Patents
Literature
63results about How to "Permit adjustment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
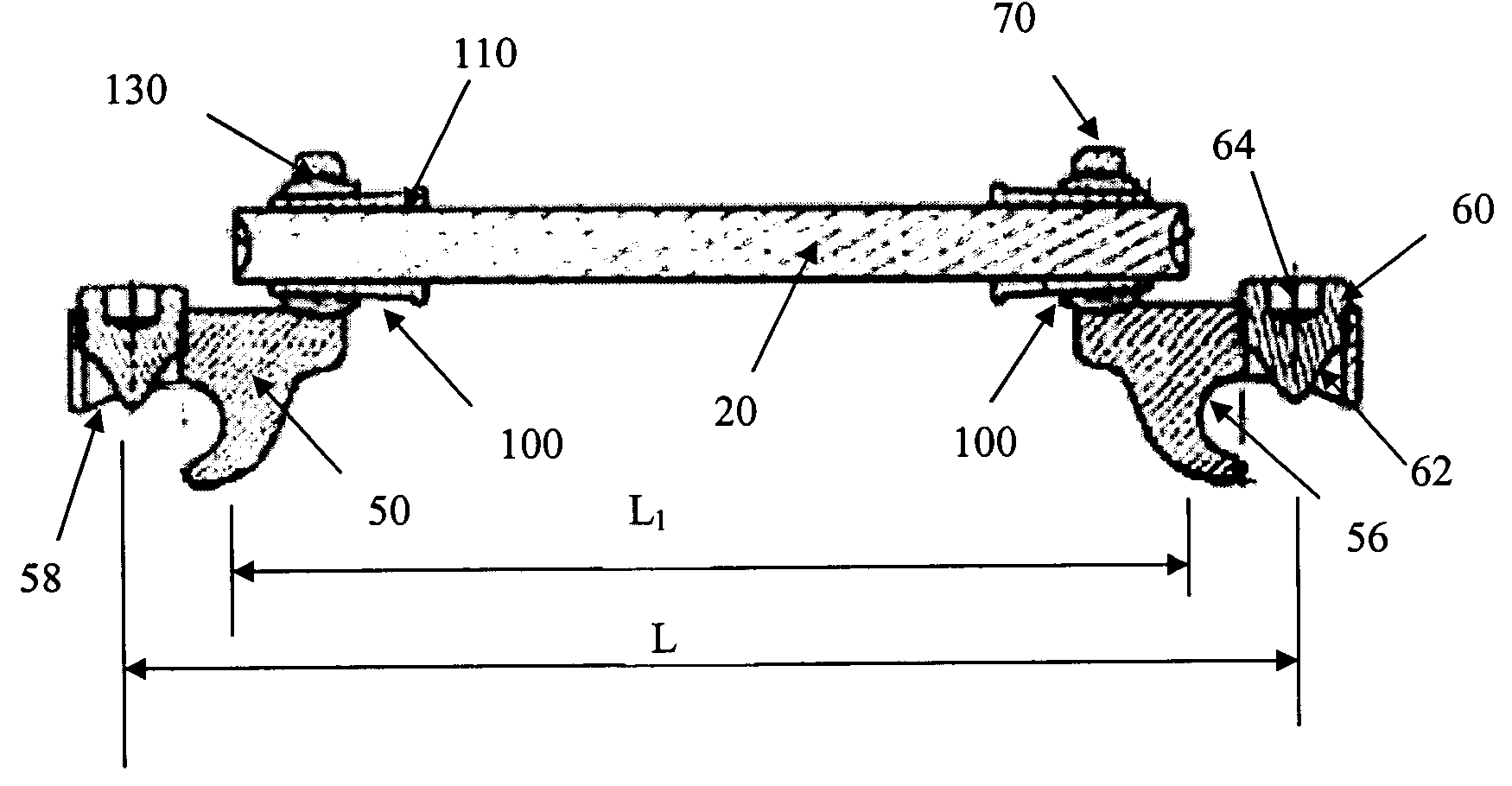
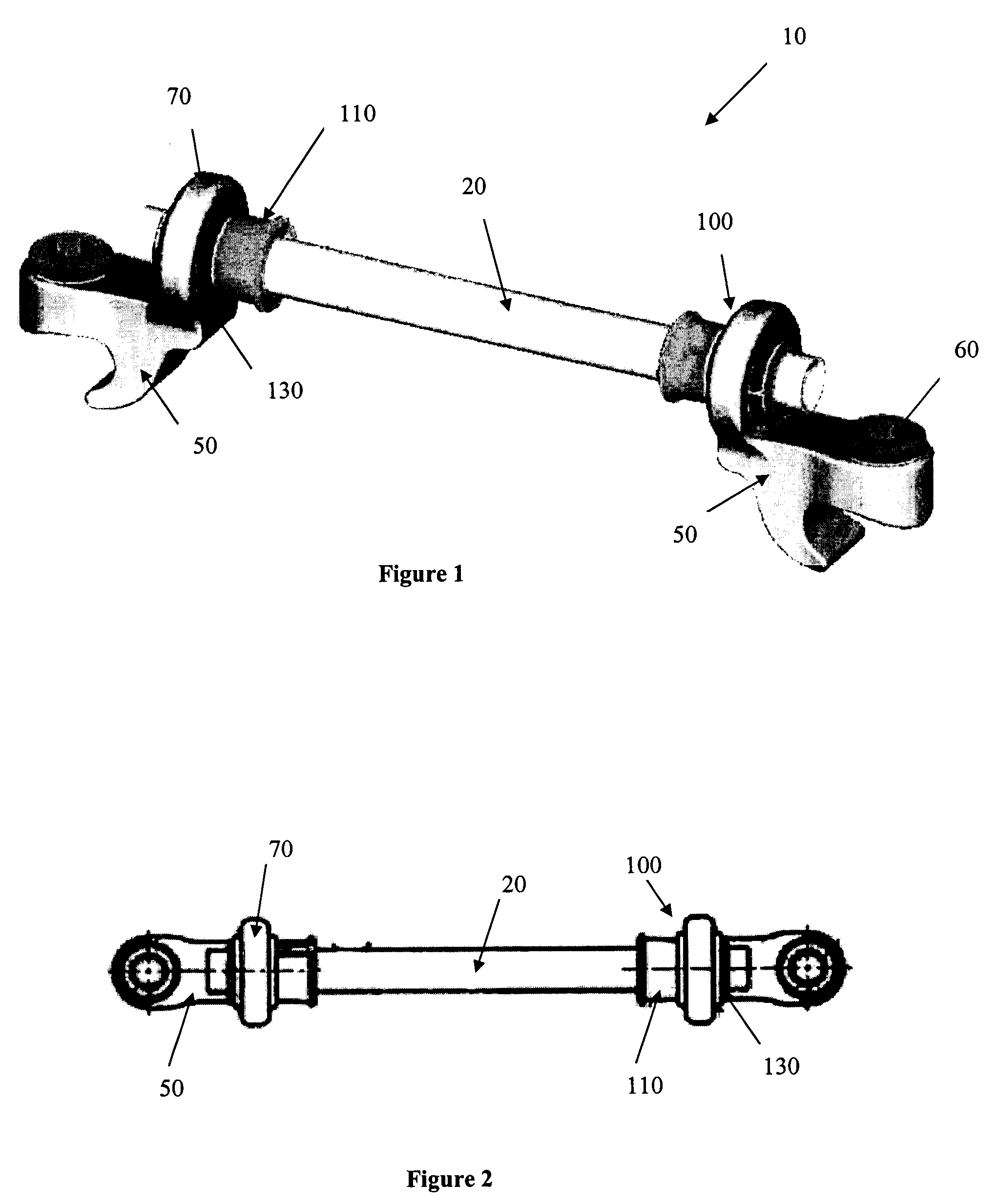
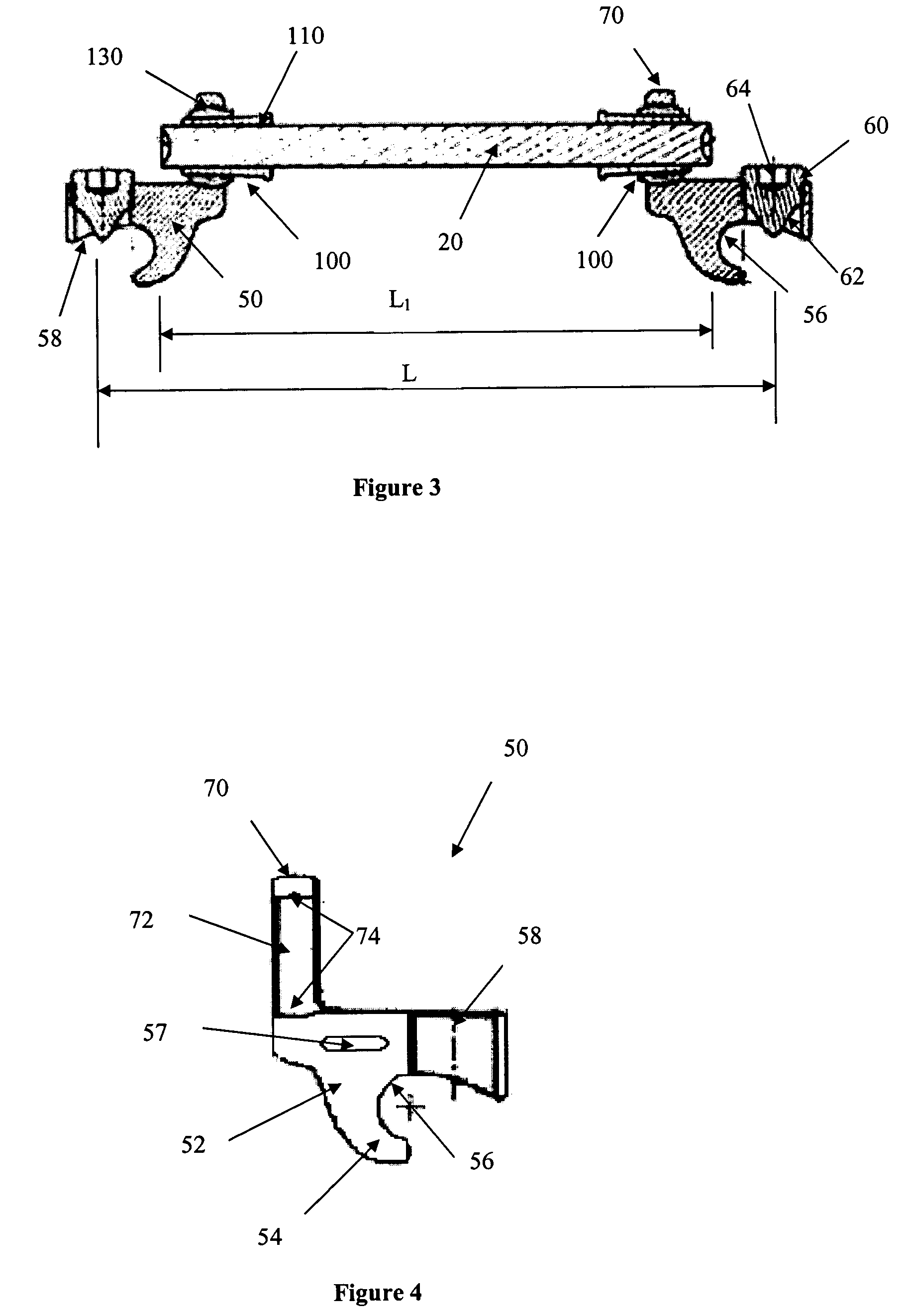
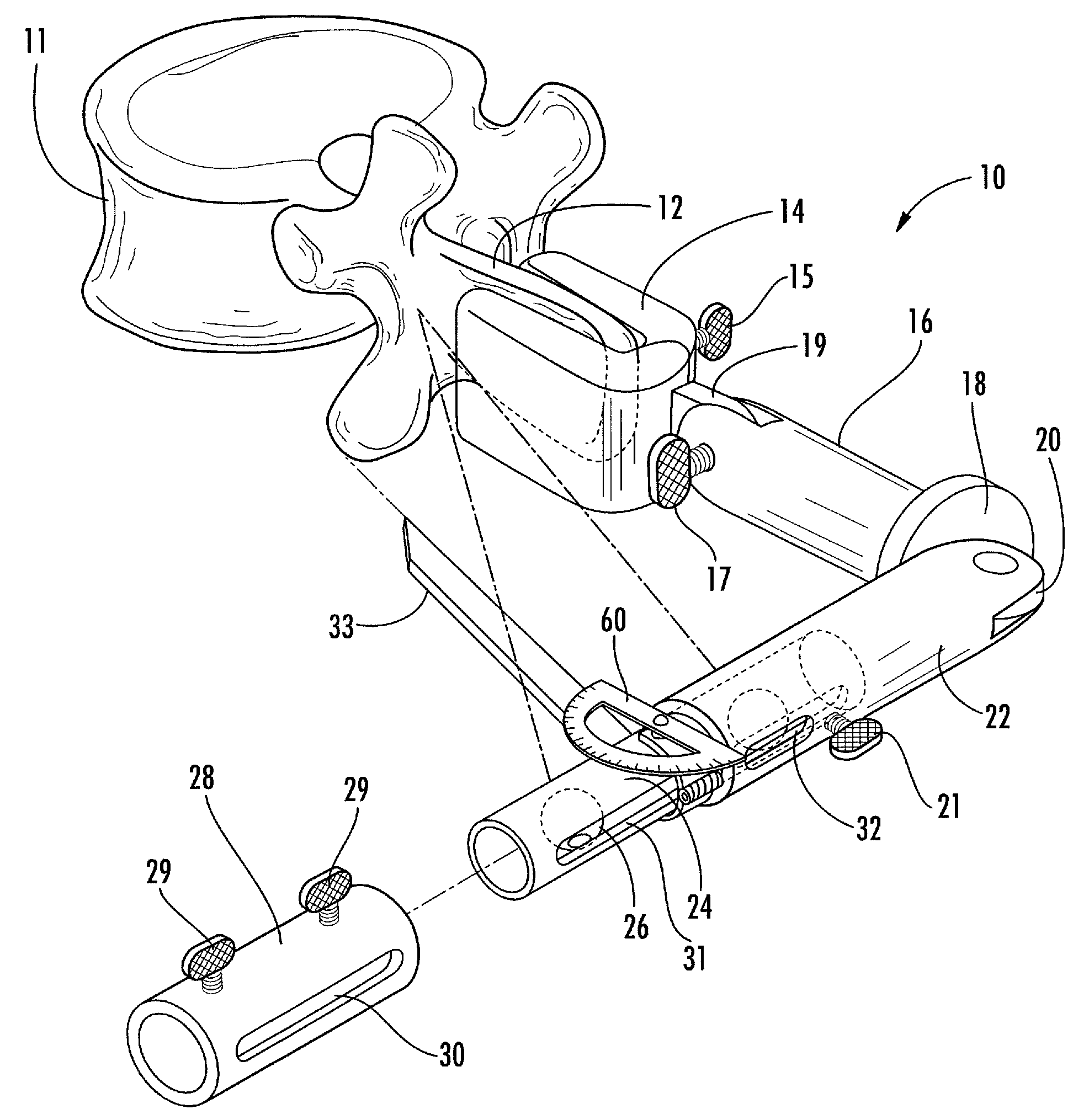
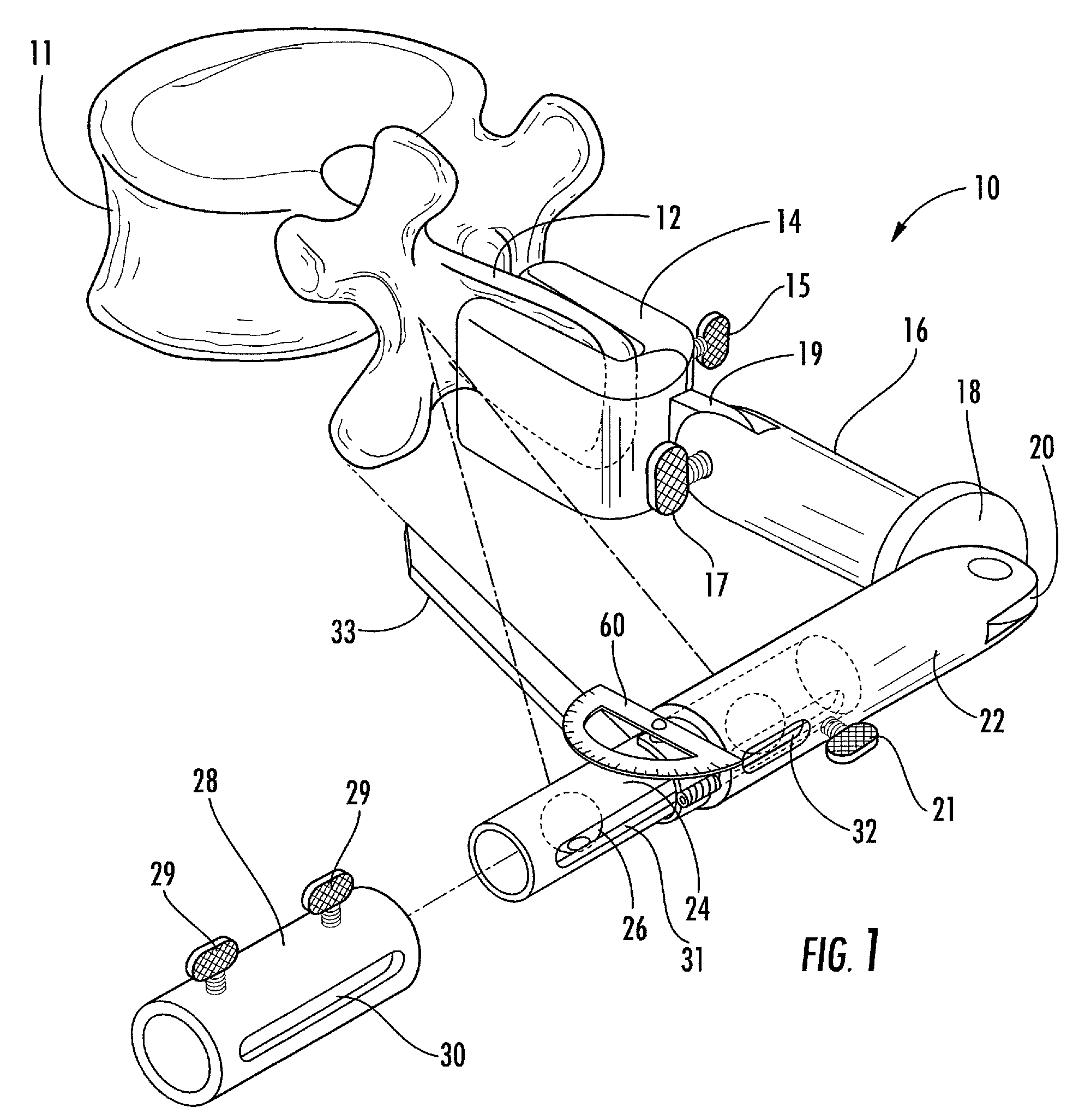
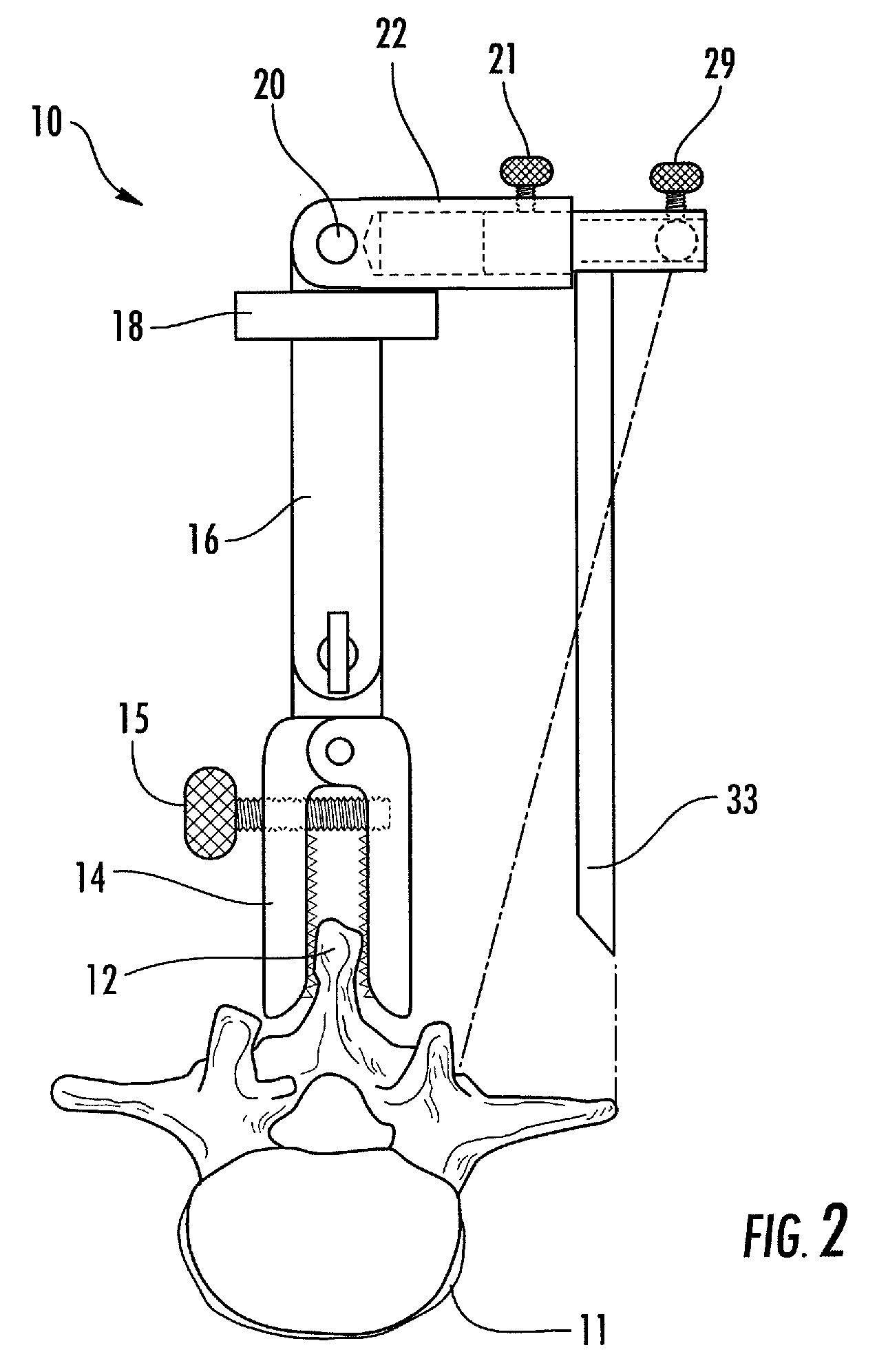
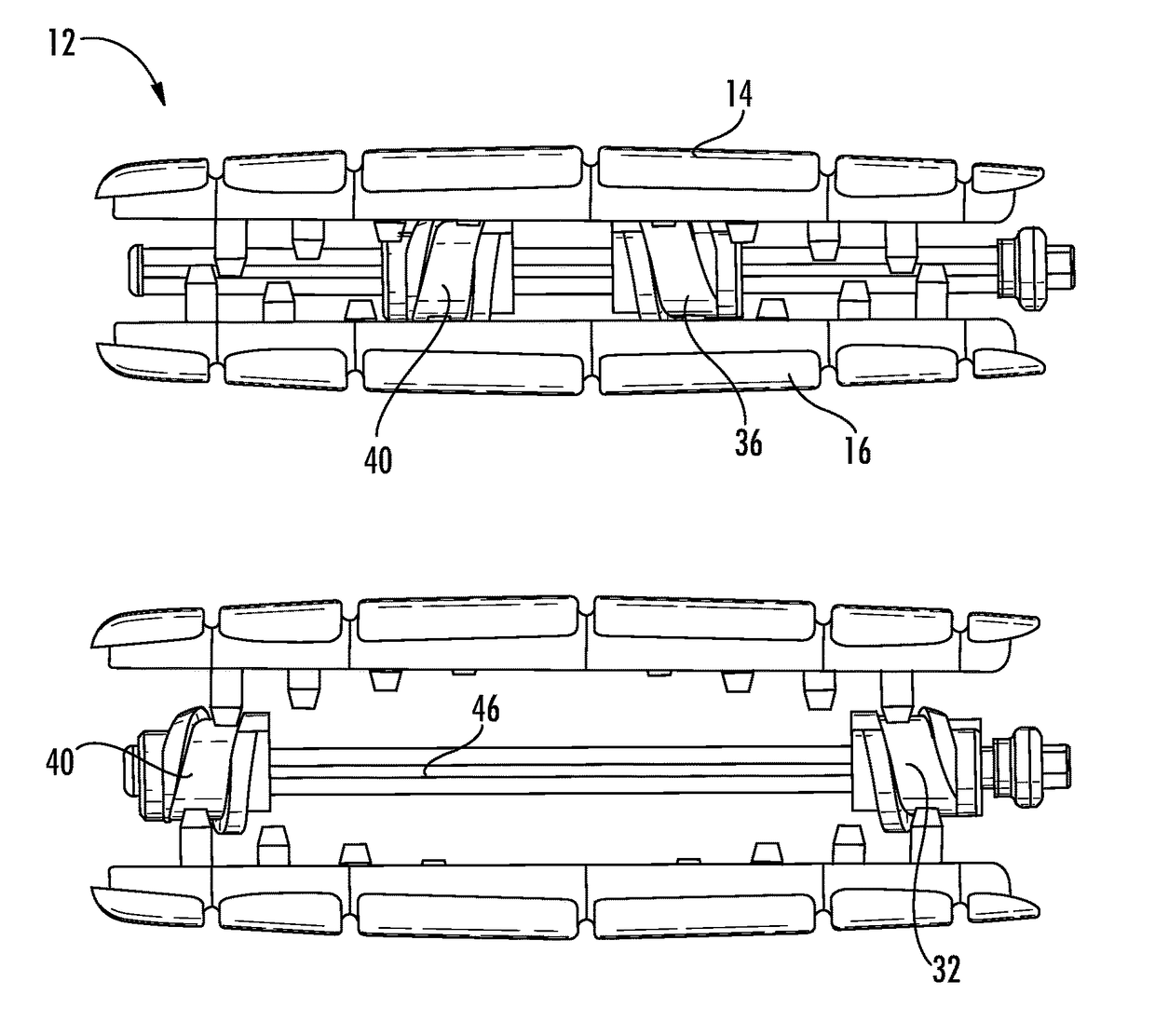
Linking transconnector for coupling spinal rods
ActiveUS20050080416A1Permit adjustmentStable positionSuture equipmentsInternal osteosythesisEngineeringMechanical engineering
A Linking Transconnector is disclosed for coupling a first longitudinal spinal rod to a second longitudinal spinal rod. The Linking Transconnector generally includes a pair of hook engaging members for engaging the longitudinal spinal rods, a lateral rod for spanning a distance between the hook engaging members, and a locking element which interconnects the hook engaging members with the lateral rod. The locking element being configured to allow for multiple degrees of adjustment to permit the Linking Transconnector to accommodate for varying spinal rod alignments. The locking element also permits the location of the lateral rod to be fixed relative to the hook engaging members once the desired position of the lateral rod with respect to the longitudinal spinal rods has been achieved. The locking element may also be able to fix the position of the lateral rod with respect to the hook engaging members by a force applied to the locking element.
Owner:SYNTHES USA
Motor-driven medical instrument with flexible shaft
InactiveUS6245086B1Low investment costLow costSuture equipmentsShaft for rotary movementMotor driveEngineering
Disclosed is a medical instrument having at least one surgical element, such as a knife or the like disposed at the distal end thereof, a motor disposed at the proximal end thereof, and a shaft which connects the shaft of the motor to the shaft of the surgical instrument in such a manner that the surgical element is rotated.According to the invention either the motor is detachably connected to said shaft of the said surgical element in an as such known manner so that a bend can be inserted between the motor shaft and said shaft disposed in the instrument or that a flexible bend is inserted between the motor and the shaft in such a manner that the motor shaft and the shaft disposed in the instrument includes an adjustable angle.
Owner:KARL STORZ GMBH & CO KG
Adjustable speed ball bearing jump rope
InactiveUS6551222B1Simple and efficient designEffectively and inexpensively cures deficiencySkipping-ropesJumping ropeBall bearing
A speed ball bearing jump rope construction with an adjustable rope length, the invention consisting of a pair of hollow handles having external grip surfaces, vent holes and a bearing assembly at one end of each handle fastened with a screw threaded into the handles. Screws mounted within each of the tops of the bearing assemblies permit the rope to slide to shorten the length.
Owner:BEAVER TERRY L
Spinous process fixated bilateral drilling guide
InactiveUS20100023018A1Precise positioningAccurate and repeatable drilling and screw placementProsthesisOsteosynthesis devicesAnatomical landmarkCoronal plane
The application describes a bilateral drilling and screw placement guide adapted for fixation to the spinous process of a vertebral body. The positioning and surgical guiding instrument is adapted for use during a spinal surgical procedure in conjunction with a drilling tool, fastening device, e.g. a pedicle screw, K-wire or the like. The guide includes an engagement device for attachment to a region of the spinous process, to which an adjustably attached support member is affixed. This allows for immobilizing the guide upon the spinous process anatomical landmark, in a specific orientation with respect thereto. The guide includes a bilaterally adjustable drill guide assembly for precise anatomical positioning of the drill and screw placement guides bilaterally about the sagittal, axial and coronal planes so as to enable the defining of a plurality of drilling axes extending toward the vertebral body. The device further provides for adjustment to account for anatomical variations in width along the axial plane, and includes pointing and angular positioning functionality to insure repeatable and reliable pilot hole and screw placement along a plurality of angles.
