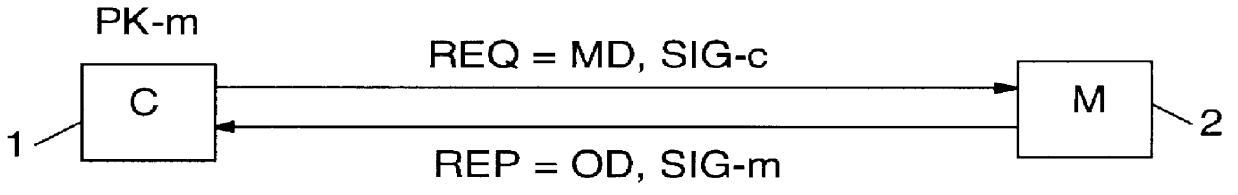Patents
Literature
105 results about "Computer network management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure anonymous information exchange in a network
InactiveUS6061789AMinimize additional effort and expenditureUser identity/authority verificationDigital data protectionSystems designData set
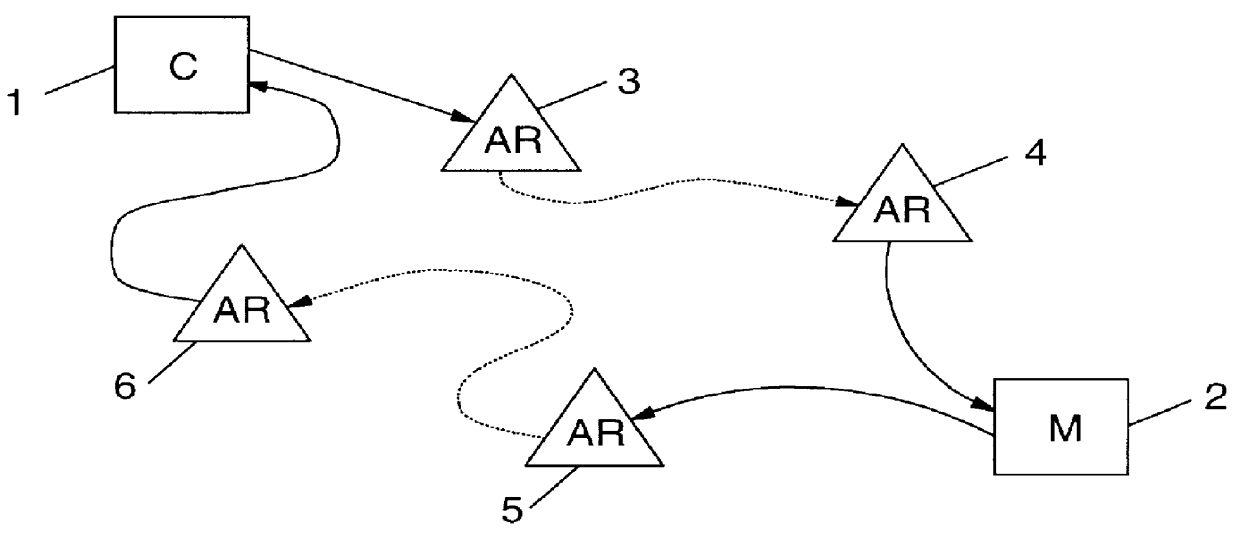
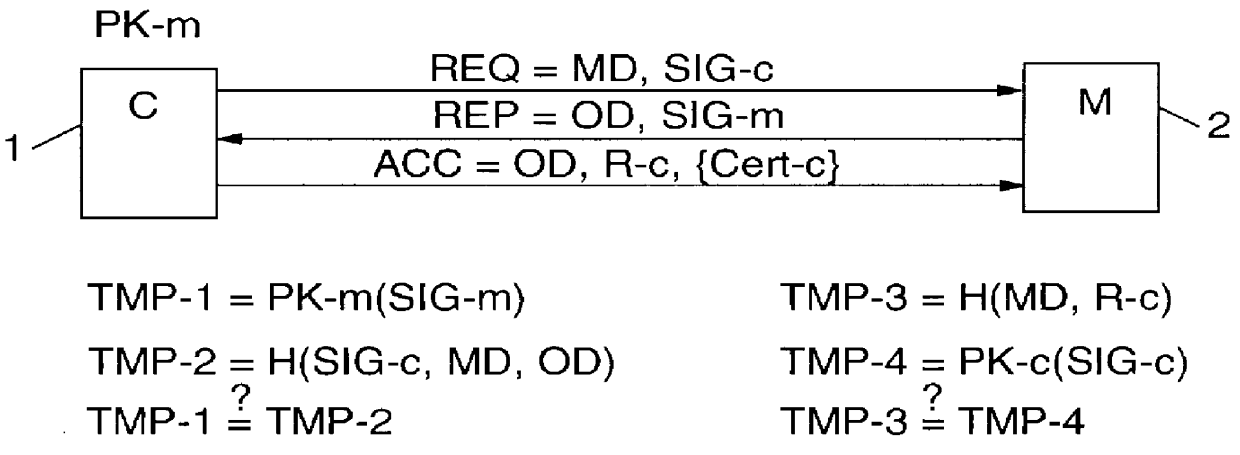
PCT No. PCT / IB96 / 00025 Sec. 371 Date Jul. 2, 1998 Sec. 102(e) Date Jul. 2, 1998 PCT Filed Jan. 12, 1996 PCT Pub. No. WO97 / 25801 PCT Pub. Date Jul. 17, 1997Computer network management for electronic commerce requires technical implementations of business processes. The process addressed here is a technical method for a communication in which two or more parties legitimately want to communicate anonymously, often before discussing a deal or closing a business, e.g. for anonymous bidding or auctioning in electronic commerce. Essentially, the invention is a method, described by a protocol, for safely exchanging data in a network that provides a public key infrastructure and an anonymous communication possibility between network users. It consists of a sequence of steps in which both sender (e.g. customer) and addressee (e.g. merchant) compose data sets (i.e., requests and replies) that are based on received data and / or prior knowledge. The data sets are enciphered to provide anonymity, and digitally signed to provide proof of the partner. The invention is also a system designed to implement the invented method.
Owner:GOOGLE LLC
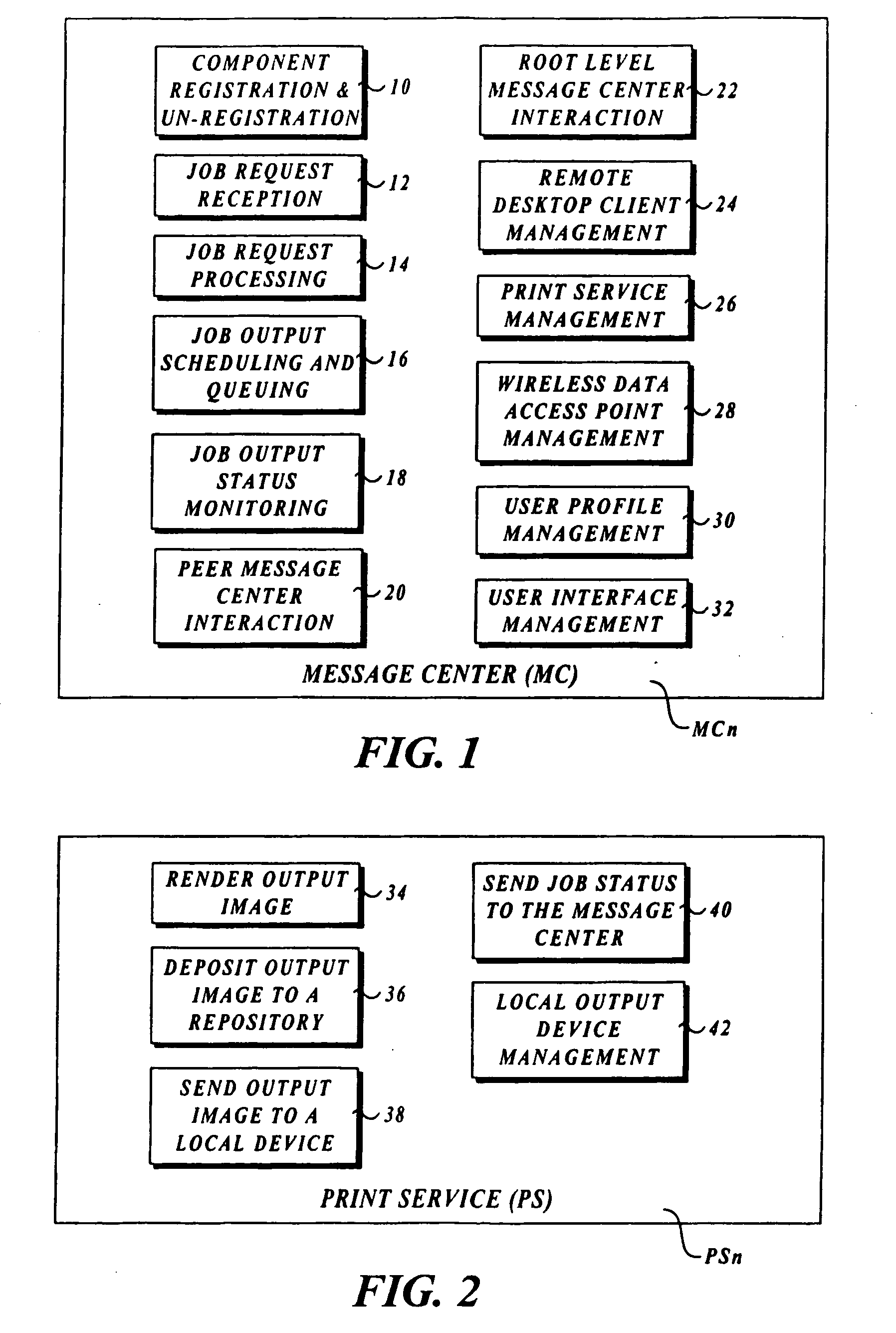
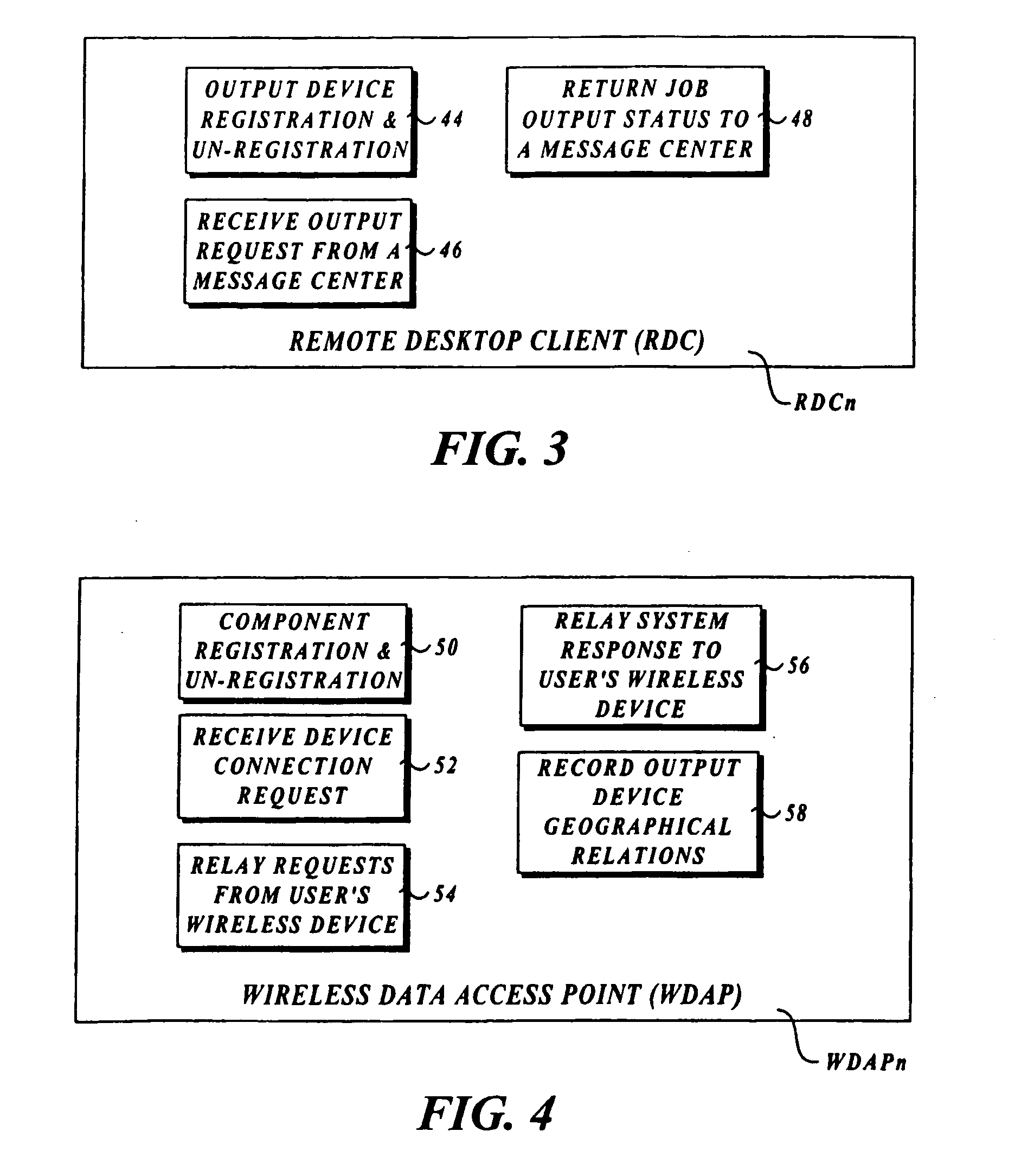
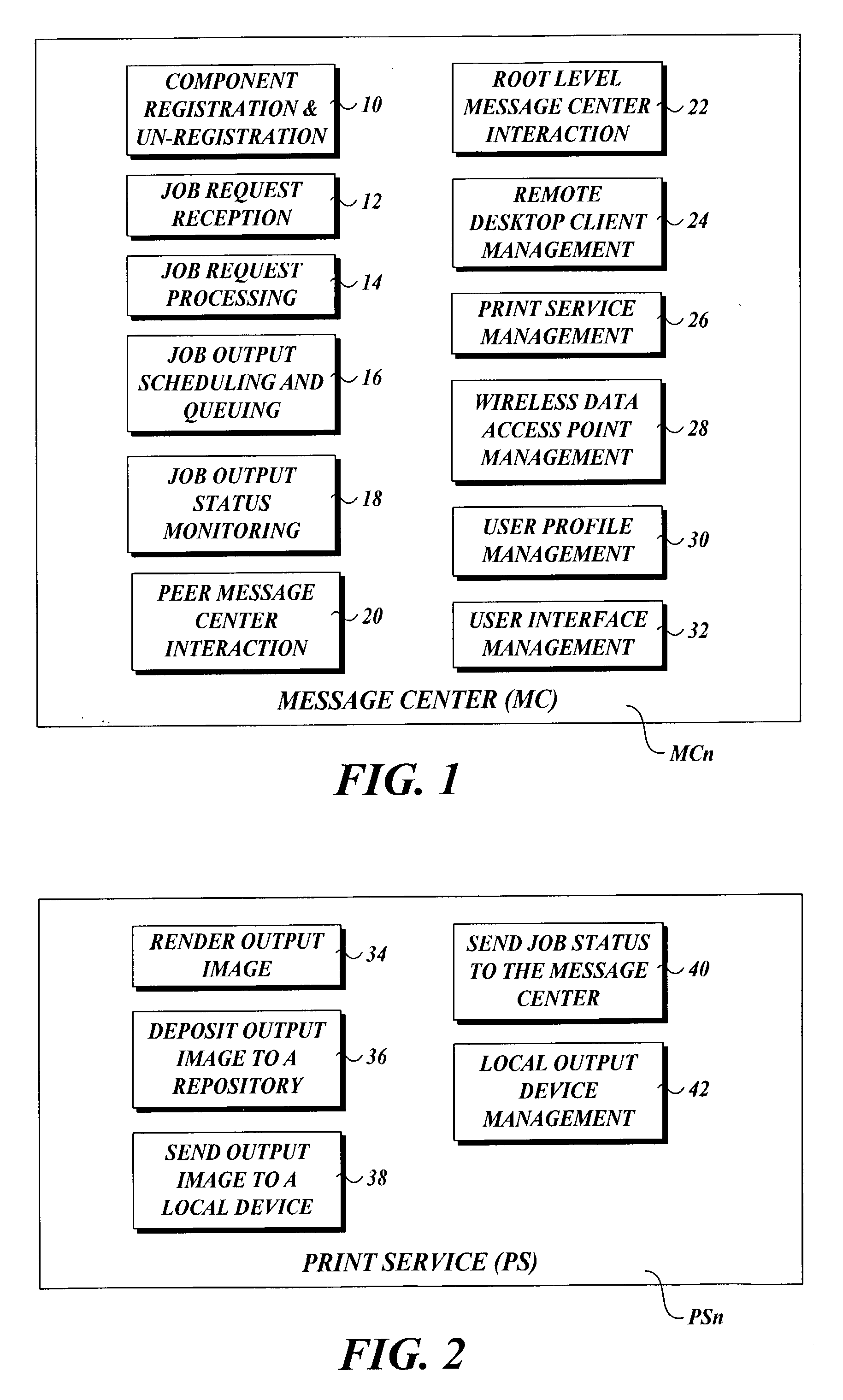
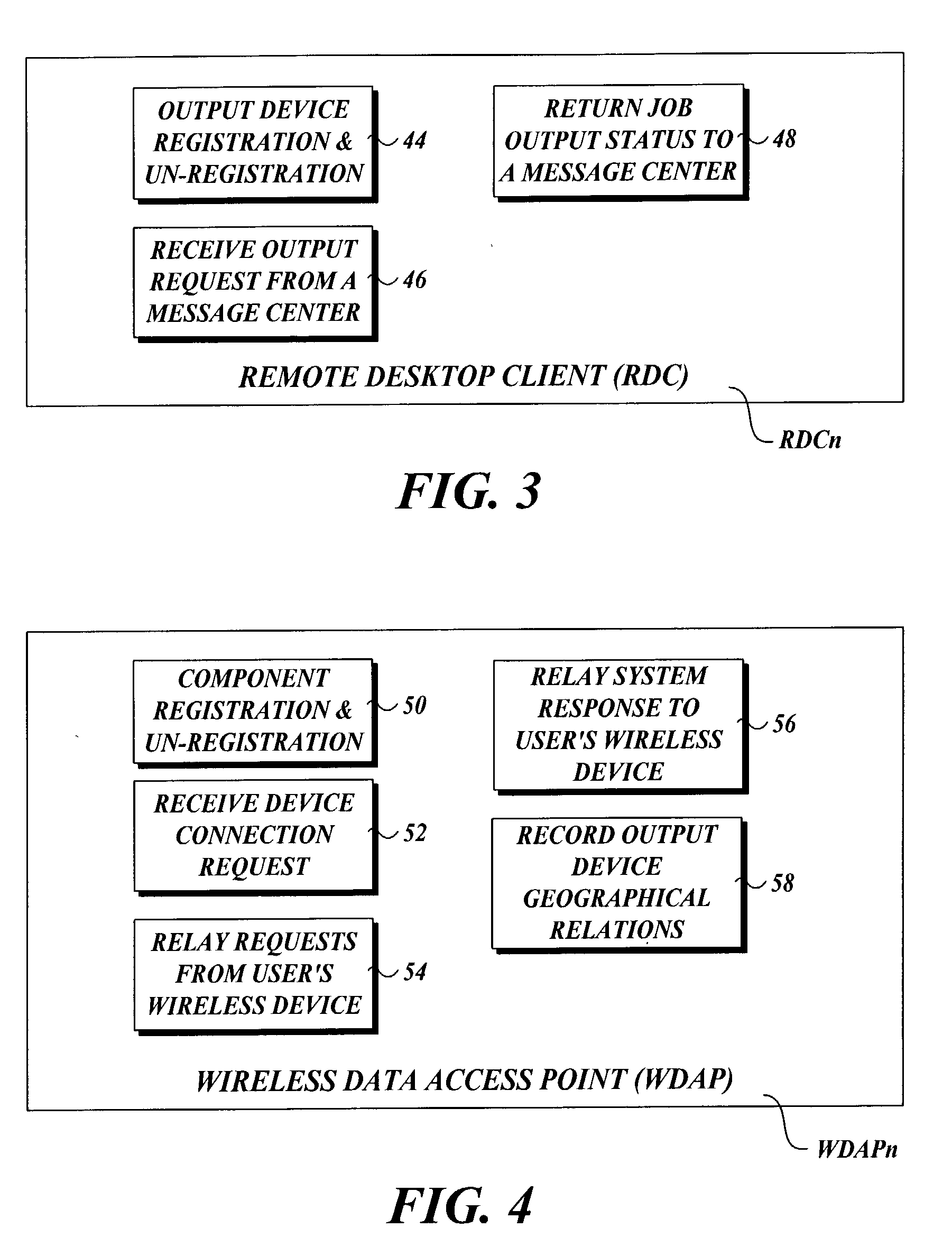
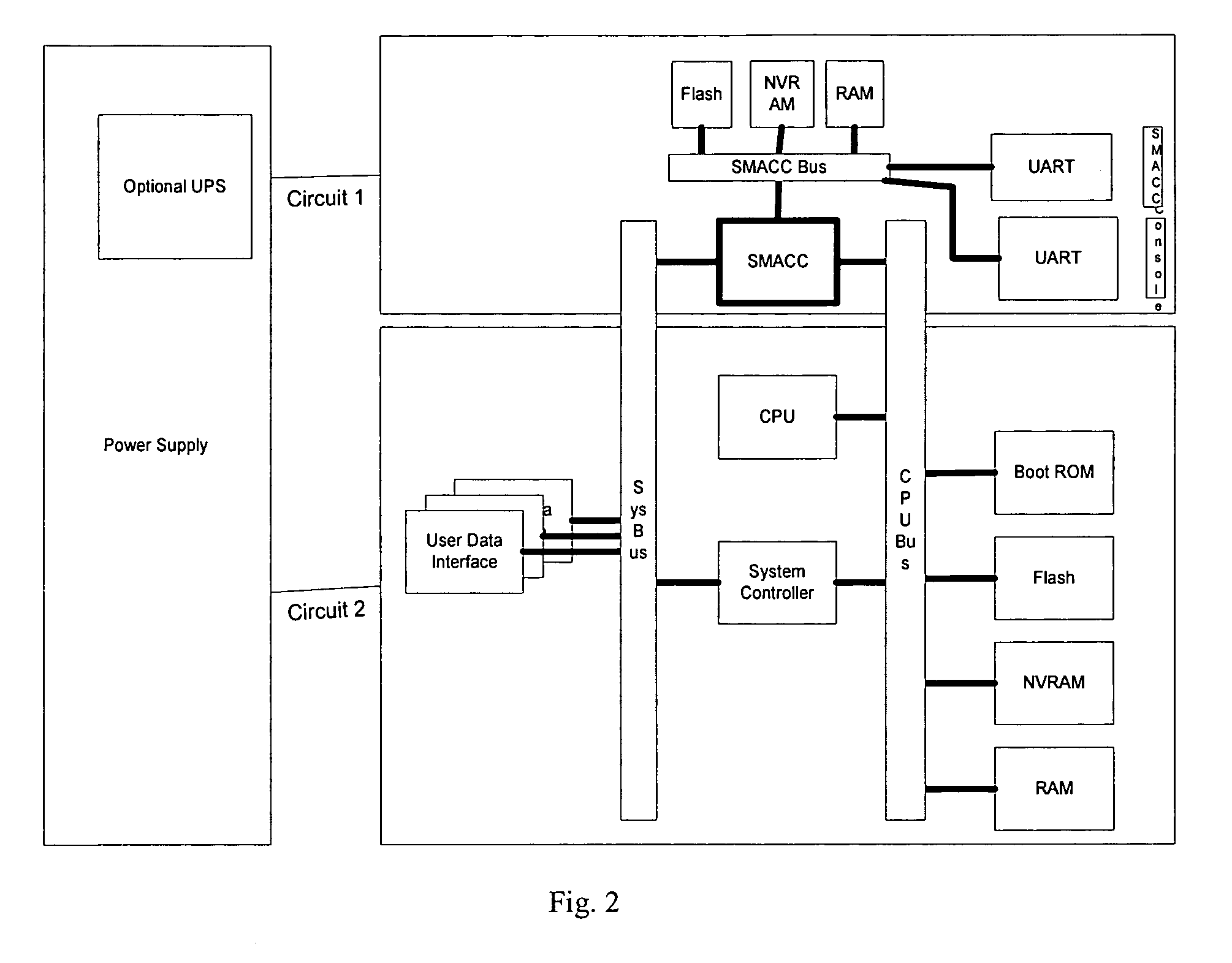
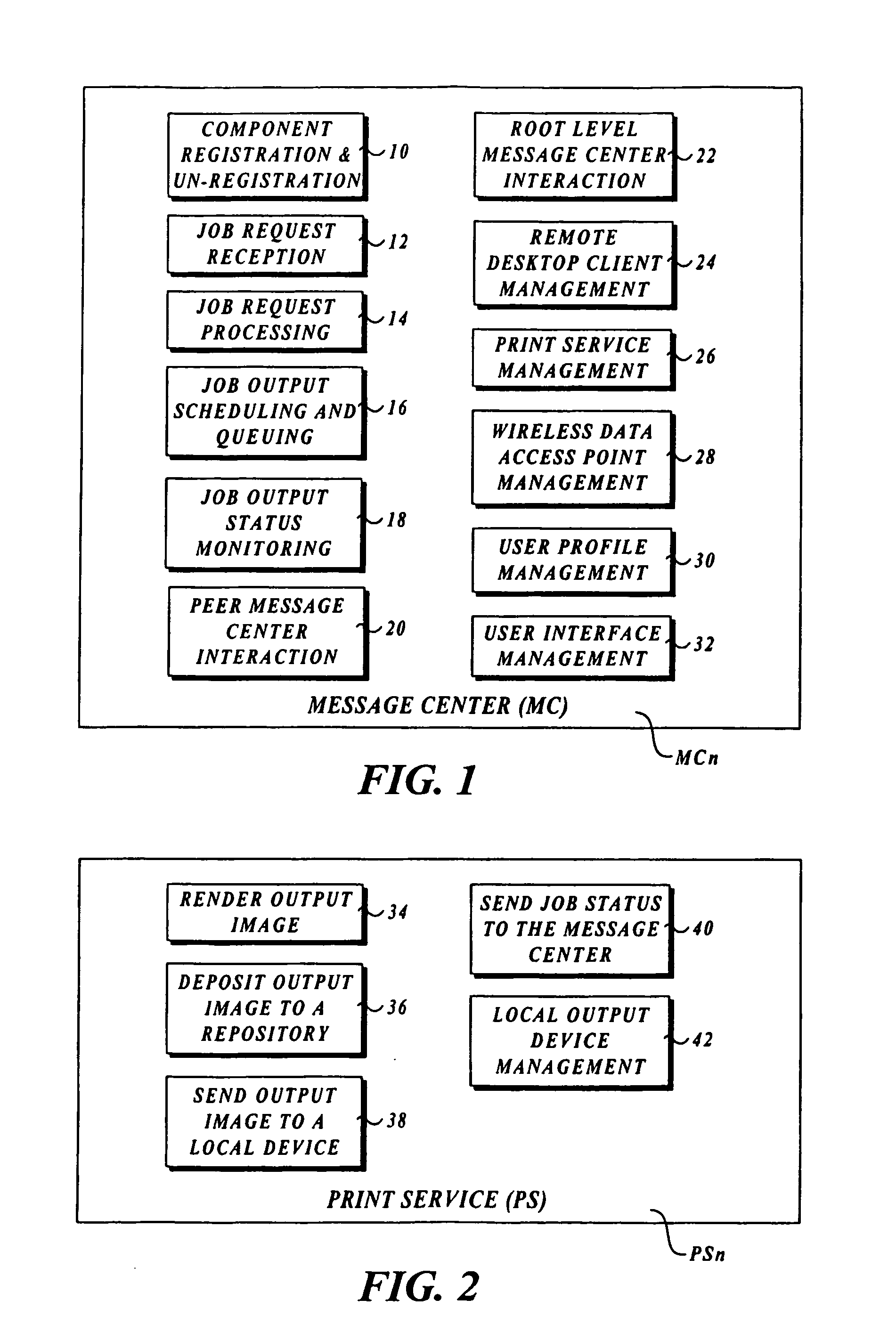
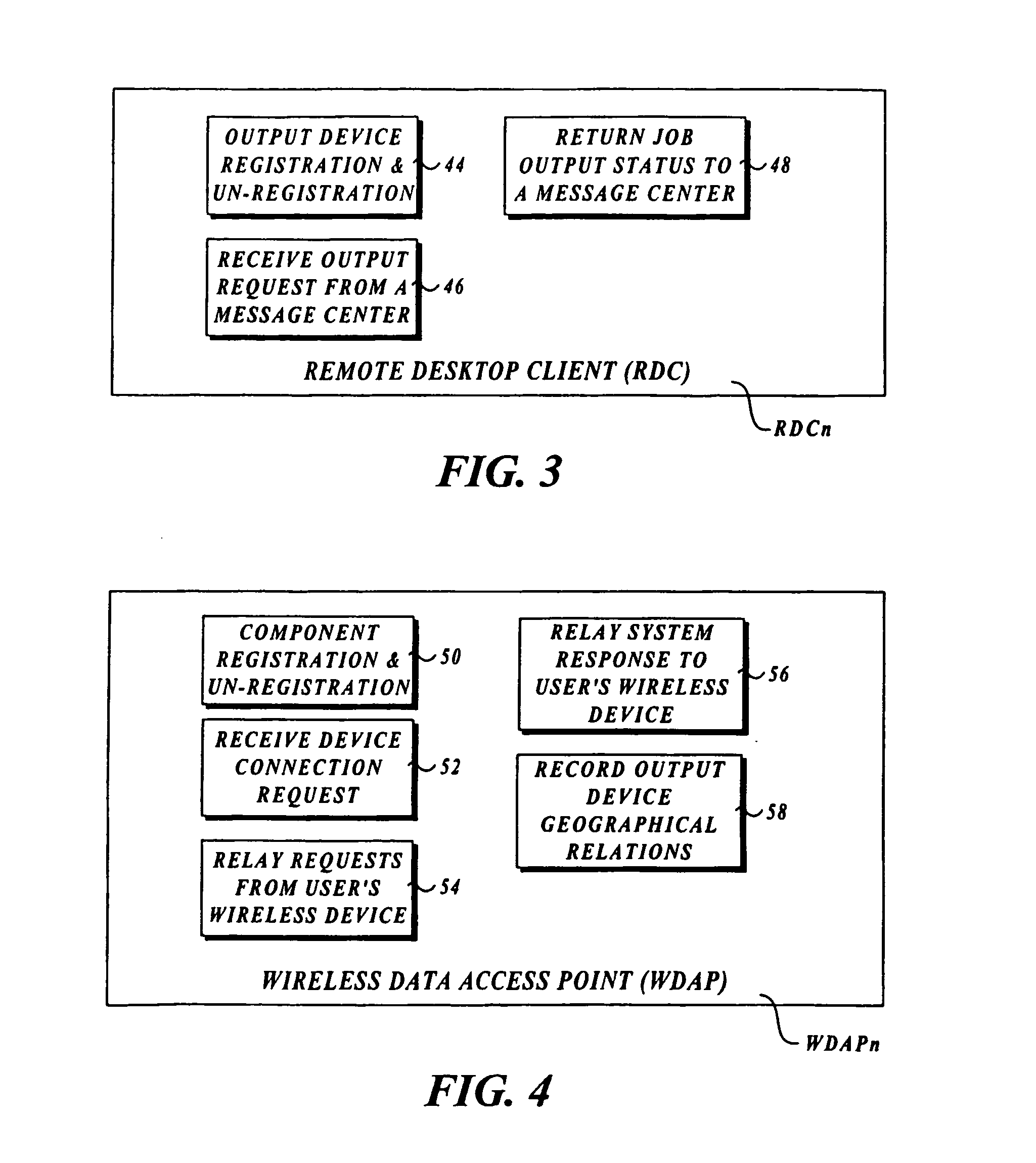
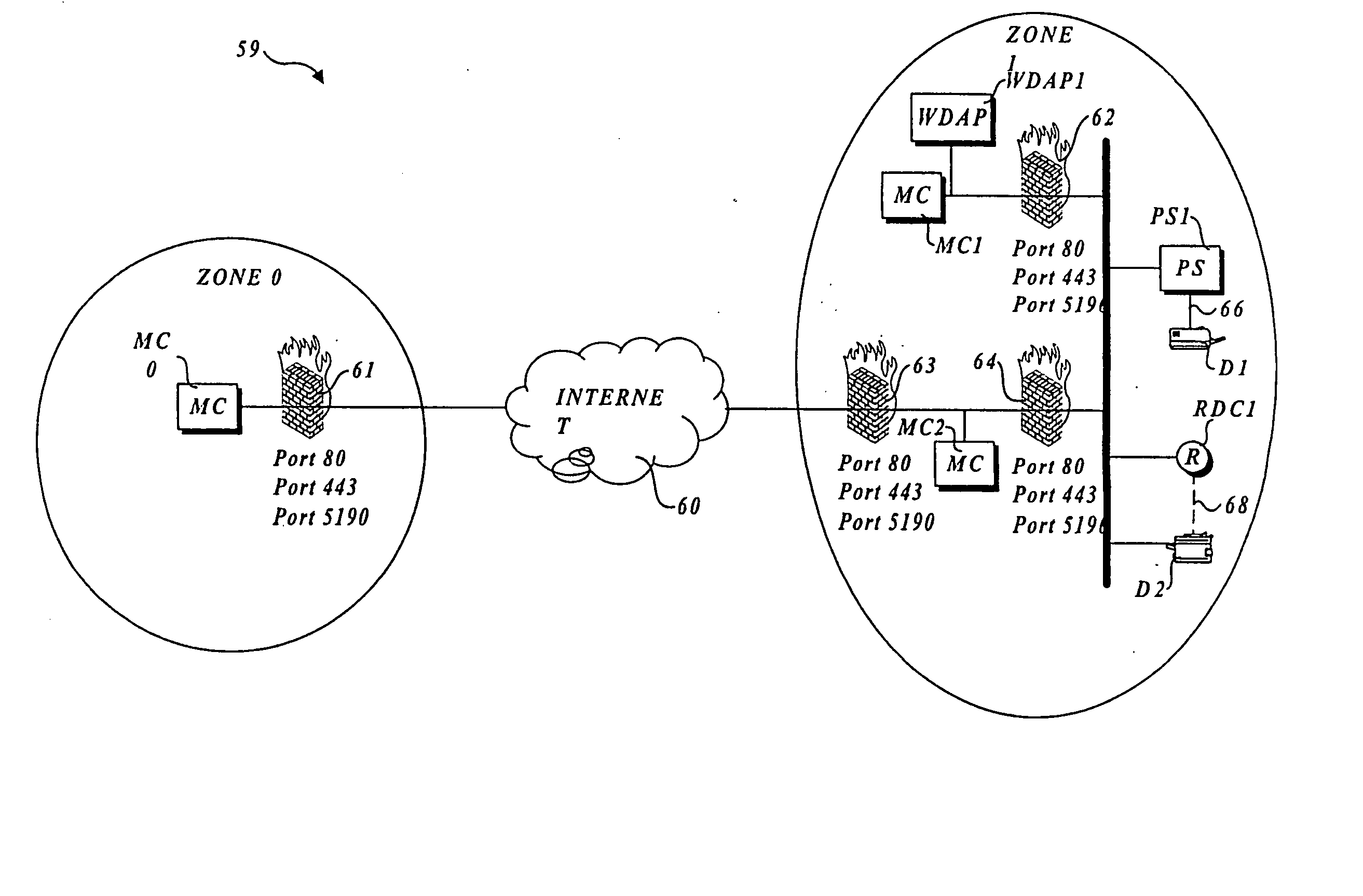
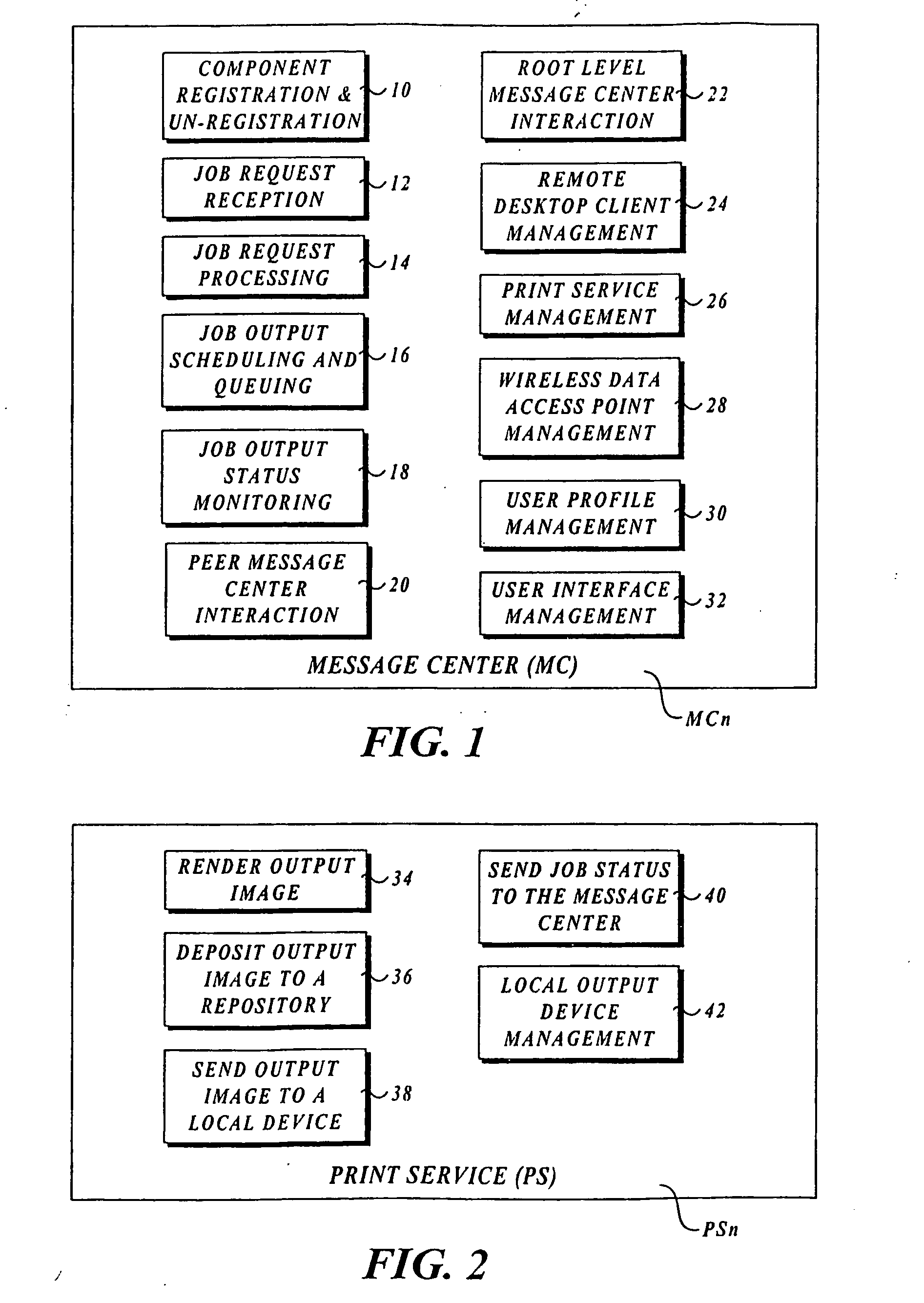
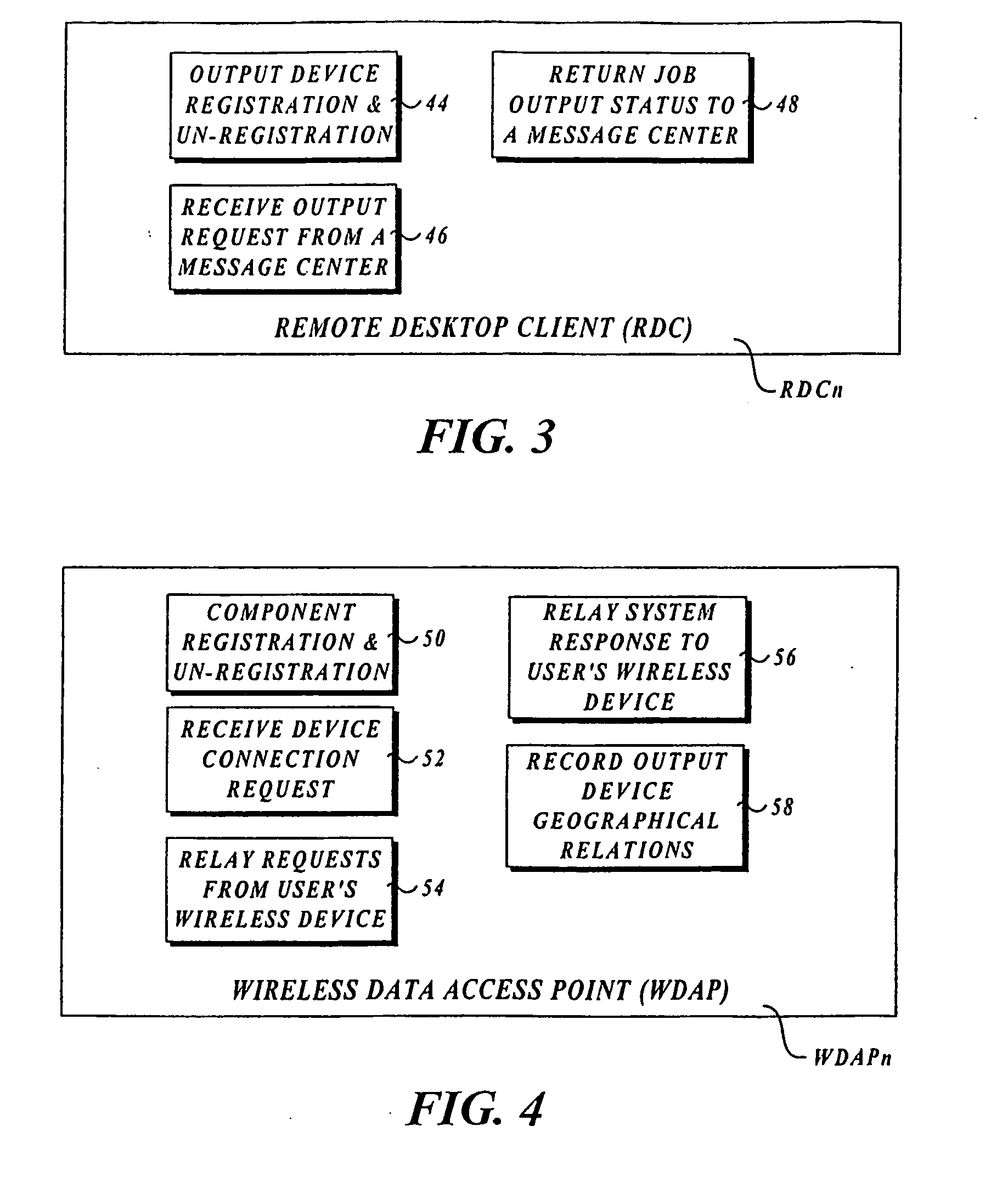
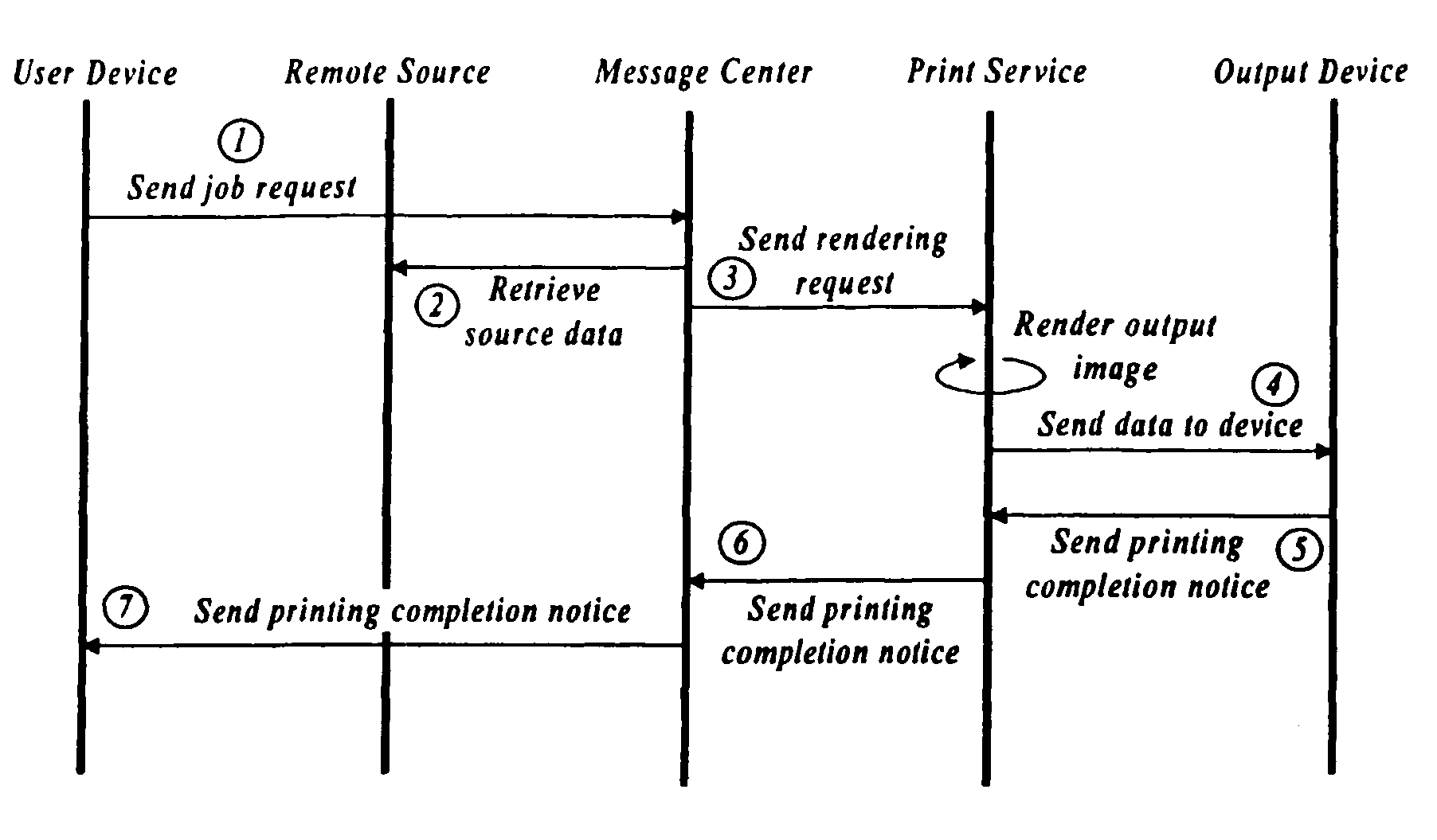
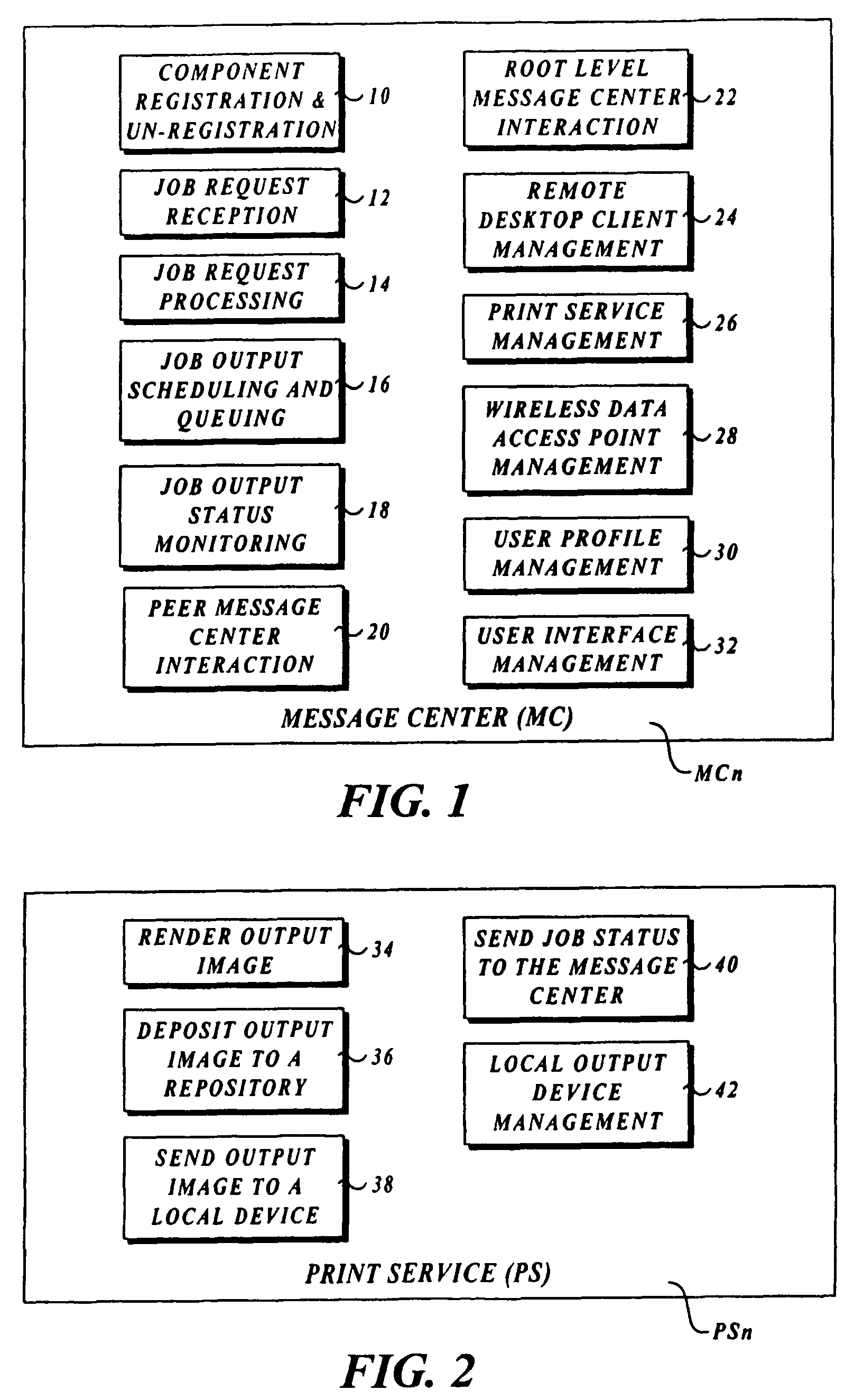
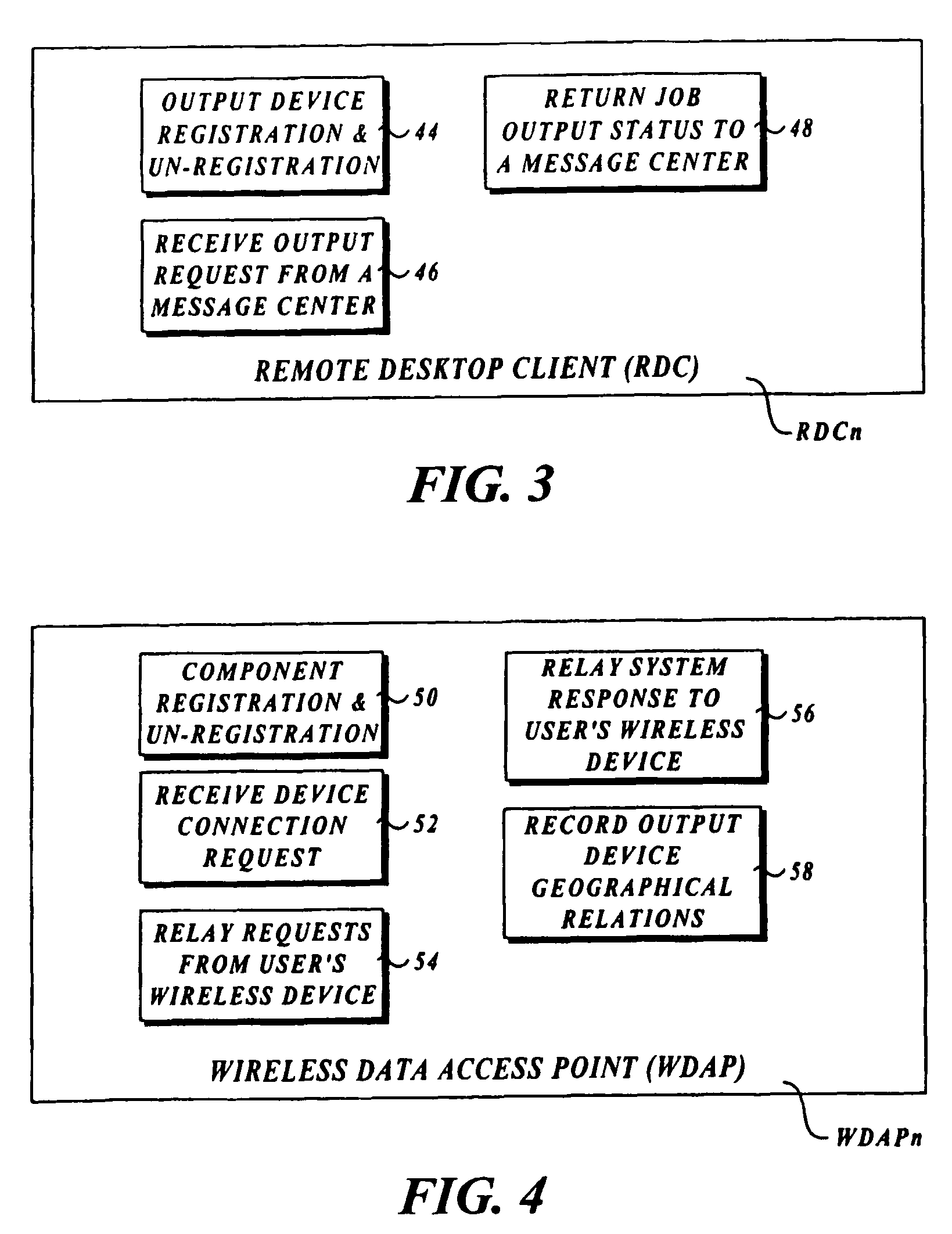
Output management system and method for enabling printing via wireless devices
InactiveUS20070022180A1Data switching by path configurationMultiple digital computer combinationsStore and forwardOutput device
A system and method for managing output such as printing, faxing, and e-mail over various types of computer networks. In one aspect, the method provides for printing via a wireless device. The system provides renderable data to the wireless device by which a user-interface (UI) may be rendered. The UI enables users to select source data and an output device on which the source data are to be printed. The source data are then retrieved from a