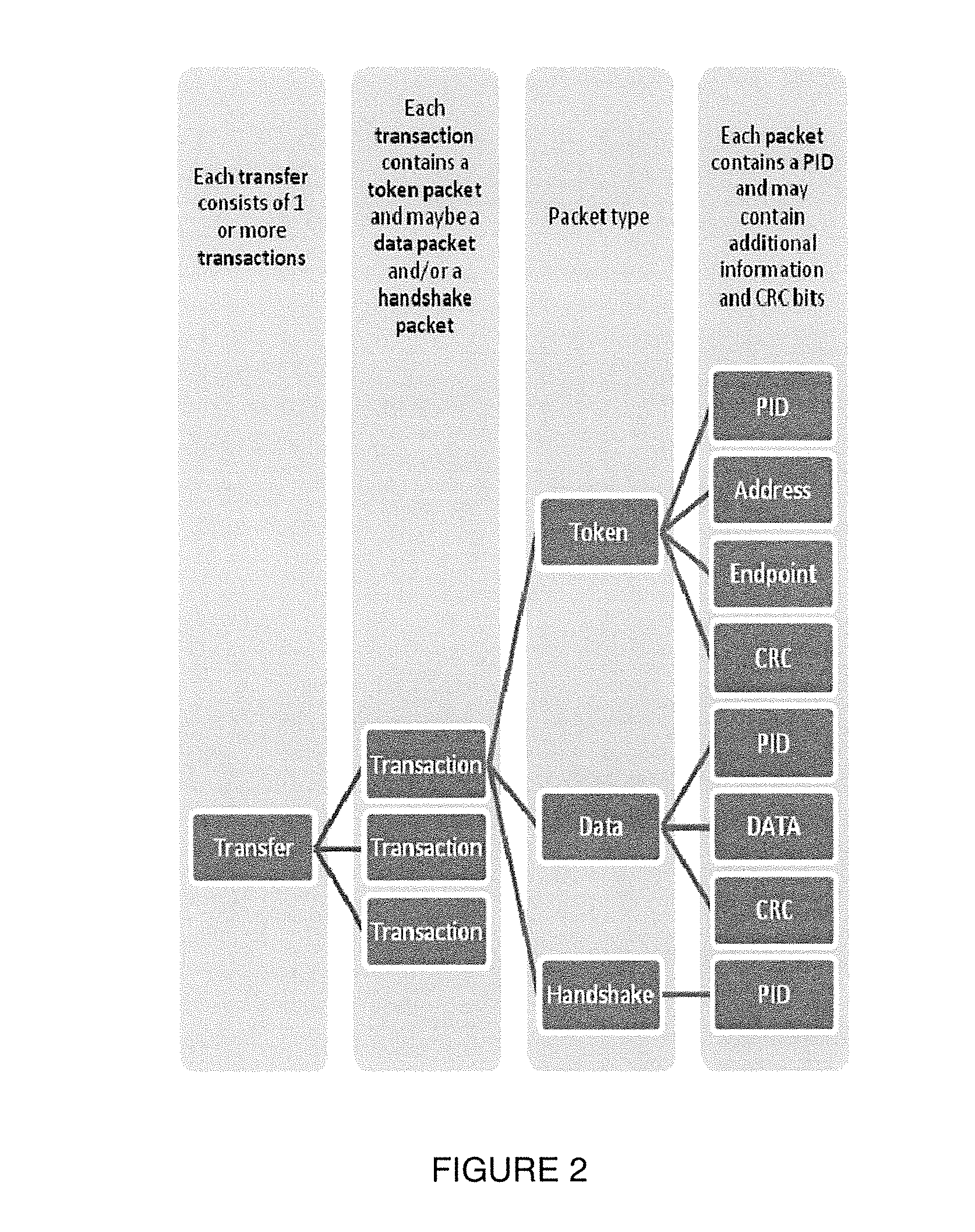
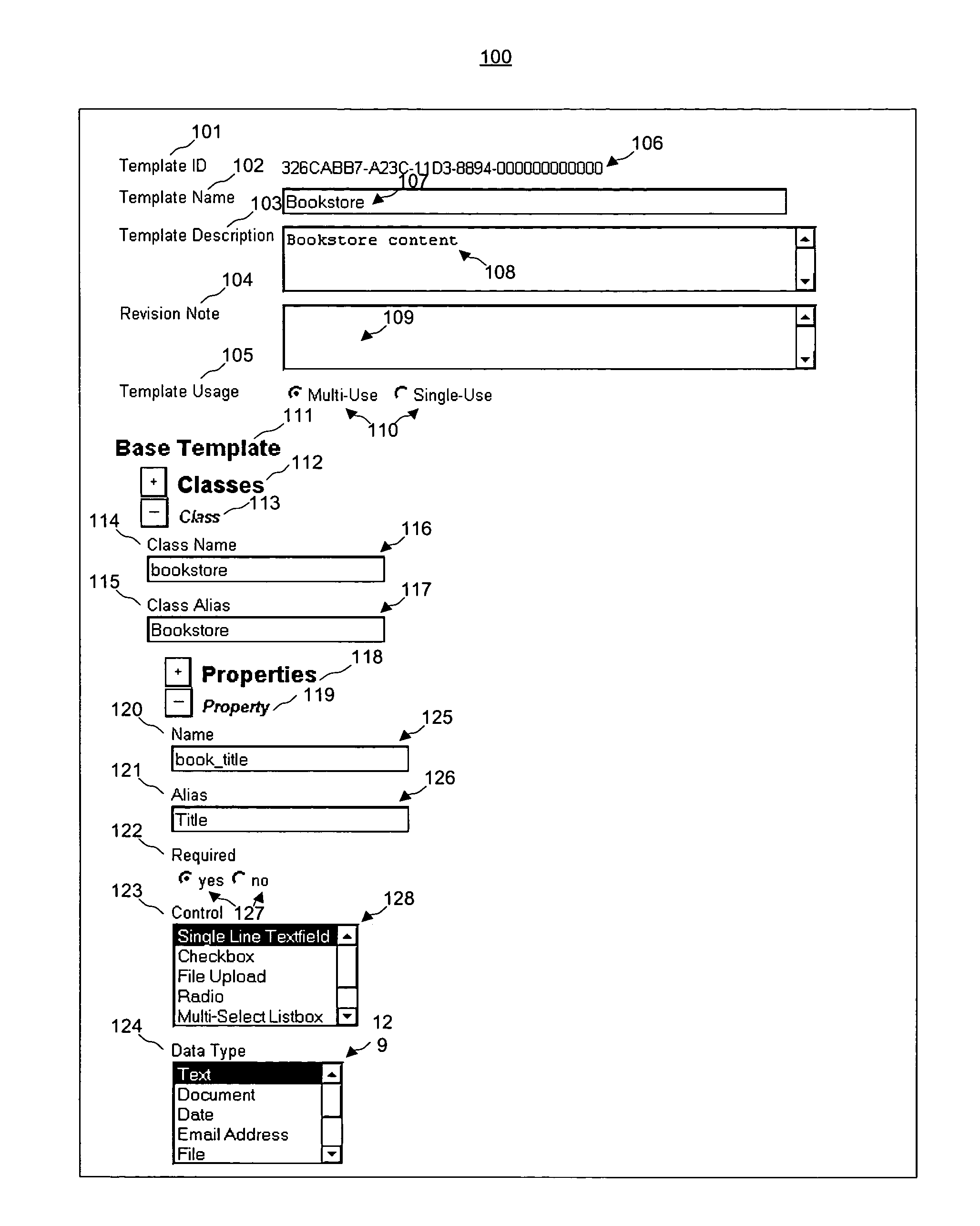
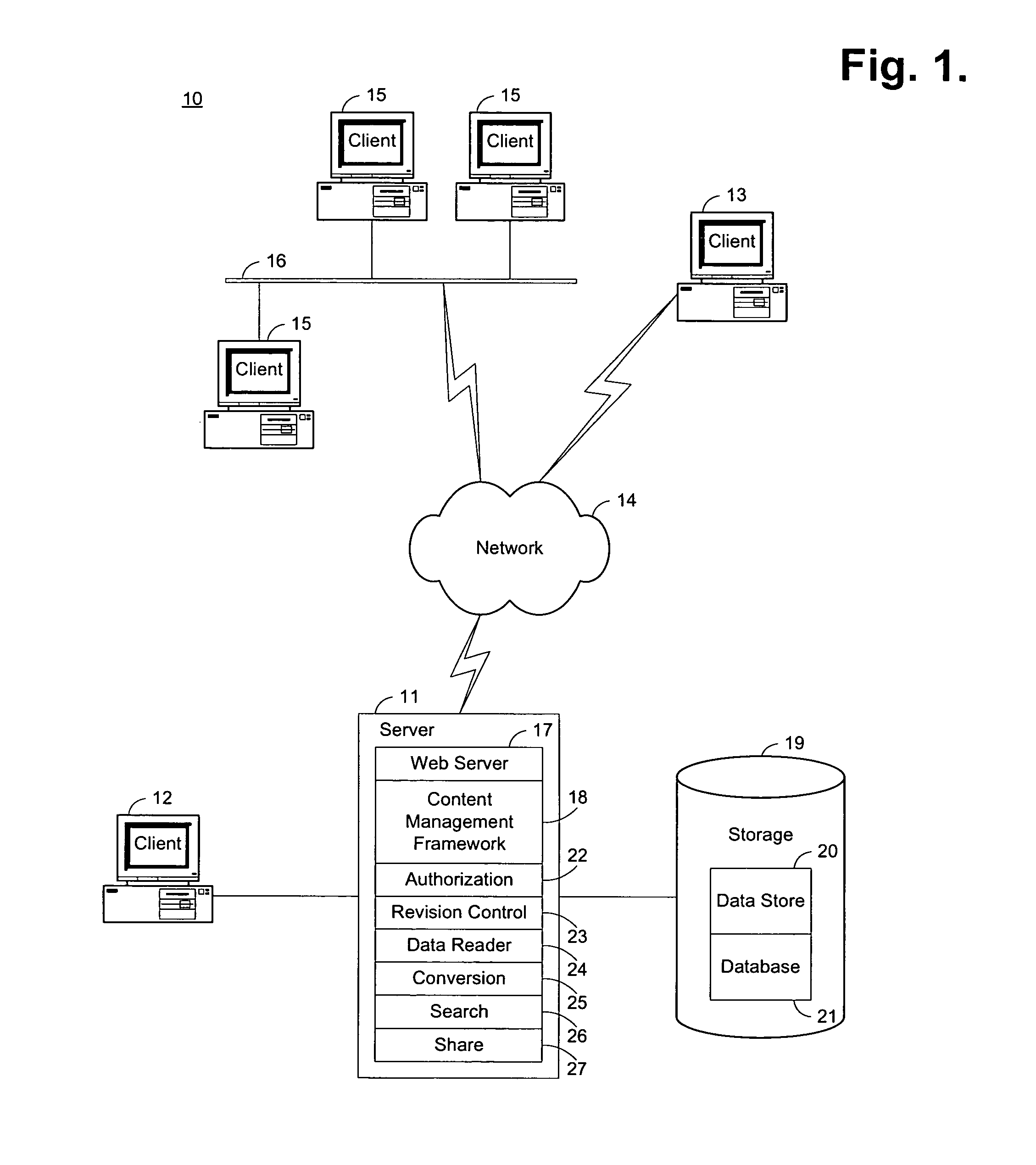
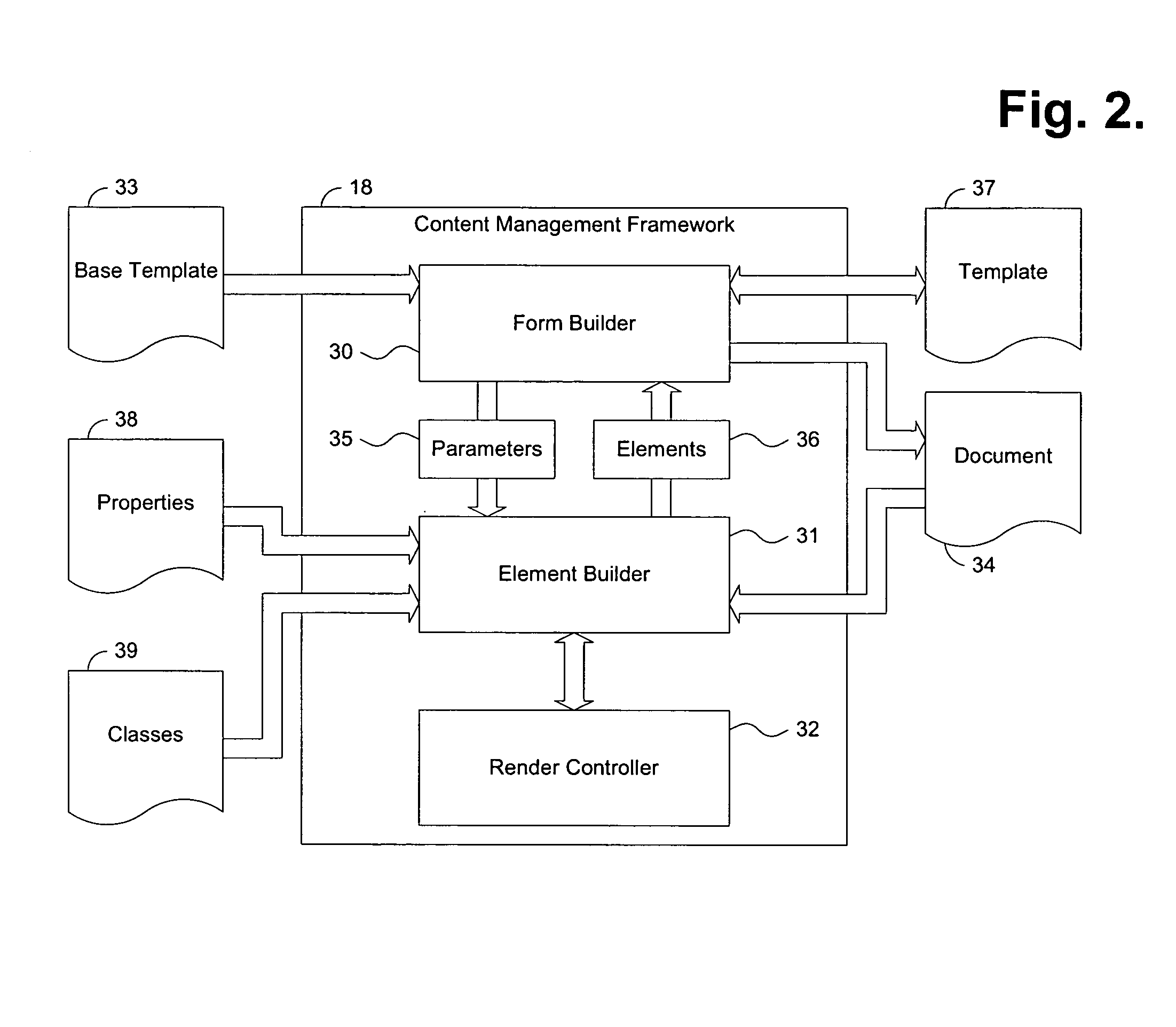
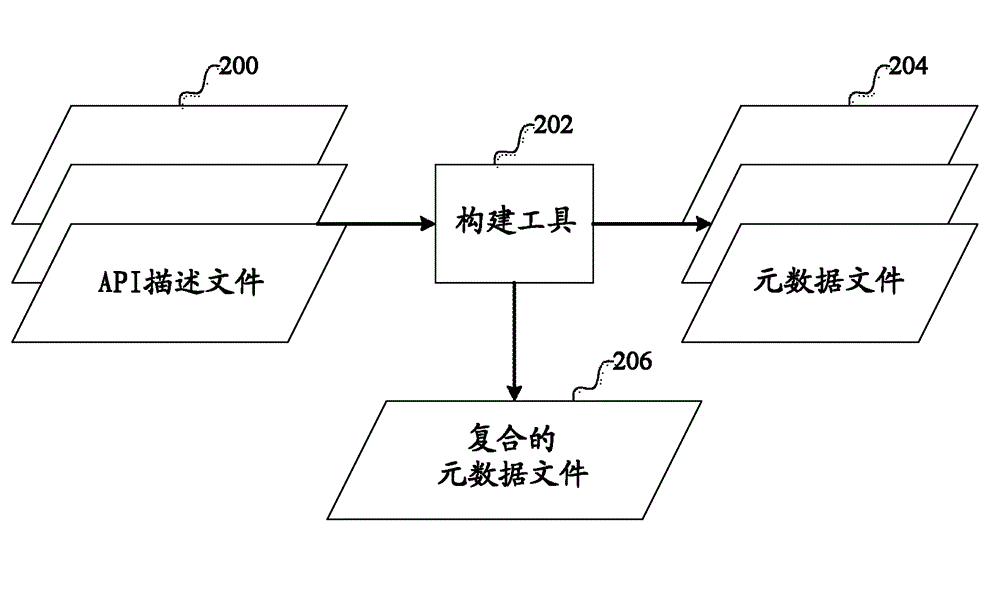
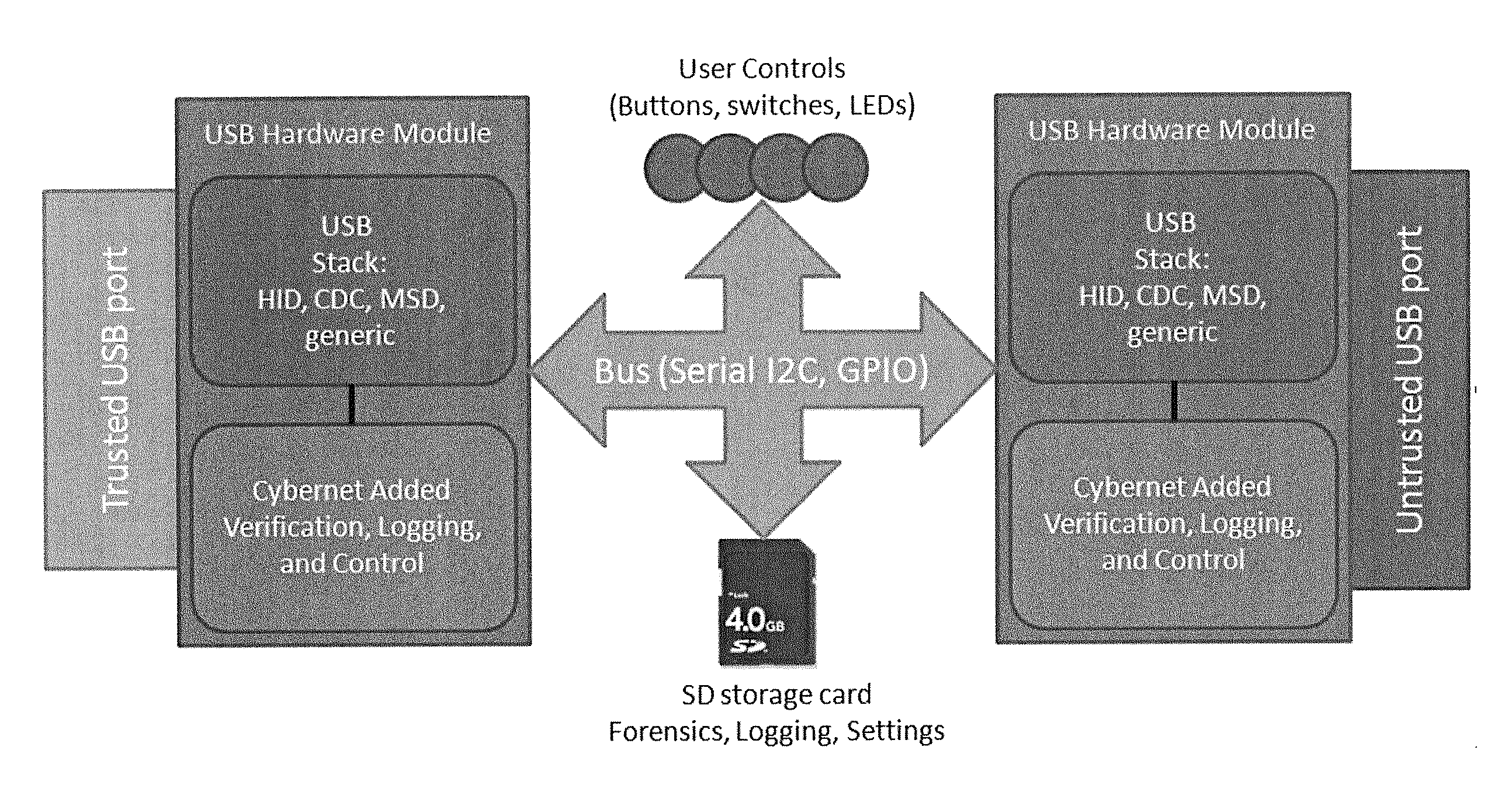Patents
Literature
80 results about "Enumerated type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, an enumerated type (also called enumeration, enum, or factor in the R programming language, and a categorical variable in statistics) is a data type consisting of a set of named values called elements, members, enumeral, or enumerators of the type. The enumerator names are usually identifiers that behave as constants in the language. An enumerated type can be seen as a degenerate tagged union of unit type.
