Patents
Literature
34 results about "Demand creation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Demand creation is the process of increasing the demand for a product or service using marketing techniques. The term is typically applied to unsought products that have little demand because it's they are unknown to customers.
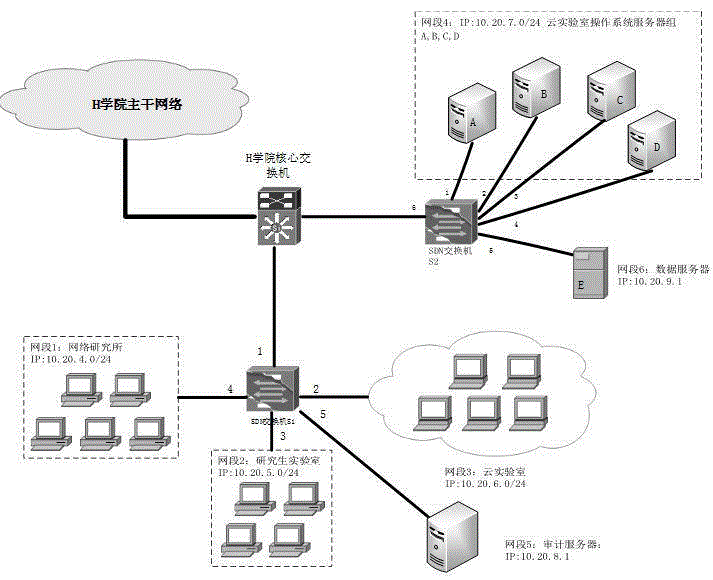
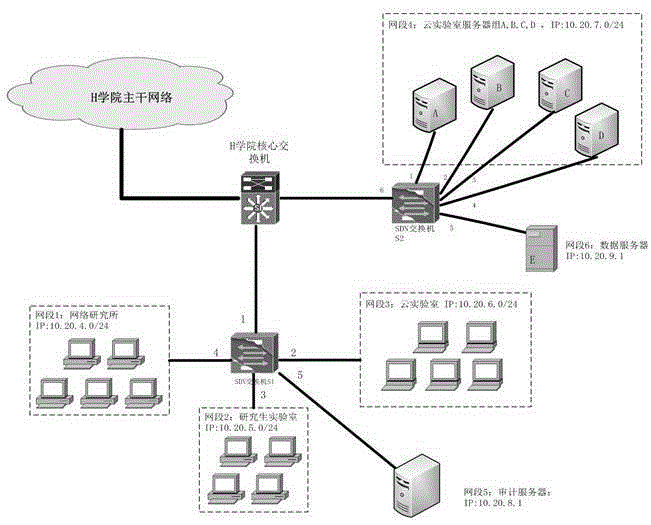
Business requirement transformation and deployment method for SDN (Software Defined Network)
ActiveCN105406992AThe combination is valid and correctCorrect combinationData switching networksNODALBusiness requirements
The invention discloses a business requirement transformation and deployment method for a SDN (Software Defined Network). The method mainly comprises the following steps: 1) a service function chain is built according to network business requirements raised by a user; 2) a local controller reports resource conditions of a bottom network node to a root controller; 3) the root controller designs a service function instance chain; 4) each service function instance is analyzed to be a multistate network strategy selection mechanism; 5) according to the current network state, the root controller selects a proper network strategy to be issued to a corresponding local controller; 6) the local controller combines instances from different service function instance chains on the same network node; 7) the local controller transforms a complicated condition strategy in the same network strategy into a plurality of simple condition strategies; 8) the local controller compiles the combined strategy into an OpenFlow flow table; and 9) the local controller issues the flow table to the bottom network nodes, and the strategy is deployed.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
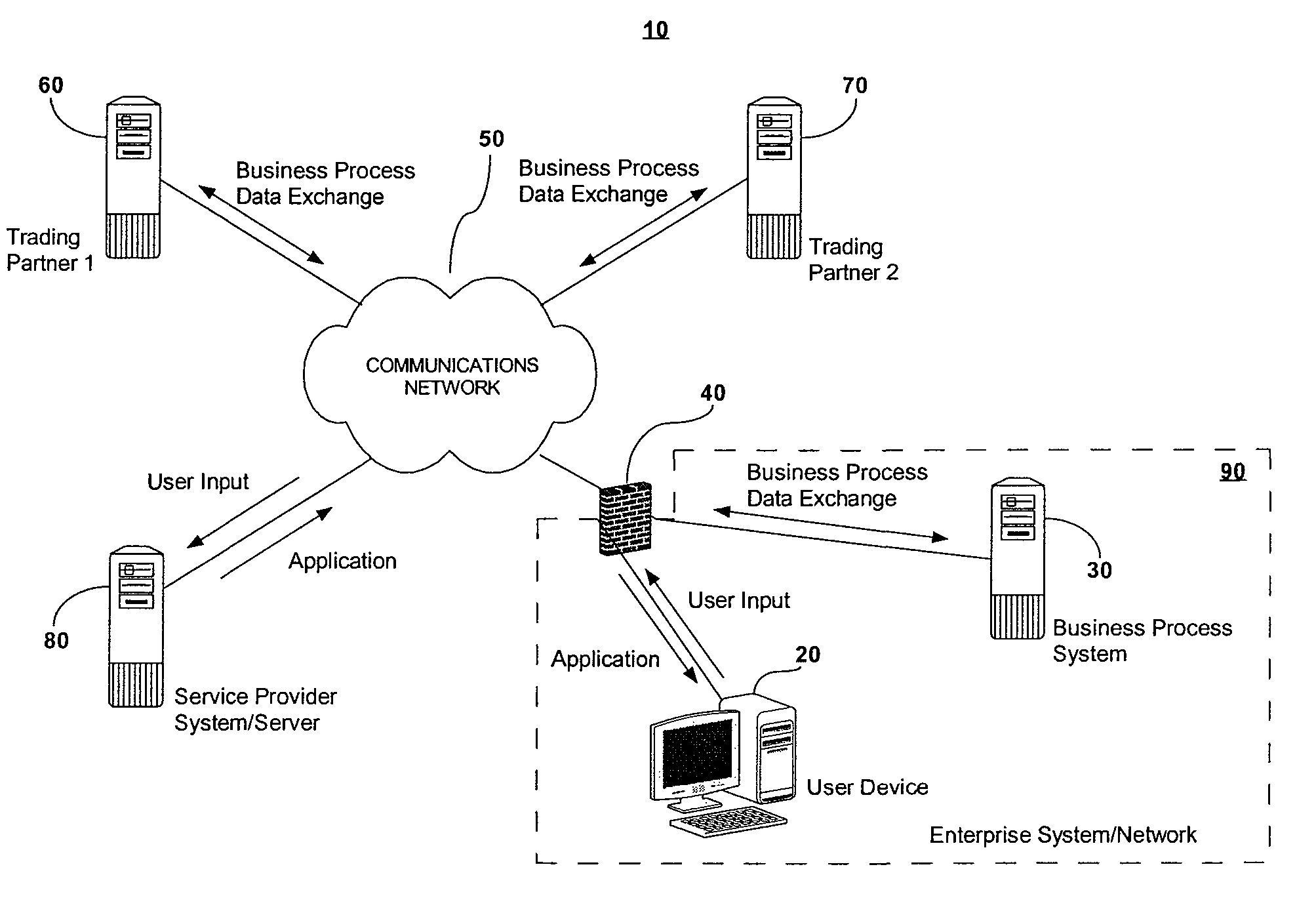
System and method for automated on-demand creation of a customized software application
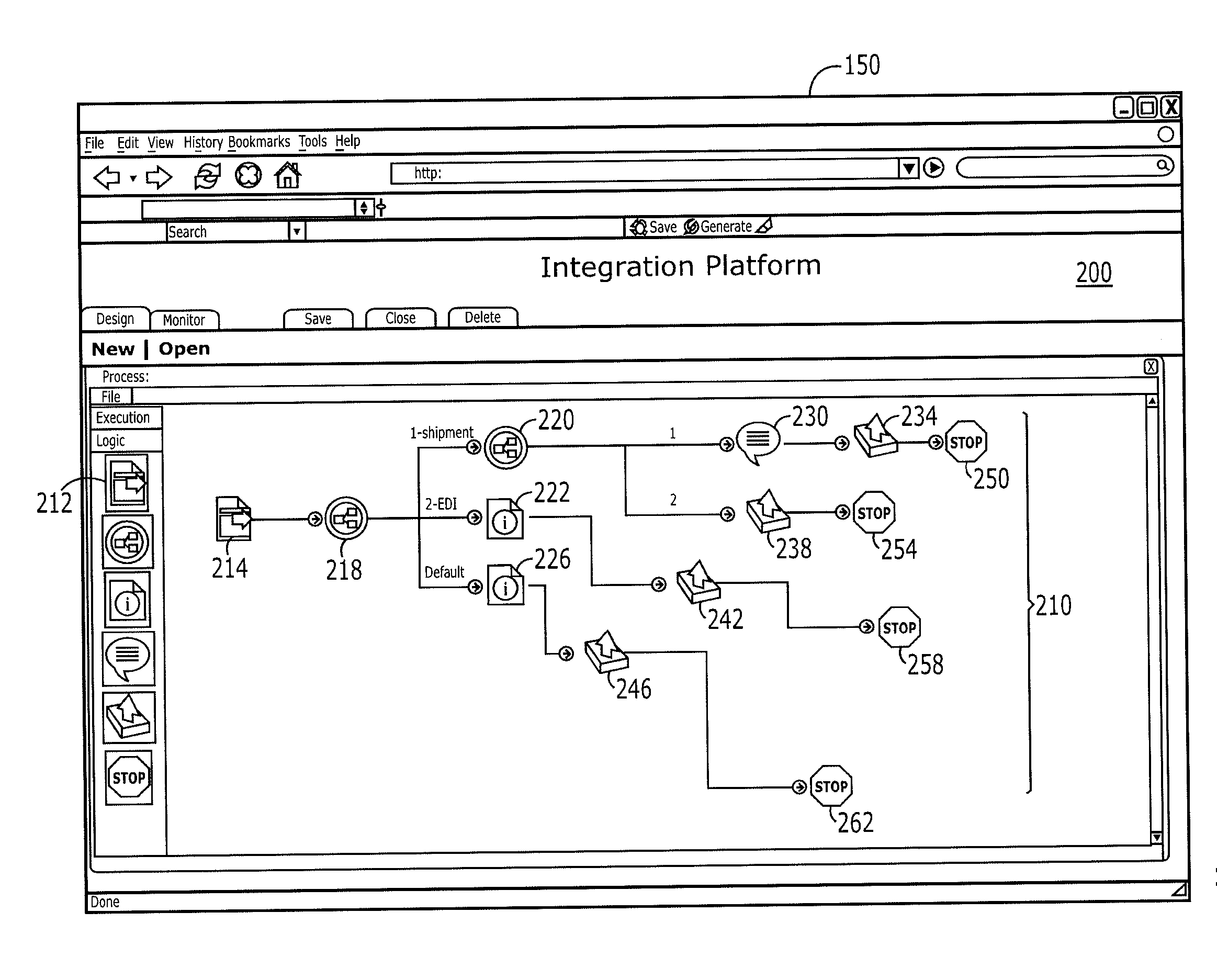
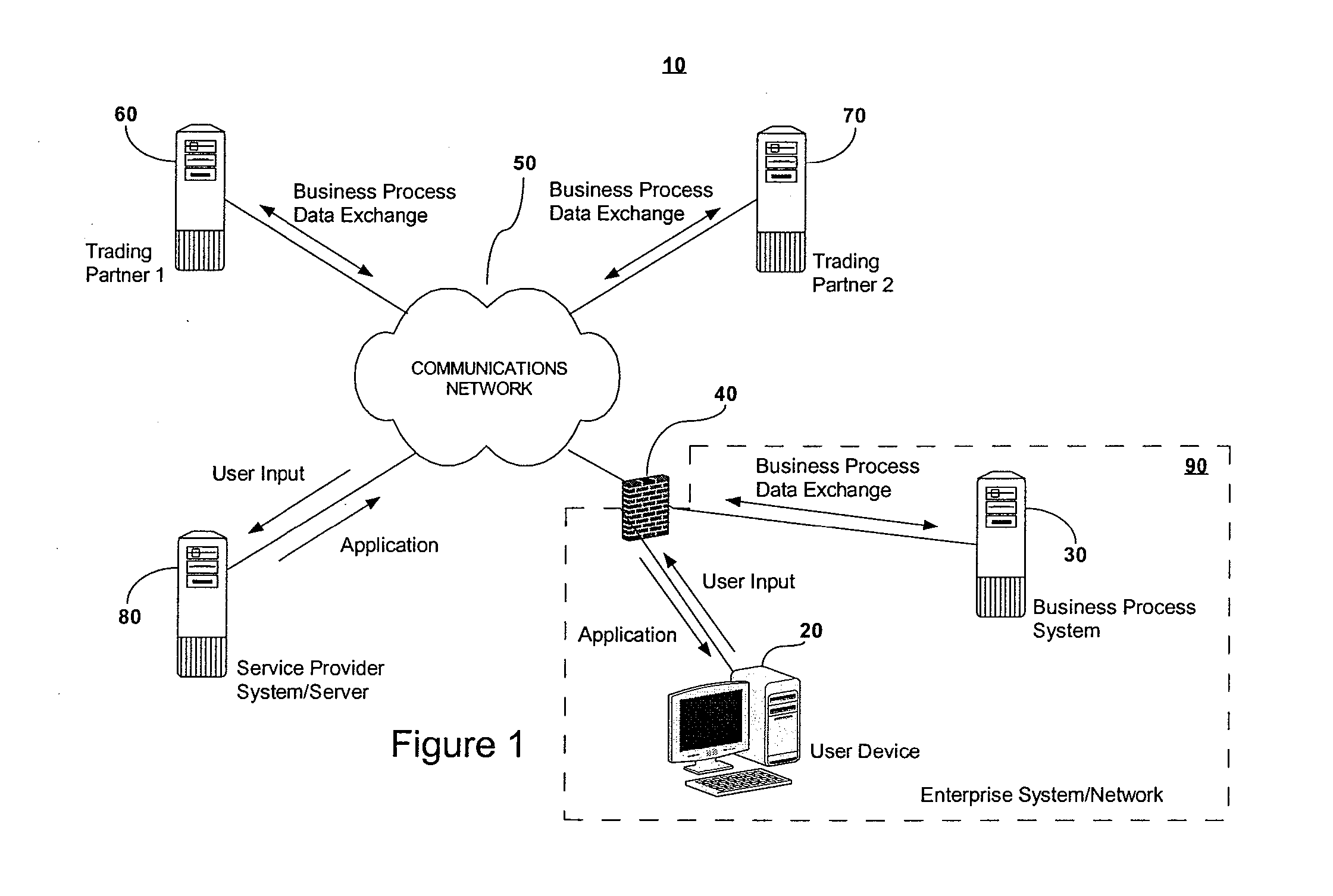
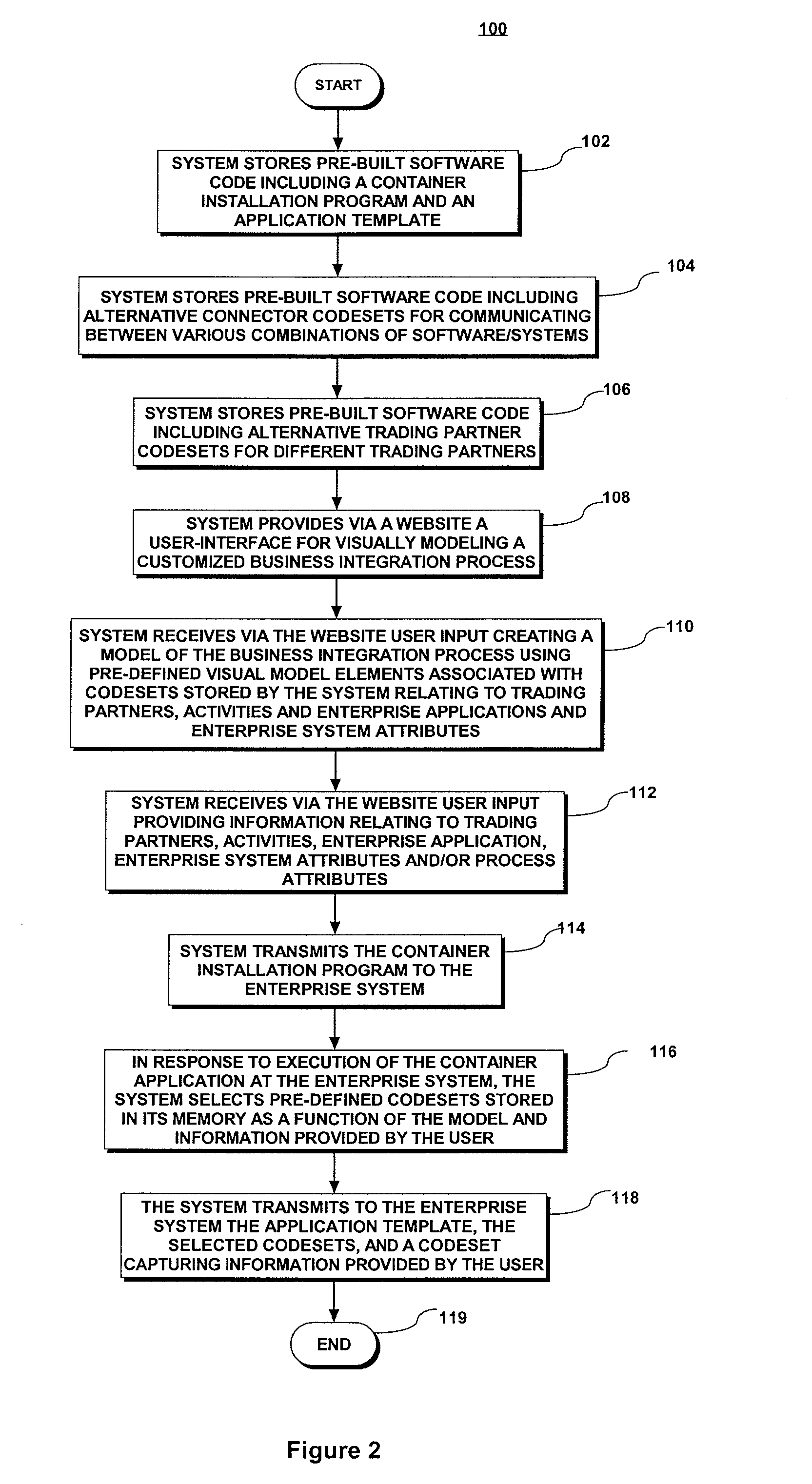
ActiveUS8533661B2Software designVisual/graphical programmingBusiness-to-businessApplication software
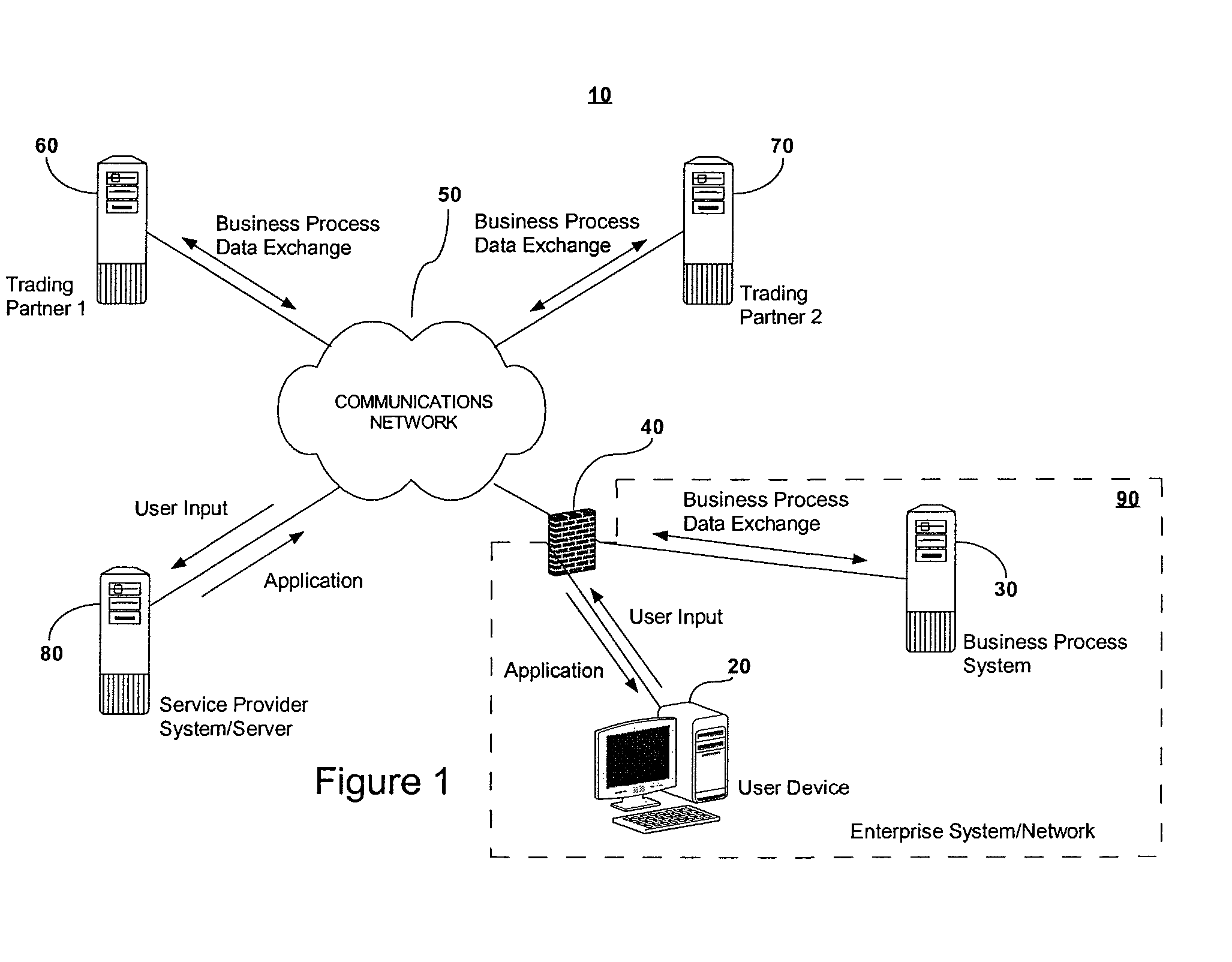
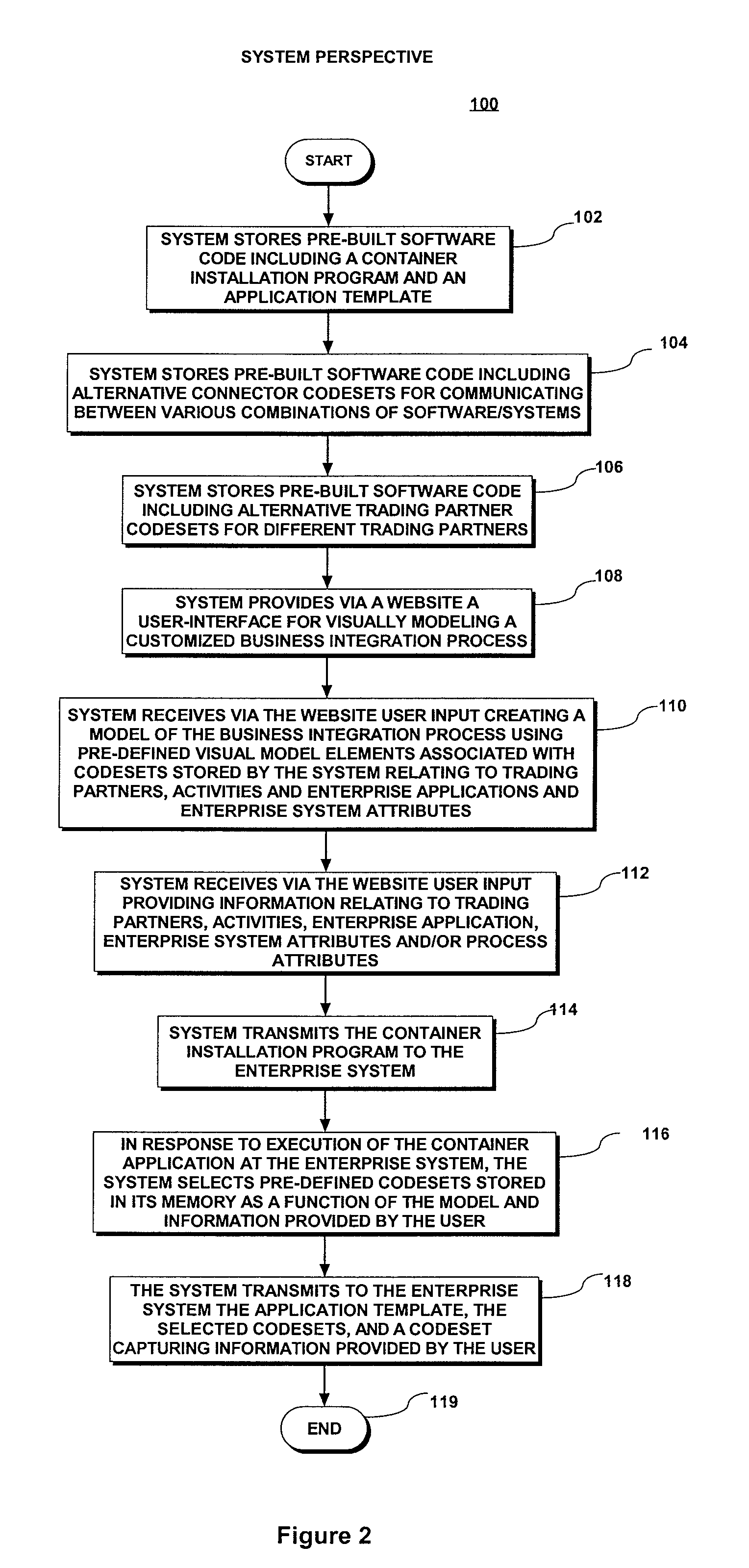
A web-based interface is provided for visually modeling a business-to-business or application integration process by selecting and associating predetermined process-representing visual elements. A customized, enterprise-specific executable software application (“dynamic runtime engine”) is automatedly produced by software running remotely. The dynamic runtime engine is created to include a generic application template, predefined “stock” codesets selected as a function of the modeled process, and a data profile codeset that includes input provided by the user for customizing the stock components for a specific integration process of a specific enterprise. The application template and selected codesets may subsequently be downloaded to provide an executable dynamic runtime engine software application that is customized to perform a specific integration process for a specific enterprise. Thus, the dynamic runtime engine software application is created automatedly outside of an enterprise's computing network, but is customized for a specific enterprise before it arrives within the enterprise's computing network or other destination network.