local or remote store and forwarded to a print service, which renders output image data corresponding to the source data and the output device that was selected. The output image data are then submitted to the output device to be physically rendered. The user-interfaces enable wired and wireless devices to access the system. The system enables documents to be printed by reference, and enables access to resources behind firewalls.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
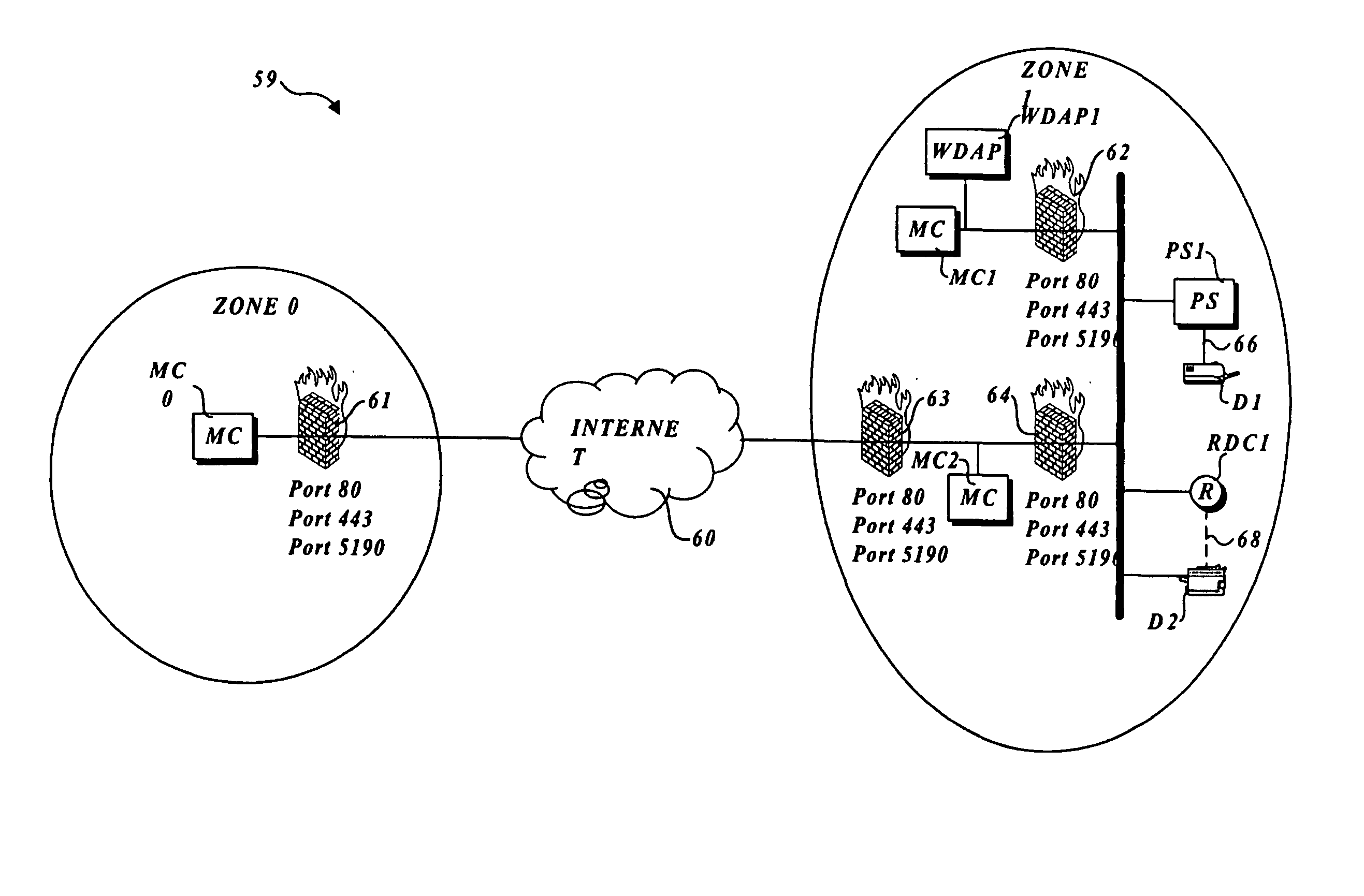
Output management system and method for enabling access to private network resources
InactiveUS20030079030A1Connection managementData switching by path configurationTelecommunications linkPrivate network
A system and method for managing output such as printing, faxing, and e-mail over various types of computer networks. In one aspect, the system and method provides for accessing print and / or document resources located on private networks behind firewalls. A pass-through communication link is established between system components located on opposing sides of a firewall. A system-served user-interface enables users to select source data and an output device on which the source data are to be printed, either or both of which may reside behind the firewall. The source data are then retrieved and forwarded to a print service, which renders output image data corresponding to the source data and the selected output device. The output image data are then submitted to the output device to be physically rendered. Access to private resources is provided by the pass-through communication link. The system also enables documents to be printed by reference.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
Distribution-based hierarchical network topology discovery method
InactiveCN102143007AEfficient Reactive Topology StatusData switching networksNetworking protocolData center
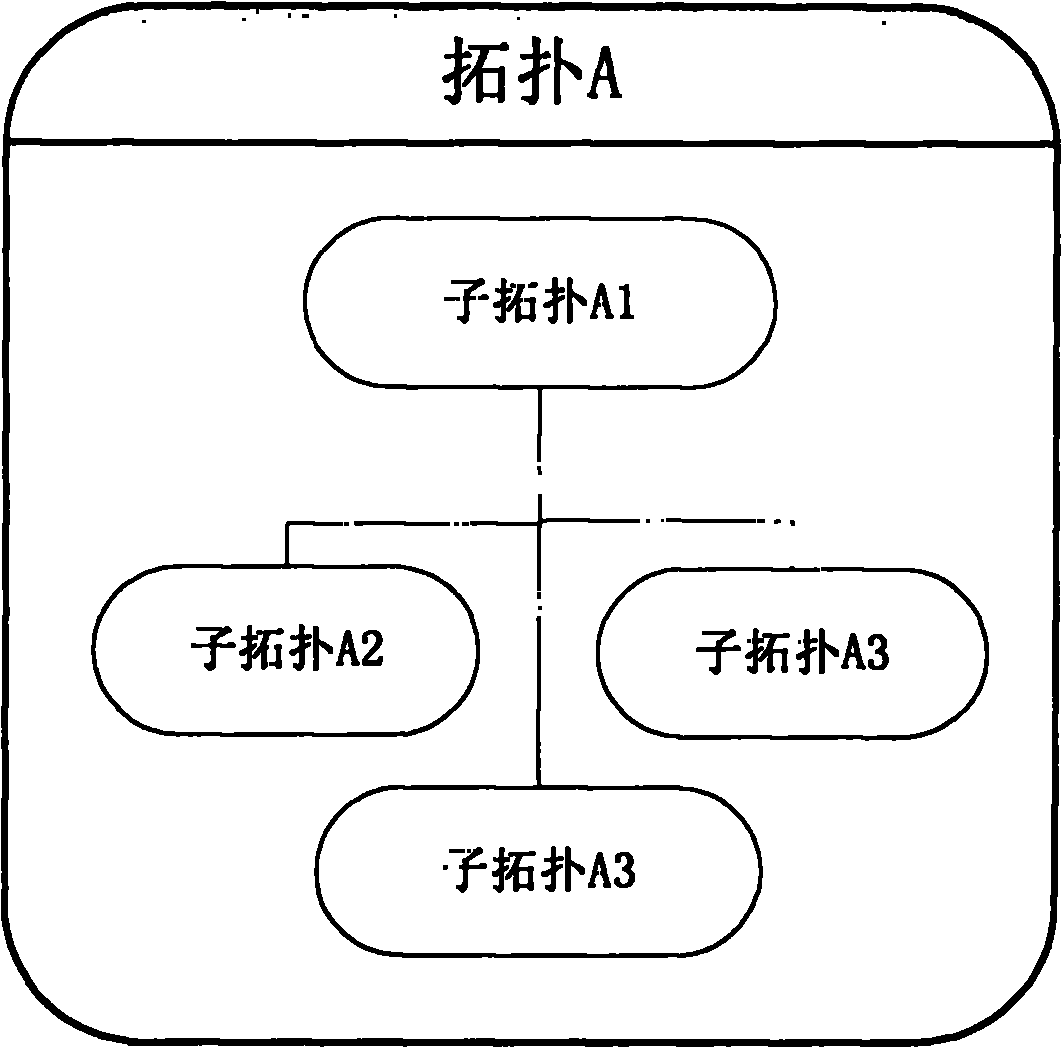
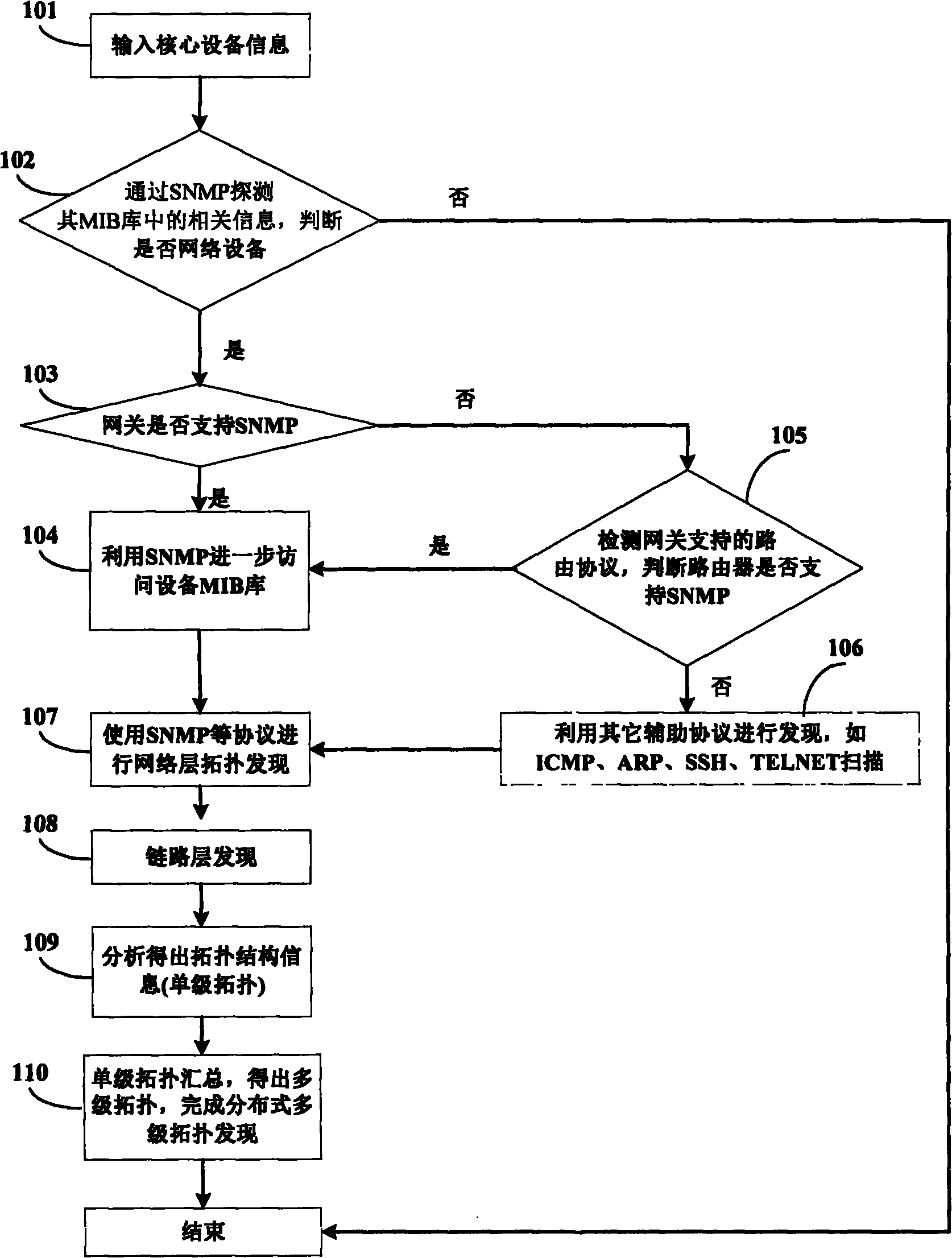
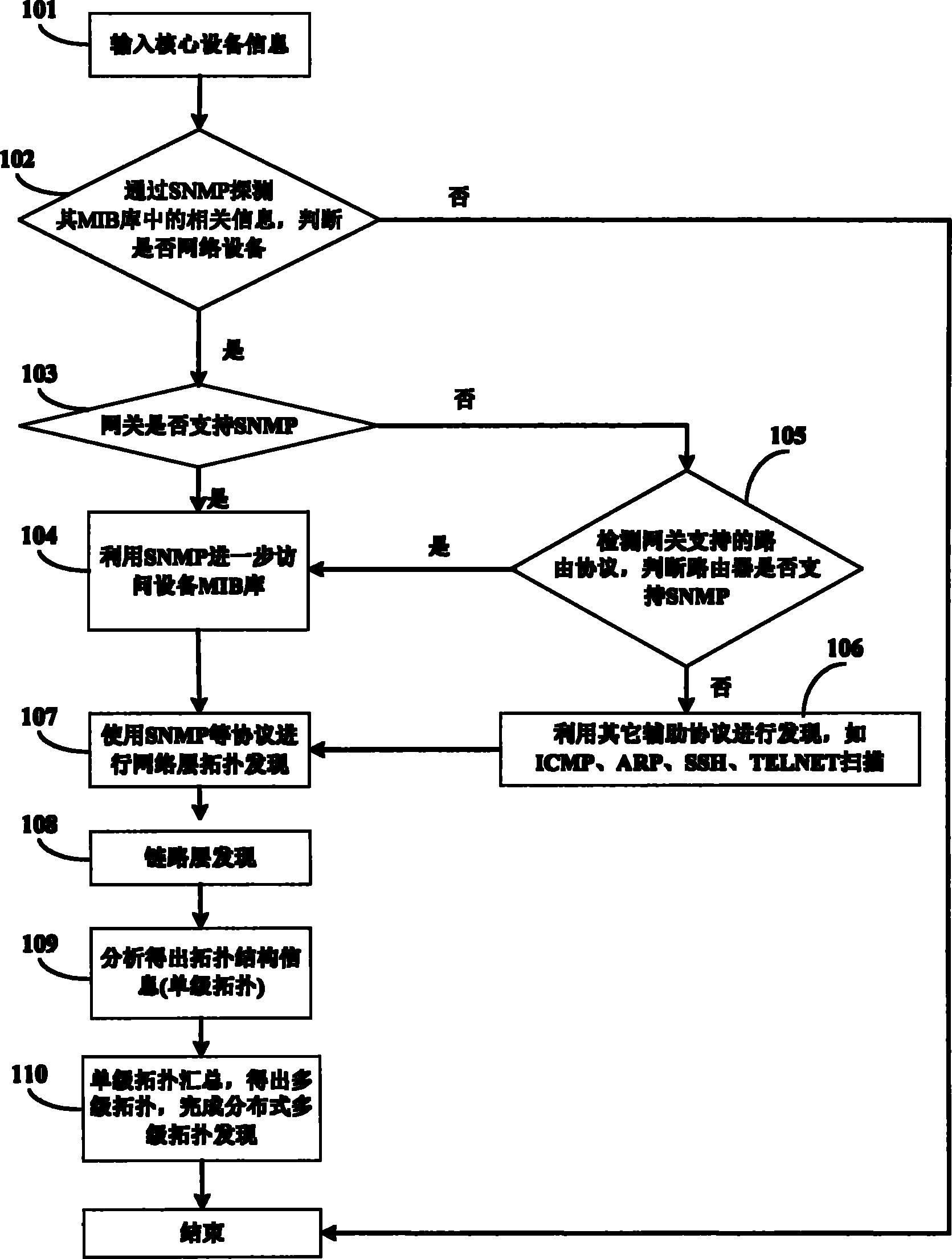
The invention discloses a distribution-based hierarchical network topology discovery method, which belongs to the field of computer network management. In the method, discovery is divided into first-level topology discovery and second-level topology discovery, wherein the first-level topology discovery is mainly the discovery of backbone routing, and comprises the discovery of connection relationships between each of routers, switches and interfaces thereof and sub-networks; and the second-level topology discovery mainly comprises the discovery of the connection relationships between each sub-network and a gateway and among different pieces of equipment in the sub-networks. The method is implemented specifically by the