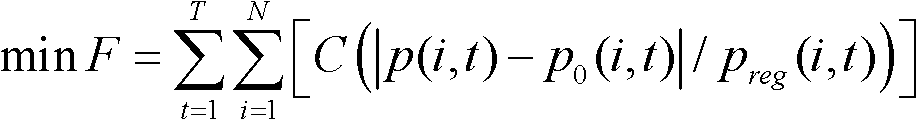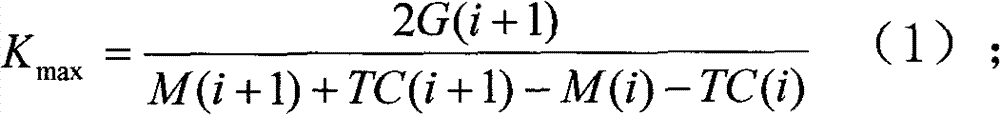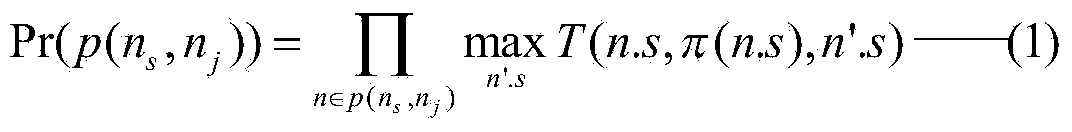Patents
Literature
48 results about "Execution planning" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Execution planning. The phase of the Joint Operation Planning and Execution System crisis action planning process that provides for the translation of an approved course of action into an executable plan of action through the preparation of a complete operation plan or operation order.
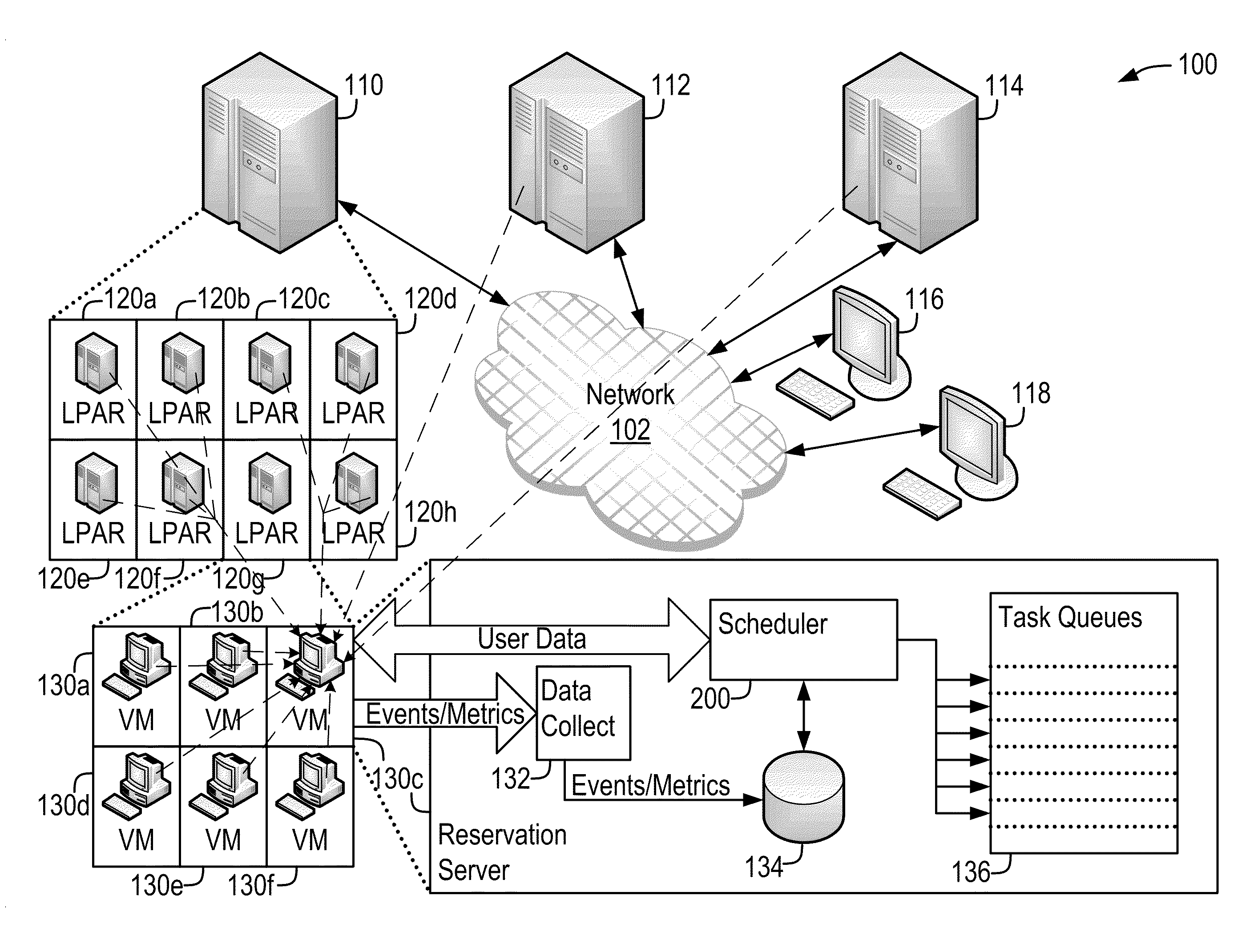
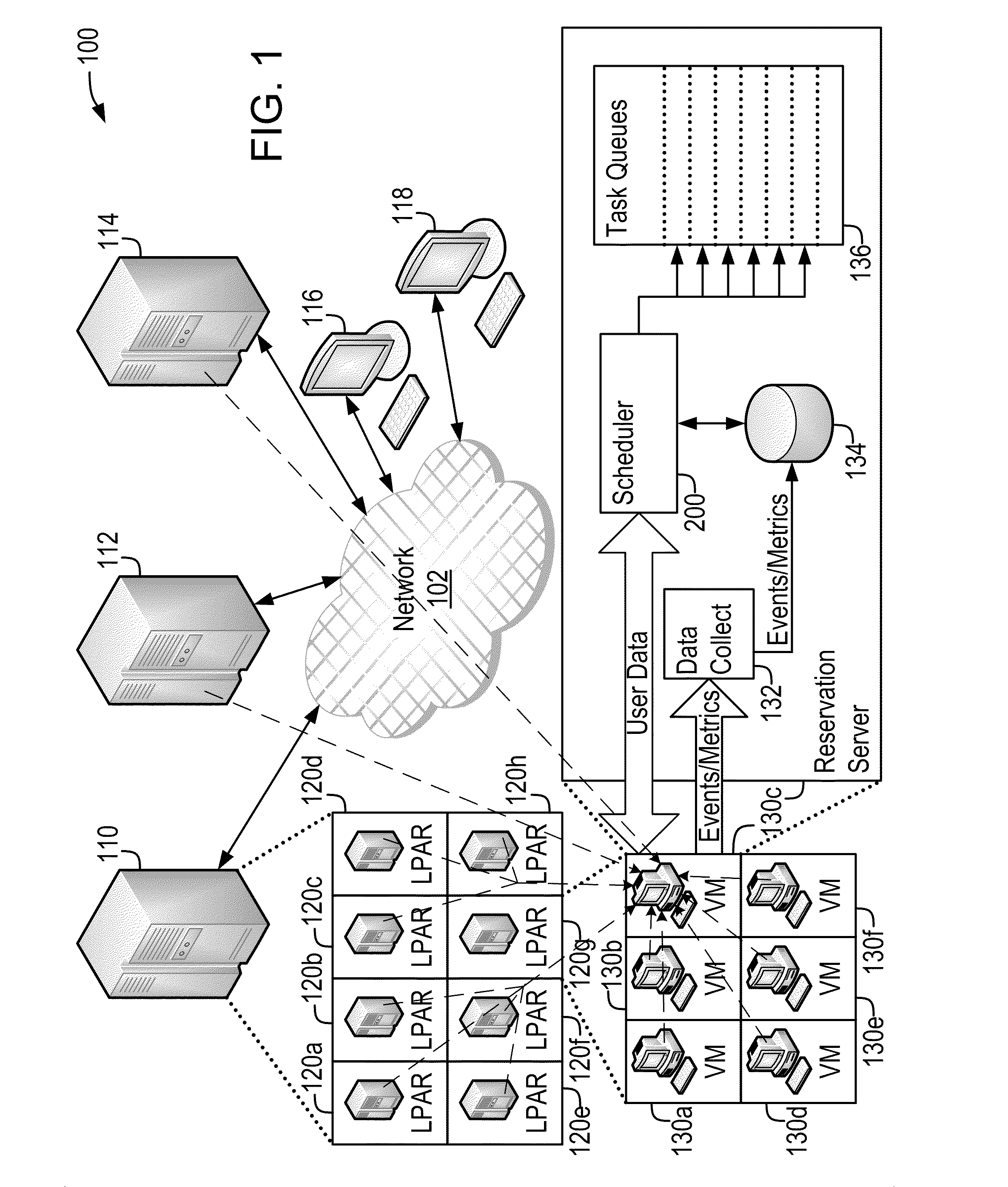
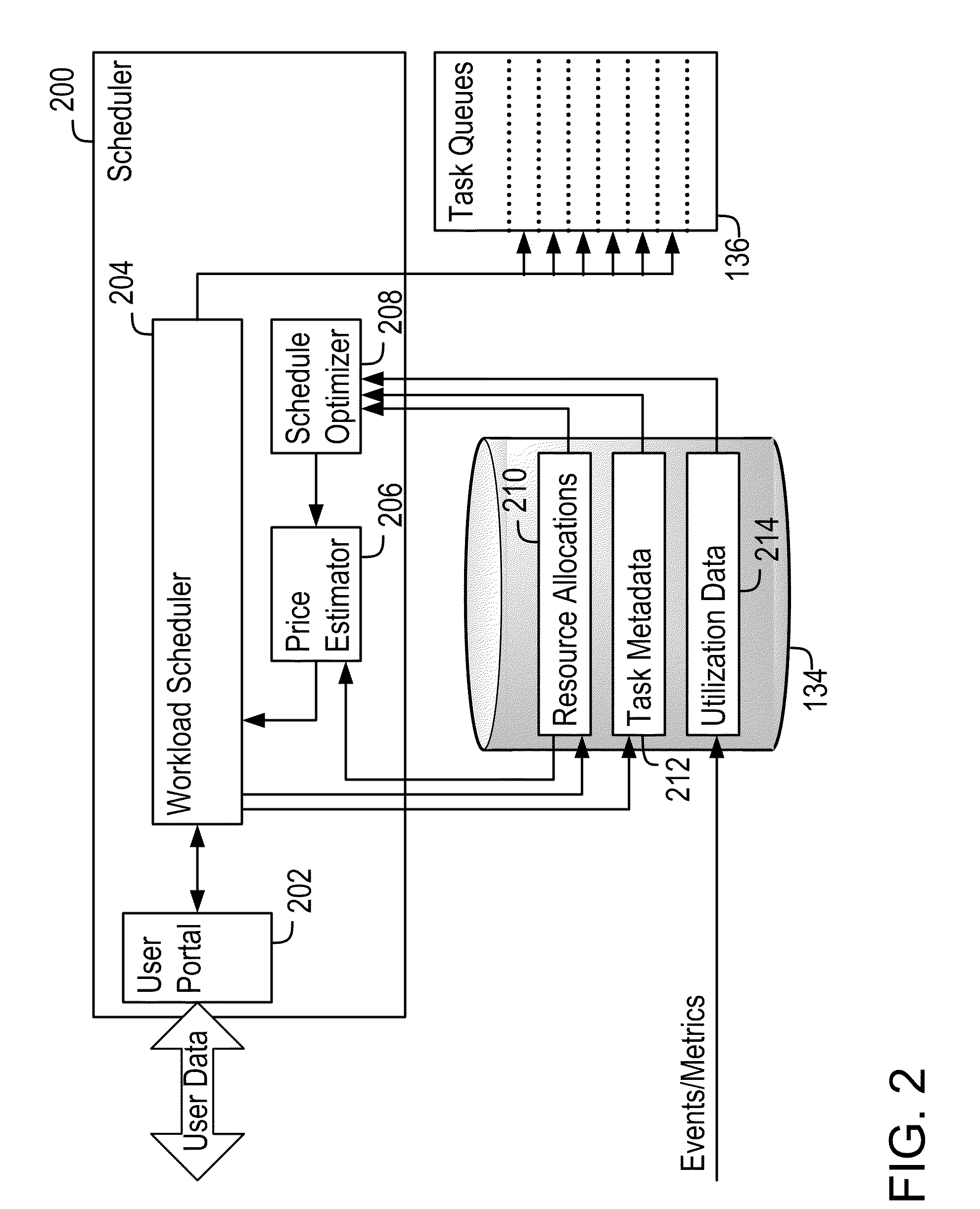
Demand-Driven Workload Scheduling Optimization on Shared Computing Resources
InactiveUS20110154353A1Low costHinder taskResource allocationMemory systemsTime scheduleProgram planning
Systems and methods implementing a demand-driven workload scheduling optimization of shared resources used to execute tasks submitted to a computer system are disclosed. Some embodiments include a method for demand-driven computer system resource optimization that includes receiving a request to execute a task (said request including the task's required execution time and resource requirements), selecting a prospective execution schedule meeting the required execution time and a computer system resource meeting the resource requirement, determining (in response to the request) a task execution price for using the computer system resource according to the prospective execution schedule, and scheduling the task to execute using the computer system resource according to the prospective execution schedule if the price is accepted. The price varies as a function of availability of the computer system resource at times corresponding to the prospective execution schedule, said availability being measured at the time the price is determined.
Owner:BMC SOFTWARE
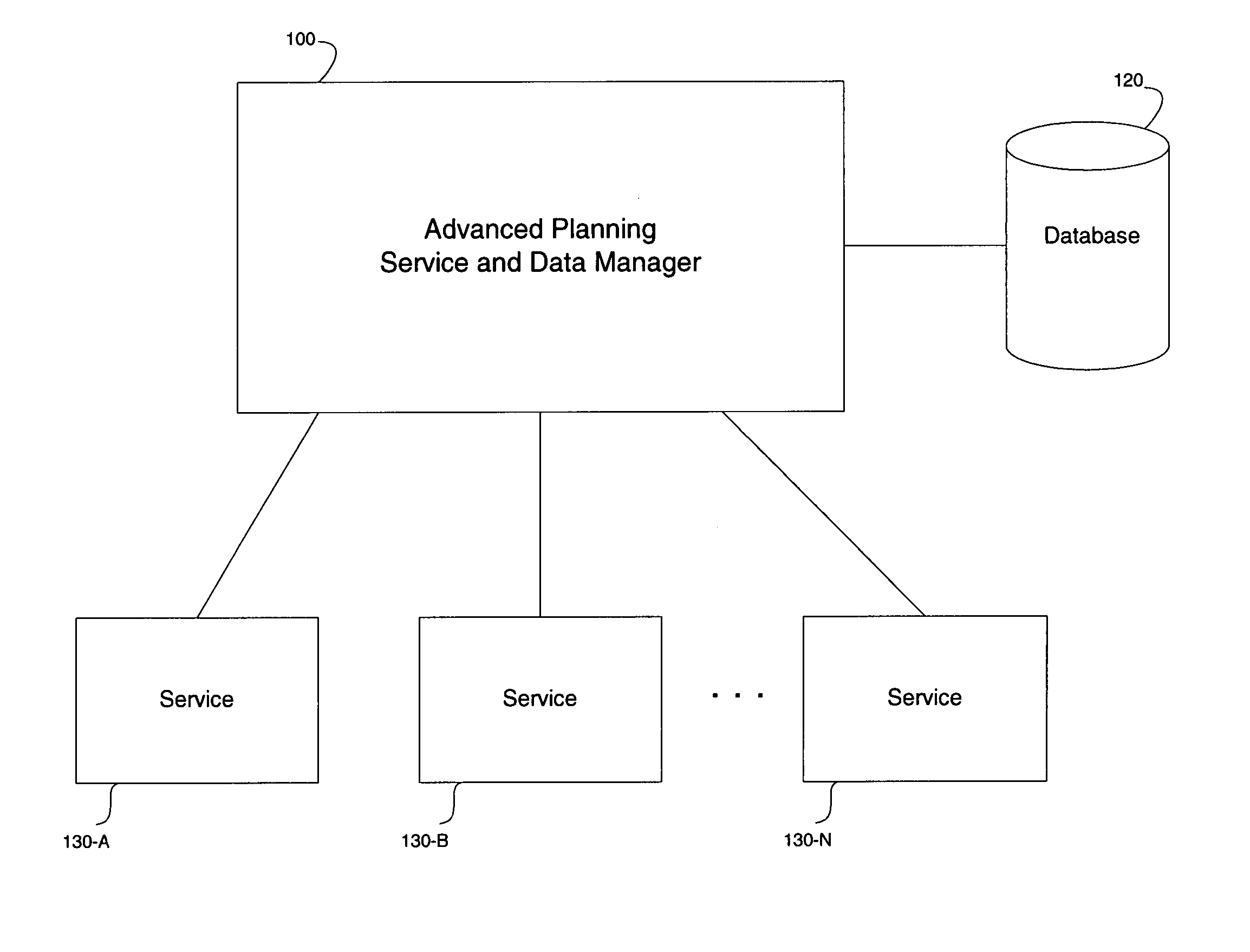
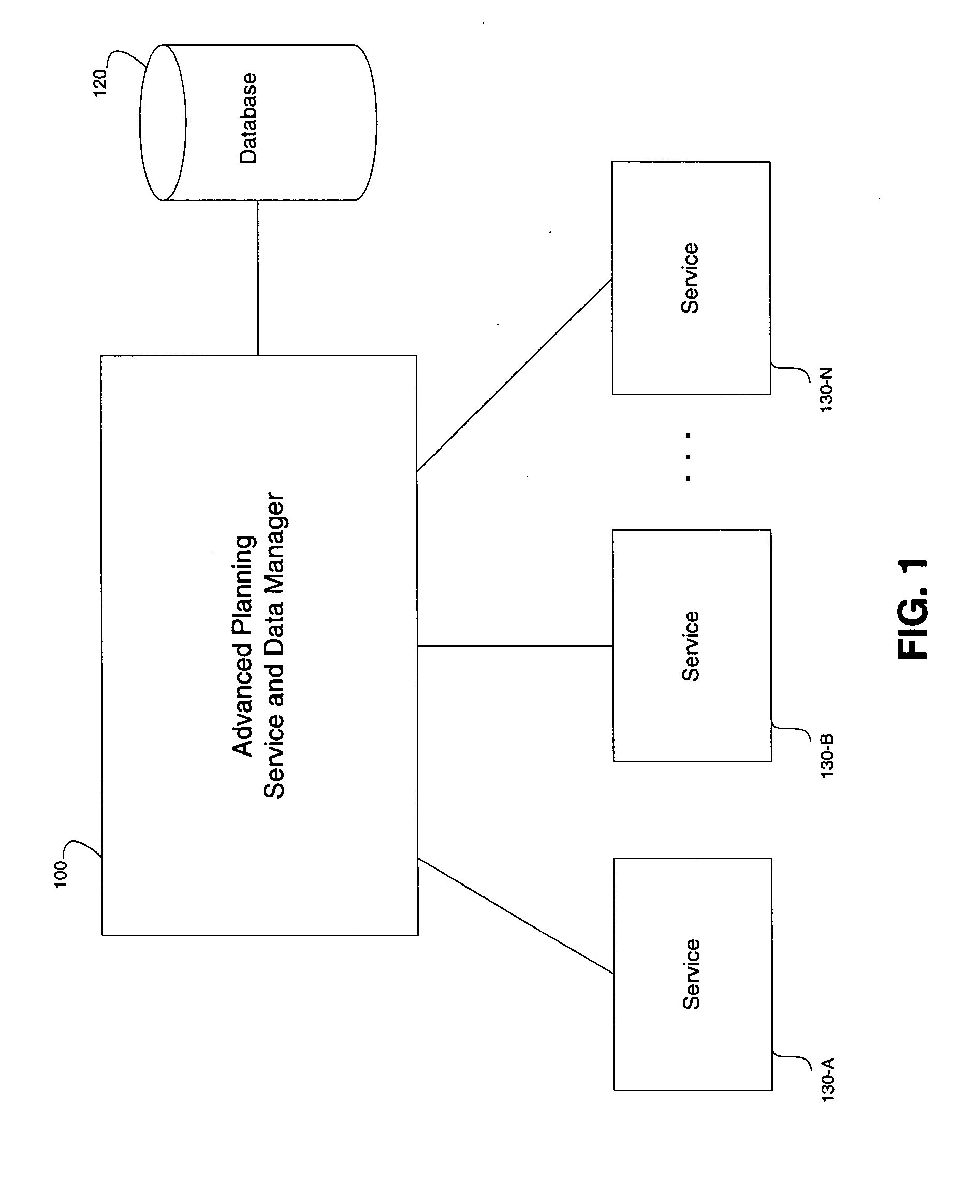
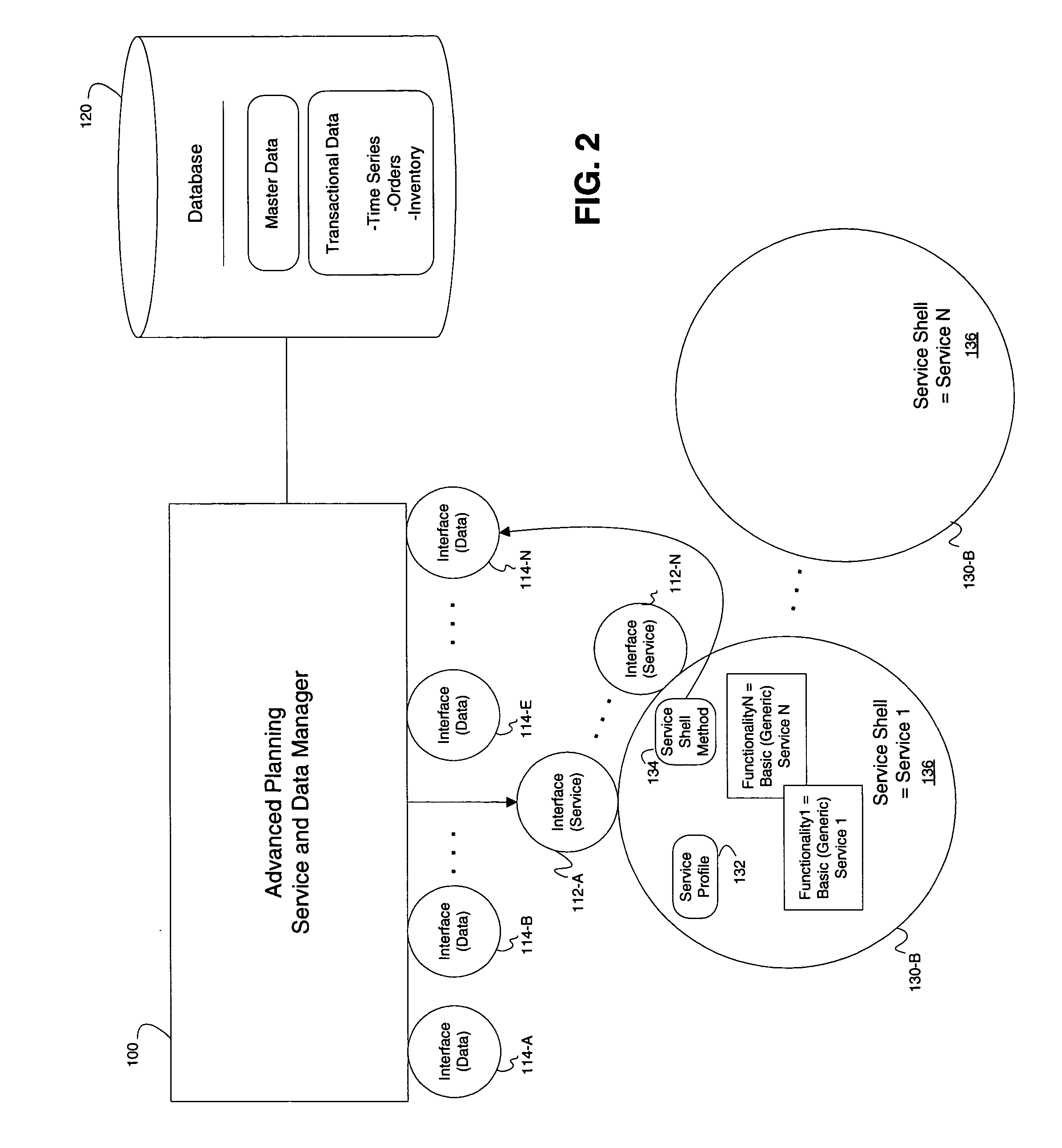
Systems and methods for executing planning services
Systems and methods are disclosed for executing services in an advanced planning environment. The services may comprise planning service that are executed using one or more objects stored in a database. Further, a planning profile may be provided, the planning profile including at least one process block containing a list of planning services to be executed. A method for executing services may include reading the planning profile, including a selection profile of the at least one process block of the planning profile. The selection profile may comprise selection criteria for specifying which of the objects stored in the database are required for processing the at least one process block. Further, the method may include accessing the objects stored in the database based on the selection criteria of the selection profile, and executing each planning service in accordance with the list of planning services and the objects accessed from the database.
