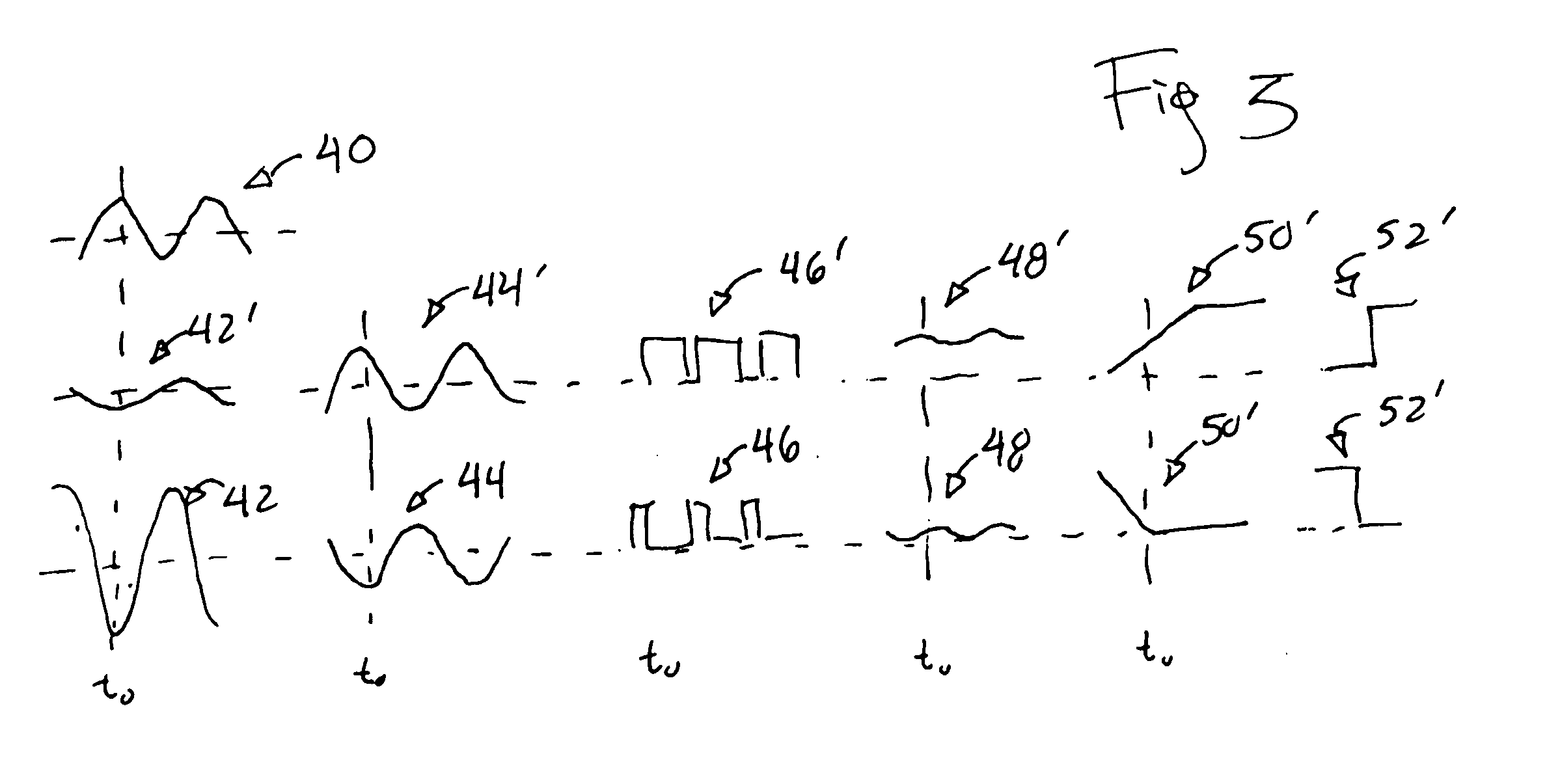Patents
Literature
30results about How to "Change its value" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
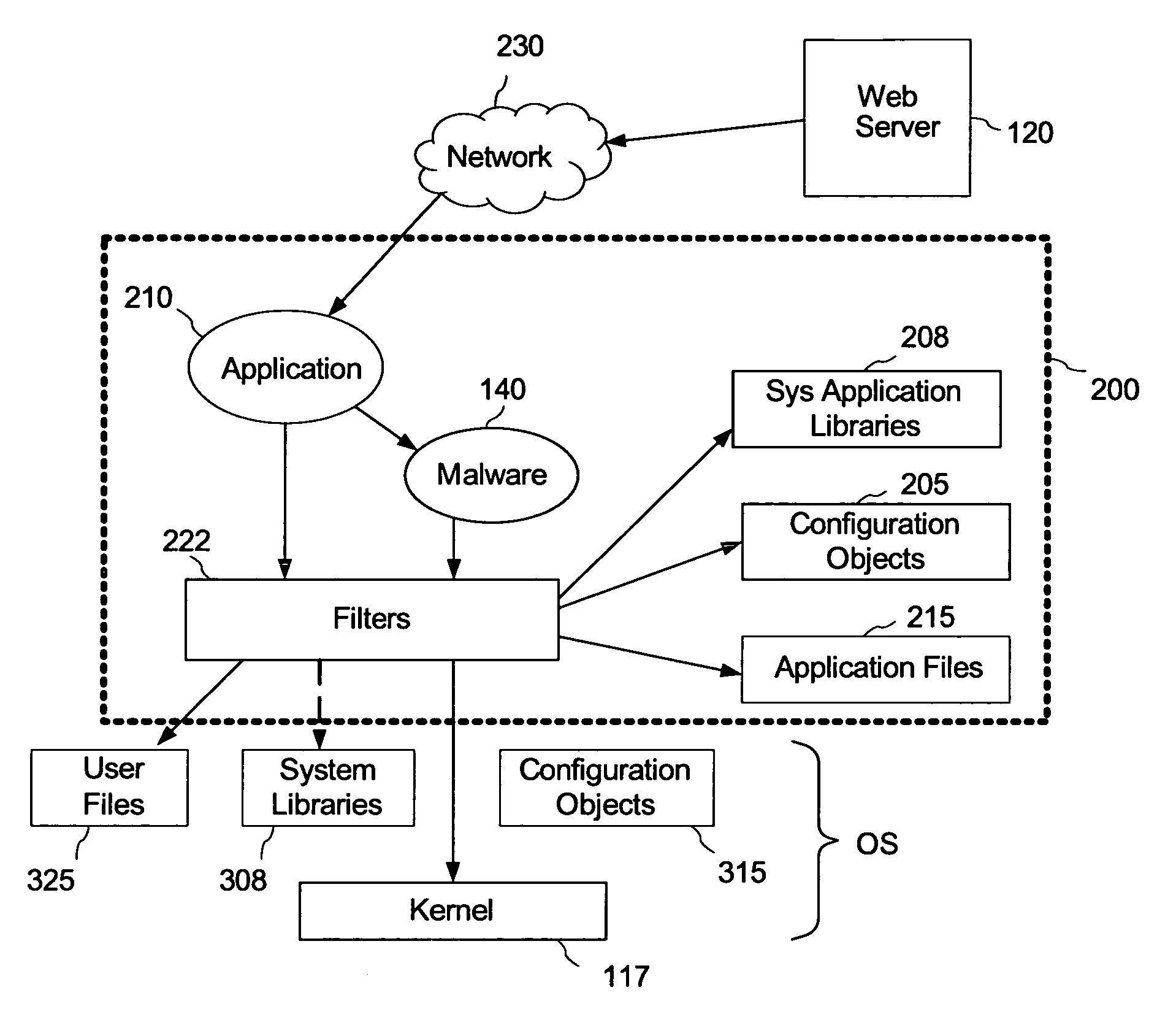
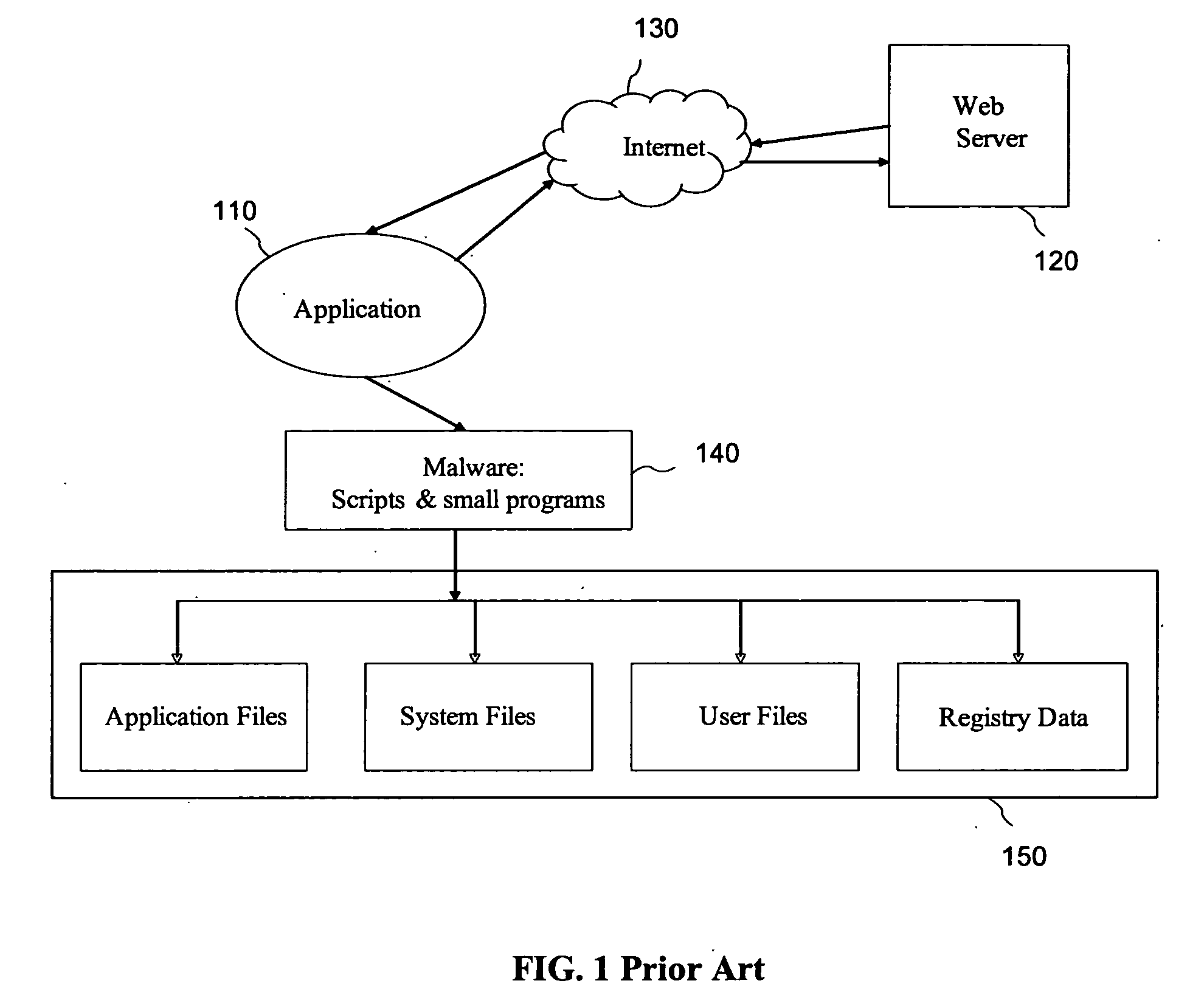
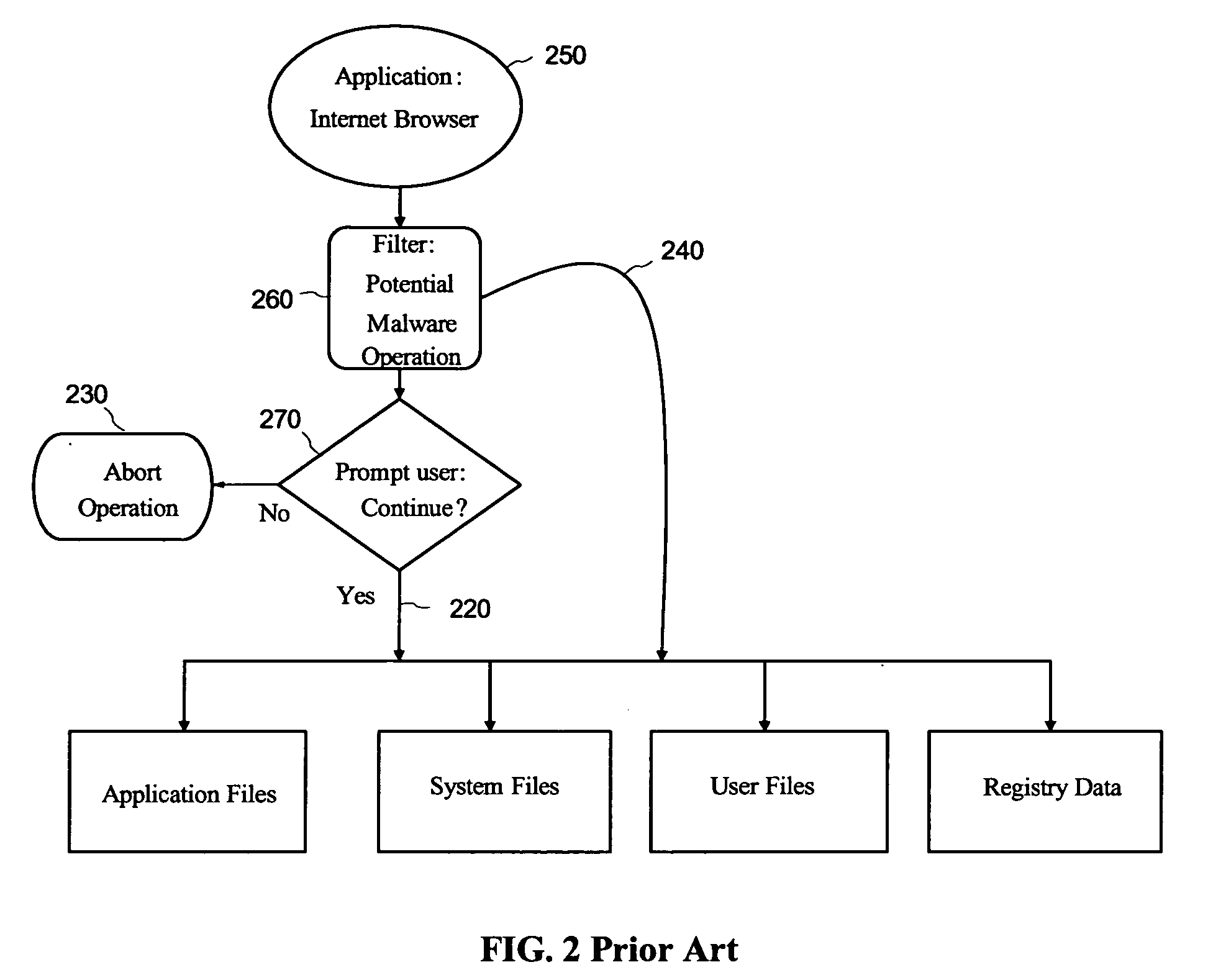
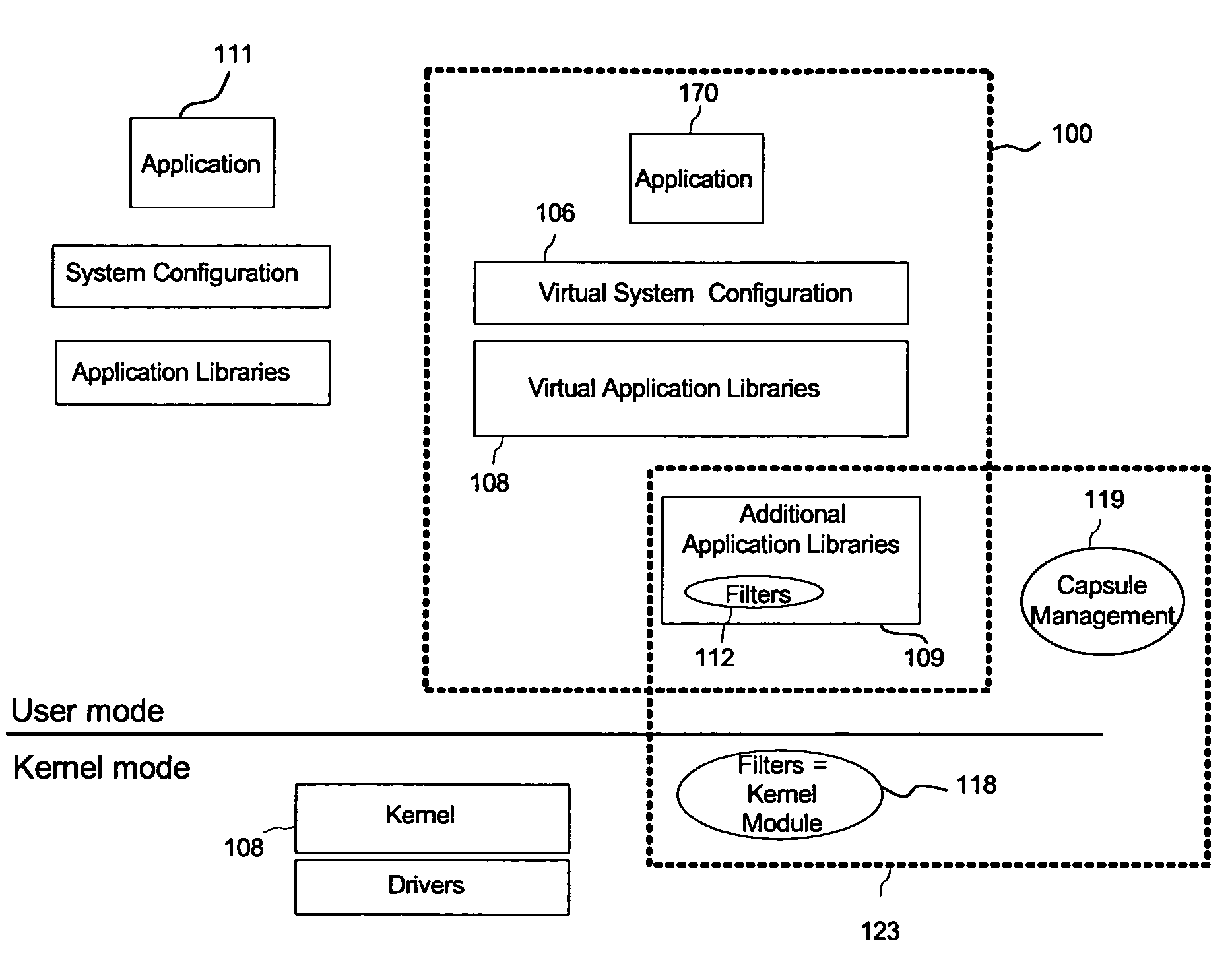
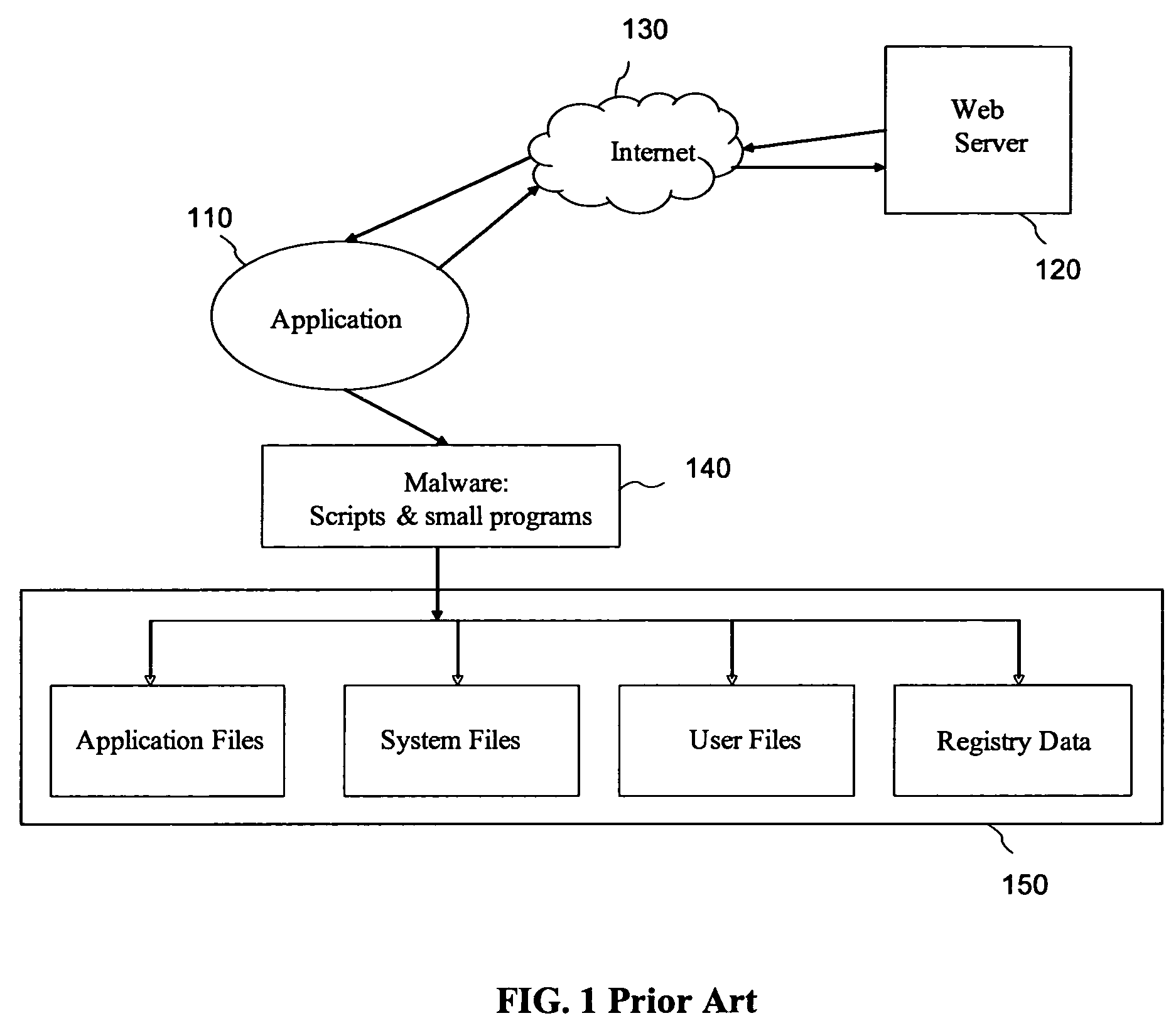
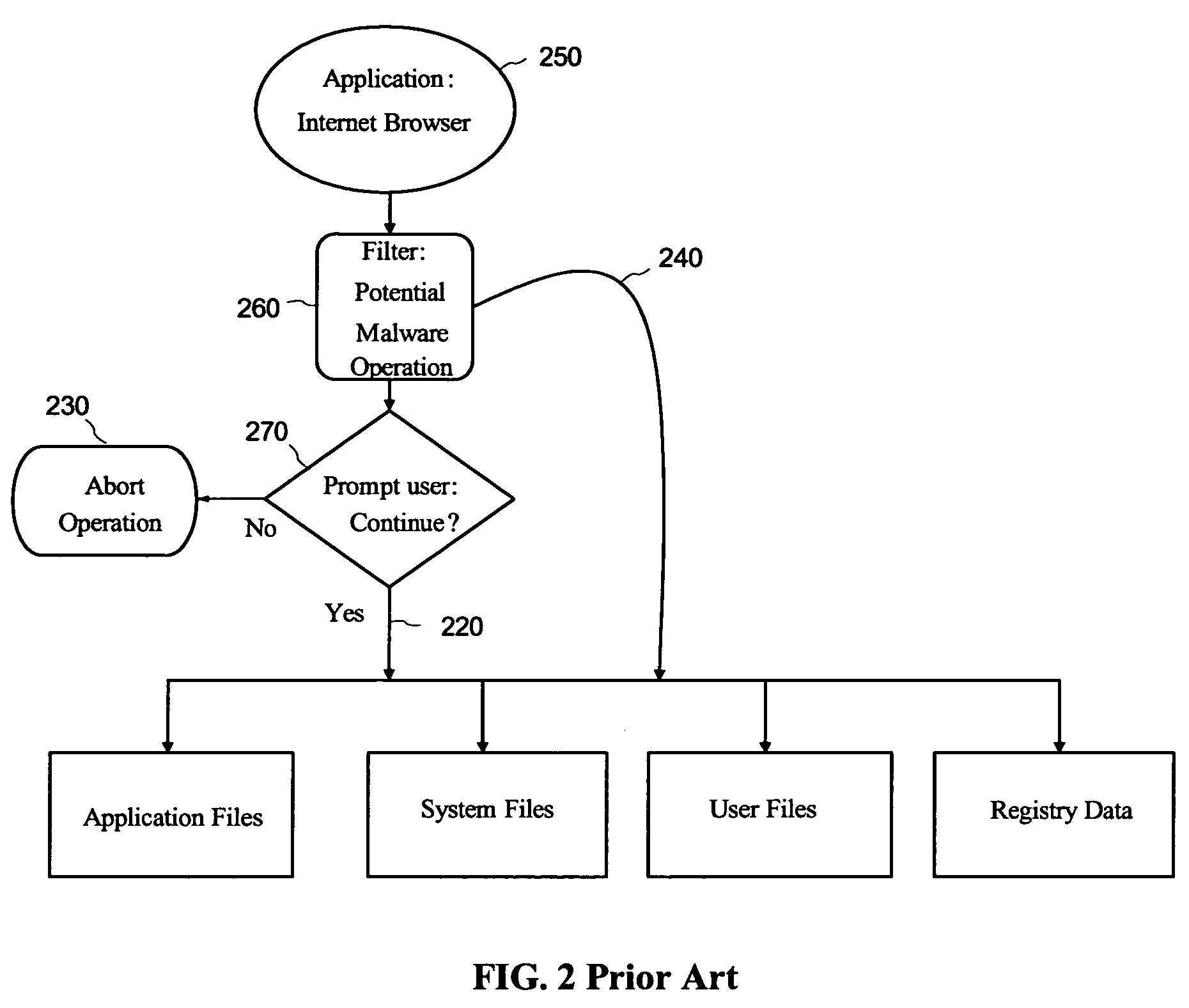
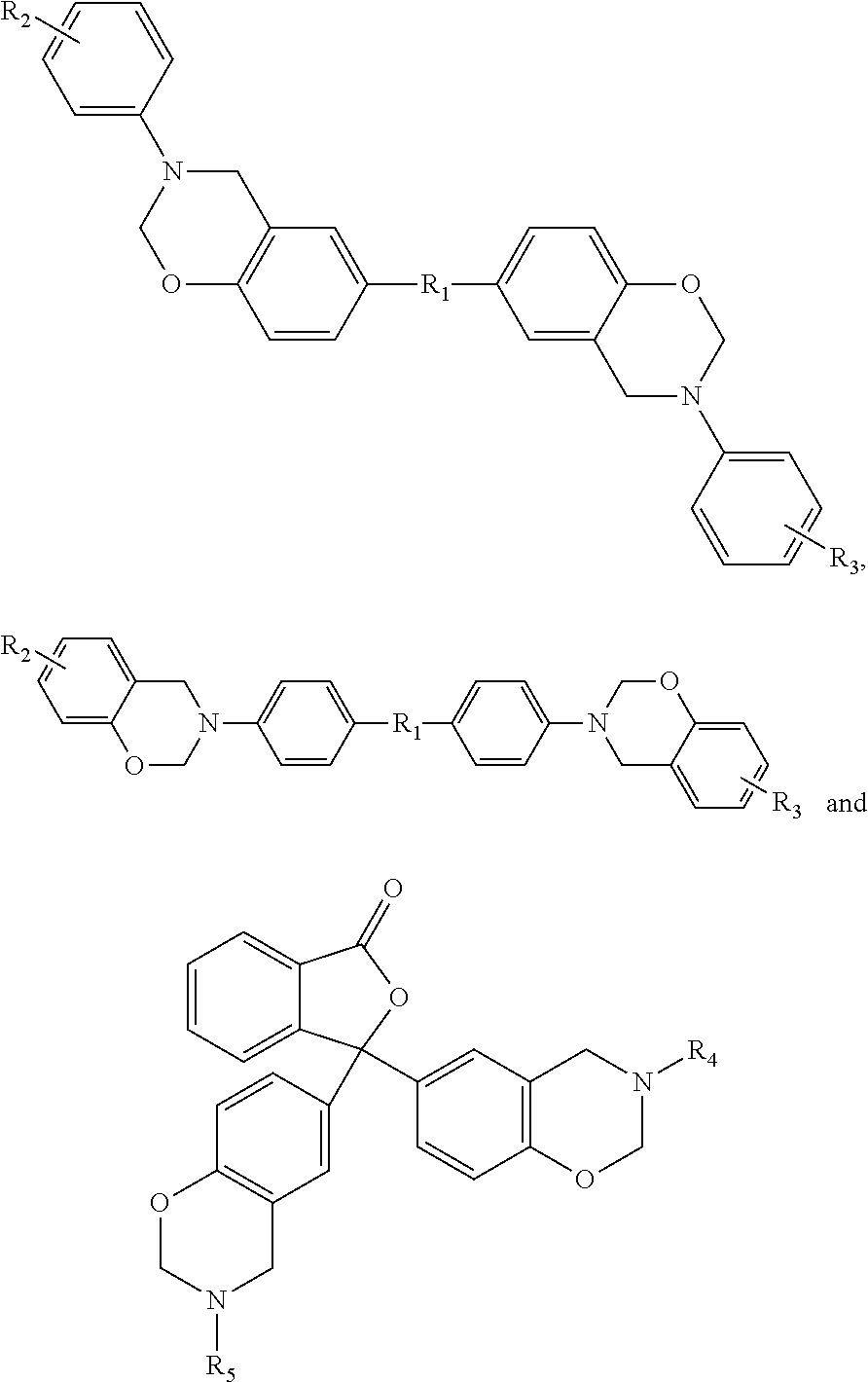
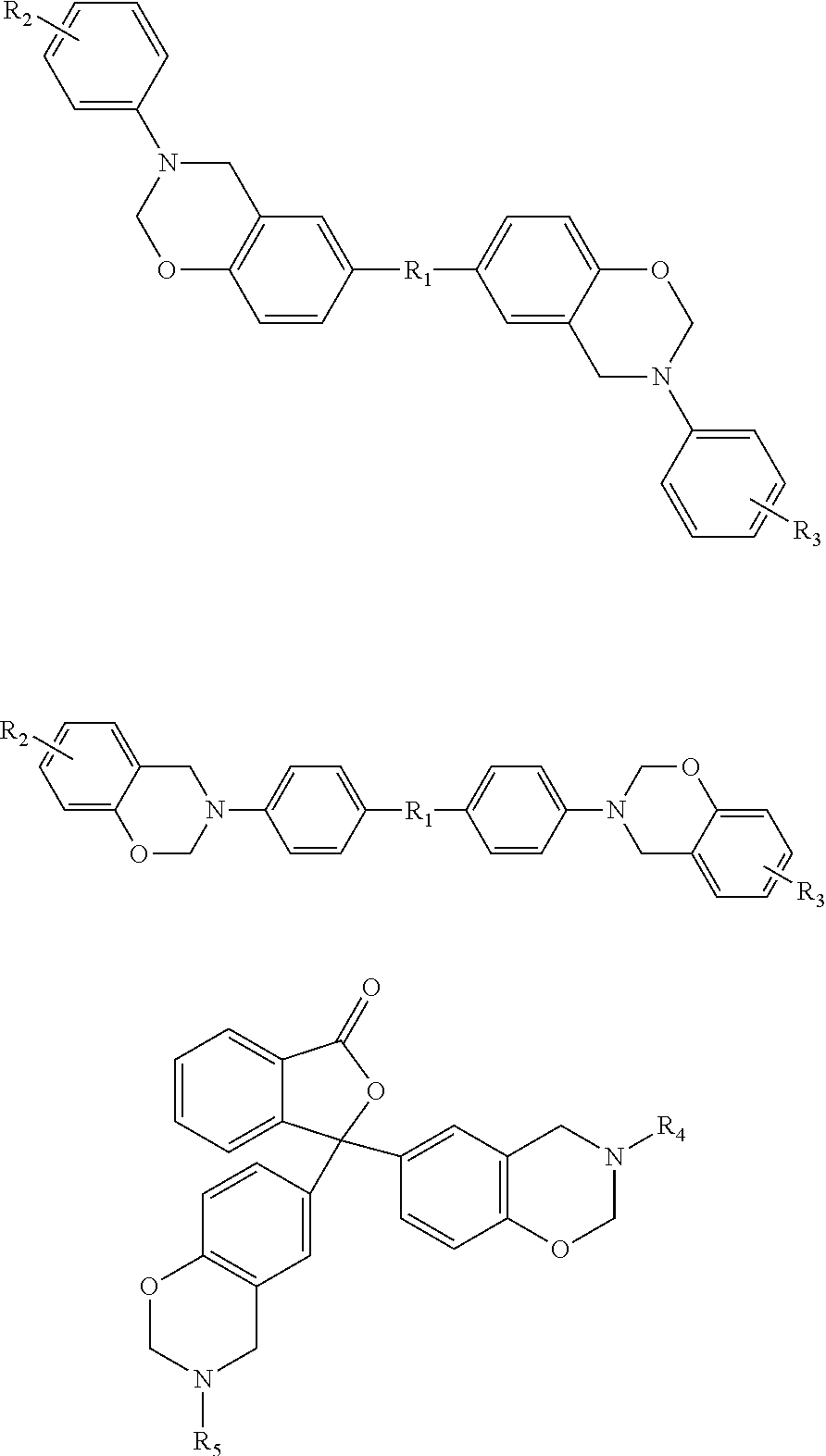
Malware containment by application encapsulation
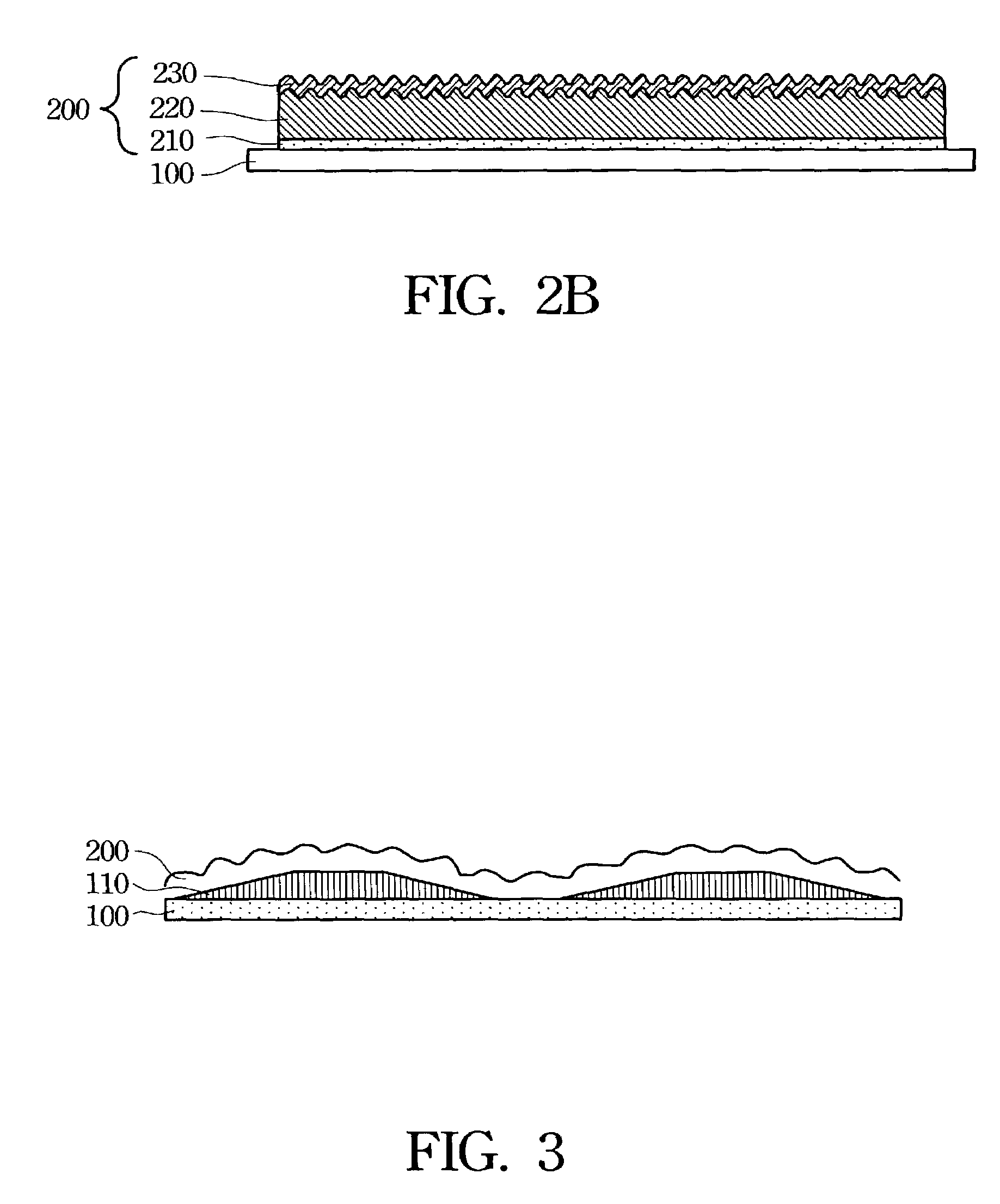
ActiveUS20060265761A1Avoid changePrevent malwareMemory loss protectionError detection/correctionOperational systemMalware
The invention discloses a method and system for protecting a computer platform from malware. The protection is achieved by encapsulating an application that can serve as a malware conduit within a protected capsule environment, so as to prevent the conduit application or any processes originated therefrom from accessing and making changes to objects associated with an operating system (OS) of the computer platform or with other applications running on the computer platform outside of the capsule environment, thereby preventing the malware provided via the conduit application from contaminating the computer platform outside of said secure protected environment, or capsule. Capsule runtime software manages the dynamic state of the encapsulated application, and re-directs system service requests generated by the application and associated processes from OS-provided system objects to corresponding object libraries provided within the capsule object set, so that any malware induced changes remain local to the capsule. Protection of the operating system and most applications running on the computer platform is thus provided by the isolation of the conduit applications within a secure capsule environment, which can be safely removed from the computer platform, together with any changes introduced by the malware to the computer platform, without affecting the computer operation.