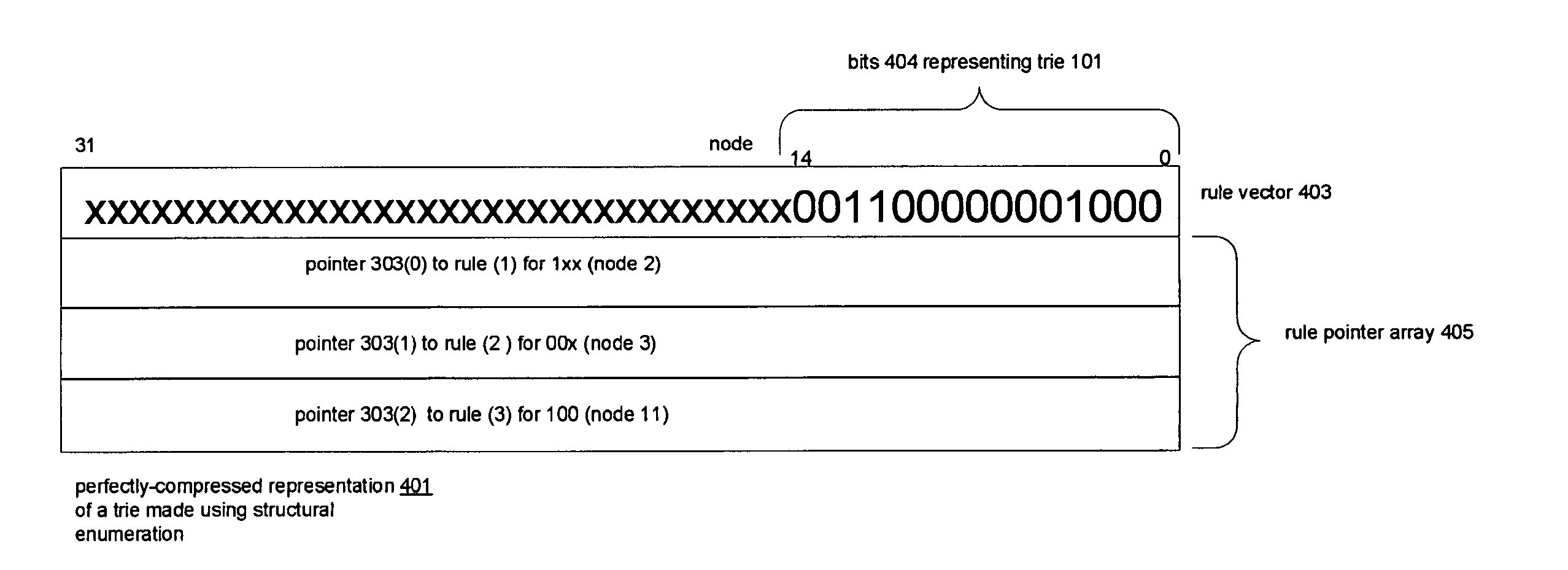
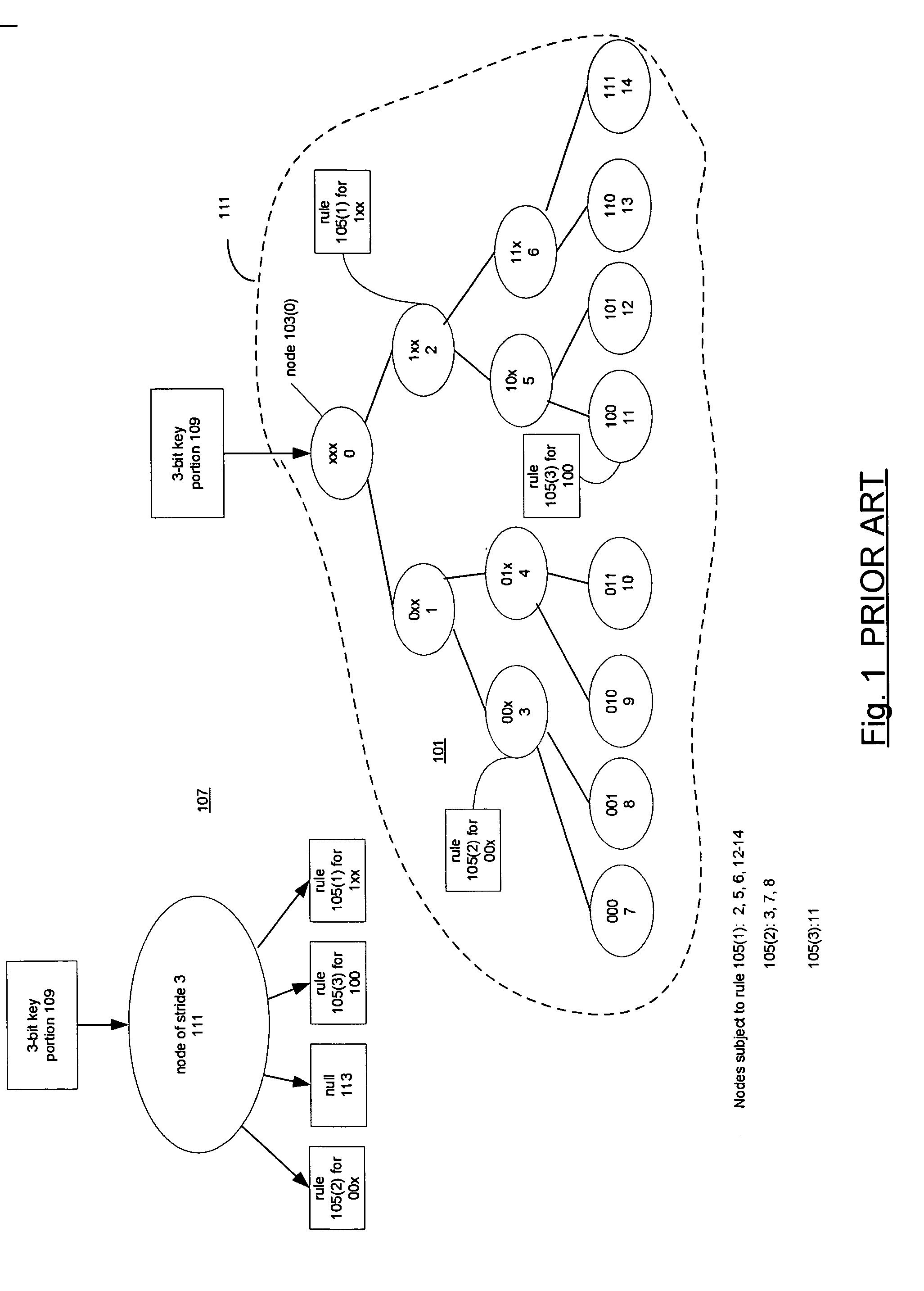
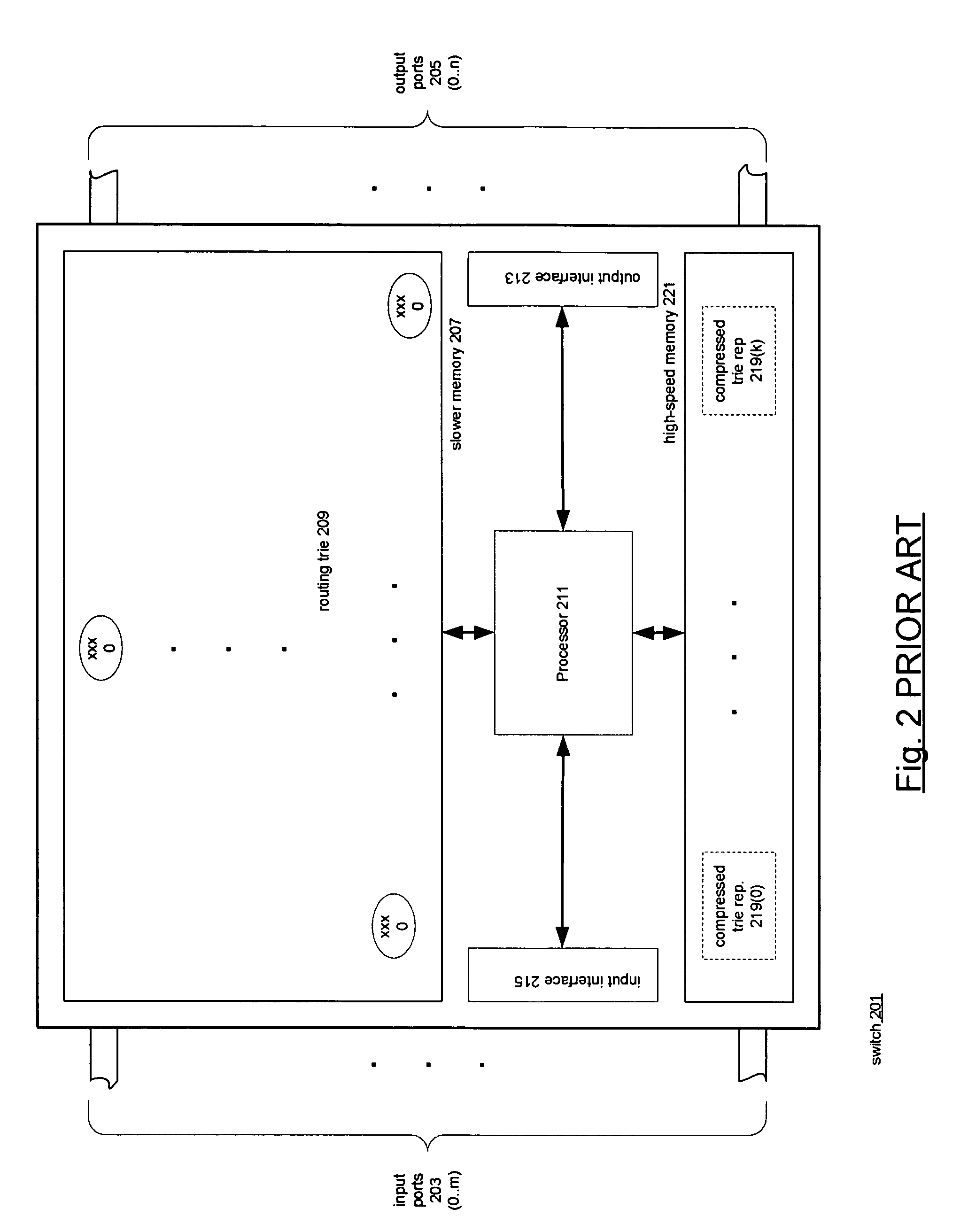
Compressed representations of tries
InactiveUS20060288024A1Digital data processing detailsTransmissionArray data structureTheoretical computer science
Techniques for representing nodes of tries. Associated with the nodes are keys and rules. A node of a trie having a stride n>1 is represented by a trie having a stride of 1 and the stride 1 trie is represented by a bit string termed a structural enumeration. The structural enumeration has a bit for each node of the trie of stride 1. If the node has a key and rule associated with it, the bit is set; otherwise it is not. The representation of a node of stride n>1 includes the node's structural enumeration and an array of rule pointers. The array has an entry for each rule associated with the node and the entries have the same order in the array as the set bits for their keys in the structural enumeration. Nodes having large strides may be represented by subdividing them into subtries.
Owner:FREESCALE SEMICON INC
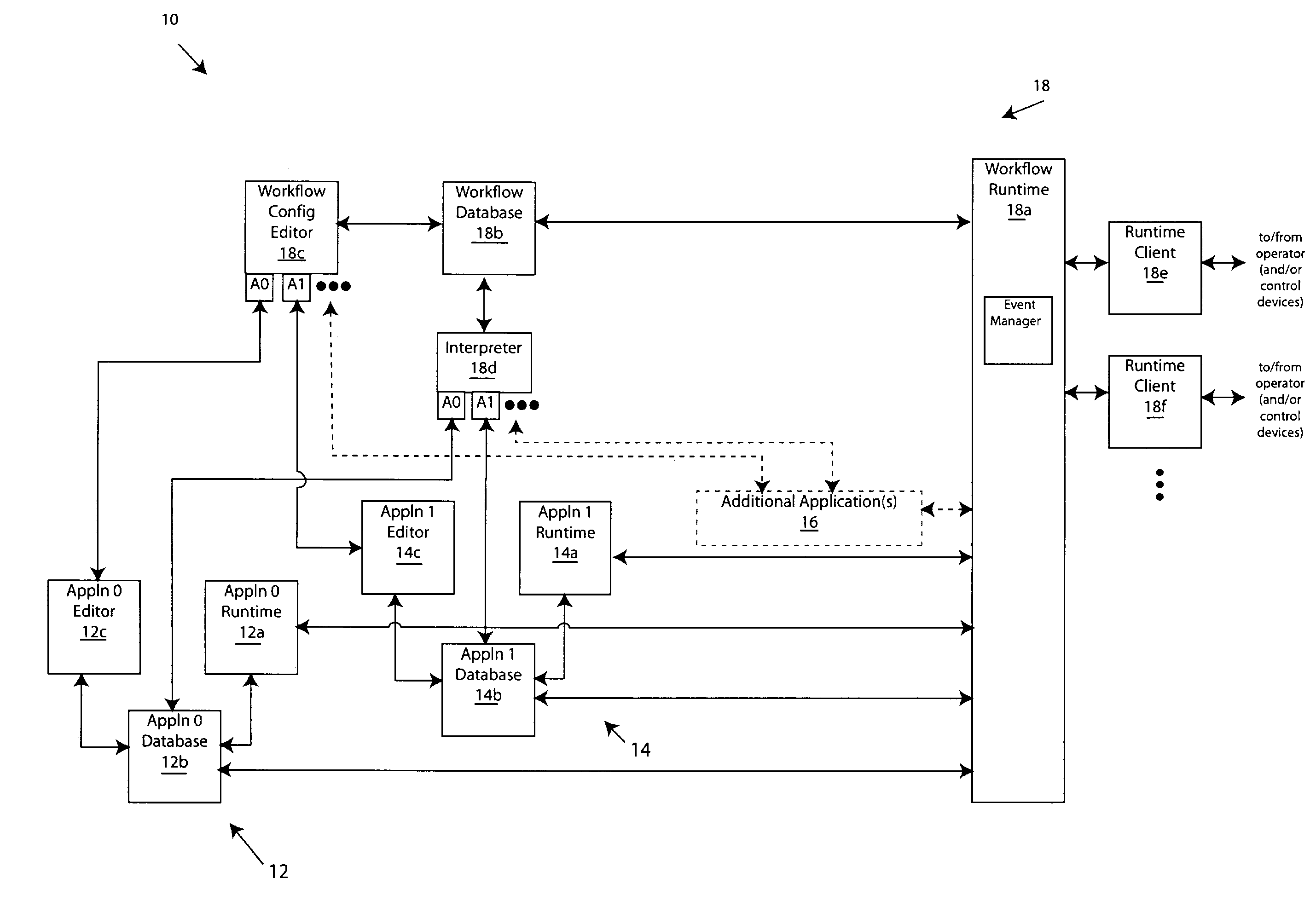
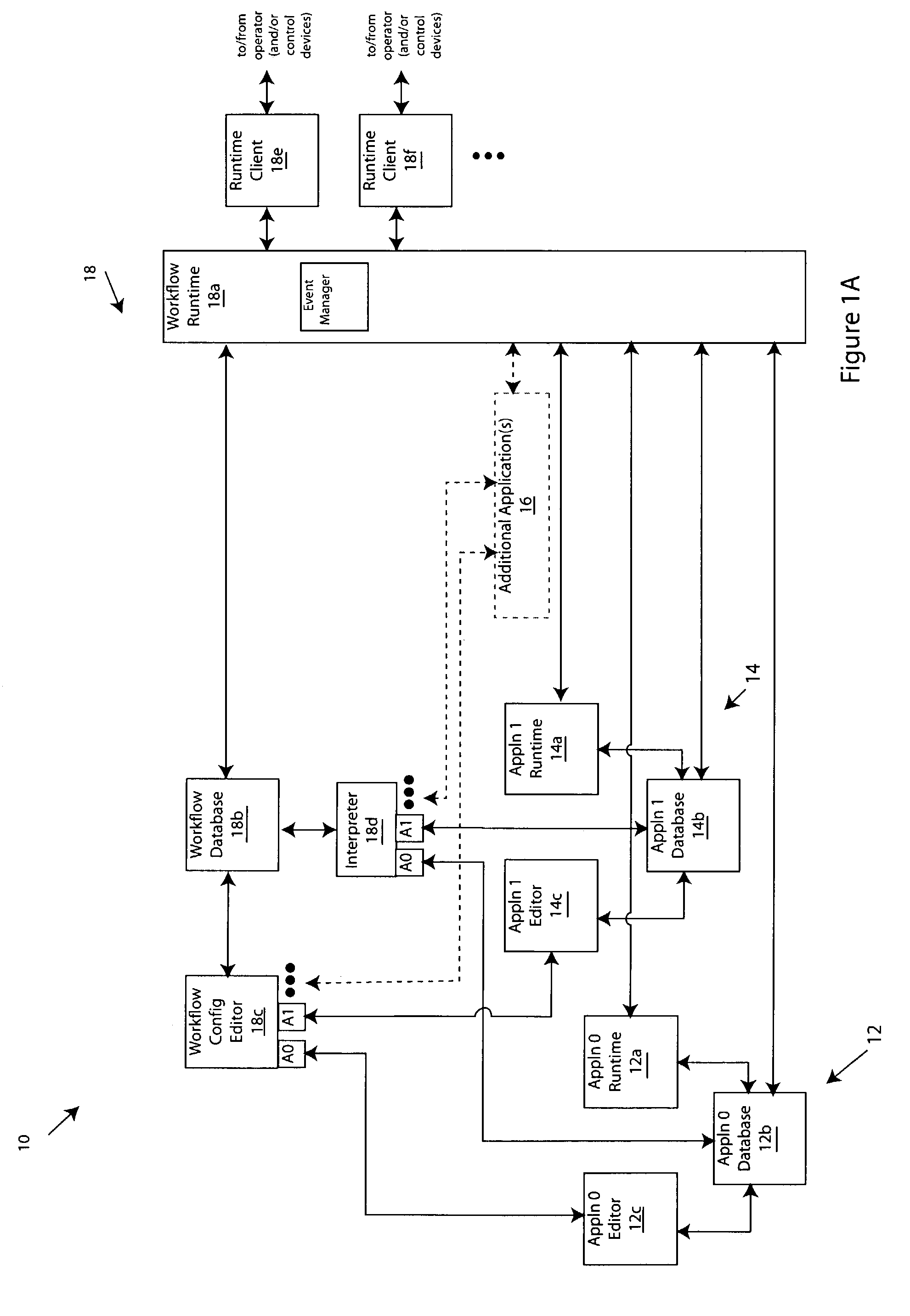
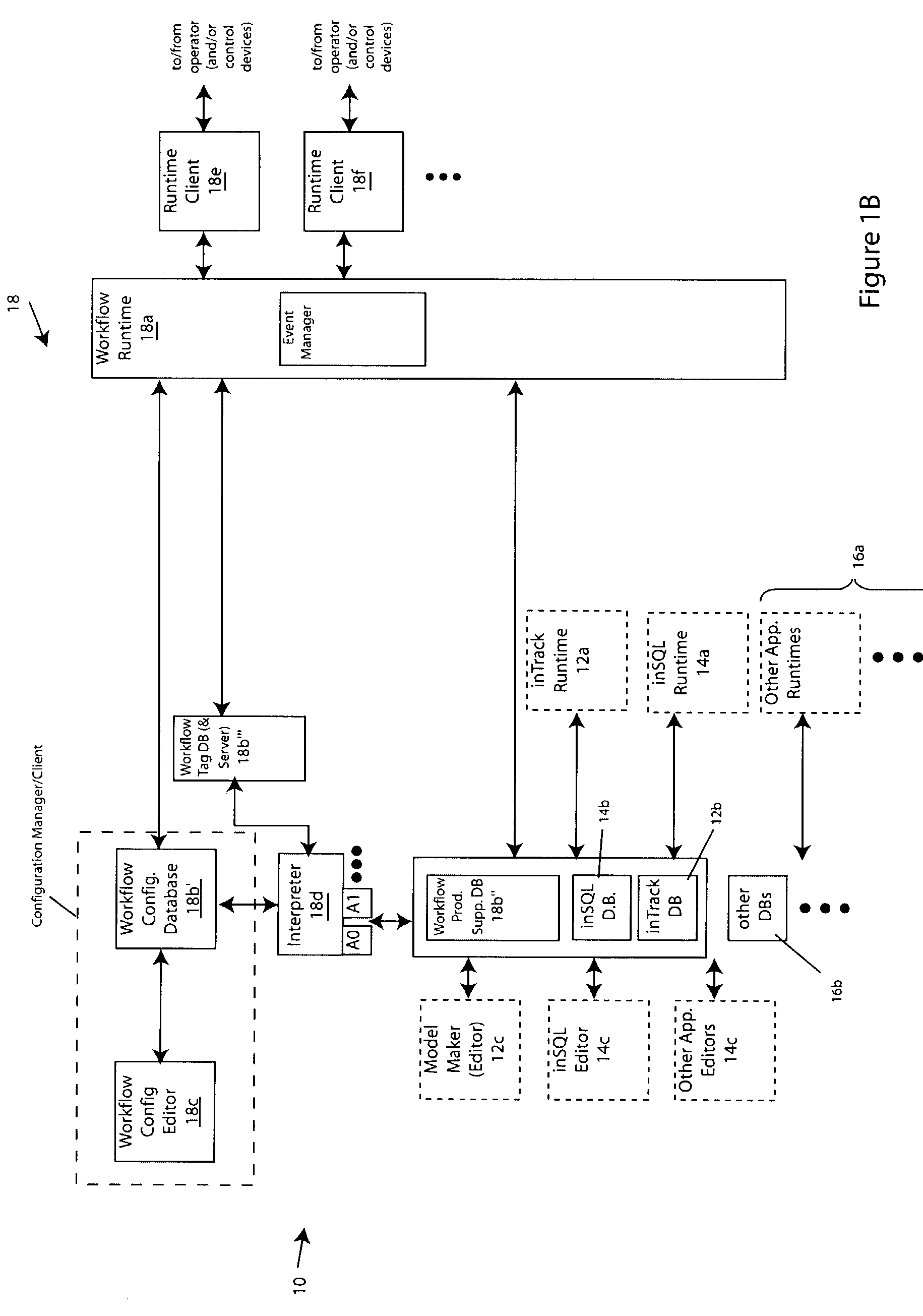
Workflow control configurator for use with process, factory-floor, environmental, computer aided manufacturing-based or other control system
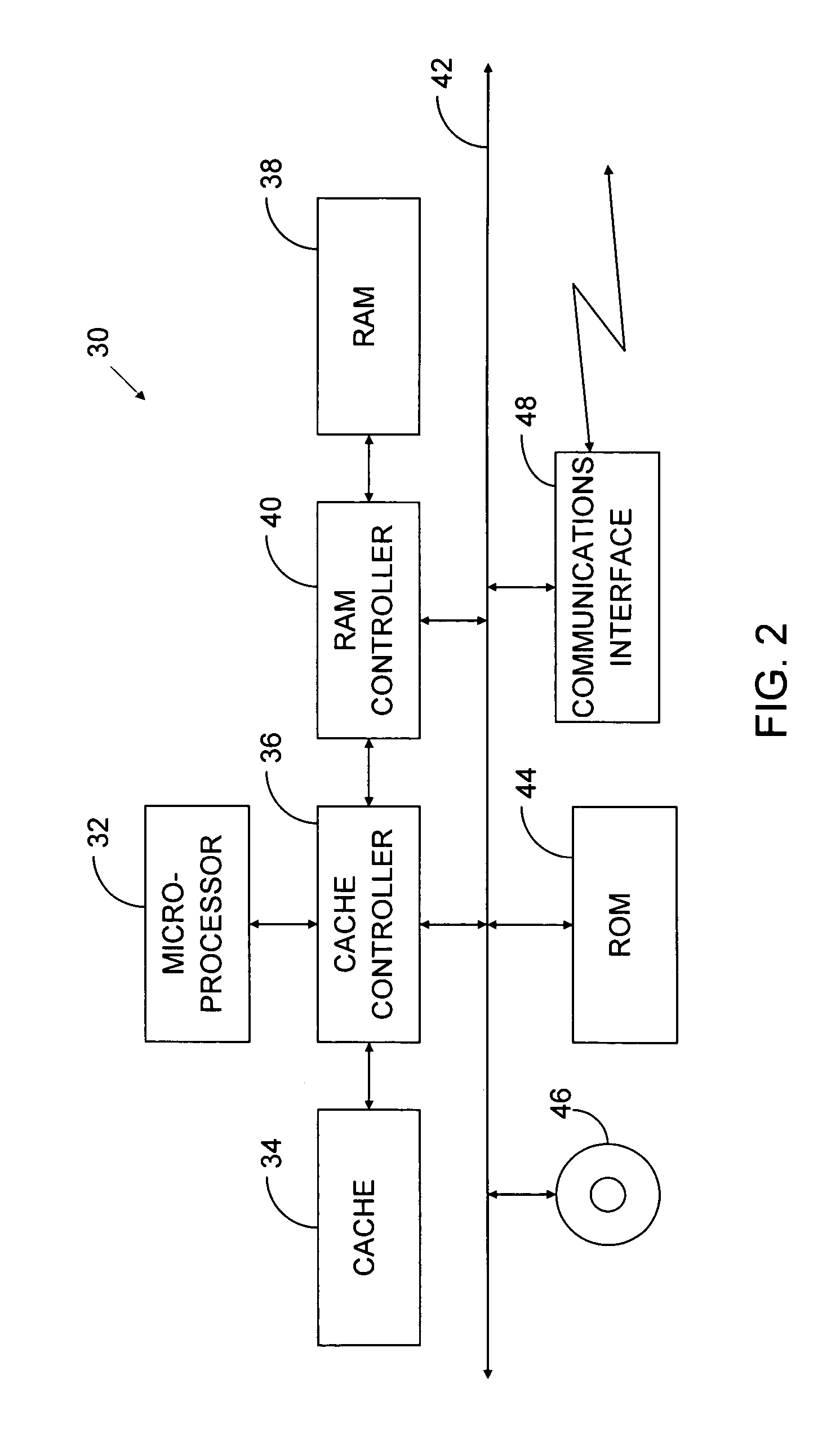
ActiveUS7242991B2Enhancement in definitionFacilitate communicationComputer controlDigital data processing detailsMessage deliveryControl system
The invention provides improved methods and apparatus for workflow editing. Such methods and apparatus permit, for example, user-defined and / or other tasks to be combined in any combination or combinations to specify a workflow. The tasks can be linked for direct, serial processing and / or for conditional processing that includes branching and / or looping. The invention also improved methods and apparatus of workflow definition and processing with extensible actions. The invention provides, further, improved methods and apparatus for workflow definition and processing which utilize workflow variables for communication of data and control information among tasks within a workflow. The invention provides, still further, improved methods and apparatus of workflow definition and processing with enhanced messaging. The invention provides, still yet further, improved methods and apparatus for workflow definition and processing which permit definition of hierarchically enumerated data types and for for definition of “plans” to collect, e.g., for storage, data such as the aforementioned hierarchical data types.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
Fast, practically optimal entropy coding
InactiveUS7161507B2Reduce computing costSacrifice little in compression ratioCode conversionAlgorithmAdditional values
Owner:1STWORKS CORP
System, method, and computer-readable medium for multilevel shaping for wireless communication systems
InactiveUS20080273614A1Error prevention/detection by using return channelDigital data processing detailsCommunications systemSignal-to-noise ratio (imaging)
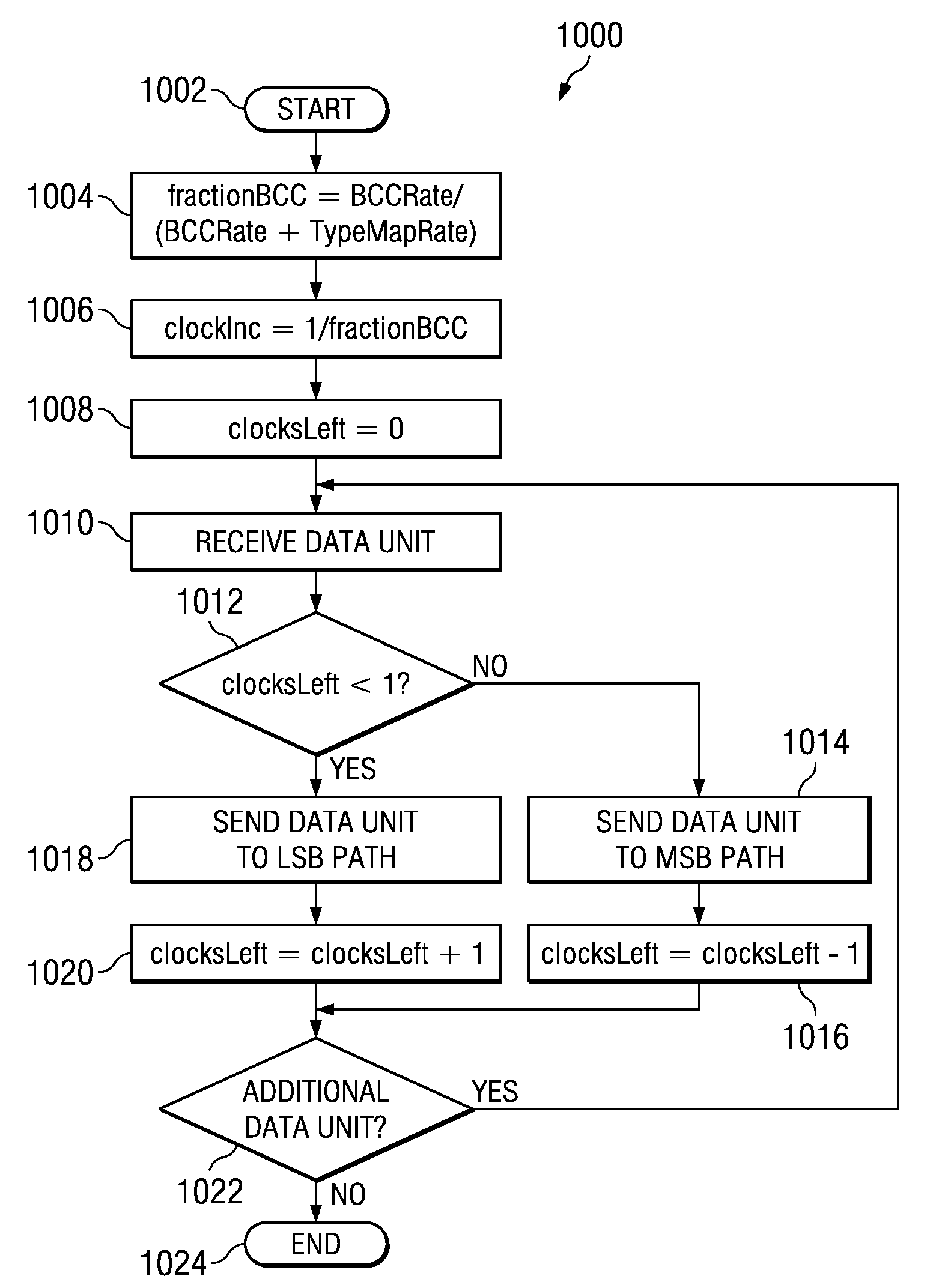
A system, method and computer-readable medium for encoding and decoding digital information over a channel is provided. Type Mapping is employed and is based on the partitioning of vectors over an alphabet into “types” and using enumeration for the encoding and decoding process. Type mapping allows for signal alphabets of arbitrary size and date rate flexible coding. Tradeoffs between optimal rate versus Signal to Noise Ratio are provided and works as a compliment to the Forward Error Control that may be employed in communications products.
