Patents
Literature
84 results about "AN codes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
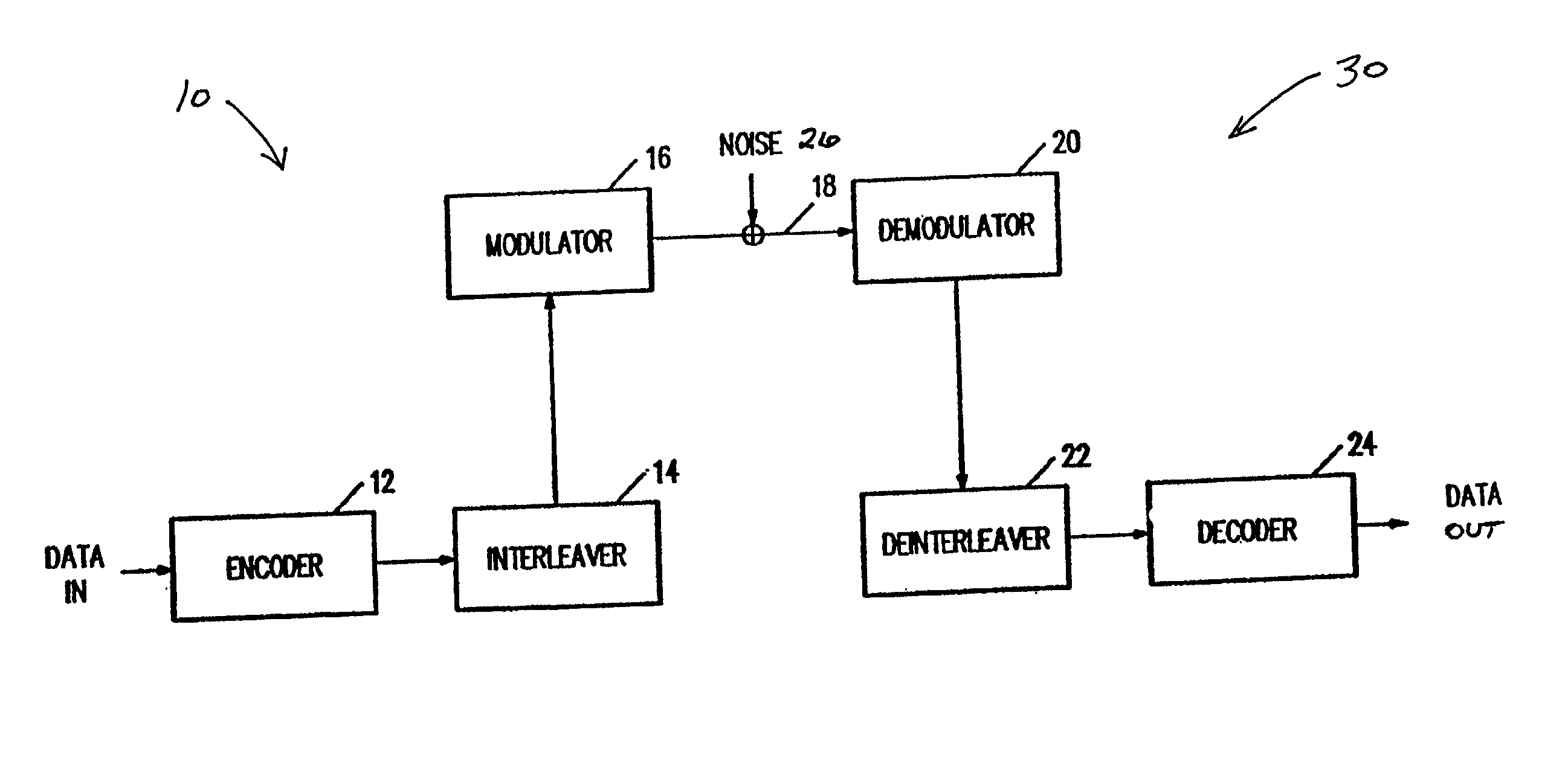
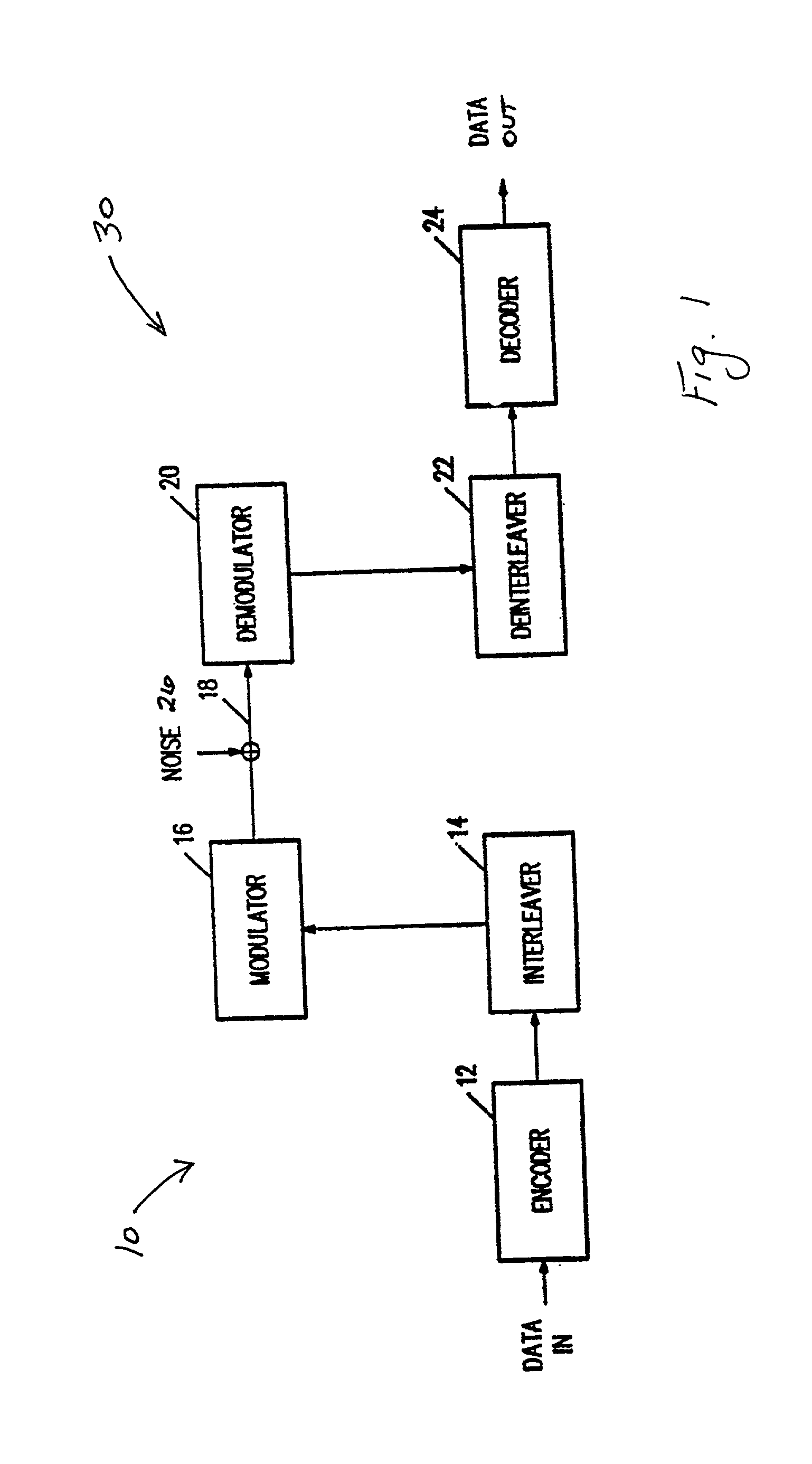
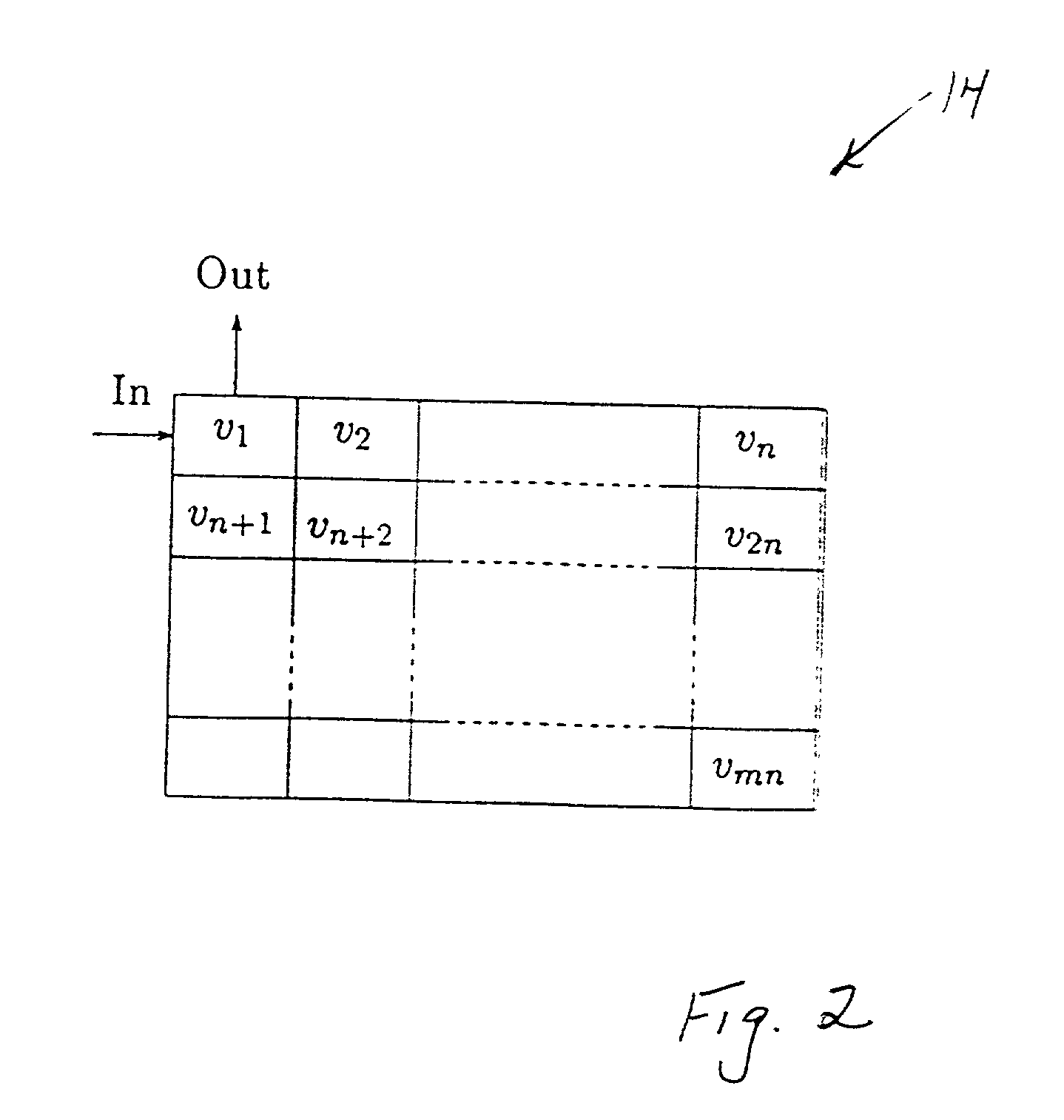
AN codes are error-correcting code that are used in arithmetic applications. Arithmetic codes were commonly used in computer processors to ensure the accuracy of its arithmetic operations when electronics were more unreliable. Arithmetic codes help the processor to detect when an error is made and correct it. Without these codes, processors would be unreliable since any errors would go undetected. AN codes are arithmetic codes that are named for the integers and that are used to encode and decode the codewords.
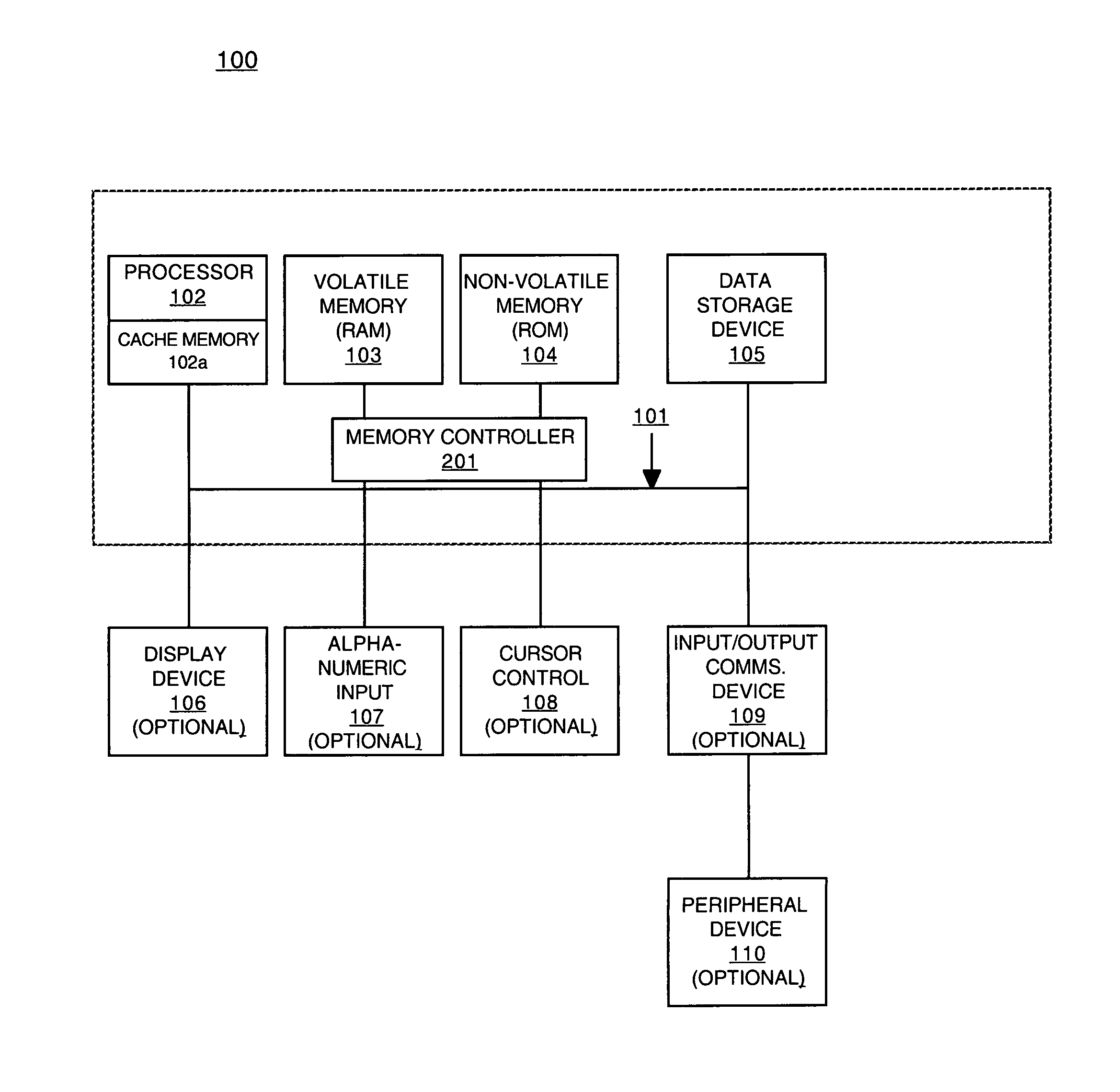
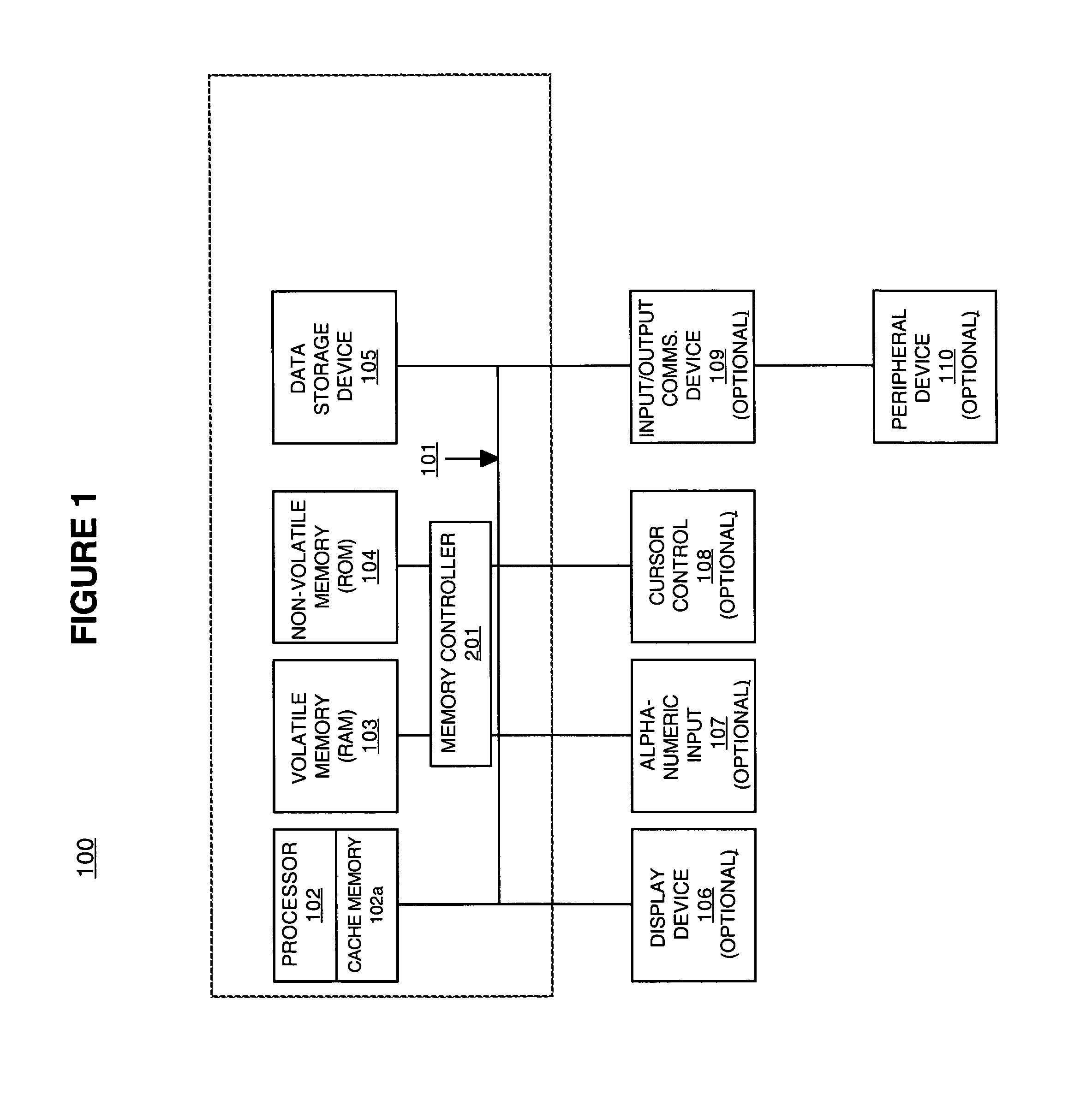
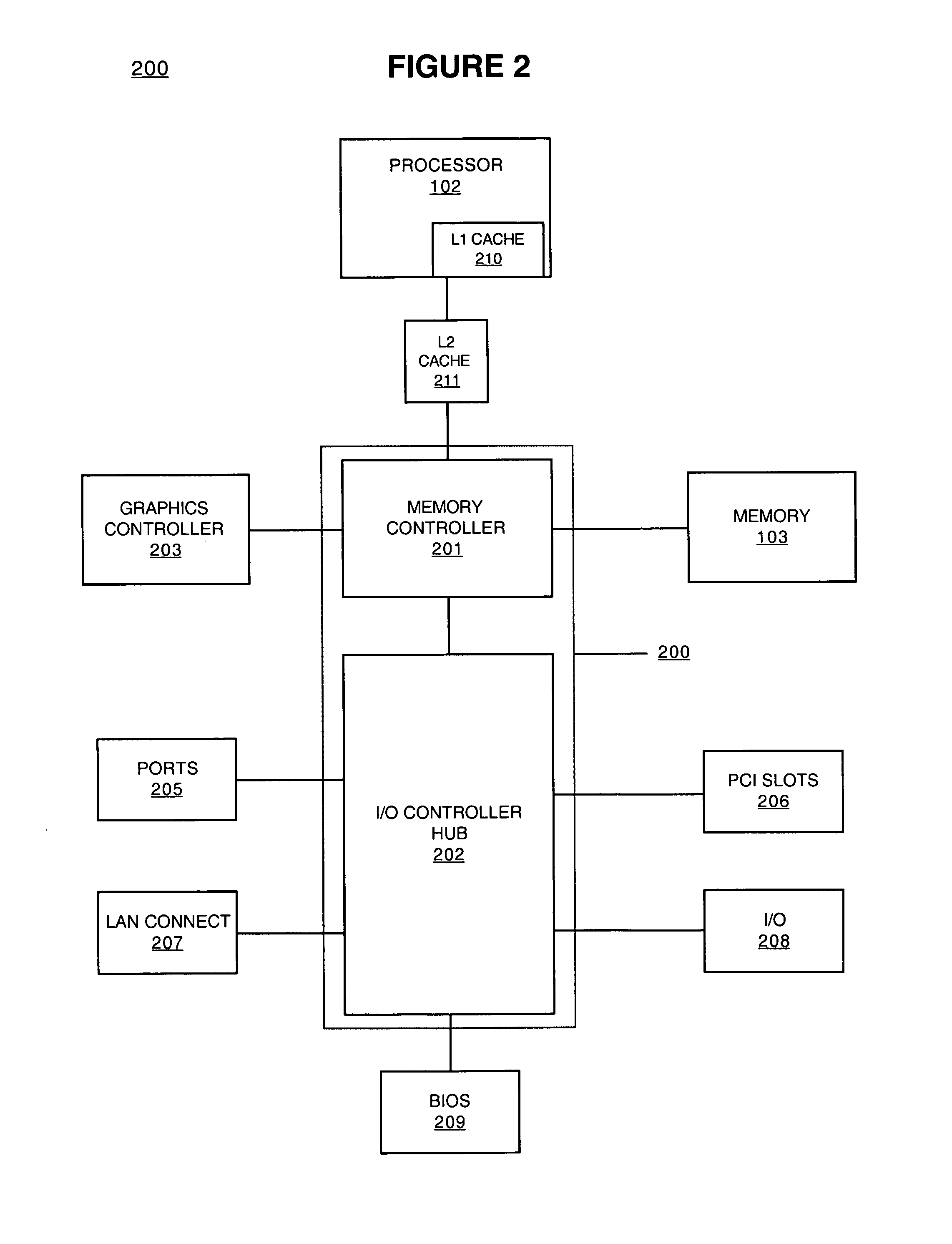
Method and system for pre-loading and executing computer instructions within the cache memory
Embodiments of the present invention recite a method and system for pre-loading and executing code within the cache. In one embodiment, an indication to operate an electronic device in a sleep state is received. At least one instance of code is loaded into a cache memory in response to receiving the indication. The at least one instance of code is for causing the electronic device to operate in said sleep state. In embodiments of the present invention, the at least one instance of code further comprises a registry setting for a memory controller. The at least one instance of code is then accessed from the cache memory.
Owner:NVIDIA CORP
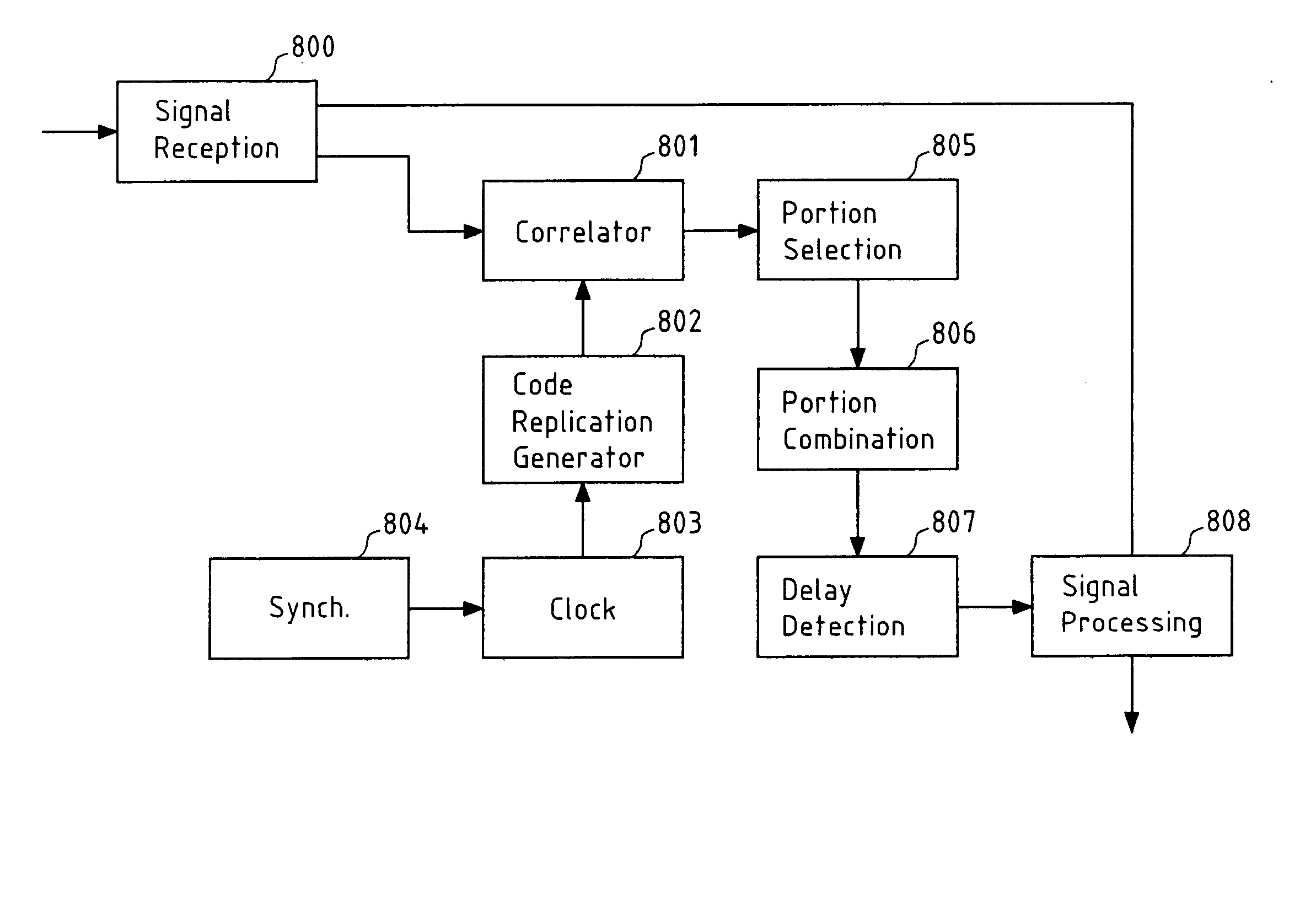
Multiple access using different codes lengths for global navigation satellite systems
InactiveUS20050129096A1Reduce impactEnhance the auto-correlation peaksCode division multiplexBeacon systemsParallel computingCorrelation function
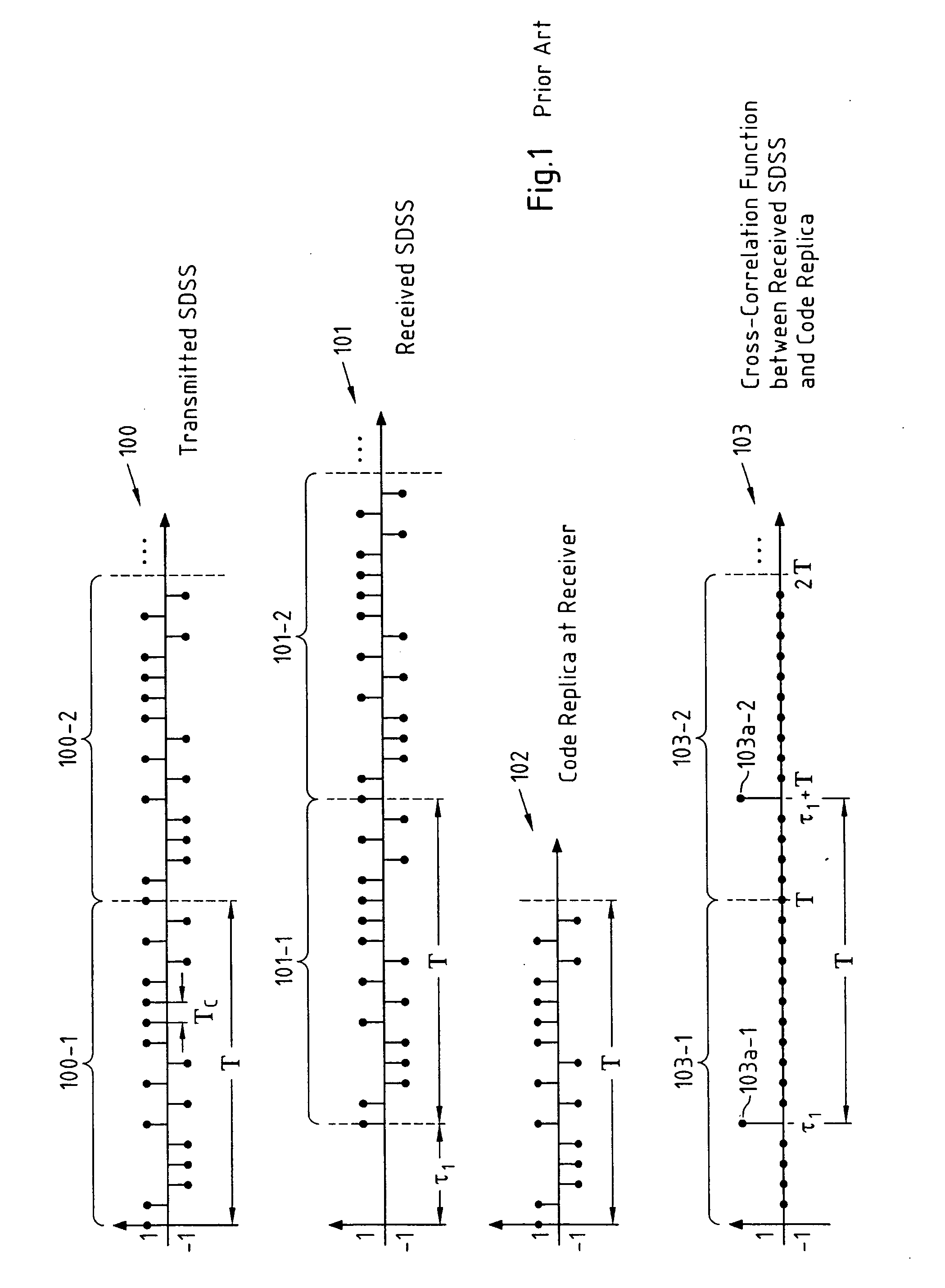
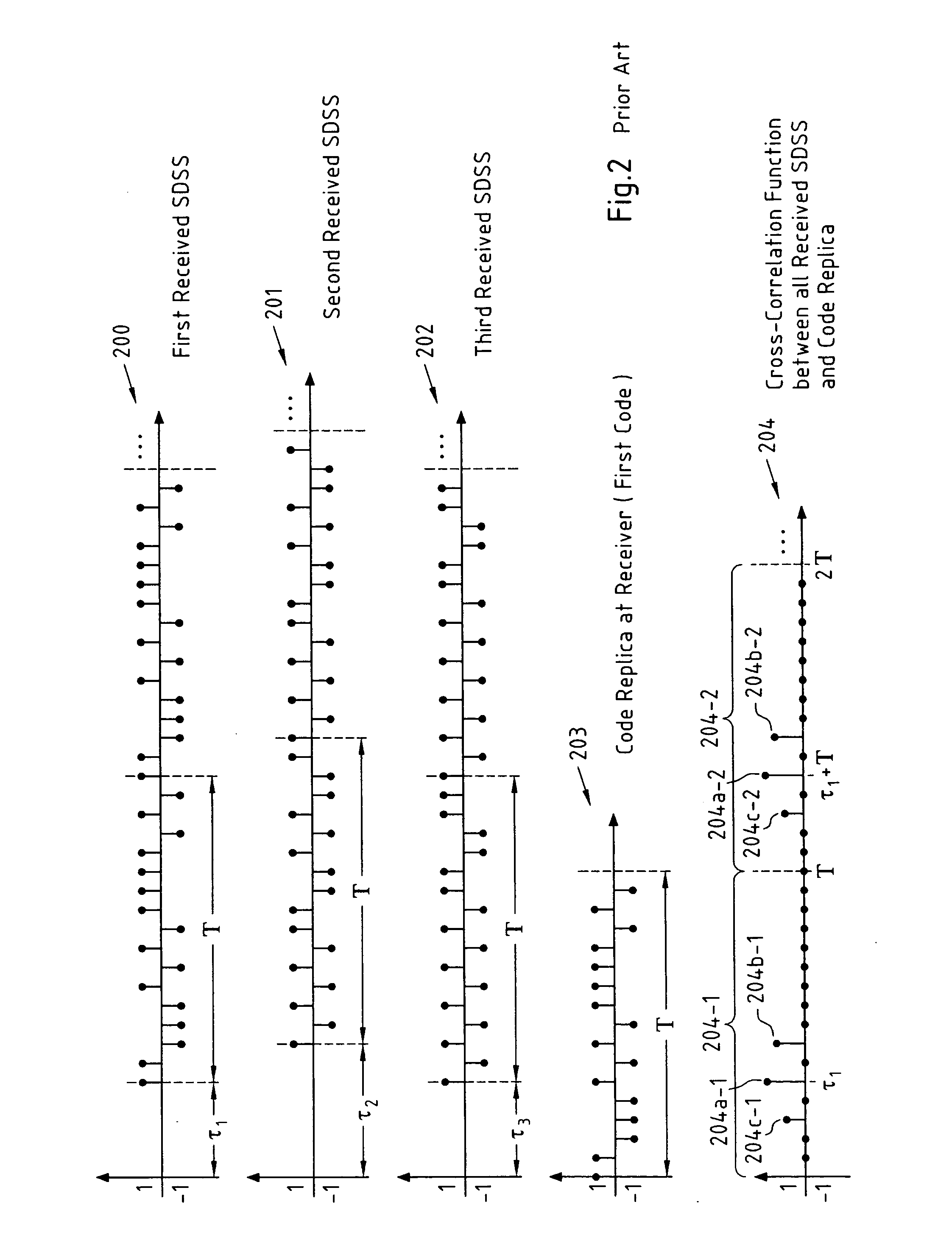
A method for determining a delay of a spread data symbol stream comprises the steps of at least partially correlating a signal, which comprises at least first and second spread data symbol streams (300, 301) that are obtained by spreading at least a first and second data symbol stream with a respective first (302) and second code, with said first code (302) to obtain at least two portions (303-1, 303-2) of a Cross-Correlation Function CCF (303), and combining said at least two portions (303-1, 303-2) of said CCF (303) to obtain a combined CCF portion from which a first delay of said first spread data symbol stream is determined, wherein said first code (302) and said second code are composed of chips and wherein the number of chips of said first code (302) is different from the number of chips of said second code. The invention further relates to a computer program, a computer program product, a device and a system.
