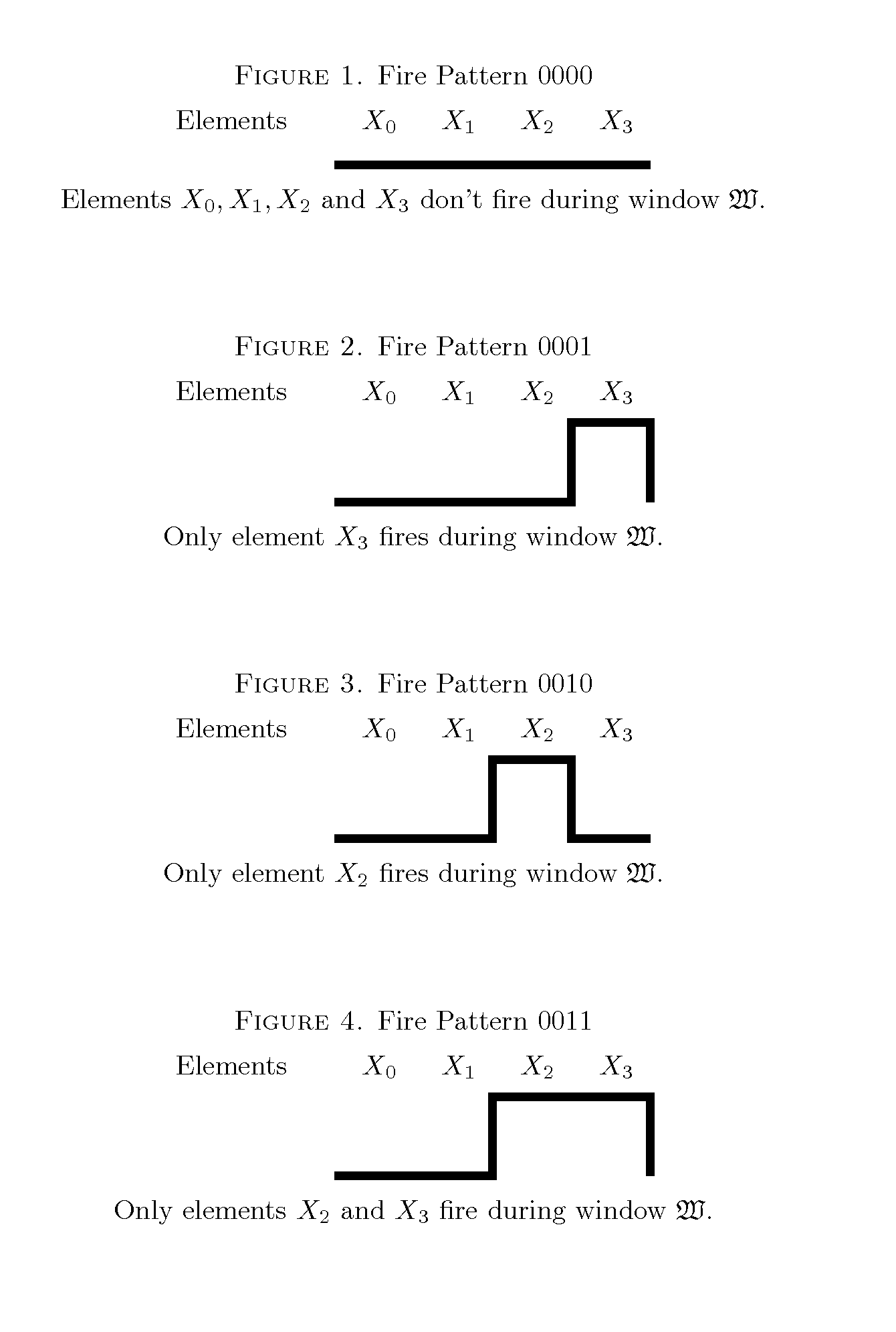
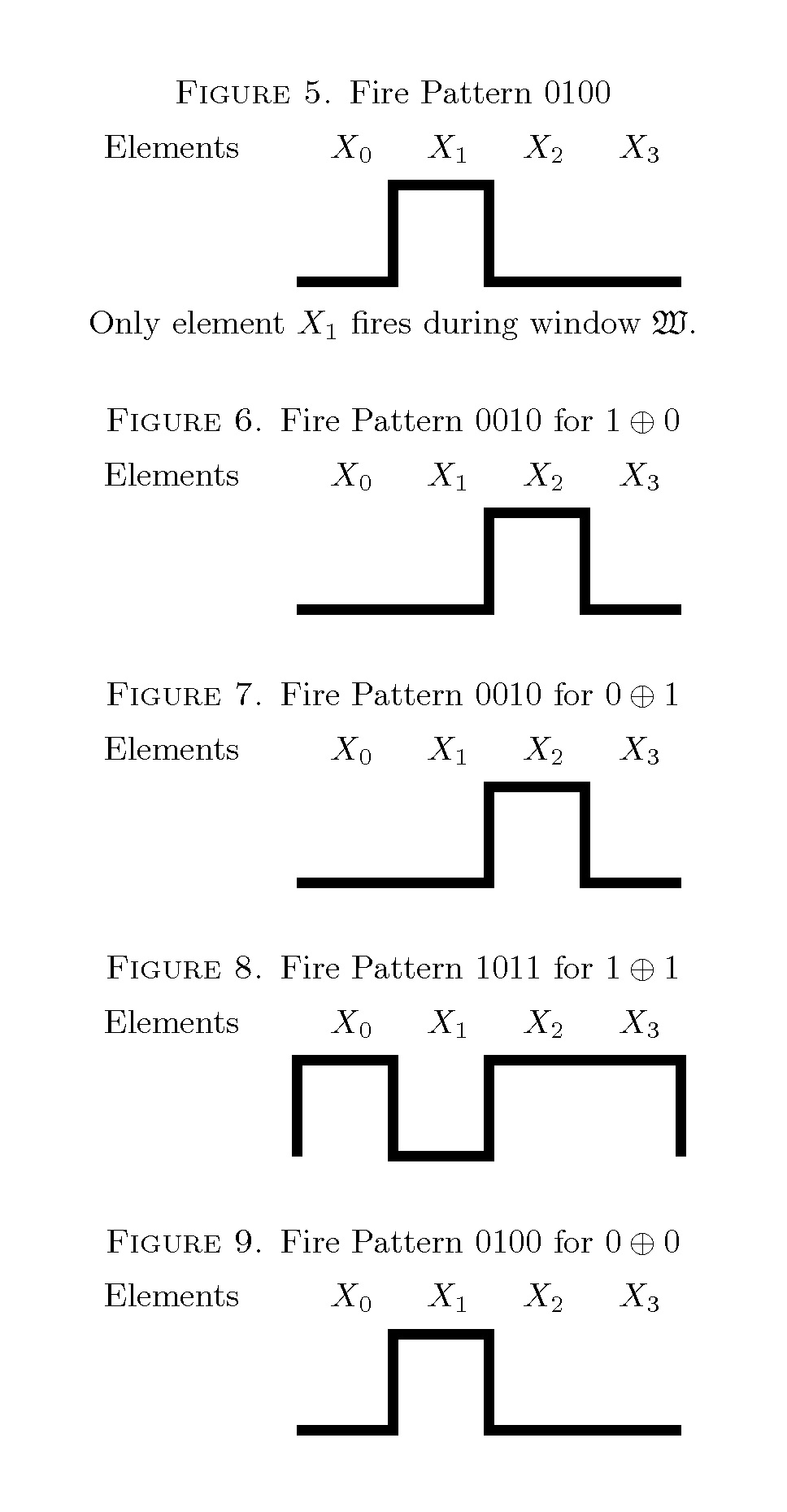
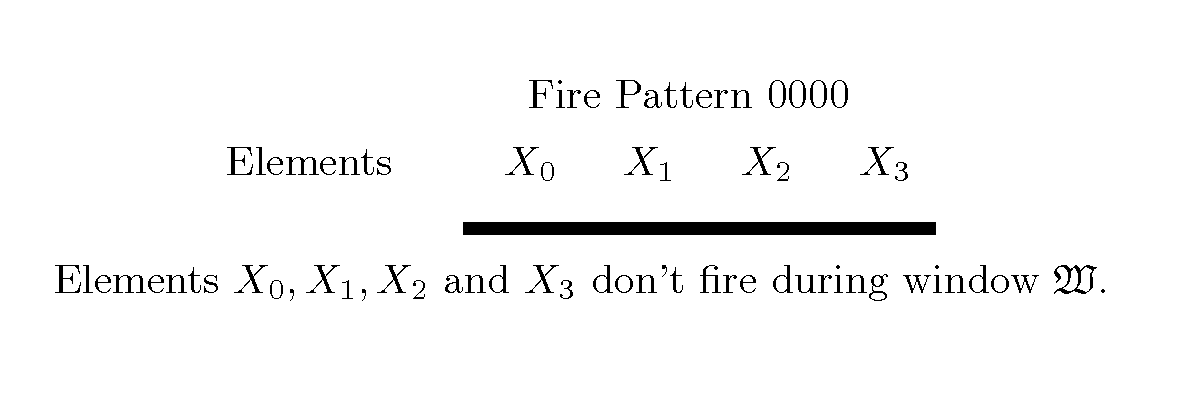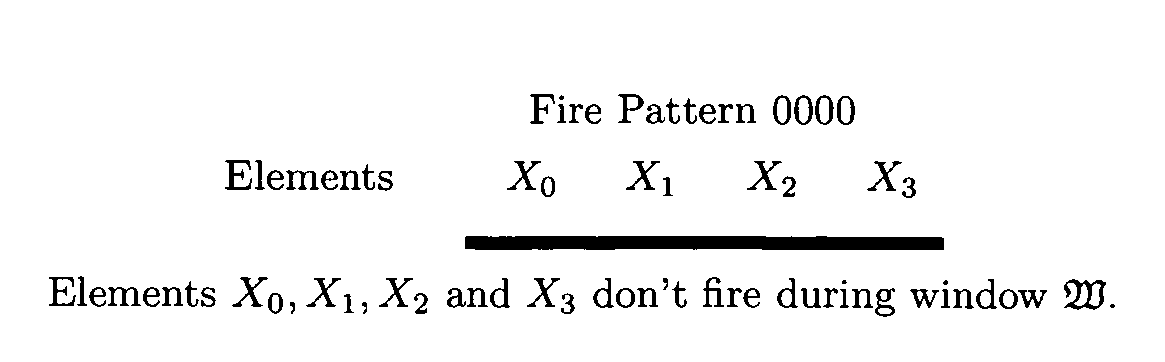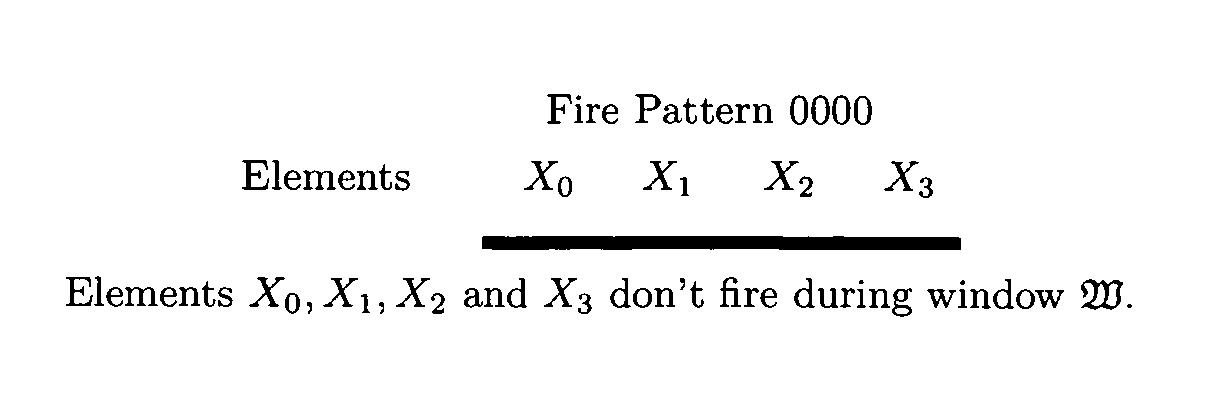Patents
Literature
32 results about "Register machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
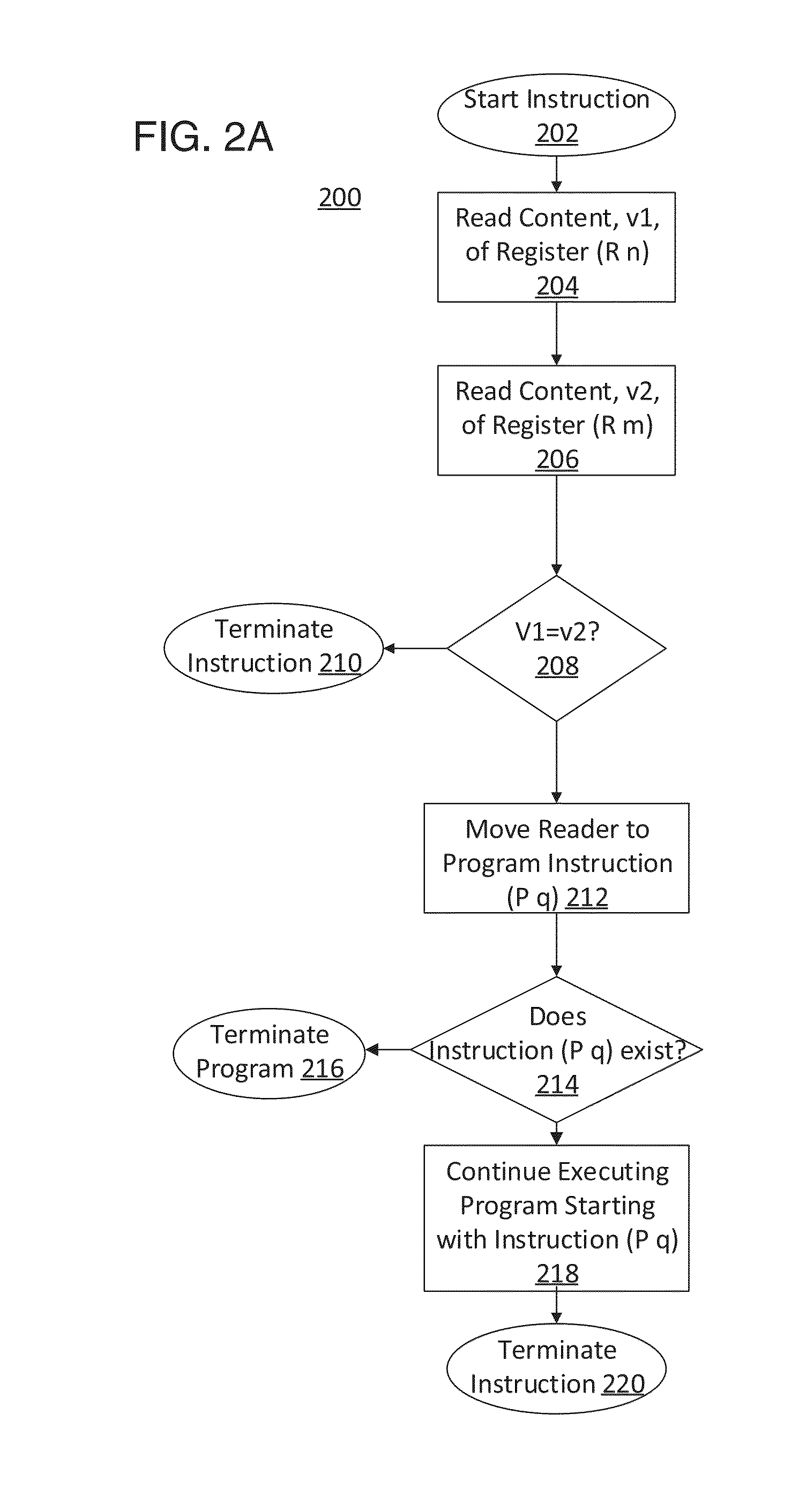
In mathematical logic and theoretical computer science a register machine is a generic class of abstract machines used in a manner similar to a Turing machine. All the models are Turing equivalent.
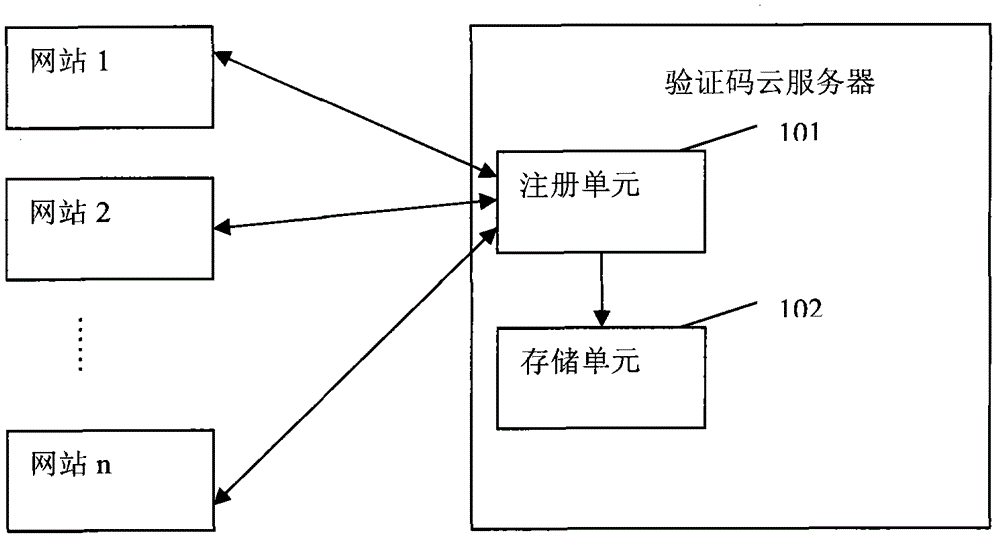
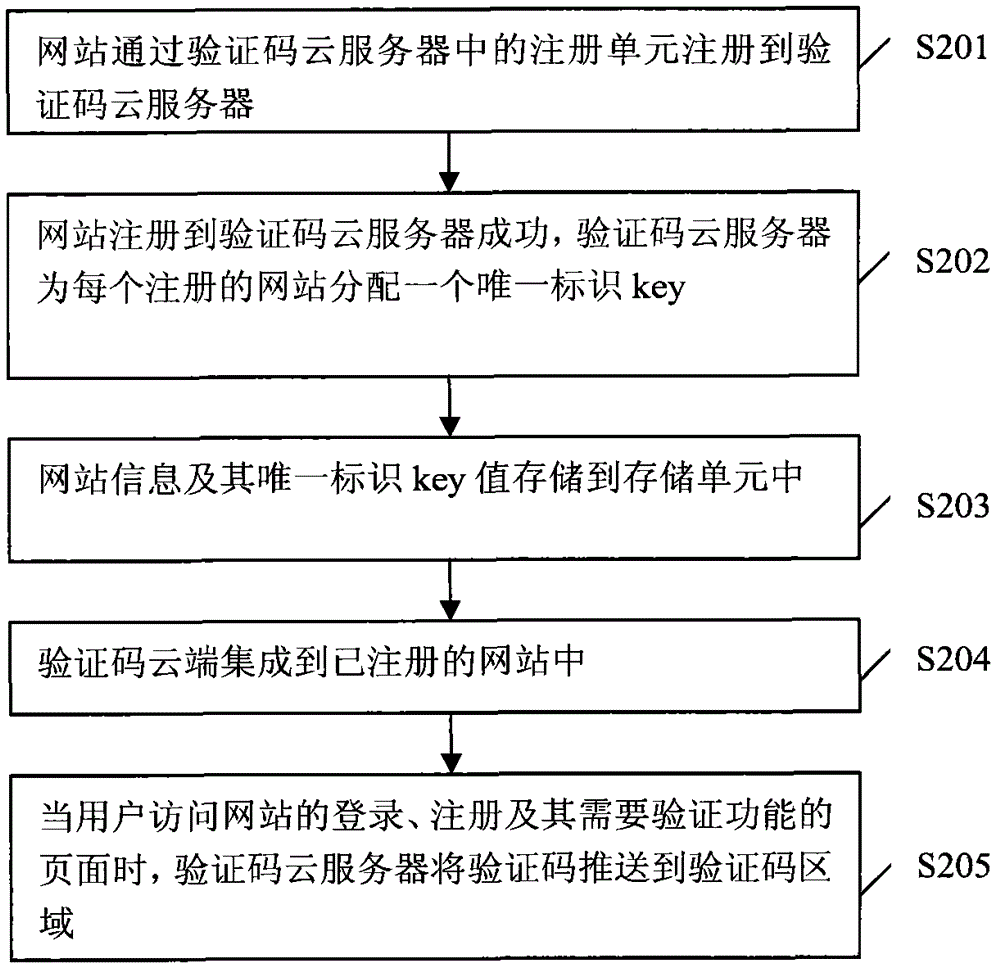
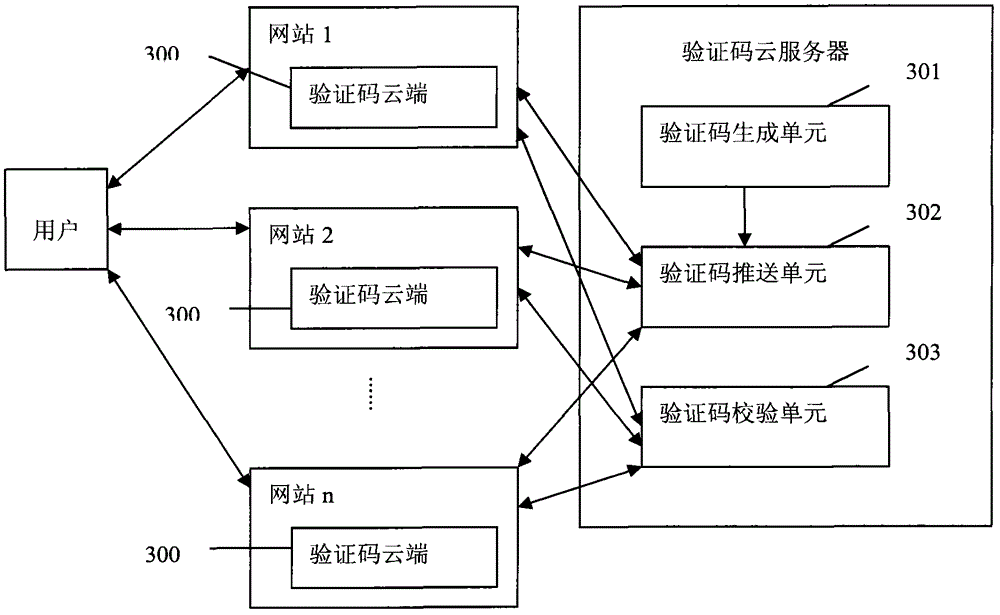
Verification code service method and system based on cloud computing
InactiveCN102752276AIncrease the difficulty of crackingImprove technical levelTransmissionRegister machineCloud server
The invention discloses a verification code service method and a system based on cloud computing. Verification code functions of a plurality of websites are provided by the verification code cloud service method and the system which are independent of website servers. The verification code cloud service system comprises a verification code cloud end and a verification code cloud server, wherein the verification code cloud end is used for being embedded into verification code areas of the websites and displaying verification codes, and the verification code cloud server is used for providing a verification code cloud service and comprises a register unit, a storage unit, a verification code generation unit, a verification code pushing unit and a verification code verifying unit. According to the verification code service method and the system based on the cloud computing, the uniform verification code cloud service is provided for the plurality of the websites, unified management is facilitated, the safety is improved, decoding difficulties are increased, attacks are prevented, registering machines can't attack the website servers, the verification code cloud server performs behavioral analysis, and simultaneously, the development and maintenance costs of the websites on the verification codes are reduced; and the verification code cloud service system can provide various verification code services so that user experiences are greatly improved.
