Patents
Literature
86 results about "Life-critical system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A safety-critical system (SCS) or life-critical system is a system whose failure or malfunction may result in one (or more) of the following outcomes...
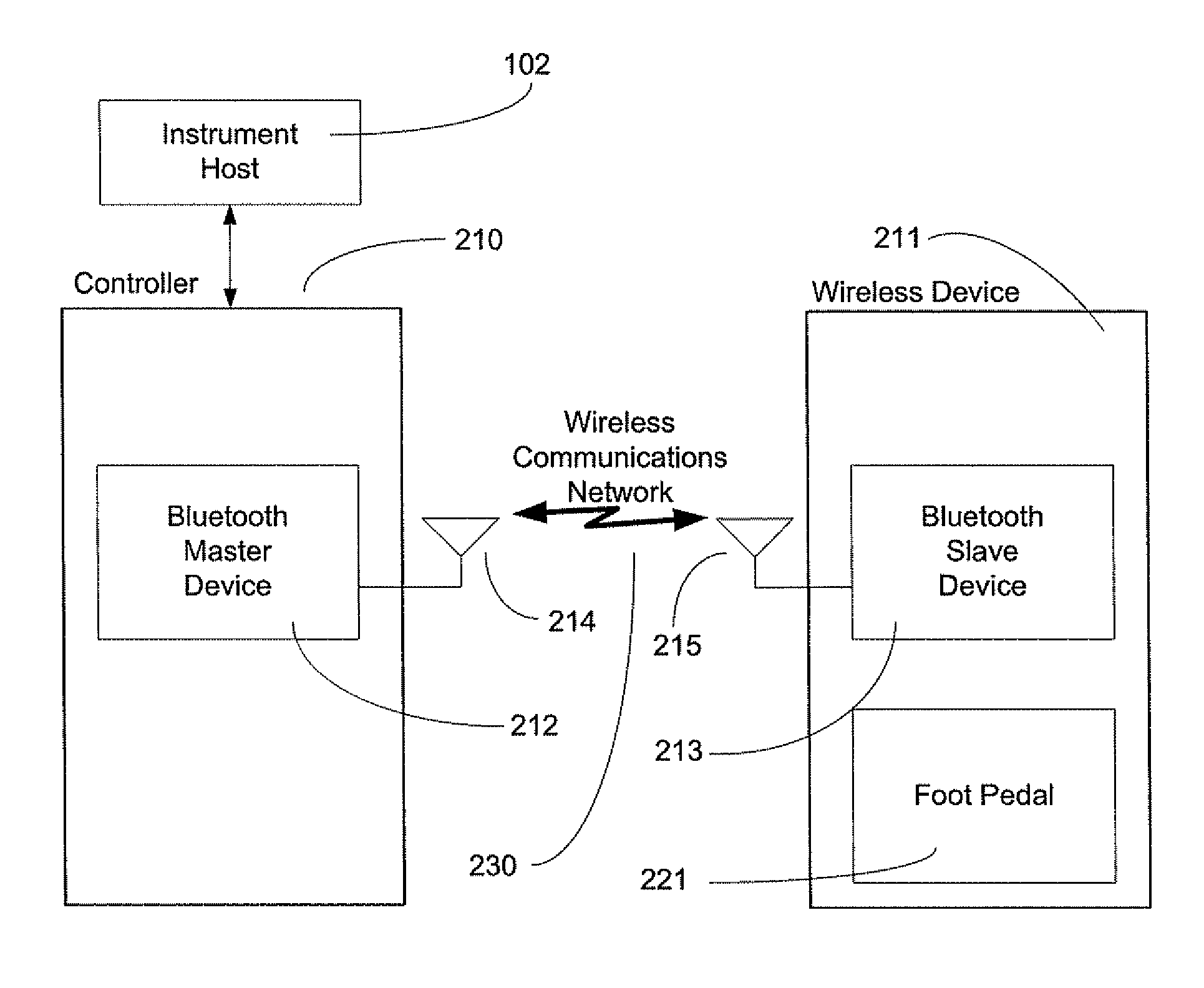
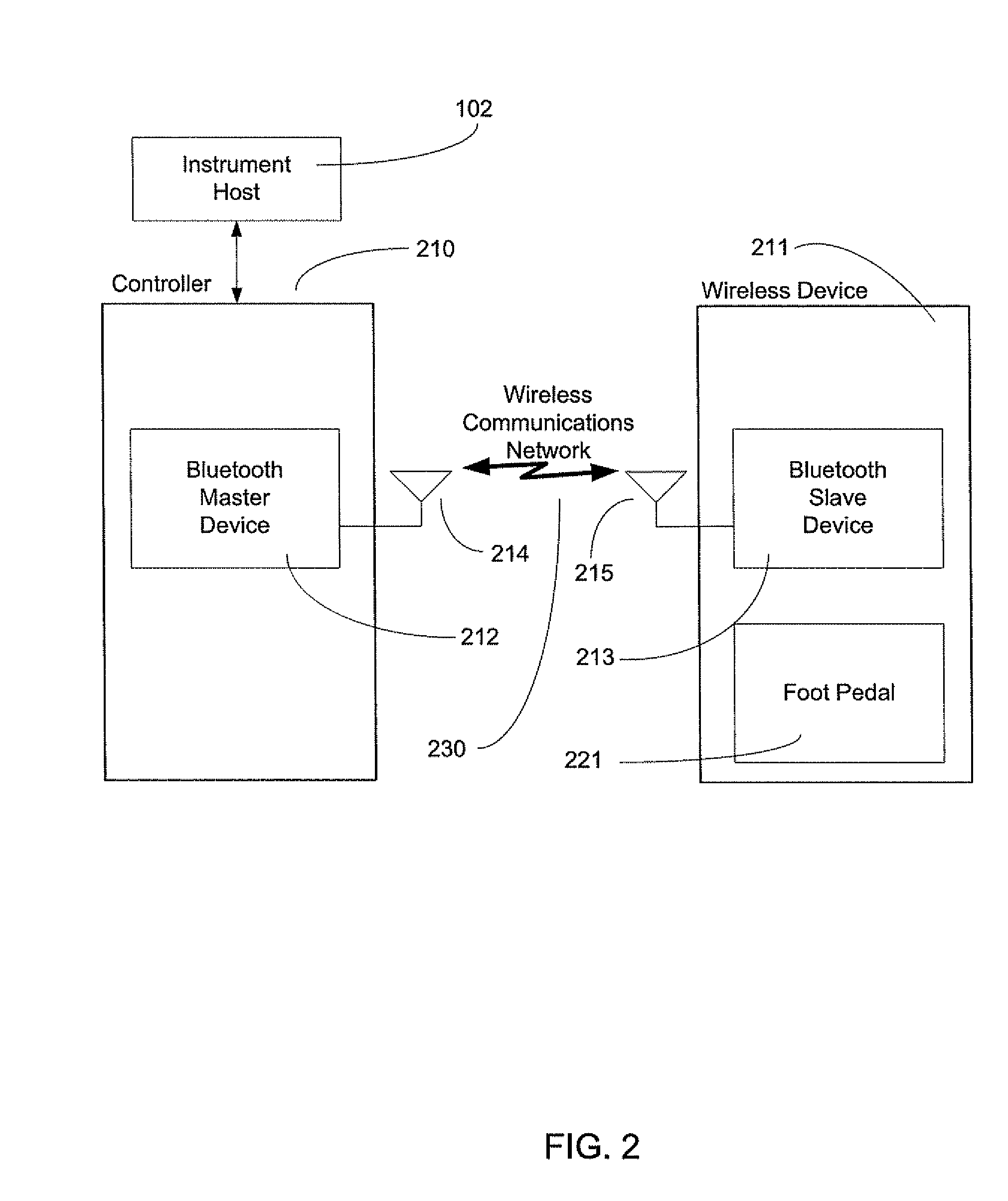
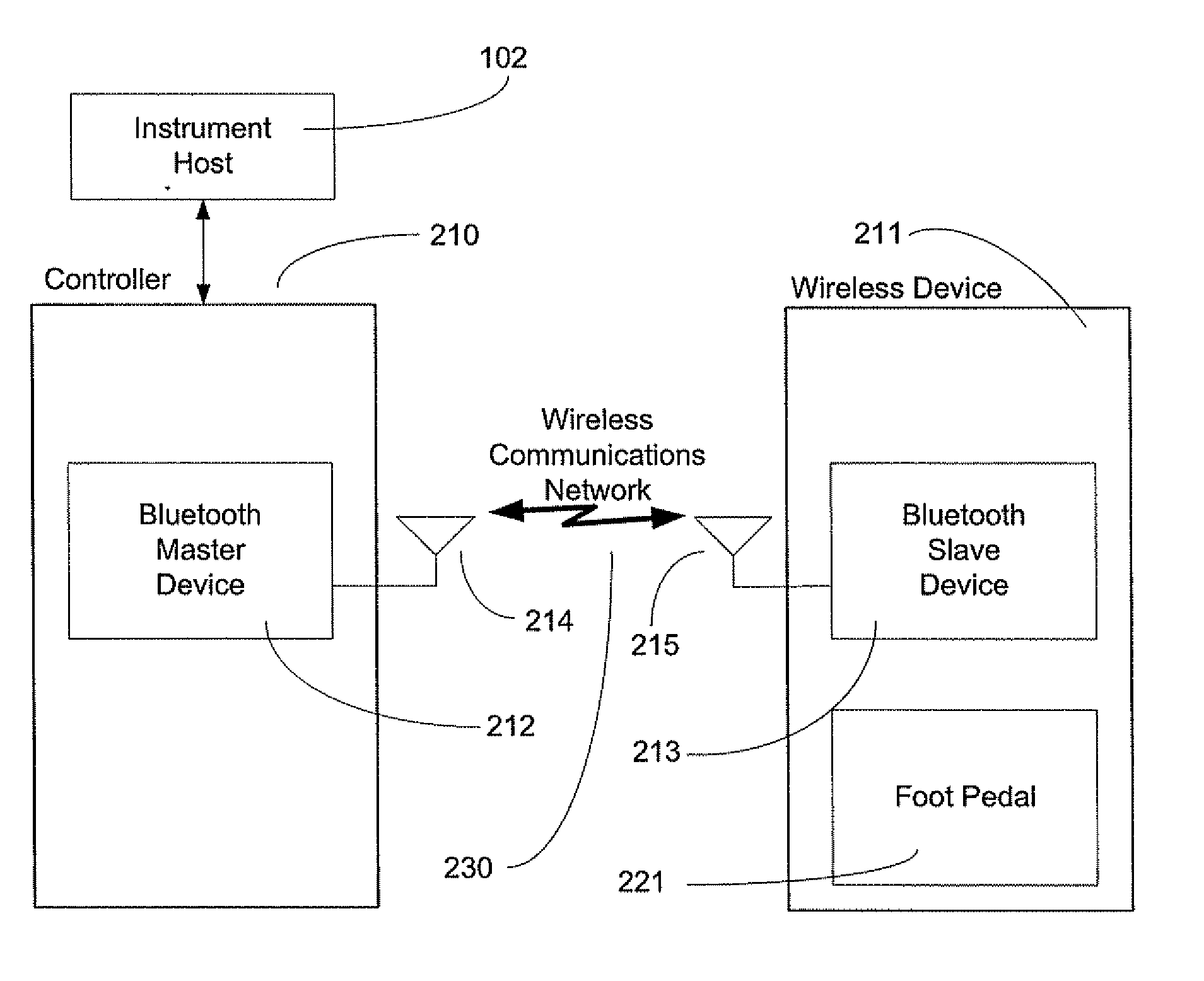
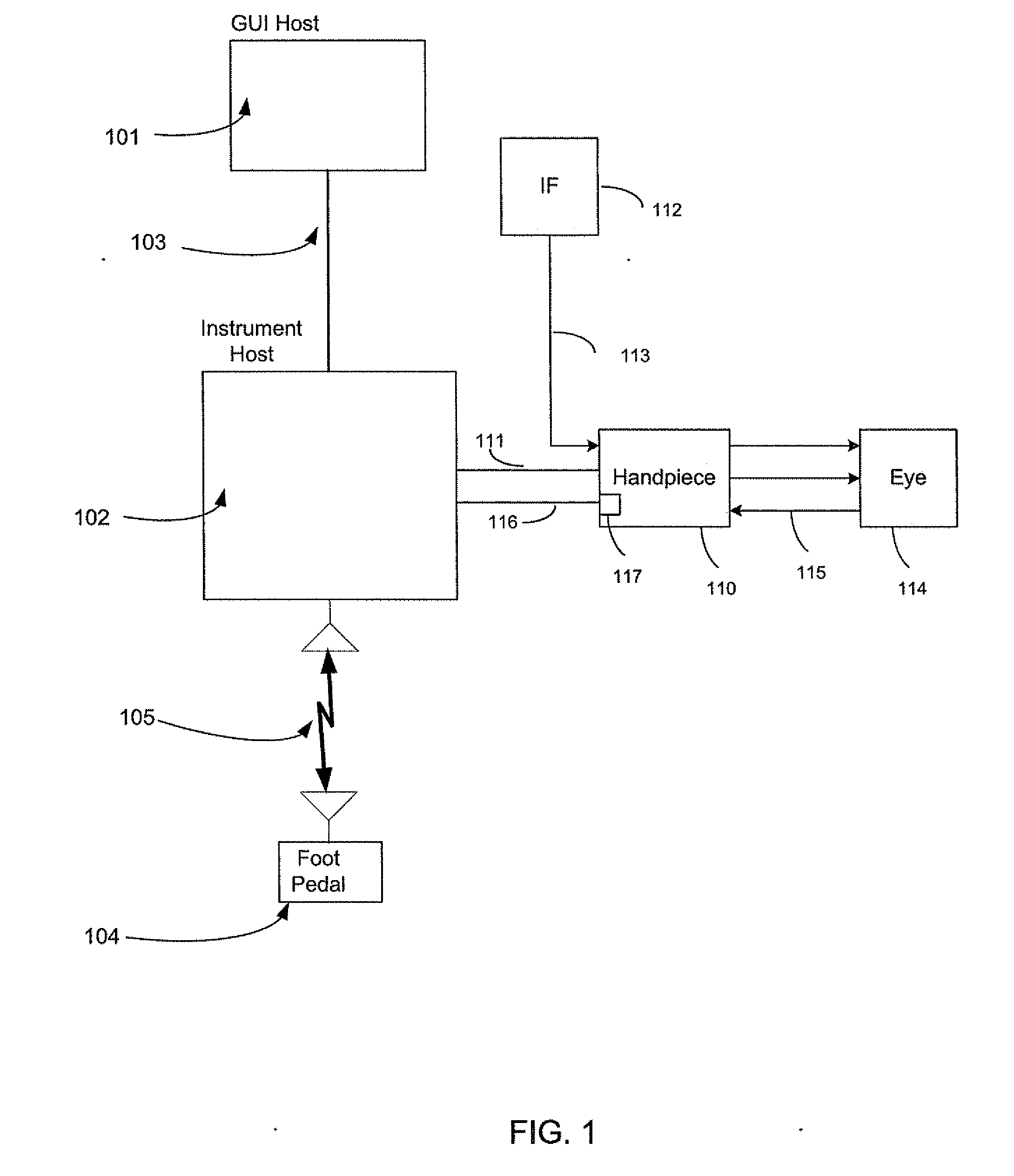
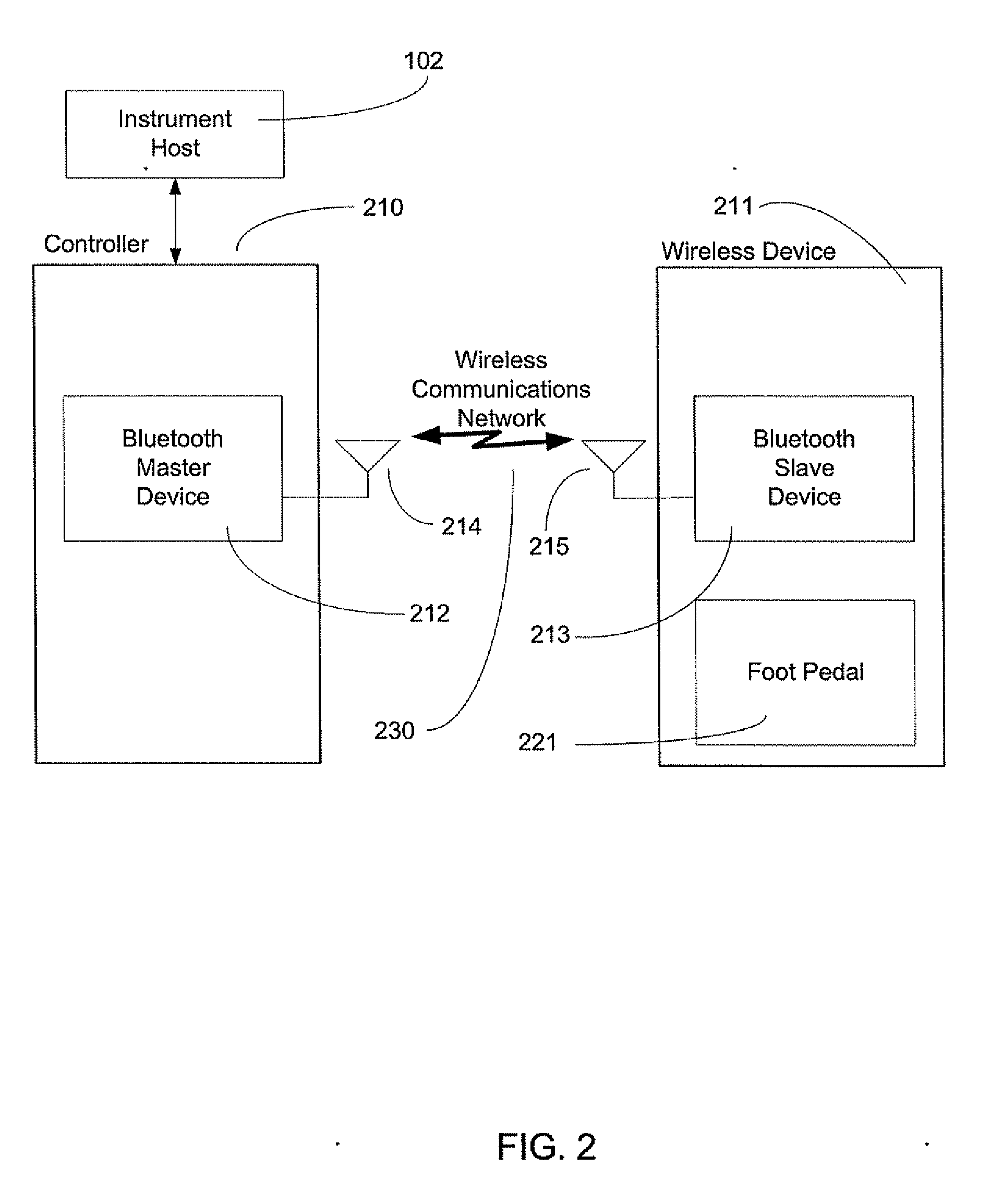
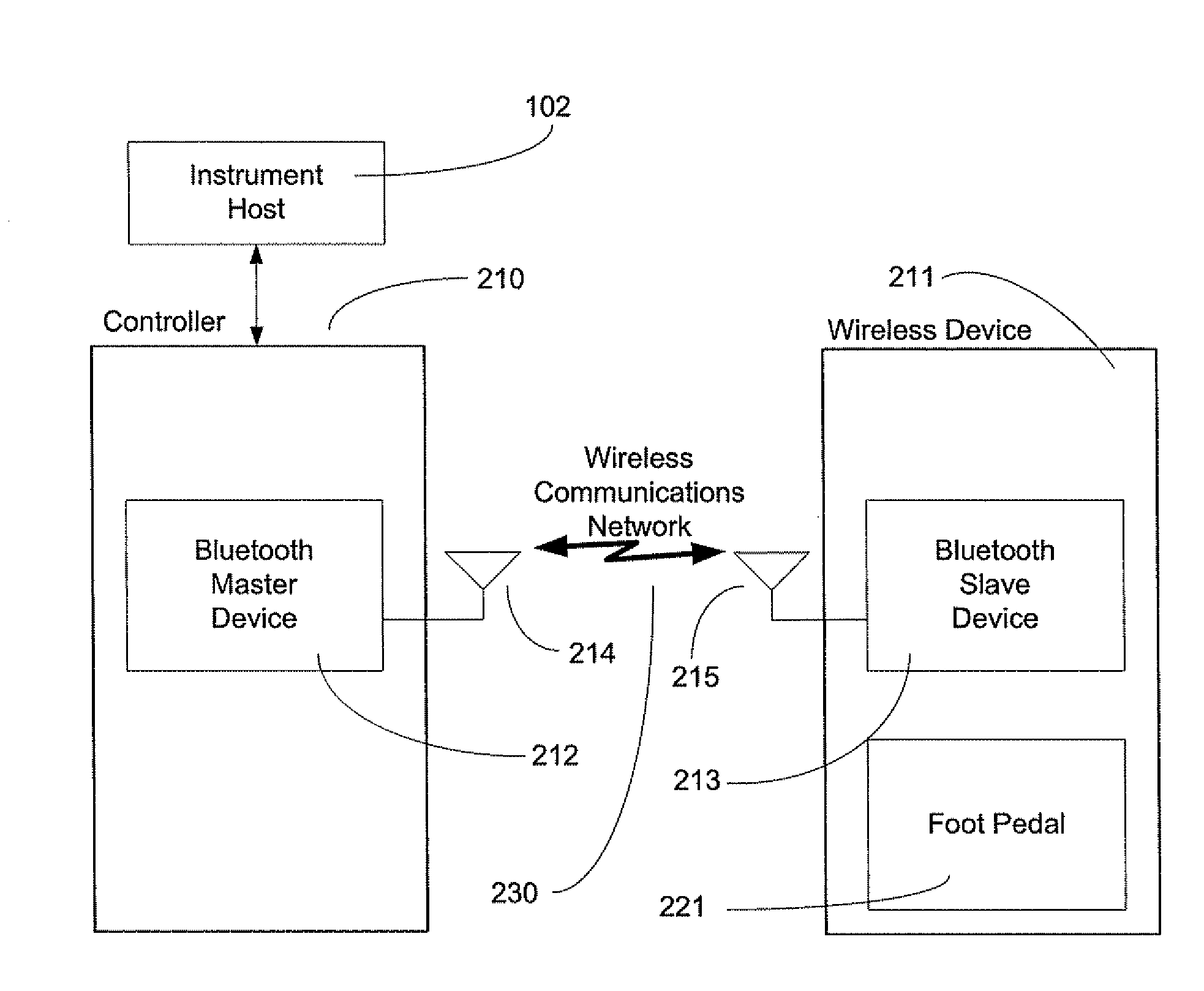
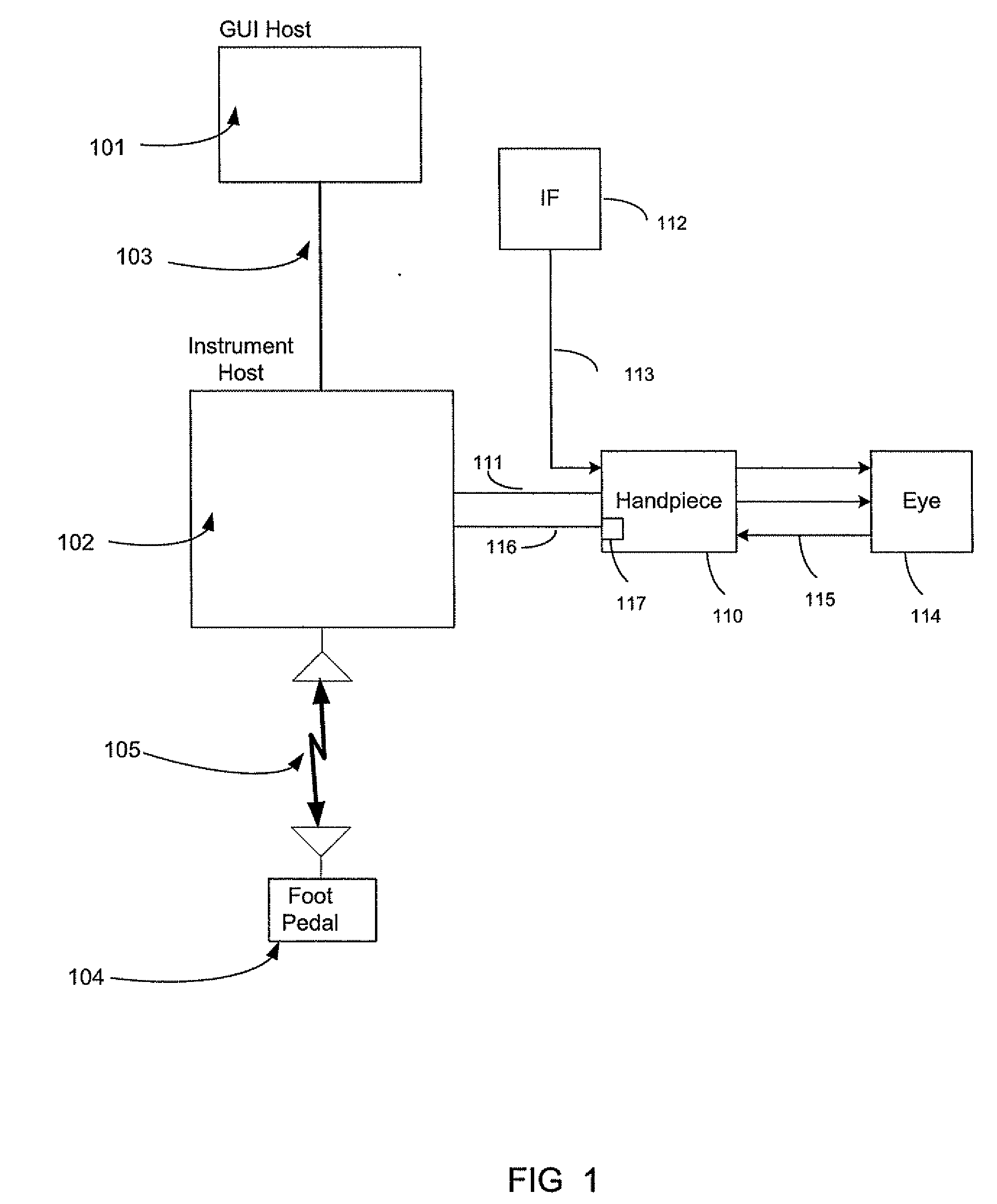
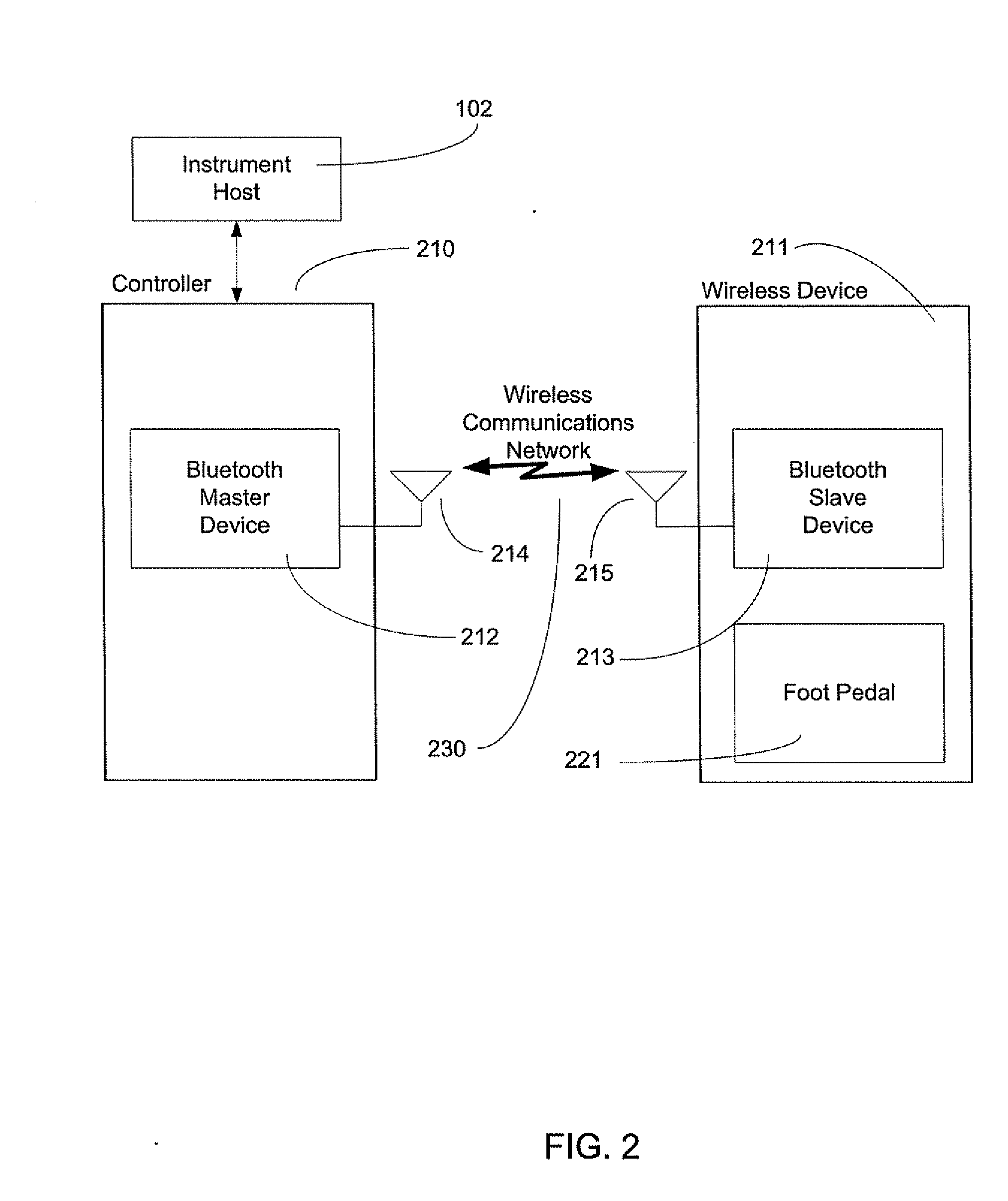
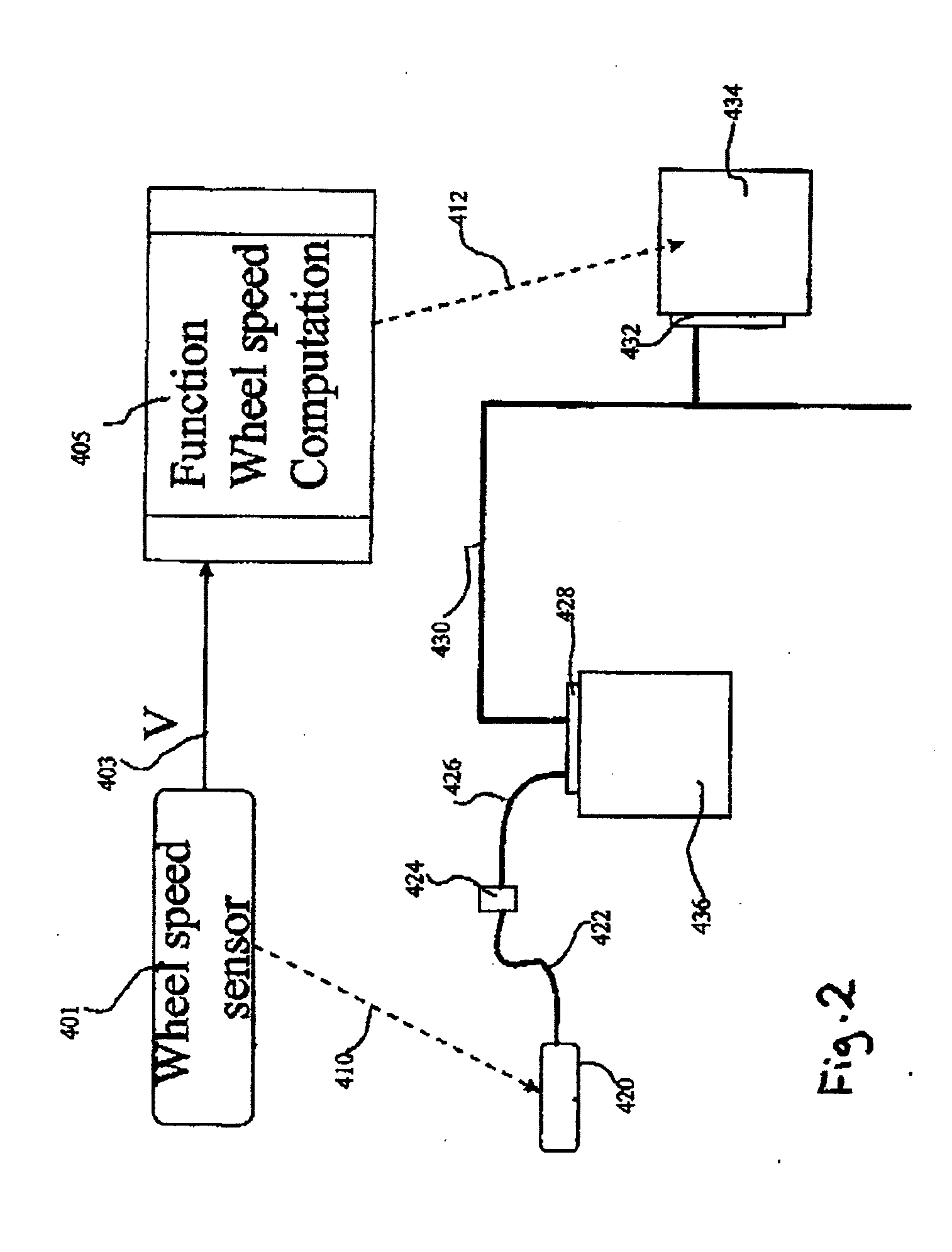
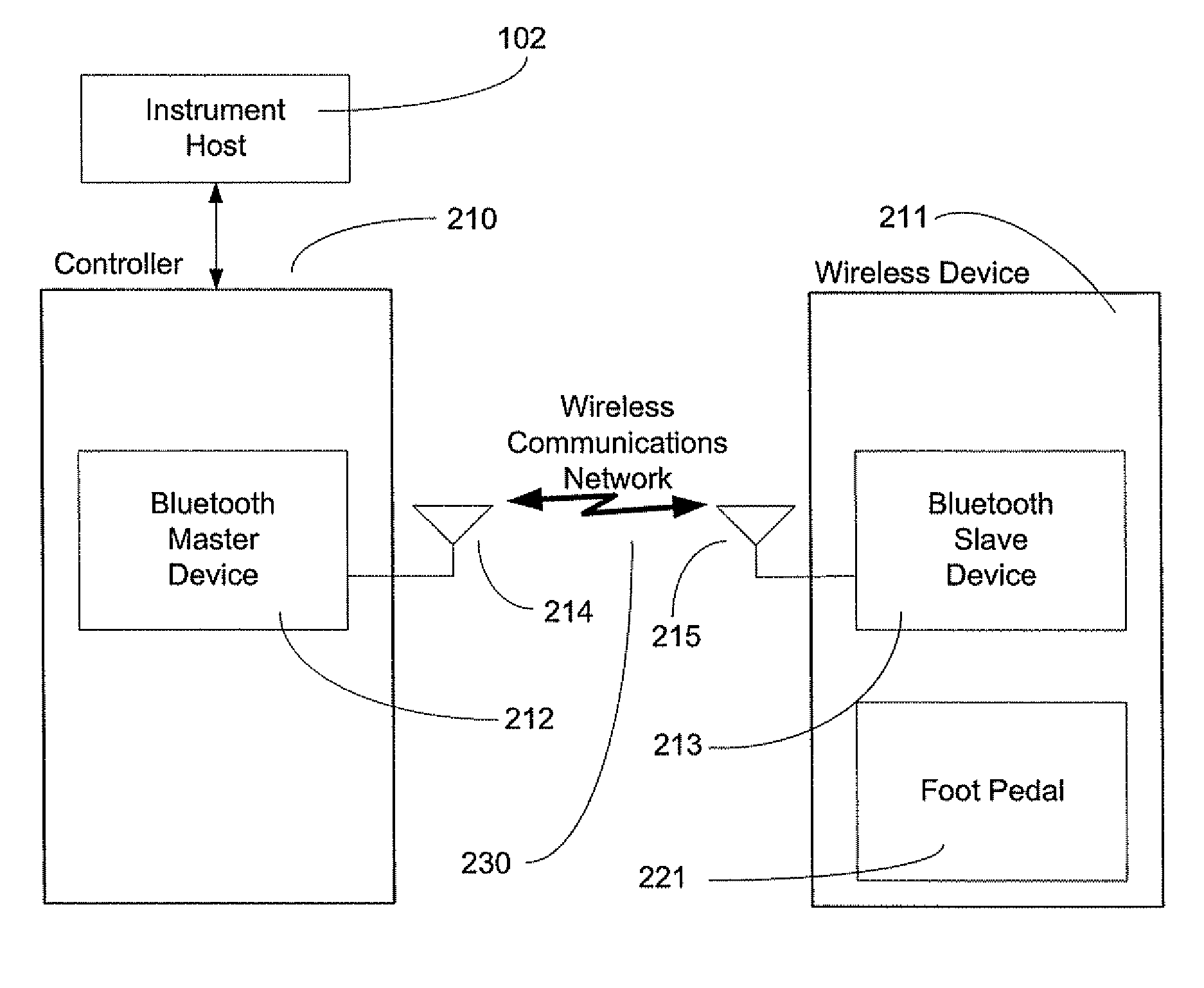
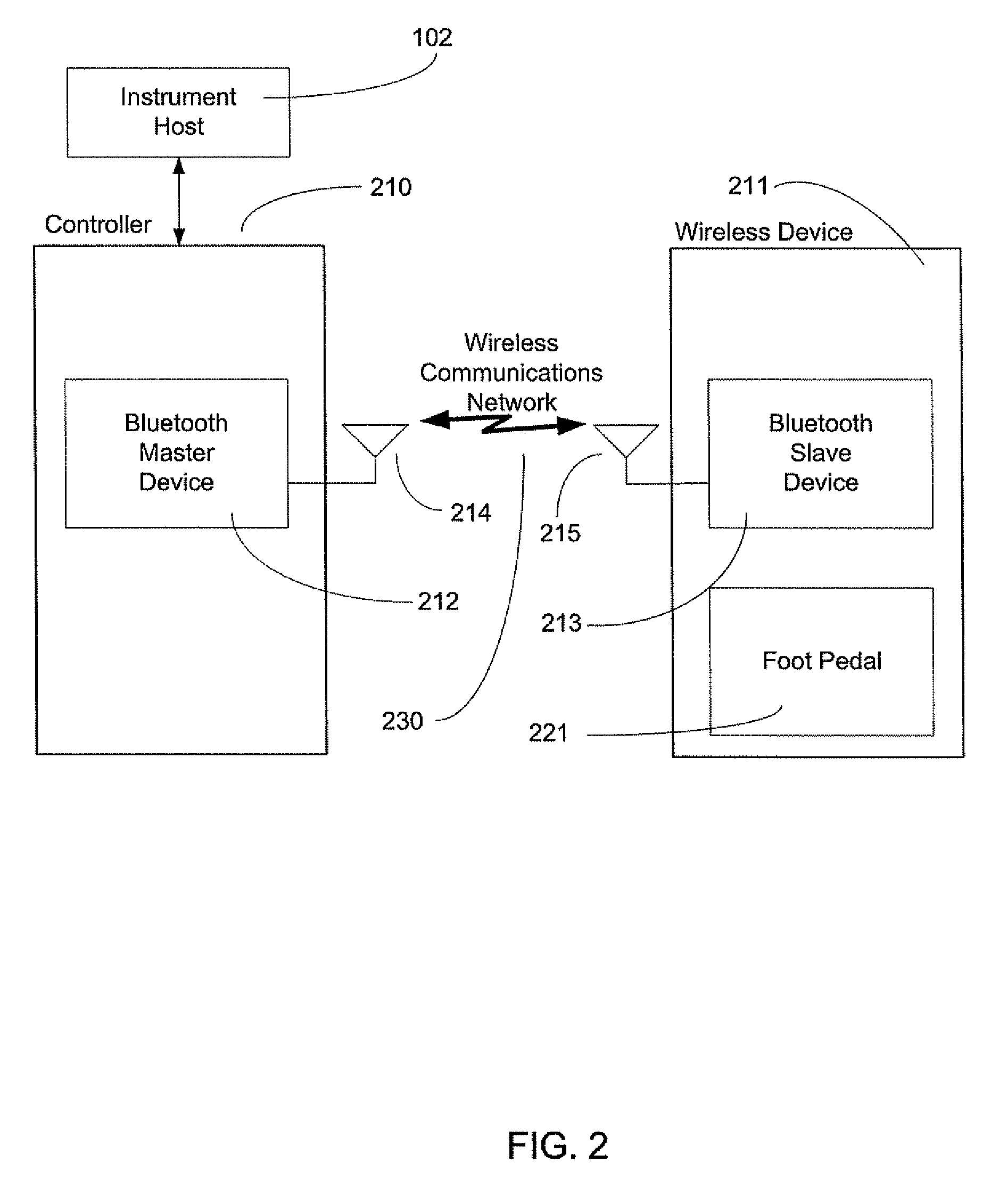
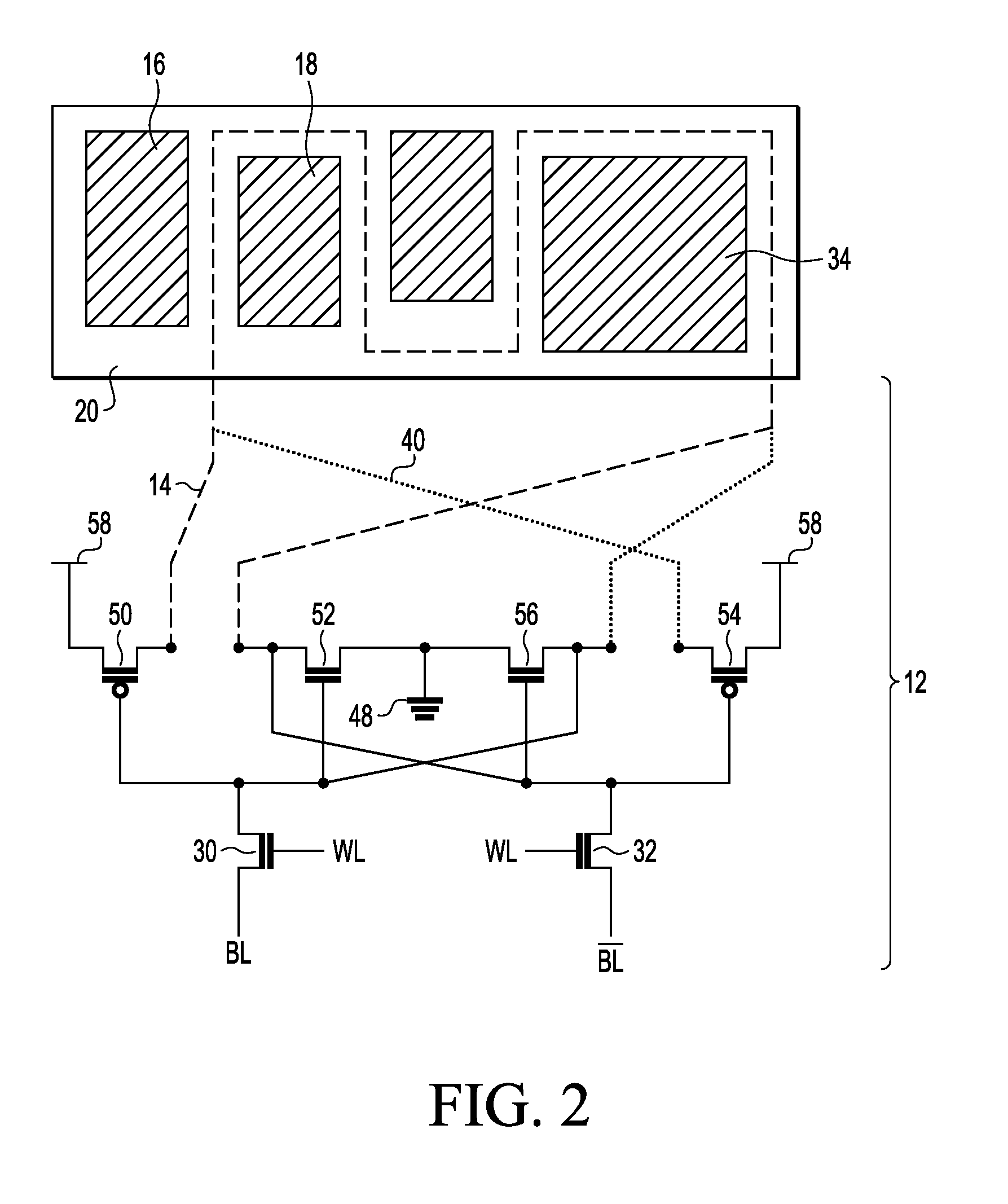
Exclusive pairing technique for Bluetooth compliant medical devices
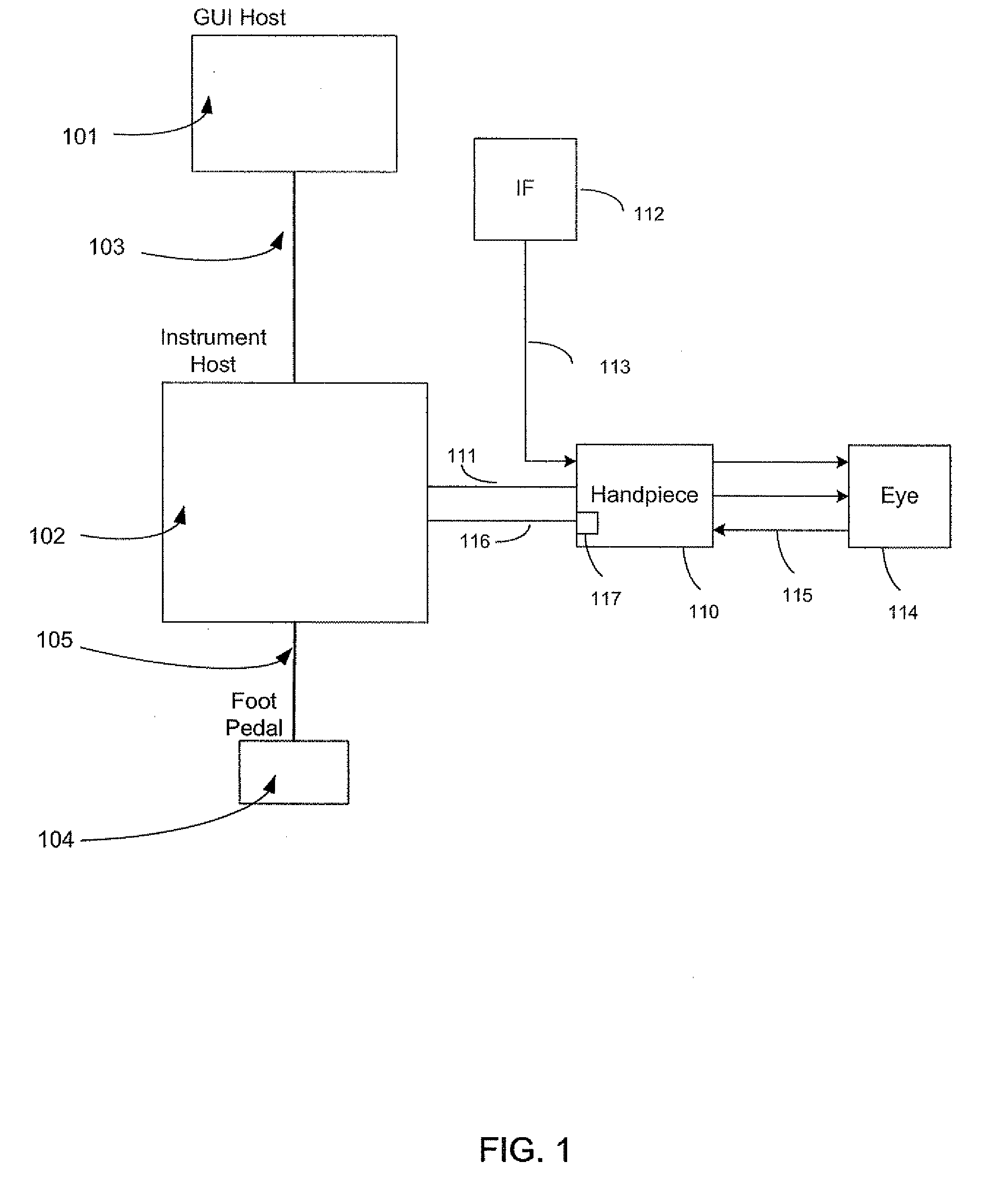
A method and system of establishing communications between at least two independent software modules in a safety critical system, such as a medical system, is provided. The design comprises providing an exclusive Bluetooth connection between at least two wireless devices. A master wireless device is configured with Bluetooth master device functionality and a slave wireless device is configured with Bluetooth slave device functionality. The wireless devices are employed in performing a medical procedure. The method further comprises acquiring a stored unique address from the slave wireless device over the Bluetooth connection, comparing the stored unique address to a master wireless device unique address available at the master wireless device, and exclusively pairing the master wireless device and the slave wireless device when the unique address acquired from the slave wireless device is found to identically match the master wireless device unique address.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
Exclusive pairing technique for bluetooth compliant devices
A method and system of establishing communications between at least two independent software modules in a safety critical system, such as a medical system, is provided. The design comprises providing an exclusive Bluetooth connection between at least two wireless devices. A master wireless device is configured with Bluetooth master device functionality and a slave wireless device is configured with Bluetooth slave device functionality. The wireless devices are employed in performing procedures in a safety critical environment. The method further comprises acquiring a stored unique address from the slave wireless device over the Bluetooth connection, comparing the stored unique address to a master wireless device unique address available at the master wireless device, and exclusively pairing the master wireless device and the slave wireless device when the unique address acquired from the slave wireless device is found to identically match the master wireless device unique address.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
Exclusive pairing technique for bluetooth compliant medical devices
A method and system of establishing communications between at least two independent software modules in a safety critical system, such as a medical system, is provided. The design comprises providing an exclusive Bluetooth connection between at least two wireless devices. A master wireless device is configured with Bluetooth master device functionality and a slave wireless device is configured with Bluetooth slave device functionality. The wireless devices are employed in performing a medical procedure. The method further comprises acquiring a stored unique address from the slave wireless device over the Bluetooth connection, comparing the stored unique address to a master wireless device unique address available at the master wireless device, and exclusively pairing the master wireless device and the slave wireless device when the unique address acquired from the slave wireless device is found to identically match the master wireless device unique address.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