Owner:NOKIA CORP
Familial correction with non-familial double bit error detection for directory storage
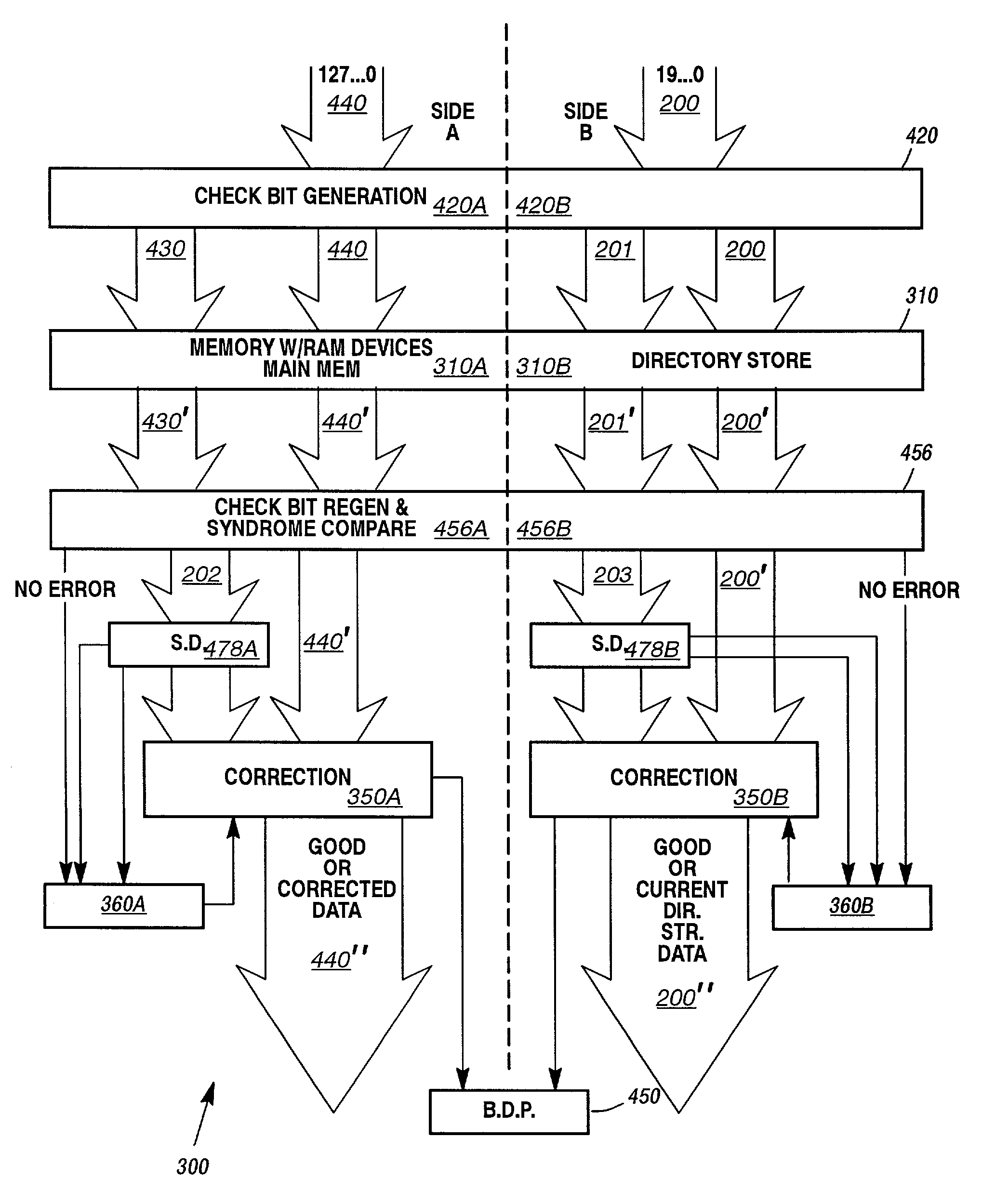
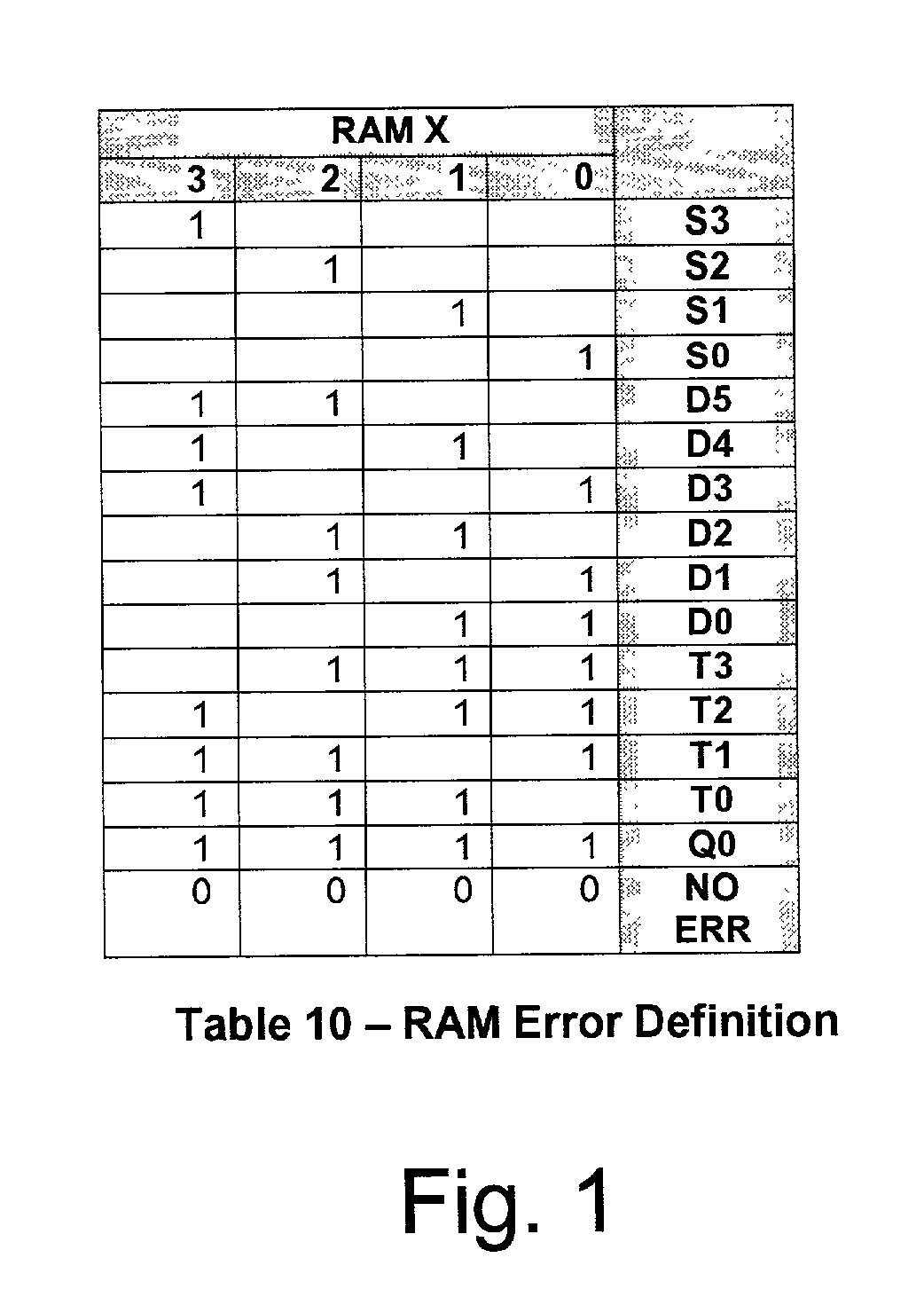
Error correction and error detection related to DRAM chip failures, particularly adapted server memory subsystems. The application of a code for 128 bit memories is applied to a 20 bit directory store to improve reliability of the directory store memory of the computer system. The code uses ×4 bit DRAM devices organized in a code word of 20 data bit words and 12 check bits. These 12 check bits provide a code capable of 4 bit adjacent error correction within a family (i.e., in a ×4 DRAM) and double bit non-adjacent error detection across the entire 20 bit word, with single bit correction across the word as well. Each device can be though of as a separate family of bits, errors occurring in more than one family are not correctable, but may be detected if only one bit in each of two families is in error. Syndrome generation and regeneration are used together with a specific large code word. Decoding the syndrome and checking it against the regenerated syndrome yield data sufficient for providing the features described.
Owner:UNISYS CORP
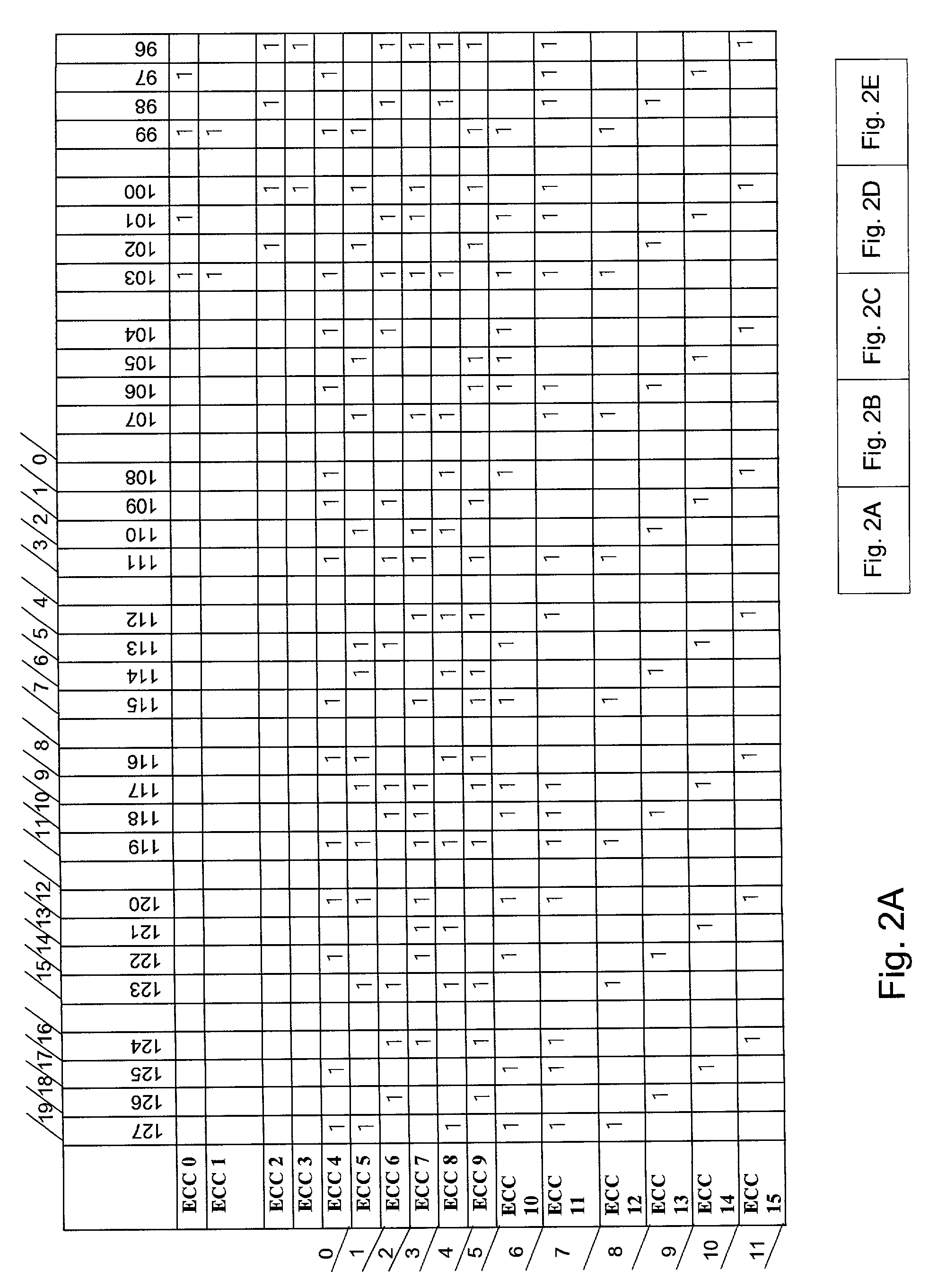
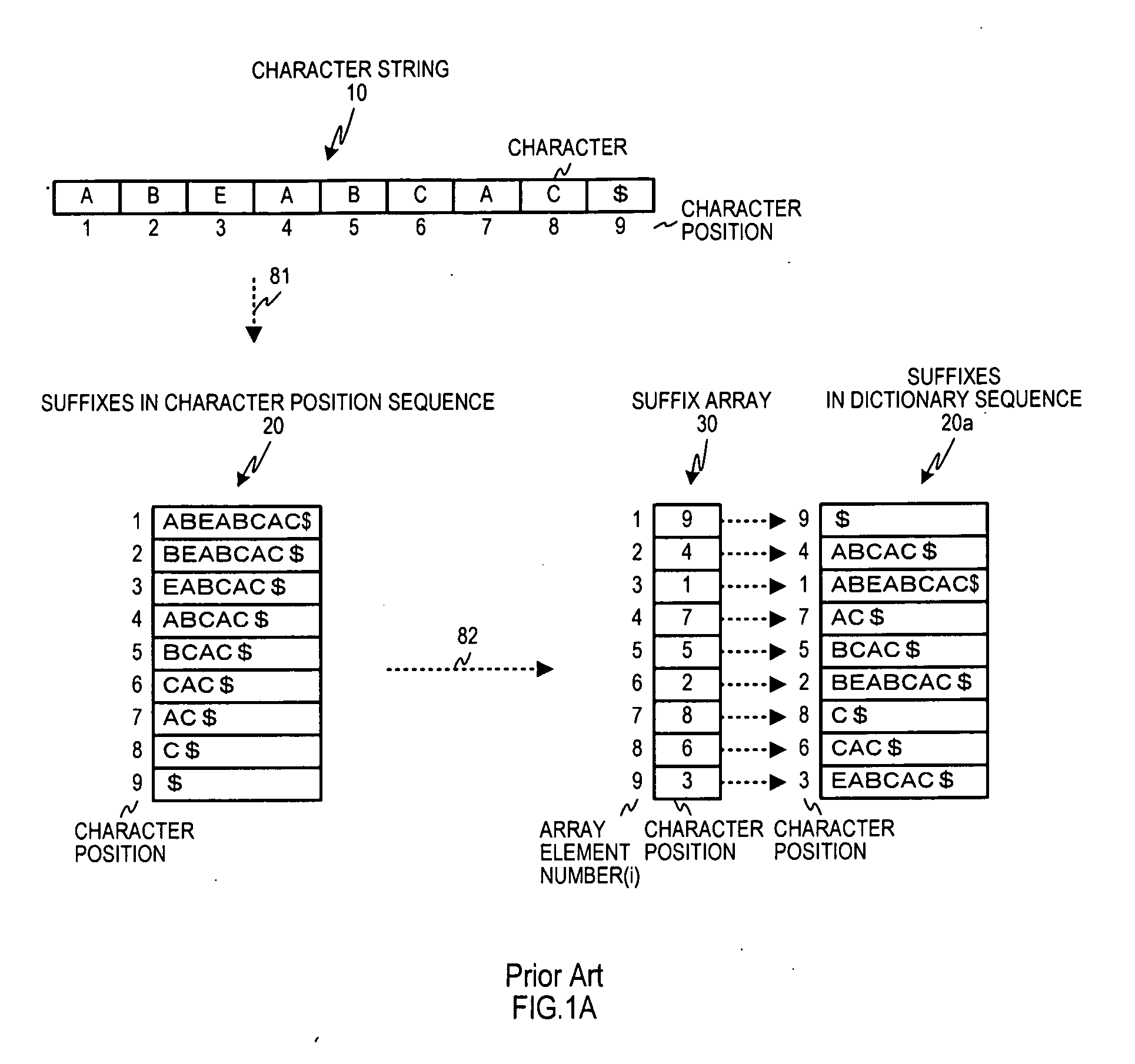
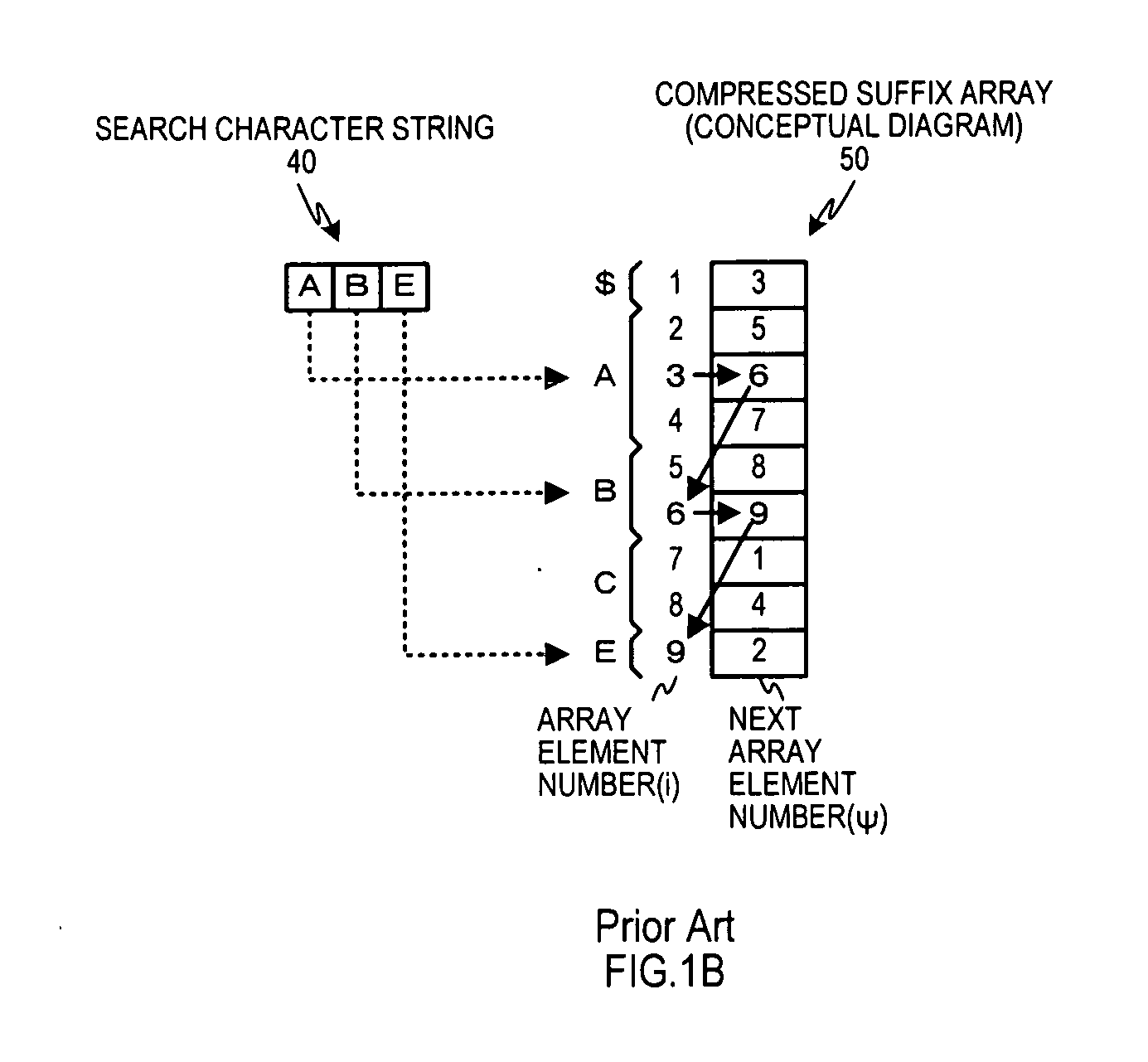
Code string search apparatus, search method, and program
ActiveUS20110191756A1Simple structureReduce processing burdenProgram controlSpecial data processing applicationsProgramming languageDead code
Owner:KOUSOKUYA
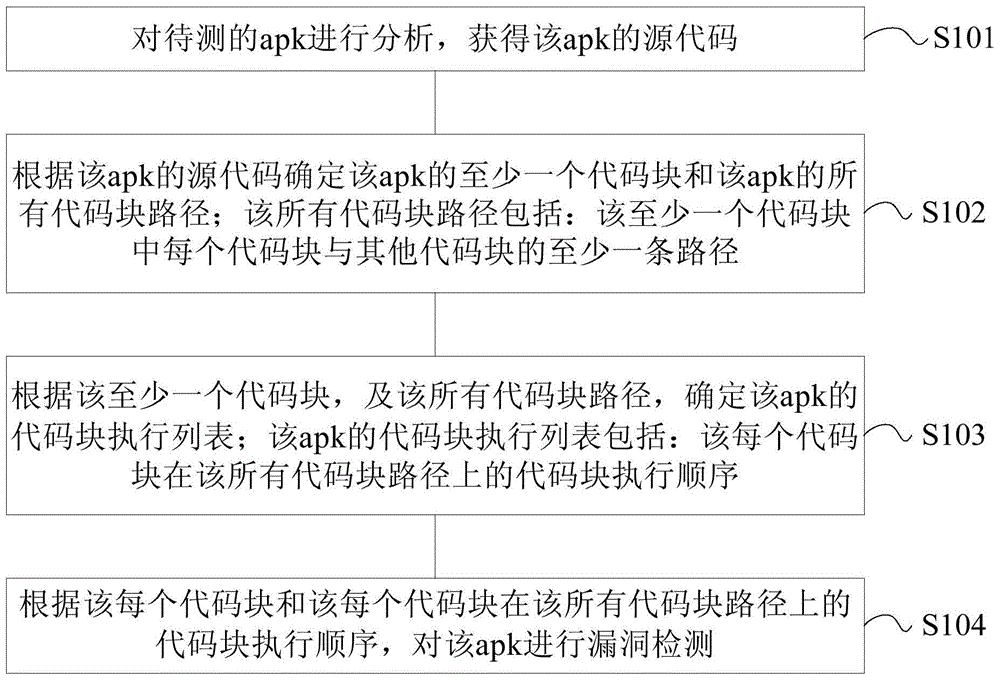
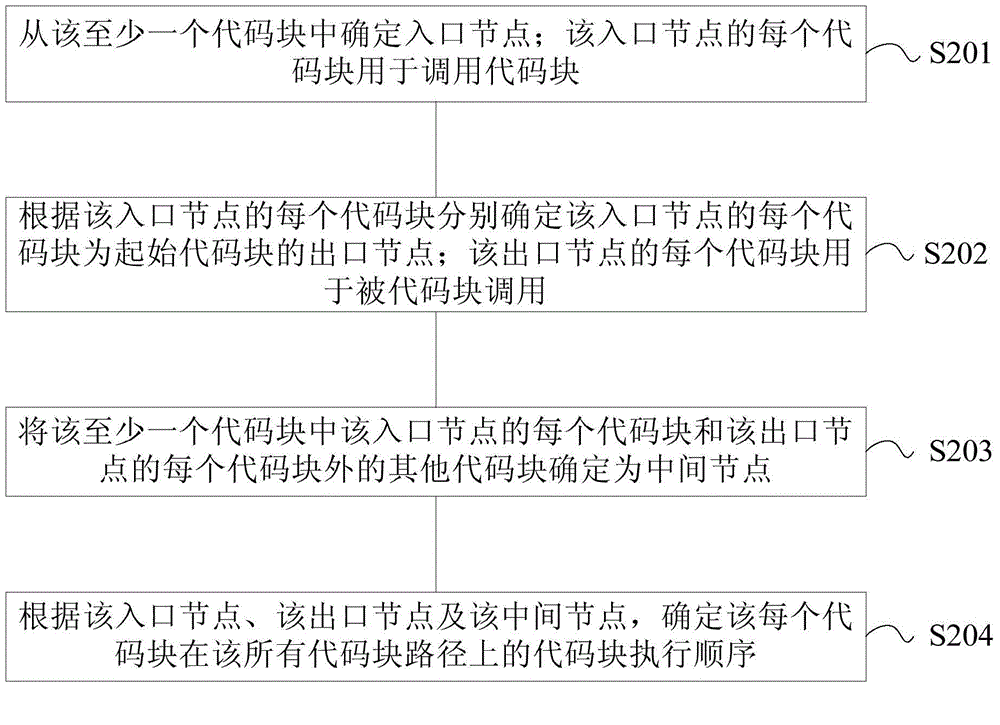
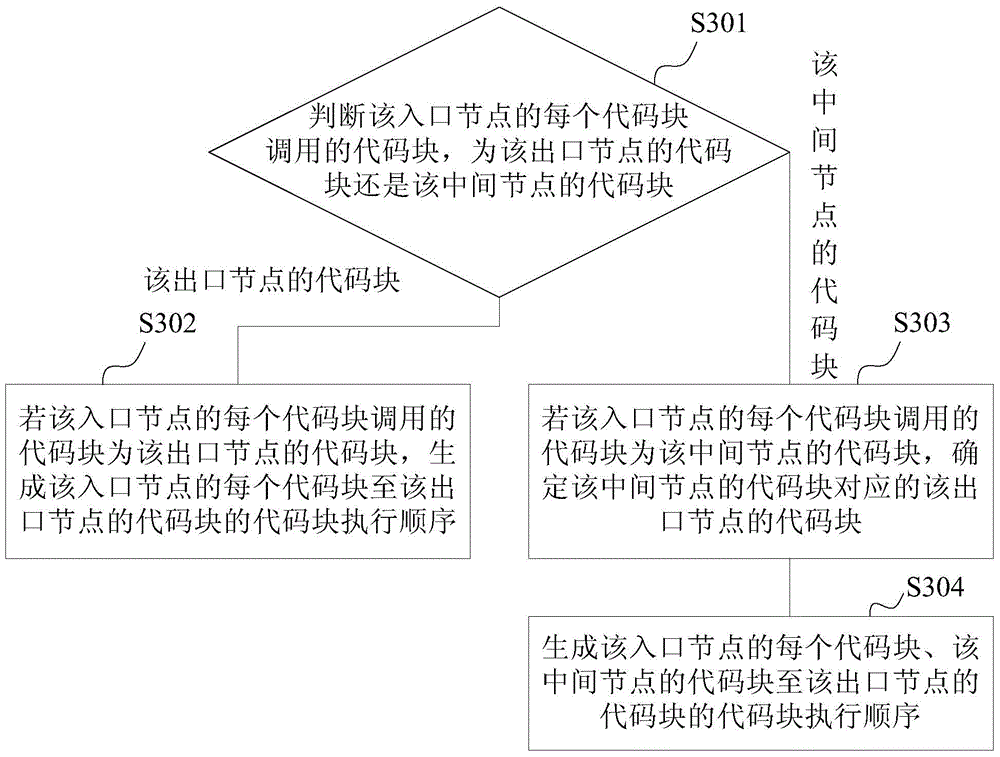
Detection method and apparatus for Android package
ActiveCN105989294AImprove detection accuracyPlatform integrity maintainanceCoding blockParallel computing
Embodiments of the invention provide a detection method and apparatus for an Android package. The detection method for the Android package provided by the embodiment of the invention comprises the steps of analyzing a to-be-detected apk (Android package) to obtain the source code of the apk; determining at least one code block of the apk and all code block paths of the apk according to the source code of the apk, wherein all the code block paths comprise at least one path of each code block and other code blocks in at least one code block; determining a code block execution list of the apk according at least one code block and all the code block paths, wherein the code block execution list of the apk comprises the code block execution sequence of each code block on all the code block paths; and performing vulnerability detection on the apk according to each code block and the code block execution sequence of each code block on all the code block paths. By adoption of the embodiments of the invention, the detection accuracy of vulnerability detection of the apk can be improved.