Owner:BOOMI
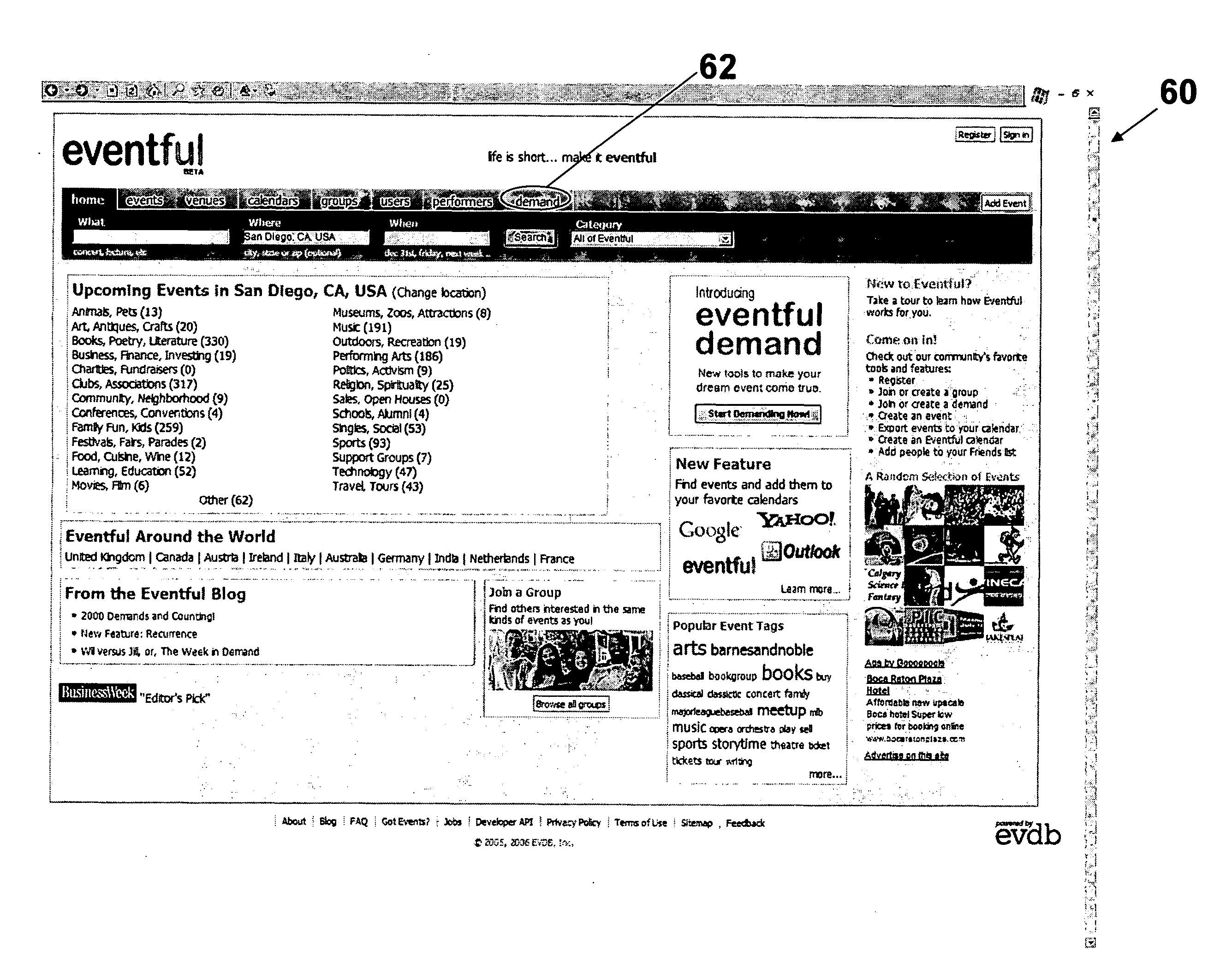
Event demand system and method
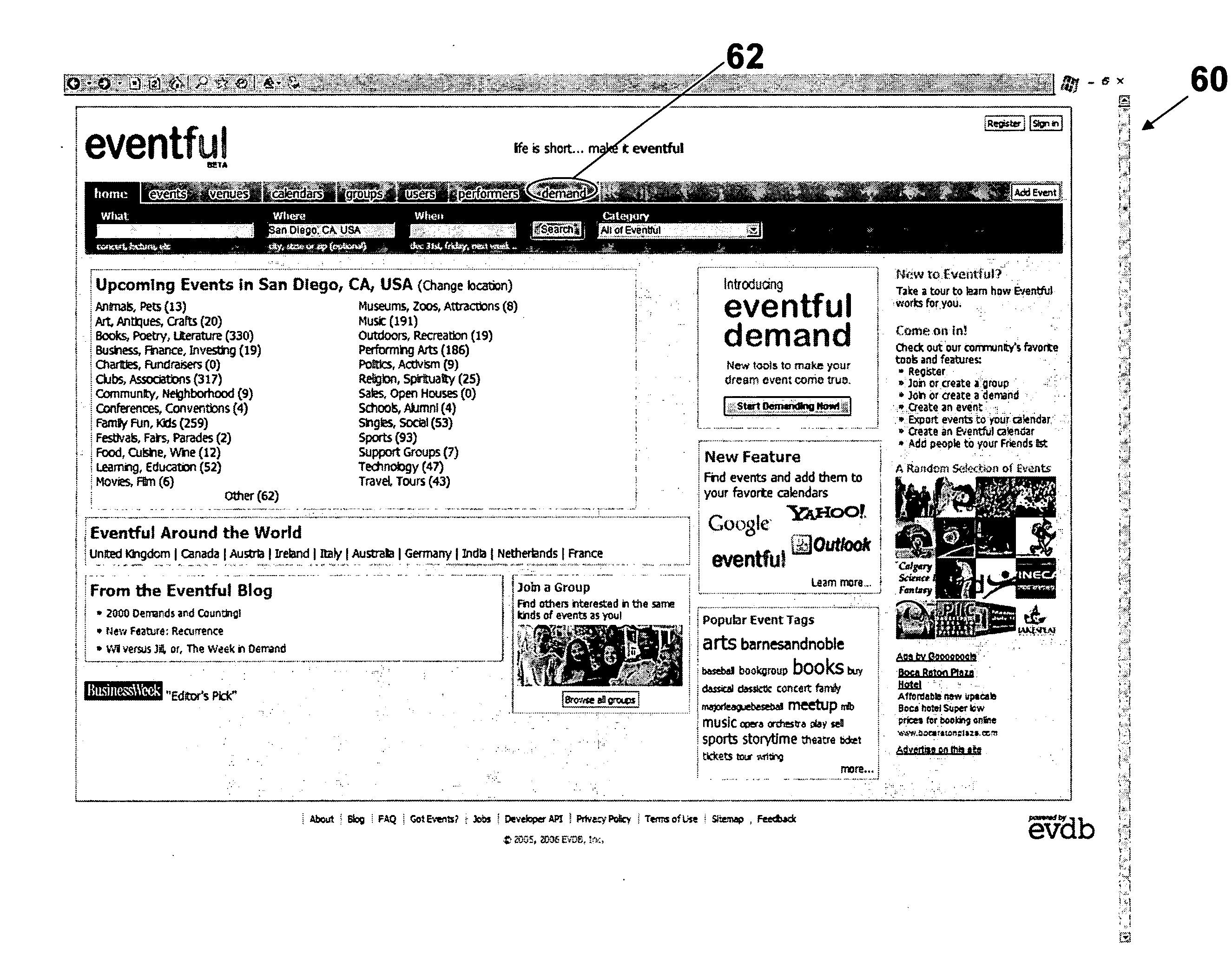
A system and method for event demand creation and event organization is provided in which an interested party can create a demand for an event at a particular location and then encourage other people to join the demand. Once the demand reaches critical mass, the event provider is notified of the demand and asked to agree to the demanded event.
Owner:EVENTFUL LLC
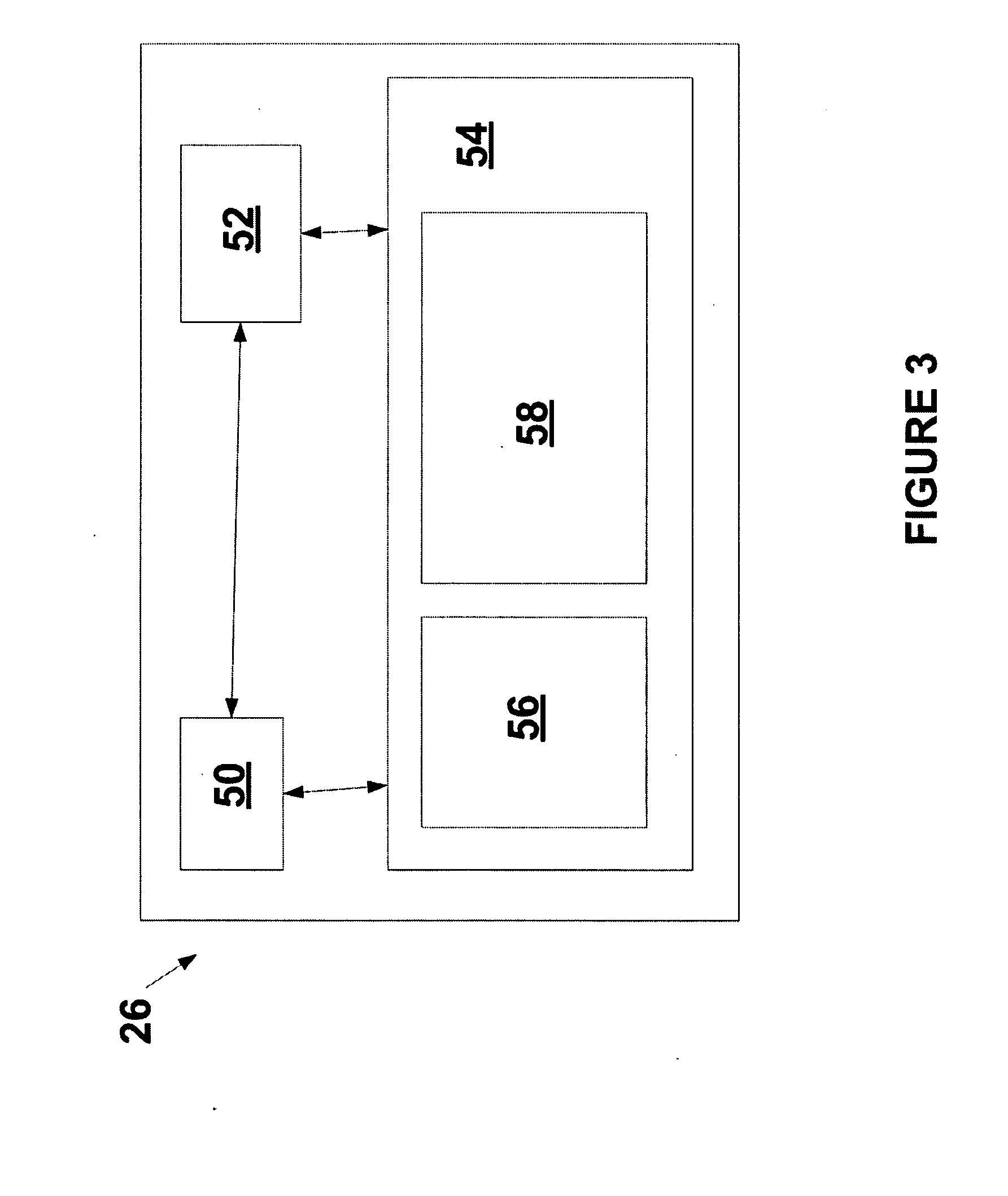
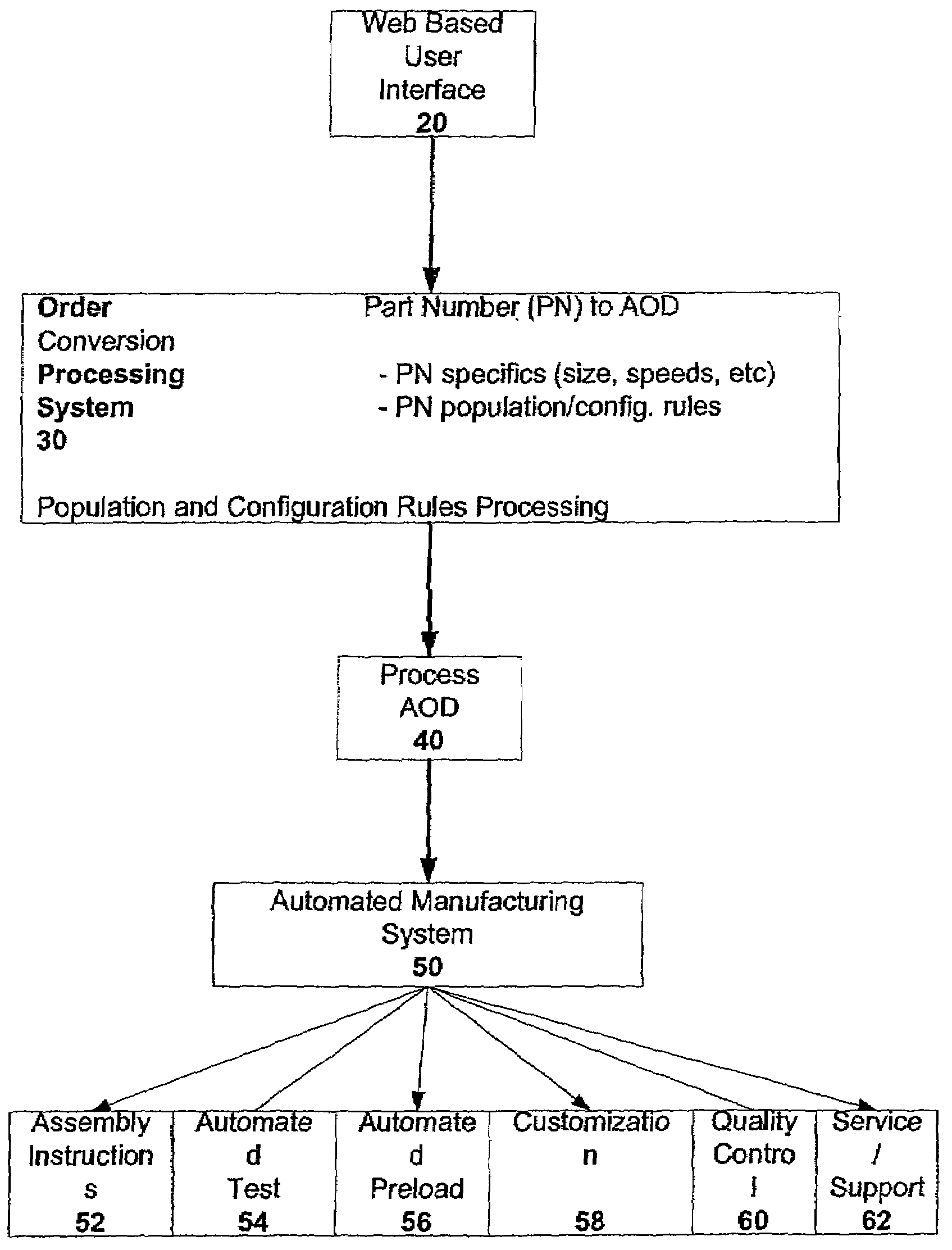
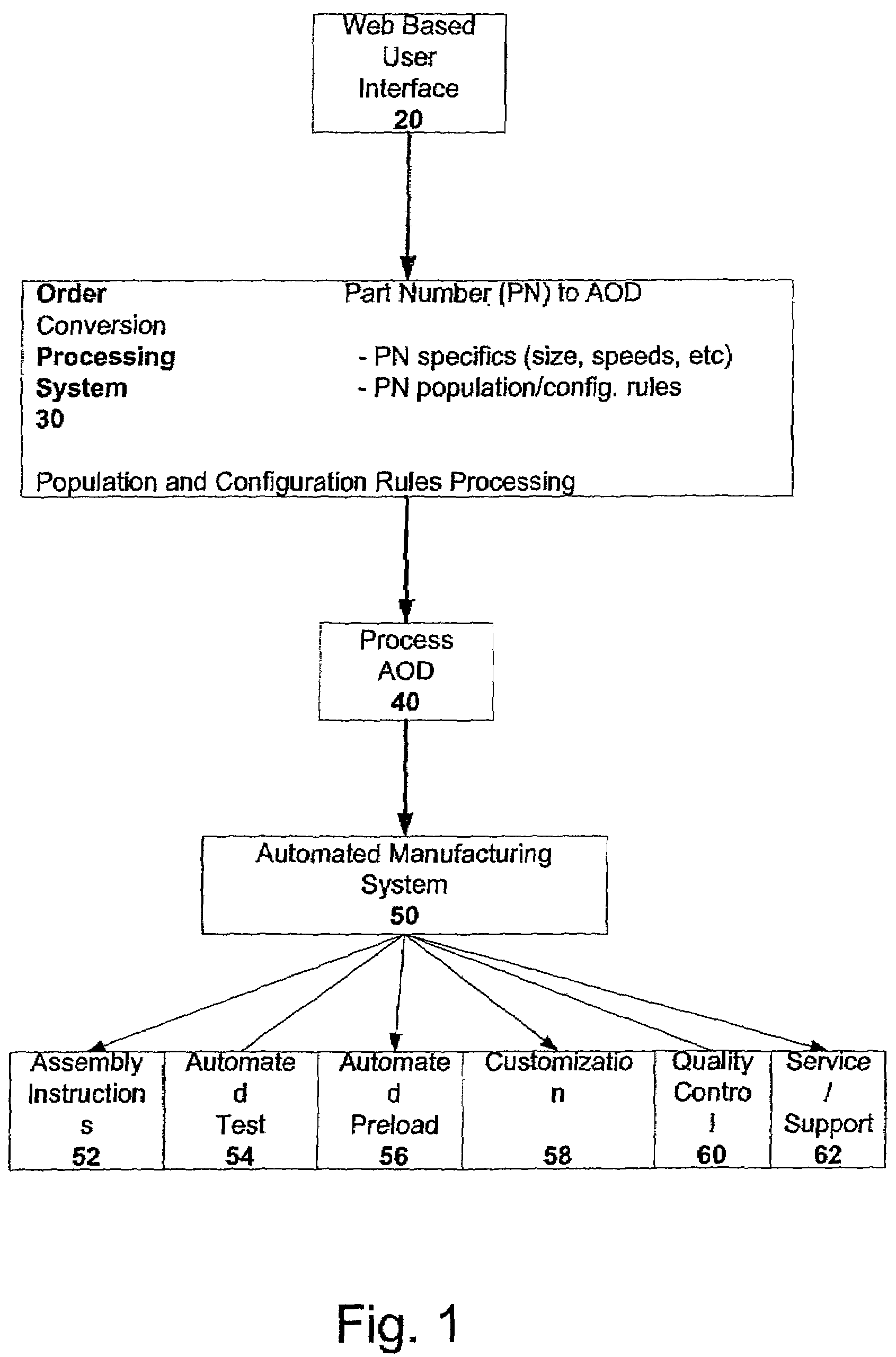
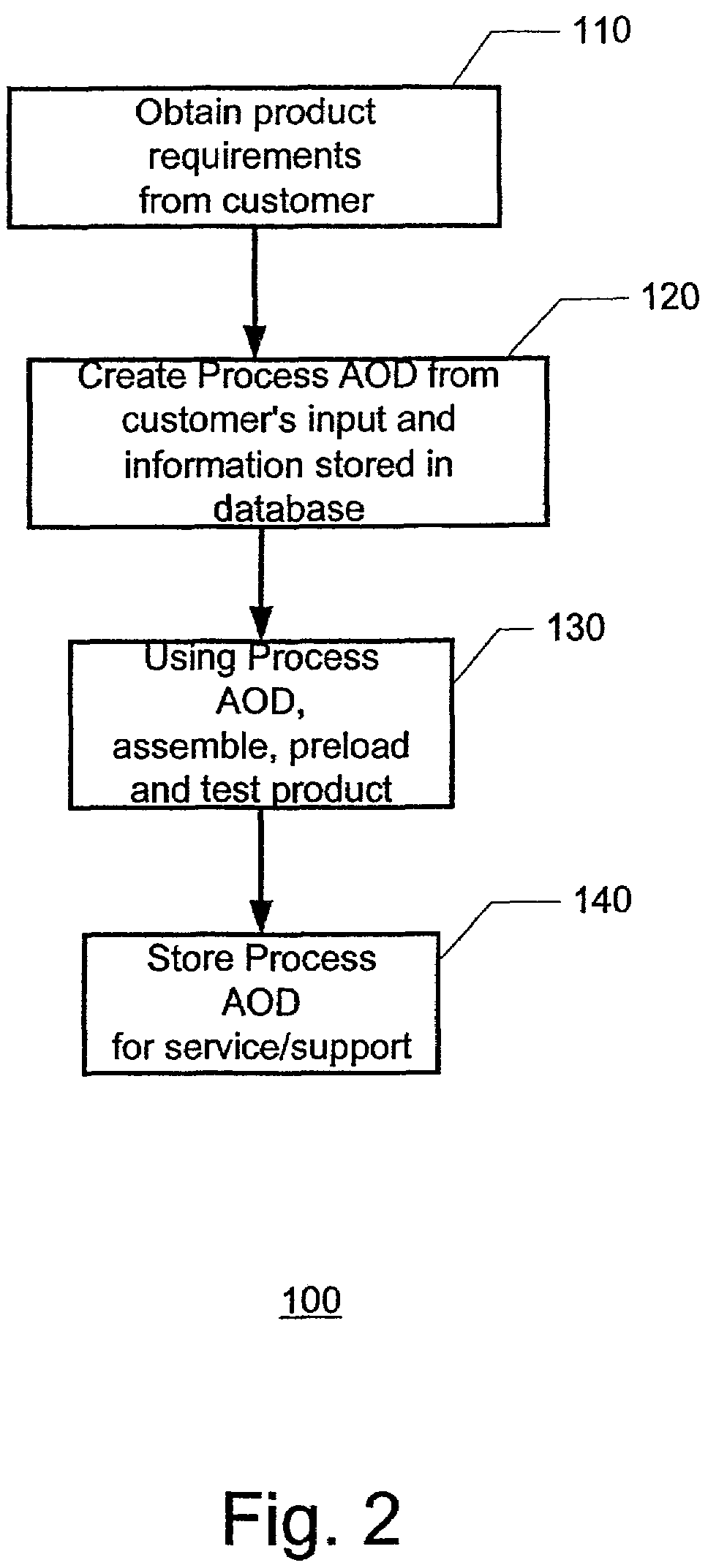
Method and system for object oriented approach and data model for configure-to-order manufacturing system
ActiveUS7194323B2Follow-up calls to the customer are eliminated or greatly reducedCost-effectiveLogisticsPoint-of-sale network systemsManufacturing systemsDescriptive language
A method and system for product fulfillment in an automated manufacturing system is disclosed. The method and system of the present invention includes obtaining requirements for a product from a customer. The method and system further includes creating a plan from the requirements using a descriptive language. The plan is then conveyed to an automated manufacturing system for use in manufacturing the product.
