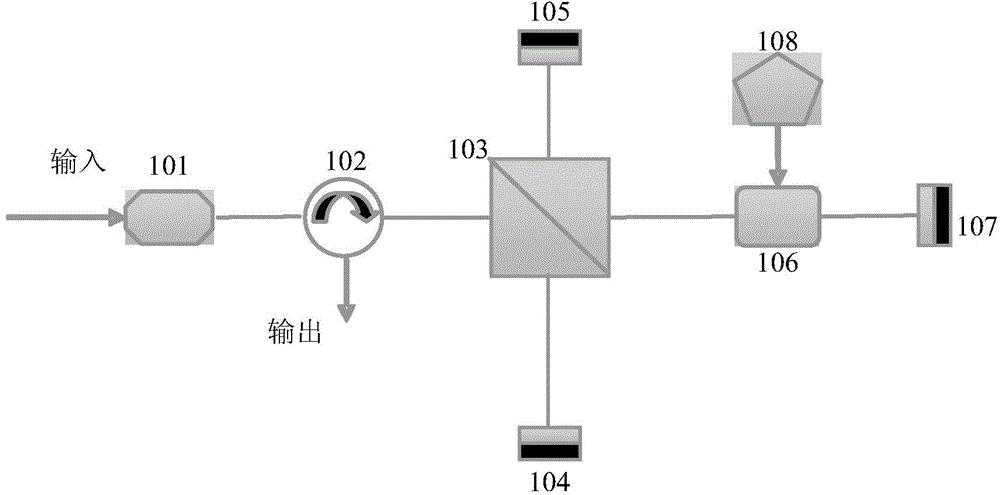
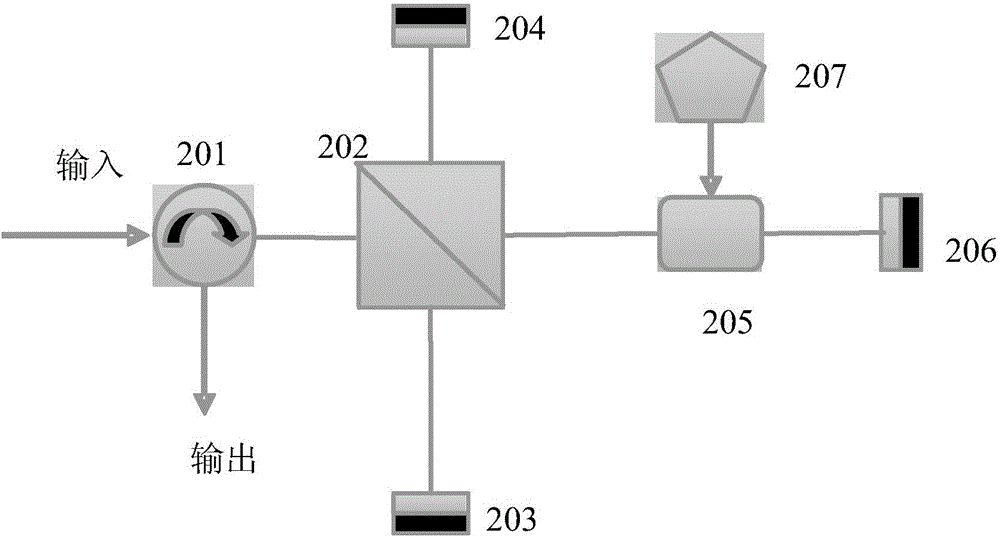
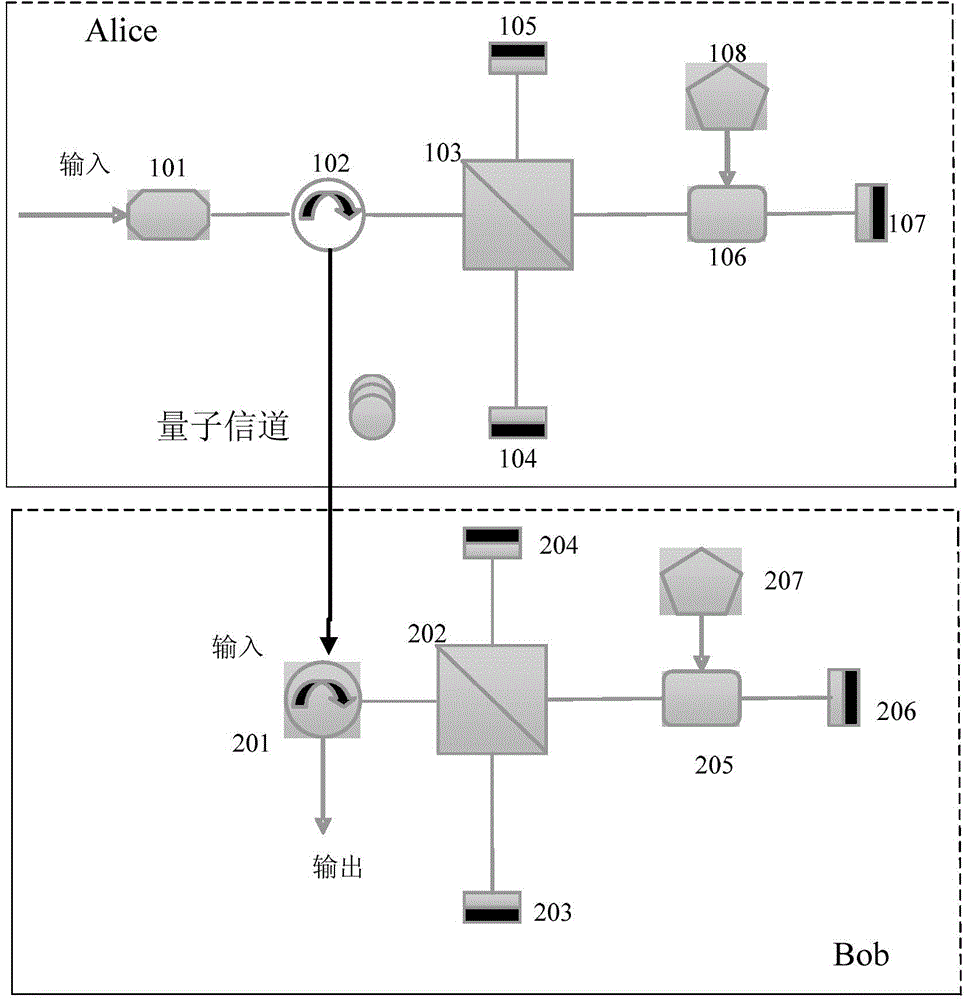
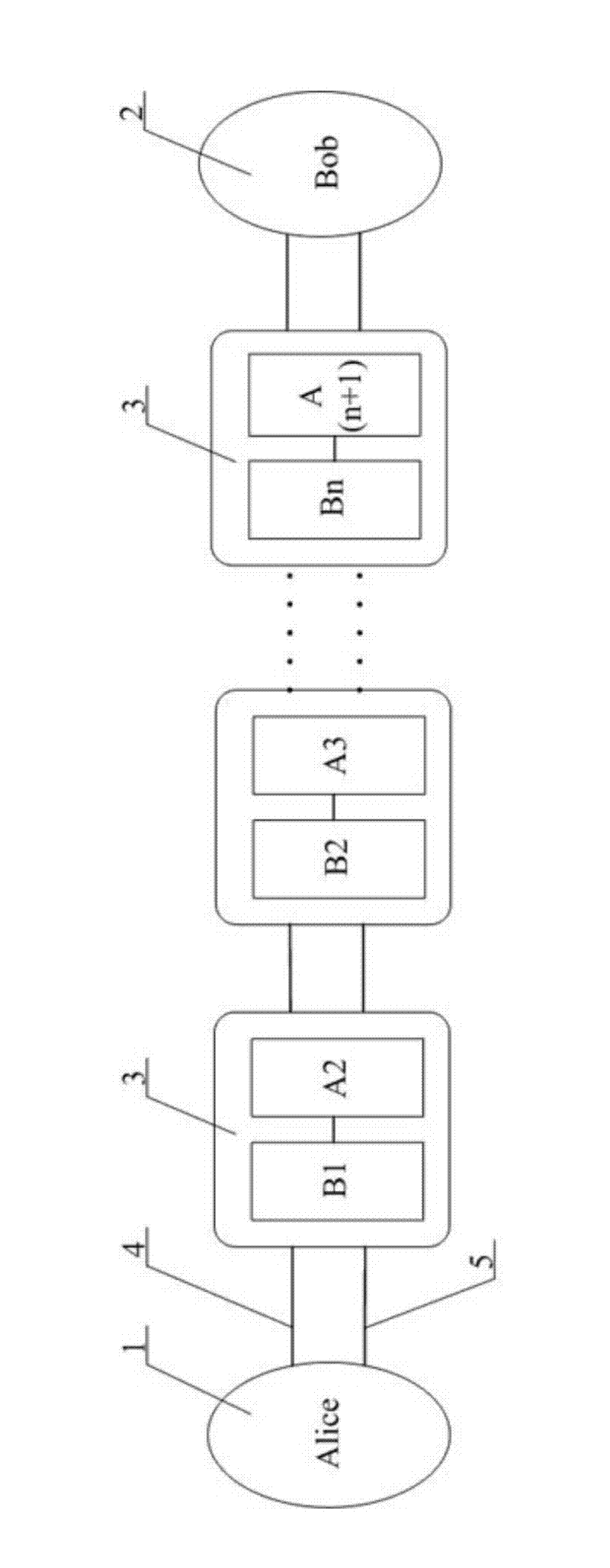
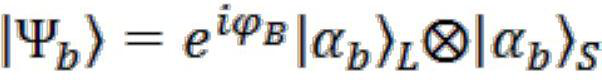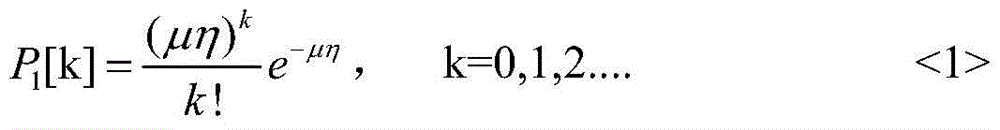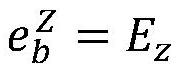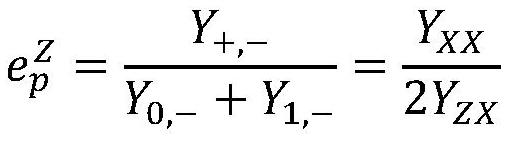Patents
Literature
44 results about "BB84" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
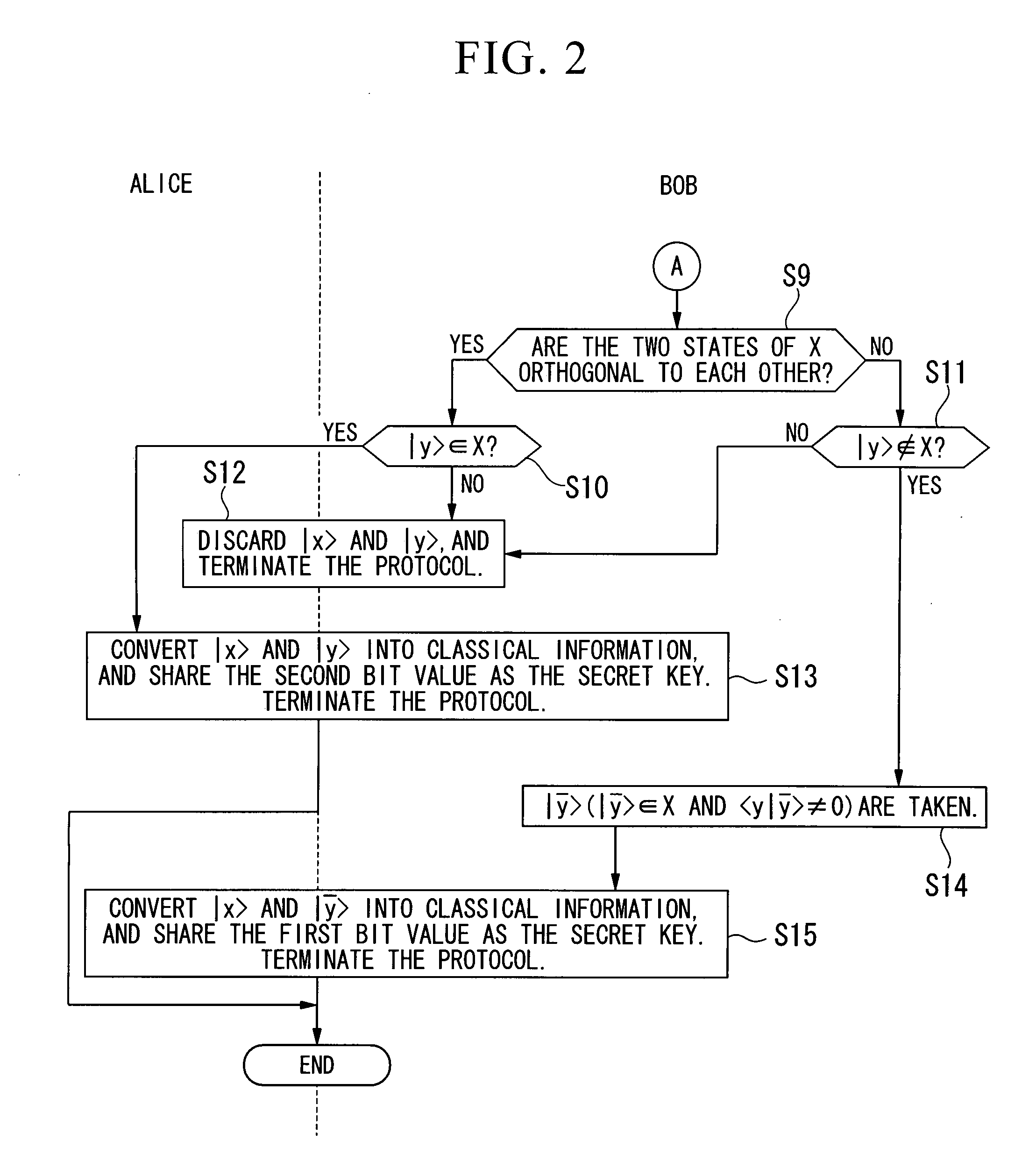
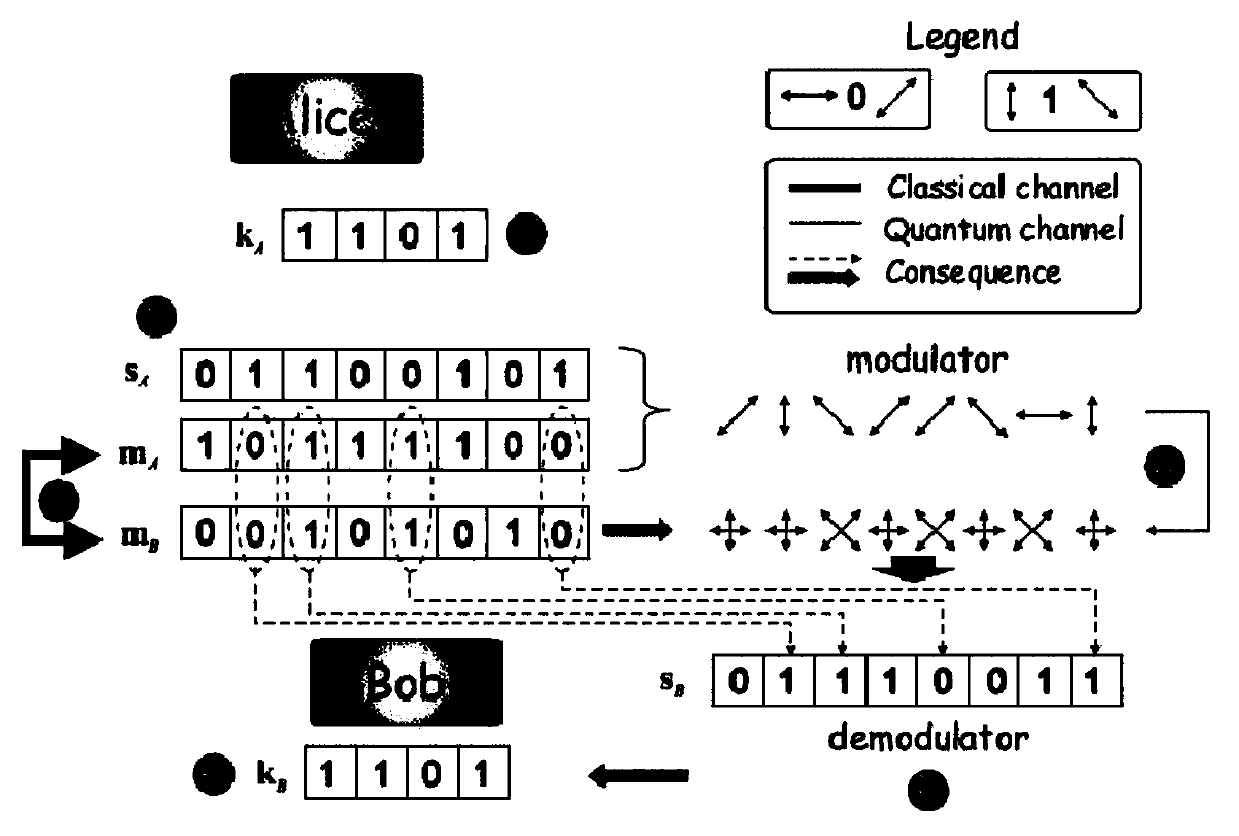
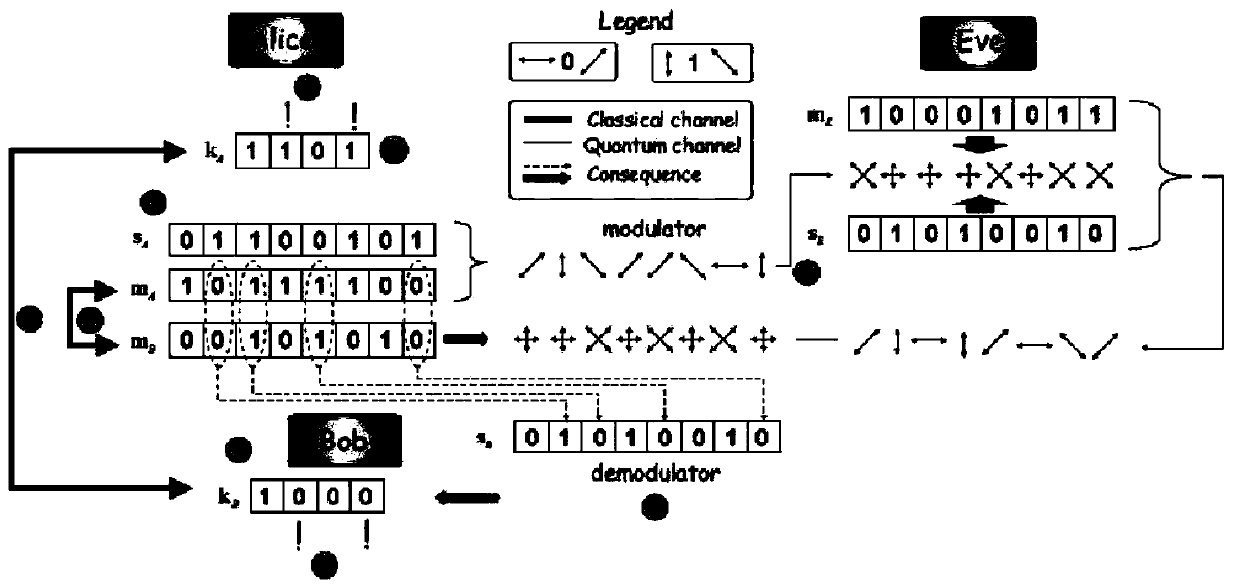
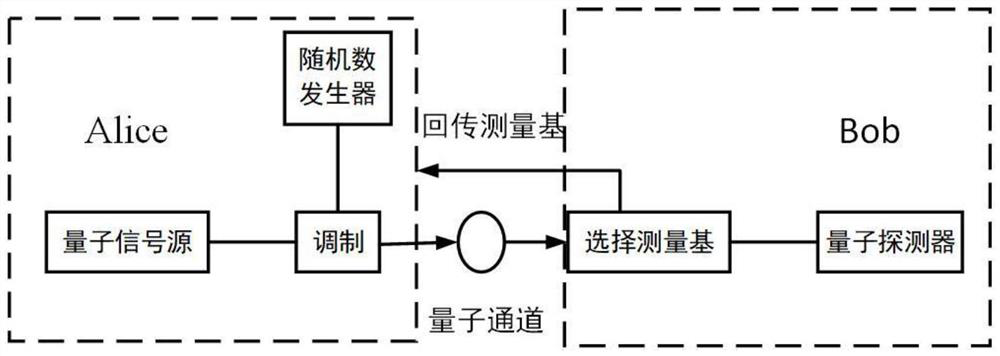
BB84 is a quantum key distribution scheme developed by Charles Bennett and Gilles Brassard in 1984. It is the first quantum cryptography protocol. The protocol is provably secure, relying on the quantum property that information gain is only possible at the expense of disturbing the signal if the two states one is trying to distinguish are not orthogonal (see no-cloning theorem) and an authenticated public classical channel. It is usually explained as a method of securely communicating a private key from one party to another for use in one-time pad encryption.
