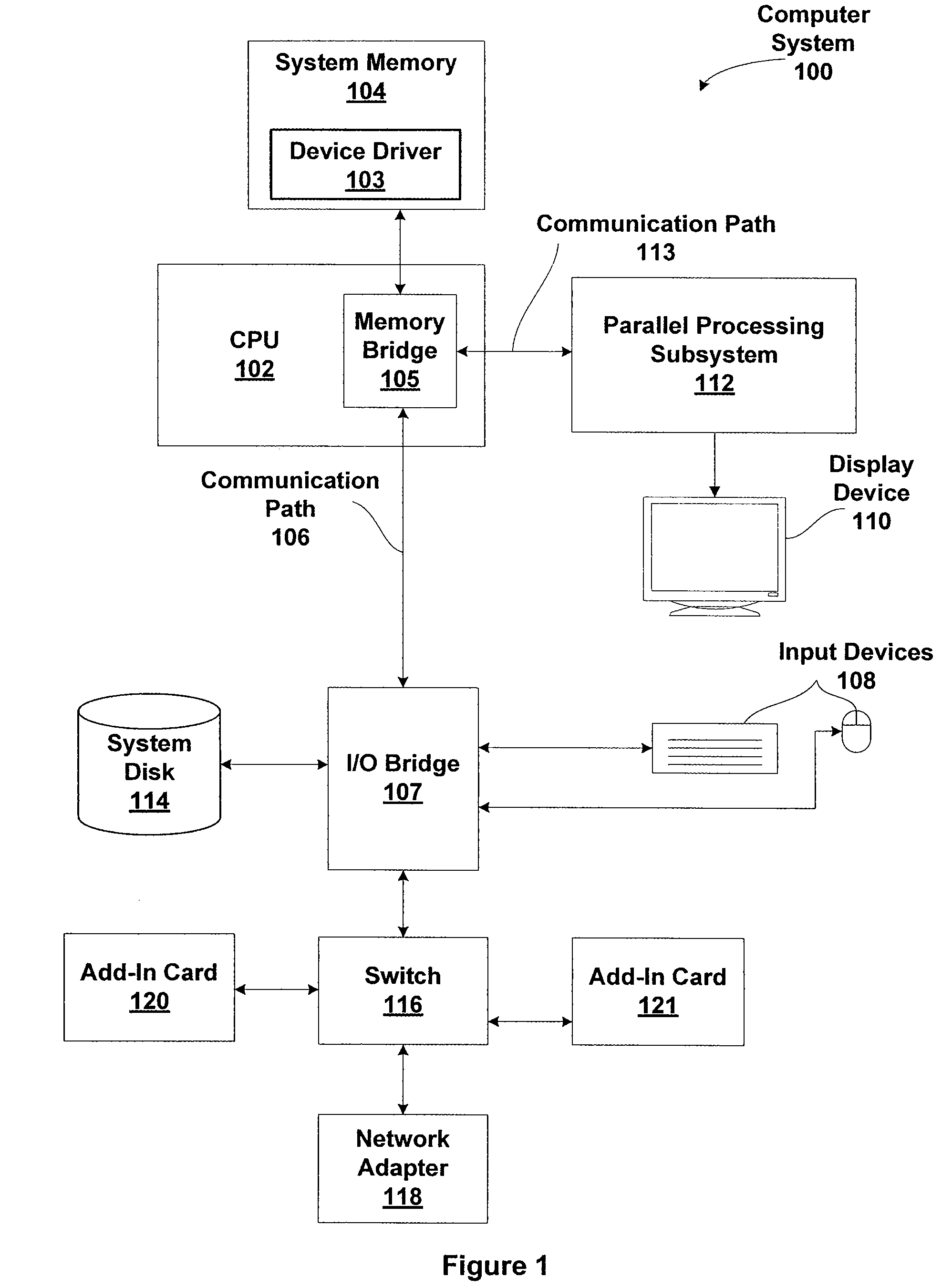
Patents
Literature
30results about How to "Waste of bandwidth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
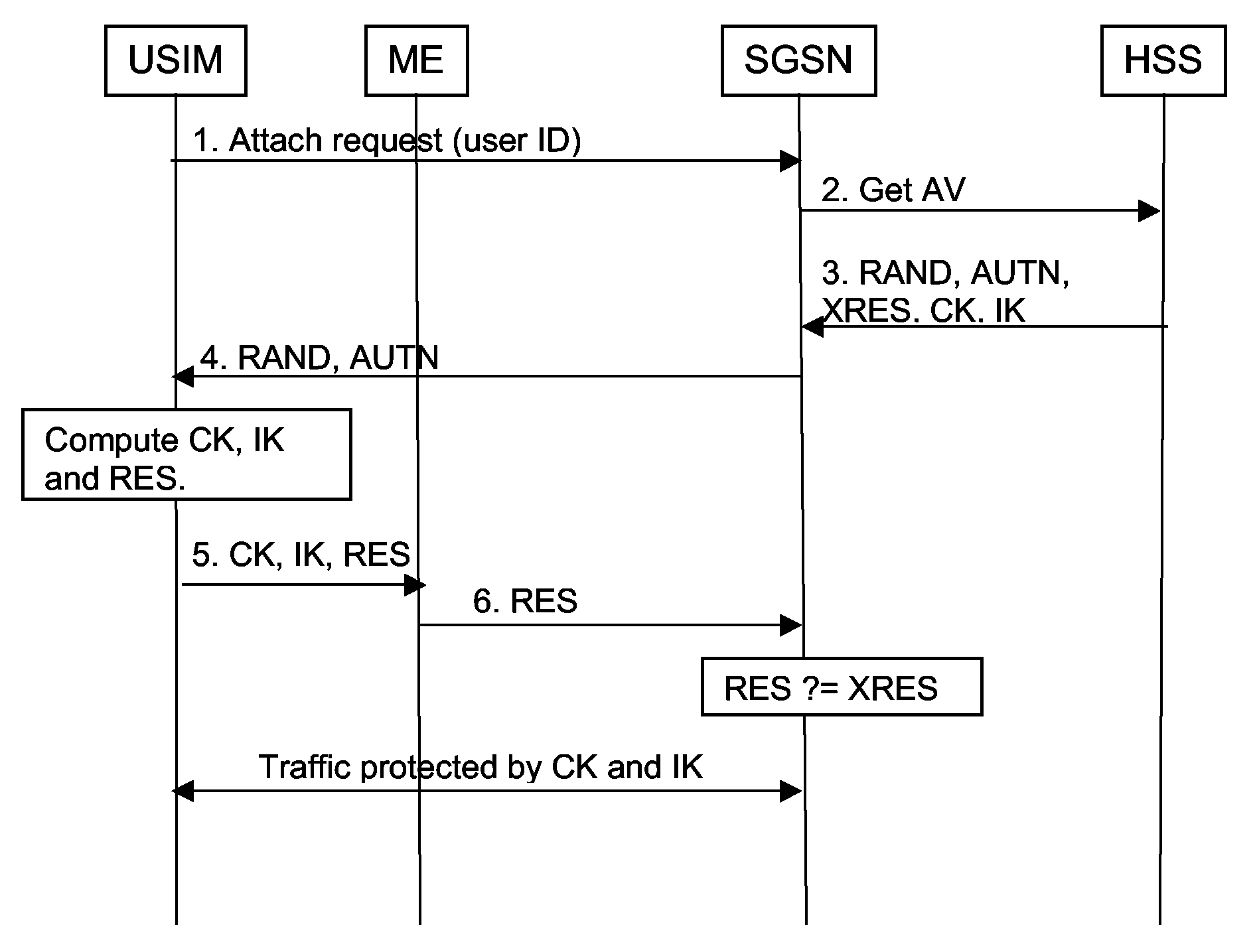
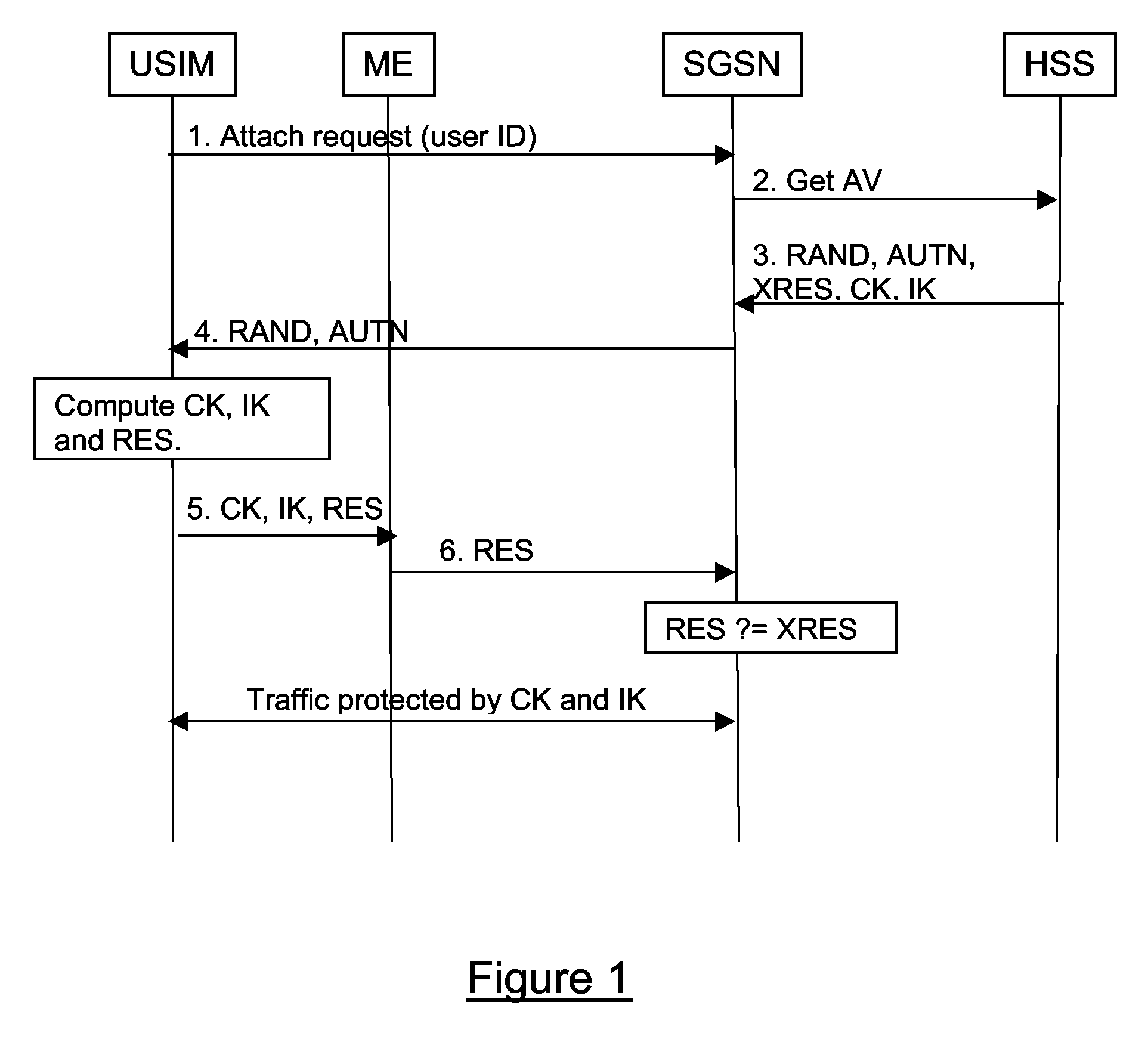
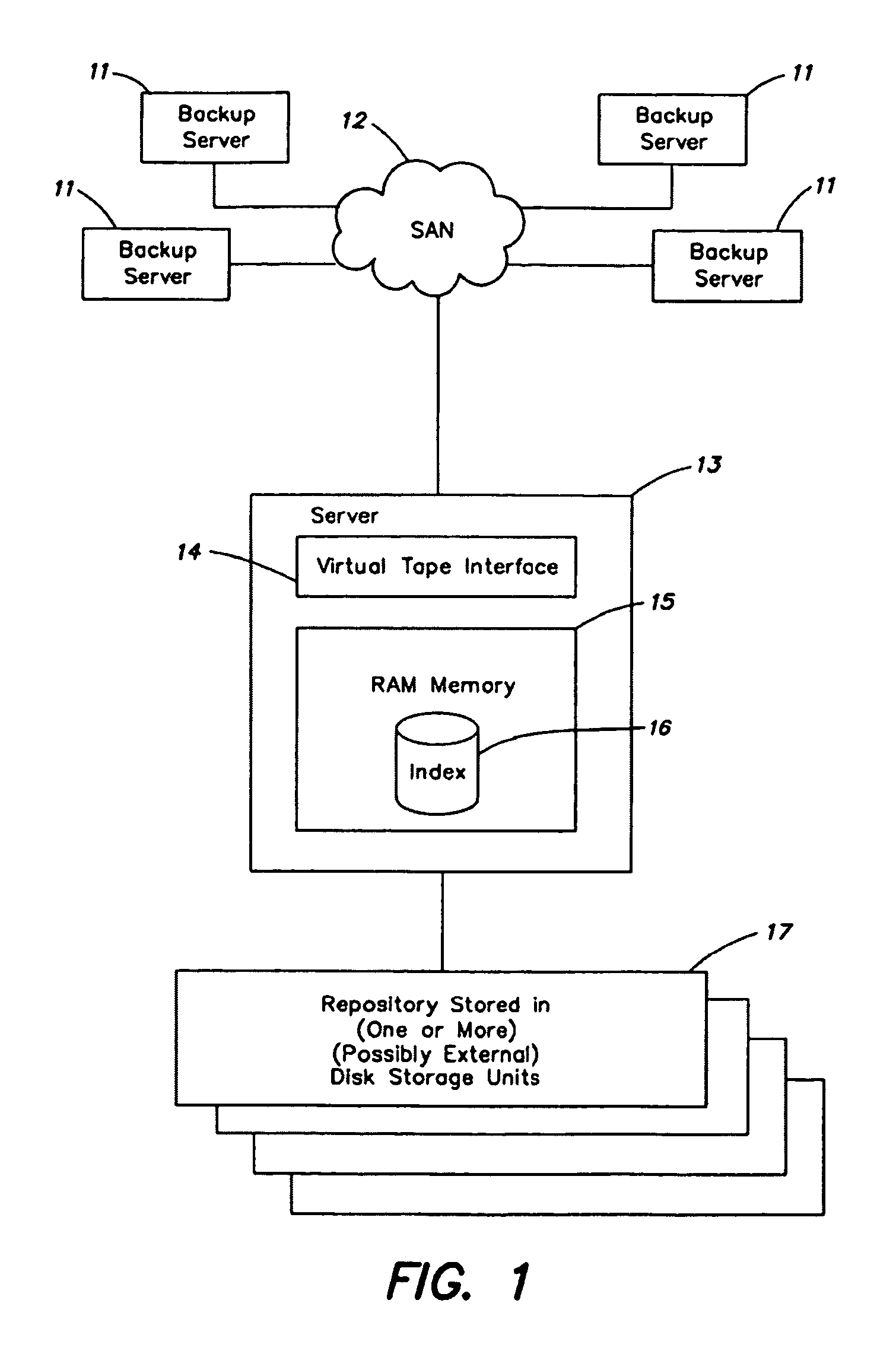
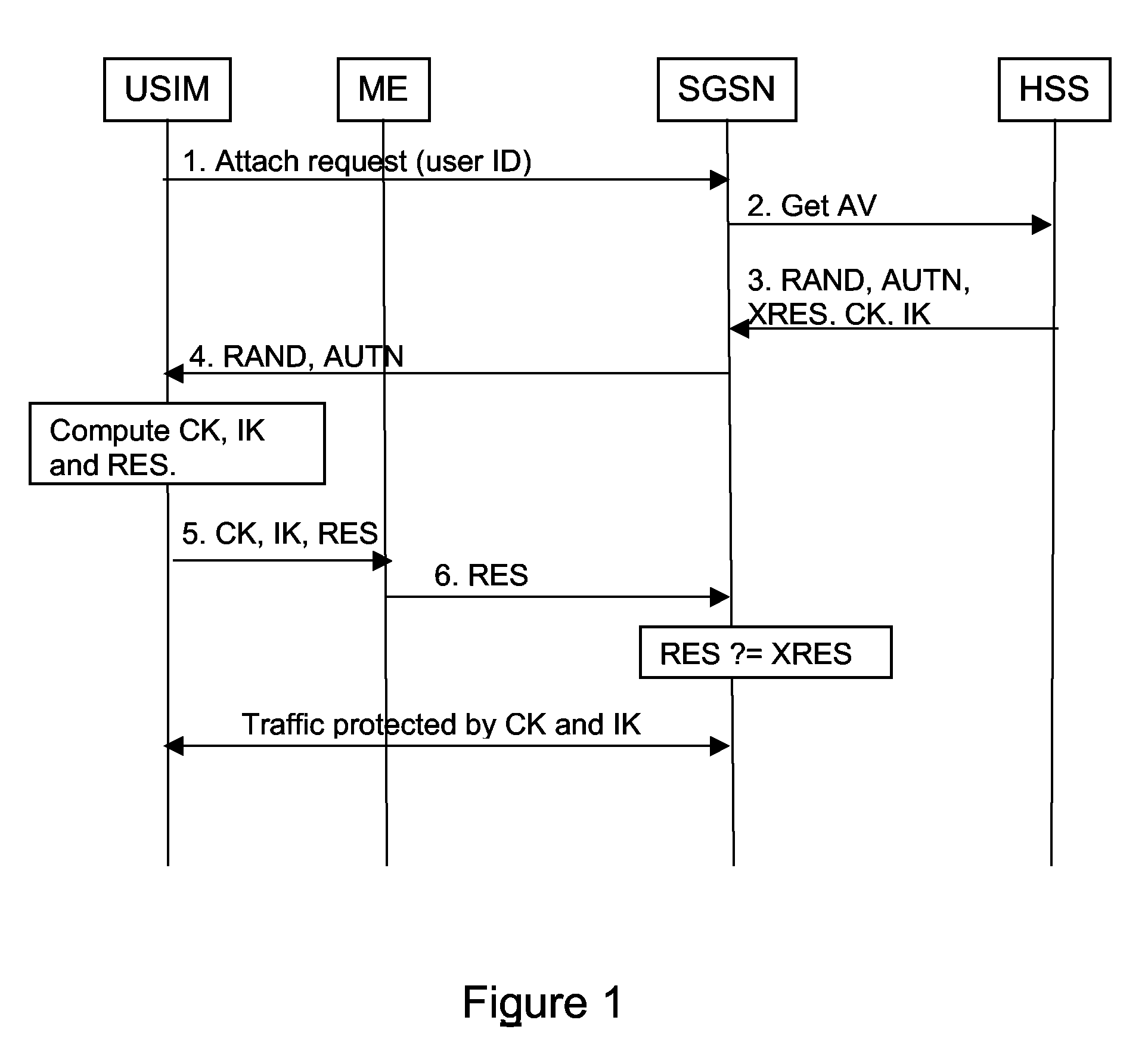
Method and Apparatus for Delivering Keying Information
ActiveUS20080273704A1Adds to session setup timesWaste of bandwidthKey distribution for secure communicationSecurity arrangementApplication serverUser equipment
A method of delivering an application key or keys to an application server for use in securing data exchanged between the application server and a user equipment, the user equipment accessing a communications network via an access domain. The method comprises running an Authentication and Key Agreement procedure between the user equipment and a home domain in order to make keying material available to the user equipment and to an access enforcement point. At least a part of said keying material is used to secure a communication tunnel between the user equipment and the access enforcement point, and one or more application keys are derived within the home domain using at least part of said keying material. Said application key(s) is(are) provided to said application server, and the same application key(s) derived at the user equipment, wherein said access enforcement point is unable to derive or have access to said application key(s).
Owner:TELEFON AB LM ERICSSON (PUBL)
Systems and Methods of QoS for Single Stream ICA
ActiveUS20120230345A1Service quality is excessiveImprove latencyData switching by path configurationHigh level techniquesQuality of serviceTransport layer
The present solution provides quality of service (QoS) for a stream of protocol data units via a single transport layer connection. A device receives via a single transport layer connection a plurality of packets carrying a plurality of protocol data units. Each protocol data unit identifies a priority. The device may include a filter for determining an average priority for a predetermined window of protocol data units and an engine for assigning the average priority as a connection priority of the single transport layer connection. The device transmits via the single transport layer connection the packets carrying those protocol data units within the predetermined window of protocol data units while the connection priority of the single transport layer connection is assigned the average priority for the predetermined window of protocol data units.