Owner:青岛印象派信息技术有限公司
Non-Deterministic Secure Active Element Machine
ActiveUS20150186683A1Computing performance that isDigital data processing detailsAnalogue secracy/subscription systemsIntellectual propertyComputation process
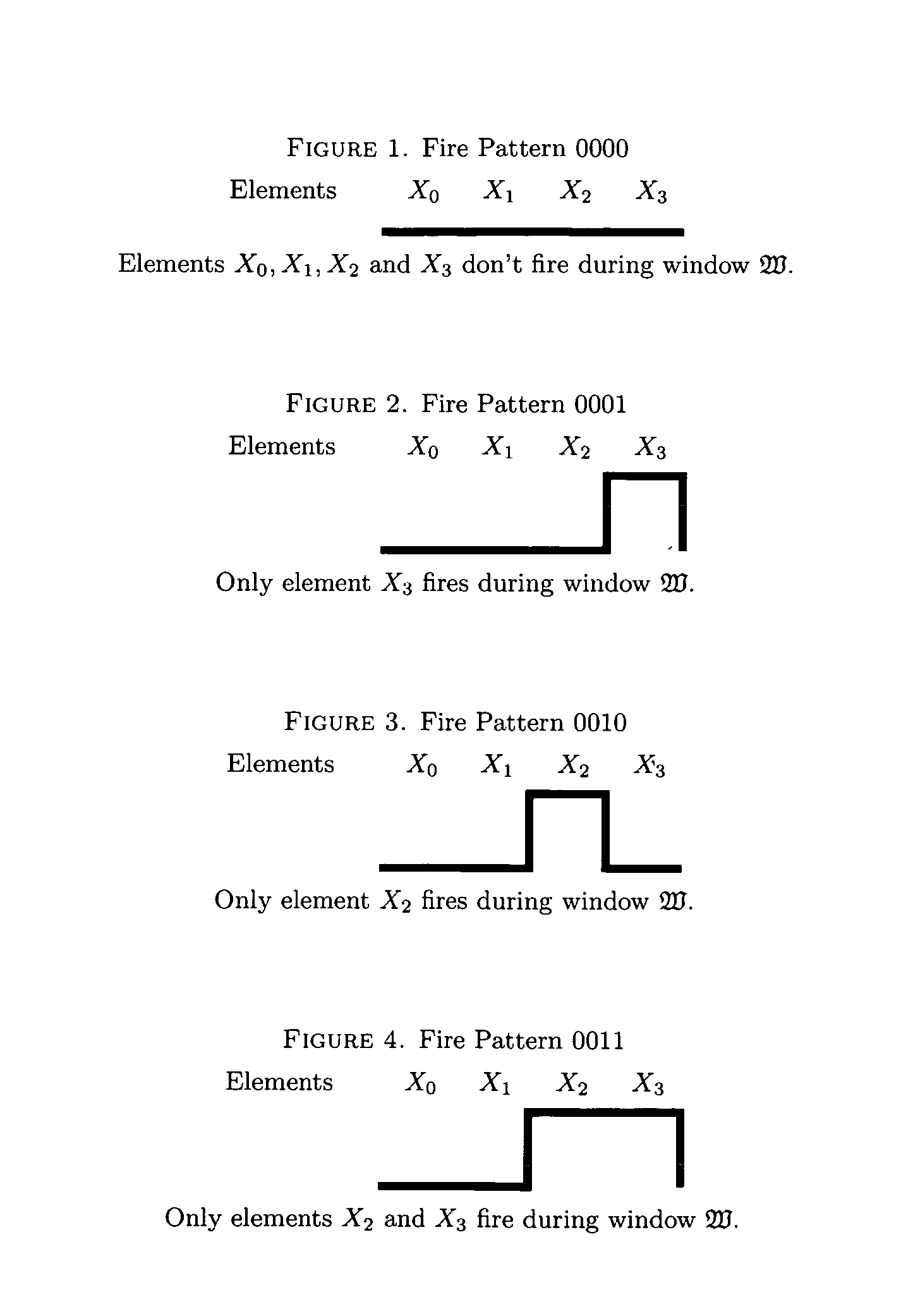
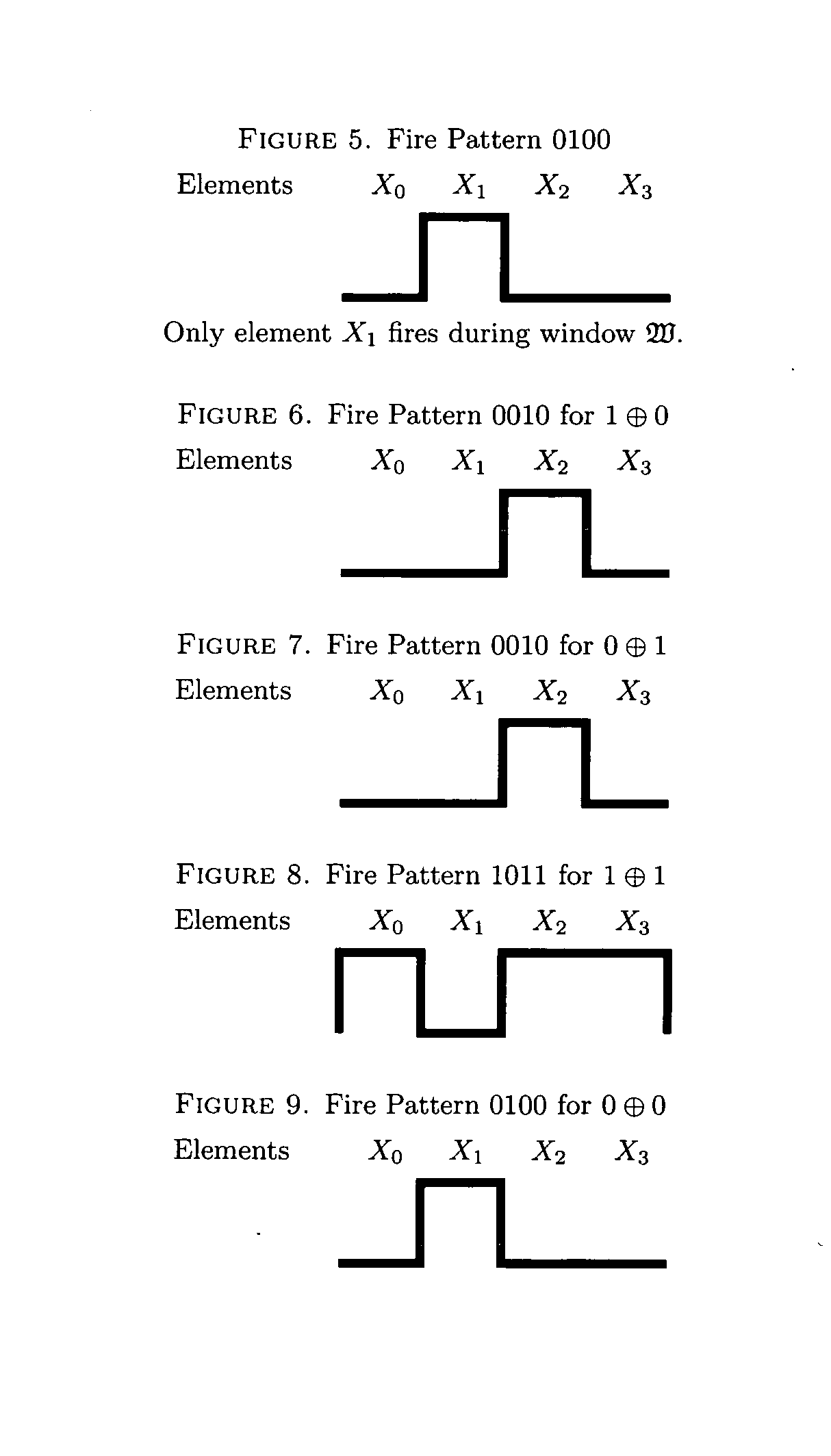
Based upon the principles of Turing incomputability, connectedness and novel properties of the Active Element Machine, a malware-resistant computing machine is constructed. This new computing machine is a non-Turing, non-register machine (non von-Neumann), called an active element machine (AEM). AEM programs are designed so that the purpose of the AEM computations are difficult to apprehend by an adversary and hijack with malware. These methods can also be used to help thwart reverse engineering of proprietary algorithms, hardware design and other areas of intellectual property.Using quantum randomness, the AEM can deterministically execute a universal Turing machine (universal digital computer program) with active element firing patterns that are Turing incomputable. In an embodiment, a more powerful computational procedure is created than Turing's computational procedure (equivalent to a digital computer procedure). Current digital computer algorithms and procedures can be derived or designed with a Turing machine computational procedure. A novel computer is invented so that a program's execution is difficult to apprehend.
Owner:AEMEA
High-safety electronic detonator initiation system and method thereof
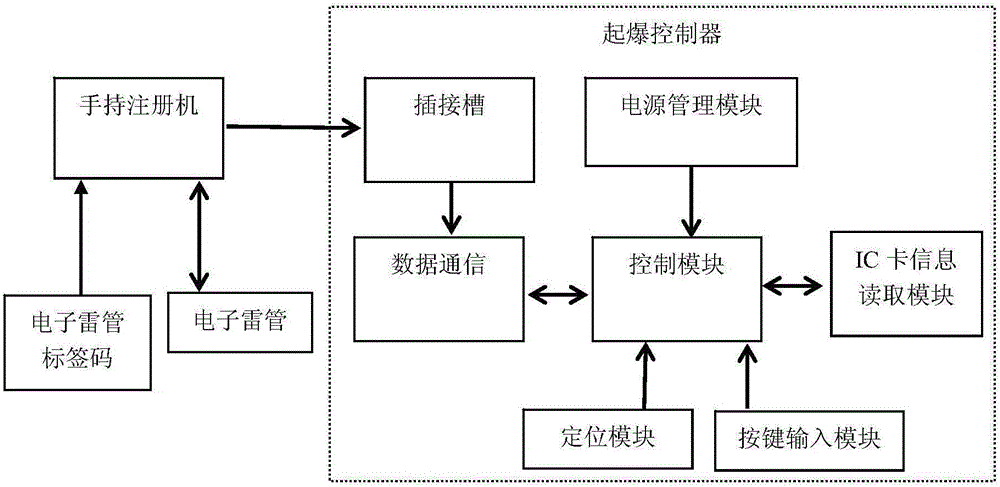
The invention discloses a high-safety electronic detonator initiation system and a method thereof. The system comprises an initiation controller, a handheld register machine and a password IC card; the initiation controller includes a handheld register machine information reading module for transmitting an initiation operation table in the handheld register machine to a control module; an IC card information reading module obtains initiation password information in the password IC card and compares with ID code information; and when the obtained initiation password information is the same with the ID code information, the control module controls electronic detonators to be initiated according to the initiation operation table. The system separates the functions of the handheld register machine, the initiation controller and the password IC card, cannot finish initiation if one of the three lacks, needs to combine the three for use, enhances the safety and the quick operability, achieves multiple protection by using a power-on password and an authorized initiation password, prevents risks by illegal use, and totally improves the use safety and controllability of digital electronic detonators.
Owner:CHINA GEZHOUBA GRP YIPULI CO LTD
Secure active element machine
ActiveUS20120198560A1Simple and safe processComputing performance that isDigital data processing detailsAnalogue secracy/subscription systemsComputational problemComputation process
Based upon the principle of Turing incomputability, and novel properties of the Active Element Machine, a malware-resistant computing machine is constructed. This new computing machine is a non-Turing, non-register machine (non von-Neumann), called an Active Element Machine (AEM). AEM programs are designed so that the purpose of the computation is difficult to apprehend by an adversary and hijack with malware. These methods can help hinder reverse engineering of proprietary algorithms and hardware design.Using quantum randomness, the AEM can deterministically execute a universal digital computer program with active element firing patterns that are Turing incomputable. In some embodiments, a more powerful computational procedure is demonstrated than Turing's computational procedure (digital computer procedure). Current digital computer algorithms can be derived or designed with a Turing machine computational procedure. A novel class of computing machines is built where the purpose of the program's execution is difficult to apprehend (Turing incomputable).
Owner:AEMEA
Dynamic register machine
InactiveUS20150261541A1Register arrangementsDigital computer detailsProgram instructionParallel computing
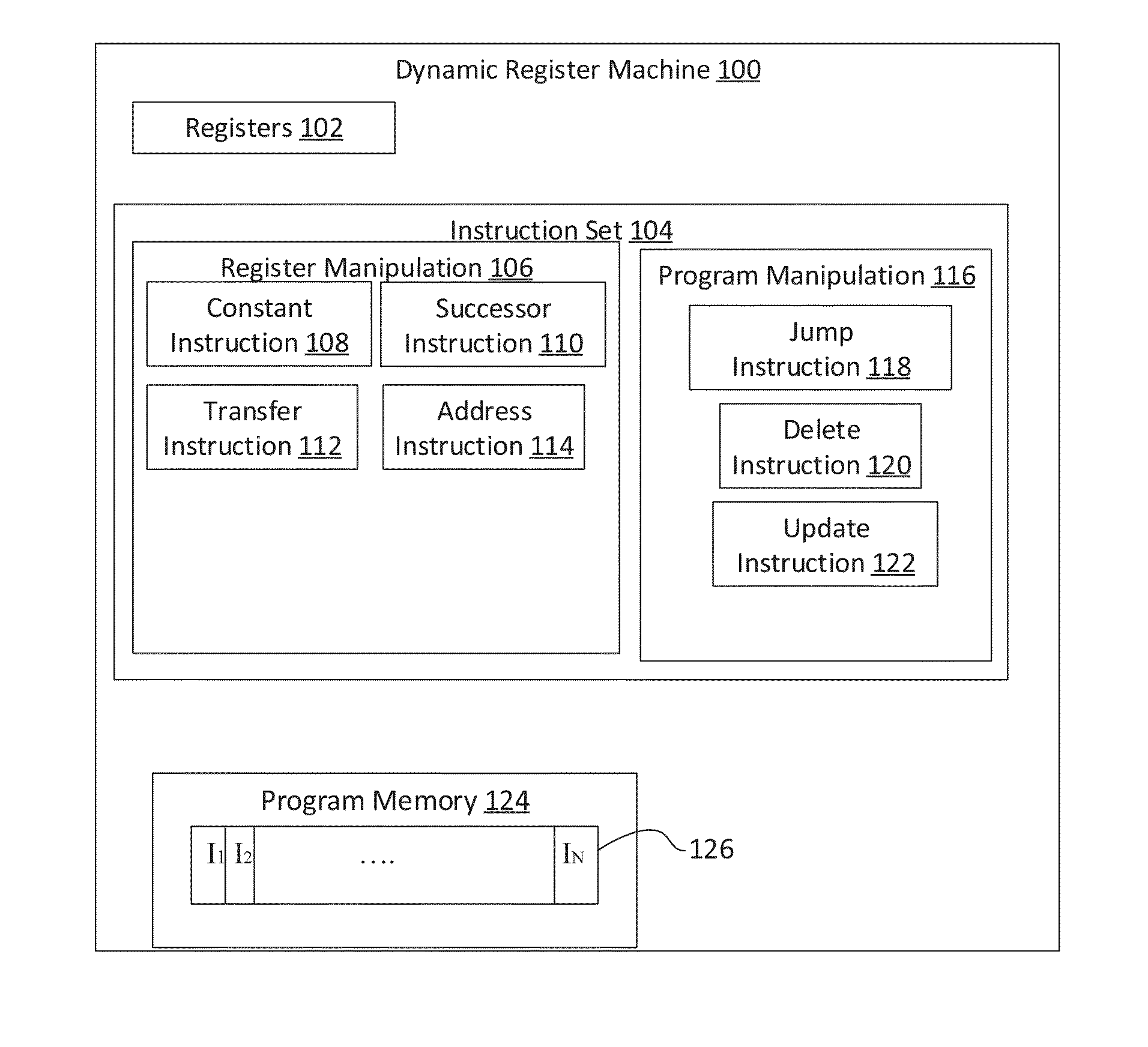
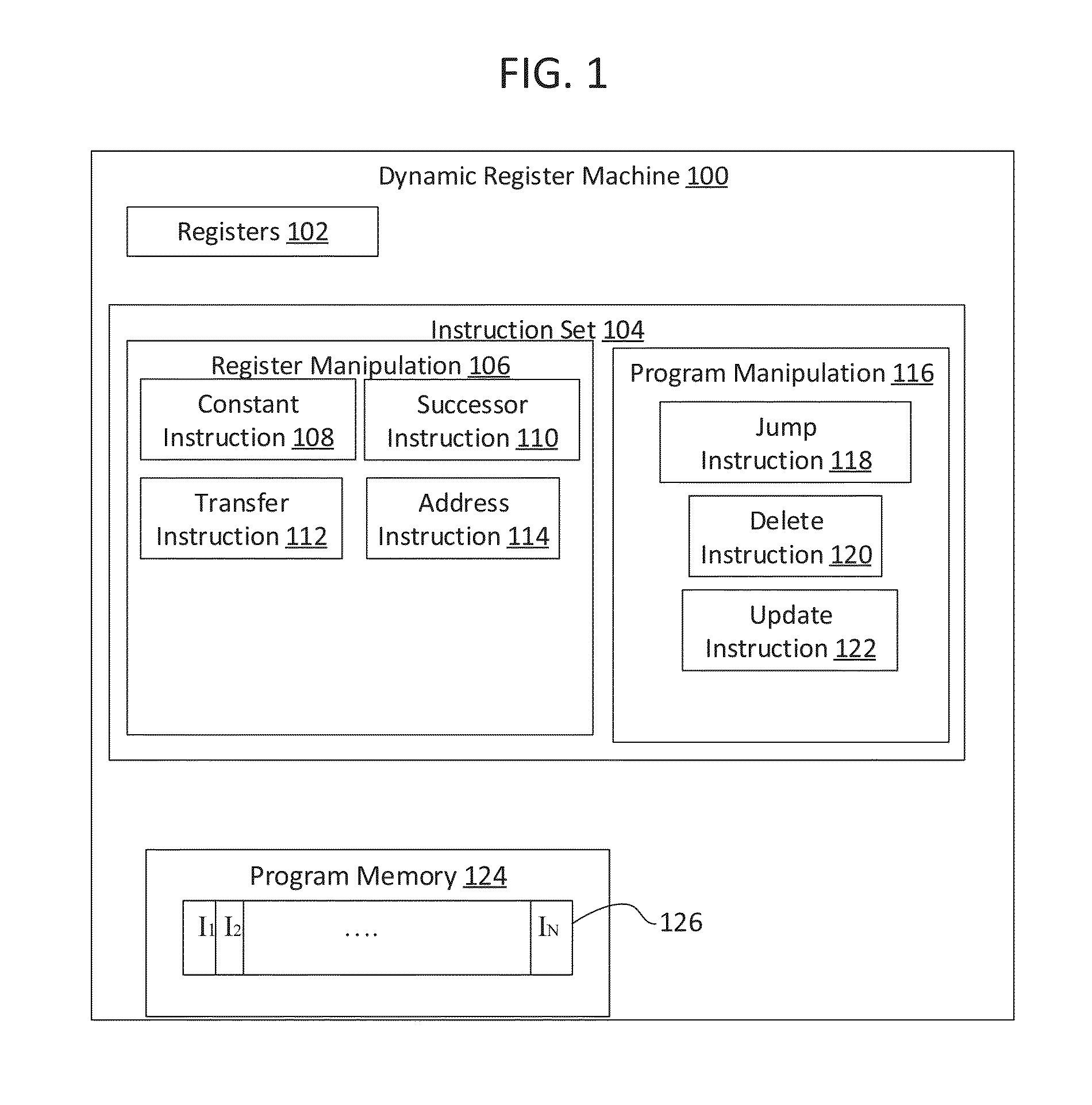
In one embodiment, a dynamic register machine that edits program instructions while the instructions are running on the machine is disclosed. In another embodiment, an execution node pair machine is disclosed that represents programs as collections of execution node pairs. In another embodiment, computer program instructions are represented as matrices, which are multiplied together to represent sequences of instructions applied to specific input data, which facilitate finding situations resulting in infinite loops having a periodic behavior. In an embodiment, infinite loops in a general computer program are detected, via the dynamic register machine, by exploring combinations of sequences of linked execution-node-pairs, thereby obtaining the results of executing sequence of computer program instructions is disclosed.
Owner:AEMEA
Fingerprint-control elevator system
The invention discloses a fingerprint-control elevator system which comprises a floor button module, a fingerprint detection module and a bar-type sliding unlocking module. The bar-type sliding unlocking module comprises a touch control screen which is used for detecting a sliding operation instruction of a user to control state conversion of the fingerprint detection module and feeding back and displaying current operation state, and the bar-type sliding unlocking module can further comprises a self-help registering machine. One of main objectives to be achieved by the elevator system is that along with increase of operation steps caused by newly adding a fingerprint recognition function module (or other personal identity recognition function modules) into the elevator system, operation cognition burden caused to the user is avoided, using experience of the user is improved, and a safety enhancing mode can be set while experience is guaranteed. In addition, a self-help registering system convenient for the user to use is designed in the elevator system, so that the elevator system can be used more conveniently and more quickly through the self-help registering machine.
Owner:何佰骏 +2
Church-turing thesis: the turing immortality problem solved with a dynamic register machine
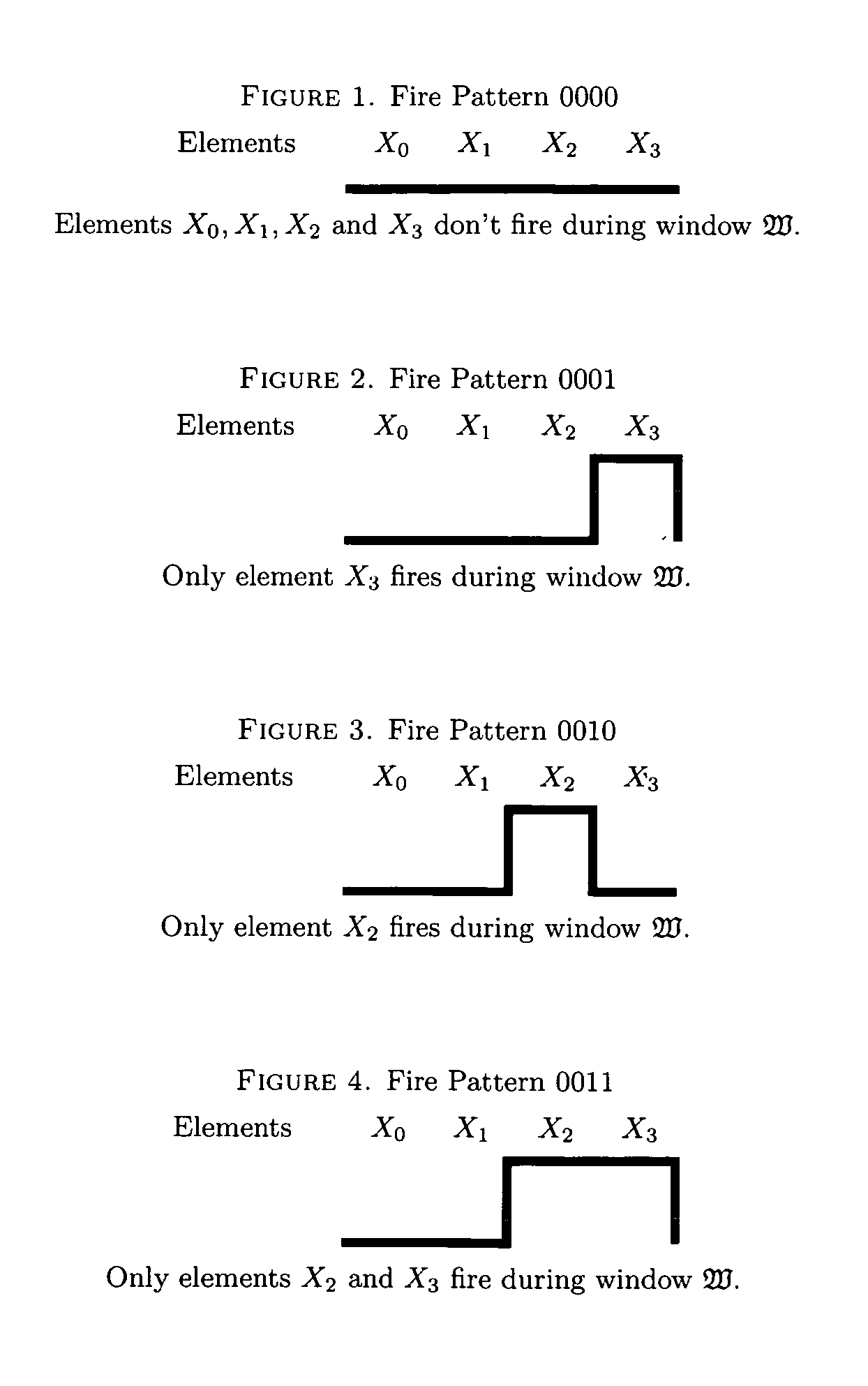
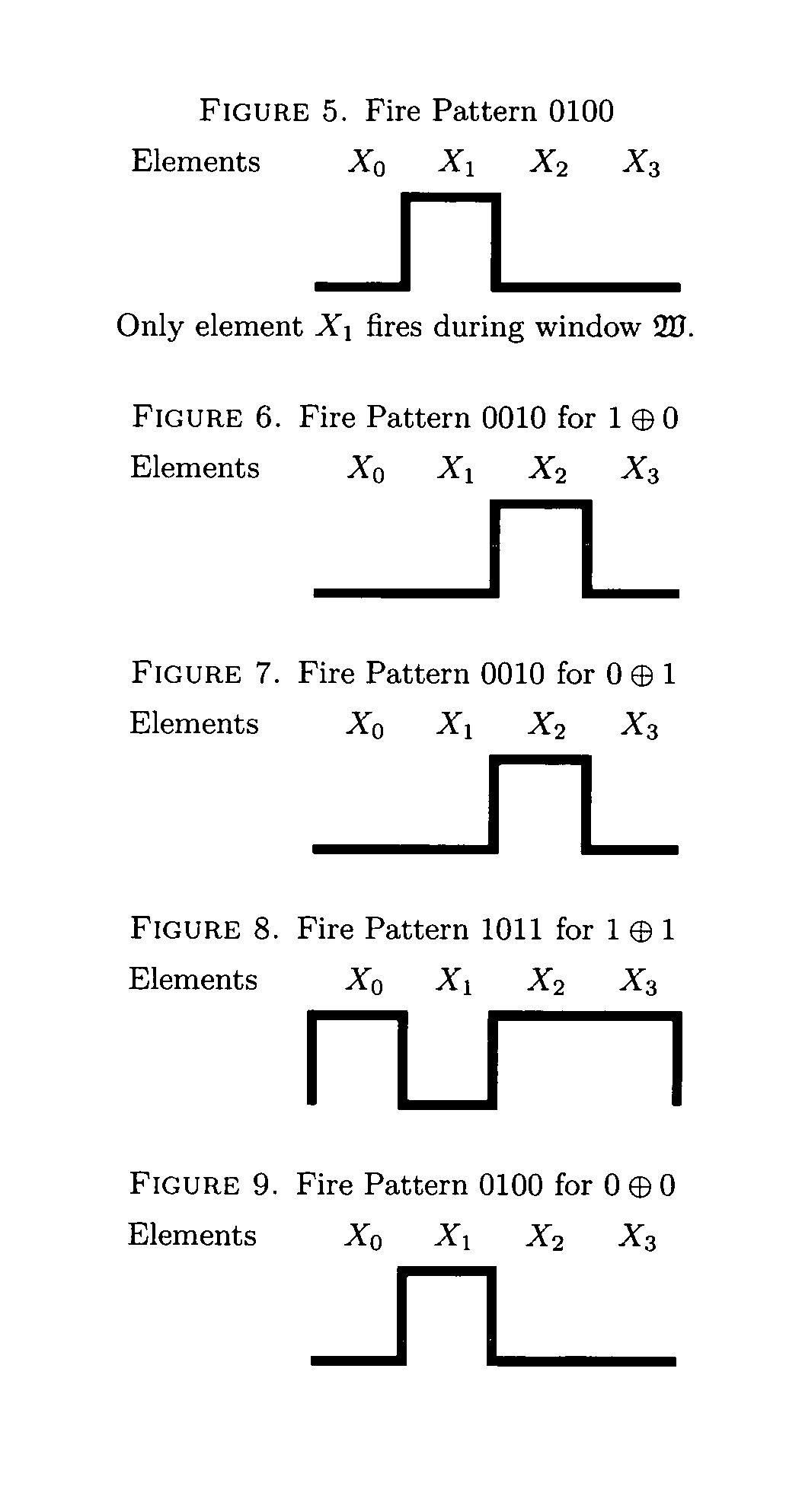
ActiveUS20110066833A1Dataflow computersSpecific program execution arrangementsComputational problemParallel computing
A new computing machine and new methods of executing and solving heretofore unknown computational problems are presented here. The computing system demonstrated here can be implemented with a program composed of instructions such that instructions may be added or removed while the instructions are being executed. The computing machine is called a Dynamic Register Machine. The methods demonstrated apply to new hardware and software technology. The new machine and methods enable advances in machine learning, new and more powerful programming languages, and more powerful and flexible compilers and interpreters.