Owner:RED HAT
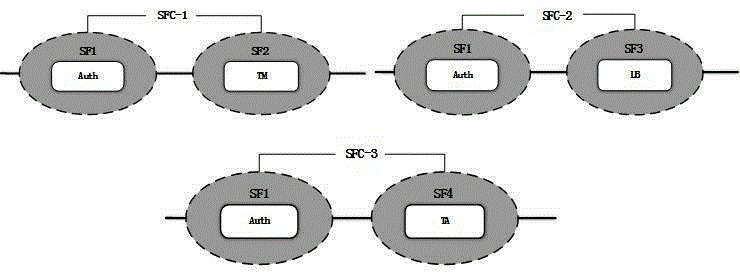
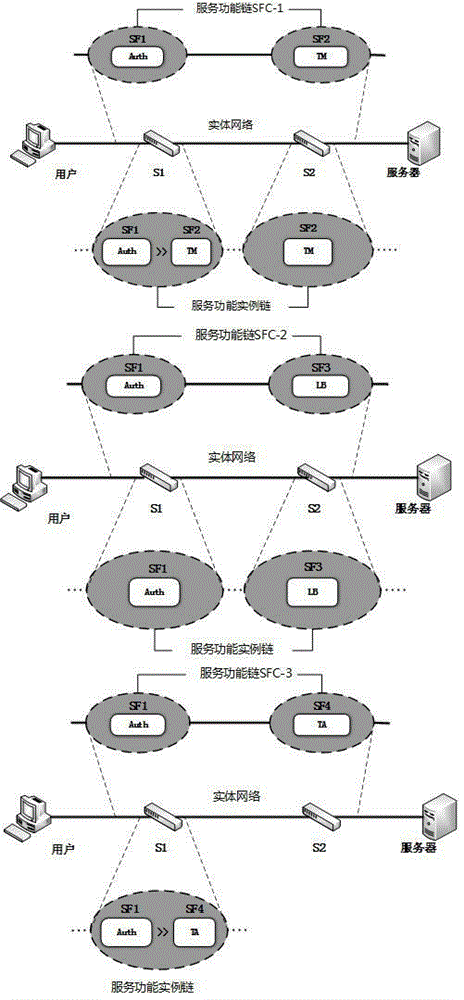
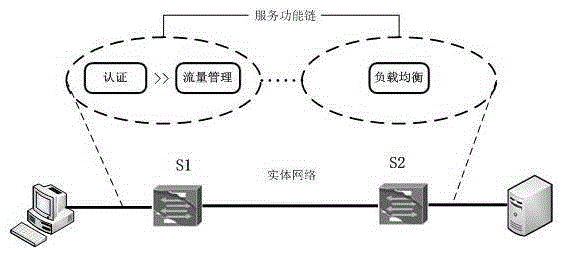
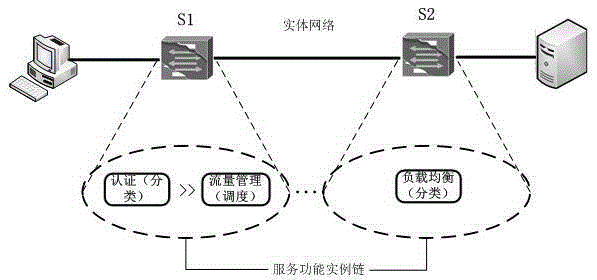
Service function chaining construction method for SDN
The invention discloses a service function chaining construction method for a SDN (Software Defined Network), which can dispose a network service function blocks (SFB) instance at a network node specific to a network service request. The method comprises: first, a controller creating a service function chaining according to a network service demand provided by a user; and creating a service function instance chaining according to network node information, wherein the service function chaining is composed of service functions, and the service function instance chaining is composed of SFBs. The service function is supported by SFBs; the main task of a classification SFB type is classifying data packets according to metadata; the main task of a scheduling SFB type is performing scheduling treatment on data packets; if a plurality of data streams have to go out from a same port, the sending order sequence and rhythm for the data streams are set. The classification greatly simplifies current SFB types, and guarantees SFB type conciseness.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
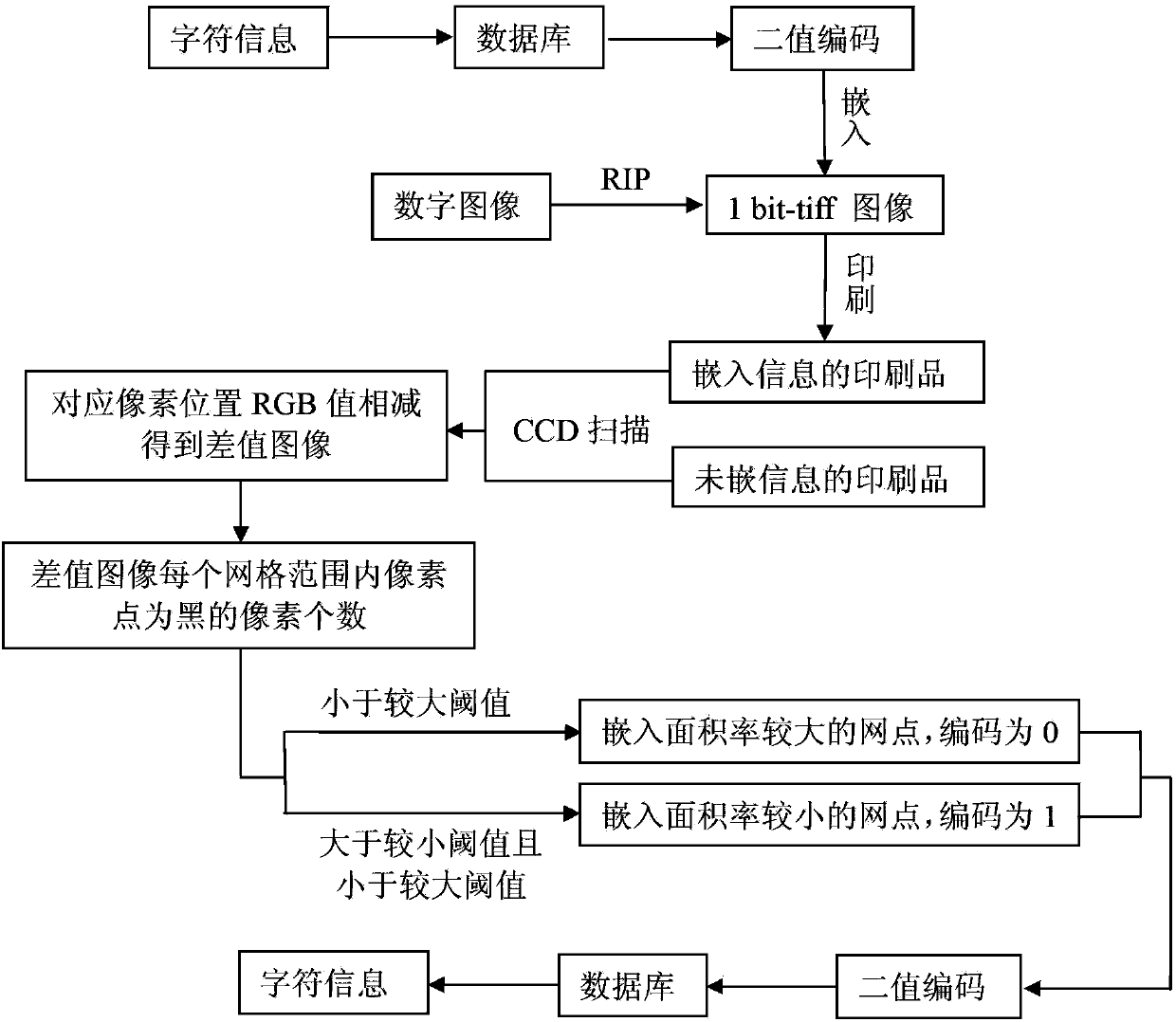
Anti-counterfeiting method of print pictures based on CCD detection
InactiveCN103426014ARealize detectionNo increase in printing costsCo-operative working arrangementsProgram/content distribution protectionData matchingFeature extraction
The invention discloses an anti-counterfeiting method of print pictures based on CCD detection and belongs to the field of presswork forgery prevention. The method includes: establishing an anti-counterfeiting information database, embedding anti-counterfeiting information, and detecting the anti-counterfeiting information. Recording in the anti-counterfeiting information database can be established according the need of a unit. The anti-counterfeiting information is embedded by embedding mesh points different in area rate into a half-tone picture, and the mesh points different in area rate are used to express character information. A detection method of the anti-counterfeiting information includes: using CCD equipment to acquire a print picture with embedded anti-counterfeiting information and a print picture with no embedded anti-counterfeiting information, extracting the embedded anti-counterfeiting information by a feature extraction method, determining a printed matter is true if the data matching with that in the database, and determining the printed matter is counterfeited if the data matching with that in the database is not obtained. The method has the advantages that forgery prevention for printed matters such as package and certificates in practical production can be achieved and copying difficulty is increased greatly.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
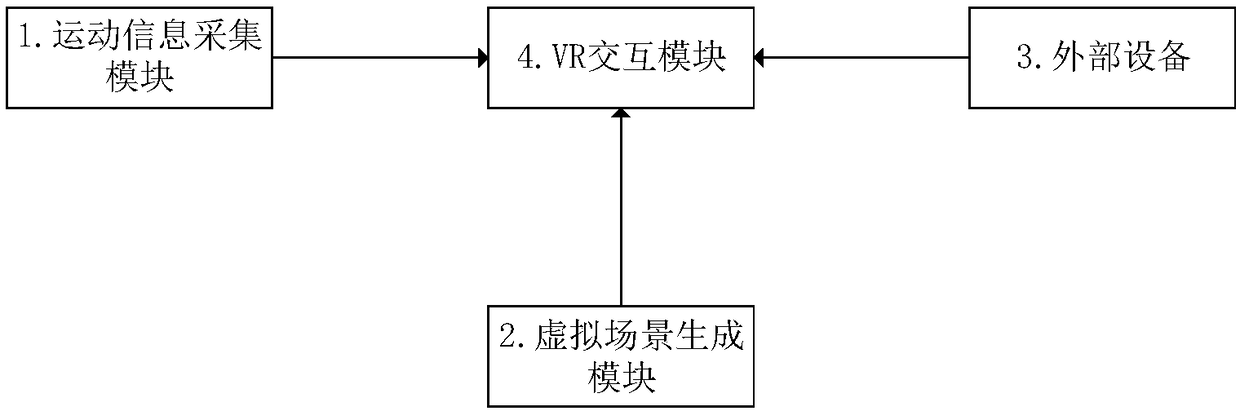
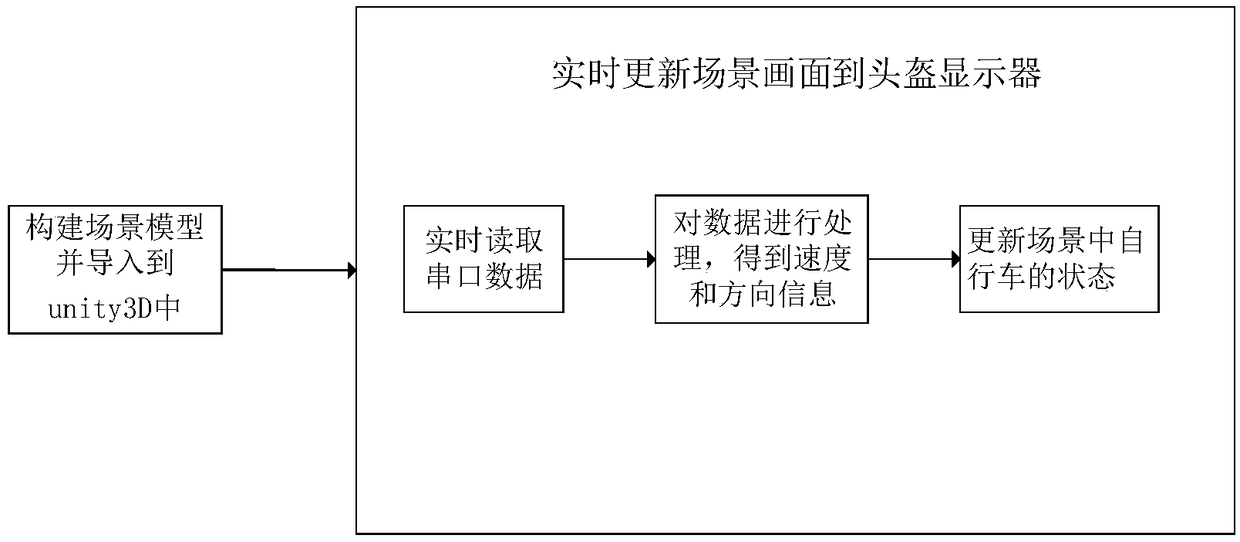
VR fitness interaction system based on unity 3D
ActiveCN108939418AAchieve diversificationGet rid of the requirement of deep customizationVideo gamesMovement coordination devicesInteraction systemsSports equipment
The invention provides a VR fitness interaction system based on unity 3D. A sport information collecting module is used for collecting bicycle sport speed and angle information, a virtual scene generating module is used for generating a scene simulating an actual fitness scene, external equipment is used for displaying a virtual scene and capturing moving information of a user, and a VR interaction module is used for the user to interact with objects in the virtual scene. By means of the system, VR fitness scene diversification is achieved, diversified scenes are created by using developing tools, specific scenes are created according to demands, the system has lower hardware cost, the demand that current VR sport equipment must be deeply customized is not needed, the system is assembled by using a normal bicycle and the external equipment, a general solving scheme is provided, the cost is greatly reduced, the system has interactivity and interestingness, a virtual reality technology is combined, the user can immerse in diversified virtual scenes by wearing a helmet when the user does fitness exercises, which is like being in a real outdoor environment.
Owner:陕西鑫禾普光电有限公司
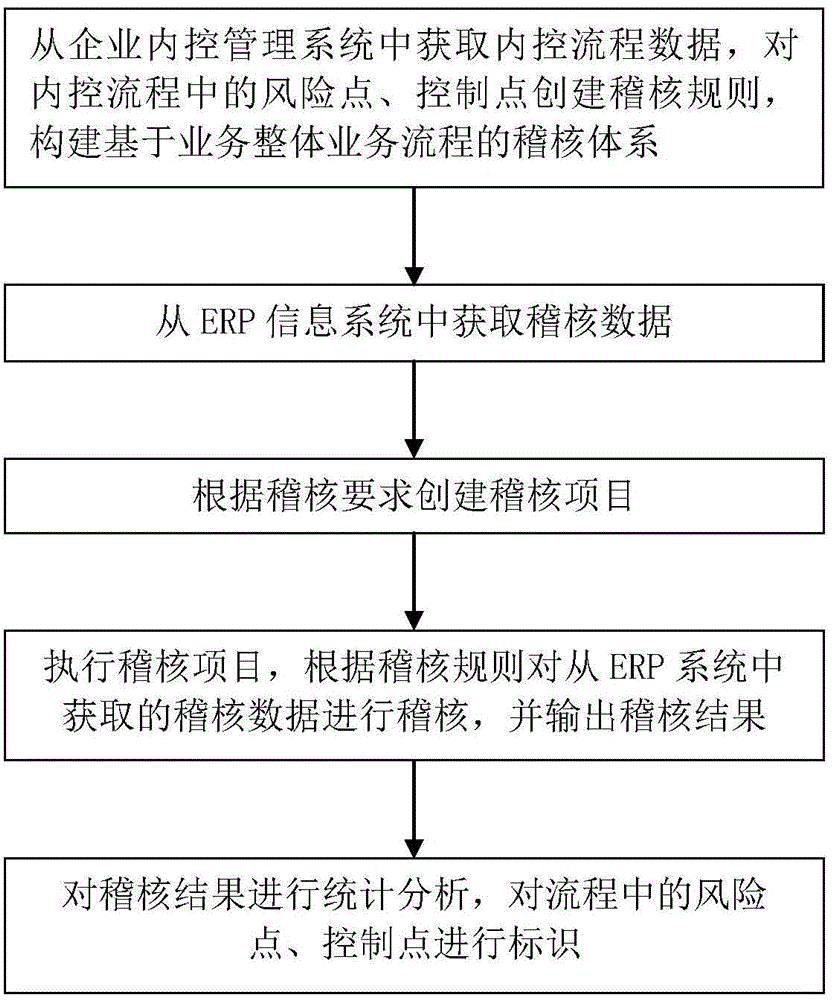
Online auditing method based on enterprise overall business process system and system thereof
InactiveCN103606038AEnsure complianceCompliant and effectiveResourcesStatistical analysisBusiness process
The invention provides an online auditing method based on an enterprise overall business process system and a system thereof. The method comprises an audit system creating step of obtaining internal control process data from an enterprise internal control management system, constructing an audit rule according to a risk point and a control point in an enterprise internal control process and auditing an audit system, an audit data obtaining step of obtaining audit data from an ERP information system, an audit program creating step of creating an audit program according to the audit need of an enterprise, an audit program executing step of auditing audit data obtained from the ERP information system according to the audit rule in an audit range and outputting an audio result, and an audit result statistical analysis step of showing each business process audit result and identifying the risk point and the control point in a business process. According to the method and the system, the audit system is created based on an enterprise overall business process, the online audit rule is established for the focused control point and risk point in a process link, and the audit has the advantages of strong pertinence and wide coverage.
Owner:YGSOFT INC
Network section optimization method in wireless access network
InactiveCN109379754AEasy to controlAchieve separationWireless communicationWireless mesh networkNon convex optimization
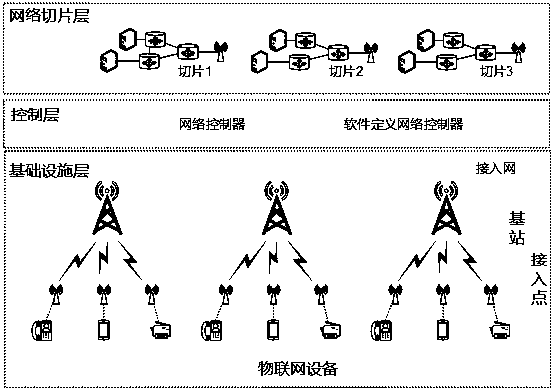
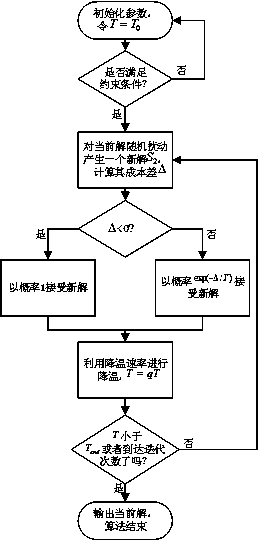
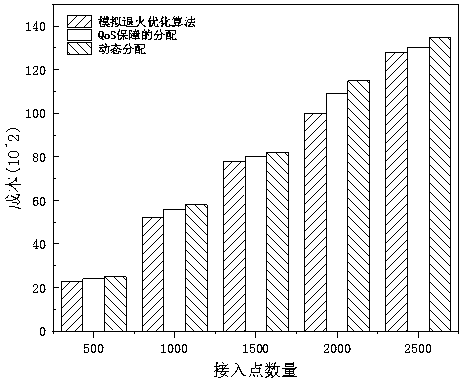
The invention relates to a network section optimization method in a wireless access network, and belongs to the field of mobile communications. The network section optimization method comprises the following steps: Step I, building a combined and non-convex optimized model in combination with the cost, service isolation and return capacity constraints; and Step II, solving the model by using a simulated annealing optimization algorithm according to the theory of an iterative adaptive heuristic probability search algorithm. The invention discloses a network resource optimized distribution method for a wireless virtual resource distribution mechanism; separation of control and forwarding is realized through an SDN (Software Defined Network) technology; and network resources are sensed and scheduled by using a network control plane. Customization of end-to-end services is supported on the basis of an SDN and a network section; independent and mutually isolated virtual networks are established according to network service requirements; and hardware resources in a network are dynamically deployed, which enables a plurality of virtual networks to share one physical network, thereby realizing sharing of the hardware resources of the network.
Owner:STATE GRID CORP OF CHINA +1
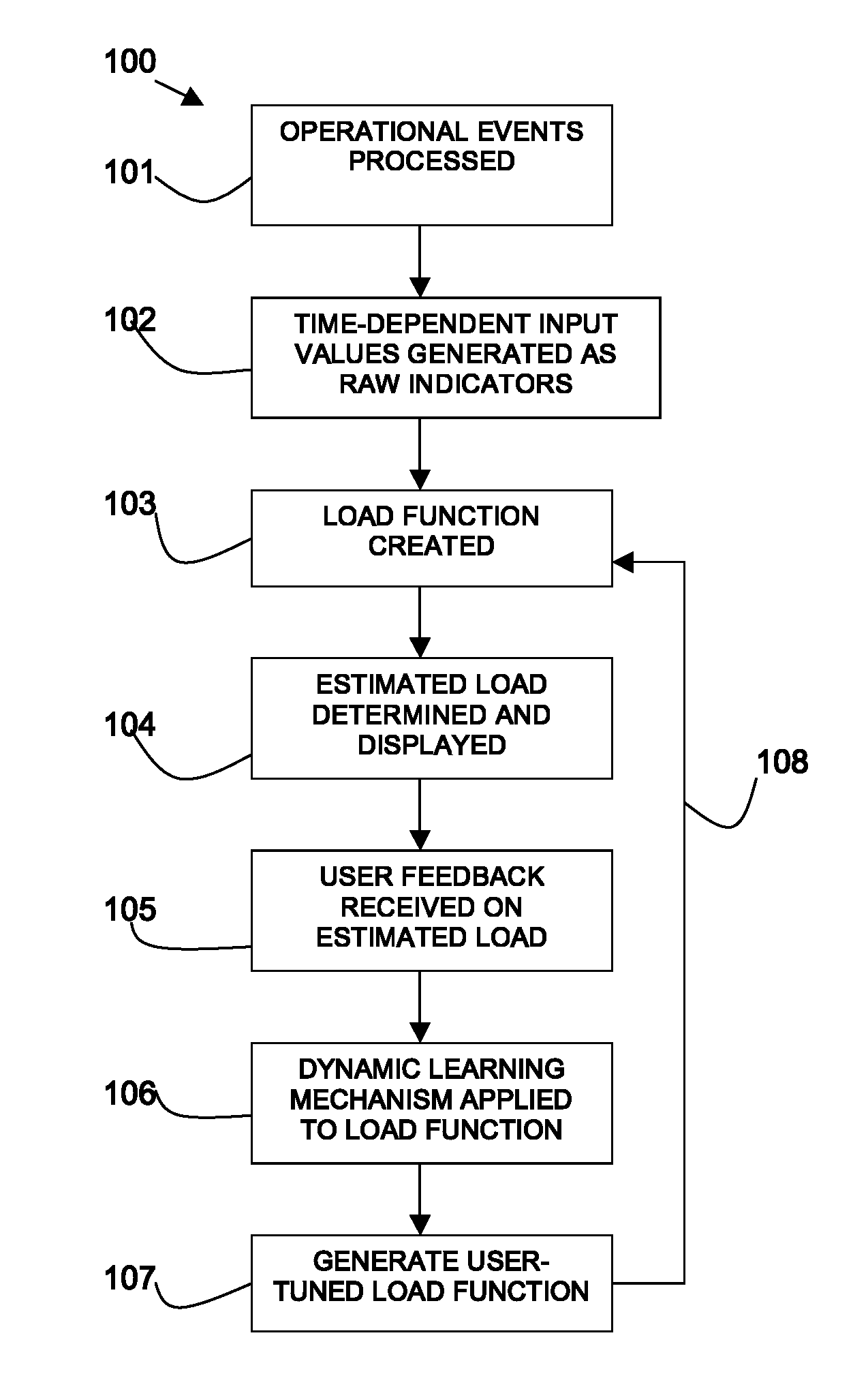
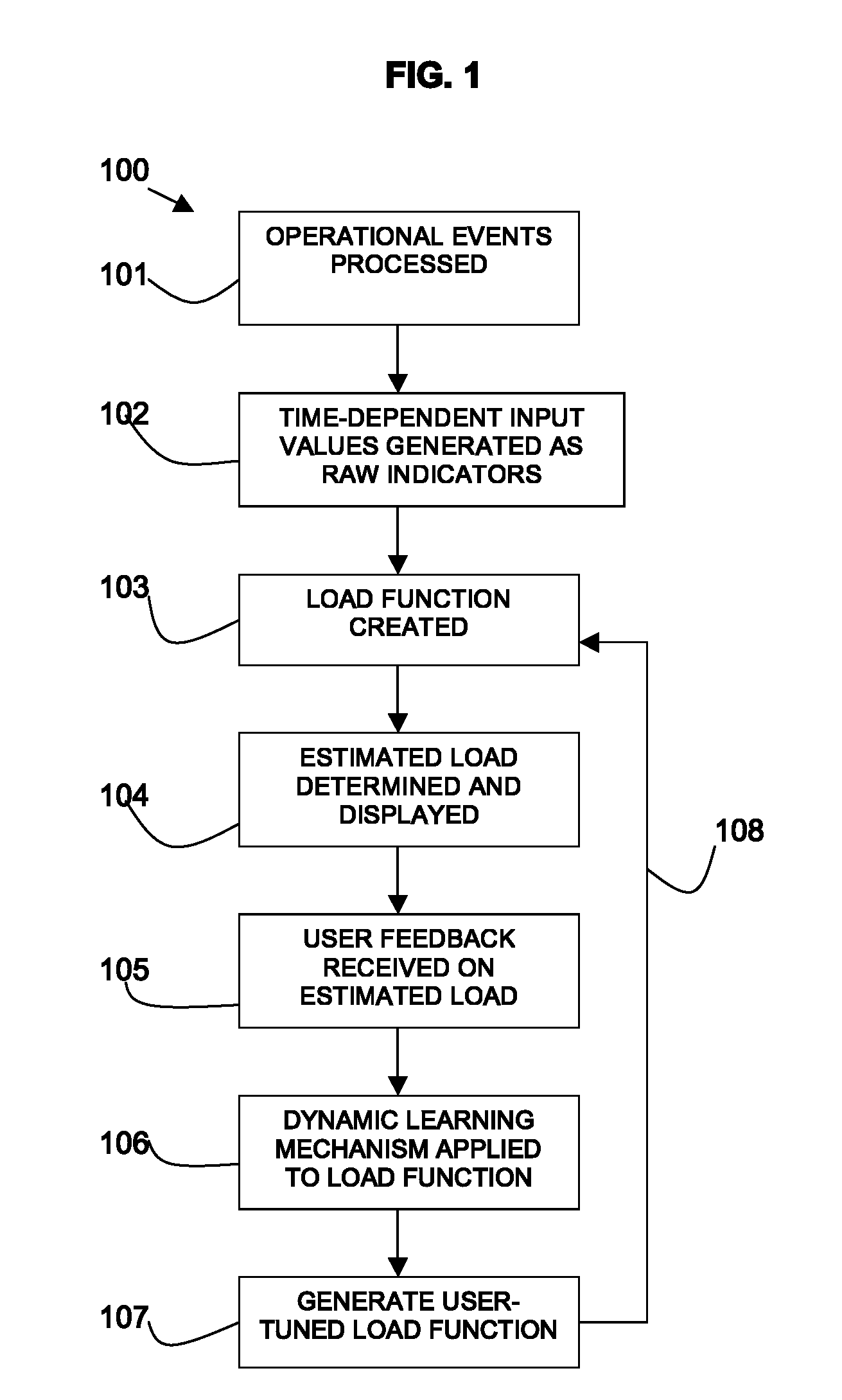
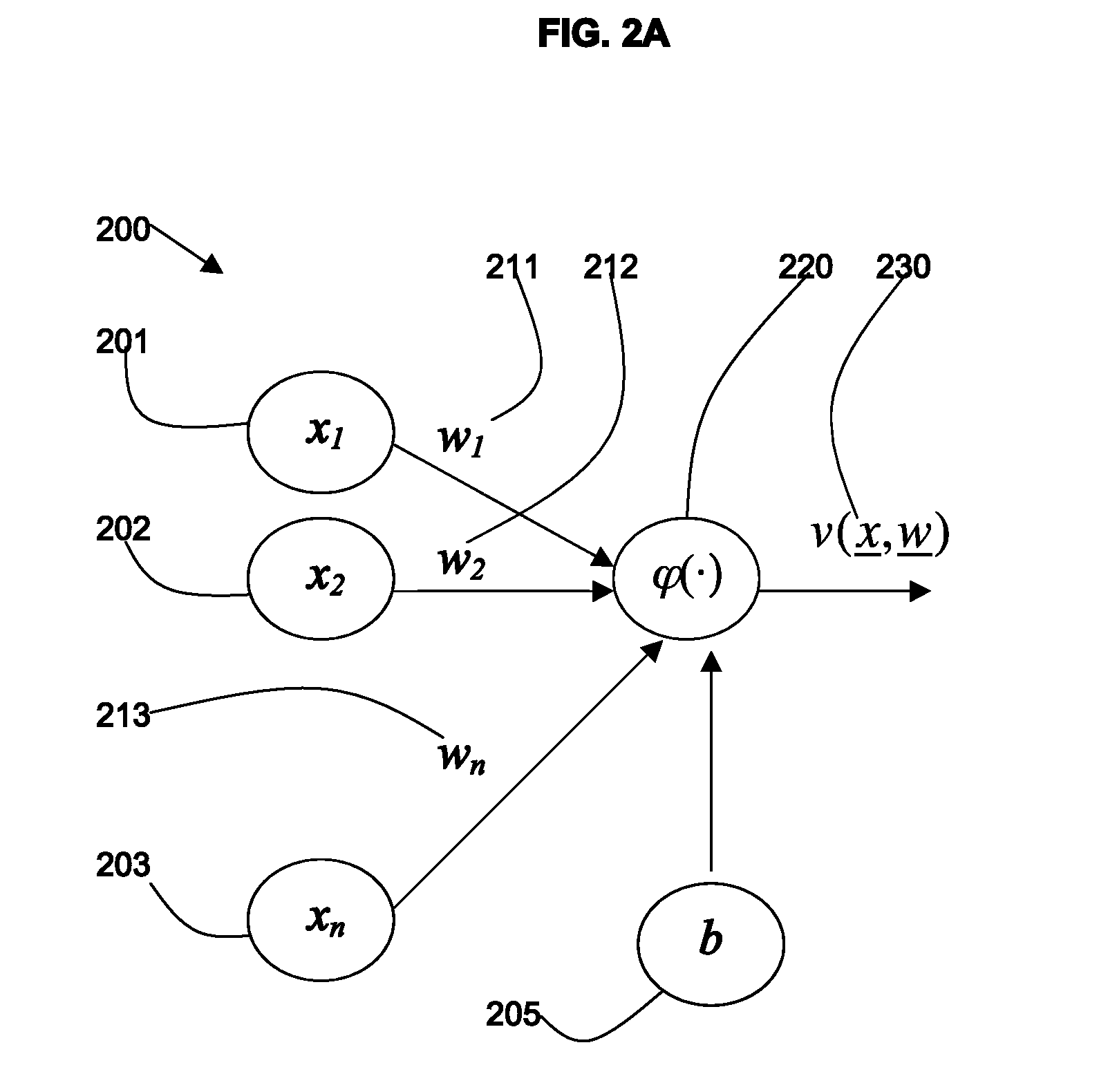
Load estimation in user-based environments
InactiveUS20120185416A1Digital computer detailsBiological neural network modelsDynamic learningComputer program
Method, system, and computer program product for load estimation in a user-based environment. The method includes: inputting a set of time-dependent, raw operational indicators of the environment; creating a load function according to the specific needs of the environment; displaying an estimated load; receiving user feedback on the estimated load; and applying a dynamic learning mechanism to generated a user-tuned load function for estimating load on the environment. The dynamic learning mechanism may be an informative mechanism that supports backtracking to solve user-adaptability problems.
