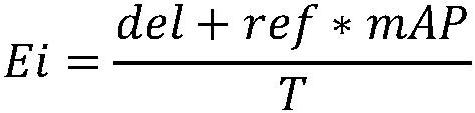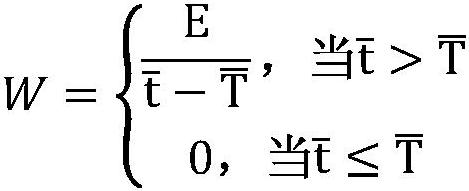Patents
Literature
33results about How to "Monitor behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
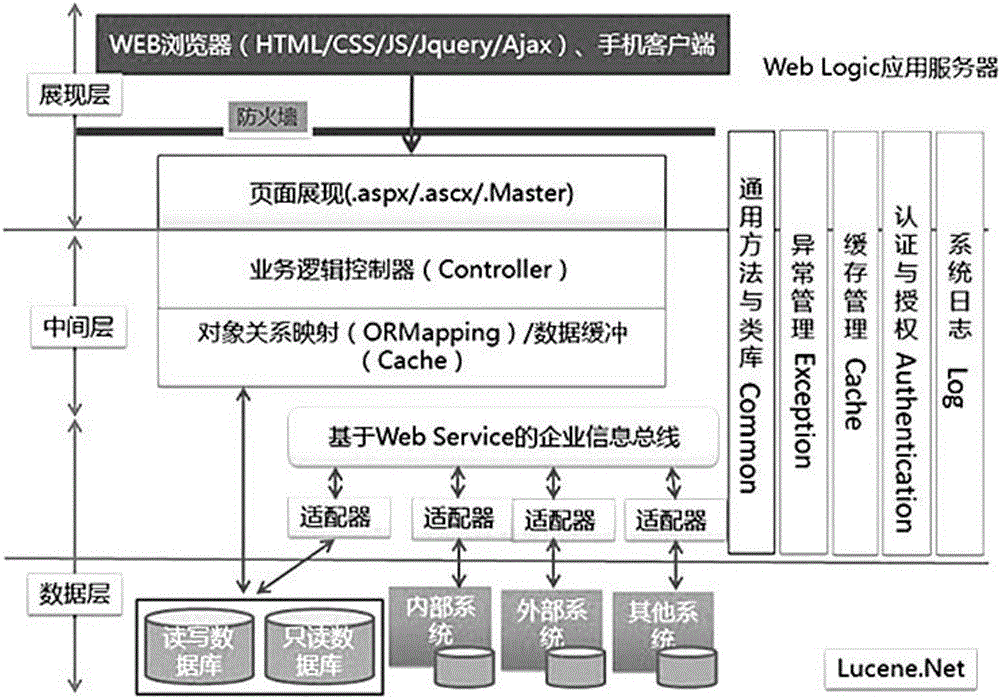
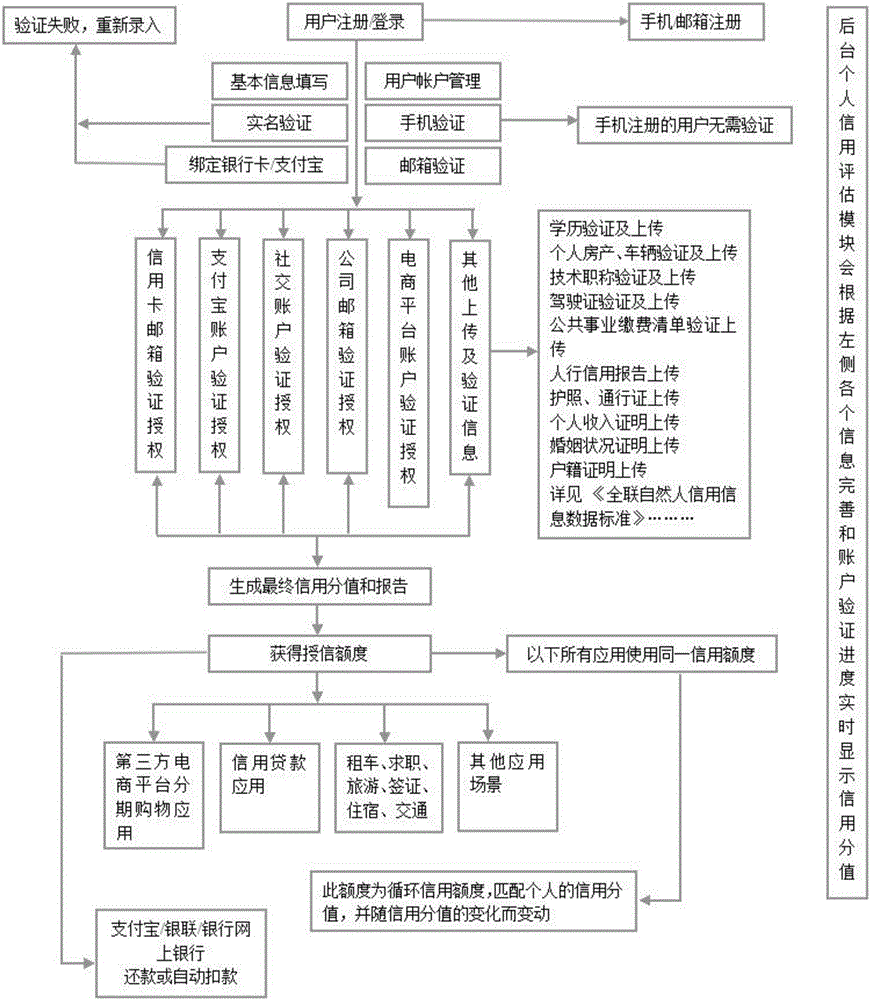
Personal credit ecological platform
InactiveCN106447434AData quality freshImprove accuracyFinanceCredit schemesComputer scienceSustainable development
The invention discloses a personal credit ecological platform, which is structured by a display layer, a middle layer and a data layer; the display layer is a front client platform, the middle layer is a background service platform, and the data layer is a data warehouse system; the whole ecological platform consists of a management end, a personal credit module, a merchant module, a payment flow, and a mobile APP. The platform data base is deep, the data quality is alive, the accuracy is high, the scale is wide, and the time track is rich, the data volume is huge and the dimension is wide. The platform deeply excavates the personal credit data, realizes the credit evaluation, provides the complete personal credit status, realizes the personal credit tracking management, and further controls the risk; besides, the client complaint procedure is added. The platform achieves the recommendation of potential and sustainable developed individual client for merchant users, and realizes the bidirectional push.
Owner:全联征信有限公司
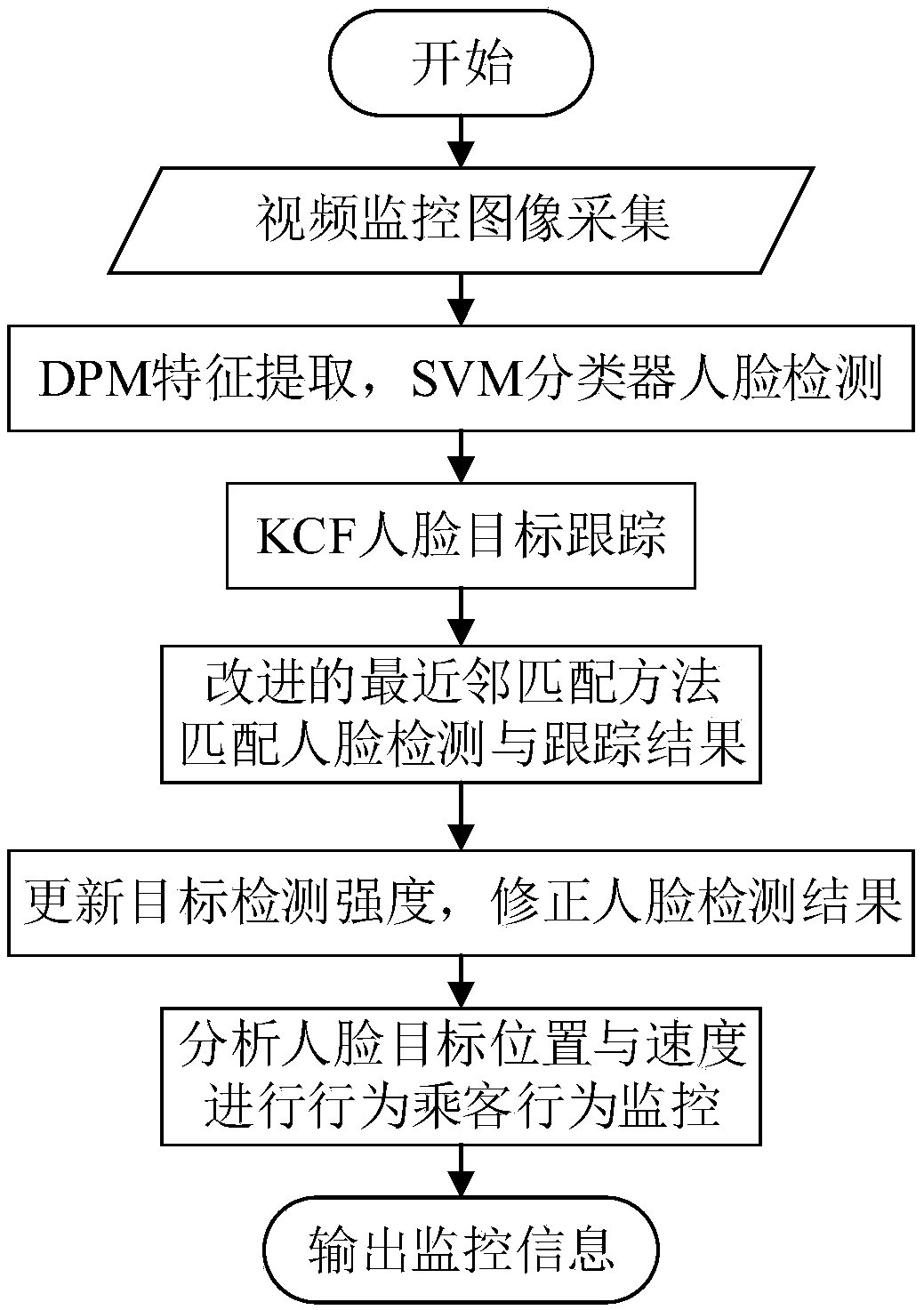
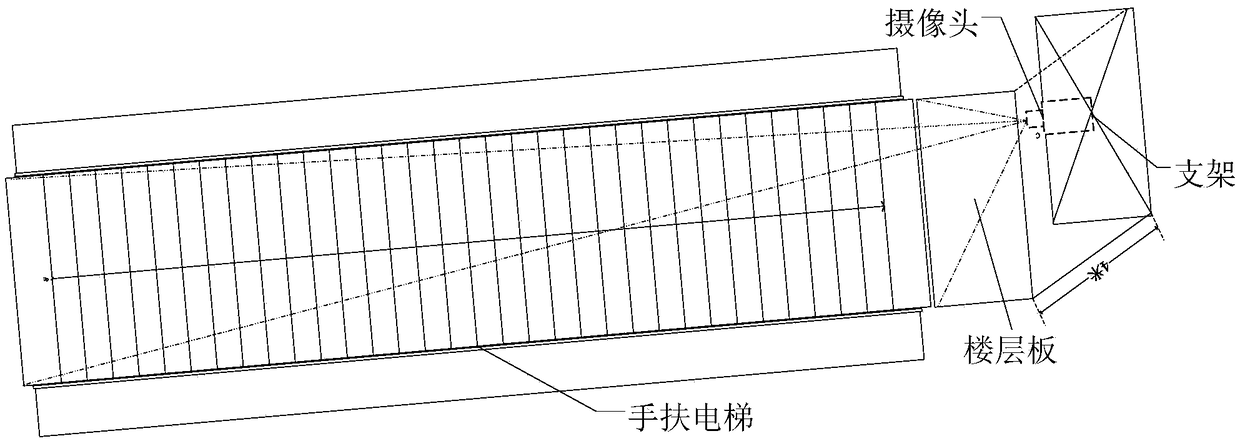
Passenger behavior monitoring method based on machine vision
ActiveCN109359536AMonitor behaviorAvoid safety accidentsCharacter and pattern recognitionFace detectionPattern recognition
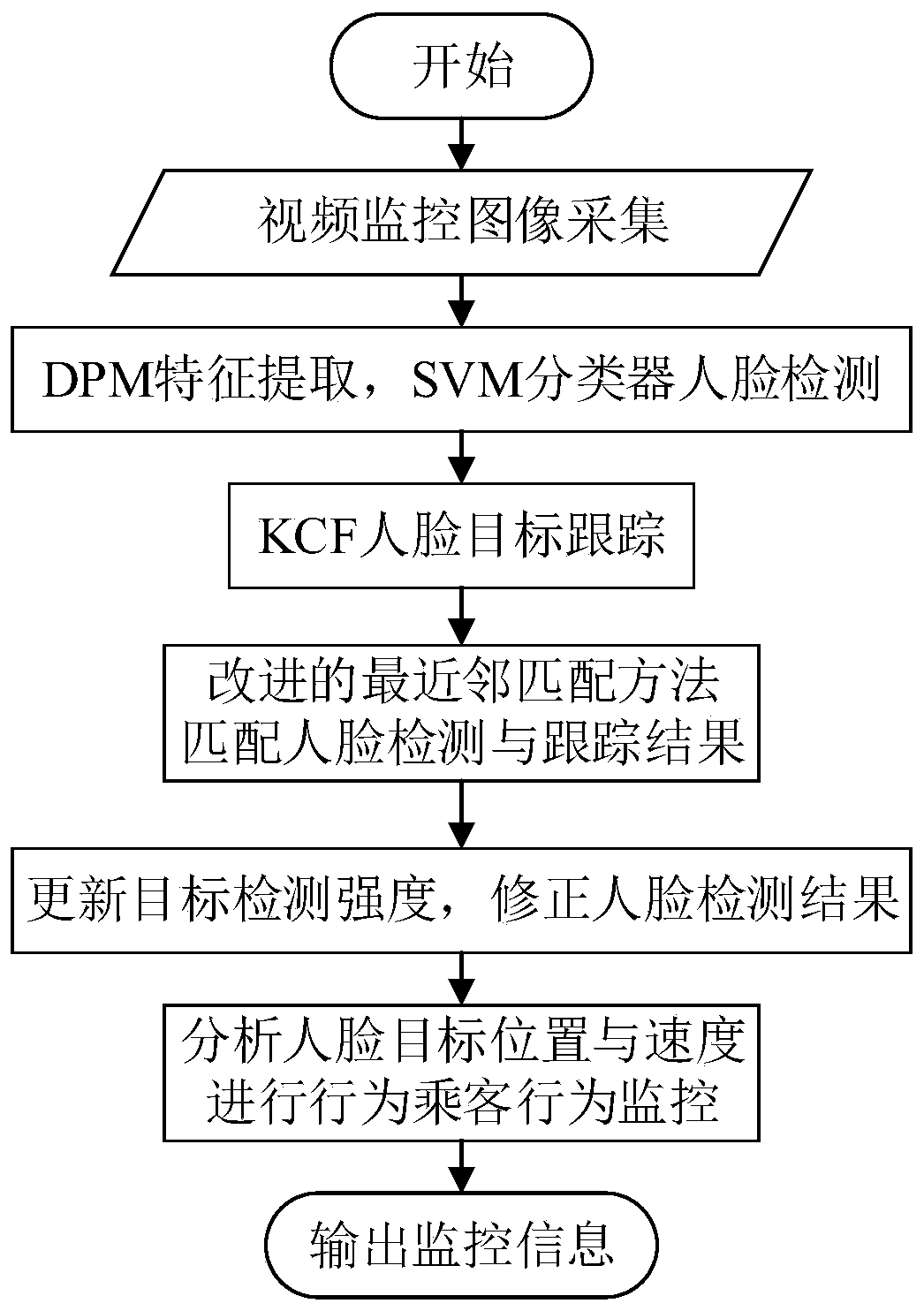
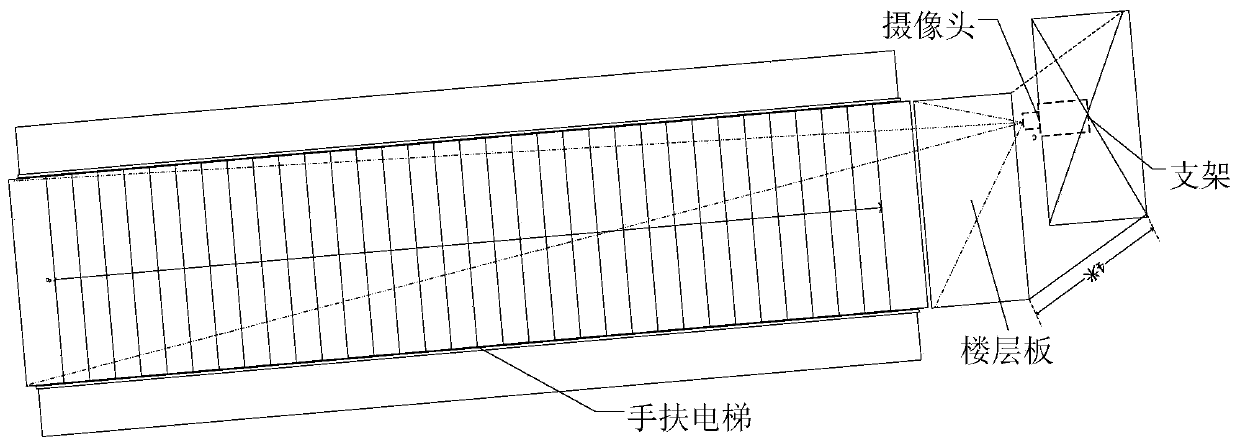
The invention discloses a passenger behavior monitoring method based on machine vision, which comprises the following steps: 1) acquiring video images of a passenger riding on an escalator; 2) extracting that DPM feature of the deformable component model to describe the passenger face; 3) detecting that passenger face of an escalator by using an SVM; 4) tracing that passenger face of the hand elevator by using the KCF; 5) using an improved nearest neighbor matching method to match the face detection and tracking results; 6) establishing a face target detection intensity model and correcting aface detection result; 7) monitoring that behavior of passengers in the escalator by analyze the detection intensity, speed magnitude and speed direction of passengers. The method of the invention candetect and track the face target of passengers riding on the escalator in real time, stably and accurately, and carry out behavior monitoring based on the face target information.