Owner:CITRIX SYST INC
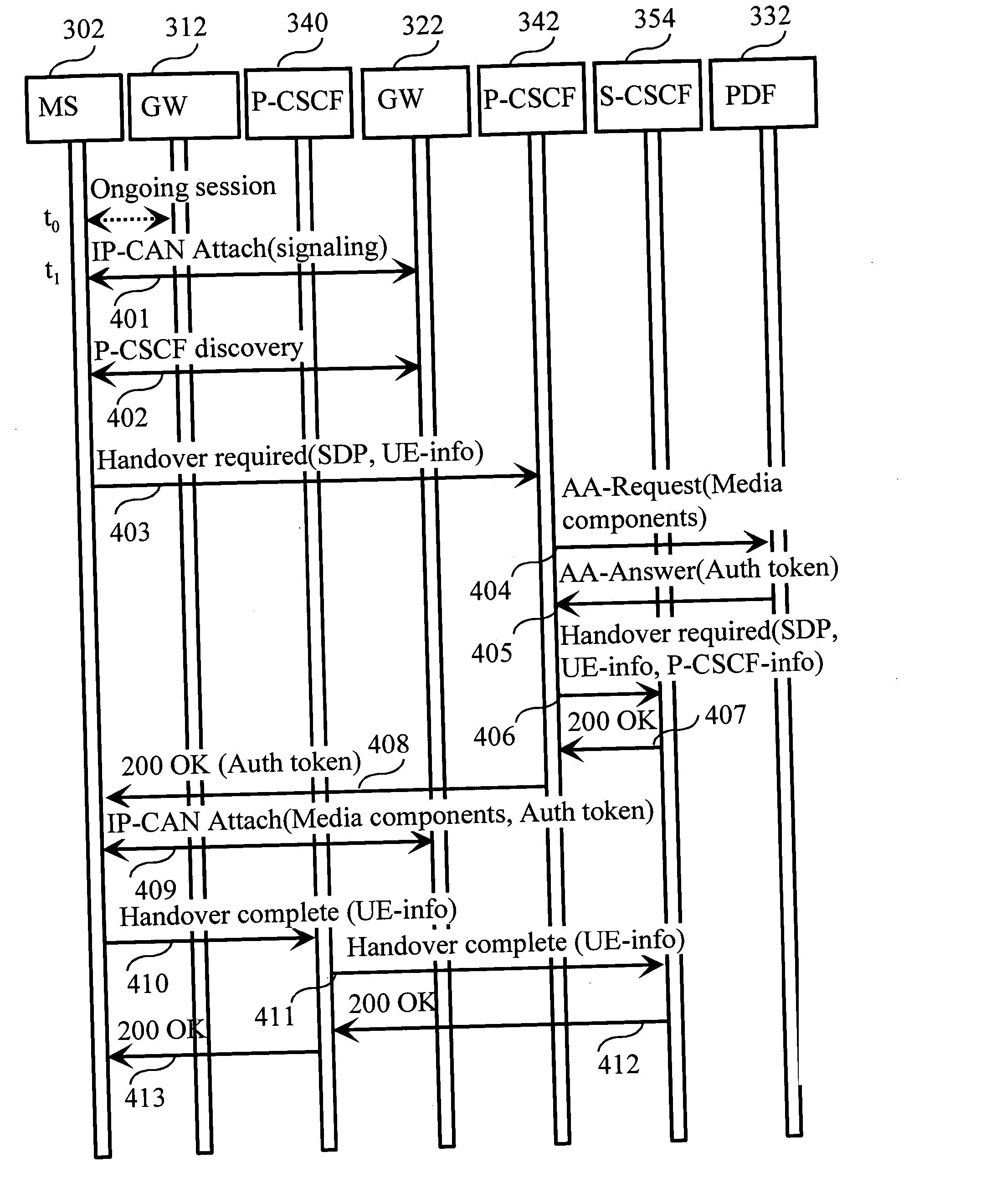
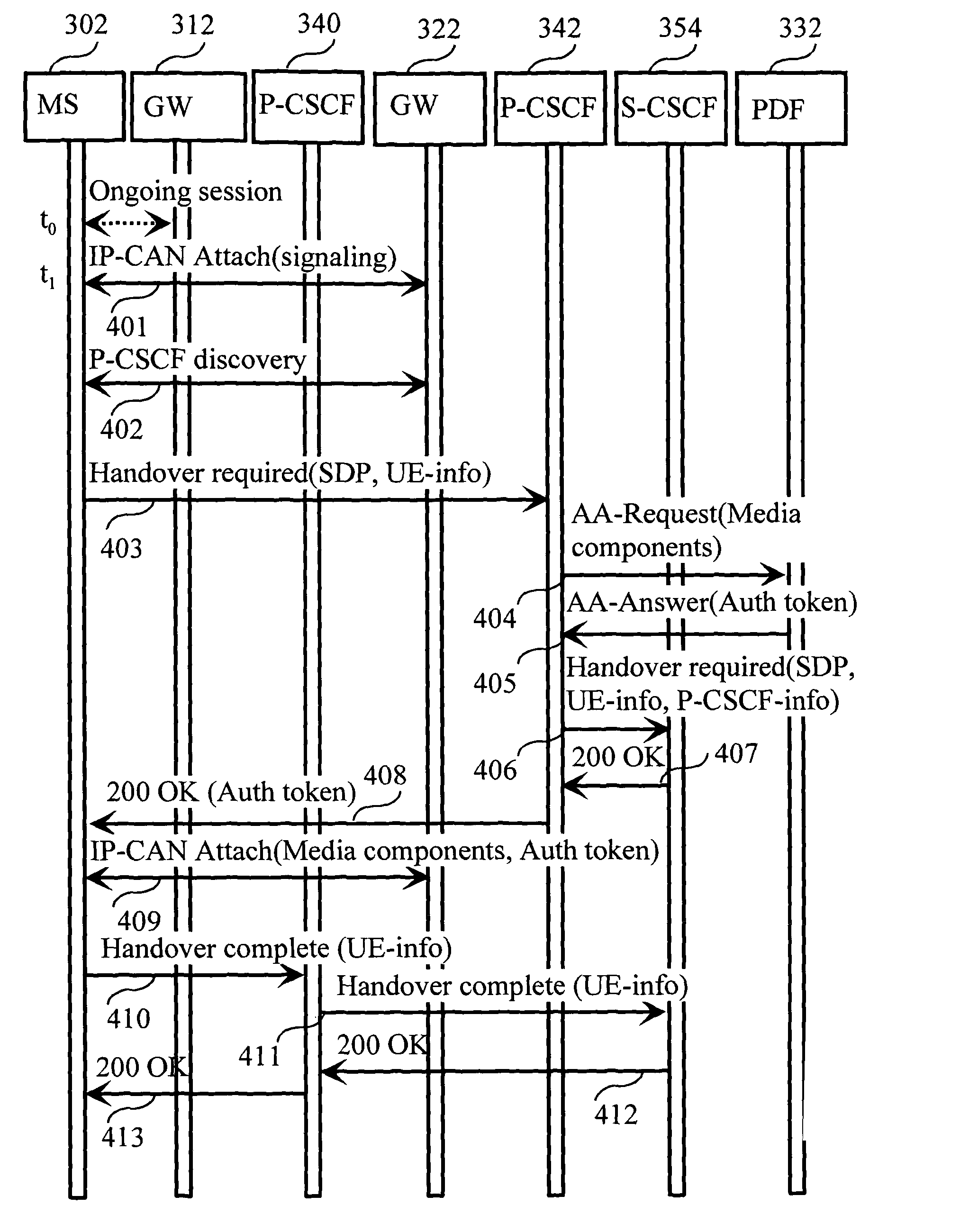
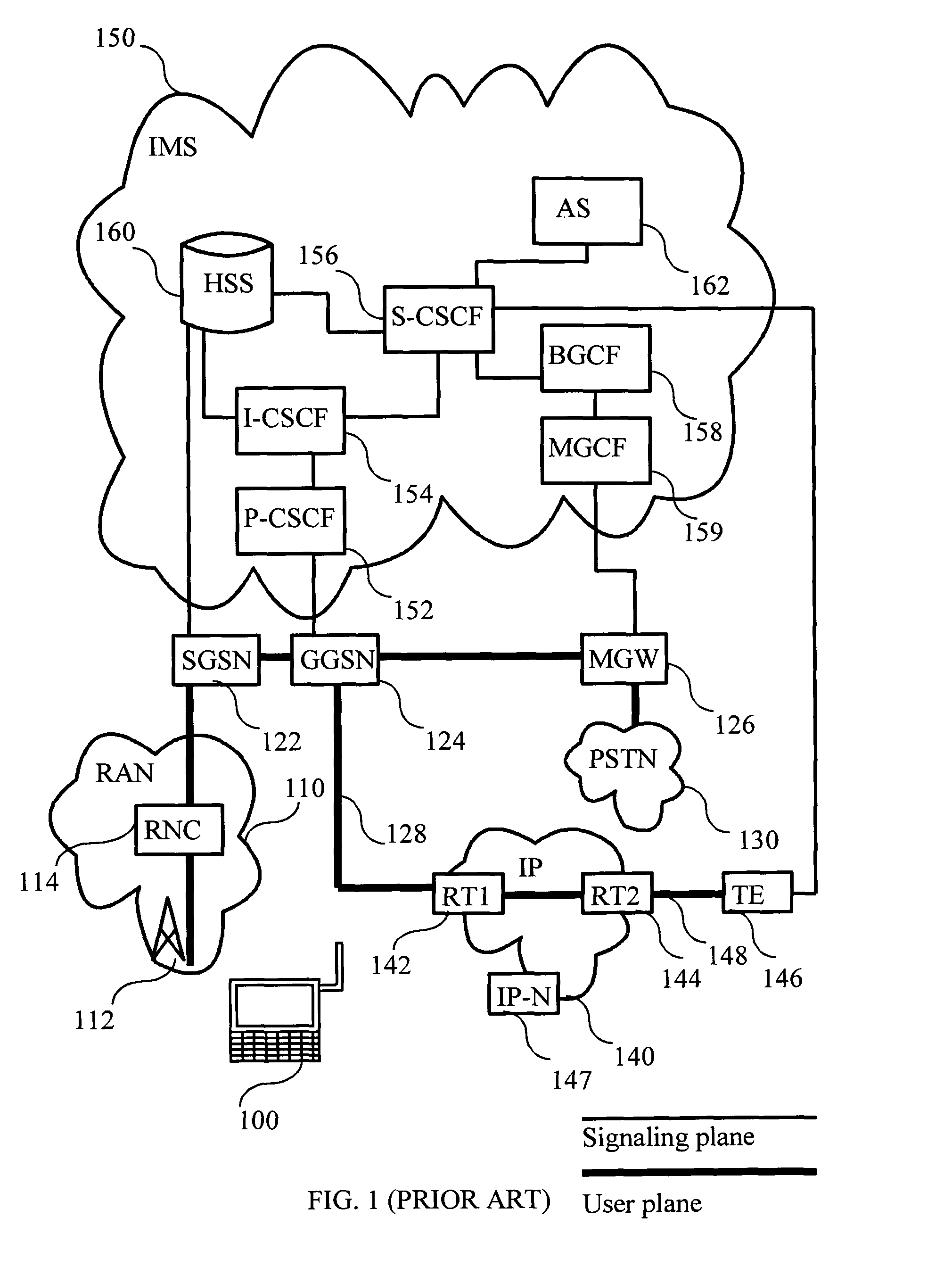
Method for the transfer of information during handovers in a communication system
ActiveUS20070211694A1Reliable functionFair and justified share of resourceTime-division multiplexConnection managementPolicy decisionCommunications system
The invention relates to a method for the transfer of policy control information during handover in a communication system. A session between a terminal and a remote node via a first network node has been established previously. The session comprising media components transmitted via the first gateway using first media component bearers. A handover condition is detected and a signaling connection is established between the terminal and the second gateway. Information on a second network node is obtained by the terminal, which determines if a proxy for the session has changed. If it has, information on media components is sent to a policy decision entity associated with the second network node. The policy decision entity authorizes second media component bearers with the information provided. Finally, the second media component bearers are established between the terminal and the second gateway.
Owner:NOKIA TECHNOLOGLES OY
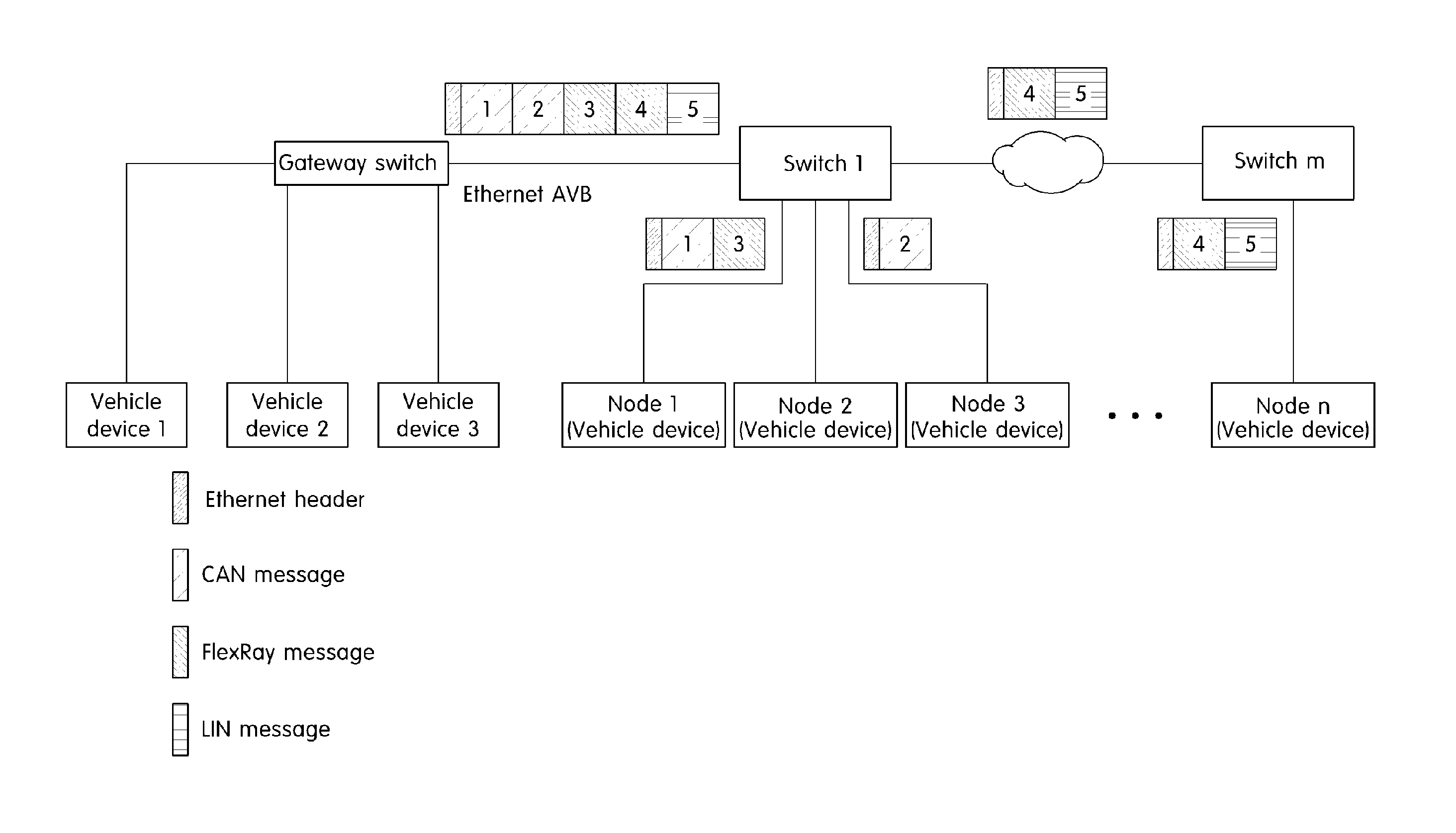
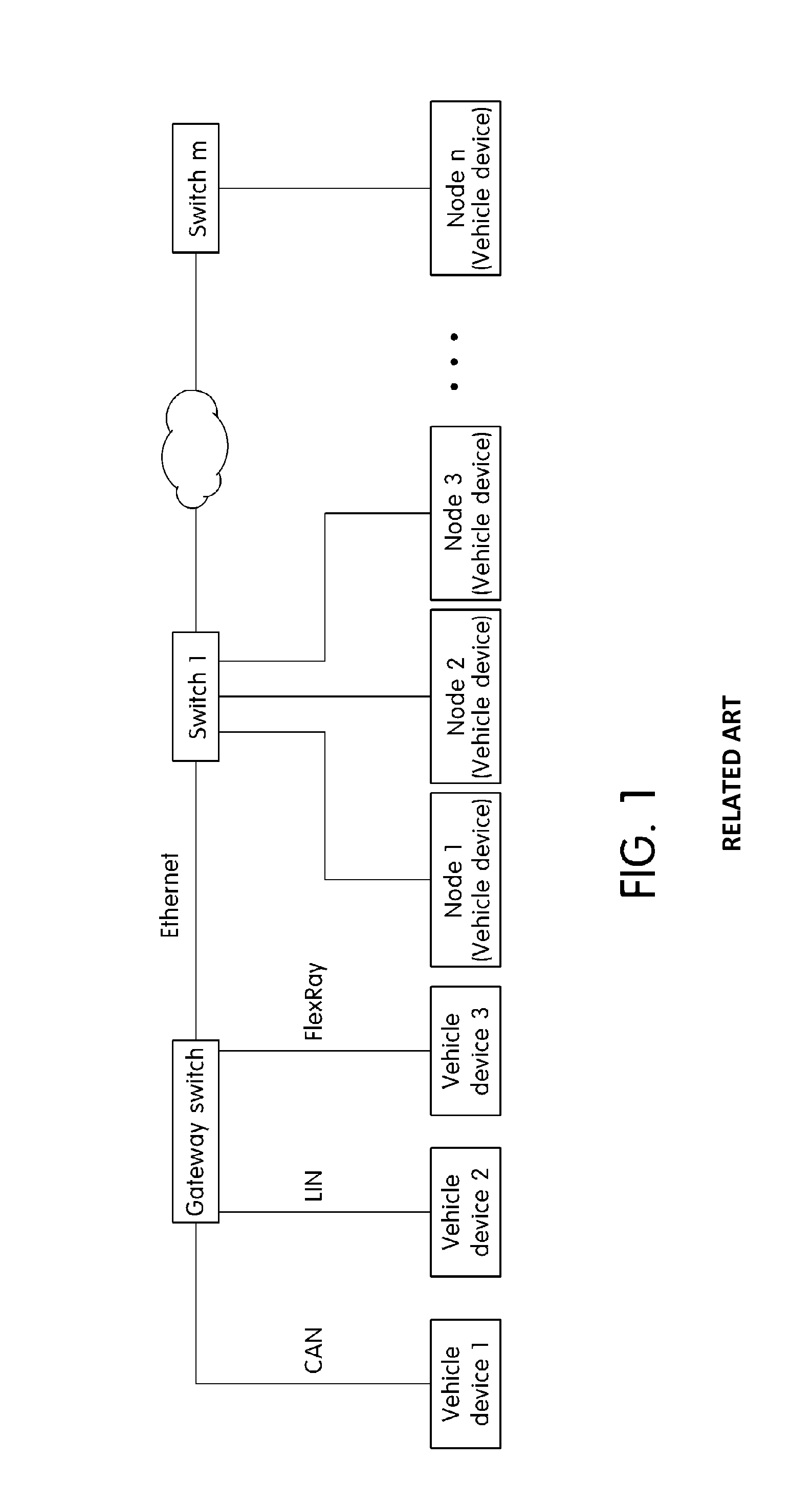
System and method for transferring message in ethernet based vehicle network
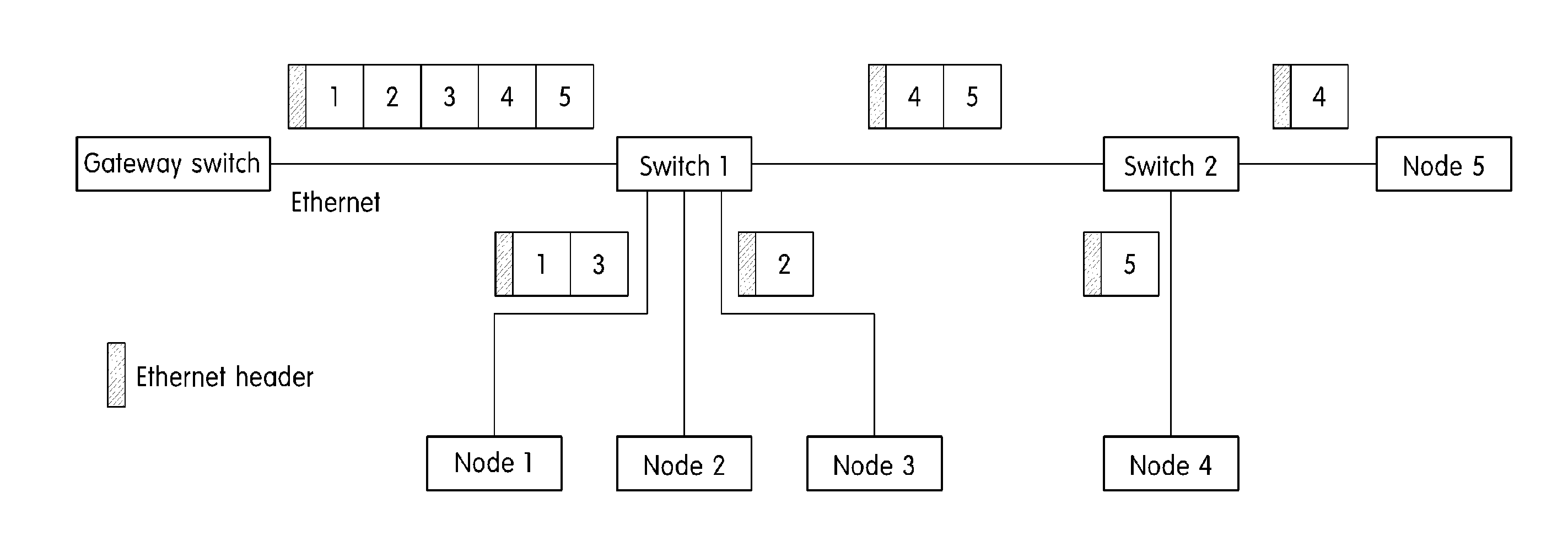
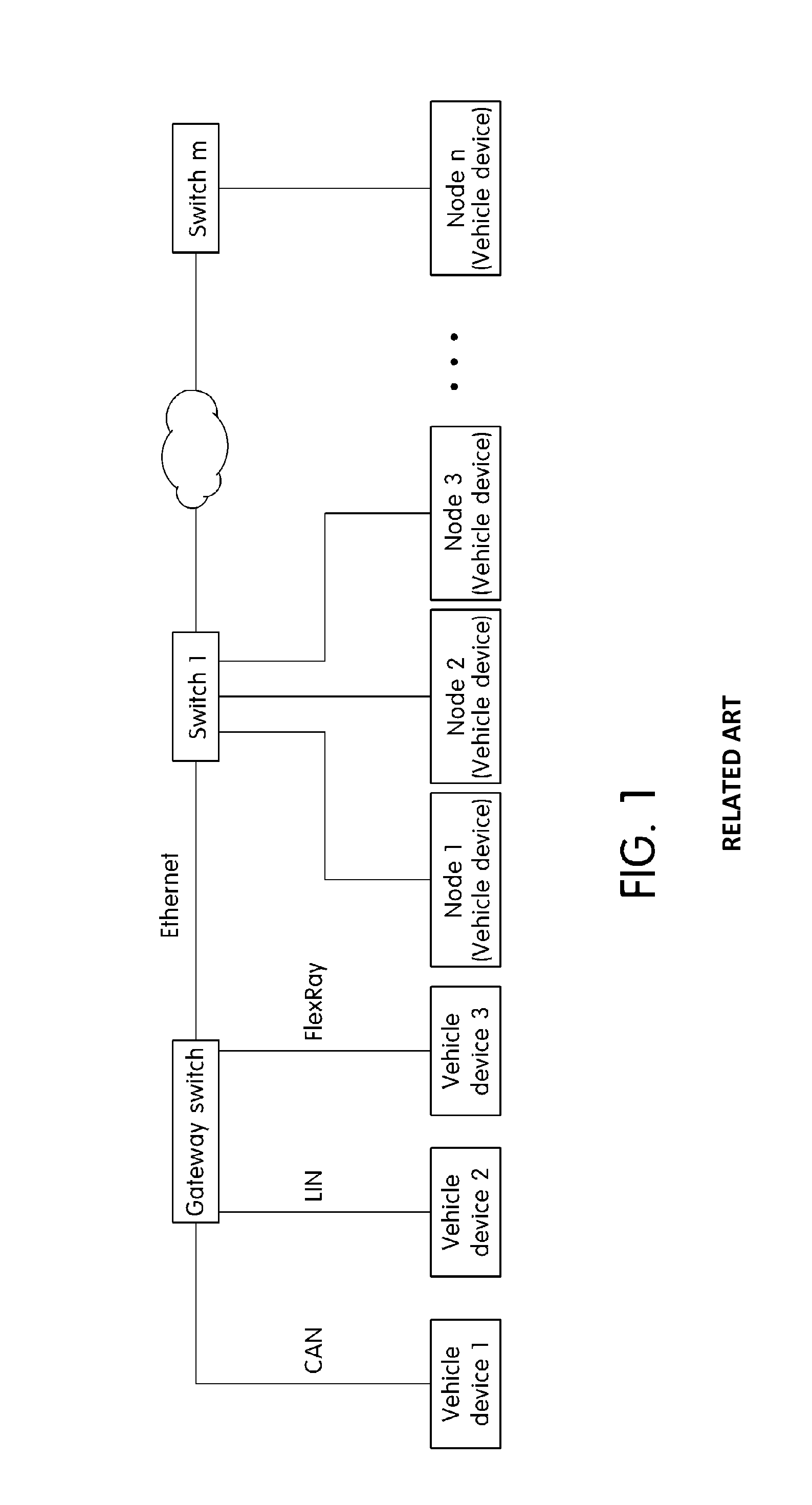
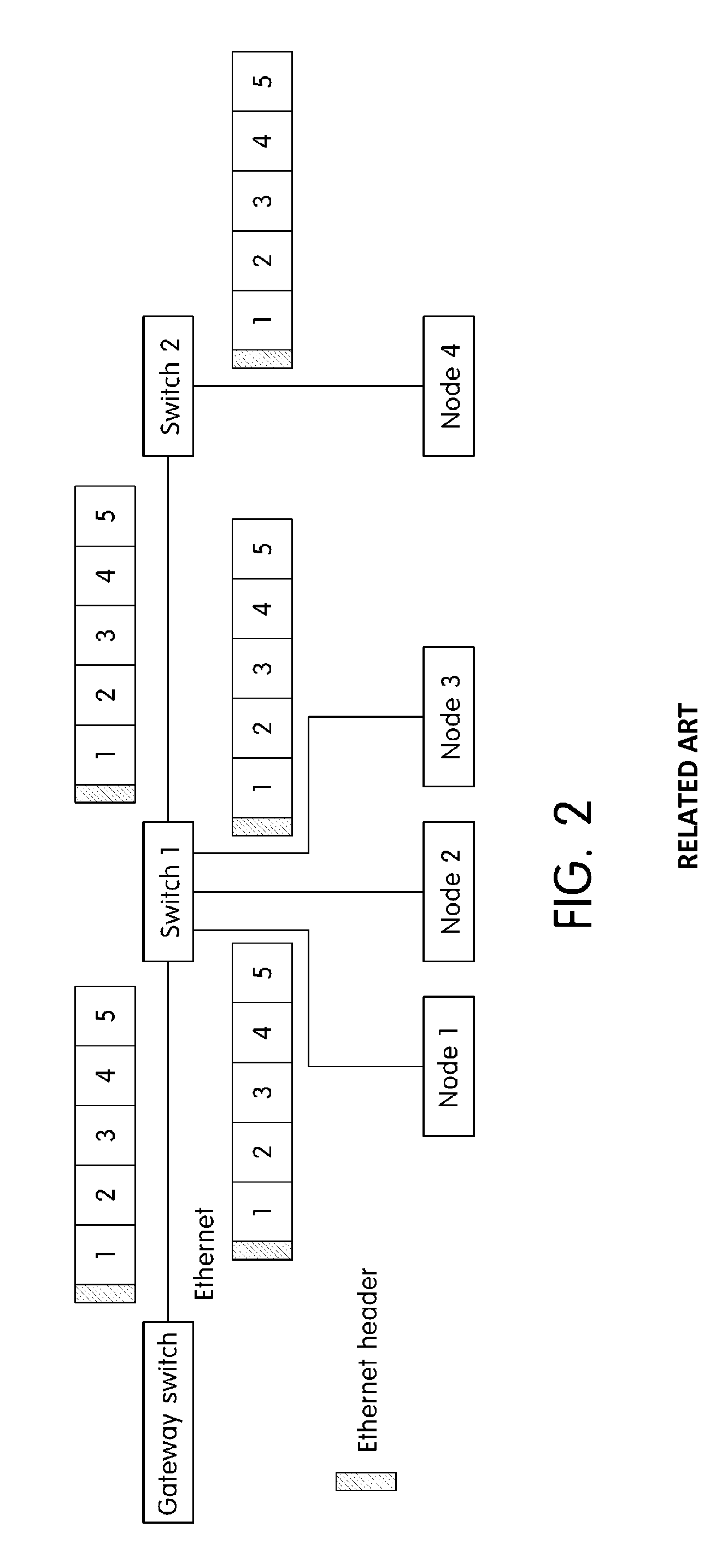
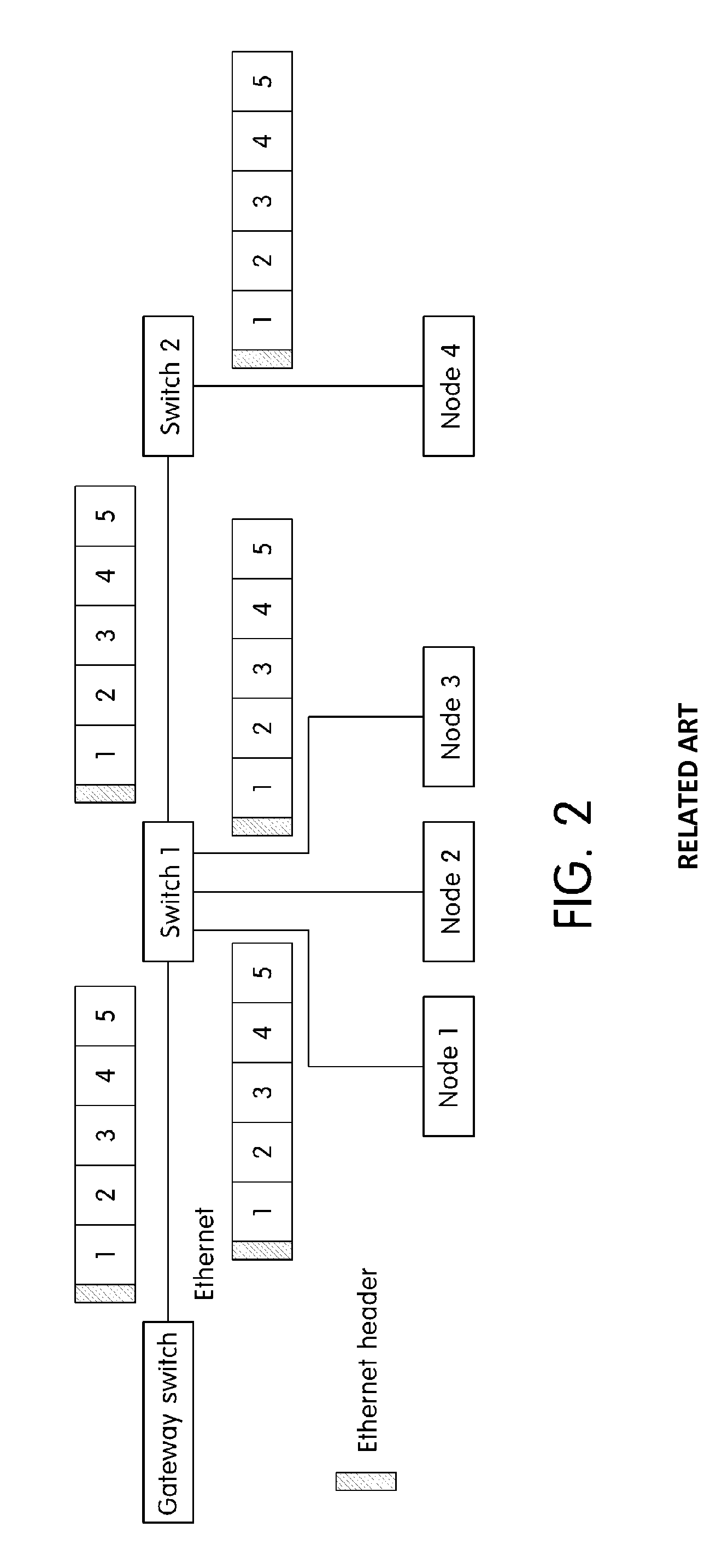
ActiveUS20150003456A1Transmit and receive messages more efficientlyWaste of bandwidthData switching by path configurationNetwork connectionsTransfer systemComputer science
An Ethernet based vehicle network message transferring system is provided that includes a gateway switch that connects the Ethernet to vehicle networks having different protocols and an Ethernet switch that switches Ethernet messages between the gateway switch and vehicle devices to transfer the Ethernet messages. The Ethernet switch includes a processing module that transfers the Ethernet messages received via the gateway switch in the different vehicle networks, a vehicle network process module that switches the messages transferred from the processing module, and a lookup table in which information necessary for switching the vehicle network process module is stored. The vehicle network process module analyzes an Ethernet message transferred via the processing module in the gateway switch to identify destinations of individual messages in the Ethernet message and divides the Ethernet message including information regarding the individual message according to destinations to transmit the divided Ethernet messages to vehicle devices of destinations.
