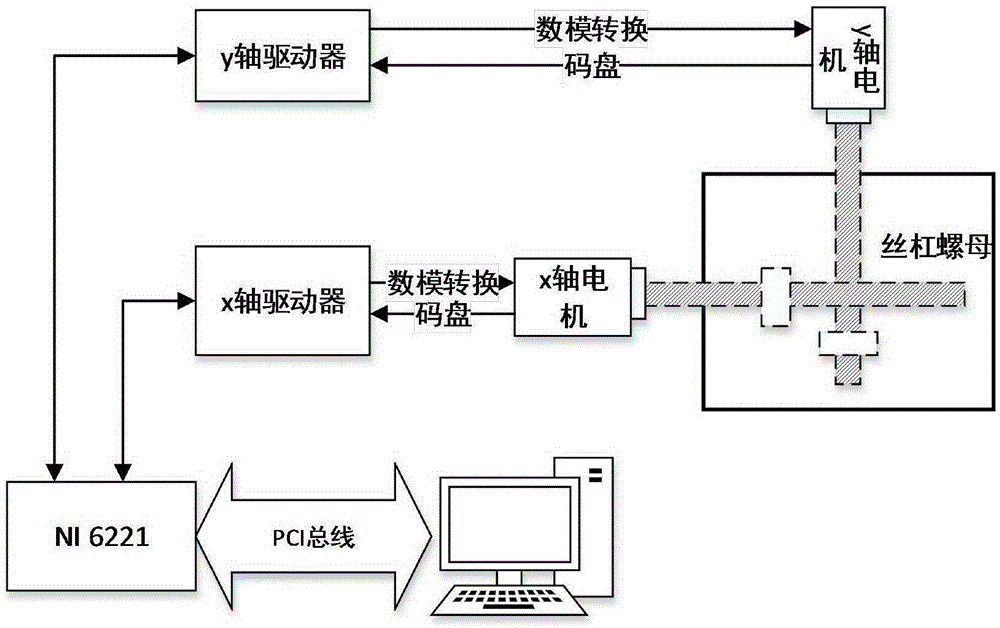
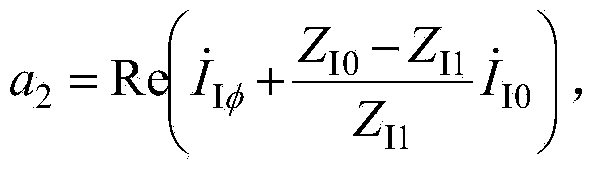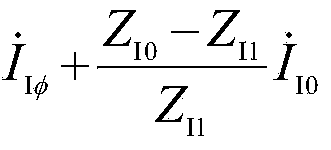Patents
Literature
86 results about "Dichotomic search" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a dichotomic search is a search algorithm that operates by selecting between two distinct alternatives (dichotomies) at each step. It is a specific type of divide and conquer algorithm. A well-known example is binary search.
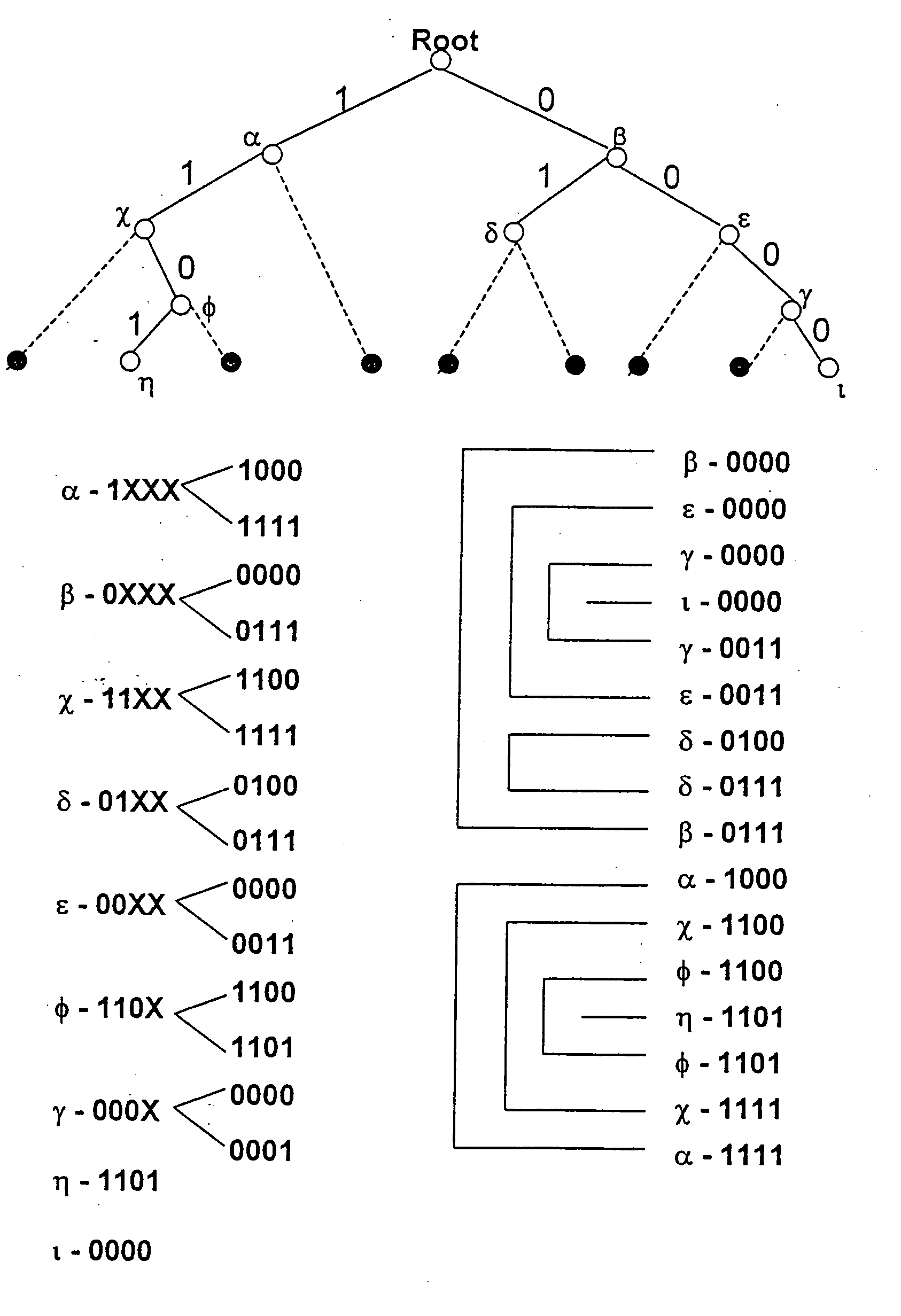
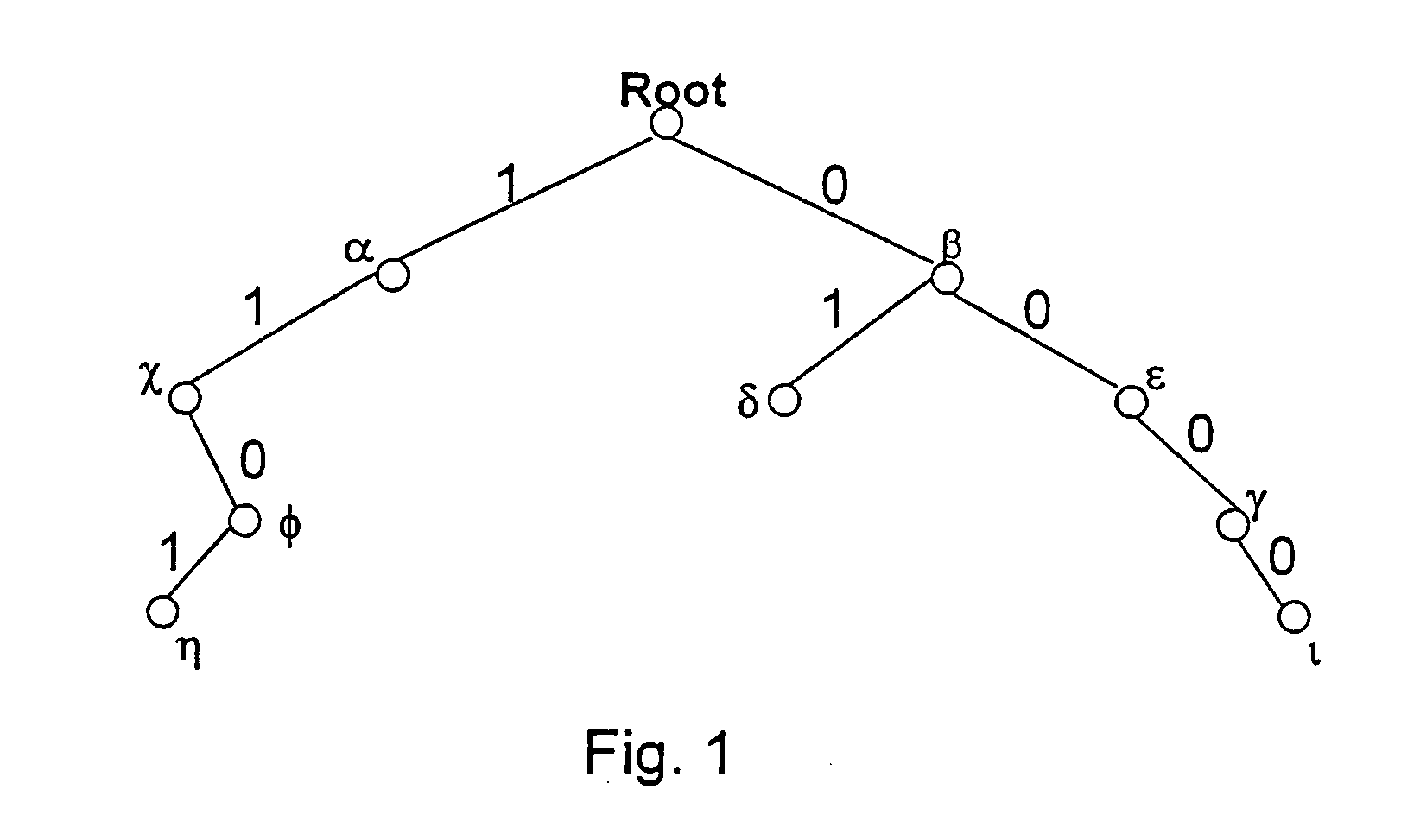
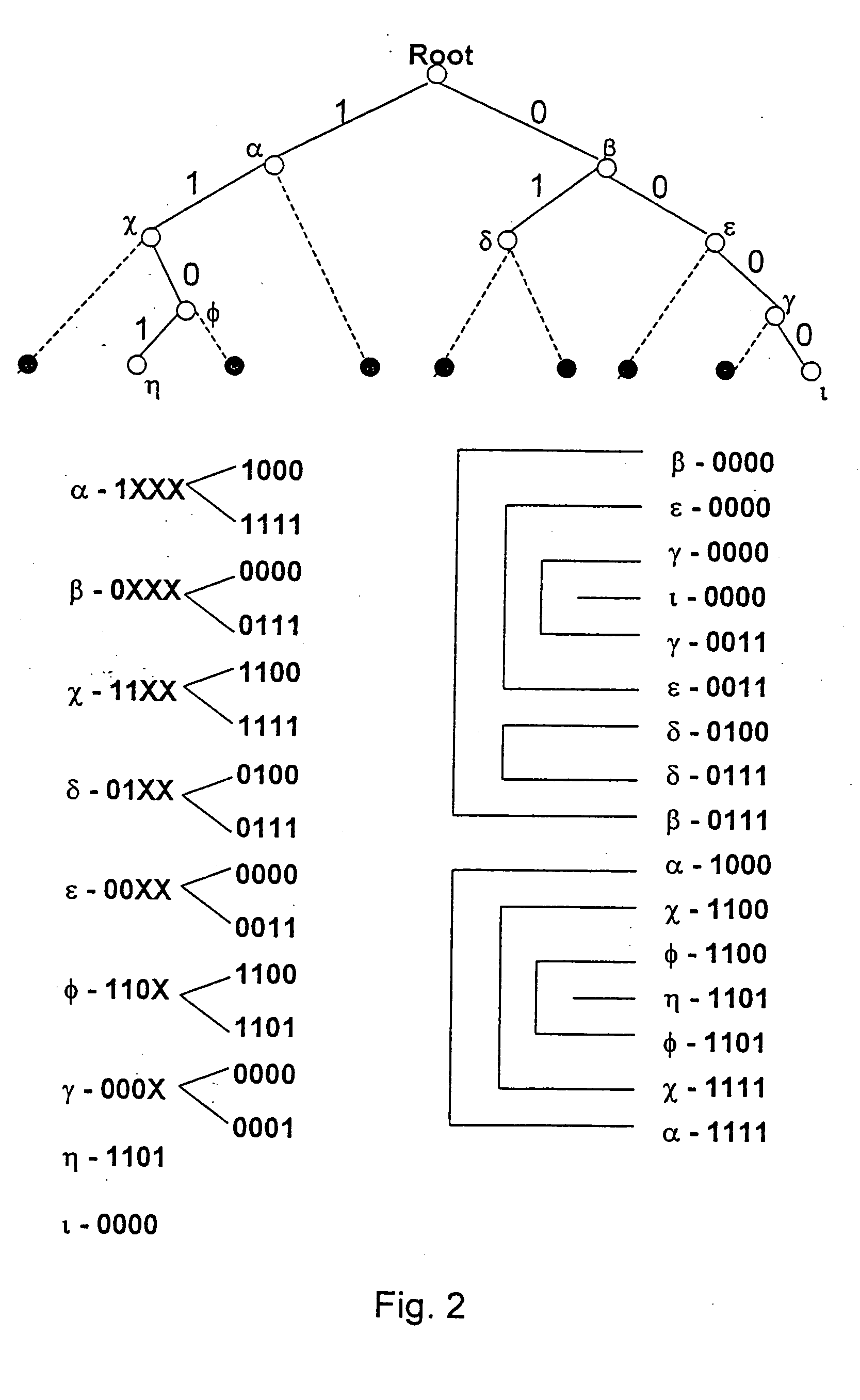
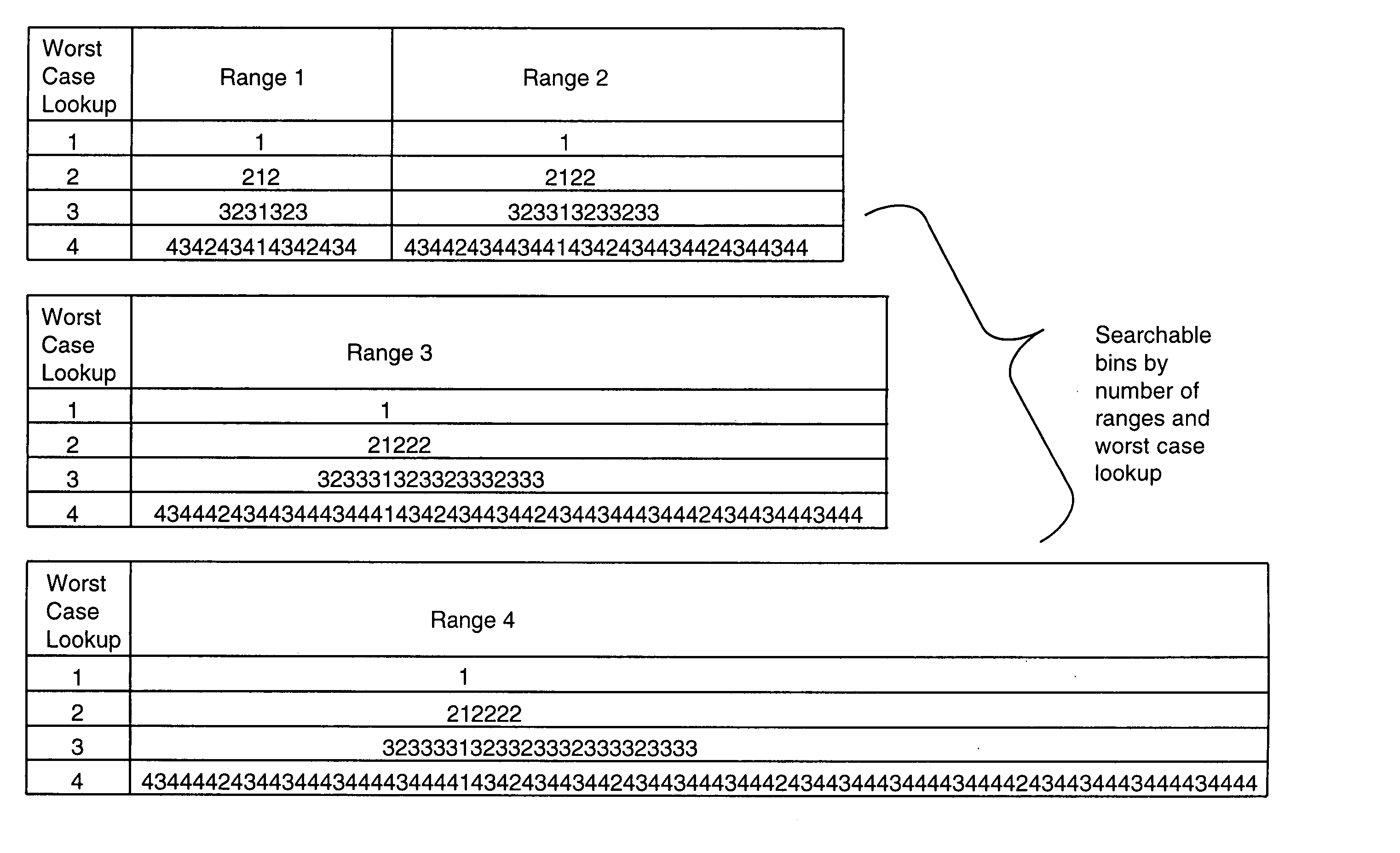
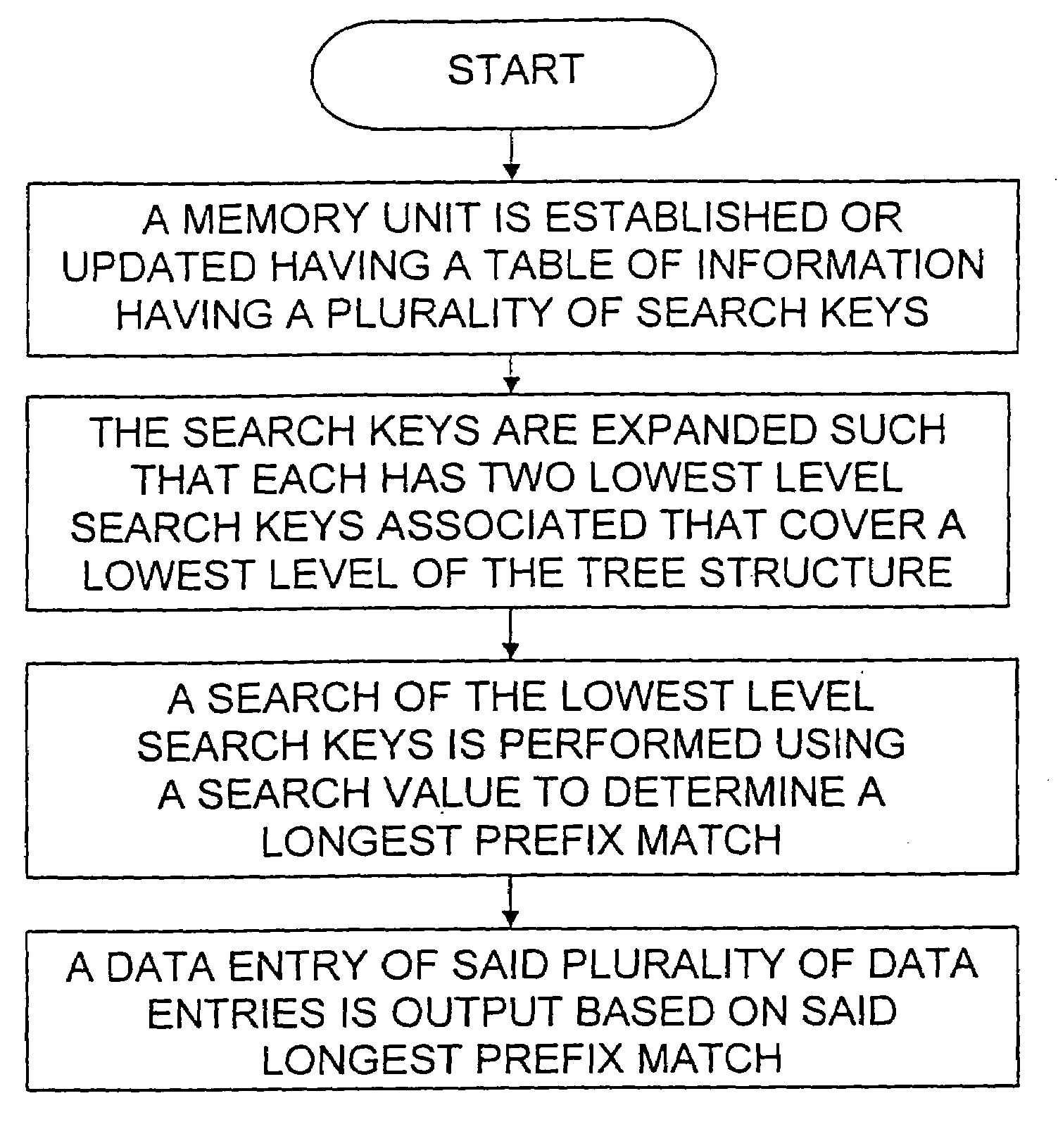
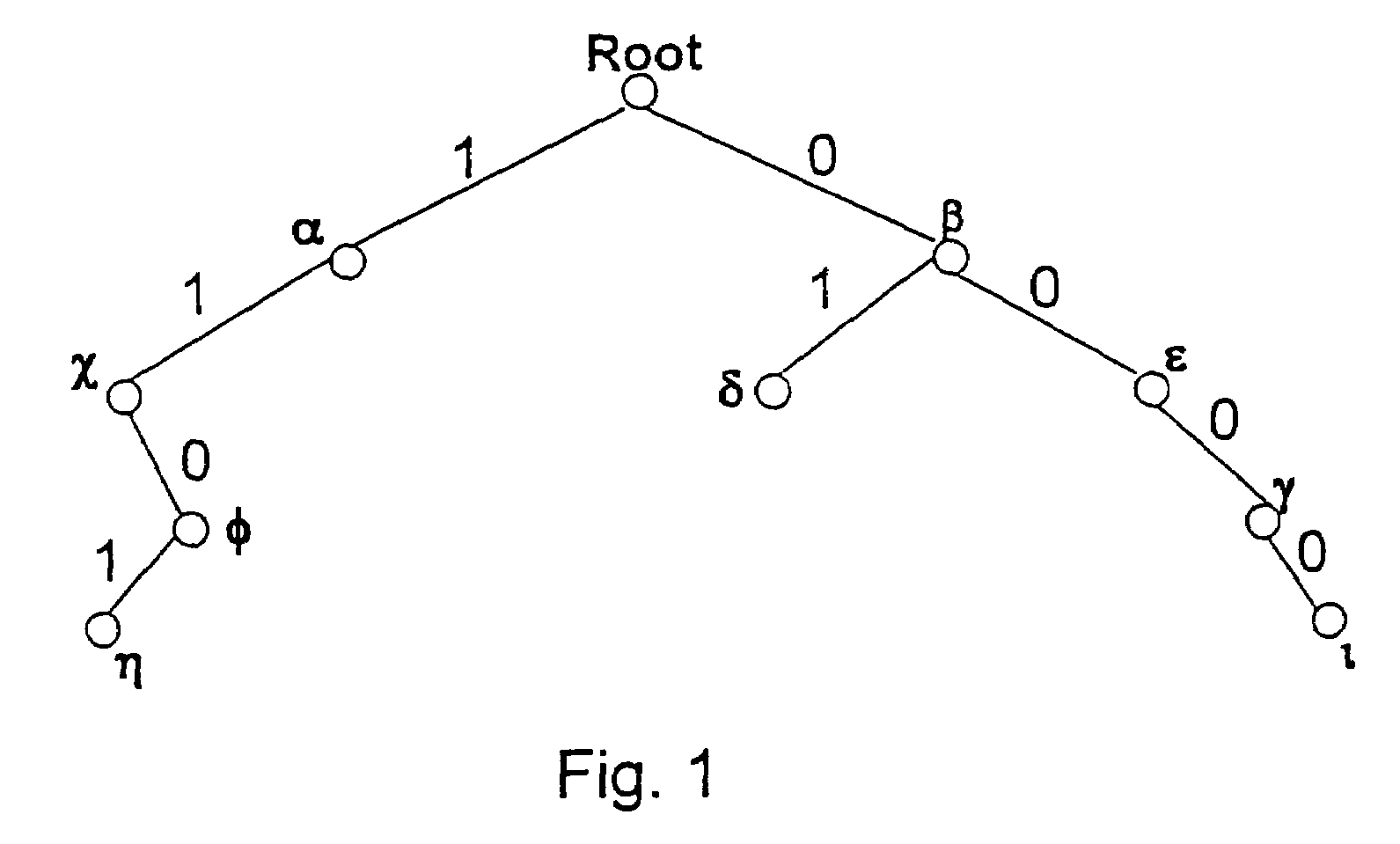
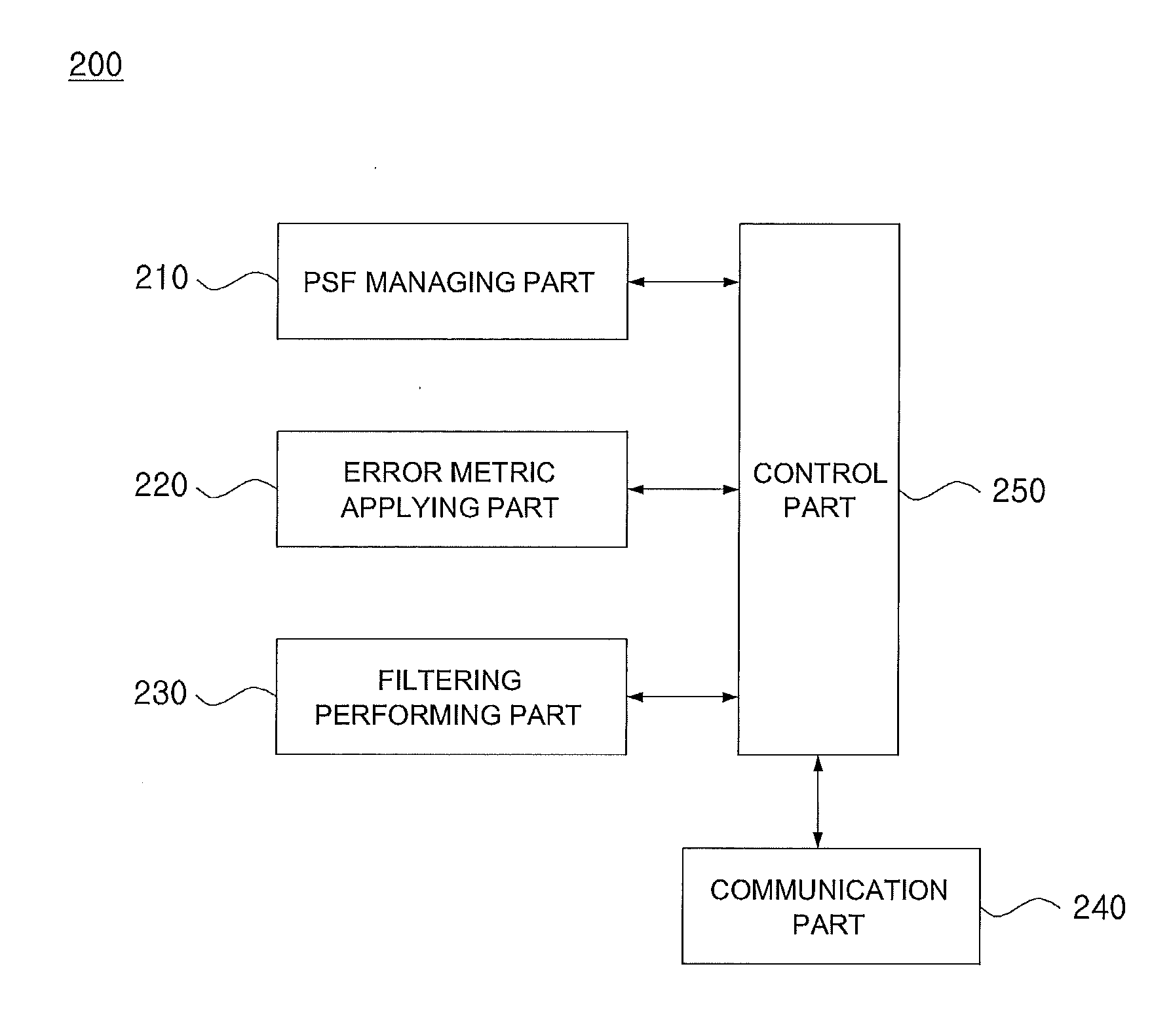
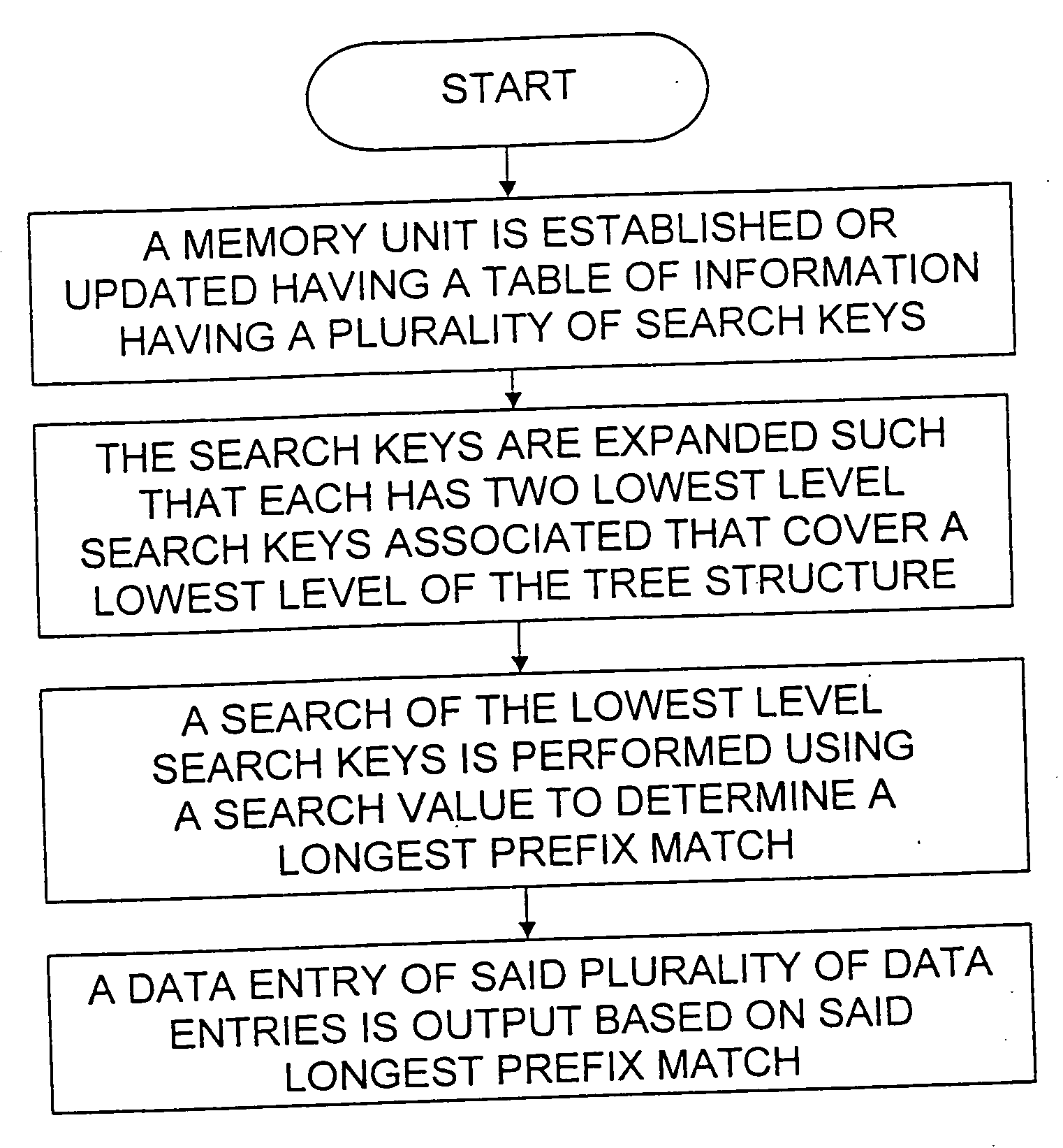
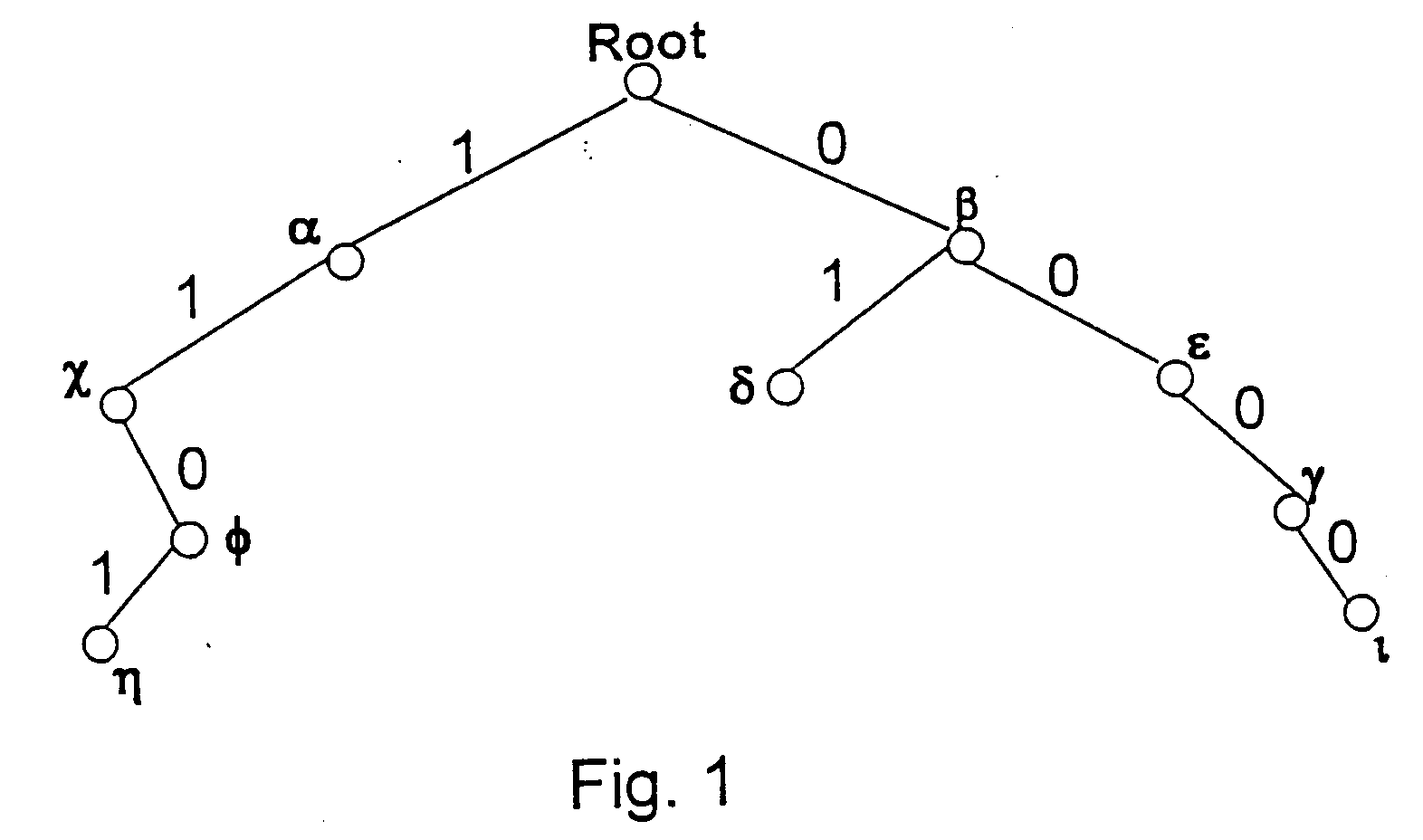
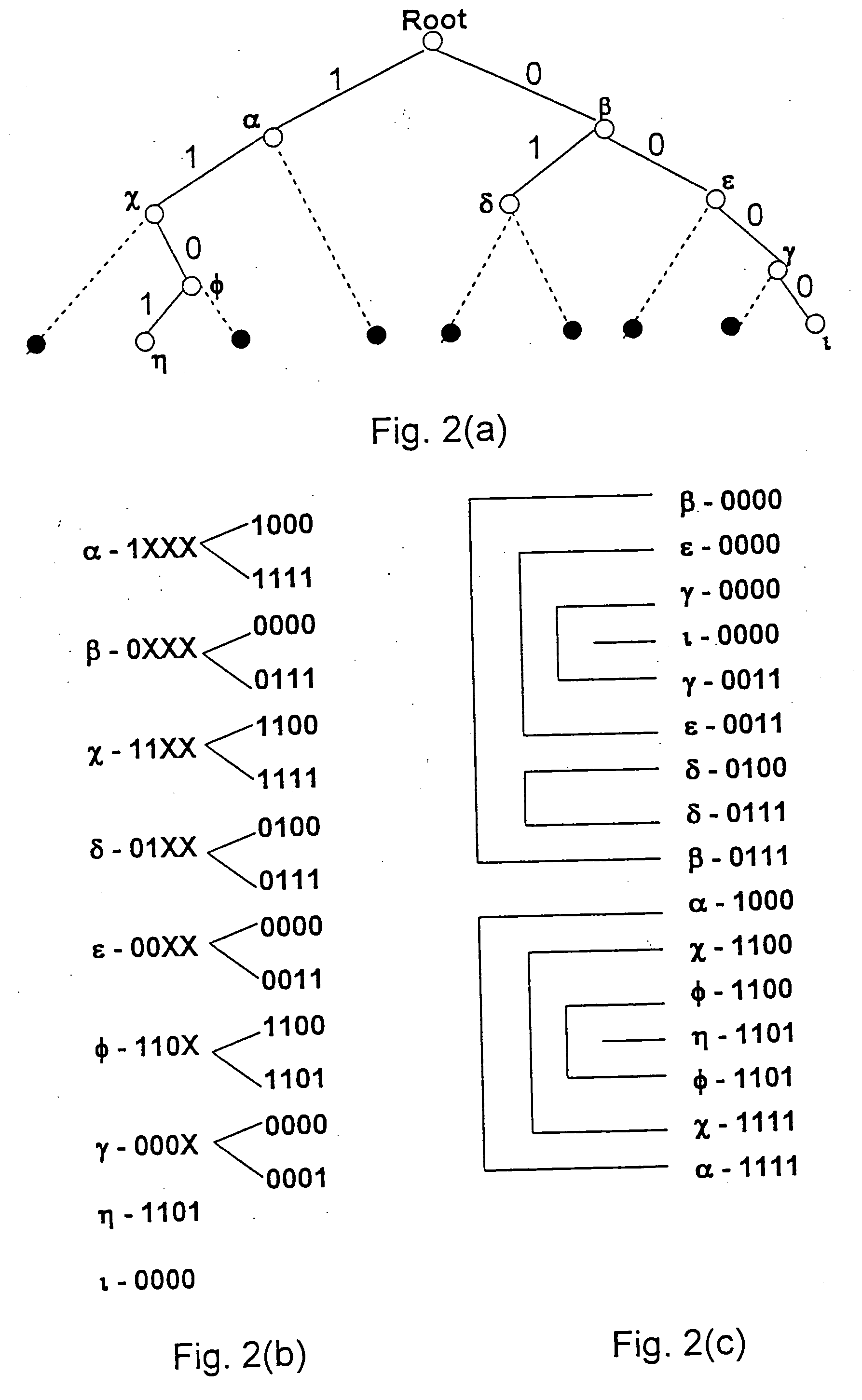
Method and apparatus for performing a binary search on an expanded tree
InactiveUS20050033740A1Increase speedHigh performance and cost-effectiveDigital data information retrievalData processing applicationsTheoretical computer scienceLongest prefix match
A method and apparatus for searching an electronically stored table of information including a plurality of table entries and facilitating high speed searching of a table to provide a longest matching entry. The table searching method uses at least one memory unit having a table of information including a plurality of data entries. The table of information has a plurality of search keys associated with the plurality of data entries and the plurality of search keys form a tree structure based on a prefix length for each of the search keys. The plurality of search keys are expanded such that each of the plurality of search keys has two lowest level search keys associated therewith that cover a lowest level of the tree structure. A binary search of the lowest level search keys is performed based on a search value to determine a longest prefix match. A data entry of the plurality of data entries is output based on said longest prefix match. The method is also applicable to routing data in an internet router where the routing of data packets depends on address information stored in the table of information.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
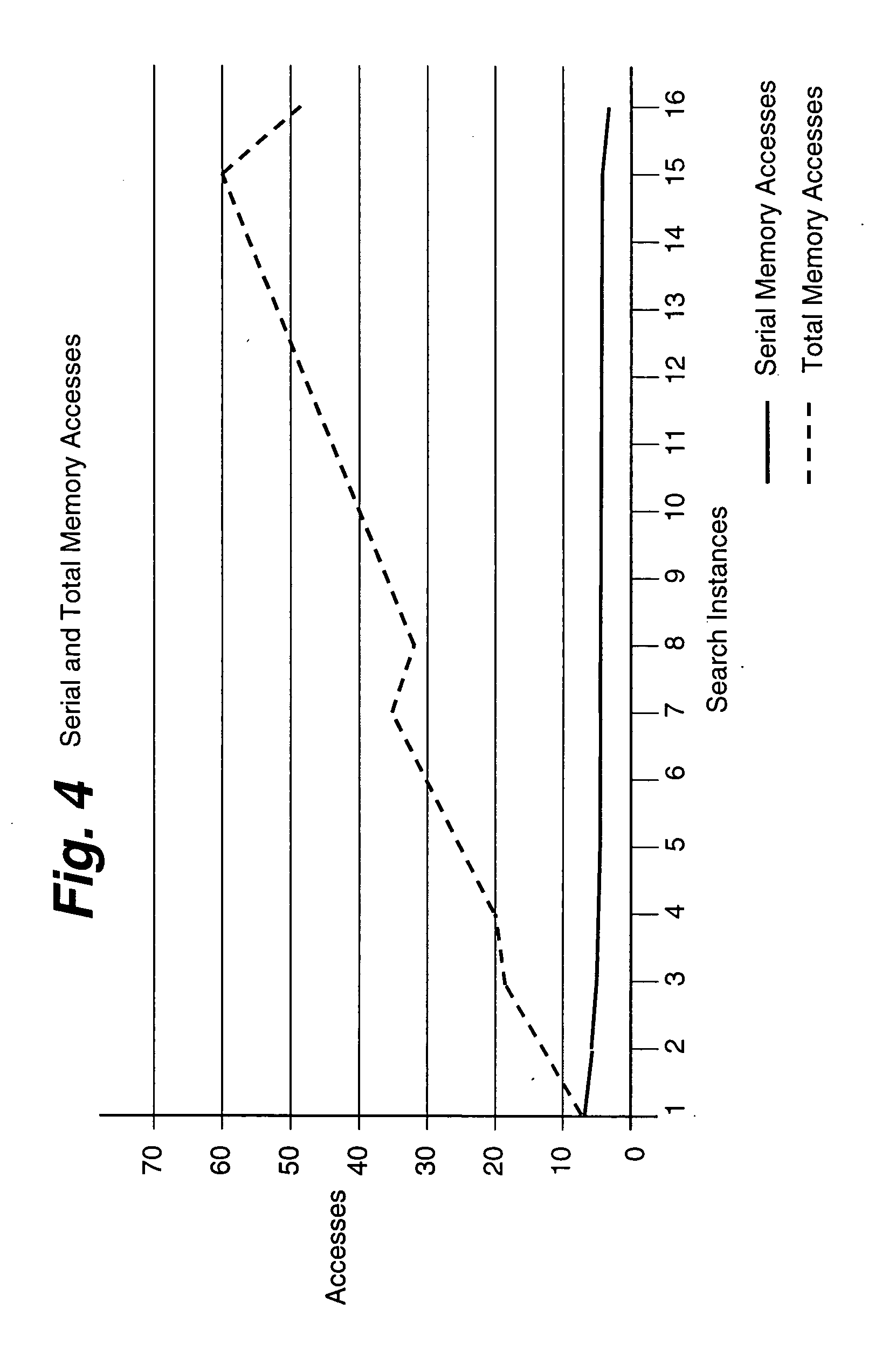
Parallel asymmetric binary search on lengths
InactiveUS20050131867A1Reduce latencyScale better to longer addressesData processing applicationsData switching networksTheoretical computer scienceParallel search
Parallel binary searches on lengths using hash tables is described. The parallel search uses more than one search instance. The search instances probe in parallel mutually different contiguous ranges of a search area during each round of searches. After each round, a new search area is defined and one or more search instances are redeployed into the new search area. The search instance for a range of shorter lengths can be redirected to help those of the longer lengths. Due to the help from other search instances, some ranges can be made large without sacrificing the performance. The invention realizes faster address lookups even for longer address lengths.