Owner:SOUTH CHINA UNIV OF TECH +1
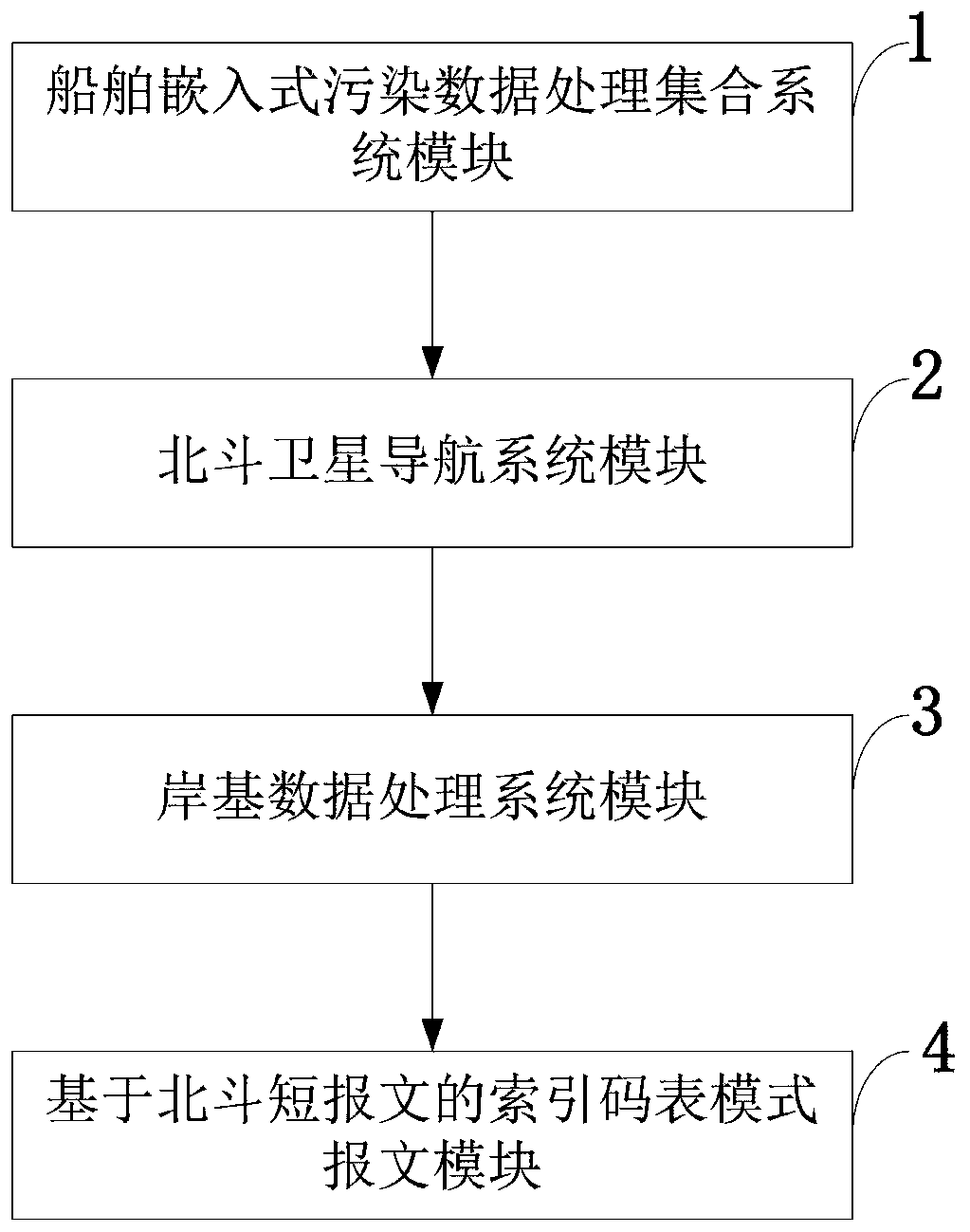
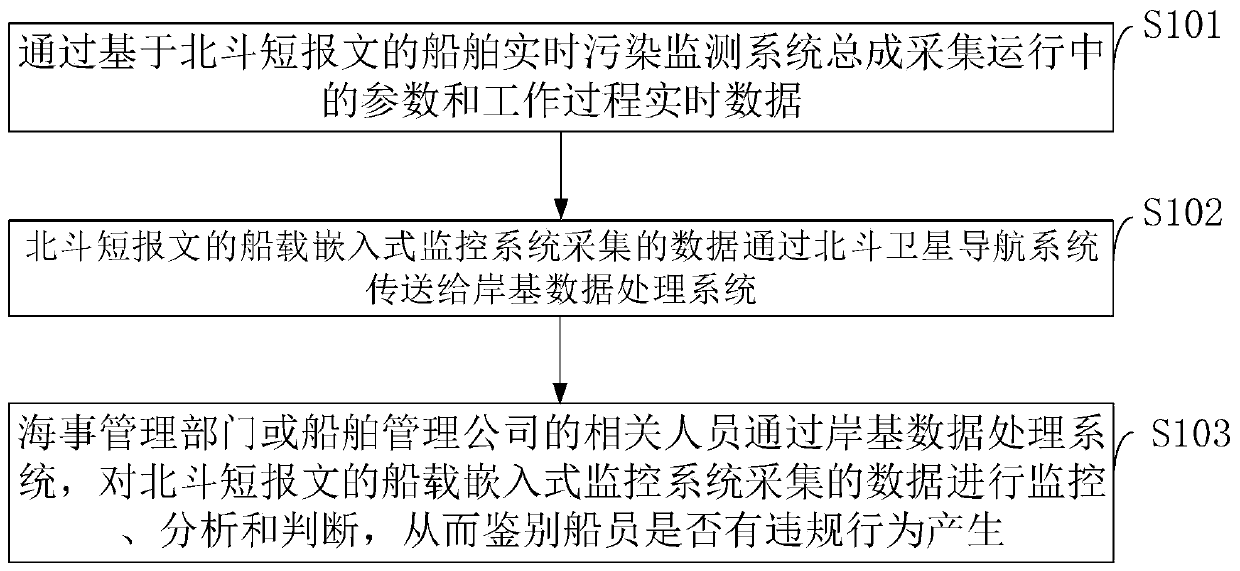
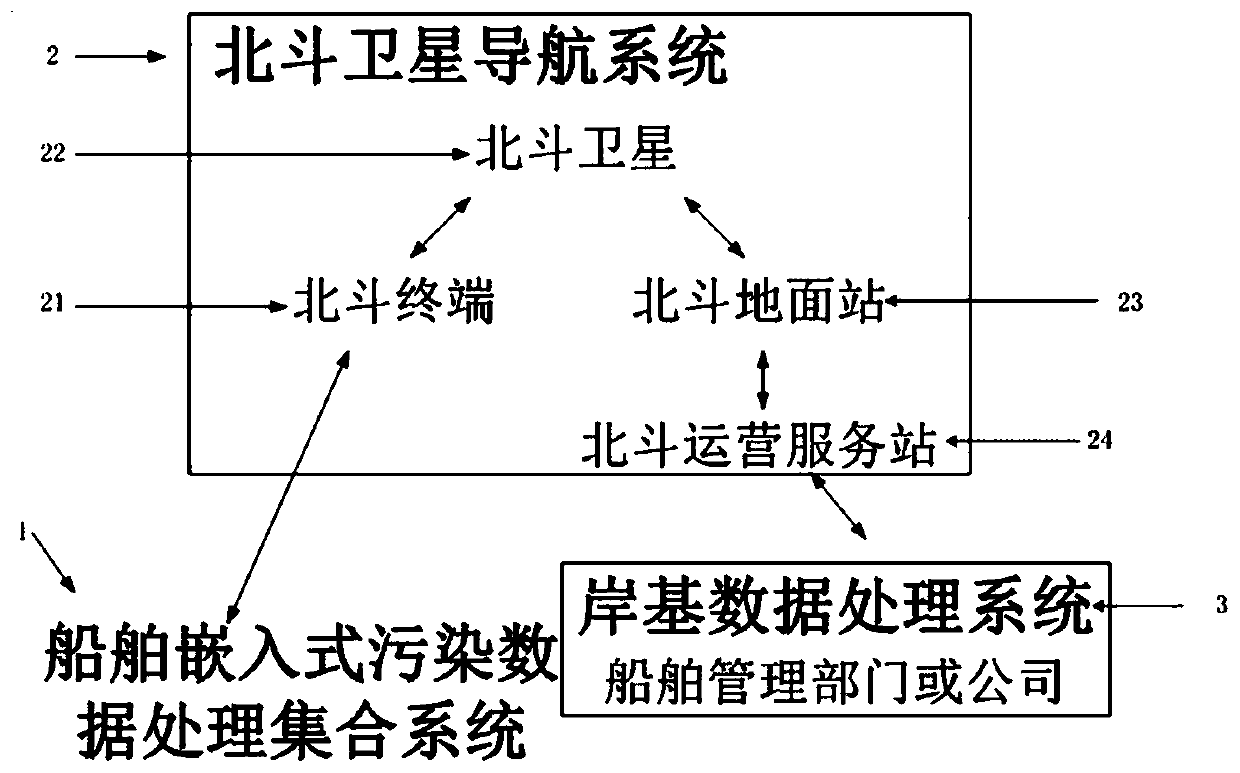
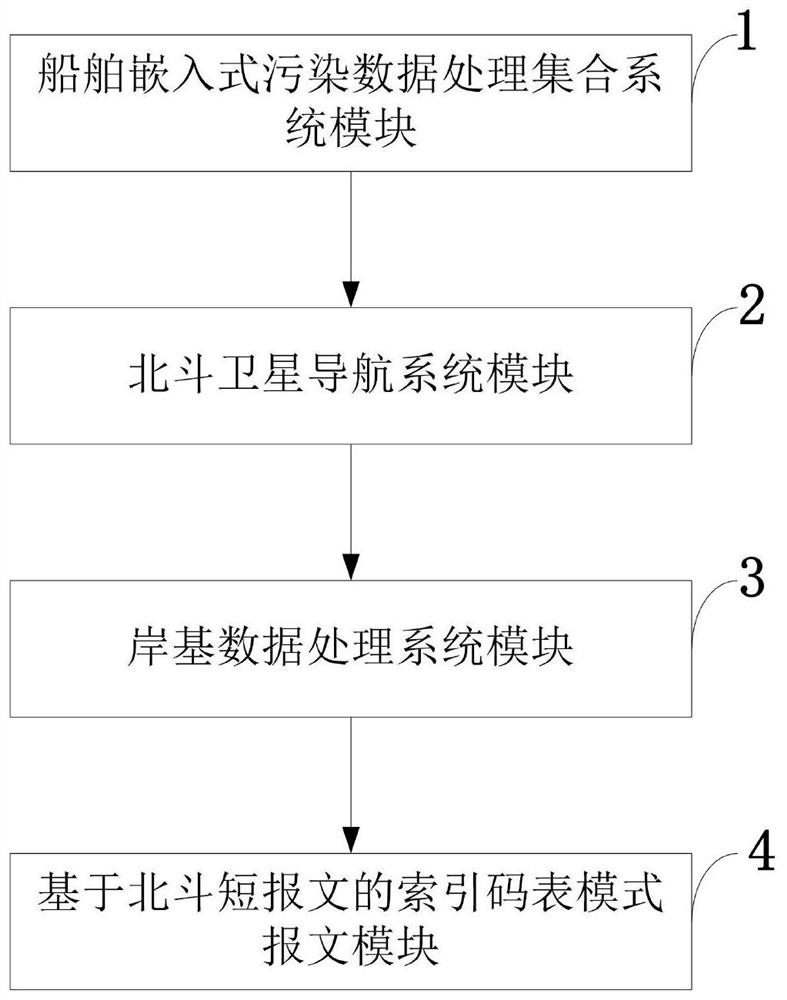
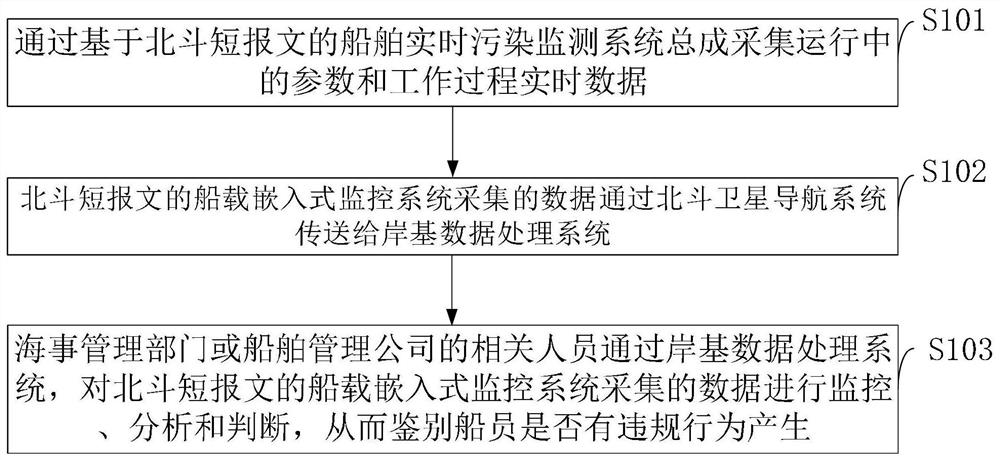
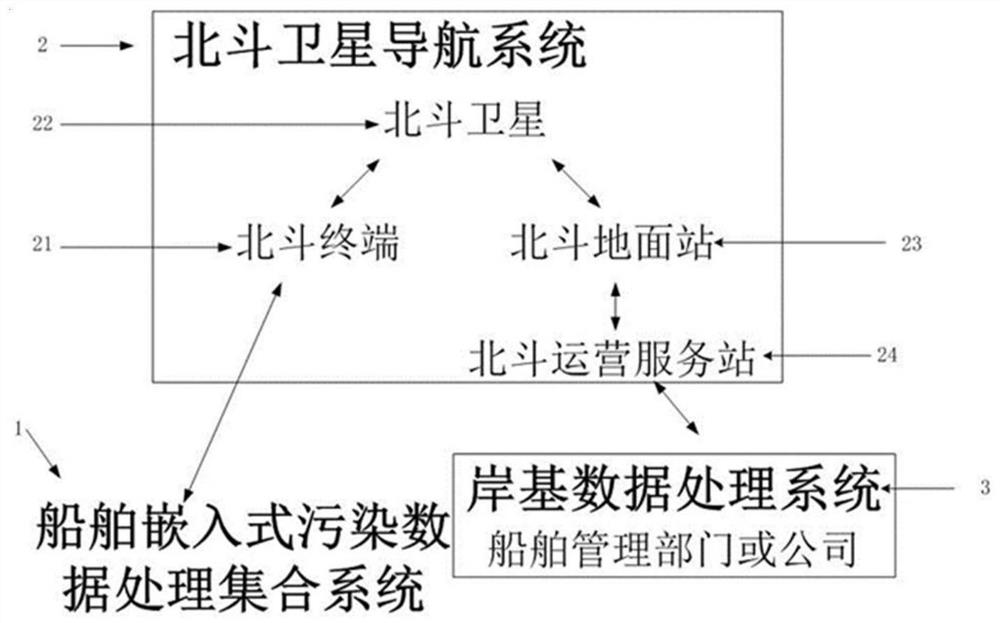
Ship real-time pollution monitoring system and method based on Beidou short message
InactiveCN110146129ASimplify the inspection inspection processInspection inspection process reductionSatellite radio beaconingMessaging/mailboxes/announcementsData processing systemCollection system
The invention belongs to the pollution monitoring technology field and discloses a ship real-time pollution monitoring system and method based on a Beidou short message. The system comprises a ship embedded pollution data processing collection system module, a Beidou satellite navigation system module, a shore-based data processing system module and an index code table mode message module based onthe Beidou short message. In the invention, for various pollution detection data of a ship, a message function of a Beidou satellite navigation system is used to carry out ship-shore two-way data transmission, ship-shore integration real-time monitoring is realized, and a demand of a shore-based management department or company to monitor various pollution gas or liquid emission conditions in real time can be satisfied. The system and the method have effects of reducing direct emission of polluted water and harmful gases during navigation of the ship and simultaneously reducing marine environmental pollution and air environmental pollution. In the invention, a problem that a mariner or a shipowner does not comply with prescribed discharge of international maritime organization (IMO) relevant anti-pollution conventions (such as a MARPOL convention) so that the pollution from ships is serious is effectively solved.
Owner:GUANGZHOU MARITIME INST
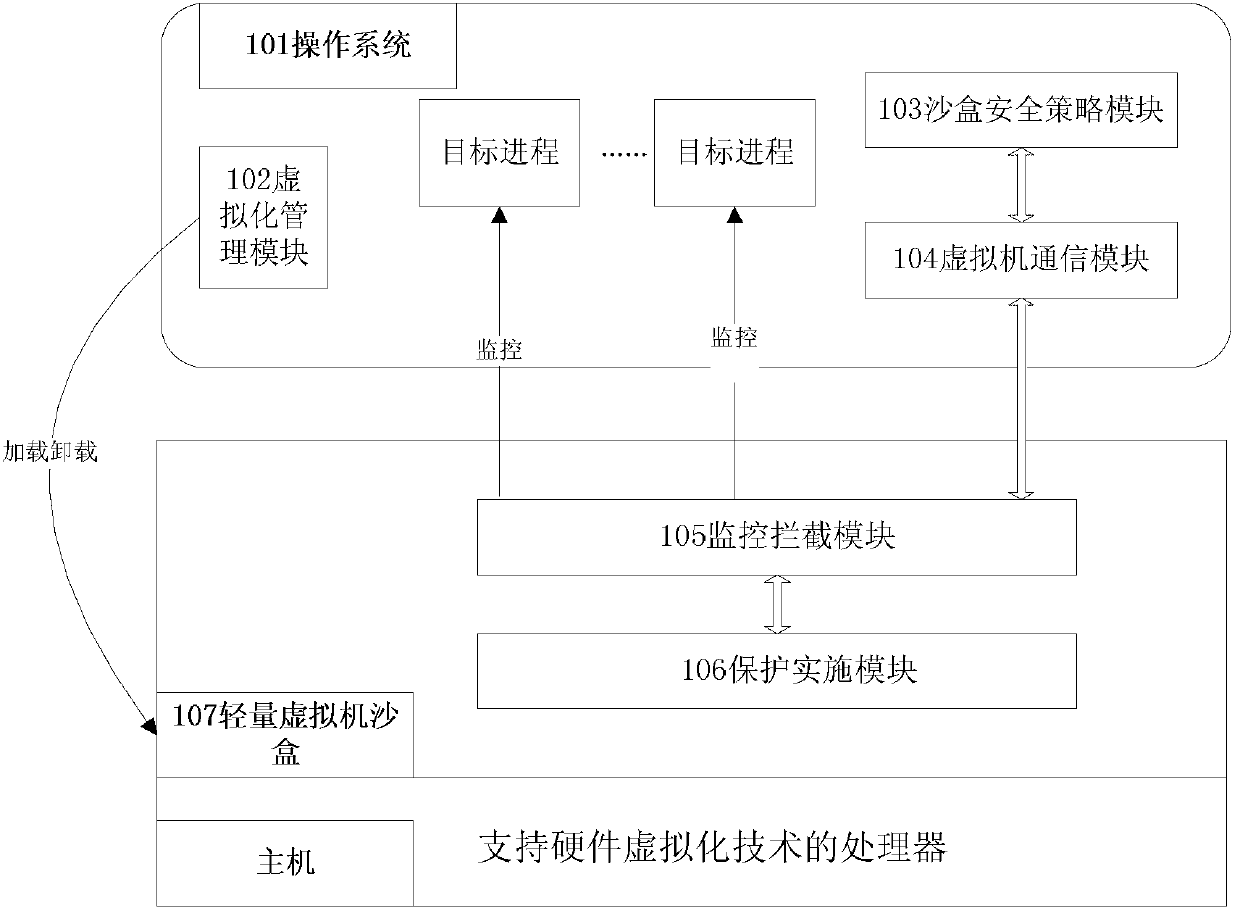
Sandbox system based on light-weight virtual machine monitor and method for monitoring OS with sandbox system
InactiveCN103345604AMonitor behaviorReduce the amount of codePlatform integrity maintainanceVirtualizationVirtual machine
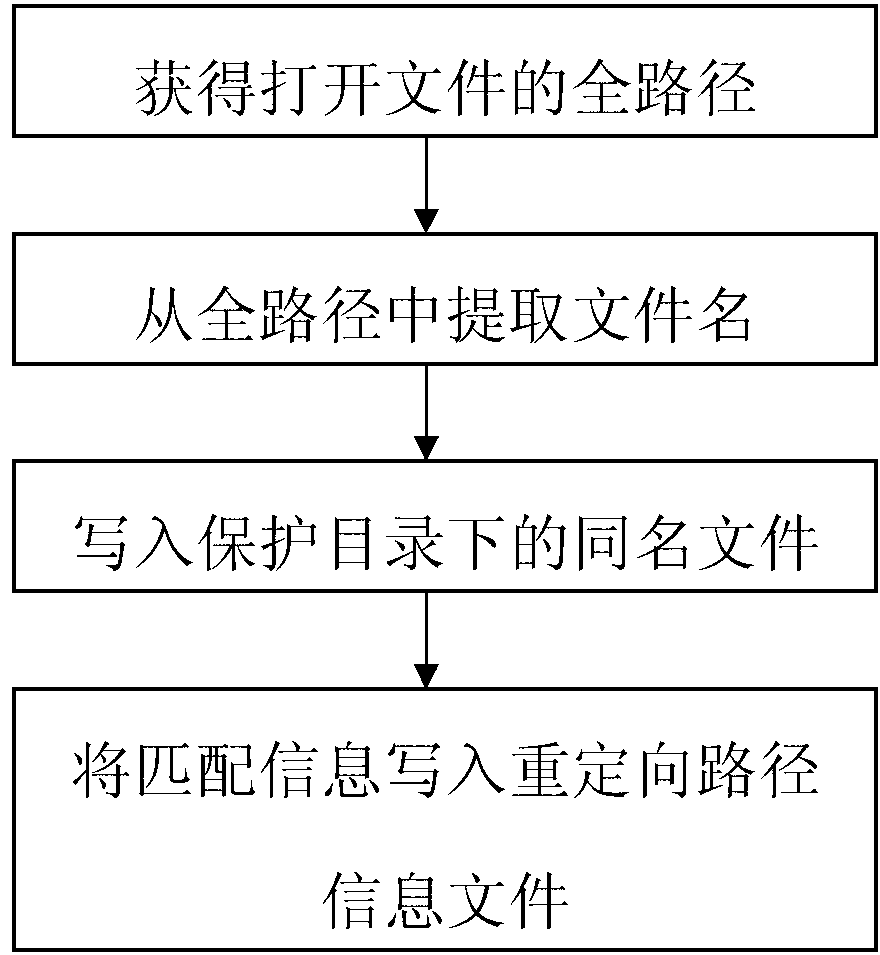
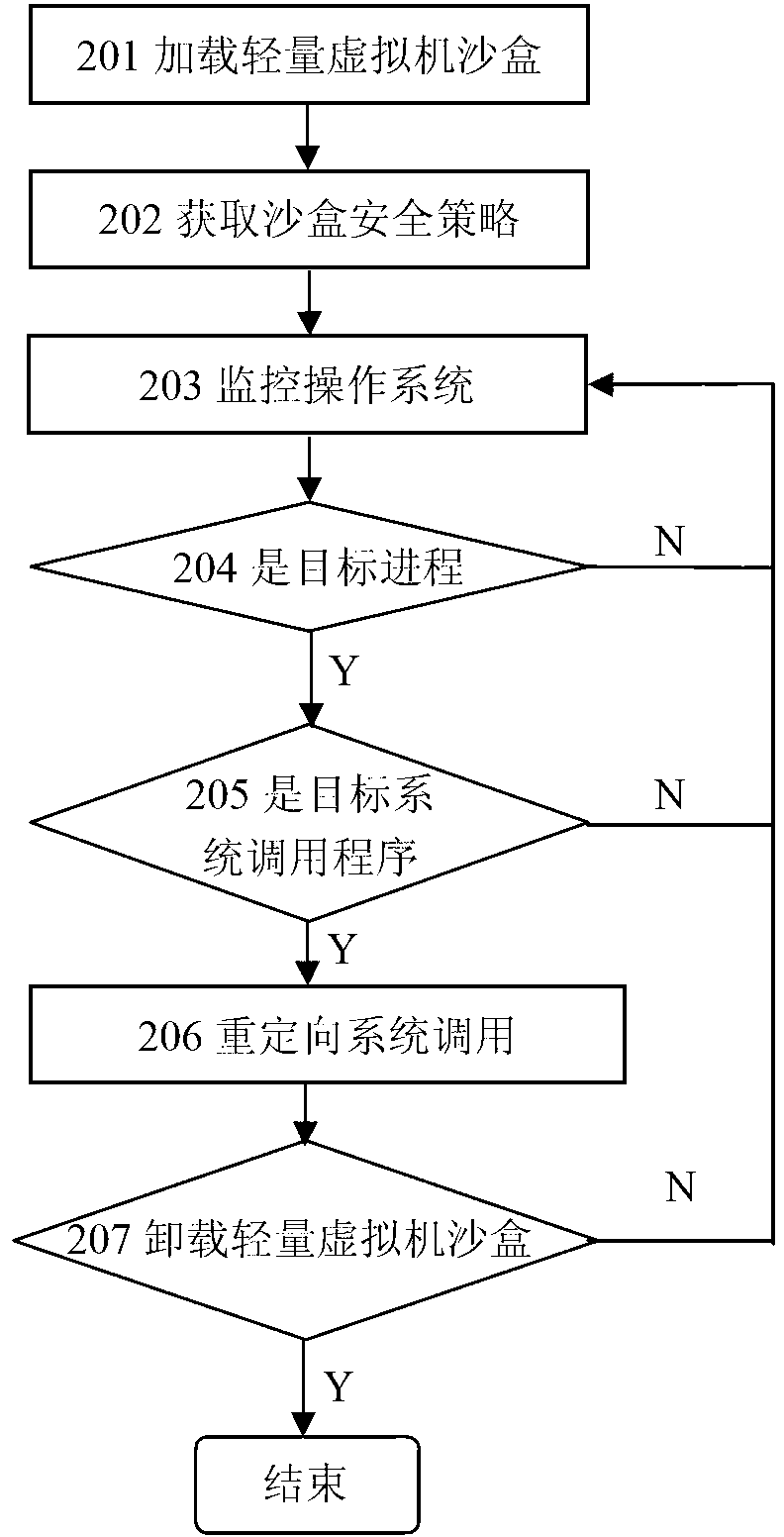
The invention discloses a sandbox system based on a light-weight virtual machine monitor and a method for monitoring an OS with the sandbox system. The sandbox system comprises a virtualization management module, a sandbox strategy module, a virtual machine communication module and a light-weight virtualization sandbox module, as shown in the figure 1. According to the sandbox system, a light-weight virtual machine sandbox which is designed for the purpose of sandbox safety can be loaded dynamically according to the protective needs of a user. The light-weight virtual machine sandbox migrates the operation system into the light-weight virtual machine sandbox, system calling of a target course is monitored and intercepted, and suspicious operation on a file system from the target course is redirected under a sandbox protective route. The sandbox system has the advantages of being transparent to the operation system, small in code number, small in virtualization expenditure and the like.