Owner:SAP AG
State-based configuration management for distributed systems
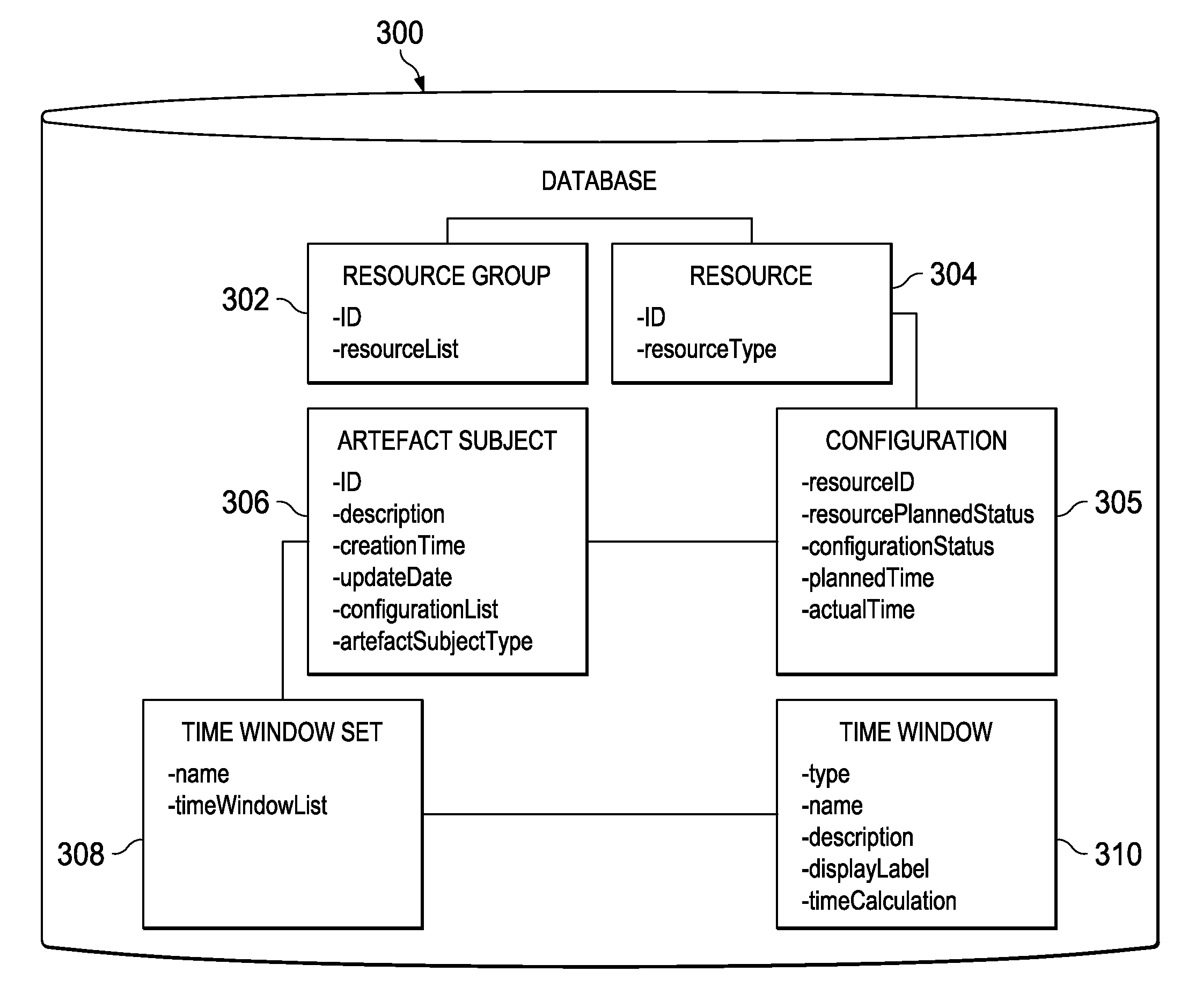
An electronic system is provided for facilitating configuration management of a service or application distributed over a plurality of nodes that can be in single datacenter or network or span multiple ones The system includes a receiver for receiving a system model, a reasoner, and a workflow engine. The reasoner automatically processes the system model received by the receiver to produce an executable plan for the distributed service. The workflow engine includes a temporal sequencer for dispatching commands to the nodes to carry out the executable plan in a temporally coordinated manner, thereby providing the distributed service. Also provided is a method for facilitating configuration management of a distributed service.
Owner:REACTOR8
Network resource configurations
ActiveUS20120290715A1Improve performanceSave capacityDigital computer detailsHybrid transportTime rangeNon compliance
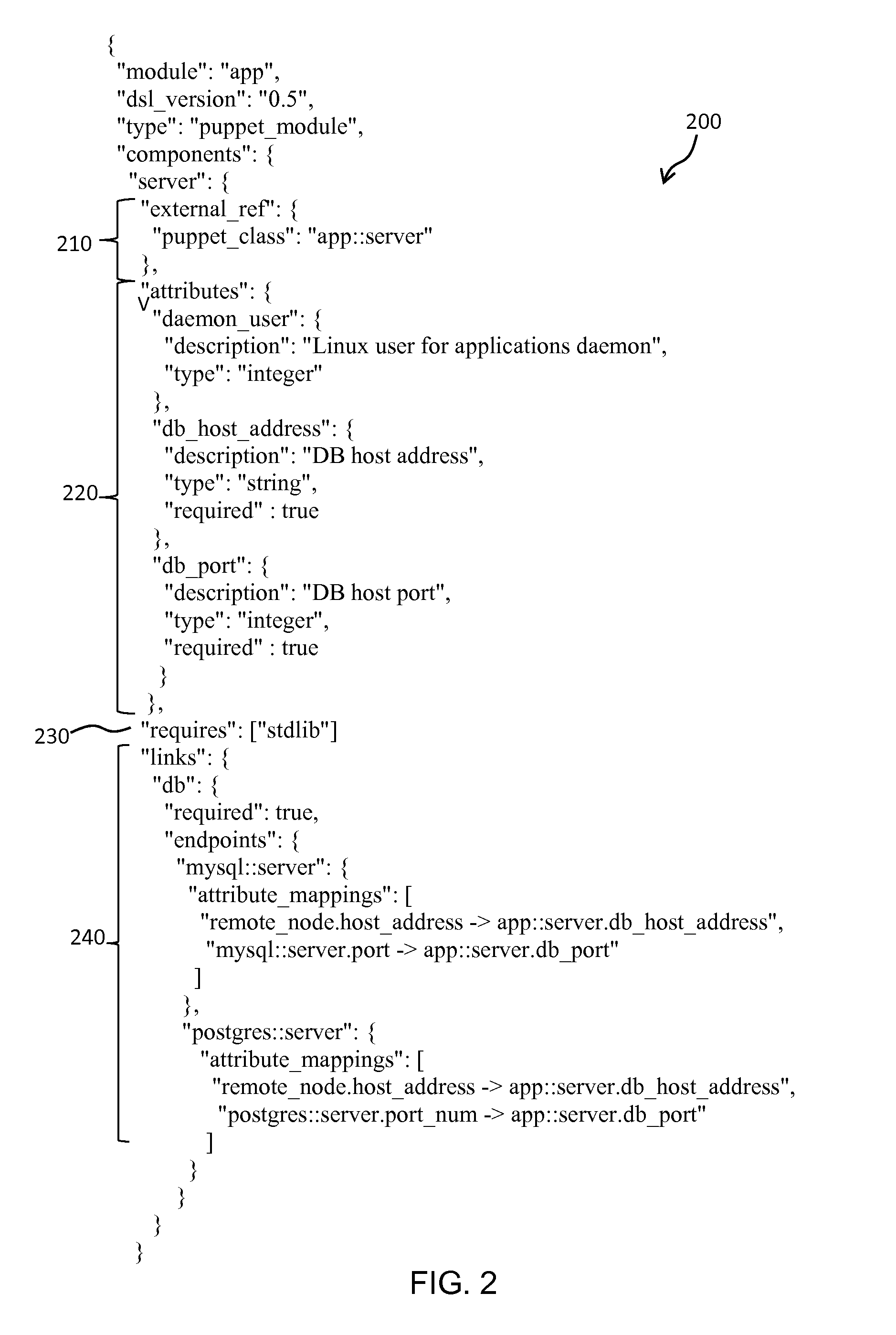
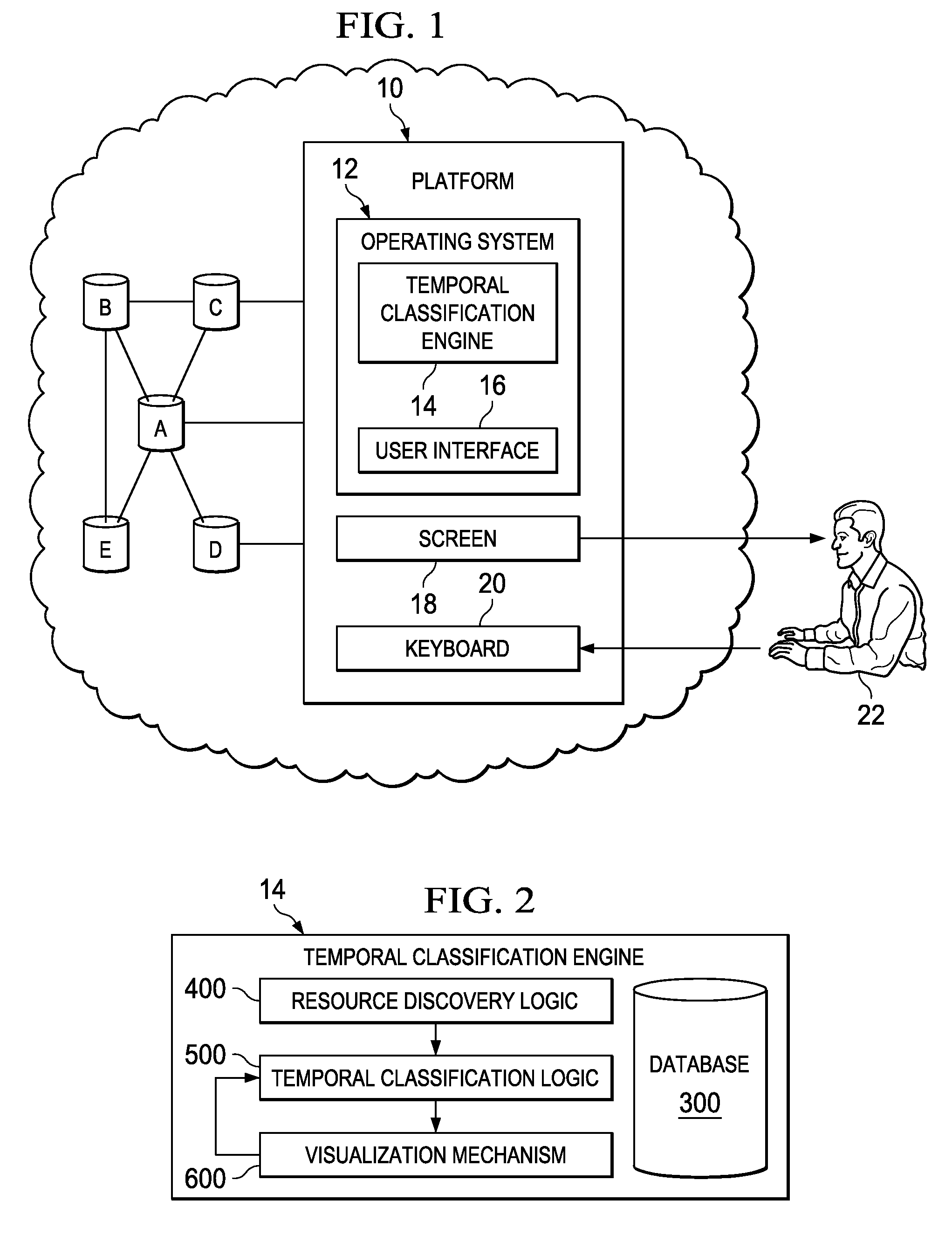
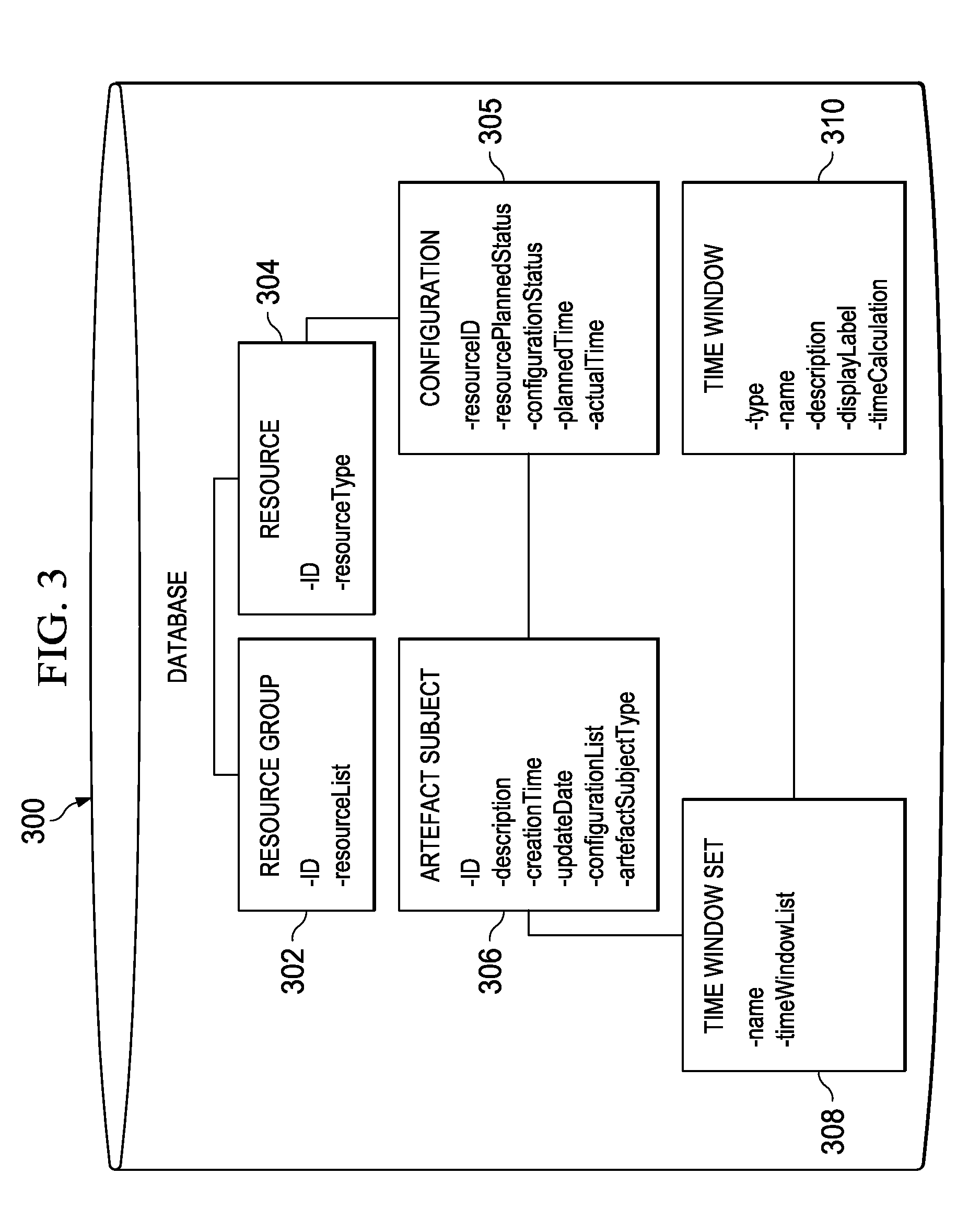
Temporally classifying and visually representing network and IT infrastructure with planned or occurred configuration activities and / or policy compliance or non-compliance of network and IT resources, including a method, apparatus and computer program for gathering and classifying observable configuration aspects of resources and relationships in a network of resources, wherein the method comprises: analyzing the network of resources to collect planned configuration times and actual resource status; monitoring actual resource status to make determinations if planned configurations are executed; and updating a network configuration status with the determinations. Planned and actual configurations are collected and monitored over a defined time range extending before and / or after a time zero. Each planned or actual configuration is categorized with respect to one or more time windows in the defined time range.
Owner:IBM CORP
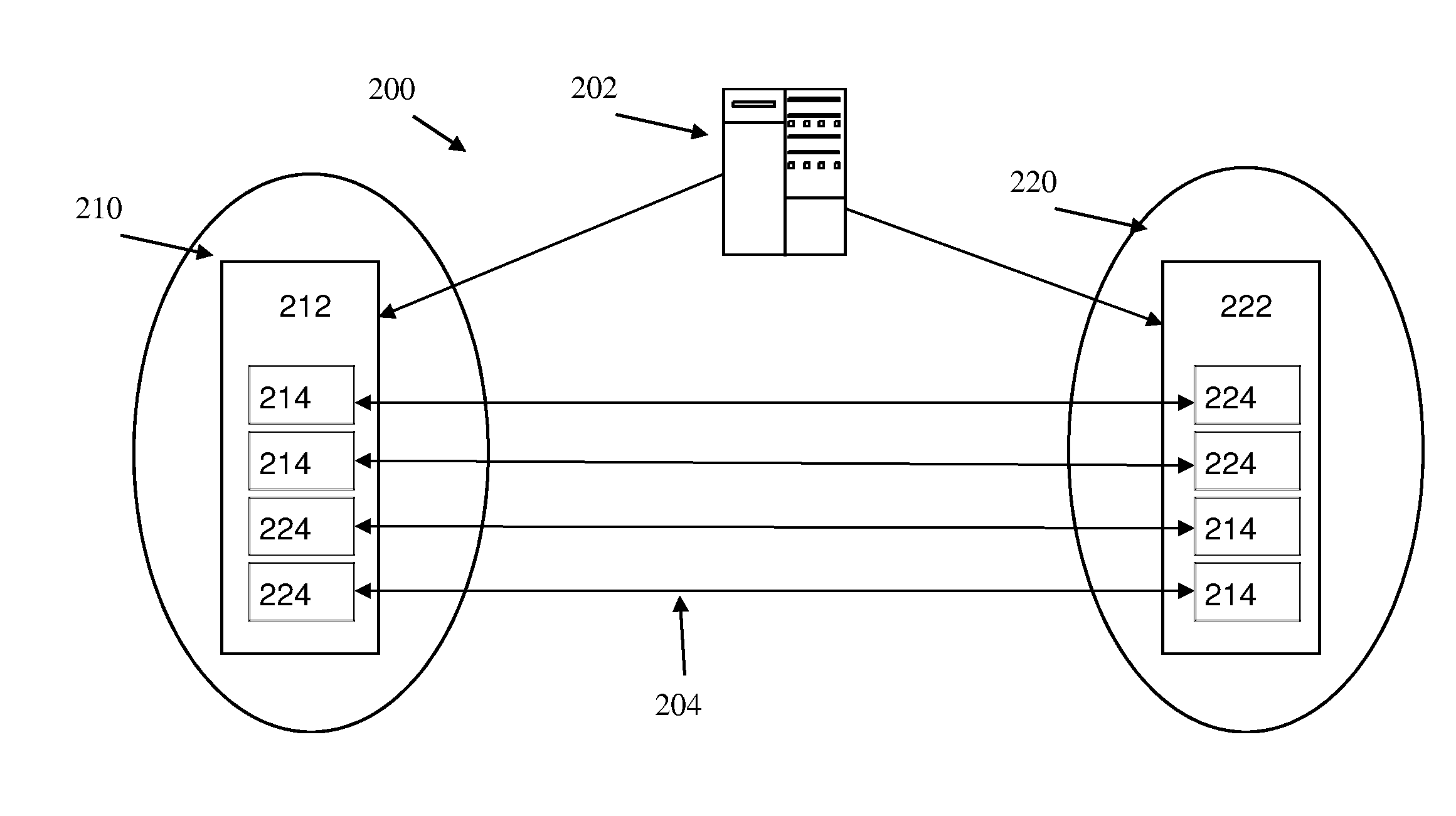
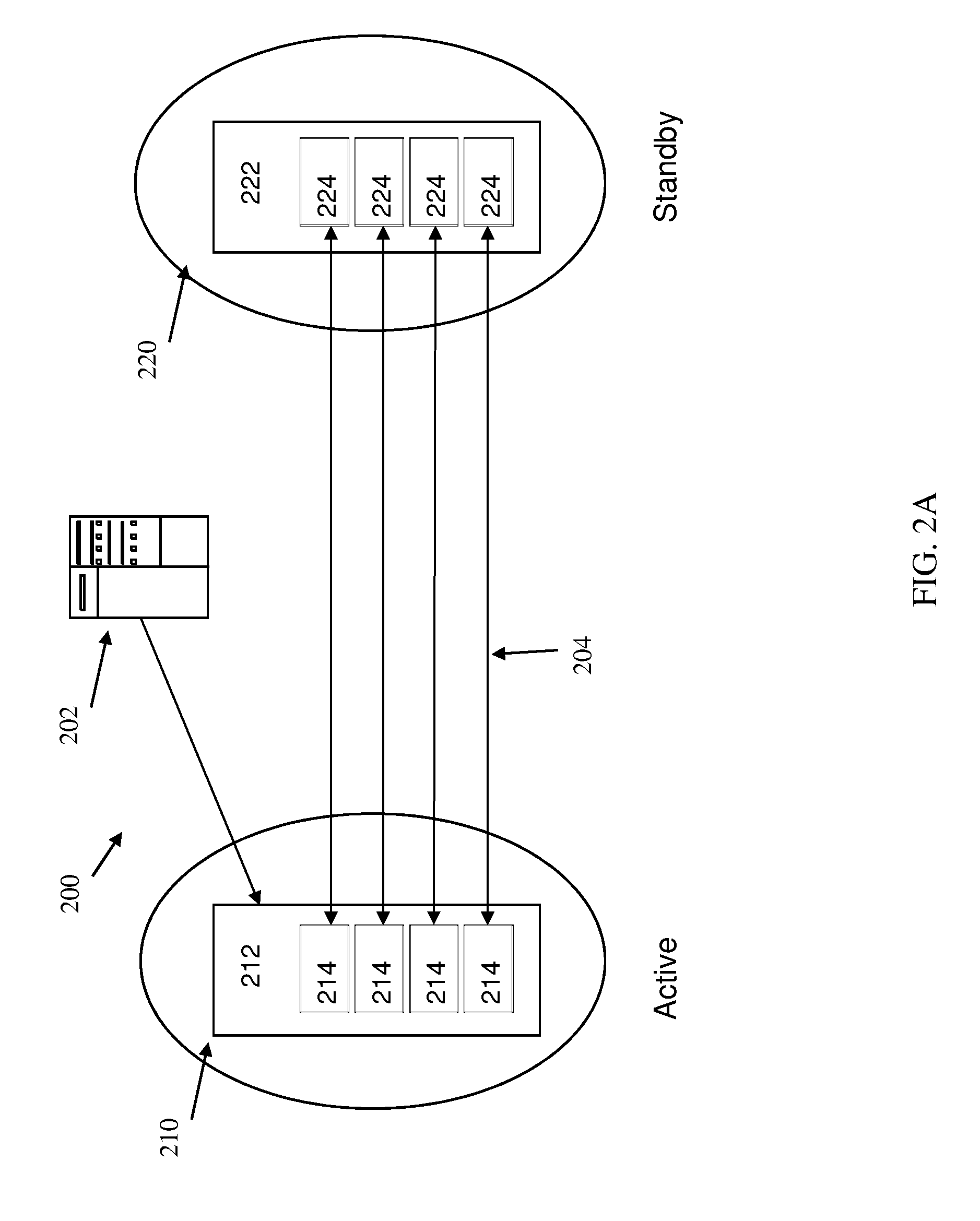
Achieving continuous availability for planned workload and site switches with no data loss
InactiveUS20140282596A1More transactionAvoid accessProgram initiation/switchingResource allocationNetwork connectionExecution planning
Embodiments of the disclosure are directed to methods, systems and computer program products for performing a planned workload switch. A method includes receiving a request to switch a site of an active workload and stopping one or more long running processes from submitting a new request to the active workload. The method also includes preventing a new network connection from accessing the active workload and processing one or more transactions in a queue of the active workload for a time period. Based on a determination that the queue of the active workload is not empty after the time period, the method includes aborting all remaining transactions in the queue of the active workload. The method further includes replicating all remaining committed units of work to a standby workload associated with the active workload.
Owner:IBM CORP
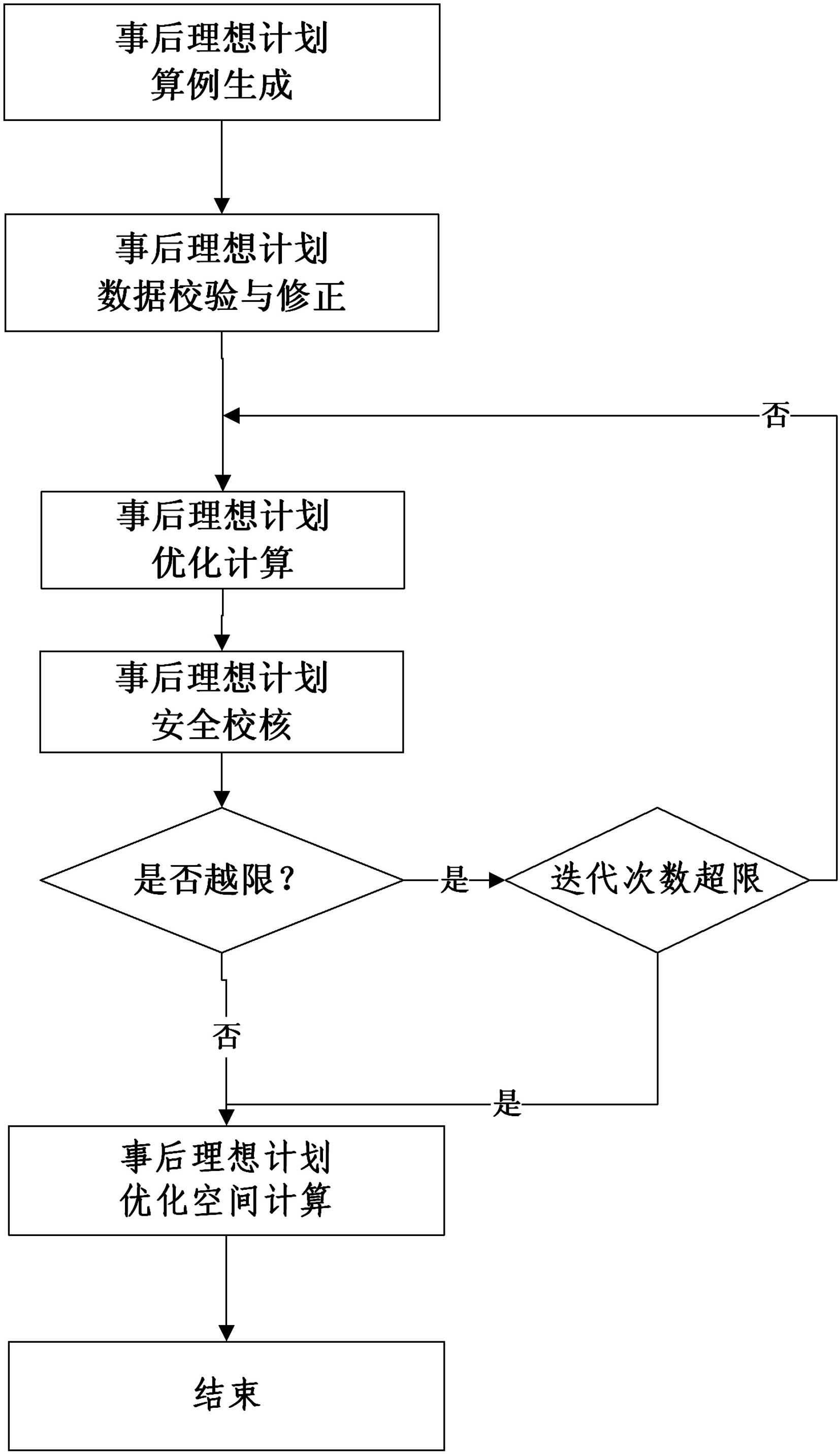
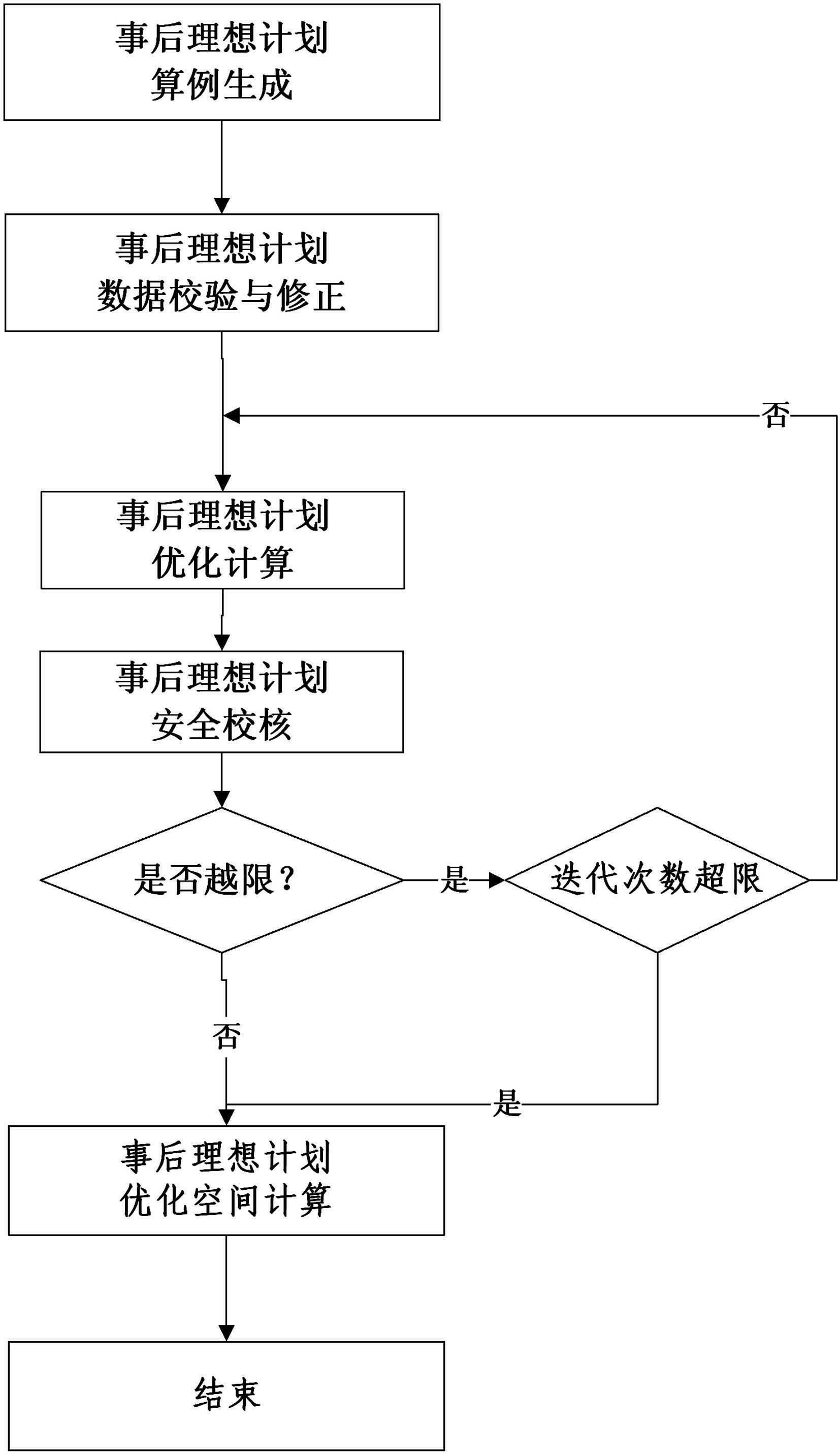
Posterior ideal plane analyzing method based on actual power grid operation data
ActiveCN102567815AImprove practicalityPromote engineering applicationForecastingInformation technology support systemSimulationPower grid
The invention discloses a posterior ideal plane analyzing method based on actual power grid operation data. The method comprises the following steps of: by using information, such as operation mode, load requirement, standby requirement and the like, in the power grid actual operation, as input information of power generation plane optimization, figuring out an optimal ideal dispatching plan according to a set optimization target; and comparing the difference between the ideal dispatching plan and an actual executing plan so as to evaluate an ideal dispatching optimization space. And by using the posterior ideal plane analyzing method based on the actual power grid operation data, disclosed by the invention, is used for analyzing the reasonability and effectiveness of SCUC / SCED (Security Constrained Unit Commitment / Security Constrained Economic Dispatch) model and algorithm, reflecting the instruction degree of the power generation plan to the actual production and promoting the practical and engineering applications of SCUC / SCED.