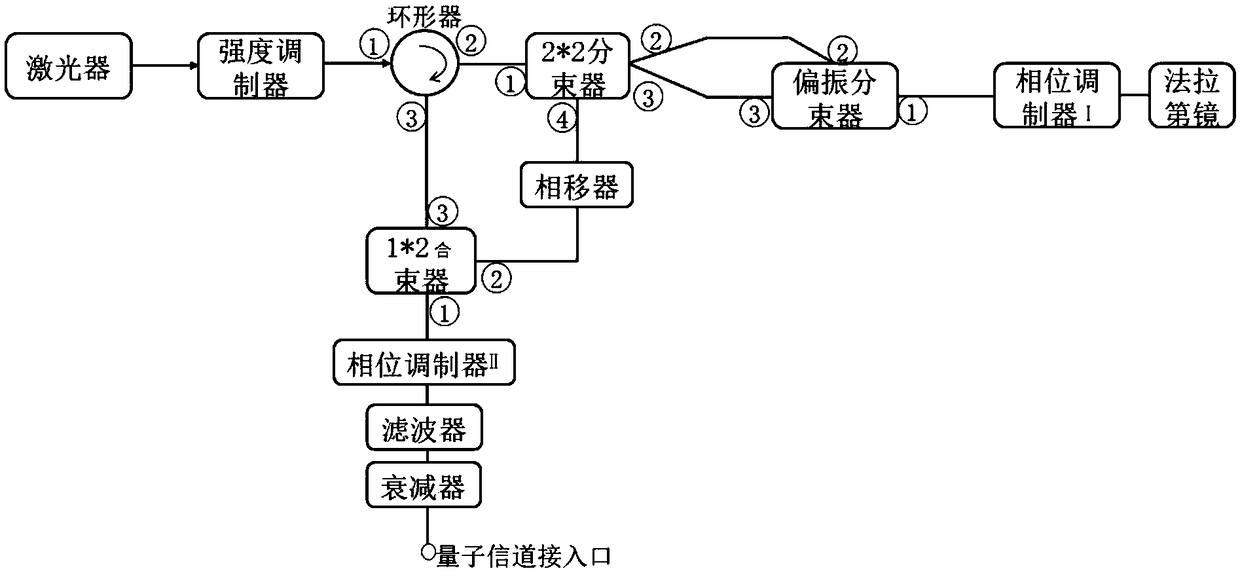
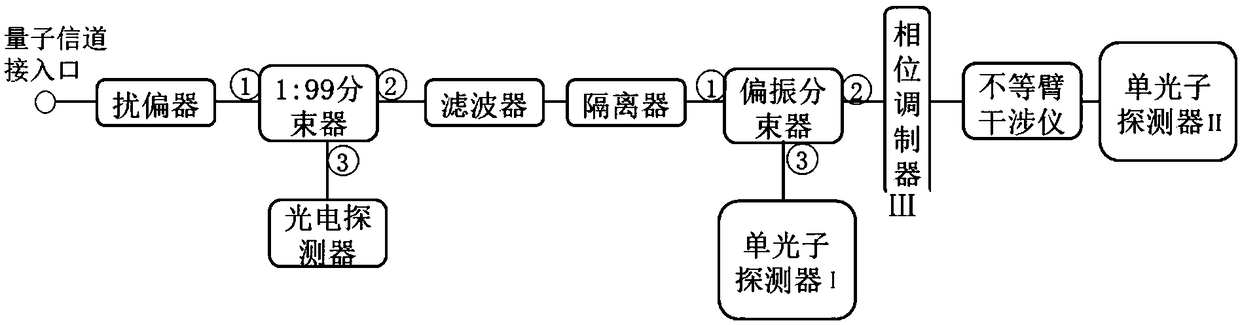
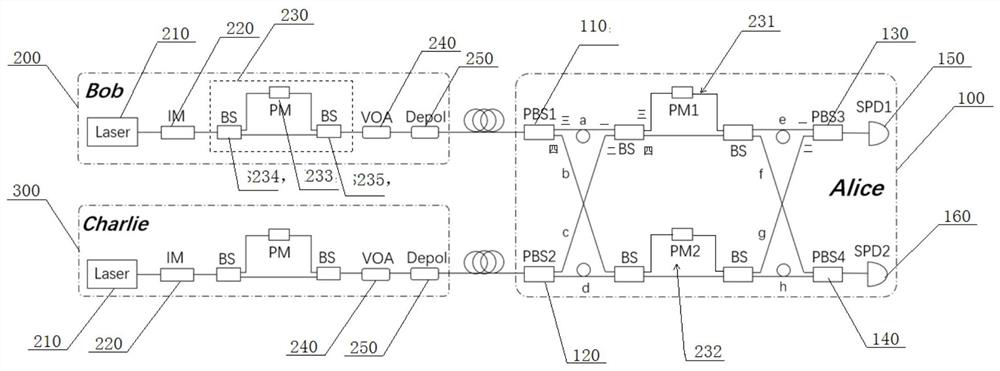
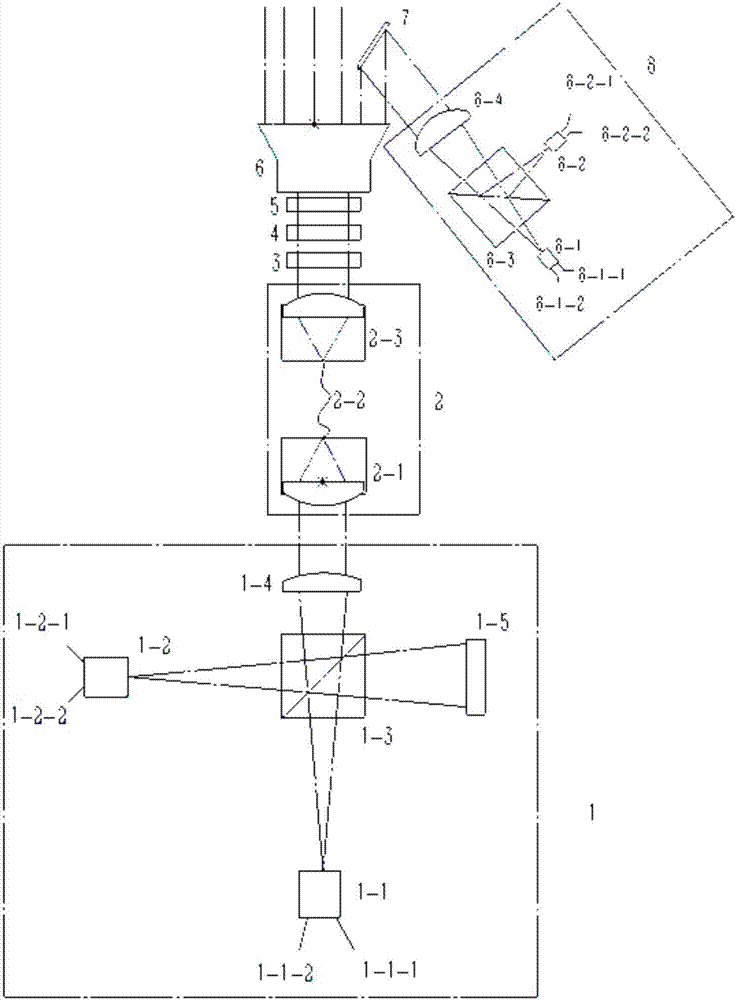
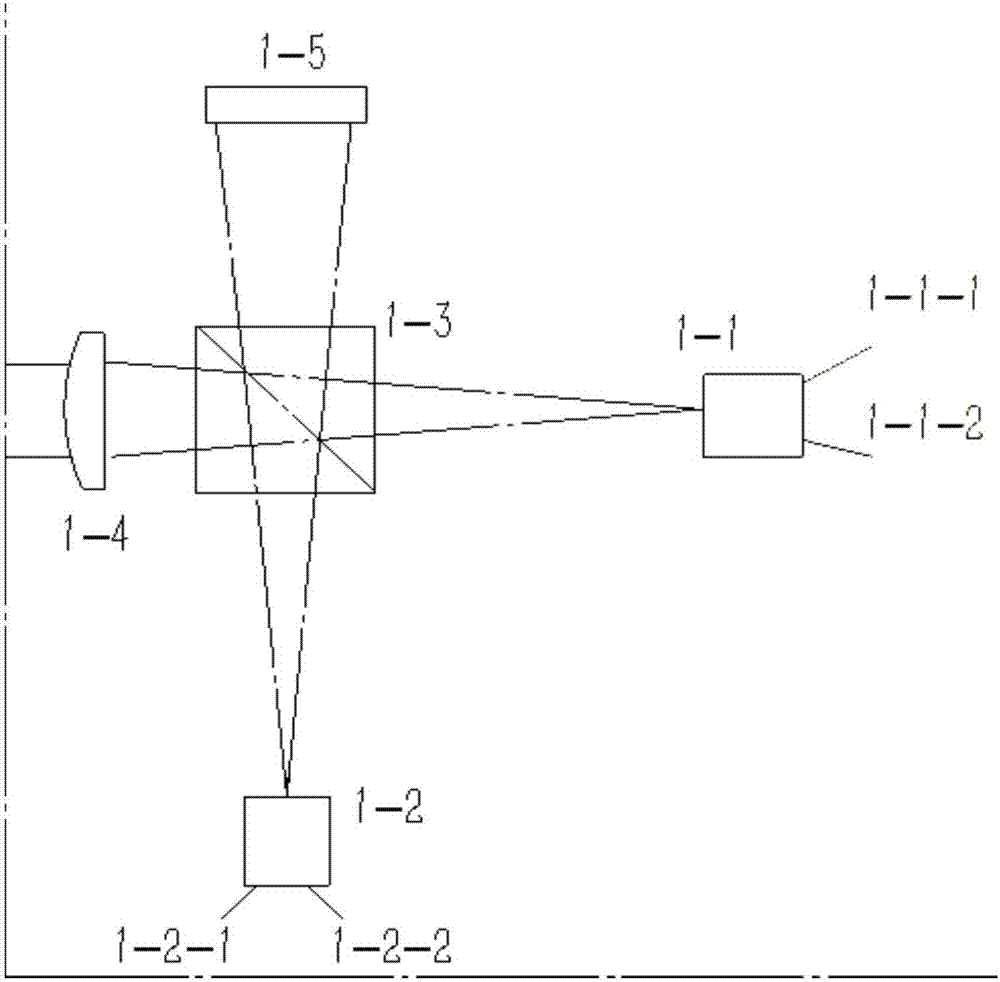
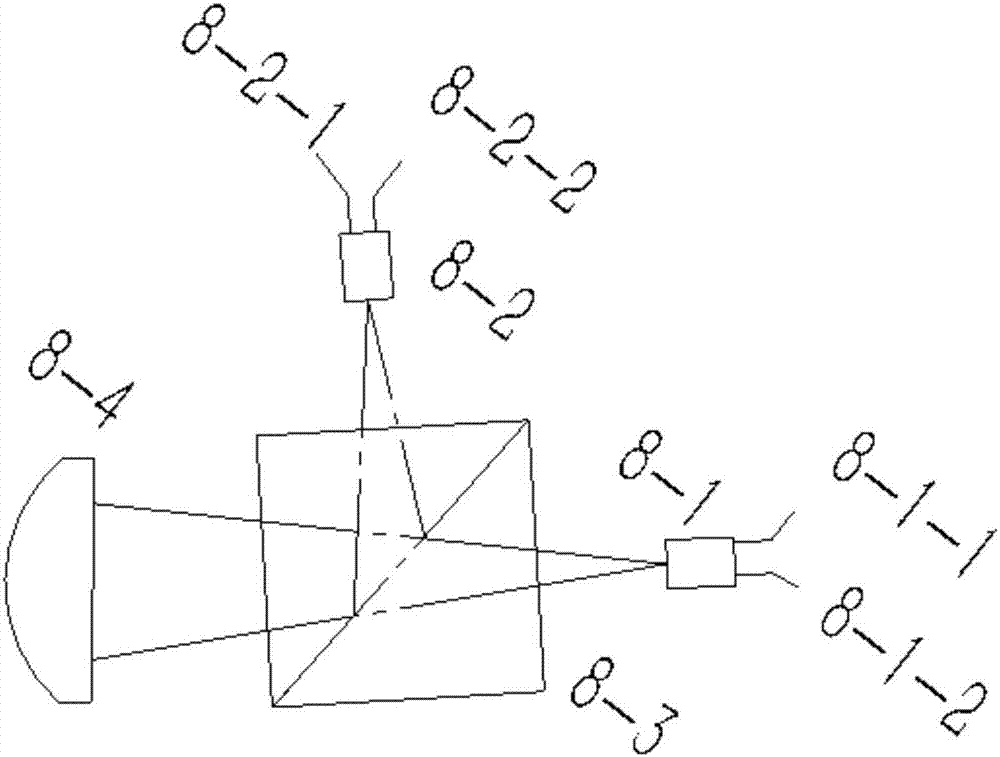
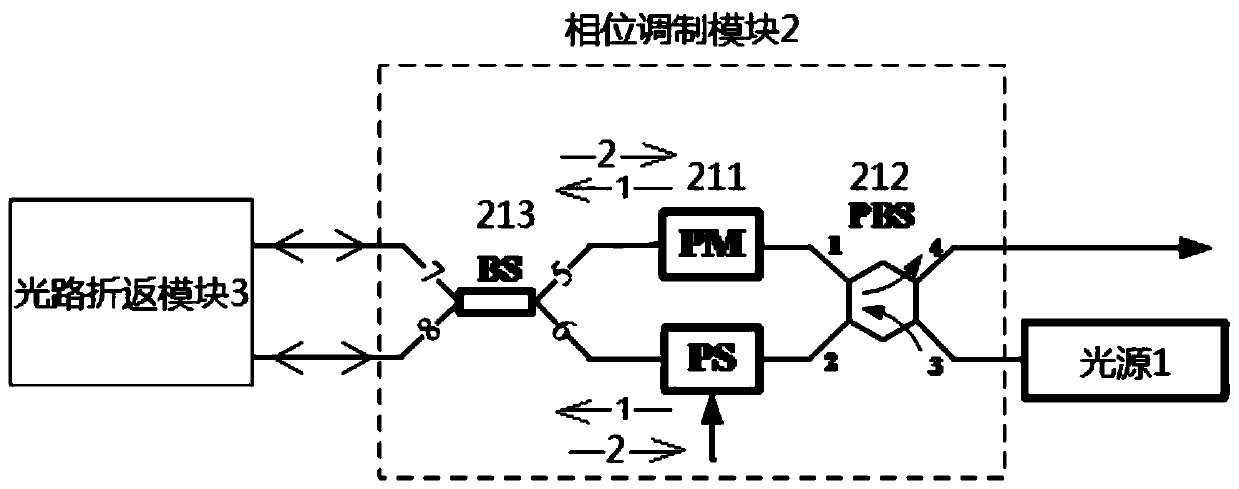
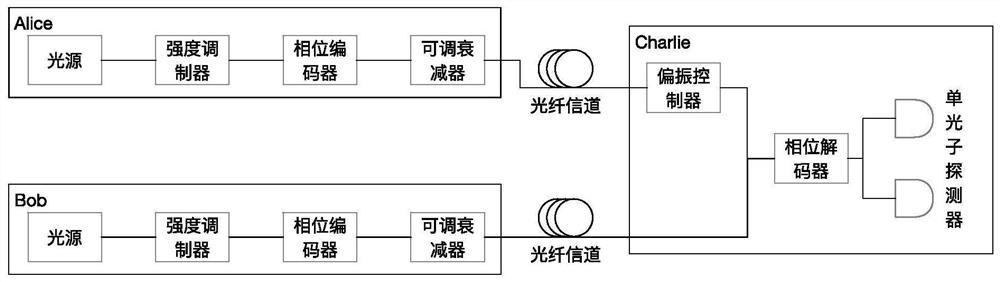
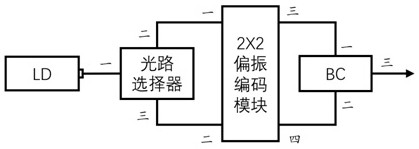
Four-state quantum encoder and decoder for phase modulation polarization encoding and quantum key distribution system
ActiveCN104579564AStability impactEasy to processKey distribution for secure communicationError preventionPolarization-maintaining optical fiberOptical polarization
The invention discloses a four-state quantum encoder and decoder for phase modulation polarization encoding and a quantum key distribution system. The encoder and the decoder have intrinsic stability, namely, the working stability is not influenced by the external environment or connecting optical fibers which can be common mono-mode optical fibers. The quantum encoder and decoder can be applied to the field of quantum key distribution, the whole system comprises a transmitting end and a receiving end, and the transmitting end and the receiving end are connected through a quantum channel to complete the key distribution process. The quantum encoder and decoder can achieve BB84 protocol four-state quantum key encoding and decoding with intrinsic stability. The common mono-mode optical fibers can be used as all the connecting optical fibers without using polarization-maintaining optical fibers, and interference with the phase drift and polarization change of the system from the external environment has no influence on the encoding or decoding process at all.