Owner:ALCATEL LUCENT SAS
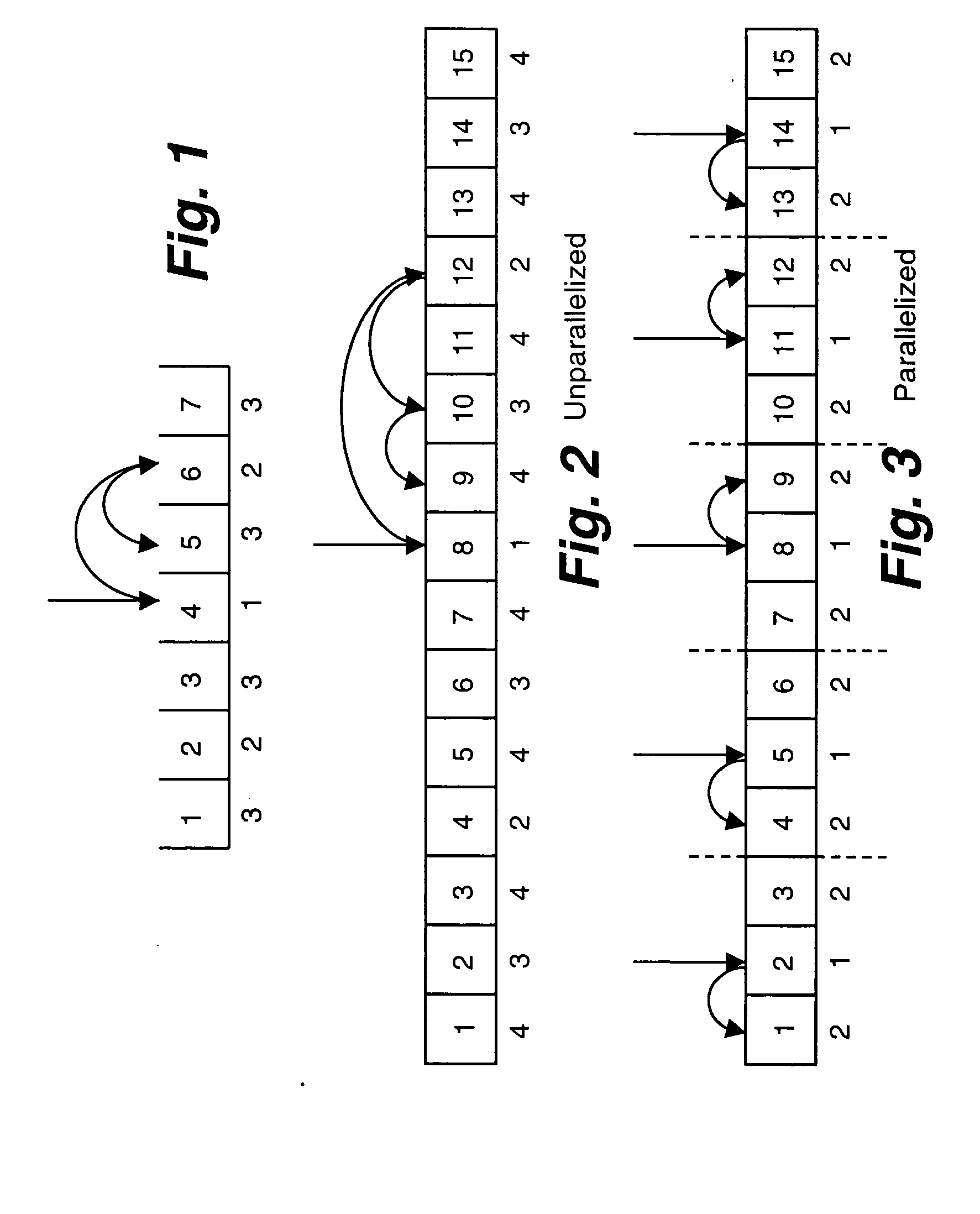
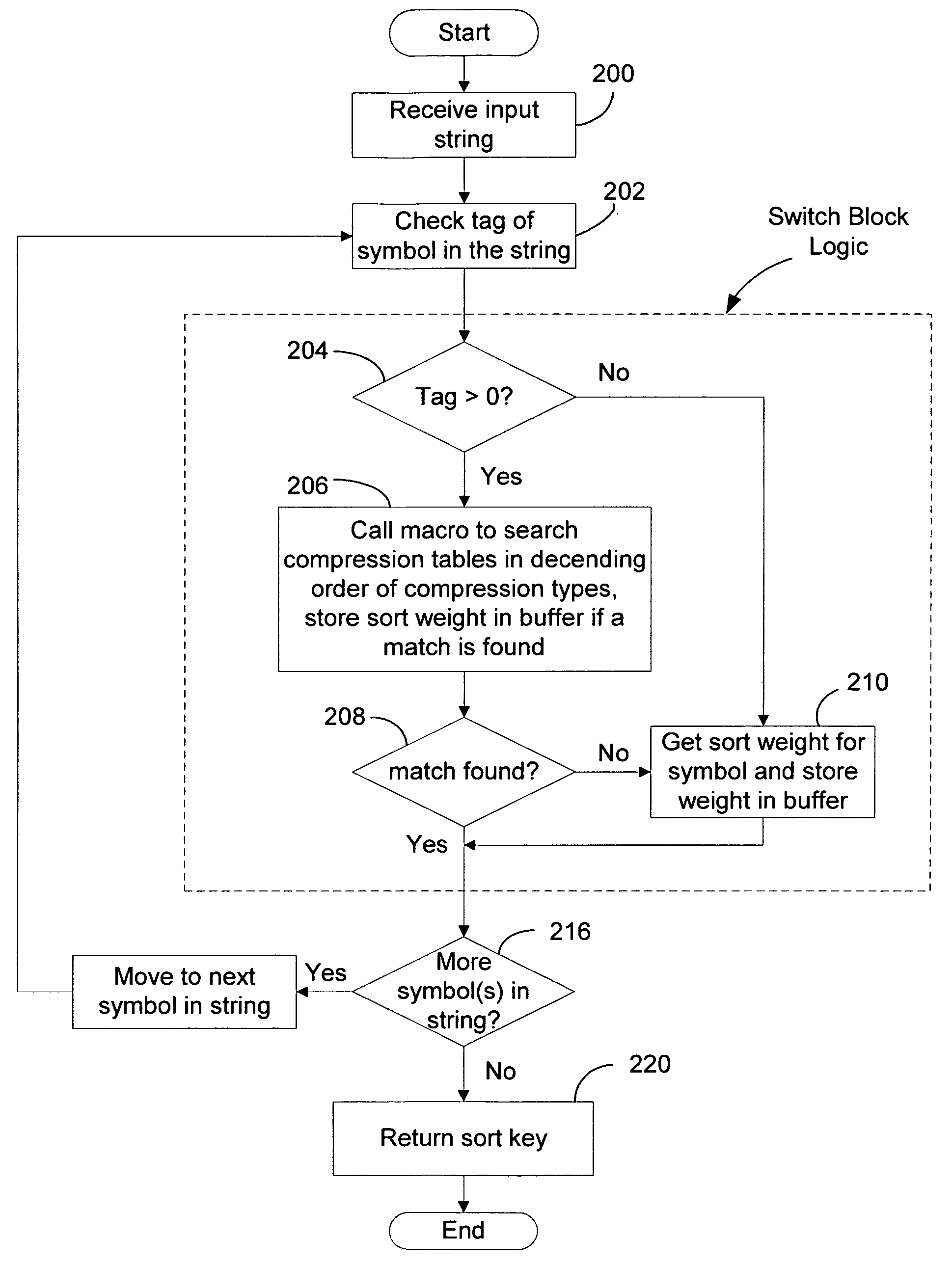
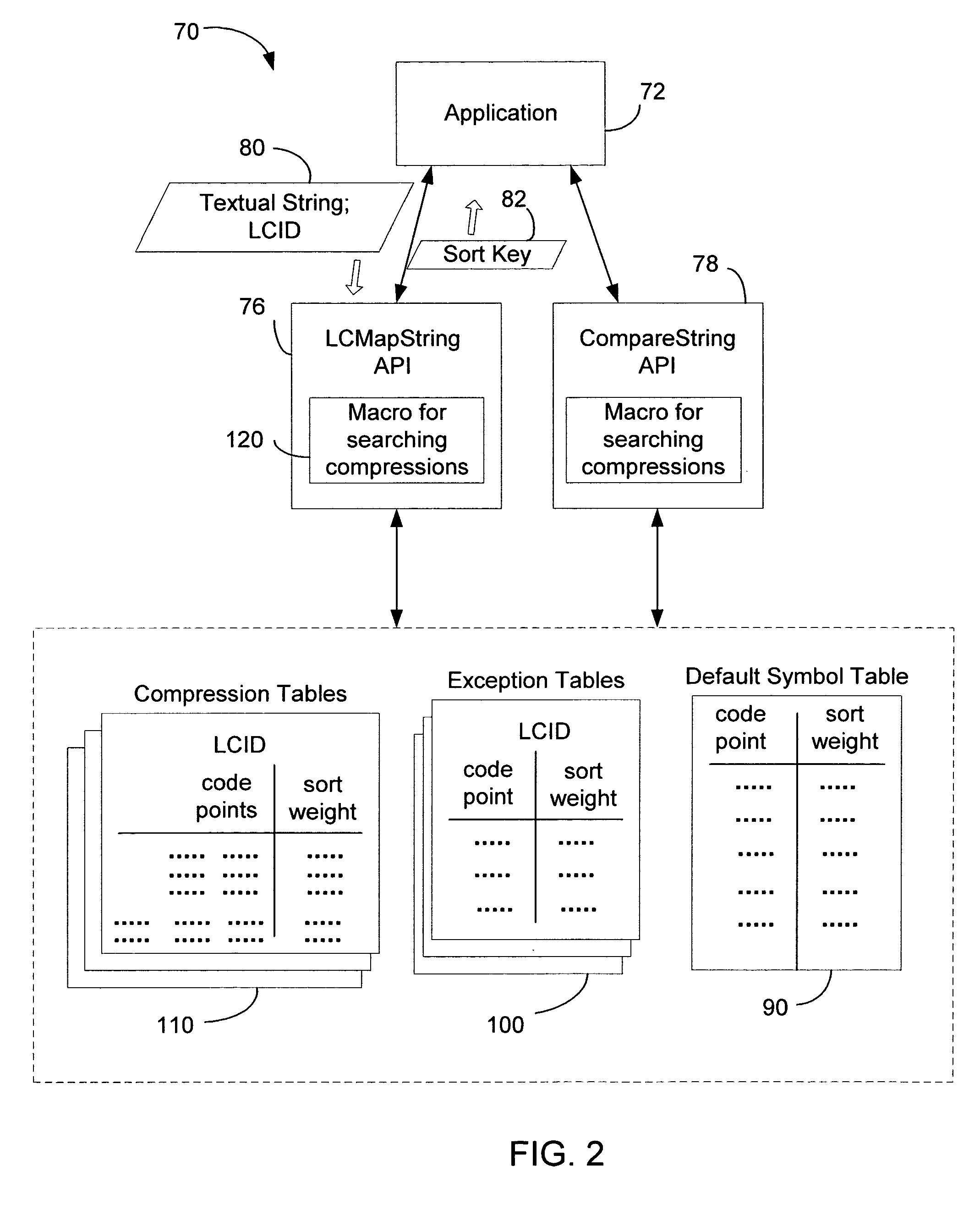
System and method for linguistic collation
A system and method is provided for handling the collation of linguistic symbols of different languages that may have various types of compressions (e.g., from 2-to-1 to 8-to-1). A symbol table of the symbols identified as Unicode code points is generated, with each symbol tagged with a highest compression type of that symbol by sorting the compression tables of the various languages. During a sorting operation with respect to a given string, the tag of a symbol in the string is checked to identify the highest compression type of compressions beginning with that symbol, and the compression tables for the language with compression types equal or lower than the highest compression type of the symbol are searched using a binary search method to find a matching compression for the symbols in the string. A common search module is used to perform binary searches through compression tables of different compression types.
Owner:MICROSOFT TECH LICENSING LLC
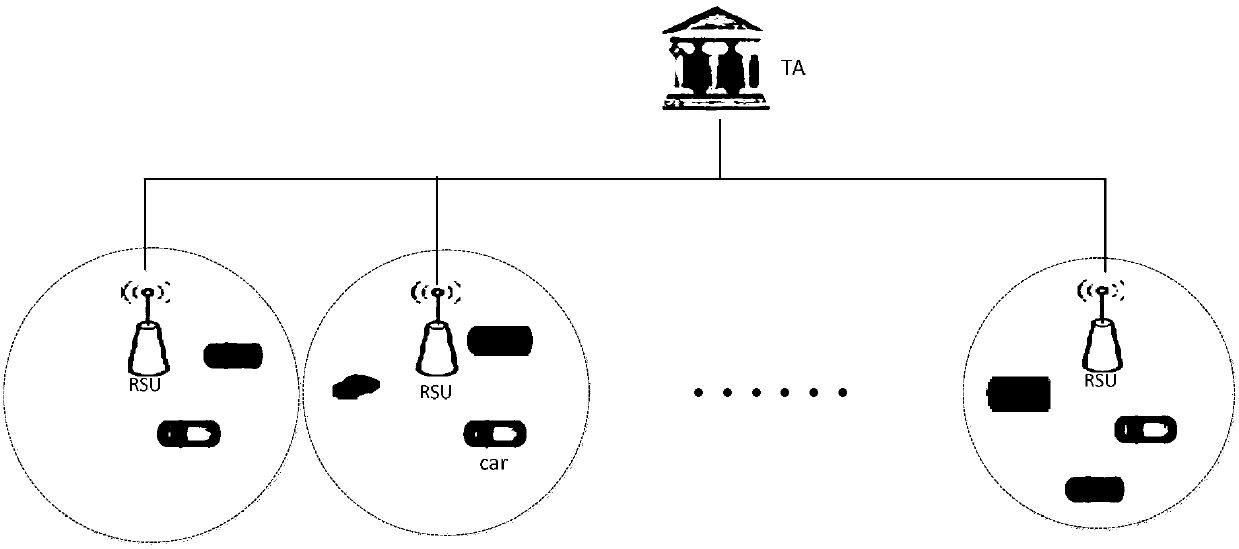
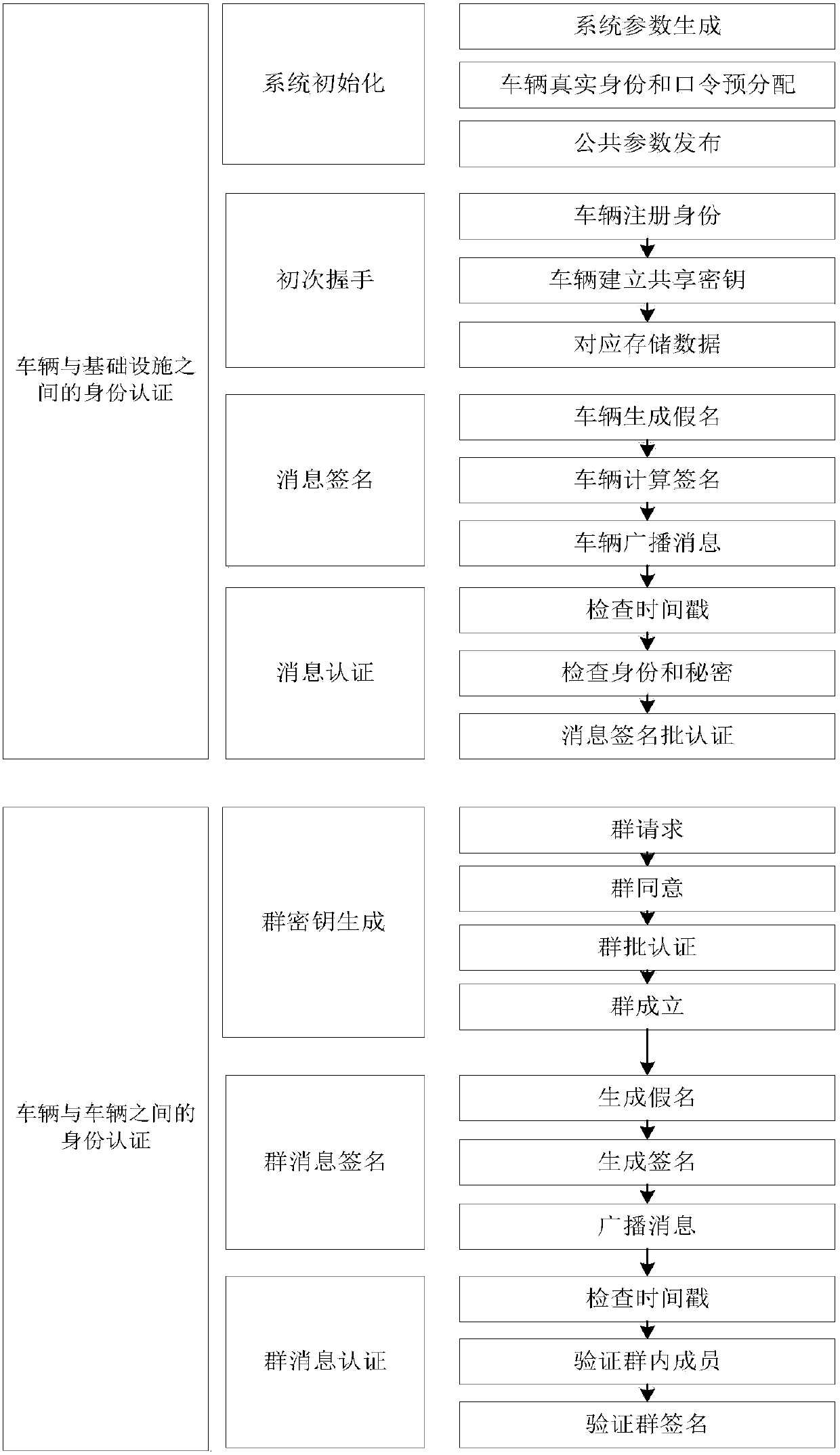
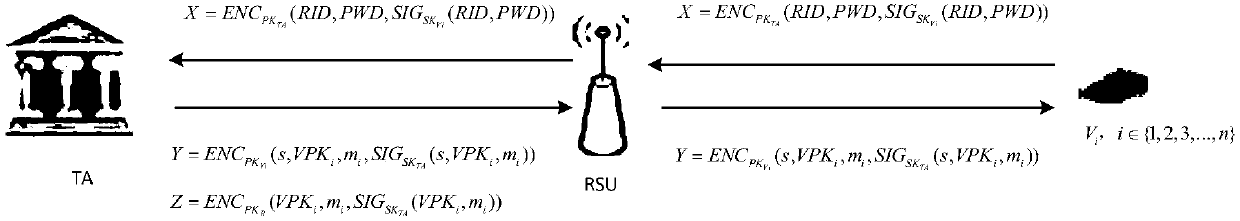
Vehicle-mounted ad hoc network security authentication method based on Cuckoo filter
ActiveCN105959117AMeet the identity authentication functionSatisfy the information integrity functionKey distribution for secure communicationPublic key for secure communicationValidation methodsMassage
The invention discloses a vehicle-mounted ad hoc network security authentication method based on a Cuckoo filter. The method comprises the following two steps: 1) identity authentication between a vehicle and an infrastructure (V2I), wherein the step comprises the following four specific processes: system initialization, initial handshake, message signature and massage authentication; and 2) identity authentication between vehicles (V2V), wherein the step comprises three specific processes: group key generation, group message signature and group massage authentication. The method is realized based on software without depending on any other specific hardware equipment; an unparalleled linear pairing method is adopted in the authentication phase, and the unparalleled linear pairing authentication method is suitable for both V2I and V2V authentication, so that the method has efficient computing power and lower cost; and in the batch certification phase, the Cuckoo filter and the binary search technique are adopted to detect whether signature is effective, so that efficiency of the authentication phase is improved to a great extent.