Method and platform to implement safety critical systems
A method of monitoring and controlling plant operations, which receive input signals from sensors monitoring parameters of plant operation to generate output signals to actuators, comprising; reducing the input signals to a selected group of input functions; reducing the output signals to a selected group of output functions; processing the input signals using FPGA to generate the output signals. The invention also relates to the platform and system embodying the method.
Owner:BAKHMACH LEVGENII
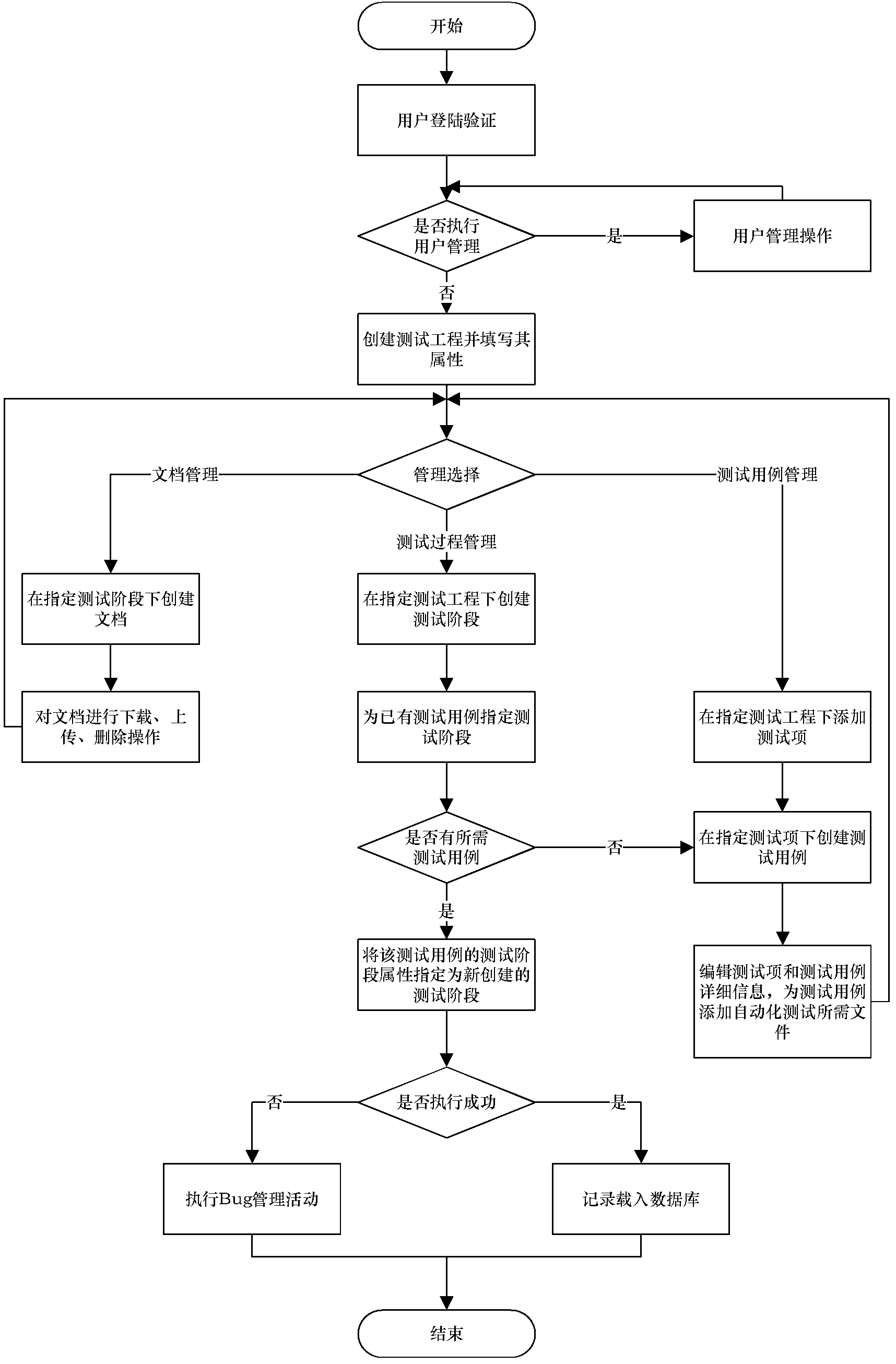
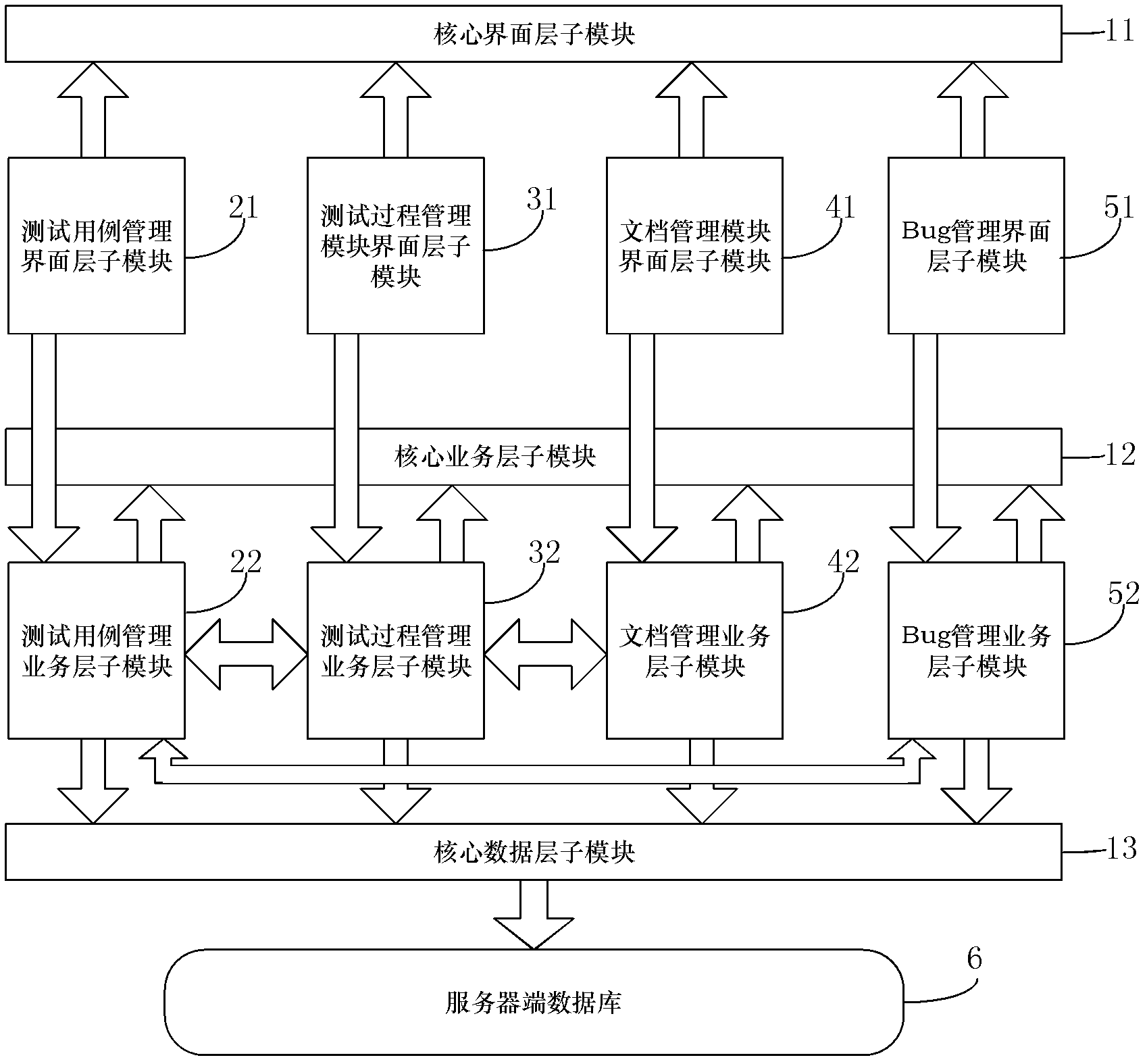
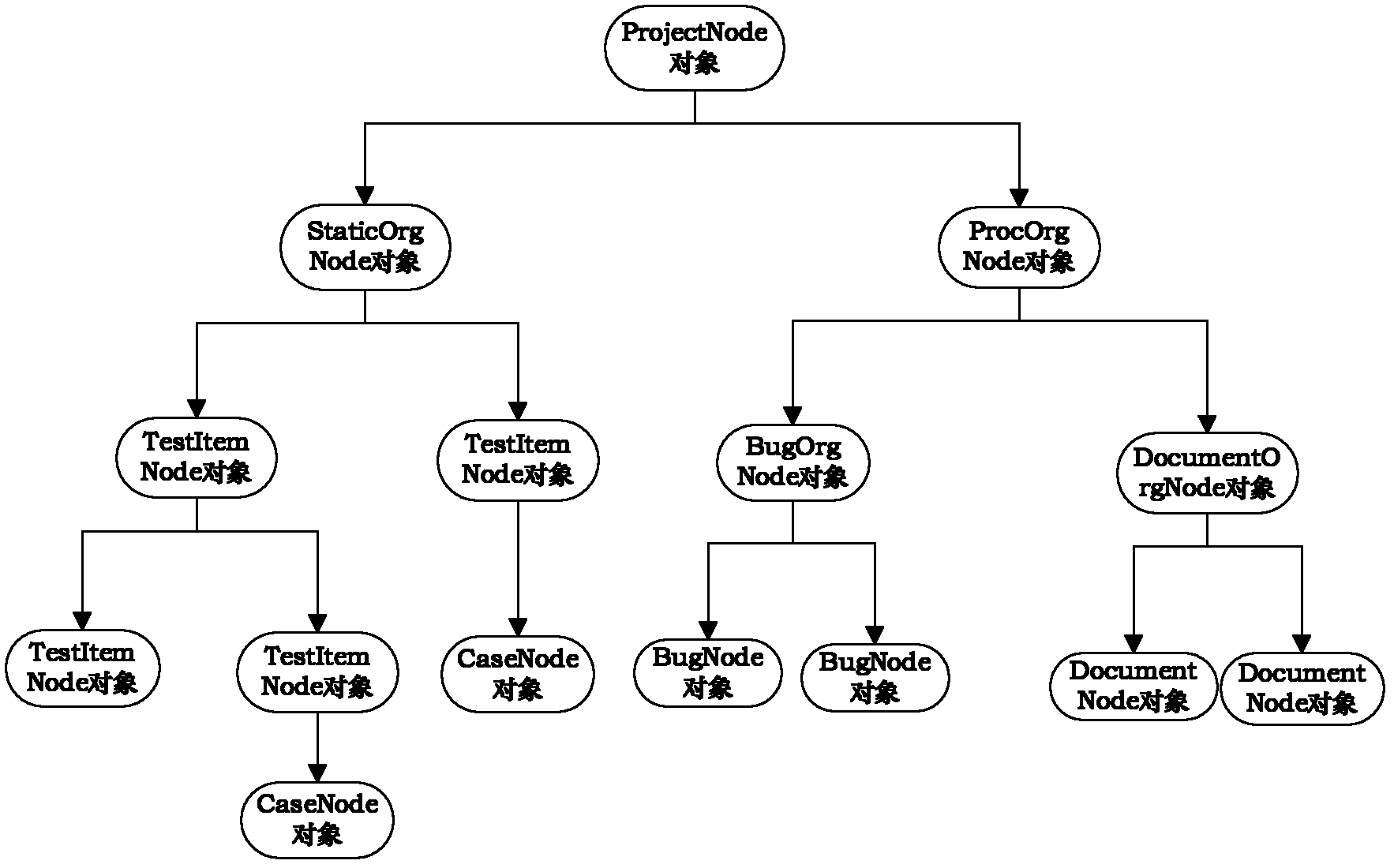
Safety critical system-oriented automatic testing resource management method and platform
InactiveCN102331970ASupport black box testingEasy to operateSoftware testing/debuggingEntity typeResource management
The invention relates to a safety critical system-oriented automatic testing resource management method and a safety critical system-oriented automatic testing resource management platform, which are applied to a huge safety critical system with a high requirement on safe reliability. In the method, a testing project is established after a user passes authentication, three management types, namely testing case management, testing process management and document management are set, and a user selects a corresponding management type to perform resource testing management. The platform has a qualification test (Qt) library-based client / server (C / S) framework on the basis of a management platform; a server is taken as a database; a client comprises a core module, a testing case management module, a testing process management module, a document management module and a Bug management module; and the tree structure and the entity type node data of testing resources and operation on the data are defined by the modules of the client. Uniform management on the automatic testing resources of the safety critical system is realized, and the resource management covers a testing stage from the time, so that the black box testing of the safety critical system is effectively supported.
Owner:BEIHANG UNIV
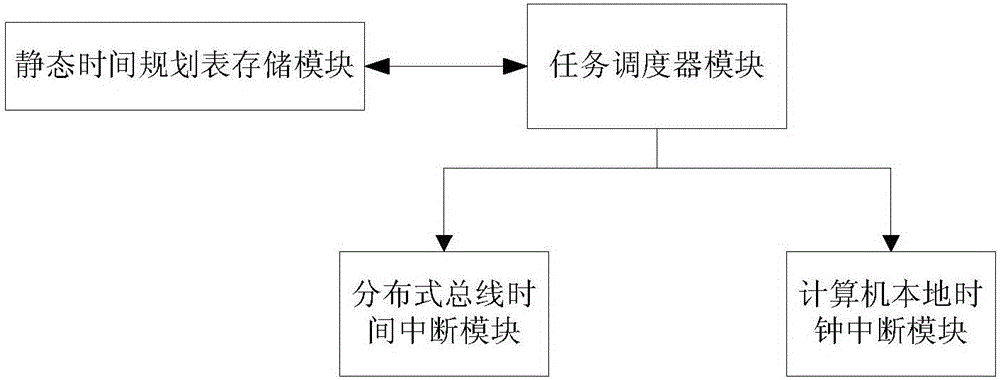
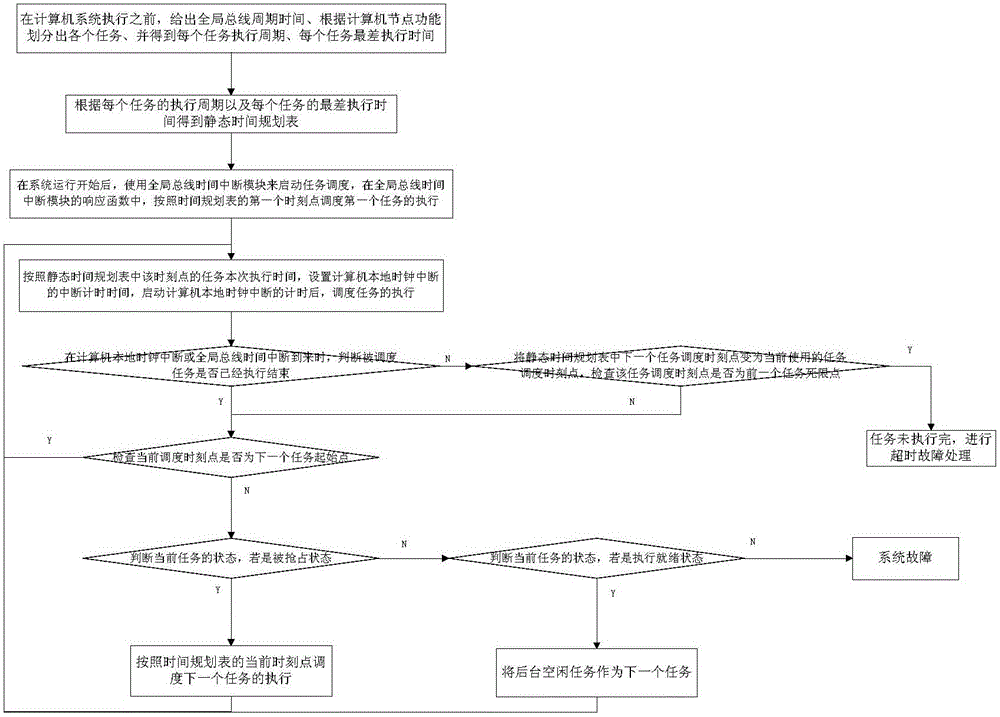
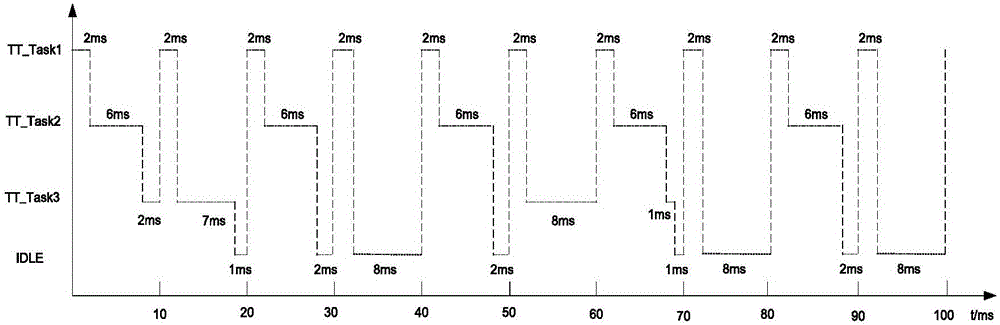
Time-triggered embedded task scheduling device and method
ActiveCN106293919AImprove safety and reliabilityProgram initiation/switchingTime scheduleCritical system
The invention discloses a time-triggered embedded task scheduling device and a time-triggered embedded task scheduling method. The device comprises a static time schedule storage module, a distributed bus time interruption module, a computer local clock interruption module and a task scheduler module. The device and the method disclosed by the invention have the advantages that the task scheduler module is used for switching attributes of a time point according to all tasks predefined in a static time schedule, realizing synchronous execution of distributed nodes by utilization of the distributed bus time interruption module, and monitoring whether task execution time is beyond the worst execution time or not by utilization of the computer local clock interruption module, so that the certainty of the operation of a safety-critical system is guaranteed by utilization of less system overhead.