Owner:XIANGTAN UNIV
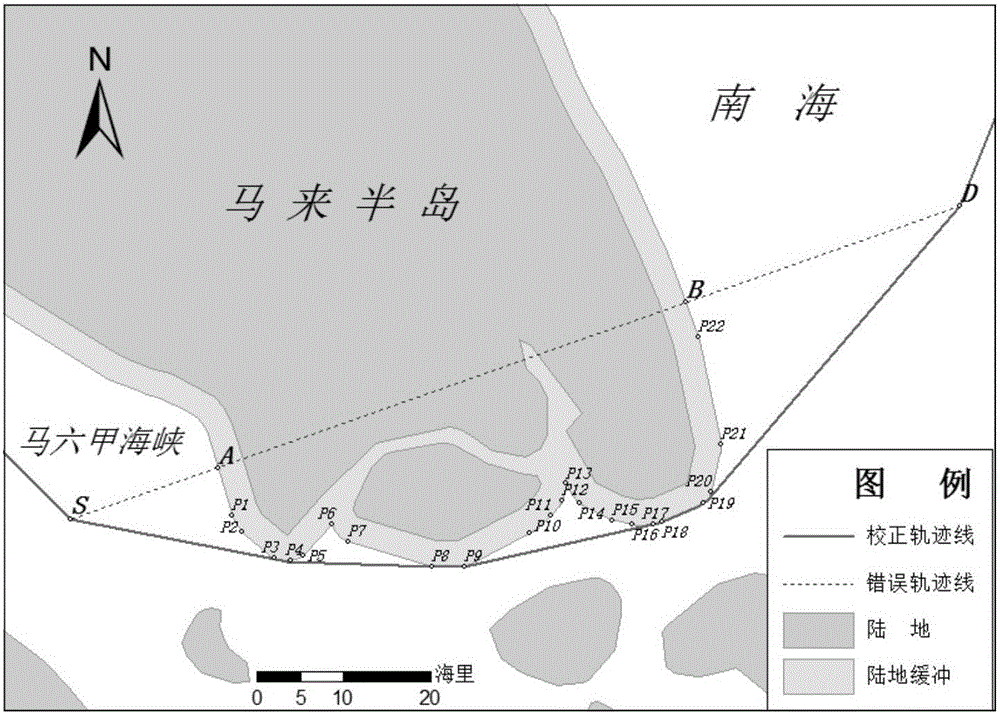
Cross-land ship track line correction method based on obstacle-avoiding path planning
InactiveCN106289255AImprove rationalityReduce the number of search nodesNavigational calculation instrumentsComputer scienceCorrection method
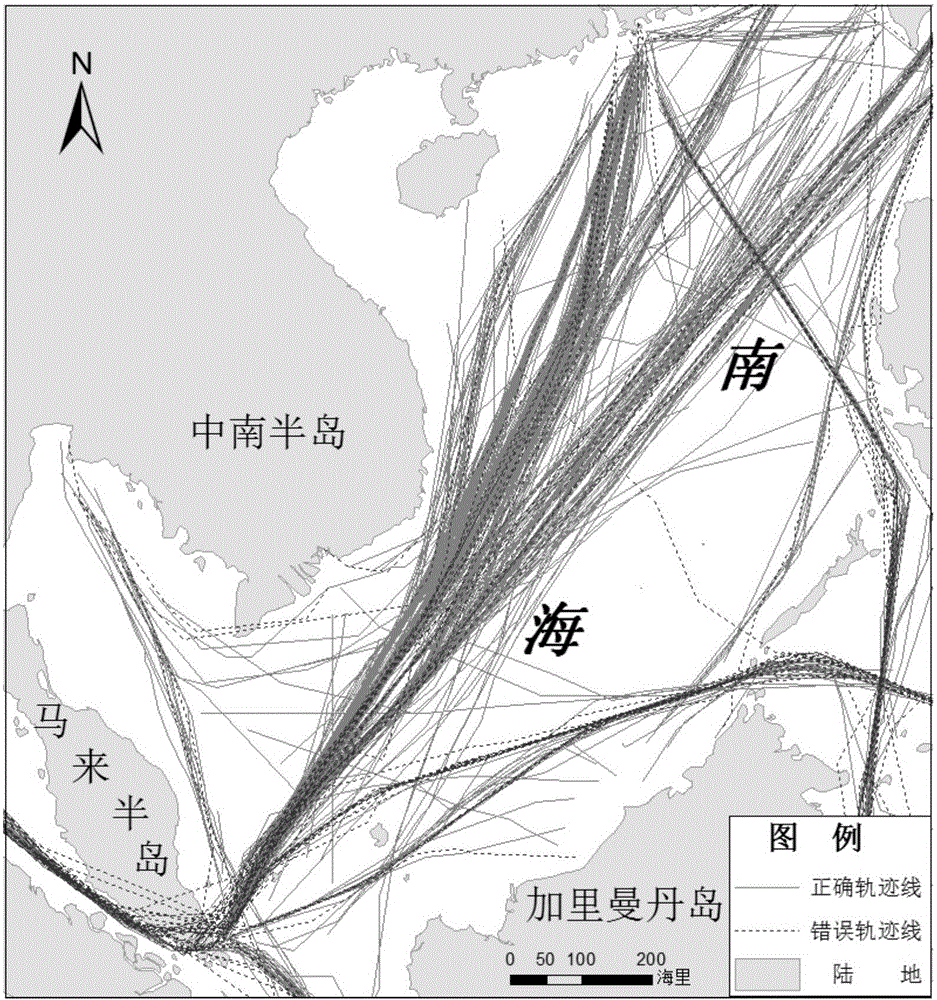
The invention discloses a cross-land ship track line correction method based on obstacle-avoiding path planning, belongs to the technical field of track analysis, and aims to solve the problems that a conventional method is low in correction efficiency on a large-area land and a great number of track lines. The cross-land ship track line correction method comprises the following steps: I, acquiring a wrong ship track line; II, analyzing a buffer range of a cross land so as to obtain a land buffer area; III, dividing the land buffer area into two parts by a wrong line section of the wrong ship track line, and forming a polygon as an obstacle-avoiding polygon by a relatively small part; IV, according to the start point and the final point of the wrong line section, acquiring a shortest obstacle-avoiding path as a modified path by using the obstacle-avoiding polygon, and replacing the wrong line section of the wrong ship track line by the modified path.
Owner:YUNNAN NORMAL UNIV
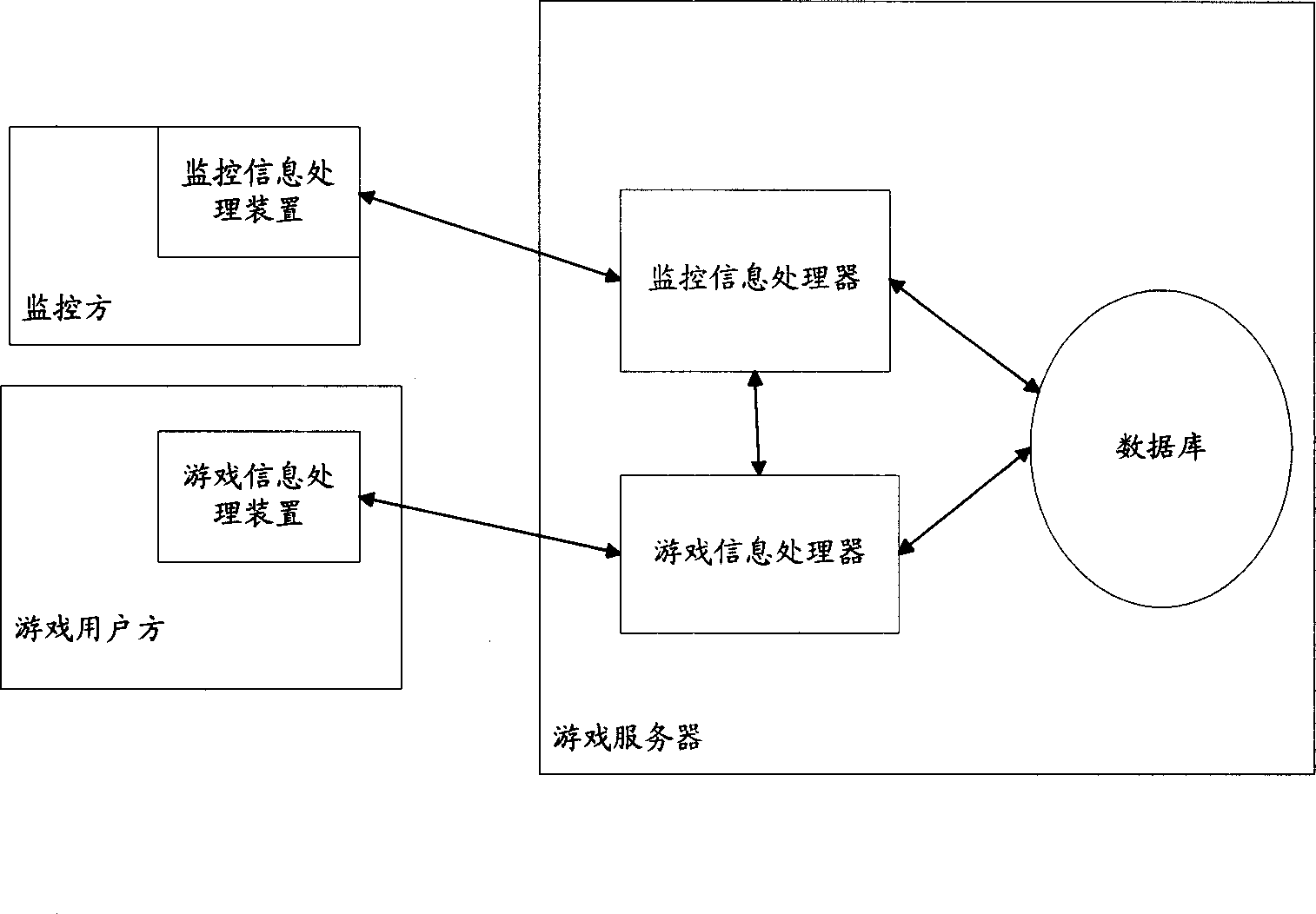
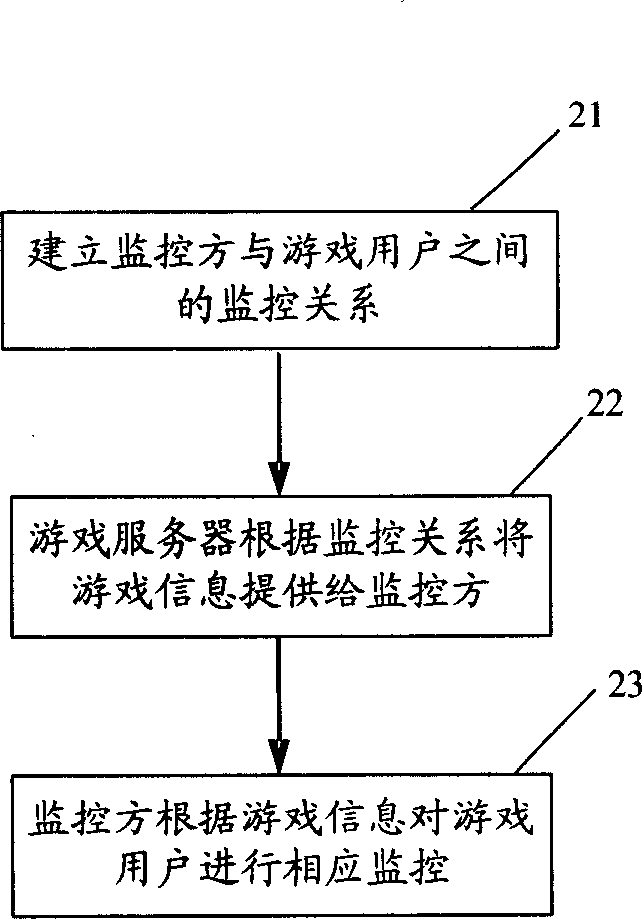
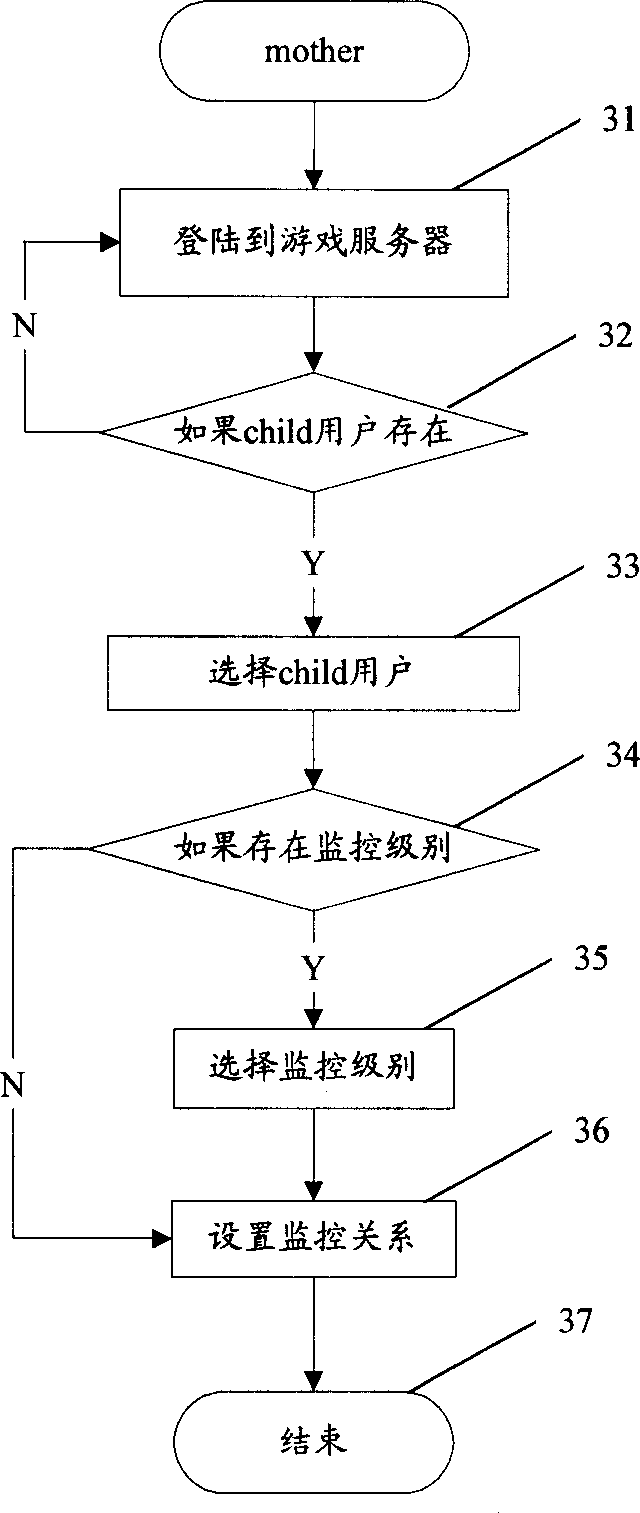
Monitoring system and method for game
InactiveCN1852139AAvoid negative effectsPlay a positive roleData switching networksSpecial data processing applicationsThird partyInformation control
The invention discloses system and method for monitoring users of playing games from third party. The monitoring system includes device of processing information of games, game server, and device of processing monitored information through the game server for monitoring users of playing games. Building monitoring relation between user of playing games and the monitoring party makes the device of processing monitored information possible to obtain game information of the device of processing monitored information. Based on obtained game information, the device of processing monitored information controls operations of the device of processing information of games. Therefore, the said third party can monitor actions of users of playing games so as to make users of playing games obtain fun from games but not abandon themselves to games. The invention prevents negative influence from games and gave play to positive influence from games.
Owner:HUAWEI TECH CO LTD
System and method for legally monitoring audio/video multimedia conference
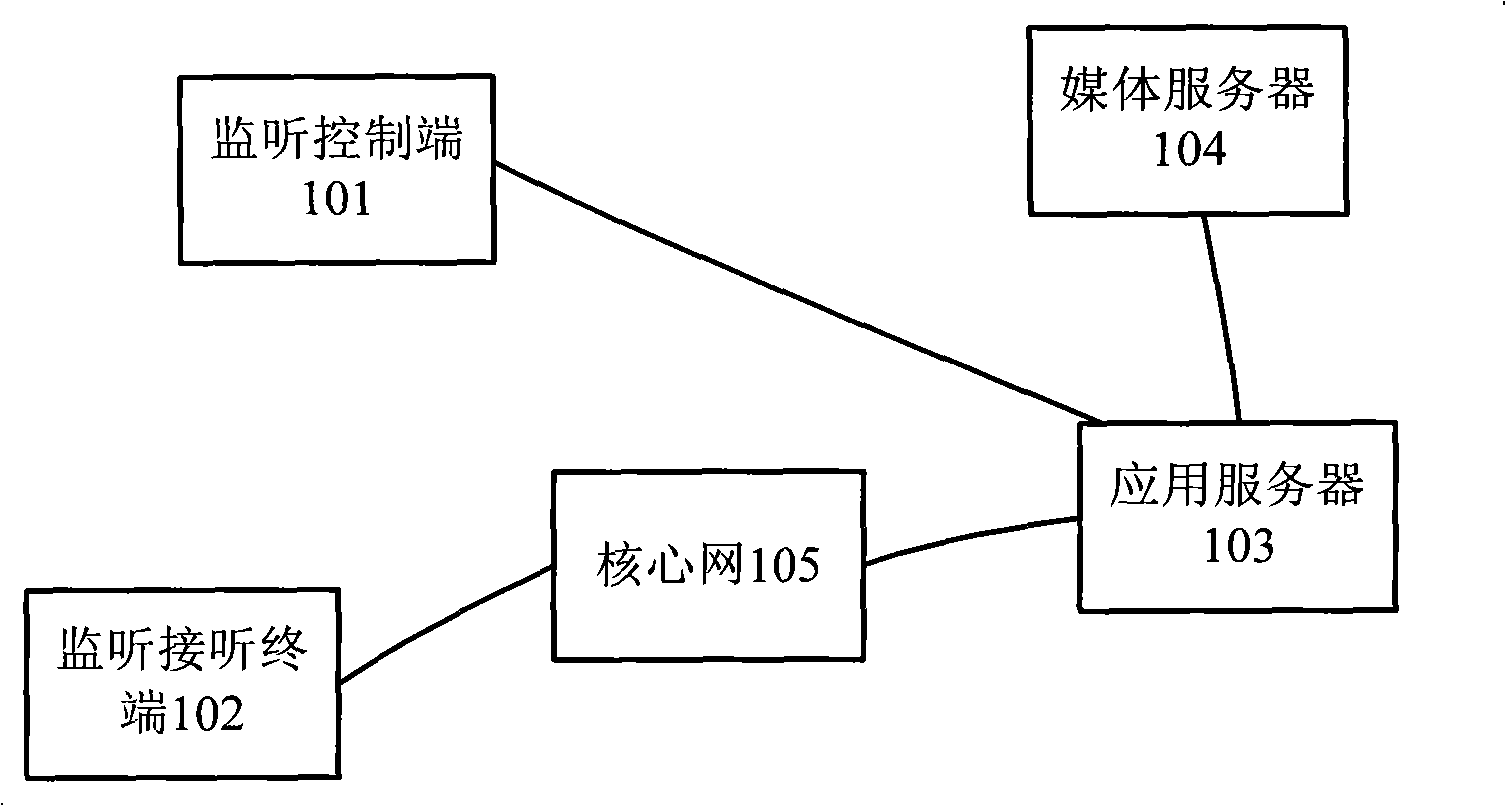
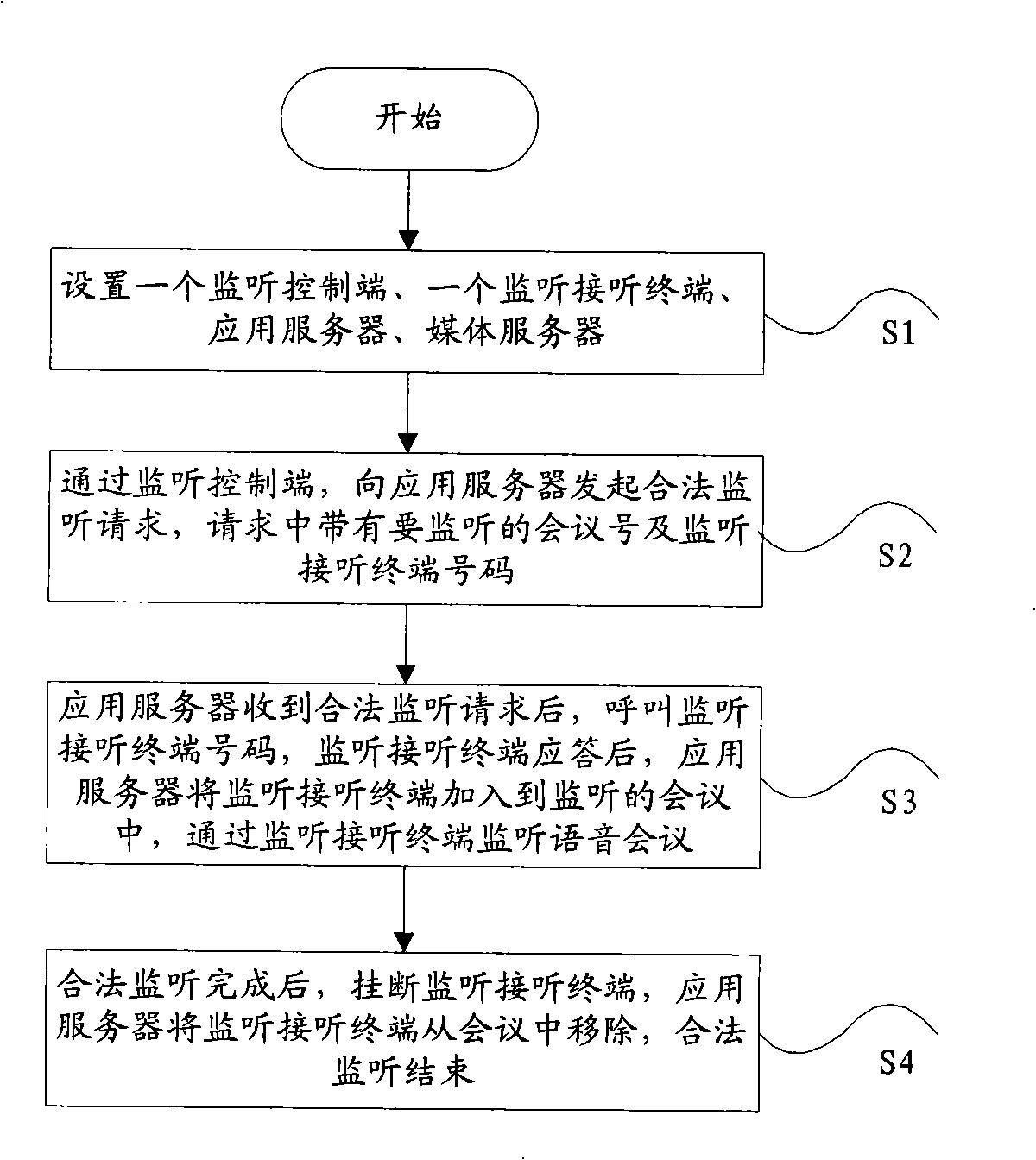
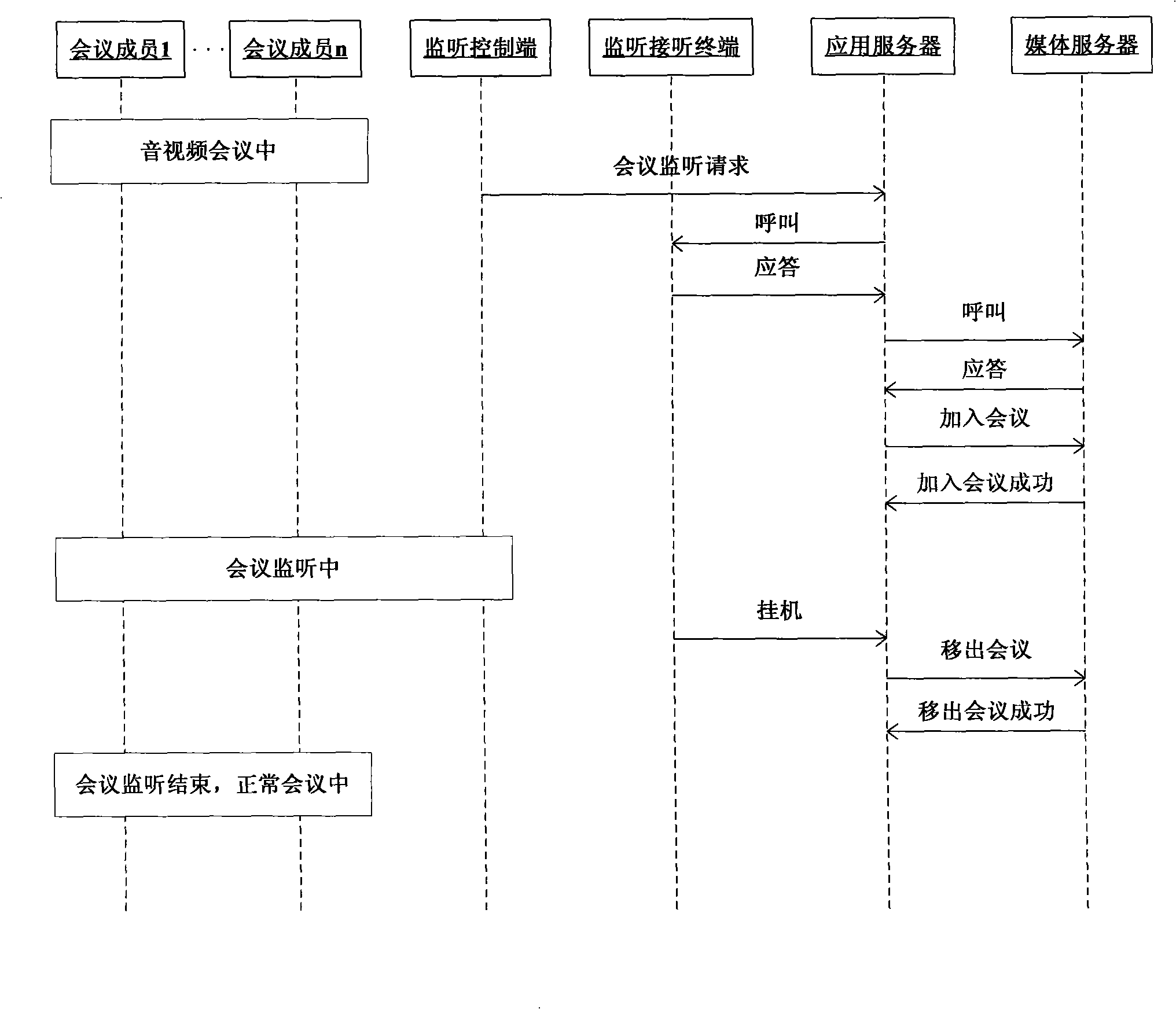
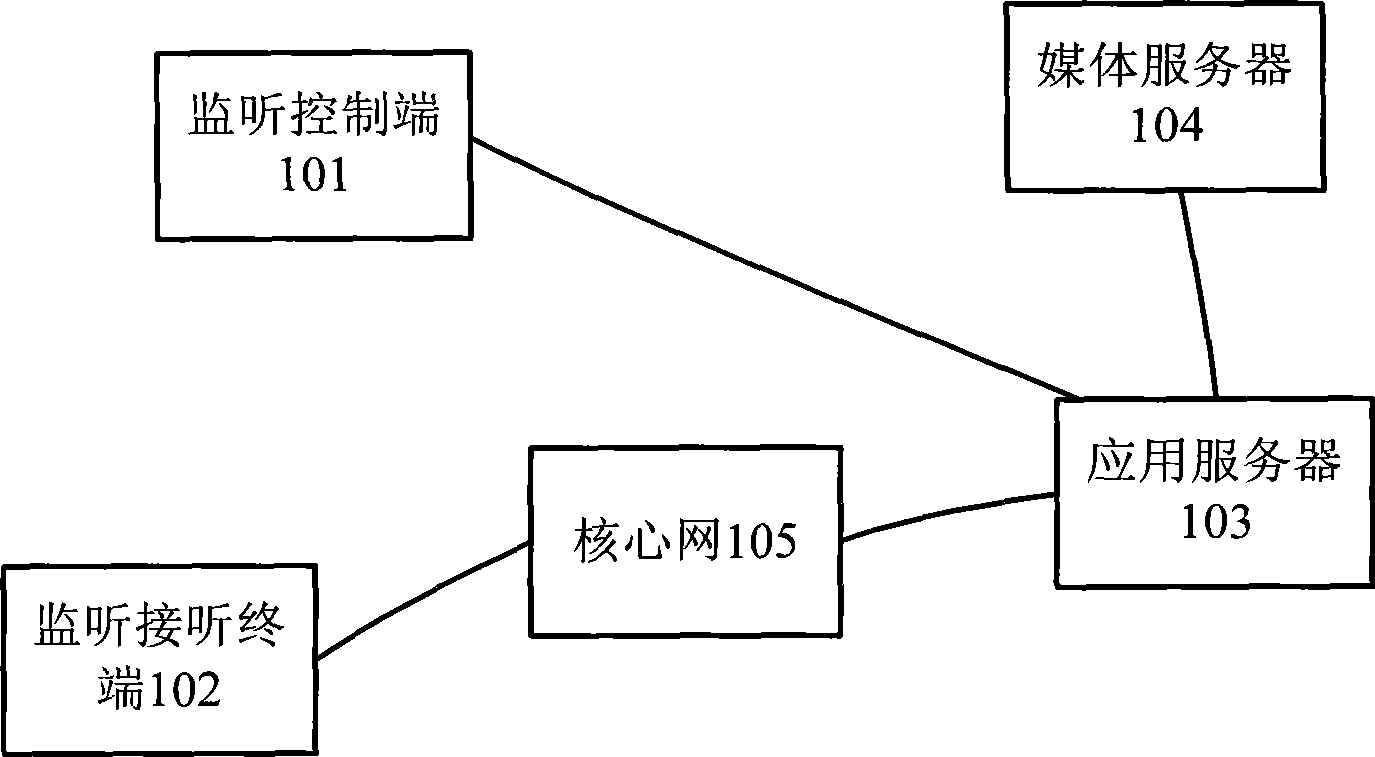