Owner:NARI TECH CO LTD +1
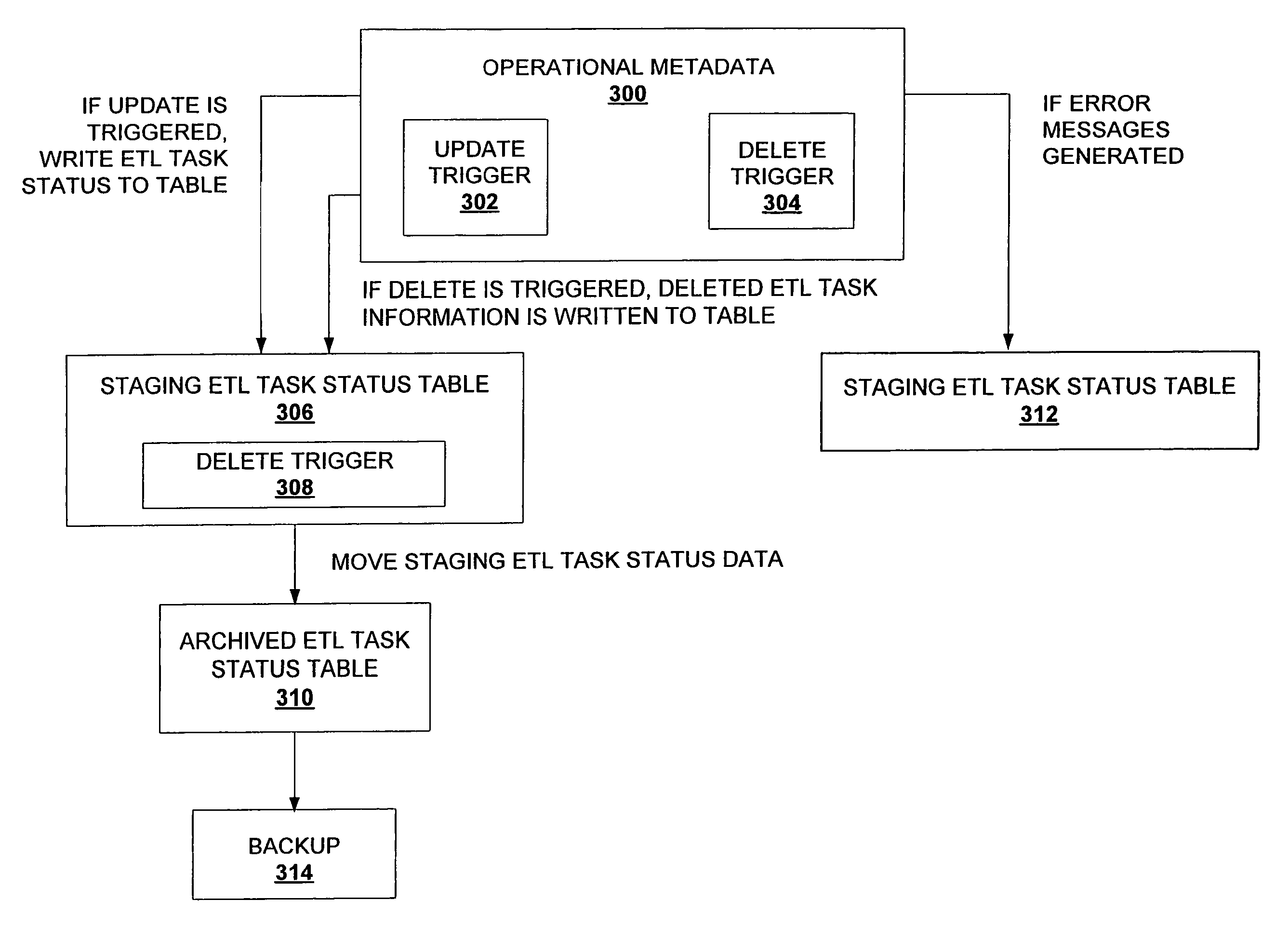
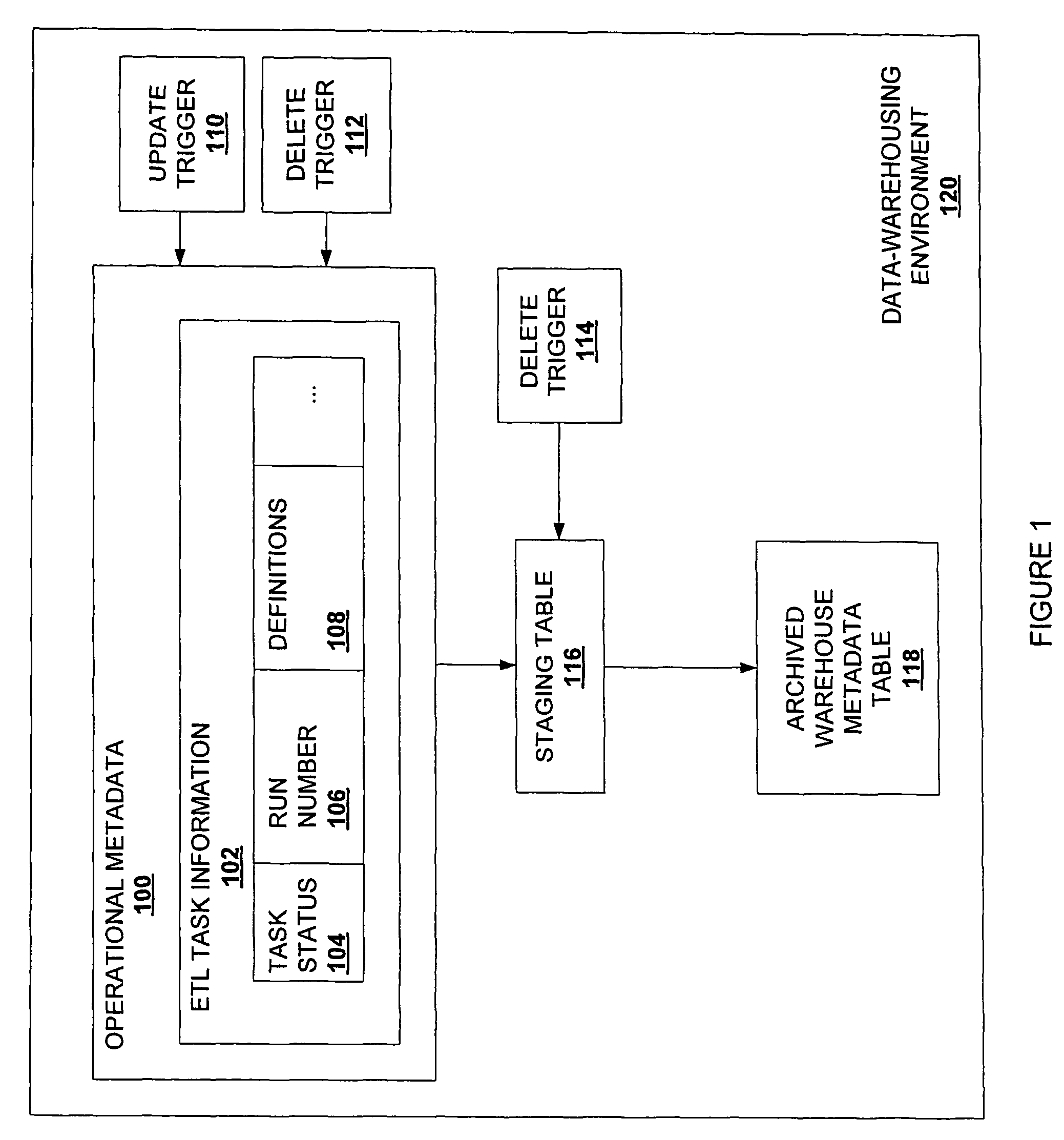
Dynamically capturing data warehouse population activities for analysis, archival, and mining
ActiveUS7941397B2Digital data information retrievalError detection/correctionControl flowData warehouse
A system comprised of trigger mechanisms, a staging area, and an archived warehouse metadata table is used to extract, store, and archive extract, transform, and load (ETL) tasks from operational metadata in a data-warehousing environment. Operational metadata is comprised of ETL information; ETL task execution statuses, run number, definitions, control flow, and execution schedules. Specified ETL information is monitored and captured so that it may be extracted from operational metadata and transformed every time a trigger mechanism activates an update of stored data. Administrator-specified ETL task information is then stored in staging table. At specified intervals a staging table is refreshed with changes in operational data for each of the administrator-specified monitored and captured ETL tasks. Overwritten data, or outdated ETL task information, is then moved and stored in an archived warehouse metadata table. In one embodiment, archives are queried to generate reports analyzing the status of ETL tasks.
Owner:WORKDAY INC
Coordination of processes in cloud computing environments
ActiveUS20150120936A1Digital computer detailsComputer security arrangementsExecution planningCloud resources
Methods and systems of managing computer cloud resources, including at least one database, at least one server configured to, act as an orchestration site, wherein the orchestration site is configured to receive at least one cloud resource management plan from at least one user and store the at least one plan in the at least one database and act as an orchestration manager. The orchestration manager is configured to retrieve the at least one plan from the at least one database and execute the plan with at least one site controller.
Owner:ORACLE INT CORP
Resource description framework distributed engine and incremental updating method
InactiveCN105447156ASupport changesSpecial data processing applicationsComputer clusterProgram planning
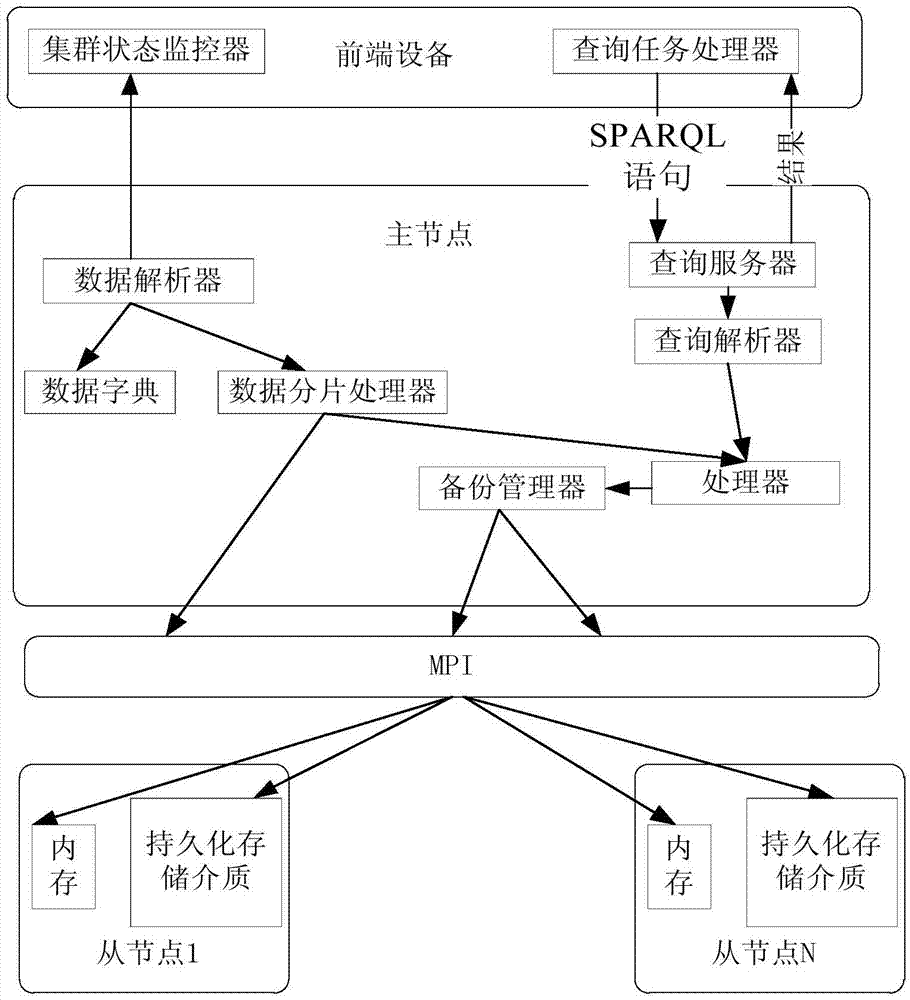
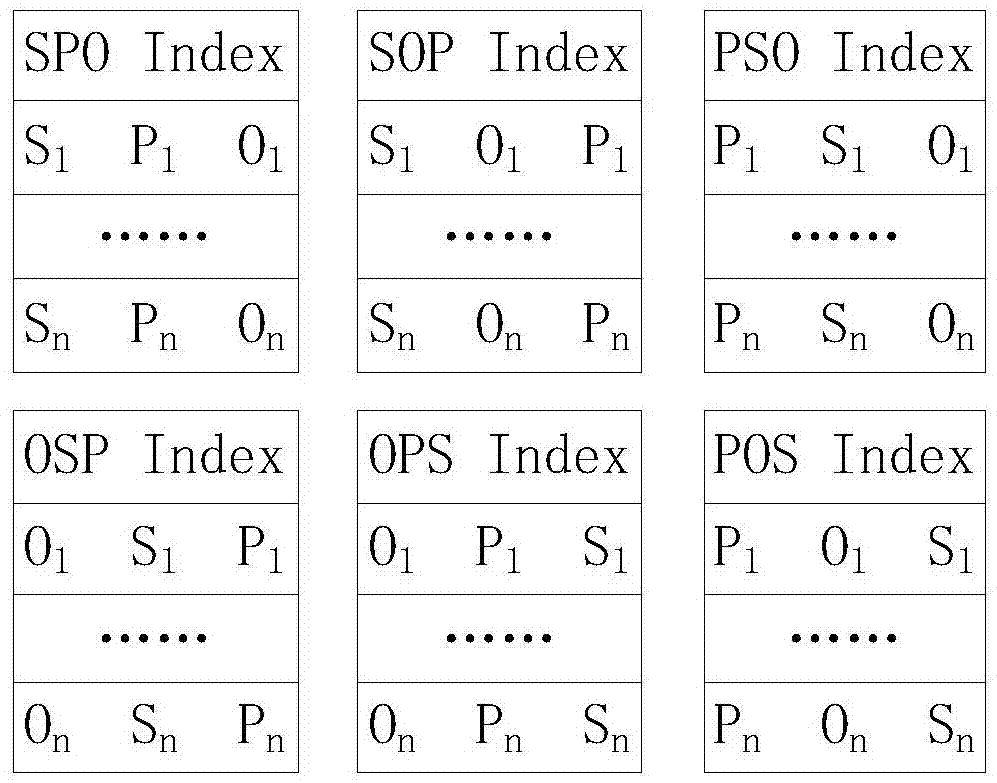
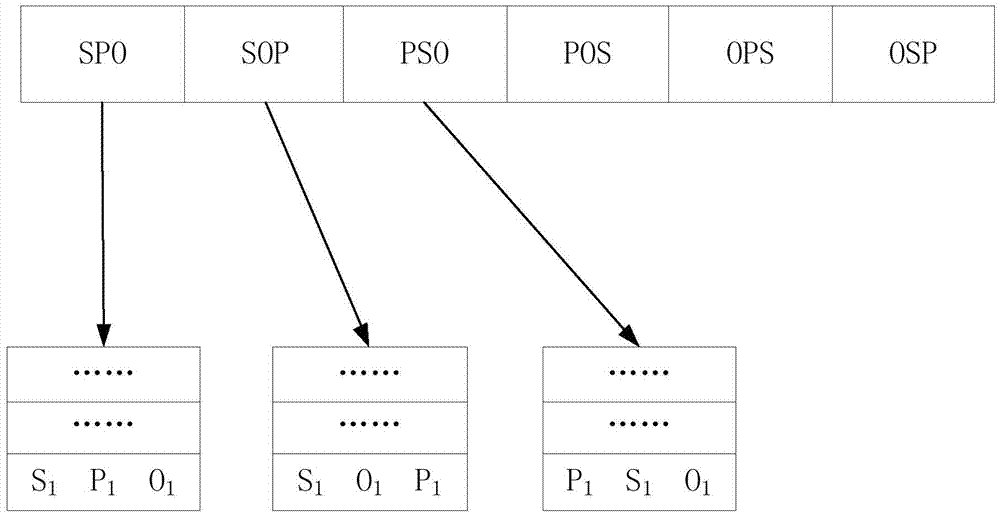
The invention provides a resource description framework (RDF) distributed engine and an incremental updating method. The RDF distributed engine is deployed on a computer cluster. The method comprises: receiving a query language and an SPARQL statement through a master node; analyzing the SPARQL statement to be converted into a query sub-graph; determining corresponding slave nodes of RDF data in the SPARQL statement from N slave nodes, and generating an operation log and an executive plan according to the query sub-graph; sending the SPARQL statement, the executive plan and the operation log to a backup manager in the master node, and sending the SPARQL statement and the executive plan to the corresponding nodes; and performing backup on the data in the corresponding slave nodes, and updating a memory in an incremental mode by the corresponding slave nodes according to the executive plan. In the process, a query analyzer capable of analyzing the SPARQL statement is added, so that the RDF distributed engine can support a data updating statement and then support a dynamic data source.
Owner:BEIHANG UNIV
Path mode inquiring system for massive image data
ActiveCN103279543AConvenient queryImprove query execution planSpecial data processing applicationsProgram planningData file
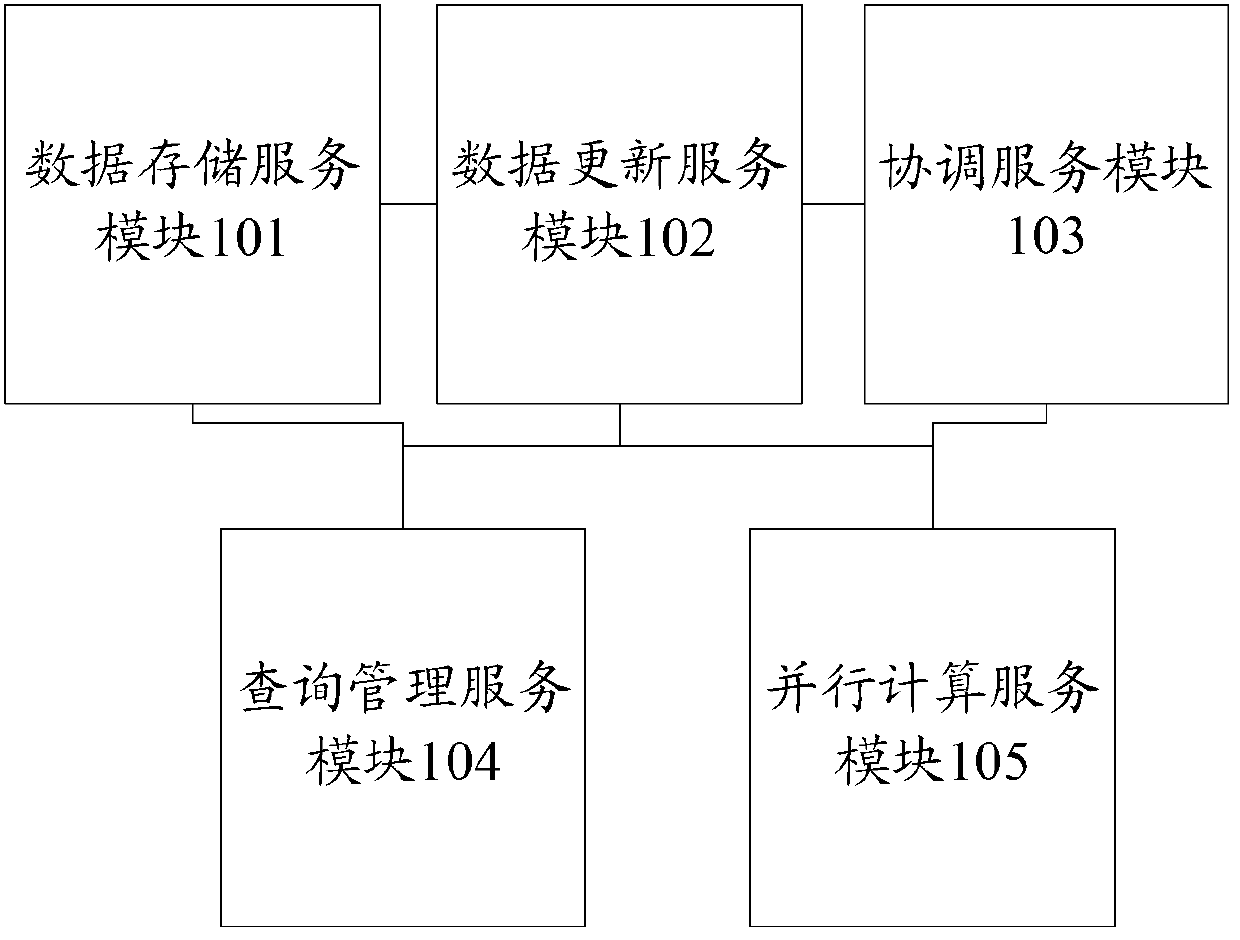
The invention provides a path mode inquiring system for massive image data. The path mode inquiring system comprises data storage service module, a data updating module, a coordination service module, an inquiring management service module and a parallel calculating service module. The data storage service module is used for storing image data at distributed clusters and providing data reading functions for other modules. The data updating module is used for combining updated blogs into data files. The coordination service module is used for coordinating status synchronization of service computers during calculating. The inquiring management service module is used for managing member computers, preprocessing inquiries, distributing inquiring tasks, and collecting inquiring results. The parallel calculating service module is used for executing actual inquiring services. By the path mode inquiring system, users' inquiring of massive image data is facilitated greatly, and inquiring execution of massive image data is improved to a great extent.