Owner:WIQUEST COMMUNICATIONS +1
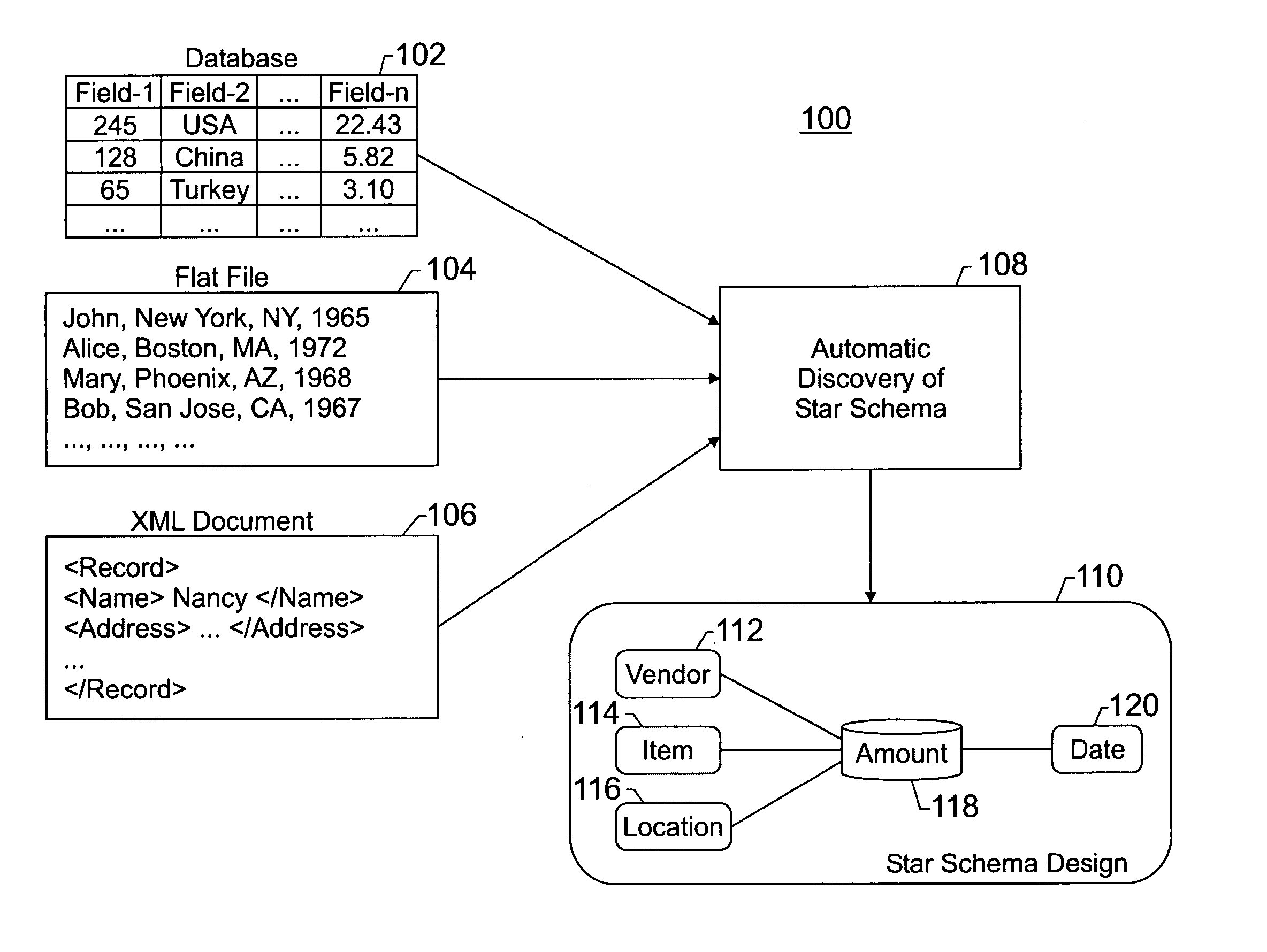
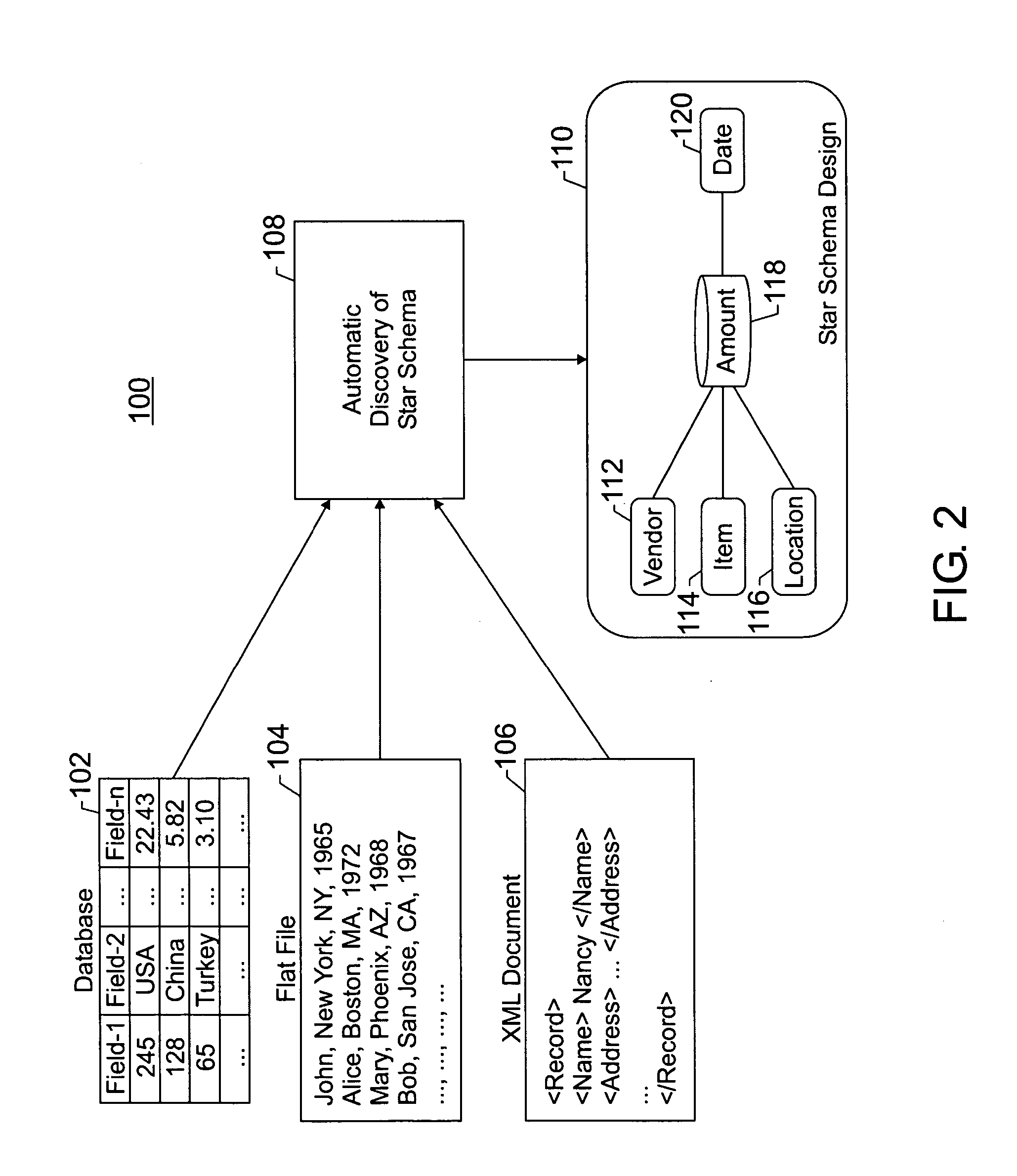
System and method for developing a star schema
ActiveUS20060036637A1Simple wayDigital data processing detailsMulti-dimensional databasesStar schemaData field
Disclosed embodiments of the present invention relate to a system and method for automatic generation of a star schema. The system and method may comprise categorizing a data field into one of a plurality of data field types, one of the data field types being an enumeration type data field. The system and method may further comprise developing dimensions for a table that represents an initial star schema design using the categorization of the data, detecting functional dependencies between the data field and other data fields, and refining the initial star schema design by modifying the table based on detected functional dependencies.
Owner:MICRO FOCUS LLC
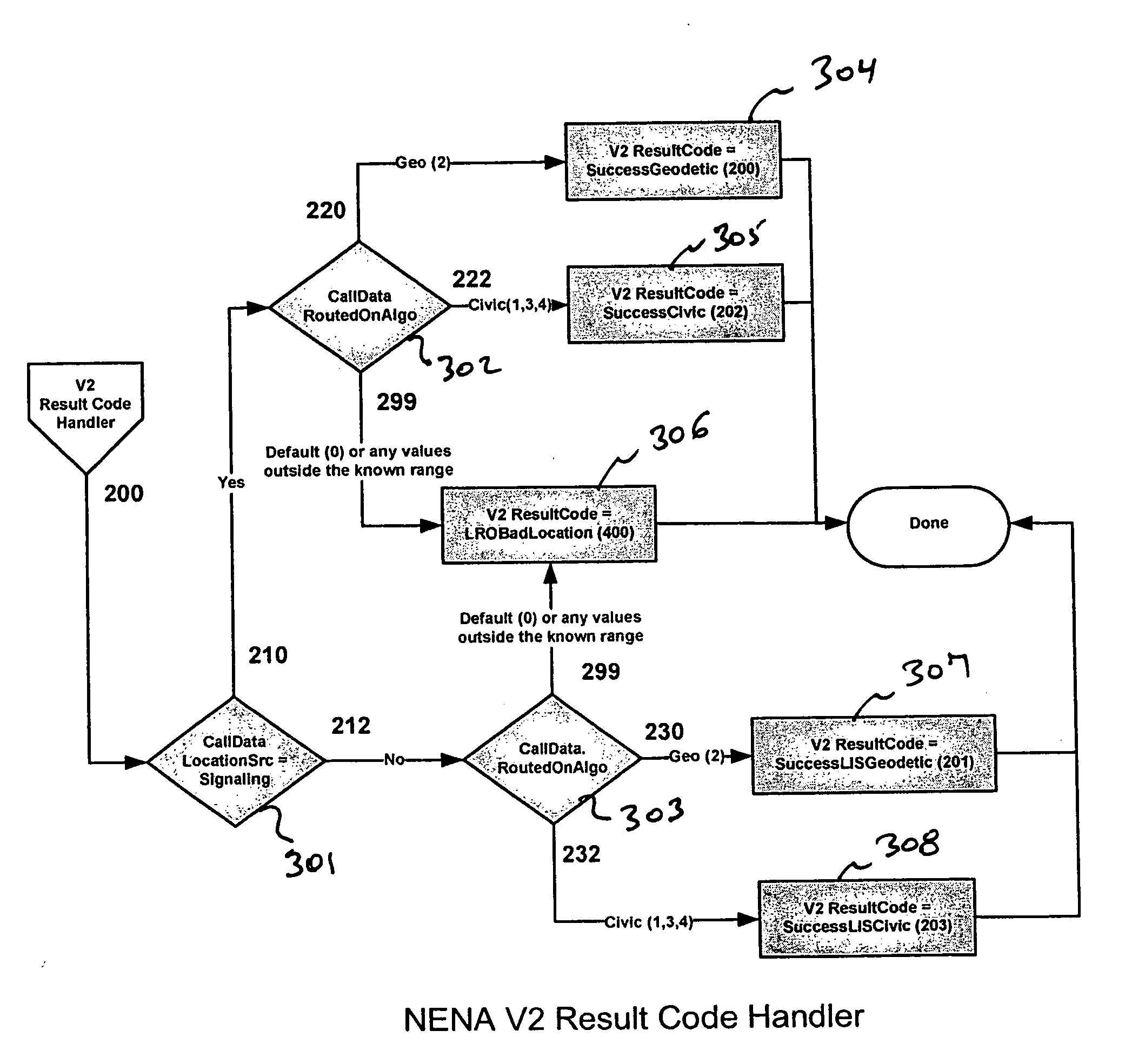
Tracking results of a v2 query in voice over internet (VoIP) emergency call systems
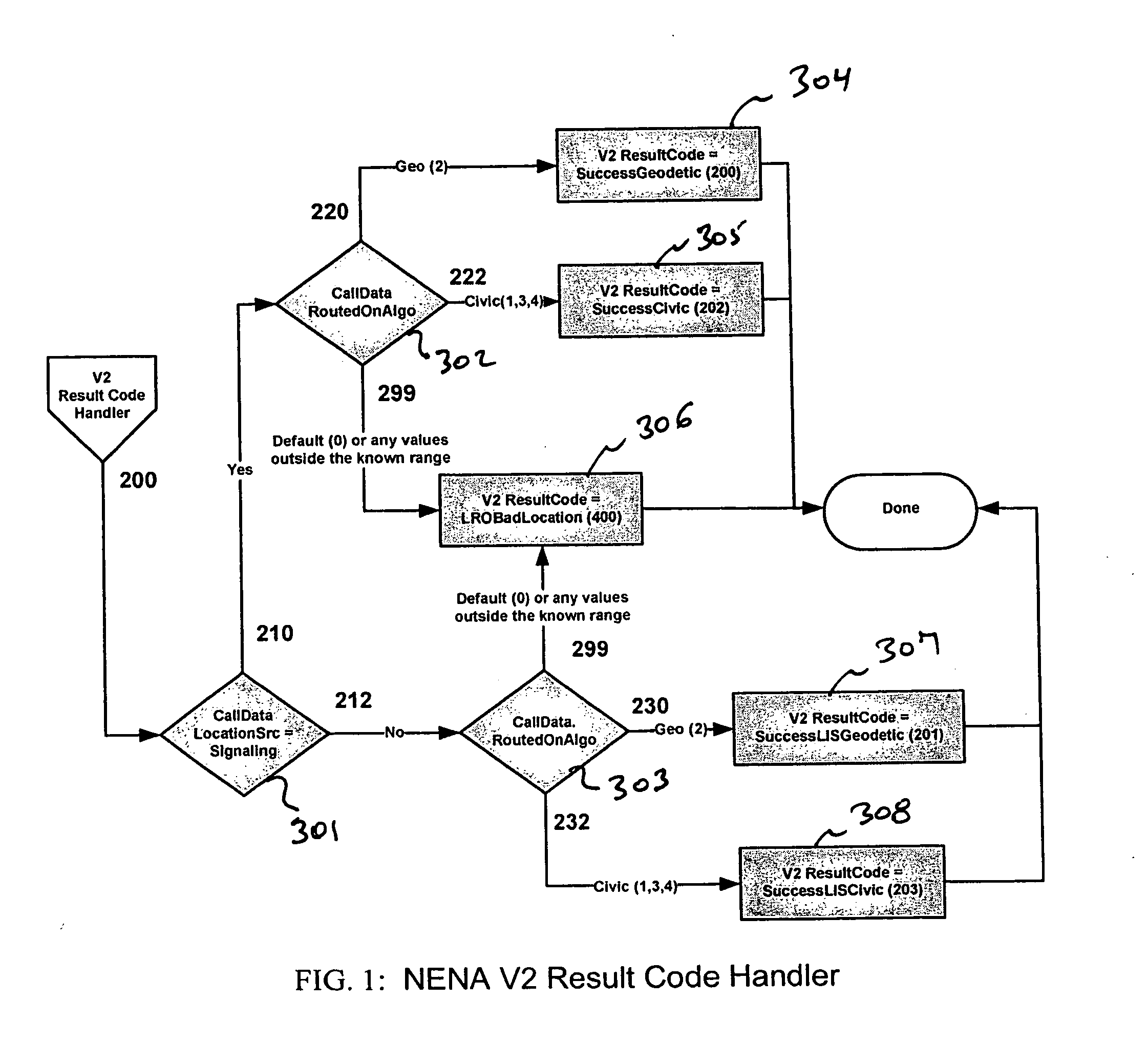
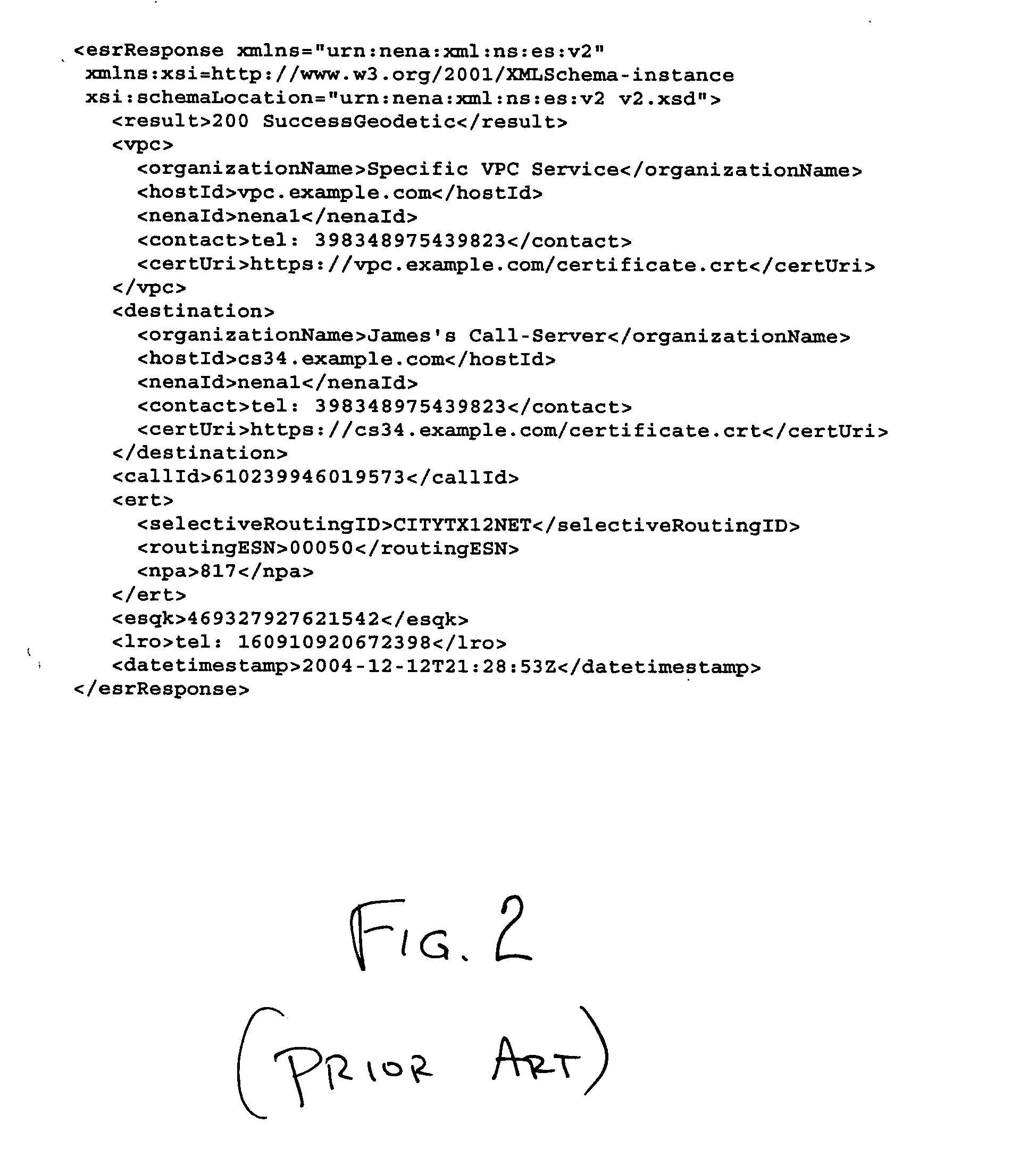
A simplified method of encoding information needed to set the NENA 08-001 v2 Result code based on two essential factors that are stored in a data store at runtime. An ESRResponse header is built with two fields created as simple enumerated types: LocationSrc and RoutedOnAlgo. For each emergency call there is one entry in this data store. The first field of the ESRResponse header comprises one of five possible unique values, as does the second field.