Owner:IBM CORP
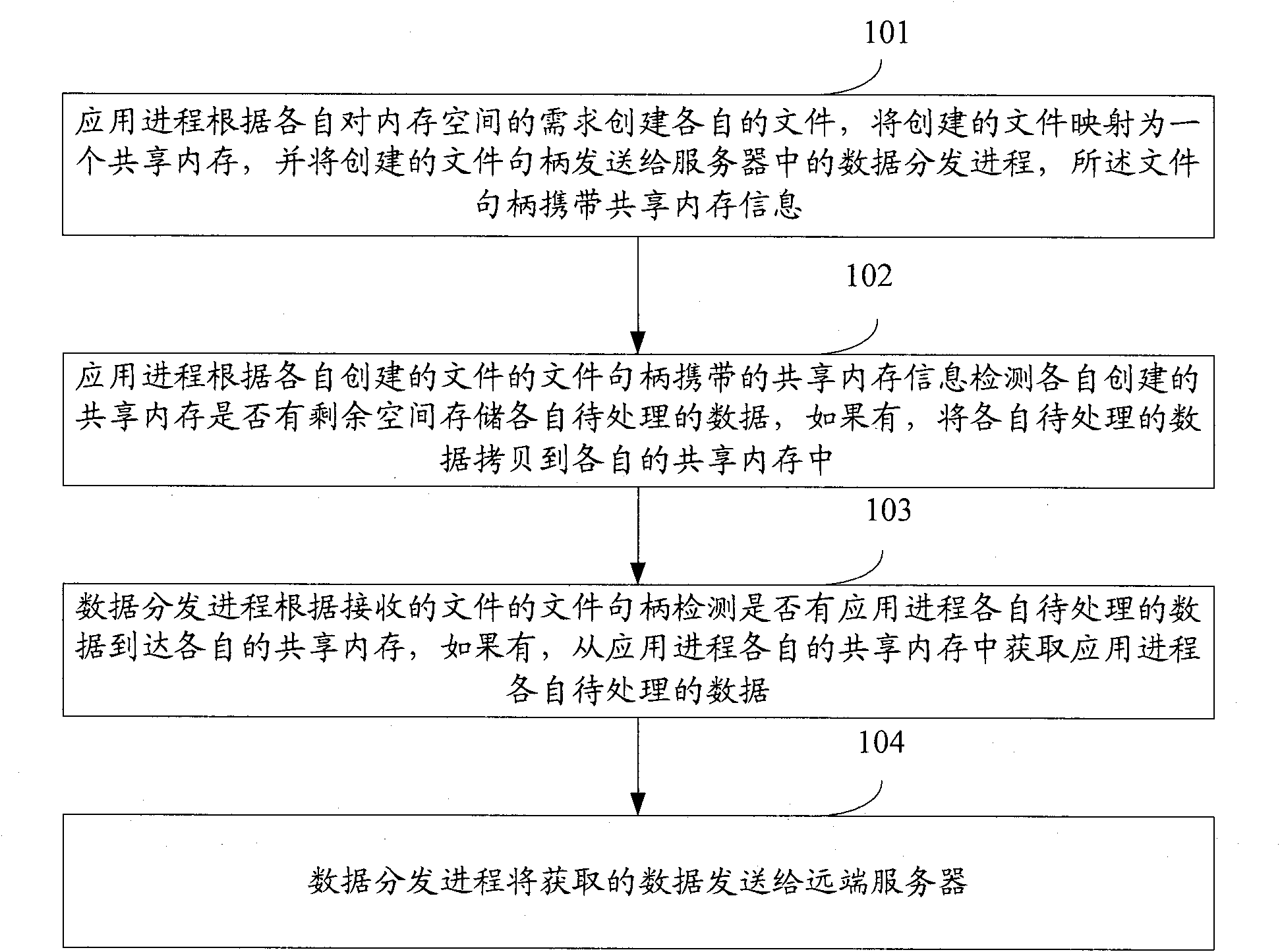
Data transmission method between servers and servers
The embodiment of the invention discloses a data transmission method between servers and servers. The method comprises the following steps of: creating respective files according to the requirement of respective internal memory spaces by an application process; mapping the files into shared memories; transmitting a created file handle to a data distribution process; detecting whether the respectively-created shared memory has residual space for storing respective data to be processed by the application process or not; if so, coping the respective data to be processed in respective shared memories; detecting whether the respective data to be processed in the application process reach the shared memory or not by the data distribution process; if so, acquiring respective data to be processed in the application process from respective shared memories of the application process; and transmitting the acquired data to a far-end server by the data distribution progress. According to the embodiment of the invention, system resources are saved while normal work of the application process is ensured and the efficiency of data transmission and the performance of the server are improved.
Owner:TAOBAO CHINA SOFTWARE
Printing system
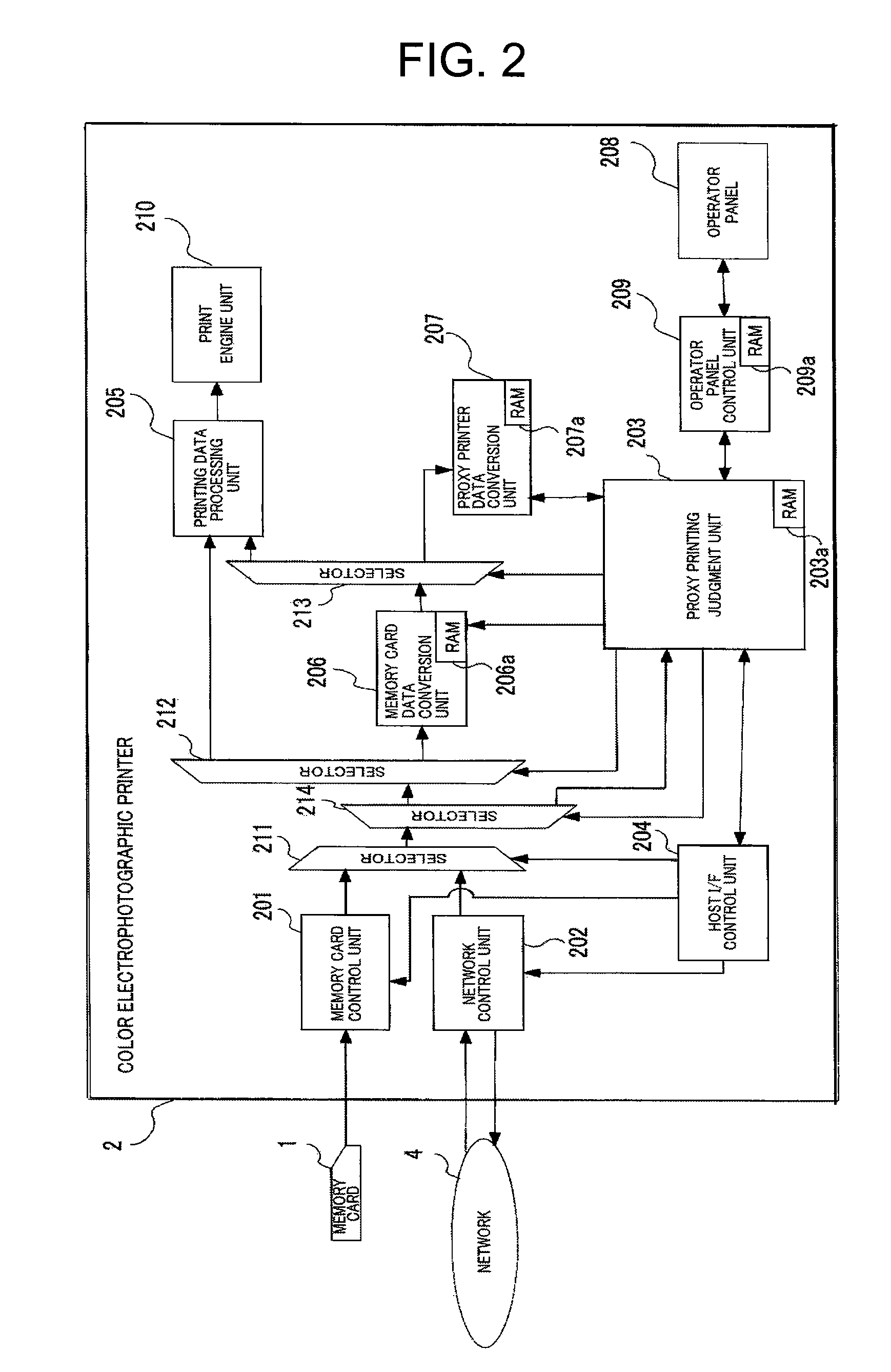
InactiveUS7760385B2Efficiently execute printingEfficient printingDigitally marking record carriersVisual presentation using printersImage resolutionEngineering
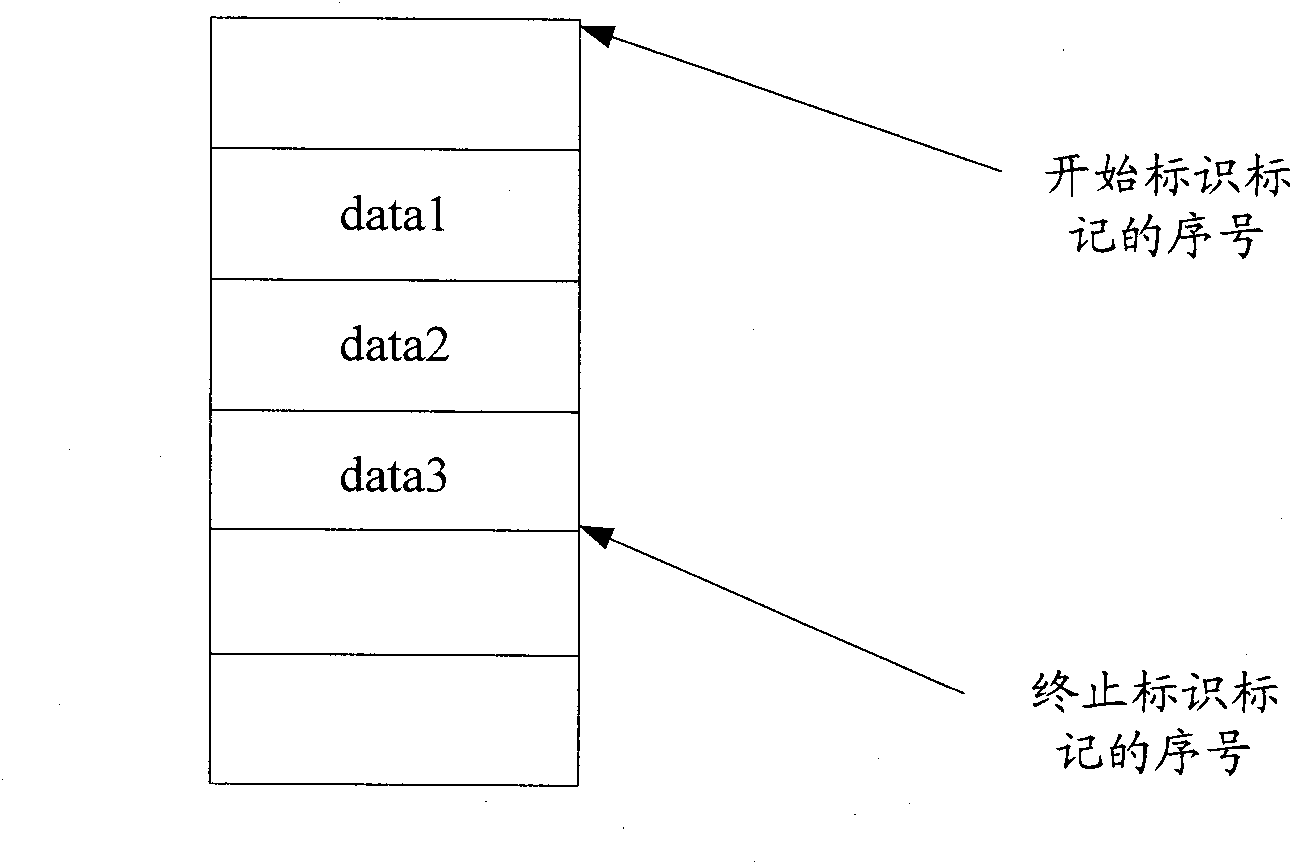
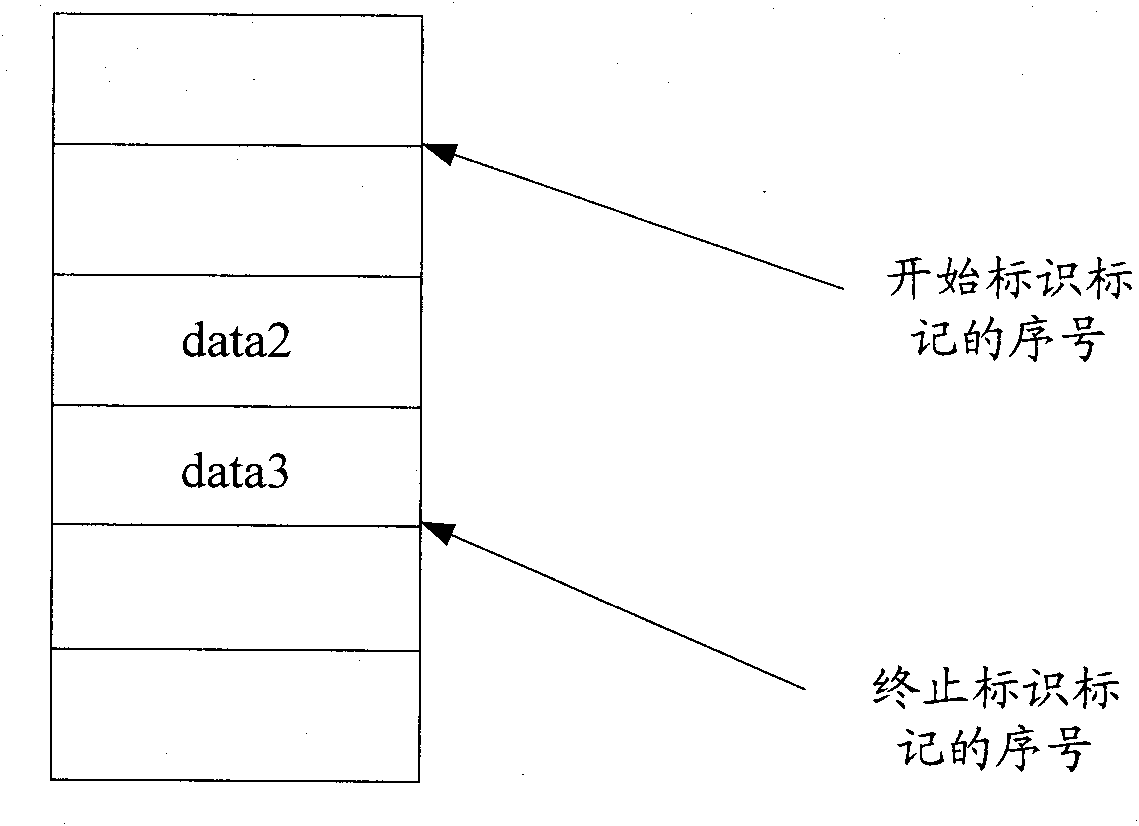
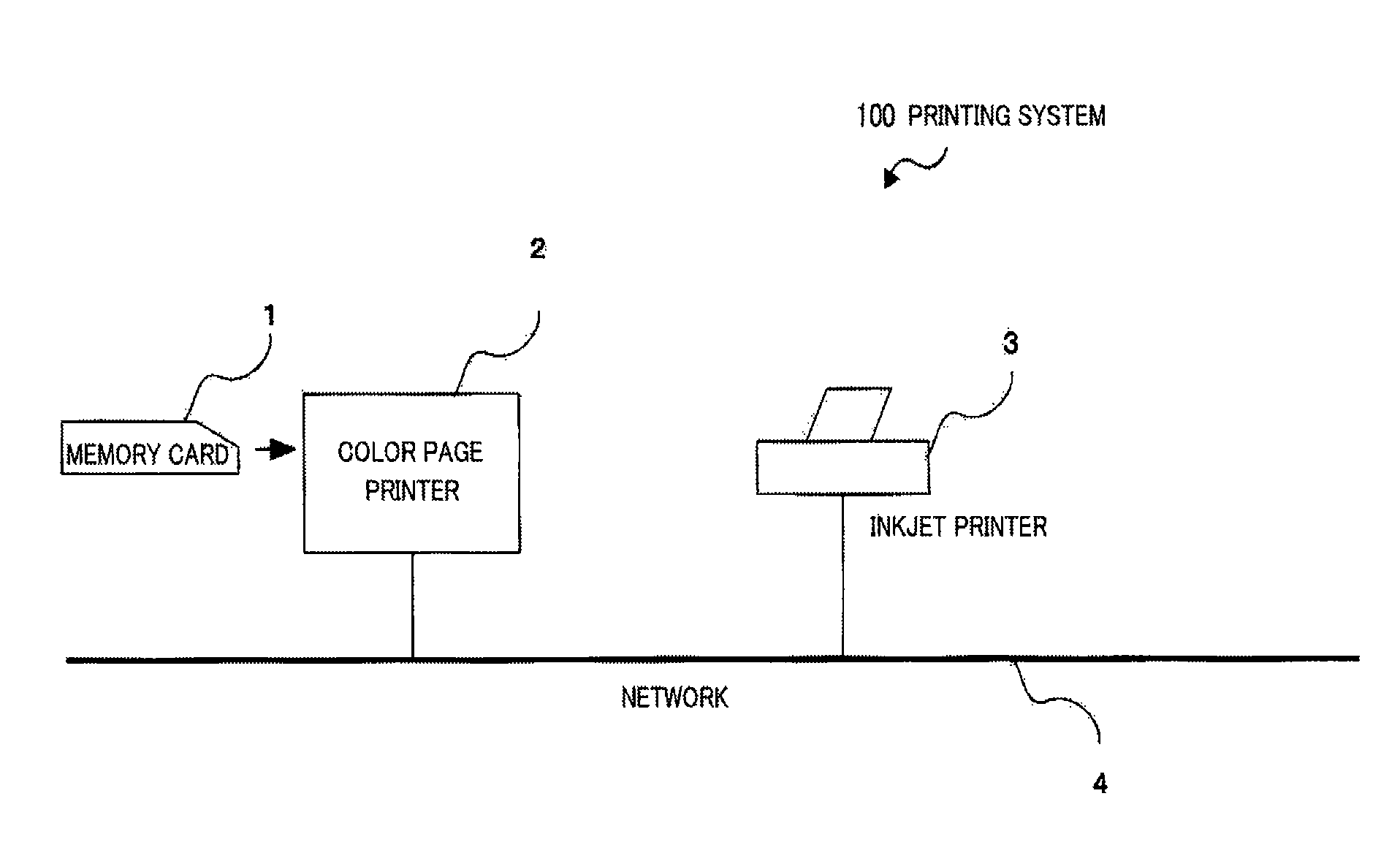
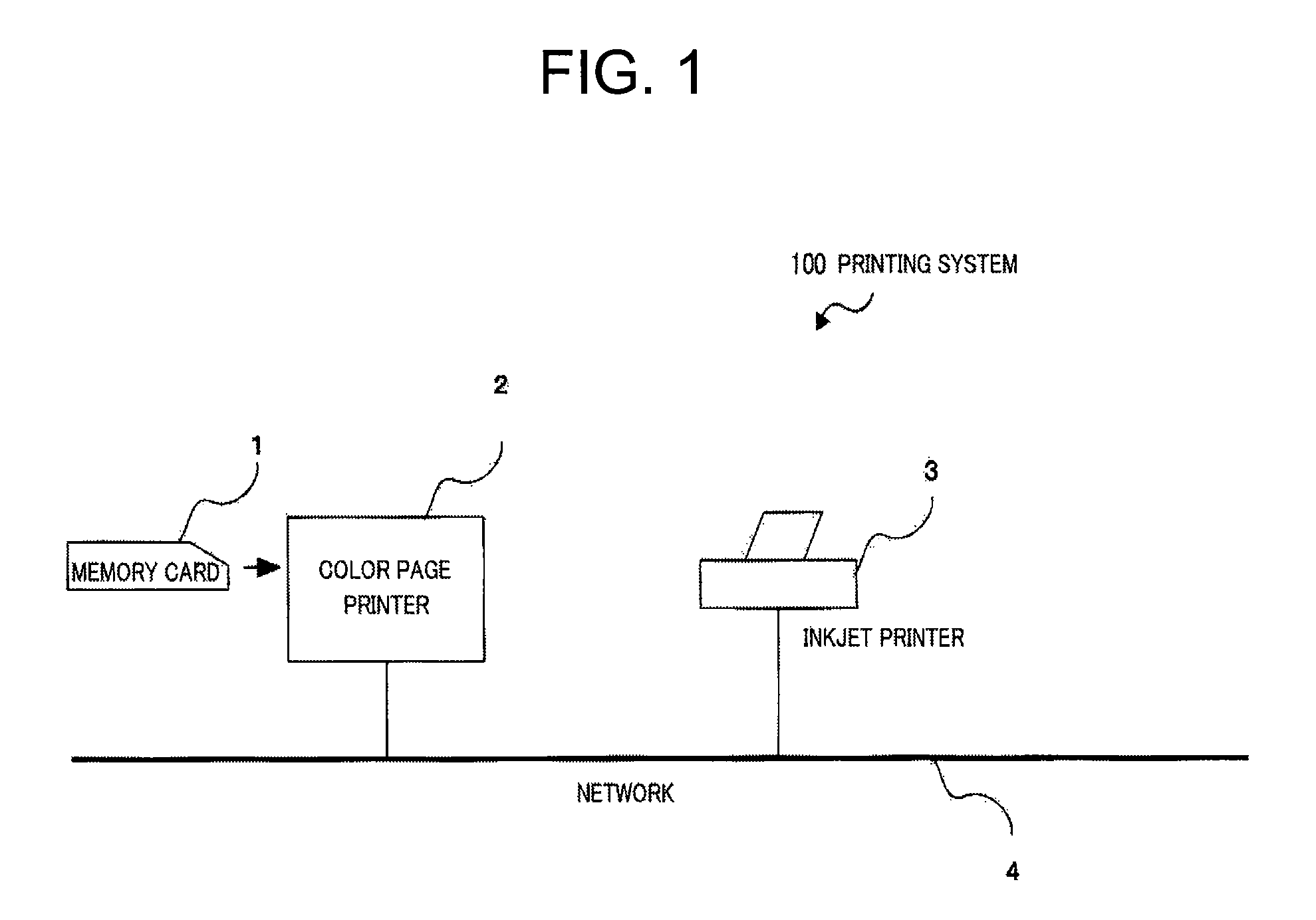
A printing system is provided capable of executing printing with a suitable printer in accordance with the printing quality assigned by the printing information that becomes the printing objective. The proxy printing judgment unit of the printer judges whether a printer exists that shows a resolution value equal to or higher than that of the resolution assigned by the printing quality information and, in a case where such a printer does not exist in the printer list, executes the process to execute the error message display. In a case where such a printer exists in the printer list, the printer showing the highest resolution value is selected. The process is then executed for demanding creation of proxy printer data from the proxy printer data conversion unit, the created proxy printing file is sent via the network to the proxy printer, and the proxy printer executes the process to perform proxy printing.