Owner:XIAN FLIGHT SELF CONTROL INST OF AVIC
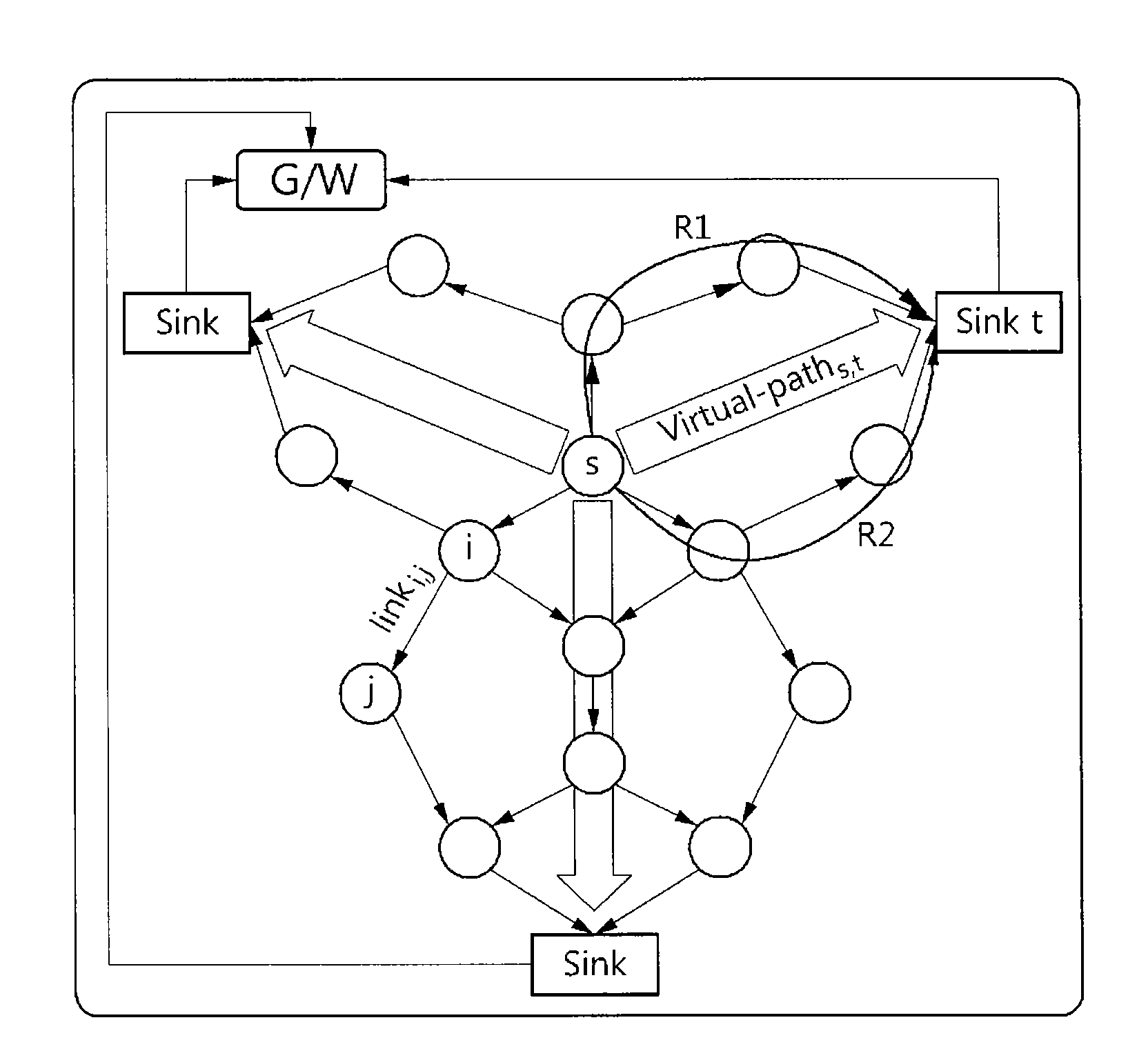
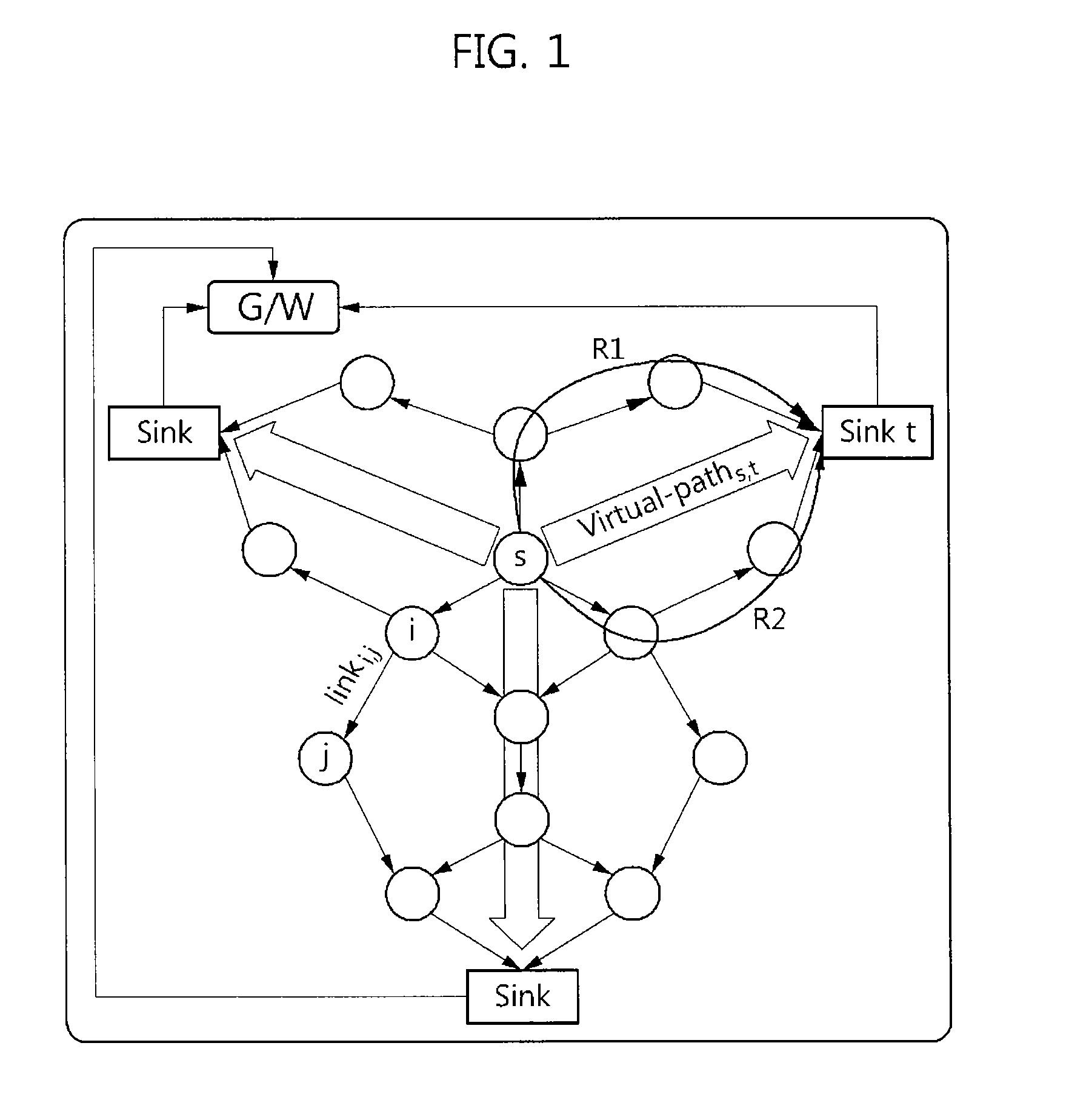
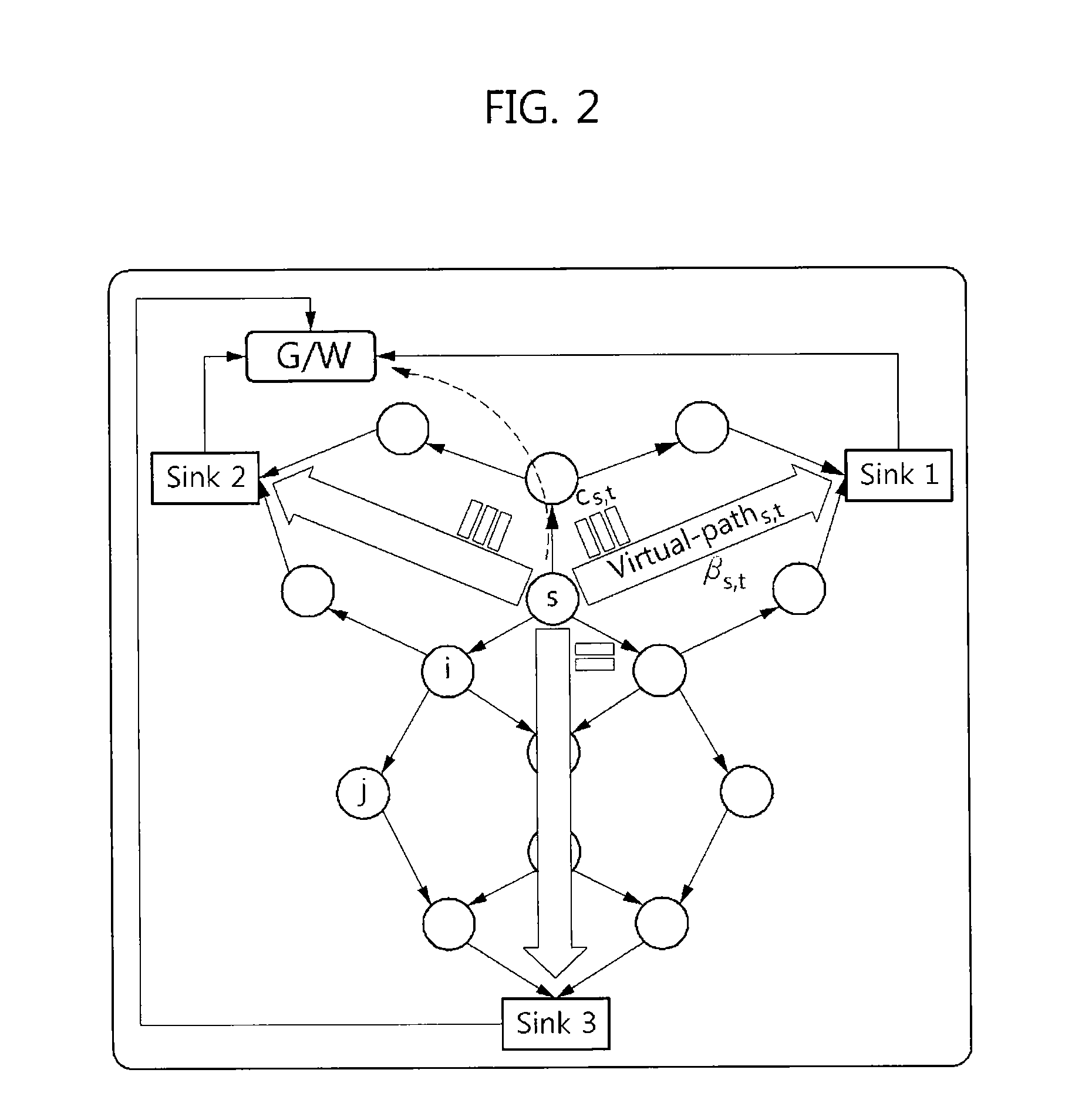
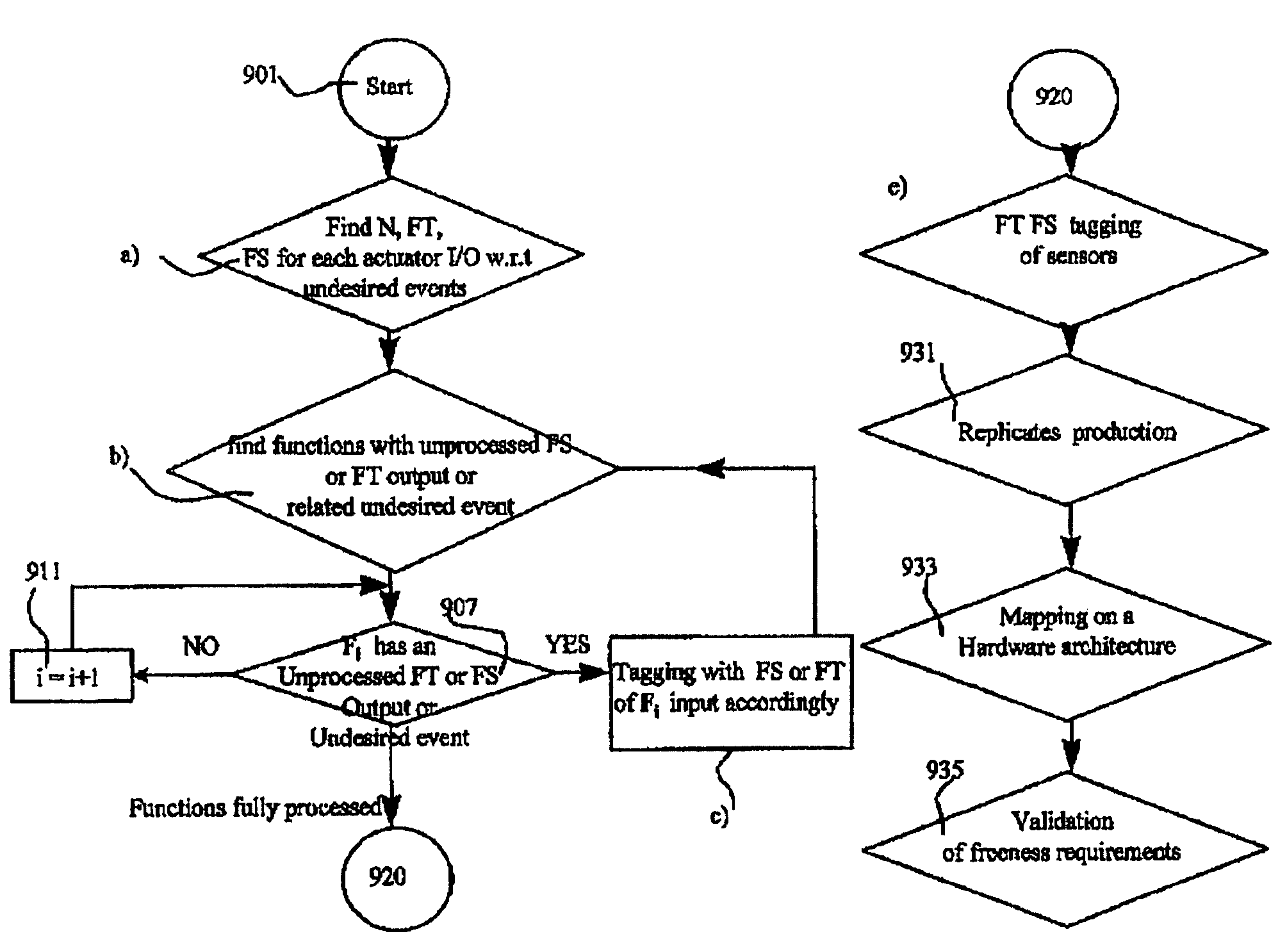
Design of safety critical systems
InactiveUS20070168096A1Produced in advanceSafety arrangmentsDigital data processing detailsHardware structureFault tolerance
A method is disclosed of producing a system architecture comprising a plurality of electrical devices connected to each other, said system preferably comprising a fault tolerant system, the method including: a) identifying a set of undesirable events and ascribing to each of said undesirable events an indicator of their severity; b) associating where possible each said undesirable event with one or more actuators of said system architecture; c) developing a functional specification of an initial architecture proposed for implementation of said system architecture; d) refining on said functional specification the fault tolerance requirements; e) producing replicates in said functional specification together with attached indicators of independence of said replicates, f) defining a hardware structure for said system architecture; g) mapping of said functional specification onto said hardware structure; and h) verifying automatically that said indicators of independence are preserved during mapping.
Owner:RENAULT SA
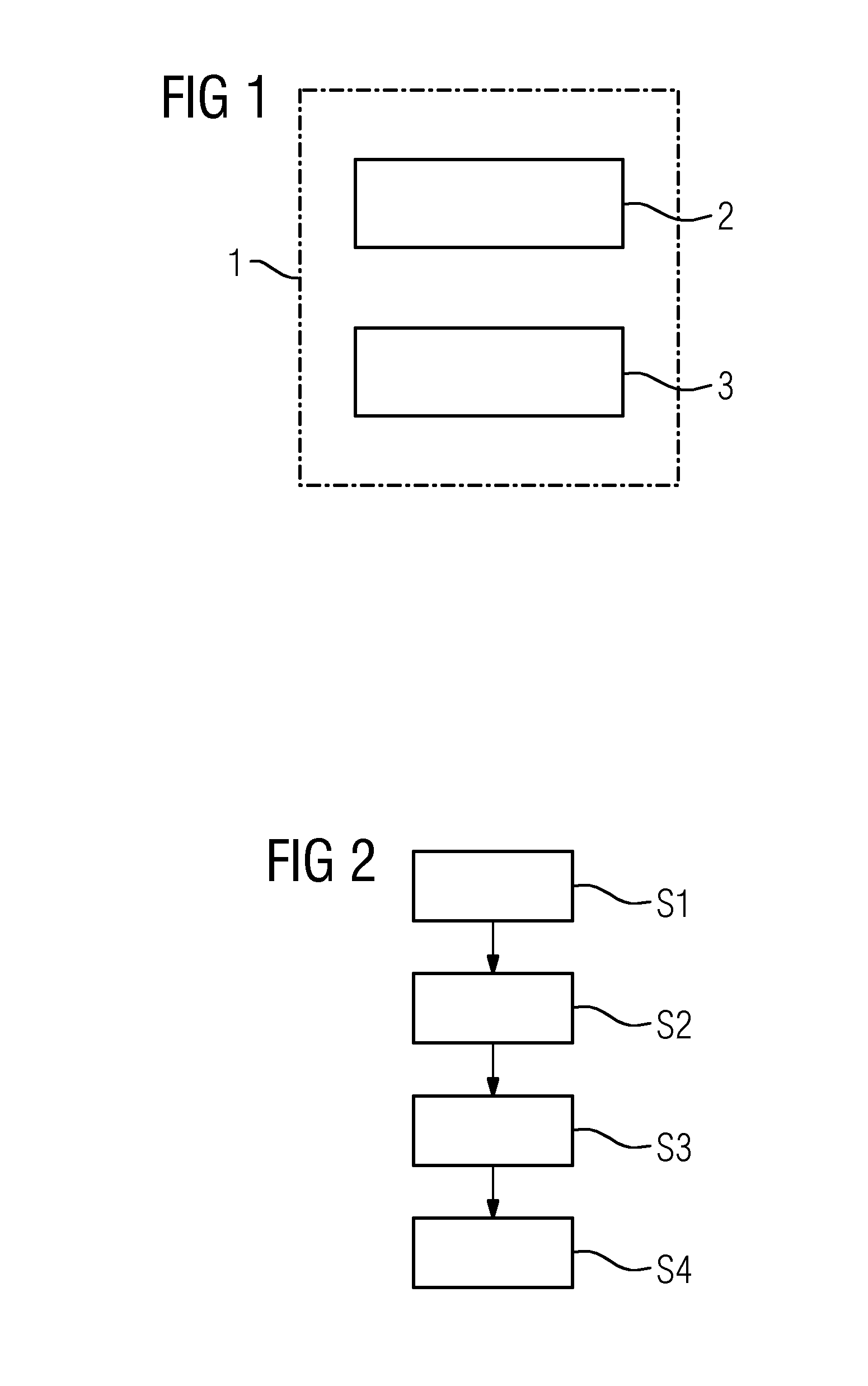
Automated Qualification of a Safety Critical System
A method for automated qualification of a safety critical system including a plurality of components is provided. A functional safety behavior of each component is represented by an associated component fault tree element. The method includes automatically performing a failure port mapping of output failure modes to input failure modes of component fault tree elements based on a predetermined generic fault type data model stored in a database.
Owner:SIEMENS AG
Exclusive pairing technique for short-range communication devices
A method and system of establishing communications between at least two independent software modules in a safety critical system, such as a medical system, is provided. The design comprises providing an exclusive Bluetooth connection between at least two wireless devices. A master wireless device is configured with Bluetooth master device functionality and a slave wireless device is configured with Bluetooth slave device functionality. The wireless devices are employed in performing procedures in a safety critical environment. The method further comprises acquiring a stored unique address from the slave wireless device over the Bluetooth connection, comparing the stored unique address to a master wireless device unique address available at the master wireless device, and exclusively pairing the master wireless device and the slave wireless device when the unique address acquired from the slave wireless device is found to identically match the master wireless device unique address.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
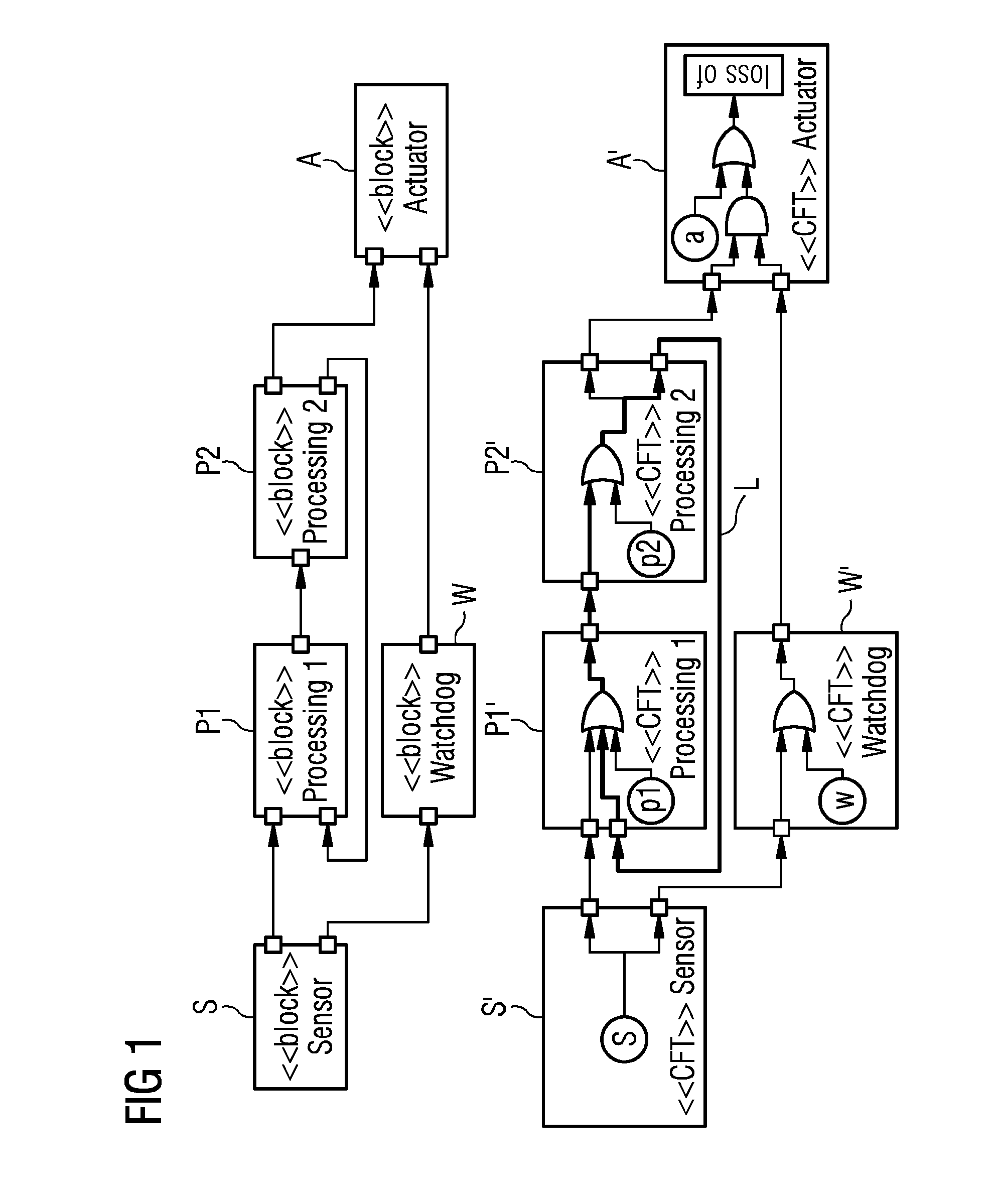
Integrated Model-Based Safety Analysis
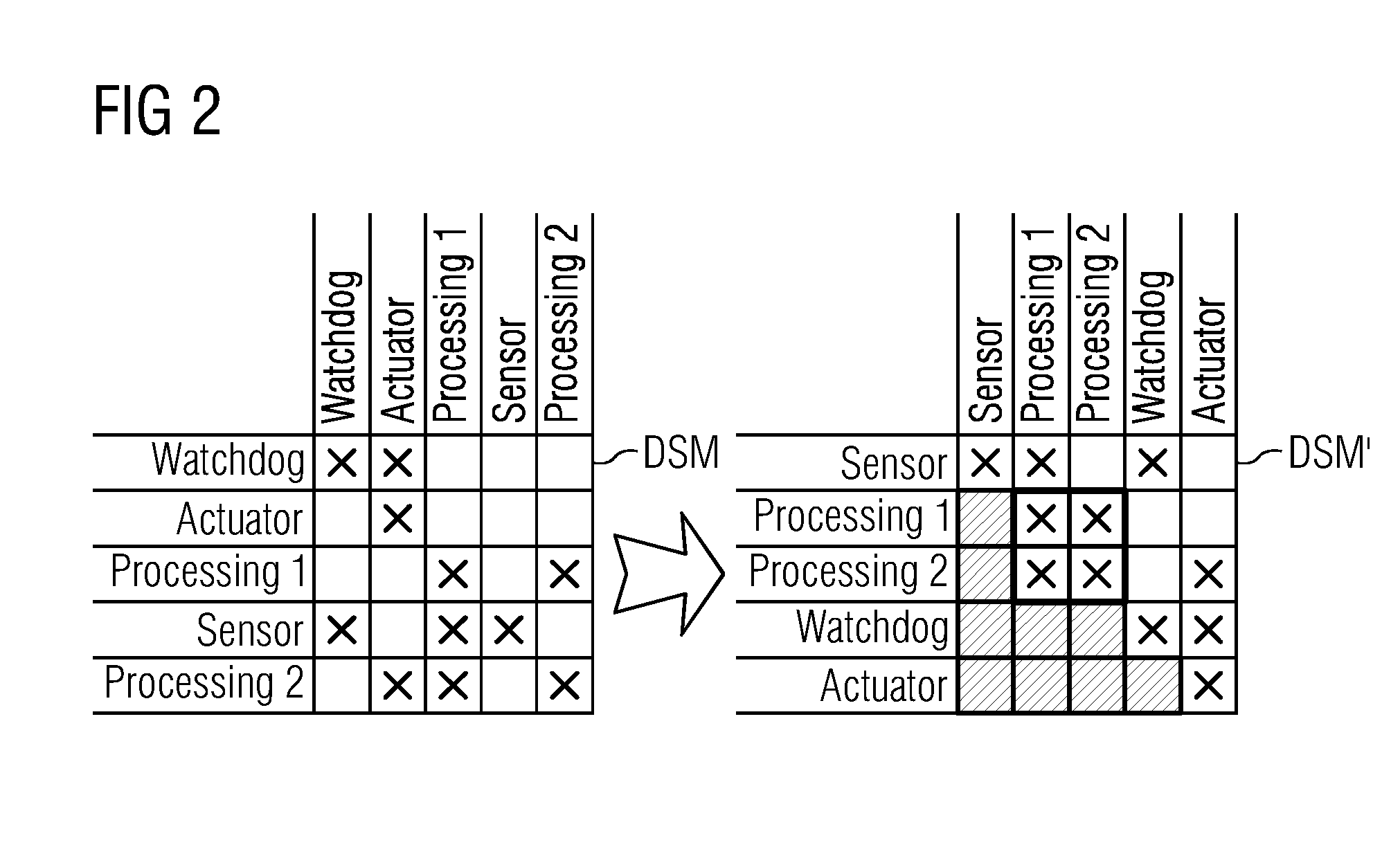
InactiveUS20150088476A1Speed up the processAvoid loopsError detection/correctionDesign optimisation/simulationSequence designSecurity analysis
A method for integrated model-based safety analysis includes integrating a safety analysis model into a system development model of a safety-critical system. The system development model includes model components. The safety analysis model models a failure logic separately for each of the model components. The method includes representing dependencies among the model components with a design structure matrix. The design structure matrix represents each of the model components with a row and a column and shows dependencies between model components with corresponding entries. The method also includes sequencing the design structure matrix, and identifying at least one dependency loop and loop components in the sequenced design structure matrix. The loop components are part of the at least one dependency loop.