Owner:TELECOMM SYST INC
USB firewall apparatus and method
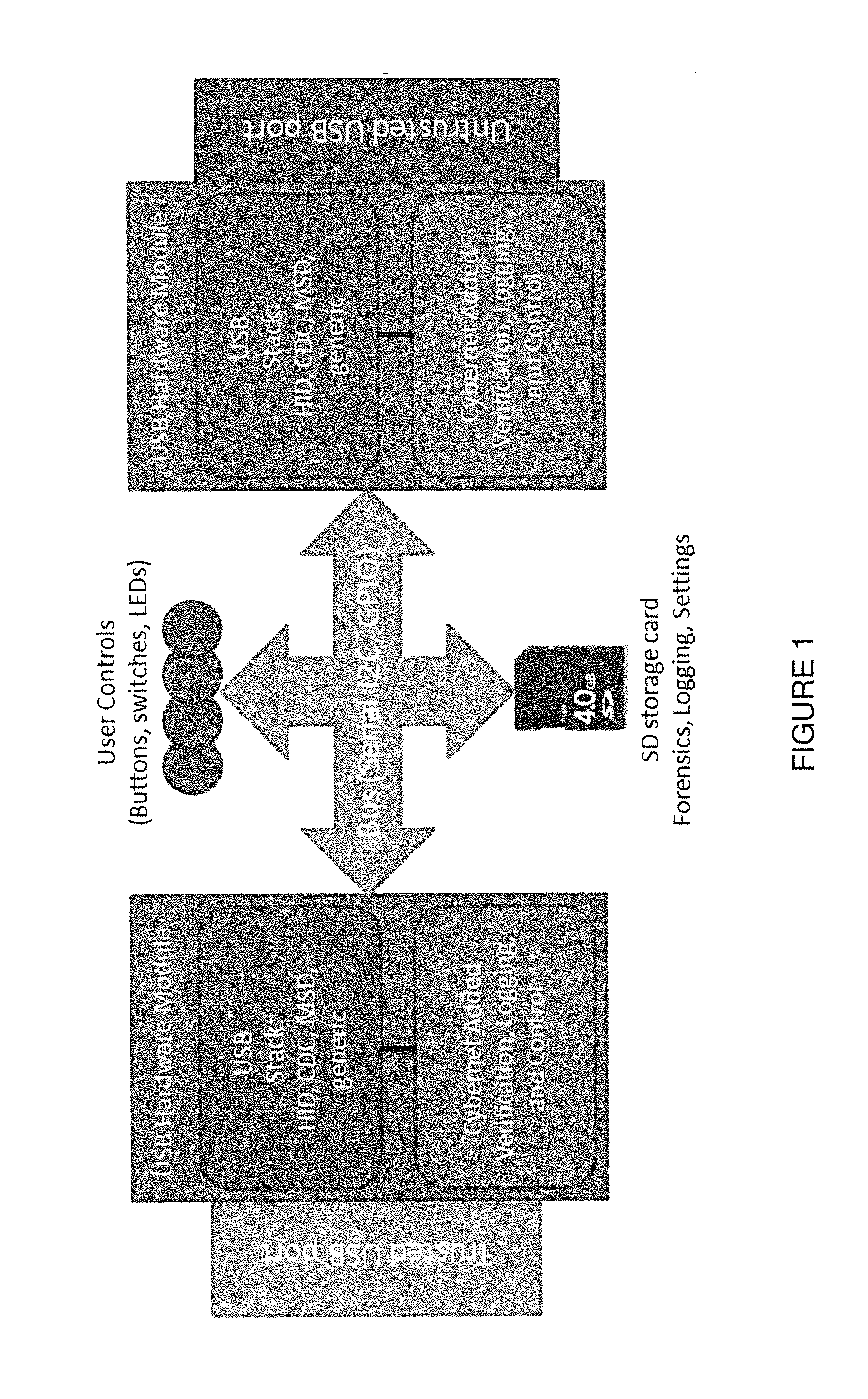
Apparatus and methods prevent malicious data in Universal Serial Bus (USB) configurations by providing a hardware firewall. A hardware device interconnected between a host and the USB monitors communication packets and blocks packets having unwanted or malicious intent. The device may act as a hub, enabling multiple devices to connect to a single host. The device may only allow mass storage packets from a device recognized as a mass storage device. The device may block enumeration of unwanted devices by not forwarding packets between the device and the host. The device may be operative to assign a bogus address to a malicious device so as not to transfer communications from the device further up the chain to the host. The device may provide shallow or deep packet inspection to determine when a trusted device is sending possible malicious data, or provide packet validation to block packets that are malformed.
Owner:CYBERNET SYST
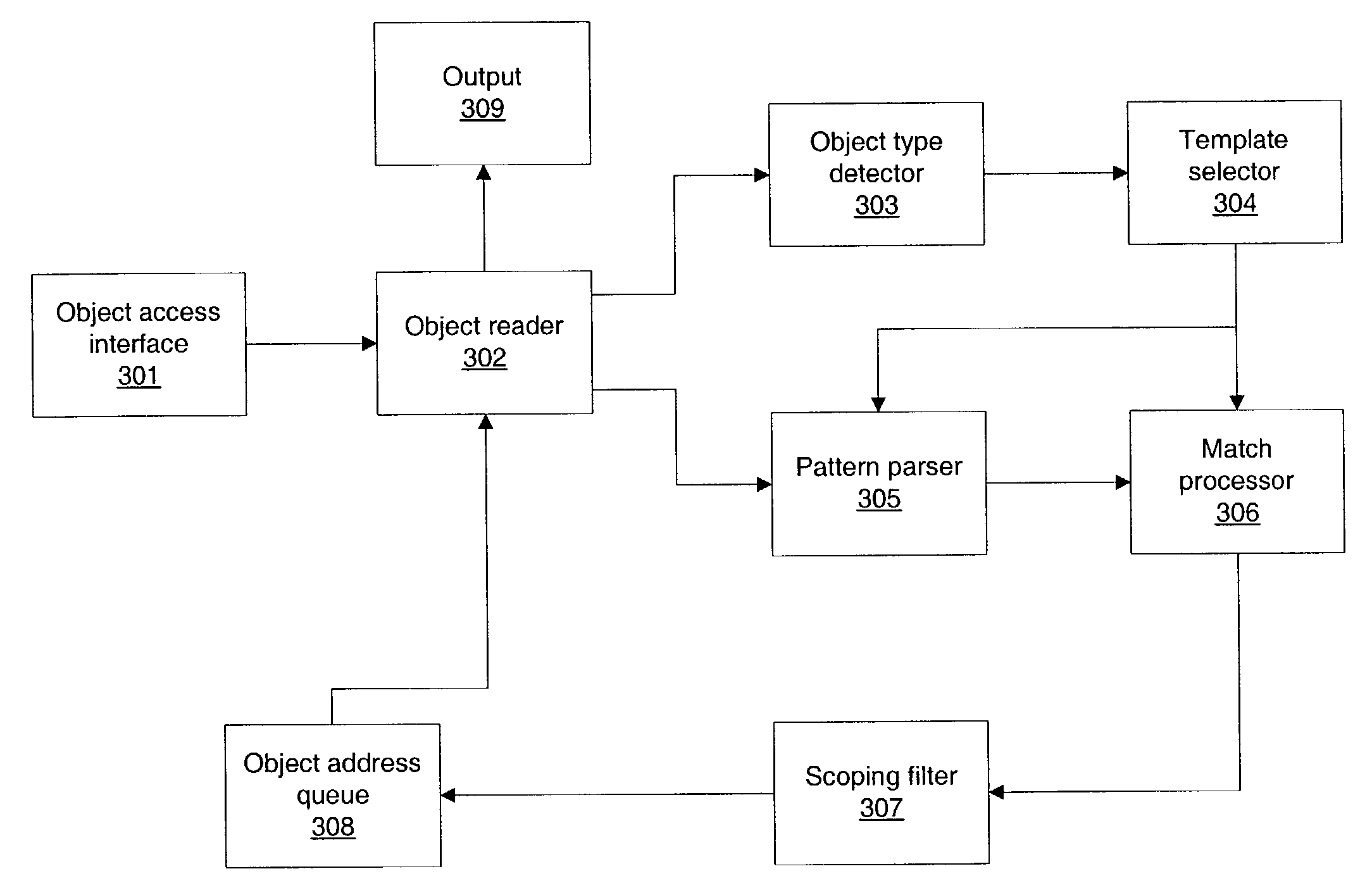
System and method for enumerating arbitrary hyperlinked structures in which links may be dynamically calculable
A system and method for dynamically enumerating the links in arbitrary hyperlinked data structures using parsing rules are provided. A hyperlinked data structure may be enumerated by reading one or more data objects through an object access interface, parsing the one or more data objects in the data structure, identifying two or more data elements in the one or more data objects, combining one or more data elements to obtain one or more hyperlink addresses, and reading the one or more hyperlink addresses to enumerate the one or more data objects. In one embodiment, hyperlinked structures such as Websites, may be enumerated using configuration templates. The templates may include heuristic parsing rules. The definition of the templates may be independent of the evolution of the data objects over time.
Owner:IORA
System and process for managing content organized in a tag-delimited template using metadata
InactiveUS8607139B2Natural language data processingWebsite content managementMetadata managementEnumerated type
A system and process for managing content organized in a tag-delimited template using metadata are described. A stored template written in a tag-delimited language is retrieved. The retrieved template is converted into an object representation of a metadata entry form. A user interface exported by the object representation is initialized. A data entry form is built including individual data entry elements responsive to user selections on the user interface of the metadata form. Each data entry element includes a set of information attributes describing the data entry element. The data entry elements of the data entry form are defined as one or more classes within the retrieved template. The data entry form is rendered by enumerating each of the one or more classes of the stored template and generating each data entry element of the one or more enumerated classes as described by the set of information attributes.
Owner:DATACLOUD TECH LLC
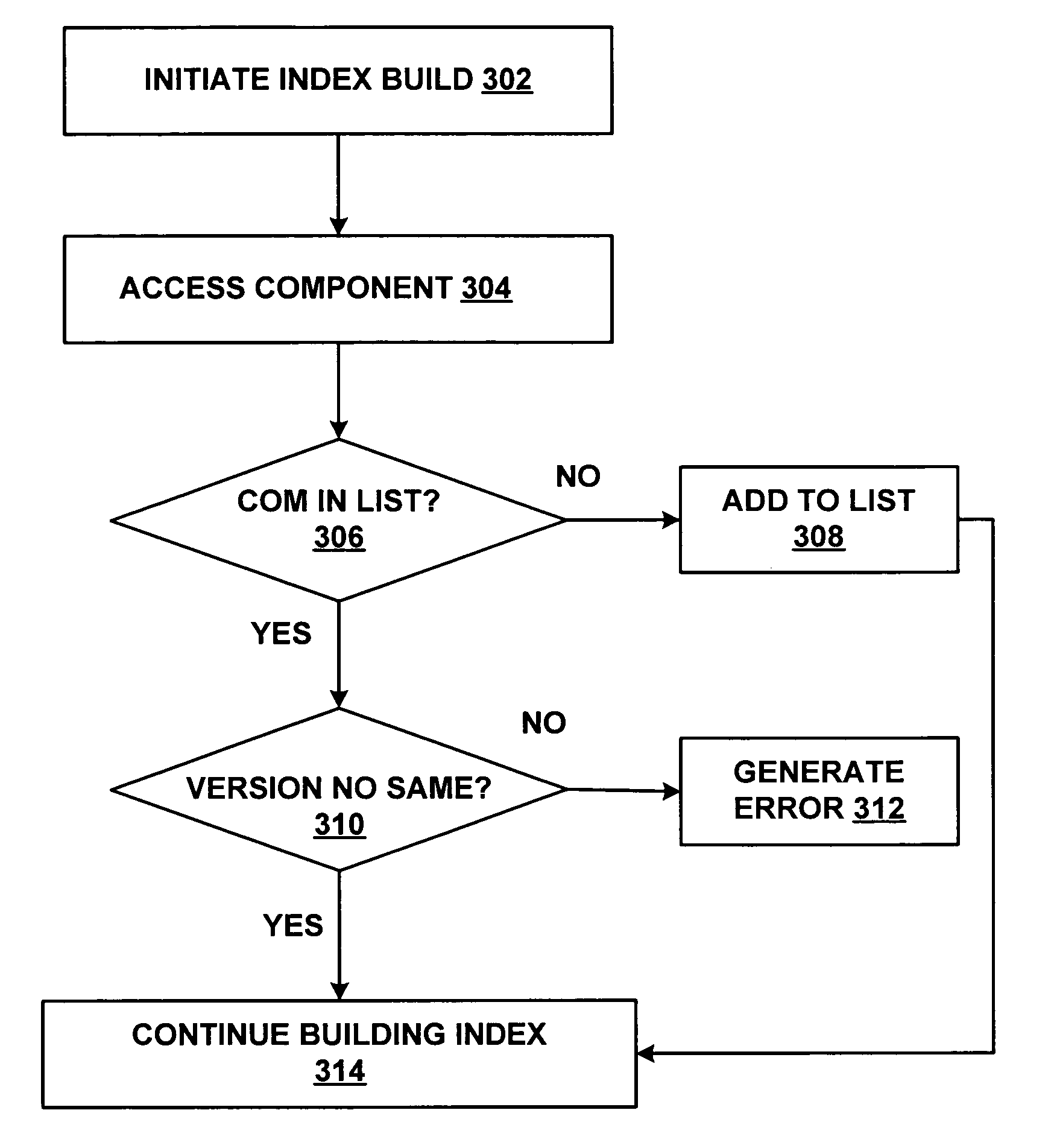
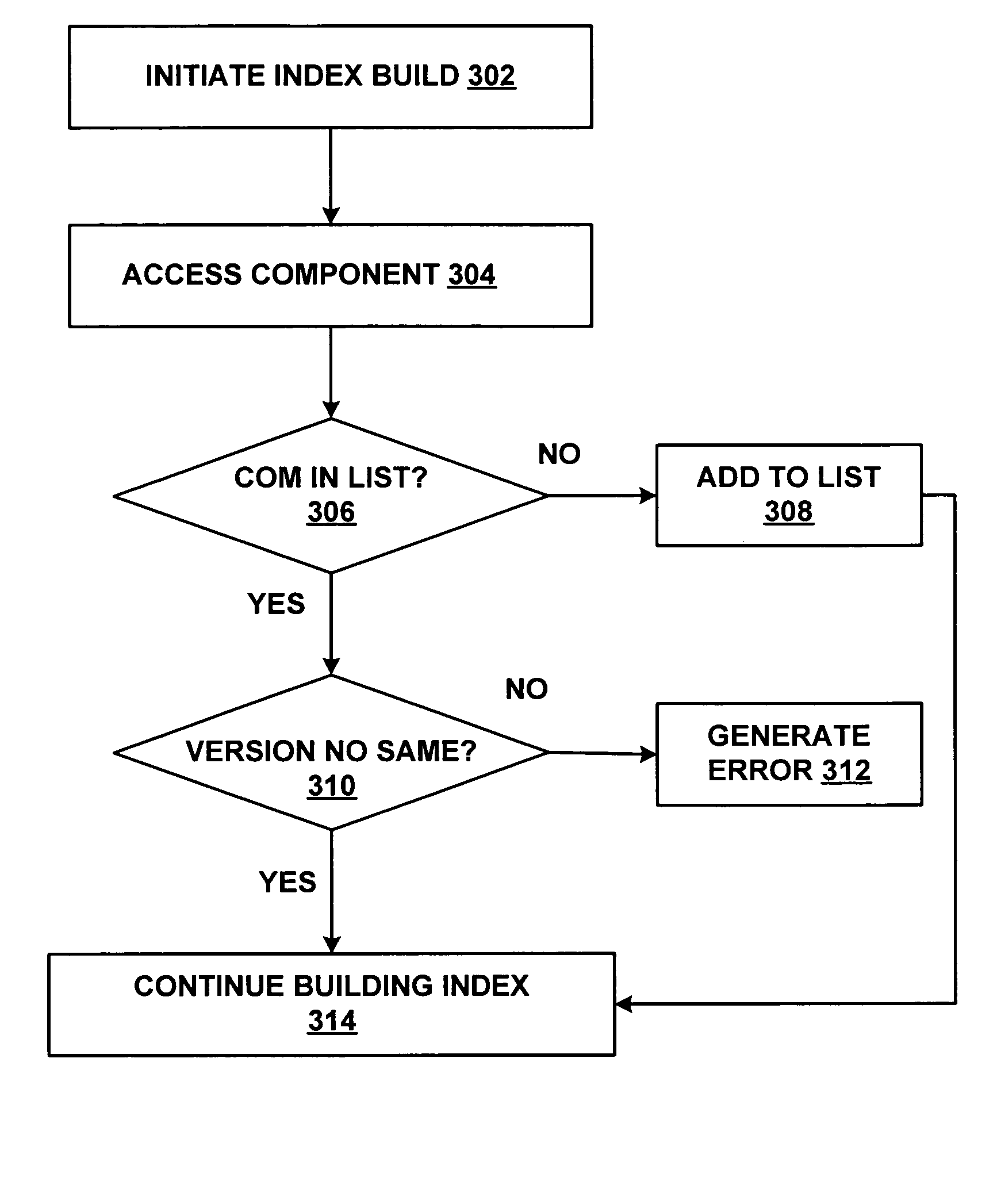
Full-text index module consistency checking
ActiveUS20050137856A1Easy to determineDigital data information retrievalNatural language data processingEnumerated typeDatabase
Consistency between the components used to generate and query a full-text index is determined and if a mismatch is detected, an error may be surfaced. A structure including information associated with each component used to build an index is programmatically compared with currently available components. The structure may be interrogated to enumerate the resources bound to a particular index. The enumeration of bound resources facilitates determination of what indexes (if any) must be regenerated for consistency as a result of a component upgrade or a move to another system.
Owner:MICROSOFT TECH LICENSING LLC
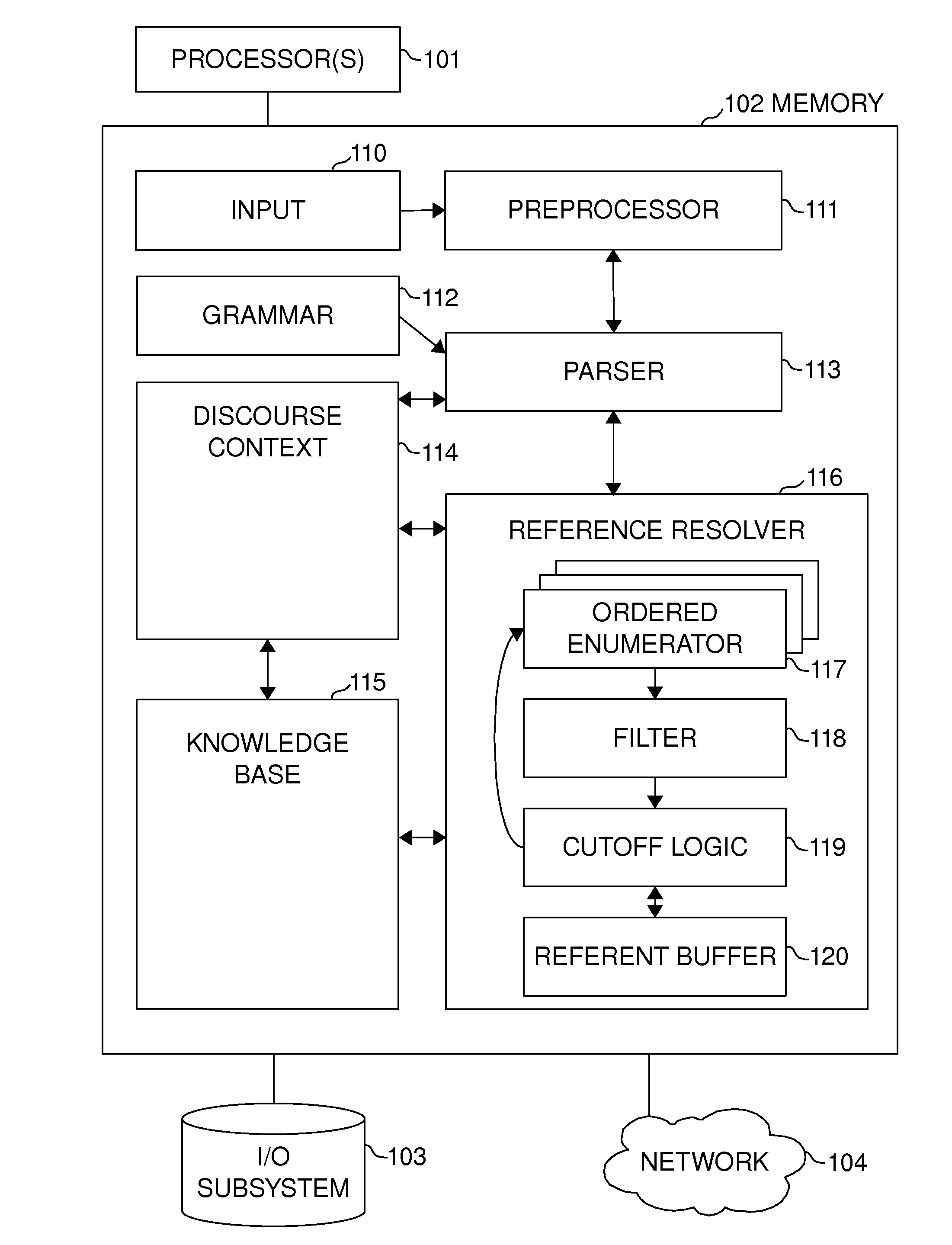
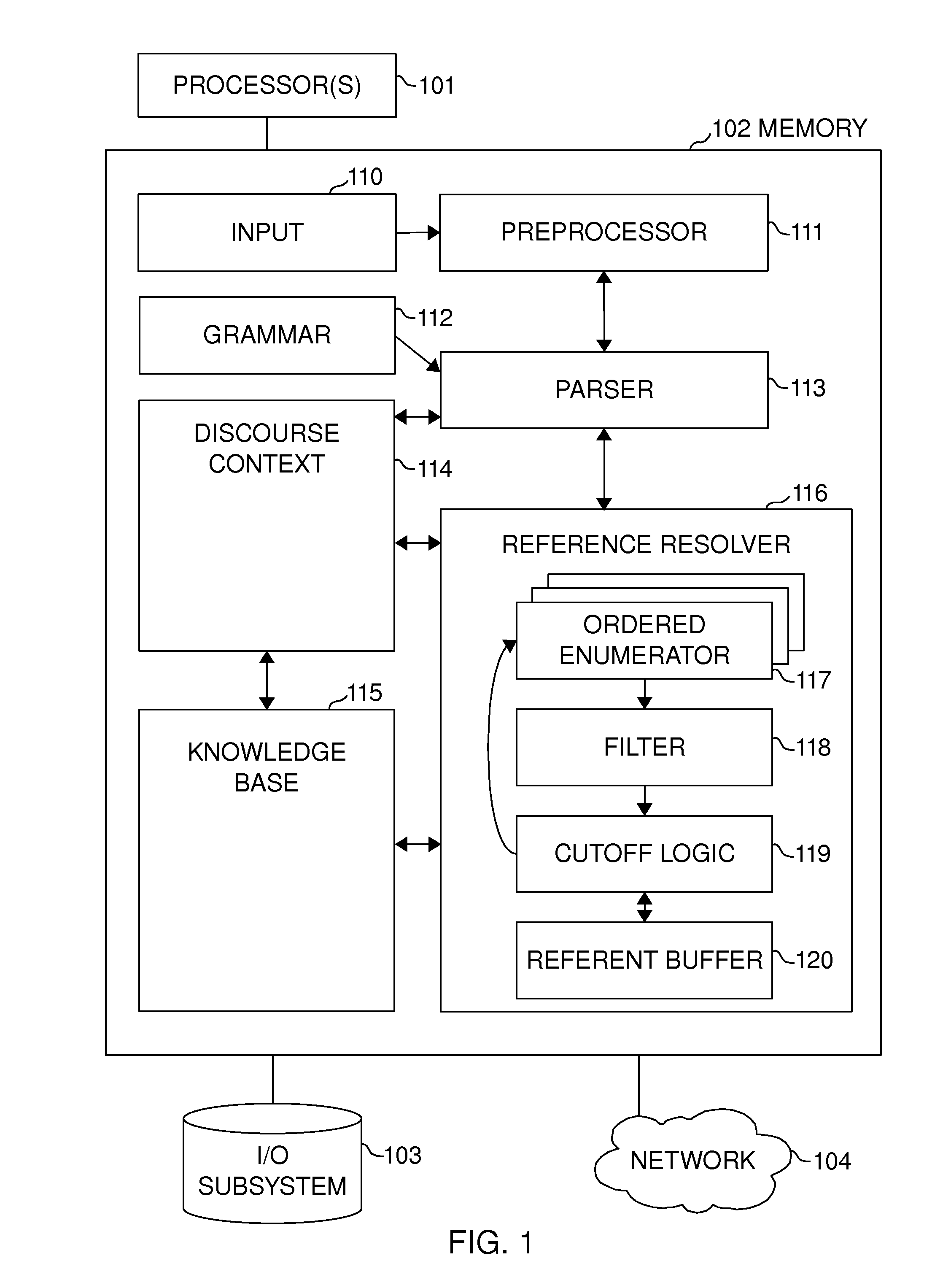
Weight-Ordered Enumeration of Referents and Cutting Off Lengthy Enumerations
InactiveUS20110131033A1Early terminationResolving referenceNatural language analysisSpecial data processing applicationsComputer scienceEnumerated type
Owner:CLAUSAL COMPUTING
Fast, practically optimal entropy coding
InactiveUS20060055569A1Small storage spaceOvercome limitationsCode conversionAlgorithmAdditional values
Owner:1STWORKS CORP
System and method for preventing race condition vulnerability
InactiveUS20080016410A1Reduce vulnerabilityMemory loss protectionError detection/correctionFile systemSystem call
A method for identifying vulnerable system call pairs is disclosed. The method is based on a model for identifying Time-Of-Check-To-Time-Of-Use (TOCTTOU) problem (called STEM), which enumerates the potential file system call pairs (called exploitable TOCTTOU pairs) that form the check / use steps. The system function calls are classified into a plurality of predefined classes and pairs of the function calls are formed according to predefined criteria, where the function calls within a pair are associated with the same file invariant.