Owner:ANHUI UNIVERSITY
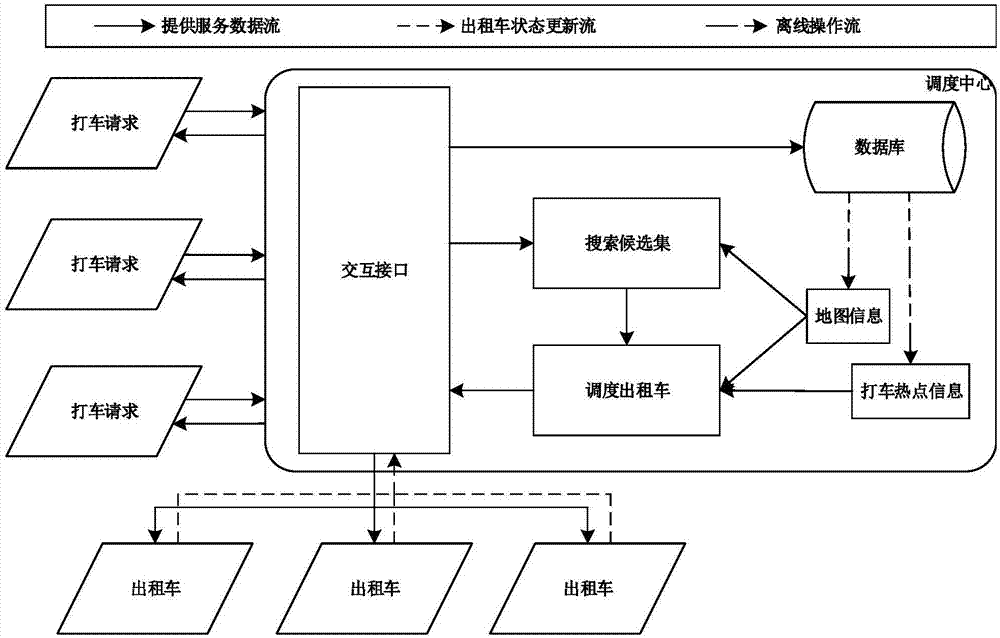
Dynamic carpooling scheduling method based on taxi-hailing hot spot
The invention belongs to the computer application technology field and discloses a dynamic carpooling scheduling method based on a taxi-hailing hot spot. The method is performed mainly through two stages: a searching stage and a scheduling stage. In the searching stage, a time-based binary search algorithm is used to quickly and efficiently retrieve taxi candidate sets that may serve passengers. In the scheduling stage, according to the given definition of dynamic carpooling scheduling problem, the conditions for each taxi in the candidate taxi sets are determined so that the taxis with the largest average satisfaction are selected to provide service for passengers, and in view of the empty car scheduling, and an optimal scheduling strategy based on hot spot is provided. This method can realize the personalized dispatching service for passengers, and it is simple and efficient, and has very strong expansibility. This provides important reference value for the study of dynamic carpooling scheduling.
Owner:DALIAN UNIV OF TECH
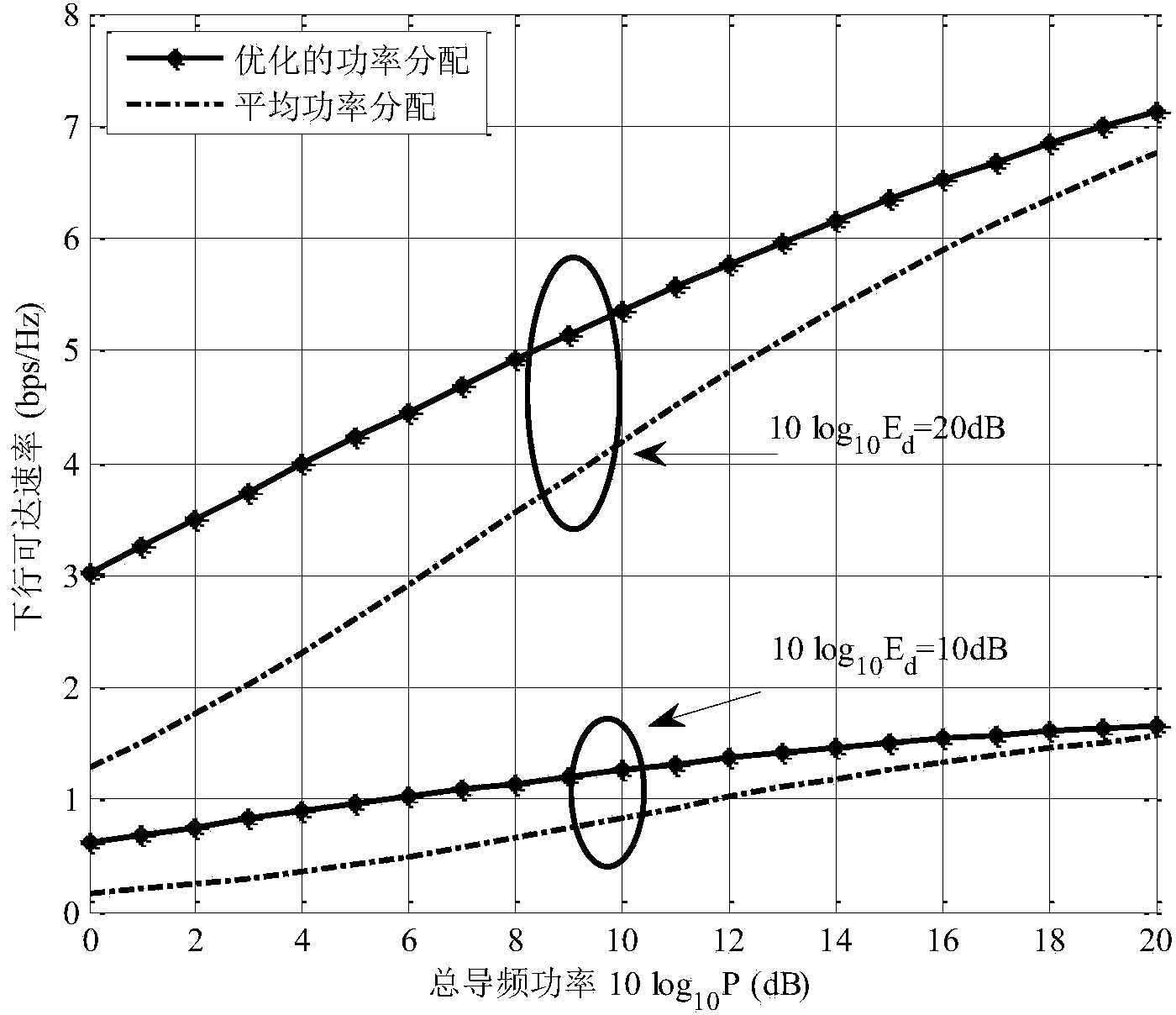
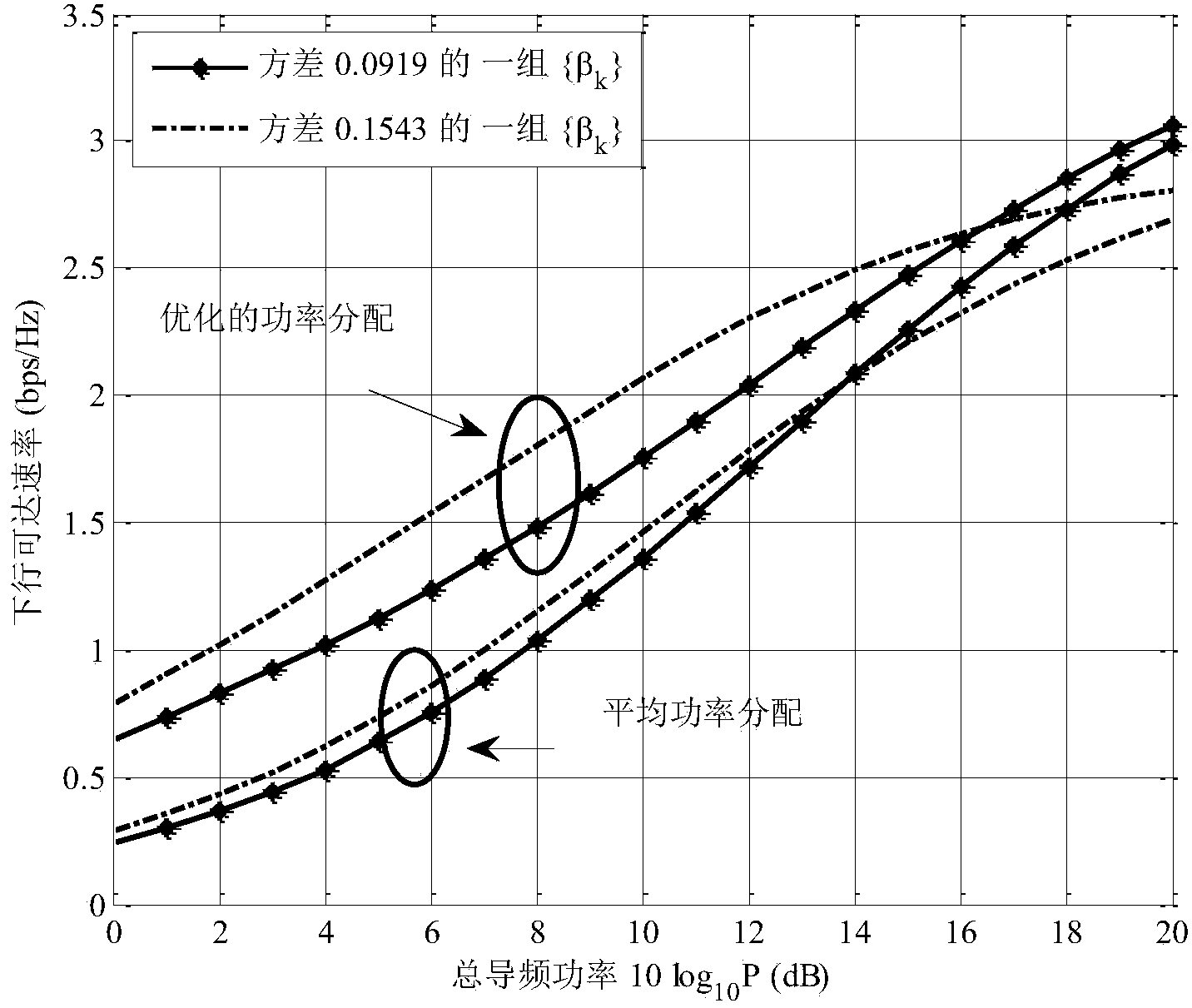
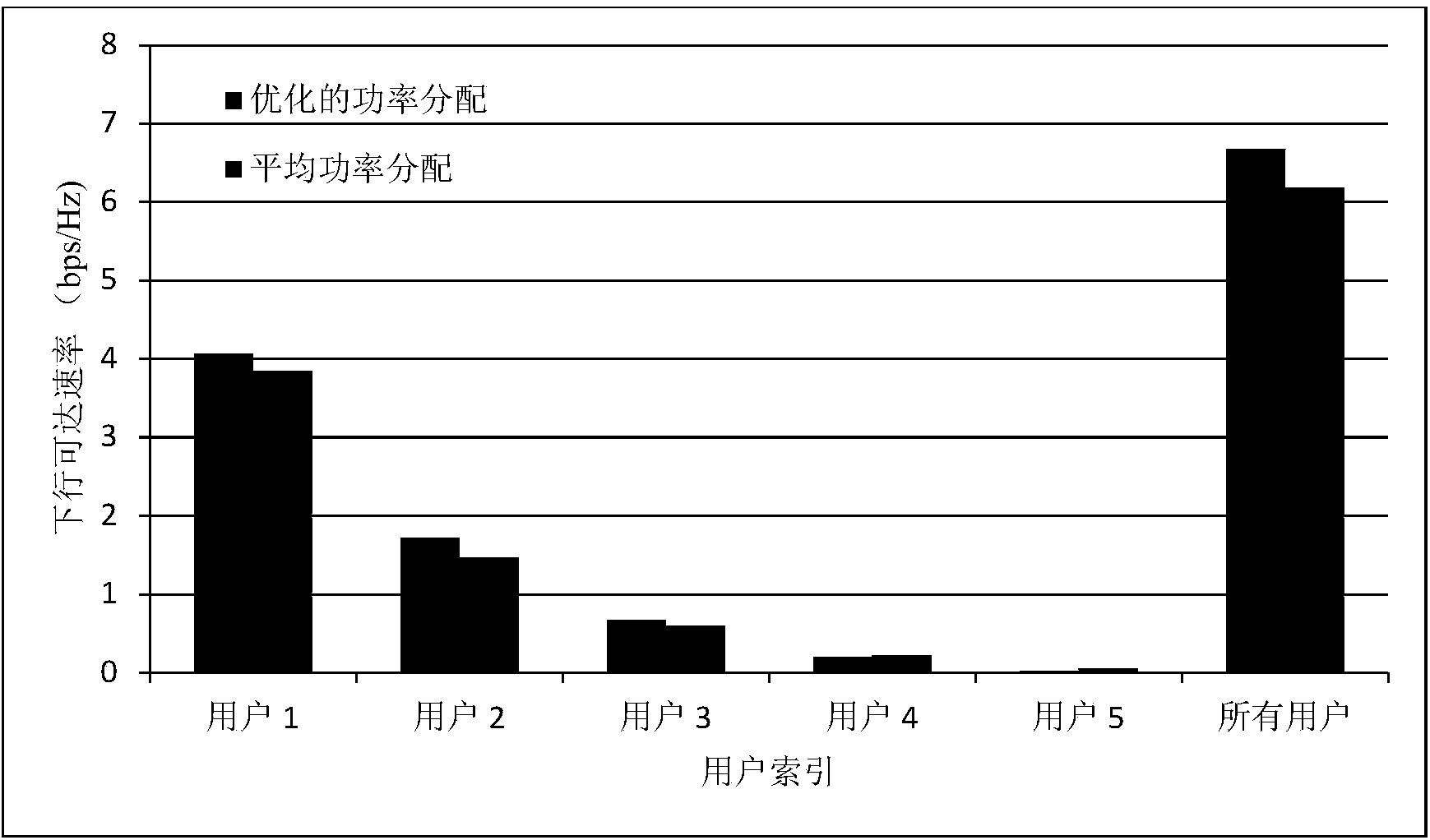
Method for heterogeneous user pilot frequency power optimal distribution in large-scale multi-input multi-output system
InactiveCN104039004AImprove data transfer performancePracticalPower managementMulti inputDistribution method
The invention discloses a method for heterogeneous user pilot frequency power optimal distribution in a large-scale multi-input multi-output system. The method comprises a first step of generating a group of randomly distributed heterogeneous users, enabling each user to undergo independent channel information, and calculating a system downlink achievable speed; a second step of forming a Lagrangian function L by the system downlink achievable speed and total power constraint conditions; a third step of assuming lambda to be a Lagrangian multiplier, performing derivation of L on pilot frequency power rhok and lambda to obtain an expression of rhok related to the lambda and the channel information; a fourth step of obtaining the value range of lambda based on the expression obtained in the third step according to the restrictions that rhok is larger than 0 and smaller than the total power; a fifth step of performing binary search according to the value range of lambda obtained in the fourth step, and obtaining an optimal pilot frequency power distribution value. According to the method, different channel information of the heterogeneous user is utilized to achieve optimal distribution of pilot frequency power, and the overall data transmission performance of the system is improved.
Owner:SOUTHEAST UNIV
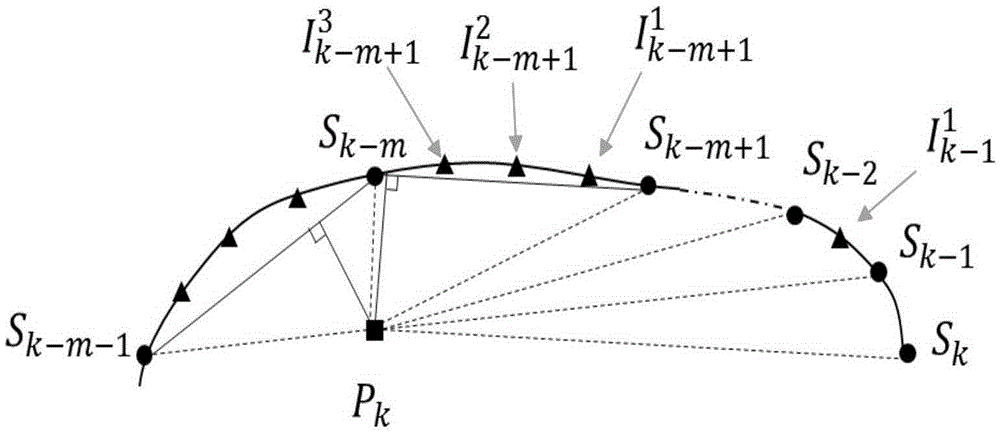
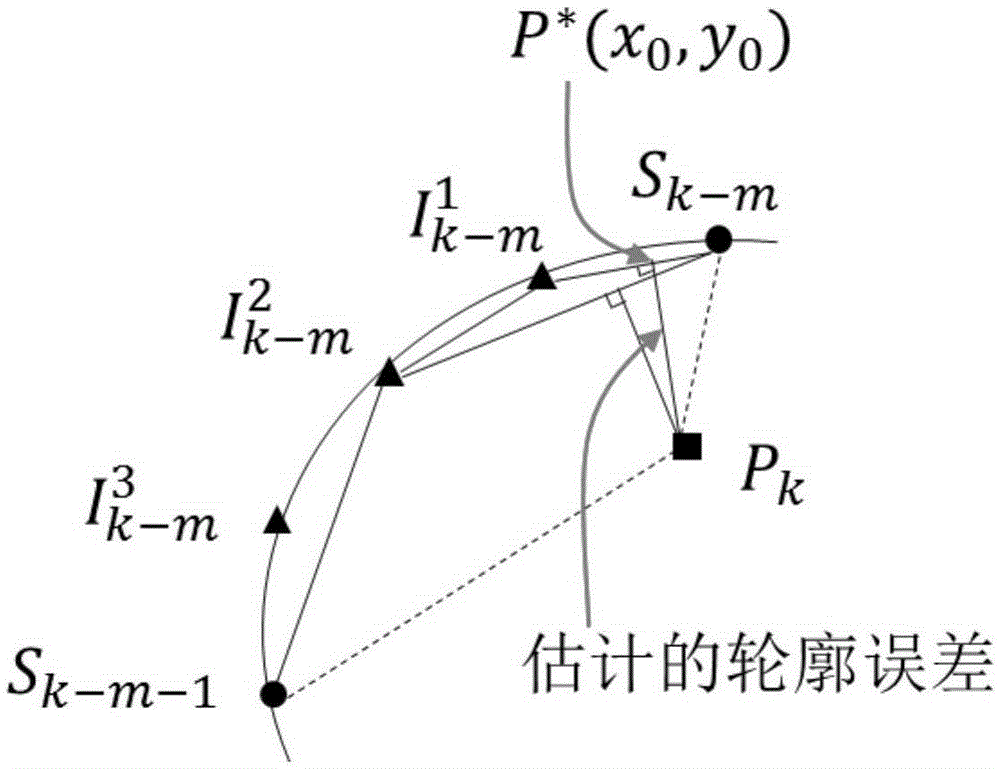
Real-time self-adaptive contour error estimation method
InactiveCN105388840AEstimated error works wellImprove robustnessNumerical controlAlgorithmEstimation methods
The invention discloses a real-time self-adaptive contour error estimation method, which can be used for a numerical control system or a contour controller of a robot. The contour error estimation method comprises the steps: generating extra interpolation points by properly modifying a conventional parameter curve interpolation method, wherein the generated extra interpolation points are only used for contour error estimation and do not serve as reference instructions of a motion controller; searching among original interpolation points the nearest point from an actual cutter position, preliminarily determining a search scope; and further determining foot points through a binary search method. A distance between the foot points and an actual cutter point is an estimated contour error. Compared with conventional estimation methods, the real-time self-adaptive contour error estimation method is more accurate in estimation precision. In particular, the method can still have a great effect and exhibit excellent algorithm robustness when the estimation effects of the conventional methods suddenly become bad in a condition with high speed movement and high curvature of a curve. Moreover, the method needs moderate computational complexity, fully meets the requirement of real-time applications, and is highly practical.
Owner:SHANGHAI JIAO TONG UNIV
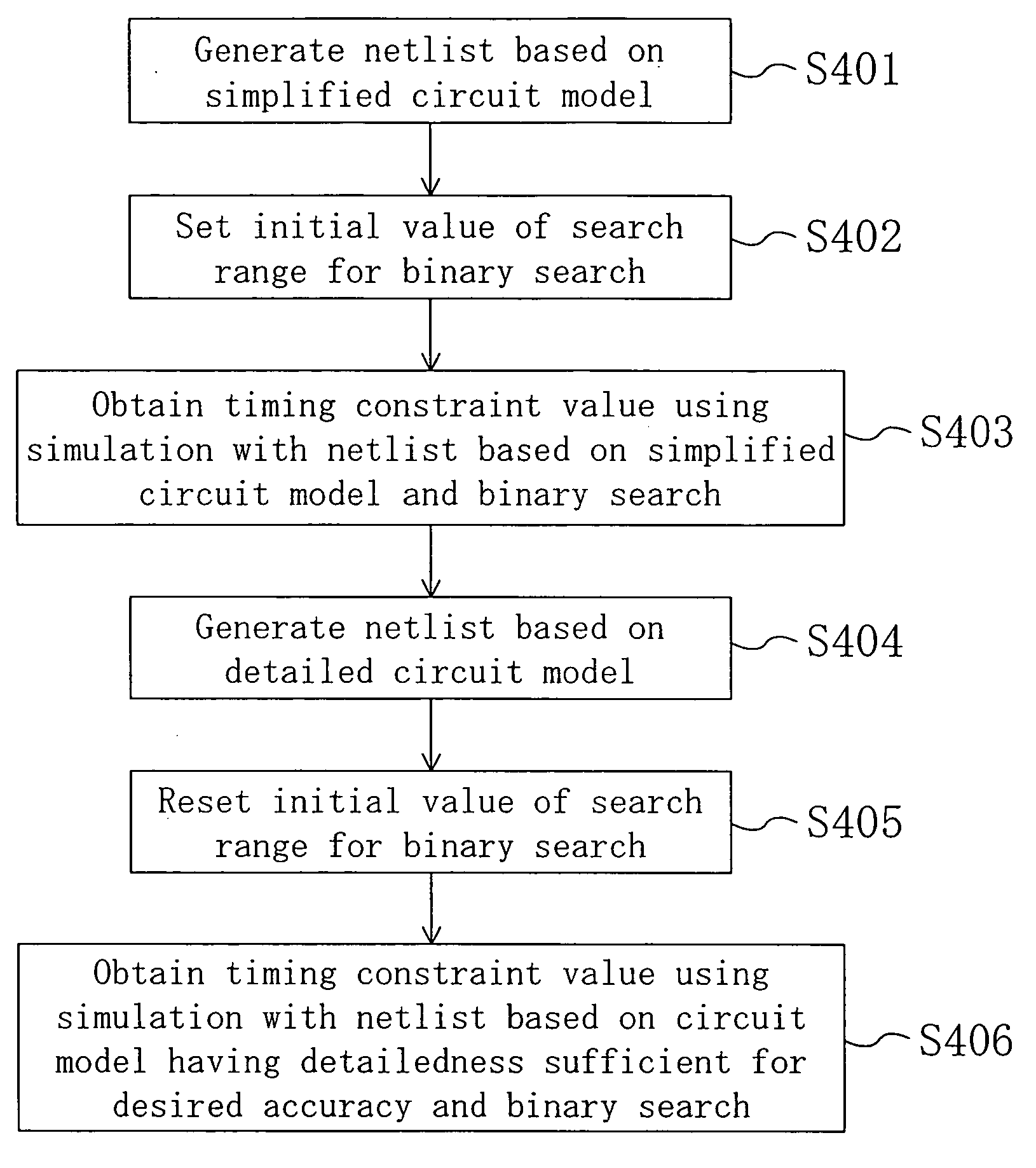
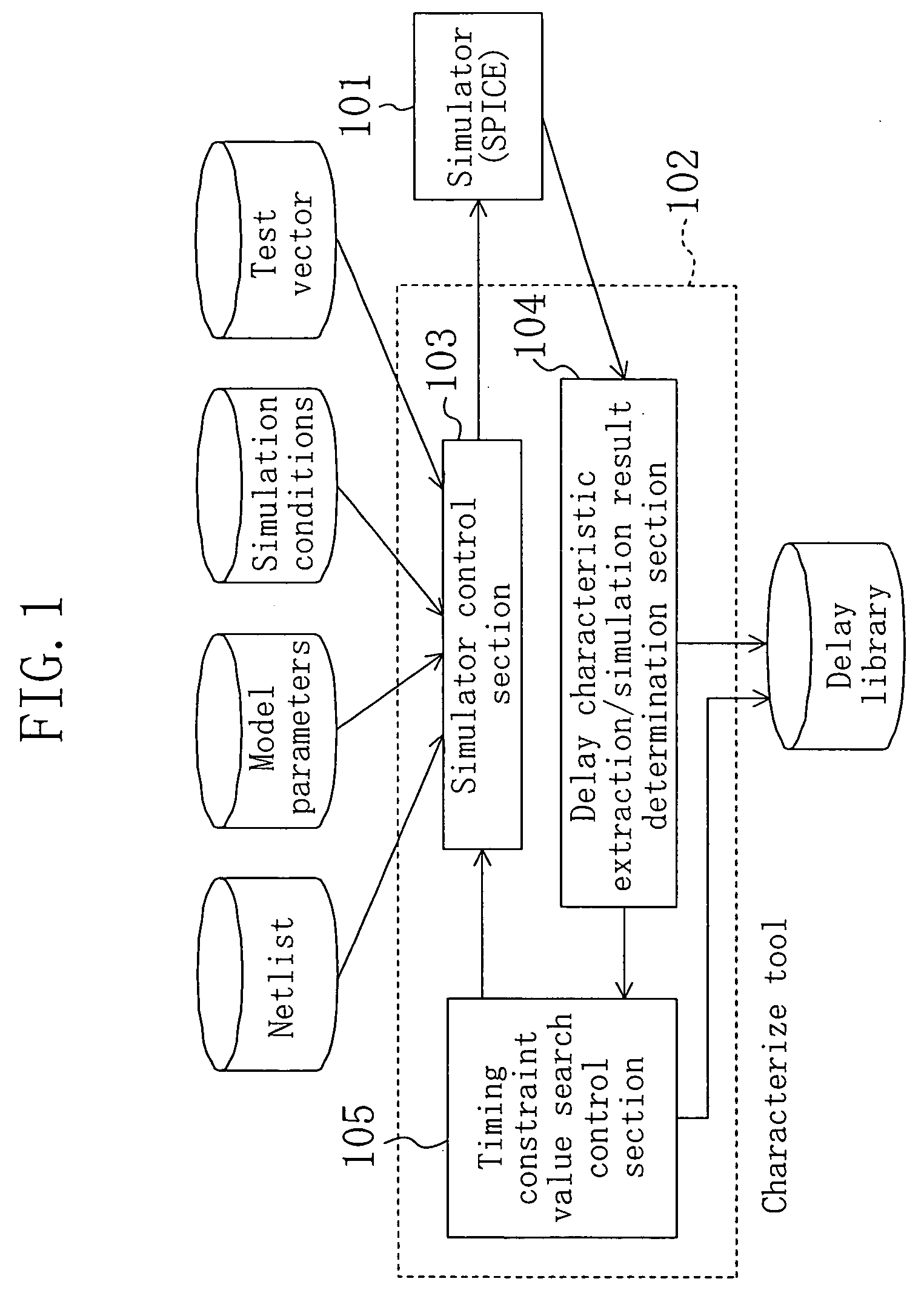
Delay library generation method and delay library generation device
InactiveUS20050149895A1Generate efficientlyImprove accuracyDetecting faulty computer hardwareSemiconductor/solid-state device manufacturingComputer scienceReal-time computing
A delay library of high accuracy is efficiently generated within a short time period. To this end, a set-up time is calculated by static analysis with no consideration of a delay caused by a wire; the initial value of the search range for the next binary search cycle is set such that the set-up time is the median value of the search range (for example, the range of 0.5 ns is set); and correct set-up time α is obtained using binary search based on the initial value of the search range.
