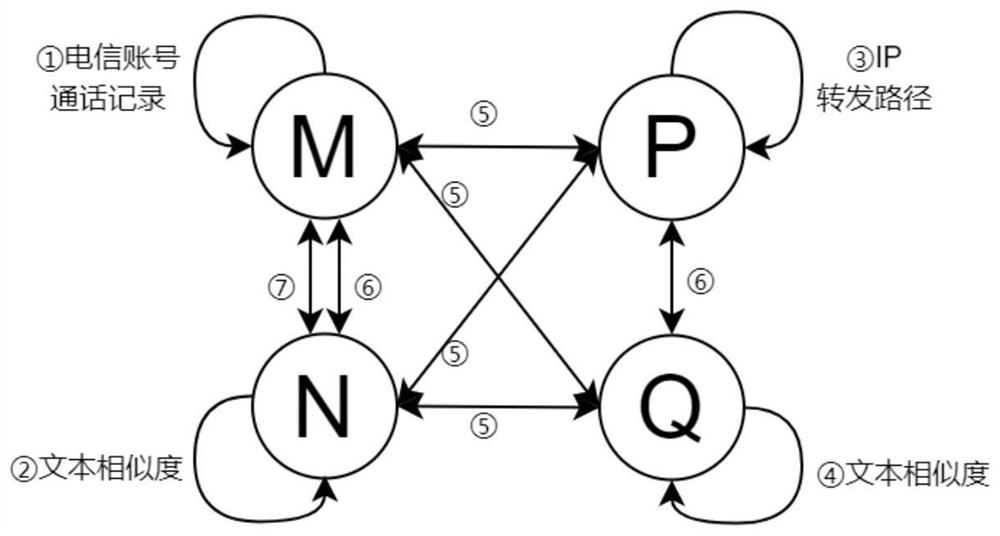
The embodiment of the invention provides a method for determining a risk account and related equipment, which can quickly and accurately identify the risk account registered in batch in the live broadcast platform, eliminate the risk account in the live broadcast platform from the registration source, and purify the network environment of the live broadcast platform. The method comprises the following steps of: constructing an undirected graph structure corresponding to a live broadcast platform, wherein the undirected graph structure indicates a corresponding relationship between a registration account and a registration device in the live broadcast platform; Determining at least one connected subgraph based on the undirected graph structure; Determining an aggregation synthesis score foreach of the at least one connected subgraphs; The registered account corresponding to the sub-graph whose aggregation comprehensive score is greater than a preset threshold value is determined as a risk account.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
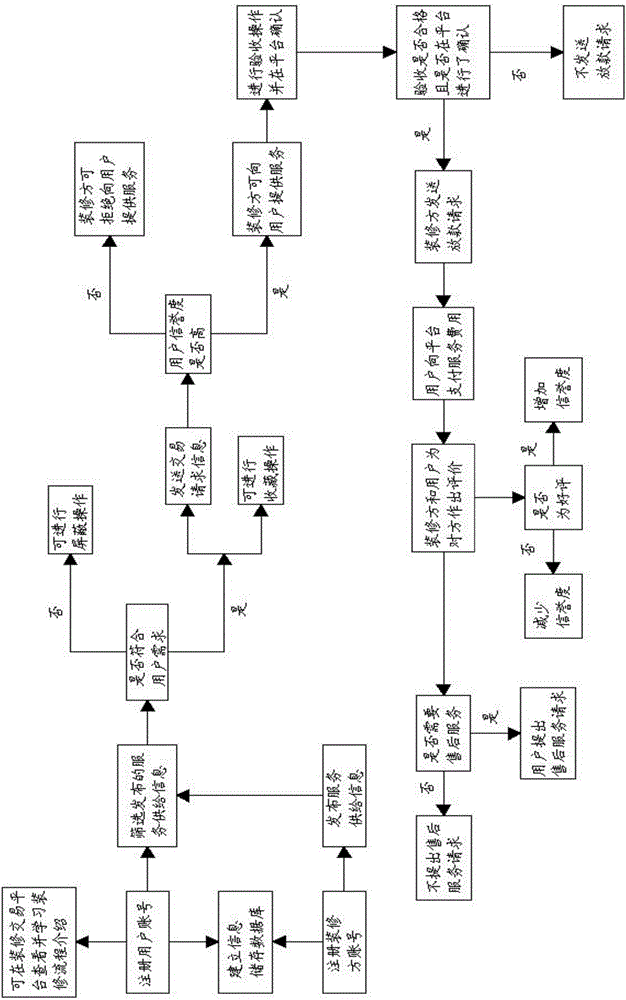
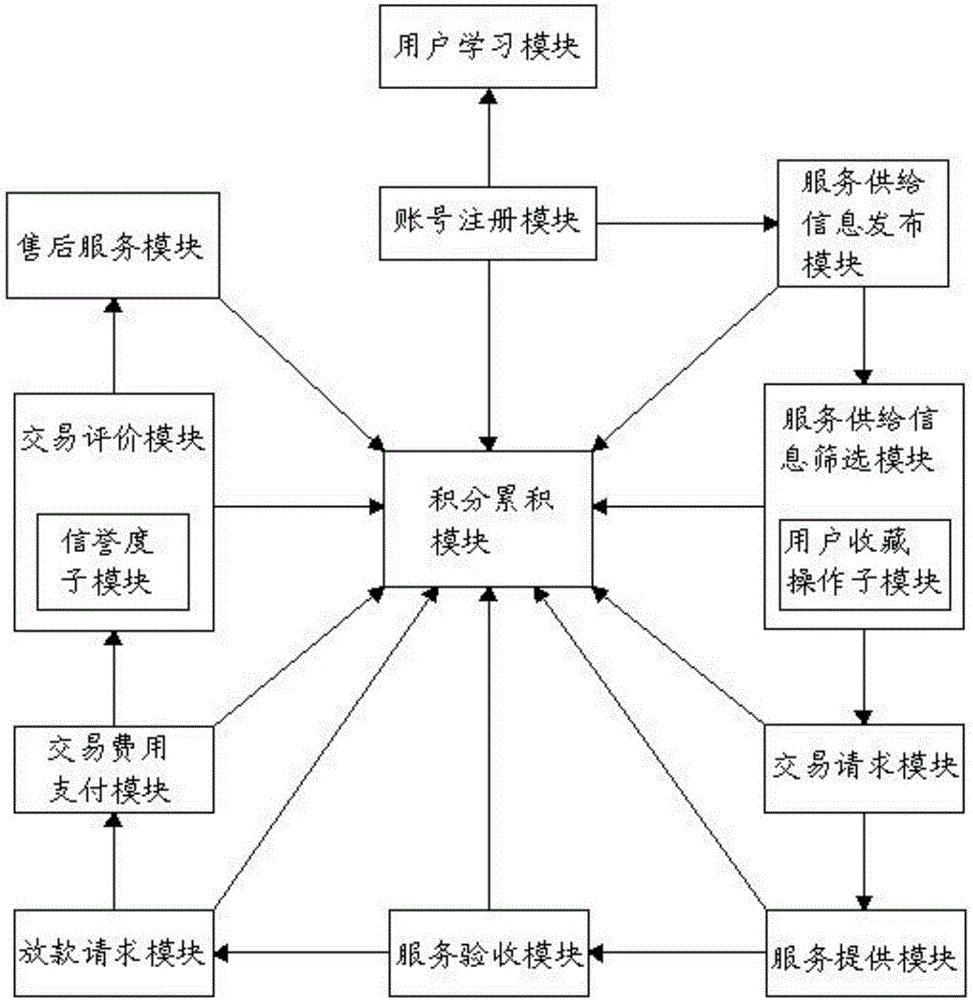
Decoration online transaction method and system
InactiveCN106372990AEasy to tradeEasy to operateBuying/selling/leasing transactionsFinancial transactionDatabase
The present invention discloses a decoration online transaction method. The method comprises: registering a user account and a decoration party account; users check and learn the decoration flow introduction on a transaction platform; a decoration party publishes service supply information to the transaction platform; the users who screen out the service supply information send a transaction request to the decoration party; the decoration party and the users perform the acceptance operation; the decoration applies for the loan to the users and the decoration transaction platform; the users pay the service cost to the decoration transaction platform; and the decoration party and the users make evaluation for the opposite side according to the completion satisfaction degree. The present invention further discloses a decoration online transaction system. The system comprises an account registration module, a user learn module, a service supply information publishing module, a service supply information screening module, a transaction request module, a service supply module, a service acceptance module, a loan request module, a transaction cost payment module and a transaction evaluation module. The operation is much simpler, the transaction is more convenient, the trustworthiness is high, the client experience is improved, the merchant operating cost is reduced, and the sense of trust between buyers and sellers is improved.
Owner:陶怡臣
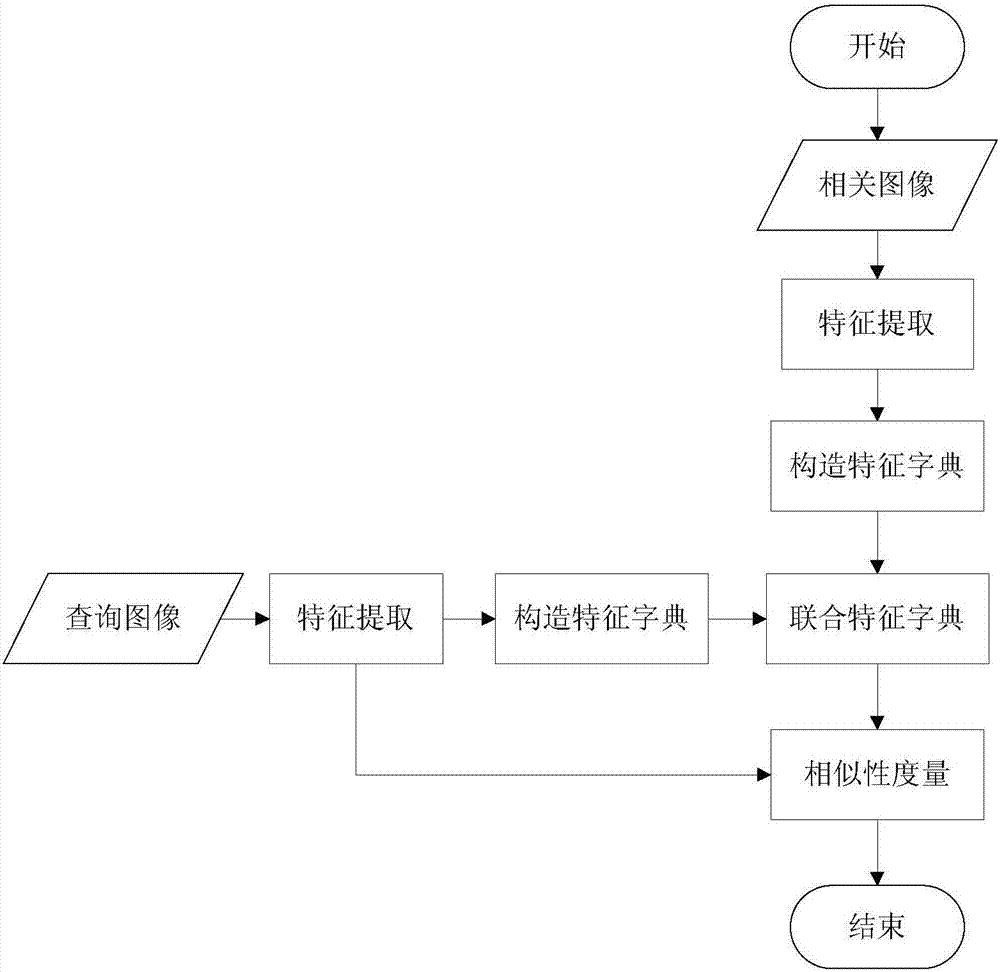
Image retrieval system and image retrieval method based on multi-feature and sparse representation
ActiveCN104142978AComprehensive descriptionFully express color informationSpecial data processing applicationsDictionary learningFeature extraction
Owner:博拉网络股份有限公司
Malicious webpage filtration system based on C/S framework and filtration method thereof
InactiveCN102043865APurify the network environmentSpecial data processing applicationsData packThe Internet
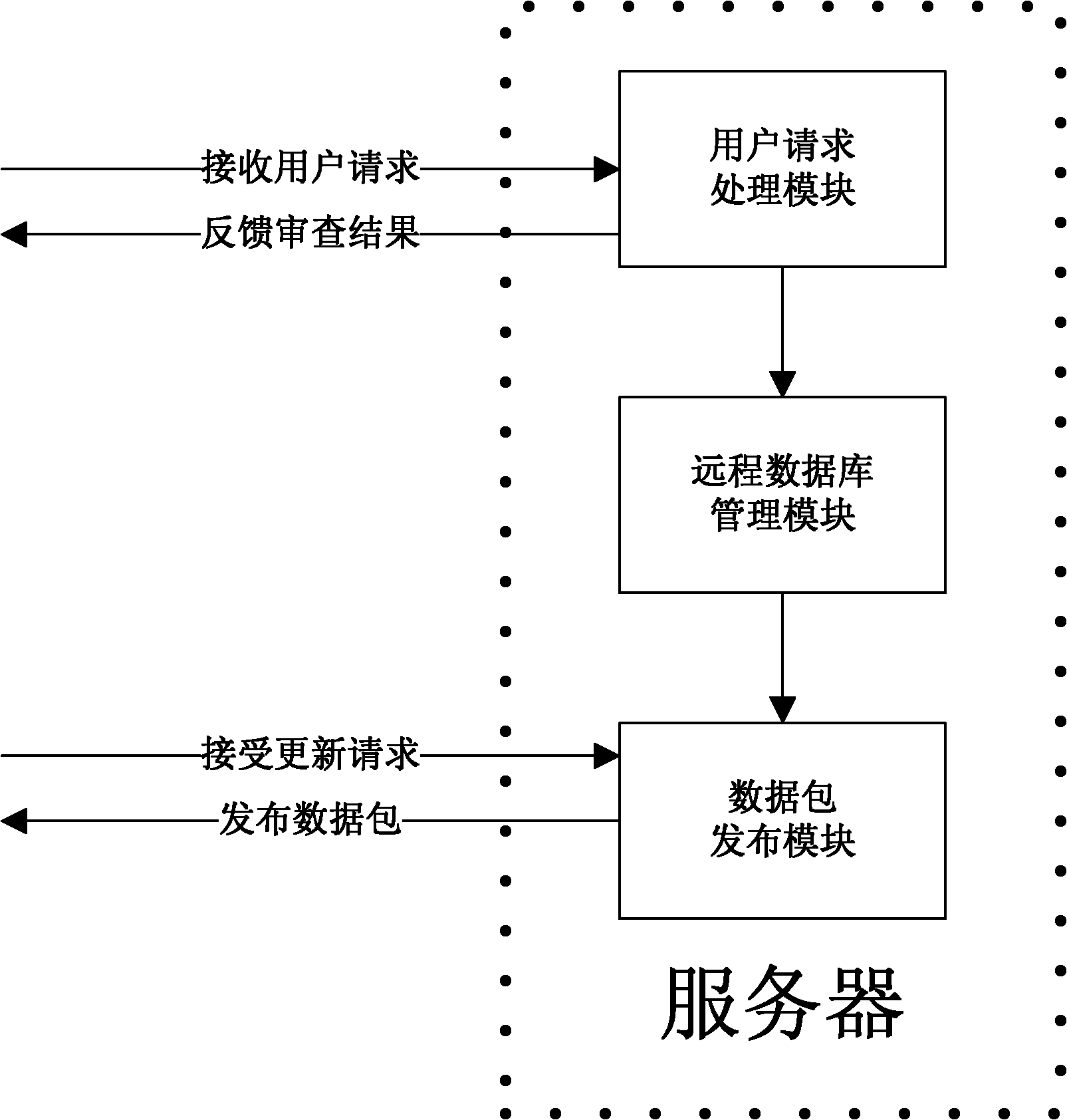
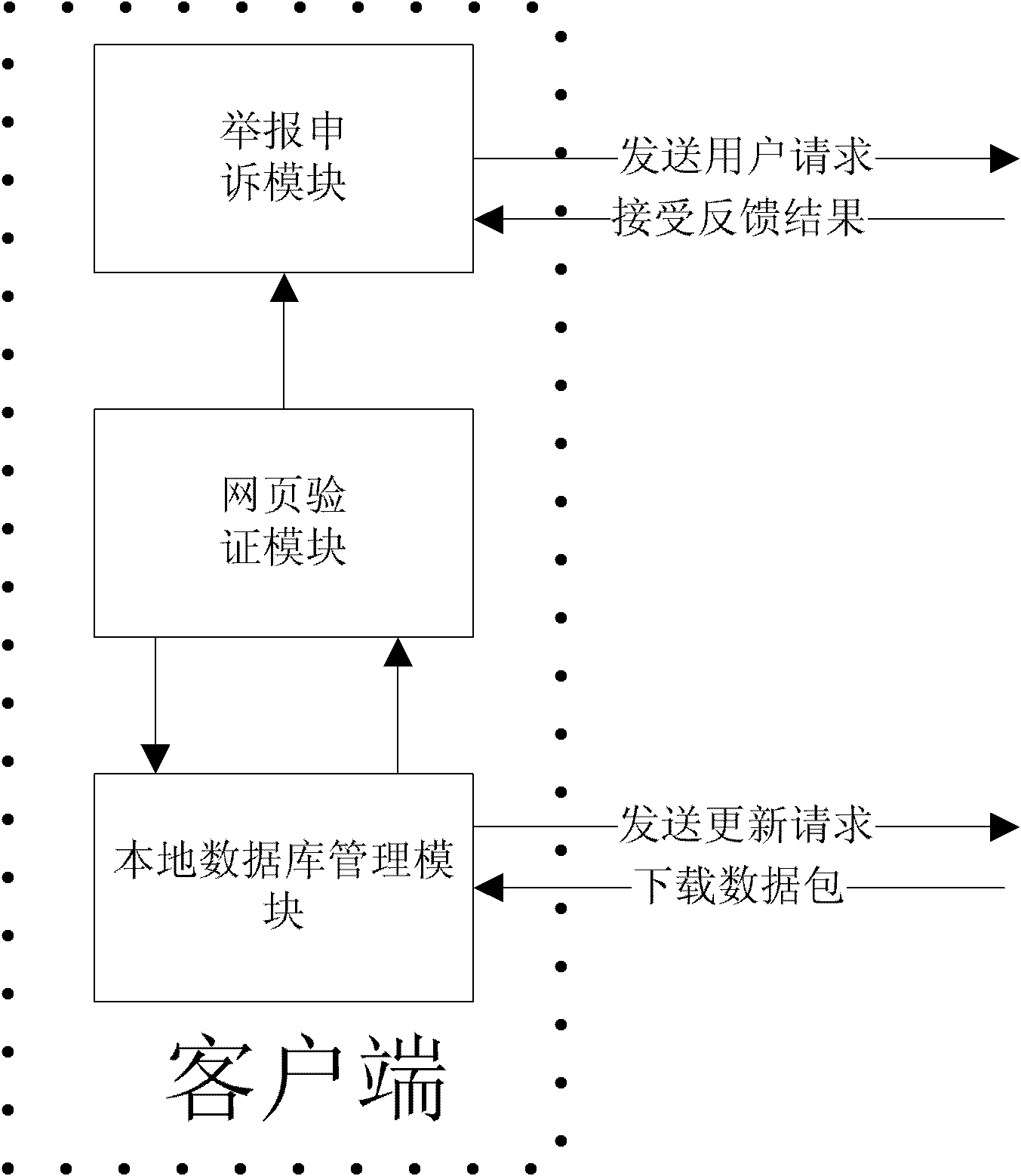
The invention discloses a malicious webpage filtration system based on C / S framework, comprising a malicious webpage monitoring server and a client bound with a browser application program and communicated with a server, wherein the client is provided with a local database management module for accepting server malicious webpage information data packet, a webpage verifying module for verifying whether the accessing webpage is the malicious webpage through the local database management module and a reporting complaint module for reporting the suspected accessing webpage to the server; the webpage verifying module searches the local malicious webpage database from the local database management module so as to determine whether the accessing webpage is the malicious webpage, if so, the webpage verifying module sounds a warning, or allows the browser to load relative webpage. The system is in favor of purifying network environment, provides a certain security guarantee for user browsing the webpage and provides an efficient way for establishing green and healthy internet environment.