Owner:SIEMENS AG
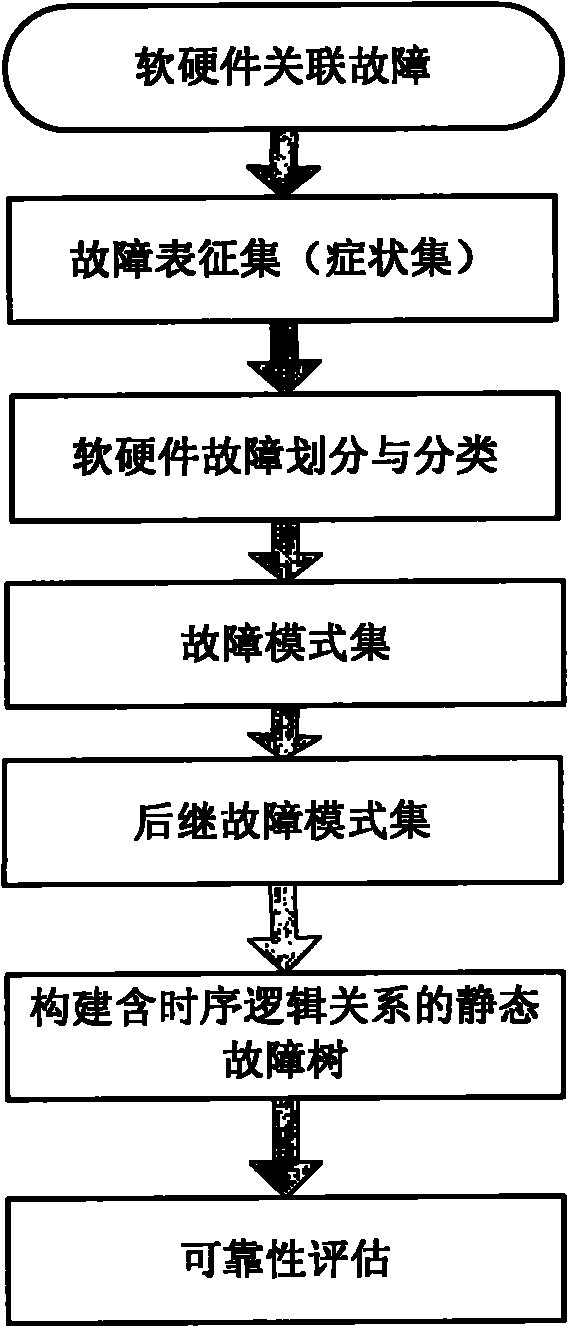
Reliability analysis method for embedded safety-critical system
InactiveCN102033789AAssessment reliabilityError detection/correctionEmbedded securityFuzzy probability
The invention relates to a reliability analysis method for an embedded safety-critical system, and belongs to the technical field of information safety. The method comprises the following steps of: constructing a software and hardware fault representation set; classifying faults in the fault representation set to acquire a software and hardware fault mode set and constructing a subsequent fault mode set by combining a fault-associated probability table; constructing a static fault tree associated with a software and hardware fault on the basis of the subsequent fault mode set; and analyzing the static fault tree to acquire a fault analysis result. In the method, software and hardware basic units of the embedded safety-critical system are subdivided, a subsequent fault mode is constructed through a fuzzy probability multi-signal flow graph model by combining association of faults of each basic unit, a static fault tree model is constructed by using time sequence logic relation between the faults reflected by the subsequent fault mode set, and the reliability of the system can be more accurately and effectively evaluated by using the model.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
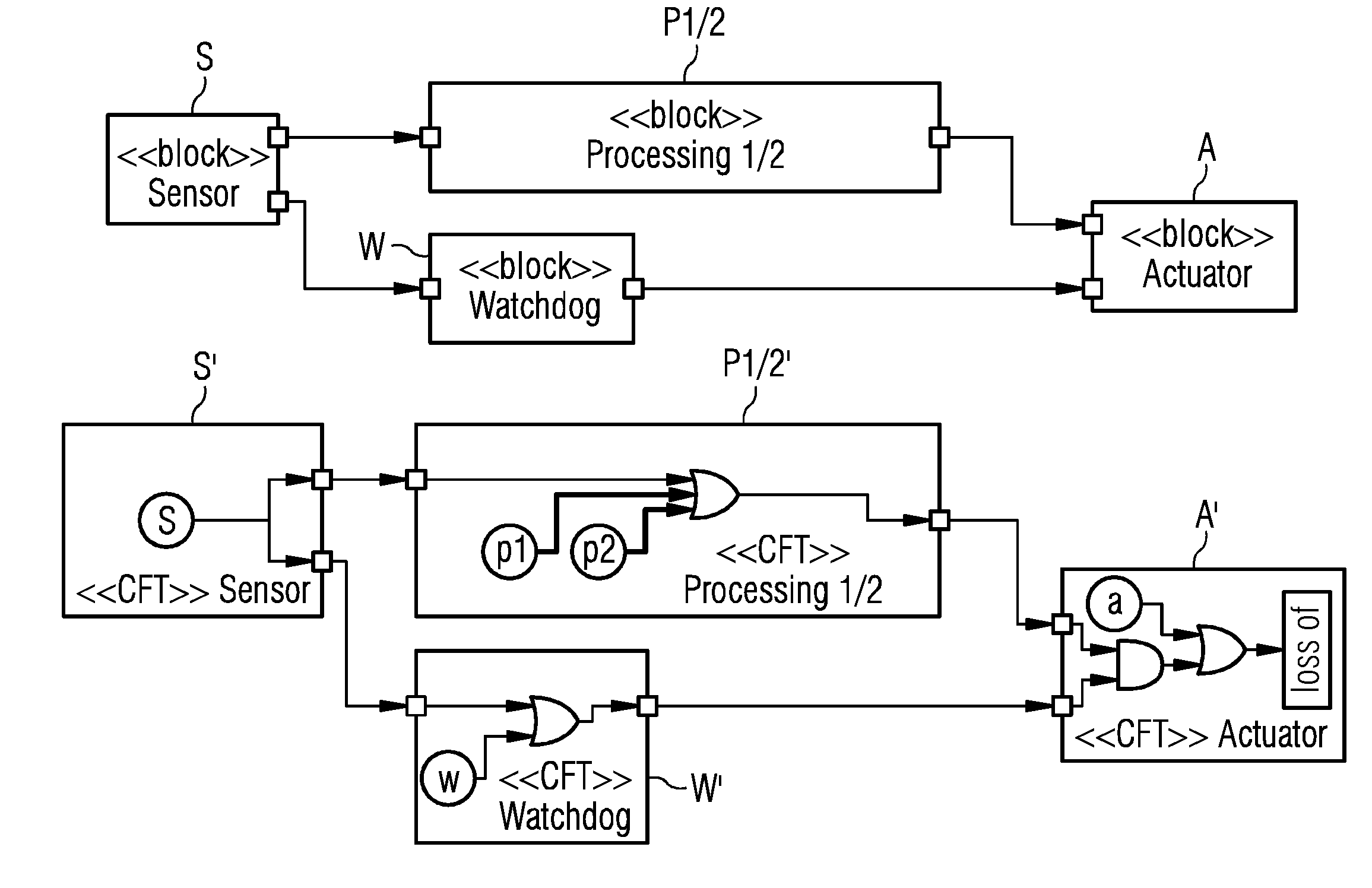
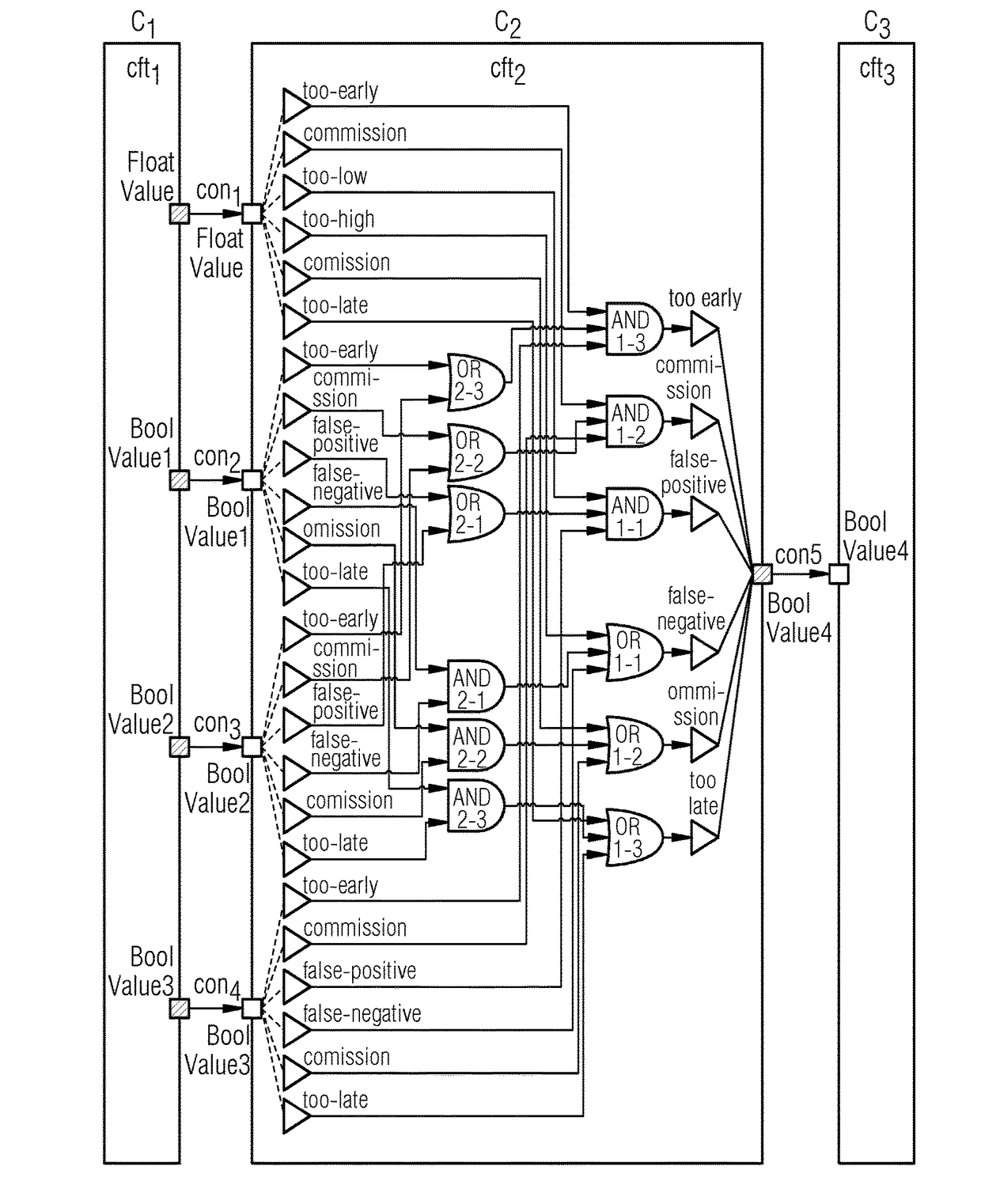
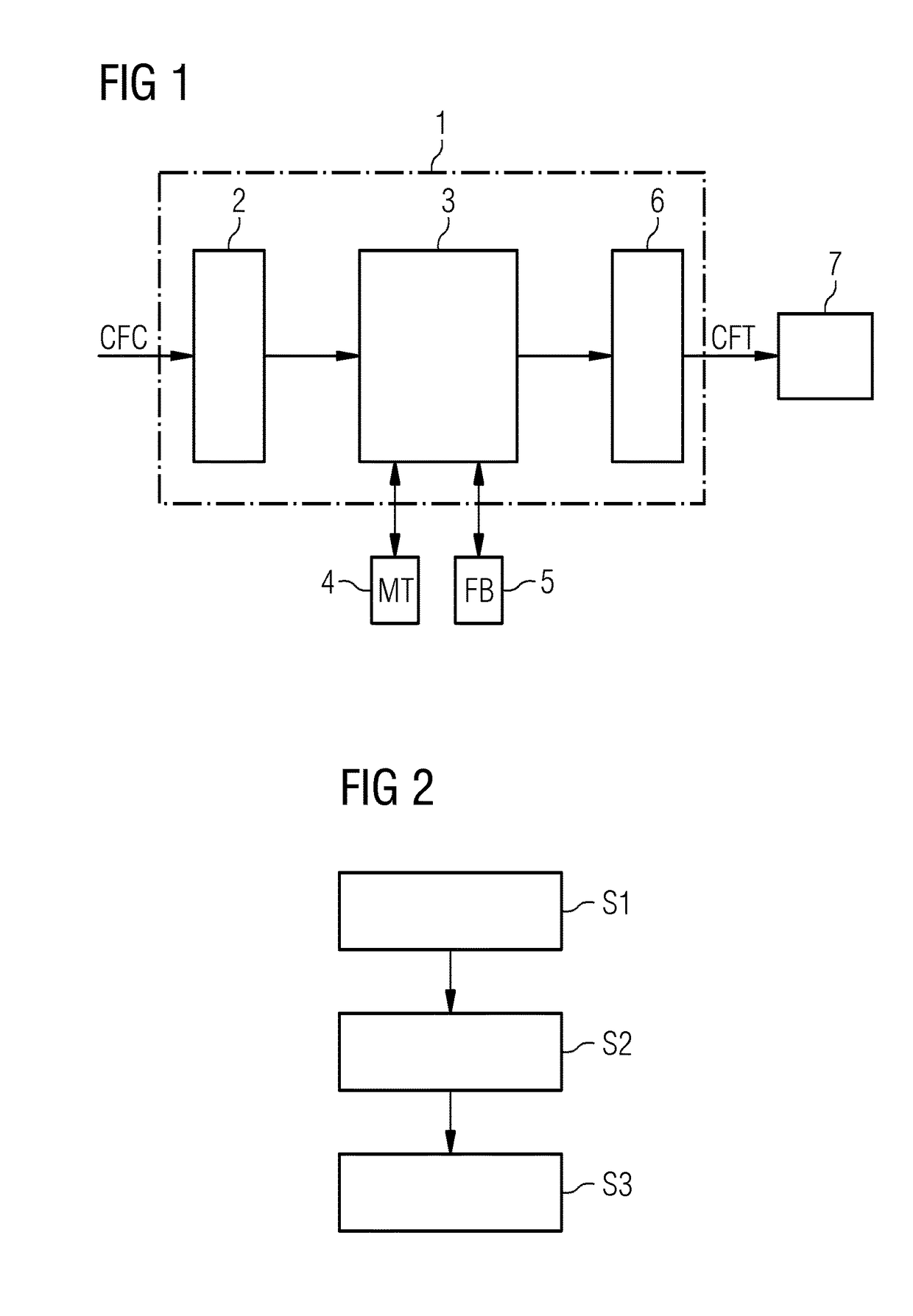
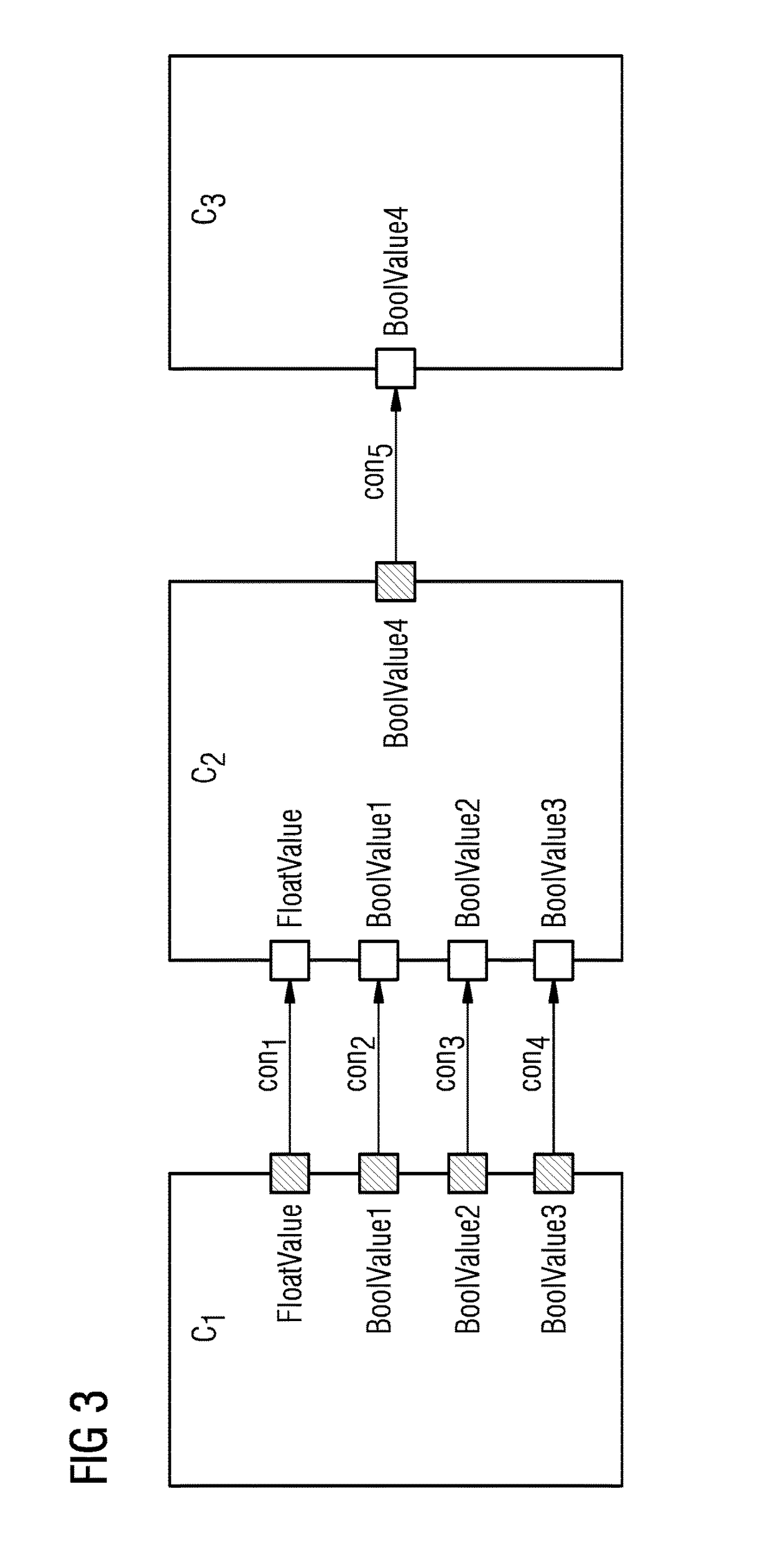
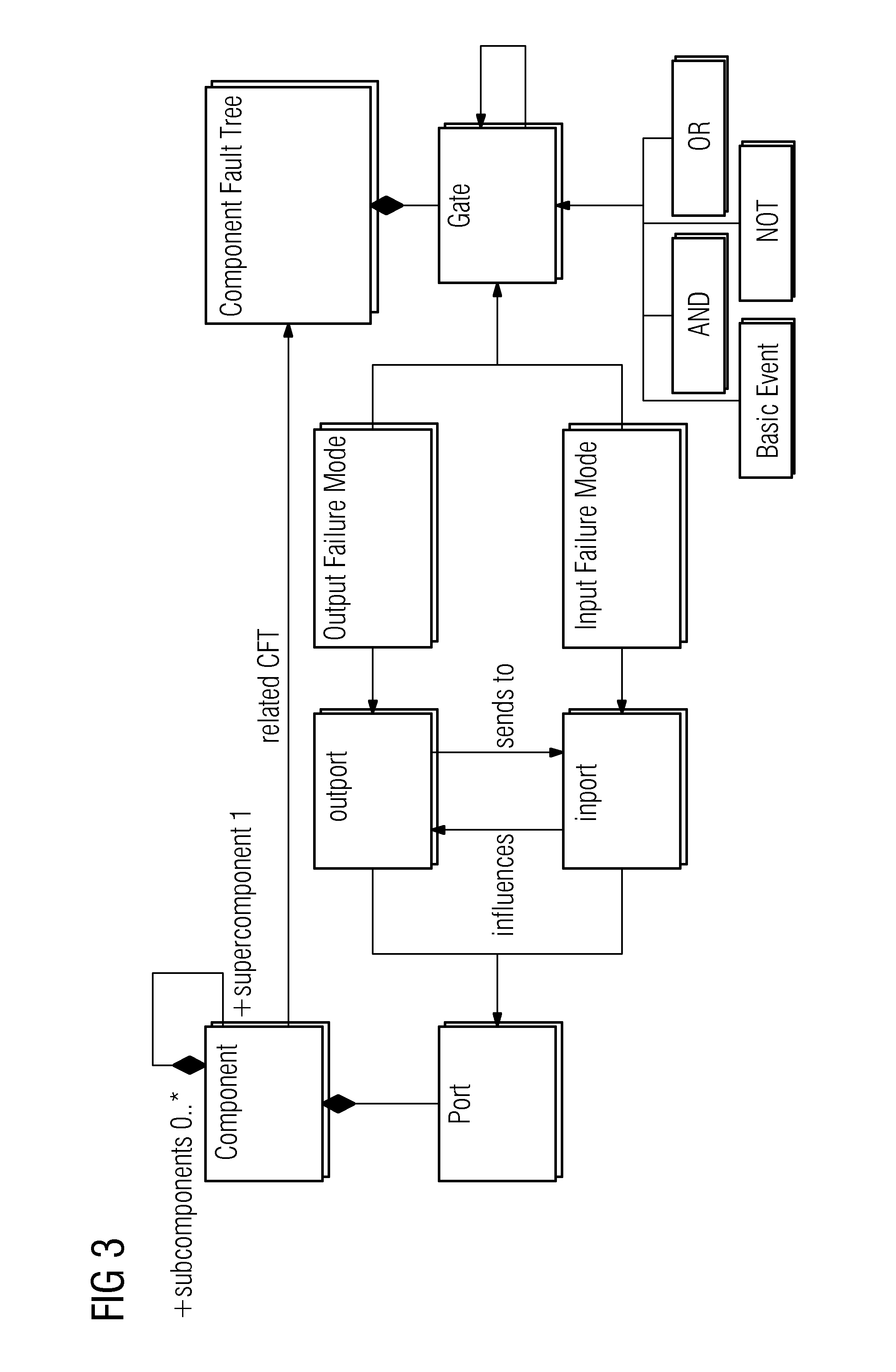
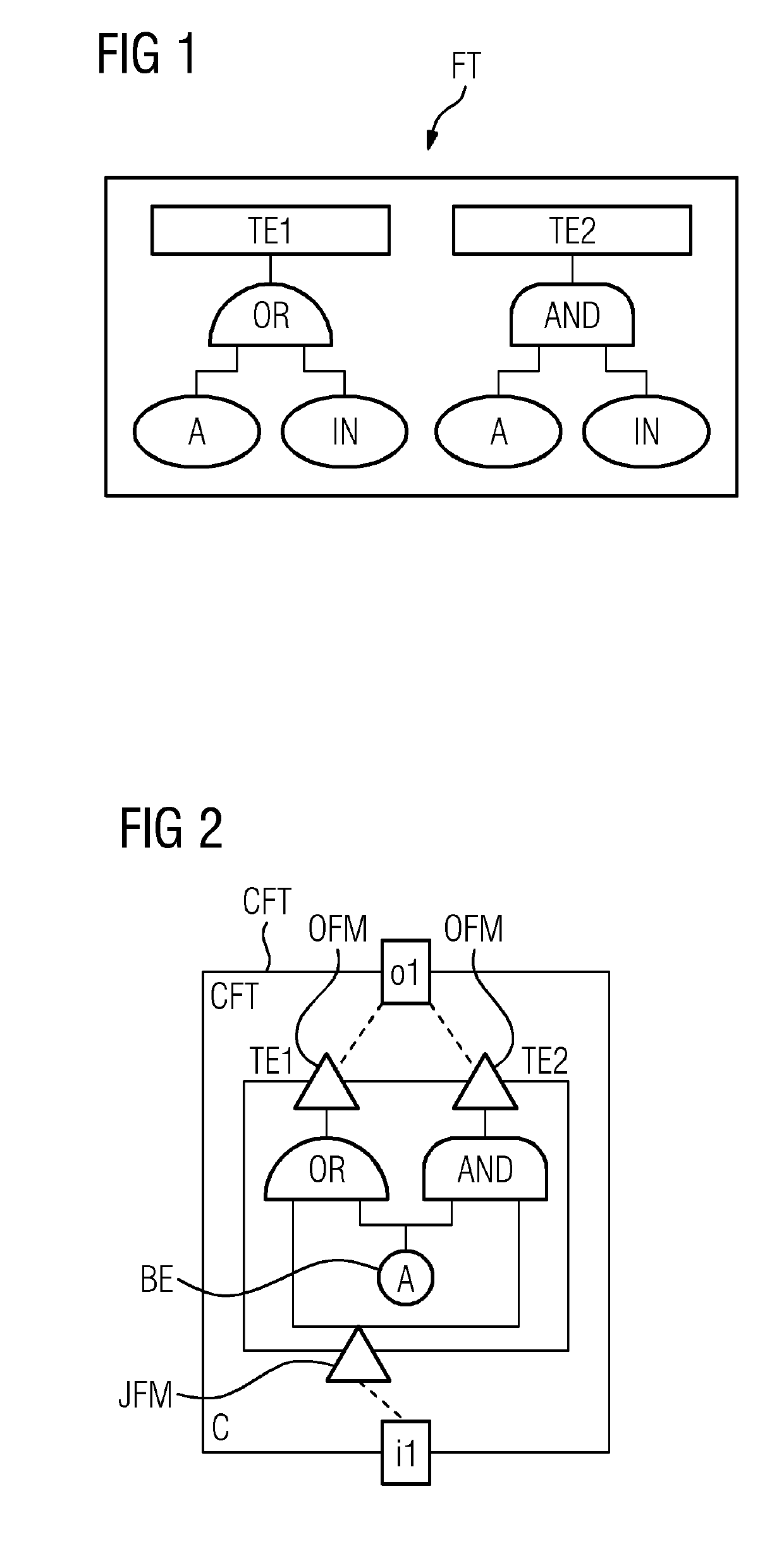
Method and apparatus for automatically generating a component fault tree of a safety-critical system
ActiveUS20170185470A1Fault responseReliability/availability analysisComputer scienceFault propagation
An apparatus includes an input that receives a continuous function chart for each component of the investigated safety-critical system. A processor generates a corresponding component fault tree element. Inports and outports of the component fault tree element are generated and interconnected based on unique names of the inputs and outputs of the corresponding continuous function chart of the respective system component. Input failure modes and output failure modes are generated based on generic mapping between connector types of the continuous function chart and failure types of failure modes of the component fault tree element. The input failure modes of a component fault tree element are connected to output failure modes of the component fault tree element via internal failure propagation paths based on interconnected function blocks of the continuous function chart of the respective system component. An output outputs the generated component fault tree of the safety-critical system.
Owner:SIEMENS AG
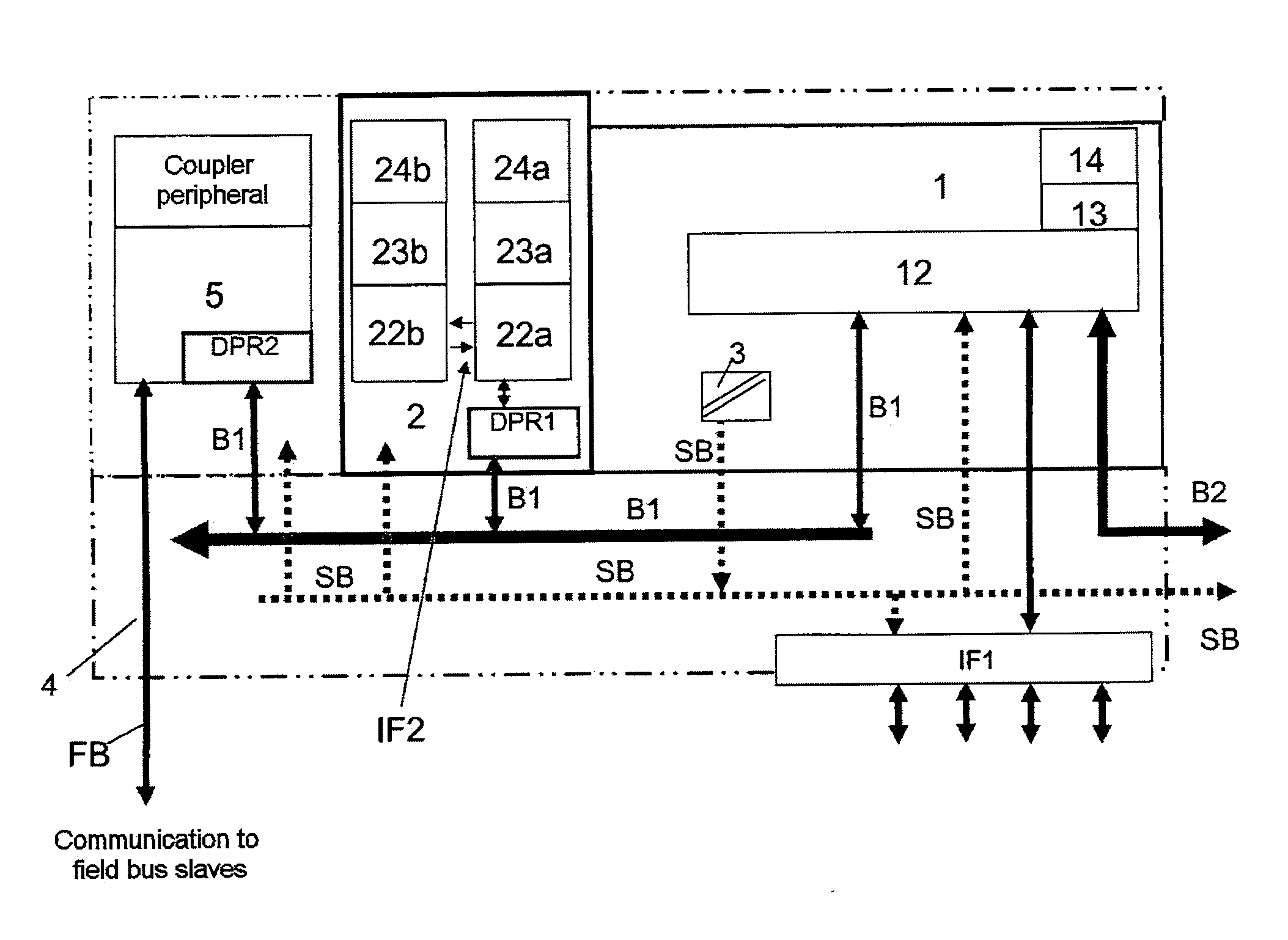
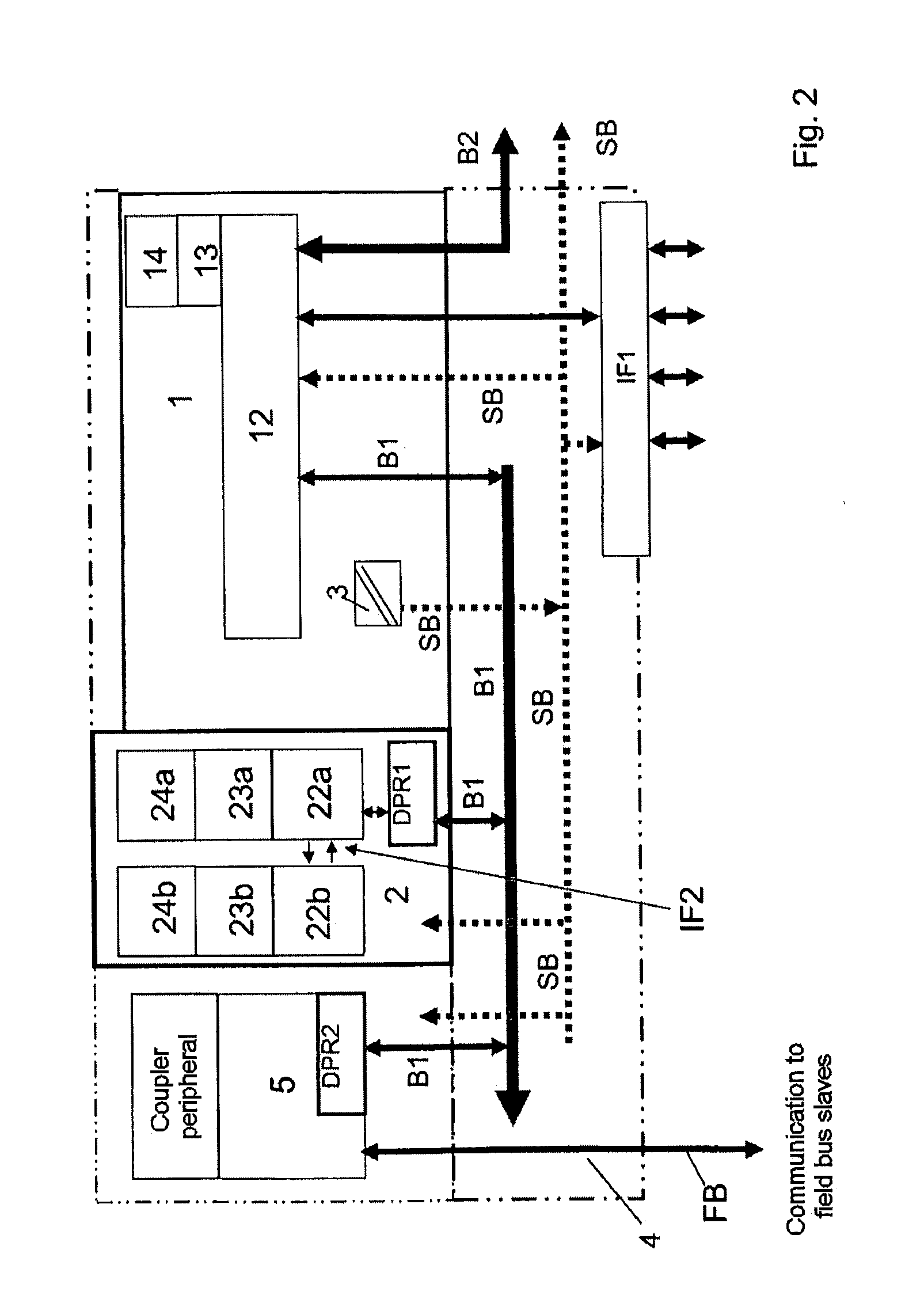
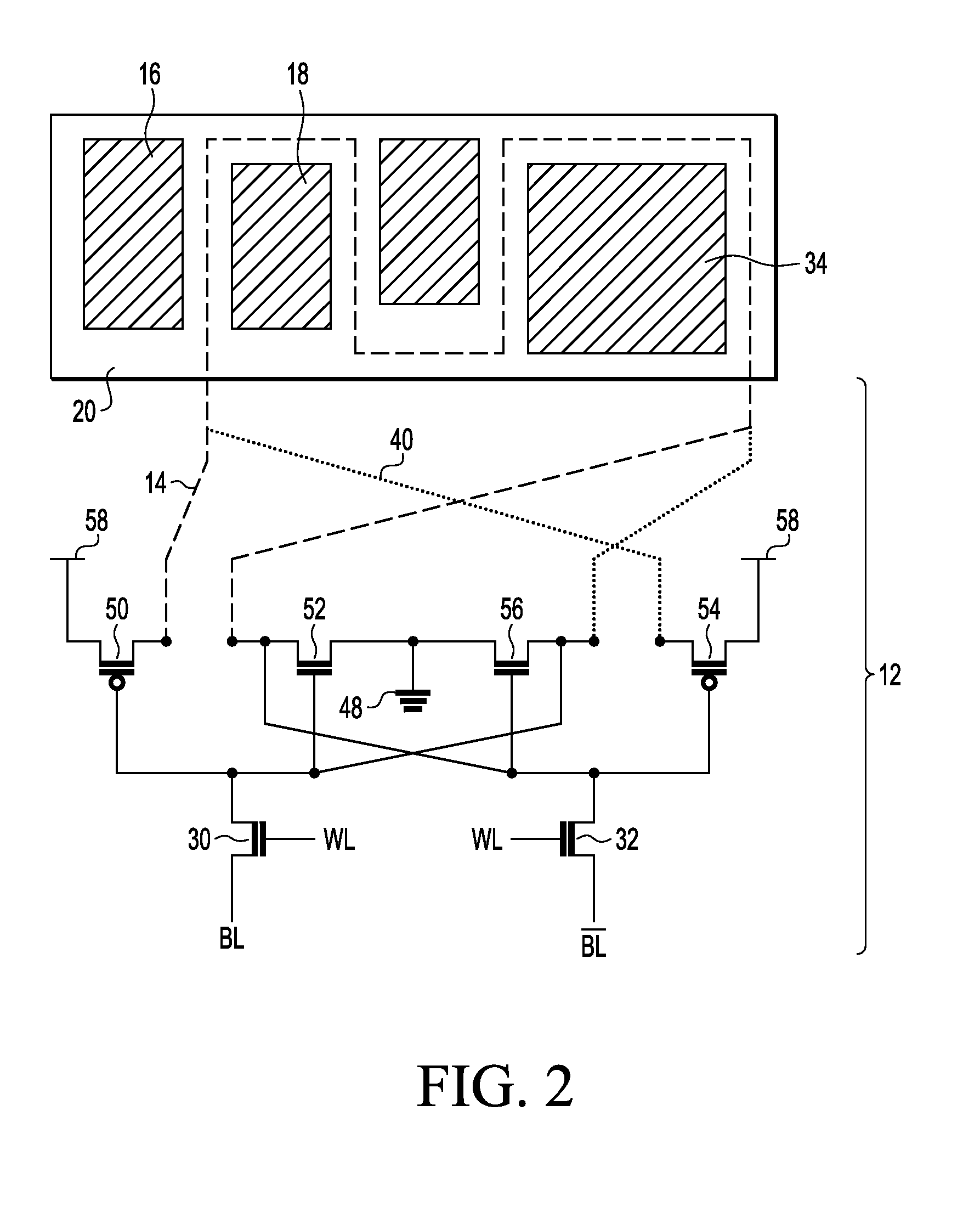
Control system for controlling safety-critical and non-safety-critical processes
ActiveUS20120296446A1Simple and cost-effectiveEnsure safetyProgramme controlComputer controlControl systemDual-ported RAM
A control system controls safety-critical and non-safety-critical processes and / or system components. The system includes a first control unit for controlling the non-safety-critical process and / or the non-safety-critical system components, at least one input / output unit connected to the first control unit, a communication coupler, which is connected to the first control unit via an internal coupler bus, and a second control unit for controlling the safety-critical process and / or the safety-critical system components. For providing safety-related functions, the second control unit includes a first dual-port RAM and at least two processors, only one of which is connected to the first dual-port RAM. The second control unit communicates with the first control unit via the first dual-port RAM and the internal coupler bus, and the first control unit transmits data from the second control unit to the communication coupler via the internal coupler bus and a second dual-port RAM integrated into the communication coupler.