Owner:PANASONIC CORP
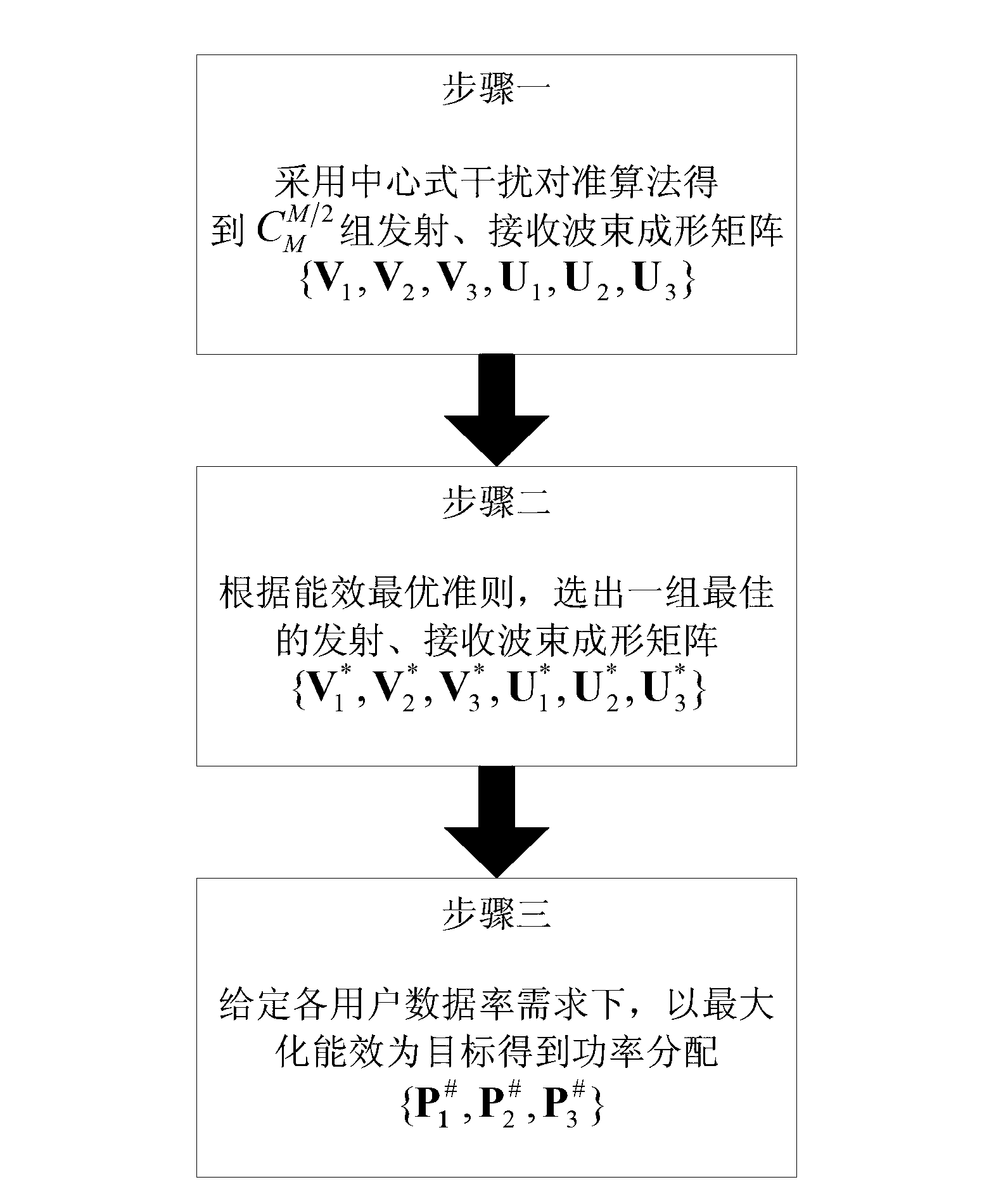
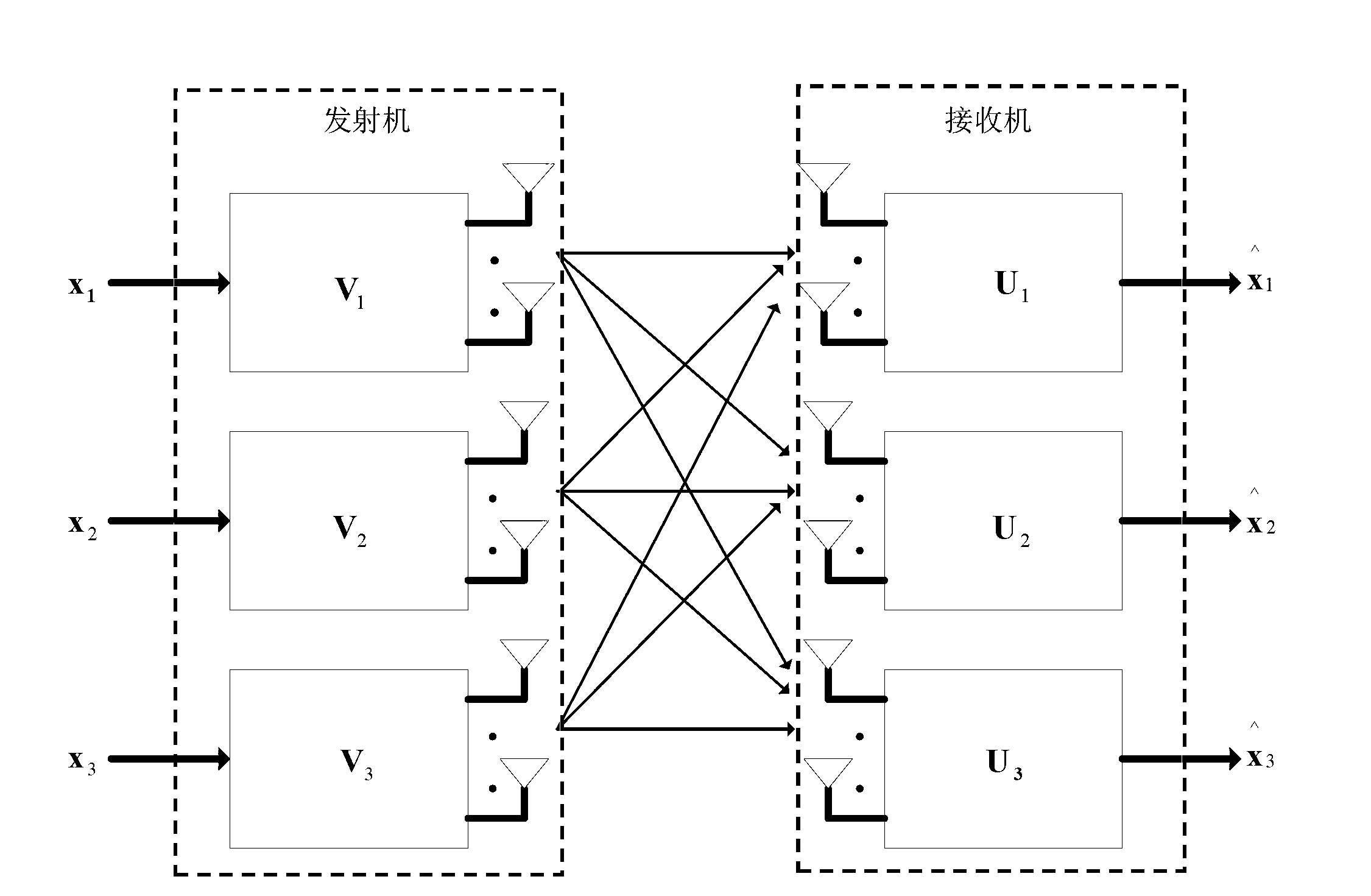
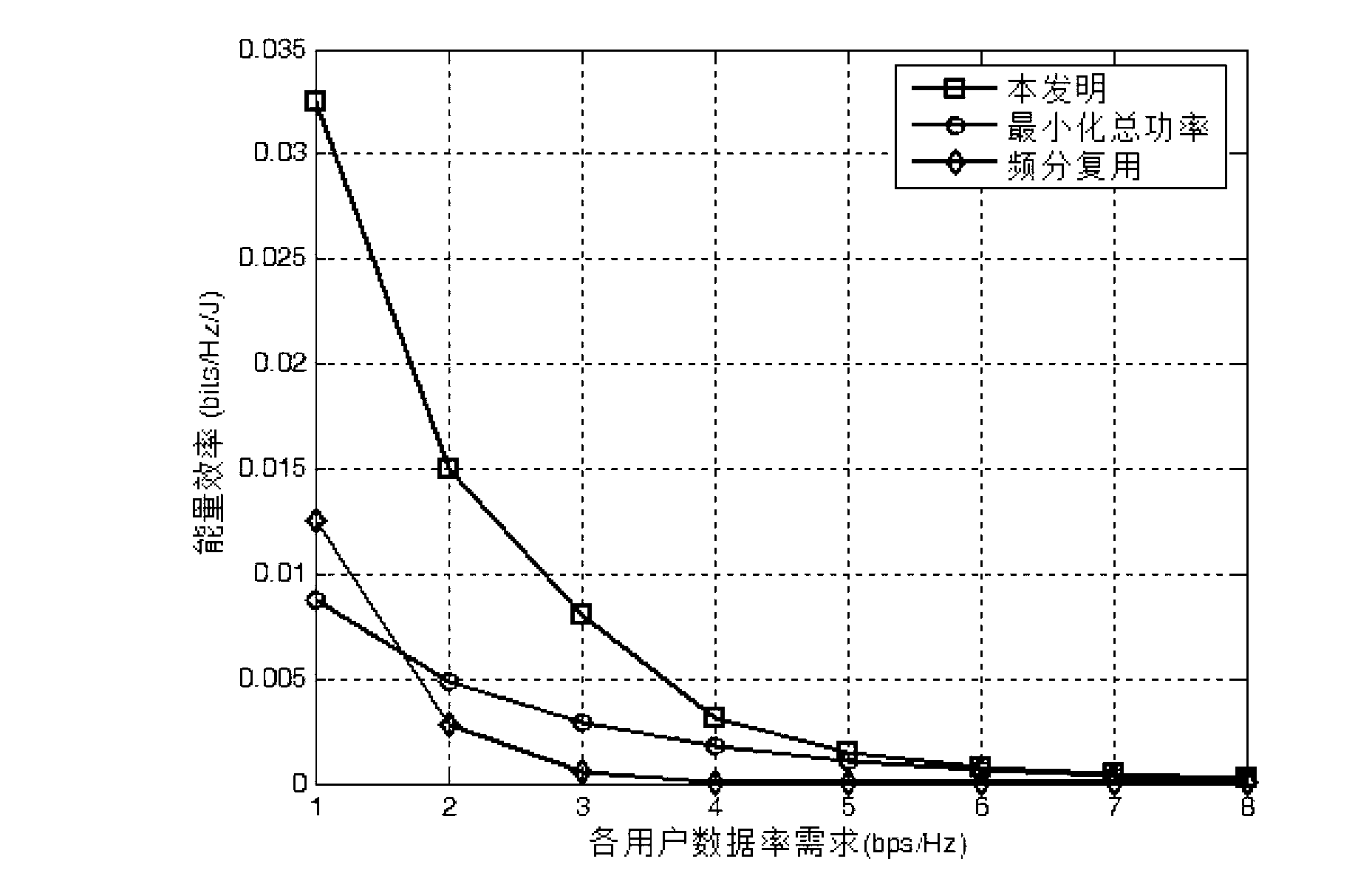
Energy-efficient interference alignment method for multi-cell MIMO (multiple-input and multiple-output) system
ActiveCN103297103AReduce complexityImprove performancePower managementSpatial transmit diversityRound complexityFrequency-division multiplexing
The invention discloses an energy-efficient interference alignment method for a multi-cell MIMO (multiple-input and multiple-output) system and belongs to the technical field of wireless communications. The method includes: firstly, interferences on a receiving end from other cells are aligned to a same space and thoroughly eliminated by a central interference alignment algorithm, and analytical solutions to a transmitting and receiving beamforming matrix are obtained; secondly, one group is selected from the analytical solutions obtained at the previous step according to energy efficient norm, and the transmitting and receiving beamforming matrix with optimal system energy efficiency is obtained under the given requirements for various user data rates; thirdly, the optimal transmitting and receiving beamforming matrix is substituted into an energy efficient expression, and optimal power matching is obtained by binary search with the goal of maximum system energy efficiency while the requirements of users for data rates are met. The method has the advantages that implementation is easier while the performance is better than that of frequency division multiplexing and that of the power matching method using minimal total transmitting power as the goal, and the method is widely applicable.
Owner:BEIHANG UNIV
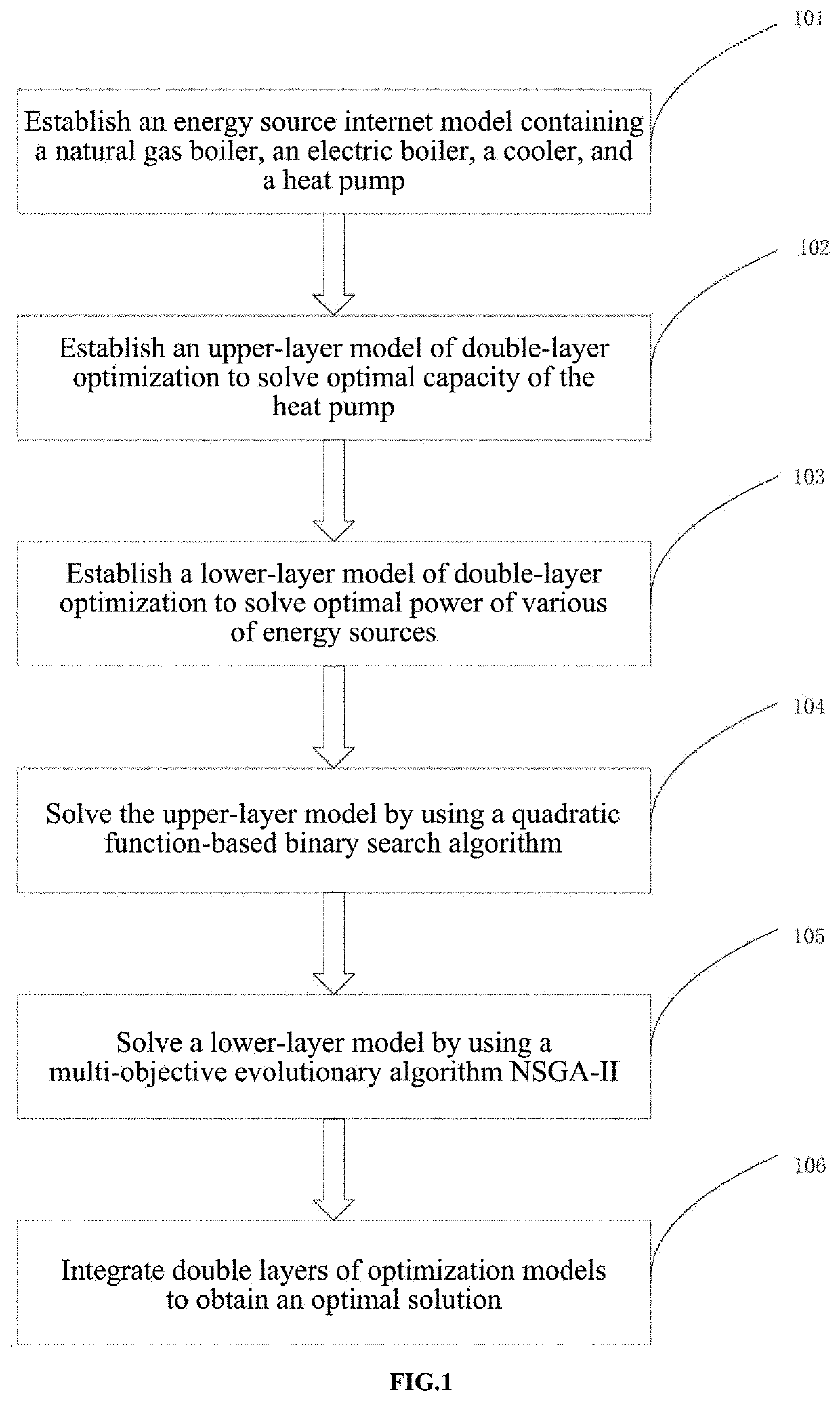
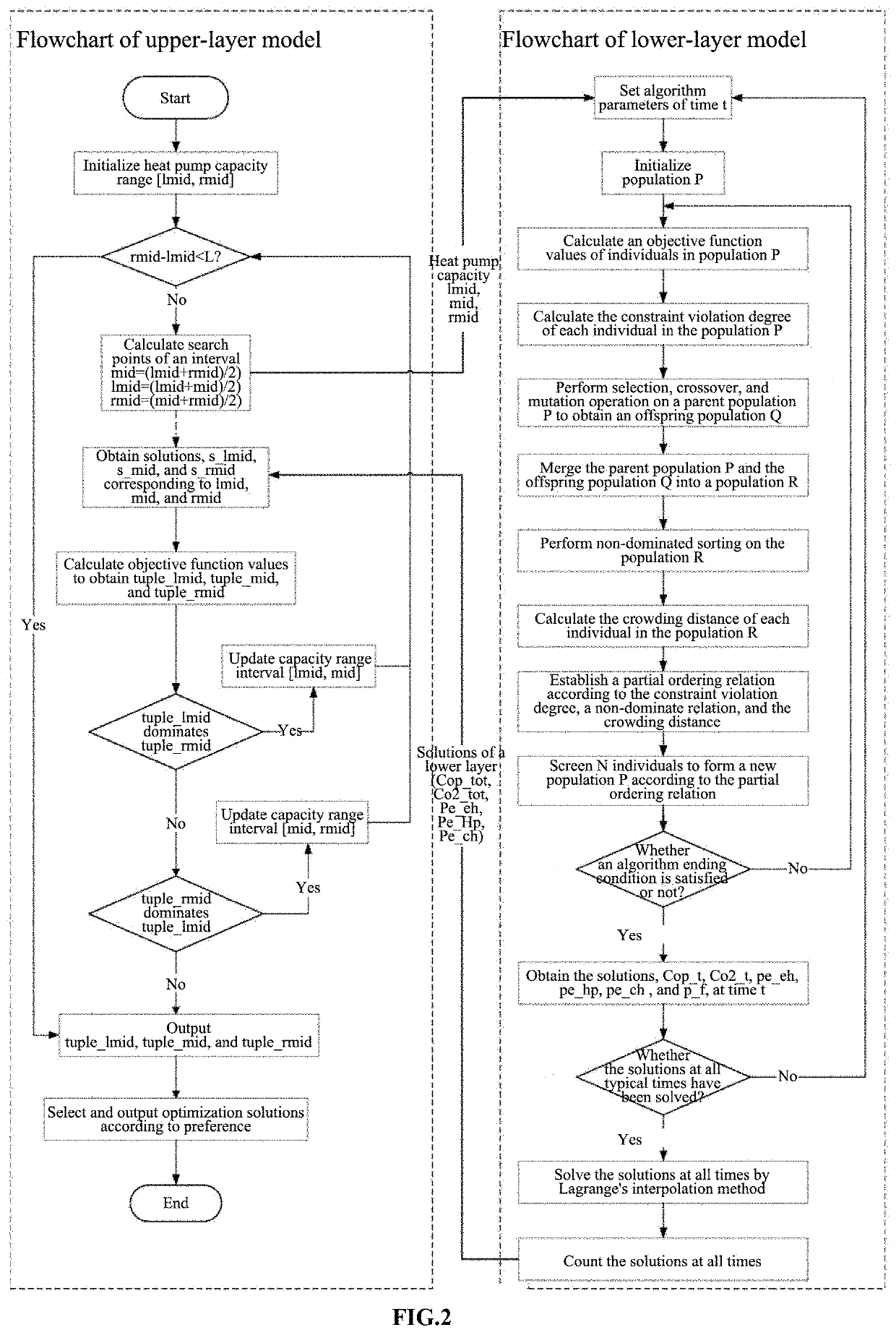
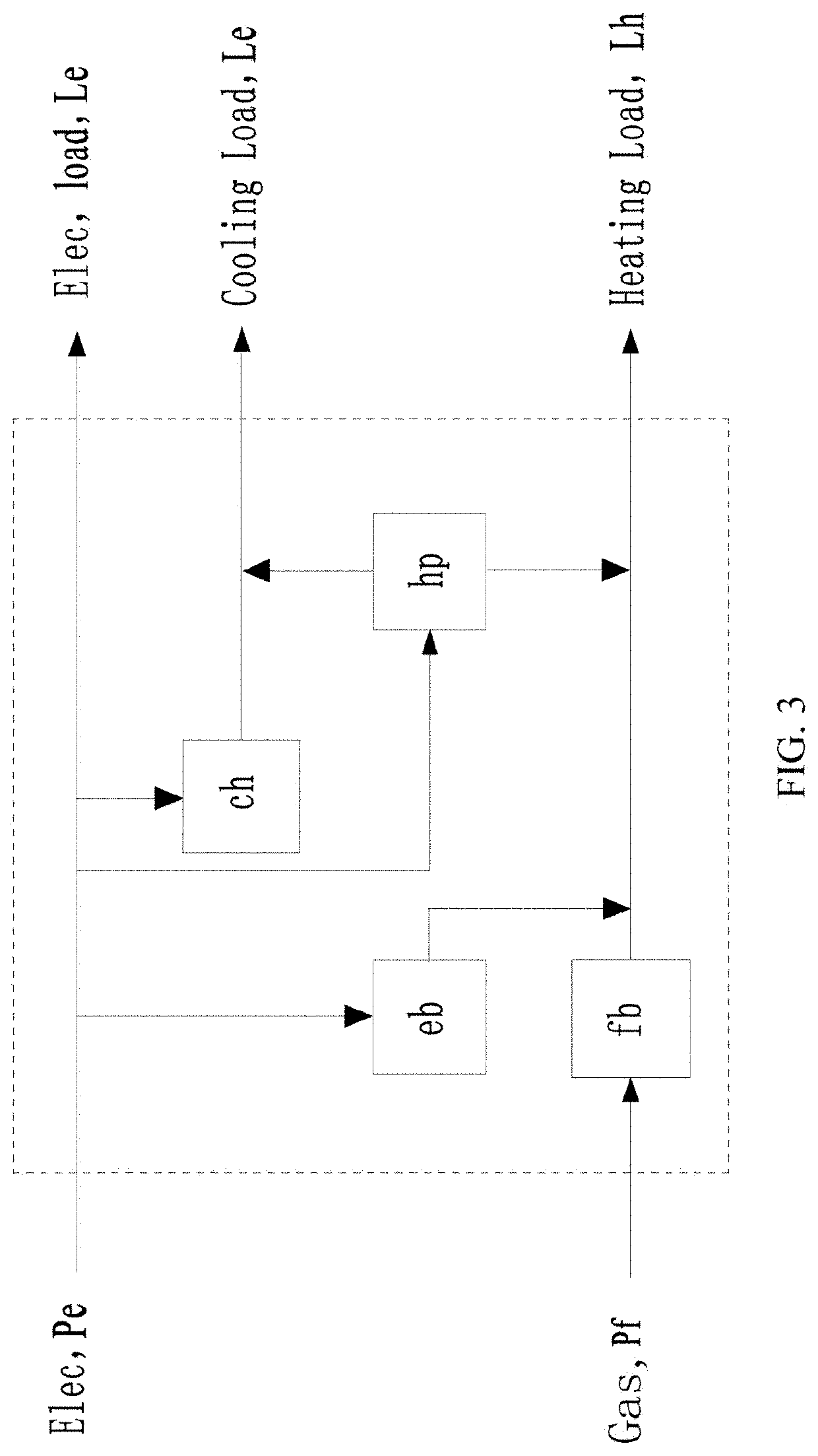
Optimization method for capacity of heat pump and power of various sets of energy source equipment in energy hub
PendingUS20210376605A1Avoid complex analysisEasy to solveGeometric CADGeneration forecast in ac networkExhaust gas emissionsIndustrial engineering
The present disclosure discloses a method for optimizing equipment capacity and equipment power of an energy hub system. The method includes establishing an energy hub model containing natural gas boilers, electric boilers, coolers and heat pumps, establishing a bilevel optimized upper model to solve the optimal heat pump capacity, and establishing a bilevel optimized lower model to solve the optimal power utilization of each energy device based on the binary search algorithm of the quadratic function solves the upper model by using the multi-objective evolutionary algorithm NSGA-II to solve the lower model. The optimization method of the present invention can solve the multi-objective bilevel model problem without the help of commercial optimization software. Obtaining a reasonable, efficient and green planning scheme makes the total operating cost and total exhaust gas emissions of the energy hub relatively optimal.
Owner:XIANGTAN UNIV
Method and apparatus for performing a binary search on an expanded tree
InactiveUS7072885B2Increase speedHigh performance and cost-effectiveDigital data information retrievalData processing applicationsTheoretical computer scienceLongest prefix match
A method and apparatus for searching an electronically stored table of information including a plurality of table entries and facilitating high speed searching of a table to provide a longest matching entry. The table searching method uses at least one memory unit having a table of information including a plurality of data entries. The table of information has a plurality of search keys associated with the plurality of data entries and the plurality of search keys form a tree structure based on a prefix length for each of the search keys. The plurality of search keys are expanded such that each of the plurality of search keys has two lowest level search keys associated therewith that cover a lowest level of the tree structure. A binary search of the lowest level search keys is performed based on a search value to determine a longest prefix match. A data entry of the plurality of data entries is output based on said longest prefix match. The method is also applicable to routing data in an internet router where the routing of data packets depends on address information stored in the table of information.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
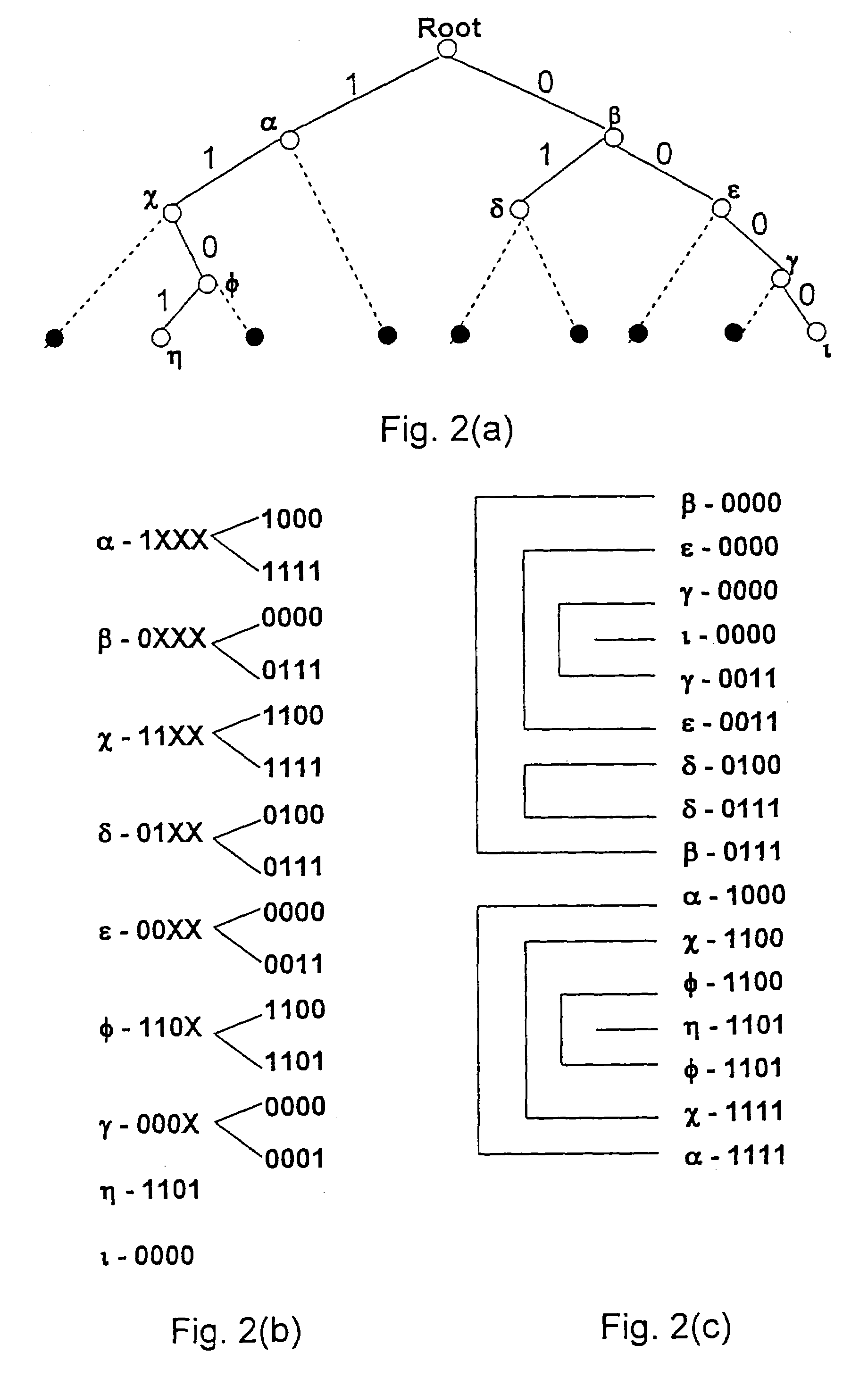
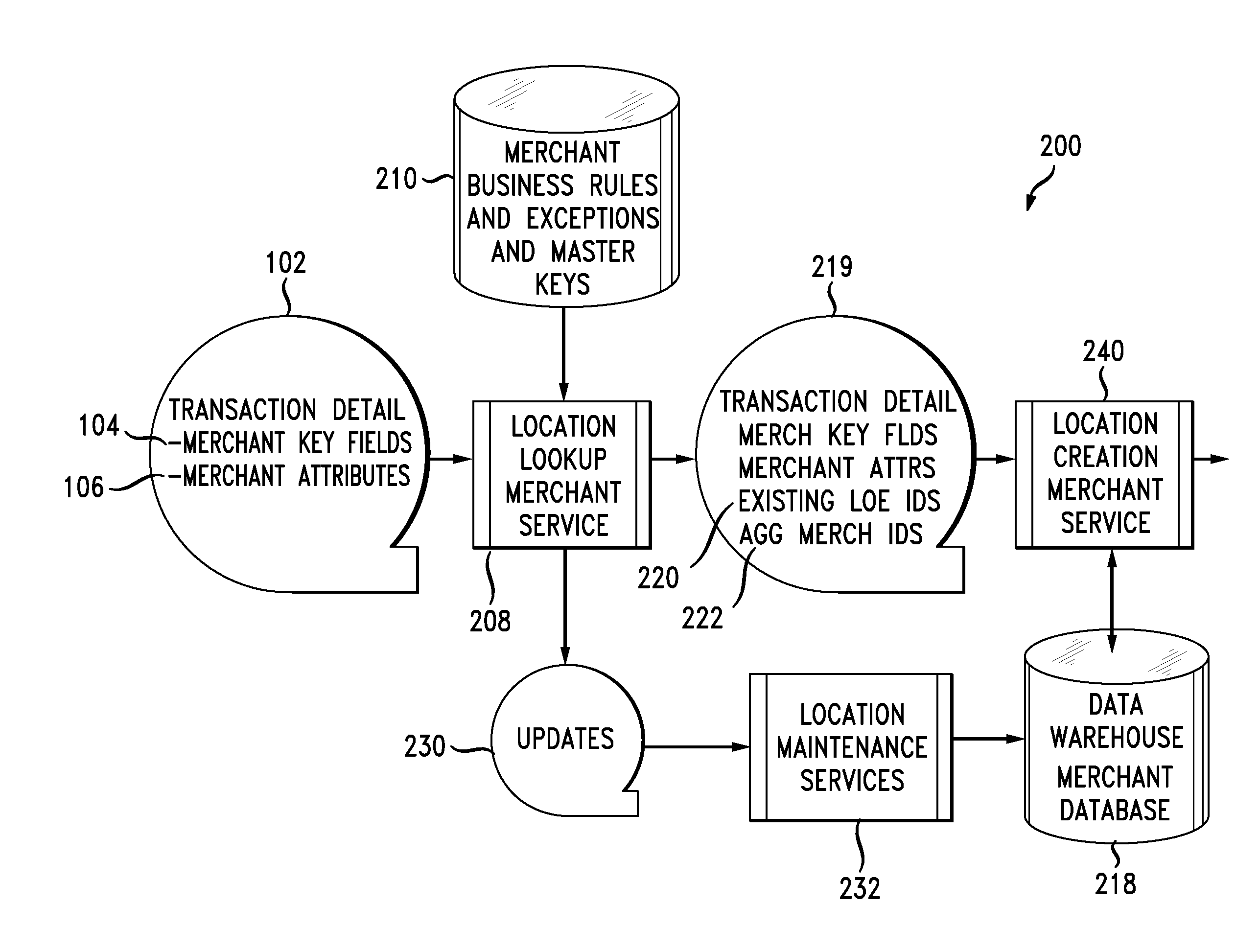
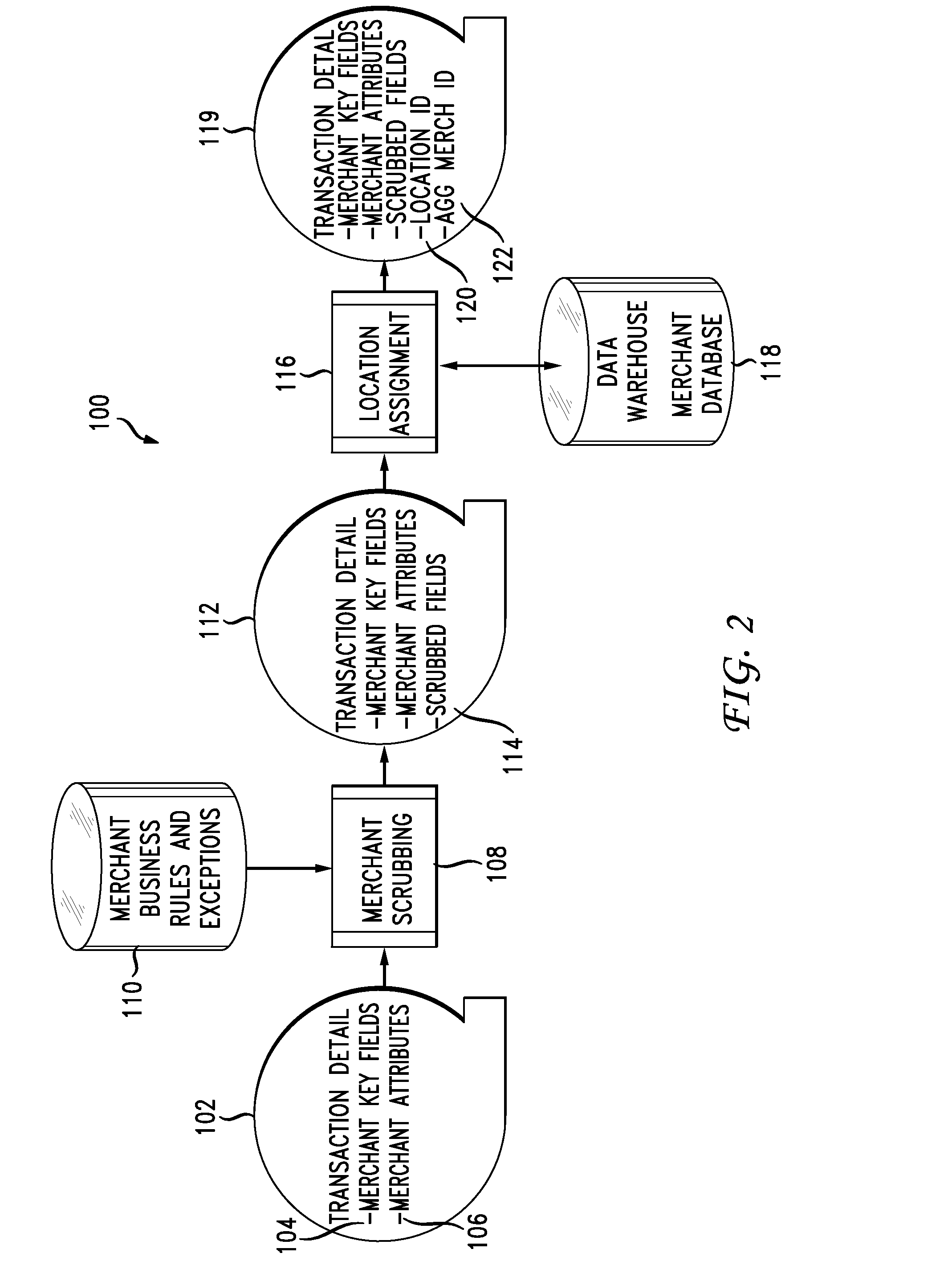
Instantaneous merchant information retrieval for financial transactions
A solution to disambiguate ambiguous merchant data in connection with processing a cashless transaction request in a real-time manner. Provided according to the present disclosure are a system and method including a binary-searchable non-transitory computer-readable medium is configure to store a first set of unambiguous merchant identification data having plural data entries therein, each entry corresponding to a merchant. A binary search of the first set of unambiguous merchant identification data is carried out using search keys based upon the ambiguous merchant identification data to determine whether one or more entries of the first set satisfies at least one of a hierarchical second set of partial match criteria for comparing the ambiguous merchant identification data with the first set of unambiguous merchant identification data. An entry of the first set of unambiguous merchant identification data is assigned to correspond with the ambiguous merchant identification data where at least a predetermined number of the second set of partial match criteria are met.