Owner:HYUNDAI MOTOR CO LTD +2
System for providing internet protocol broadcast services and a method thereof
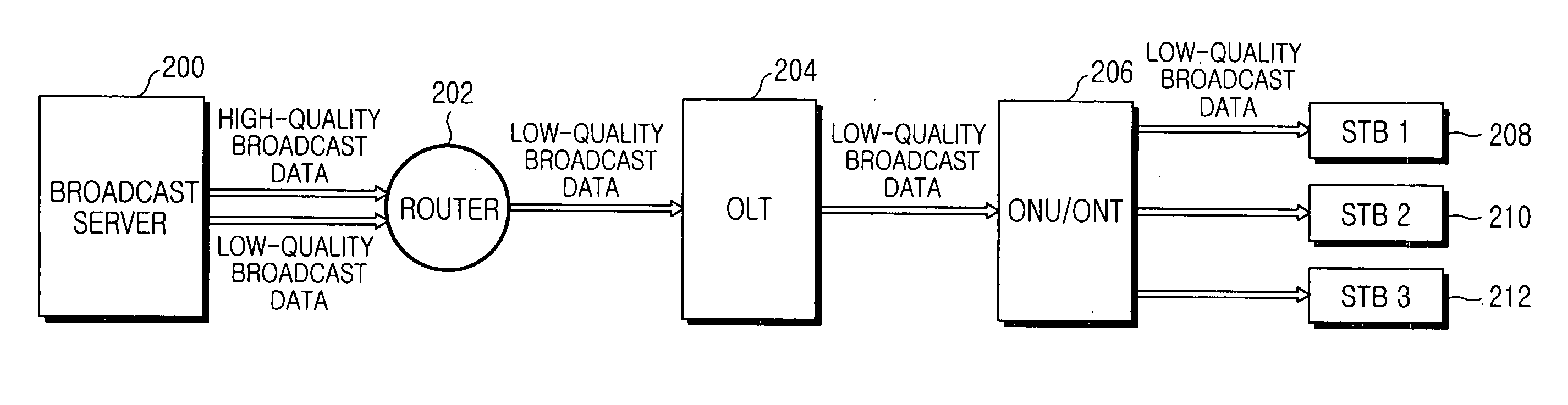
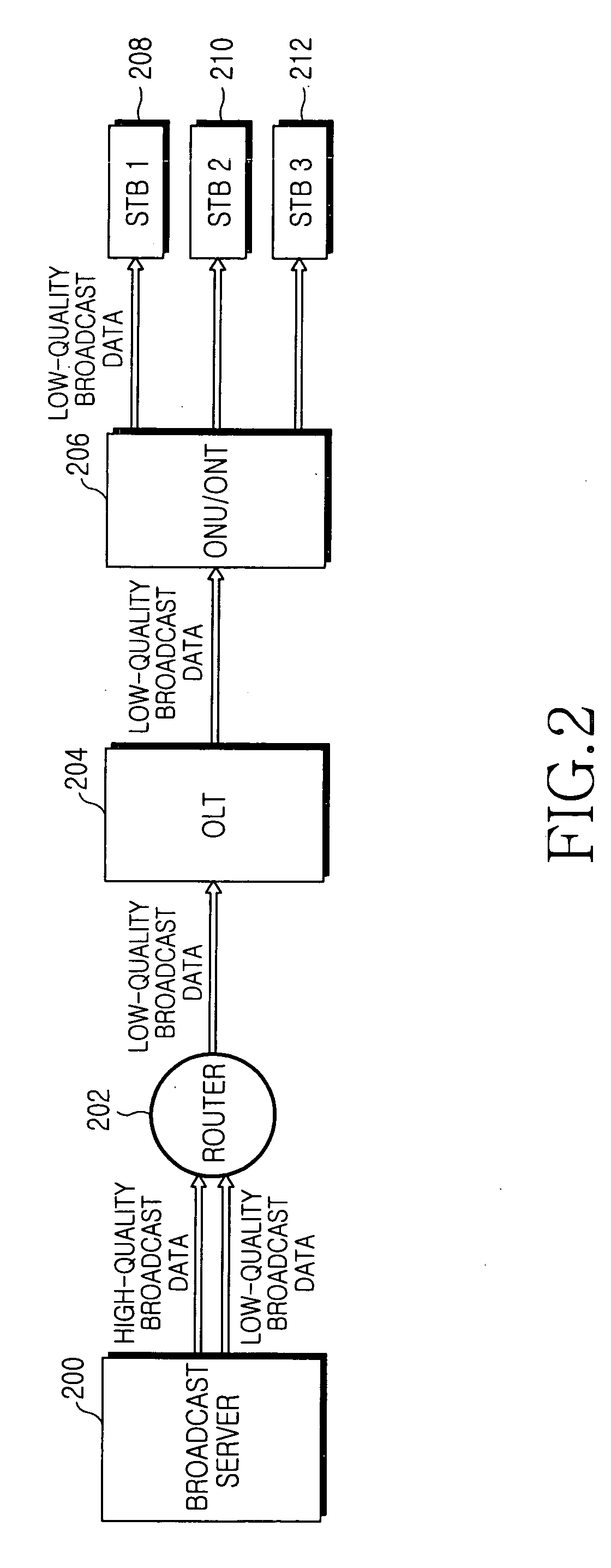
InactiveUS20060182052A1Slow changeWaste of bandwidthSpecial service provision for substationOptical transmission adaptationsBroadcast dataChannel surfing
Disclosed is an IP-based broadcast service system capable of reducing the channel zapping or changing time and the waste of bandwidths during frequent channel changes such as channel surfing. A broadcast server for providing broadcast services generates both high-quality broadcast data and low-quality broadcast data of each TV channel. The broadcast server provides the low-quality broadcast data during a simple channel surfing. When a viewer selects a channel to view, the broadcast server then provides the high-quality broadcast data of the selected channel.
Owner:SAMSUNG ELECTRONICS CO LTD
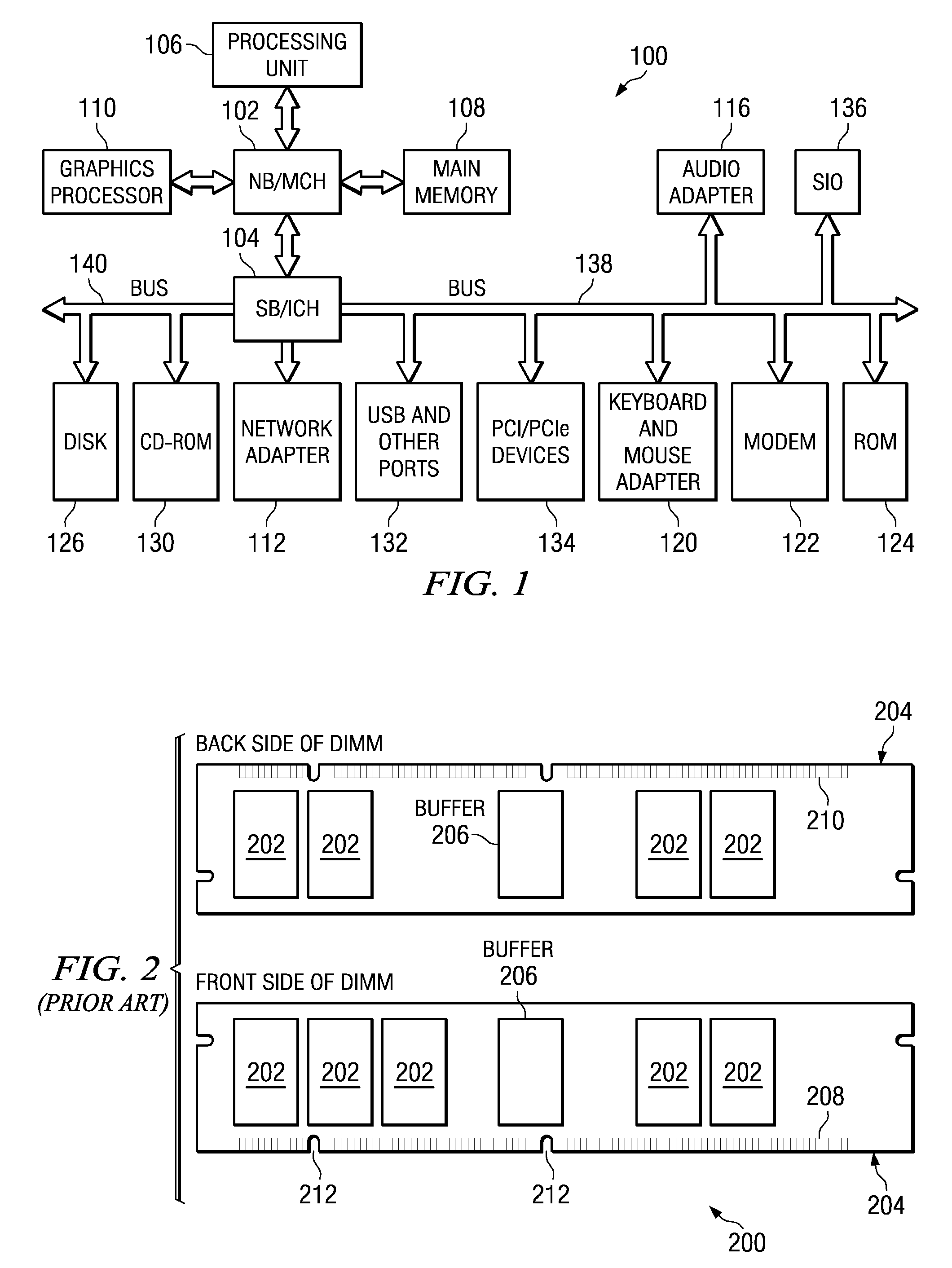
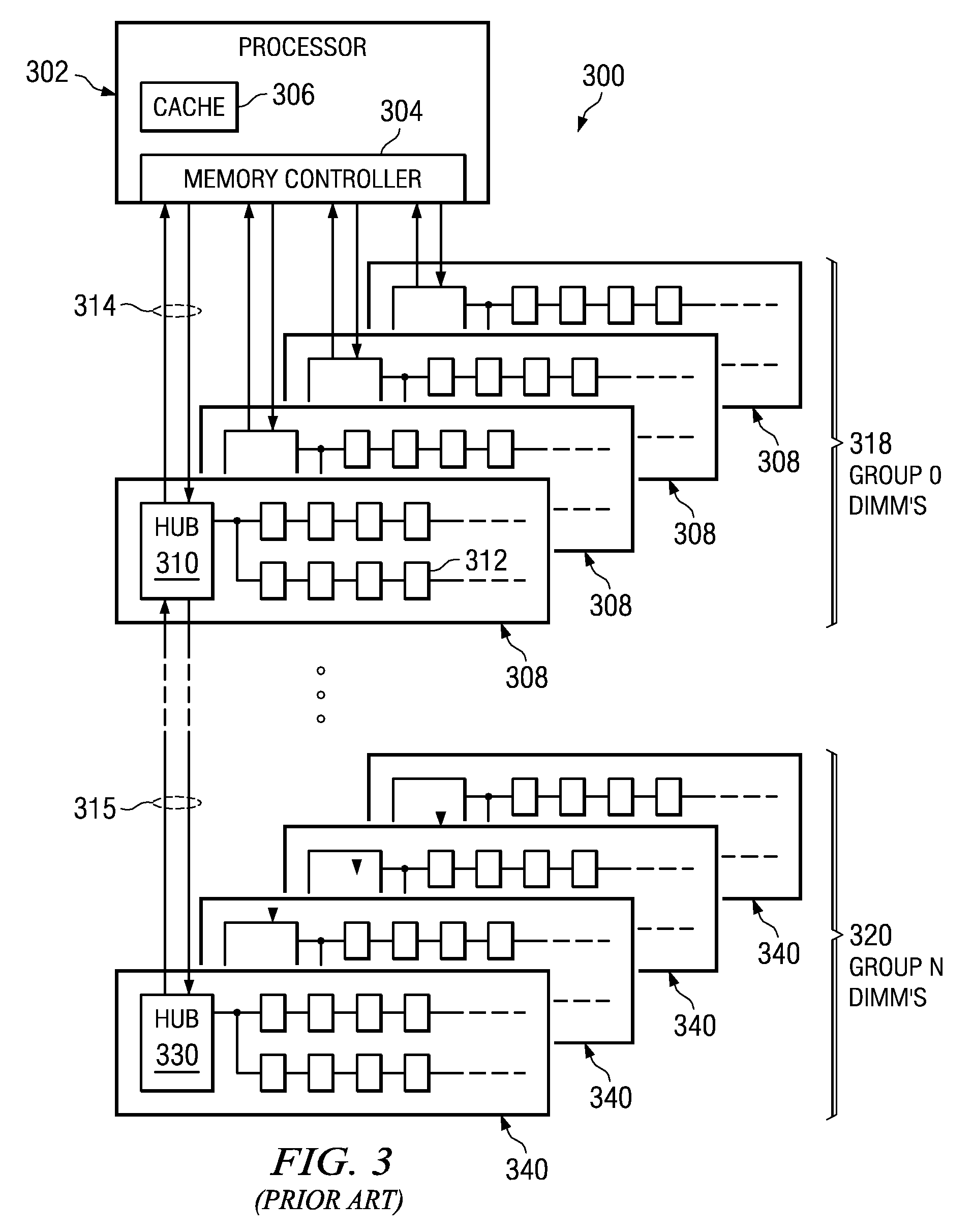
System for Supporting Partial Cache Line Read Operations to a Memory Module to Reduce Read Data Traffic on a Memory Channel
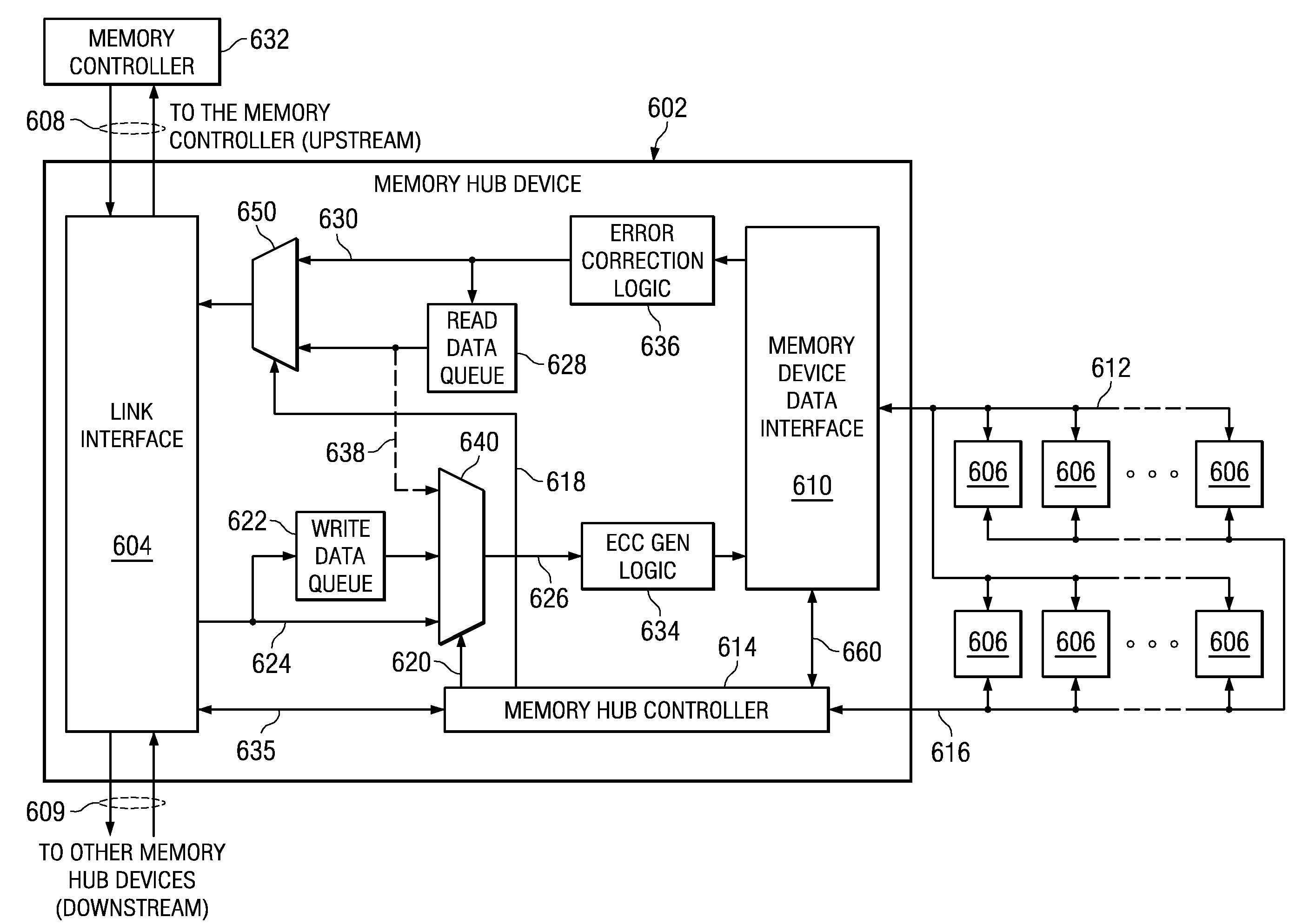
InactiveUS20090063729A1Waste of bandwidthIncreased memory bandwidthError detection/correctionMemory adressing/allocation/relocationTraffic volumeTraffic capacity
A memory system is provided that supports partial cache line read operations to a memory module to reduce read data traffic on a memory channel. The memory system comprises a memory hub device integrated in the memory module and a set of memory devices coupled to the memory hub device. The memory hub comprises burst logic integrated in the memory hub device. The burst logic determines an amount of read data to be transmitted from the set of memory devices and generates a burst length field corresponding to the amount of read data. The memory hub also comprises a memory hub controller integrated in the memory hub device. The memory hub controller controls the amount of read data that is transmitted using the burst length field. The memory hub device transmits the amount of read data that is equal to or less than a conventional data burst amount of data.