Owner:GEORGIA TECH RES CORP
Method and device for parallel enumeration of support points based on metric space
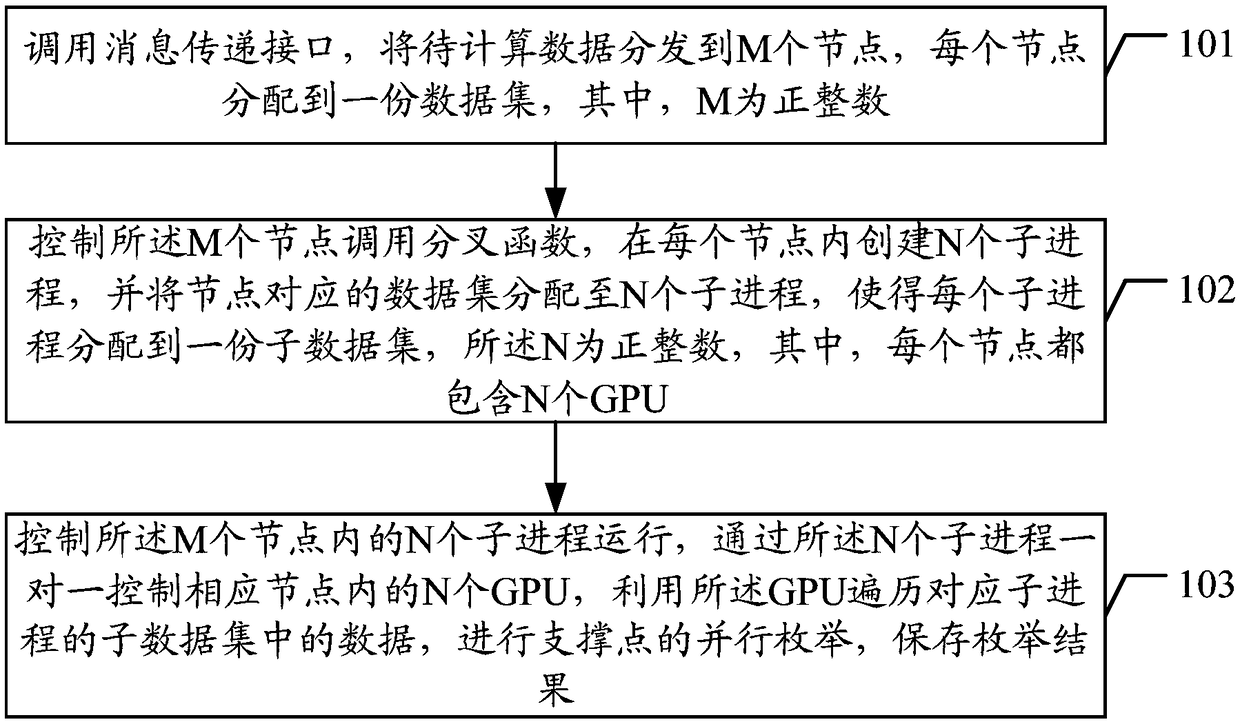
ActiveCN108804383AParallel enumeration implementationShorten the timeResource allocationComplex mathematical operationsData setMessage delivery
The invention discloses a method and a device for parallel enumeration of support points based on a metric space. The method comprises the following steps: calling a message delivery interface, distributing to-be-calculated data to M nodes, wherein each node is assigned to a data set; controlling the M nodes to respectively call a fork function, creating N child processes in each node, and assigning the data sets corresponding to the nodes to the N child processes, so that each child process is assigned to a child data set, and N is equal to the number of GPUs contained in each node; controlling the N child processes established in the M nodes to operate; controlling the N GPUs in the corresponding node one by one through the N child processes; using the GPUs to traverse the data in the sub data set corresponding to the child process; carrying out parallel enumeration of the support point and storing the enumeration result. Through the aforementioned manner, the parallel enumeration ofthe support point can be effectively realized; the time consumed by enumeration of the support point is effectively shortened; and the performance of data calculation is improved.
Owner:SHENZHEN UNIV
Method and system for implementing collection program interface for accessing a collection of data associated with a legacy enumeration application interface
InactiveUS6842905B2Quick implementationEasy to useInterprogram communicationProgram code adaptionData setJava
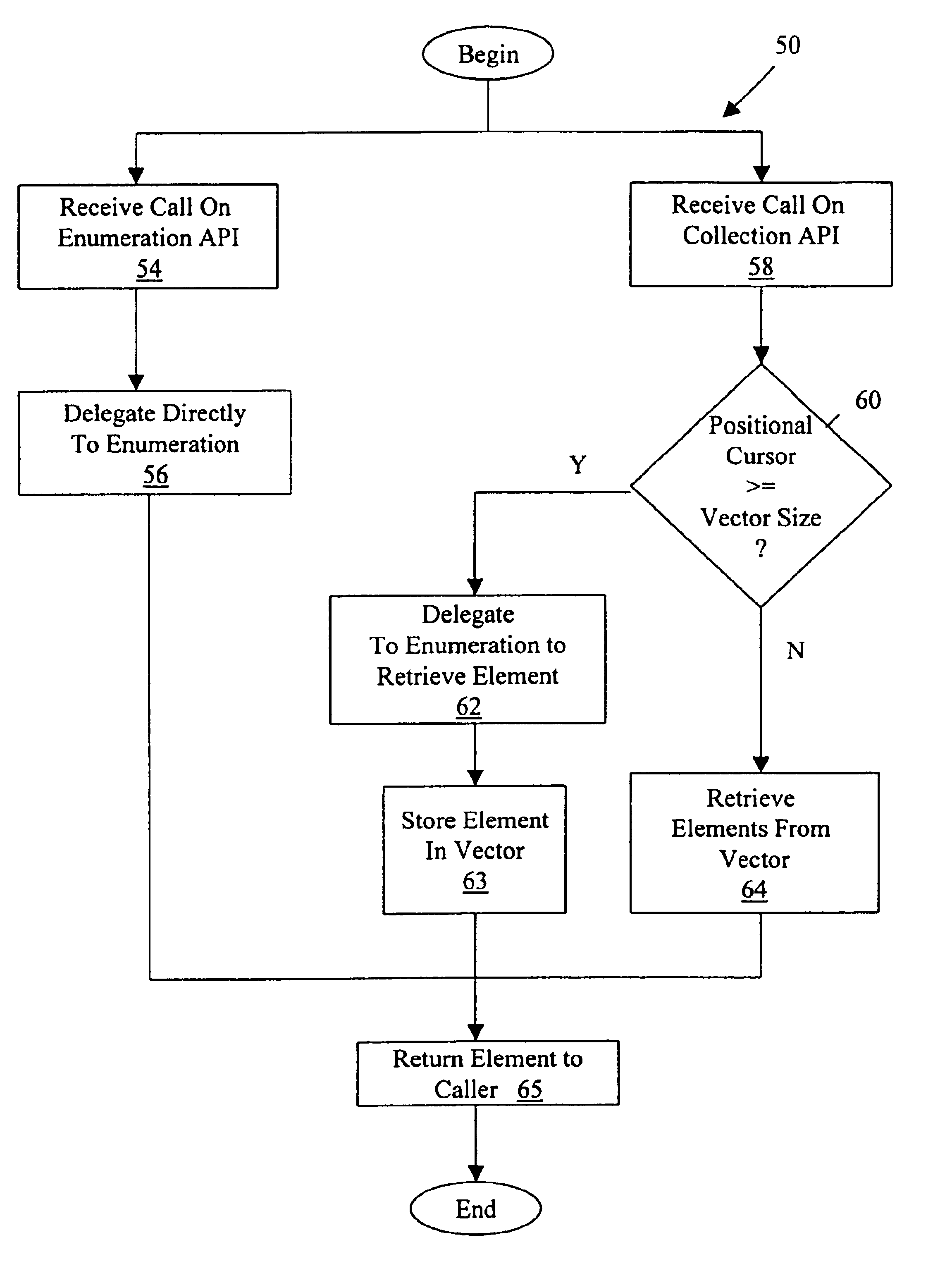
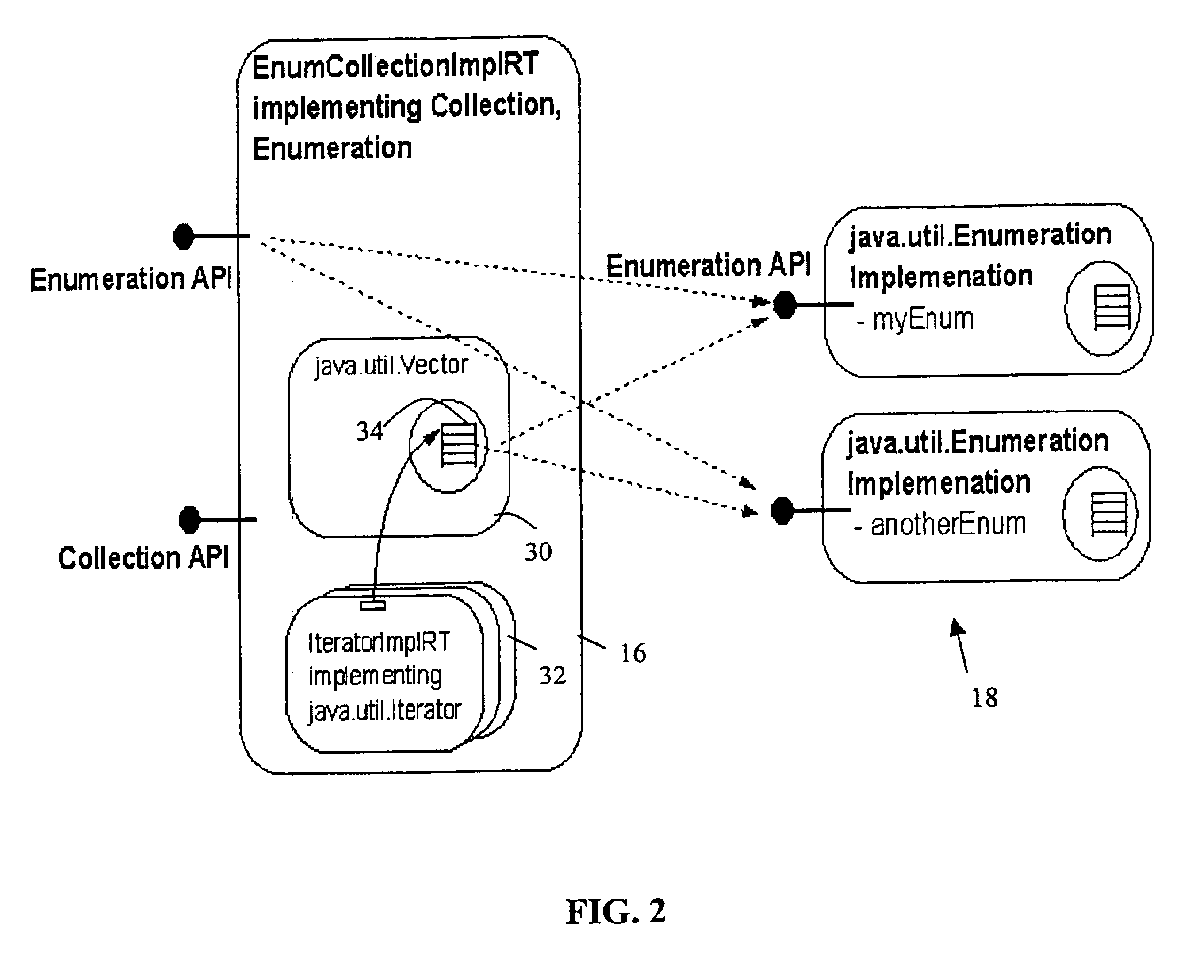
A software wrapper for interfacing to pre-existing software code is provided. The software wrapper is capable of inheriting from a first application program interface (API) and a second API. For calls to the first API, the software wrapper delegates to a pre-existing enumeration of objects. The wrapper creates a vector identifying elements of the enumeration. Iterators provided by the wrapper maintain positional cursors for calls to the second API. A comparison is made between each of the positional cursors and the vector. If a positional cursor exceeds the size of the vector, additional elements are extracted from the enumeration, placed in the vector, and returned on the second API. Otherwise, if the positional cursor is smaller than the vector size, the wrapper delegates directly to the vector. The first API can be a java-based enumeration API and the second API can be a java-based collection API.
Owner:IBM CORP
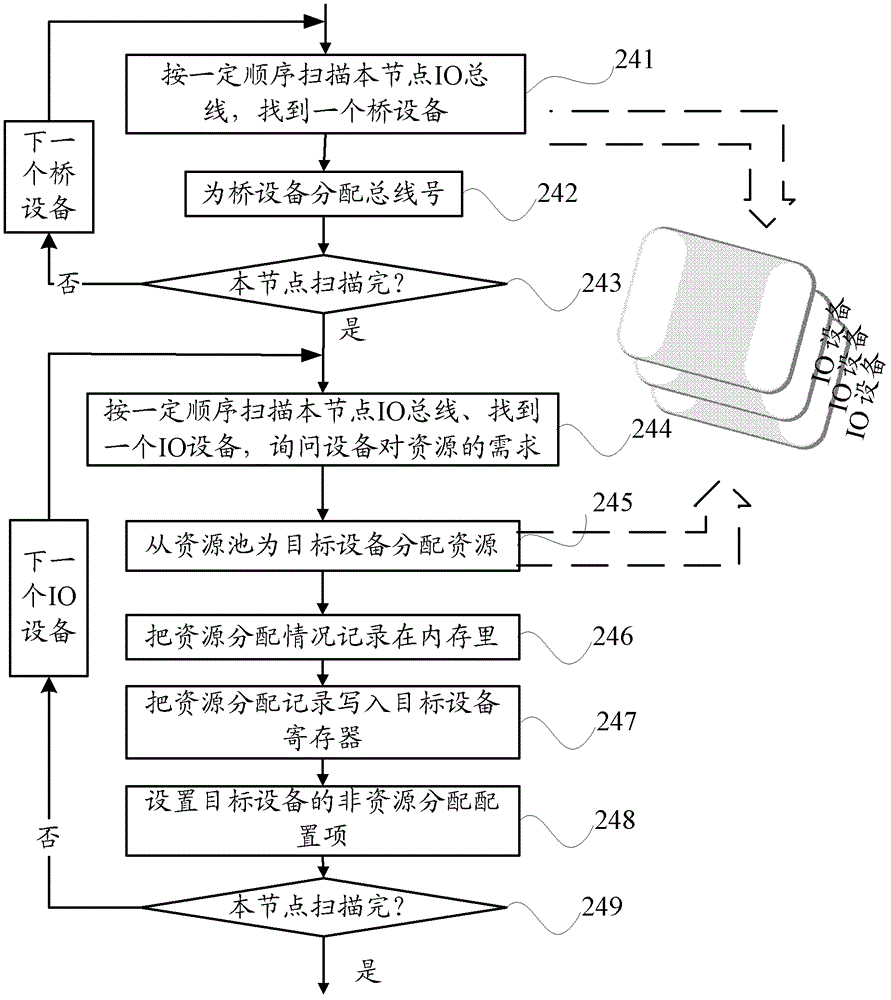
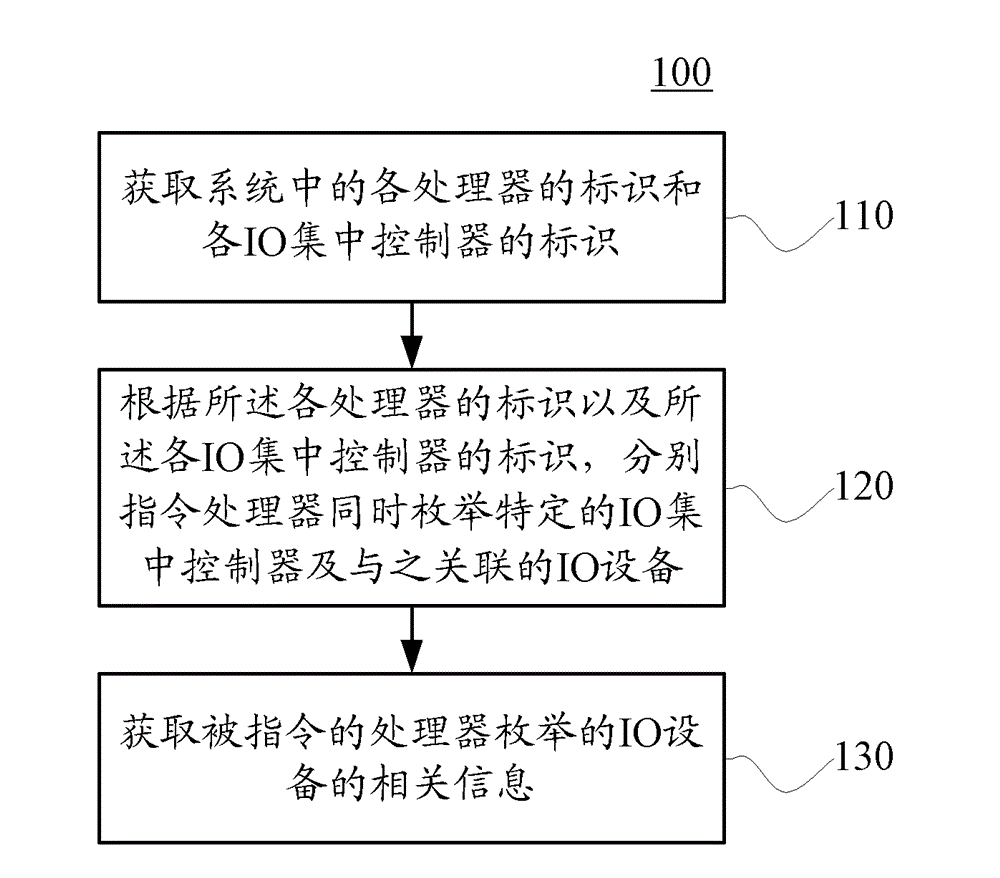
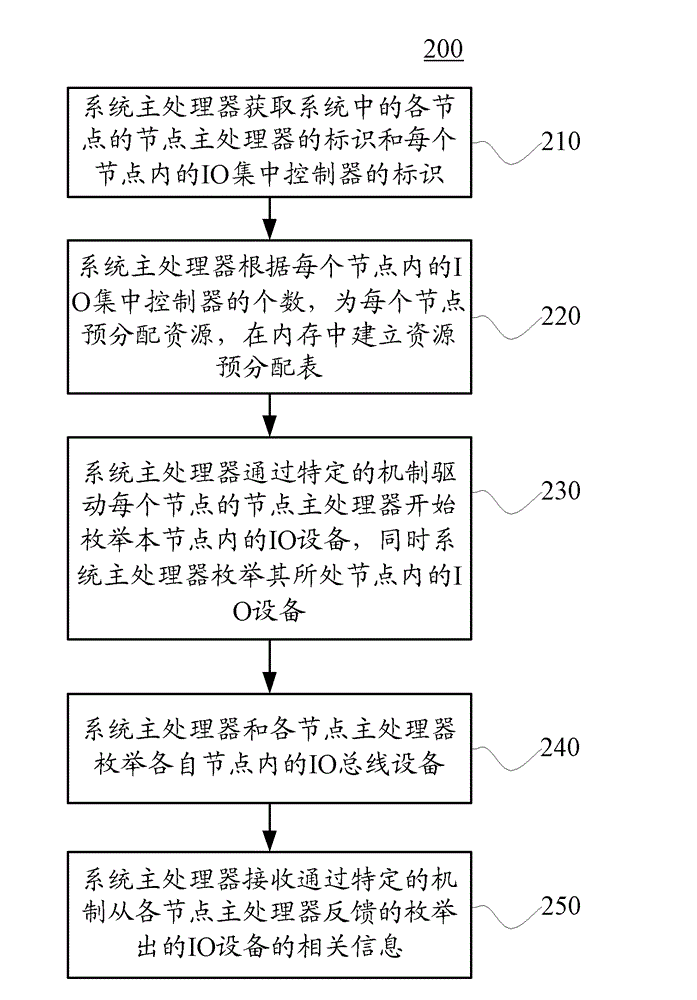
Method and device for enumerating input/output devices
ActiveCN102725749AShorten the timeSpeed up the initialization processResource allocationMultiple digital computer combinationsWork distributionRelevant information
The embodiments of the present invention relate to a method and device for enumerating Input / Output devices (IO devices). The method for enumerating input / output devices includes: obtaining the identifier of each processor and the identifier of each Input / Output (IO) hub in the system; respectively instructing each processor to simultaneously enumerate specific IO hubs and IO devices connected thereto according to the identifier of each processor and the identifier of each IO hub; and obtaining related information about the IO devices enumerated by the instructed processors. According to the embodiments of the present invention, the task of enumerating IO devices in the system can be assigned to a plurality of processors simultaneously, thus greatly shortening the time consumed by the enumeration process, and accelerating the initiation process of the system.
Owner:XFUSION DIGITAL TECH CO LTD
Describing native application programming interfaces of an operating system with metadata
InactiveCN102866910AMultiprogramming arrangementsExecution paradigmsOperational systemApplication programming interface
Native operating system application programming interfaces (APIs) are described using metadata and such descriptions are stored in a standard file format in a known location. By storing API definitions using such metadata, other applications can readily identify and use the APIs. To create such API representations, during development, a developer describes the shape of the API, including (but not limited to) the classes, interfaces, methods, properties, events, parameters, structures and enumerated types defined by the API. This API description is processed by a tool which generates a machine-readable metadata file. The machine-readable metadata file contains the same information as the API description, however in a format designed to be machine read rather than human authored.