following steps of: dividing the whole discovery process into the two main stages of network layer topology discovery and link layer topology discovery by utilizing network protocol layering, integrating the topology discovery data of each single sub-area divided from a topological field and transmitting the data to a central data center for summarization, thereby realizing the hierarchical topology discovery of a distributed network. By the method, the dynamic tracking and updating functions of topology are provided so as to more effectively reflect the current situation of the network topology and automatically record the situations of all activities of equipment.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
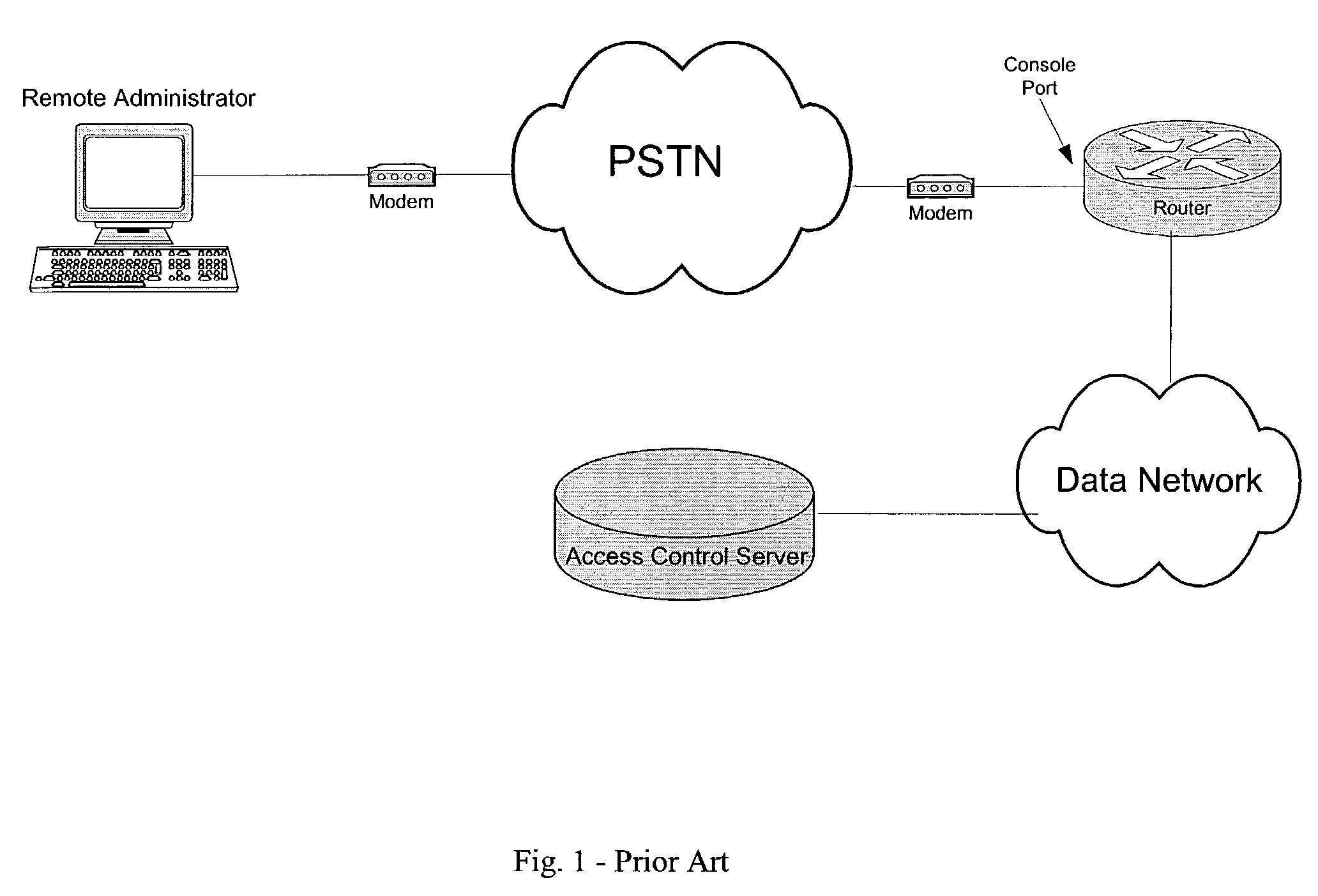
Secure management access control for computers, embedded and card embodiment
ActiveUS20050086494A1Great opportunityConvenient remote managementDigital data processing detailsMultiple digital computer combinationsDirect communicationAuthorization
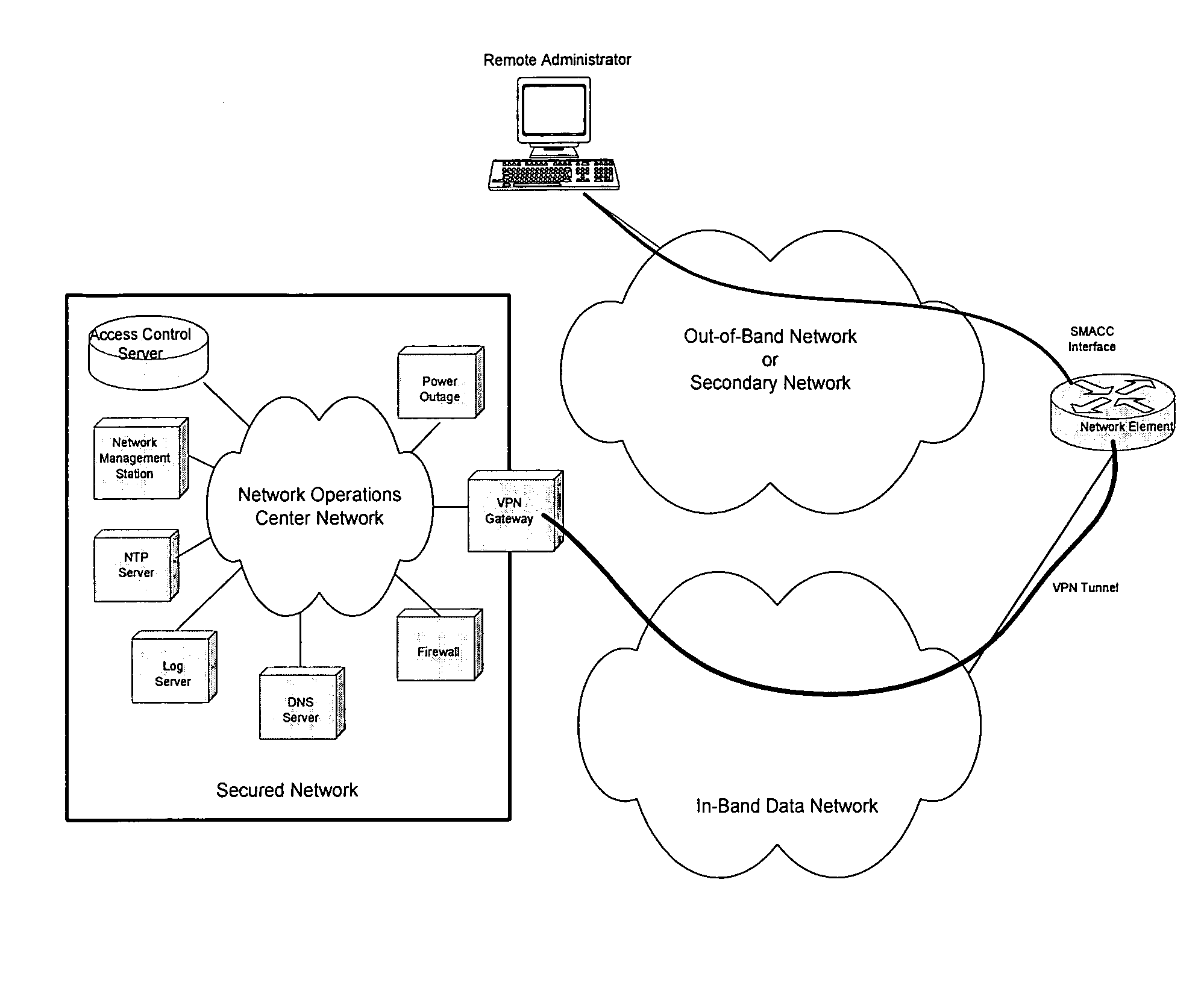
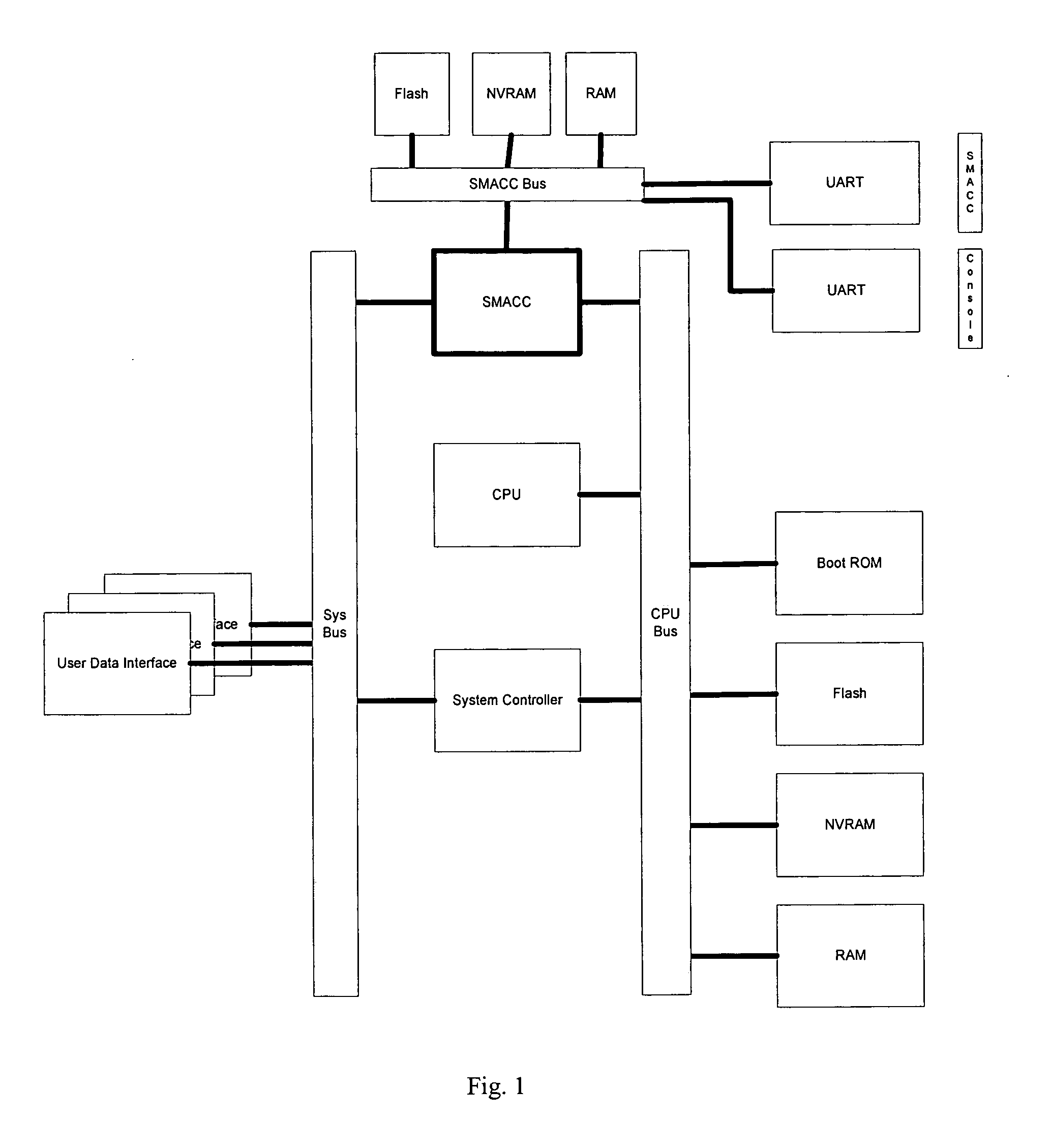
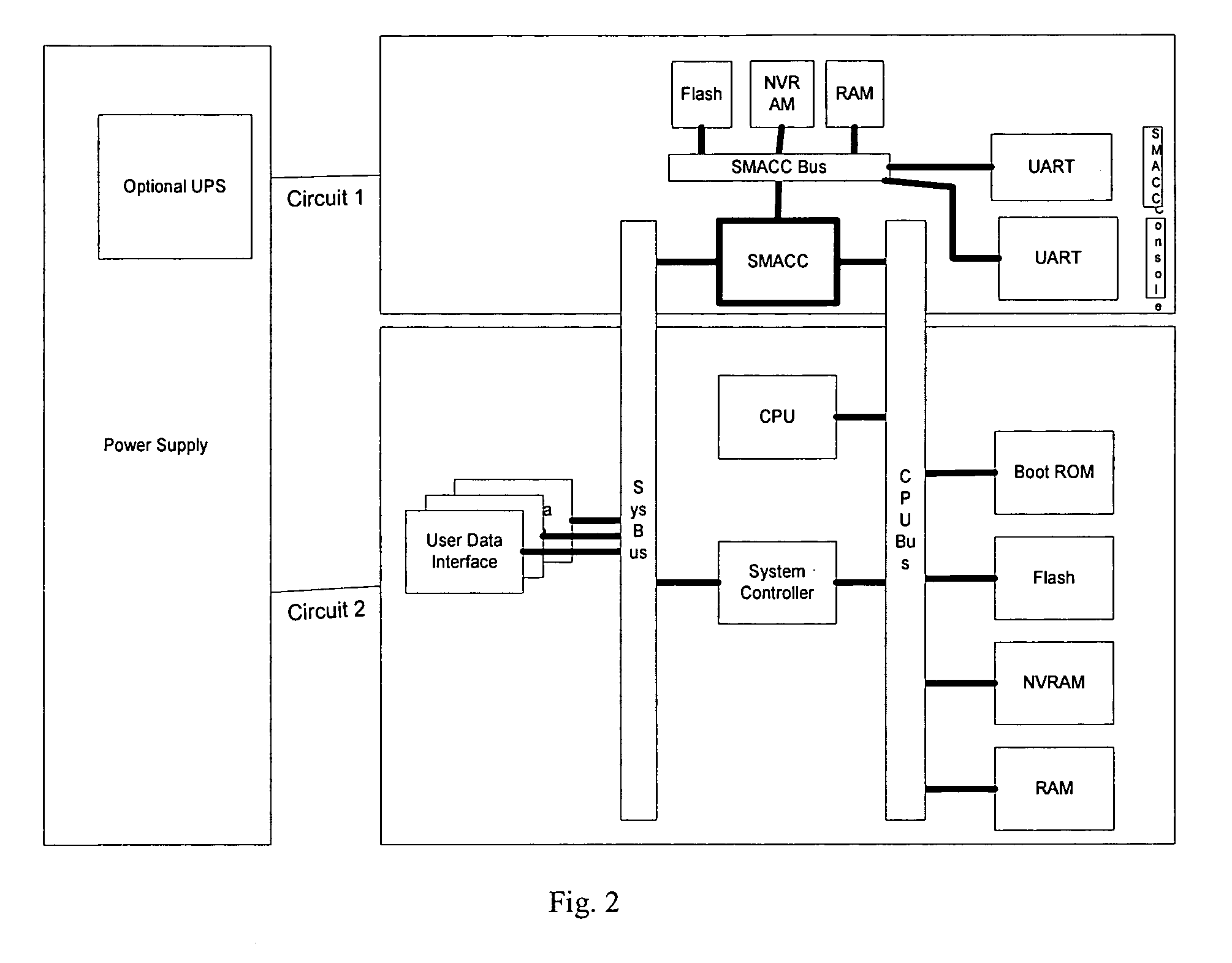
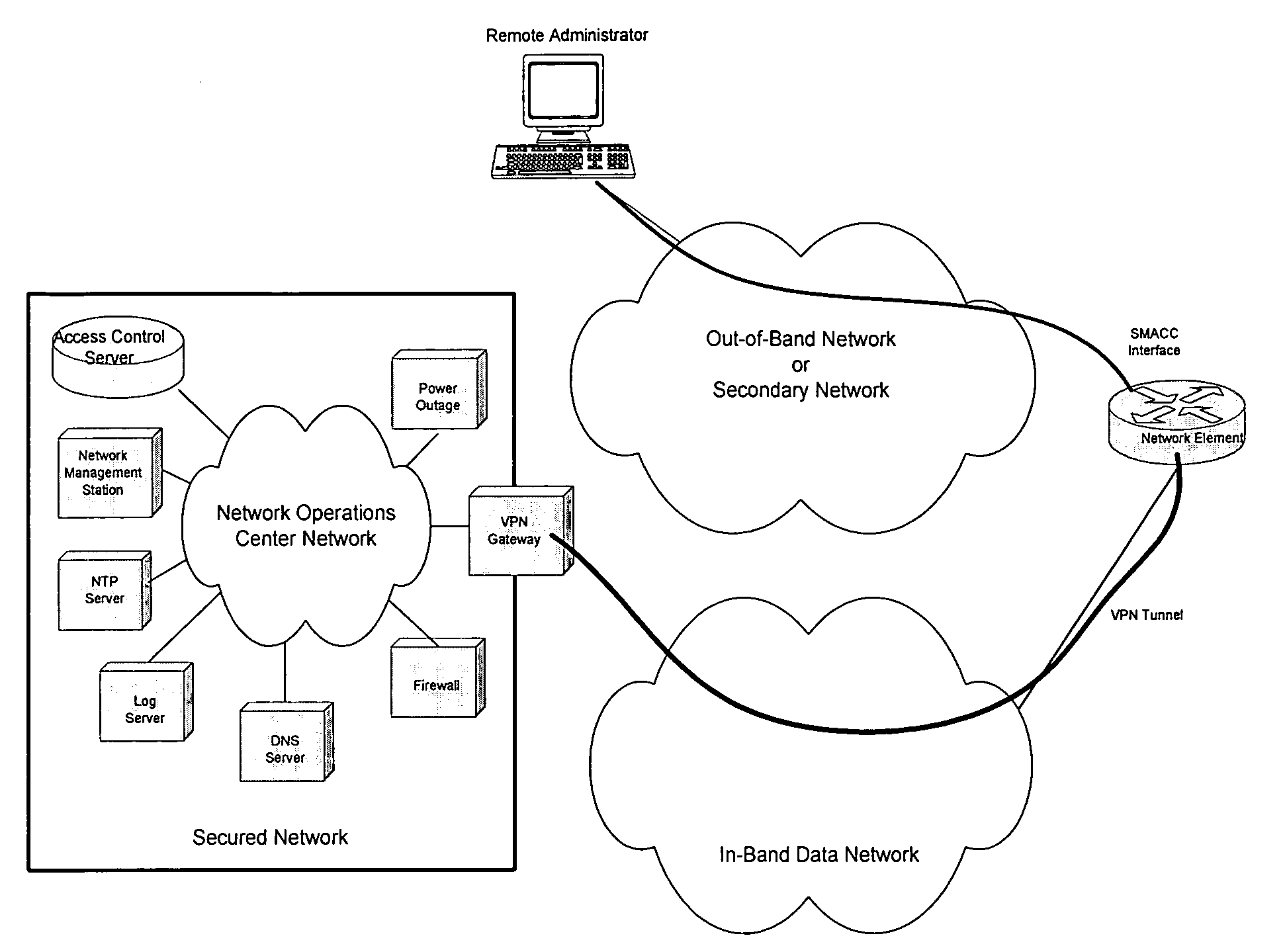
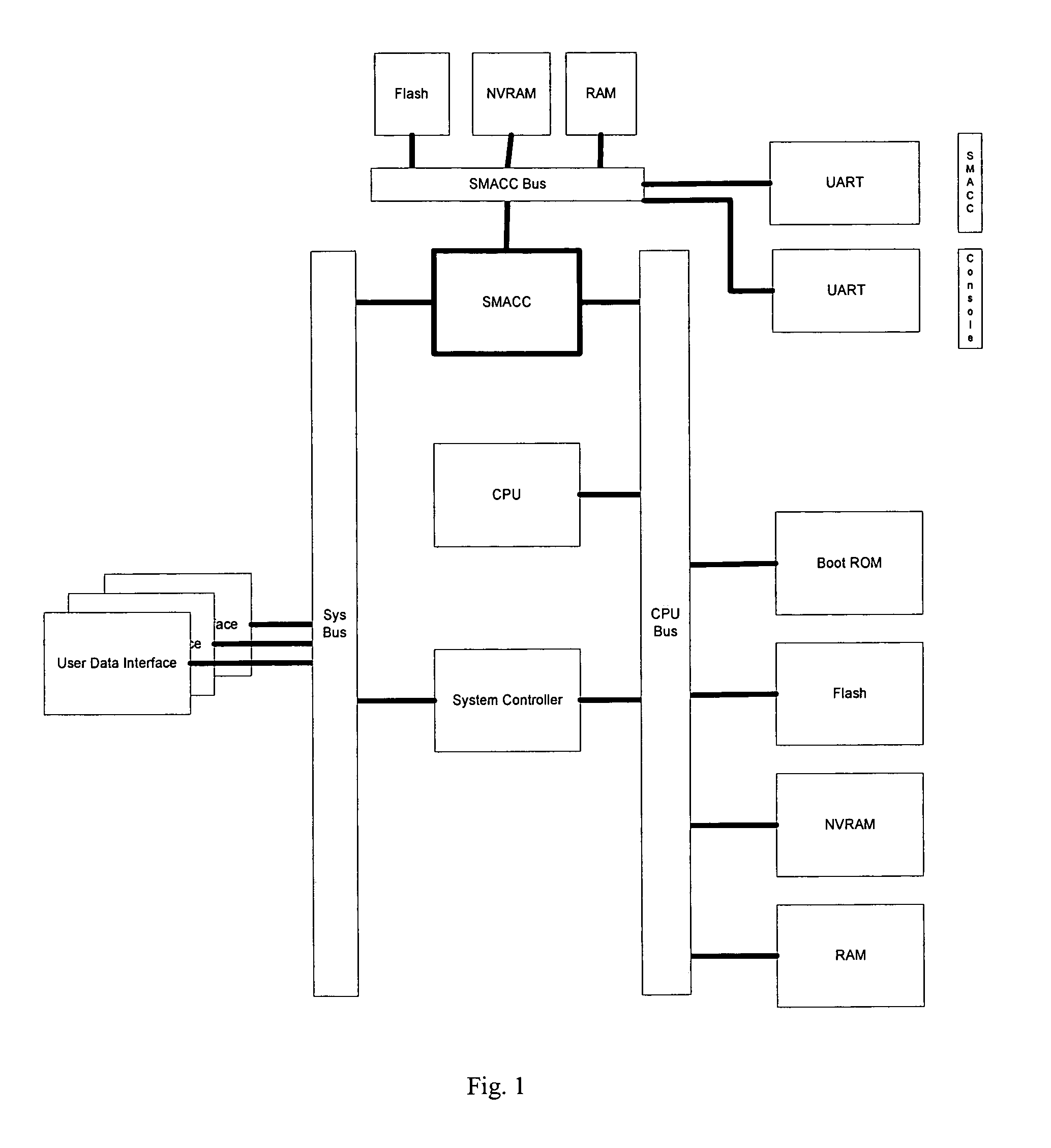
A computer network management system for remotely managing a network device. The system includes a secure management access controller which is in direct communication with the network device. The secure management access controller provides access for remotely and securely managing a network. The secure management access controller further separates management communications from user communications to ensure the security of the management communications. The system further includes network and power monitoring and notification systems. The system further provides authentication and authorization capabilities for security purposes.
Owner:INTELLECTUAL VENTURES II
Secure management access control for computers, embedded and card embodiment
ActiveUS7325140B2Convenient remote managementTransportDigital data processing detailsMultiple digital computer combinationsDirect communicationAuthorization
A computer network management system for remotely managing a network device. The system includes a secure management access controller which is in direct communication with the network device. The secure management access controller provides access for remotely and securely managing a network. The secure management access controller further separates management communications from user communications to ensure the security of the management communications. The system further includes network and power monitoring and notification systems. The system further provides authentication and authorization capabilities for security purposes.