Owner:ALPHA GUIDE HLDG LLC
Expandable and adjustable lordosis interbody fusion system
ActiveUS9889019B2Assists lordotic adjustmentEffective tool for in situ adjustmentJoint implantsSpinal implantsLumbar vertebraeEngineering
An expandable housing for an interbody fusion system has movable tapered external helical threaded members that travel along tracking to operably engage against the top and bottom shell members, urging them apart to cause expansion in the height of the housing. In an embodiment, the tapered members are disposed in a dual arrangement such that independent engagement of the tapered members along lateral portions of the top and bottom shells cause an angular tilt to the exterior surface of the housing when the tapered members are moved to different degrees. This function permits adjustment in the angular relationship between adjacent vertebrae and assists the lordotic adjustment of the patient's spine. When the functions of the device are used in combination by the surgeon, the device provides an effective tool for in situ adjustment when performing lateral lumbar interbody fusion.
Owner:ADCURA INC
Storm protection apparatus
InactiveUS20070000183A1Permit adjustmentHigh wind induced loadingHuman health protectionTents/canopiesStormEngineering
Owner:LOGAN EDWARD ALEXANDER
Office chair
A chair having an adjustable resilient back recliner mechanism, a pair of adjustable armrests, modular upper back portions and an adjustable lumbar support. The chair includes a tension control that adjusts the tension in the recliner mechanism. The tension control is cam-operated to permit adjustment throughout the entire range of adjustability with only limited rotational movement of a control knob. The chair includes a recline limit control that adjusts the limit of rearward movement in the recliner mechanism. The limit control includes a cable operated stop that interact with a stepped trackway on the seat. The chair further includes a height control for adjusting the seat height including a push-button located in the tension control knob. The armrests include height and angle adjustment mechanisms. The lumbar support includes a lumbar cam that is rotatably mounted to a lumbar pad. The lumbar cam includes a plurality of lobes that vary in radius so that rotation of the cam causes variation in the contour of the lumbar region. The chair back includes a fabric carrier with an upper back portion mounting platform that permits attachment of any of a variety of modular upper back portions.
Owner:JSJ SEATING COMPANY TEXAS
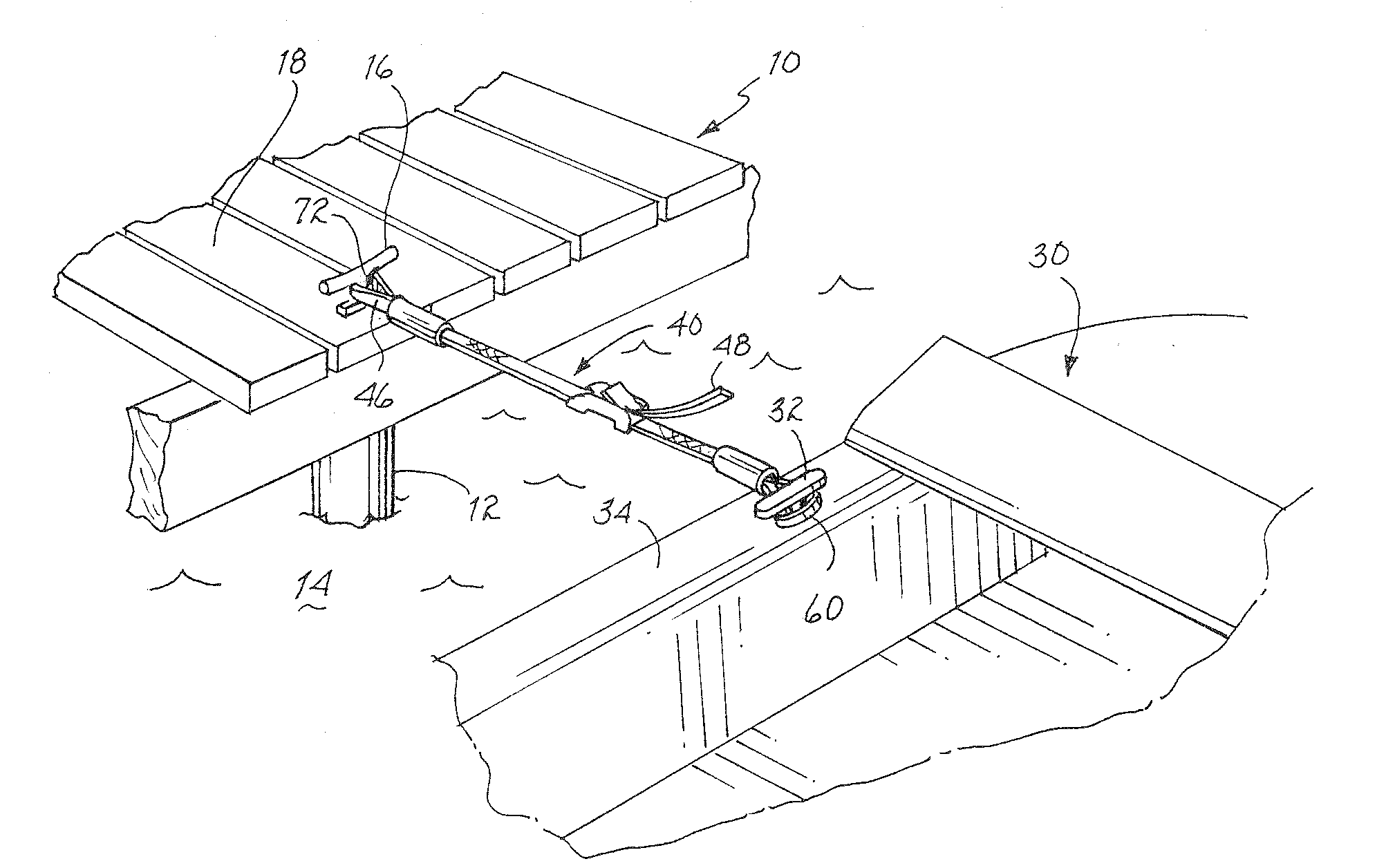
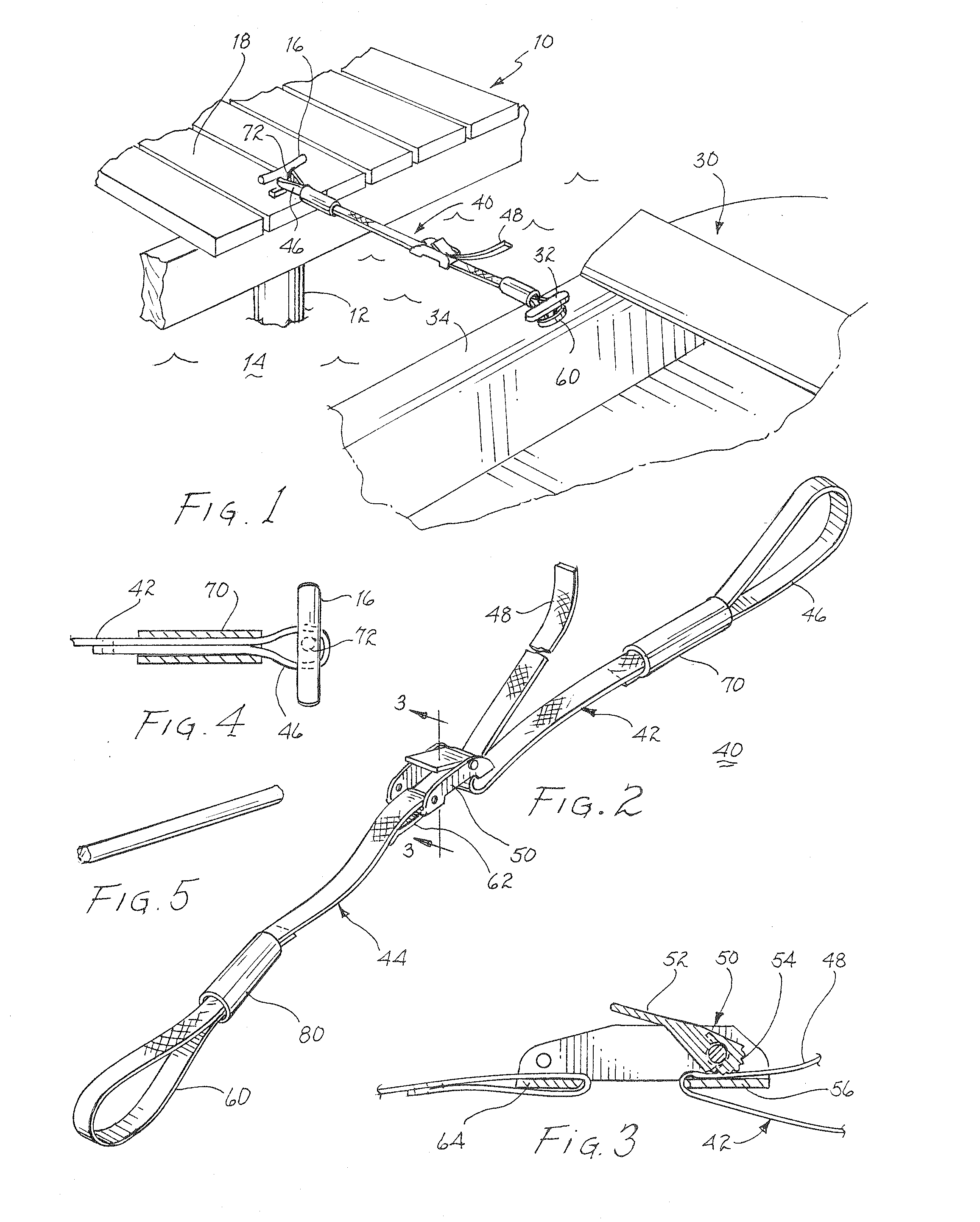
Mooring Strap
InactiveUS20080196650A1Reduce functional lengthPermit adjustmentWaterborne vesselsEngineeringMechanical engineering
A mooring strap for vessels includes a first loop for engaging a dock mounted cleat and a second loop for engaging a cleat on a vessel. A strap extending from each of the two loops is interconnected with a cam lock to permit drawing the two loops toward one another to draw the vessel toward the dock and to secure the vessel with the dock. A sleeve attendant each loop is slid toward a loop engaged cleat to reduce the functional size of the loop and thereby prevent the loop from becoming inadvertently disengaged from the cleat. Upon release of the cam lock and drawing the sleeves away from the respective engaged cleats, the mooring strap may be disengaged from the cleats.