Owner:TRIGENCE CORP
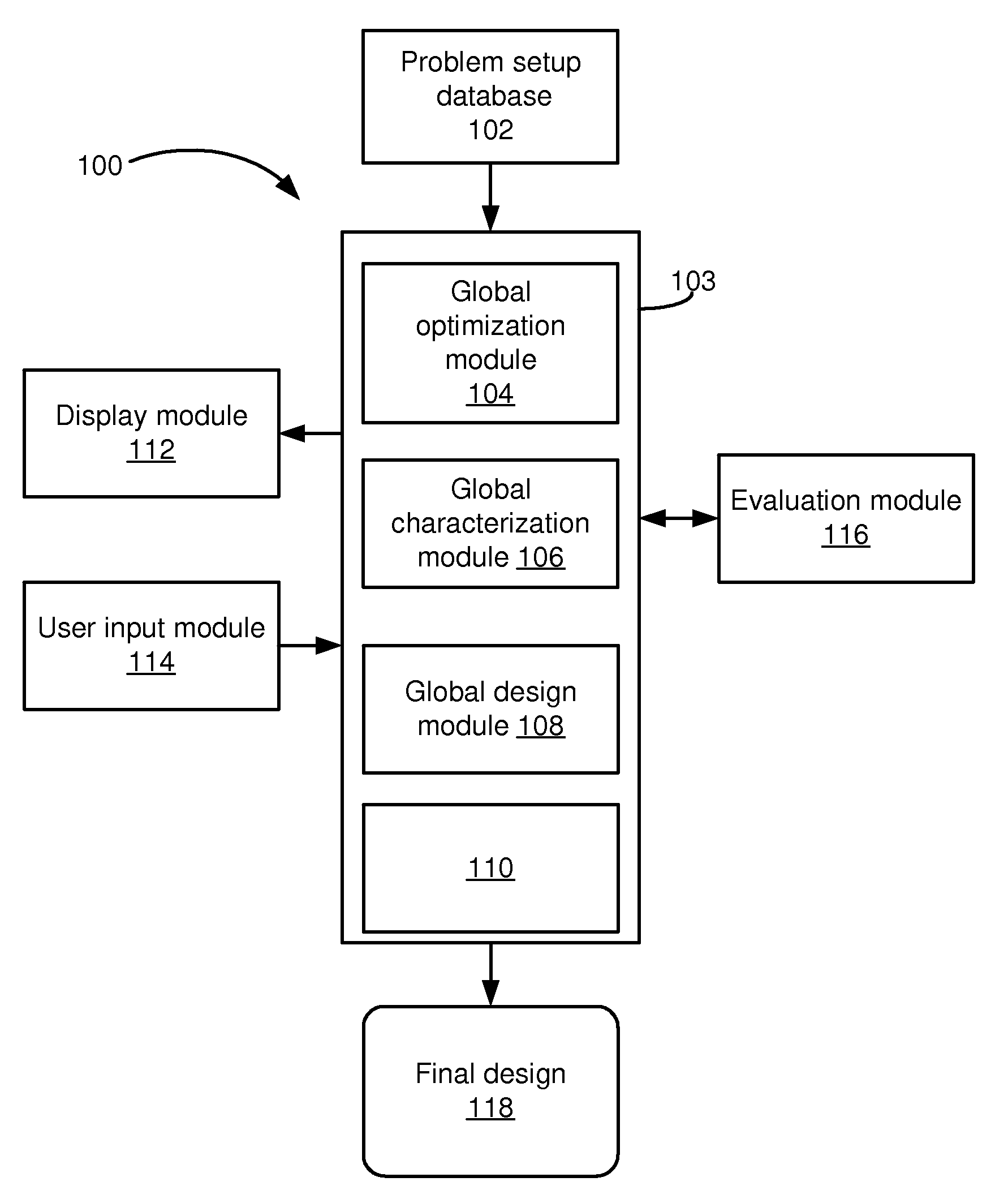
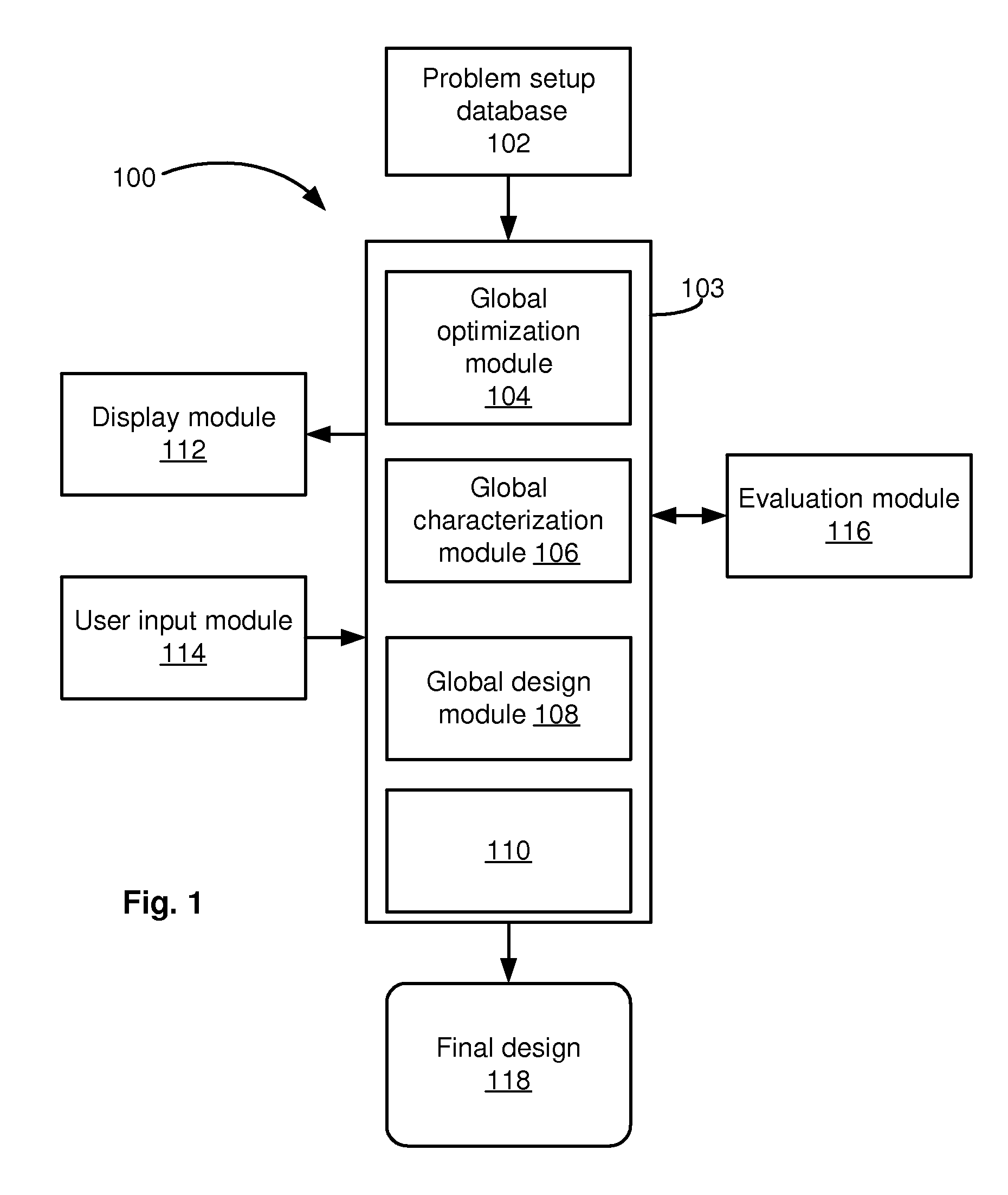
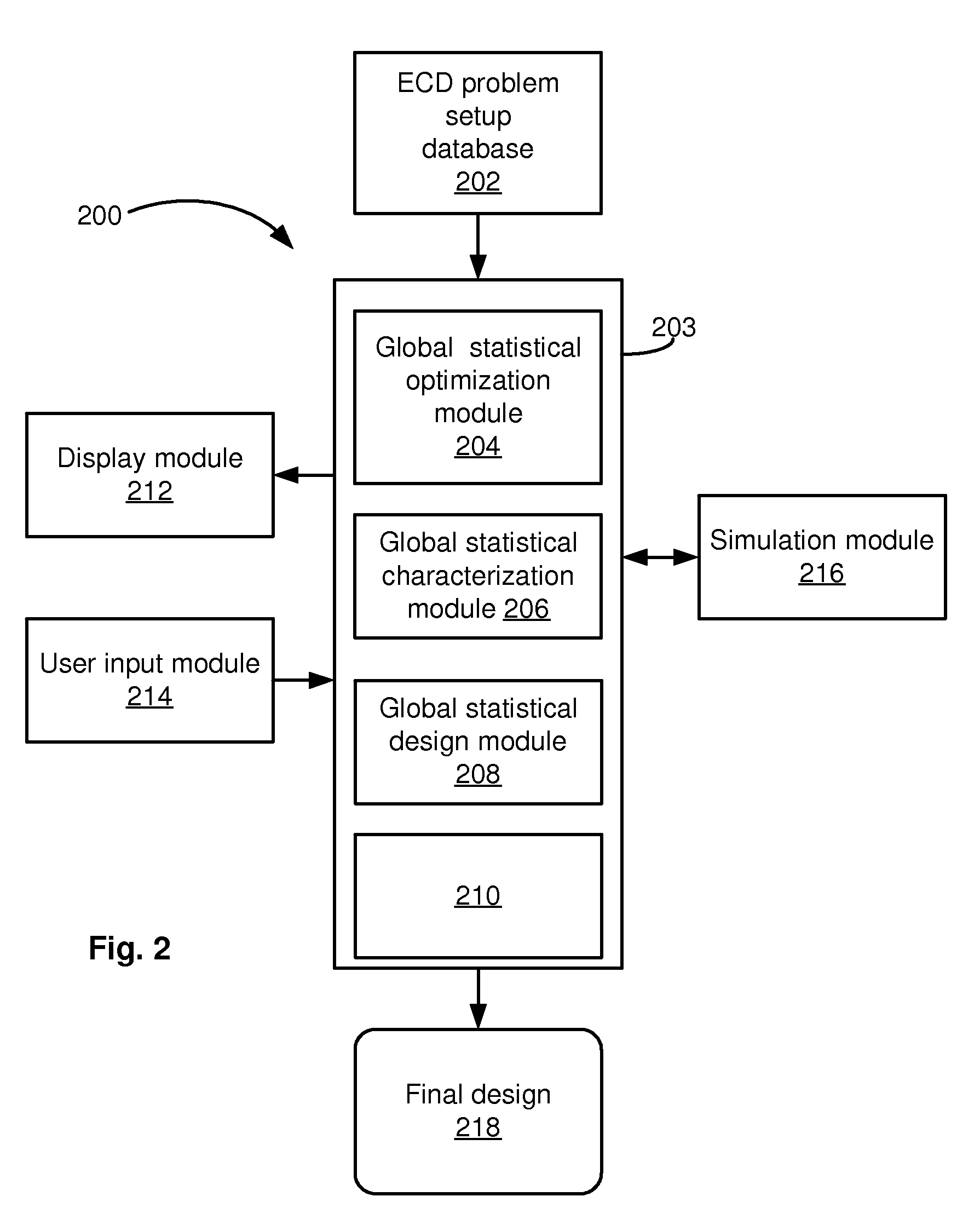
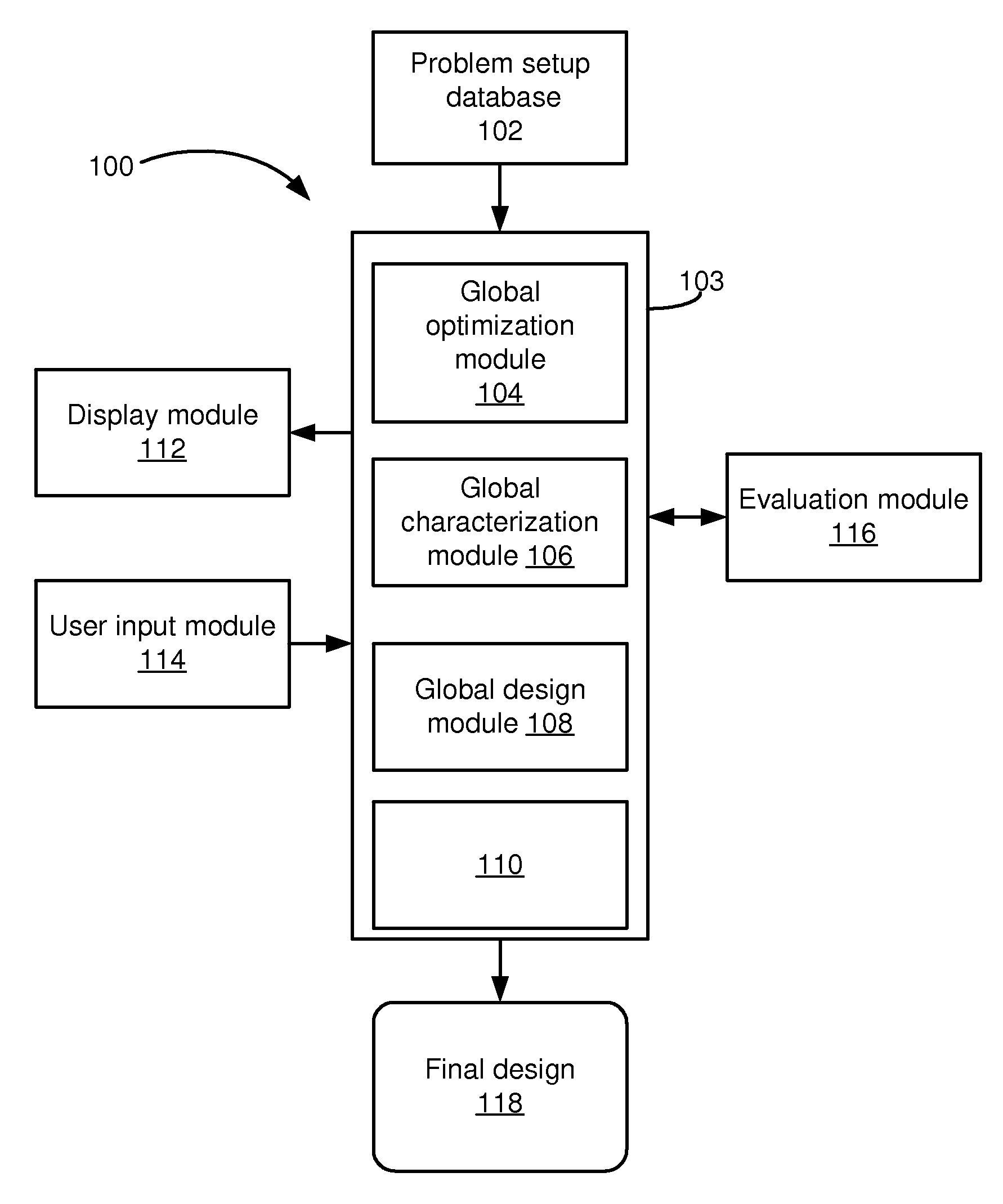
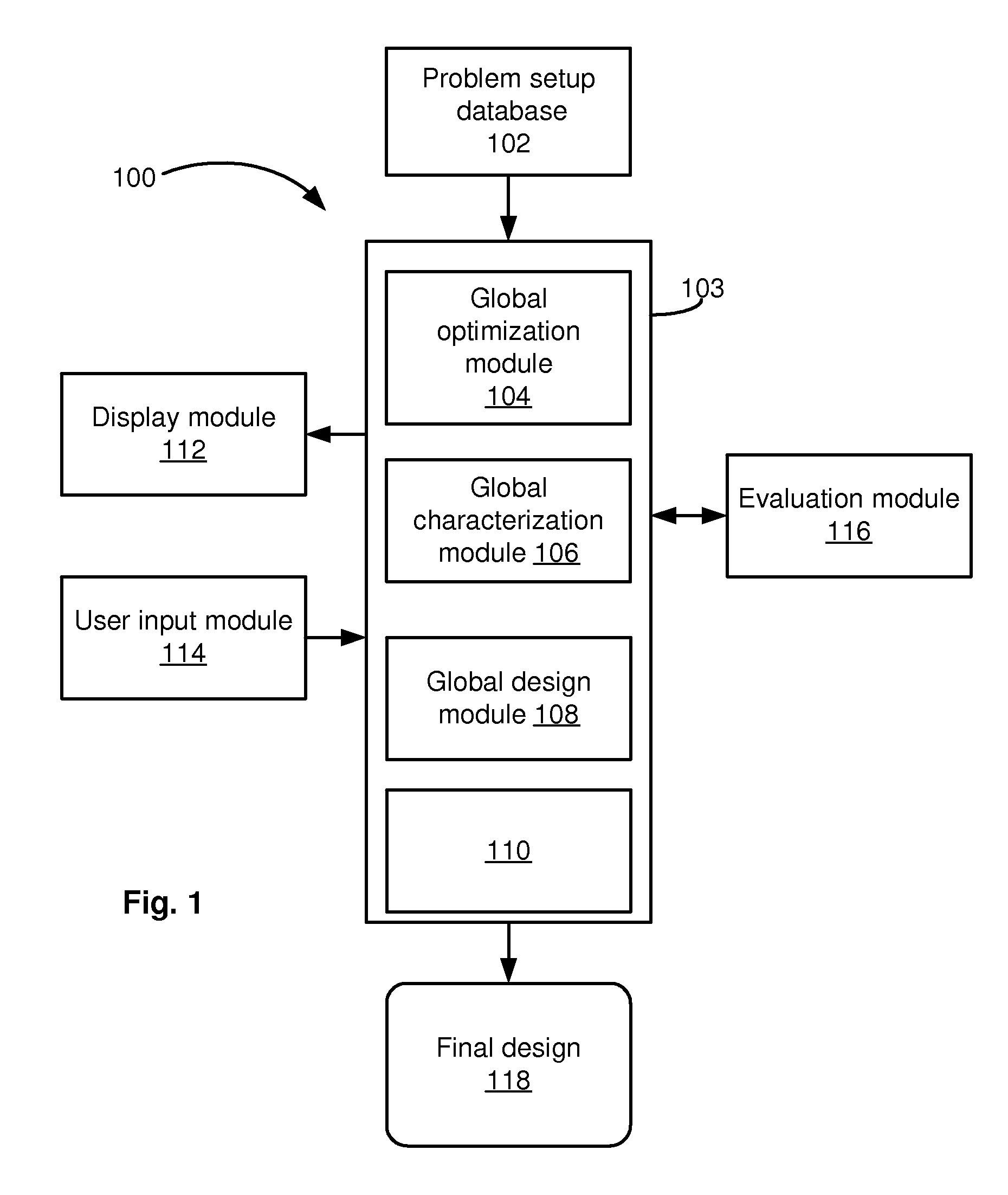
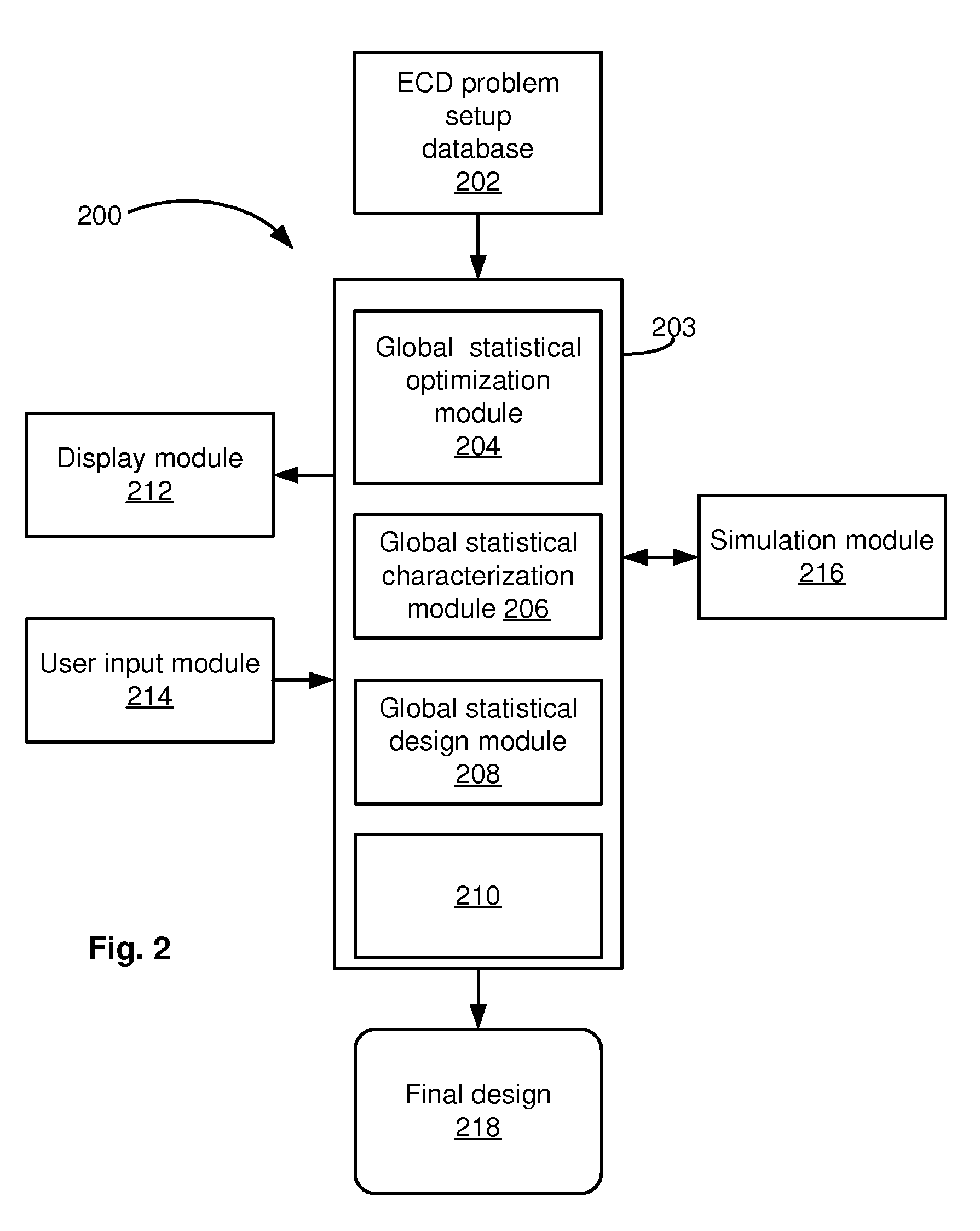
Global statistical optimization, characterization, and design
ActiveUS20090228846A1Low costChange its valueDetecting faulty computer hardwareCAD circuit designTime rangeTheoretical computer science
For application to analog, mixed-signal, and custom digital circuits, a system and method to do: global statistical optimization (GSO), global statistical characterization (GSC), global statistical design (GSD), and block-specific design. GSO can perform global yield optimization on hundreds of variables, with no simplifying assumptions. GSC can capture and display mappings from design variables to performance, across the whole design space. GSC can handle hundreds of design variables in a reasonable time frame, e.g., in less than a day, for a reasonable number of simulations, e.g., less than 100,000. GSC can capture design variable interactions and other possible nonlinearities, explicitly capture uncertainties, and intuitively display them. GSD can support the user's exploration of design-to-performance mappings with fast feedback, thoroughly capturing design variable interactions in the whole space, and allow for more efficiently created, more optimal designs. Block-specific design should make it simple to design small circuit blocks, in less time and with lower overhead than optimization through optimization.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
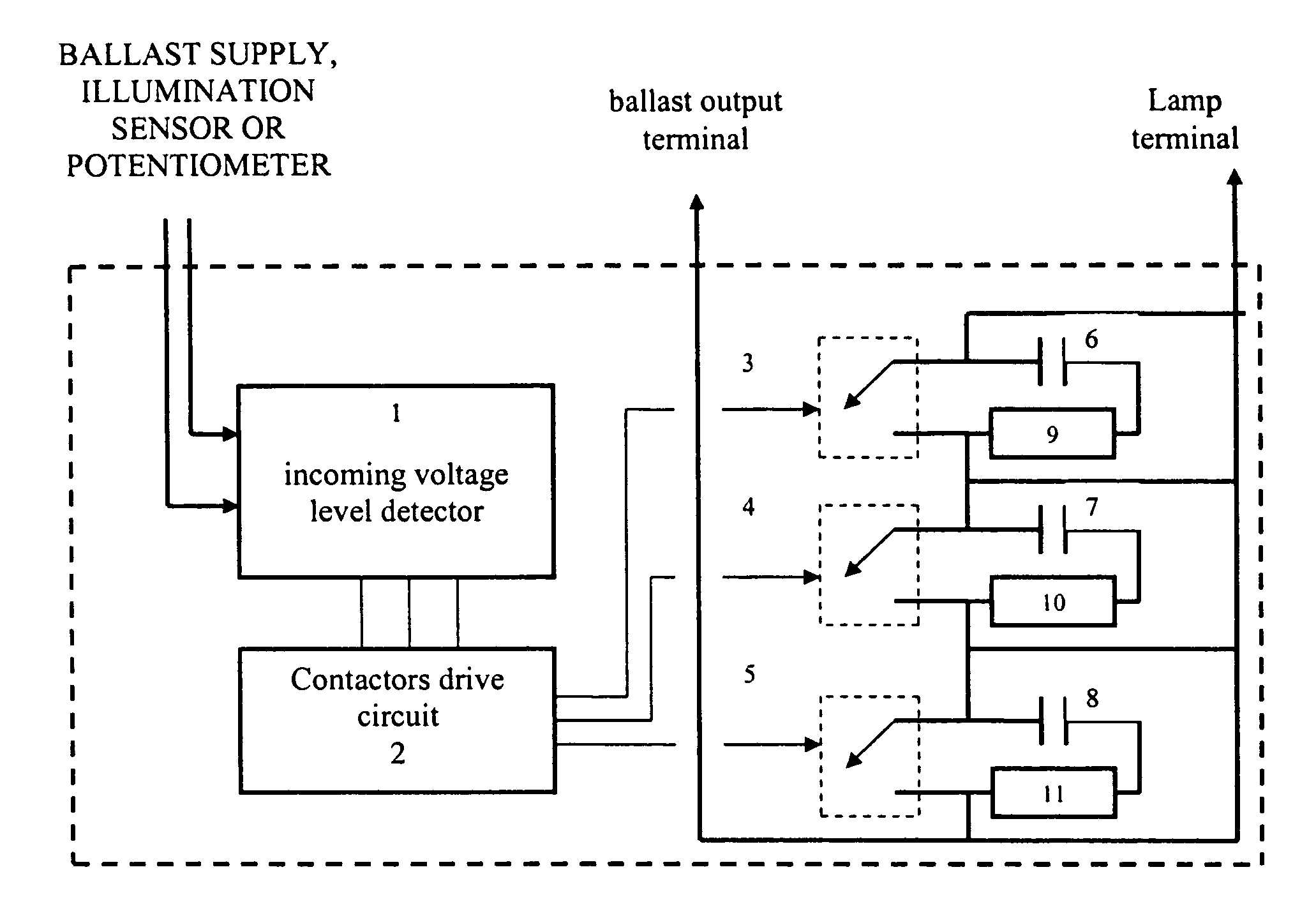
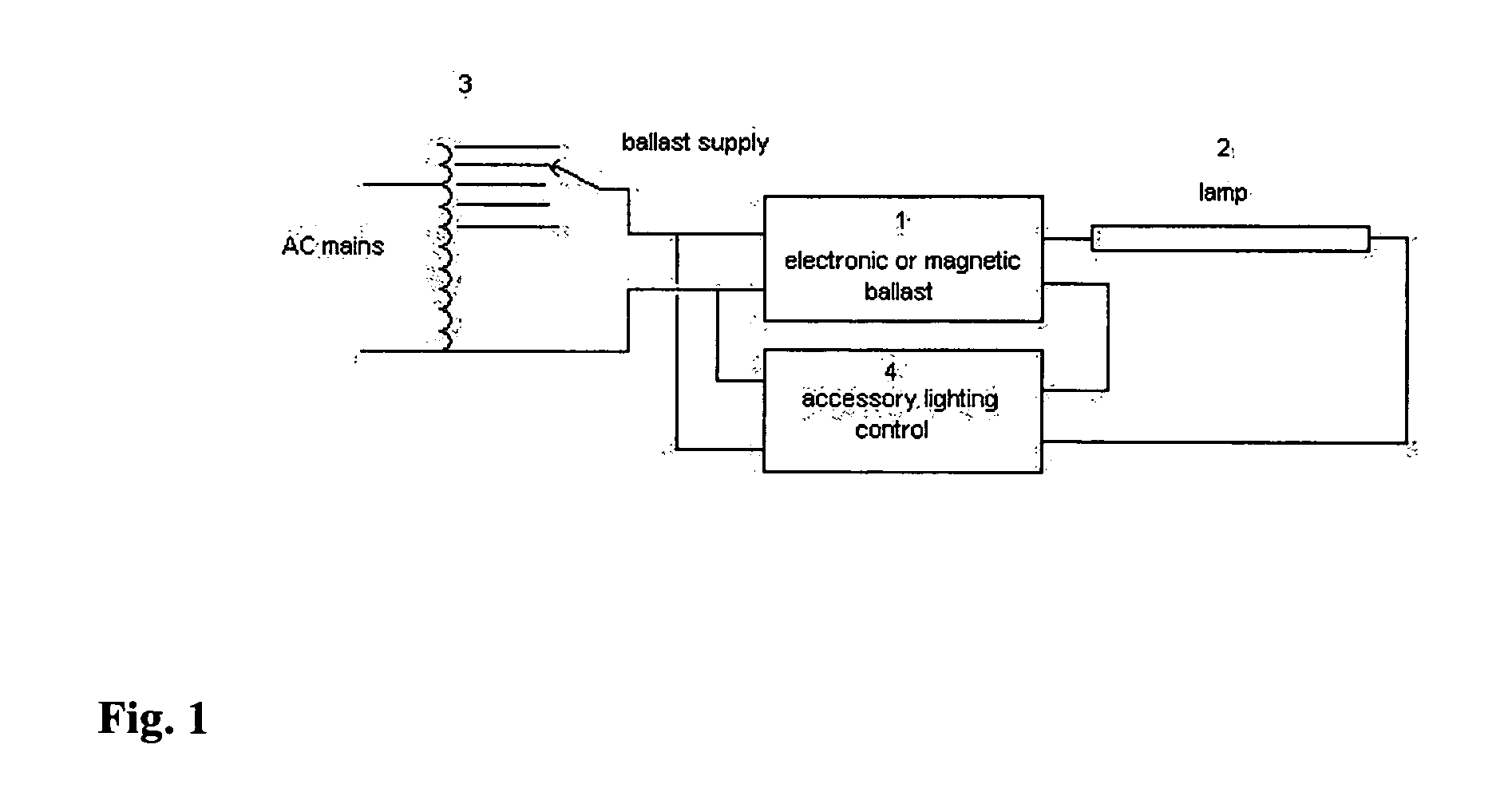
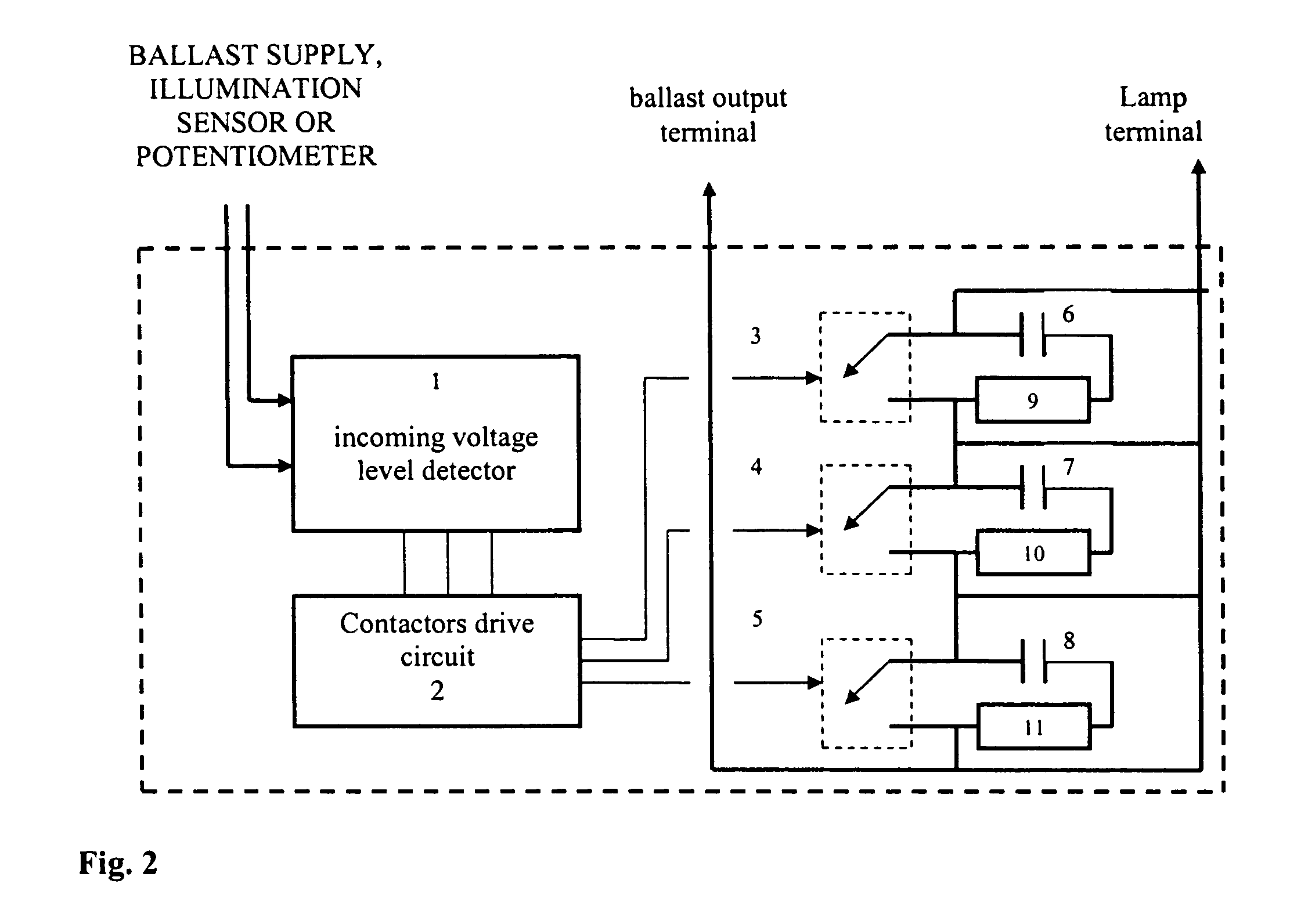
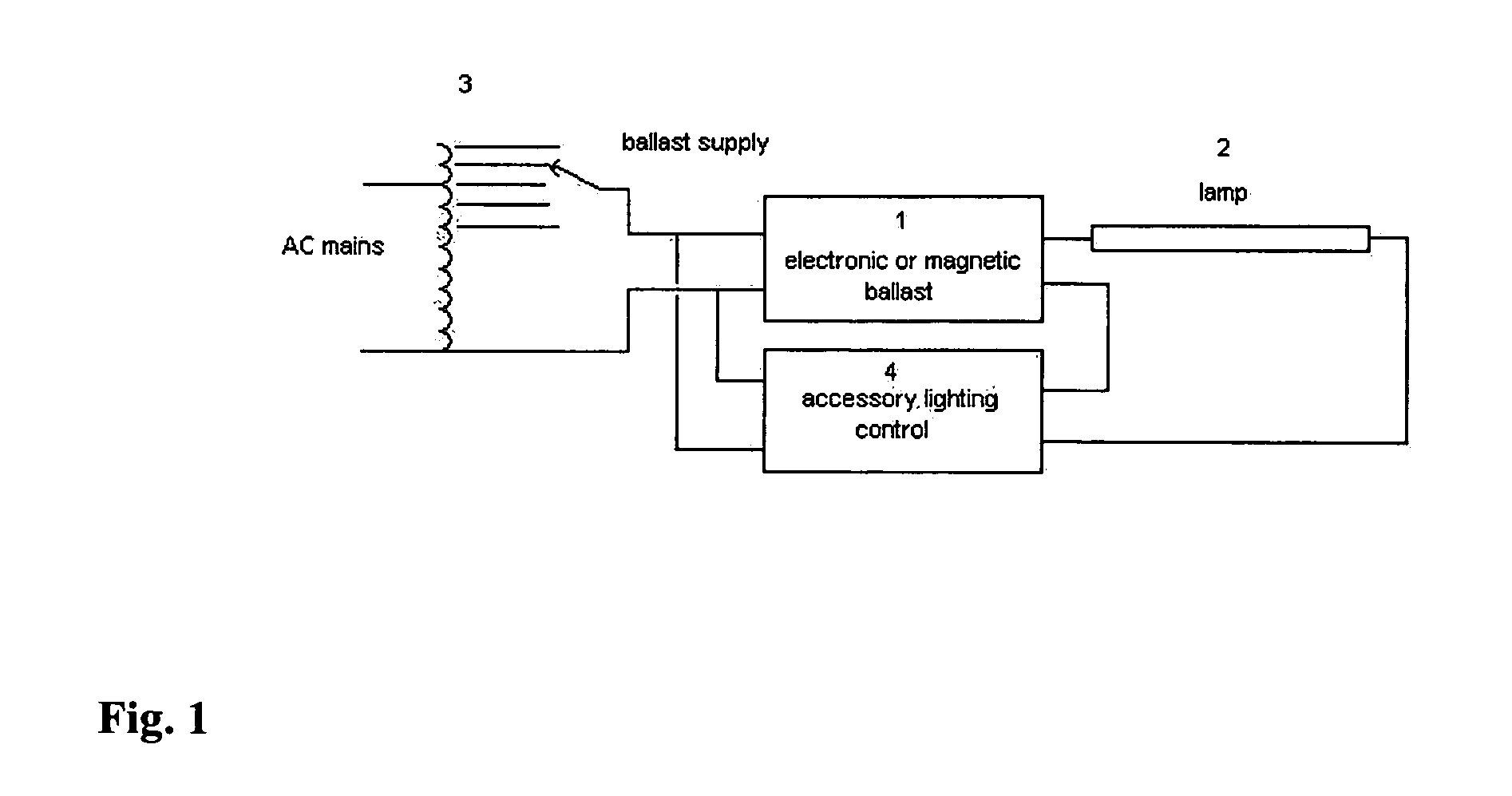
Automatic light dimmer for electronic and magnetic ballasts (fluorescent or HID)
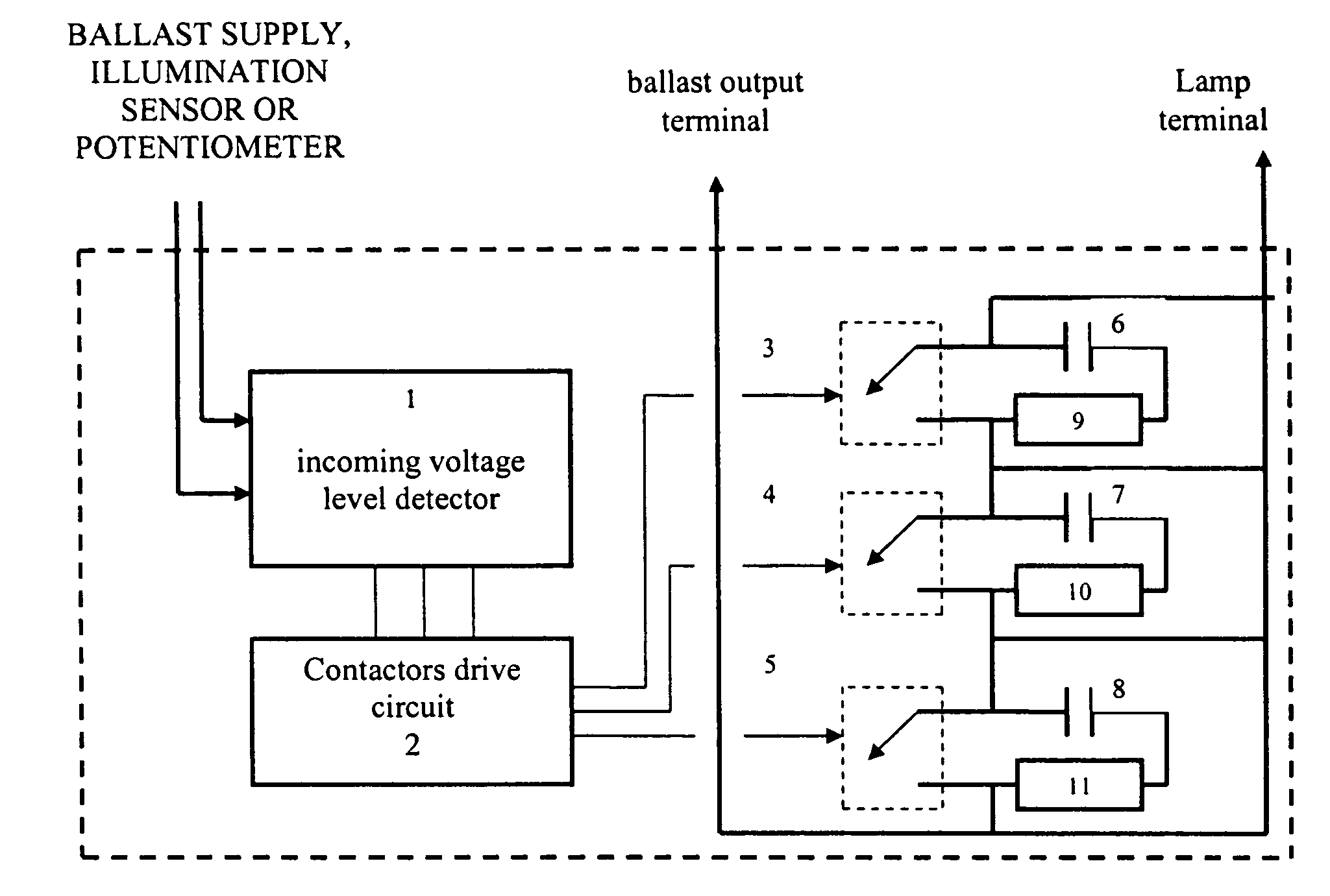
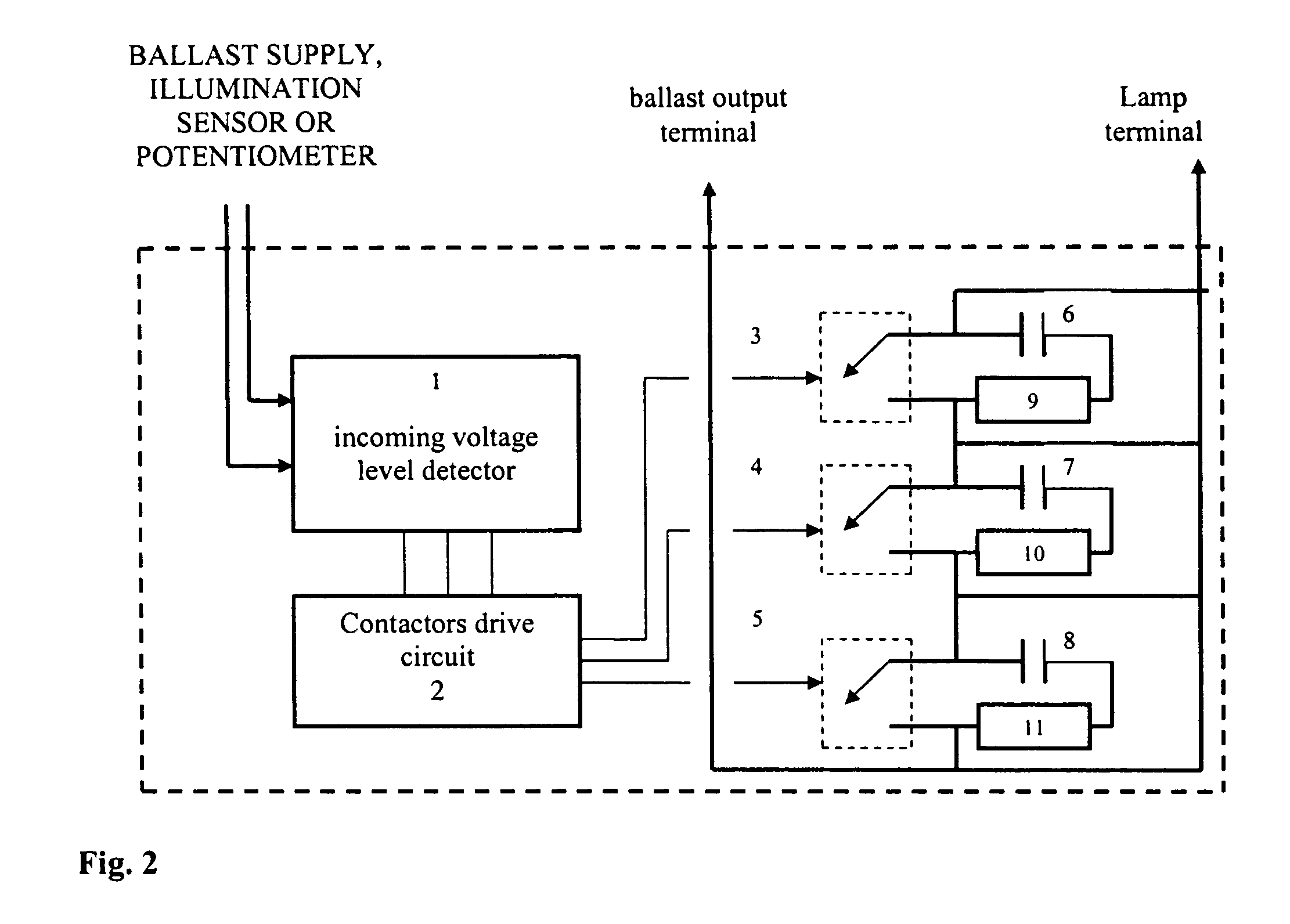