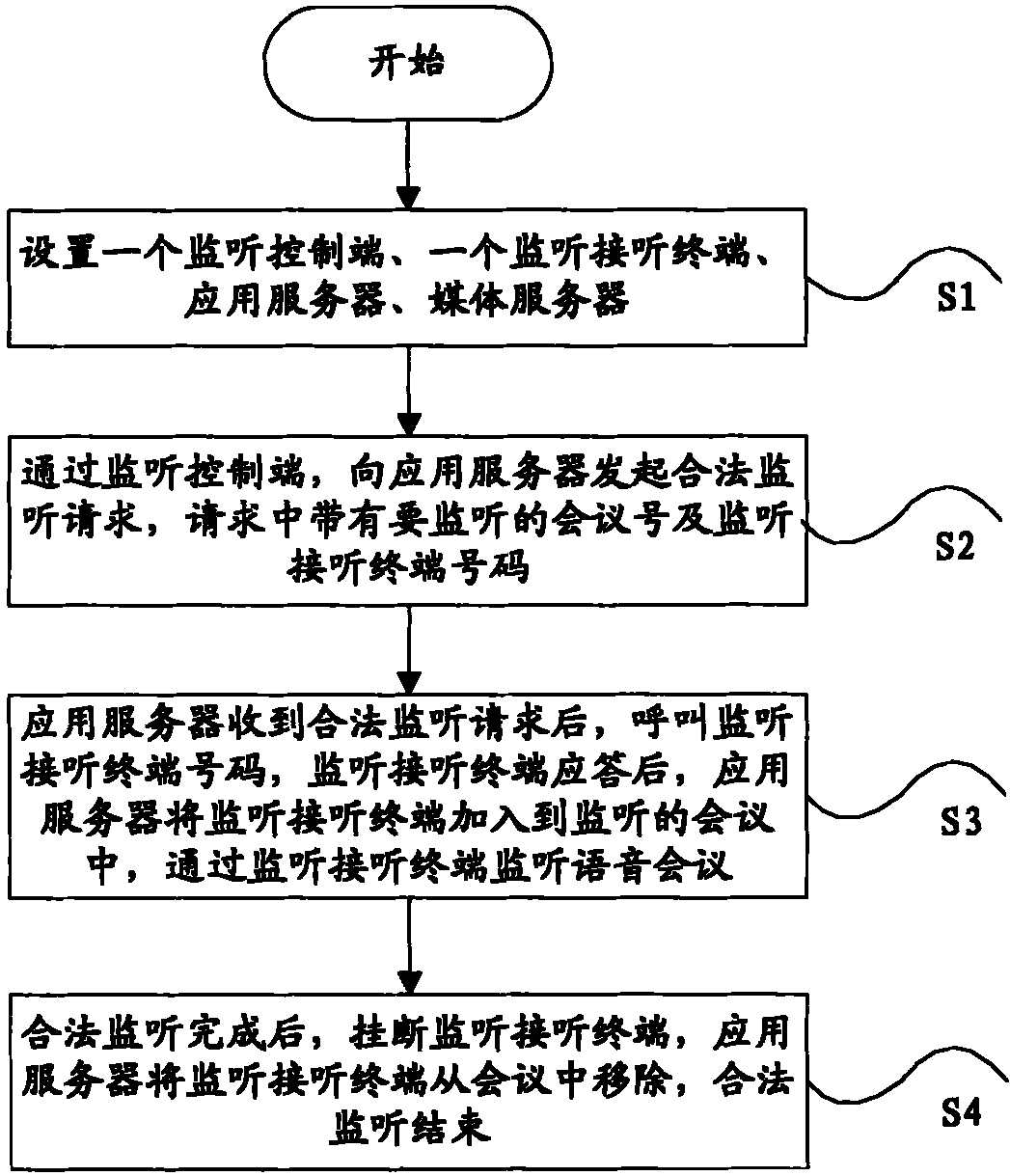
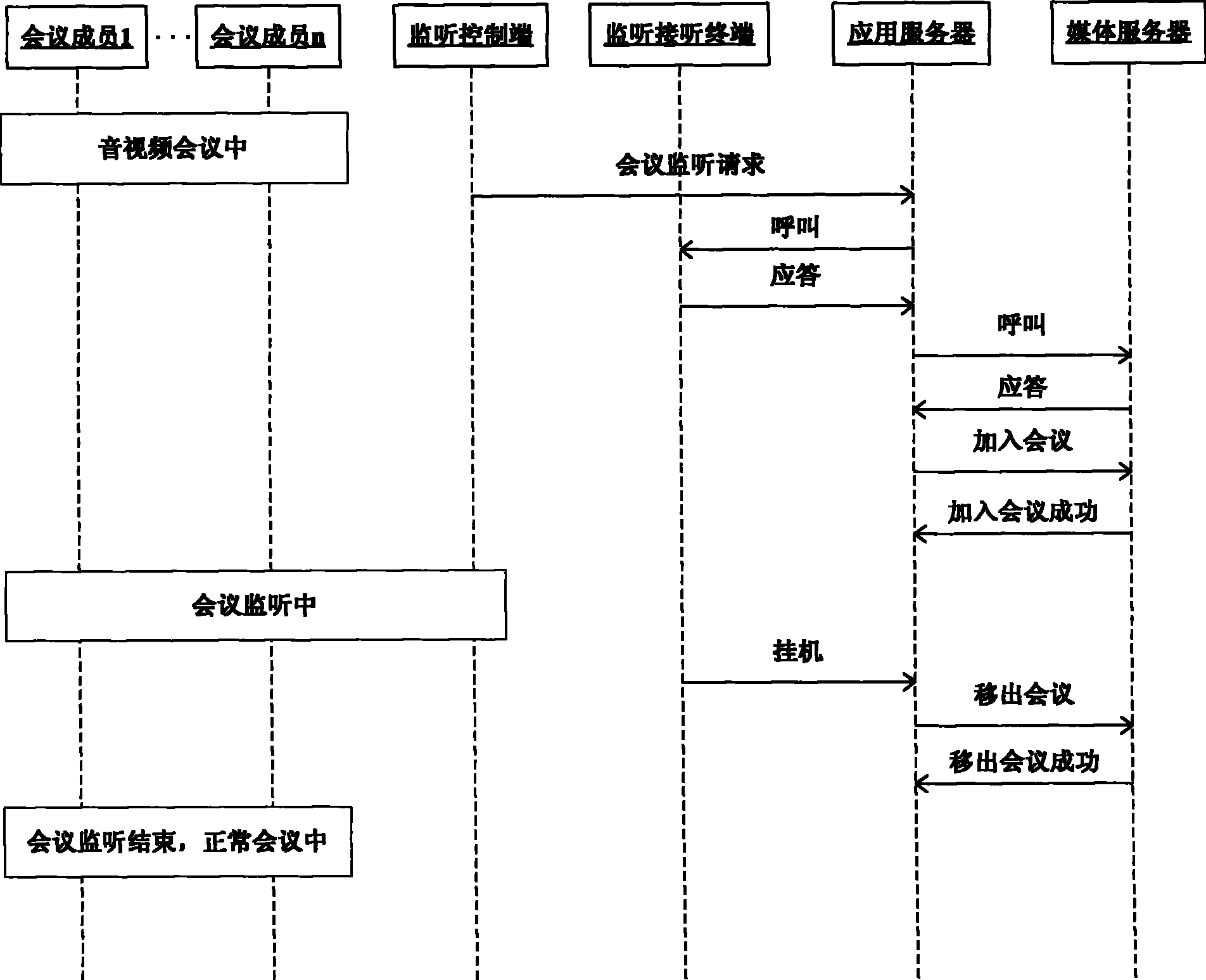
InactiveCN101345846AEffectively monitor behaviorMonitor behaviorTelevision conference systemsSupervisory/monitoring/testing arrangementsApplication serverMedia server
The present invention discloses a system for legitimately monitoring the audio and video multimedia conference, including: a monitoring control terminal, a monitoring answer terminal, an application server and a media server, wherein, the application server is used to realize the processing logic of audio and video multimedia conference service and the legitimate monitoring; the medium service apparatus can be used to realize the media processing of the audio and video multimedia conference and the legitimate monitoring; and the monitoring control terminal can be used to initiate monitor indication and perform monitor management. The present invention also discloses a method for legitimately monitoring the audio and video multimedia conference, which realizes legitimate monitoring function by using the apparatus and function in the audio and video multimedia conference service. The present invention is suitable for audio and video multimedia conference in the field of NGN or IMS communications.
Owner:ZTE CORP
Application program monitoring method and apparatus, electronic device, and readable storage medium
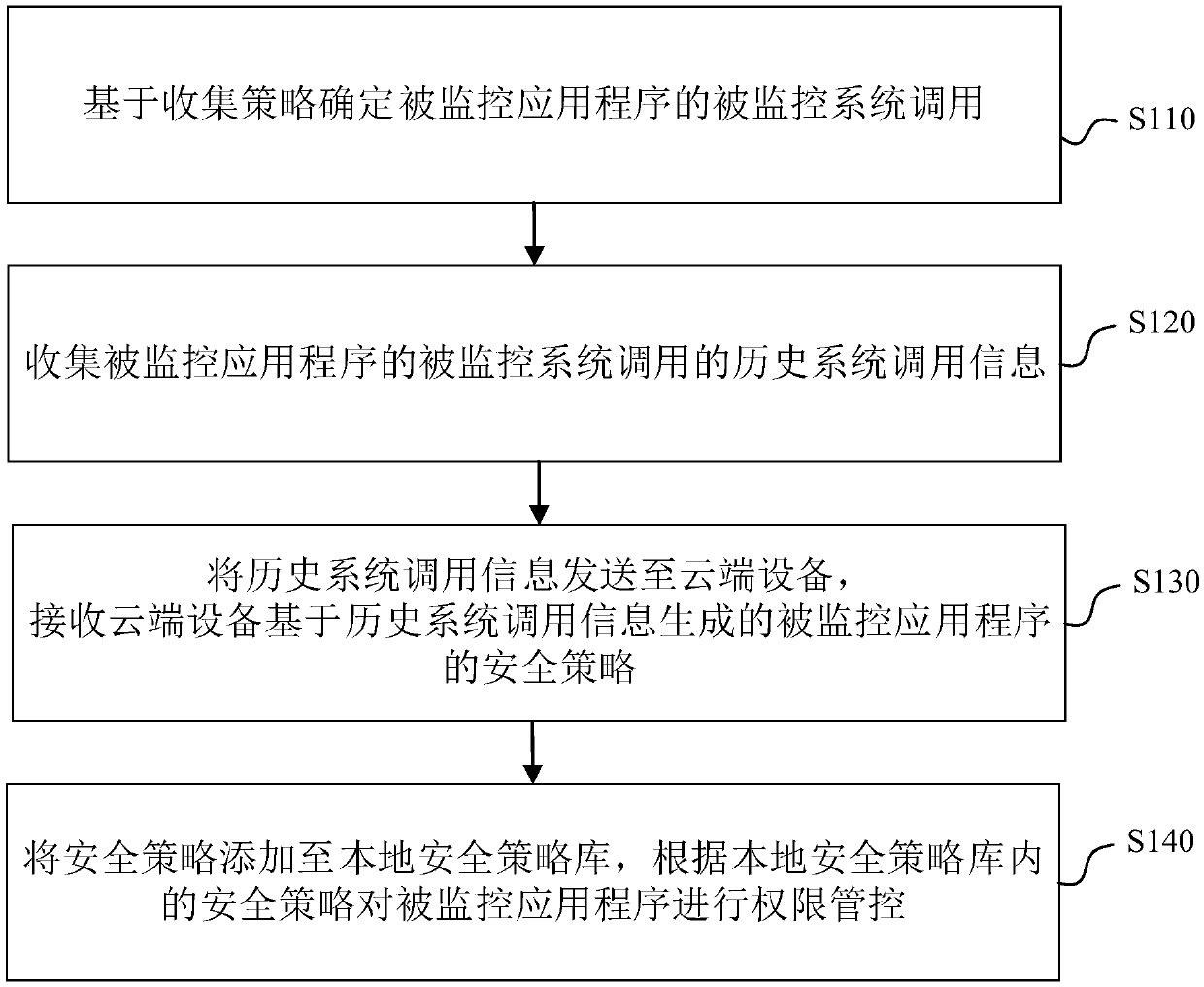
InactiveCN109543411AMonitor behaviorEnsure safetyPlatform integrity maintainanceTerminal equipmentSystem call
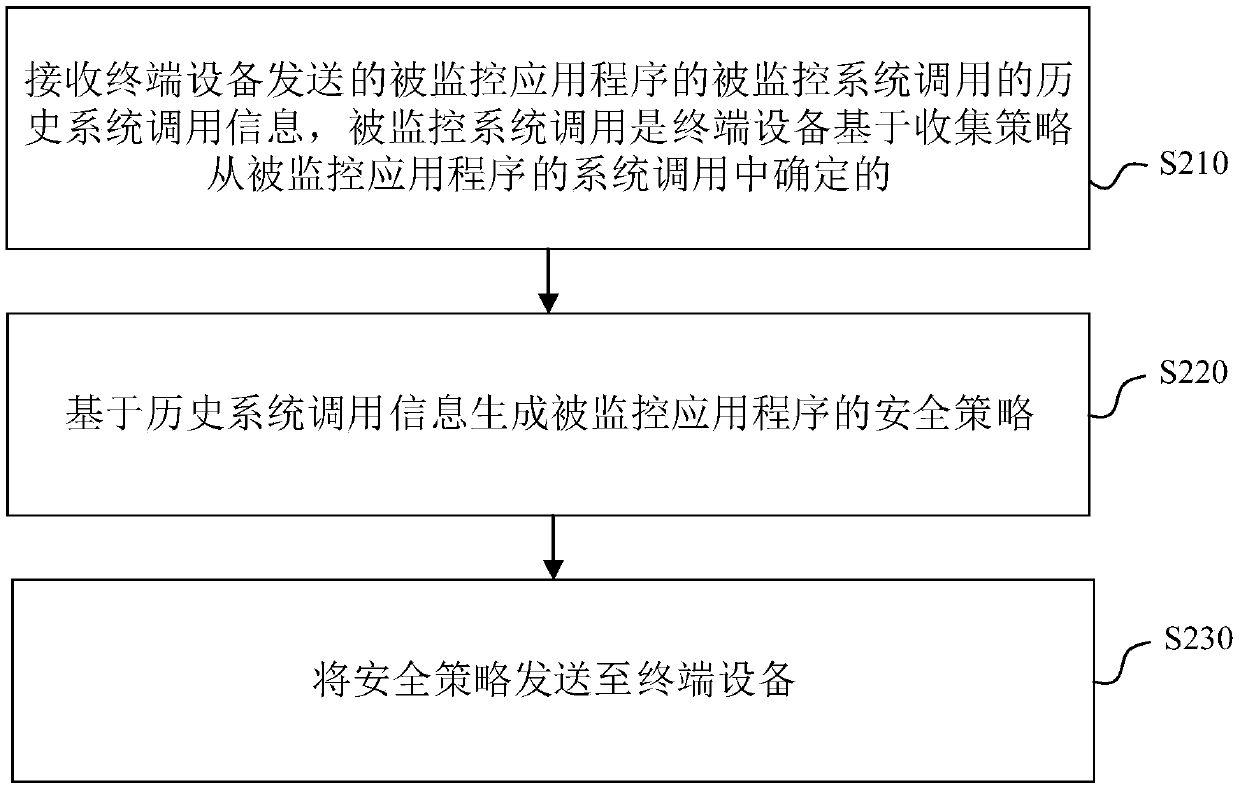
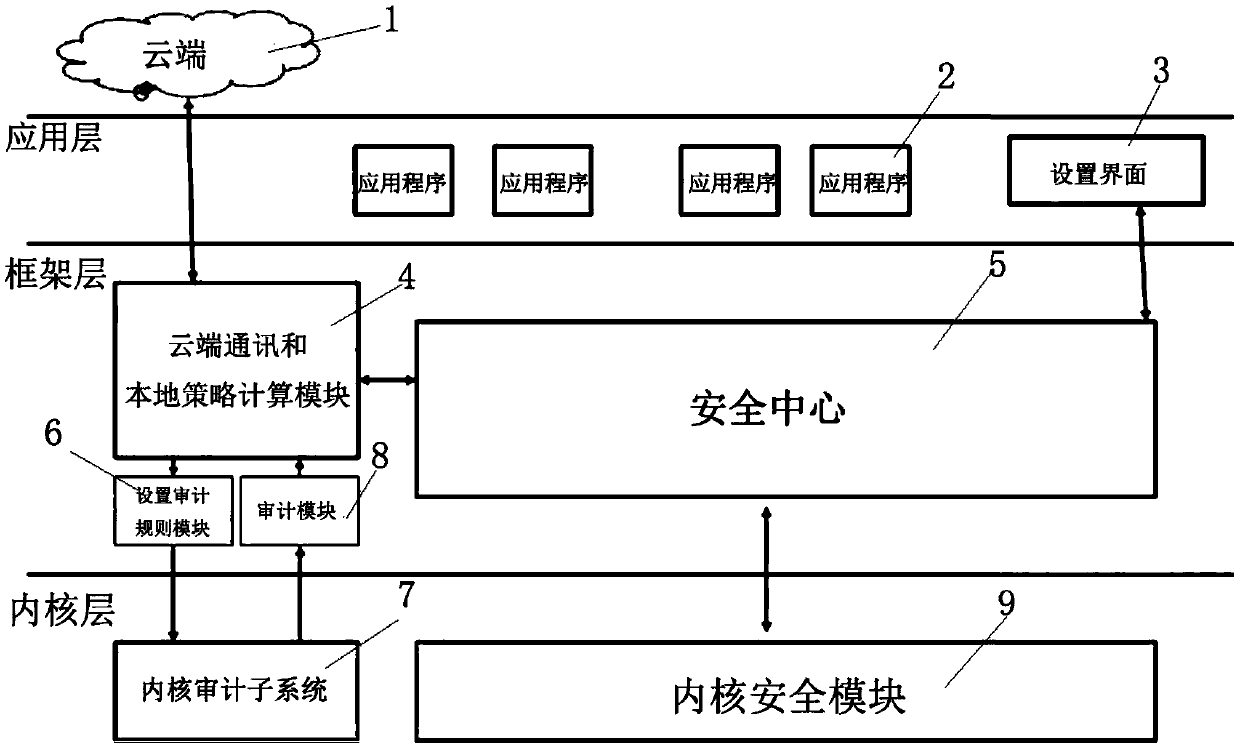
Embodiments of the present application provide an application monitoring method and apparatus, an electronic device, and a readable storage medium. The method includes: determining a monitored systemcall of a monitored application based on a collection policy; Collecting historical system call information of monitored system calls of monitored applications; Sending the history system call information to the cloud device, receiving the security policy of the monitored application generated by the cloud device based on the history system call information; Adding a security policy to the local security policy repository and controlling the permissions of monitored applications based on the security policy within the local security policy repository. The scheme of embodiments of the present application collects historical system call information of an application program, Accurately monitor the behavior of the application, and generate the corresponding security policy to update the localsecurity policy, so that the terminal equipment can control the permissions of the application according to the updated local security policy, and realize the effective monitoring of the applicationto ensure the system security.
