Patents
Literature
4179results about "Digital-analogue convertors" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
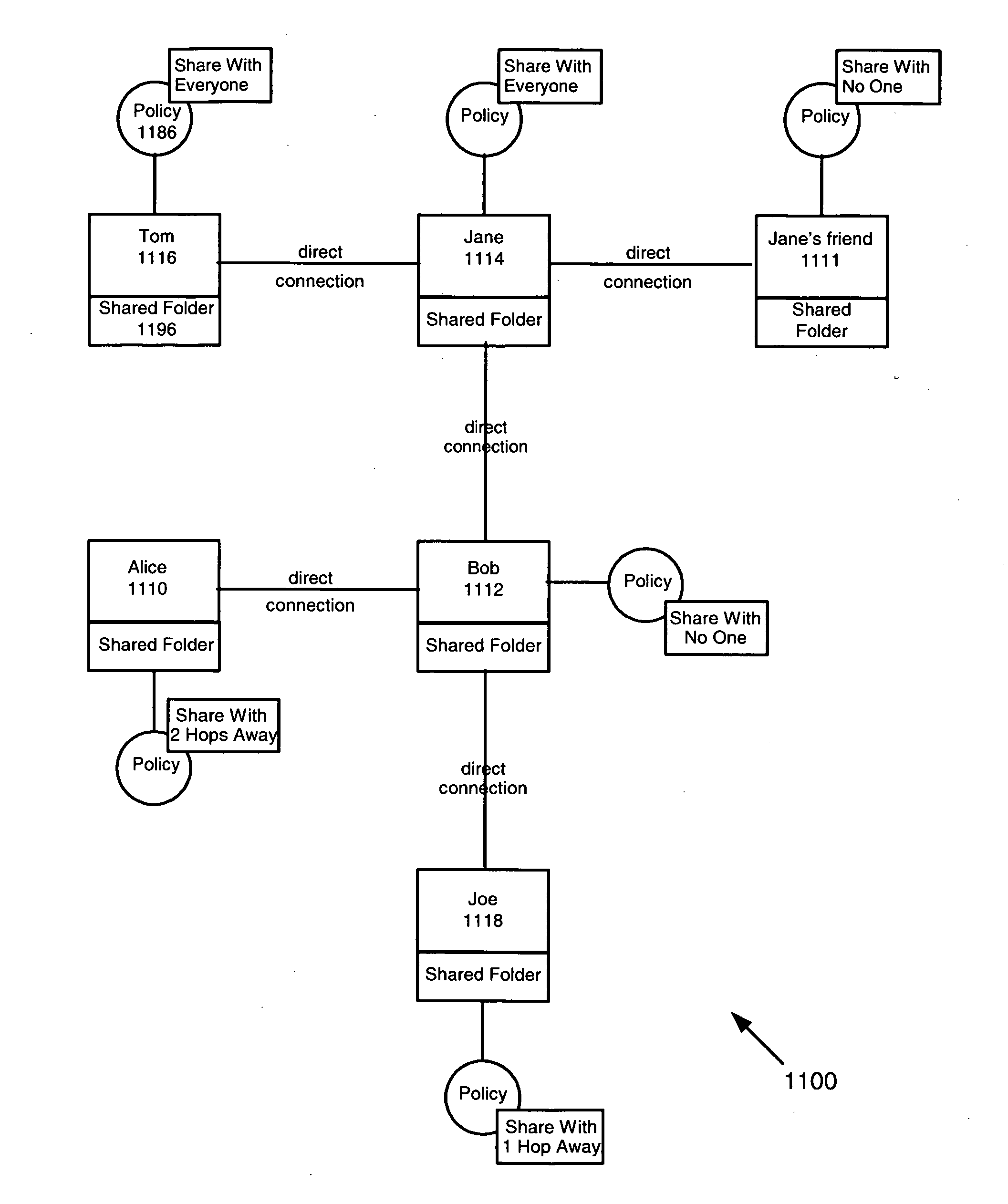
System and method for developing and using trusted policy based on a social model
InactiveUS20060248573A1Digital data processing detailsUser identity/authority verificationInternet privacyFile sharing
A trust policy is constructed based upon a social relationship between real-world entities. The trust policy may determined based upon a social network and social network maps. The social network map provides a framework to determine social distances. The trust policy provides quick and secure access to desired or trusted nodes while providing security from entities outside the trusted sphere of nodes. The trust policy determined by the social distance may be used for various types of applications including filtering unwanted e-mail, providing secure access to resources, and accessing protected services. File sharing, referral querying, advertisement targeting, announcement targeting, access control, and various applications may be limited using the constructed trust policy.
Owner:CONTENTGUARD HLDG
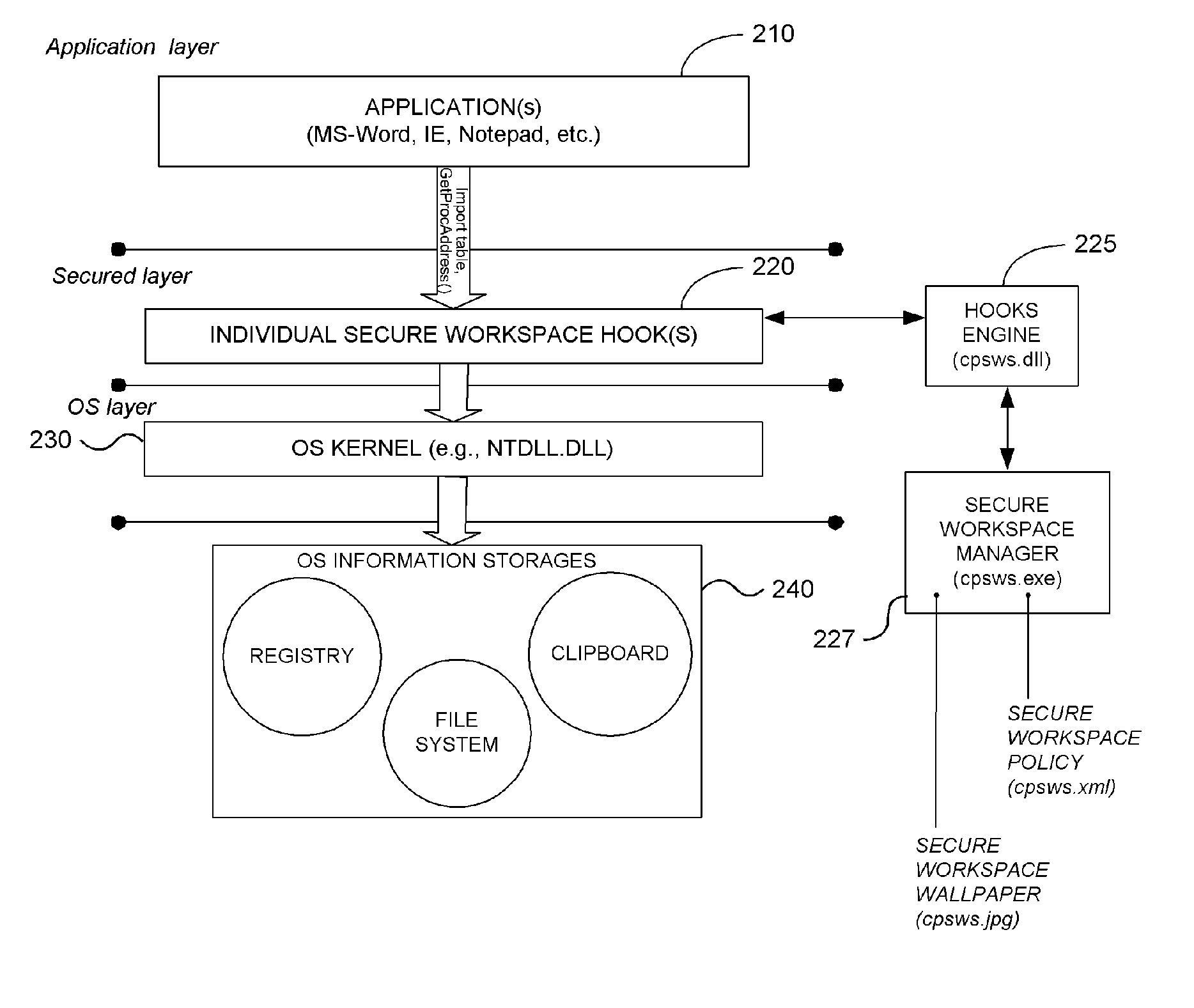
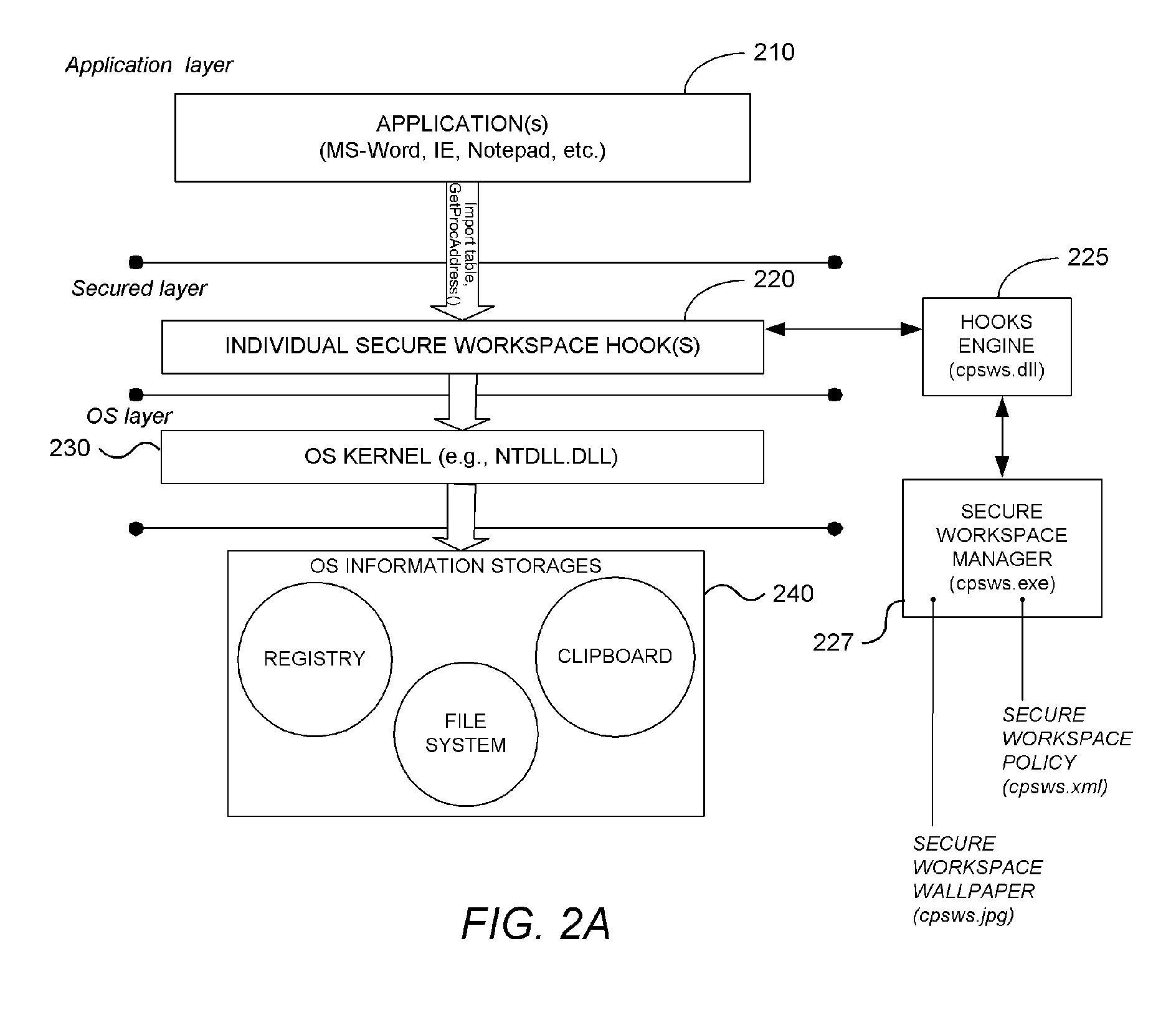
System and Methodology Providing Secure Workspace Environment
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
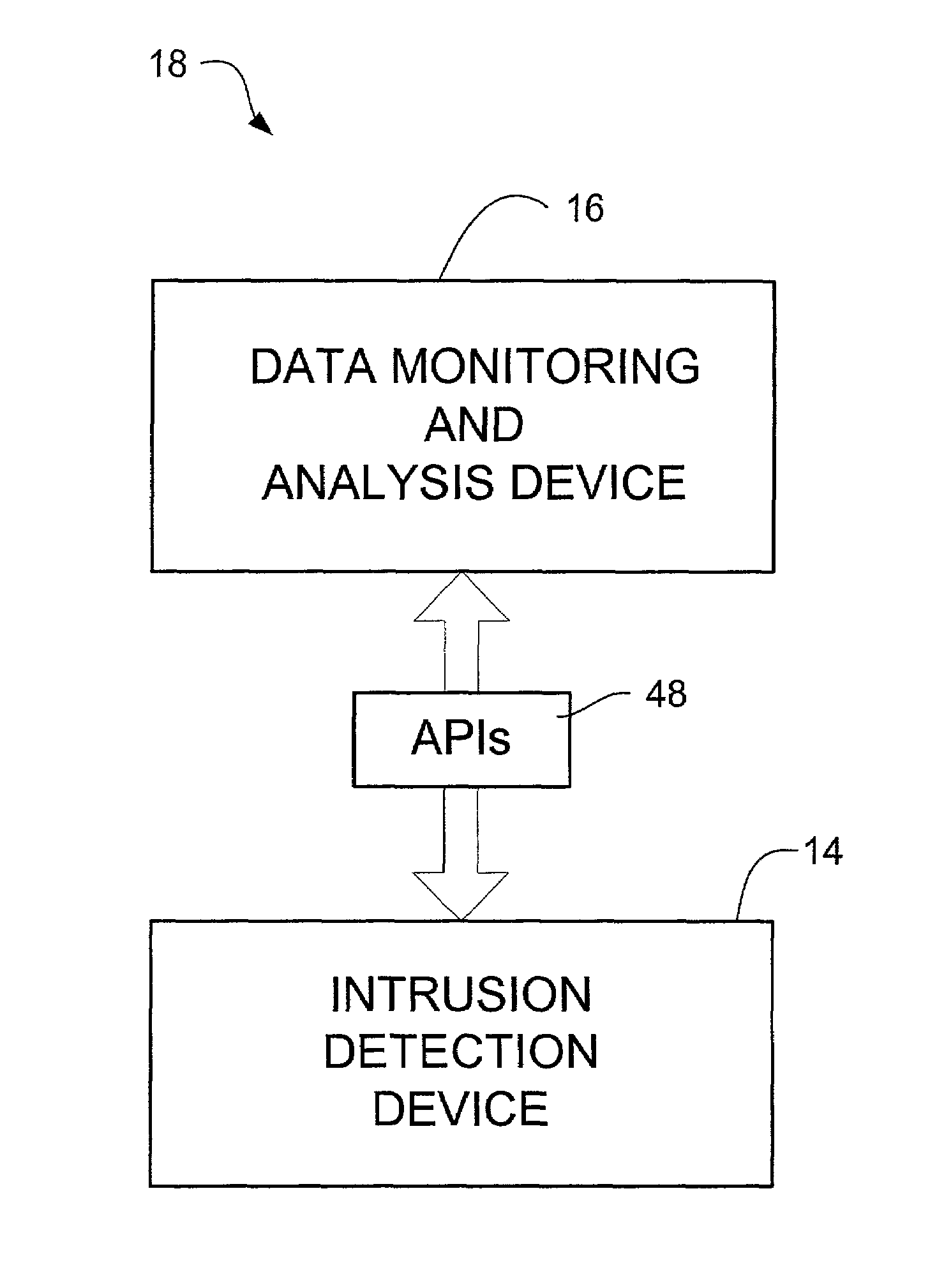
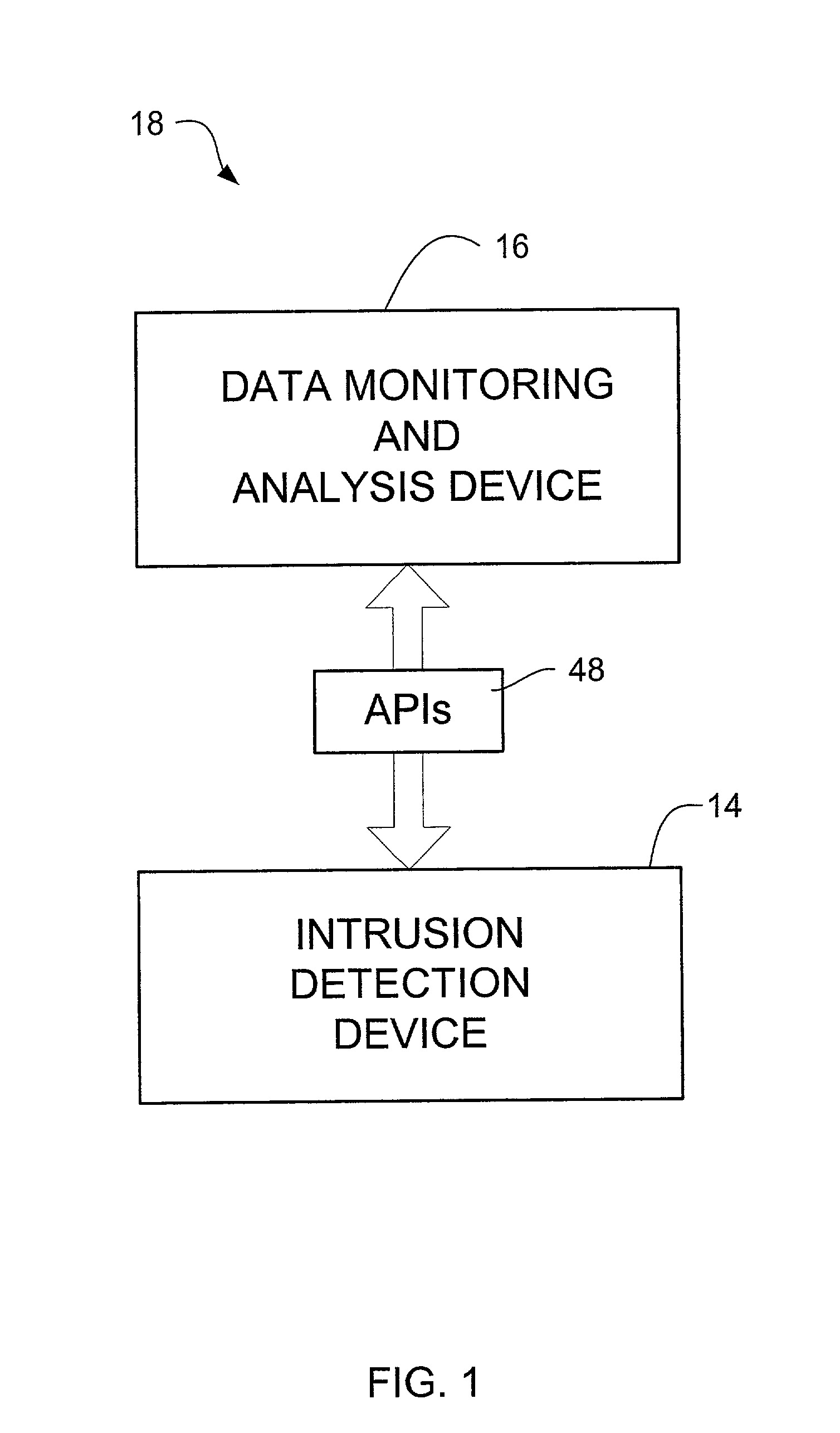
Network intrusion detection and analysis system and method
ActiveUS7493659B1Digital data processing detailsUser identity/authority verificationTraffic capacityData monitoring
An intrusion detection and analysis system and method are disclosed. The system includes a data monitoring device comprising a capture engine operable to capture data passing through the network and configured to monitor network traffic, decode protocols, and analyze received data. The system further includes an intrusion detection device comprising a detection engine operable to perform intrusion detection on data provided by the data monitoring device. Application program interfaces are provided and configured to allow the intrusion detection device access to applications of the data monitoring device to perform intrusion detection. The system also includes memory for storing reference network information used by the intrusion detection device to determine if an intrusion has occurred.
Owner:MCAFEE LLC
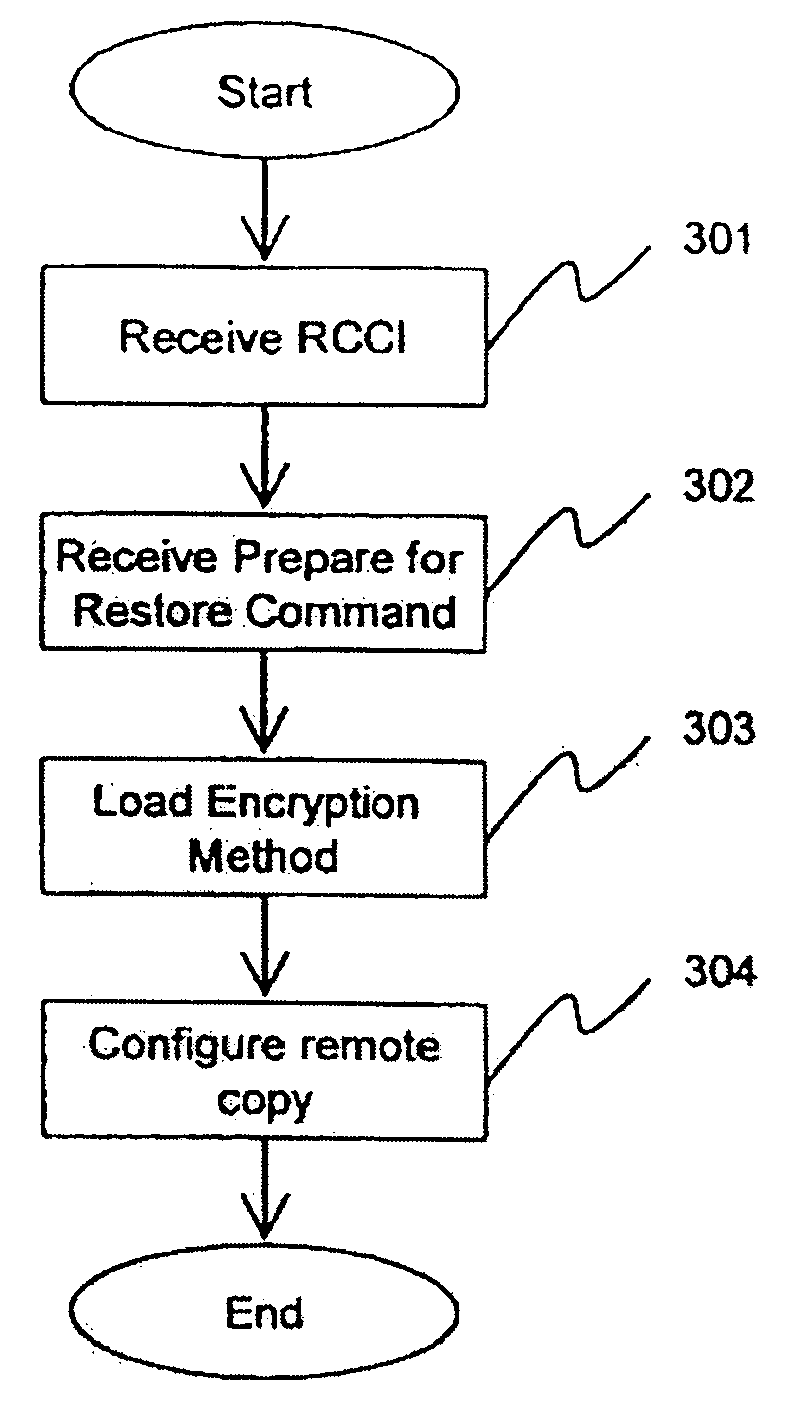
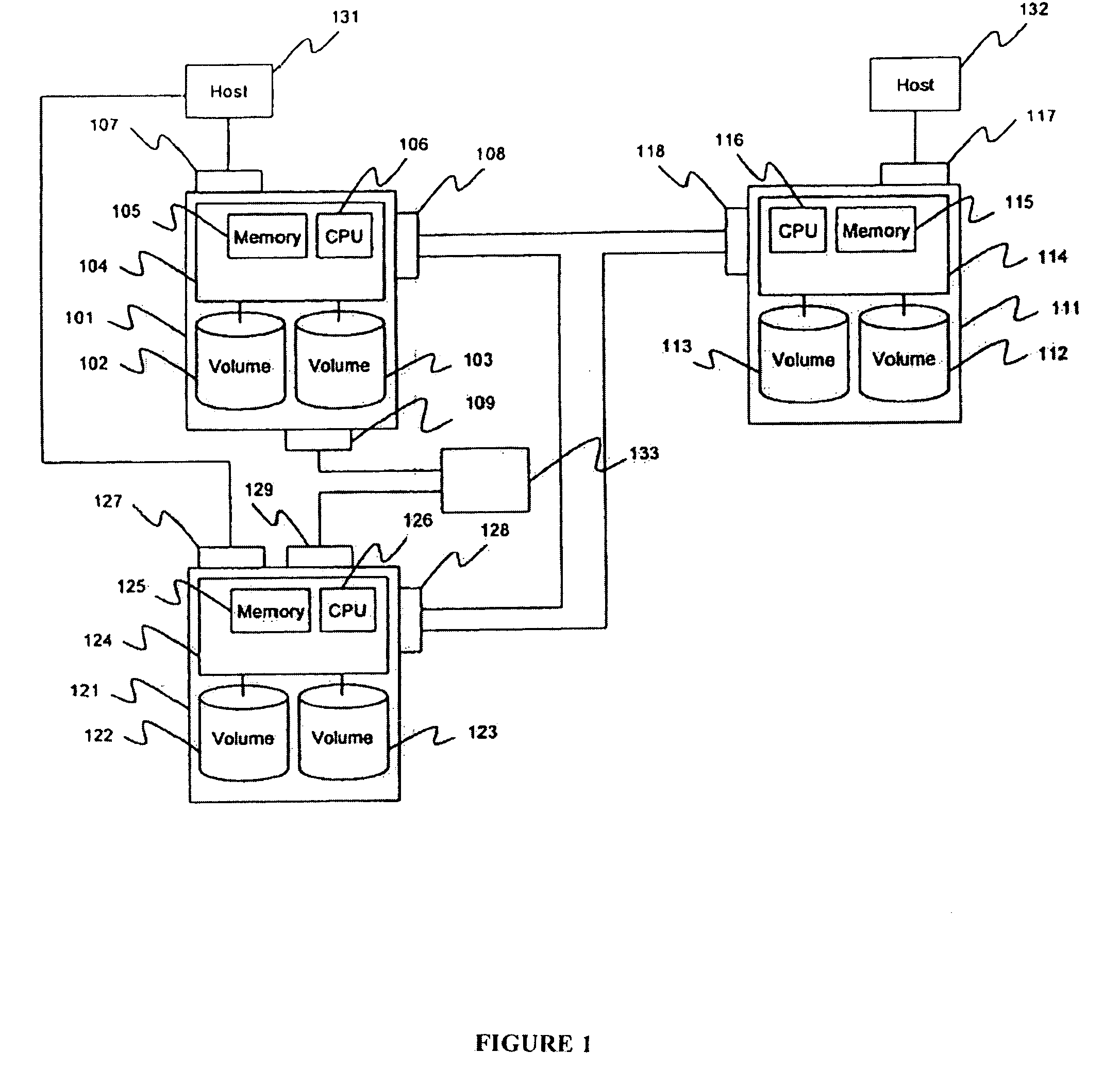
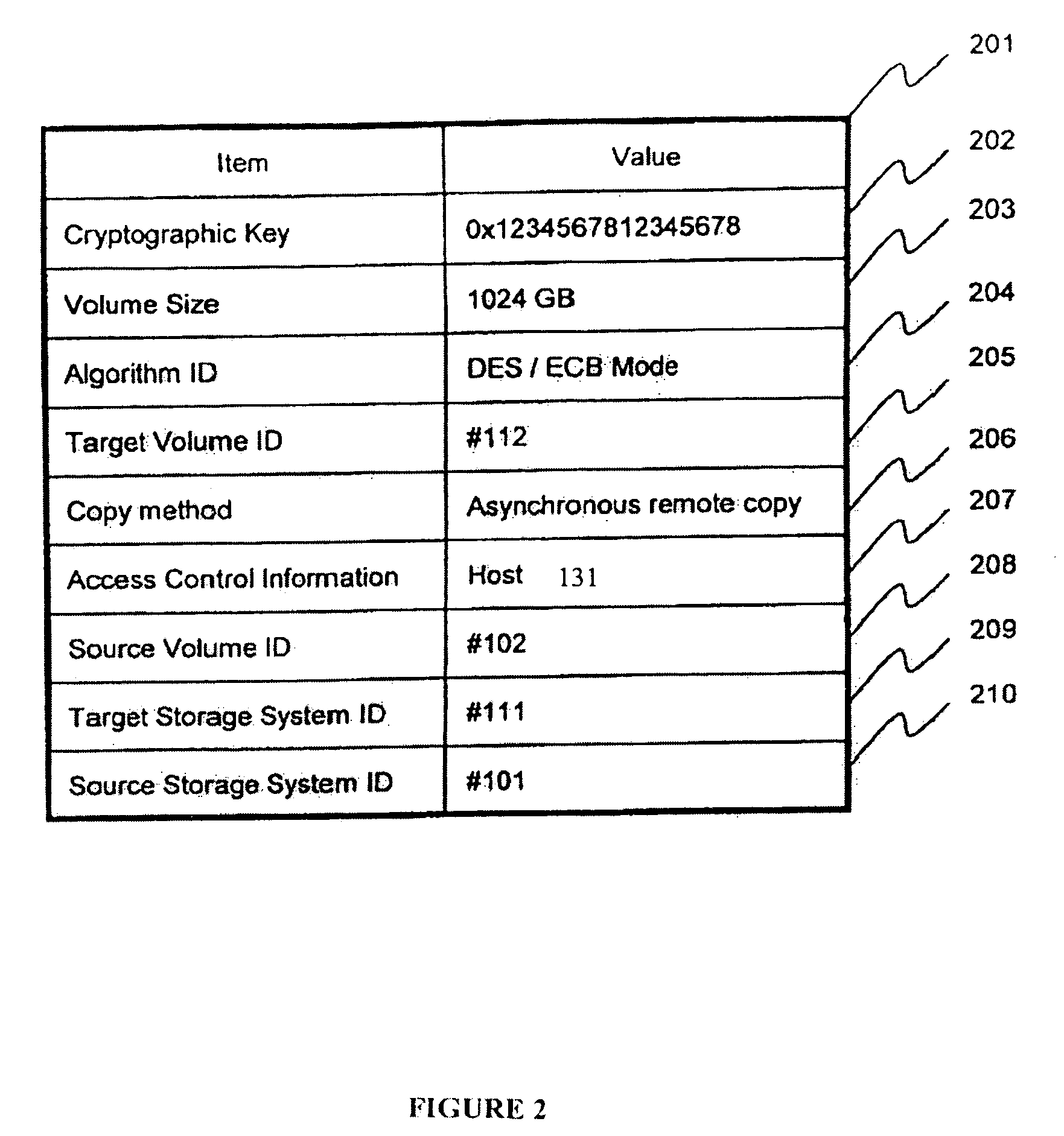
Method and apparatus for encrypted remote copy for secure data backup and restoration
InactiveUS20060005048A1Conveniently implemented in programmingDigital data processing detailsUser identity/authority verificationThird partyData source
Data at a primary storage system is encrypted and remote copied to a secondary storage system. A Remote Copy Configuration Information (RCCI) is created that identifies the encryption mechanism, keys, data source volume, and target volume for the remote copy. The RCCI is backed up on a trusted computer system. In one embodiment, the secondary storage system is an off-site data storage system managed by a third party. Upon detection of a failure in the primary storage system, the encrypted data and RCCI are transferred to a tertiary server, which is optionally created upon detection of the failure, and operations of the failed primary server are resumed by the tertiary server. In one embodiment, the failure is detected by loss of a heart beat signal transmitted from the primary storage system to a management server that initiates the transfers to the tertiary server.