InactiveUS20060119288A1Save energyReduce investmentElectric light circuit arrangementElectric discharge lampsCapacitanceElectrical ballast
An apparatus is disclosed for automatic light dimming of electronic and magnetic ballasts used for fluorescent or high intensity discharge lamps. A variable capacitant's limiting current is added in the lamps which provides lighting intensity controls without changing the ballast's operation frequency. Several capacitors are placed in line with a terminal for the lamp. The capacitor's switching capability is used to change the current received by the lamp. The amount of voltage can be controlled by either varying the supply voltage, or with an elimination sensor, or by manual potentiometer control.
Owner:INTELLISWITCH DE C V
Global statistical optimization, characterization, and design
ActiveUS8024682B2Low costChange its valueDetecting faulty computer hardwareCAD circuit designTime rangeTheoretical computer science
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
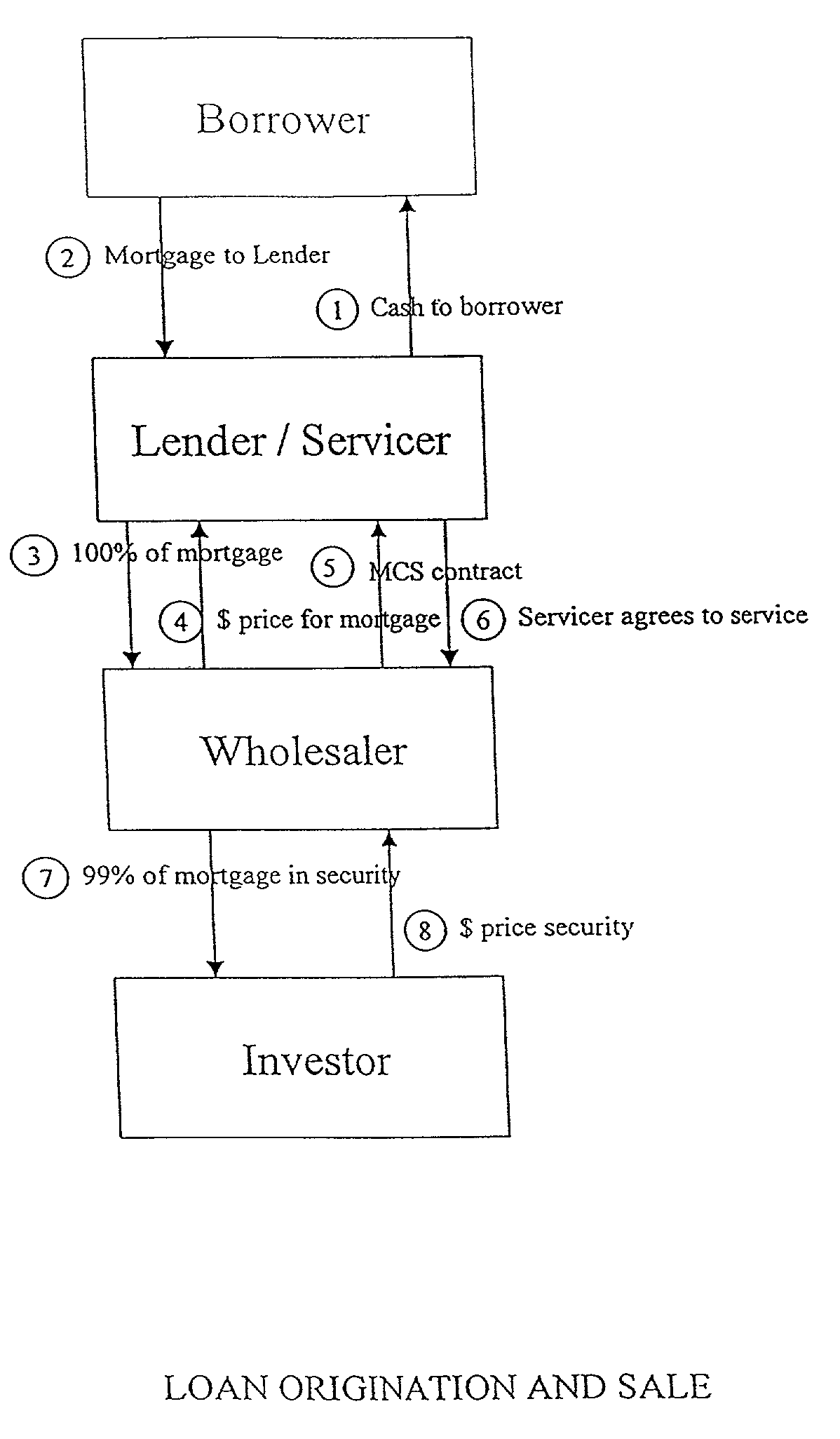
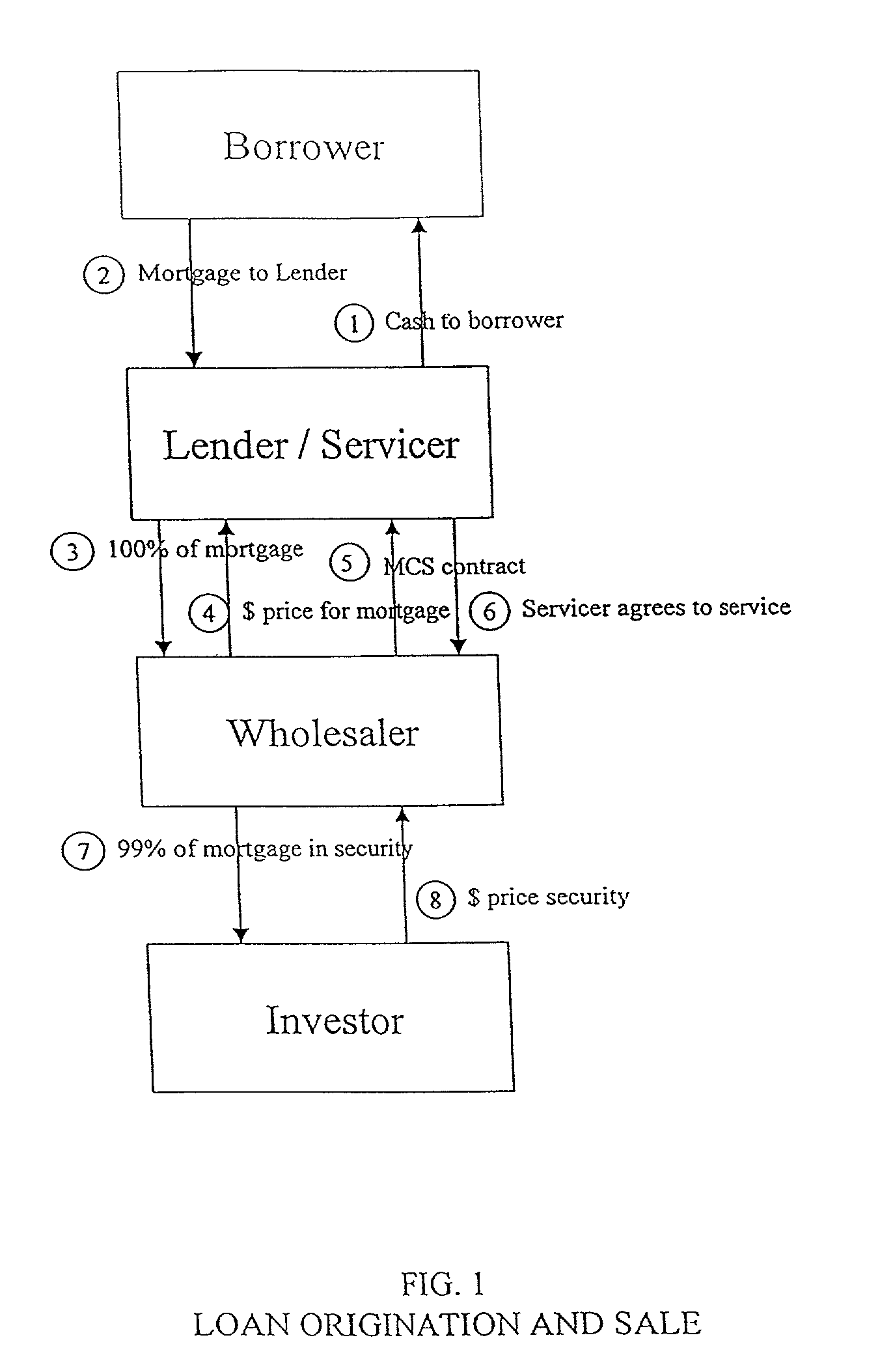
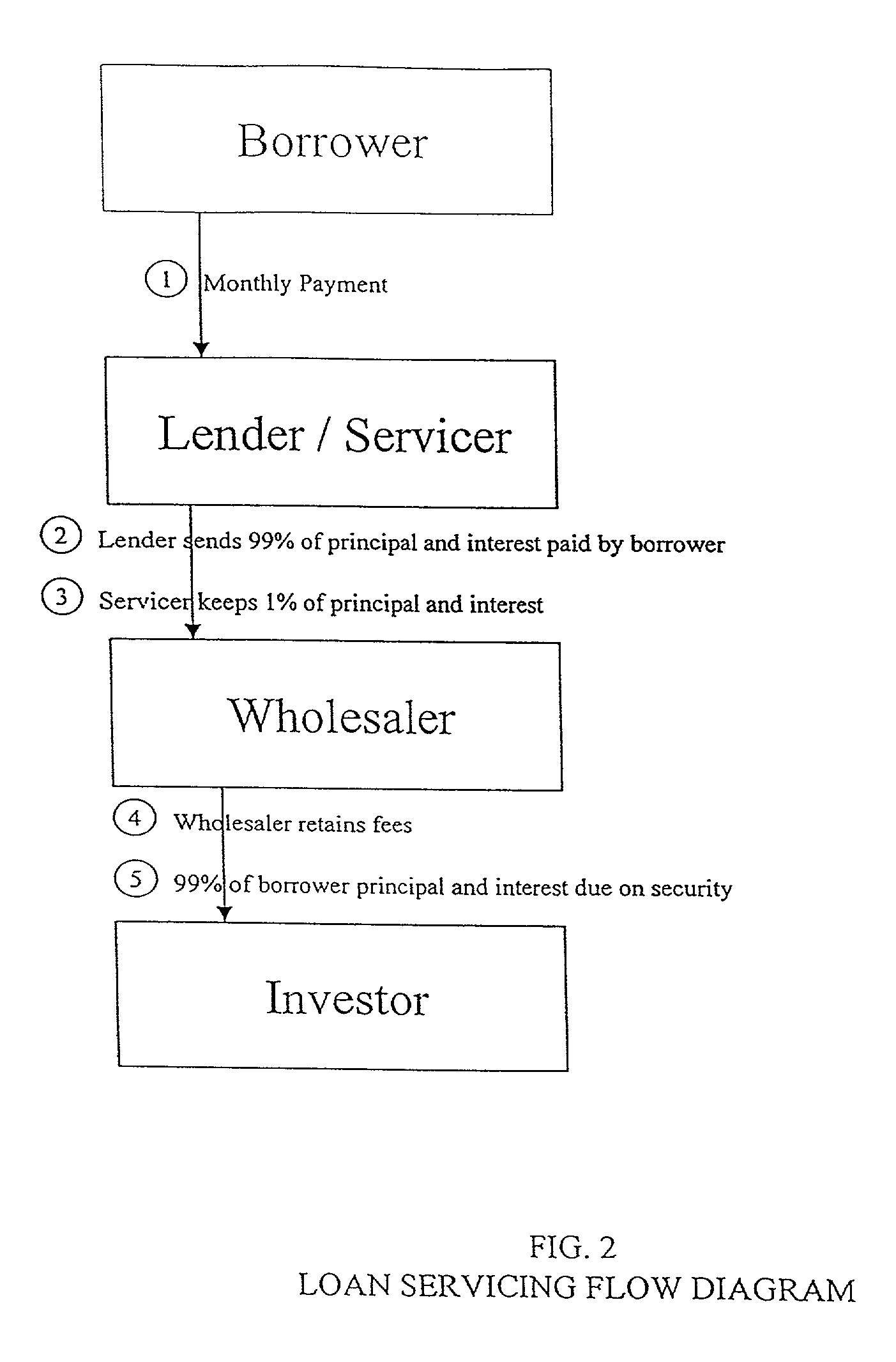
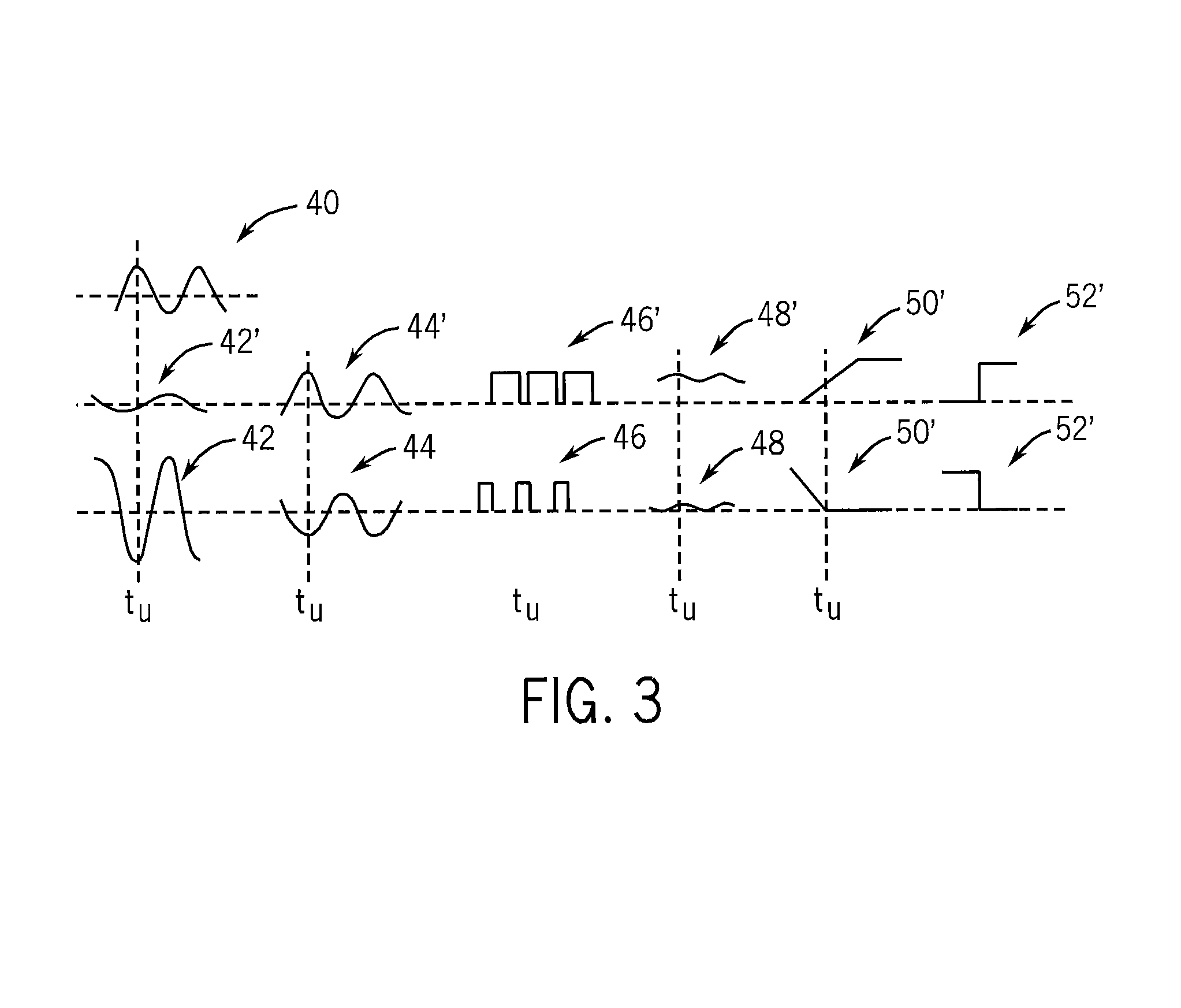
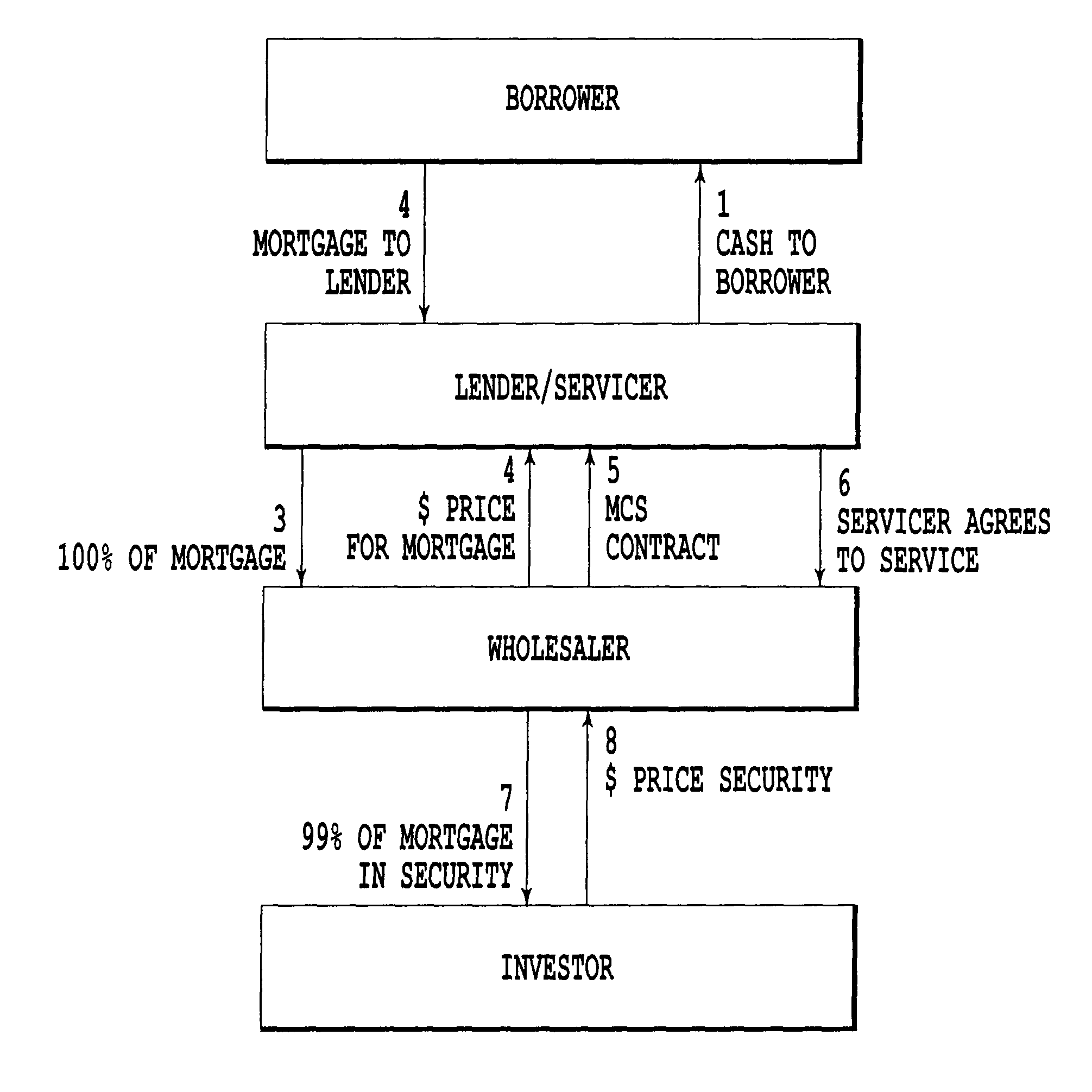
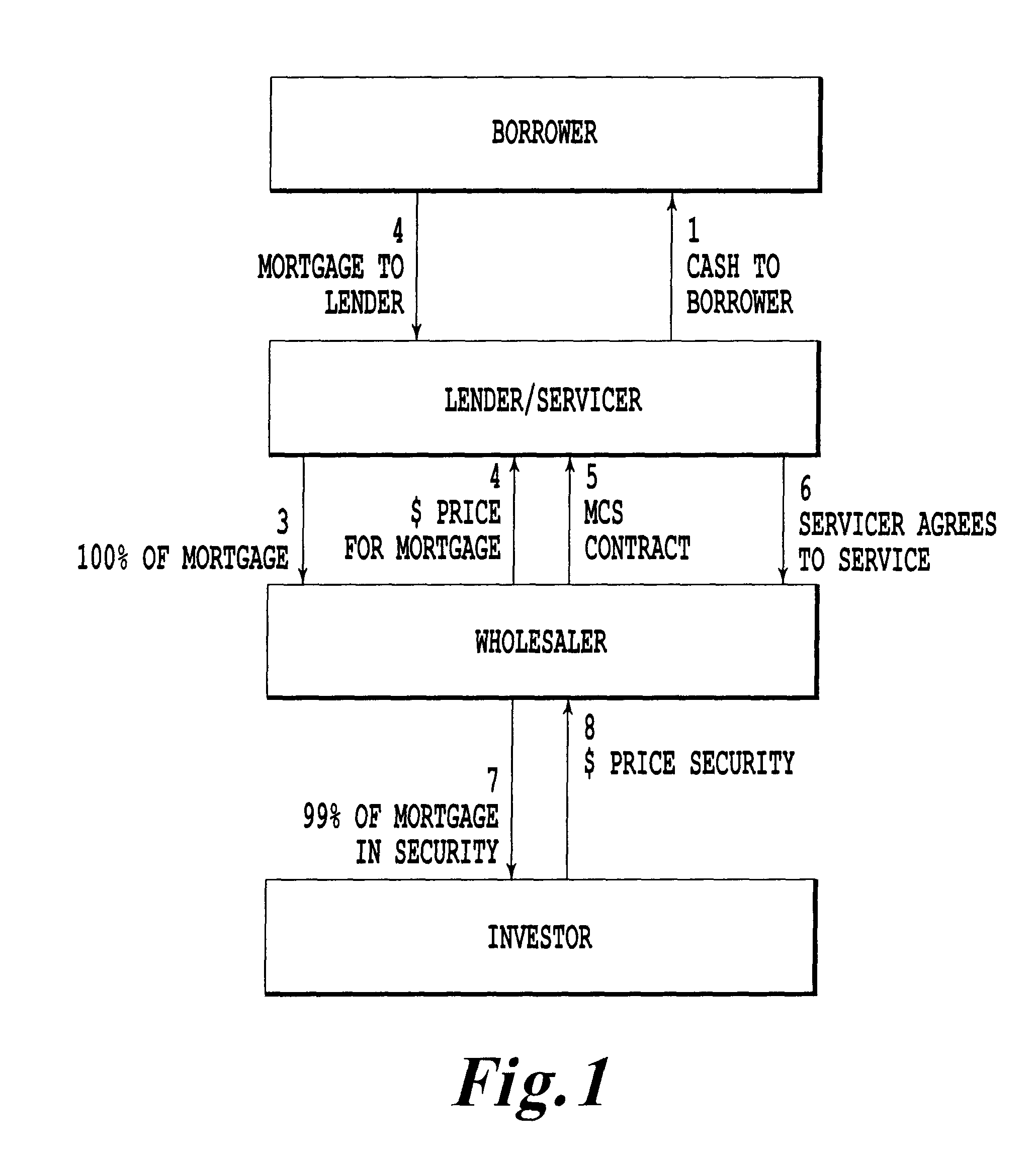
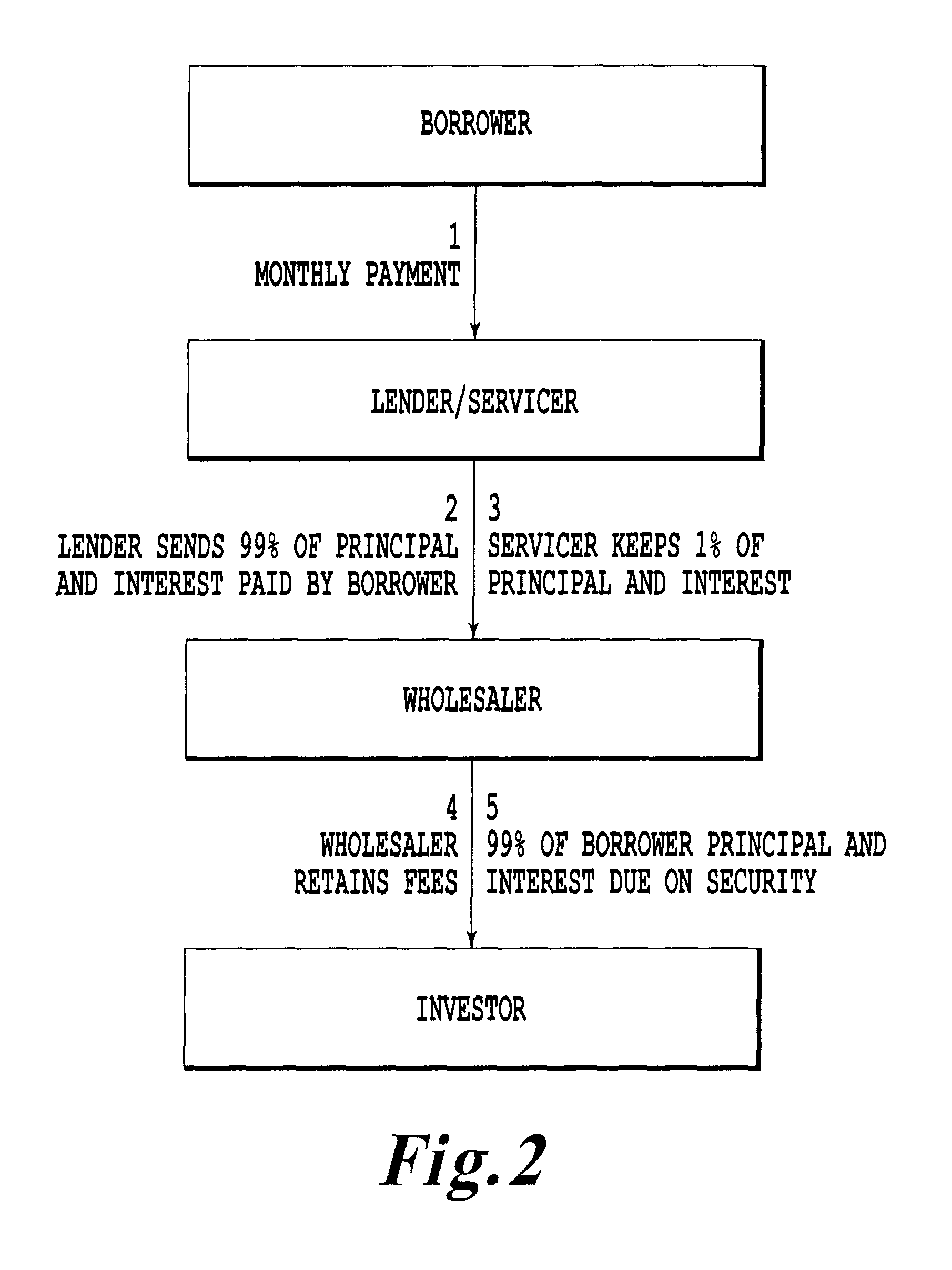
Method for structuring a mortgage servicing right asset efficiently to include a hedging component
Method for providing mortgage collateralized servicing (MCS) contracts to mortgage servicers as a tool to manage hedging risk. The MCS contracts of the present invention pays mortgage servicers for their services, while providing a “self-hedging” component that reduces (or eliminates) the need for the servicer to engage in additional investing and trading in derivatives in order to hedge against servicing contract risks. Such risks typically include default, delinquency, pre-payment, and interest rate fluctuations associated with mortgage loans. Additionally, the method preserves the tax and accounting treatment for mortgage servicing rights contracts preferred by servicers.