Owner:博视联(苏州)信息科技有限公司 +1
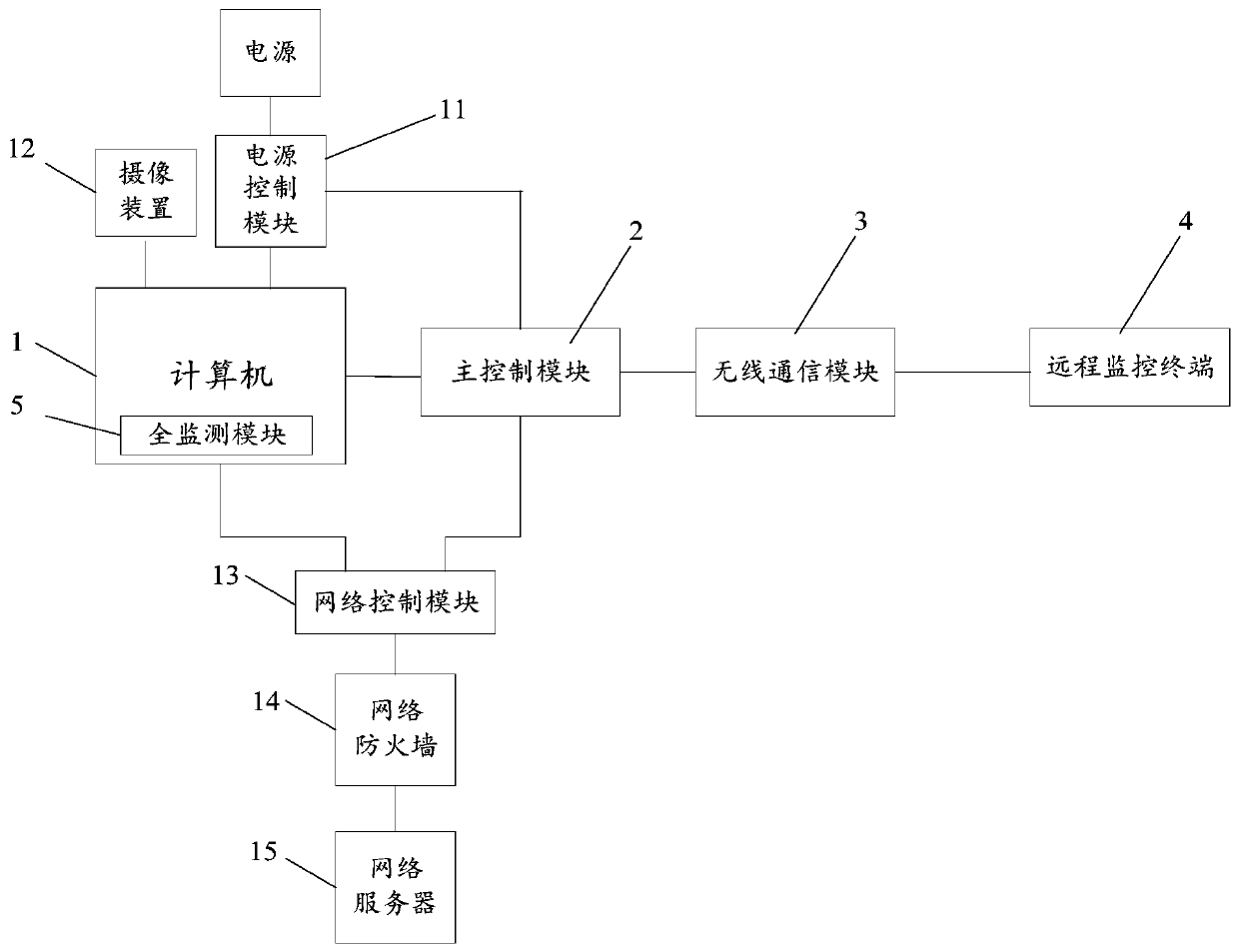
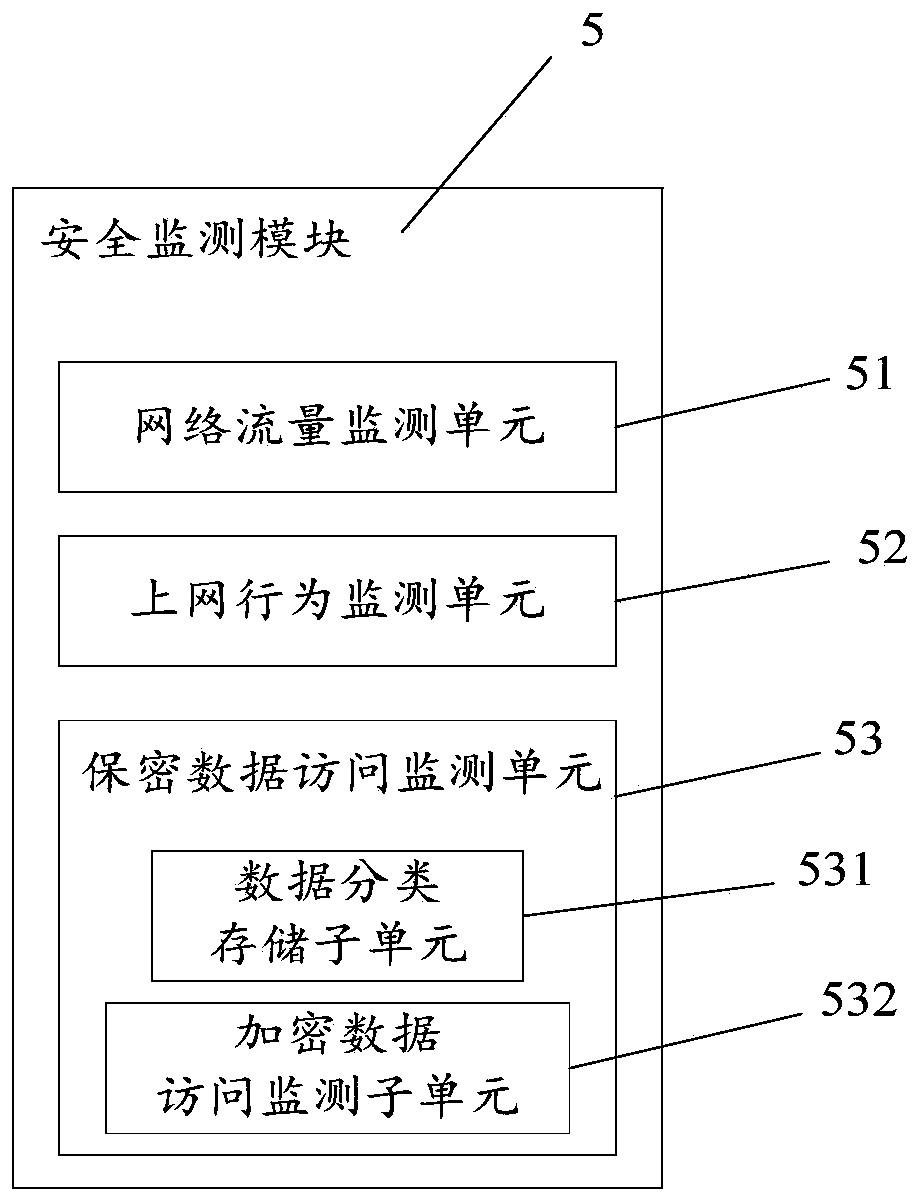
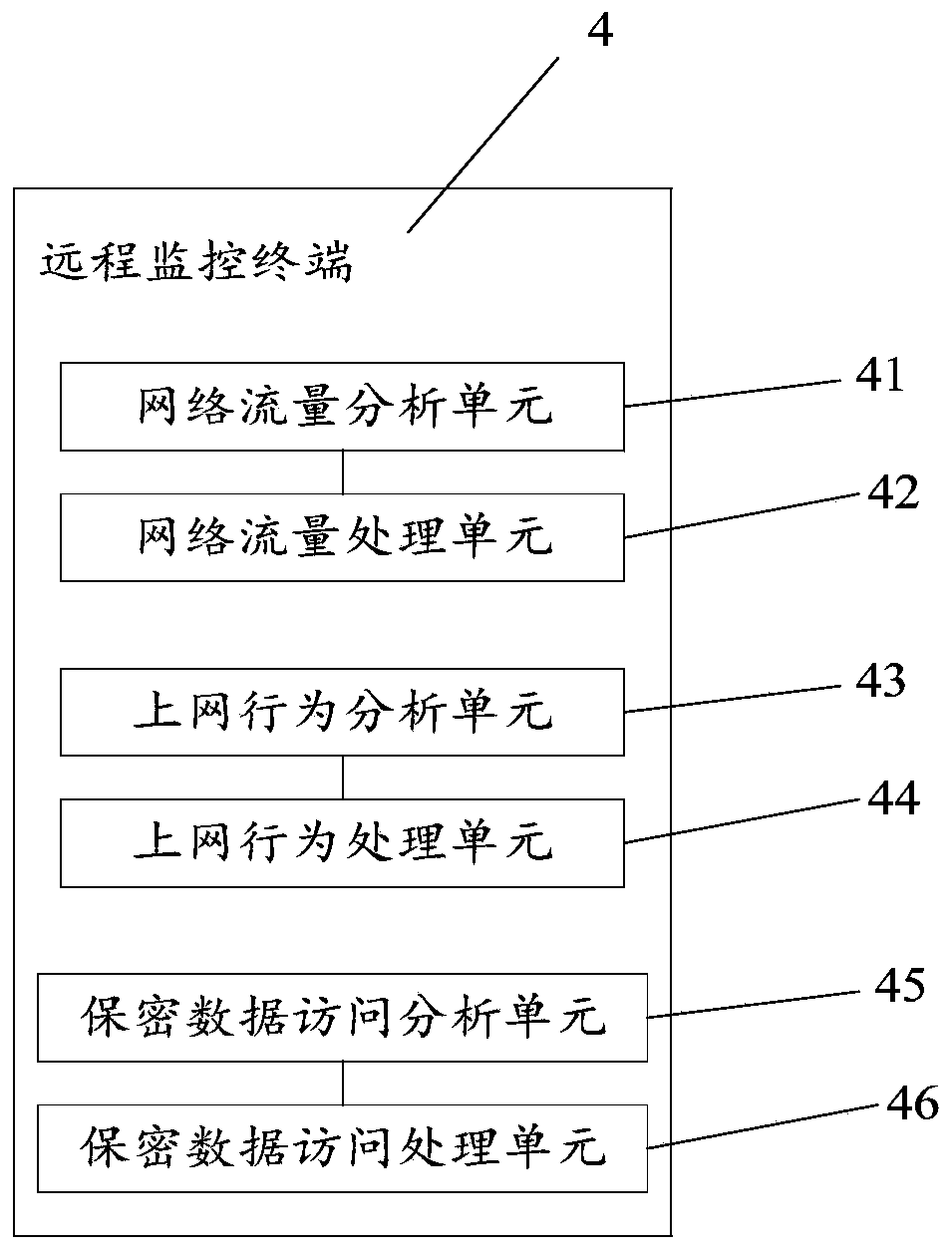
Computer network security remote monitoring device
InactiveCN110650151AAvoid underallocationPrevent theftTransmissionSecurity arrangementBehavioral analyticsInternet traffic
The invention discloses a computer network security remote monitoring device, which comprises a security monitoring module used for carrying out routing inspection statistics on network traffic, carrying out record statistics on internet surfing behaviors, and carrying out record statistics on access conditions of confidential information or access conditions of a mobile hard disk interface; the main control module is used for recording the network flow abnormal information, the internet behavior record information influencing the network environment, the access condition of the confidential information or the access condition of the mobile hard disk interface; and the remote monitoring terminal is used for analyzing the abnormal condition of the network flow, analyzing the Internet surfing behavior influencing the network environment, analyzing whether the access to the confidential information is normal access or not, and sending an adjustment scheme, network disconnection information or power failure information. The computer network security is monitored from three aspects of network flow, internet surfing behaviors and hard disk confidential data, so that the computer networksecurity is effectively ensured, the computer network security monitoring function is perfected, the practicability is enhanced, and the computer network security monitoring method and system are suitable for wide popularization.
Owner:QINGHAI UNIVERSITY
Label user identification method and related equipment
ActiveCN110222297AImprove experienceQuick identificationWebsite content managementSpecial data processing applicationsDirected graphData mining
Owner:WUHAN DOUYU NETWORK TECH CO LTD
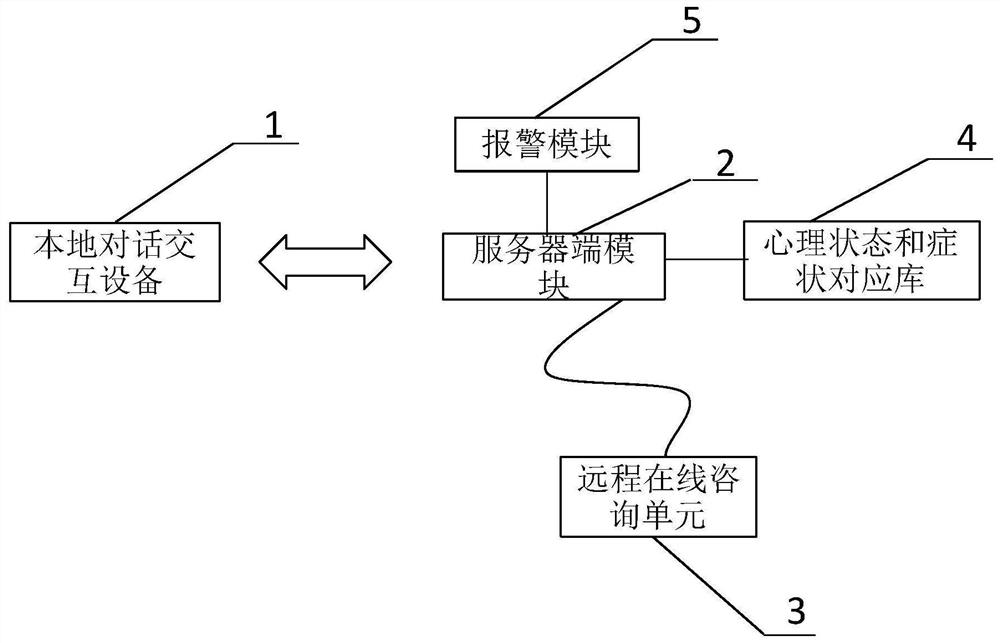
Risk control method in online psychological counseling
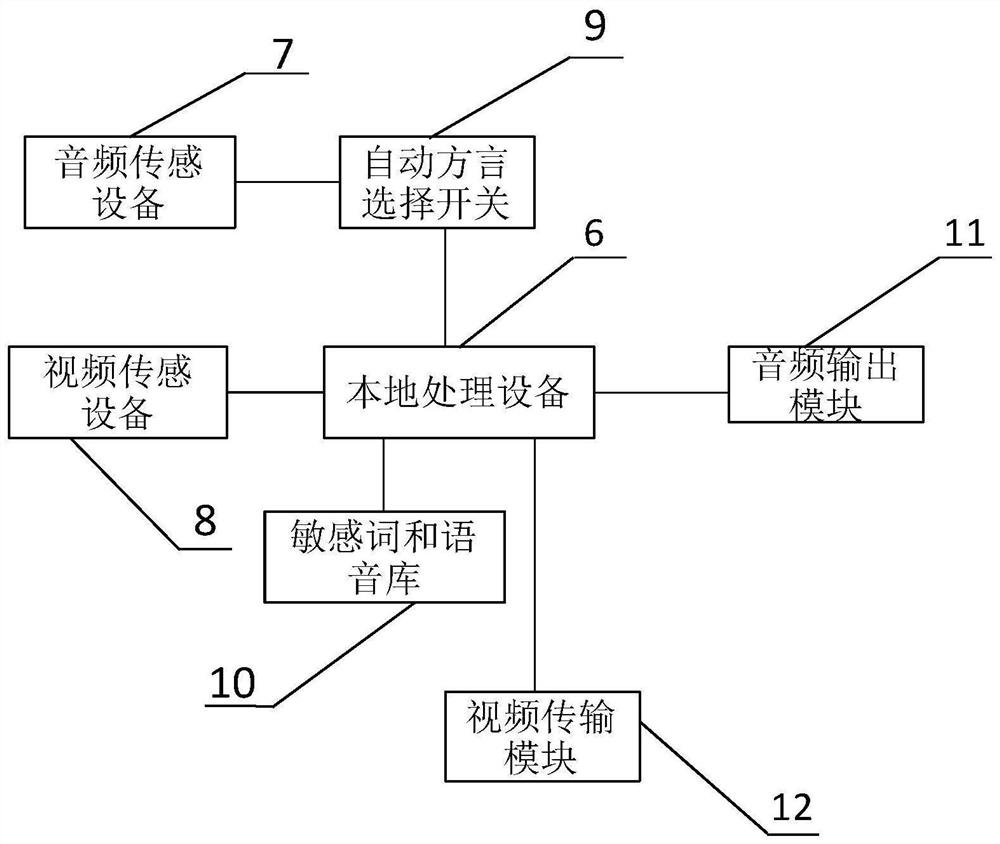
PendingCN112579744AEnsure safetyPrevent crimeSemantic analysisHealth-index calculationPsychological statusVideo transmission
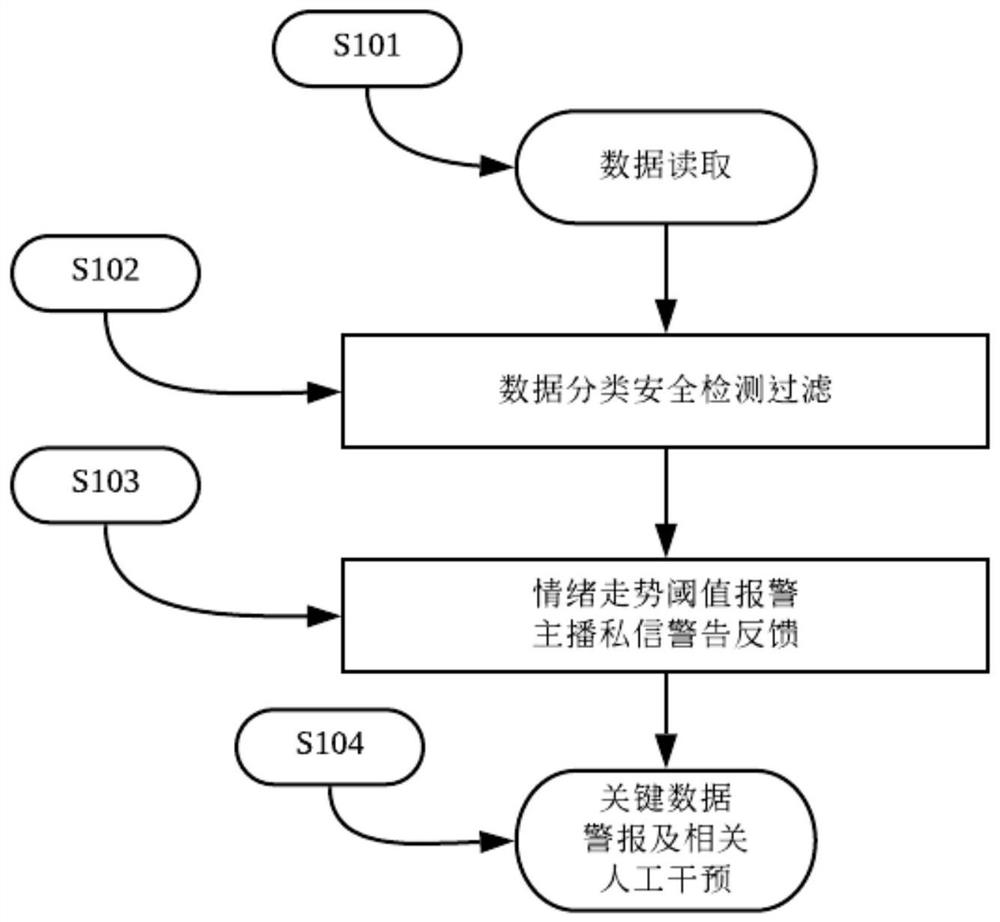
The invention discloses a risk control method in online psychological counseling. A local dialogue interaction device 1, a server module 2, a remote online counseling unit 3, a psychological state andsymptom corresponding library 4 and an alarm module 5 are included. The local dialogue interaction device 1 comprises a local processing device 6, an audio sensing device 7, a video sensing device 8,an automatic dialect selection switch 9, a sensitive word and voice library 10, an audio output module 11 and a video transmission module 12. The local dialogue interaction device 1 and the server module 2 are connected through communication signals, and the server module 2 is in communication signal connection with the remote online consultation unit 3, the psychological state and symptom corresponding library 4 and the alarm module 5. According to the invention, contrastive analysis is carried out on the audio and the video, then corresponding safety detection filtering is carried out respectively, and manual intervention is carried out on special data, so that accidents are avoided. Meanwhile, the dialect recognition mode is utilized to better perform intelligent voice recognition, sothat the consultation accuracy of the application is improved.