Owner:AEMEA
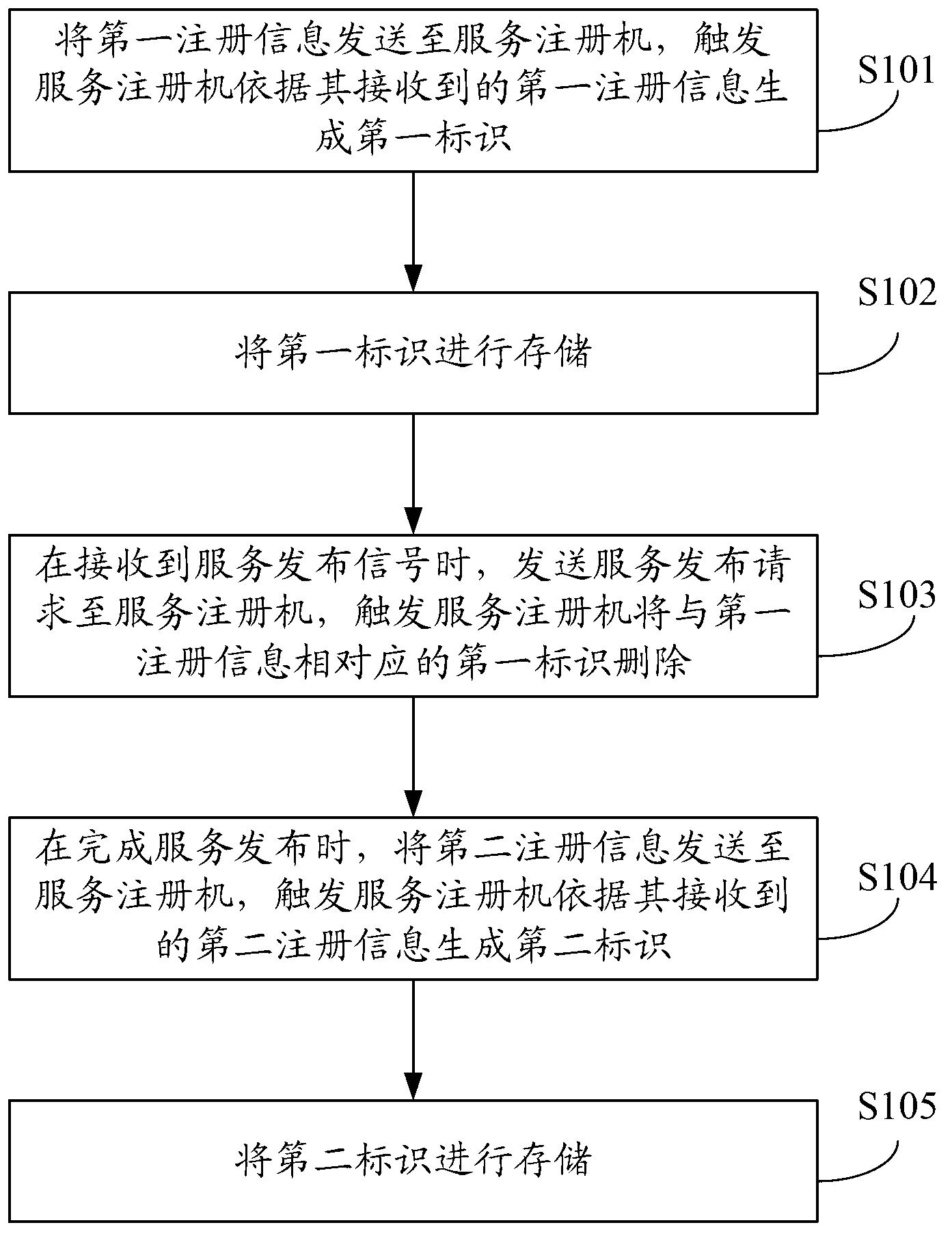
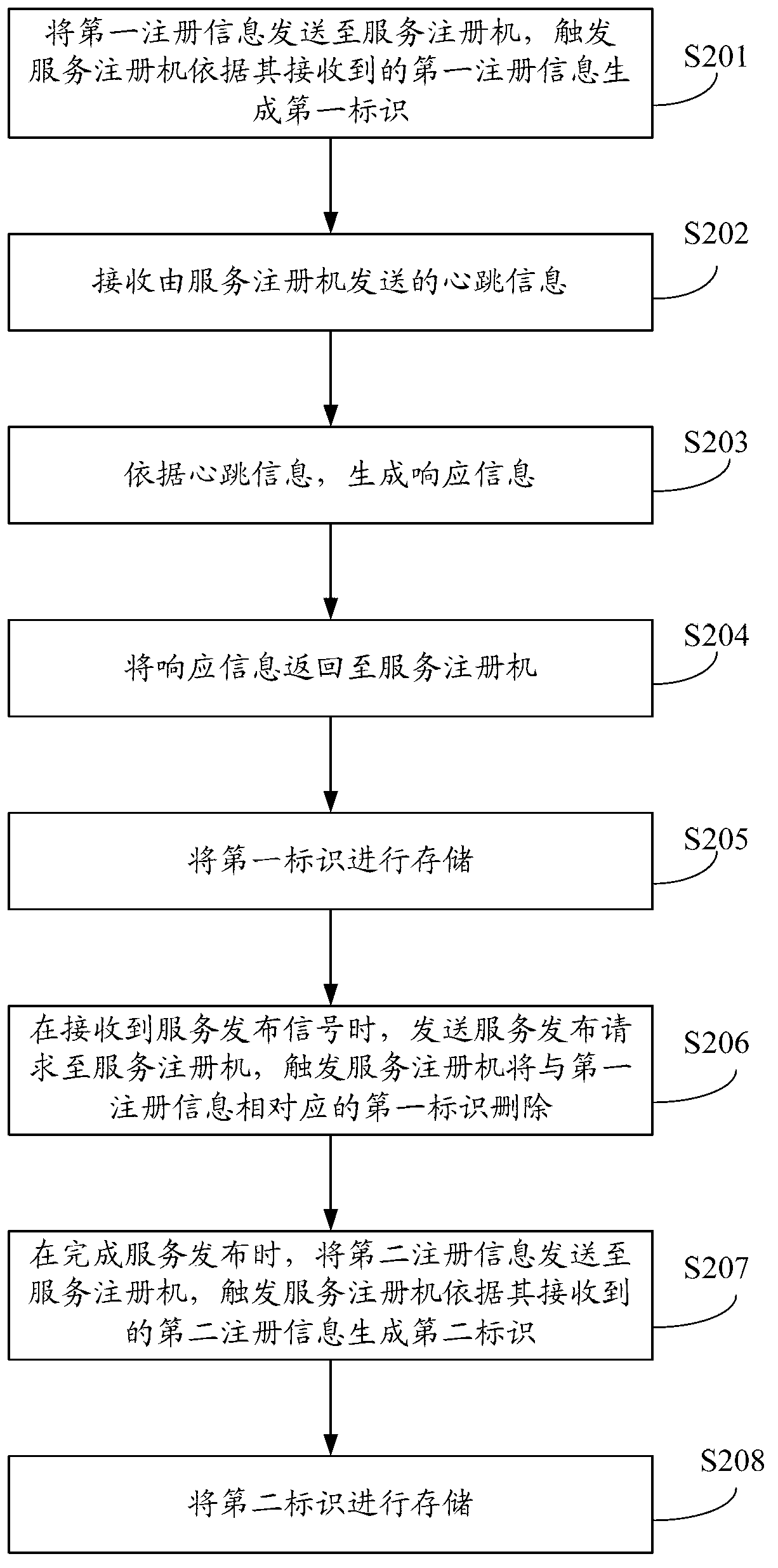
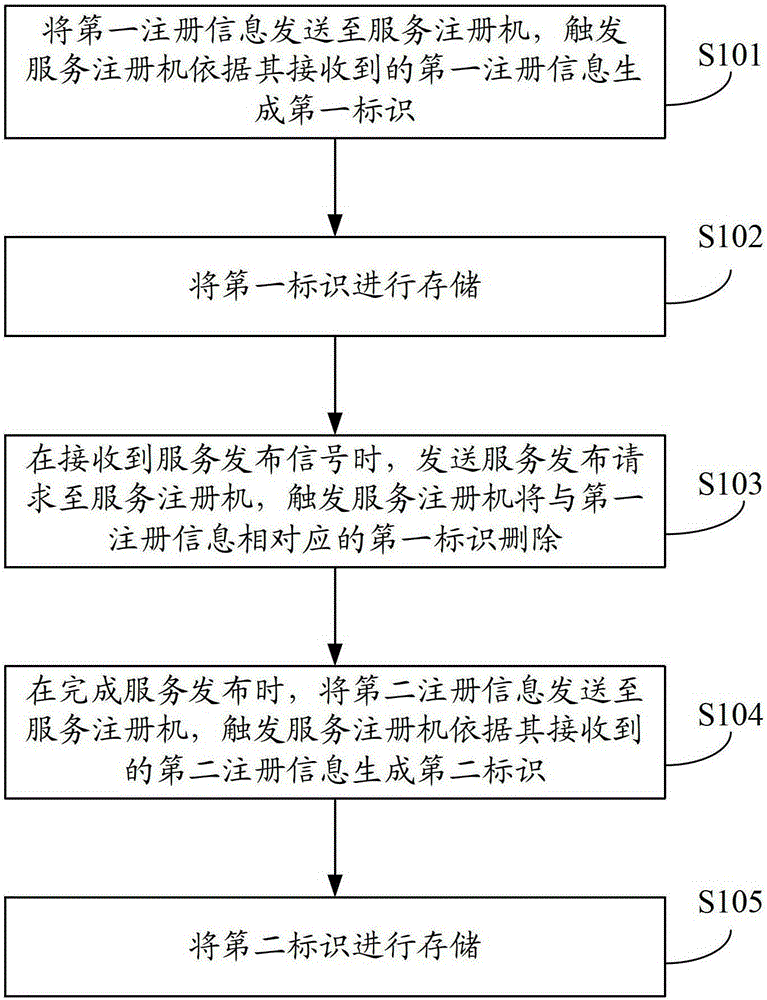
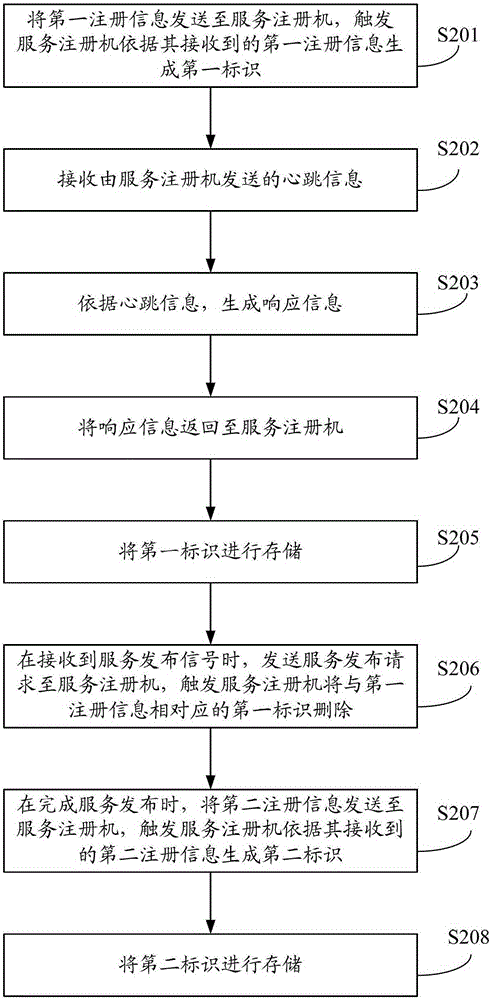
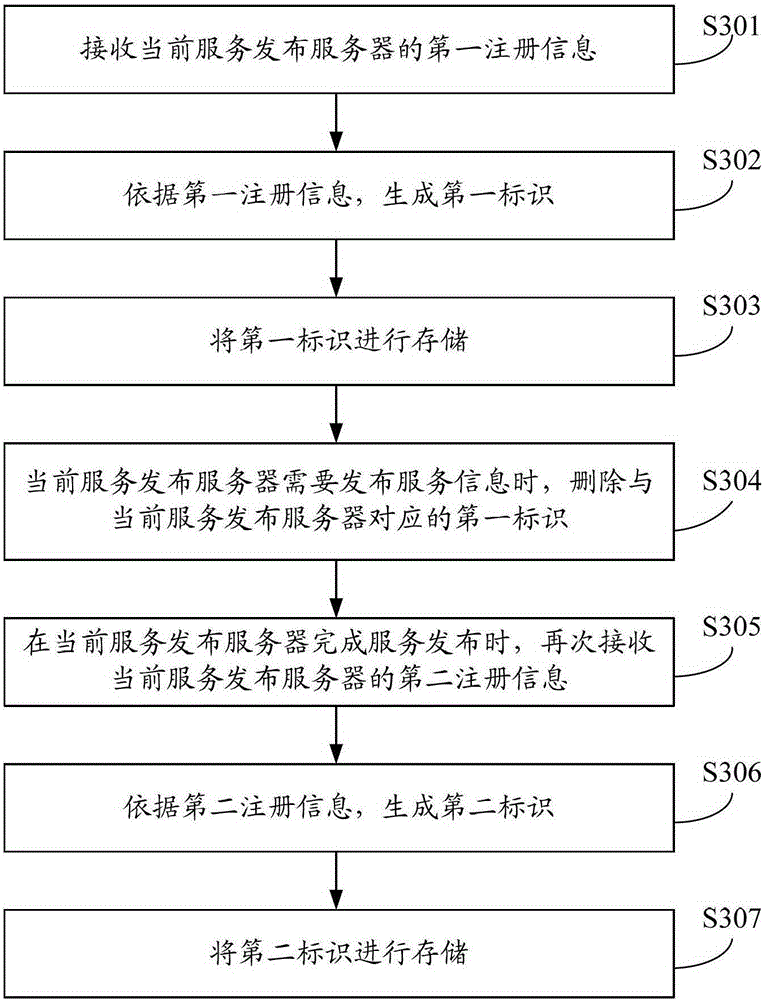
Service publication method, service publication server and service registering machine
InactiveCN103227723AImprove experienceSpecial service provision for substationService informationDistributed computing
The invention provides a service publication method, a service publication server and a service registering machine. The service publication method is applied to a current service publication server of multiple service publication servers, the multiple service publication servers cannot simultaneously publish services, the current service publication server sends first register information to the service registering machine, the service registering machine is used for producing a first mark according to the first register information and deleting the first mark when the current service publication server needs to publish service information, the current service publication server can send second register information to the service registering machine after the services are published, and the service registering machine can produce a second mark according to the second register information. Therefore, when the current service publication server publishes the services, only the work of the current service publication server is stopped without influencing the works of other service publication servers, therefore, turn-off of the whole servers is not needed, and the user experience is improved.