Owner:BEIJING YUANXIN SCI & TECH
Method for generating ship track curve based on voluntary observation ship (VOS) data
InactiveCN104680850AEasy to classifyQuick classificationMarine craft traffic controlDiscrete pointsComputer science
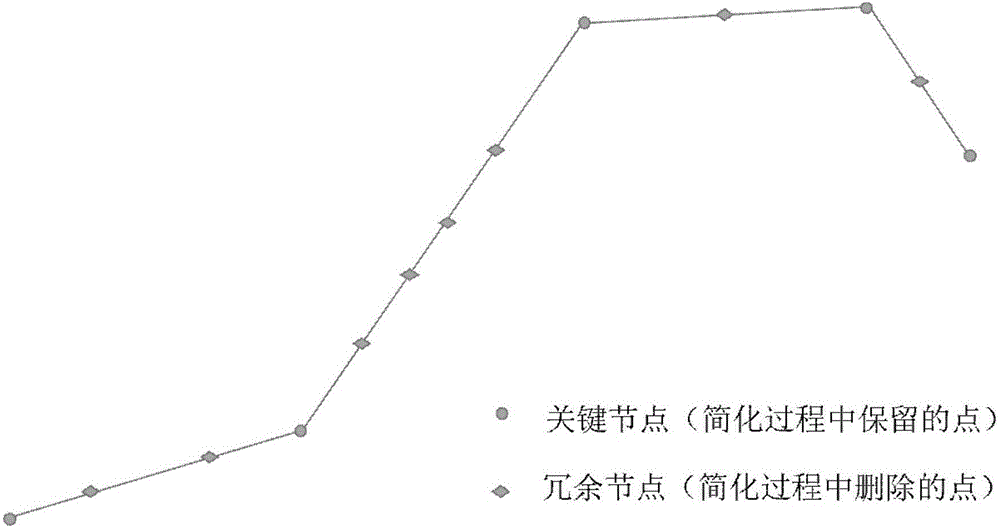
The invention relates to a method for generating a ship track curve based on voluntary observation ship (VOS) data, in particular to a method for generating the ship track curve with a large number of discrete points. The method comprises the following steps: reading VOS; recognizing the voyage according to the VOS track points; arranging the VOS track point data; connecting the VOS track curves; correcting the connection of the track curves according to the obstacle-avoiding path design; generating the VOS track curve. Through adoption of the method, the problem that the ship track curve or ship route is extracted a little can be solved; the ship track curve generation method is provided; a large number of discrete VOS point data can be used for generating into a continuous ship track curve which is beneficial for mastering the regional marine traffic distribution conditions and monitor ship behavior so as to ensure the marine traffic security as well as providing decision-making reference for the marine administrative authority; the method is of great significance on protecting the life and property of people, protecting the marine environment and ensuring the national core strategic interests.
Owner:NANJING UNIV
Method and device for automatically identifying malicious codes during software running
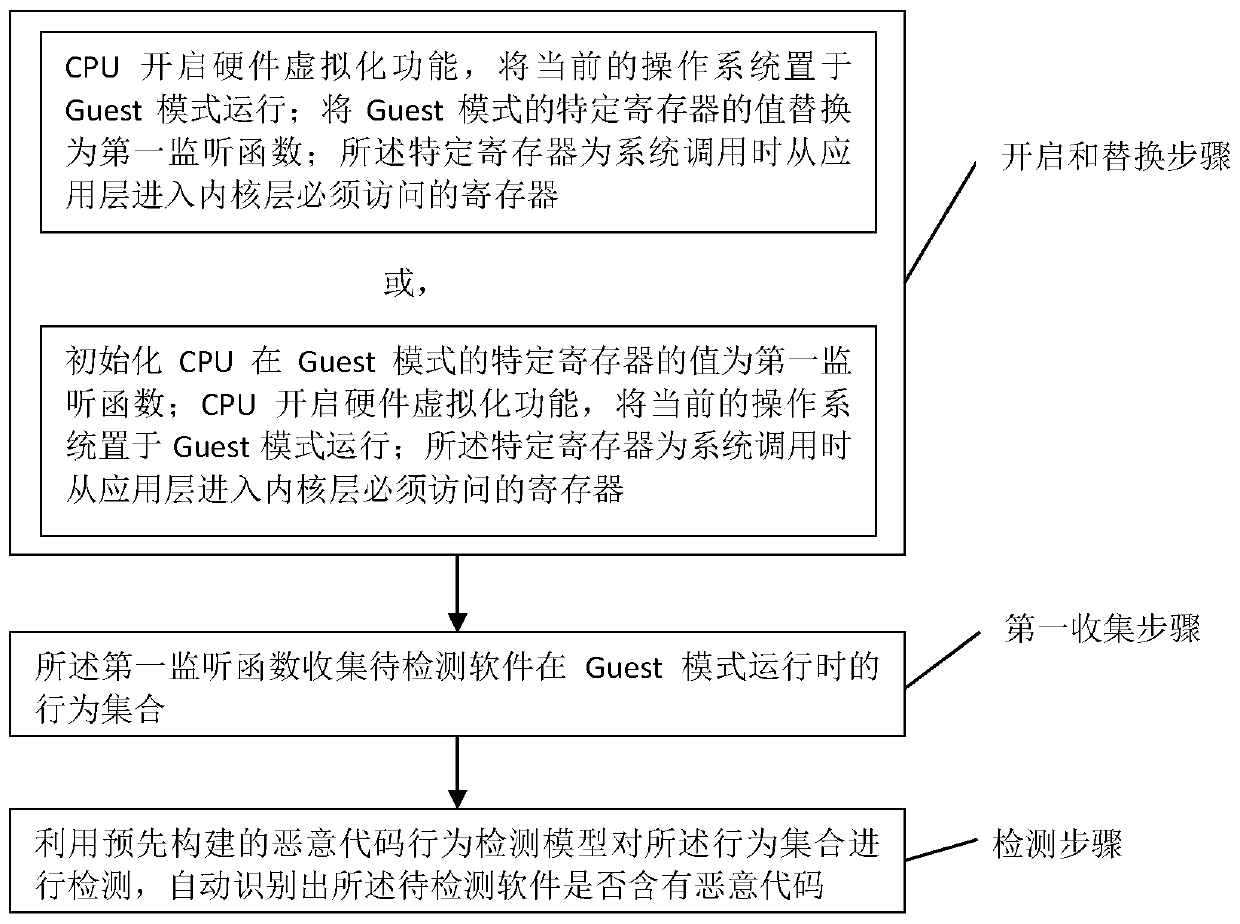
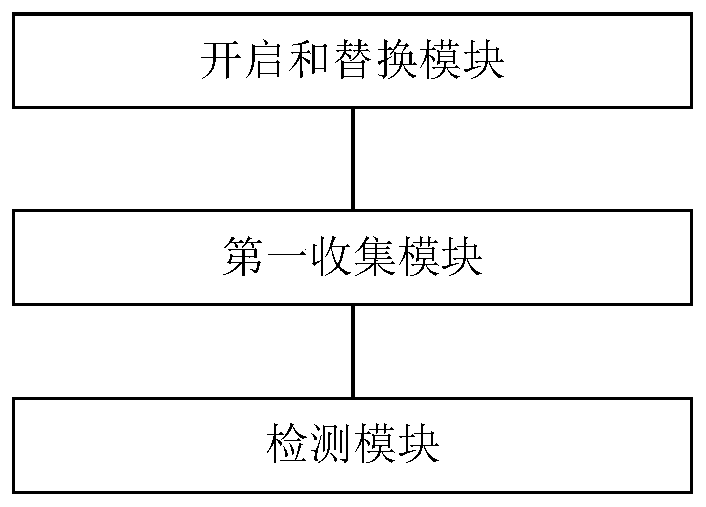
InactiveCN111444504AComprehensive monitoring of running behaviorMonitor running behaviorPlatform integrity maintainanceVirtualizationOperational system
The invention provides a method and device for automatically identifying malicious codes during software running. The method comprises the steps: starting and replacing, and enabling a CPU to start ahardware virtualization function, and enabling a current operating system to run in a Guest mode; replacing the value of the specific register in the Guest mode with a first monitoring function; or, initializing the value of the specific register of the CPU in the Guest mode as a first monitoring function; the CPU starts a hardware virtualization function, and the current operating system is set to run in a Guest mode; a first collection step, wherein the first monitoring function collects a behavior set of the to-be-detected software when the to-be-detected software runs in the Guest mode; and a detection step: detecting the behavior set by utilizing a pre-constructed malicious code behavior detection model, and automatically identifying whether the to-be-detected software contains malicious codes or not. According to the scheme of the invention, the running behavior of the software can be comprehensively monitored, and the malicious code can be automatically identified based on the running behavior of the software.
Owner:安芯网盾(北京)科技有限公司
Intelligent service terminal in train carriage
InactiveCN109685919AImprove service efficiency and real-time performanceNovel structureTicket-issuing apparatusCharacter and pattern recognitionTransmission delayInductive charging
The invention discloses an intelligent service terminal in a train carriage, which comprises an intelligent service device main body and a mainboard, wherein a camera device is arranged on the front surface of the intelligent service device main body; and a wireless charging auxiliary coil is fixedly connected to the back surface of the intelligent service device body. Through the arrangement of the intelligent service device main body, the camera device, the wireless charging auxiliary coil, a broadcasting device, a transmission device, an installation structure, a mainboard, a power supply and a voice interactive system, the terminal not only can overcome the actual situation that a prior train carriage lacks an intelligent service terminal, improves the service efficiency and real-timeperformance on the train, but also solves the problems of high relative work cost, low efficiency and multiple repeated work when the prior train manages and communicates passengers through manual service and train staffs; and the intelligent service terminal has the advantages of intelligently checking and identifying tickets, monitoring the behaviors of passengers and communicating with the passengers, and is worthy of popularization.
Owner:YANTAI ANTELOPE NETWORK TECH CO LTD
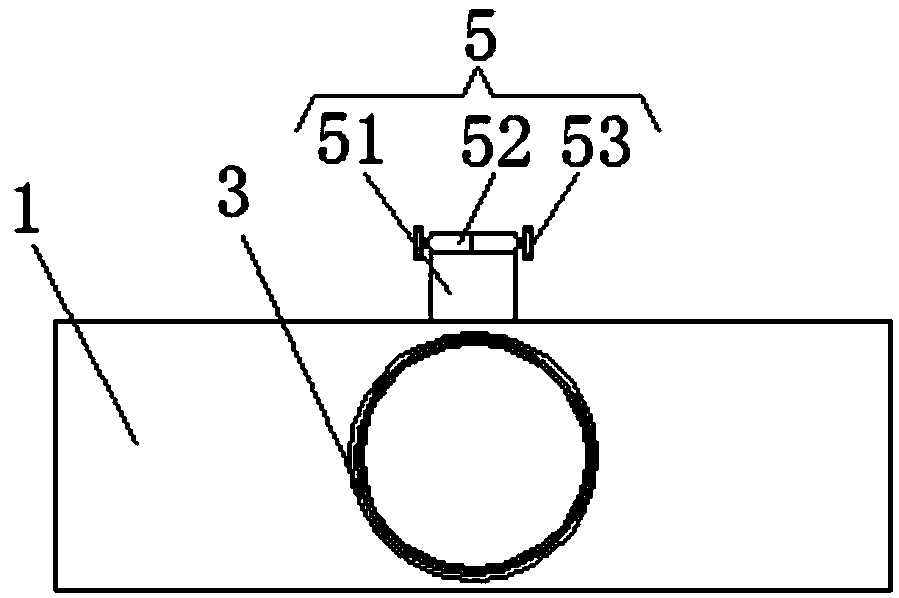
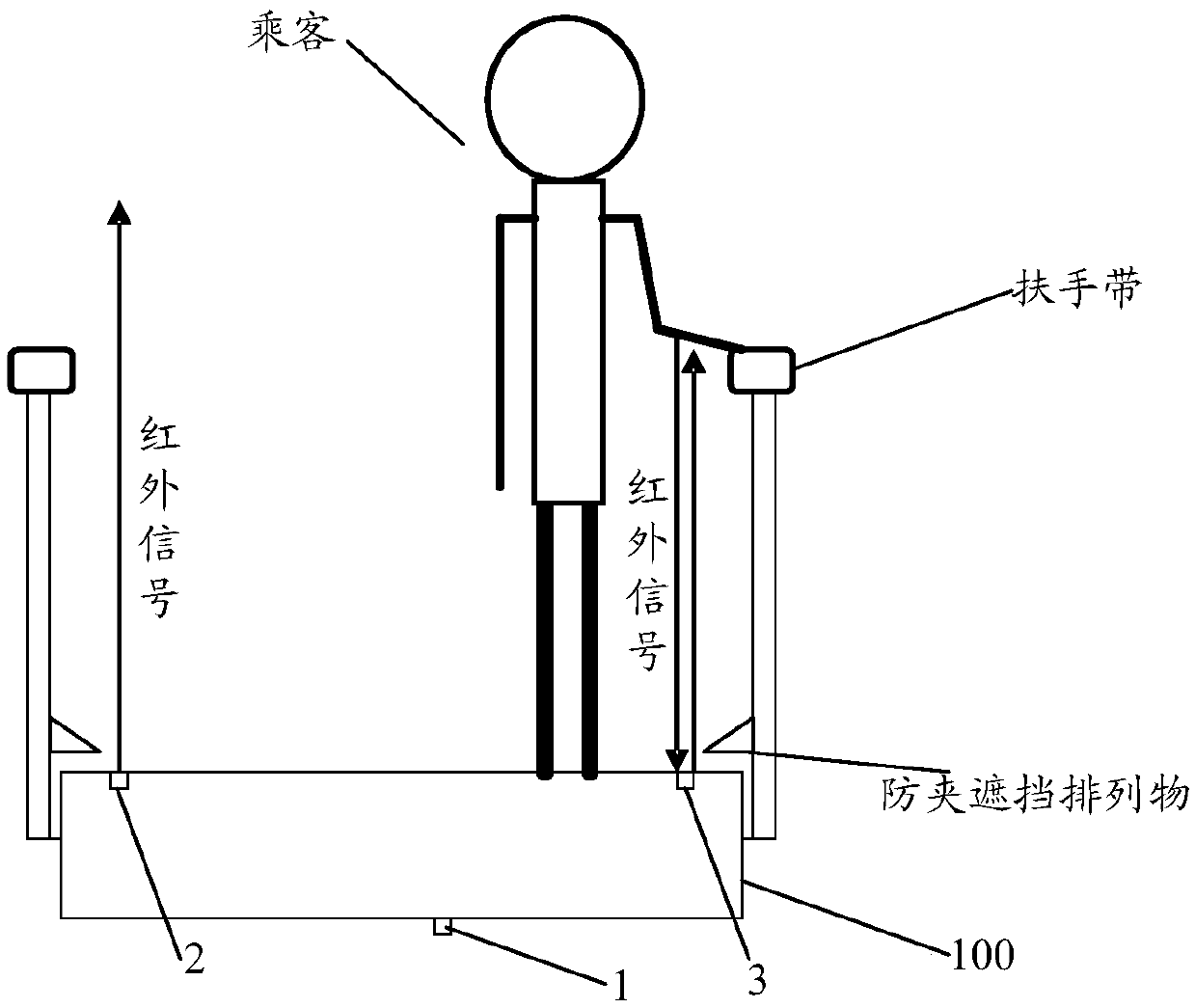
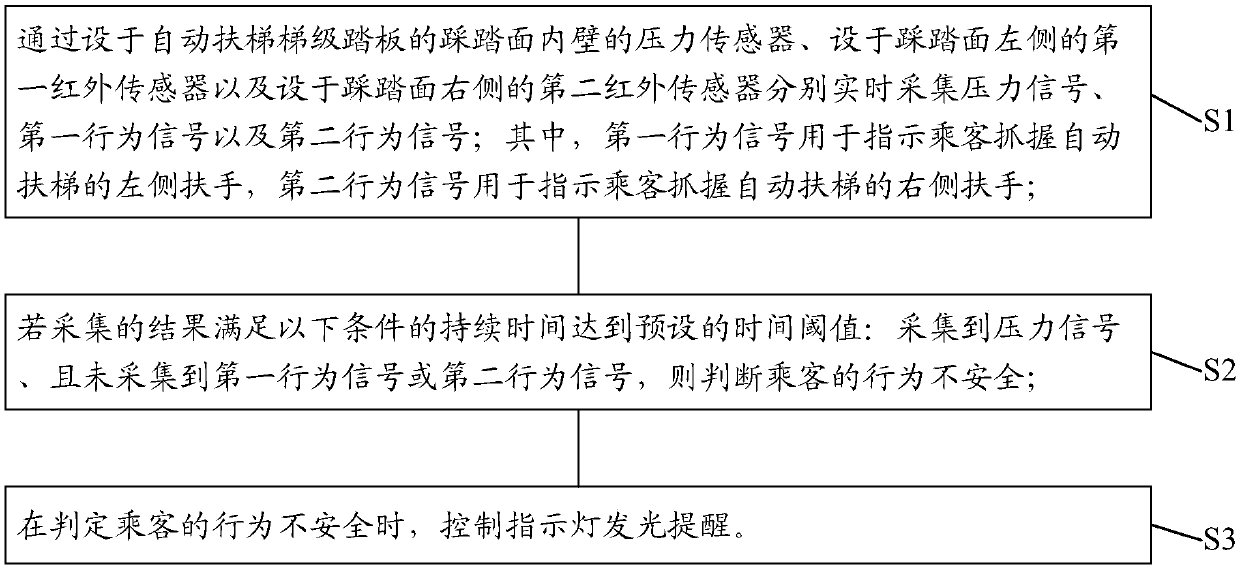
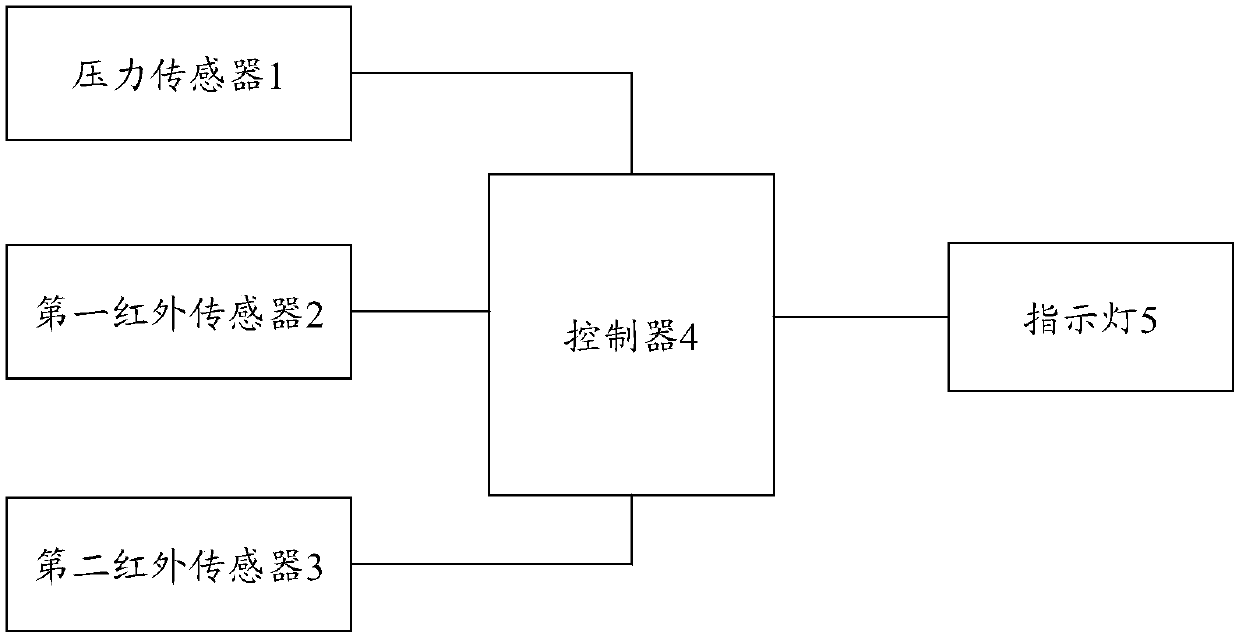
Passenger behavior monitoring method and device
The invention discloses a passenger behavior monitoring method and device. A pressure sensor arranged on the inner wall of a pedal surface of an escalator step pedal, a first infrared sensor arrangedon the left side of the pedal surface and a second infrared sensor arranged on the right side of the pedal surface are respectively used for acquiring pressure signals, first behavior signals and second behavior signals in real time; the first behavior signals are used for indicating passengers to grab an armrest on the left side of an escalator; the second behavior signals are used for indicatingthe passengers to grab an armrest on the right side of the escalator; if the lasting time of acquired results meeting the following conditions reaches a preset time threshold, the pressure signals are acquired, and the first behavior signals or the second behavior signals are not acquired to judge unsafe behaviors of the passengers; and when the unsafe behaviors of the passengers are judged, an indicating lamp is controlled to emit light for reminding. The passenger behavior monitoring method and device can effectively remind the escalator taking behaviors of the passengers to improve the escalator taking safety of the passengers.