Owner:北京智能工场科技有限公司
Method and device for filtering Internet web page information
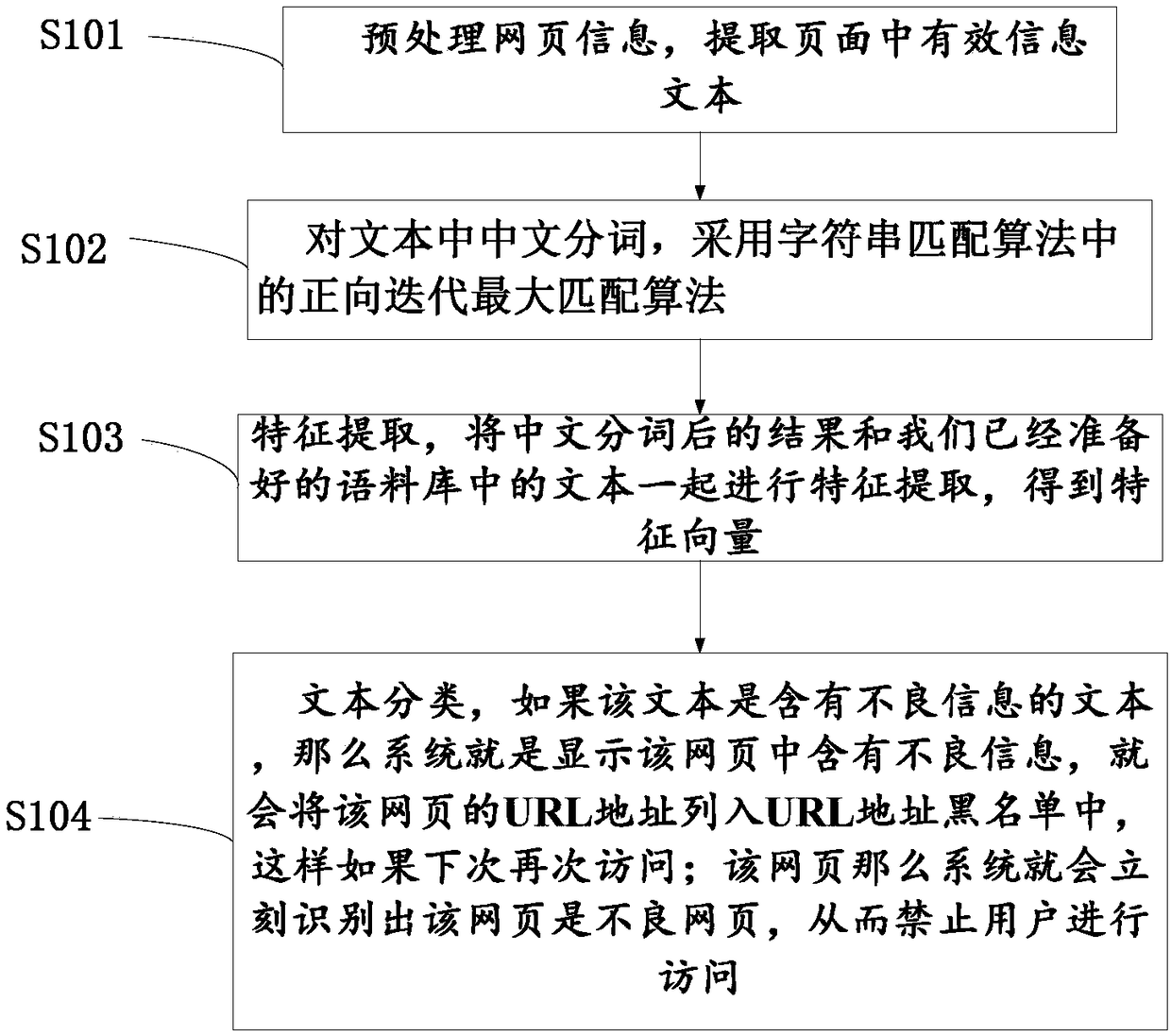
InactiveCN108153872AReduce access to bad informationAccess forbiddenNatural language data processingSpecial data processing applicationsFeature vectorFeature extraction
The invention provides a method and device for filtering Internet web page information. The method comprises the steps that a valid information text is extracted by preprocessing web page information;Chinese word segmentation is conducted on the text, and a forward iteration maximum matching algorithm of a string matching algorithm is adopted; feature extraction is conducted, and feature extraction of resulTS after Chinese word segmentation is conducted and texTS in a prepared corpus is conducted simultaneously to obtain feature vectors; text classification is conducted, if a text is the textcontaining unhealthy information, a system shows that a web page contains the unhealthy information, and the URL address of the web page is put on a URL address blacklist, so that when accessing is performed next time, the web page is immediately identified by the system as an unhealthy web page, and accessing of the web page by a user is prohibited. According to the method, the unhealthy information is filtered before the unhealthy information is viewed by the user, so that the network environment is purified to an extent, routes for a netizen to obtain the unhealthy information can be reduced, and the method is particularly important for development of physical and mental health of youths.
Owner:佛山市车品匠汽车用品有限公司
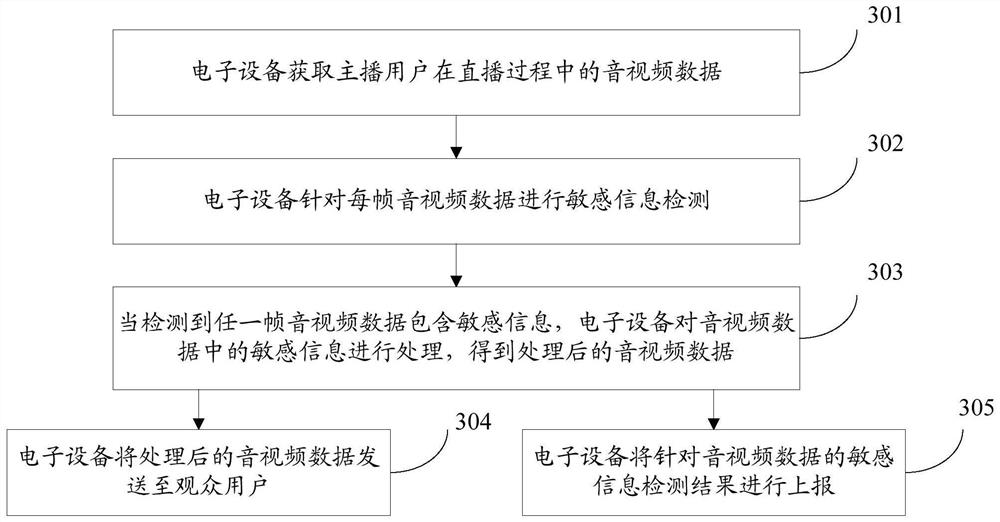
Sensitive information processing method and device, electronic equipment and storage medium
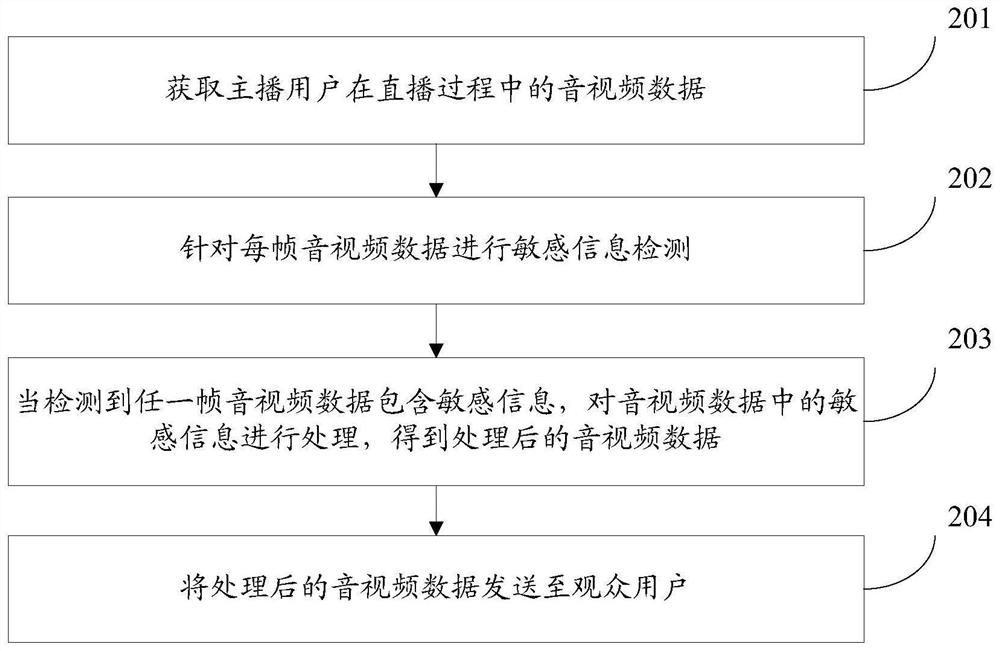
PendingCN113613035APurify the network environmentSpeech analysisSelective content distributionInformation processingData pack
The invention provides a sensitive information processing method and device, electronic equipment and a storage medium, and belongs to the technical field of Internet. The method comprises the following steps: acquiring audio and video data of an anchor user in a live broadcast process; carrying out sensitive information detection on each frame of audio and video data; when it is detected that any frame of audio and video data contains the sensitive information, processing the sensitive information in the audio and video data to obtain processed audio and video data, wherein the processed audio and video data does not contain the sensitive information; and sending the processed audio and video data to audience users. According to the method and the device, the audio and video data of the anchor user in the live broadcast process are detected in real time, and the sensitive information in the audio and video data is processed in time when it is detected that the audio and video data contains the sensitive information, so that adverse effects caused by transmission of the audio and video data containing the sensitive information on a network are avoided, and the network environment is effectively maintained.
Owner:广州繁星互娱信息科技有限公司
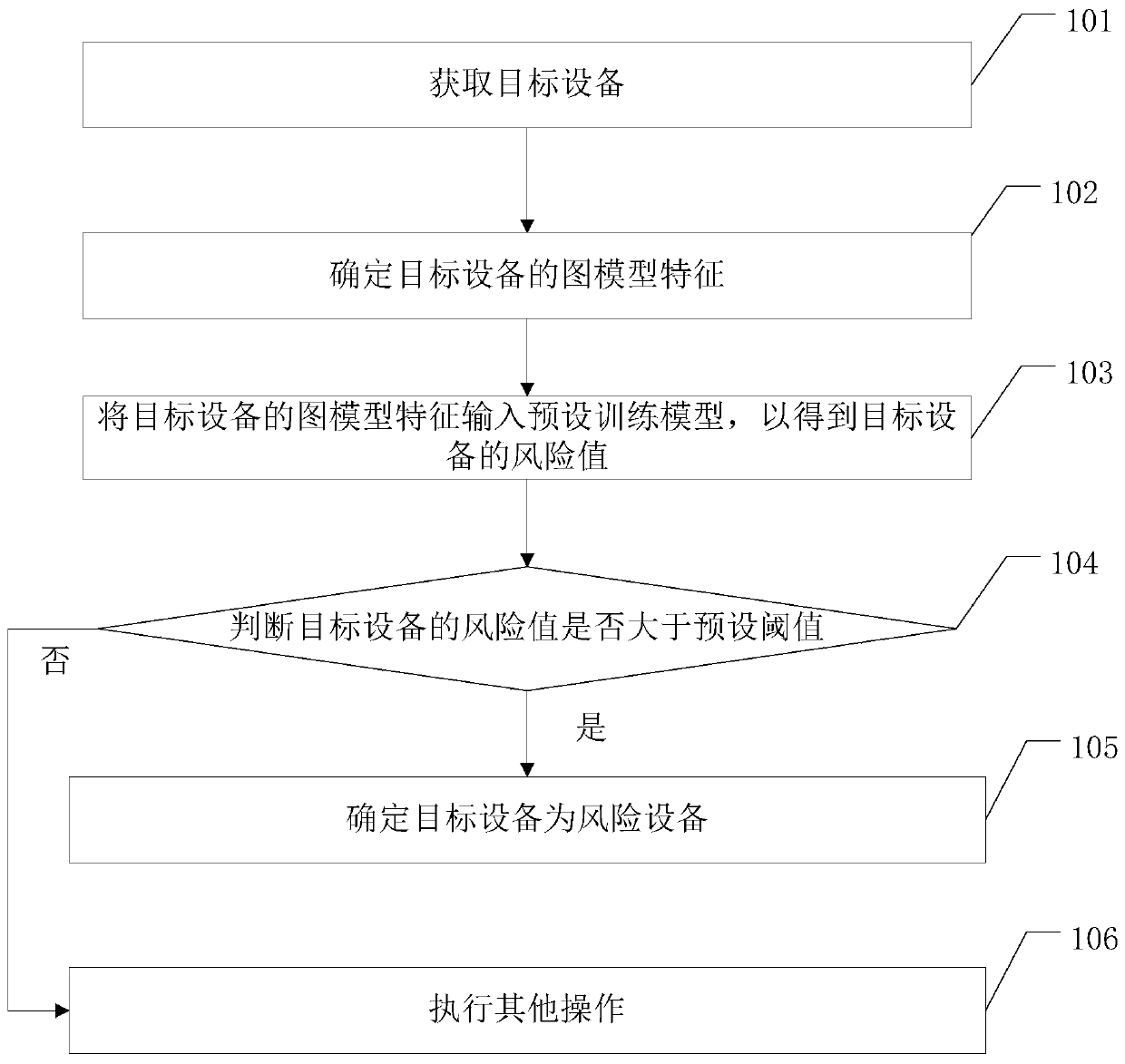
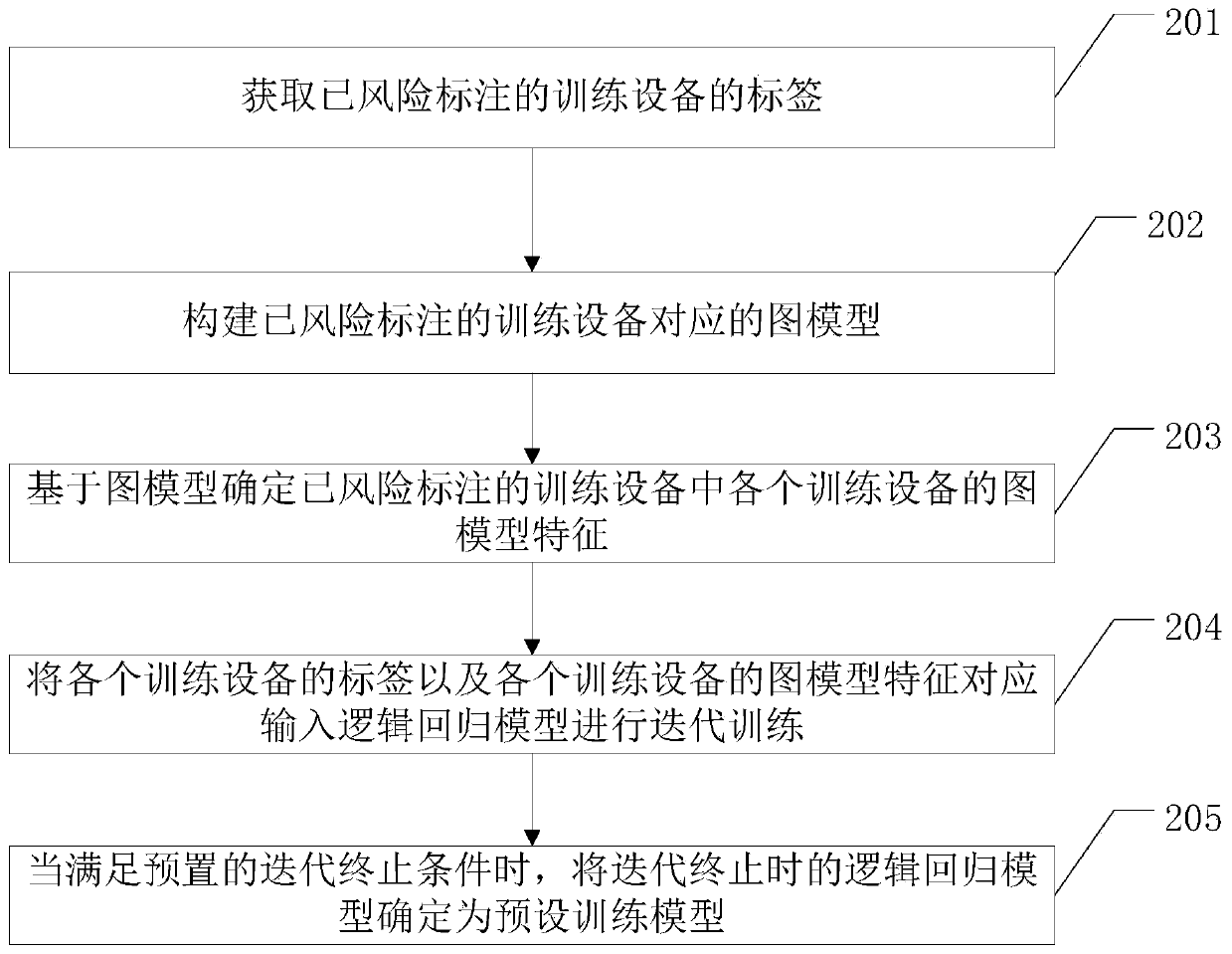
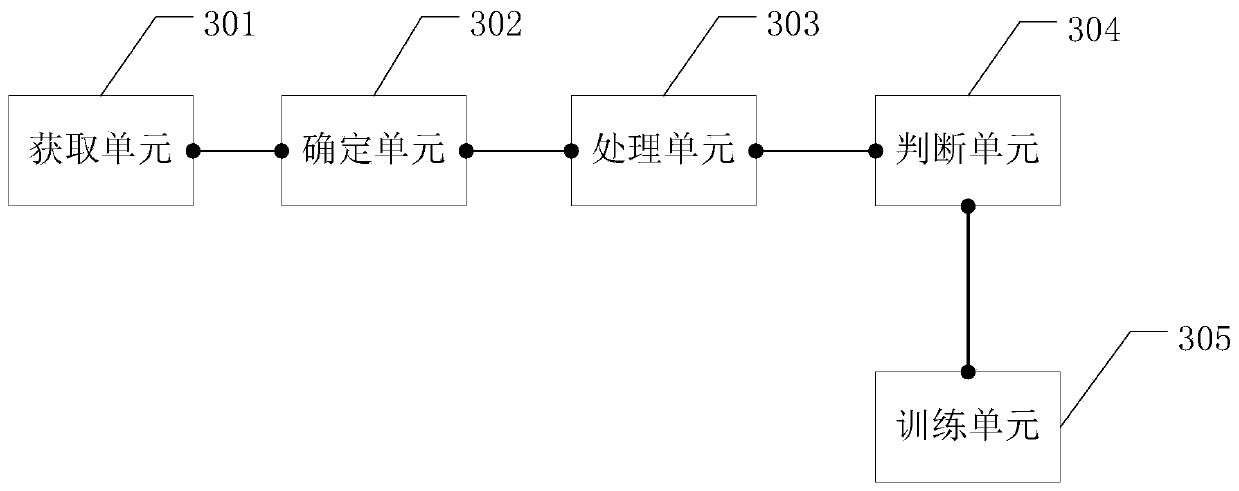
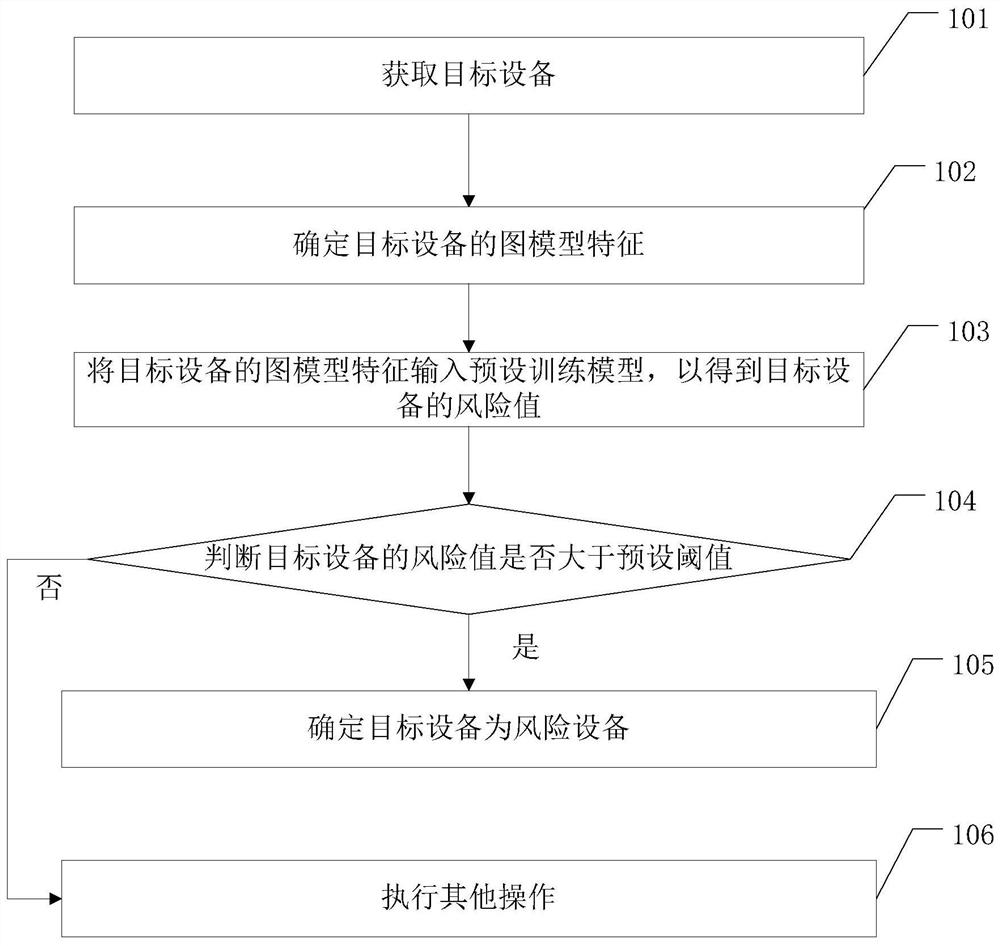
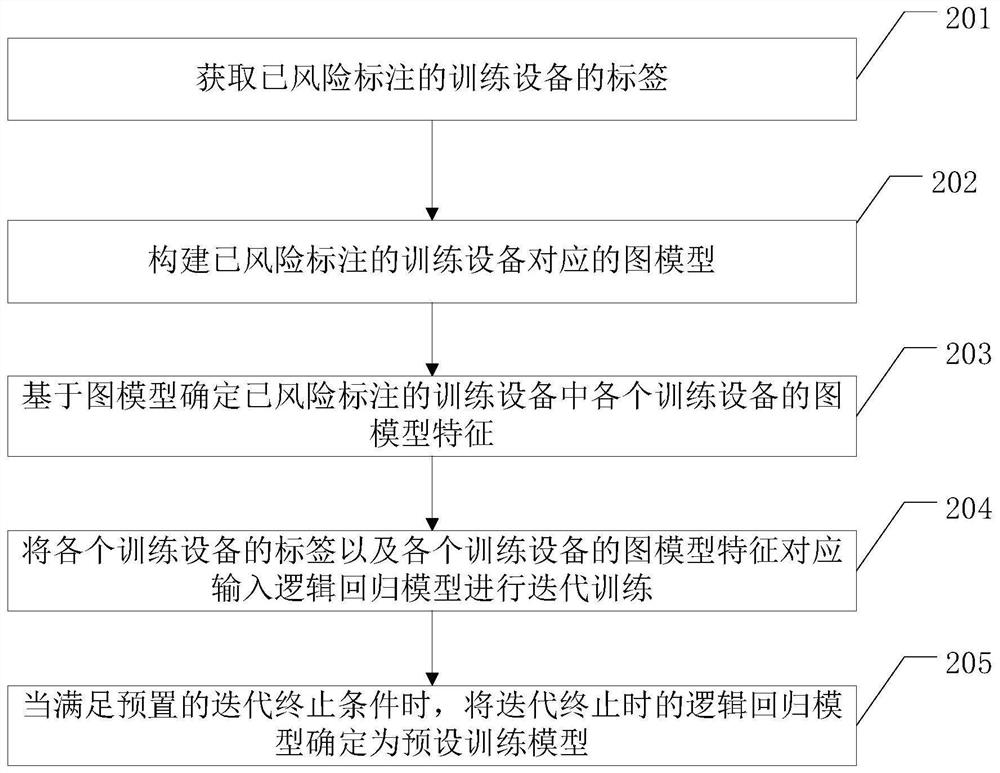
Method of identifying risk device and related device
ActiveCN109784403AAccurate identificationImprove discriminationCharacter and pattern recognitionResourcesWeb environmentEngineering
The embodiment of the invention provides a method for identifying risk device and a related device, which can accurately identify the risk equipment registered in batches in a live broadcast platformand purify the network environment of the live broadcast platform. The method comprises the steps of obtaining target equipment, wherein the target equipment is equipment with a risk to be identifiedin a live broadcast platform; determining a graph model feature of the target device; Inputting the graph model characteristics of the target equipment into a preset training model to obtain a risk value of the target equipment; judging whether the risk value of the target equipment is greater than a preset threshold value or not; And if yes, determining that the target device is a risk device.