Owner:ZHEJIANG YUTIAN TECH +2
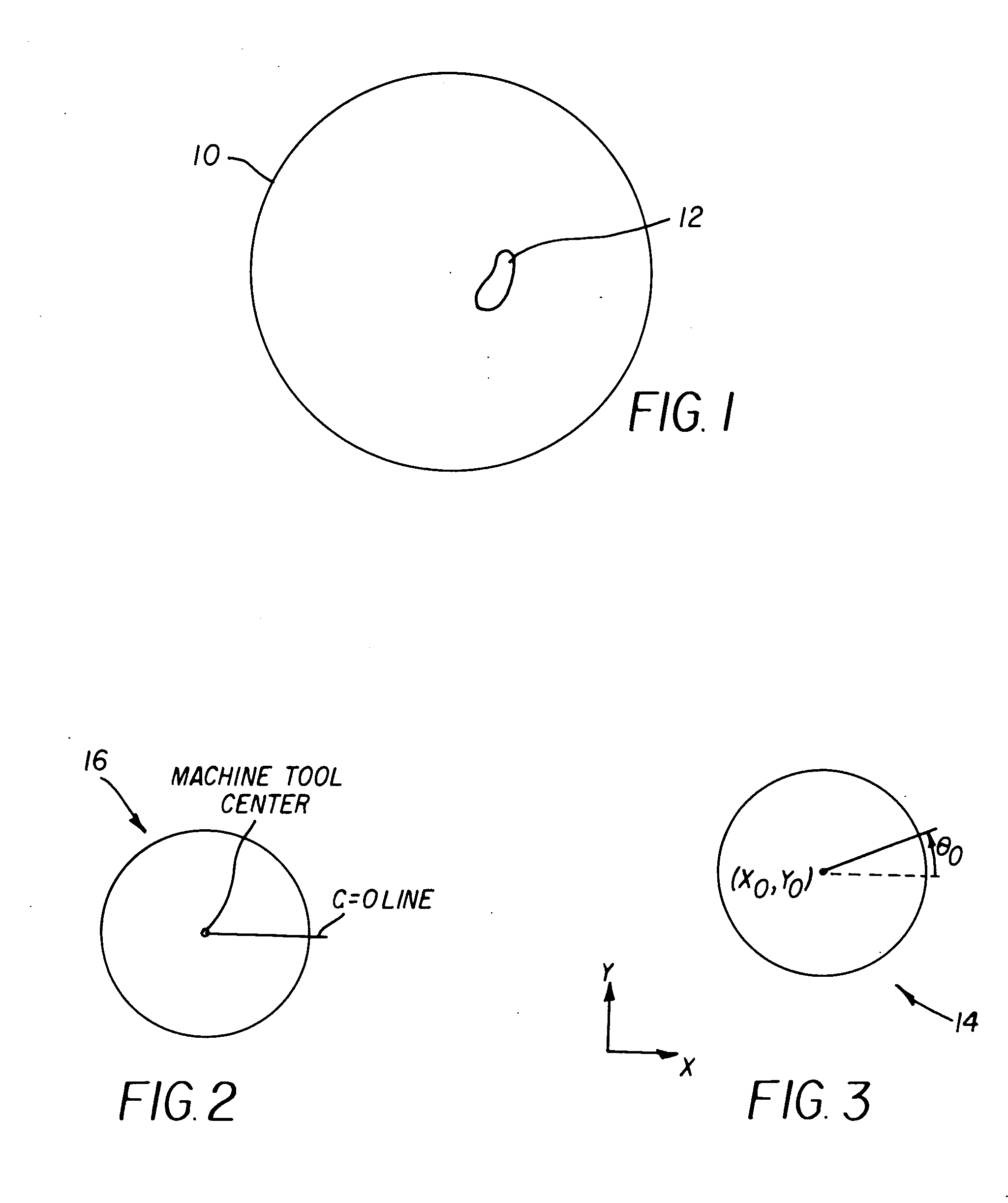
Method for machine tool and profilometer coordinate registration
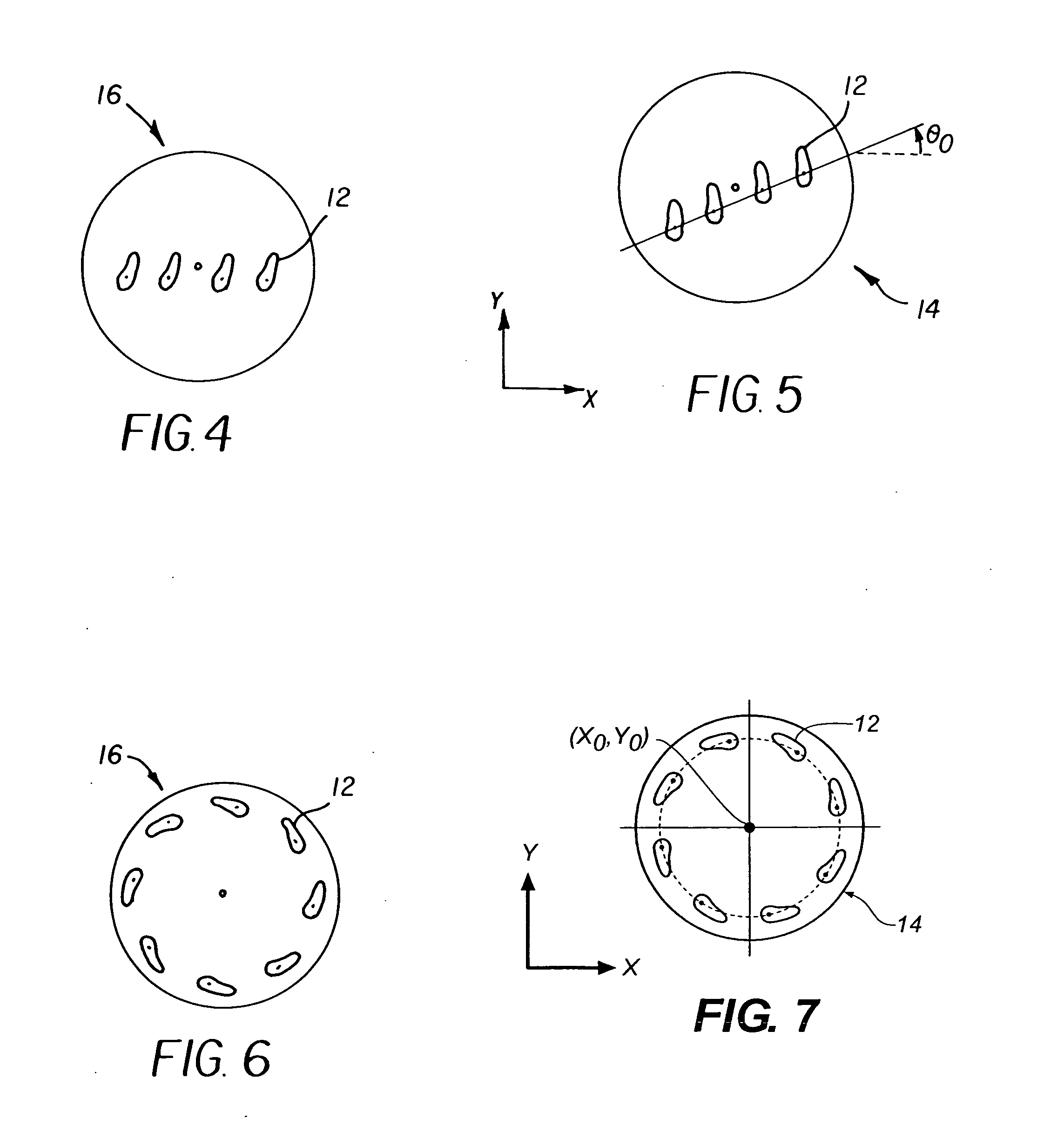
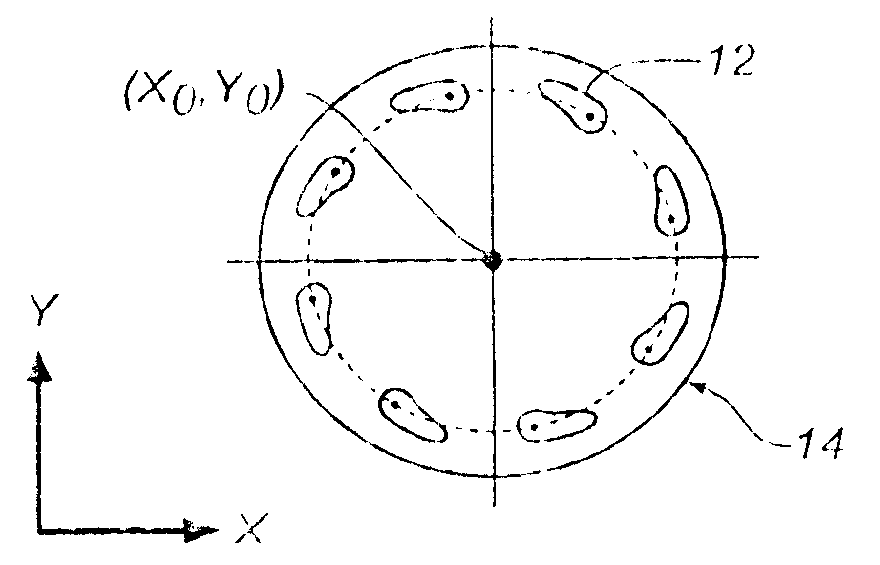
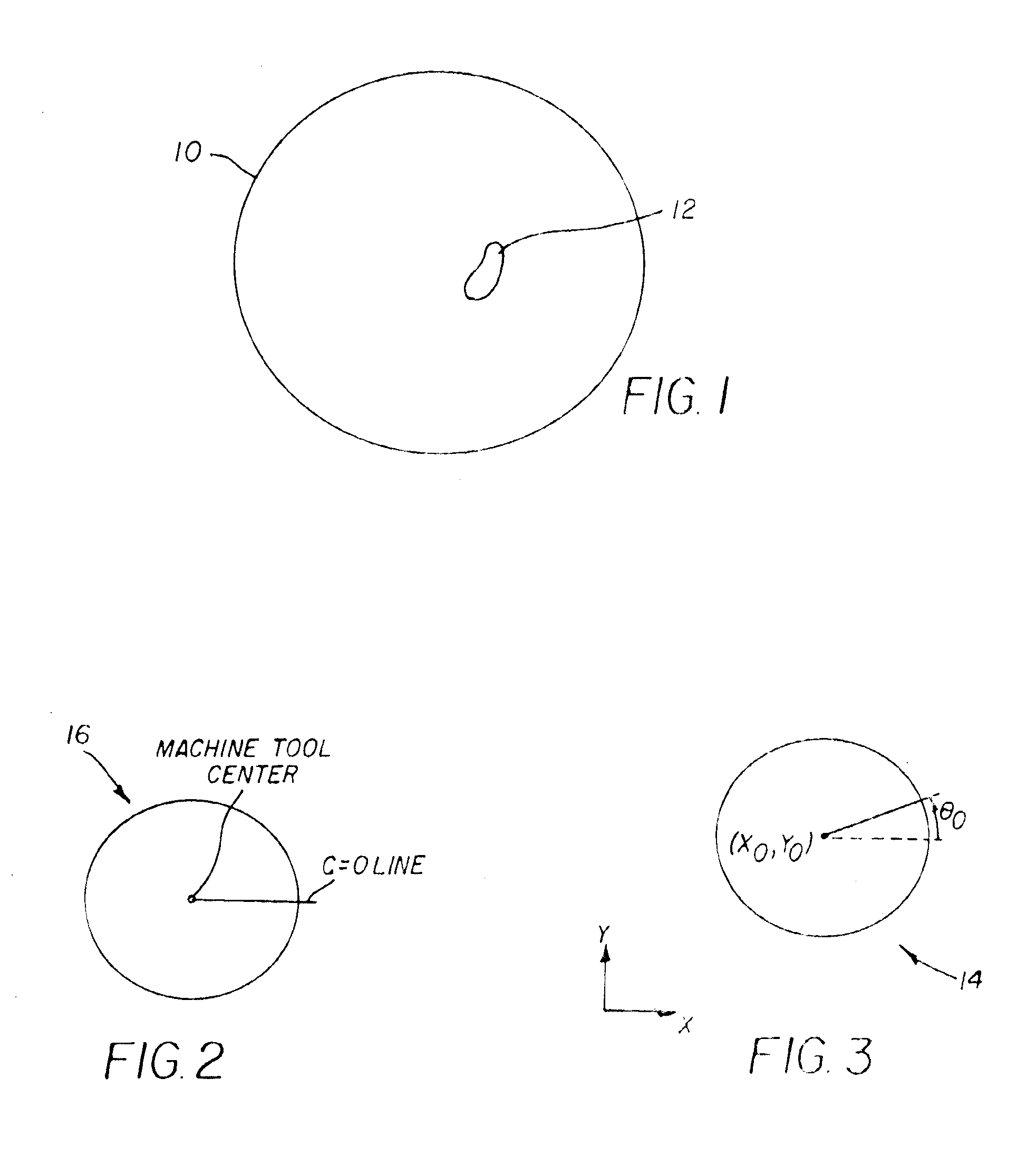
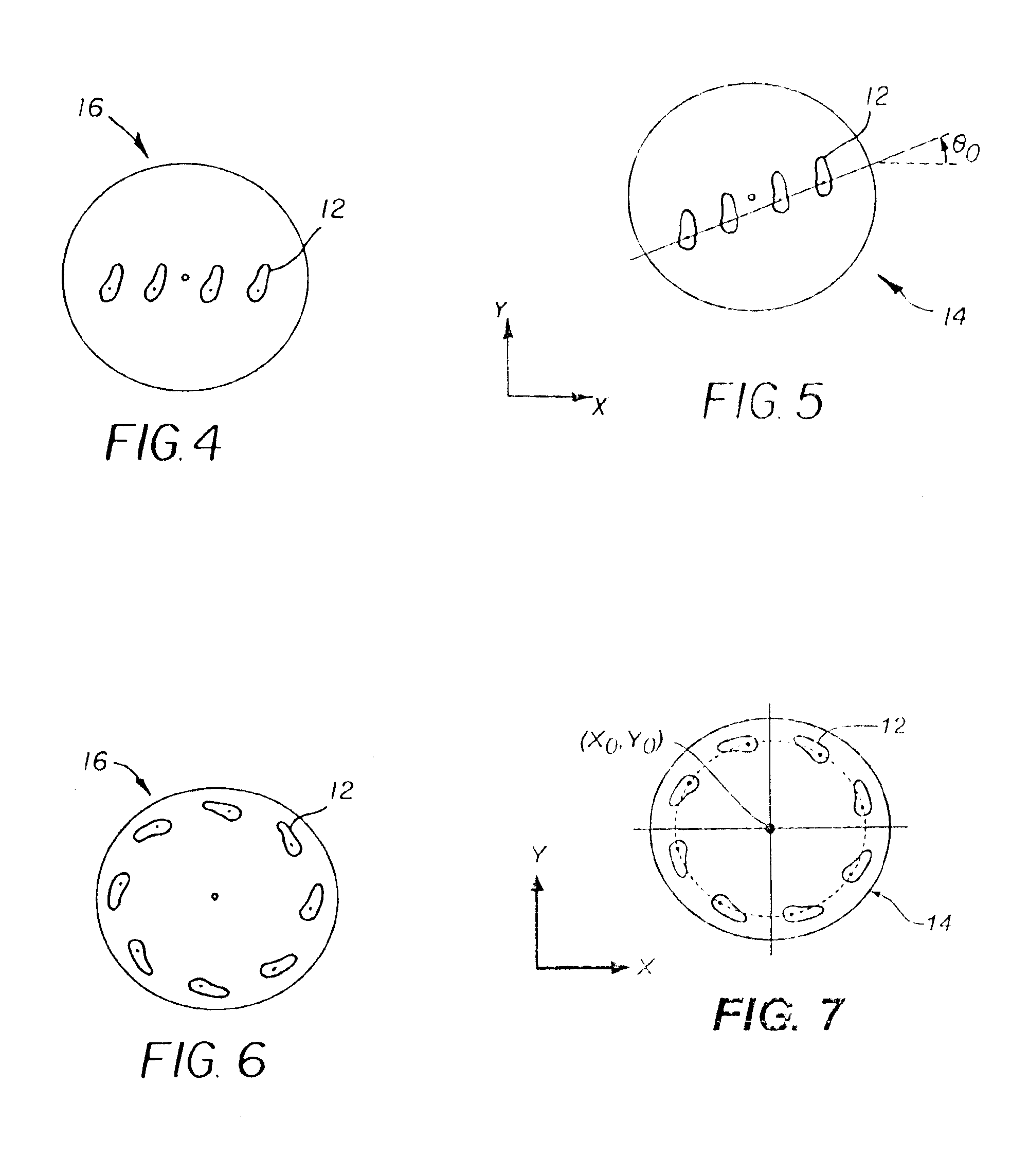
A method for registering machine tool and profilometer coordinates, wherein the machine tool defines a C-axis having a zero position, C=0, comprises loading a sacrificial workpiece into the machine tool; cutting several first features in a surface of the sacrificial workpiece and producing a linear machine tool motion across the workpiece; determining the centroid of each first cut feature; fitting a line to the centroids of the first cut features; and measuring angle θ0 of the line relative to the C-axis zero position. The angle θ0 is the departure in profilometer coordinates from the C=0 line. The method includes moving the machine tool to a fixed radius; cutting several second features in a surface of the sacrificial workpiece and producing a circular machine tool motion across the workpiece; determining the centroid of each second cut feature; fitting a circle to the centroids of the second cut features; and determining a center of the circle. The center of the circle is the machine tool center in profilometer coordinates.
Owner:EASTMAN KODAK CO
Secure active element machine
ActiveUS9032537B2Simple and safe processComputing performance that isDigital data processing detailsAnalogue secracy/subscription systemsComputational problemComputation process
Based upon the principle of Turing incomputability, and novel properties of the Active Element Machine, a malware-resistant computing machine is constructed. This new computing machine is a non-Turing, non-register machine (non von-Neumann), called an Active Element Machine (AEM). AEM programs are designed so that the purpose of the computation is difficult to apprehend by an adversary and hijack with malware. These methods can help hinder reverse engineering of proprietary algorithms and hardware design.Using quantum randomness, the AEM can deterministically execute a universal digital computer program with active element firing patterns that are Turing incomputable. In some embodiments, a more powerful computational procedure is demonstrated than Turing's computational procedure (digital computer procedure). Current digital computer algorithms can be derived or designed with a Turing machine computational procedure. A novel class of computing machines is built where the purpose of the program's execution is difficult to apprehend (Turing incomputable).
Owner:AEMEA
Intelligent side door and corresponding arrangement method thereof
InactiveCN110029932AAccurate and timely releaseImprove release efficiencyTurnstilesIndividual entry/exit registersMachine partsData information
The invention provides an intelligent side door. The intelligent side door automatically identifies people capable of passing through the side door and accurately and timely release without extra staff on duty, and the release efficiency of the intelligent side door is high; and the intelligent side door includes a multi-functional gate machine and a register machine, the multi-functional gate machine includes a gate machine part, an information identification part, a logic control part and a database, the information identification part is used for identifying the identity information of to-be-passed people, the information identification part feeds identified data information back to the logical control part, the logic control part calls data in the database and compares the identified data information with saved passage people information, if comparison is successful, the logic control part drives a gate of the gate machine part to open, and if comparison fails, the logic control part does not operate the gate; and the register machine comprises a registration information input part, a registration information judgment system and a registration information feedback system.
Owner:苏州雷格特智能设备股份有限公司
Non-deterministic secure active element machine
ActiveUS10268843B2Computing performance that isInternal/peripheral component protectionExecution paradigmsIntellectual propertyComputation process
Based upon Turing incomputability, connectedness and properties of the active element machine (AEM), a malware-resistant computing machine is constructed. The active element computing machine is a non-Turing, non-register machine. AEM programs are designed so that the purpose of the AEM computations are difficult to apprehend by an adversary and hijack with malware. These methods can also be used to help thwart reverse engineering of proprietary algorithms, hardware design and other areas of intellectual property. Using quantum randomness, the AEM can deterministically execute a universal Turing machine (universal digital computer program) with active element firing patterns that are Turing incomputable. In an embodiment, a more powerful computational procedure is created than Turing's computational procedure (equivalent to a digital computer procedure). Current digital computer algorithms and procedures can be derived or designed with a Turing machine computational procedure. A novel computer is invented so that a program's execution is difficult to apprehend.
Owner:AEMEA
Self-help time-limited free Wi-Fi management system
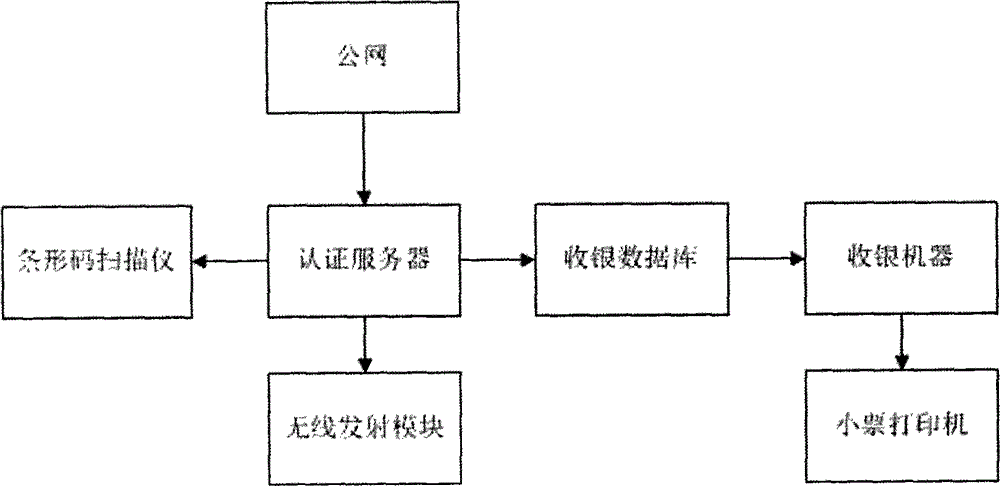
InactiveCN104680468ASpeed up the flowSave network resourcesPayment architectureWi-FiComputer network
The invention discloses a self-help time-limited free Wi-Fi management system which is characterized by comprising a barcode scanner, an authentication server, a wireless transmitting module, a cash registering database, a cash registering machine, and a receipt printer, wherein the barcode scanner is connected with the authentication server, the wireless transmitting module is connected with the authentication server, the authentication server is connected with the cash registering database, the cash registering database is connected with the cash registering machine, and the cash registering machine is connected with the receipt printer. According to the self-help time-limited free Wi-Fi management system provided by the invention, free Wi-Fi is managed, a consumption document number is printed in the form of barcode so as to associate a wireless authentication server with a cash registering system, network resources and human resources are saved because self-help free Internet surfing is realized by use of barcode, and the personnel turnover rate is improved by associating the amount of consumption with the duration of Internet surfing.
Owner:WUXI CINSEC INFORMATION TECH
WIFI password transmission method through NFC connection
The invention provides a WIFI password transmission method through a NFC connection. The method comprises the steps that in step 1, a user establishes a communications connection at the time of consumption by a business customer through a NFC module of a smartphone phone and through the NFC module of a cash register machine, a user preset payment account information is sent to the cash register machine through the NFC module of the intelligent phone; in step 2, the payment account is deducted by the payment amount through the connection of the cash register machine and a server end, after a notification message of success payment deduction is obtained from the server end, the NFC identification is saved to a WIFI permission list by the cash register machine; in step 3, when the user wishes to log in a WIFI network, the NFC module of the smartphone and the NFC module of the register machine establish a communication connection, a request is sent to access the request message in the WIFI, the request message includes the identification of the NFC module for the smartphone.
Owner:环玺信息科技(上海)有限公司
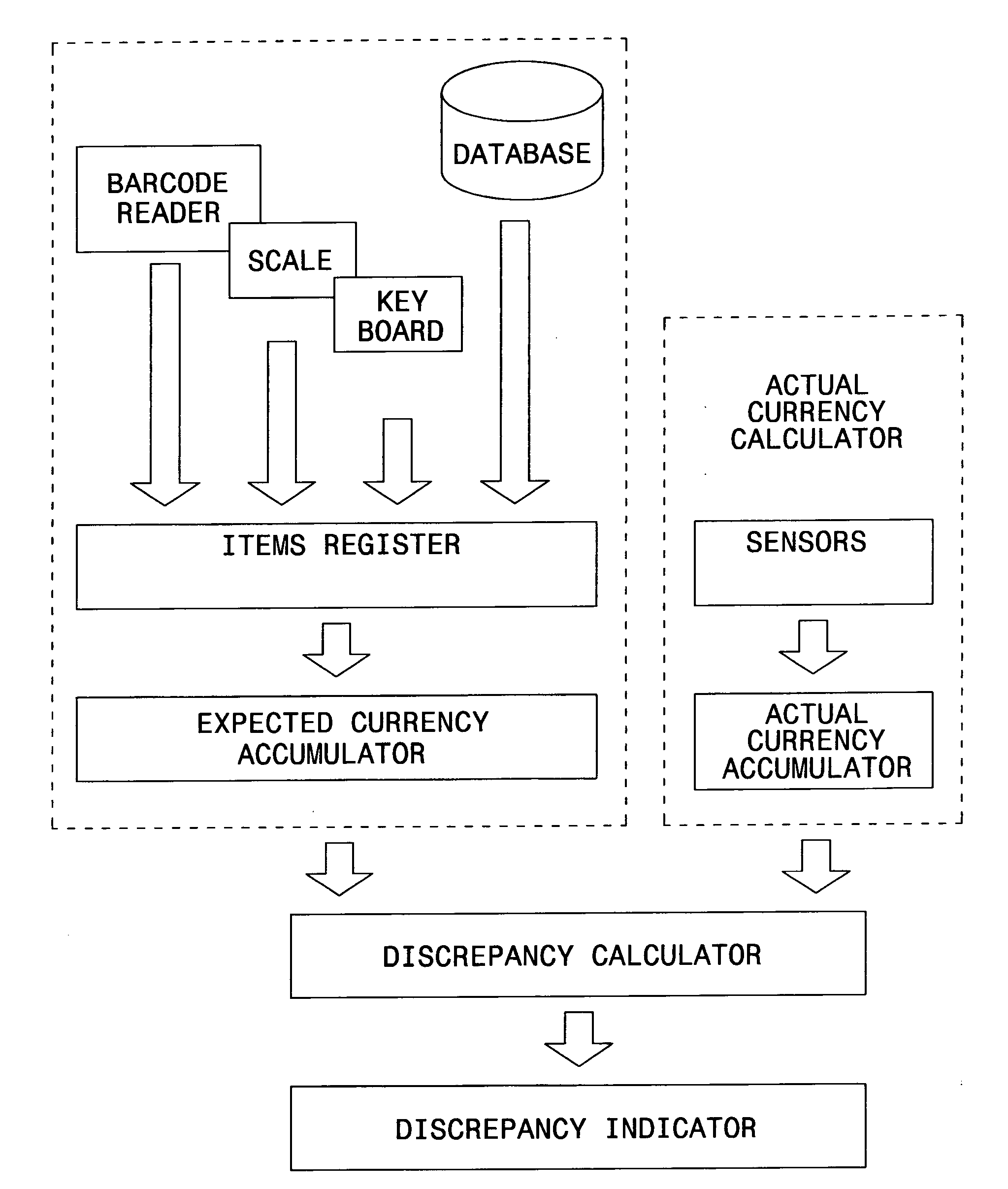
Cash register machine
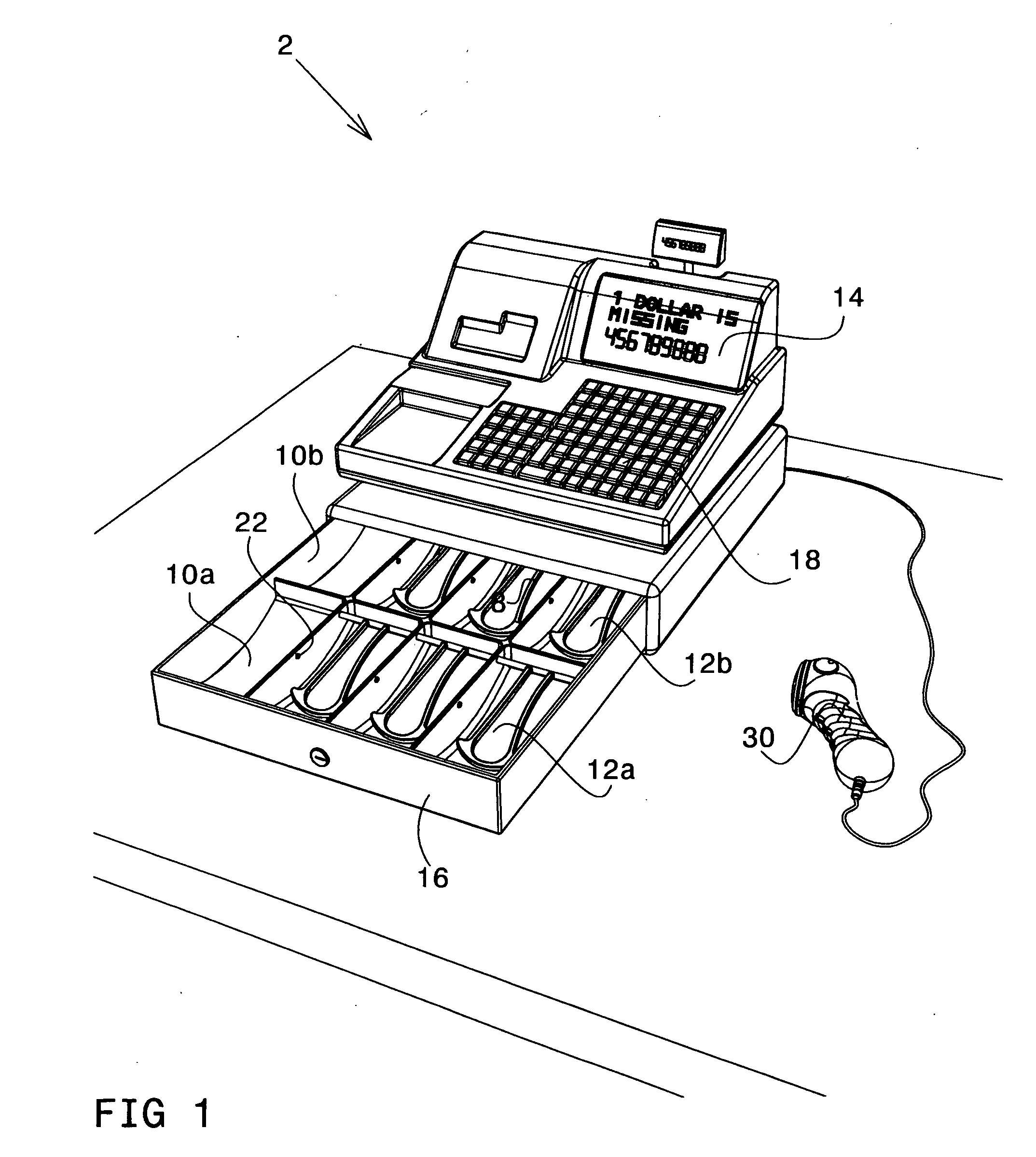
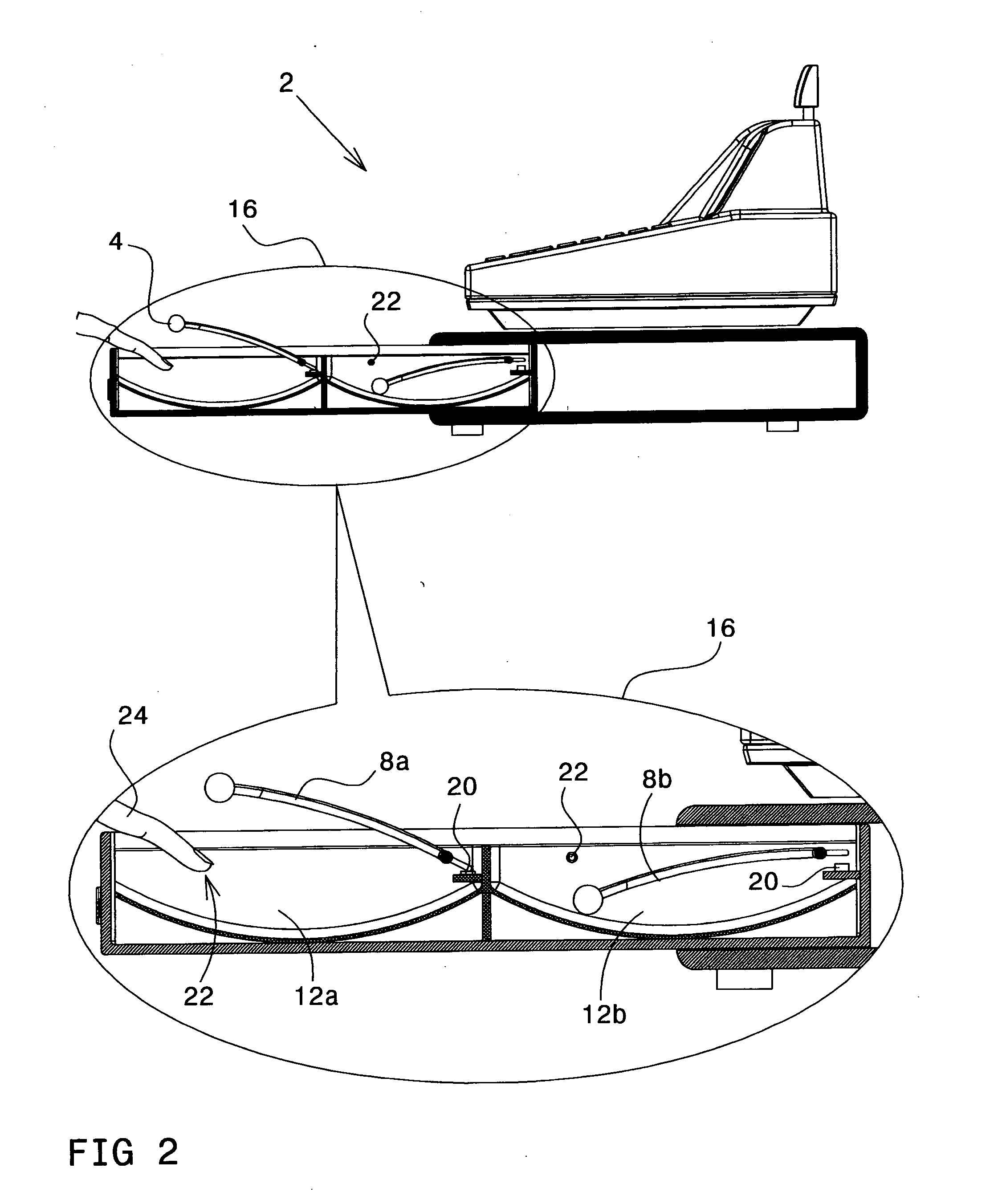
In one aspect, the present invention is directed to a cash register machine, comprising: an expected currency calculator; and an actual currency calculator, employing one or more sensors for the operation thereof. The sensor(s) may detect whether a banknote is placed into a compartment of the machine, whether a banknote is removed from a compartment of the machine, and so on. According to one embodiment of the invention, the sensors comprise: a first sensor for detecting an operation of placing or removing an object from a compartment of the machine, and a second sensor for determining whether the operation is placing or removing. The machine may further comprise image processing means. The image processing means may be employed for decoding the content of a check, credit card voucher, banknote, and so on.