Owner:MICROSOFT CORP
Method for improving game code reusability, terminal device and storage medium
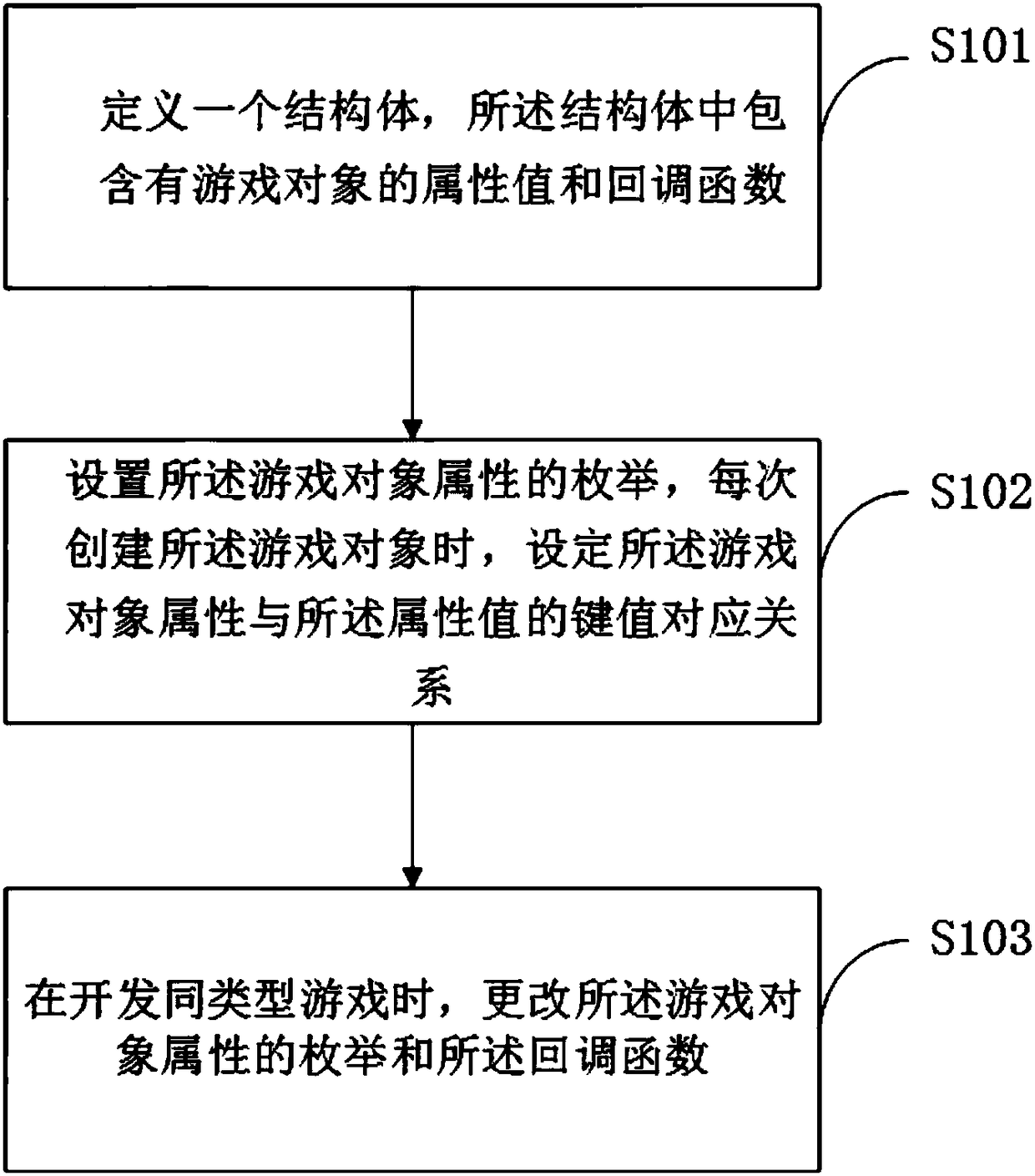
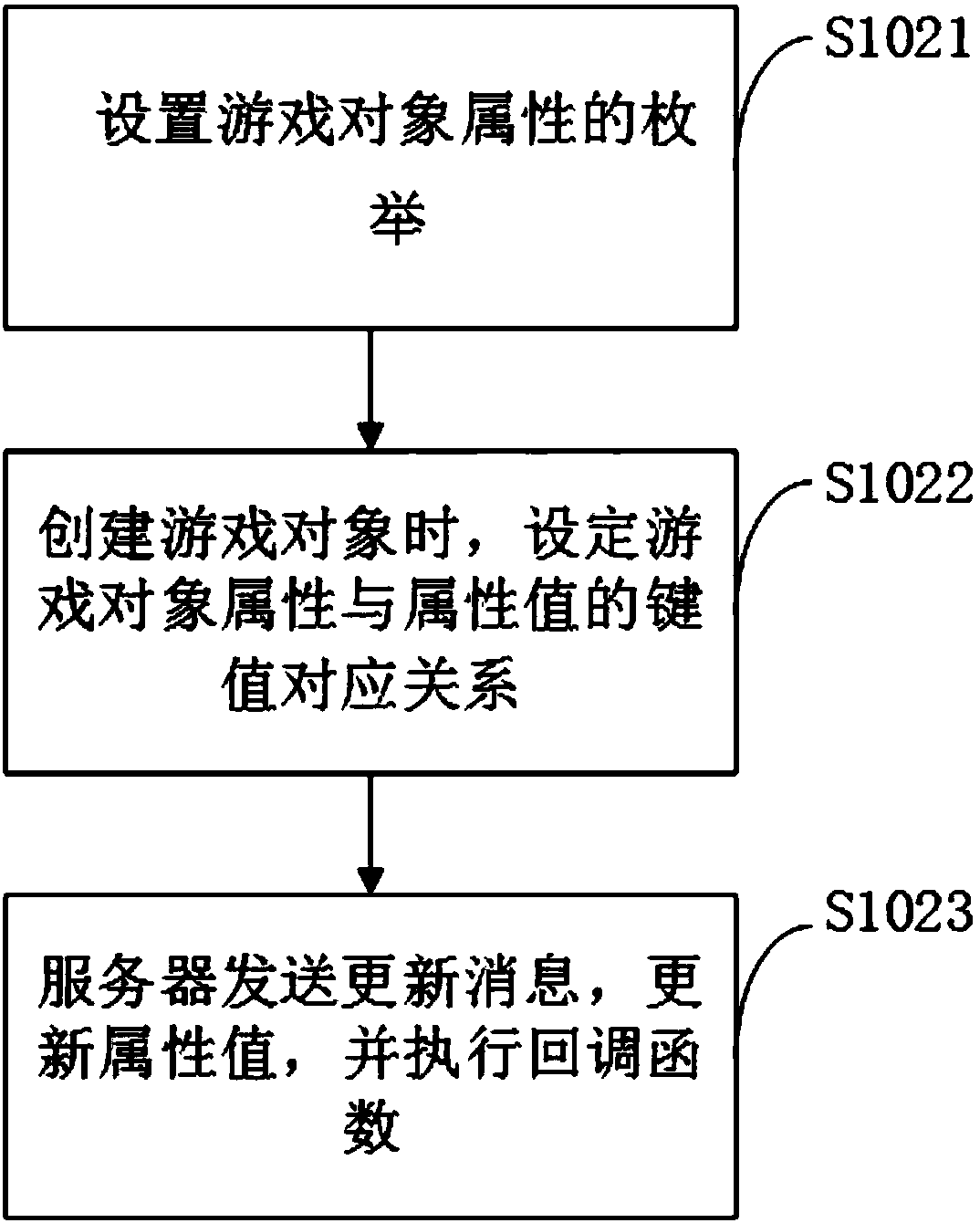
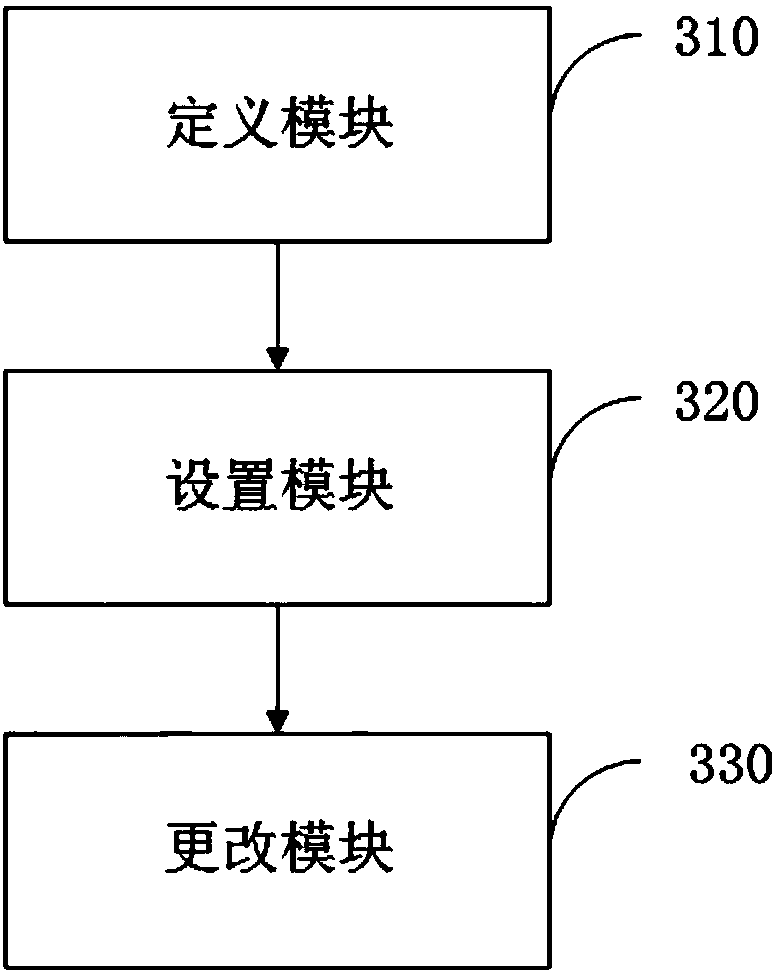
InactiveCN108595172AImprove portabilityImprove reusabilityCode refactoringSoftware reuseReusabilityTerminal equipment
The invention discloses a method for improving game code reusability, a terminal device and a storage medium, and is suitable for game software development. The method provided by the invention comprises the following steps that: defining a structural body, wherein the structural body contains the attribute value and the callback function of a game object setting the enumeration of a game object attribute, and setting a key value corresponding relationship of the game object attribute and the attribute value during the creation of the game object each time; and when the same type of game is developed, changing the enumeration and the callback function of the game object attribute. By use of the method, the structural object is defined to carry out enumeration on the game object attribute so as to establish the key value corresponding relationship of the attribute and the attribute value. When new game is developed, only the attribute of the enumeration and the call function need to bechanged, the portability and the reusability of codes can be improved, in addition, a workload can be reduced, and working efficiency is improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Design of a signal switch
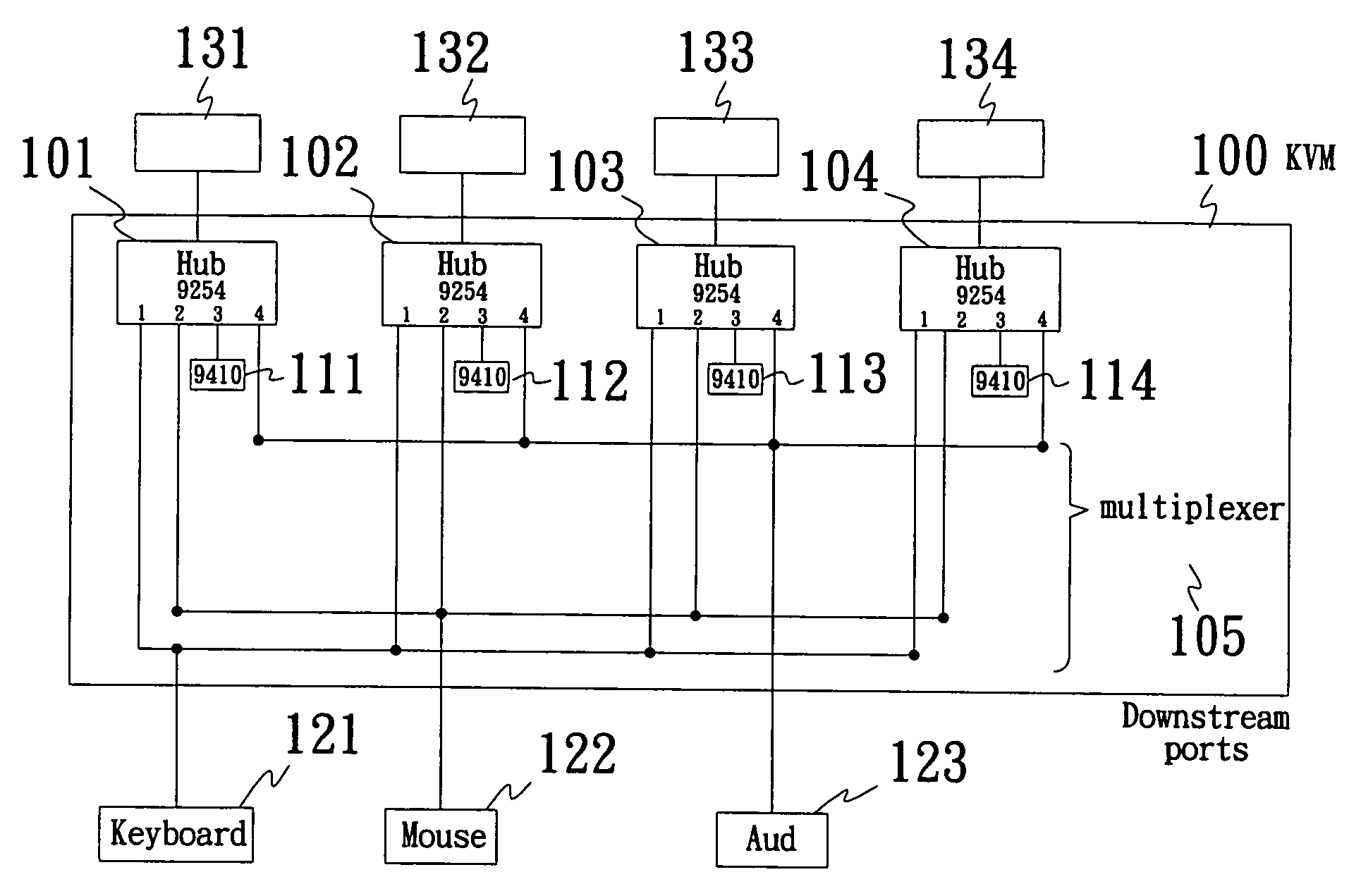
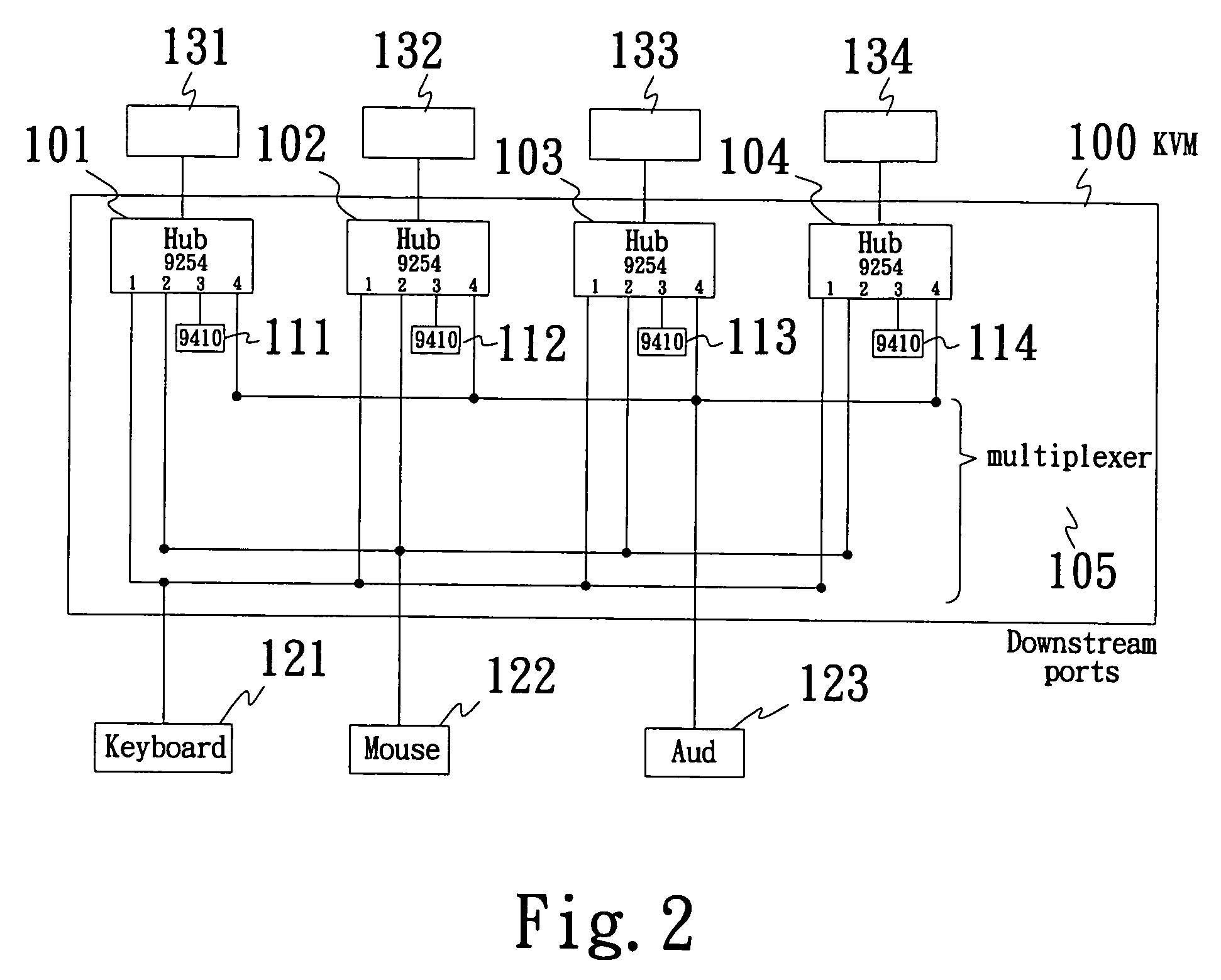
InactiveUS20070067553A1Shorten the timeIncrease speedElectric digital data processingMultiplexingMultiplexer
The present invention provides an improved design of the signal switch, wherein the signal switch comprises at least one combinational logic such as a chip, a plurality of hosts and at least one set of input control device such as a keyboard and a mouse. The chip can further comprise one or more virtual keyboard controller and a plurality of hubs and a multiplexer. The multiplexer of the present invention is utilized to detect and interpret signals. The present invention utilizes the combinational logic design of the chips and the multiplexer to provide a signal switch that can share multi-upstream devices but less downstream ports, only one set of keyboard and mouse is required. Multiplexing downstream devices among multiple hubs, which are dedicated to upstream hosts, help reducing the whole enumeration process of time. The signal switch of the present invention provides an improved design by replacing the central processing units (CPU) of a conventional design of signal switch with the combinational logics such as chips in order to increase the speed of the enumeration, as a result, the enumerating time is thus reduced.
Owner:ALCOR MICRO CORP
Full-text index module consistency checking
ActiveUS7509252B2Easy to determineDigital data information retrievalNatural language data processingEnumerated typeDatabase
Consistency between the components used to generate and query a full-text index is determined and if a mismatch is detected, an error may be surfaced. A structure including information associated with each component used to build an index is programmatically compared with currently available components. The structure may be interrogated to enumerate the resources bound to a particular index. The enumeration of bound resources facilitates determination of what indexes (if any) must be regenerated for consistency as a result of a component upgrade or a move to another system.
Owner:MICROSOFT TECH LICENSING LLC
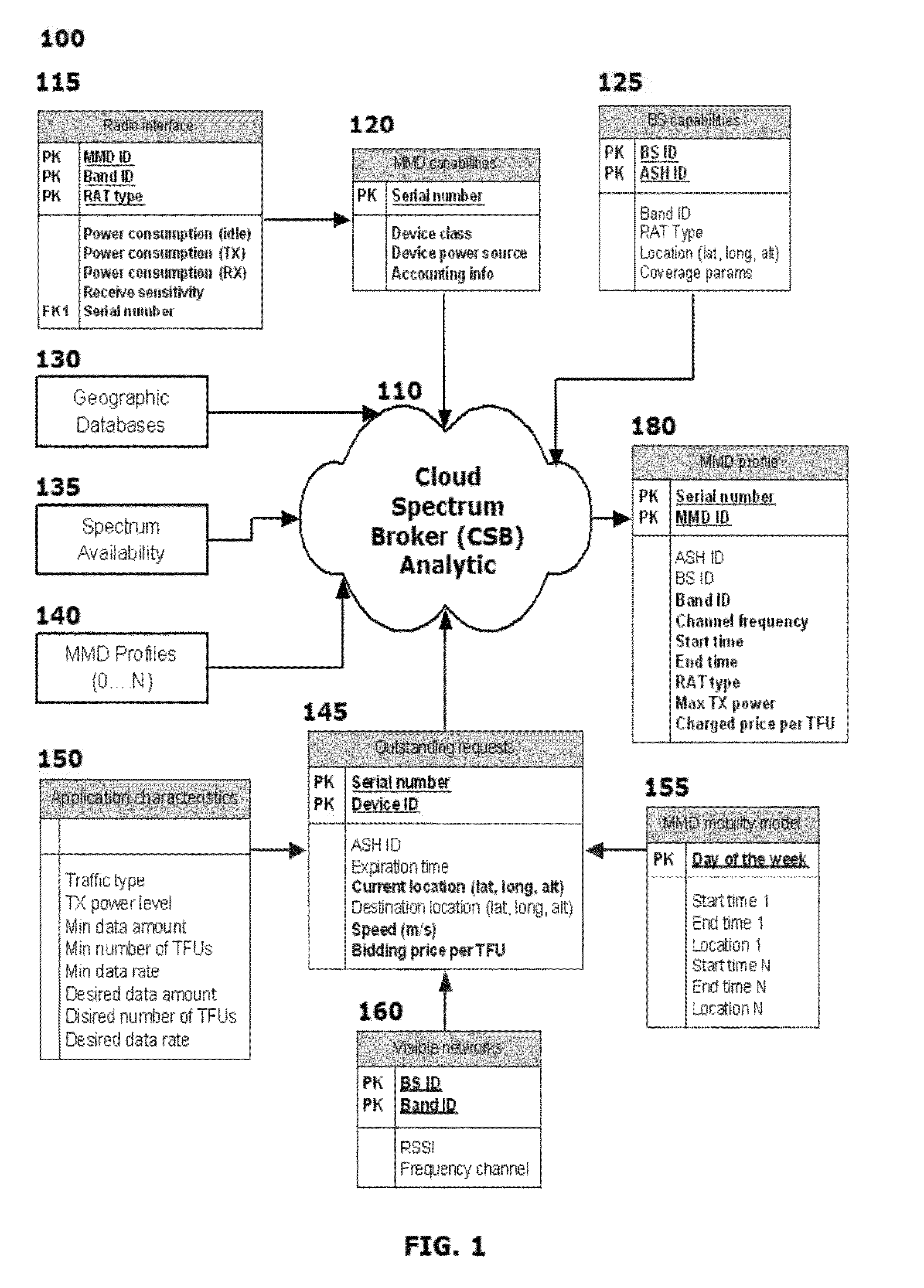
Cloud based spectrum management analytics
InactiveUS20140220999A1Efficient and scalable DSA schemeMinimal costAccounting/billing servicesNetwork traffic/resource managementFrequency spectrumCloud base
A system and method are provided for implementing a spectrum management analytics (SMA) algorithm that references a plurality of enumerated inputs to generate a set of output parameters for use in attempting to optimize spectrum. The SMA algorithm is a part of a cloud spectrum broker (CSB) analytic. The CSB analytic provides for:(1) Managing CSS transactions involving transfer of spectrum resources from participating primary spectrum holders (PSH's) to one or more alternate spectrum holders (ASH's);(2) Reclaiming spectrum resources from an ASH back to the corresponding PSH on request;(3) Initiating queries to PSH's based on requests from MMD's, or through other ASH's; and(4) Performing a series of predictive resource allocations that may optimize spectrum use as the MMD moves between a number of regions.