Owner:TSINGHUA UNIV
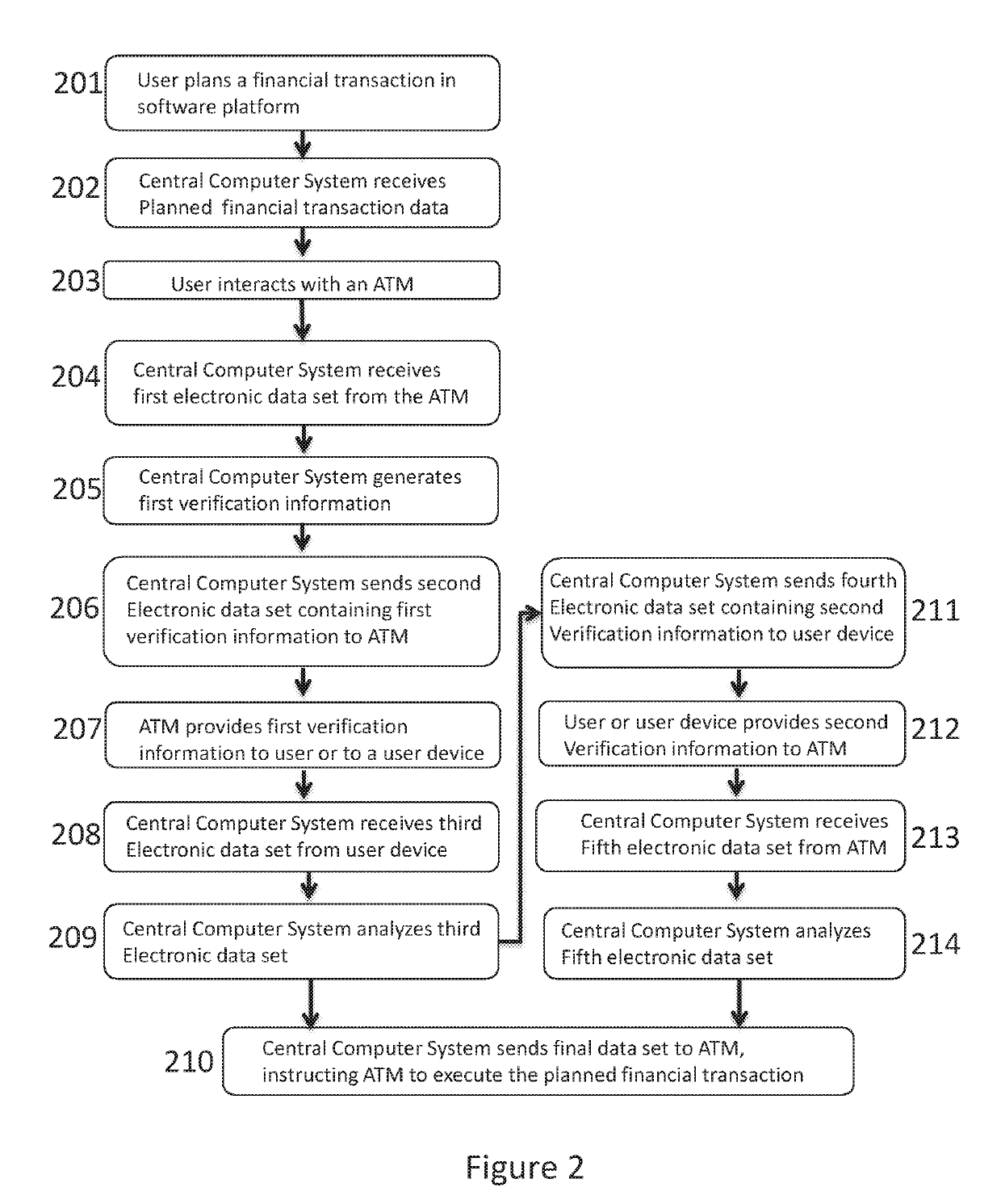
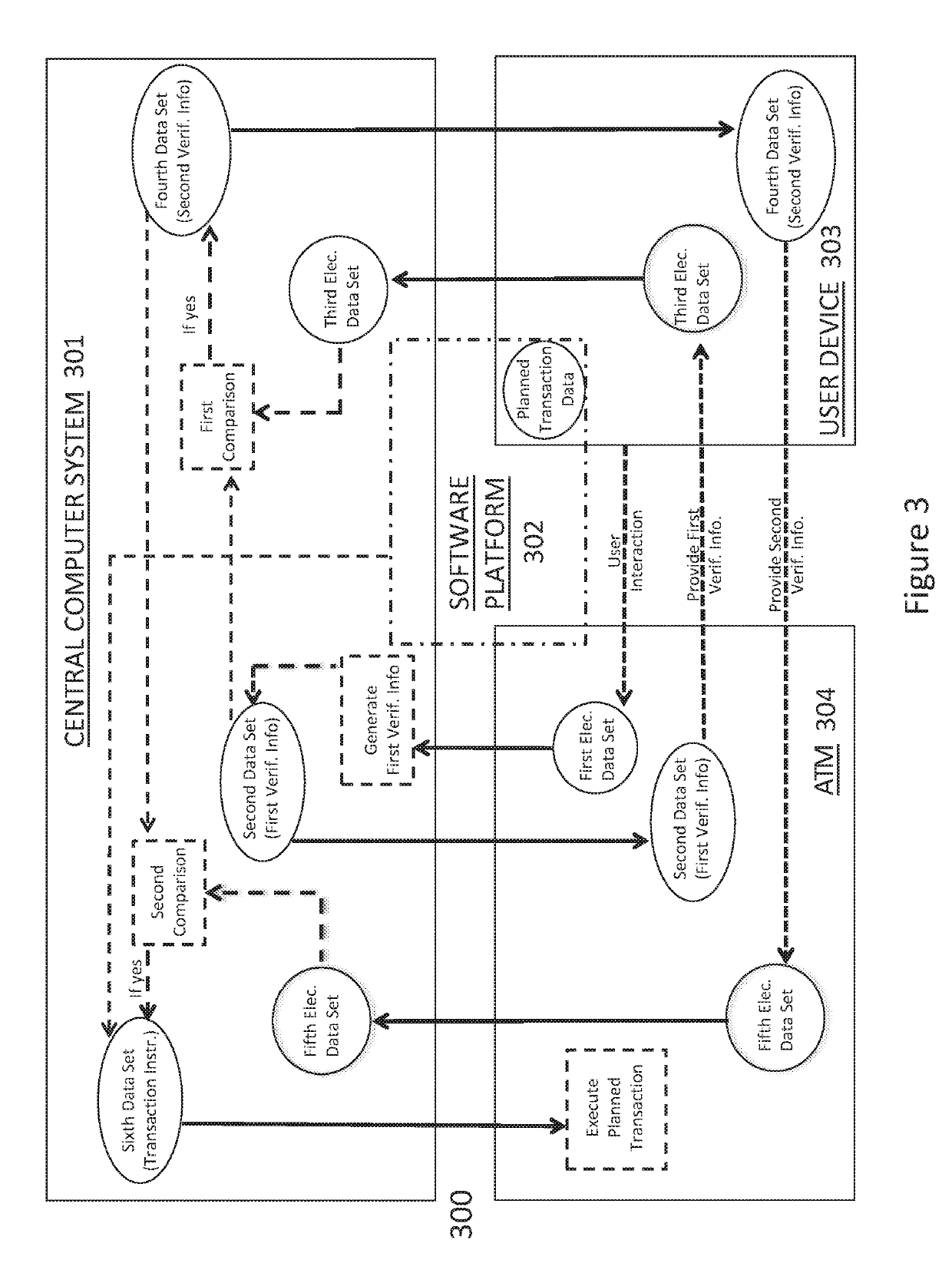
Enhanced automated teller machine, system and method for securely enabling a financial transaction at the automated teller machine
An enhanced automated teller machine (ATM), system and method for securely authenticating and enabling a financial transaction at the ATM. The method includes receiving at a central computer system, planned transaction data representing a future financial transaction. The central computer system generates first and second verification information, sends electronic data including the first verification information to the ATM, and sends electronic data including the second verification information to a user device. The central computer system receives multiple sets of electronic data from a user device and multiple sets of electronic data from the ATM. Multiple comparisons of certain sets of the electronic data from the ATM to certain sets of the electronic data from the user device are conducted at the central computer system. If the comparisons result in positive verifications, the central computer system sends electronic data including instructions for the ATM to execute the planned financial transaction.
Owner:KLEAR TECH INC
Data online gathering method in cloud computing environment
ActiveCN103699696ARealize online aggregationSave resourcesRelational databasesSpecial data processing applicationsUser needsProgram planning
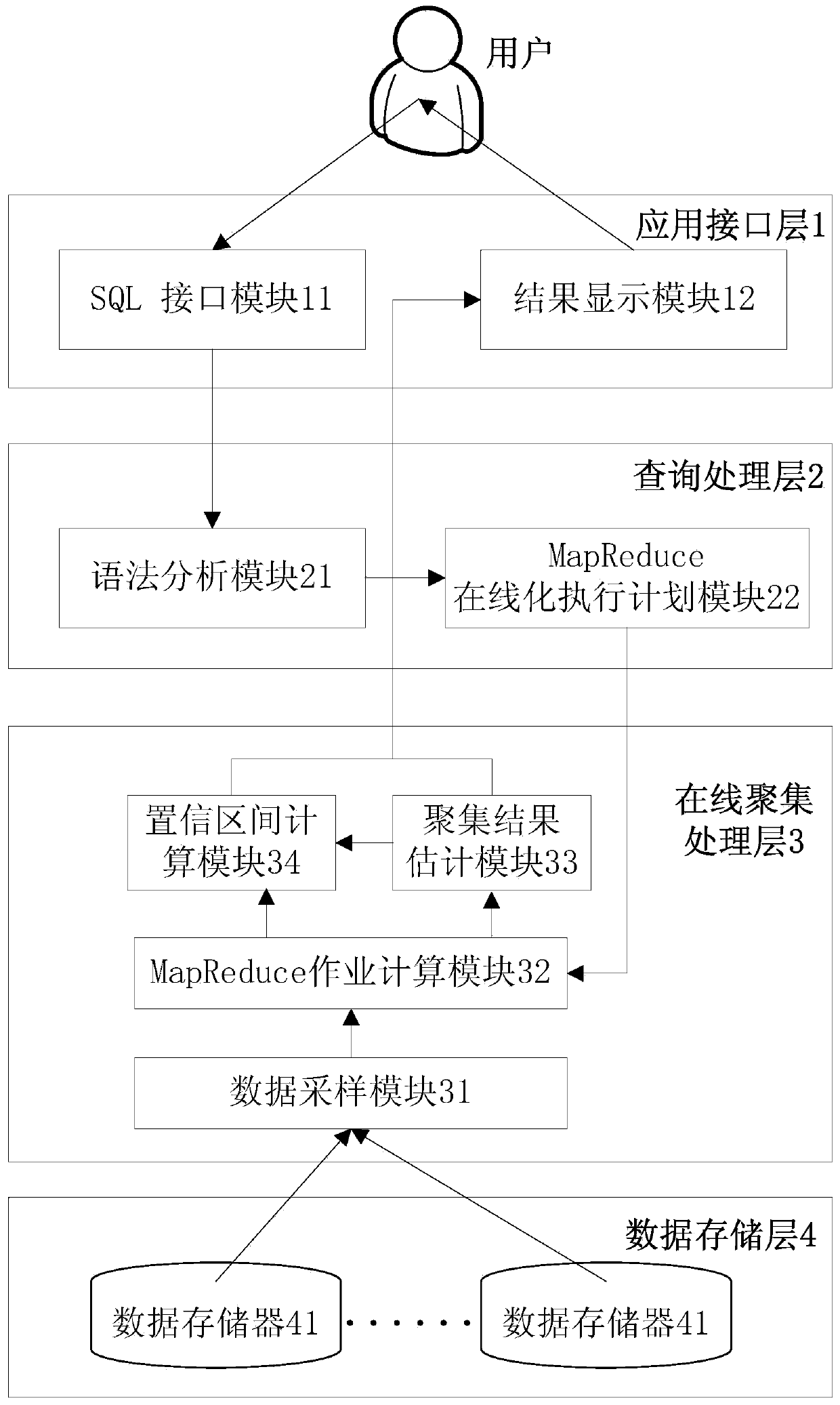
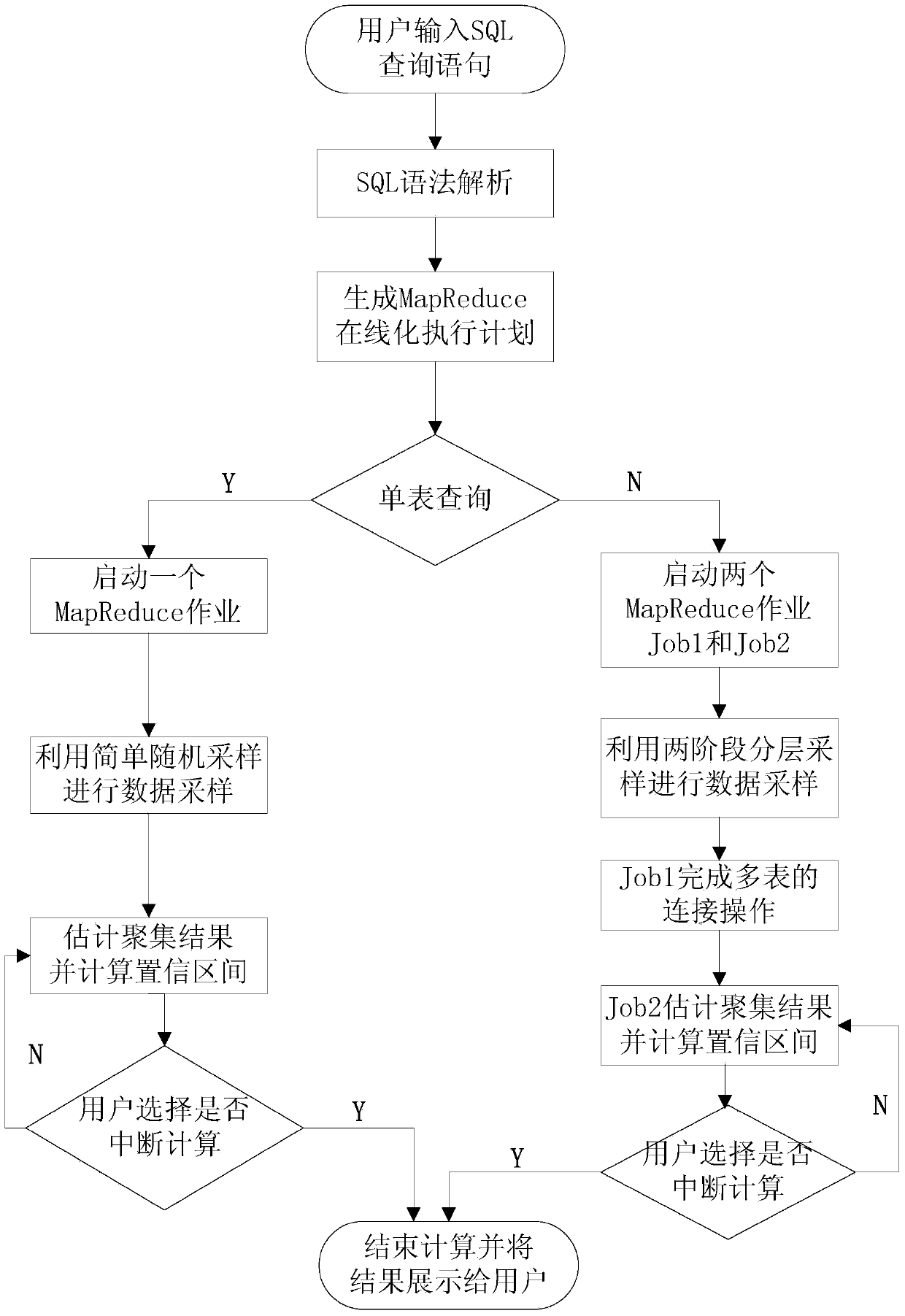
The invention relates to a data online gathering method in a cloud computing environment. The method comprises the steps of setting an SQL (Structured Query Language) query statement Q according to requirement of a user by an SQL interface module at an application interference layer, and transmitting the SQL query statement Q to a query processing layer; analyzing the received query statement Q through a grammar analyzing module, and transmitting an analyzing result to a MapReduce online performing plan module; starting MapReducer operation by the MapReduce online performing plan module if the analyzed query statement Q is query on account of a single form, starting two MapReduce operations by the MapReduce online performing plan module if the analyzed query statement Q is on account of query of a plurality of forms, processing a query request of the query statement Q through an online gathering processing layer according to one or two received MapReduce operations, and transmitting a processing result to the application interface layer for display. The data online gathering method can be widely applied to the cloud computing environment.
Owner:RENMIN UNIVERSITY OF CHINA
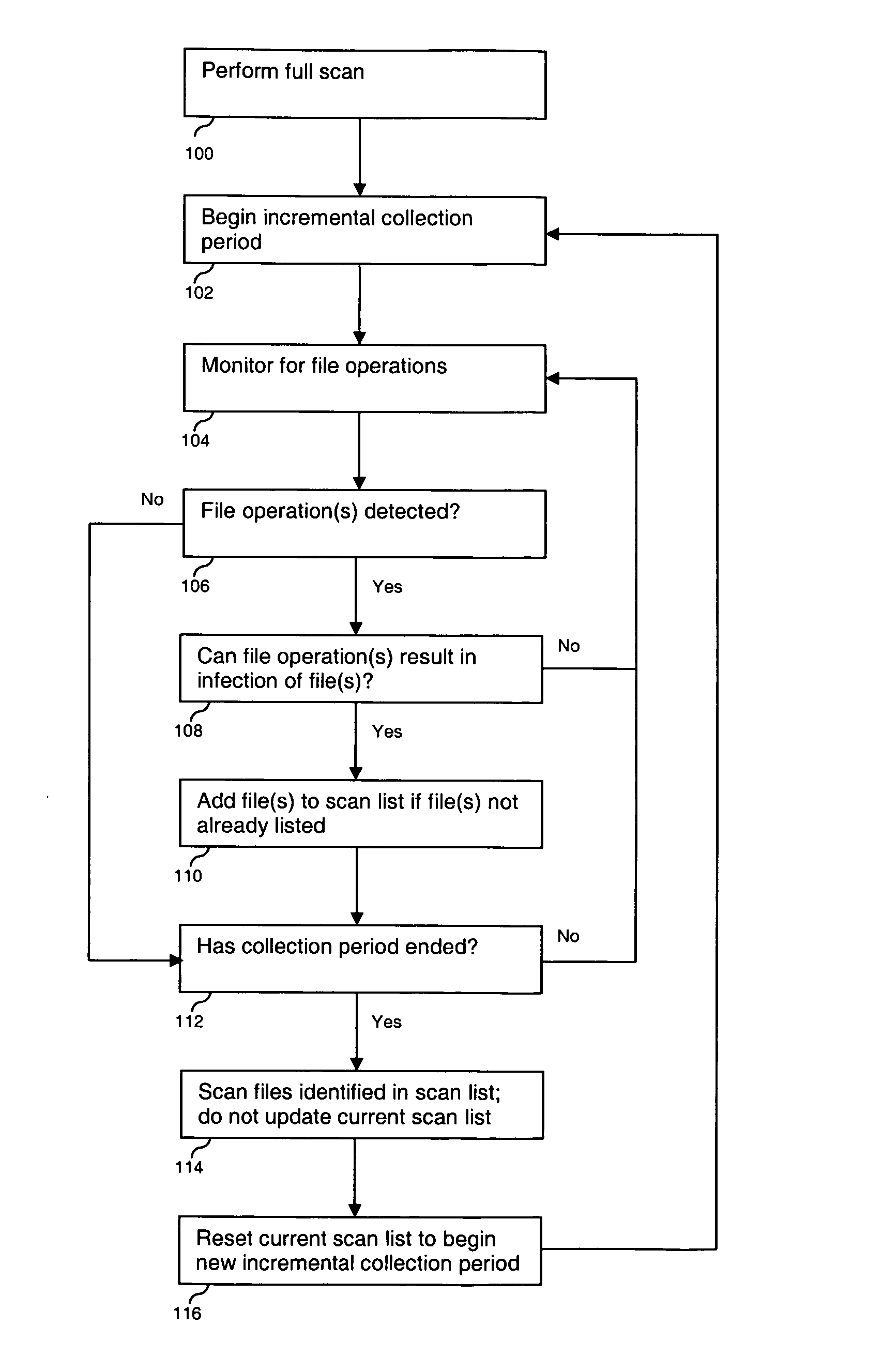
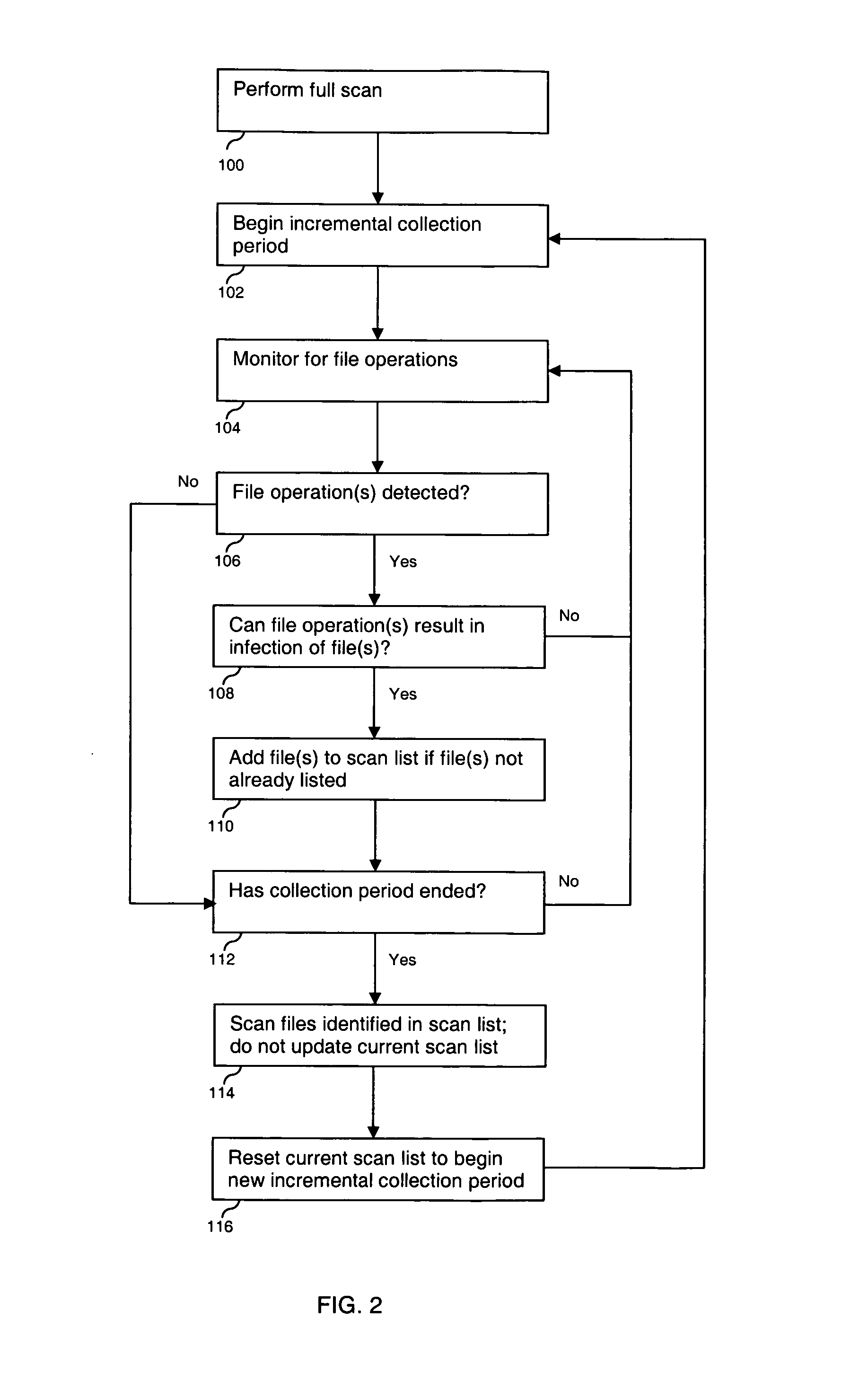
Risk-aware scanning of objects
Scanning is disclosed. A system is monitored to detect object events. A risk level is determined for an object event, and a scan is scheduled for an object associated with the object event according to the risk level. The risk level may be based on the risk level of the object type, and on the risk level of the operation. An immediate on access scan may be scheduled for a first risk range, a differential scan may be scheduled for a second risk range, and an incremental scan may be scheduled for a third risk range. The scheduled scan is performed.
Owner:EMC IP HLDG CO LLC
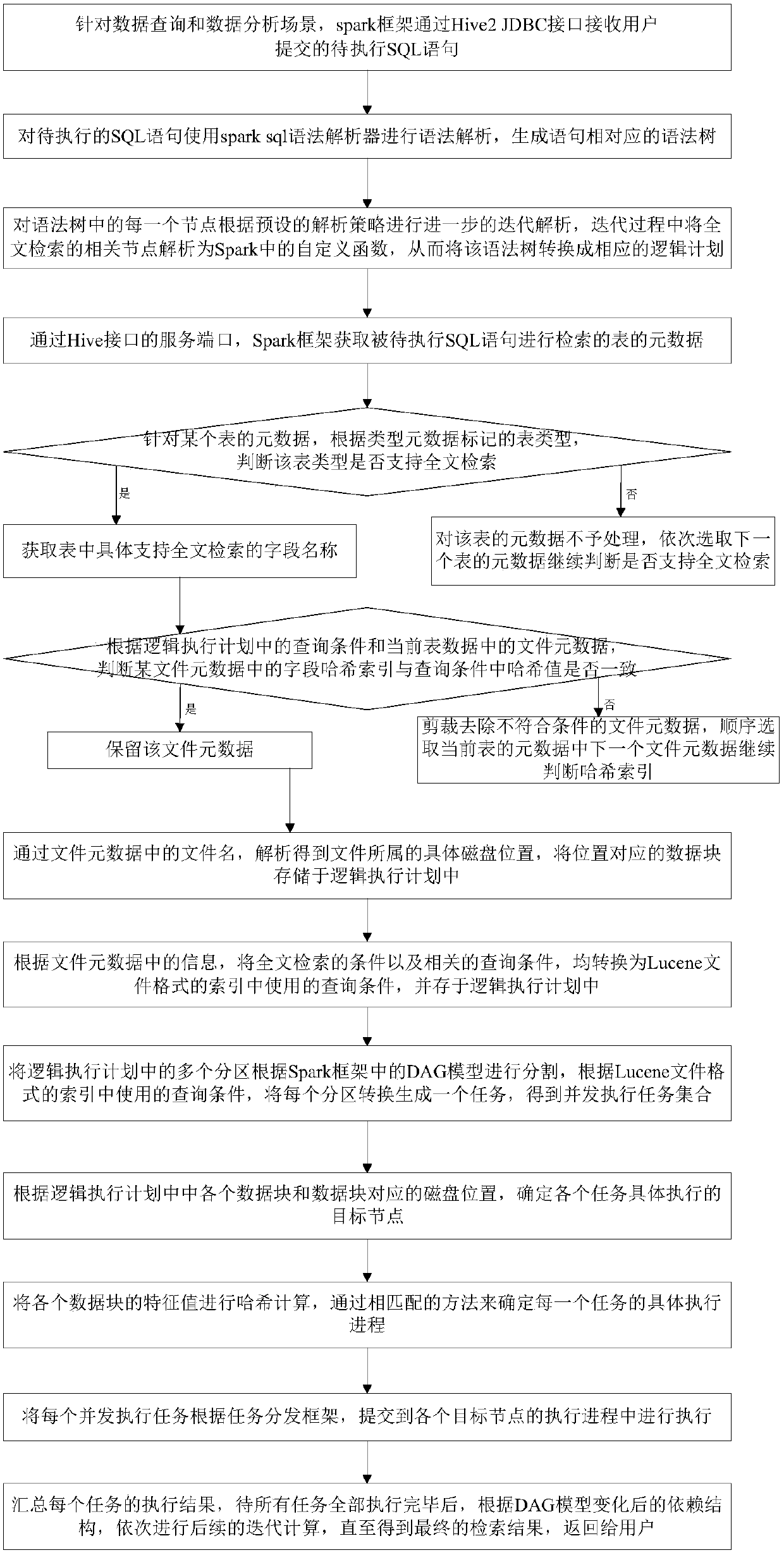
Realization method of full-text retrieval based on Spark framework
ActiveCN107943952AFast full-text searchImprove efficiencySpecial data processing applicationsNODALProgram planning
The invention discloses a realization method of full-text retrieval based on a Spark framework and belongs to the field of big-data processing. According to the method, a to-be-executed SQL statementis received, and a syntax tree is generated and converted into corresponding logic plans; metadata of retrieving all tables are retrieved from Hive, fields supporting full-text retrieval are sought, and data blocks are initially cropped through field hash indexes; disk locations where the data blocks are specifically stored are acquired from file metadata according to a query condition; the logicexecution plans are converted into a set of tasks which can be executed in a distributed manner, and target nodes and target processes where the tasks are specifically executed are determined throughall the data block locations; and the tasks are distributed and executed, execution results are summarized, and a final result is acquired by iteration. The method has higher efficiency, can quickly complete full-text retrieval of massive data, has very high practicality and a very large application range in the field of big-data processing, and has very wide application prospects.