Owner:SAMUELS SIMCHA ISRAEL
Short message platform based software authorization method
InactiveCN105844119AProtection of rights and interestsLimited use periodProgram/content distribution protectionSoftware licenseMessage processing
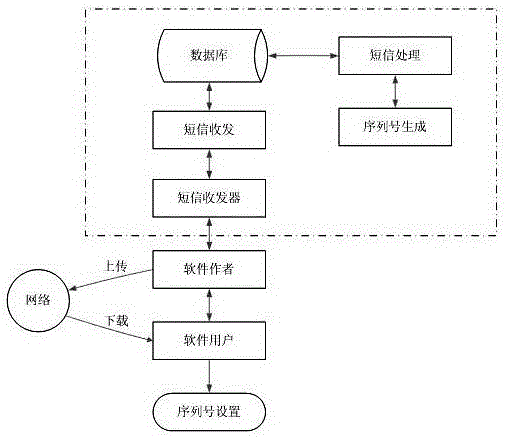
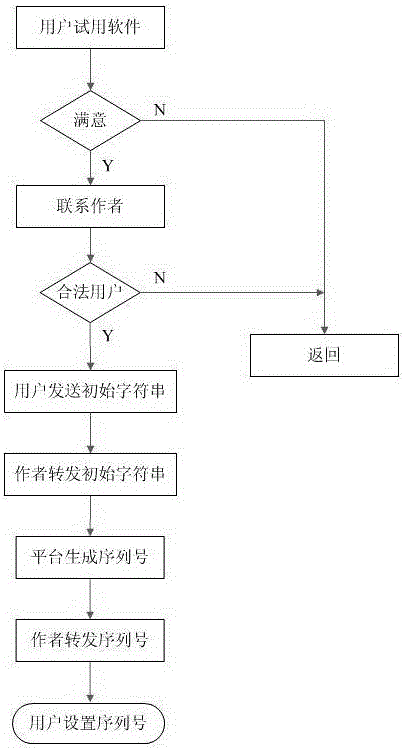
The invention discloses a short message platform based software authorization method. The method involves a short message platform, a serial number generation program, a serial number viewing and setting program, and an encrypted binary software license file containing serial number information. The method comprises the steps that a potential user downloads or obtains a software copy from a network or in other ways and tries to use the software copy, and a software author is contacted if software is needed; after it is confirmed that the user can be authorized, the software author requires the user to provide an initial character string containing unique hardware information of a corresponding device by using a short message; the software author transmits the received character string short message to the short message platform; a short message processing program of the short message platform generates an authorized serial number in combination with the received initial character string and hardware information of a registered machine, and returns the authorized serial number to the software author by a short message; the software author transmits the received serial number to the user; and the user changes the software license file by using a carried tool according to the received serial number. According to the method, the service life and a maximum user number can be limited, the security is high, and the rights and interests of the software author are protected to the maximum extent.
Owner:STATE GRID JIANGXI ELECTRIC POWER CO +1
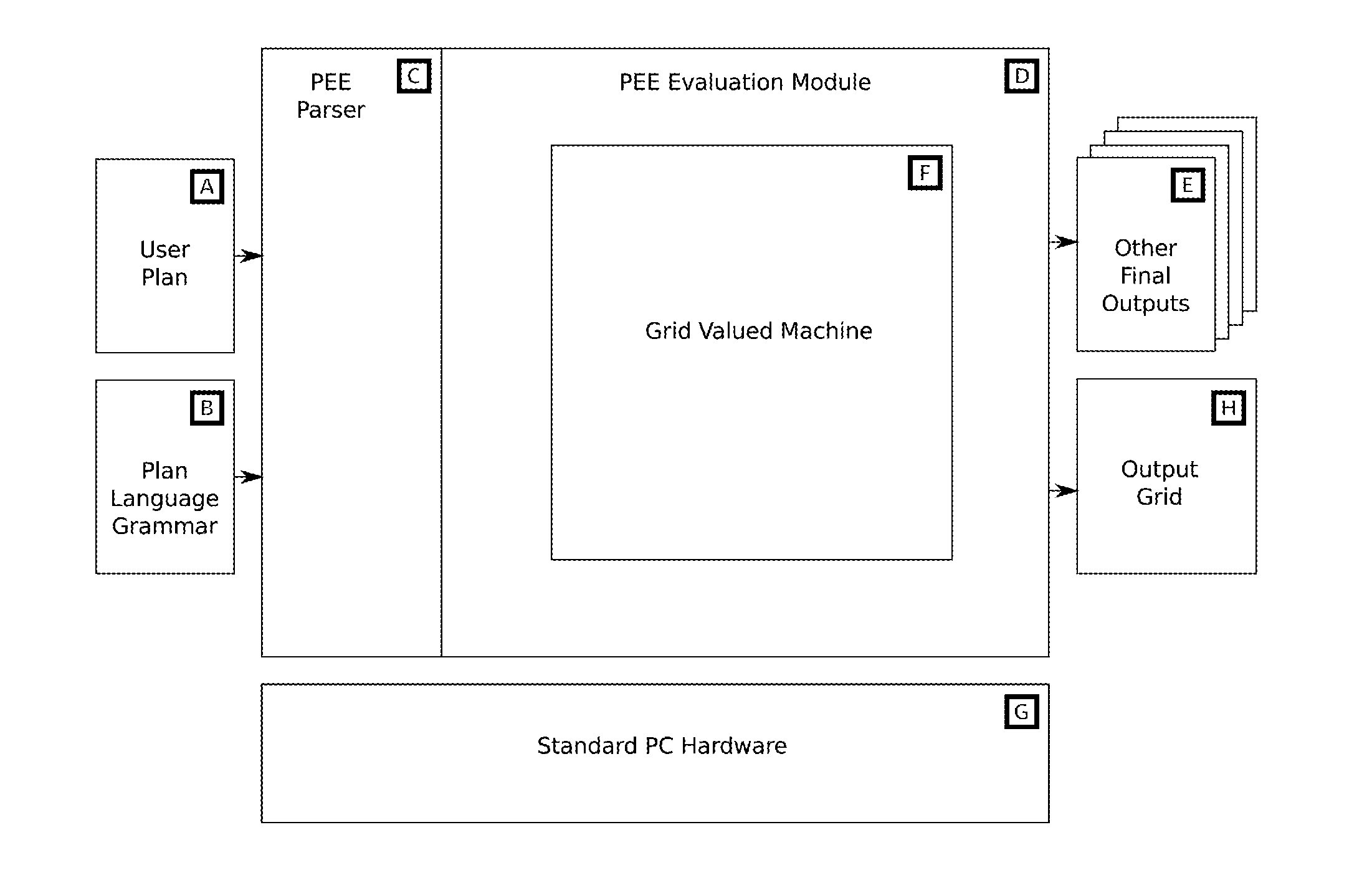
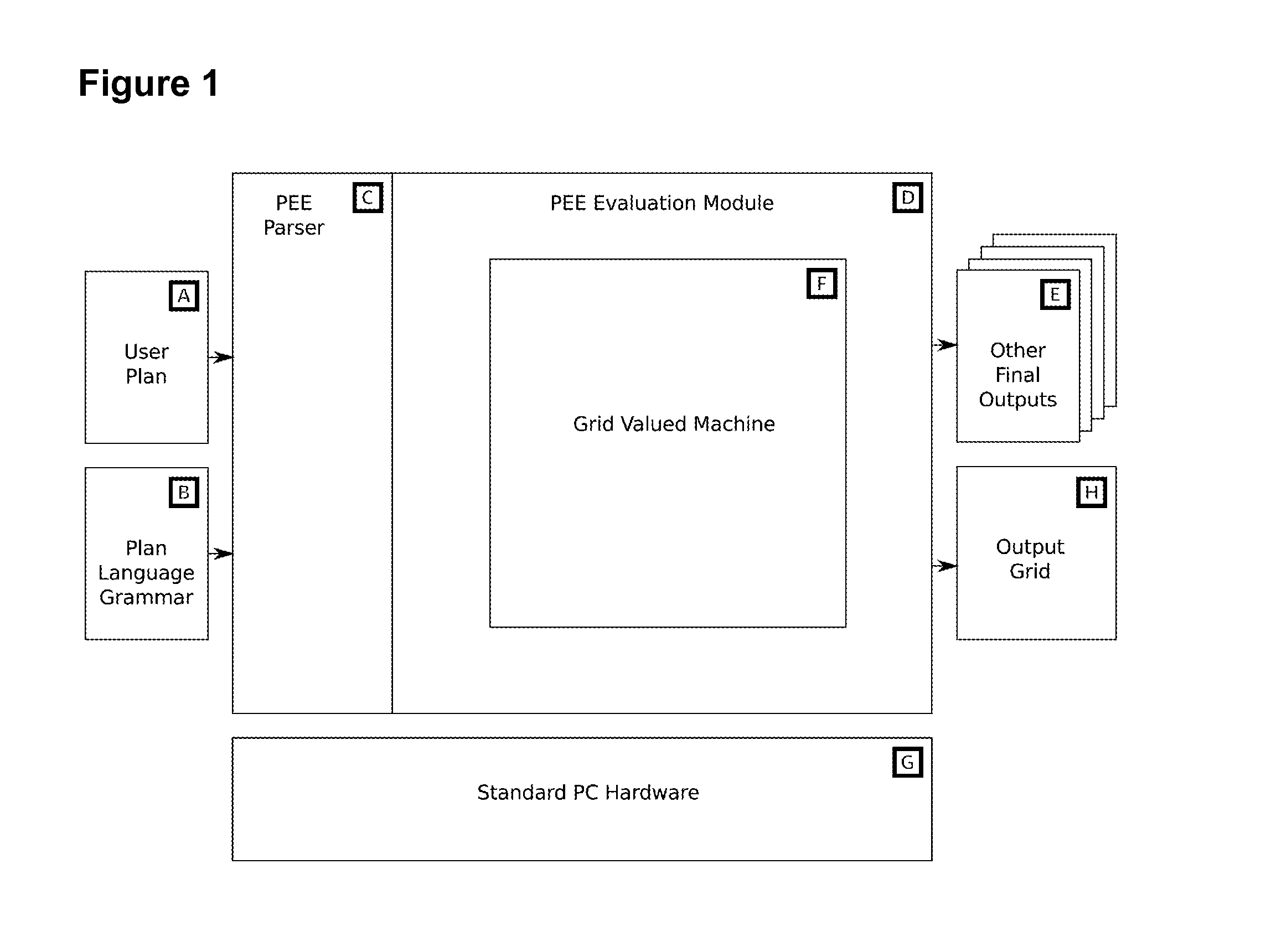
Structured domain specific language and grid valued machine for creating spreadsheets and numerical plans
The new invention is a system for specifying spreadsheets, business plans or other numerical plans using a structured text format, also known as a domain specific language (DSL), and a grid-valued machine. The DSL is both human-readable and can be interpreted by a computing system to create a spreadsheet or related outputs, including the calculation of business metrics. The grid-valued machine is a new model for a computer fitted to this purpose, where a grid of values is used as the underlying data model (i.e., as opposed to the normal register machine model). The language can include terms for describing uncertainty, allowing the specification and presentation of stochastic plans, e.g. for risk analysis. This can be supported in the grid-valued machine using a Monte Carlo approach with multiple grids.
Owner:WINTERSTEIN DANIEL BEN
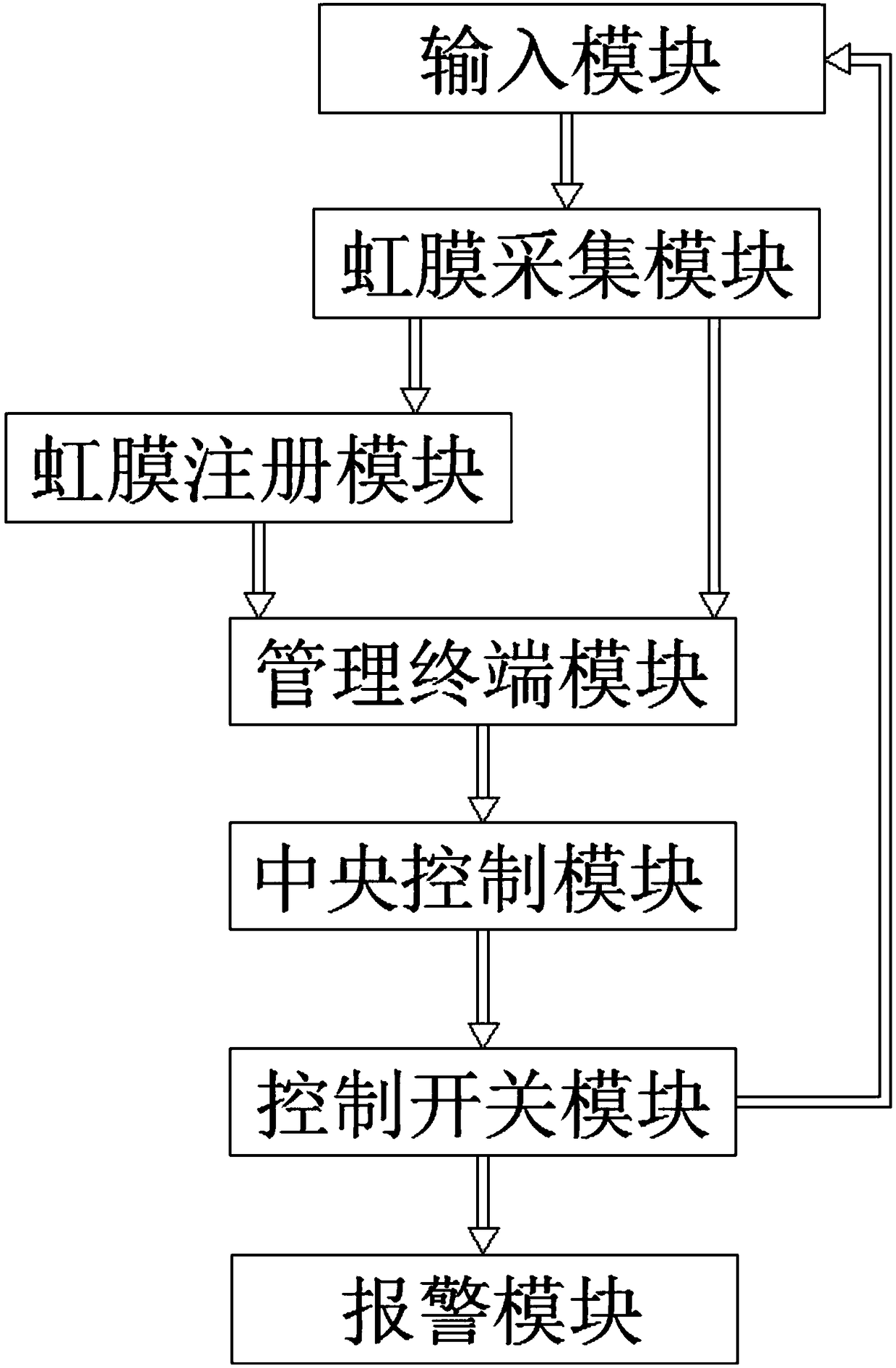
Access control system based on iris recognition
The invention relates to the technical field of smart building, and discloses an access control system based on iris recognition. The access control system based on iris recognition comprises an inputmodule, an iris collection module, an iris registration module, a management terminal module, a central control module, a control switch module and an alarm module, wherein the input module comprisesa keyboard and a display screen, and is used for inputting an issued command and sending the input command; the iris collection module comprises an iris collection unit and a command analysis unit; the command analysis unit is used for receiving the command sent by the input module and analyzing the received command; the iris collection unit is used for collecting irises of human bodies, and thensending the collected irises according to analyzed command content; and the iris registration module comprises a register machine. According to the access control system based on iris recognition, the access control system can control an access control switch via iris recognition, and thus the security of access control system is improved.
Owner:ANHUI CHAOQING INFORMATION ENG
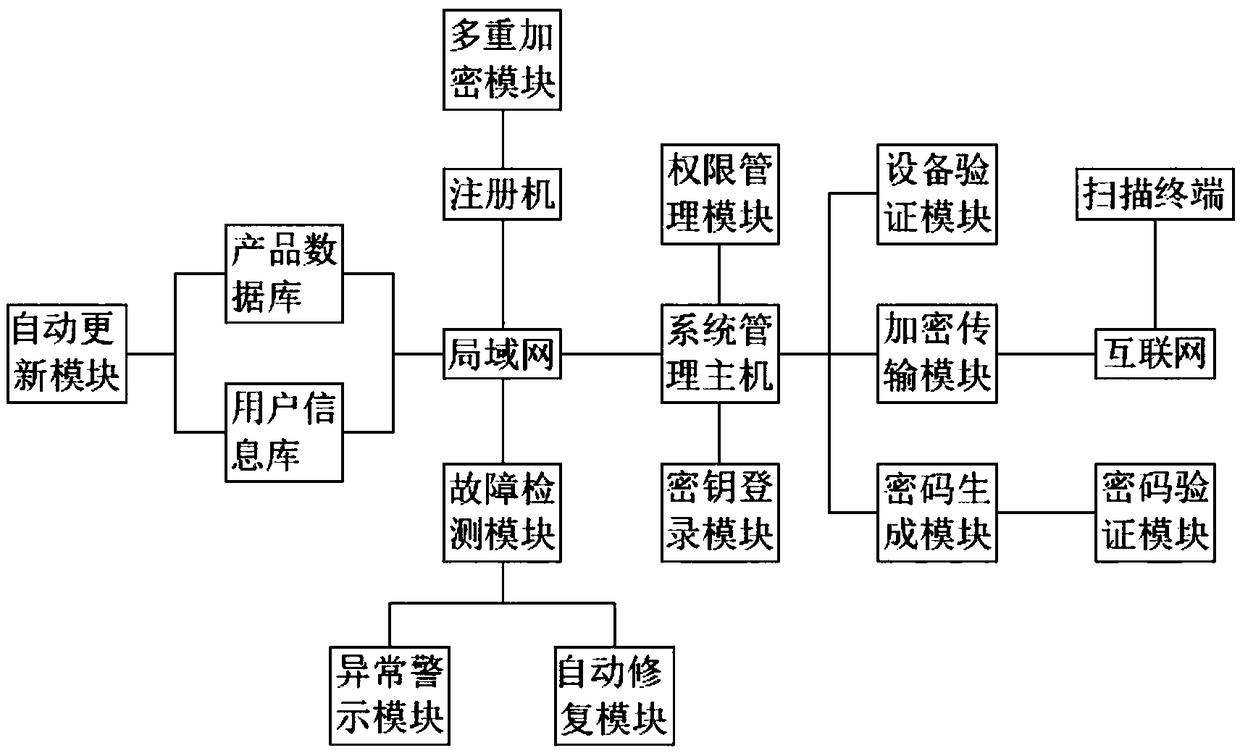
Quick verification system for electronic product code
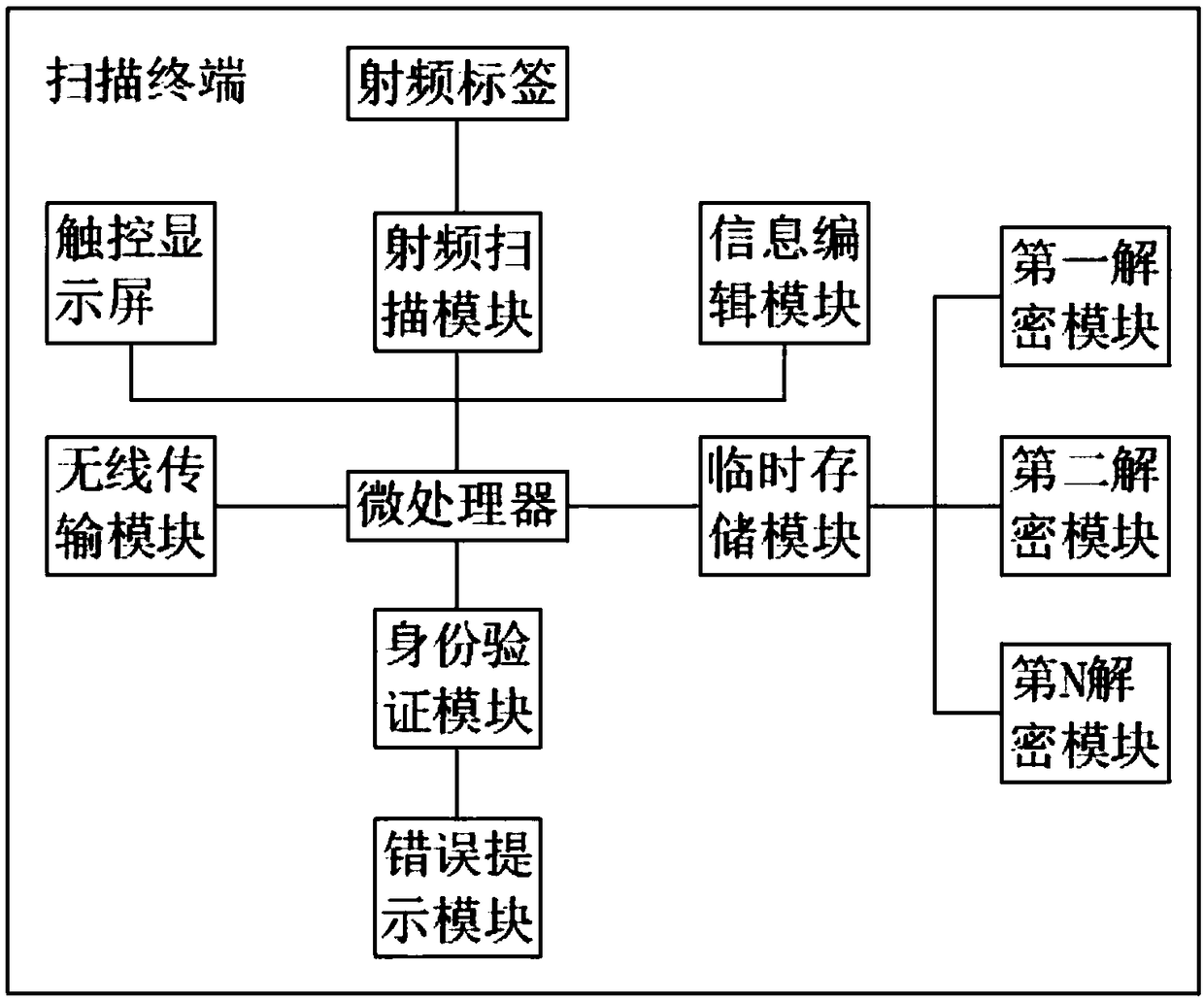
ActiveCN108595974AImprove securityHigh speedDigital data protectionInternal/peripheral component protectionMultiple encryptionInformation repository
The invention relates to the technical field of Internet of Things information security, in particular to a quick verification system for an electronic product code. The quick verification system forthe electronic product code comprises a system management host, wherein the system management host is connected with a register machine, a product database and a user information library through a local area network; the registration machine is connected with a multi-encryption module through a lead; the system management host is connected with a permission management module, a secret key login module and an encryption transmission module through a signal line; and the encryption transmission module is connected with a scanning terminal through the internet. By use of the system, multiple encryption is adopted, product information is divided into multiple segments, so that safety is improved, a corresponding secret key is sent according to user permission, a scanning terminal is provided with a plurality of decryption modules to independently decrypt each segment of secret key, and speed is improved.