Owner:武汉斗鱼鱼乐网络科技有限公司
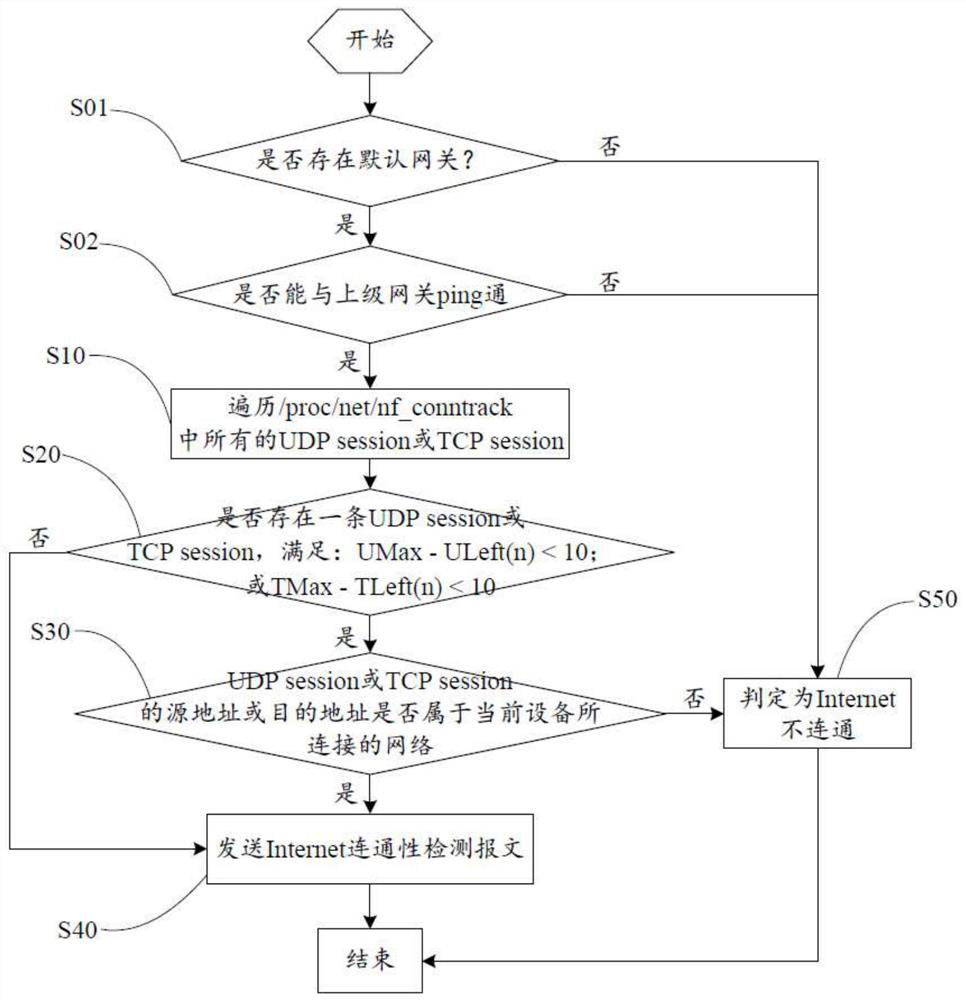
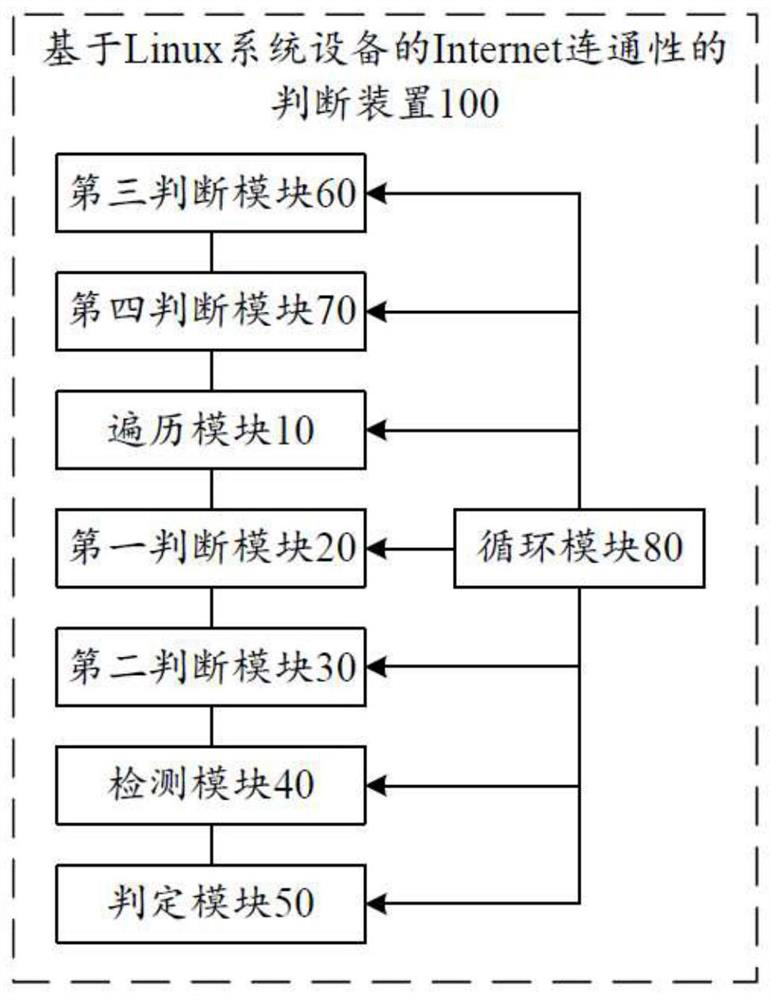
Method and device for judging Internet connectivity based on Linux system equipment
ActiveCN111917608AImprove Internet experienceReduce the burden onData switching networksCyber operationsThe Internet
The invention relates to a method and device for judging Internet connectivity based on Linux system equipment, and the method comprises the steps: traversing all UDP sessions or TCP sessions in / proc / net / nf_conntrack; judging whether a UDP session or a TCP session exists or not, and meeting the timeout time requirement; if so, judging whether a source address or a destination address of the UDP session or the TCP session belongs to a network connected with the current equipment or not; if so, sending an Internet connectivity detection message. According to the invention, the network connectivity is further judged through the receiving and sending history record of the effective data of the user, whether the network is connected is judged, and if the result cannot be judged, the Internet connectivity detection message is sent. According to the invention, the sending amount of detection data can be greatly reduced, the network environment is effectively purified, and the burden of a network server or gateway equipment is reduced, so that the operation cost of a network operator is reduced, and the internet surfing experience of a user is improved.
Owner:深圳市友华软件科技有限公司
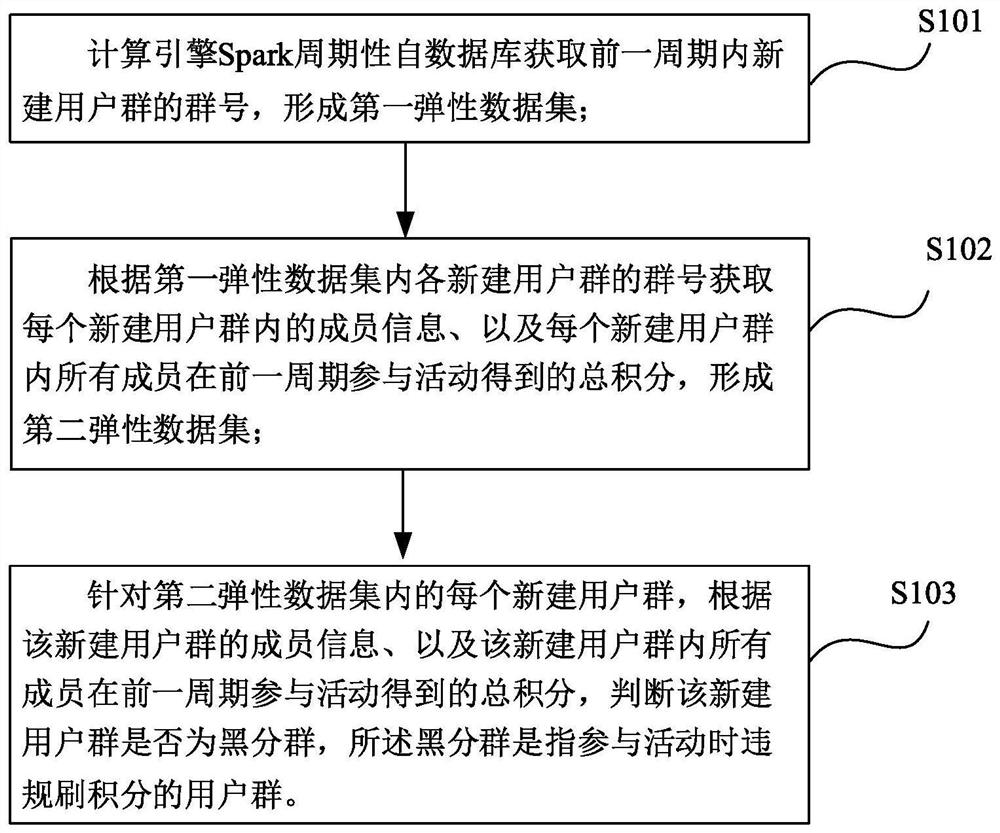
Method and system for determining black groups based on Spark
PendingCN111984695APurify the network environmentSpecial service provision for substationDigital data information retrievalData setThe Internet
The embodiment of the invention provides a method and system for determining black grouping based on Spark, and the method comprises the steps: enabling a calculation engine Spark to periodically obtain the group number of a newly-built user group in a previous period from a database, and forming a first elastic data set; according to the group number of each newly-built user group in the first elastic data set, obtaining member information in each newly-built user group and a total integral obtained by all members in each newly-built user group participating in an activity in a previous period, and forming a second elastic data set; and for each newly-built user group in the second elastic data set, judging whether the newly-built user group is a black sub-group or not according to the member information of the newly-built user group and the total integral obtained by all the members in the newly-built user group participating in the activity in the previous period. The black groups are mined by adopting Spark, so that data analysis, statistics and exception authentication for judging whether all newly-built groups are black groups or not can be carried out on a large internet platform within a period of time.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
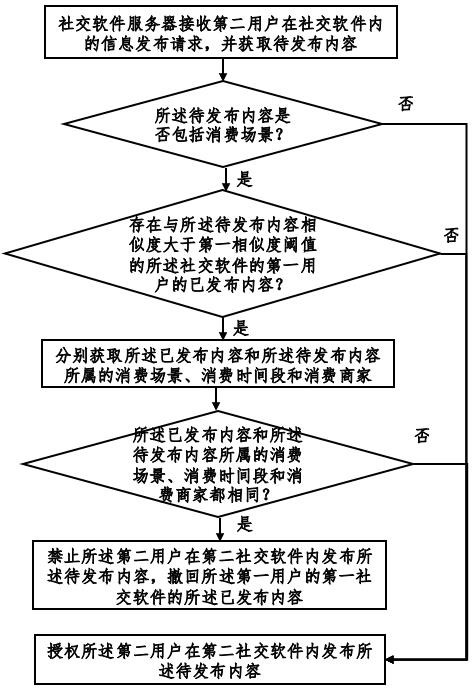
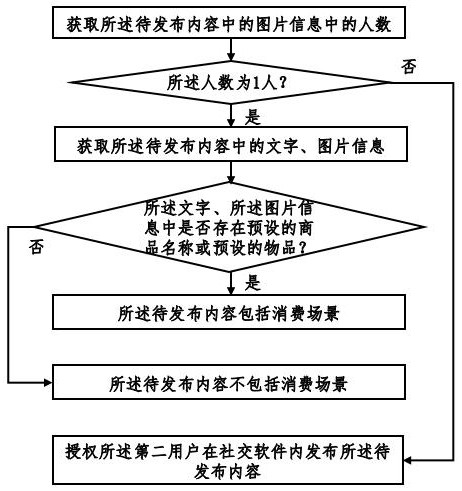
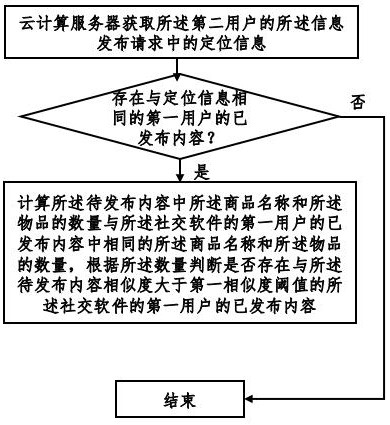
Social software information publishing method and system based on block chain
InactiveCN112330478AAvoid misleadingPurify the network environmentDigital data information retrievalData processing applicationsData scienceWeb environment
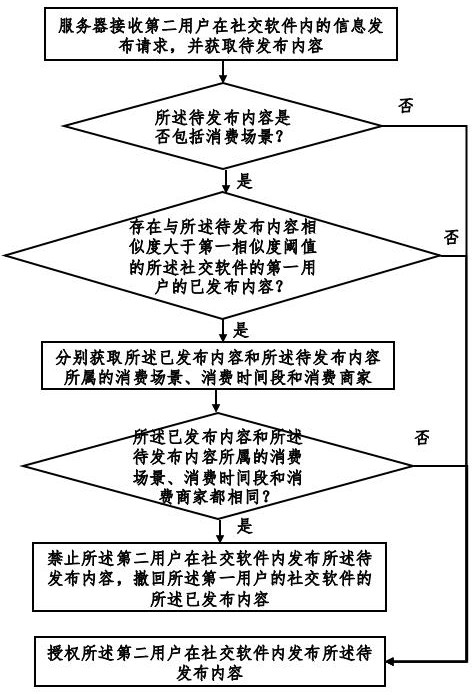
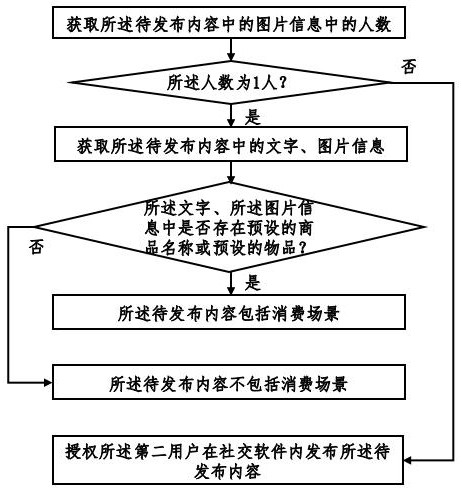
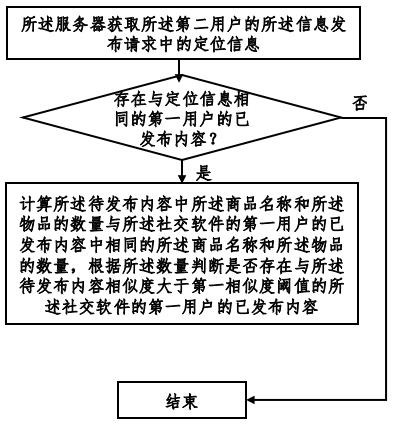
The invention provides a social software information publishing method and system based on a blockchain, and the method comprises the steps: searching for contents which are published by other users and have the higher similarity with the second user based on the contents requested to be published by the second user, and judging whether the two contents belong to the same consumption scene, consumption time period and consumption merchant or not; and judging order sharing consumption behaviors of a plurality of users, so that the content published by order sharing consumption is forbidden or withdrawn, misleading of audiences is avoided, and the network environment is purified. In addition, whether an order sharing behavior exists or not is accurately discriminated according to informationsuch as commodities or articles of published content, the number of people in pictures, publishing time and consumption places, so that the identification accuracy is improved. Finally, the order sharing evidence among the users is further locked through the account transfer behaviors among the different users, so that the identification accuracy is further improved.
