Patents
Literature
55 results about "Converged infrastructure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
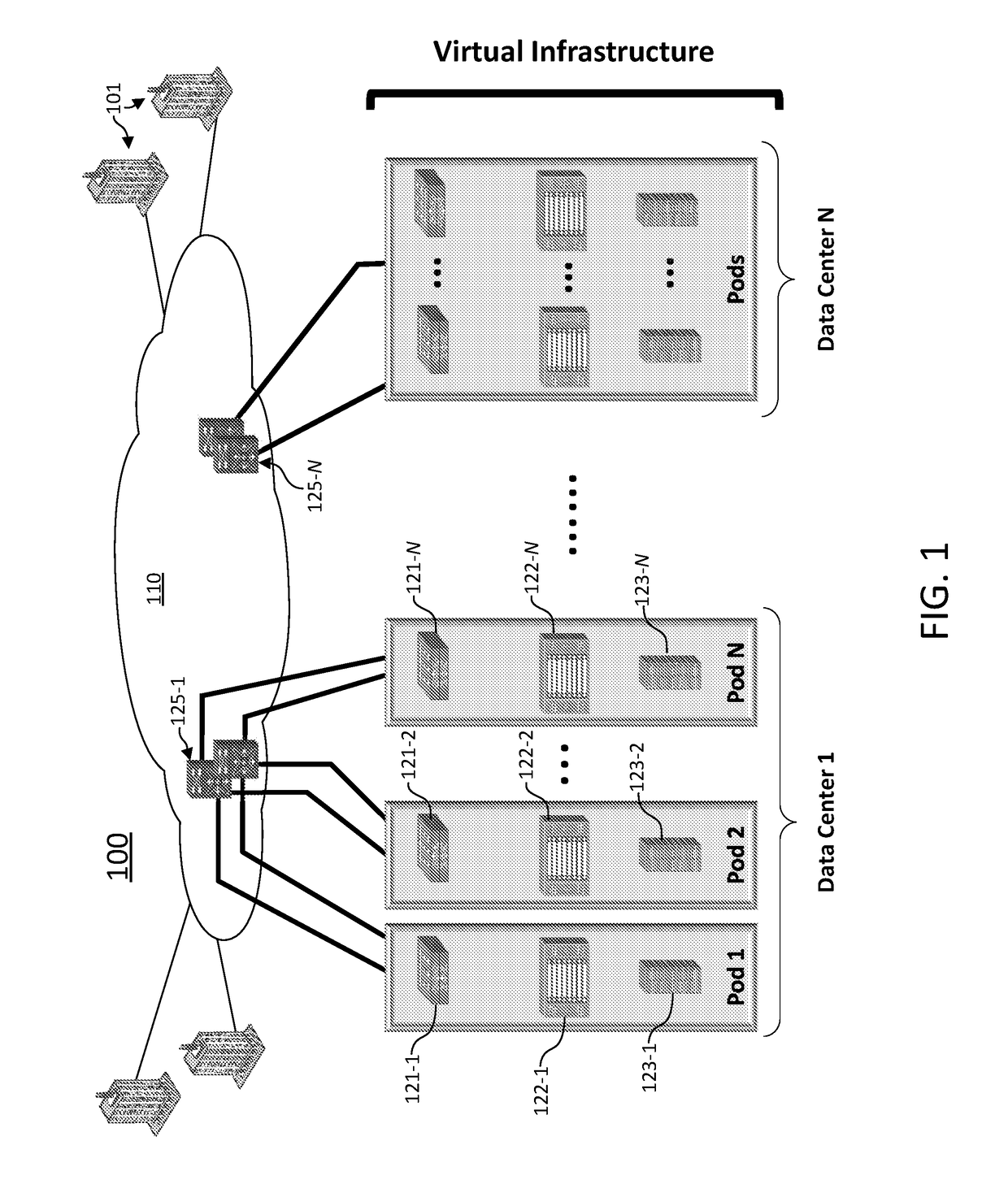
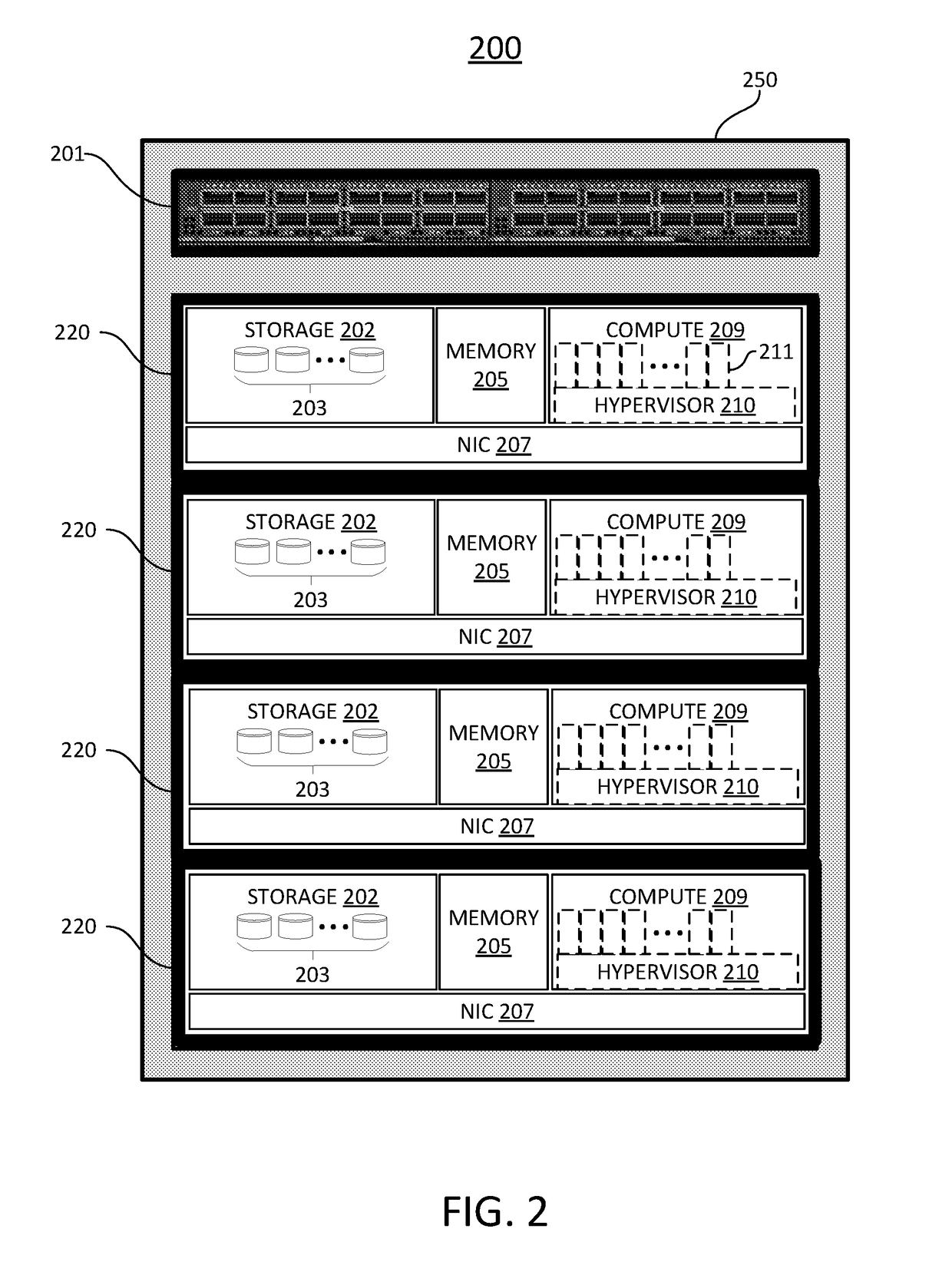
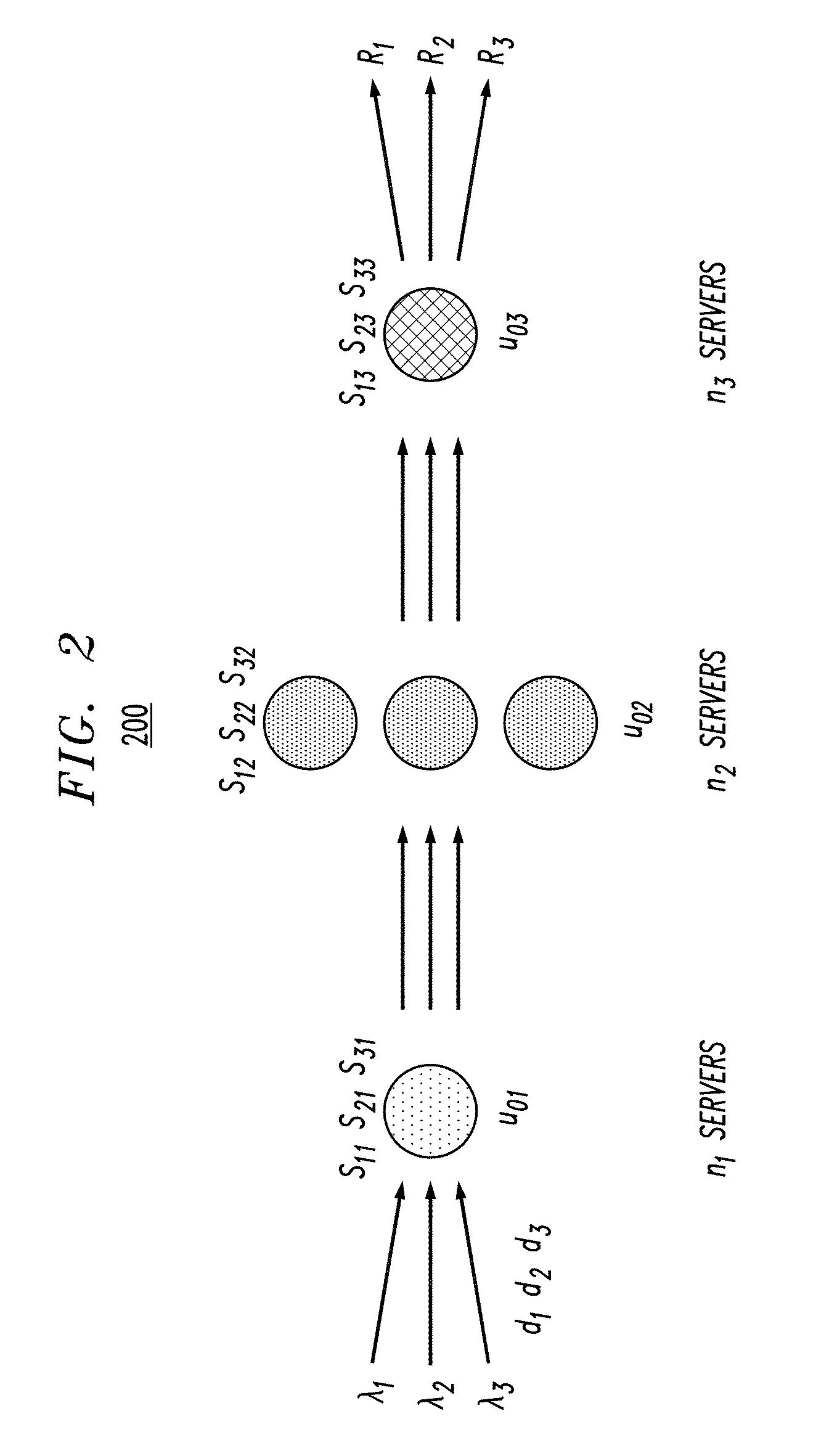
Converged infrastructure is a way of structuring an information technology (IT) system which groups multiple components into a single optimized computing package. Components of a converged infrastructure may include servers, data storage devices, networking equipment and software for IT infrastructure management, automation and orchestration.
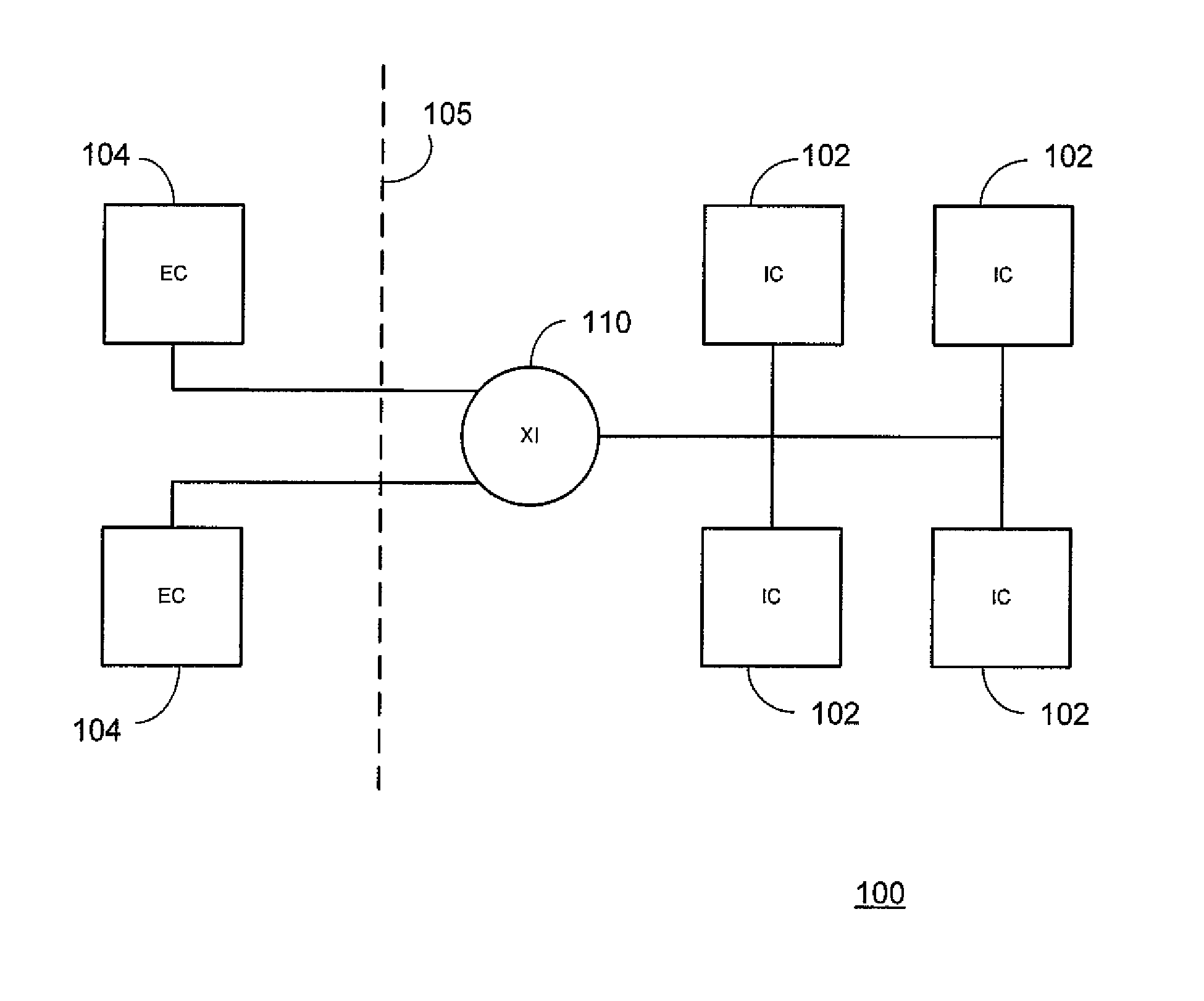
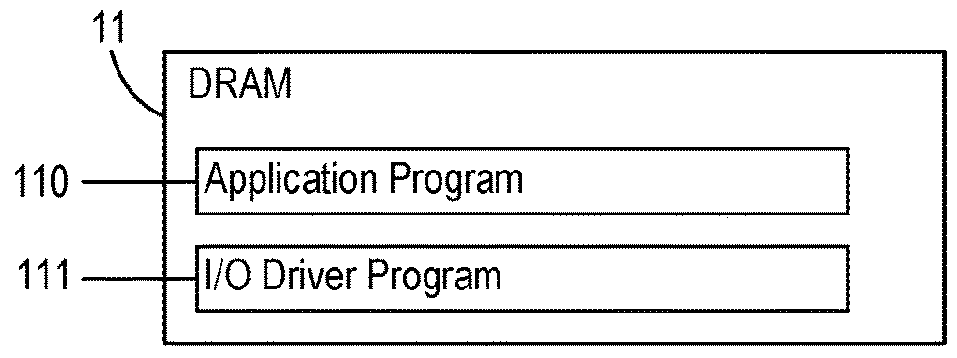
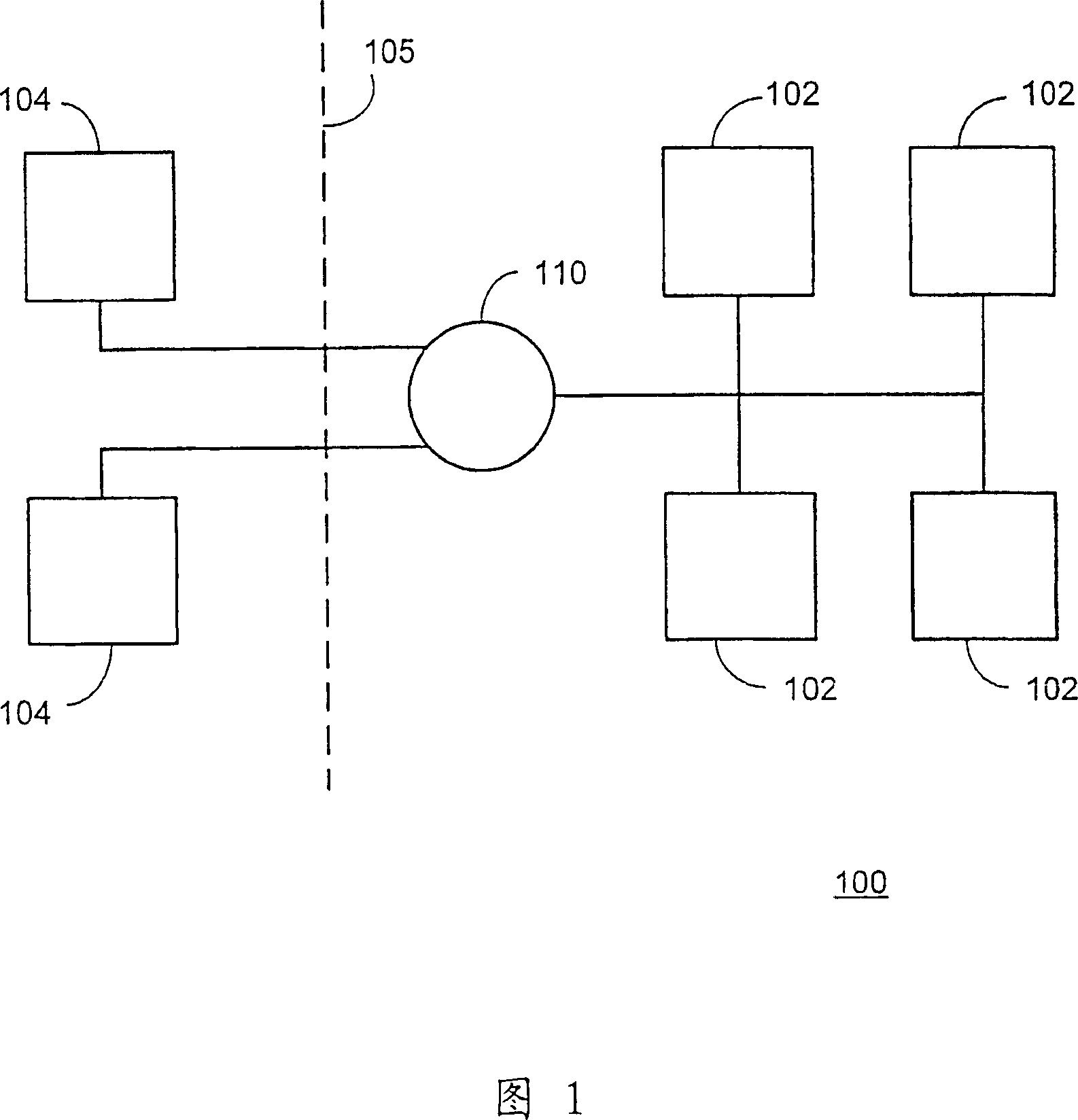
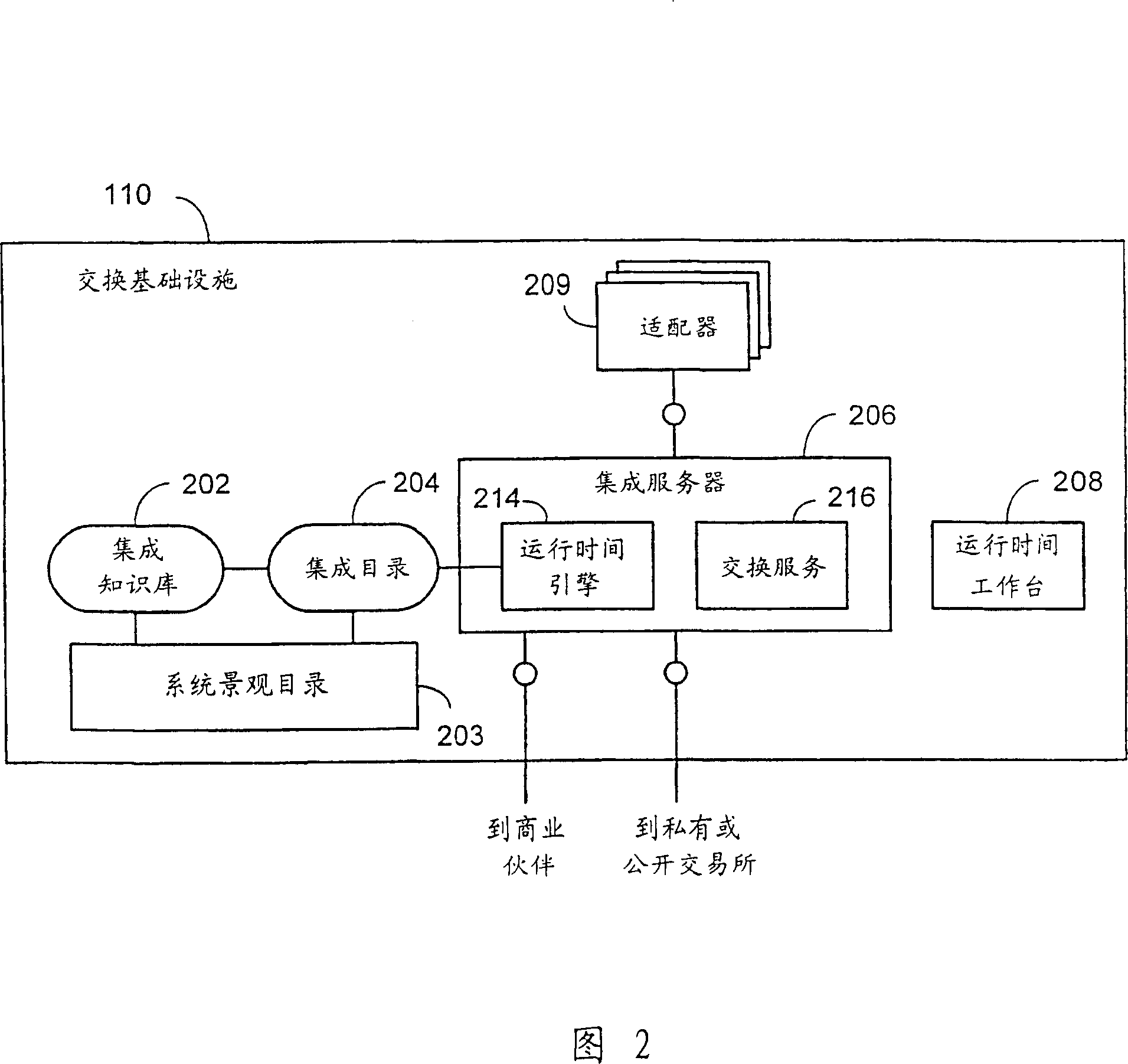
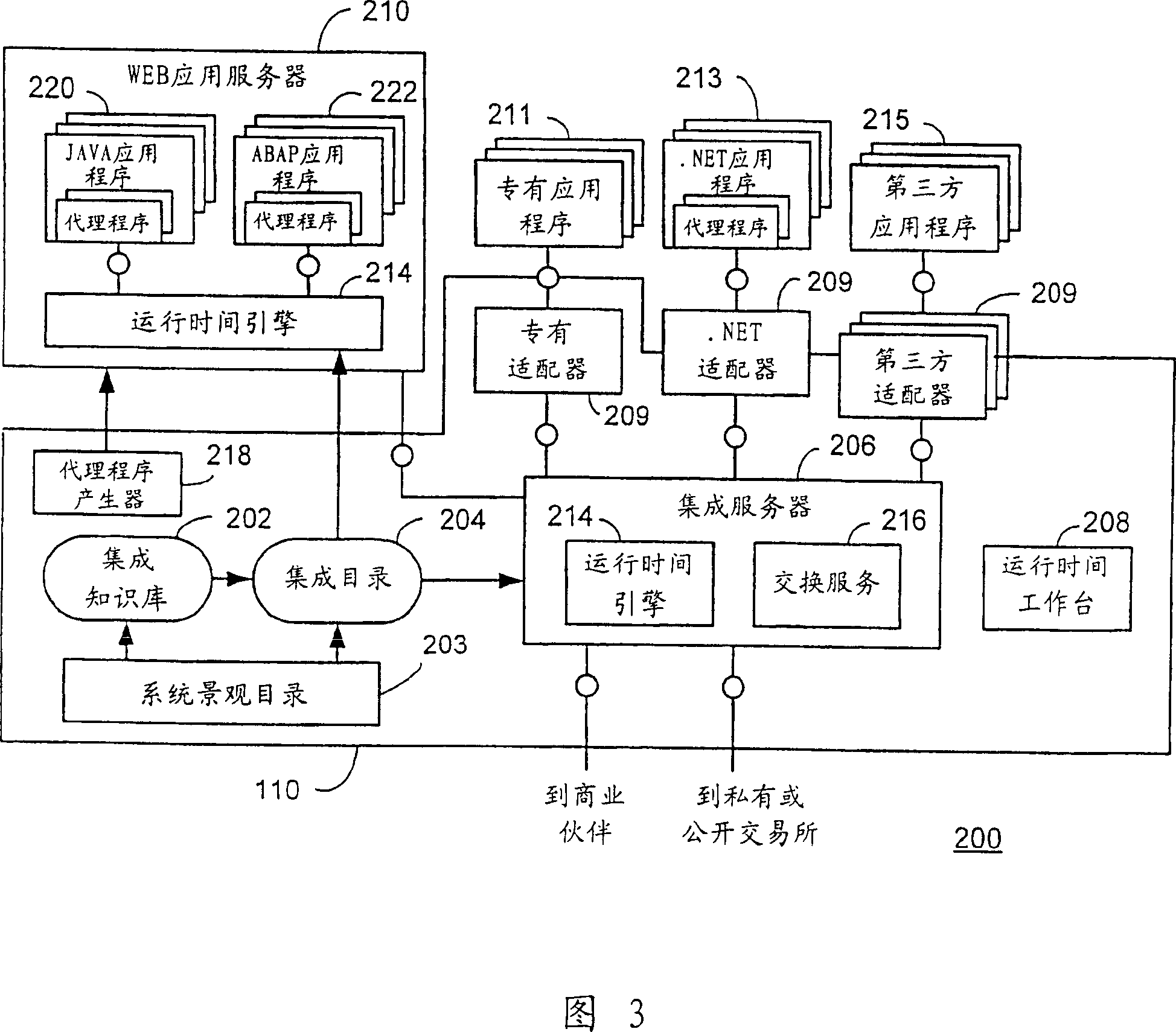
Business process management for a message-based exchange infrastructure
Methods and systems for managing integration of a heterogeneous application landscape are disclosed. The landscape is defined by one or more business process. A business process management system includes an integration server connected between two or more applications in the landscape. The integration server includes a business process engine configured to execute one or more business processes that define message-based interactions between the two or more applications. The business process management system further includes a runtime engine, under direction of the business process engine, for executing one or more messaging services on the message-based interactions between the two or more applications.