Owner:INTELLECTUAL VENTURES II
Output management system and method for enabling printing via wireless devices
InactiveUS20070168514A1Digital computer detailsData switching by path configurationOutput deviceImaging data
A system and method for managing output such as printing, faxing, and e-mail over various types of computer networks. In one aspect, the method provides for printing via a wireless device. The system provides renderable data to the wireless device by which a user-interface (UI) may be rendered. The UI enables users to select source data and an output device on which the source data are to be printed. The source data are then retrieved from a local or remote store and forwarded to a print service, which renders output image data corresponding to the source data and the output device that was selected. The output image data are then submitted to the output device to be physically rendered. The user-interfaces enable wired and wireless devices to access the system. The system enables documents to be printed by reference, and enables access to resources behind firewalls.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
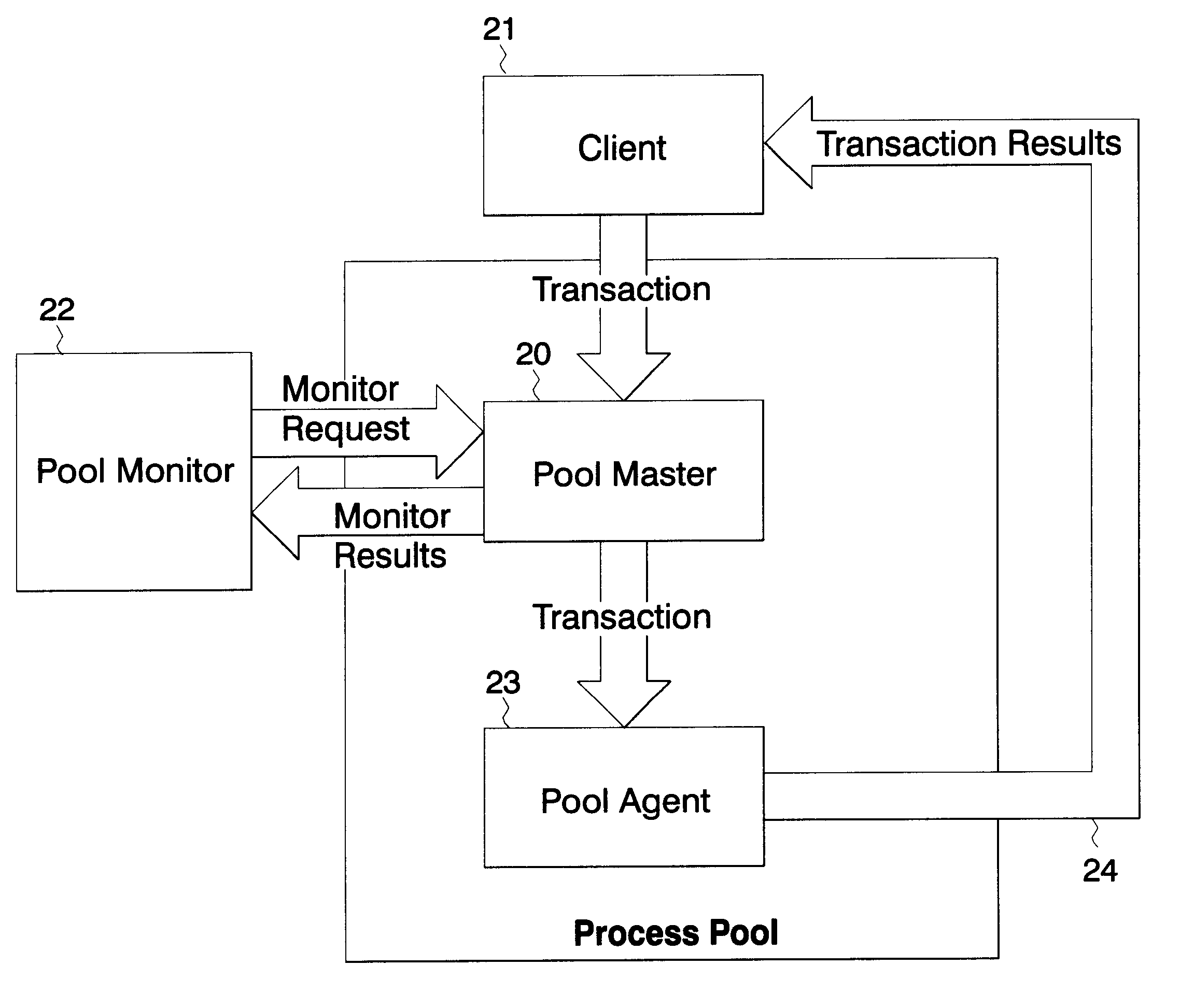
Method and apparatus for computer network management
InactiveUS6477569B1Multiprogramming arrangementsMultiple digital computer combinationsApplication specificDistributed computing
A method and apparatus for managing a computer network which utilizes a process pool. A pool master dispatches agents for transaction processing. The agents are application specific and utilize a common interface. The process pool grows as transactions increase and contracts as transactions decrease.
Owner:SAYAN EUGENE +1
Method and system for customizing a project
ActiveUS20130185646A1Easy to assistQuality improvementTransmissionInput/output processes for data processingUser profileProject selection
A method, system, and computer readable media for managing a project over a computer network is disclosed. A project selection is received. Data associated with the project is retrieved in response to the selection. Data associated with a user profile is also retrieved, and compared to the data associated with the project to detect inconsistencies between the project and the user profile. In an embodiment, substitutions are determined based on the inconsistencies and automatically incorporated into the project. Data associated with the project including the substitutions is then delivered to the user over a computer network. In another embodiment, data associated with the project and the inconsistencies is delivered to the user over a computer network. In some embodiments, data associated with alternative project inputs and / or project actions consistent with the user profile is delivered to the user for substitution into the project. In some implementations, a selection of one or more alternative project inputs and / or project actions may be received from the user over a computer network.
Owner:CAELO MEDIA
System and method for unified configuration of network equipment
InactiveCN101582794AReduce the burden onReduce configuration workloadData switching networksWorkloadModel Number
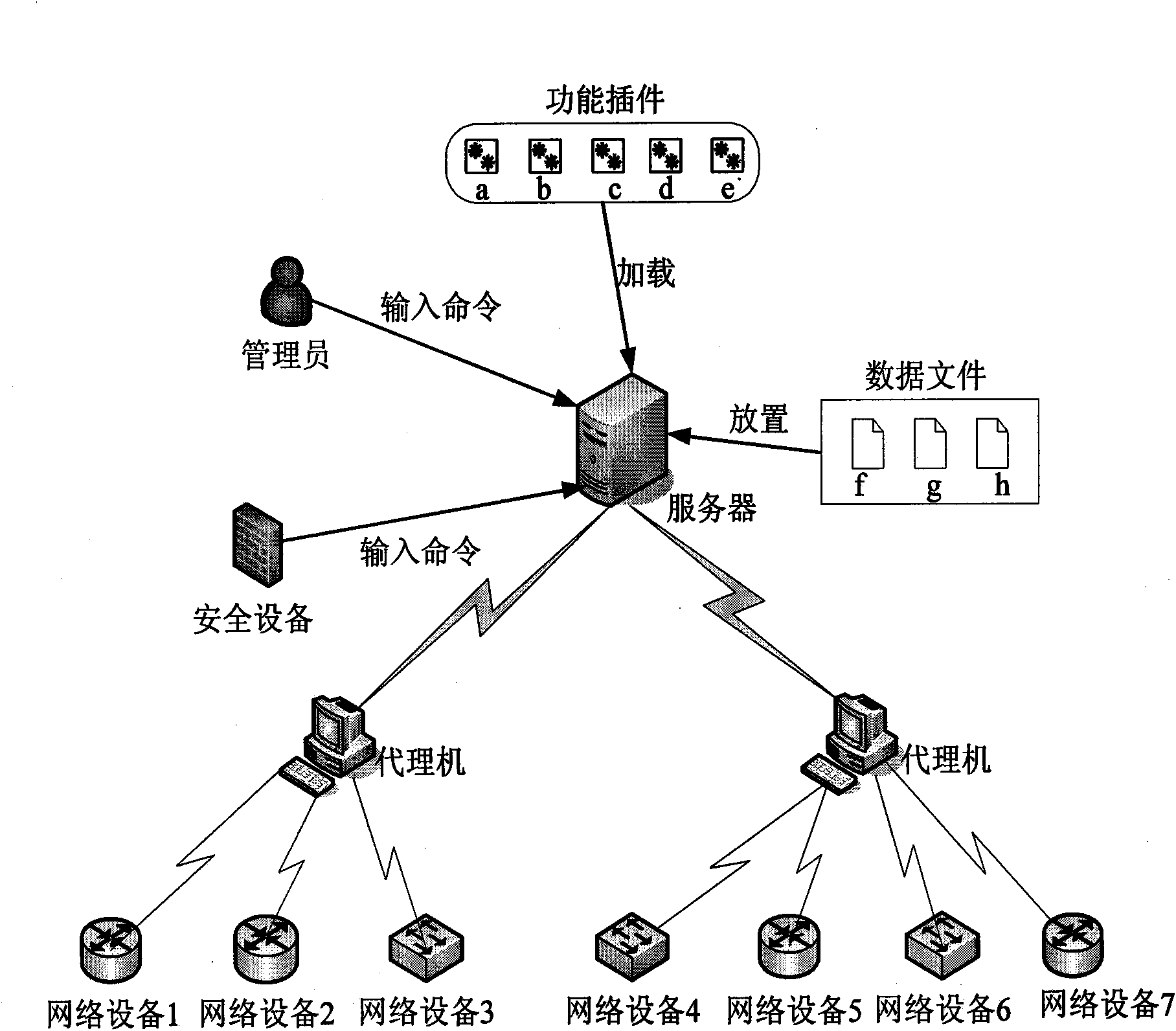
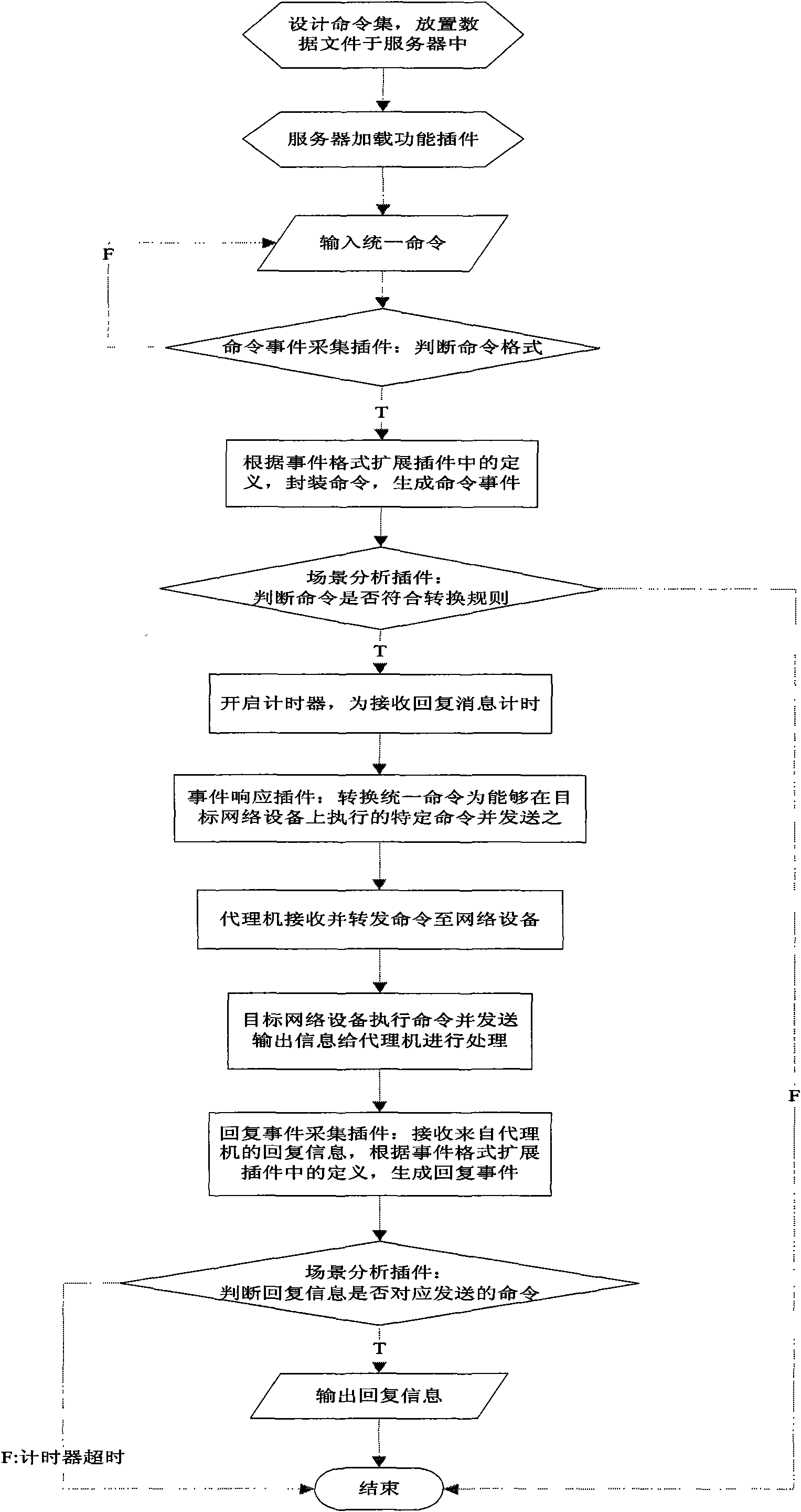
The invention discloses a system and a method for unified configuration of network equipment, and mainly solves the problems of huge workload and the lack of security function for configuring the network equipment in the prior configuration method. A self-designed command set is used for the unified configuration of network equipment from different factories and in different models. The system mainly comprises a server, an agent and the network equipment, wherein the server is loaded with a command event acquisition plug-in, a reply event acquisition plug-in, an event format extension plug-in, a scene analysis plug-in, an event response plug-in, an equipment information file, a command conversion information file and a command conversion rule file. The elf-designed command is converted into a special command which can be executed in the target network equipment by the server, and forwarded to the network equipment for execution through the agent, and after execution, the output information of the network equipment is transmitted to the agent for processing and then returned to the server. The system and the method have the advantages of convenient centralized and unified configuration of the network equipment, and can be widely applied in the field of computer network management.
Owner:XIDIAN UNIV
System and method for enterprise policy management
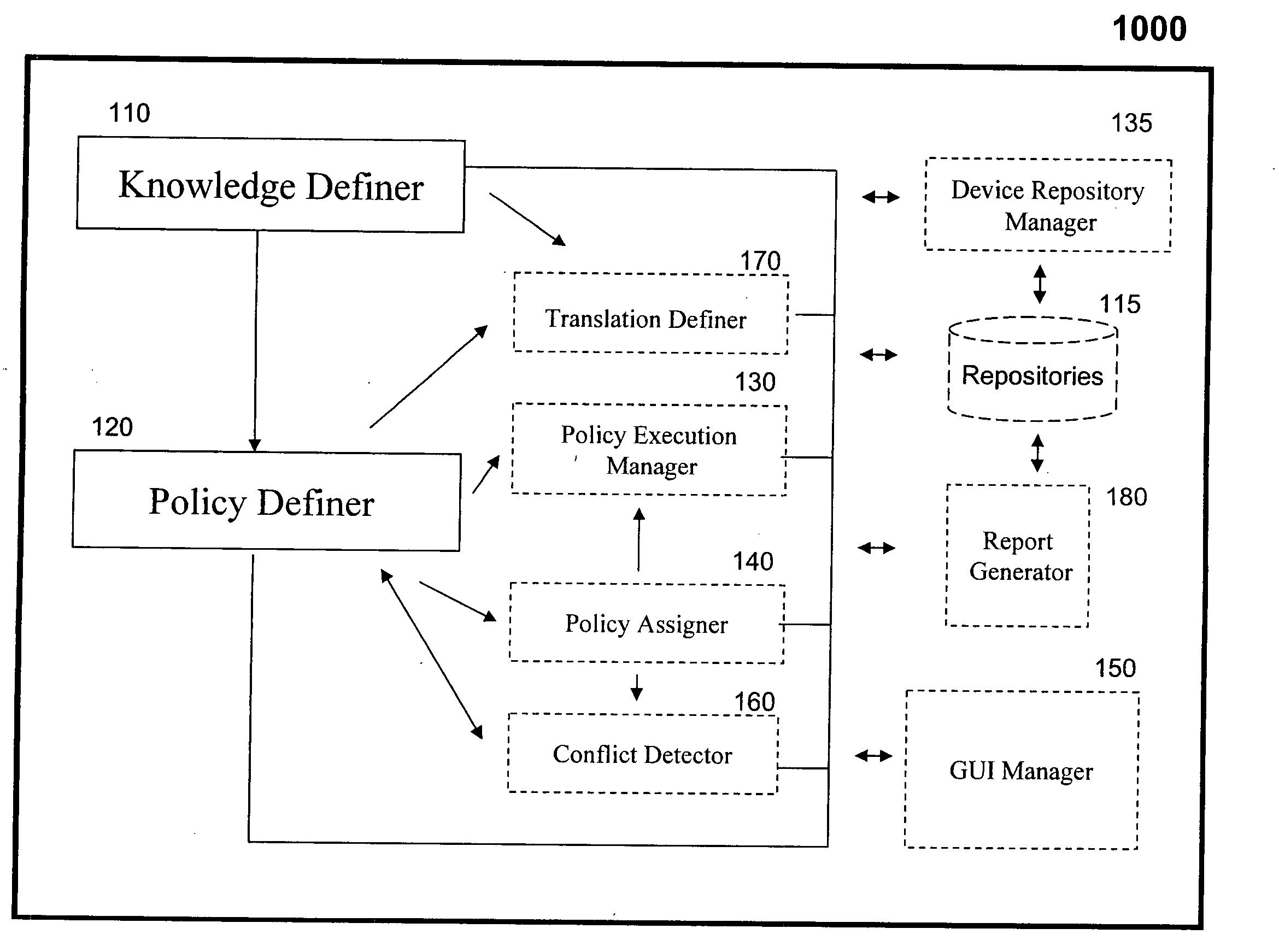
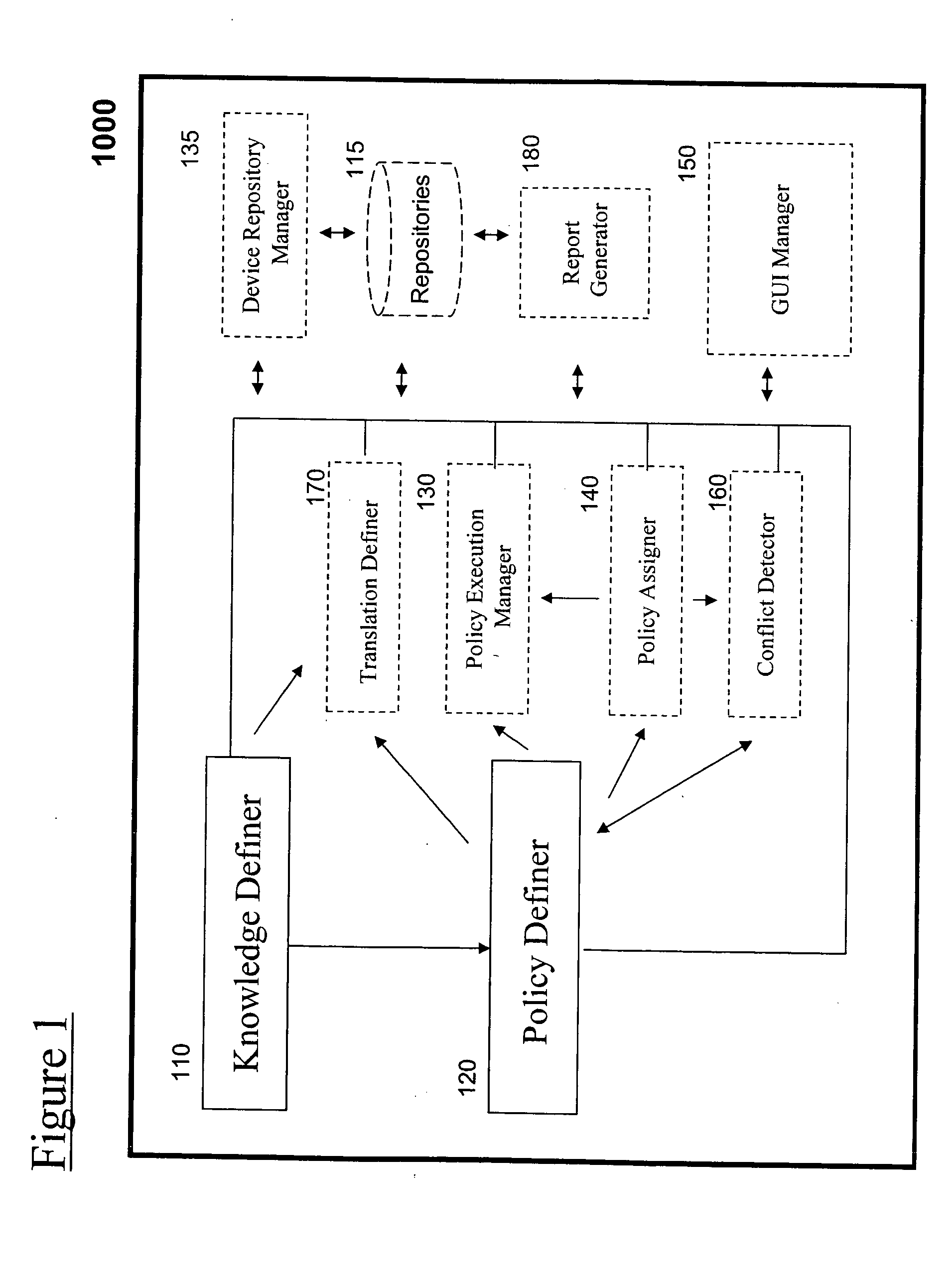
Apparatus for computer network management, comprising: a knowledge definer, operable for defining a knowledge module comprised of a plurality of knowledge items, hierarchically arranged according to technologies, each of the knowledge items comprising possible values for a configuration activity of one of the technologies. The apparatus further includes a policy definer, associated with the knowledge definer, operable for defining at least one technical policy based on the knowledge module, usable for overriding selected values of the possible values while keeping remaining values of the possible values, the technical policy inheriting from the knowledge module.
Owner:TRISIXTY SECURITY
Method and system for secure use of services by untrusted storage providers
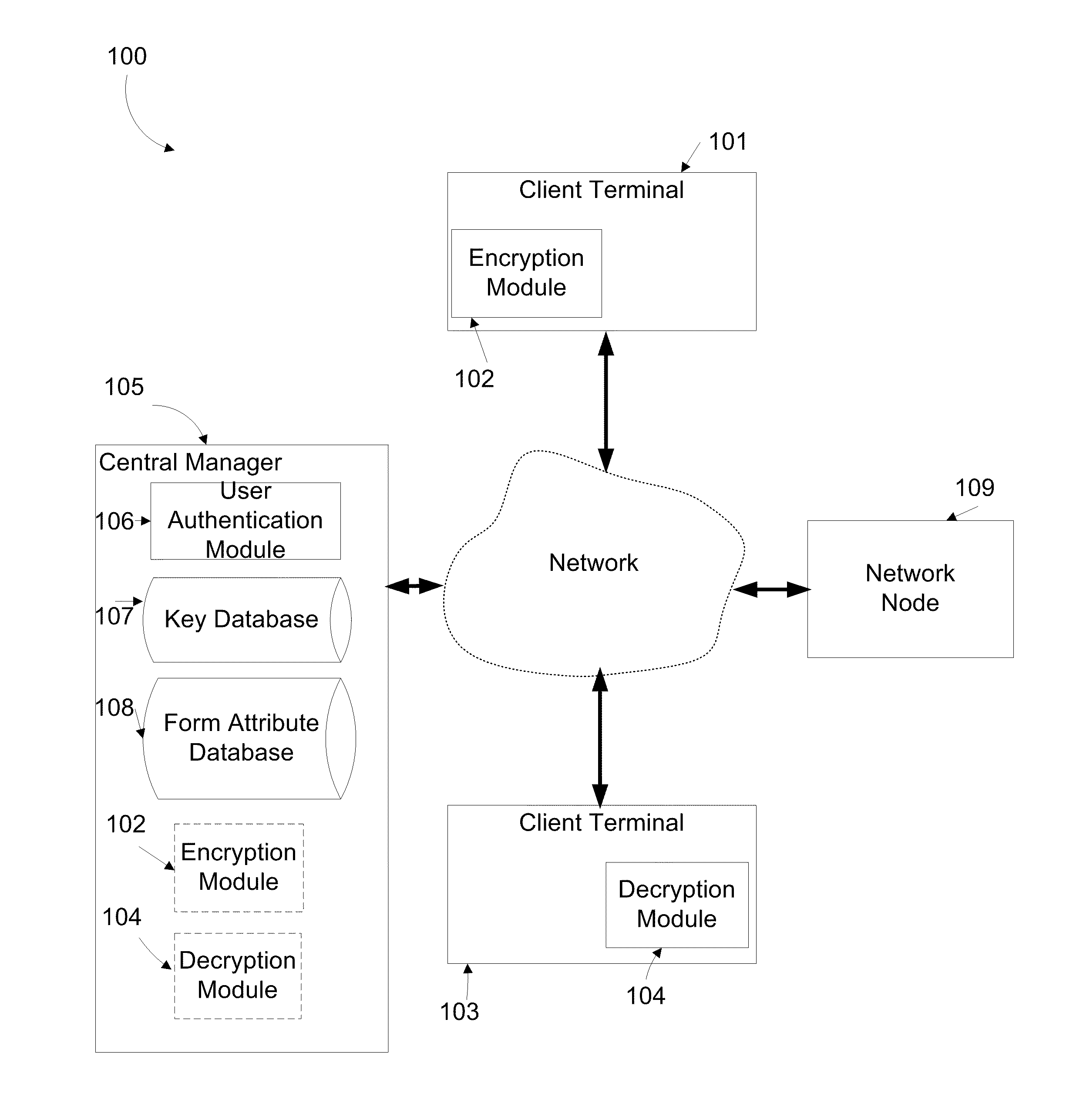
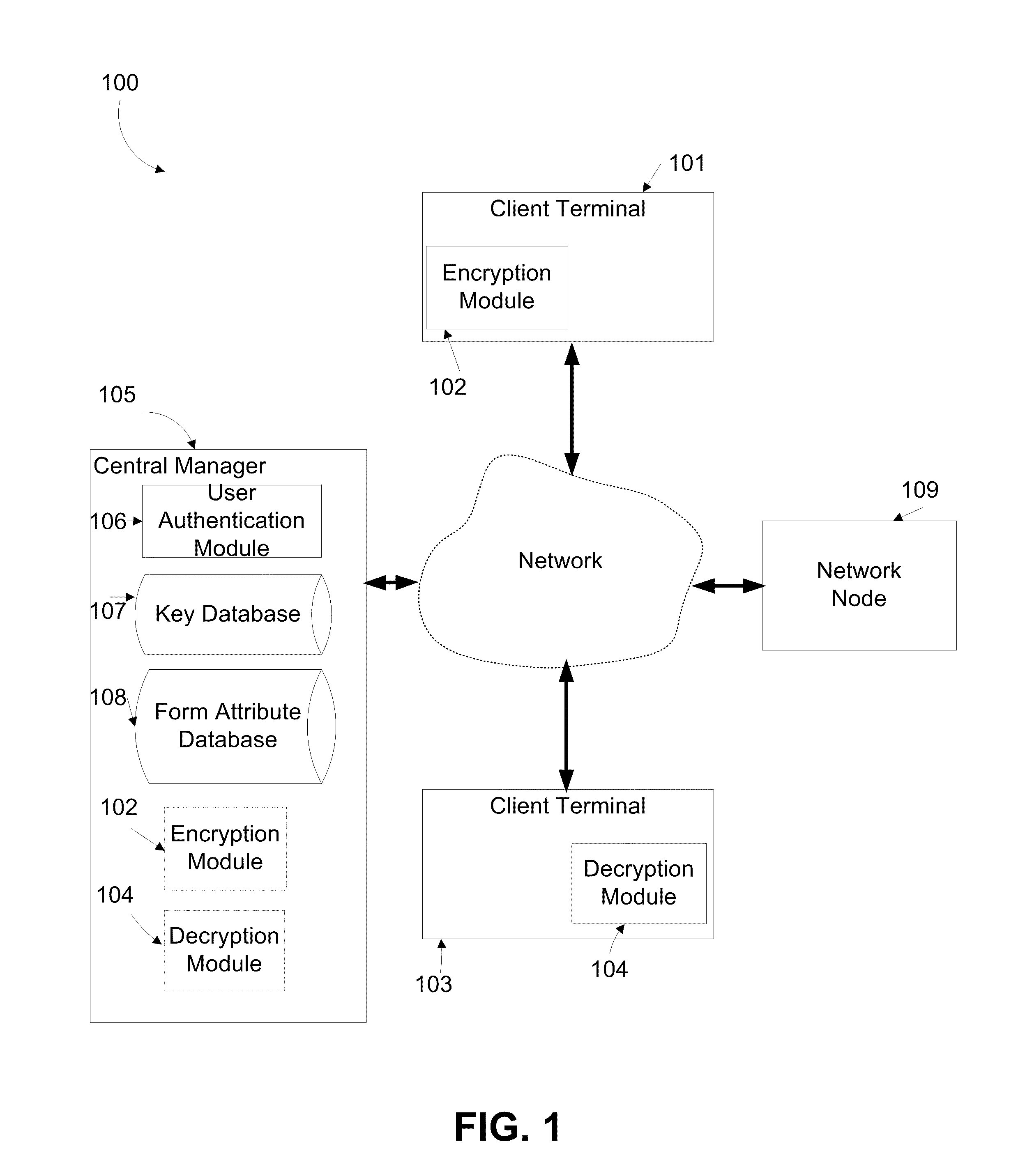
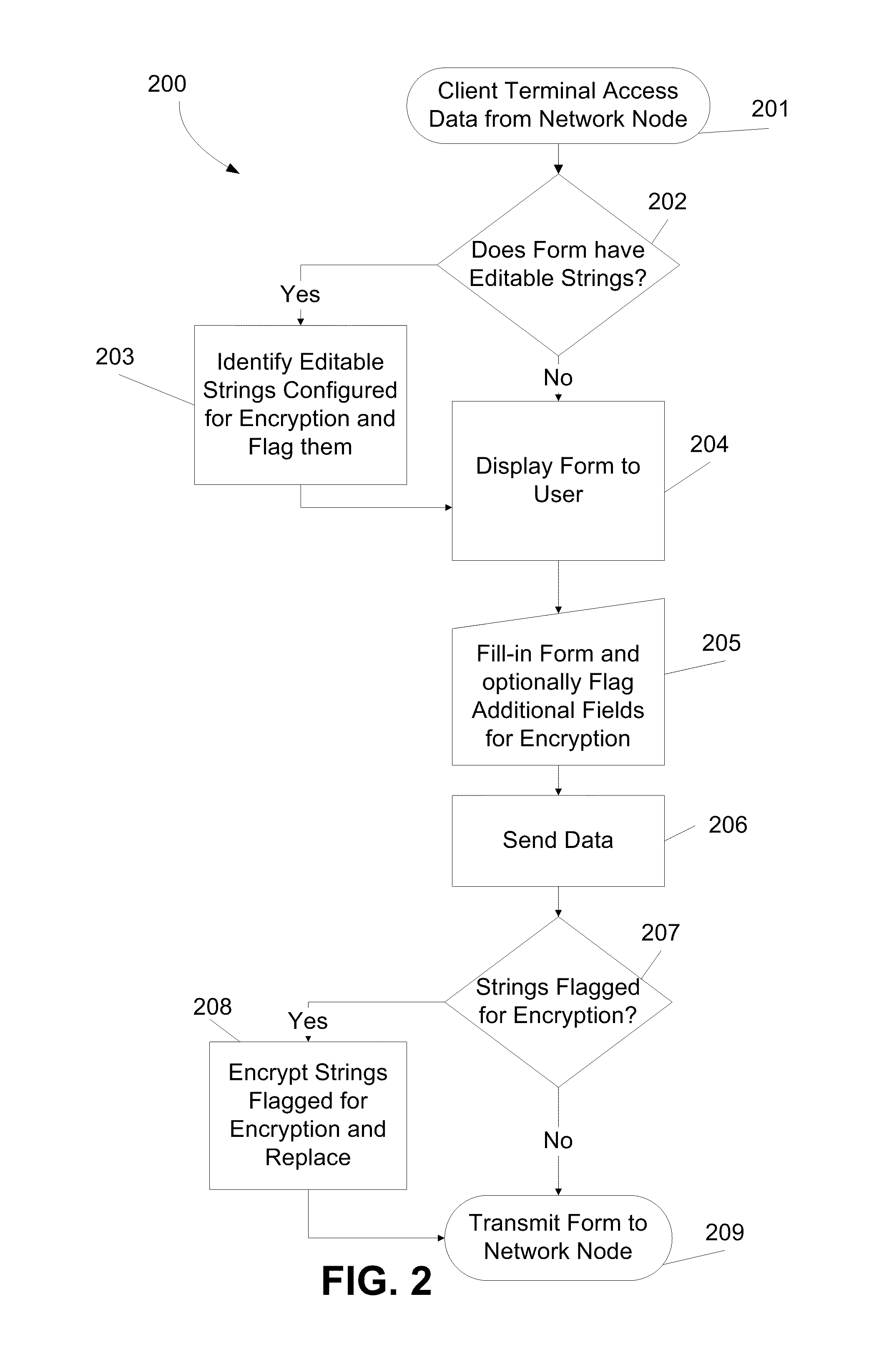
ActiveUS20110173438A1Multiple keys/algorithms usageDigital data protectionComputer networkDigital content
A method for encrypting data. The method comprises receiving, from a user, via a client terminal, digital content including at least one textual string for filling in at least one field in a document managed by a network node via a computer network, encrypting the at least one textual string, and sending the at least one encrypted textual string to the network node via the computer network so as to allow filling in the at least one field with the at least one encrypted textual string. The network node is configured for storing and retrieving the at least one textual encrypted string without decrypting.