Owner:FERNUNG RICK E
Expandable and adjustable lordosis interbody fusion system
ActiveUS20200078190A1Facilitate insertionPrevent from rotateJoint implantsSpinal implantsSpinal implantBiomedical engineering
A spinal implant device for placement between vertebral bodies includes a housing, at least one screw member in the housing, and at least one drive shaft operably engageable with the screw member. The housing includes a first shell member and a second shell member. At least the first shell member has step tracking comprising a plurality of individual riser members for receiving the at least one screw member. The height of the plurality of individual riser members may change along the step tracking. The drive shaft may be operable to rotate the at least one screw member, causing the at least one screw member to move on the plurality of individual riser members. The at least one screw member comprises an external helical thread having a thickness configured to fit in the gaps between adjacent individual riser members, and is engageable with the first and second shell members, whereby the first and second shell members move relative to each other in response to the rotation of the at least one screw member to effect an expansion of the housing or a contraction of the housing from the expansion by reversing the rotation of the at least one screw member.
Owner:ADCURA INC
Image pickup lens, image pickup apparatus and method for forming image pickup lens
InactiveUS7092174B2Permit adjustmentSpeed up the flowRecord information storageMountingsOptical axisObject point
The present invention relates to an image pick-up lens, an image pick-up apparatus comprising the image pick-up lens and a producing method of the image pick-up lens, and the image pick-up lens comprising: a lens part to form an image point of an object point at predetermined distance; and a supporting part to support the lens part and integrally formed with the lens part in a tubular form extended from the periphery of the lens part along the optical axis of the lens part, and the tip end of the tubular form is included in an ideal plain surface perpendicular to the optical axis of the lens part, wherein the image point is located in the ideal plain surface.
Owner:KONICA CORP
Mirror with adjustable detent
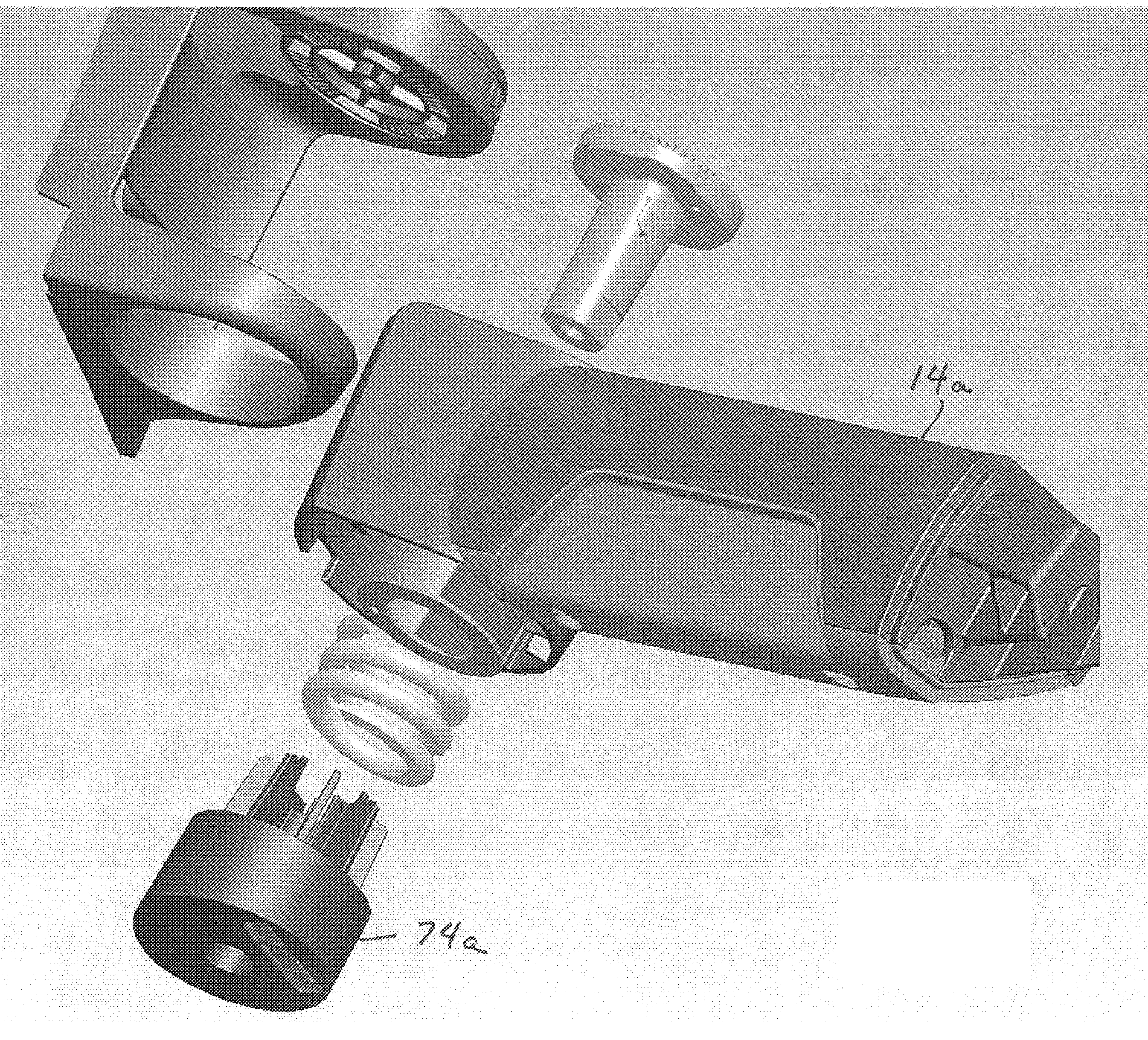
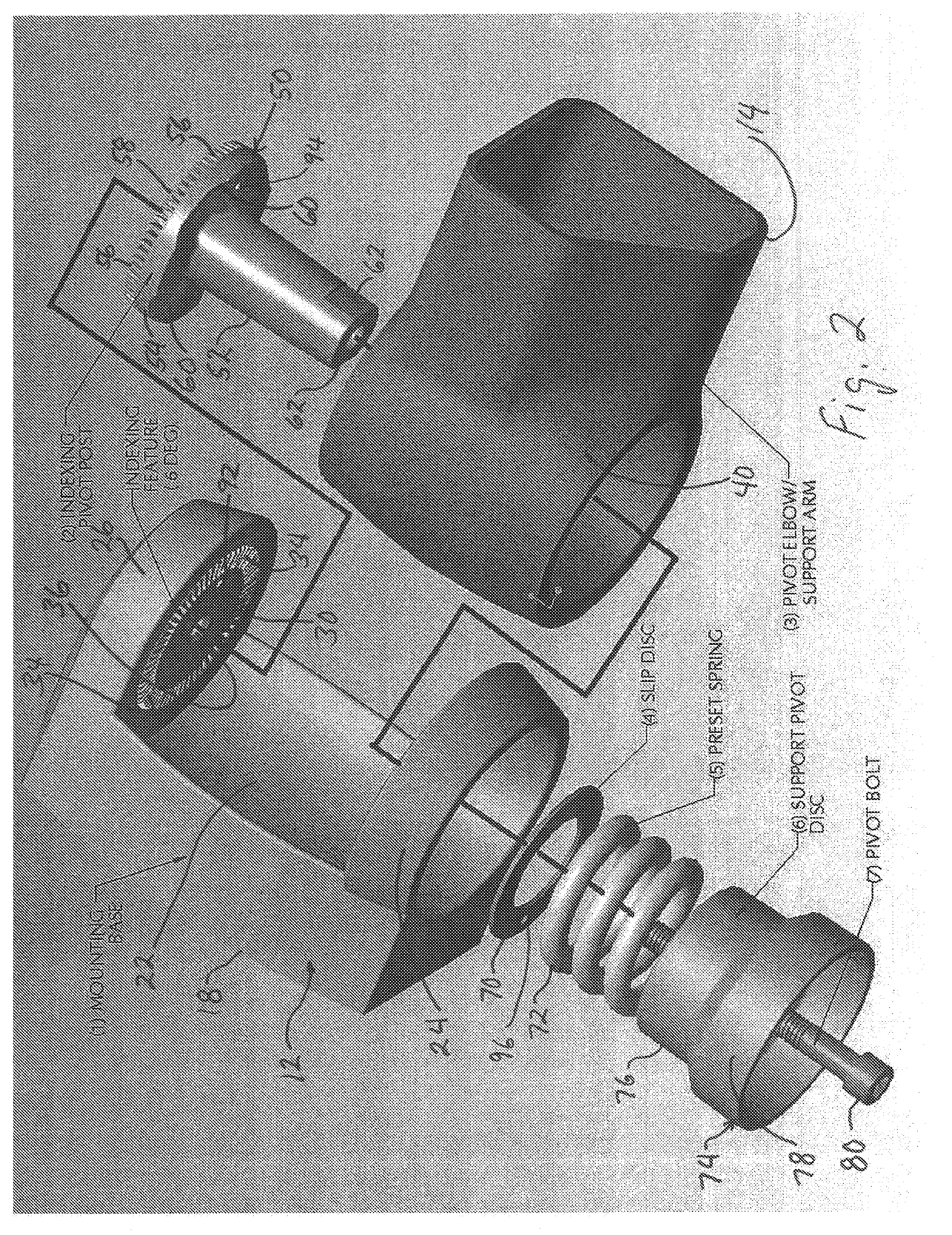
A mirror unit for a vehicle includes a base from which extends an arm holding a mirror housing. The arm is pivotably mounted in the base to permit the mirror to be pivoted toward the vehicle in the event that the mirror is struck, for example. The extended position of the mirror when not folded is defined by a detent in the pivoting movement. The detent position of the mirror is the result of a bolt that presses a spring. The spring in turn presses a hub on the arm against an indexing pivot post, so that ramps on the hub bear against ramps on the indexing pivot post and define the detent position of the mirror. The indexing pivot post has an arrangement of teeth that engage into tooth recesses on the base when pressed thereagainst by the spring. The detent position of the mirror can be changed by the user by the user releasing the bolt to relieve spring pressure on the teeth so that the teeth of the indexing pivot post disengage from the tooth recesses and can be pivoted to a new detent position. The new detent position is ensured by tightening the bolt so that the spring presses the teeth into the tooth recesses.
Owner:VELVAC
Method and device for assembling optical components or an optical component and a substrate
InactiveUS20020118908A1Good low temperaturePermit adjustmentCoupling light guidesMulticore optical fibreEngineeringPhysical chemistry
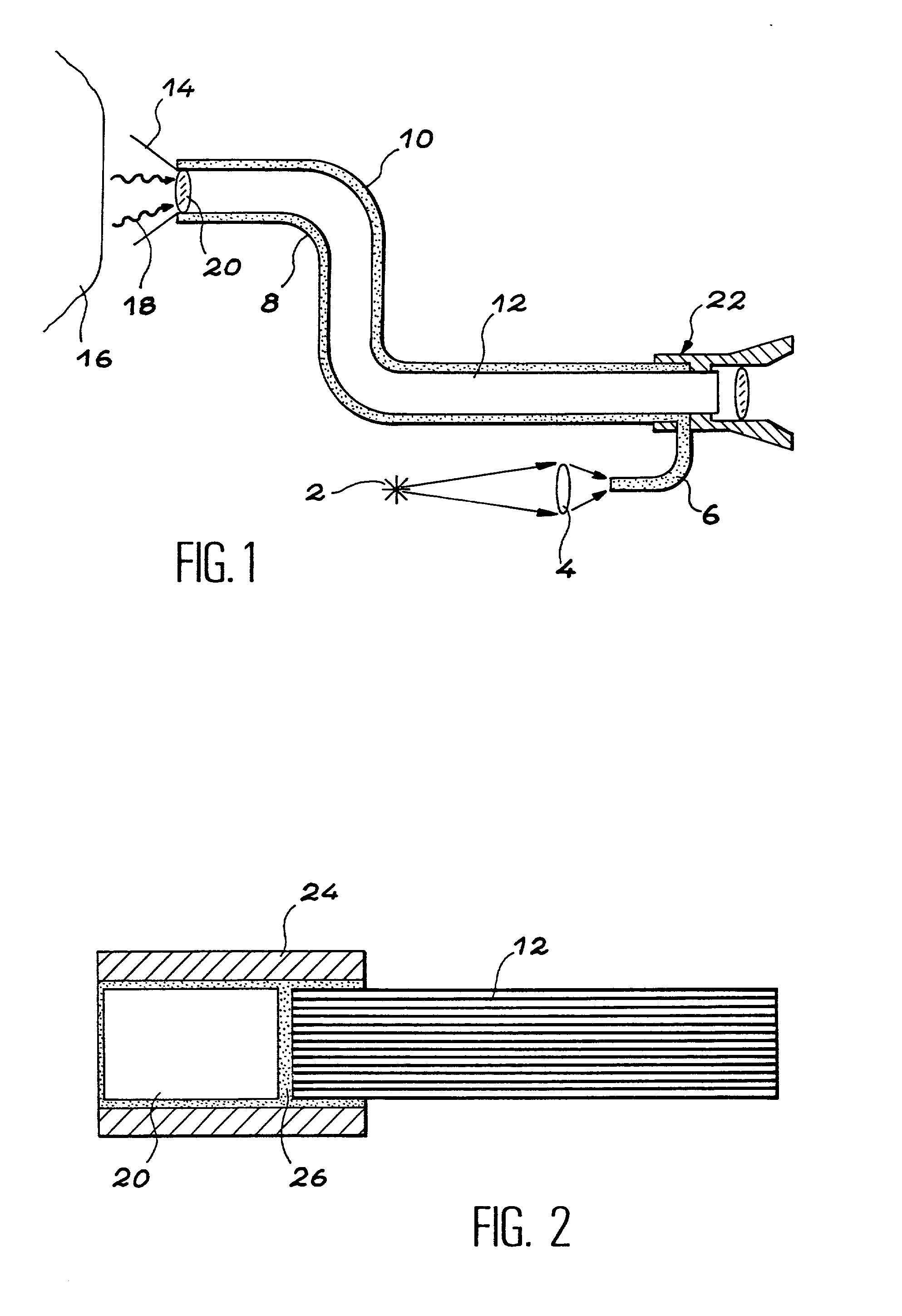
The invention relates to an assembly of an optical component (30) and a substrate (32) comprising: the optical component, the substrate, a glass layer (34) located at the interface between the optical component and the substrate. The invention also relates to an assembly between two optical components, which is particularly appropriate for use in the field of imaging, especially in endoscopy.
Owner:ANDROMIS
Rearview device with moveable head assembly
InactiveUS20180126910A1Ensure maintenanceSmall mirror sizeOptical viewingMobile vehicleMotorized vehicle
A rear view device for a motor vehicle includes a base assembly for arrangement on the motor vehicle, a moveable head assembly attached to the base assembly, and an actuation mechanism, the actuation mechanism including a fixed part attached to the base assembly and a moveable part attached to the head assembly, where the actuation mechanism allows movement of the moveable part with respect to the fixed part in one or more axes.