Owner:SAP AG
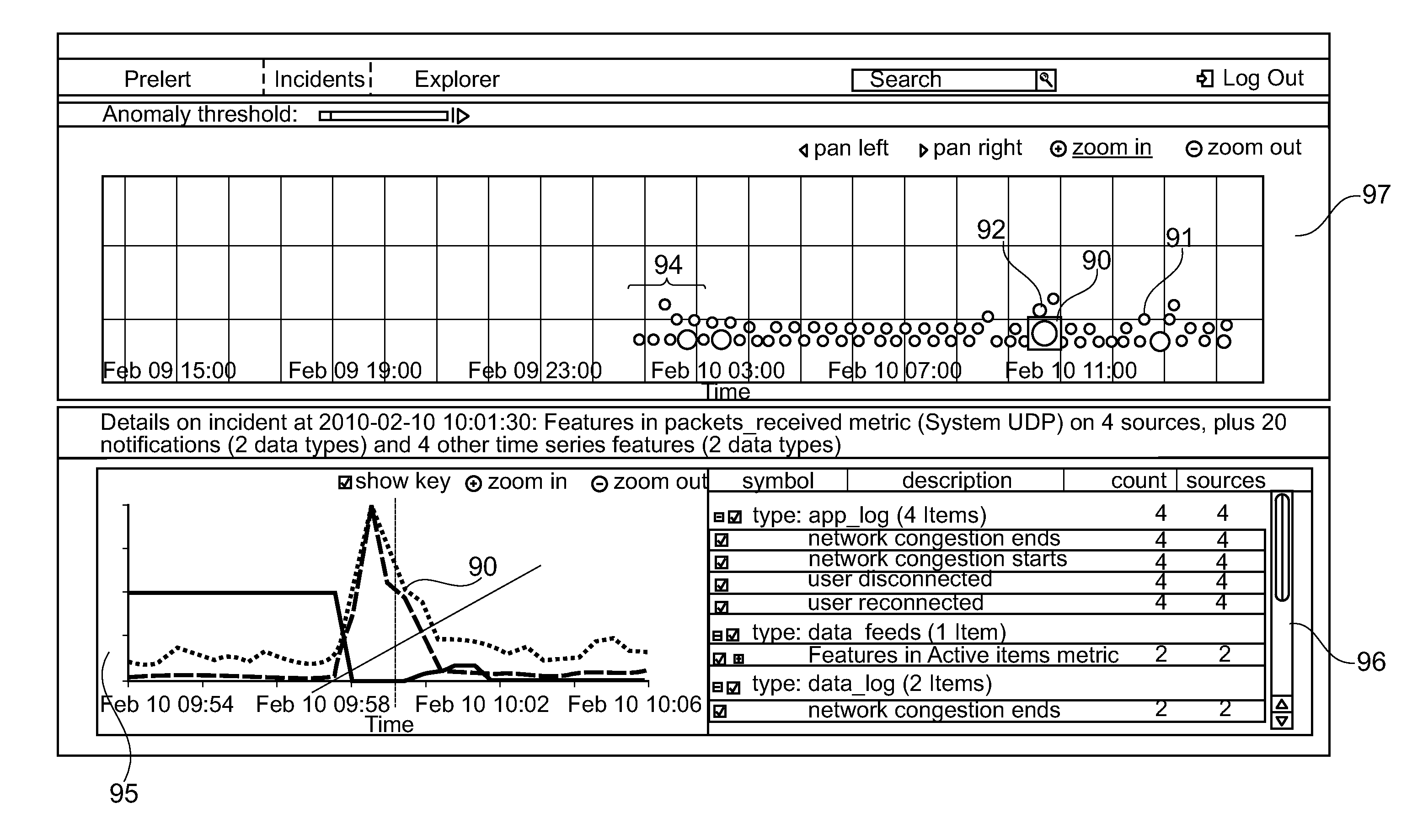
System and Method for Visualisation of Behaviour within Computer Infrastructure
ActiveUS20130262347A1Easy to detectAvoid expensive and time-consumingMathematical modelsError detection/correctionGraphicsAsynchronous data
The field of the disclosure relates generally to a method and system for analysing behaviour of a computer infrastructure and the displaying the behaviour of the computer infrastructure in a graphical manner. The system comprises an analytical engine connected to agents running on devices in the computer infrastructure and analysing continuous data and asynchronous data.
Owner:ELASTICSEARCH BV
Control infrastructure
Owner:SYSTECH CORP
Connected-media end user experience using an overlay network
ActiveUS20140195653A1Facilitate “ second screen ”Multiple digital computer combinationsTransmissionService provisionThe Internet
An Internet infrastructure delivery platform (e.g., operated by a service provider) provides an overlay network (a server infrastructure) that is used to facilitate “second screen” end user media experiences. In this approach, first media content, which is typically either live on-demand, is being rendered on a first content device (e.g., a television, Blu-Ray disk or other source). That first media content may be delivered by servers in the overlay network. One or multiple end user second content devices are then adapted to be associated with the first content source, preferably, via the overlay network, to facilitate second screen end user experiences (on the second content devices).
Owner:AKAMAI TECH INC
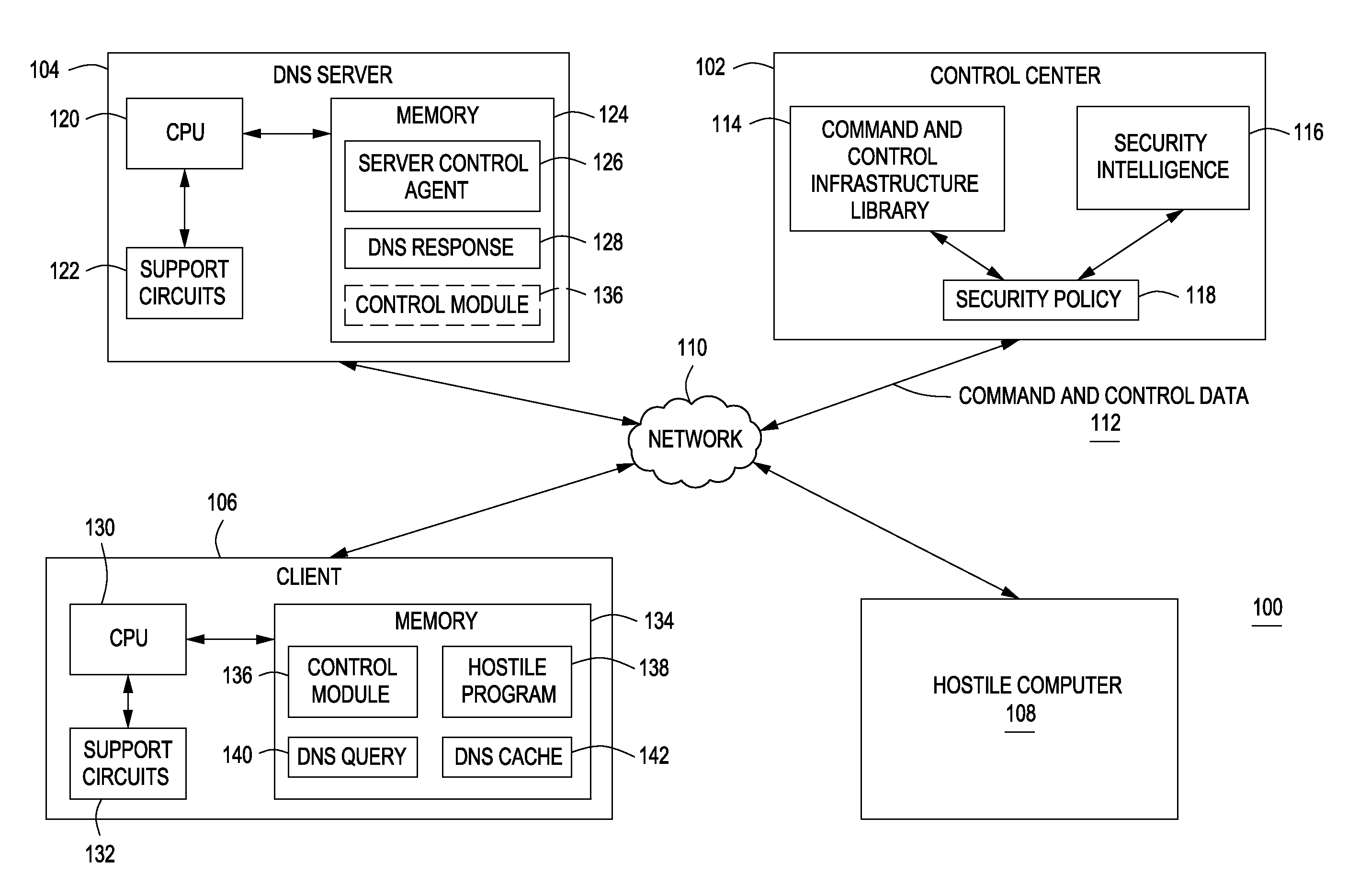
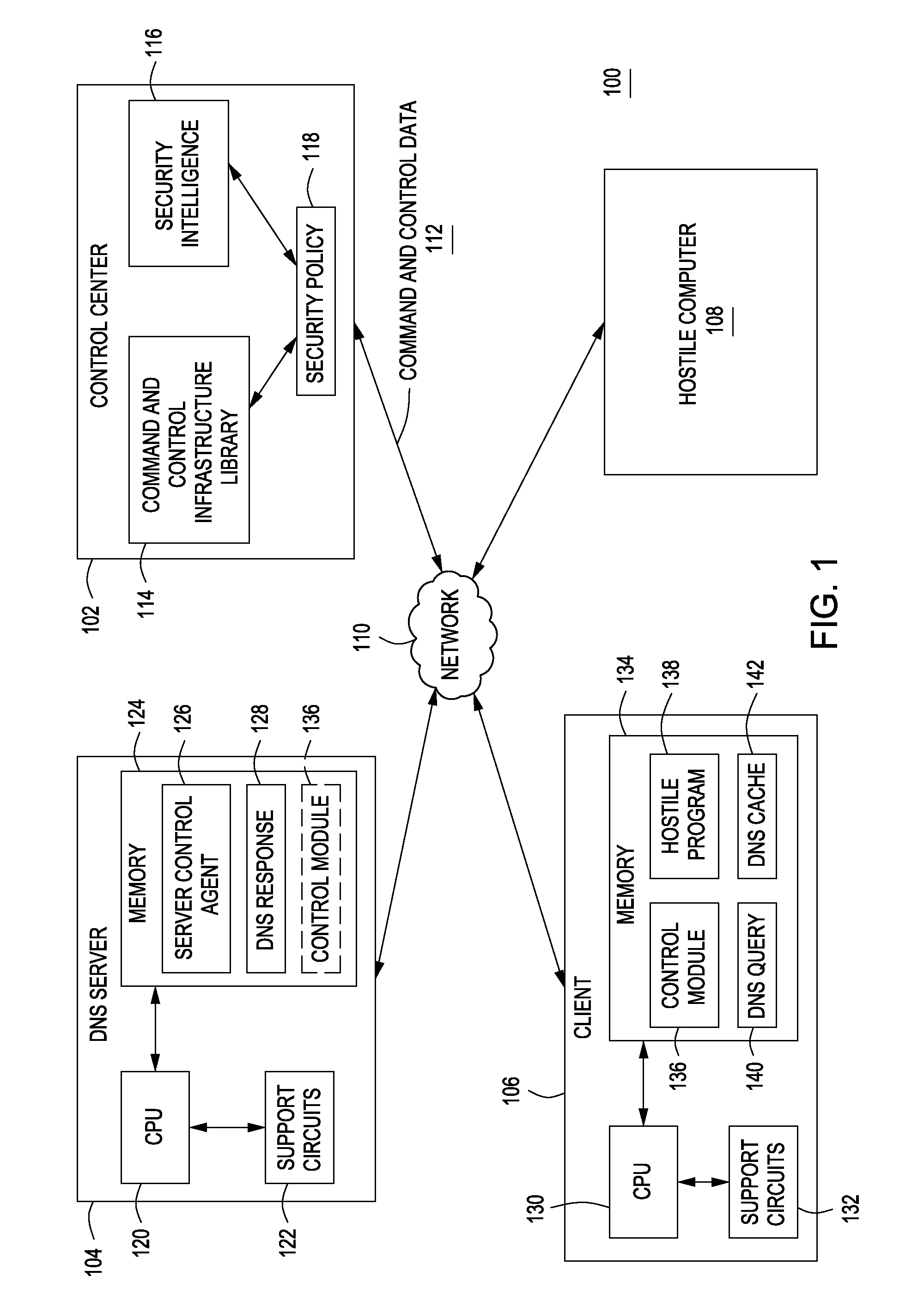
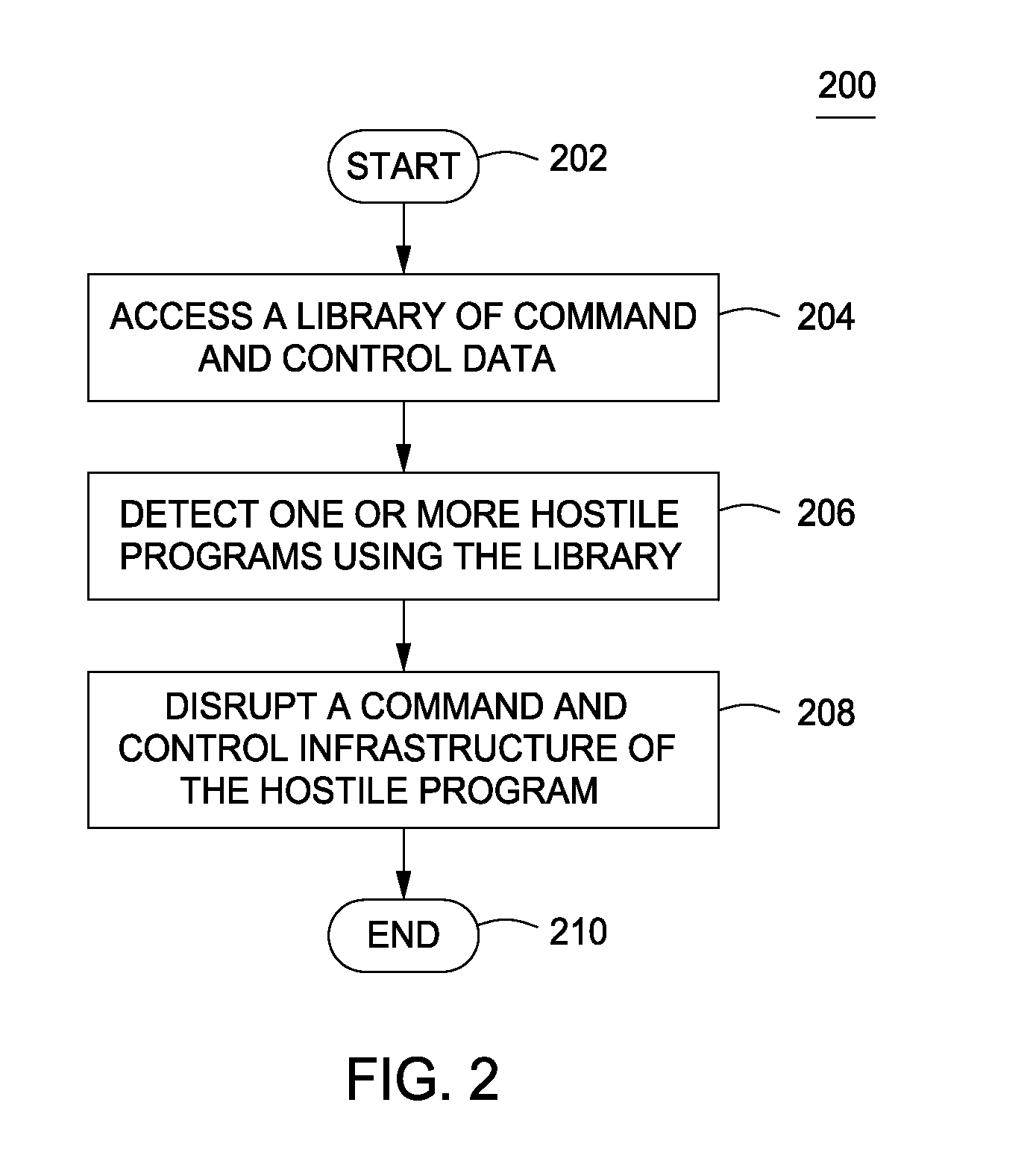
Method and apparatus for disrupting the command and control infrastructure of hostile programs
ActiveUS8869268B1Memory loss protectionError detection/correctionCommand and controlStructure of Management Information
A method and apparatus for securing a computer is described. The method and apparatus comprise detecting one or more hostile programs residing upon a computer using a command and control infrastructure library and disrupting a command and control infrastructure of the one or more hostile programs.
Owner:NORTONLIFELOCK INC
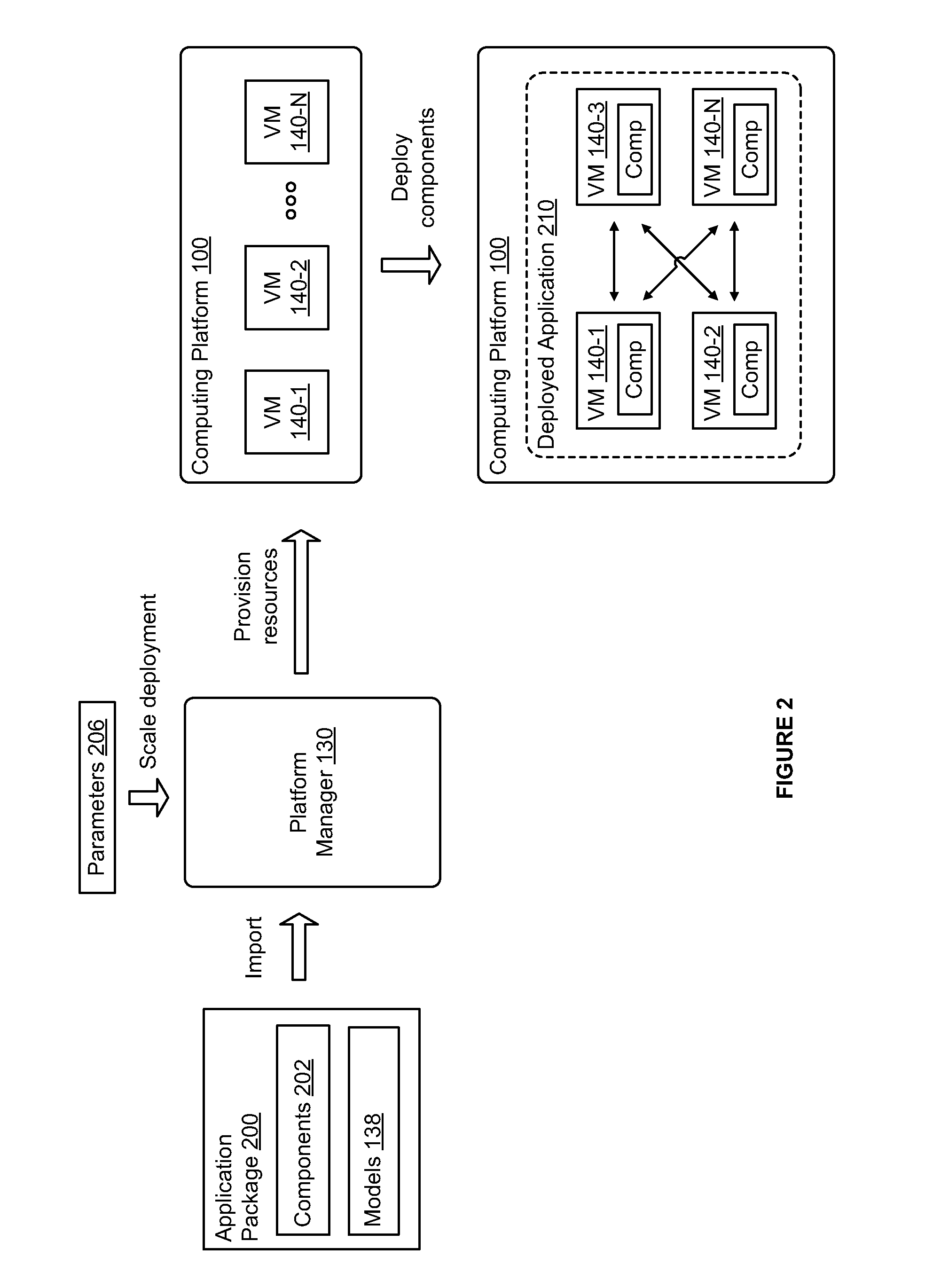
Packaged application delivery for converged infrastructure
ActiveUS20140068599A1Software simulation/interpretation/emulationMemory systemsGood practiceApplication software
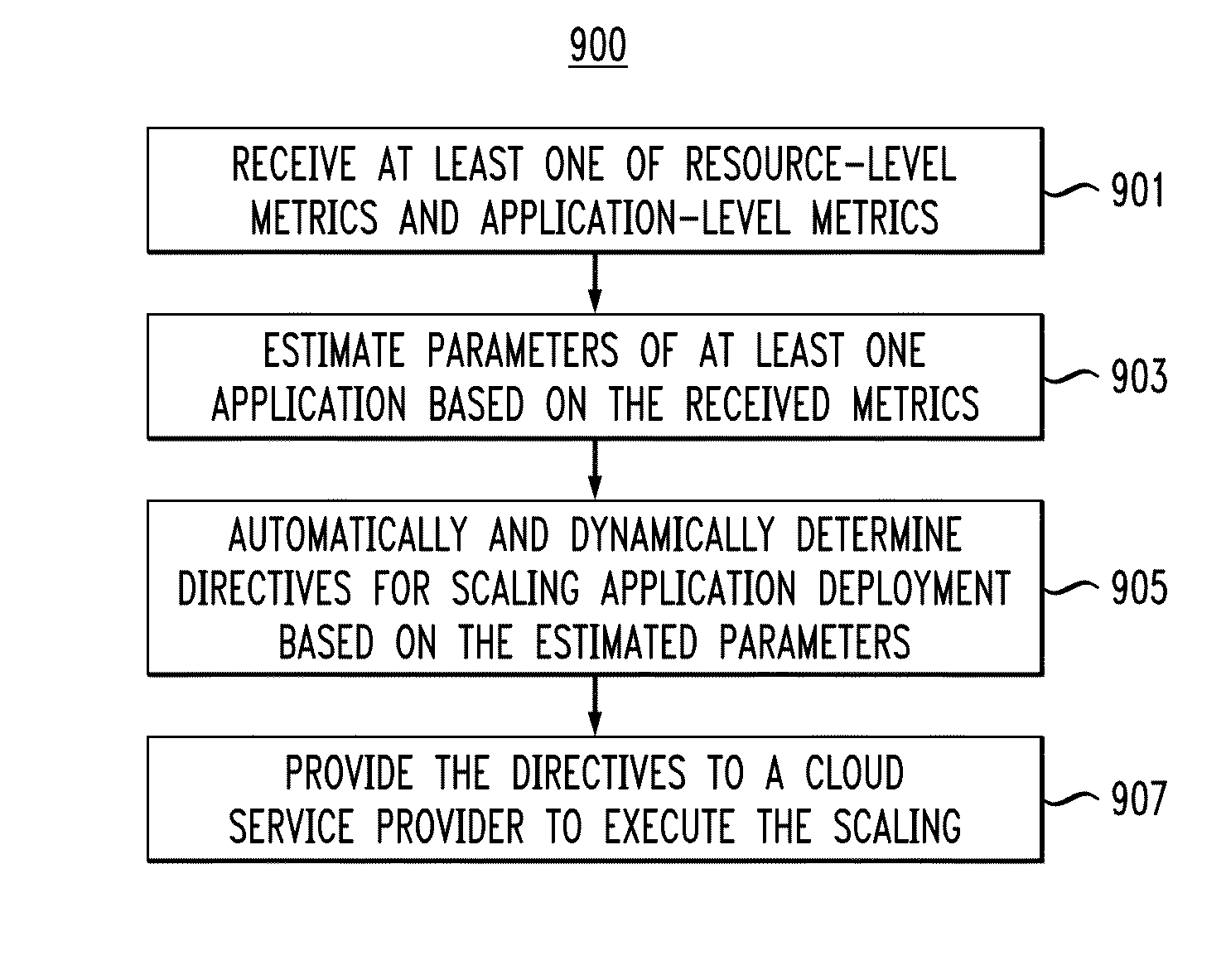
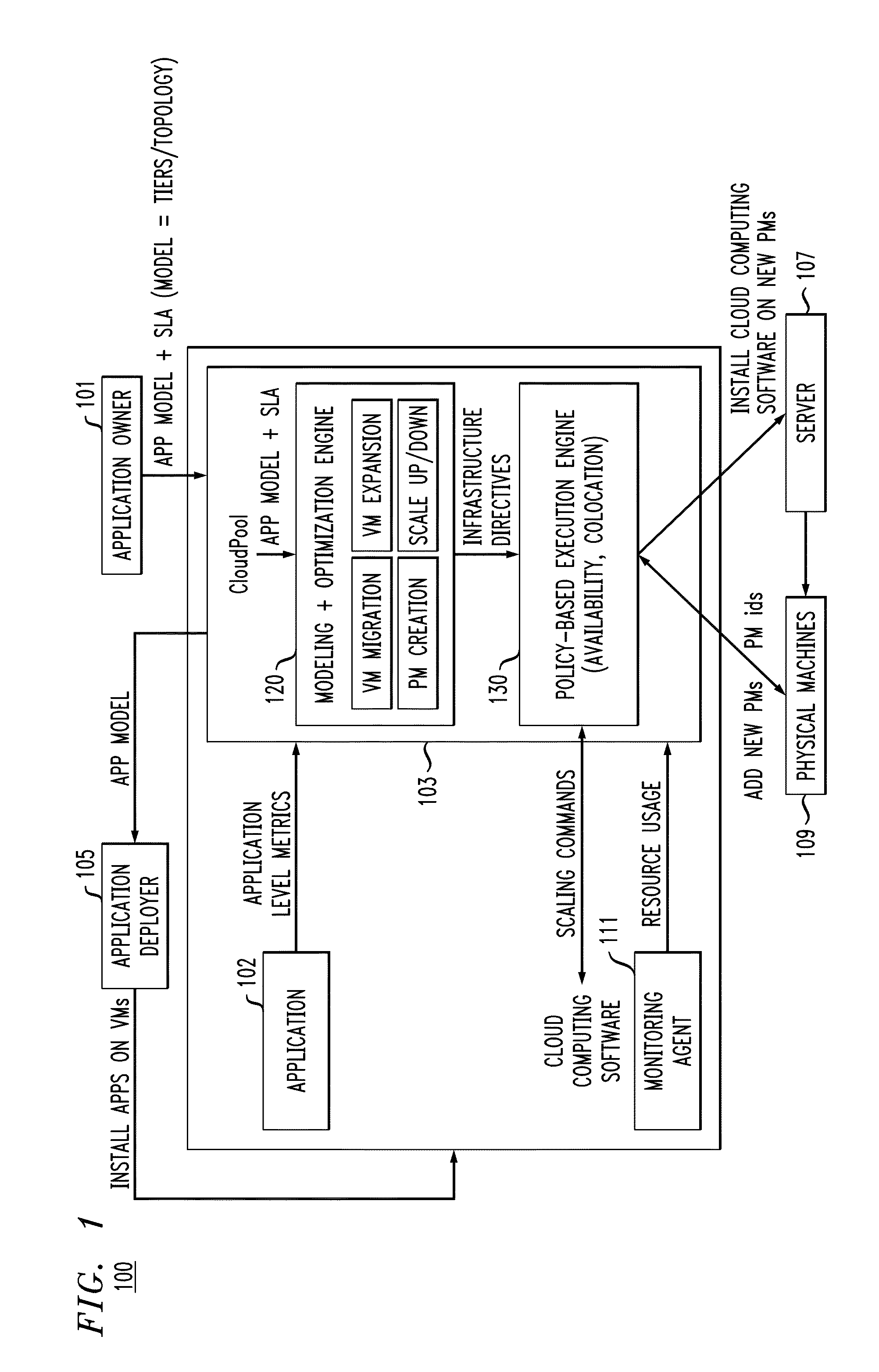
A method and apparatus for deploying an application in a converged infrastructure is described. The application may be deployed according a model that specifies deployment of the application on resources allocated from the converged infrastructure. The model may be used to scale and adjust the deployment of the application according to pre-determined best practices and according to deployment-specific parameters provided by a system administrator.