Owner:MASTERCARD INT INC
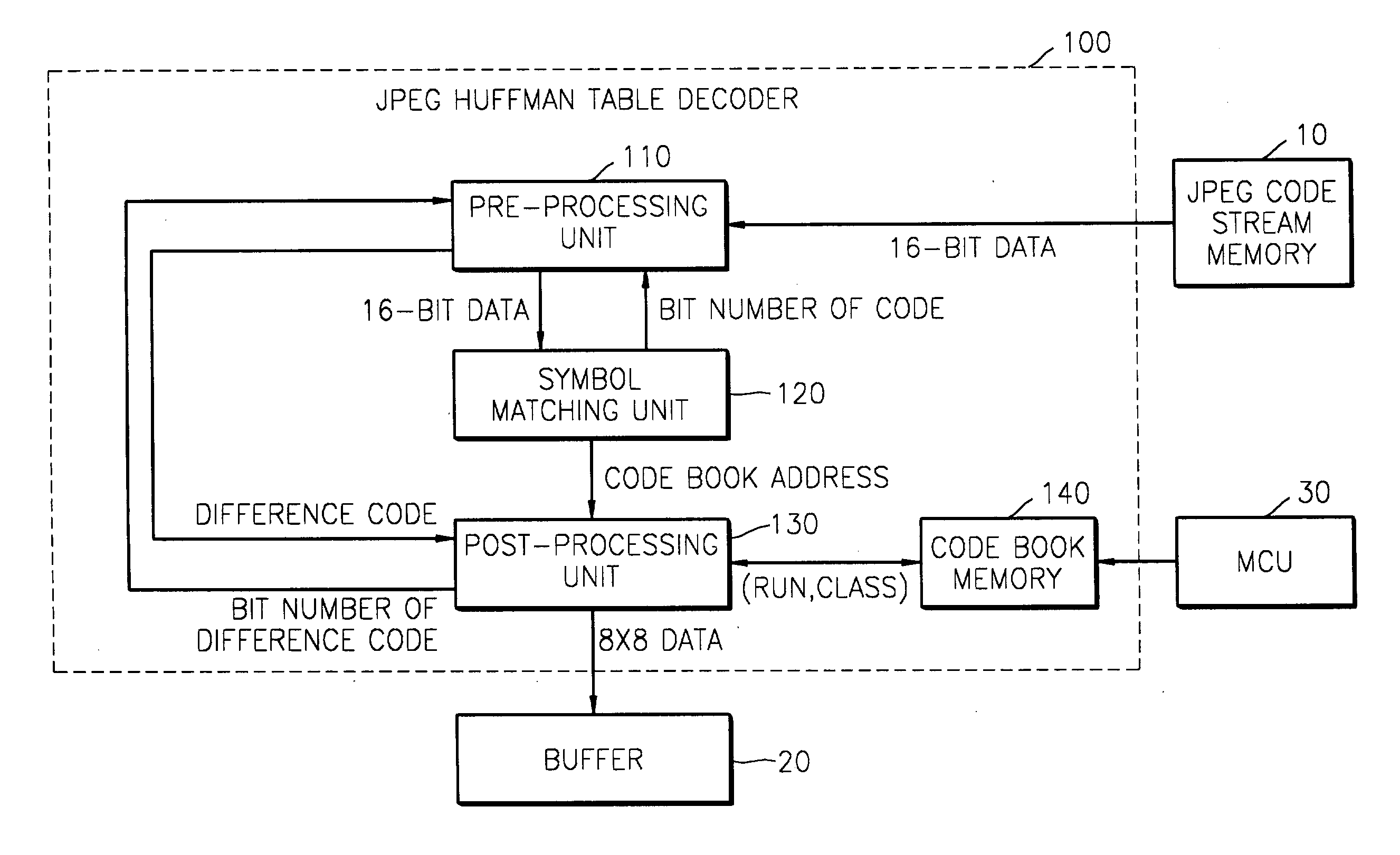
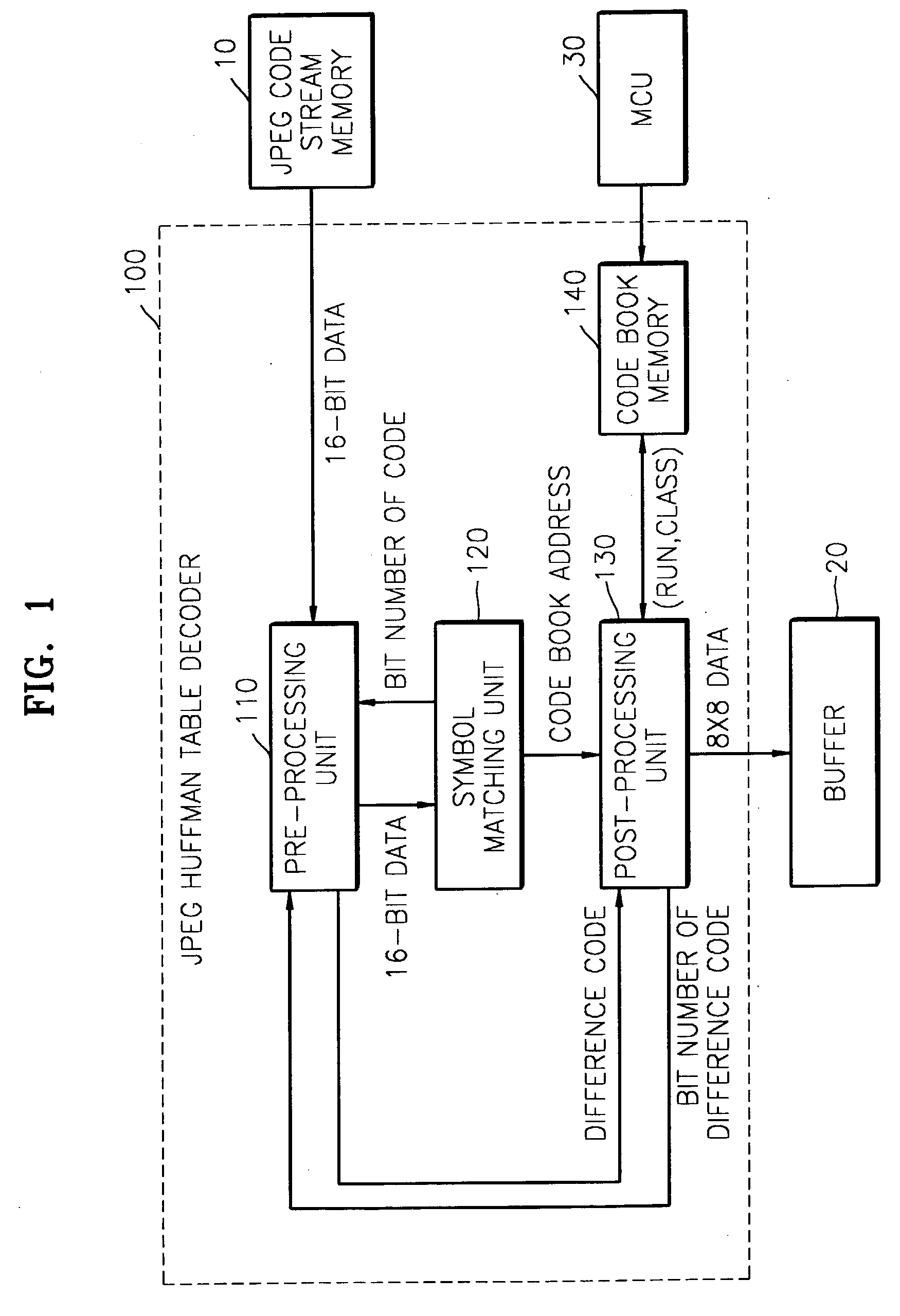
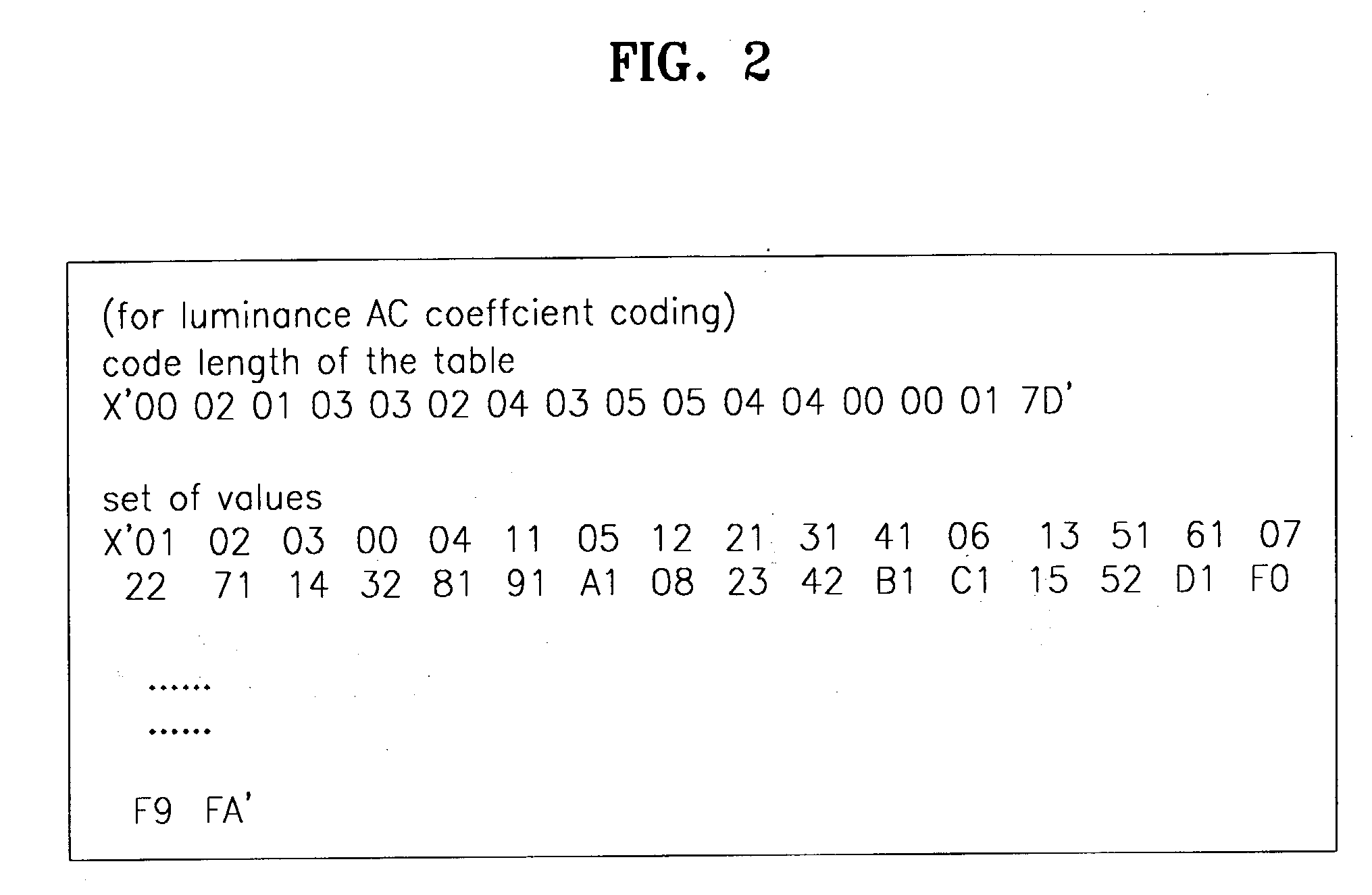
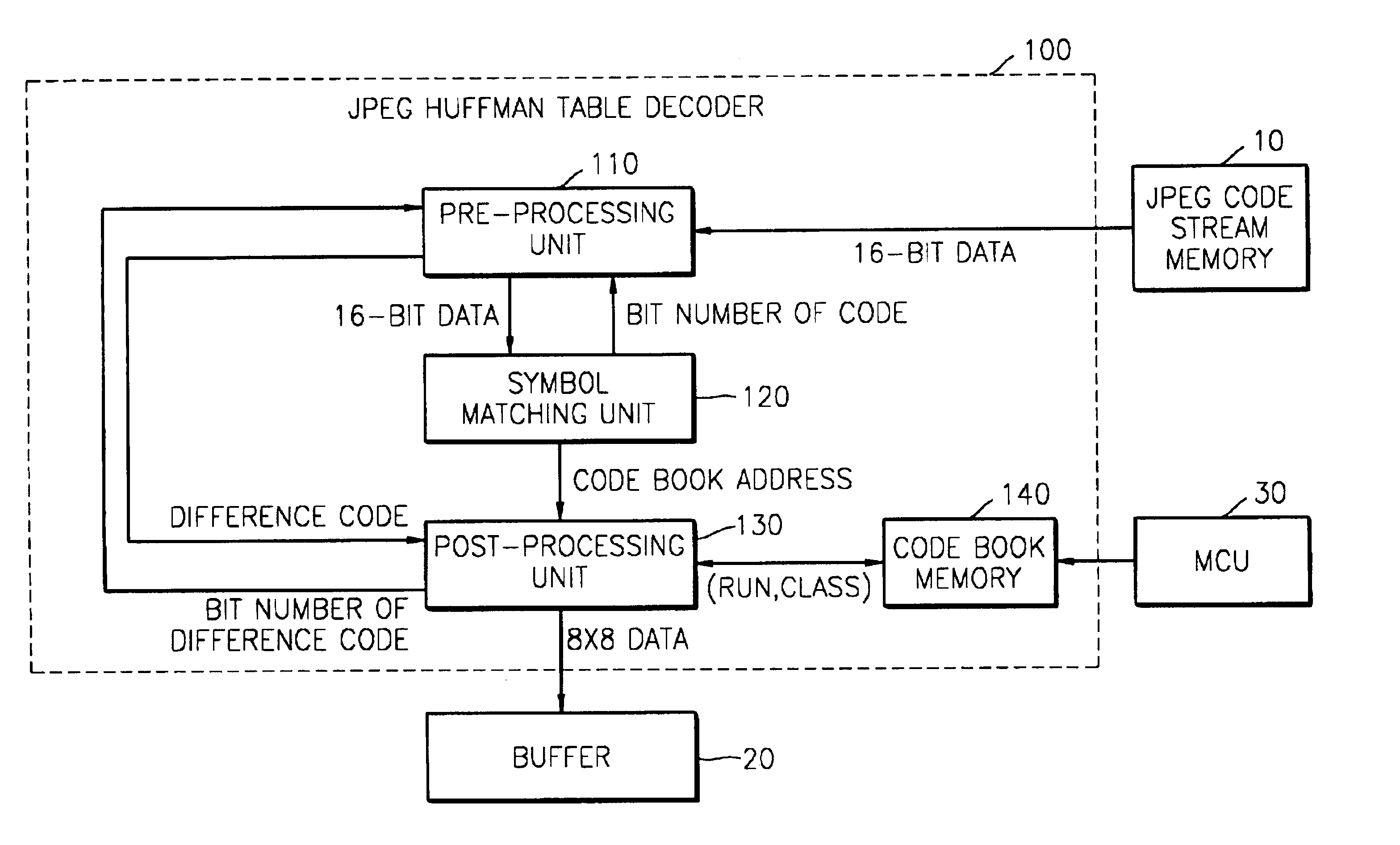
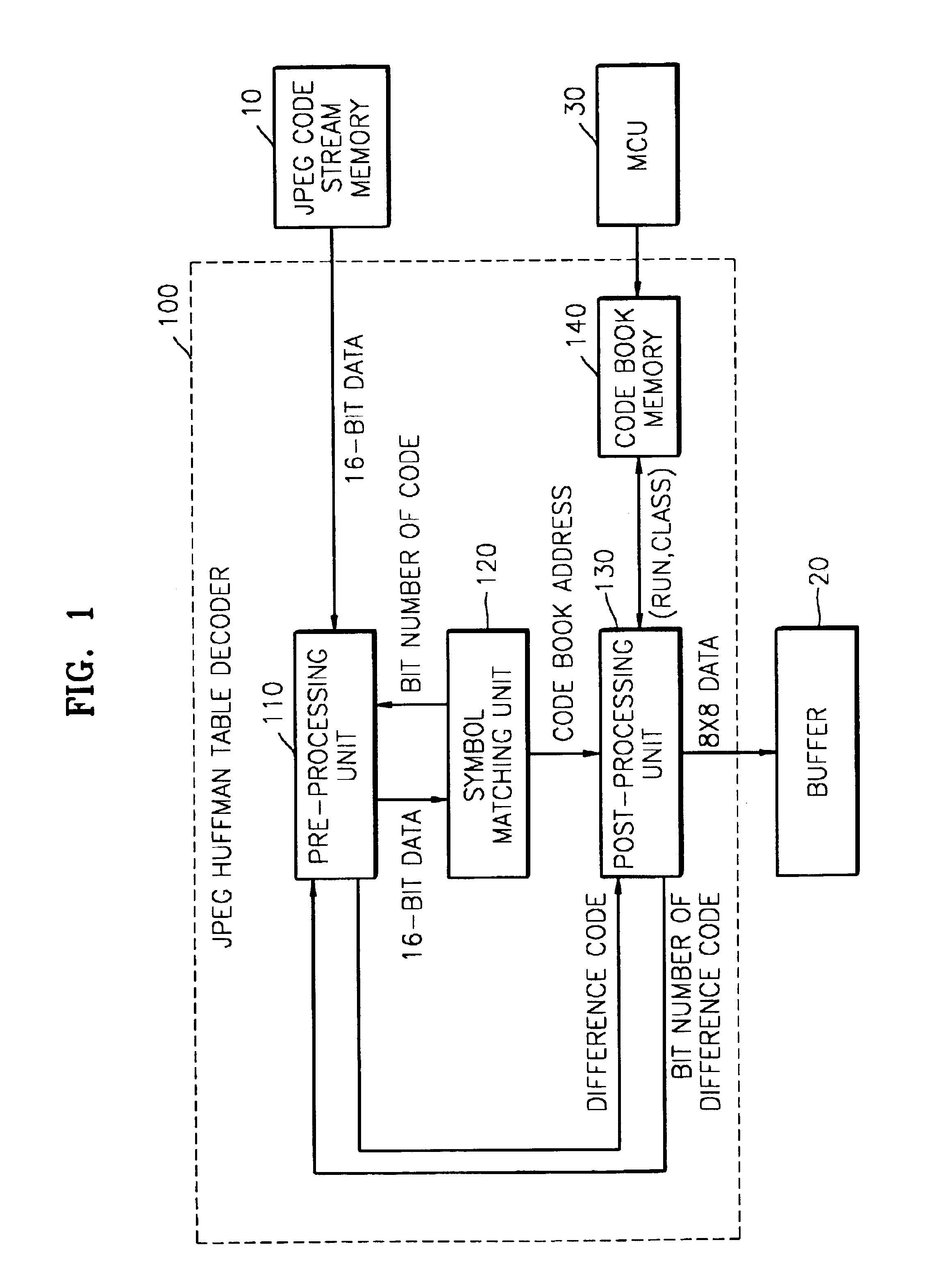
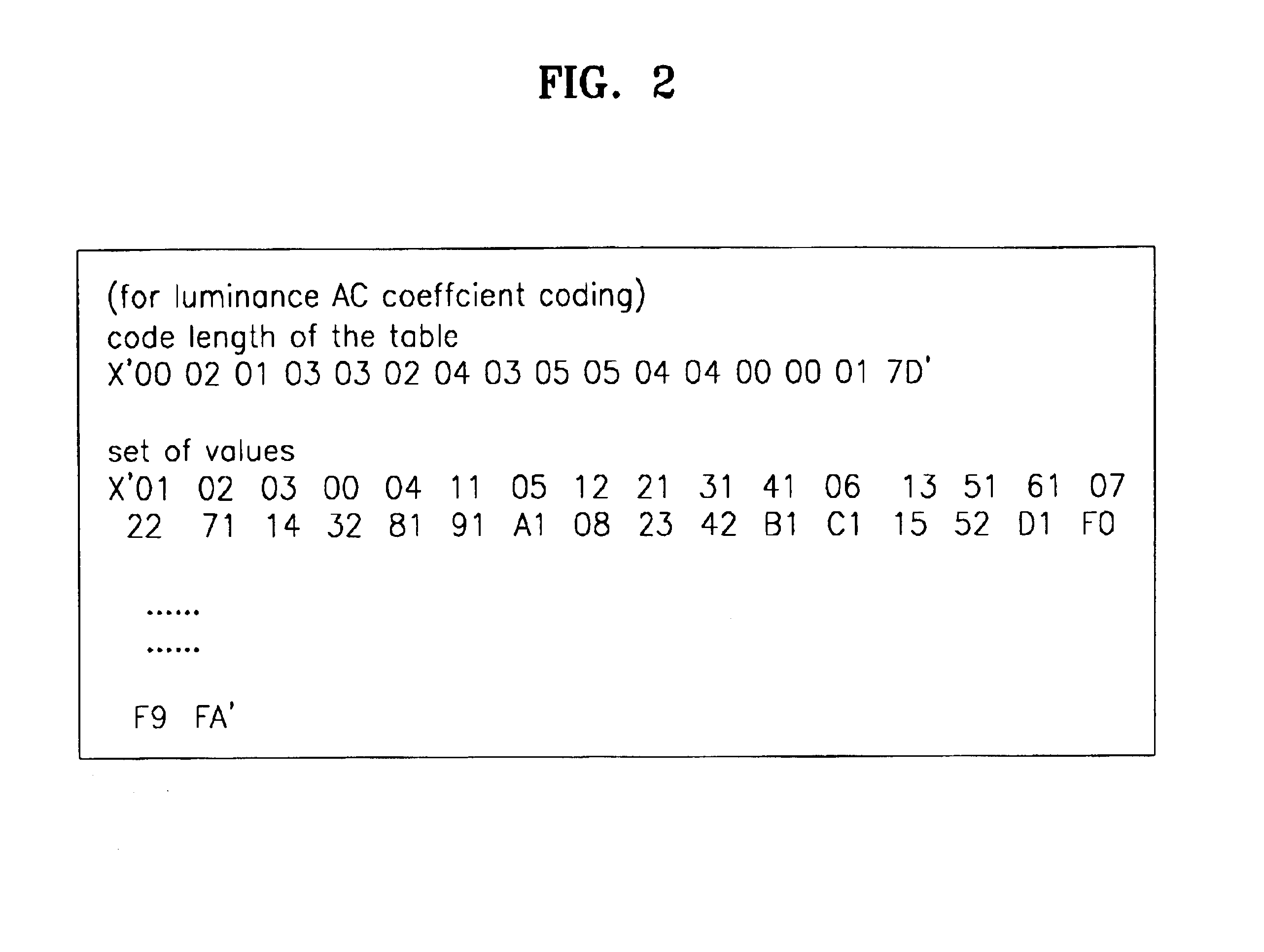
JPEG Huffman table decoder and method thereof based on binary search technique
A joint photographic expert group (JPEG) Huffman table decoder and a method thereof based on a binary search technique. The JPEG Huffman table decoder performs symbol matching based on the binary search and calculates an address of the matched symbol in code book data. Comparison time and an amount of memory required for searching the symbols are reduced.