Owner:王小燕
VoIP malicious behavior detection method and system based on heterogeneous neural network technology
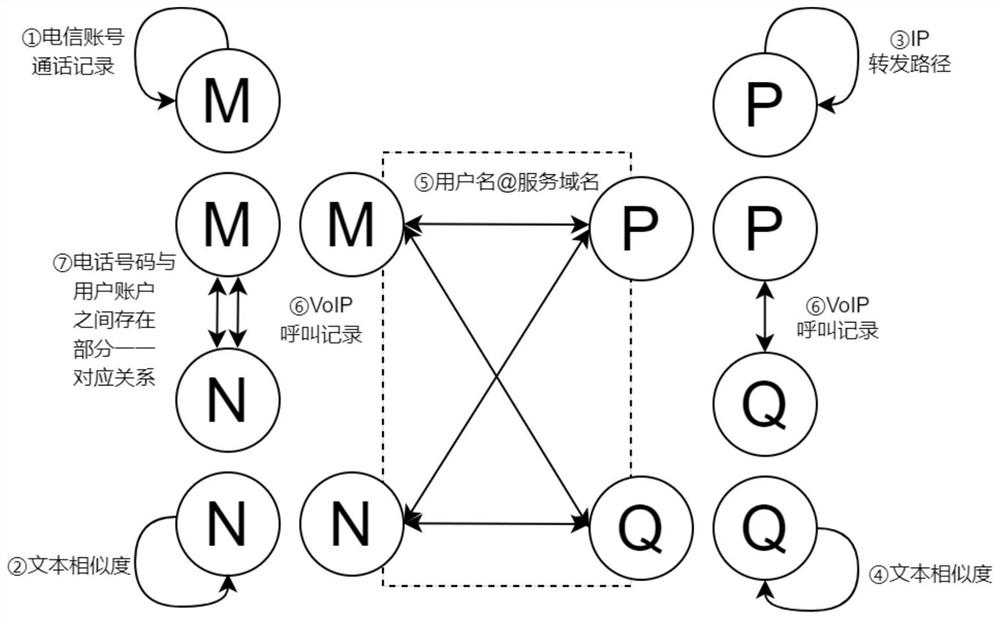
PendingCN114826735AEasy to detectFacilitates implicit relationsSecuring communicationInformation objectInformation networks
The invention discloses a VoIP malicious behavior detection method and system based on a heterogeneous neural network technology, and relates to the field of network information security. An information object is extracted from a VoIP multi-data source, a heterogeneous information network is constructed, and node vector representation is obtained by using a GEM model; clustering is carried out by calculating the similarity between different nodes, training data are enriched by labeling the same class of nodes with the same label, and then supervised learning classification is carried out on a classification algorithm to obtain harmful VoIP nodes. According to the method, the information of various data sources can be utilized, and the harmful VoIP behavior can be found by mining the implicit relationship and the hidden mode in the heterogeneous information network.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
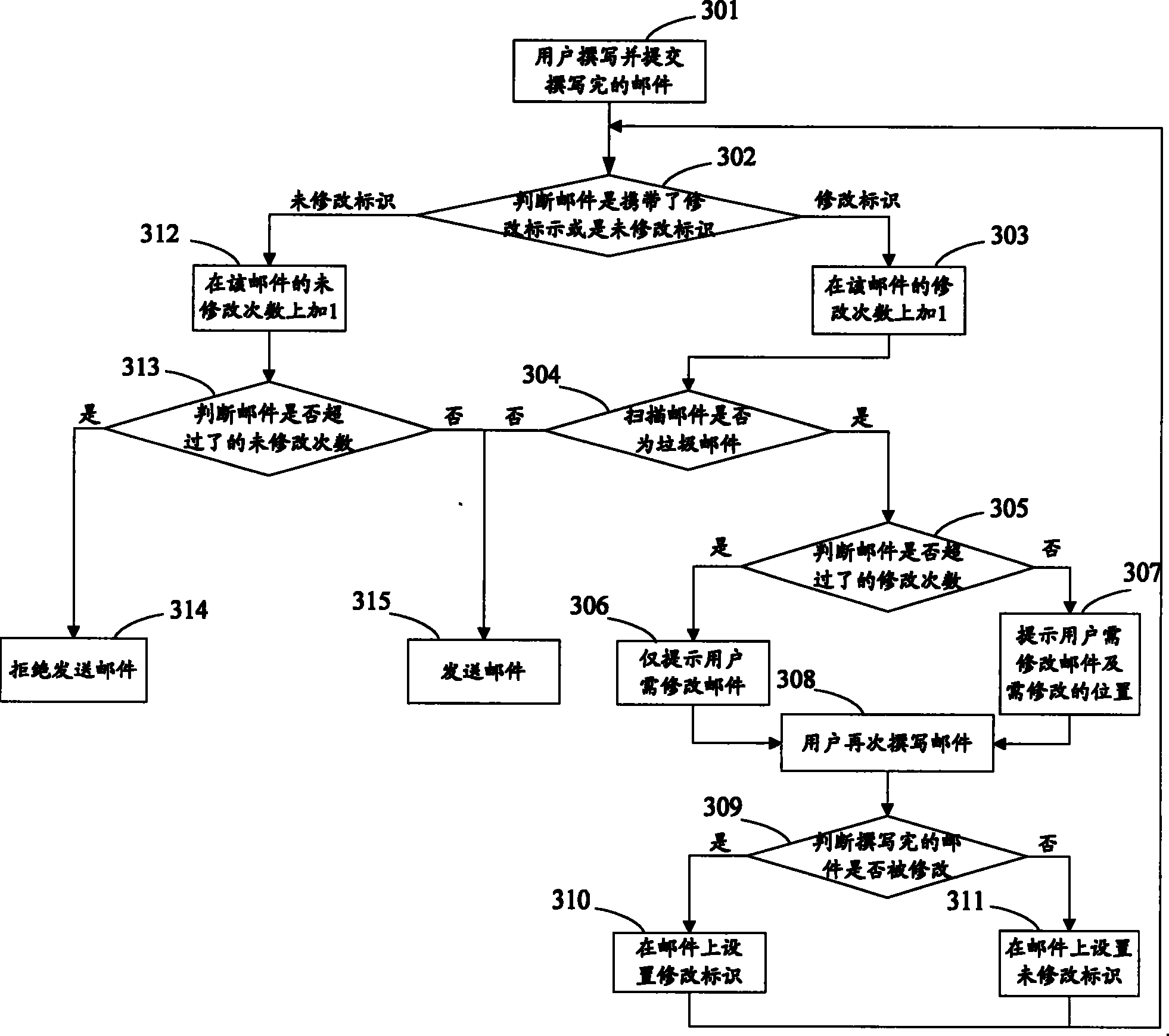
A mail sending control system and method
ActiveCN101009666BAvoid the bad luck of deletionAvoid sendingData switching networksControl systemComputer engineering
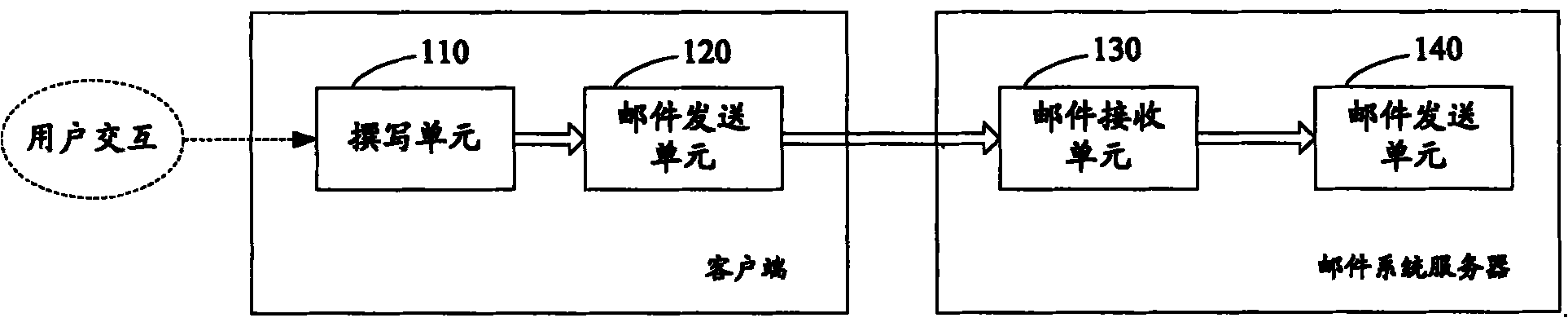
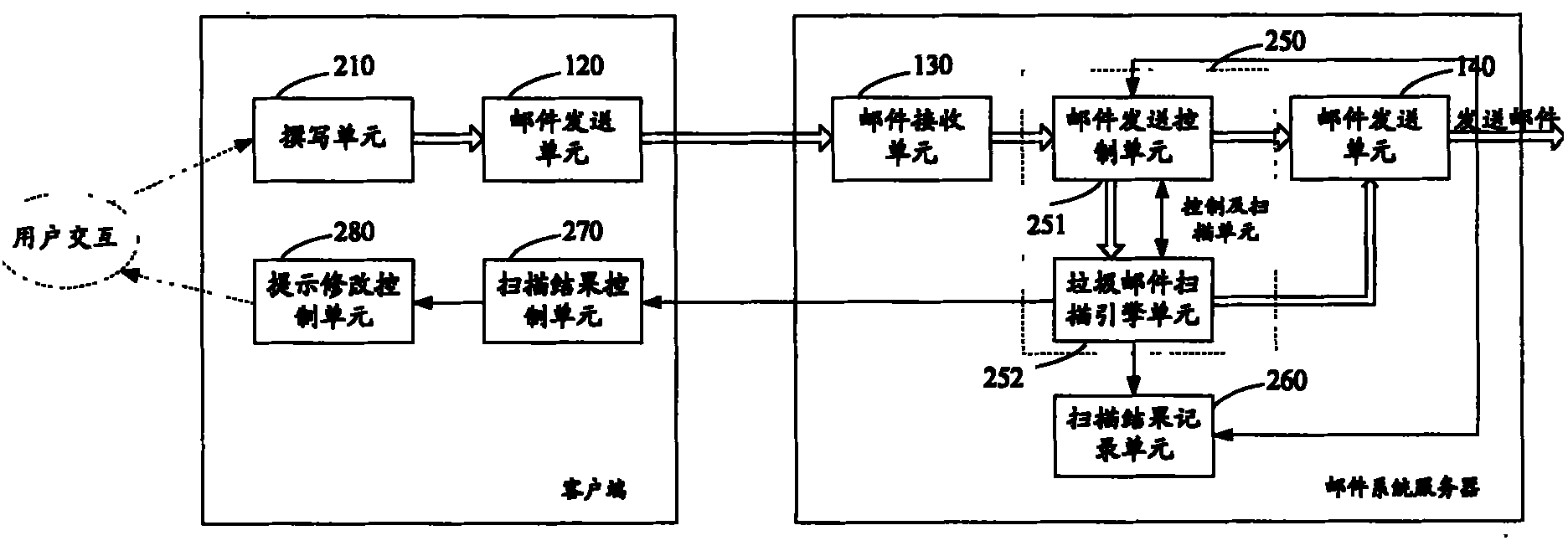
The invention discloses a mail sending control method, comprising the following steps: A. Scanning the spam mail currently submitted by the user to be sent, judging whether it is a spam mail, if not, sending the currently scanned mail, and ending the current processing flow ; Otherwise, prompt the user to modify the currently submitted mail; B. Scan the spam mail that the user resubmits; C. Send the mail that meets the sending conditions. The invention also discloses a mail sending control system at the same time. By applying the system and method, the mail sending process can be controlled, so that legal mails of legal users can avoid the bad luck of being deleted due to the characteristics of spam mails. Try to prevent spam from being sent out from the mail system, purify the network environment, and improve the efficiency of mail users in using mail.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A method of identifying risk equipment and related equipment
ActiveCN109784403BAccurate identificationImprove discriminationCharacter and pattern recognitionResourcesGraph modelData mining
The embodiments of the present invention provide a method for identifying risk equipment and related equipment, which can accurately identify risk equipment registered in batches in a live broadcast platform and purify the network environment of the live broadcast platform. The method includes: acquiring a target device, which is a device with a risk to be identified in a live broadcast platform; determining a graph model feature of the target device; inputting the graph model feature of the target device into a preset training model to obtain the target device. determining the risk value of the target device; judging whether the risk value of the target device is greater than a preset threshold; if so, determining that the target device is a risk device.
Owner:武汉斗鱼鱼乐网络科技有限公司
Visual analysis data processing system
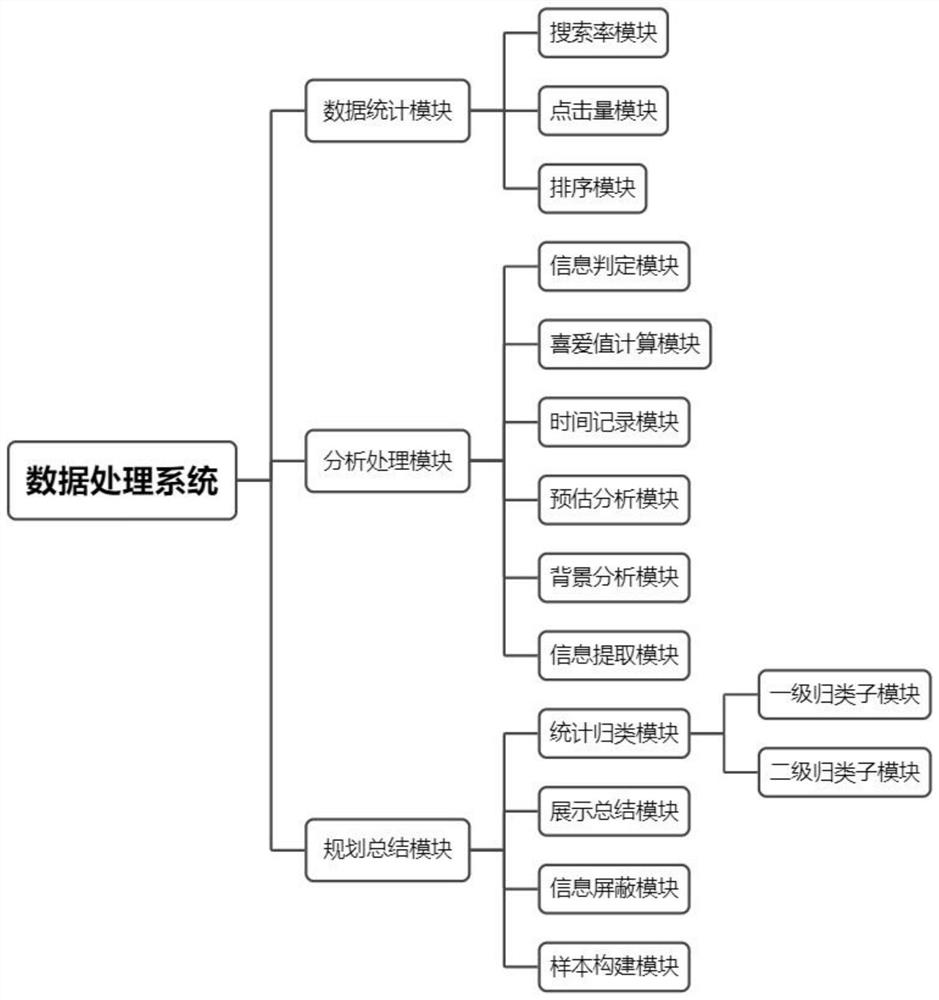
PendingCN114691925AReflect likingTo tasteVideo data browsing/visualisationVideo data clustering/classificationData processing systemAnalysis data
The invention discloses a visual analysis data processing system, which comprises a data statistics module, an analysis processing module and a planning summary module, and is characterized in that the data statistics module is electrically connected with the analysis processing module, and the analysis processing module is electrically connected with the planning summary module; the data statistics module is used for carrying out statistical analysis on the short video watching condition of a user on a short video platform, the analysis processing module is used for carrying out calculation analysis on data information, and the planning summarization module is used for carrying out planning summarization on the short video watching data information of the user; the data statistics module comprises a search rate module, a click rate module and a sorting module, the search rate module is electrically connected with the click rate module, the click rate module is electrically connected with the sorting module, and the sorting module is in network connection with the search rate module.
Owner:陈燕飞
Webpage health rating control system
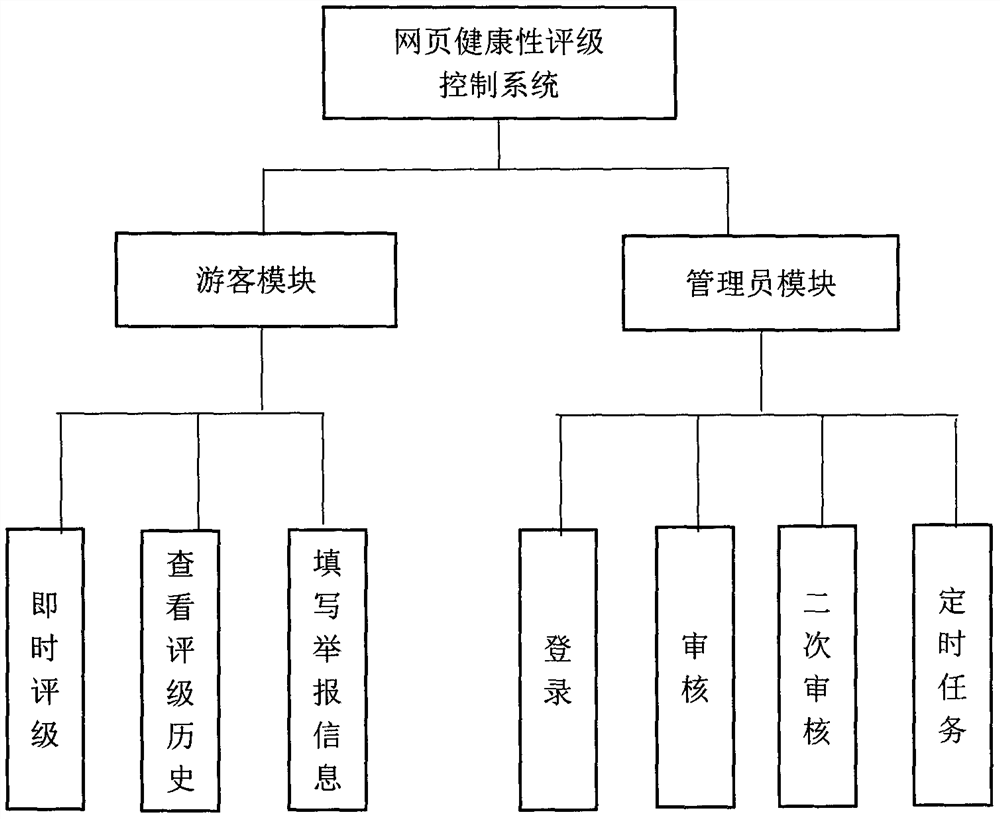
InactiveCN111984897AAchieving Healthy RatingsPurify the network environmentWebsite content managementSpecial data processing applicationsInteraction controlWeb application
The invention relates to a webpage health rating control system, which comprises function modules adopting an interactive control mode through a client and a server, and the function modules comprisea tourist module and an administrator module. The web page health rating control function is achieved in a Web application mode, through PC Web application, a user can conveniently conduct health rating on a web page on a computer, a supervision department is assisted, and a civilized network environment is created.