Owner:EMC IP HLDG CO LLC
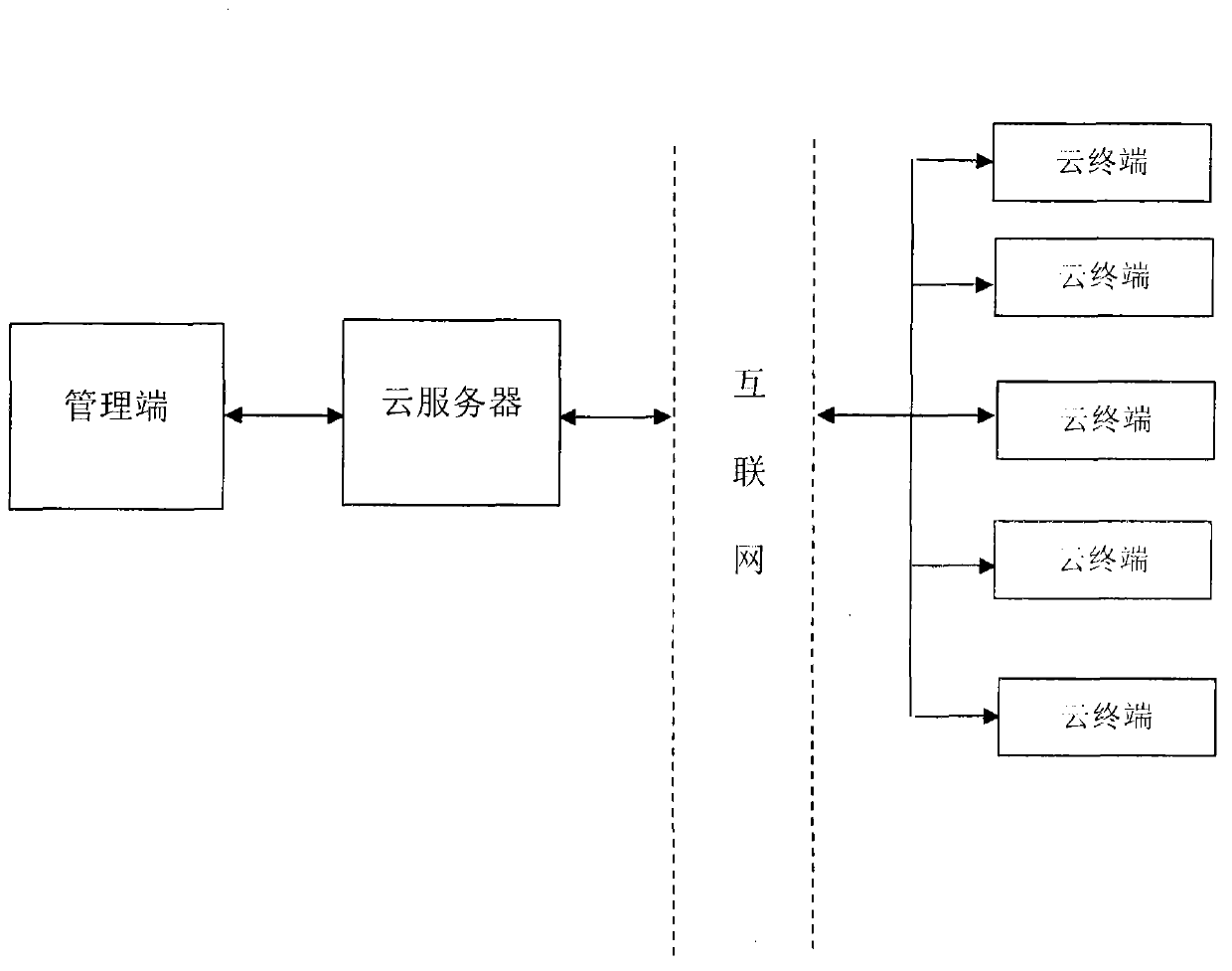
Cloud desktop system and operating method
InactiveCN103281359AReduce operating costsLow failure rateTransmissionSoftware simulation/interpretation/emulationOperating pointOperational costs
A cloud desktop system comprises a management end, a cloud server and cloud terminals; the cloud server forms a physical machine for a plurality of virtual machines, and the cloud terminals correspond to the virtual machines on the cloud server. An operating method for the cloud desktop system includes the following steps: users are connected with the cloud server through the cloud terminals, each user corresponds to a different virtual machine, and when the users use the cloud terminals to work, data are actually processed by the cloud server, while the local cloud terminals only assume the work of data transmission and display. Compared with the conventional working mode, the cloud infrastructure can more sufficiently utilize resources, excessive hardware investment on the local end is avoided, the operating cost of work is saved, the pressure of hardware upgrading is avoided, and since the structure of the cloud terminal is relatively simple and the fault rate is low, the cost of later maintenance is further reduced as well.
Owner:北京启创卓越科技有限公司
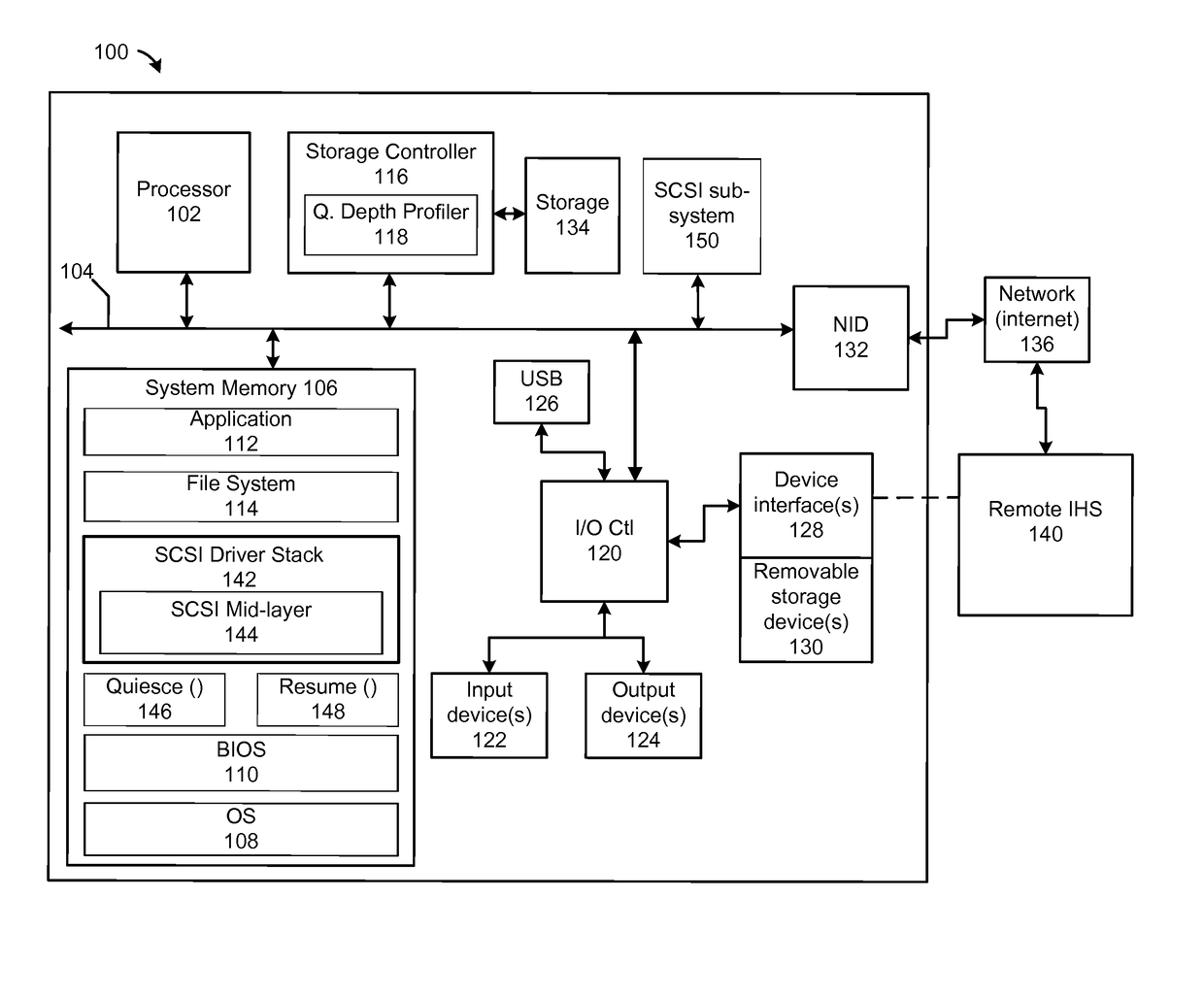
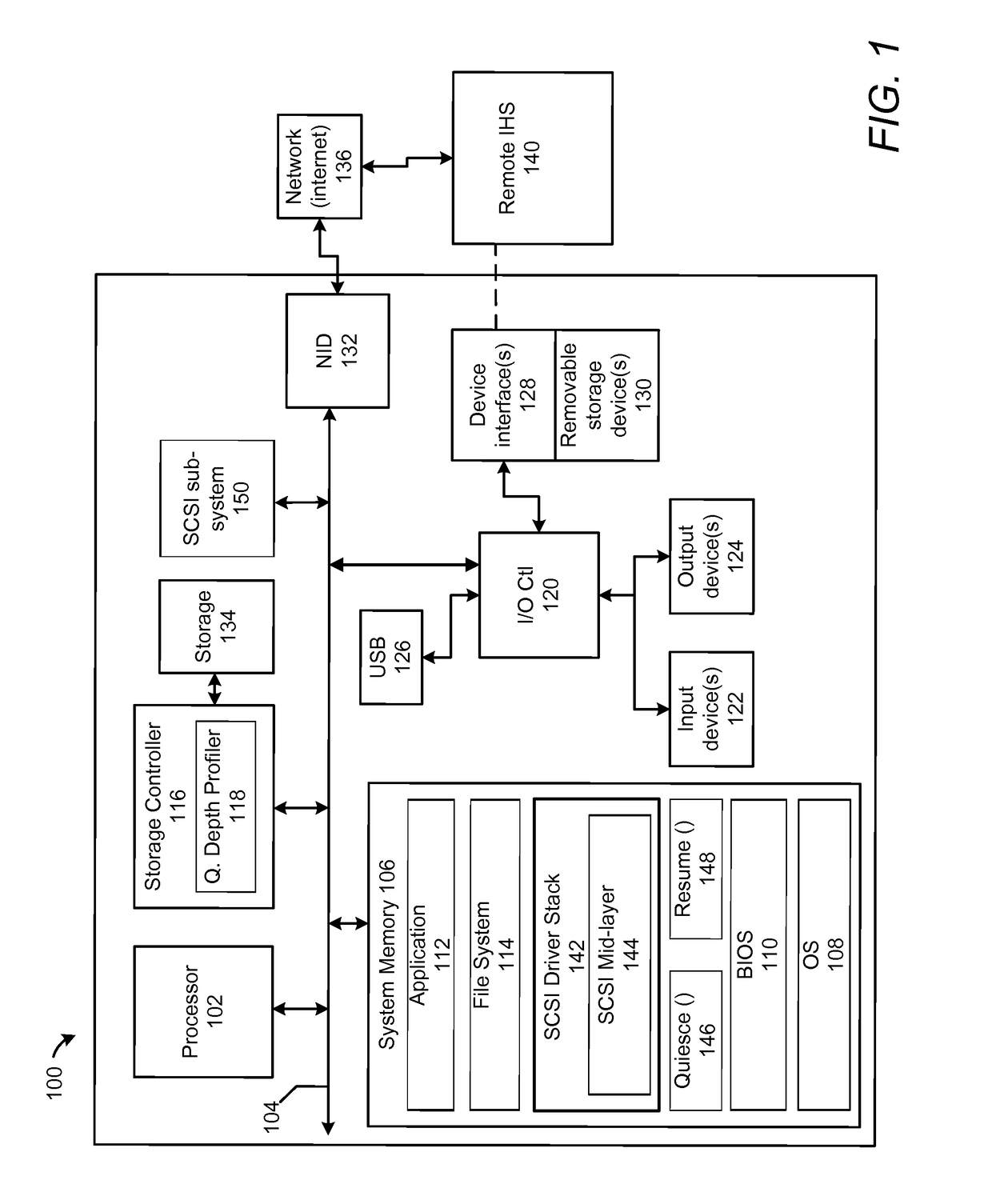
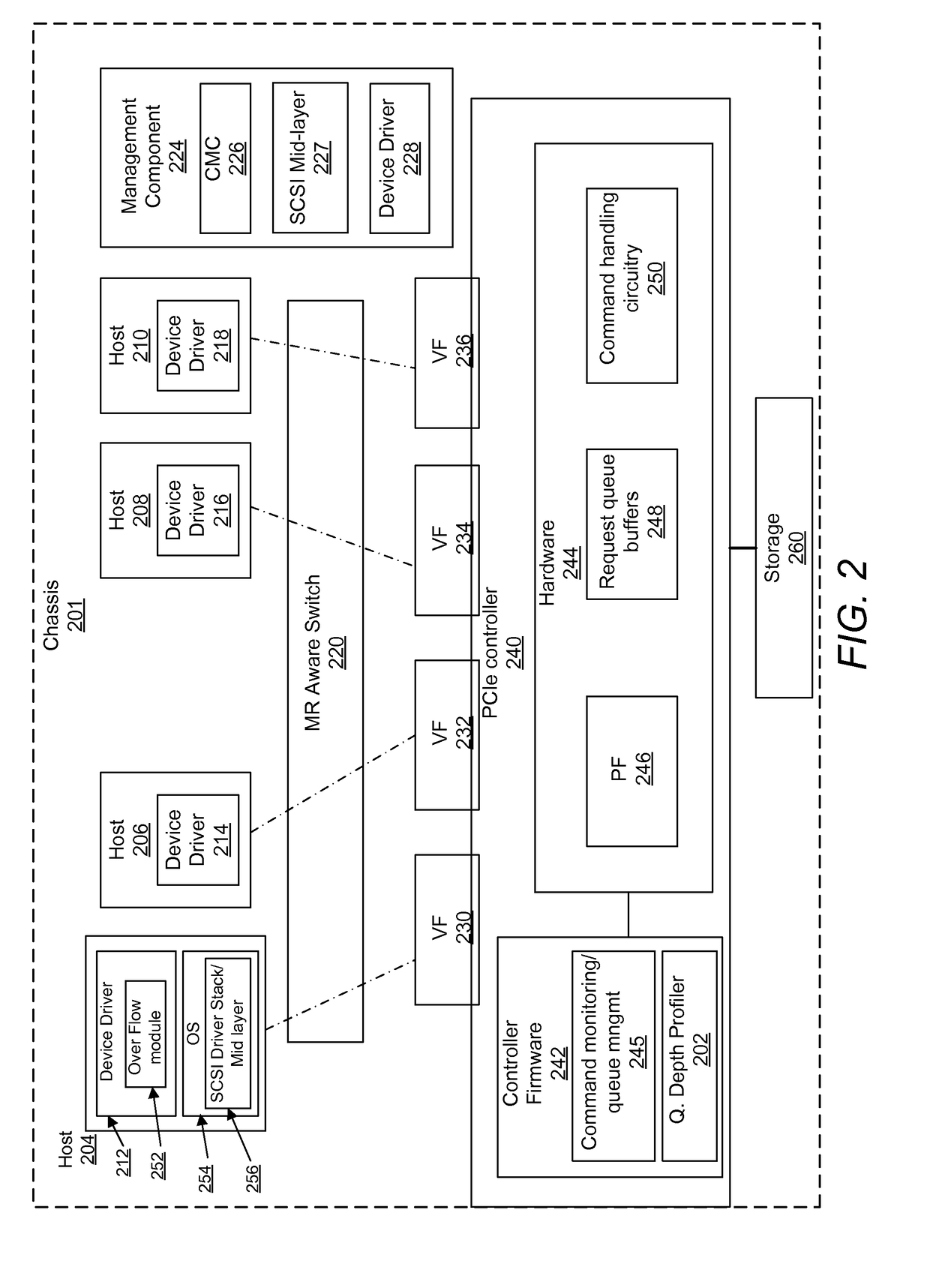
Dynamic allocation of queue depths for virtual functions in a converged infrastructure
ActiveUS20170134310A1Data switching networksSoftware simulation/interpretation/emulationHandling systemWorkload
A method and an information handling system (IHS) dynamically modifies queue depth values based on changing relative workload demands of virtual functions. A controller, executing code of a queue depth profiler, determines, for each virtual function, an average number of total unfulfilled, outstanding requests. The controller compares values for an average number of total outstanding requests across the plurality of virtual functions. The controller determines a relative demand for request queue depth corresponding to each respective virtual function based on the compared values. The controller calculates desired queue depth values for each virtual function, based on the relative demand. The controller triggers completion of pending requests for a first processing state. In response to successful completion of the first processing state, the controller enables initiation of a second processing state in which request processing continues using the desired queue depth values.