Owner:BEIJING SCISTOR TECH +1
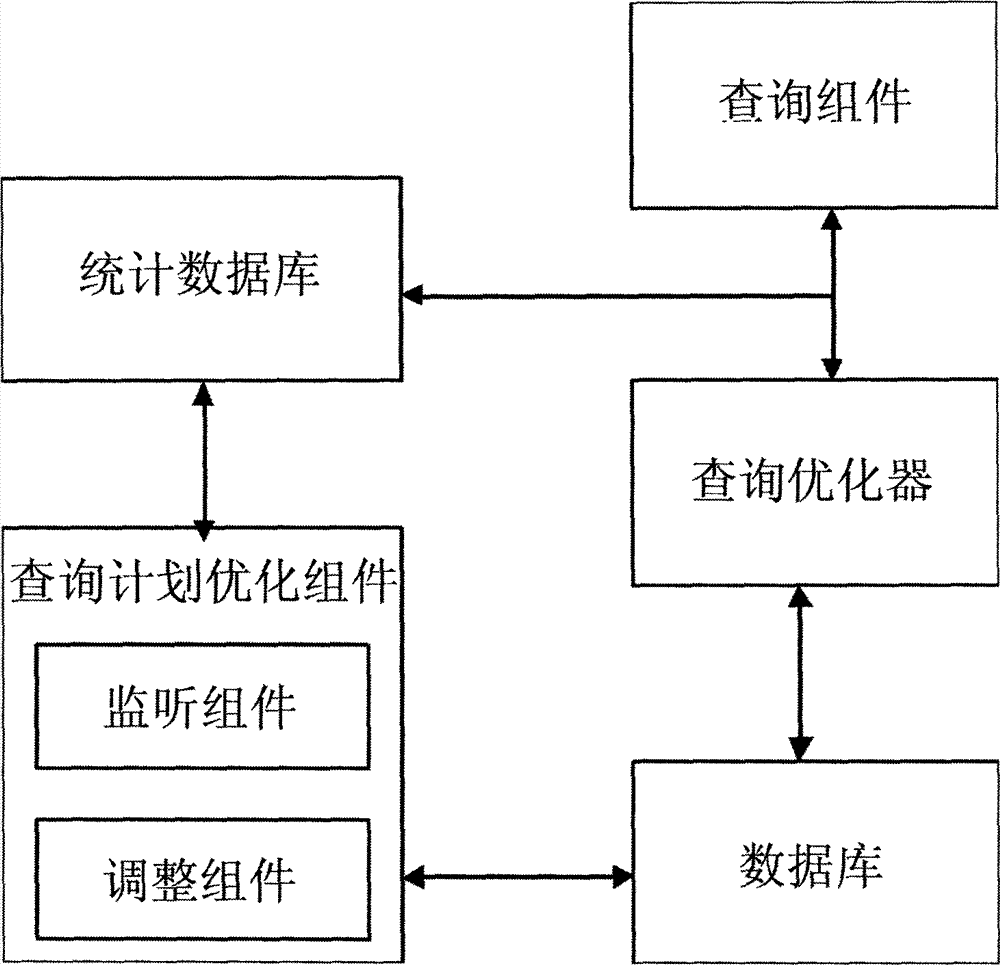
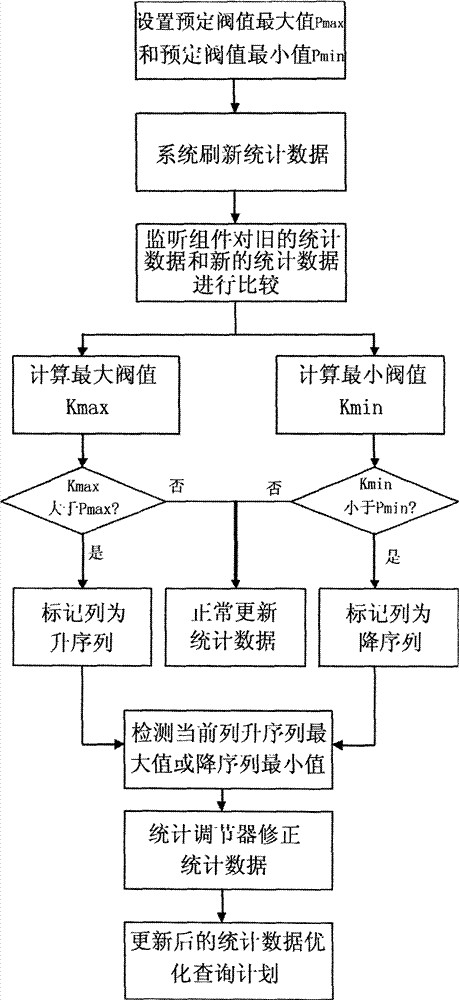
Database query plan optimization system and method
InactiveCN102930003ALow costGuaranteed reliabilitySpecial data processing applicationsStatistical databaseQuery plan
The invention relates to database technologies and specifically relates to a database query plan optimization system and method. The system comprises a database, a statistical database, a query optimizer, a query assembly and a query plan optimization assembly, wherein the query plan optimization assembly comprises a monitoring component and an adjusting component; the monitoring component is used for detecting the changes of the database; the adjusting component is used for submitting a query based on a middle process according to feedback information of the monitoring component and completing the updating of the statistical database; and the query optimizer is used for constructing a query plan according to the statistical database and finishing the query plan by virtue of the query assembly. The database query plan optimization system and method have the beneficial effects of reducing the cost for executing the plan, avoiding time-consuming data scanning, timely updating statistical data, preventing query contents exceeding a known range, improving accuracy of cardinality estimation so as to improve query efficiency, allowing the optimized query plan to be executed, and ensuring the reliability, accuracy and high efficiency of the query plan.
Owner:浙江图讯科技股份有限公司
Coordination of processes in cloud computing environments
ActiveCN104335179AResource allocationComputer security arrangementsExecution planningCloud resources
Methods and systems of managing computer cloud resources, including at least one database, at least one server configured to, act as an orchestration site, wherein the orchestration site is configured to receive at least one cloud resource management plan from at least one user and store the at least one plan in the at least one database and act as an orchestration manager. The orchestration manager is configured to retrieve the at least one plan from the at least one database and execute the plan with at least one site controller.
Owner:ORACLE INT CORP
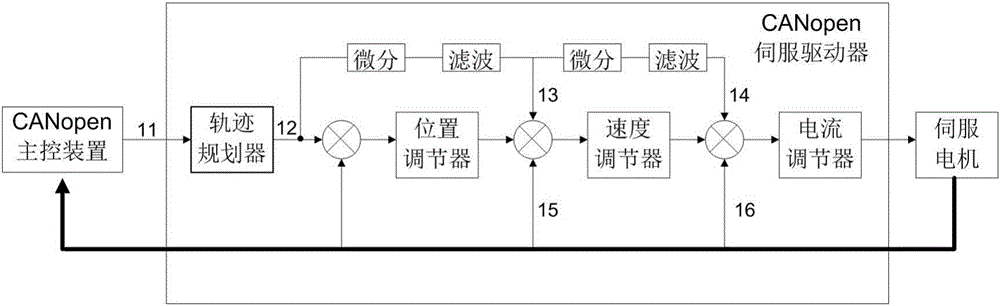
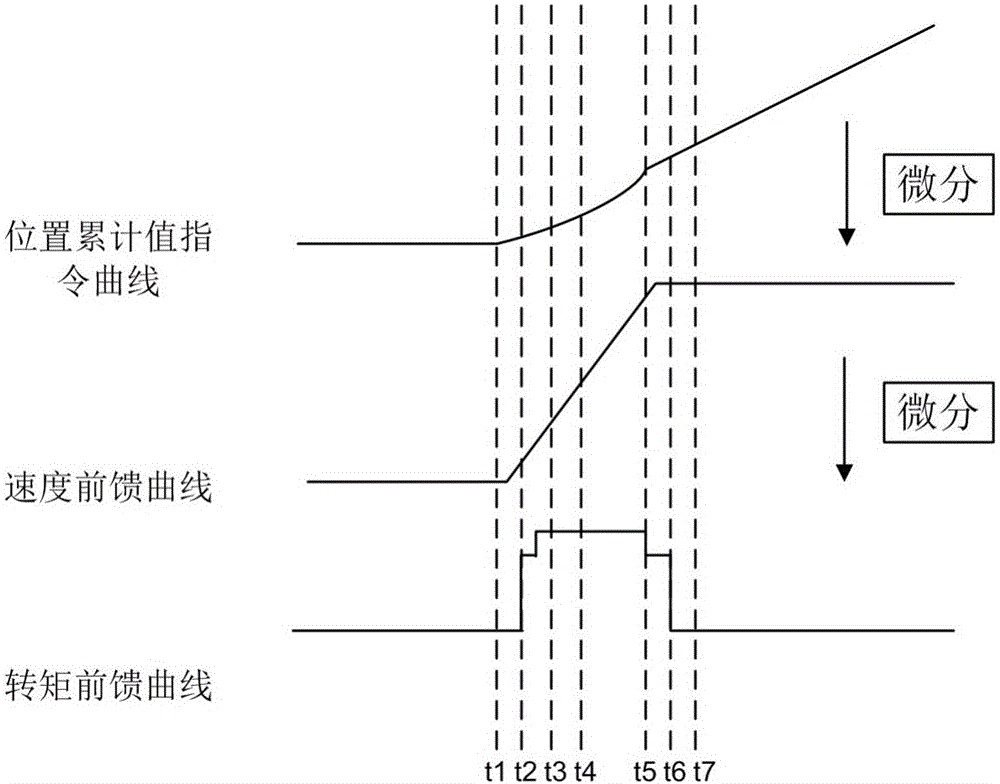
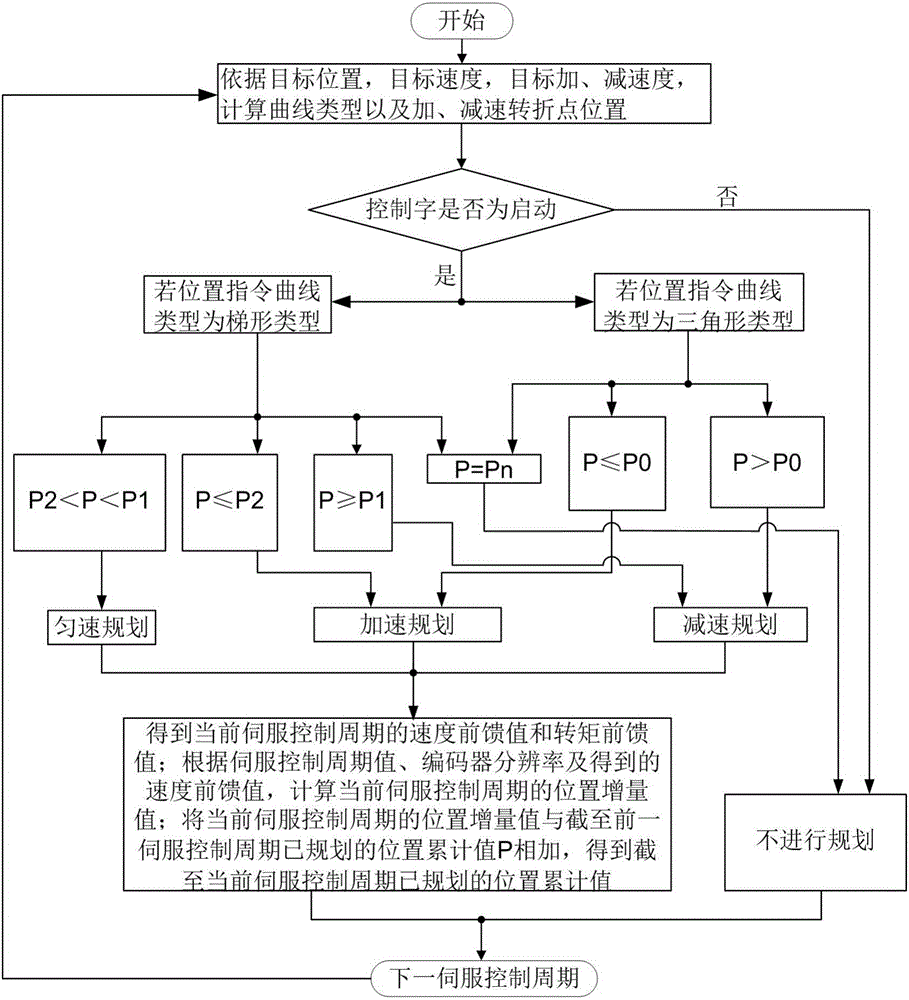
Processing method for speed feedforward and torque feedforward in CANopen servo system
ActiveCN105955203AEliminate the impact of dynamic following performanceExcellent dynamic follow performanceNumerical controlTarget controlCANopen
The invention relates to a processing method for speed feedforward and torque feedforward in a CANopen servo system, which comprises the steps that a trajectory planner receives a target control command and calculates the type of position instruction curves, the position of an acceleration turning point and the position of a deceleration turning point; the trajectory planner judges whether servo control is started or not; if not, a speed feedforward curve, a torque feedforward curve and the position instruction curves are all zero; if so, a position accumulated value planned up to the previous servo control period is compared with the acceleration turning point position, the deceleration turning point position and a target position, acceleration planning, deceleration planning, constant speed planning or non-execution planning is executed according to a comparison result so as to acquire a speed feedforward value and a torque feedforward value of the current servo control period; a position increment value of the current servo control period and a position accumulated value planned up to the current servo control period are calculated; a plurality of position increment values form a position increment instruction curve, a plurality of position accumulated values form a position accumulated value instruction curve, a plurality of speed feedforward values form a speed feedforward curve, and a plurality of torque feedforward values form a torque feedforward curve.
Owner:深圳市雷赛软件技术有限公司 +1
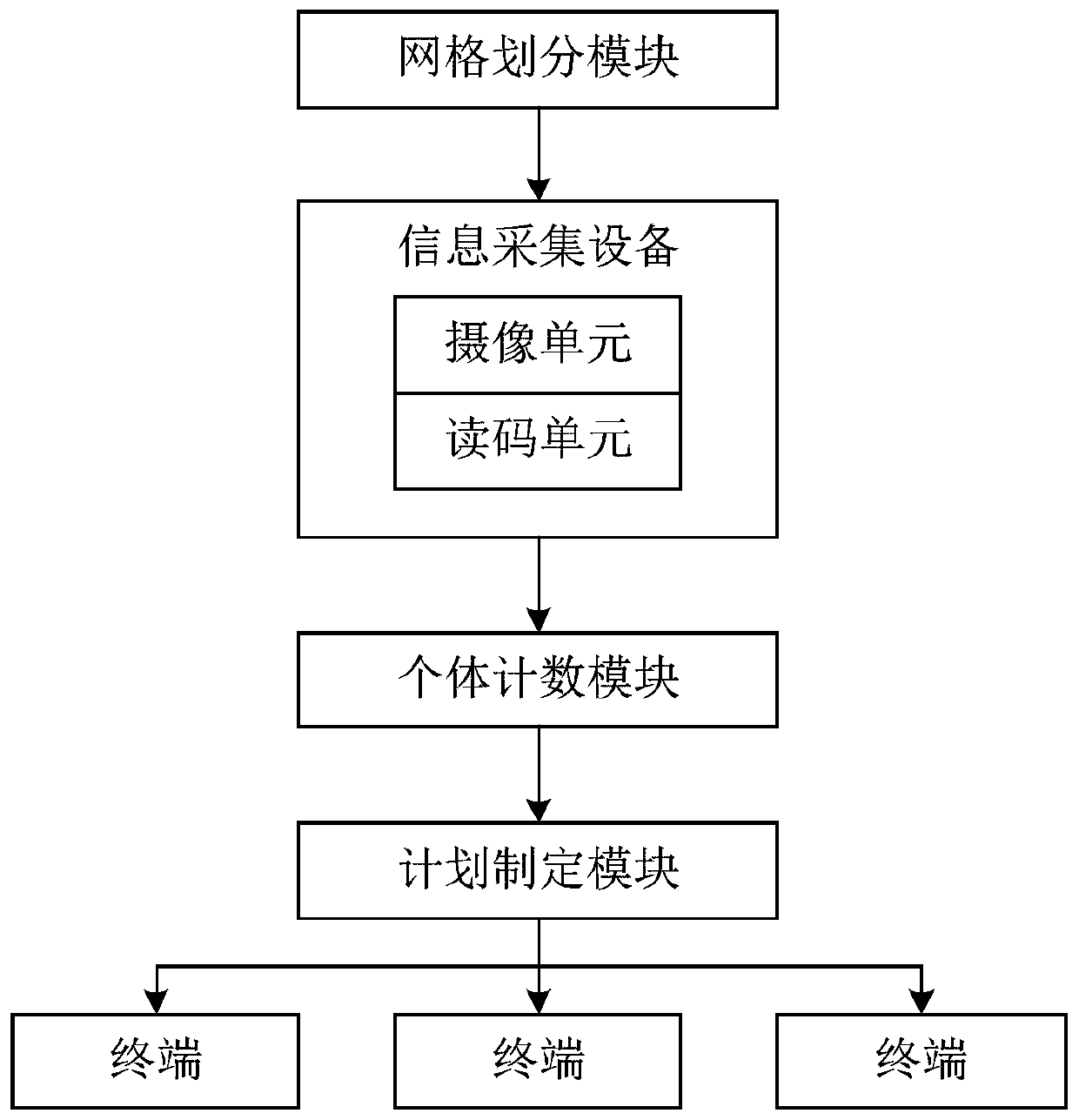
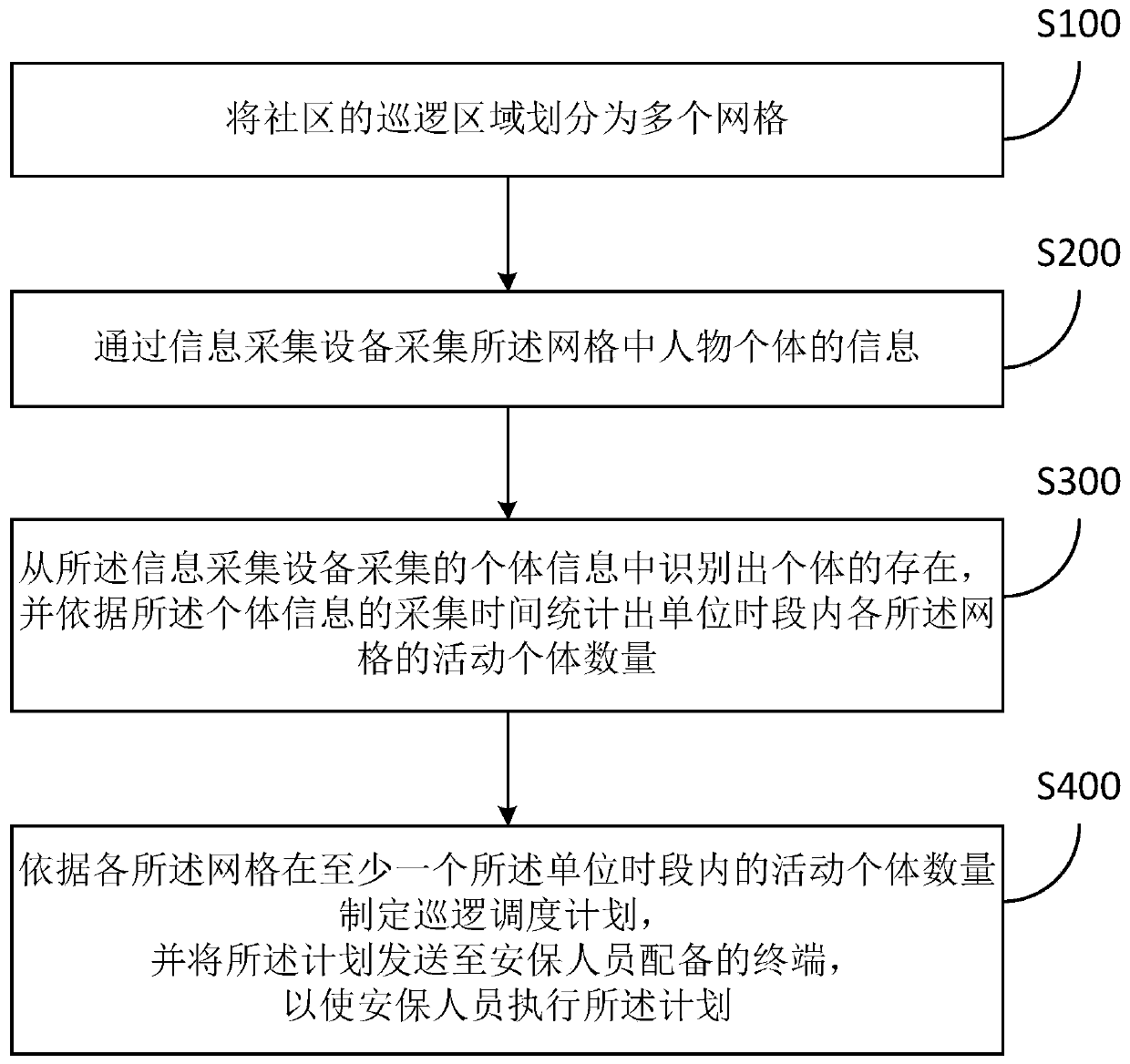
Community security personnel scheduling method based on gridding, and method
ActiveCN110378552AWaste of human resourcesDetect and solve crimesResourcesTraffic capacityAcquisition time
The invention discloses a community security personnel scheduling method based on gridding. The method comprises the following steps: firstly, dividinga patrol area of a community into a plurality ofgrids; then, collecting information of character individuals in the grids through information collection equipment; identifying the existence of the individual from the individual information acquiredby the information acquisition equipment; counting the number of activity individuals of each grid in a unit time period according to the acquisition time of the individual information, finally making a patrol scheduling plan according to the number of activity individuals of each grid in at least one unit time period, and sending the plan to a terminal equipped for security personnel to enable the security personnel to execute the plan. According to the method, the patrol plan is formulated in a more scientific manner, so that patrol personnel matched with the required number can perform security work in regions with different pedestrian flows, manpower resources are not wasted, and more personnel can be arranged for patrol in regions with large pedestrian flows so as to discover and solve crimes and accidents in time.