Owner:ABB (SCHWEIZ) AG
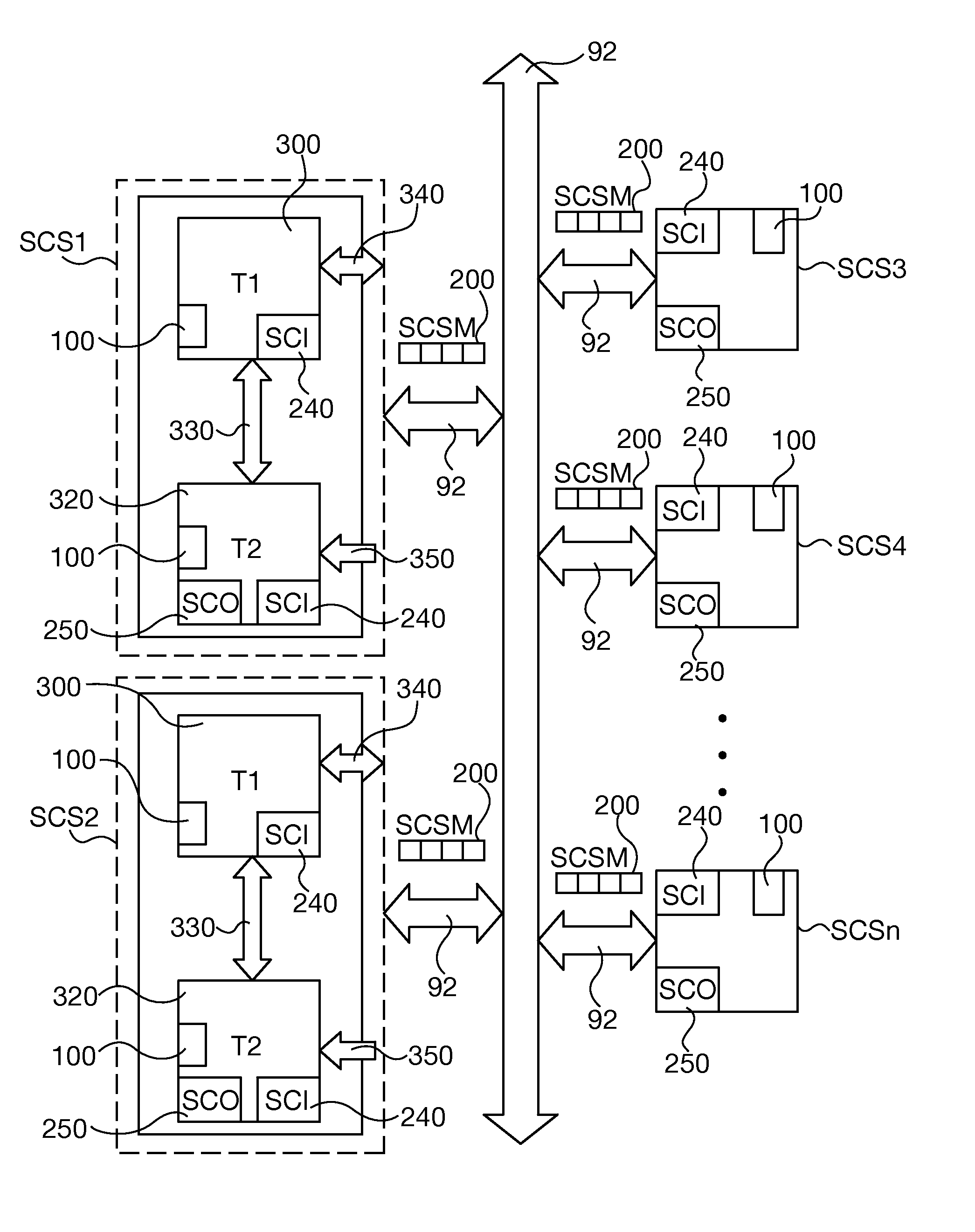
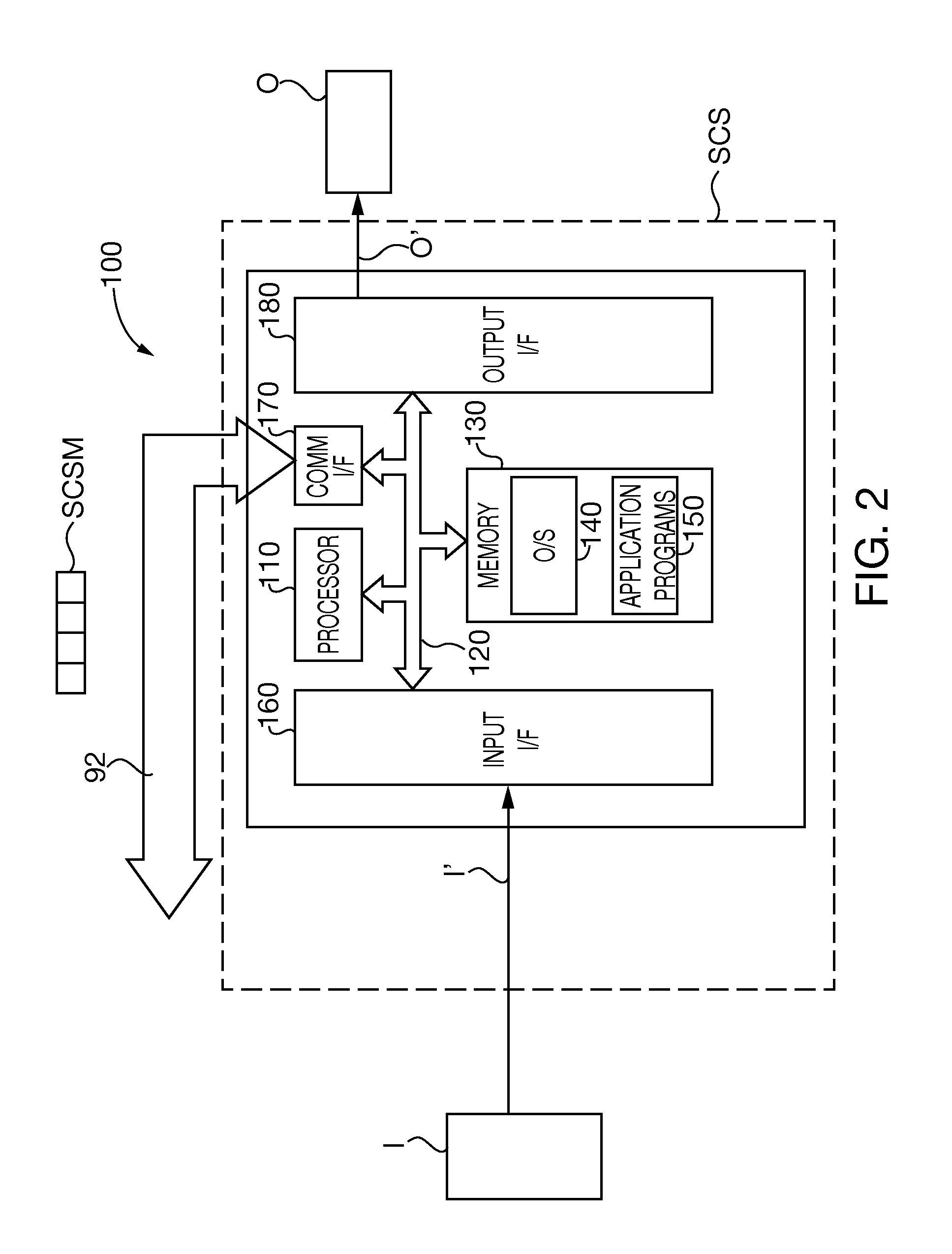
Maintaining vitality of data in safety-critical systems
Owner:AUSTRALIAN RAIL TRACK CORP
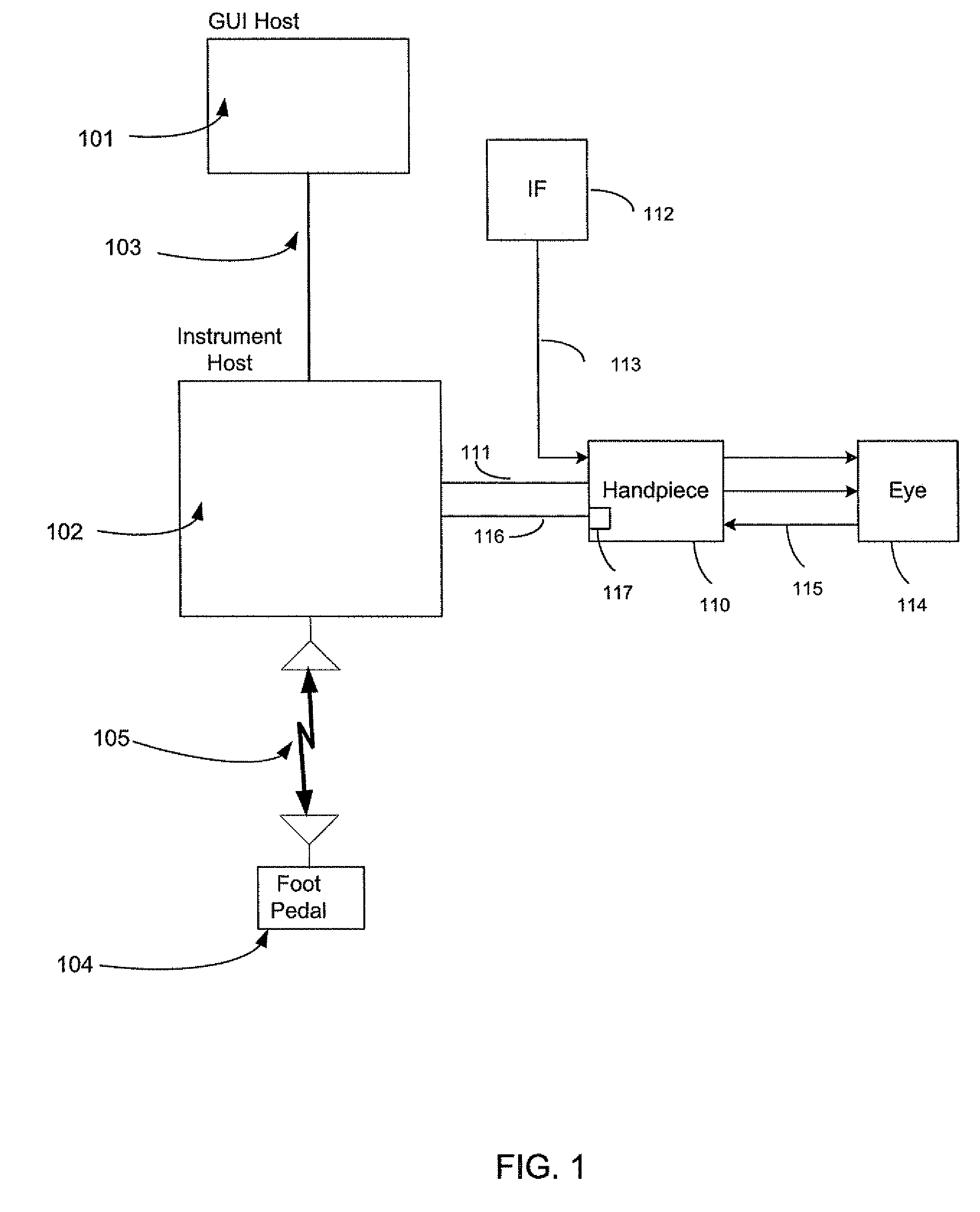
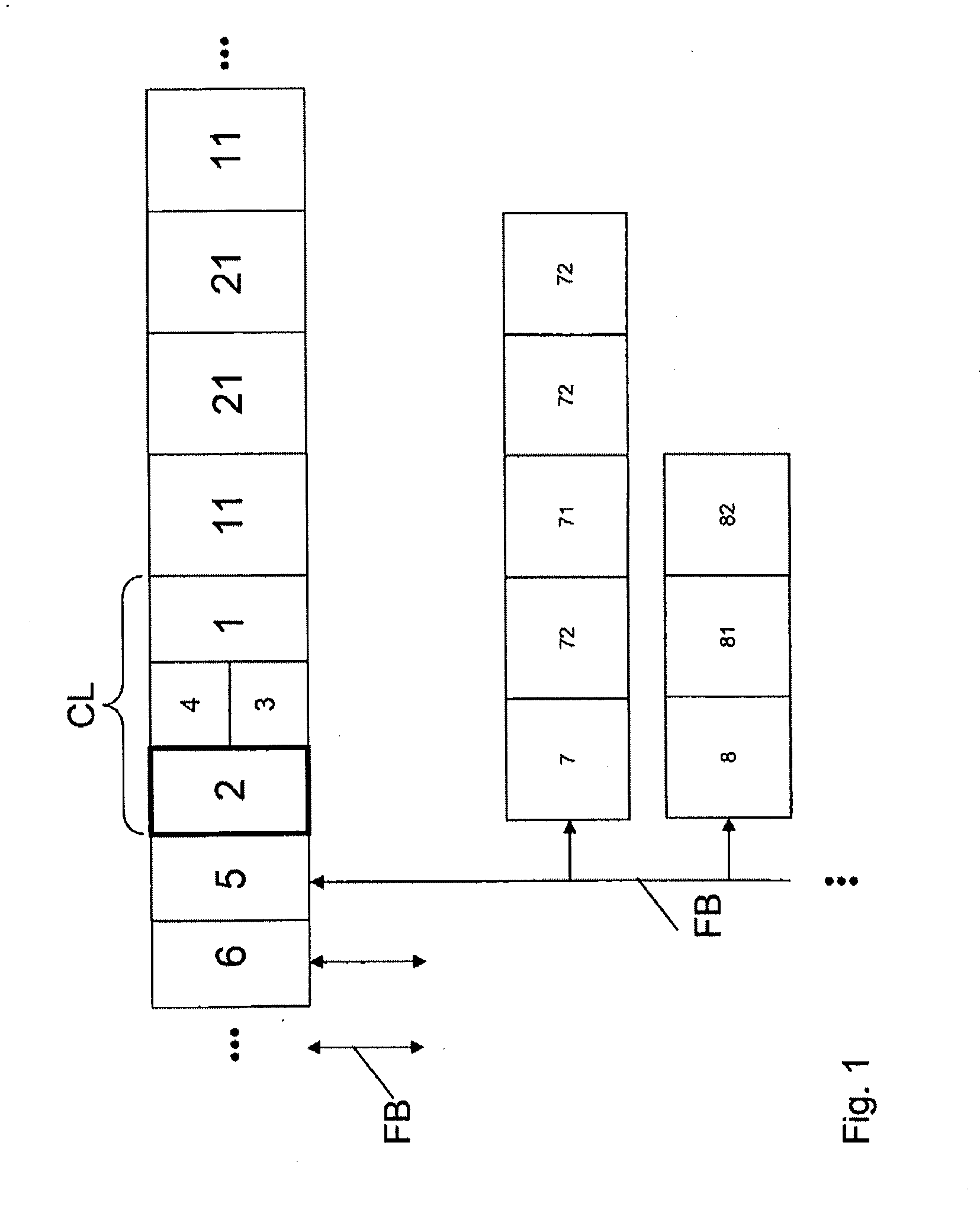
Serial communications protocol for safety critical systems
ActiveUS20080115146A1Multiprogramming arrangementsTransmissionNetwork Communication ProtocolsDirectional antenna
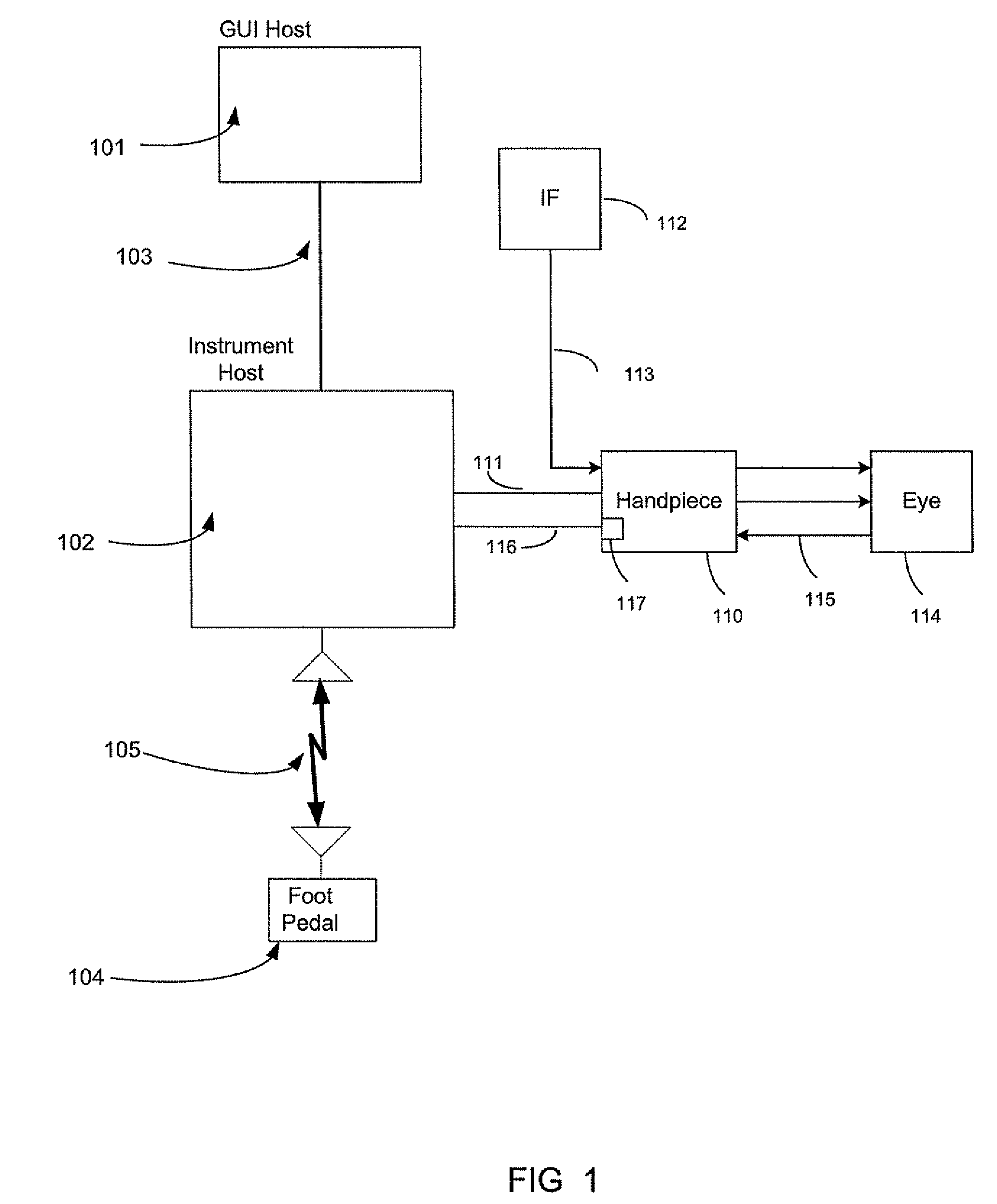
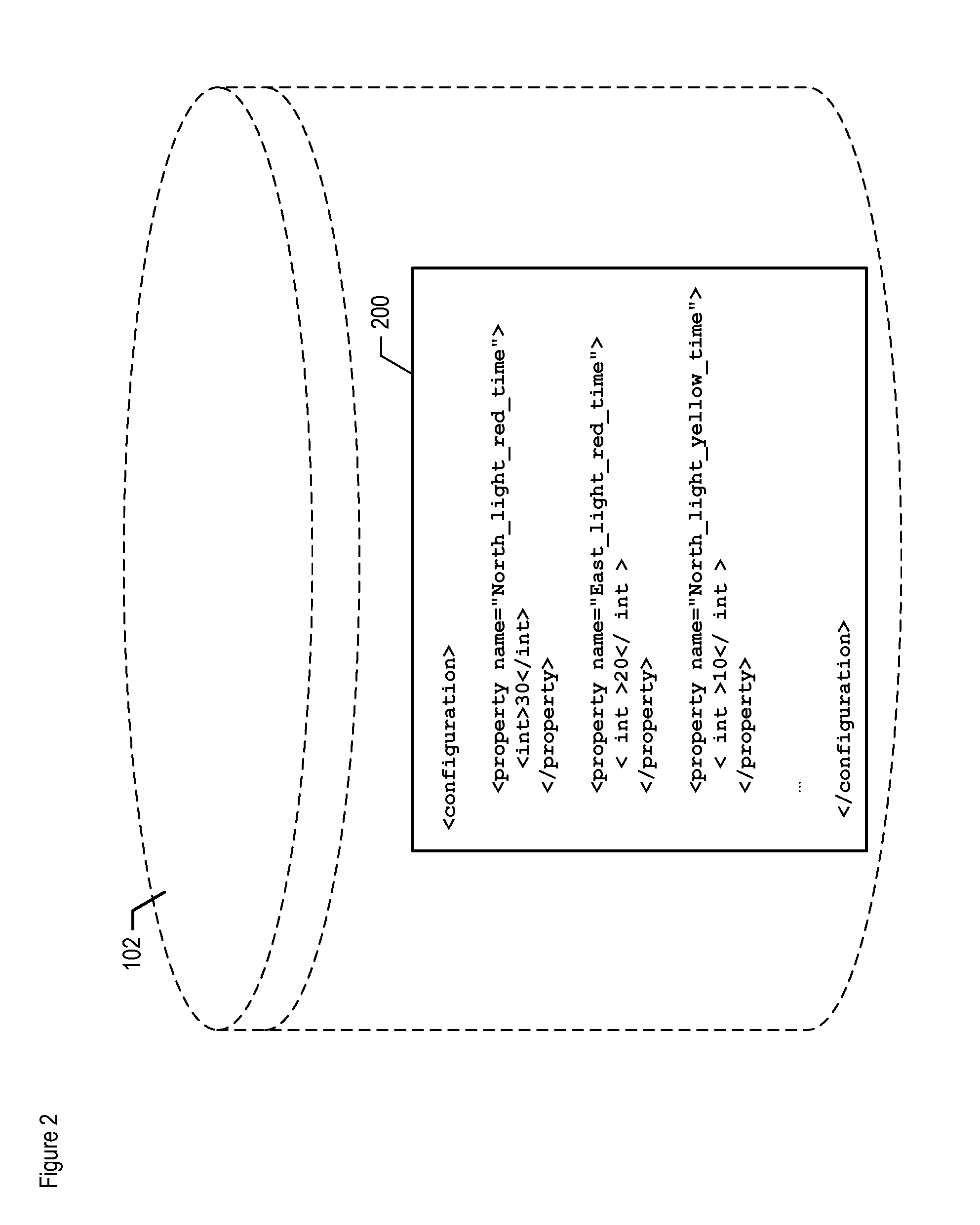
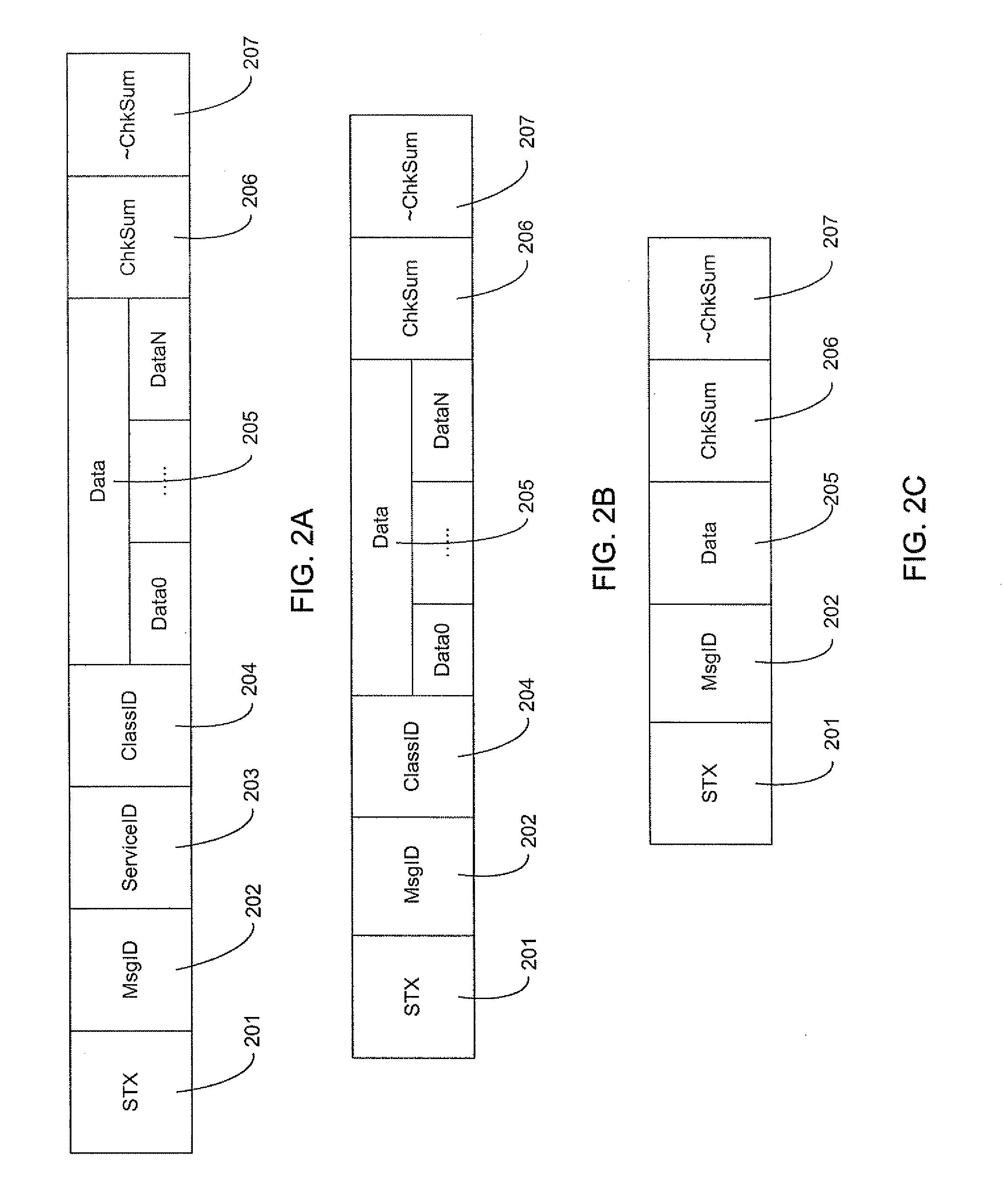
A method and system of establishing communications between at least two independent software modules in a safety critical system, such as a medical system, is provided. The design comprises providing a media connection between software modules, wherein the software modules employ a communications protocol and participate in a bi-directional master-slave relationship between a master module and a slave module. The design further comprises sending arbitrary data between the master and slave modules, wherein the arbitrary data is used by the master module to control and obtain status from the slave module, and sending arbitrary data further enables the slave module to return data and status information to the master module. The design also employs a safety critical communications watchdog between the master and slave modules, wherein the safety critical communications watchdog monitors communications quality between the master and slave modules. The bandwidth efficient communications protocol comprises bytes transmitted using a packet consisting of a start indication, a message identifier, an optional service identifier, a class identifier, an optional length of data pertinent to the medical device, a checksum, and a checksum complement.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
Method for controlling multi-sink/multi-path routing sensor network and sensor network using the same
ActiveUS20120236855A1Network topologiesData switching by path configurationTraffic capacitySensing data
A method for controlling a multi-sink / multi-path routing sensor network and a sensor network system using the same are provided. The method for controlling the sensor network includes generating, at a sensor node, sensing data; transmitting, at the sensor node, the sensing data to a plurality of sink nodes; and forwarding, at the sink nodes receiving the sensing data from the sensor node, the sensing data to a gateway. Hence, it is possible to satisfy the reliability required in the safety-critical system with the minimum traffic. Both of the two conflicting requirements which are the reliability enhancement of the sensor network and the minimization of the network traffic in the repeated data transmission, can be satisfied adequately.