Owner:IBM CORP
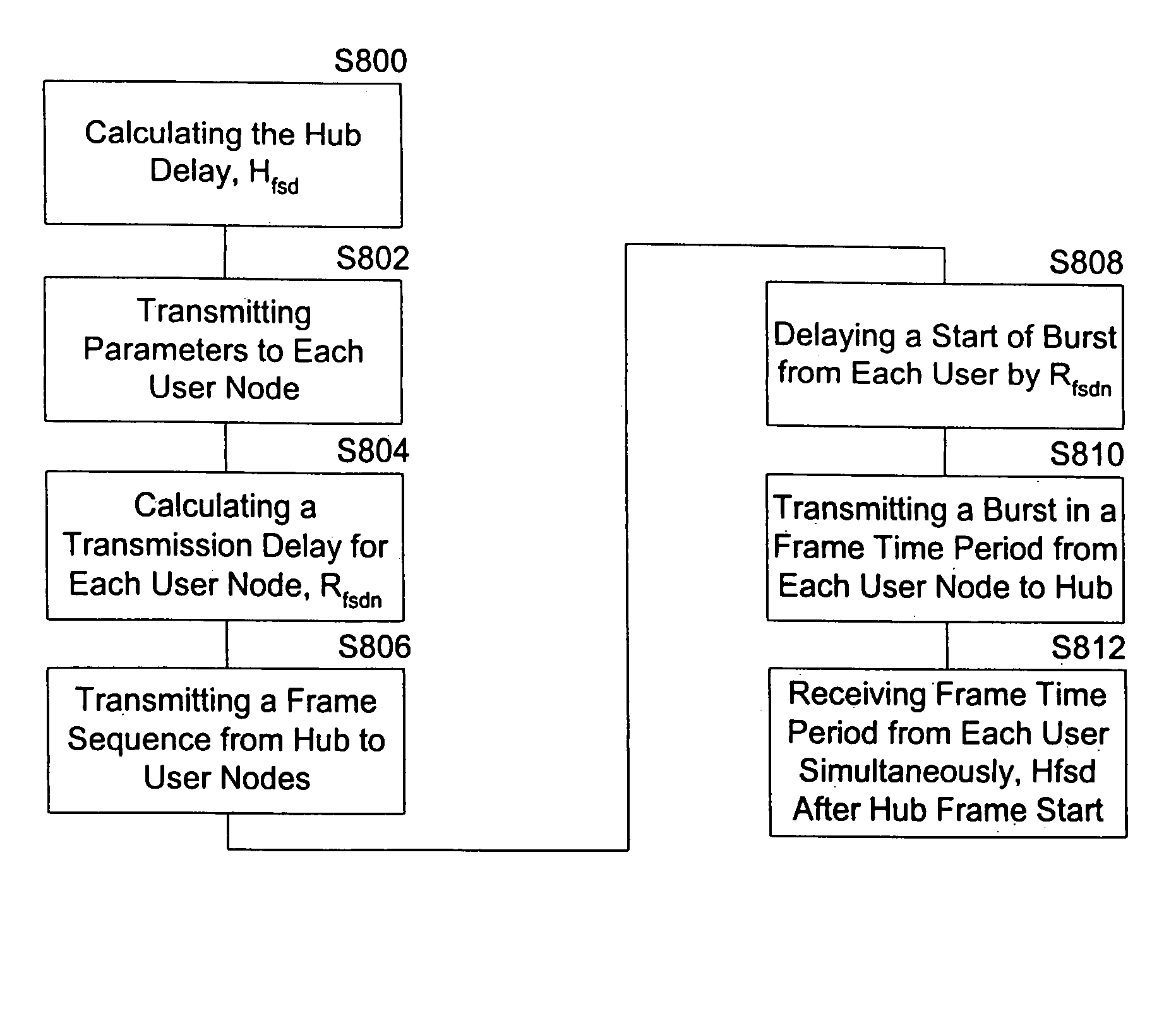
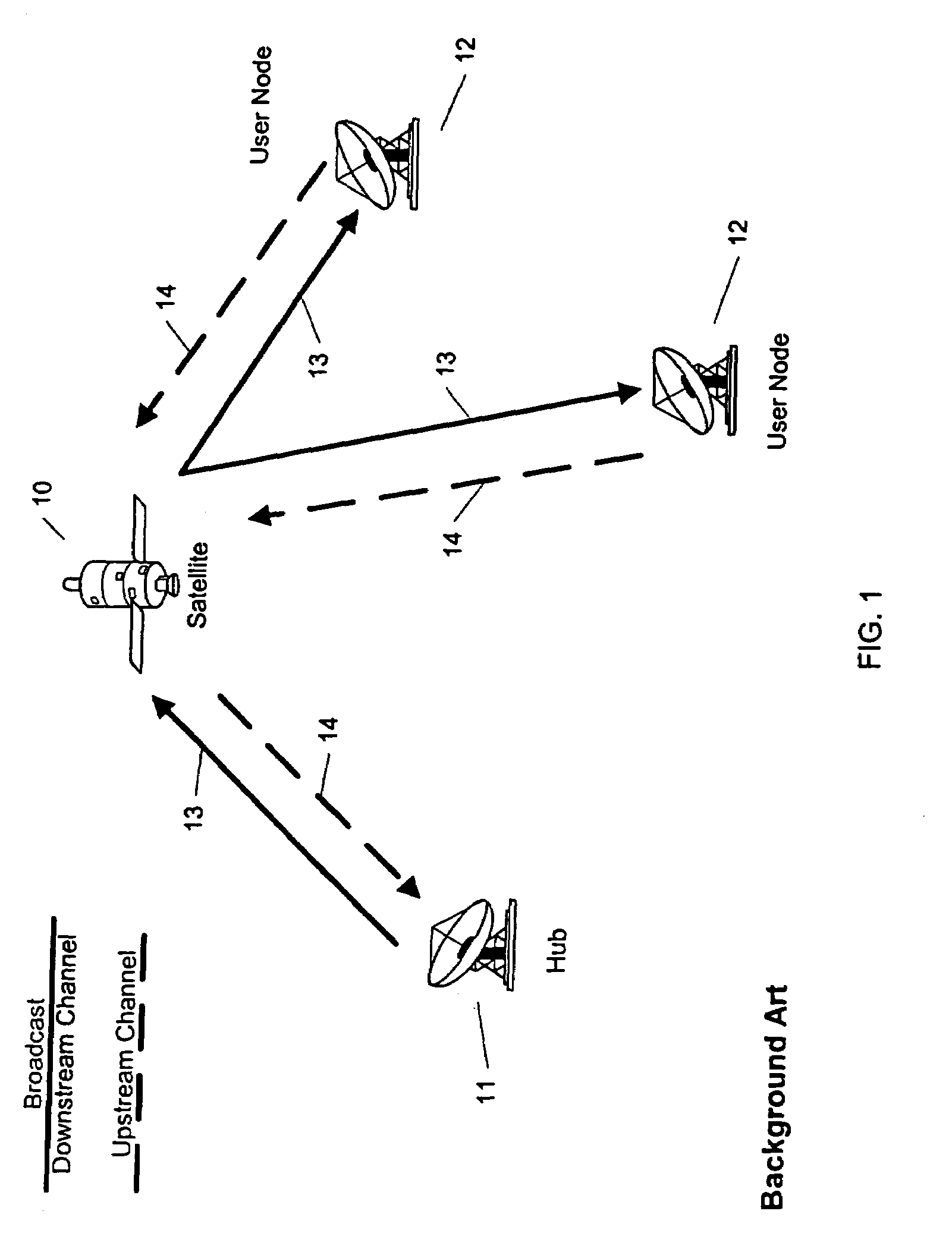
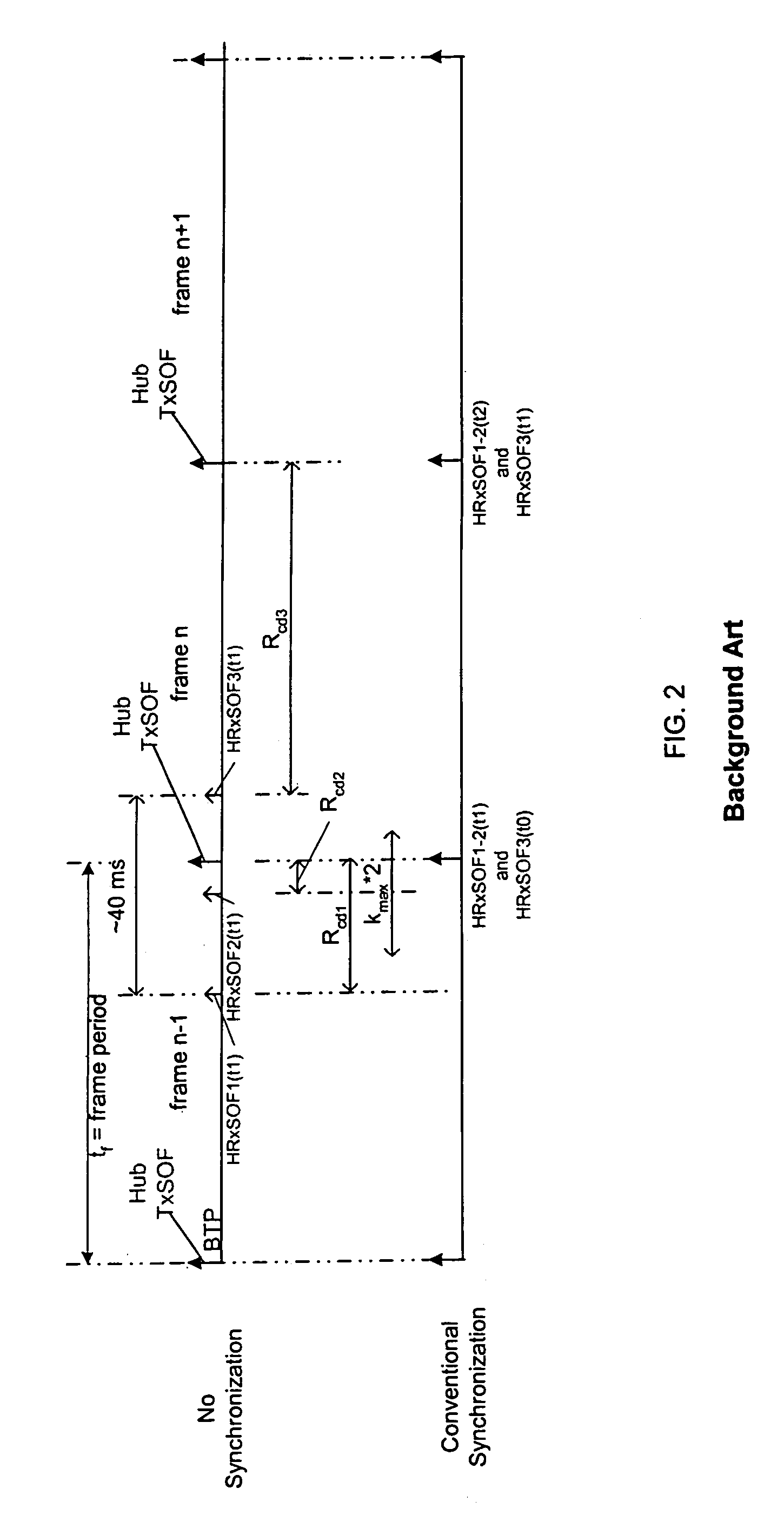
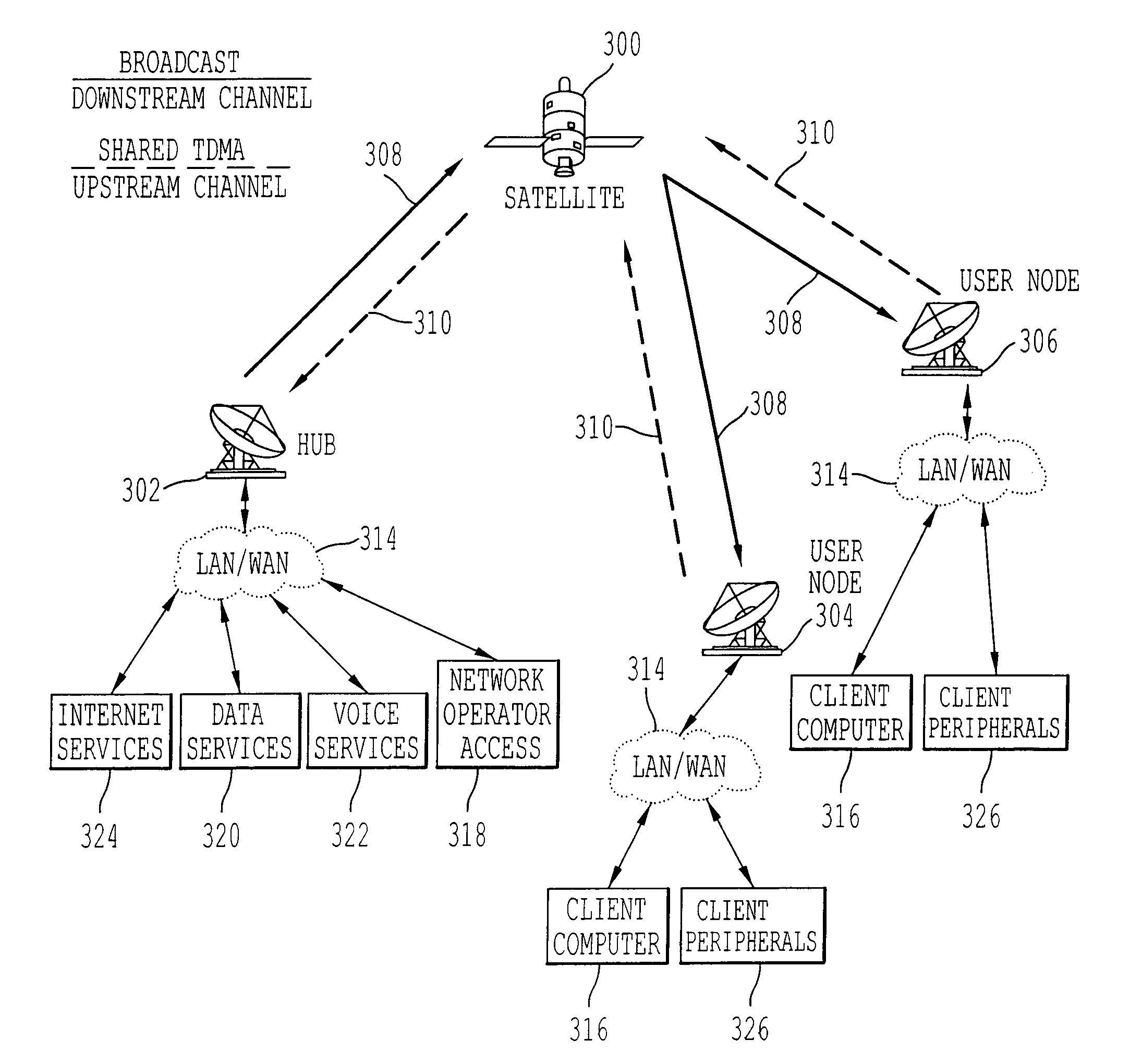
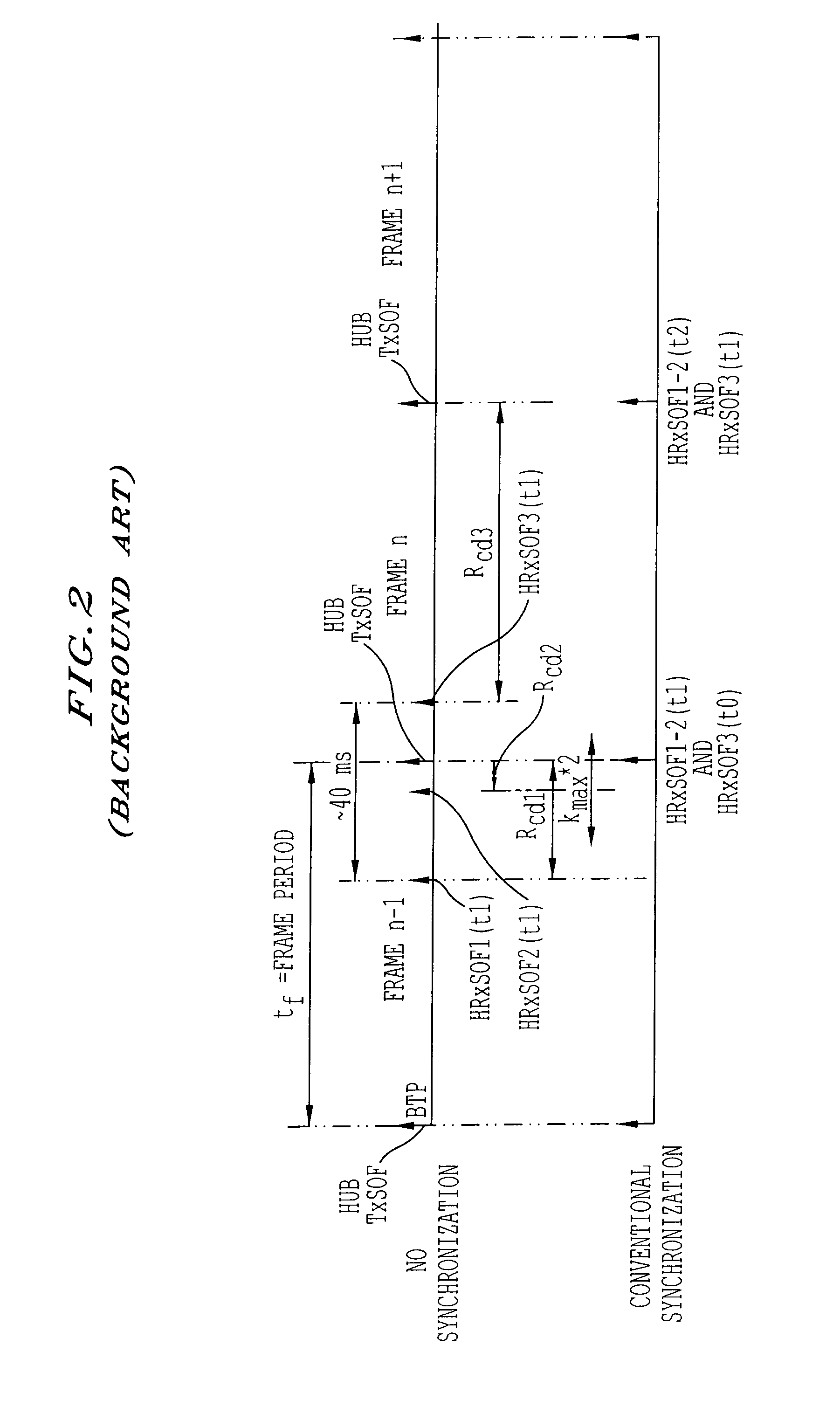
Method, apparatus, and system for using a synchronous burst time plan in a communication network
ActiveUS7257371B1Maximize qualityWork reliablyActive radio relay systemsTime-division multiplexData rateNetwork control
A communication network control method for a communication network including a hub and a plurality of user nodes includes adjusting system parameters to maximize communication data rate and minimize bit error rate given current conditions of the wireless channel, current loading of the network, and user constraints. In particular, the method includes transmitting a first and second frame with first and second control information from the hub to each user node, and transmitting a first and second respective data burst from each of the user nodes to the hub according to the first and second control information. The first data burst from each user node arrives simultaneously at the hub, and the second data burst from each user node arrives simultaneously at the hub. Further, the second data burst from each user node arrives immediately following the arrival of the first data burst from each user node.
Owner:ST ENG IDIRECT INC
Mapping table loading method, memory control circuit unit and memory storage apparatus
ActiveUS20170315925A1Easy to useImprove performanceMemory architecture accessing/allocationVirtual memory detailsComputer moduleOperation mode
A mapping table loading method, a memory control circuit unit and a memory storage apparatus are provided. The method includes: receiving a first command; loading a first sub-logical address-physical address mapping table corresponding to the first command if an operating mode of a non-volatile rewritable memory module is a first operating mode; and loading a first logical address-physical address mapping table corresponding to the first command if the operating mode of the non-volatile rewritable memory module is a second operating mode, wherein the first logical address-physical address mapping table includes the first sub-logical address-physical address mapping table.
Owner:PHISON ELECTRONICS
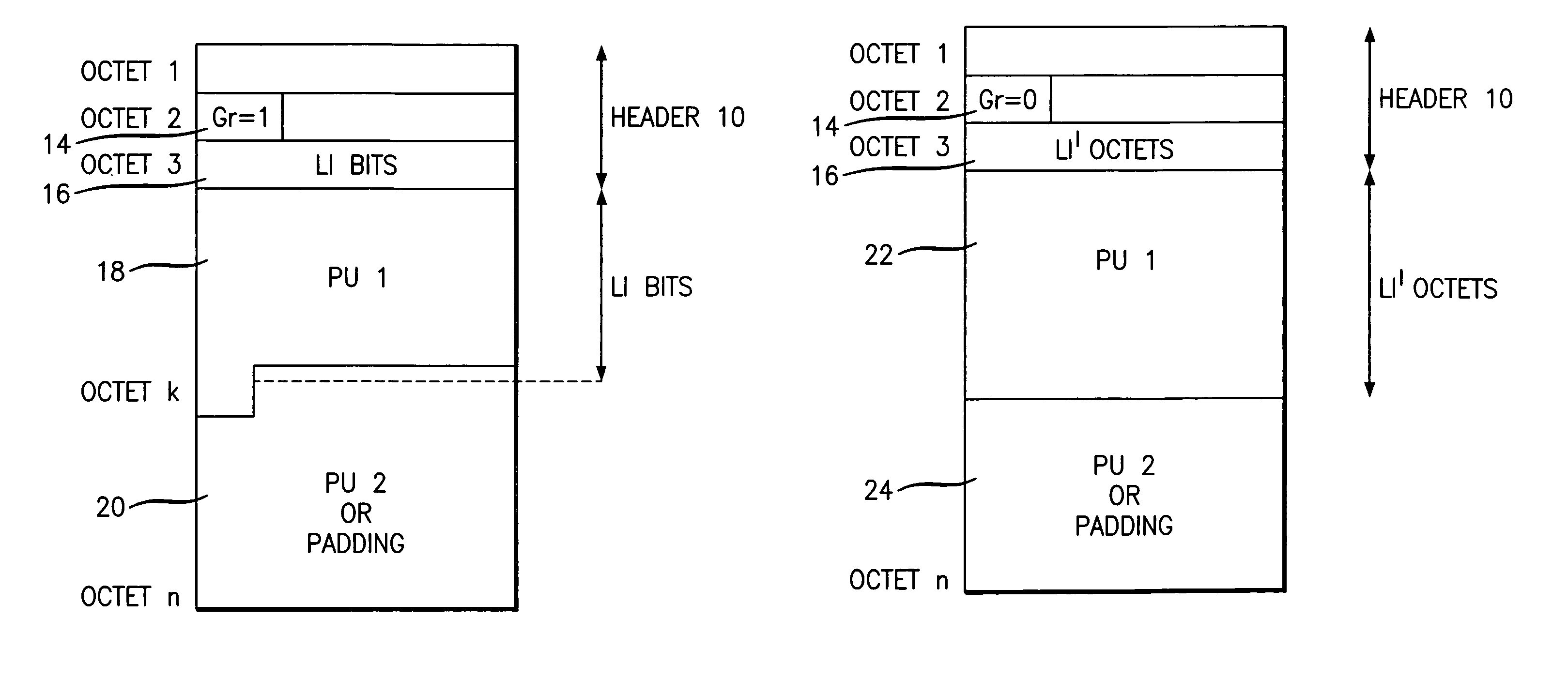
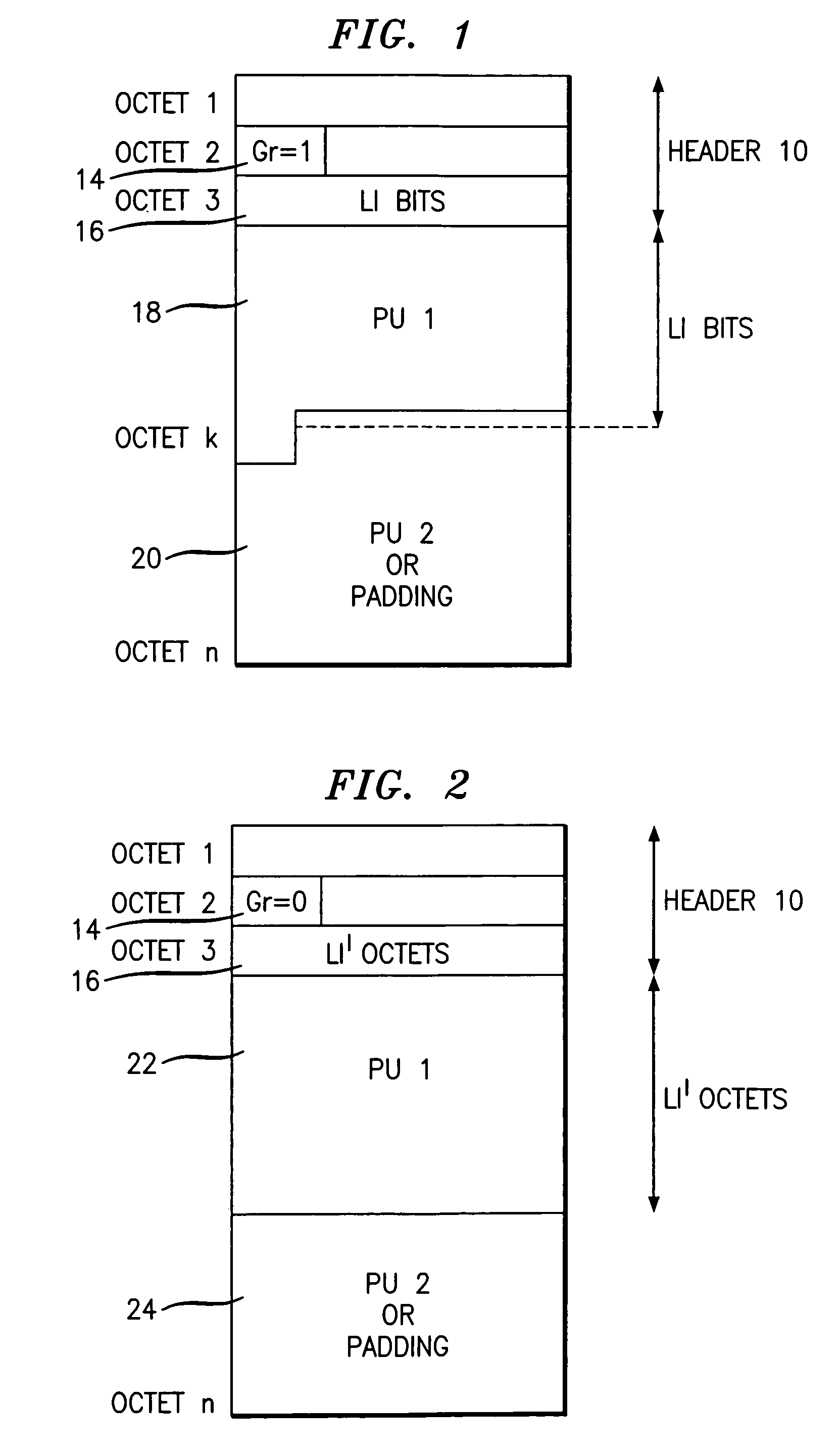
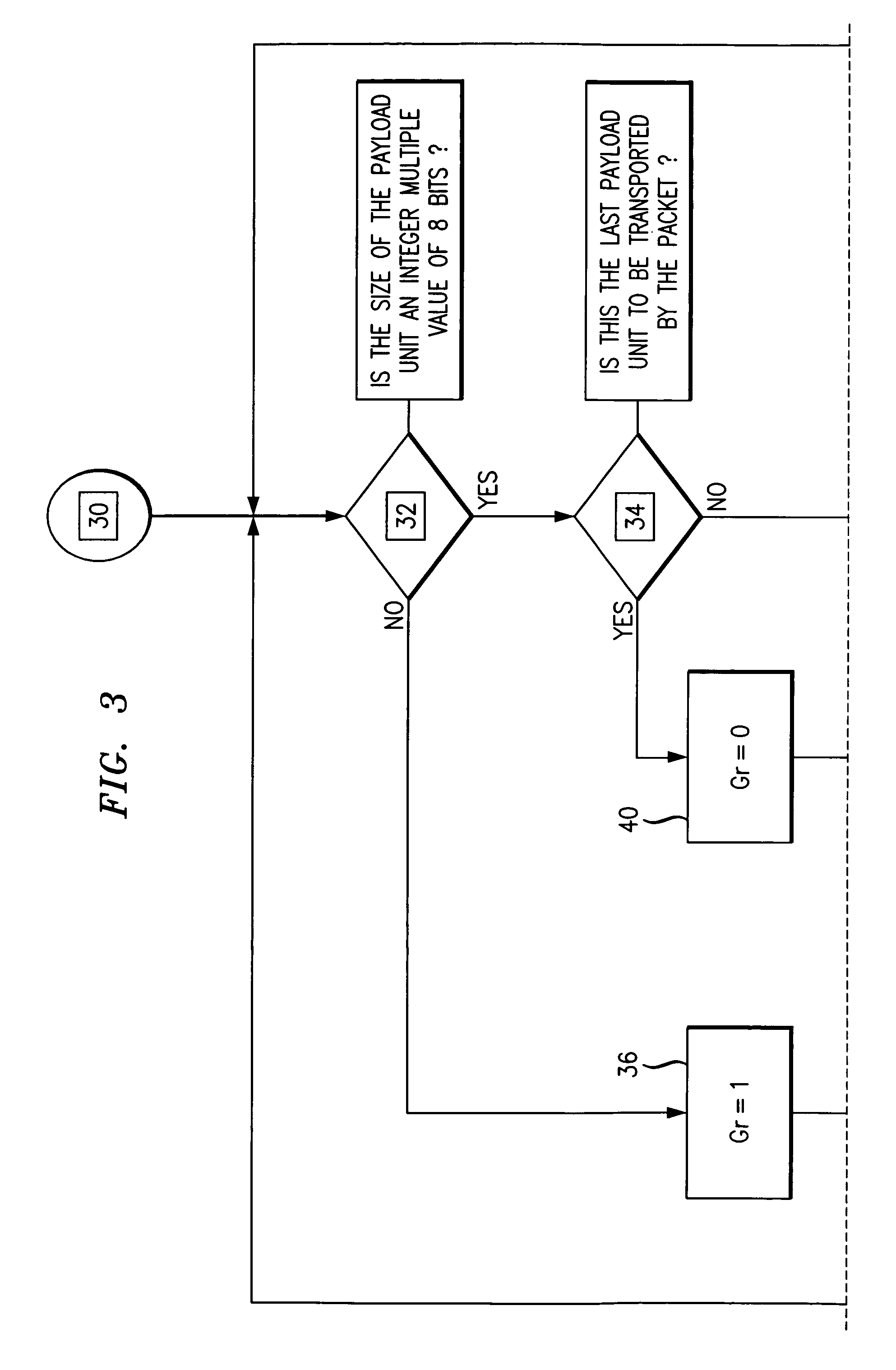
Data packet length indication for mobile telecommunications systems
InactiveUS6956870B1Decrease in LI granularityWaste of bandwidthNetwork traffic/resource managementTime-division multiplexGranularityNetwork packet
In a data packet, e.g. a PDU of the UMTS, a length indicator field of variable granularity is created, depending on the exact length of the payload to be transmitted. An additional field is provided, a single bit in length, to indicate the granularity of the length indicator field. This increases the resolution of the header, whilst keeping low an overhead of extra field bits. The method comprises: assessing the length of the data to determine the appropriate units, from a plurality of possible units, in which the length should be expressed; setting the granularity field to define the appropriate units in which the length of the data is to be indicated; and setting the length indicator field to indicate the data length.