Owner:OKI DATA CORP
System and Method for Automated On-Demand Creation of a Customized Software Application
ActiveUS20130339925A1Software designVisual/graphical programmingBusiness-to-businessSoftware engineering
A web-based interface is provided for visually modeling a business-to-business or application integration process by selecting and associating predetermined process-representing visual elements. A customized, enterprise-specific executable software application (“dynamic runtime engine”) is automatedly produced by software running remotely. The dynamic runtime engine is created to include a generic application template, predefined “stock” codesets selected as a function of the modeled process, and a data profile codeset that includes input provided by the user for customizing the stock components for a specific integration process of a specific enterprise.
Owner:BOOMI
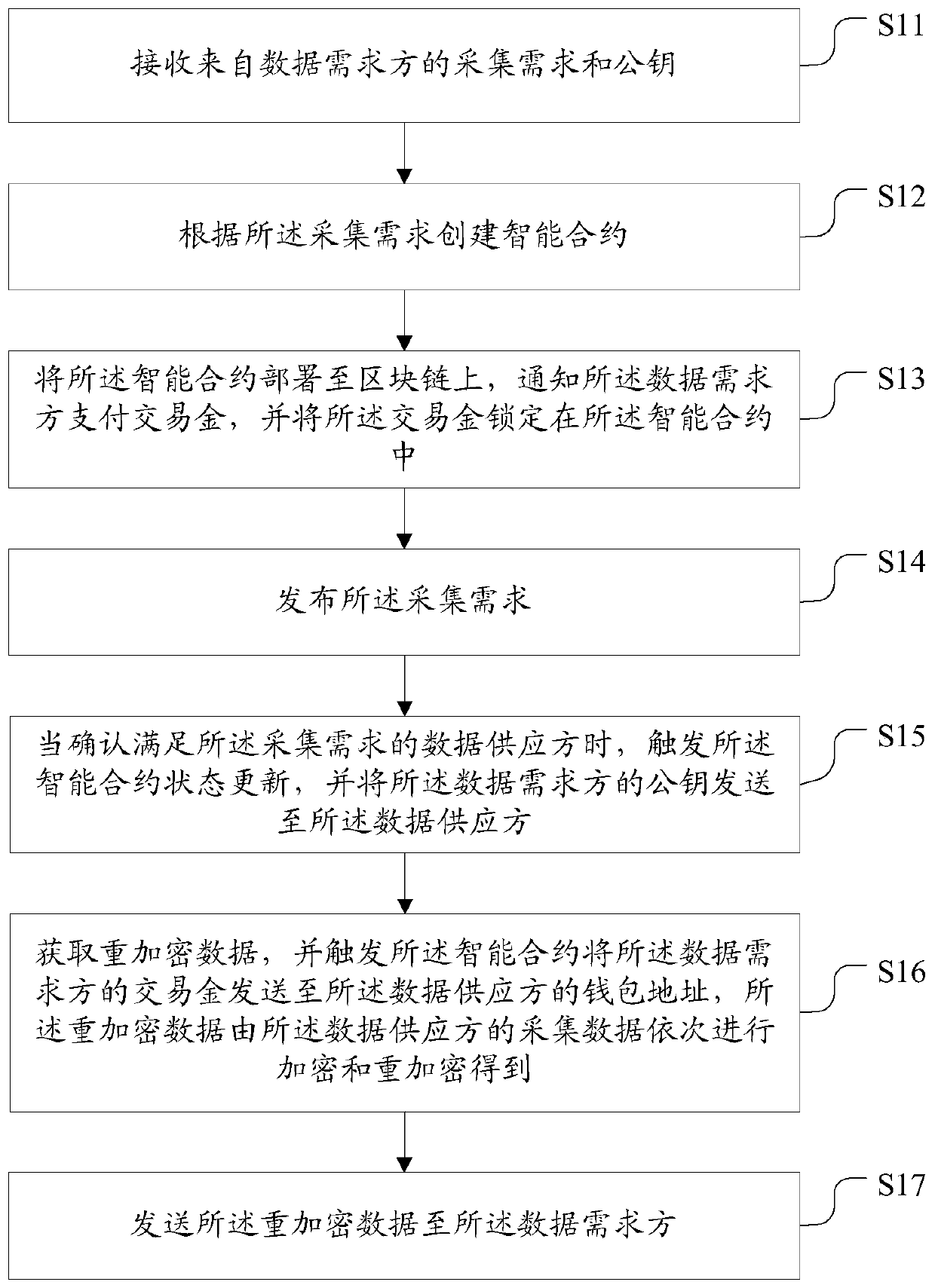
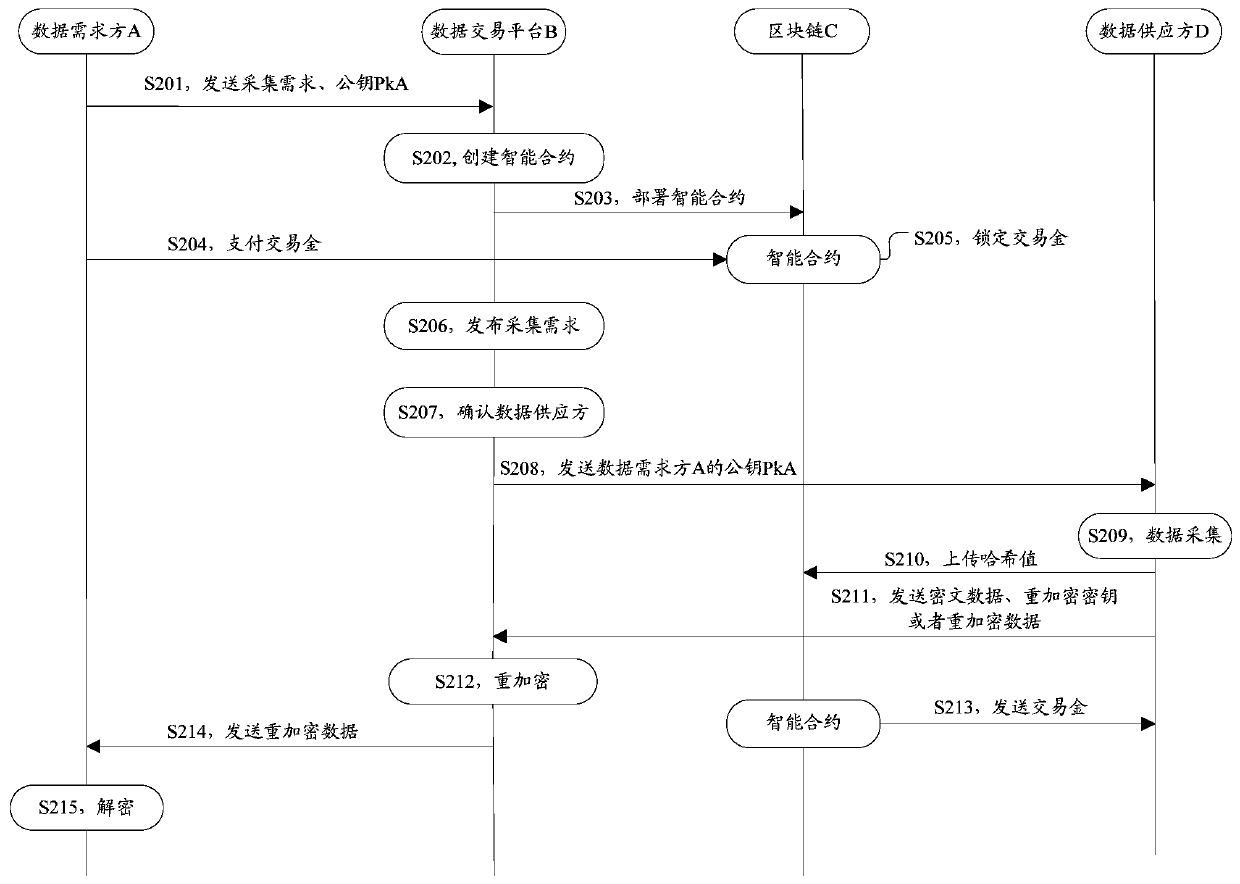
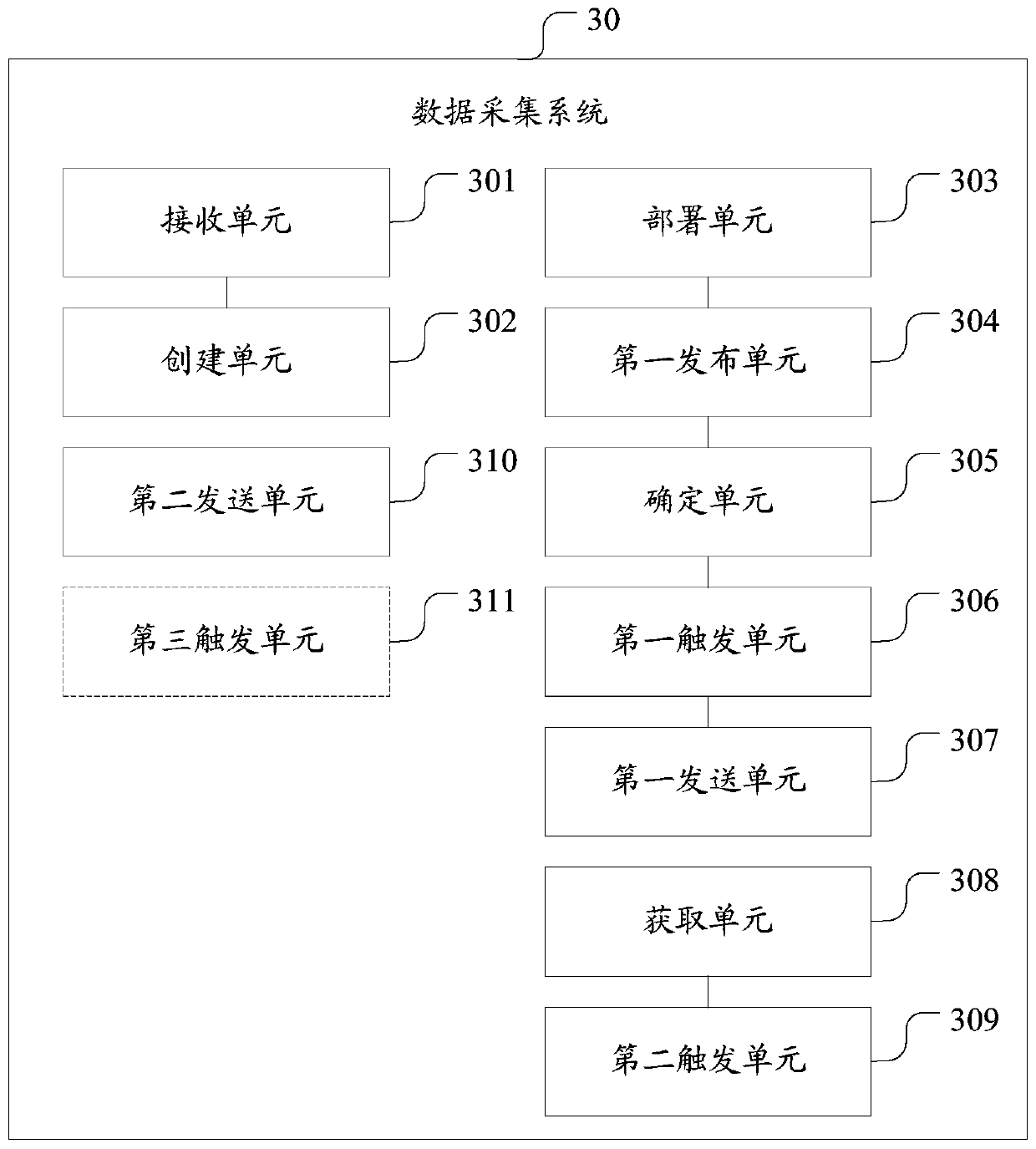
Data acquisition method and system, platform and storage medium
InactiveCN109741057AImprove collection efficiencyTake advantage ofFinanceDigital data protectionData acquisitionData needs
The invention discloses a data acquisition method and system, a platform and a storage medium. The data acquisition method comprises the following steps: receiving an acquisition demand and a public key from a data demander; creating an intelligent contract according to the collection requirement of the data demander, deploying the intelligent contract to a block chain, notifying the data demanderto pay a transaction fund, and locking the transaction fund in the intelligent contract; issuing an acquisition demand of the data demander, triggering the state updating of the smart contract when determining that a data supplier meeting the acquisition demand is satisfied, and sending a public key of the data demander to the data supplier; and obtaining re-encrypted data, triggering the smart contract to send the transaction money of the data demander to the wallet address of the data supplier, and sending the re-encrypted data to the data demander, so that the data demander decrypts the re-encrypted data to obtain collected data. By adopting the data acquisition method, the data acquisition efficiency can be improved.
Owner:石更箭数据科技(上海)有限公司
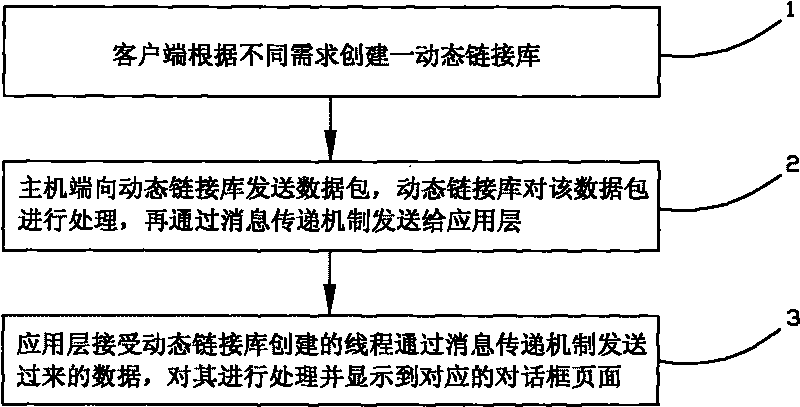
Method for realizing remote data monitoring
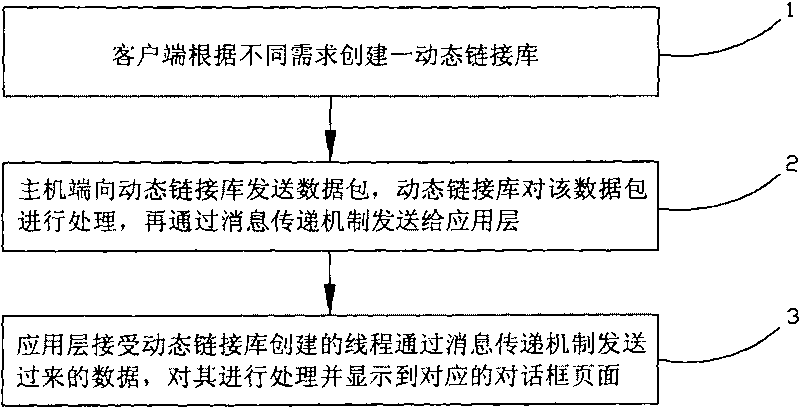
InactiveCN101707622AAvoid lossPowerfulTransmissionSpecial data processing applicationsInformation transmissionNetwork packet
The invention relates to a method for realizing remote data monitoring, which comprises the following steps: step (1), establishing a dynamic link library by a client terminal according to different requirements; step (2), transmitting a data packet to the dynamic link library by a host machine terminal, processing the data packet by the dynamic link library and then transmitting the data packet to an application layer by an information transmission mechanism; and step (3), receiving threads established by the dynamic link library through the application layer, processing the threads by data transmitted by the information transmission mechanism and displaying the threads in the page of the corresponding dialog box. By establishing one dynamic link library and establishing each functional thread according to the requirement of the user, the invention carries out connection communication and data transmission or reception with a host machine in a single-thread or multi-thread mode, the selectivity of the data transmission mode of the invention is multiple, data transmission is safer and more reliable, the invention can upgrade a plurality of host machines simultaneously, the update and upgrade time of a system is short, and the efficiency is high.
Owner:深圳市深视音电子技术有限公司
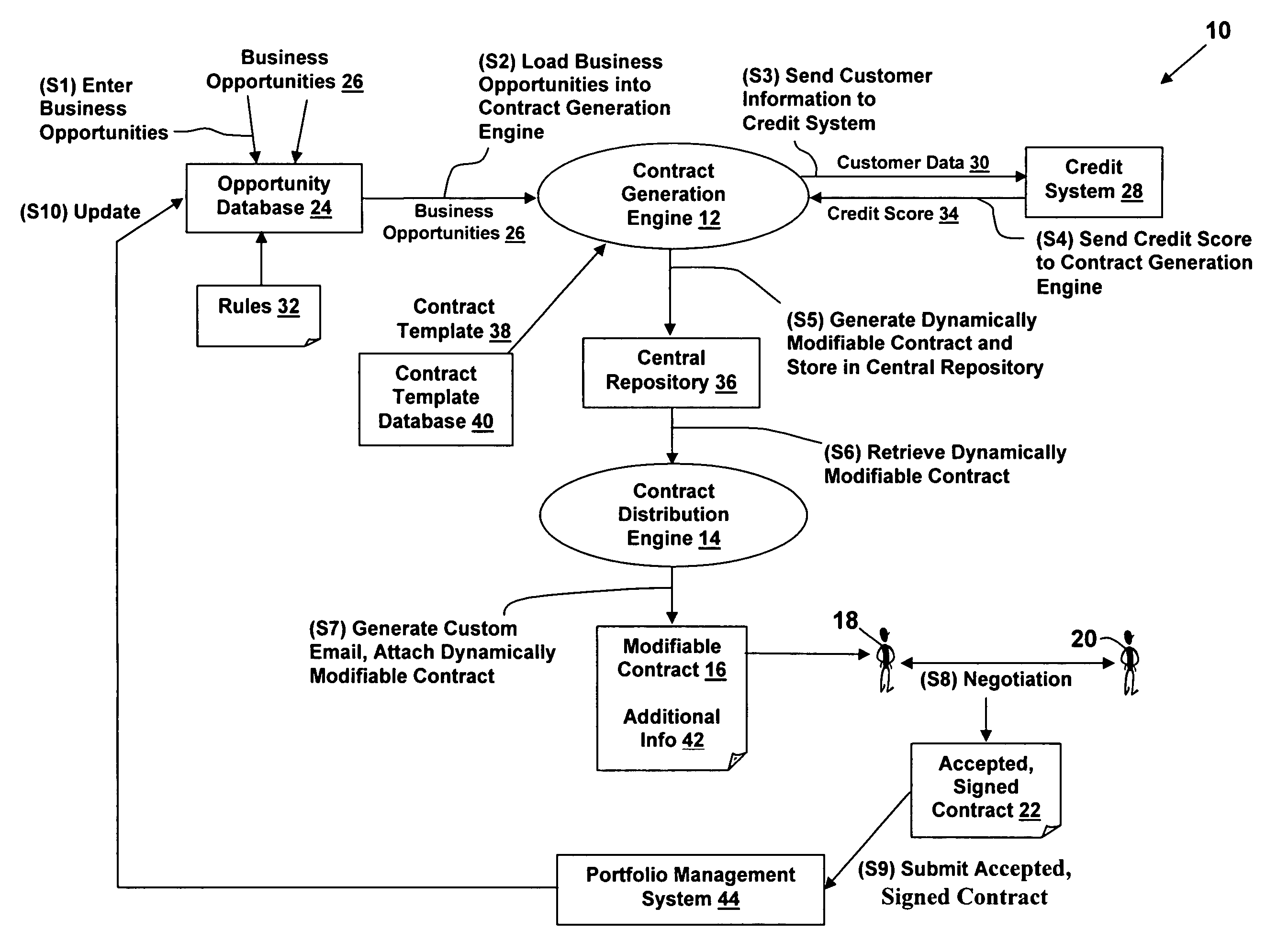
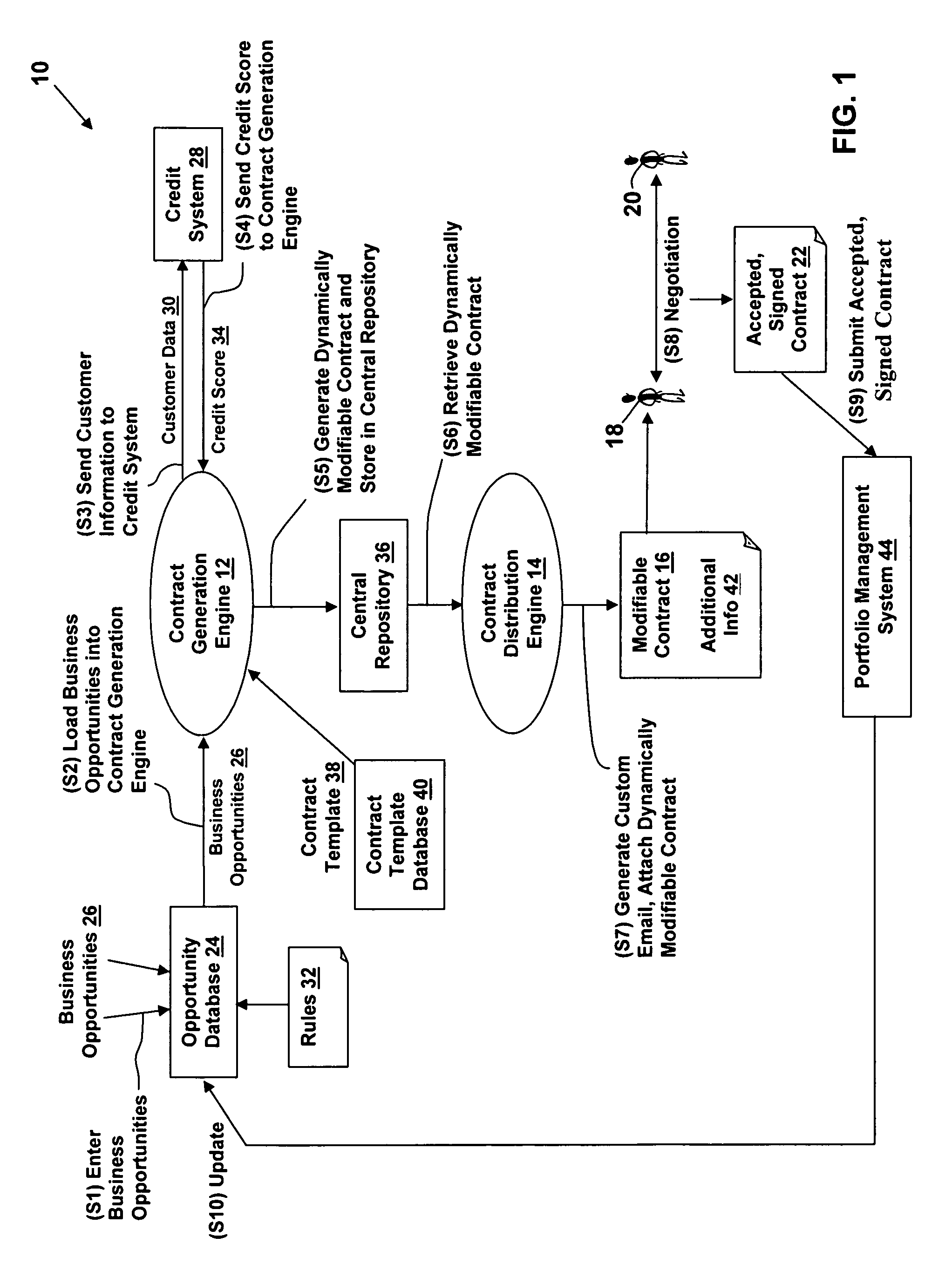
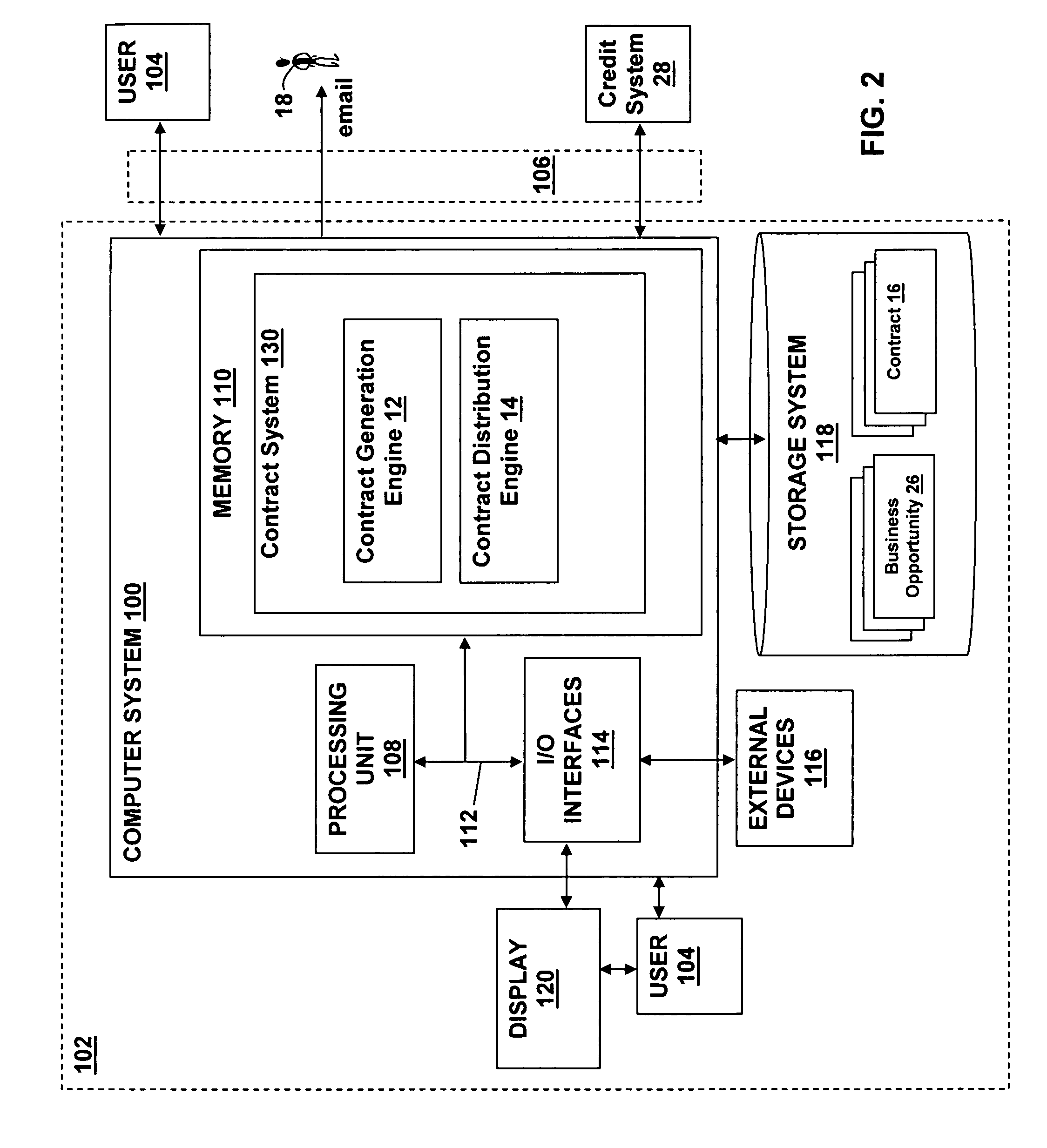
Method, system, and computer program product for on-demand creation and distribution of customized dynamic contracts
The present invention provides a method, system, and computer program product for the on-demand creation and distribution of customized dynamic contracts. At least one business opportunity is extracted from an opportunity database. For each extracted business opportunity, a credit score for a customer associated with the extracted business opportunity is obtained and a dynamically modifiable contract for the extracted business opportunity is generated. The dynamically modifiable contract is distributed to a contact associated with the extracted business opportunity, who presents the dynamically modifiable contract to the customer associated with the extracted business opportunity. The contact can modify the dynamically modifiable contract, if necessary, during negotiations with the customer, to provide a contract that is acceptable to the contact and the customer.