Owner:HONOR DEVICE CO LTD
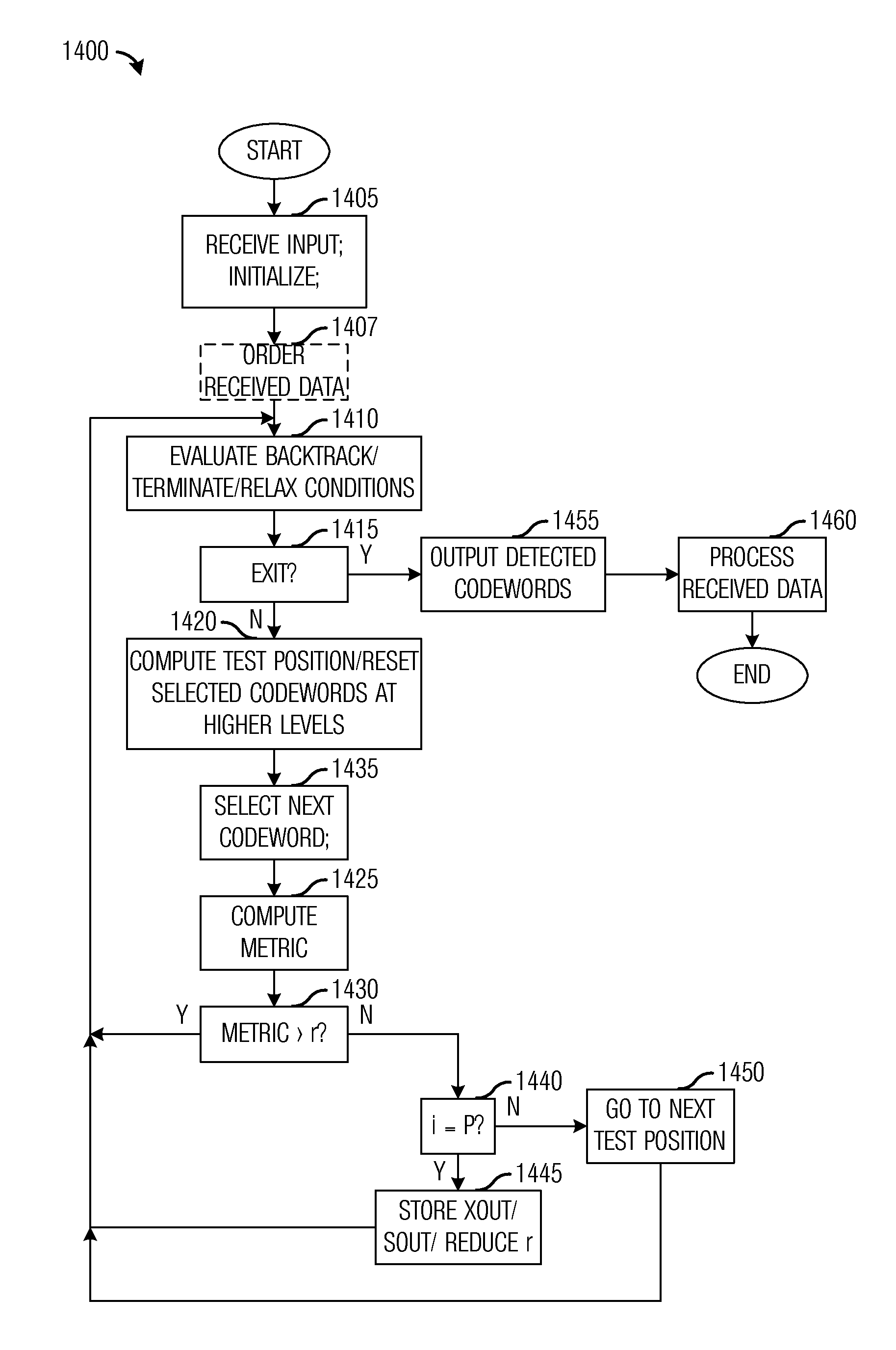
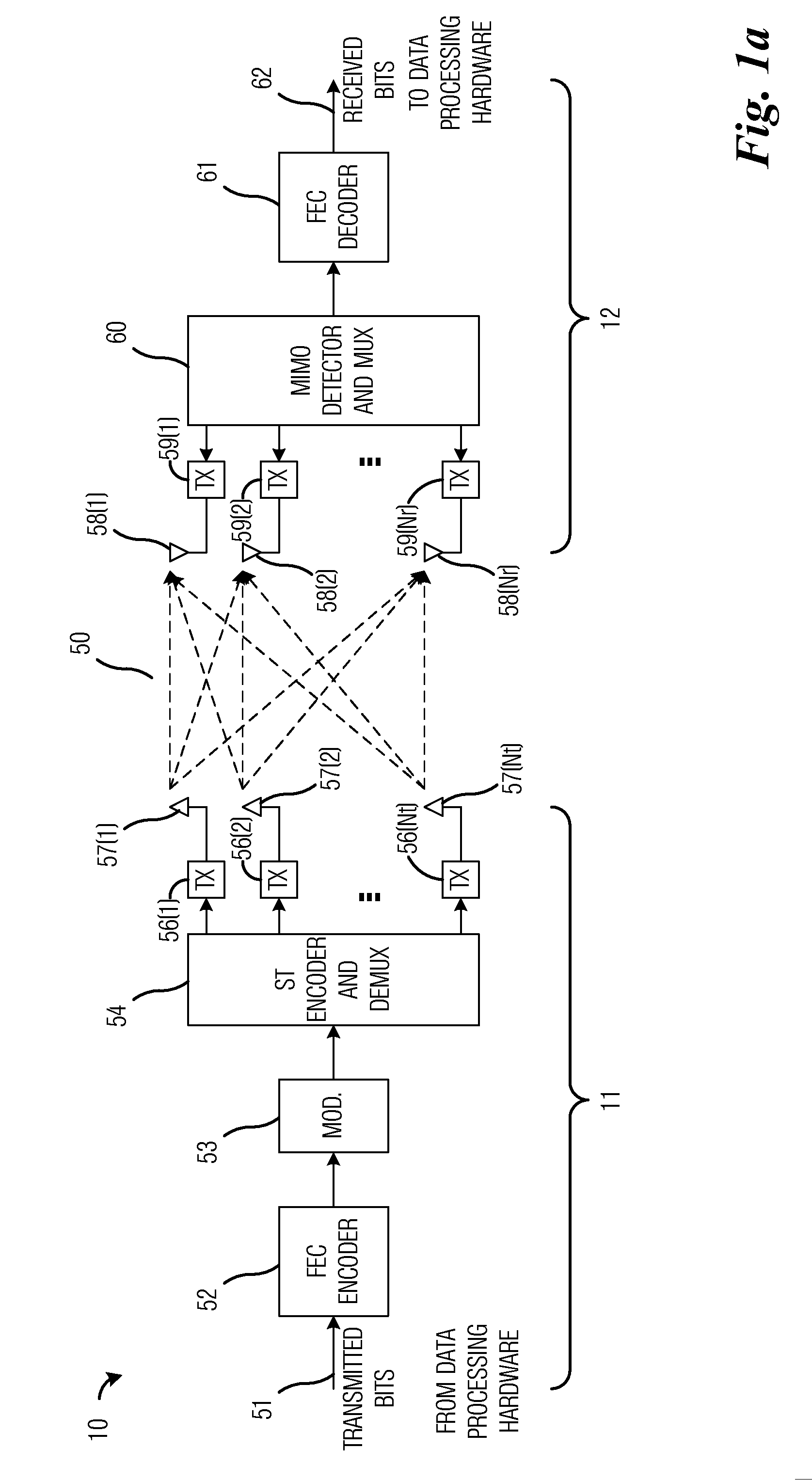
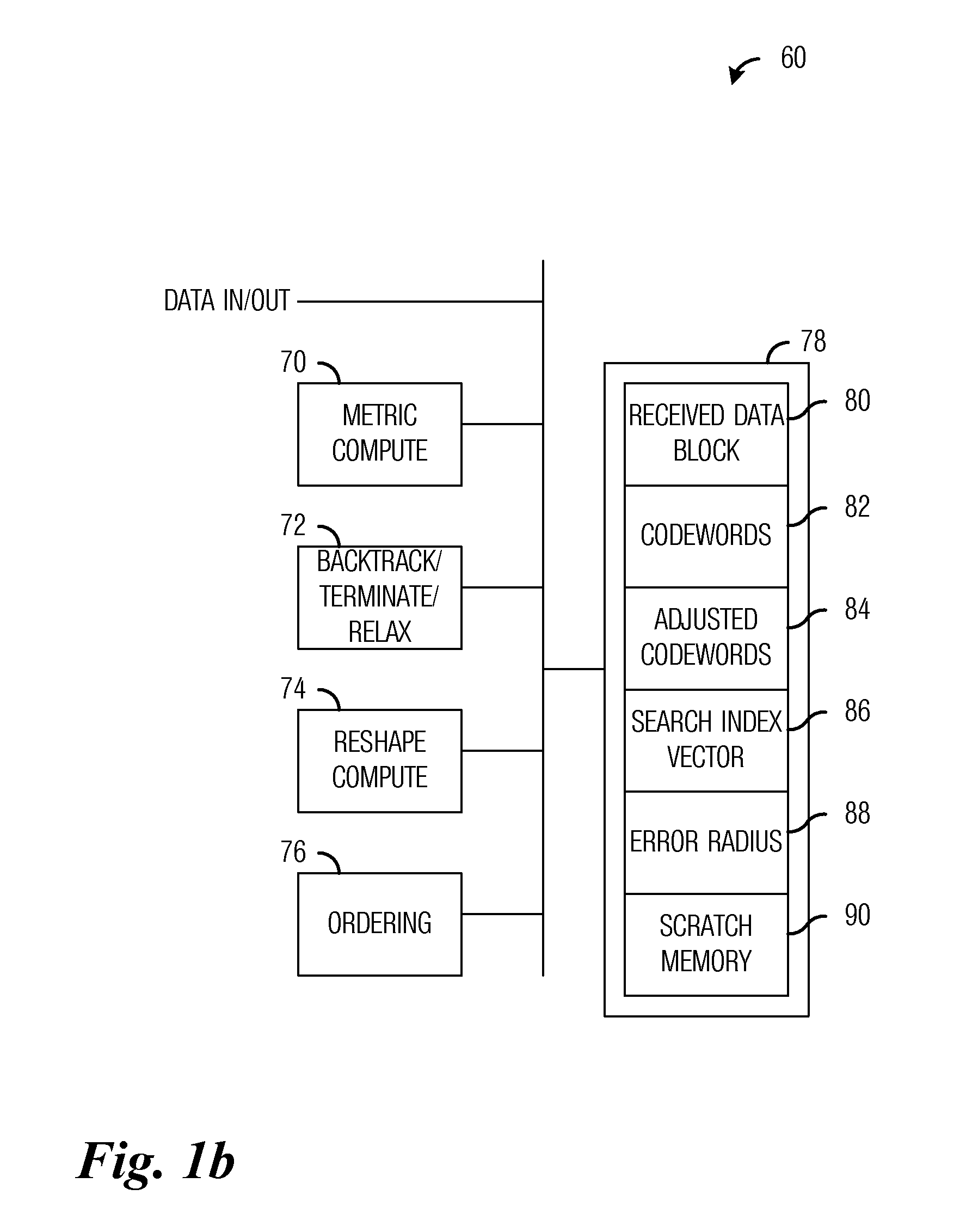
System and Method for Multiple Input, Multiple Output (MIMO) Communications
ActiveUS20110126067A1Reduce communication overheadIncrease communication channel capacityError prevention/detection by using return channelSpatial transmit diversityComputer hardwareMimo communication
A system and method for MIMO communications is provided. A method includes receiving a data block of P matrices from a transmitter, and determining if operating conditions are met. The method also includes if operating conditions are not met, computing a test position, selecting a codeword based on the test position, and computing a metric. The metric may then be compared with an error radius to determine a validity of the codeword. If the codeword is invalid, another codeword is selected. If the codeword is valid, then the codeword is stored if all matrices have been evaluated, else another matrix is selected for evaluation. If matrices earlier in the data block have untested codewords while all codewords for a matrix being evaluated have been tested, backtracking may be performed. After the codewords for the data block have been found, the stored data may be outputted and processed.
Owner:FUTUREWEI TECH INC
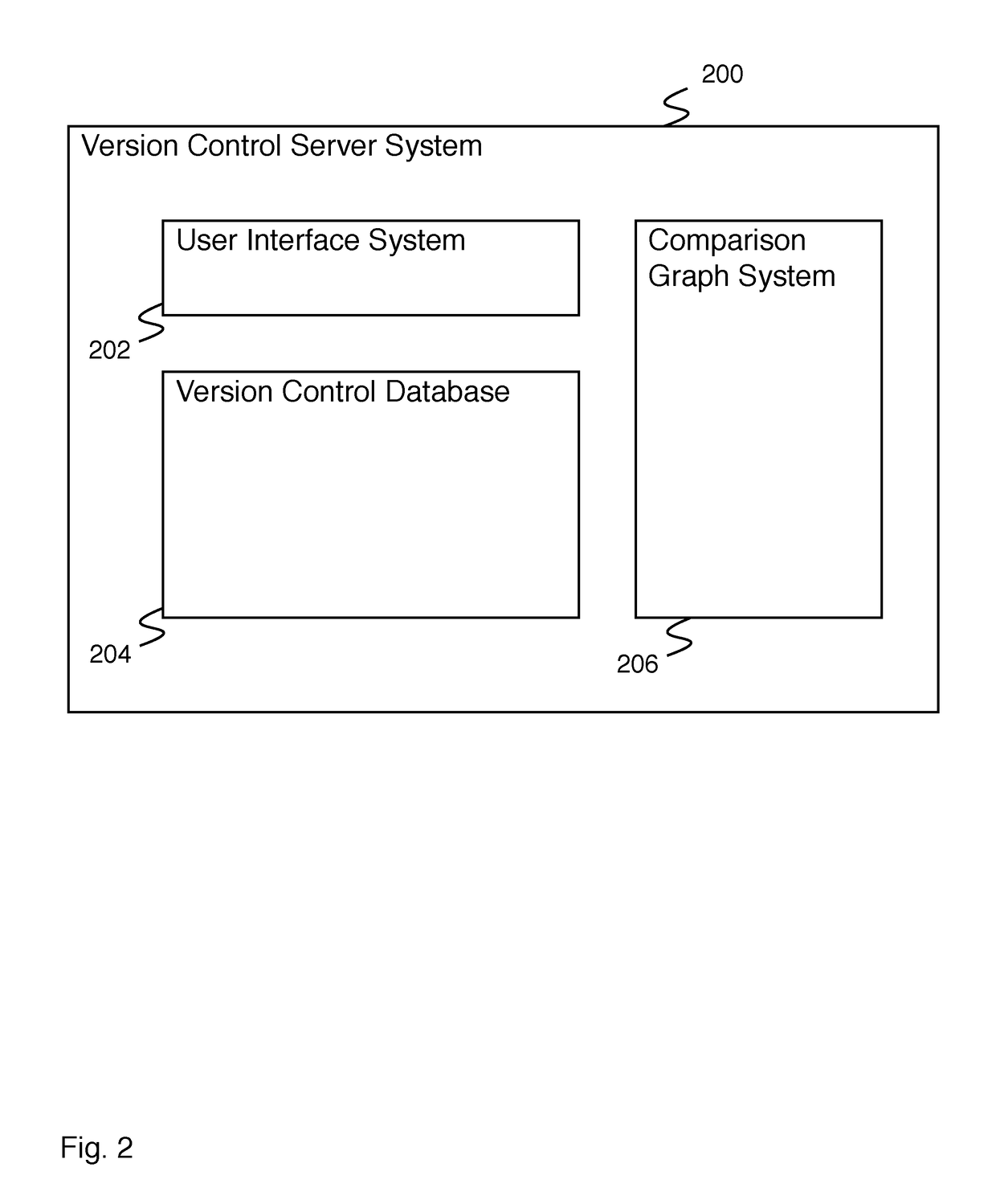
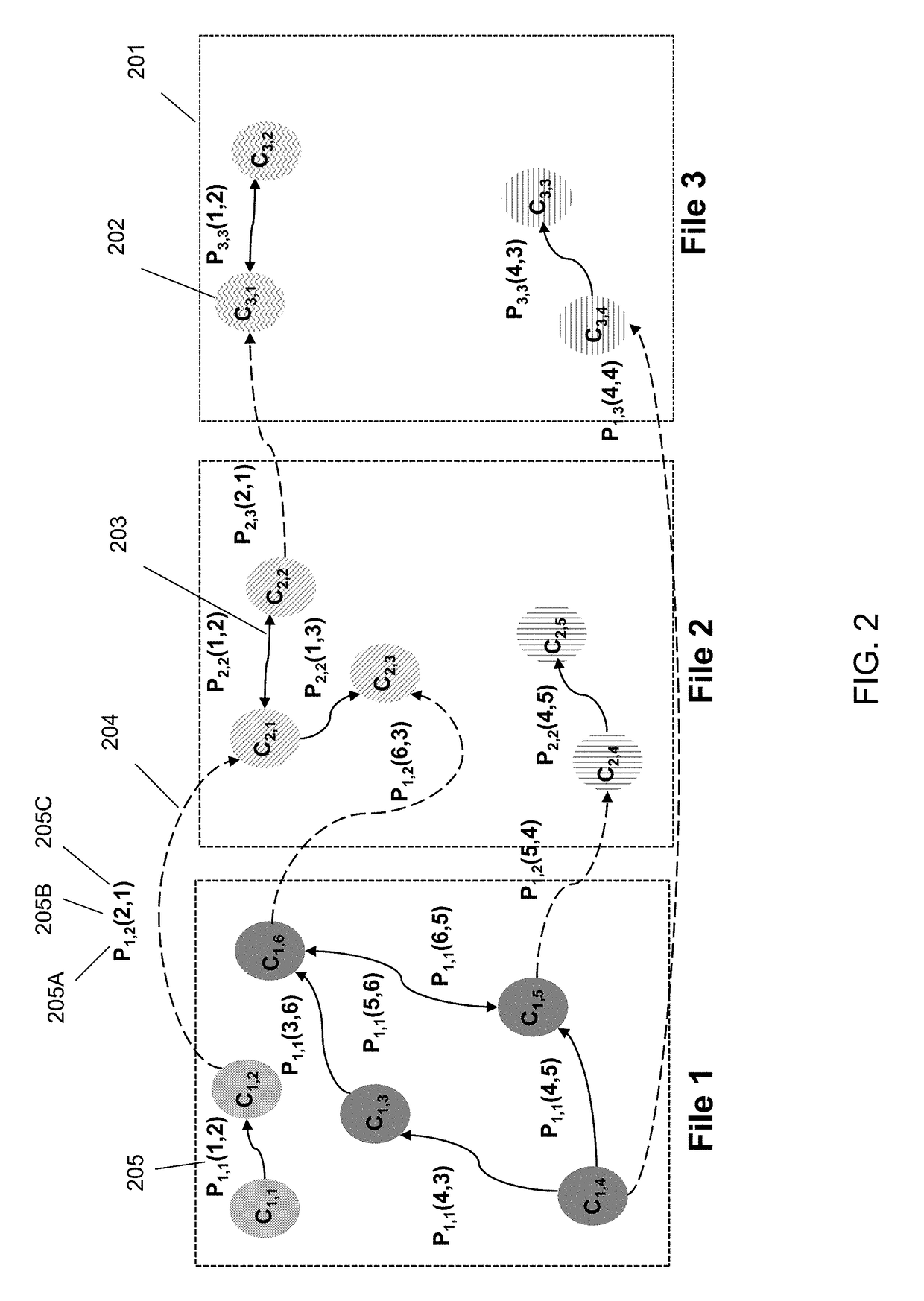
Comparison graph
A comparison graph is disclosed. A system for comparing code branches comprises a code branch separator for determining a first set of commits in a first code branch that are not common to a second code branch, and determining a second set of commits in the second code branch that are not common to the first code branch; and a user interface determiner for determining a display of the first set of commits and the second set of commits.
Owner:MICROSOFT TECH LICENSING LLC
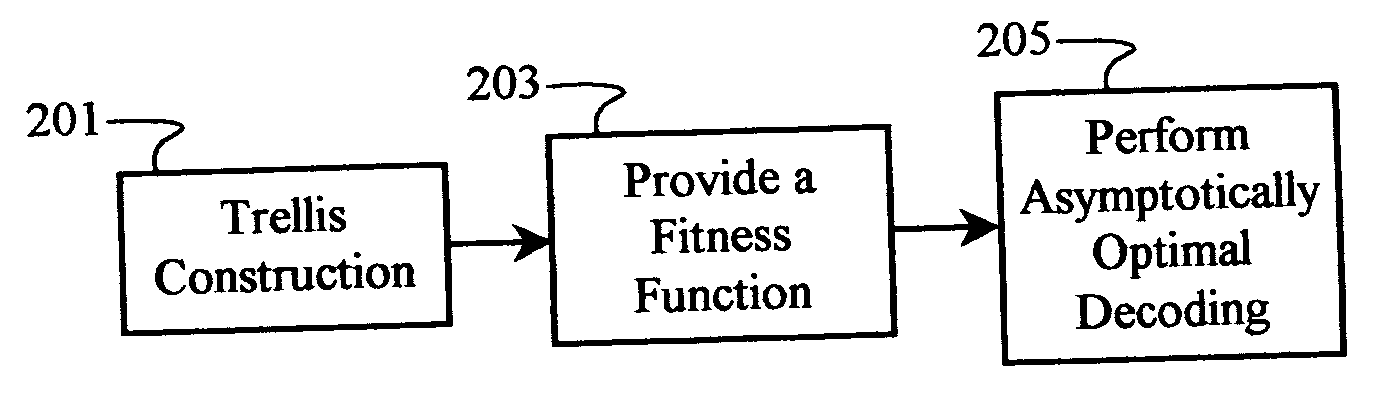
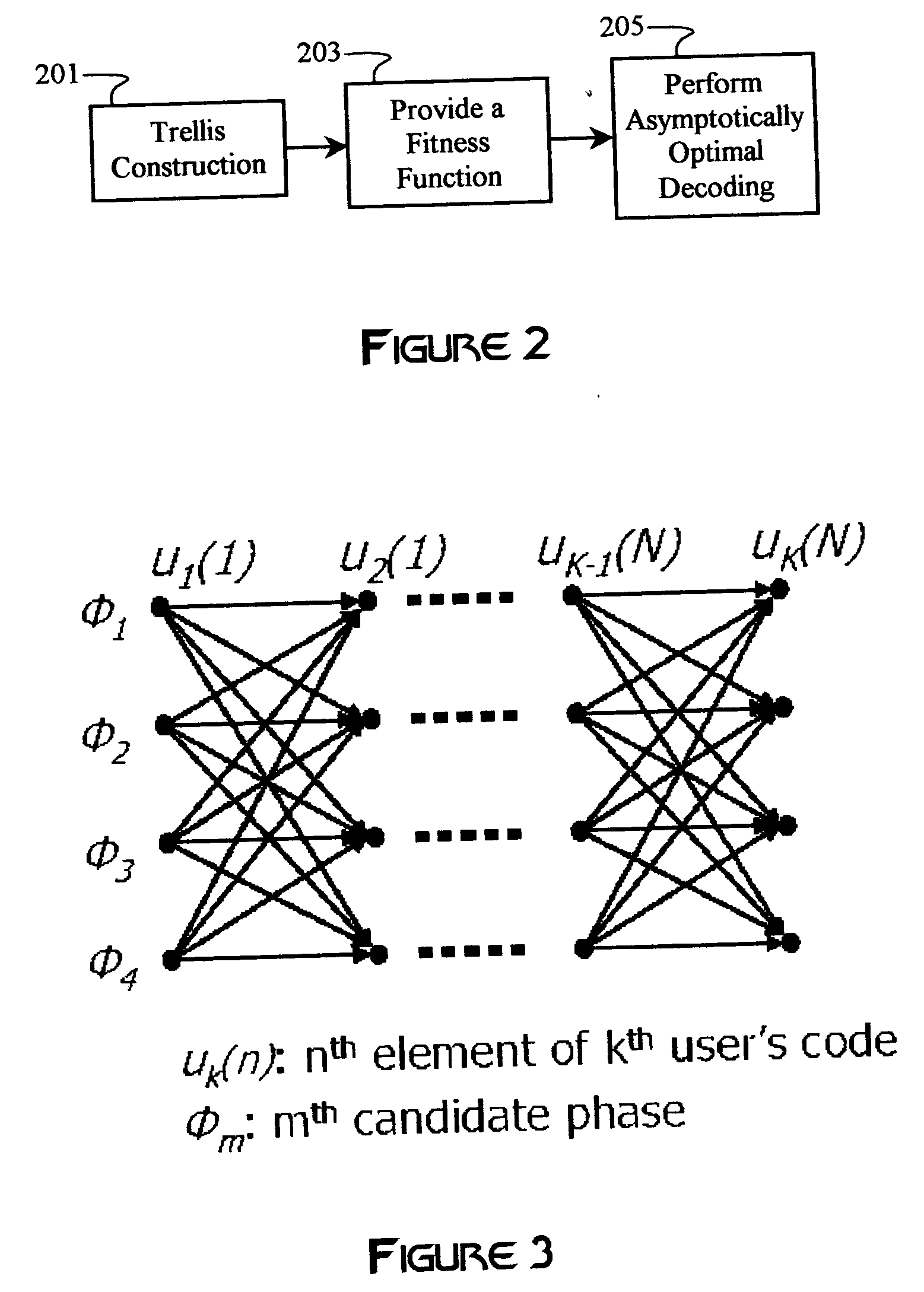
Multiple-access code generation
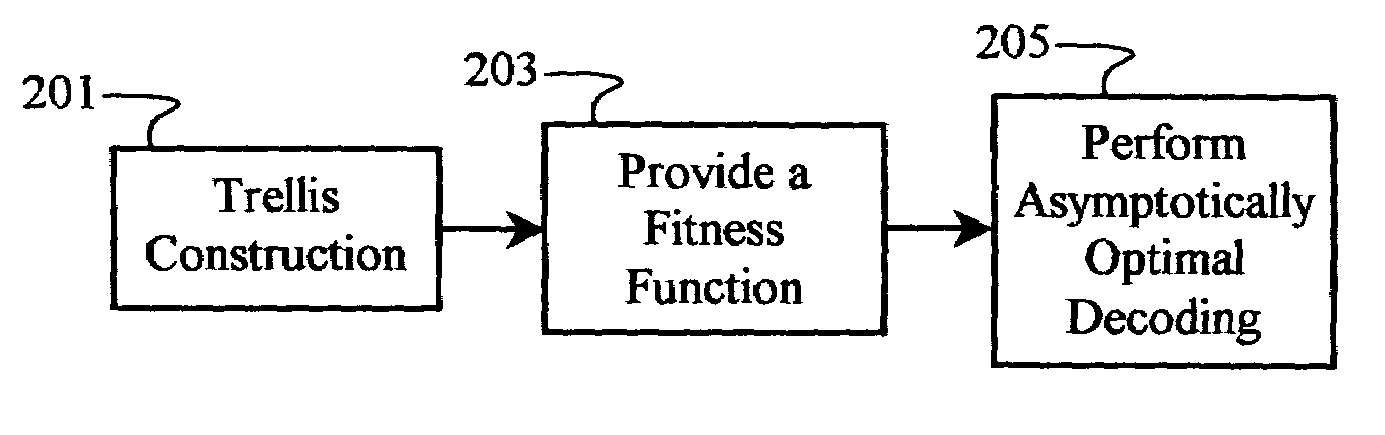
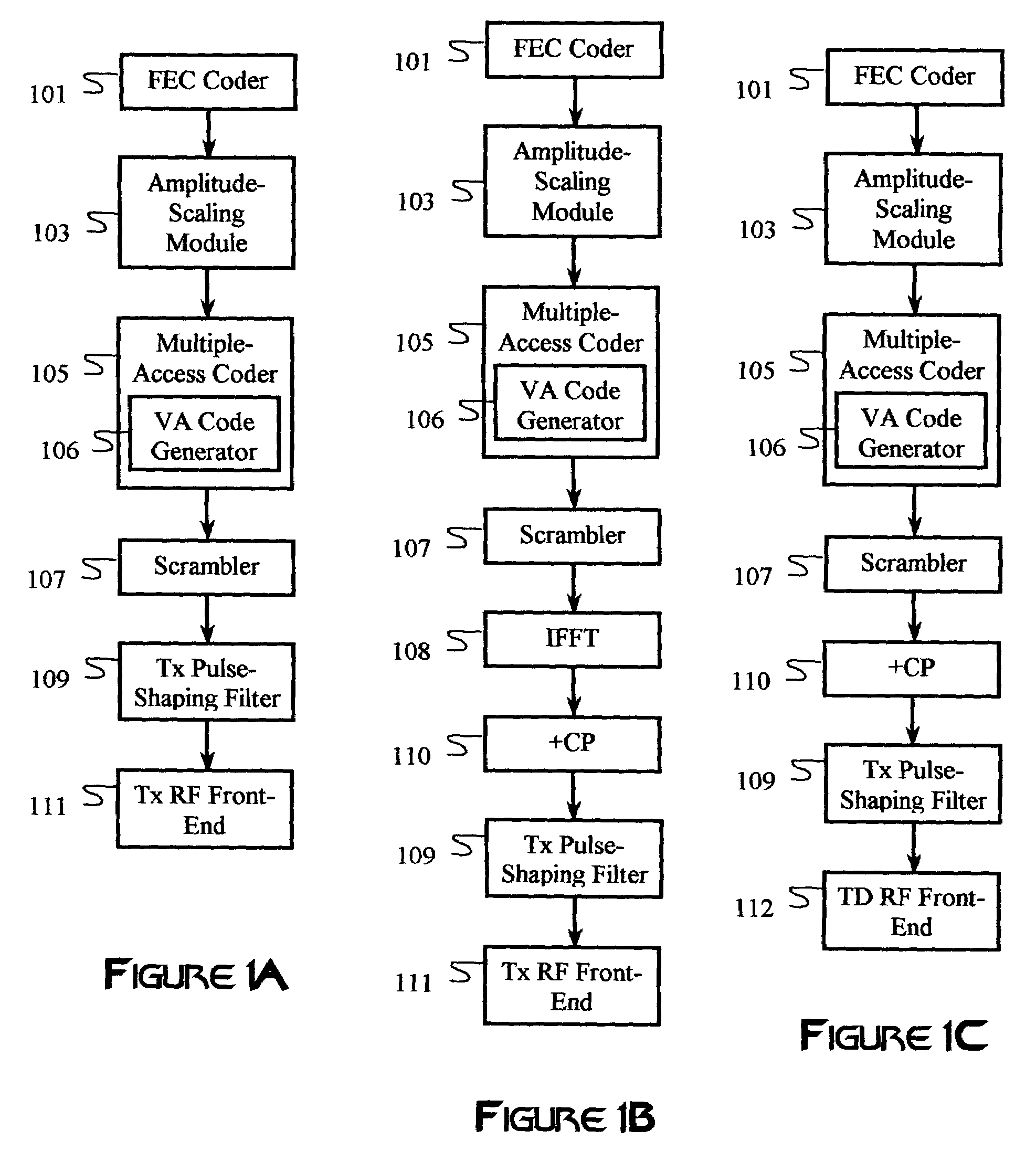
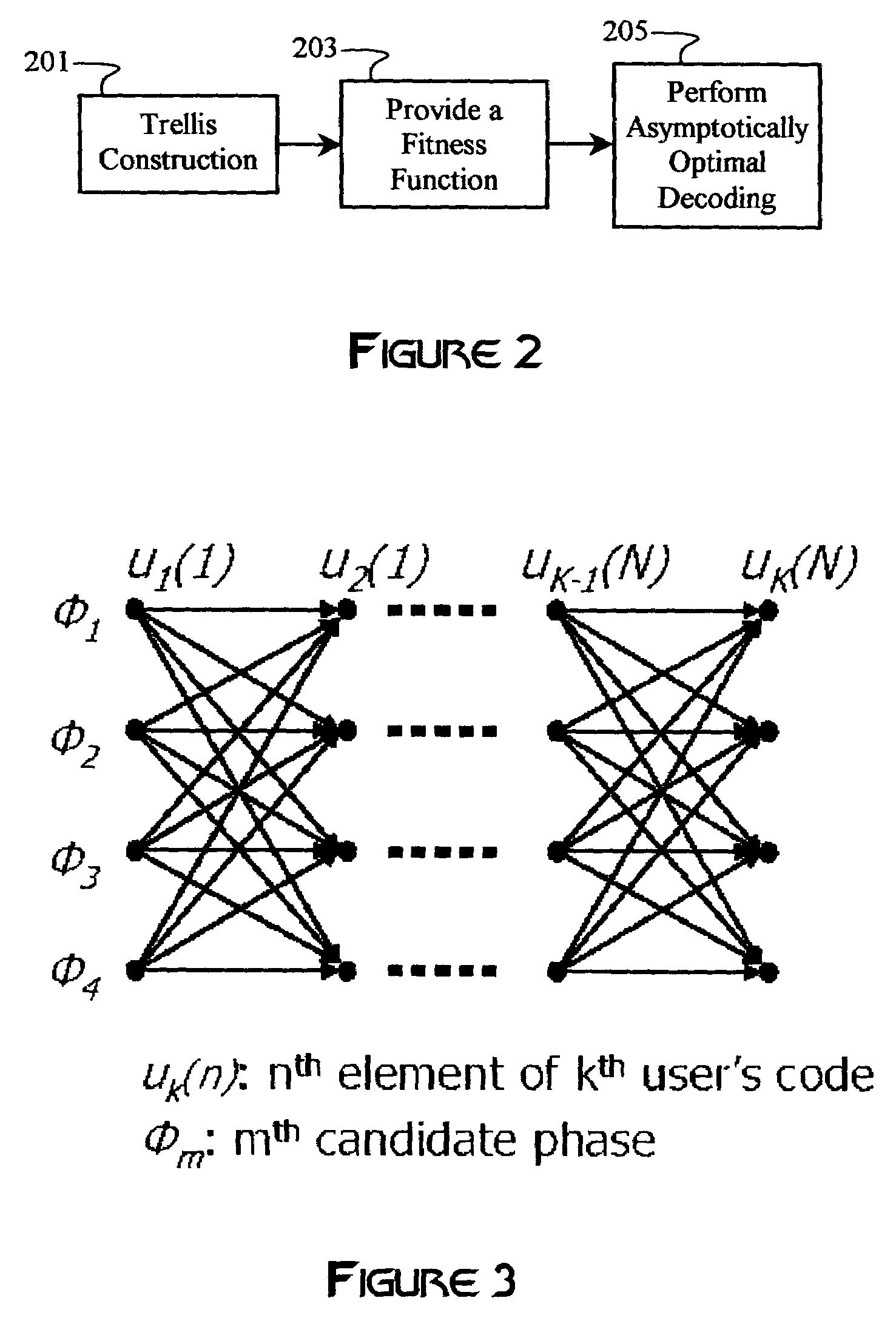
InactiveUS20060239371A1Solve complex processQuick updateData representation error detection/correctionError preventionTheoretical computer scienceViterbi algorithm
Multiple-access codes are generated using an asymptotically optimal decoding algorithm, such as the Viterbi algorithm. A trellis may be constructed using a number of desired users, at least one code length, and a number of code-chip parameters. A fitness function is derived from a mathematical relationship between the multiple-access codes, and may include some measure of correlation of the codes. The multiple-access codes correspond to paths having optimal path metrics derived from the fitness function. Multiple iterations through the trellis may be performed to refine a selection of multiple-access codes.