Owner:GUANGZHOU GUANGRI ELEVATOR IND
Safe production management method
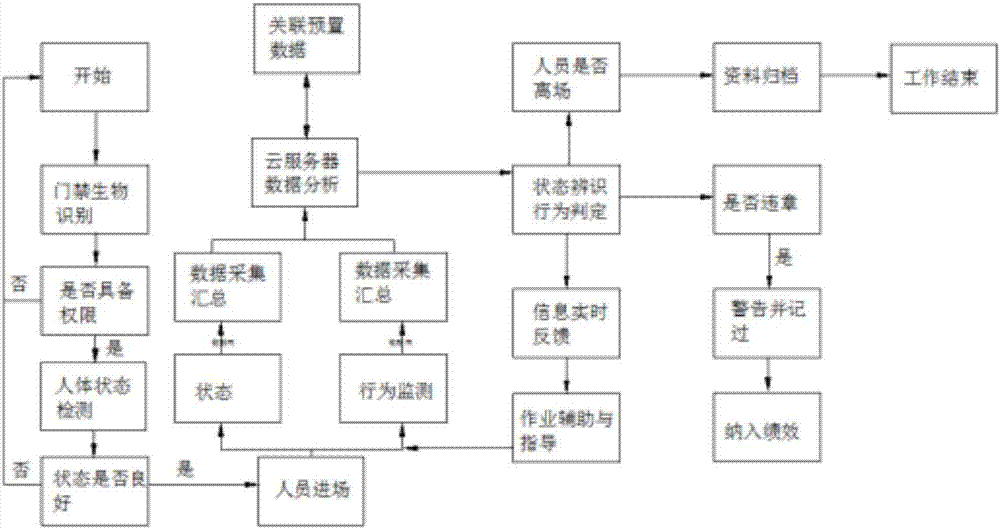
ActiveCN107464317AMonitor working statusMonitor behaviorIndividual entry/exit registersResourcesElectromagnetic lockIdentification device
The invention discloses a safe production management method. The safe production management method comprises the following steps of S1, mounting an electromagnetic lock onto the door plank of every workshop, forming a lock slot matched with the locking piece of the electromagnetic lock in one side of a door frame hinged to the door plank, according to the operation level of the production requirements in the workshop, numbering the level of the workshop, mounting an identification device corresponding to the level of the workshop onto the door plank of the workshop, wherein the identification device on the corresponding door plank is connected with a controller, and the controller is connected with the electromagnetic lock on the corresponding door plank; S2, ensuring that every worker needs identity identification through the identification device before entering a workshop to avoid entering a workshop without sufficient authority. The safe production management method can monitor behaviors of workers, ensure safe production and assess work of the workers; the workers can query problems during the working process via receiving computers to timely solve the problems. The safe production management method can improve the working efficiency of the workers.
Owner:STATE GRID SHANDONG ELECTRIC POWER CO JIMO POWER SUPPLY CO
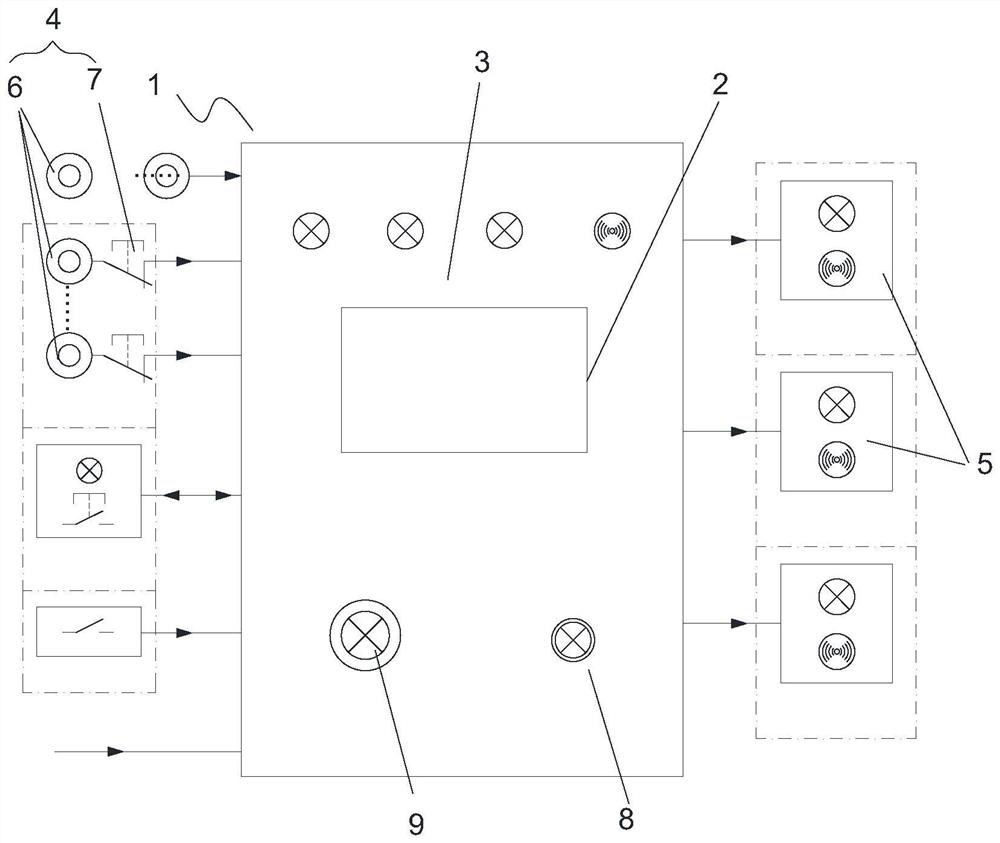
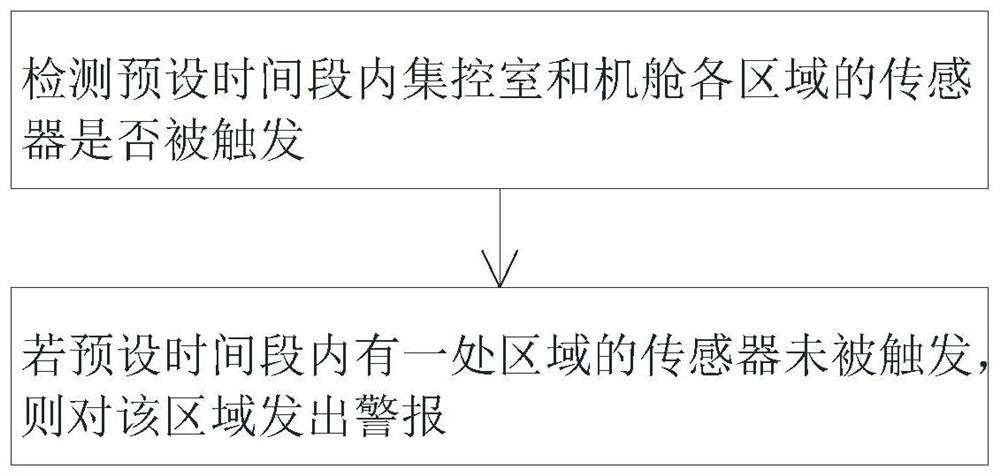
Ship engine room on-duty monitoring alarm system and alarm method
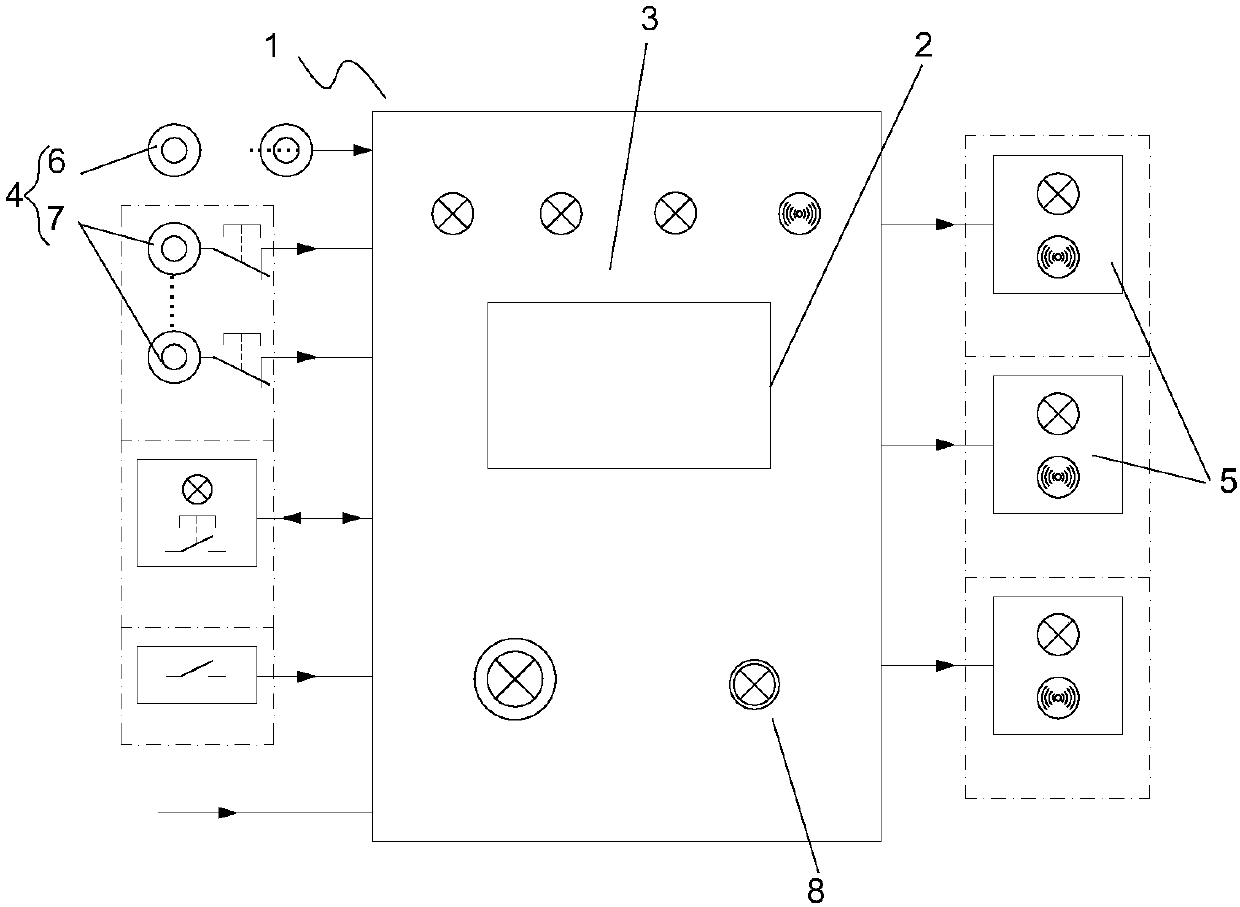
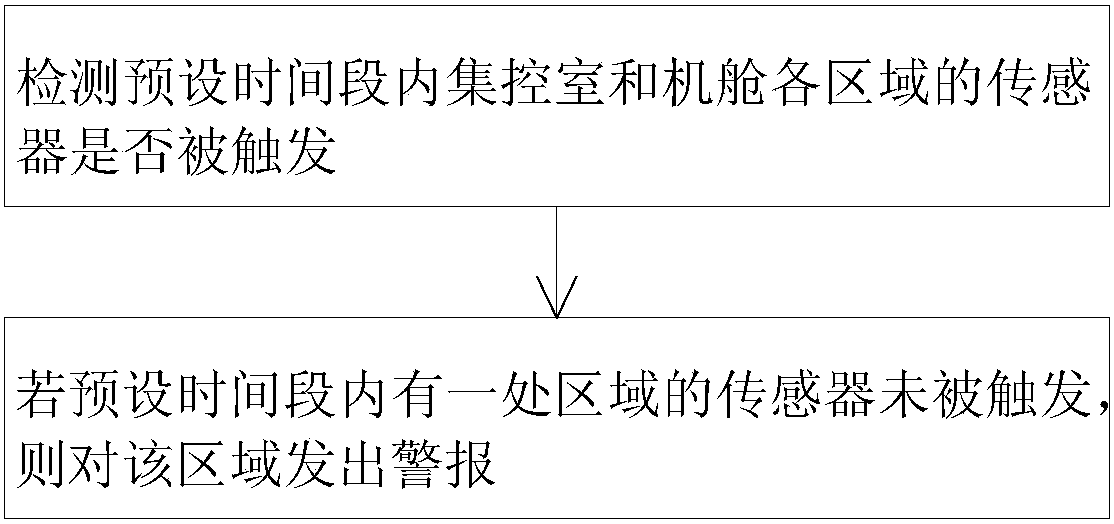
ActiveCN107665563AMonitor behaviorAvoid the problem of not performing inspectionsAlarmsRemote controlEngineering
The invention discloses a ship engine room on-duty monitoring alarm system and alarm method. The ship engine room on-duty monitoring alarm system comprises a master control box (1), a remote control resetting device (4) and extension alarms (5), the master control box (1) is provided with a panel (3) and a touch screen (2), a controller is arranged in the master control box (1), the remote controlresetting device (4) is connected to the controller and used for monitoring behaviors of engine room personnel and sending monitoring results to the controller, the extension alarms (5) are connectedto the controller, and the controller controls the extension alarms (5) to emit alarms if the behaviors of the engine room personnel are not monitored at any monitoring position in a specified time.According to the ship engine room on-duty monitoring alarm system, the problem that on-duty personnel cannot be effectively monitored in the prior art can be solved.
Owner:于斐 +1
Automatic software test management system and method based on artificial intelligence
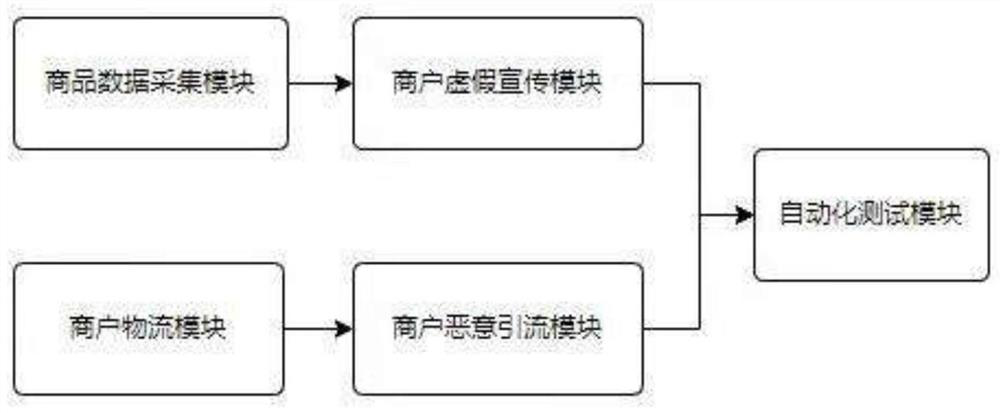
ActiveCN114819985AMonitor behaviorMaintain reputationCharacter and pattern recognitionSoftware testing/debuggingTest managementData mining
The invention discloses a software automatic test management system and method based on artificial intelligence, and belongs to the technical field of artificial intelligence. A false propaganda module is arranged to identify commodities actually sold by merchants based on a deep learning algorithm, calculate differences between the commodities actually sold by the merchants and commodities propagandized by the merchants, and judge whether the merchants propagandize falsely; setting a merchant malicious drainage module to construct a malicious drainage judgment model, and judging whether the merchant is maliciously drained or not; an automatic test module is arranged to realize that one script adapts to multiple sets of environment scenes through a parameterization mechanism of the system and packaged diversified components; by setting a merchant false propaganda module and a merchant malicious drainage model to assess and monitor merchant behaviors and maintain the reputation of the platform, by setting an automatic test module and modularly managing test scenes, the scenes are combined according to specific test requirements to automatically output a test report, and normal operation of the system after multiple times of data debugging is guaranteed.
Owner:北京网鲜供应链科技有限公司
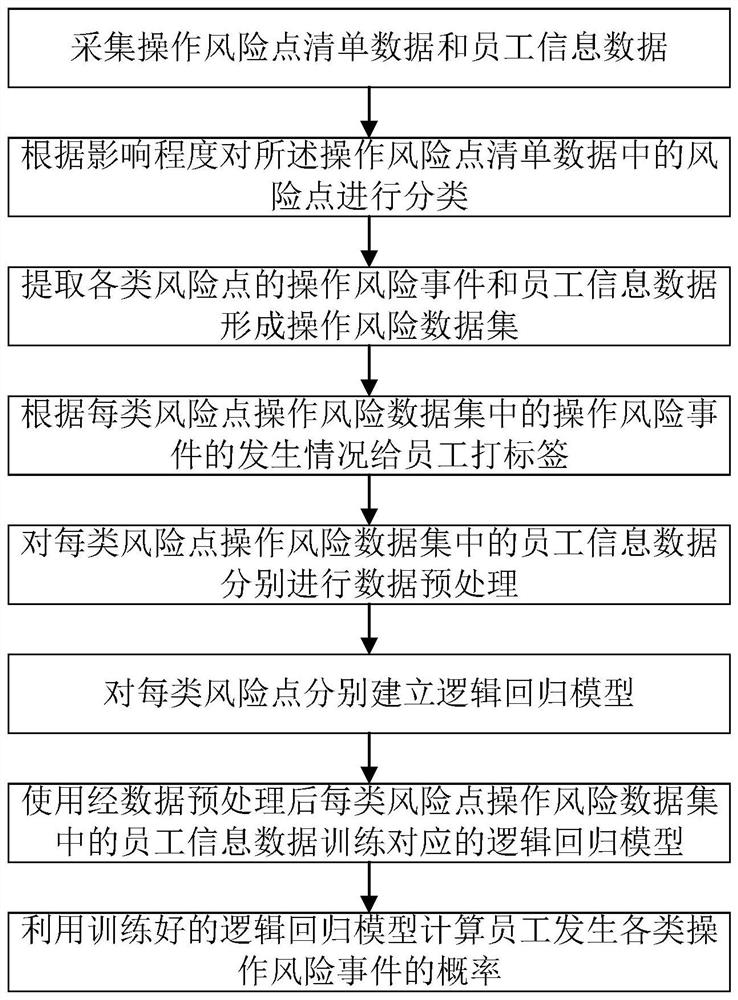
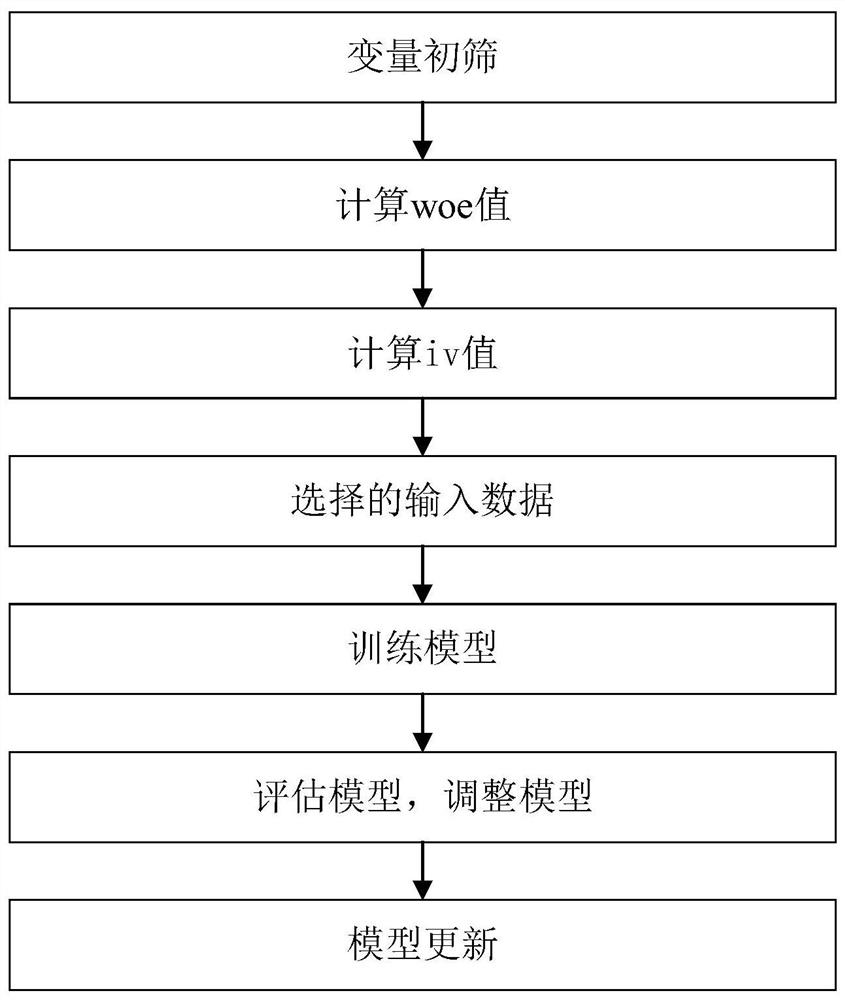
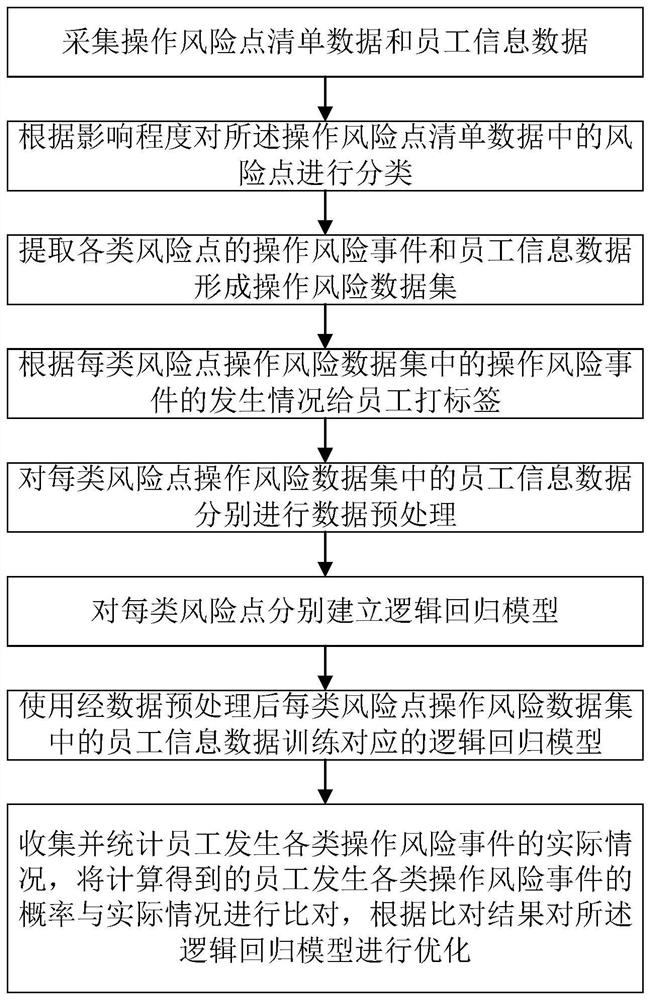
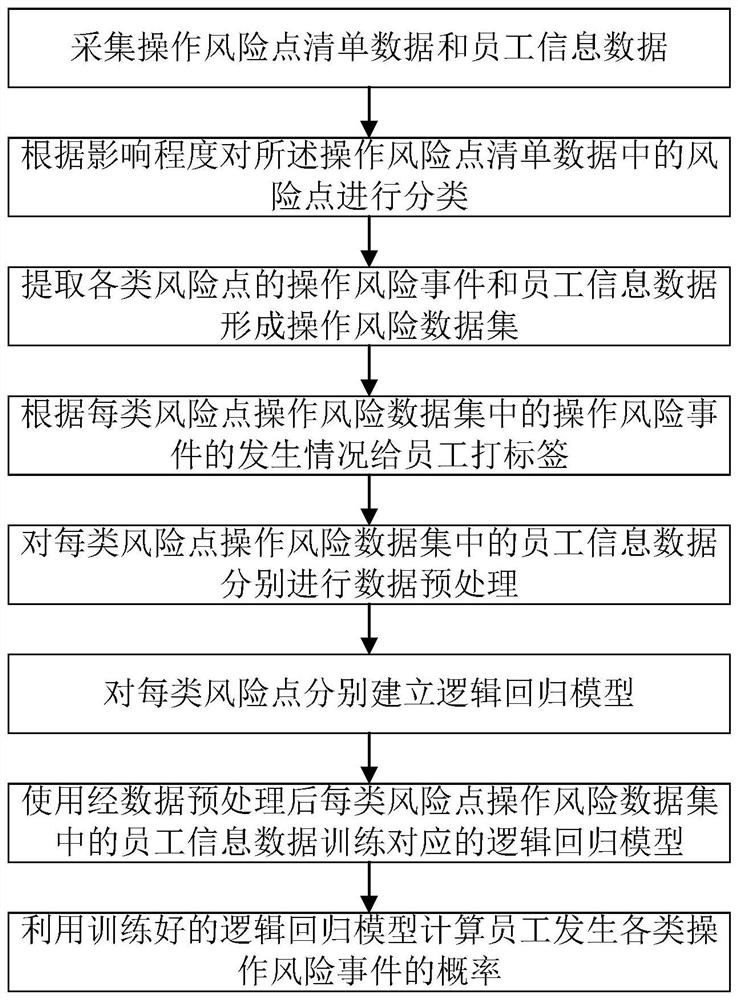
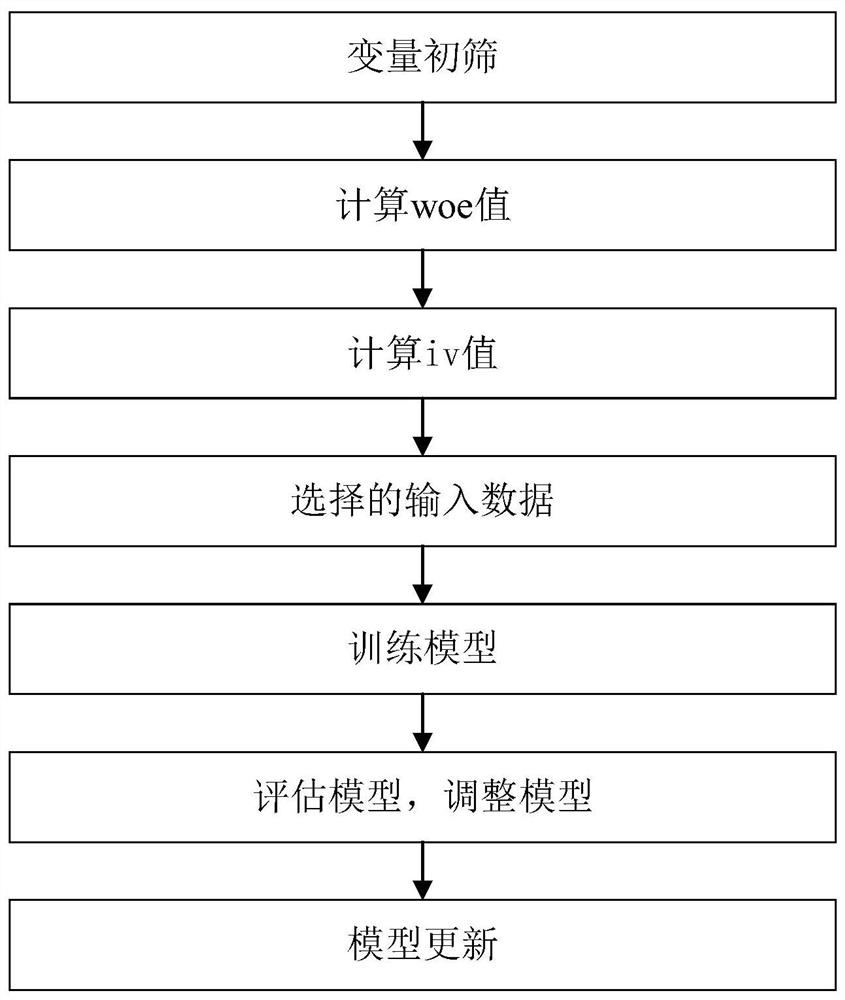
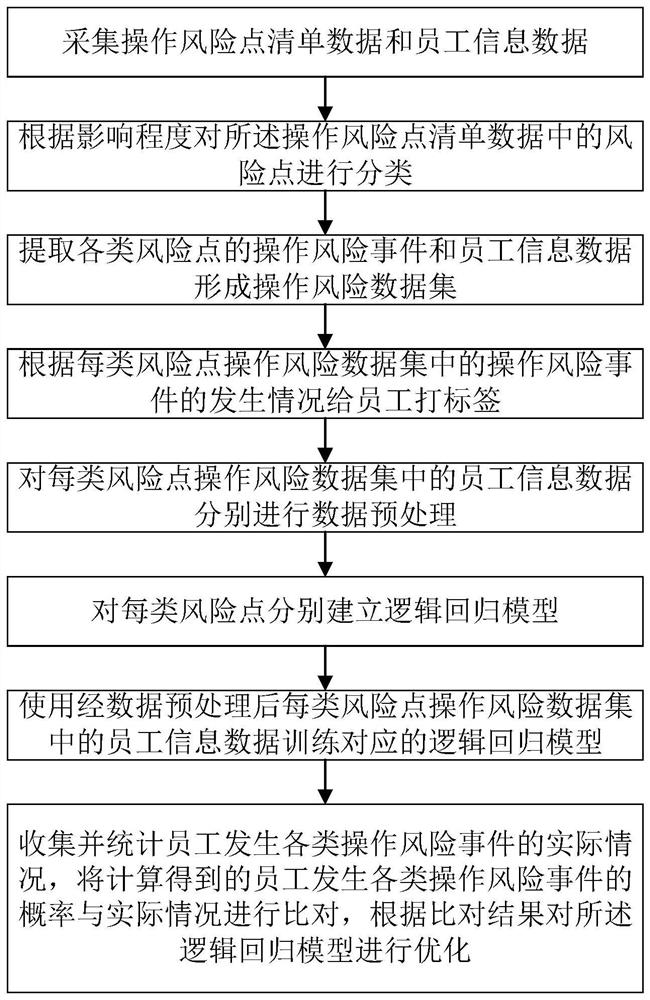
Employee operation risk prediction method based on logistic regression
The invention provides an employee operation risk prediction method based on logistic regression. The employee operation risk prediction method comprises the steps of S1, collecting operation risk point list data and employee information data; S2, classifying risk points in the operation risk point list data; S3, extracting operation risk events and employee information data of various risk pointsto form an operation risk data set; S4, labeling the staff according to the occurrence condition of the operation risk event; S5, performing data preprocessing on employee information data in each type of risk point operation risk data set; S6, based on employee tags, establishing a logistic regression model for each type of risk points; S7, training a corresponding logistic regression model by using employee information data in each type of risk point operation risk data set after data preprocessing; and S8, the trained logistic regression model being utilized to calculate the probability ofoccurrence of various operation risk events of the employees. According to the invention, employee information data is collected, employee behaviors are monitored, manual on-site inspection is not needed, and the labor cost is reduced.