Owner:HEUER JOAN D +6
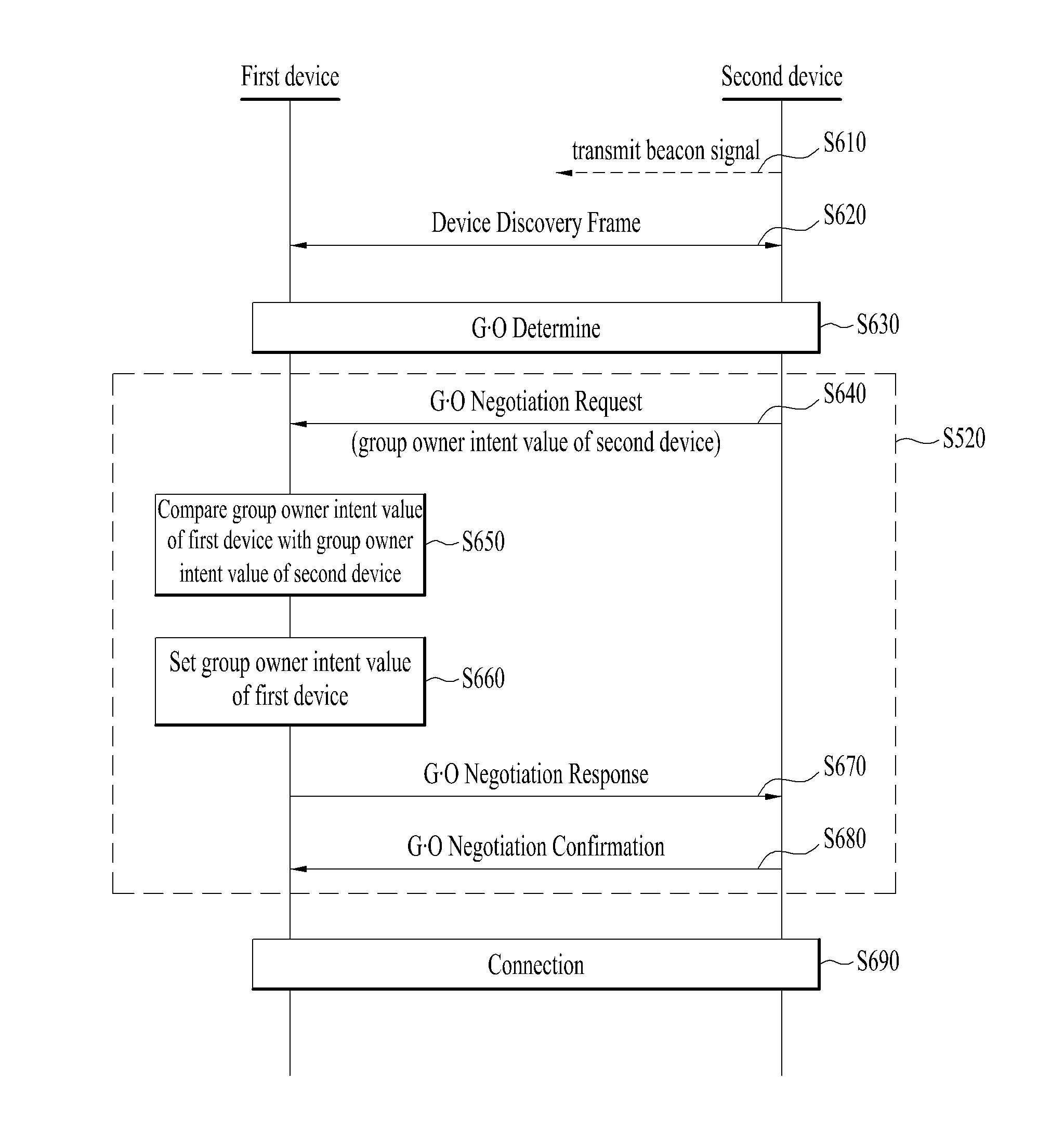
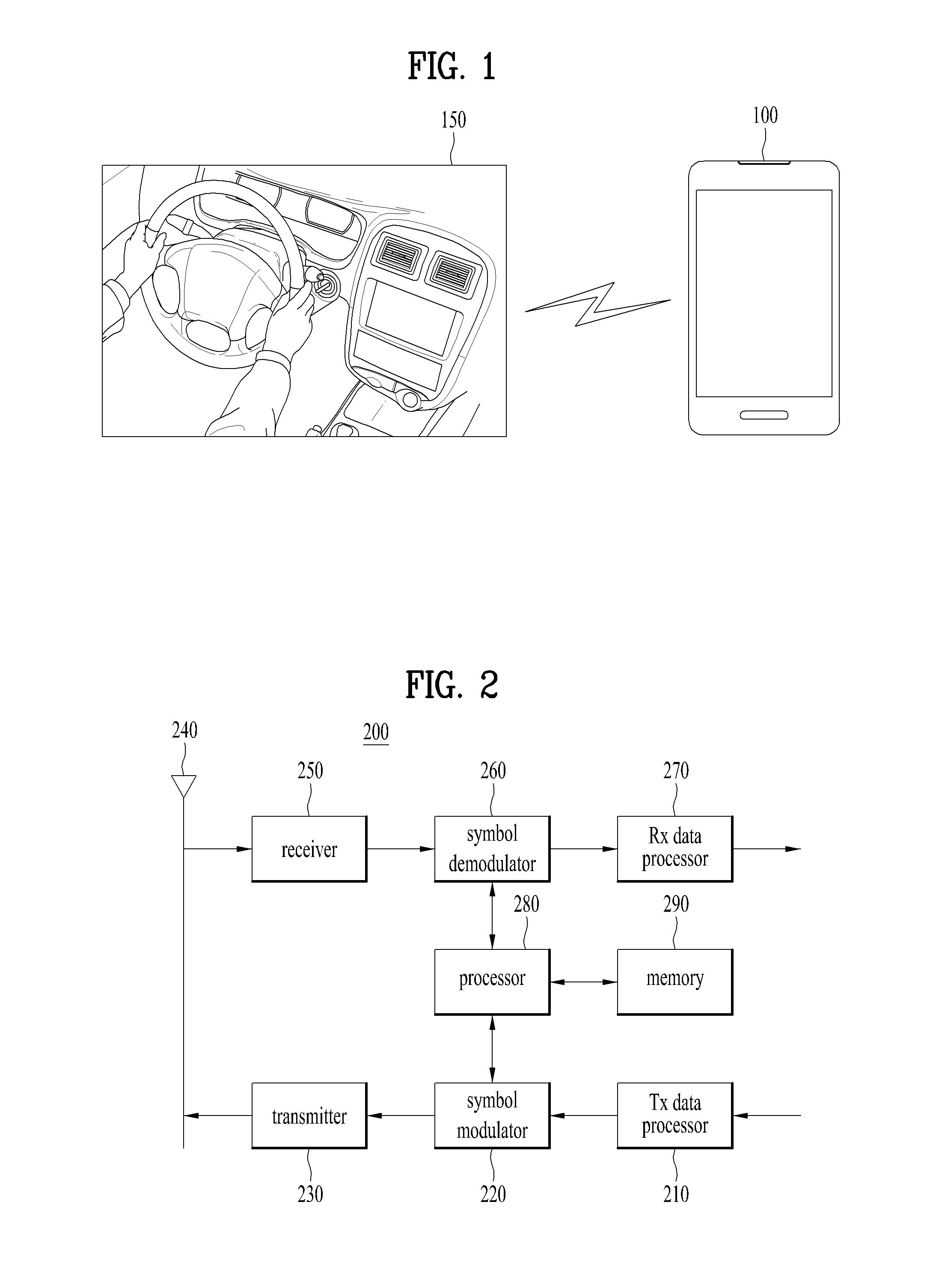
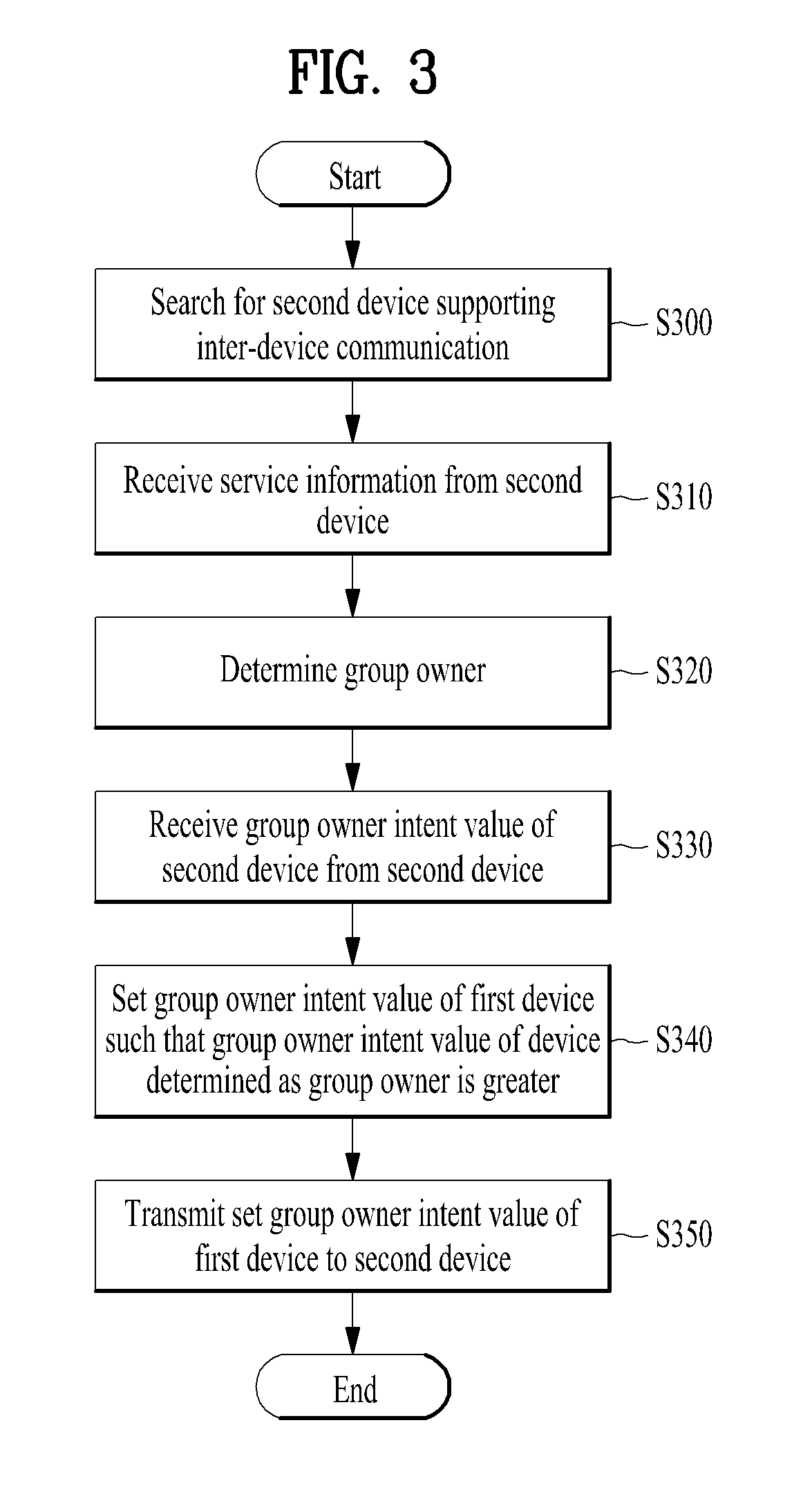
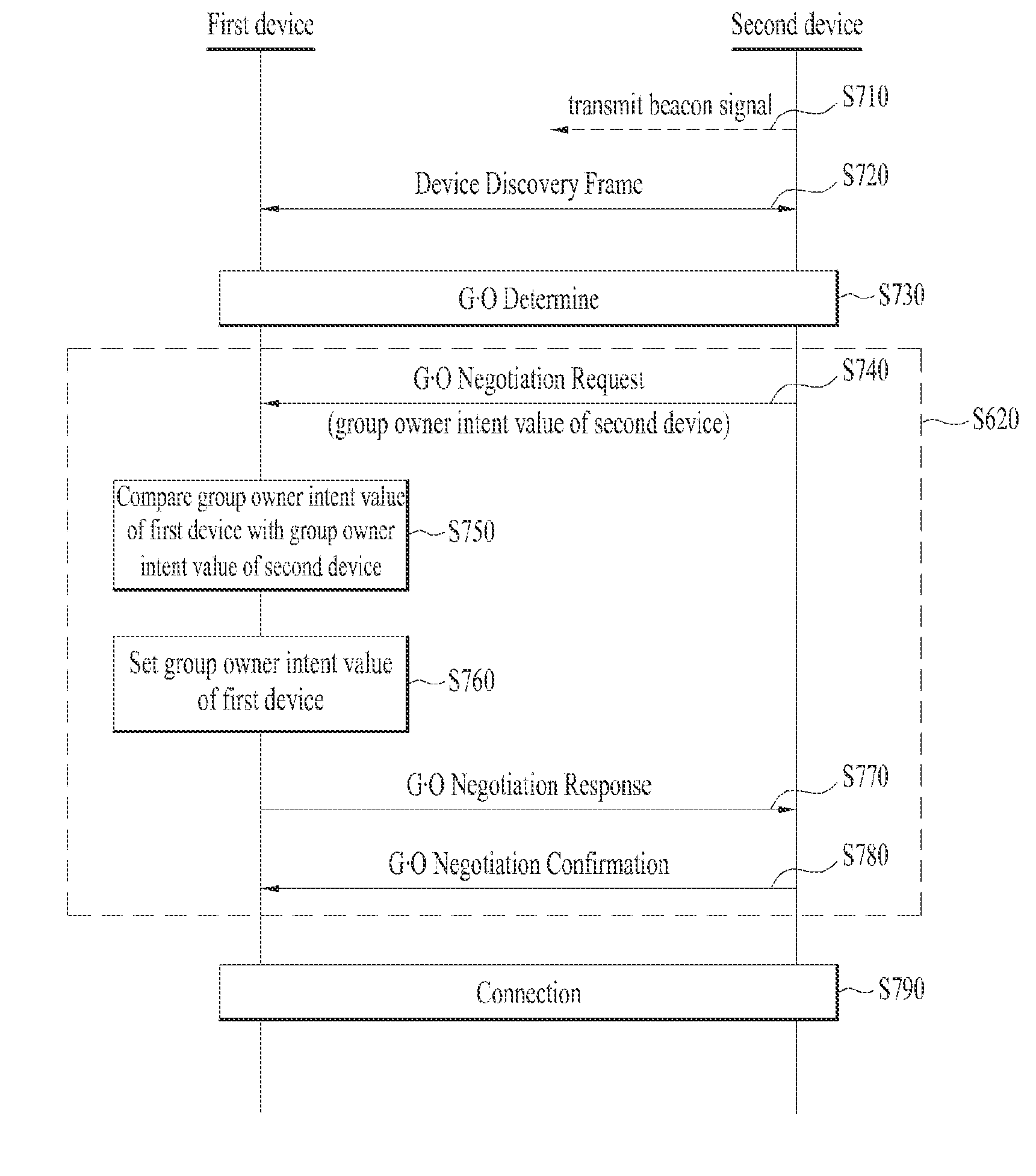
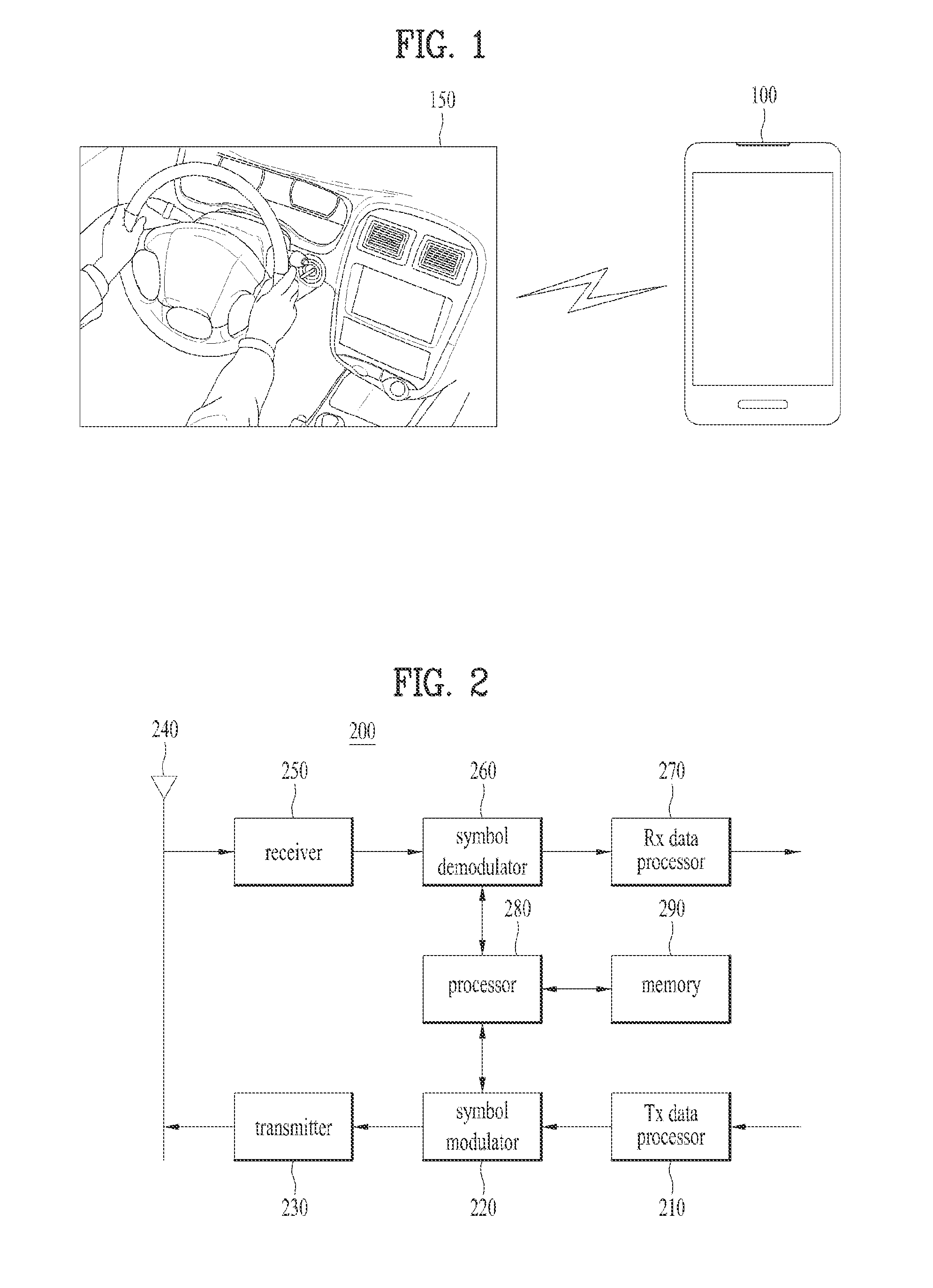
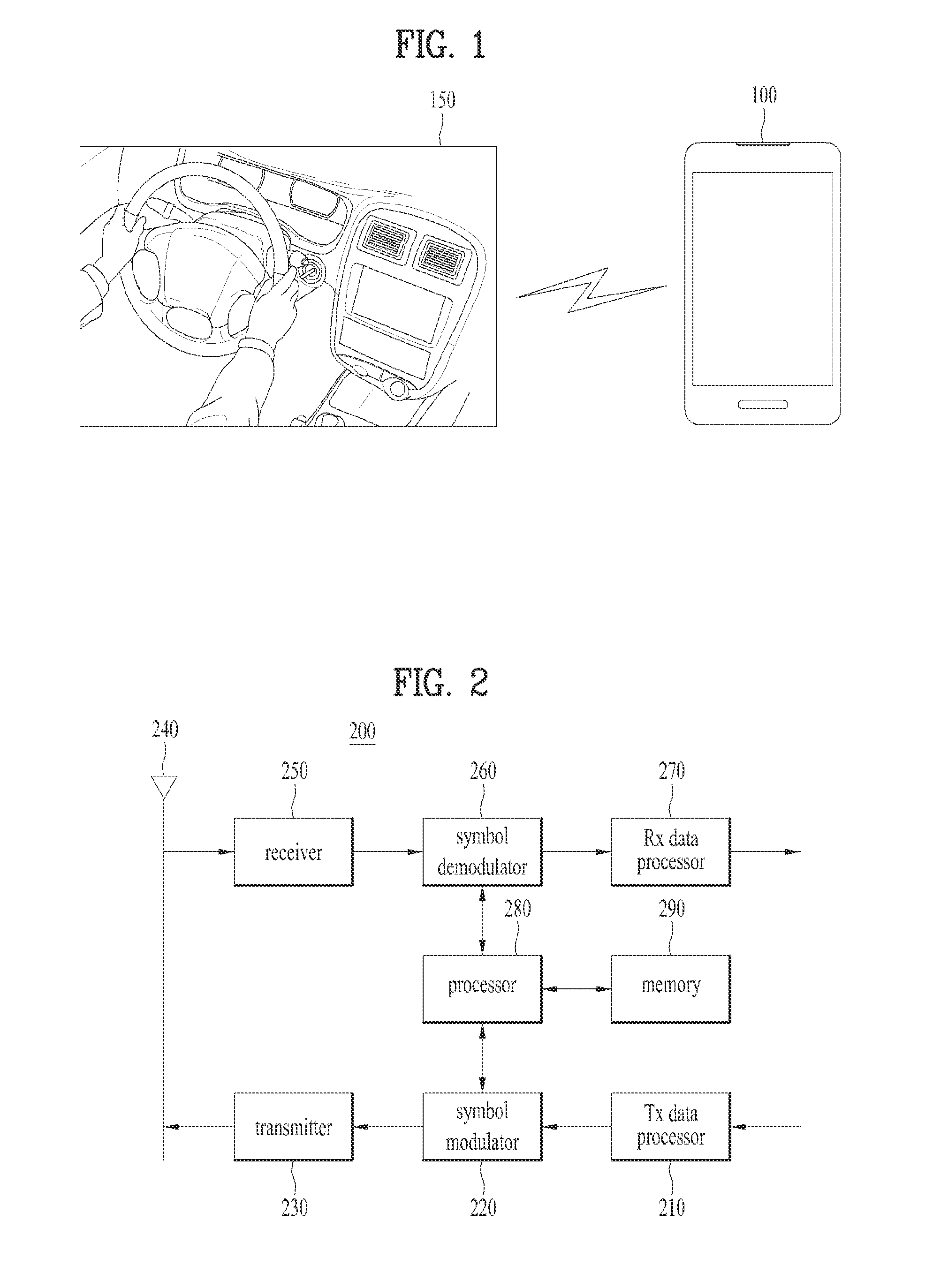
Device and method for performing inter-device communication
ActiveUS20140051360A1Change its valueConnection managementBroadcast service distributionService informationOperating system
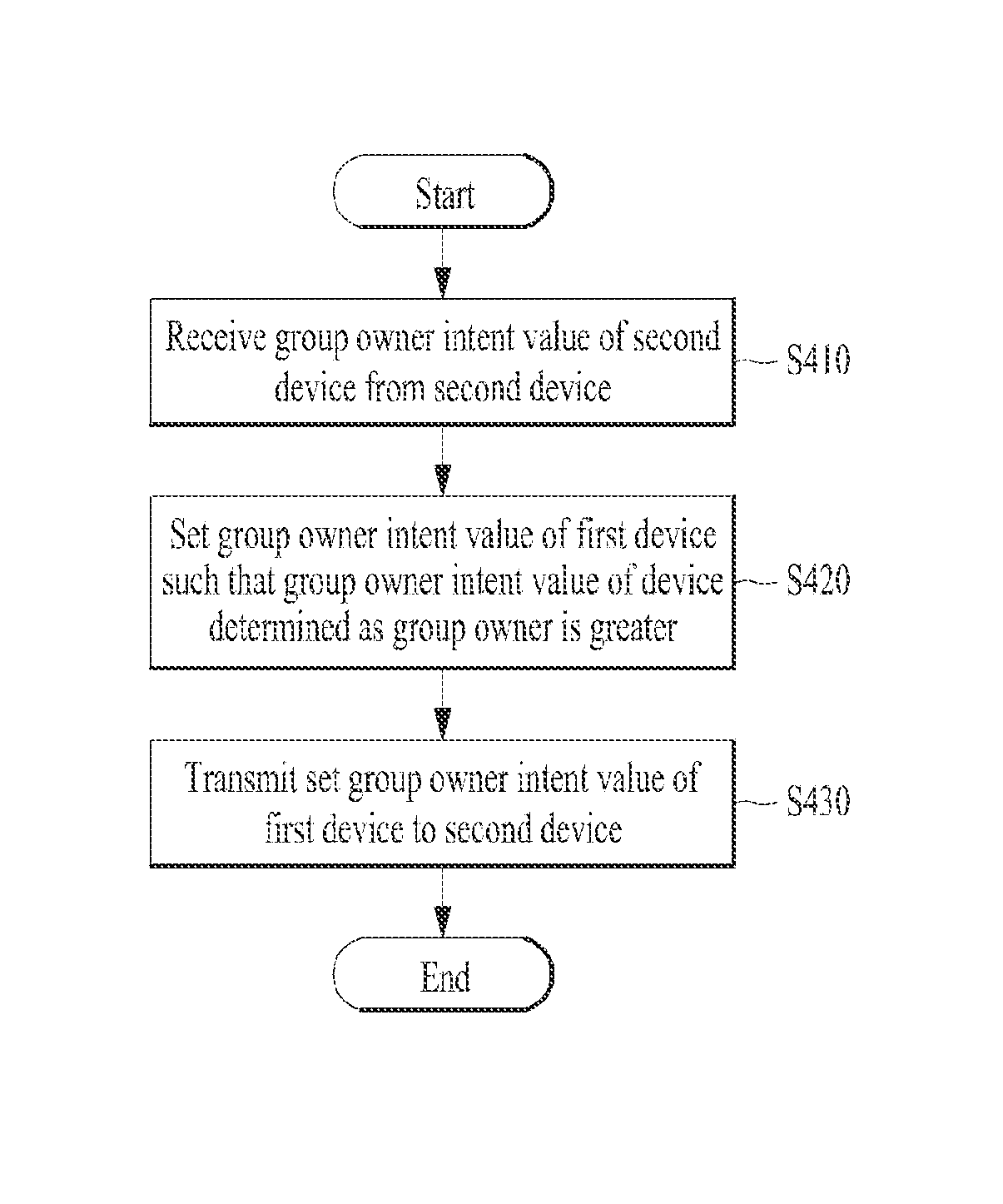
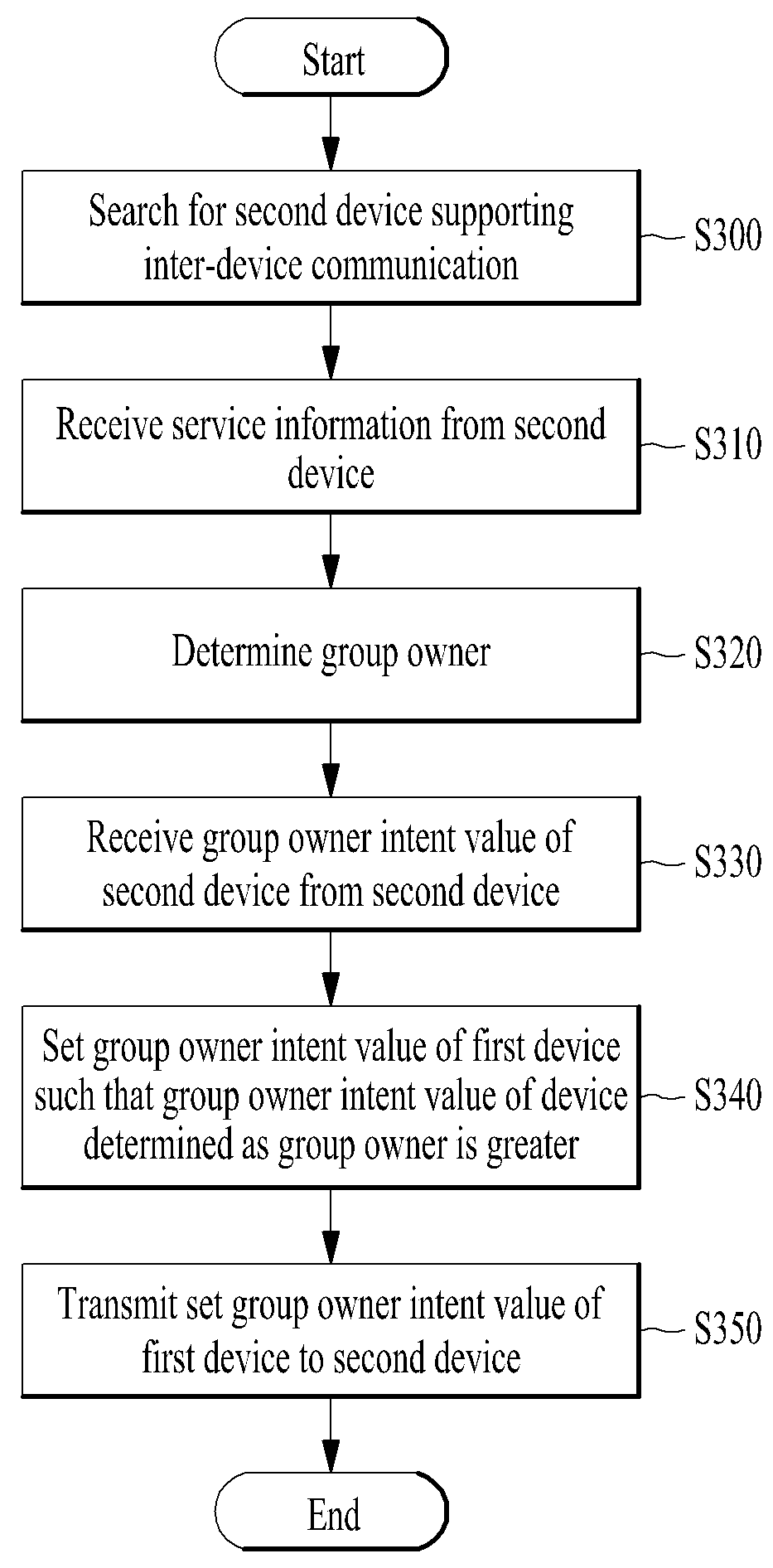
A device and method for performing inter-device communication are disclosed. The inter-device communication method includes searching for a second device supporting inter-device communication, receiving service information from the searched second device, determining that one of the first and second devices is a group owner and the other is a group client to compare the received service information of the second device with service information of a first device, receiving a group owner intent value of the second device from the second device, and setting a group owner intent value of the first device such that the group owner intent value of the device determined as the group owner is greater than the group owner intent value of the device determined as the group client to compare the group owner intent value of the first device with the group owner intent value of the second device.
Owner:LG ELECTRONICS INC
Driving device, light amount controller and shutter
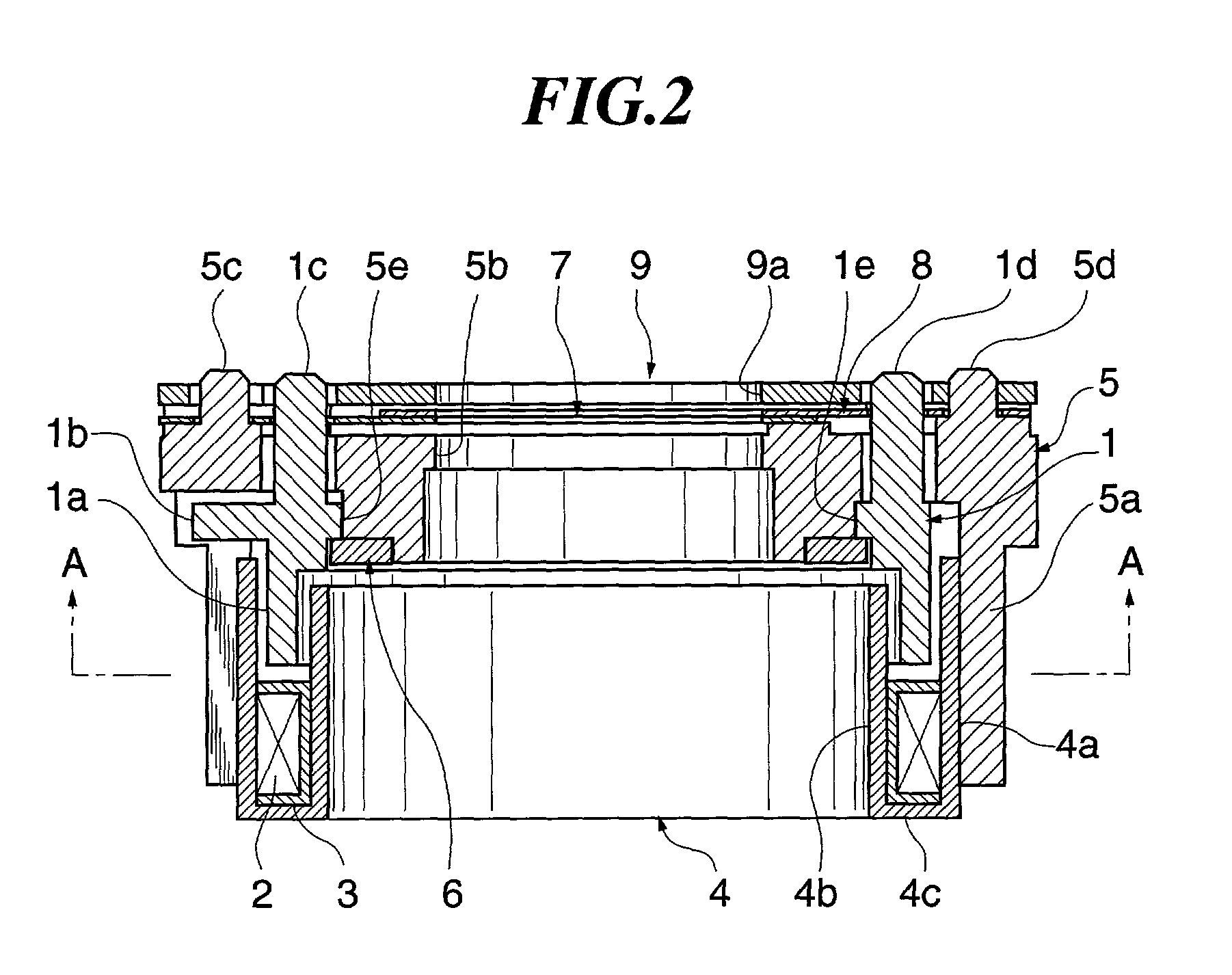
InactiveUS20020127013A1Easy to manufactureIncrease productionComputer controlSimulator controlRotational axisMagnetic poles
There is provided a small-sized and slim driving device which is easy to manufacture and capable of producing high output. A magnet has a cylindrical shape, and at least the outer peripheral surface of the magnet is circumferentially divided into n sections magnetized so as to have alternately different poles. The magnet can rotate about a rotational axis of the cylindrical shape. A coil is arranged axially of the magnet and parallel thereto. An outer magnetic pole portion is disposed to be magnetized by the coil, and has a plurality of hair comb tooth-shaped portions opposed to the magnet and arranged around the magnet such that an angle corresponding to the circumferential width of each of the hair comb tooth-shaped portions opposed to the magnet about the rotational axis of the hollow cylindrical shape of the magnet is equal to a predetermined angle A. An inner magnetic pole portion is disposed to be magnetized by the coil, and has a hollow cylindrical shape opposed to the inner peripheral surface of the magnet. The predetermined angle A is set to such a value that a rotational force acts on the magnet to return to a position in which a circumferential center of each of n magnetized sections on the outer peripheral surface of the magnet is opposed to a circumferential center of a corresponding one of the hair comb tooth-shaped portions of the outer magnetic pole portion, when the circumferential center of each of n magnetized sections shifts from the position.