Owner:HITACHI LTD
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
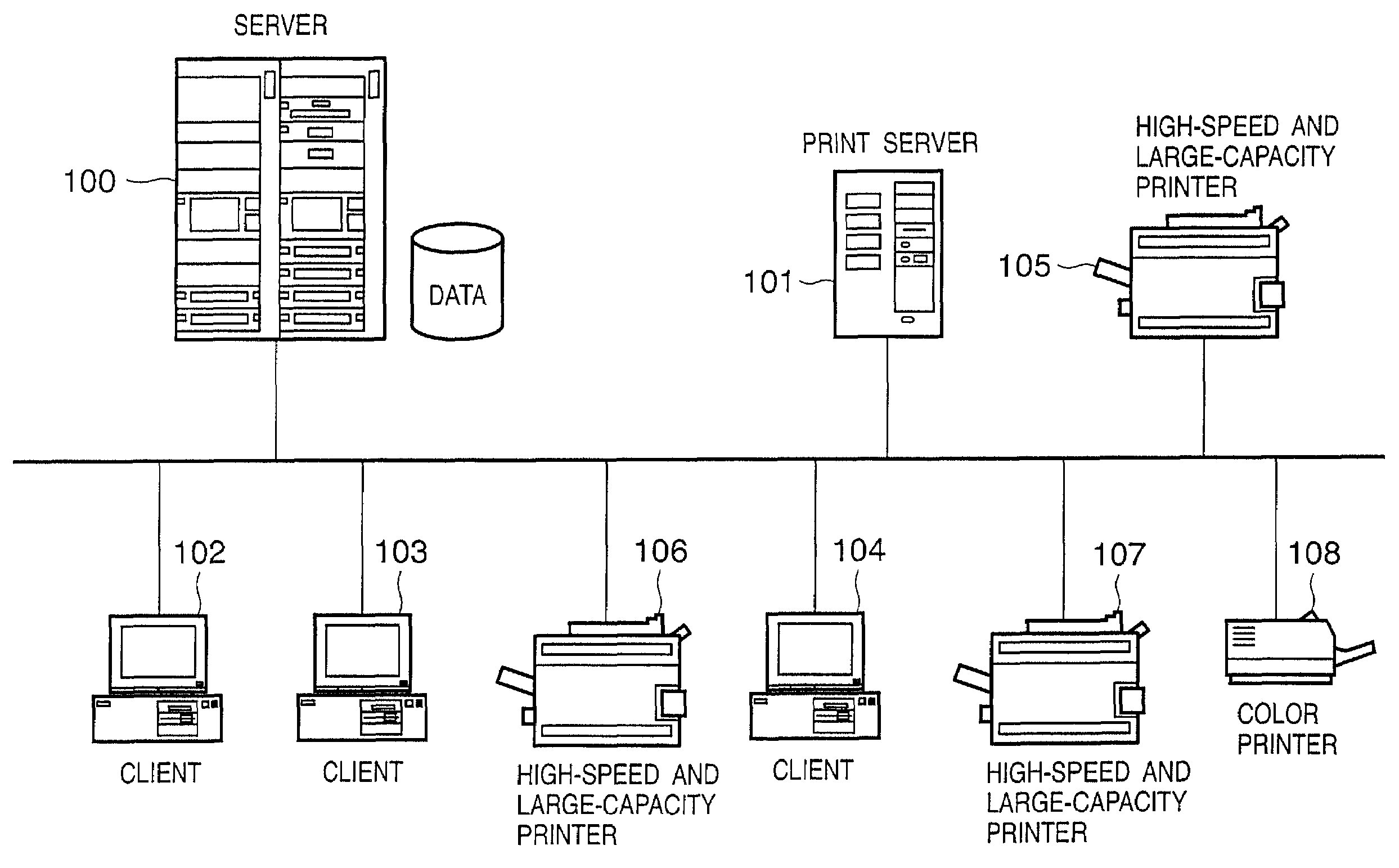
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
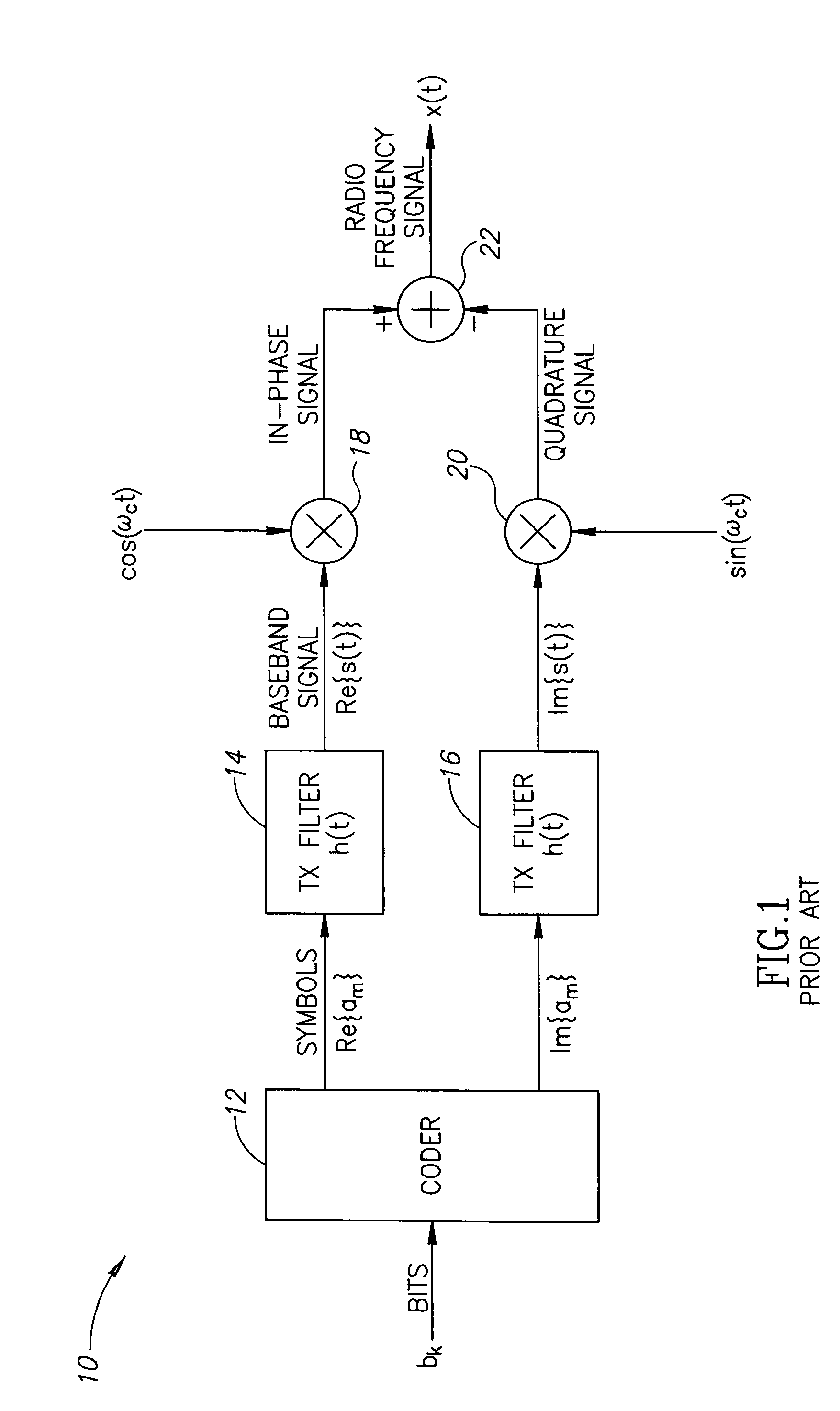
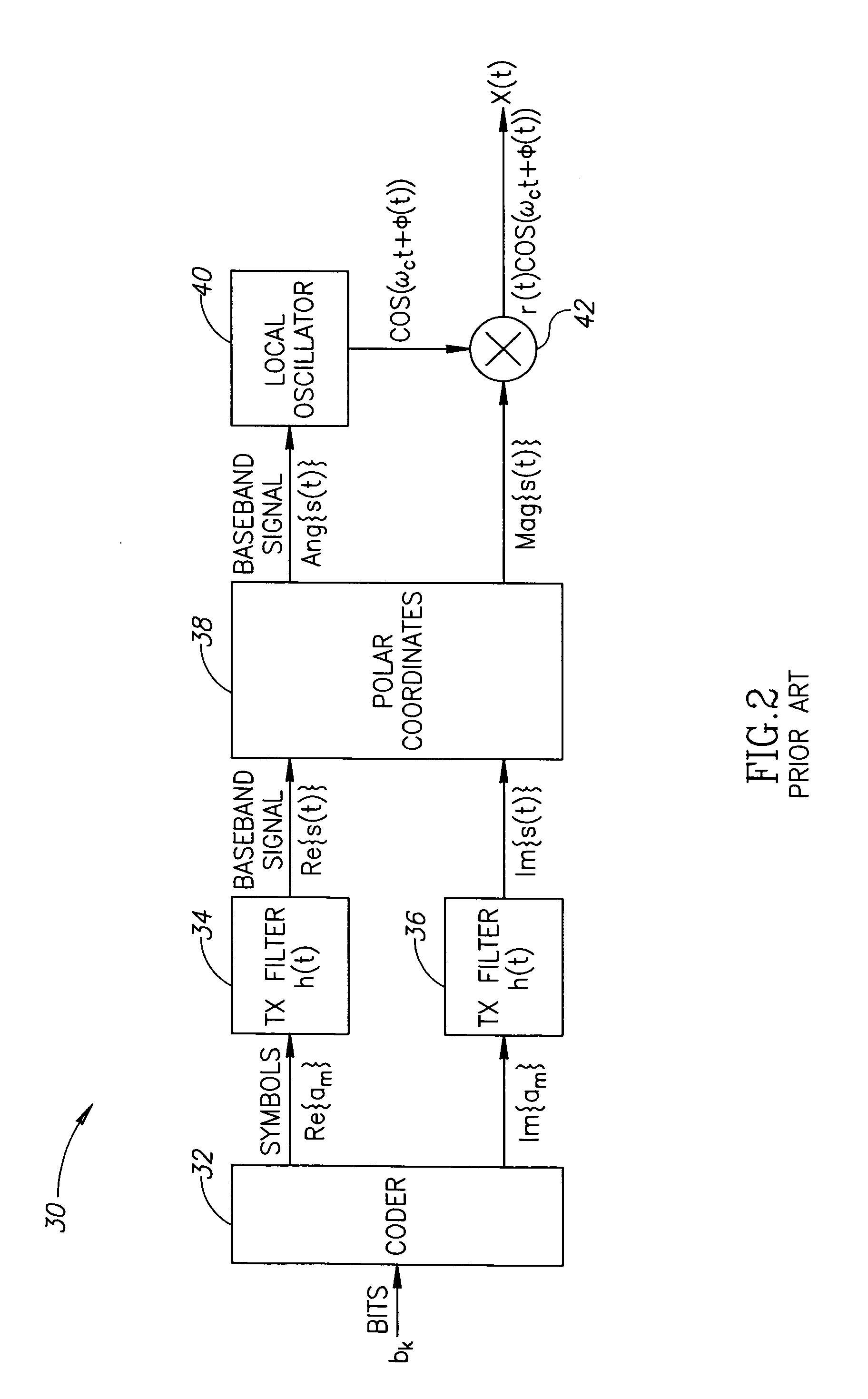
Hybrid polar/cartesian digital modulator
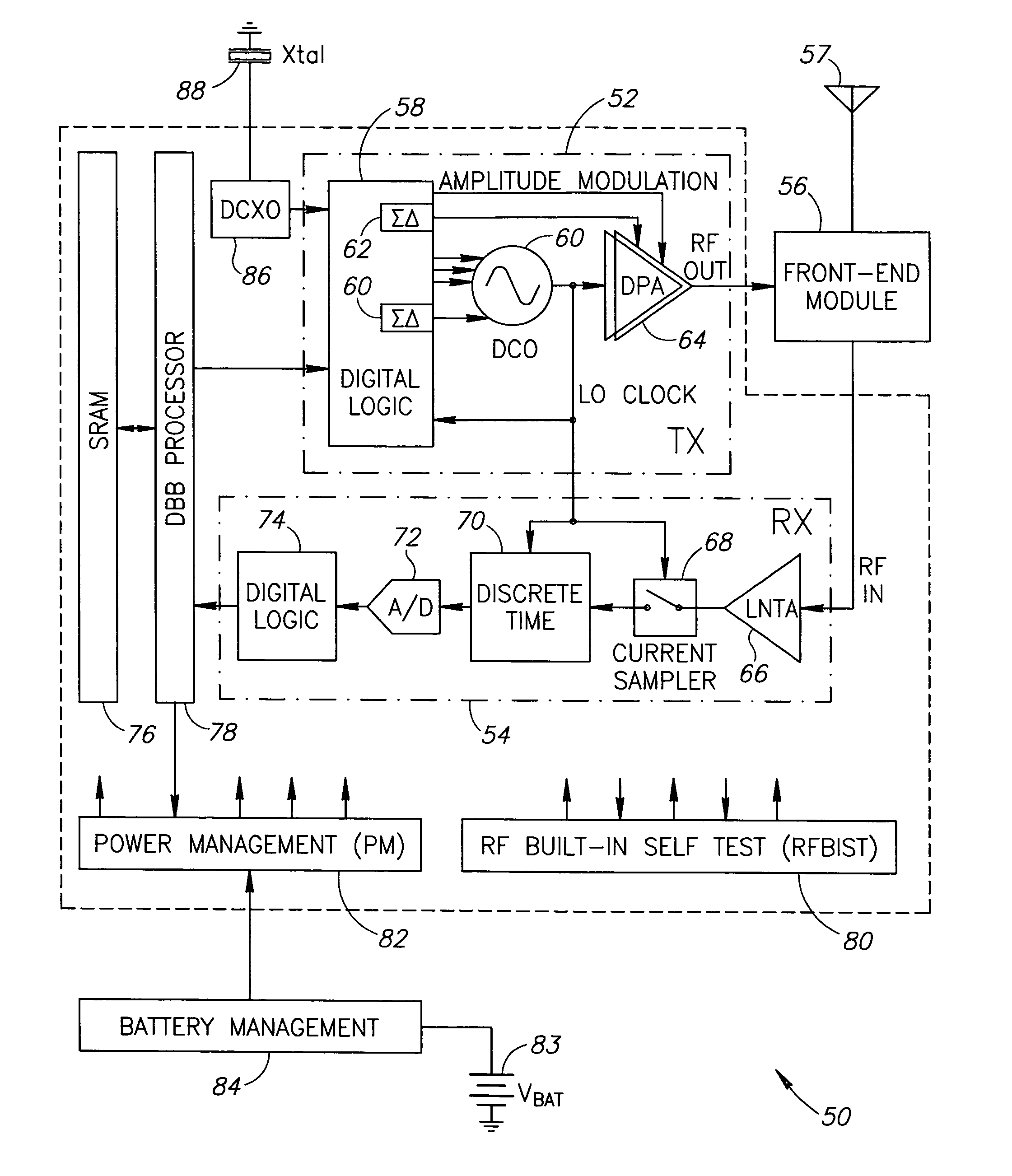
ActiveUS20060038710A1Reconfigurable analogue/digital convertersAnalogue conversionControl powerEngineering
A novel apparatus and method for a hybrid Cartesian / polar digital QAM modulator. The hybrid technique of the present invention utilizes a combination of an all digital phase locked loop (ADPLL) that features a wideband frequency modulation capability and a digitally controlled power amplifier (DPA) that features interpolation between 90 degree spaced quadrature phases. This structure is capable of performing either a polar operation or a Cartesian operation and can dynamically switch between them depending on the instantaneous value of a metric measured by a thresholder / router. In this manner, the disadvantages of each modulation technique are avoided while the benefits of each are exploited.
Owner:TEXAS INSTR INC
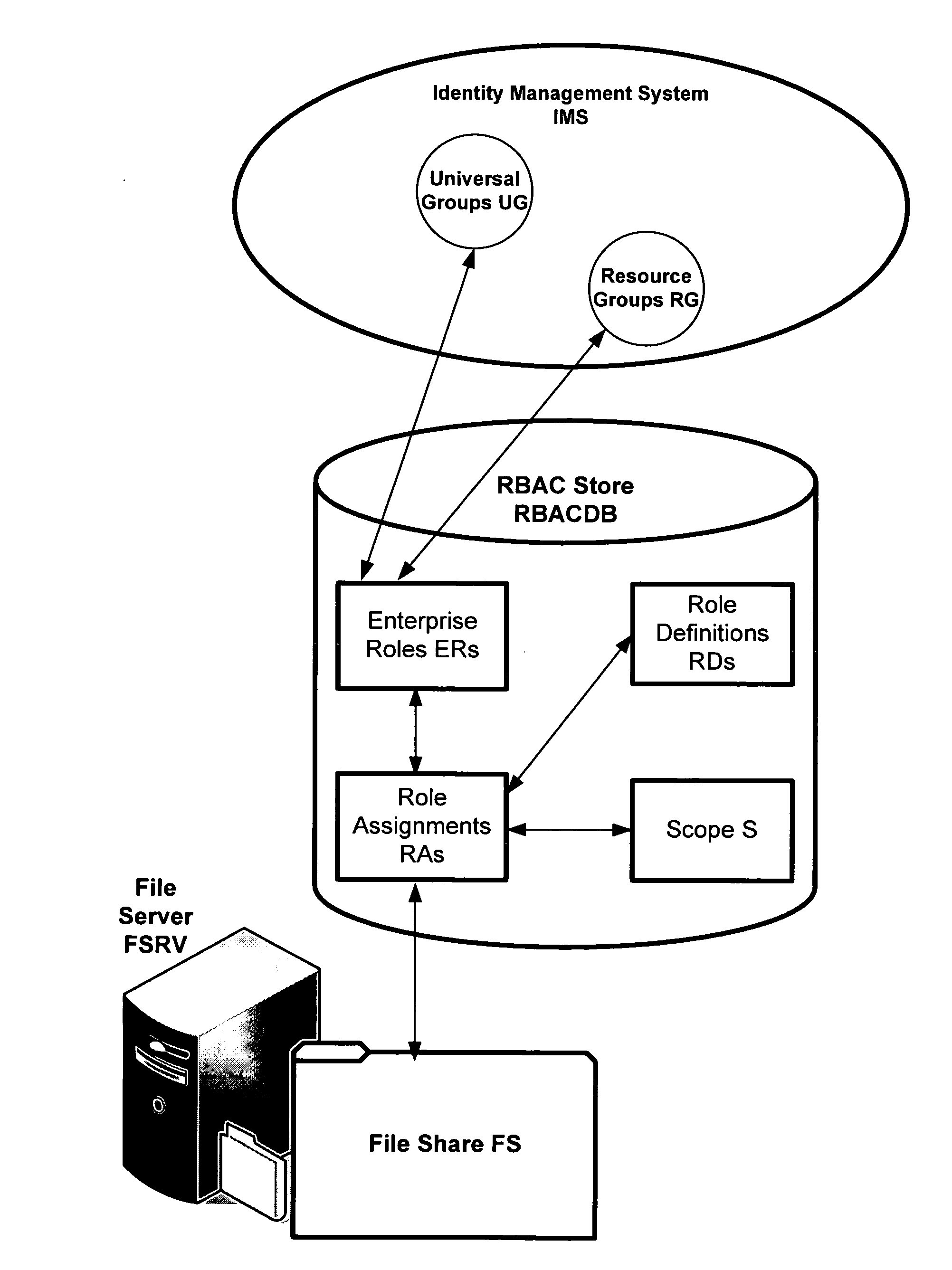
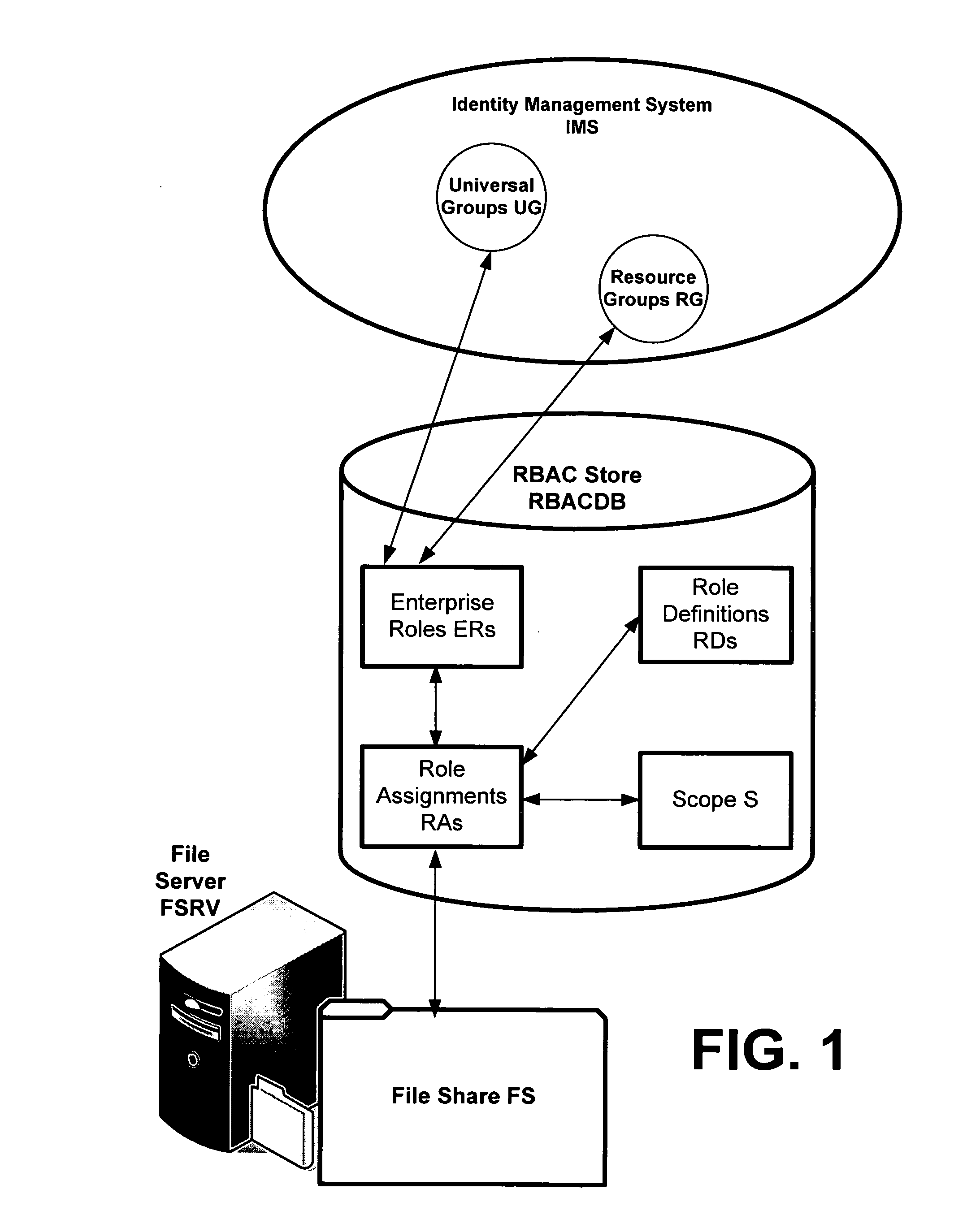
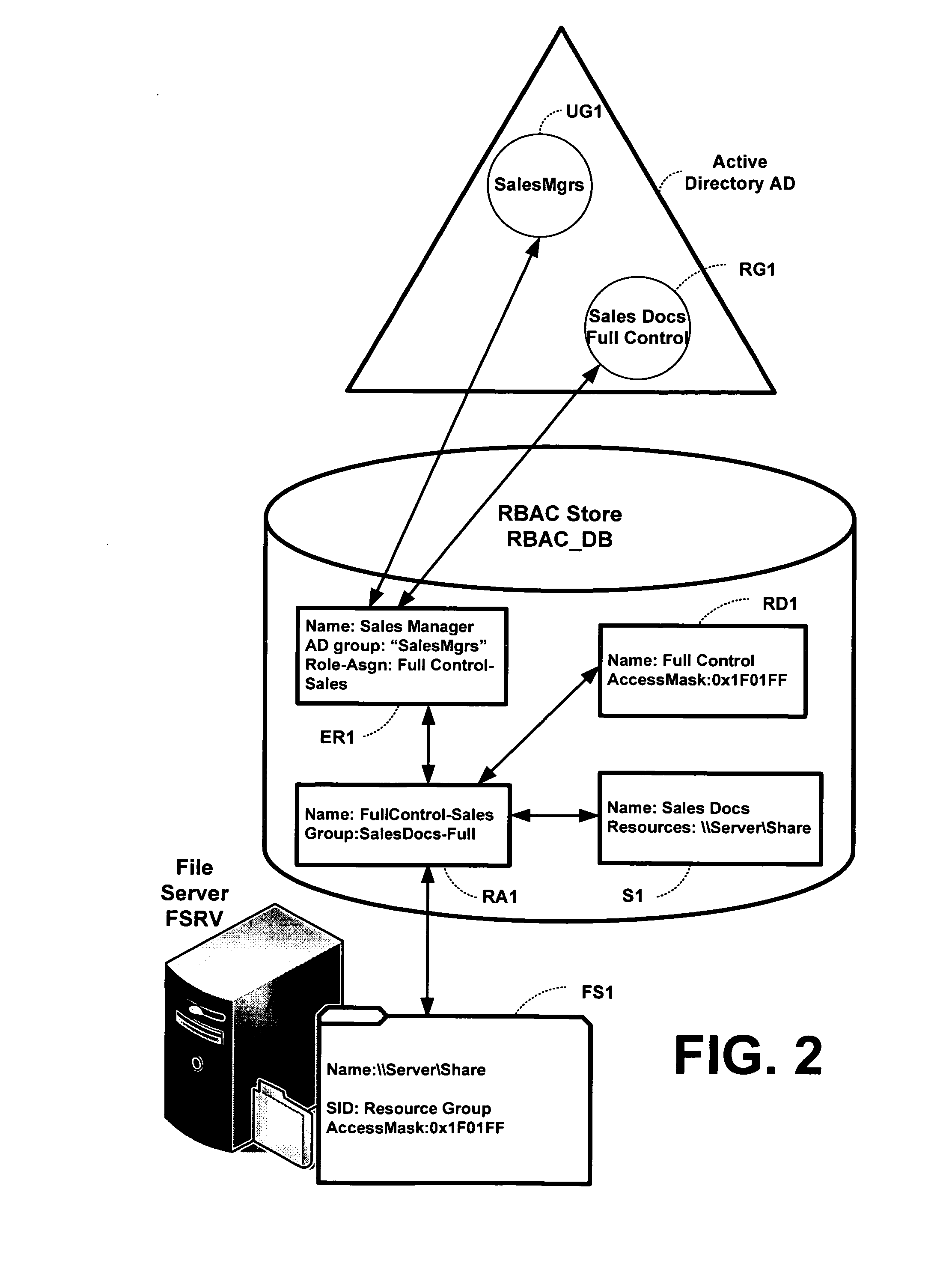
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
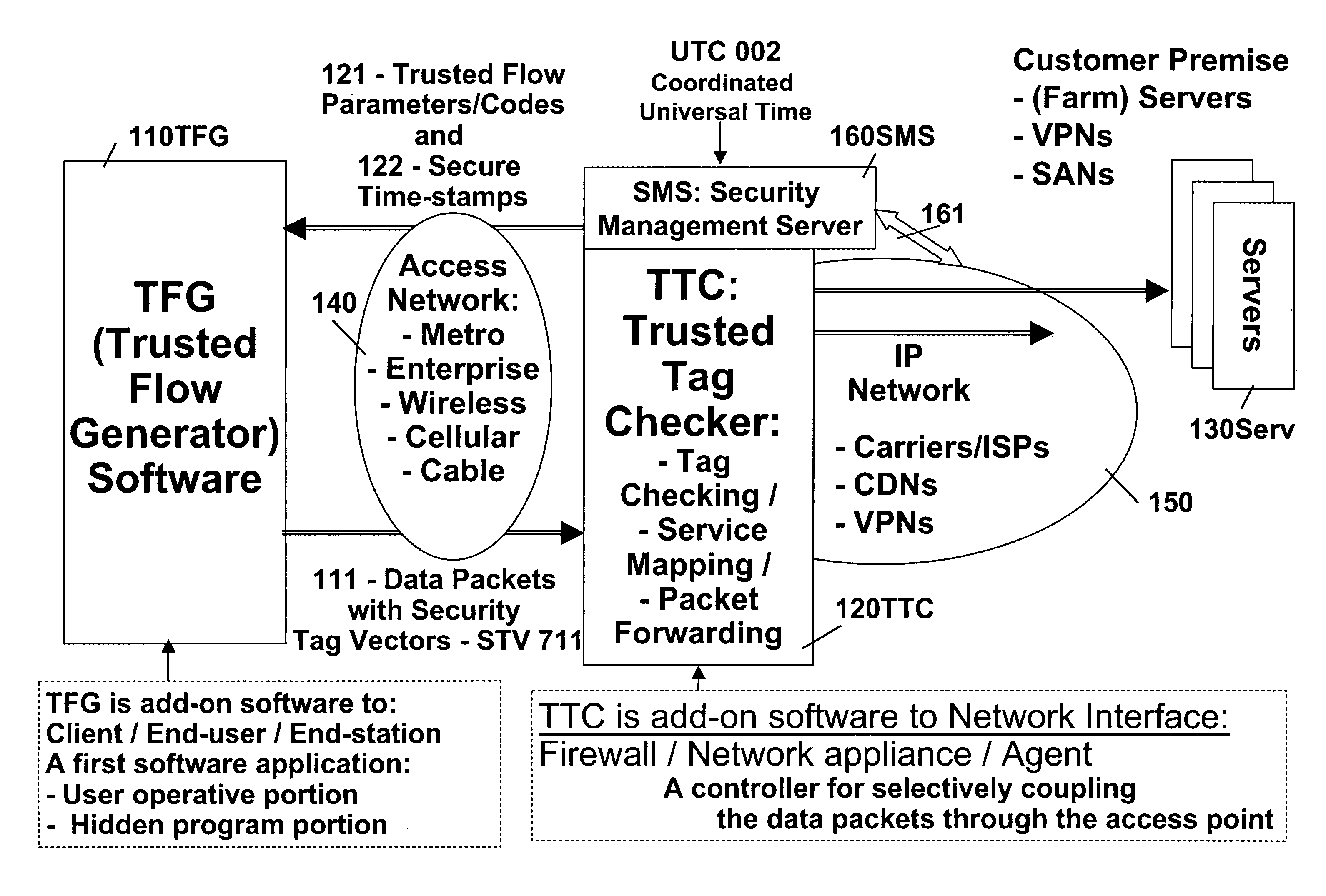
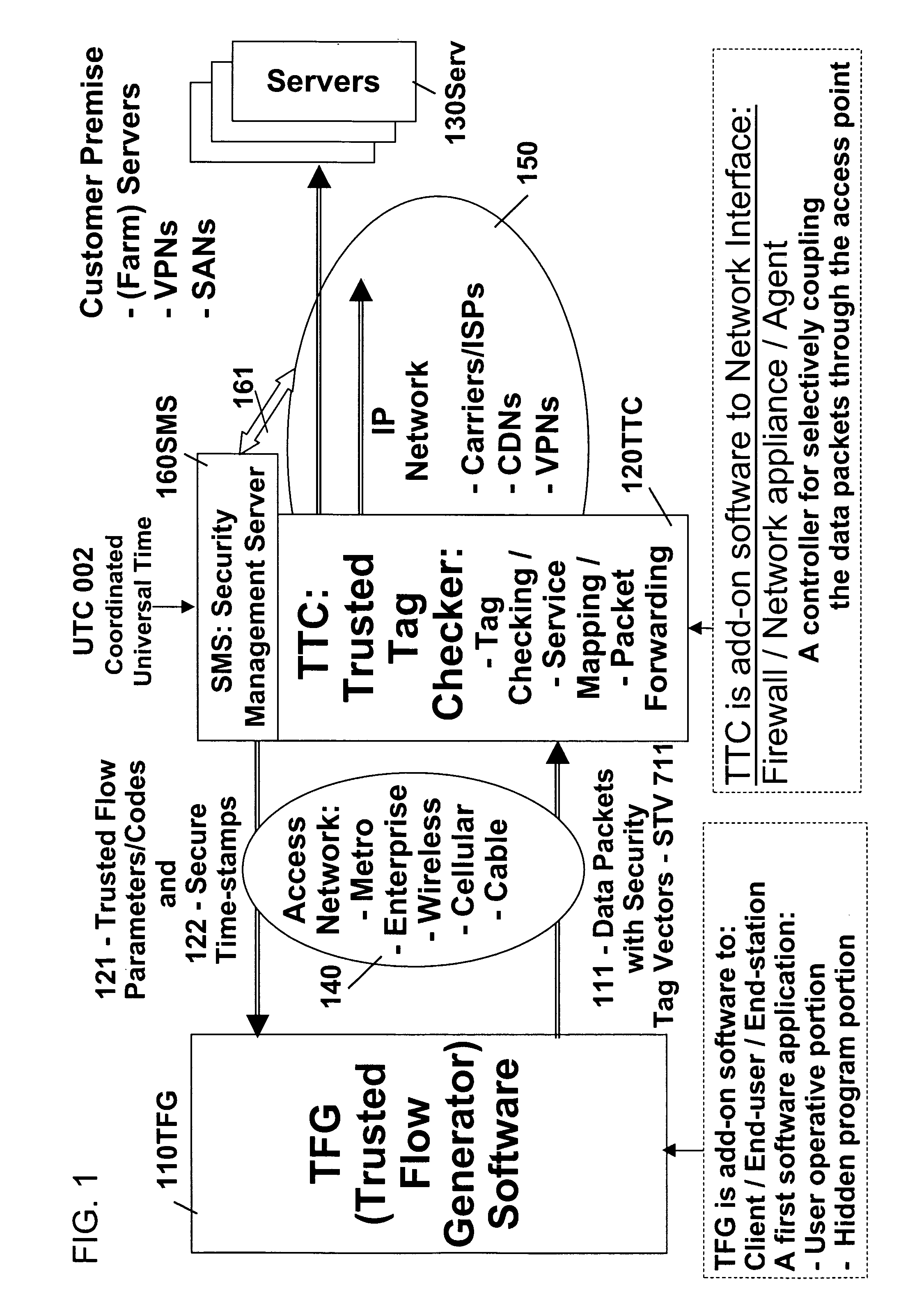
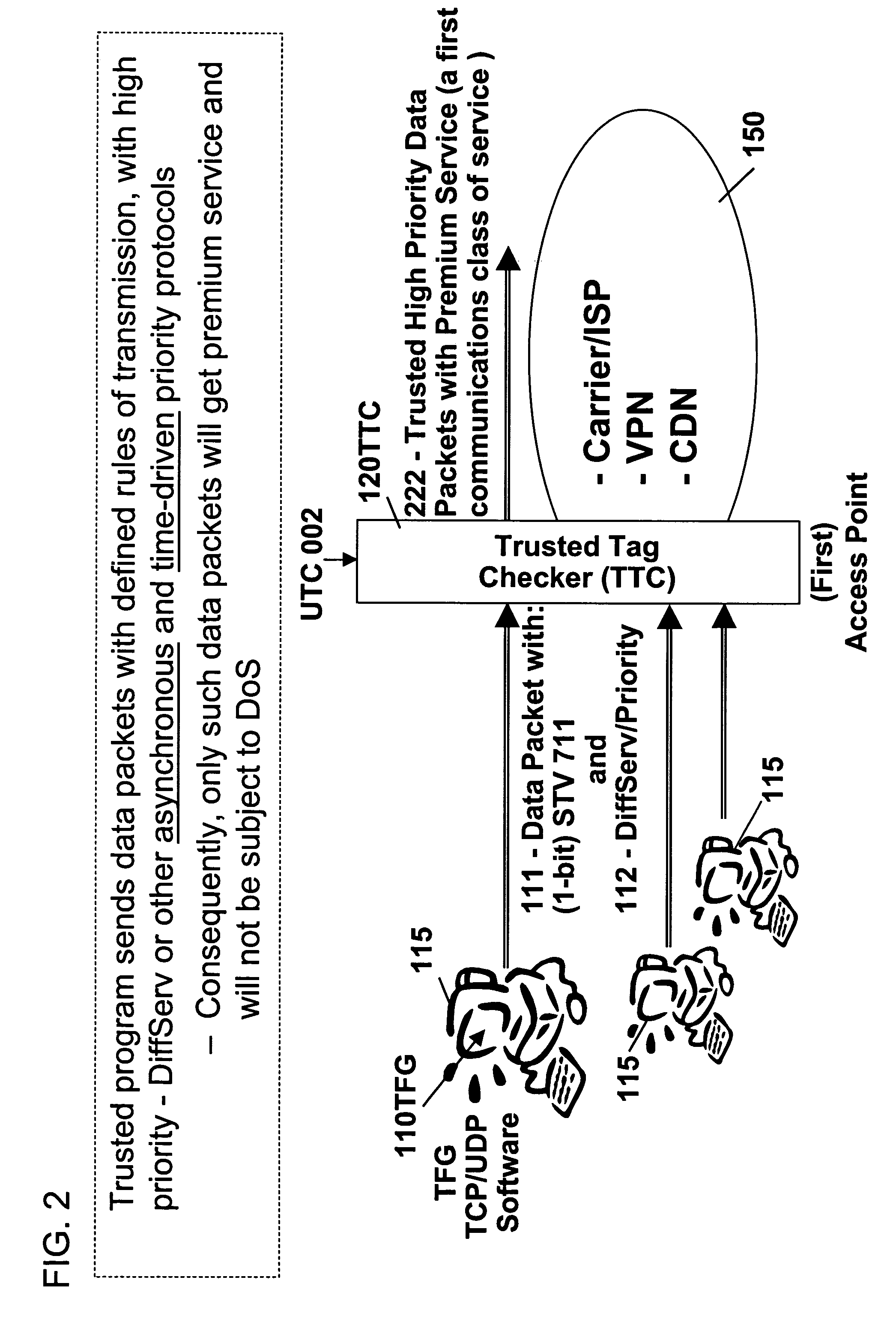
Remotely authenticated operation method
InactiveUS7509687B2Improvement effortsEfficient use ofDigital data processing detailsUser identity/authority verificationTrusted ComputingMedia server
The objective of this invention is to provide continuous remote authenticated operations for ensuring proper content processing and management in remote untrusted computing environment. The method is based on using a program that was hidden within the content protection program at the remote untrusted computing environment, e.g., an end station. The hidden program can be updated dynamically and it includes an inseparable and interlocked functionality for generating a pseudo random sequence of security signals. Only the media server that sends the content knows how the pseudo-random sequence of security signals were generated; therefore, the media server is able to check the validity of the security signals, and thereby, verify the authenticity of the programs used to process content at the remote untrusted computing environment. If the verification operation fails, the media server will stop the transmission of content to the remote untrusted computing environment.