Owner:ALCATEL-LUCENT USA INC +1
Systems and methods for searching of storage data with reduced bandwidth requirements
InactiveUS8725705B2Amount of data can be transmittedReduce the amount requiredDigital data information retrievalError detection/correctionTheoretical computer scienceLinearity
Owner:INT BUSINESS MASCH CORP
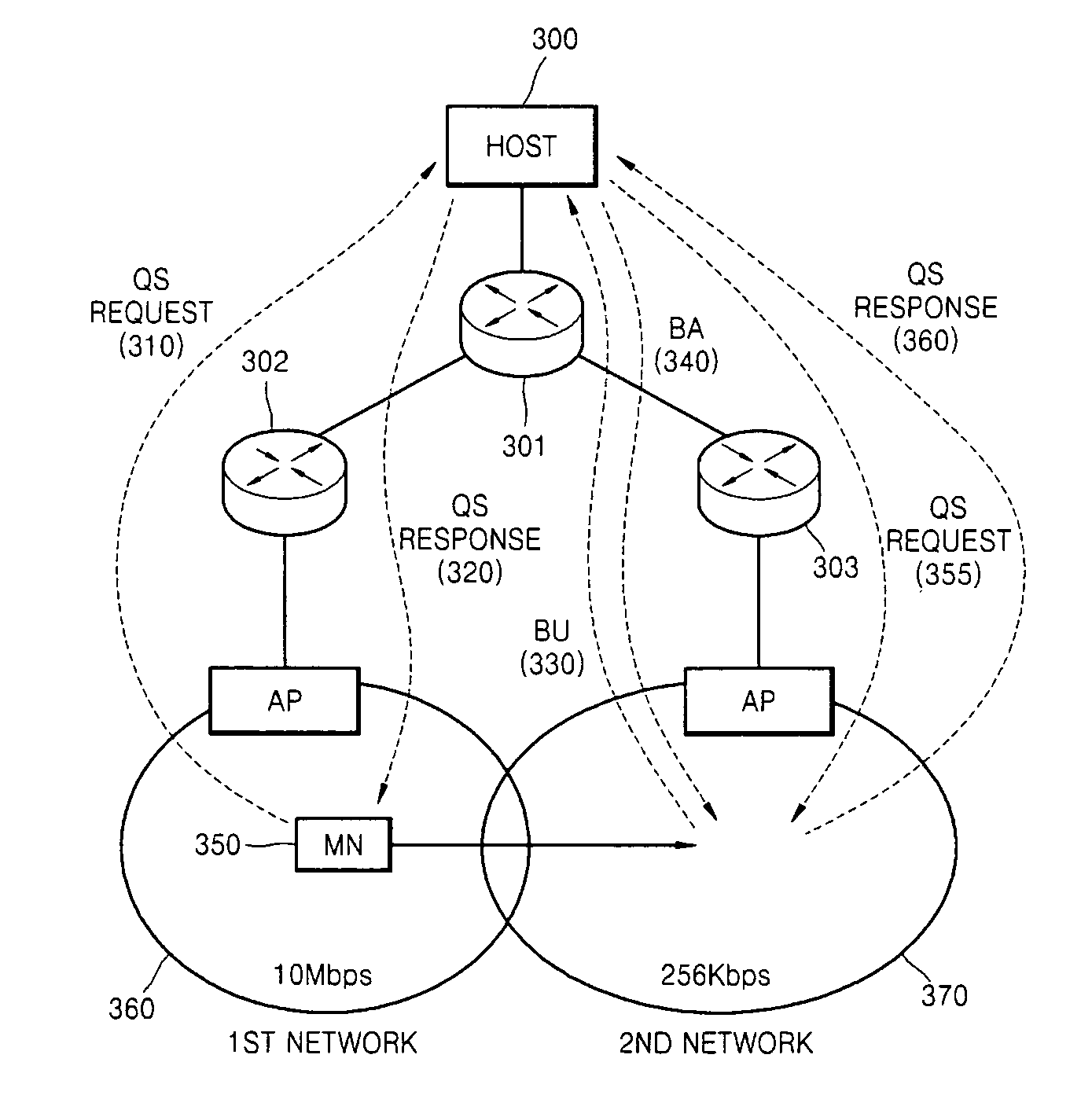
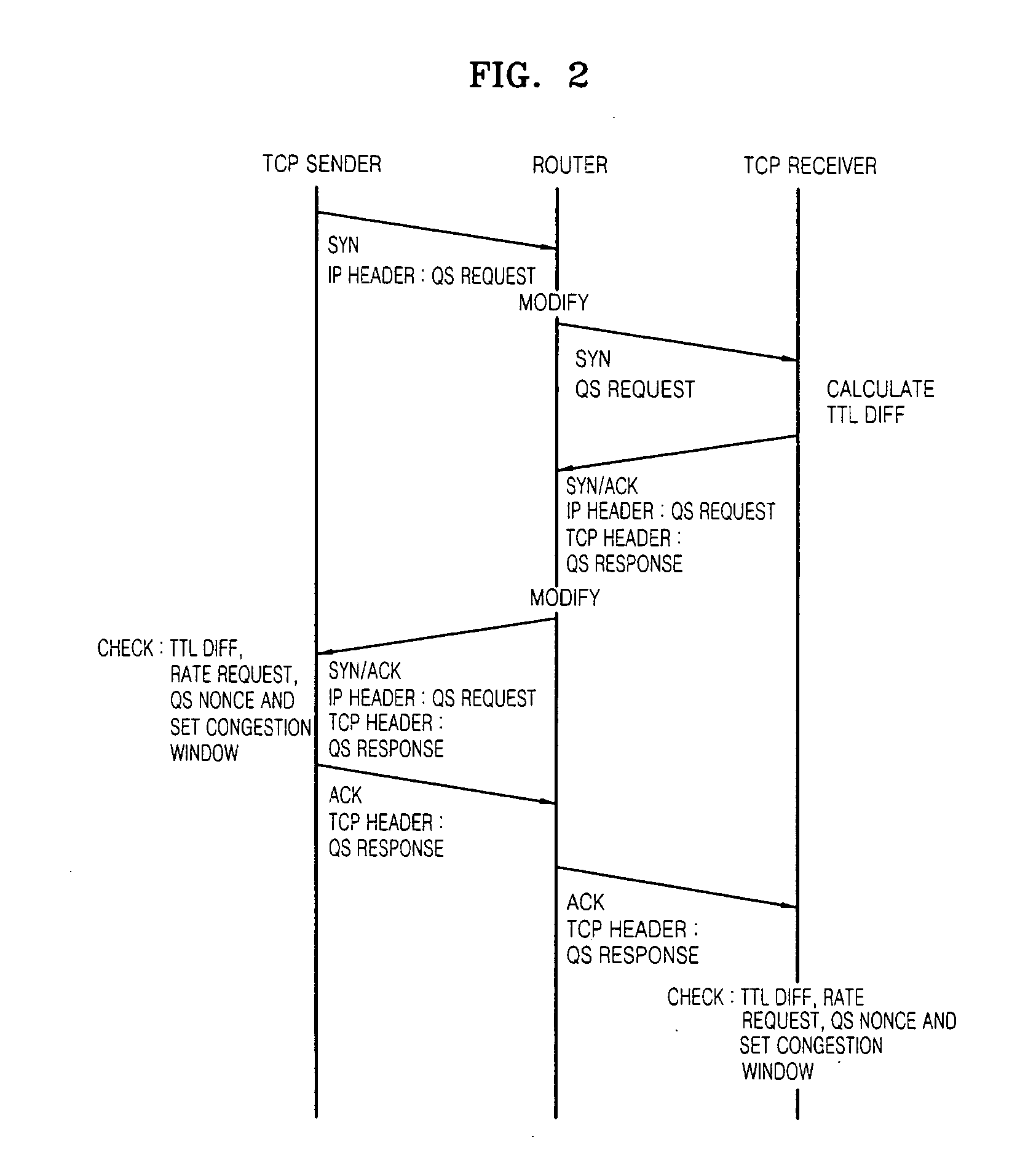
Method and apparatus to perform handover enhancing throughput
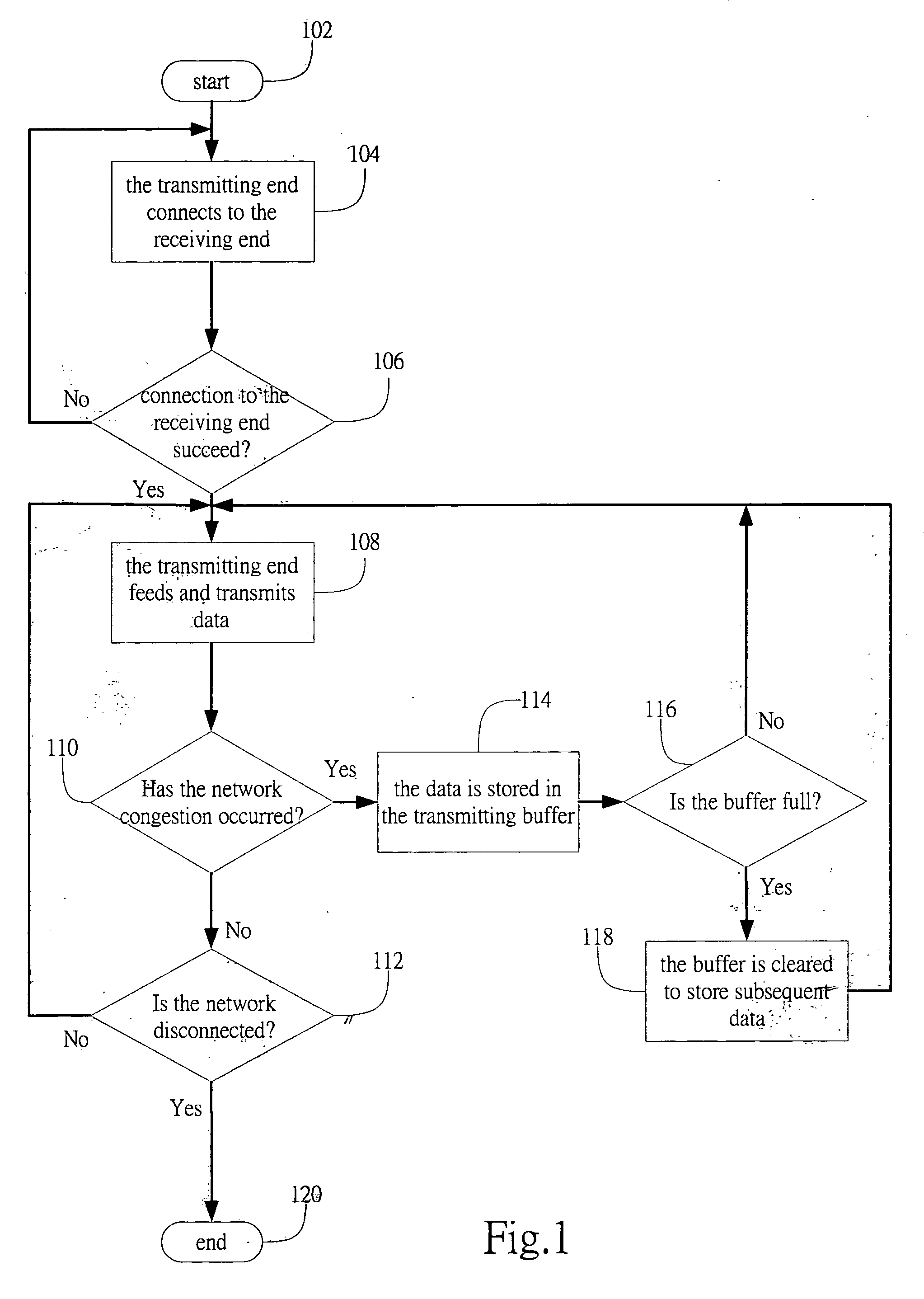
InactiveUS20070280273A1Waste of bandwidthLow costError preventionTransmission systemsCongestion windowPacket loss
A method and apparatus to perform a handover of a mobile terminal that is receiving data, wherein before the handover is performed, the mobile terminal receiving data from a host provides information about a new network to the host by using a quick-start (QS) request message. Accordingly, the host recognizes that a packet loss caused by the handover is not caused by network congestion, and sets the size of a congestion window based on the information on the new network. Accordingly, waste of bandwidth can be reduced compared to that of a conventional slow-start algorithm.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for data transmission
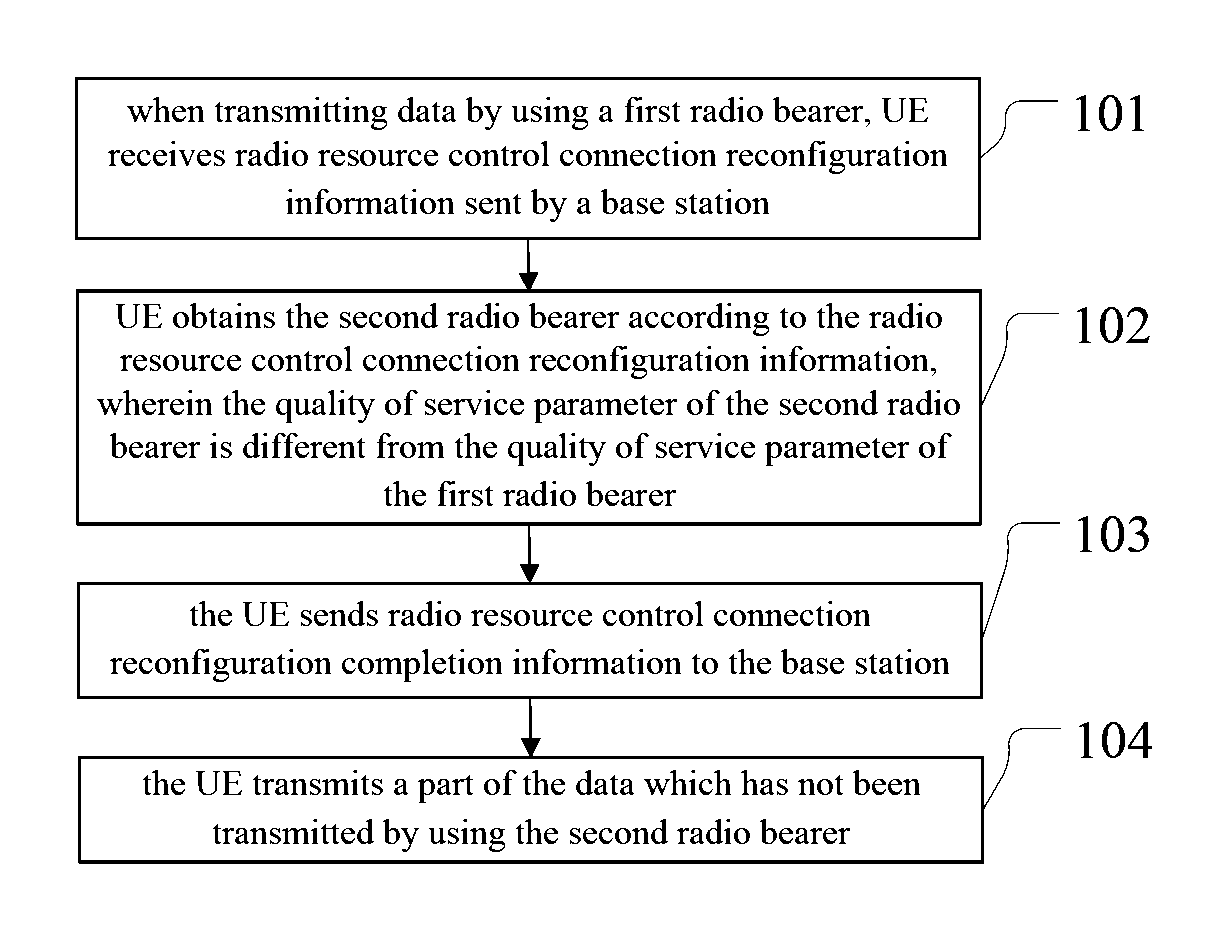
ActiveUS20150296559A1Improve user experienceDecreased video qualityMetering/charging/biilling arrangementsNetwork traffic/resource managementData transmissionRadio Resource Control
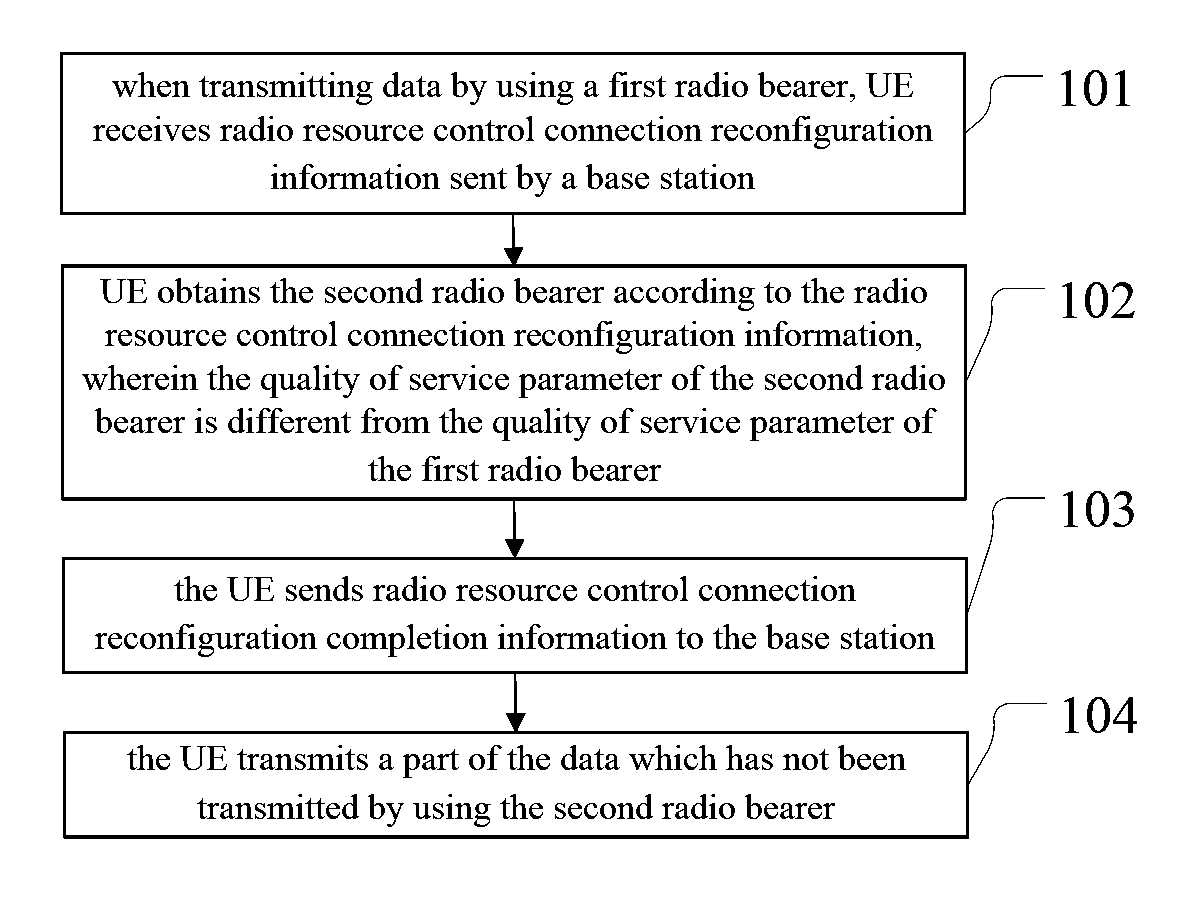
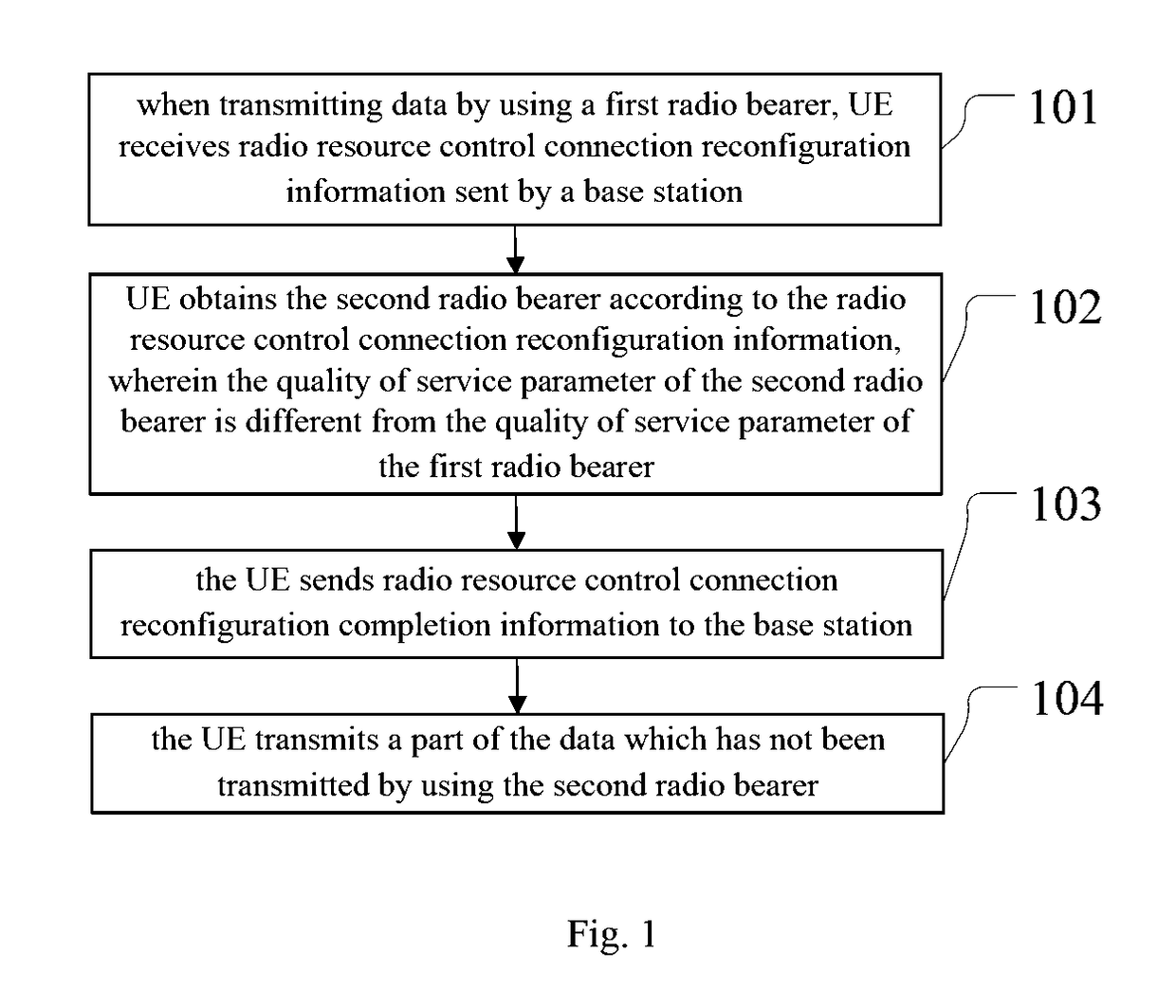
The present invention discloses a data transmission method and apparatus. According to the present invention, when transmitting data by using a first radio bearer, a UE receives radio resource control connection reconfiguration information sent by a base station; the UE obtains a second radio bearer according to the radio resource control connection reconfiguration information; the UE sends radio resource control connection reconfiguration completion information to the base station; the UE transmits a part of the data which has not been transmitted by using the second radio bearer. The solutions provided by the embodiments of the present invention are suitable to be adopted during switch between an adaptive streaming mode and a progressive download mode.