Owner:KANSAS STATE UNIV RES FOUND
Method and apparatus for conveying messages and simple patterns in communications network
InactiveUS20050195927A1Small sizeLoading of pattern can be fastTelevision system detailsError preventionComputer networkTheoretical computer science
Owner:NOKIA CORP
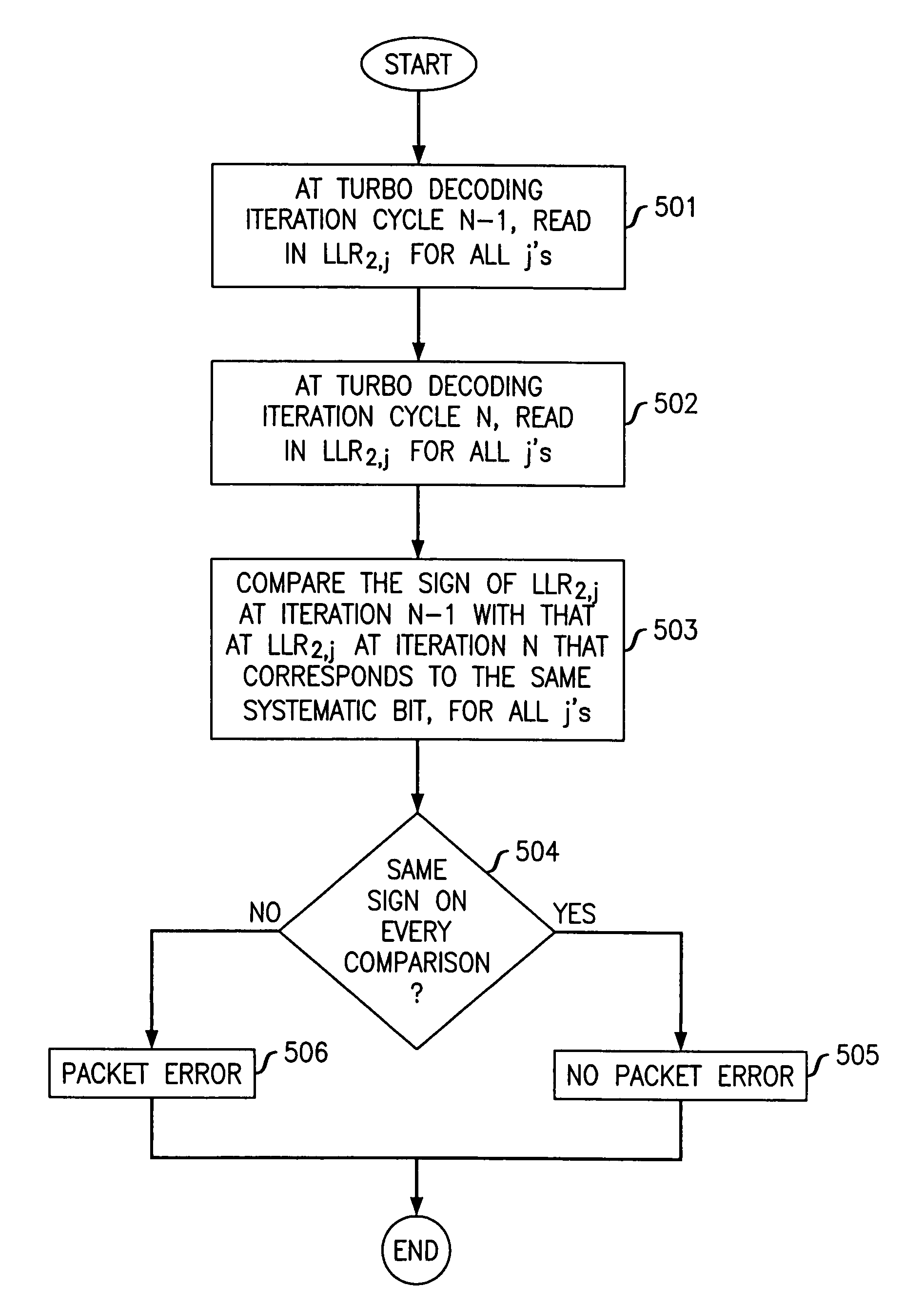
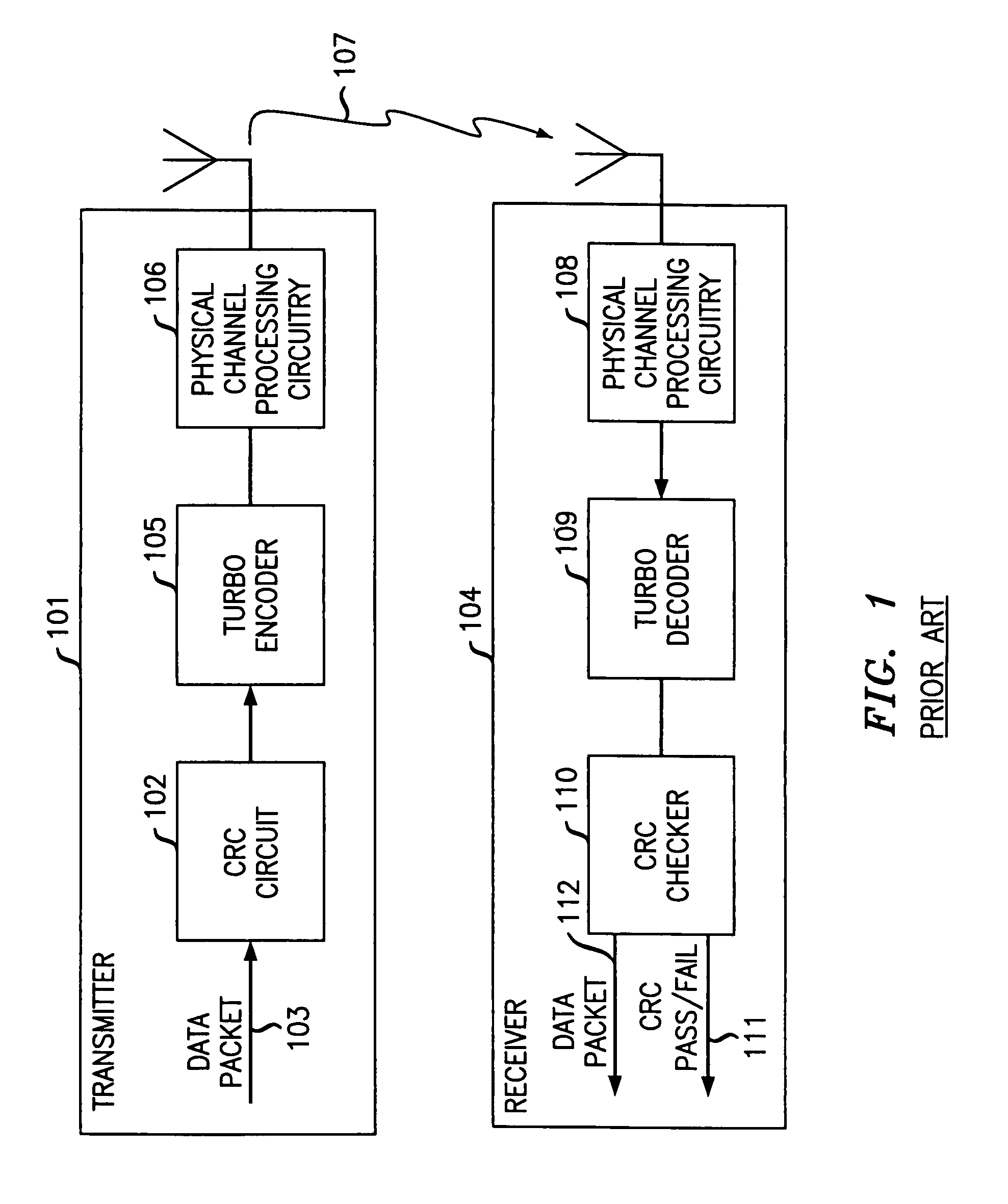
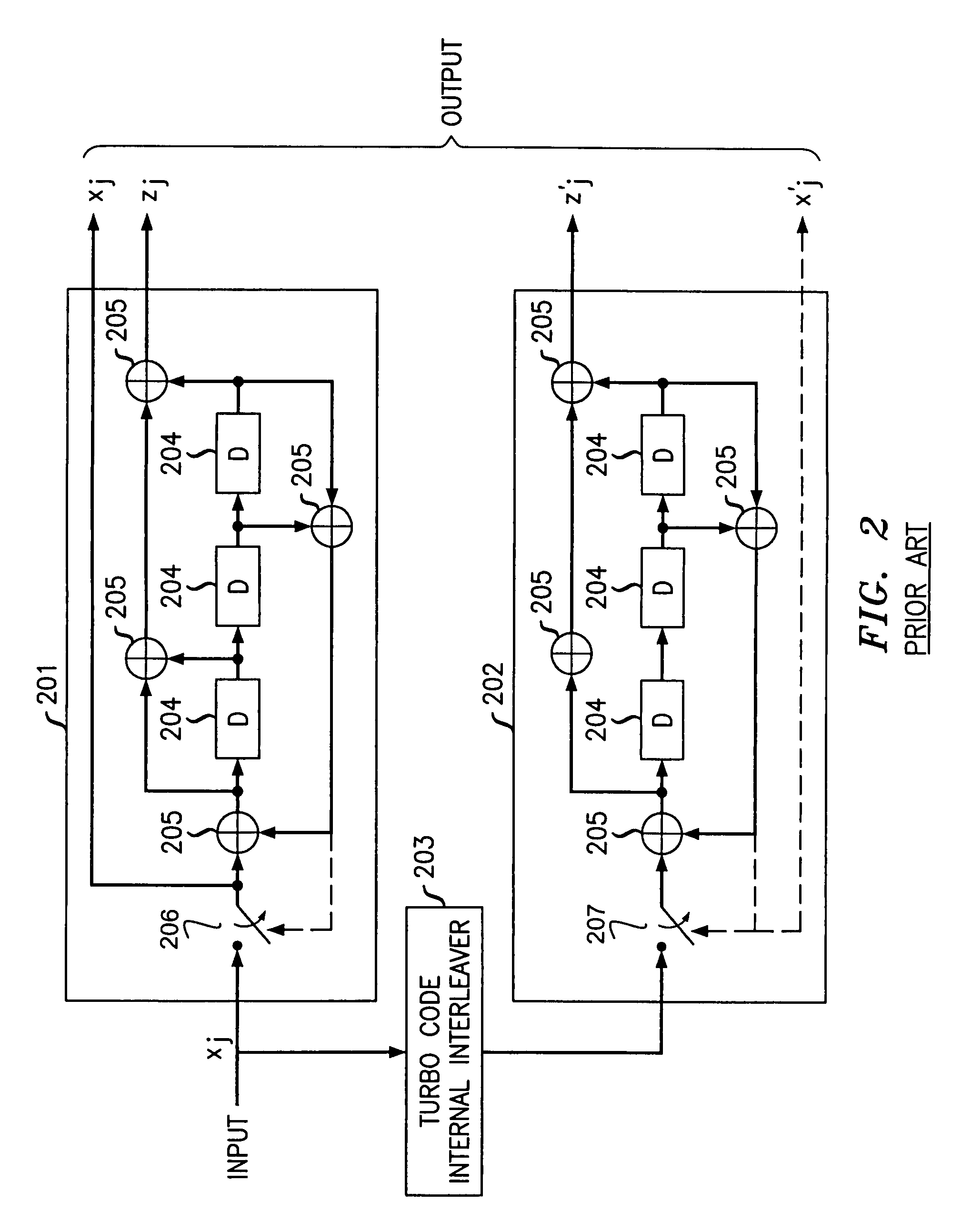
Method and apparatus for detecting a packet error in a wireless communications system with minimum overhead using embedded error detection capability of turbo code
InactiveUS7565594B2Data representation error detection/correctionCode conversionComputer hardwareCommunications system
The need for separate CRC bits is eliminated by taking advantage of what has been determined to be an embedded error detection capability in a turbo code itself to perform error detection following turbo decoding. Specifically, since the two constituent encoders of a turbo encoder that are used to encode a data packet produce two systematic codes that share the same systematic bits one code, one is used to serve as the parity check for the other. The sign of the log likelihood ratio (LLR) of each systematic bit in a block of decoded data calculated at the end of a turbo decoding cycle is compared with the sign of the LLR of each corresponding bit that was calculated at a previous turbo decoding cycle. If the signs of the LLRs for each comparison do not agree, then a packet error is determined to have occurred; otherwise no packet error is detected.
Owner:WSOU INVESTMENTS LLC
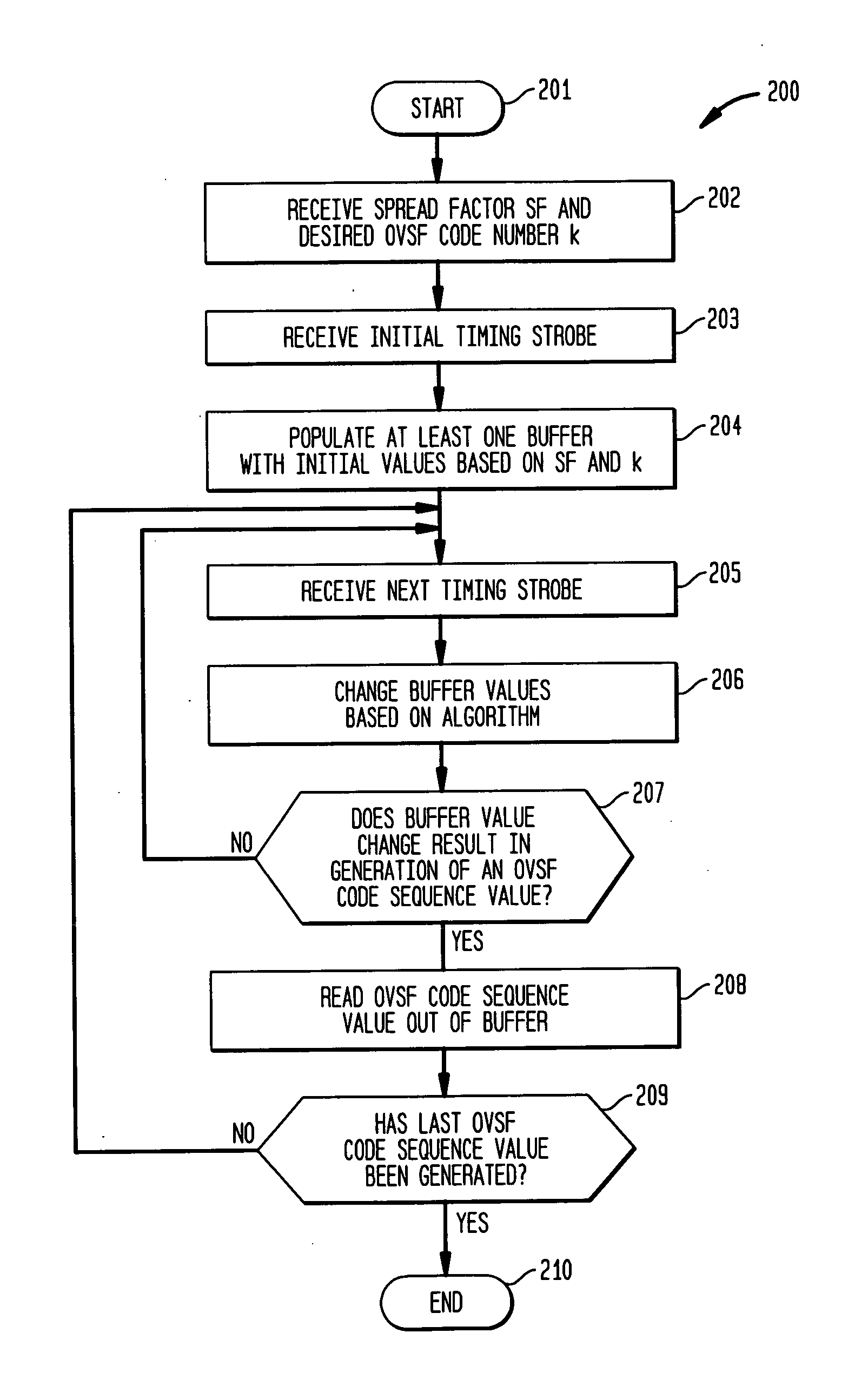
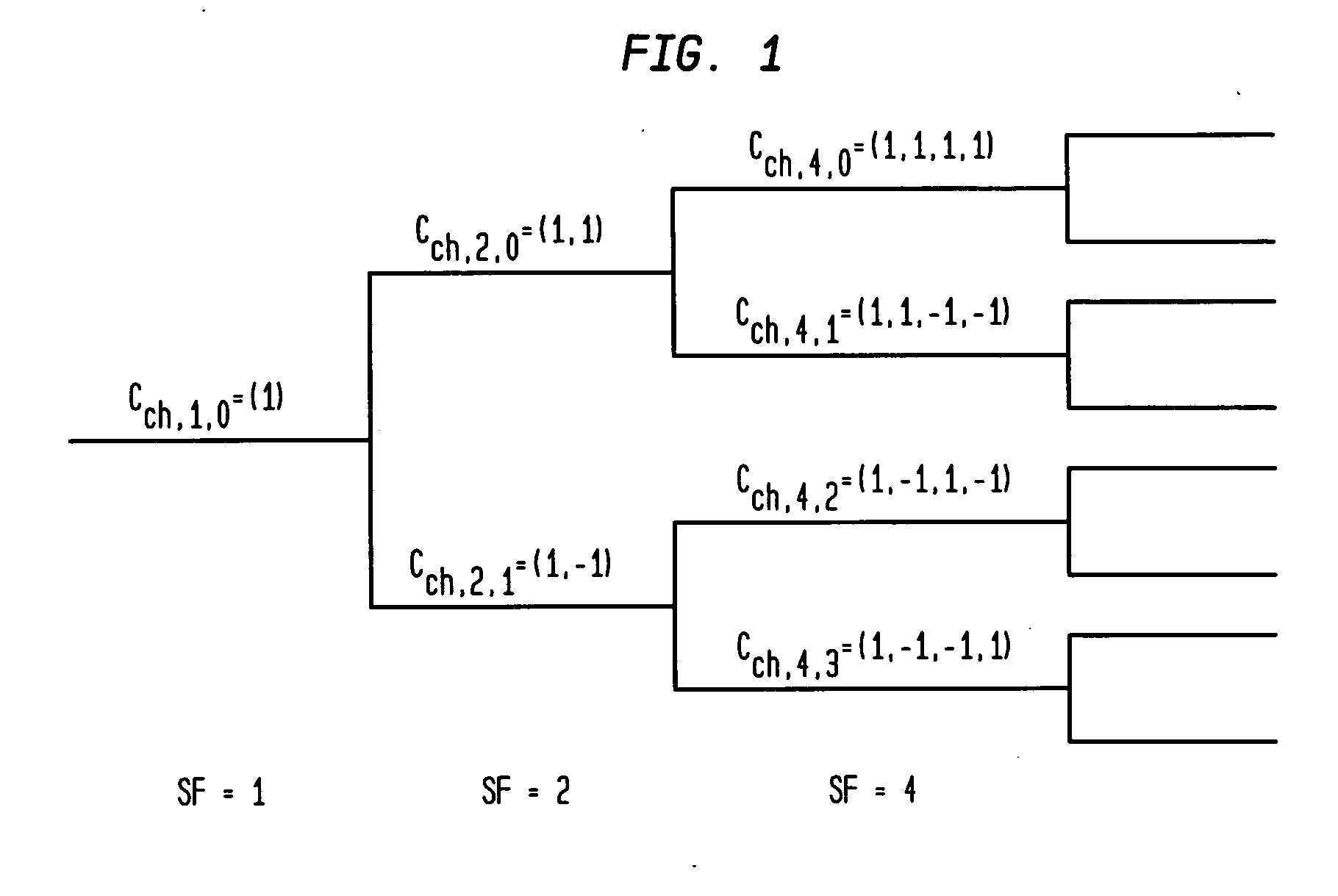
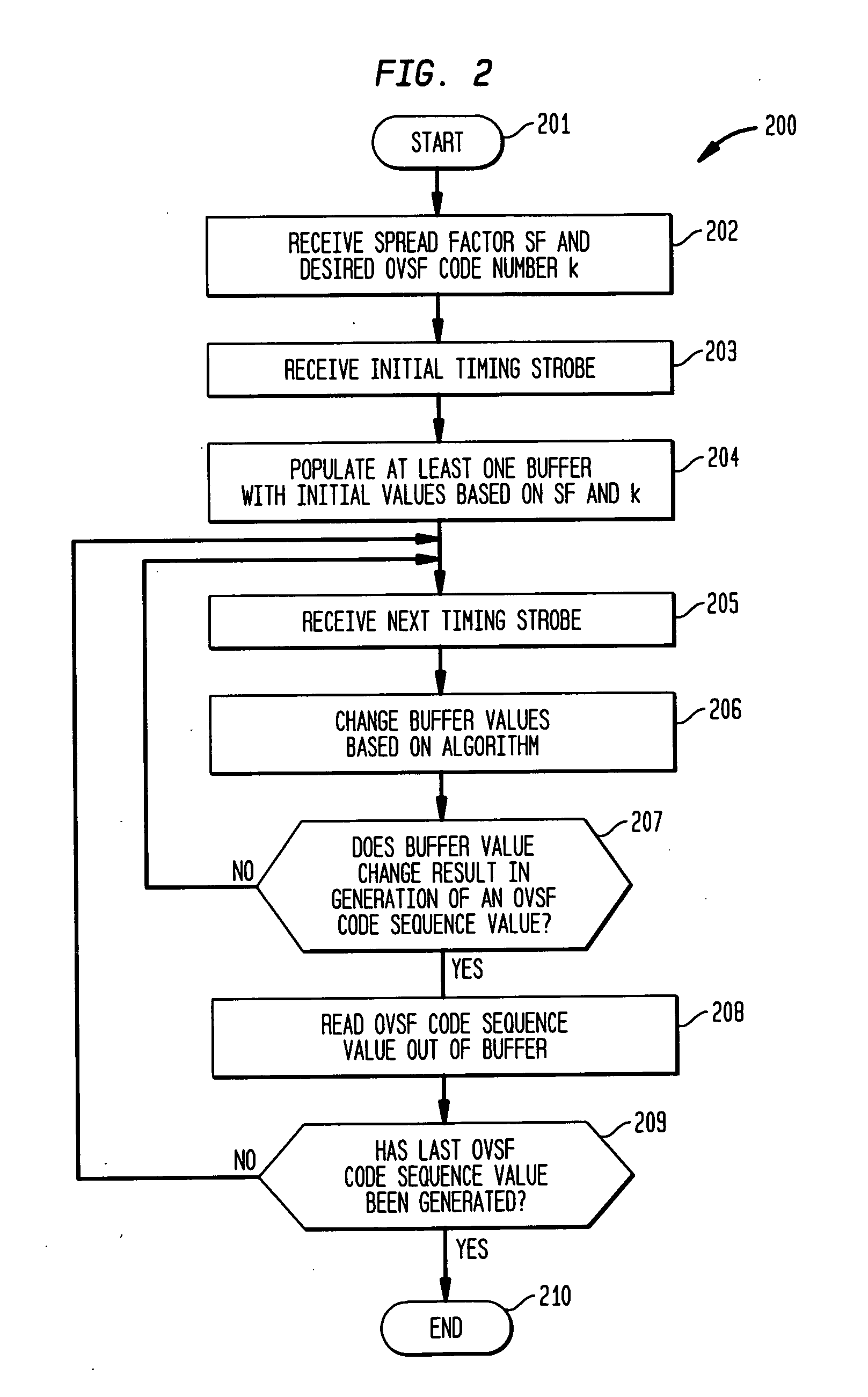
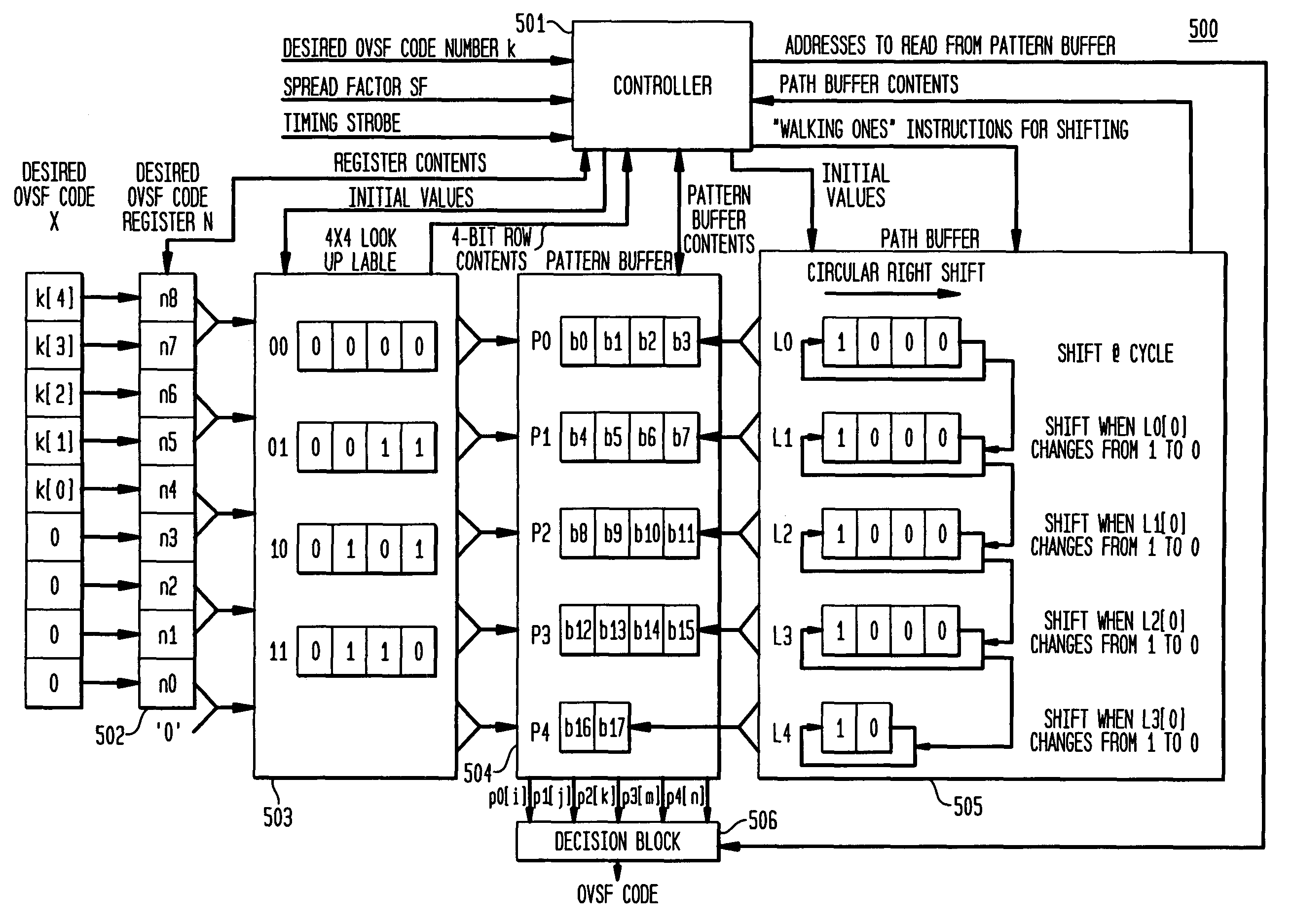
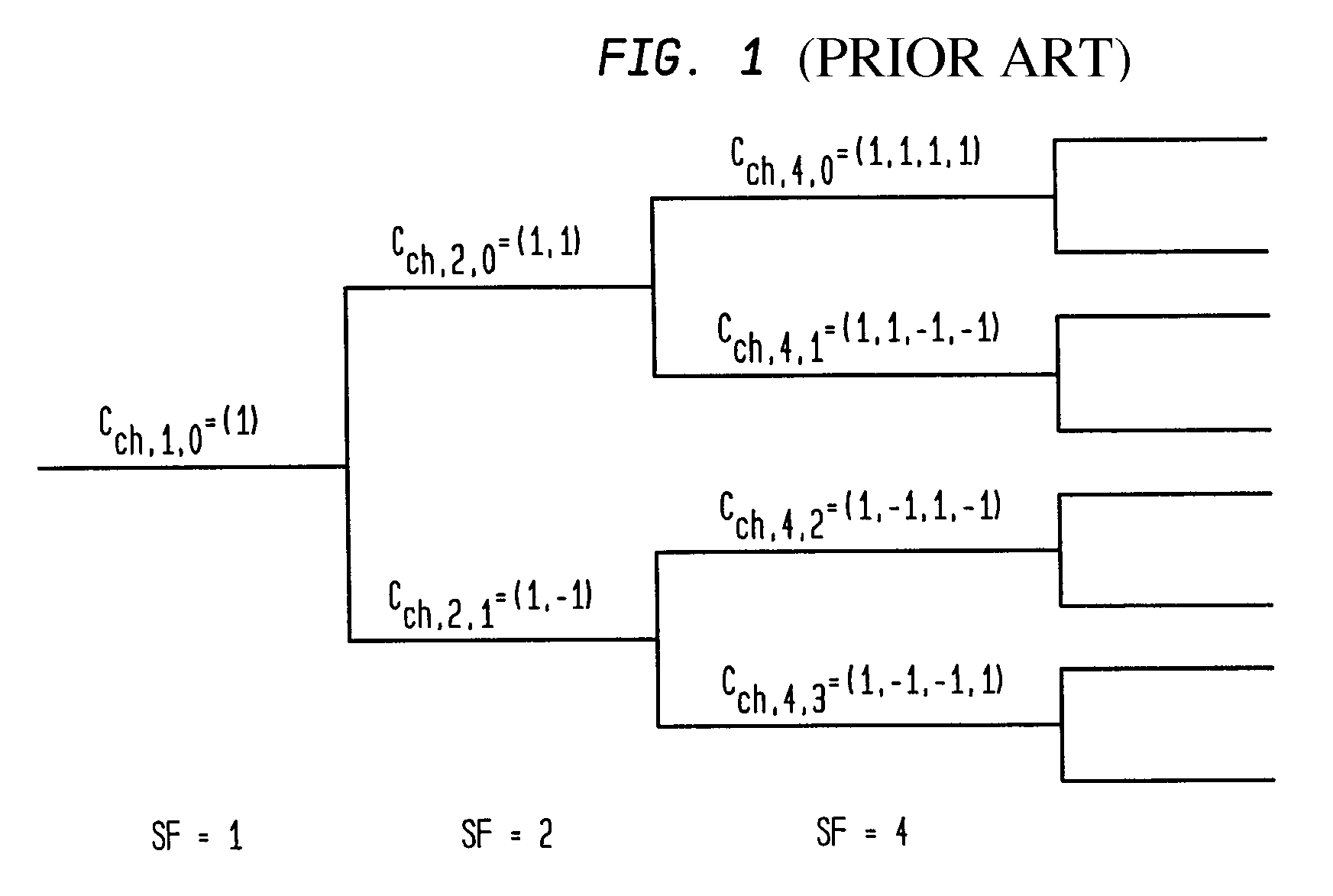
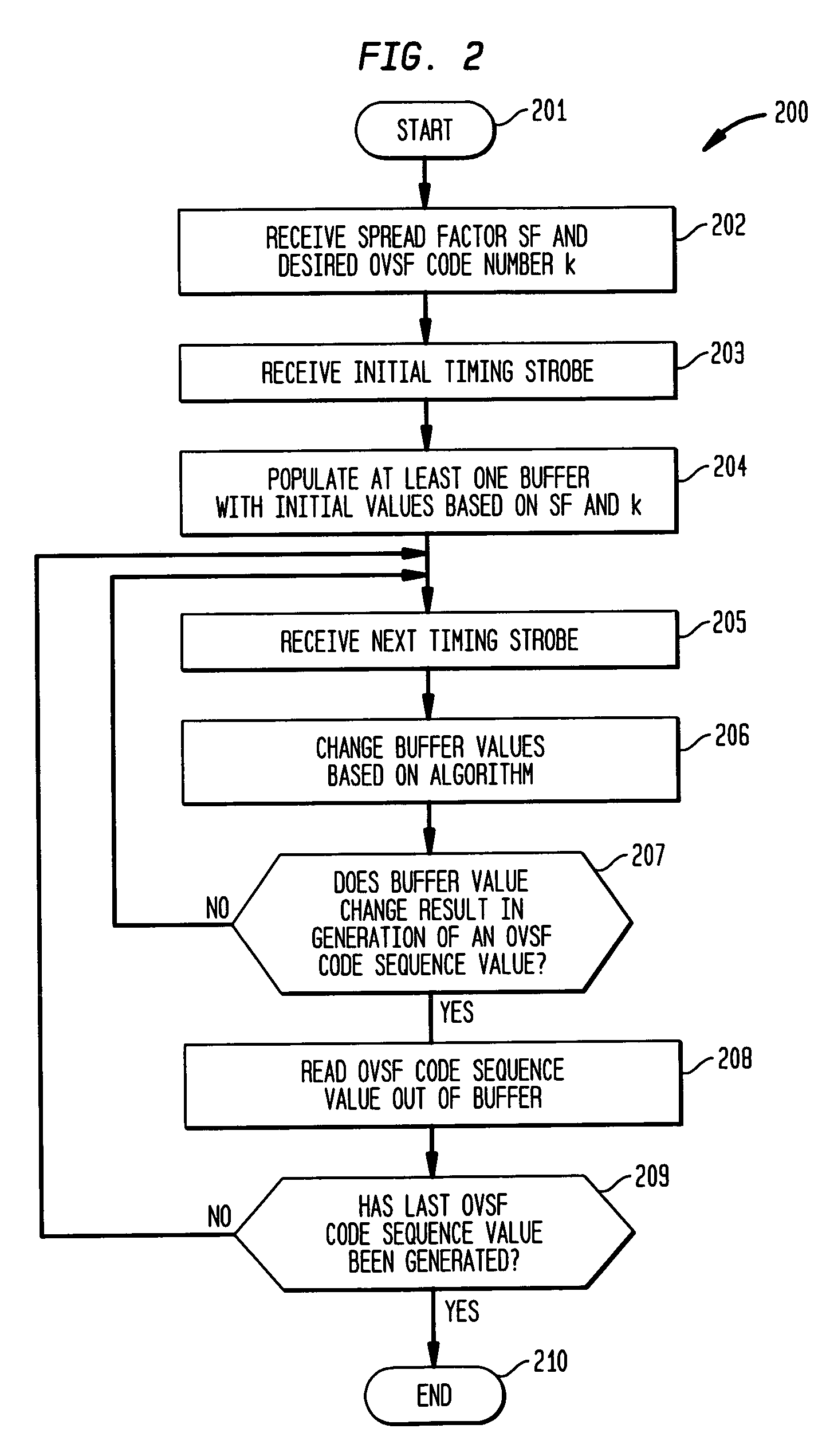
Buffer-based generation of OVSF code sequences
A method of generating a code sequence comprises populating at least one buffer with initial values based on a received spreading factor and desired code index; receiving a timing strobe; changing the values in the at least one buffer upon receipt of the timing strobe based on an algorithm that is independent of any count value associated with the timing strobe; and outputting at least one code sequence value based on the values in the at least one buffer. An apparatus for generating a code sequence comprises means for populating at least one buffer with initial values based on a received spreading factor and desired code index; means for receiving a timing strobe; means for changing the values in the at least one buffer upon receipt of the timing strobe based on an algorithm that is independent of any count value associated with the timing strobe; and means for outputting at least one code sequence value based on the values in the at least one buffer.