Owner:DELL PROD LP
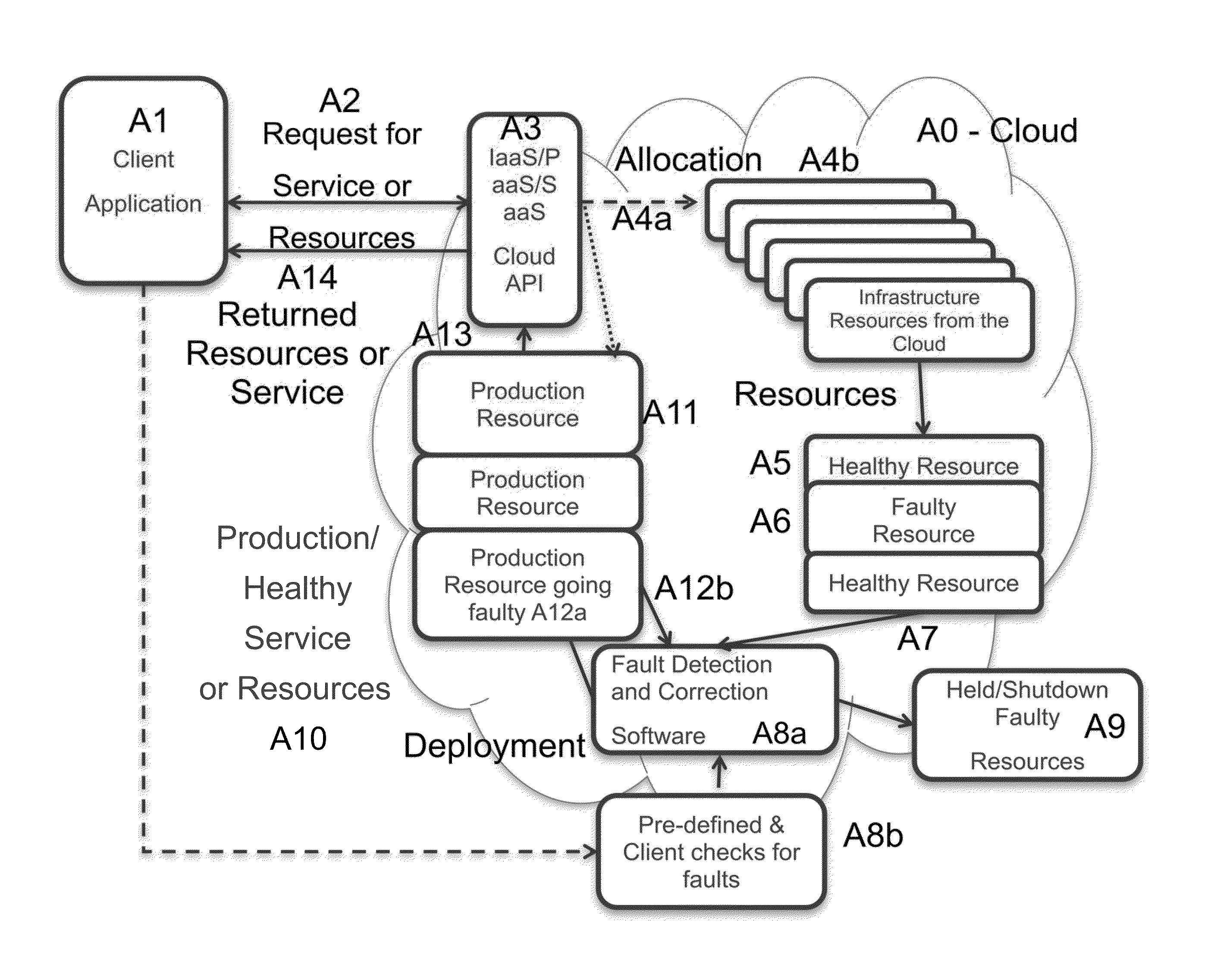
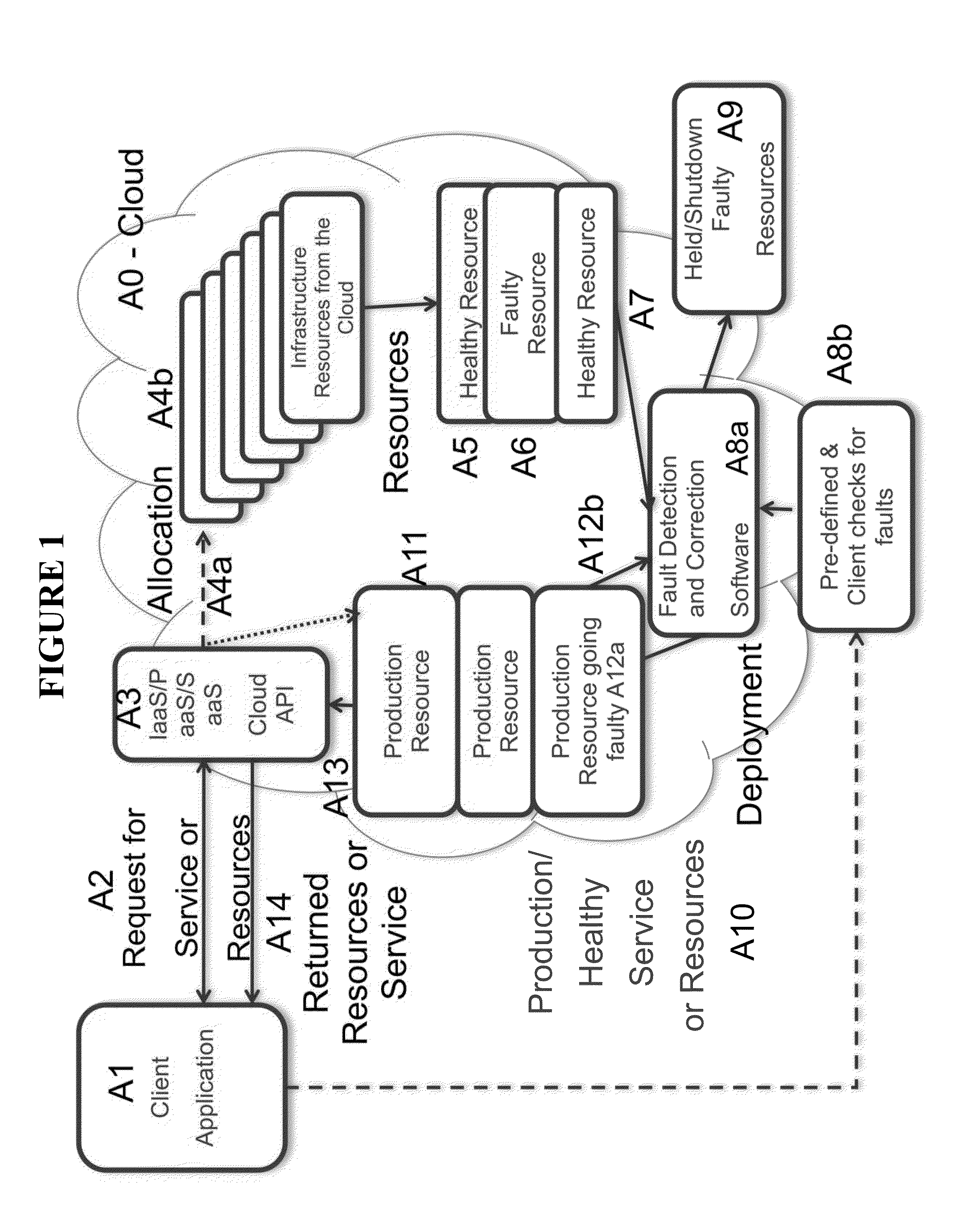
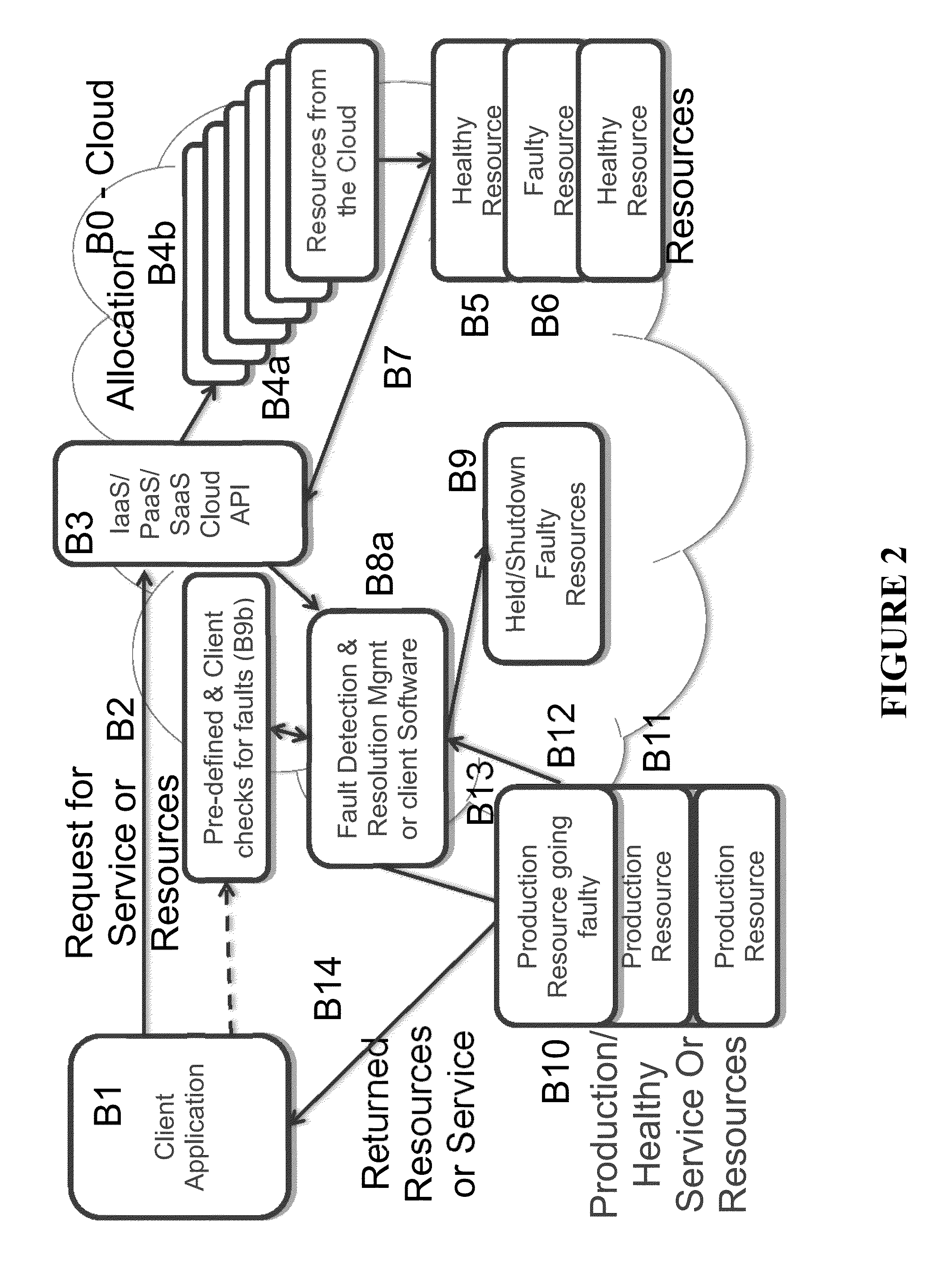
Method and system for automatically detecting and resolving infrastructure faults in cloud infrastructure
ActiveUS20140006844A1Eliminate needStay healthySoftware testing/debuggingNon-redundant fault processingCloud providerWorkload
Systems and methods are provided for any party in a cloud ecosystem (cloud providers of such resources, the intermediate management software for such resources, and the end user of such resources) to detect and resolve faulty resources synchronously or asynchronously, before said faults adversely affect the users' workloads. The system requests a service or set of one or more resources within a cloud, automatically checking the infrastructure for various faults that would cause it to be non-functional, including pre-defined and user-defined checks, and resolving them before including the infrastructure in the working service cluster of resources. The system presents an API to the user that returns only functional, production-quality resources that are not in a faulty state. An API that tests and resolves bad infrastructure can be registered during the request or a preceding / subsequent API call, removing the need for the end-user to deal with various types of infrastructure faults.
Owner:CYCLE COMPUTING
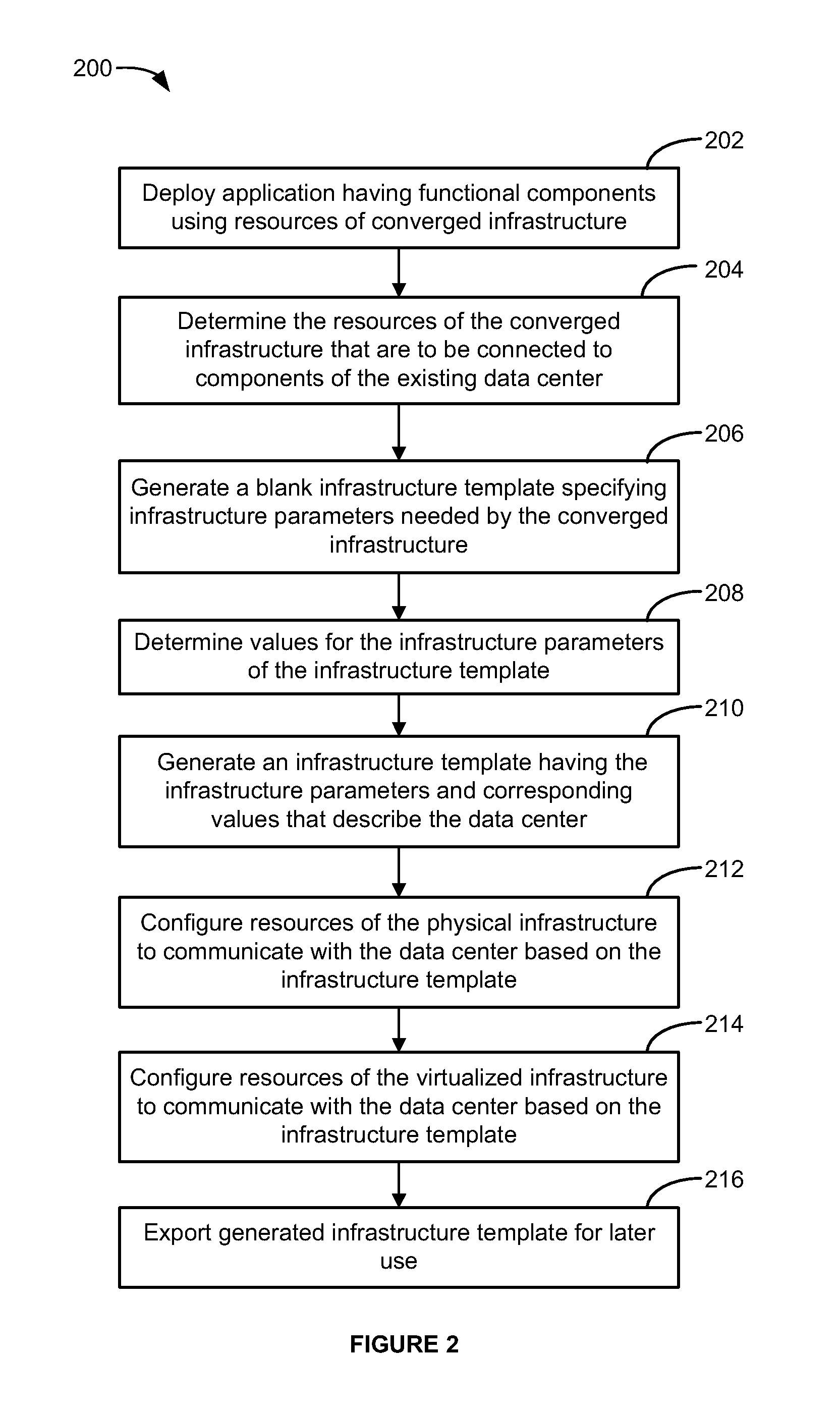
Application dependent data center integration
ActiveUS20140068032A1Facilitate communicationDigital computer detailsProgram controlData centerNetwork integration
A method and apparatus for integrating a converged infrastructure platform in a data center is provided. The described apparatus configures the physical and virtual resources that run on the converged infrastructure to communicate with the rest of the data center. The network integration process understands the data center network already in place and extends the set up into the converged infrastructure to enable communication between the converged infrastructure and the rest of the network in the data center. The apparatus uses an infrastructure template that describes the data center and that may be pre-defined for a specific application deployed within the converged infrastructure platform.
Owner:EMC IP HLDG CO LLC
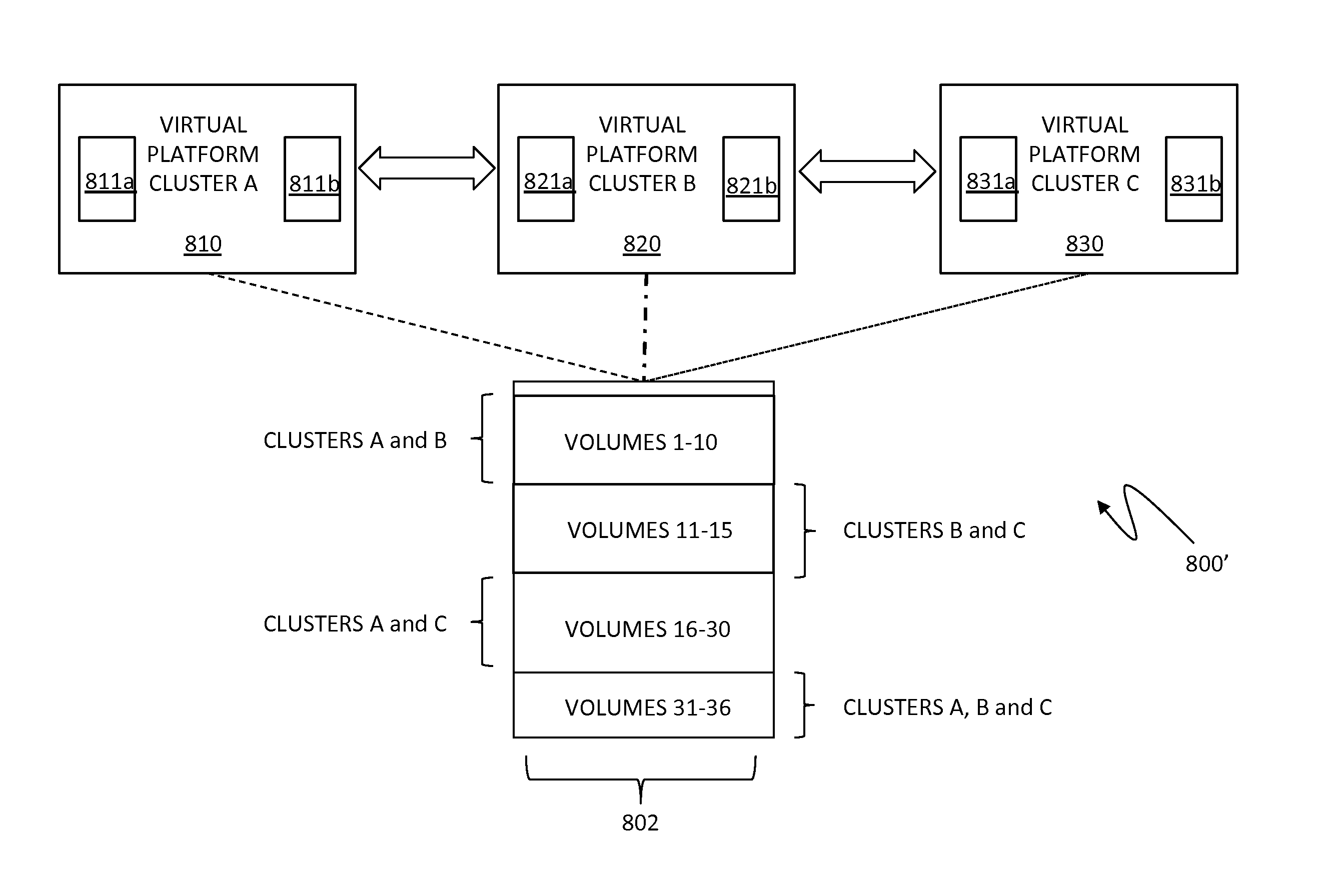
Distributed dynamic federation between multi-connected virtual platform clusters
ActiveUS9348627B1Interprogram communicationSoftware simulation/interpretation/emulationFailoverData center
Dynamic mobility of virtual data centers and converged infrastructure components, such as Vblocks, may be provided using a virtual platform product that federates and / or coordinates virtual storage. The system described herein enables sharing of distributed resources between multi-connected virtual platform clusters, such as VPLEX clusters, in a dynamic sharing arrangement. A virtual platform cluster may include one or more pairs of directors that enables failover from one director of the pair(s) to the other director of the pair(s) in a cluster in the case of hardware or path failure.
Owner:EMC IP HLDG CO LLC
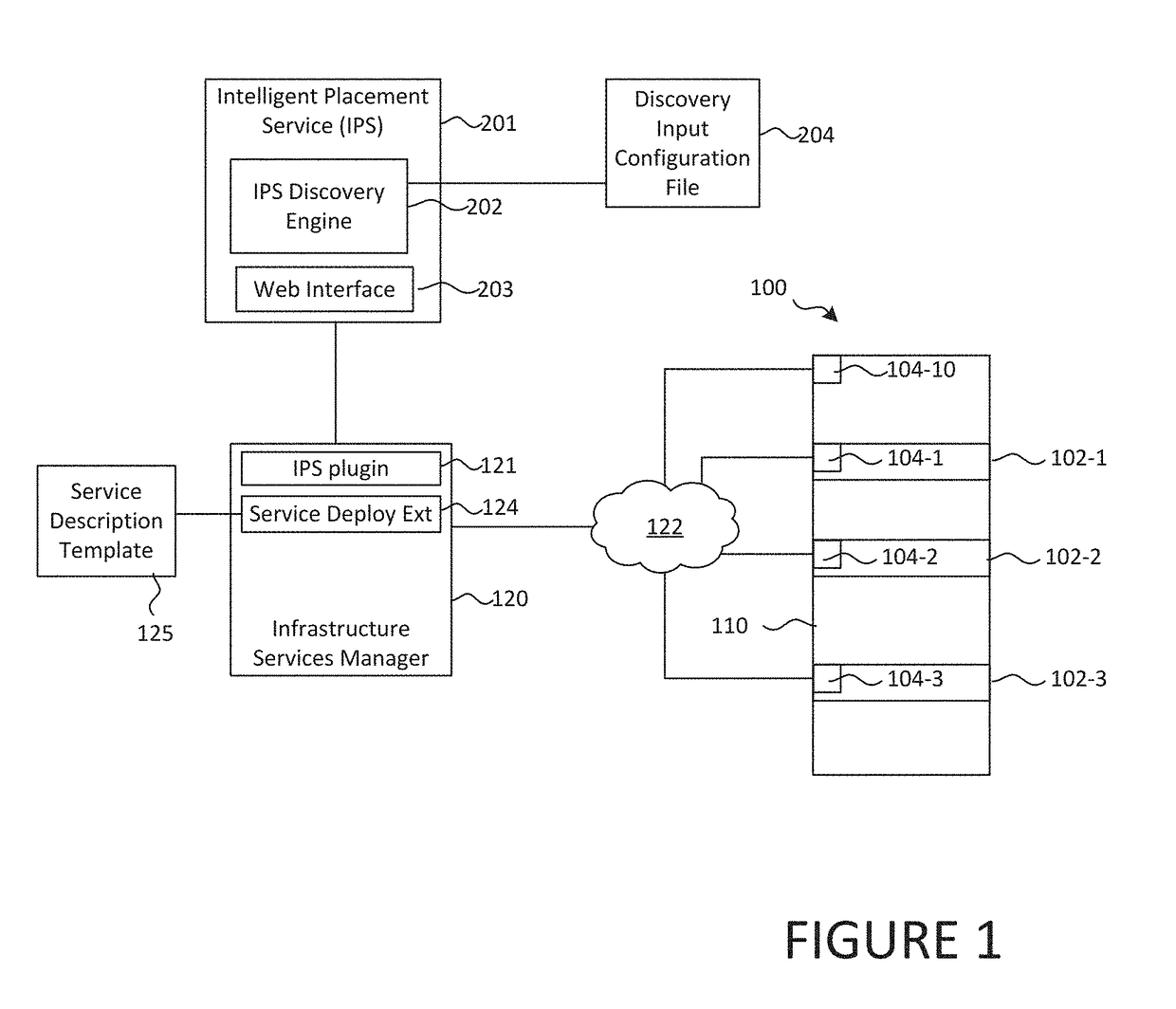
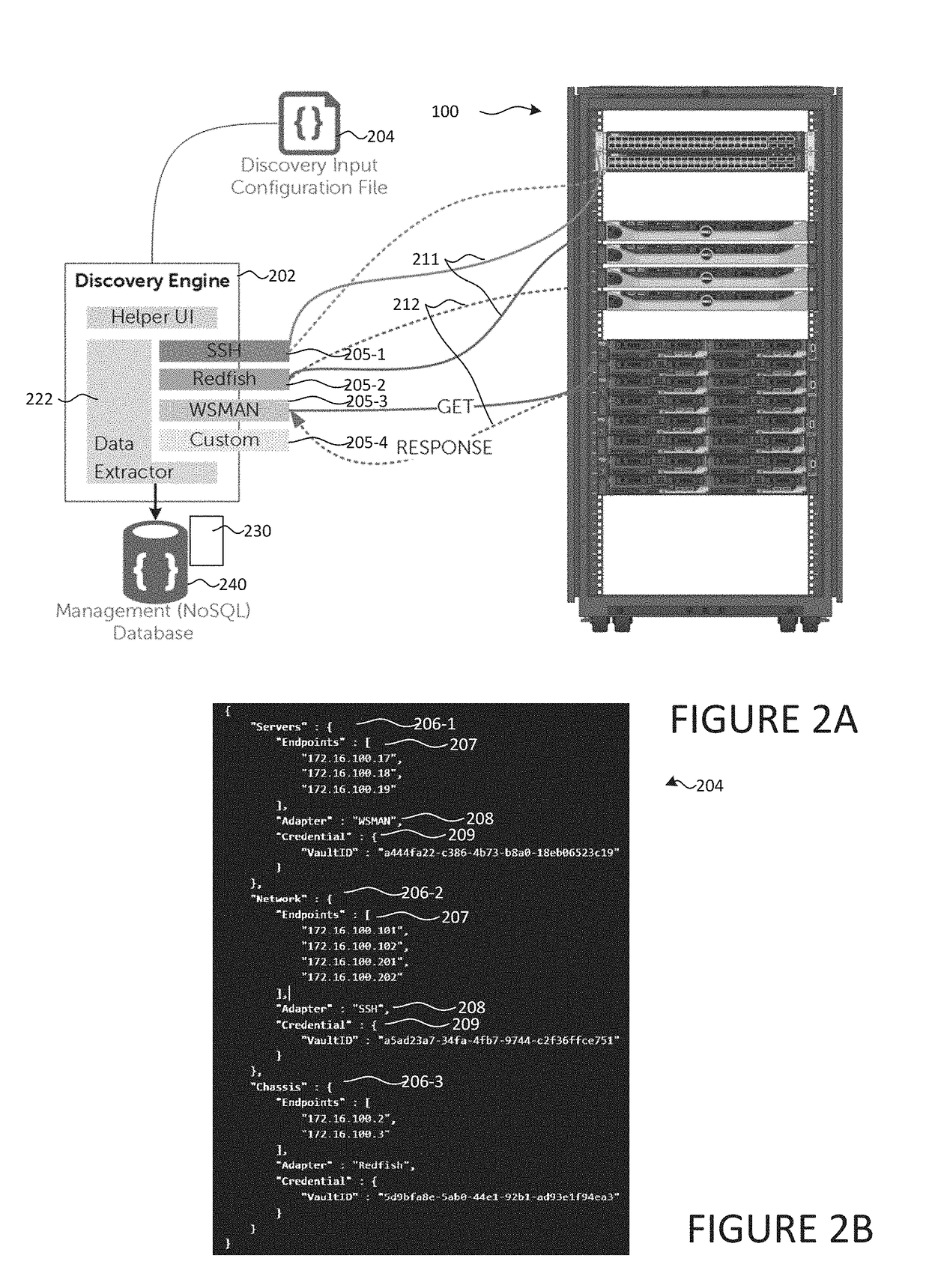
Discovery of hyper-converged infrastructure devices
A system may include a database, where a managed network includes a computing cluster that provides networking, storage, and virtualization services distributed across a plurality of computing devices, where each computing device can execute one or more respective software applications and comprises: (i) a respective controller, and (ii) a respective storage device, and where the storage devices of the plurality of computing devices collectively form a storage pool. The system may also include a proxy server application configured to: request and receive computing cluster data that identifies the computing cluster; request and receive storage pool data that identifies the storage pool; request and receive storage container data that identifies storage containers of the storage pool; request and receive controller data that identifies the controllers of the plurality computing devices; and provide, to the database, the computing cluster data, the storage pool data, the storage container data, and the controller data.