Owner:TAHOE RES LTD
Coding and decoding method applicable to ASN.1 recursive solution data structure description
ActiveCN105843663ALow cost transferSave memory spaceProgram controlMemory systemsDecoding methodsArray data structure
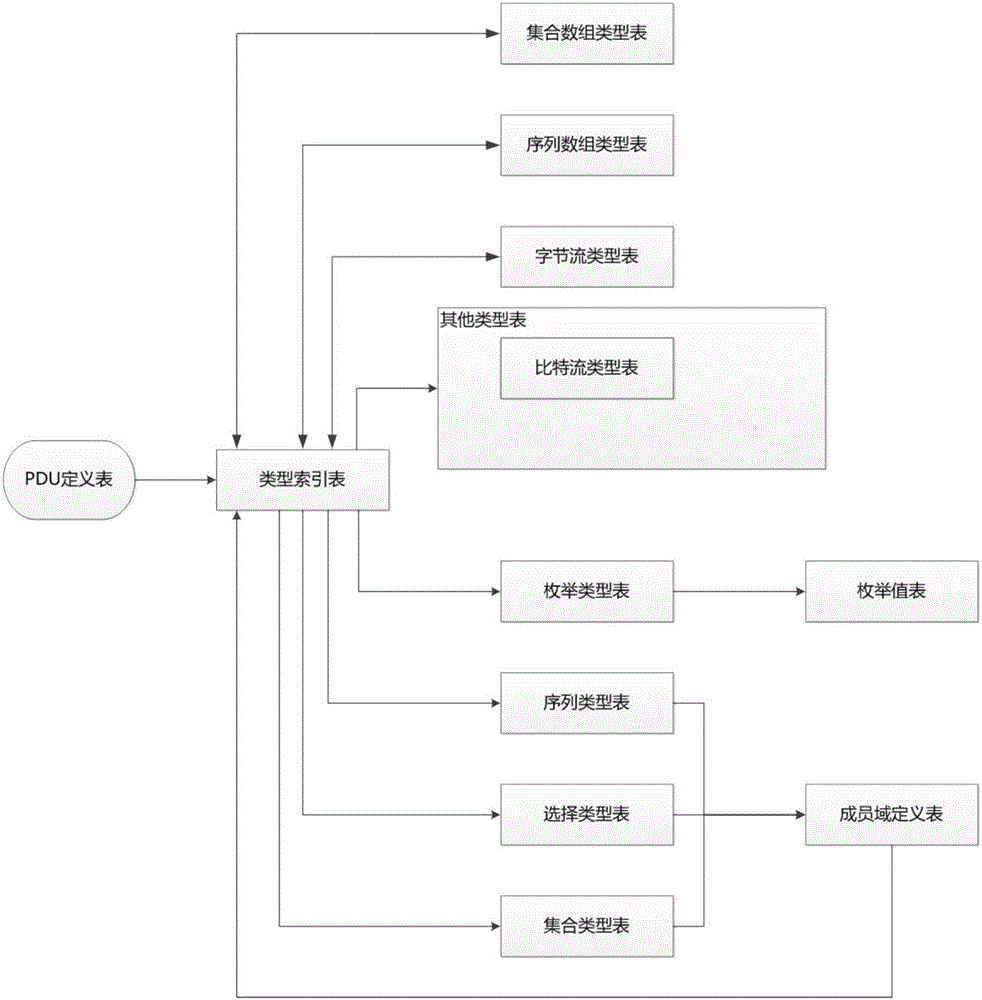
The invention relates to a coding and decoding method applicable to ASN.1 recursive solution data structure description. The coding and decoding method is characterized in that an ASN.1 compiler establishes an enumeration value table and a member definition table for an enumerated type and a compound type; a type definition table is established independently for each ASN.1 basic data type, an enumeration definition table is linked with the enumeration value table, and a compound type table is linked with the member definition table; extended data types defined in all ASN.1 grammar form a table entry in each type definition table, and all table entries are collected into one type index table; the member definition table, a sequence array definition table, a set array definition table and a CONTAINING defined octet string type definition table are linked with the type index table; meanwhile, all PDUs are listed independently, and a PDU definition table is formed and linked with the type index table. A coding and decoding library scheme independent from concrete ASN.1 grammar can be set and realizes coding and decoding of the PDUs by traversing the net-shaped data tables in a recursive manner.
Owner:苏州简约纳电子有限公司
Graphical concept modeling method and device and computer equipment
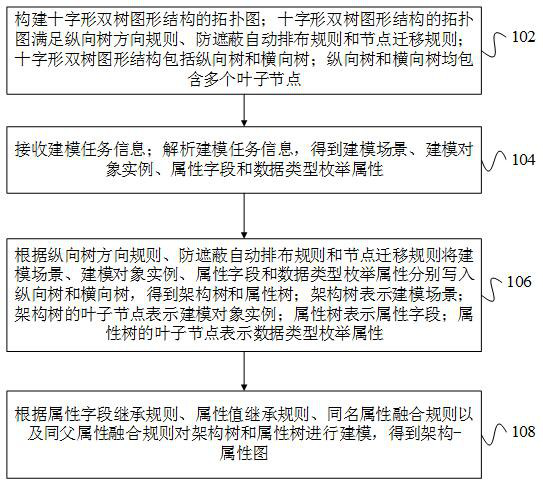
ActiveCN114417638AEasy to hideImprove good performanceGeometric CADDesign optimisation/simulationGraphicsData class
The invention relates to a graphical concept modeling method and device, computer equipment and a storage medium. The method comprises the following steps: constructing a topological graph of a cross-shaped dual-tree graphic structure; the cross-shaped double-tree graphic structure comprises a longitudinal tree and a transverse tree and is used for receiving modeling task information; analyzing the modeling task information to obtain a modeling scene, a modeling object instance, an attribute field and a data type enumeration attribute; respectively writing the modeling scene, the modeling object instance, the attribute field and the data type enumeration attribute into a longitudinal tree and a transverse tree according to a longitudinal tree direction rule, an anti-shielding automatic arrangement rule and a node migration rule to obtain an architecture tree and an attribute tree; and modeling the architecture tree and the attribute tree according to an attribute field inheriting rule, an attribute value inheriting rule, a homonymous attribute fusion rule and a same parent attribute fusion rule to obtain an architecture-attribute graph. By adopting the method, the simulation modeling efficiency can be improved.
Owner:HUNAN GAOZHI SCI & TECH CO LTD
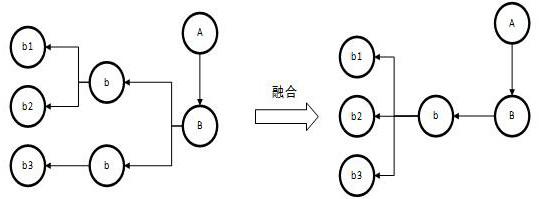
Enumeration type design method and device
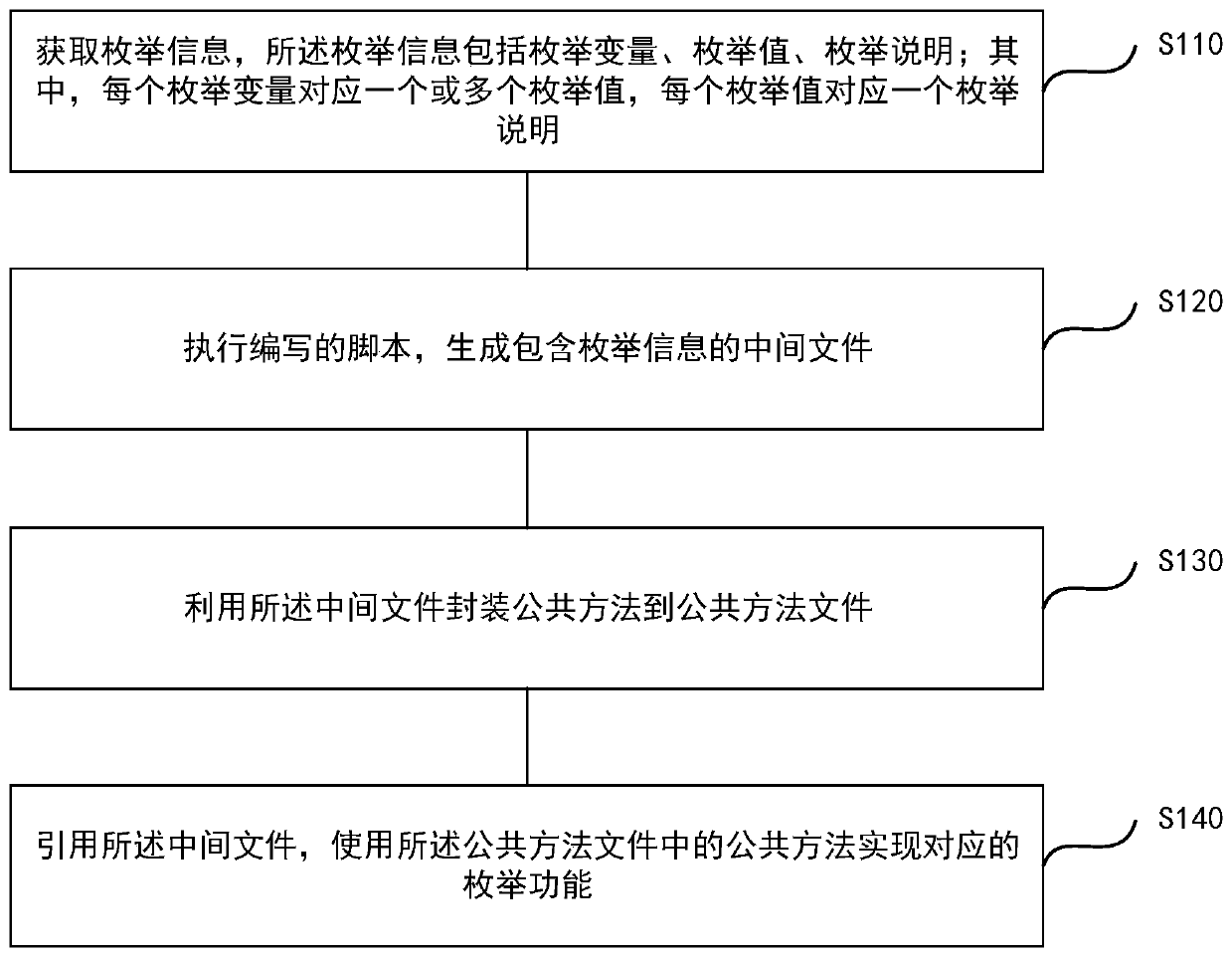
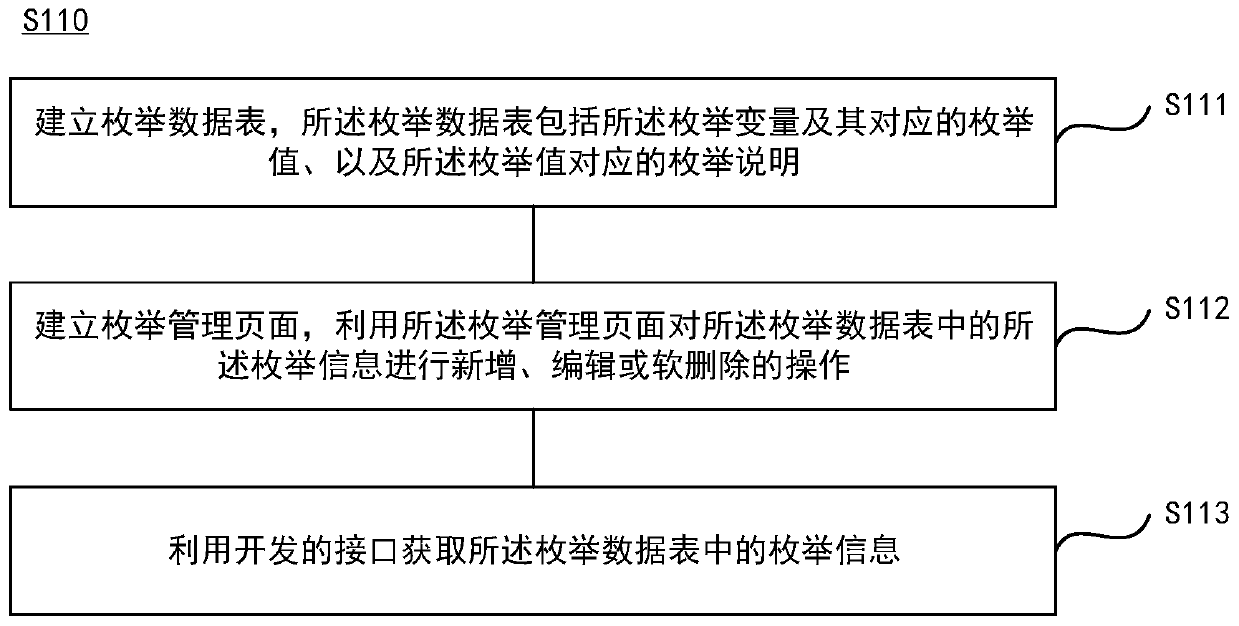
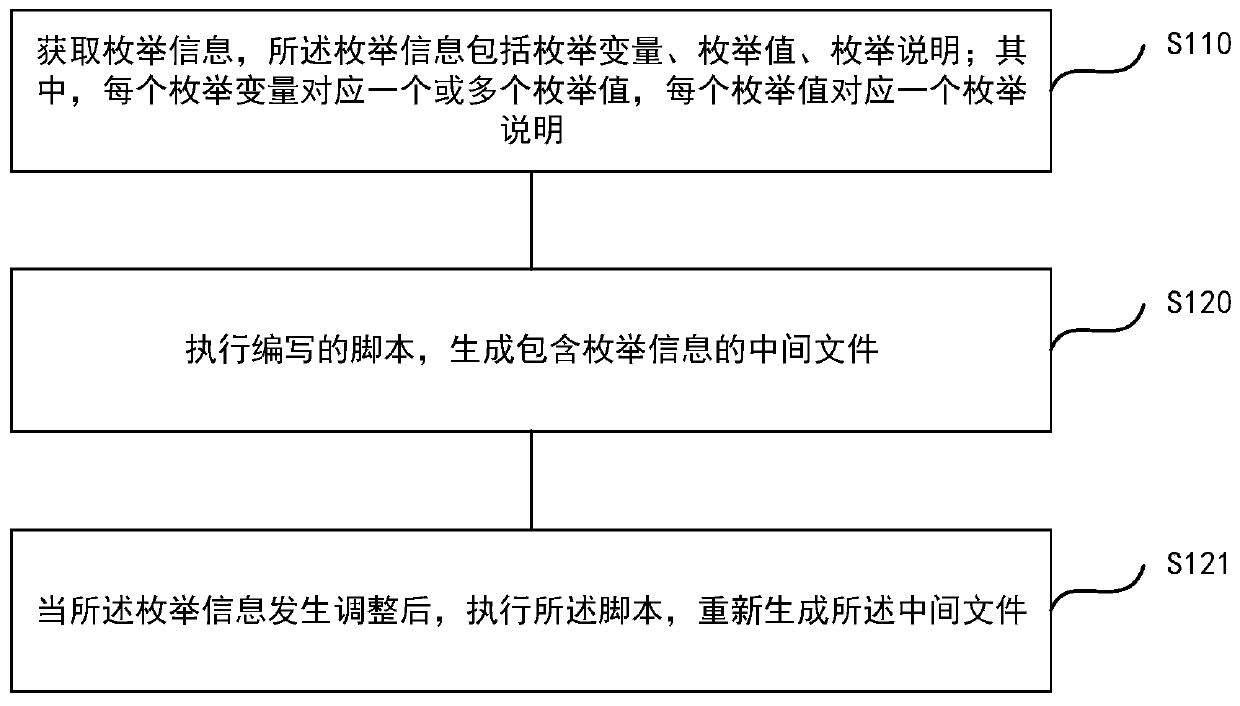
ActiveCN111367524AEasy to manageImprove recoverabilitySoftware engineeringProgramming languageSoftware engineering
The invention discloses an enumeration type design method and device, electronic equipment and a computer storage medium, and the method comprises the steps: obtaining enumeration information which comprises an enumeration variable, an enumeration value and an enumeration description; executing the written script to generate an intermediate file containing enumeration information; packaging the public method to a public method file by utilizing the intermediate file; and quoting the intermediate file, and realizing a corresponding enumeration function by using a public method in the public method file. According to the method, enumeration-related processing scripts are developed in the early development stage, and if enumeration information is adjusted in the later development process, only script files need to be executed again, and related intermediate files are generated again; when an enumeration function needs to be used, a related intermediate file is quoted, and an encapsulatedpublic method is used in a code, so that the enumeration function corresponding to the public method can be realized, the development efficiency is improved, and different reports, page presentation and data related to the same enumeration are highly unified.
Owner:SHANGHAI DONGPU INFORMATION TECH CO LTD
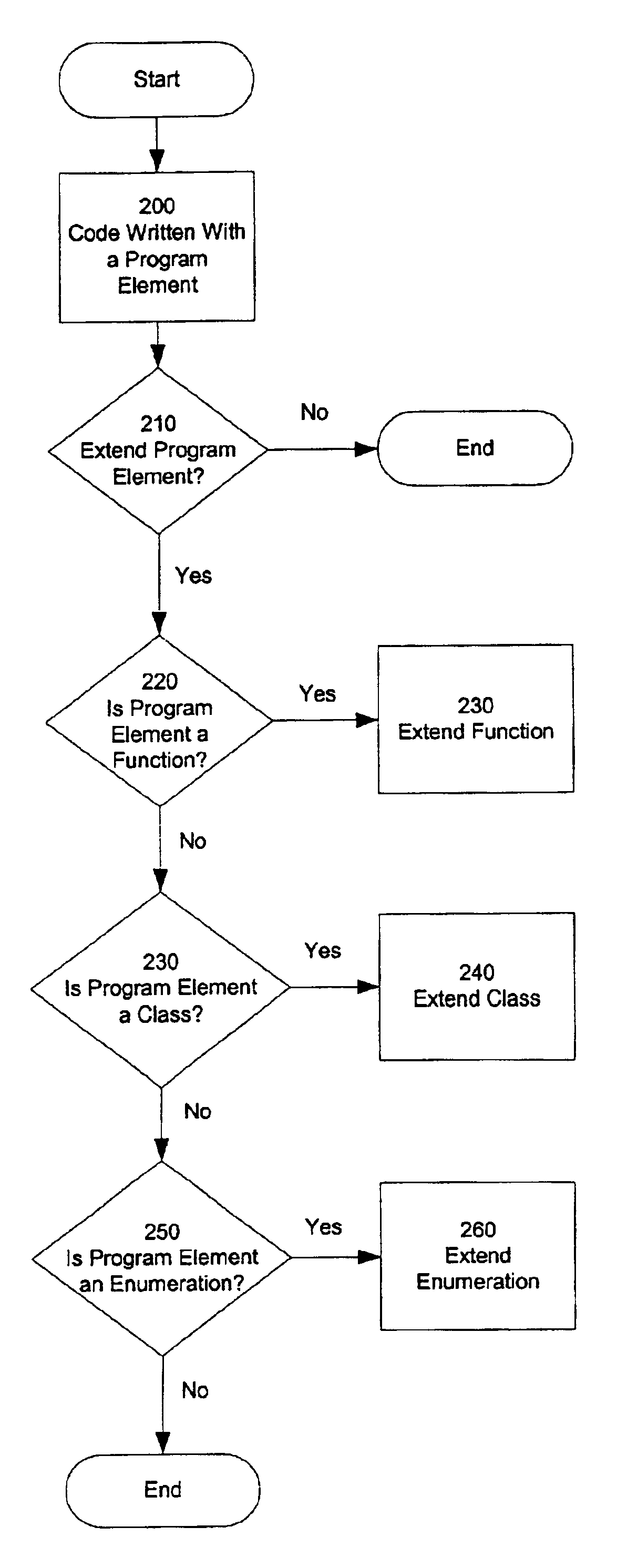
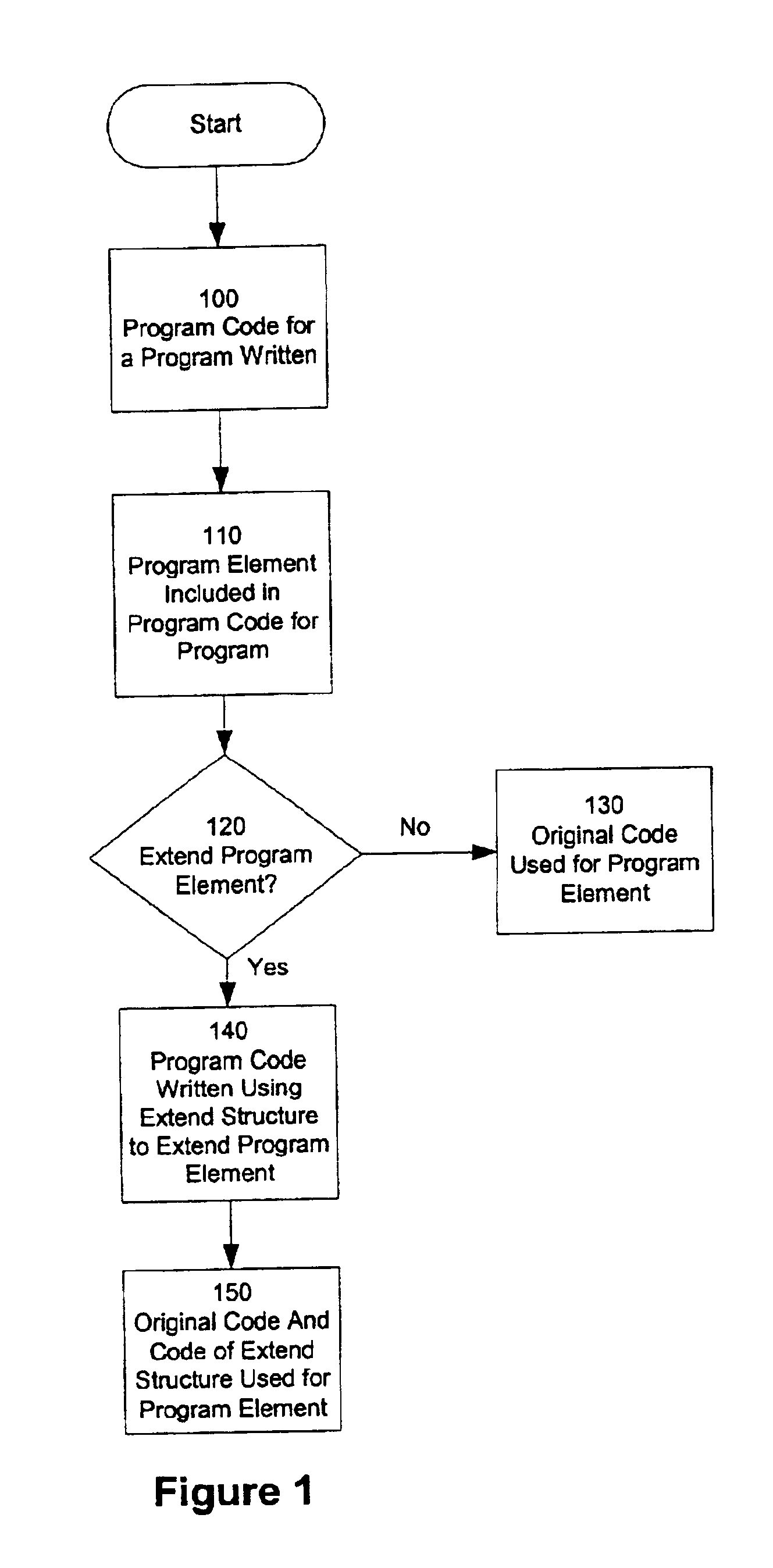
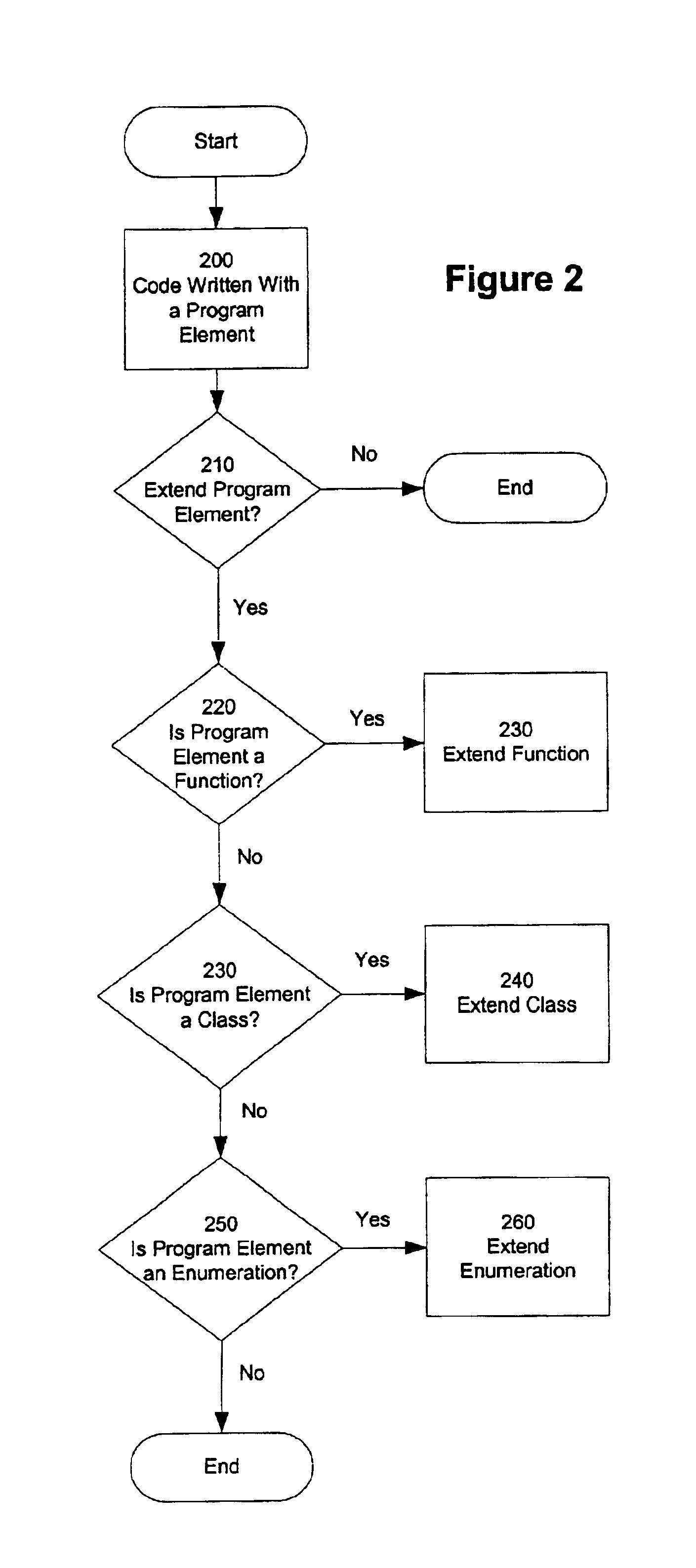
Method and apparatus for extending a program element in a dynamically typed programming language
Embodiments of the present invention are directed to a method and apparatus for extending a program element in a dynamically typed programming language. In one embodiment, a program element is extended without altering the source code defining the program element. An extend structure is used to extend a program element in a particular program. In one embodiment, the program element is a function. The function is extended by adding code to be executed by the function. In another embodiment, the program element is an enumeration. The enumeration is extend by adding additional constants to the enumeration. In another embodiment, the program element is a class. In one embodiment, a class is extended by adding code to the constructor of the class. In another embodiment, a class is extended by adding member variables to the class. In yet another embodiment, a class is extended by adding member functions to the class.