Owner:AVAGO TECH INT SALES PTE LTD
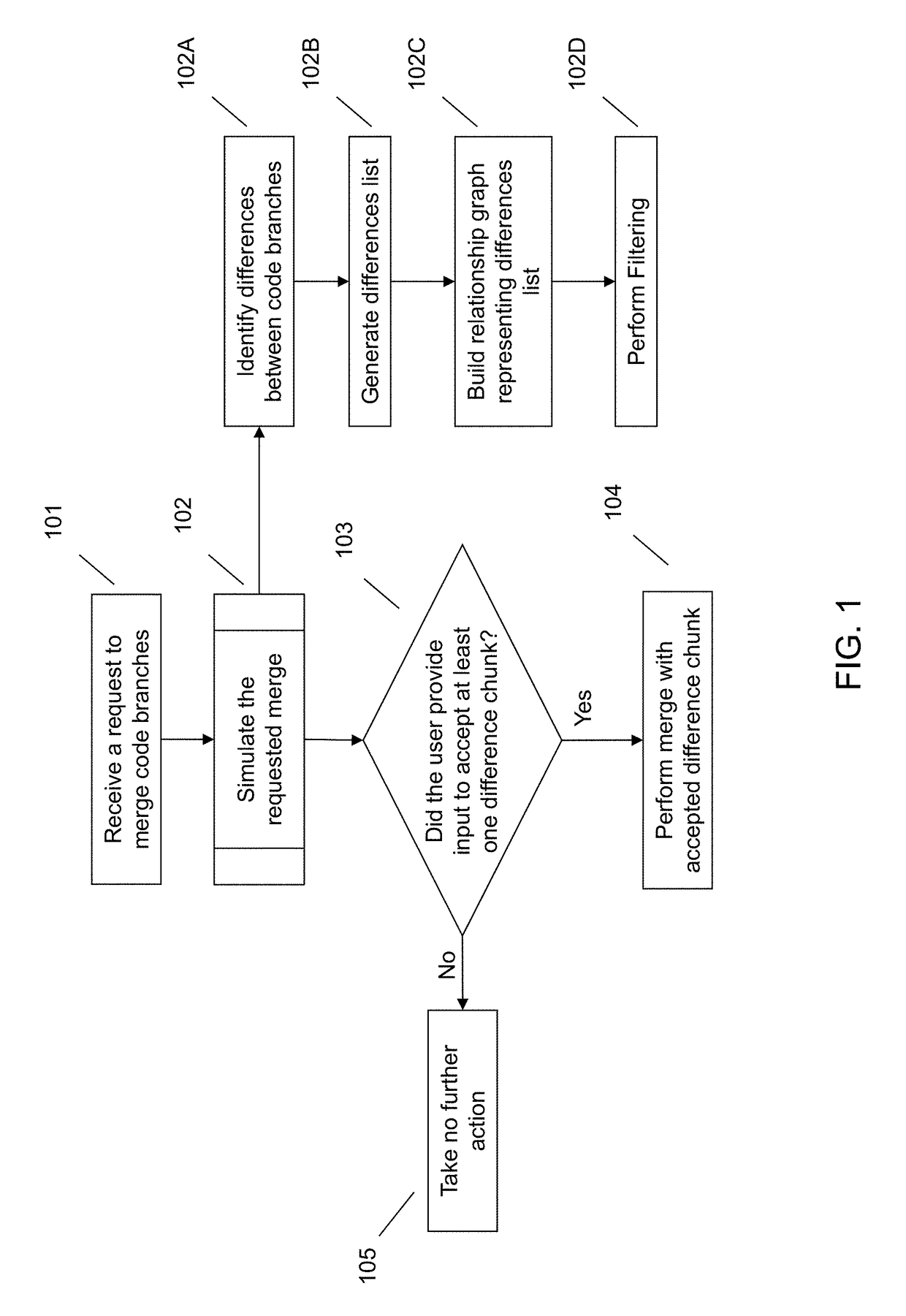
Simulating and evaluating code branch merge
One embodiment provides a method, including: receiving a request to merge at least one code branch with a first code branch, wherein the at least one code branch and the first code branch comprise different versions of software code; and simulating the merge via: identifying the differences between the at least one code branch and the first code branch; generating a differences list comprising a list of (i) added code snippets, (ii) deleted code snippets, and (iii) changed code snippets, wherein code snippets are clustered in the differences list by difference chunks comprising connected code snippets; and building a relationship graph comprising a plurality of nodes and a plurality of edges, wherein each of the plurality of nodes represent a difference chunk and wherein each of the plurality of edges comprise a relationship between two of the plurality of nodes; each of the plurality of edges comprise a cost vector.
Owner:IBM CORP
Mixed video fault tolerance method based on multiple description encoding and error hiding
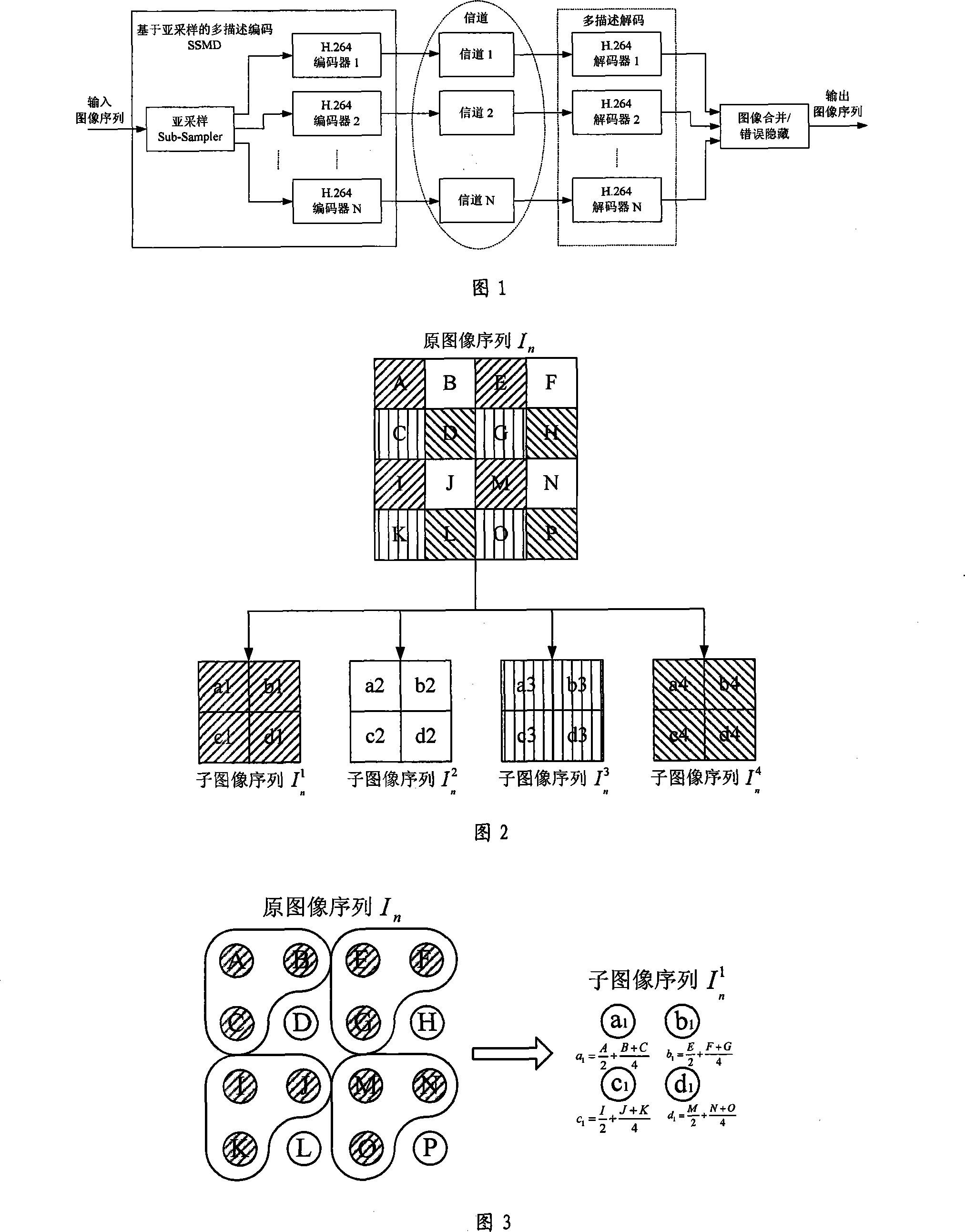
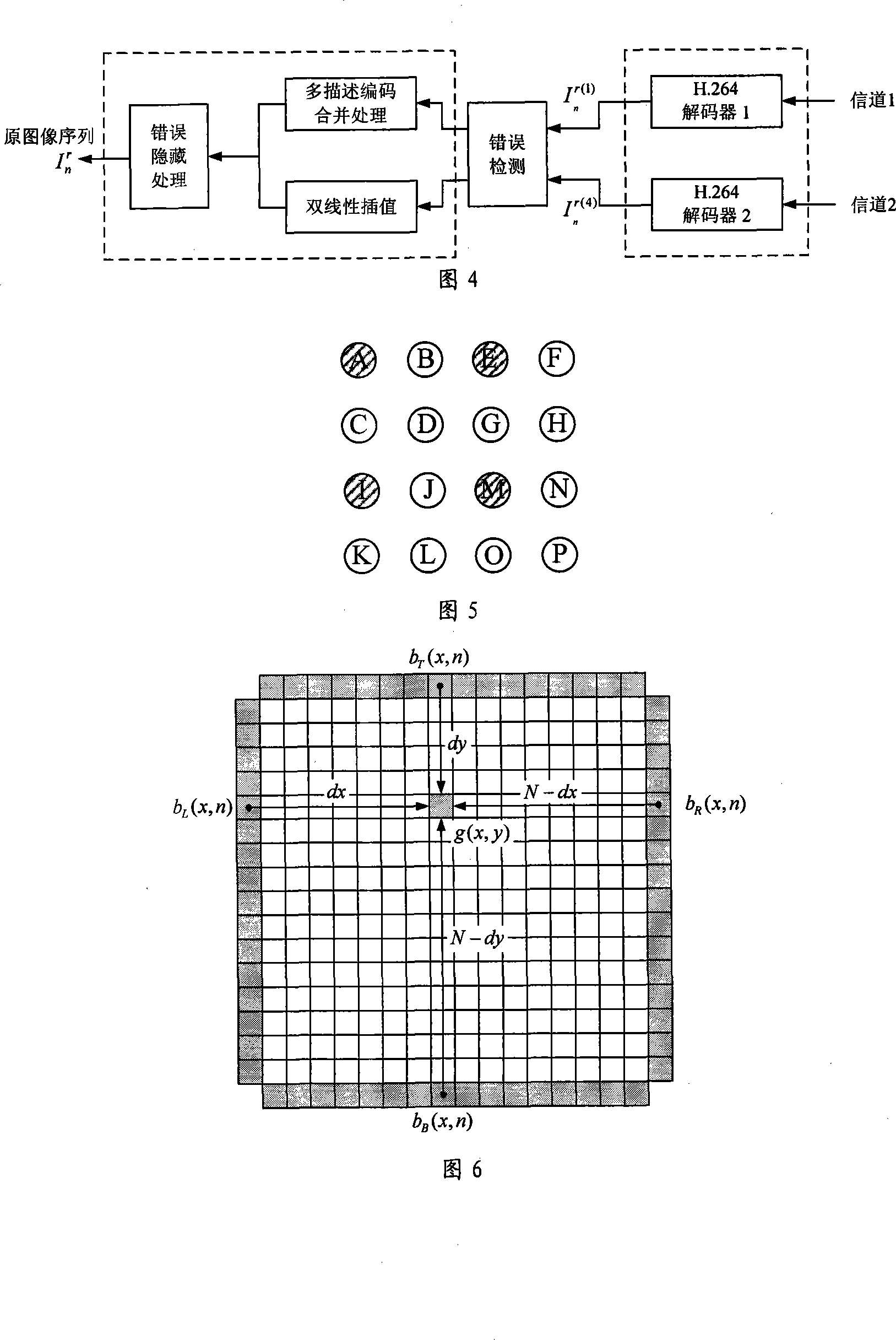
InactiveCN101175216AImprove efficiencyImprove fault toleranceTelevision systemsDigital video signal modificationFault toleranceComputer architecture
The present invention provides a mixed video fault-tolerance method based on multiple description coding and fault concealment. In the method, the imported image sequence firstly undergoes multiple description coding to form N independent video compression coding code streams; the N descriptions are simultaneously transmitted via independent channels; after a receiving end receives the N descriptions, the N descriptions are sent into a decoder for being decoded in order to obtain N image subsequences. According to packet loss, the decoder demarcates an image area; the image subsequences are merged, and finally, a reconstructed image sequence is obtained. Because the present invention exerts the complementarity between the multiple description coding technology and the fault concealment technology, the better effect of system performance is achieved in comparison with the sole utilization of one of the two technologies; wherein, the framework of the multiple description coding of an coding end carries out processing aiming at a sampling environment and can be combined with the newest coding standards, thus resolving the problems of the low-efficiency coding and the complex realization of most prior multiple description coding systems and the defects of the inadequate compatibility of the prior coding criteria.
Owner:NANJING UNIV
Iterative decoding of differentially modulated symbols
InactiveUS20020138793A1Other decoding techniquesError detection/correctionAlgorithmTheoretical computer science
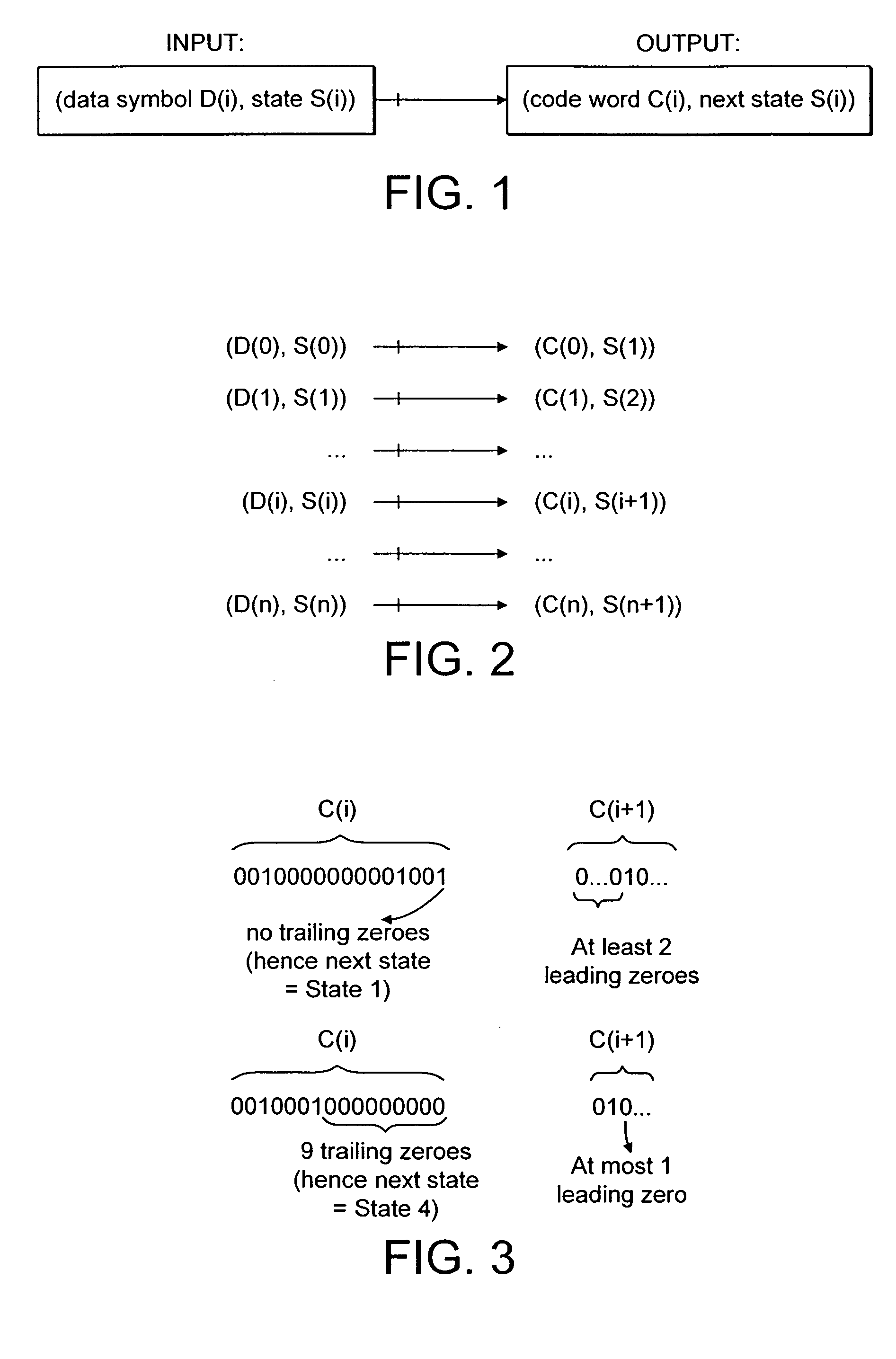
Method and apparatus for decoding block-coded data which has been transmitted by means of differential modulation. The method first attempts to decode all codewords using an error correcting code, and if at least one codeword is still not decoded, uses a correctly decoded codeword to locate a possibly erroneous code symbol in the at least one codeword, alters the possibly erroneous code symbol, and again attempts to decode the at least one codeword. The invention recognizes that errors in such data typically occur in pairs, and utilizes this property to improve the decoding process.
Owner:TELEFON AB LM ERICSSON (PUBL)
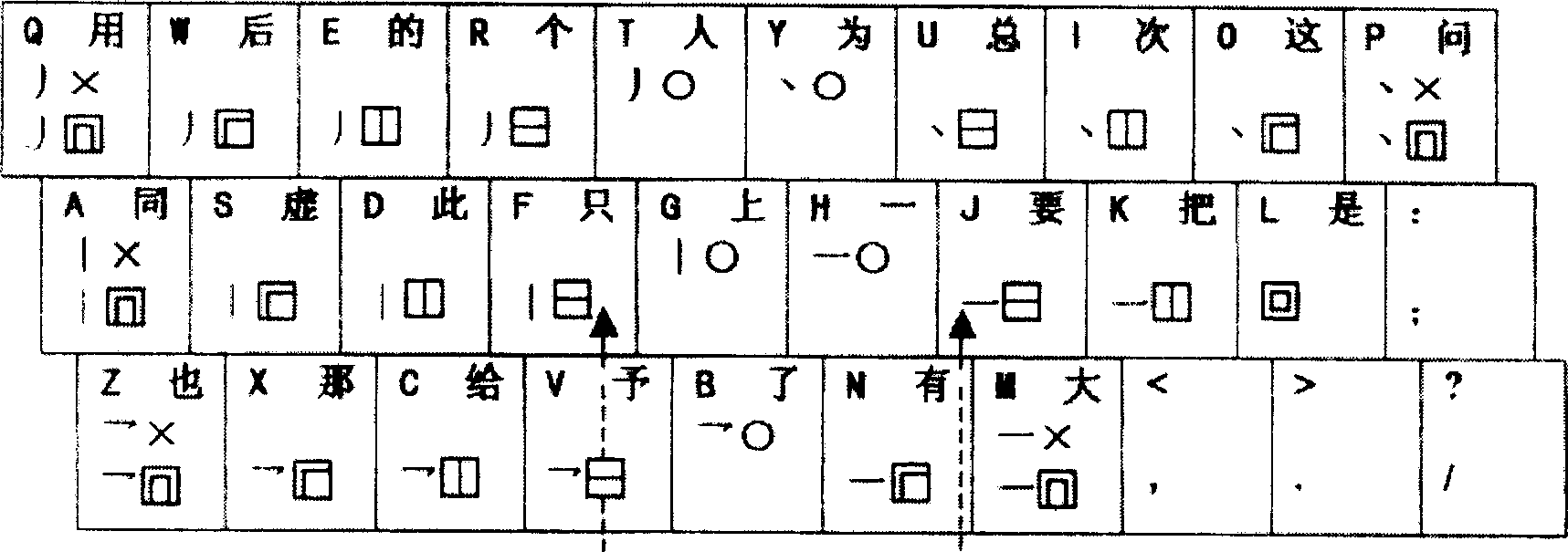
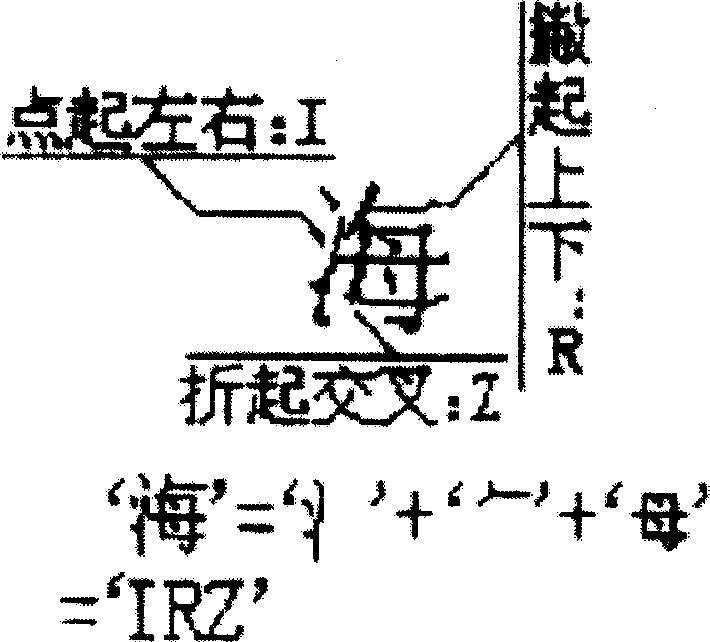
Structural code Chinese-character input method
InactiveCN1641547AThe coding method is simple and easy to rememberReasonable distribution of keysInput/output processes for data processingProgramming languageChinese characters
The invention relates to structure code Chinese character input method. The code includes structure code and stroke code. Structure code is used to encode complex character. Separating different zone according the start stroke of each component of the complex character and classifying according to the structure of every component and its afterward component every combination has a code called structure code. Strode code is used to encode simple character. The invention is easy to be memorized and has a reasonable key mapping. Moreover, it has low coincident code ratio and the input speed is very fast.
Owner:荣敬曾
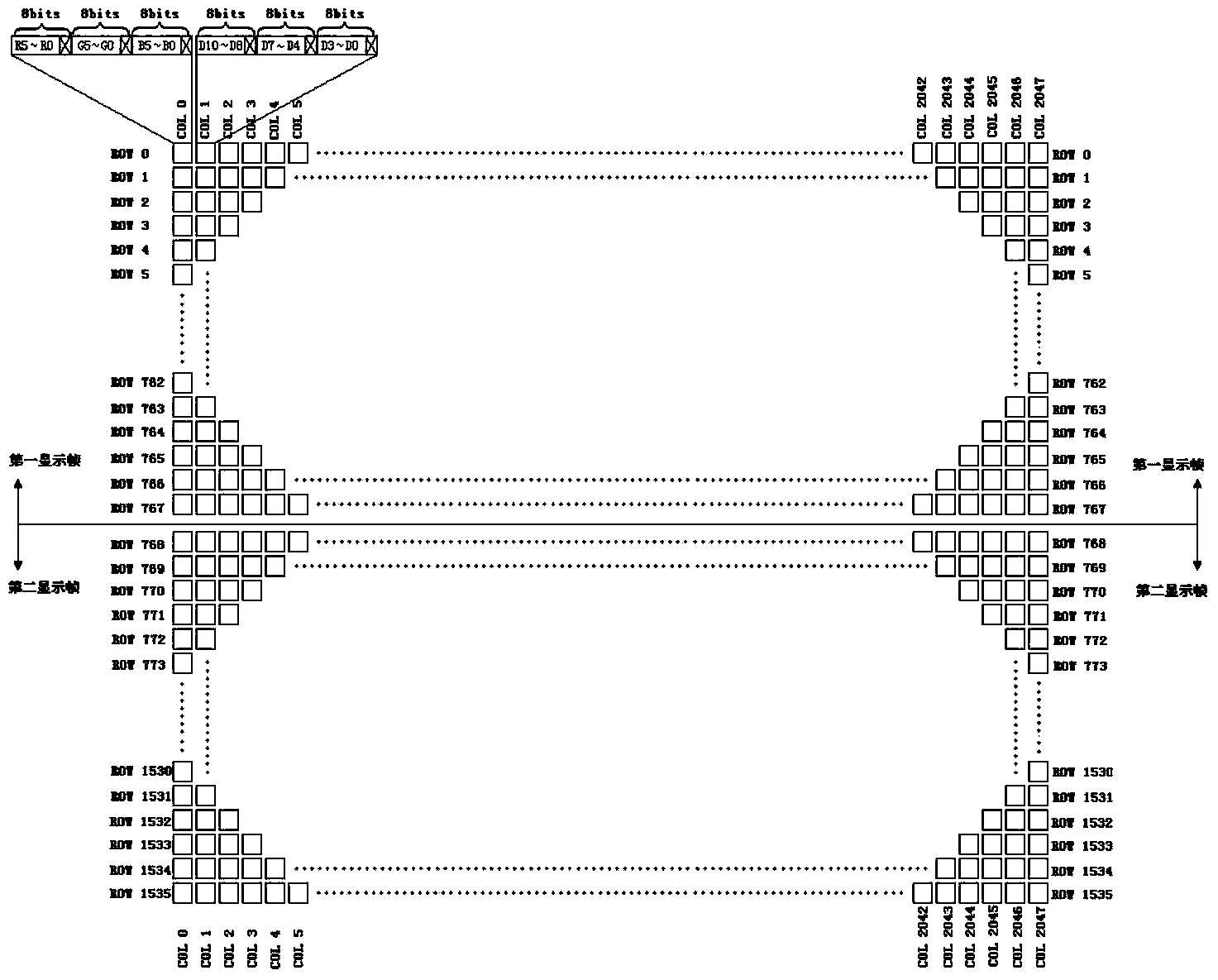
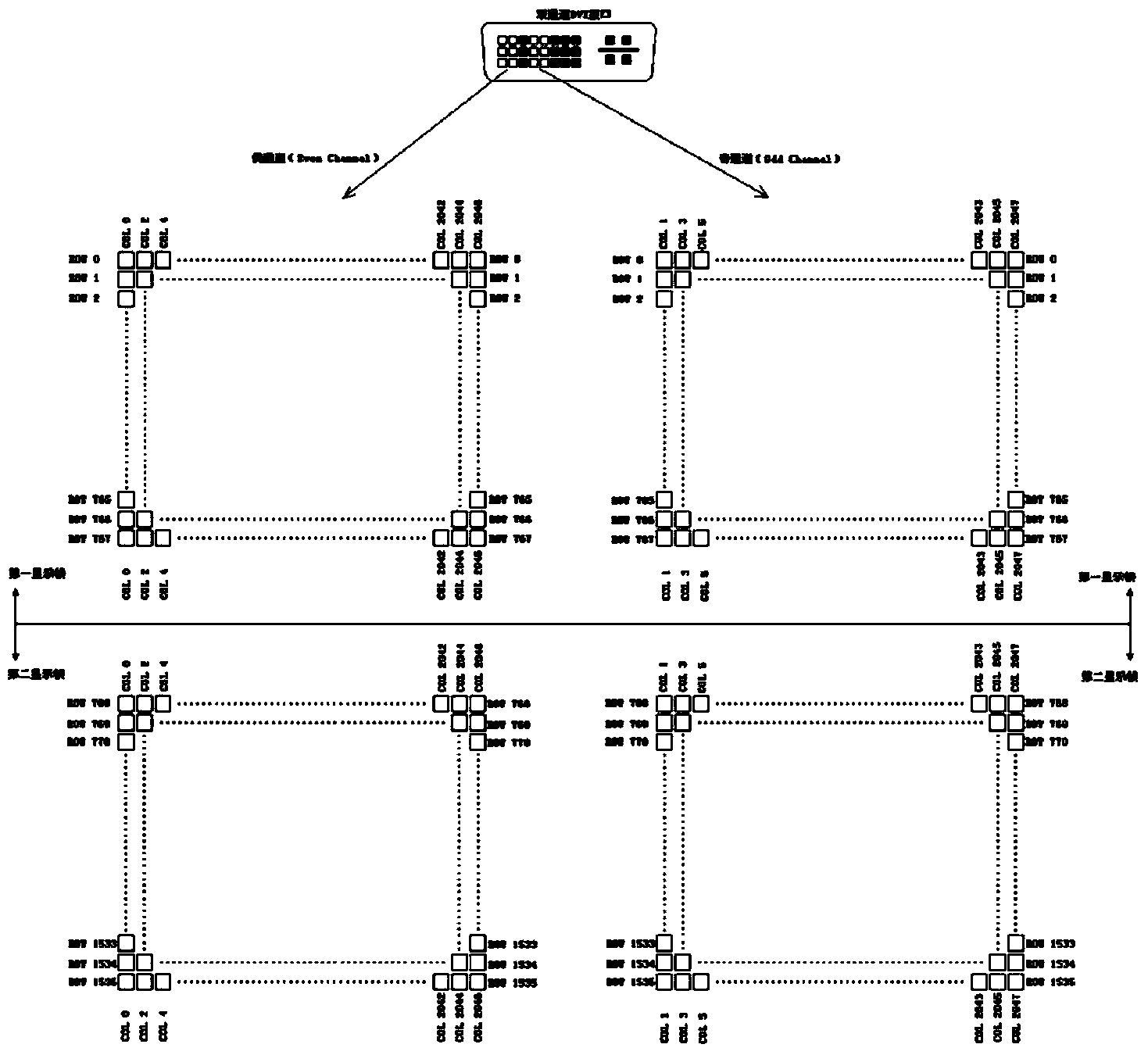
Solid real three-dimension voxel coding and transmission method based on dual-channel DVI interface
The invention discloses a solid real three-dimension voxel coding and transmission method based on a dual-channel DVI interface. The method is characterized in that a computer system codes real three-dimension display data in 2048*1536 pixels per frame, and the RGB gray value and depth value of a display voxel are respectively coded to pixels in even-numbered rows and pixels in odd-numbered rows of an coding frame. When data is transmitted in DVI dual channels, the even channel and the odd channel are respectively used for transmitting the RGB gray value and depth value. Display voxel coding of which the sum of the RGB gray value and depth value is greater than 24 bits is realized, the dual channels are separated and respectively used for transmitting the RGB gray value and depth value to facilitate rear-end data receiving and processing, the display data transmission frame frequency is multiplied, and the method adapts to the constantly-improving color bit depth coding and transmission requirement of a solid real three-dimension system.