Owner:SERVICENOW INC
Method and system for media content transmission based on CDN (Content Distribution Network) and P2P (Peer to Peer) converged infrastructure
InactiveCN102868912AGuaranteed privacyPrevent human tamperingSelective content distributionContent distributionTraffic capacity
Owner:北京视博数字电视科技有限公司
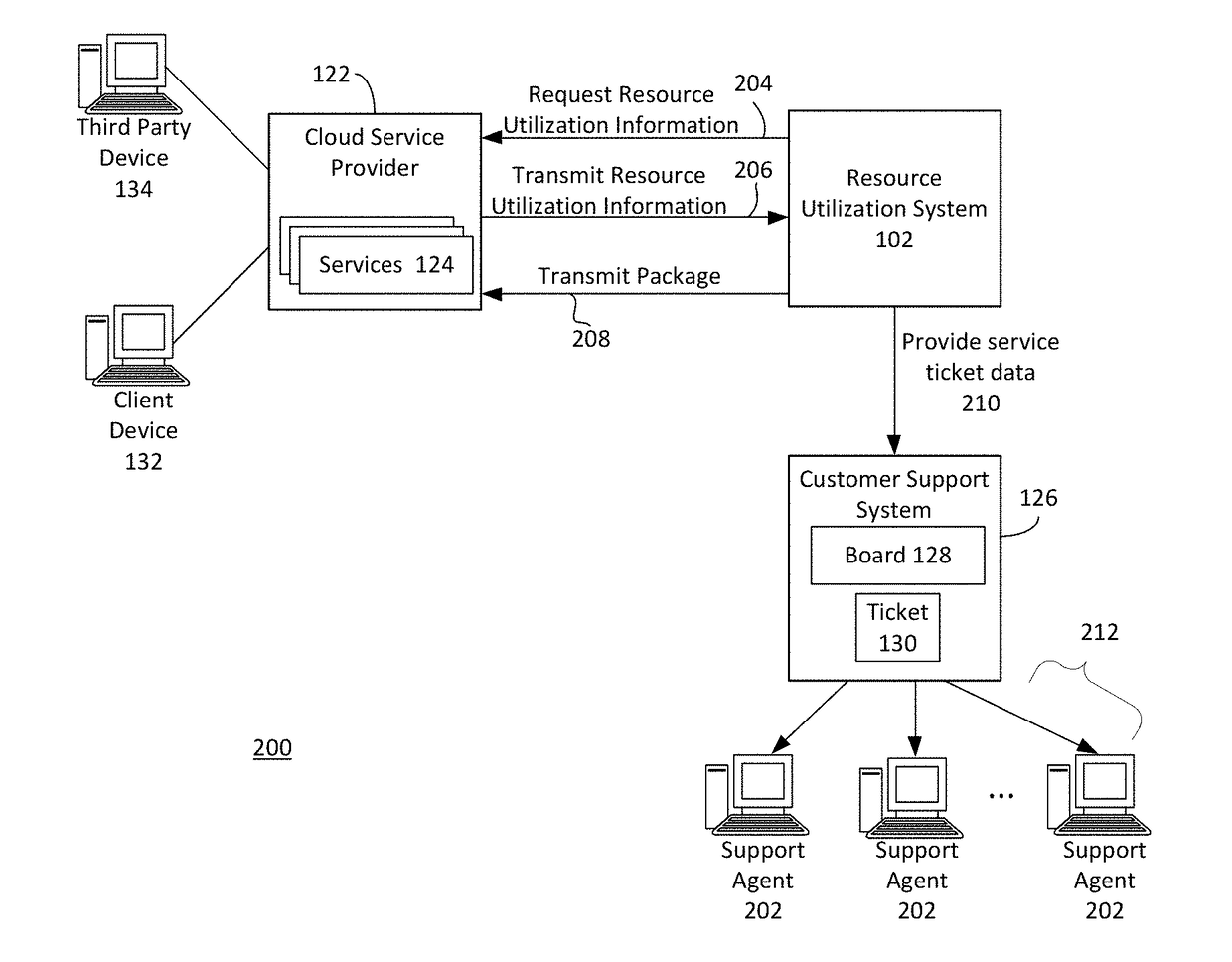
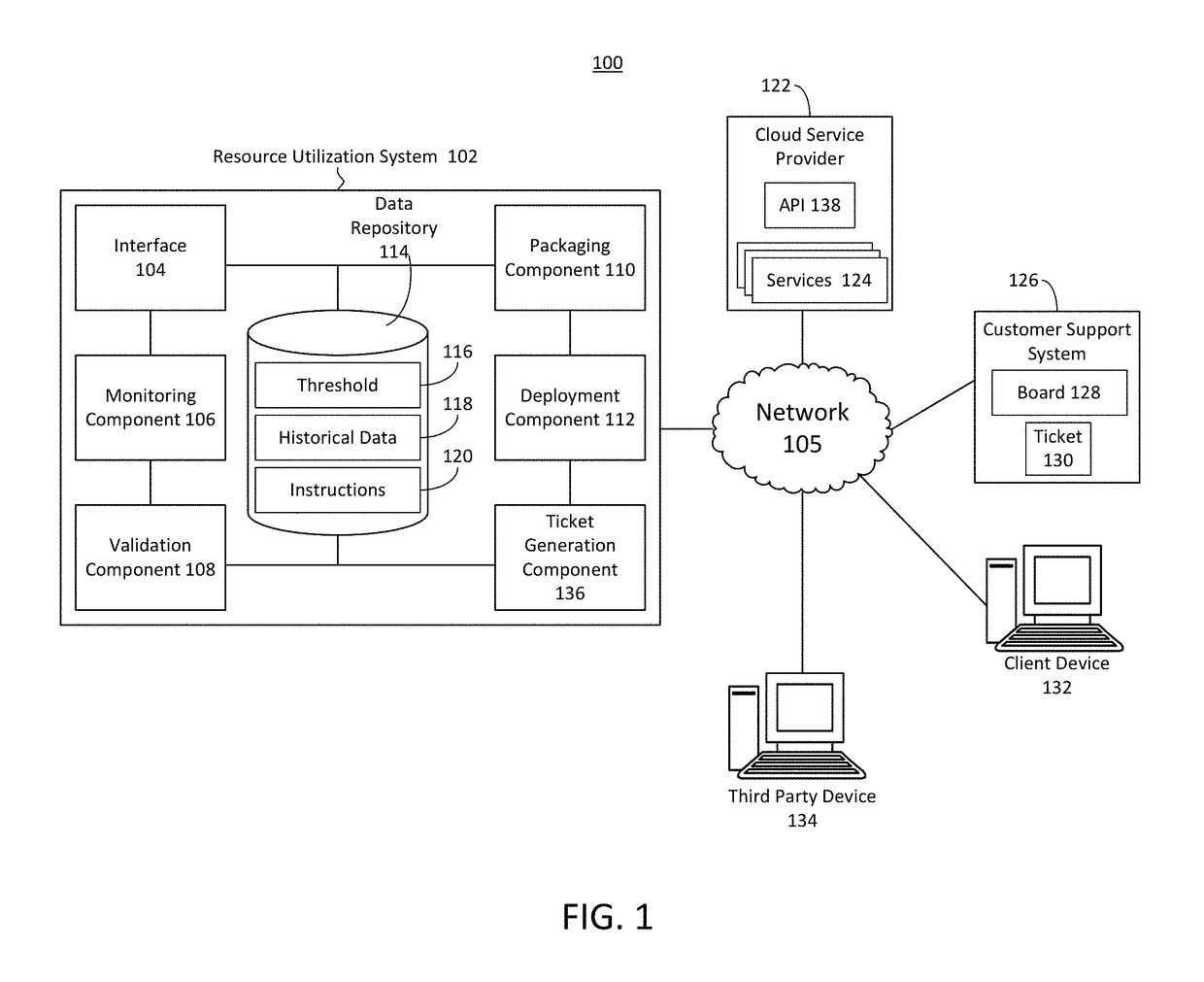
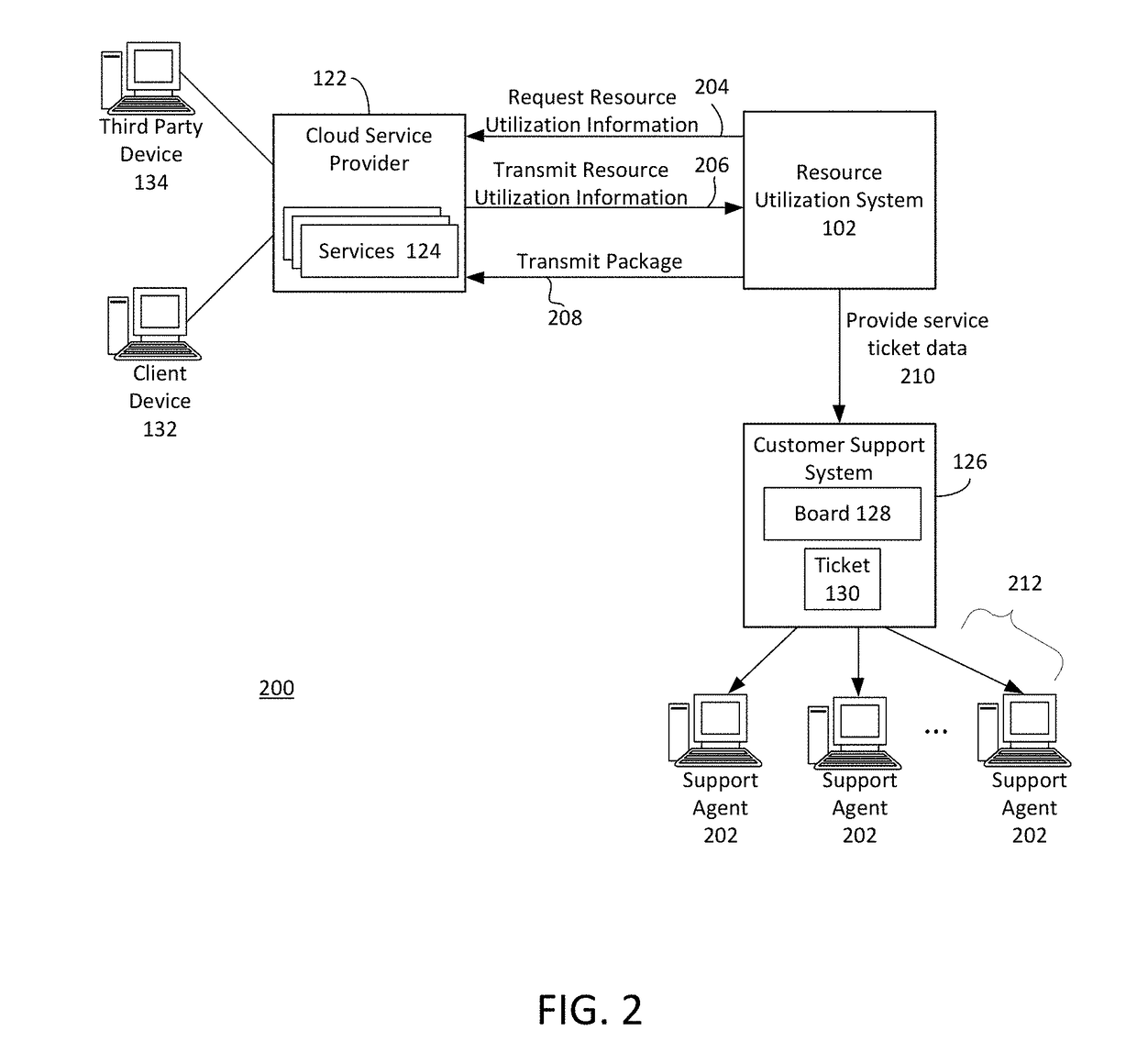
Systems and methods for managing resource utilization in cloud infrastructure
The present disclosure relates to managing resource utilization in cloud service infrastructure. A device can monitor the cloud service. The cloud service can be configured with an automatic scaling function based on a threshold. The device can determine, based on the monitoring, that a utilization value of the cloud service during a time interval exceeds the threshold. The device can generate, using a policy based on the utilization value and the threshold, an instruction to disable the automatic scaling function of the cloud service by the one or more servers. The device can transmit the instruction to the one or more servers via a second cloud application programming interface. The device can generate, responsive to the policy, a service ticket data structure with an indication of the utilization value and the time interval. The device can provide the service ticket data structure to an electronic board.
Owner:CONNECTWISE LLC
Network attack and defense virtual simulation system based on hyper-converged infrastructure
ActiveCN106790046ALow costImprove service capabilitiesData switching networksWeb applicationBusiness efficiency
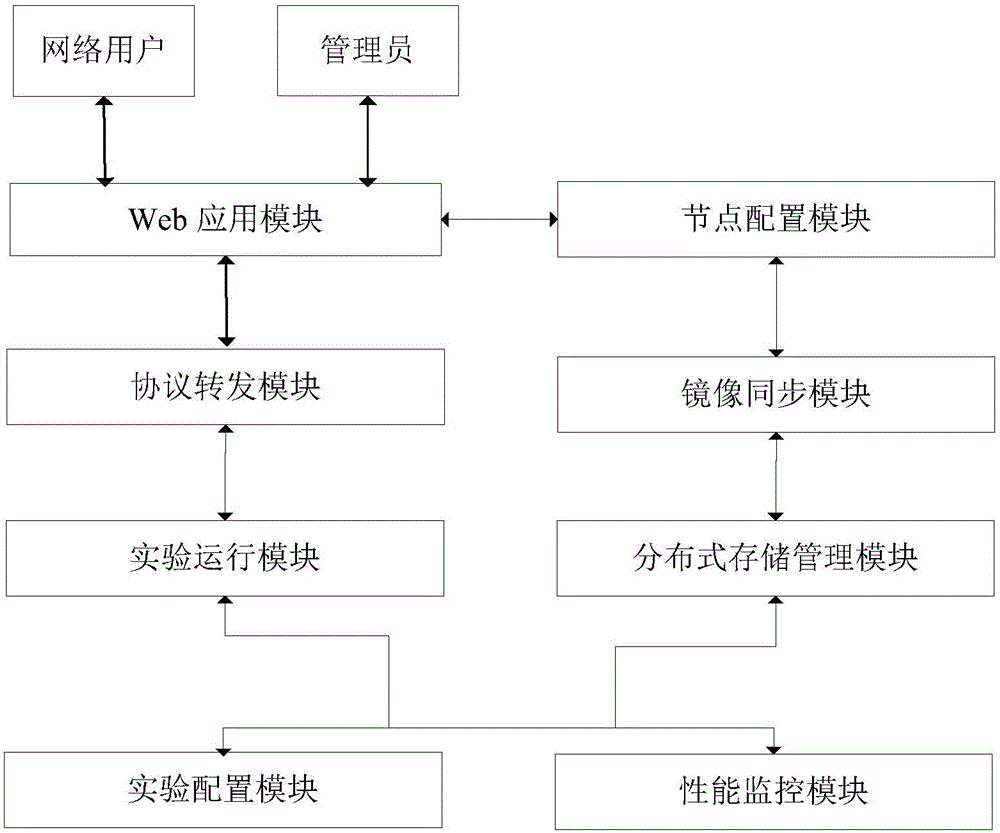
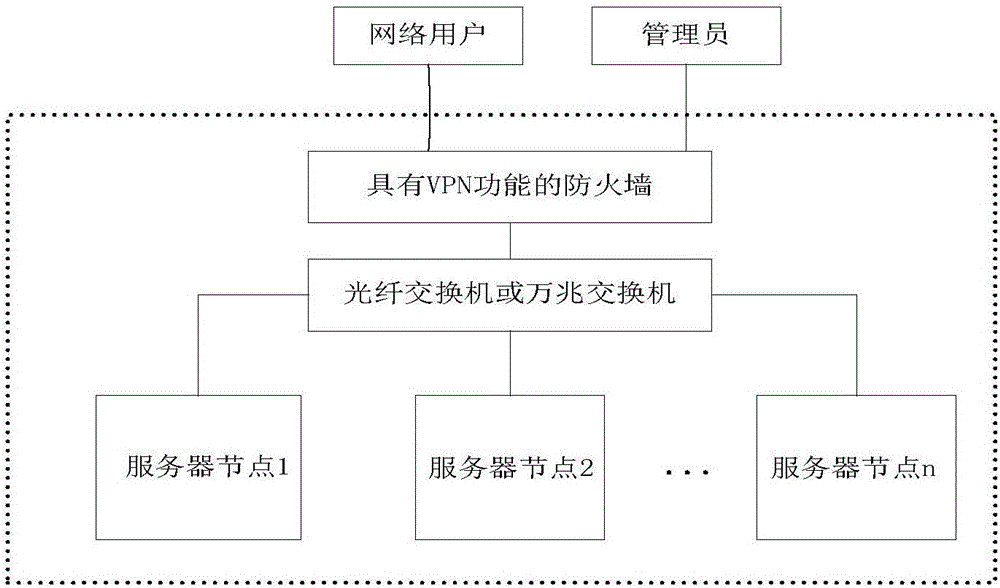
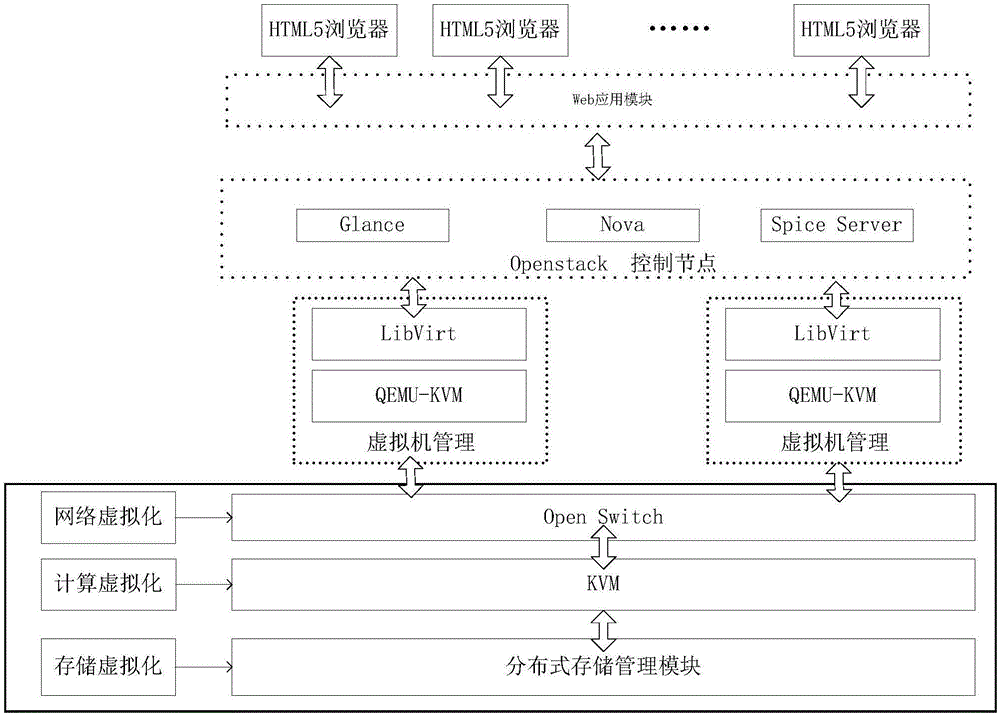
The invention discloses a network attack and defense virtual simulation system based on hyper-converged infrastructure, relates to the field of network security and solves the problems that an existing network security virtual simulation system is low in expansibility and low in efficiency ratio and is difficult to manage. The system comprises a Web application module, a protocol forwarding module, an experiment configuration module, an experiment operation module, a node configuration module, a mirror synchronization module and a performance monitoring module. According to the network attack and defense virtual simulation experiment system established through adoption of the hyper-converged infrastructure, a plurality of server nodes are interconnected through a high-speed network; the server nodes are computing nodes and also are storage nodes; the service capability of the system is expanded horizontally by increasing the number of the service nodes; the plurality of server nodes are arranged in the system, so when software and hardware faults occur in partial server nodes, the operation of the system is not influenced; the fault server nodes can be directly replaced; and when the server nodes are newly increased, mirror resources can be automatically synchronized to the newly increased server nodes by the system, and the service capability of the system can be rapidly improved.
Owner:CHANGCHUN UNIV OF SCI & TECH
Ethernet-leveraged hyper-converged infrastructure
ActiveUS10108560B1Increase ratingsEliminate wasteInput/output to record carriersResource poolExtensibility
Systems and methods are provided for enabling extensibility of discrete components (e.g., memory, storage, cache (hardware- or software-based), network / fabric, capacity, etc.) within a hyper-converged infrastructure. In the context of extending the storage component, an external storage device is connected to a hyper-converged appliance (“node” or “host”) via an Ethernet-based host bus adapter (“HBA”). Utilizing ATA over Ethernet (“AoE”) as the communication protocol, storage drives within the external storage device appear as direct-attached storage to the hypervisor of the hyper-converged appliance, extending the pool of storage resources available for allocation by the hyper-visor.
Owner:BIN 2022 SERIES 822 OF ALLIED SECURITY TRUST I
Scaling a cloud infrastructure
InactiveUS9300553B2RobustnessImprove superioritySoftware designSoftware metricsUrban infrastructureSocial infrastructure
Owner:INT BUSINESS MASCH CORP
Method for designing multi-path server QPI clamp based on converged infrastructure
InactiveCN104899179AEasy to switch between downgrade and downgradeReduce wiringMultiple digital computer combinationsShortest distanceInterconnection
The invention discloses a method for designing a multi-path server QPI clamp based on converged infrastructure, and belongs to the field of server mainboard design. For a situation in which each computing node only has two CPUs and computing nodes are the same, the multi-path server QPI clamp is mounted at a position of a computing node of a mainboard; when only one computing node exists, a shortest distance QPI connection is performed for the two CPUs in the computing node, and two CPUs outside the computing node are connected by means of QPI; and when more than one computing node exists, a shortest distance QPI connection is performed for the two CPUs in the computing node, and a QPI interconnection is performed for each CPU outside the computing node and two CPUs in another computing node. According to the method for designing a multi-path server QPI clamp based on converged infrastructure, the QPI clamp is designed in front of a server for convenience of detachment, and costs are reduced; the invention has a commercial value, system switching is convenient, and backboard wiring is reduced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
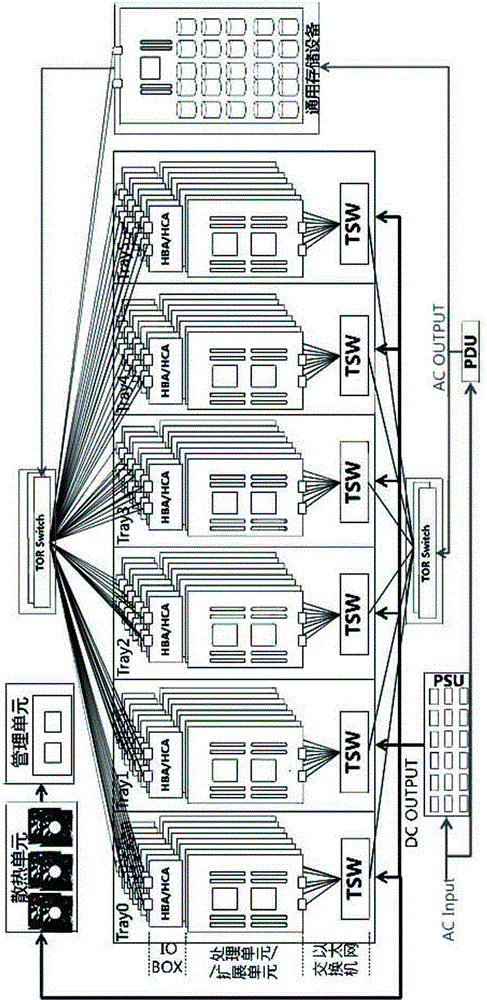
Converged-infrastructure cloud server system architecture
ActiveCN104951251AImprove utilization efficiencyEasy to operate and manageInput/output to record carriersData exchangeComputer science
The invention relates to converged-infrastructure cloud server system architecture, and relates to the technical field of cloud server architecture. A whole system for the cloud server is composed of a processing unit or an extension unit, an IO BOX unit, a TSW data exchange unit, a universal storage equipment, a TOR data exchange unit, a power supply unit, a heat dissipation unit, a monitoring and managing unit and an infrastructure. A whole cabinet state is utilized in the architecture, heat dissipation is unified, power supply is unified, and management is unified, so that the energy use efficiency can be improved greatly, and management operation is simplified.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
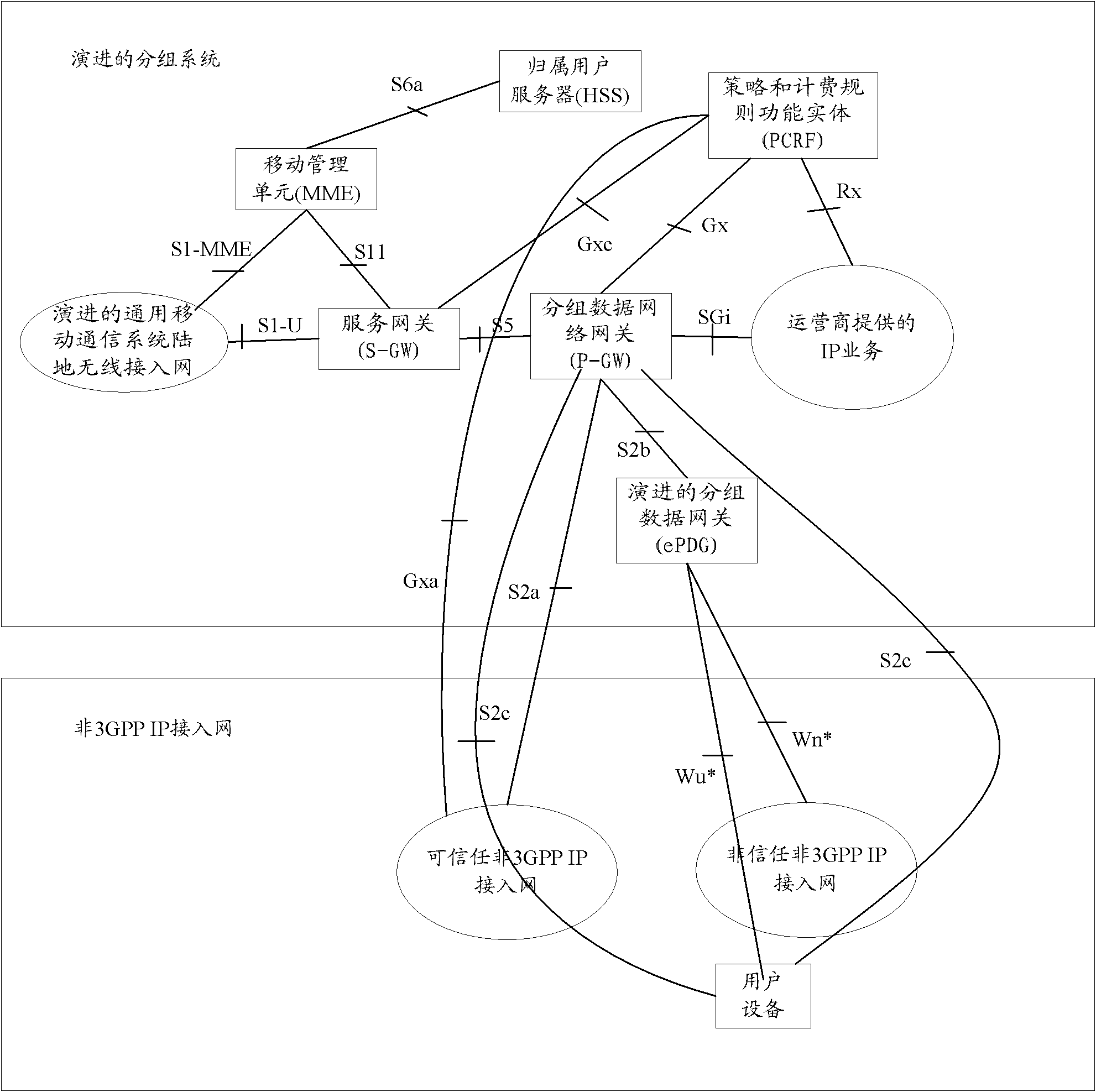
Method and system for obtaining roaming information
InactiveCN102761852AAchieve deliveryConnection managementNetwork data managementTelecommunicationsPublic land mobile network
The invention discloses a method and system for obtaining roaming information. The method comprises the steps of: transmitting the roaming information to a P-GW (Packet Data Network Gateway) by a gateway connected with the P-GW, and forwarding the received roaming information to an H-PCRF (Home-Policy and Charging Rules Function) by the P-GW. Therefore, a VPLMN ID (Public Land Mobile Network) is extracted from the obtained roaming information by the H-PCRF. According to the invention, in a fixed network mobile converged infrastructure, the roaming information is transmitted, so as to ensure that a proper V-PCRF (Visited-Policy and Charging Rules Function) is determined by the H-PCRF.