Owner:SOUTH CHINA NORMAL UNIVERSITY
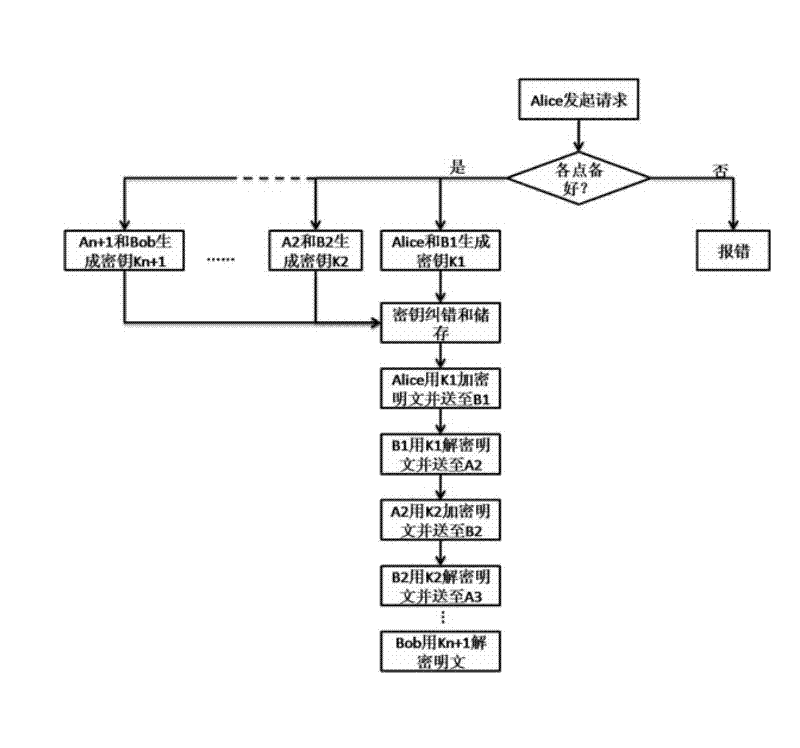
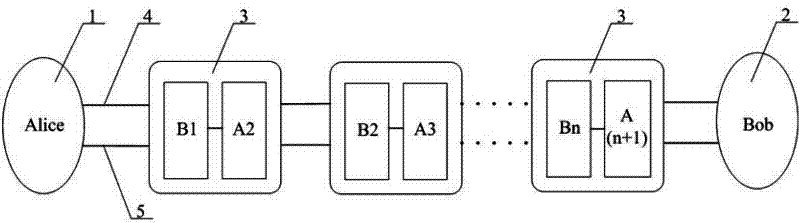
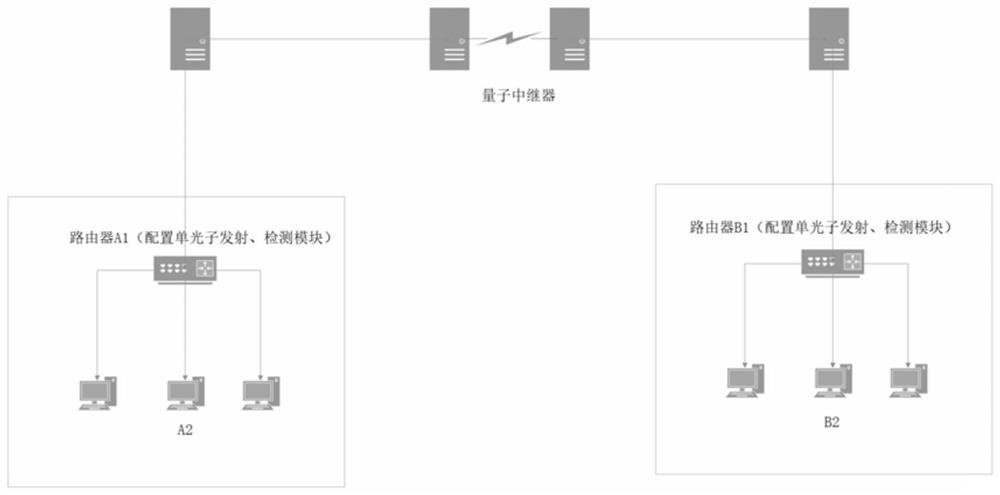
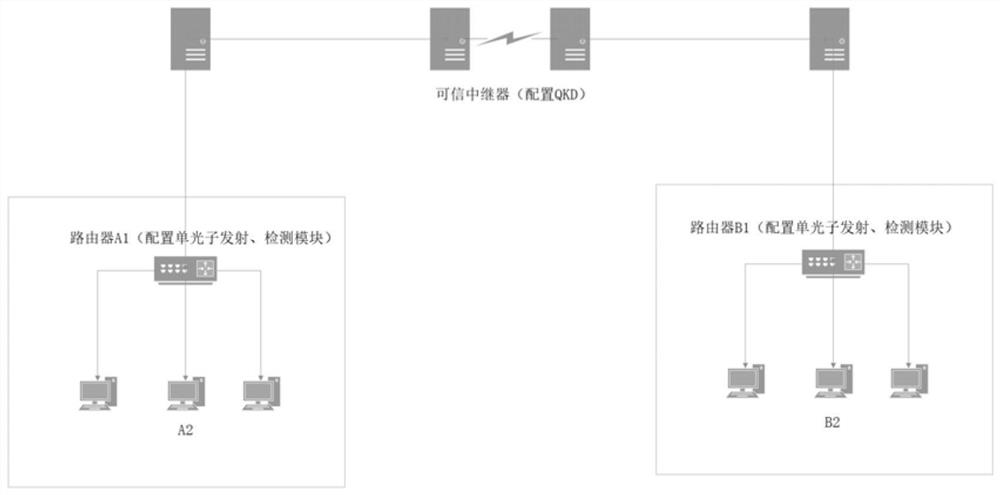
Relaying method for remote secure quantum communication
InactiveCN102238005AImprove confidentialityImprove the effective transmission distanceKey distribution for secure communicationElectromagnetic repeatersPeer-to-peerComputer security
The invention discloses a relaying method for remote secure quantum communication. The method is characterized in that: at least more than one relay station is arranged on a link for connecting two user terminals by a quantum channel and a high speed optical module channel, generates own relatively more independent key by adopting a phase encoding BB84 protocol, encrypts once transmitted information and generates a corresponding key in the connection of each time, and performs connection and integration by the distribution of a plurality of peer-to-peer keys to realize ultra-long range secure quantum communication. Compared with the prior art, the invention has the advantages of peer-to-peer remote secure quantum communication, high security, high system security and high transmission efficiency; and by the method, the effective transmission range of the quantum communication is greatly prolonged, and the problems of limitations to a single-system secure communication range are solved.
Owner:SHANGHAI LANGYAN OPTOELECTRONICS TECH
Quantum Key Distribution Protocol
InactiveUS20080101612A1Easily realizedIncrease the number ofKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareTransmitter
A quantum key distribution protocol is provided that reduces the maximum value of the leaked information amount over the same distance when an adversary makes a photon number splitting attack more than the reduction by the BB84 protocol and the SARG protocol, by making use of the advantages of the BB84 protocol and the SARG protocol. By properly proportioning the existing BB84 protocol and the SARG protocol in accordance with the rate determined by the communication distance between the sender and the receiver of the coherent light, a protocol that is more robust against photon number splitting attack than the known existing protocols can be realized, and long distance quantum key distribution, which was not possible until now, becomes possible.
Owner:THE FOUND FOR THE PROMOTION OF IND SCI +1
Quantum secret data chain communication system
ActiveCN110247765ACapable of monitoringHave a certain defensive abilityKey distribution for secure communicationPhotonic quantum communicationCommunications systemKey issues
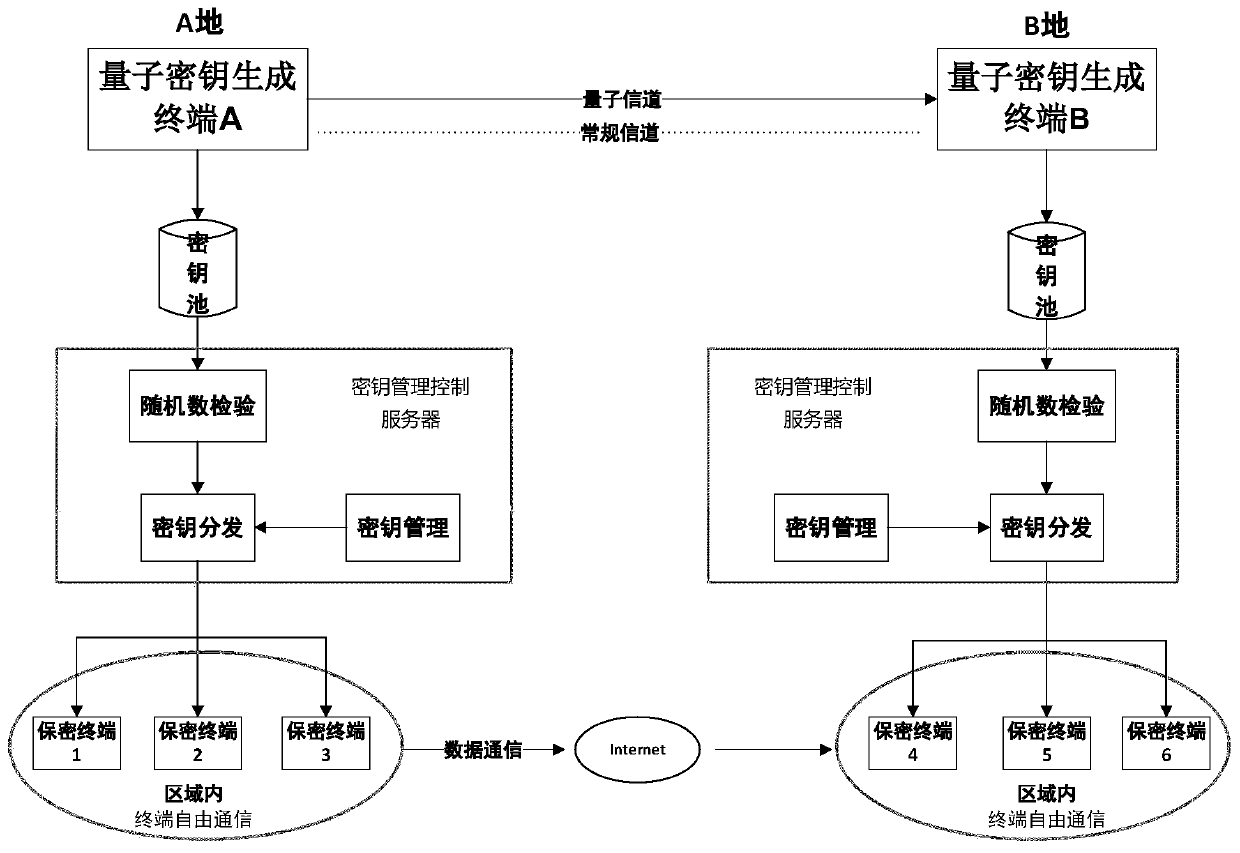
The invention discloses a quantum secret data link communication system, which comprises two identical quantum secrecy devices, each quantum secrecy device comprises quantum key generation equipment, a key management control server and a plurality of secrecy terminals, wherein each key management control server is bound with a plurality of confidential terminals; the two pieces of quantum key generation equipment are used for transmitting the partial normal single light quantum through a channel, operating a BB84 protocol and generating symmetrical quantum keys; putting into respective key pools; then respectively issuing to the secret key management control servers which are respectively connected with the server; the key management control server is used for receiving and verifying the quantum key issued by the key pool and then distributing the quantum key to a plurality of bound confidential terminals; and the security terminal is used for establishing a binding connection with the key management control server through a built-in authentication key, and receiving and storing the quantum key. The system disclosed by the invention has the advantages of high security, high independence, and convenience, rapidness and simplicity in deployment.
Owner:湖北凯乐量子通信光电科技有限公司
Quantum secure communication optical path
InactiveCN109257109AImplement passive random selectionAvoid Modulation Bandwidth LimitationsPhotonic quantum communicationElectromagnetic transmission optical aspectsCommunications systemRound complexity
The invention relates to a quantum secure communication optical path. Only two phase modulators are required to realize the preparation of all quantum states required for quantum communication, thereby reducing the complexity of the system. Meanwhile, the quantum secure communication realization scheme provided by the invention can be compatible with different quantum secure communication protocols such as BB84, reference frame irrelevance and the like, so as to truly realize the free switching of multiple protocols of a system. The problem of loss mismatch between the two arms of the interferometer is solved. It not only reduces the complexity of the existing quantum secure communication system and improves the stability of the system, but also can be compatible with different quantum secure communication protocols, which can better meet various application needs and promote the practicality and commercialization of quantum secure communication.
Owner:NAT UNIV OF DEFENSE TECH
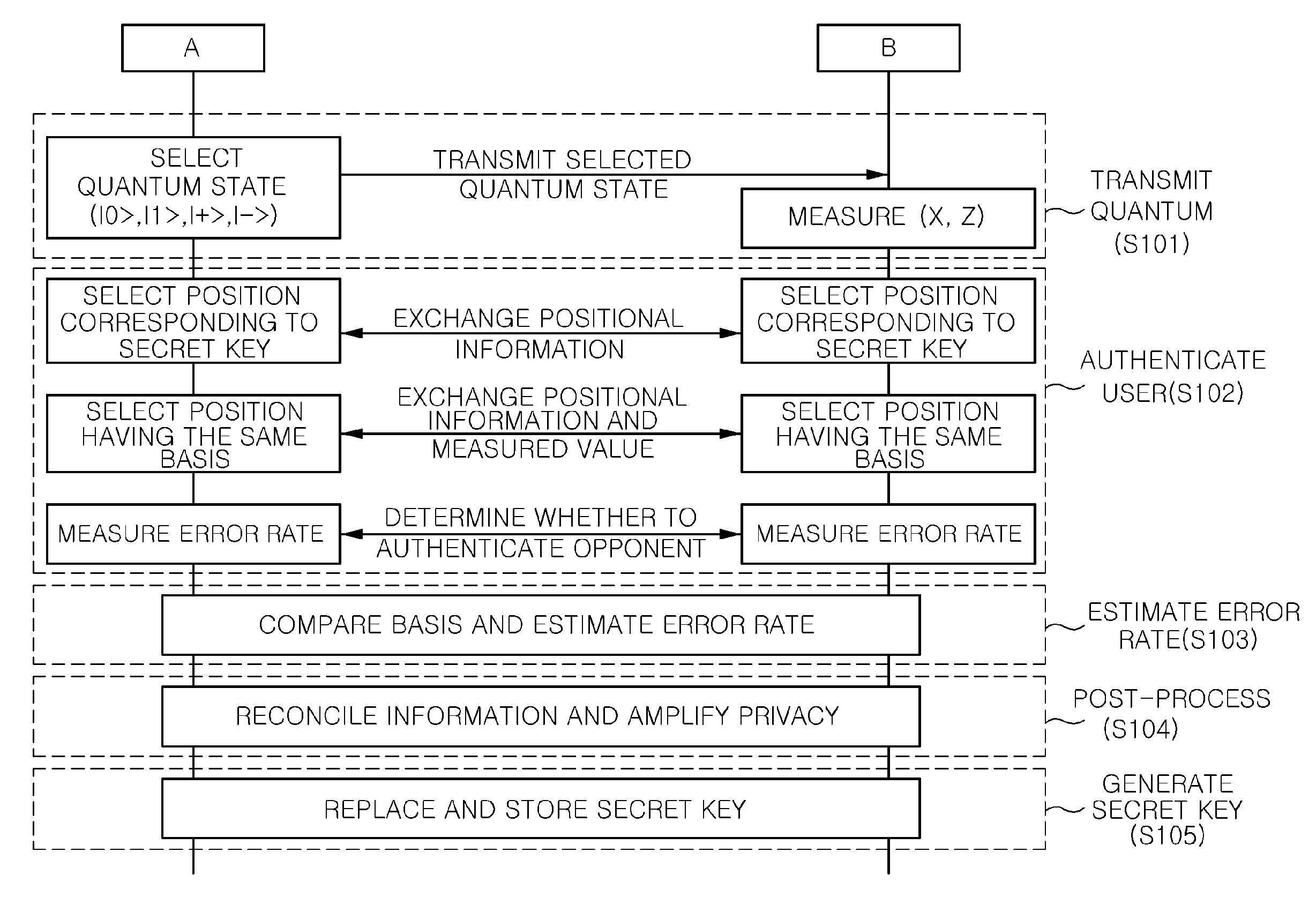
Method of user-authenticated quantum key distribution
InactiveUS8639927B2Efficient use ofPublic key for secure communicationUser identity/authority verificationMan-in-the-middle attackKey distribution
A method of user-authenticated quantum key distribution according to the present invention shares a position having the same basis without making public basis information using previously shared secret keys and authenticates a quantum channel by confirming whether there is the same measured outcome at that position, in order to secure unconditional security of BB84 quantum key distribution (QKD) protocols vulnerable to man-in-the-middle attack.
Owner:ELECTRONICS & TELECOMM RES INST
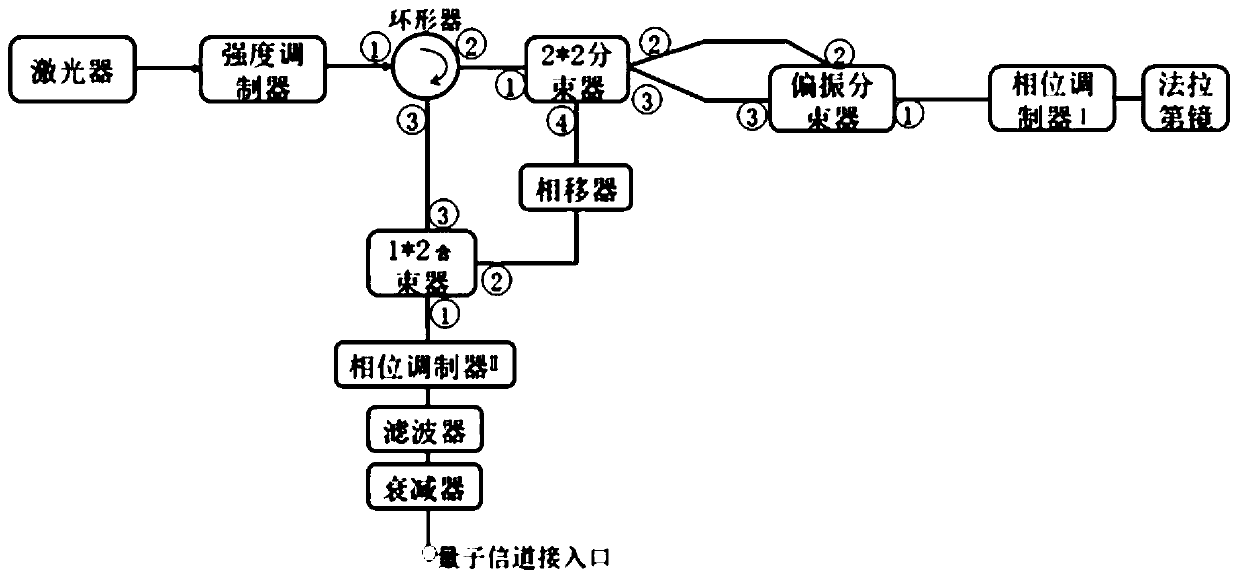
Polarization coding device used for quantum key distribution and quantum key distribution system
ActiveCN113708931AReduce complexitySolve the problem of wavelength inconsistencyKey distribution for secure communicationPhotonic quantum communicationSoftware engineeringHemt circuits
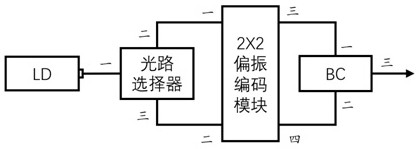
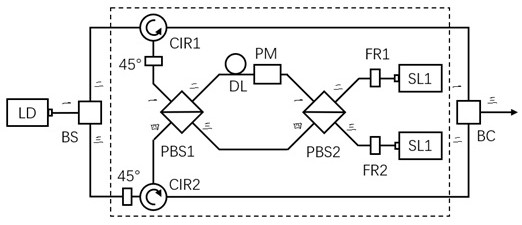
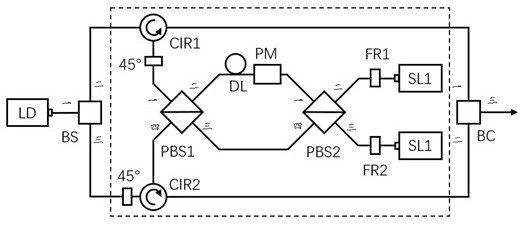
The invention discloses a polarization coding device used for quantum key distribution, the polarization coding device comprises a laser LD, an optical path selector, a 2X2 polarization coding device and a beam combiner BC, the 2X2 polarization coding device is provided with two input ports and two output ports, and the invention also provides a quantum key distribution system. Compared with the prior art, the polarization encoding device adopts the 2X2 polarization encoding module, only one phase modulator is needed, the modulation phase is 0 or pi, and four BB84 polarization states can be prepared. The problem that the wavelengths of multiple lasers are inconsistent can be solved, and the requirement for a phase modulator driving circuit is lowered. The safety of quantum state preparation is ensured, and the complexity of the coding device is reduced.