Owner:ATTESTWAVE LLC
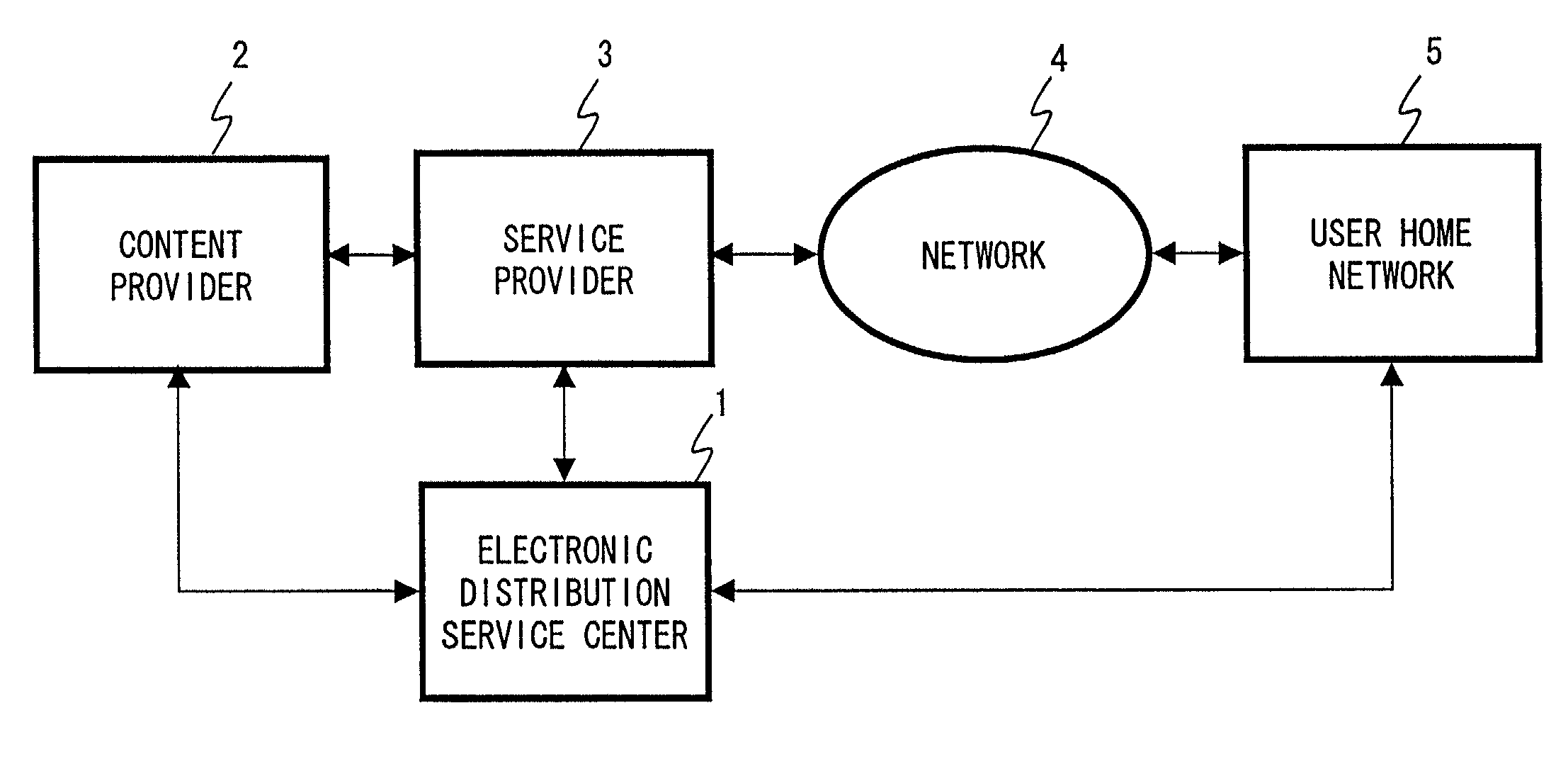
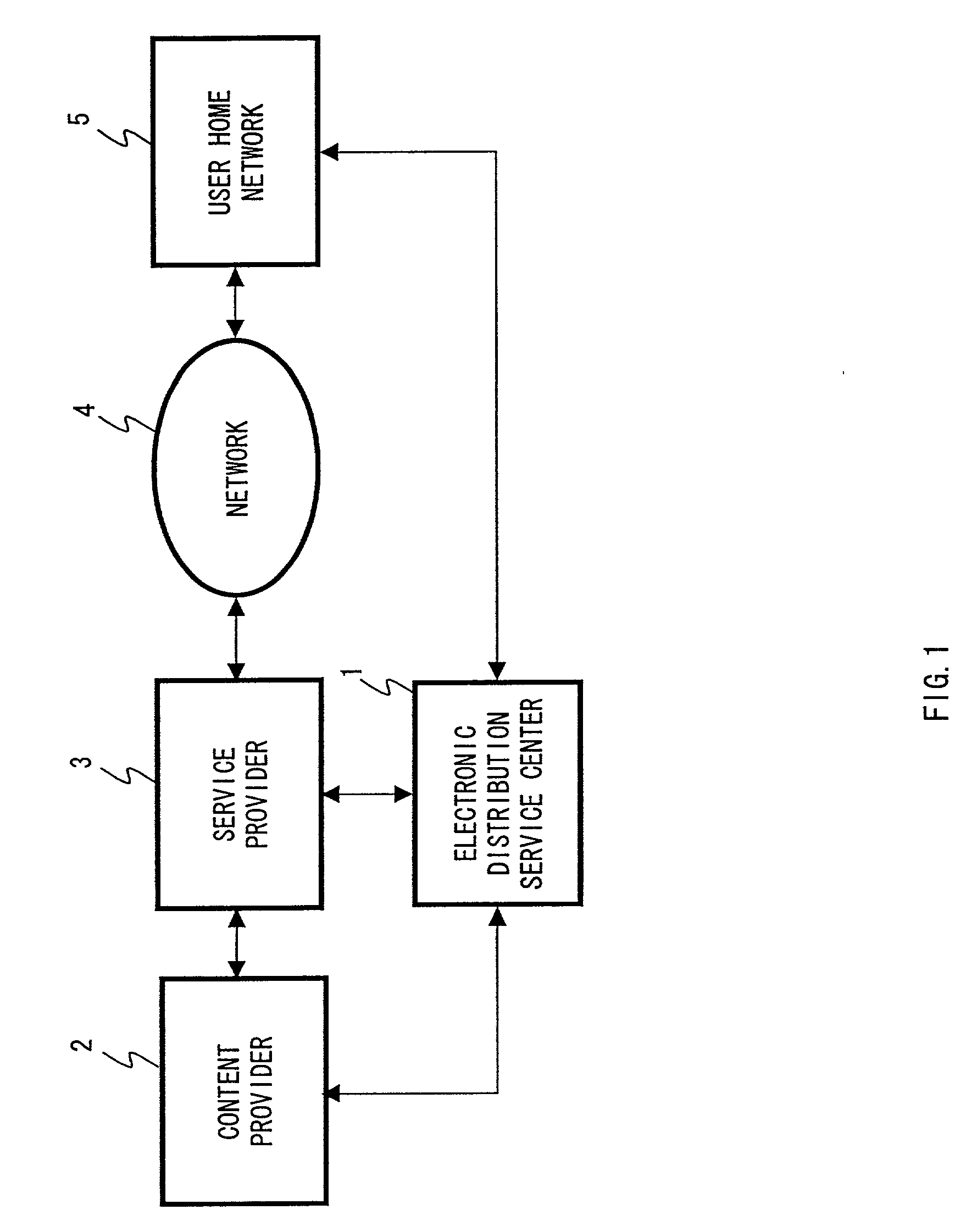
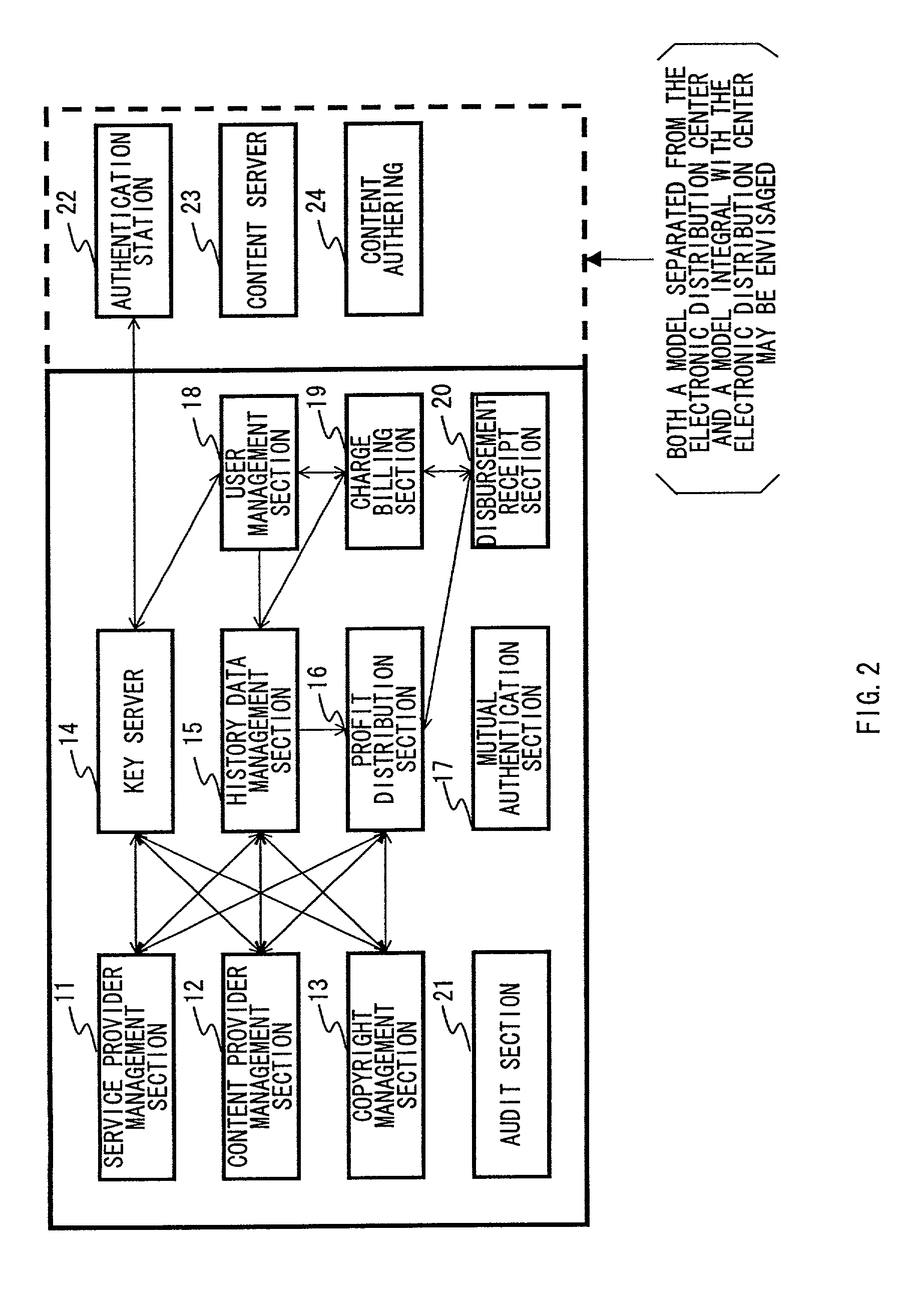
Systems and methods for content distribution using one or more distribution keys
InactiveUS7353541B1Inhibited DiffusionTelevision system detailsDigital data processing detailsContent distributionData store
Owner:SONY CORP
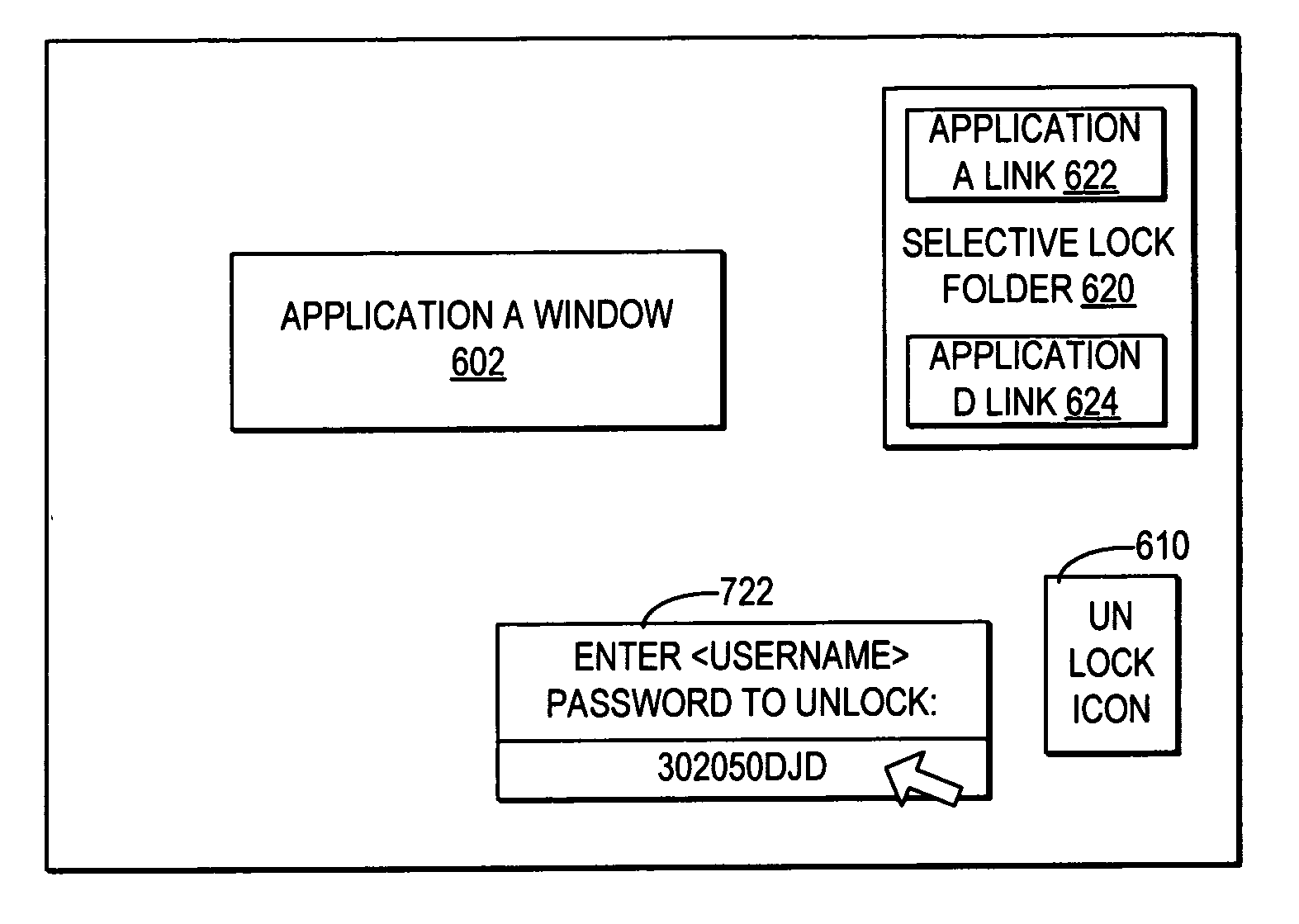
Allowing any computer users access to use only a selection of the available applications
InactiveUS20070016958A1Reduce usageDigital data processing detailsUser identity/authority verificationComputer usersUser input
A computer system operates in normal mode where all applications and files are accessible to an authorized user, where an authorized user enters a required log in to access all applications. When a trigger to change the control access from normal mode to selective lock mode is detected, access to the applications and files is blocked and the content within the user interface is cleared to initiate the selective lock mode. Next, content is added to the user interface including a folder with only a selection of the applications each accessible through a separate selectable link, where the selectable links are designated in the particular folder by an authorized user during normal mode. During selective lock mode, any user may only select to open one of the selection of applications by selecting a displayed selectable link for the application. Responsive to a selection of a selectable link, a wrapper function is called that opens the application, wherein any user is enabled to fully access only the wrappered application and the wrapper blocks access to the remainder of the computer system, such that during selective lock mode any user is presented with access, without first logging in, to a fully functioning version of each of the selection of applications designated by the authorized user in the particular folder.