Owner:TERMINUSBEIJING TECH CO LTD
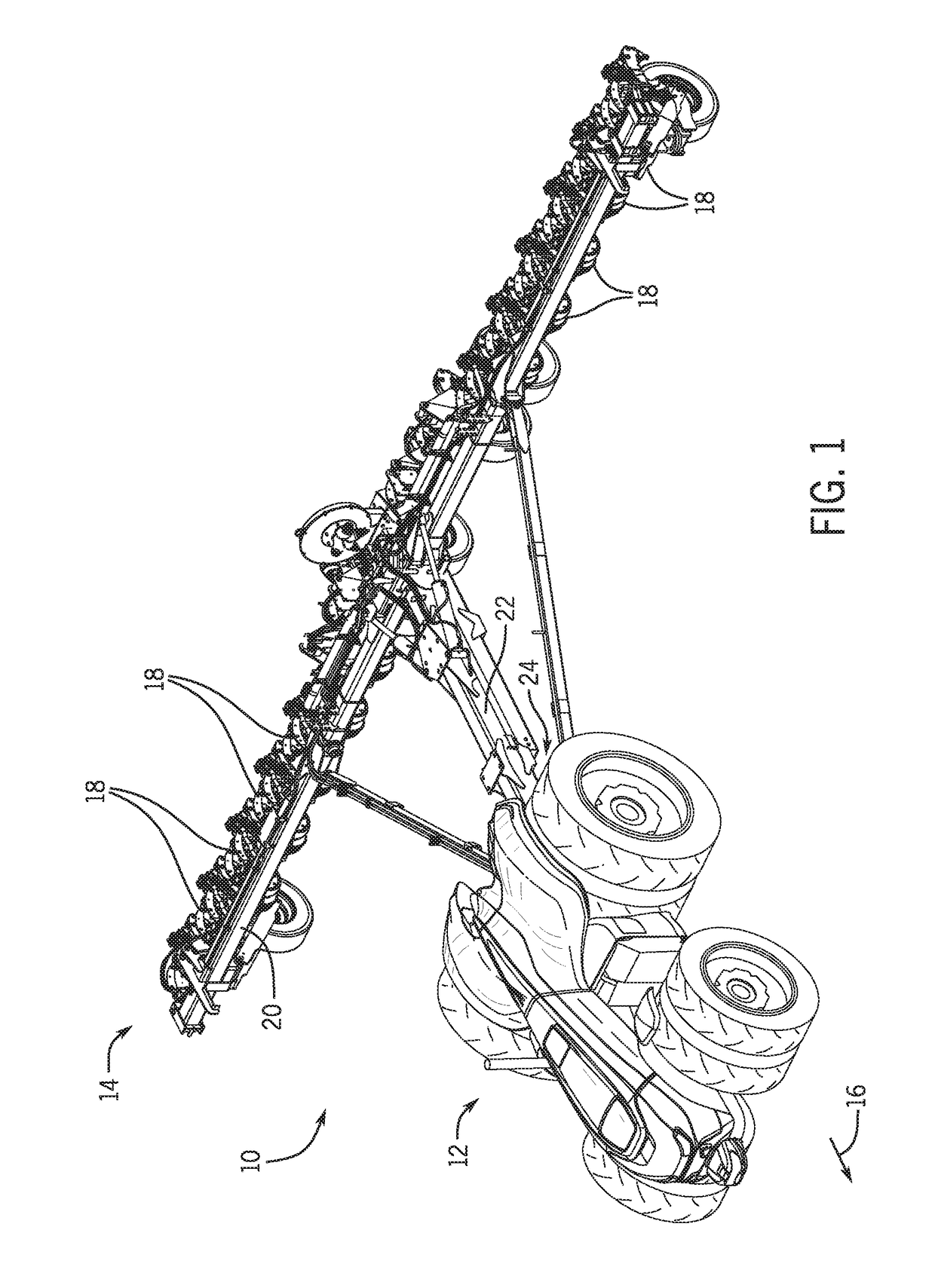
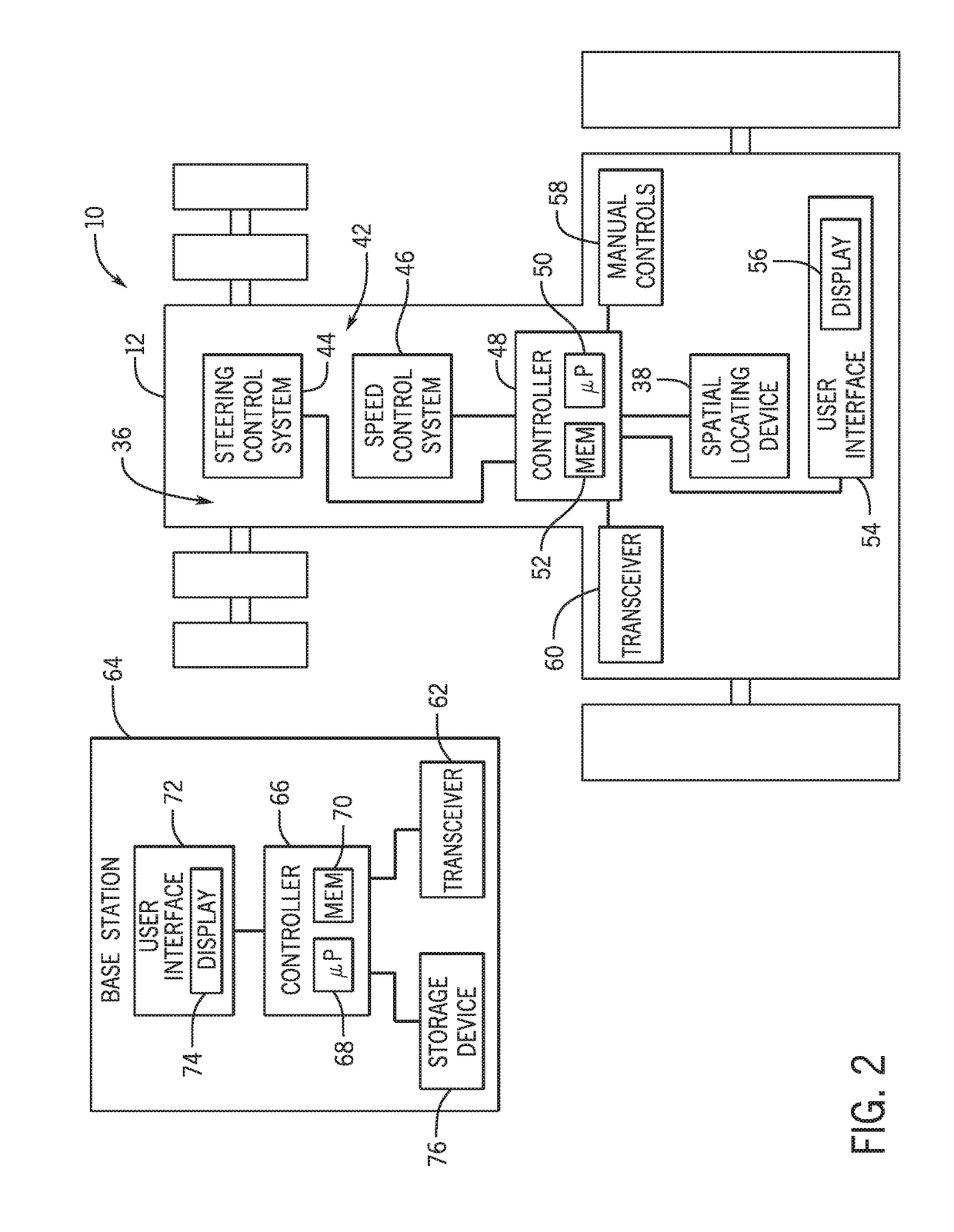
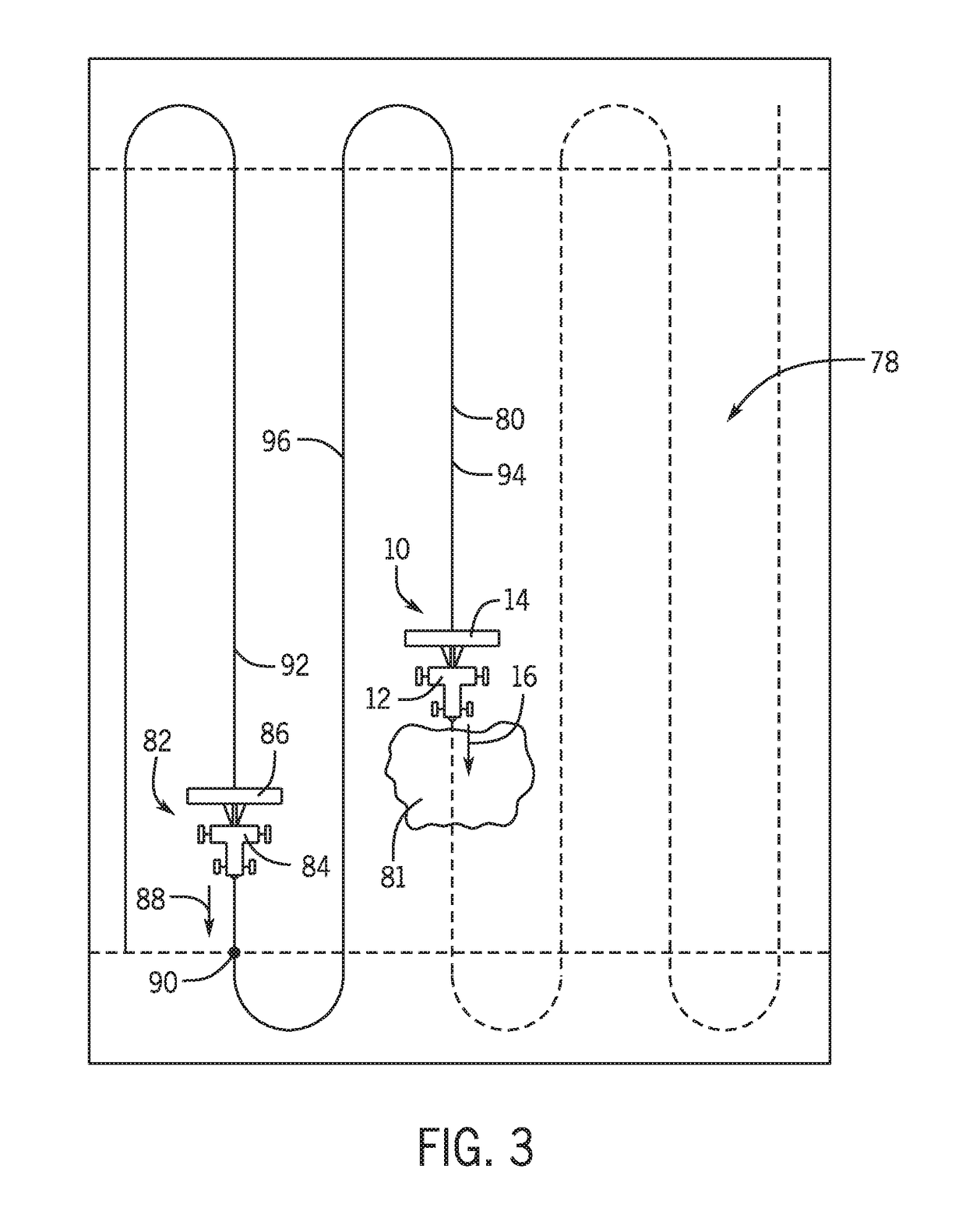
Planning system for an autonomous work vehicle system
ActiveUS20180359906A1Decreasing overall cost functionGuiding agricultural machinesResourcesExecution planningScheduling system
A planning system for an autonomous work vehicle system includes a controller configured to determine a plan for the autonomous work vehicle system by reducing a cost function, and to output one or more signals indicative of the plan and / or instructions to execute the plan. The plan includes a route of the autonomous work vehicle system through a field, and the cost function includes multiple costs associated with operation of the autonomous work vehicle system.
Owner:AUTONOMOUS SOLUTIONS +1
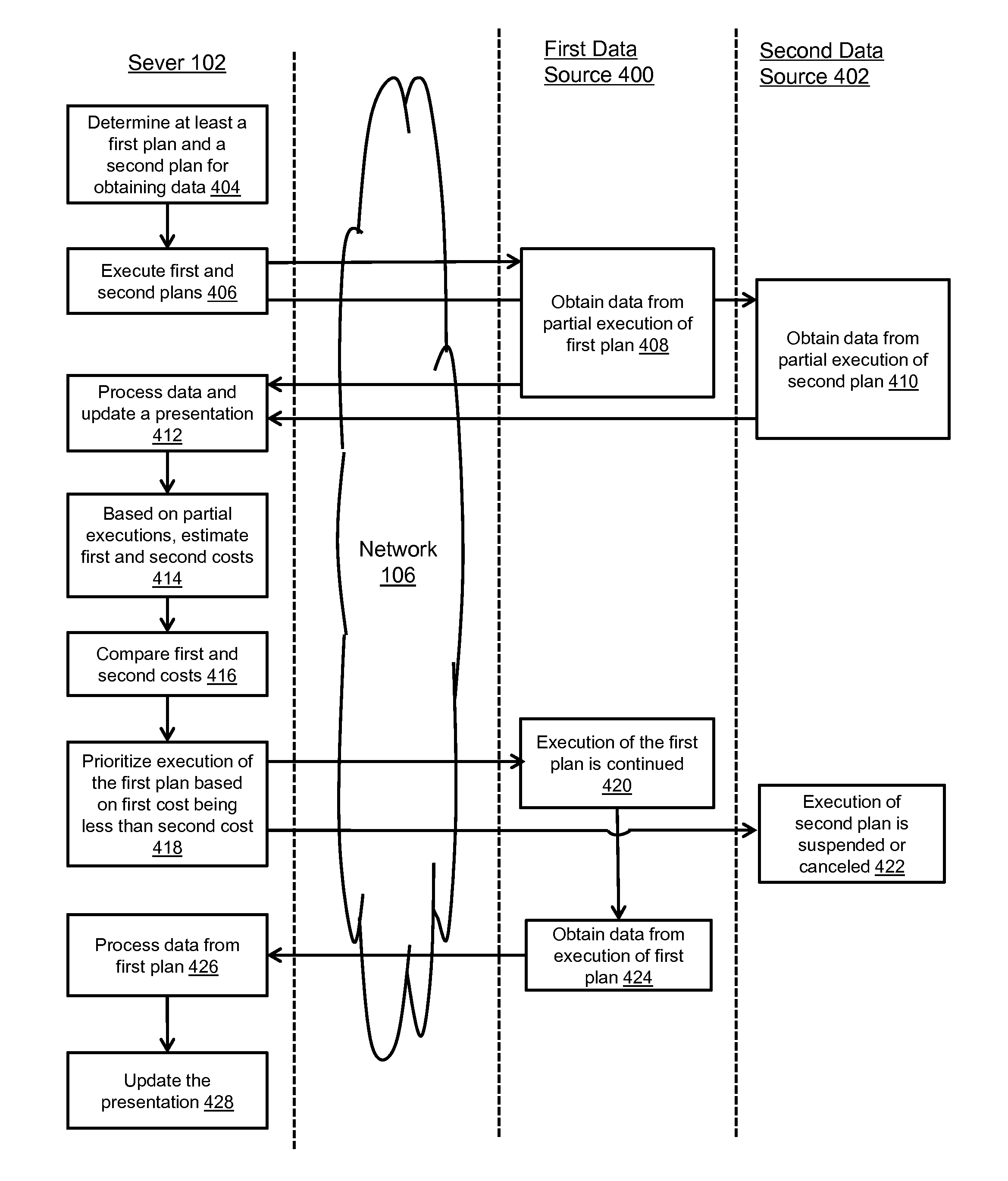
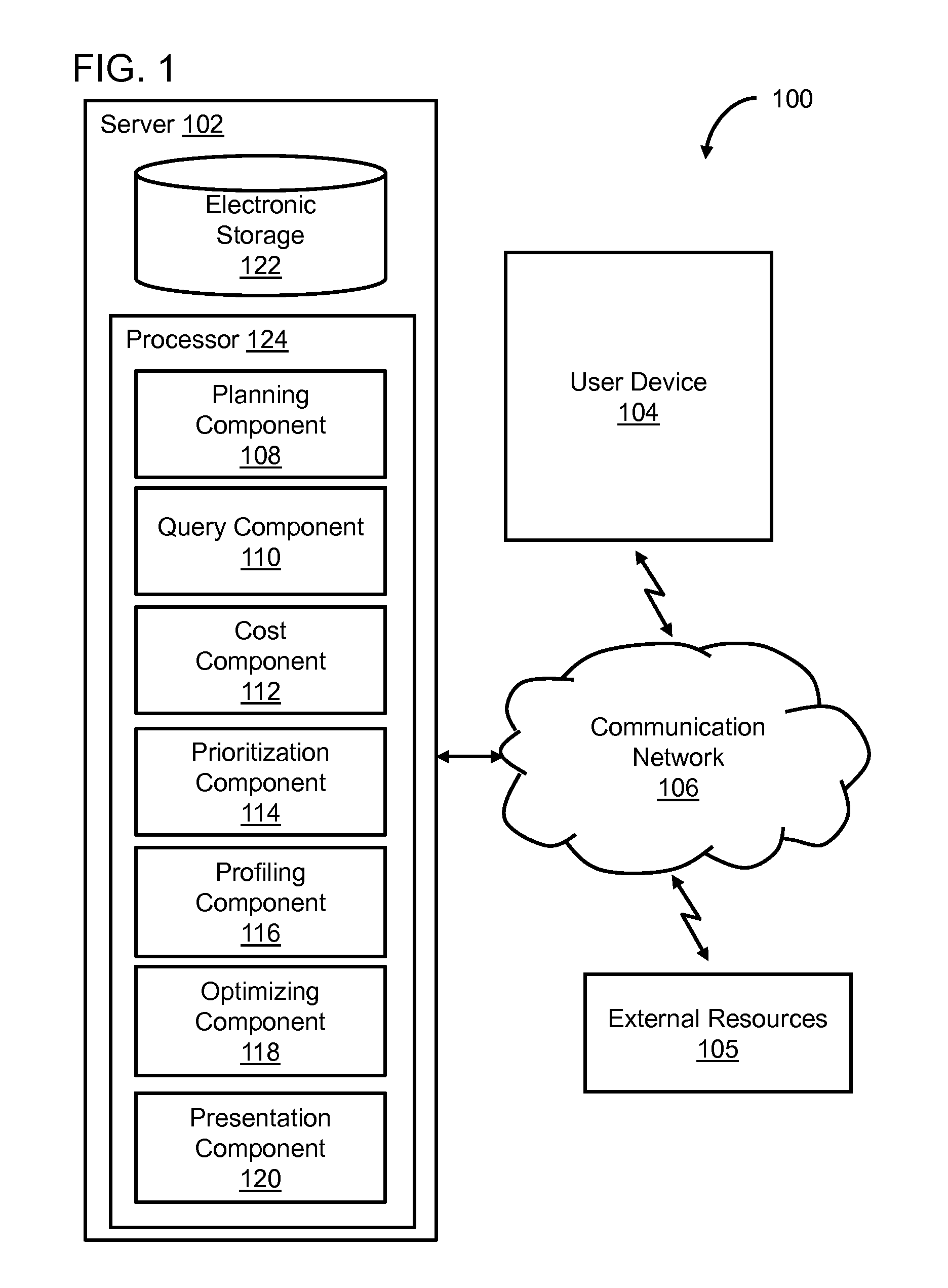
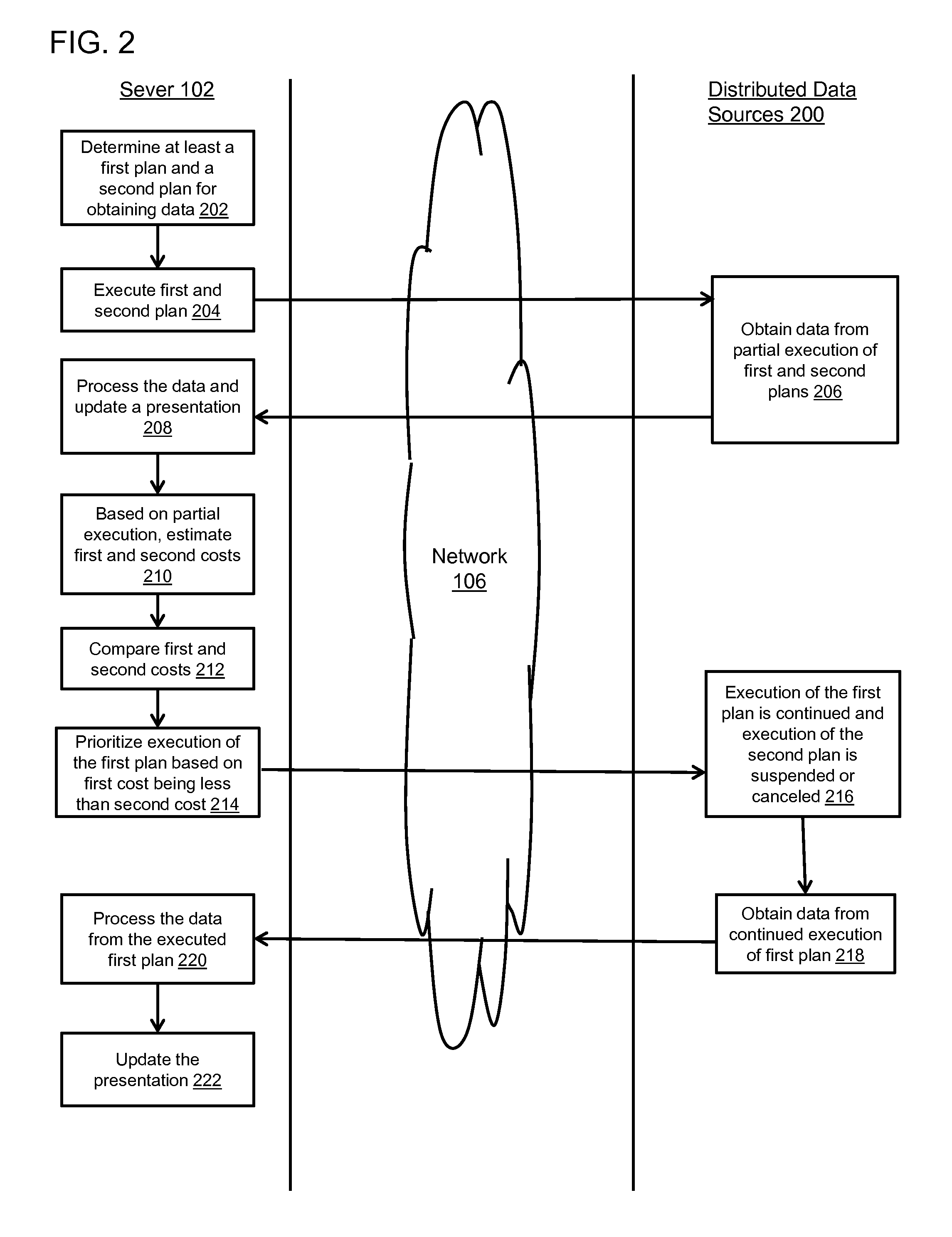
Prioritized execution of plans for obtaining and/or processing data
ActiveUS9389909B1Low costFacilitate minimizing delayProgram initiation/switchingResource allocationProgram planningExecution planning
Systems and methods of prioritizing execution of plans for obtaining and / or processing data based on partial execution of the plans are presented herein. In certain implementations, one or more plans may be executed. Costs associated with individual ones of the plans may be estimated based on partial execution of respective ones of the plans. Based on a comparison between the estimated costs, the execution of at least one of plans may be prioritized over at least the execution of the other ones of the plans.
Owner:ZOOMDATA
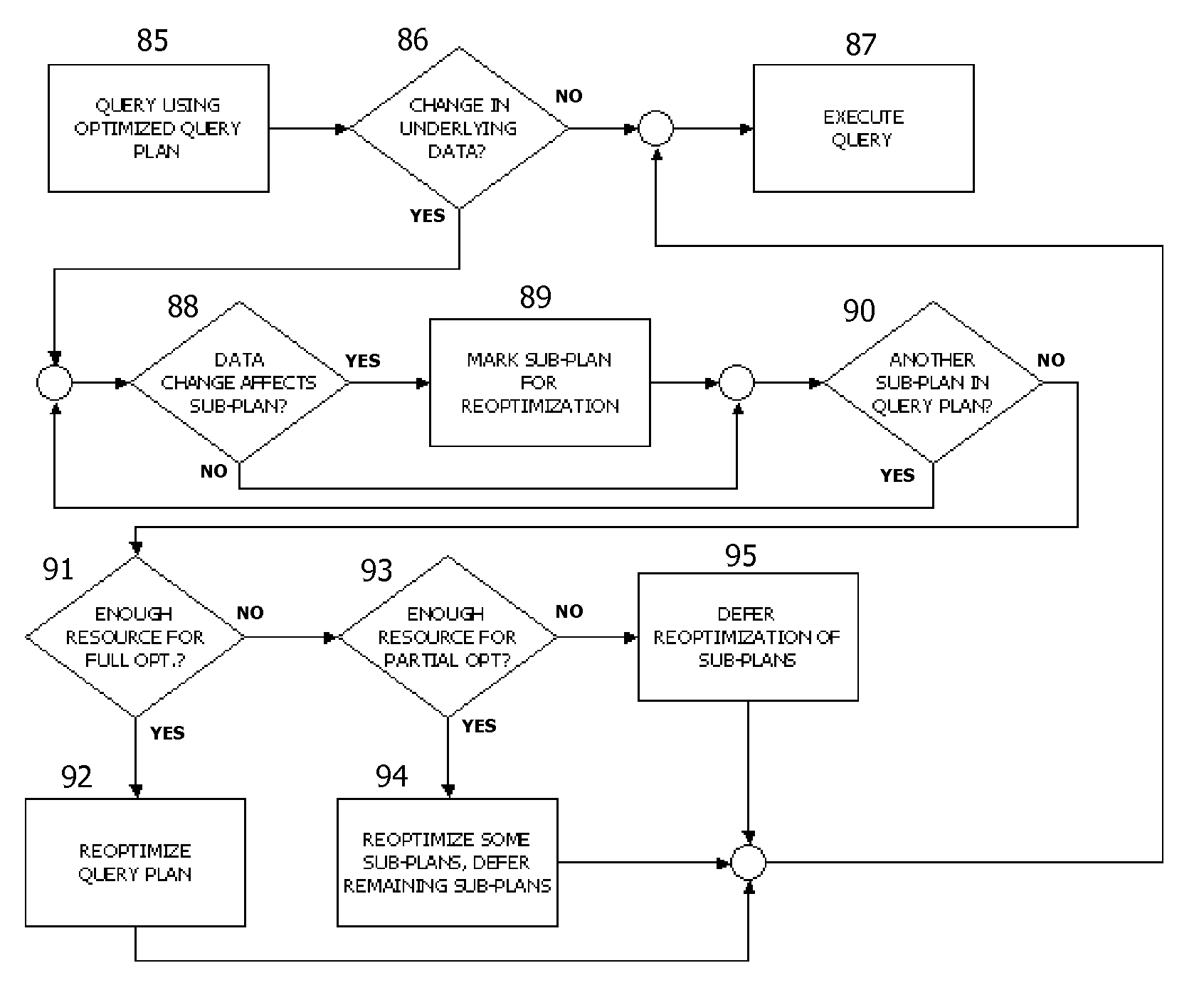
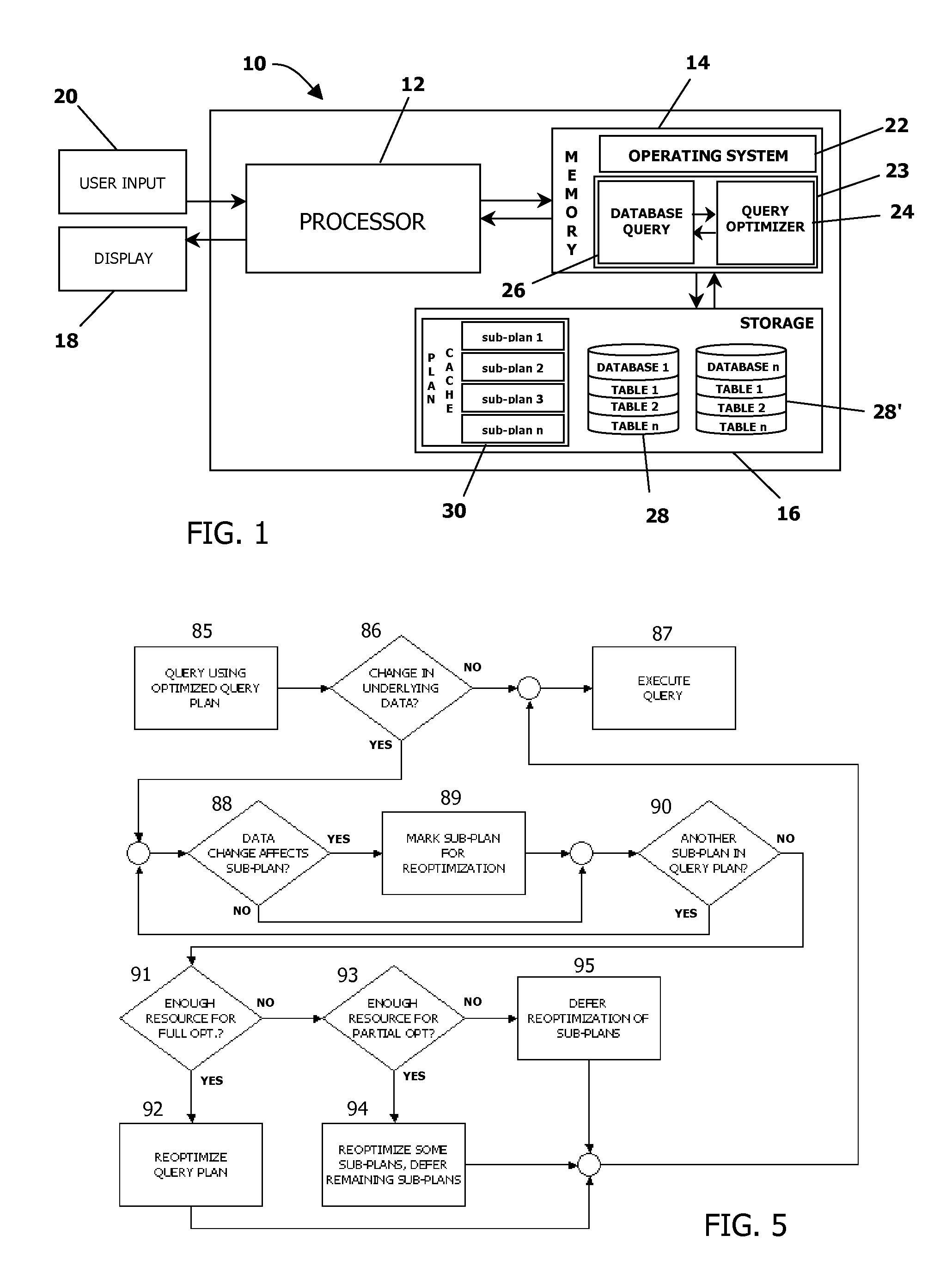
Portable and iterative re-usable suboptimization of database queries
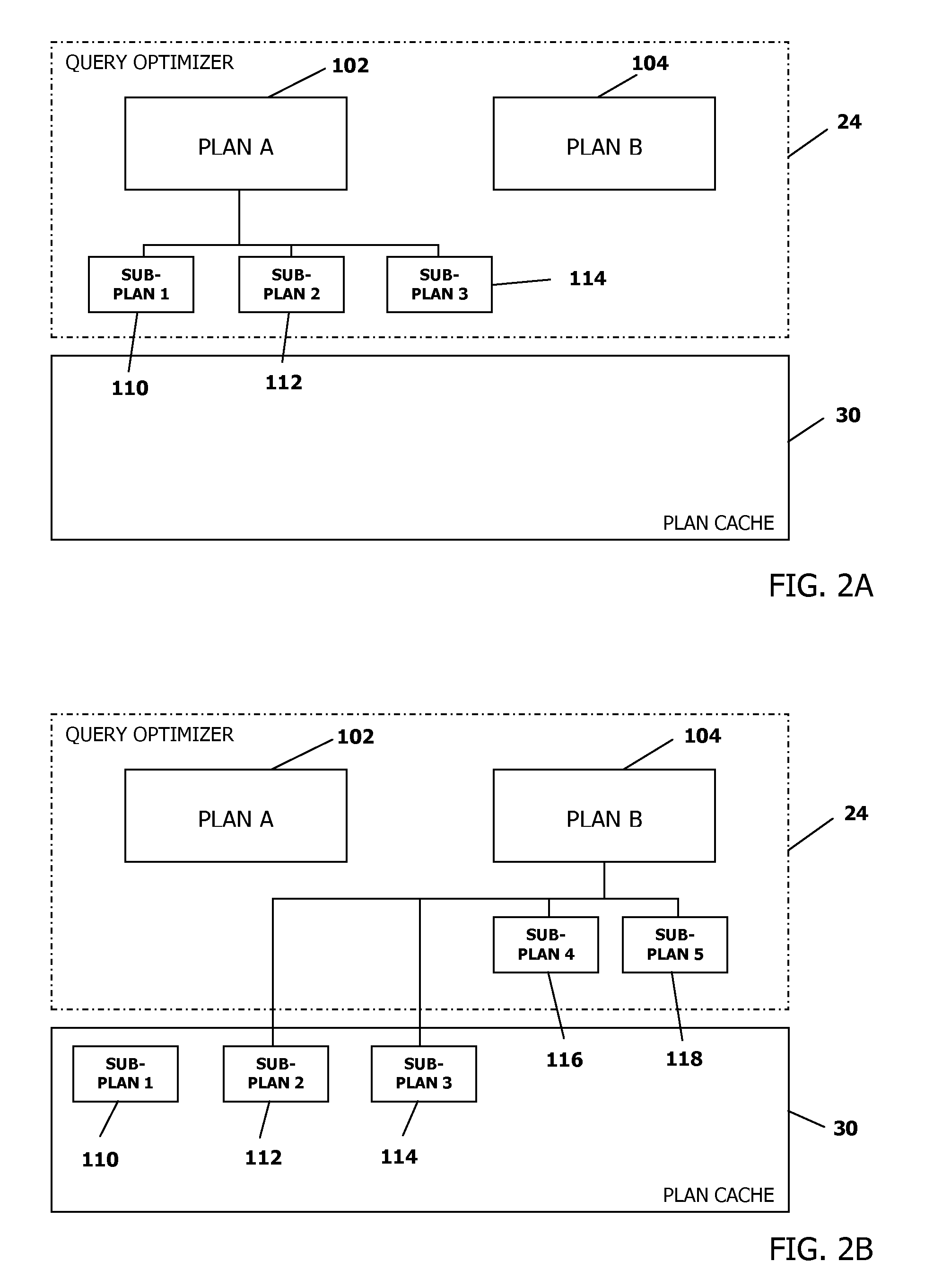
InactiveUS8126873B2Digital data information retrievalDigital data processing detailsDatabase queryQuery plan
A method, apparatus and program product to optimize a database query. A query plan is generated for the database query where the query plan includes first and second subplans. Cached optimization data associated with the first subplan and generated during evaluation of another query plan for a previous query that uses the first subplan is retrieved. The first subplan is evaluated for resource cost using the retrieved optimization data. The second subplan is also evaluated for resource cost. The query plan is then evaluated for resource cost based upon the evaluations of resource cost for the first and second subplans. A query plan is selected based on evaluations of resource cost and the plan is executed to generate a result set.