Owner:ZHEJIANG QUANTUM TECH CO LTD
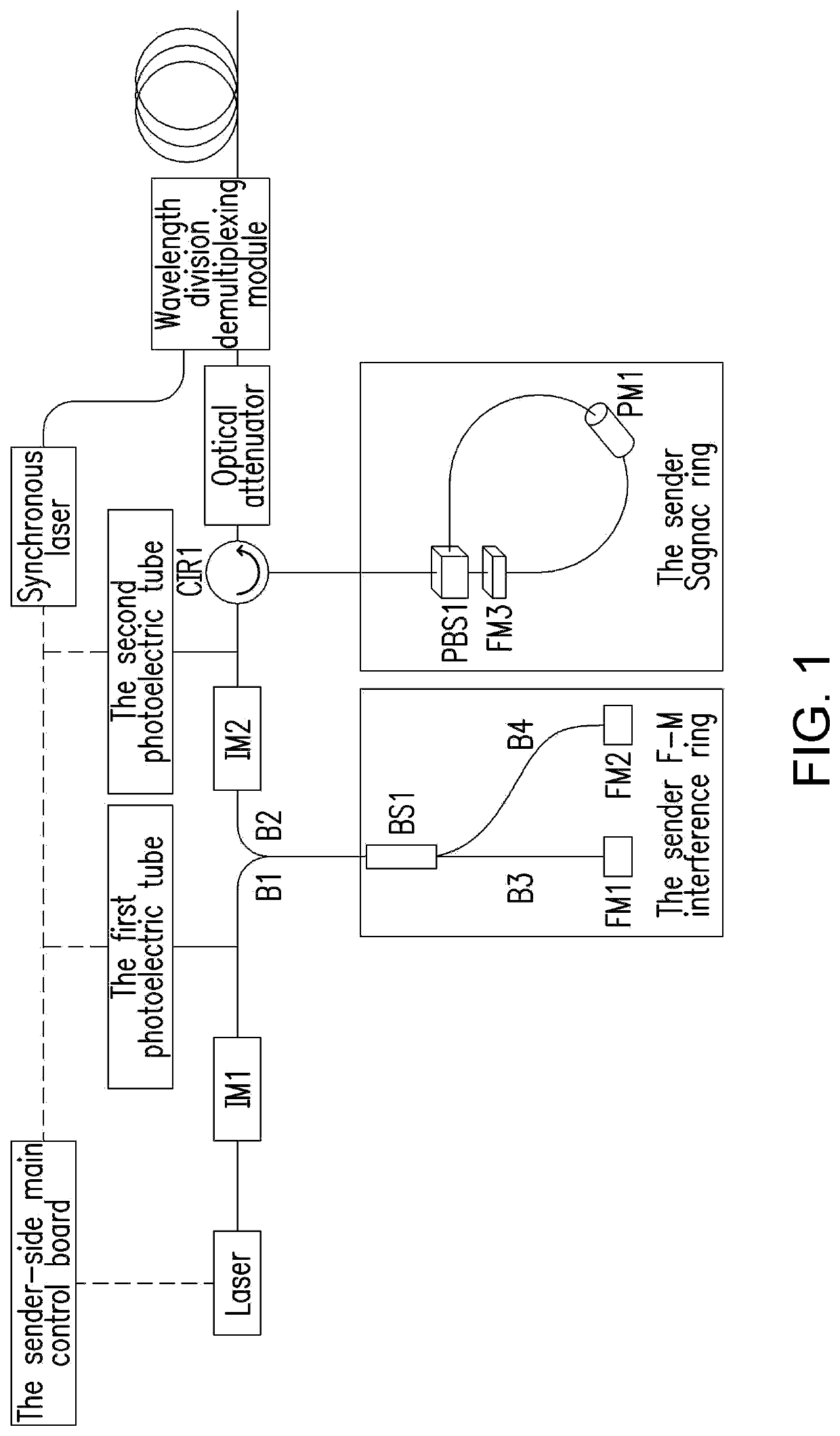
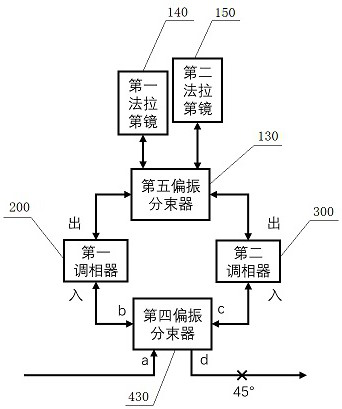
Quantum key distribution device capable of configuring multiple protocols
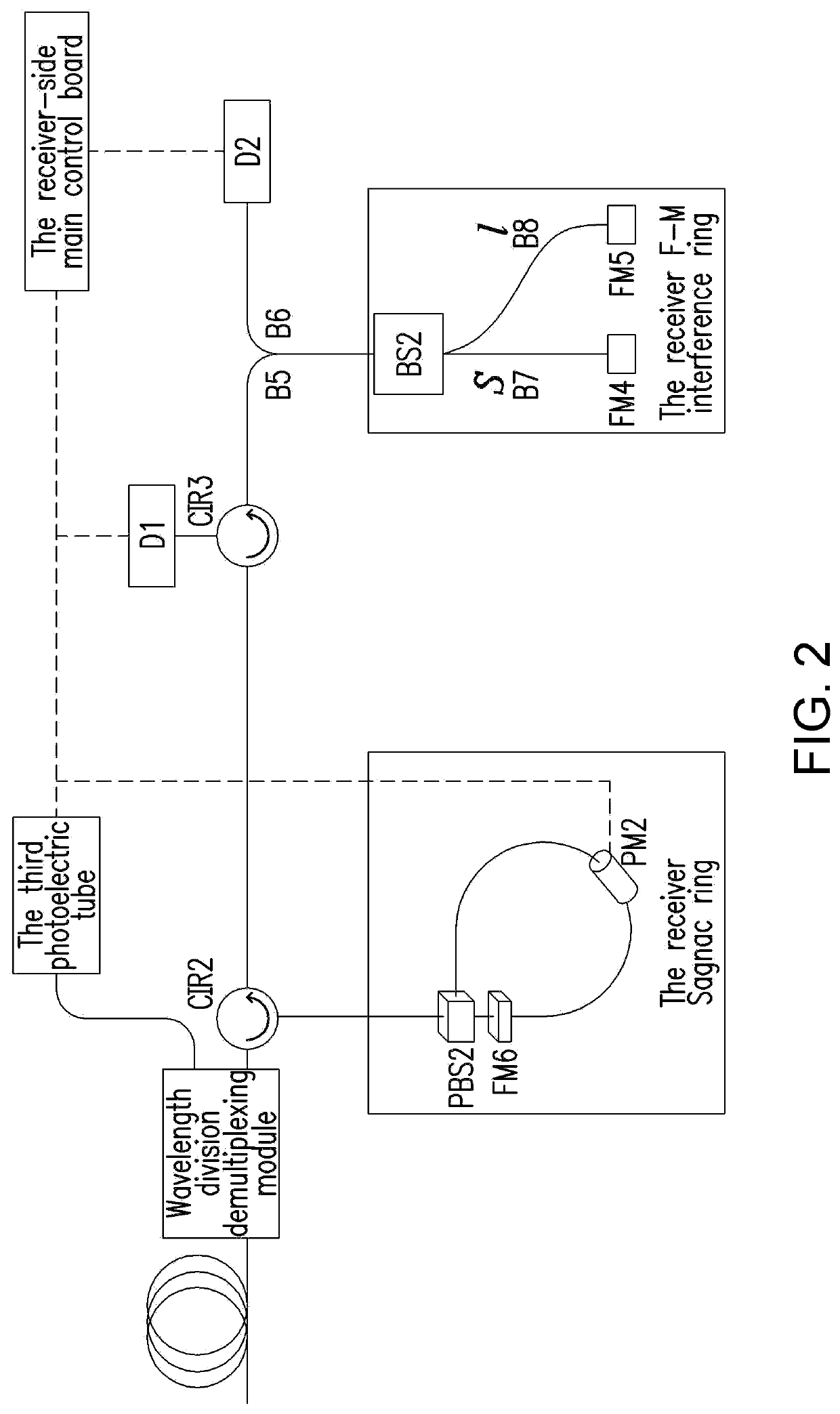
ActiveCN112448815AAvoid Polarization Selectivity EffectsLow insertion lossQuantum computersKey distribution for secure communicationTimestampSoftware engineering
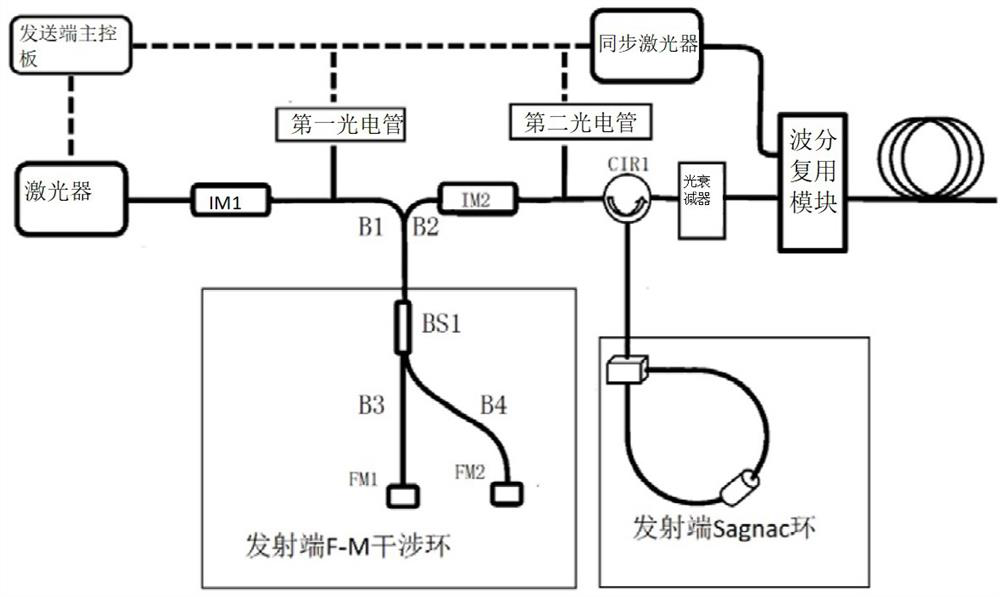
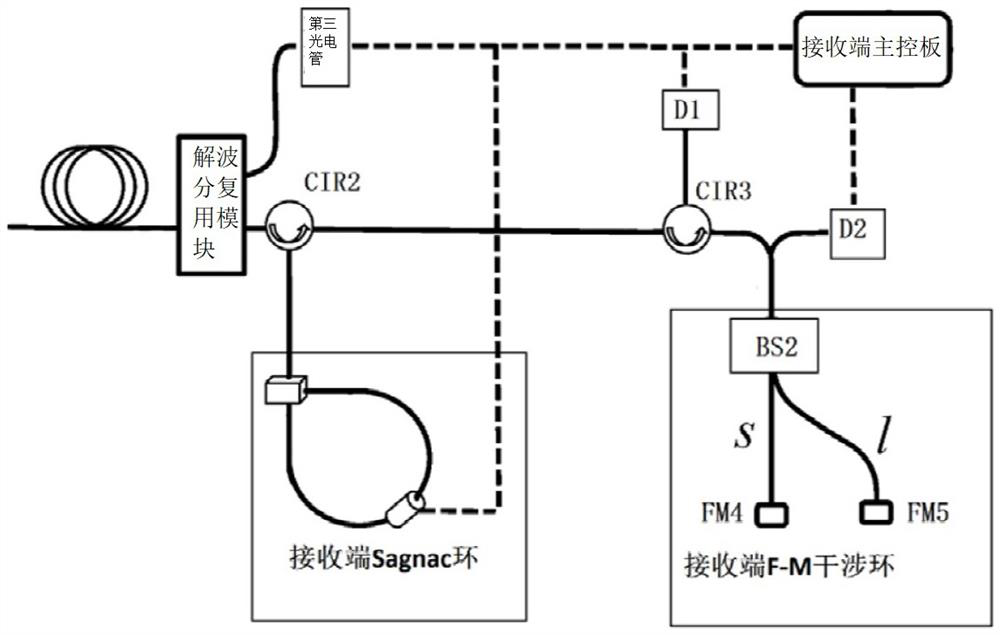
The invention relates to the field of quantum communication, in particular to a quantum key distribution device capable of configuring multiple protocols, which utilizes a simplified Faraday Michelsoninterference ring combined with an intensity modulator to finish timestamp coding in a chopping mode. Phase modulation is completed through a Sagnac ring device composed of a single-polarization phase modulator, a polarization beam splitter and a Faraday rotator, so that the purpose of composite encoding and decoding is achieved, and the quantum key distribution device capable of configuring multiple protocols and multiple decoy state schemes is achieved. The device can be compatible with various protocols including a BB84 protocol, a reference system independent protocol, a six-state protocol, a SARG protocol and the like, and has the characteristics of phase modulation polarization independence, low system complexity and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
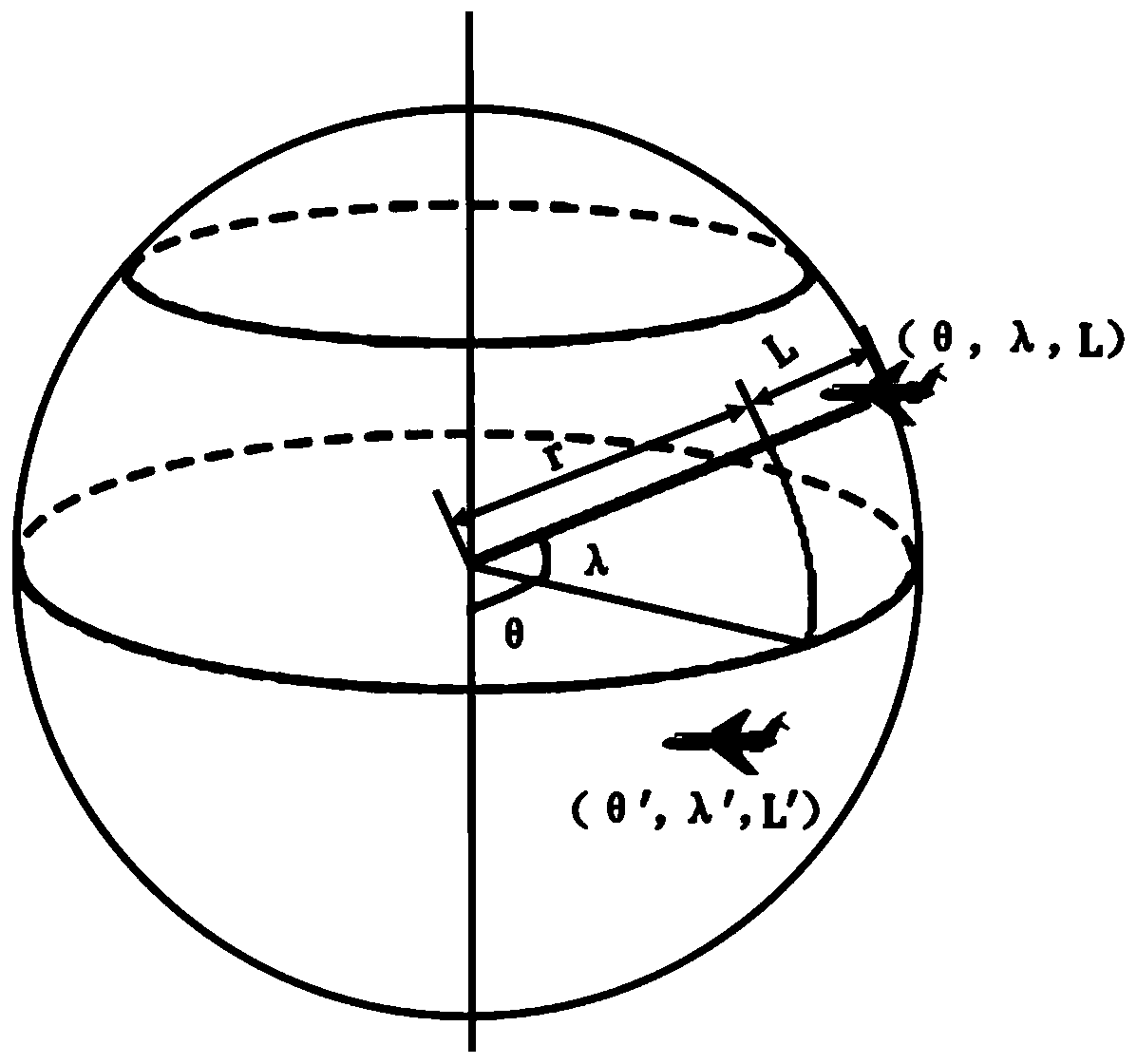
Free space quantum key distribution system and method for aircraft
PendingCN111162903AEnsure safetyKey distribution for secure communicationPhotonic quantum communicationGround stationRecipient side
The invention discloses a free space quantum key distribution system and method for an aircraft. Theoretically absolutely safe point-to-point quantum secret communication can be realized between an aircraft carrying the quantum key distribution equipment and any aircraft or ground station carrying the equipment. A communication sender attenuates strong laser to obtain quasi-single-photon laser with an average photon number in the single-photon level, then performs polarization state modulation on the quasi-single-photon laser according to a polarization BB84 protocol, and sends the quasi-single-photon laser to a receiver through an optical antenna via a free space. And the receiver receives the single photon from the sender through the optical antenna, and demodulates key information carried by the single photon through a quantum signal receiving system. Because the single photon in the unknown quantum state has the characteristics of non-replicability and non-divisibility, the third party cannot steal the key information of the two communication parties without being discovered, and the security of the aircraft communication information is ensured.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
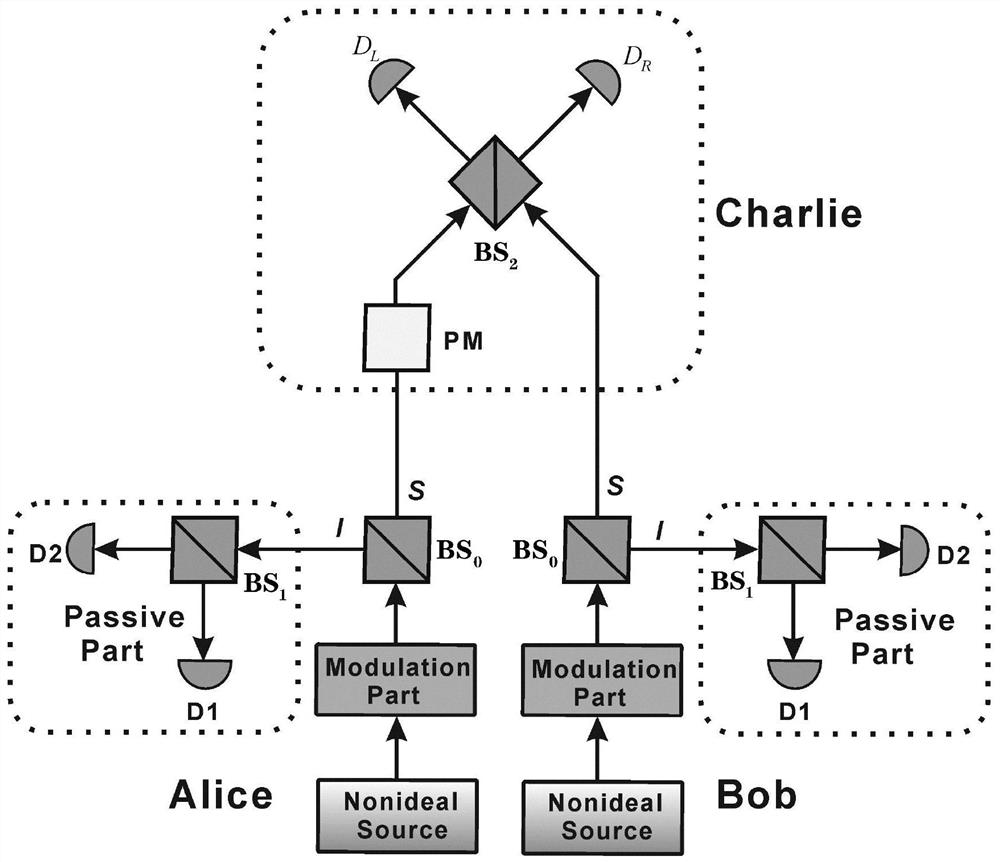
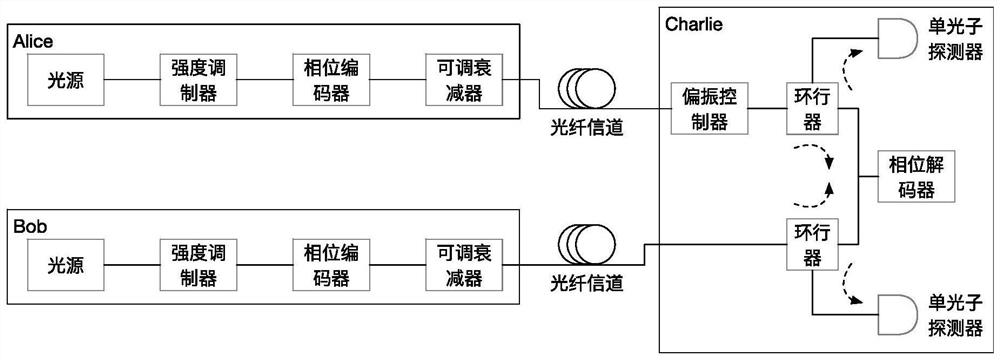
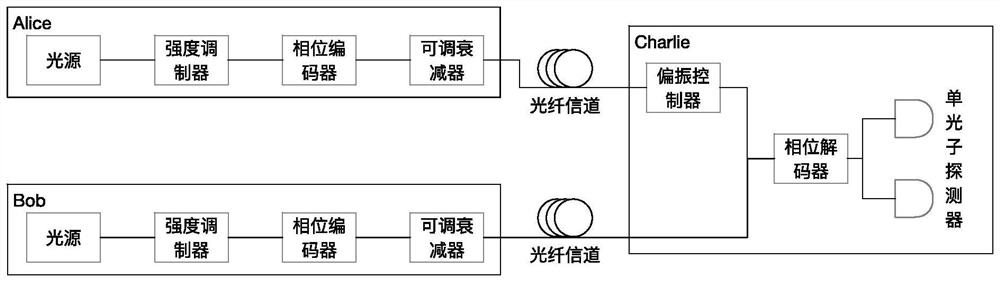
Quantum digital signature system resistant to polarization disturbance
PendingCN113347005AThe structure is simple and identicalEasy to prepare in large batchesKey distribution for secure communicationUser identity/authority verificationTelecommunicationsDigital signature
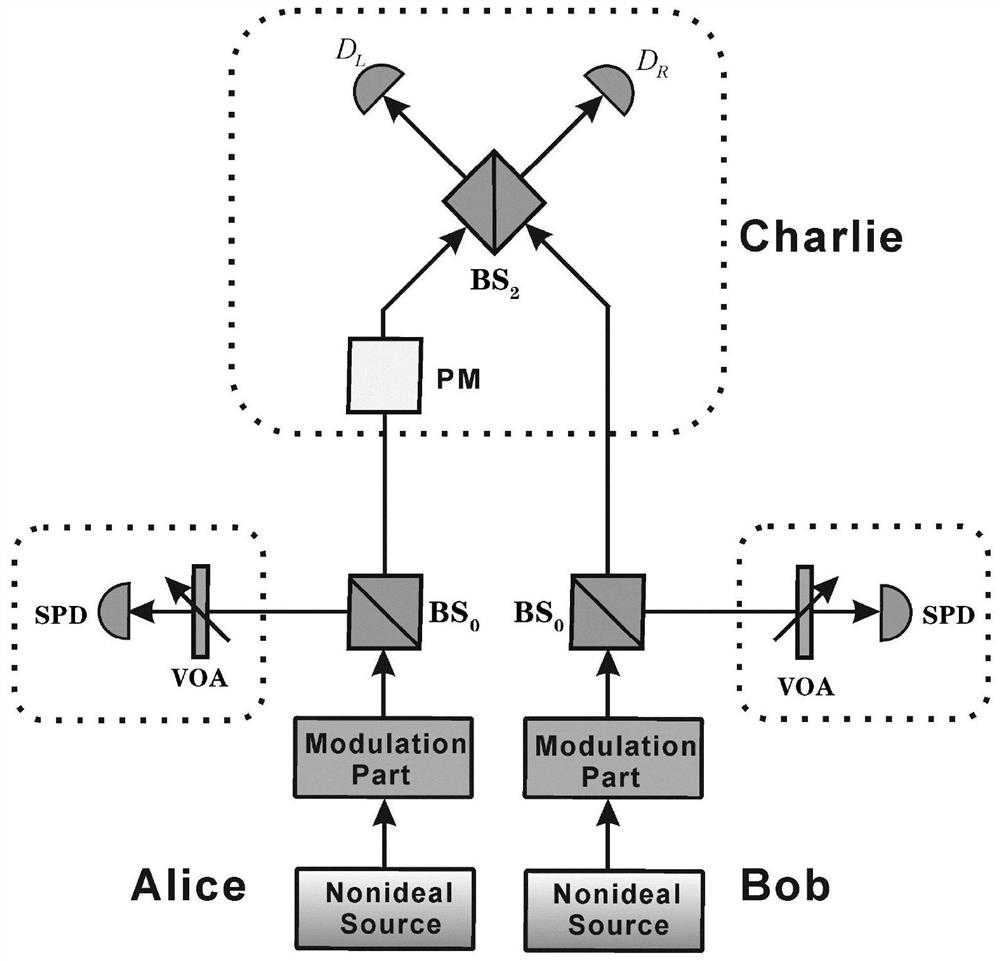
A quantum digital signature system resistant to polarization disturbance comprises a message sender Alice, two message receivers Bob and a receiver Charlie, the sender Alice sends a message to the receiver Bob and the receiver Charlie in combination with a digital signature, the receiver Bob serves as a message authenticator and forwards information sent by the sender Alice to the receiver Charlie, and the composition of the receiver Charlie is completely the same as that of the receiver Bob. Compared with the prior art, the quantum digital signature scheme based on the phase coding BB84 quantum key distribution system can resist channel polarization disturbance. The photon polarization state change caused by channel disturbance does not influence the final interference result of the system, namely, the stability of the system can be ensured.
Owner:神盾迅波(北京)量子科技发展有限公司
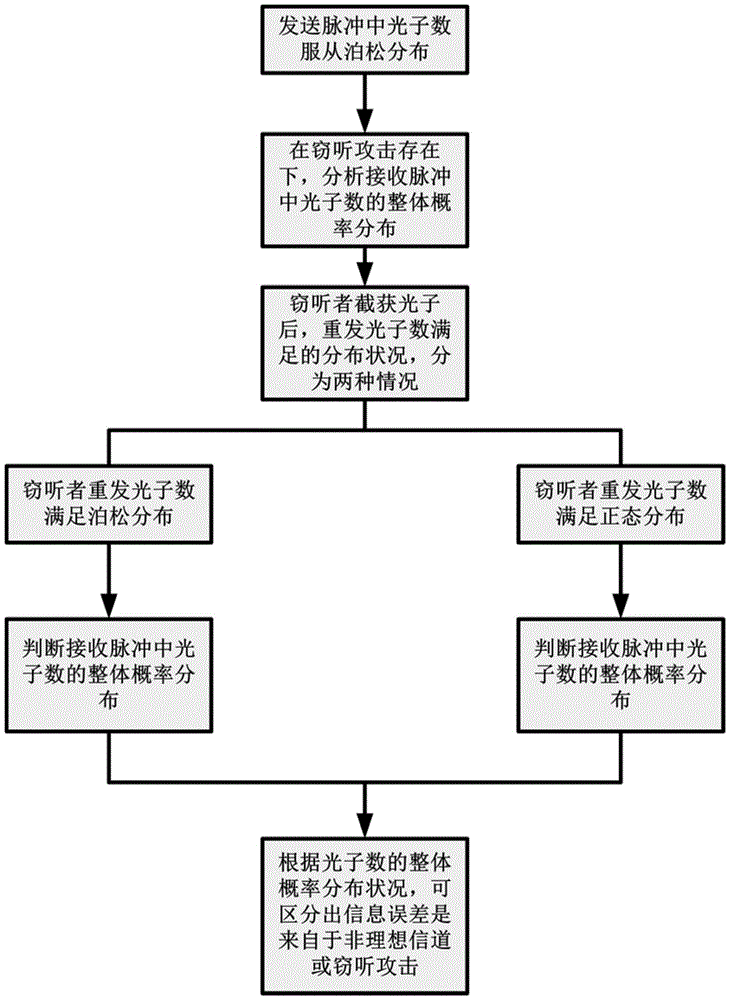