Owner:LINKEDIN
Tree data structure based universal UI interface generating method and device
InactiveCN106815022ASimple structureStrong expandabilitySoftware engineeringSpecific program execution arrangementsExtensibilityTree (data structure)
The invention relates to a tree data structure based universal UI interface generating method and device. The generating method includes: allowing a user to create a personalized tree data structure describing his project according to the demand of the user on a preset basic tree structure, completing a whole data frame and definition of each node data type, and automatically generating a configuration file; analyzing the completed configuration file, and acquiring the whole tree data structure and configuration information of each node; and invoking a tool to execute a configuration command, acquiring control attribute data, dynamically creating a control, and generating a targeted personalized UI interface. The method and device can achieve terminal UI interface customization, have excellent extensibility and university, can simplify a code structure, and can improve the development efficiency of a UI interface.
Owner:CHINA UNIV OF PETROLEUM (BEIJING)
Method and device for supporting multi-tenancy network transmission
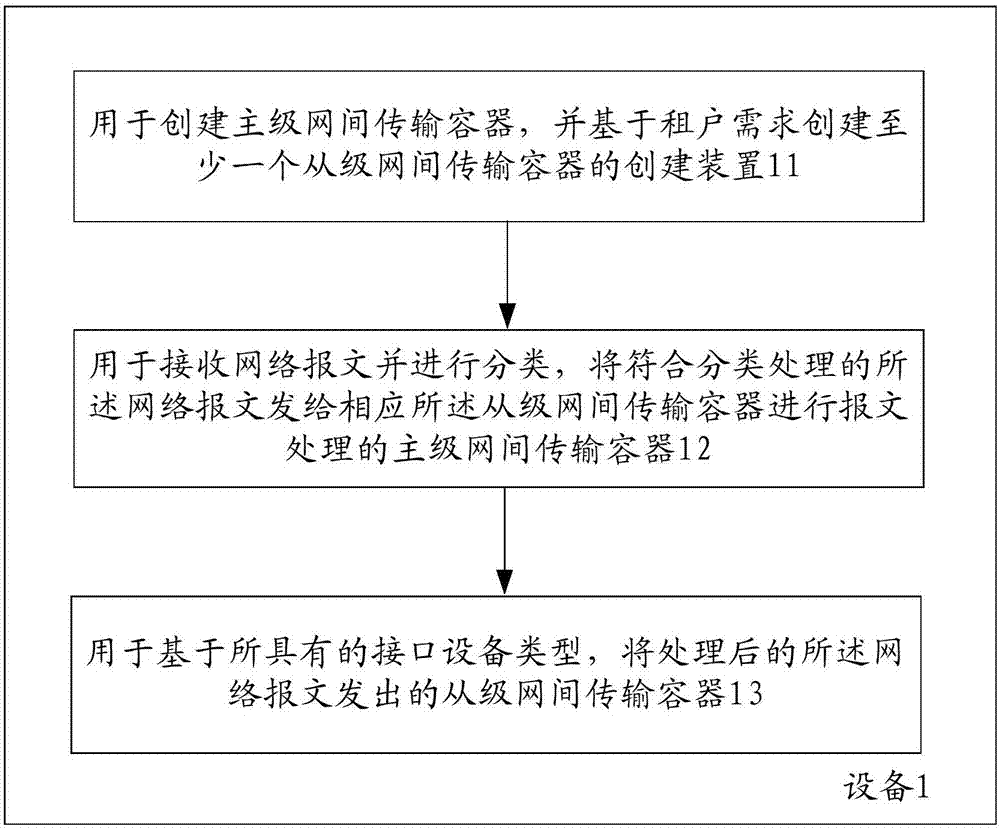
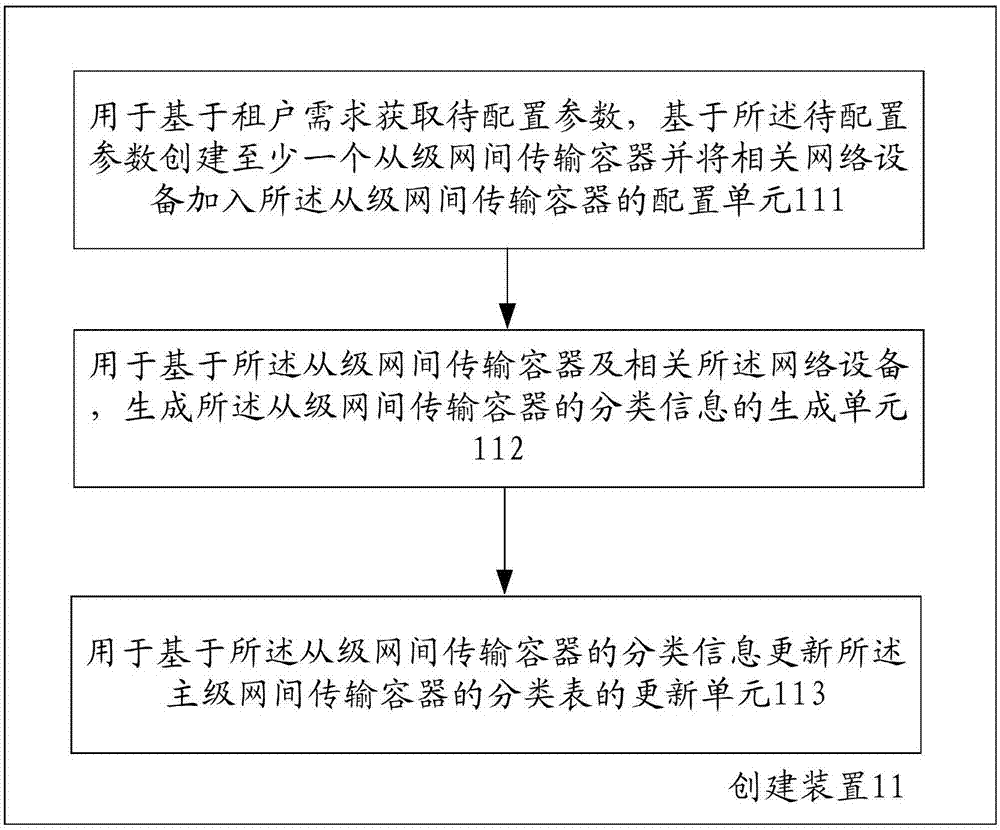
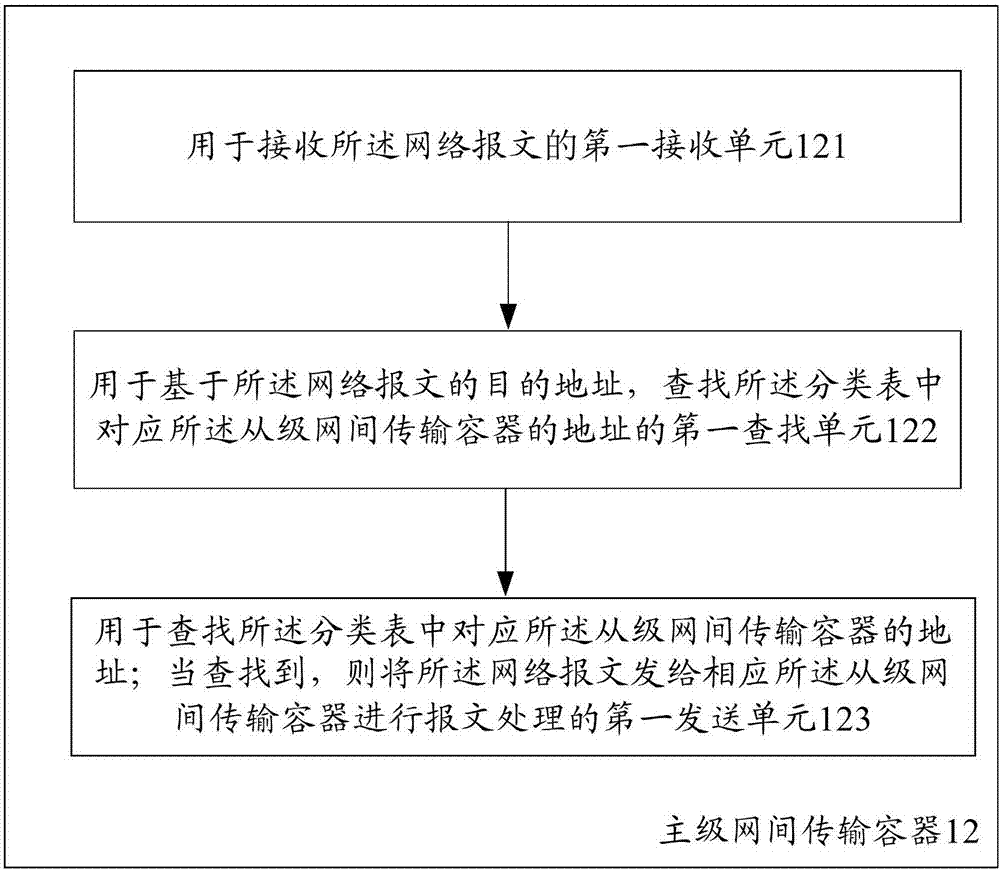
ActiveCN107454132AReduce workloadPerformance advantageData switching networksDevice typeVirtualization
The invention provides a method and device for supporting multi-tenancy network transmission. The method comprises the following steps: creating a primary-level inter-network transmission container, and creating at least one secondary-level inter-network transmission container based on a tenant demand; receiving network packets and classifying the network packets by the primary-level inter-network transmission container, and sending network packets conforming to classification processing to the corresponding secondary-level inter-network transmission container for packet processing; and based on an interface equipment type, sending the processed network packets by the secondary-level inter-network transmission container. According to the invention, functions of boarder routing devices of different virtual networks are integrated and abstracted into one, the workload of operation management is reduced, and the workload of subsequent development testing is decreased. Besides, through only virtualization of network functions, only network packets are forwarded, forwarding protocol stacks are optimized, it is unnecessary to configure such virtual functions of a CPU, a memory, a hard disk and the like which are similar to a virtual machine, and therefore, the performance and capacity advantages are remarkable.
Owner:ALIBABA GRP HLDG LTD
Multi-protocol acquiring and scheduling method for comprehensive network management
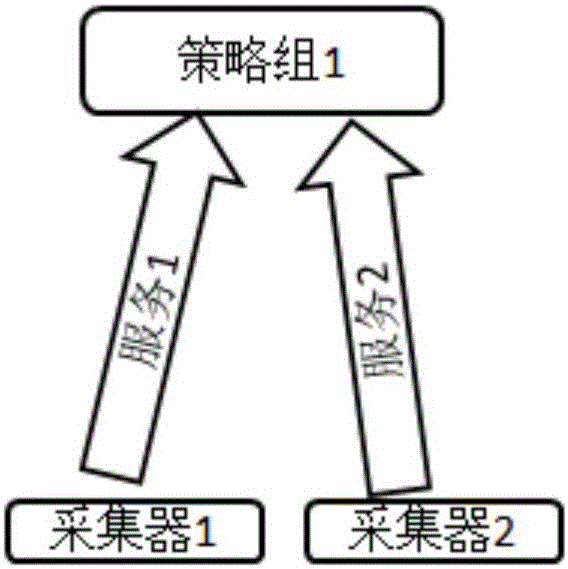
ActiveCN105681100AReduce workloadRealize unified callData switching networksMulti languageInterface protocol