Owner:SAMSUNG ELECTRONICS CO LTD
JPEG Huffman table decoder and method thereof based on binary search technique
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and method for information access, search, rank and retrieval
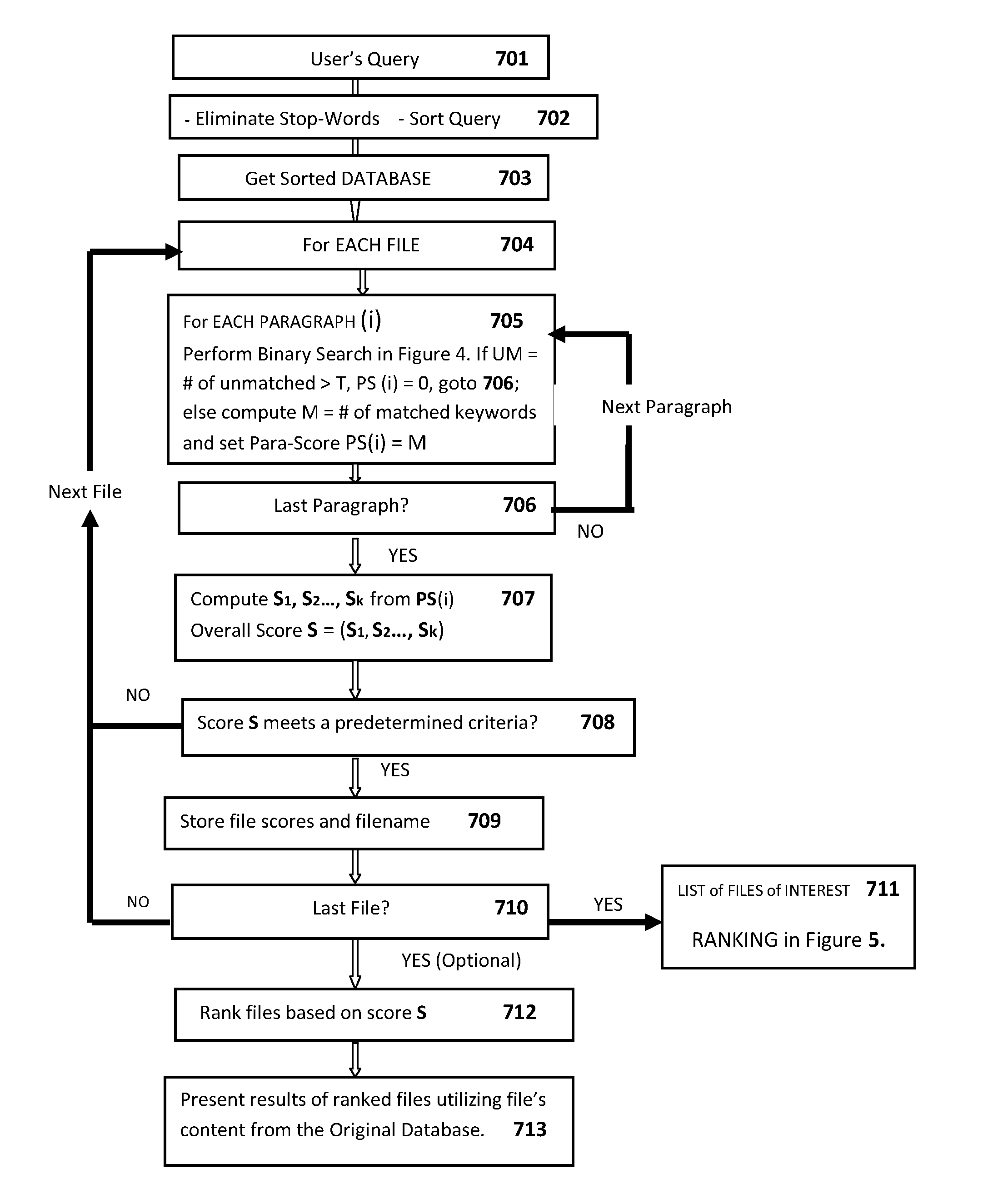
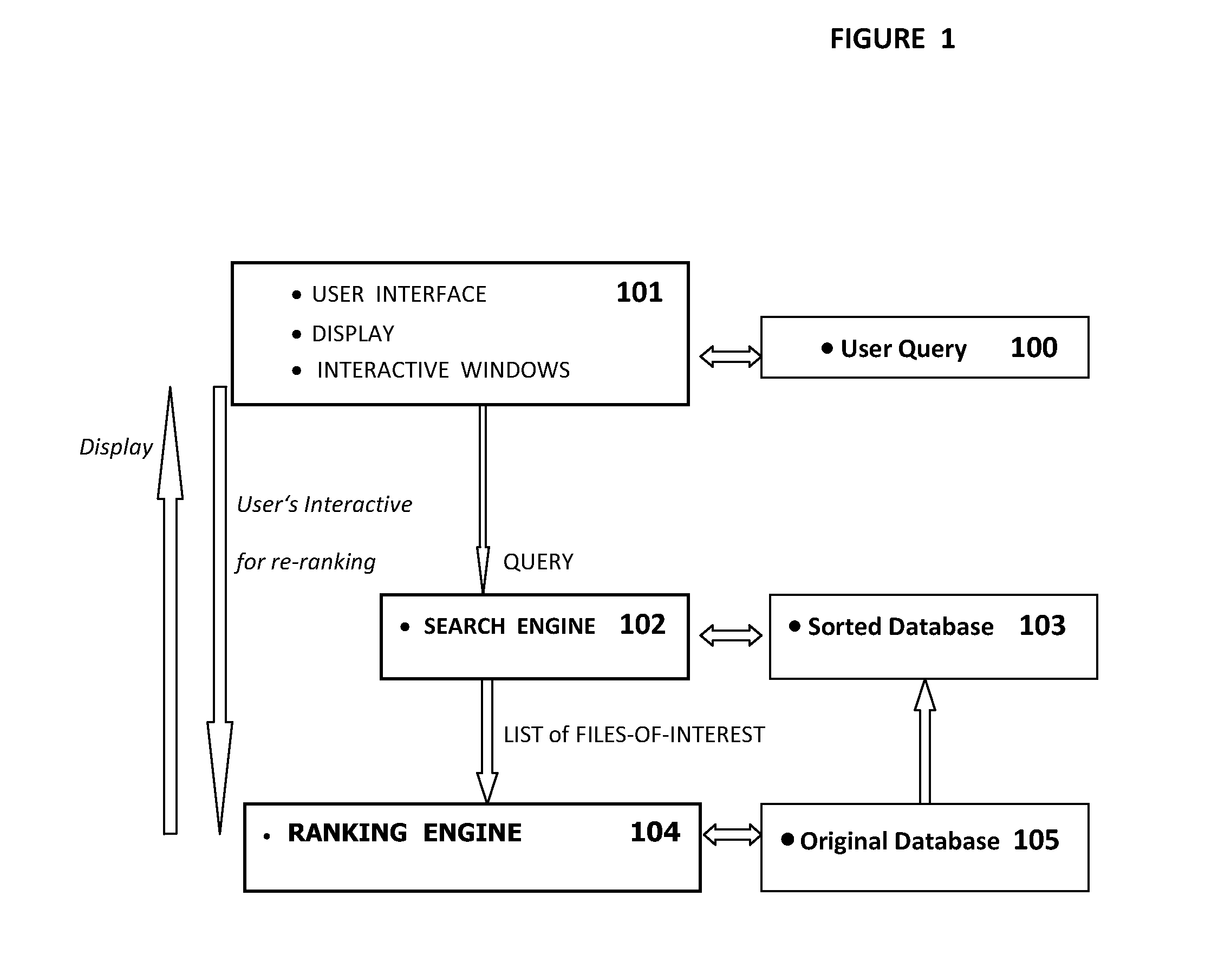
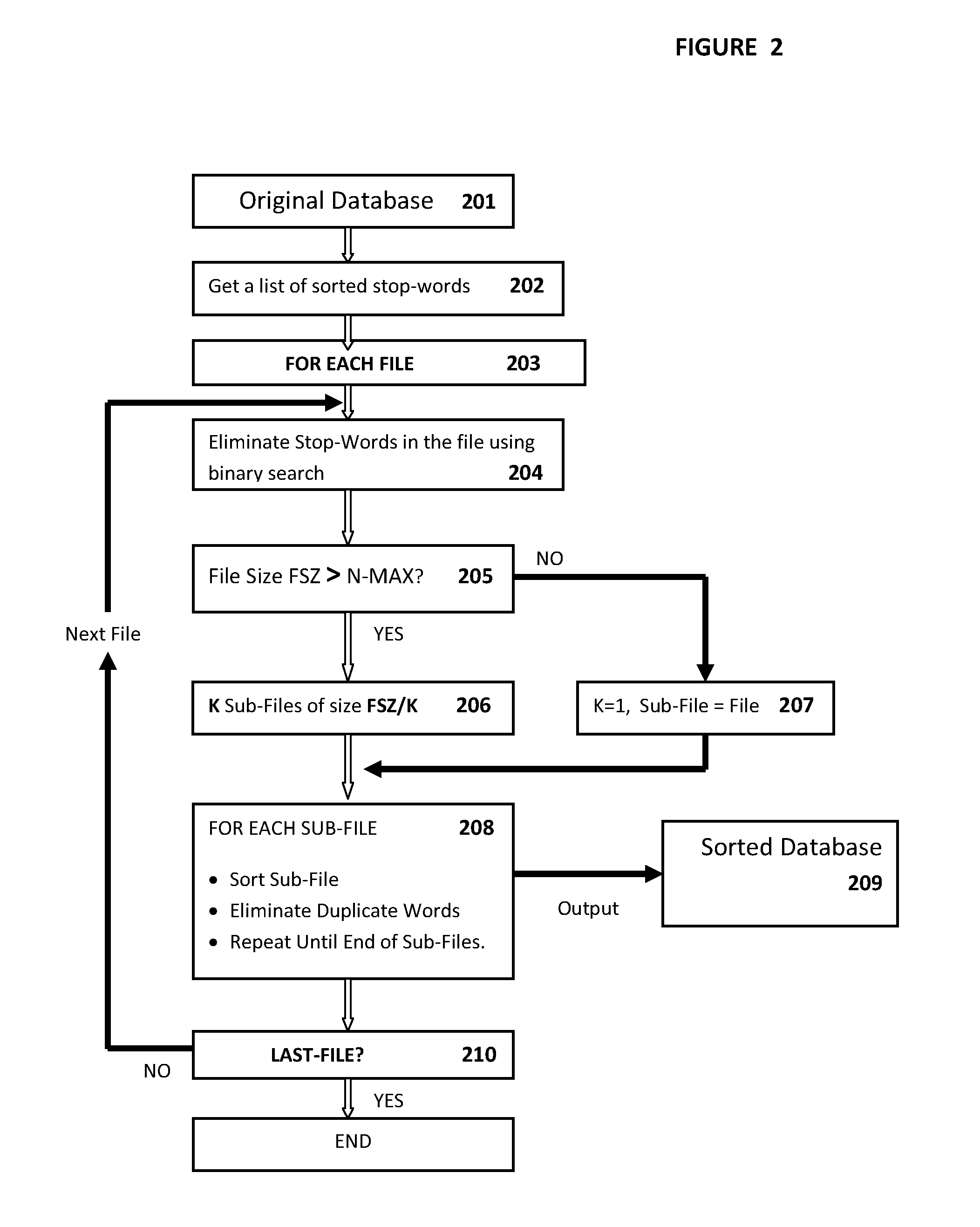
InactiveUS8965904B2Shorten the timeScore and rank files more accuratelyDigital data information retrievalDigital data processing detailsUser inputInformation access
The invention discloses an apparatus and method for quickly searching and ranking related documents in a database based on user input queries. In operation, a user interface receives a query comprising a plurality of keywords input thereto from a user, the search engine receives the query, retrieves the sorted database which has been sorted in advance, performs a binary search on the sorted database to quickly produce a list of files-of-interest. The ranking engine uses the list of files-of-interest to search corresponding files in the list from the original database, score corresponding files based on a plurality of paragraph scores, where each paragraph score is calculated based on a number of matched keywords and adjacent distances between matched keywords within each paragraph, ranked files based on overall scores are then presented to the user on a display which further comprises an interactive window that allows the user to dynamically reselect a priority of a score among a plurality of scores for re-ranking corresponding files.
Owner:DINH LONG VAN +1
Threshold search failure analysis
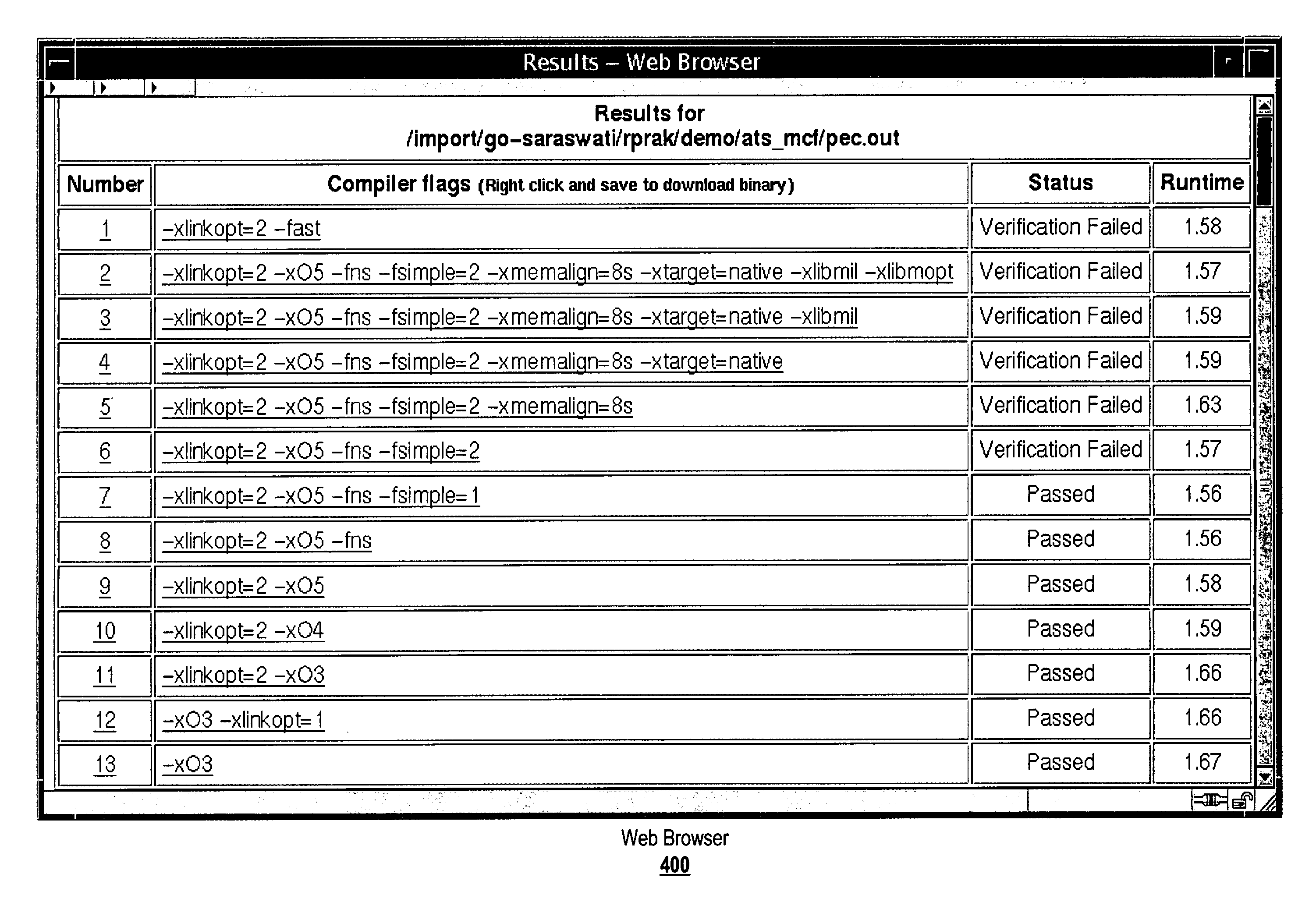
A value range for a code development option, which results in an error when applied to a given code, can be automatically searched to intelligently identify a threshold for the error within the value range. Instead of completely abandoning the optimizations offered by a code development option with a value range, the code development option as applied to a given code can be limited to a subrange of the value range, thus imbuing the given code with at least the optimizations offered by the code development option with the subrange. A failure analysis tool searches, for example according to binary search, a value range. Subranges are applied to the given code and results examined to influence successive selections of subranges. Eventually, a threshold, if any, is discovered that separates a subrange that does not result in error from a subrange that results in error.
Owner:ORACLE INT CORP
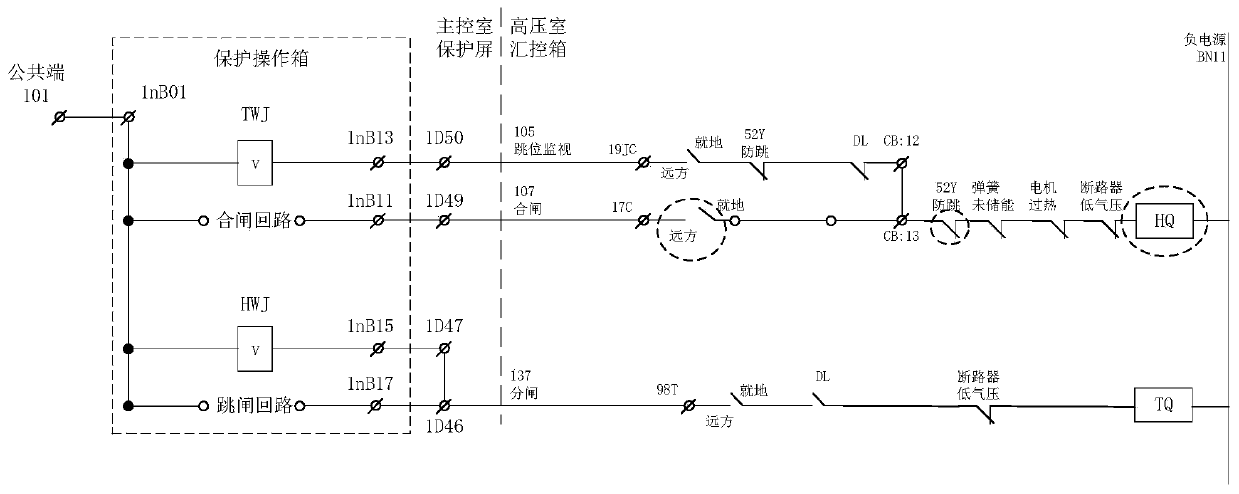
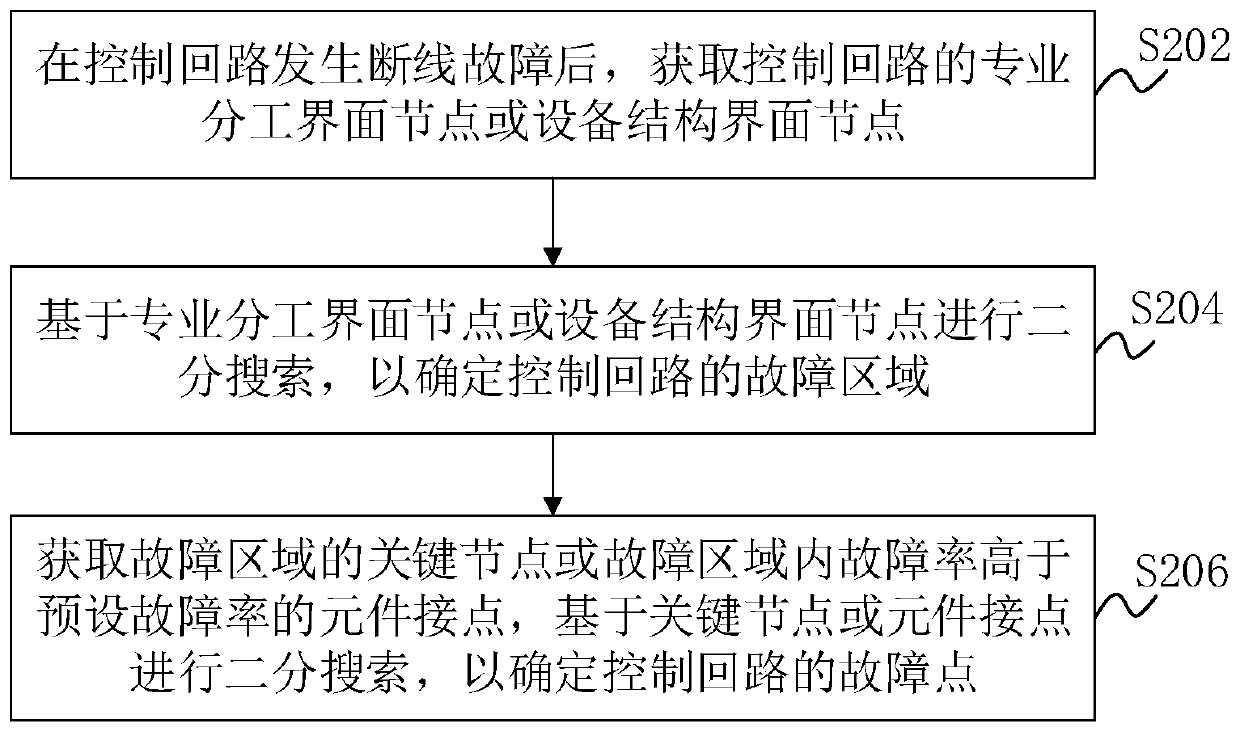
Breakage fault positioning method, device and equipment for circuit breaker control loop
PendingCN111580011AQuick classification and troubleshootingImprove accuracyContinuity testingControl engineeringCircuit breaker
The invention relates to a circuit breaker control loop disconnection fault positioning method, device and equipment. The method comprises steps of obtaining a professional division interface node oran equipment structure interface node of a control loop after a disconnection fault happens to the control loop; performing binary search based on the professional division interface node or the equipment structure interface node to determine a fault area of the control loop; acquiring key nodes of the fault area or element contacts with the fault rate higher than the preset fault rate in the fault area, and carrying out binary search based on the key nodes or the element contacts so as to determine fault points of the control loop. The method is advantaged in that binary processing is carriedout based on professional division interface nodes or equipment structure interface nodes of the control loop, compared with a point-by-point electricity measurement method and a simple dichotomy, fault location is fast, accuracy is high, and universality is strong.
Owner:SHENZHEN POWER SUPPLY BUREAU
Method for locating non-homonymic phase overline earth fault of double-circuit line based on binary search
ActiveCN104062550AImprove accuracyEliminate the effects ofFault locationPhase currentsElectrical resistance and conductance
The invention discloses a method for locating a non-homonymic phase overline earth fault of a double-circuit line based on binary search. The method includes the steps that firstly, fault phase voltage, fault phase current and zero-sequence current of the protection installing position of a I-circuit line of the double-circuit line on the same pole are measured, lumped parameter modeling is adopted, zero-sequence current of an II-circuit line of the double-circuit line on the same pole is calculated, zero-sequence compensating current of the I-circuit line of the double-circuit line on the same pole is calculated, the non-homonymic phase overline earth fault of the double-circuit line is accurately located by the adoption of a binary search method and through the characteristic that a relative coefficient of the positions in front of and behind the non-homonymic phase overline earth fault point is abruptly changed into a value smaller than 0 from a value larger than 0, the influences of interline zero-sequence mutual inductance, transition resistance and load current on fault locating accuracy are eliminated, high capacity for resisting the influences of the transition resistance and the load current is achieved, and no fault location dead zones exist when the non-homonymic phase overline earth fault of the double-circuit line is generated at a protection positive direction outlet.
Owner:STATE GRID PUTIAN ELECTRIC POWER SUPPLY +3
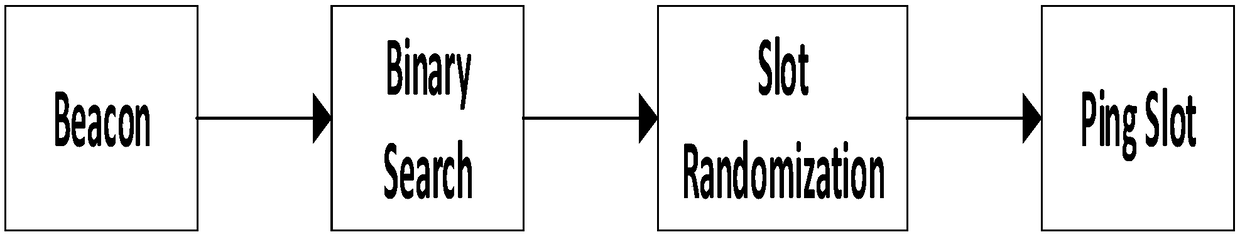
Lora terminal energy-saving method based on binary search time slot randomization communication mechanism
ActiveCN108934063AShorten communication timeSave energyPower managementHigh level techniquesStart timeCommunications system
The invention discloses a Lora terminal energy-saving method based on a binary search time slot randomization communication mechanism, which comprises an algorithm adopted by a Lora terminal, an MCU used by a terminal, and a Lora radio frequency module. The algorithm adopted by the Lora terminal Class B includes the following steps: S1: using the binary search algorithm to select and set an appropriate PingNb when a node receives a Beacon; S2: obtaining the offset PingOffset of a start time point of a Ping Slot of each node through time slot randomization; S3: entering the Ping Slot for data reception. The terminal algorithm uses the binary search algorithm to select and set the appropriate PingNb. Each time, the selection range can be reduced by half, and the set PingNb can be quickly andaccurately selected, which greatly shortens the communication time and saves more energy. The time slot randomization is adopted to obtain a cheap amount, it can be ensured that only one node in thePing Slot performs data, and additional energy consumption due to communication system collision or monitoring overload cannot be caused. The Lora terminal energy-saving method can effectively reducepower consumption and achieve energy saving.
Owner:FOSHAN SHUNDE SUN YAT SEN UNIV RES INST +2
Stream data-oriented quick indexing method, streaming data-oriented quick indexing device, streaming data-oriented quick indexing equipment and storage medium
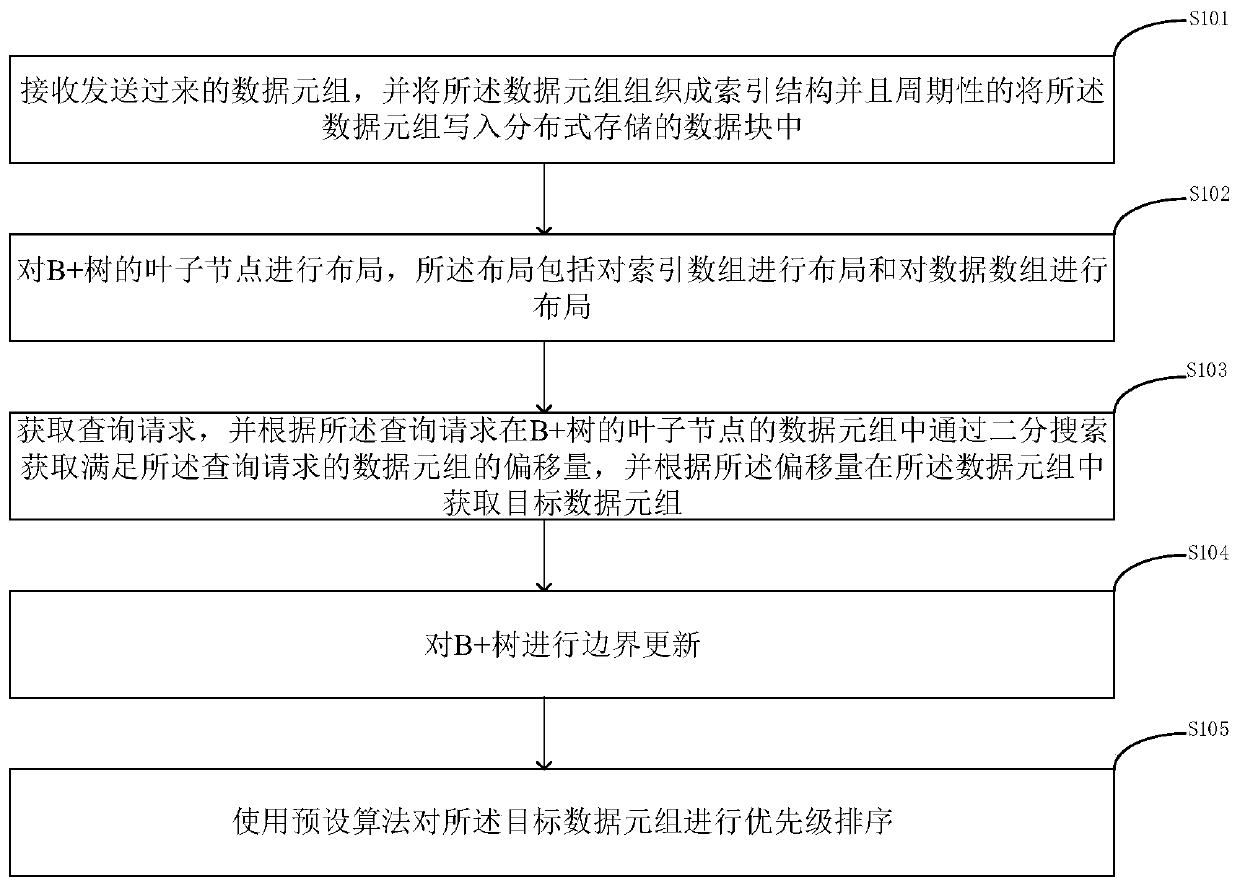
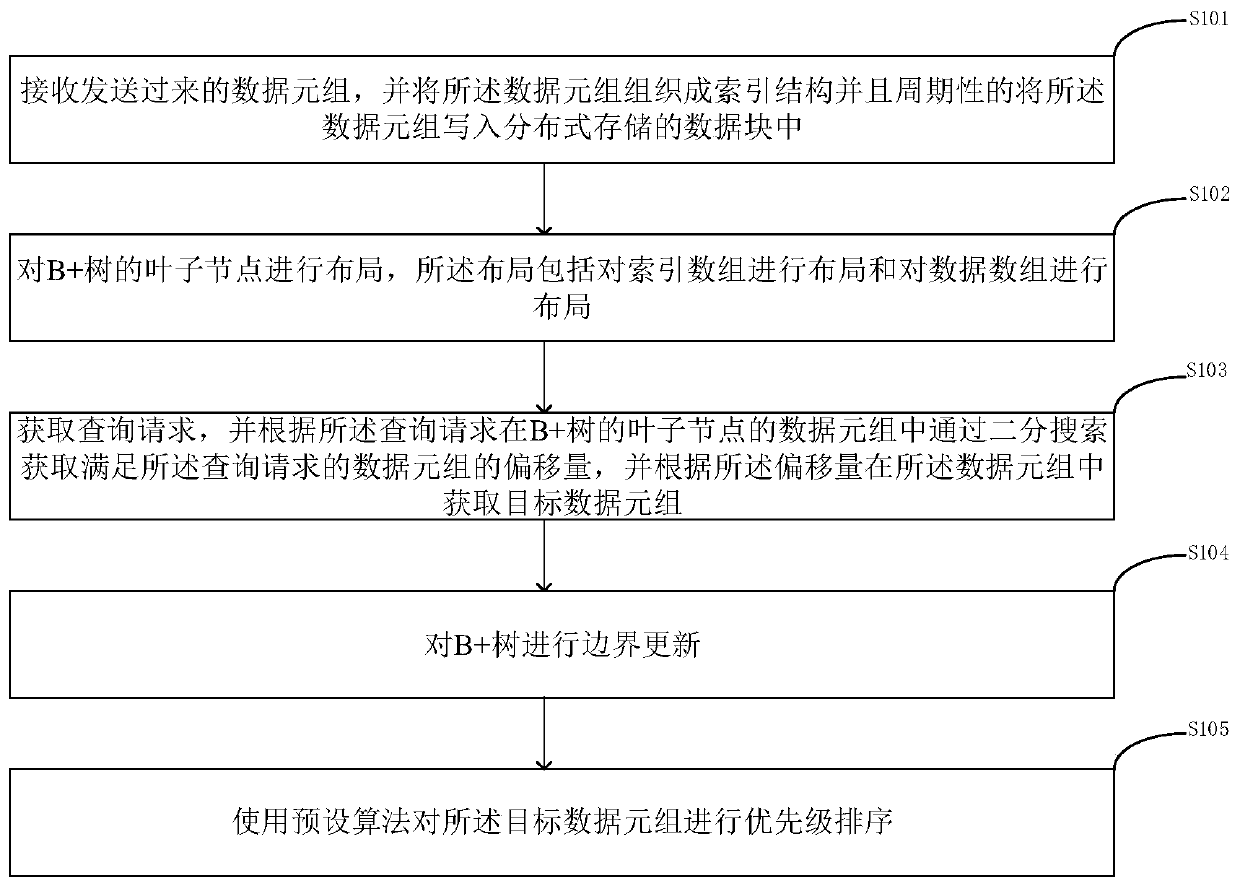
ActiveCN111125120AReduce overheadEfficient use ofDatabase distribution/replicationSpecial data processing applicationsStreaming dataEngineering
The invention discloses a streaming data-oriented quick indexing method. The method comprises the following steps: receiving sent data tuples, organizing the data tuples into an indexing structure, and periodically writing the data tuples into a distributed storage data block; carrying out layout on leaf nodes of a B + tree, wherein the layout comprises layout of an index array and layout of a data array; obtaining a query request, obtaining the offset of data tuples satisfying the query request through binary search in the data tuple of the leaf node of the B + tree according to the query request, and obtaining a target data tuple in the data tuple according to the offset; carrying out boundary updating on the B + tree; and performing priority ranking on the target data tuple by using a preset algorithm. High-speed insertion of data can be realized, and the real-time retrieval capability can be improved.