Owner:襄阳市尚贤信息科技有限公司
Pattern dimension measurement method using electron microscope, pattern dimension measurement system, and method for monitoring changes in electron microscope equipment over time
InactiveUS9671223B2Electric discharge tubesScanning probe techniquesTemporal changeElectron Microscopy Facility
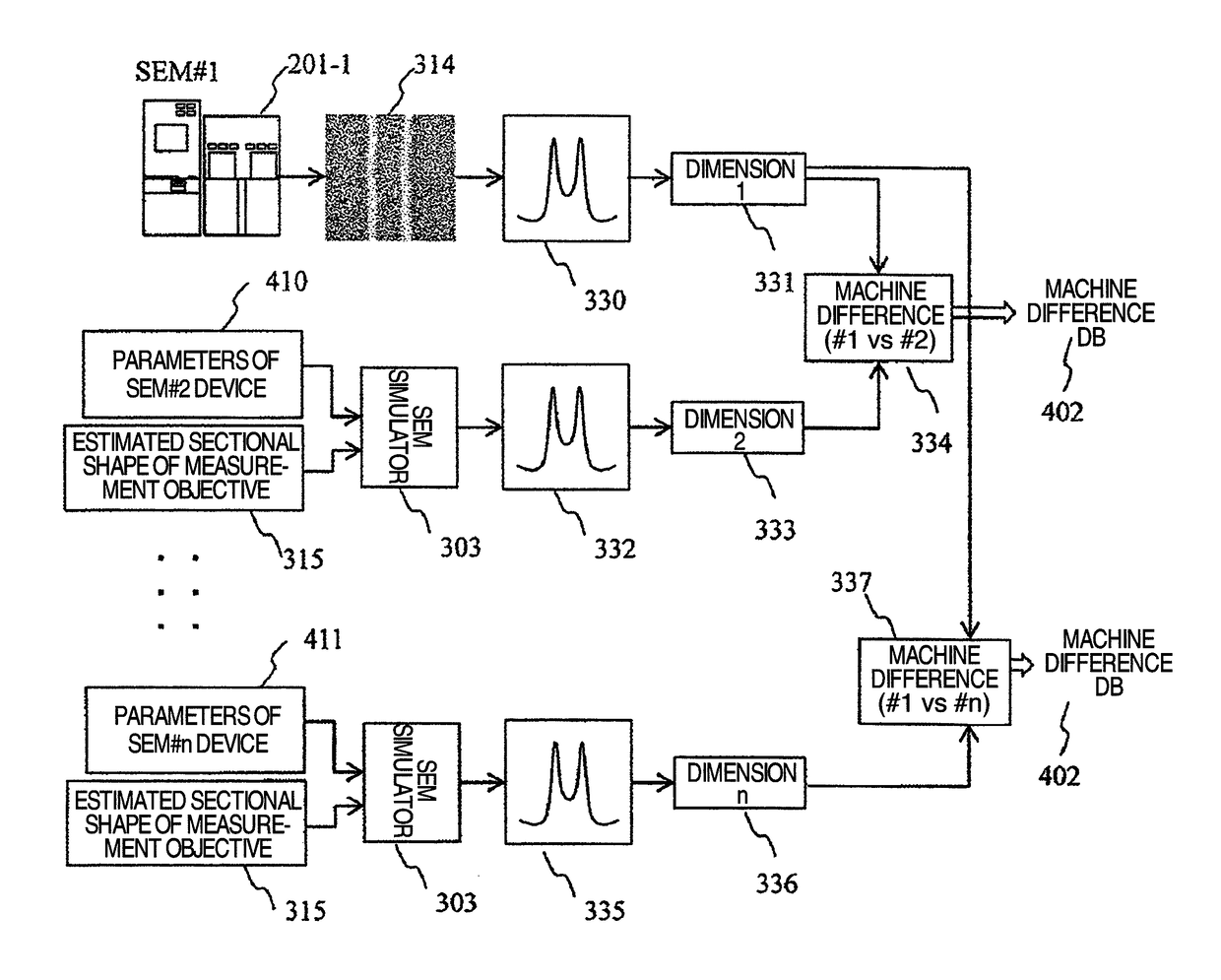
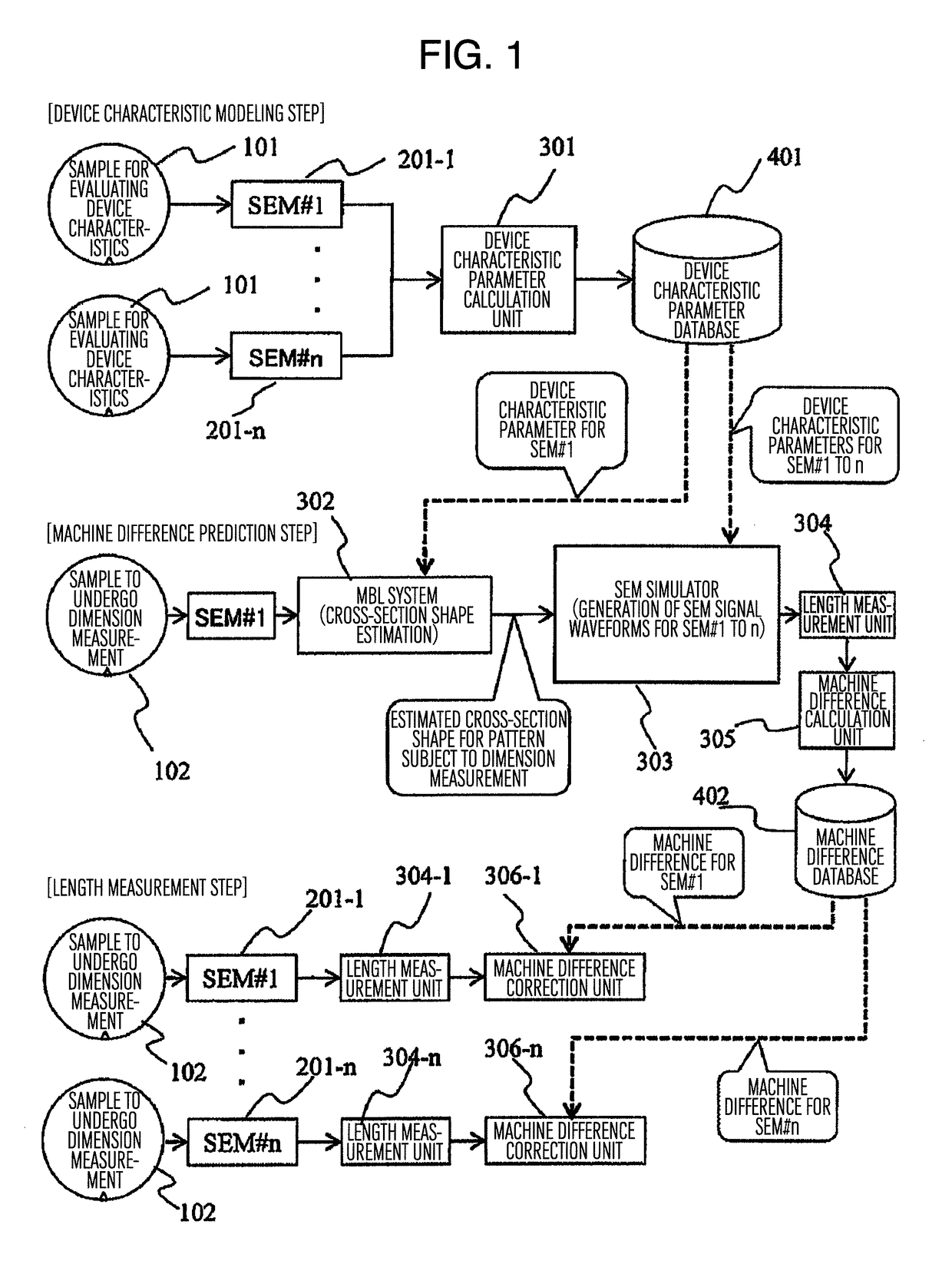
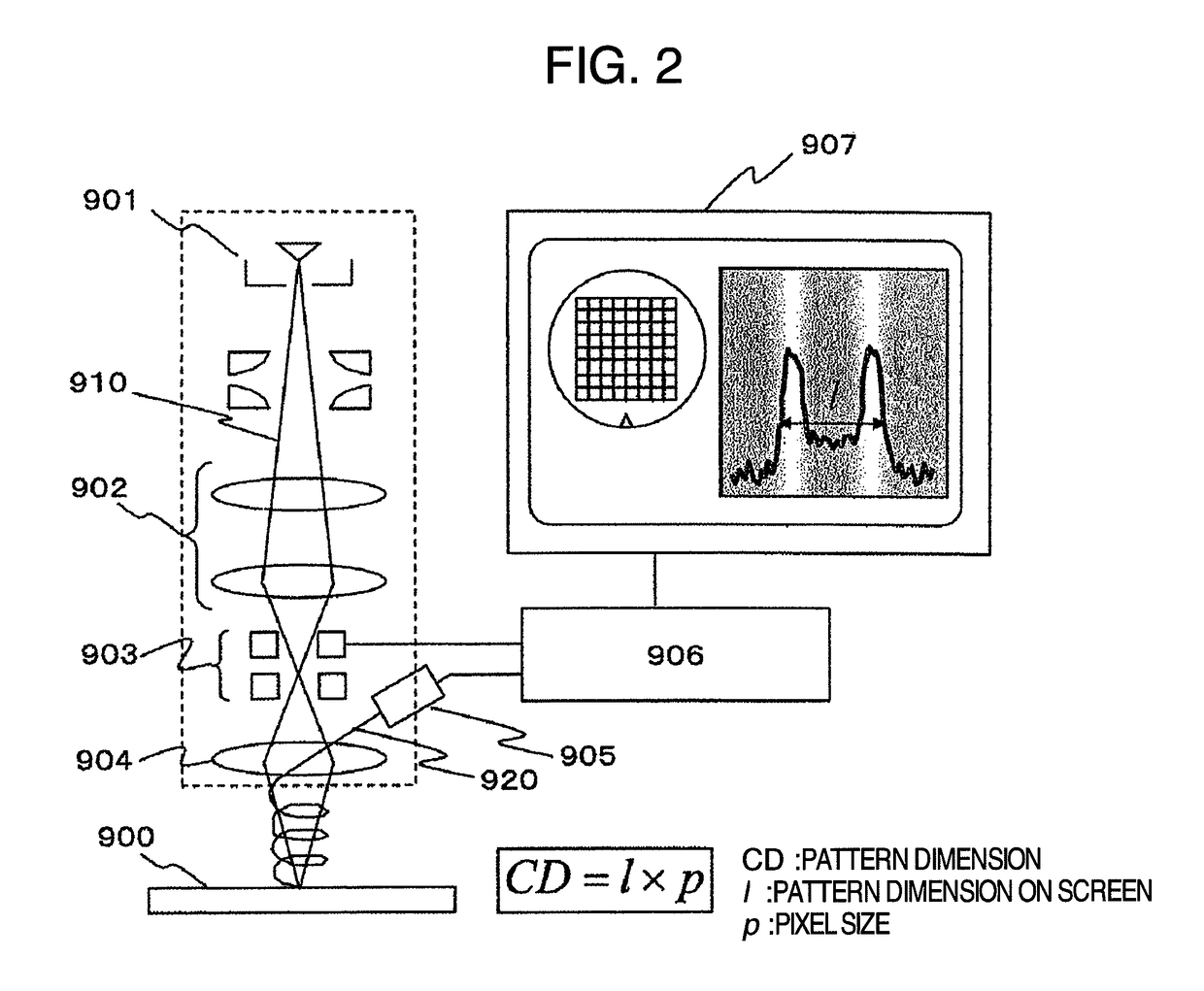
Beforehand, the device characteristic patterns of each critical dimension SEM are measured, a sectional shape of an object to undergo dimension measurement is presumed by a model base library (MBL) matching system, dimension measurements are carried out by generating signal waveforms through SEM simulation by inputting the presumed sectional shapes and the device characteristic parameters, and differences in the dimension measurement results are registered as machine differences. In actual measurements, from the dimension measurement results in each critical dimension SEM, machine differences are corrected by subtracting the registered machine differences. Furthermore, changes in critical dimension SEM's over time are monitored by periodically measuring the above-mentioned device characteristic parameters and predicting the above-mentioned dimension measurement results. According to the present invention, actual measurements of machine differences, which require considerable time and effort, are unnecessary. In addition, the influence of changes in samples over time, which is problematic in monitoring changes in devices over time, can be eliminated.
Owner:HITACHI HIGH-TECH CORP
Intelligent medical auxiliary diagnosis system based on deep learning
PendingCN110136826AReduce the difficulty of diagnosisReduce misdiagnosis rateMedical automated diagnosisMedical imagesDiseaseDiagnostic system
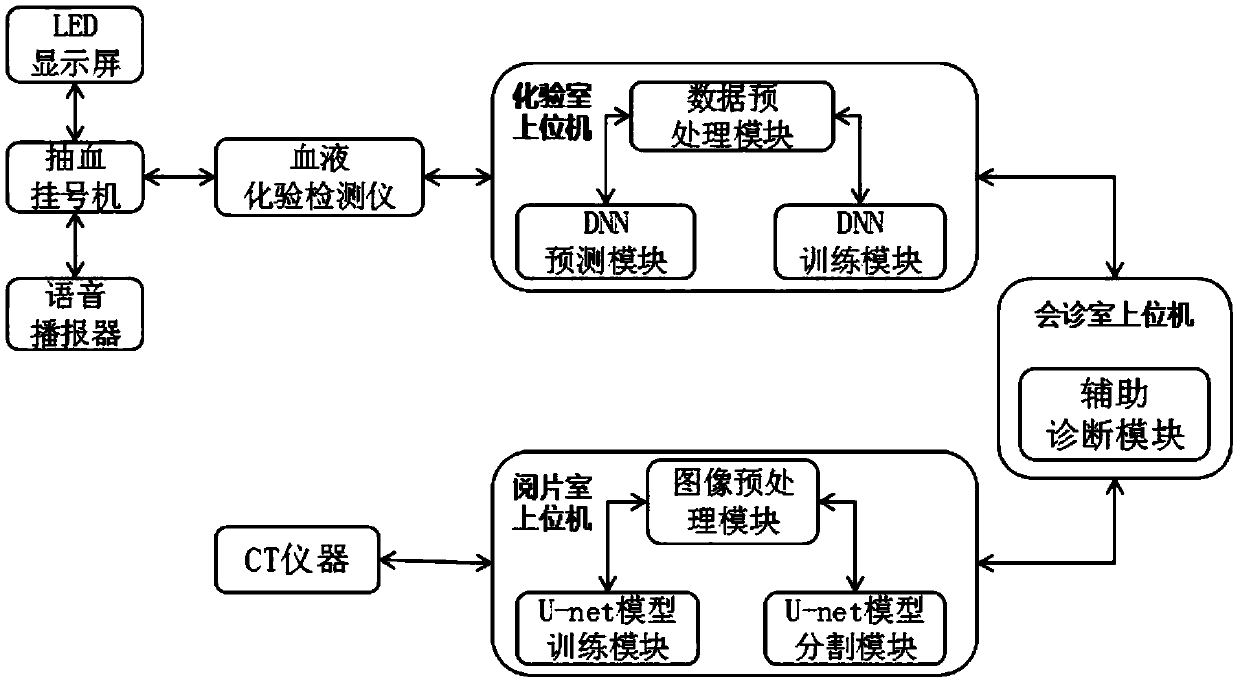
The invention discloses an intelligent medical auxiliary diagnosis system based on deep learning, wherein the system relates to the field of intelligent medical technology. The system comprises a consultation room upper computer, a laboratory upper computer, a film reading room upper computer, a blood drawing registering machine, a blood examination instrument and a CT instrument. The consultationroom upper computer is in wireless communication connection with the laboratory upper computer and the film reading room upper computer. The laboratory upper computer is in communication connection with the blood examination instrument. The film reading room upper computer is in communication connection with the CT instrument. According to the intelligent medical auxiliary diagnosis system, a blood examination analysis result is obtained through a DNN predicting module of the laboratory upper computer by means of a DNN characteristic model, and furthermore a U-net model segmenting module of the film reading room upper computer utilizes a U-net model for performing segmenting processing on a CT image for obtaining a segmenting graph. Finally an auxiliary diagnosis module of the consultation room upper computer analyzes a disease suffering probability according to the blood examination analysis result, the CT image and the segmenting graph thereof by means of a medical knowledge database, thereby reducing diagnosis difficulty, reducing error diagnosis probability and improving diagnosis accuracy.
Owner:安徽蔻享数字科技有限公司
Search Infrastructure Supporting Identification, Setup and Maintenance of Machine to Machine Interactions
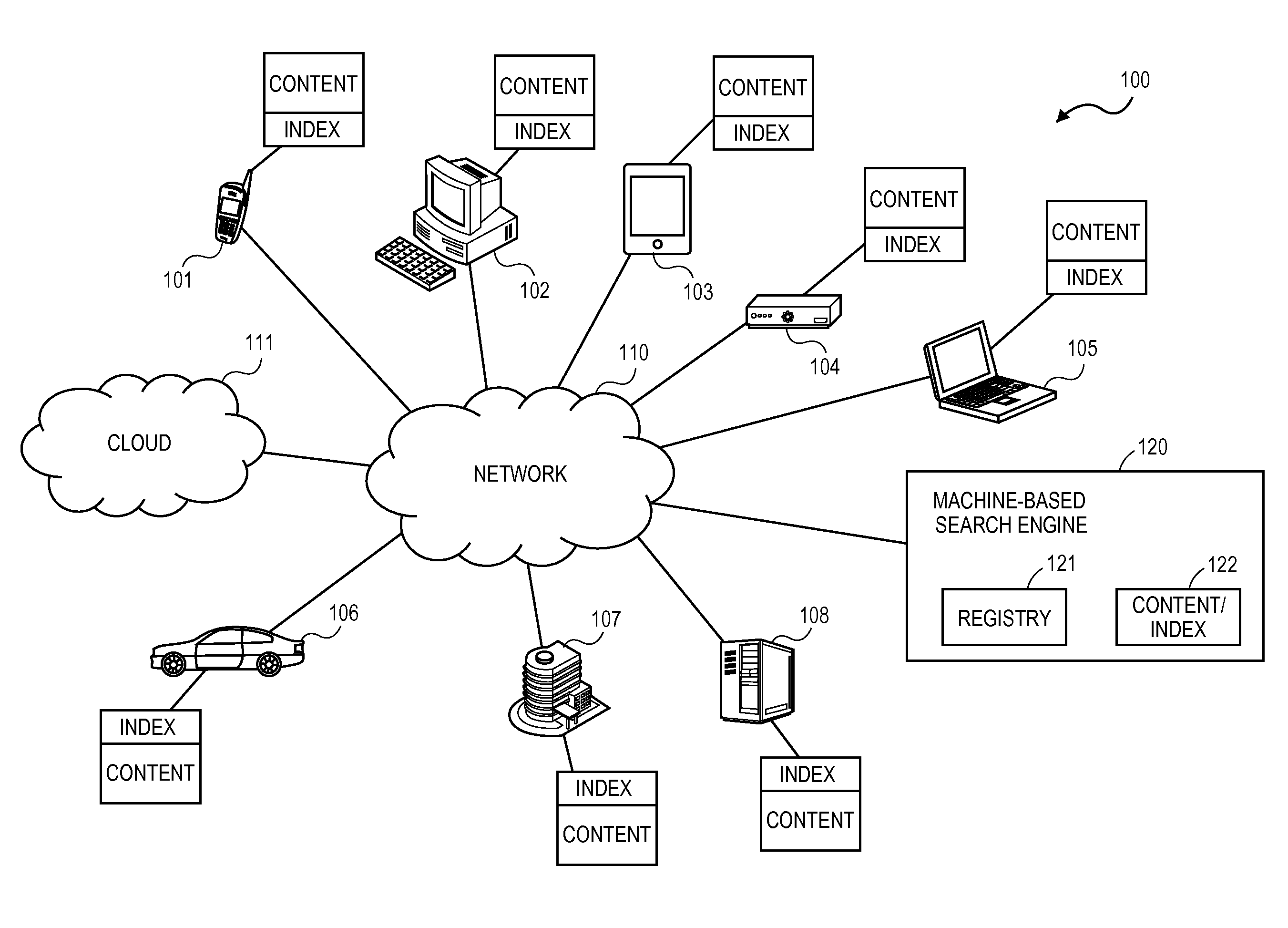
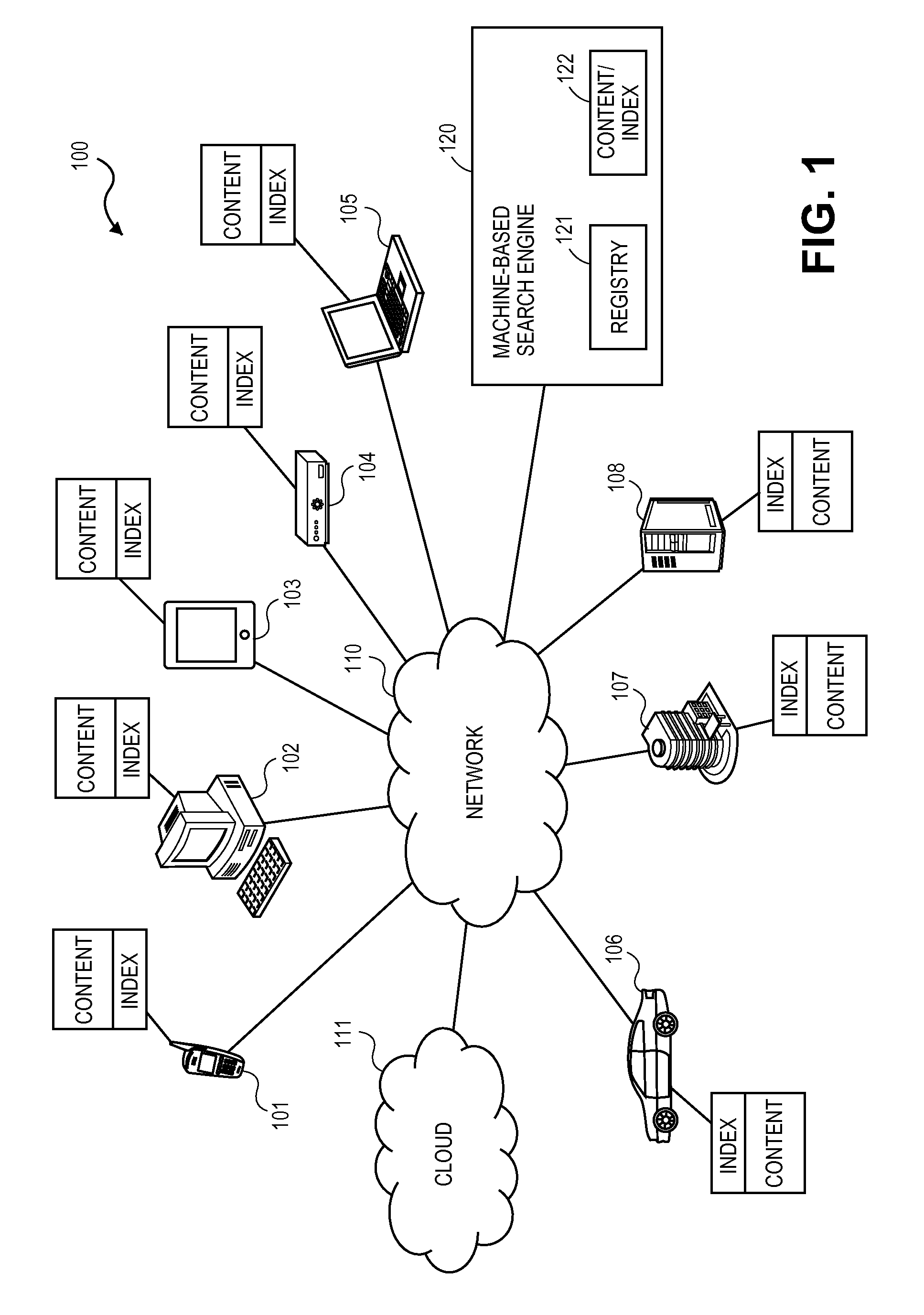
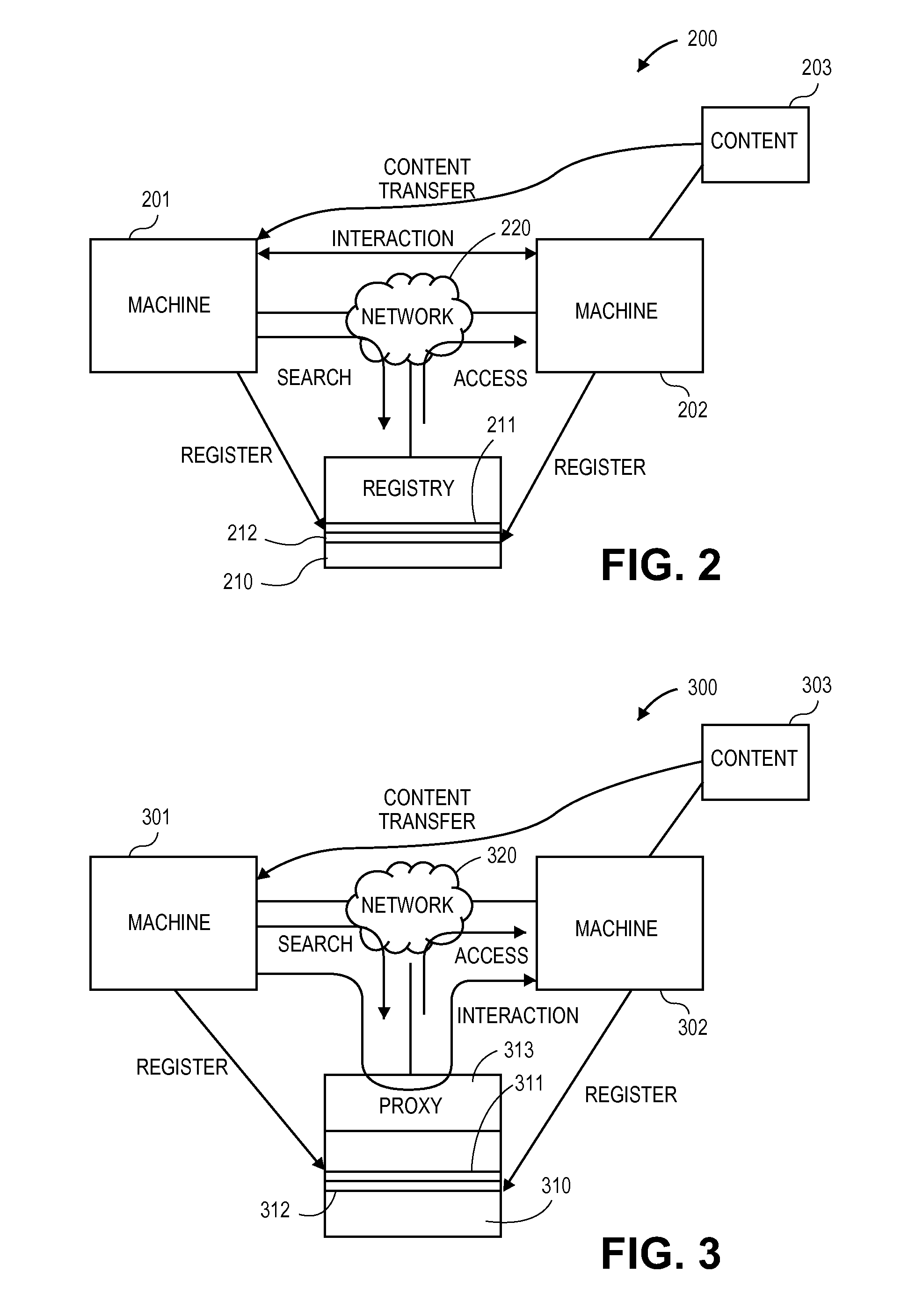
A technique in which autonomous machine-to-machine interactions are identified, setup and maintained between machines by utilizing a registry that may be searched to identify a registered machine. The search may be for a particular target machine or for content. By identifying a target machine, the registry may provide an address to connect two machines for the two machines to interact, such as the download of content stored on one of the machines.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Program code compiling method and device, electronic equipment and storage medium
The embodiment of the invention provides a program code compiling method and device, electronic equipment and a storage medium, in the embodiment of the invention, a callee register mechanism is introduced in the program code compiling process, so that when a program runs, if a called function needs to modify a register in a callee storage register set, the callee storage register set can be modified, and the program code compiling efficiency is improved. If the value of the register does not need to be modified, the value of the register is stored to the call stack and recovered to the register when the call is finished, and if the value of the register does not need to be modified, the value of the register can not be stored to the call stack, so that the instruction consumption can be reduced to a great extent, and the computing power resource consumed by storing the register is reduced; the register modification frequency is reduced, and the program code performance and size are improved.