Owner:IBM CORP
Search Hit URL Modification for Secure Application Integration
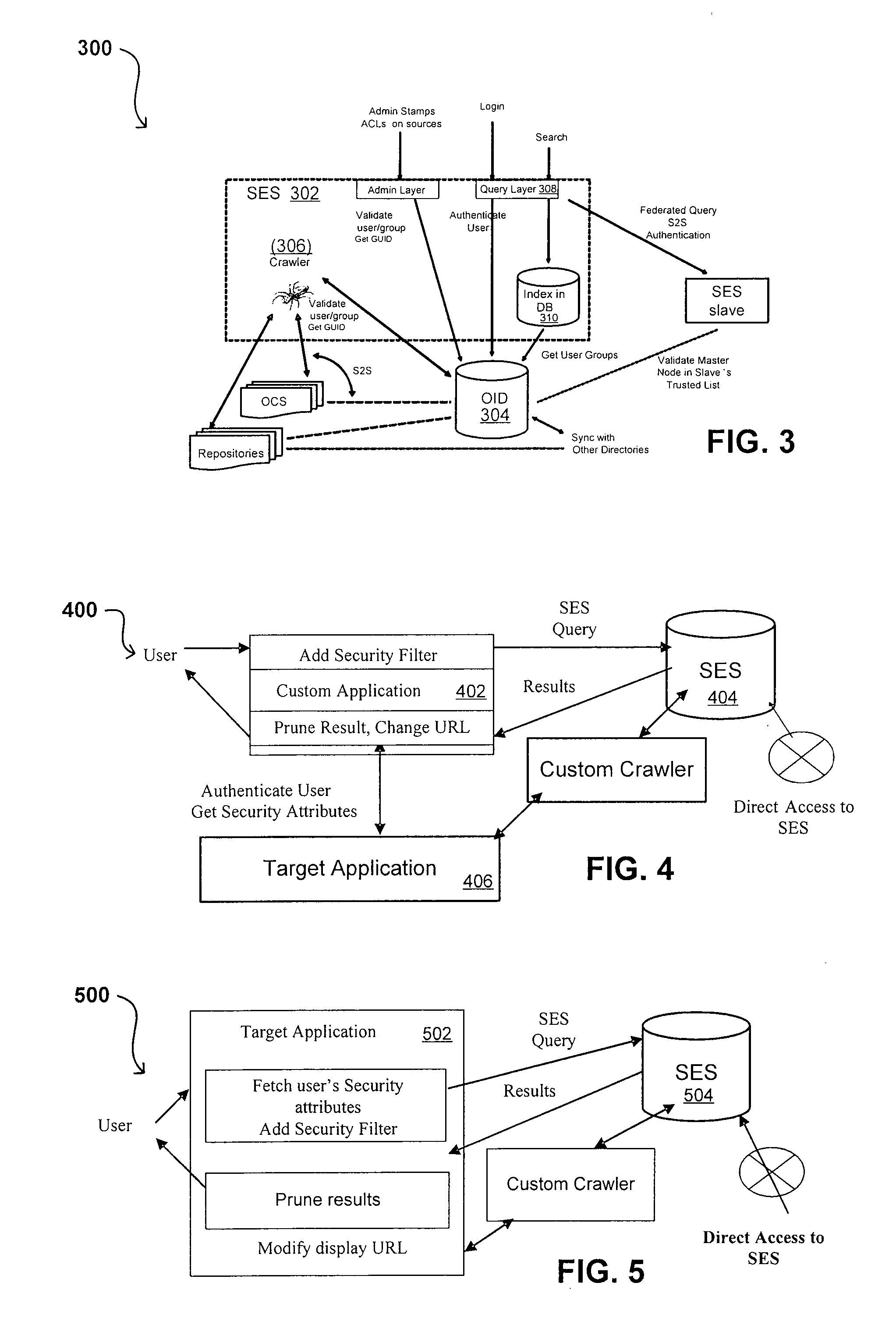
ActiveUS20070209080A1Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Method and system for providing a secure multi-user portable database
ActiveUS20070006322A1Easy to useLimited storage capabilityFinanceDigital data processing detailsMedical recordFile allocation
A system and method for providing, managing, and accessing a multi-user secure portable database using secure memory cards is provided. The database has a secure portion for storing security keys and a non-secure portion for encrypted data files. Access to the encrypted data files is controlled by assigning access rights through an access control matrix to each encrypted data file according to a hierarchical structure of users. A user requesting access is identified in the hierarchy, associated with a key for allowing the requested access, and the requested access allowed to a file in accordance with the rights allocated through the access control matrix. A patient can selectively grant access to encrypted medical records on his card to a physician. Authentication of the owner / patient is preferably required. Other records required by emergency medical personnel are readable from the same card without requiring permission from the patient.
Owner:PRIVAMED
Platform and service for management and multi-channel delivery of multi-types of contents
ActiveUS20060272028A1Random number generatorsUser identity/authority verificationIdentity managementContent management
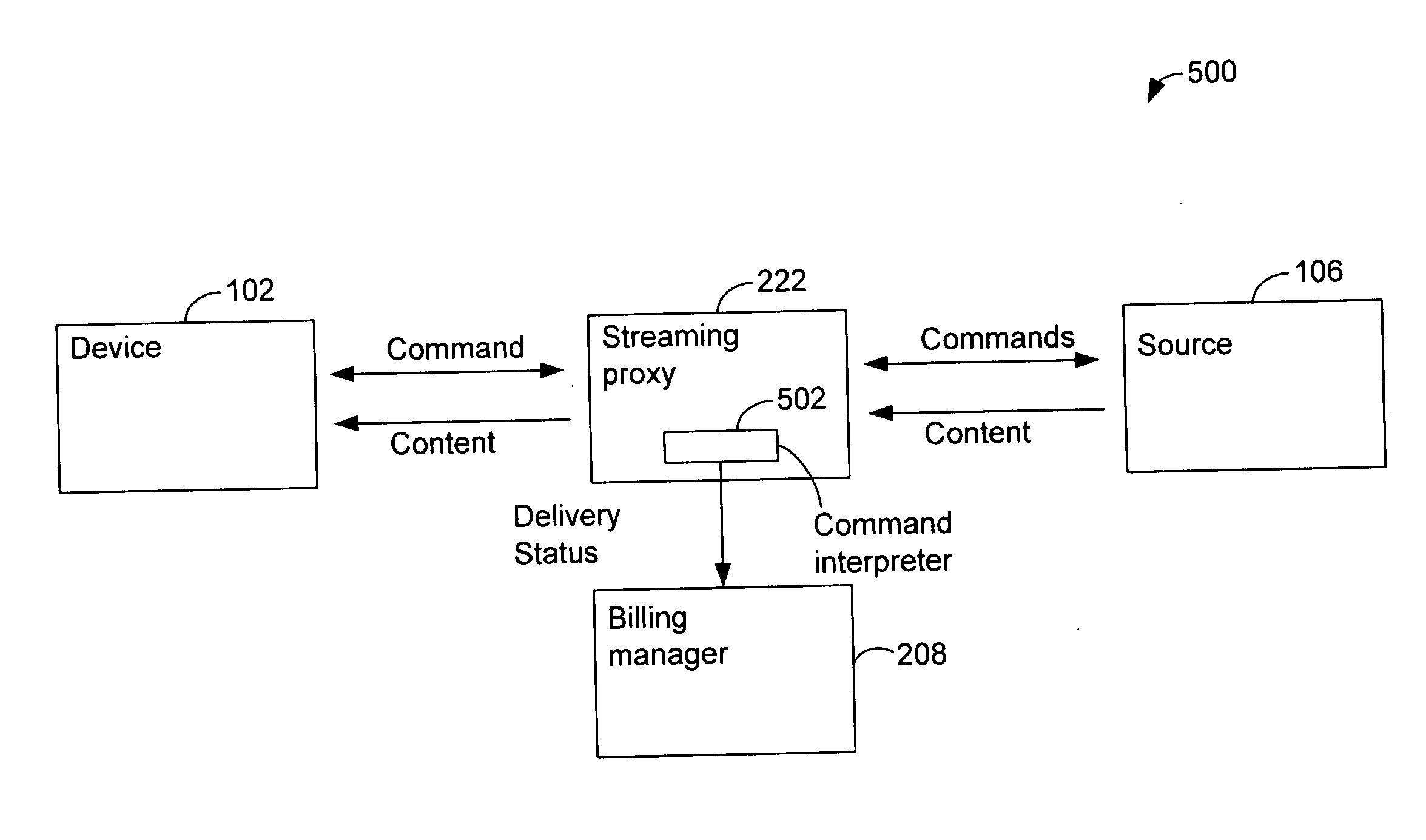
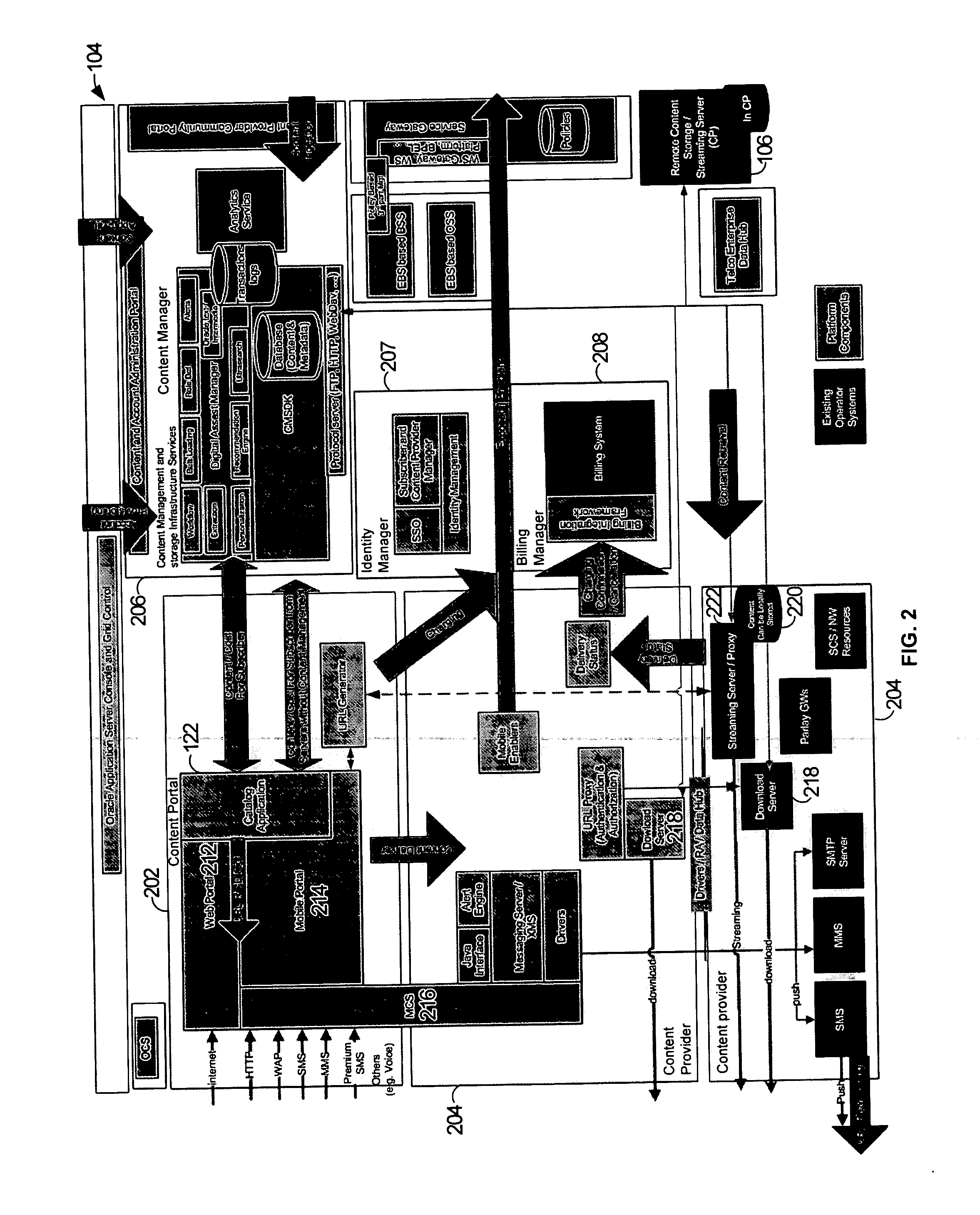
A platform for managing delivery of content originating from one or more content providers to users is provided. The platform includes a portal that is configured to support access through a plurality of access channels configured to receive requests through one or more access channels. A request for content is received from an access device through an access channel. An identity management module is configured to determine a user associated with the message. A content manager is configured to manage content for delivery through the plurality of access channels and configured to determine eligible content for the user. A billing module is configured to process billing for the user and content provider based on the content provided to the user. The content manager is then configured to deliver the requested content to the user's access device through the access channel.
Owner:ORACLE INT CORP
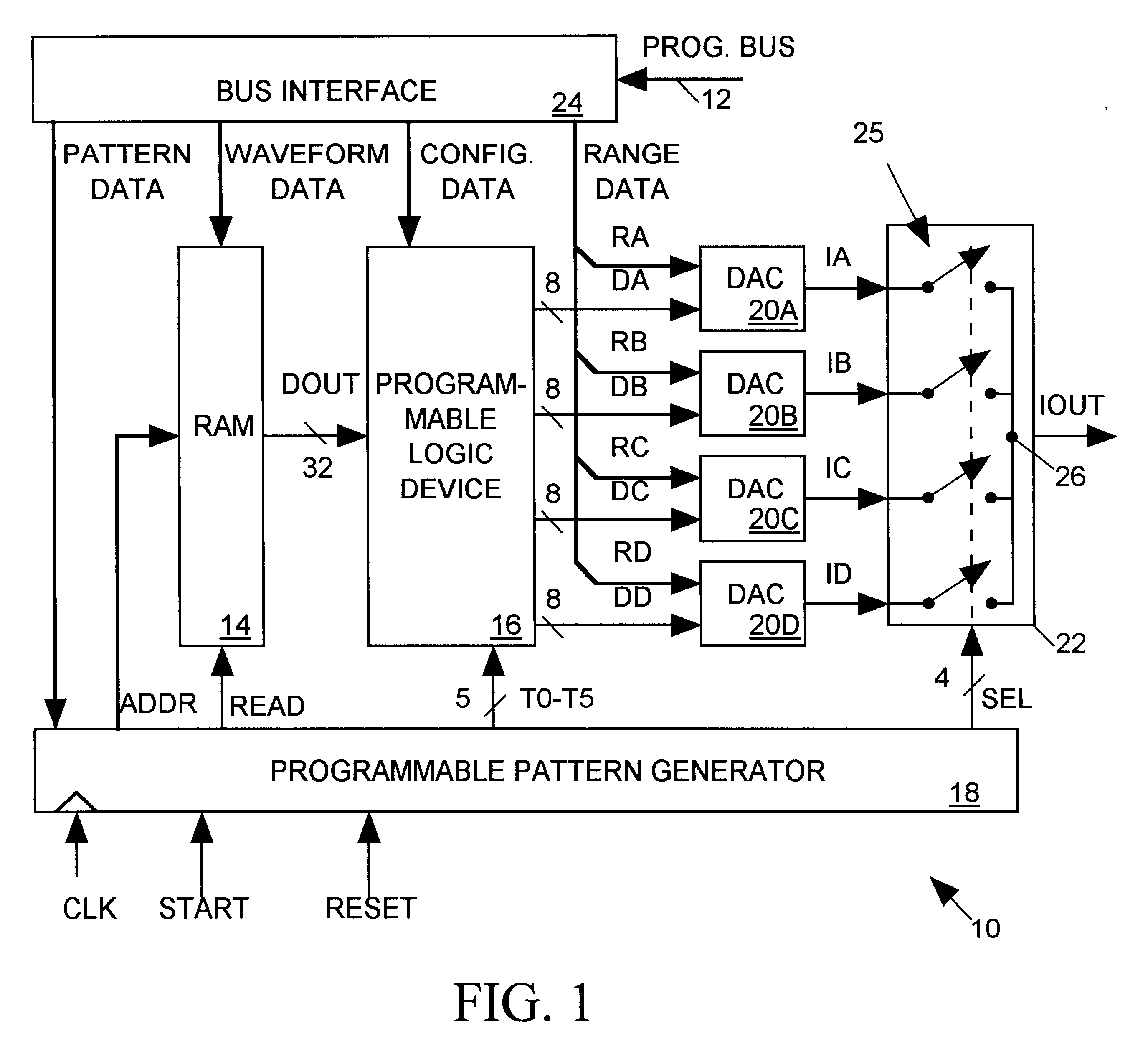
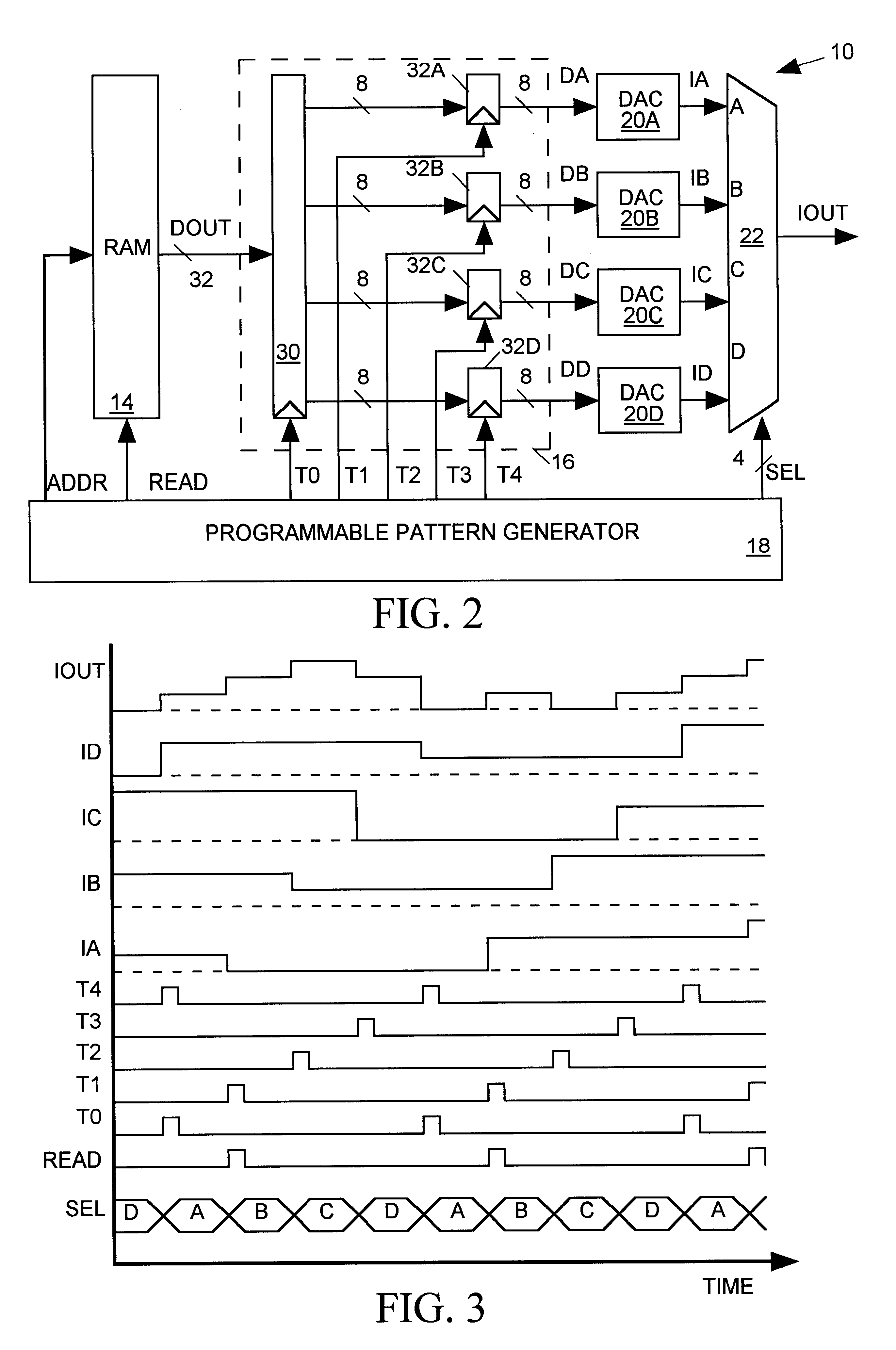
Arbitrary waveform generator having programmably configurable architecture
InactiveUS6356224B1Electric signal transmission systemsOscillations generatorsDigital analog converterMultiplexer
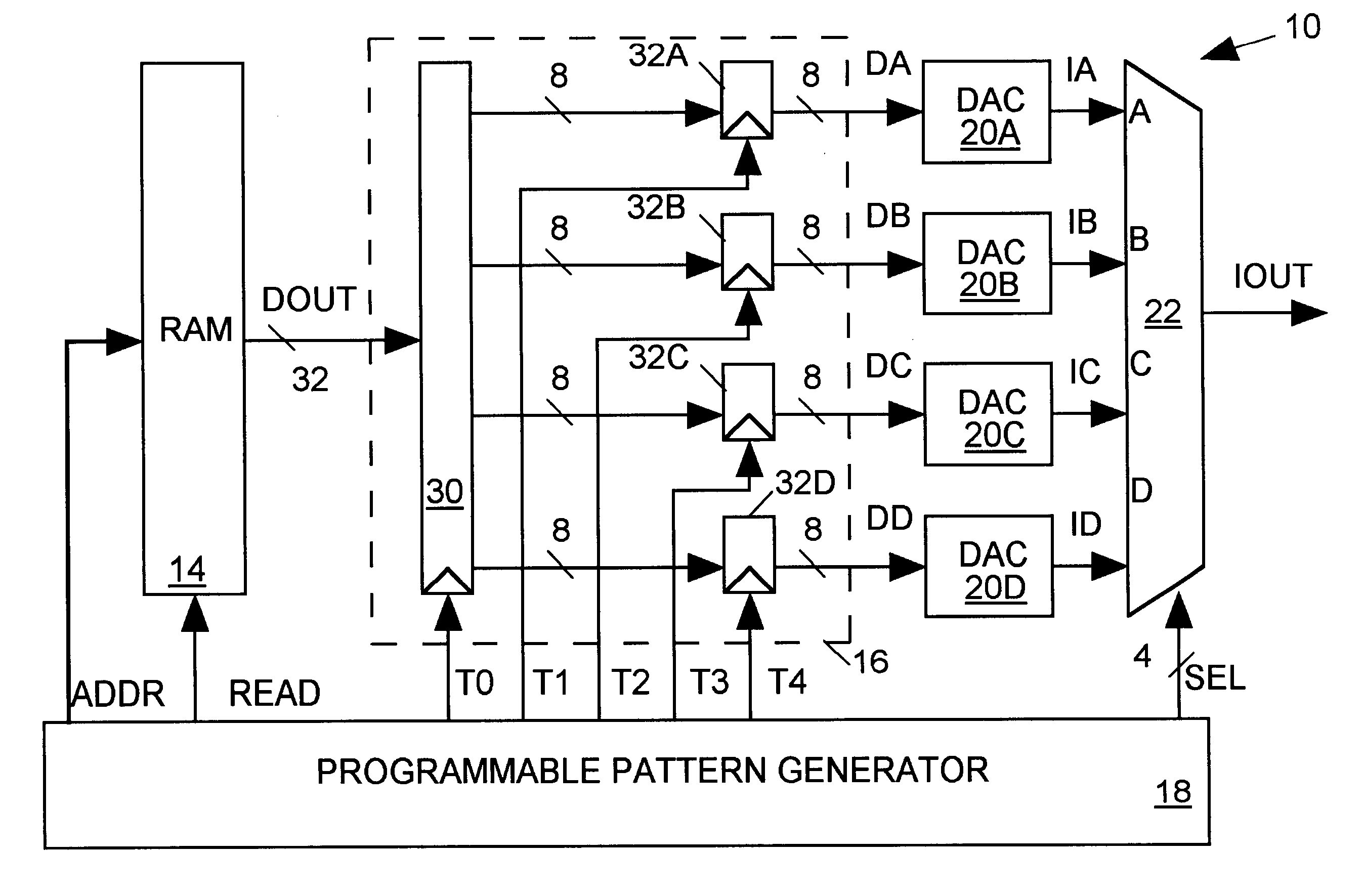
An arbitrary waveform generator (AWG) for producing an analog output current signal includes a random access memory (RAM), a programmable logic device (PLD), a programmable pattern generator, several digital-to analog converters (DACS) and a current multiplexer. The RAM store data sequences representing the analog waveform to be generated. The pattern generator read addresses the RAM causing it to sequentially read out its stored data sequence to the PLD. The PLD routes selected fields of each data sequence word to one or more of the DACs in response to timing signals provided by the pattern generator. Each DAC produces an output current of magnitude determined by its input waveform and range data. The pattern generator also signals the analog multiplexer to sum currents produced by one or more selected DACs to produce the AWG output waveform. The nature of the AWG output waveform is flexibly determined by the nature of the data sequence and the frequency at which it is read out of the RAM, the manner in which the PLD routes the data sequence to the DACs, the value of the range data supplied to each DAC, and the output pattern generated by the pattern generator. The flexible AWG architecture permits the AWG to be appropriately configured for various combinations of output waveform frequency, bandwidth and resolution requirements.
Owner:CREDENCE SYSTEMS
Method and apparatus for simplifying the deployment and serviceability of commercial software environments
InactiveUS20060047974A1Component can be removedEliminate redundancyDigital data processing detailsUser identity/authority verificationComputer hardwareCommercial software
Owner:IBM CORP
Systems and methods of securing resources through passwords
InactiveUS20060041756A1Mitigates password coordination problemMitigating password coordination problemDigital data processing detailsUser identity/authority verificationPasswordData file
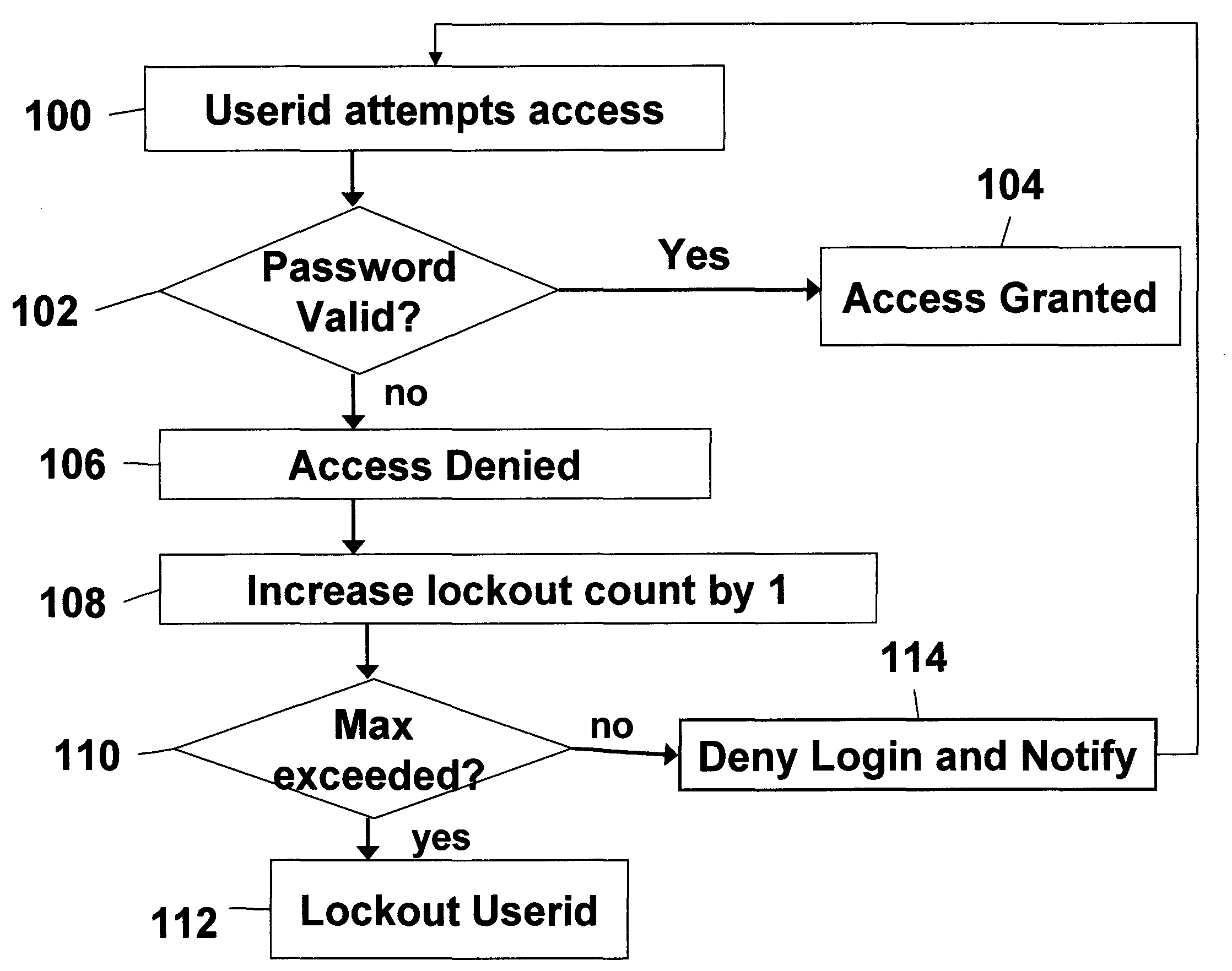
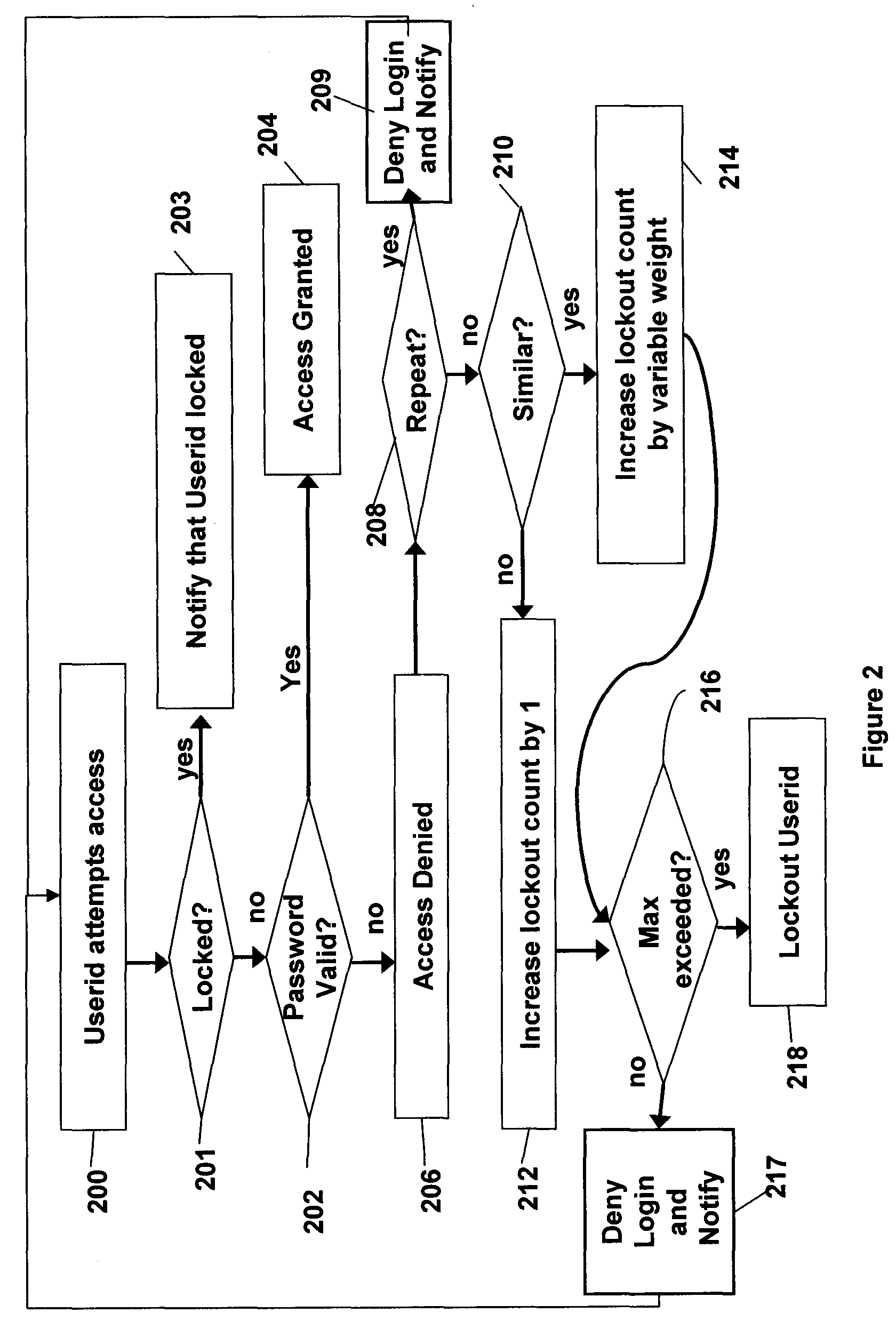
Disclosed is a method of authorizing access to an item that maintains a lockout count and blocks access to the item if the lockout count exceeds a predetermined value. One feature is that the invention “variably” increments the lockout count if the presented password fails to exactly match the stored password. In this process the invention increments the lockout count different amounts depending upon how closely the presented password matches the stored password. The invention also provides a methodology that allocates a plurality of the same passwords to a plurality of users who share the same userid. The invention allows continuous operation of the item being accessed by providing that each of the passwords has a different expiration date. Also, when dealing with situations where a plurality of users who share the same userid also share the same password, the invention maps information associated with the users to the password in a data file and periodically updates the data file.