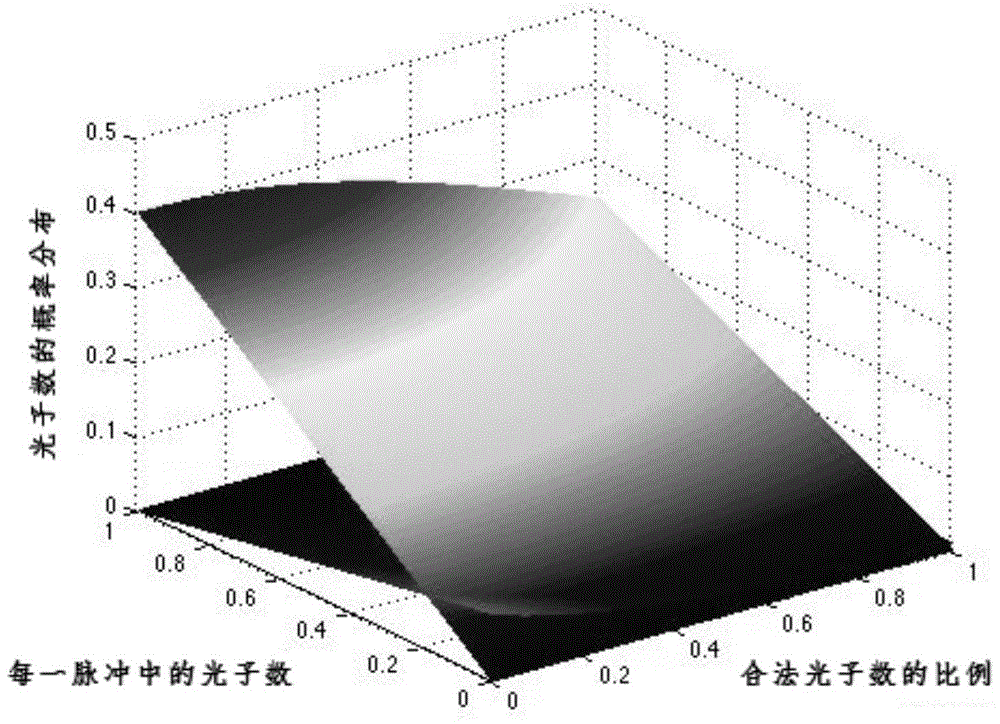
Quantum key distribution eavesdropping judgment method based on BB84 protocol
ActiveCN105743882ADifferentiate sources of errorImprove transmission efficiencyKey distribution for secure communicationSkew normal distributionMatrix normal distribution
The invention discloses a quantum key distribution eavesdropping judgment method based on a BB84 protocol, and mainly aims to solve the safety problem in quantum encryption caused by non-ideal devices and imperfect experimental conditions. According to the technical scheme, the method comprises the following steps: the overall probability distribution of photon number in a received pulse sequence is judged according to the Poisson distribution followed by the number of photons in sent pulses and the Poisson distribution or normal distribution satisfied by the number of retransmitted photons after an eavesdropper intercepts part of photons; the source of received information error is judged according to the overall probability distribution of photon number; if the overall probability distribution of photon number is damaged, that the information error is from an eavesdropping attack is judged, legitimate participants believe that the communication is unsafe and cancel the communication; or, that the information error is from a non-ideal channel is judged, and legitimate participants adjust the parameters of the non-ideal channel to reduce information error. The method improves the efficiency and safety of quantum key distribution, and can be used in the BB84 protocol.
Owner:XIDIAN UNIV
Four-way coaxial free space quantum communication coding device
ActiveCN107147442AImprove coaxialityImprove stabilityPolarisation multiplex systemsPhotonic quantum communicationTelecommunicationsMiniaturization
The invention discloses a four-way coaxial free space quantum communication coding device. According to the device, four-way coding signals are coupled to a single mode fiber for transmission, so high-precision coaxiality of four-way quantum light is ensured; moreover, through utilization of the polarization property that the single mode fiber has unitary transformation, the polarization transformation introduced into the fiber is compensated through adoption of a 1 / 4, 1 / 4 and 1 / 2 wave plate combination scheme, so a polarization state of emergent light is ensured; and the polarization compensation is monitored through utilization of a BB84 decoding module, thereby ensuring a polarization compensation effect. The device is characterized by high coaxiality, high stability and high confidentiality. The device is applicable to urgent demands for miniaturization, high polarization-maintenance and high reliability of the coding module in space quantum communication.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
Passive light source monitoring method suitable for twin-field protocol
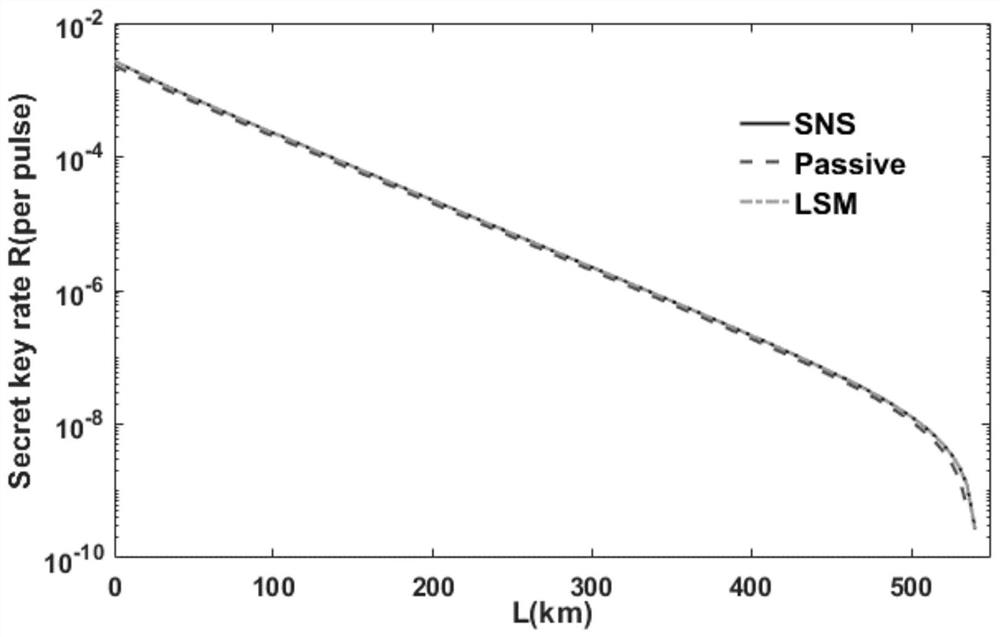
ActiveCN113300762AImprove performanceReduce the difficulty of experimentsKey distribution for secure communicationPhotonic quantum communicationLight beamEngineering
The invention discloses a passive light source monitoring method suitable for a twin-field protocol. The method comprises the following steps: acquiring signal light and idle light obtained by splitting a light pulse subjected to intensity modulation; dividing the idle light into two light beams, detecting the two light beams, and obtaining four different counting events according to a detection result; estimating the parameters of the signal light through four different counting events so as to obtain a safe coding rate under a untrusted light source. Parameters of devices in a light source monitoring module do not need to be adjusted, the experiment difficulty is reduced, and safety reduction caused by modulation errors is avoided. The method is introduced by taking a twin-field quantum key distribution protocol as an example, is not only limited to be applied to a quantum key distribution process of the twin-field protocol, but also is suitable for quantum key distribution and quantum communication processes involving an untrusted light source, such as a BB84 protocol and a measurement equipment irrelevant protocol.