Owner:UCWEB
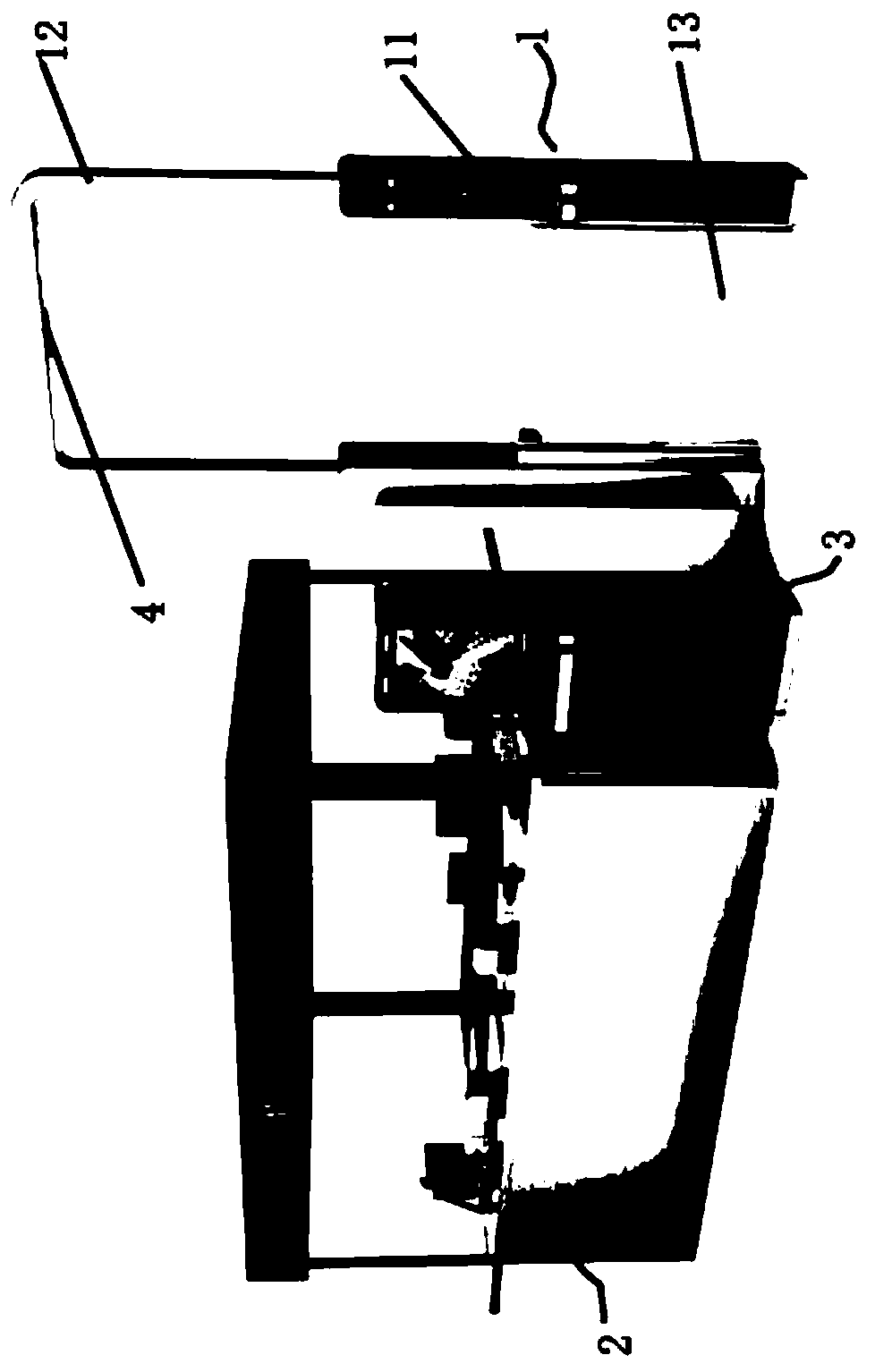
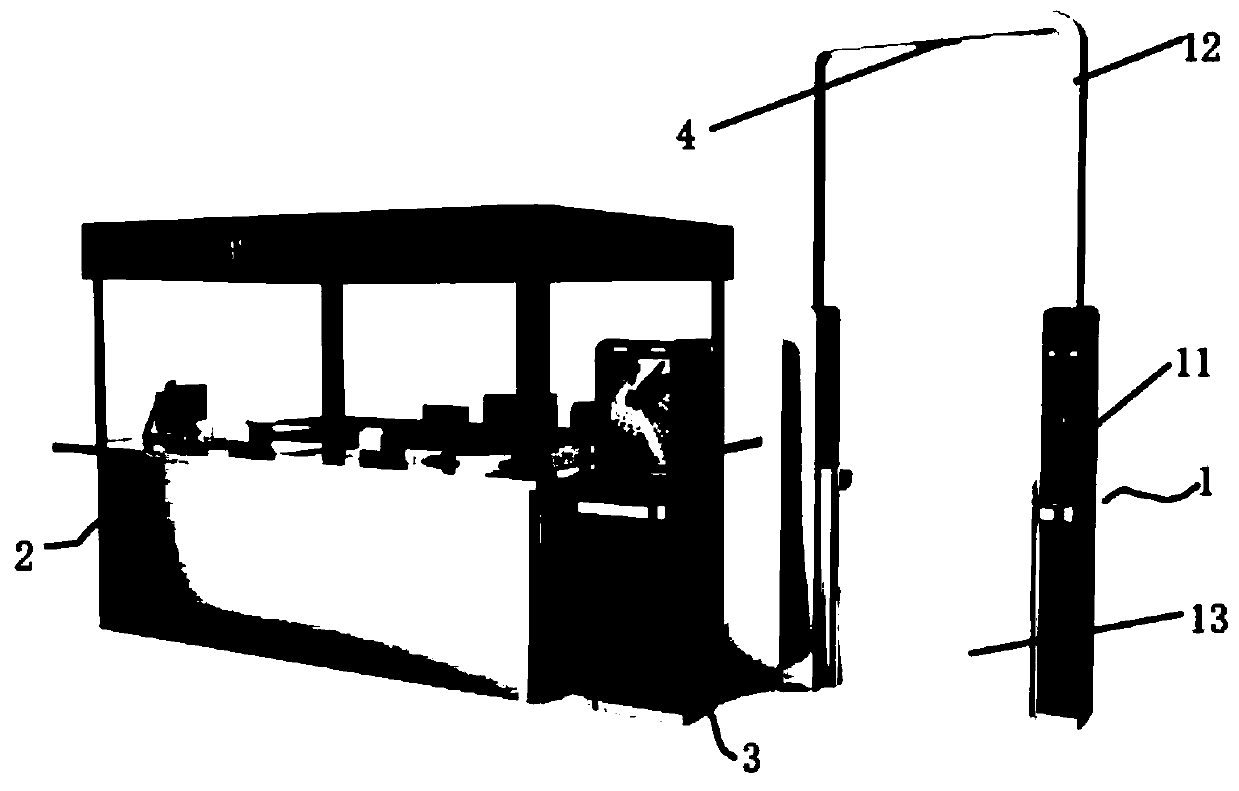
Intelligent cash register all-in-one machine
The present invention relates to the field of machinery, in particular to an intelligent cashier integrated machine, which includes a code scanner bracket, a POS machine frame, and a POS machine and a base installed thereon. The code scanner is connected to the base. The code scanner bracket includes a bottom plate, a side plate and a rotating connector. The bottom plate is provided with a camera hole, and the side plate is provided with a first fixing piece and a second fixing piece. , the rotating slot is arranged on the back of the base, and the code scanner bracket can rotate around the base frame; it provides a good installation and placement structure of the tablet computer type code scanner and the entire bracket of the cash register, and the bottom of the frame The bases are set as a stretchable structure through the bearings and the connecting shafts set on the bases that match the bearings, which can facilitate consumers of different heights. Such an invention will be more conducive to the use of consumers and provide better customer experience.
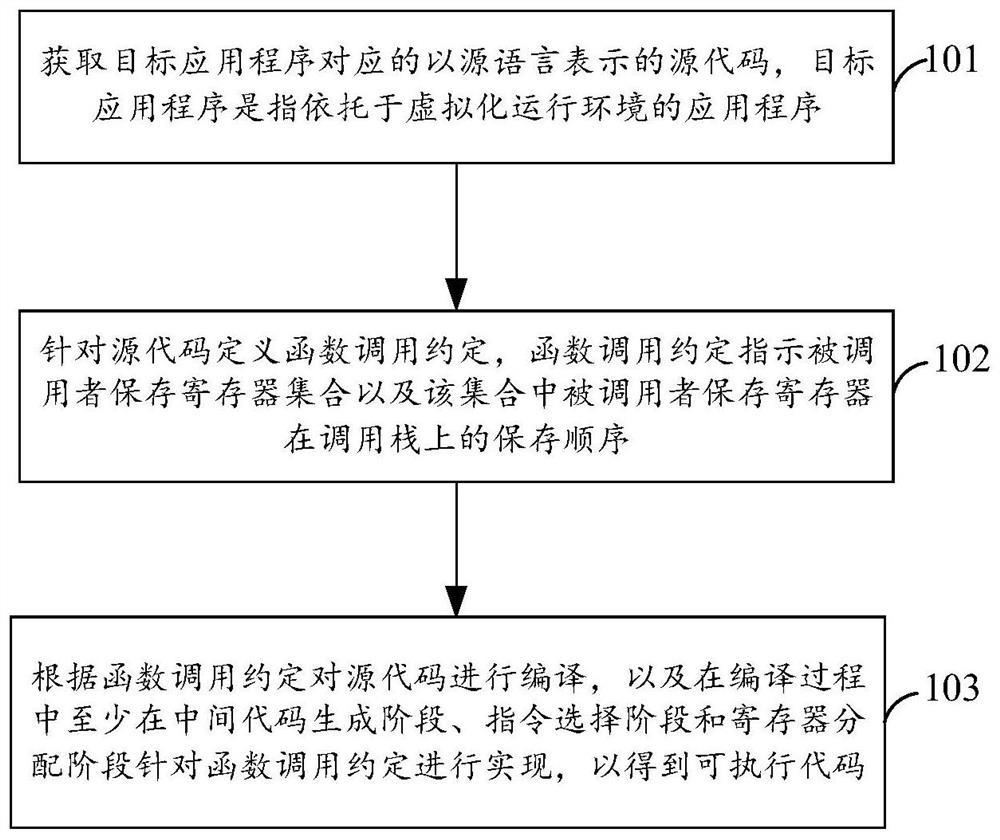
Owner:ZHEJIANG XKESHI NETWORK TECH
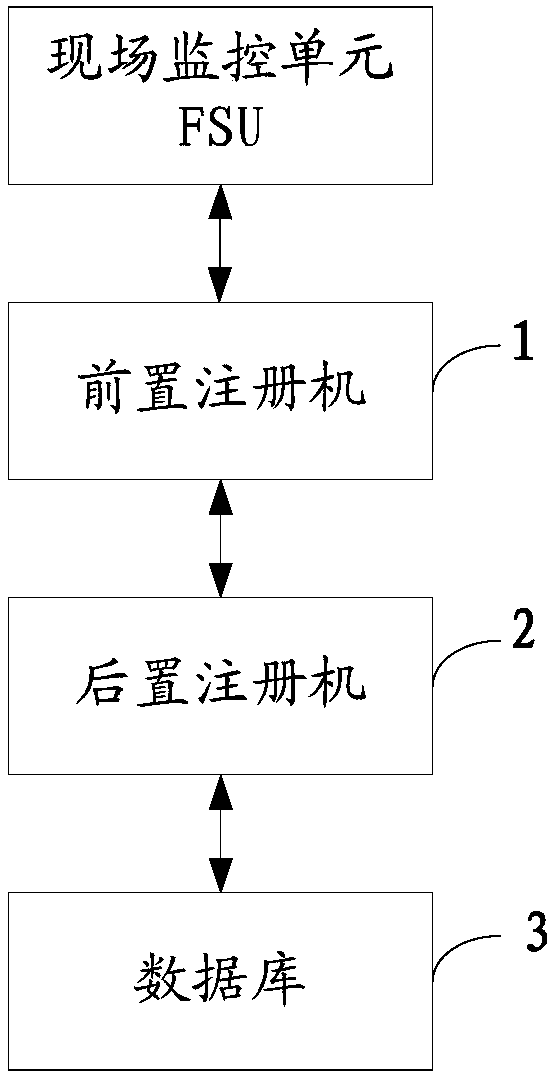
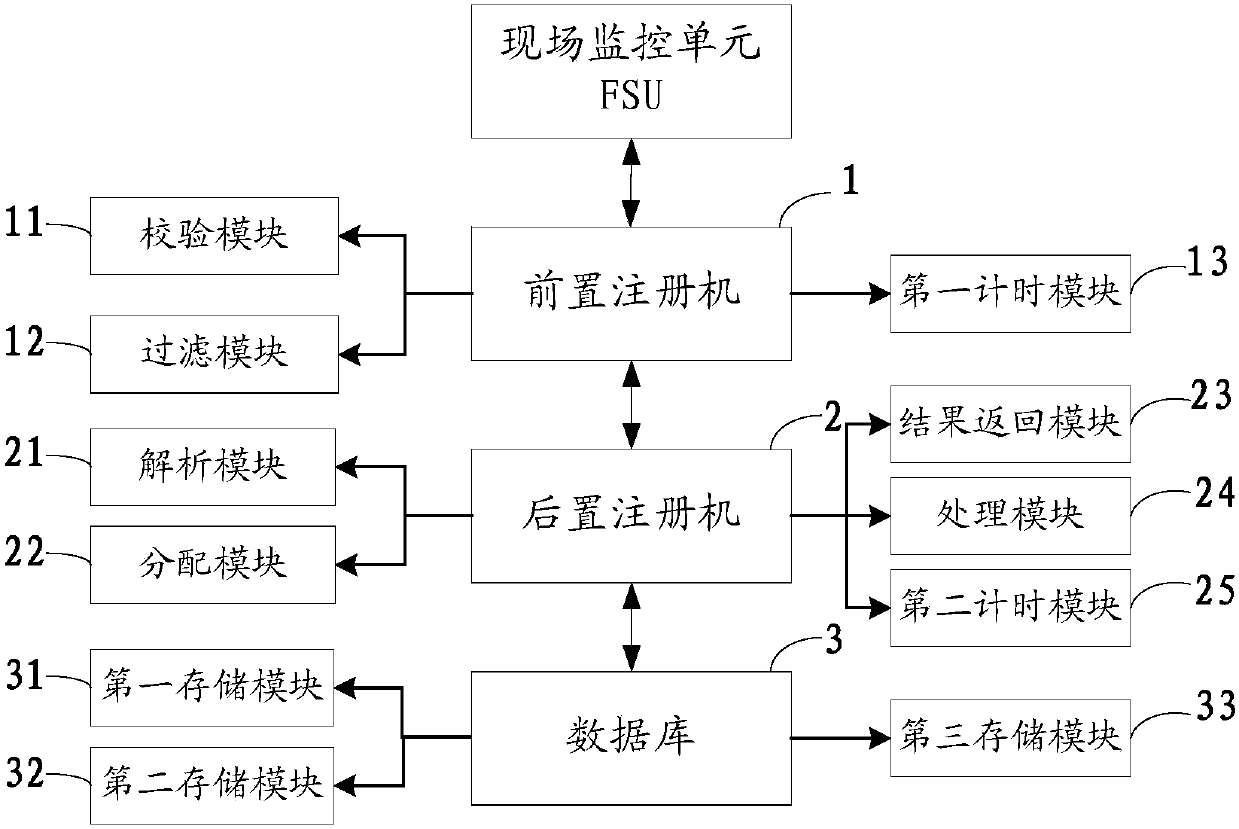
Field supervision unit registration system and method
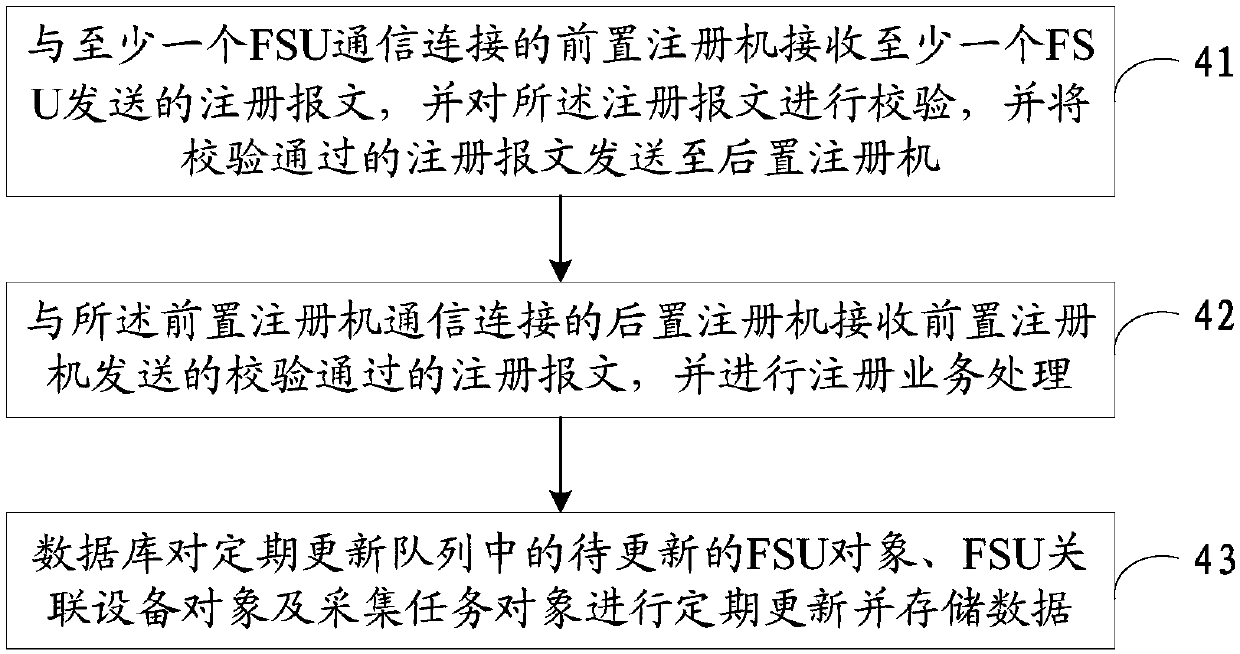
ActiveCN107634963AGuaranteed continuityImprove concurrent access performanceTransmissionStart up timeField monitoring
The invention discloses a field supervision unit registration system and method. The field supervision unit registration system comprises a pre-posed register machine which is connected with at leastone field supervision unit FSU through a transmission control protocol TCP; a post-posed register machine which is connected with the pre-posed register machine through a user datagram protocol UDP, wherein the pre-posed register machine receives a register message transmitted by at least one FSU, verifies the register message, and transmits the verified register message to the post-posed registermachine; and the post-posed register machine receives the verified register message transmitted by the pre-posed register machine, and performs registered business processing. The field supervision unit registration system provided by the invention greatly improves the concurrent access capability of the FSU, and the start-up time is short, so that the continuity of the registered business and the stability of the running state of the register machines are effectively guaranteed.
Owner:CHINA TOWER CO LTD
Method for machine tool and profilometer coordinate registration
A method for registering machine tool and profilometer coordinates, wherein the machine tool defines a C-axis having a zero position, C=0, comprises loading a sacrificial workpiece into the machine tool; cutting several first features in a surface of the sacrificial workpiece and producing a linear machine tool motion across the workpiece; determining the centroid of each first cut feature; fitting a line to the centroids of the first cut features; and measuring angle θ0 of the line relative to the C-axis zero position. The angle θ0 is the departure in profilometer coordinates from the C=0 line. The method includes moving the machine tool to a fixed radius; cutting several second features in a surface of the sacrificial workpiece and producing a circular machine tool motion across the workpiece; determining the centroid of each second cut feature; fitting a circle to the centroids of the second cut features; and determining a center of the circle. The center of the circle is the machine tool center in profilometer coordinates.