Owner:IBM CORP
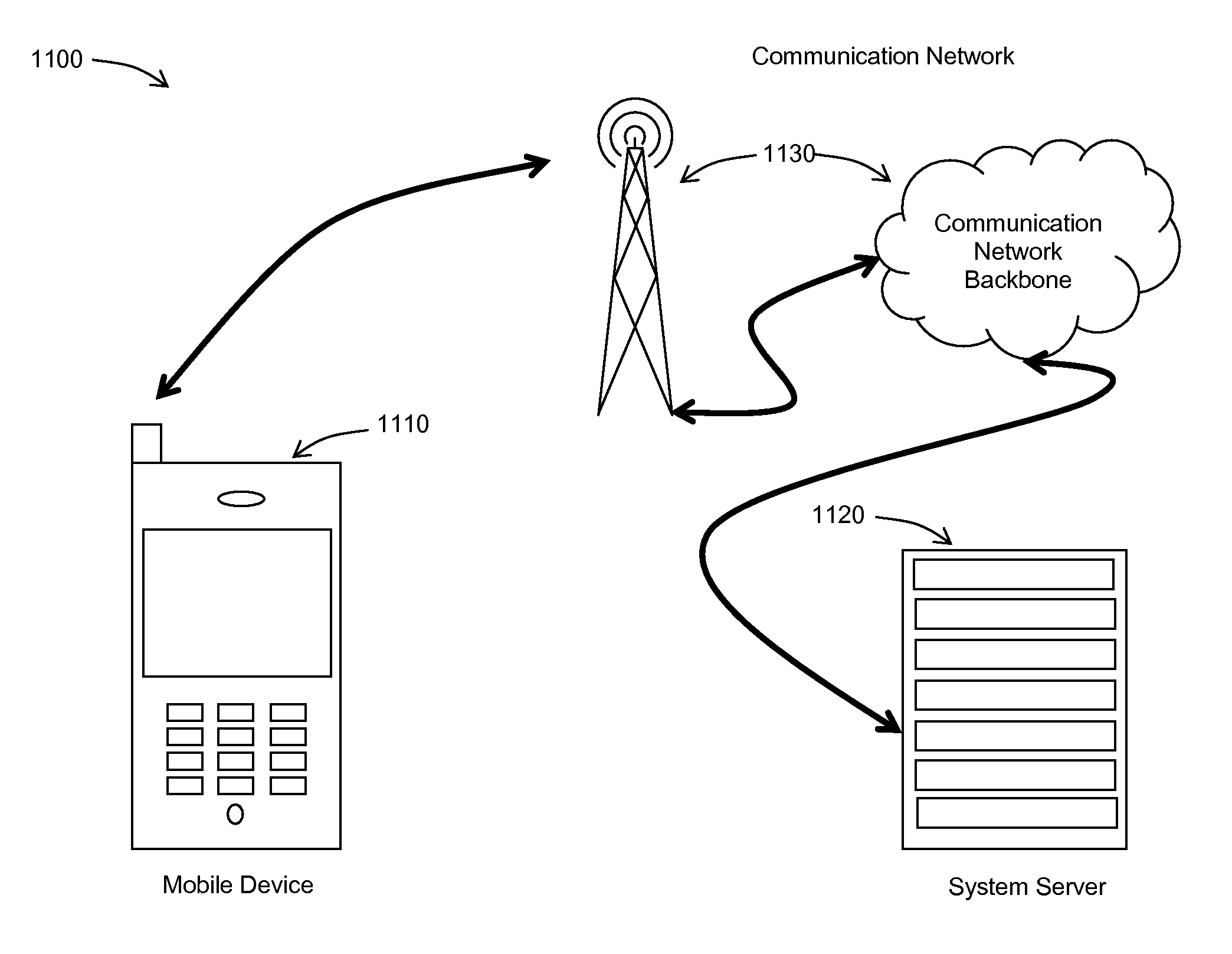
System and Method for Providing Digital Content on Mobile Devices
InactiveUS20070079383A1Multimedia data browsing/visualisationDigital data processing detailsDigital contentNumber content
A system and methods for providing digital content on mobile devices is described. User interfaces and methods for requesting, presentation, communication and storage of digital content are also described.
Owner:TAHOE RES LTD
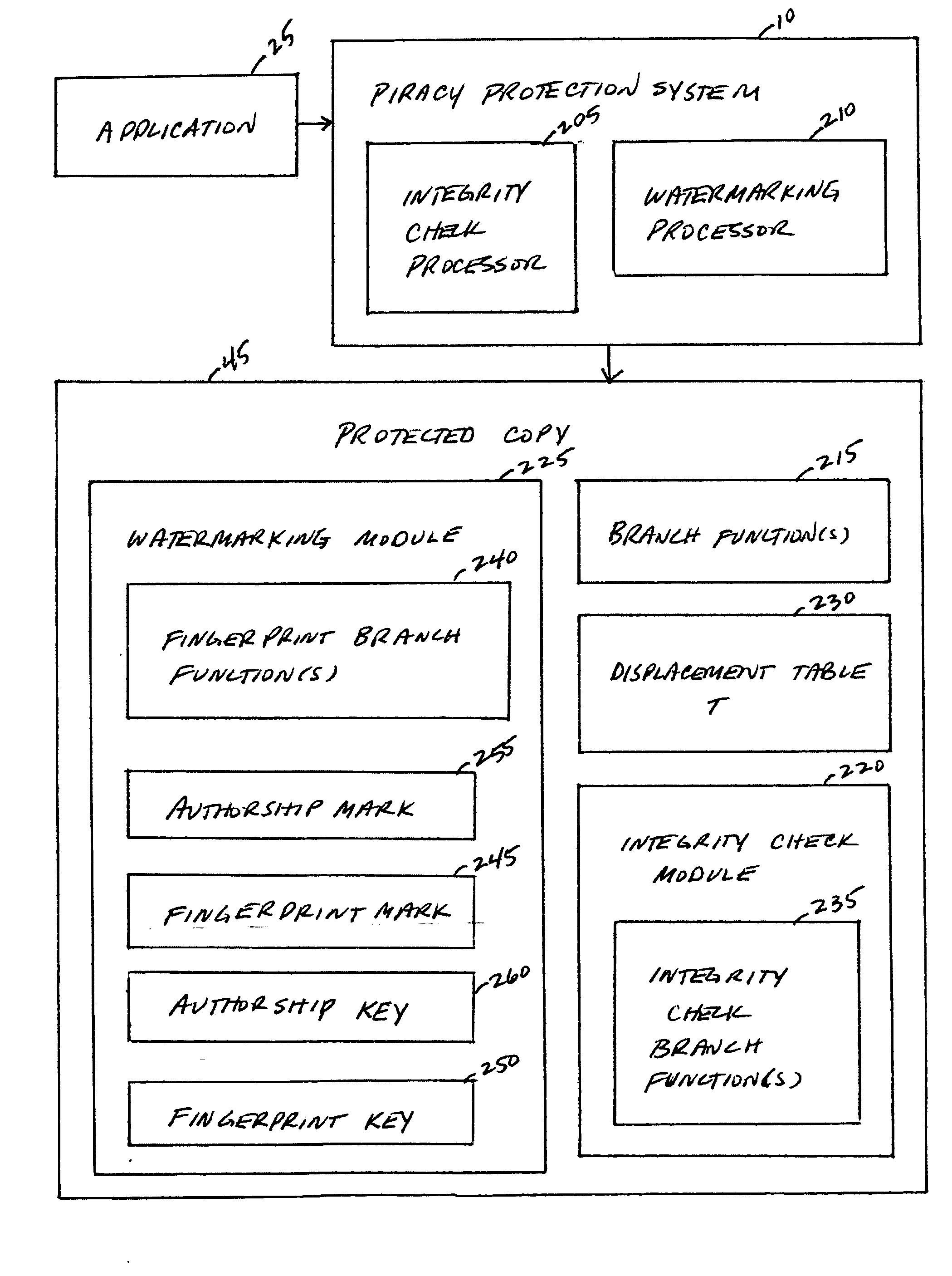
System, method, and service for detecting improper manipulation of an application
InactiveUS20060195906A1Eliminate loopholesMore robustnessDigital data processing detailsUser identity/authority verificationObfuscationApplication procedure
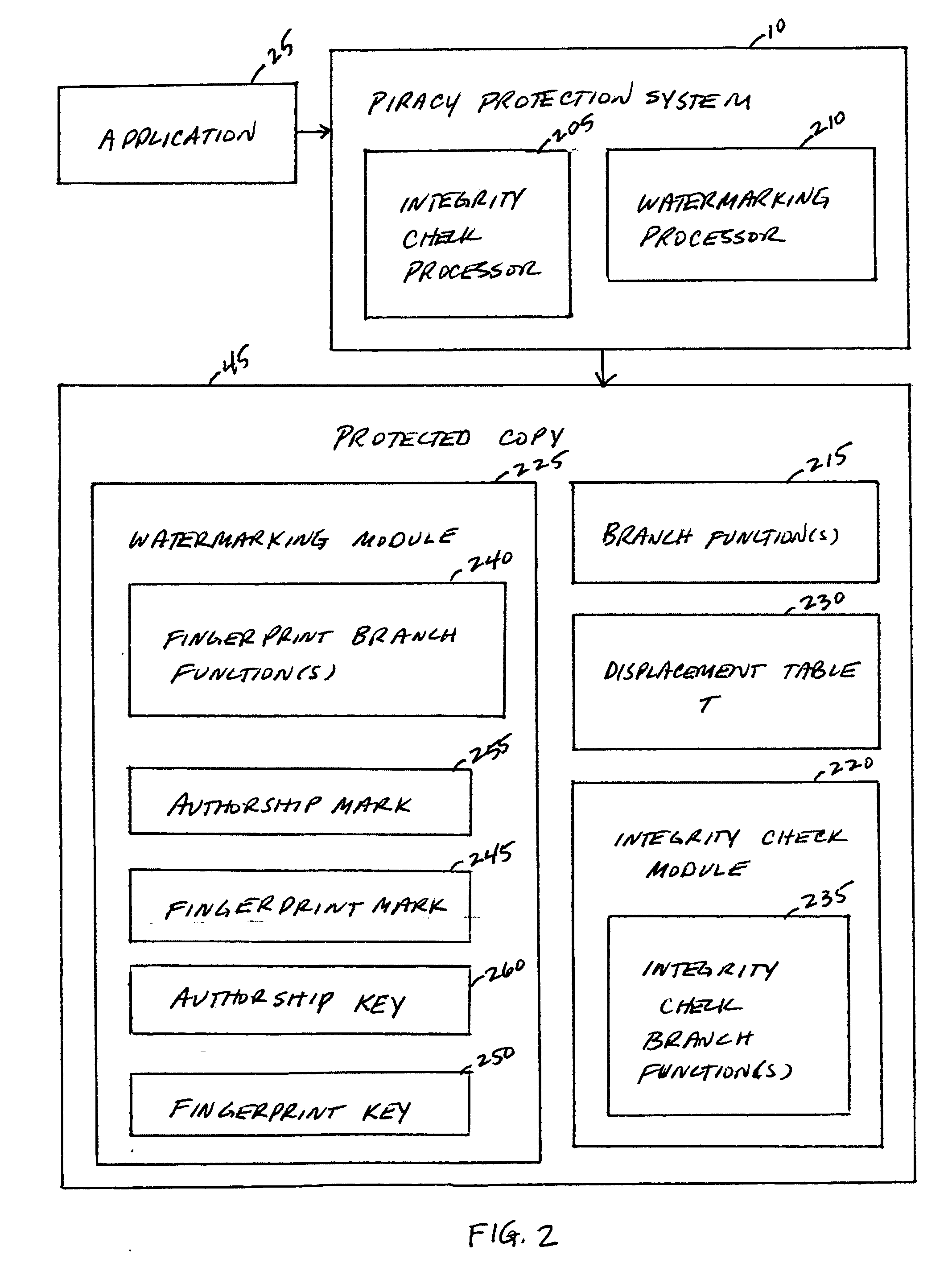
A piracy protection system incorporates tamper detection capabilities into a protected copy of an application by disassembling a statically linked binary of the application, modifying some of the instructions in the application, and then rewriting all of the modified and unmodified instructions to a new executable file, a protected copy. The piracy protection system comprises an offline tamper detection technique in which the software itself detects the tampering and causes the program to fail, therefore protecting itself from malicious attacks. The system further comprises a dynamic software-watermarking process that incorporates code obfuscation to prevent reverse engineering.
Owner:IBM CORP
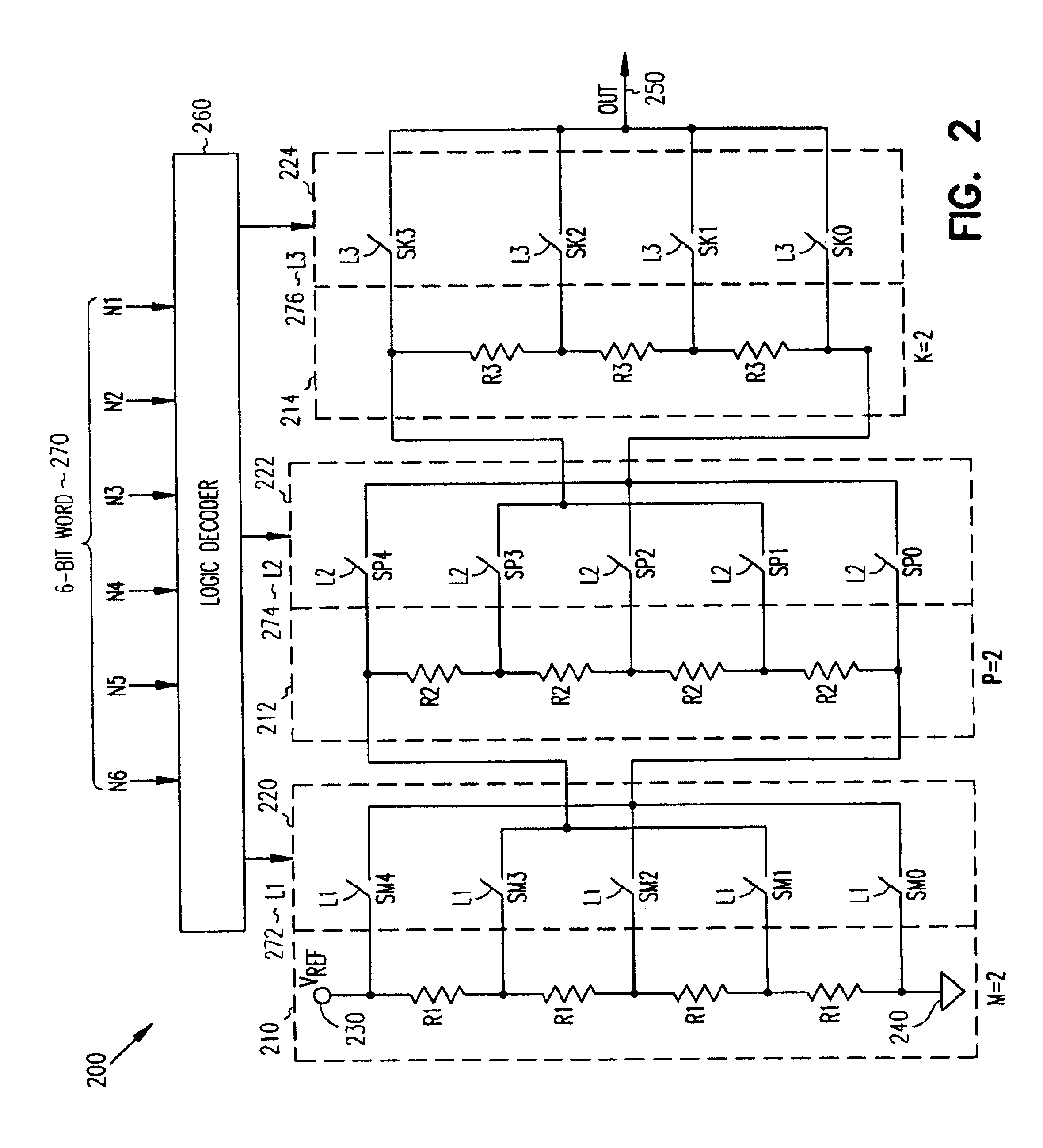
Triple resistor string DAC architecture
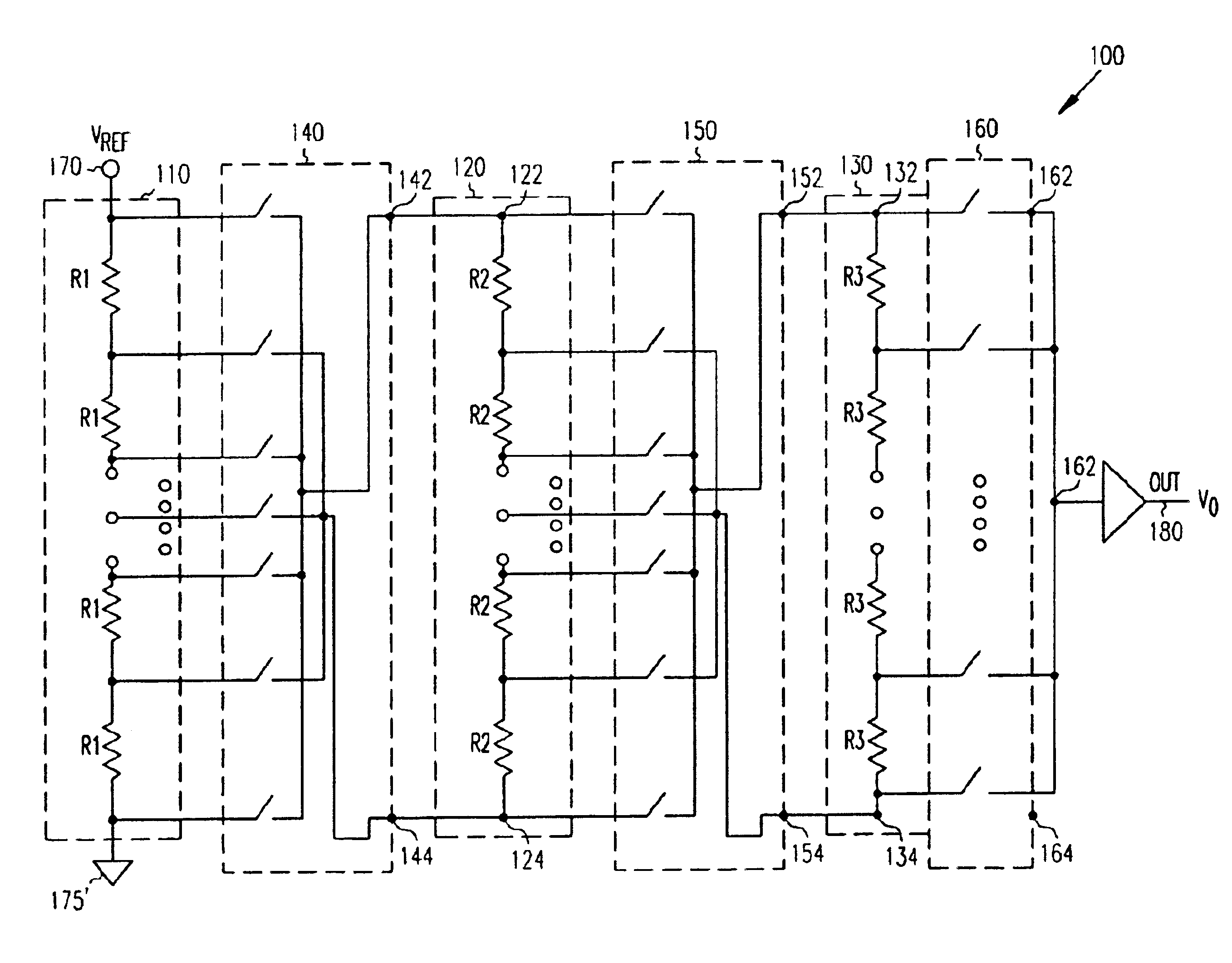
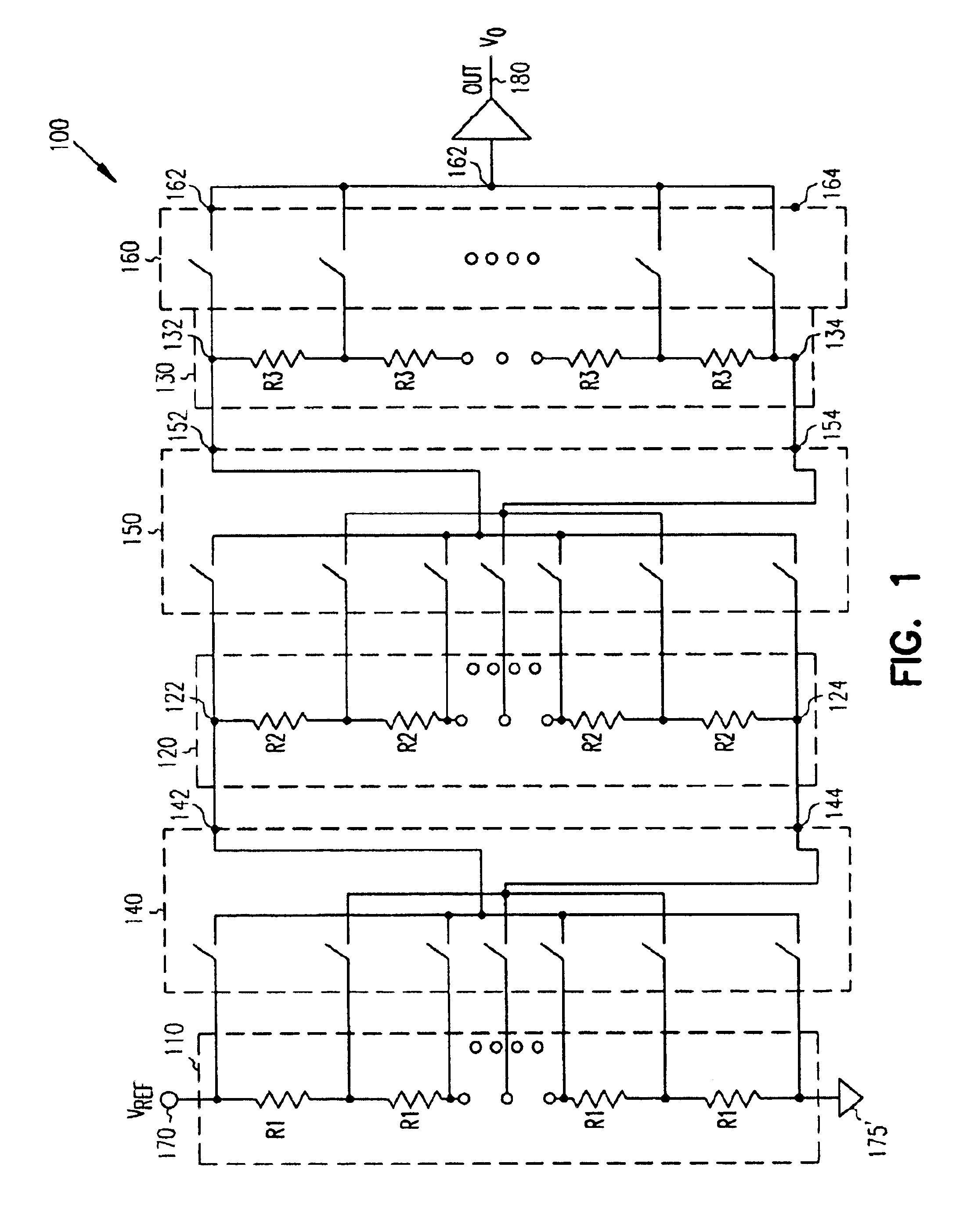
ActiveUS6914547B1Electric signal transmission systemsDigital-analogue convertorsCapacitanceImage resolution
A technique to provide a higher resolution DAC architecture for converting an N-bit digital word to a corresponding analog voltage signal without increasing chip area and switching capacitance. In one example embodiment, this is accomplished by using a triple string converter. In the triple string converter, a triple switching tree is coupled to a triple resistor string and to an analog output. Each switching tree includes a plurality of switches and each resistor string includes a plurality of corresponding resistors. A logic decoder coupled to the triple switching tree receives an N-bit digital word and generates a digital signal. The plurality of switches in each switching tree is substantially simultaneously controlled by the digital signal to output a range of corresponding analog voltage signals when the triple resistor string is connected across a voltage supply.