Owner:CANON KK
Automatic light dimmer for electronic and magnetic ballasts (fluorescent or HID)
InactiveUS7336041B2Change its valueTotal current dropElectric light circuit arrangementElectric discharge lampsDimmerHigh intensity
An apparatus is disclosed for automatic light dimming of electronic and magnetic ballasts used for fluorescent or high intensity discharge lamps. A variable capacitant's limiting current is added in the lamps which provides lighting intensity controls without changing the ballast's operation frequency. Several capacitors are placed in line with a terminal for the lamp. The capacitor's switching capability is used to change the current received by the lamp. The amount of voltage can be controlled by either varying the supply voltage, or with an elimination sensor, or by manual potentiometer control.
Owner:INTELLISWITCH DE C V
Malware containment by application encapsulation
ActiveUS7757291B2Prevent malwareChange its valueMemory loss protectionError detection/correctionOperational systemApplication software
Owner:TRIGENCE CORP
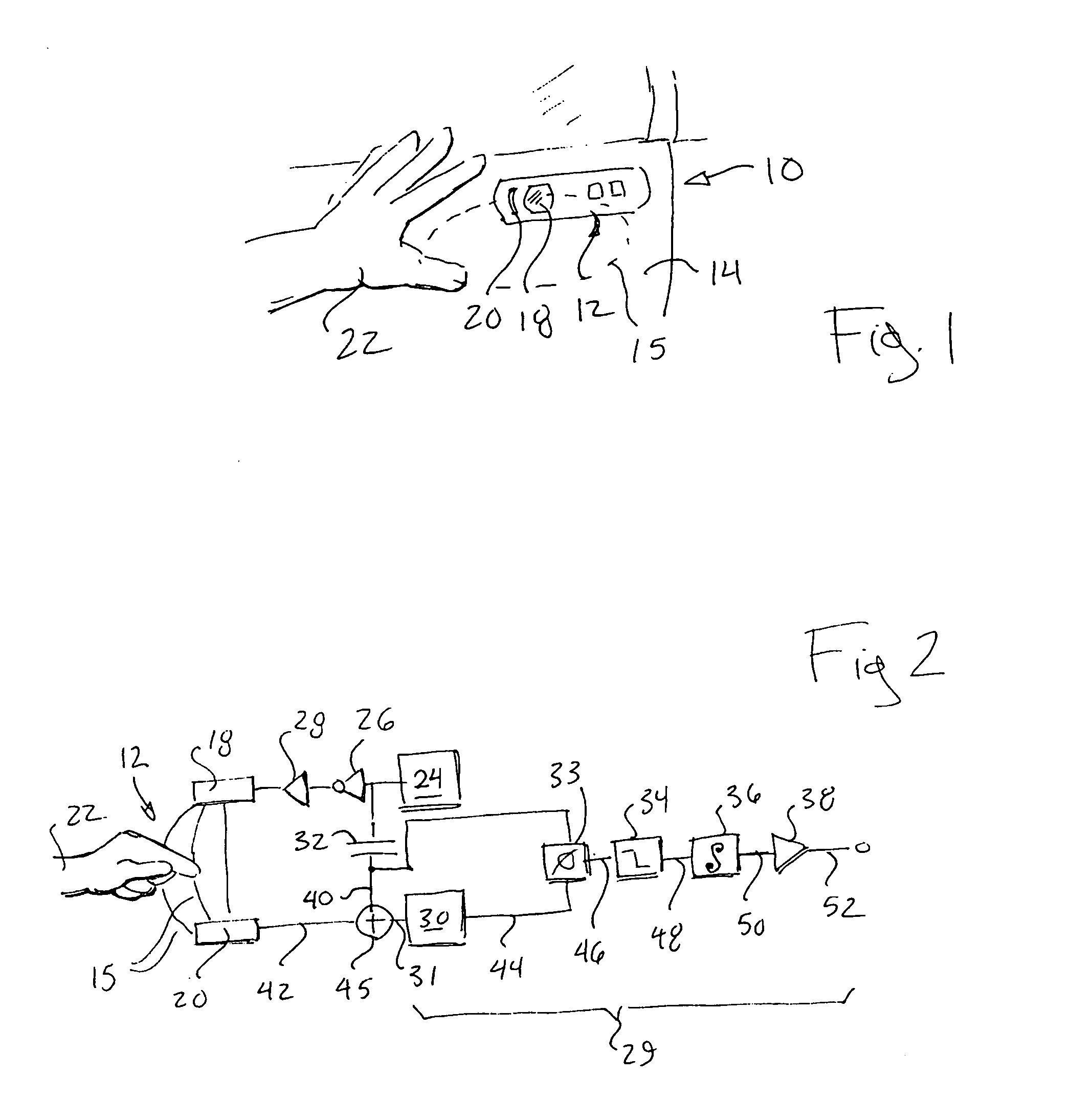
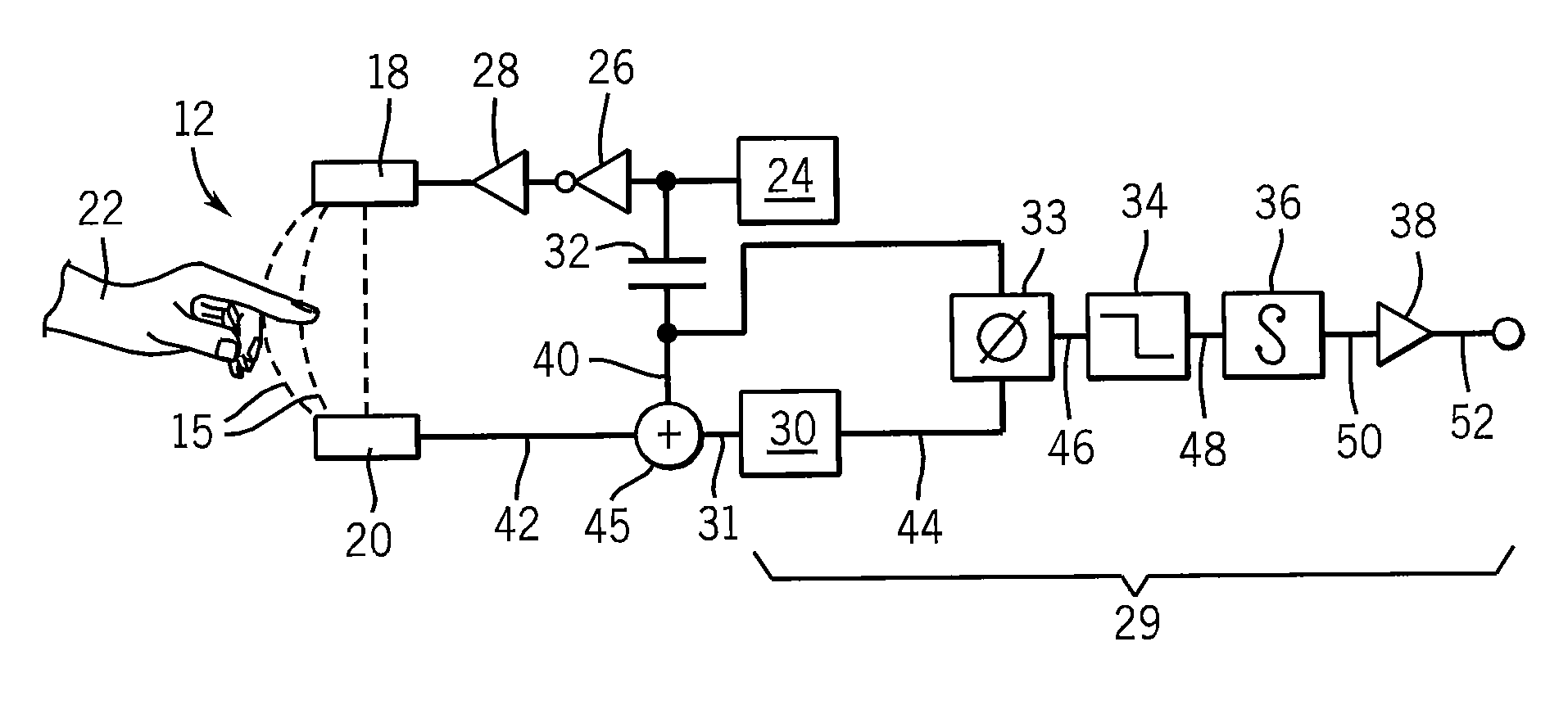
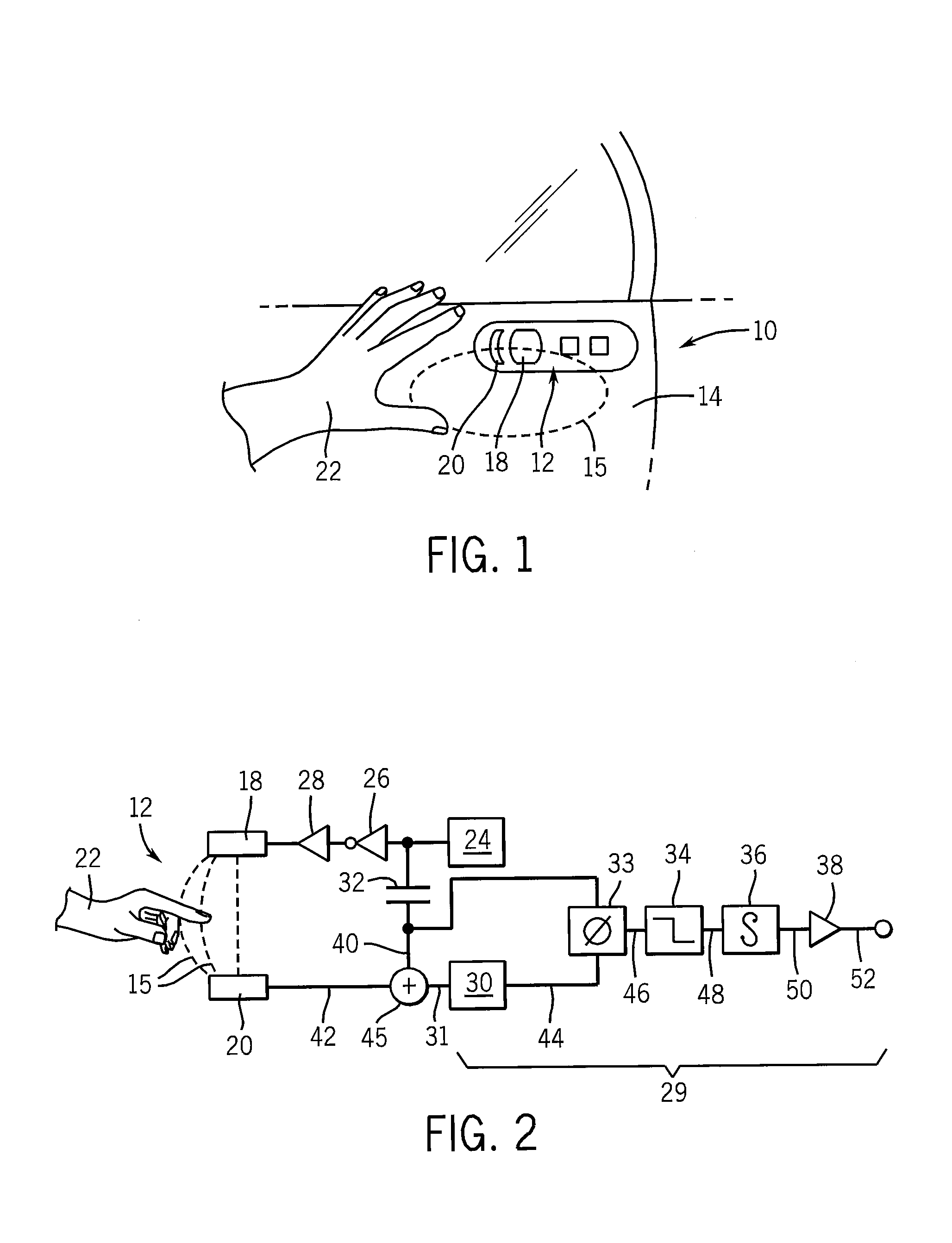
Electronic proximity switch
ActiveUS20070247299A1Increase resistanceChange its valueElectronic switchingPower-operated mechanismPhase shiftedCoupling
An electronic proximity switch employs two oscillators coupled through two electrical paths, one associated with an antenna serving as a proximity switch sensor. Absorption by an object near the antenna changes the coupling between the oscillators producing a dramatic phase shift that may be detected and used for switching purposes.
Owner:ILLINOIS TOOL WORKS INC
Electronic proximity switch
ActiveUS7394368B2Increase resistanceChange its valueBurglar alarm by openingElectronic switchingPhase shiftedProximity sensor
An electronic proximity switch employs two oscillators coupled through two electrical paths, one associated with an antenna serving as a proximity switch sensor. Absorption by an object near the antenna changes the coupling between the oscillators producing a dramatic phase shift that may be detected and used for switching purposes.
Owner:ILLINOIS TOOL WORKS INC
Method for structuring a mortgage servicing right asset efficiently to include a hedging component
Method for providing mortgage collateralized servicing (MCS) contracts to mortgage servicers as a tool to manage hedging risk. The MCS contracts of the present invention pays mortgage servicers for their services, while providing a “self-hedging” component that reduces (or eliminates) the need for the servicer to engage in additional investing and trading in derivatives in order to hedge against servicing contract risks. Such risks typically include default, delinquency, pre-payment, and interest rate fluctuations associated with mortgage loans. Additionally, the method preserves the tax and accounting treatment for mortgage servicing rights contracts preferred by servicers.
Owner:FREDDIE MAC
Halogen-Free Epoxy Resin Composition, Prepreg, Laminate and Printed Circuit Board Containing the Same
ActiveUS20170298218A1Ensures Df value stabilityLow dielectric constantPlastic/resin/waxes insulatorsSynthetic resin layered productsEpoxyDielectric loss
Owner:GUANGDONG SHENGYI SCI TECH
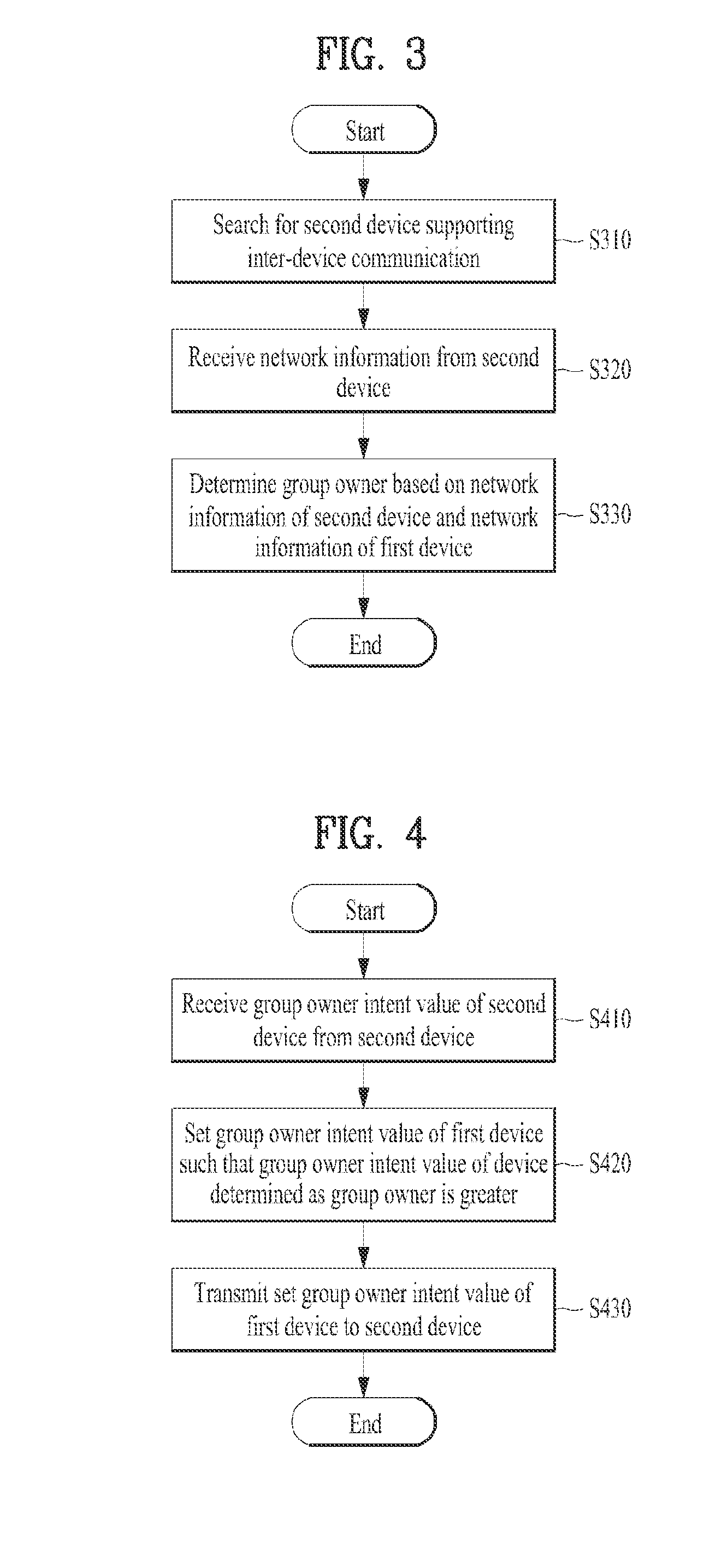
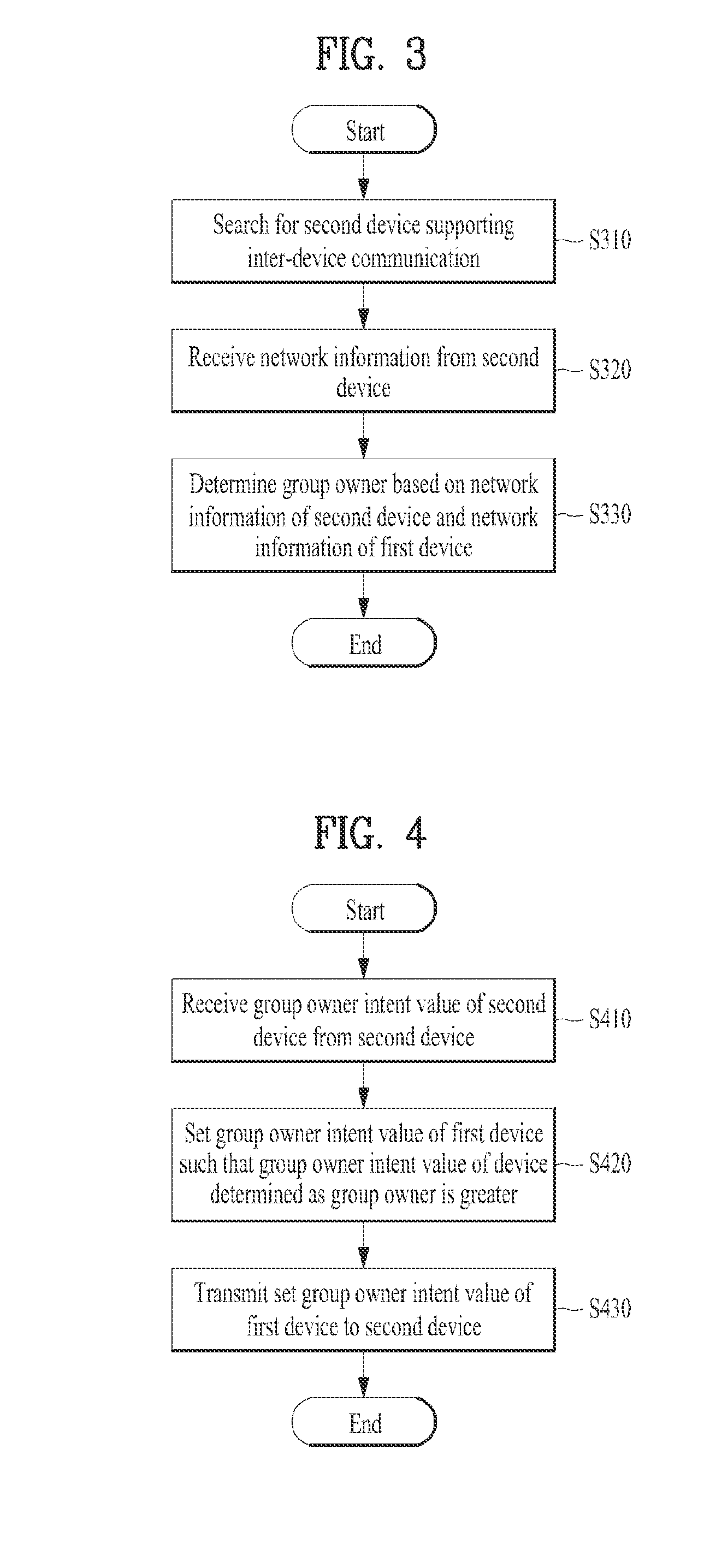
Device and method for performing inter-device communication
ActiveUS20140079045A1Change its valueNetwork topologiesServices signallingServer applianceReal-time computing
A device and method for performing inter-device communication are disclosed. An inter-device communication method of a first device includes searching for a second device supporting inter-device communication, receiving network information from the searched second device, and determining that one of the first and second devices is a group owner based on the received network information of the second device and network information of the first device. The network information includes at least one selected from among type information indicating a server device or a client device, network support information, network necessity information, and network setting information.
Owner:LG ELECTRONICS INC
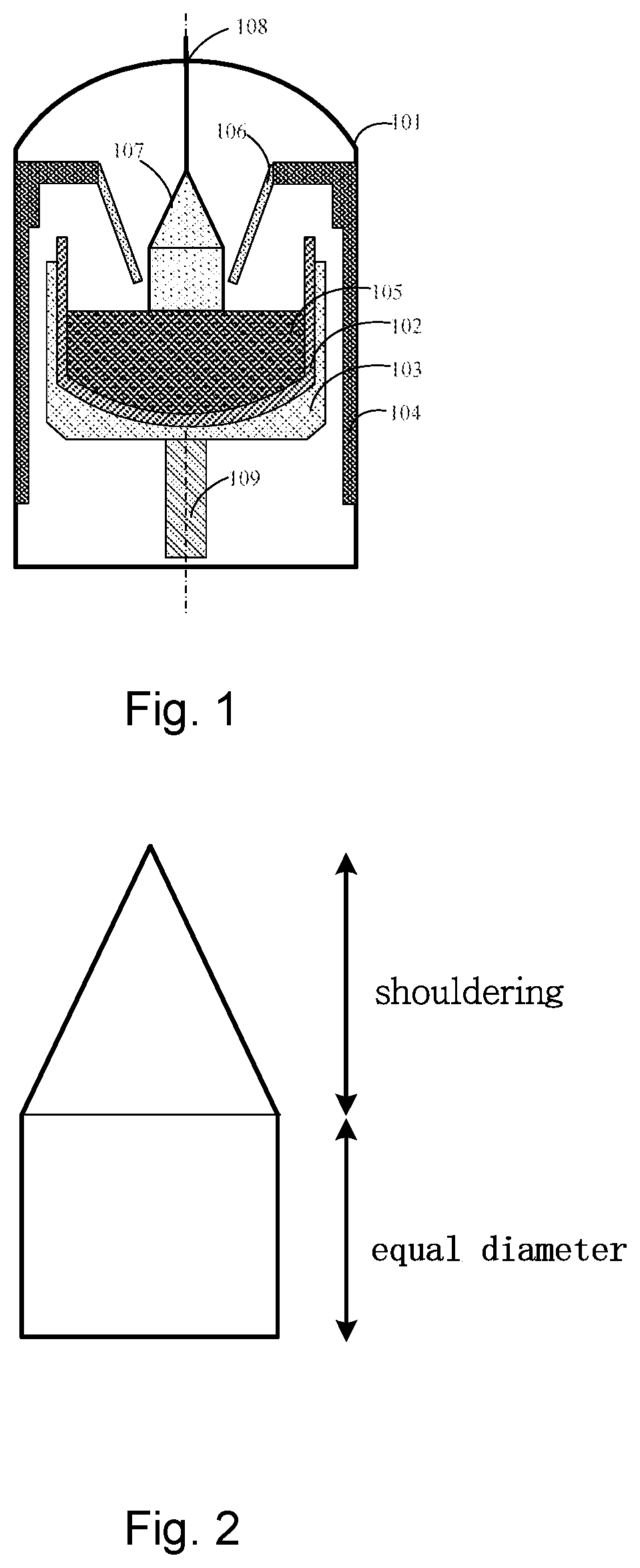
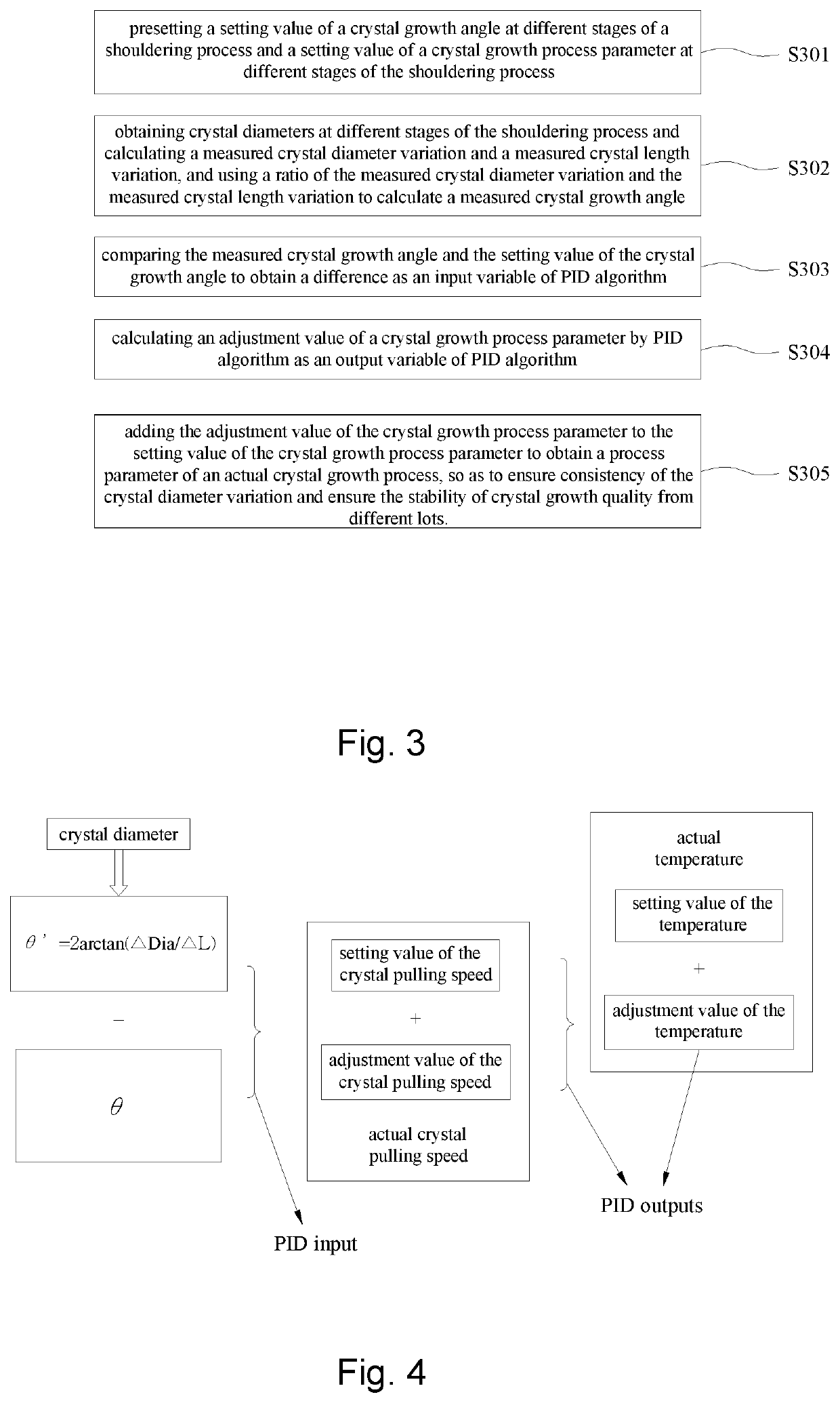
Method, device, system, and computer storage medium for crystal growing control
InactiveUS20200291541A1Improved process stabilityEnsure stabilityPolycrystalline material growthBy pulling from meltComputational physicsEngineering
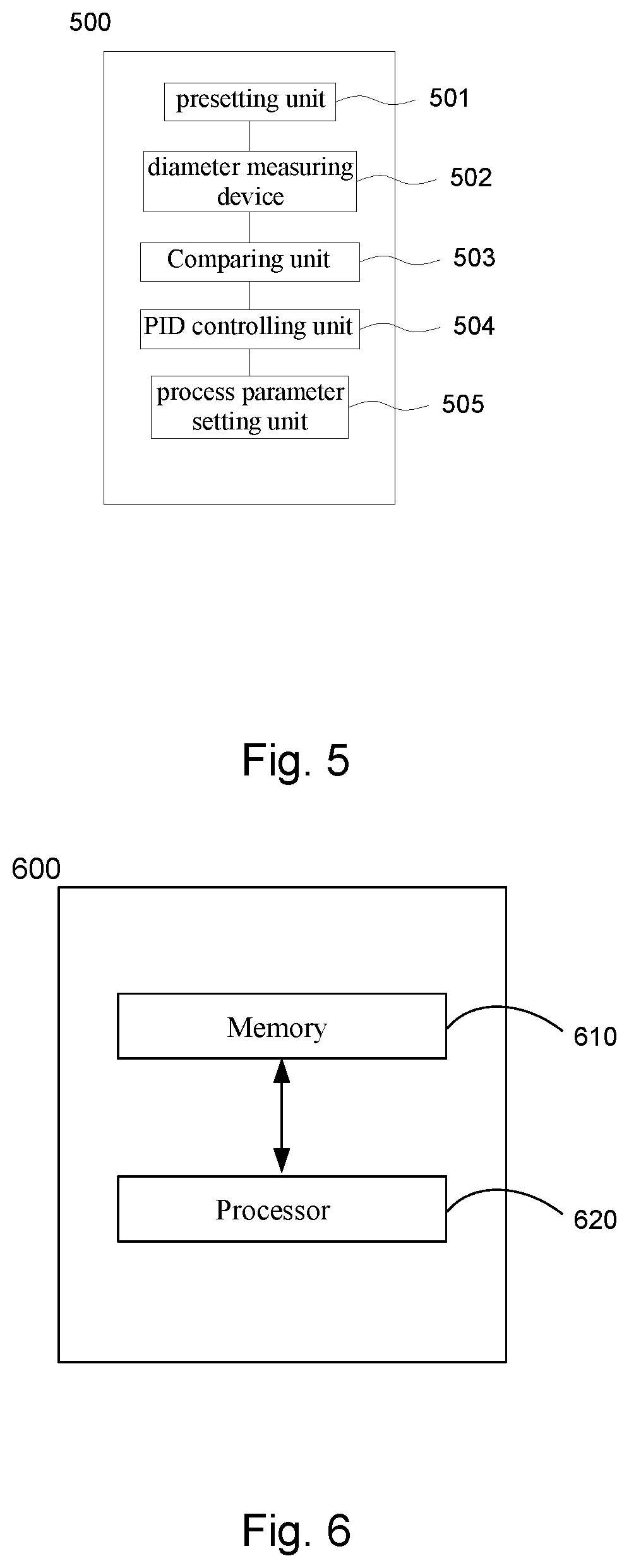
This invention provides method, device, system, and computer storage medium for crystal growth control of a shouldering process. The method comprises: presetting a setting value of a crystal growth angle at different stages of a shouldering process and a crystal growth process parameter at different stages of the shouldering process; obtaining crystal diameters at different stages of the shouldering process and calculating a measured crystal diameter variation and a measured crystal length variation, and using a ratio of the measured crystal diameter variation and the measured crystal length variation to calculate a measured crystal growth angle; comparing the measured crystal growth angle with the setting value of the crystal growth angle to obtain a difference as an input variable of PID algorithm; calculating an adjustment value of a crystal growth process parameter by PID algorithm as an output variable of PID algorithm; adding the adjustment value of the crystal growth process parameter and the setting value of the crystal growth process parameter to obtain a process parameter of an actual crystal growth process.