Owner:GUANGZHOU SHURUI INTELLIGENT TECH CO LTD
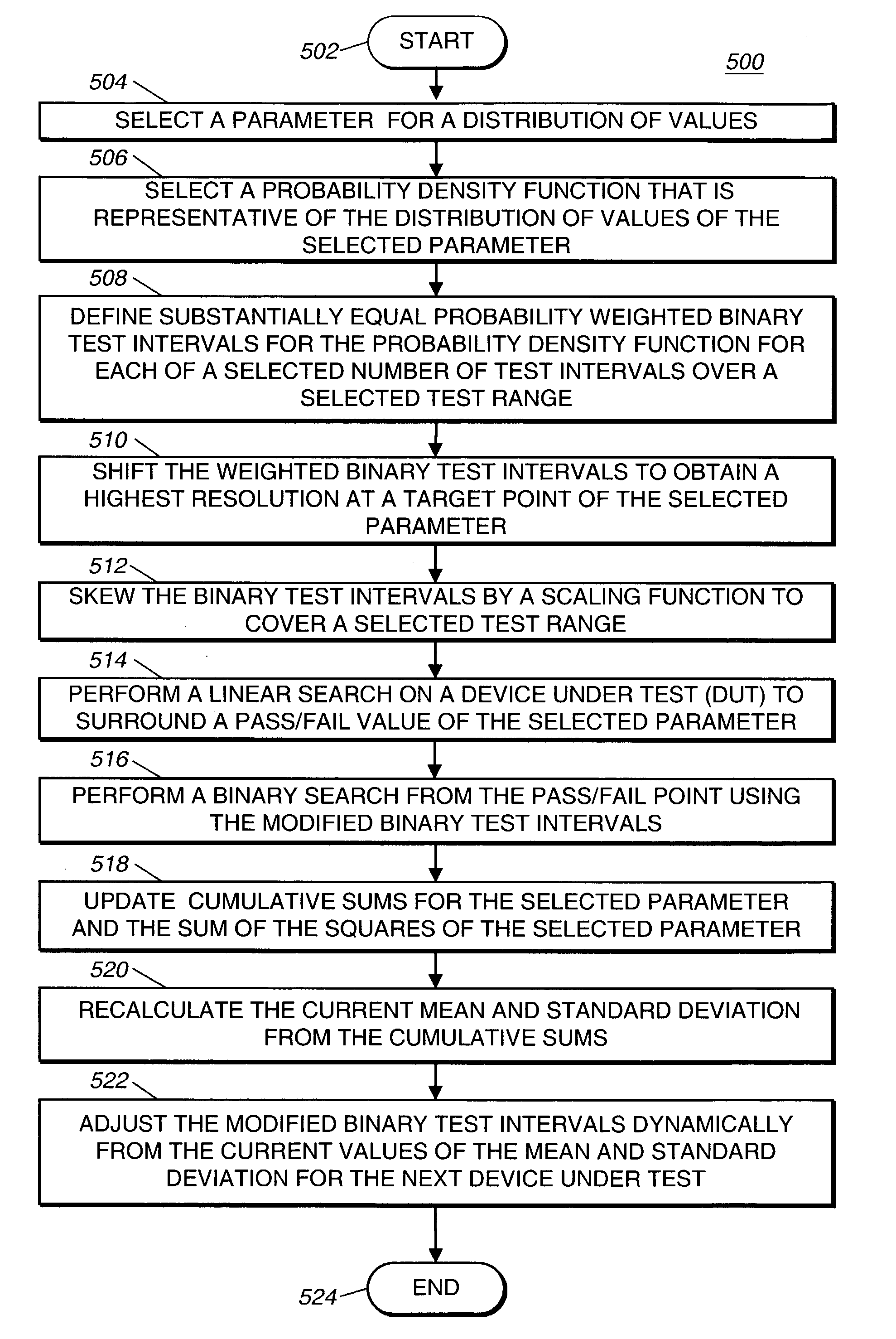
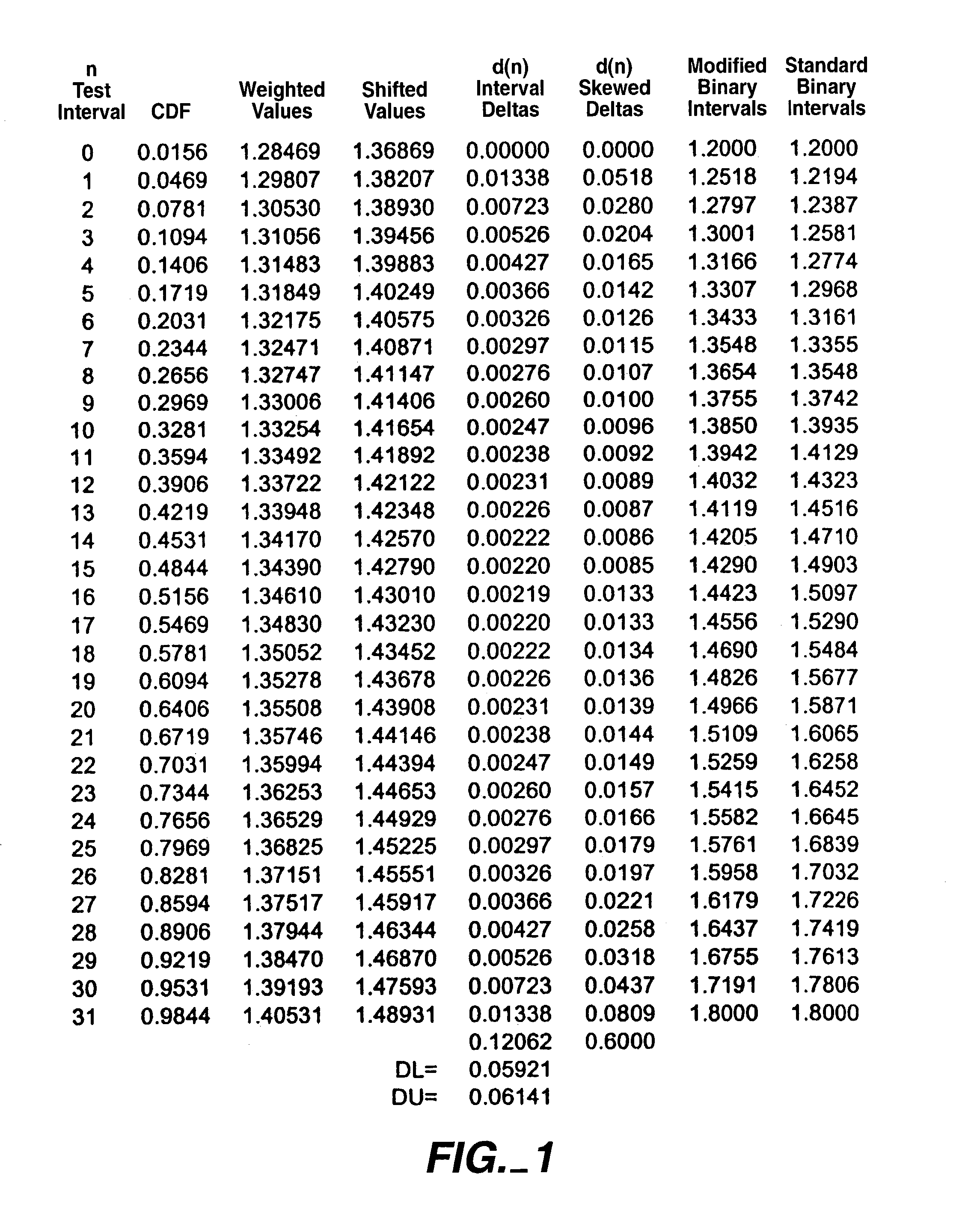
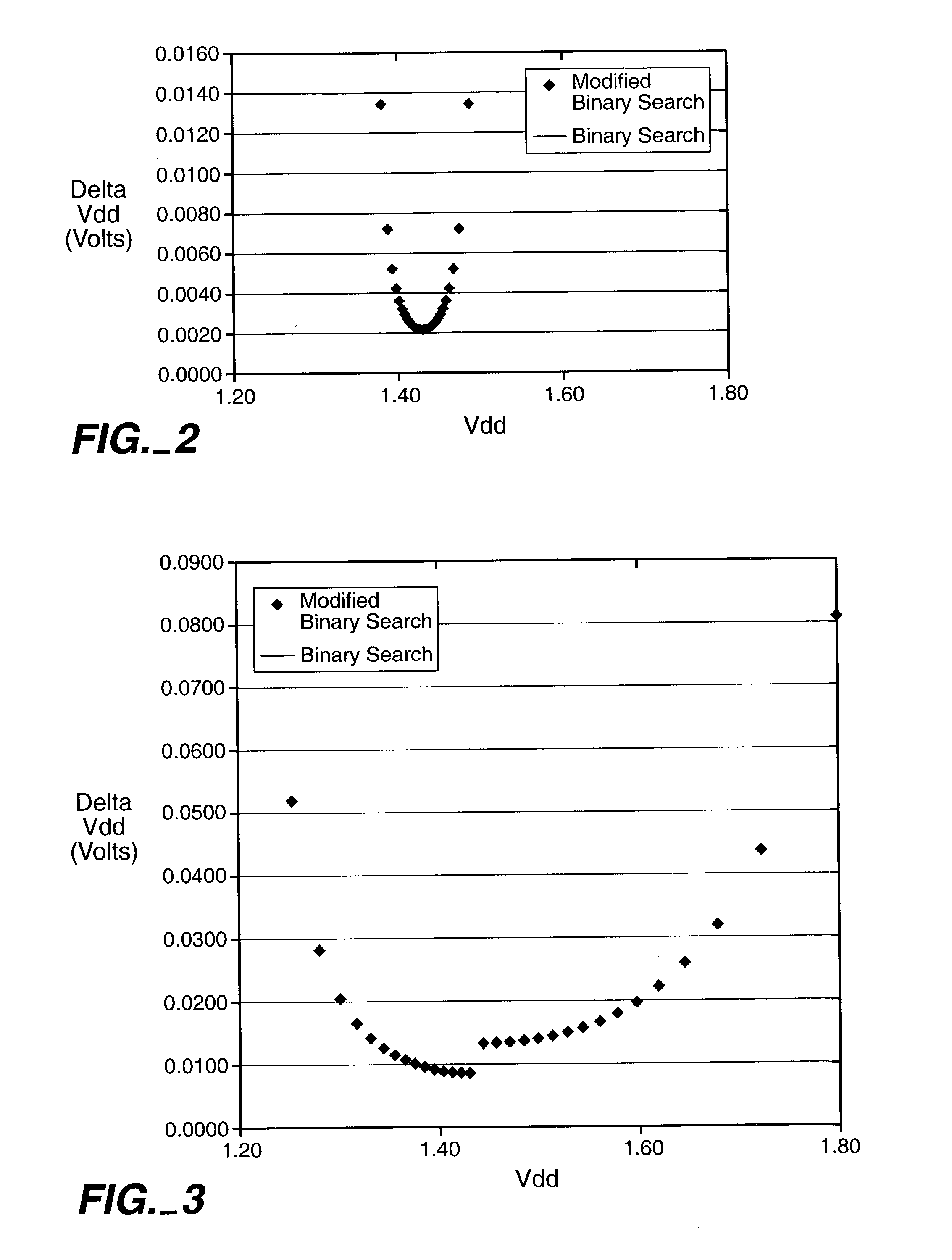
Modified binary search for optimizing efficiency of data collection time
A method for a modified binary search includes steps of: selecting a parameter having a distribution of values, selecting a probability density function representative of the distribution of values of the selected parameter, defining a substantially equal probability weighted binary test interval from the probability density function for each of a selected number of test intervals over a selected test range, translating the weighted binary test intervals to obtain a highest resolution at a target point of the selected parameter, and skewing the translated and weighted binary test intervals by a selected scaling function to generate a modified binary test interval for each of the selected number of test intervals over the selected test range.
Owner:BELL SEMICON LLC
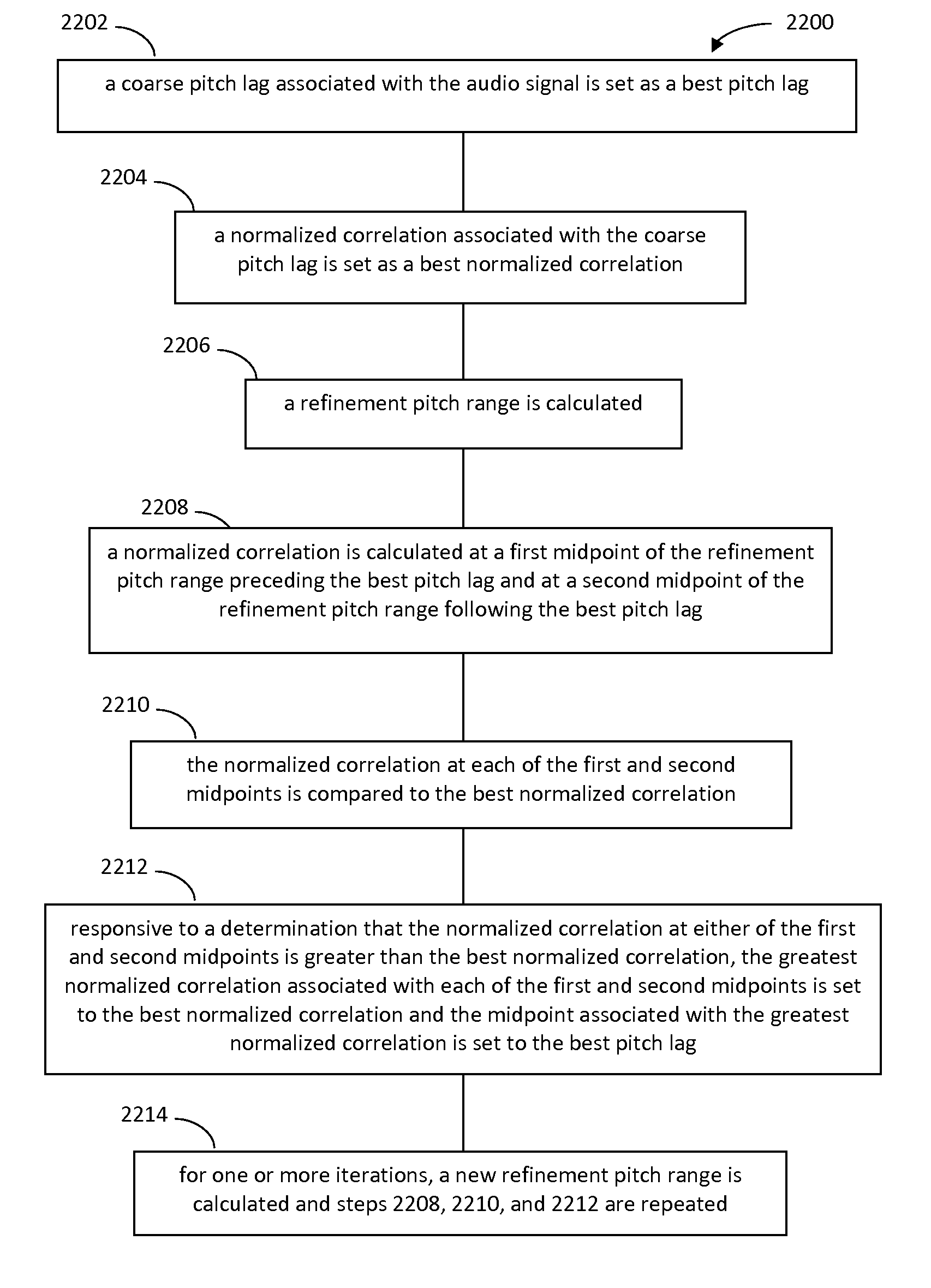
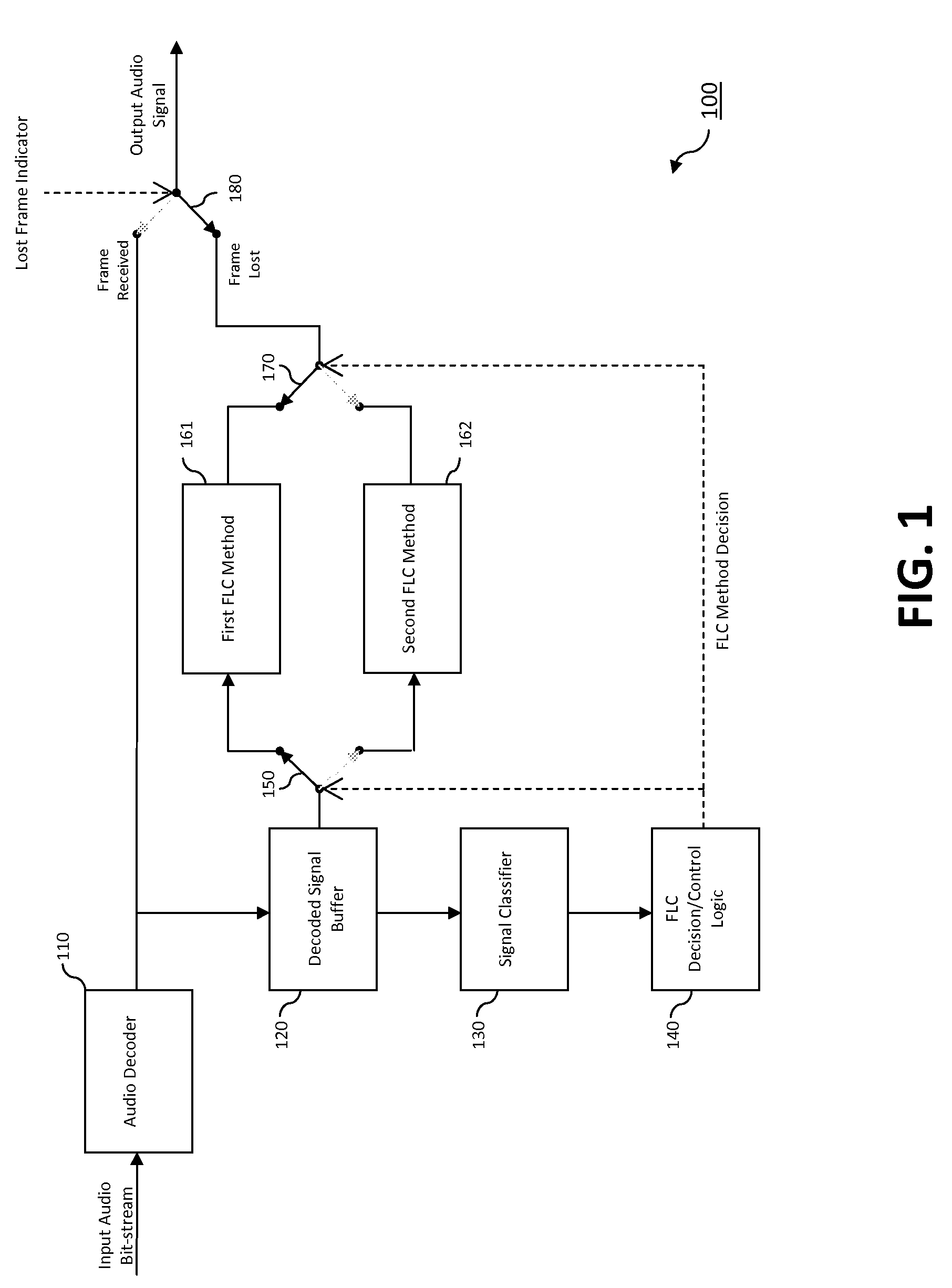
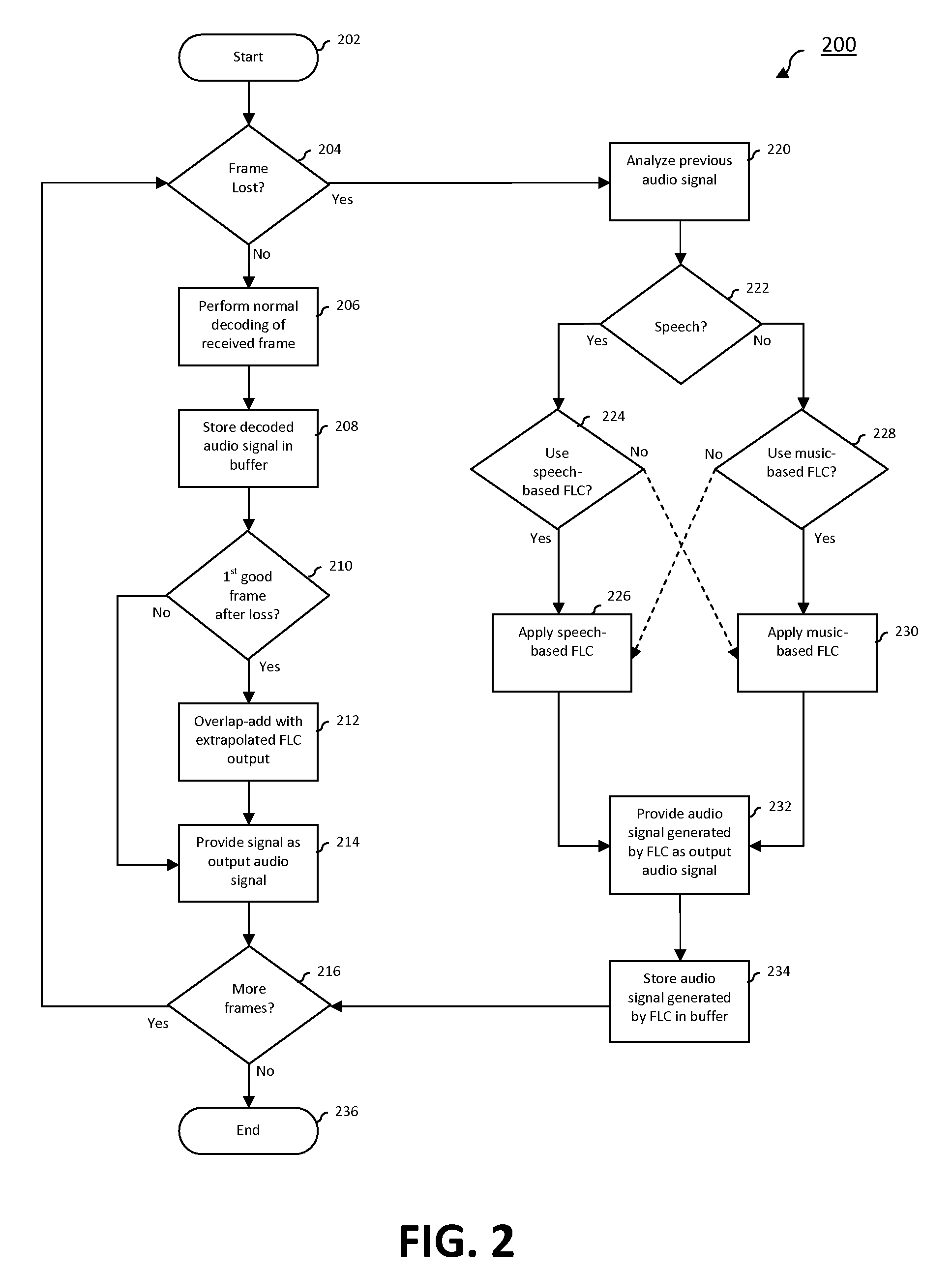
Decimated bisectional pitch refinement
A method and system for refining an estimated pitch period estimate based on a coarse pitch useful for performing frame loss concealment in an audio decoder as well as for other applications. A normalized correlation at the coarse pitch lag is computed and used as the current best candidate. The normalized correlation is then evaluated at the midpoint of the refinement pitch range on either side of the current best candidate. If the normalized correlation at either midpoint is greater than the current best lag, the midpoint with the maximum correlation is selected as the current best lag. After each iteration, the refinement range is decreased by a factor of two and centered on the current best lag. This bisectional search continues until the pitch has been refined to an acceptable tolerance or until the refinement range has been exhausted. During each step of the bisectional pitch refinement, the signal is decimated to reduce the complexity of computing the normalized correlation.
Owner:AVAGO TECH INT SALES PTE LTD
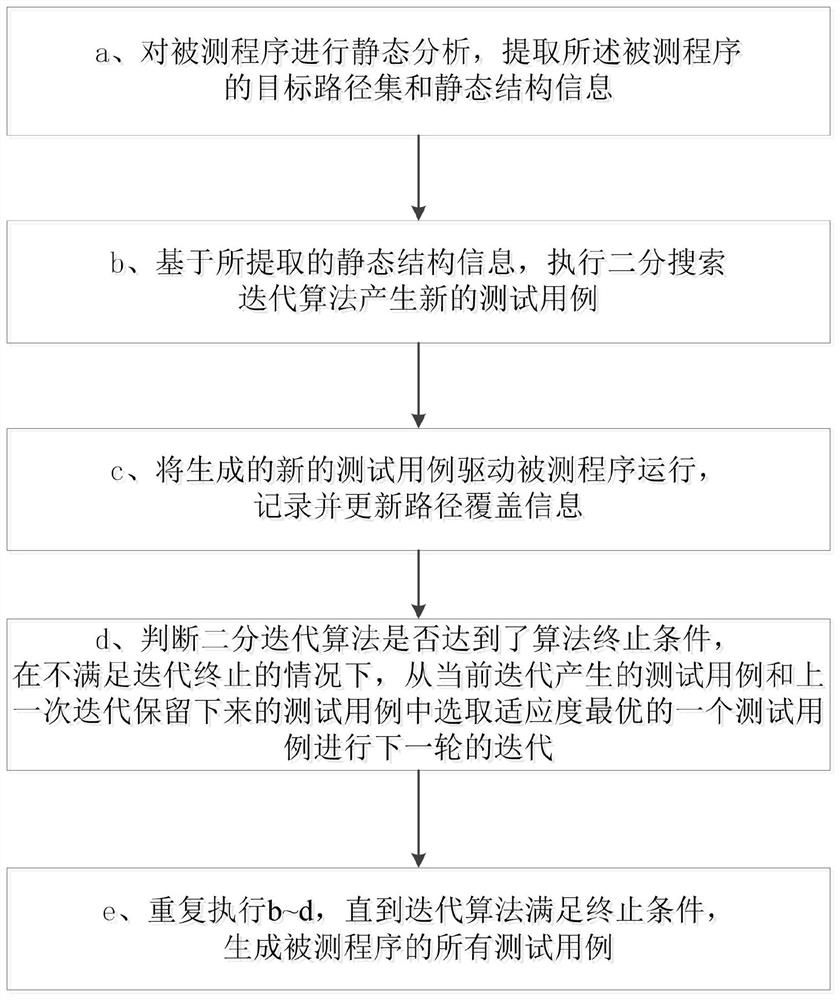
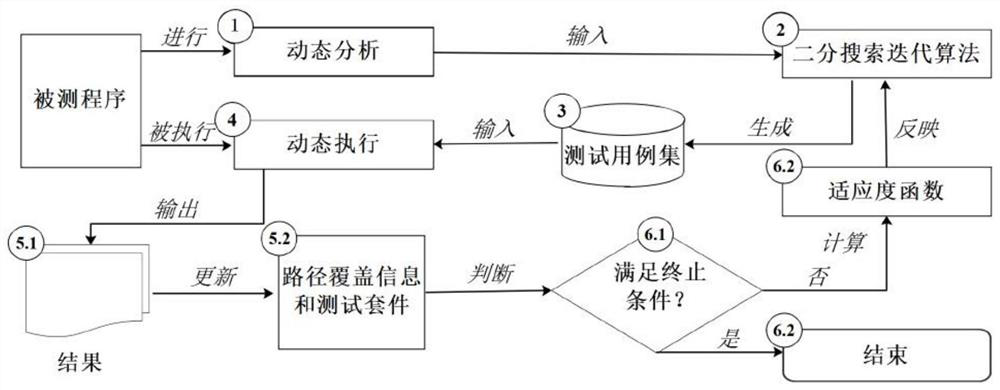
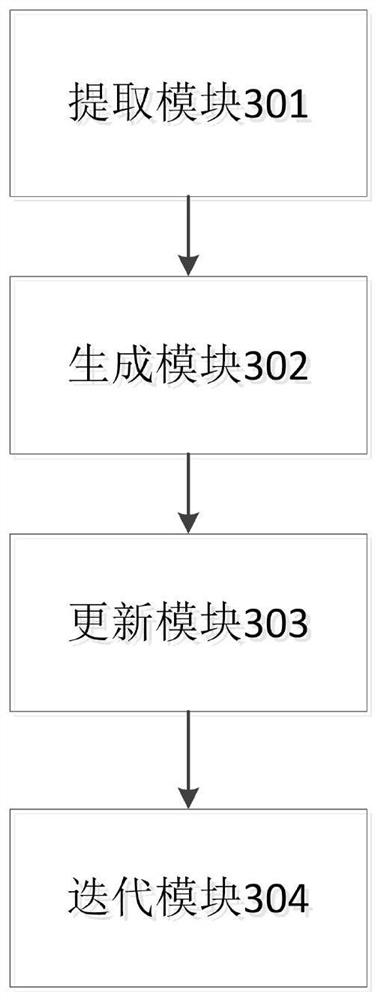
Test case generation method and system based on binary search iteration and electronic equipment
ActiveCN112286824AImprove search efficiencyImprove production efficiencySoftware testing/debuggingSoftware deploymentPathPingAlgorithm
The embodiment of the invention provides a test case generation method and system based on binary search iteration and electronic equipment. The method comprises the steps: carrying out the static analysis of a tested program, and extracting a target path set and static structure information; based on the extracted static structure information, executing a binary search iterative algorithm to generate a new test case; driving the tested program to run via the generated test case, and recording and updating path coverage information; selecting the test case with the optimal fitness from the test cases generated by the current iteration and the test cases reserved by the last iteration to carry out the next round of iteration til the iterative algorithm meets the termination condition. According to the binary search iterative algorithm provided by the embodiment of the invention, the potential relationship between the paths is fully utilized, and the test cases of other paths are quicklyfound by utilizing the existing test cases. The binary search has relatively high search efficiency, so that the test case generation efficiency for path coverage is improved, and the test cost is reduced.
Owner:YANGTZE UNIVERSITY
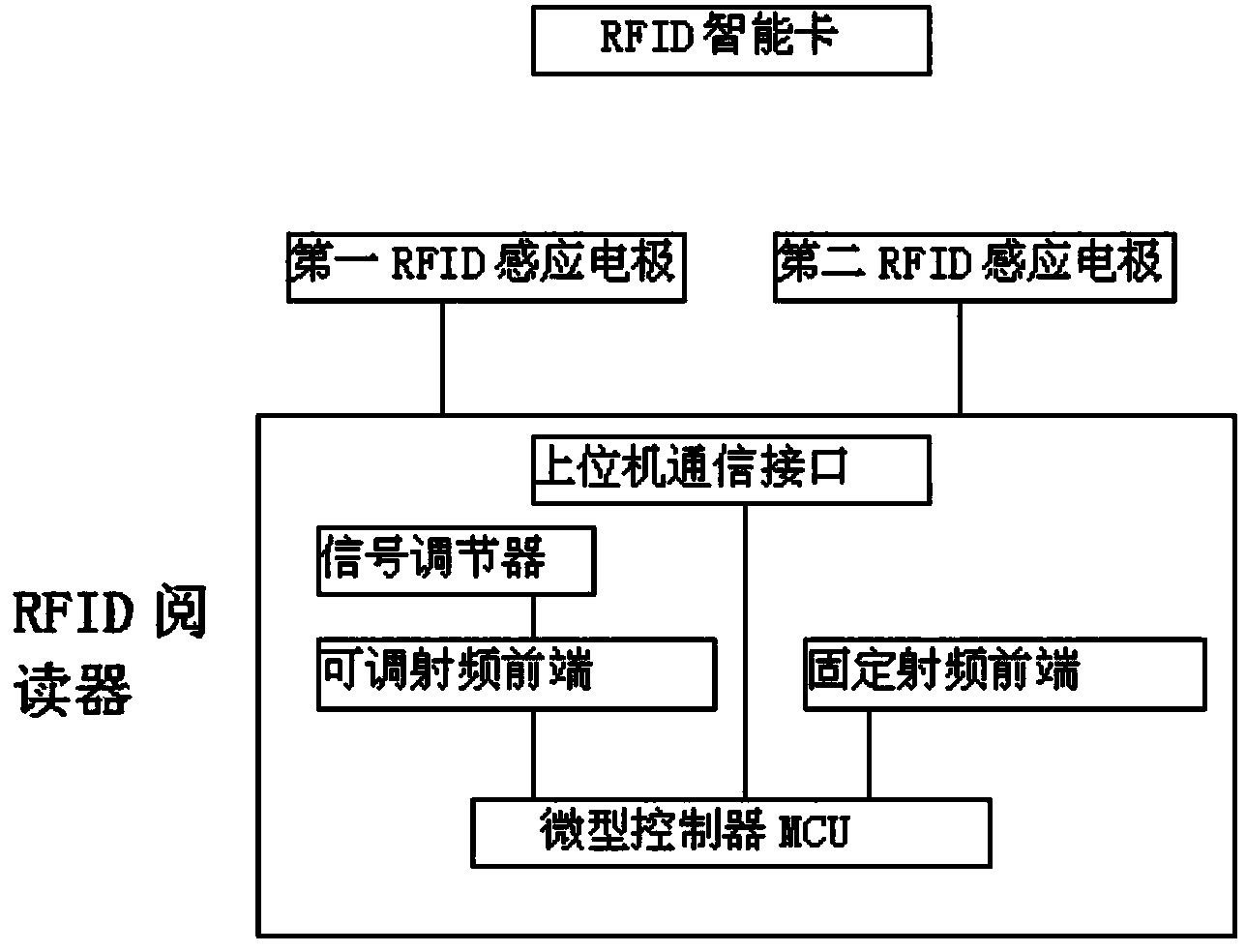
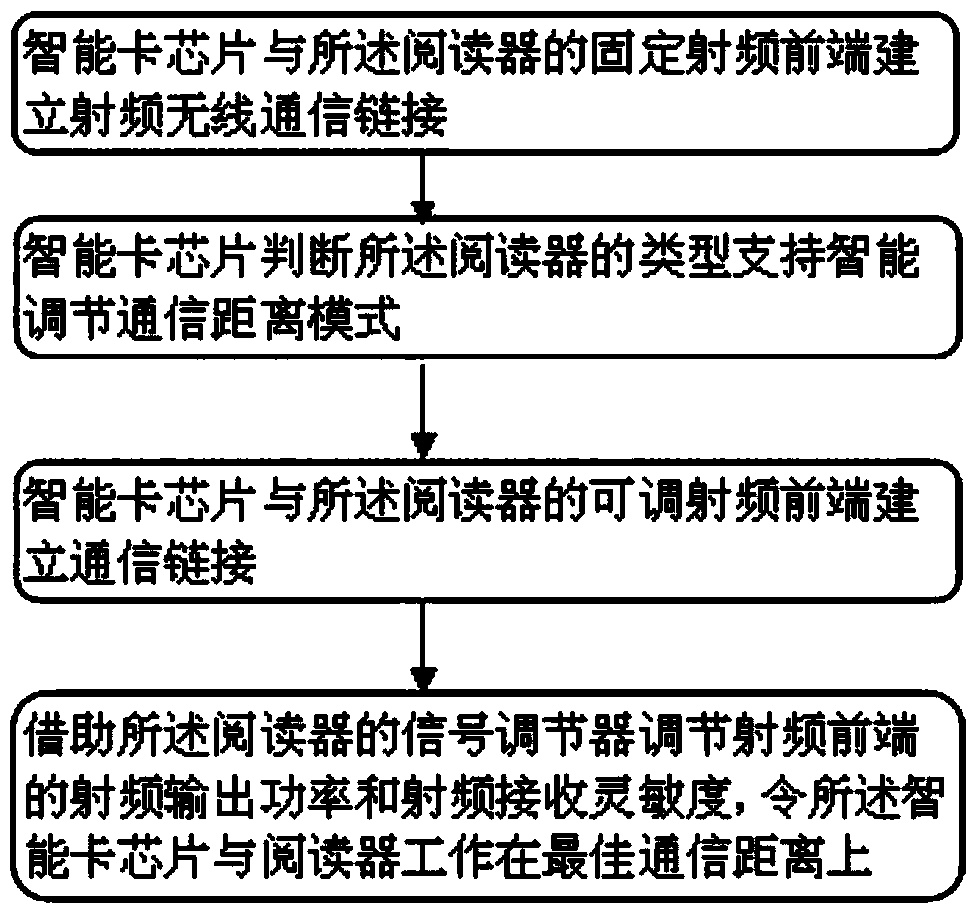
Mobile payment system based on radio frequency identification (RFID)
InactiveCN104063787ASensitivity adjustableEasy to usePayment architectureSensing record carriersPower controlSelf adaptive
A mobile payment system based on RFID provided by the present invention detects the distance change among objects by comparing the difference among the signal intensity of different frequencies when a first RFID induction electrode and a second RFID induction electrode work, and controls the power of an emission signal and adjusts the sensitivity of a reception signal by employing a double-channel radio frequency front end and by a signal regulator, searches a current optimum communication distance by a binary search method, and realizes the adaptive communication distance adjustment, so that the mobile payment system based on RFID can work under the best work mode in different environments, is more energy-saving, and is convenient for users to use.