Owner:SMR PATENTS S A R L
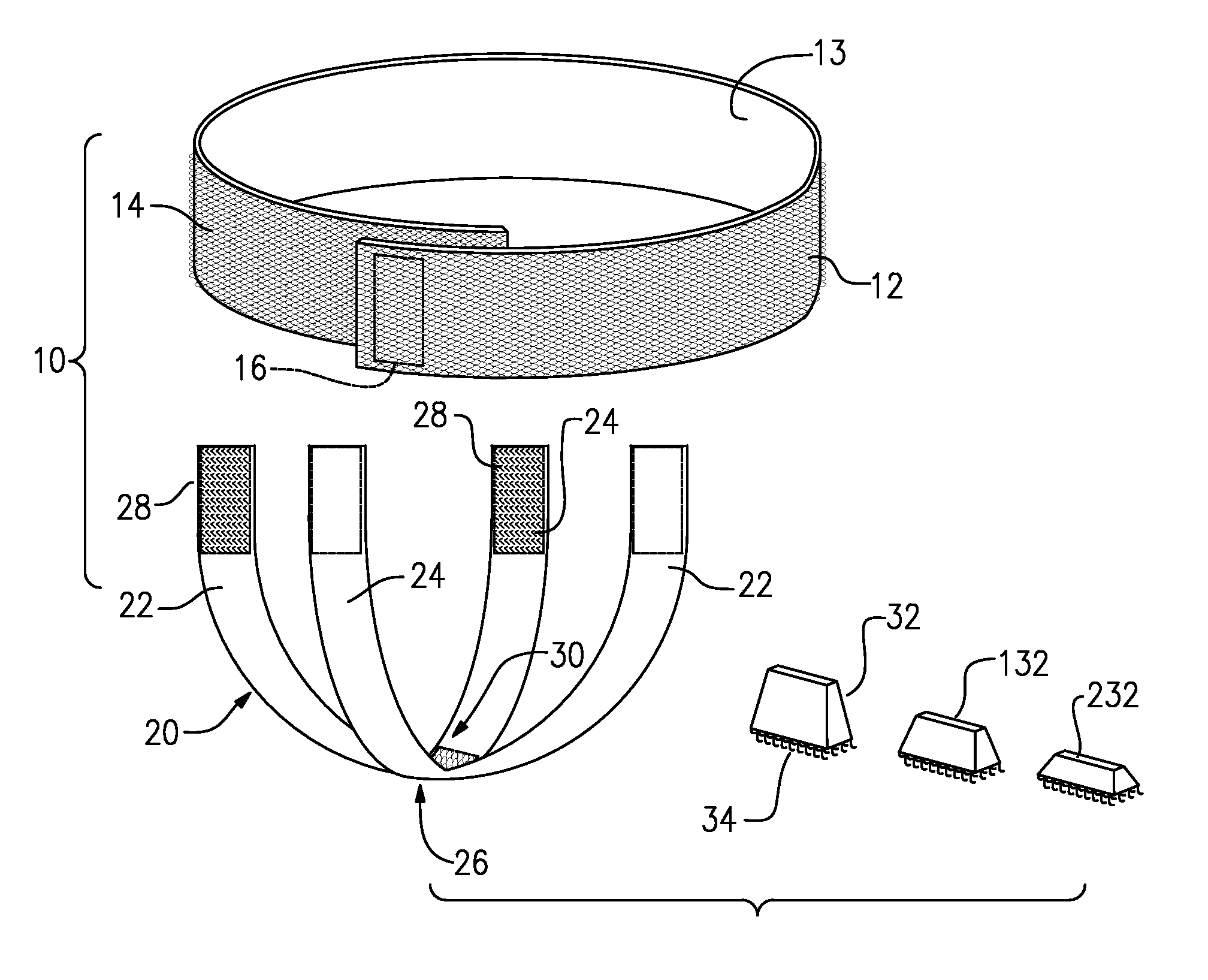
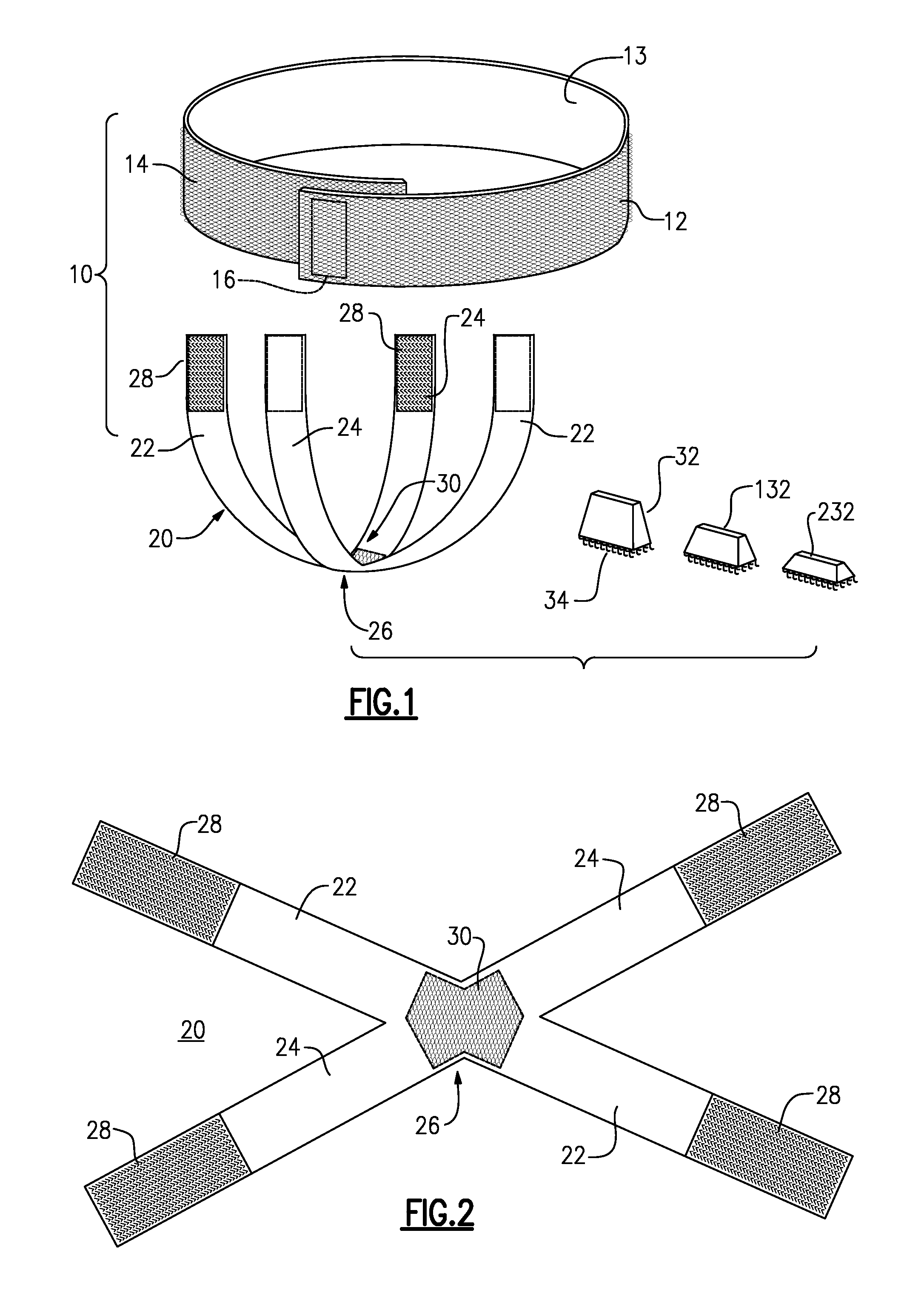
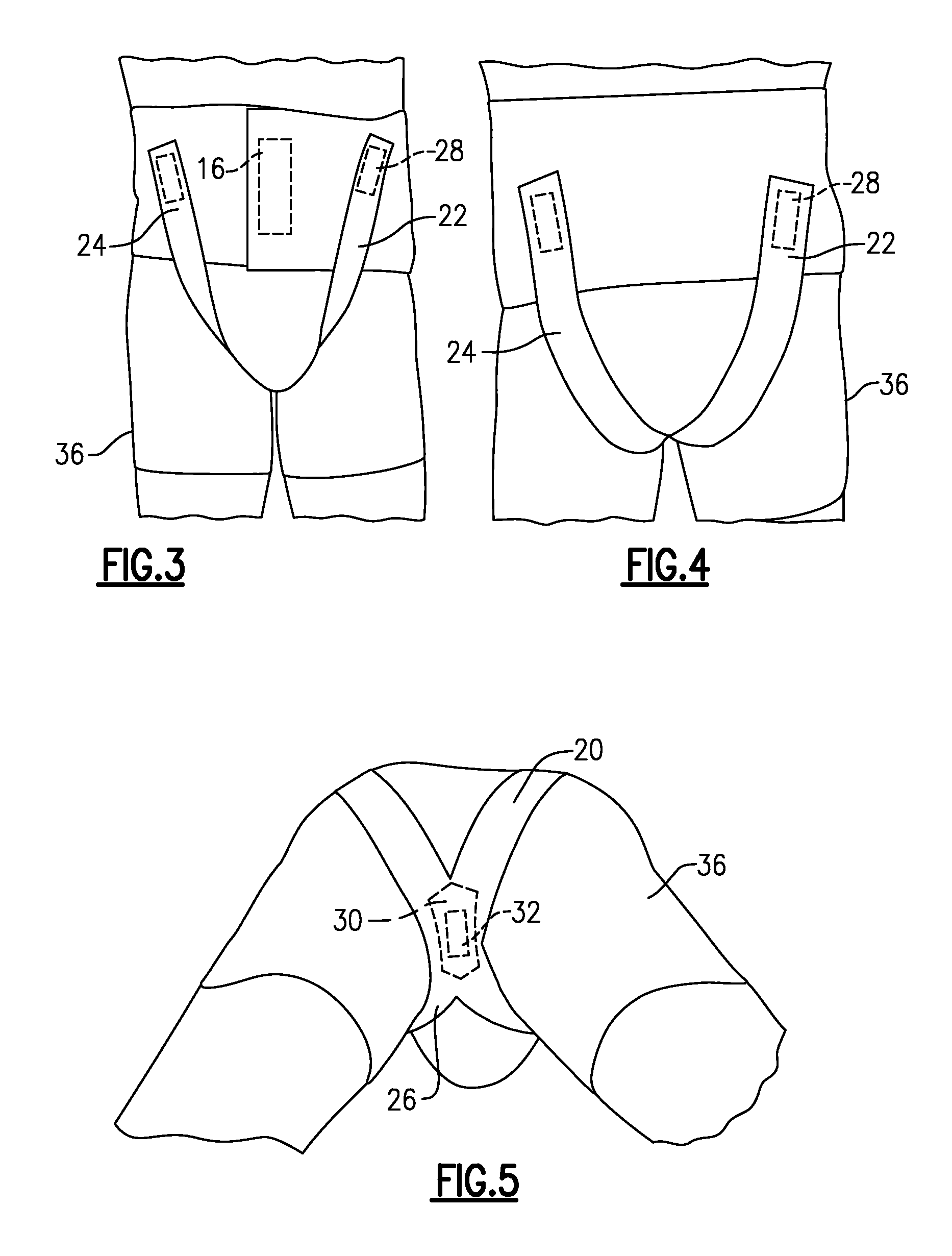
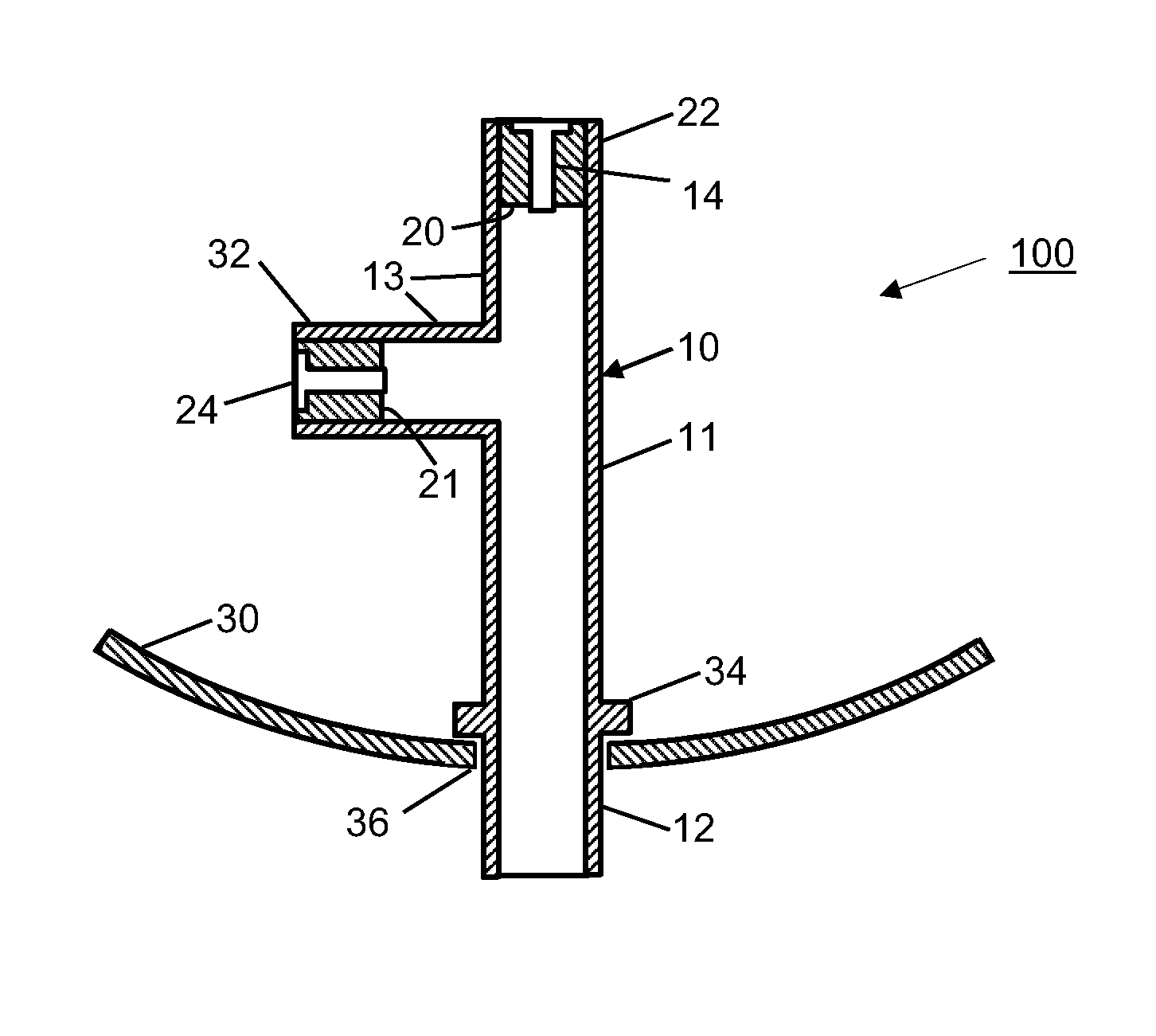
Male incontinence aid
InactiveUS8672910B1Reliable and comfortable to wearEasy to disassembleMale contraceptivesBreast bandagesMale genderUrethra
An external urinary incontinence aid in the form of a pelvic floor support sling has three components. A belt or girdle encircles the patient at or above the waist. An X-shaped elastic cross strap has hook / loop fastener strips at its ends to attach removably to the outer surface of the girdle, and hook / loop material at the crossing or intersection. A pressure block or pad is attached removably to the crossing portion of the cross strap, and presses against the perineum or pelvic floor, applying pressure to occlude the urethra and prevent or reduce involuntary leakage.
Owner:KAUFMAN KENNETH M
Two-port tire valve stem
A two-port tire valve stem has a body, preferably of substantially rigid construction, with a first end portion adapted to be mounted to a wheel rim and a second end portion with at least two ports in a branched configuration, each supporting a valve. One of the valve ports may be used for inflation or deflation concurrently with the other being coupled to a pressure sensor for monitoring the air pressure in the tire. The two-port tire valve stem is adapted to be rigidly mounted to an outer of a pair of adjacent wheels, using a bracket, while its first end is adapted to be connected in fluid communication with the inner of the pair of wheels.
Owner:HAWKSHEAD SYST
Collapsible pan
InactiveUS20100133142A1Facilitate pivotable movementPermit adjustmentBaking ovenCooking vesselsAlong edgeMechanical engineering
Owner:EDISON NATION
Color Cosmetics Containing Isoalkane Mixture and Effect Pigments
InactiveUS20090196841A1Improve compatibilityPleasant feelCosmetic preparationsHair cosmeticsPigmentChemistry
The invention provides compositions for color cosmetic formulations comprising a specially formulated isoalkane mixture and effect pigments, and optionally, one or more cosmetically acceptable auxiliary agents, and methods for making the color cosmetics formulations.
Owner:BASF CATALYSTS LLC
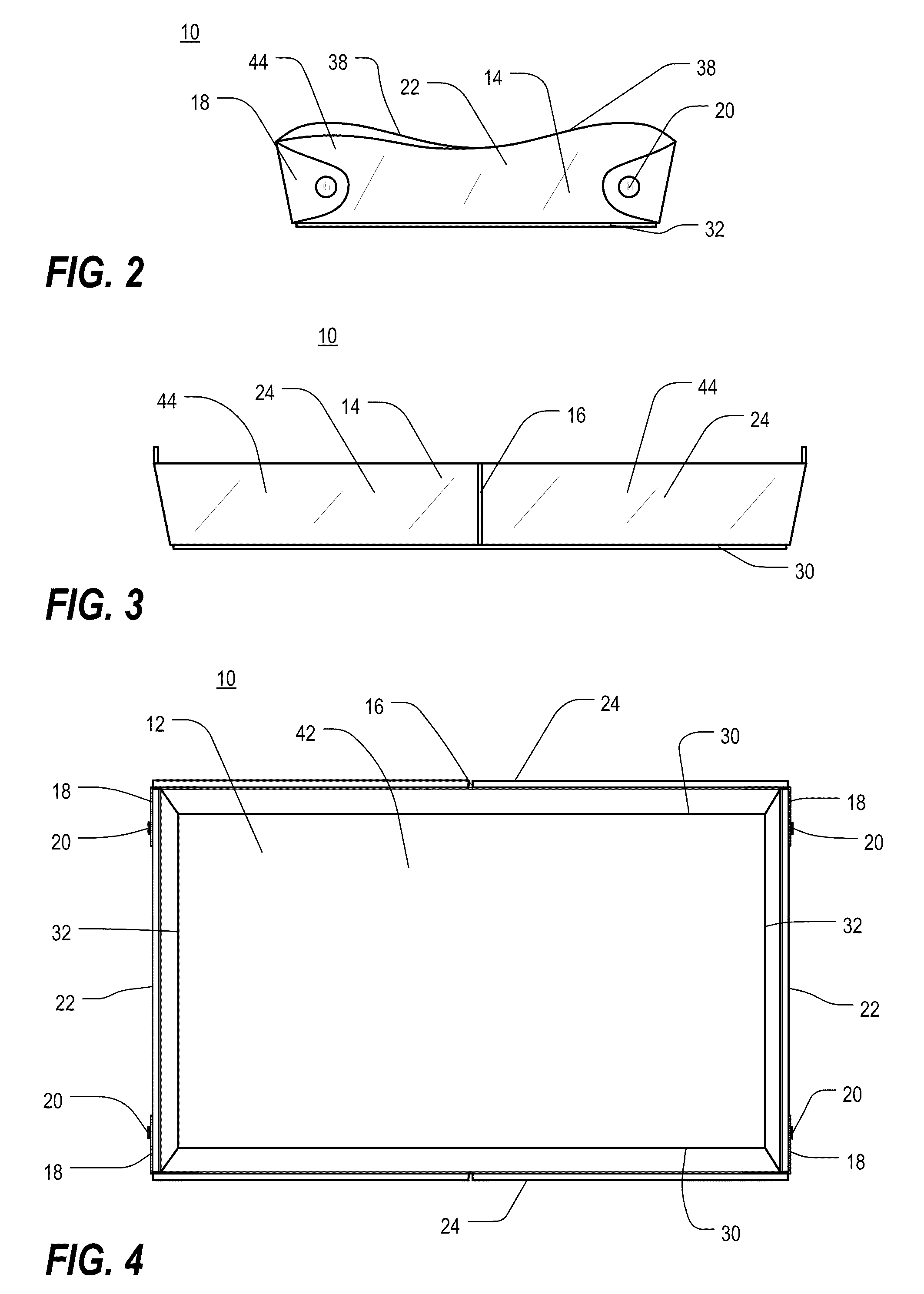
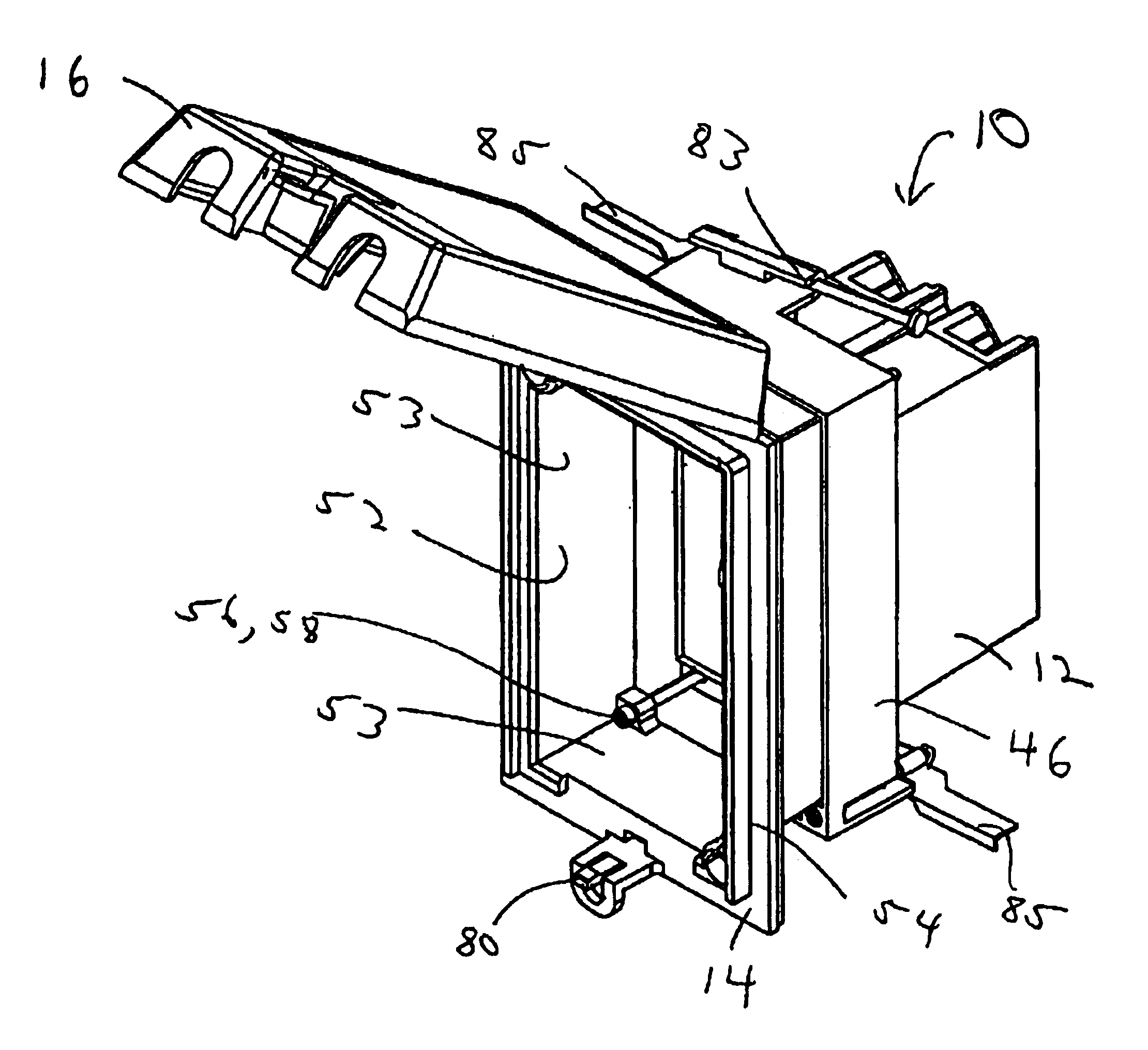