Owner:HEFEI UNIV OF TECH
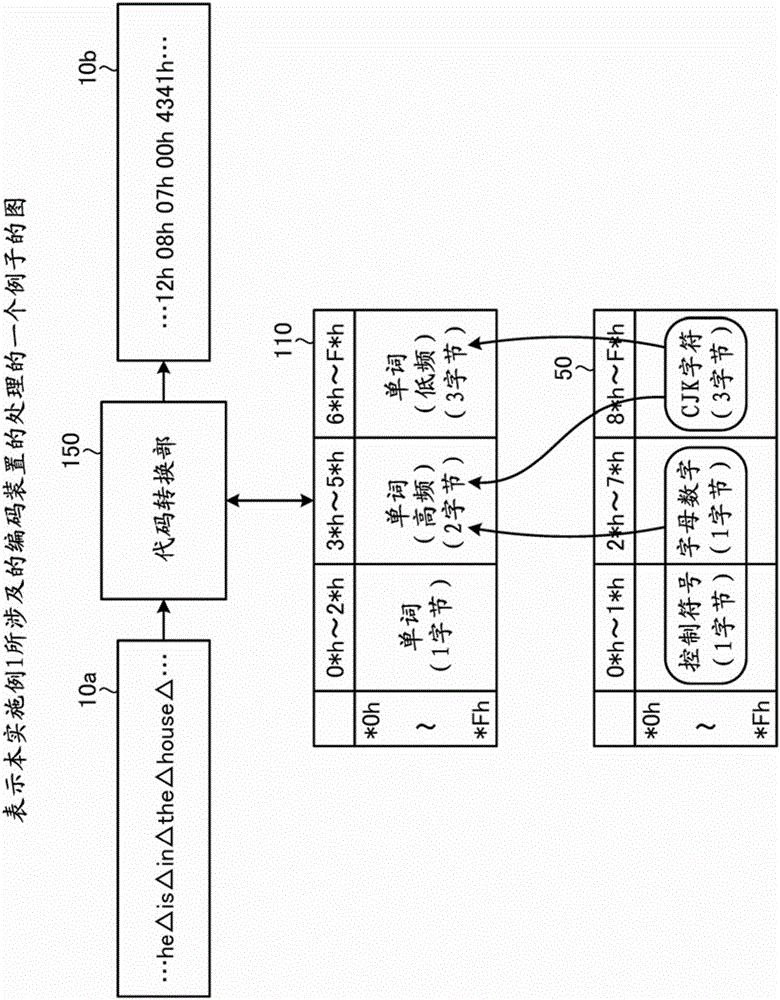
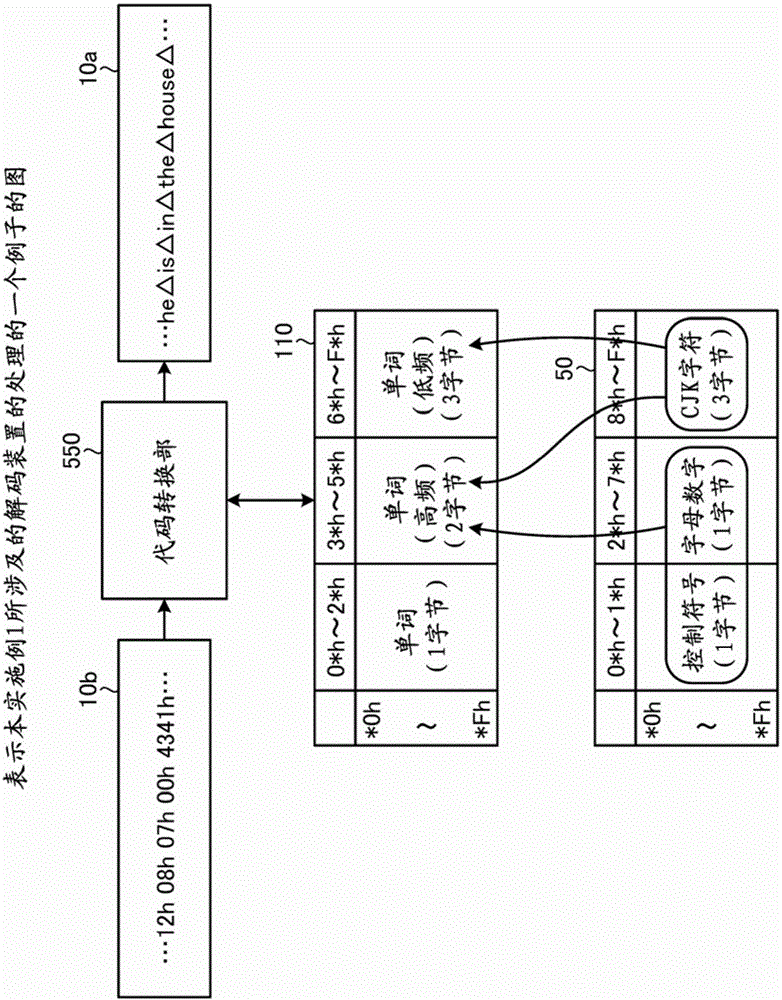
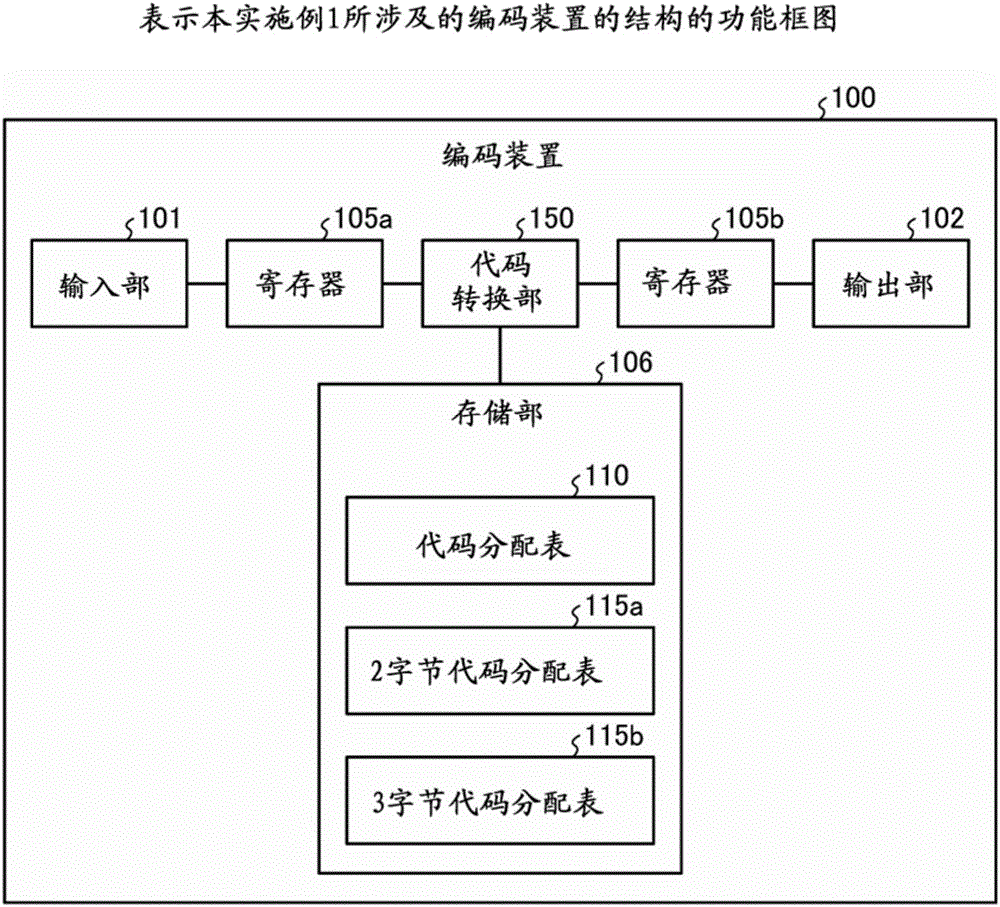
Encoding computer program, encoding method, encoding apparatus, decoding computer program, decoding method, and decoding apparatus
ActiveCN106354699ADistribute quicklyNatural language translationCode conversionDecoding methodsTheoretical computer science
A code converting unit(150, 250, 350) encodes input text data based on an code assignment table stored in a storage device that defines a conversion rule for encoding text data, wherein; the code assignment table being generated by assigning a part of character strings assigned to a 1-byte region of a first code assignment table to a 2-byte region of the code assignment table, and by assigning one or more codes each having two or more bytes to at least a part of character strings assigned to the 2-byte region of the code assignment table.
Owner:FUJITSU LTD
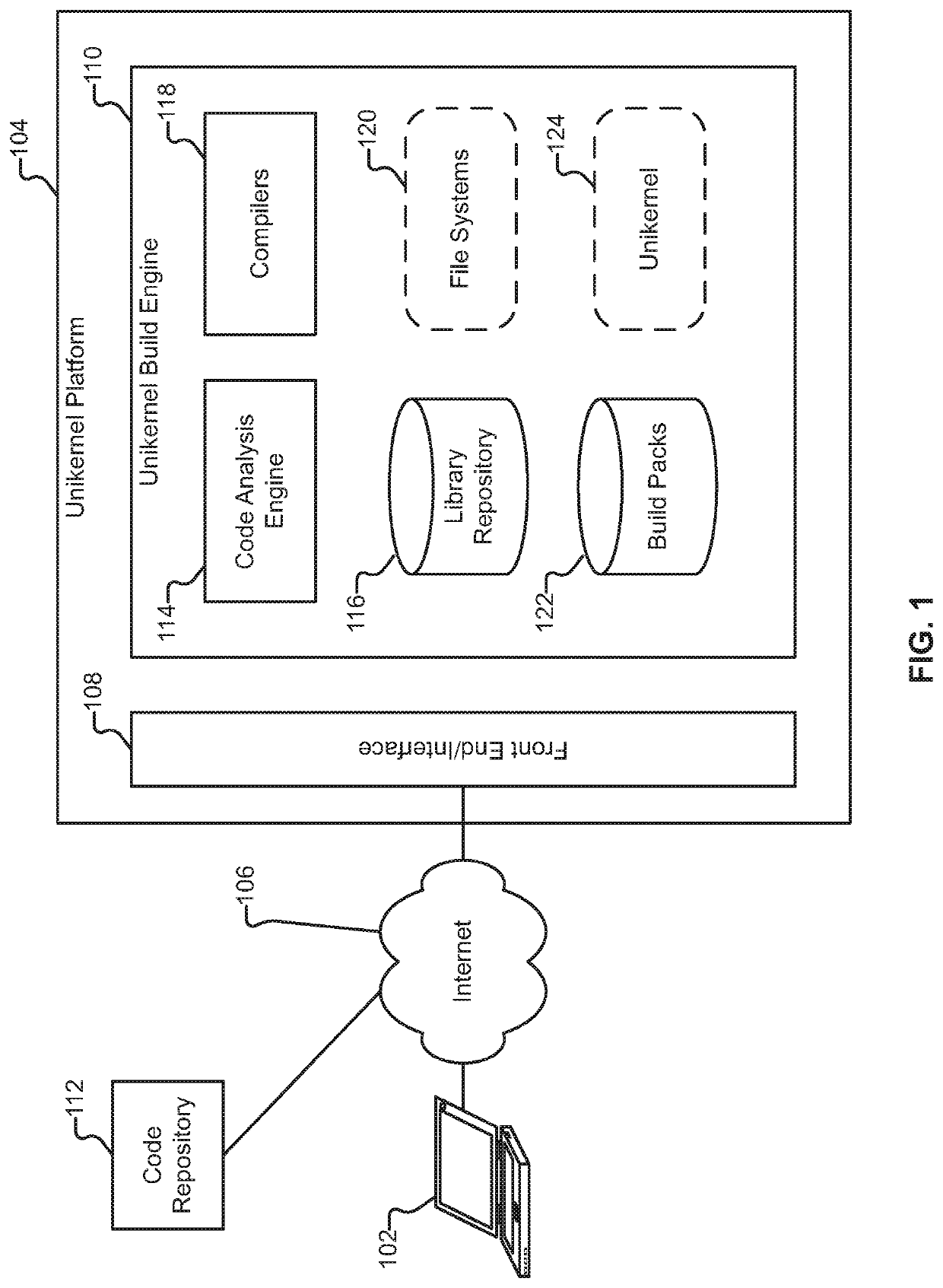
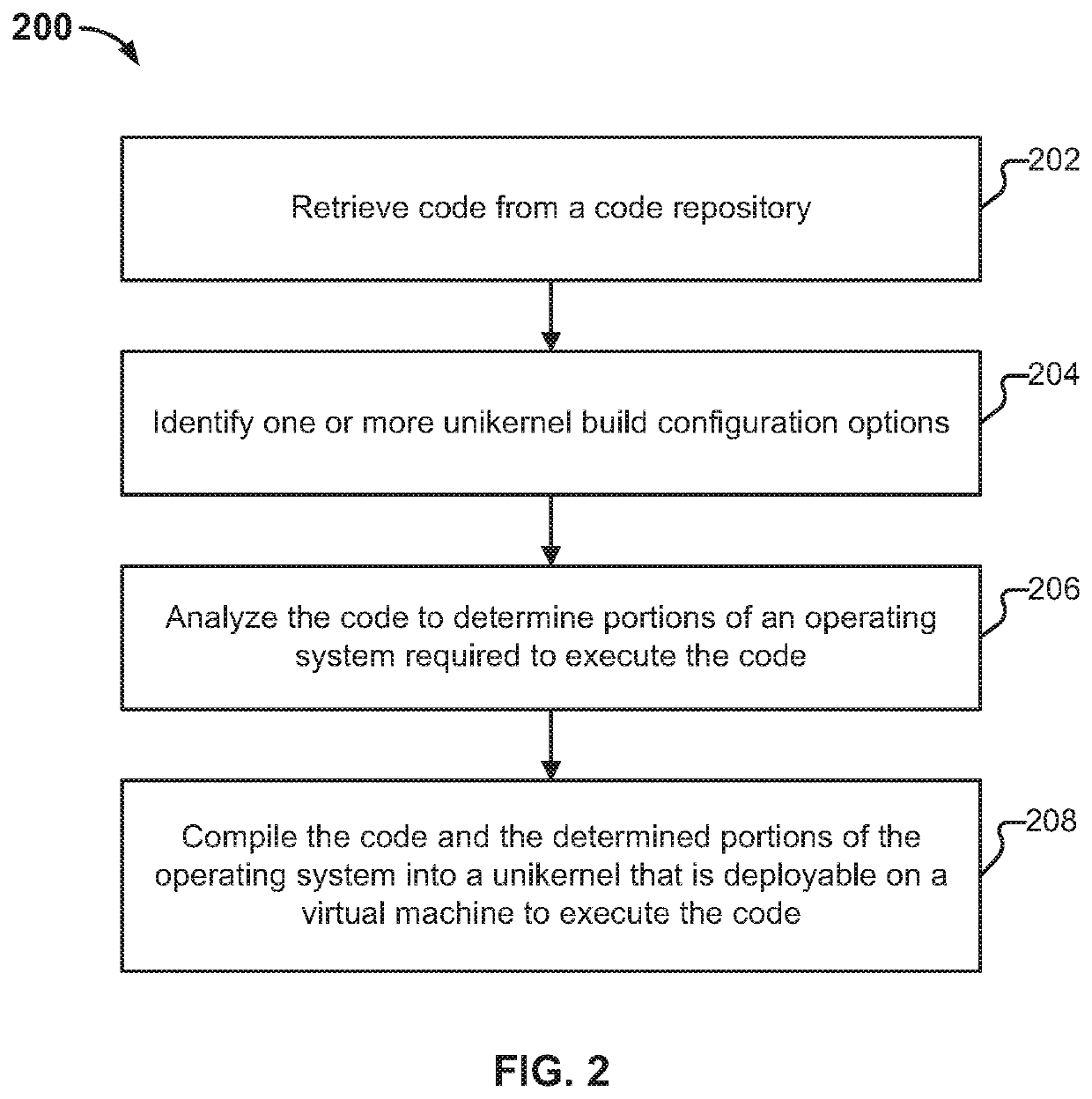
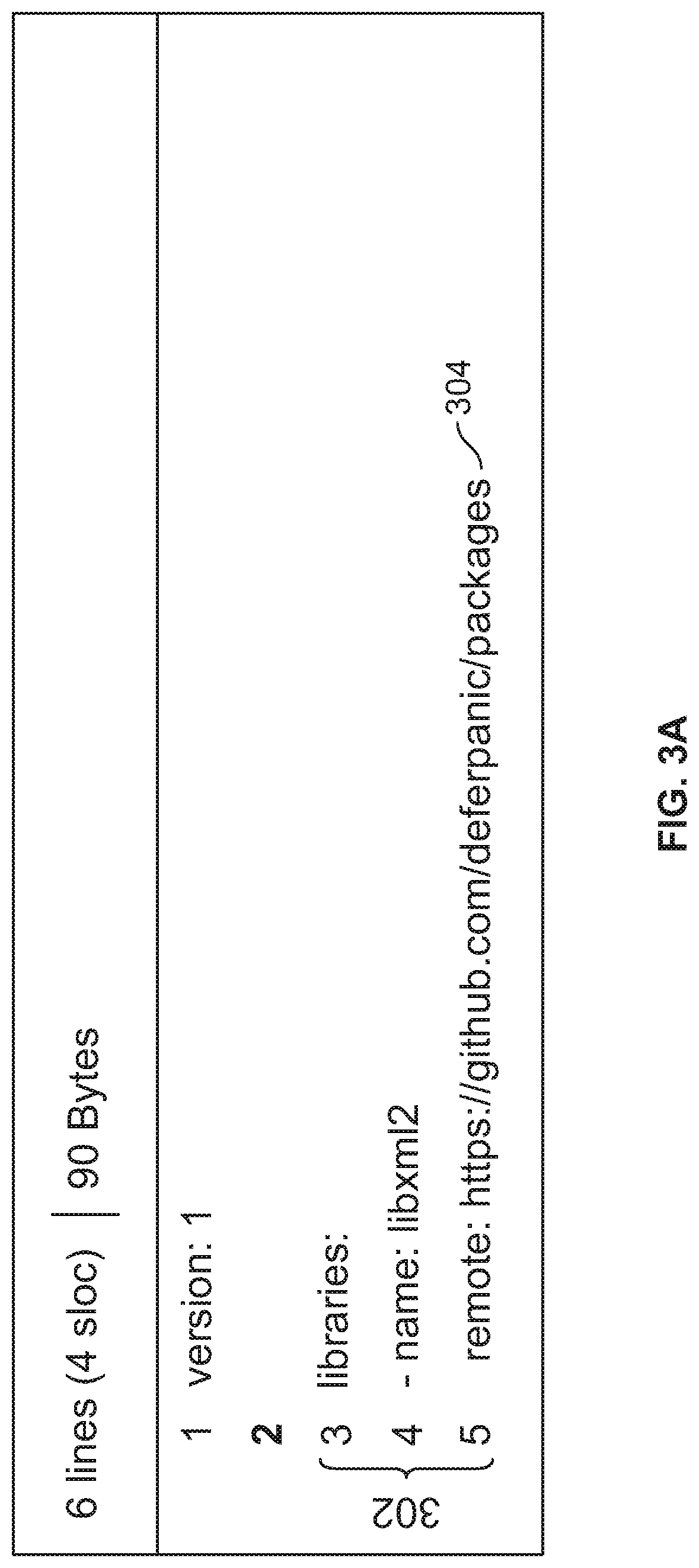
Unikernel cross-compilation
Building a unikernel is disclosed. Code is retrieved from a code repository. One or more unikernel build configuration options are identified. The code is analyzed to determine portions of an operating system required to execute the code. The code is compiled with the determined portions of the operating system into a unikernel that is deployable on a virtual machine to execute the code.
Owner:NANOVMS INC
Buffer-based generation of OVSF code sequences
A method of generating a code sequence comprises populating at least one buffer with initial values based on a received spreading factor and desired code index; receiving a timing strobe; changing the values in the at least one buffer upon receipt of the timing strobe based on an algorithm that is independent of any count value associated with the timing strobe; and outputting at least one code sequence value based on the values in the at least one buffer. An apparatus for generating a code sequence comprises means for populating at least one buffer with initial values based on a received spreading factor and desired code index; means for receiving a timing strobe; means for changing the values in the at least one buffer upon receipt of the timing strobe based on an algorithm that is independent of any count value associated with the timing strobe; and means for outputting at least one code sequence value based on the values in the at least one buffer.
Owner:AVAGO TECH INT SALES PTE LTD
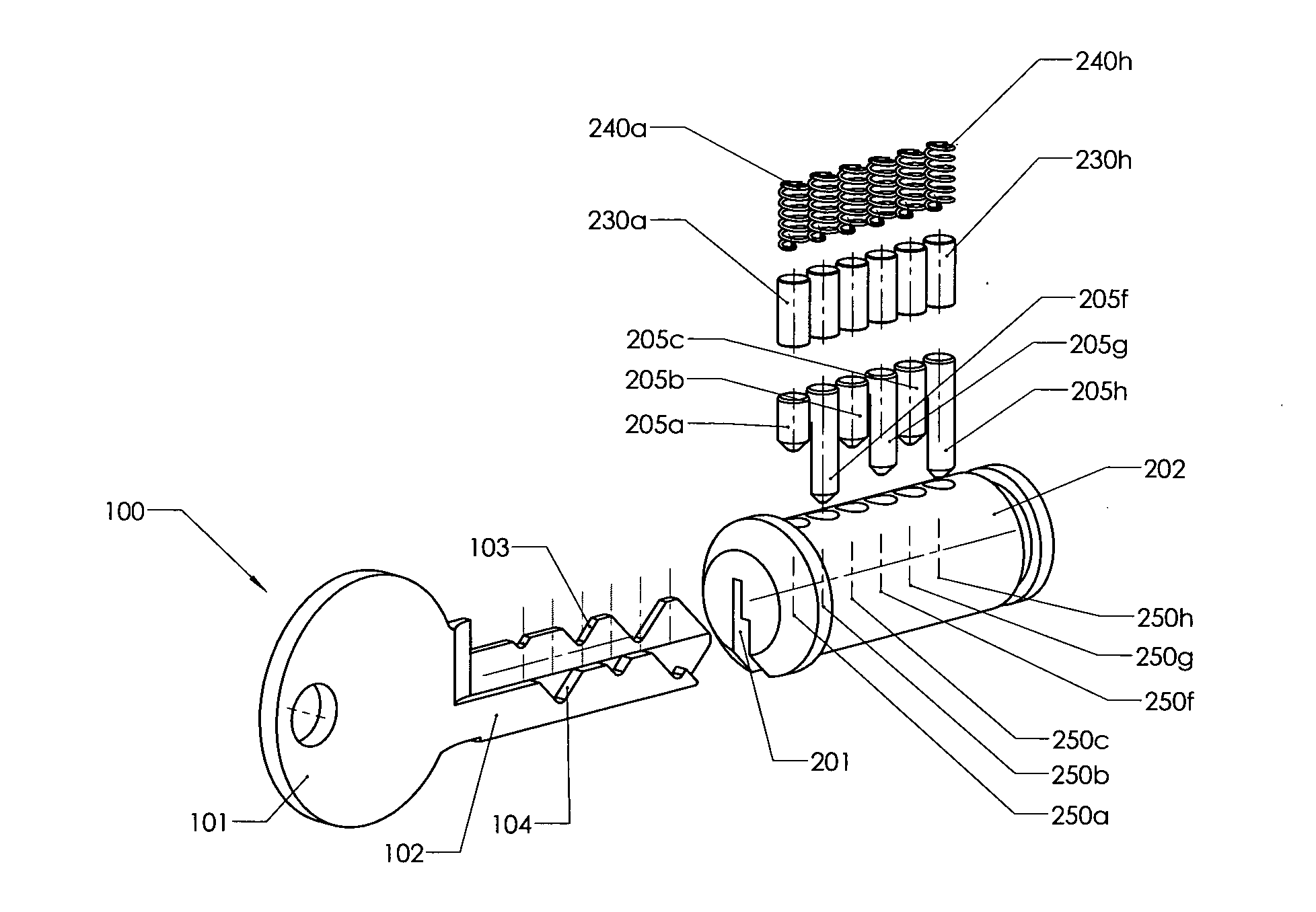
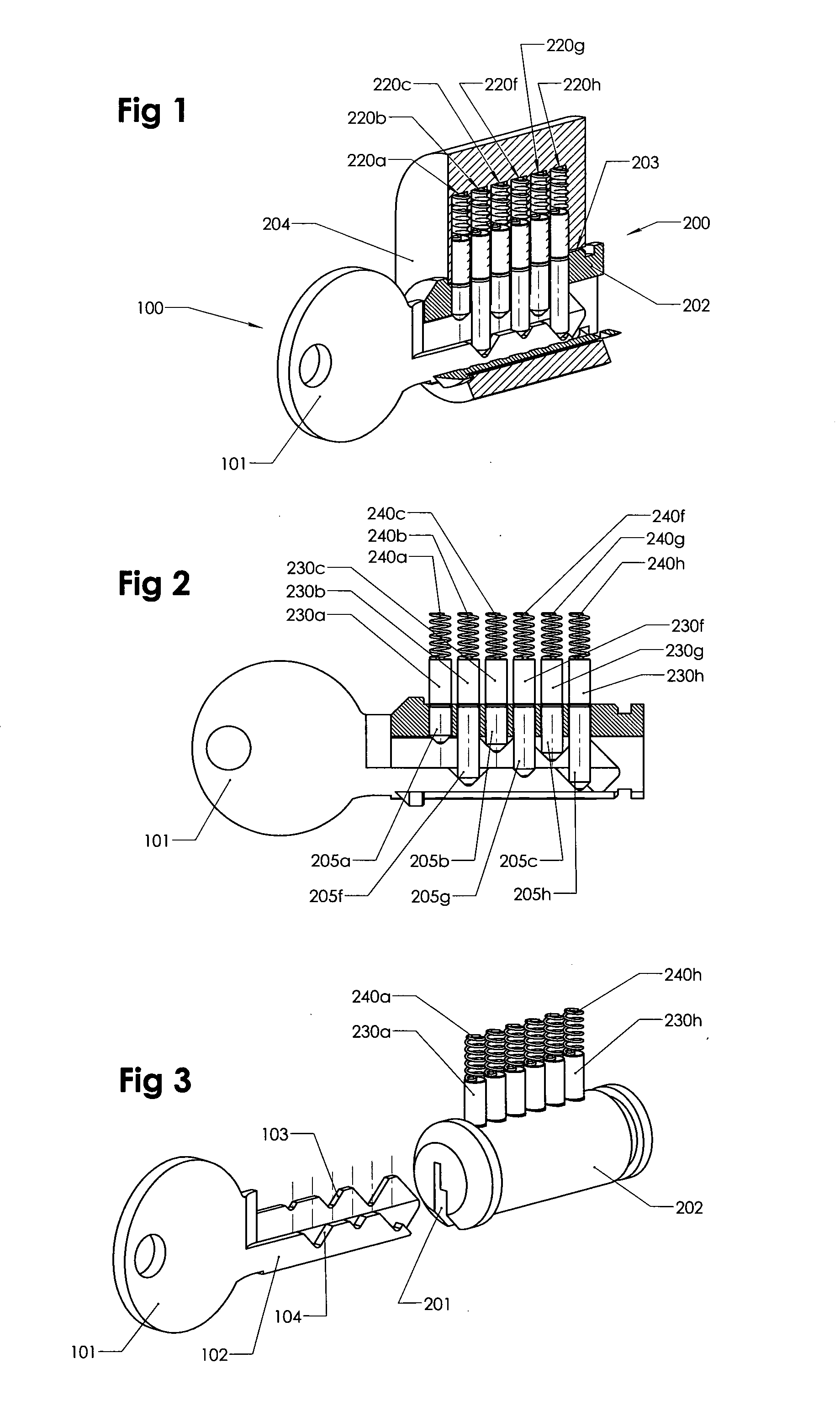
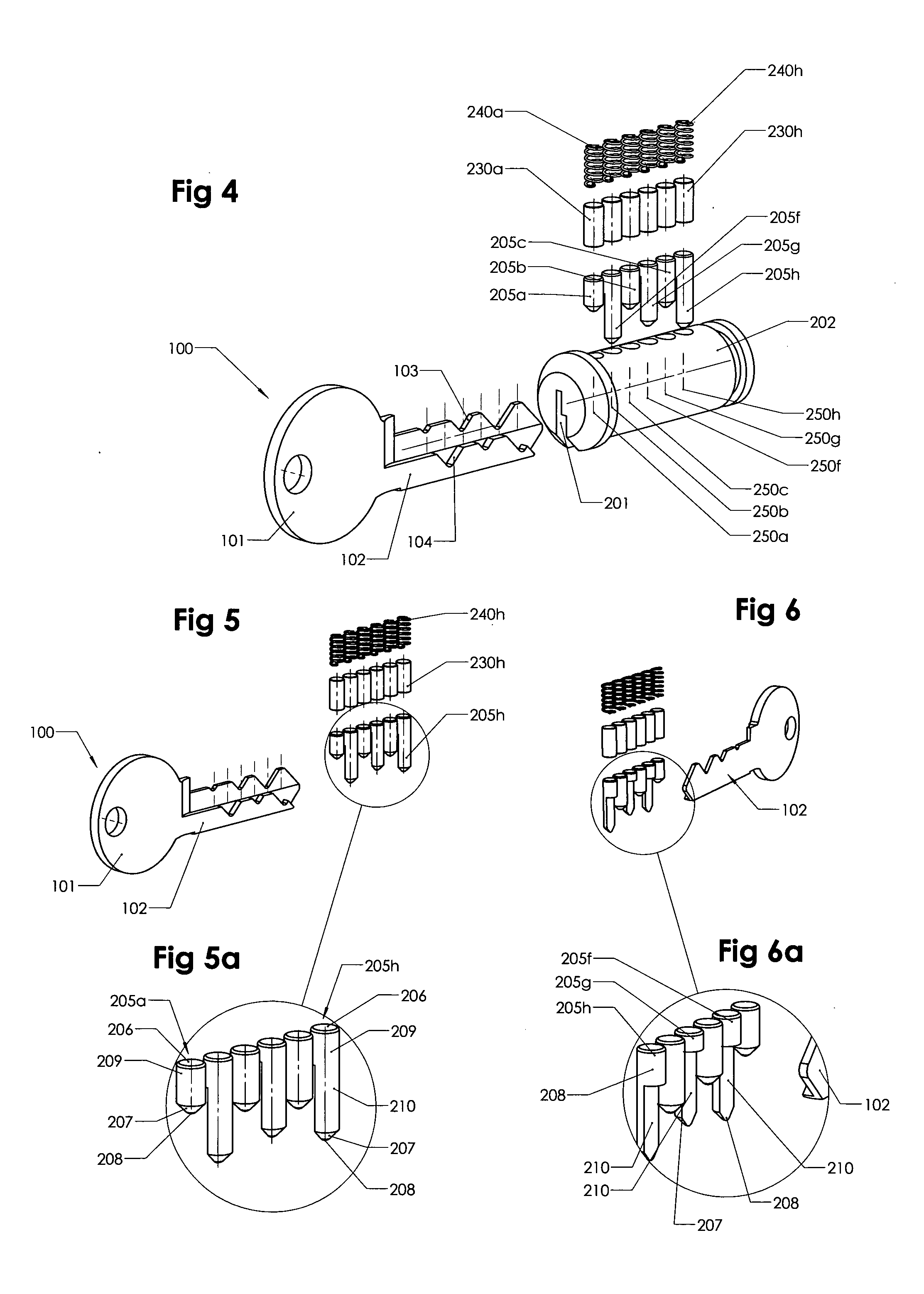
Lock and key combination with a large number of codes
ActiveUS20110219833A1Easy to manufactureIncrease the number ofKeysCylinder locksComputer hardwareKey pressing
Owner:WINLOC
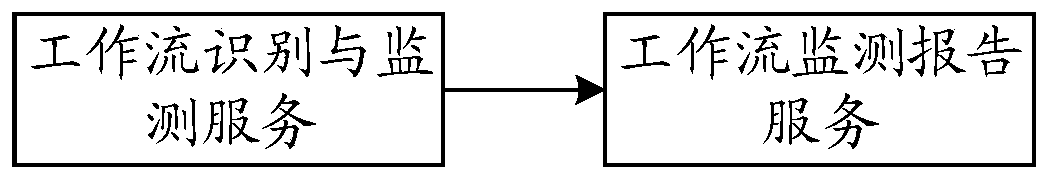
Code processing method and device, server and storage medium
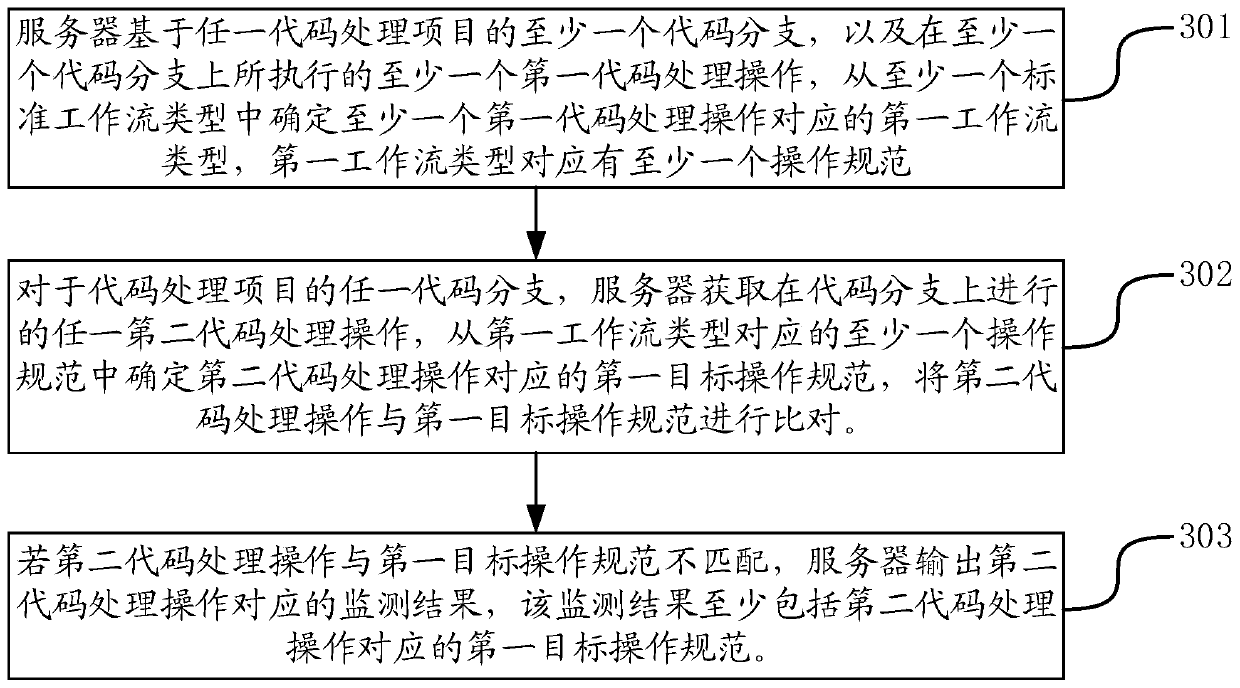
ActiveCN110865806AAccurate timingImprove collaborative development efficiencyEnergy efficient computingCreation/generation of source codeProgramming languageSoftware engineering
The invention provides a code processing method and device, a server and a storage medium, and belongs to the technical field of computers. The method comprises: based on at least one code branch of any code processing item and a first code processing operation executed on the code branch, determining a first workflow type from at least one standard workflow type, and the first workflow type corresponding to at least one operation specification; for any code branch of the code processing project, obtaining any second code processing operation performed on the code branch, determining a first target operation specification corresponding to the second code processing operation from the at least one operation specification, and comparing the second code processing operation with the first target operation specification; and if the second code processing operation is not matched with the first target operation specification, outputting a monitoring result. In the application, the server can assist the development team to apply the standard workflow more accurately and efficiently, so that the collaborative development efficiency of the development team is higher.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multiple-access code generation
InactiveUS7587660B2Solve complex processQuick updateData representation error detection/correctionError preventionTheoretical computer scienceRelevance measure
Multiple-access codes are generated using an asymptotically optimal decoding algorithm, such as the Viterbi algorithm. A trellis may be constructed using a number of desired users, at least one code length, and a number of code-chip parameters. A fitness function is derived from a mathematical relationship between the multiple-access codes, and may include some measure of correlation of the codes. The multiple-access codes correspond to paths having optimal path metrics derived from the fitness function. Multiple iterations through the trellis may be performed to refine a selection of multiple-access codes.