The invention relates to a multi-protocol acquiring and scheduling method for comprehensive network management. An acquiring and scheduling service is a bridge for connecting a data presentation layer to an acquiring adapter, and is responsible for operating a task and feeding back a result; an acquirer of the acquiring and scheduling service is a program developed according to different interface protocols; by means of the acquirer, acquisition of all data described by the interface protocols is realized; the task to be operated comes from the presentation layer; users can see all kinds of operations supported by an interface in an interface configuration interface and create all kinds of acquisition tasks according to practical requirements in a task management interface; the acquiring and scheduling service operates the configured task in a timed manner; an acquisition service is adapted according to information described by the task; then, the acquisition service is invoked through a standard inlet; operation of the acquisition service is monitored; and an operation result is fed back to the presentation layer or directly written in a data storage layer. According to the invention, uniform invoking of multi-protocol and multi-language processes is realized; the various interface protocols are thoroughly isolated from the presentation layer; and thus, qualification requirements of constructors and maintainers are greatly reduced.
Owner:BEIJING ENOVELL TECH
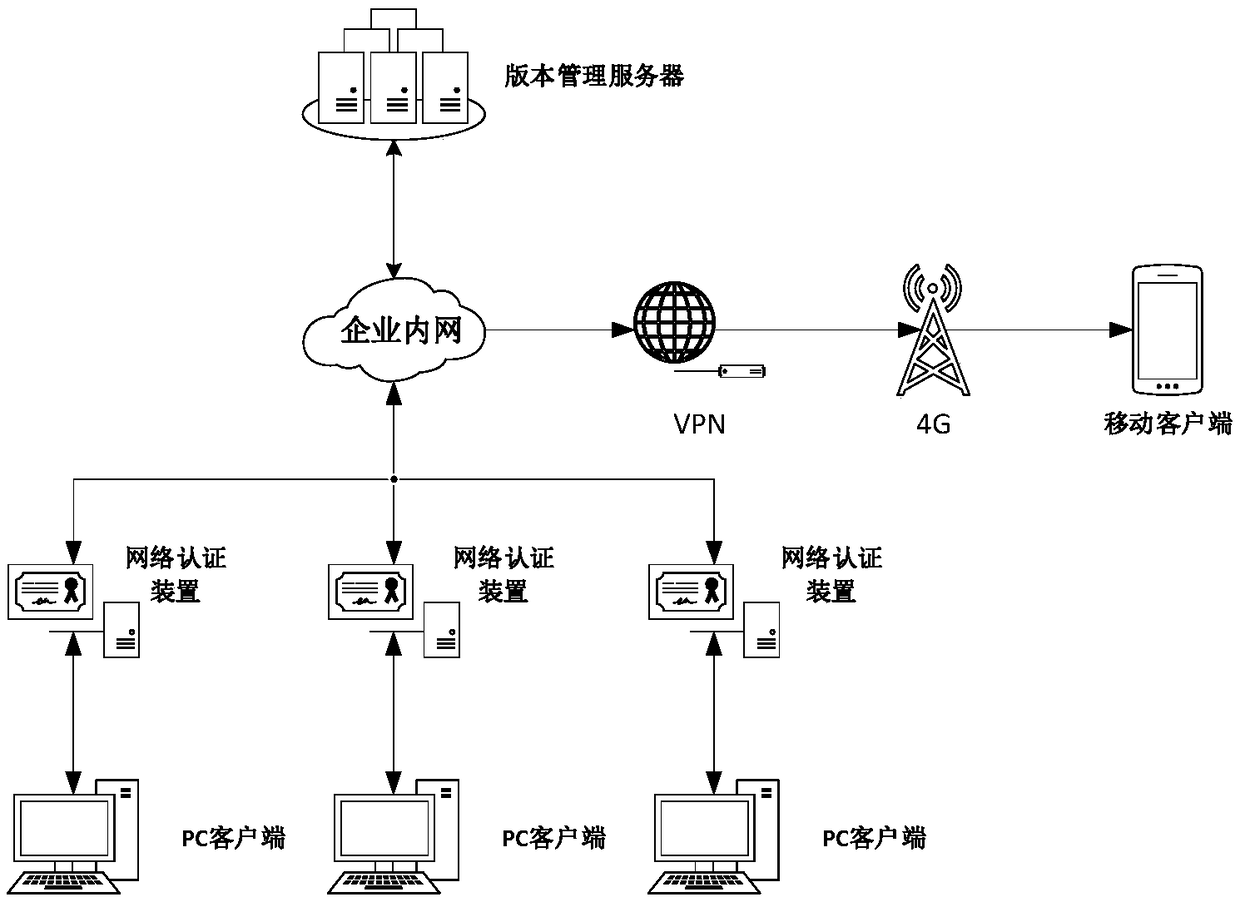
A substation file version management method and system
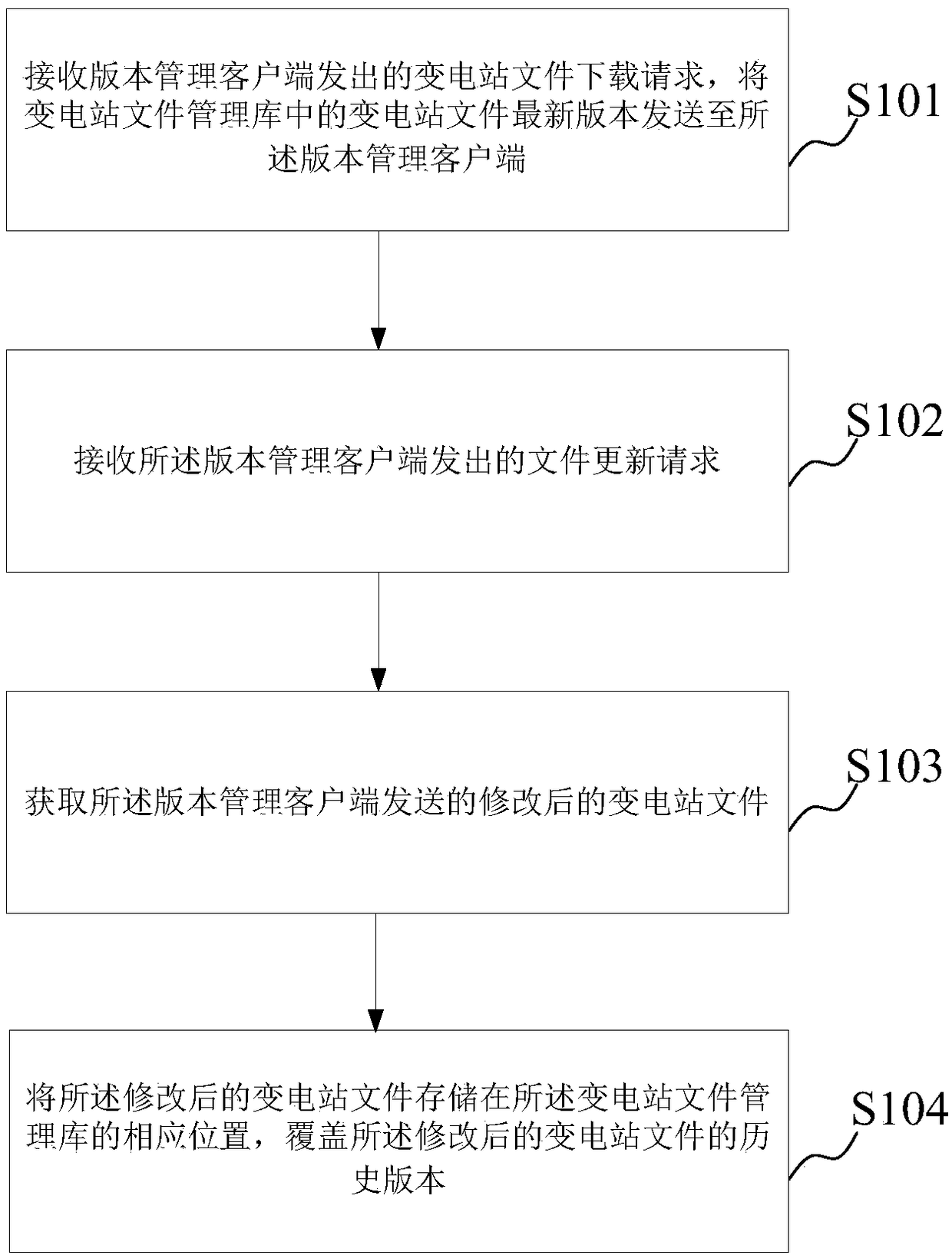
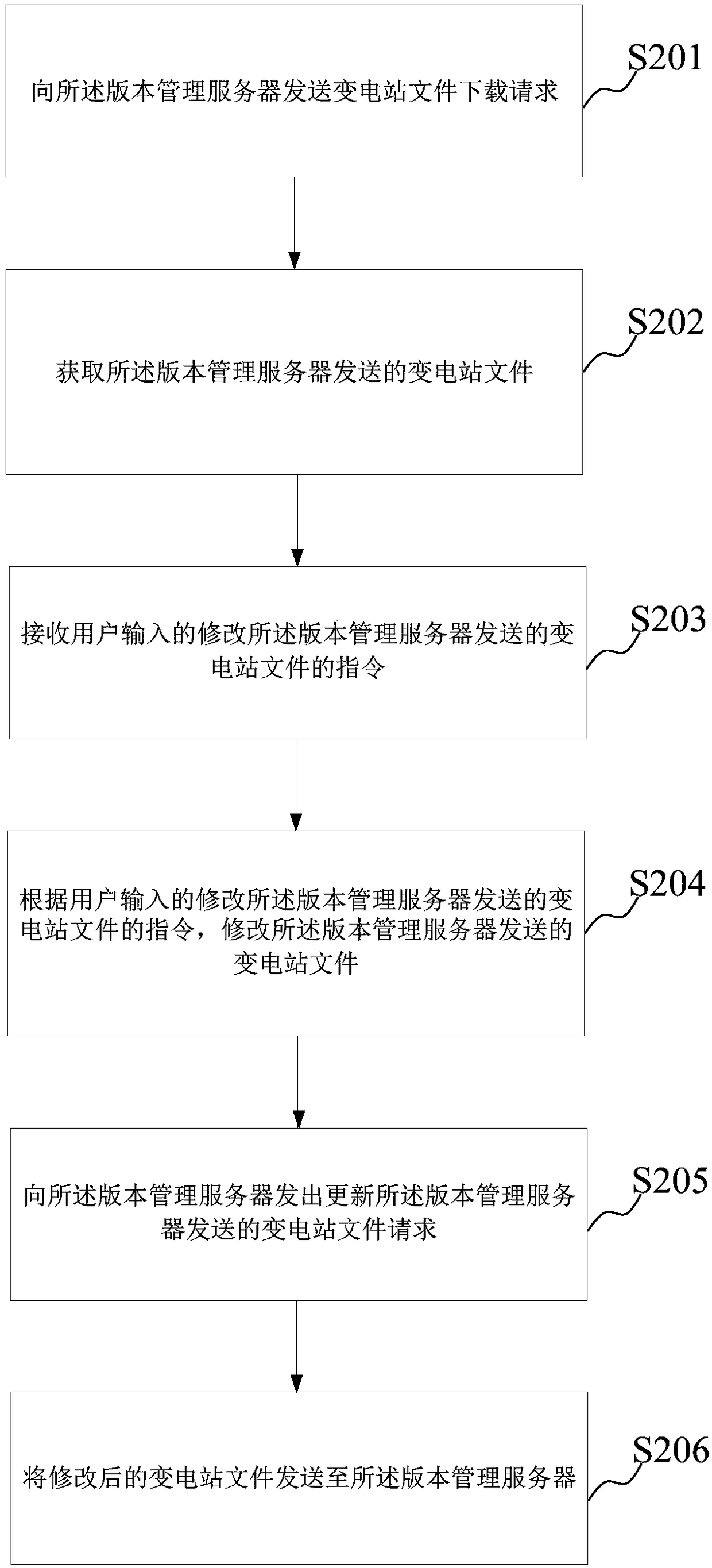
ActiveCN109086062AImprove management efficiencyData processing applicationsSoftware deploymentFile systemUser input
A method and system for version management of a substation file are provided in embodiments of that present disclosure. According to the characteristics of substation equipments and the requirements of operation and maintenance, after the version management client sends a substation file download request to the version management server, the version management server sends the substation file to the version management client, based on the user input instructions for modifying the substation file, after modifying the substation file, the version management client sends a file update request tothe version management server, and the version management server obtains the modified substation file sent by the version management client, stores the modified substation file in the corresponding location of the substation file management library, and overwrites the historical version of the modified substation file. The invention provides a substation file version management method and a substation file version management system, which can realize unified and standardized version management of a complex substation file system and improve the file management work efficiency.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
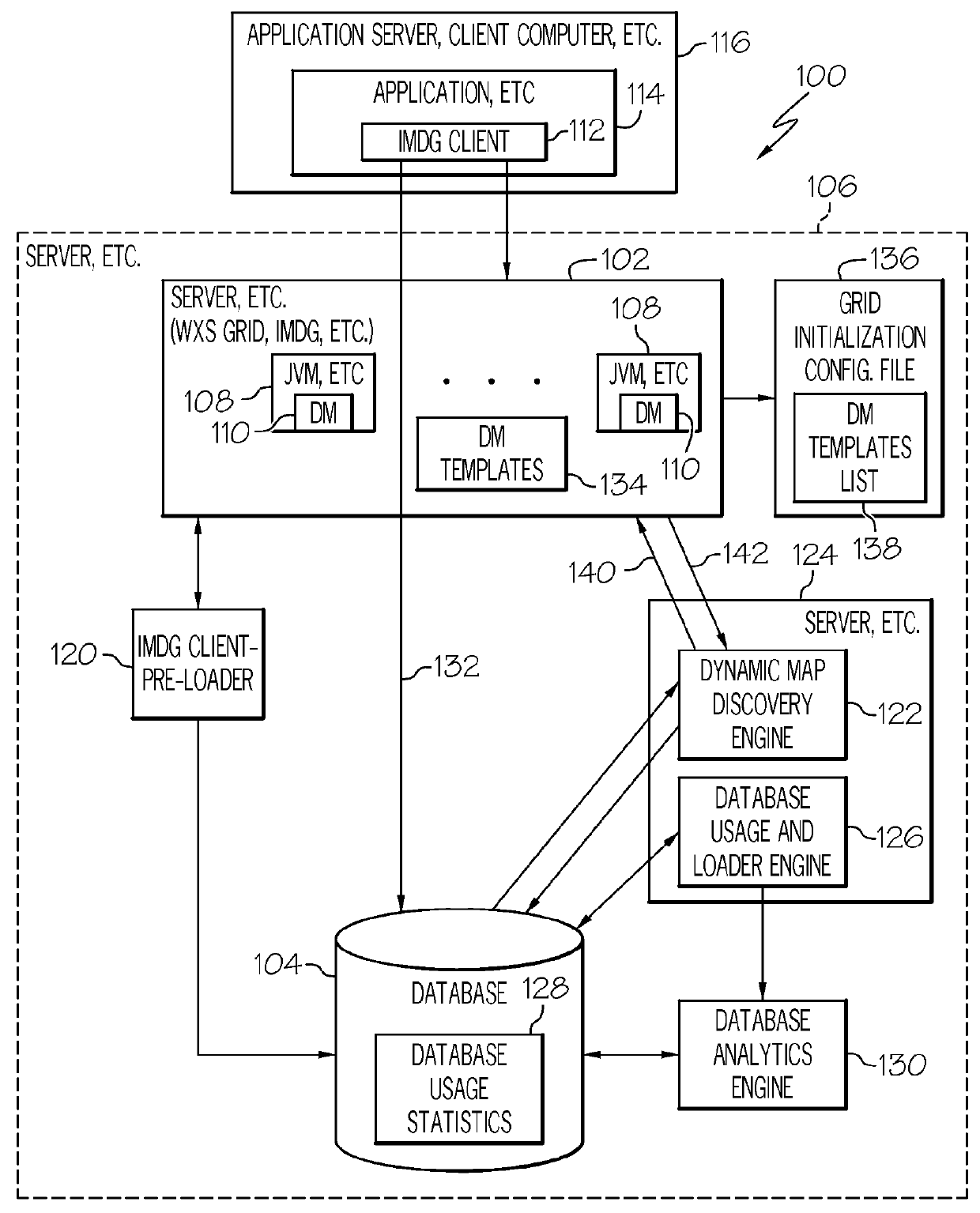
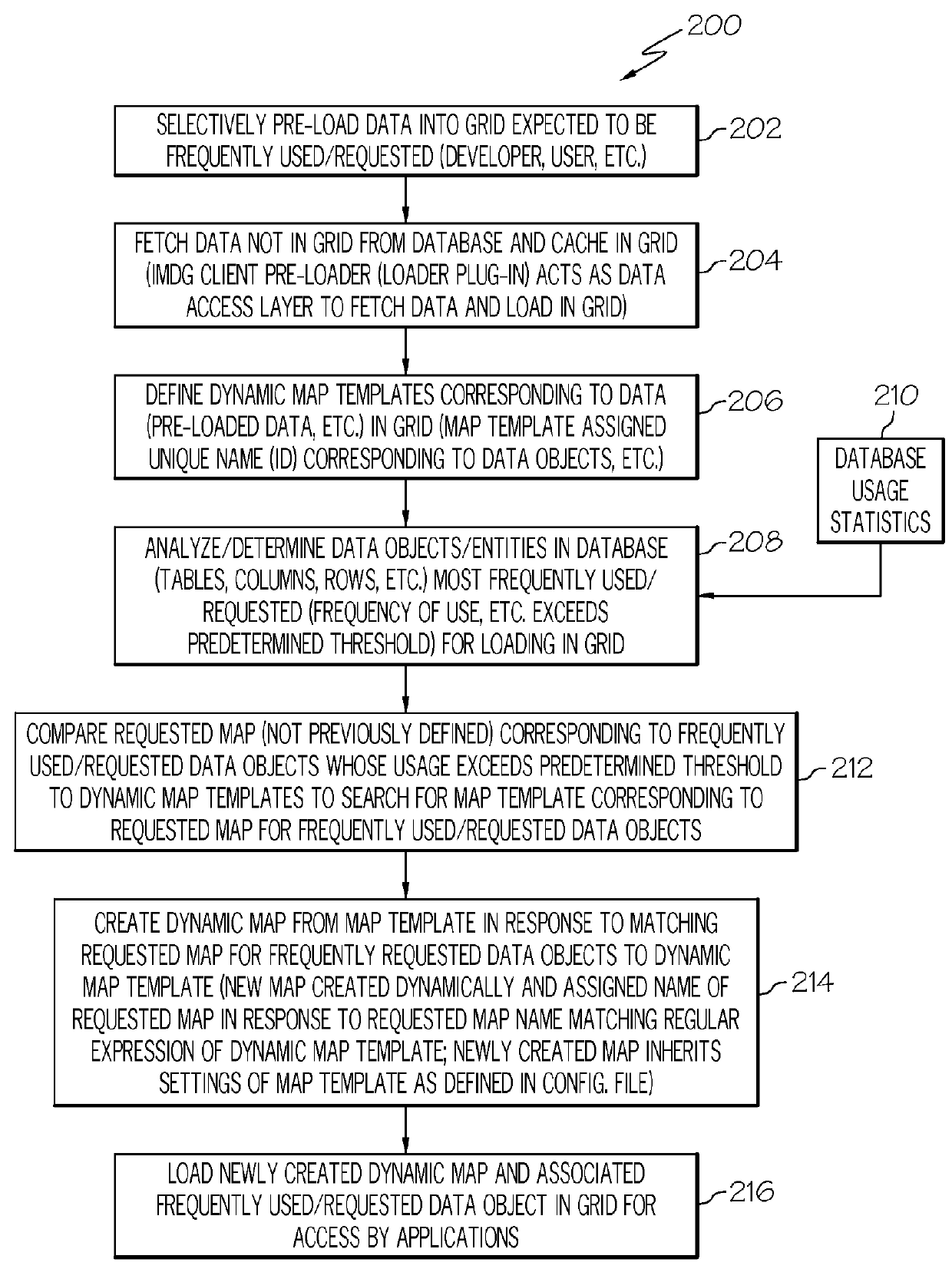
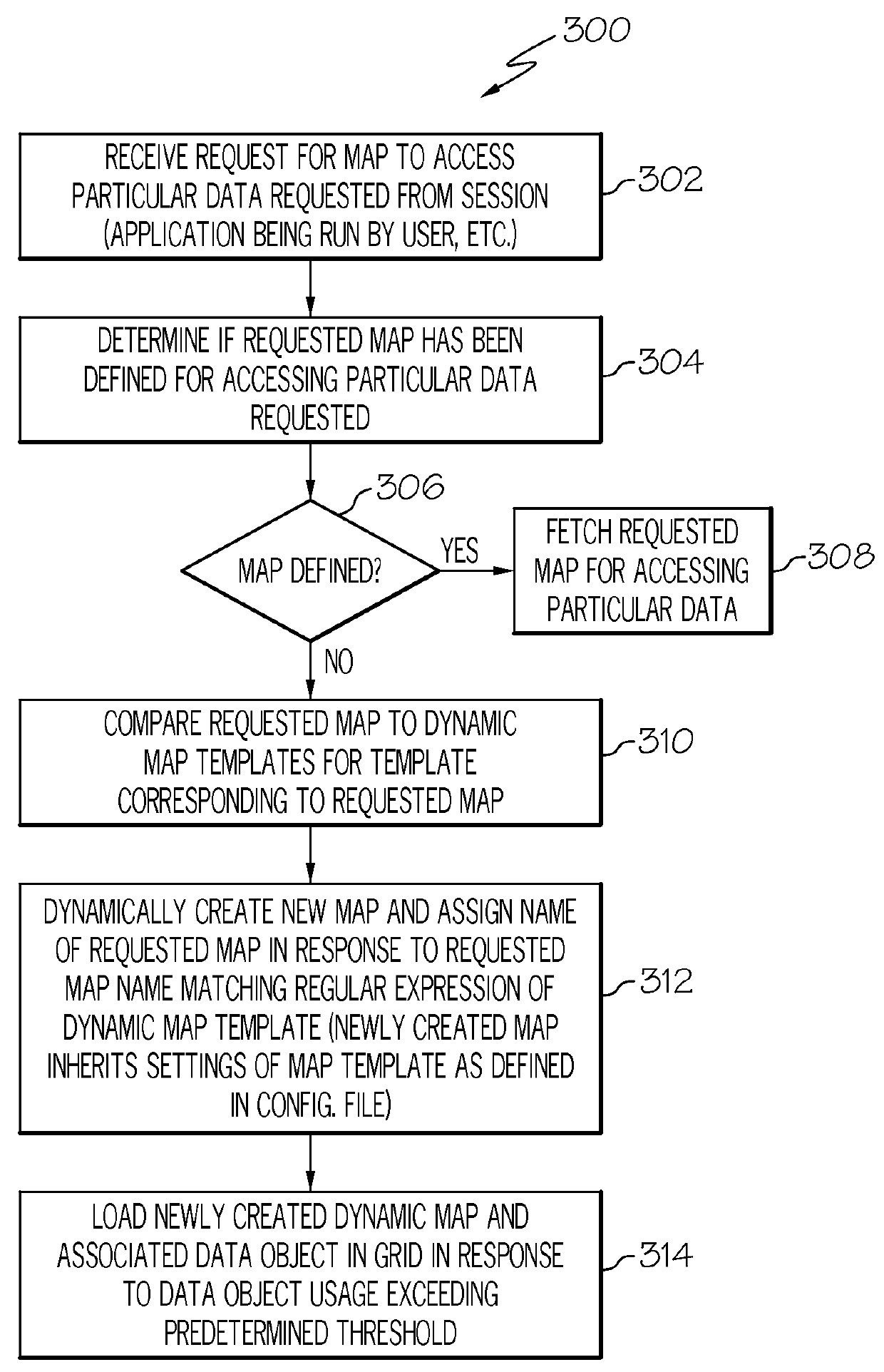
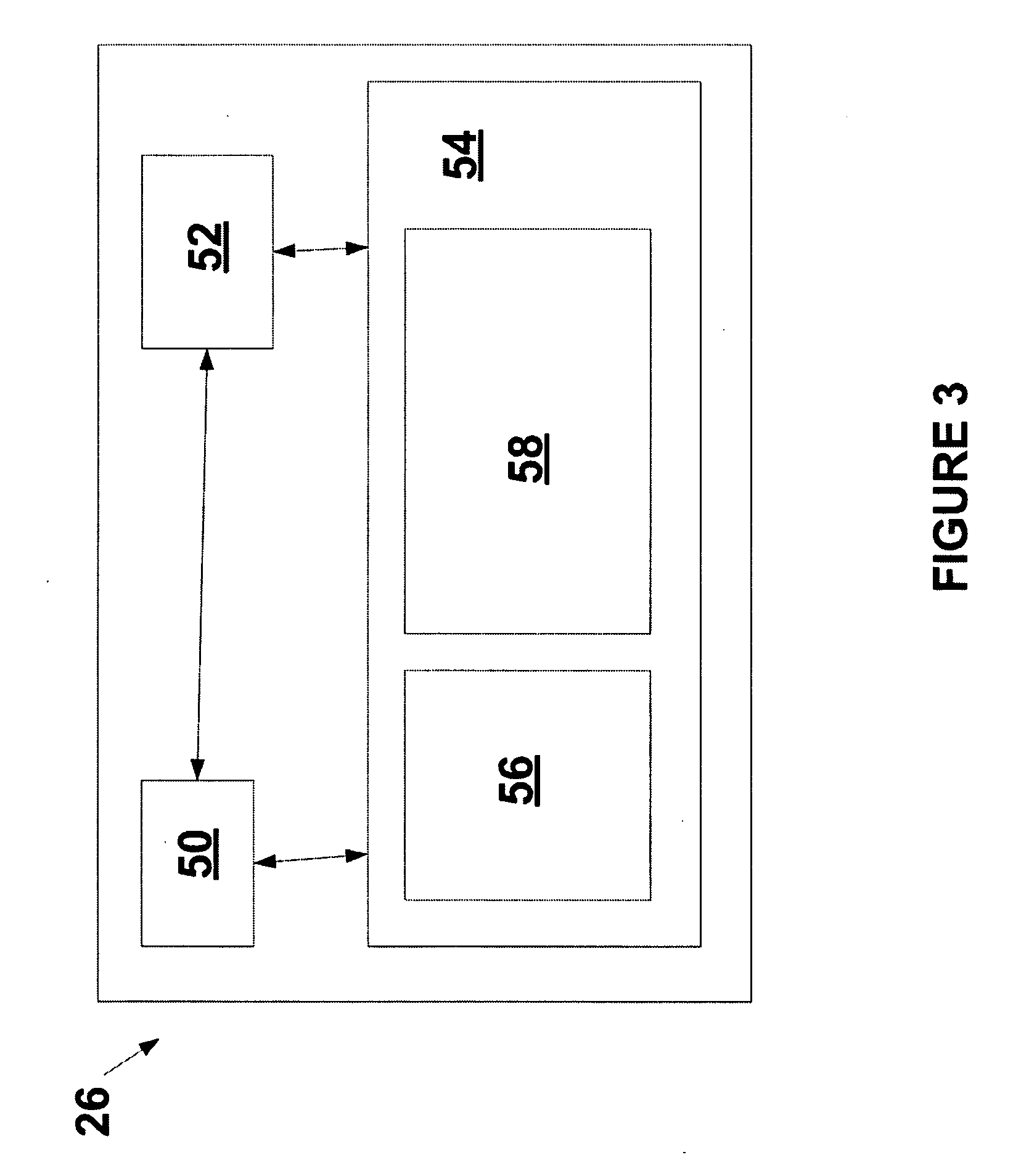
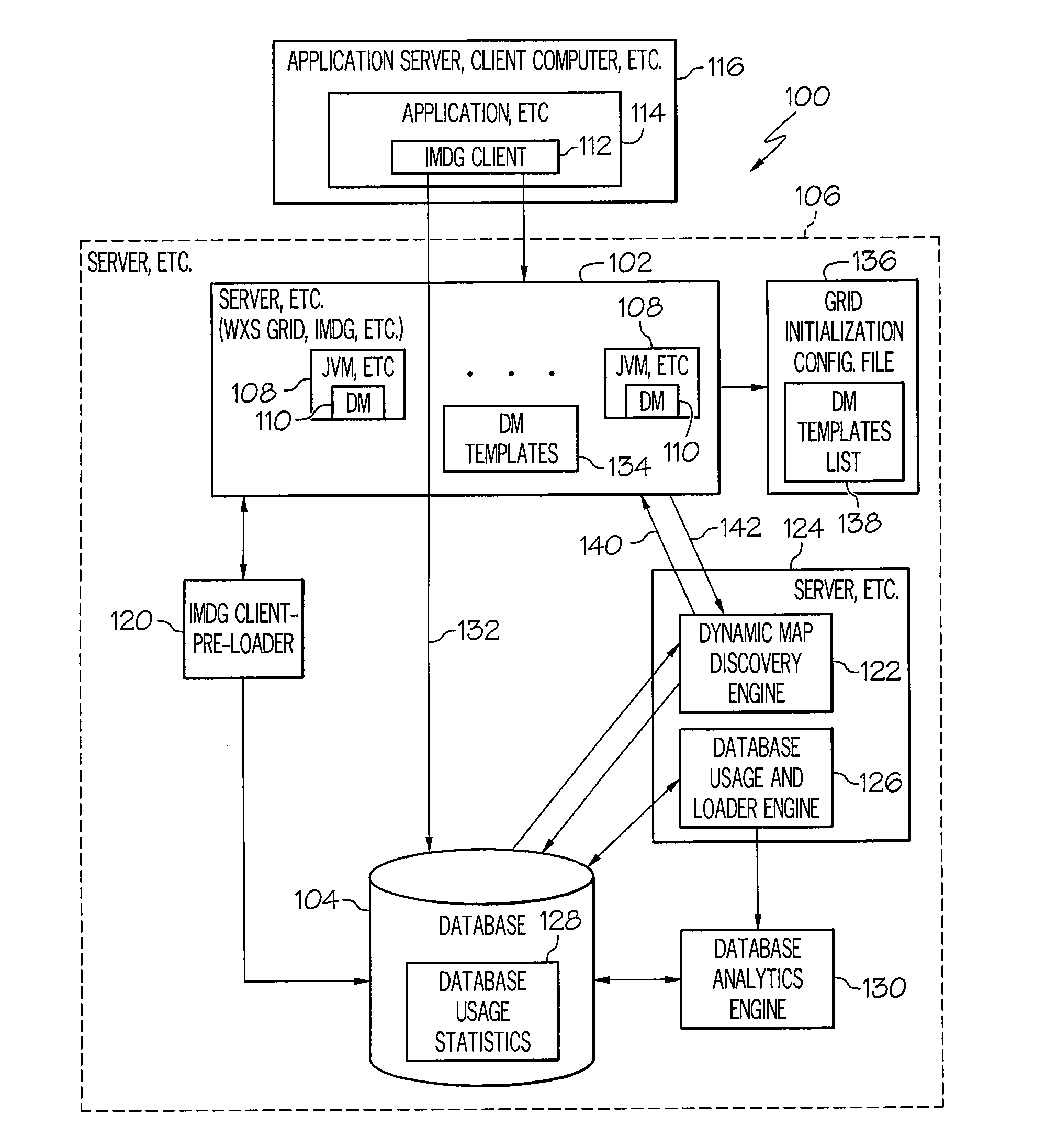
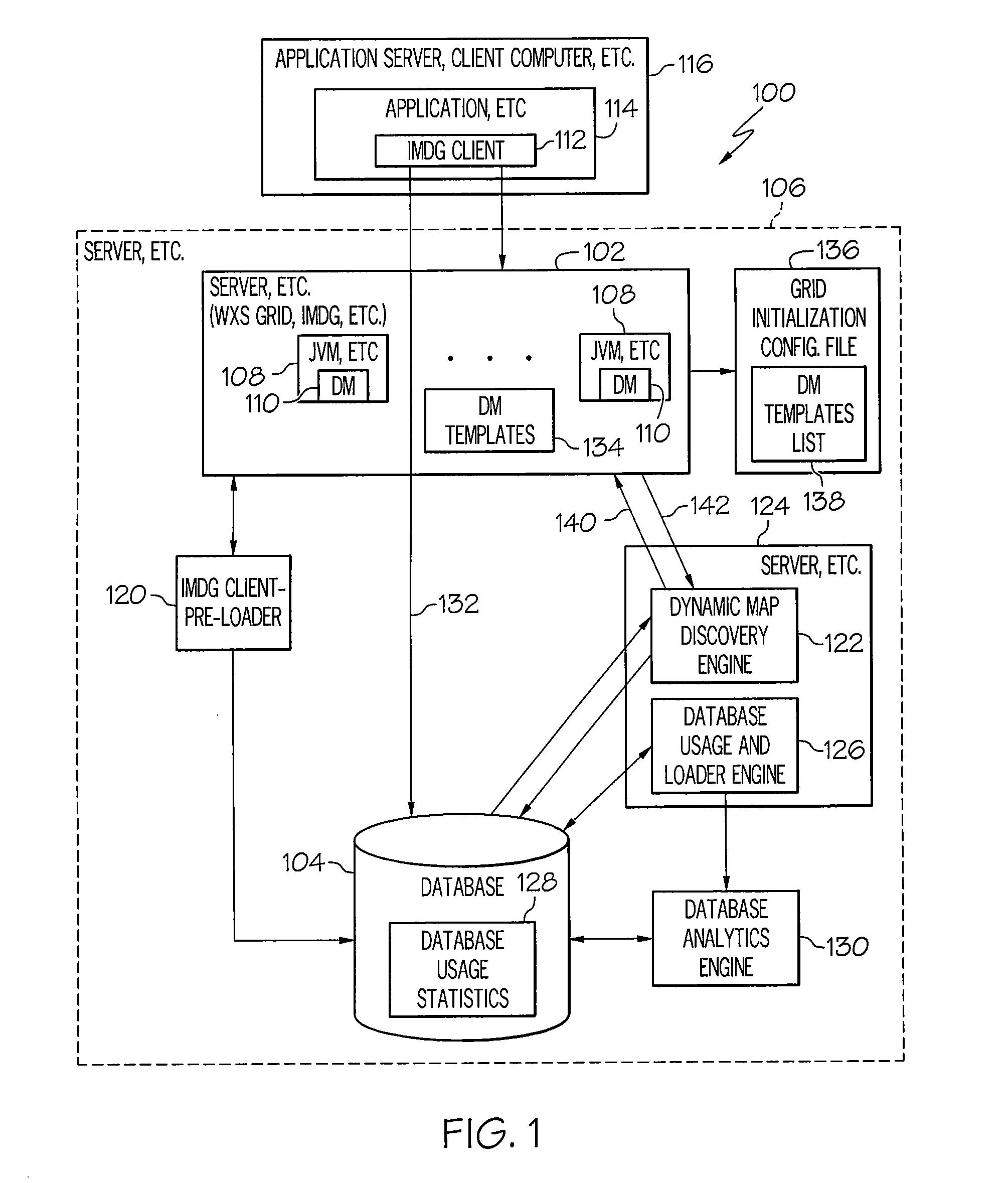
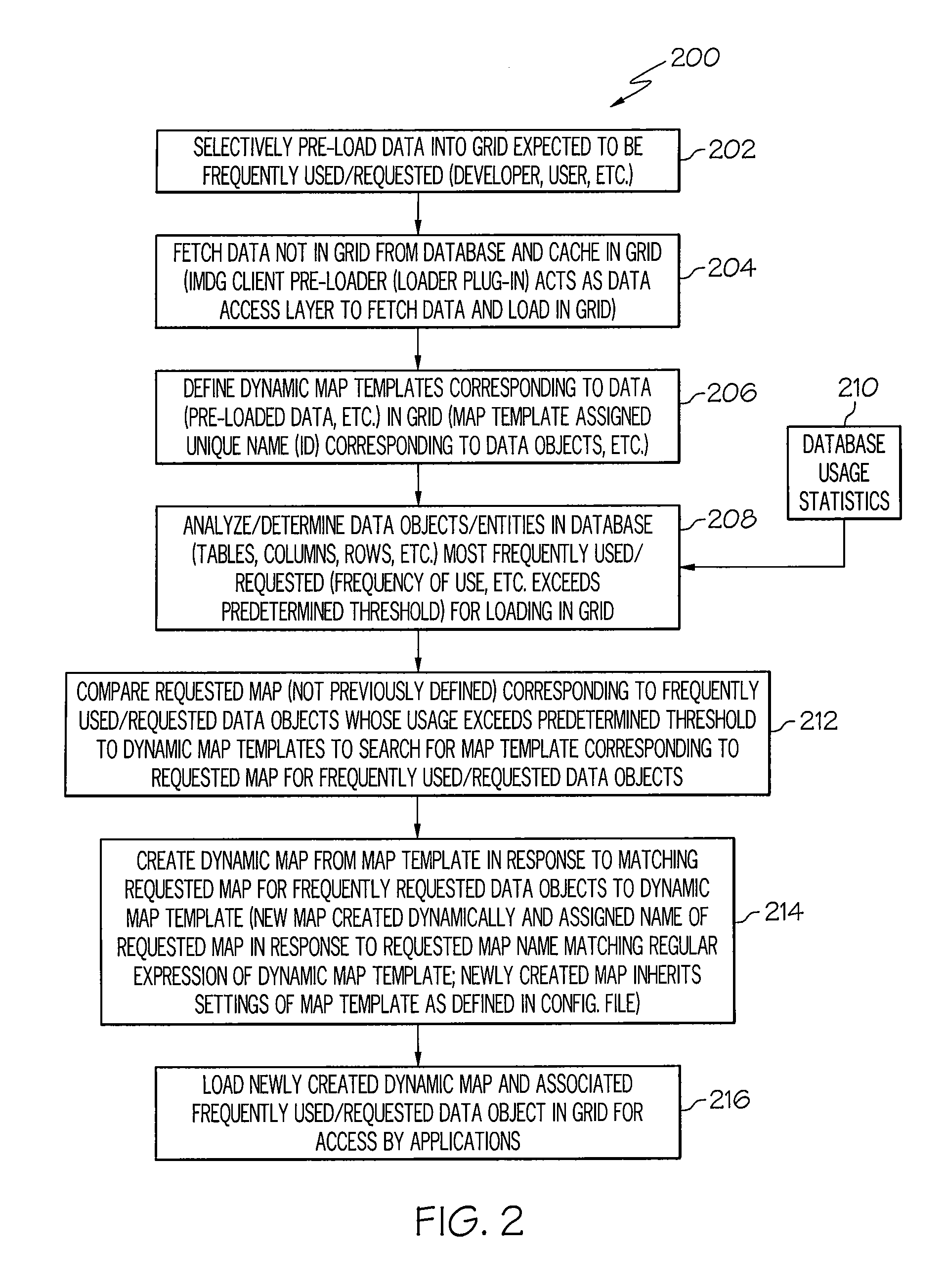
Dynamic map template discovery and map creation
InactiveUS9251181B2Digital data information retrievalDigital data processing detailsData miningDigital object
A method, system and computer program product for dynamic map template discovery and map creation may include determining a frequency of use of a data object in a database and discovering a dynamic map template corresponding to the data object based on the frequency of use of the data object. The method may also include creating a dynamic map from the dynamic map template in response to discovering the dynamic map template.