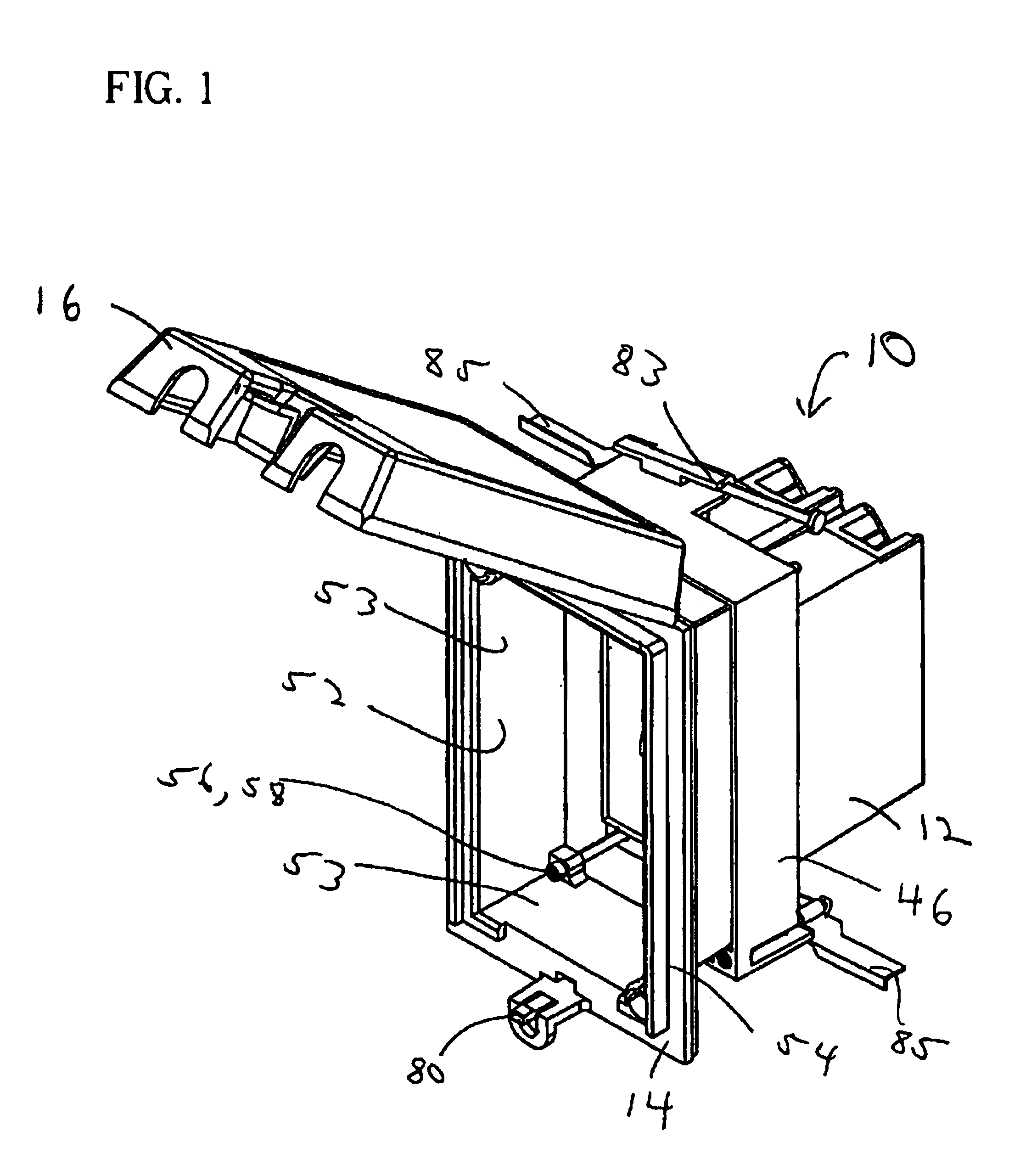
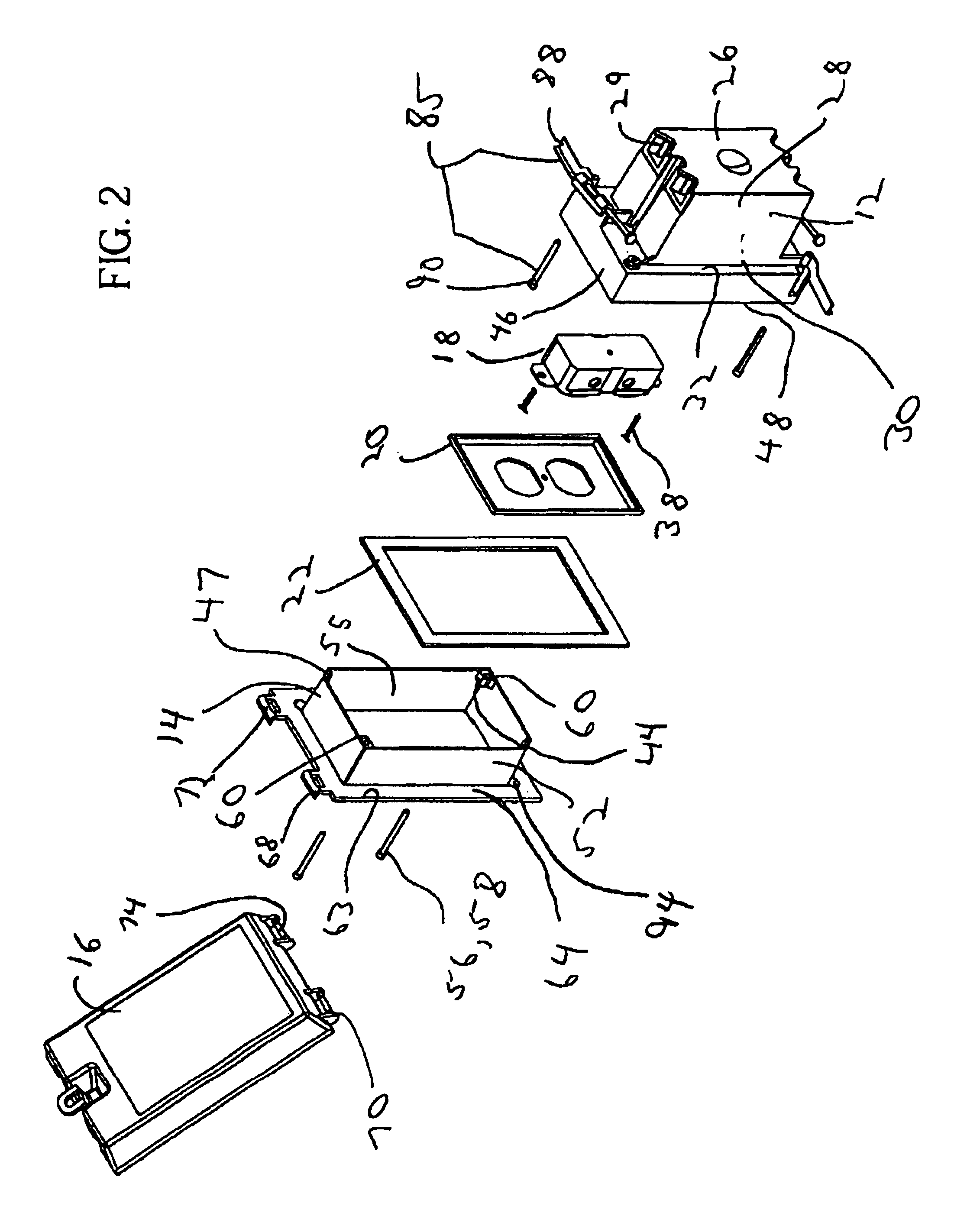
Electrical box assembly
InactiveUSRE41661E1Easy to installPermit adjustmentSubstation/switching arrangement detailsCouplings bases/casesEngineeringShaft collar
An electrical box assembly including a box having a base wall perimetrically bounded by a sidewall extending therefrom forming a housing adapted to receive an electrical component. The sidewall having an upper portion and a flange extending outwardly in a transverse direction from the upper portion. An electrical component attachment point is disposed adjacent the sidewall upper portion and adapted for securing an electrical component to the box. The flange is perimetrically bounded by a collar extending outwardly therefrom. A securement device disposed on the box for securing the box to a support structure is provided. A frame is further provided which is in telescopic engagement with the collar and movable relative thereto. The frame has an abutment surface for abutting against a facing surface. An adjustment device is provided for moving the frame relative to the box and urges the abutment surface against the facing surface.
Owner:THOMAS & BETTS INT INC
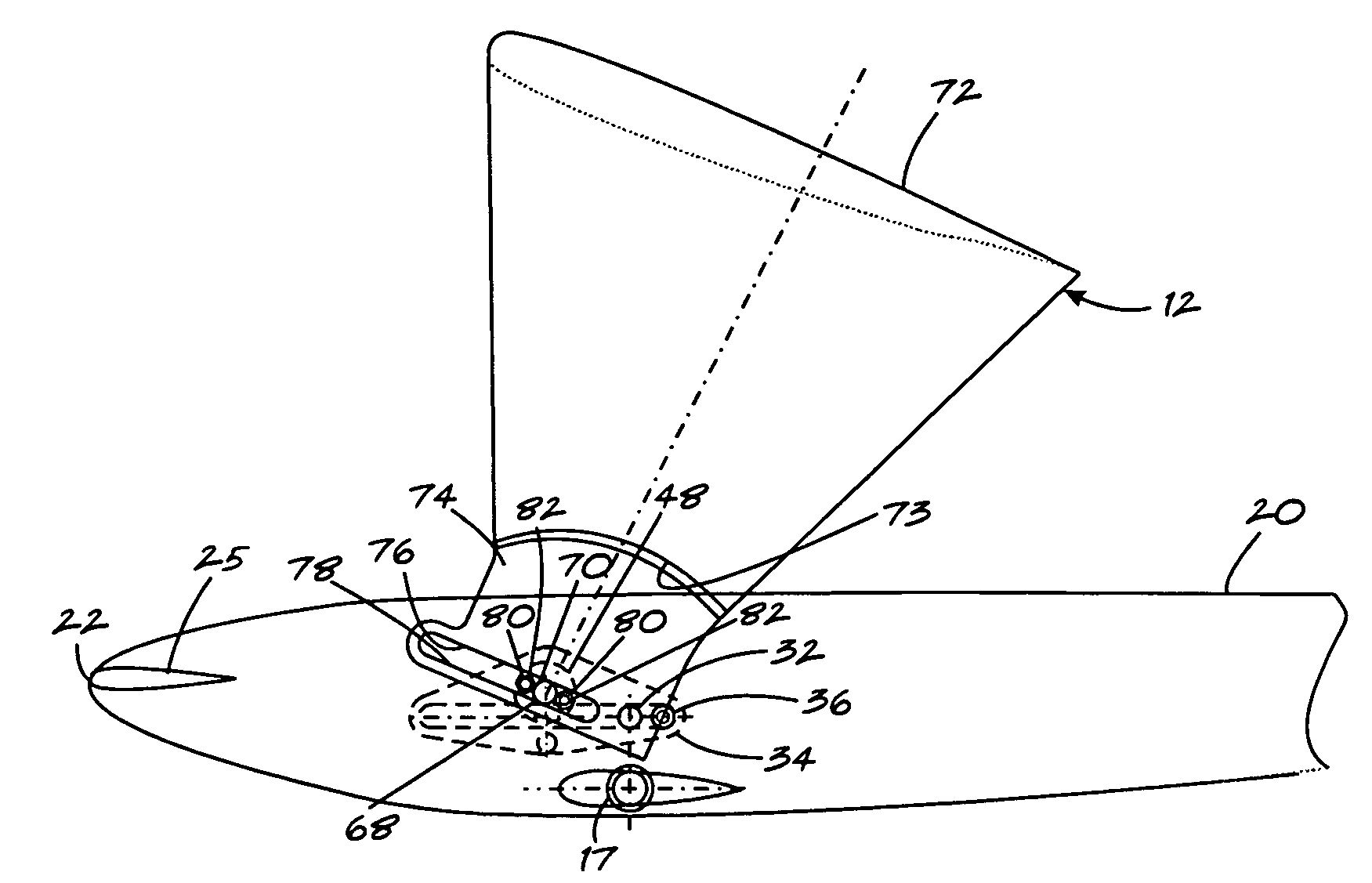
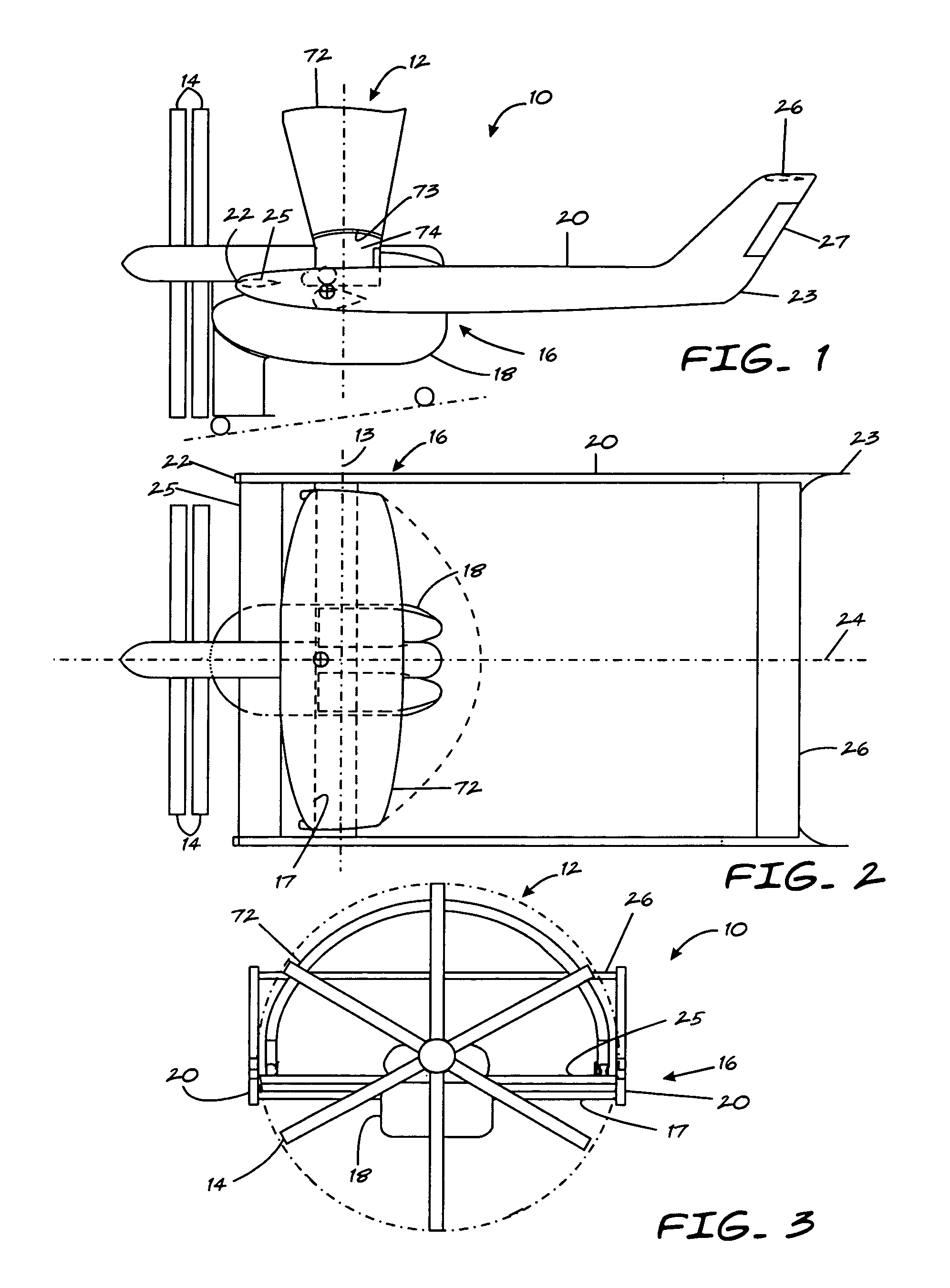
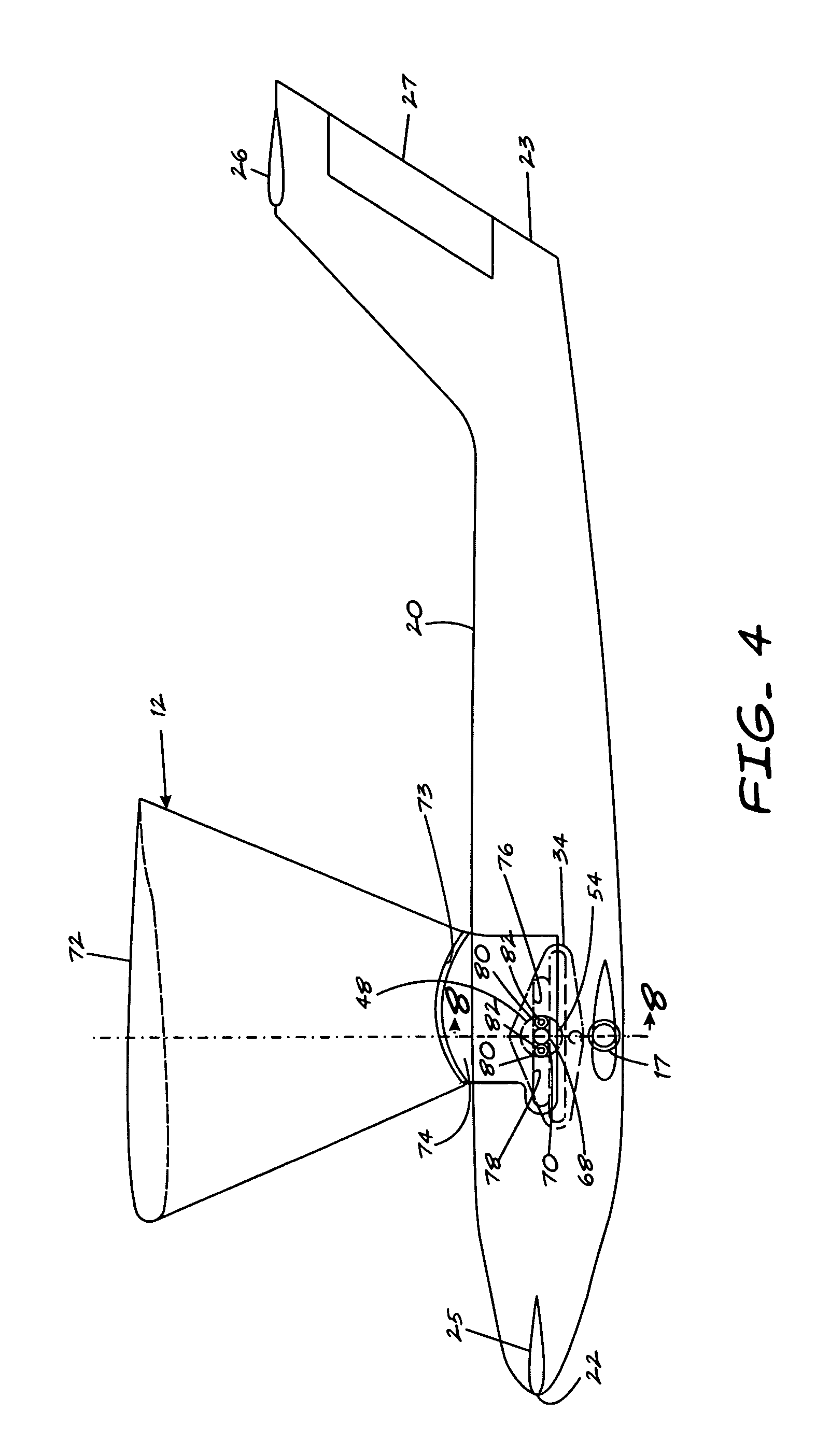
Wing assembly and aircraft
ActiveUS7510143B1Easy to reachPermit adjustmentAircraft stabilisationEfficient propulsion technologiesFlight vehicleEngineering
An aircraft is provided with a wing assembly mounted in a slipstream of a source of propulsion of the aircraft. The aircraft includes a body having a longitudinal axis, a wing assembly carried by the body and including a moveable portion moveable relative to the body and a wing carried by the moveable portion. A first actuator is coupled to the moveable portion to move it relative to the body in a direction generally parallel to the axis of the body. A second actuator is coupled to the wing to move the wing relative to the moveable portion and between first and second positions. The second actuator at least selectively permits uninhibited pivoted movement of the wing relative to the body in response to aerodynamic forces acting on the wing so that the wing may pivot to a position wherein the forces acting on the wing are balanced.