Owner:HUAWEI TECH CO LTD
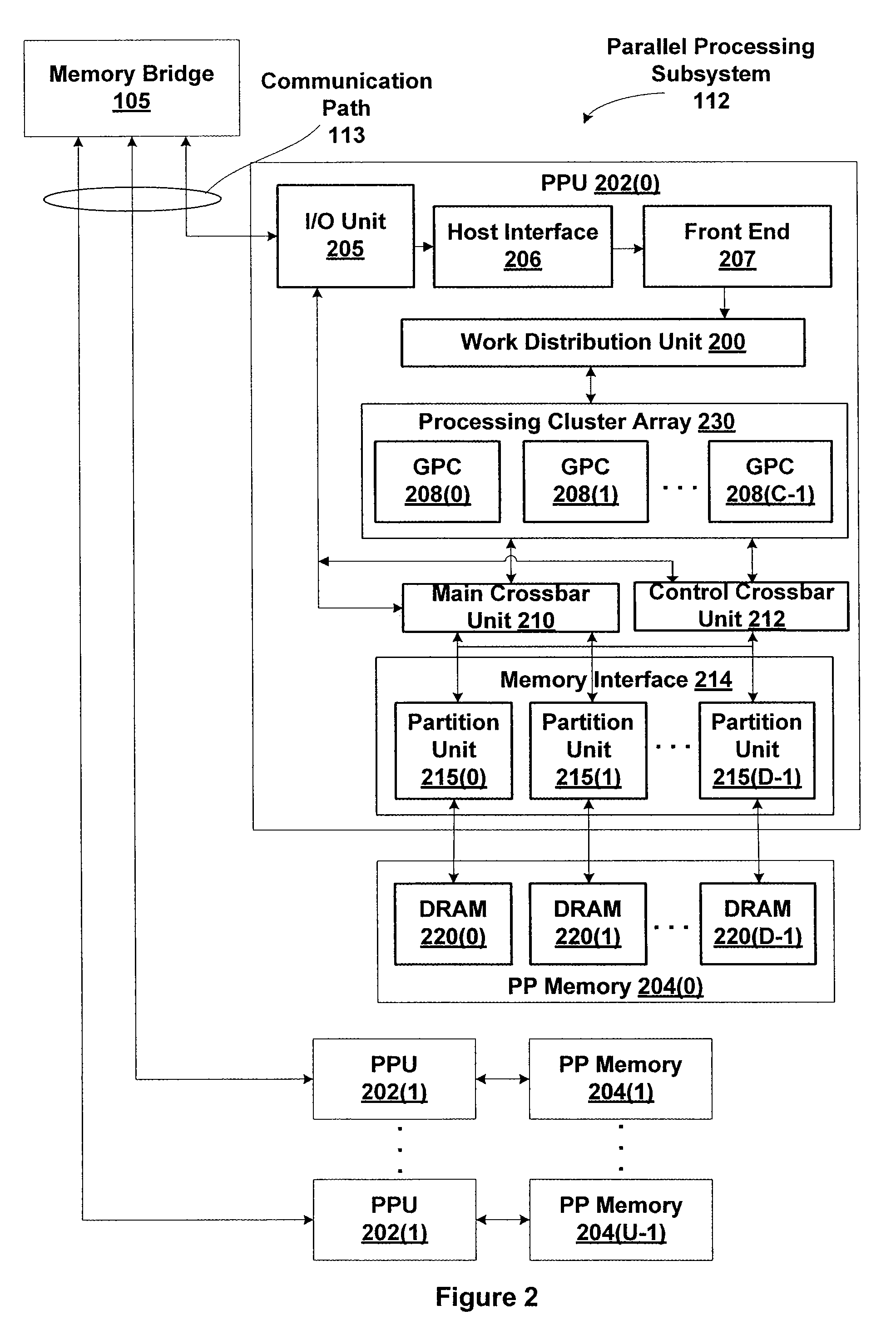
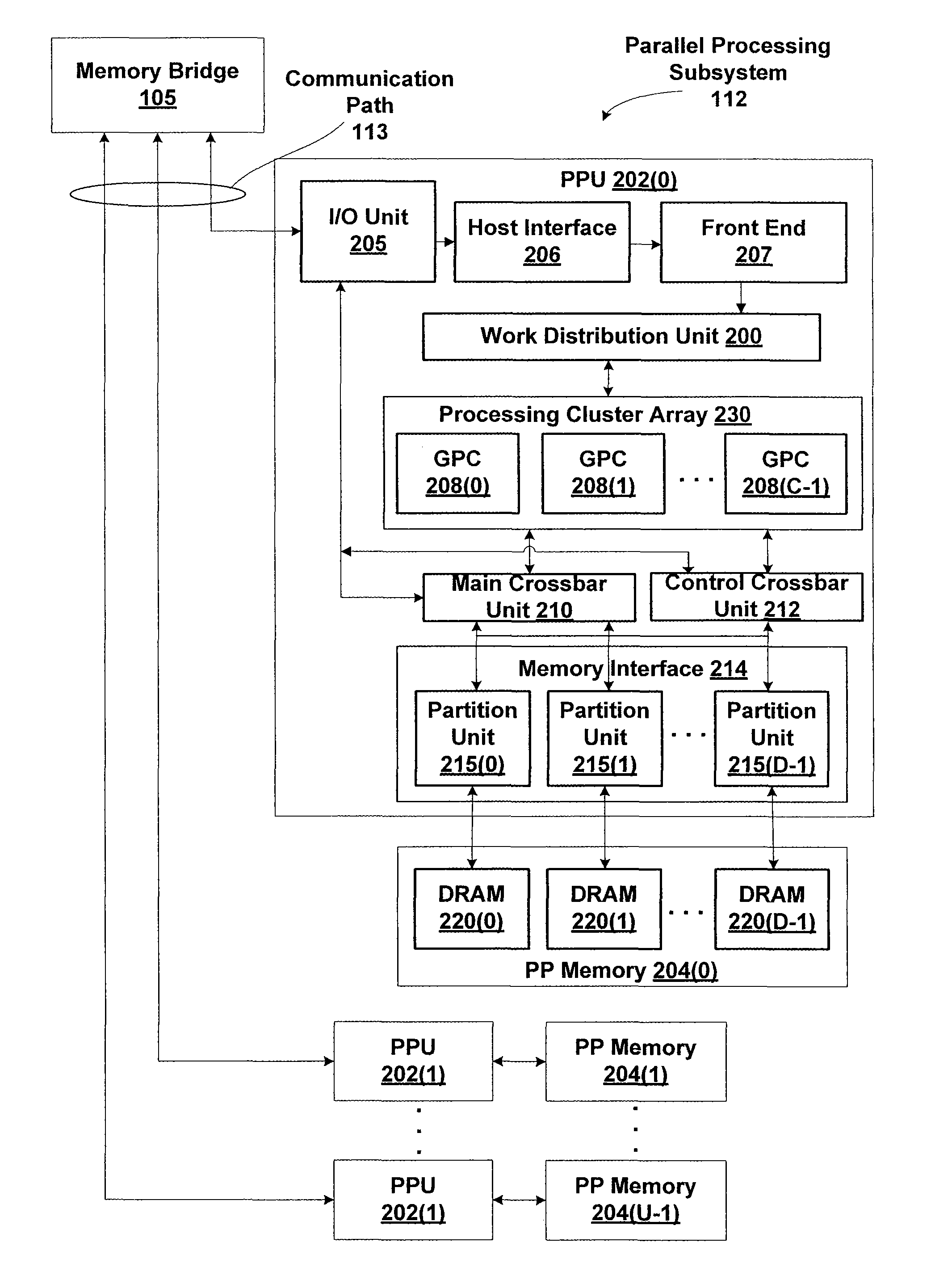
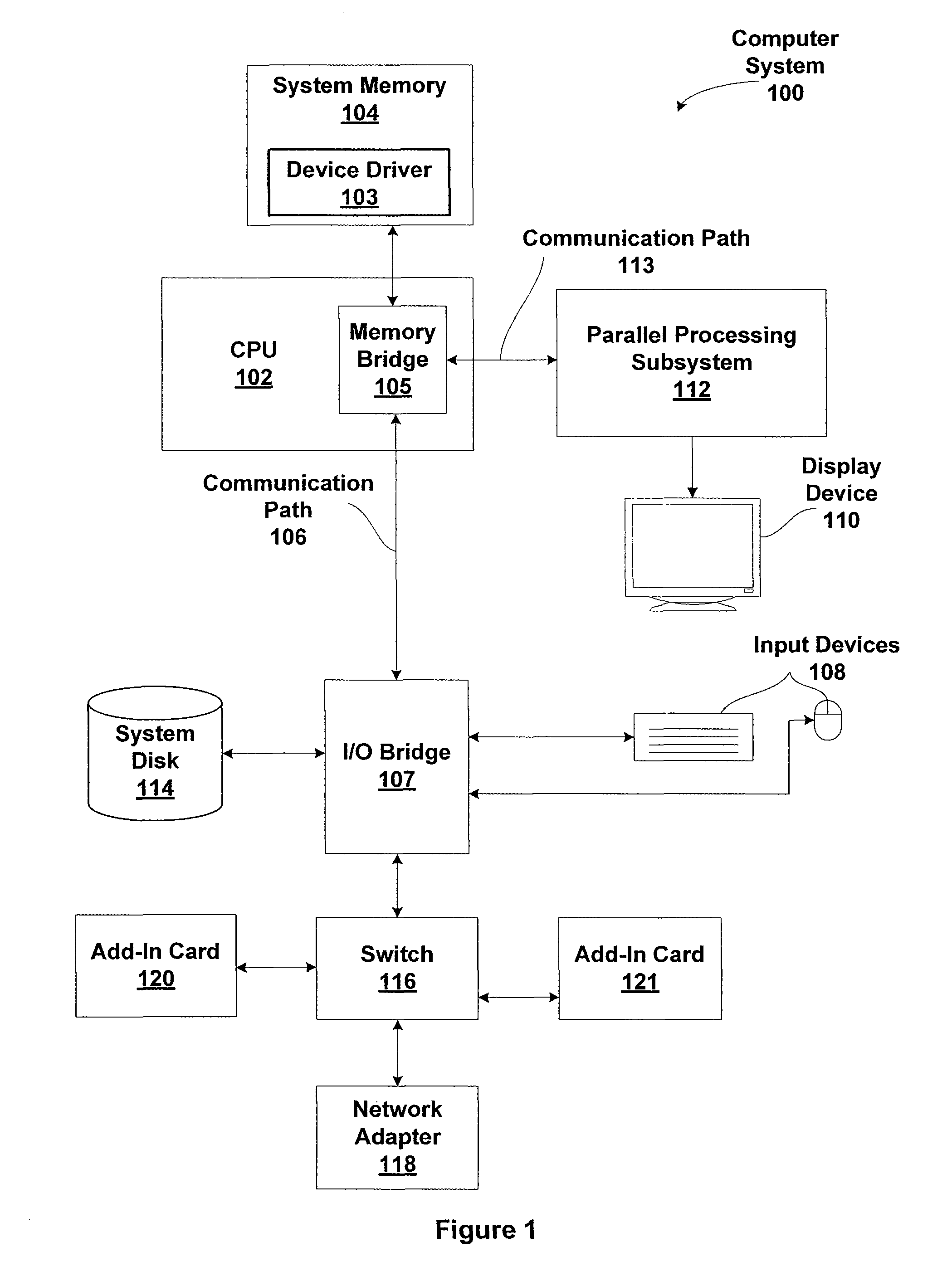
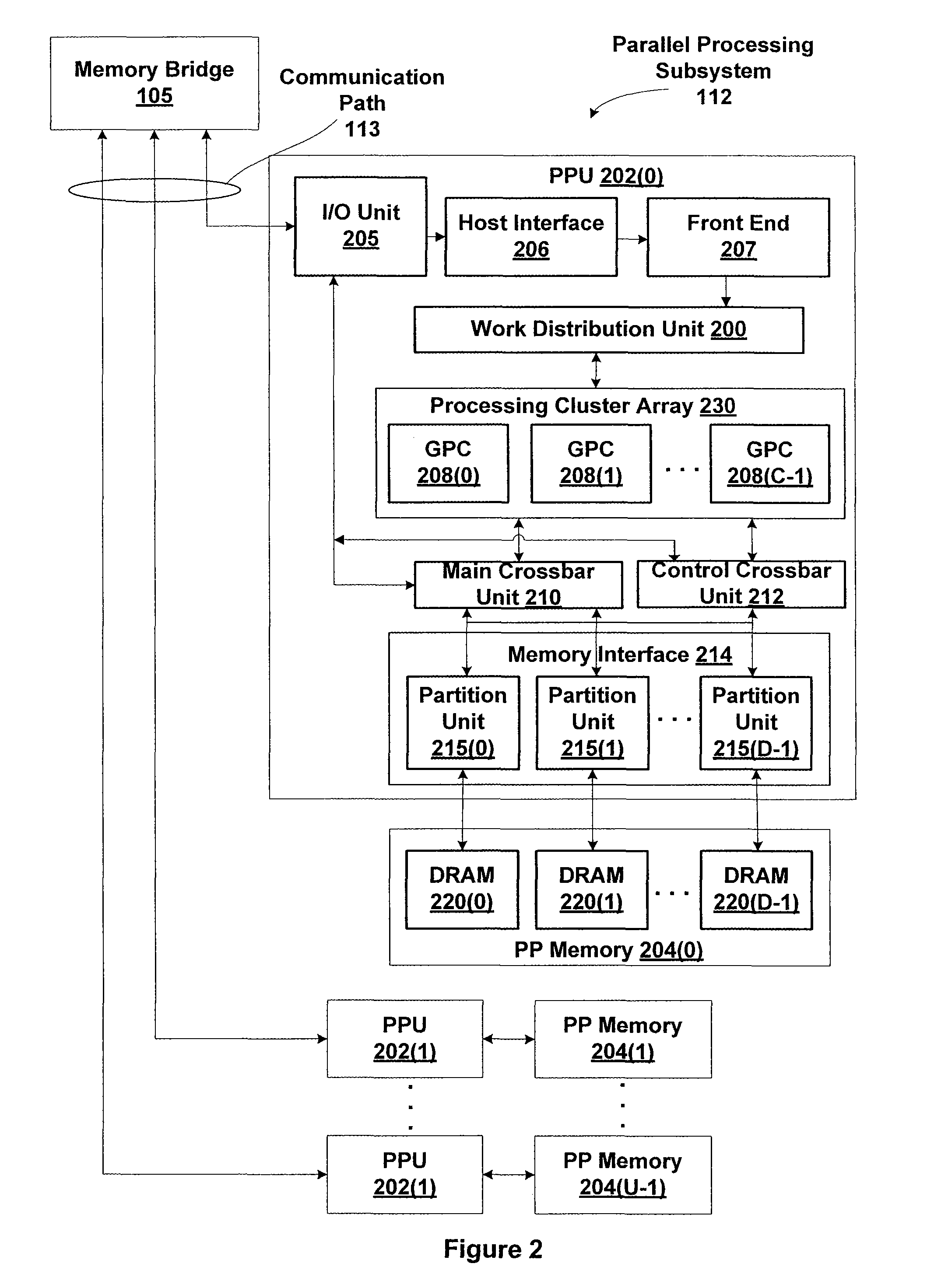
Mitigating main crossbar load using dedicated connections for certain traffic types
ActiveUS8325194B1Reduce loadWaste of bandwidthElectric digital data processingTraffic capacityComputerized system
One embodiment of the invention sets forth a control crossbar unit that is designed to transmit control information from control information generators to destination components within the computer system. The control information may belong to various traffic paradigms, such as short-latency data traffic, narrow-width data traffic or broadcast data traffic. The physical connections within the control crossbar unit are categorized based on the different types of control information being transmitted through the control crossbar unit. The physical connections belong to the following categories: one-to-one (OTO) connections, one-to-many (OTM) connections, valid-to-one (VTO) connections, valid-to-many (VTM) connections wire-to-one (WTO) connections and wire-to-many (WTM) connections.
Owner:NVIDIA CORP
Method, apparatus, and system for transmitting control information in a communication network
ActiveUS7675879B1Maximize qualityWork reliablyEnergy efficient ICTFrequency-division multiplex detailsComputer networkComputer science
Owner:VT IDIRECT
Apparatus, method, system and software product for a scheduling synchronization mechanism in a multi-hop environment
InactiveUS20080043747A1No delayWaste of bandwidthNetwork topologiesData switching by path configurationMulti hop relayWireless network
A method is disclosed for commencing distributed scheduling of uplink communication, in a component of a multihop relay system of a wireless network. The component sends information that is related to the scheduling, to a direct downlink neighbor along a multihop path. This information at least indicates a time interval available for the uplink communication, that time interval corresponding to a hop of the path between the neighbor and the component. The time interval is shorter for a hop that is downstream from another hop which corresponds to a longer time interval.
Owner:NOKIA CORP
Numerical controller for communication with I/O units
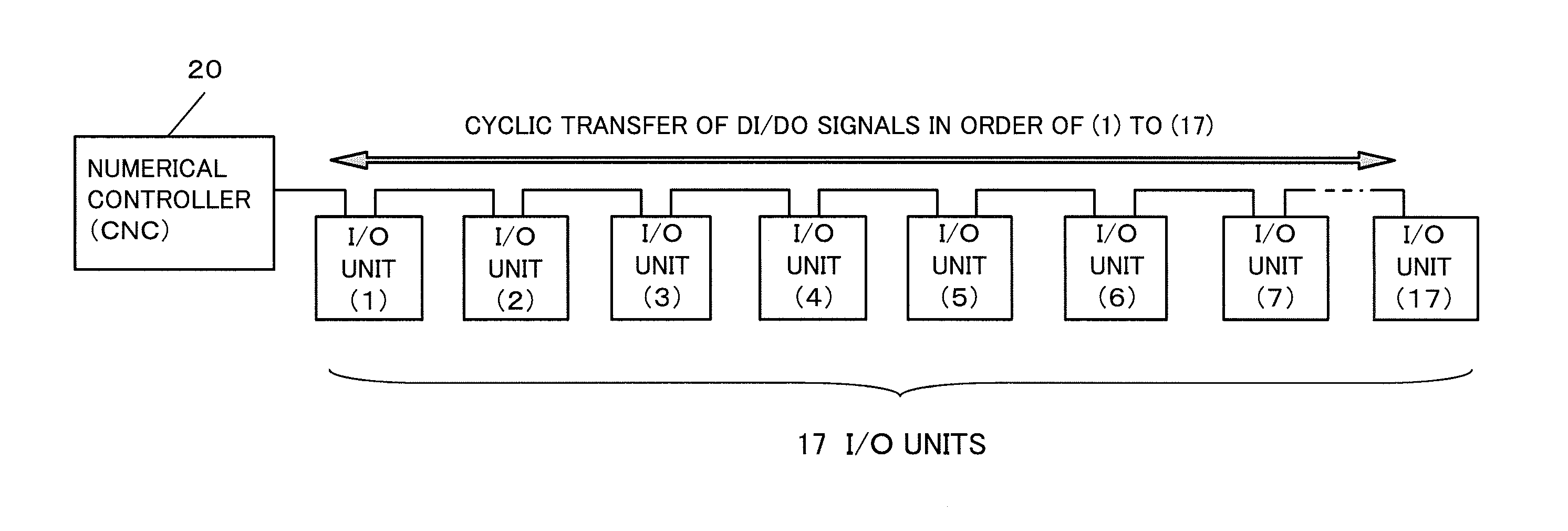
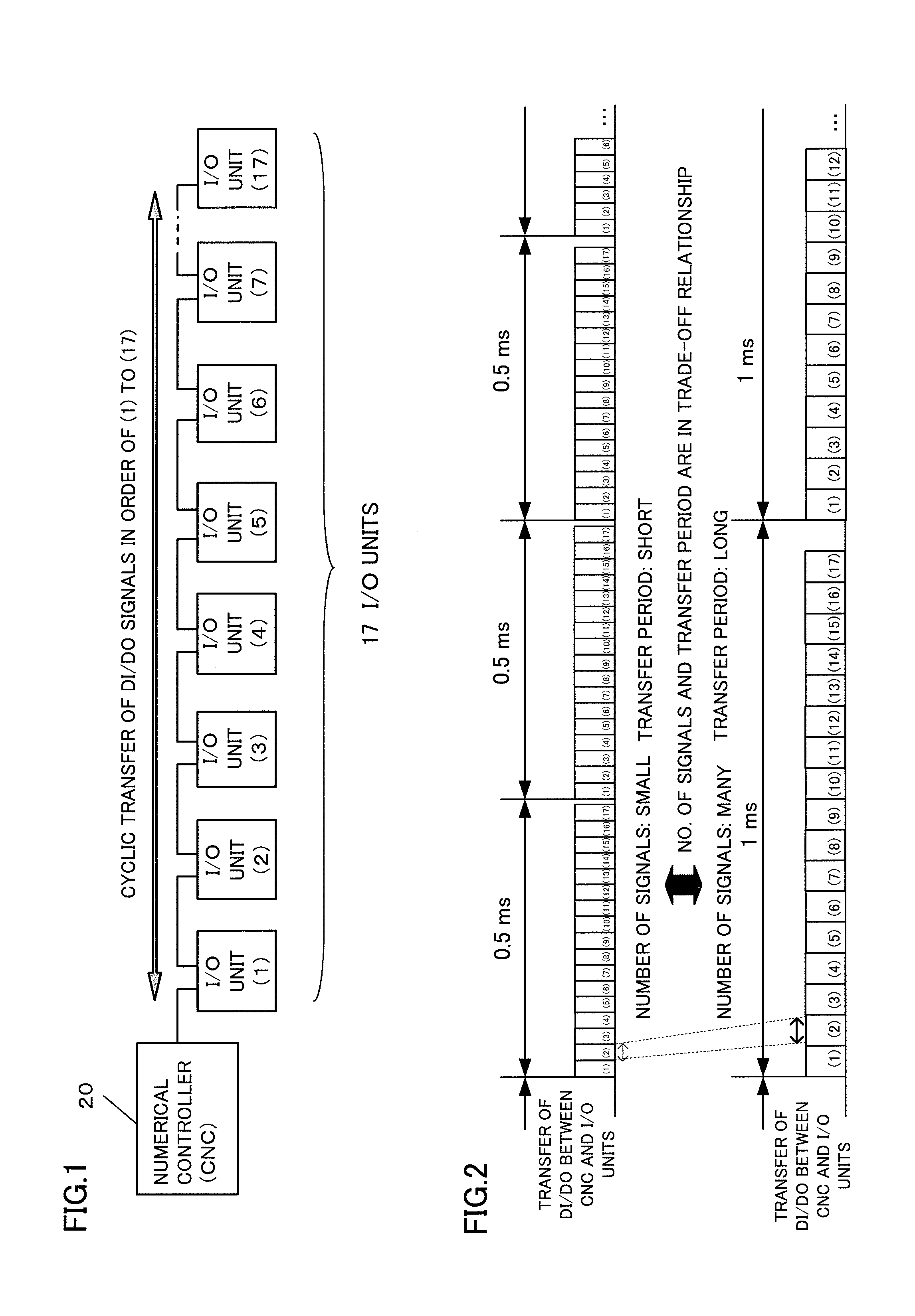
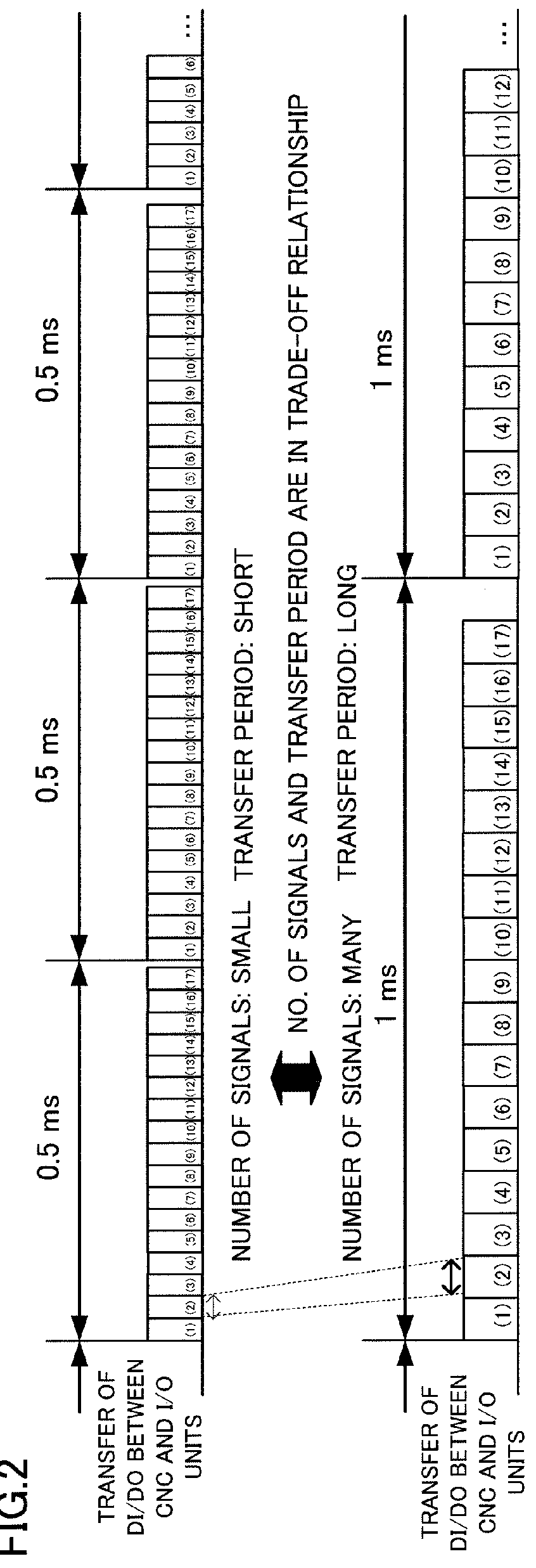
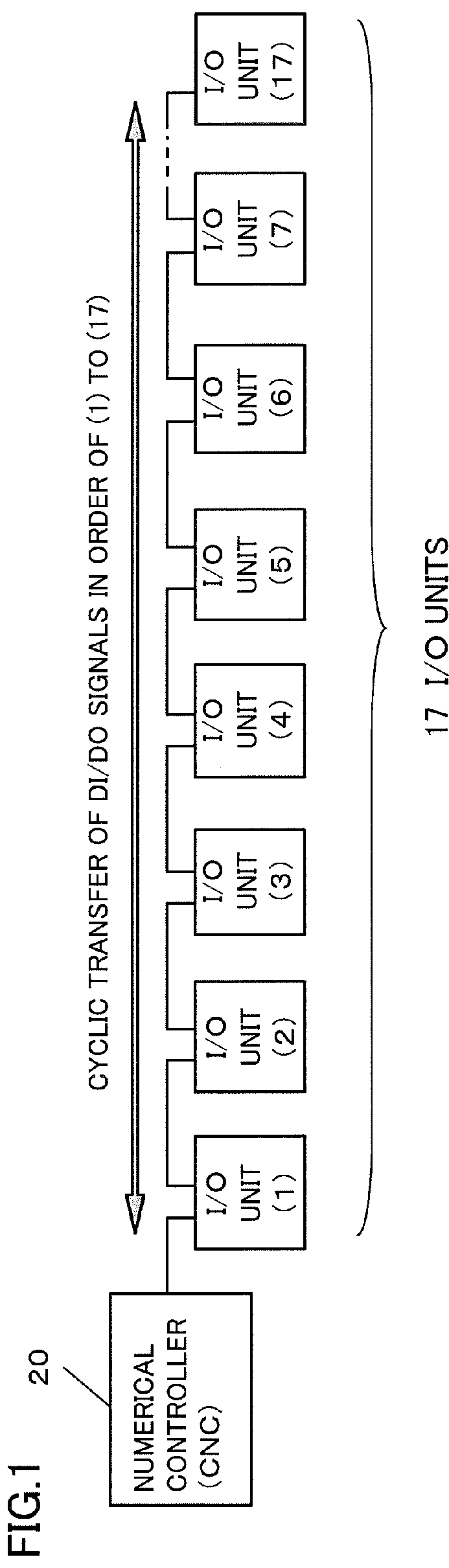
ActiveUS20140025185A1Waste of bandwidthLong waiting timeComputer controlSimulator controlTimerComputer science
A numerical controller is chain-connected with a plurality of I / O units so that it transmits DI / DO signals to and receives DI / DO signals from the I / O units by master-slave communication. The numerical controller counts signals generated by a timer circuit up to a predetermined number and sets, from among the plurality of I / O units, an I / O unit with which transfer of the DI / DO signals is to be performed for each count value. The DI / DO signals of the set I / O units are transferred according to the count value.