Owner:KOREA ELECTRONICS TECH INST
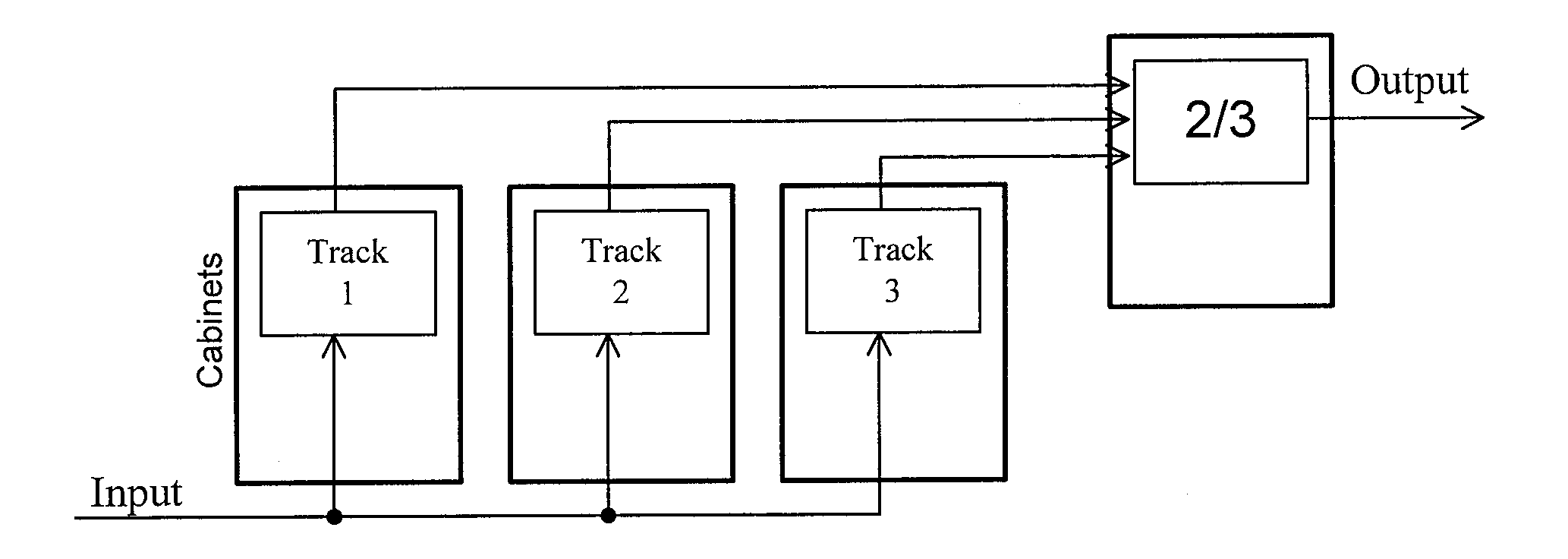
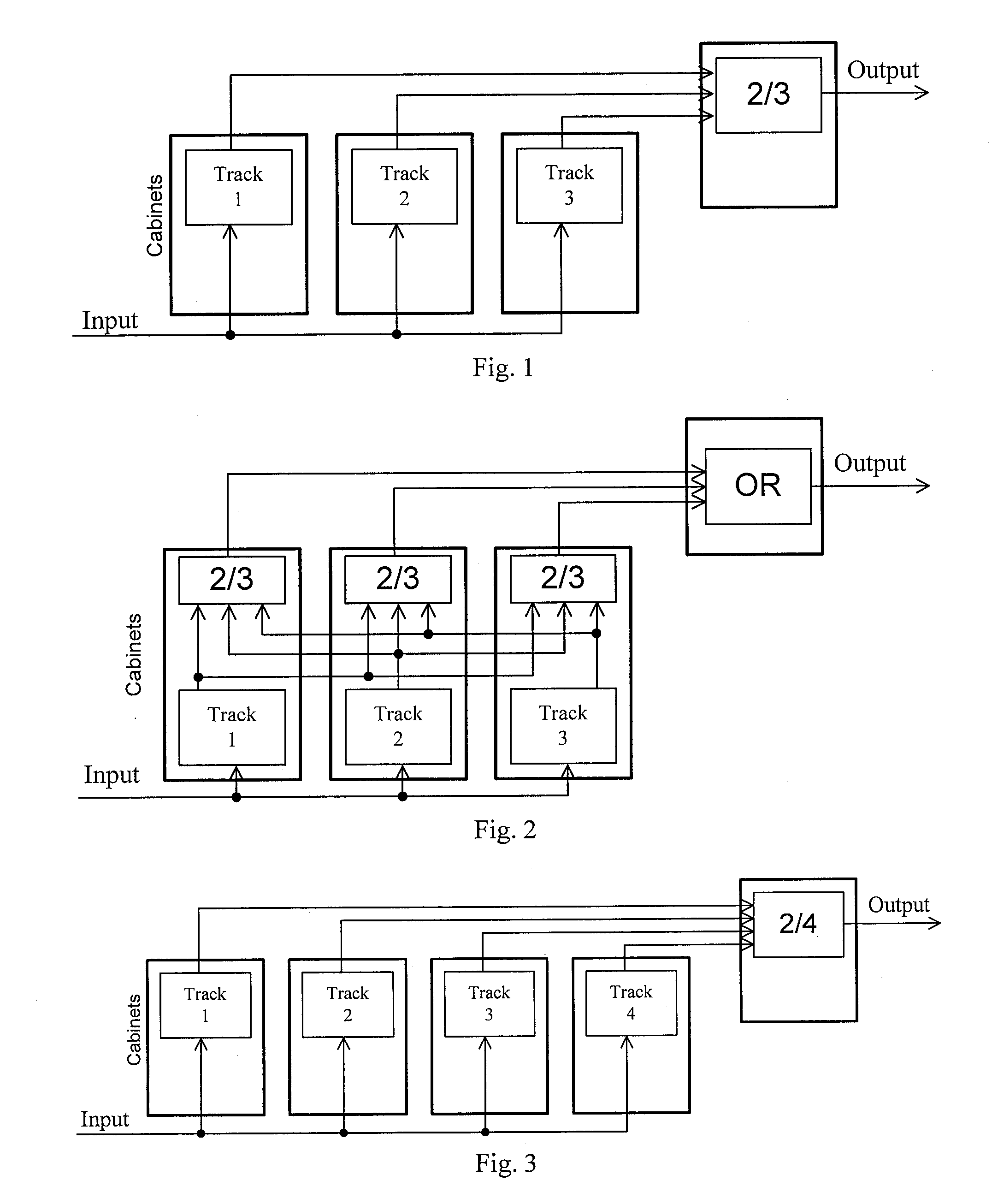
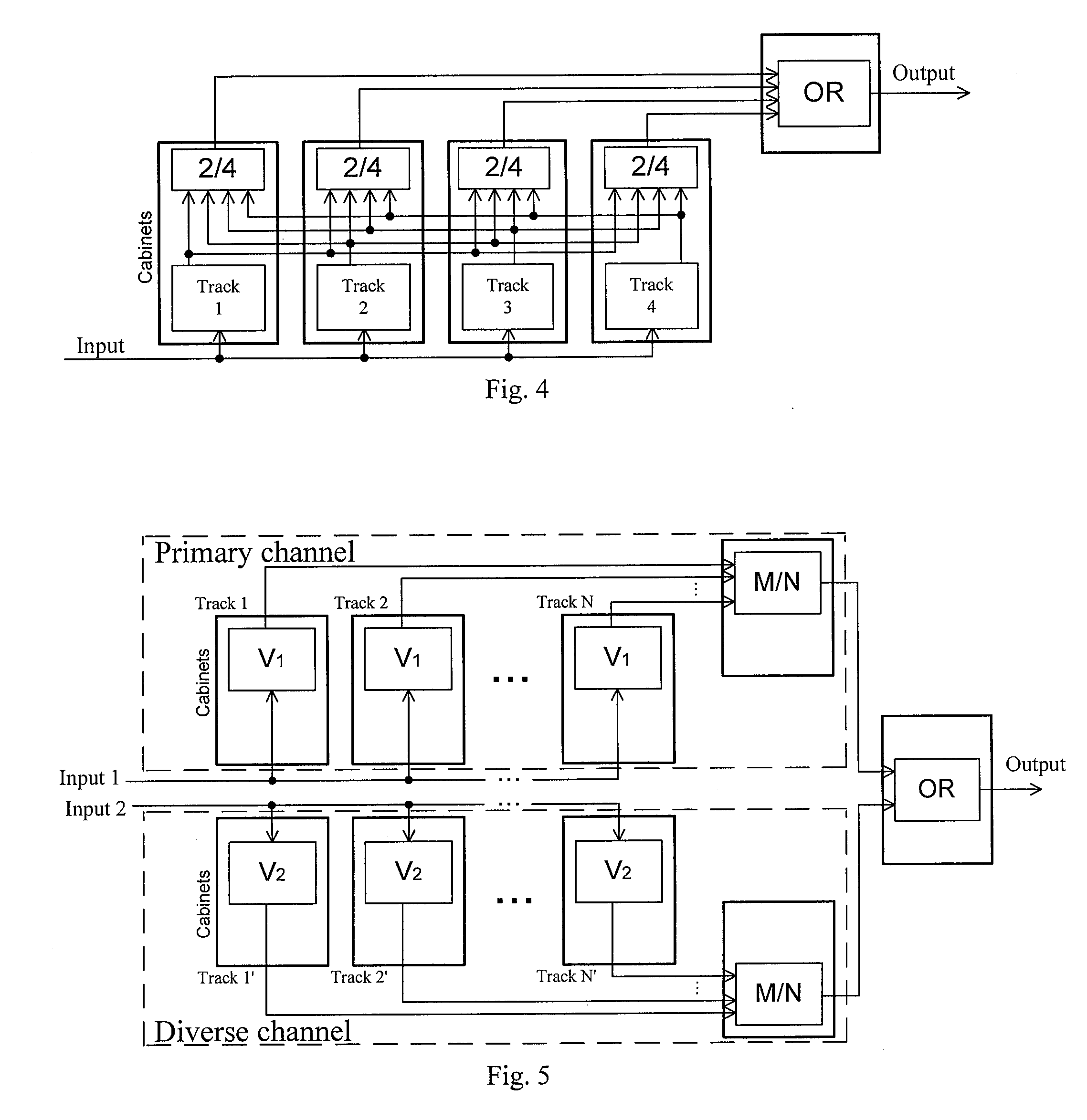
Method for design and verification of safety critical systems
InactiveUS7694250B2Produced in advanceSafety arrangmentsDigital data processing detailsHardware structureFault tolerance
A method of producing a system architecture comprises identifying a set of undesirable events and ascribing to each of the undesirable events an indicator of their severity, associating the undesirable events with one or more actuators of the system architecture, developing a functional specification of an initial architecture proposed for implementation of the system architecture, refining fault tolerance requirements associated with the severity of each of the undesirable events and issuing refined fault tolerance requirements, producing replicates in the functional specification together with attached indicators of freeness of the replicates from other of the replicates, the indicators reflecting the refined fault tolerance requirements, defining a hardware structure for the system architecture, mapping the functional specification onto the hardware structure, and verifying automatically that the indicators of freeness are preserved during the mapping. The method can be stored on a computer readable storage medium or implemented by a design tool.
Owner:RENAULT SA
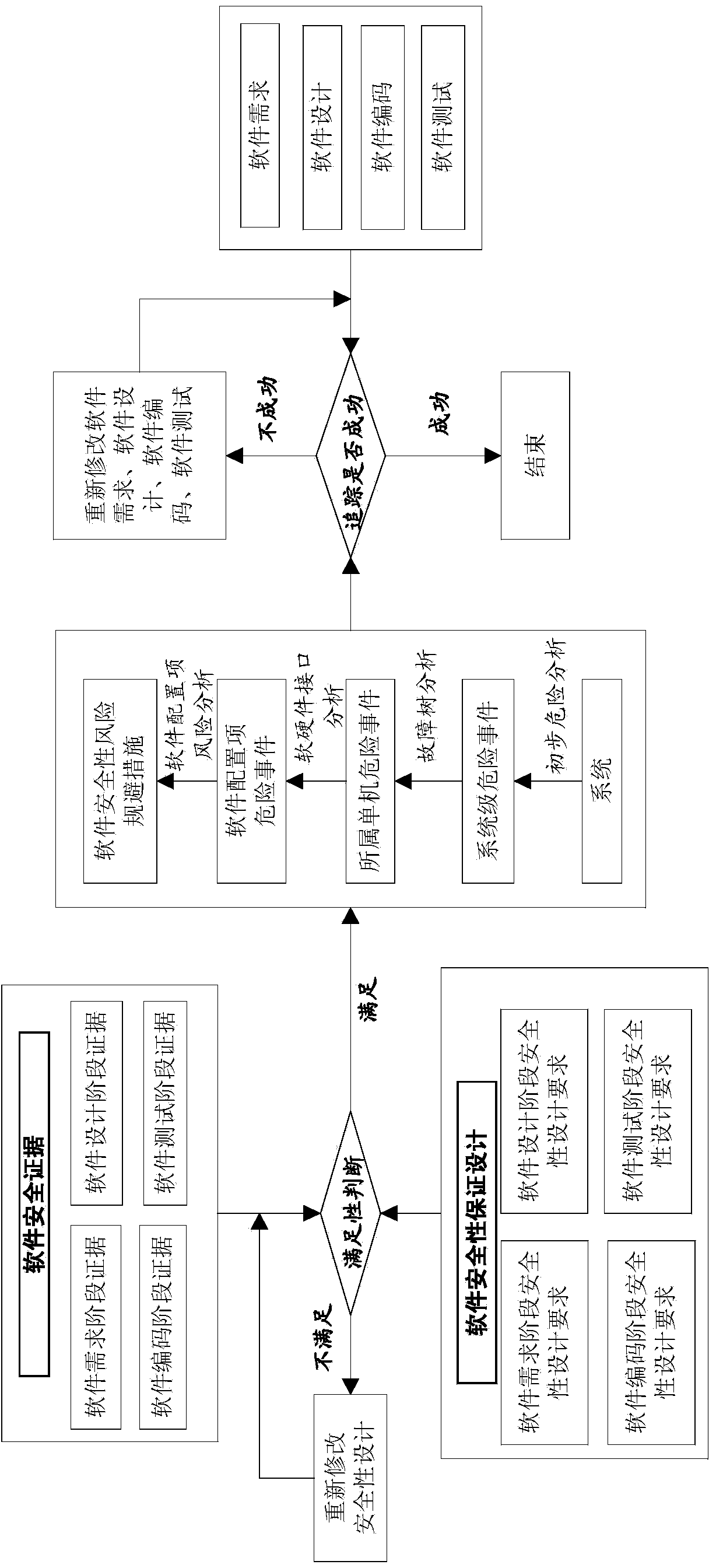
Realizing method for software safety guarantee of safety-critical system
ActiveCN103955427AEnsure safetyImprove securitySoftware testing/debuggingSoftware designSoftware engineering
A realizing method for the software safety guarantee of a safety-critical system comprises the following steps: (1), defining the software safety design requirements of the system, including safety design requirements in a software demand stage, safety design requirements in a software design stage, safety design requirements in a software encoding stage and safety design requirements in a software test stage; (2) according to software safety grades, truncating the safety design requirements in step (1), and implementing safety design about software demand, software design, software encoding and software test according to all the requirements; (3) acquiring software safety evidences, and judging whether the safety evidences meet all the safety design requirements in step (2); (4) acquiring the software safety risk avoidance measures of the system; (5) verifying whether the software safety risk avoidance measures can trace to software demand, software design, software encoding and software test. The software safety guarantee capability is improved, and the technical blank in the software safety guarantee of aerospace major engineering is filled.
Owner:探月与航天工程中心 +1
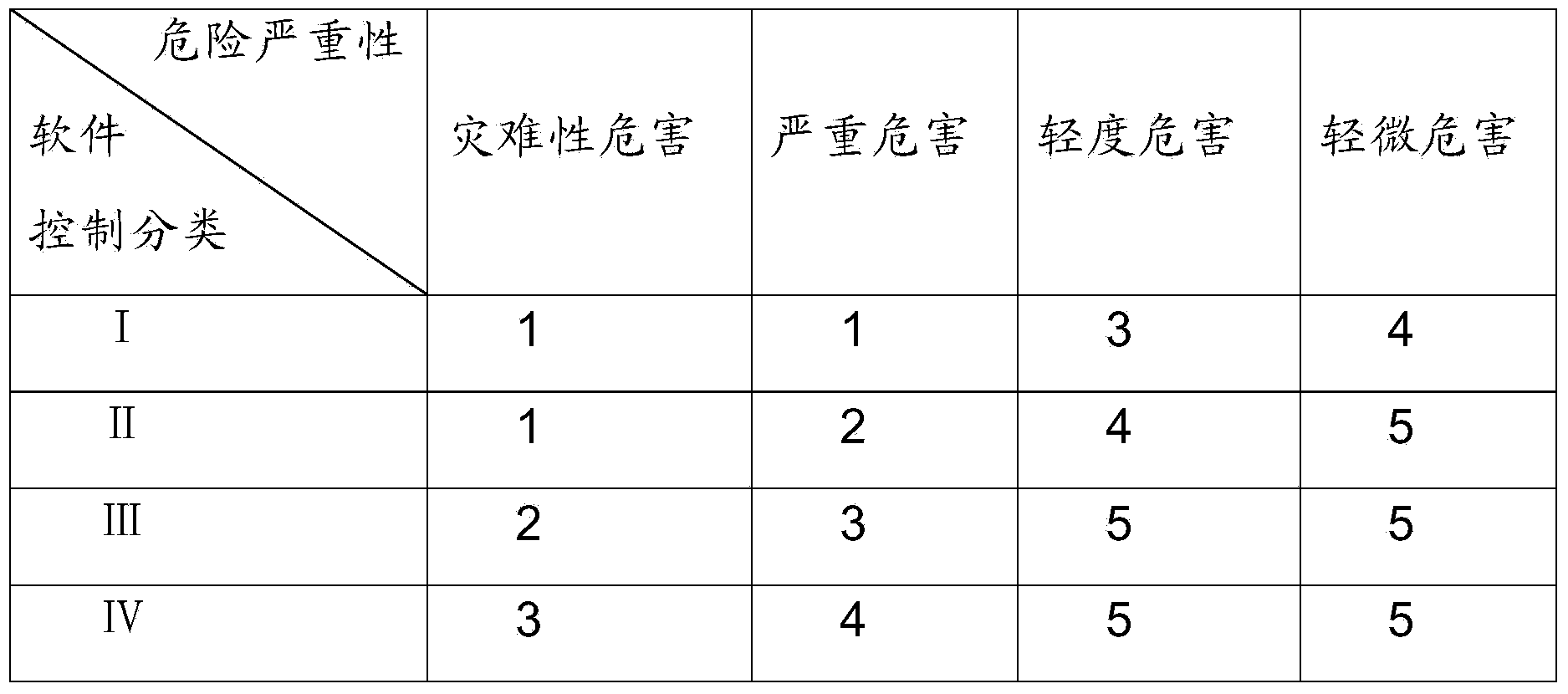
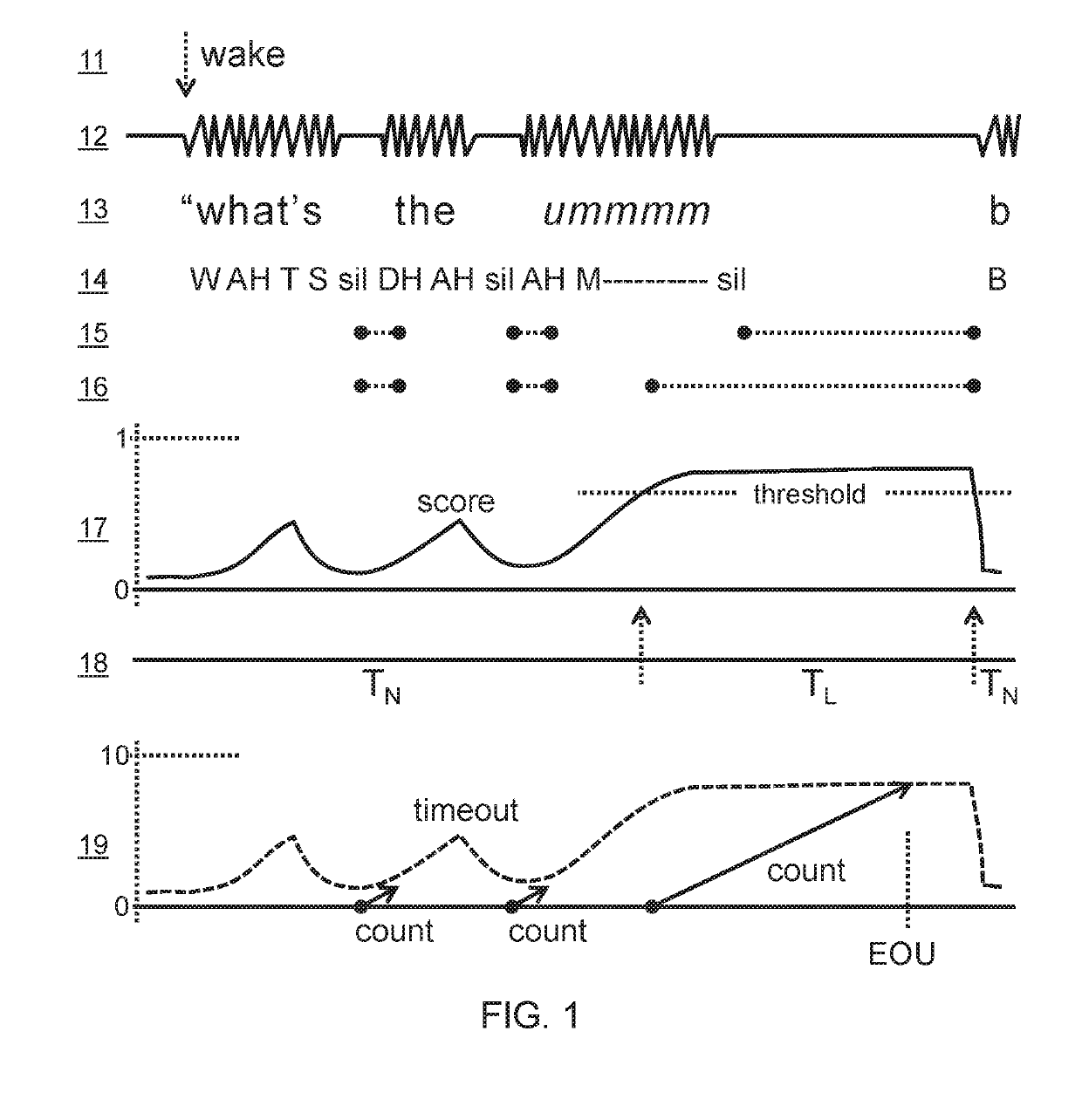
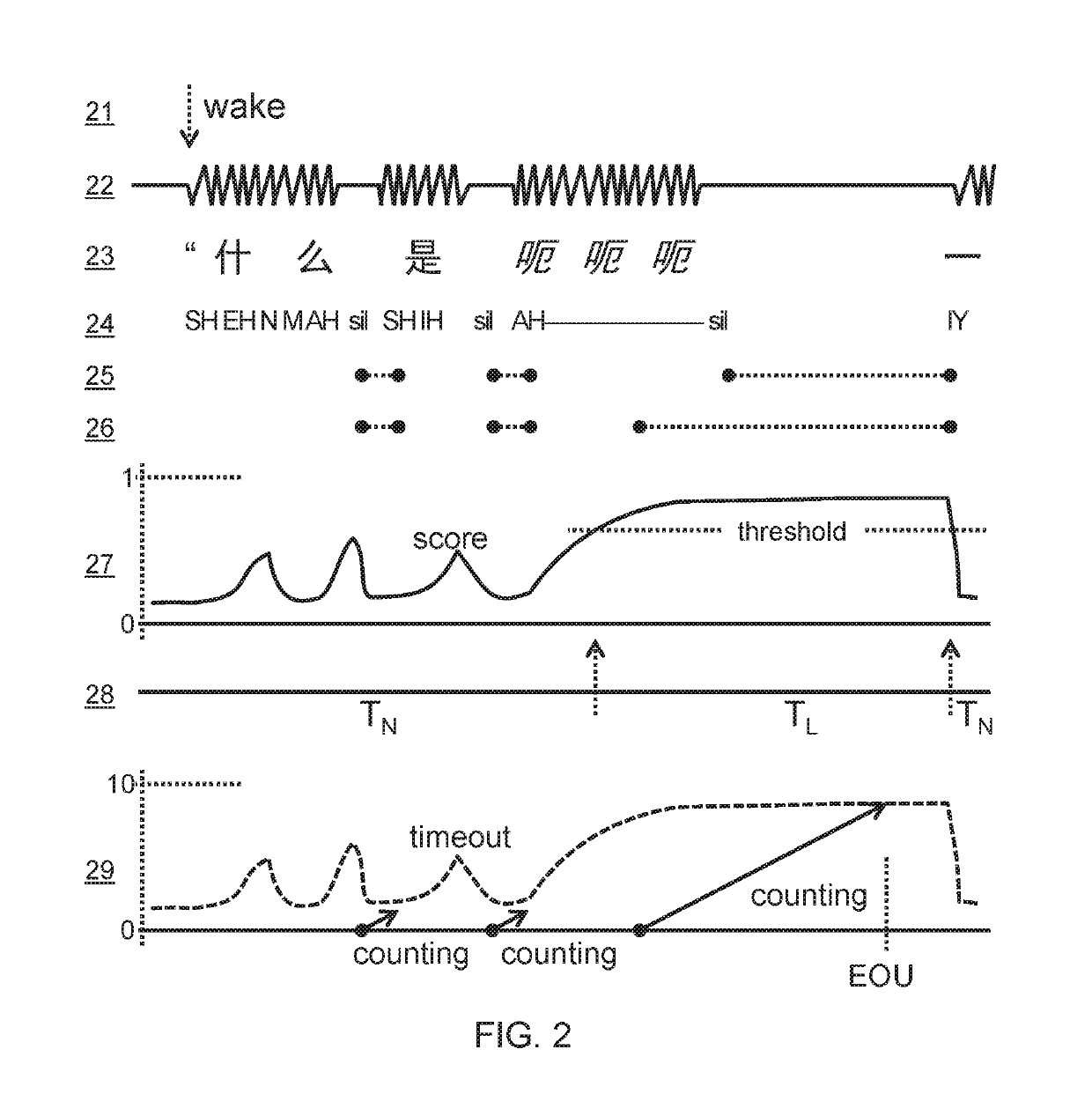
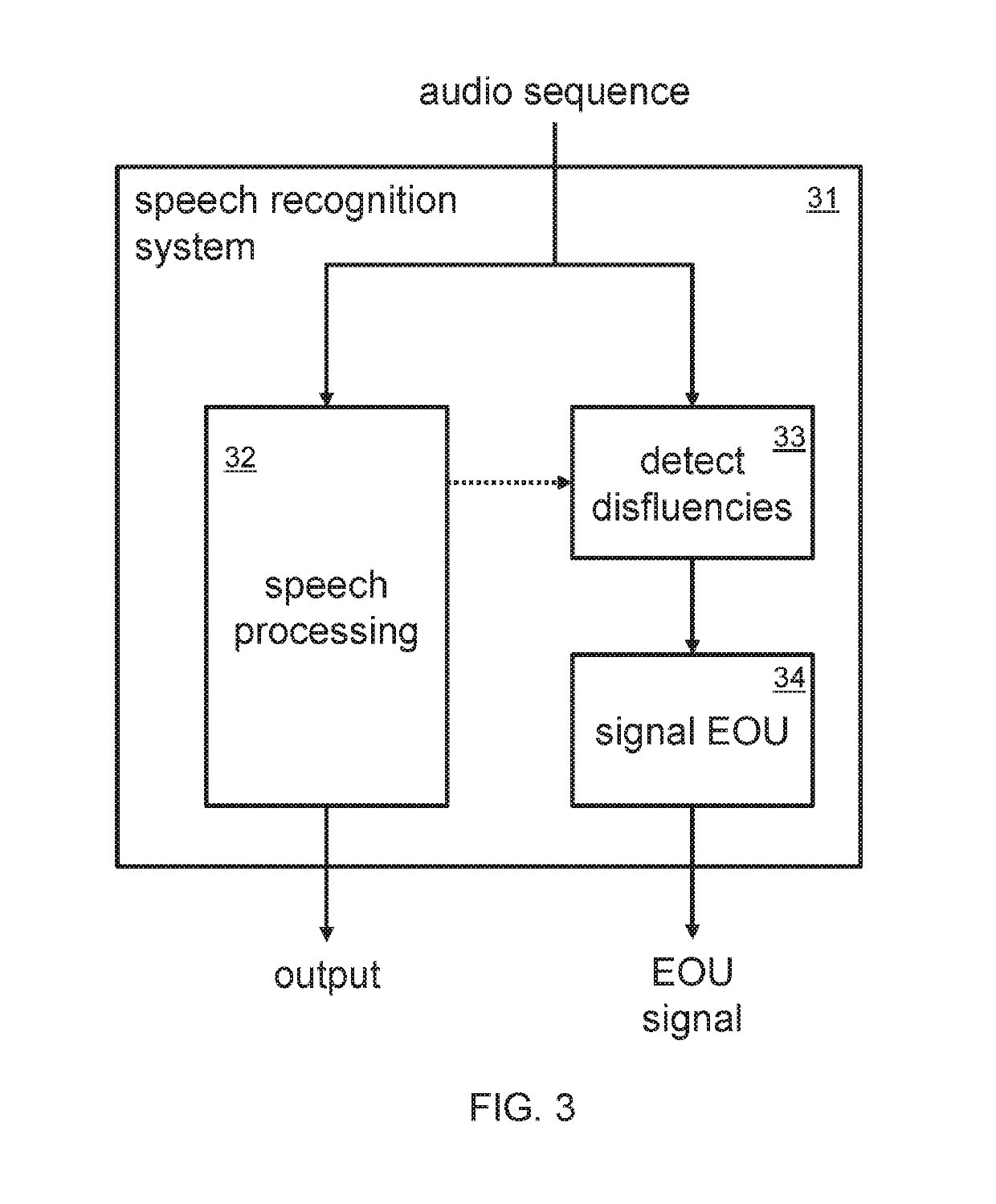
Adaptive end-of-utterance timeout for real-time speech recognition
InactiveUS20190325898A1Improve accuracySemantic analysisSpeech recognitionAcoustic modelSpeech sound
Real-time speech recognition systems extend an end-of-utterance timeout period in response to the presence of a disfluency at the end of speech, and by so doing avoid cutting off speakers mid-sentence. Approaches to detecting disfluencies include the application of disfluency n-gram language models, acoustic models, prosody models, and phrase spotting. Explicit pause phrases can also be detected to extend sentence parsing until relevant semantic information is gathered from the speaker or another voice. Disfluency models can be trained such as by searching by successive deletion of tokens, phonemes, or acoustic segments to convert sentences that cannot be parsed into ones that can. Disfluency-based timeout adaptation is applicable to safety-critical systems.
Owner:SOUNDHOUND AI IP LLC
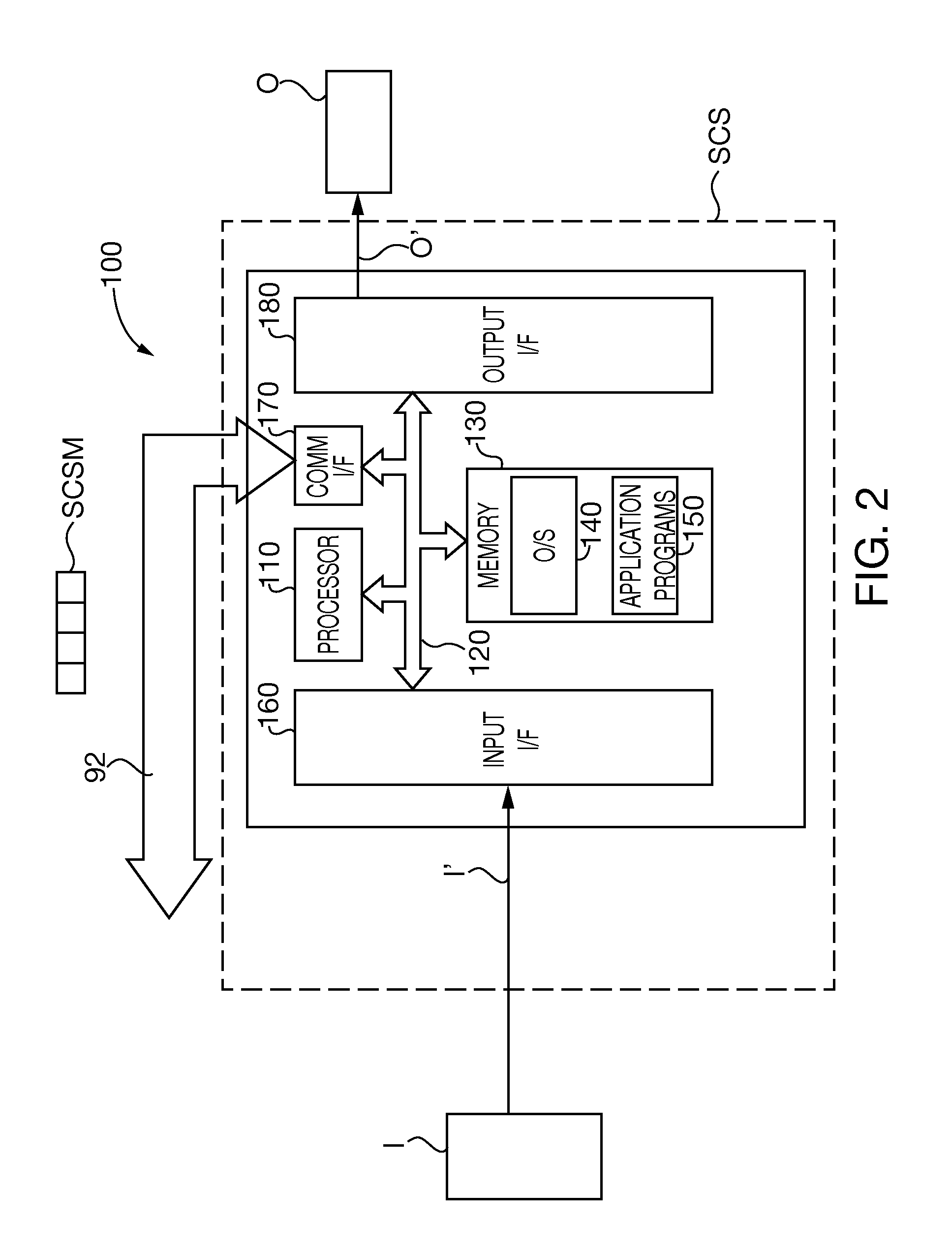
Method and software product for managing data exchange in a high-dynamics safety-critical system
InactiveUS20090138097A1Overcomes drawbackInterprogram communicationElectric controllersData exchangeCritical system
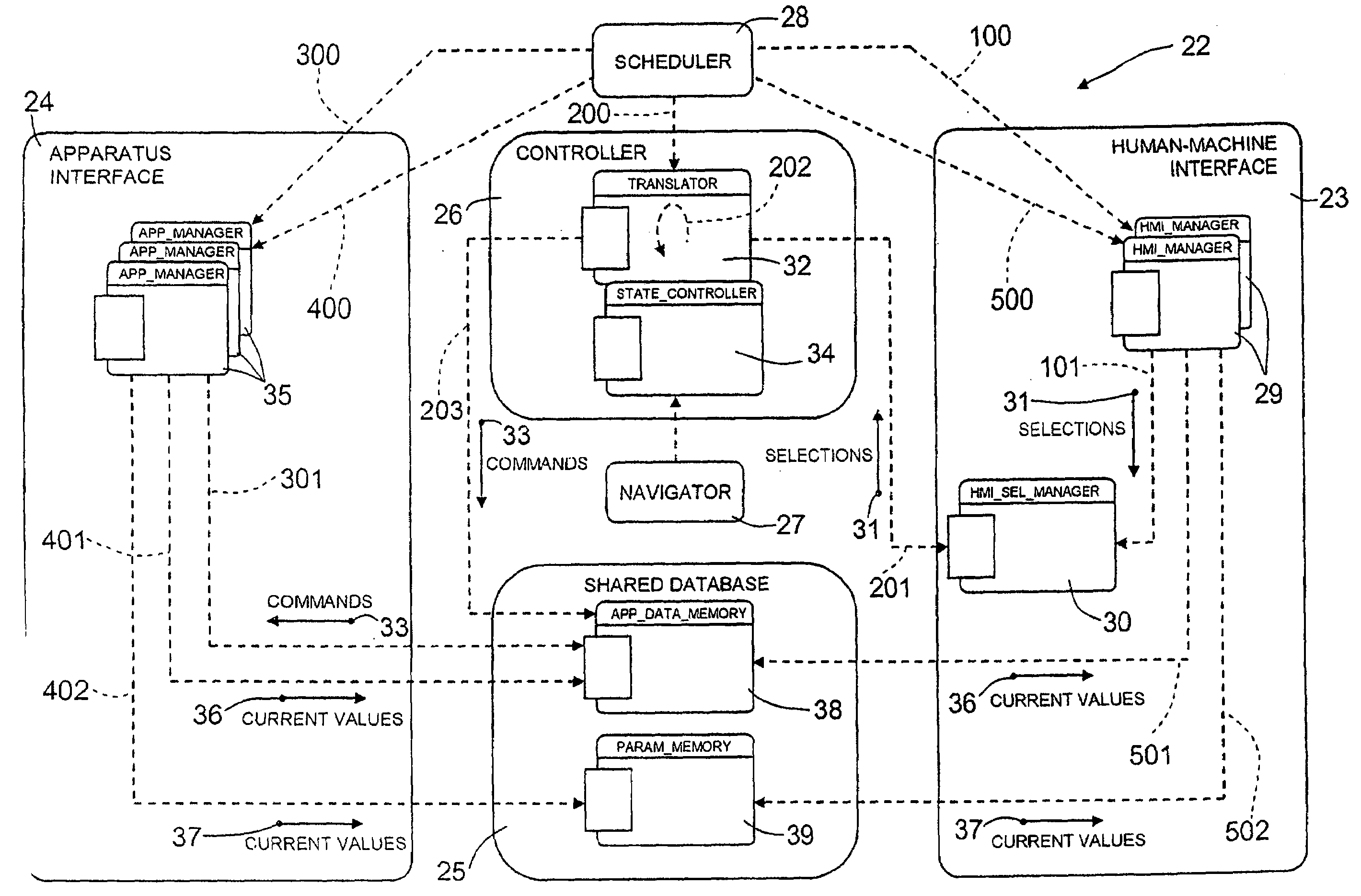
Disclosed herein is a high-dynamics safety-critical system, comprising a plurality of apparatuses, a plurality of interface devices through which a user can interact with the apparatuses, and a control computer connected to the apparatuses and the interface devices and on which there is installed a software product designed to implement and manage the data exchange between management modules for the apparatuses and management modules for the interface devices, in which the management modules for the interface devices acquire the selections made by a user via the interface devices, the selections are then transformed into commands for the apparatuses, and the commands thus generated are then stored in a shared database in such a way as to be usable by the management modules of the apparatus and actuated on the latter.