Owner:INT BUSINESS MASCH CORP
Method and apparatus for managing security vulnerability lifecycles
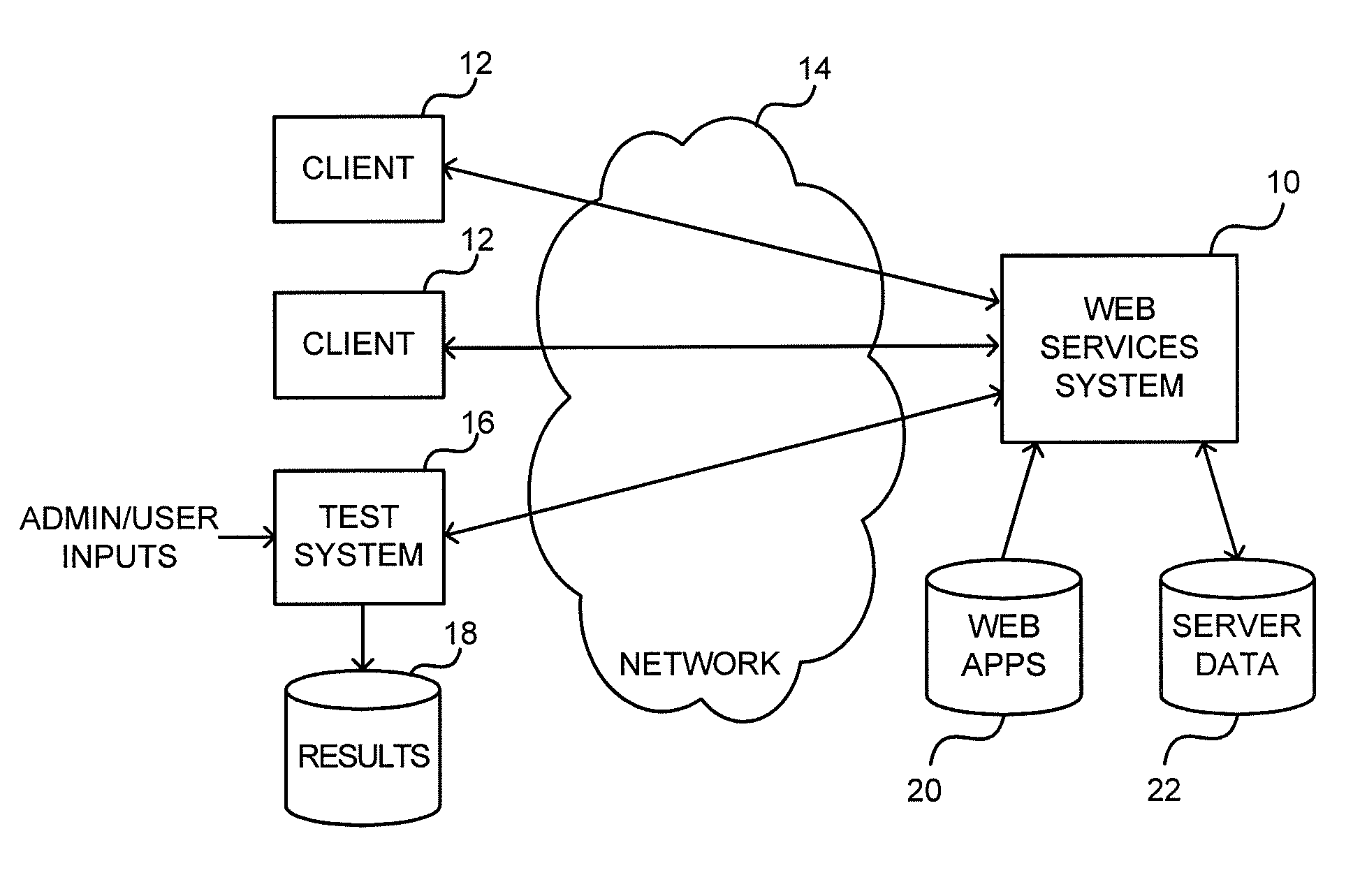
ActiveUS9239745B1Computer security arrangementsSoftware testing/debuggingWeb applicationExecution planning
Vulnerability testing of a web application can be done using external testing, wherein an external test system runs with permissions of a user of the web application and interacts with the web application over a network, the external test system might obtain a schedule for a vulnerability test, execute the schedule using the external test system, log at least portions of responses of the web application to interactions of the external test system with the web application, compare portions of the responses to expected possible responses associated with particular possible vulnerabilities of the web application, thereby detecting possible vulnerabilities of the web application and, for at least one detected possible vulnerability, generating a retest script that comprises at least instructions to place the web application in a state at least similar to the state at which the at least one detected possible vulnerability was detected during execution of the schedule and that comprises at least instructions to interact with the web application in an attempt to recreate the detection without requiring reexecution of the schedule.
Owner:SYNOPSYS INC
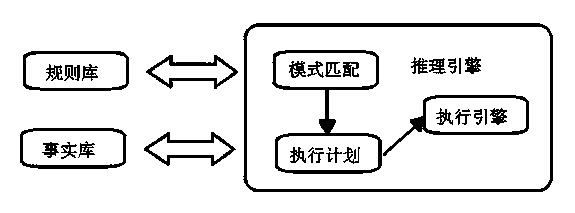
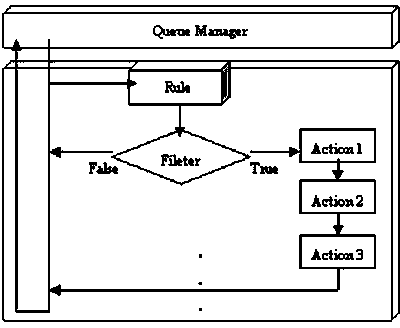
EHK rule engine and realization method of EHK rule
InactiveCN104239038AAvoid repeated operationsImprove execution efficiencySpecific program execution arrangementsProgram planningExecution planning
The invention discloses an EHK rule engine and a realization method of the EHK rule. The EHK rule engine comprises a rule base, a fact base and an inference engine, wherein the inference engine caries out mode matching, plan execution and engine execution, the rule engine sequentially receives an information element from a queue manager and checks rules in a rule set carried by the information element according to the defined sequence of the rule, after the checking on all of the rules in the information element is completely executed, the information element isdestroyed, and the rule engine continuously receives a next information element from the queue manager. The EHK rule engine and the realization method have the advantages that various scenes can be intelligently triggered according to the equipment state, the operation can be freely defined by a user, relevant operation is executed according to specific conditions, and in addition, the executing efficiency is very high.
Owner:倪成胜
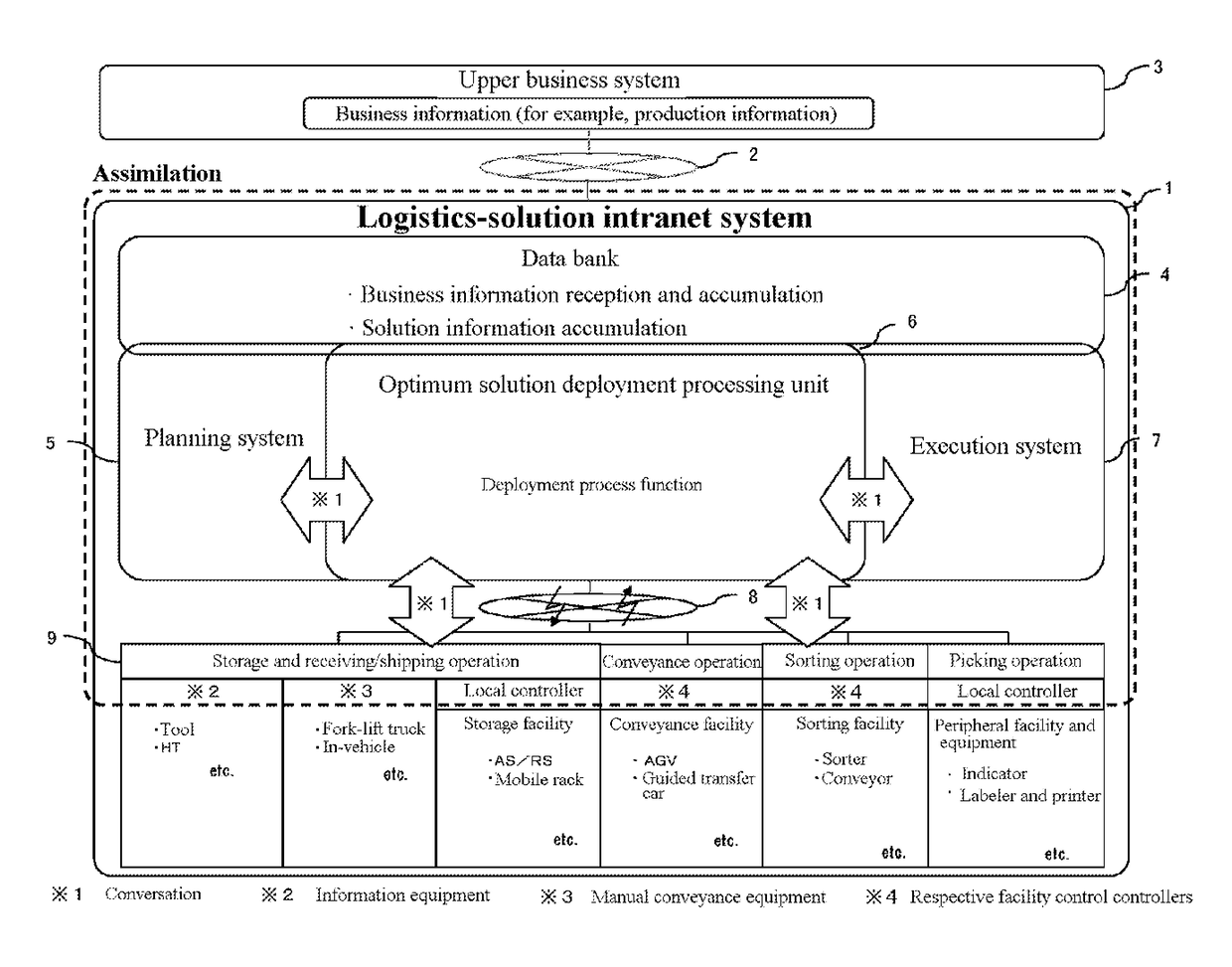
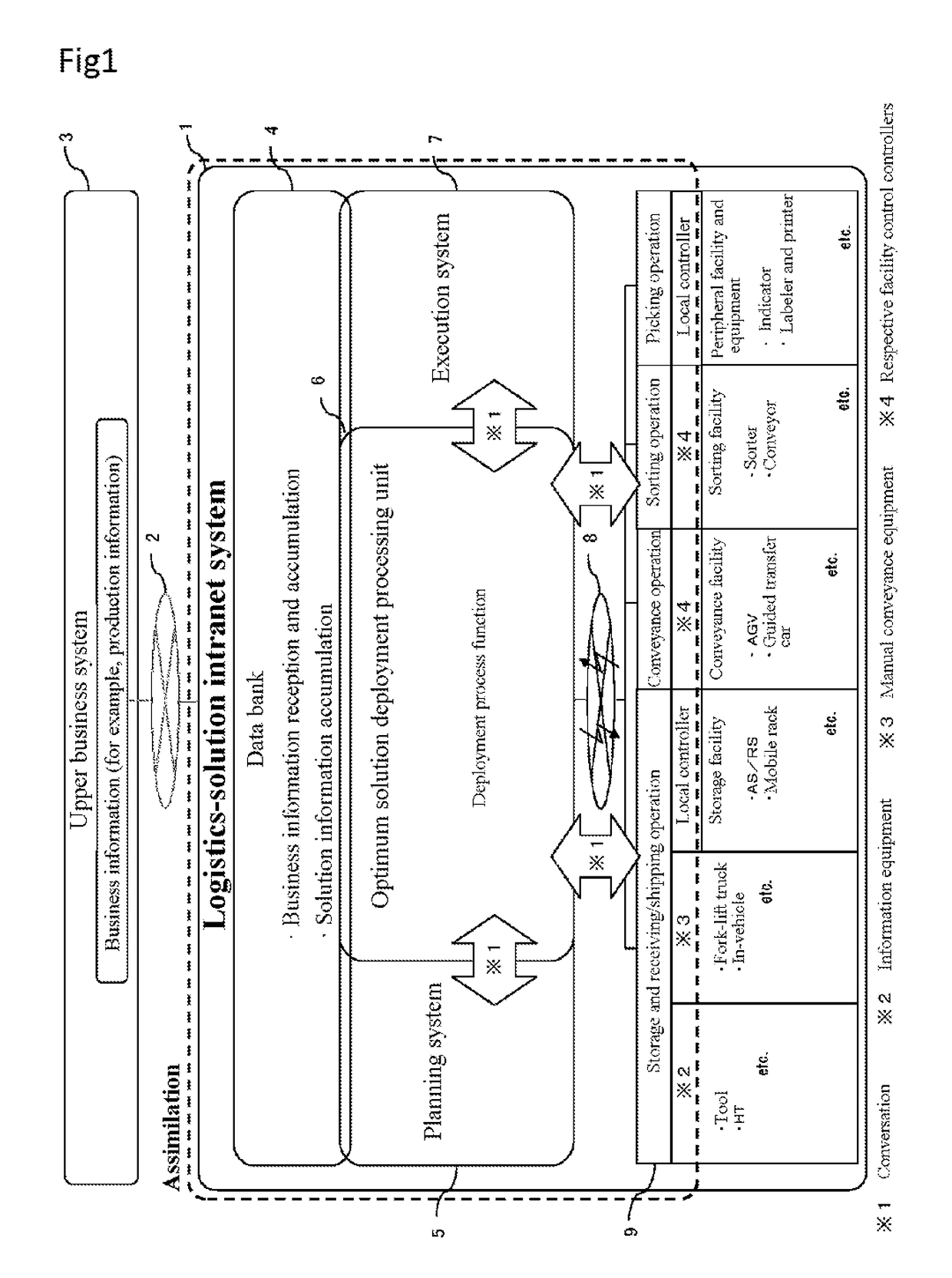
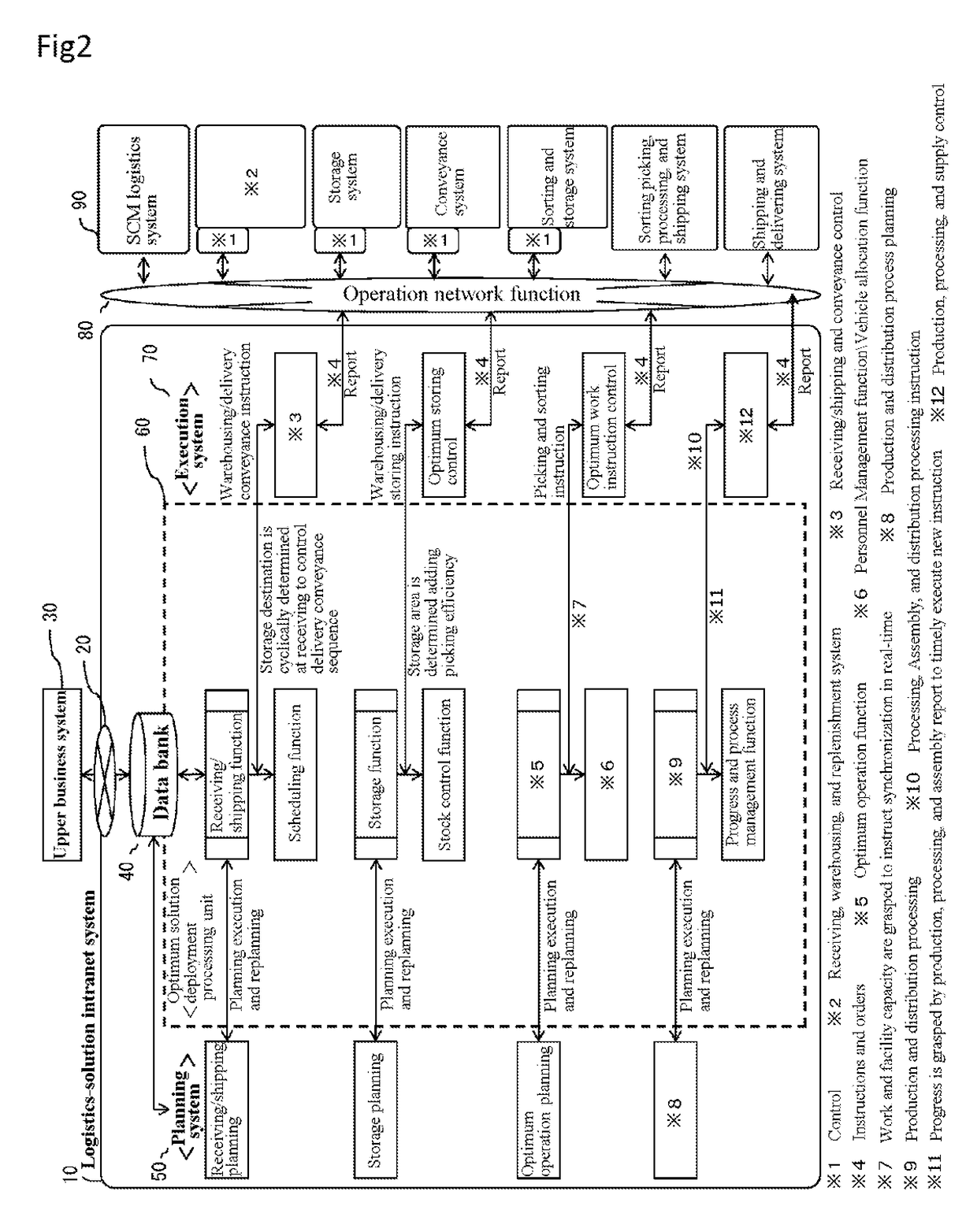
Logistics solution and intranet system
ActiveUS20170220994A1Efficient system operationEasy to operateHardware monitoringResourcesOperational systemLogistics management
A logistics-solution intranet system of the present invention includes a data bank that stores information regarding predetermined logistics, planning means that plans a process of a logistics solution based on the information regarding the predetermined logistics, execution means that transmits execution process information that an operation target device executes, based on the process planned by the planning means, a controller that transmits a work state of the operation target device, optimum process deployment means that controls the entire logistics-solution intranet system based on the information regarding the predetermined logistics, and a network that mutually communicatively couples the planning means, the execution means, and the optimum process deployment means to the controller, and the planning means, the execution means, and the optimum process deployment means are executed in a communication information process (a conversation method), and use identical hardware to be configured using an identical operating system.
Owner:ALE
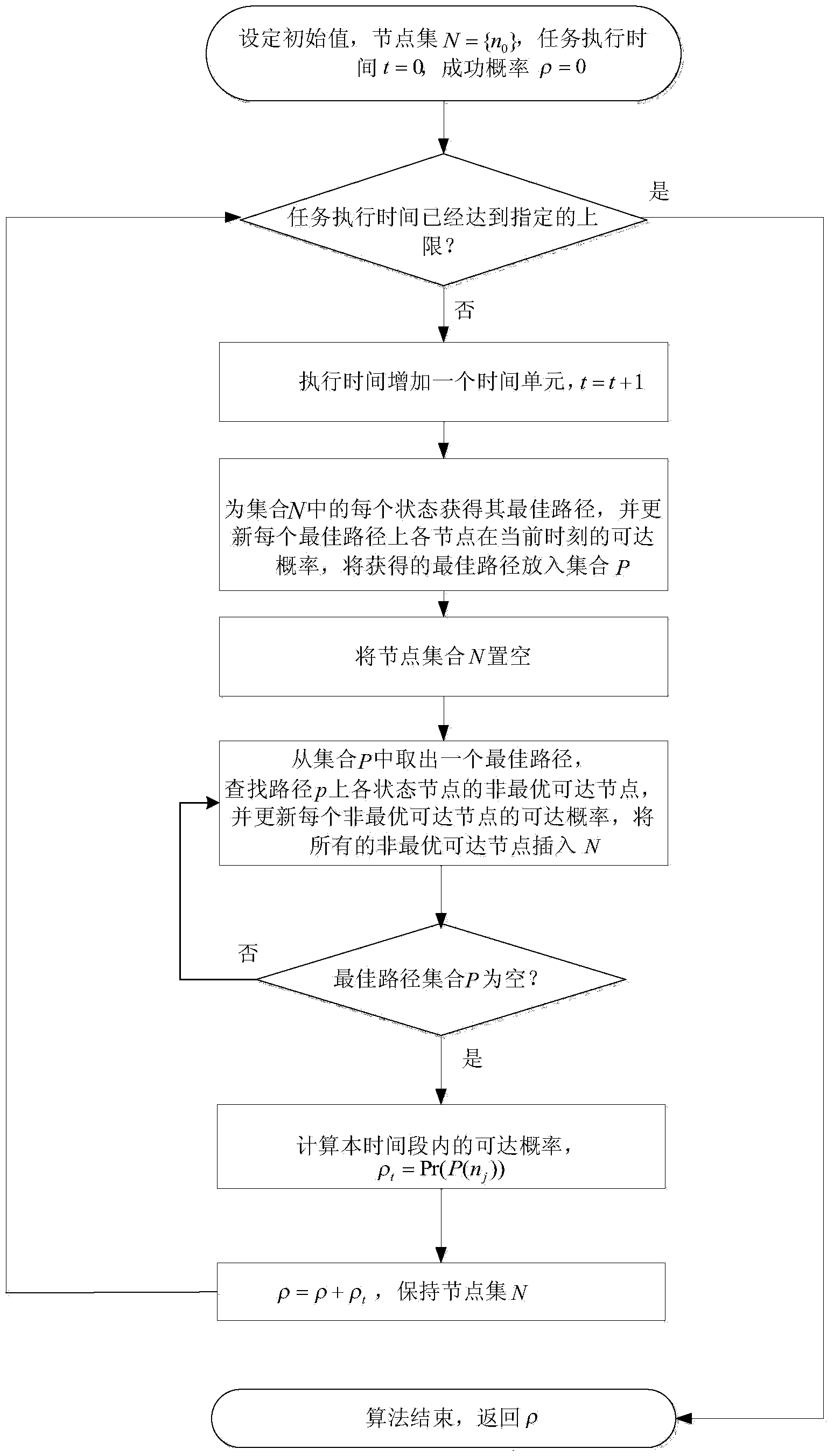
Measuring and risk evaluation method of executive capability of scheduled task
The invention relates to a measuring and risk evaluation method of executive capability of a scheduled task. The method comprises the following steps that firstly, a Markov decision-making process of the scheduled task is built, and the optimal solution of the Markov decision-making process is calculated in an existing method; secondly, the optimal execution path of each state is calculated, and calculation results are stored in an optimal execution path set; finally, according to a task execution time unit, a plan trace and evaluation method (PlaTE for short) is executed repeatedly until the task success rate reaches an expected index or time consumed by task execution exceeds an appointed limitation. The method is beneficial to improving a commanding, dispatching and management decision level, and has positive practical significance.