Owner:NANJING UNIV OF POSTS & TELECOMM
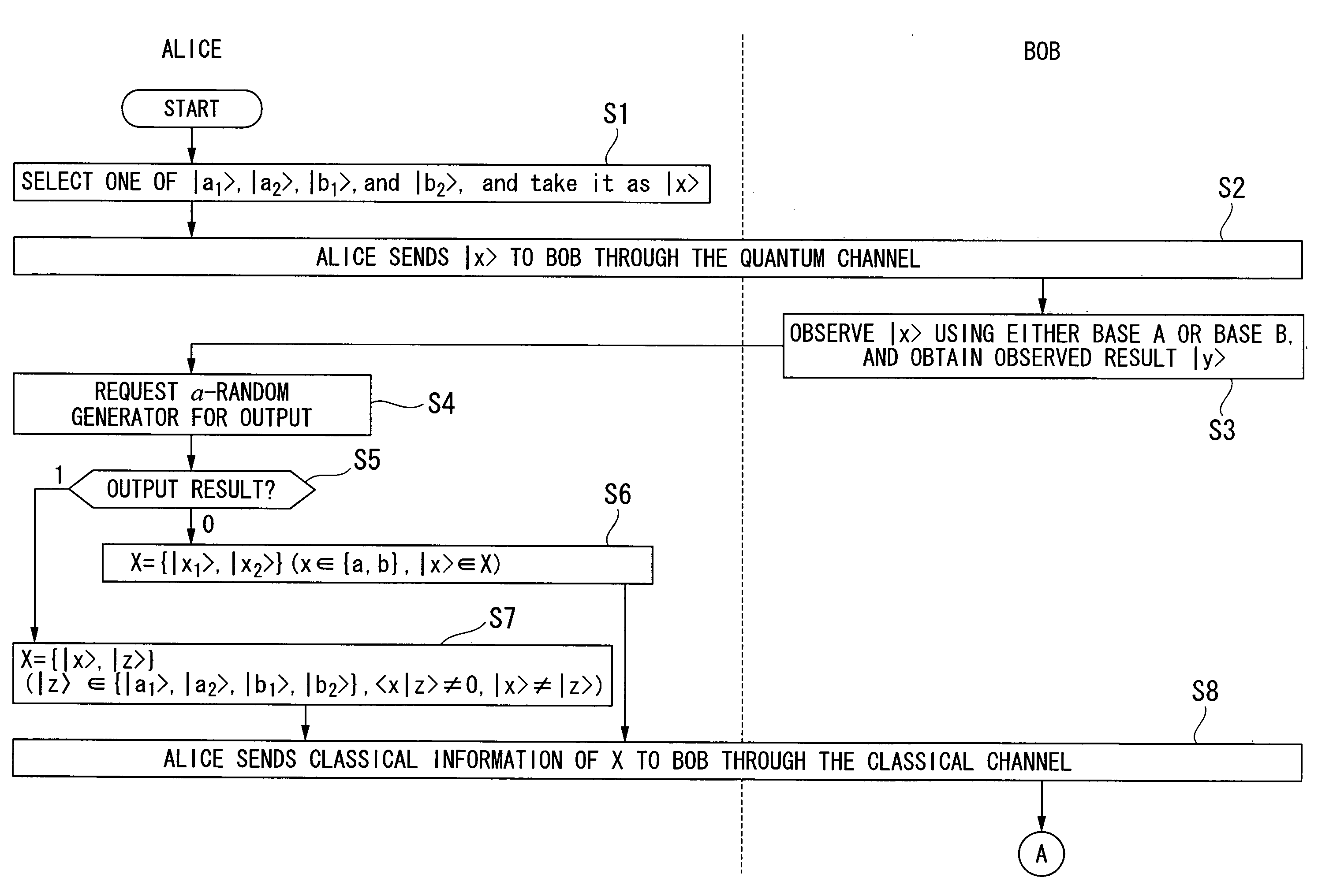
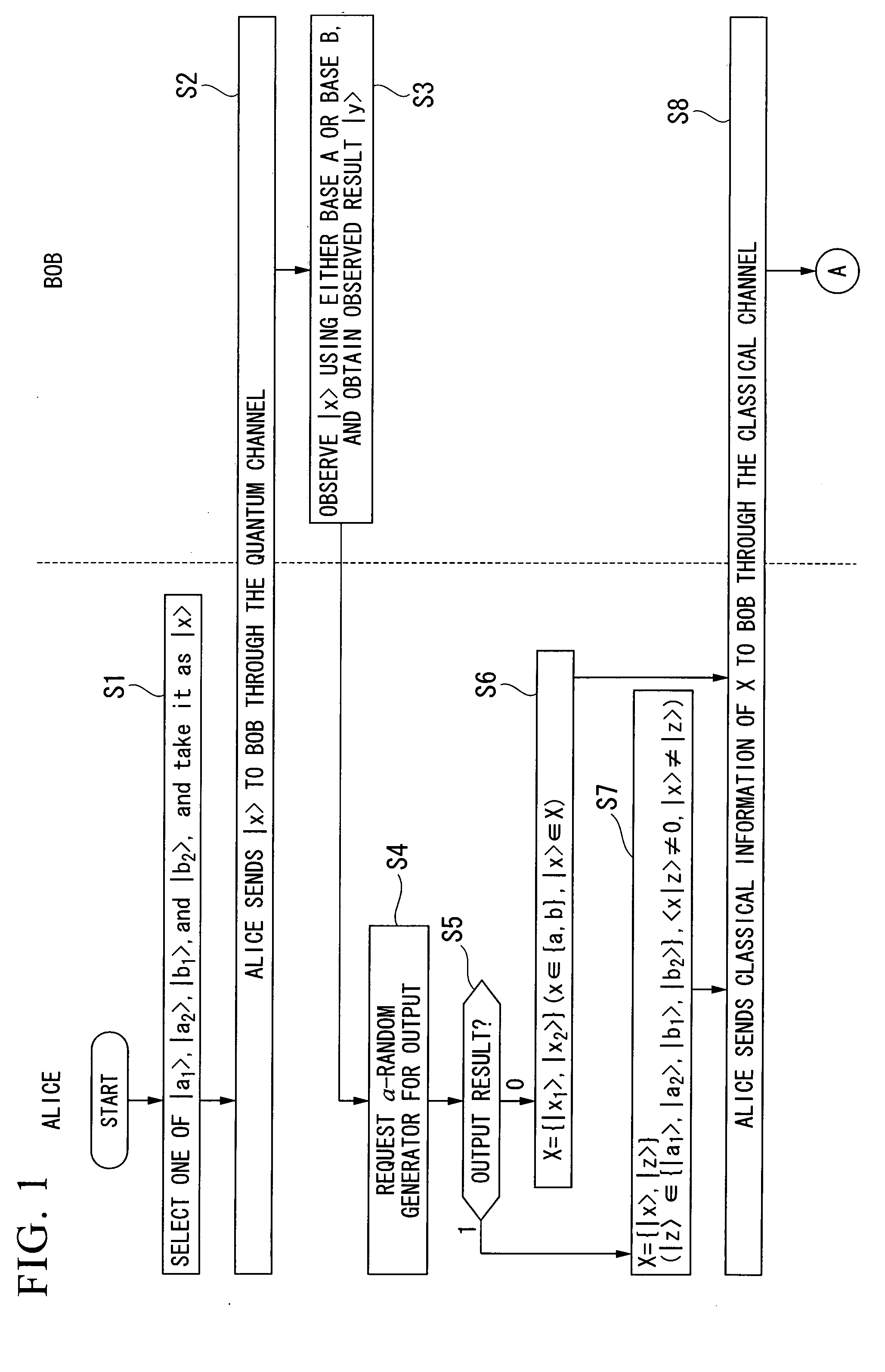
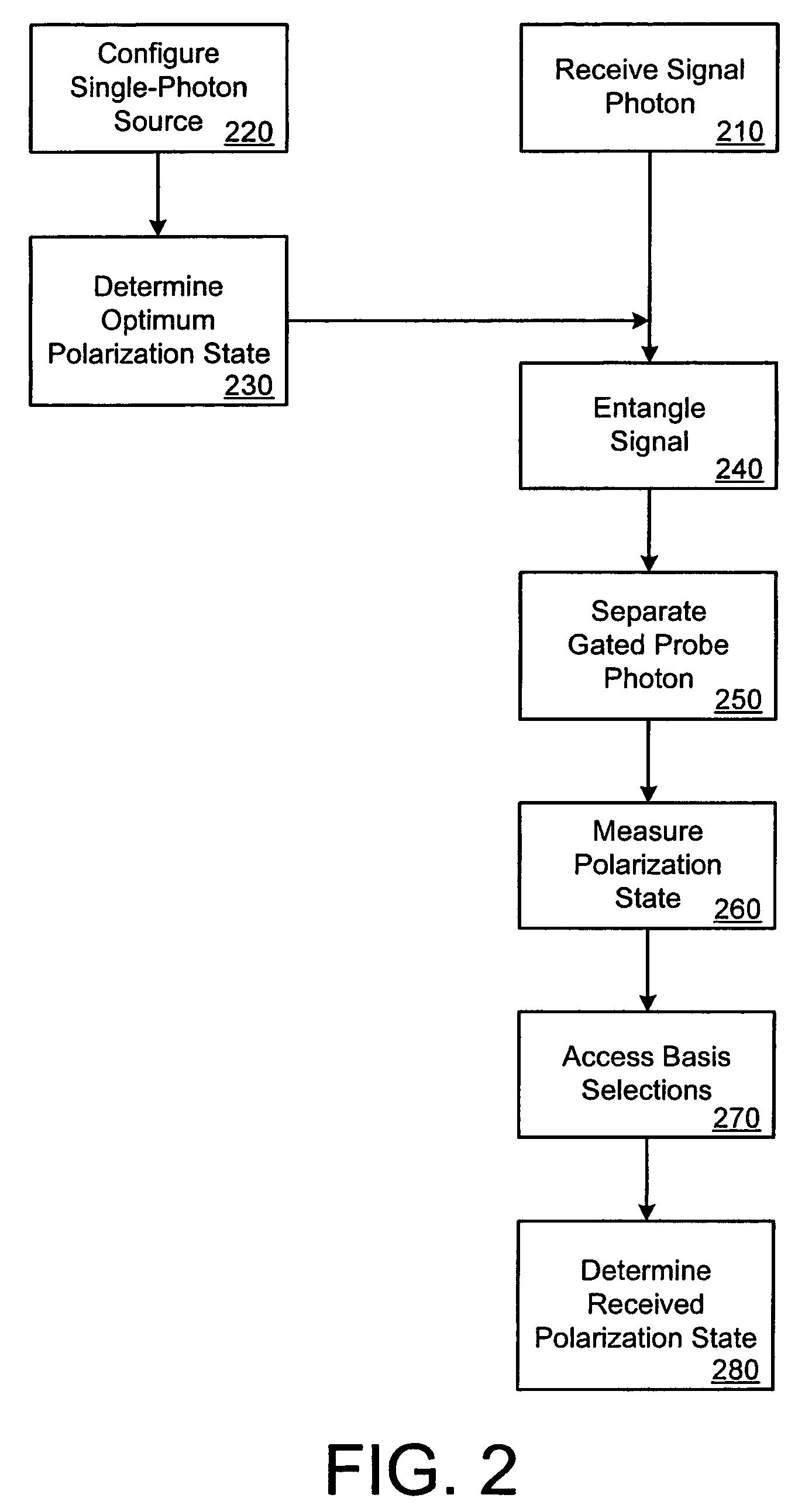
Systems and methods for obtaining information on a key in BB84 protocol of quantum key distribution
InactiveUS7920704B2Key distribution for secure communicationRadiation pyrometryWollaston prismPhotodetector
Systems and methods for obtaining information on a key in the BB84 (Bennett-Brassard 1984) protocol of quantum key distribution are provided. A representative system comprises a quantum cryptographic entangling probe, comprising a single-photon source configured to produce a probe photon, a polarization filter configured to determine an initial probe photon polarization state for a set error rate induced by the quantum cryptographic entangling probe, a quantum controlled-NOT (CNOT) gate configured to provide entanglement of a signal with the probe photon polarization state and produce a gated probe photon so as to obtain information on a key, a Wollaston prism configured to separate the gated probe photon with polarization correlated to a signal measured by a receiver, and two single-photon photodetectors configured to measure the polarization state of the gated probe photon.
Owner:US SEC THE ARMY THE
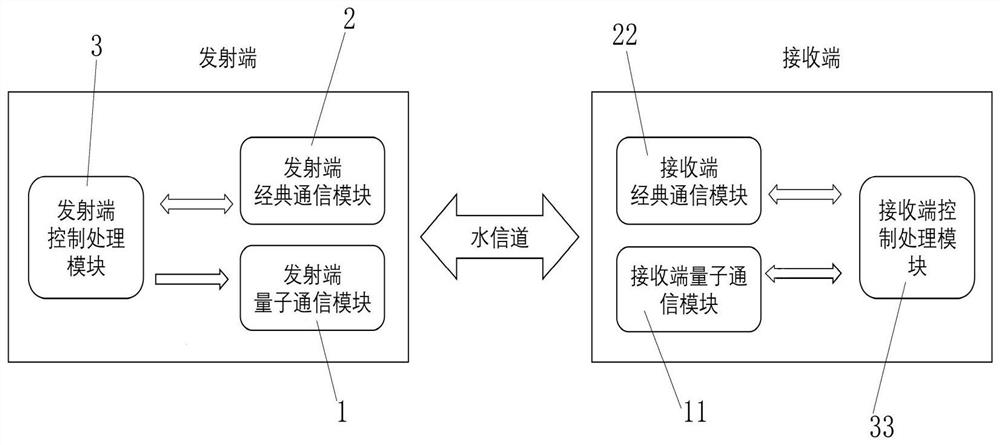
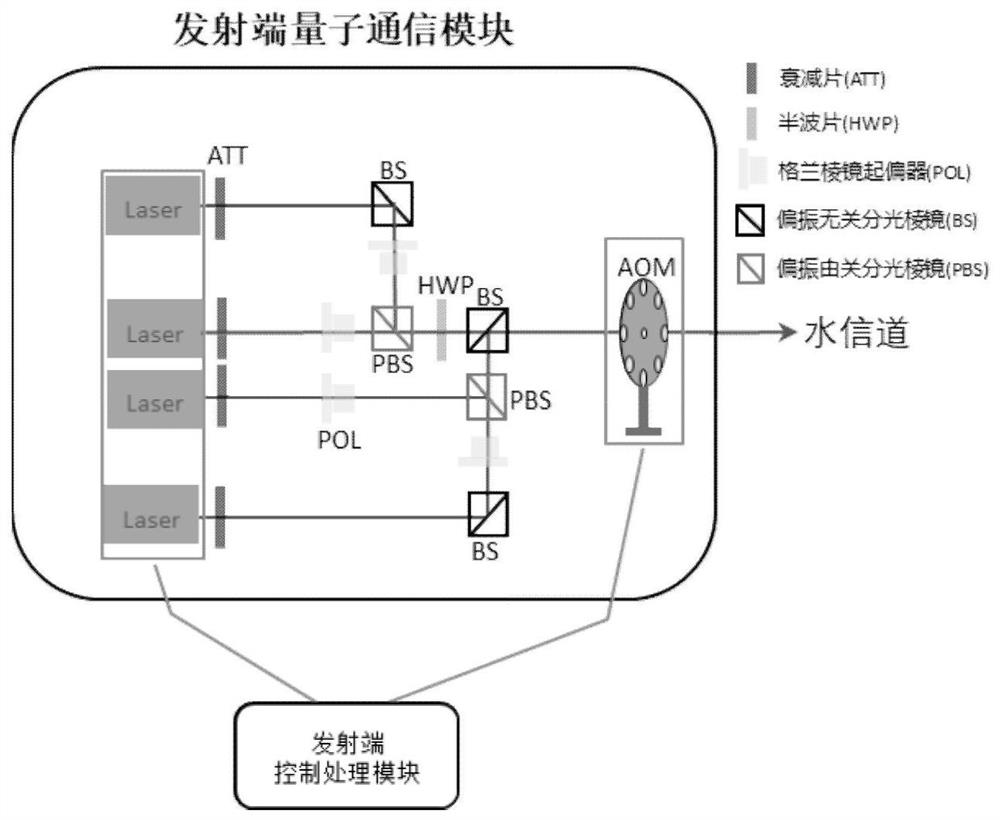
Self-adaptive multiband underwater wireless quantum key distribution system and method
PendingCN111726229AIncrease spawn rateImprove communication efficiencyKey distribution for secure communicationPhotonic quantum communicationSignal lightOptical communication
The invention discloses a self-adaptive multiband underwater wireless quantum key distribution system and method. The system comprises a transmitting end and a receiving end. Based on a BB84 communication protocol, the transmitting end and the receiving end interact with each other in real time, and generate quantum optical signals and classic optical signals with different wavelengths through theadjustable optical module to perform underwater wireless quantum key distribution and underwater wireless classic optical communication according to the change condition of quantum bit error rate QBER caused by real-time change of a channel; based on the real-time change conditions of water channels of different water bodies or the same water body water channel, the signal light wavelength can beautomatically adjusted, the change of the water channel is adapted in real time, the bit error rate is reduced, and finally the maximum key generation rate of the underwater wireless quantum key distribution system under the current channel is achieved.
Owner:OCEAN UNIV OF CHINA
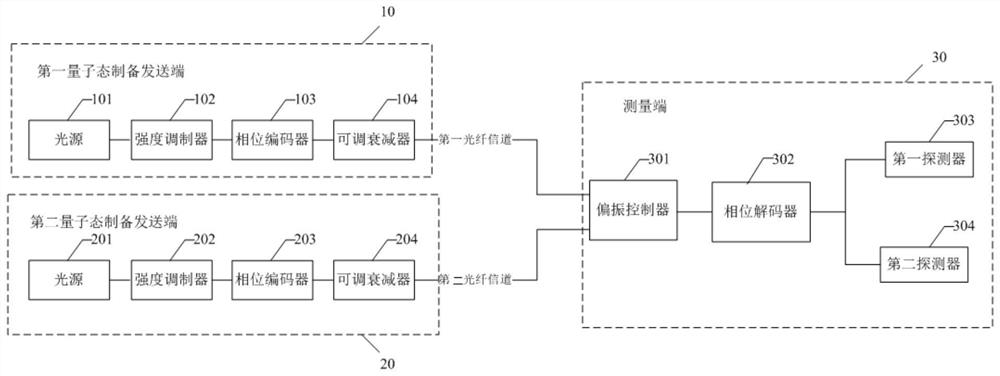
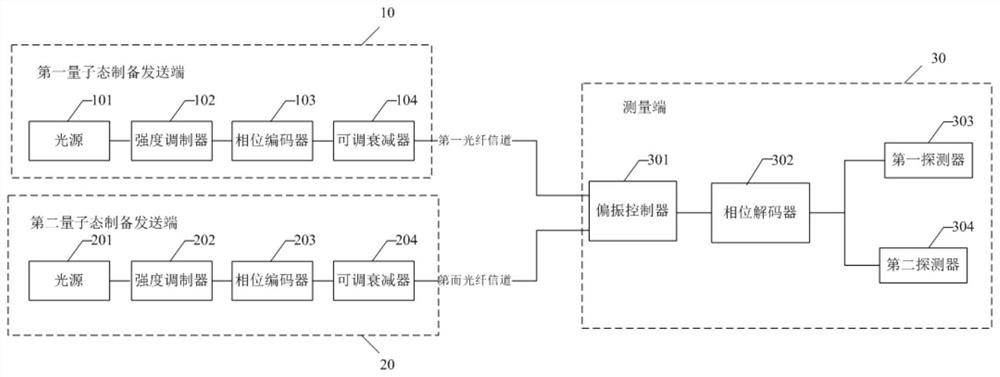
A quantum key distribution networking system and quantum key distribution method
ActiveCN113438077BImprove compatibilityImprove practicalityKey distribution for secure communicationPhotonic quantum communicationPhase differenceEngineering
The invention discloses a quantum key distribution networking system and a quantum key distribution method. The system comprises: a first quantum state preparation sending end, a second quantum state preparation sending end and a measuring end, and the quantum state preparation includes: a light source , an intensity modulator, a phase encoder and an adjustable attenuator; the phase encoder is used to modulate each optical pulse according to the target phase encoding mode, so that each optical pulse is divided into two pulses with a target delay, and modulated The phase difference of the two pulses; the phase decoder in the measurement end is used to modulate the phase difference of the two pulses; the polarization controller modulates the polarization state of the light quantum input by the first fiber channel when executing the first target protocol mode. The phase difference between the two pulses is modulated by the phase decoder, which eliminates the difference between the MDI protocol and the BB84 protocol in encoding and detection, realizes the compatibility of the MDI protocol and the BB84 protocol in the same system, and improves the quantum key distribution. usability of the network.