Owner:FANUC CORP
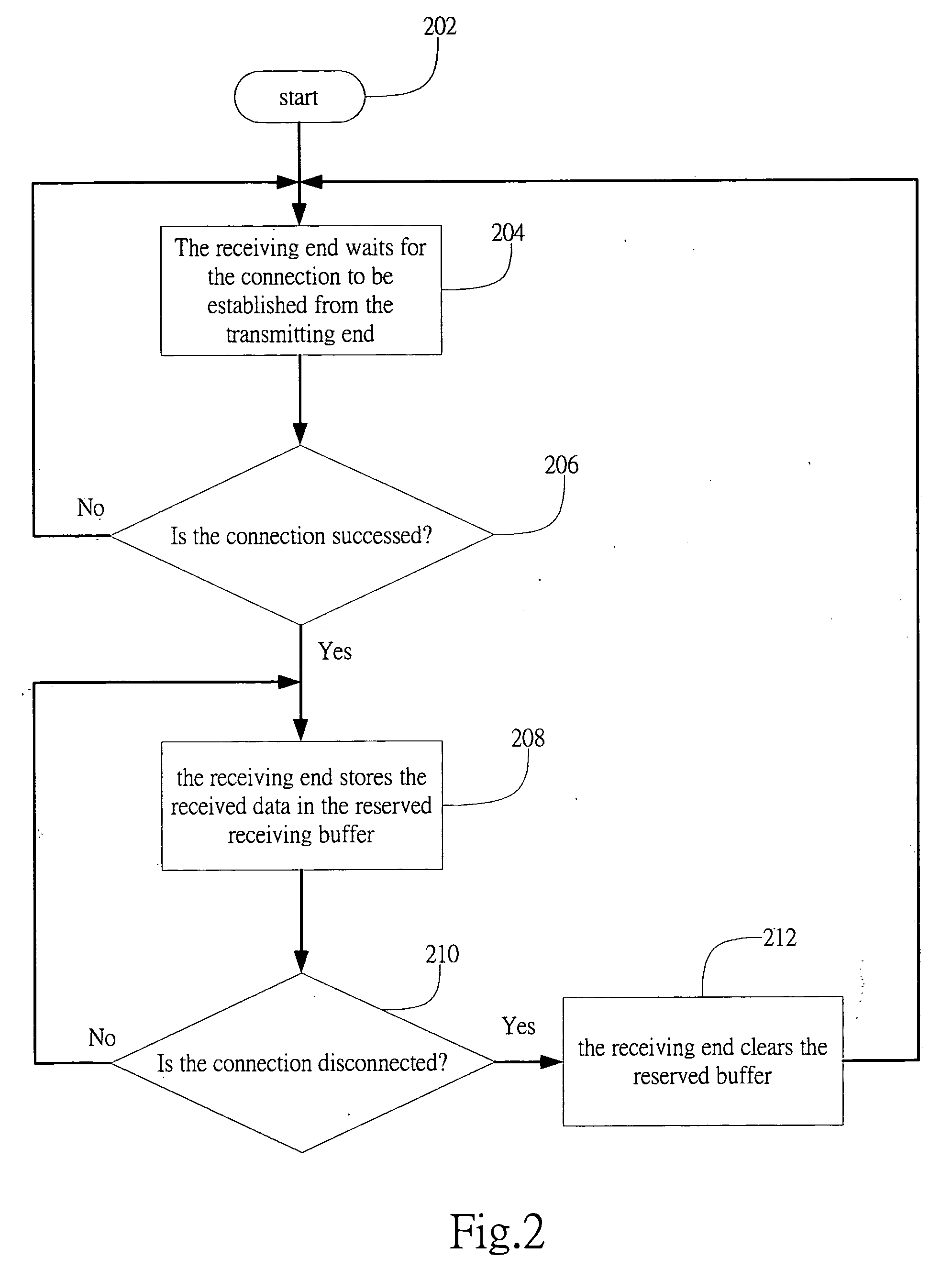
Real-time and reliable method for transporting data
InactiveUS20060251076A1Improve efficiencyOvercomes drawbackData switching by path configurationReal-time dataData transmission
A method for transporting data is provided. The method can manage the buffer and communicate between a sender and a receiver by protocol to improve the performance of data transportation and real-time data playing. Moreover, the size of the buffer in the sender equals to that of the pre-buffer in the receiver, and the total amount of data held therefore is constant, thereby fixes the delay period to keep the real-time data played at a steady speed.
Owner:AZUREWAVE TEHNOLOGIES INC
Method for the transfer of information during handovers in a communication system
ActiveUS8577368B2Reliable functionFair and justified share of resourceAnalogue secracy/subscription systemsConnection managementPolicy decisionCommunications system
The invention relates to a method for the transfer of policy control information during handover in a communication system. A session between a terminal and a remote node via a first network node has been established previously. The session comprising media components transmitted via the first gateway using first media component bearers. A handover condition is detected and a signaling connection is established between the terminal and the second gateway. Information on a second network node is obtained by the terminal, which determines if a proxy for the session has changed. If it has, information on media components is sent to a policy decision entity associated with the second network node. The policy decision entity authorizes second media component bearers with the information provided. Finally, the second media component bearers are established between the terminal and the second gateway.
Owner:NOKIA TECH OY
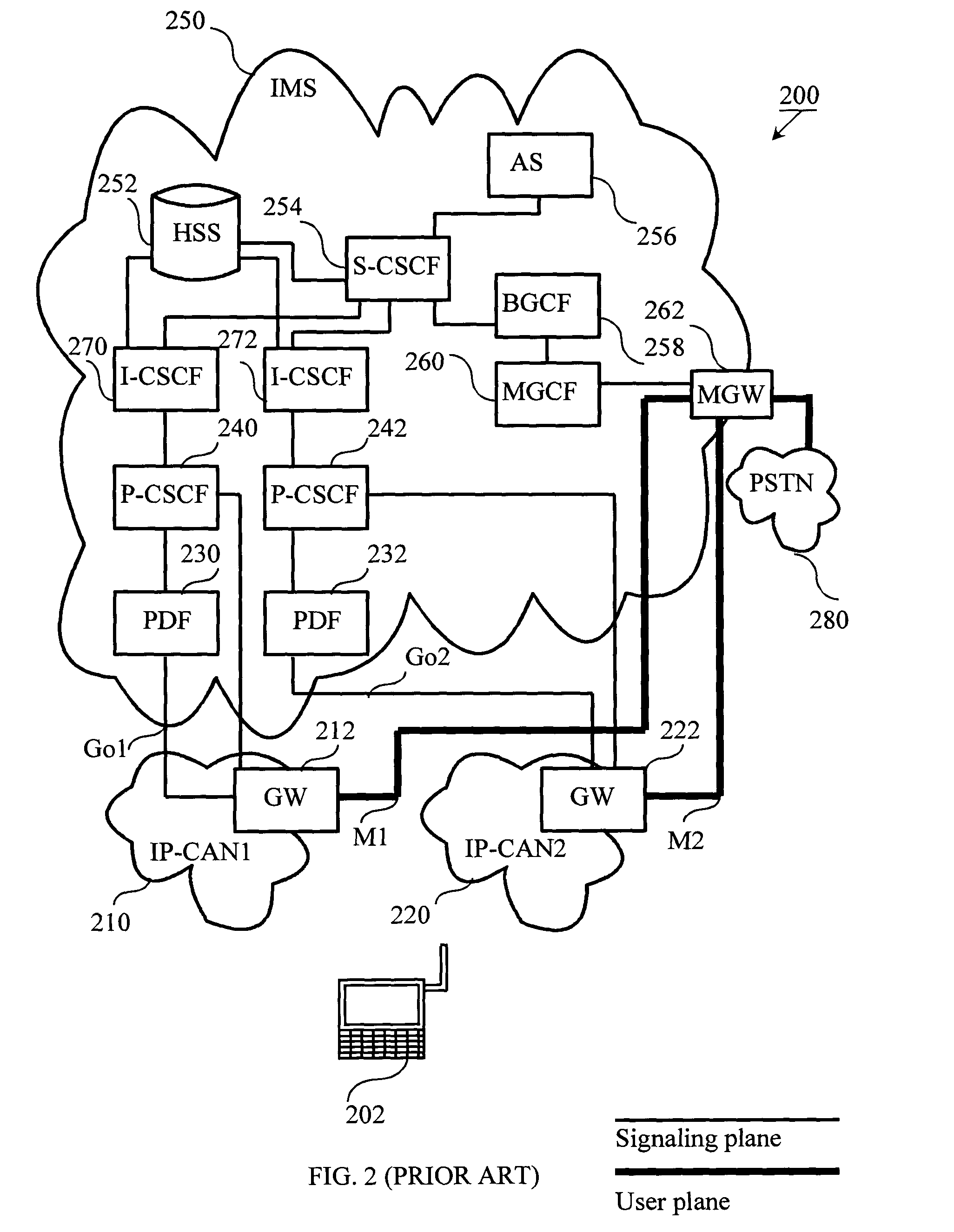
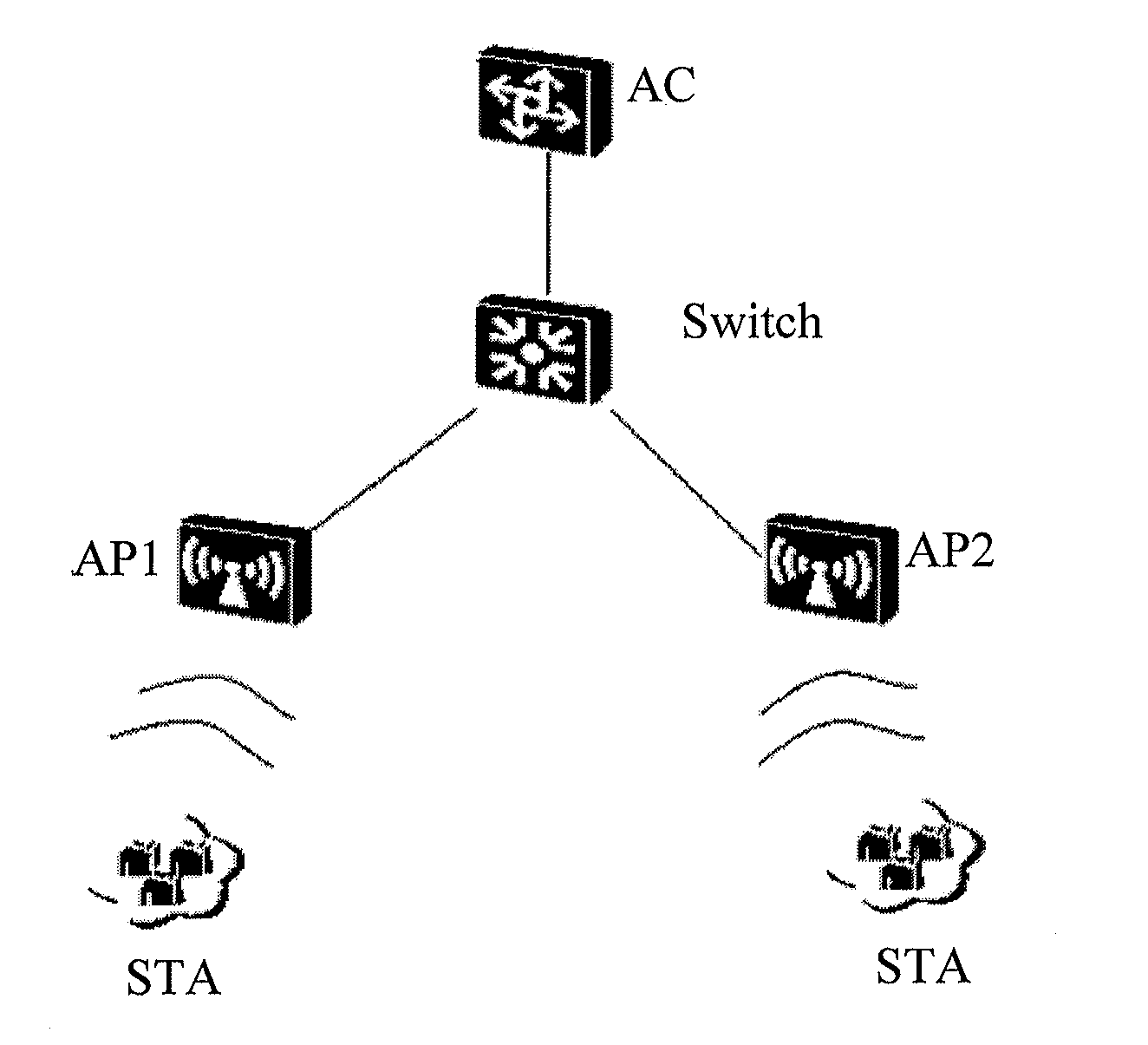
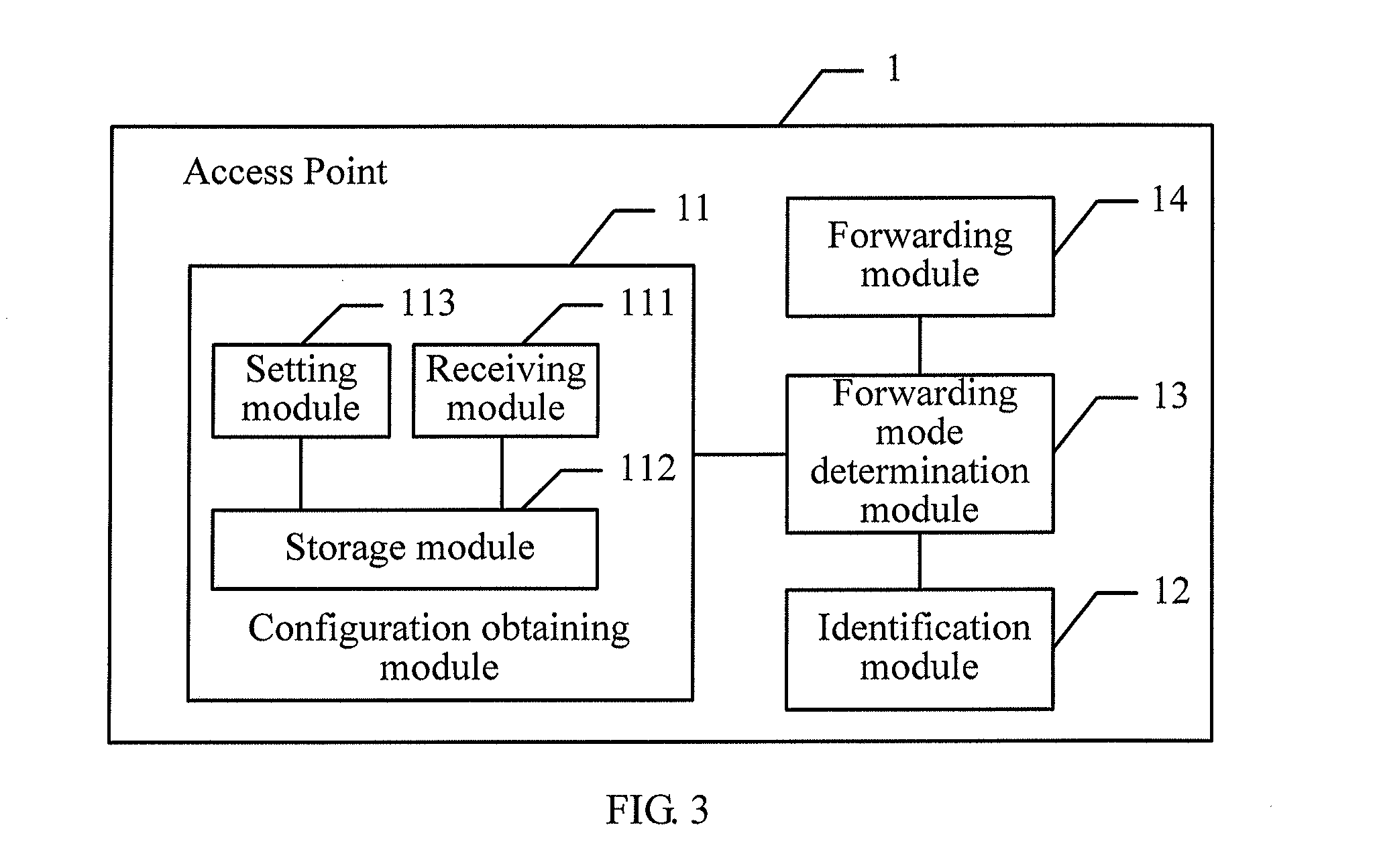
Message forwarding method, access point, and system
ActiveUS20130059530A1Waste of bandwidthAssess restrictionRadio transmission for post communicationAir interfaceMessage type
The present disclosure discloses a message forwarding method, an Access Point, and a system. An Access Point obtains a forwarding configuration table, where the forwarding configuration table includes message types and forwarding modes; receives a message sent by a user station and obtains a message type of the message; determines the forwarding mode of the message according to the message type of the message and the forwarding configuration table; encapsulates and forwards the message according to the forwarding mode of the message. Through the present disclosure, forwarding control of messages of wireless users can be implemented on the Access Point, thereby avoiding the problem that wireless air interface control is separated from user access control on an AP controller (AC) in the local forwarding mode and the problem of waste of bandwidth between the AP and the AC in the tunnel forwarding mode.
Owner:HUAWEI TECH CO LTD
Method and system for controlling reading transfer among buses with different speeds
ActiveCN101694646AEasy accessWaste of bandwidthElectric digital data processingComputer hardwareEngineering
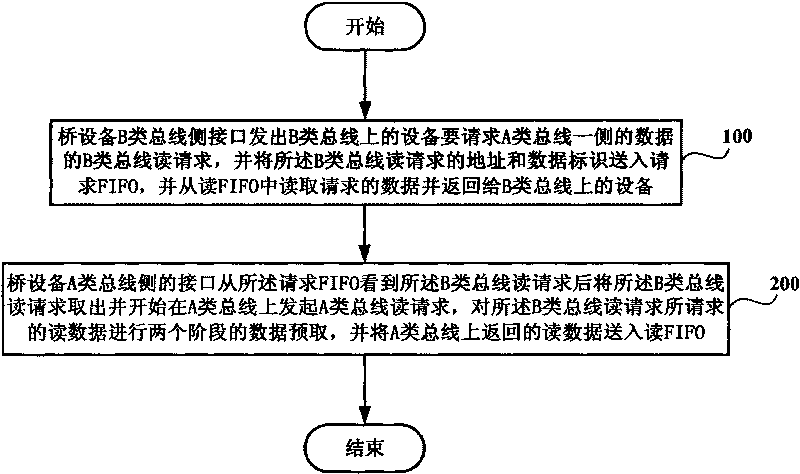
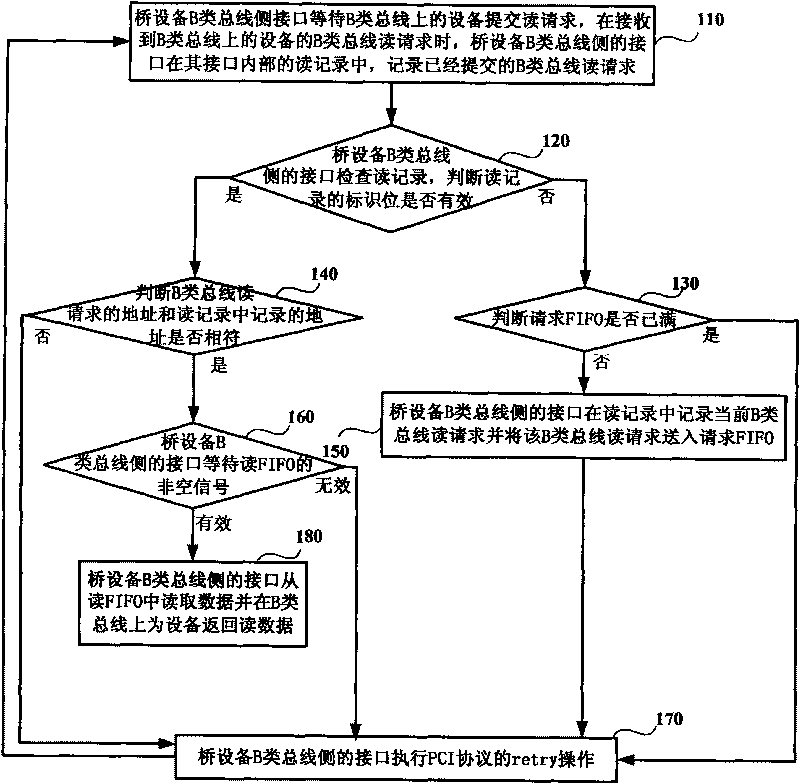
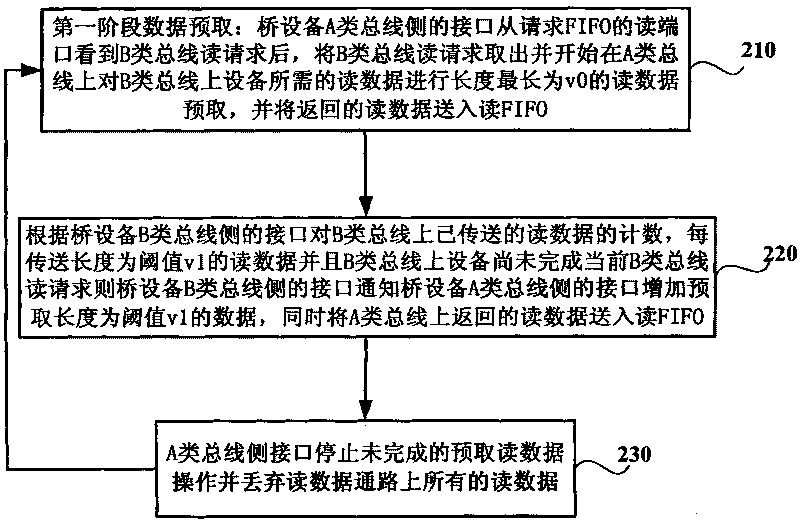
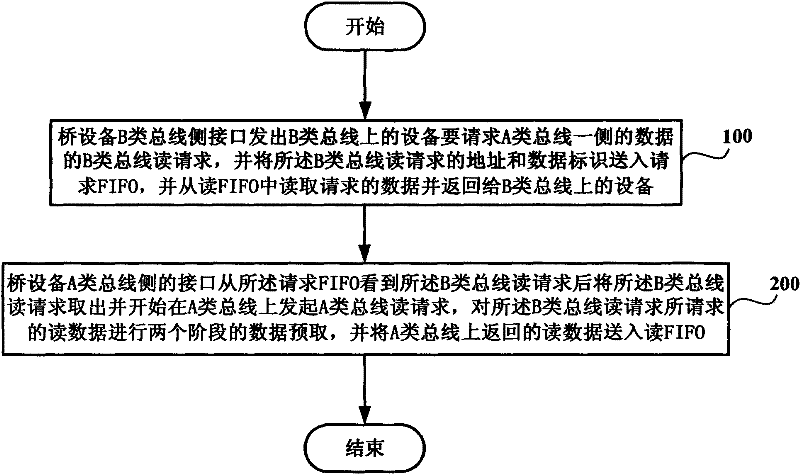
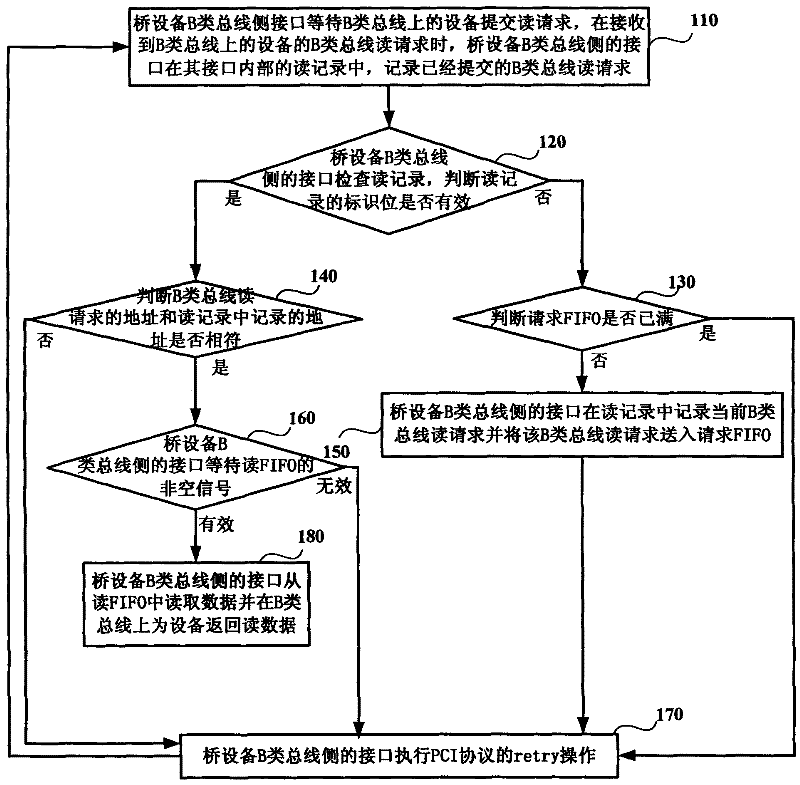
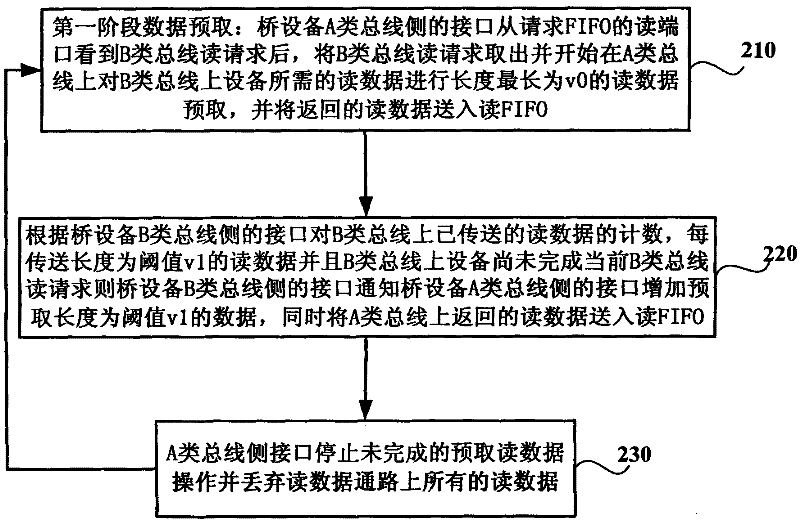
The invention discloses a method for controlling reading transfer among buses with different speeds, which includes following steps that a lateral interface of a bridge equipment B-class bus sends a B-class bus reading request of data on one side of an A-class bus requested by equipment on a B-class bus, sends an address of the reading request of the B-class bus and data identification to request FIFO, reads request data from reading FIFO and returns the data to the equipment on the B-class bus; and a lateral interface of a bridge equipment A-class bus takes out the reading request of the B-class bus after seeing the reading request of the B-class bus from the request FIFO, begins to send reading request of an A-class bus on the A-class bus, performs data prefetch of two stages for reading data request by reading request of the B-class bus, and sends the reading data returned from the A-class bus to the reading FIFO.