Owner:ANALOG DEVICES INC
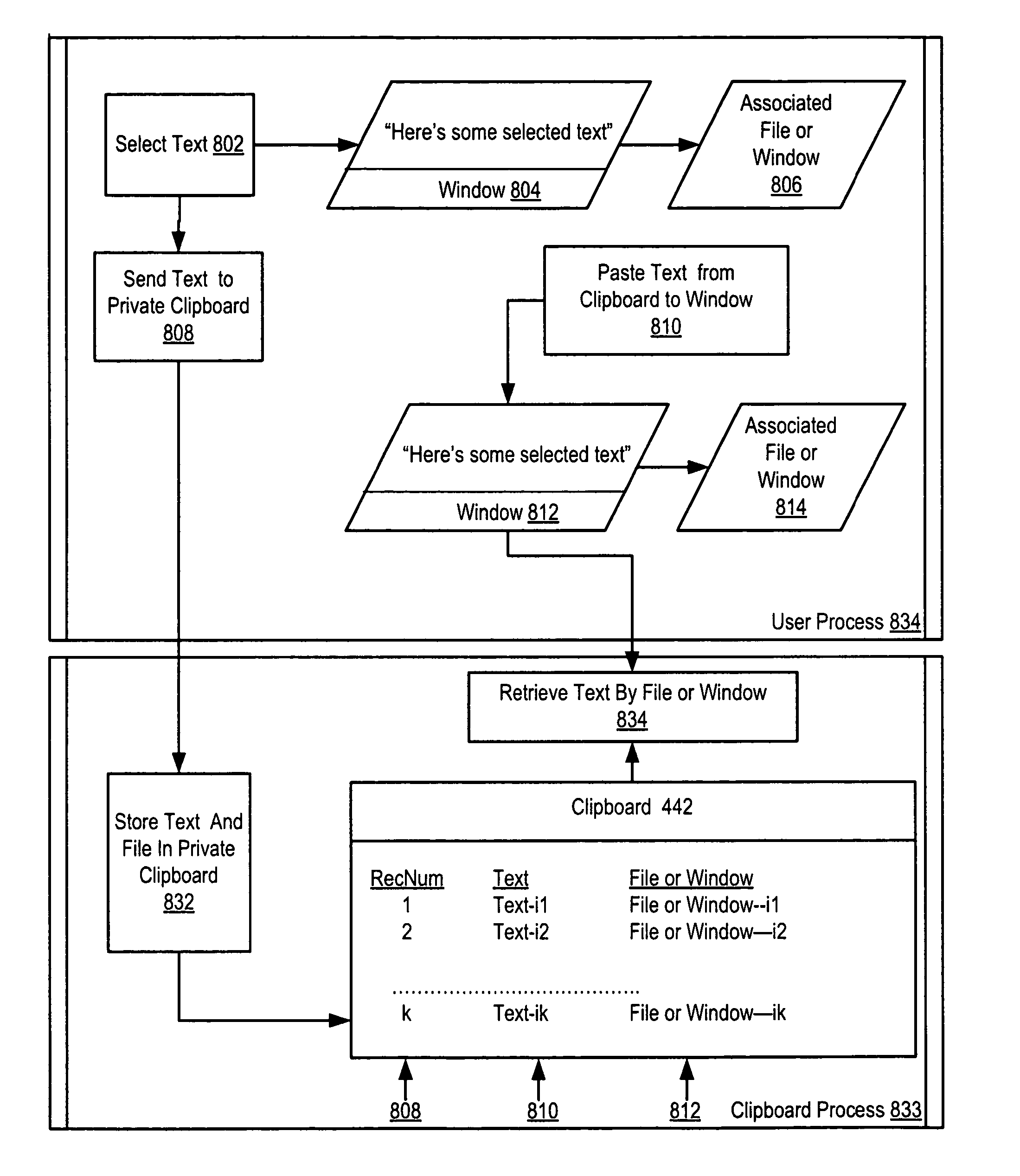
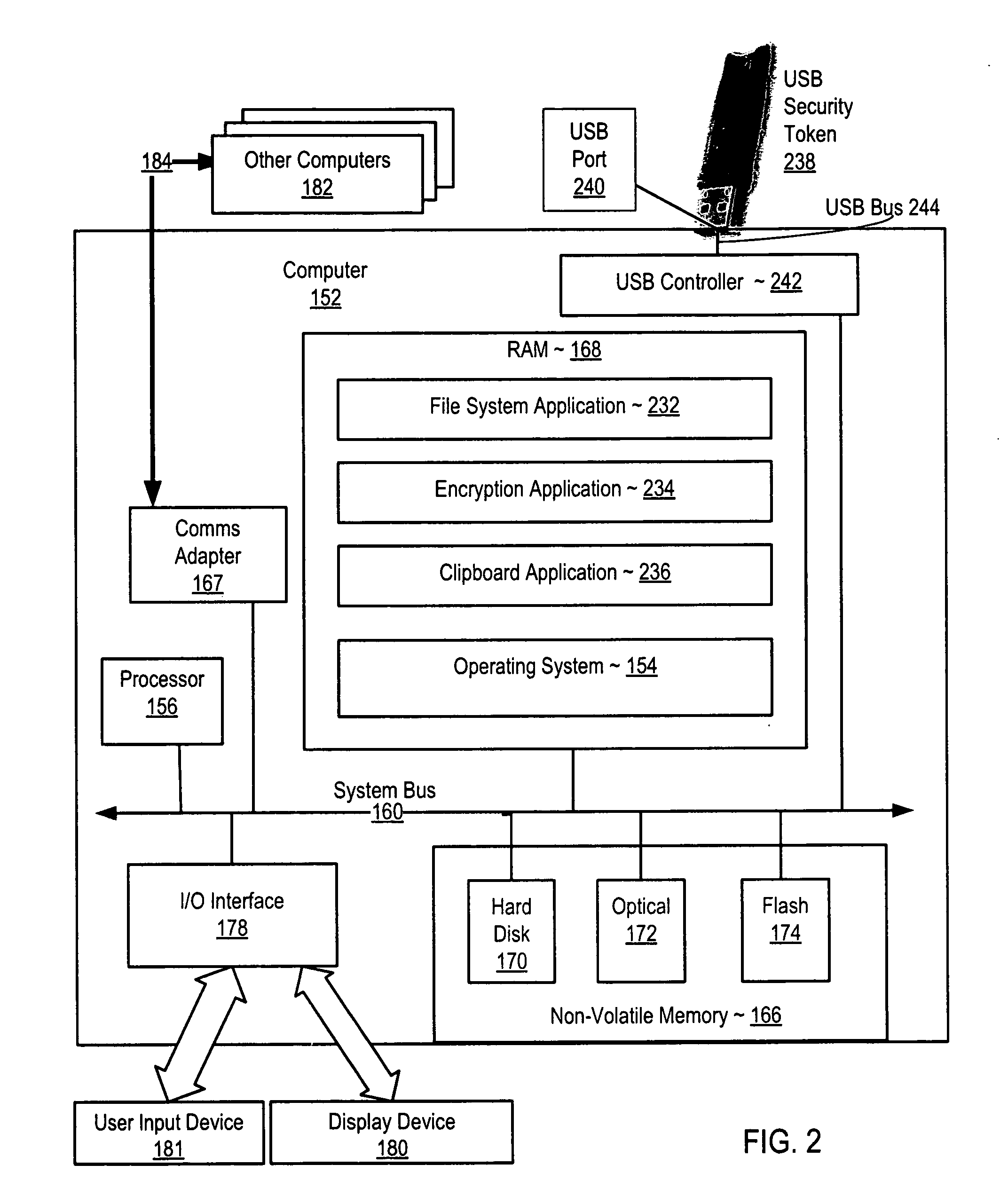
Secure clipboard function
InactiveUS20070011749A1Digital data processing detailsUser identity/authority verificationFile systemUSB
Securing computer files in which a publish permission is present in a file system. Upon receiving a request to write data from one file to another, the file system determines whether publish permission is needed. If so and the user lacks the publish permission, the request is rejected. Disclosed is securing computer files which include encrypting metadata about an encrypted file and storing both the encrypted file and the encrypted metadata. The metadata includes a key for decrypting the encrypted file. The key for decrypting the metadata is stored in a USB security token. Disclosed is securing computer files which include copying material from a window displaying the contents of a file to a clipboard application. The file or window is associated with the material. The clipboard application can deny a request to paste material associated with one file to a window displaying the contents of a different file.
Owner:SIMDESK TECH INC
Smart radio incorporating Parascan(R) varactors embodied within an intelligent adaptive RF front end
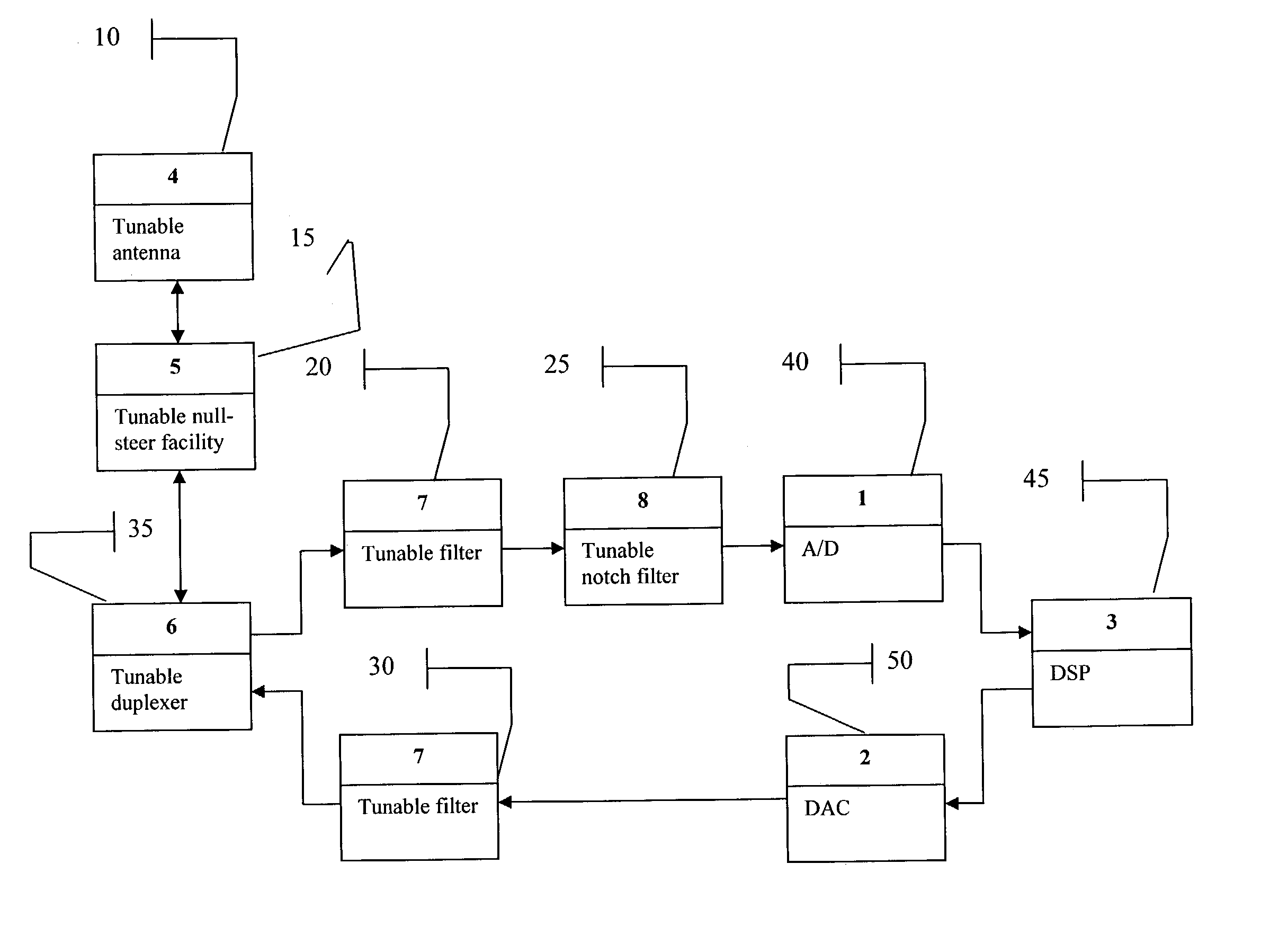
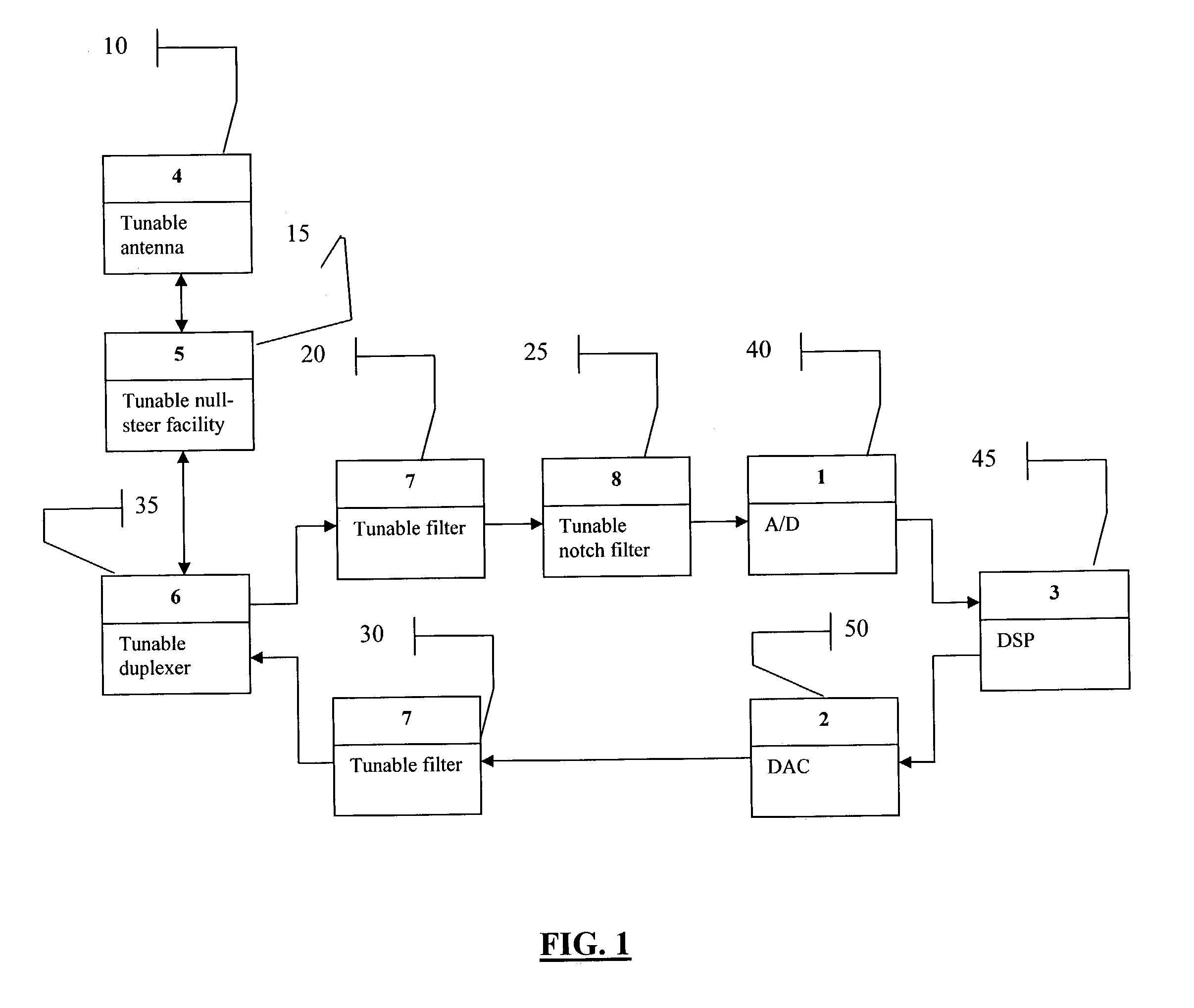
ActiveUS7107033B2Electric signal transmission systemsAnalogue conversionDigital analog converterRF front end
A smart radio incorporating Parascan® varactors embodied within an intelligent adaptive RF front end. More specifically, this is provided for by a smart radio incorporating Parascan® varactors embodied within an intelligent adaptive RF front end that comprises at least one tunable antenna; at least one antenna null steering facility associated with said at least on tunable antenna; at least one tunable duplexer receiving the output from and providing input to said at least one antenna null steering facility; a first tunable RF filter receiving the output from said at least one tunable duplexer and providing the input to an analog to digital converter, said analog to digital converter providing the input to a digital signal processor, the output of which is input for a digital to analog converter; a second tunable RF filter receiving the analog output of said digital to analog converter and providing an input to said at least one tunable duplexer.
Owner:NXP USA INC
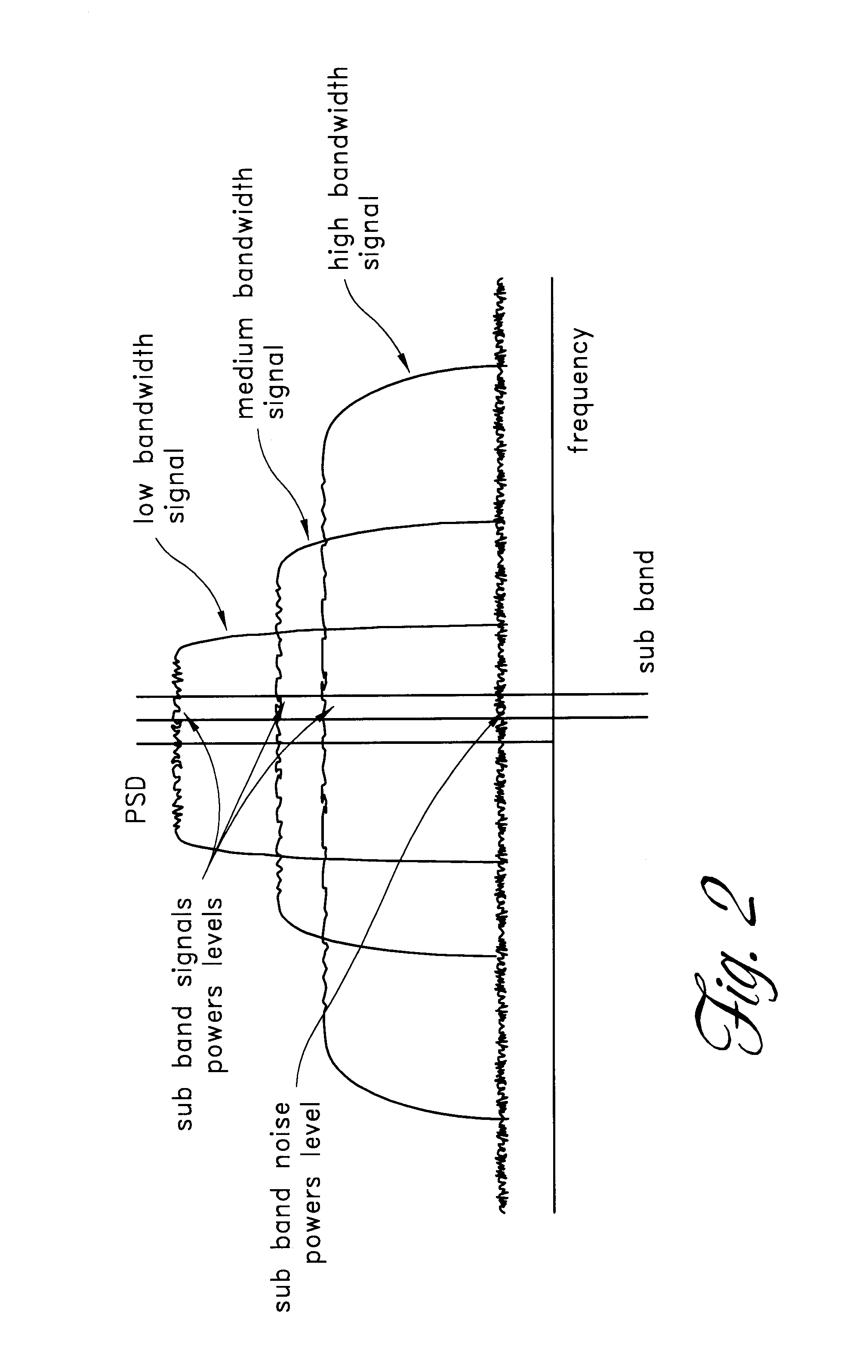
Low noise wideband digital predistortion amplifier
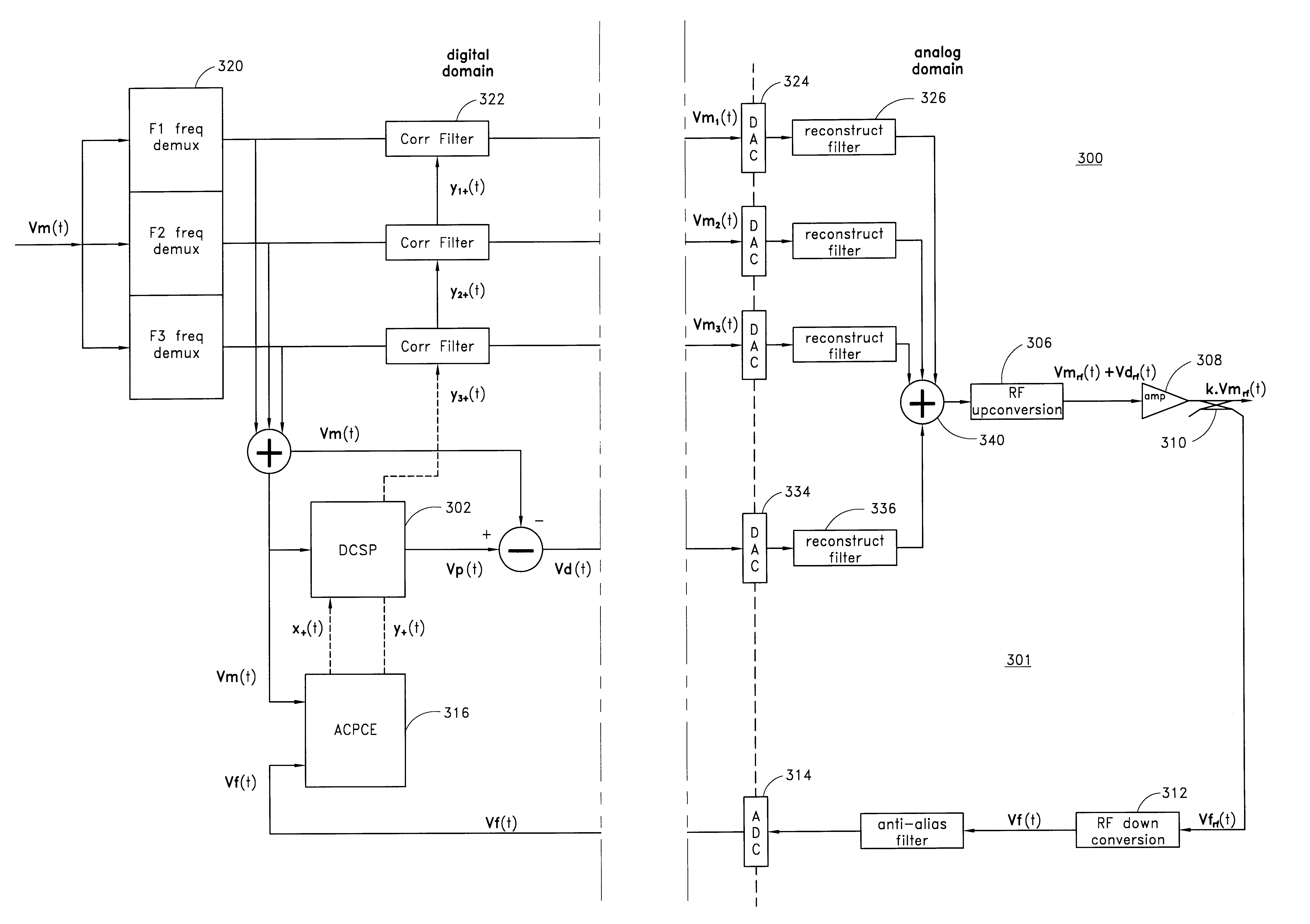
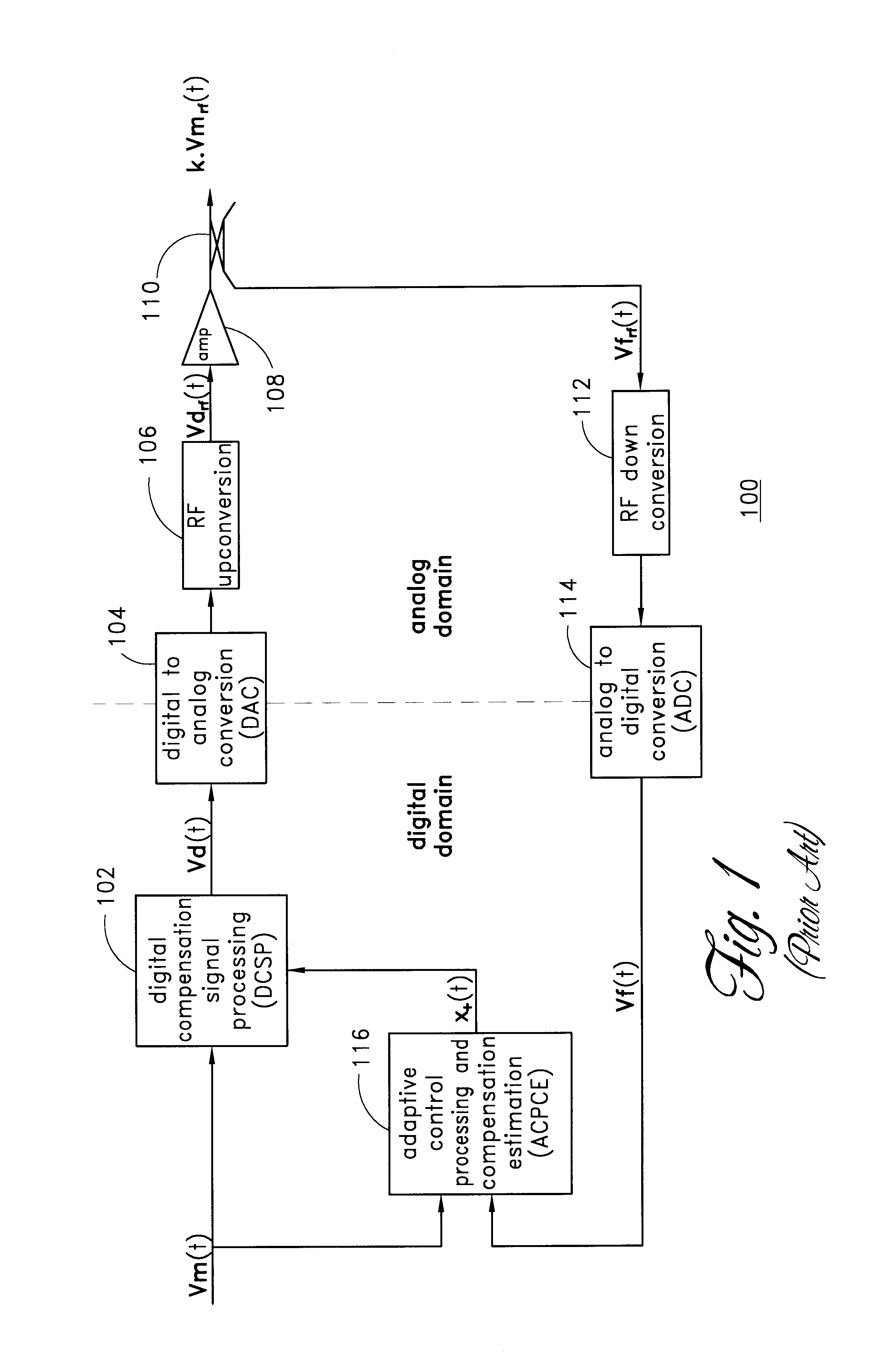
InactiveUS6570444B2Low bandwidthReduce total powerAmplifier modifications to reduce non-linear distortionElectric signal transmission systemsLow noiseSignal-to-noise ratio (imaging)
A digital predistortion amplifier design compensates for non-linear amplification of an input signal using predistortion techniques. The design provides a reduced noise floor by using separate digital to analog converters (DAC) to separately convert the input signal and an error correction signal. Furthermore, the input signal can be separated into two or more subbands of narrower bandwidth. Each of the subbands are converted to analog using a separate DAC. By reducing the power and / or bandwidth to be handled by any one DAC, the available levels of quantization of the DAC are applied to a lower power signal and therefore the signal to noise ratio resulting from the conversion process is improved. In addition, each digital subband is passed through a correction filter, which is driven by an adaptive control processing and compensation estimator to compensate for relative gain, phase, and delay inconsistencies between the different subbands.