Owner:KANSAS STATE UNIV RES FOUND
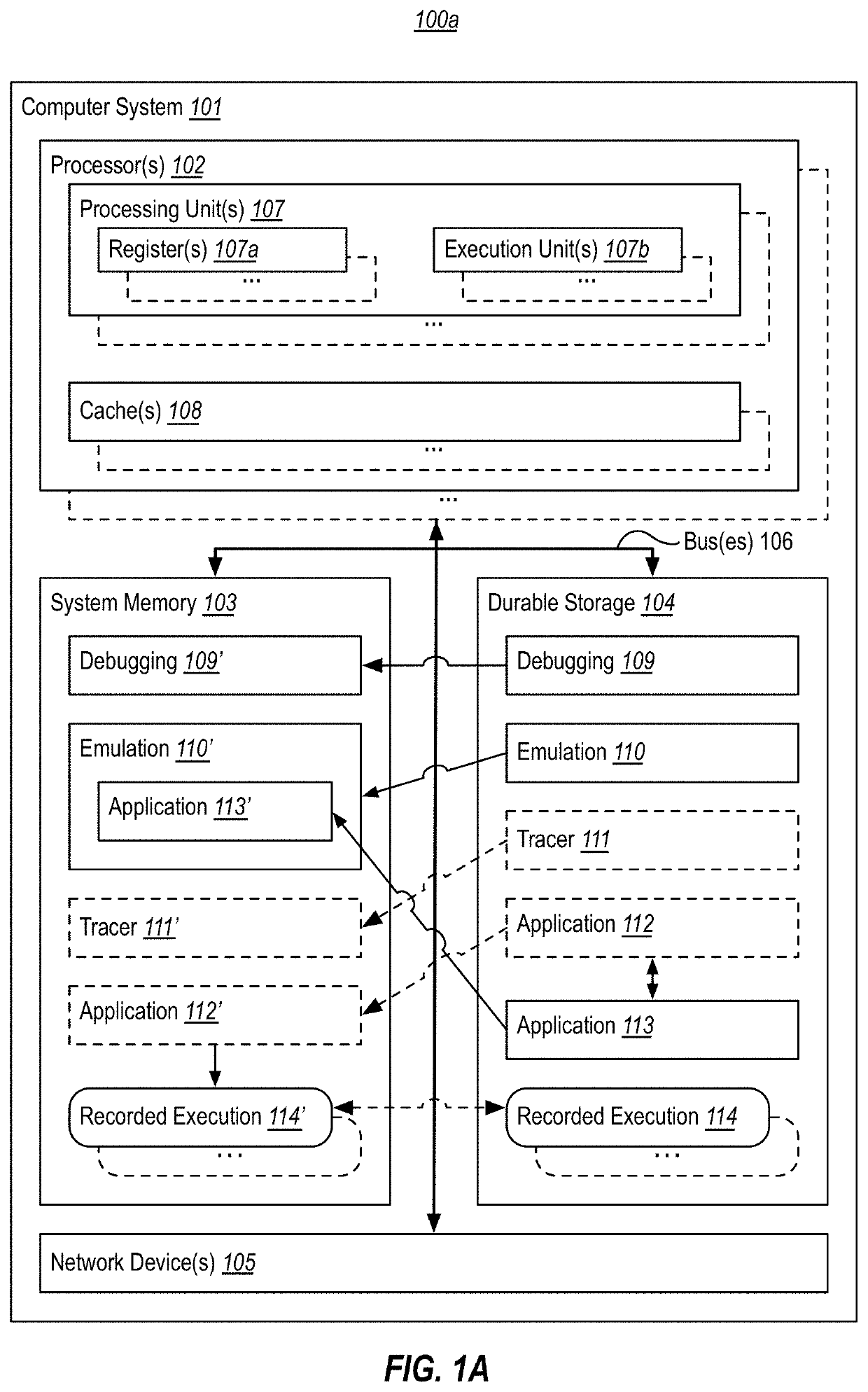
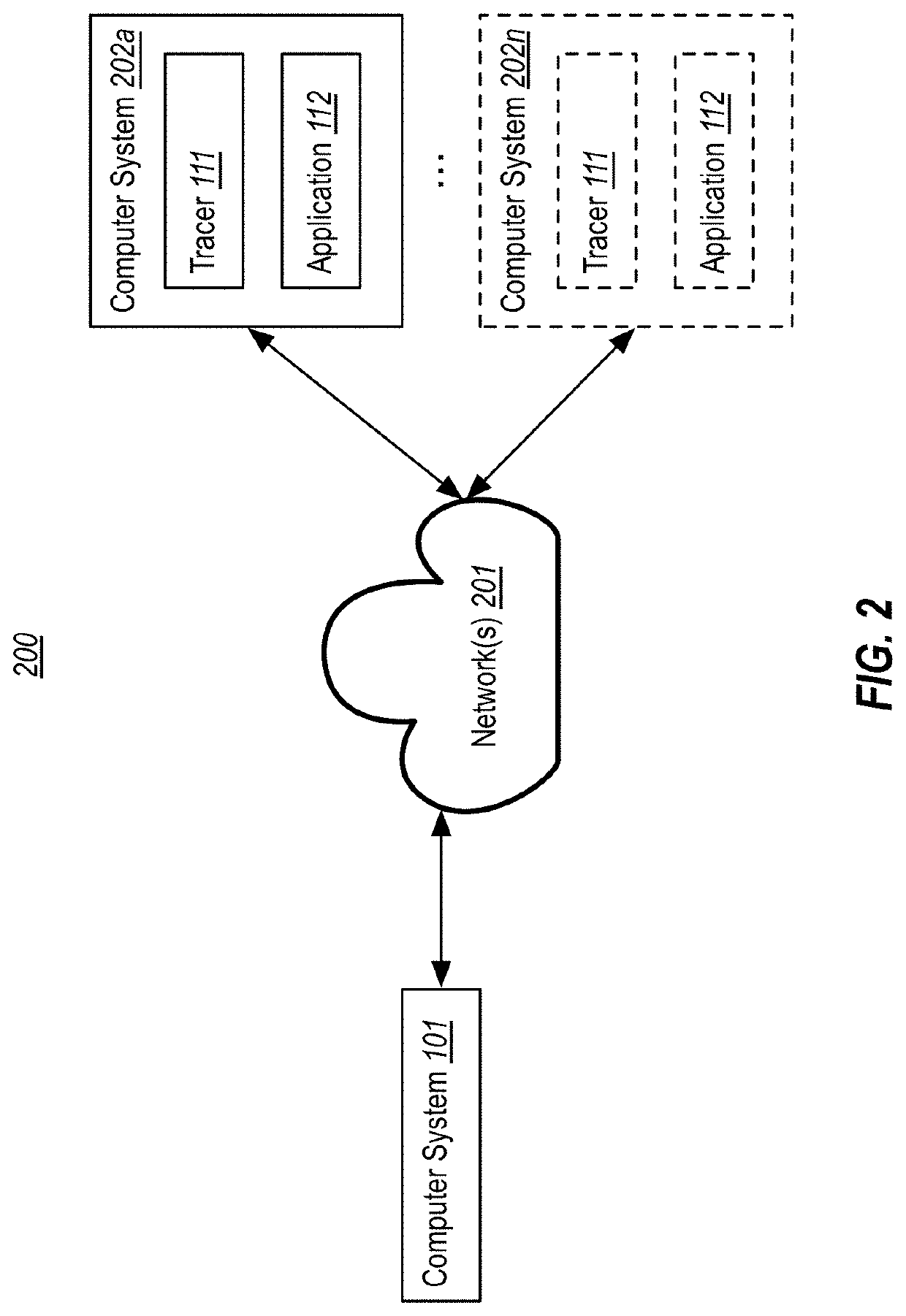
Using synthetic inputs to compare execution of different code versions
InactiveUS20200301815A1Increasing code execution coverage of codeVersion controlSoftware testing/debuggingPathPingRecord
Using synthetic inputs to determine if different versions of executable code execute equivalently. First and second versions of code are accessed. Based on recorded execution(s), a first code path is identified in the first code version that lacks execution coverage. A second code path is identified in the second code version that maps to the first code path. Synthetic inputs are generated for the first code path. The first and second code paths are emulated using the generated synthetic inputs, resulting in first outputs for the first code path and second outputs for the second code path. It is determined if there are any differences between the first and second outputs. If so, it is reported that the first and second code paths do not execute equivalently when supplied with the synthetic inputs. Otherwise, it is reported that the first and second code paths execute equivalently.
Owner:MICROSOFT TECH LICENSING LLC
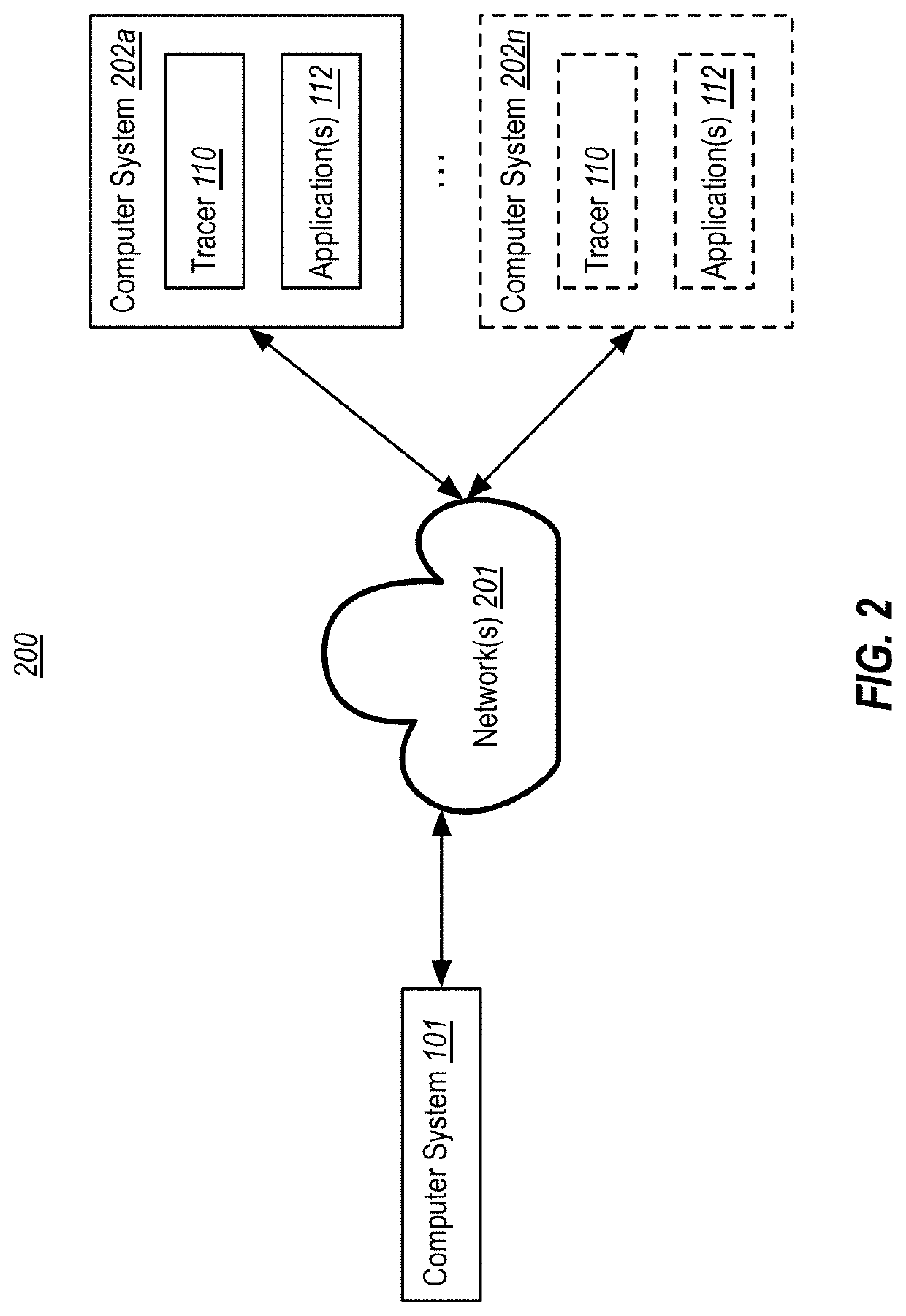
Instruction set architecture transformations when emulating non-traced code with a recorded execution of traced code
InactiveUS20200301821A1Well formedRegister arrangementsSoftware testing/debuggingInstruction setRecord
Emulating execution of second code of a second instruction set architecture (ISA) using a trace of execution of first code of a first ISA. The stores data of an input that was consumed by the first code when executing on the first ISA. It is determined that the stored data of the input is usable as an input to the second code. Difference(s) in location / size / format of the stored data as used by the first code, compared to a location / size / format expected by the second code, is identified. Based on the identified difference(s), transformation(s) are determined that would enable the second code to access and consume the stored data when being emulated on the second ISA. Execution of the second code is emulated on the second ISA using the stored data, including projecting the transformation(s) to enable the second code to access and consume the stored data.
Owner:MICROSOFT TECH LICENSING LLC
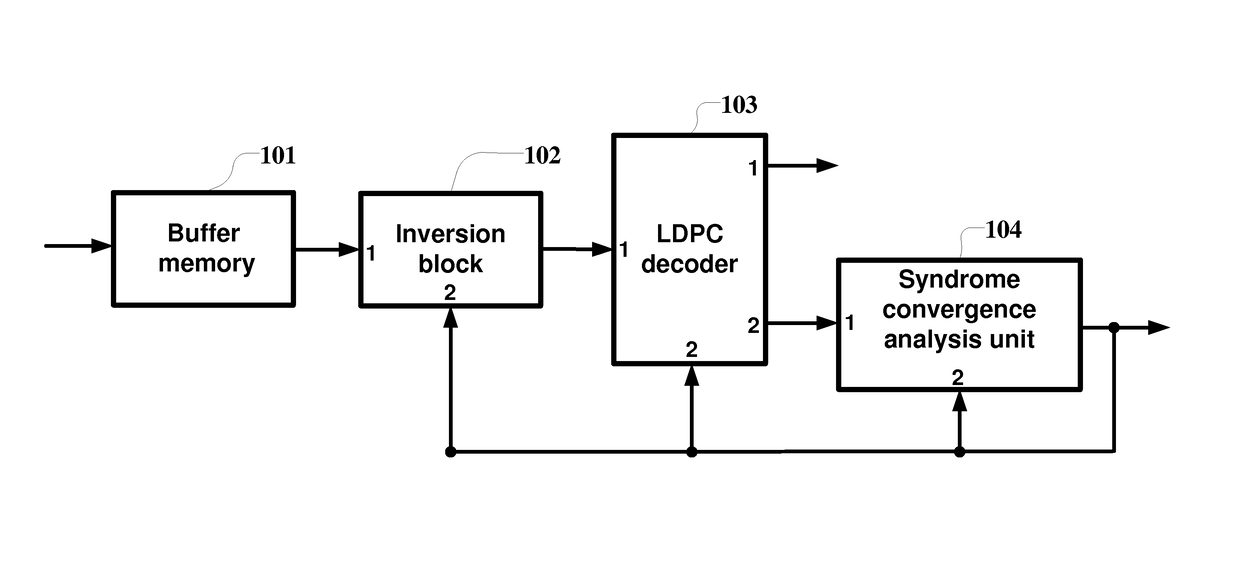
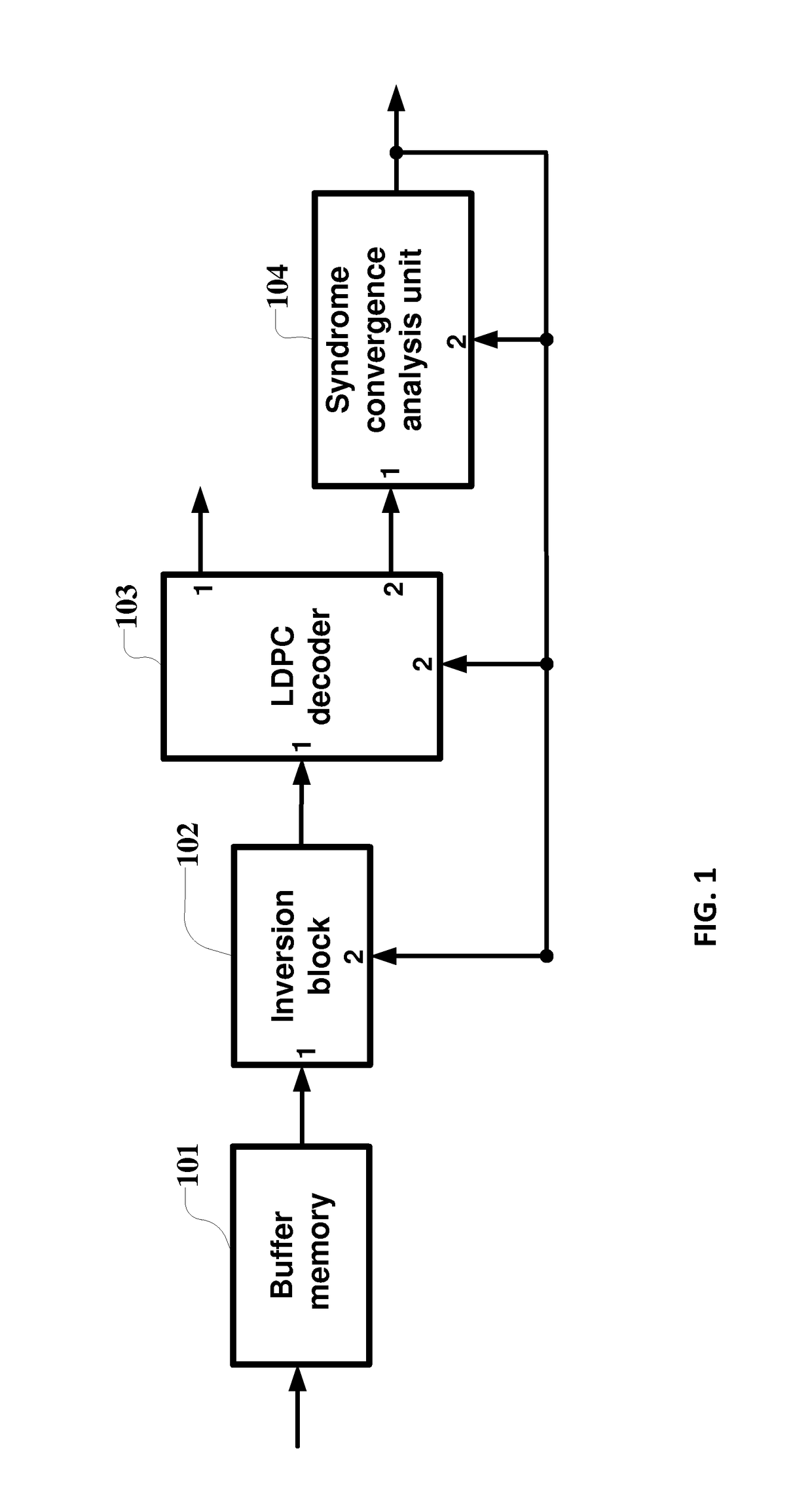
Method and apparatus for identification and compensation for inversion of input bit stream in Ldpc decoding
ActiveUS9621189B2Improving interference immunity and efficiencyImproving interference suppressionOther decoding techniquesError correction/detection using multiple parity bitsParallel computingLdpc decoding
Method of identification and compensation for inversion of the input bit stream when decoding LDPC codes includes obtaining a code word of the LDPC code from a demodulator output and writing the code word into a buffer memory, decoding the code word, calculating a syndrome for each iteration when decoding, making an analysis of converging the weight of the syndrome, generating an inversion feature for the input bit stream based on this analysis, continuing the decoding, if the inversion feature for the input bit stream does not give evidence of detecting inversion, resetting, if the inversion feature for the input bit stream shows inversion, the LDPC decoder and analysis parameters for the convergence of the weight of the syndrome, reading next code word from the buffer memory, and producing an inversion of this code word, and feeding the word to the decoder input to implement the next decoding operation.
Owner:TOPCON POSITIONING SYST INC
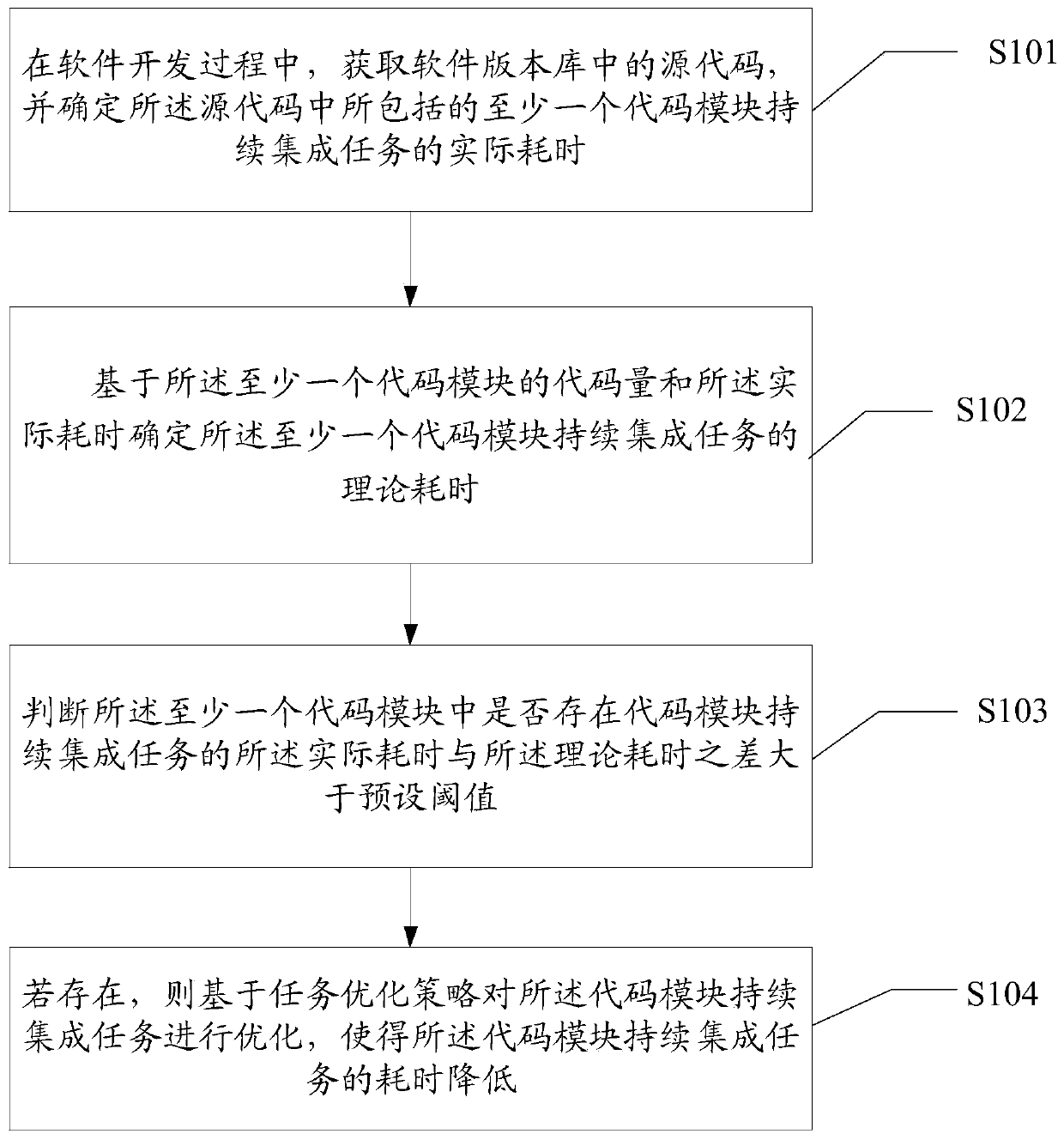
Continuous integration task optimization method and device
ActiveCN111324353AImprove the efficiency of continuous deliveryShort timeCode compilationSoftware development processCode module
The invention discloses a continuous integration task optimization method and device. The method comprises the following steps: in a software development process, obtaining a source code in a softwareversion library, determining actual consumed time of continuous task integration of at least one code module included in the source code; determining theoretical time consumption of continuous task integration of the at least one code module based on the code quantity of the at least one code module and the actual time consumption, and judging whether the difference between the actual time consumption and the theoretical time consumption of the continuous integration task of the code module in the at least one code module is greater than a preset threshold, and if so, optimizing the continuous integration task of the code module based on a task optimization strategy, so that the time consumption of the continuous integration task of the code module is reduced. The technical problem that in the prior art, the software continuous delivery efficiency is low is solved.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
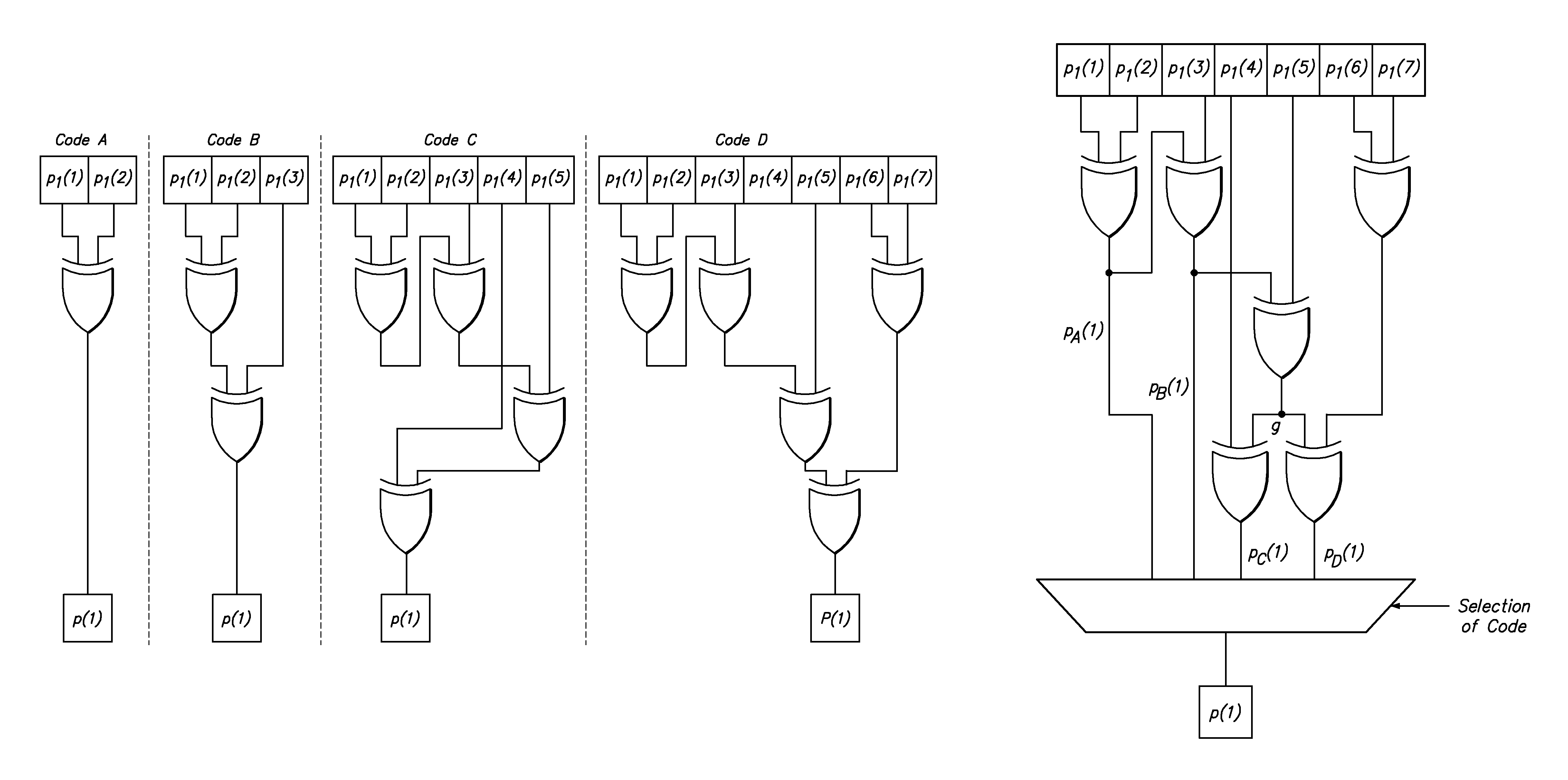
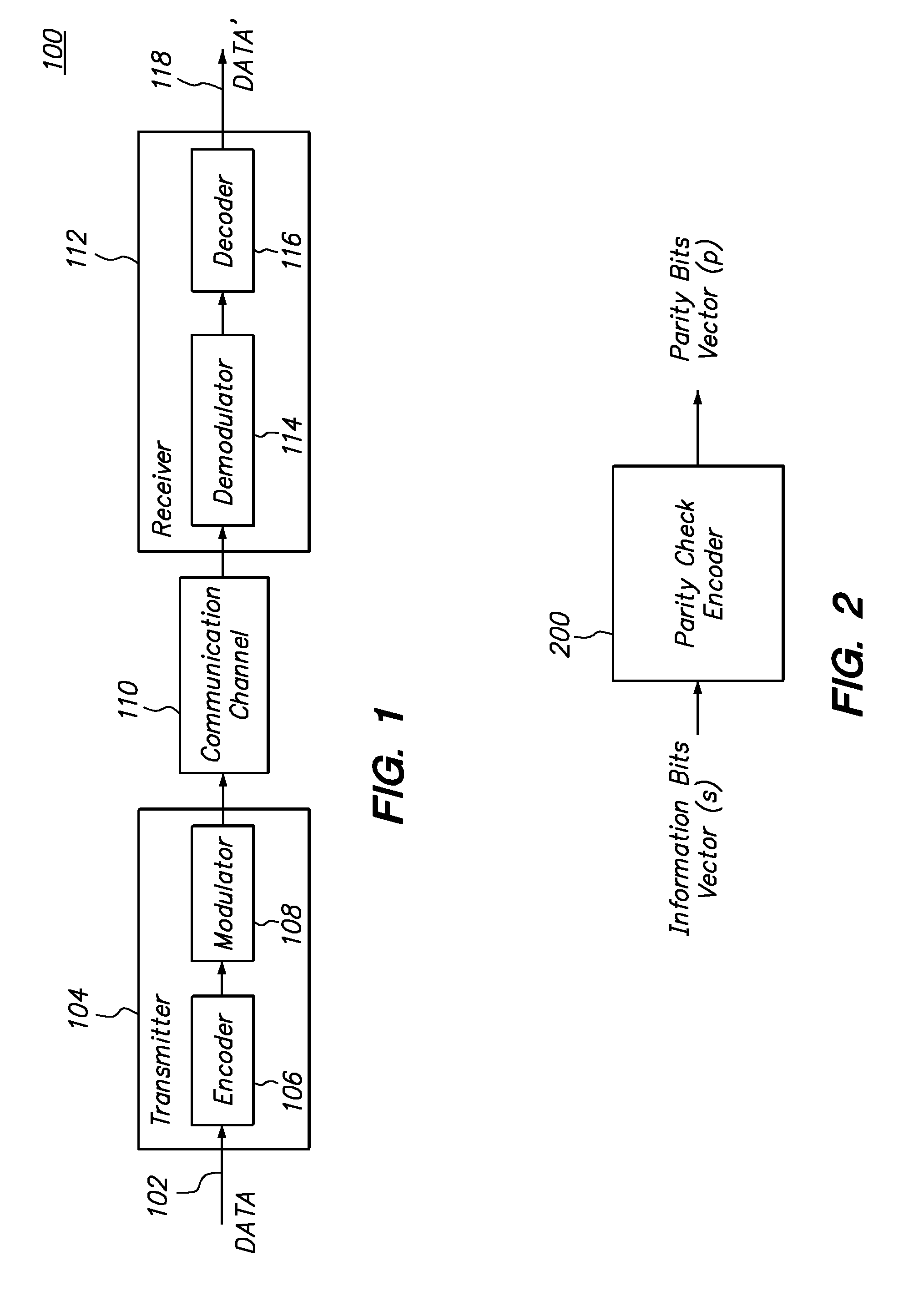
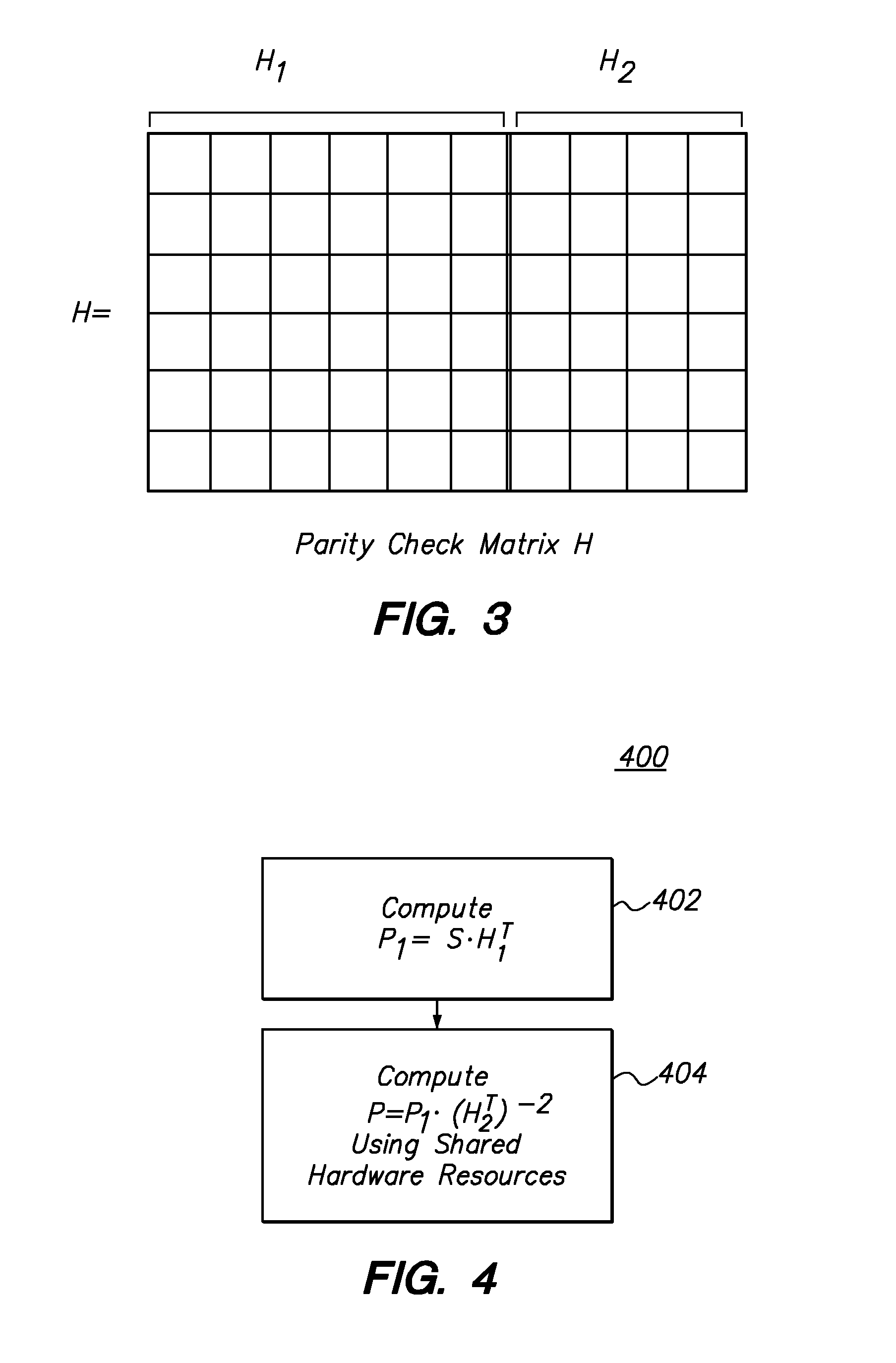
Low density parity check encoder and encoding method
ActiveUS9003257B1Error correction/detection using multiple parity bitsCode conversionParity-check matrixLow density
The present invention is directed toward a parity check encoder for low density error correction codes and to an encoding method. In accordance with an embodiment, an encoder for error correction coding comprises: first hardware resources configured to receive a message bits vector and to compute an intermediate parity bits vector from the message bits vector wherein the intermediate parity bits vector is computed based on a sub-matrix of a parity check matrix; and second hardware resources configured to compute a parity bits vector from the intermediate parity bits vector, wherein the second hardware resources are configured to compute parity bits for multiple different codes, and wherein portions of the hardware resources that are configured to compute the parity bits for a particular one of the codes are commonly shared with portions of the hardware resources that are configured to compute the parity bits for another particular one of the codes.