Owner:IBM CORP
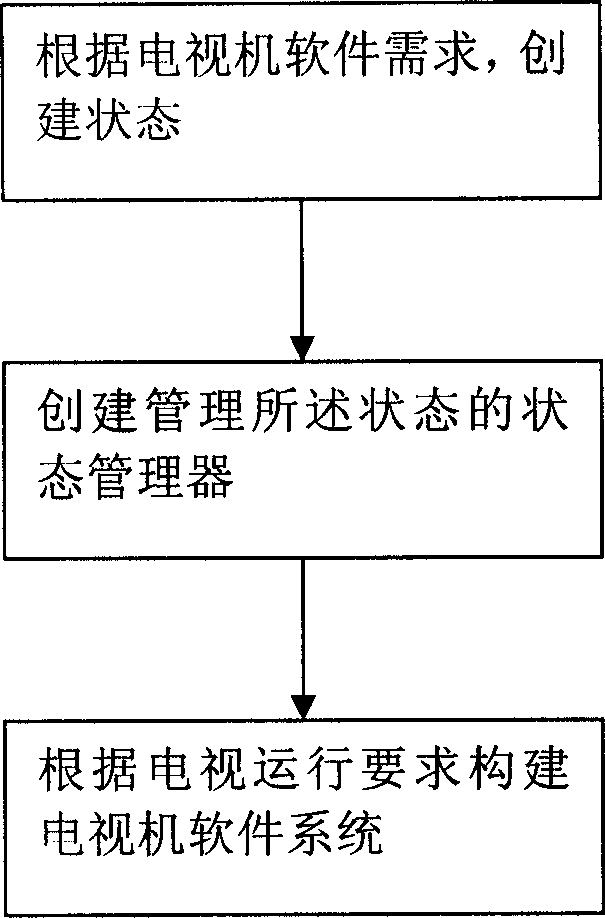
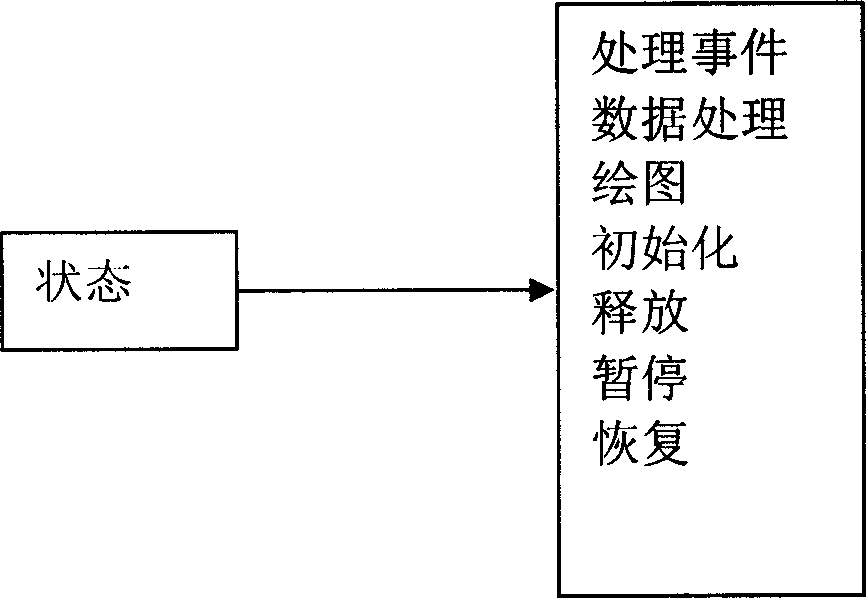
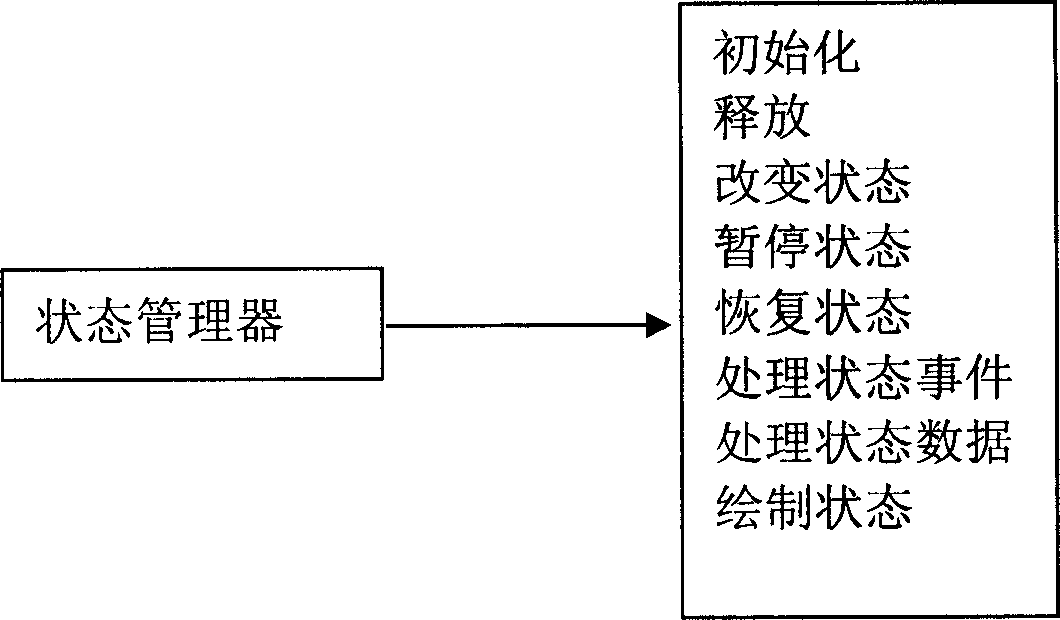
Method for constituting television software system using mode machine
InactiveCN1889644AQuick buildRun fast and stableTelevision system detailsColor television detailsSoftware systemModularity
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
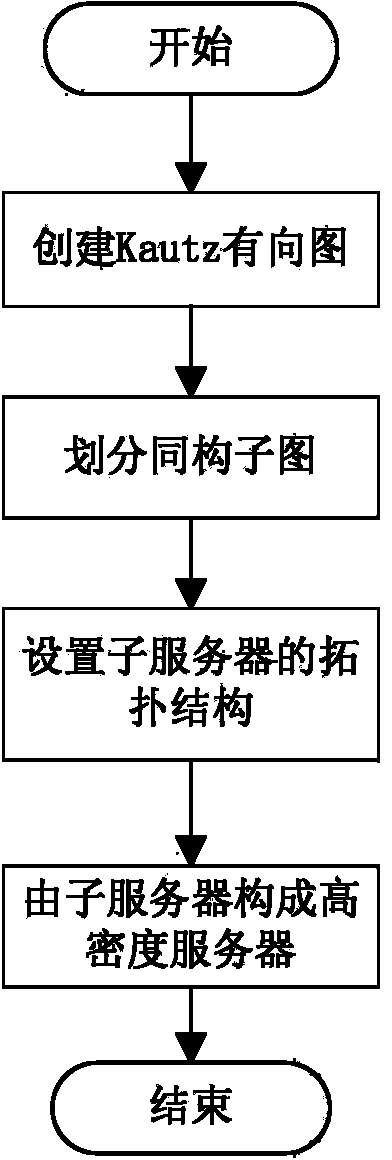
Topology construction method of high-density server and system thereof
ActiveCN104022928AImprove fault toleranceSave manufacturing costEnergy efficient ICTData switching by path configurationFault toleranceHigh density
The invention provides a topology construction method of a high-density server and a system thereof. The method comprises the following steps: a Kautz digraph for a topological structure of a high-density server is created according to requirements on network size, and the Kautz digraph is divided into multiple isomorphic sub-graphs; and switch chips are arranged on a subserver according to the isomorphic sub-graphs, and multiple subservers are arranged in the high-density server according to the Kautz digraph such that the switch chips on the multiple subservers are corresponding to nodes in the Kautz digraph one to one and the connection mode between the switch chips is consistent with the connection mode between the corresponding nodes in the Kautz digraph. Based on the Kautz digraph, the subservers with the same topological structure are used to form the high-density server. Thus, the high-density server has characteristics of high efficiency, good fault tolerance and extendibility. In addition, batch production of the subservers can be realized, thus saving manufacturing cost and time cost.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Event demand system and method
A system and method for event demand creation and event organization is provided in which an interested party can create a demand for an event at a particular location and then encourage other people to join the demand. Once the demand reaches critical mass, the event provider is notified of the demand and asked to agree to the demanded event.
Owner:EVENTFUL LLC
Dynamic map template discovery and map creation
InactiveUS20130339393A1Digital data information retrievalDigital data processing detailsData miningDigital object
A method, system and computer program product for dynamic map template discovery and map creation may include determining a frequency of use of a data object in a database and discovering a dynamic map template corresponding to the data object based on the frequency of use of the data object. The method may also include creating a dynamic map from the dynamic map template in response to discovering the dynamic map template.
Owner:IBM CORP
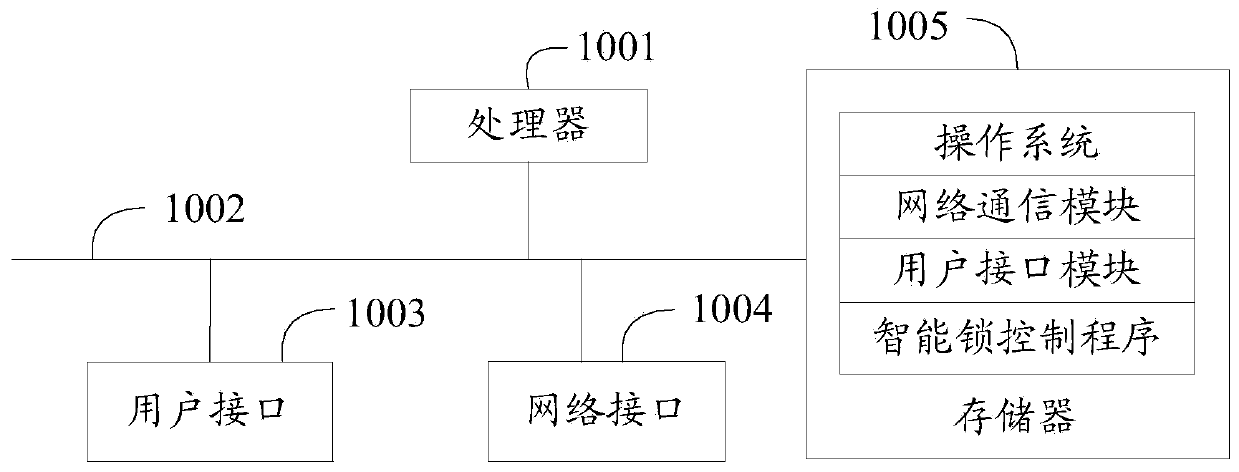
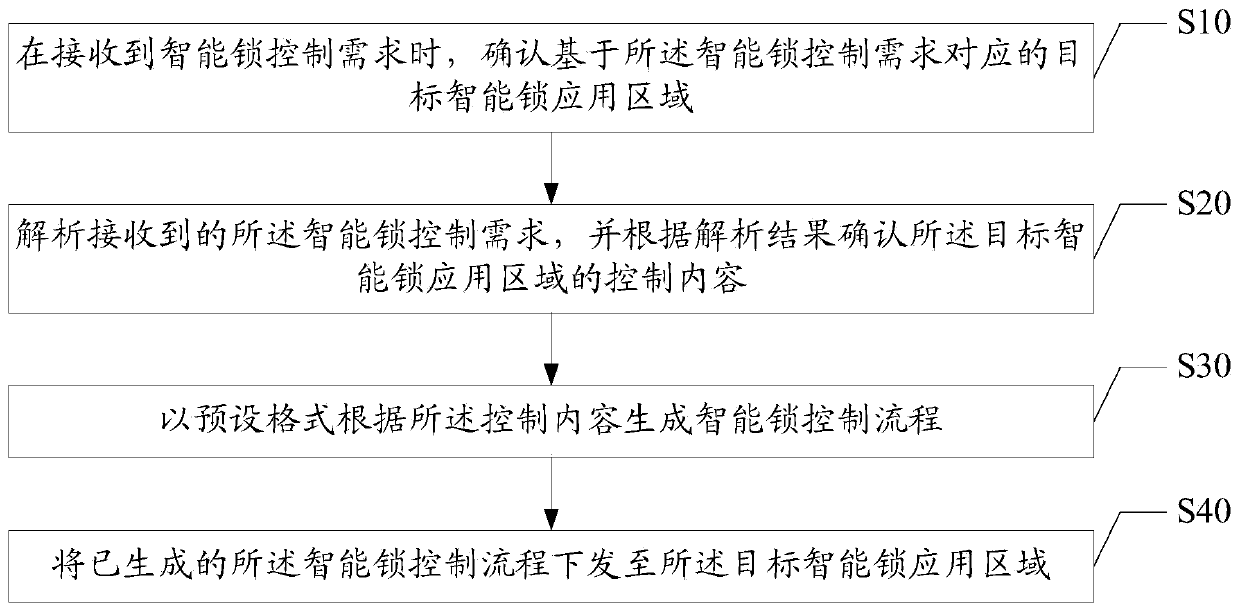
Intelligent lock control method, device and system, and computer readable storage medium
InactiveCN110246255AImprove industrial application securityIndividual entry/exit registersIndustrial areaApplication areas
The invention discloses an intelligent lock control method, which comprises the following steps that: when an intelligent lock control requirement is received, confirming a corresponding target intelligent lock application area based on the intelligent lock control requirement; analyzing the received intelligent lock control requirement, and according to an analysis result, confirming the control contents of the target intelligent lock application area; by a preset format, according to the control contents, generating an intelligent lock control process; and issuing the generated intelligent lock control process to the target intelligent lock application area. The invention also discloses a device, a computer readable storage medium and a system. The intelligent lock control method is constructed in an industrial area where the intelligent lock is deployed, and on the basis of the intelligent lock control requirement, an intelligent lock control process based on the current intelligent lock industrial application area is configured. Since the intelligent lock control process is created on the basis of the current control requirement, the method comprises intelligent lock control logic and a control sequence to realize a beneficial effect that the industrial application safety of the intelligent lock is improved.
Owner:SHENZHEN SHENG YU MIN PHOTOELECTRIC TECH CO LTD
Asset/equipment operation and maintenance management realization method
The invention discloses an asset (equipment) operation and maintenance management realization method, and belongs to the field of operation and maintenance management. A system corresponding to the method comprises an enterprise platform network management center user PC, an enterprise platform background administrator PC, an enterprise equipment administrator mobile phone client, and an enterprise equipment usage mobile phone client. The system mainly performs targeted operations on usage conditions of fixed assets in enterprise management as follows: 1, the enterprise platform network management center user PC can create a corresponding department and a corresponding pc account according to a demand; 2, the enterprise platform background administrator PC can view usage conditions of equipment at any time; 3, the enterprise equipment administrator mobile phone client can view repair history of the equipment at any time; 4, equipment management of enterprise users is all deployed to a cloud terminal, so that the security risk is controlled to be lowest; 5, equipment repair records of equipment with running faults can be viewed at any time; and 6, enterprise administrator users can view whether the equipment runs normally or not and who uses the equipment at any time.
Owner:无锡益教服网络技术有限公司
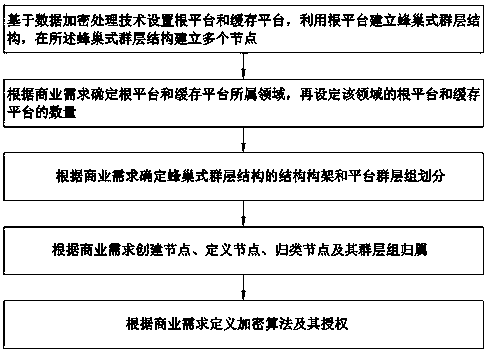
Honeycomb architecture application implementation method based on data encryption processing technology
ActiveCN110247799ALarge amount of processingImprove processing efficiencyData switching networksStructure of Management InformationHoneycomb
The invention discloses a honeycomb architecture application implementation method based on a data encryption processing technology, and the method comprises the following steps: 1, setting a root platform and a cache platform based on the data encryption processing technology, building a honeycomb group layer structure by using the root platform, and building a plurality of nodes in the honeycomb group layer structure; 2, determining the fields to which the root platforms and the cache platforms belong according to commercial requirements, and then setting the number of the root platforms and the cache platforms in the field; 3, determining a structure framework and platform group division of the honeycomb type group layer structure according to commercial requirements; 4, creating nodes according to commercial requirements, and defining nodes, classification nodes and group attribution of the nodes and the classification nodes; and 5, defining an encryption algorithm and authorization thereof according to commercial requirements. The honeycomb architecture application realization method can meet the business requirements of scientific and technological upgrading and daily extraordinary business, the solution after information integration is accurate, and the method can control the cost cause of the operation project on the platform timely and accurately.
Owner:郑勇
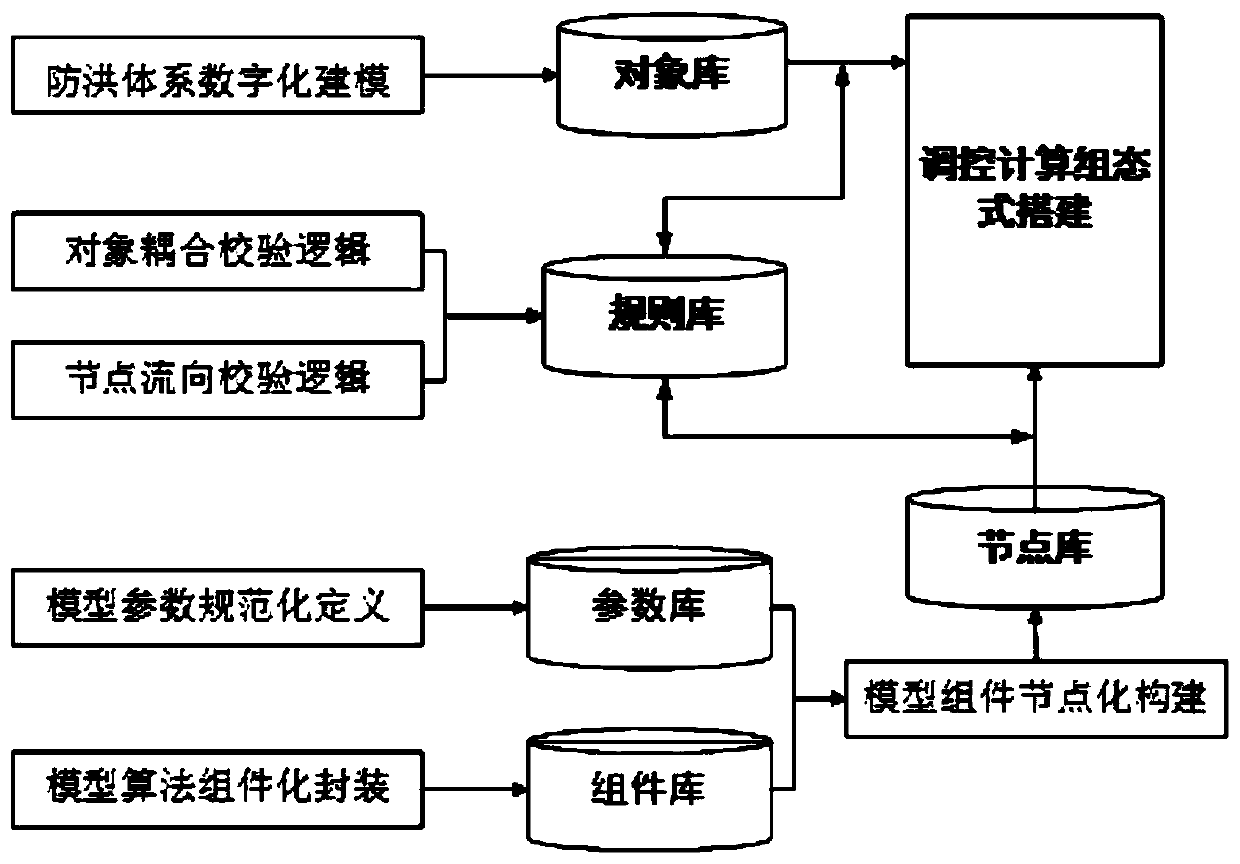
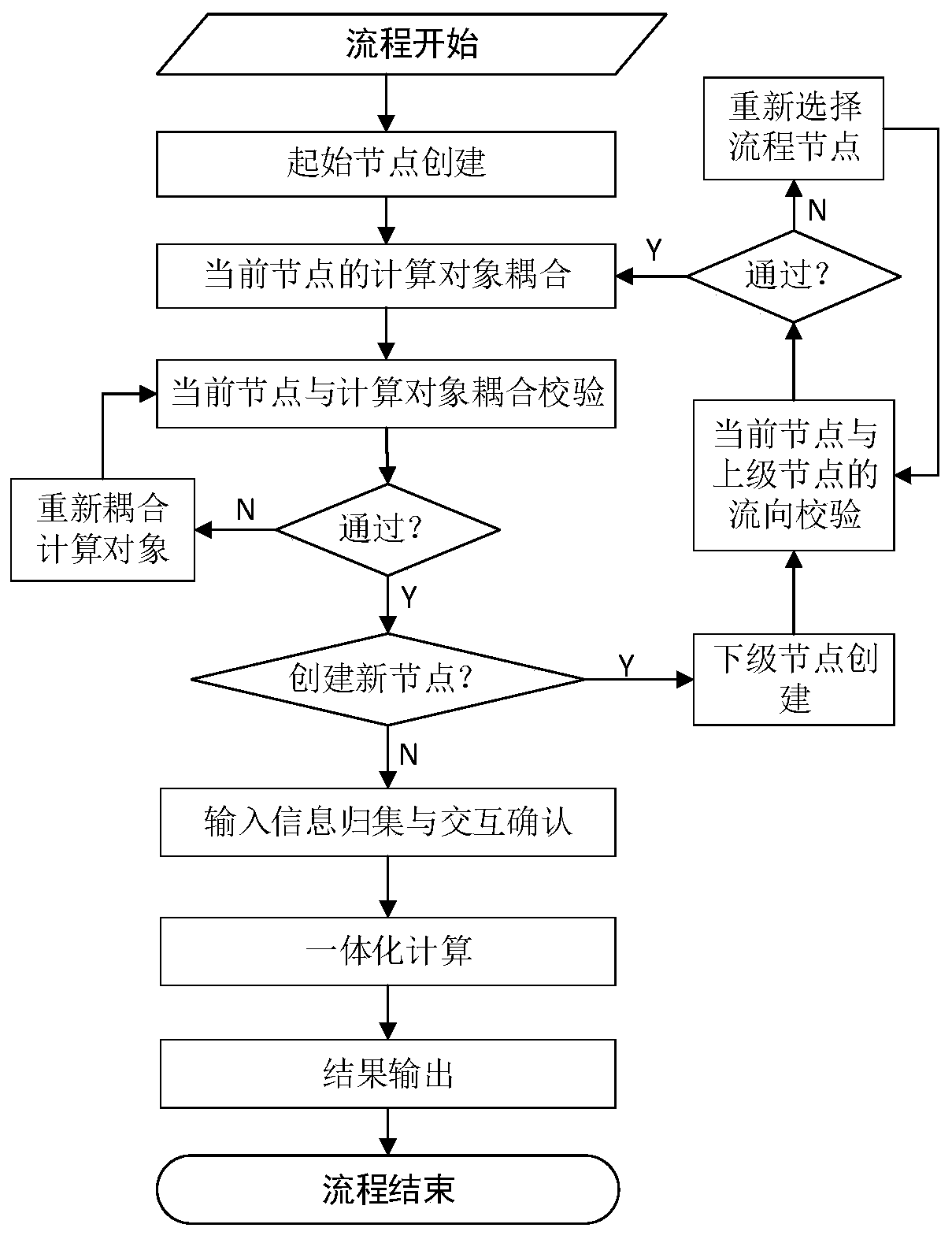
Agile configuration method for over-standard flood multi-combination regulation and control calculation
ActiveCN110377993ASolve the segmentation problemSolve curing problemsData processing applicationsClimate change adaptationNODALCoupling
Modularization, configuration and process engine technologies are introduced into the field of basin flood scheduling control. The invention provides an agile configuration method for over-standard flood multi-combination regulation and control calculation. The agile configuration method comprises the following steps: packaging various model algorithm components into a node library; selecting onenode from the node library as a starting point node of the process; calculating an object for the initial node coupling, and verifying whether the current node and the object coupling are valid according to a rule base; creating subordinate nodes according to the combination requirements; coupling a calculation object for the subordinate node; repeating the steps to circularly create a new subordinate node according to the combined calculation requirement, and completing the corresponding node flow direction and object coupling verification until the node is completely created; and collectingall input information of the node flow, starting a calculation task, and outputting a summary result.
Owner:CHANGJIANG SURVEY PLANNING DESIGN & RES
A multi-protocol acquisition and scheduling method for integrated network management
The invention relates to a multi-protocol acquiring and scheduling method for comprehensive network management. An acquiring and scheduling service is a bridge for connecting a data presentation layer to an acquiring adapter, and is responsible for operating a task and feeding back a result; an acquirer of the acquiring and scheduling service is a program developed according to different interface protocols; by means of the acquirer, acquisition of all data described by the interface protocols is realized; the task to be operated comes from the presentation layer; users can see all kinds of operations supported by an interface in an interface configuration interface and create all kinds of acquisition tasks according to practical requirements in a task management interface; the acquiring and scheduling service operates the configured task in a timed manner; an acquisition service is adapted according to information described by the task; then, the acquisition service is invoked through a standard inlet; operation of the acquisition service is monitored; and an operation result is fed back to the presentation layer or directly written in a data storage layer. According to the invention, uniform invoking of multi-protocol and multi-language processes is realized; the various interface protocols are thoroughly isolated from the presentation layer; and thus, qualification requirements of constructors and maintainers are greatly reduced.
Owner:BEIJING ENOVELL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com