Owner:ZING SEMICON CORP
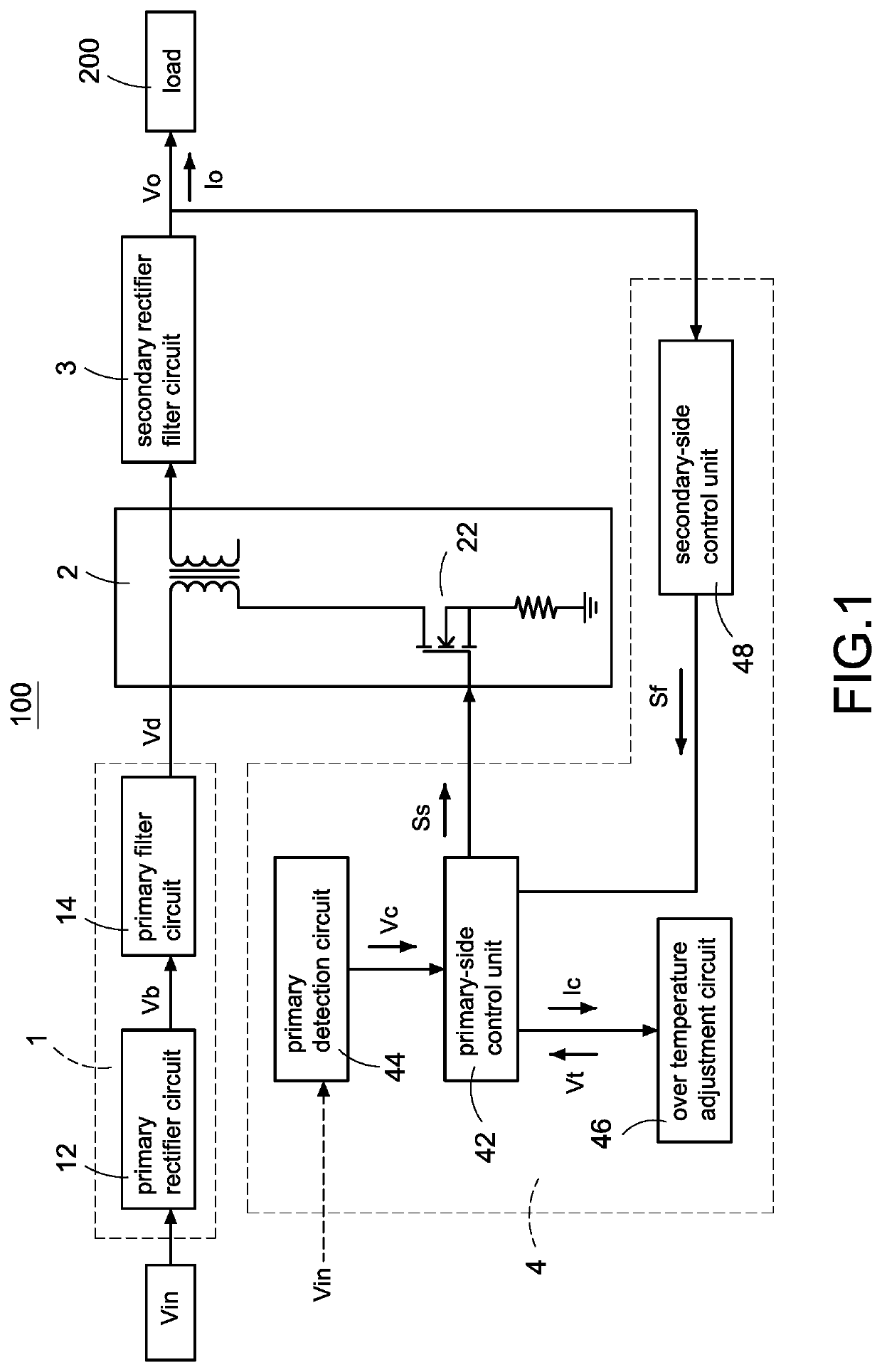
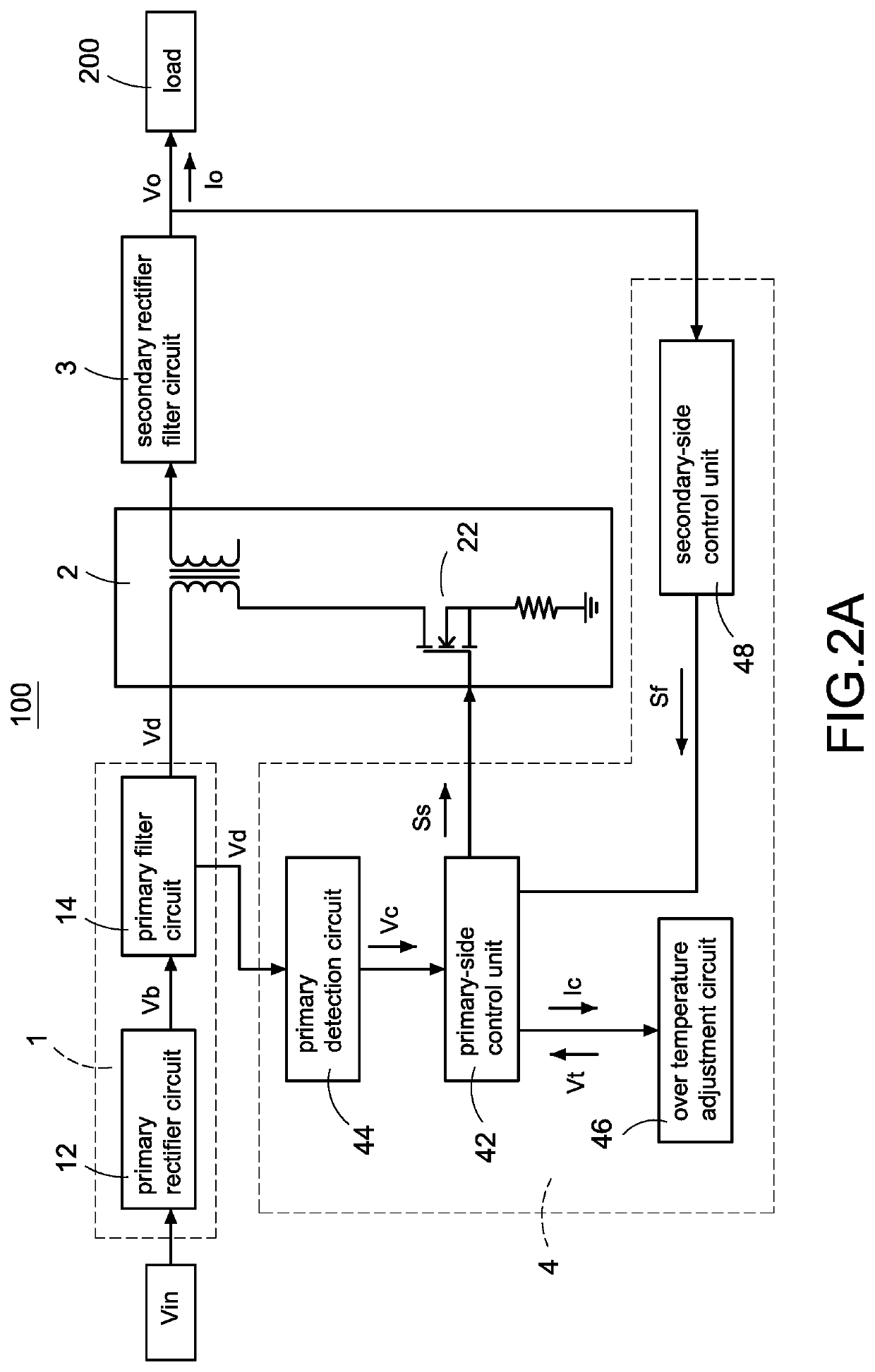
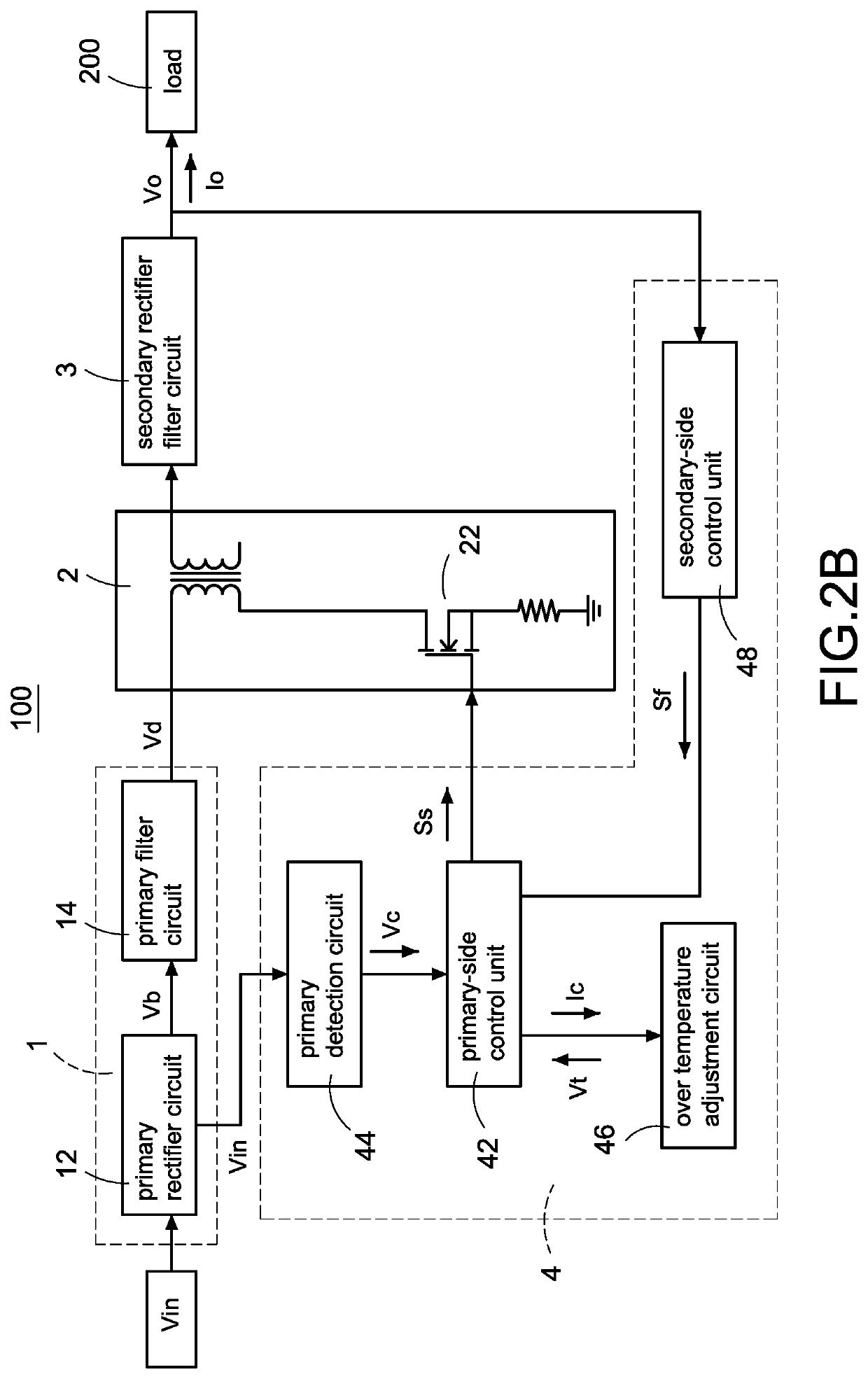
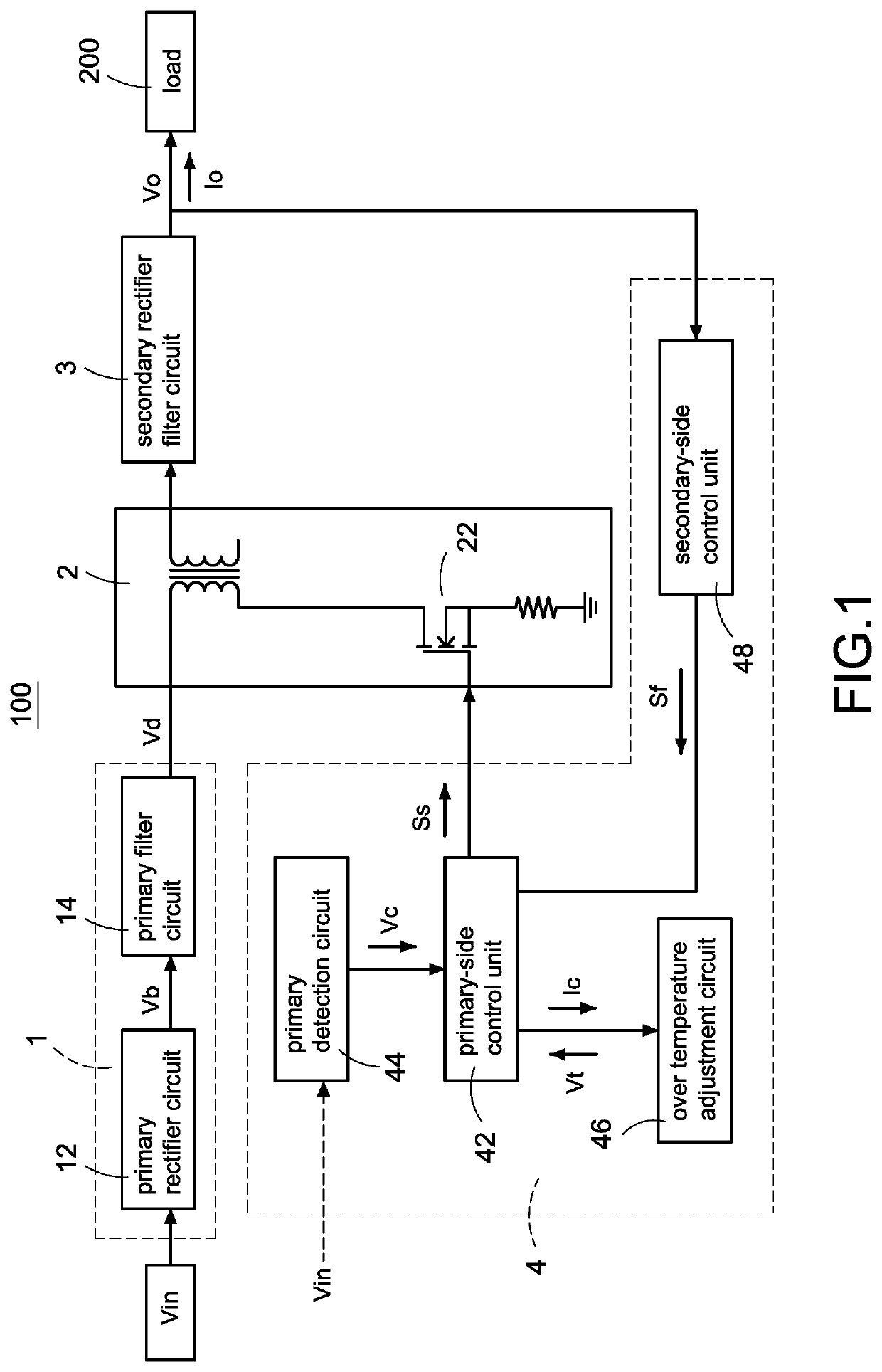
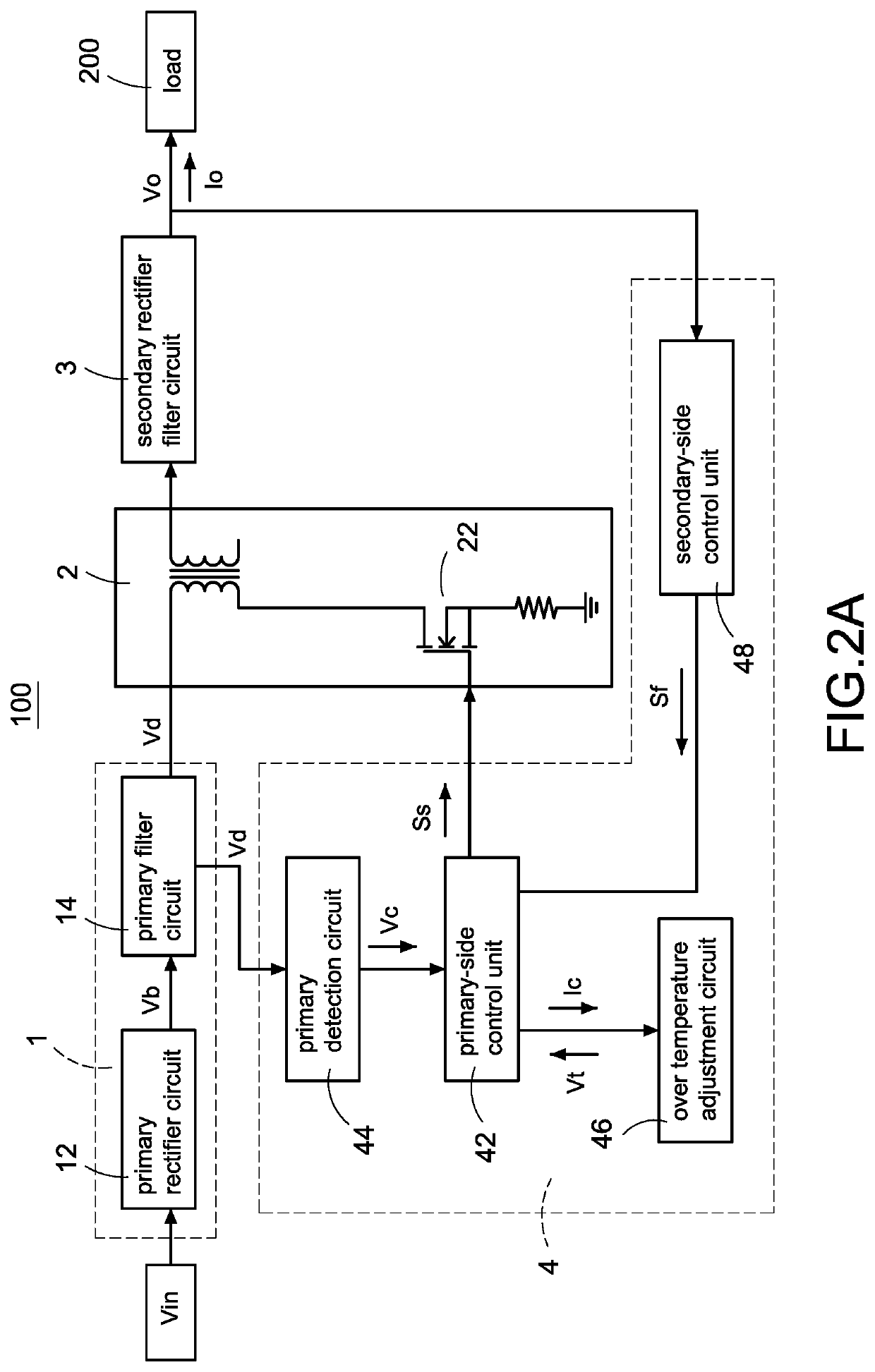
Power converter with over temperature protection compensation
ActiveUS11050342B2Change its valueEmergency protective circuit arrangementsDc-dc conversionConvertersTemperature control
Owner:CHICONY POWER TECH CO LTD
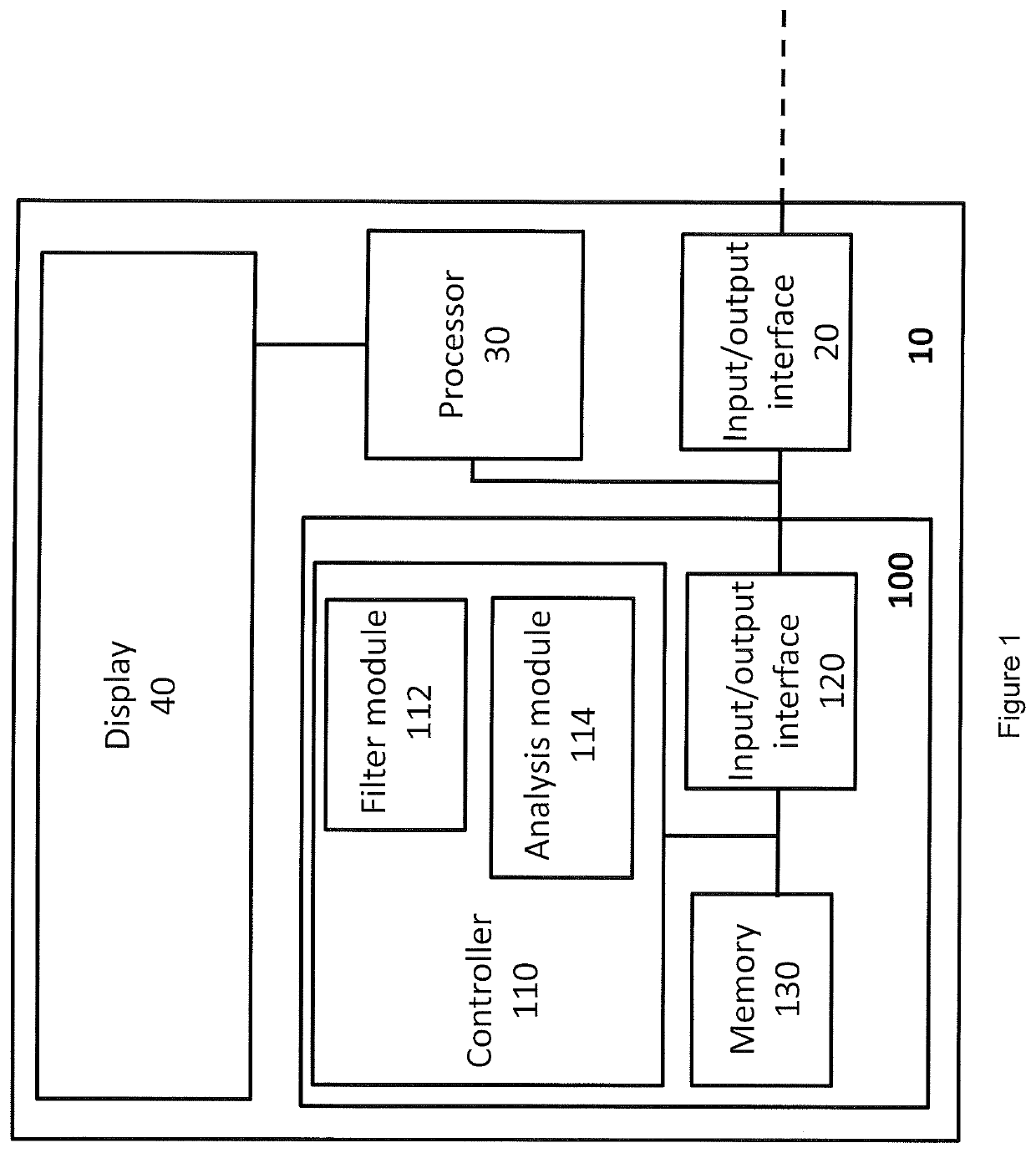
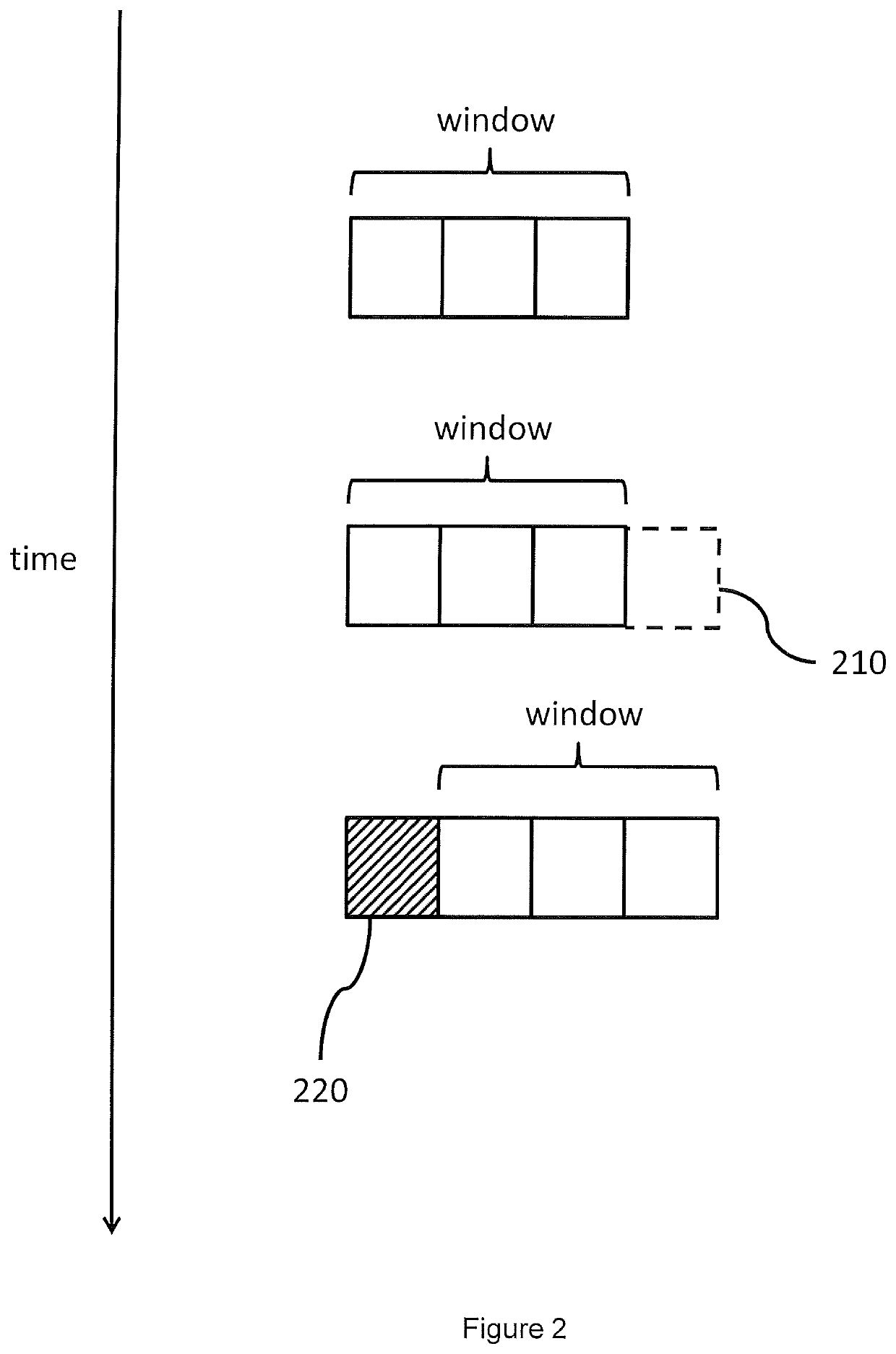
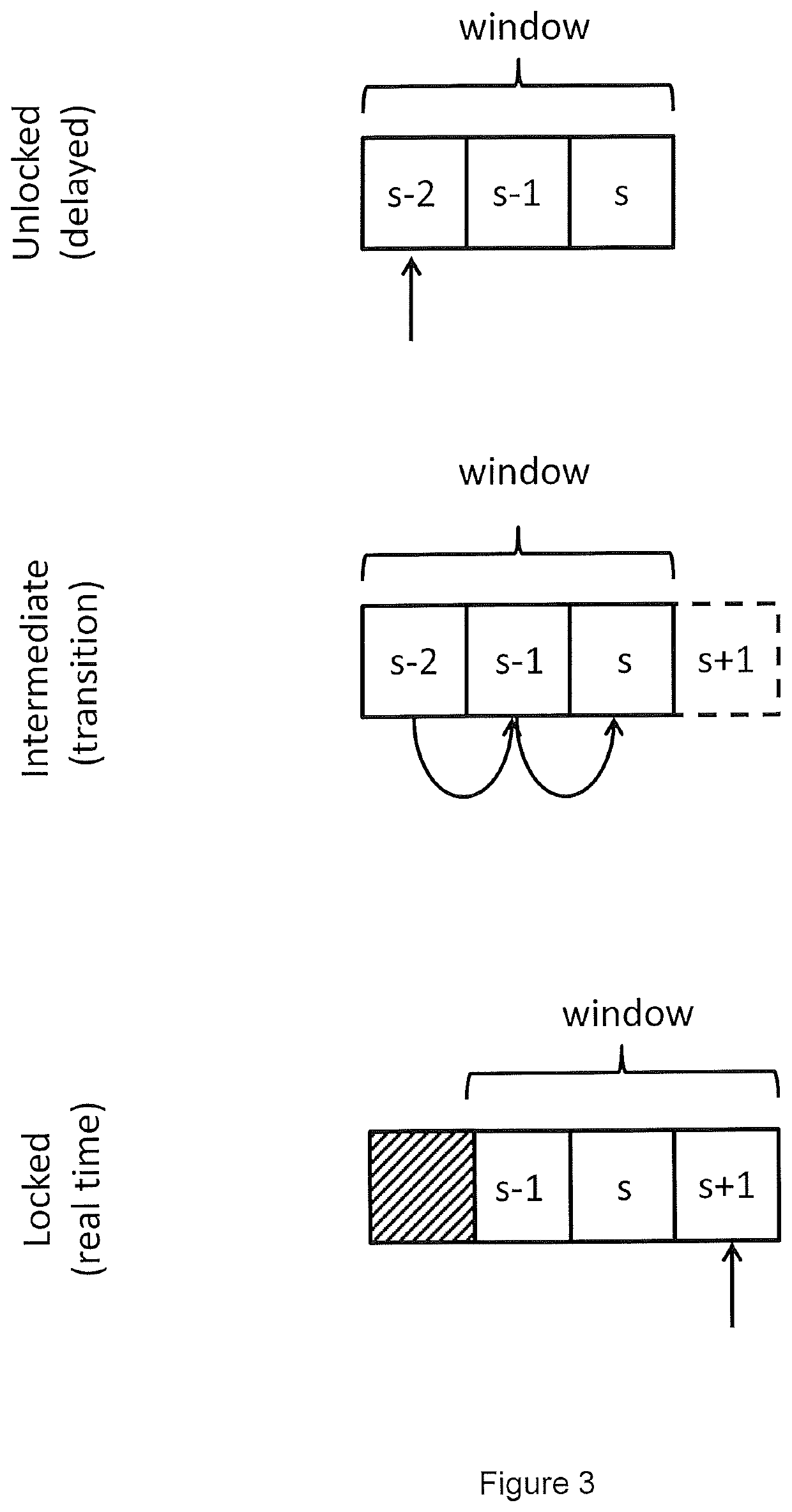
Haemodynamic monitor with improved filtering
ActiveUS11382567B2Analyse data moreChange its valueDiagnostic signal processingEvaluation of blood vesselsPhysiological valuesMedicine
There is provided a device and method of filtering outliers from physiological values. The method comprises: (a) populating a window with n physiological values taken, in sequence, from a sequence of physiological values, wherein n is a positive integer; (b) determining whether the variability in the physiological values within the window is less than a predetermined threshold; (c) responsive to the variability in the physiological values within the window being less than a predetermined threshold, determining that the window comprises no outliers, and / or responsive to the variability in the physiological values within the window not being less than a predetermined threshold, determining that the window comprises at least one outlier.
Owner:LIDCO GROUP +1
Power converter with over temperature protection compensation
ActiveUS11050341B2Change its valueEmergency protective circuit arrangementsDc-dc conversionConvertersTemperature control
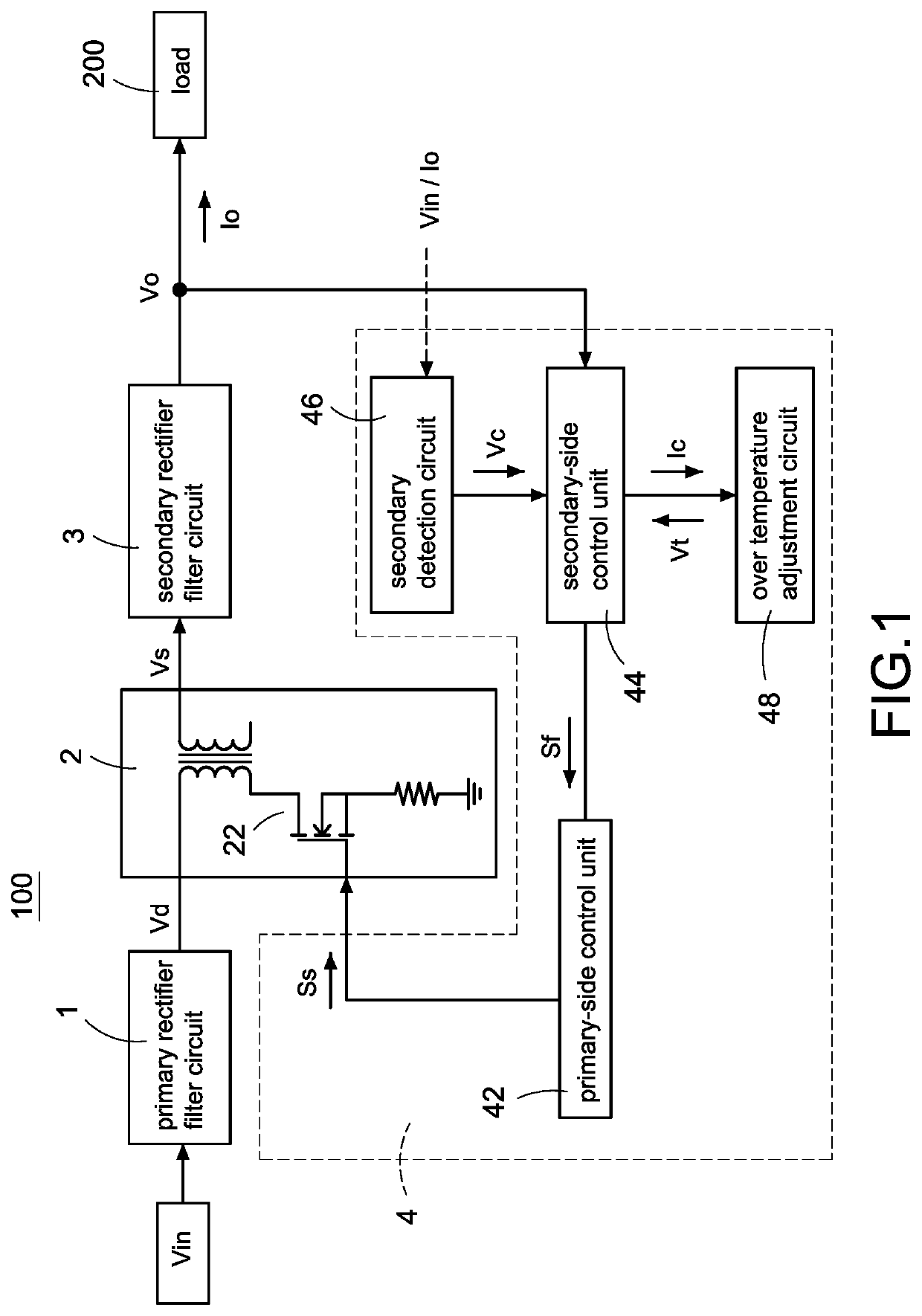
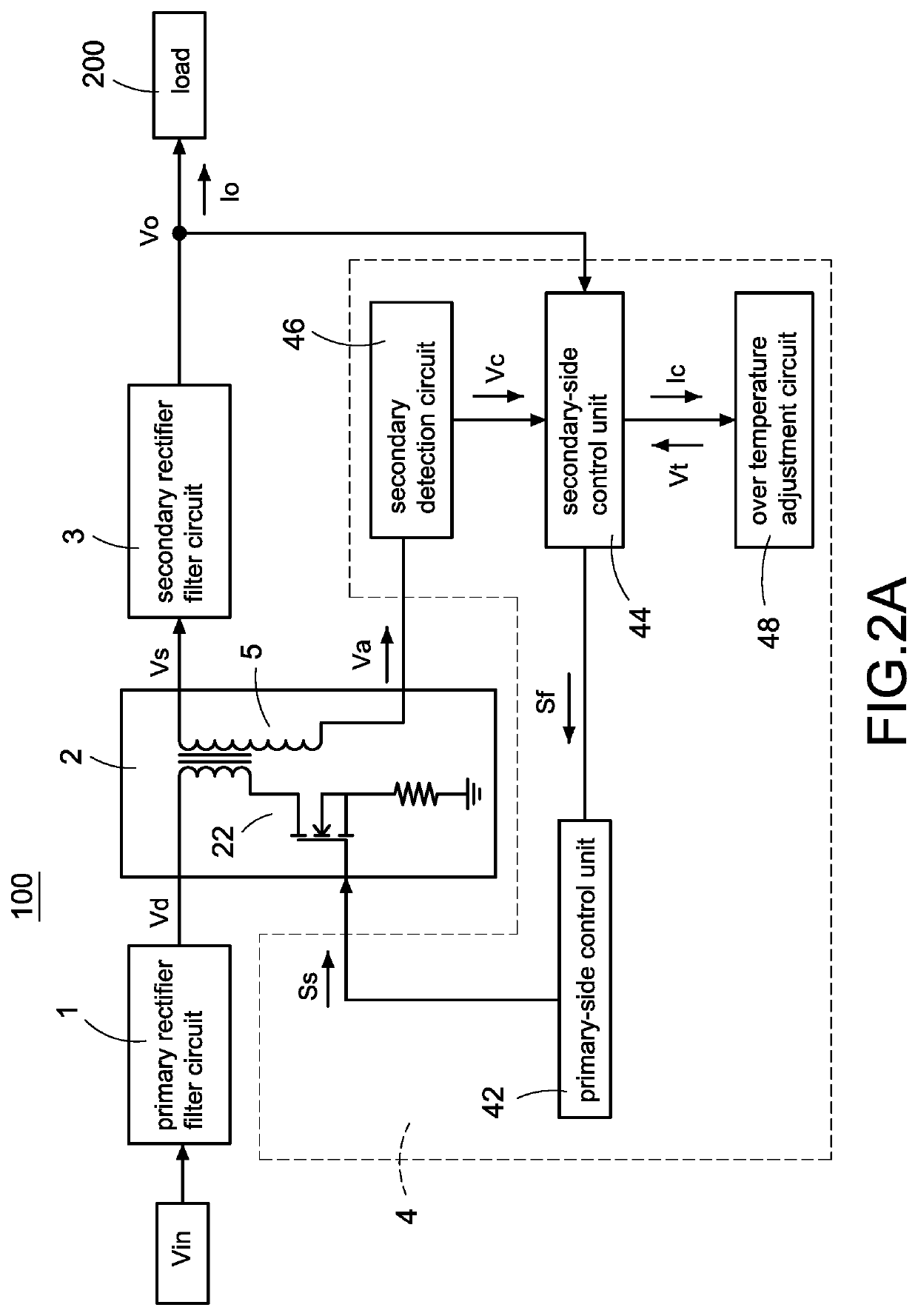
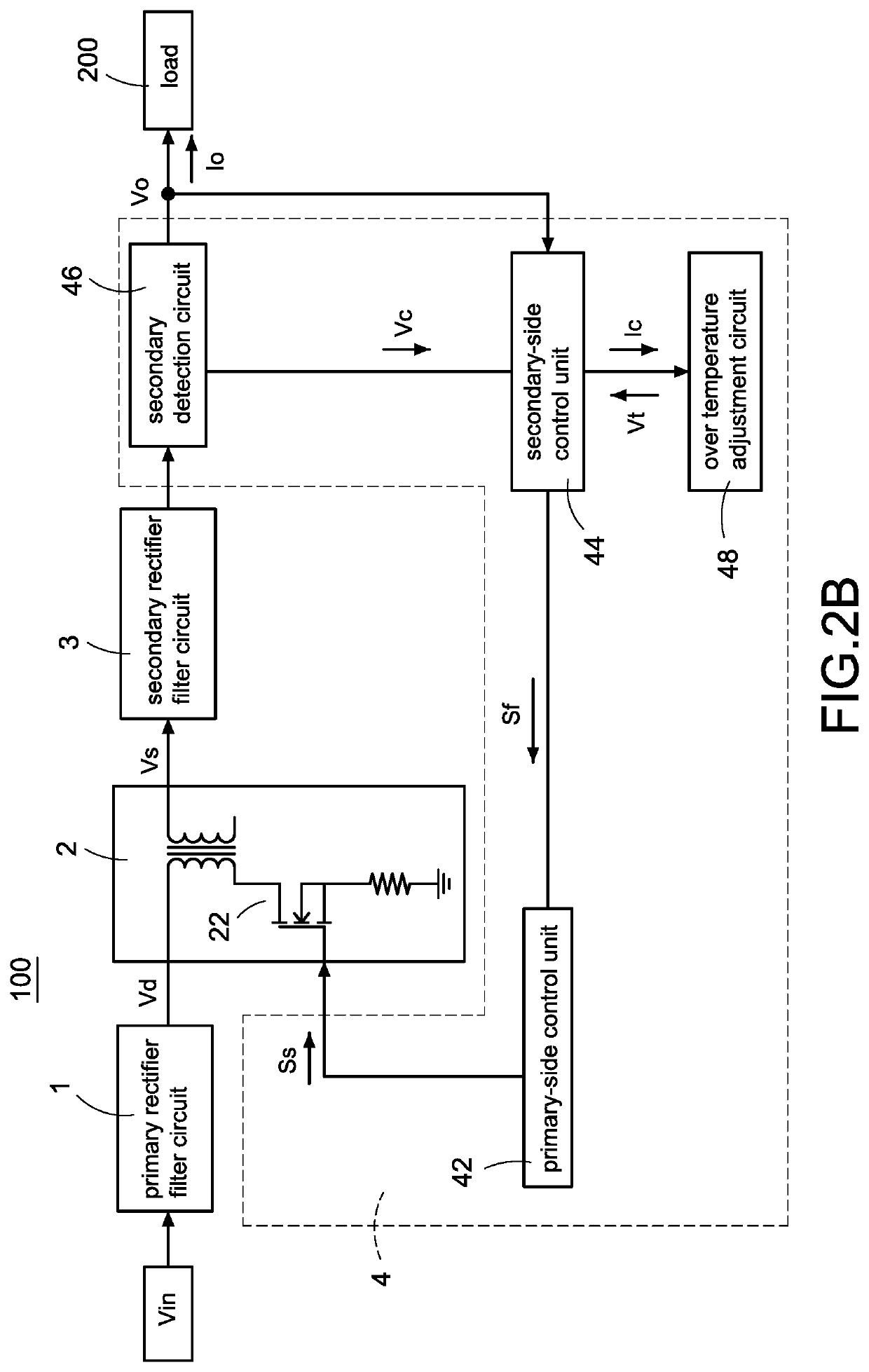
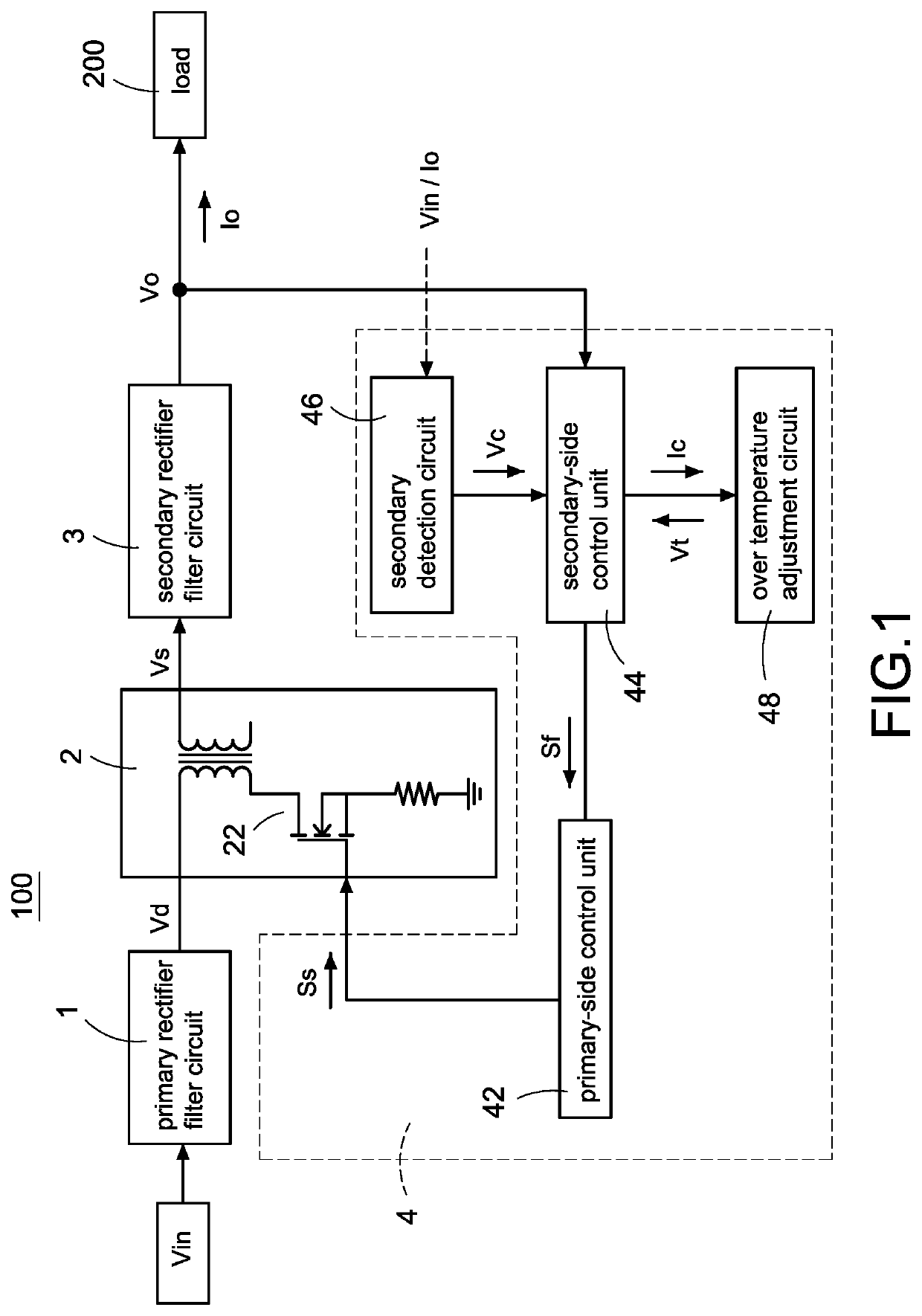
A power converter with over temperature protection compensation includes a main conversion unit, a primary-side control unit, a primary detection circuit, and an over temperature adjustment circuit. The primary-side control unit obtains a primary voltage change value through the primary detection circuit, and the primary-side control unit correspondingly provides a current change value to the over temperature adjustment circuit according to the primary voltage change value. The over temperature adjustment circuit provides a temperature control voltage according to the current change value so that the primary-side control unit determines whether an over temperature protection is activated according to the temperature control voltage.