Owner:MAXLINEAR ASIA SINGAPORE PTE LTD
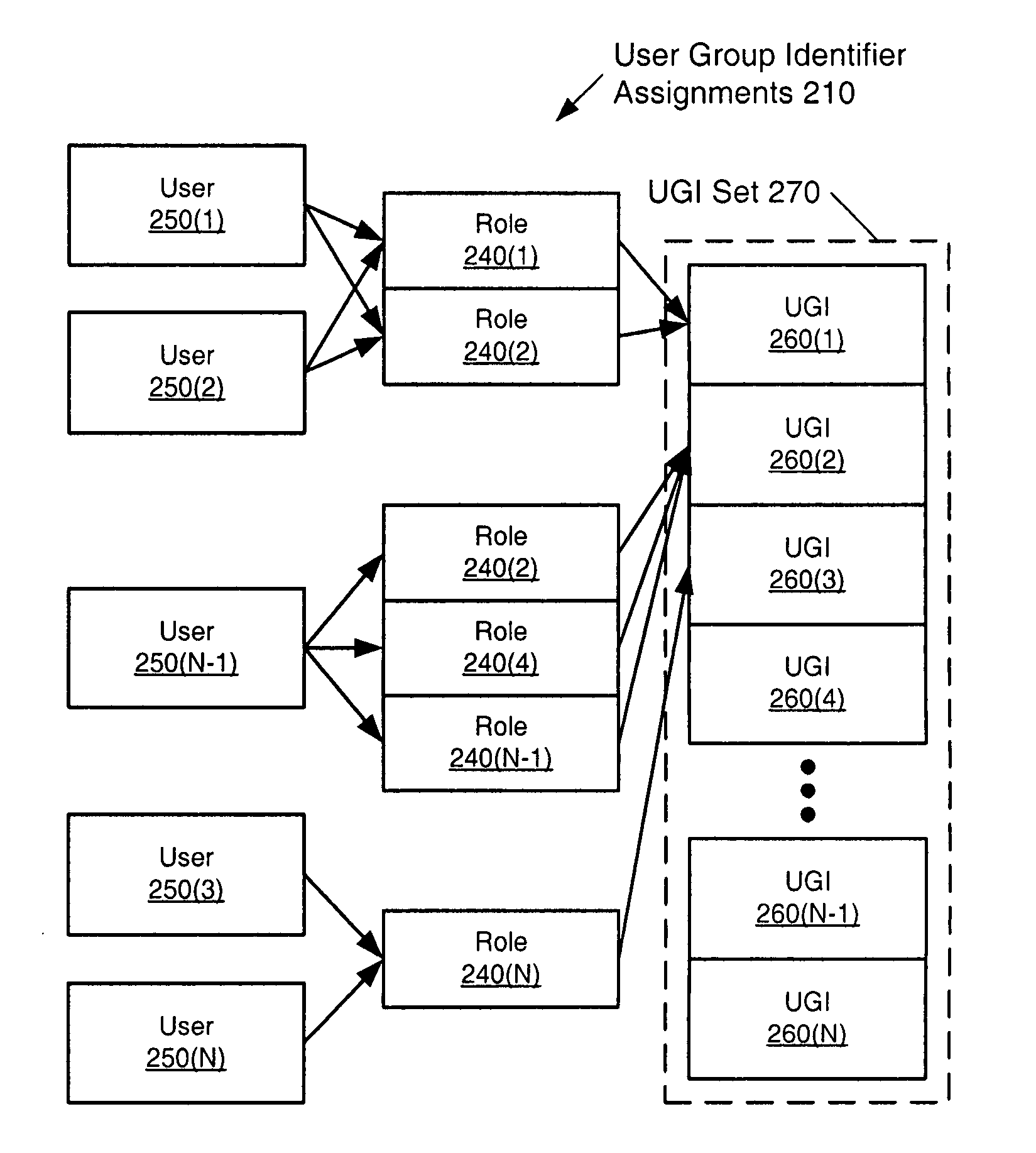
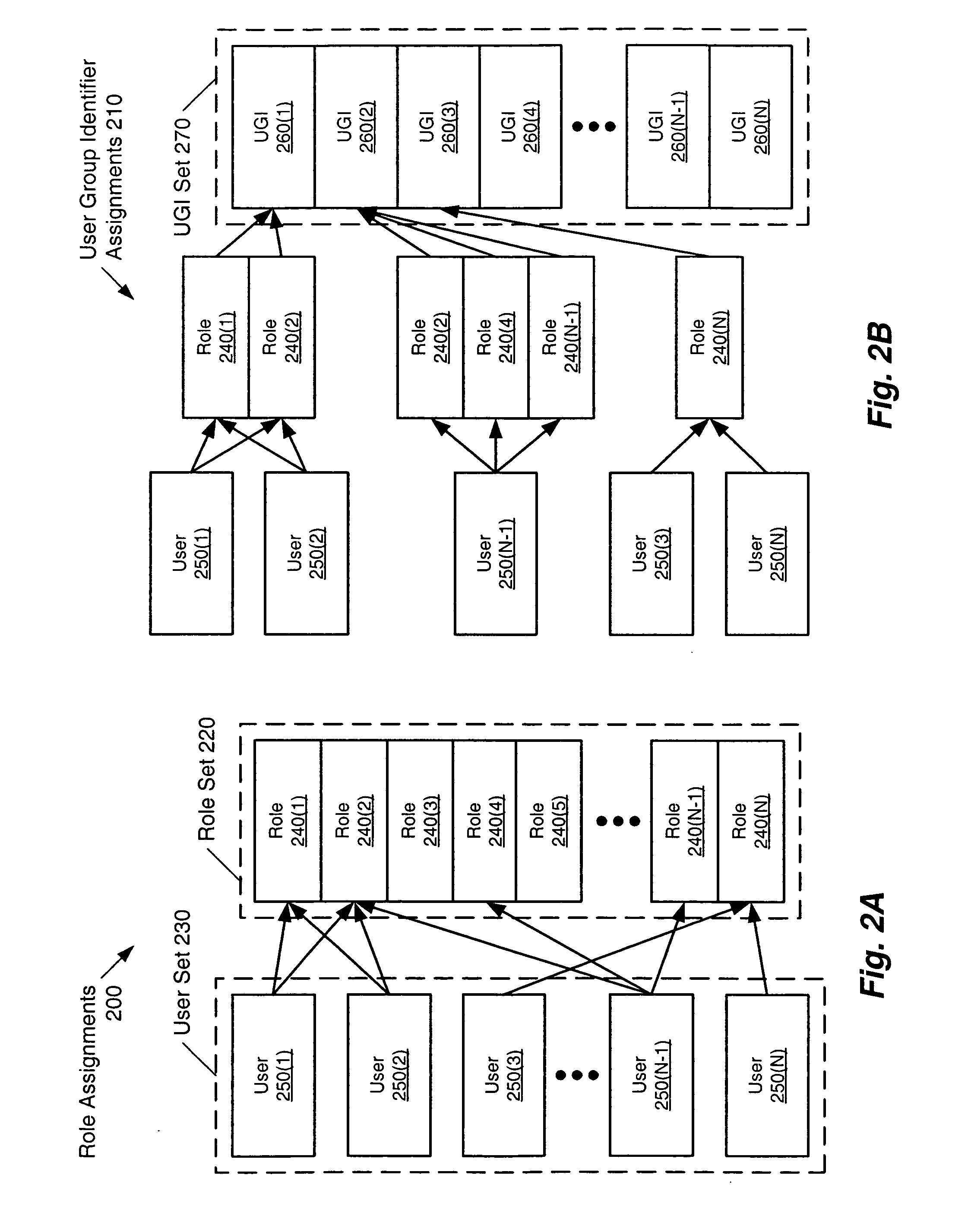
Method and system for generating user group identifiers
ActiveUS20060090208A1Digital data processing detailsUser identity/authority verificationWorld Wide WebData structure
A method and apparatus for generating user group identifiers using a permissions matrix is disclosed. The permissions matrix includes an entry that is associated with a row and a column of the permissions matrix. The row of the permissions matrix is indexed with a first role and the column of the permissions matrix is indexed with a second role. A data structure implementing such a method can include, for example, a user group identifier matrix. Alternatively, a method is disclosed in which the expiration of a user group identifier is detected. In such a case, the user group identifier is updated by accessing a user group identifier matrix.
Owner:CISCO TECH INC
Method and apparatus for preparing signals to be compared to establish predistortion at the input of an amplifier
InactiveUS20030156658A1Improve electricity efficiencyImprove performance efficiencyAmplifier modifications to reduce non-linear distortionElectric signal transmission systemsAudio power amplifierUnit of time
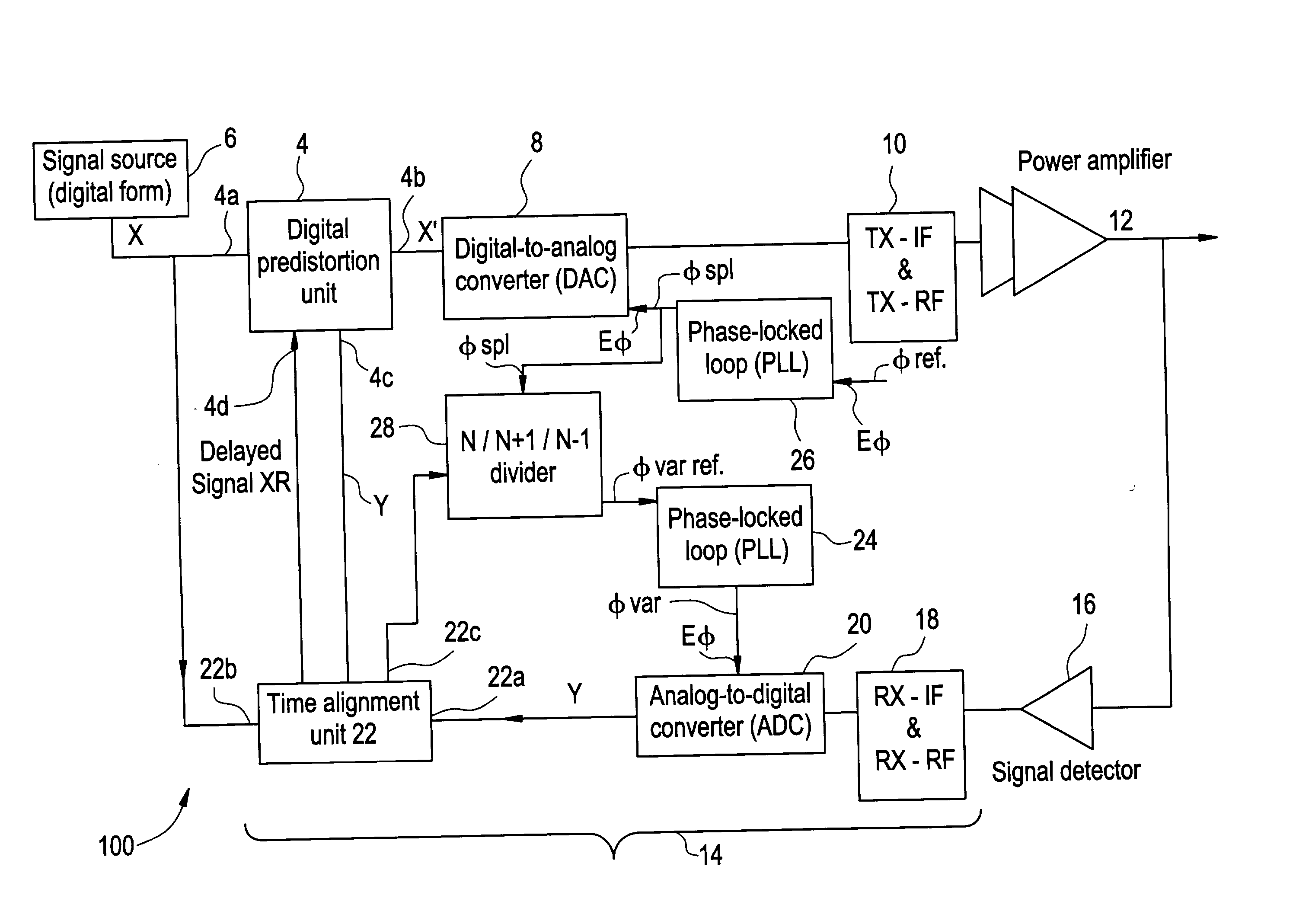
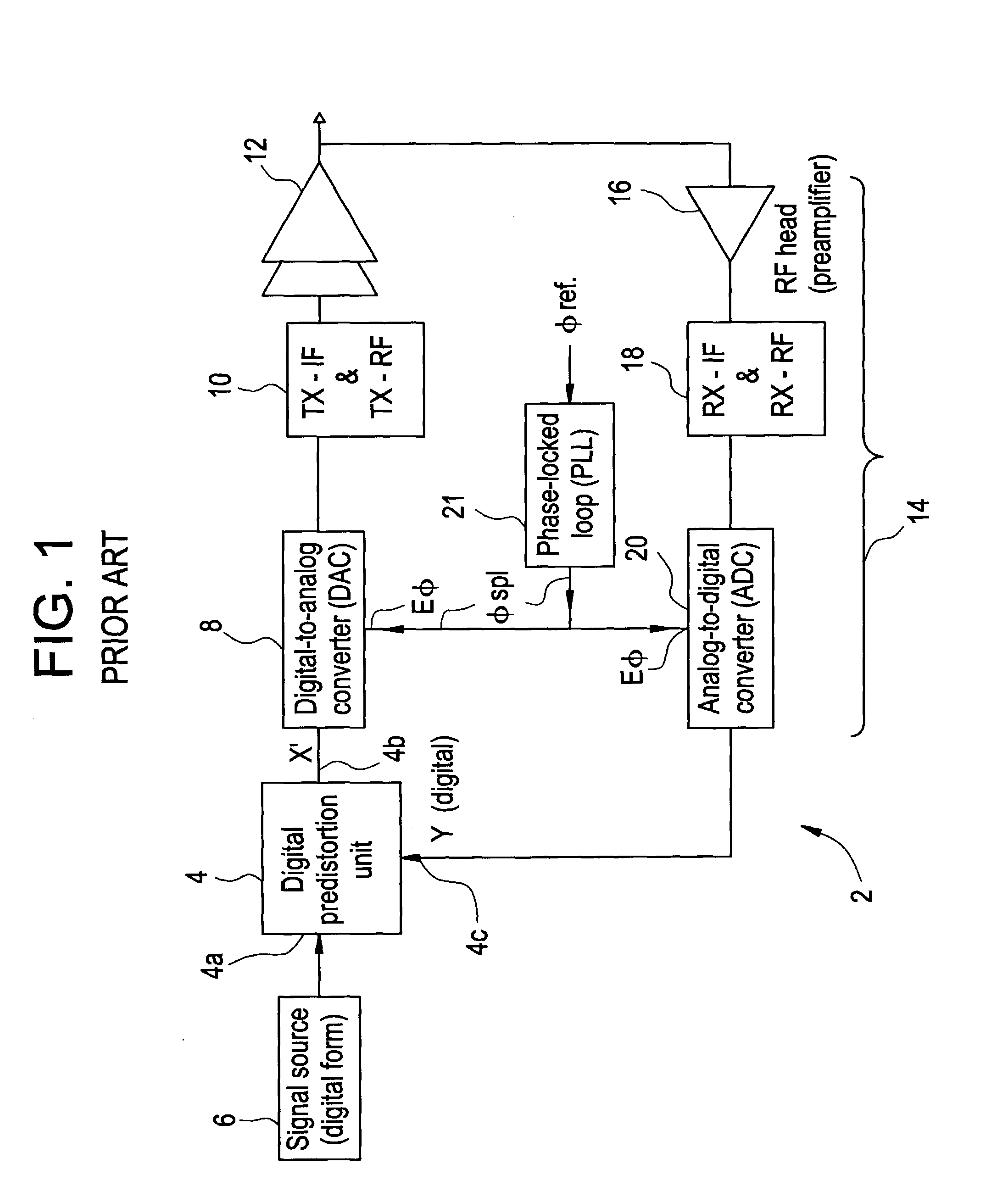
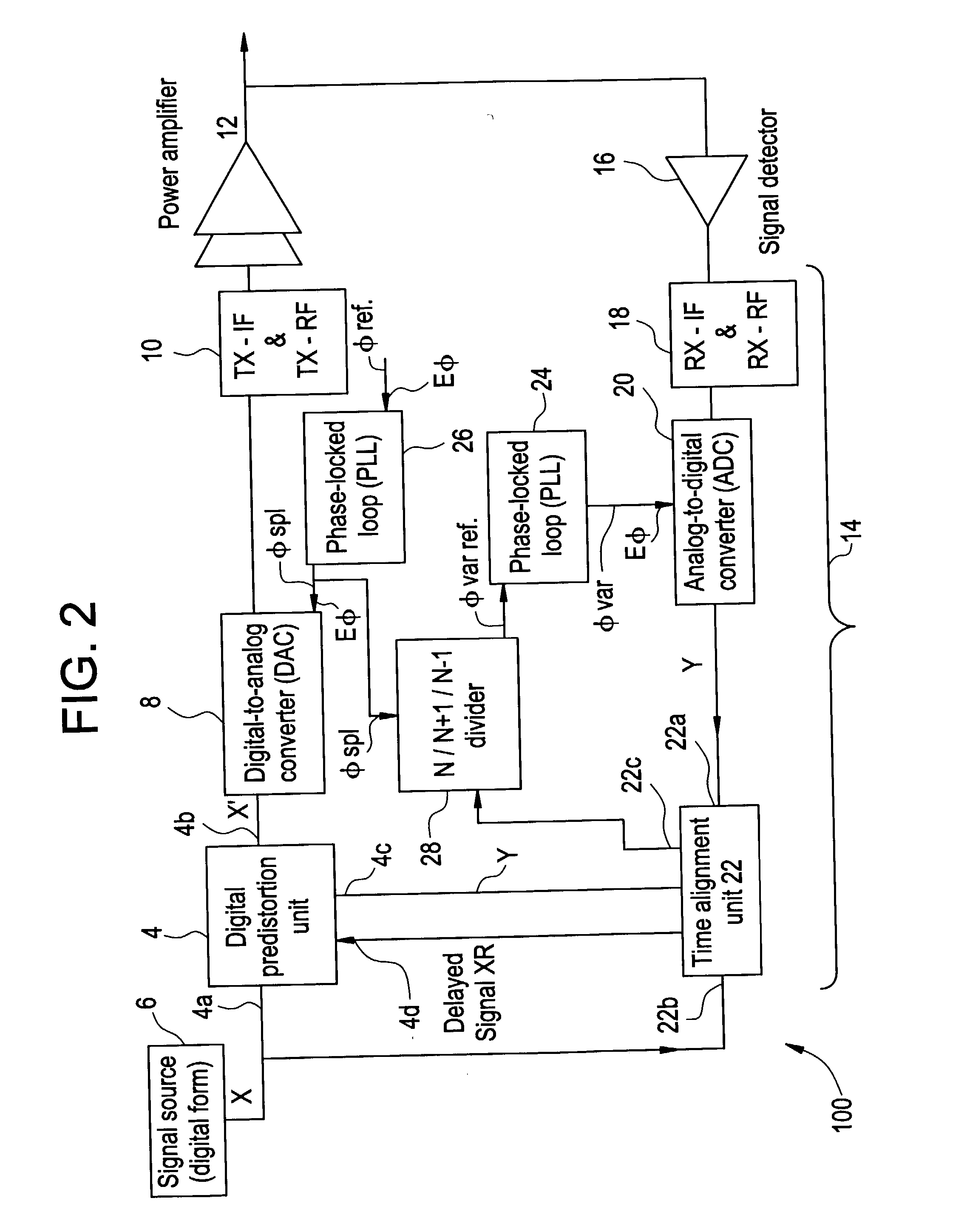
The invention relates to a method of preparing signals (X and Y) to be compared to establish predistortion at the input of an amplifier (12), the signals comprising a signal (X) before amplification and a signal (Y) after amplification by said amplifier. Preparation includes time aligning (22) the signal before amplification (X) with the signal after amplification (Y) before using them to establish said predistortion. The invention preferably operates in two stages, namely a stage of coarse time alignment, in which the signal before amplification (X) is subjected to a time delay comprising an integer number of first time units, and a stage of fine time alignment, in which a delay or advance value of a fraction of the first time unit is determined.
Owner:EVOLIUM
Secure e-mail services system and methods implementing inversion of security control
InactiveUS20080098237A1Digital data processing detailsUser identity/authority verificationComputerized systemRecipient side
A secure e-mail service, executable on a recipient e-mail server or associated computer system, implements inverted security control over recipient content stored by the recipient e-mail server. Recipient content is received in conjunction with e-mail messages transmitted directed to recipients from sender computer systems unassociated with the secure e-mail service. The secure e-mail service includes a policy engine that operates on e-mail messages, as received from a communications network, to evaluate metadata features of the message and select a corresponding encryption key. The service further includes a content processing engine that operates to encrypt a portion of the message in a manner that allows subsequent decryption of said portion using the selected encryption key. A service interface enables transfer of the e-mail message, including the portion as encrypted, to the recipient e-mail server, which supports access by the recipients.
Owner:DUNG TRUNG T +2
System and method for controlling distribution of electronic information
InactiveUS20070061889A1Conveniently adding security featureInformation can be usedDigital data processing detailsUser identity/authority verificationElectronic documentPaper document
A method for managing access to electronic documents, wherein the documents include code scripts executable by, the documents being viewable by recipients only when viewed in a the document viewer upon satisfaction of an access policy embedded in the document, the method comprising the steps of opening the document for viewing in the document viewer by the recipient; executing the code to obscure viewing of selected pages of a the document upon the document being opened; communicating with an authentication server, by the viewer, for authenticating the recipient upon the recipient attempting to read the document; and unobscuring the selected pages by the viewer upon receipt of the recipient authentication.
Owner:SAND BOX TECH
Content data distributing system, content data distributing method, and commodity selling method
InactiveUS20070174198A1Inhibit inputSimple inputDigital data processing detailsUser identity/authority verificationCcd cameraWorld Wide Web
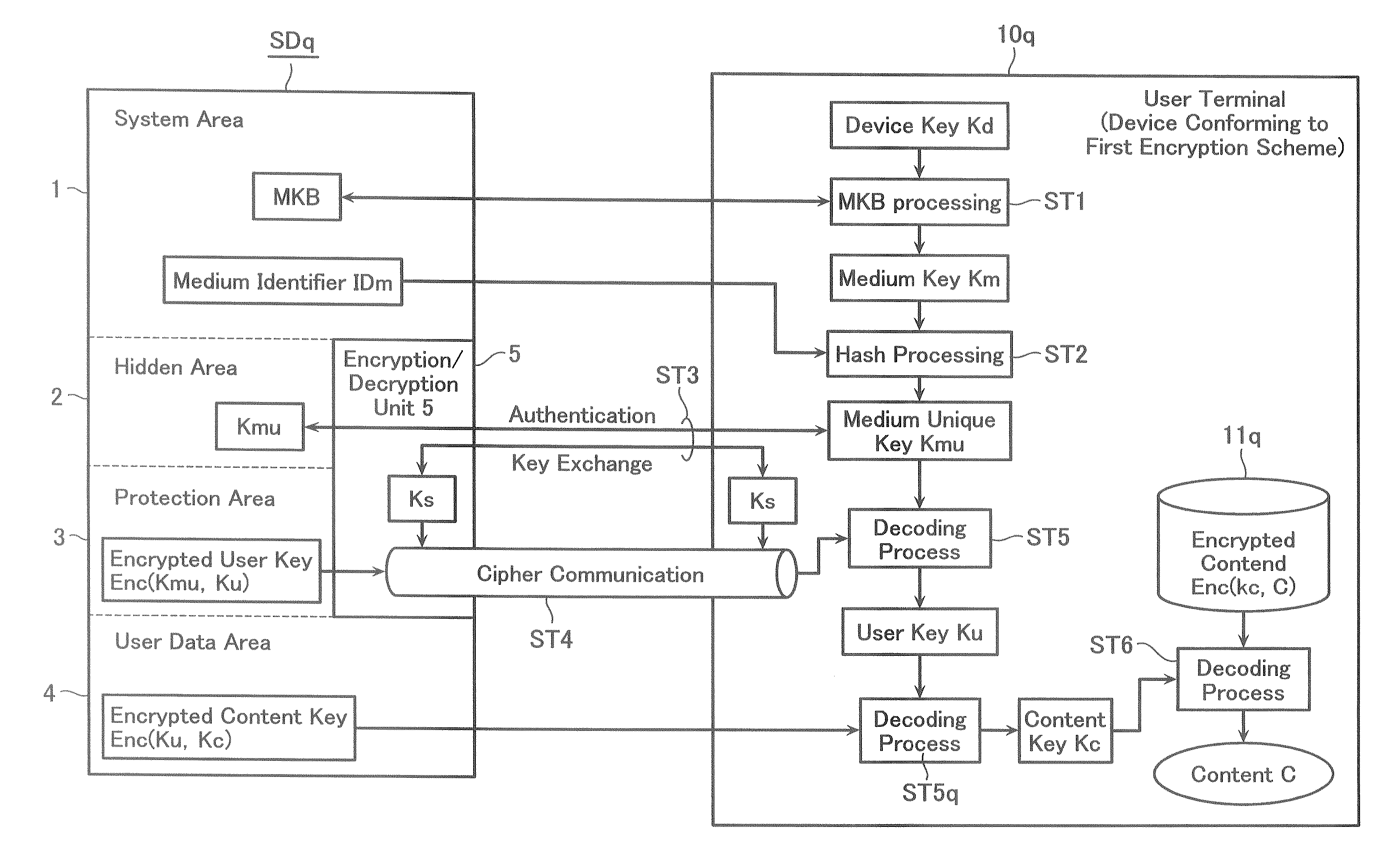
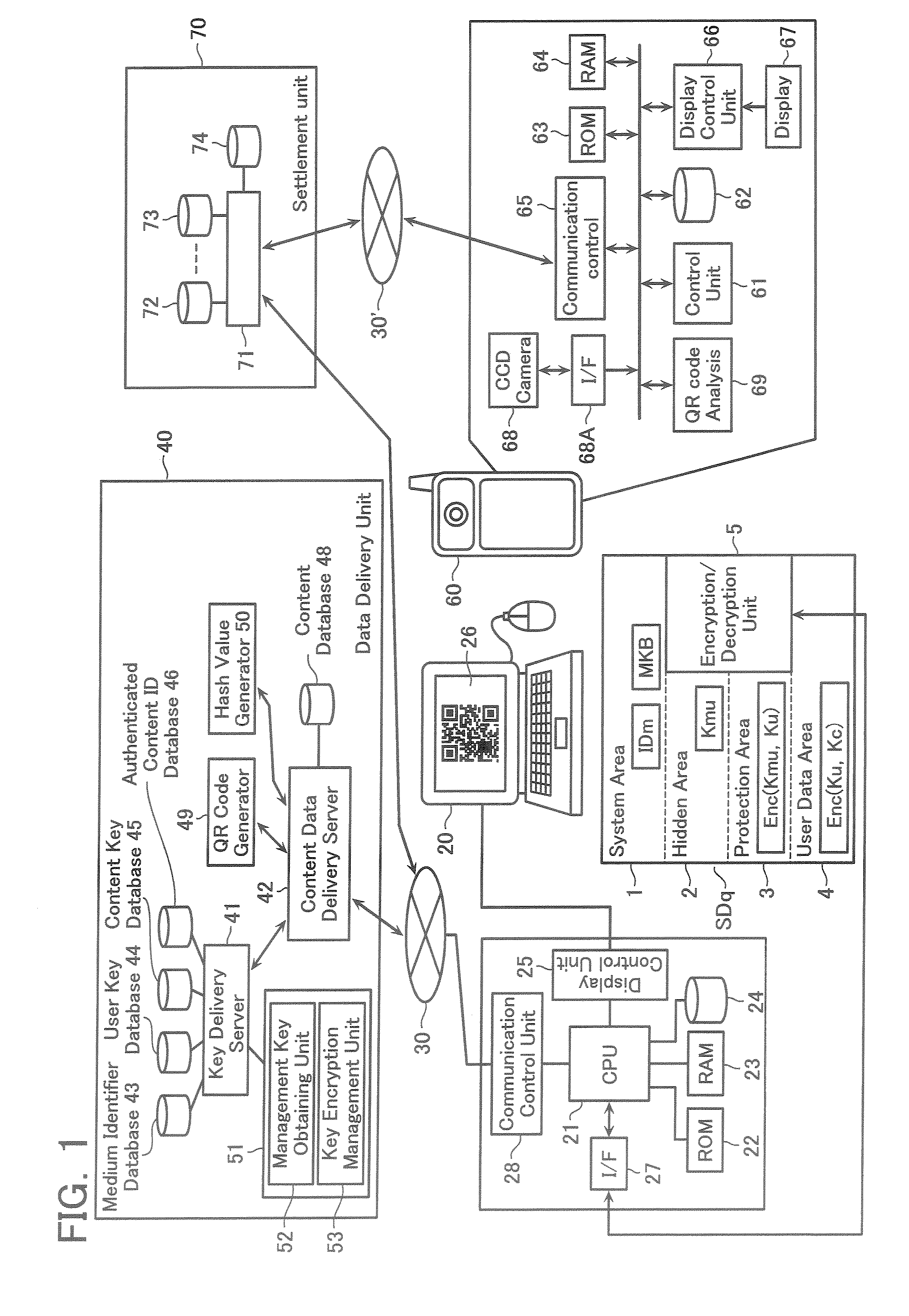
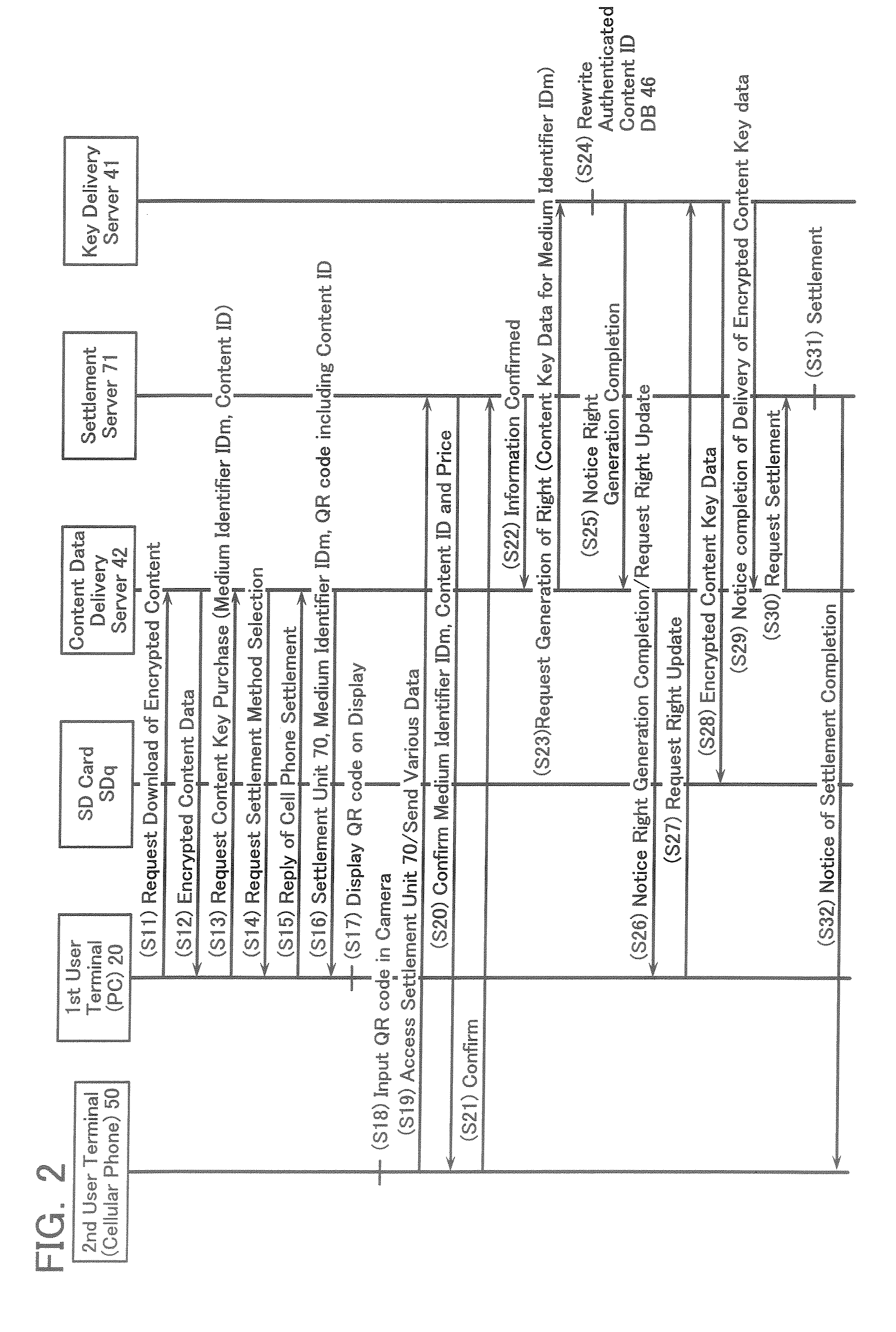
When settling a purchase price, a troublesome input is omitted and an input mistake or the like is prevented. The content data delivery server 42 makes the QR code generation unit 49 generate a QR code including encoded URL data of the settlement unit 70, a medium identifier data IDm and so forth. The QR code is displayed on a display 26. After imaging the displayed QR code by a CCD camera 58, the QR code is analyzed and a data is read therefrom. It is transmitted to a settlement server 71 and a settlement request is performed.