Owner:TIANJIN UNIV OF SCI & TECH
Method for filtering network messages of process level of intelligent substation
InactiveCN103378654BEffective smooth transmissionSmooth transmissionCircuit arrangementsData switching networksSmart substationPhysical layer
Provided is a method for filtering network messages of a process level of an intelligent substation. A network of the process level of the intelligent substation is connected with various devices which comprise a merging unit, an intelligent terminal, a switchboard, a protection device and a measuring and control device, wherein the devices are used for sending and receiving SV messages and GOOSE messages, message filtering modules are additionally arranged between network interfaces and physical layers of the devices, the received messages are filtered additionally in a message filtering mode, traffic limitation is performed on the messages with MAC addresses assigned by the devices, key fields of the messages with the MAC addresses assigned by the devices are recognized, repeated messages are filtered, the messages without the MAC addresses assigned by the devices are discarded or forwarded, and broadcasting messages are discarded or forwarded. According to the method, the accurate management of the GOOSE messages and the SV messages can be achieved through the merging unit, the intelligent terminal, the switchboard, the protection device and the measuring and control device in the intelligent substation.
Owner:NR ELECTRIC CO LTD +1
Network security detection method and device
PendingCN114244561AImprove website utilizationIncrease profitSpecial data processing applicationsSecuring communicationWeb environmentEngineering
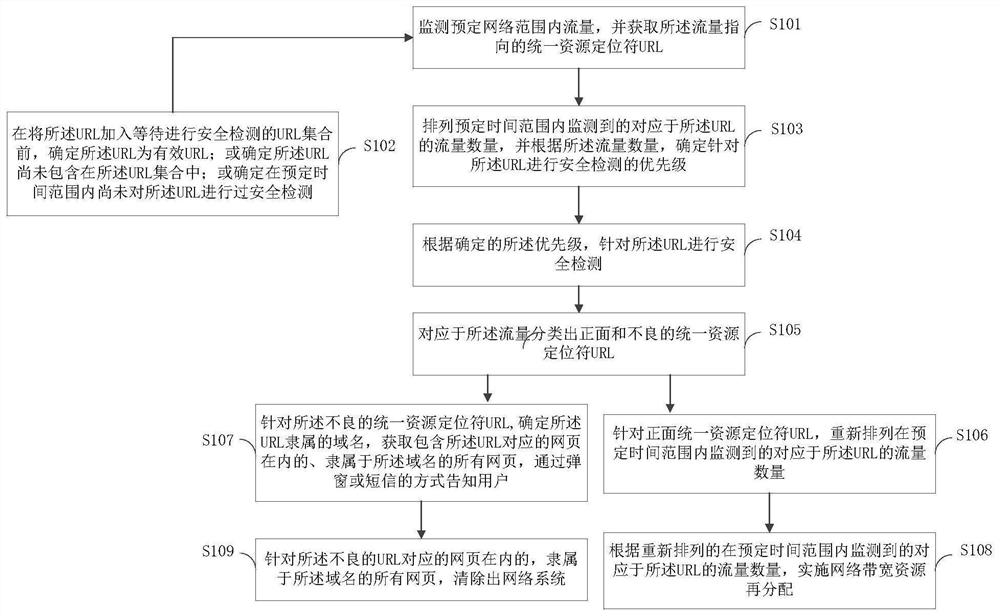
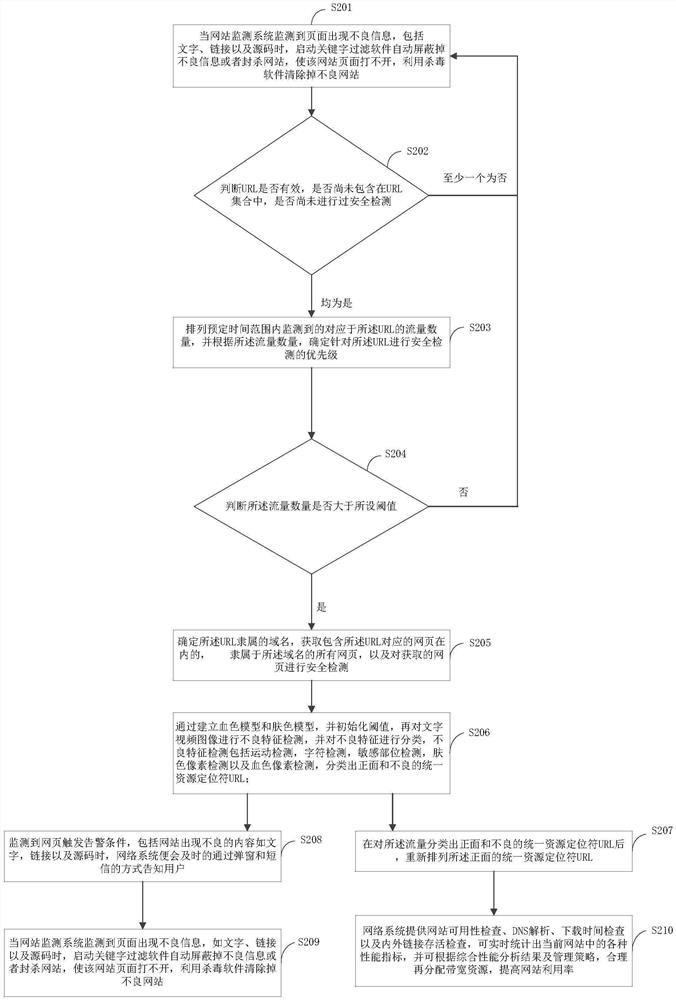
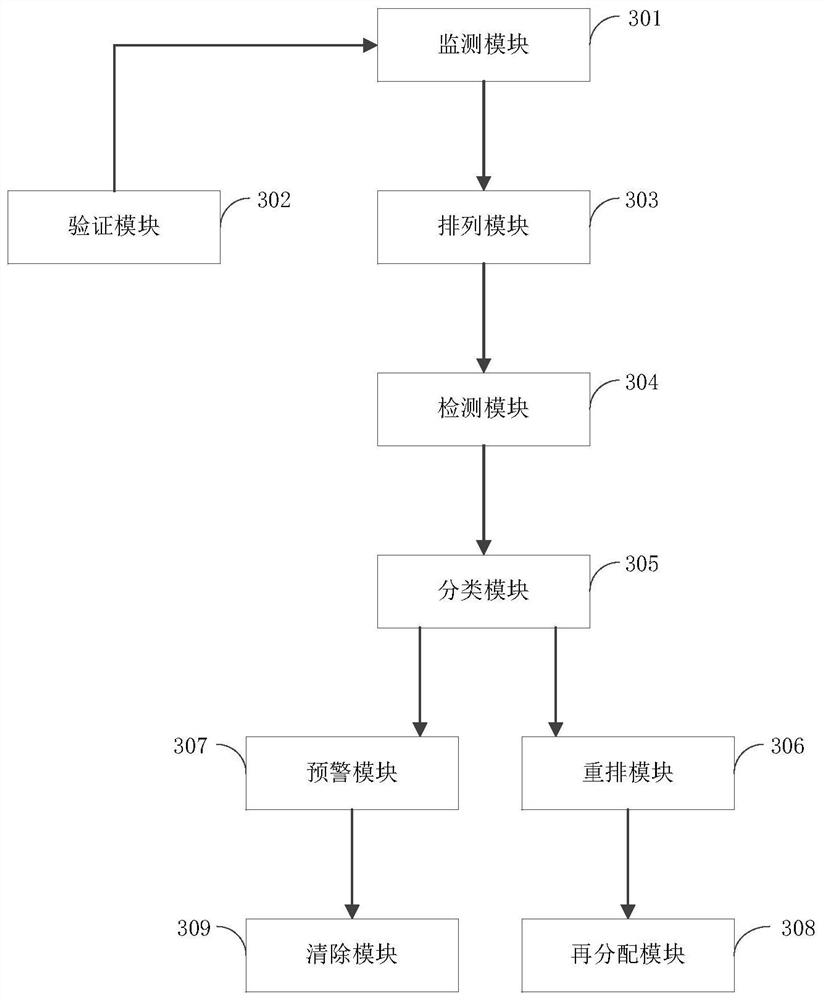
The invention provides a network security detection method and device, and the method comprises the steps: monitoring the flow in a preset network range, and obtaining a URL (Uniform Resource Locator) pointed by the flow; before the URL is added into a URL set waiting for security detection, determining that the URL is an effective URL; or the URL is not included in the URL set; or the URL is not subjected to security detection; determining a priority for performing security detection on the URL; according to the arranged priority, performing security detection on the URL; classifying positive and negative URLs corresponding to the traffic; aiming at the front URL, rearranging the flow quantity of the URL; aiming at the bad URL, determining all webpages of the URL, and informing a user through a popup window mode; according to the flow quantity of the rearranged URLs, implementing network bandwidth resource redistribution; and clearing out the network system. The method has the advantages that the website utilization rate is increased, more network space is released, and the network environment is purified.
Owner:安徽健坤通信股份有限公司
Detecting and positioning method of spam server
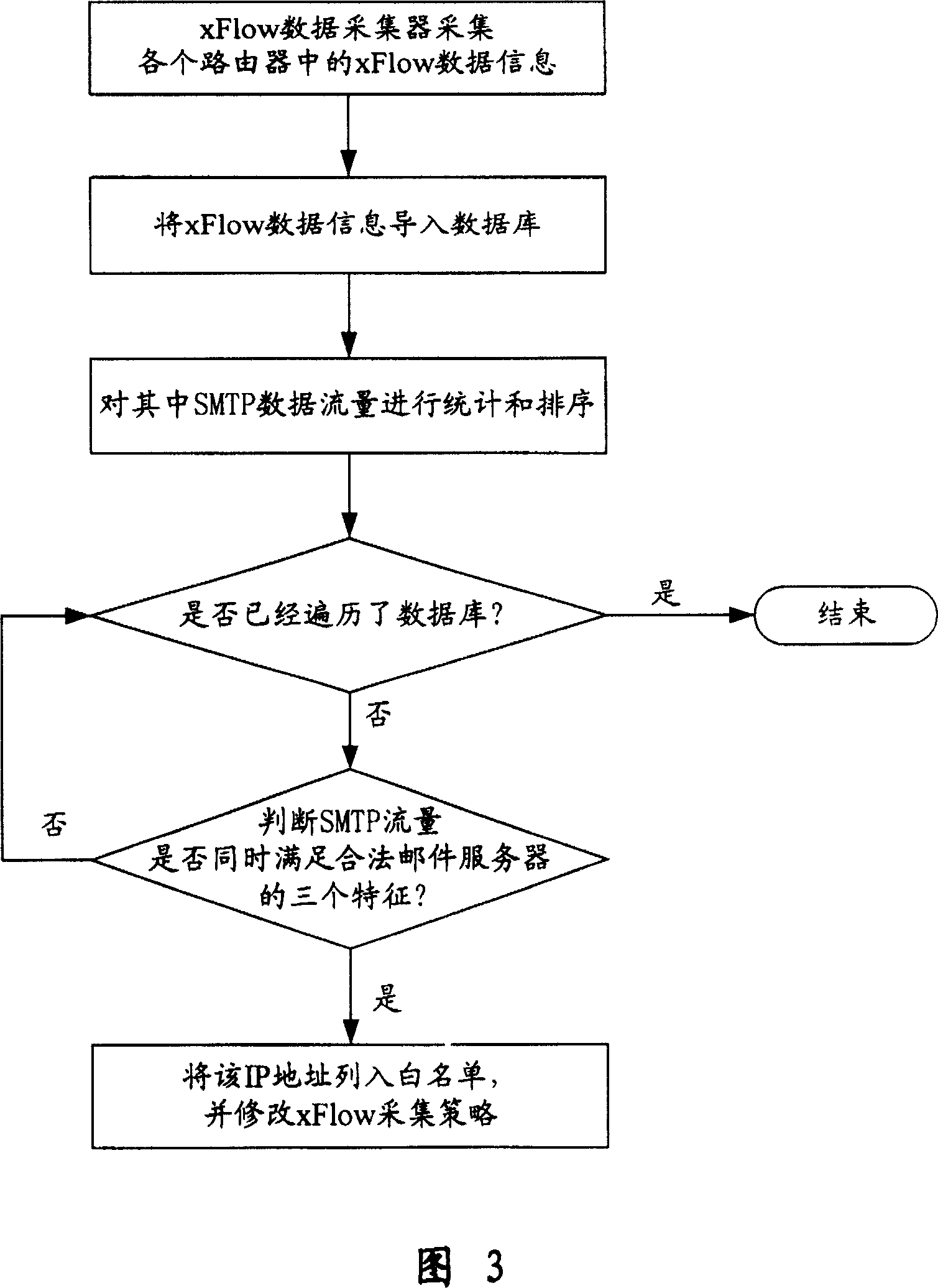
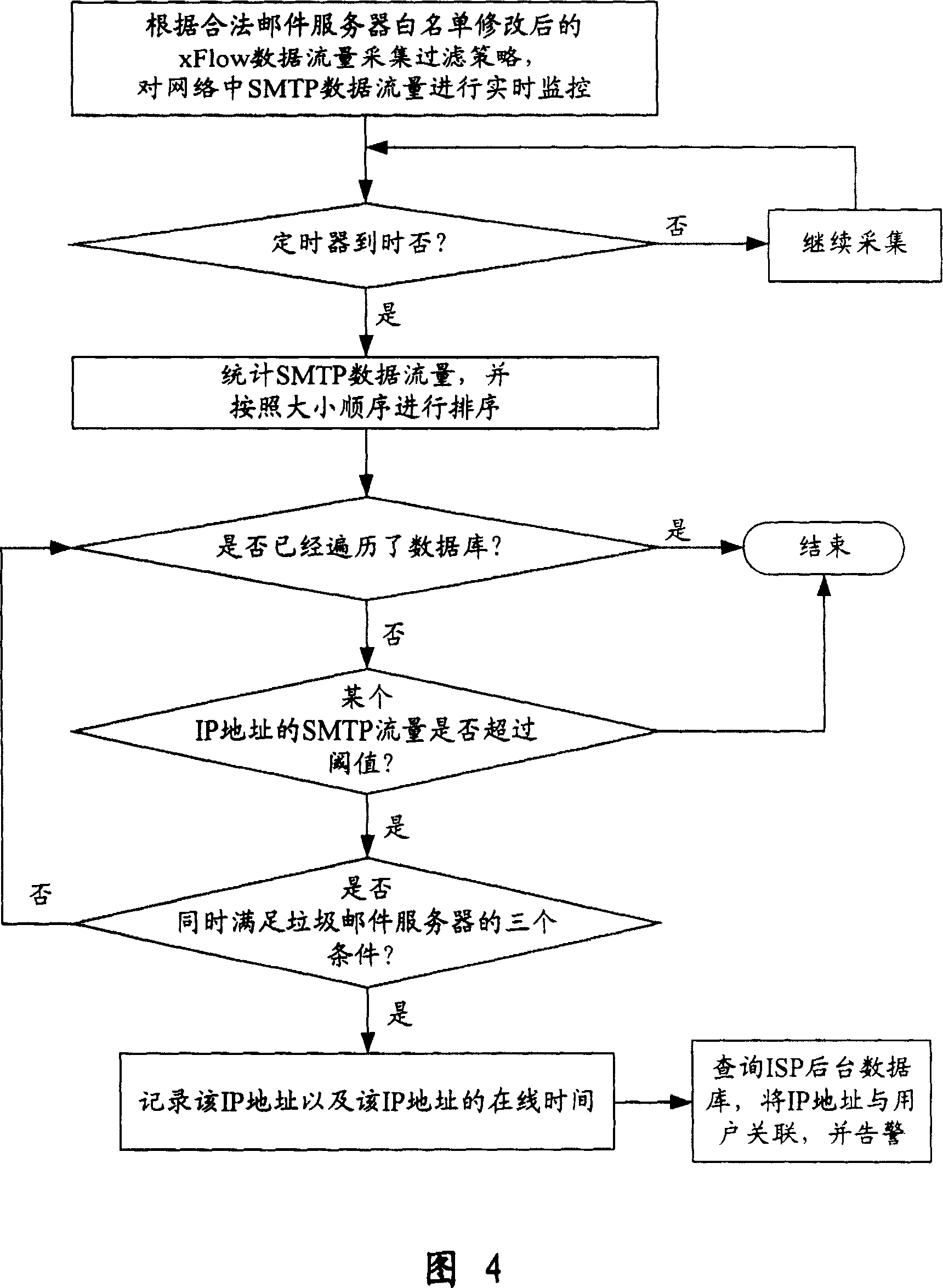
ActiveCN100349421CEffective positioningEnsure safetyData switching networksComputer scienceTraffic volume
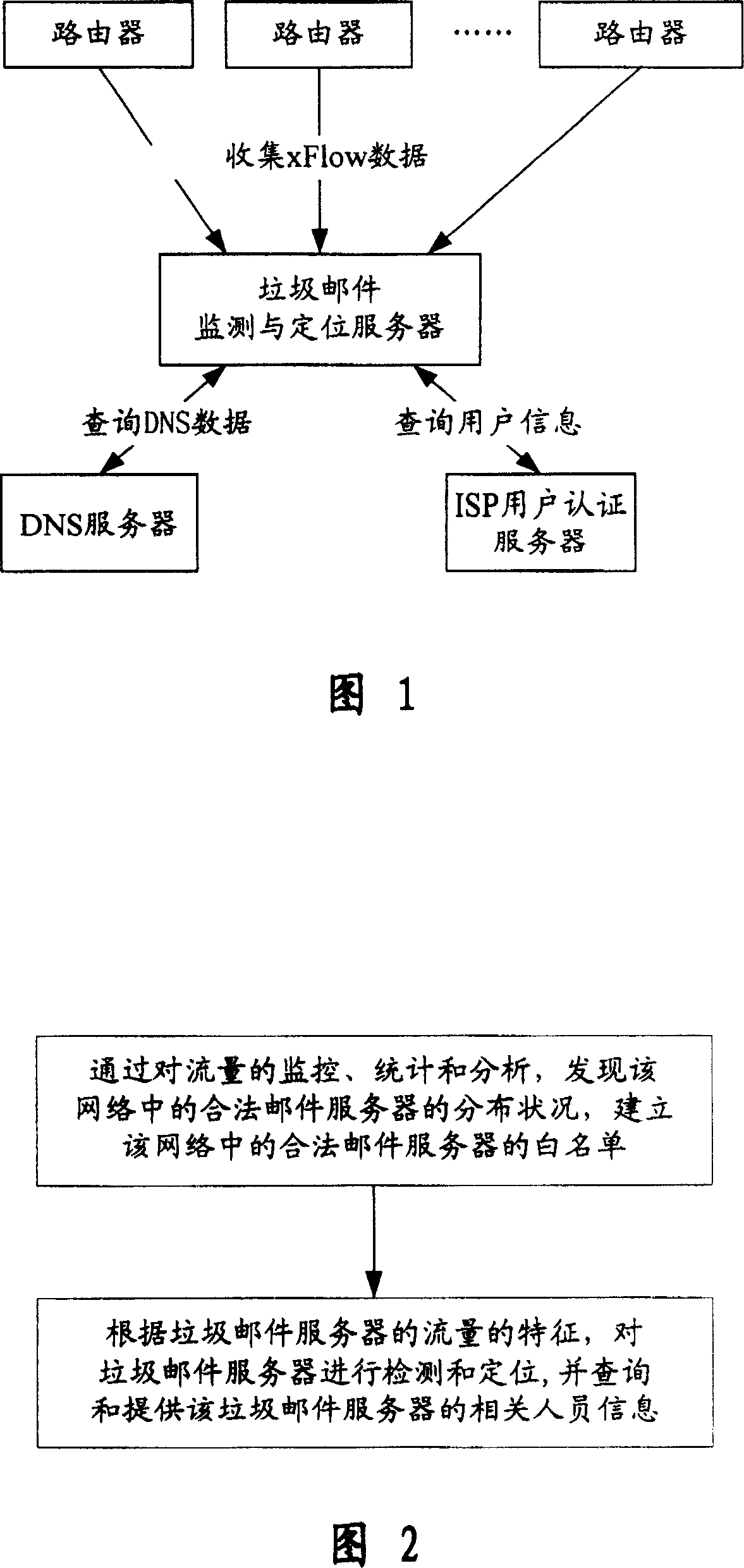
This invention relates to one garbage servo testing and positioning method, which comprises the following steps: a, finding the legal emails servo distributions and establishing the white list of the legal email servo and preventing the mistaking the legal emails as garbage servo through flow monitoring, statistics and analyzing; b, testing and positioning the garbage email servo according to the garbage servo flow characteristics and requiring and providing the servo relative human information.