Owner:CHICONY POWER TECH CO LTD
Roughness reflective layer for pixel designed thin film transistor and liquid crystal display
InactiveUS6980269B2Reduce variationImprove reflection efficiencyNon-linear opticsRough surfaceLiquid-crystal display
A thin-film transistor and a liquid crystal display having an ultra minimal rough reflective layer on pixel design are described. An ultra minimal rough reflective layer with an ultra minimal rough surface is formed on a substrate. The ultra minimal rough reflective layer includes an amorphous or partial crystalline indium tin oxide layer and a silicon-containing rugged layer to form the ultra minimal rough surface. A reflective layer conformal to the rugged layer is then formed thereon to obtain an ultra minimal roughness reflective surface, thereby to enhance reflective results.
Owner:WISTRON CORP
Device and method for setting a group owner intent value based on a comparison of group owner intent values
ActiveUS9179486B2Change its valueNetwork topologiesServices signallingInformation networksClient-side
A device and method for performing inter-device communication are disclosed. An inter-device communication method of a first device includes searching for a second device supporting inter-device communication, receiving network information from the searched second device, and determining that one of the first and second devices is a group owner based on the received network information of the second device and network information of the first device. The network information includes at least one selected from among type information indicating a server device or a client device, network support information, network necessity information, and network setting information.
Owner:LG ELECTRONICS INC
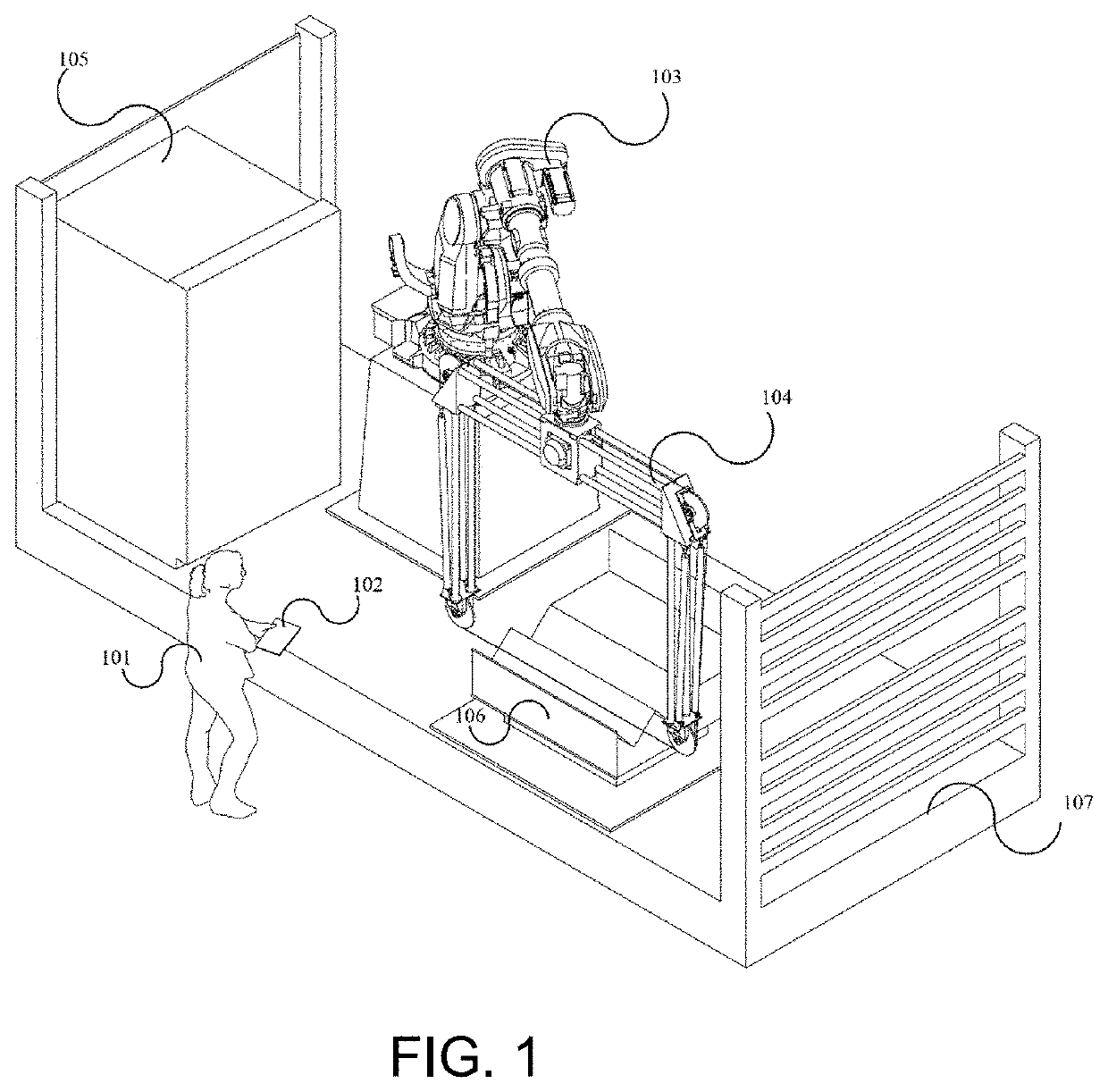
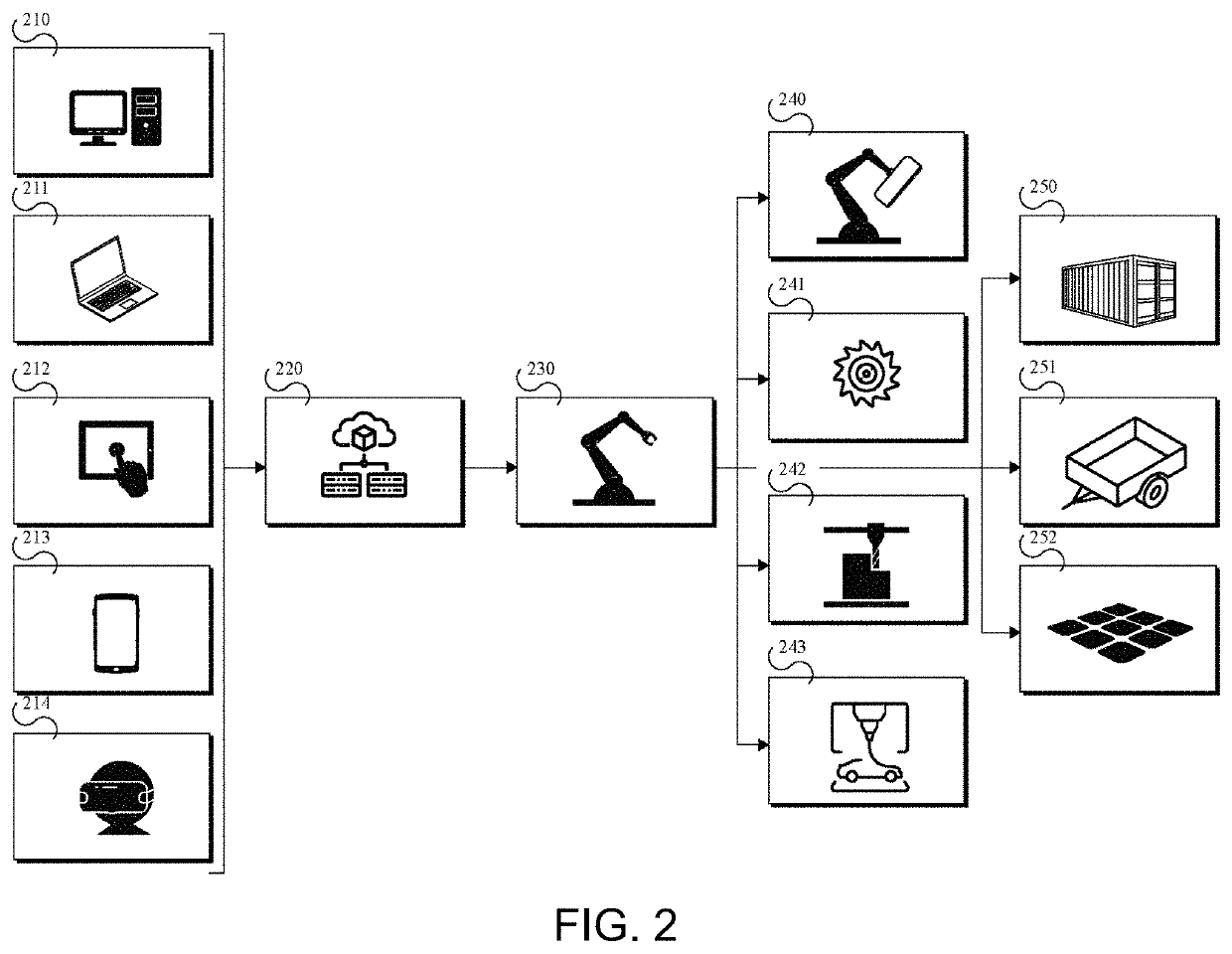
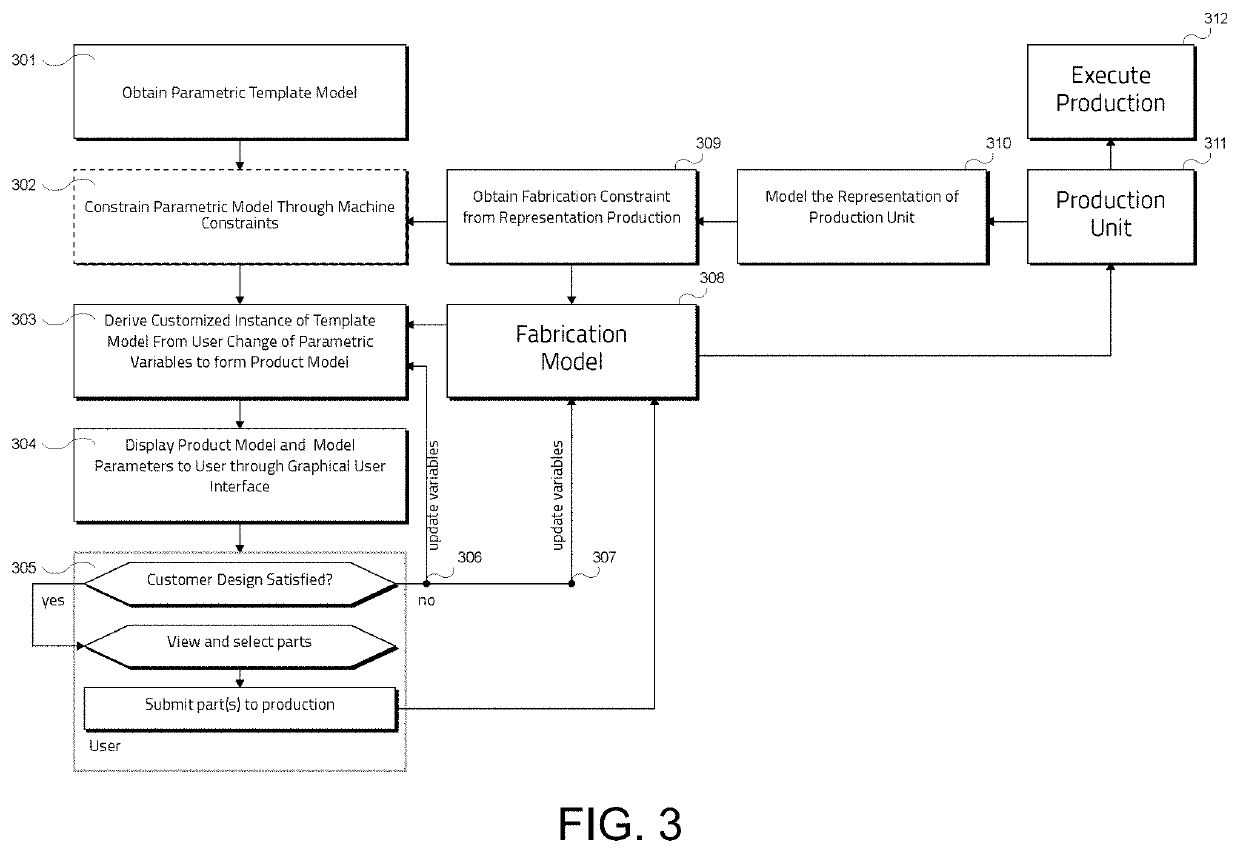
Smart manufacturing framework
PendingUS20220155752A1Safely make any design choiceQuickly reconfiguredComputer controlSimulator controlProcess engineeringAutonomation
The present disclosure relates to a computer-implemented method for customizing an automated product manufacturing process. It further relates to a robotic manufacturing system for manufacturing a product based on a fabrication model generated by means of the aforementioned computer-implemented method. One embodiment relates to a computer-implemented method for customizing a parametric design and manufacturing process of a physical product, the method comprising the steps of: obtaining a configurable parametric 3D product model representing a template of the physical product; customizing by a user the parametric 3D product model to provide a product instance describing the desired geometry of the physical product; automatically updating a fabrication model based on the parametric 3D product model; and optionally submitting the fabrication model to a manufacturing machine for fabricating the physical product or a mould for the physical product.
Owner:ODICO AS
Heat transfer medium composition
The present invention provides a pH stabilizing heat transfer medium composition comprising a main component of water, glycol, alcohol or glycol ether, and a pH buffer agent. The pH buffer agent is comprised of an alicyclic compound where a single ring-constituting carbon atom is bonded to two identical members or two different members selected from the group consisting of carboxymethyl and its salts, or where at least two ring-constituting neighboring carbon atoms are each bonded to a single member selected from the group consisting of carboxymethyl and its salts.
Owner:CCI CORPORATION
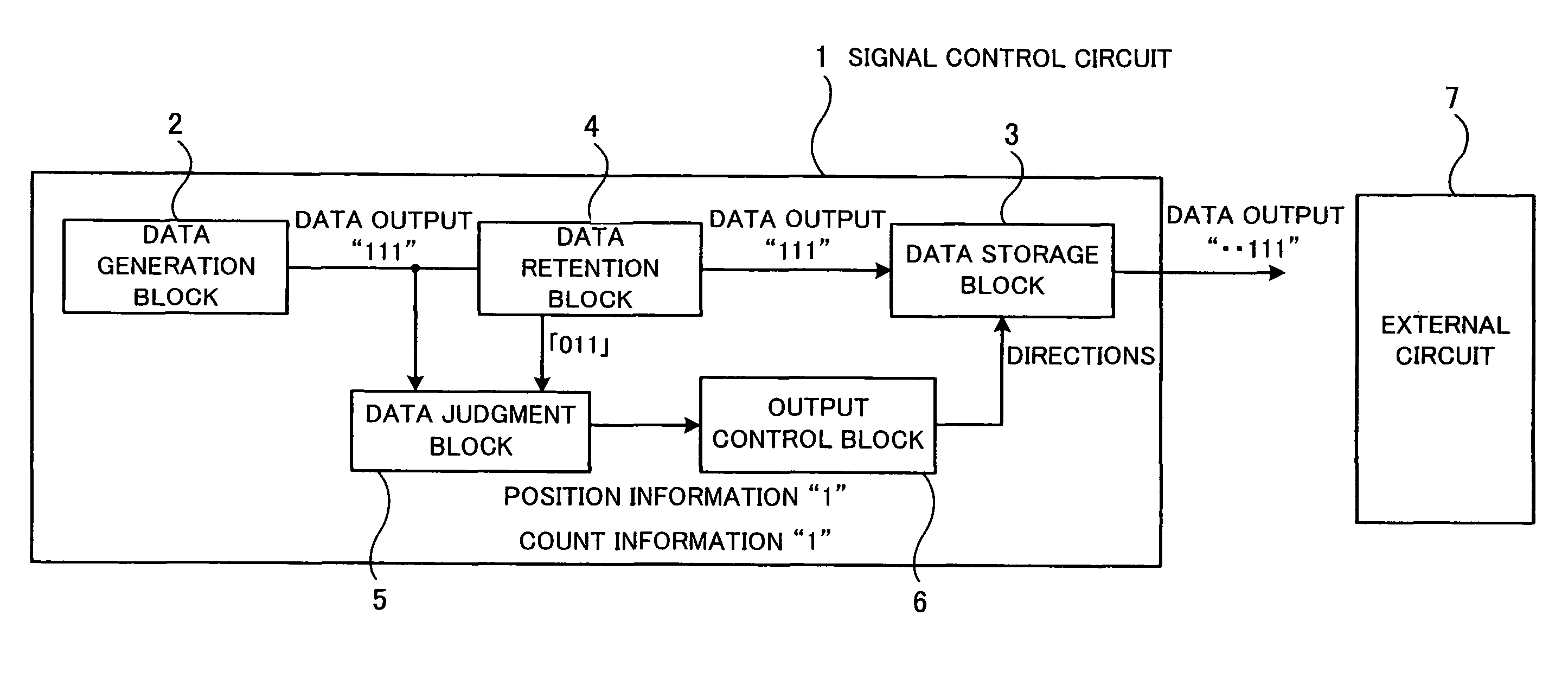
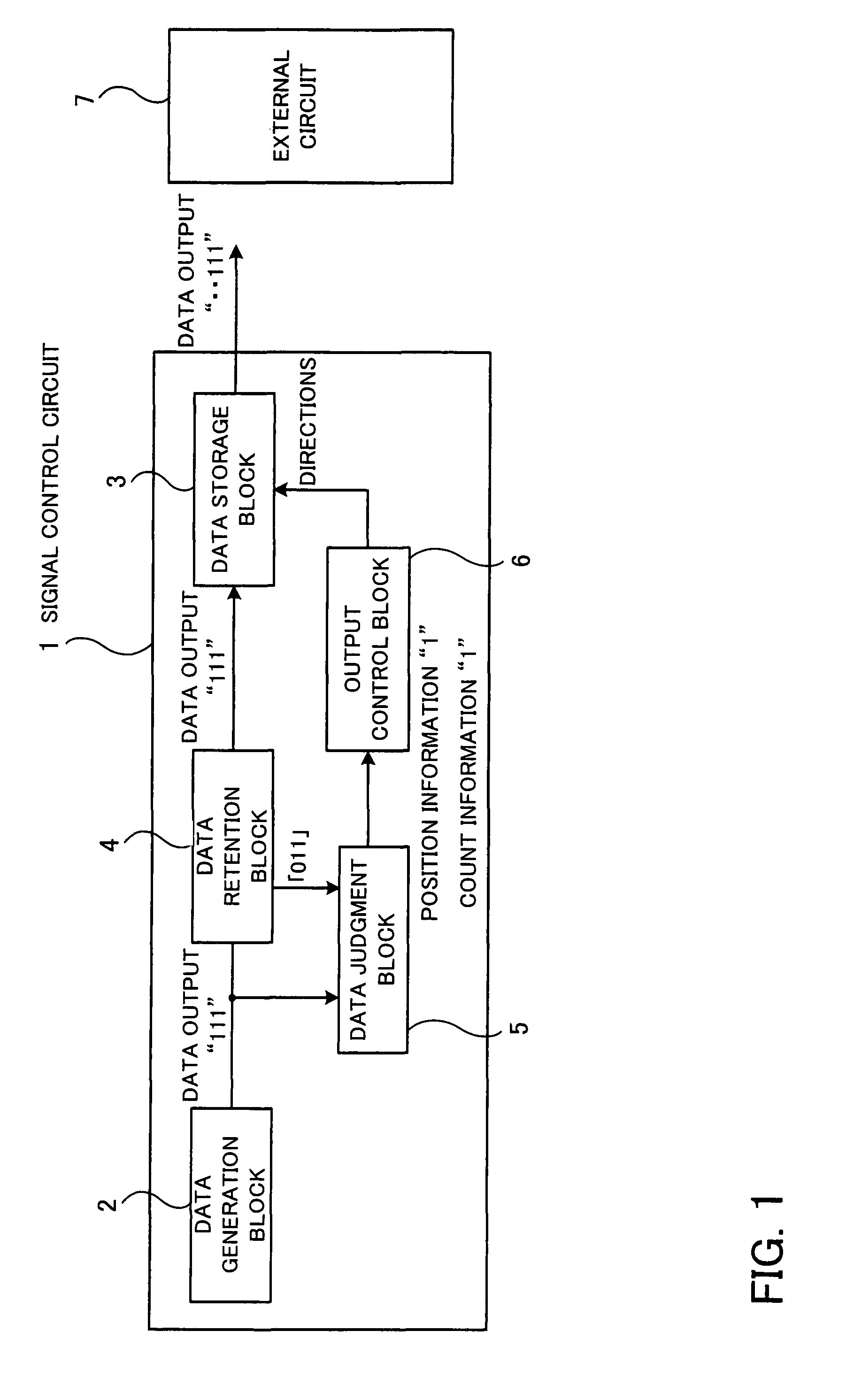
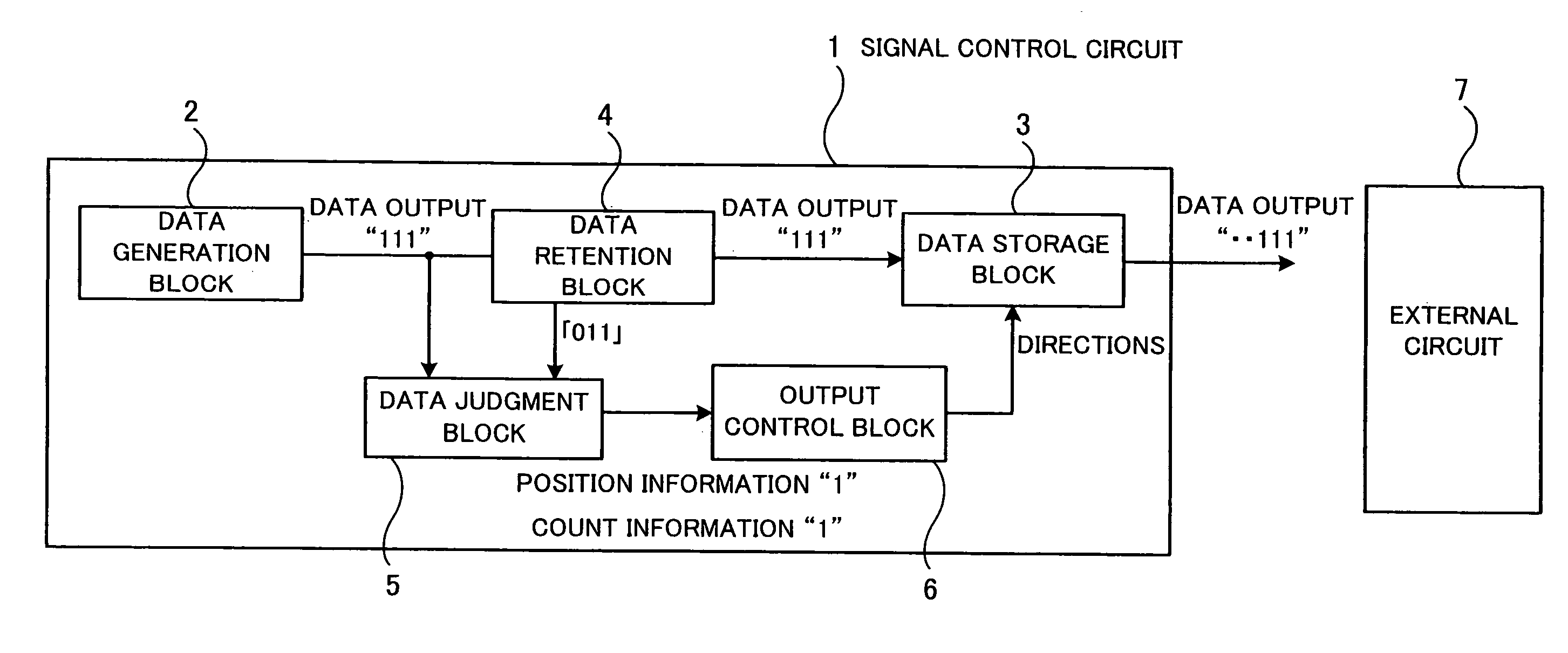
Signal control circuit and signal control apparatus
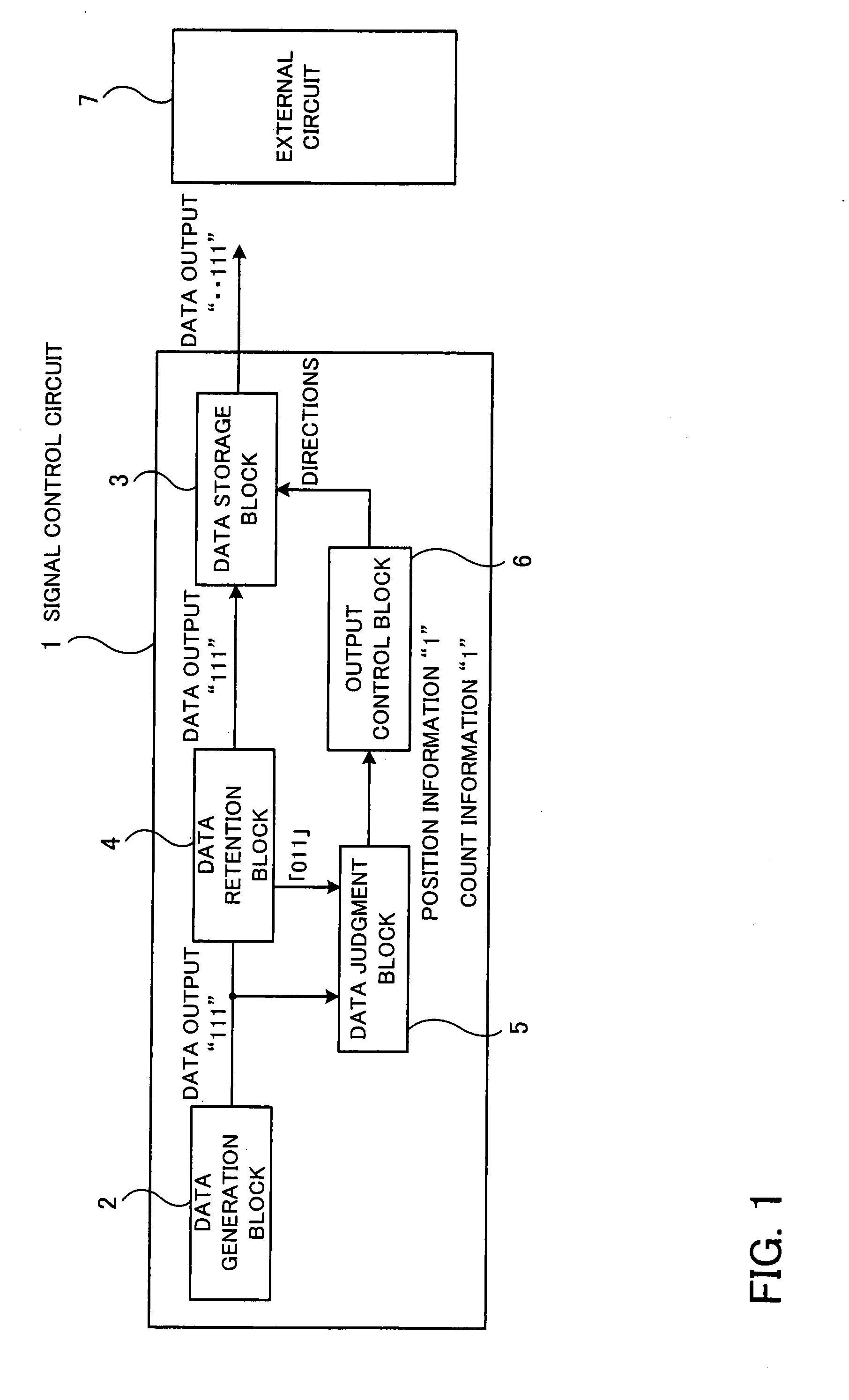
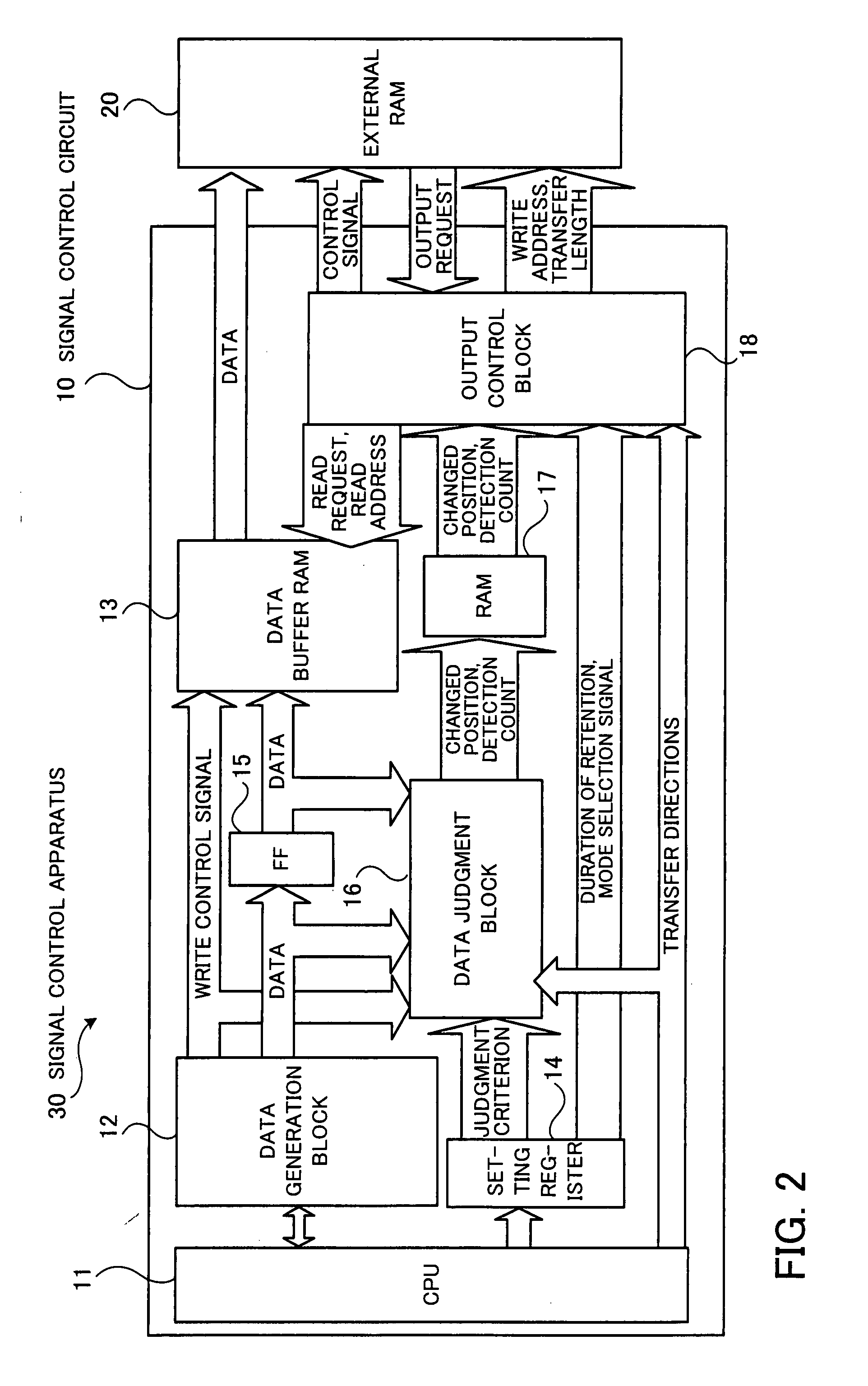
InactiveUS8245121B2Change its valueError detection/correctionCode conversionComputer hardwareControl circuit
A signal control circuit and a signal control apparatus that can reduce processing time and can send or receive correct data with reliability. When a data generation block outputs data, a data judgment block judges the number of changed bits by comparing each bit of the data output in the preceding session with the corresponding bit of the data to be sent in the current session and outputs position information indicating the position of each changed bit and the number of changed bits when the number of changed bits has reached a predetermined level. An output control block keeps a time period for stabilizing the change in value of the bit corresponding to the position information when the data is output, and directs a data storage block to send the value of the bit corresponding to the position information to an external circuit after the kept period has passed.