Owner:EASTMAN KODAK CO
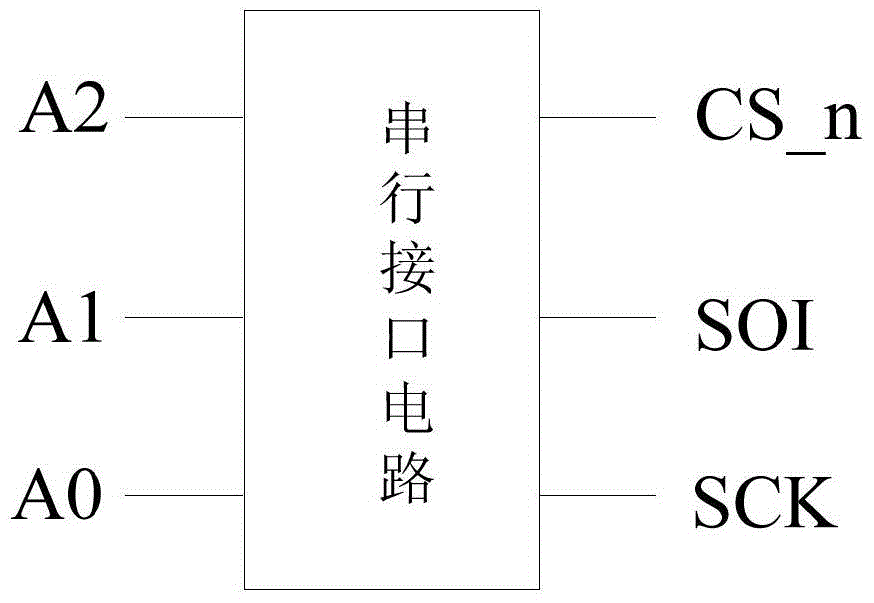
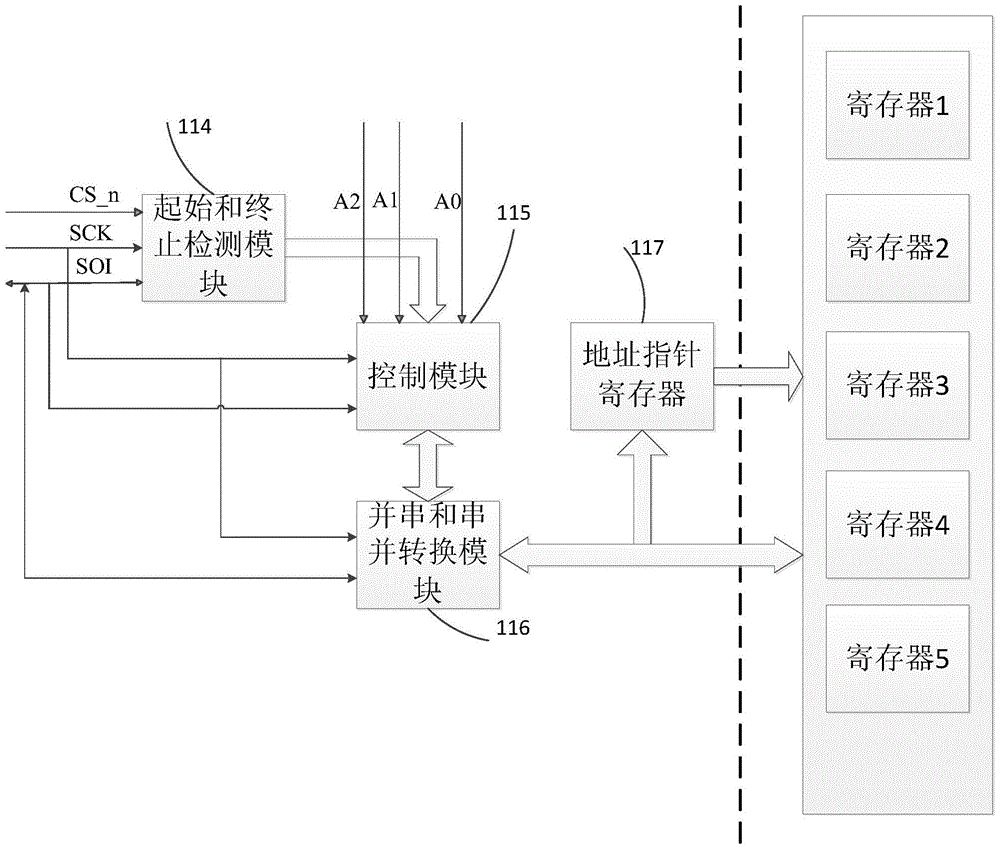
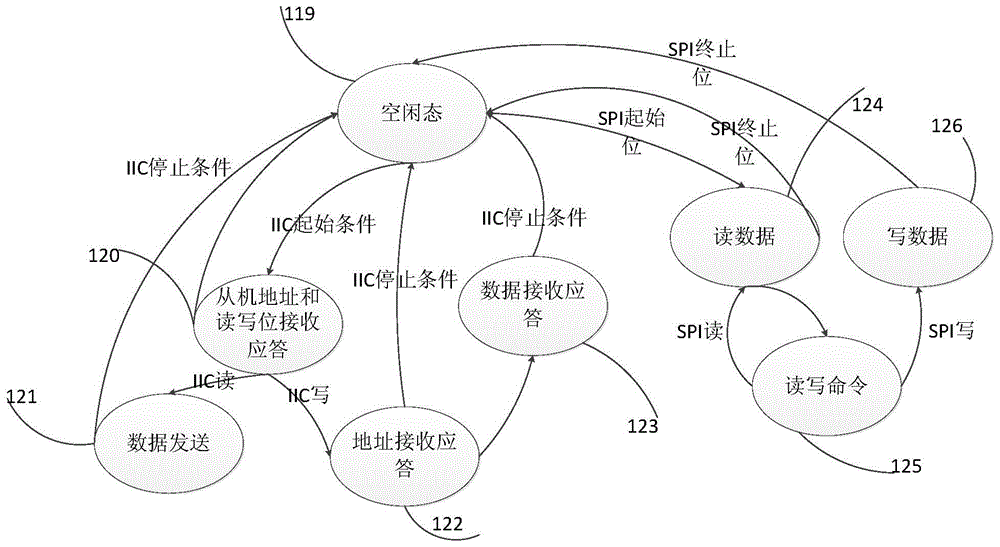
Universal Slave Synchronous Serial Interface Circuit
ActiveCN103488600BSave internal logic resourcesReduce the number of interfacesElectric digital data processingProcessor registerExternal data
The invention provides a synchronous serial interface circuit of a universal slave, comprising a start and stop detection module, which is used to detect and output the effective bit of the SPI bus protocol, the start condition and the stop condition of the IIC bus protocol; The output signal of the start and end detection module determines the bus data transmission mode of the serial interface circuit, and controls the parallel-serial and serial-parallel conversion modules; the parallel-serial and serial-parallel conversion modules are controlled by the control module and are used to transfer slave Serial output of multiple register data inside the machine and external serial data are converted into internal register data of the slave machine; the address pointer register is used to address multiple registers inside the slave machine. The invention realizes a universal slave synchronous serial interface circuit supporting bus data transmission compatible with the IIC protocol and the SPI protocol, and can meet the application requirements of different occasions.
Owner:中科芯未来微电子科技成都有限公司
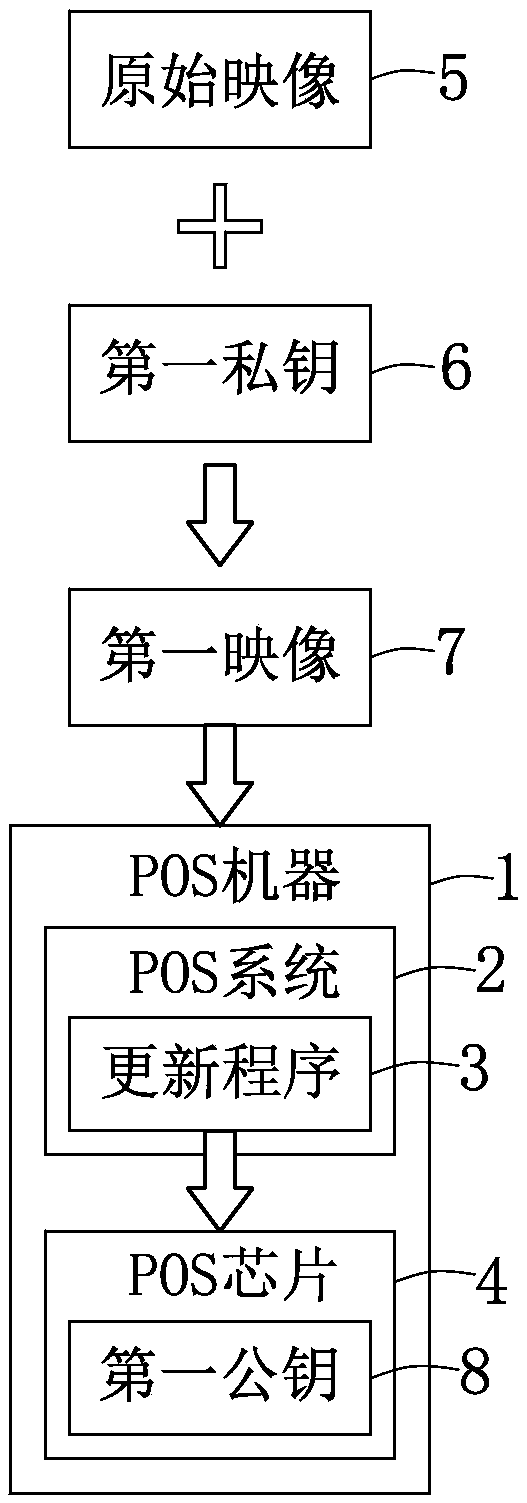
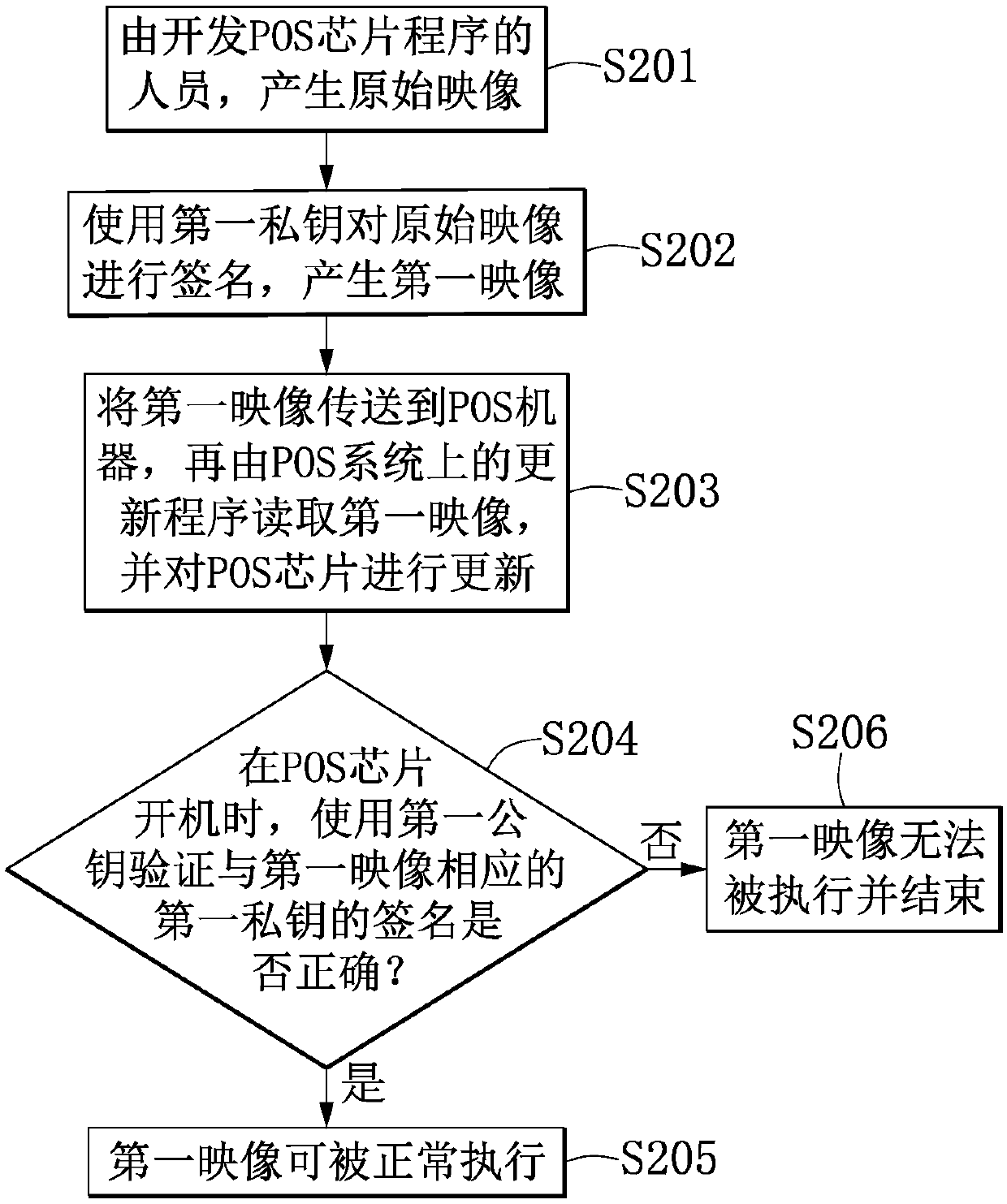
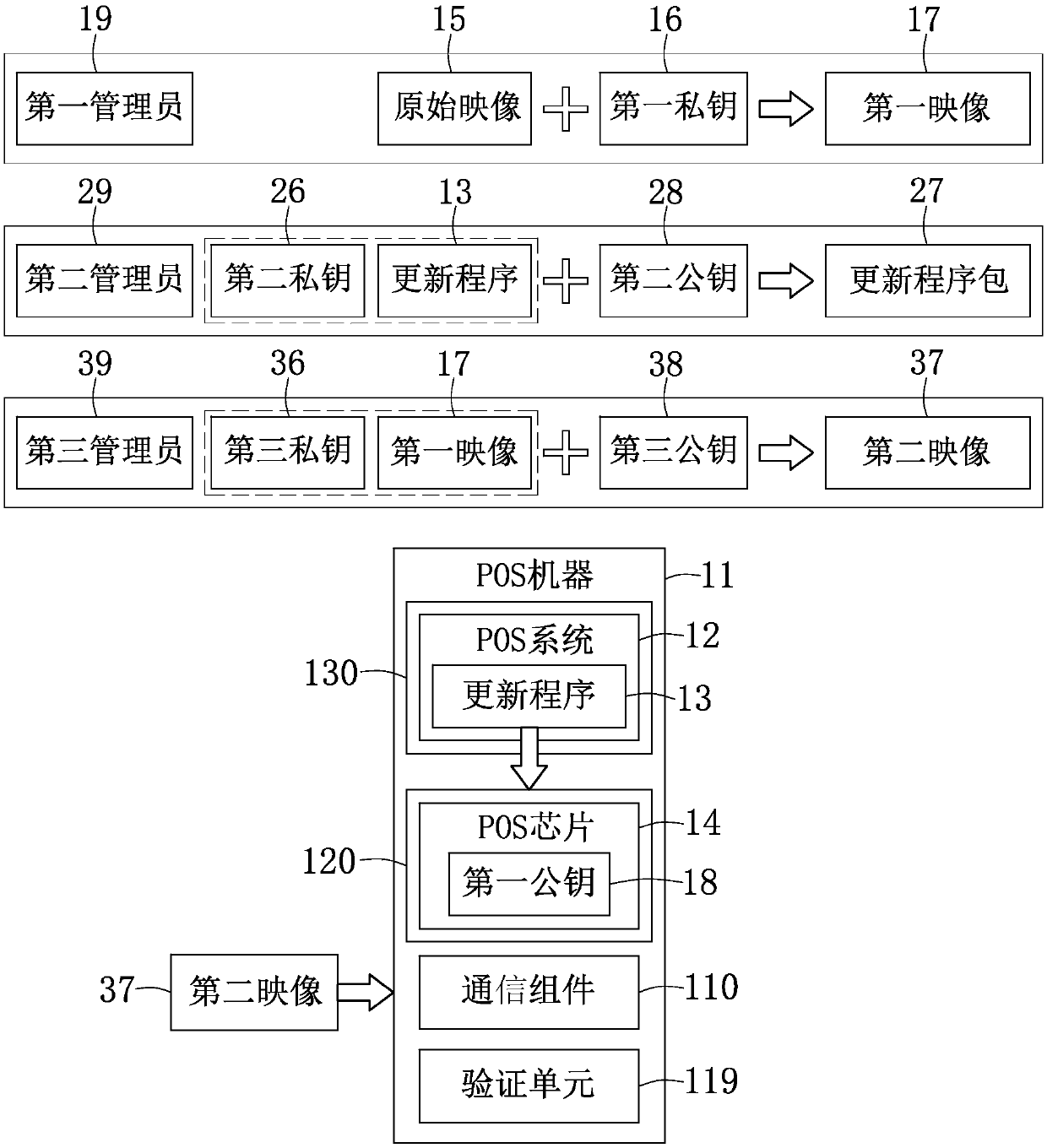
Cash register and method for verifying security of cash register
ActiveCN109671229AImprove securityUser identity/authority verificationCash registersSecurity validationComputer science
The invention provides a method for verifying the security of a cash register. The method comprises the following steps: when a cash register machine starts up, the cash register machine receives an update program package and verifies whether the update program package uses a second private key to sign or not, and if so, an updating program is installed on the cash register machine, wherein the update program package is generated by using the second private key to sign the updating program and packaging a second public key and the updating program; after the updating program is installed, a third private key matched with a third public key to sign a second image so as to decide whether to update the cash register machine or not, wherein the second image is generated by packaging a third public key and a first image; and a first public key is used for verifying whether a signature of a first private key corresponding to the first image is correct or not, and if so, the first image is set to be capable of being executed by the cash register machine, wherein the first image is generated by using the first private key to sign an original image through.
Owner:USI SCI & TECH (SHENZHEN) CO LTD
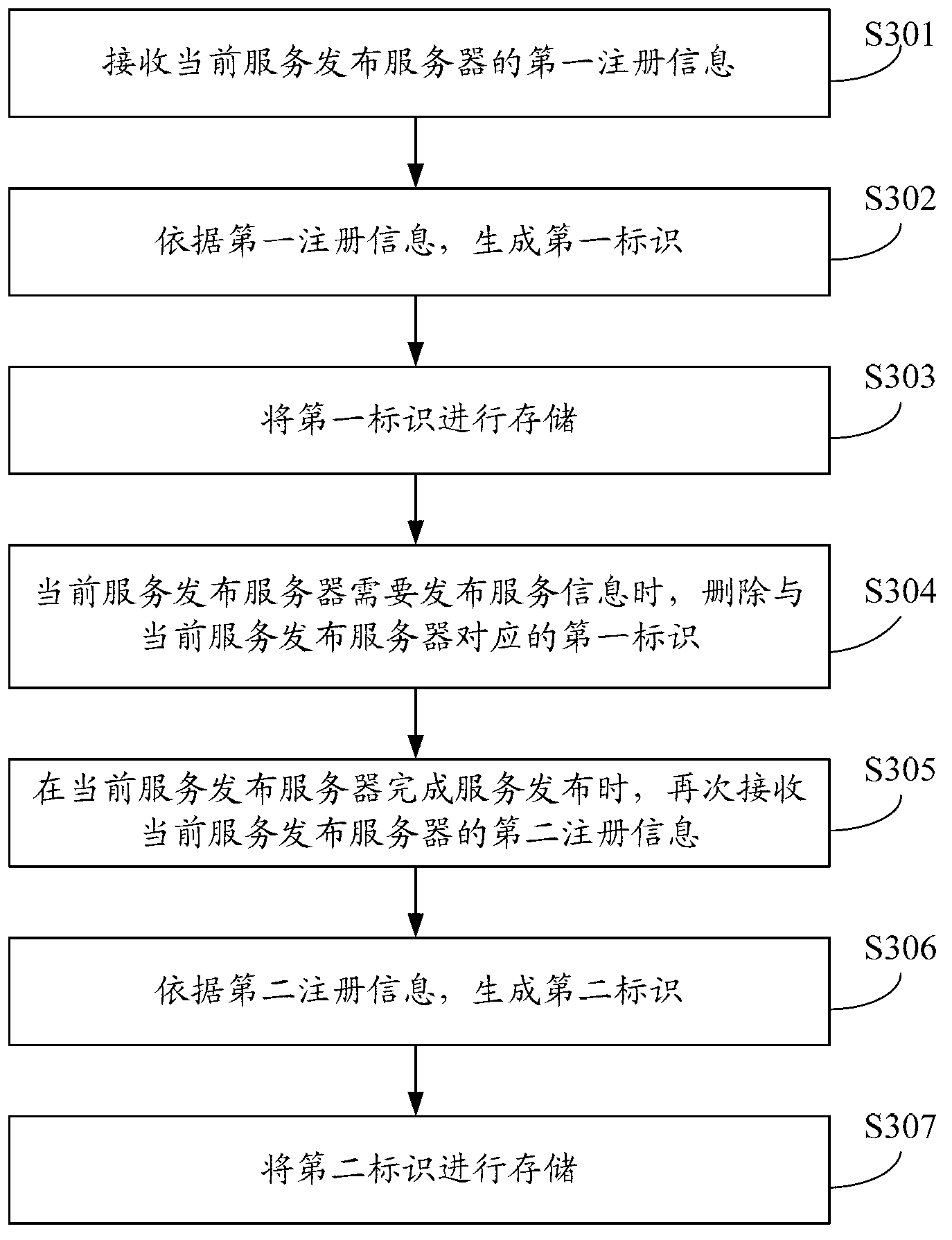
A service publishing method, service publishing server and service registration machine
InactiveCN103227723BImprove experienceSpecial service provision for substationService informationDistributed computing
The invention provides a service publication method, a service publication server and a service registering machine. The service publication method is applied to a current service publication server of multiple service publication servers, the multiple service publication servers cannot simultaneously publish services, the current service publication server sends first register information to the service registering machine, the service registering machine is used for producing a first mark according to the first register information and deleting the first mark when the current service publication server needs to publish service information, the current service publication server can send second register information to the service registering machine after the services are published, and the service registering machine can produce a second mark according to the second register information. Therefore, when the current service publication server publishes the services, only the work of the current service publication server is stopped without influencing the works of other service publication servers, therefore, turn-off of the whole servers is not needed, and the user experience is improved.
Owner:ZHEJIANG YUTIAN TECH +2
A system and method for connecting ip terminal to dvb video network
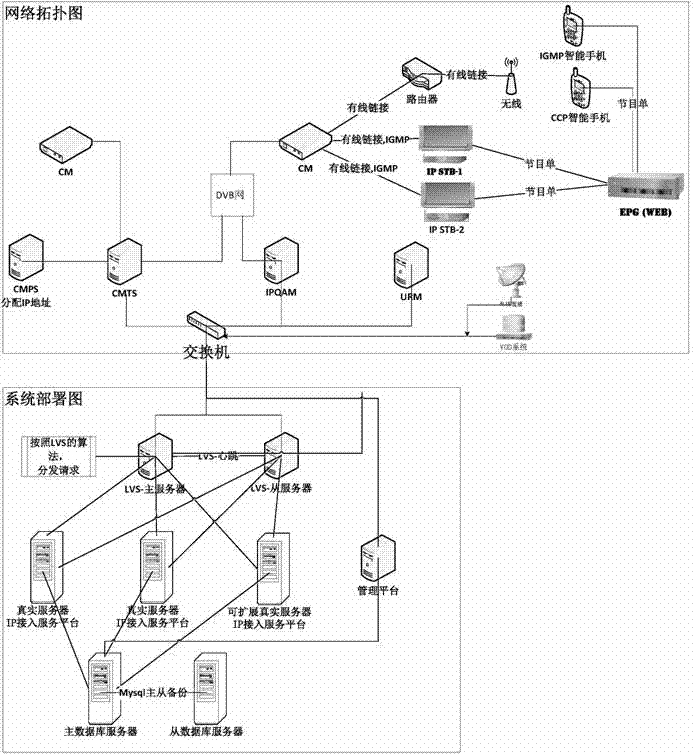
ActiveCN104038777BImprove market resilienceSave resourcesTransmissionSelective content distributionAccess networkComputer terminal
The invention discloses access of an IP (Internet Protocol) terminal to a DVB (Digital Video Broadcasting) video network system. An IP access service platform, a management platform, a URM (Unlimited Register Machine), an IPQAM, an IP terminal, a DVB terminal, a VOD (Video-On-Demand) background and a live video source are provided; the IP access service platform, the management platform, the URM, the IPQAM, the VOD background and the live video source are interconnected through an IP network, the DVB terminal is connected with the IPQAM through a DVB network, and the DVB terminal is connected with the IP terminal through the IP network. Meanwhile, the conventional around-the-clock broadcast live video is changed into on-demand live video, resources are allocated and played according to the demand of a user, and programs are transmitted in a video-on-demand form, thereby effectively saving these resources, providing more abundant video programs under the same resource background, and wining the user.
Owner:华数传媒网络有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com