Owner:CHINA TELECOM CORP LTD
Digital education software application technology
InactiveCN113360137APurify the network environmentHas the unique characteristicData processing applicationsSoftware designEngineeringApplication software
The invention relates to the technical field of software, in particular to a digital education software application technology which comprises special character setting, special image setting, special scene setting and special voice setting; the special image setting is designed according to a required unique game image, the special scene setting is designed according to a required unique game scene, and the special voice setting is designed according to a required unique voice. The invention has the beneficial effects that an entertainment software user can obtain educational enlightenment significance which cannot be achieved by other entertainment software in the entertainment process of the application software; according to the invention, the comprehensive application of characters, images, voice and the like is emphasized, so that the developed whole software application reaches the unprecedented network application height, and the network environment is purified; compared with market online game application software, the invention has the multi-body characteristics of playing, learning, practicability and the like; according to the invention, the application of characters and images has uniqueness; the invention relates to the fields of games and education, in particular to a content application mode and method of application software which are indispensable in the current life of people.
Owner:襄阳特杰沸腾软件开发有限公司
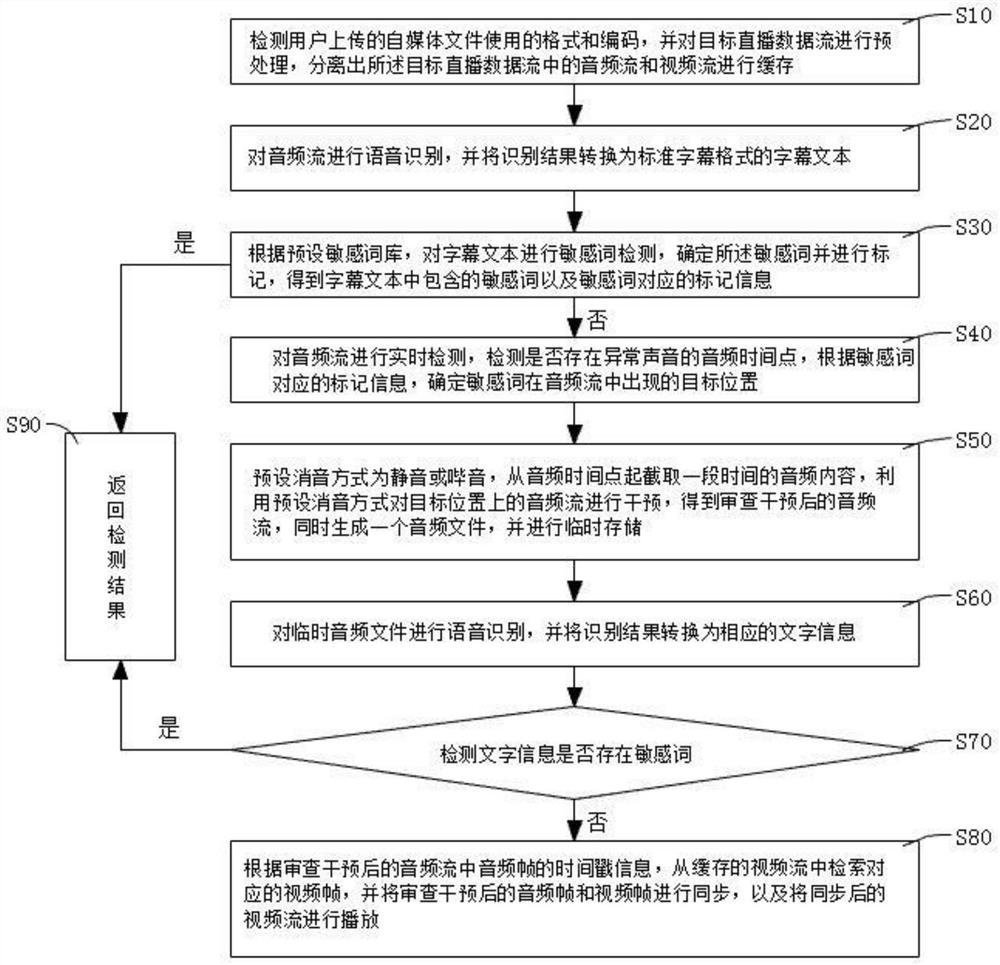
Method for intelligently examining self-media audio and video contents
PendingCN114845130AReduce manual laborPurify the network environmentCharacter and pattern recognitionSelective content distributionTextual informationMediaFLO
Owner:武汉景冠科技有限公司
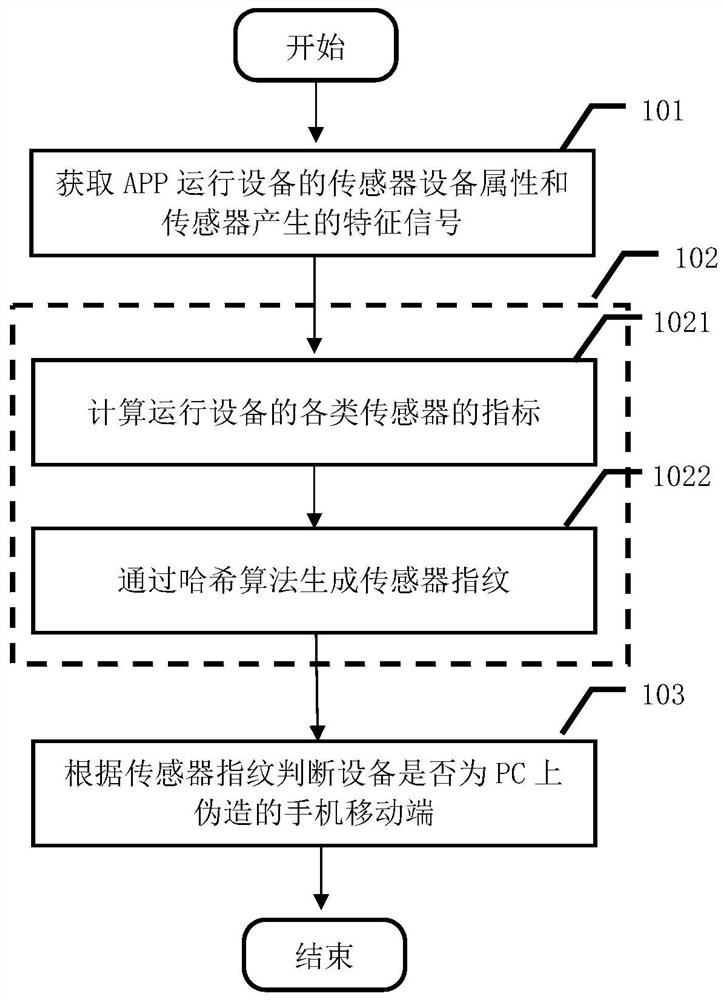
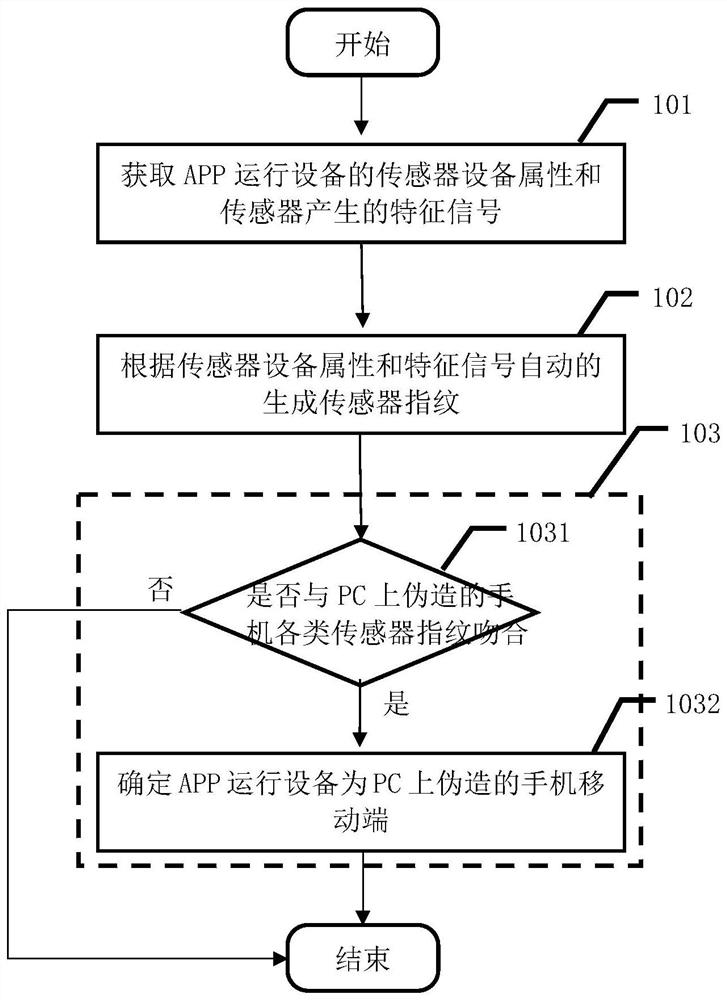
A method and device for identifying counterfeit mobile terminals based on mobile phone sensor fingerprints
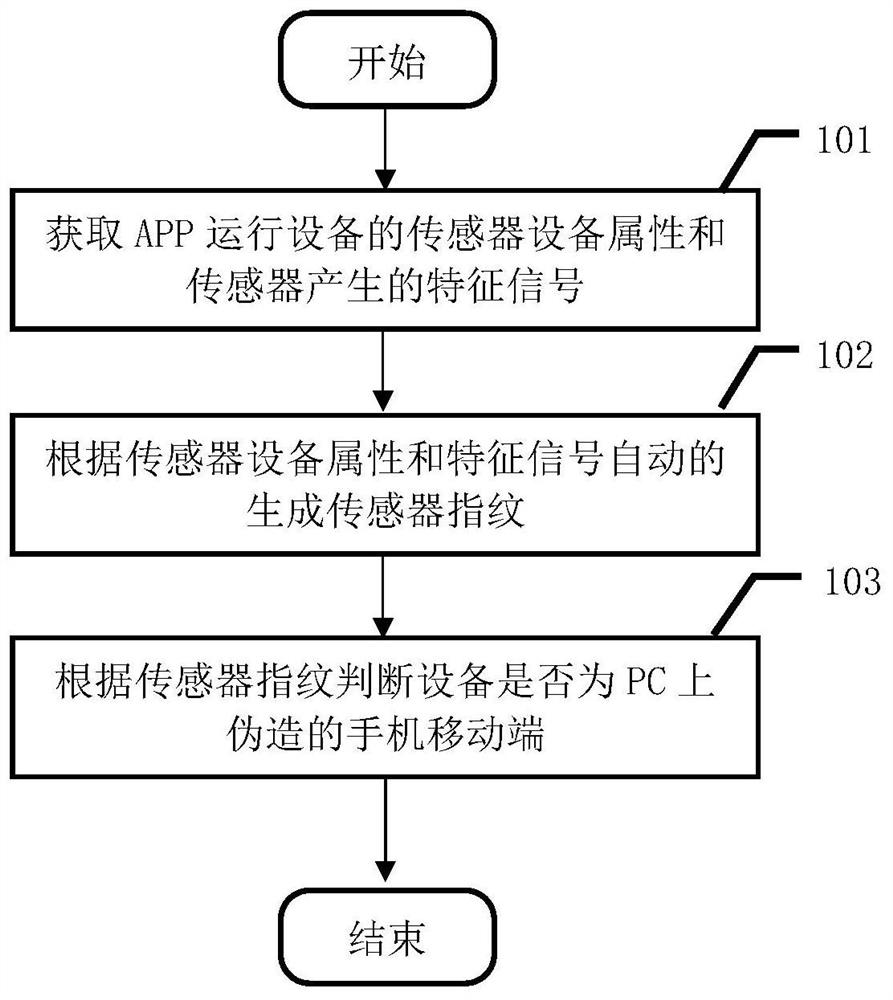
ActiveCN108712253BProtection of legitimate interestsCurb floodingKey distribution for secure communicationDevices with sensorPersonal computerHacker
The present invention provides a method and device for identifying counterfeit mobile terminals based on mobile phone sensor fingerprints, including: based on the device attributes of the sensors (including but not limited to acceleration sensors, gyroscopes, magnetic field sensors, etc.) that come with the mobile phone and the signal characteristics generated by the sensors Automatically generate sensor fingerprints, and judge whether the application access device is a personal computer terminal or a mobile terminal based on the sensor fingerprint. The method and device provided by the present invention can accurately judge those computer programs disguised as mobile terminals, ensure the legitimate interests of the application program owner in the process of operation and promotion, and protect the application program owner's assets from being illegally exploited by hackers and others. Suffer losses by means of theft.
Owner:北京人人云图信息技术有限公司
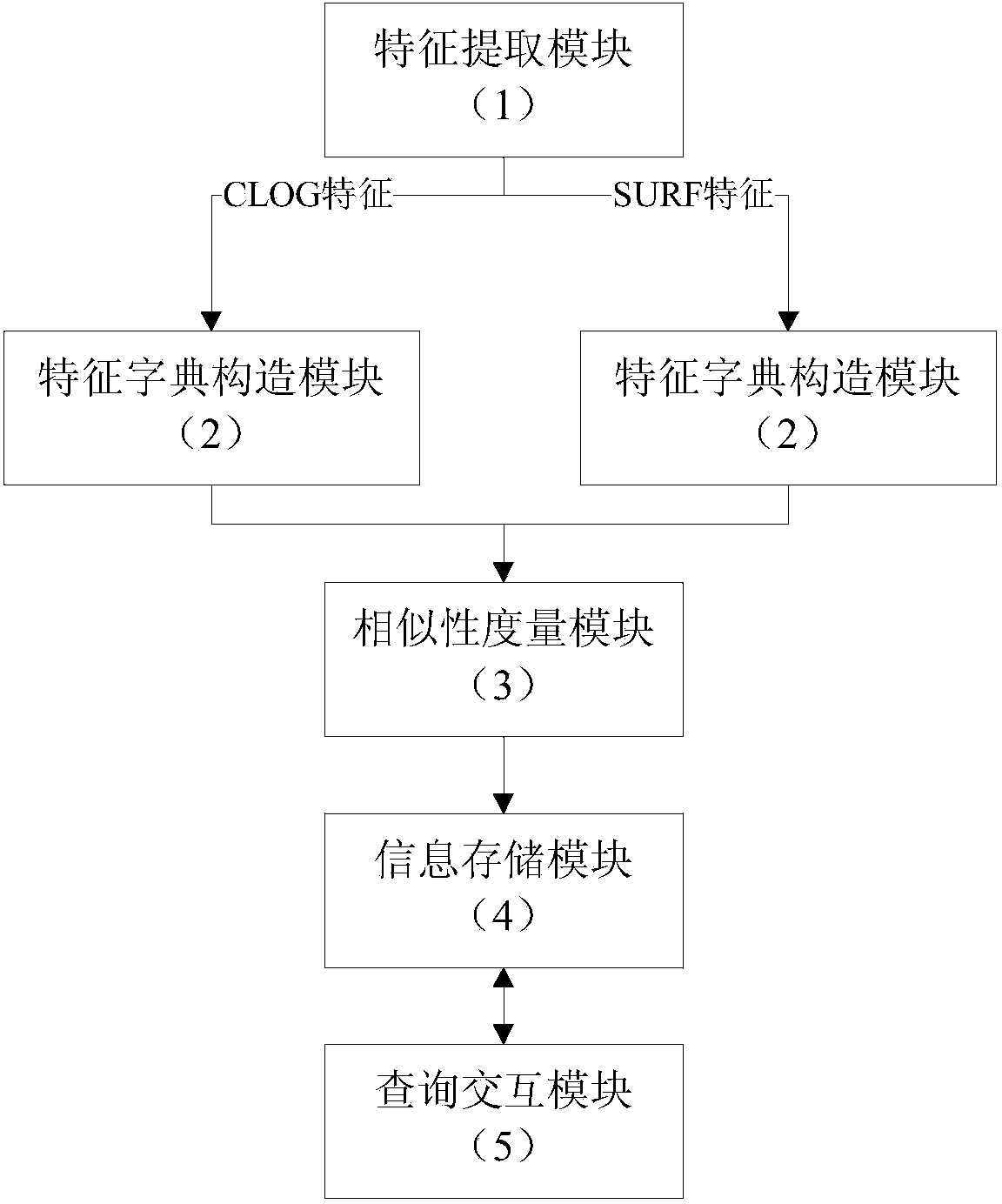
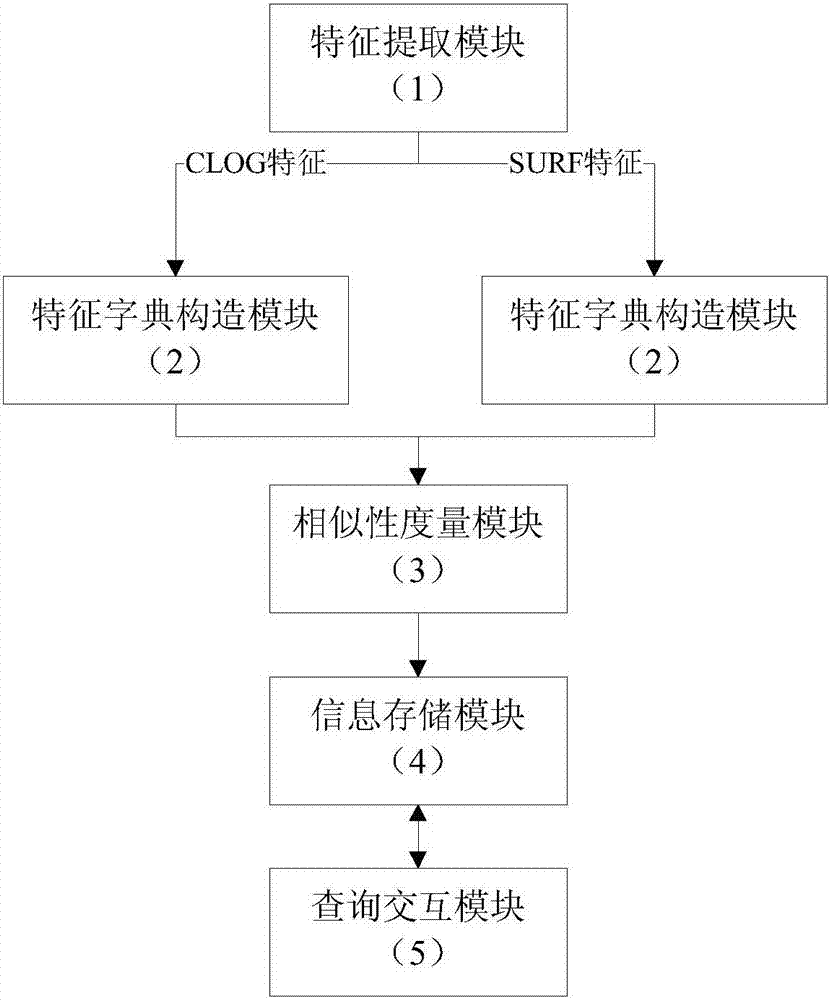
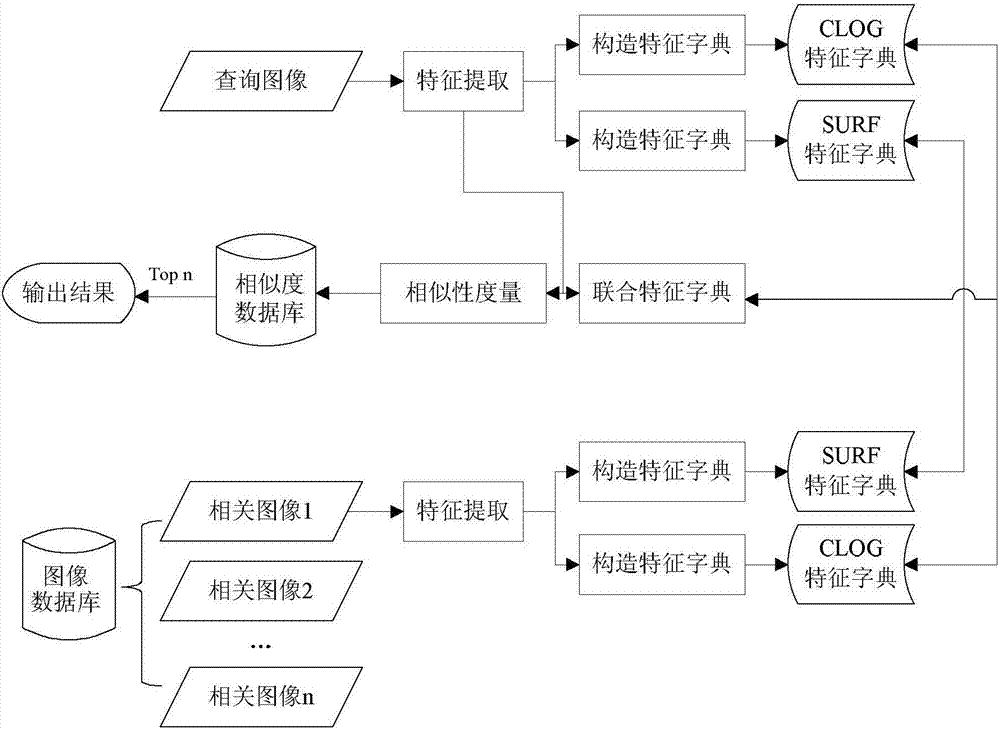
An image retrieval system and method based on multi-features and sparse representation
ActiveCN104142978BComprehensive descriptionFully express color informationSpecial data processing applicationsDictionary learningFeature extraction
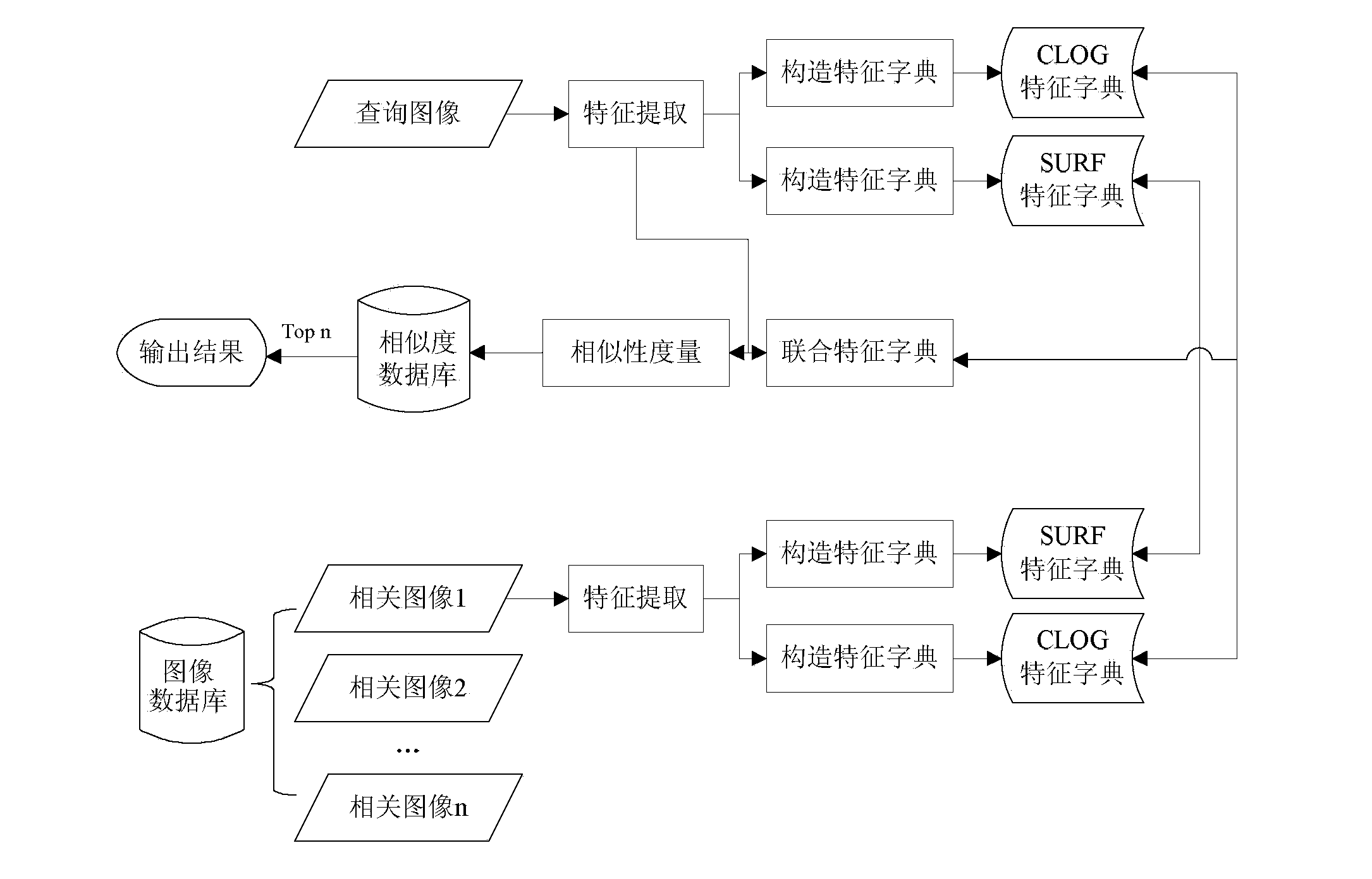
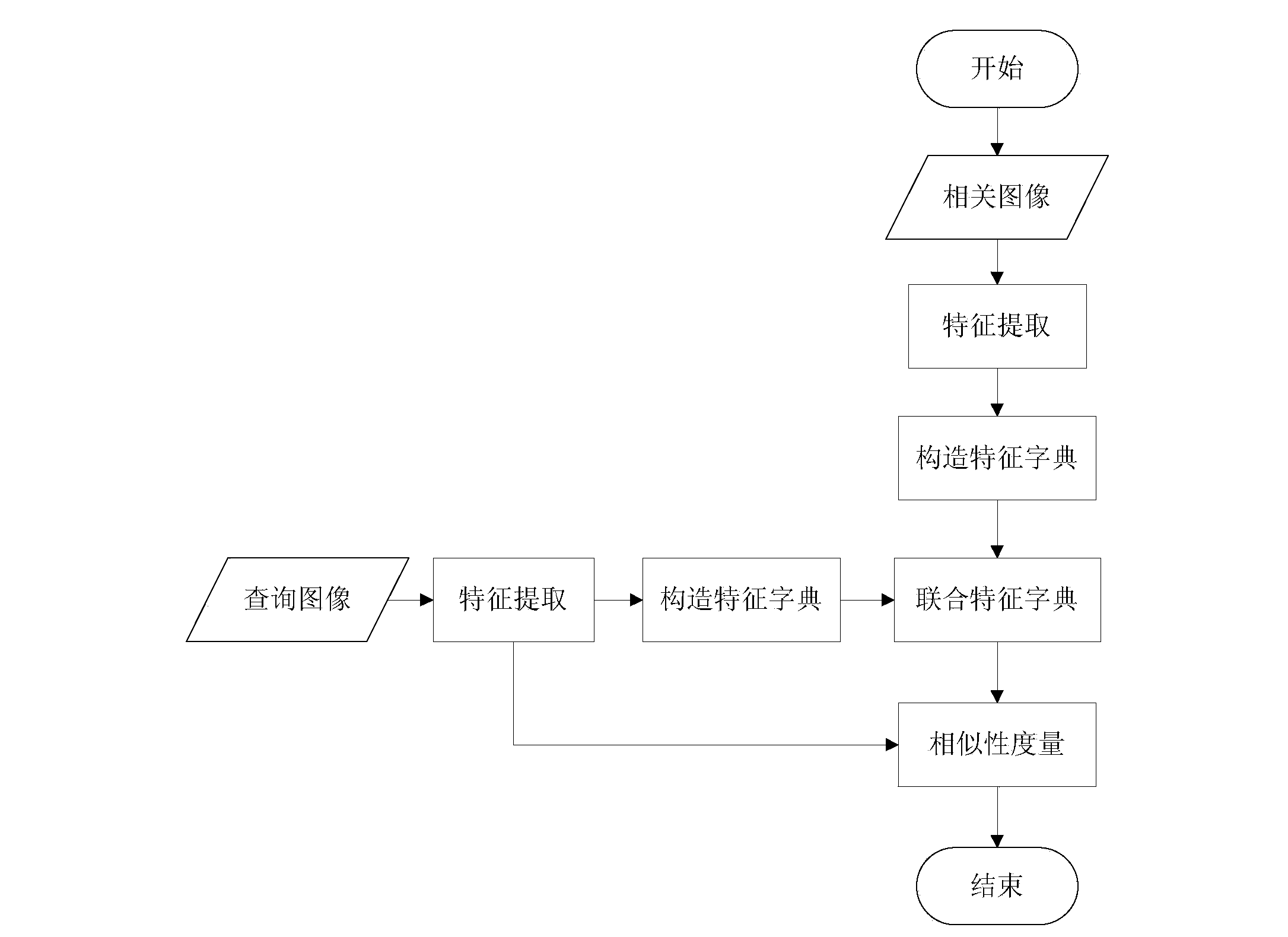