Owner:SELEX GALILEO
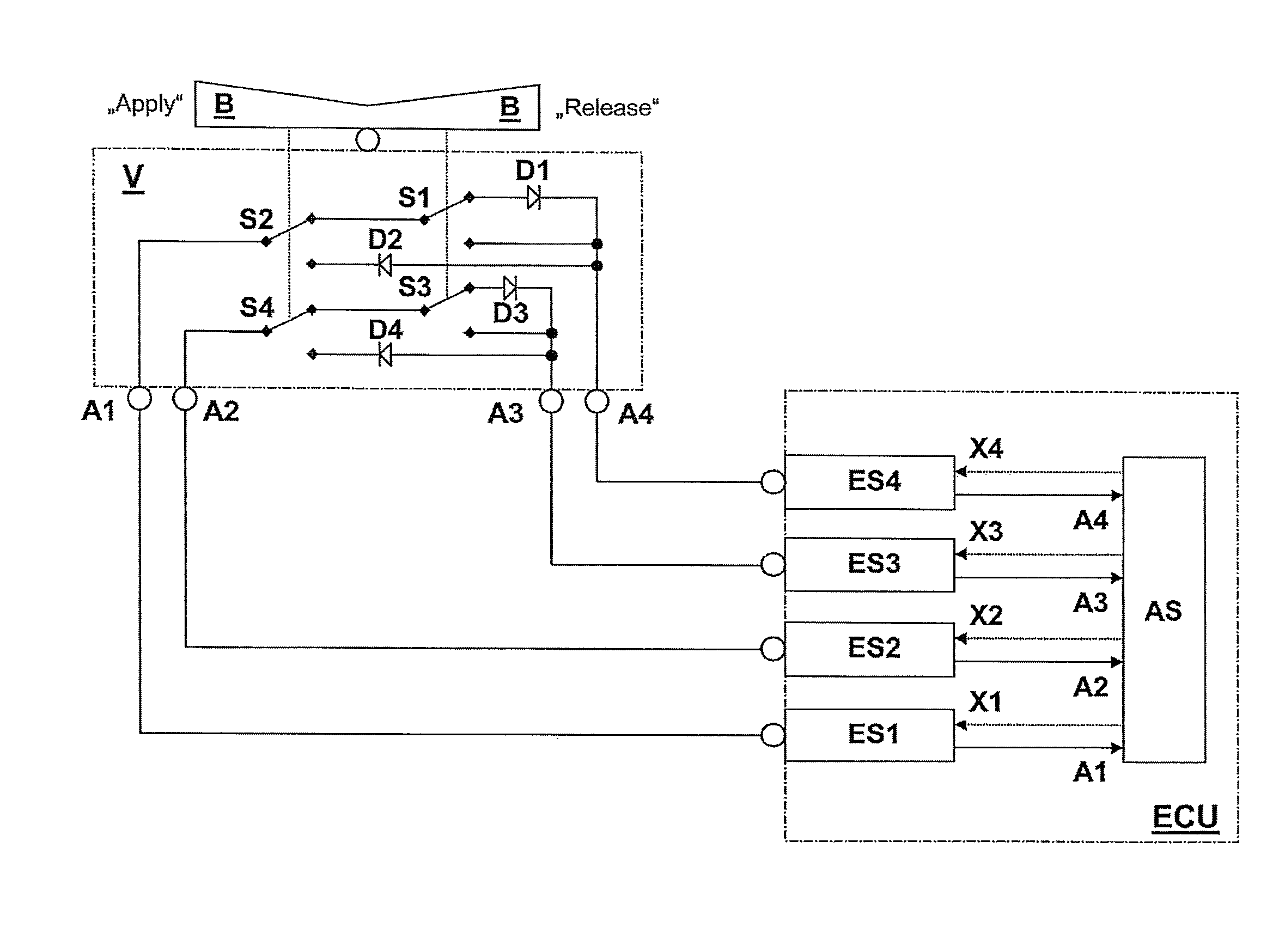
Device for the electric actuation of a safety-critical system
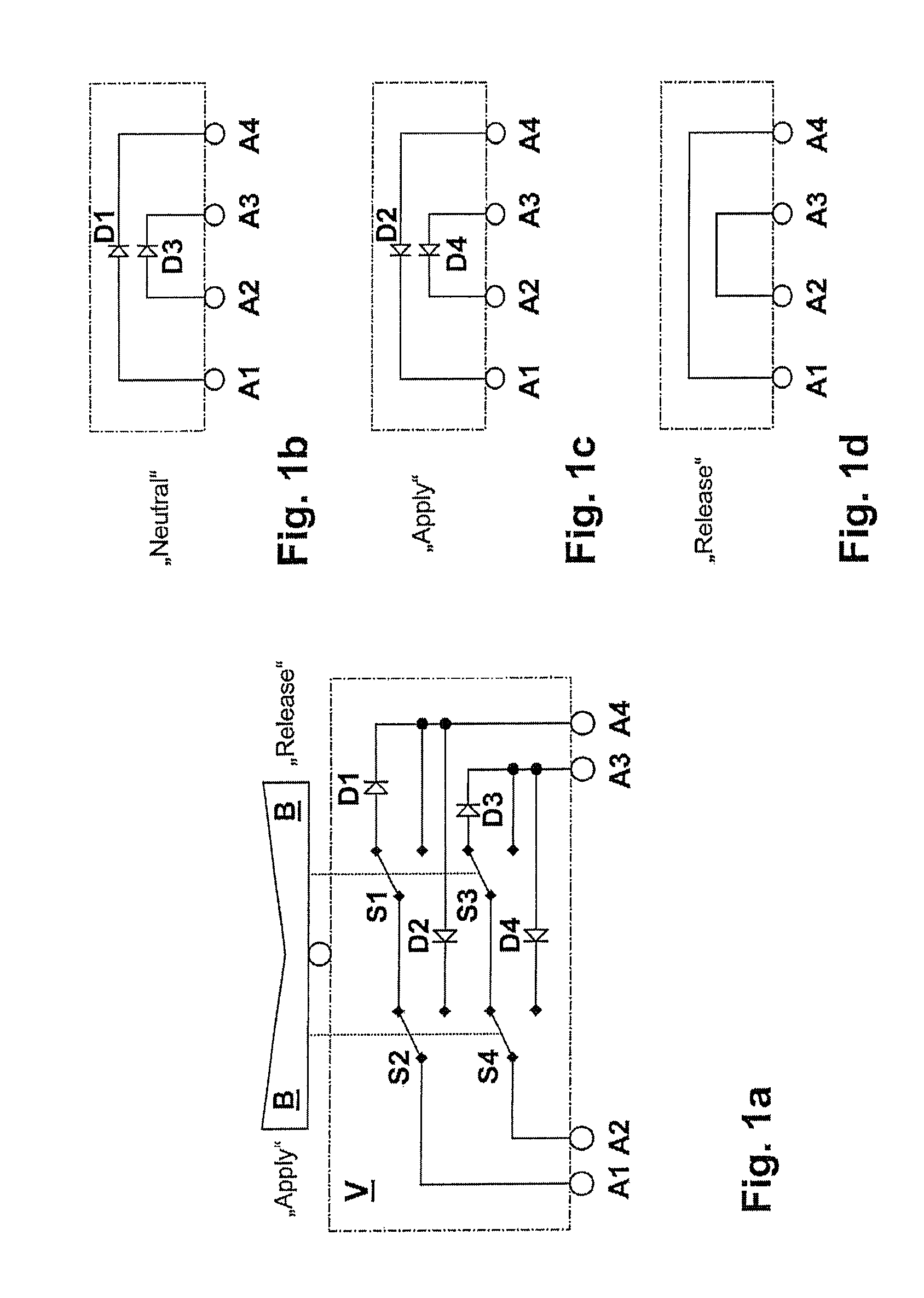
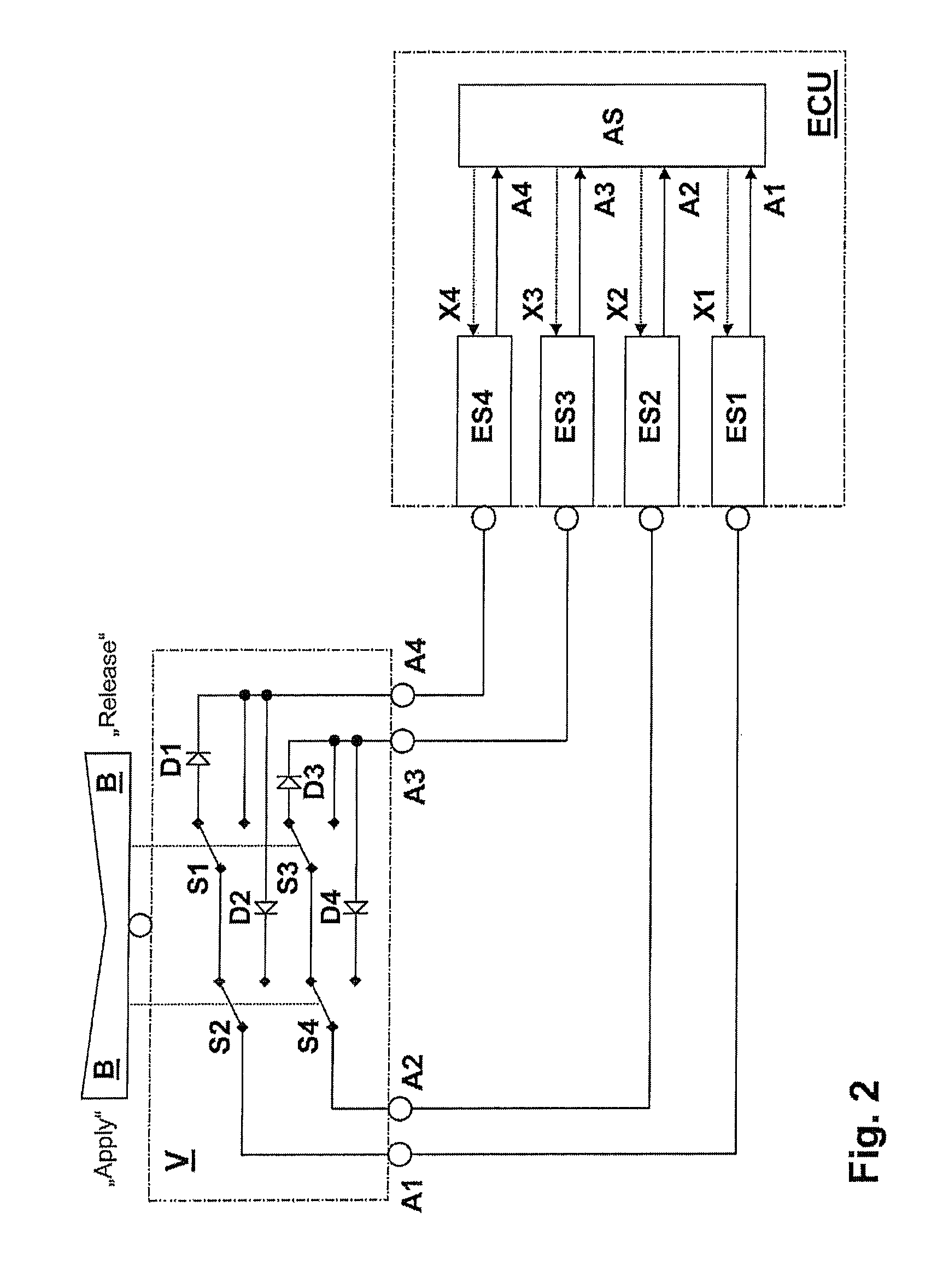
ActiveUS8432060B2High redundancy and fault toleranceSafely and reliably determined and identifiedBoards/switchyards circuit arrangementsElectric devicesSelection systemElectrical current
For a device for the electrical actuation of a safety-critical system, having at least two terminals, at least one switch, an operator control element, by means of which at least two operating states for the system are selectable, by means of which switching positions of the at least one switch are determined, it is proposed that at least one current direction element is provided, so that for at least one of the at least two operating states a unidirectional current flow occurs between the at least two terminals.
Owner:LUCAS AUTOMOTIVE GMBH
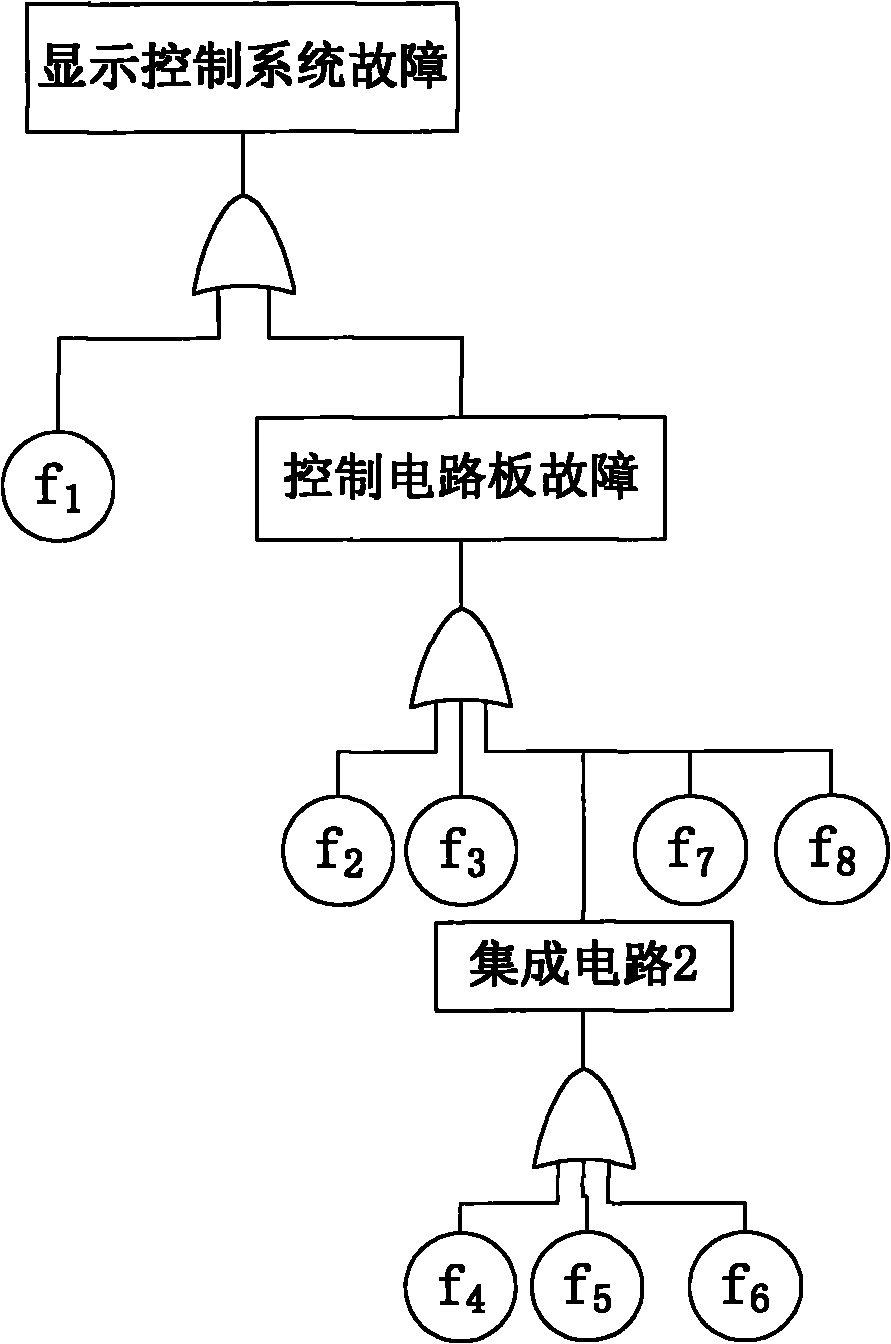
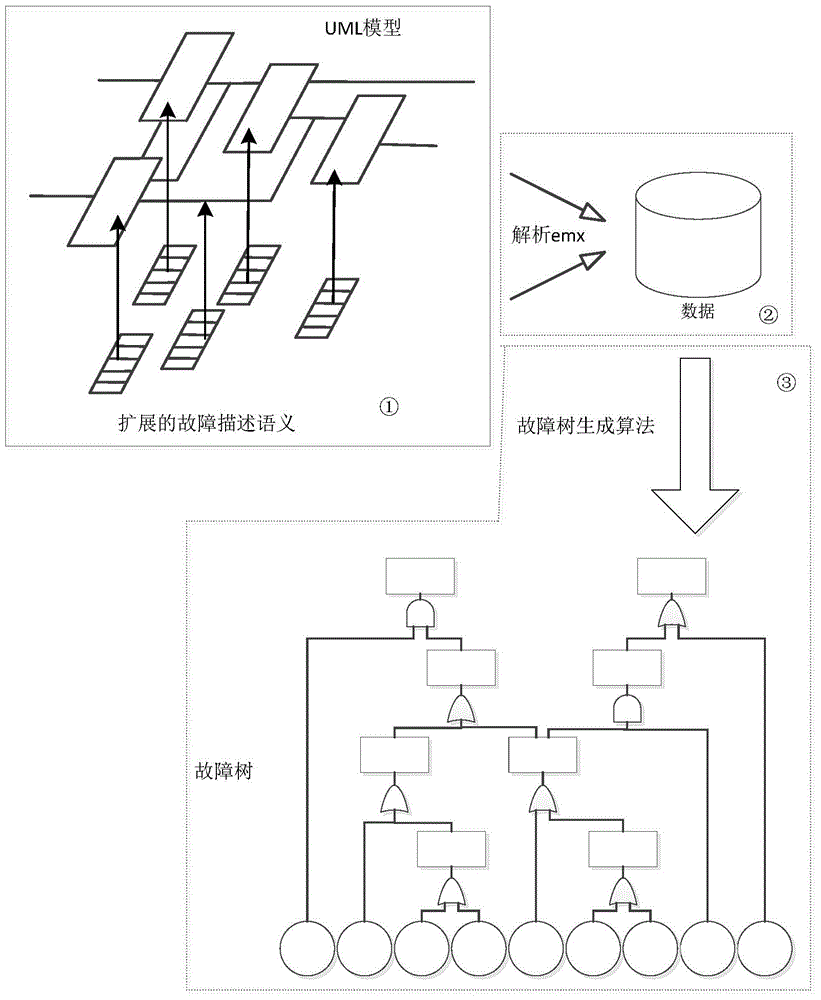
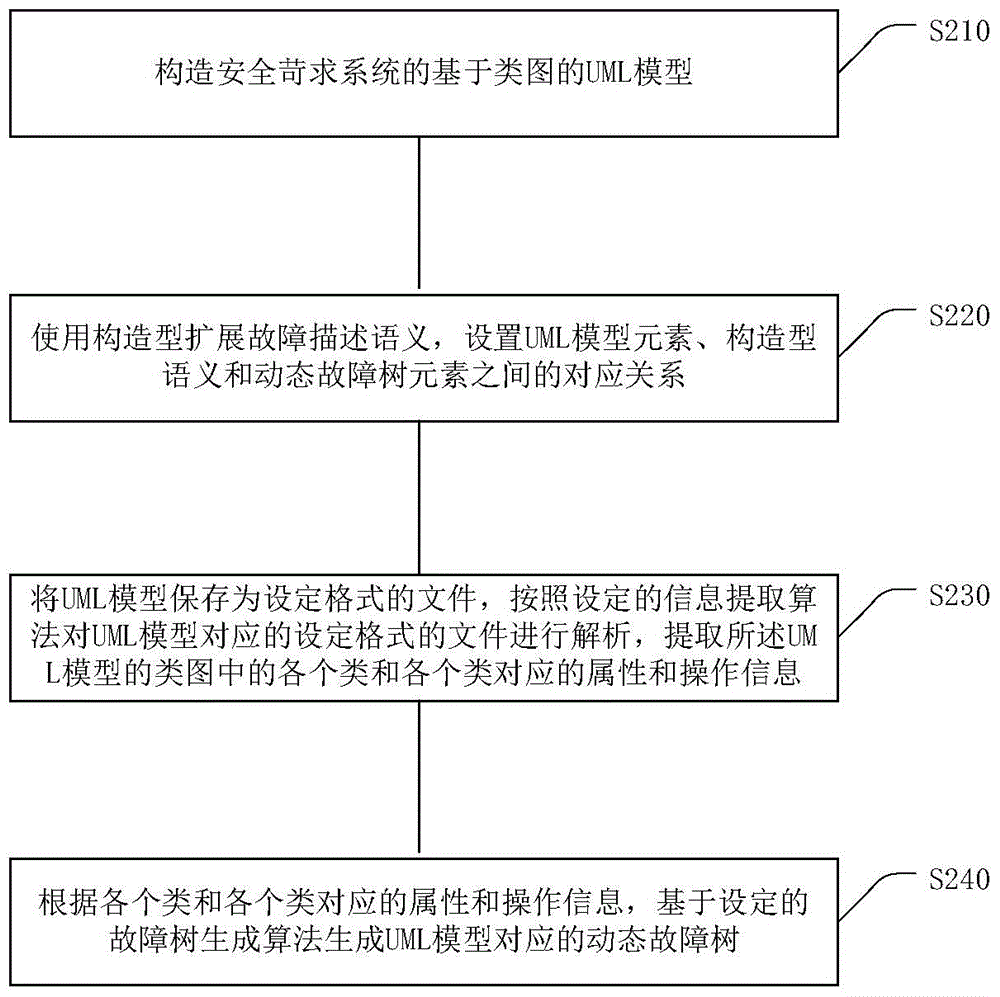
Fault tree generation method for extended UML class diagram model of safety-critical system
InactiveCN104679510AOvercoming design failuresImplement automatic conversionSpecific program execution arrangementsSystems designSemantics
The embodiment of the invention provides a fault tree generation method for an extended UML class diagram model of a safety-critical system. The method comprises the steps of constructing the UML class diagram model of the safety-critical system, wherein all classes in the UML class diagram model comprise attributes and operations and have a certain relation, and the element semantics of the model is extended by a stereotype; storing the UML class diagram model into a file with a set format, analyzing the file with the set format corresponding to the UML class diagram model by a set information extraction algorithm to extract all the classes and the attributes and the operation information which correspond to all the classes in the UML class diagram model, and generating a fault tree of the UML class diagram model according to a set fault tree generation algorithm. According to the method disclosed by the embodiment of the invention, relevant safety analysis information is successfully embedded into the designed model of the safety-critical system, so that automatic conversion between the designed model of the system and a safety model of the system is realized, and the design fault of the safety-critical system can be effectively overcome.
Owner:BEIJING JIAOTONG UNIV
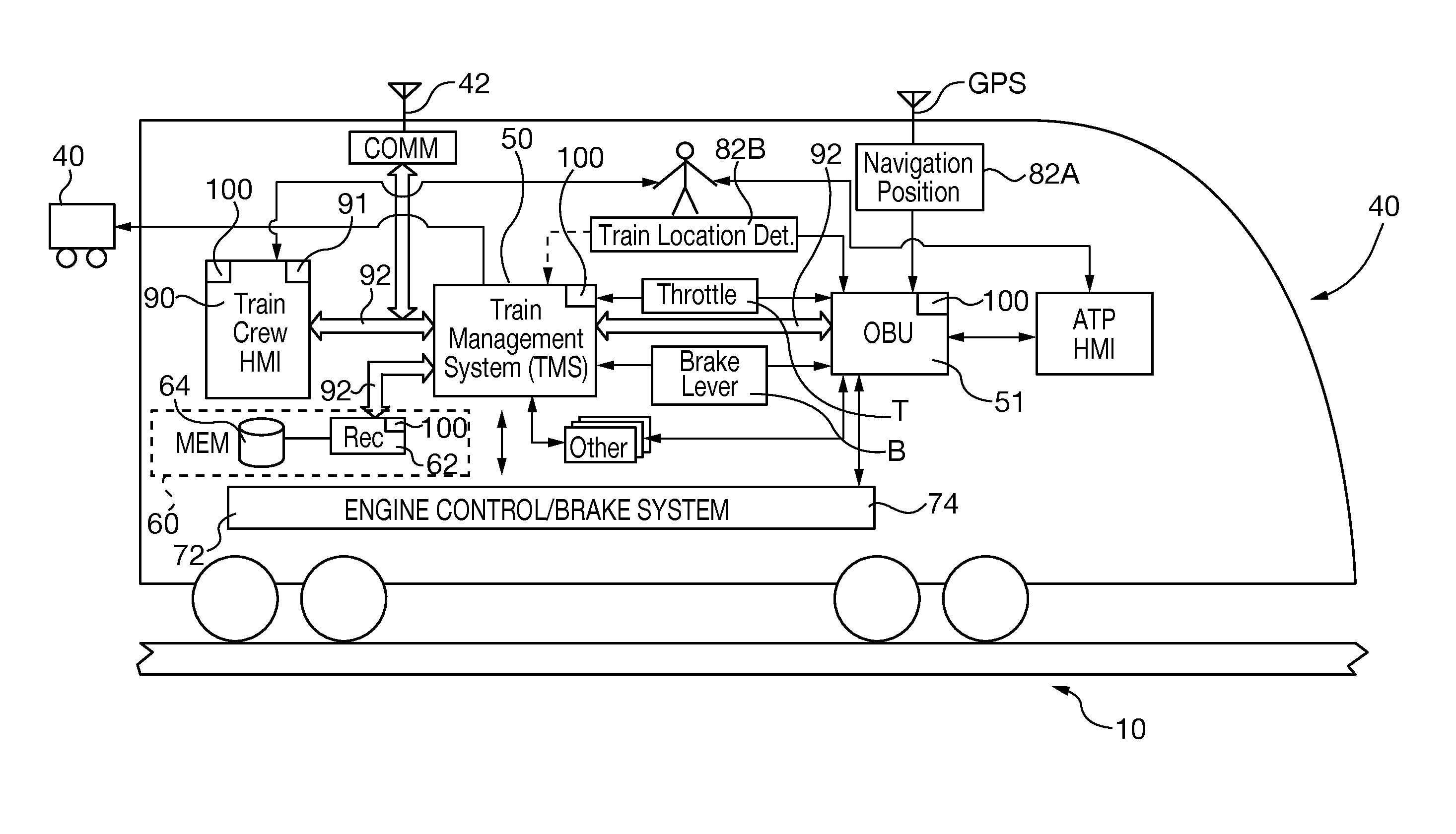
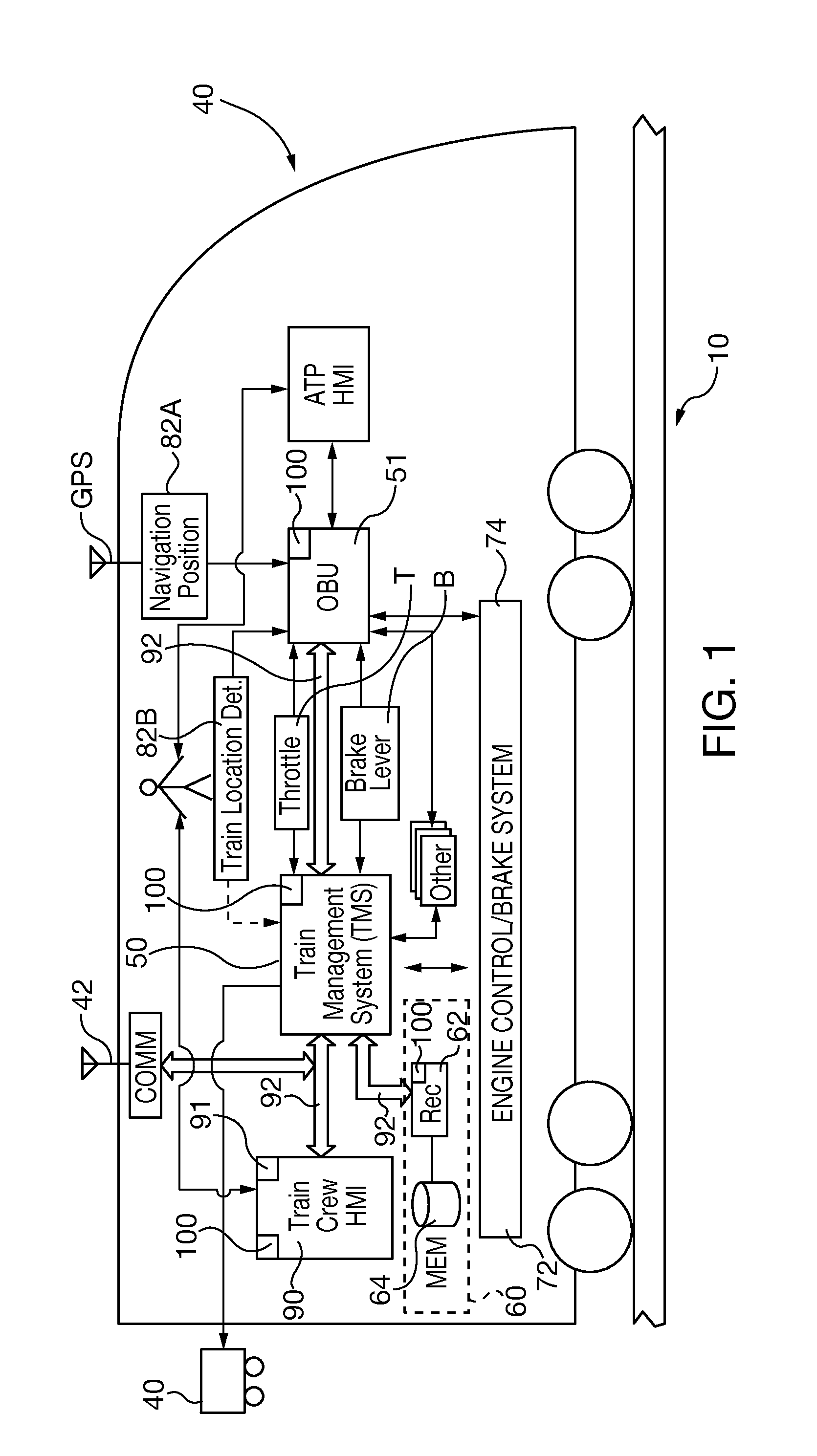
Railway safety critical systems with task redundancy and asymmetric communications capability
ActiveUS20140229040A1Reduce safety critical system control system procurement costIncrease the number ofAutomatic systemsDigital data processing detailsTechnical standardPersonal computer
A railway safety critical application system substitutes commercial off-the-shelf (COTS) hardware and / or software for railway-domain specific product components, yet is validated to conform to railway safety critical system failure-free standards. The safety critical system uses a pair of tasks executed on a controller of a COTS personal computer or within a virtual environment with asymmetric communications capability. Both tasks receive and verify safety critical systems input message data and security code integrity and separately generate output data responsive to the input message. The first task has sole capability to send complete safety critical system output messages, but only the second task has the capability of generating the output security code. A failure of any of systems hardware, software or processing capability results failure to transmit a safety critical system output message or an output message that cannot be verified by other safety critical systems.