Owner:NINGBO KAISHITONG INFORMATION TECH CO LTD
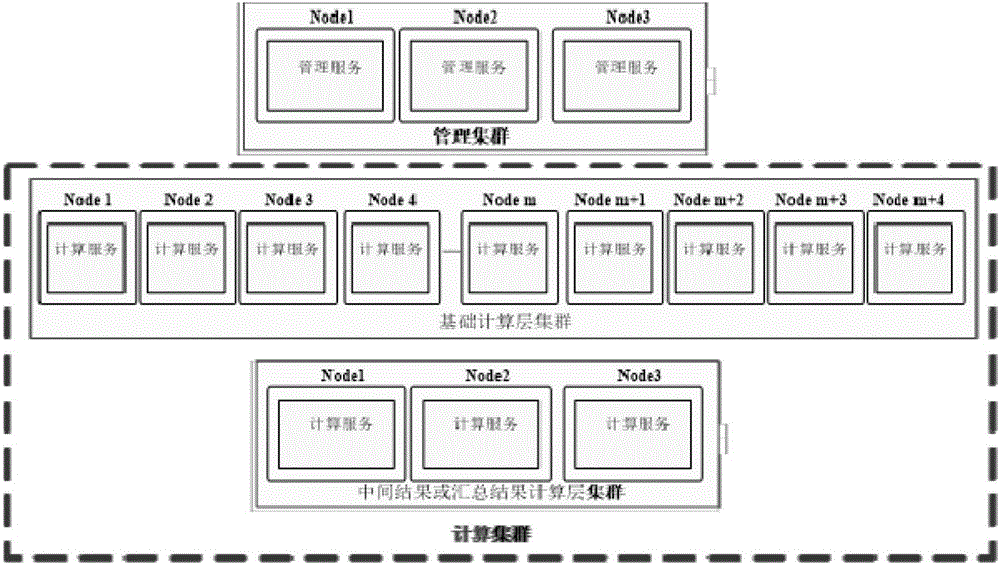
Distributed database and management method for data operation of same
InactiveCN106250566AReduce usageOperational balanceDatabase distribution/replicationSpecial data processing applicationsProgram planningData operations
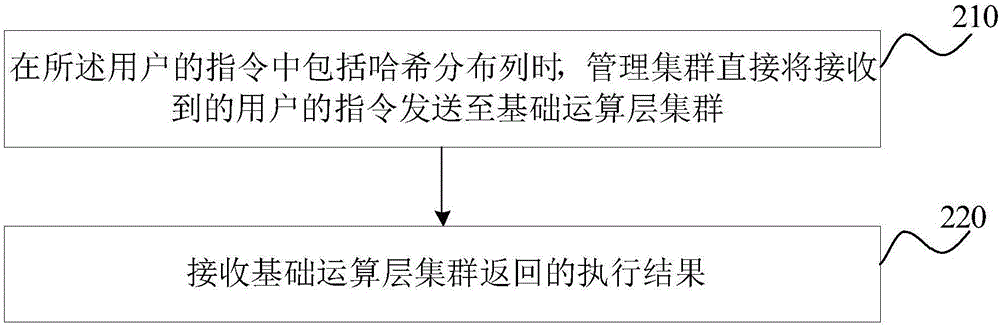
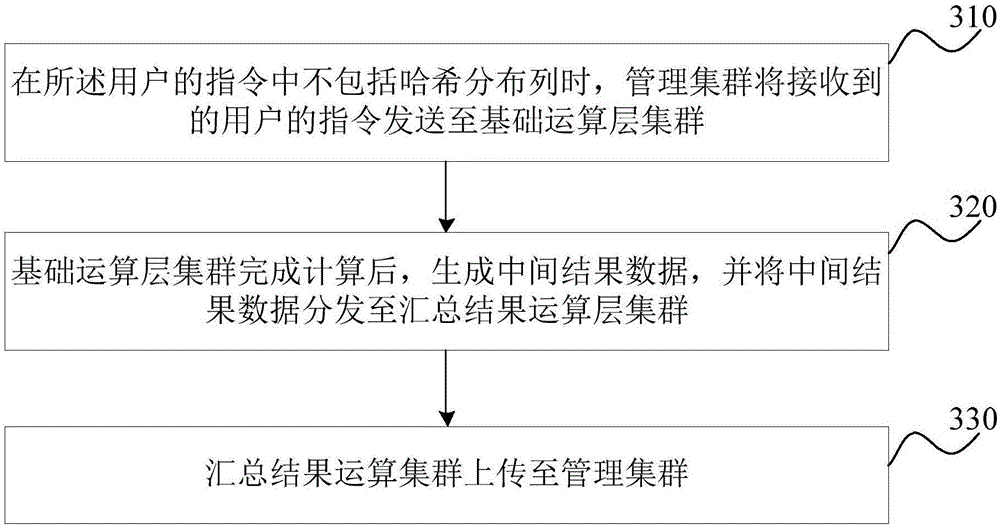
The invention provides a distributed database and a management method for data operation of the same. The distributed database comprises a management cluster used for receiving an instruction of a user, analyzing and optimizing the instruction and generating executive plan and schedule, a basic operation layer cluster used for receiving the executive plan from the management cluster and performing operation based on business tables distributed on nodes, and a summarized result operation layer cluster used for receiving data distributed by the basic operation layer cluster to perform operation. When the data does not have locality, data summarization and interaction can be realized, the use of network resources between the nodes can be reduced, and operation node resources of the distributed database can be more balanced.
Owner:TIANJIN NANKAI UNIV GENERAL DATA TECH
Wearable equipment as well as task execution control method and device thereof
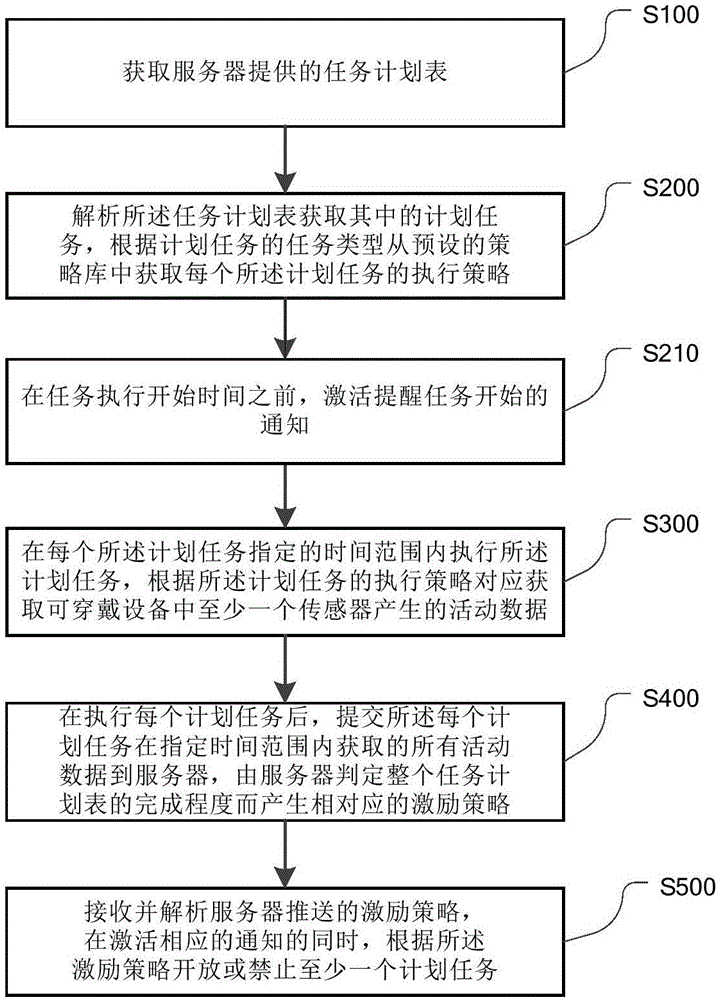
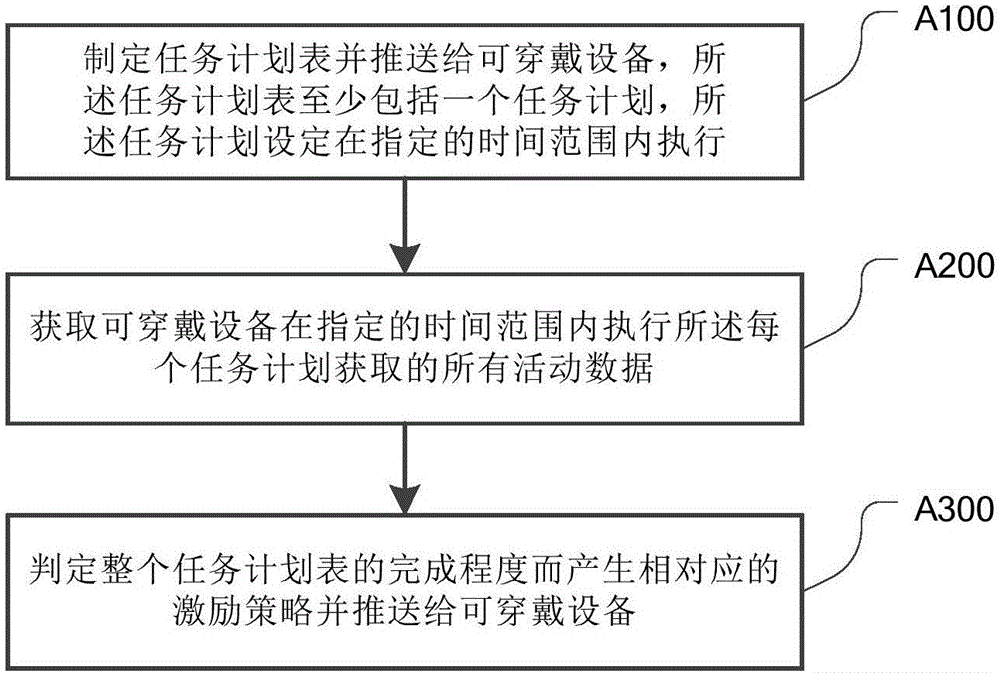
InactiveCN106776073AHumanizeDevelop behavioral habitsInterprogram communicationTime rangeProgram planning
The invention discloses a task execution control method and device of wearable equipment. The method comprises the following steps: acquiring a task schedule provided by a server; analyzing the schedule to obtain planned tasks, and obtaining execution strategies of the planned tasks from a preset strategy library according to the types of the planned tasks; executing the planned tasks within a time range designated by the planned tasks, and correspondingly acquiring activity data generated by a sensor in the wearable equipment according to the execution strategies of the planned tasks; after each planned task is executed, submitting all the activity data acquired by each planned task within the designated time range to the server, and judging the completion degree of the task schedule by the server to generate a corresponding excitation strategy; receiving and analyzing the excitation strategy pushed by the server, and during activation of corresponding notifications, allowing or forbidding at least one planned task according to the excitation strategy. The wearable equipment disclosed by the invention is more humanized; the time point of task setting to the time point of completion of tasks to the time point after the tasks are completed are in cohesive relation; the wearable equipment has continuity in habit development.
Owner:BEIJING QIHOO TECH CO LTD
Abnormal behavior detection and guide safety method for control software of wind generation set
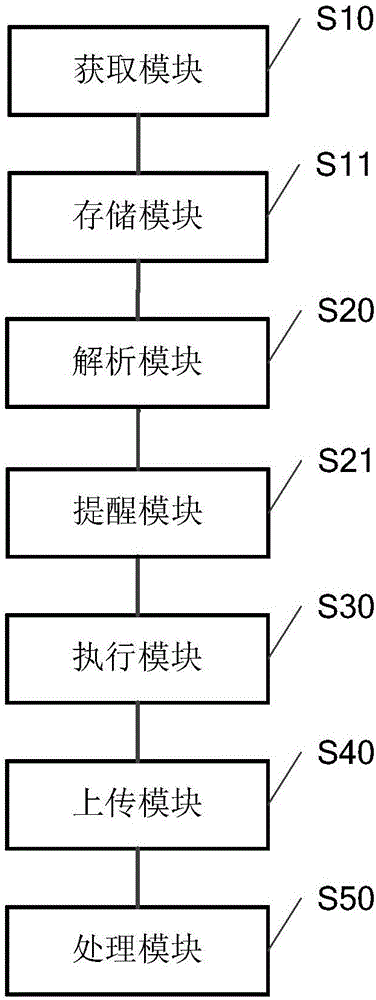
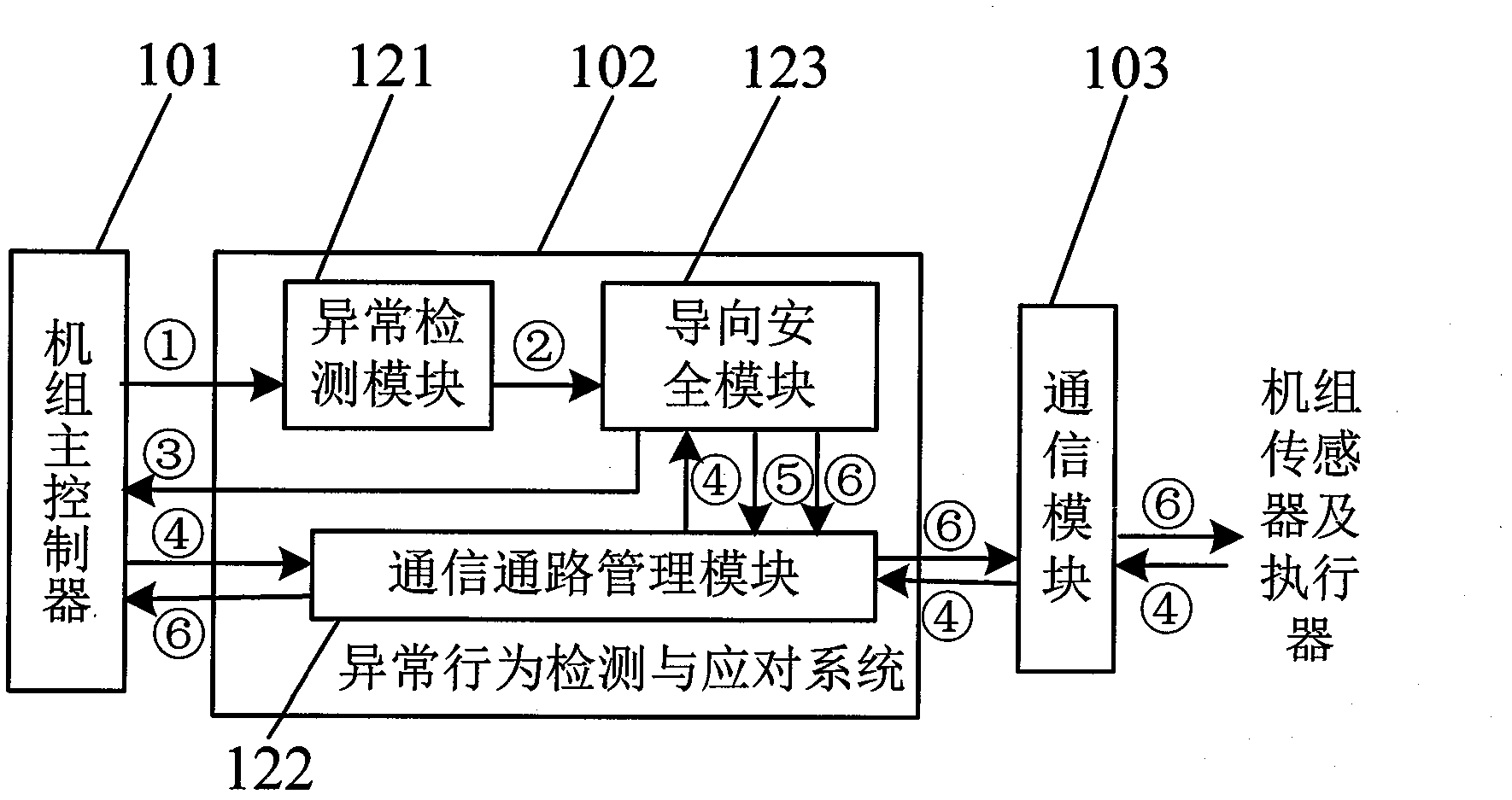
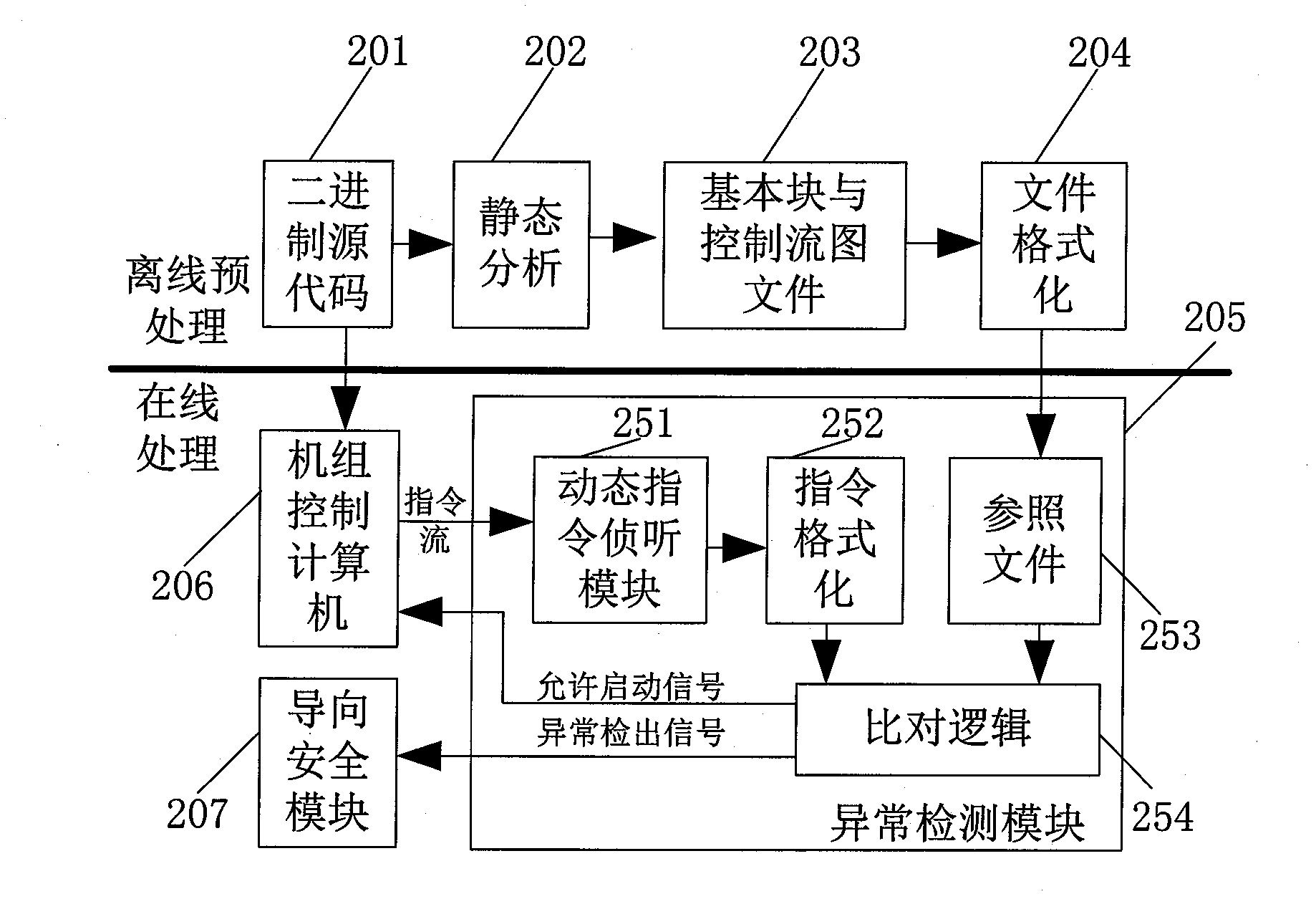
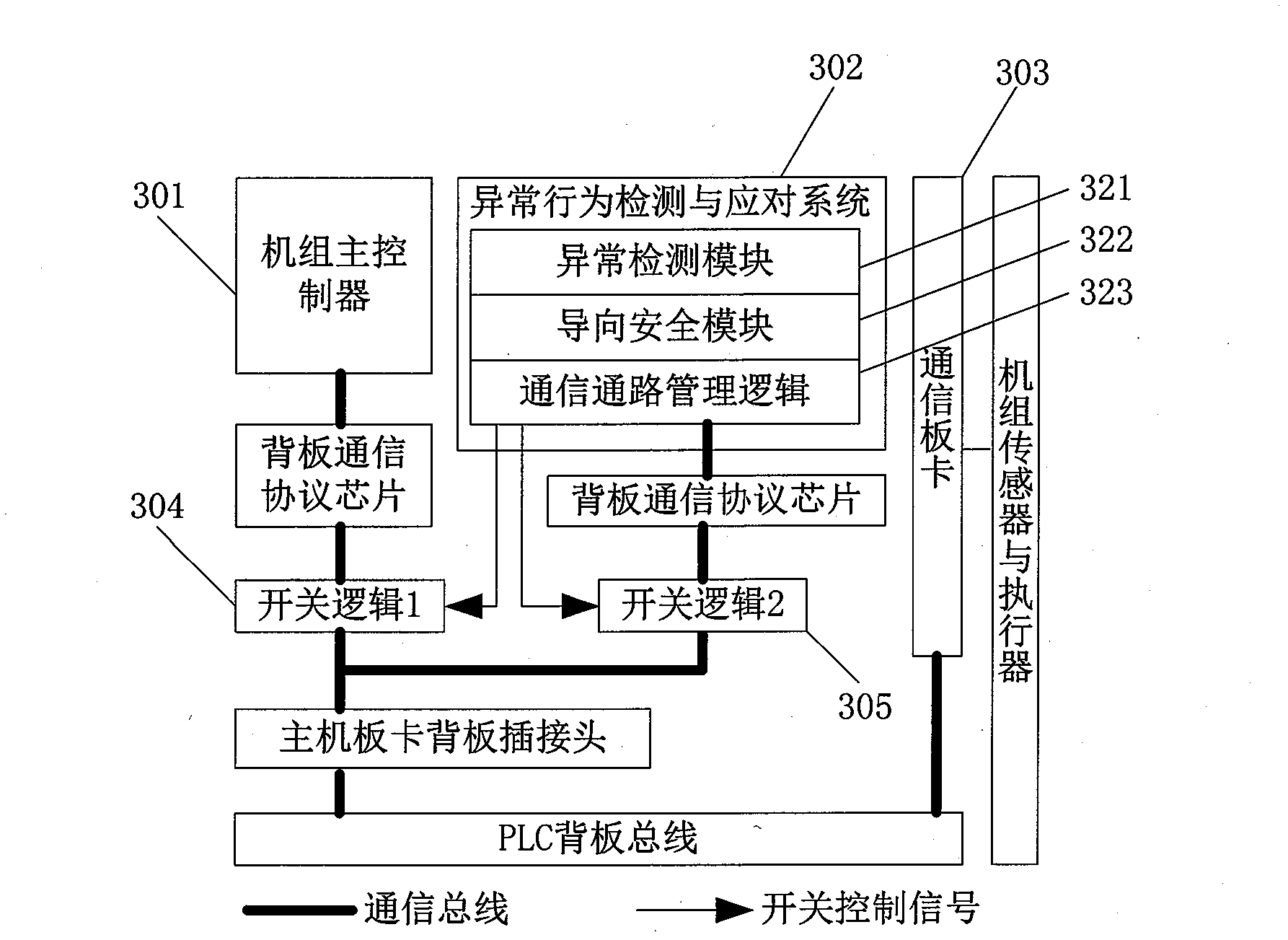
The invention discloses an abnormal behavior detection and guide safety method for a control software of a wind generation set for safety detection and treatment when a main control software of the wind generation set is operated. The method comprises the following main points of: 1) firstly, taking a instruction stream executed and output by a main controller of the wind generation set to an abnormal behavior detection and handling system independent of the main controller of the wind generation set, wherein the system detects that the software is abnormal in behavior as the command executed by the main controller of the wind generation set is deviated from a binary source code of the control software; 2) after detecting an abnormal behavior, switching a communication path by the abnormal behavior detection and handling system to achieve takeover of the wind generation set; and 3) after controlling the abnormal behavior detection and handling system taking charge of control of the wind generation set, the main controller of the wind generation set is shut down firstly, and the wind generation set is shut down in a normal shutdown mode. The technical scheme provided by the invention can detect abnormal behaviors of a main controller software of the wind generation set which goes wrong or executes a code out of a plan, and guides the wind generation set to be safe.
Owner:XIANGTAN UNIV
Engine control system designed to manage schedule of engine control tasks
InactiveUS7912623B2Chance of of evenlyGuaranteed smooth executionElectrical controlDigital data processing detailsProgram planningControl system design
An engine control system for managing a schedule of execution of engine control tasks is provided. The system works to schedule execution of the engine control tasks upon receipt of requests to initiate the engine control tasks. The system determines a sequence of execution of the engine control tasks and allocates execution times for which the engine control tasks are to be executed so as to provide chances of execution of the engine control task as evenly as possible. The system may determine required time-sharing ratios of the engine control tasks based on statuses of execution of the engine control tasks.
Owner:DENSO CORP
Method and system for supervising execution of scheme
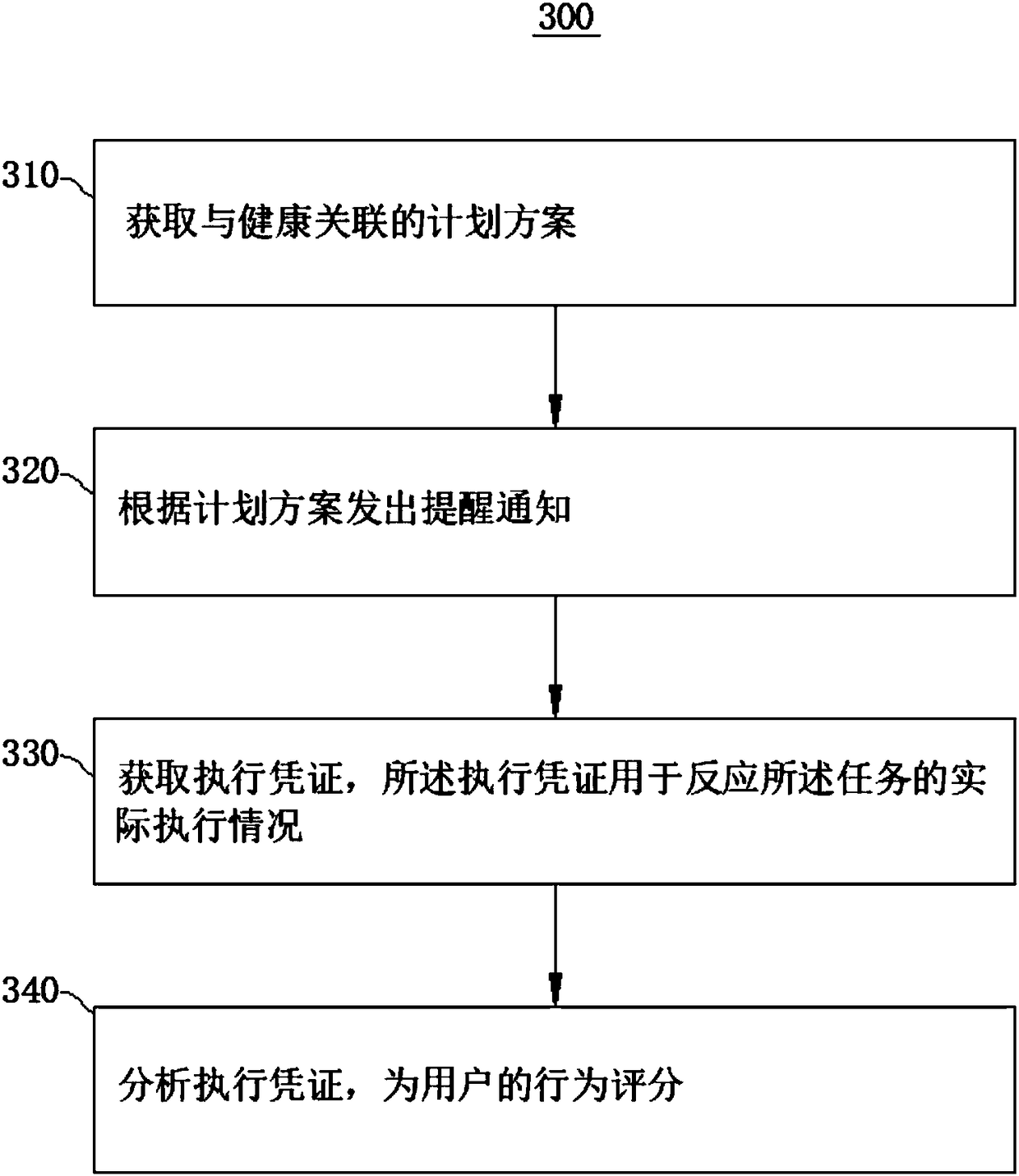
InactiveCN108364673APhysical therapies and activitiesHealth-index calculationProgram planningExecution planning
The application provides a method and system for supervising the execution of a scheme, and relates to the field of intelligent terminals. The method comprises acquiring a planned scheme associated with health; giving a reminder notification according to the planned scheme, wherein the reminder notification is configured to remind the user to execute a certain task on time; obtaining an executioncredential for reflecting the actual execution state of the task; analyzing the execution credential to score a user's behavior. The method and system for supervising the execution of a scheme, on theone hand, prompts the user to execute the planned scheme by the reminder notification, and on the other hand, can promote the user to execute the planned scheme by scoring the behavior of the user.
Owner:SHANGHAI IUV SOFTWARE DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com