Owner:ZTE CORP
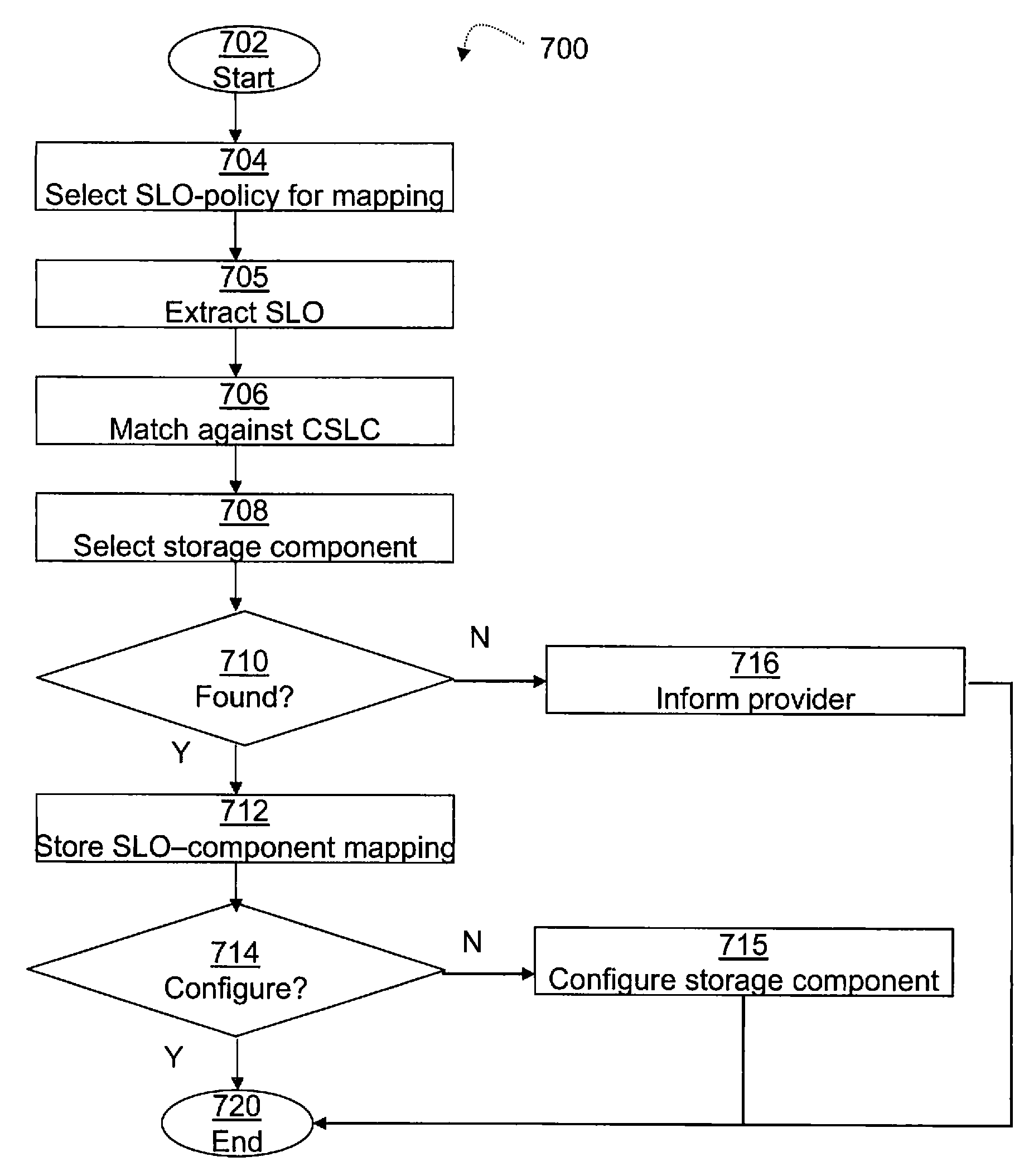
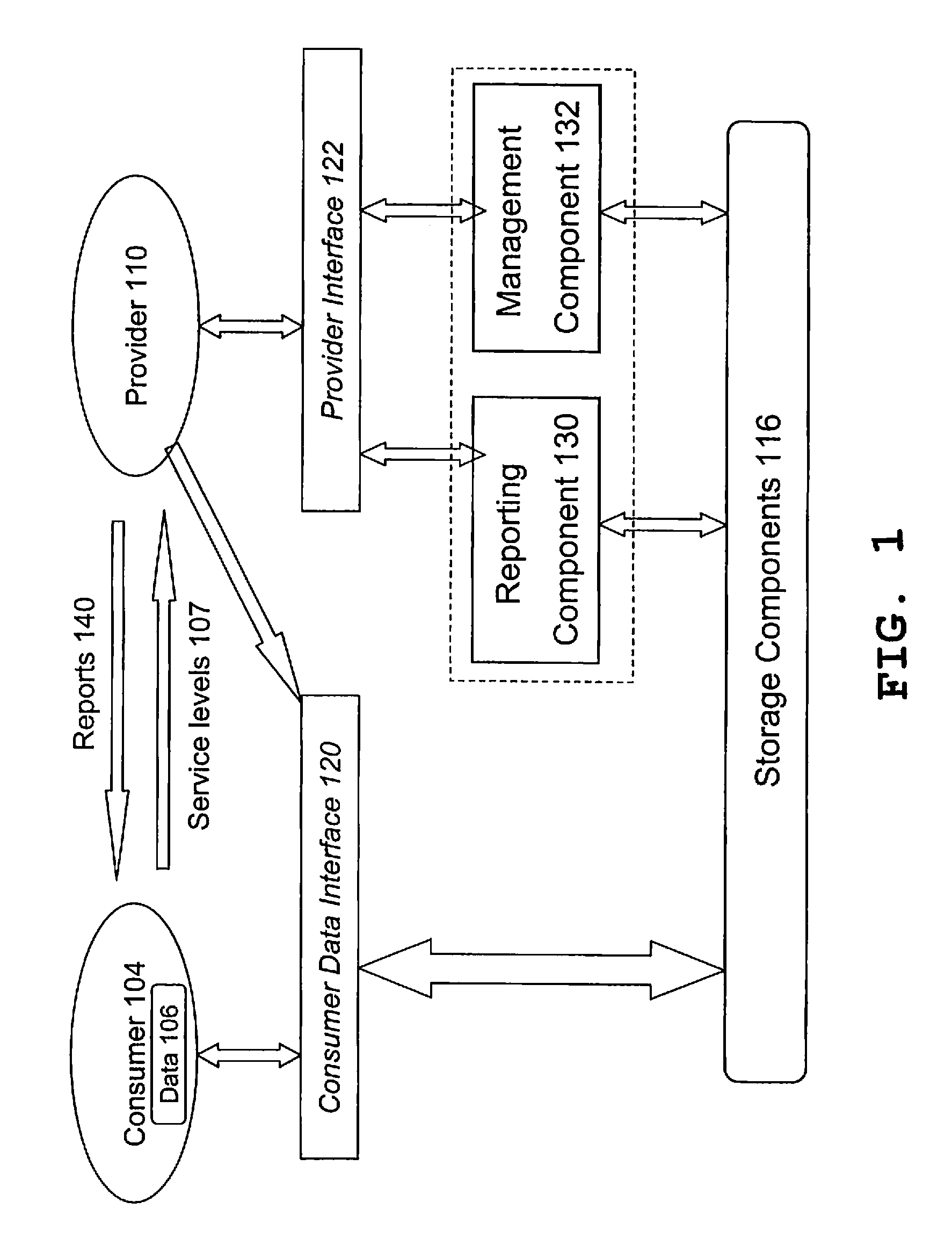
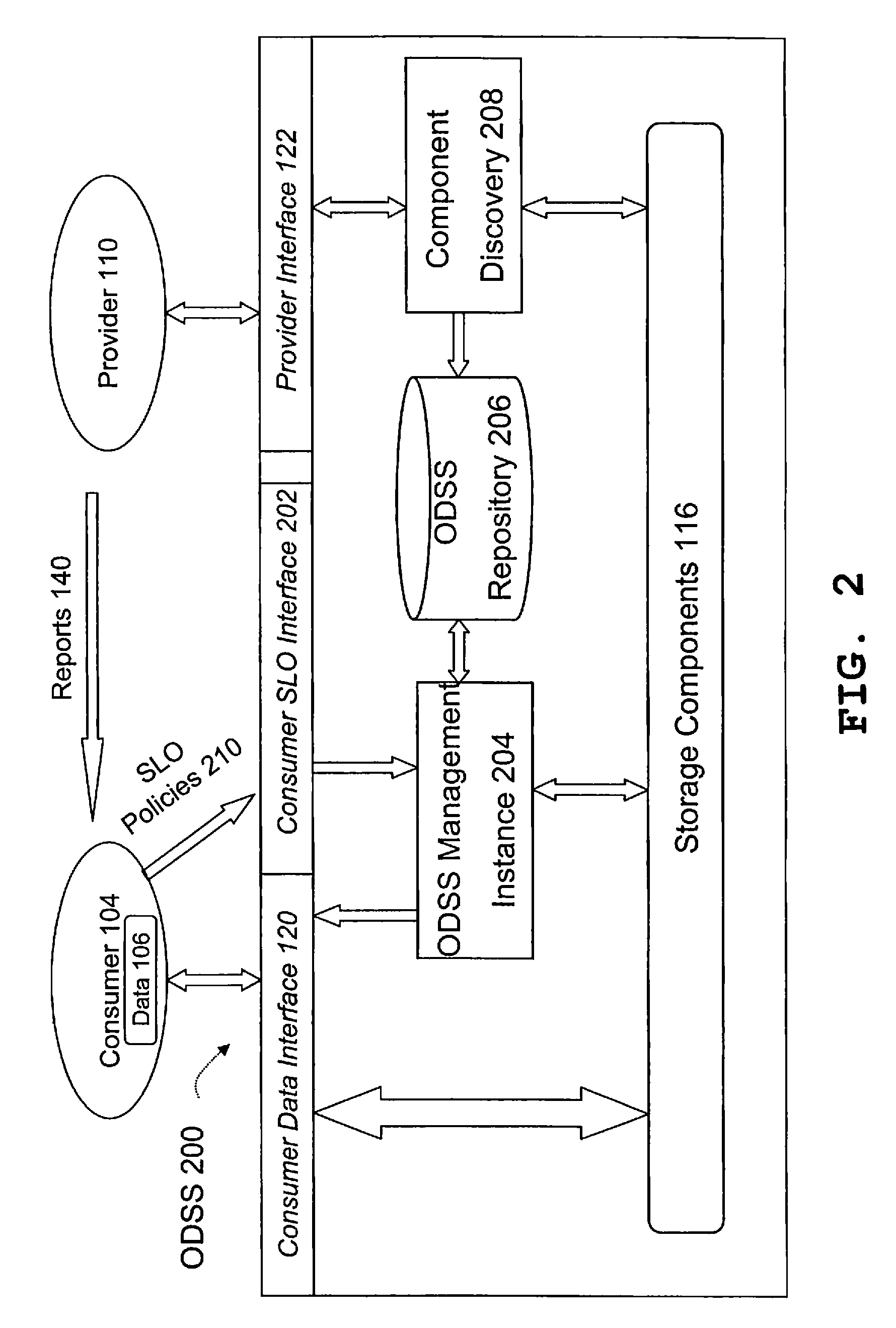
Automatically Managing a Storage Infrastructure and Appropriate Storage Infrastructure
InactiveUS20090182777A1Data processing applicationsSpecial data processing applicationsData classAuto-configuration
With the present invention means are provided for automatically managing a storage infrastructure with a plurality of storage components in compliance with consumer service level objectives (SLOs). Therefore, the claimed method comprises: automated identification of available storage components, which are appropriate for storing consumer data under consideration of specified service level objectives (SLOs); automated mapping of said consumer SLO policies to said available storage components to select available storage components for specified data classes; and automated configuration of said selected storage components according to said mapping of consumer SLO policies.
Owner:IBM CORP
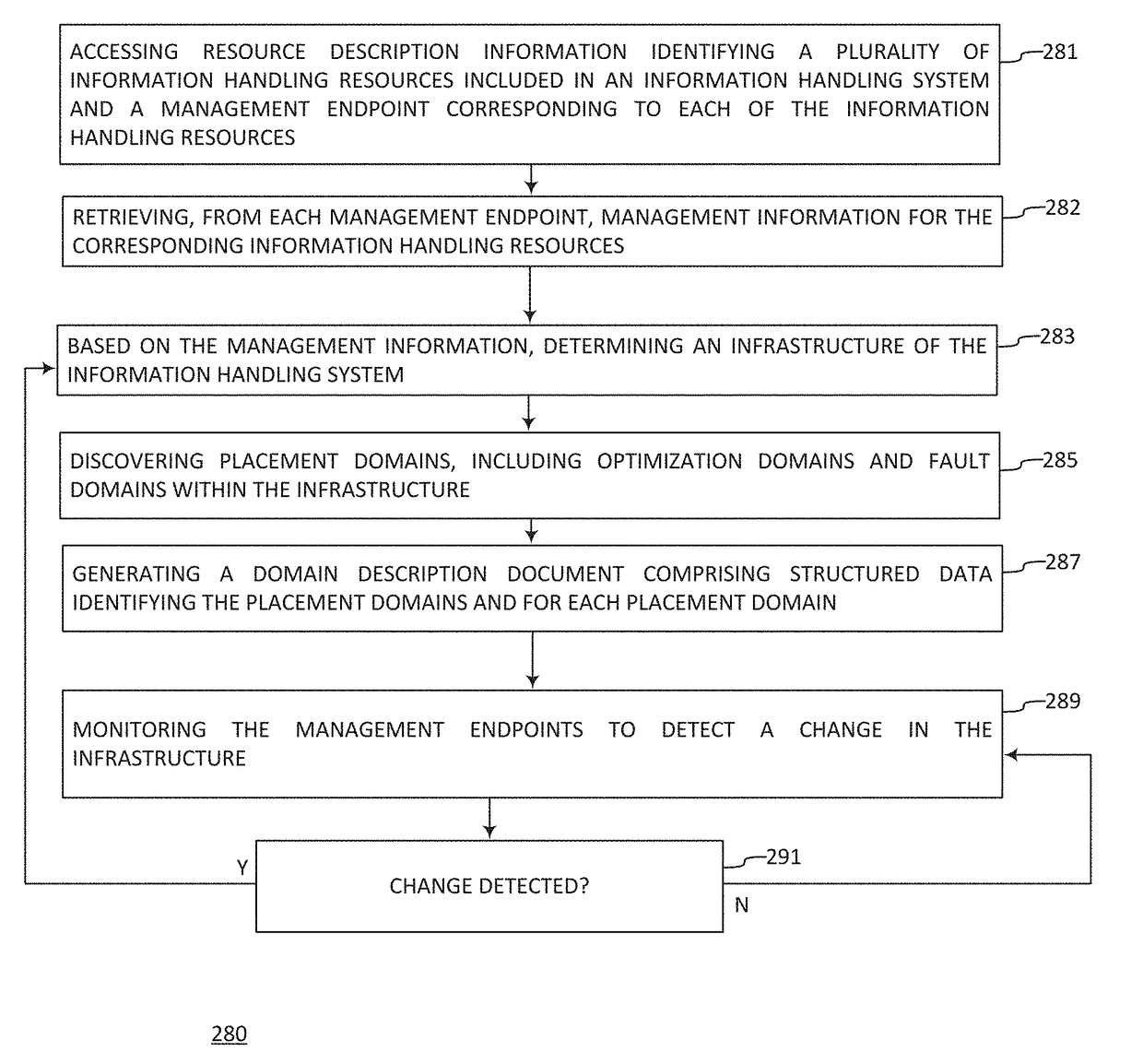
Storage isolation domains for converged infrastructure information handling systems
ActiveUS20180248758A1Low costImprove resource utilizationData switching networksStructure of Management InformationHandling system
A storage management method includes obtaining storage configuration information corresponding to a storage infrastructure of an information handling system, determining, from the storage configuration information, one or more storage and isolation fault domains within the storage infrastructure, wherein each of the one or more storage and isolation fault domains comprises an independently available and physically isolated storage resource, and placing an application workload data store within the storage infrastructure in accordance with the storage and isolation fault domains to comply with a physical isolation requirement applicable to the data store. Obtaining the storage configuration may include discovering the storage configuration information by accessing resource description information identifying a plurality of storage resources and a management endpoint corresponding to each of the one or more storage resources, and retrieving, from each management endpoint, storage configuration information for a storage resource associated with the management endpoint.
Owner:DELL PROD LP
Method and apparatus for defining storage infrastructure
InactiveUS20180267713A1Input/output to record carriersFile system administrationStorage managementOperating system
Example implementations are directed to systems and methods for how an application defines storage infrastructure. Such example implementations described herein may be used by application programmers to develop applications quickly and flexibly, without having to communicate with storage administrators to make storage infrastructure changes. In an example implementation, there is an application configured to perform storage management operations that change the storage resources allocated to the application.
Owner:HITACHI LTD
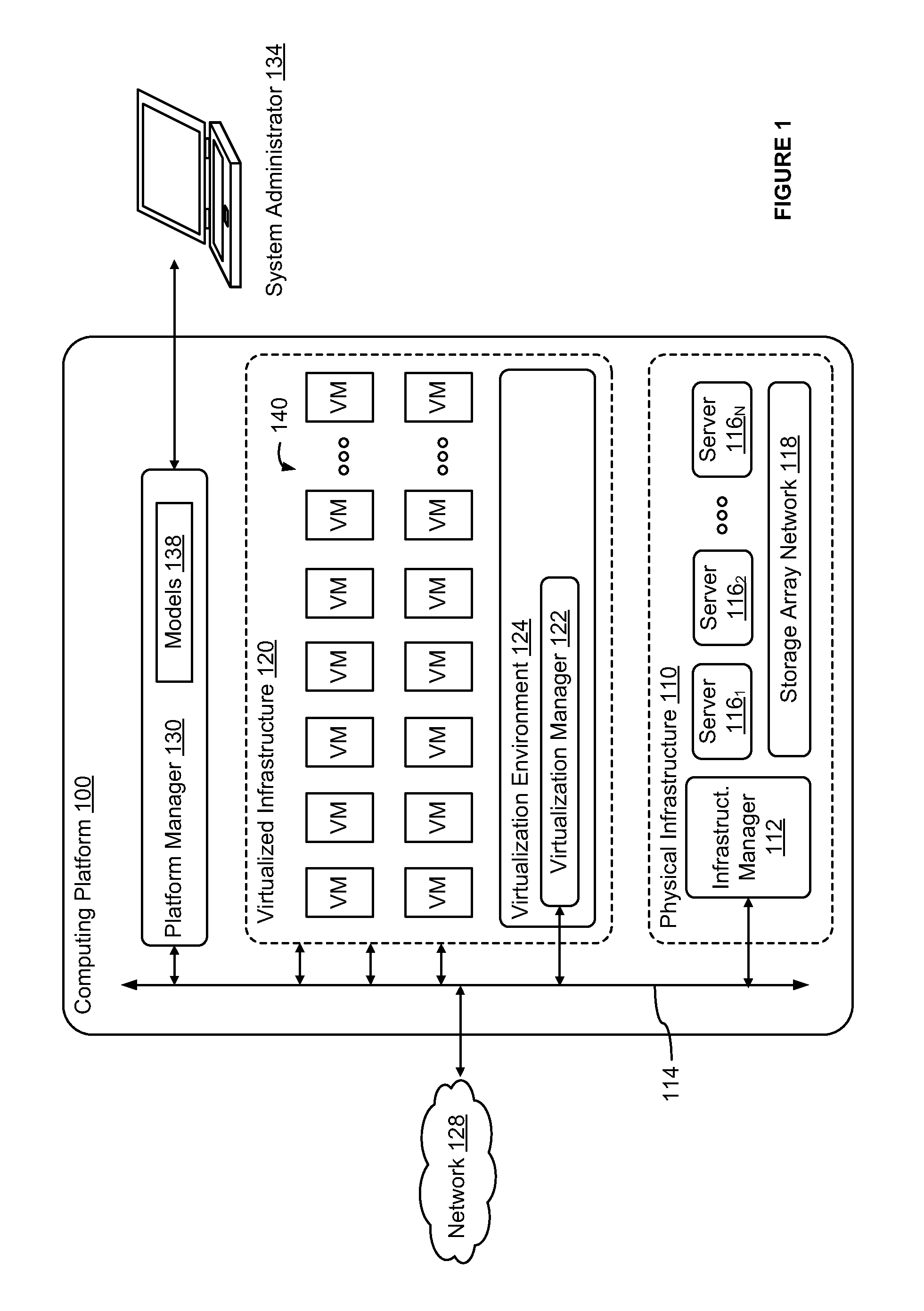
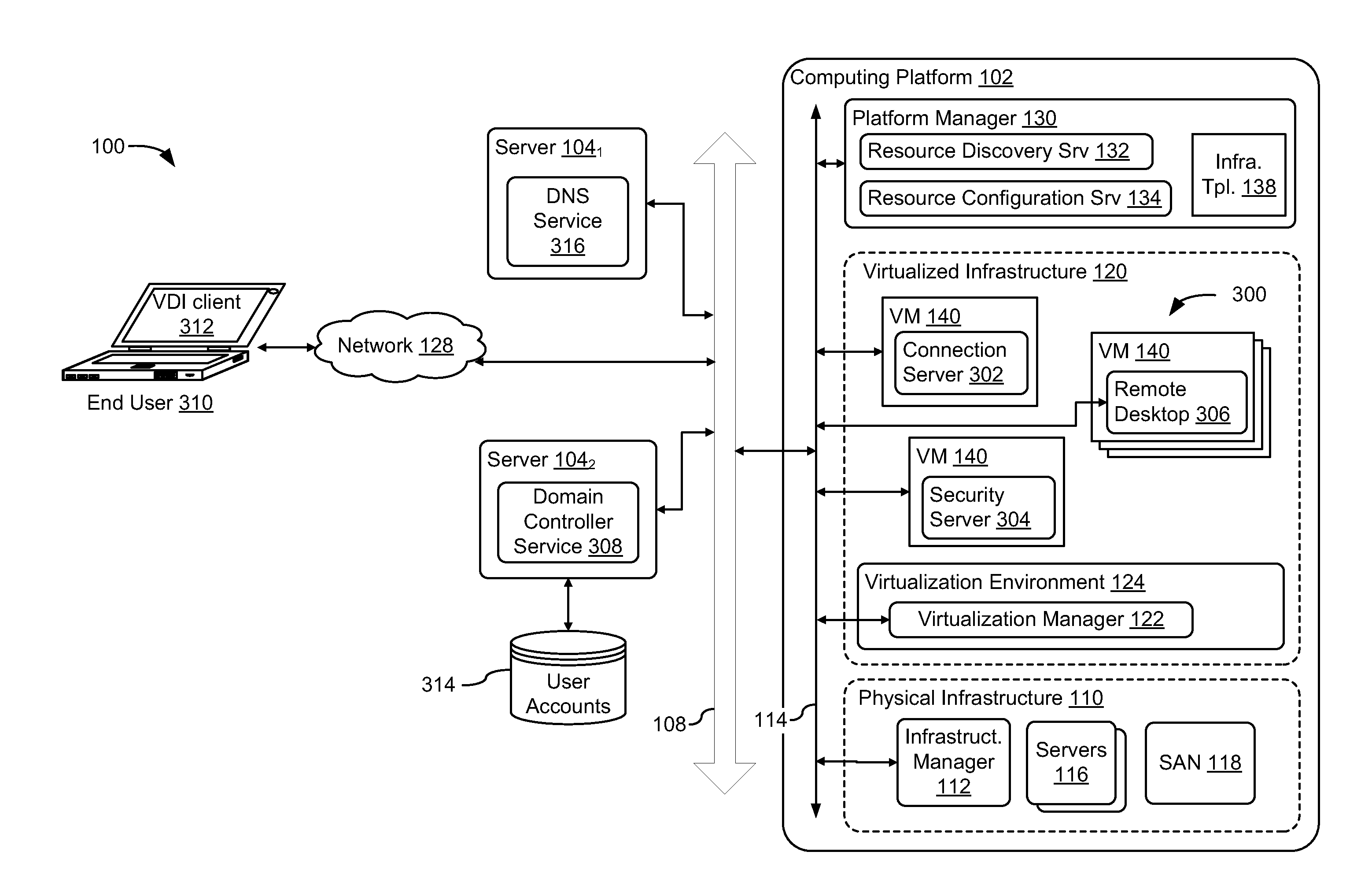
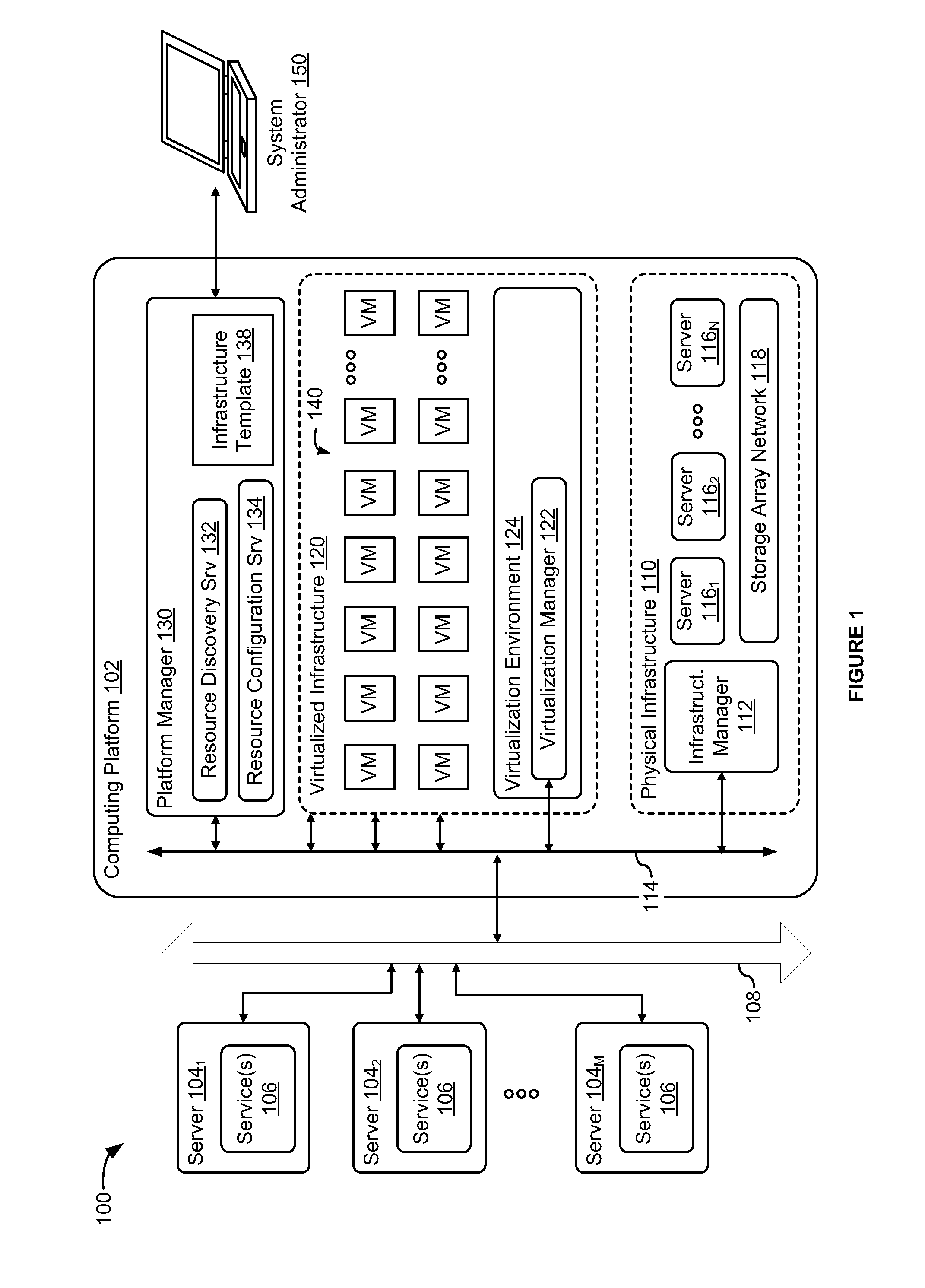
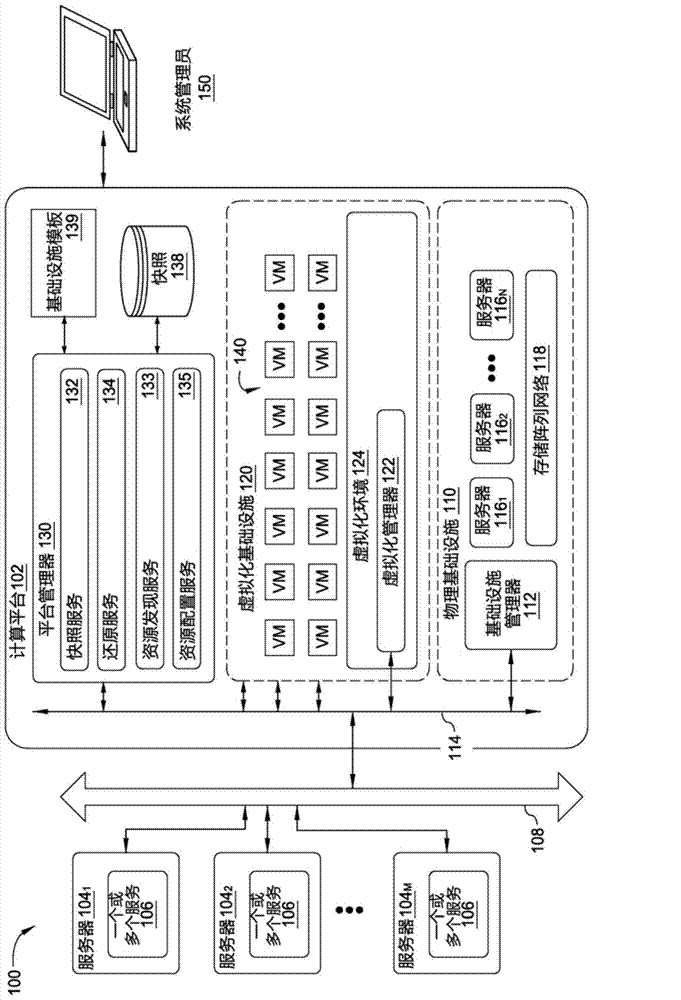
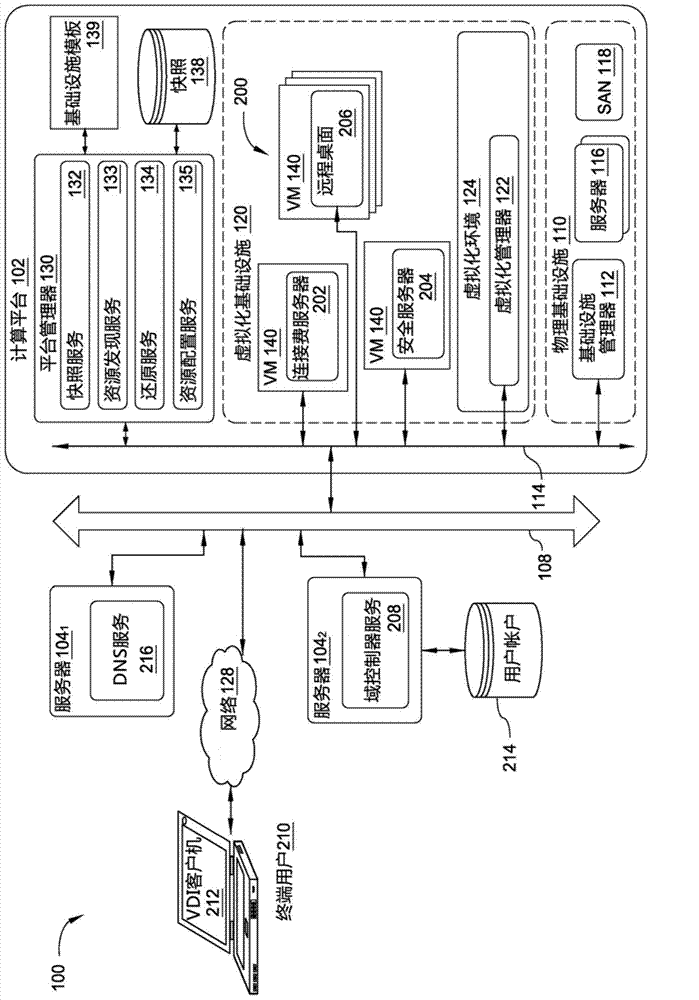
Integrated computing platform deployed in an existing computing environment
A method and apparatus for integrating a converged infrastructure platform in a data center is provided. The described apparatus configures the physical and virtual resources that run on the converged infrastructure to communicate with the rest of the data center. The described apparatus further enables a system administrator to rollback configurations of the physical and virtual resources of the converged infrastructure to restore the converged infrastructure to a factory state.