Owner:泸州银行股份有限公司 +2
Method and device for automatically obtaining suspected card raising channel
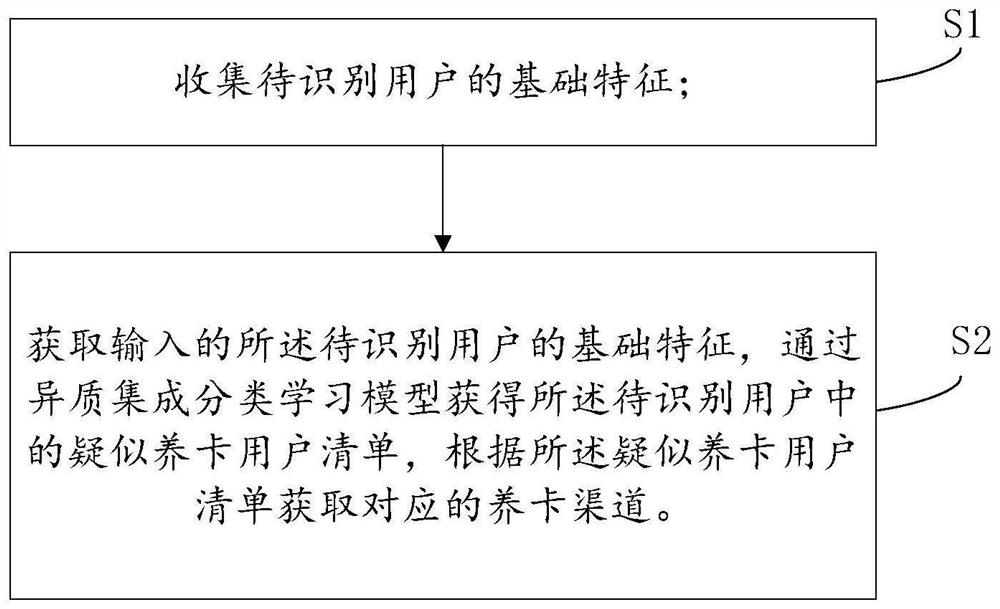
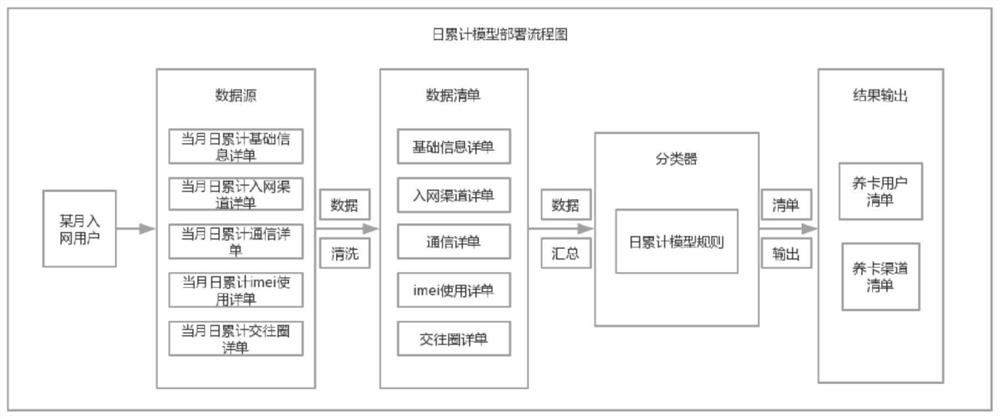
PendingCN112446425AHave diversityBreach ControlEnsemble learningCharacter and pattern recognitionData ingestionEngineering
The invention discloses a method and device for automatically obtaining a suspected card raising channel, and relates to the field of intelligent risk control. The method comprises the steps of collecting basic features of a to-be-identified user; acquiring input basic characteristics of a user to be identified, performing weighted fusion through a trained random forest model with acquired suspected card raising rules in combination with a trained linear regression model to acquire a suspected card raising user list in the user to be identified, and acquiring a corresponding card raising channel according to the suspected card raising user list. A random forest learning base algorithm fused by a plurality of decision tree classifiers is applied to extract potential suspected card raising rules from sample data, weighted fusion is carried out on the potential suspected card raising rules and a linear regression classification model, the integration generalization ability is enhanced, and the suspected card raising rules have diversity. Supervision and management of a card raising phenomenon in a daily operation process of a market department are satisfied so that a channel violationbehavior is effectively controlled.
Owner:北京思特奇信息技术股份有限公司
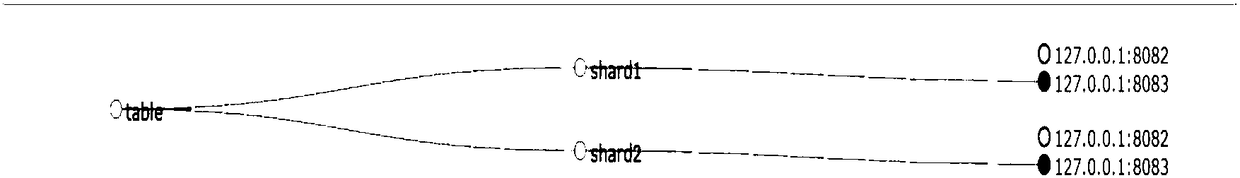
Distributed retrieval method based on Solr
InactiveCN108073617AEvenly distributedLoad balancingDatabase distribution/replicationSpecial data processing applicationsDistributed retrievalLogfile
The invention discloses a distributed retrieval method based on Solr. The method comprises the following steps that: establishing a zookeeper in each server, carrying out cluster management through the zookeeper, and automatically recommending master and slave clusters via the server; adopting solrCloud distributed deployment, establishing at least one solr in each server according to actual requirements, uniformly submitting the solr to the zookeeper for management, or manually adding nodes; carrying out customized selection on index fields by a user according to actual requirements; generating a corresponding configuration file by the system according to the selection of the user, and carrying out indexing; automatically distributing an index by the zookeeper to enable each solr to be evenly distributed in the node to achieve load balancing; and according to different users, distributing the access permission of different tables to manage user query permission, meanwhile, generatinga log file according to a user query record, monitoring user behaviors, and avoiding the illegal operation of the user.
Owner:CHINA CHANGFENG SCI TECH IND GROUPCORP
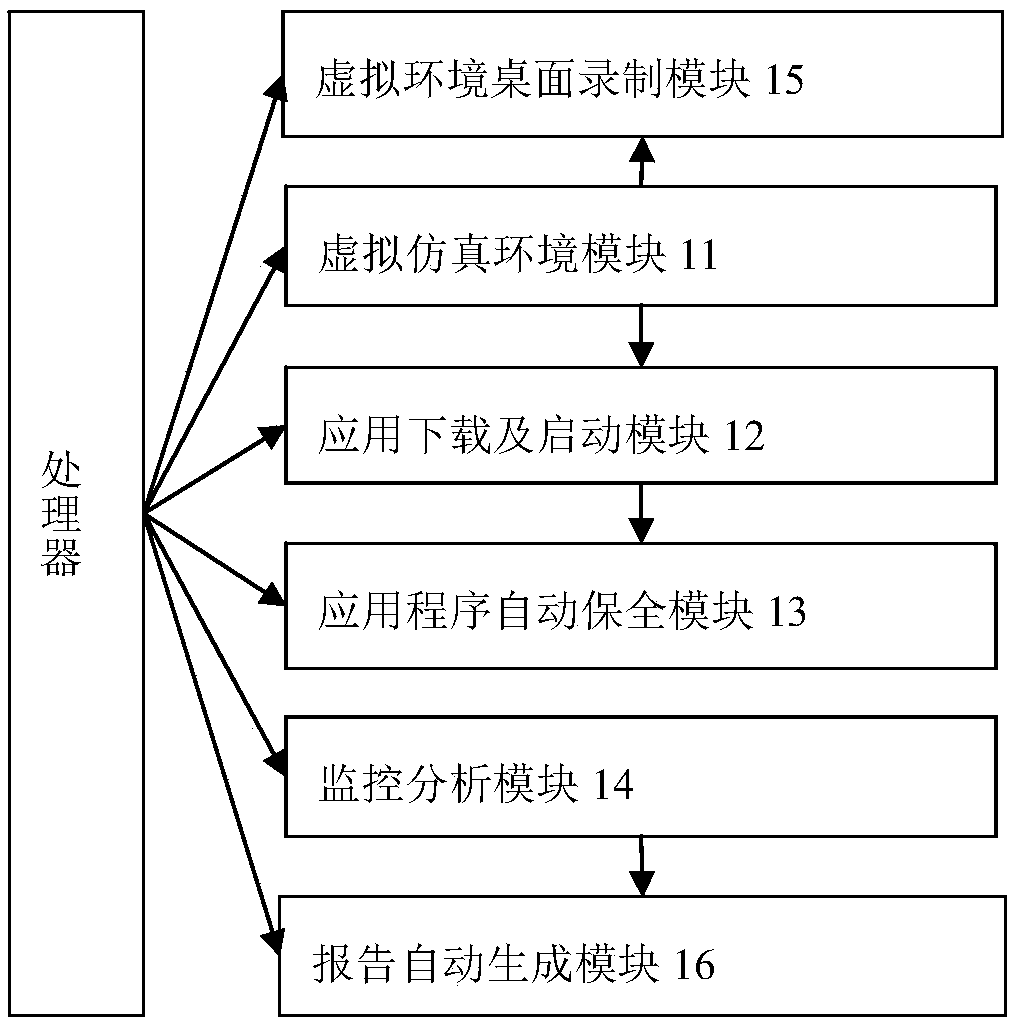
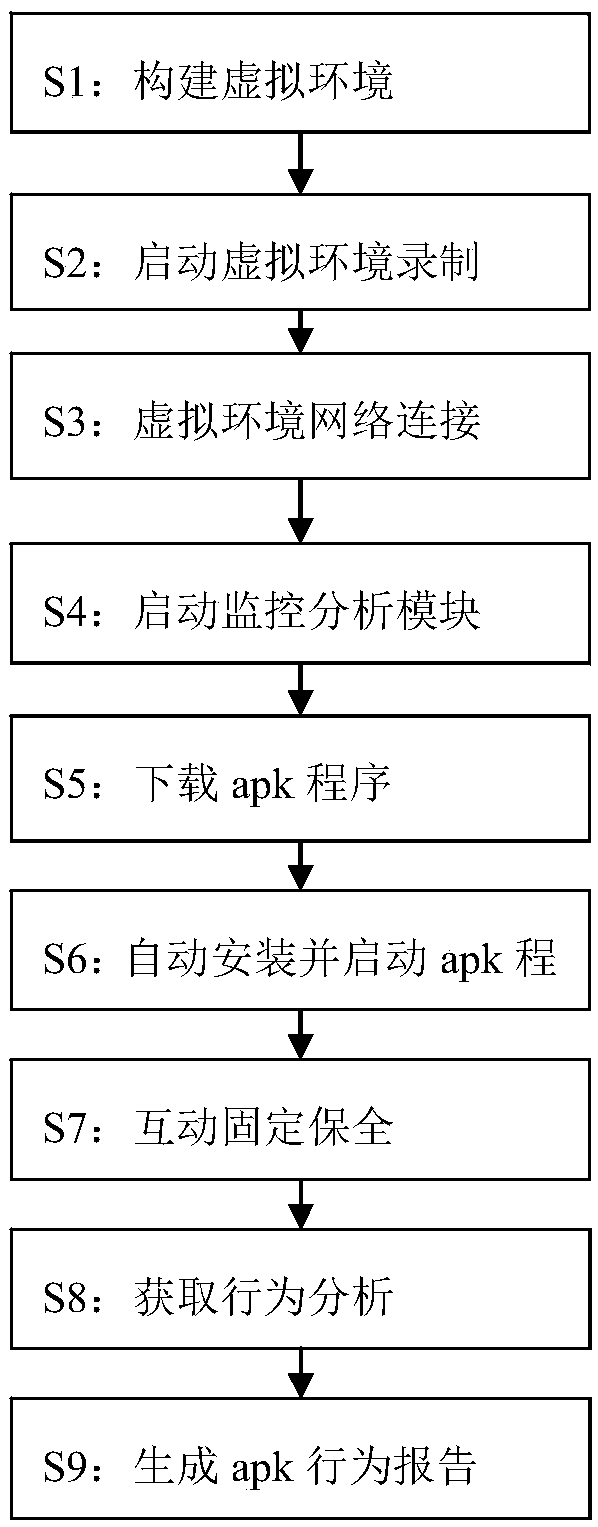
A mobile terminal application fixed security system and method based on simulation
InactiveCN109583192AMonitor behaviorHardware monitoringPlatform integrity maintainanceOperating systemSecurity system
The invention discloses a mobile terminal application fixed security system and method based on simulation. According to the scheme, a virtual simulation environment for operation of a mobile terminalapplication is constructed; Downloading is carried out in a virtual simulation environment, and a mobile terminal application is installed; The method comprises the following steps: operating a mobile terminal application in a virtual simulation environment, identifying and triggering each functional unit in the mobile terminal application, carrying out simulation interaction with the mobile terminal application to realize a function corresponding to each functional unit, and carrying out fixed security on an interactive operation process of the mobile terminal application in the virtual simulation environment. Compared with the prior art, the scheme provided by the invention has the advantages that interaction is automatically carried out on the mobile terminal application by constructing the virtual simulation environment, and evidence collection and preservation are synchronously carried out.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Passenger behavior monitoring method based on machine vision
ActiveCN109359536BMonitor behaviorAvoid safety accidentsCharacter and pattern recognitionFace detectionMachine vision
The invention discloses a method for monitoring passenger behavior based on machine vision, comprising the steps of: 1) collecting video images of passengers riding an escalator; 2) extracting deformable component model DPM features to describe passengers' faces; 3) using SVM to walk the escalator Passenger face detection; 4) Use KCF to track the face of the escalator passenger; 5) Use an improved nearest neighbor matching method to match the face detection and tracking results; 6) Establish a face target detection intensity model, correct the face Face detection results; 7) Monitor the behavior of passengers in the escalator by analyzing the passenger detection intensity, speed and speed direction. The method of the invention can detect and track the facial objects of passengers taking the escalator in a real-time, stable and accurate manner, and conduct behavior monitoring based on the facial object information.
Owner:SOUTH CHINA UNIV OF TECH +1
Ship trajectory generation method based on voluntary observation ship data
InactiveCN104680850BEasy to classifyQuick classificationMarine craft traffic controlShip tracksComputer science
The invention relates to a method for generating a ship track curve based on voluntary observation ship (VOS) data, in particular to a method for generating the ship track curve with a large number of discrete points. The method comprises the following steps: reading VOS; recognizing the voyage according to the VOS track points; arranging the VOS track point data; connecting the VOS track curves; correcting the connection of the track curves according to the obstacle-avoiding path design; generating the VOS track curve. Through adoption of the method, the problem that the ship track curve or ship route is extracted a little can be solved; the ship track curve generation method is provided; a large number of discrete VOS point data can be used for generating into a continuous ship track curve which is beneficial for mastering the regional marine traffic distribution conditions and monitor ship behavior so as to ensure the marine traffic security as well as providing decision-making reference for the marine administrative authority; the method is of great significance on protecting the life and property of people, protecting the marine environment and ensuring the national core strategic interests.