Owner:CYBERARK SOFTWARE LTD
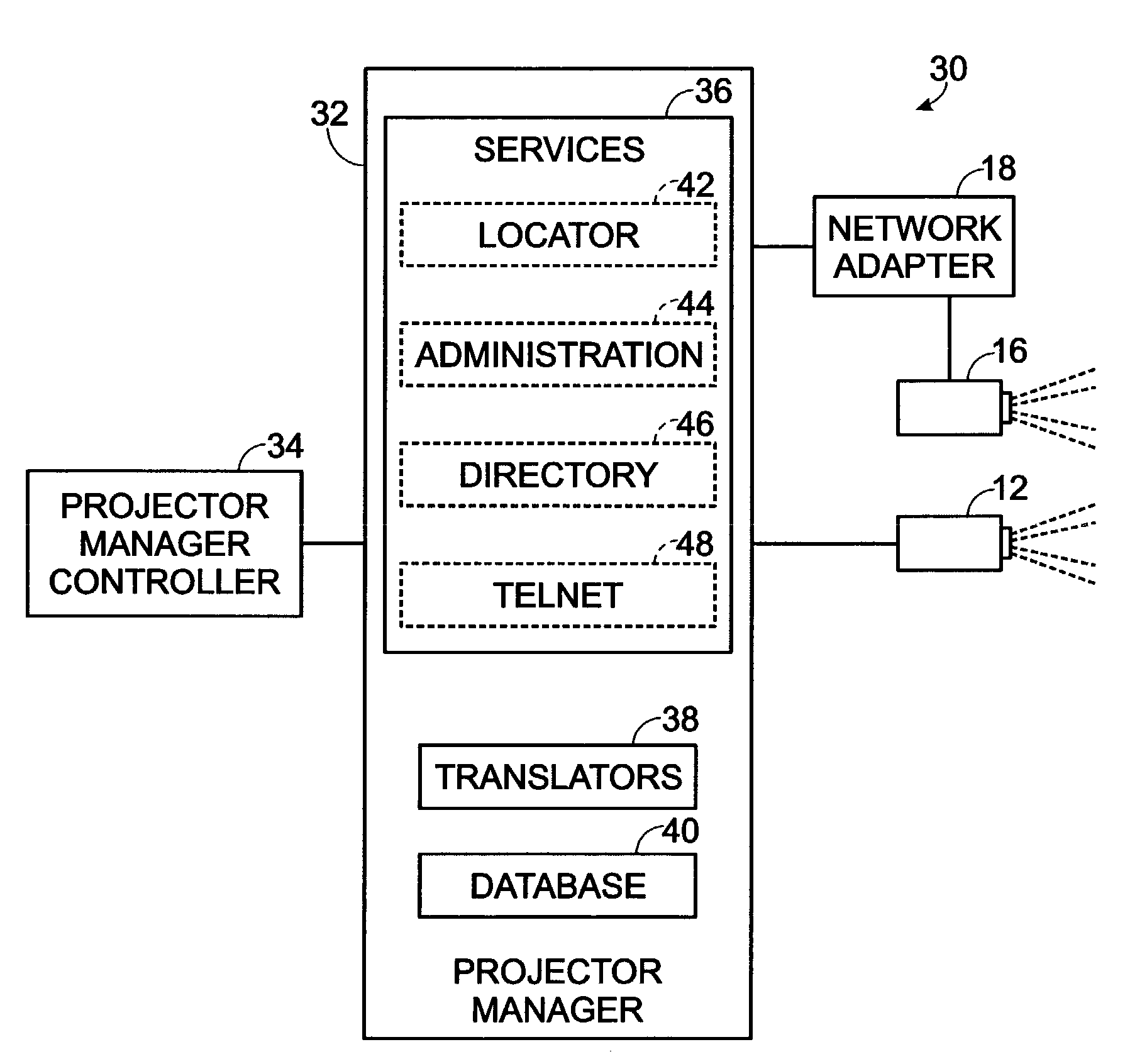
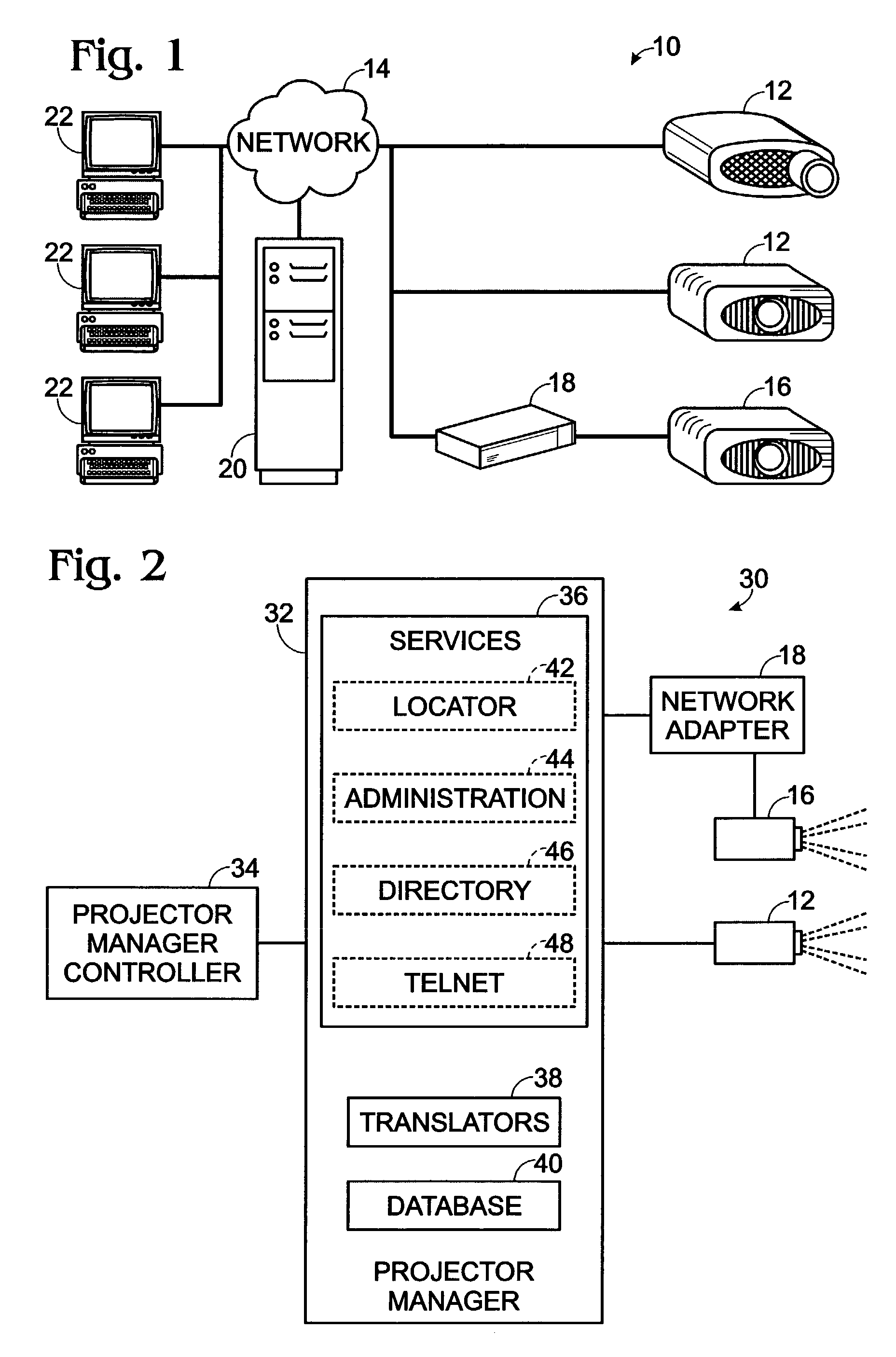
Projector device management system
ActiveUS7197562B2Multiple digital computer combinationsTransmissionComputer scienceManagement system
A system and methods for managing a plurality of projector devices over a computer network are provided. The system includes a projector manager linked to a computer network, wherein the projector manager is configured to monitor over the network a status of a selected feature of a selected projector device, and to change the status of the selected feature when requested. The system also includes a projector manager controller linked to the computer network, wherein the projector manager controller is configured to request the projector manager to perform at least one of the functions of reporting the status of the selected feature and requesting the selected projector device to change the status of the selected feature.
Owner:SEIKO EPSON CORP
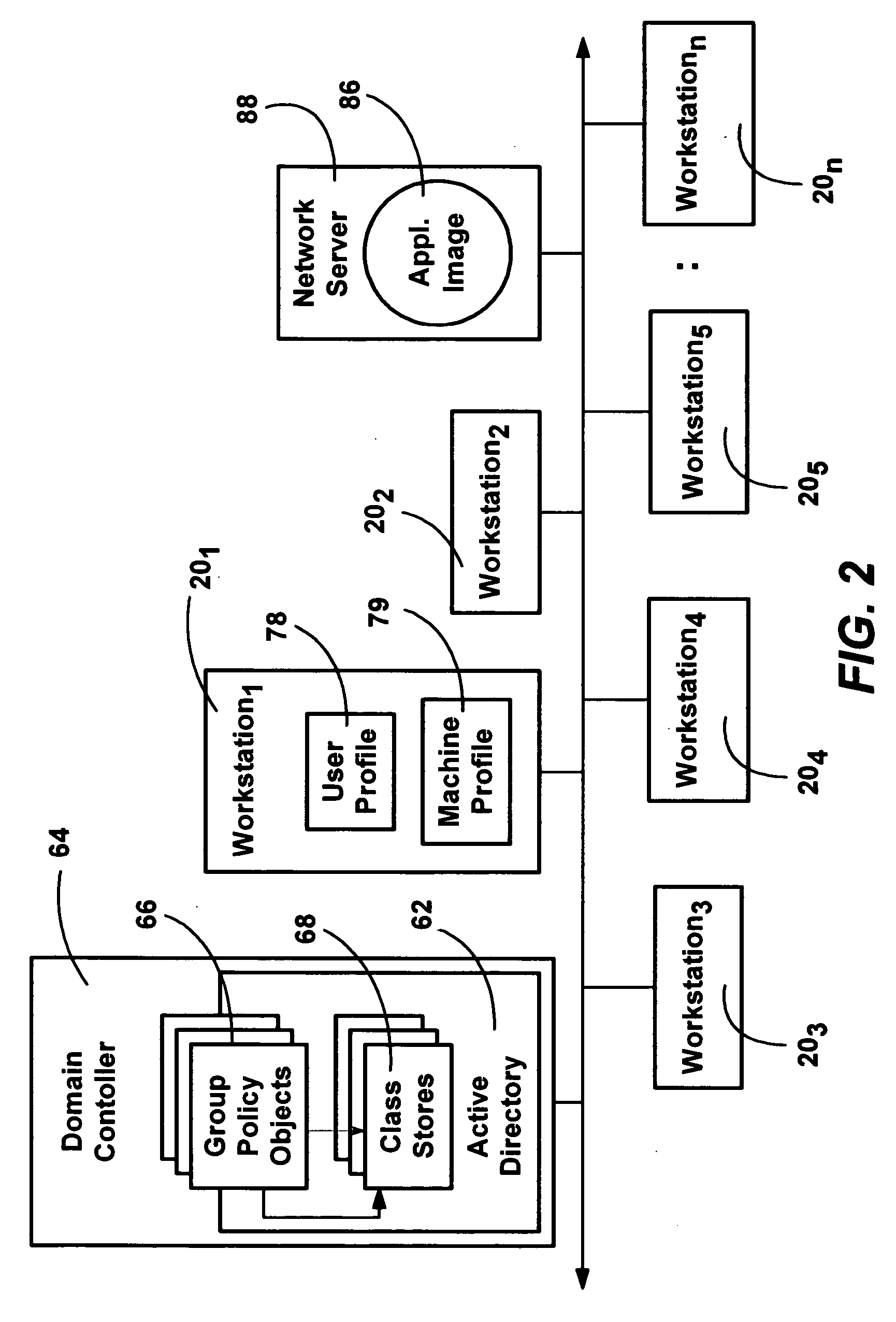
Method and system for assigning and publishing applications
InactiveUS20050108688A1Automatically deployingDigital computer detailsProgram loading/initiatingWorkstationWindows Registry
A method and system for managing and deploying applications across a computer network by assigning and publishing applications to user and computer policy recipients. Assigned applications are automatically applied via a script to the policy recipients, thereby ensuring that the recipient has an administrator-specified workstation configuration. Assigned applications are advertised so as to appear available to the user, by adding an application shortcut to the start menu, and by populating the machine registry with appropriate application information. Other applications may be published to users, whereby those applications are optionally available for use by users. Published application information is maintained in a centralized store of information on the network. Assigned and published applications may be installed on demand, such as when the application is activated.
Owner:MICROSOFT TECH LICENSING LLC
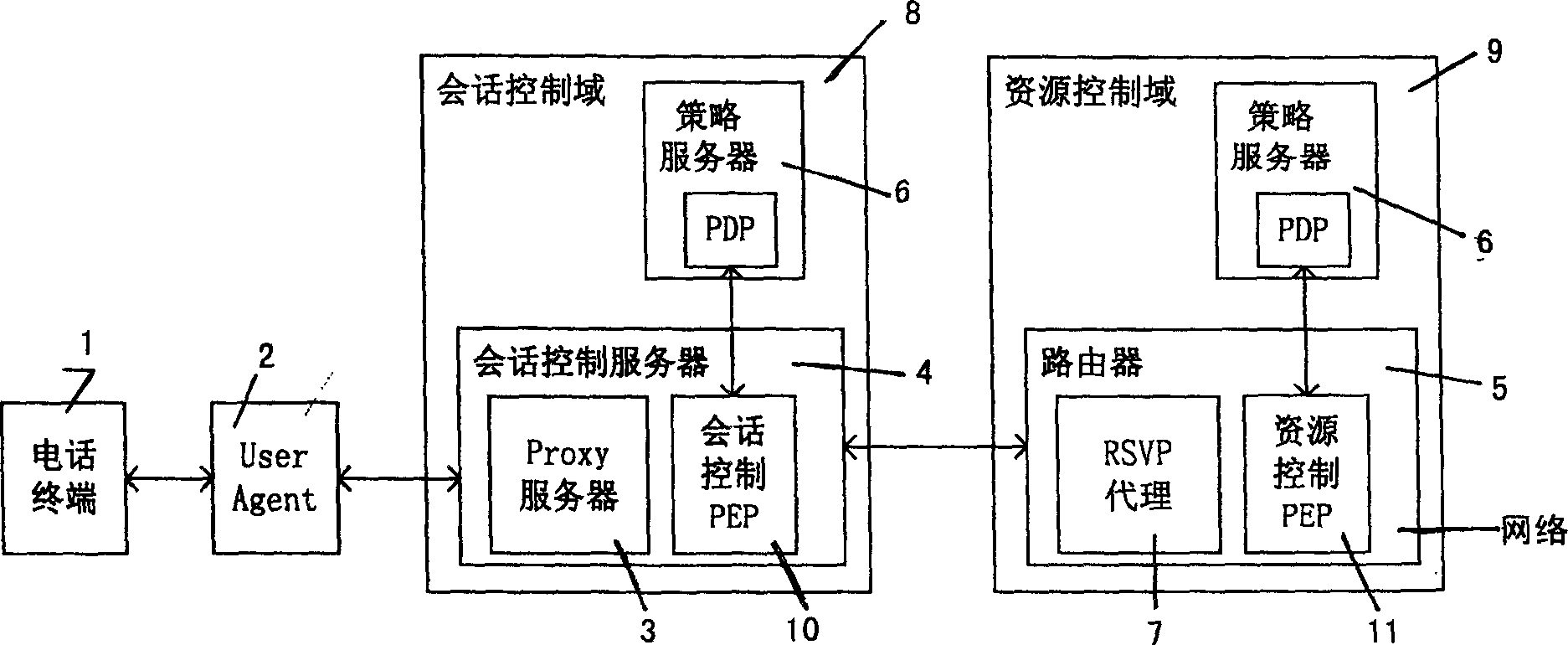
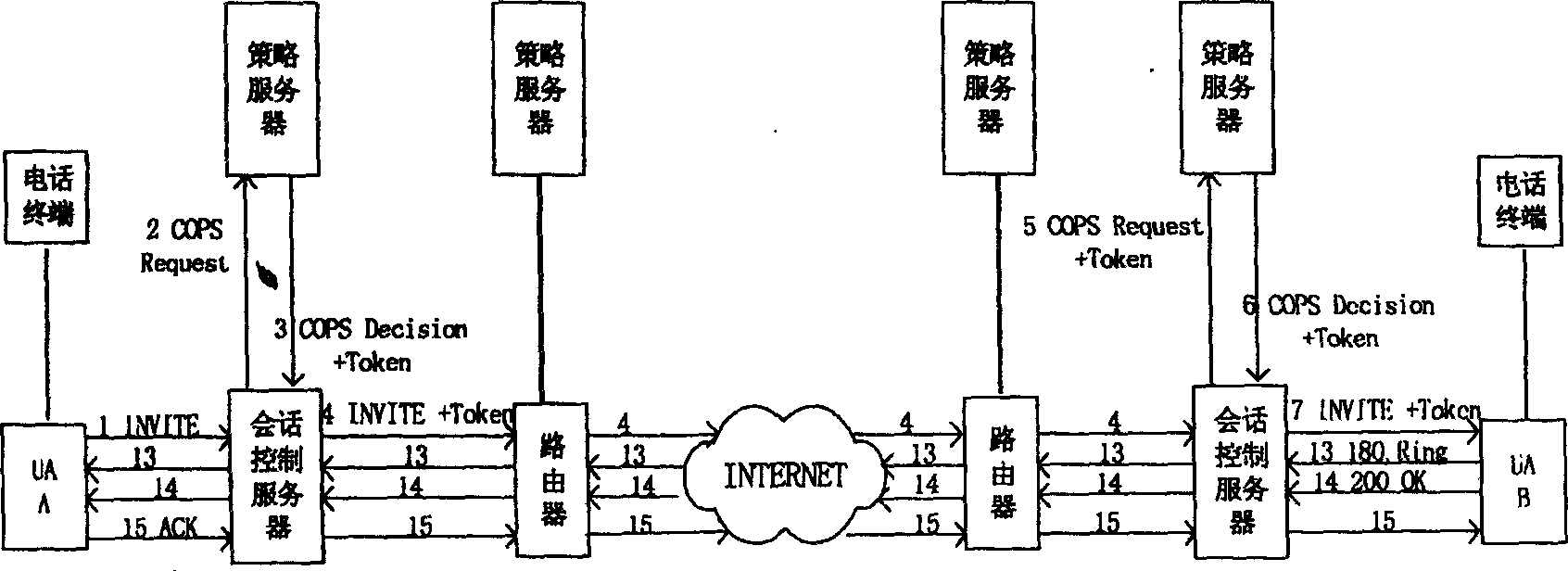
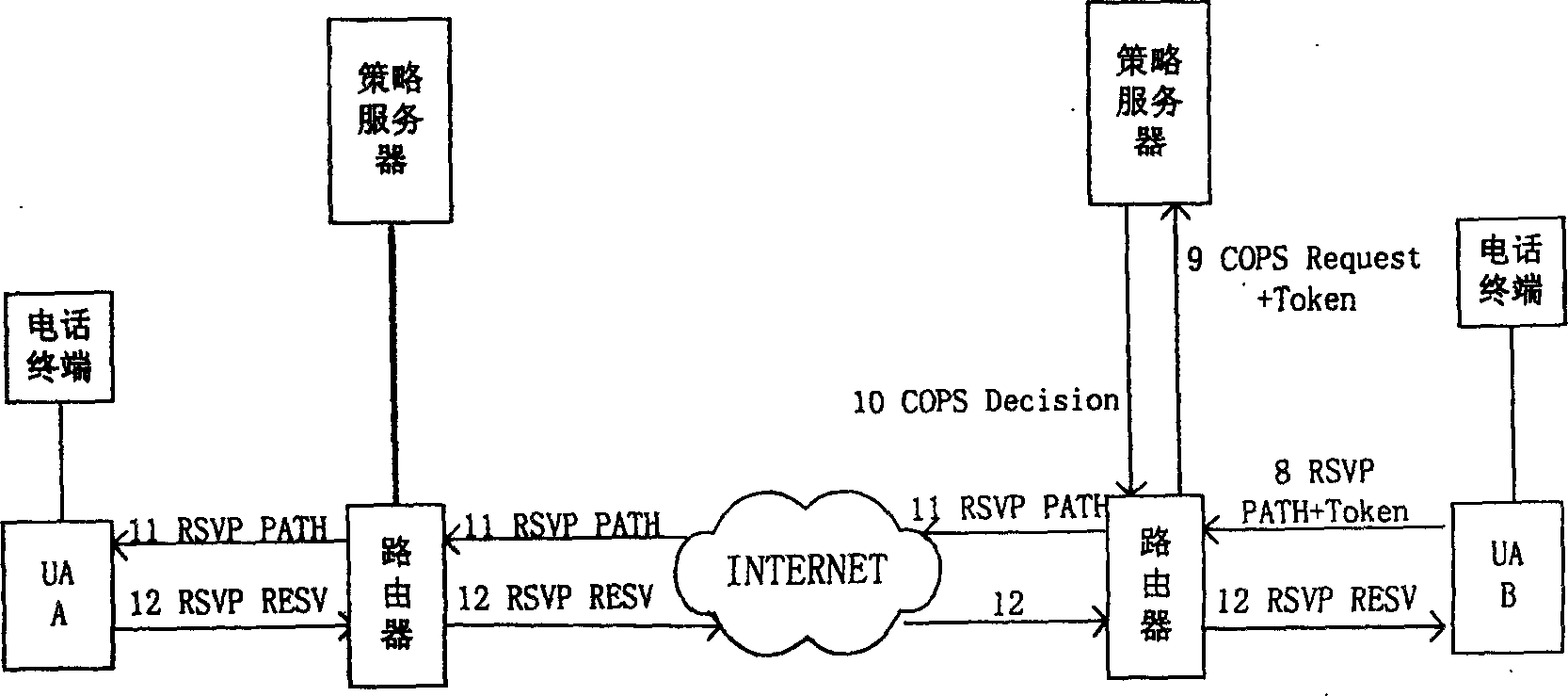
Session and medium authorization method in IP video telephone system based on session start protocol
InactiveCN1469585AEasy to manageReduce pre-trust relationshipsTelephonic communicationData switching networksSession controlNetwork management
The present invention relates to computer network management technology, and is one session and medium authorization method in IP video telephone system based on session initialization protocol. Thepresent invention adopts network management technology based on strategy in realizing session authorization, and one strategy server is used in generating management command to inform the session control server to execute management action. The present invention solves the session and medium authorization problem in IP video telephone system and can control effectively the session occupied network resource. The present invention features that during session course, all the network entities exchange authorization message via transmitting authorization token to reduce message exchange times, decrease the mutual independence between the network entities and obtain even more flexibility.
Owner:陈弟桂
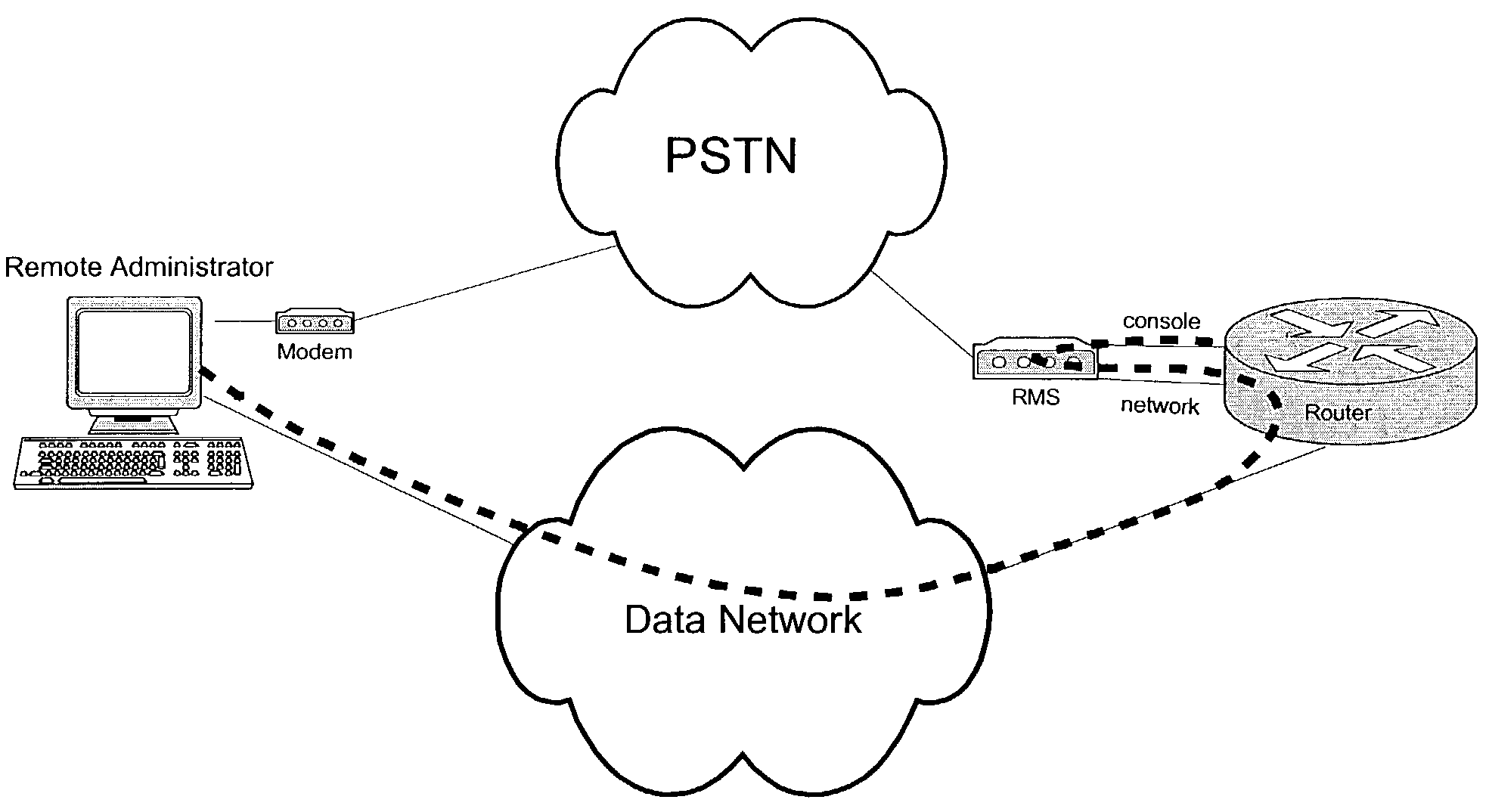
Out-of-band remote management station
InactiveUS7171467B2Eliminate security concernsProtect informationDigital computer detailsSupervisory/monitoring/testing arrangementsModem deviceDigital interface
A computer network management system with an embedded processor, an analog communication means and a digital interface for network management provides a system for remotely and securely managing a network. Backup power in the form of an uninterrupted power supply, or other power means as appropriate, allows the modem to provide power outage notification to a remote site. The system further provides authentication and authorization capabilities for security purposes.
Owner:INTELLECTUAL VENTURES II
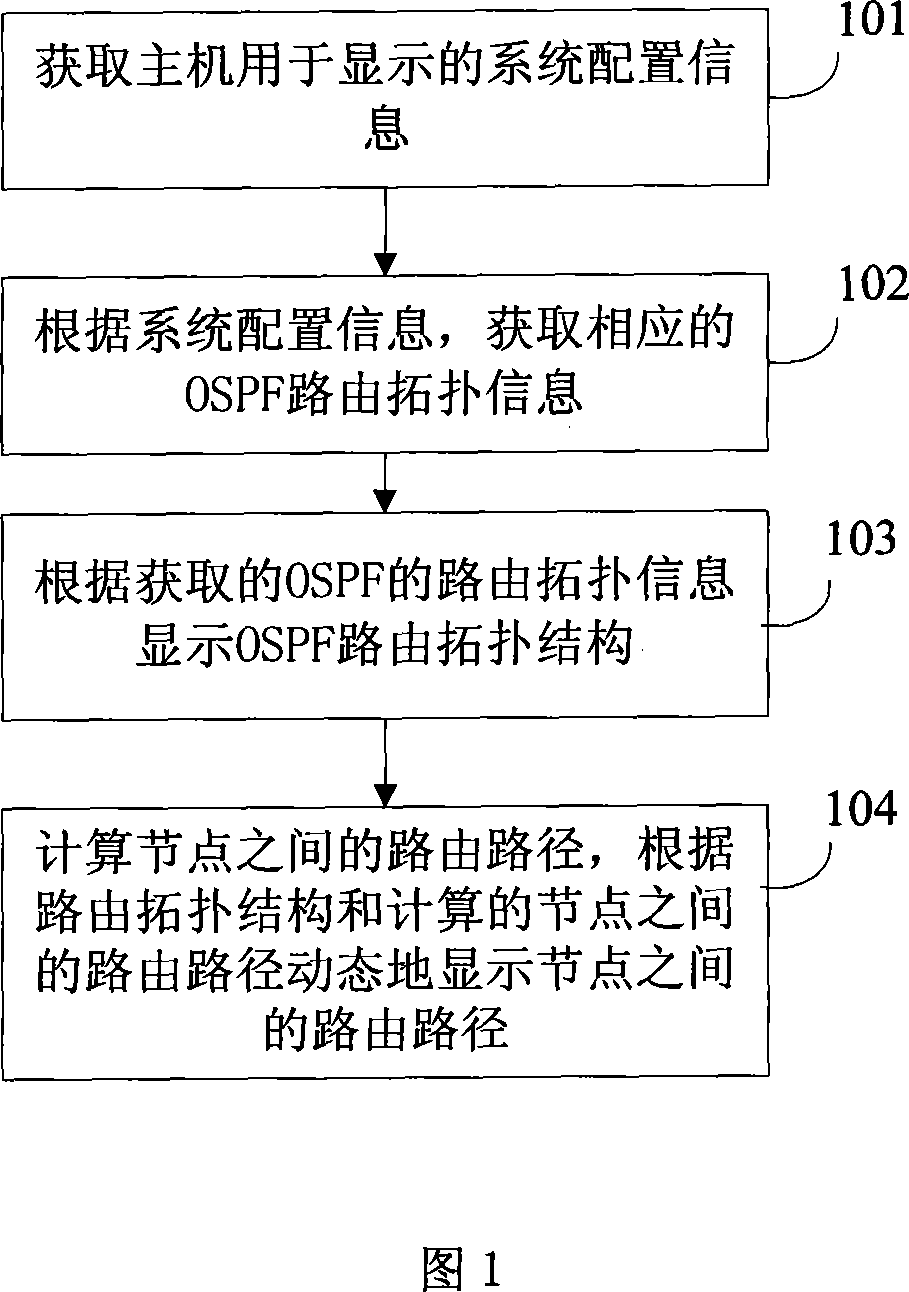
A routing path display method
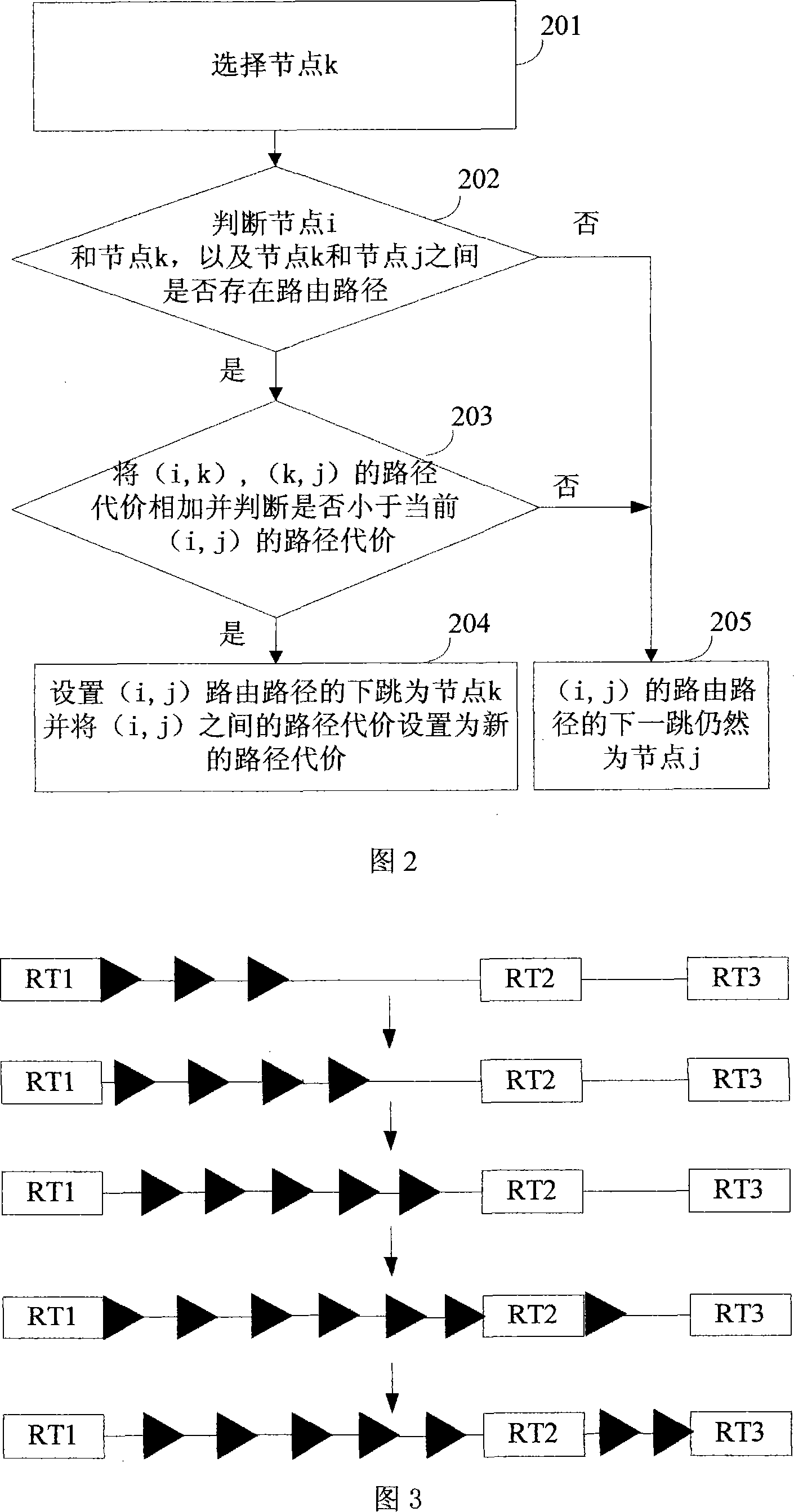
InactiveCN101145974AStay abreast of internal changesMaster the operationData switching networksGraphicsSystem configuration
The invention discloses a route path display method, belonging to the technical field of computer network management. The invention is characterized in acquiring system configuration information; acquiring the route topological information according to the system configuration information; displaying the route topological structure according to the topological information; calculating the route path among nodes in the route topological information, and dynamically and visually displaying the route path among the nodes. The invention can display the message of the route path in a pattern form, and represent the progress movement of the message visually in pattern form so as to dynamically display the route process of the message from one router to another router. The invention can provide users with a plurality of selections of display manners; the administrator user can monitor the internal operation process of the network through the invention and know the internal change and control the operation condition of the network immediately; and the common user can gain a better understanding of the internal operation mechanism of the network through the visualized route path, thereby developing a deeper and more direct-viewing perception of the network.