Owner:UNIV OF SCI & TECH OF CHINA
Quantum key distribution device capable of being configured with multiple protocols
ActiveUS20220247557A1Maintain stabilityExtra componentQuantum computersKey distribution for secure communicationInterference (communication)Particle physics
The present invention relates to the field of quantum communication, especially a quantum key distribution device that can be configured with multiple protocols. It uses the simplified Faraday-Michelson interference ring in combination with the intensity modulator to perform timestamp encoding in a chopping manner. The phase modulation is completed with a Sagnac ring device composed of a single-polarization phase modulator, a polarization beam splitter and a Faraday rotator, so as to achieve the purpose of composite encoding and decoding, thus realizing a quantum key distribution device which can be configured with multiple protocols and multiple decoy state schemes. This device can be compatible with multiple protocols including BB84 protocol, the reference frame-independent protocol, the six-state protocol and SARG protocol and is characterized with polarization-independent phase modulation and low system complexity.
Owner:NANJING UNIV OF POSTS & TELECOMM
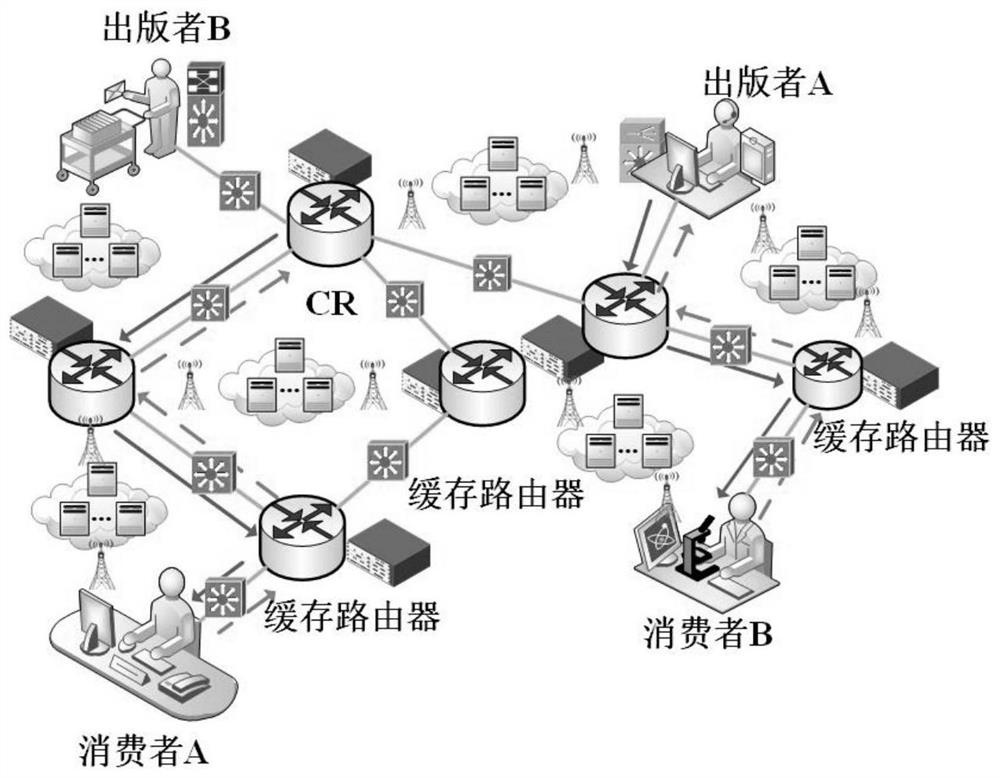
Quantum-based content centric network privacy protection method
ActiveCN113346996ATroubleshoot secure distribution issuesWith absolute privacyKey distribution for secure communicationCiphertextConfidentiality
The invention provides a quantum-based content centric network privacy protection method, which comprises the following steps of: encrypting and aggregating a classical ciphertext by using an ELGamal algorithm: generating a main public key according to public and private key pairs generated by all participants, generating a ciphertext according to plaintext information of the participants, sending the ciphertext to a cloud server, aggregating according to the ciphertext to obtain an aggregated ciphertext, and generating a classic message to be shared according to the aggregated ciphertext; in the quantum encryption stage, in all interaction processes with the cloud server, enabling a data owner to convert classic information into quantum information and negotiate a shared key with the cloud server through a BB84 key negotiation protocol, wherein each data person encrypts the quantum information by using the shared key; and detecting the eavesdropping behavior through adoption of a method of randomly inserting the decoy particles, so that the safety has double assurance. According to the method, confidentiality of sensitive content exchange between a publisher and a user is guaranteed, the method can be effectively executed under the condition that any privacy information is not leaked, and the content can be safely shared and aggregated.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
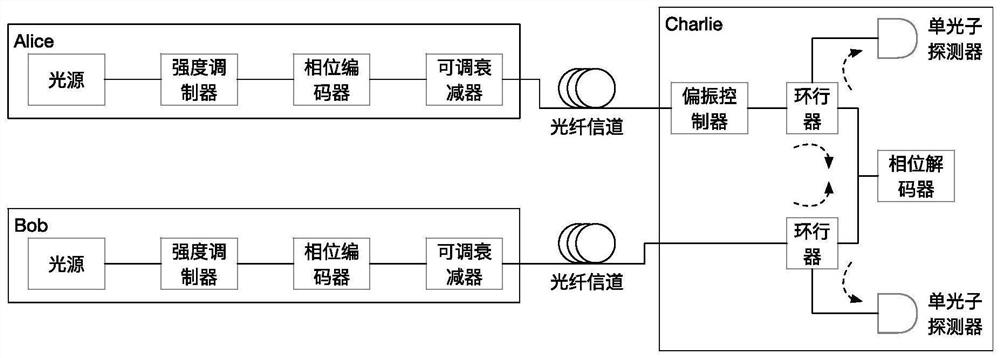
Sending end for realizing encoding of six polarization states, encoding method and quantum communication system
ActiveCN111585747AKey distribution for secure communicationPhotonic quantum communicationCommunications systemSoftware engineering
The invention discloses a sending end for realizing encoding of six polarization states, a coding method and a quantum communication system. The present invention relates to the sending terminal for the quantum communication system, an encoding method, and the quantum communication system, which enable encoding of four polarization states, such as H and V, commonly used in the preparation of a BB84 protocol to be achieved with a minimum number of optical elements and in a most stable manner, and also enable encoding of two other polarization states, such as H and V, to be prepared.
Owner:QUANTUMCTEK +1
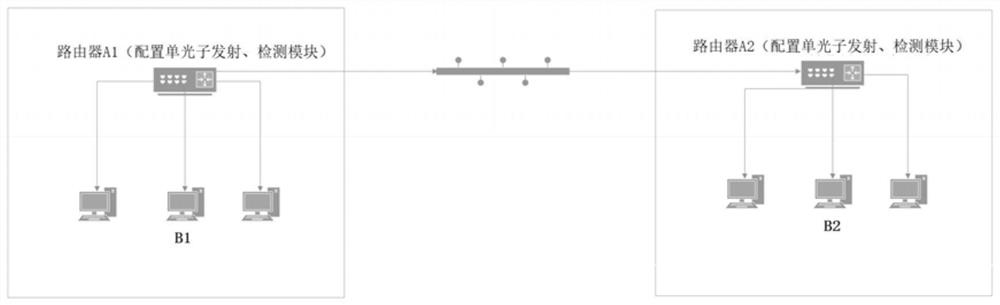
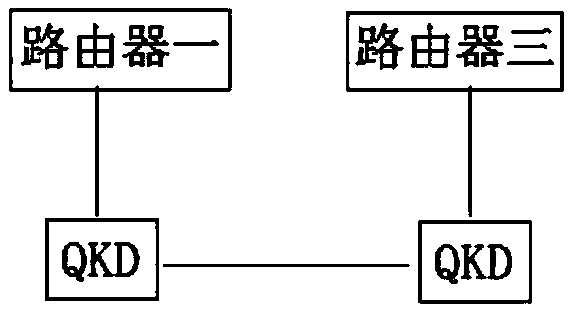
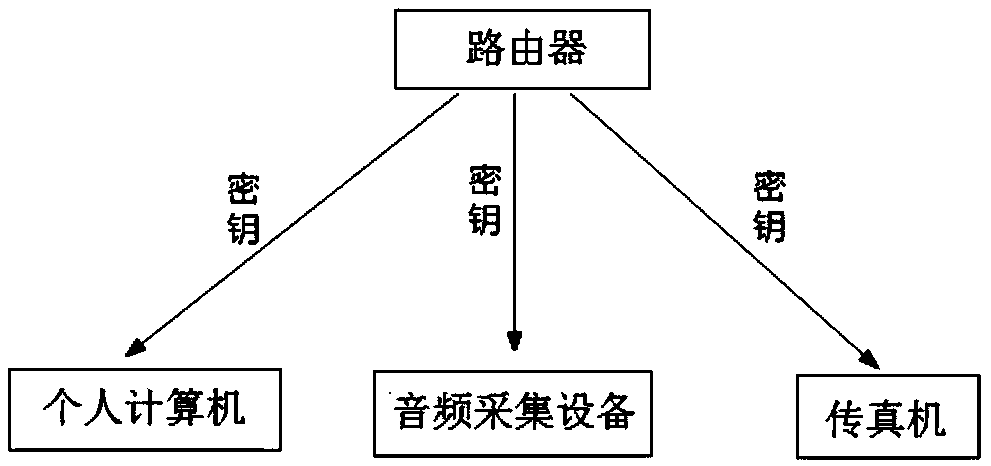
Router-based local area network terminal quantum communication method and system
ActiveCN111934785AImprove communication securityLow costKey distribution for secure communicationPhotonic quantum communicationCommunications securityTrunking
The invention provides a router-based local area network terminal quantum communication method and system. According to the invention, the router is used as a relay of the terminal, so that two terminals which are located in different local area networks and are not provided with quantum key distribution equipment can realize BB84-based quantum communication through the router, and the communication security between mobile terminals such as mobile phones in the local area networks is greatly improved.
Owner:南京如般量子科技有限公司 +1
IPv6 network node data security transmission method
InactiveCN109302285ASecure relay pathEnsure safetyKey distribution for secure communicationShort range communication serviceIp addressCryptosystem
The invention discloses an IPv6 network node data security transmission method. The IPv6 network node data security transmission method comprises the following steps of: a network node A sends an encrypted communication request packet to a network node B according to a routing path order; the network node B performs key sharing on key data K with the network node A through a key relay path consistent with the routing path; the network node A performs combinatorial computing on the key data K, the IP address of the network node A, and the IP address of the network node B to obtain a new key K<AB>; and the network node A encrypts the data to be sent by using the new key K<AB>. The IPv6 network node data security transmission method uses the BB84 protocol to perform quantum key distribution,and the key generated by a quantum key distribution terminal is transmitted to a router, which is more secure than a traditional cryptosystem; moreover, the new key K<AB> is calculated through a combined operation mode, therefore, the key utilization and encryption security are improved; and the data security problem of the IPv6 network node can be effectively solved, and the economic loss of thesociety and an individual caused by leakage of network data is reduced.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
Quantum key distribution networking system and quantum key distribution method
ActiveCN113438077AImprove compatibilityImprove practicalityKey distribution for secure communicationPhotonic quantum communicationParticle physicsKey distribution
The invention discloses a quantum key distribution networking system and a quantum key distribution method. The system comprises a first quantum state preparation sending end, a second quantum state preparation sending end and a measurement end. The quantum state preparation comprises a light source, an intensity modulator, a phase encoder and an adjustable attenuator; the phase encoder is used for modulating each light pulse according to a target phase encoding mode, so that each light pulse is divided into two pulses with target delay, and the phase difference of the two pulses is modulated; a phase decoder in the measuring end is used for modulating the phase difference of the two pulses; and the polarization controller modulates the polarization state of the light quantum input by the first optical fiber channel when the first target protocol mode is executed. The phase difference between the two pulses is modulated through the phase decoder, so that the difference between the MDI protocol and the BB84 protocol in coding and detection is eliminated. The compatibility of the MDI protocol and the BB84 protocol in the same system is realized, and the practicability of the quantum key distribution network is improved.
Owner:UNIV OF SCI & TECH OF CHINA
Mobile communication terminal quantum communication method and system based on base station
ActiveCN111917537AImprove communication securityLow costKey distribution for secure communicationPhotonic quantum communicationCommunications securityTrunking
The invention provides a mobile communication terminal quantum communication method and system based on a base station, and the method employs the base station as a relay of a mobile communication terminal so that two mobile communication terminals which are not provided with quantum key distribution equipment to achieve quantum communication based on BB84 through the base station. According to the invention, a mobile communication scheme based on the base station is provided for different application scenes, and the communication security between mobile terminals such as a mobile phone and the like is greatly improved.
Owner:南京如般量子科技有限公司 +1
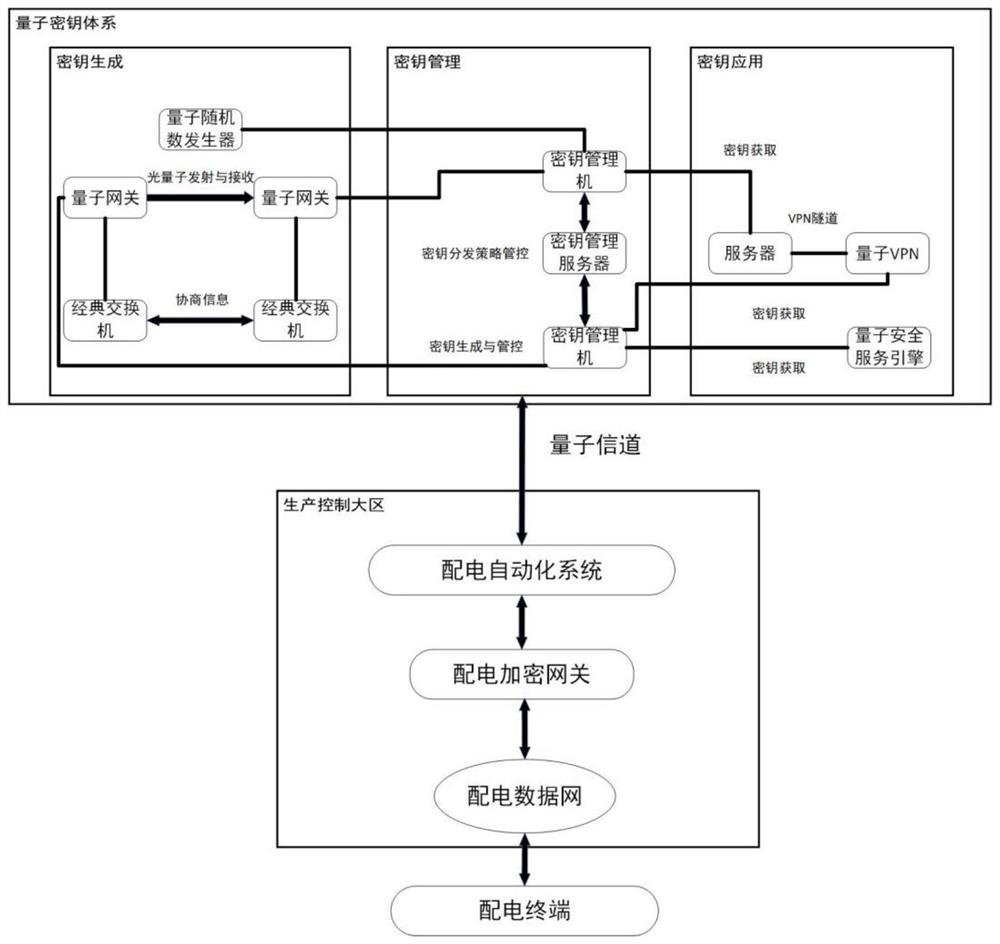
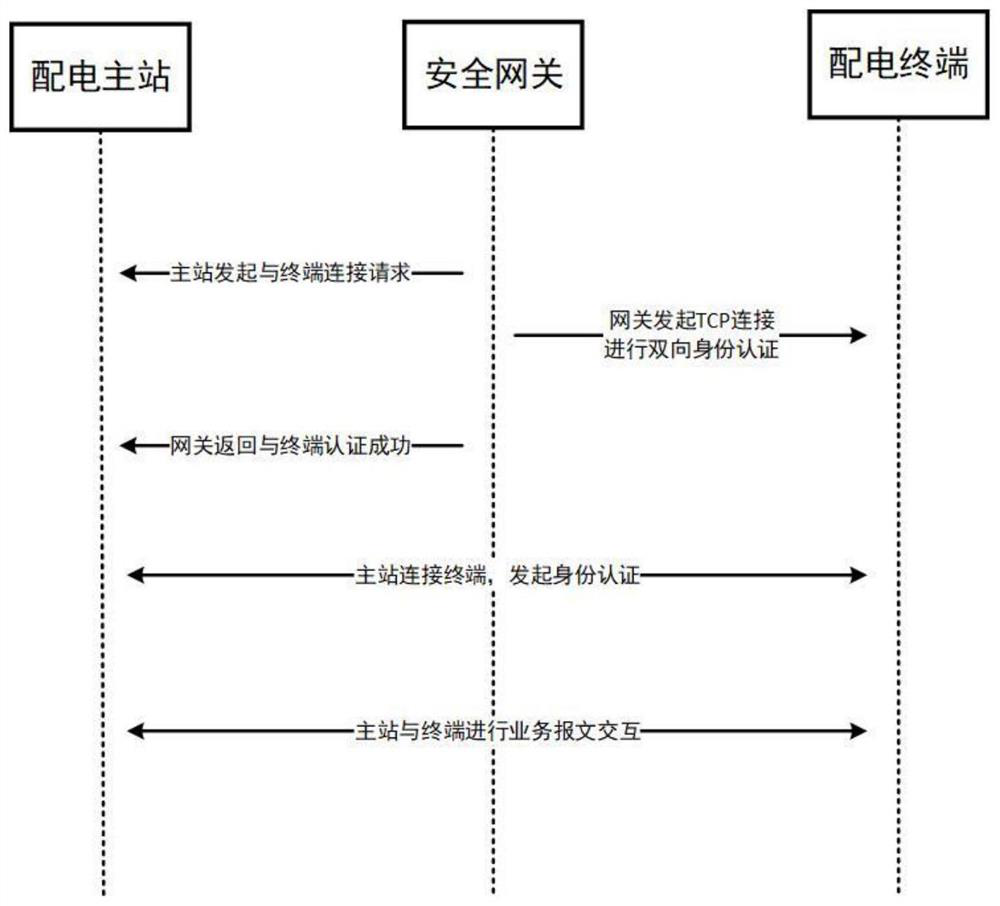
Power distribution longitudinal encryption method and system based on quantum encryption
PendingCN114553404AEnsure safetyRealize timelinessKey distribution for secure communicationMultiple keys/algorithms usageConfidentialityAttack
The invention discloses a power distribution longitudinal encryption method and system based on quantum encryption, and the method comprises the steps: generating an absolutely safe quantum key based on a BB84 principle through employing quantum characteristics; based on a bidirectional authentication technology of a digital certificate, bidirectional identity authentication between the power distribution terminal and the power distribution master station and between the power distribution terminal and the security gateway is realized, and attack forms such as terminal identity counterfeiting and replay attack are effectively prevented; and the confidentiality and integrity of service data are ensured by using a data encryption and message authentication technology based on a symmetric cryptographic algorithm.