Owner:云思易有限责任公司
Multi-plane exchange network equipment of converged infrastructure-oriented server
ActiveCN104486256AExtended Network Expansion CapabilitiesIncrease profitData switching networksInformation processingExchange network
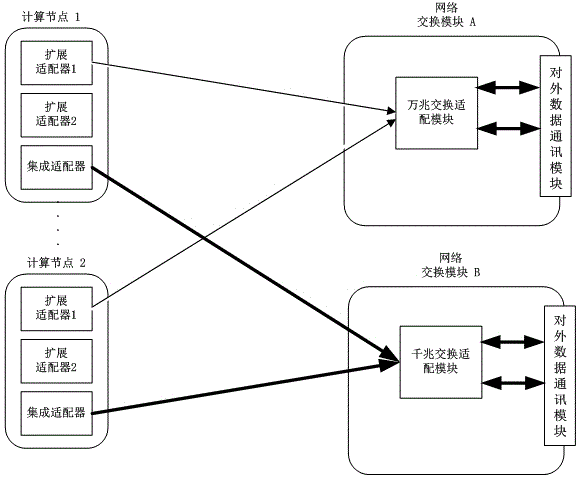
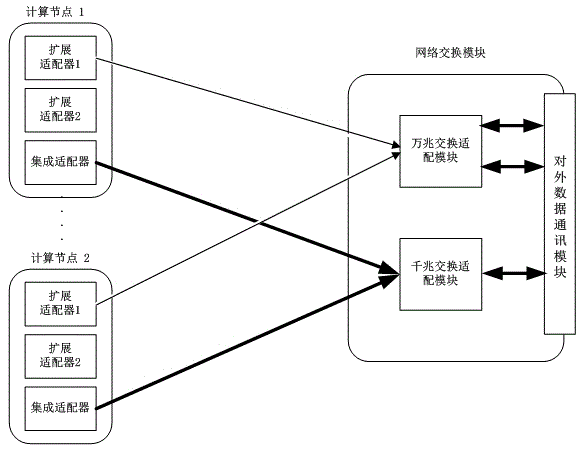
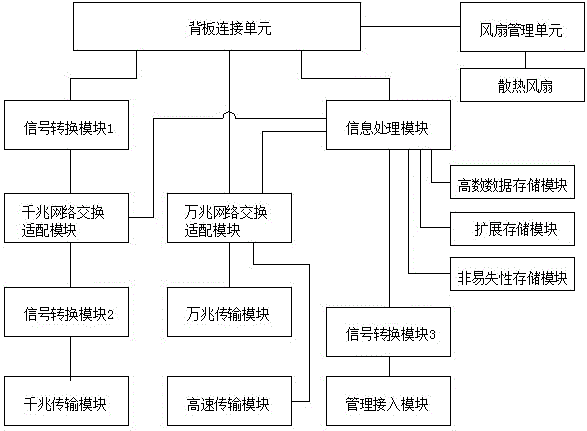
The invention discloses multi-plane exchange network equipment of a converged infrastructure-oriented server, and provides a converged exchange module capable of supporting multi-network plane exchange. The converged exchange module comprises an information processing module, a signal conversion module, a network exchange module and a backboard connection unit, wherein the information processing module interacts with the network exchange module; a kilomega network exchange adapter module and a 10-gigabit network exchange adapter module are integrated in the network exchange module; the kilomega network exchange adapter module is connected with an integrated adapter of a computational node via the backboard; the 10-gigabit network exchange adapter module is connected with an expansion adapter of the computational node via the backboard connection unit. A low-speed network and a high-speed network can be simultaneously or independently supported on the same exchange module, and are separated, a data path bandwidth between the computational node and the exchange network is widened, the use ratio of the network equipment is effectively improved, and the application and management cost of a client is simplified.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Security evaluating and detecting method used for cloud infrastructure
ActiveCN104735063AImprove utilization efficiencyReduce unnecessary occupationTransmissionDevice formComputer module
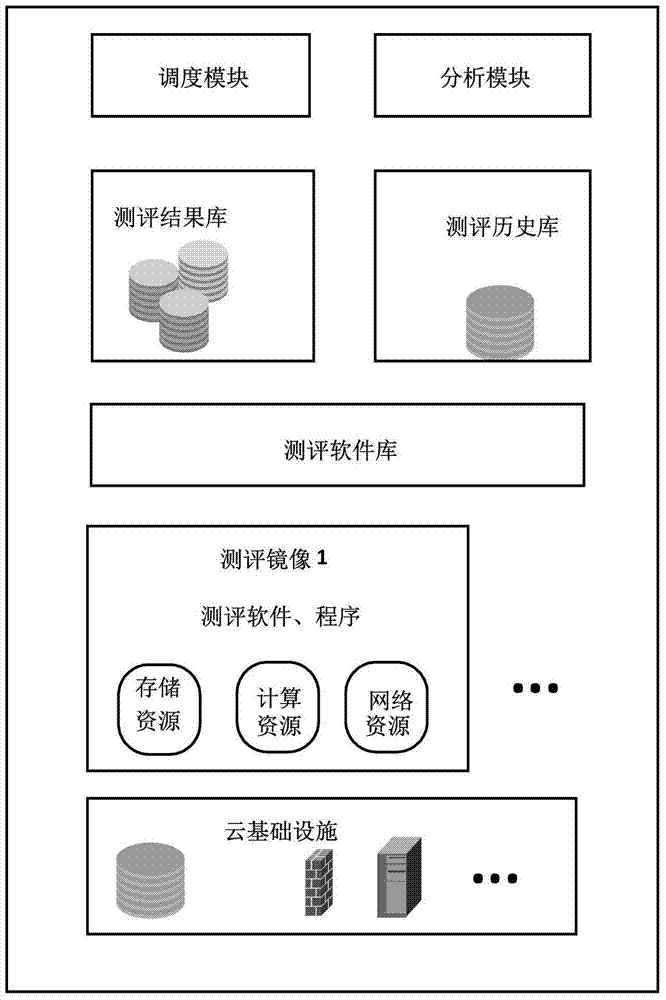
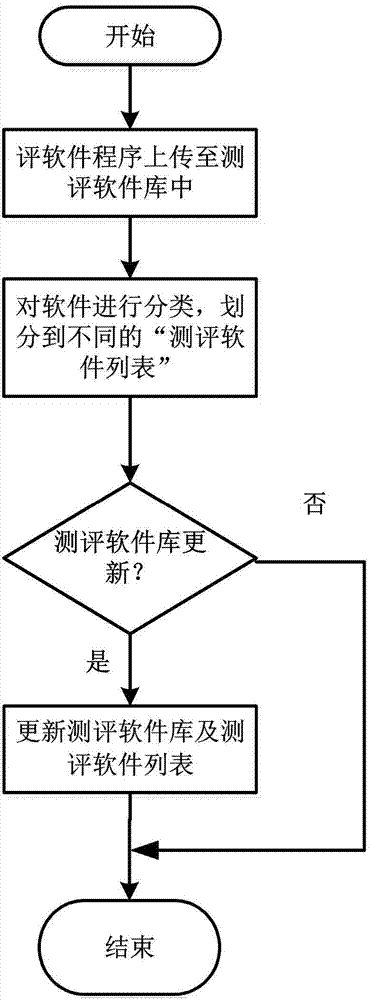
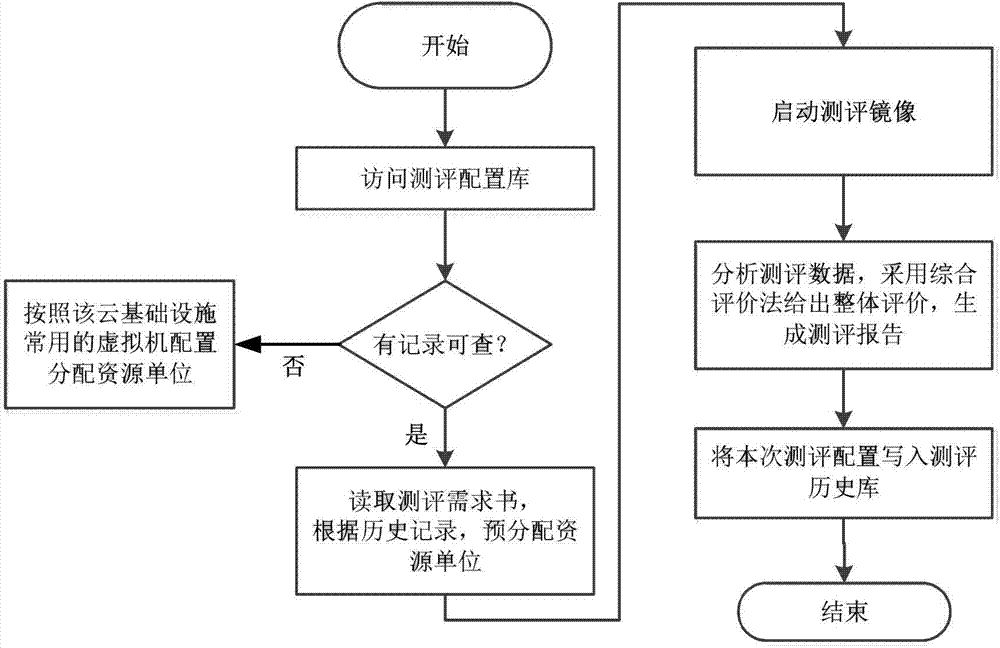
The invention relates to the technical field of the information security, in particular to a security evaluating and detecting method used for a cloud infrastructure. The method is completed by a device formed by a dispatching module, a testing software library, a testing mirror, a testing configuration library, a testing result library, an analysis module, a testing requirement docment, a testing report and other modules. Configuration operating is carried out on the testing software library by a user in advance before testing; security testing software which exists in the market and aims at the cloud infrastructure and independently programmed testing software programs are uploaded to the testing software library; classification is carried out on the software according to the usual classification, namely the system security, the network security, the data security, the behavior security and the like, and the software is partitioned to different 'testing software lists'; the testing software library can be continuously updated, and the advancement and the maturity of the testing software are guaranteed. The problem of compatibility of the information security testing method and the cloud calculation is solved, and the method can be used for security evaluating and testing of the cloud infrastructure.
Owner:GUANGDONG ELECTRONICS IND INST
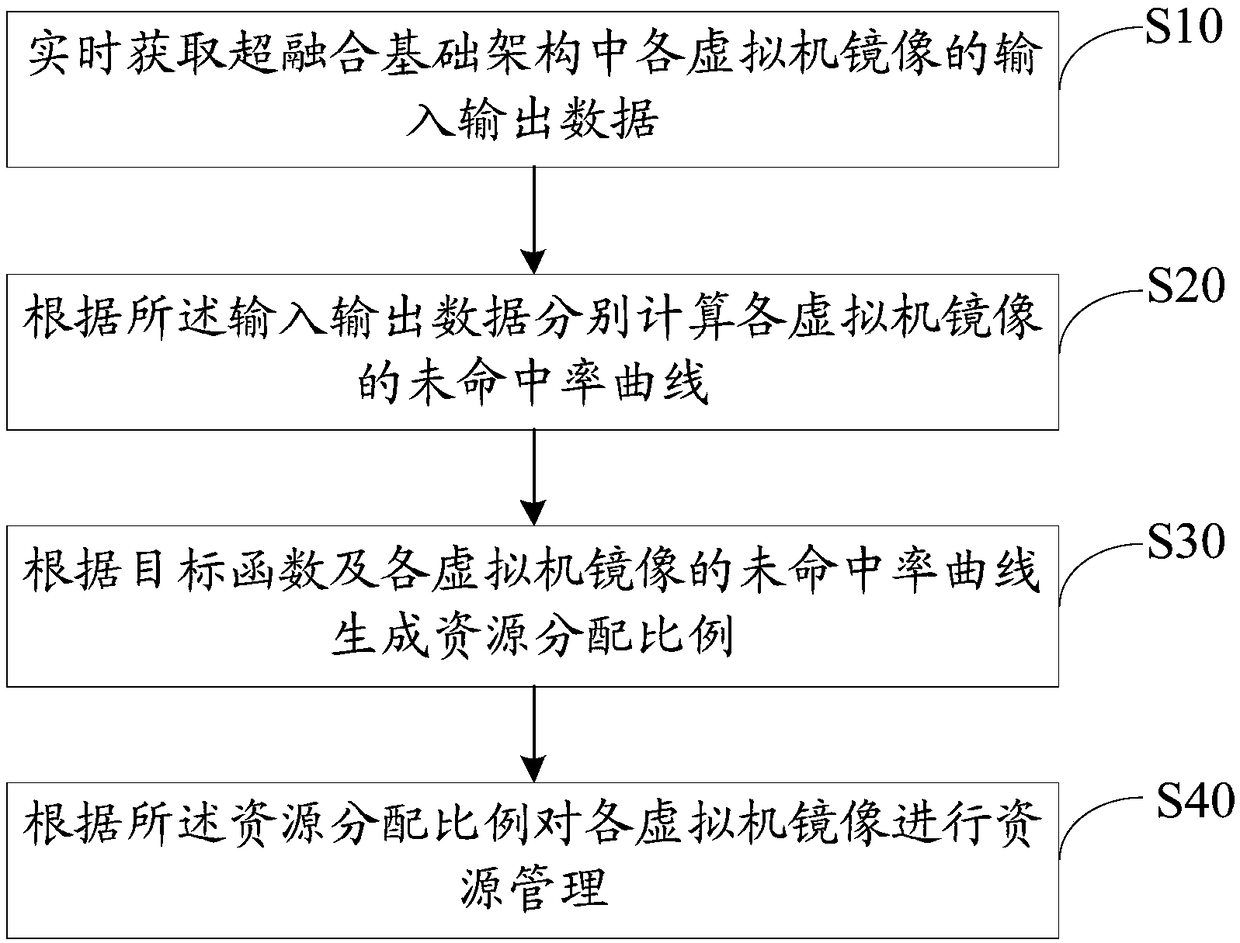
Hierarchical resource management method, device and system for hyper-converged infrastructure
ActiveCN108073457AReach resourcesTo achieve the purpose of maximizing storage performanceResource allocationSoftware simulation/interpretation/emulationResource isolationResource management
The invention discloses a hierarchical resource management method, device and system for a hyper-converged infrastructure and a computer readable storage medium. According to the hierarchical resourcemanagement method, device and system, input and output data of each virtual machine image in the hyper-converged infrastructure is obtained in real time, and then a miss rate curve of each virtual machine image is calculated according to the input and output data; the miss rate curve can represent hierarchical resource usage efficiency of the virtual machine image; an appropriate resource allocation proportion is generated according to an objective function generated in real time and the miss rate curve of each virtual machine image; finally resource management is performed on each virtual machine image according to the resource allocation proportion, appropriate hierarchical resources are distributed for different virtual machine images intelligently, to achieve the goal of resource isolation and storage performance maximization, and the storage performance and service quality can be improved without significantly increasing memory and computing overhead.