Owner:LINKSILICON INNOVATION PTE
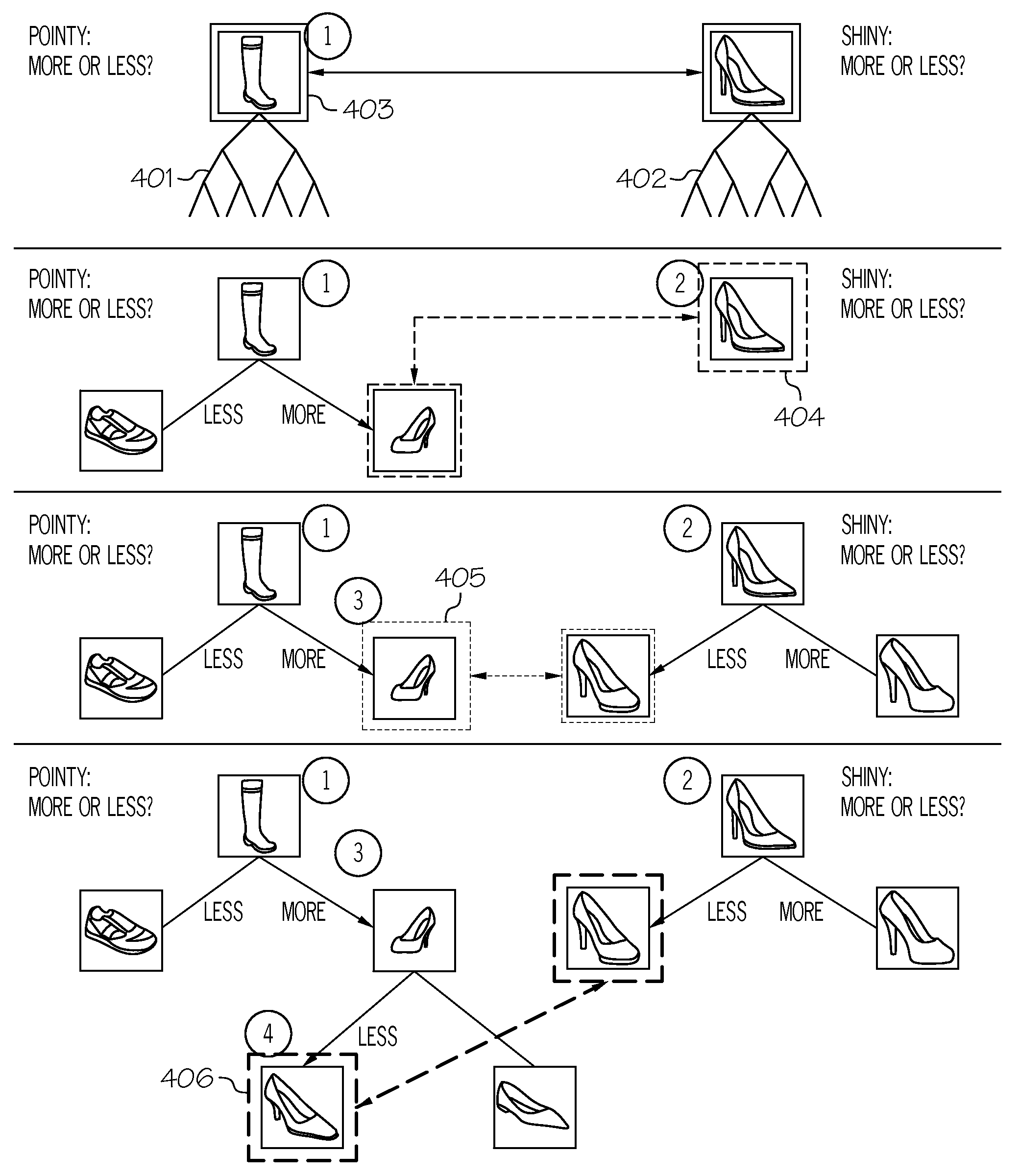
Efficiently identifying images, videos, songs or documents most relevant to the user using binary search trees on attributes for guiding relevance feedback
InactiveUS9176993B2Efficient identificationStill image data browsing/visualisationSpecial data processing applicationsInformation gainBinary tree
A method, system and computer program product for efficiently identifying images, videos, audio files or documents relevant to a user using binary search trees in attribute space for guiding relevance feedback. A binary tree is constructed for each relative attribute of interest. A “pivot exemplar” (at a node of the binary tree) is set for each relative attribute's binary tree as corresponding to the database image, video, audio file or document with a median relative attribute value among that subtree's child examples. A pivot exemplar out of the available current pivot exemplars that has the highest expected information gain is selected to be provided to the user. Comparative attribute feedback is then received from the user regarding whether a degree of the attribute in the user's target image, video, audio file or document is more, less or equal with the attribute displayed in the selected pivot exemplar.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
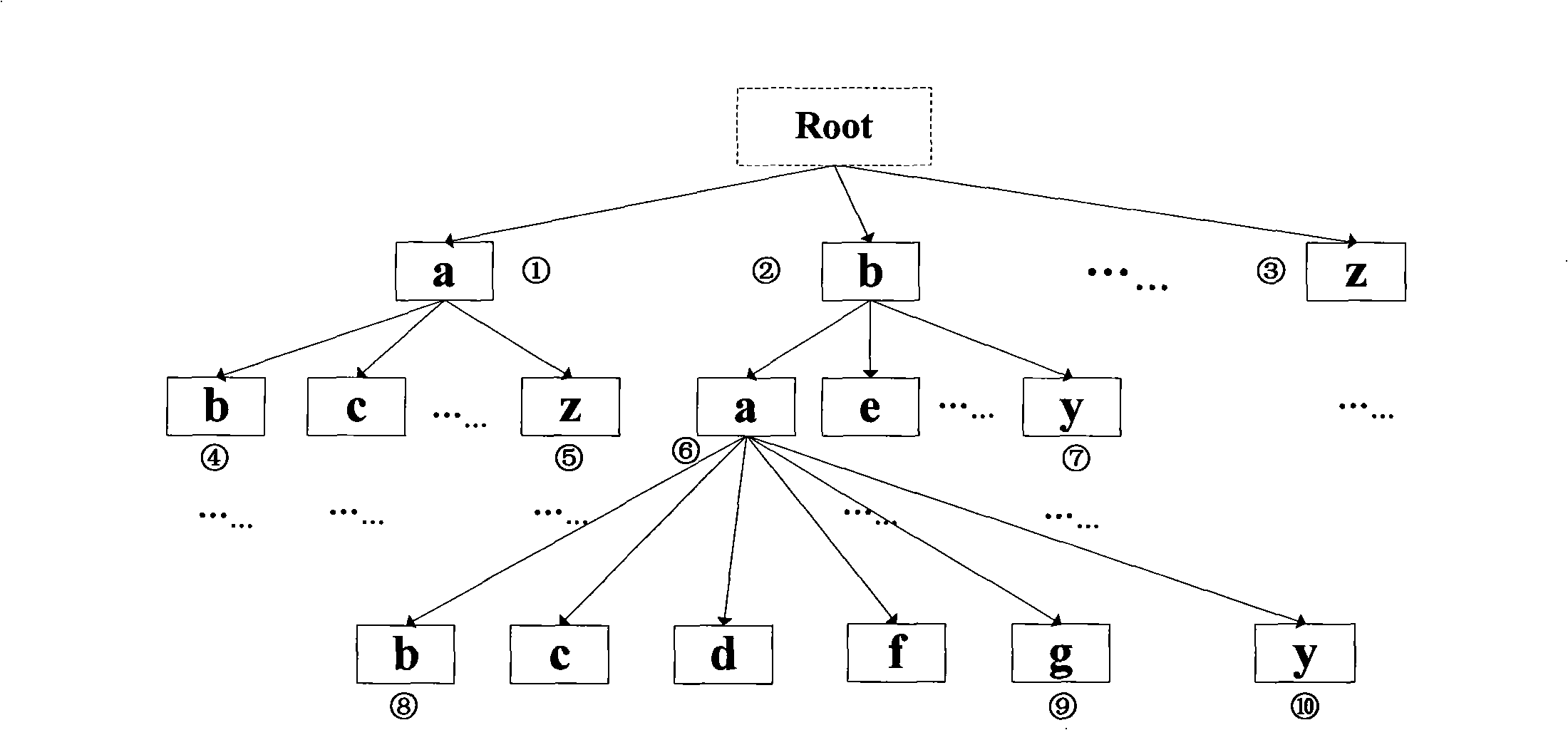
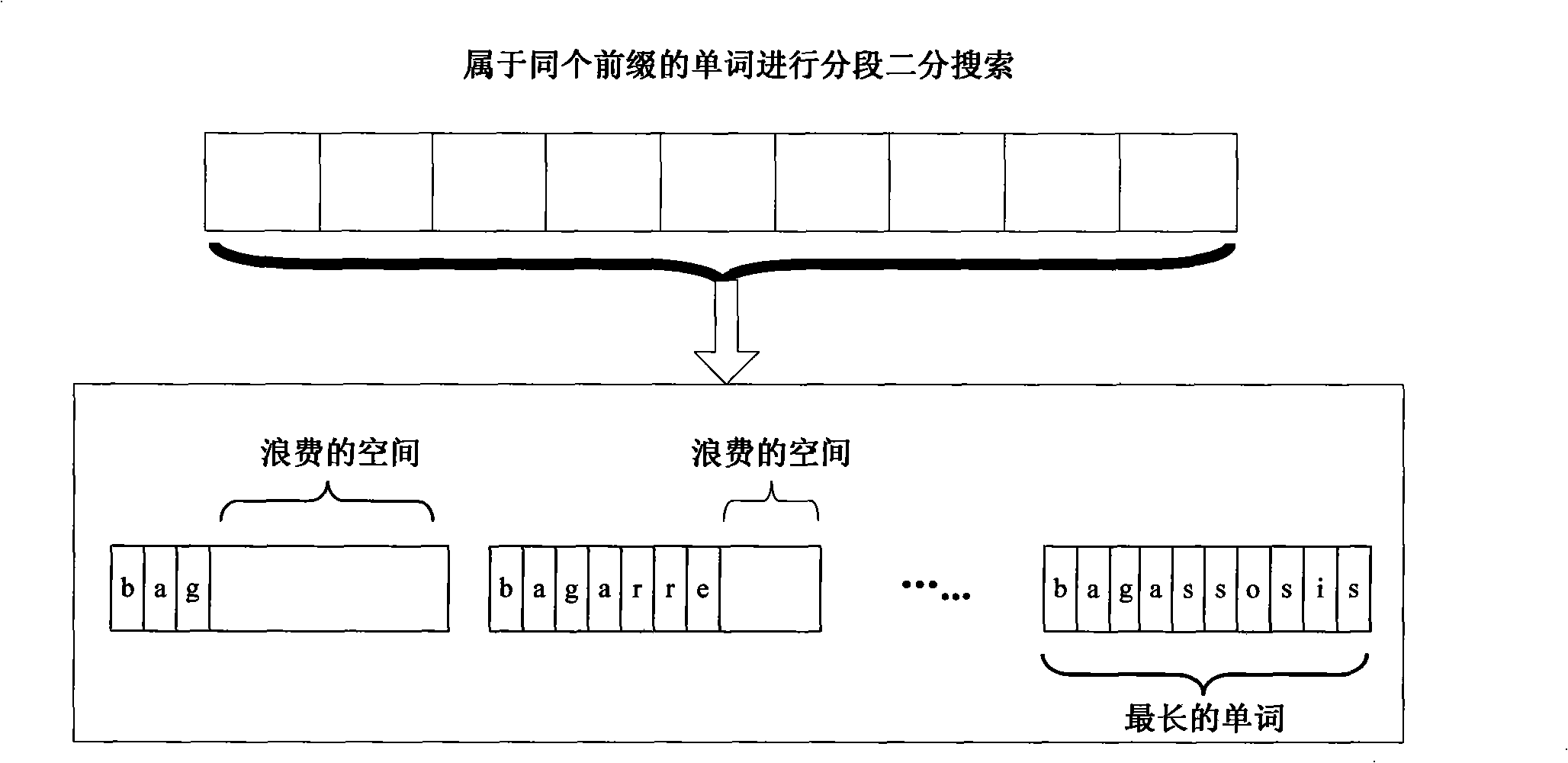
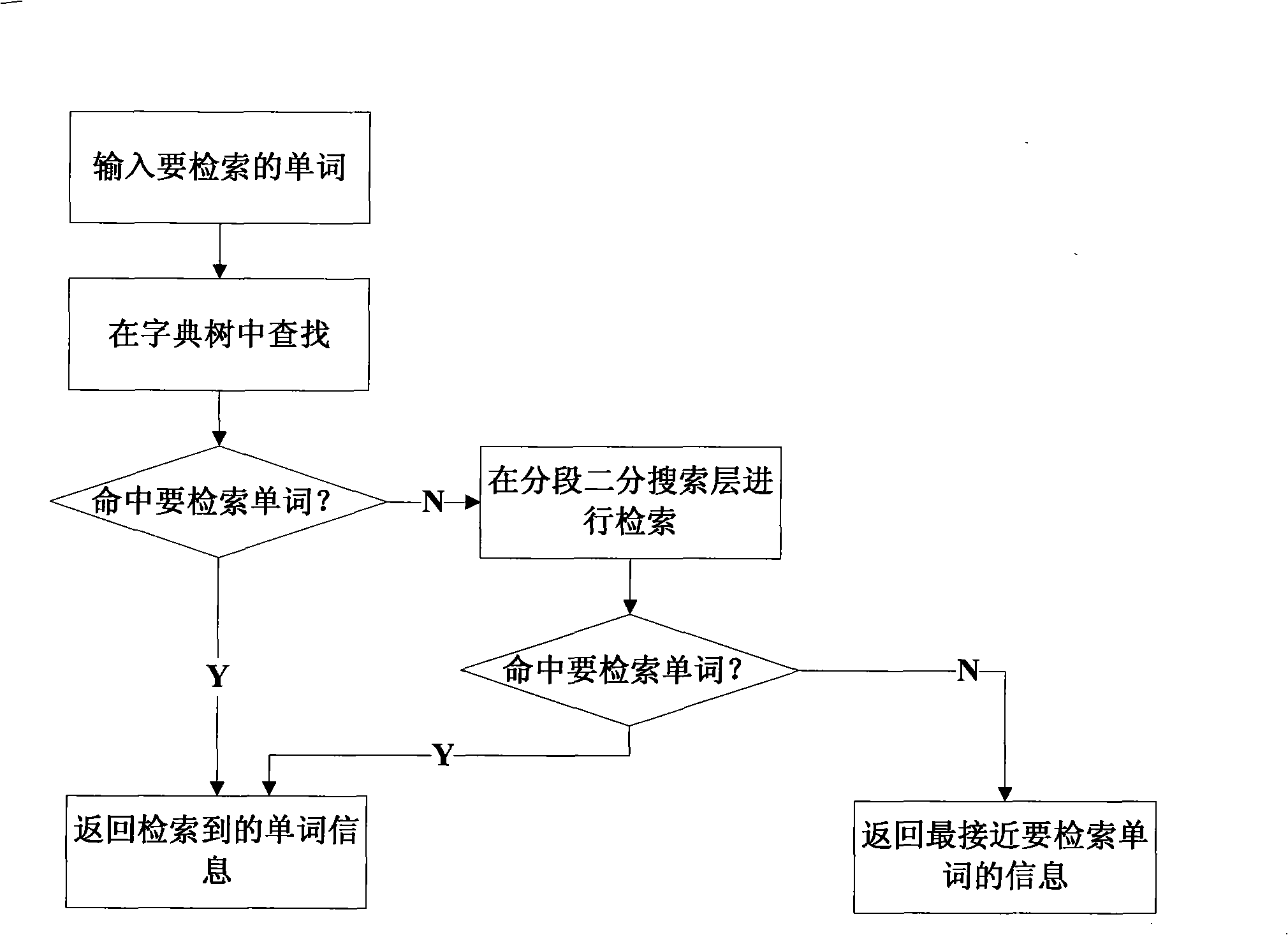
Electronic dictionary work retrieval method based on self-adapting dictionary tree
InactiveCN101271466ASmall footprintImprove retrieval efficiencySpecial data processing applicationsWord searchSelf adaptive
The invention discloses an electronic dictionary words retrieval method based on a self-adaptive dictionary tree and relates to a words retrieval technology in an electronic dictionary. The method defines a retrieval structure with two levels which includes a prefix matching level of the self-adaptive dictionary and a complete words matching level for a piecewise dichotomy search. The retrieval method is that the matching of words prefixes is firstly implemented in the self-adaptive dictionary tree, and if the words prefixes are hit, the information of the words is returned. Otherwise, the piecewise dichotomy search level is started for the search, and the words to be searched for or the information of the words which is nearest to the words to be searched for is found out and returned. The electronic dictionary words retrieval method can be used for effectively improving the efficiency of the words search and ensuring the balance of time efficiency and space occupation.
Owner:SUN YAT SEN UNIV
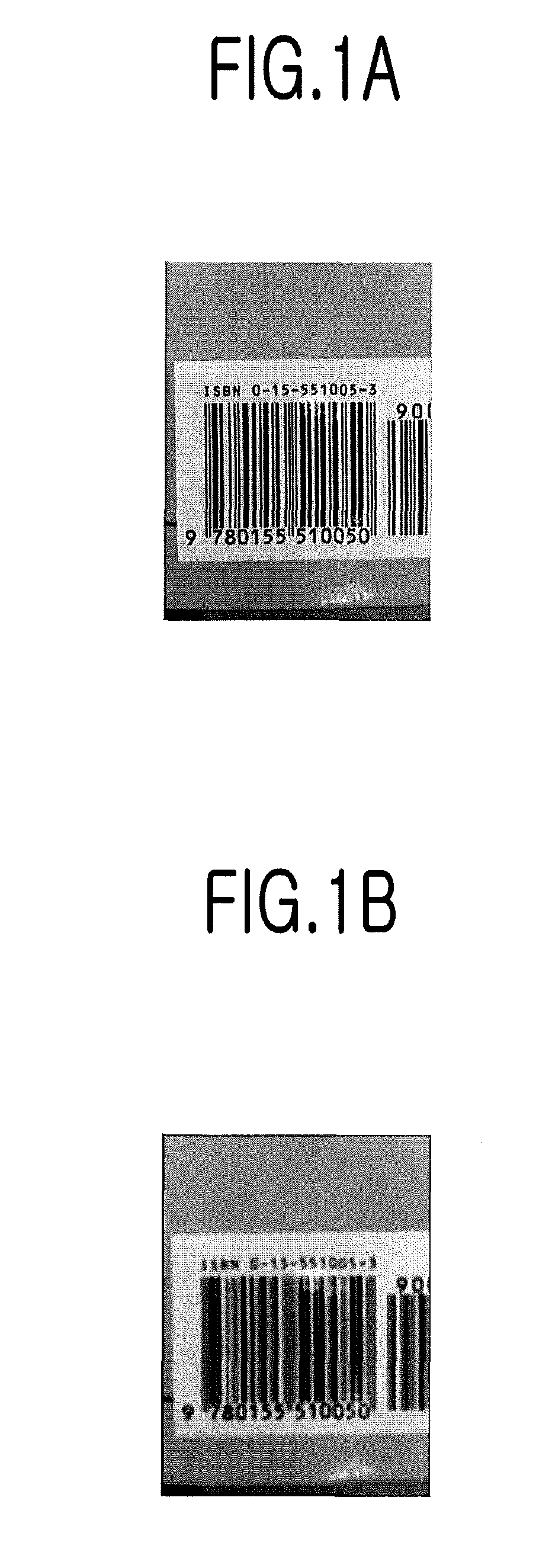
Method, terminal and computer-readable recording medium for deblurring barcode image
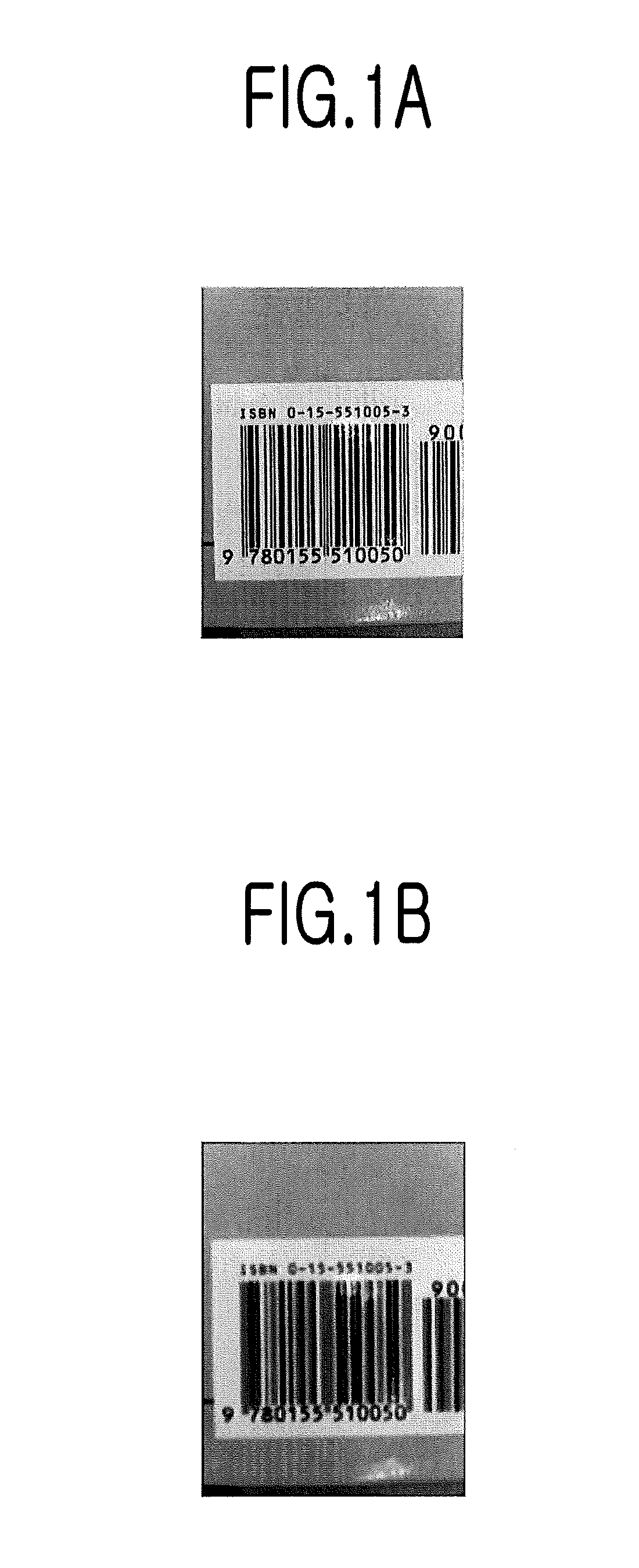
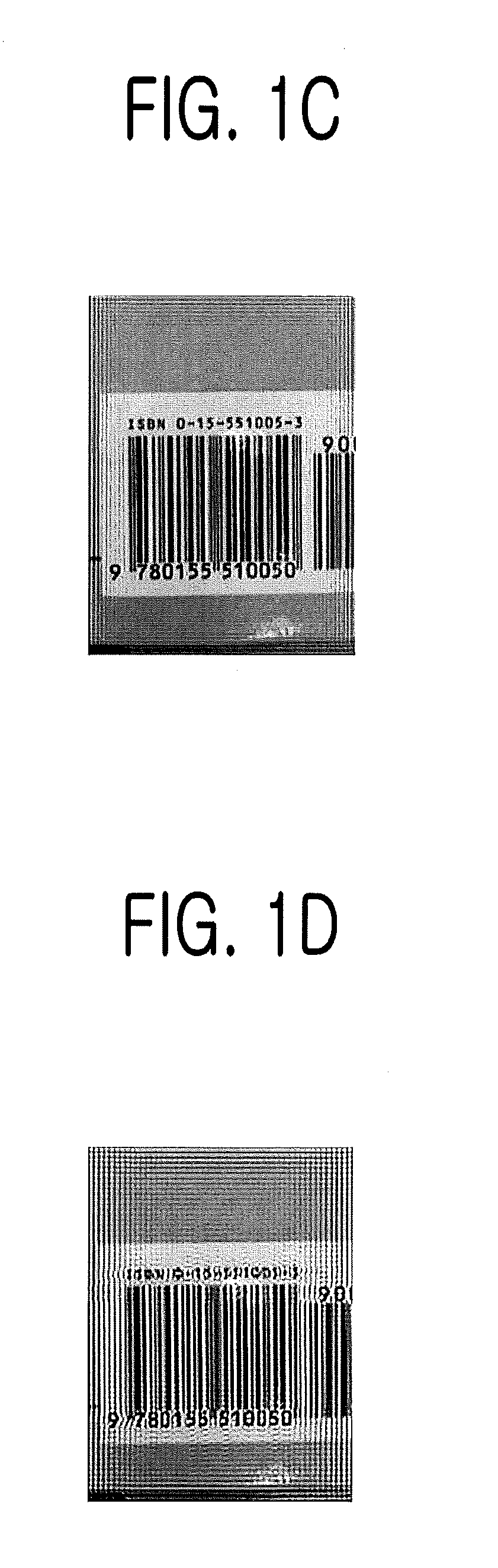
InactiveUS8320695B2Shorten the timeThe solution function is relatively simpleImage enhancementCharacter and pattern recognitionBarcodeComputer terminal
The present invention relates to a method for deblurring a barcode image. The method includes the steps of: acquiring the terminal's n OTFs calculated by varying focal lengths for a subject; if a barcode image is inputted through the mobile terminal, fixing a specific value among NSRs as a value to be applied to an error metric of Wiener filtering, applying n PSFs calculated from the n OTFs to the error metric by a binary search algorithm and determining whether the result of the application to the error metric is not exceeding the pre-set threshold or not; and selecting a PSF value and an NSR value as values of Wiener filtering if the result of the application to the error metric is not exceeding the pre-set threshold and then performing the Wiener filtering to the inputted barcode image by using the selected PSF value and the selected NSR value.
Owner:INTEL CORP
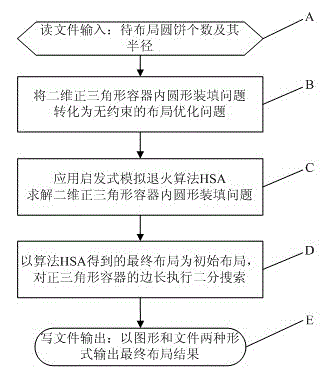
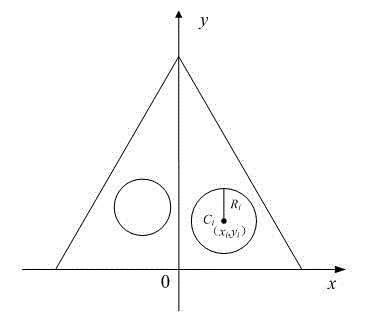
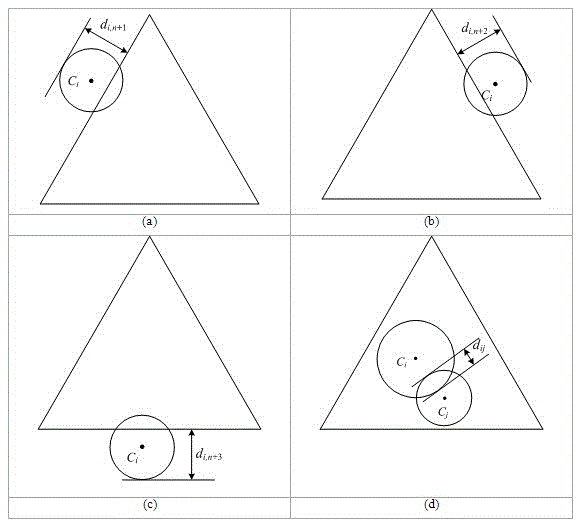
Annealing strategy-based layout method for circle packing problem
The invention relates to an annealing strategy-based layout method for a circle packing problem, and the problem is that n given round cakes are arranged in a regular triangle container in a way that every two round cakes are not embedded mutually, wherein the side length of the triangle is L, and the minimal value of the L is determined. The method comprises the following steps: A, reading an input file, namely, data including the number of the round cake to be arranged and the Ri thereof (i is larger than or equal to 1 and smaller than or equal to n) for test cases; B, converting the problem of the circle packing problem in the triangular container into an unconstrained layout optimization problem through a quasi content strategy; C, solving the circle packing problem in the triangular container through a heuristic simulated annealing algorithm; D, taking the final layout obtained from the algorithm as an initial layout, and carrying out binary search to the side length L; and E, outputting the final result in a way of graphics and documents. The method provided by the invention has high feasibility and high processing speed, can obtain the result closer to a global optimal solution, and can be widely used to solve other layout optimization problems.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Method, terminal and computer-readable recording medium for deblurring barcode image
InactiveUS20120170862A1Shorten the timeThe solution function is relatively simpleImage enhancementCharacter and pattern recognitionDeblurringBarcode
The present invention relates to a method for deblurring a barcode image. The method includes the steps of: acquiring the terminal's n OTFs calculated by varying focal lengths for a subject; if a barcode image is inputted through the mobile terminal, fixing a specific value among NSRs as a value to be applied to an error metric of Wiener filtering, applying n PSFs calculated from the n OTFs to the error metric by a binary search algorithm and determining whether the result of the application to the error metric is not exceeding the pre-set threshold or not; and selecting a PSF value and an NSR value as values of Wiener filtering if the result of the application to the error metric is not exceeding the pre-set threshold and then performing the Wiener filtering to the inputted barcode image by using the selected PSF value and the selected NSR value.
Owner:INTEL CORP
Method and apparatus for performing a binary search on an expanded tree
InactiveUS20050071501A1Increase speedHigh performance and cost-effectiveData processing applicationsDigital data information retrievalTheoretical computer scienceLongest prefix match
A method and apparatus for searching an electronically stored table of information including a plurality of table entries and facilitating high speed searching of a table to provide a longest matching entry. The table searching method uses at least one memory unit having a table of information including a plurality of data entries. The table of information has a plurality of search keys associated with the plurality of data entries and the plurality of search keys form a tree structure based on a prefix length for each of the search keys. The plurality of search keys are expanded such that each of the plurality of search keys has two lowest level search keys associated therewith that cover a lowest level of the tree structure. A binary search of the lowest level search keys is performed based on a search value to determine a longest prefix match. A data entry of the plurality of data entries is output based on said longest prefix match. The method is also applicable to routing data in an internet router where the routing of data packets depends on address information stored in the table of information.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com