The invention discloses an image retrieval system and an image retrieval method based on multi-feature and sparse representation. The system comprises a feature extraction module, a feature dictionary building module, a similarity measurement module, an information storage module and an inquiry interaction module, wherein the feature extraction module adopts shape and color combining image features, color enhanced Gaussian Laplace features (CLOG features) and SURF features; the feature dictionary building module compresses original features into overcomplete overcomplete features through an on-line dictionary learning algorithm, and overcomes the defect that the original features are too dense; the similarity measurement module introduces a sparse representation theory, compares the residual error size generated by original dictionary and relevant dictionary representation, and judges the similarity of the two images, and the problem of higher feature dependence of the traditional similarity measurement method is solved. The system and the method provided by the invention have the advantages that rotating, noise and illumination change images can be effectively retrieved, and the image retrieval robustness is obviously improved.
Owner:博拉网络股份有限公司
Social software information publishing method and system based on cloud computing
InactiveCN112330479AAvoid misleadingPurify the network environmentData processing applicationsDigital data information retrievalEngineeringDegree of similarity
The invention provides a social software information publishing method and system based on cloud computing, and the method comprises the steps: searching contents which have been published by other users and are higher in similarity with the second user based on the contents requested to be published by the second user, and judging whether the two contents belong to the same consumption scene, consumption time period and consumption merchant or not; judging order sharing consumption behaviors of a plurality of users, so that the content published by order sharing consumption is forbidden or withdrawn, misleading of audiences is avoided, and the network environment is purified. In addition, whether an order sharing behavior exists or not is accurately discriminated according to informationsuch as commodities or articles of published content, the number of people in pictures, publishing time and consumption places, so that the identification accuracy is improved. Finally, the order sharing evidence among the users is further locked through the account transfer behaviors among the different users, so that the identification accuracy is further improved.
Owner:王小燕
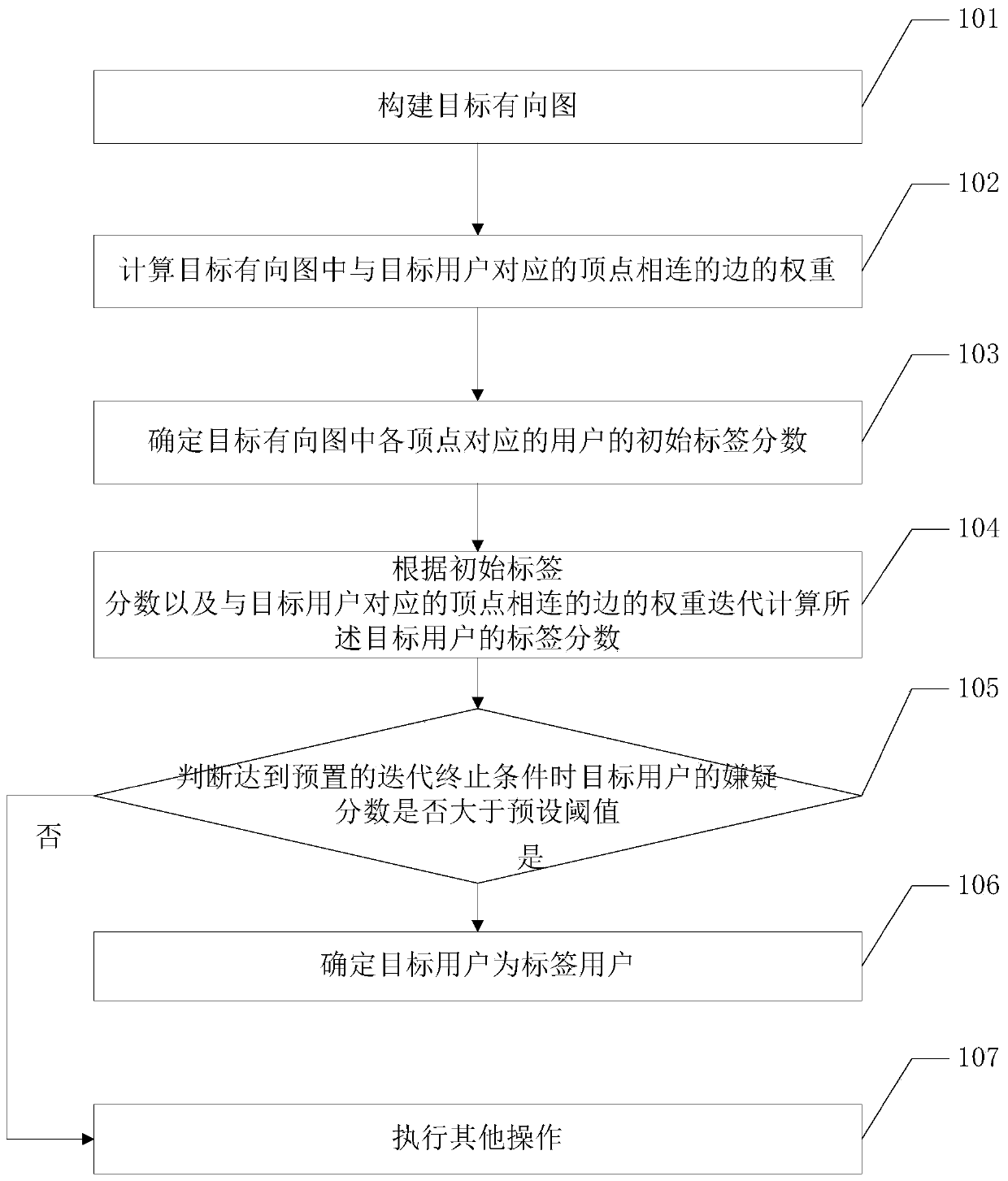
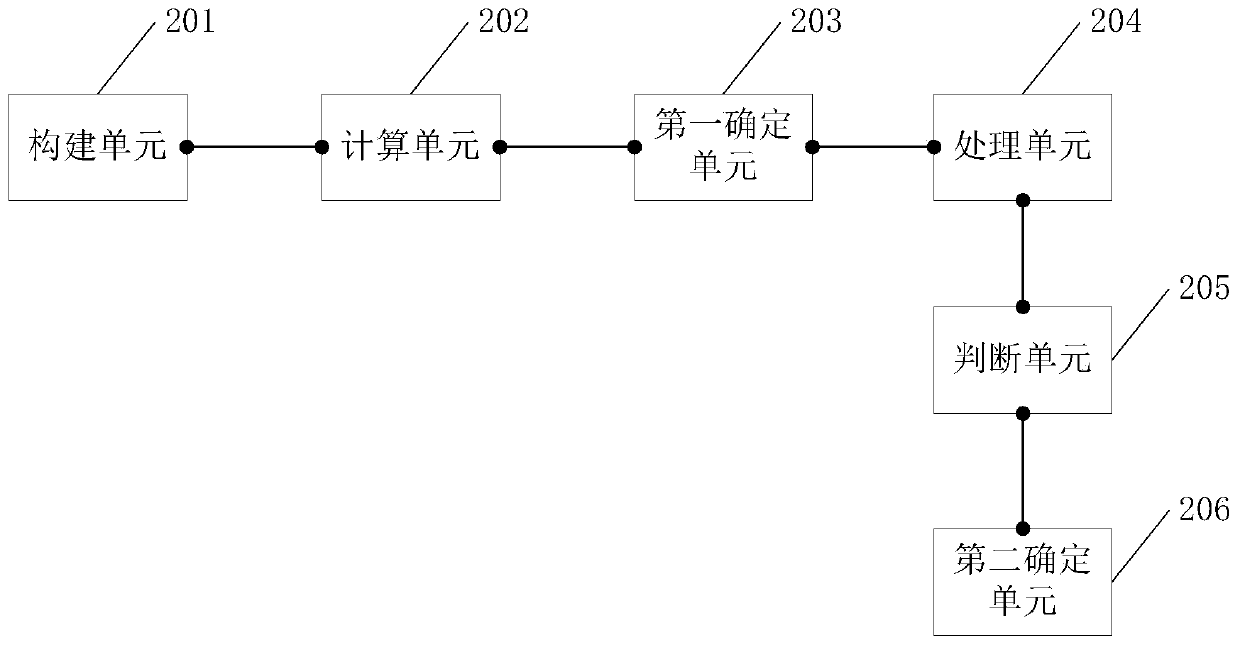
A tag user identification method and related equipment
ActiveCN110222297BImprove experienceQuick identificationWebsite content managementSpecial data processing applicationsEngineeringData mining
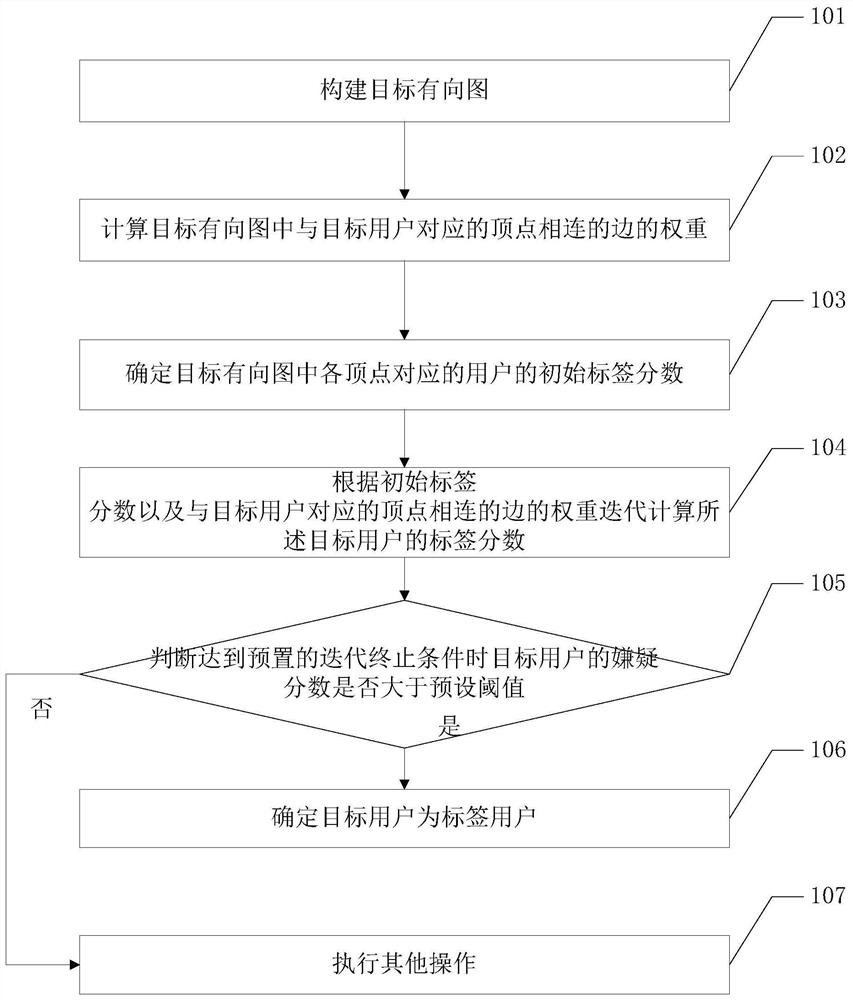
Embodiments of the present invention provide a label user identification method and related equipment, which are used to quickly identify label users on a live broadcast platform, purify the network environment, and provide user experience on the platform. The method includes: constructing a target directed graph, the target directed graph indicating the information interaction relationship between any two users in the live broadcast platform; calculating the weight of an edge connected to a vertex corresponding to the target user in the target directed graph , the target user is the user of the label to be identified; determine the initial label score of the user corresponding to each vertex in the target directed graph; according to the initial label score and the weight of the edge connected to the vertex corresponding to the target user Iteratively calculating the label score of the target user; judging whether the label score of the target user is greater than a preset threshold when the preset iteration termination condition is reached; if so, determining that the target user is a label user.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com