Owner:SIEMENS MOBILITY INC
Railway safety critical systems with task redundancy and asymmetric communications capability
ActiveUS9233698B2Simplify railway safety critical systems overall designReduce procurement costsAutomatic systemsPoint-signal interlocking arrangmentsTechnical standardPersonal computer
A railway safety critical application system substitutes commercial off-the-shelf (COTS) hardware and / or software for railway-domain specific product components, yet is validated to conform to railway safety critical system failure-free standards. The safety critical system uses a pair of tasks executed on a controller of a COTS personal computer or within a virtual environment with asymmetric communications capability. Both tasks receive and verify safety critical systems input message data and security code integrity and separately generate output data responsive to the input message. The first task has sole capability to send complete safety critical system output messages, but only the second task has the capability of generating the output security code. A failure of any of systems hardware, software or processing capability results failure to transmit a safety critical system output message or an output message that cannot be verified by other safety critical systems.
Owner:SIEMENS MOBILITY INC
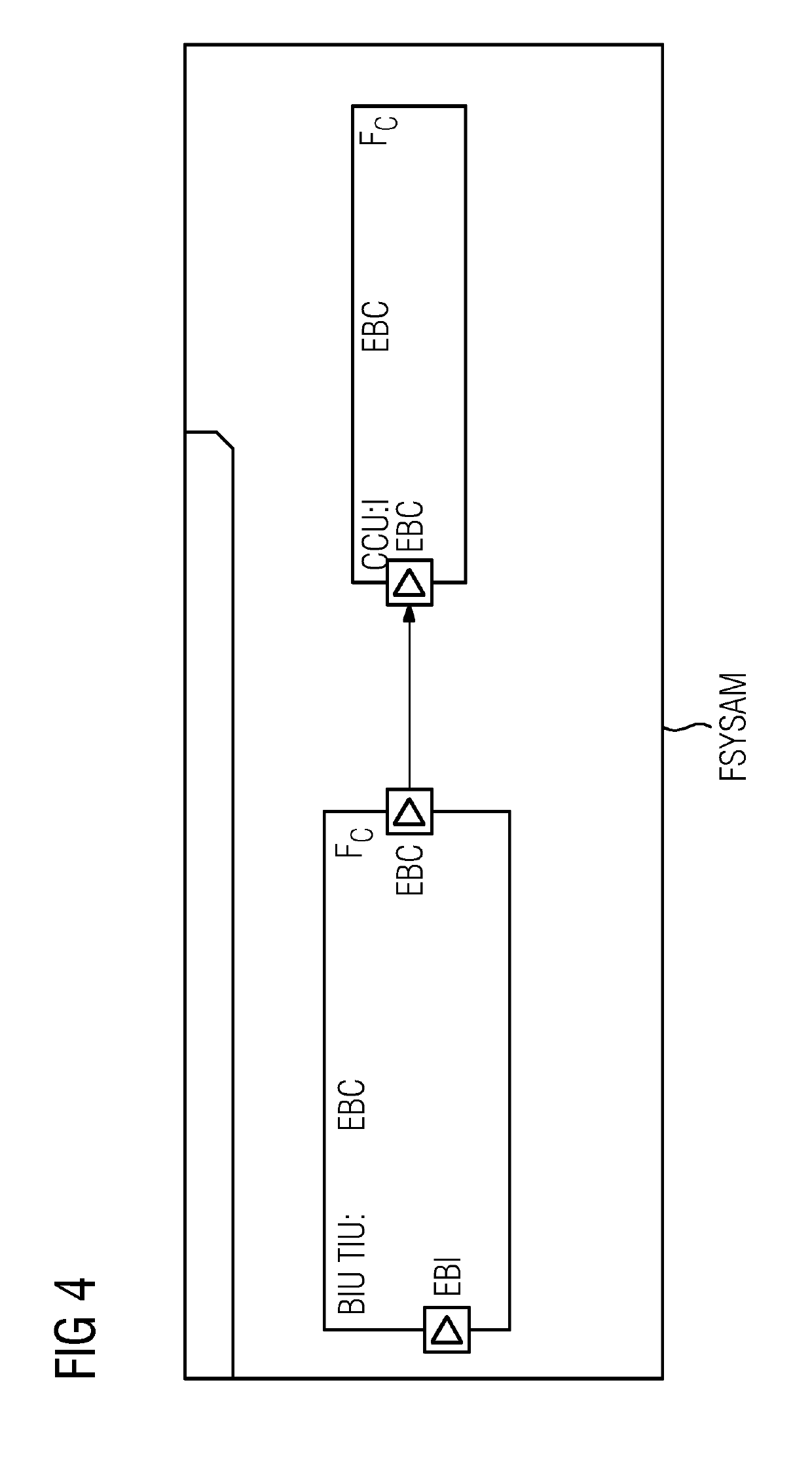
Automated Recertification of a Safety Critical System
A method for automated recertification of a safety critical system with at least one altered functionality is provided. The method includes providing a failure propagation model of the safety critical system. The method also includes updating the failure propagation model of the safety critical system according to the at least one altered functionality using inner port dependency traces between inports and outports of a failure propagation model element representing the at least one altered functionality. The method includes calculating top events of the updated failure propagation model, and comparing the calculated top events with predetermined system requirements to recertify the safety critical system.
Owner:SIEMENS AG
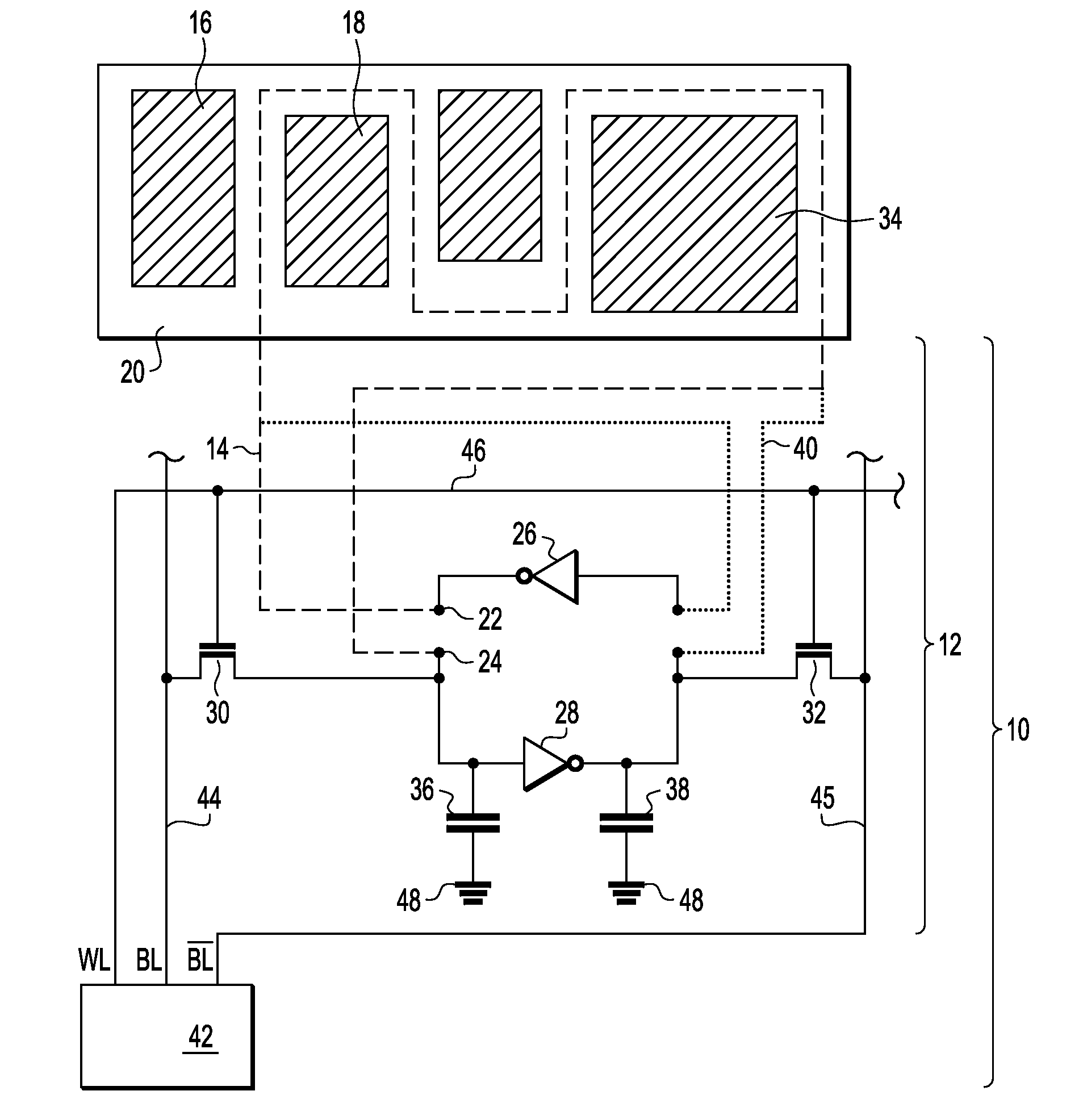
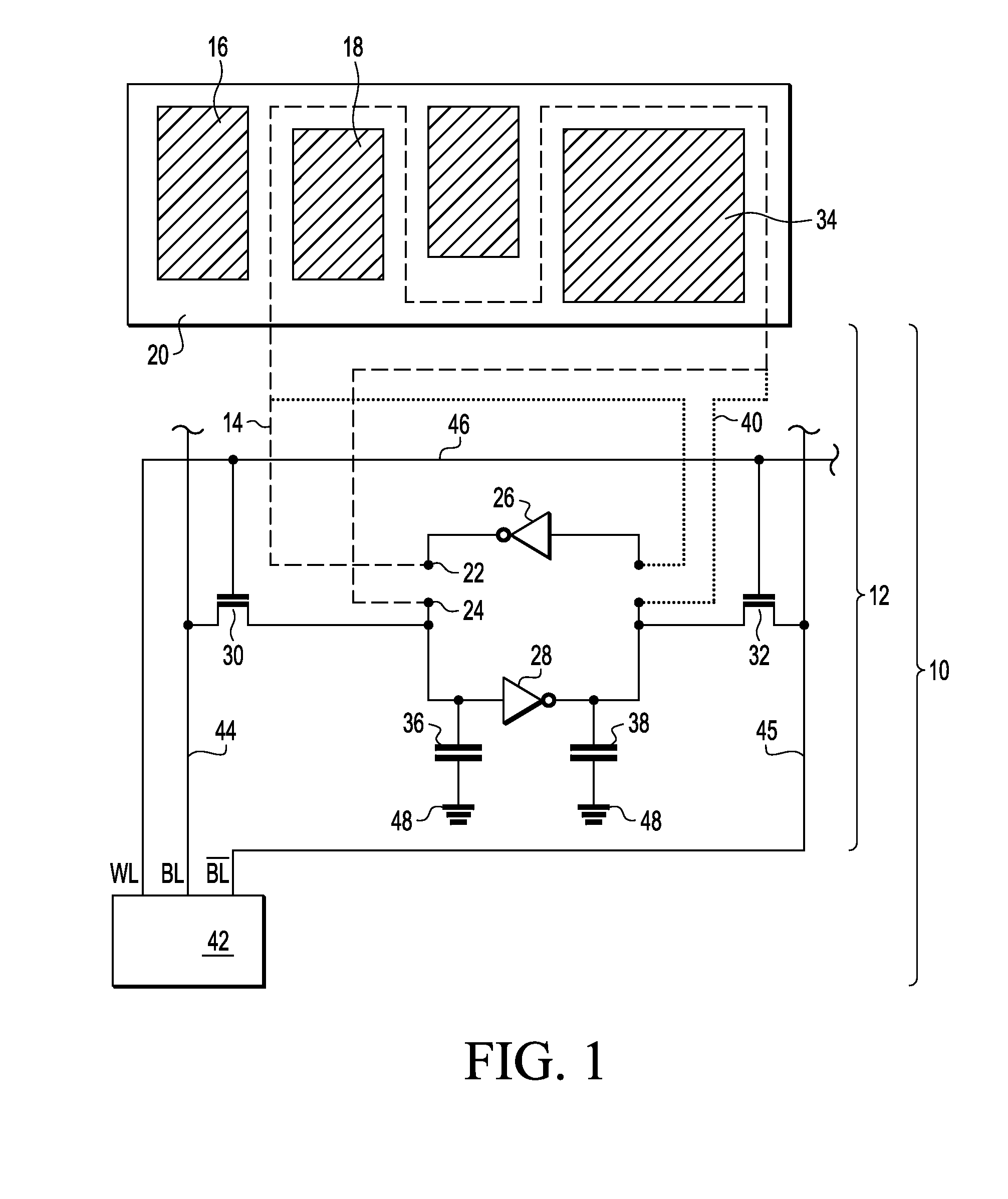
Chip damage detection device for a semiconductor integrated circuit
ActiveUS9157955B2Digital circuit testingSemiconductor/solid-state device detailsBistable circuitsStable state
A chip damage detection device is provided that includes at least one bi-stable circuit having a first conductive line passing through an observed area of a semiconductor integrated circuit chip for damage monitoring of the observed area. The at least one bi-stable circuit is arranged to flip from a first stable state into a second stable state when a potential difference between a first end and a second end of the first conductive line changes or when a leakage current overdrives a state keeping current at the first conductive line. Further, a semiconductor integrated circuit device that includes the chip damage detection device and a safety critical system that includes the semiconductor integrated circuit device or the chip damage detection circuit is provided.
Owner:NXP USA INC
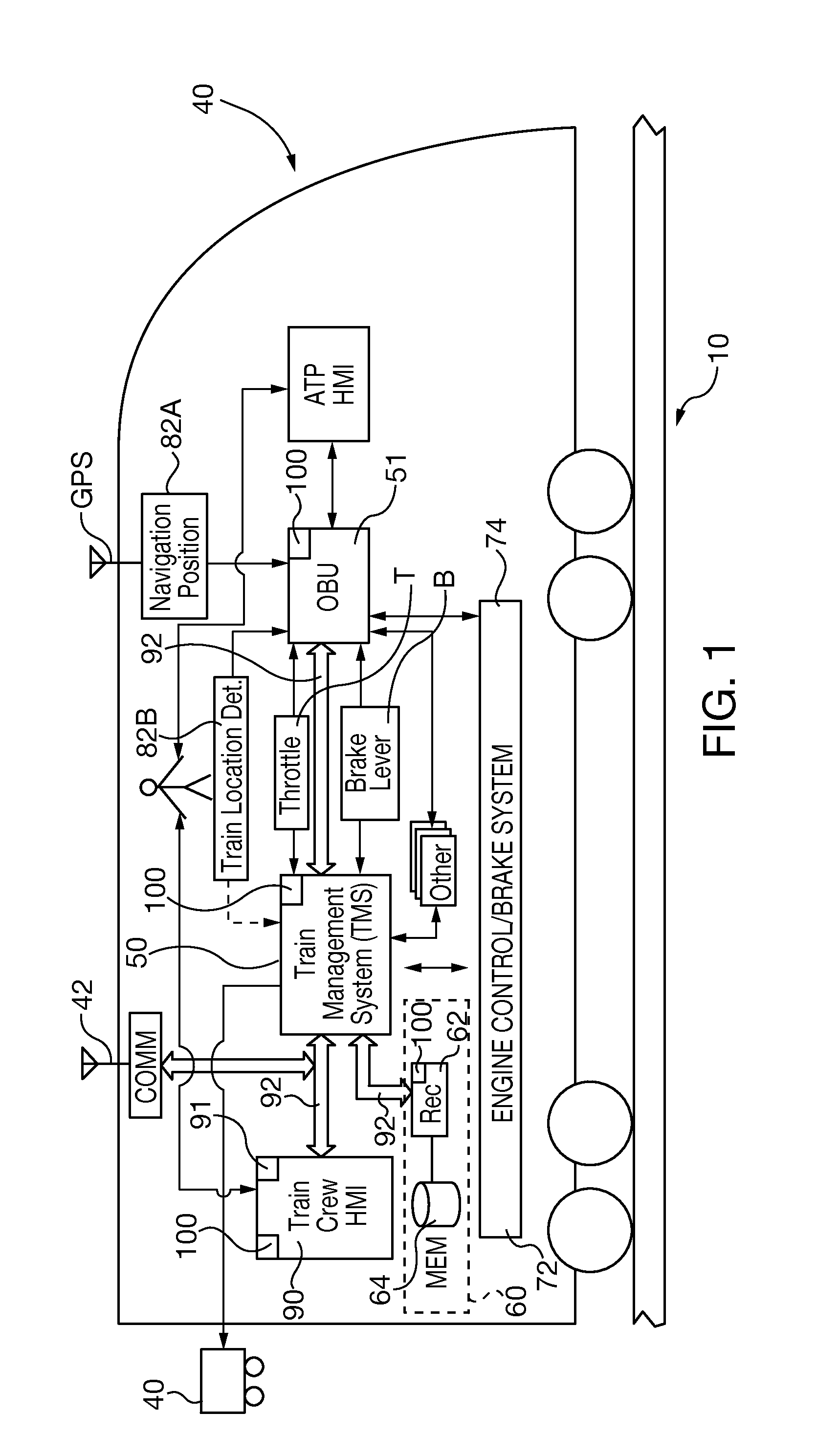
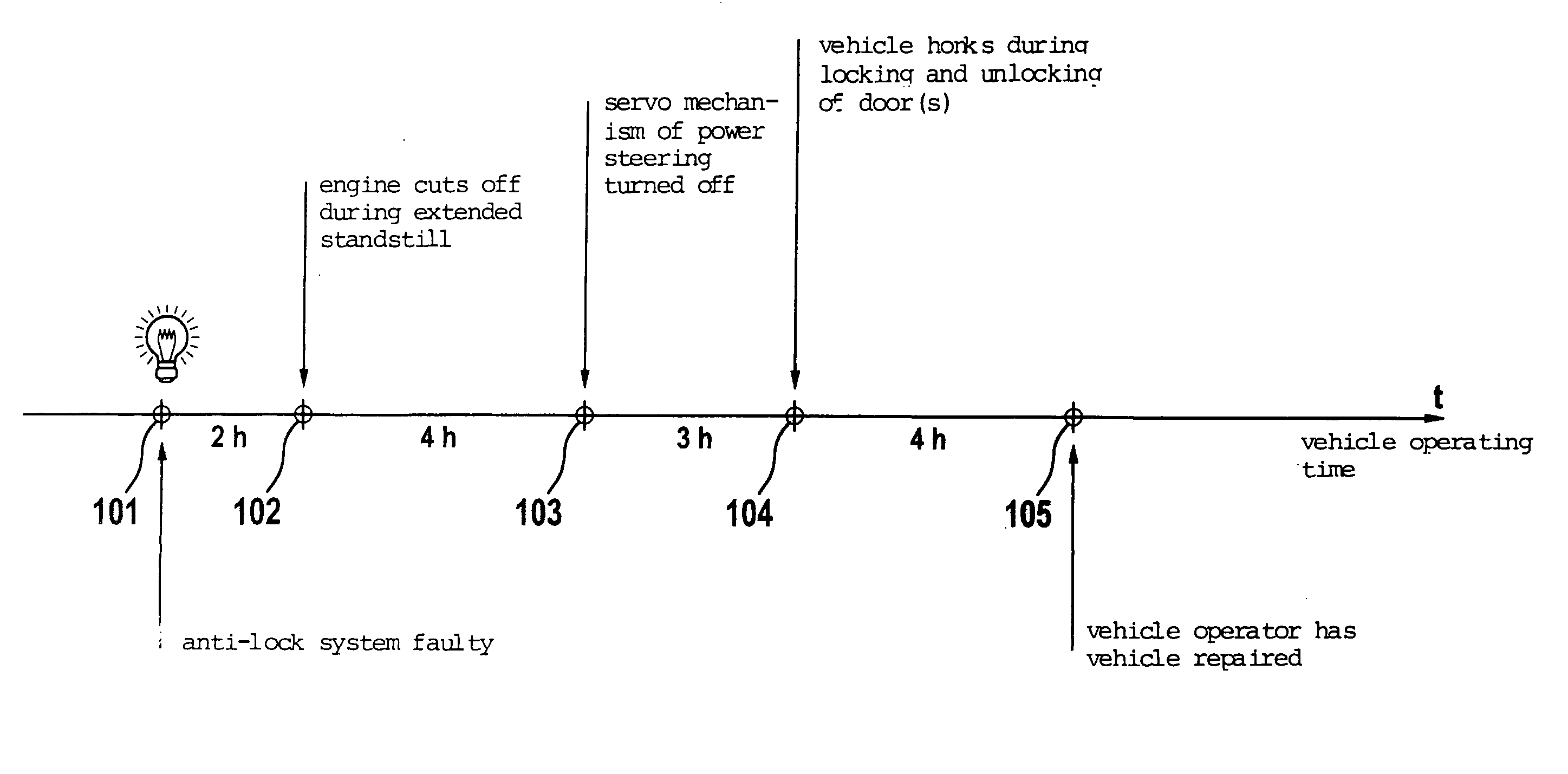
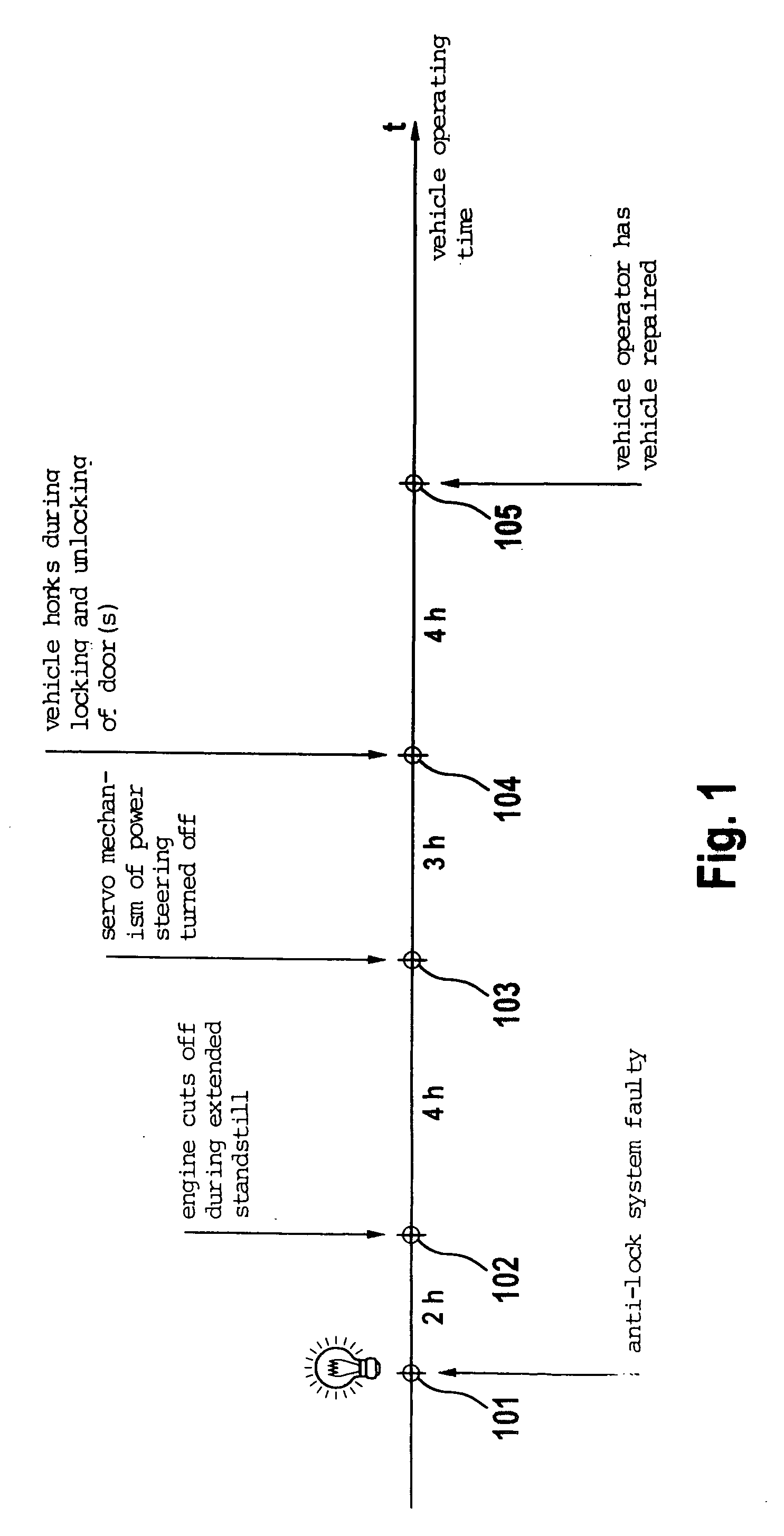
Method and device for transmitting safety-critical operating conditions of a motor vehicle
InactiveUS20060113138A1Electric devicesPedestrian/occupant safety arrangementMobile vehicleDriver/operator
The present invention relates to a method for transmitting a safety-critical operating condition of a safety-critical system of a motor vehicle to the driver, and a device for implementing the method. Transmission of a safety-critical operating condition to the driver by means of a control lamp can be disrupted if the control lamp is broken or the driver ignores the control lamp. To this end, measures are provided which reduce the driving comfort of the driver and draw his attention to the safety-critical operating condition.
Owner:CONTINENTAL TEVES AG & CO OHG
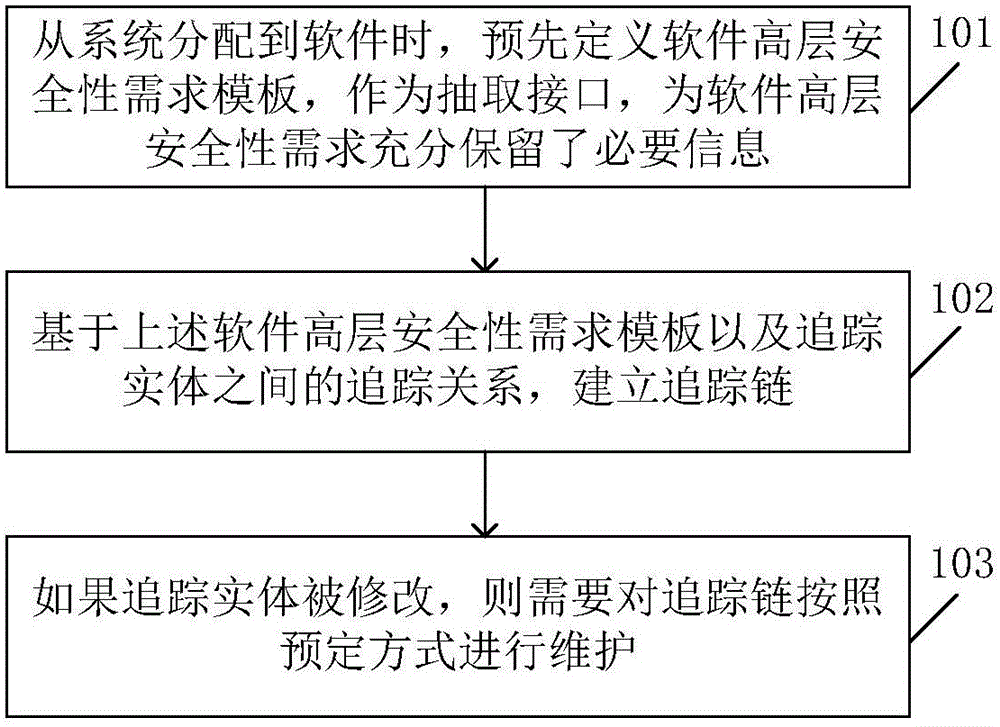
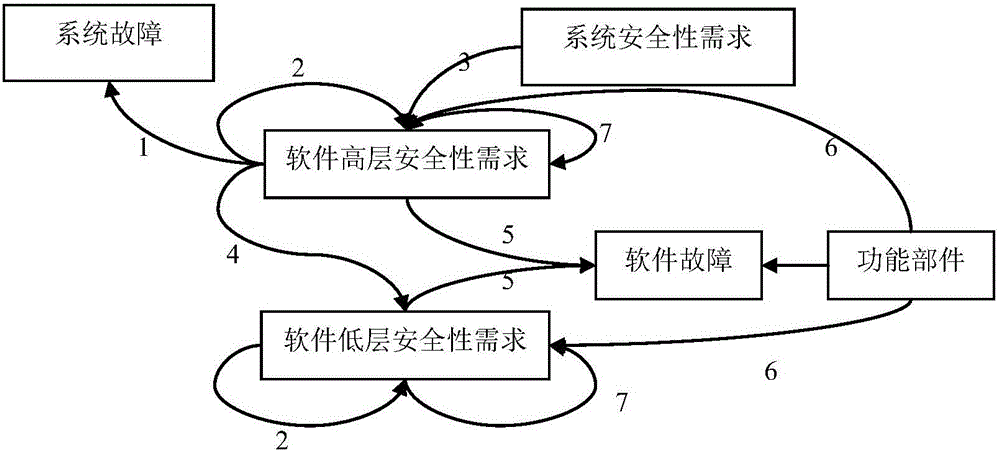
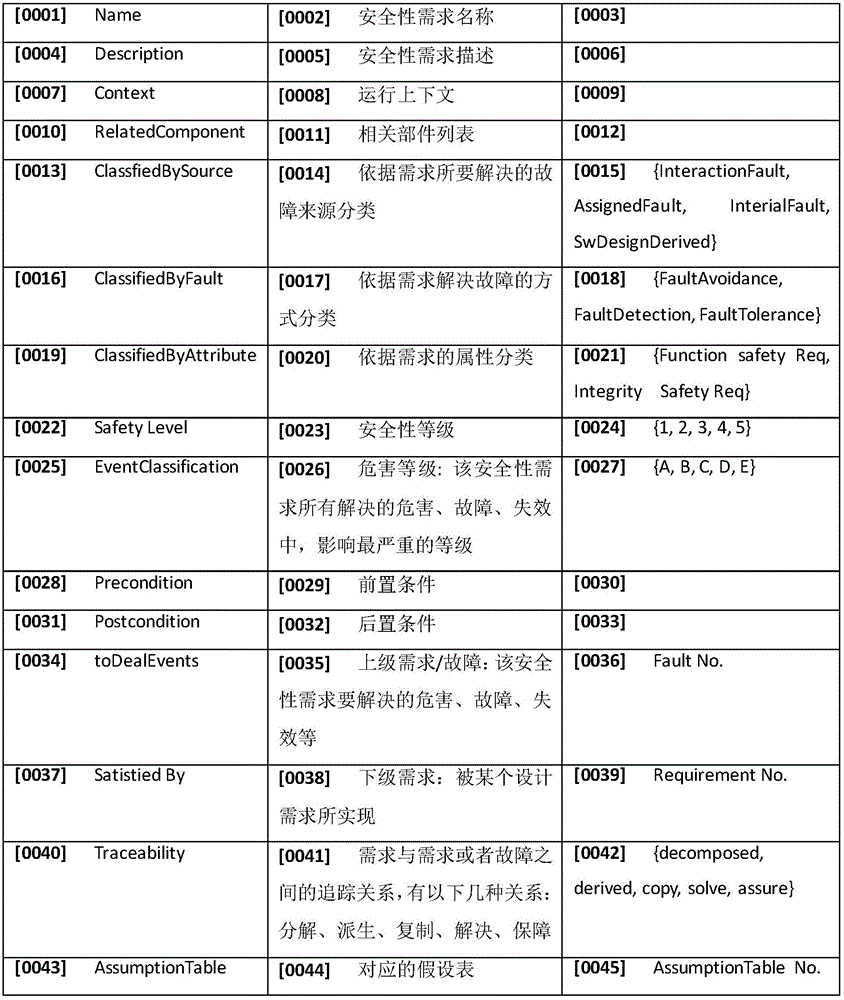
Airborne safety-critical system security requirement tracking chain establishment and maintenance method
ActiveCN105955719ASolve the problem of not describing the elements of software securityEmphasize entitiesReverse engineeringPlatform integrity maintainanceSystem safetyComputer security
The invention relates to an airborne safety-critical system security requirement tracking chain establishment and maintenance method comprising the following steps: preliminarily defining a software high level security requirement template when system distributes to software; building a tracking chain according to the software high level security requirement template and a preliminarily defined tracking entity. The method can keep sufficient information in a process in which system security requirement is distributed to software high level security requirement; the method can solve the problems that a present software high level requirement template cannot describe software security essential factors; the method provides a tracking chain build model, considers software different level (from high level to low level) requirements and tracking relation between requirements, and emphasizes to-be-tracked entities and relations in a parse process; the method can provide basis for parsing security requirement consistency and integrity, and verifying whether the security requirement is satisfied or not.
Owner:BEIHANG UNIV
Chip damage detection device for a semiconductor integrated circuit
ActiveUS20120286269A1Semiconductor/solid-state device detailsSolid-state devicesBistable circuitsStable state
A chip damage detection device is provided that includes at least one bi-stable circuit having a first conductive line passing through an observed area of a semiconductor integrated circuit chip for damage monitoring of the observed area. The at least one bi-stable circuit is arranged to flip from a first stable state into a second stable state when a potential difference between a first end and a second end of the first conductive line changes or when a leakage current overdrives a state keeping current at the first conductive line. Further, a semiconductor integrated circuit device that includes the chip damage detection device and a safety critical system that includes the semiconductor integrated circuit device or the chip damage detection circuit is provided.
Owner:NXP USA INC
Method for analyzing a physical system architecture of a safety-critical system
ActiveUS20190138416A1Testing/monitoring control systemsReliability/availability analysisFailure ratePhysical system
Provided is a method for analyzing and designing a physical system architecture of a safety-critical system, wherein a physical system analysis model representing the physical system architecture of the safety-critical system is modified incrementally until calculated failure rates of failure modes of the physical system analysis model are less or equal to failure rates of corresponding failure modes of a functional system analysis model representing a functional system architecture of the safety-critical system.
Owner:SIEMENS AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com