Owner:ORACLE INT CORP
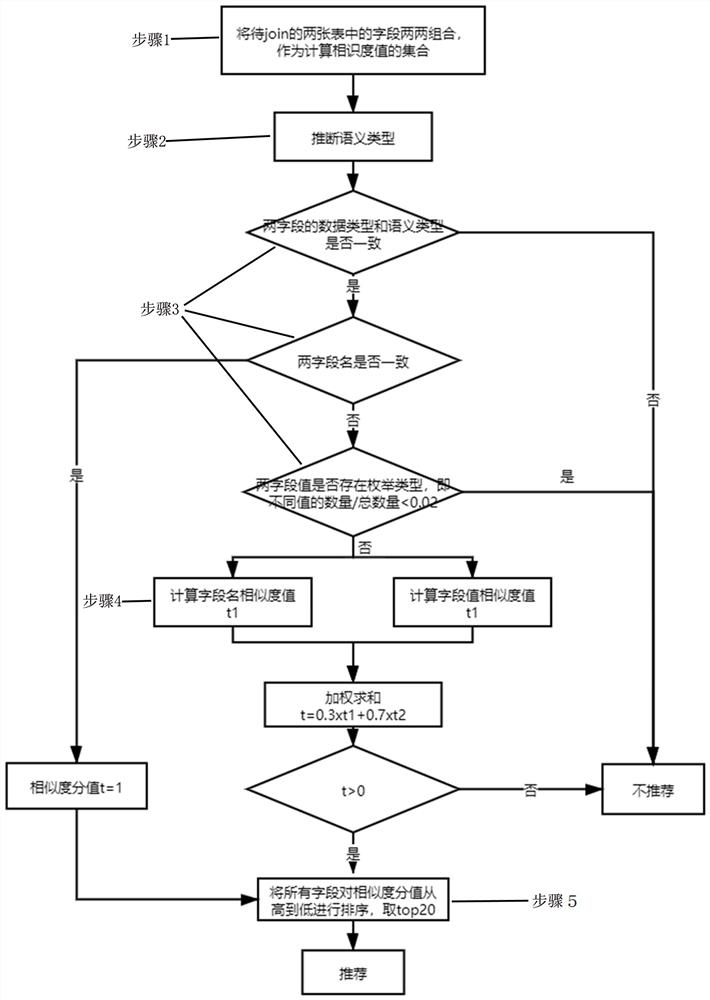
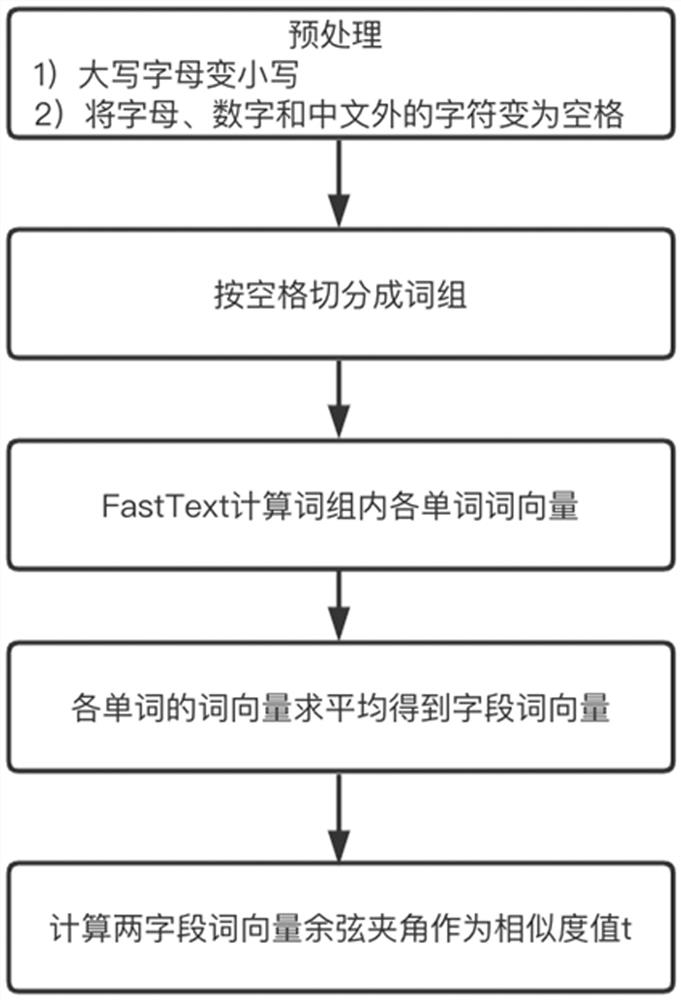
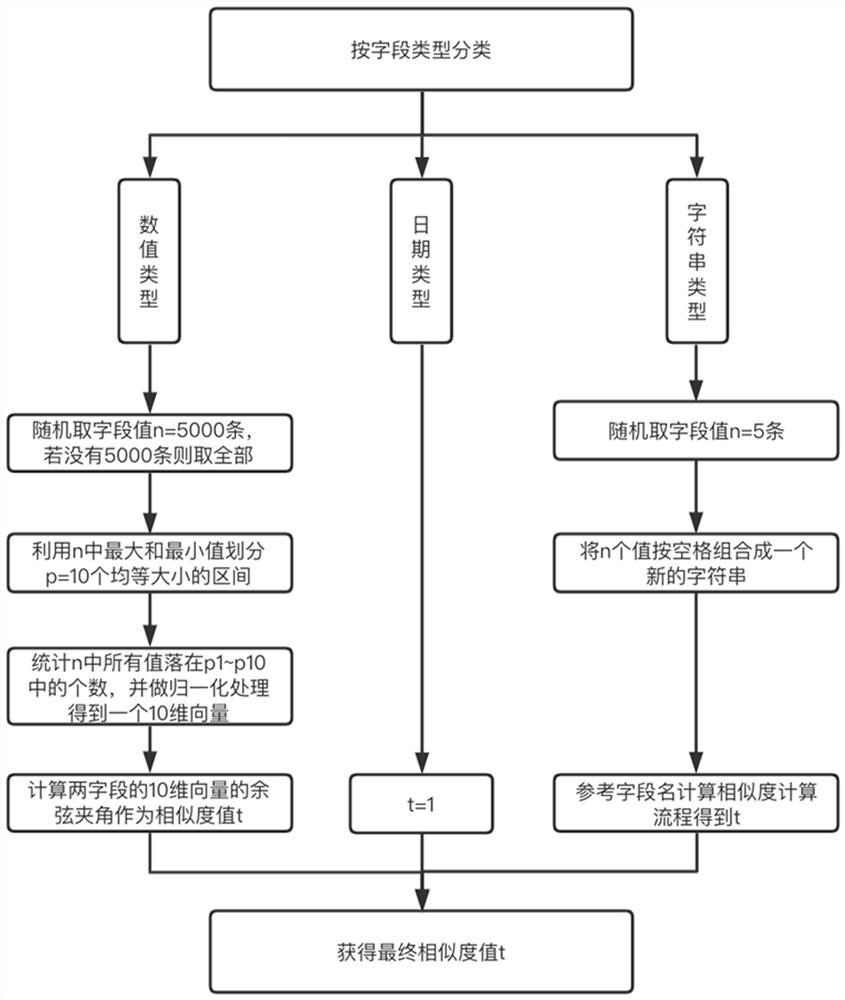
Data table automatic join recommendation method based on field semantics
PendingCN113673252AImprove the level of intelligenceAccurate and more comprehensive discoverySemantic analysisCharacter and pattern recognitionDatasheetData class
The invention relates to the field of multi-dimensional data analysis, in particular to a data table automatic join recommendation method based on field semantics. The method comprises the following steps of: 1, combining fields in two to-join data tables in pairs as a set for calculating similarity values; 2, inferring the semantic type of the field; 3, judging whether the data types and the semantic types of the two fields are consistent or not, then judging whether the names of the two fields are consistent or not, and then judging whether enumeration classes exist in the values of the two fields or not; 4, respectively calculating the similarity of the field names and the similarity of the field values, and then obtaining a matching coefficient through weighted summation, namely the similarity of the two fields; and 5, sorting the scores of the similarity of all the fields from high to low, and outputting and extracting the first 20 items as recommendation. According to the method, the join connection clauses are recommended by analyzing the field names and the field values of the data tables, so that a user is more accurately and comprehensively helped to find associated information hidden by multi-dimensional data, and the intelligent level of a big data analysis system is effectively improved.
Owner:ZHEJIANG LAB
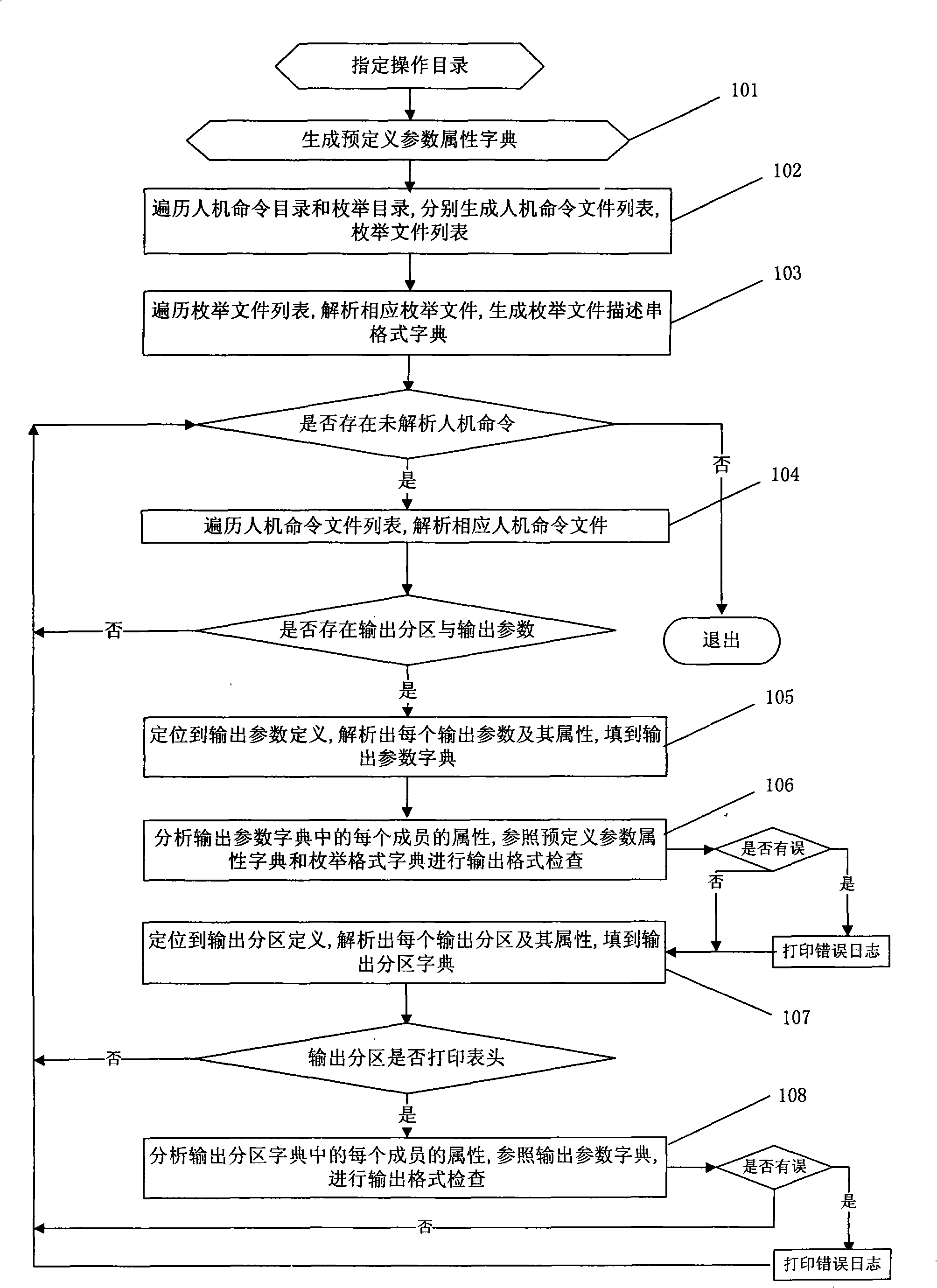
Human machine command output formats checking procedure based on text
InactiveCN101339504ASolve the problem of displaying illegalReduce difficultySpecific program execution arrangementsAlgorithmTheoretical computer science
The invention discloses an inspection method which is based on textual output format of man-machine command, including the following steps: output parameter type of the man-machine command is added to a parameter attribute dictionary and enumeration of the man-machine command is added to an enumeration attribute dictionary; a script file of the man-machine command is traversed and definitions including output parameters and output partition in the script file are respectively added to an output parameter attribute dictionary and an output partition attribute dictionary; content of the parameter attribute dictionary and the enumeration attribute dictionary and that of the output parameter attribute dictionary and the output partition attribute dictionary are compared and inspected to judge whether the output parameter format is correct or not. As the parameter format inspection method which is based on dictionaries and regular expression is adopted, the inspection of legality of the parameter format is completed by the program, thus solving the problem of illegal display of the output parameter information; problems discovered can be obviously seen and pointedly solved by opening error log, thus reducing difficulty of program development and maintenance.
Owner:ZTE CORP
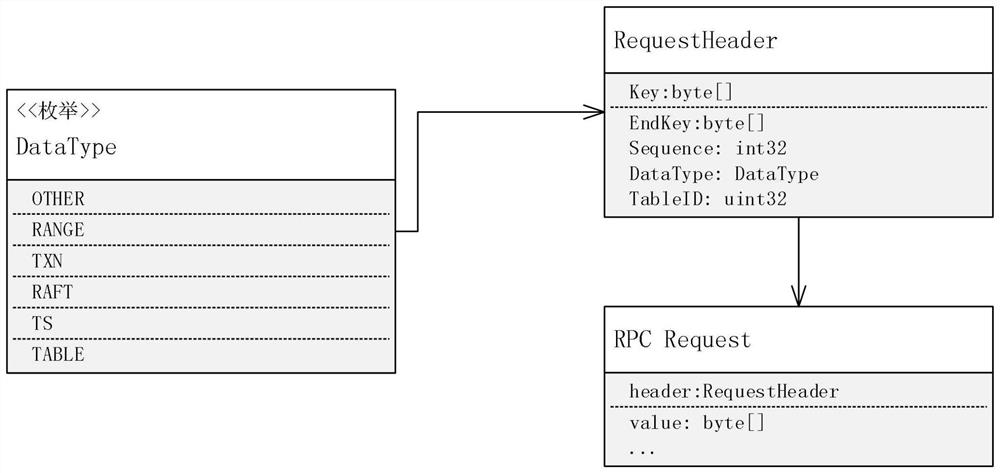
Data classification optimization method based on Cockroach DB bottom layer key value
InactiveCN112364278AOptimizing read and write amplification problemsImprove read and write performanceSpecial data processing applicationsWeb data browsing optimisationTable (database)Data class
The invention discloses an underlying key value data classification optimization method based on Cockroach DB, and belongs to the technical field of distributed databases. According to the invention,an enumeration type DataType is newly added in the header of an RPC request in a distributed database Cockroach DB, and underlying data classification identifiers and table identifiers are analyzed ina request processor to obtain data types and table identifiers and transmitted to a storage engine; and the storage engine adopts different data optimization strategies for different types of read-write characteristics. According to the invention, the read-write amplification problem of the database can be optimized, so that the read-write performance of the database is improved, and the method has very good popularization and application values.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Method for preventing conflict of initial code
The invention discloses a method for preventing occurrence of pseudo initial code in a coded data stream. An initial code in the data stream is changed into another enumeration conflict code whose length is the same as that of the initial code, and modification information is written in the head or tail of the coded data stream. The method successively solves the problem of occurrence of pseudo initial code in the coded data stream.
Owner:朱洪波
ASN.1-PER dynamic and static encoding and decoding method based on 3GPP protocol
ActiveCN111625244AReduce complexitySimplified volumeNetwork traffic/resource managementHigh level techniquesDecoding methodsParallel computing
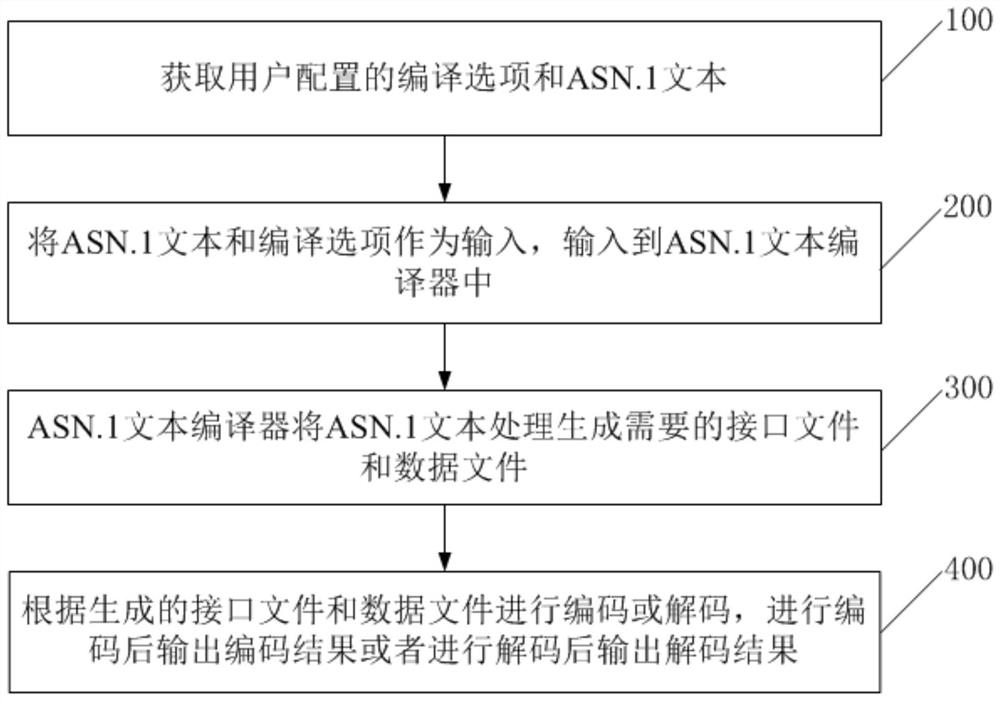
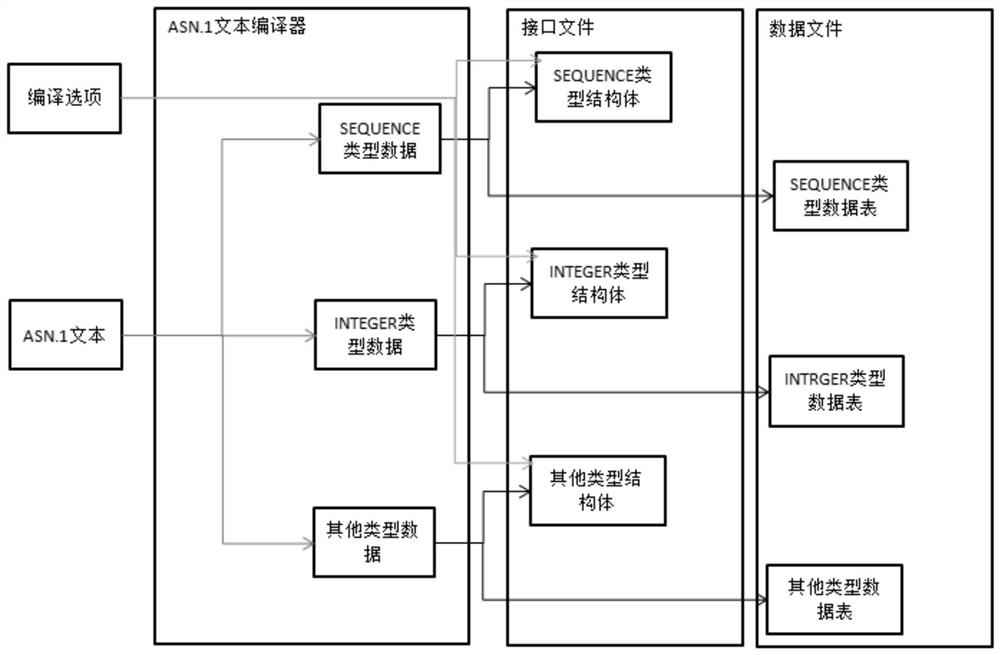
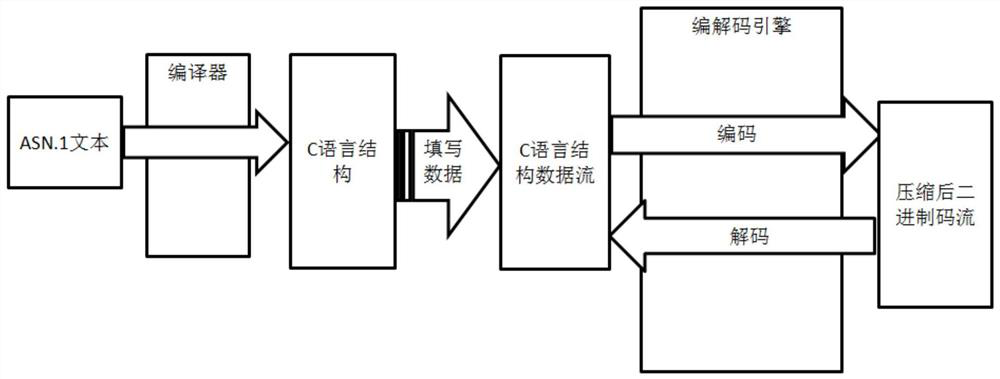
The invention relates to the technical field of communication, and provides an ASN.1-PER dynamic and static encoding and decoding method based on a 3GPP protocol, and the method comprises the steps: 100, obtaining a compiling option and an ASN.1 text configured by a user, wherein the compiling option comprises a protocol name, a structural body prefix, a constant type prefix, a macro definition prefix, an enumeration type prefix and dynamic and static information for controlling dynamic and static states; step 200, taking the ASN.1 text and the compiling options as input, and inputting the ASN.1 text and the compiling options into an ASN.1 text compiler; step 300, enabling the ASN.1 text compiler to process the ASN.1 text to generate a required interface file and a data file; and 400, performing encoding or decoding according to the generated interface file and data file, and outputting an encoding result after encoding or outputting a decoding result after decoding. The method can improve the flexibility of a product, and has the advantages of small size of a dynamic structure and high efficiency of a static structure.
Owner:华畅科技(大连)股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com