Owner:NANJING UNIV
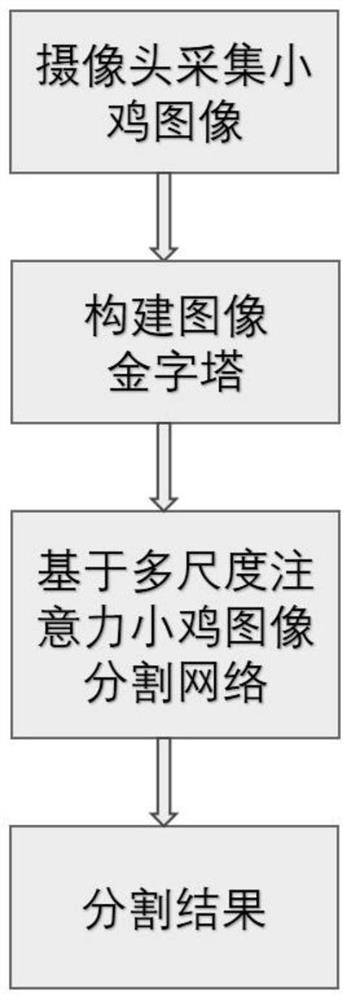
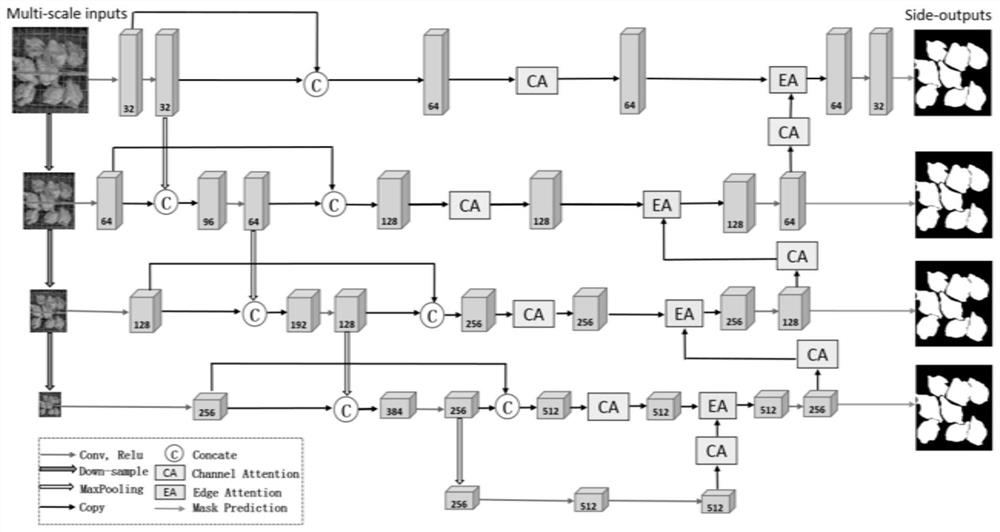
Chicken image segmentation method and system based on multi-scale attention network
ActiveCN113052848AImprove segmentationHelp to deal withImage enhancementImage analysisPattern recognitionImage segmentation
The invention discloses a chick image segmentation method and system based on a multi-scale attention network. The method comprises the steps of performing multi-scale downsampling on an acquired chick image and then constructing an image pyramid; constructing a segmentation network based on a multi-scale attention mechanism, extracting a multi-scale feature map in the segmentation network through a coding network, carrying out global and local feature enhancement through a double attention mechanism, and carrying out decoding prediction on the enhanced features to obtain a segmentation result of each layer; and obtaining multi-scale joint loss based on the segmentation result of each layer, optimizing the multi-scale attention segmentation network based on the multi-scale joint loss, and obtaining an image segmentation result by using the optimized multi-scale attention segmentation network. The chick image segmentation effect is effectively improved.
Owner:SHANDONG UNIV
A system and method for real-time pollution monitoring of ships based on Beidou short messages
InactiveCN110146129BSimplify the inspection inspection processInspection inspection process reductionSatellite radio beaconingMessaging/mailboxes/announcementsNavigation systemData transmission
The invention belongs to the technical field of pollution monitoring, and discloses a ship real-time pollution monitoring system and method of a Beidou short message; it includes a ship embedded pollution data processing set system module, a Beidou satellite navigation system module, a shore-based data processing system module, and a system based on The index code table mode message module of Beidou short message. The invention uses the message function of the Beidou satellite navigation system to transmit the various pollution detection data of the ship to the two-way data transmission between the ship and the shore, realizes the integrated real-time monitoring of the ship and the shore, and satisfies the requirements of the shore-based management department or the company on various pollution gases or pollutants of the ship. The demand for real-time monitoring of liquid discharge has the effect of reducing polluted water and direct discharge of harmful gases while reducing marine environmental pollution and atmospheric environmental pollution during ship navigation. The invention effectively solves the problem that the crew or the shipowner do not discharge in accordance with the regulations of the International Maritime Organization (IMO) related pollution prevention convention (such as the MARPOL convention), which makes the pollution of the ship more serious.
Owner:GUANGZHOU MARITIME INST
A general-purpose face recognition security door
The invention discloses a universal face recognition safety door. The door opening and closing device comprises an opening and closing door and a power device located in the opening and closing door.The power device comprises a power cavity; a motor is arranged in the right end wall of the power cavity; a recognition device located in the opening and closing door is arranged above the power device. The recognition device comprises a telescopic moving cavity; a conversion groove is formed in the lower end wall of the telescopic moving cavity; according to the device, the height of a person canbe automatically sensed, so that the device hidden in a door is telescopically moved to recognize a human face, password recognition is automatically switched when human face recognition fails, and when password recognition fails, a monitor hidden above pops up to monitor the behavior of the person.
Owner:广东创宇信息工程有限公司
System and method for legally monitoring audio/video multimedia conference
InactiveCN101345846BEffectively monitor behaviorMonitor behaviorTelevision conference systemsSupervisory/monitoring/testing arrangementsApplication serverMedia server
The present invention discloses a system for legitimately monitoring the audio and video multimedia conference, including: a monitoring control terminal, a monitoring answer terminal, an application server and a media server, wherein, the application server is used to realize the processing logic of audio and video multimedia conference service and the legitimate monitoring; the medium service apparatus can be used to realize the media processing of the audio and video multimedia conference and the legitimate monitoring; and the monitoring control terminal can be used to initiate monitor indication and perform monitor management. The present invention also discloses a method for legitimately monitoring the audio and video multimedia conference, which realizes legitimate monitoring function by using the apparatus and function in the audio and video multimedia conference service. The present invention is suitable for audio and video multimedia conference in the field of NGN or IMS communications.
Owner:ZTE CORP
Monitoring and alarm system and alarm method for ship engine room on duty
ActiveCN107665563BMonitor behaviorAvoid the problem of not performing inspectionsAlarmsTouchscreenReliability engineering
Owner:于斐 +1
A Logistic Regression Based Employee Operational Risk Prediction Method
The present invention provides a method for predicting employee operational risks based on logistic regression, comprising: S1, collecting operational risk point list data and employee information data; S2, classifying the risk points in the operational risk point list data; S3, extracting Operational risk events and employee information data of various risk points form an operational risk data set; S4, label employees according to the occurrence of operational risk events; Preprocessing; S6, based on the employee label, establish a logistic regression model for each type of risk point; S7, use the employee information data in the operation risk data set of each type of risk point after data preprocessing to train the corresponding logistic regression model; S8, use The trained logistic regression model calculates the probability of employees having various operational risk events. The invention collects employee information data, monitors employee behavior, does not need manual on-site inspection, and reduces labor costs.
Owner:泸州银行股份有限公司 +2
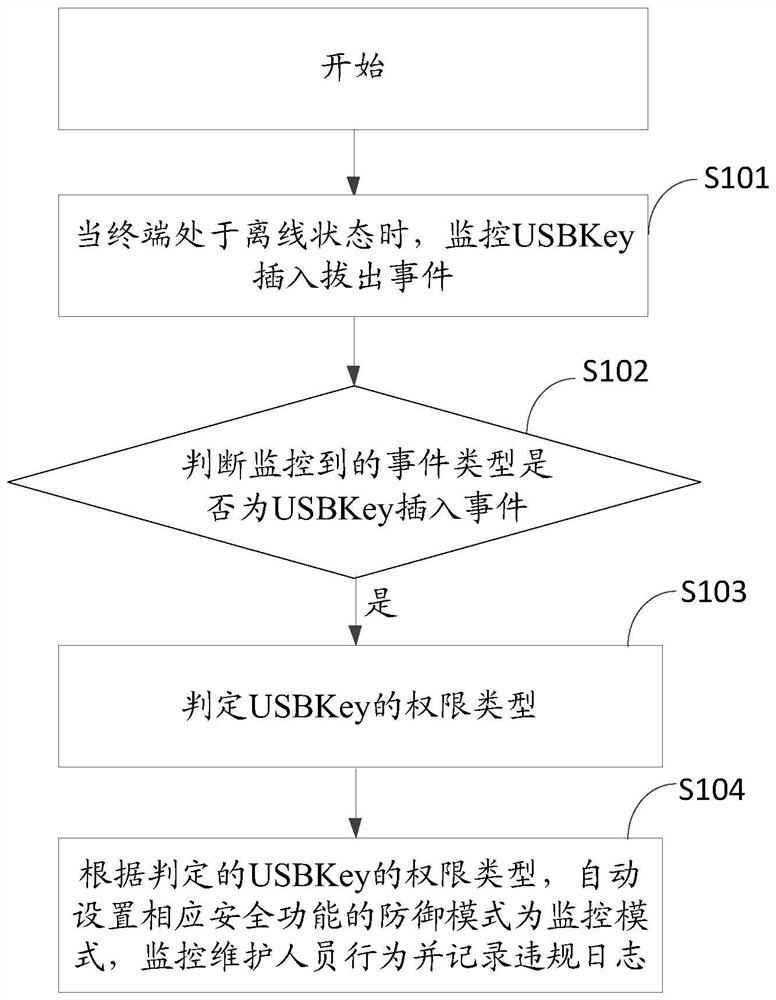
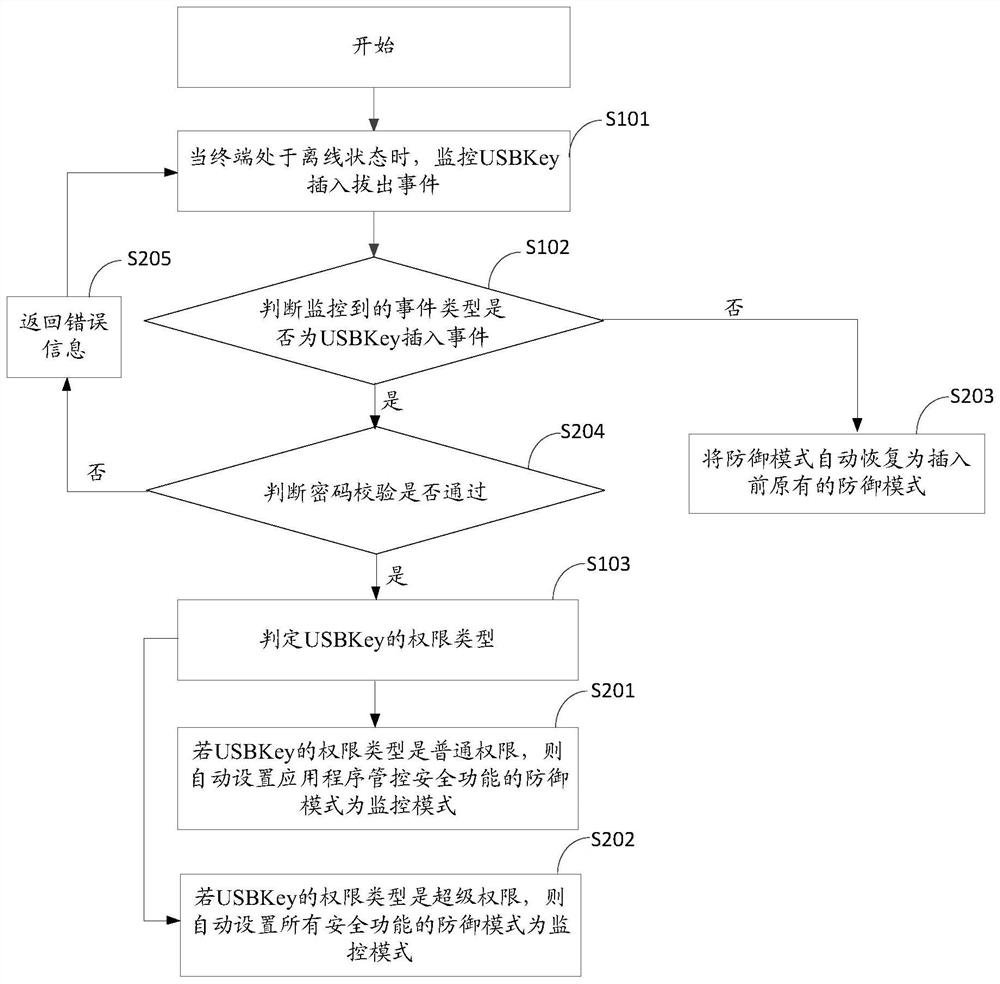
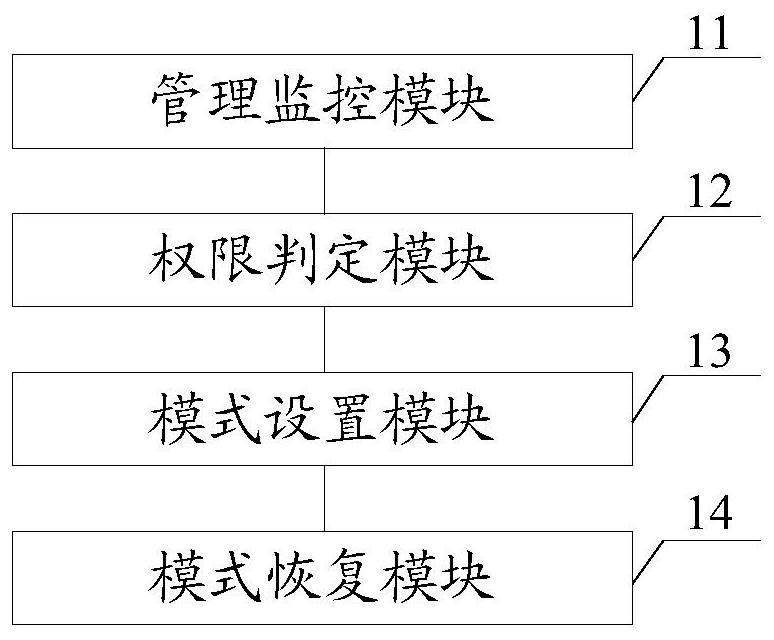
A terminal maintenance management method, device, equipment and storage medium
ActiveCN110750779BMonitor behaviorAffect normal operationDigital data authenticationPlatform integrity maintainanceMonitor modeMaintenance management
Owner:北京浪潮数据技术有限公司
Android ransomware detection and defense method, device and equipment and readable storage medium
PendingCN113886824AFree from harmEfficient analysisPlatform integrity maintainanceRansomwareSoftware engineering
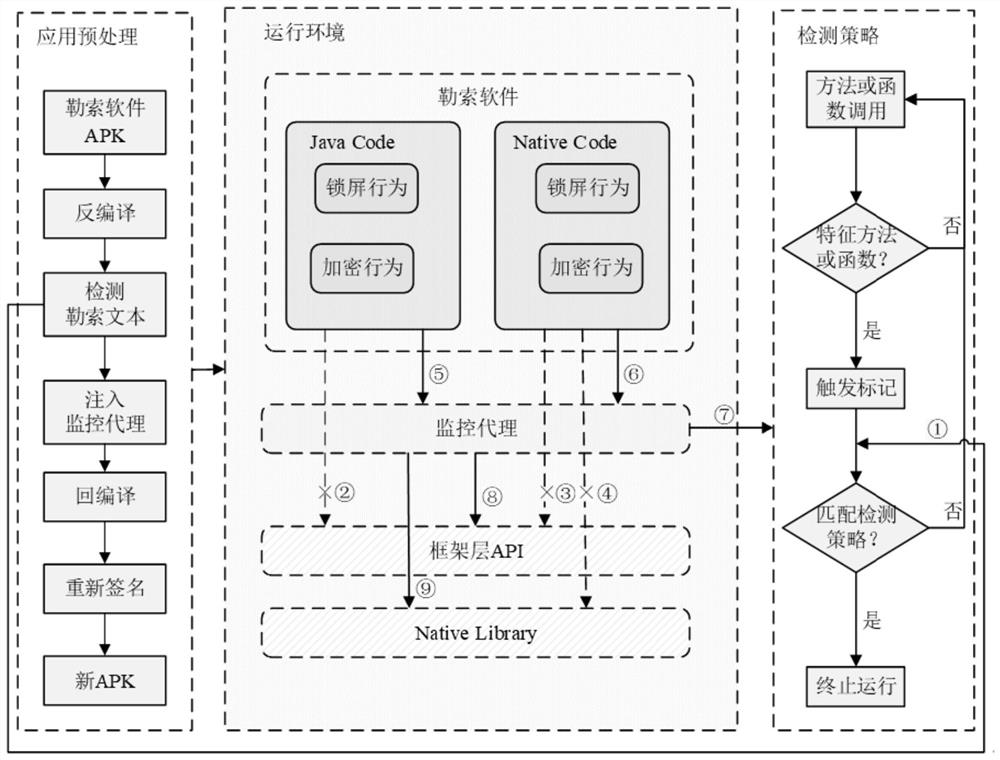
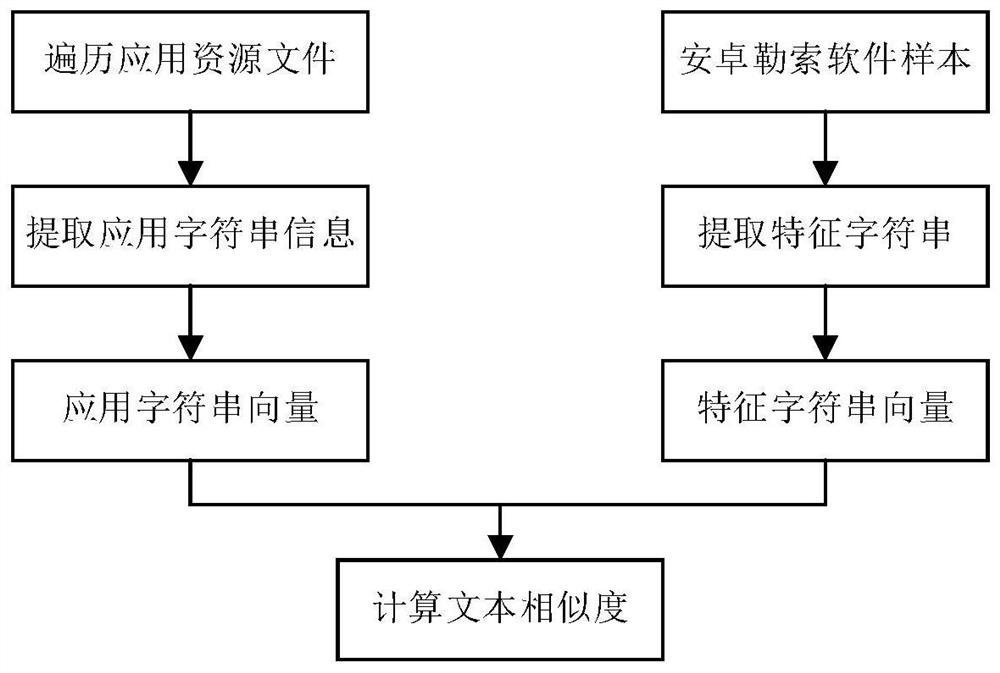
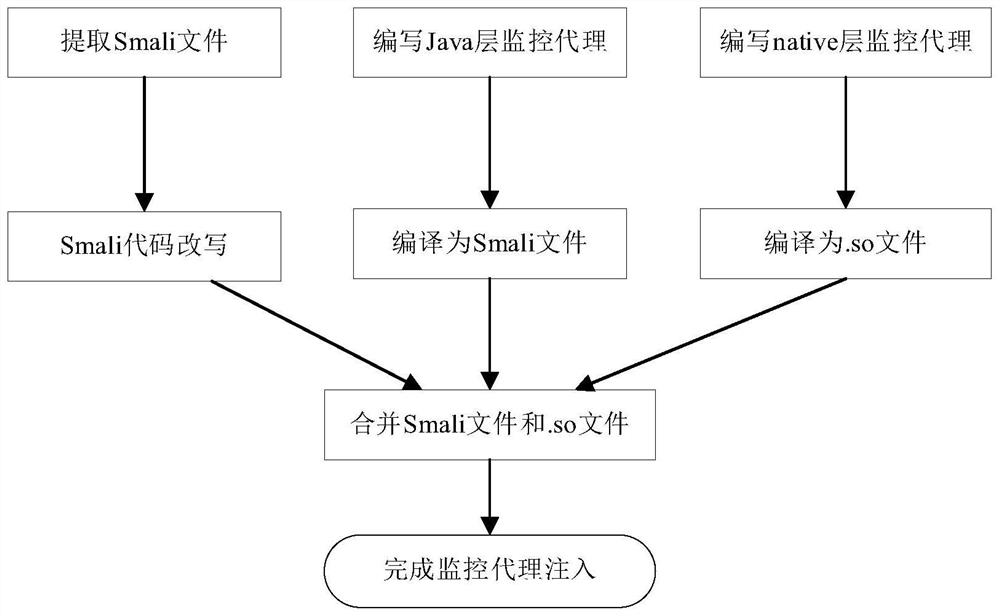
The invention discloses an android ransomware detection and defense method, device and equipment and a readable storage medium. The method comprises three parts of to-be-detected android application preprocessing, operation environment detection and detection strategy. The preprocessing of the to-be-detected Android application mainly comprises the steps of detecting a ransomware in the to-be-detected Android application and injecting a monitoring agent into the to-be-detected Android application; the operation environment detection mainly comprises the steps that the monitoring agent detects calling of the ransomware to a framework layer API and Native Library so as to monitor behaviors of the ransomware; the detection strategy is mainly used for judging whether the application is the android ransomware or not according to the android application behavior to be detected. According to the invention, the ransomware in the application can be effectively detected, and malicious behaviors during application running can be analyzed; therefore, Android ransomware attacks are resisted, the user equipment is protected from being damaged by the ransomware, and the safety of the user equipment is protected.
Owner:XIDIAN UNIV
Android program real-time behavior analysis method and system based on kernel
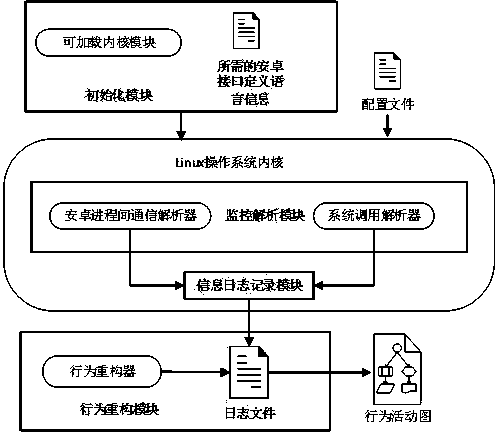
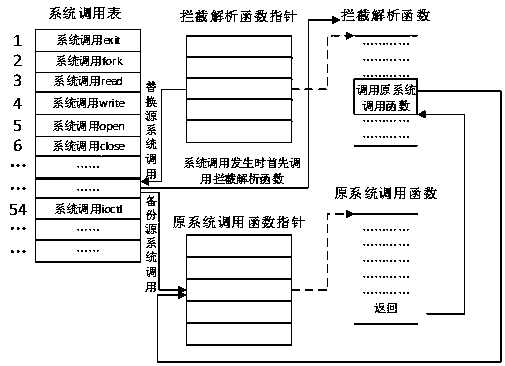
InactiveCN105184166BImprove accuracyMonitor behaviorPlatform integrity maintainanceBehavioral analyticsSystem call
The invention discloses a kernel-based Android application real-time behavior analysis method and a behavior analysis system capable for implementing the method. The method comprises a system call monitoring initialization step, a kernel system call interception monitoring and parsing step, a parsing result-based information logging step and an information log-based application behavior reconstruction step. A system call is intercepted and parsed in a kernel, so that an application file, a network as well as inter-process communication and other particular behaviors of the Android system are reconstructed; the whole behavior analysis process is monitored in real time in the kernel, so that the accuracy of behavior obtaining is guaranteed; meanwhile, the kernel has the highest authority, so that malware is hard to evade the kernel; according to the method, no code in the Android system is modified, so that the performance loss is low; practice proves that a result of the method can serve as key evidence to be obtained and provides a reference for malware detection.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com