Owner:LOONGSON TECH CORP
Mitigating main crossbar load using dedicated connections for certain traffic types
ActiveUS9367487B1Reduce loadWaste of bandwidthDigital computer detailsConcurrent instruction executionCrossover switchTraffic volume
One embodiment of the invention sets forth a control crossbar unit that is designed to transmit control information from control information generators to destination components within the computer system. The control information may belong to various traffic paradigms, such as short-latency data traffic, narrow-width data traffic or broadcast data traffic. The physical connections within the control crossbar unit are categorized based on the different types of control information being transmitted through the control crossbar unit. The physical connections belong to the following categories: one-to-one (OTO) connections, one-to-many (OTM) connections, valid-to-one (VTO) connections, valid-to-many (VTM) connections wire-to-one (WTO) connections and wire-to-many (WTM) connections.
Owner:NVIDIA CORP
System and method for transferring message in ethernet based vehicle network
ActiveUS9432207B2Transmit and receive messages more efficientlyWaste of bandwidthNetworks interconnectionNetwork connectionsProcess moduleTransfer system
An Ethernet based vehicle network message transferring system is provided that includes a gateway switch that connects the Ethernet to vehicle networks having different protocols and an Ethernet switch that switches Ethernet messages between the gateway switch and vehicle devices to transfer the Ethernet messages. The Ethernet switch includes a processing module that transfers the Ethernet messages received via the gateway switch in the different vehicle networks, a vehicle network process module that switches the messages transferred from the processing module, and a lookup table in which information necessary for switching the vehicle network process module is stored. The vehicle network process module analyzes an Ethernet message transferred via the processing module in the gateway switch to identify destinations of individual messages in the Ethernet message and divides the Ethernet message including information regarding the individual message according to destinations to transmit the divided Ethernet messages to vehicle devices of destinations.
Owner:HYUNDAI MOTOR CO LTD +2
Mapping table loading method, memory control circuit unit and memory storage apparatus
ActiveUS10152426B2Improving usage efficiency and performanceWaste of bandwidthMemory architecture accessing/allocationMemory adressing/allocation/relocationOperation modeControl circuit
A mapping table loading method, a memory control circuit unit and a memory storage apparatus are provided. The method includes: receiving a first command; loading a first sub-logical address-physical address mapping table corresponding to the first command if an operating mode of a non-volatile rewritable memory module is a first operating mode; and loading a first logical address-physical address mapping table corresponding to the first command if the operating mode of the non-volatile rewritable memory module is a second operating mode, wherein the first logical address-physical address mapping table includes the first sub-logical address-physical address mapping table.
Owner:PHISON ELECTRONICS
Numerical controller for communication with I/O units
ActiveUS9377771B2Waste of bandwidthKeep for a long timeSpecial data processing applicationsNumerical controlComputer scienceTimer
Owner:FANUC LTD
Method and apparatus for data transmission
ActiveUS9936534B2Improve video qualitySave bandwidth resourcesMetering/charging/biilling arrangementsNetwork traffic/resource managementData transmissionComputer science
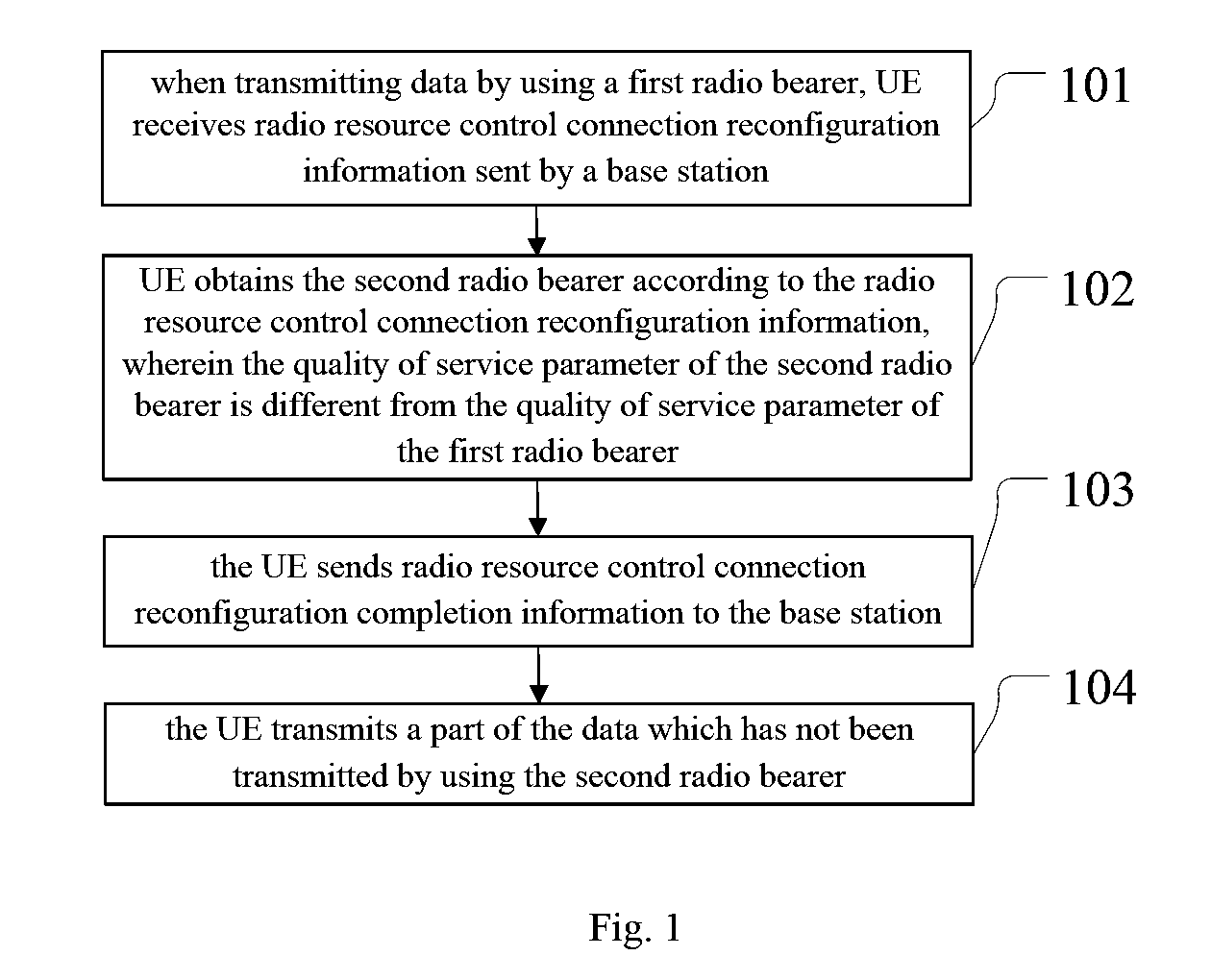
The present invention discloses a data transmission method and apparatus. According to the present invention, when transmitting data by using a first radio bearer, a UE receives radio resource control connection reconfiguration information sent by a base station; the UE obtains a second radio bearer according to the radio resource control connection reconfiguration information; the UE sends radio resource control connection reconfiguration completion information to the base station; the UE transmits a part of the data which has not been transmitted by using the second radio bearer. The solutions provided by the embodiments of the present invention are suitable to be adopted during switch between an adaptive streaming mode and a progressive download mode.
Owner:HUAWEI TECH CO LTD
Block chain token login method
InactiveCN112749381ARule out the possibility of hijackingImprove securityDigital data protectionDigital data authenticationSystem verificationBank account
The invention discloses a block chain token login method. The method comprises the following steps: S1, firstly, making and uploading a public key to a block chain; s2, calculating a private key through an RSA algorithm; s3, generating different private keys through the public key by using an RSA algorithm; distributing and storing the private key into different hardware devices (such as an intelligent id card); and S4, if a user wants to log in the bank account checking system, only when the hardware verification is passed and the face system verification is passed, the user can log in the bank account checking system after double verification. The method has the following advantages: 1, for the security problem, external hardware and face recognition are combined for permission login, so that the security is greatly improved, and the possibility of network virus or illegal software hijacking is eliminated; 2, since external software performs matching key login according to an algorithm, waste bandwidth and CPU performance do not need to be considered at all; and 3, if attacked, the public key cannot be destroyed or changed.
Owner:中证瑞通(上海)科技有限公司
Method and system for controlling reading transfer among buses with different speeds
ActiveCN101694646BEasy accessWaste of bandwidthElectric digital data processingEmbedded systemData request
The invention discloses a method for controlling reading transfer among buses with different speeds, which includes following steps that a lateral interface of a bridge equipment B-class bus sends a B-class bus reading request of data on one side of an A-class bus requested by equipment on a B-class bus, sends an address of the reading request of the B-class bus and data identification to requestFIFO, reads request data from reading FIFO and returns the data to the equipment on the B-class bus; and a lateral interface of a bridge equipment A-class bus takes out the reading request of the B-class bus after seeing the reading request of the B-class bus from the request FIFO, begins to send reading request of an A-class bus on the A-class bus, performs data prefetch of two stages for reading data request by reading request of the B-class bus, and sends the reading data returned from the A-class bus to the reading FIFO.
Owner:LOONGSON TECH CORP
Speech data processing method, system and medium
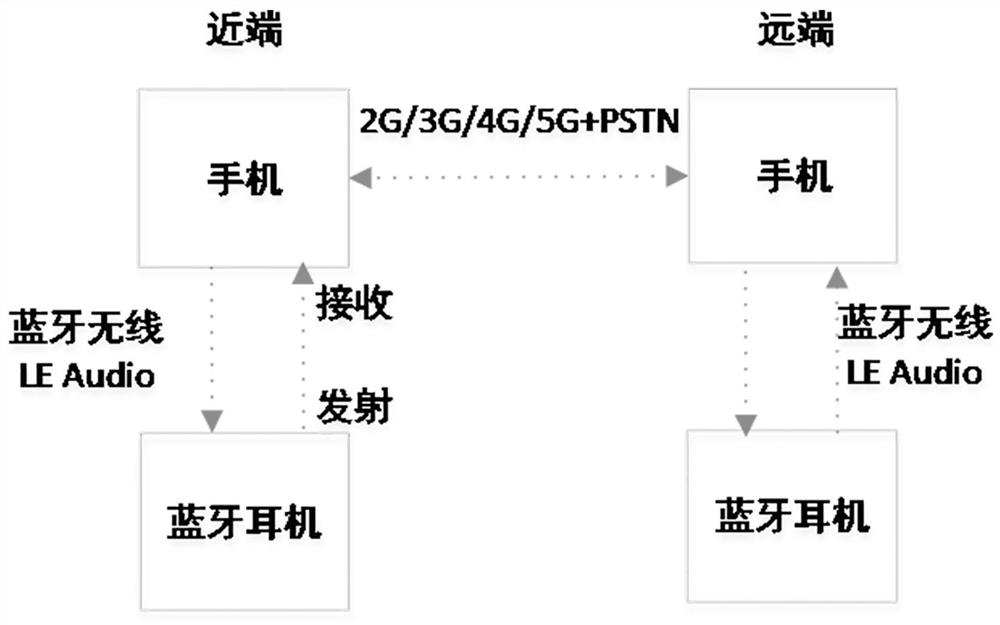
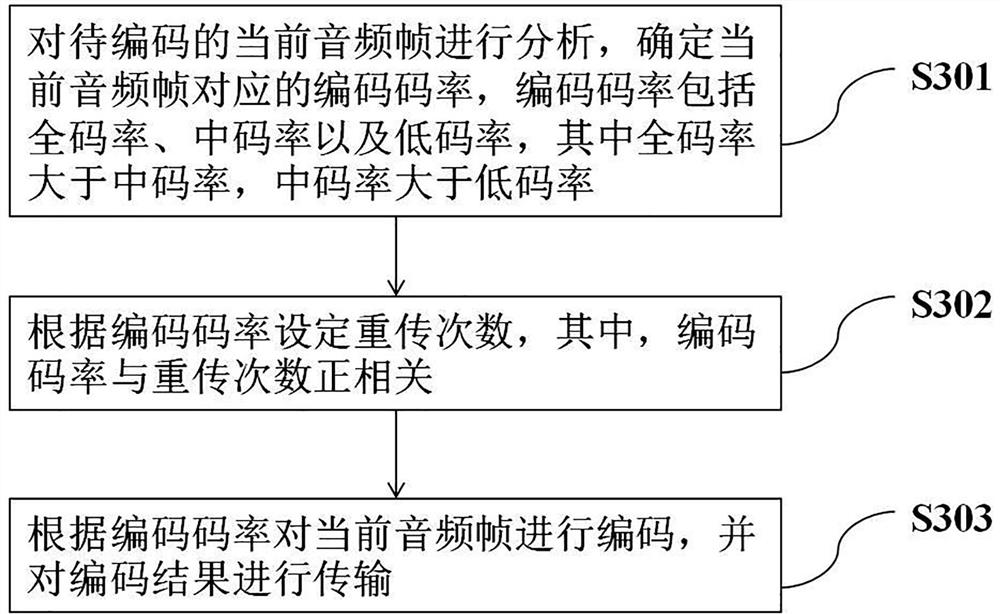
ActiveCN113450809BWaste of bandwidthReduce the number of retransmissionsSpeech analysisComputer hardwareDelay
The application discloses a voice data processing method, system and medium, belonging to the technical field of bluetooth audio data processing. The method includes: analyzing the current audio frame to be encoded, and determining the encoding bit rate corresponding to the current audio frame, the encoding bit rate includes a full bit rate, a medium bit rate and a low bit rate, wherein the full bit rate is greater than the medium bit rate, and the medium bit rate The rate is greater than the low bit rate; the number of retransmissions is set according to the encoding bit rate, where the encoding bit rate is positively correlated with the number of retransmissions; the current audio frame is encoded according to the encoding bit rate, and the encoding result is transmitted. According to the characteristics of the audio frame, the present application selects the corresponding encoding rate to encode the audio frame, and sets different retransmission times correspondingly. It reduces the number of retransmissions or even does not retransmit some audio frames for which there is no valid voice, avoiding wasting audio transmission bandwidth, reducing power consumption and delay.
Owner:BEIJING BAIRUI INTERNET TECH CO LTD
Method and apparatus for delivering keying information
ActiveUS9503890B2Adds to session setup timesWaste of bandwidthKey distribution for secure communicationUser identity/authority verificationApplication serverUser equipment
A method of delivering an application key or keys to an application server for use in securing data exchanged between the application server and a user equipment, the user equipment accessing a communications network via an access domain. The method comprises running an Authentication and Key Agreement procedure between the user equipment and a home domain in order to make keying material available to the user equipment and to an access enforcement point. At least a part of said keying material is used to secure a communication tunnel between the user equipment and the access enforcement point, and one or more application keys are derived within the home domain using at least part of said keying material. Said application key(s) is(are) provided to said application server, and the same application key(s) derived at the user equipment, wherein said access enforcement point is unable to derive or have access to said application key(s).
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and system for unlocking mobile terminal on the basis of a high-quality eyeprint image
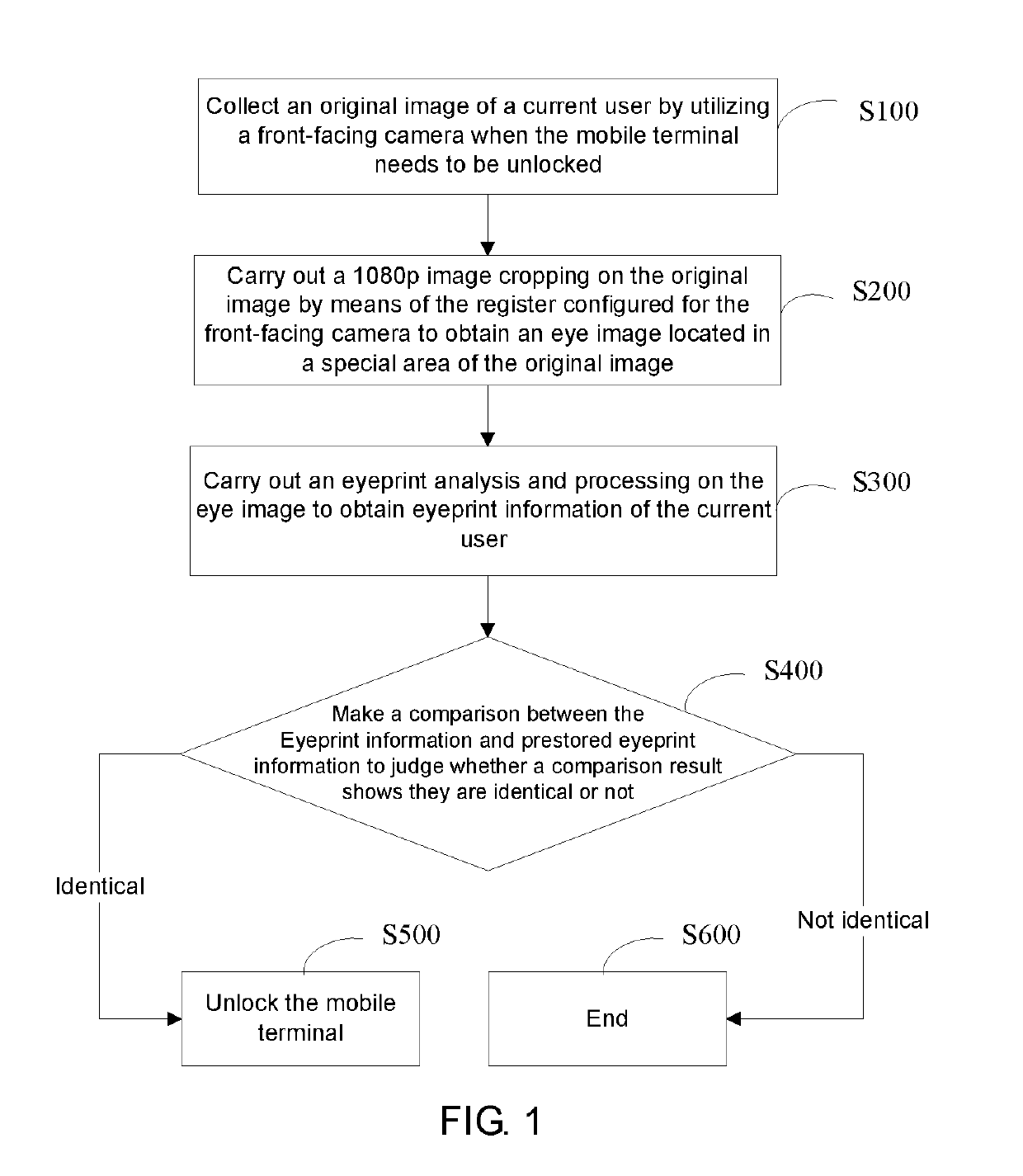
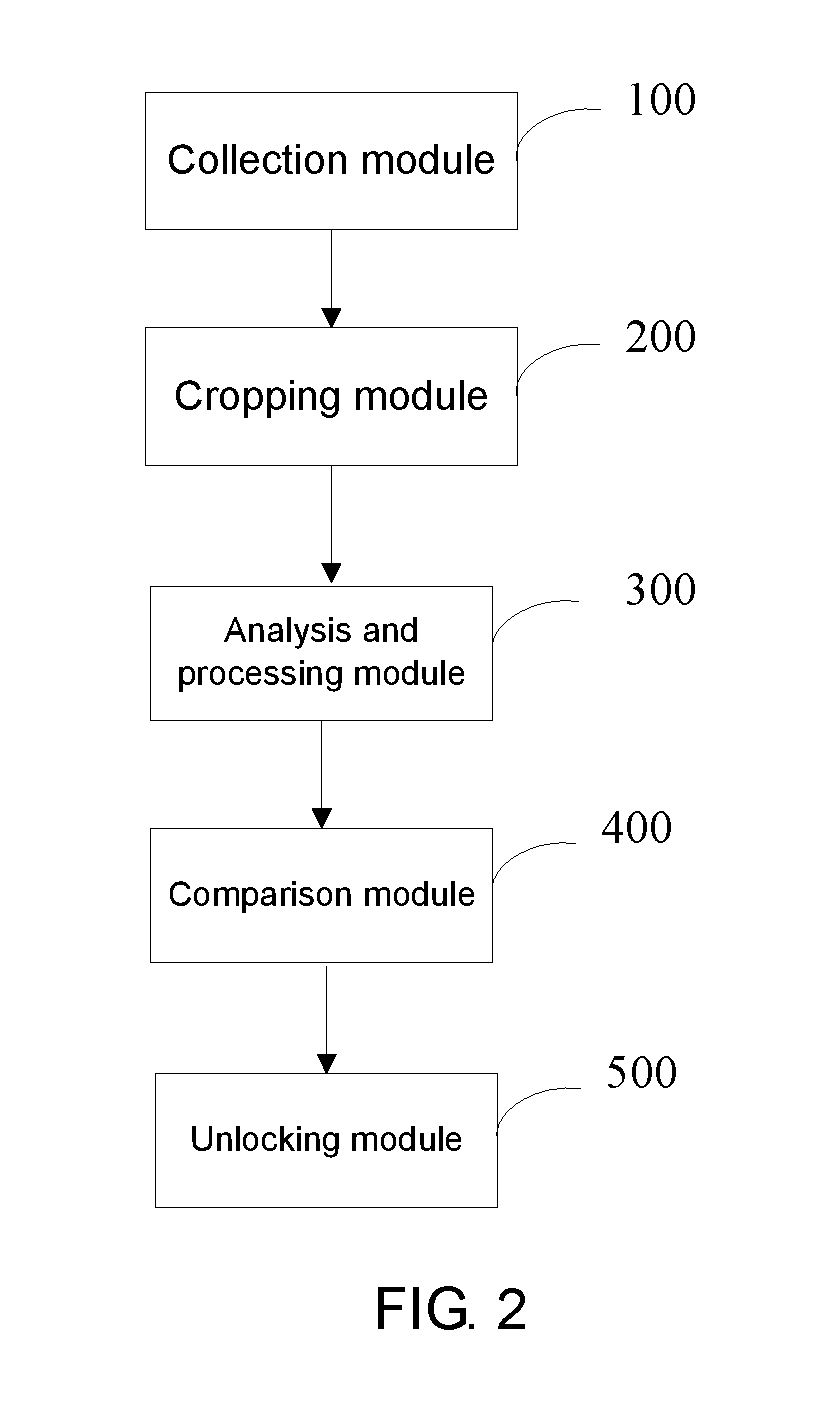
ActiveUS10275584B2Waste of bandwidthShorten speedCharacter and pattern recognitionDigital data authenticationComputer graphics (images)Processor register
A method and a system for unlocking a mobile terminal on the basis of a high-quality eyeprint image may include collecting an original image of a current user by utilizing a front-facing camera when the mobile terminal needs to be unlocked; carrying out a 1080p image cropping on the original image by means of a register configured for the front-facing camera to obtain an eye image located in a special area of the original image; carrying out an eyeprint analysis and processing on the eye image to acquire eyeprint information of the current user; making a comparison between the eyeprint information and prestored eyeprint information to judge whether the comparison result shows that they are identical or not; and unlocking the mobile terminal if it is judged that they are identical.
Owner:JRD COMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com