Owner:BERTELSEN DEISGN
Collapsible pan
Owner:EDISON NATION
System for mounting wall panels to a wall
InactiveUS10253507B1Easy to installPermit adjustmentCovering/liningsThree degrees of freedomEngineering
A system for mounting wall panels to an existing wall, includes a base assembly adapted to be secured to the existing wall; a wall panel securement arrangement adapted to be secured to a wall panel; and an adjustment arrangement for adjustably securing the securement arrangement to the base assembly at a position with three degrees of freedom, the adjustment arrangement including a sliding member slidably received in the base support for movement in a first lengthwise direction of the base support and in a second transverse direction of the base support, the sliding member including two parallel, spaced apart capture walls extending from a central member thereof, and the adjustment positioning member includes an adjustment plate positioned adjustably between the capture walls for adjustment in a direction orthogonal to the first and second directions.
Owner:BILGE HENRY H
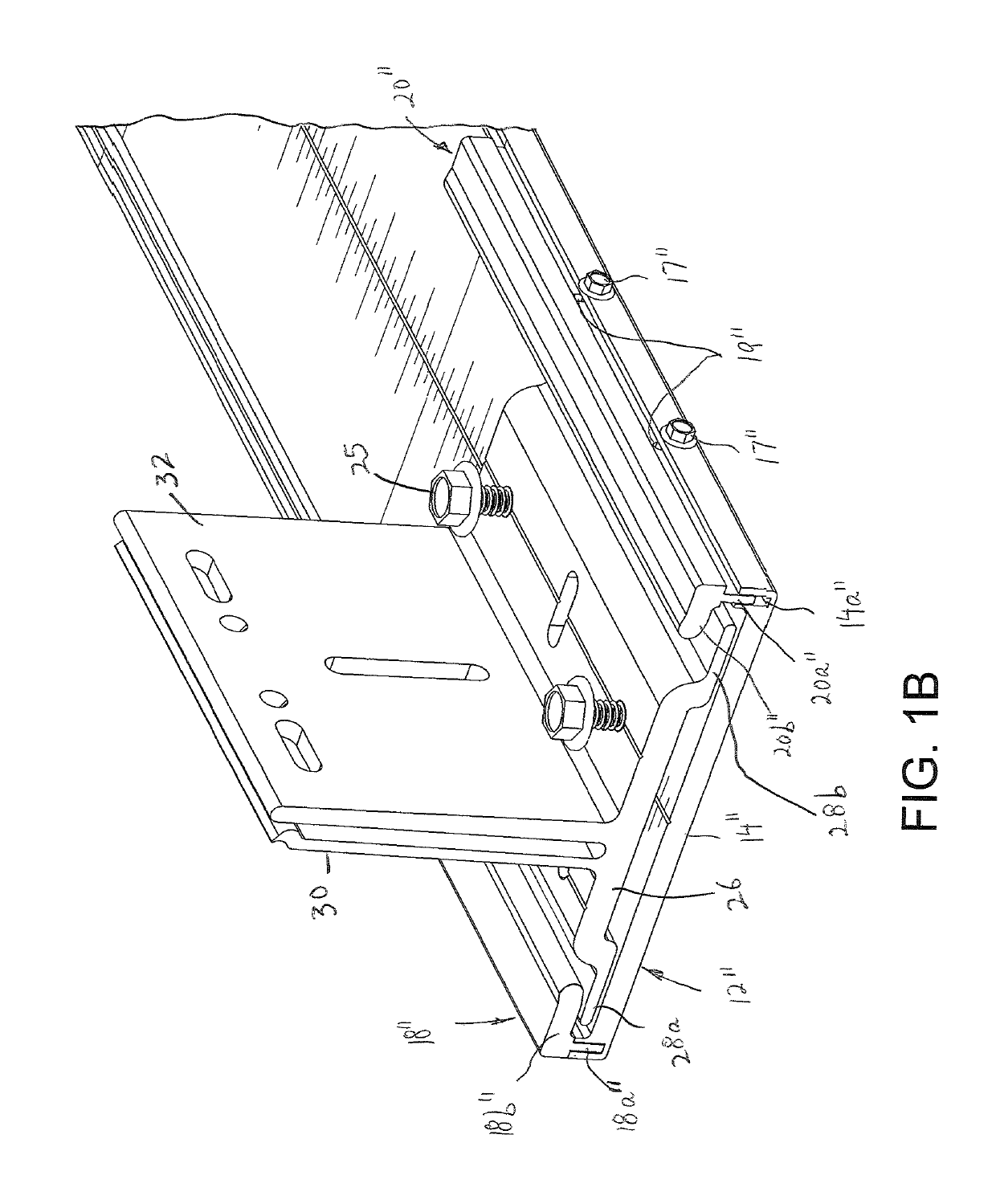
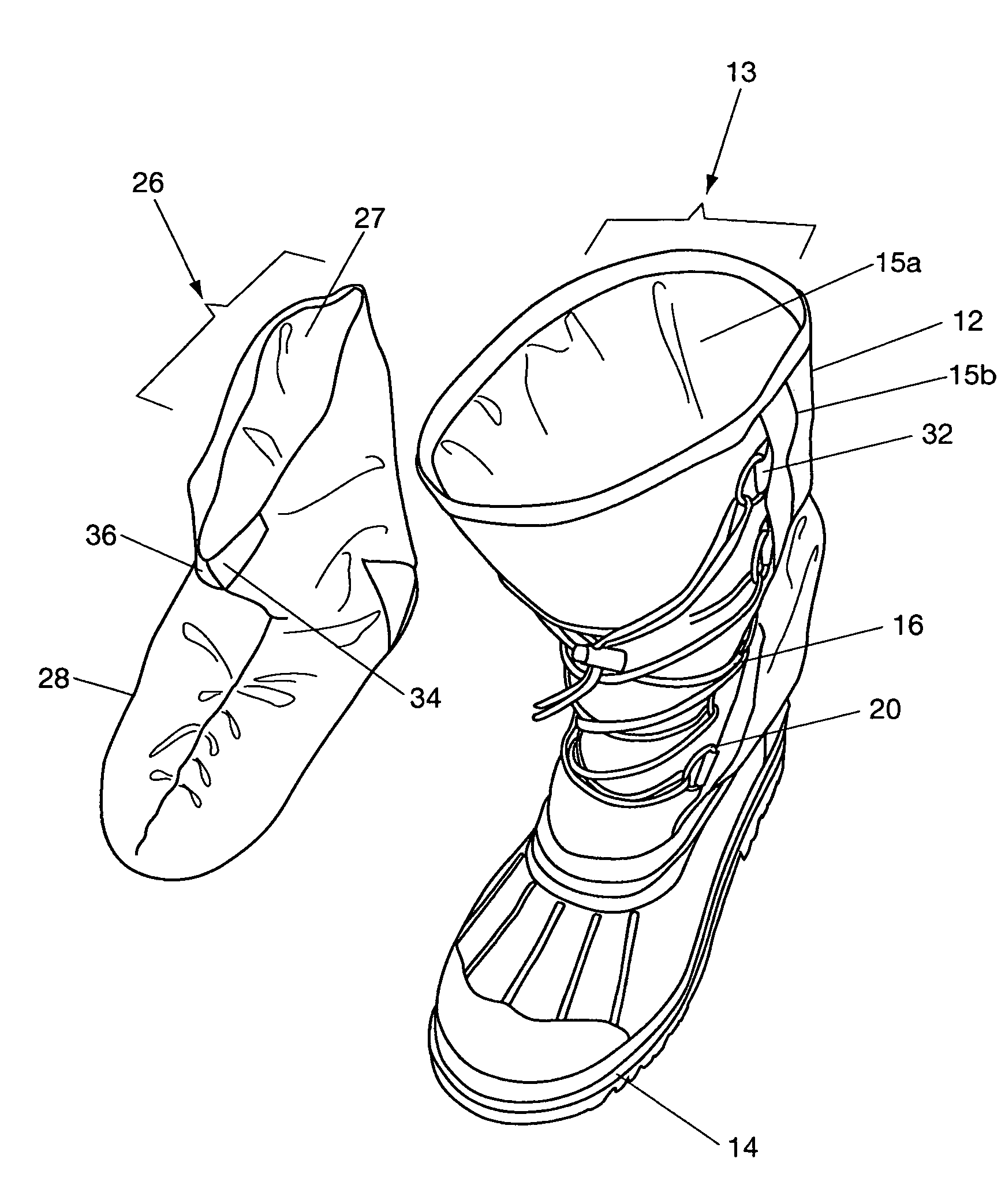
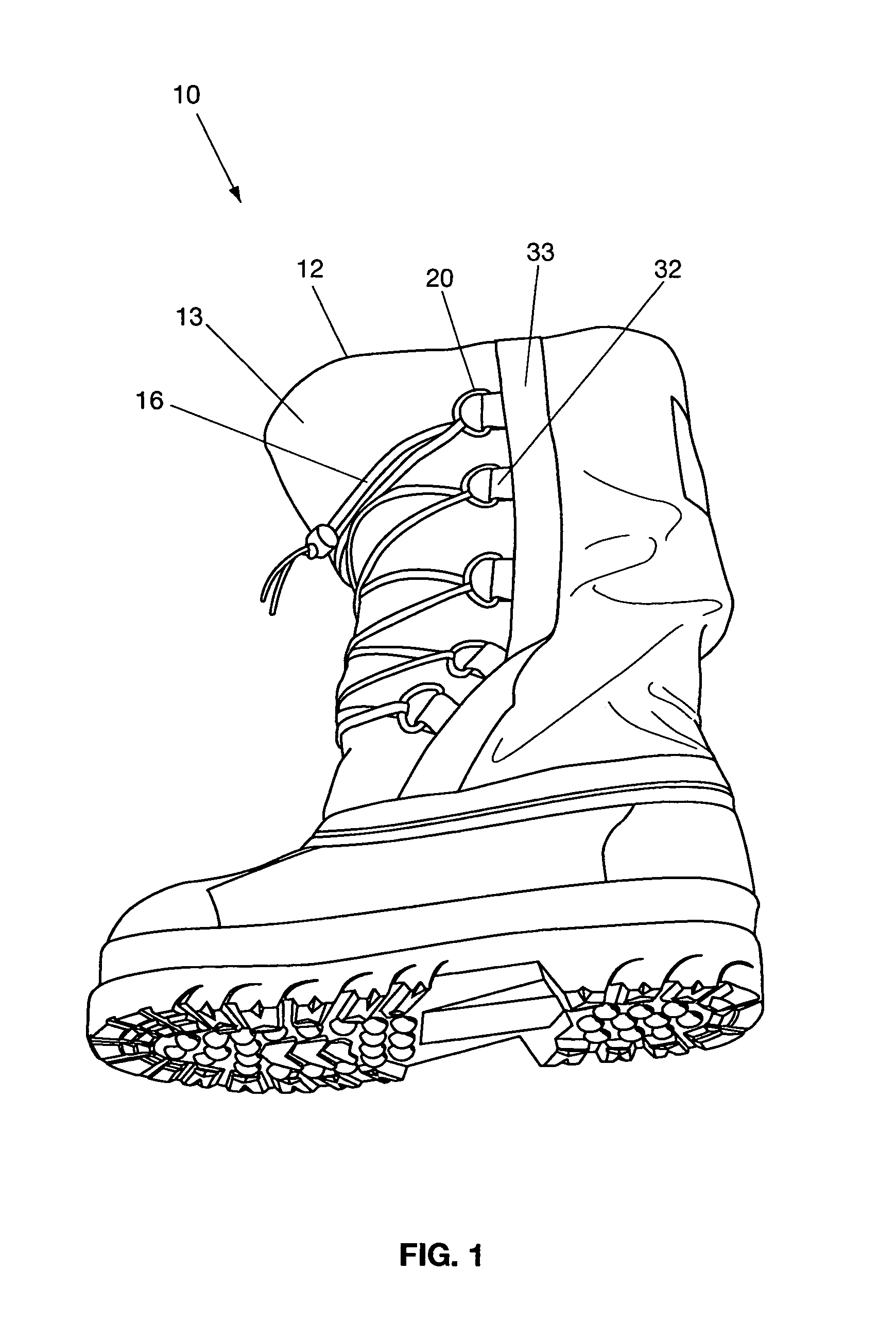
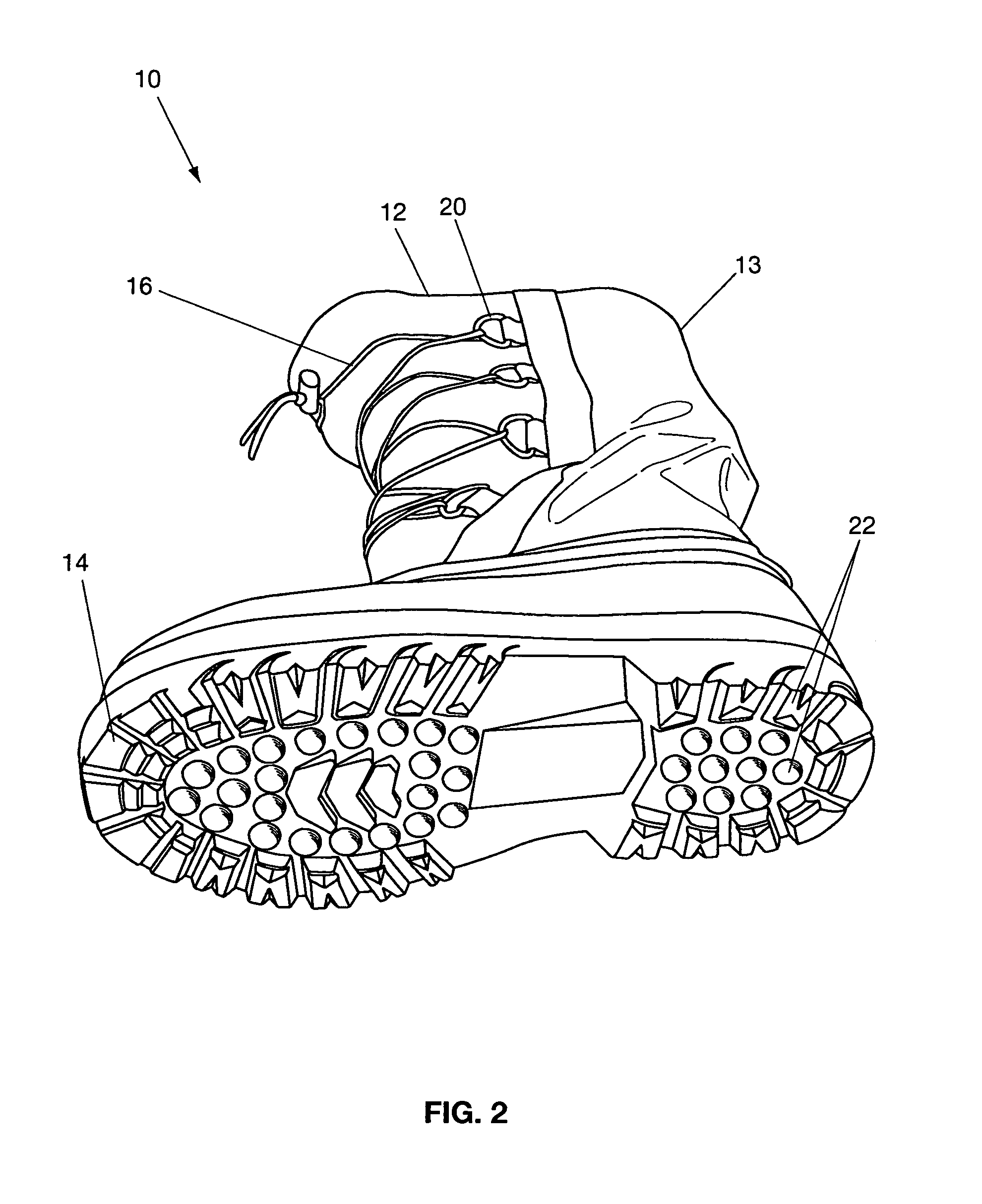
Insulated lightweight pack boot
A lightweight cold and wet weather pack boot comprising an outer boot including an upper boot with an exterior material layer constructed of waterproofing coated polyester, an interior layer of oxford nylon with insulation batting between the exterior and interior layers, further including a molded rubber bottom with cleats, and an inner bootie with outer and inner layers of oxford nylon with insulations between said outer and inner layers.