Owner:KK TOSHIBA
Method and apparatus for generating one-time password on hand-held mobile device
InactiveUS20060136739A1Easy to useSimple and easySynchronising transmission/receiving encryption devicesUnauthorised/fraudulent call preventionKey exchangeWeb service
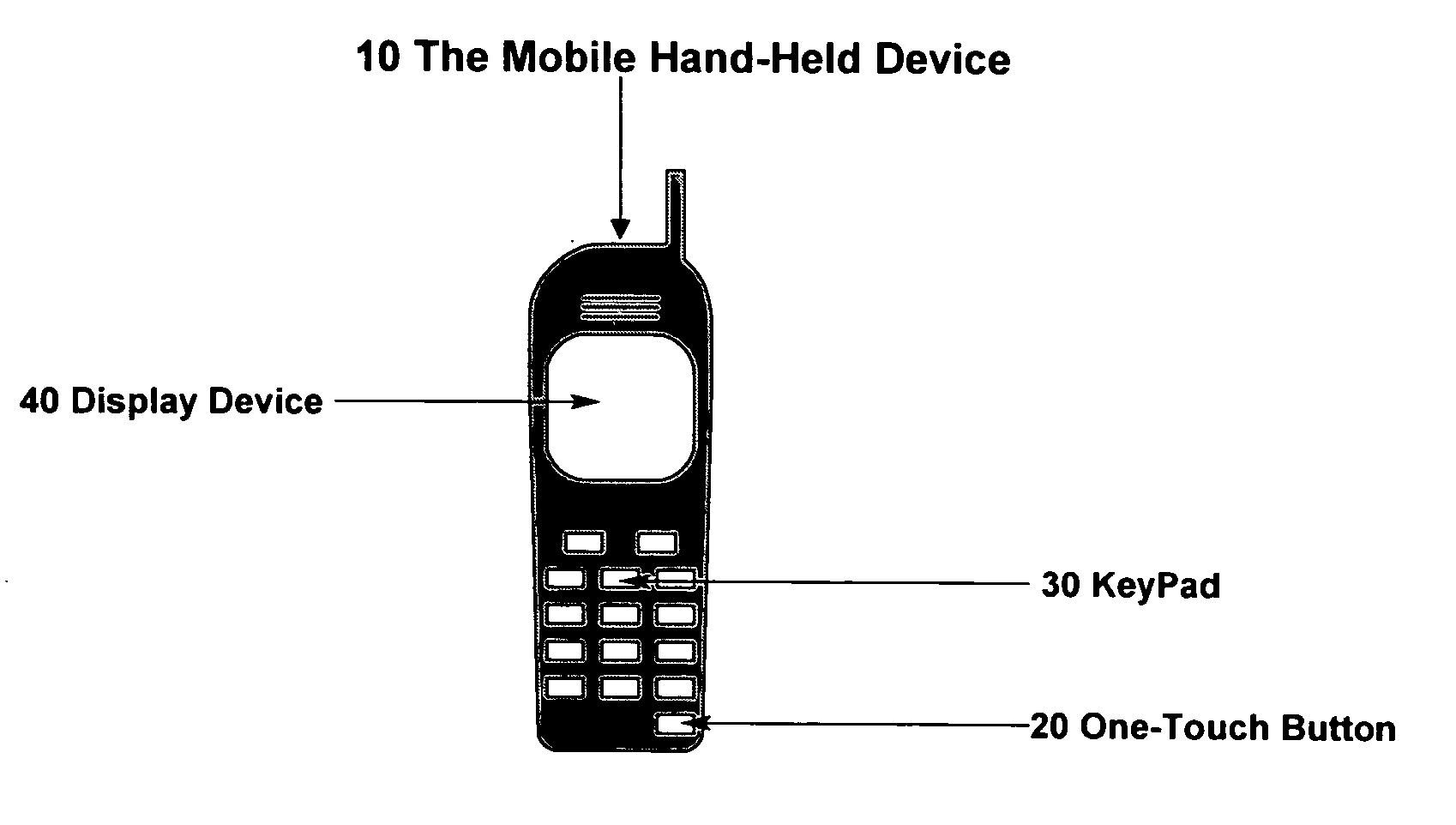
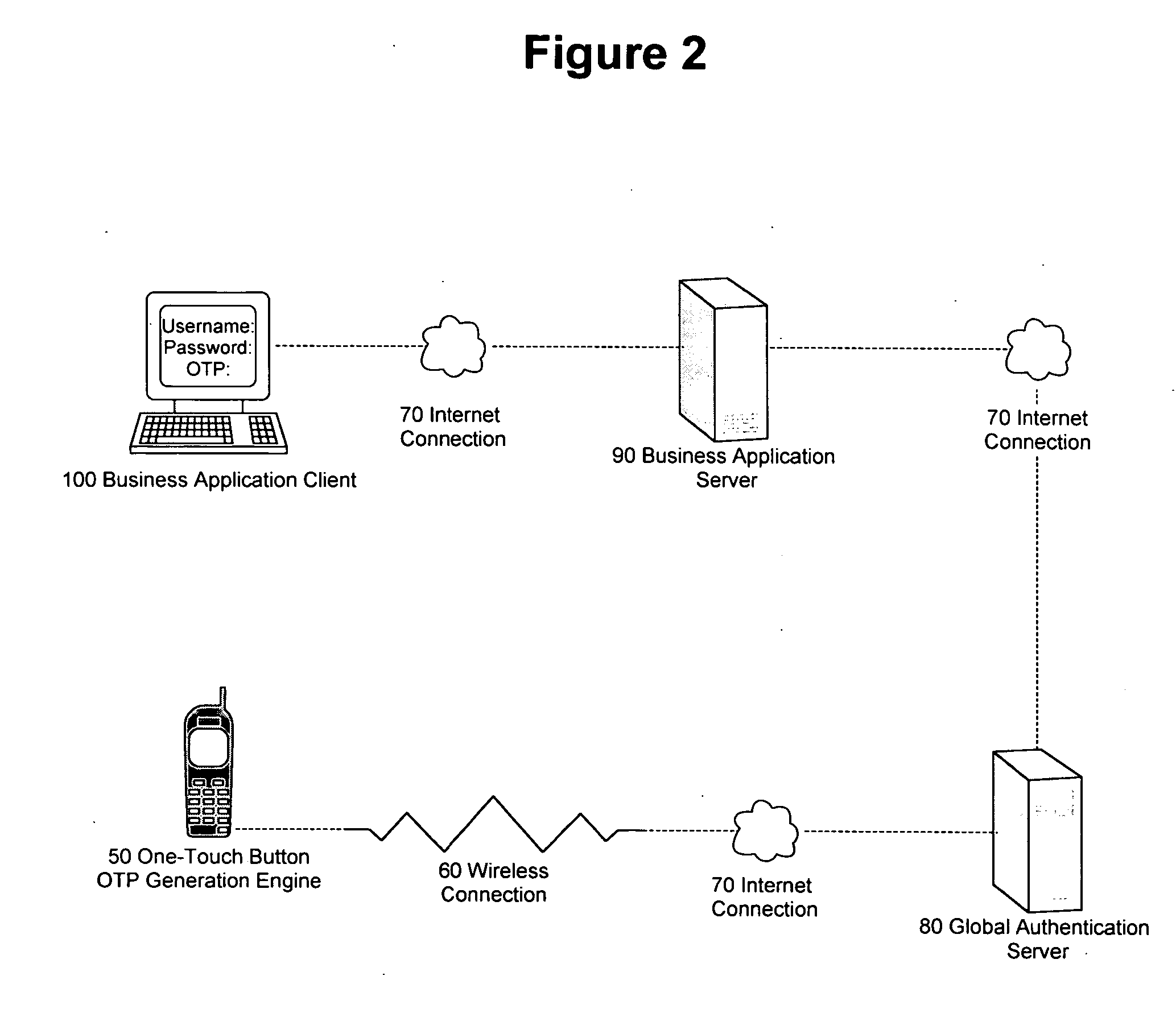
According to the invention, a system and an apparatus to use the One-Touch button on a mobile hand-held device to generate one time passwords (OTP) are disclosed. Components of this system comprise: a mobile hand-held device, a built-in One-Touch button on the mobile device, a Global Authentication Server, and an OTP Generation engine installed and ran on the mobile device. The mobile device user only needs to push the One-Touch button and an OTP is generated. The OTP is generated on the mobile device by the OTP generation engine after a secure key exchange process is performed between the remote Global Authentication Server and the mobile device. The mobile device is registered to use online web services that recognize the OTP through the Global Authentication Service. Online web services require that the user enter a combination of the user's known password and OTP for identity assurance. As a result of this invention, users will quickly adopt the two-factor authentication method as a central means to identify themselves.
Owner:BROCK CHRISTIAN +1
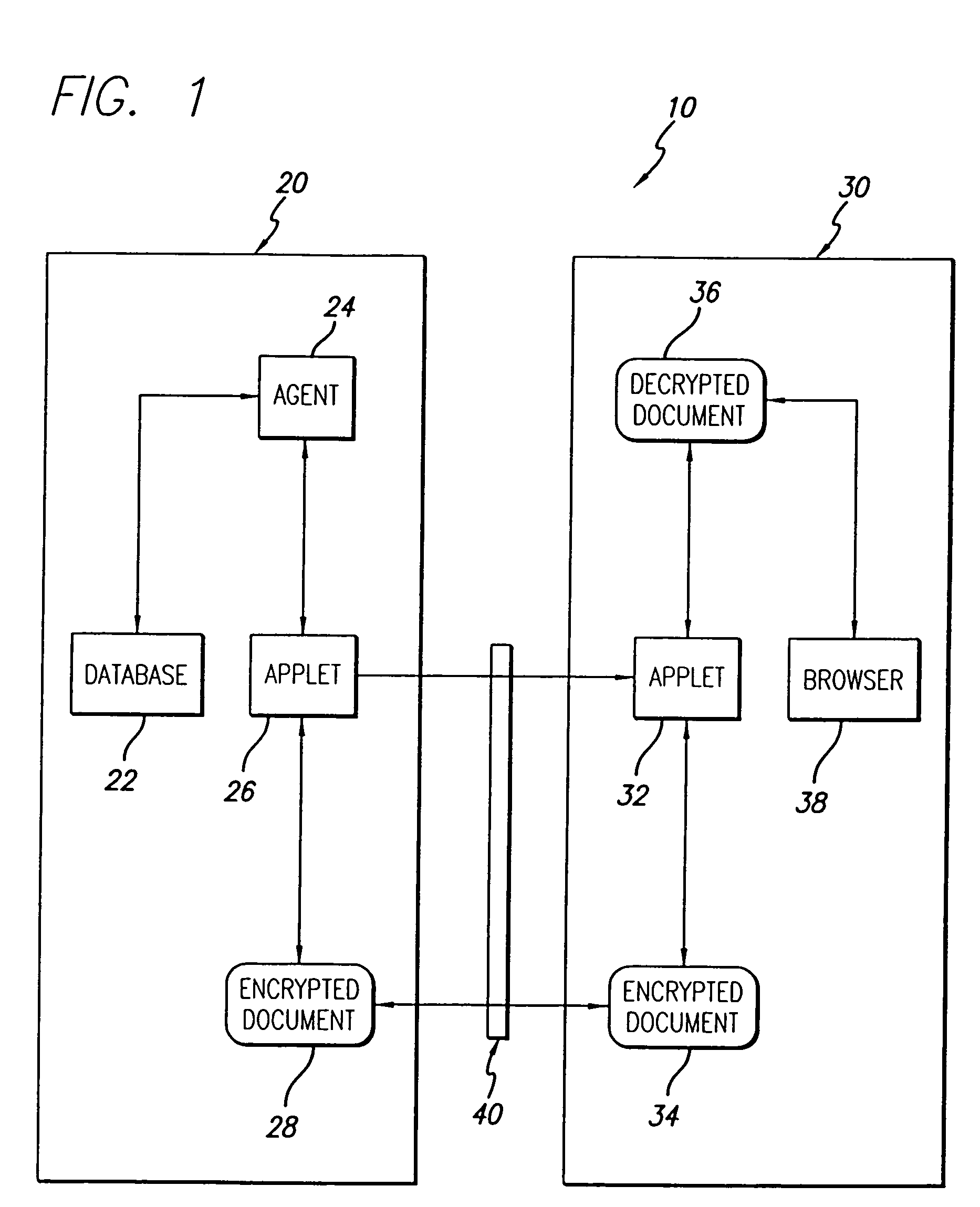
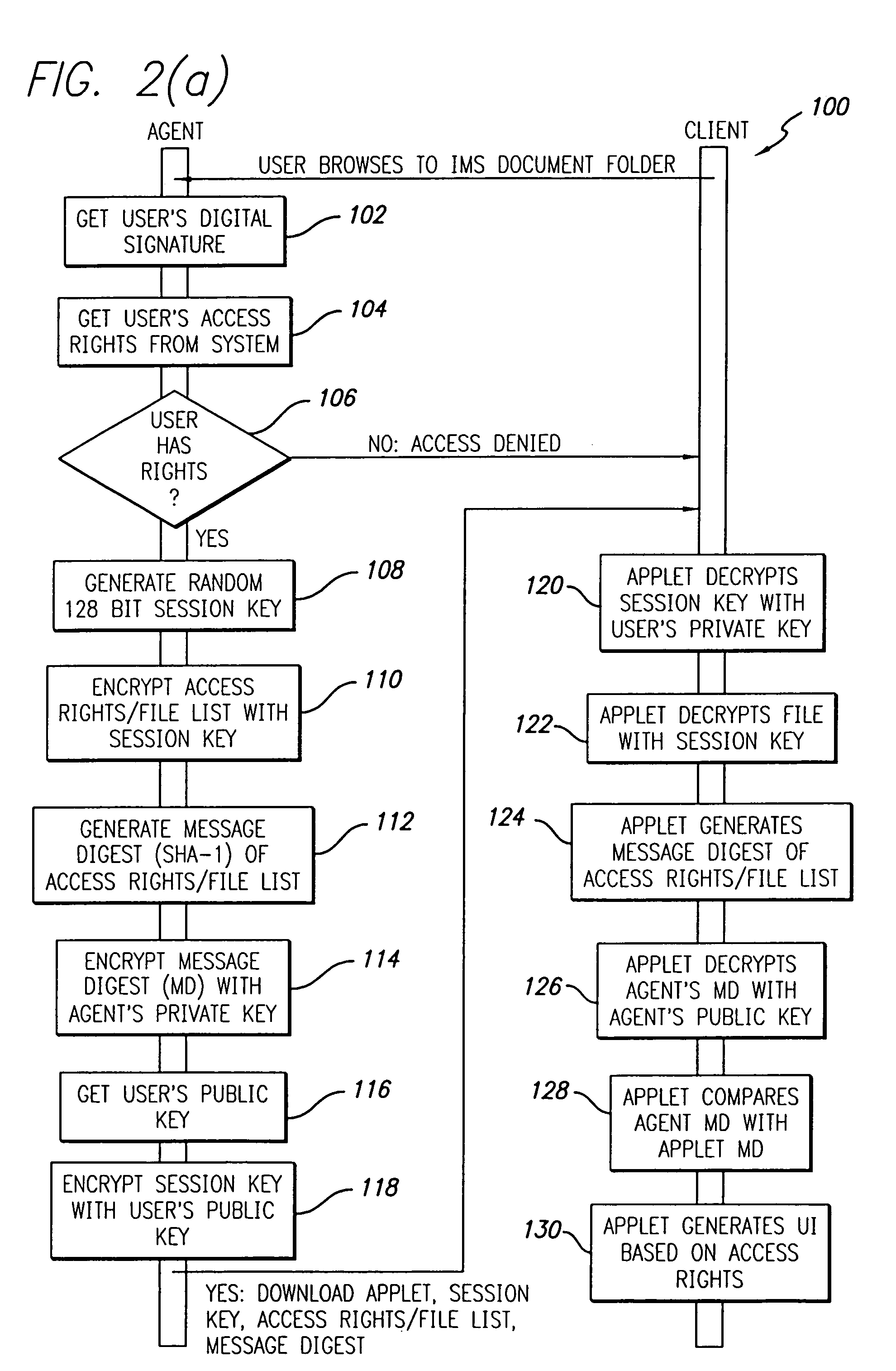
System and method for providing customized secure access to shared documents
InactiveUS7299502B2Key distribution for secure communicationDigital data processing detailsDigital signatureClient-side
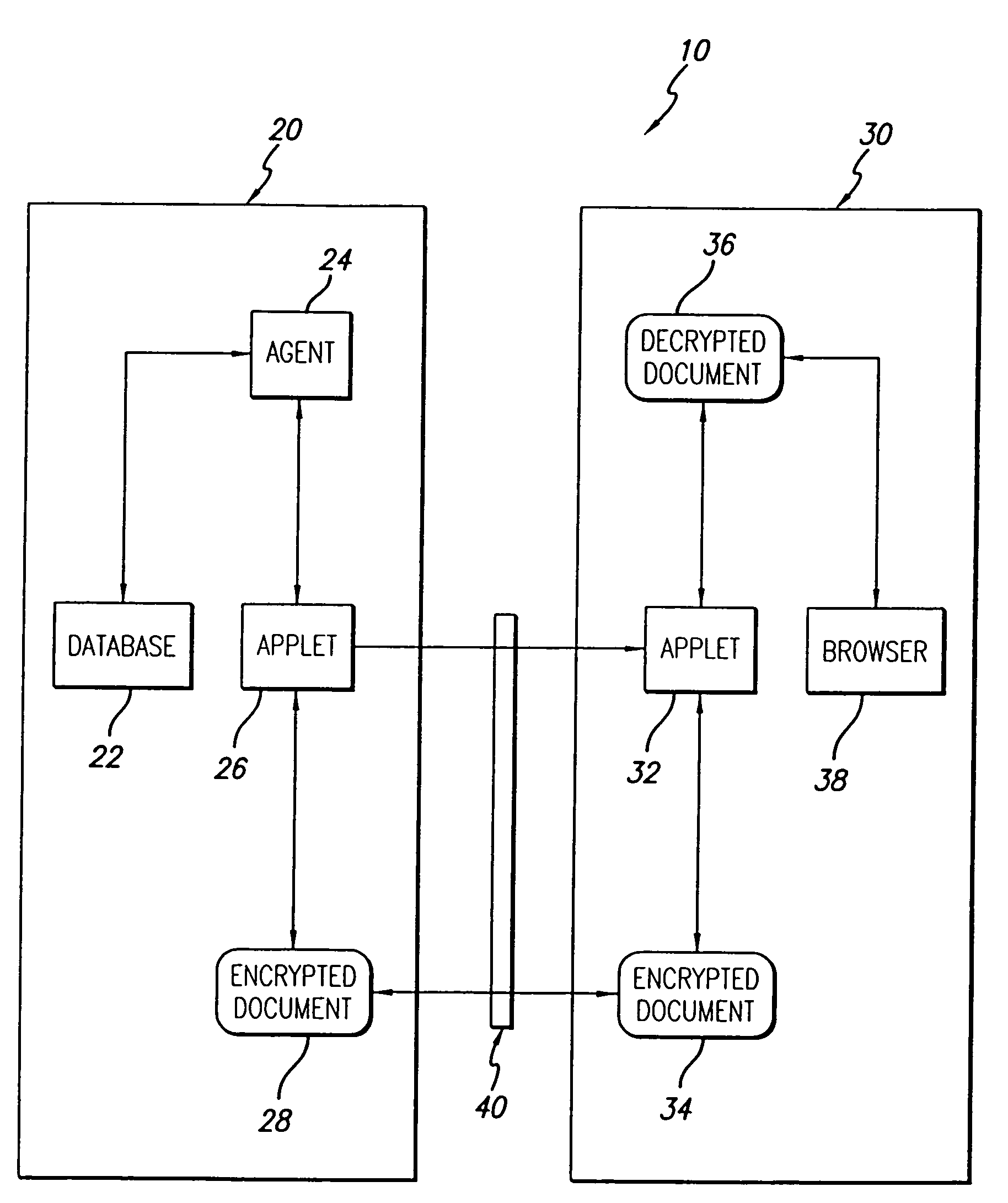
A document management system and method. The inventive system includes a server for providing data from a stored document. Software is provided on the server for encrypting the data. A communications subsystem is included for transporting the encrypted data from the server to the client. Software is provided at the client for decrypting the encrypted data. The inventive method includes the steps of: using a client machine to access a server via a network and to request data therefrom; encrypting at least a portion of said data on said server; communicating said encrypted data from said server to said client; and decrypting said data on said client. In the illustrative embodiment, the inventive method operates under the control of an agent residing on the server. The encrypting software is a first applet residing on the server and the decrypting software is a second applet residing on the client. In the illustrative implementation, the second applet is communicated from the server to the client. Several mechanisms are included for verifying the user's identity including a digital signature, a private key and a public key. In accordance with the invention, software is included for customizing the data based on the user's access rights; providing for secure modification of the shared document; and tracking submission, access, and changes in the document.
Owner:HEWLETT PACKARD DEV CO LP
Method for controlling security function execution with a flexible, entendable, and non-forgable block
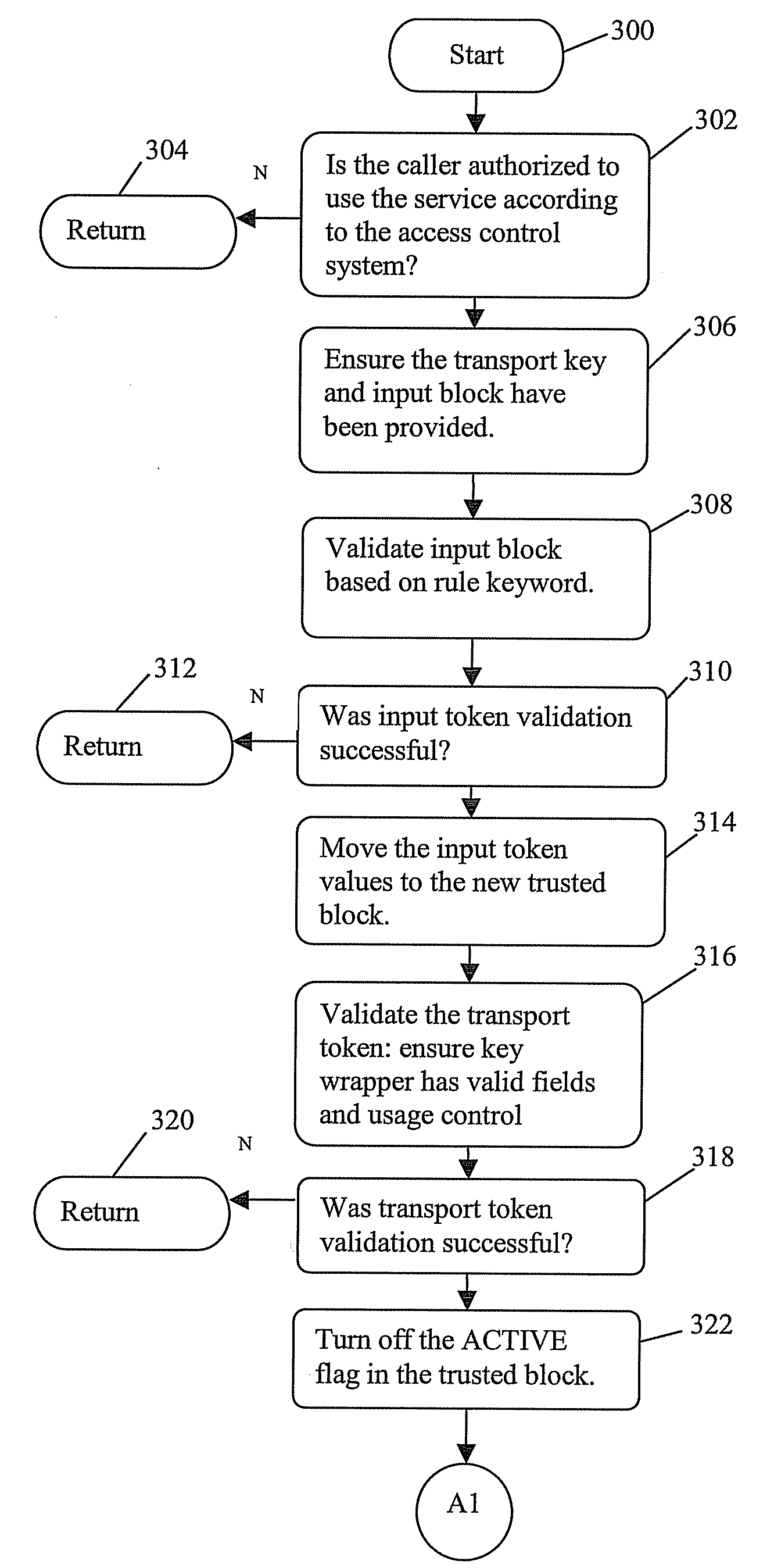
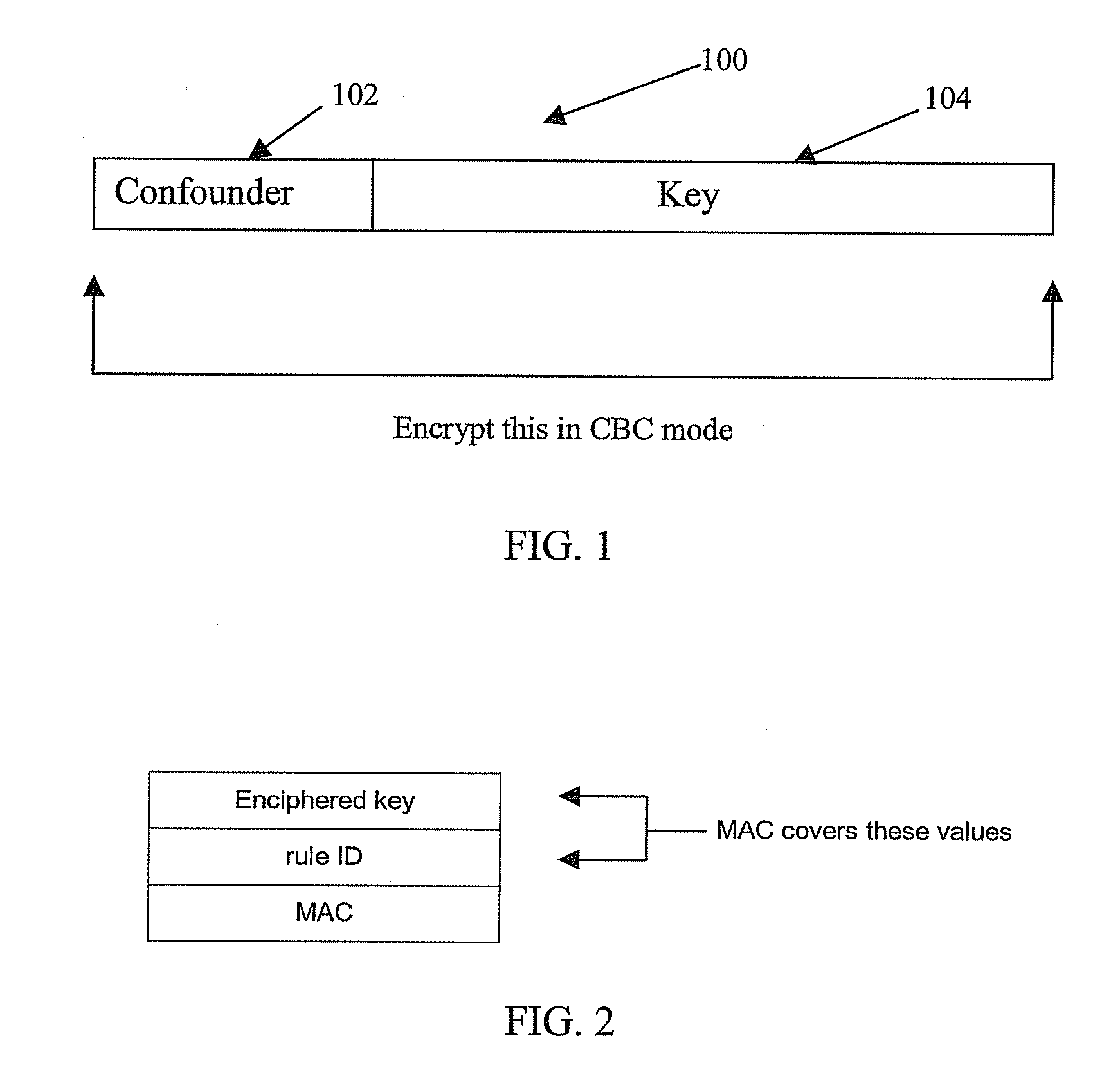
InactiveUS20080077794A1Reduce riskDigital data processing detailsUser identity/authority verificationApplication programming interfaceApplication procedure
A method, article, and system for providing an effective implementation of data structures, and application programming interface (API) functions that allow secure execution of functions behind a secure boundary. The controlling mechanism is a flexible, extendable, and non-forgeable block that details how values and parameters behind the secure boundary can be changed. The invention allows for one entity to execute a security function that will normally require extensive authorizations or dual or multiple control. The method and system comprise instructions that are cryptographically protected against alteration or misuse, wherein the instructions further comprise a trusted block that defines security policies that are permitted when an application program employs the trusted block in APIs. The trusted block has a number of fields containing rules that provide an ability to limit how the trusted block is used, thereby reducing the risk of the trusted block being employed in unintended ways. This trusted block controls the critical values or parameters behind the secure boundary. Cryptographically secured data structures are provided that allow for breaking up the instructions in the trusted blocks in a number of steps without reducing the level of security. Systems that make use of the trusted block must provide two API functions; one that encapsulates the block under at least dual control, and one that process the instructions or rules in the trusted block. In particular the invention provides a method, article, and system for the effective implementation for securely transferring symmetric encryption keys to remote devices, such as Automated Teller Machines (ATMs), PIN entry devices, and point of sale terminals. It may also be used to exchange symmetric keys with another cryptographic system of any type, such as a Host Security Module (HSM) in a computer server.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com