Owner:SOCIONEXT INC
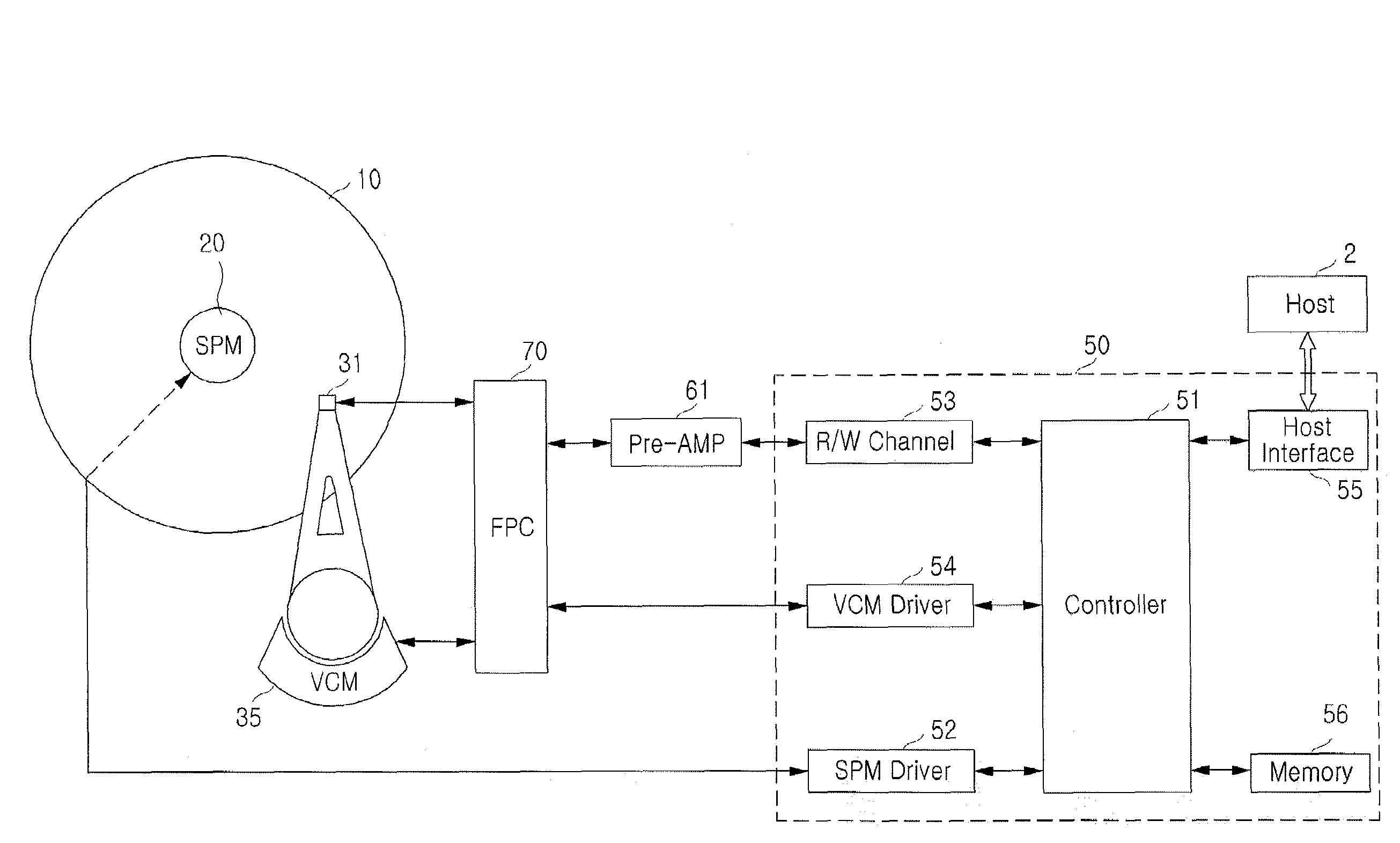
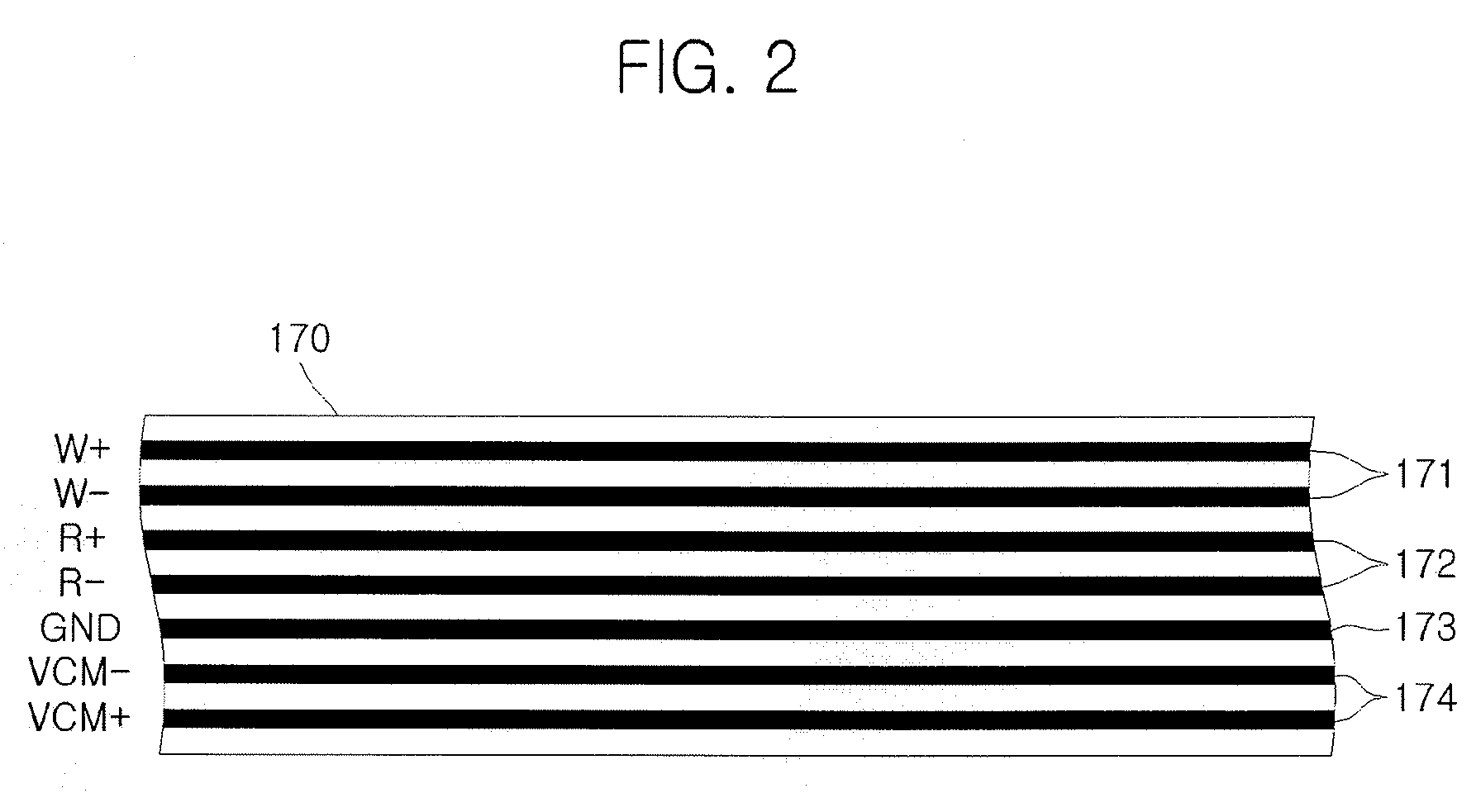
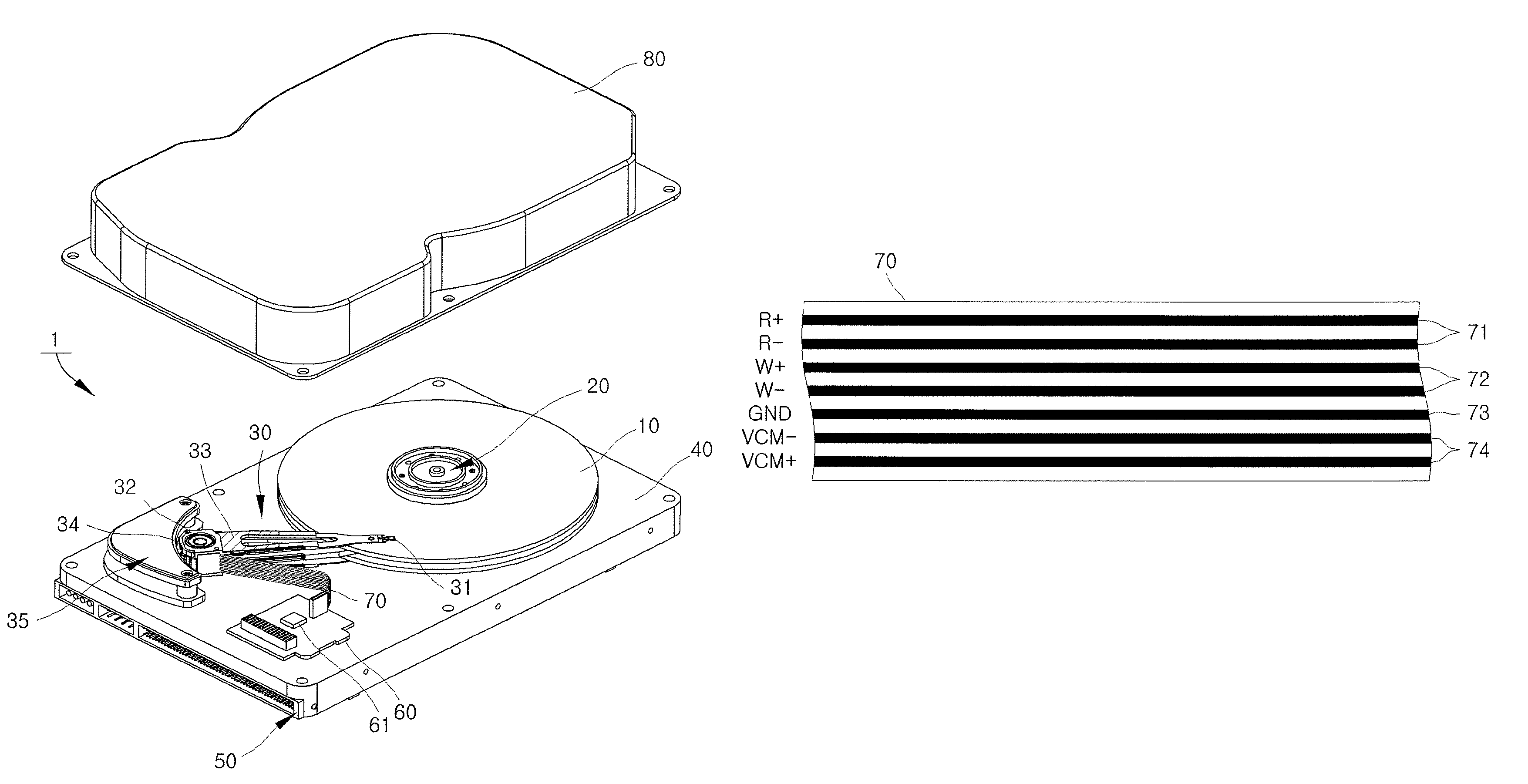
Hard disk drive apparatus
InactiveUS20080204931A1Change its valueConstruction of head windingsPrinted circuit aspectsHard disc driveEngineering
A hard disk drive apparatus includes a magnetic head having a write head to record data on a disk and a read head to read the data recorded on the disk, at least one actuator arm on which the magnetic head is mounted, a voice coil motor to rotate the at least one actuator arm across the disk, a printed circuit board electrically connected to the write head, the read head, and the voice coil motor, and a flexible printed circuit having at least one write trace to electrically connect the write head and the printed circuit board, at least one read trace to electrically connect the read head and the printed circuit board, and a voice coil motor trace to electrically connect the voice coil motor and the printed circuit board. In the hard disk drive, the write trace is arranged between the read trace and the voice coil motor trace.
Owner:SEAGATE TECH INT
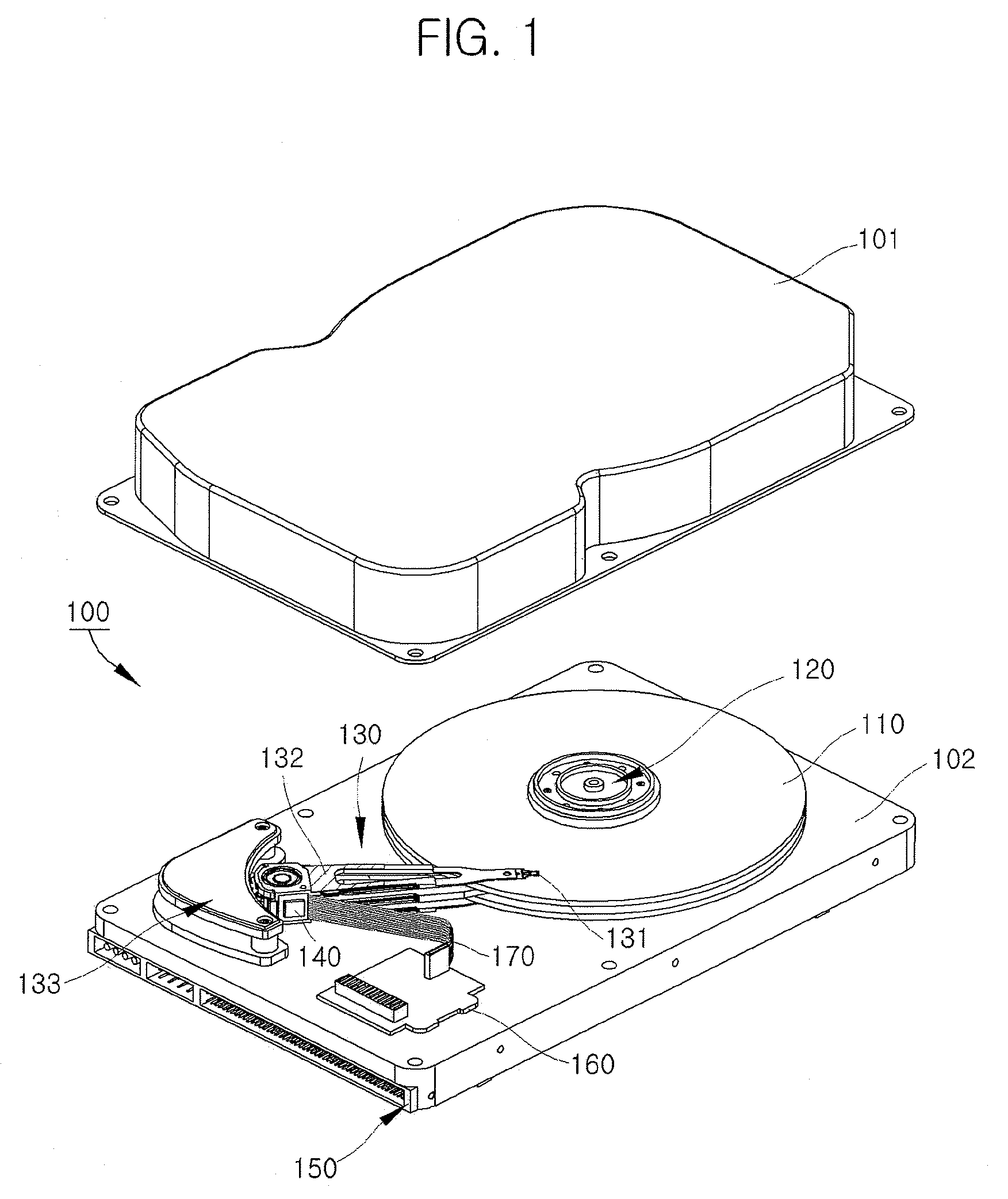
Hard disk drive apparatus having a flexible printed circuit with a plurality of traces in a specified order
InactiveUS8149543B2Change its valueConstruction of head windingsPrinted circuit aspectsElectricityHard disc drive
A hard disk drive apparatus includes a magnetic head having a write head to record data on a disk and a read head to read the data recorded on the disk, at least one actuator arm on which the magnetic head is mounted, a voice coil motor to rotate the at least one actuator arm across the disk, a printed circuit board electrically connected to the write head, the read head, and the voice coil motor, and a flexible printed circuit having at least one write trace to electrically connect the write head and the printed circuit board, at least one read trace to electrically connect the read head and the printed circuit board, and a voice coil motor trace to electrically connect the voice coil motor and the printed circuit board. In the hard disk drive, the write trace is arranged between the read trace and the voice coil motor trace.
Owner:SEAGATE TECH INT
Heat transfer medium composition
The present invention provides a pH stabilizing heat transfer medium composition comprising a main component of water, glycol, alcohol or glycol ether, and a pH buffer agent. The pH buffer agent is comprised of an alicyclic compound where a single ring-constituting carbon atom is bonded to two identical members or two different members selected from the group consisting of carboxymethyl and its salts, or where at least two ring-constituting neighboring carbon atoms are each bonded to a single member selected from the group consisting of carboxymethyl and its salts.
Owner:SHISHIAI KK
Power converter with over temperature protection compensation
ActiveUS20200251993A1Change its valueEmergency protective circuit arrangementsDc-dc conversionConvertersTemperature control
A power converter with over temperature protection compensation includes a main conversion unit, a primary-side control unit, a primary detection circuit, and an over temperature adjustment circuit. The primary-side control unit obtains a primary voltage change value through the primary detection circuit, and the primary-side control unit correspondingly provides a current change value to the over temperature adjustment circuit according to the primary voltage change value. The over temperature adjustment circuit provides a temperature control voltage according to the current change value so that the primary-side control unit determines whether an over temperature protection is activated according to the temperature control voltage.
Owner:CHICONY POWER TECH CO LTD
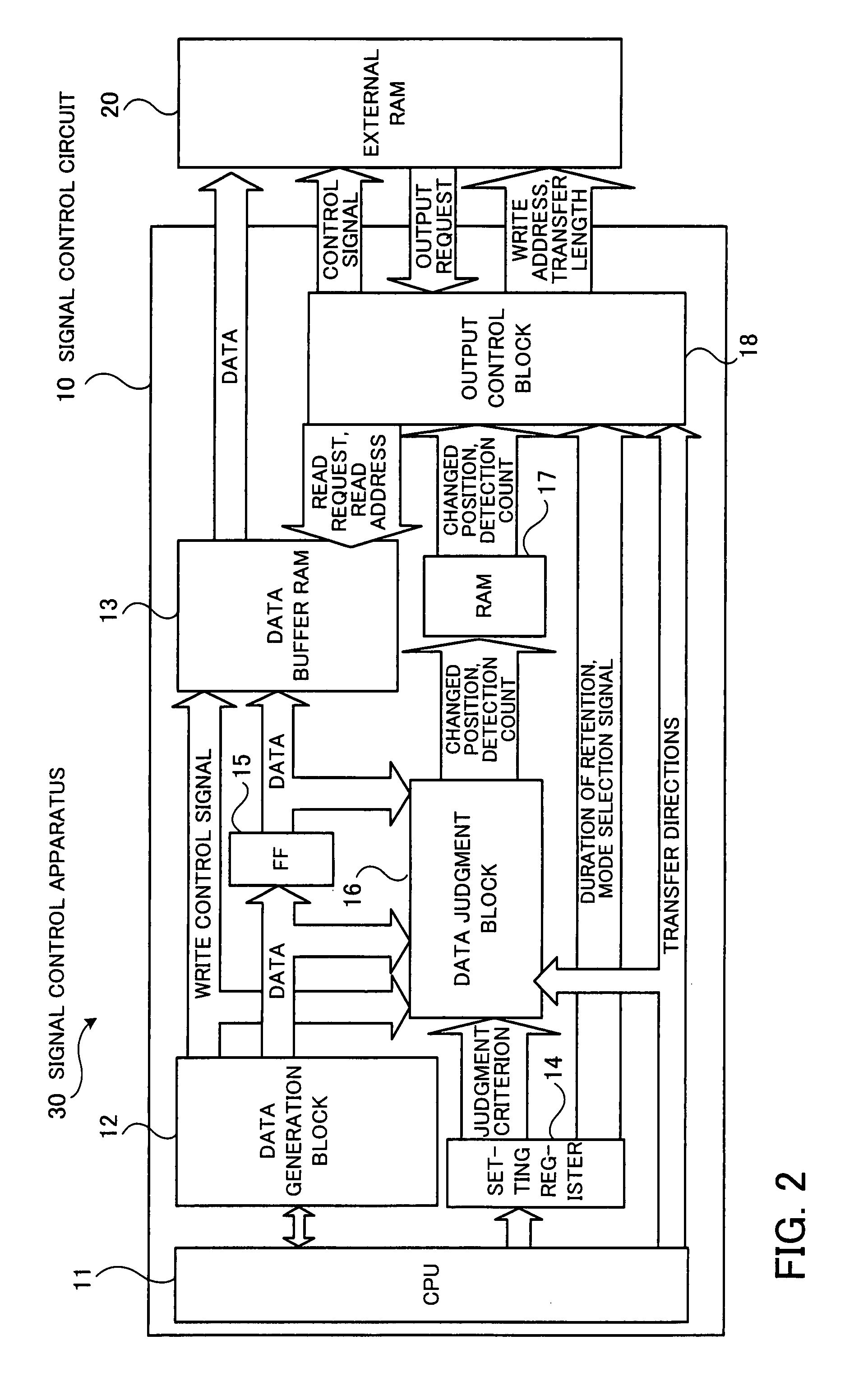
Signal control circuit and signal control apparatus
InactiveUS20080163037A1Change its valueFault responseCode conversionComputer hardwareControl circuit
A signal control circuit and a signal control apparatus that can reduce processing time and can send or receive correct data with reliability. When a data generation block outputs data, a data judgment block judges the number of changed bits by comparing each bit of the data output in the preceding session with the corresponding bit of the data to be sent in the current session and outputs position information indicating the position of each changed bit and the number of changed bits when the number of changed bits has reached a predetermined level. An output control block keeps a time period for stabilizing the change in value of the bit corresponding to the position information when the data is output, and directs a data storage block to send the value of the bit corresponding to the position information to an external circuit after the kept period has passed.
Owner:SOCIONEXT INC
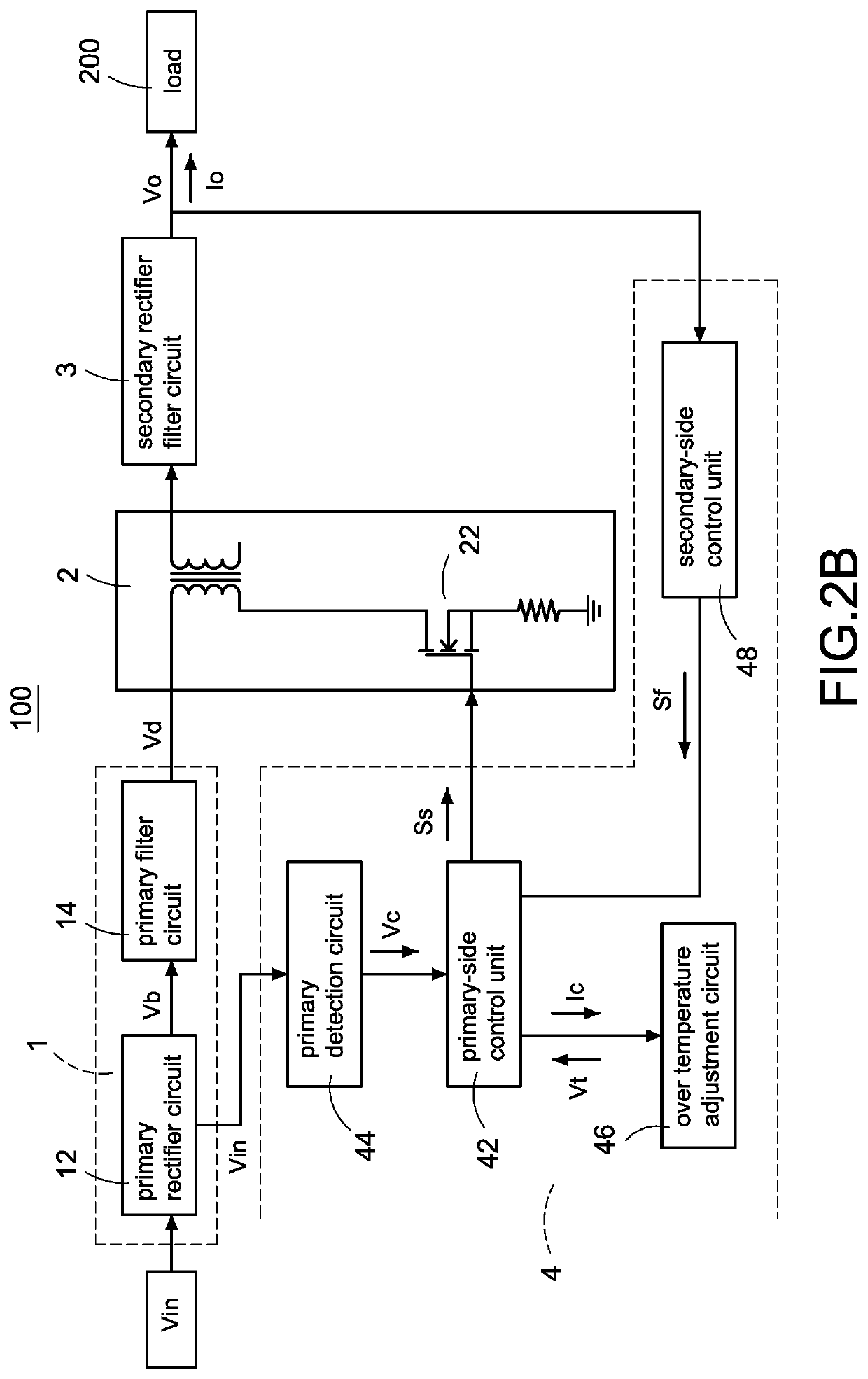
Power converter with over temperature protection compensation
ActiveUS20210281162A1Change its valueEmergency protective circuit arrangementsDc-dc conversionConvertersTemperature control
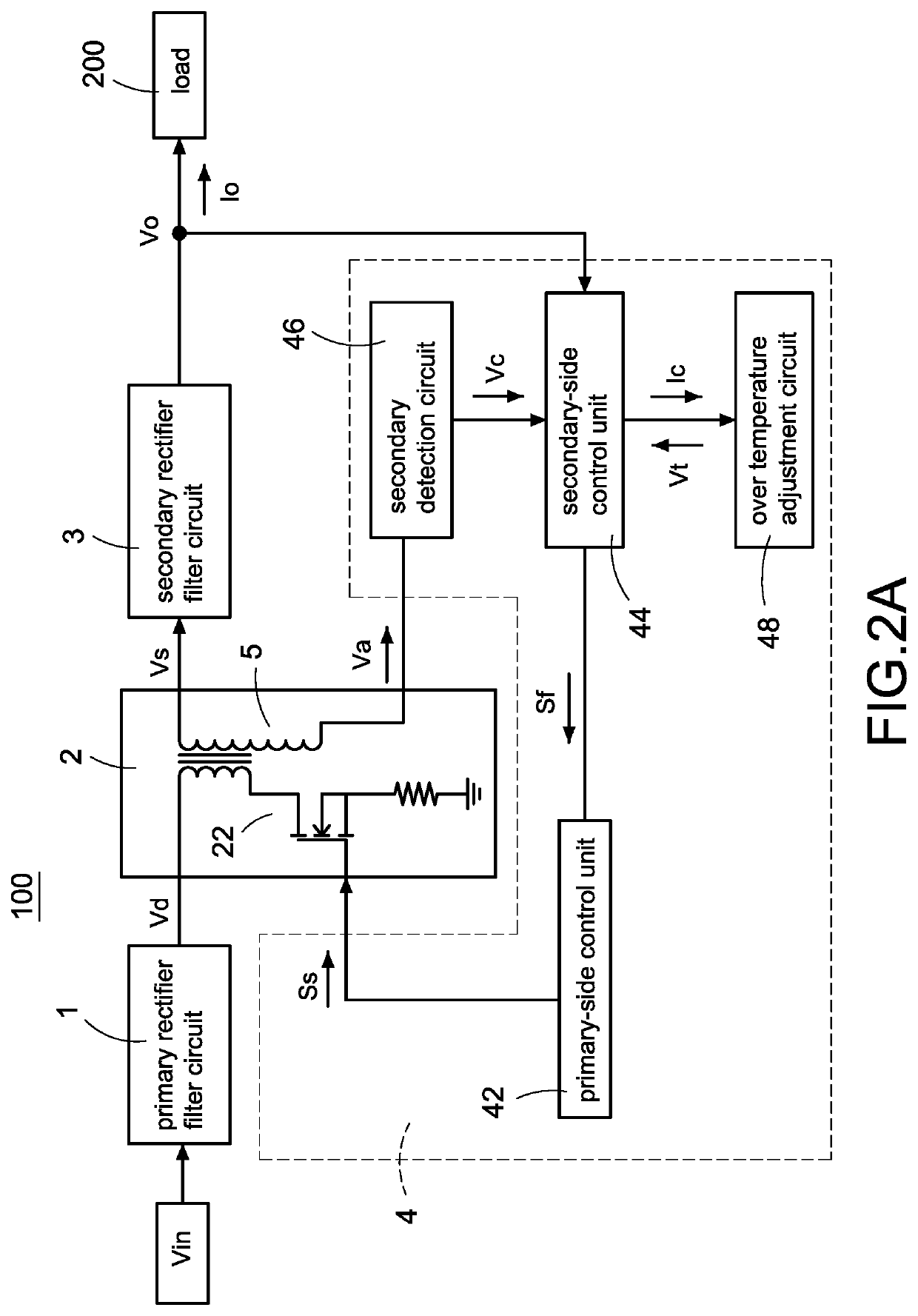
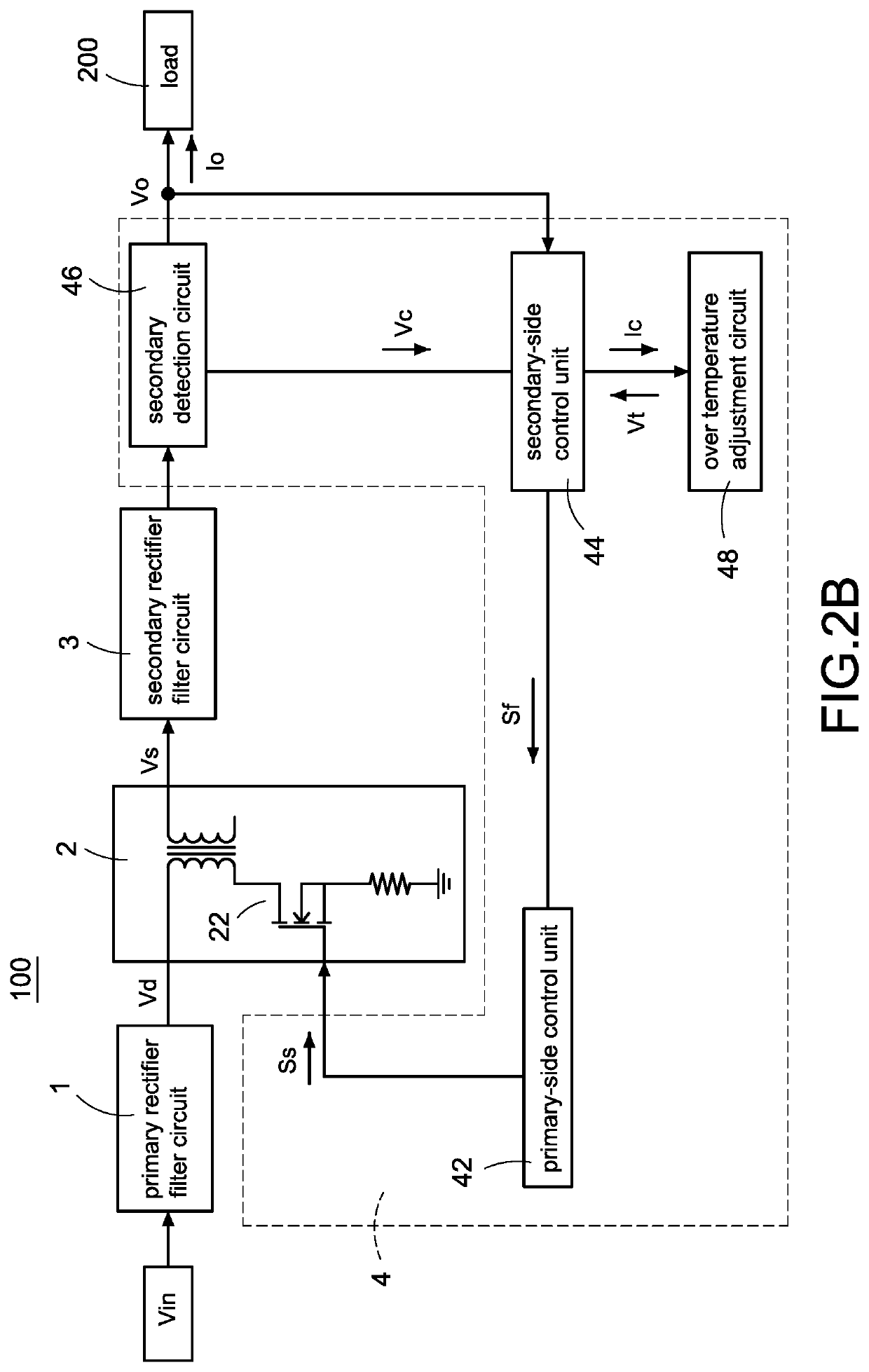
A power converter with over temperature protection compensation includes a main conversion unit, a primary-side control unit, a secondary-side control unit, a secondary detection circuit, and an over temperature adjustment circuit. The secondary-side control unit obtains a secondary voltage change value through the secondary detection circuit, and the secondary-side control unit correspondingly provides a current change value to the over temperature adjustment circuit according to the secondary voltage change value. The over temperature adjustment circuit provides a temperature control voltage according to the current change value so that the secondary-side control unit determines whether an over temperature protection is activated according to the temperature control voltage.
Owner:CHICONY POWER TECH CO LTD
Device and method for performing inter-device communication
ActiveUS9386616B2Change its valueNetwork topologiesConnection managementService informationOperating system
Owner:LG ELECTRONICS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com