Owner:TSINGHUA UNIV
Output management system and method for enabling access to private network resources
InactiveUS20060294251A1Connection managementData switching by path configurationTelecommunications linkPrivate network
A system and method for managing output such as printing, faxing, and e-mail over various types of computer networks. In one aspect, the system and method provides for accessing print and / or document resources located on private networks behind firewalls. A pass-through communication link is established between system components located on opposing sides of a firewall. A system-served user-interface enables users to select source data and an output device on which the source data are to be printed, either or both of which may reside behind the firewall. The source data are then retrieved and forwarded to a print service, which renders output image data corresponding to the source data and the selected output device. The output image data are then submitted to the output device to be physically rendered. Access to private resources is provided by the pass-through communication link. The system also enables documents to be printed by reference.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
System and method for implementing Java-based software network management objects
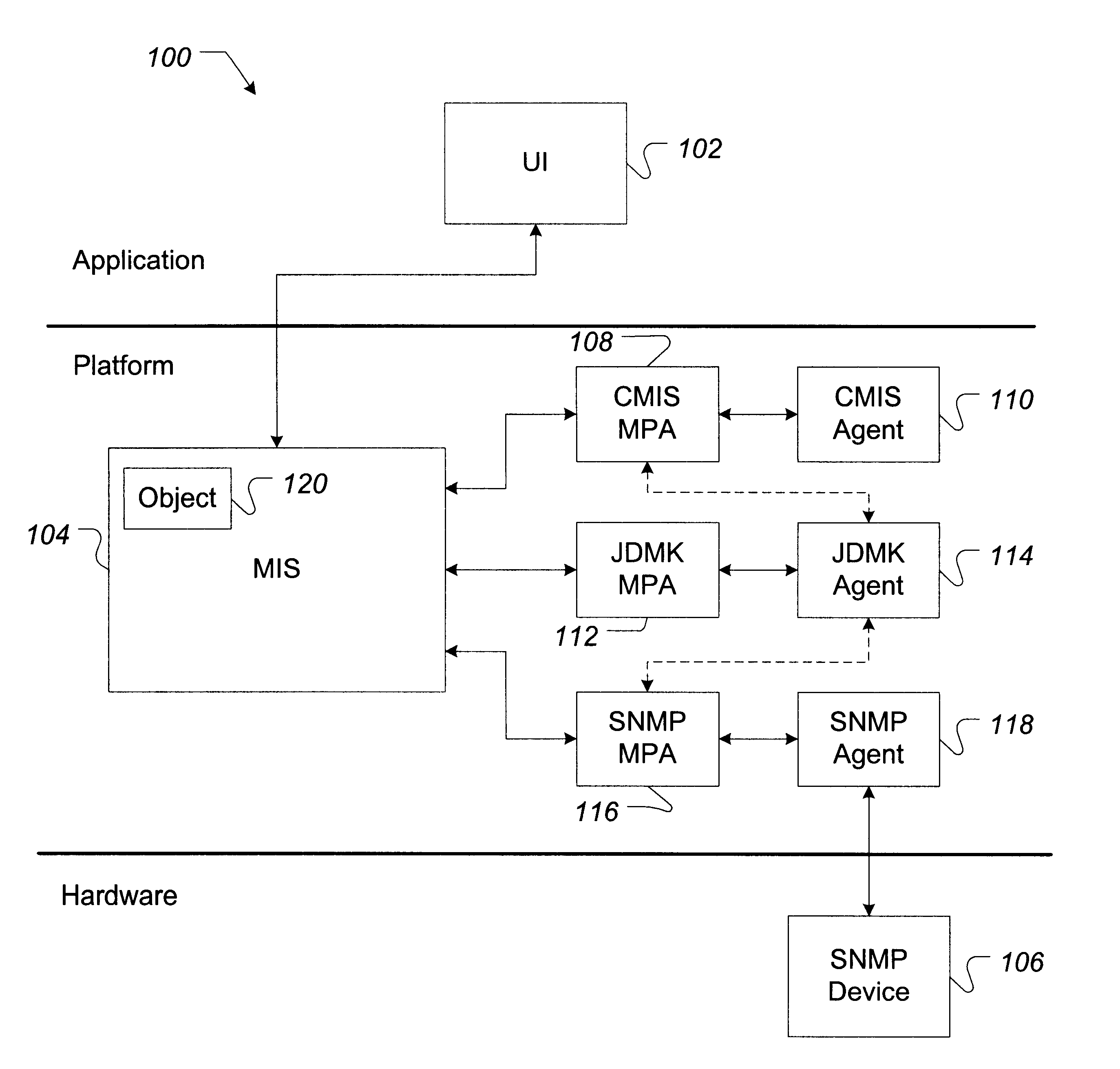
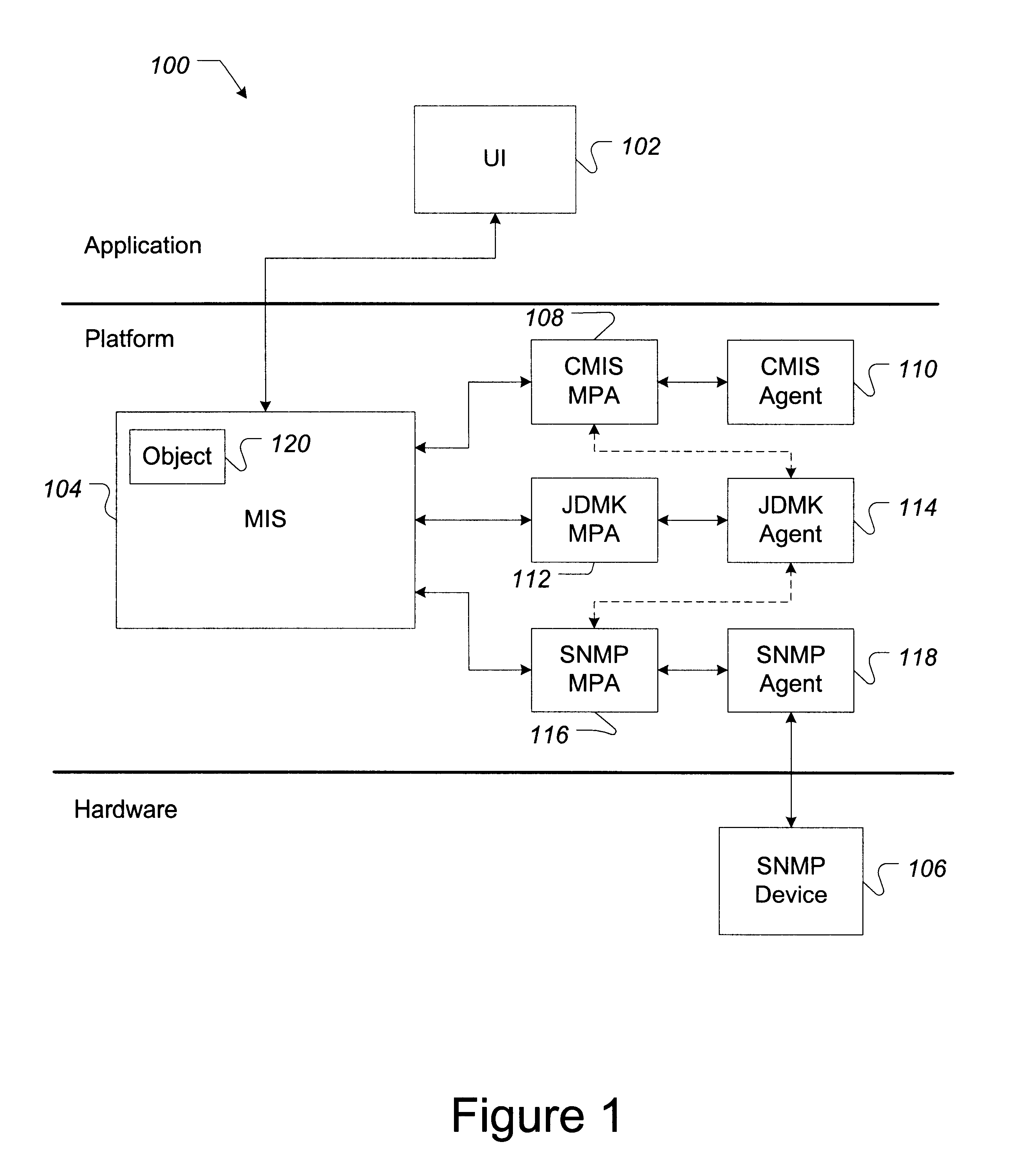
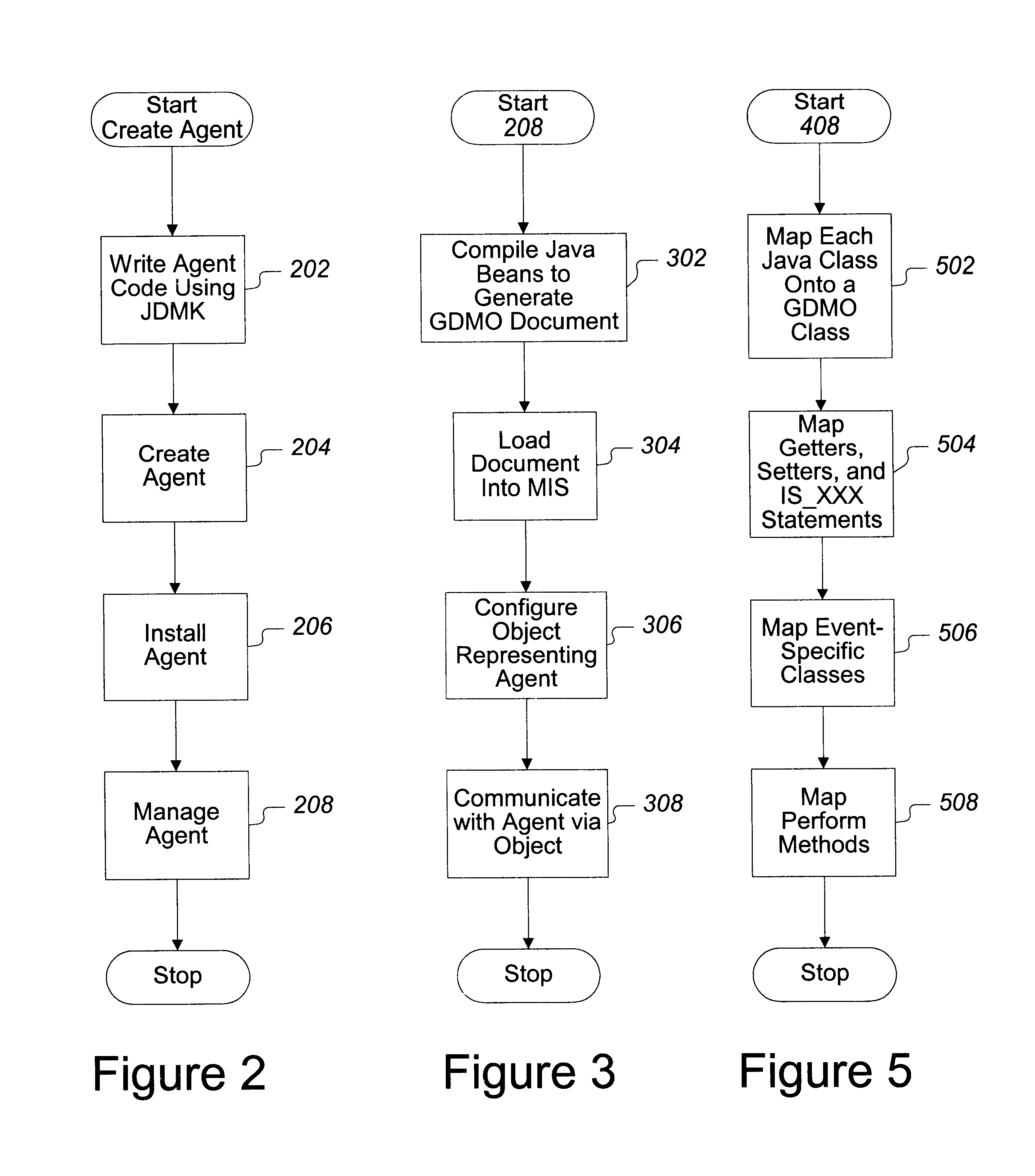
InactiveUS6427153B2Easy accessRapid development timeMultiple digital computer combinationsOffice automationSoftware networkManagement object
Software, systems, and methods for facilitating the development and implementation of computer network management software containing Java-based instructions is provided. In one aspect, the invention includes a system for implementing Java-based software network management objects configured to implement computer network management functions on a computer network. In one embodiment, the system of the invention includes a computer network management information server. The network management server performs communications using a first computer network management communications protocol. The system further includes a Java development management kit ("JDMK") methods protocol adapter ("MPA") that is configured to translate the first computer network management communications protocol into a JDMK communications protocol. A JDMK agent that is configured to communicate with the JDMK MPA using the JDMK communications protocol also is included.
Owner:ORACLE INT CORP
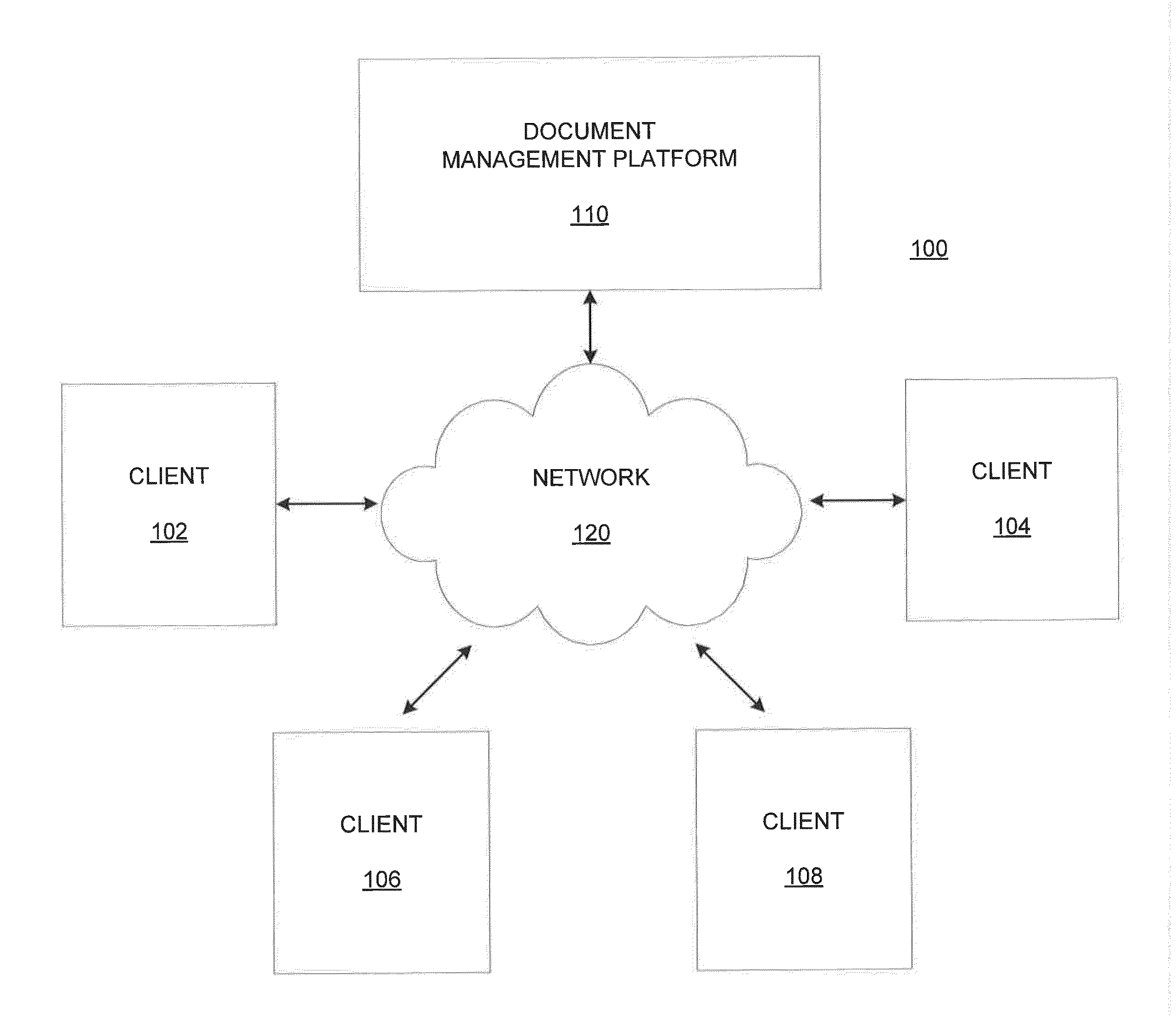
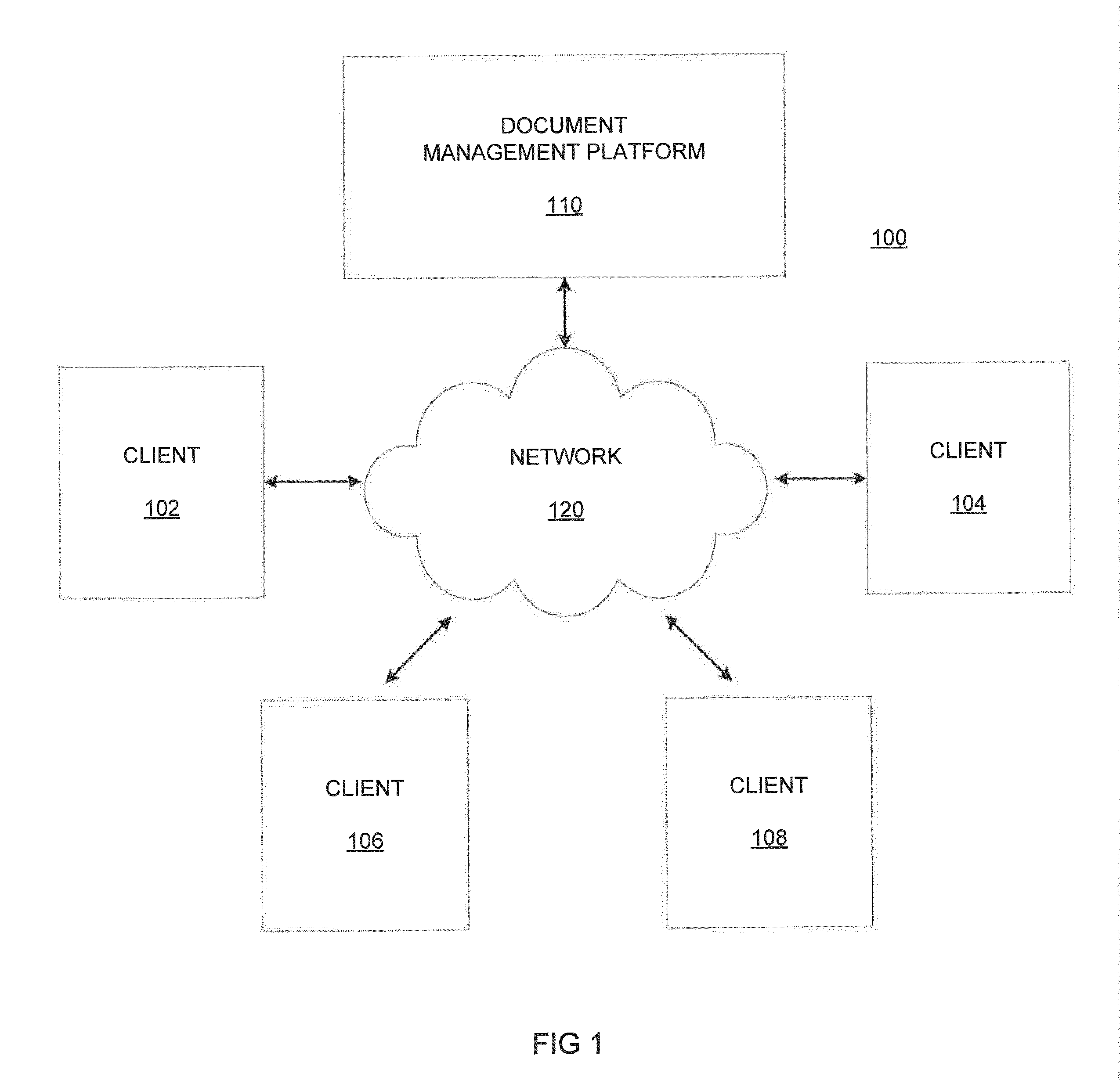
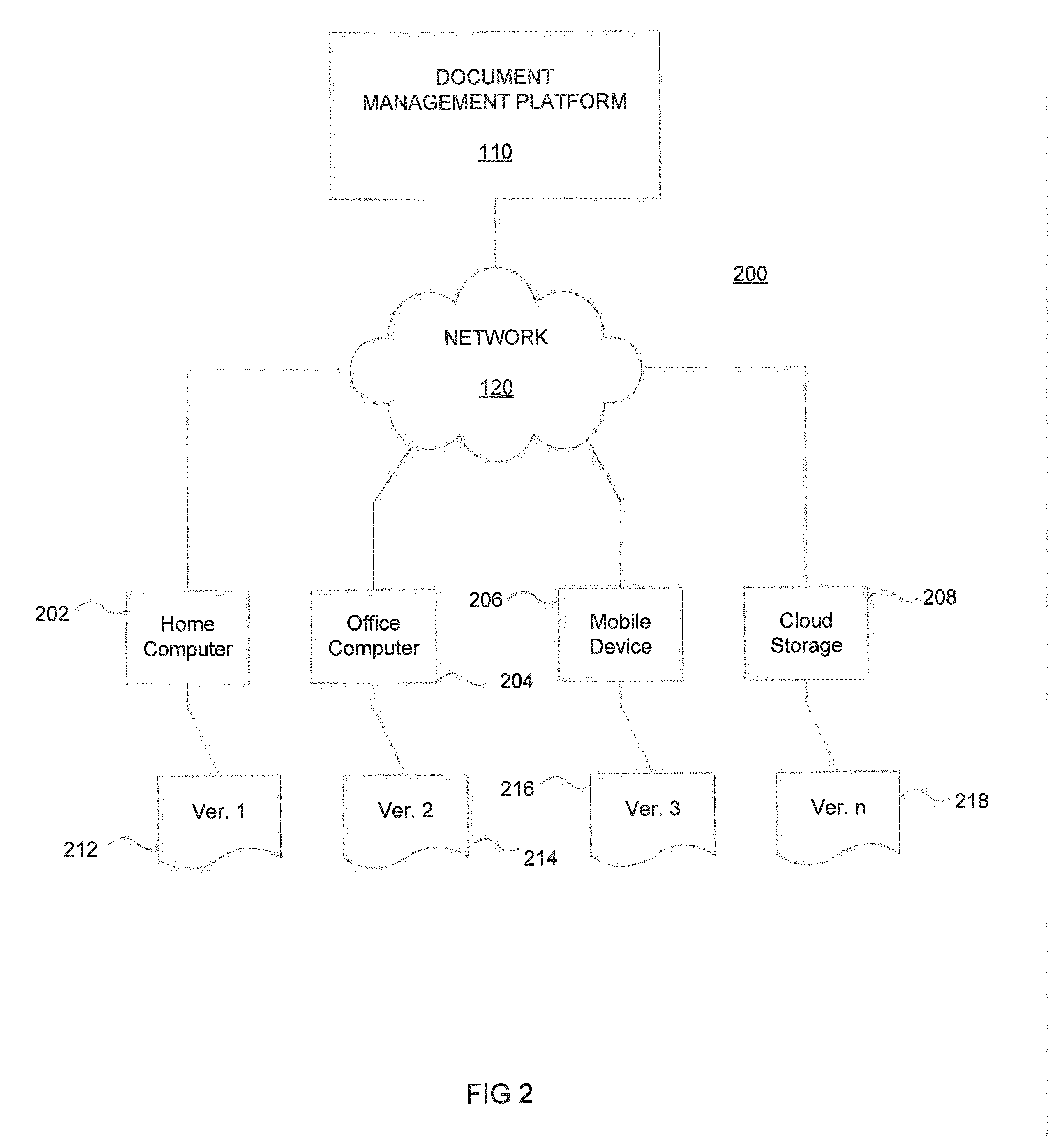
Systems and methods for multiple document version collaboration and management
ActiveUS20140372370A1Digital data processing detailsSpecial data processing applicationsDocumentation procedureRemote computer
Owner:LITERA CORP
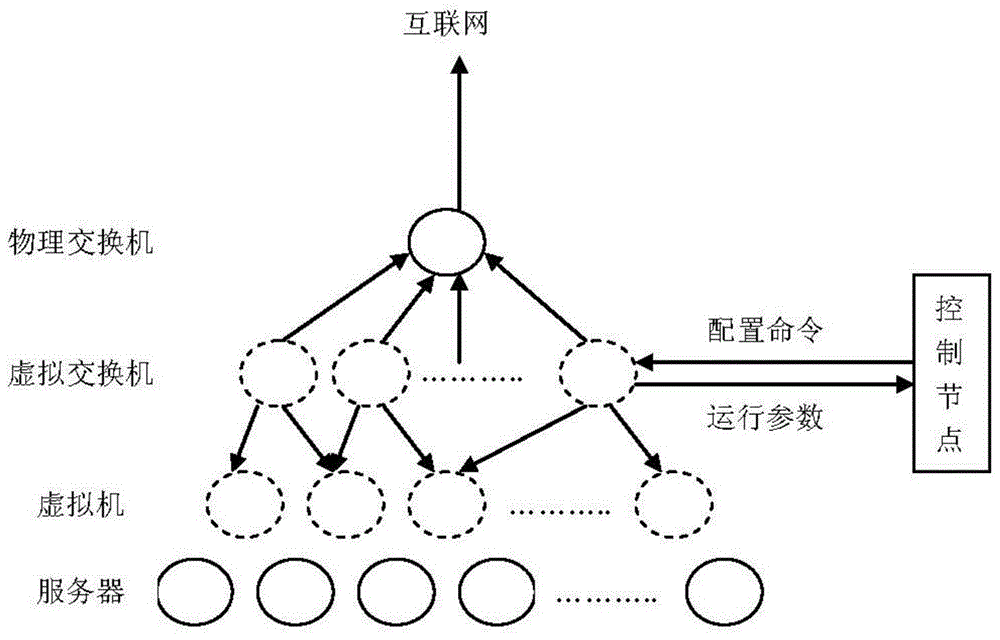
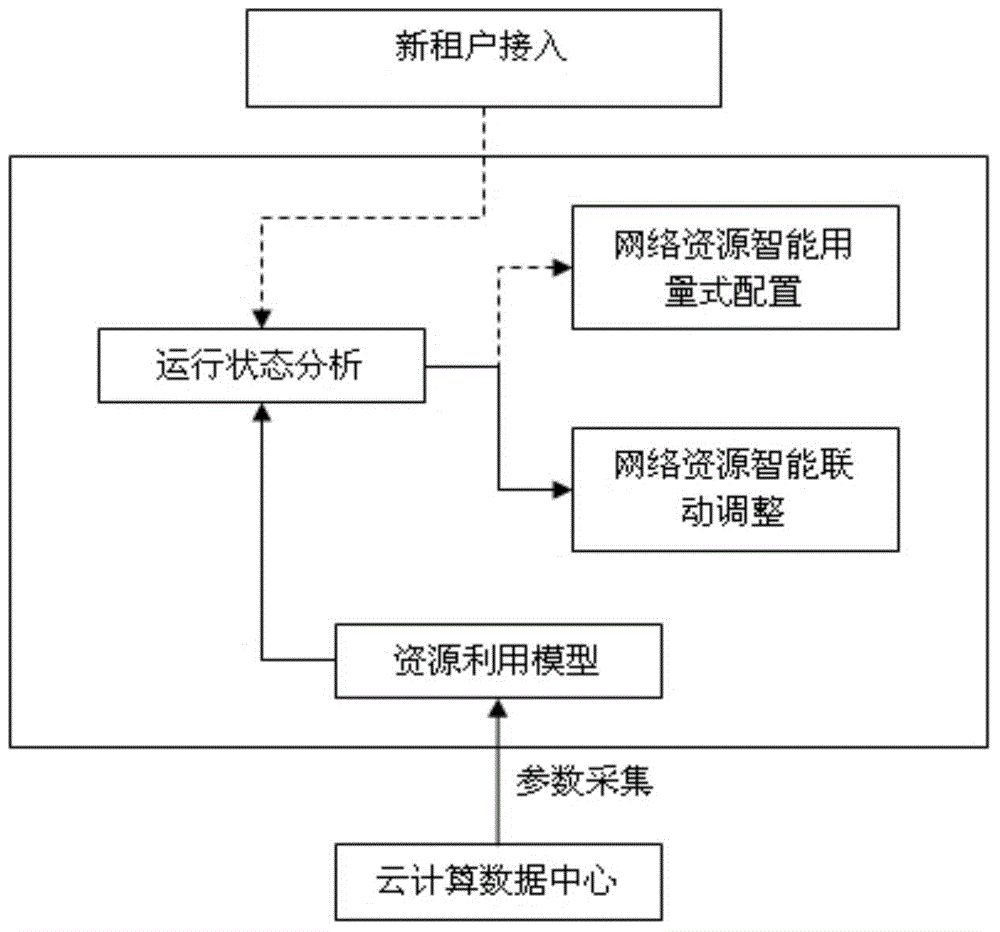
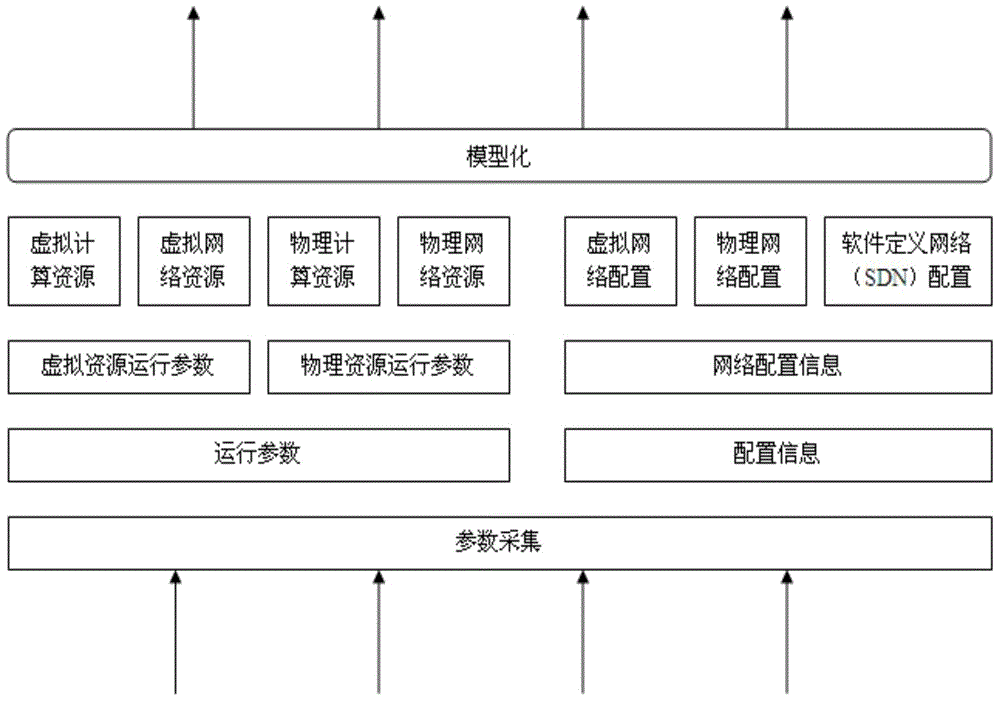
Cloud computing data center network intelligent linkage configuration method and system
InactiveCN104468212AImprove resource utilizationGuaranteed service qualityData switching networksResource utilizationData center
The invention discloses a cloud computing data center network intelligent linkage configuration method and system and relates to the technical field of computer network management. The cloud computing data center network intelligent linkage configuration method comprises the steps of extracting resource operation information and resource configuration information in a cloud computing data center network, performing analysis according to the resource operation information and the resource configuration information to obtain state information of a server and state information of a link in the cloud computing data center network, and performing adjustment by migrating the position of a virtual machine in the server according to the state information of the server and the state information of the link when the CPU utilization rate of the server or the utilization rate of the link is abnormal. The problem that a current cloud computing virtualized data center network is inflexible in strategy configuration and high in complexity and cannot sense the cloud computing platform resource utilization situation is effectively solved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Output management system and method for enabling printing via wireless devices
InactiveUS8019829B2Digitally marking record carriersVisual presentation using printersStore and forwardOutput device
A system and method for managing output such as printing, faxing, and e-mail over various types of computer networks. In one aspect, the method provides for printing via a wireless device. The system provides renderable data to the wireless device by which a user-interface (UI) may be rendered. The UI enables users to select source data and an output device on which the source data are to be printed. The source data are then retrieved from a local or remote store and forwarded to a print service, which renders output image data corresponding to the source data and the output device that was selected. The output image data are then submitted to the output device to be physically rendered. The user-interfaces enable wired and wireless devices to access the system. The system enables documents to be printed by reference, and enables access to resources behind firewalls.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
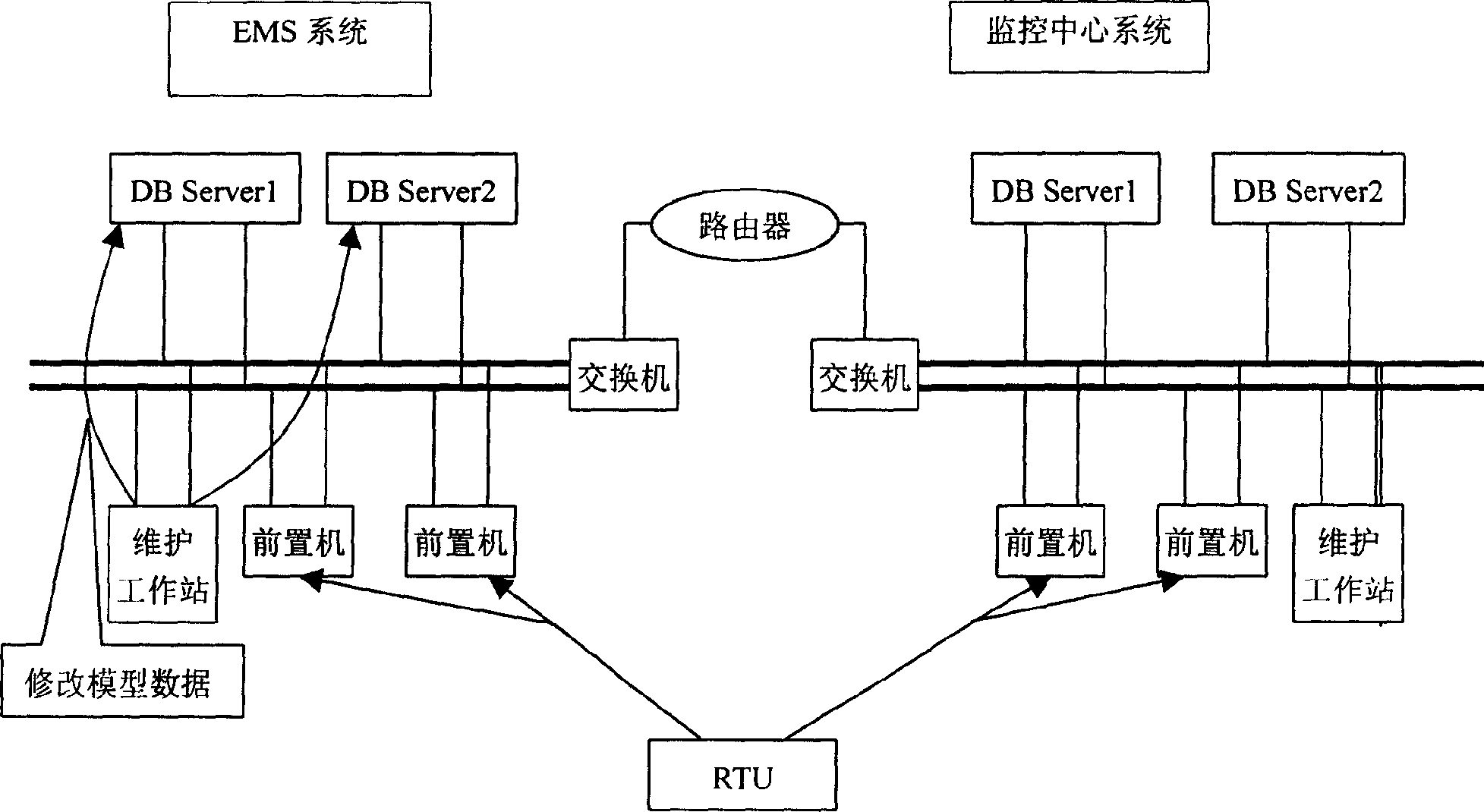
Method for establishing electric network monitoring disaster back-up system
InactiveCN1630160ASolve the problem of remote backupThe problem of off-site backup ensures thatCircuit arrangementsMultiple digital computer combinationsData synchronizationNetwork connection
An optical semiconductor device contains P type semiconductor substrate, P type epitaxy layer, N type cathode surface layer, optical receiving component formed of P type epitaxy layer and cathode surface layer, micro reflection mirror area formed from channel part, semiconductor laser chip fixed on bottom of channel part, and anode buried layer, so the optical receiving component having high speed action and high optical receiving sensitivity and luminous component having semiconductor laser chip can be integrated in one substrate.