Owner:HAAS STEPHAN
S-video signal loss compensation processing apparatus and method
InactiveUS6480241B1Enhance signalPermit adjustmentTelevision system detailsColor signal processing circuitsPhysicsTransmission line
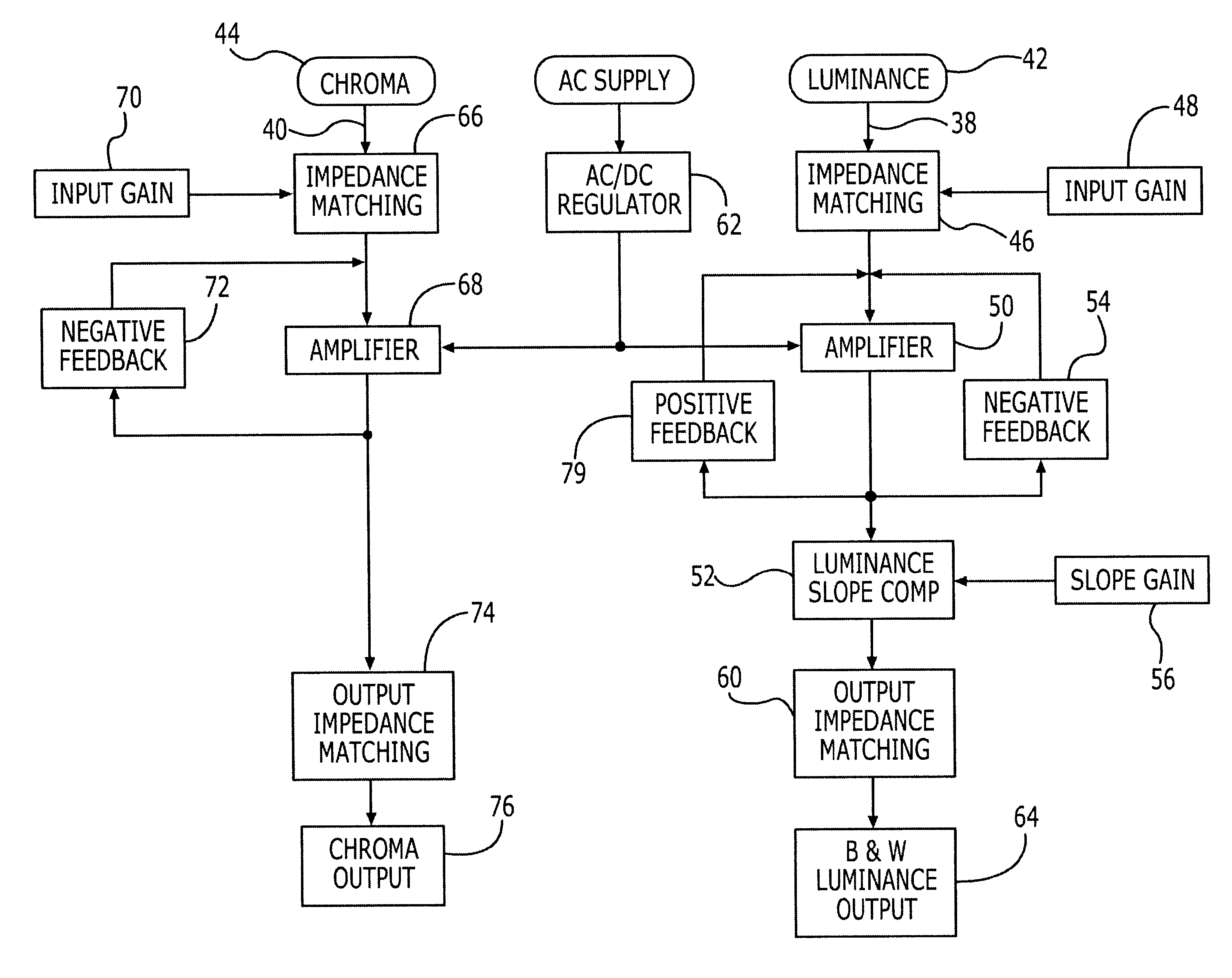
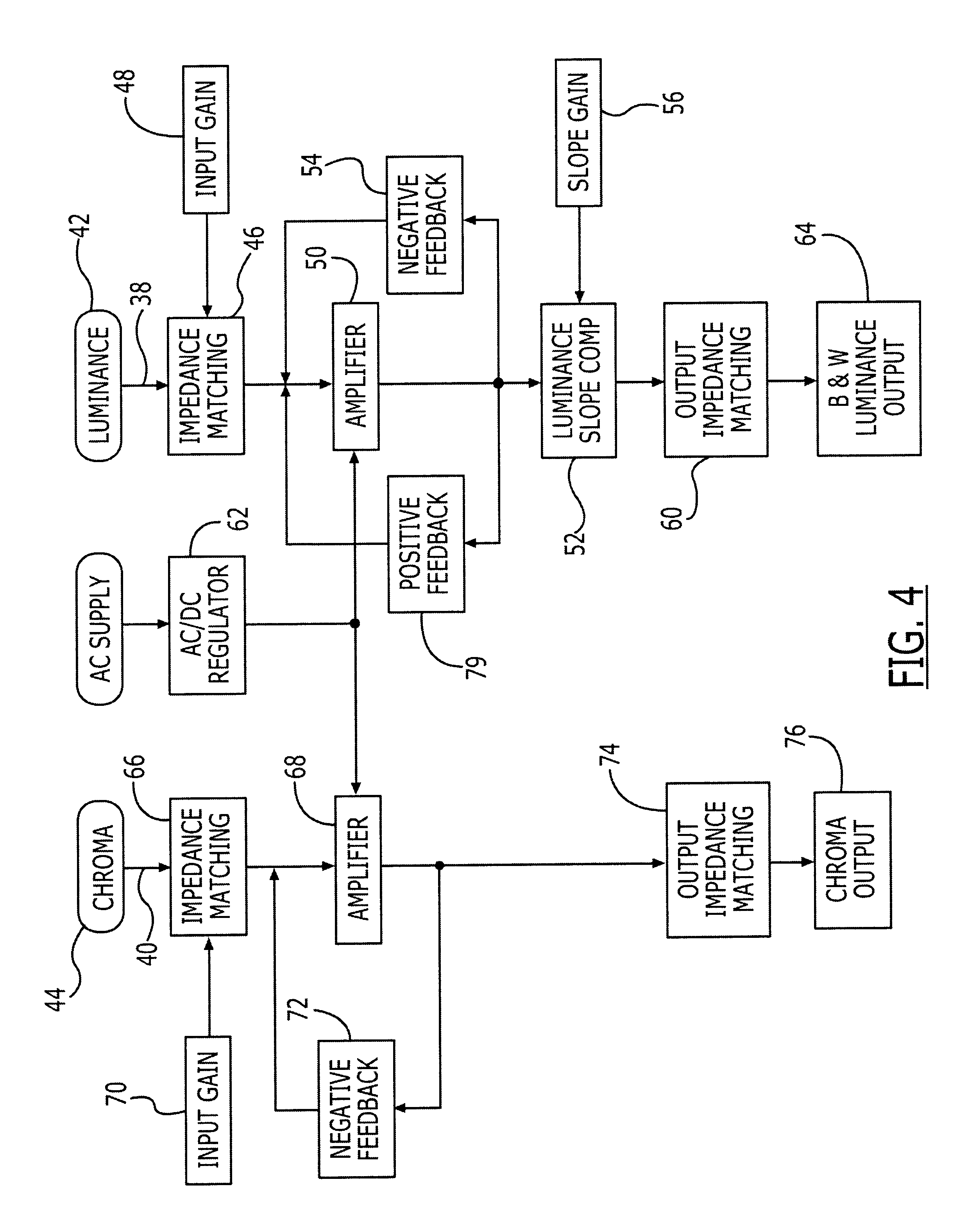
In an S-video signal processor, the luminance signal is amplified and adjusted over selected frequency ranges using a parallel signal for shaping the S-video signal response and permitting the S-video signal to be transmitted over exceptionally long transmission lines while providing a quality picture. In separate channels, chrominance and luminance signals are amplified and impedance matched. A luminance band pass filter permits manual adjustments to a lower range of video signal frequencies and thus changes to white level picture information. One version of the S-video signal processor includes a positive feedback network which permits user adjustments in an upper video signal frequency range having picture super detail information for providing a picture of high resolution and thus pleasing to the user. In a second version a compensation amplifier is used to alter the frequency response of the luminance signal. A clear picture, brighter and sharper, rather than simply a brighter picture is available whether transmitted over a few or few hundred feet from a video source to a video monitor.
Owner:GORDON J GOW TECH
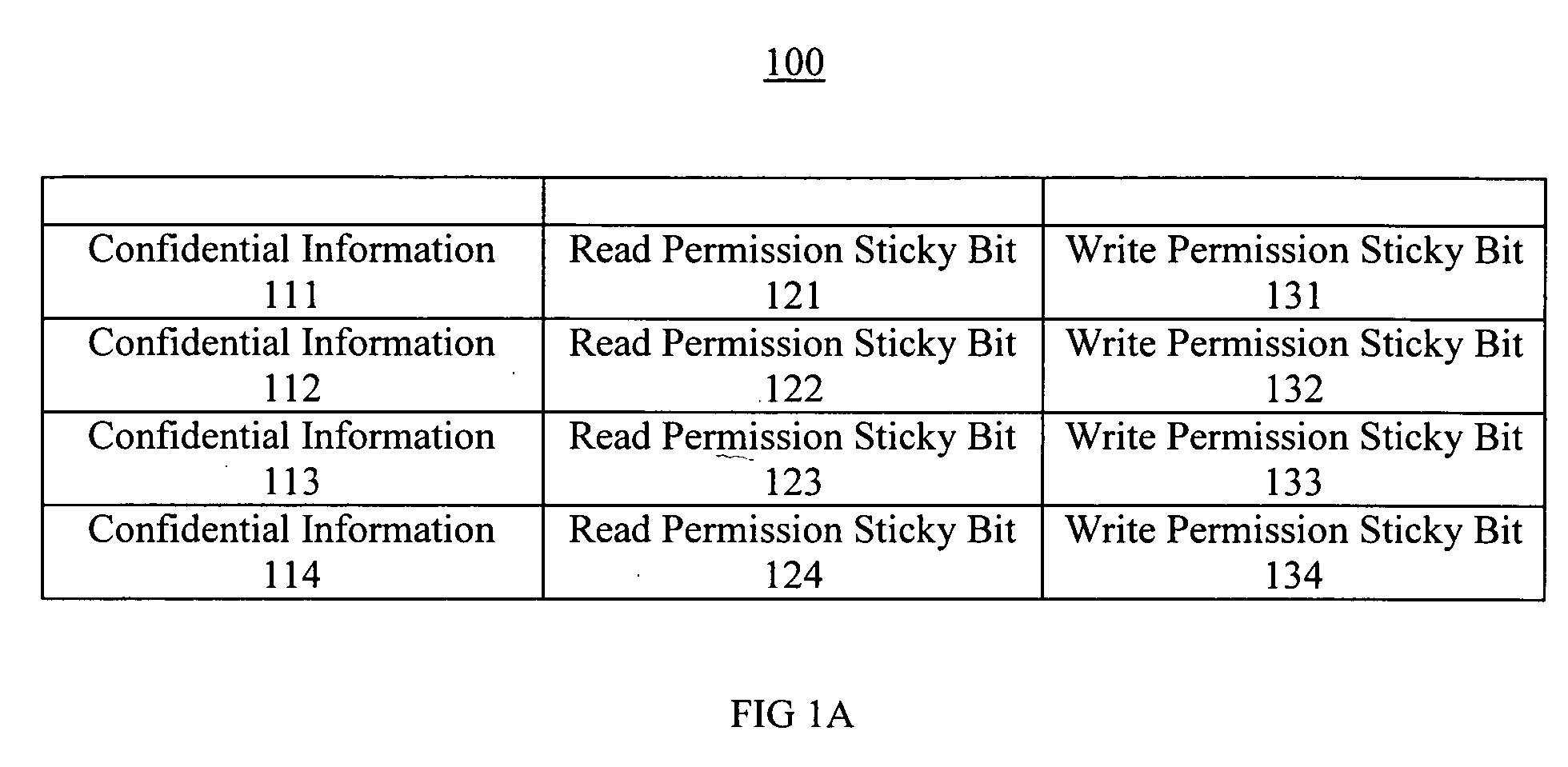
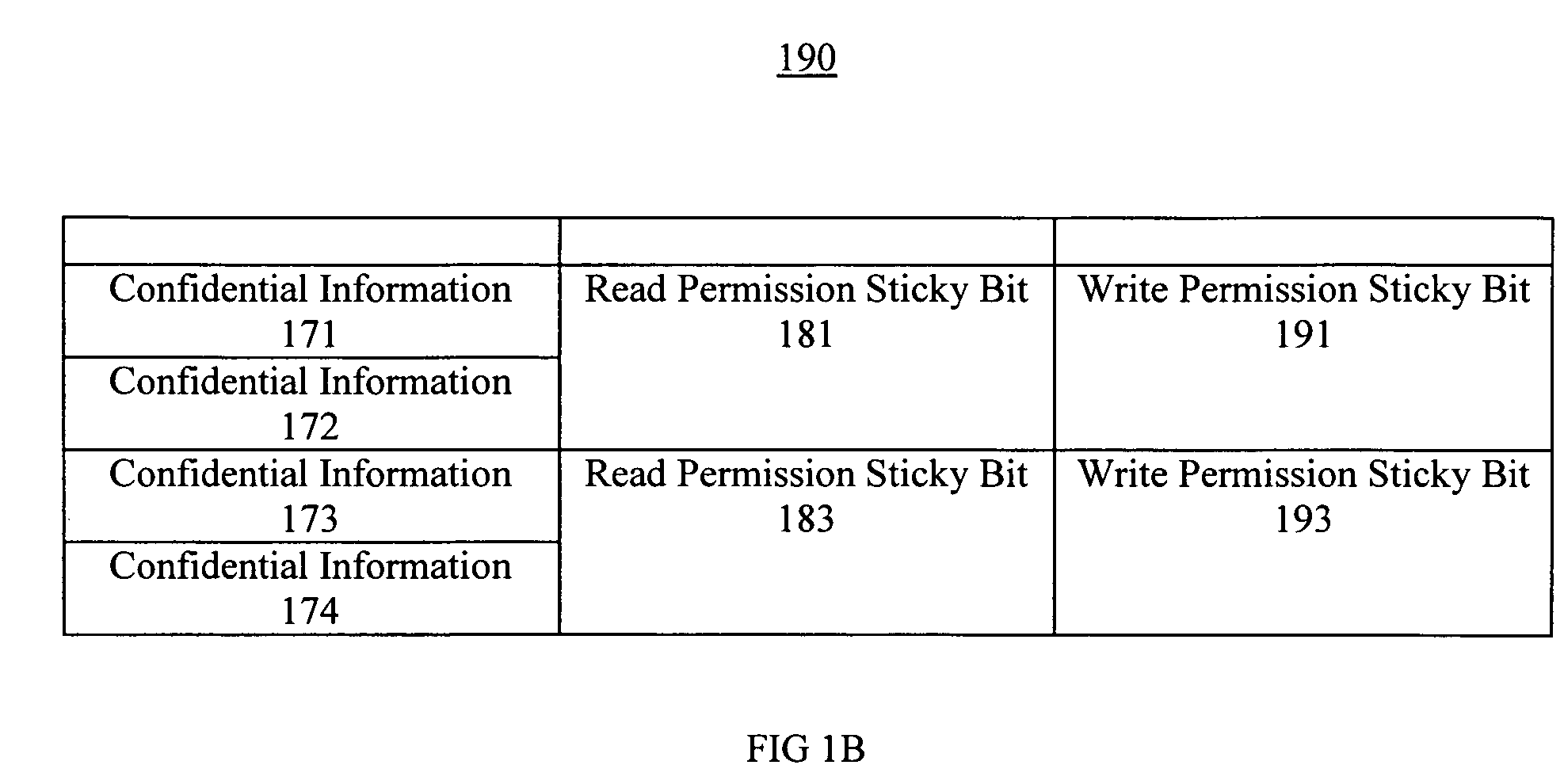
Confidential information protection system and method
ActiveUS20090205053A1Easy to storeImprove protectionDigital data processing detailsAnalogue secracy/subscription systemsOperational systemInitialization vector
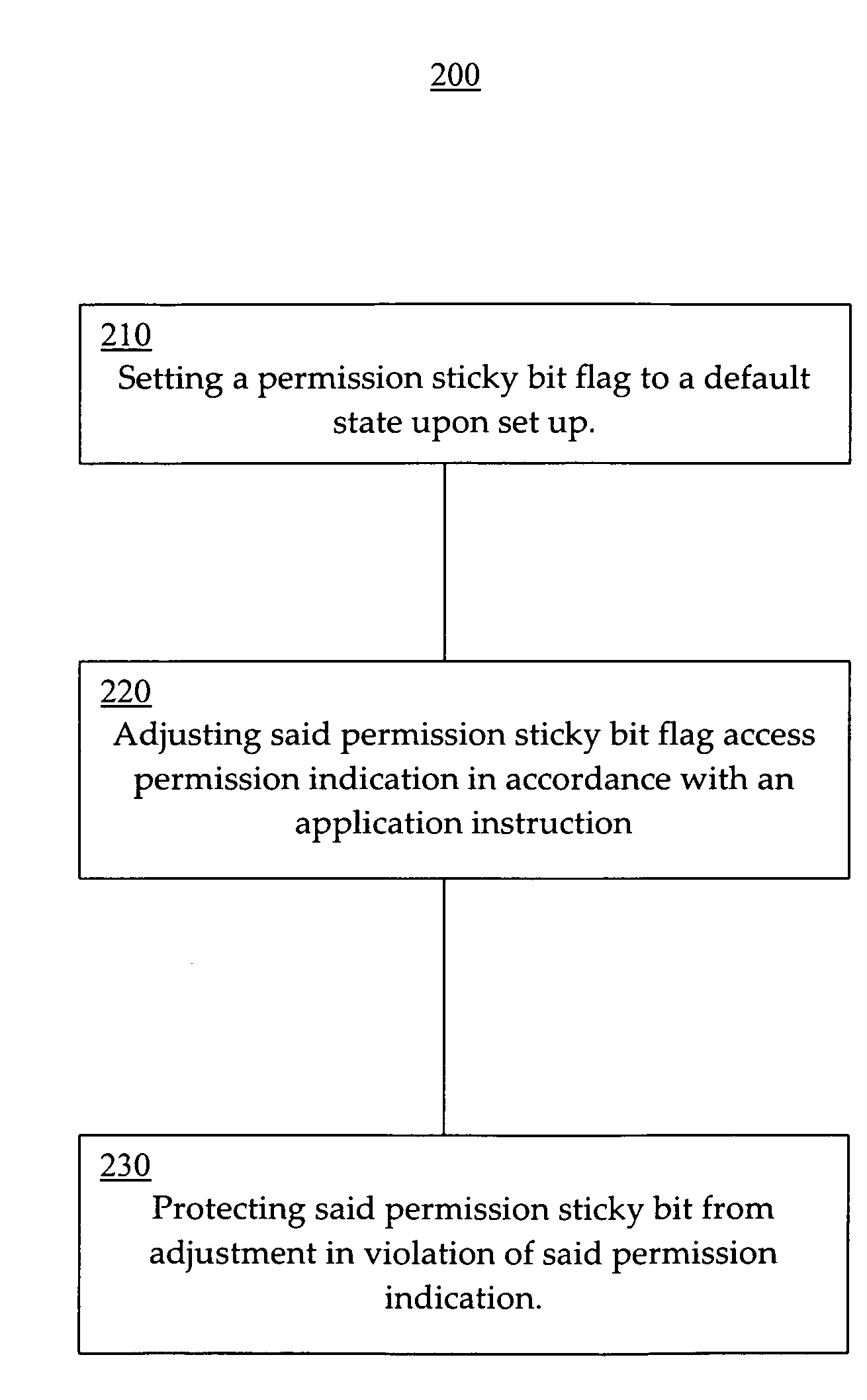
Efficient and effective permission confidential information protection systems and methods are described. The secure information protection systems and methods facilitate storage of confidential information in a manner safe from rogue software access. In one embodiment, a confidential information protection method is implemented in hardware and facilitates protection against software and / or Operating System hacks. In one exemplary implementation, a confidential information protection method includes setting a permission sticky bit flag to a default state upon system set up. The permission sticky bit flag access permission indication is adjusted at system reset in accordance with an initial application instruction. Access to the confidential information is restricted in accordance with the permission sticky bit and the permission sticky bit is protected from adjustments attempting to violate the permission indication. For example, another software application can not access or alter confidential information (e.g., an encryption key, initialization vector, etc.) if a permission sticky bit is designated as the highest security rating (e.g., disabling read permission and write permission until system reset).