Owner:U-BLOX
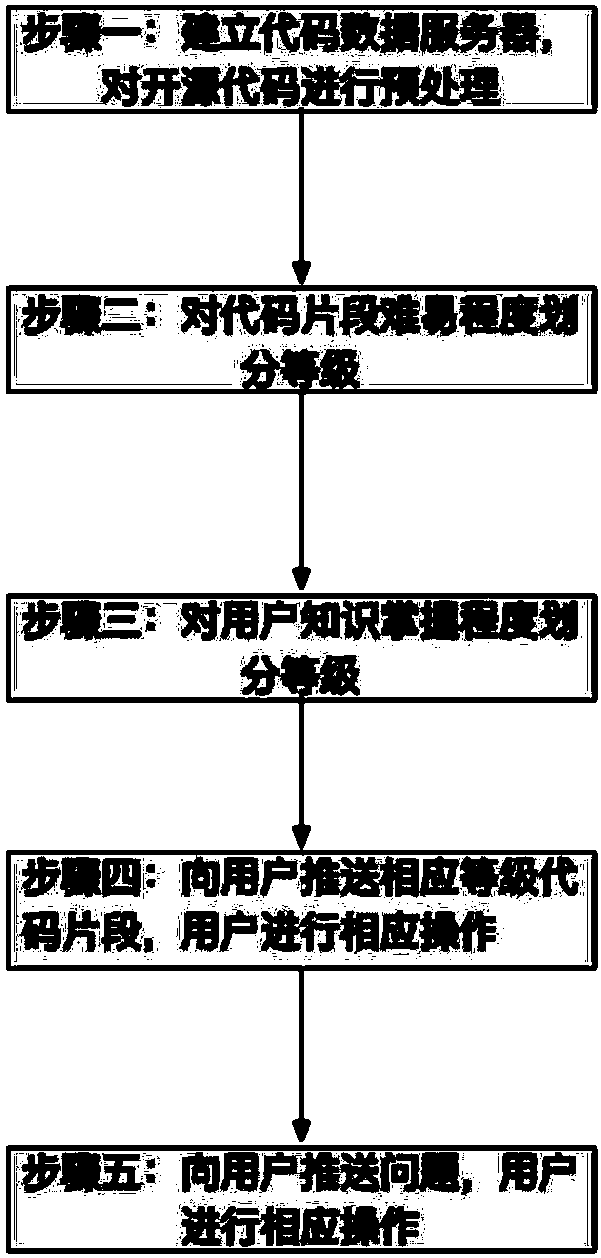
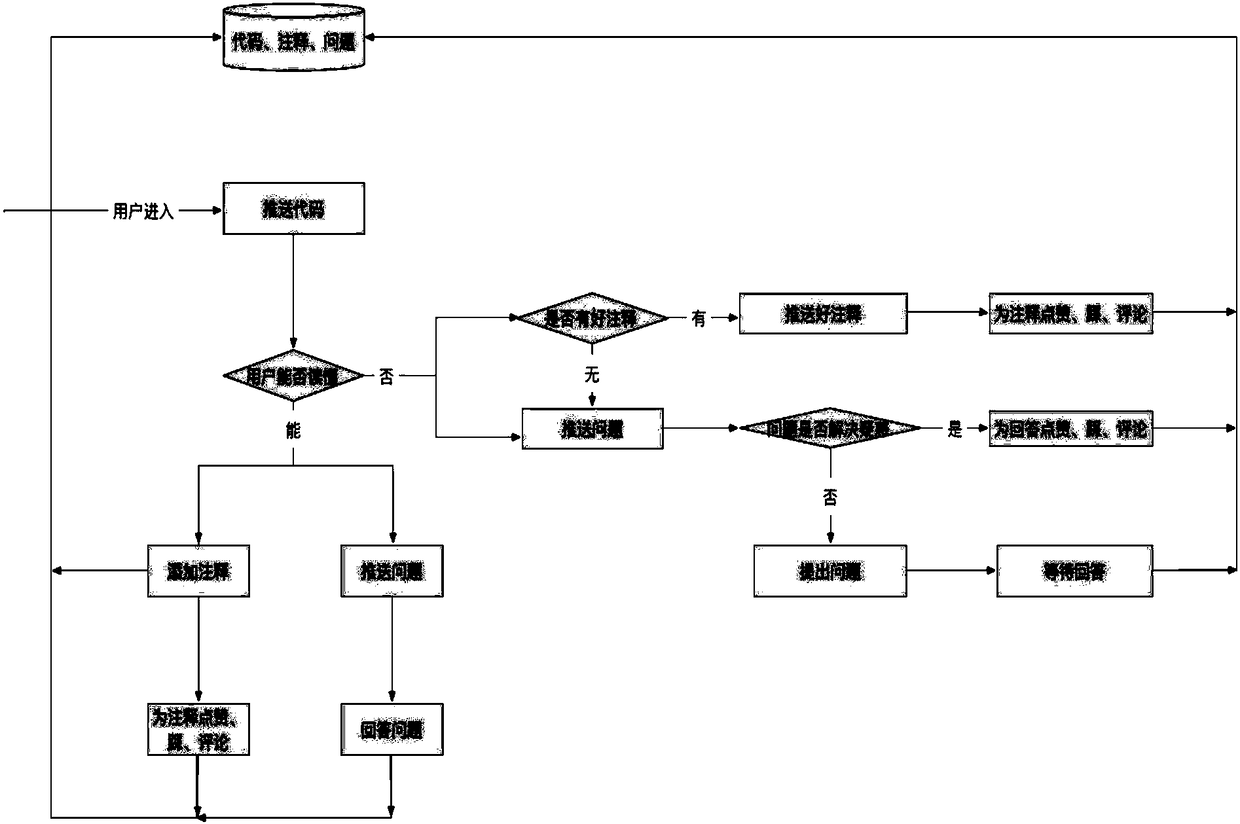
Method for improving annotation rate and annotation quality of open source codes
ActiveCN108459873AImprove retrieval efficiencyImprove reuse rateProgram documentationSoftware development processOpen source
The invention provides a method for improving annotation rate and annotation quality of open source codes. The method comprises the following steps of 1, establishing a code data server, and preprocessing the open source codes; 2, grading difficulty levels of code segments; 3, grading knowledge mastery levels of users; 3, pushing the code segments to the users of the corresponding levels accordingto the levels, thereby enabling the users to perform corresponding operations; and 5, pushing questions automatically generated for the code segments by a system to the users, performing answering bythe users, and if the answering is correct, displaying that the answering of the users is correct, and highlighting answers of the users; and if the answering is not correct, displaying that the answering of the users is wrong, and providing reference answers. According to the method, a batch of code segments with annotations and high-quality code annotations are formed after multi-time cyclic pushing; rich resources are provided for code reuse; the code retrieval efficiency of developers and the code reuse rate in a software development process are effectively improved; and the development efficiency is greatly improved.
Owner:NAT UNIV OF DEFENSE TECH
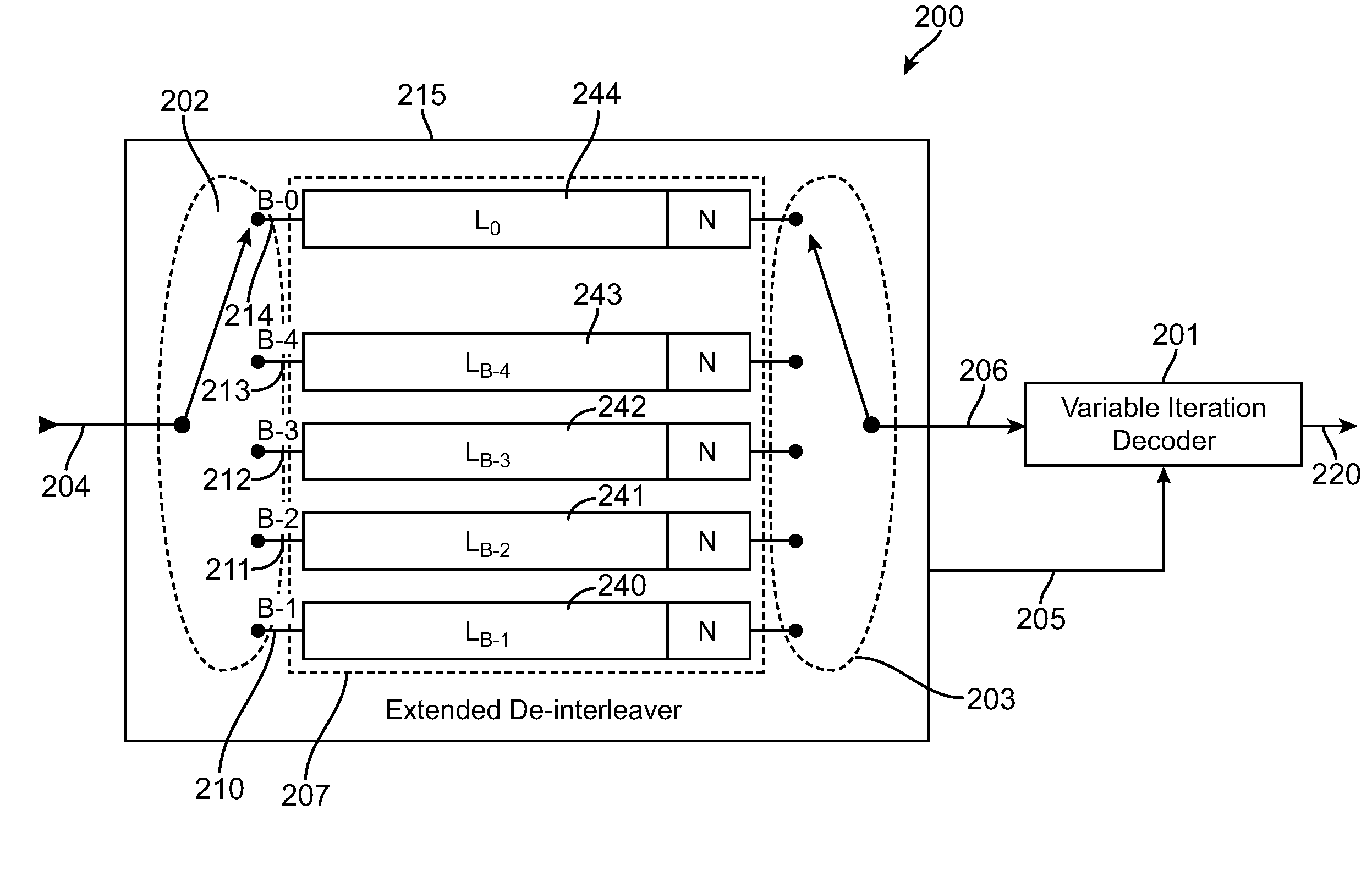
Extended deinterleaver for an iterative decoder
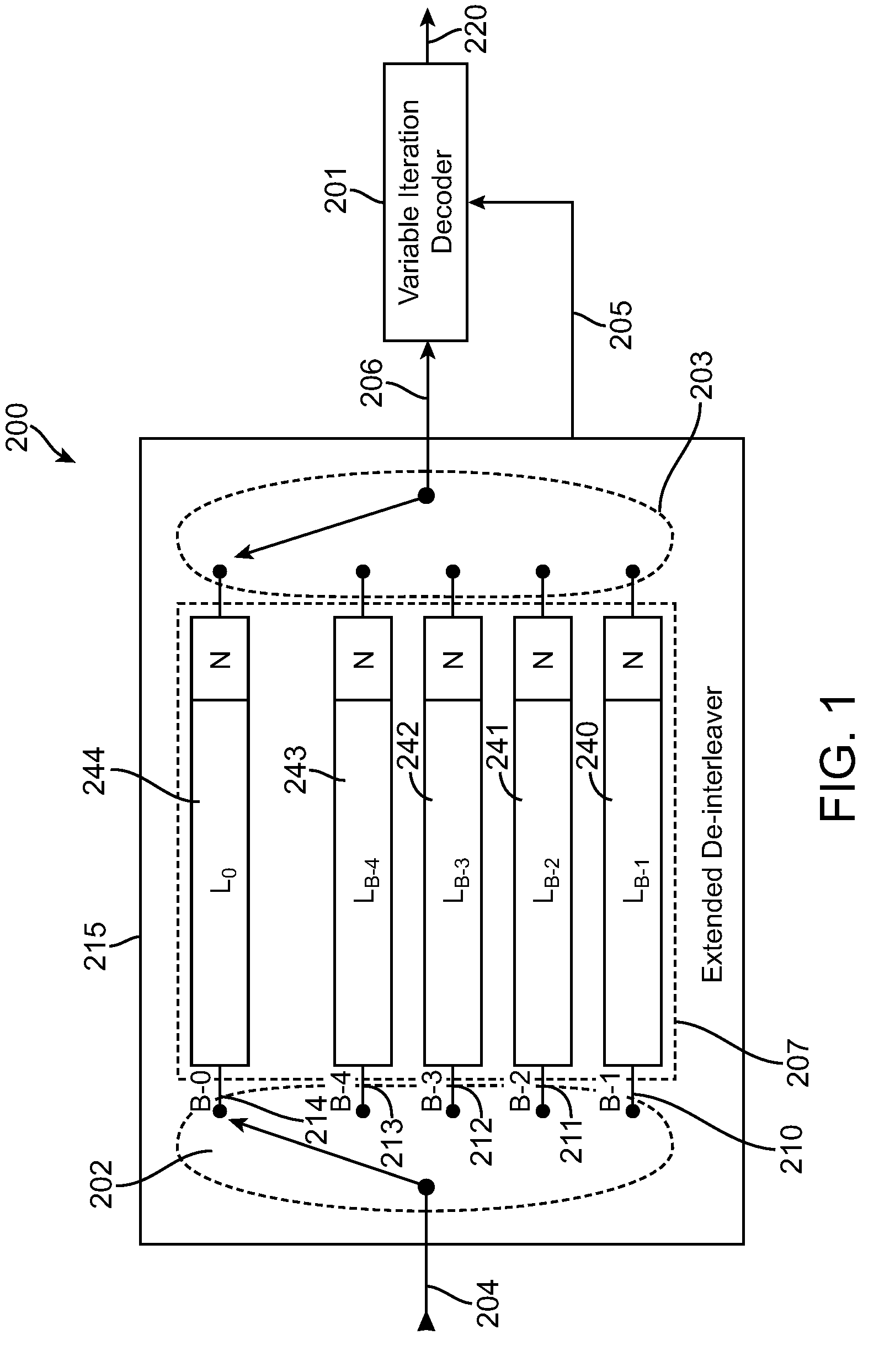
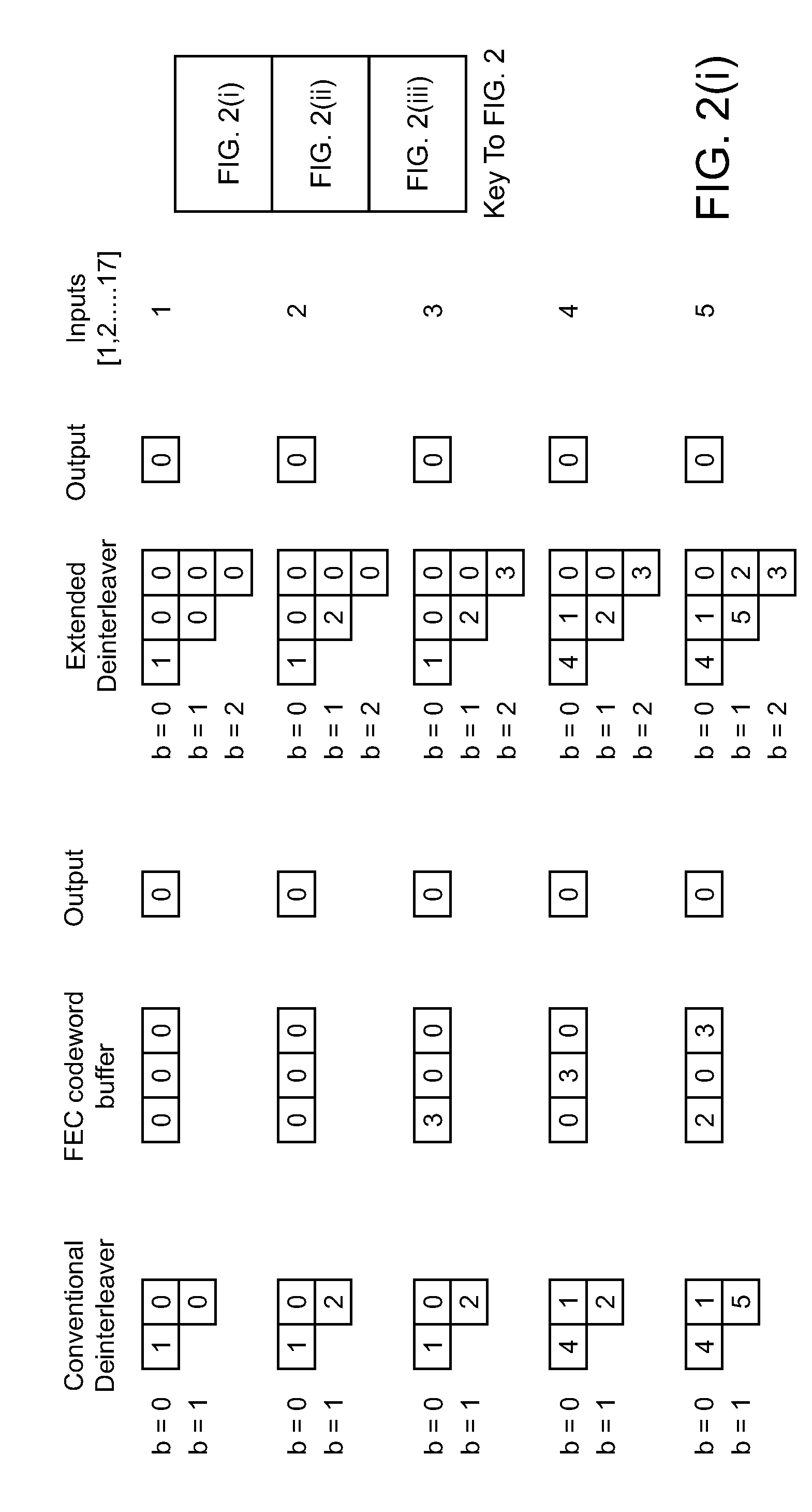
An extended deinterleaver the extended deinterleaver being responsive to at least one input signal, comprised of codewords, and operative to generate a deinterleaved output signal. The extended deinterleaver comprising a storage space organized into B number of appended storage branches, at least one appended storage branch having a storage branch and at least one element N, the received codewords being deinterleaved and buffered by the extended deinterleaver prior to being provided to the variable iteration decoder. Each appended storage branch further having a length that is extended by the length of N, N being at least one element, wherein as a codeword is provided to the variable iteration decoder, other codewords are provided to subsequent appended storage branches, and further wherein each appended storage branch, indexed by ‘b’, has a length of Lb+N, wherein Lb is the length of the storage branch prior to appending N.
Owner:CSR TECH INC
Copy protection of optical discs
ActiveUS7788504B2Quick changeTelevision system detailsDigital data processing detailsComputer hardwareCopy protection
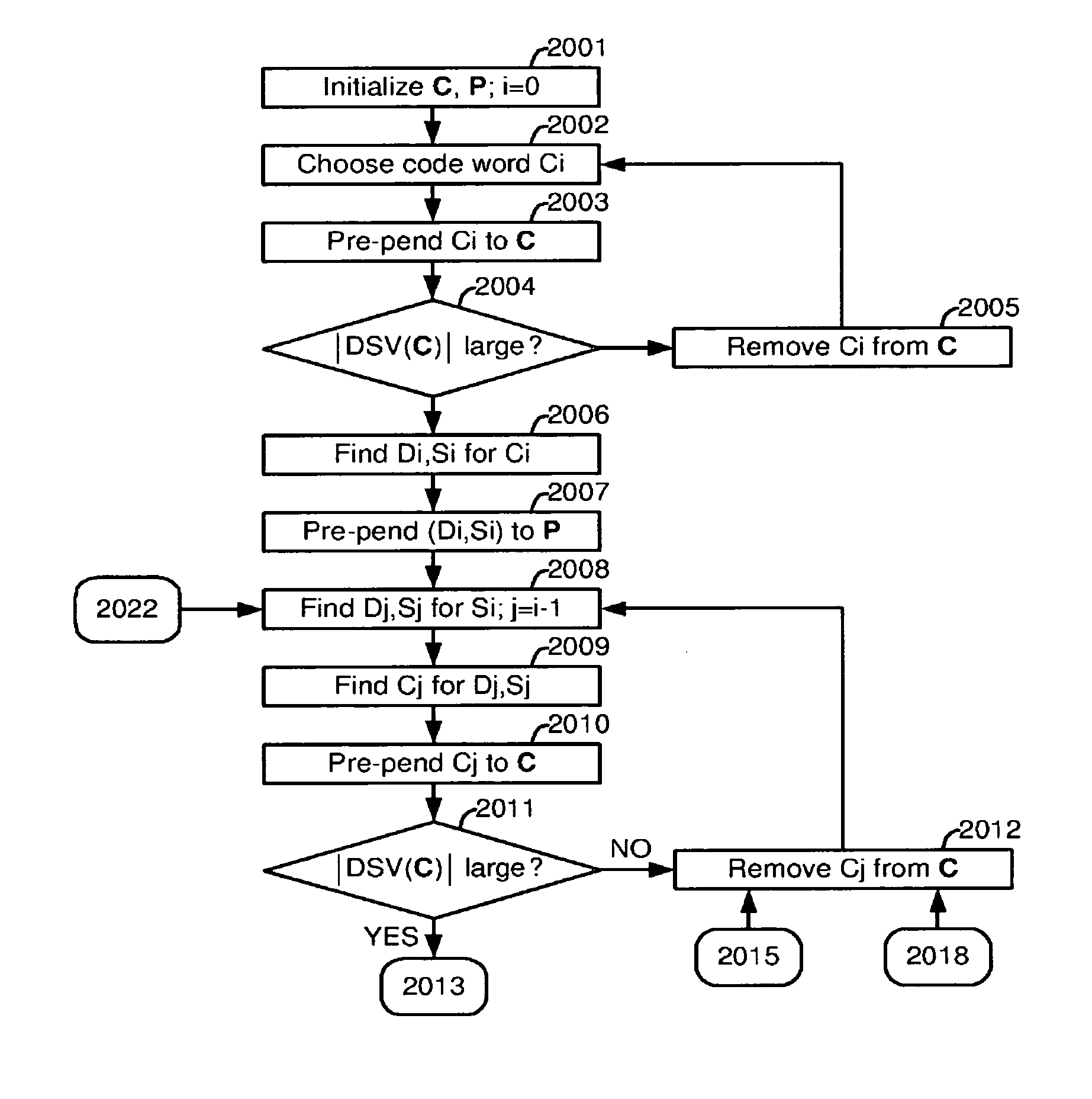
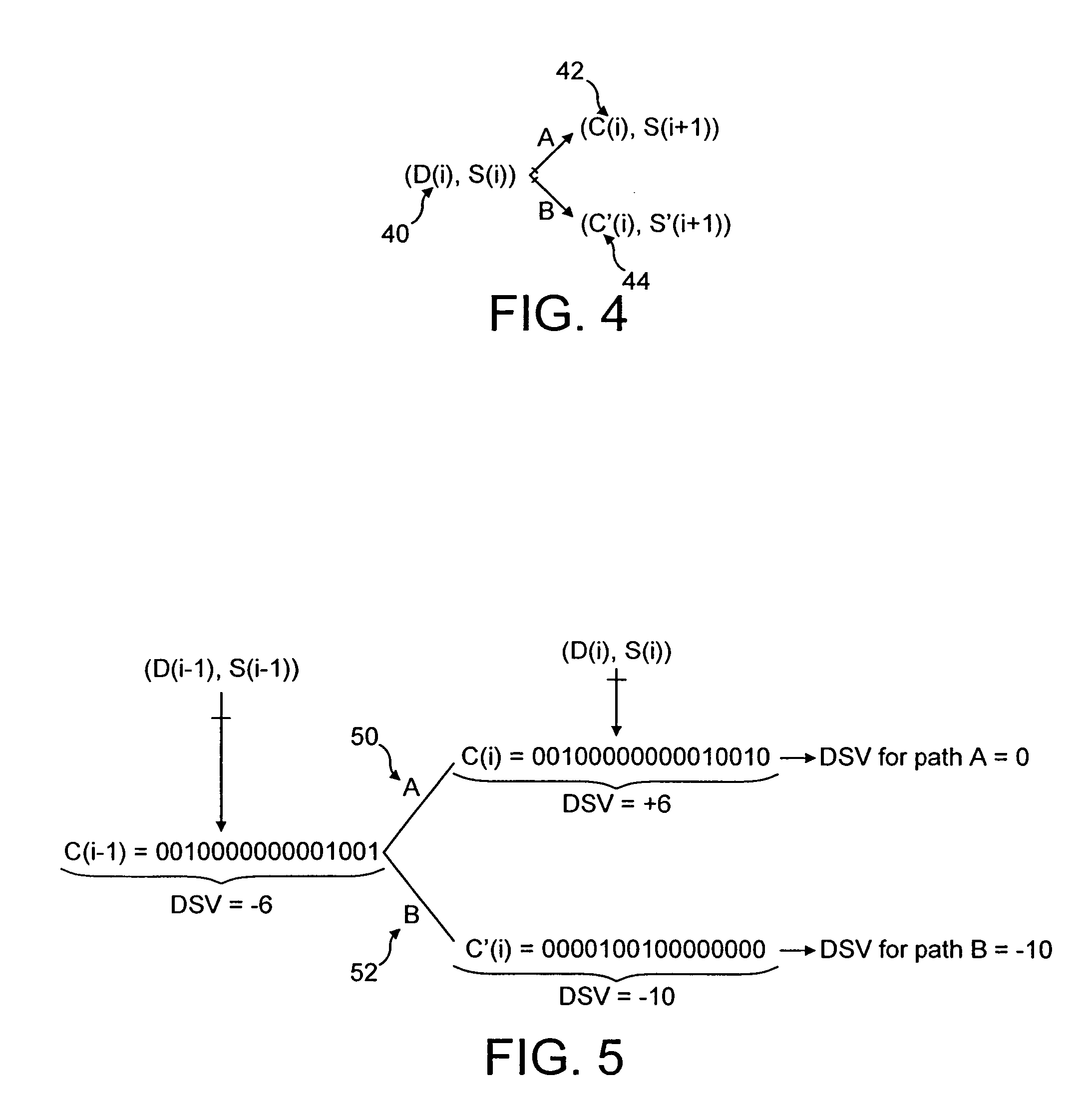
Subversive DSV (SDSV) sequences of data symbols having a large absolute value of DSV are extremely valuable in the copy protection of optical discs as they can induce uncorrectable read errors. However, very few SDSV sequences of data symbols can be found in multimodal codes such as Eight-to-Sixteen Modulation (ESM) utilised in DVDs. It is required to select data symbols, for encoding using a multimodal code, which are capable of forcing an encoder to produce at least one subversive sequence of code words. A possible code word for a data symbol is selected if the code word has a large absolute value of DSV and there are no alternative code words, or all alternative code words are equivalent, or all alternatives except one are ruled out by RLL rules.
Owner:ROVI SOLUTIONS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com