Owner:JIANGSU ELECTRIC POWER CO
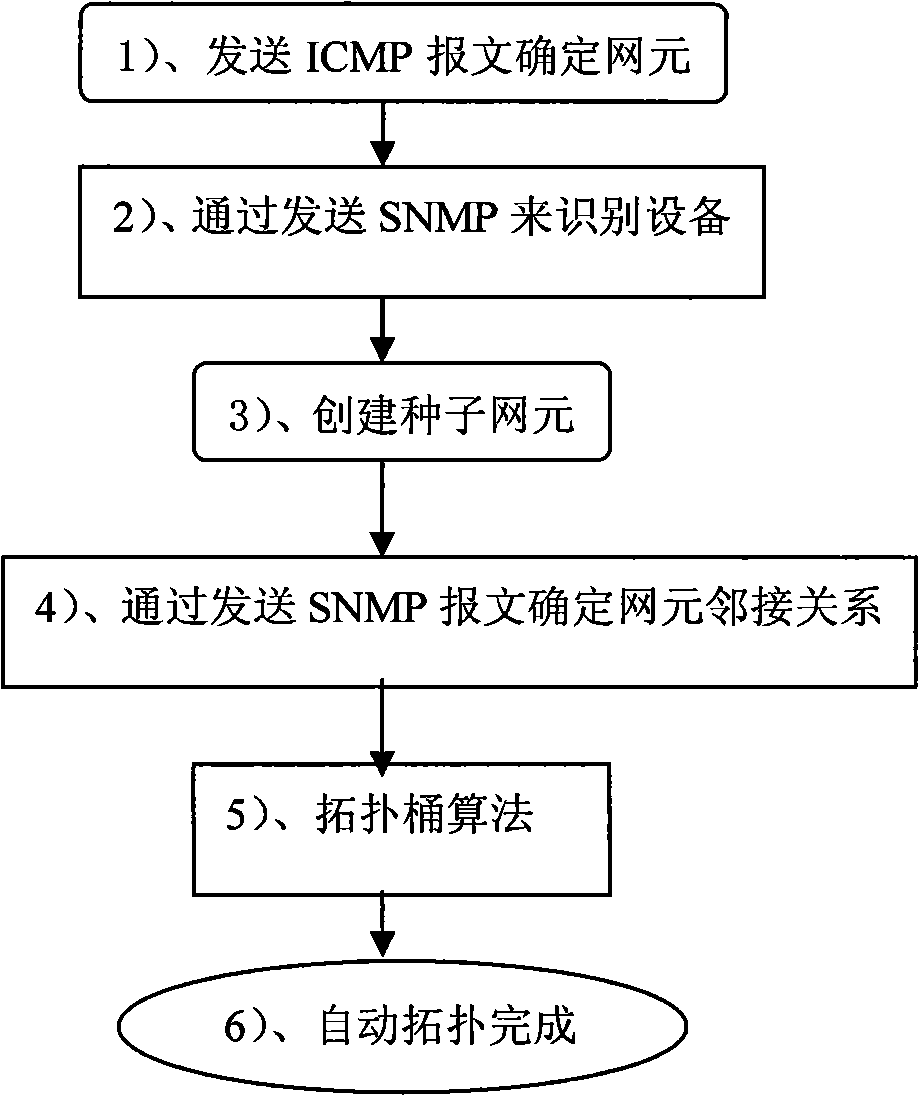
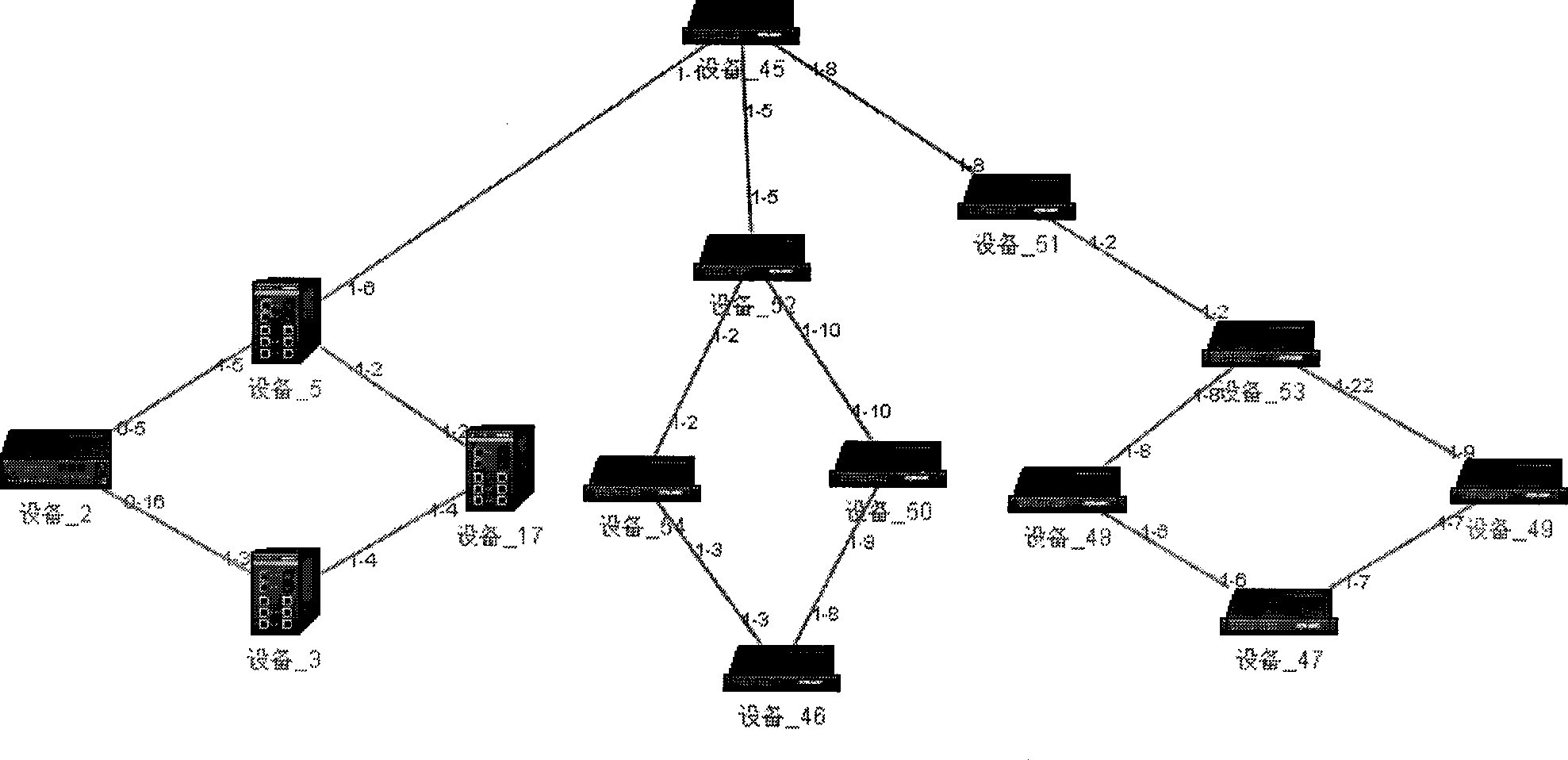
Automatic topology realisation method based on topological bucket algorithm
ActiveCN101534216ASimplified managementAutomatically discover connectionsEnergy efficient ICTData switching networksAdjacency relationComputer science
The invention discloses an automatic topology realisation method based on topological bucket algorithm, belongs to the field of computer network management, and is particularly suitable for network topology management of an Ethernet exchanger. The invention solves the technical problem of quick formation of wide area automatic topology. The invention comprises the steps of optionally selecting a network apparatus in a topological seed bucket as a seed net element, sending a message for inquiring apparatus adjacency relation to the seed net element, obtaining the apparatus adjacency relation, adding the inquired adjacent apparatus in a temporary topological queue, orderly constructing net elements and apparatus icons on a topological plane, and establishing a topological relation; comparing the apparatuses in the temporary topological queue with the apparatuses in the topological bucket and the topological seed bucket, then orderly taking out the adjacent apparatuses as seed net elements from the to-be-topological queue, continuously searching and circulating, and accomplishing topology until the temporary topological queue, the to-be-topological queue and the topological seed bucket are blank. The technical proposal of the invention has the advantages of high efficiency, high flexibility and high accuracy, and the topology is relatively intuitive.
Owner:东土科技(宜昌)有限公司
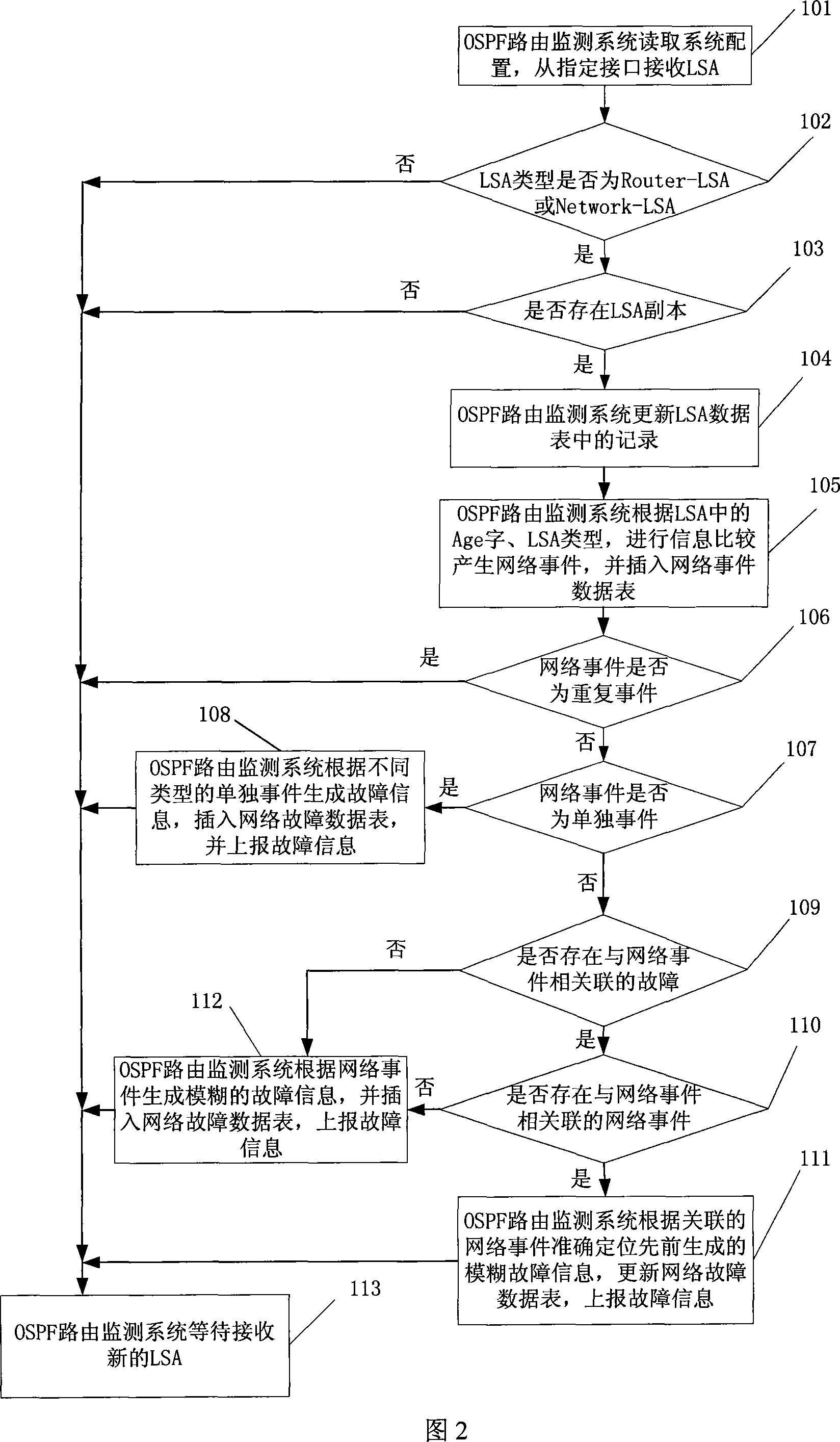
Method and device for IPv4 and IPv6 network failure detection and location
ActiveCN101188530ATimely detection and positioningData switching networksEvent dataMonitoring system
The invention discloses an Ipv4 and Ipv6 network failure detecting and locating method and the apparatus thereof, and belongs to the technical field of the computer network management The method comprises the steps that a route monitoring system receives the chain circuit state broadcasting which identifies a network state, generates a network incident through analyzing the type of the chain circuit state broadcasting and the signal change, and then inserts the network incident into a network incident data table; according to the attribution of the network incident, the route monitoring system makes a relevant analysis on the network incident and the prior network incident to generate failure information; the route monitoring system inserts the failure information into a network failure data table, and reports the failure information to a network manager. The apparatus comprises a receiving module, an analysis generating module, a generation module, and a reporting module. The invention uses the route monitoring system to collect the chain circuit state broadcasting which identifies the network state, and to store and analyze the chain circuit state broadcasting, thereby realizing the purpose of timely detecting and locating the failure which arises in the network.
Owner:TSINGHUA UNIV
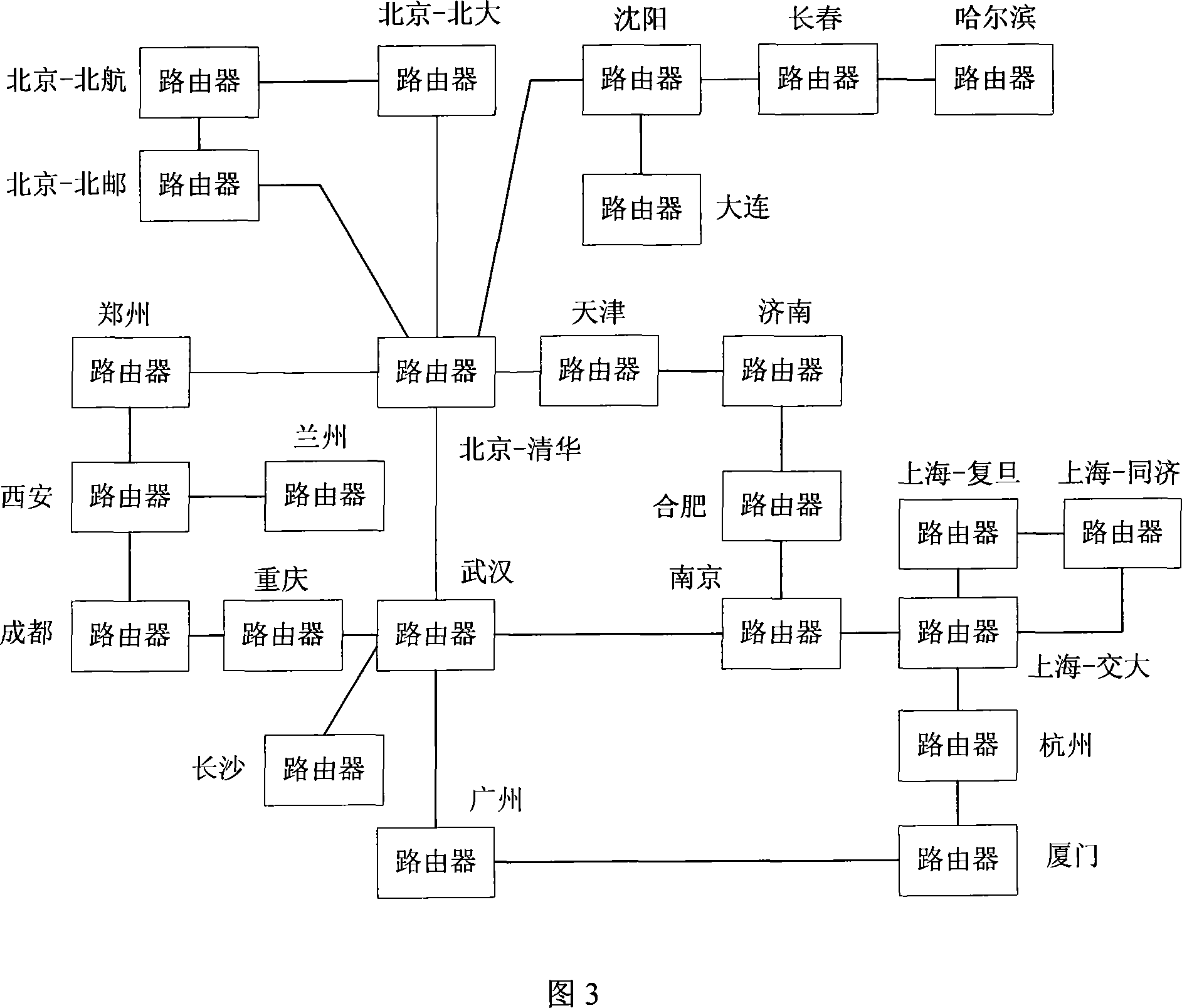
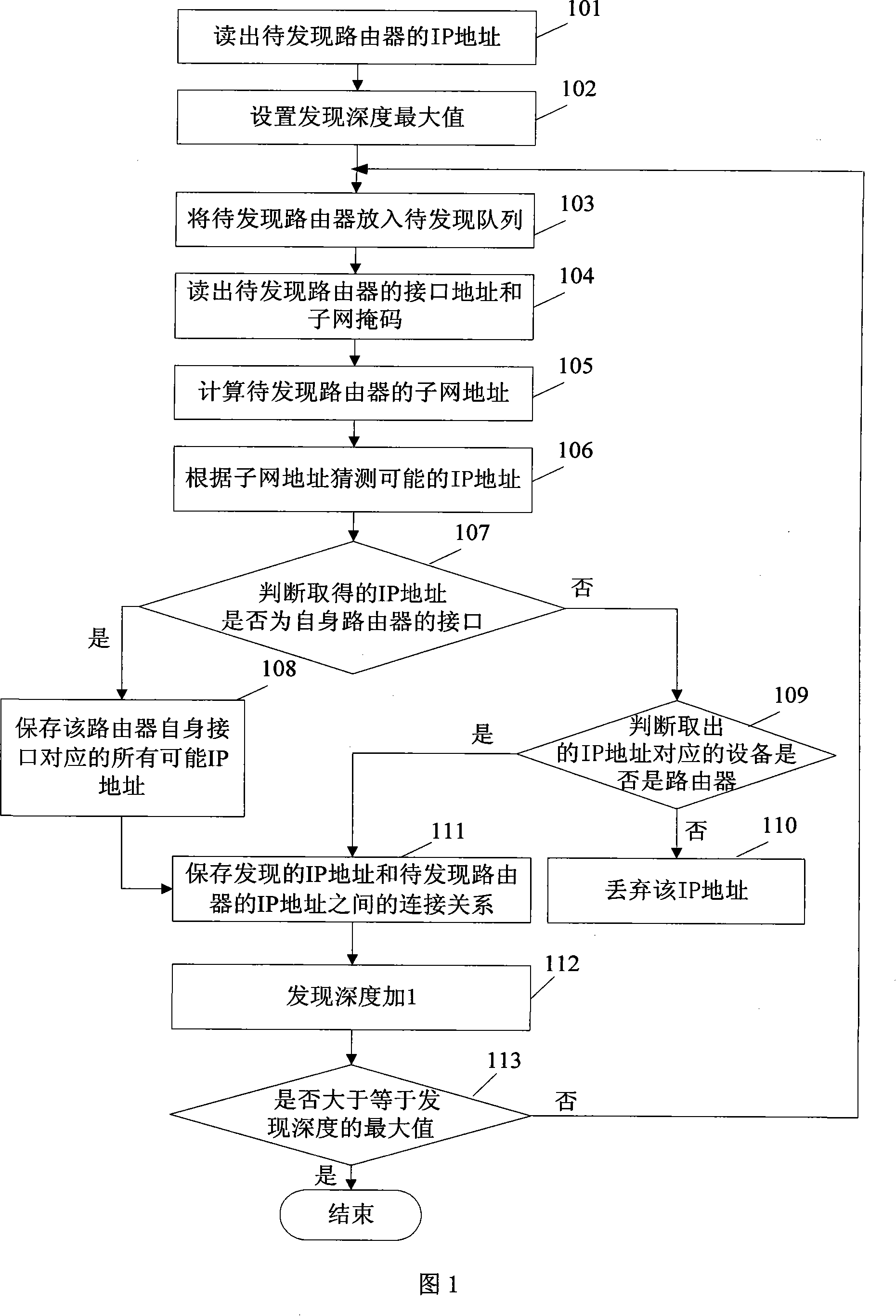
Topology discovering method of IP backbone network
InactiveCN101141308AAccurate discoveryEfficient discoveryData switching networksIp addressNetwork addressing
The utility model discloses an IP backbone topology discovery method, pertaining to the field of computer network administration. The method can pre-set the maximal value of the discovery depth and read IP address of the seed router to obtain all of the port address and sub-net mask code of the router. As per the port address and the sub-net mask code, the sub-network address can be calculated. Such sub-network address is connected with the router. Based on the calculated sub-network address, deducing the IP address which is correspondent to the sub-net; the deduced IP address is chosen as the IP address for the router to conduct the respective self-adapting and intelligent judgment & analyzing; the connected relation for the discovered router IP address shall be kept; the discovered depth is added with 1 to judge whether the discovered depth is no less than the maximal value. If yes, it is over, or the router subjecting to the discovered IP address shall be placed in the list to be discovered. The utility model gradually extends from the router to be discovered to the outside, so as to self-adapt and discover various IP backbones' topology connection relation accurately and effectively.