Owner:NVIDIA CORP
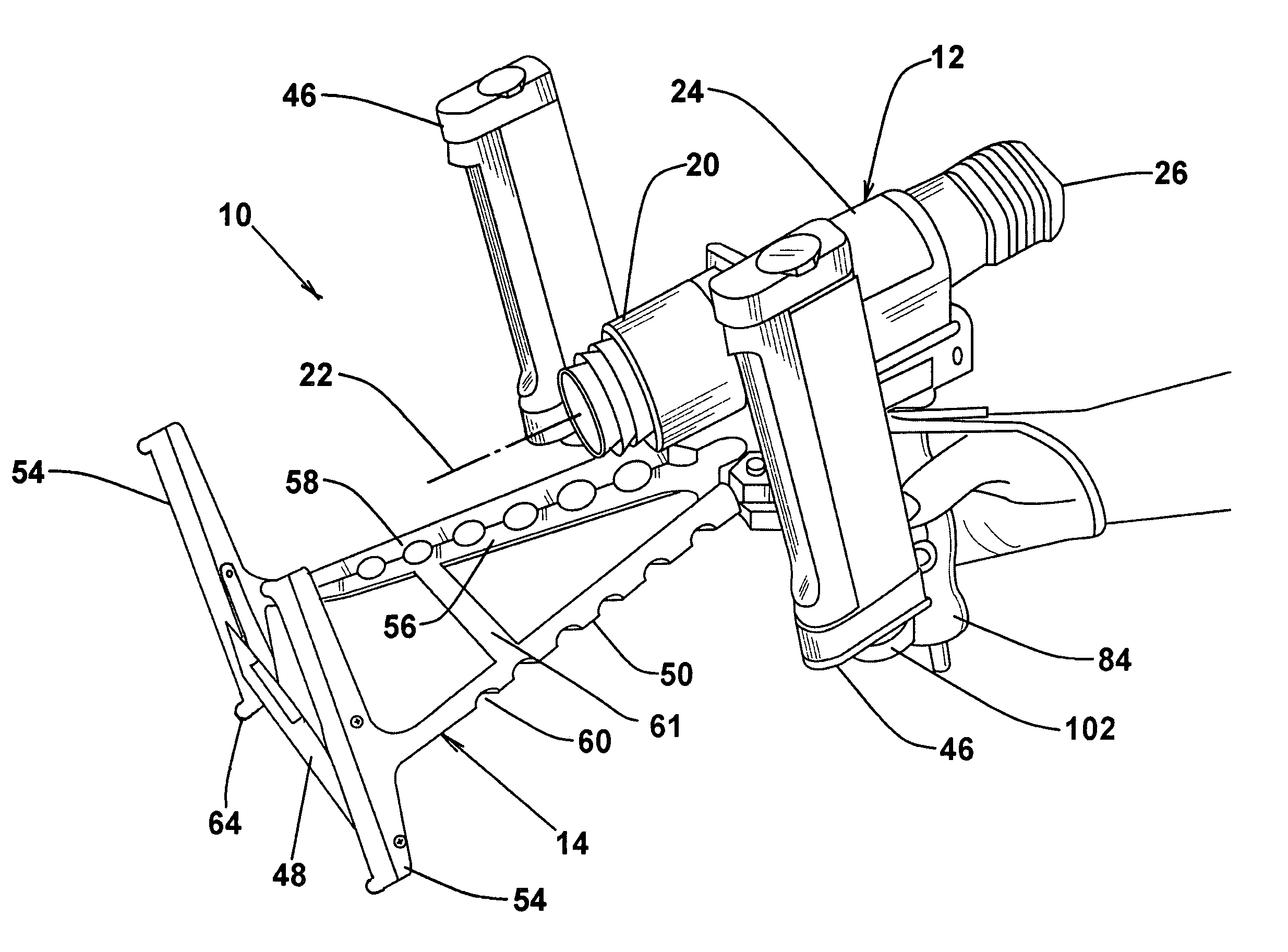
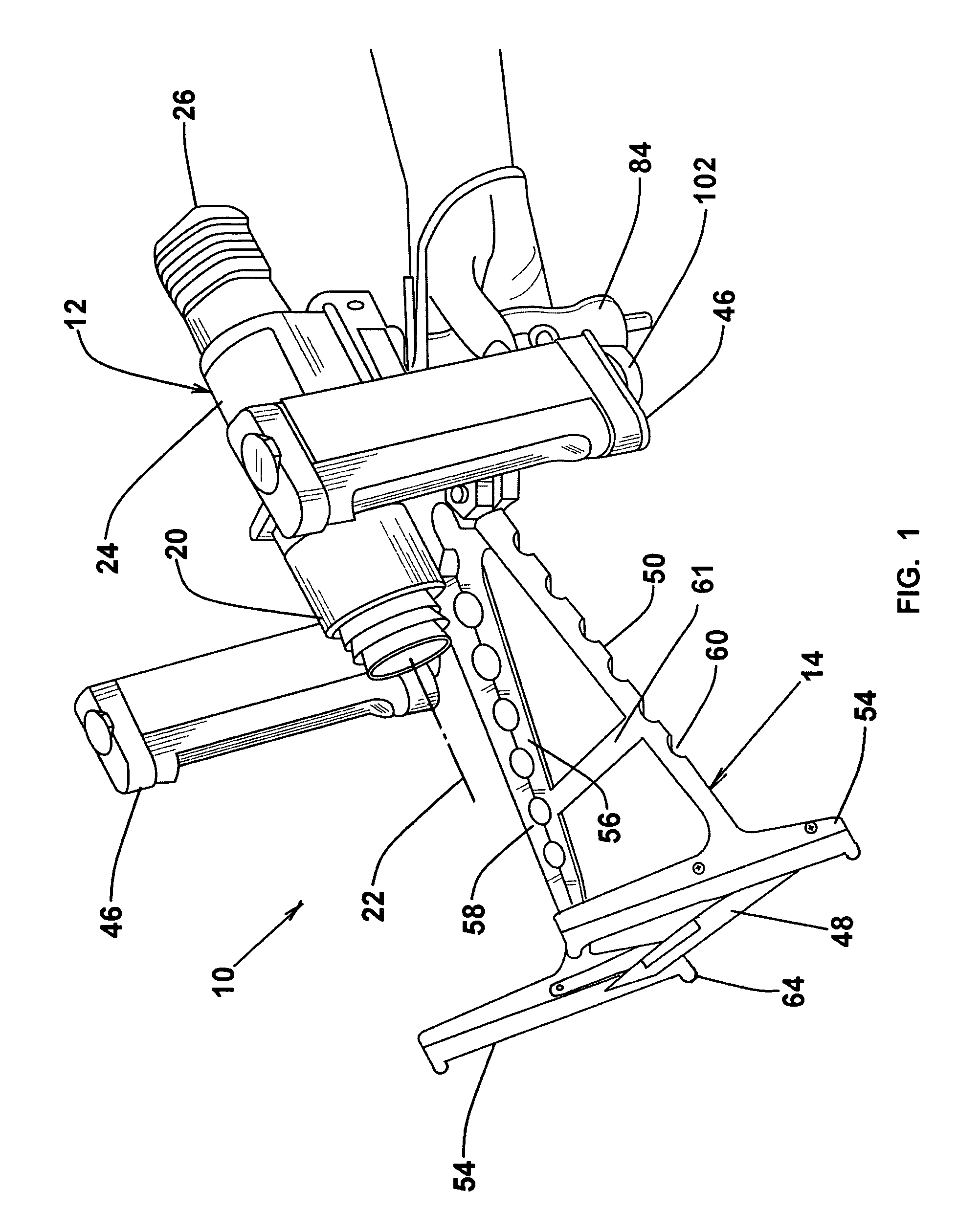
Forensic visualization and recording apparatus
ActiveUS7050715B1Stable focusStable recorded imageCamera body detailsPhotographyEngineeringSliding scale
An integrated imager and camera mounting assembly that allows a single operator to scan the crime scene for prints without assistance, and to attain an optimally illuminated and stably focused recorded image with single handed adjustments. The assembly includes an A-frame stand which carries a pair of UV lights on adjustable arms for single handled adjustment by the operator in the scanning and recording modes. The stand includes a footed base that allows the operator to securely engage the frame against vertical, horizontal and irregular surfaces using the imager handle thereby locating the imager at a fixed distance from the print area and permitting ready focusing of the image with the other hand. The base further includes a sliding scale for placement in the field of view for dimensional referencing.
Owner:SIRCHIE ACQUISITION COMPANY
Portable Mountable Upper-Body Exercise Device
InactiveUS20100056348A1Permit adjustmentTherapy exerciseFrictional force resistorsRotational axisEngineering
An exercise apparatus includes a handle bar and a resistance assembly, coupled to the handle bar. The resistance assembly includes a housing having first and second opposed parts, and permitting movement of the handle bar about a rotational axis upon applying force to the handle bar. A resistance mechanism resists movement of the handle bar about the rotational axis. A screw, mounted lengthwise along the rotational axis, and engaging a threaded receptacle, adjustably compresses the spacing between the housing parts and modifies resistance to movement of the handle bar. One of the screw and the receptacle is coupled to an adjustment knob setting a user-defined resistance. A clamp, coupled to the housing, removably attaches the exterior of the first housing part to a member. A user grasps the handle bar and moves it by applying force corresponding to the resistance setting. The clamp can be utilized without operating the knob.
Owner:GOLDBERG ELLIOTT
Wire Retainer for Surgical Device
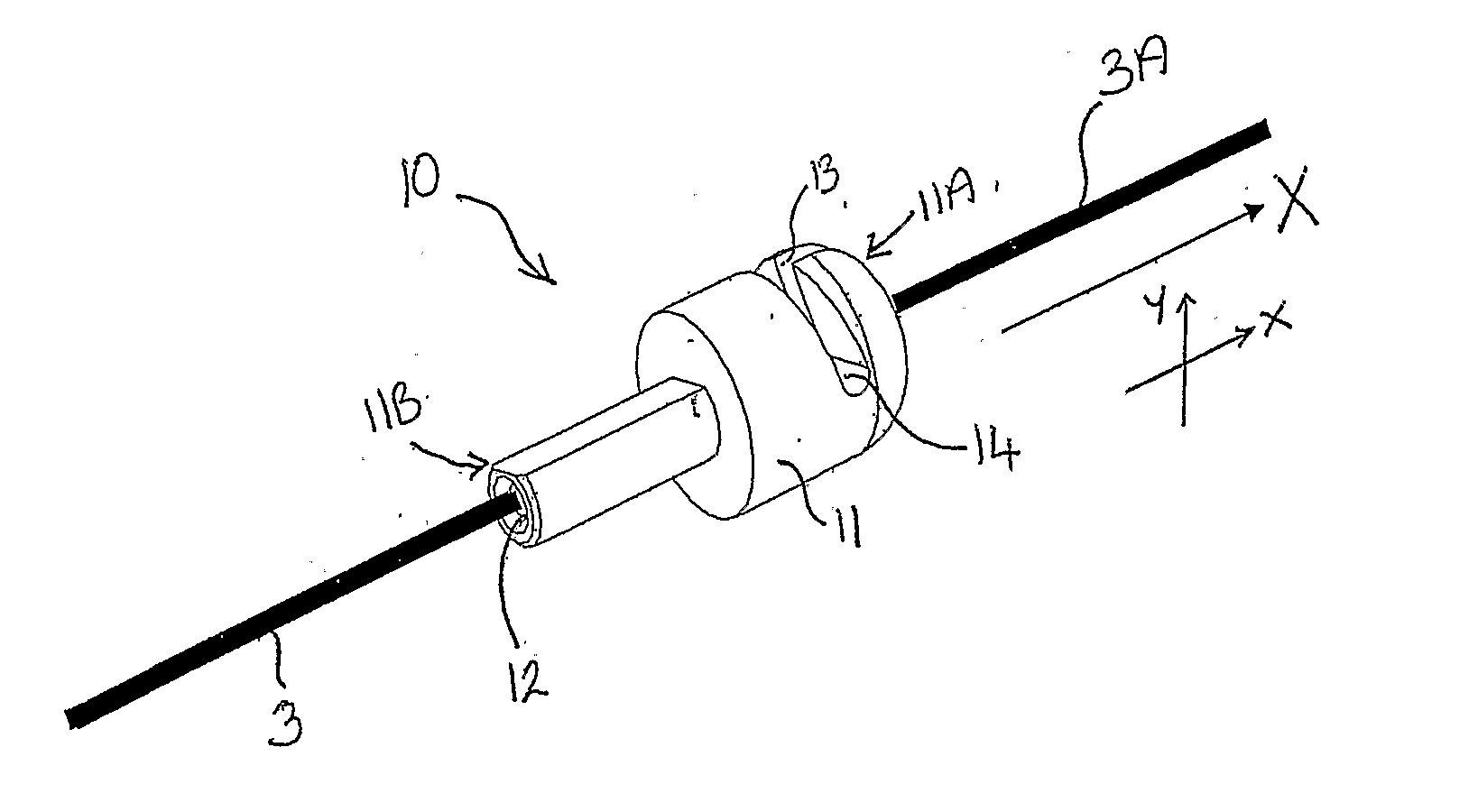
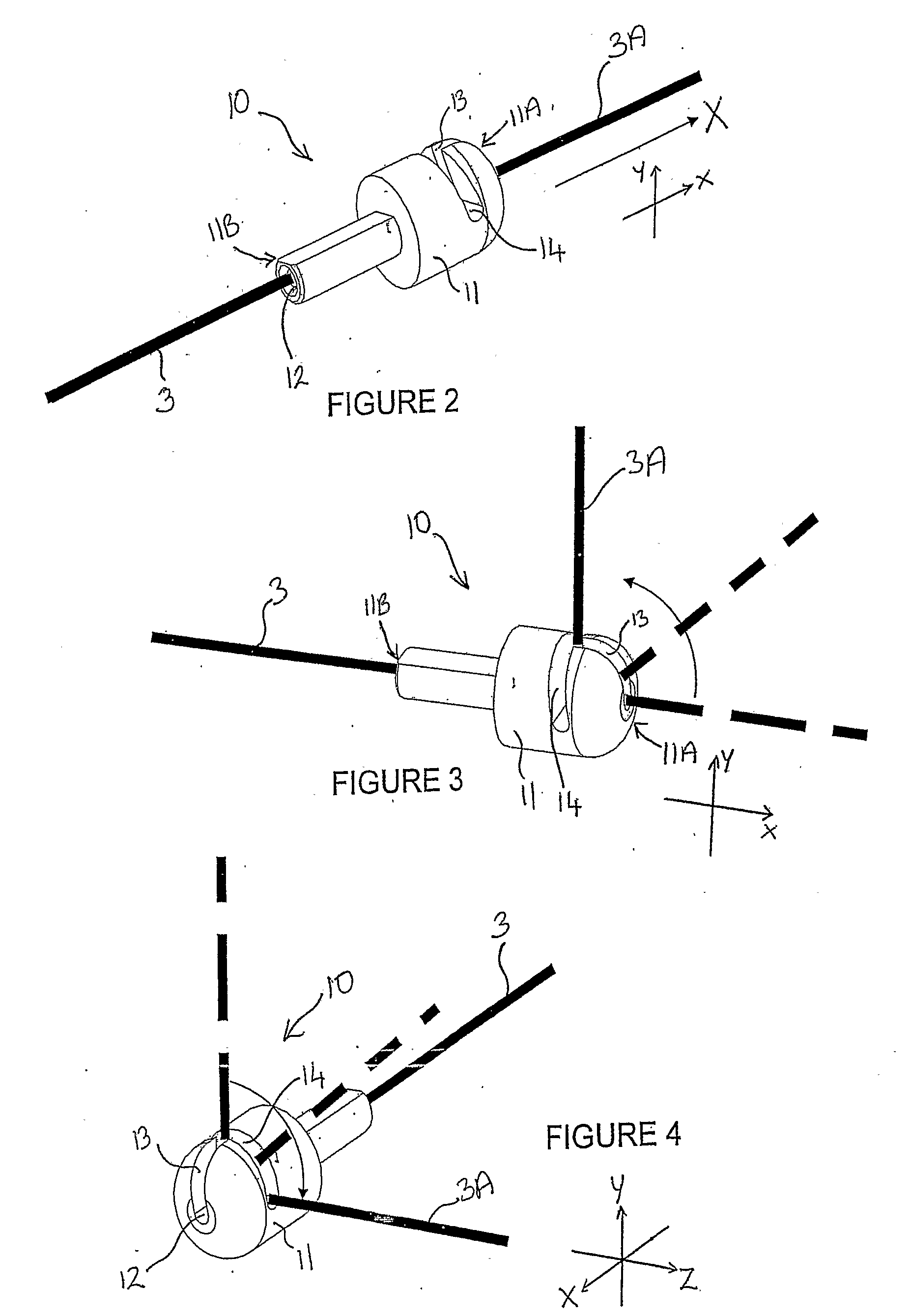
InactiveUS20080300606A1Permit adjustmentRopes and cables for vehicles/pulleyJoint implantsEngineeringSurgical device
A wire retainer (10) for securing wire under tension comprising a body (11) having an exterior surface and a far end (11a) and a near end (11b) and a bore (12) extending therebetween in the general direction of a first axis (X) in a first plane (XY), the bore receiving an end of the wire (3) in use, a first slot (13) substantially in said first plane and having a far end which coincides with the far end of the body and a near end intermediate the far and near ends of the body, the first slot extending between said bore and said exterior surface and a second slot (14) intersecting said first slot at the near end thereof and at said bore.
Owner:INTELLIGENT ORTHOPAEDICS
System for mounting wall panels to a wall
InactiveUS10260240B1Easy to installPermit adjustmentCeilingsCovering/liningsEngineeringMechanical engineering
A system for mounting wall panels to an existing wall, includes adjustment support members to be secured either directly or indirectly to an existing wall; connecting panels for connecting together spaced apart adjustment support members, with each connecting panel adapted to support a wall panel thereon; each adjustment support member including a central platform wall, and two U-shaped tracks extending along opposite side edges thereof, each U-shaped track including an upper exposed surface arranged parallel to the existing wall when the adjustment support member is secured to the existing wall and first and second end walls extending at orthogonally from opposite sides of the upper exposed surface so as to define a channel therebetween; and each connecting panel including a main panel wall and two opposite slide walls extending from opposite side edges of the main panel wall to be positioned in the channel for sliding movement therein.
Owner:BILGE HENRY H
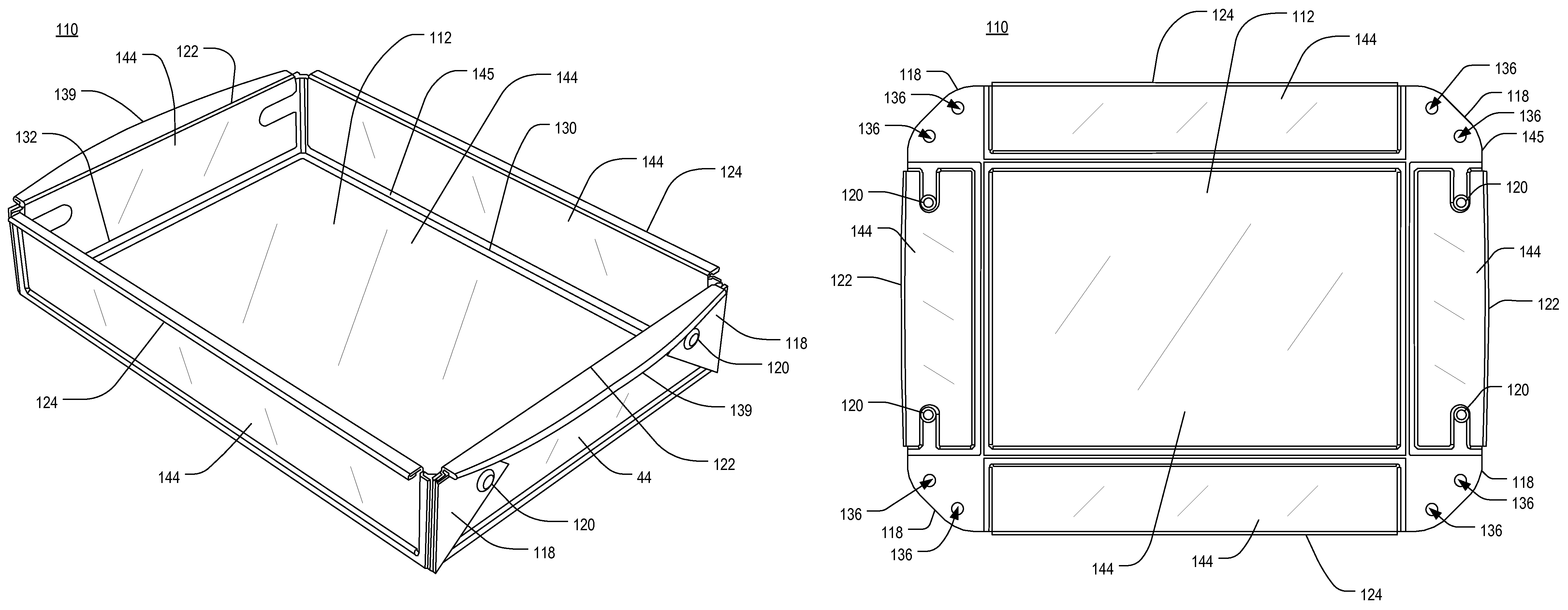
Expandable luggage with locking expansion mechanism
An item of expandable luggage having a main body and an expandable member. A locking expansion means connects the main body to the expandable member, and includes at least one fixed plate and corresponding slidable plate slidably coupled together. Each fixed plate is fixedly mounted to the main body and includes a plurality of locking apertures. Each slidable plate is fixedly mounted to the expandable member and includes an expansion control mechanism for controlling displacement of the slidable plate with respect to its corresponding fixed plate. Each expansion control mechanism includes an actuator for engaging a first end of a rotatable crank. A locking element includes opposing first and second ends. The second end of the locking element engages the second end of the crank. The first end of the locking element slidably engages with one of the apertures of the first fixed plate in response to the actuator engaging the corresponding crank.
Owner:BRIGGS & RILEY TRAVELWARE
System for mounting wall panels to a wall
InactiveUS10407917B1Easy to installPermit adjustmentCovering/liningsStructural engineeringWall plate
A system for mounting wall panels to an existing wall, includes adjustment support members secured to an existing wall and including a platform and a side wall extending from a side thereof and including elongated slots therein; connecting panels connecting together spaced apart adjustment support members, each connecting panel including a main panel and a side wall having a slot therein which opens at one edge of the side wall for receipt in an elongated slot; and a hook member including a securing section to which a wall panel is mounted, an L-shaped hook wall so as to receive a connecting panel in a space between the L-shaped hook wall and the securing section, and an adjustment arrangement for adjusting a position of the hook wall on the securing section so as to move the hook wall toward and away from the securing section.
Owner:BILGE HENRY H
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com