Owner:SANGFOR TECH INC
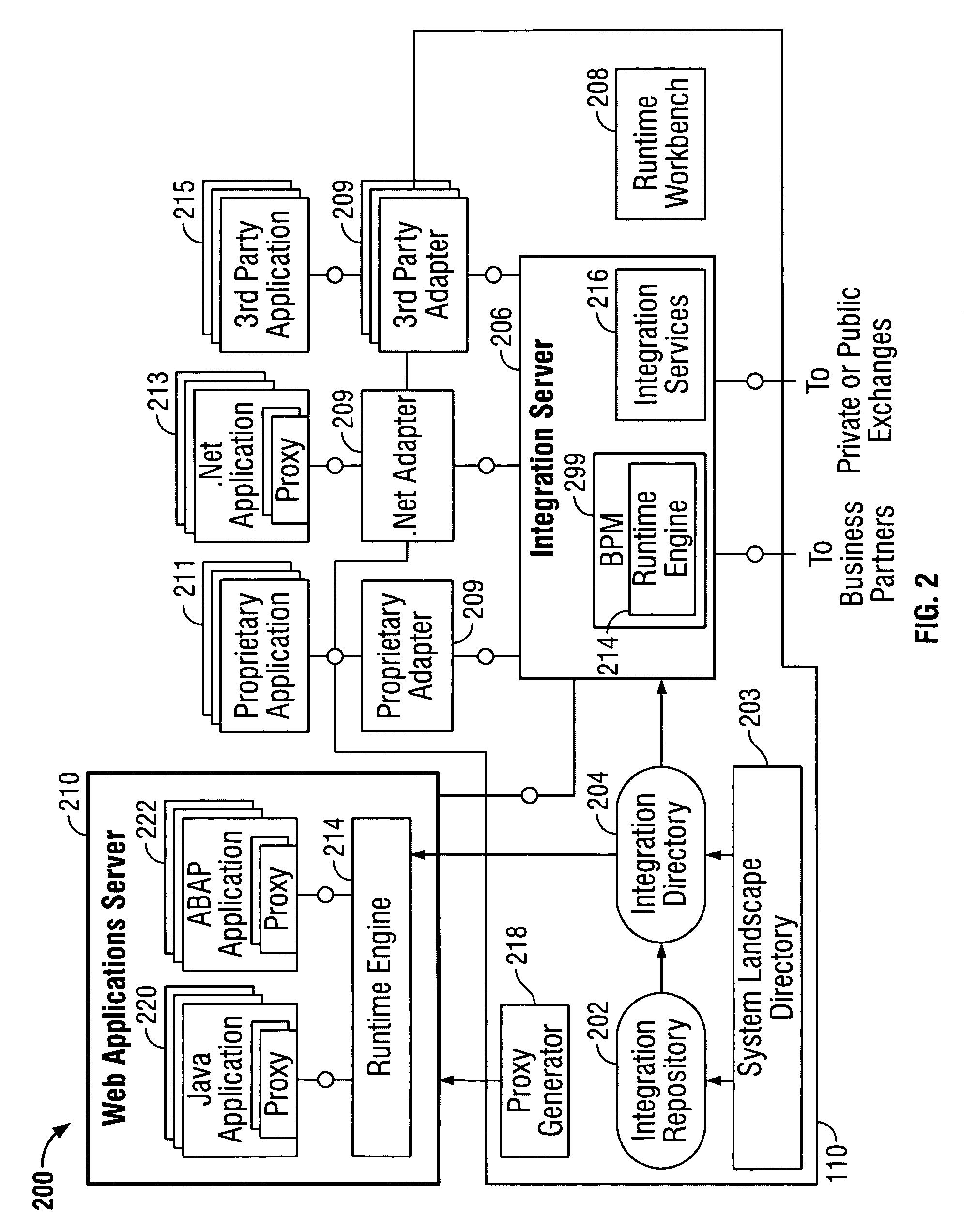
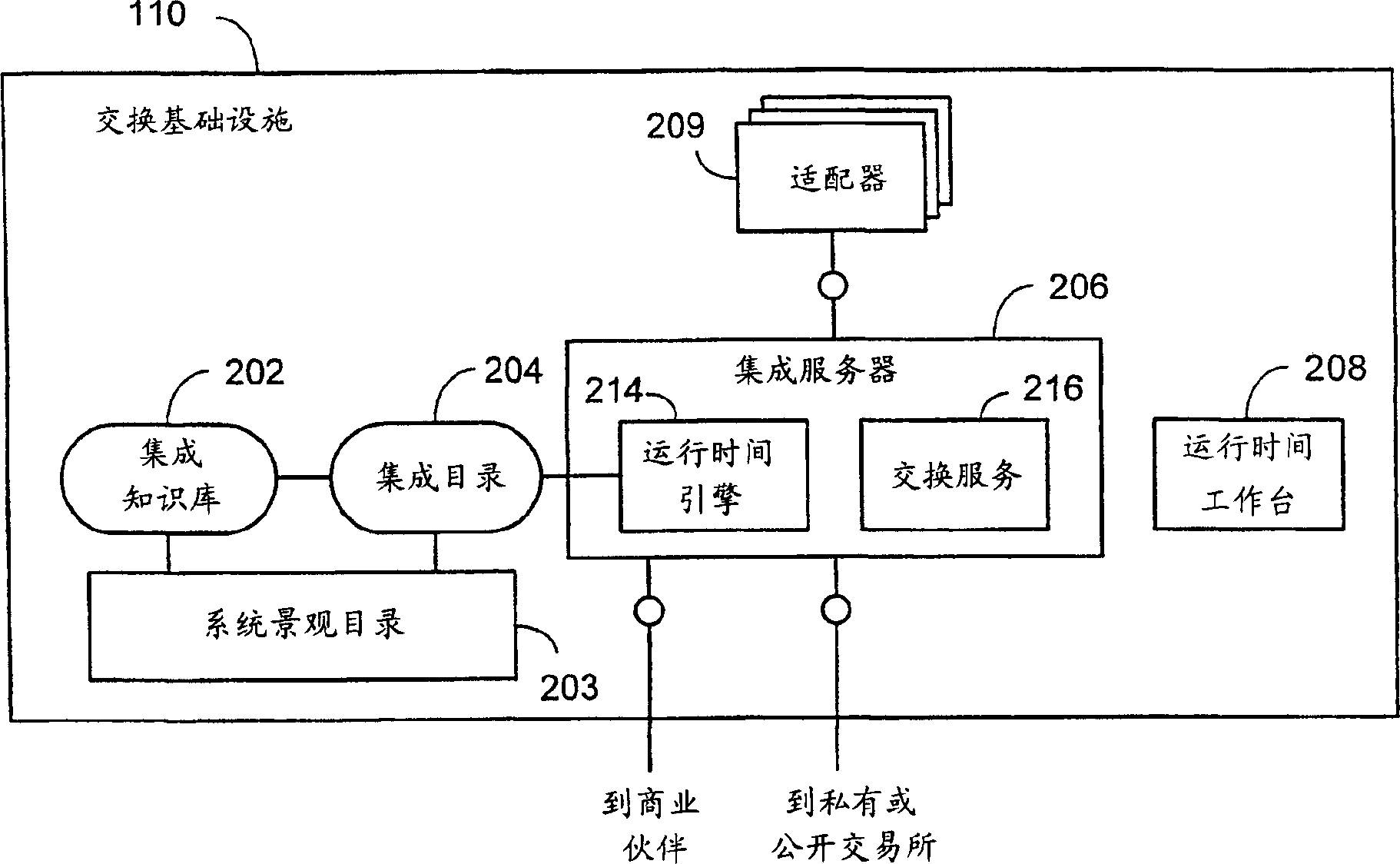
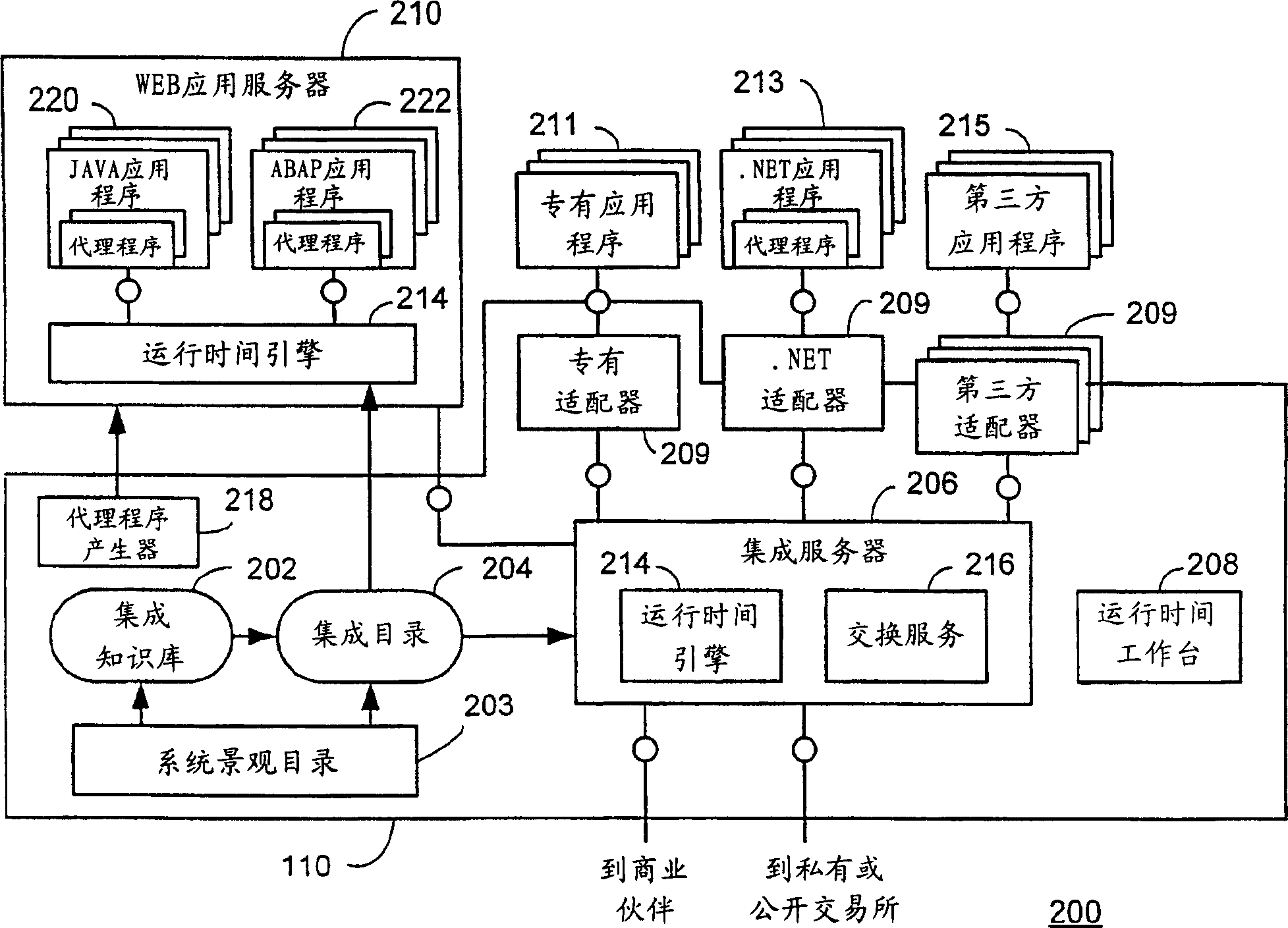
Exchange infrastructure system and method
An exchange infrastructure for message-based exchange and integration of a collection of heterogeneous software components is disclosed. The exchange infrastructure includes a repository for storing design-time collaboration descriptions of a plurality of software components, and a directory for storing configuration-specific collaboration descriptions of a runtime system landscape. The exchange infrastructure further includes a runtime engine configured for message-based exchange of information based on the configuration-specific collaboration descriptions. At runtime, the runtime engine receives messages, and resolves intended or required receivers based on message content and parameters provided by the configuration-specific collaboration descriptions from the directory.
Owner:SAP AG
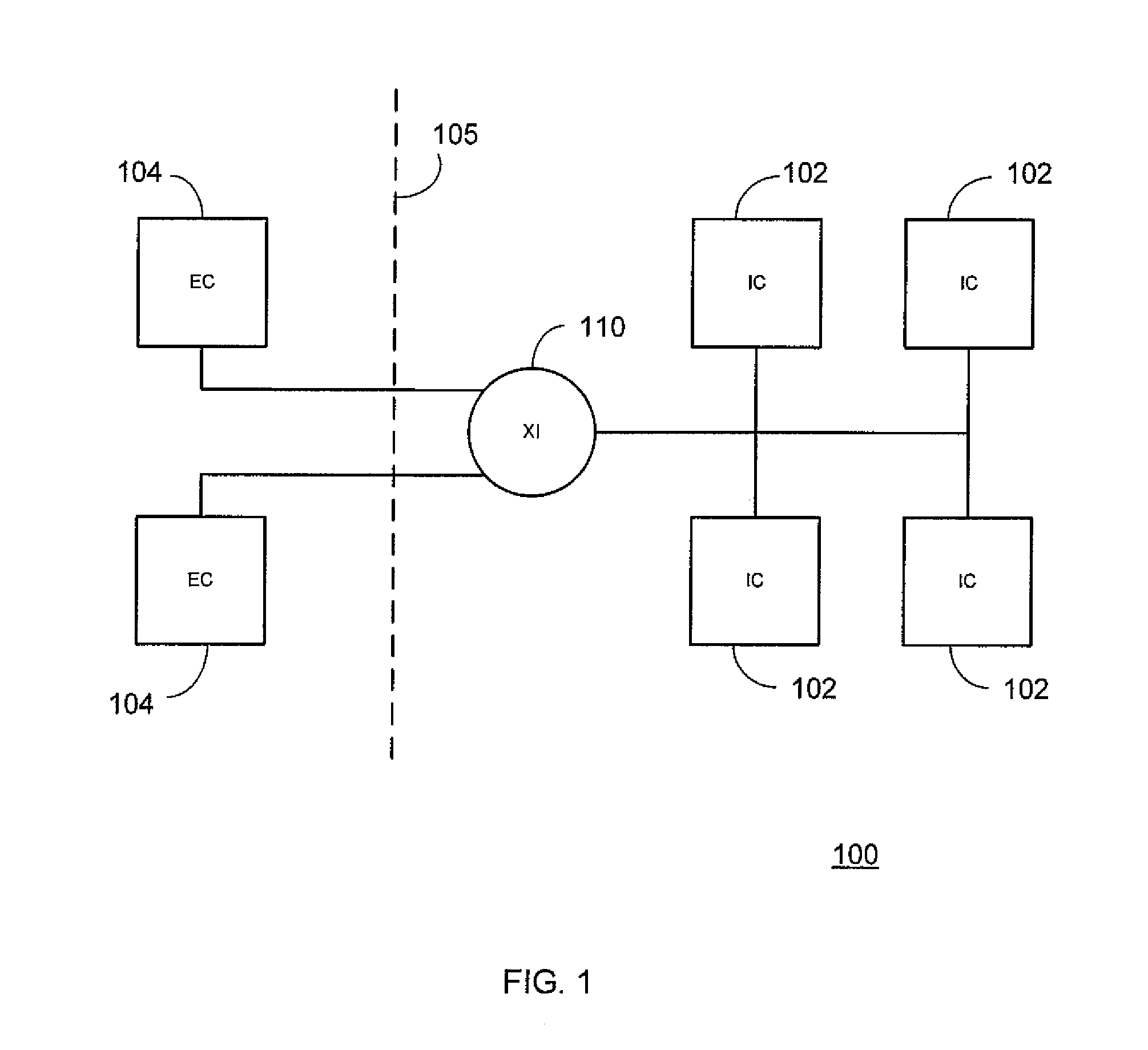
Exchange infrastructure system and method
An exchange infrastructure for message-based exchange and integration of a collection of heterogeneous software components is disclosed. The exchange infrastructure includes a repository for storing design-time collaboration descriptions of a plurality of software components, and a directory for storing configuration-specific collaboration descriptions of a runtime system landscape. The exchange infrastructure further includes a runtime engine configured for message-based exchange of information based on the configuration-specific collaboration descriptions. At runtime, the runtime engine receives messages, and resolves intended or required receivers based on message content and parameters provided by the configuration-specific collaboration descriptions from the directory.
Owner:SAP AG
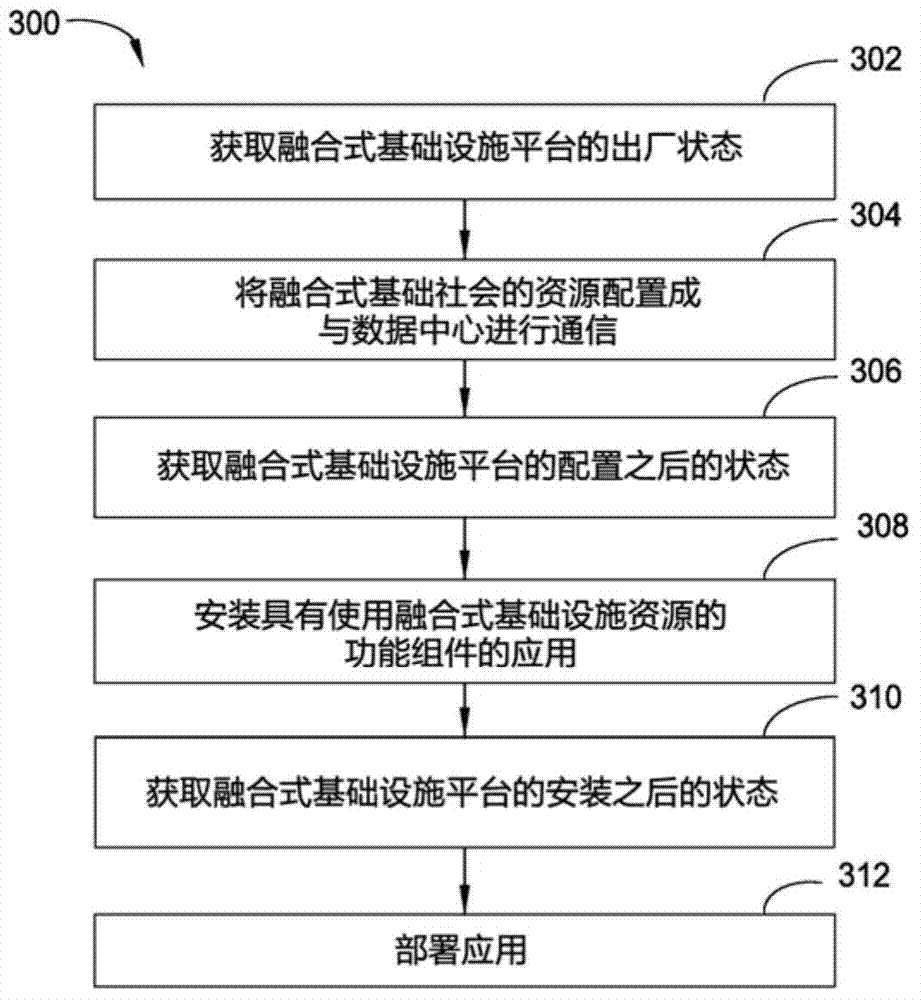
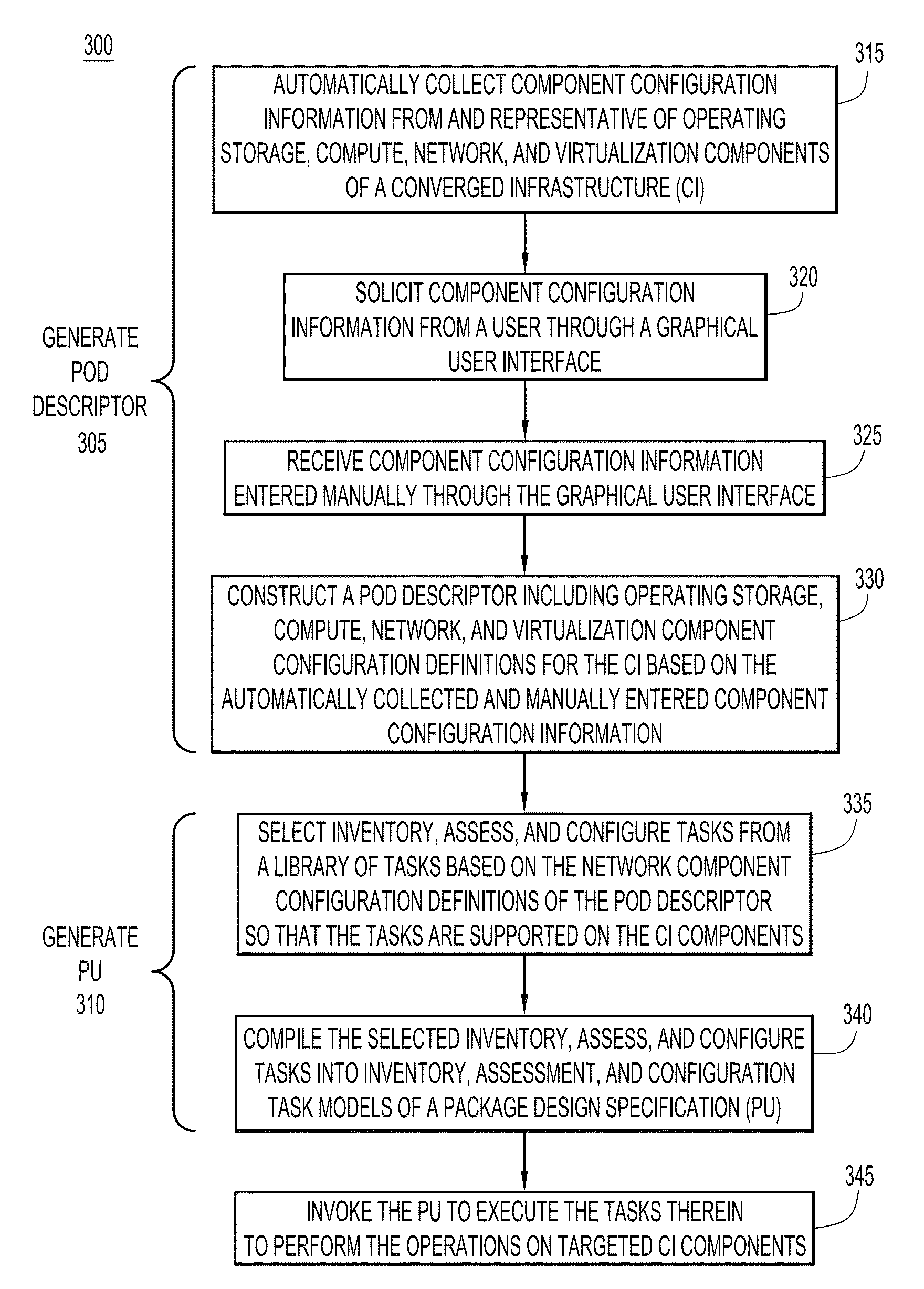
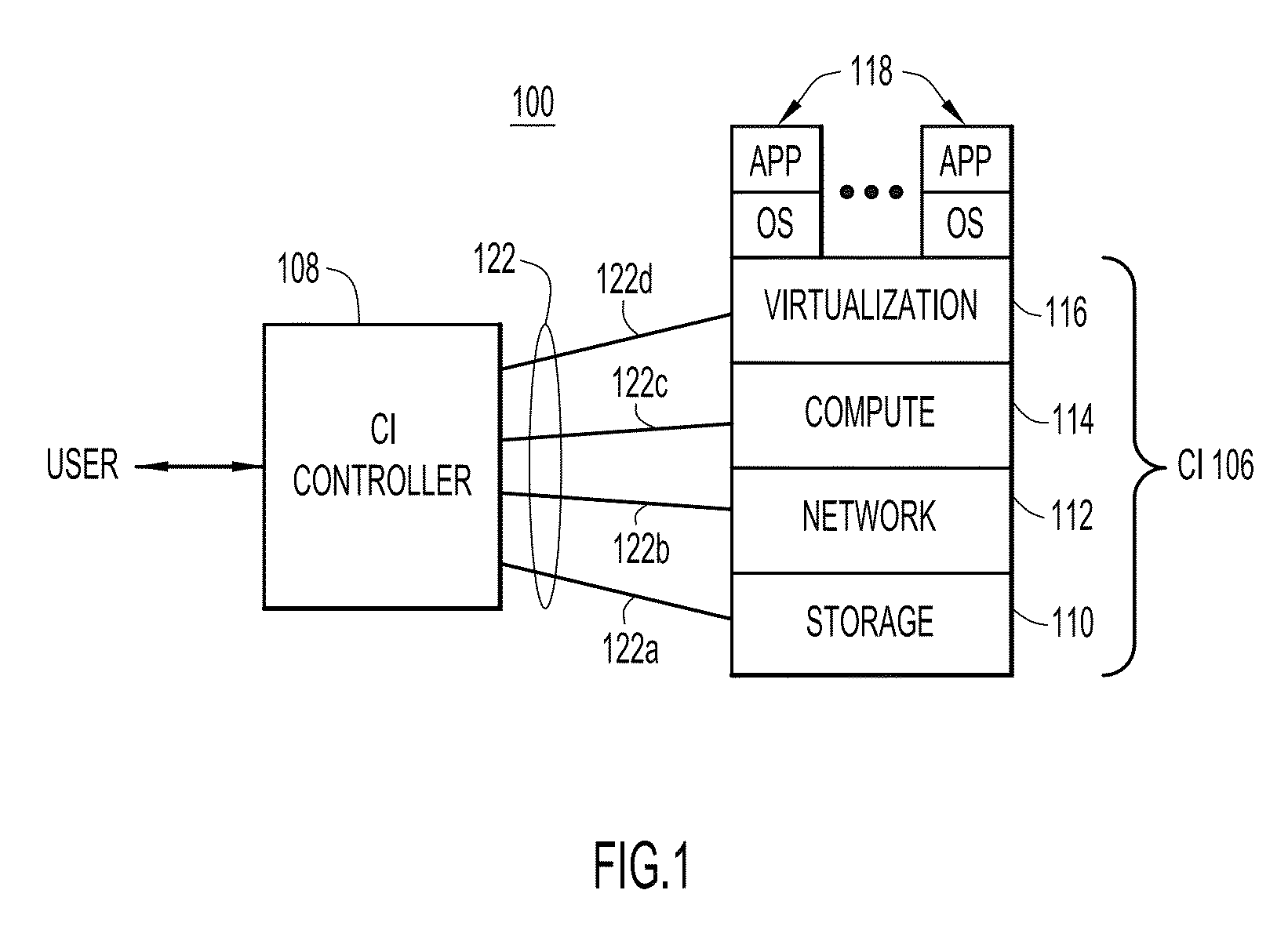
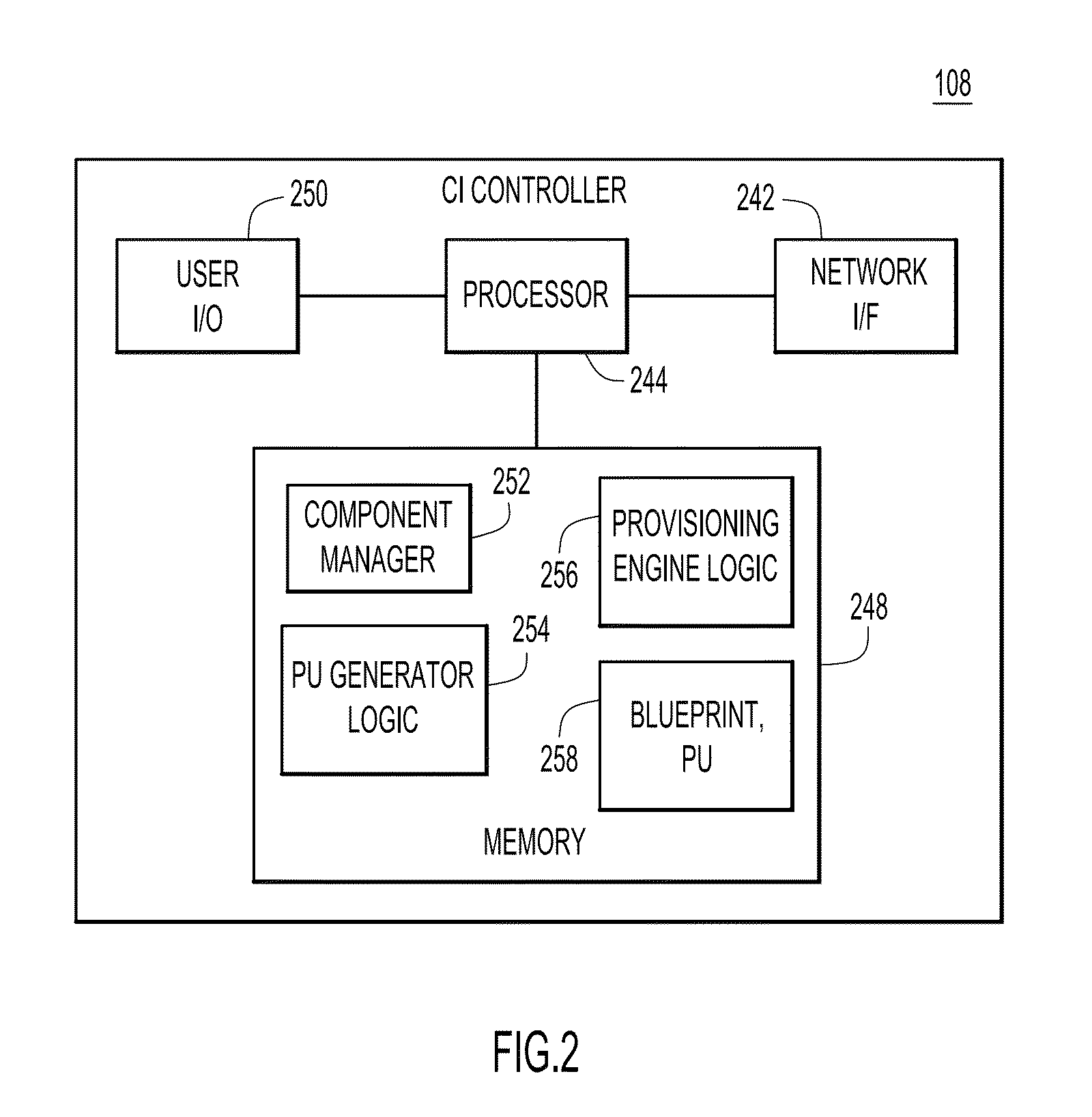
Automated techniques to deploy a converged infrastructure having unknown initial component configurations
A technique to adaptively configure components of a converged infrastructure (CI). Component configuration information is collected from and representative of operating storage, compute, and network components of the CI. A pod descriptor is constructed from the collected information. The pod descriptor includes operating storage, compute, and network component configuration definitions for the CI based on the collected component configuration information. A package specification unit is generated based on the component configuration definitions of the pod descriptor. The package specification unit includes tasks that, when executed, automatically inventory, assess, and configure targeted ones of the CI components. The technique executes the tasks in the package specification unit to perform corresponding operations on targeted ones of the CI components.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com