Owner:NARI NANJING CONTROL SYST +3
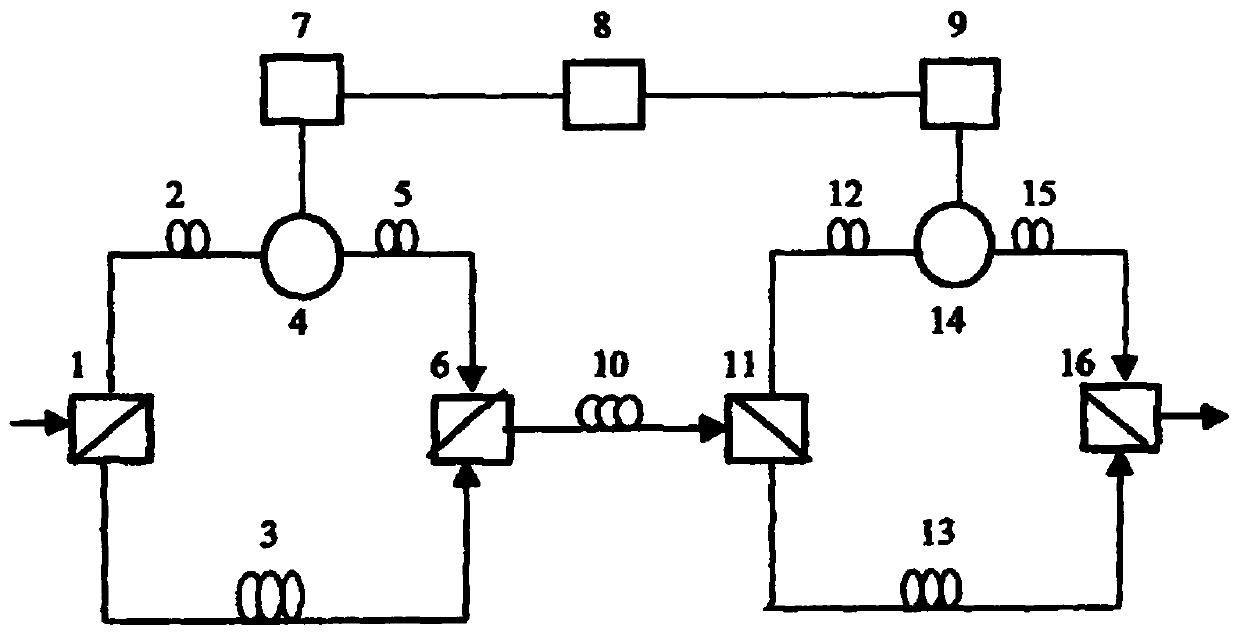
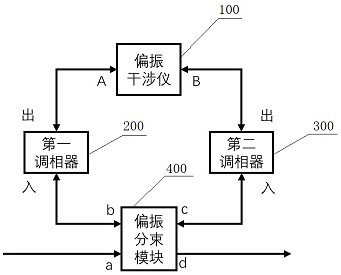
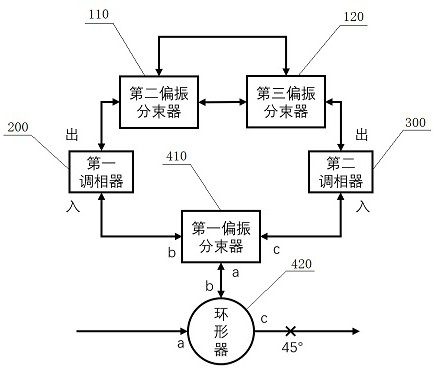
Quantum key distribution coding device
ActiveCN114465725AAchieve preparationIncrease the amount of informationKey distribution for secure communicationPhotonic quantum communicationBeam splittingErbium lasers
A quantum key distribution encoding device comprises a polarization interferometer, a first phase modulator, a second phase modulator and a polarization beam splitting module, and a port a of the polarization beam splitting module is an input port of the encoding device; a port b of the polarization beam splitting module and a port A of the polarization interferometer are respectively connected with an input port of the first phase modulator and an output port of the first phase modulator, and a port c of the polarization beam splitting module and a port B of the polarization interferometer are respectively connected with an input port of the second phase modulator and an output port of the second phase modulator to form a Sagnac ring. Compared with the prior art, six polarization states can be stably prepared, multiple lasers are not needed, safety loopholes caused by inconsistent wavelengths of the multiple lasers are eliminated, the prepared polarization states are very stable, any compensation is not needed, a receiving end only needs two single-photon detectors, and the complexity and cost of the system are reduced. In addition, the polarization coding device can be used for realizing a BB84 protocol, a 6-state protocol and a reference system independent protocol.
Owner:北京中科国光量子科技有限公司
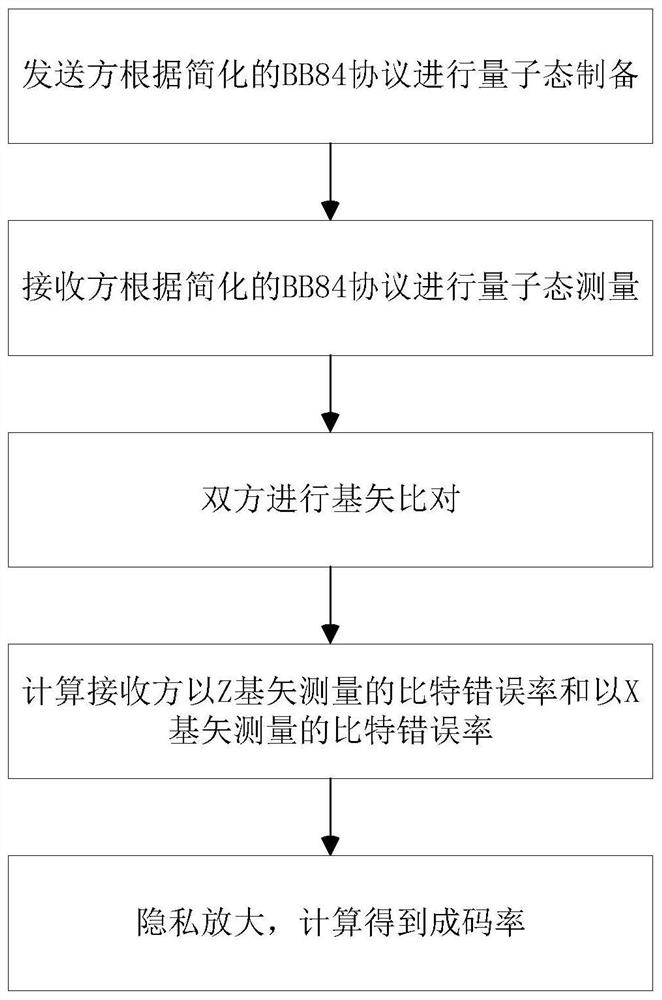
Calculation method for coding error rate of quantum key generation system
ActiveCN112929156AEstimates are tightImprove bit rateKey distribution for secure communicationCommunications systemKey generation
The invention provides a calculation method for the coding error rate of a quantum key generation system, the calculation method can be used for calculation of the coding error rate of a simplified BB84 protocol, the coding rate of a communication system is given, the calculation method does not need to depend on a basic detection efficiency condition, the estimated value of the phase error rate is more compact, and the detection efficiency is improved. And the calculation mode is relatively simple. The method mainly comprises the following steps: step 1, a sender and a receiver of quantum key distribution perform preparation, transmission and measurement of a quantum state according to a simplified BB84 protocol; step 2, the sender and the receiver carry out basis vector comparison; step 3, the sender and the receiver carry out error correction to obtain a bit error rate measured by the receiver by using the Z basis vector; step 4, calculating a phase error rate measured by the receiver by using the Z basis vector; and 5, carrying out privacy amplification on the secret key after the basis vector information is discarded to obtain a code rate.
Owner:BEIJING ZHONGCHUANGWEI NANJING QUANTUM COMM TECH CO LTD
Transmitter, encoding method and quantum communication system for realizing encoding of six polarization states
ActiveCN111585747BKey distribution for secure communicationPhotonic quantum communicationCommunications systemSoftware engineering
A sending end, an encoding method, and a quantum communication system for realizing encoding of six polarization states. The present invention relates to a sending end, an encoding method, and a quantum communication system for a quantum communication system, which can use the fewest optical elements and the most A stable way to realize the four polarization state codes commonly used in the preparation of the BB84 protocol, such as H, V, and other two polarization state codes, such as
Owner:QUANTUMCTEK +1
Polarization state ambiguity resolution method when evolutionary reconstruction is incomplete
ActiveCN108173647BEliminate the ambiguity of polarization state evolutionKey distribution for secure communicationPhotonic quantum communicationState predictionComputational physics
A polarization state ambiguity elimination method when the evolution reconstruction is incomplete. When the quantum key distribution system is implemented according to the protocol of BB84 using two sets of non-orthogonal bases, the method of the present invention can combine the steps of polarization compensation to eliminate from The ambiguity of the polarization state evolution reconstructed from the measurement results of quantum communication provides accurate historical data for real-time polarization state prediction and compensation.
Owner:ARMY ENG UNIV OF PLA
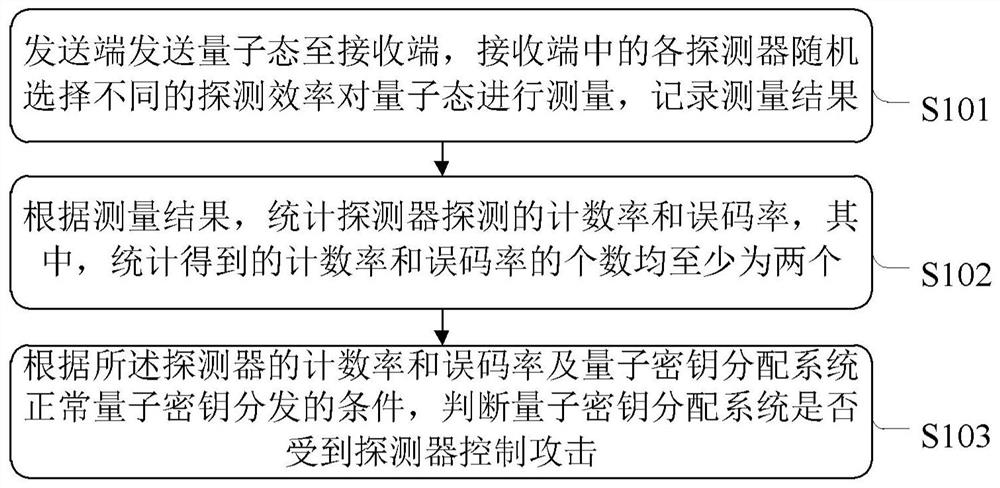
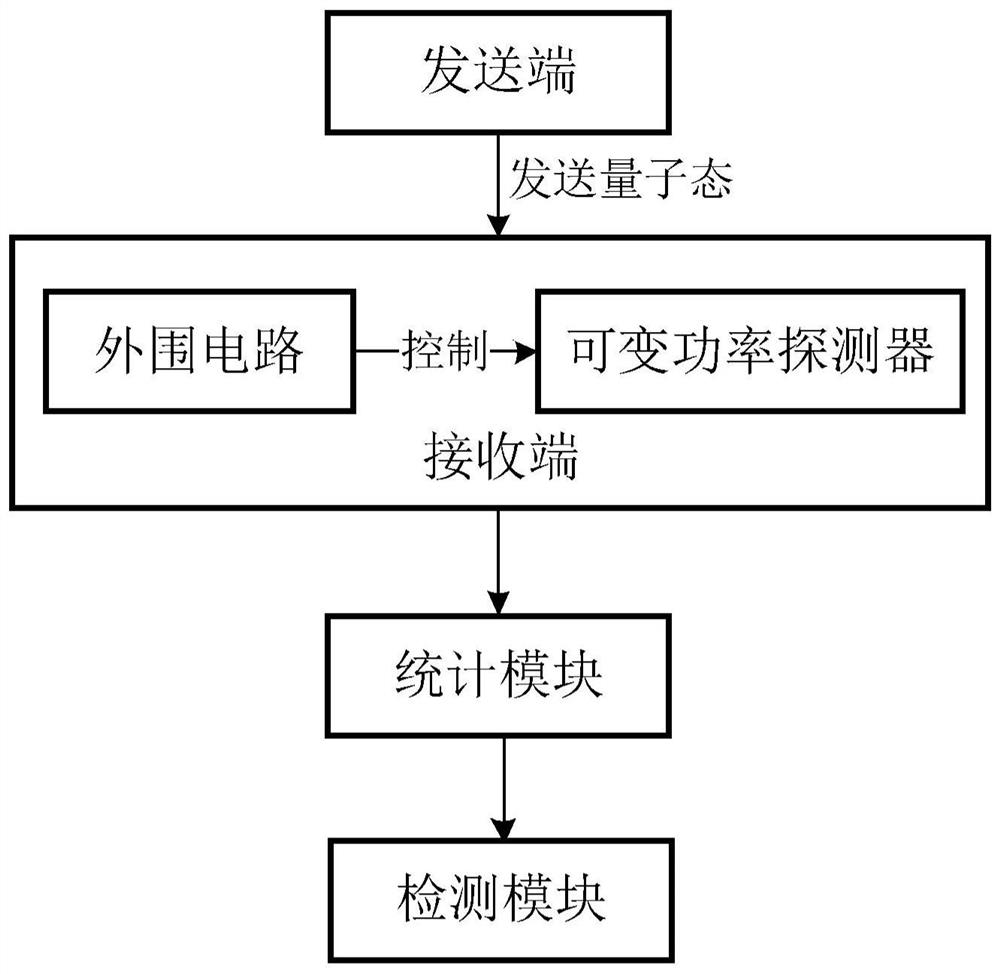
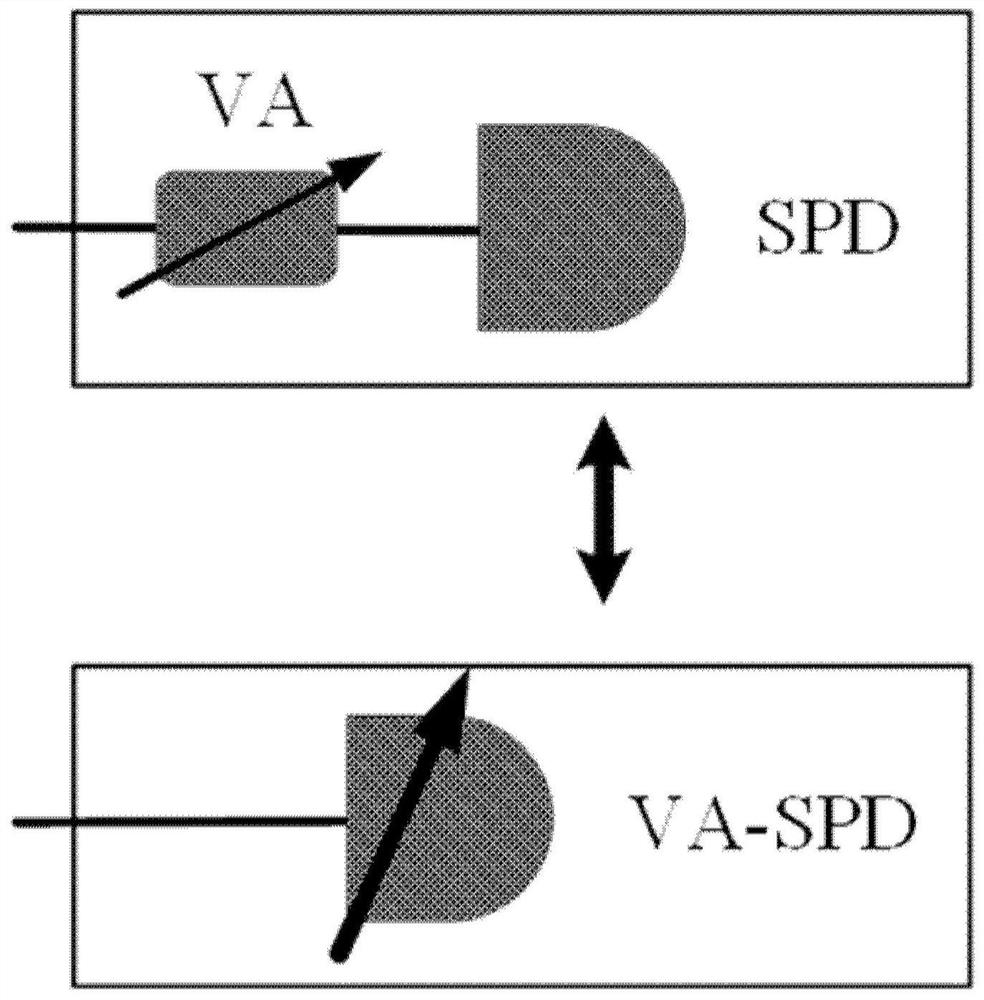
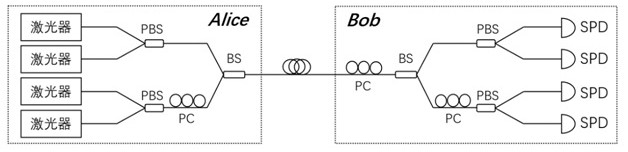
A detection method and system for a detector control attack
ActiveCN110535640BKey distribution for secure communicationPhotonic quantum communicationCounting rateEngineering
Owner:UNIV OF SCI & TECH OF CHINA
Polarization encoding device and quantum key distribution system for quantum key distribution
ActiveCN113708931BReduce complexitySolve the problem of wavelength inconsistencyKey distribution for secure communicationPhotonic quantum communicationHemt circuitsEngineering
The invention discloses a polarization encoding device for quantum key distribution, including a laser LD, an optical path selector, a 2X2 polarization encoding device and a beam combiner BC, wherein the 2X2 polarization encoding device has 2 input ports and 2 output ports , the present invention also provides a quantum key distribution system. Compared with the prior art, a polarization encoding device of the present invention adopts a 2X2 polarization encoding module, only needs one phase modulator, and modulates the phase 0 or π to prepare 4 kinds of BB84 polarization states. It can not only solve the problem of inconsistent wavelengths of multiple lasers, but also reduce the requirements on the driving circuit of the phase modulator. It not only ensures the safety of quantum state preparation, but also reduces the complexity of the encoding device.
Owner:ZHEJIANG QUANTUM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com