Owner:TSINGHUA UNIV +1
Organization and maintenance method based on GIS for computer network map
InactiveCN1474297ADigital computer detailsSpecial data processing applicationsTopological consistencyNetwork structure
The organization method of hierarchical computer network GIS map includes the following steps: constituting hierarchical network structure in practical requirement; constituting relevant GIS maps foreach network in the hierarchical structure; and adding corresponding practical links to the hierarchical network GIS map for all connections in the network topology while maintaining the consistency between the practical link and upper convergent link. The hierarchical network GIS map provides hierarchical network topology and state information converging and de-converging method. The present invention provides the topological updating and state updating algorithm for hierarchical network GIS map and can maintain the topological consistency and state consistency of network GIS map. The present invention may be used widely in computerized network management system and network monitoring system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
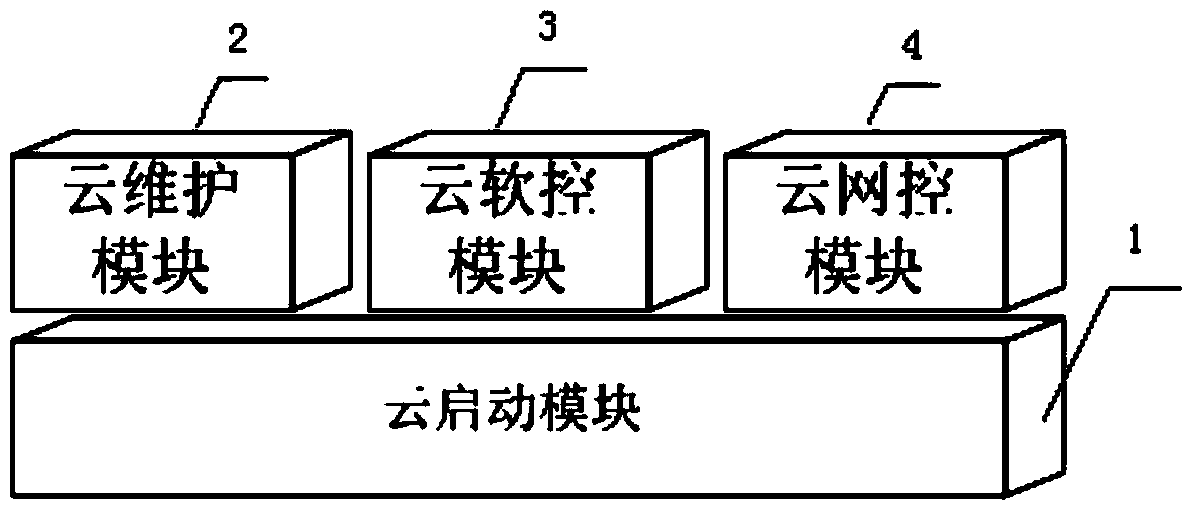
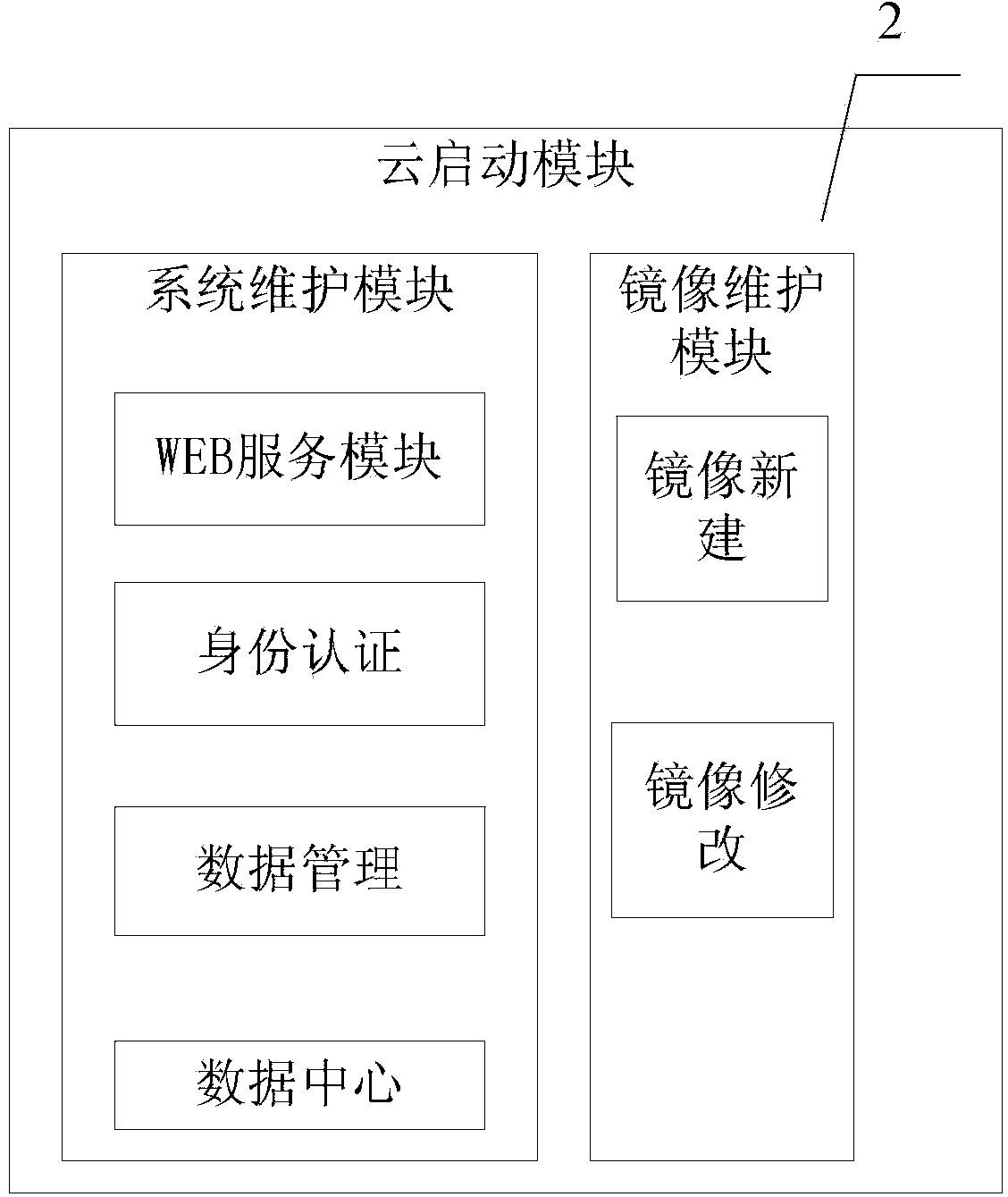
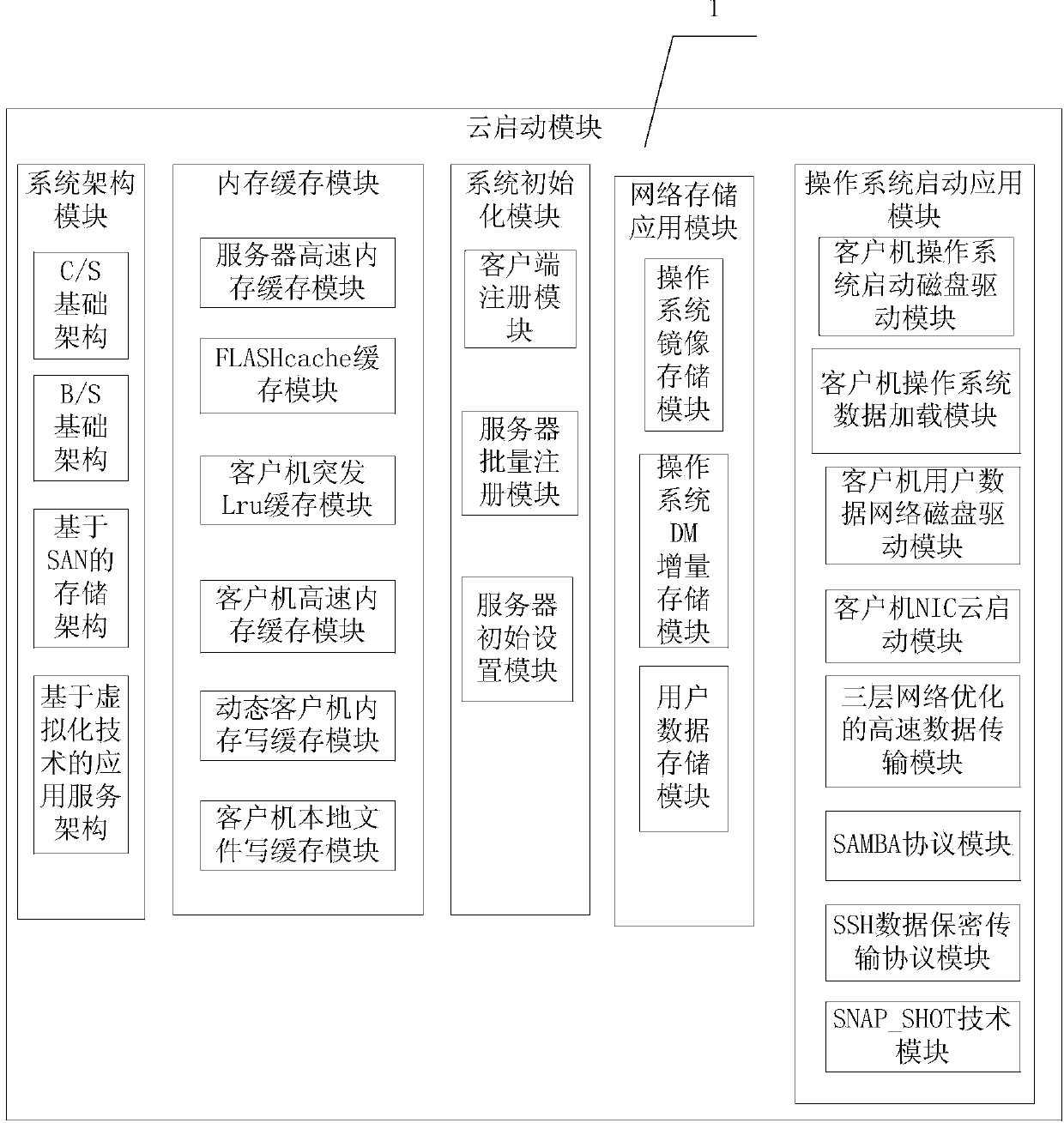
Computer network cloud start-up system
InactiveCN103595574AMake sure not to be poisonedImprove transmission efficiencyData switching networksOperational systemSystem maintenance
The invention discloses a computer network cloud start-up system which is characterized by comprising a cloud start-up module, a cloud maintaining module, a cloud software control module and a cloud network control module. The cloud start-up module is used for completing client system construction with network mirror image starting, setting an abandoning area, separately storing normal operational data and system temporary data, separating user data and operational system data, abandoning the temporary data related to an operation system through shutdown, and normally storing normal operational data of a user; heterogeneous networking protocols are adopted to network data transmission; the cloud maintaining module is used for system maintenance and software installation of a computer in a network; synchronous maintaining and synchronous updating on all systems or software of the computer are completed through one-time operation by logging in a server; as for a computer requiring to customize individual software and individual systems, a computer maintenance mode is provided in an independent mirror image mode. The computer network cloud start-up system can be widely applied to computer network management in occasions such as schools, factories and offices.
Owner:CHONGQING SUNWARD TECH
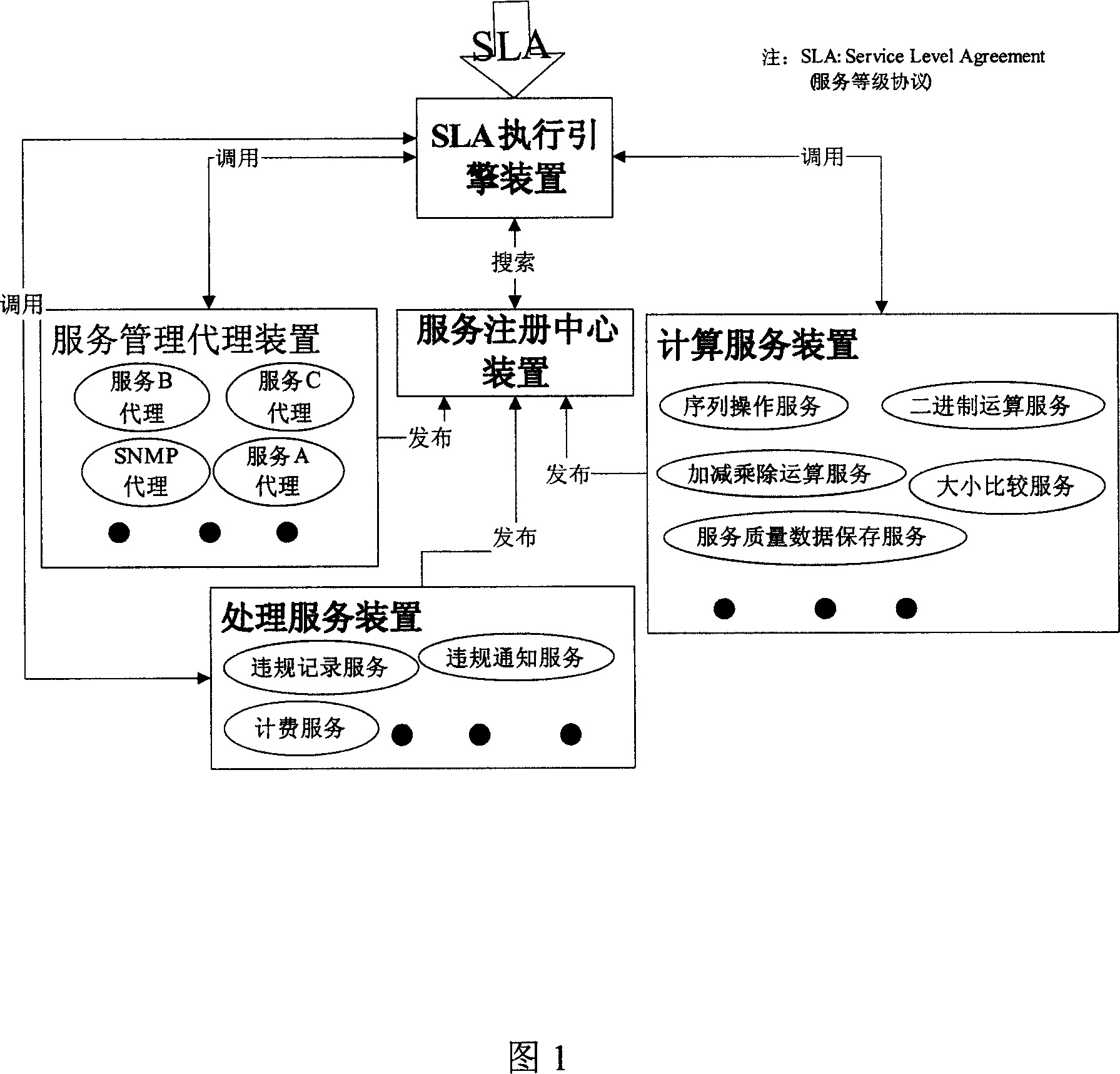
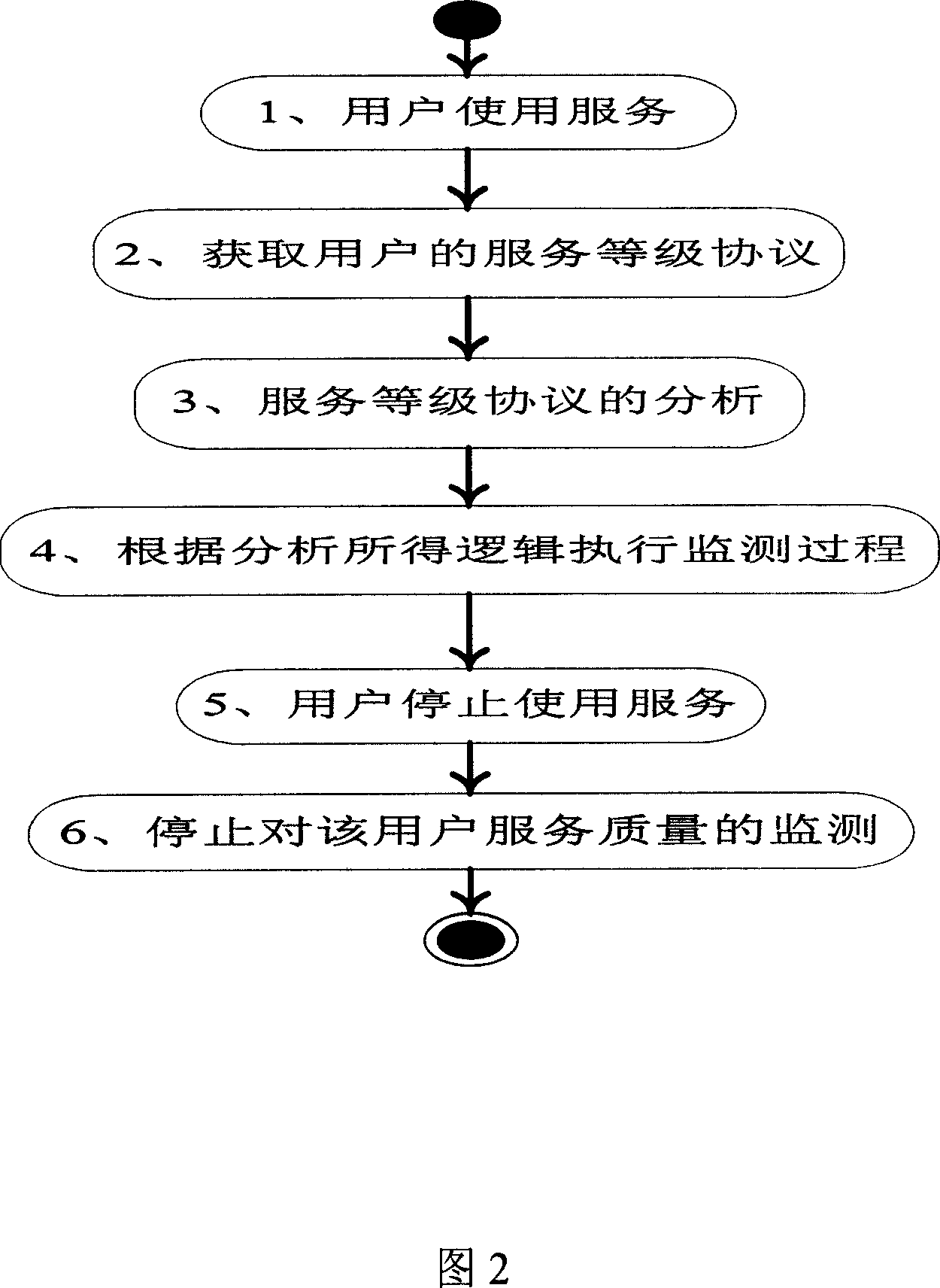
Method for monitoring network service quality and system thereof
ActiveCN1949714AAdapt to different needsReduce the impactData switching networksGrade of serviceMonitoring system
The invention relates to computer network management technical field, especially a network QoS monitoring system and method based on service grade protocol. And the courses: resolving the whole monitoring courese into parts of plural monitoring functional servcies, determining service grade protocol, analyzing service grade and obtaining QoS monitoring logic, and processing the monitoring functional services according to the obtained logic. And the system comprises: service management agency, calculation service, processing service, service registering center, and SLA executing engine. And the method has very high flexibility and self- adaptivity and can be applied to monitoring qualities of various services.
Owner:SHENZHEN ACSNO INFORMATION TECH
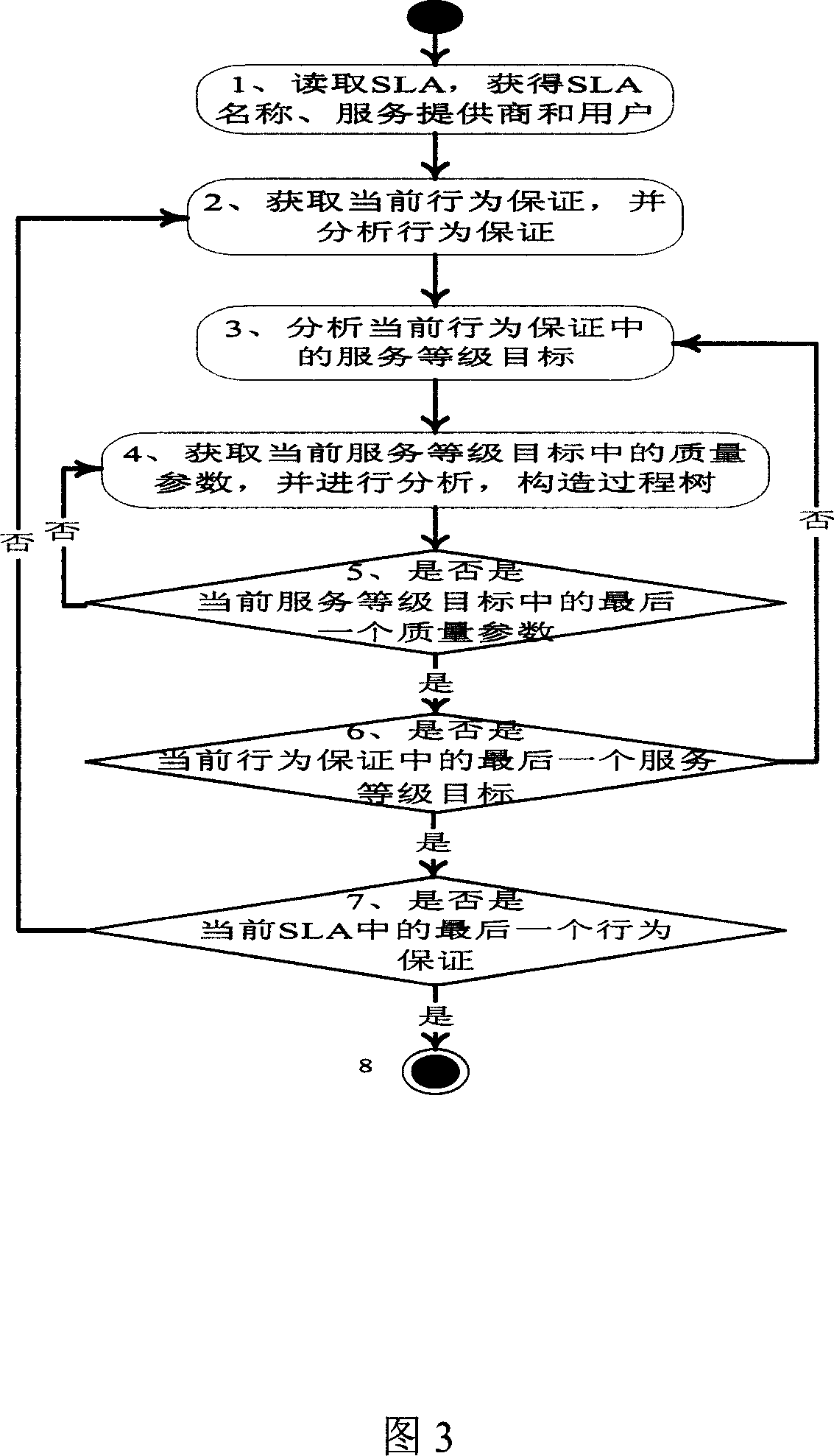
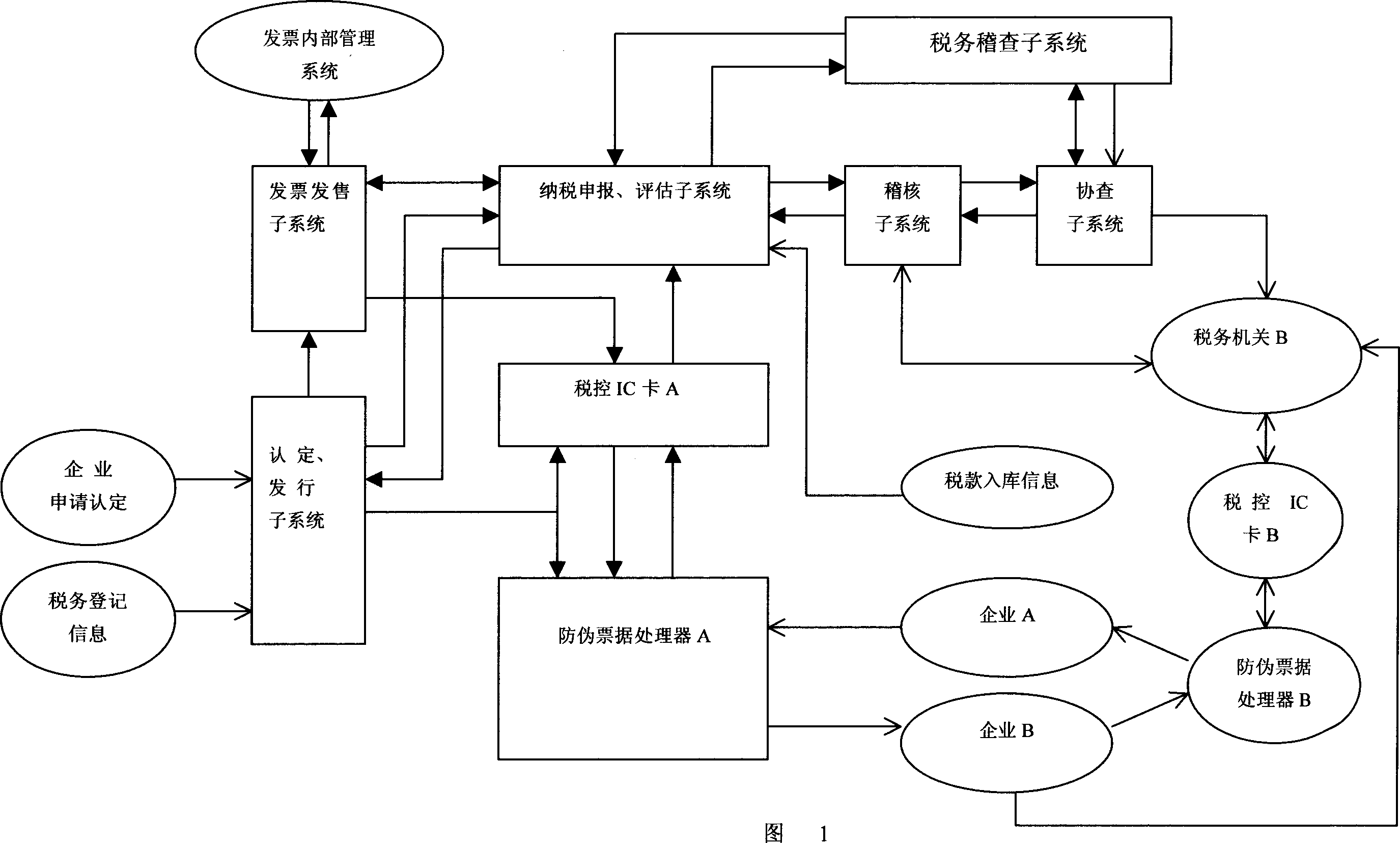
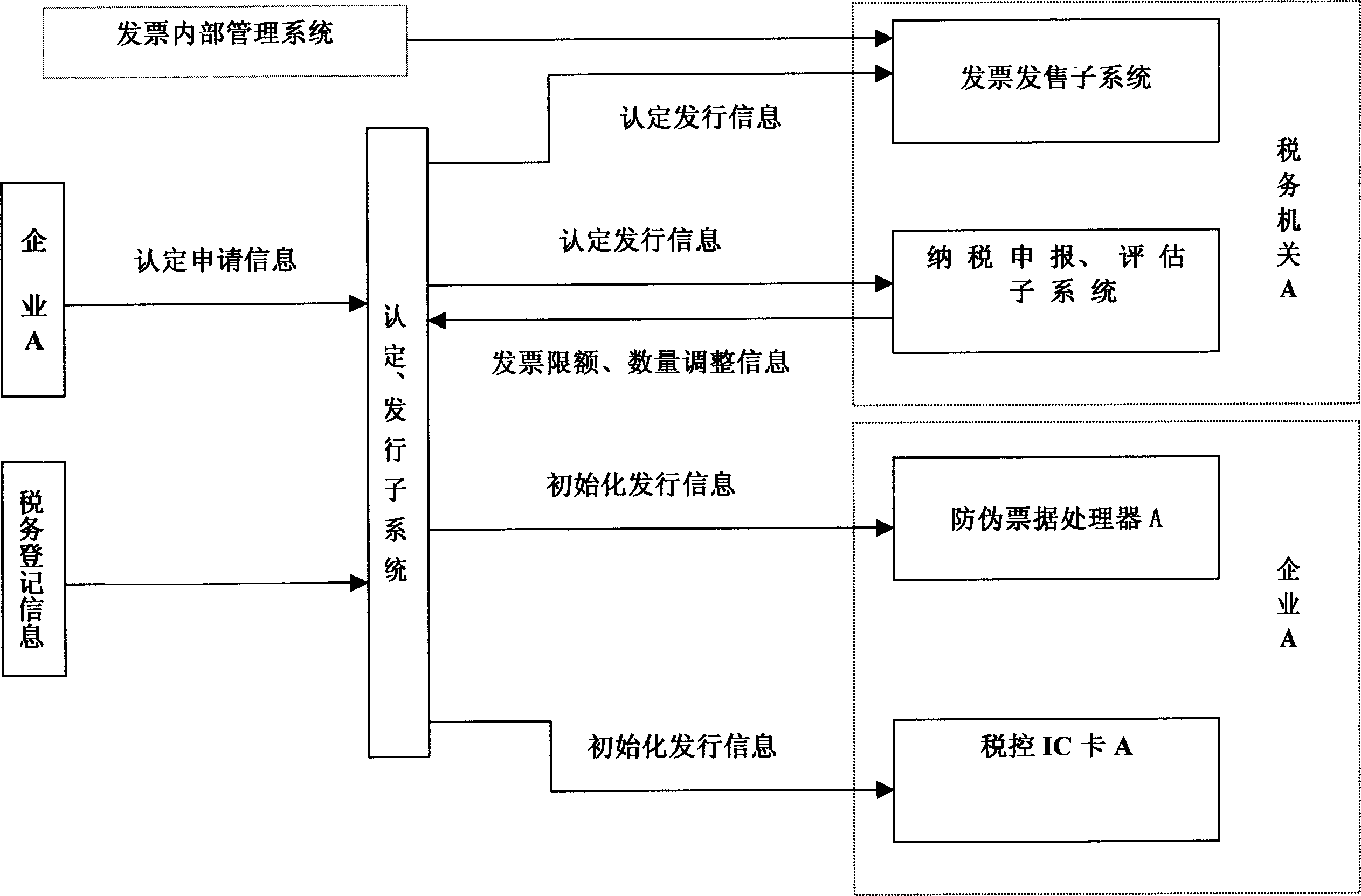
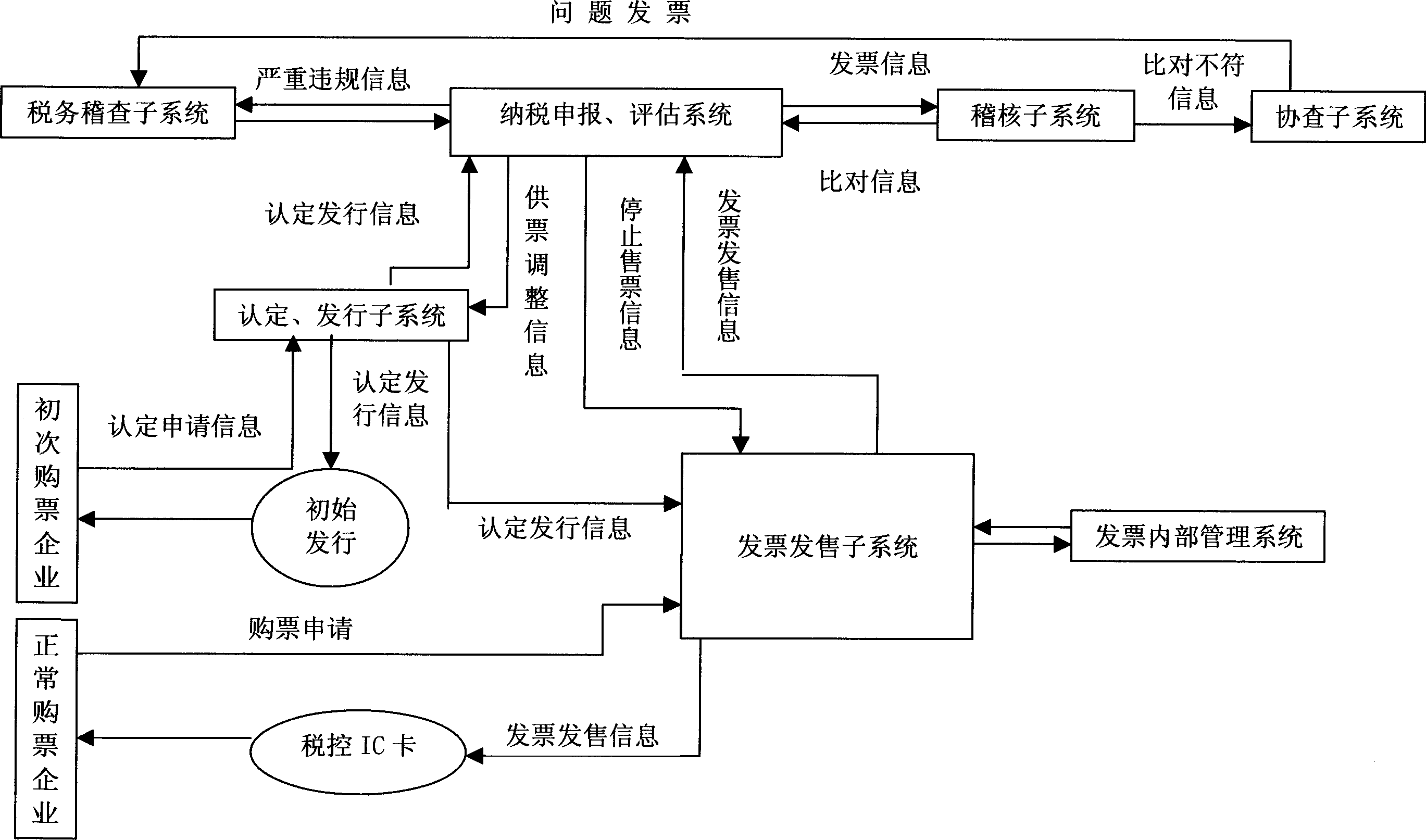
Tax-controlled invoice check management method
InactiveCN1776748AEfficient managementStrengthen unified managementPaper-money testing devicesDigital dataInvoice
The method is related to technical area of electronic digital data process applicable to administrative department. Main technical features are as following: through processor of anti false bill, enterprise draws a bill and verifies received invoice; when tax declaration, through tax controlled IC card, the method sends data stored in the said processor to sub systems of tax declaration and sub system of evaluation; then data are transferred to verification sub system to carry out verification and comparison between information of bill drawn by one enterprise and information of invoice received by another enterprise so as to realize closing management for invoice. Using computer network for managing invoice with magnetic strip, the invention manages invoice strictly. Features are: low cost, easy of operation.
Owner:柴杰生
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com