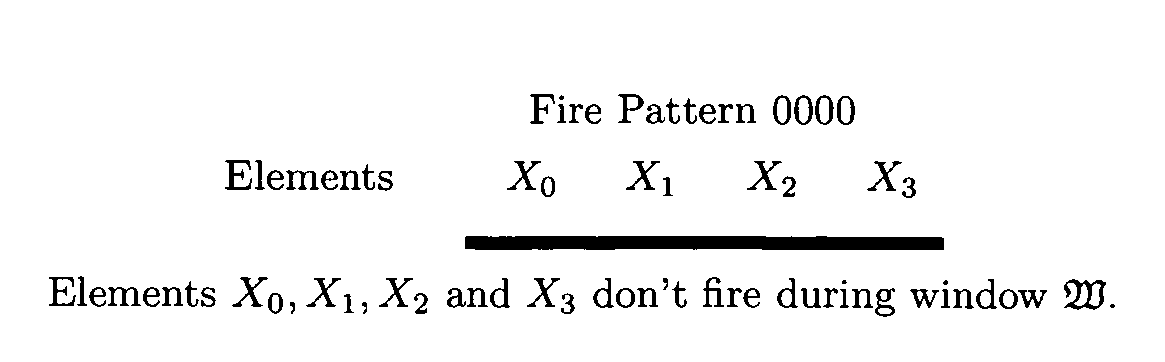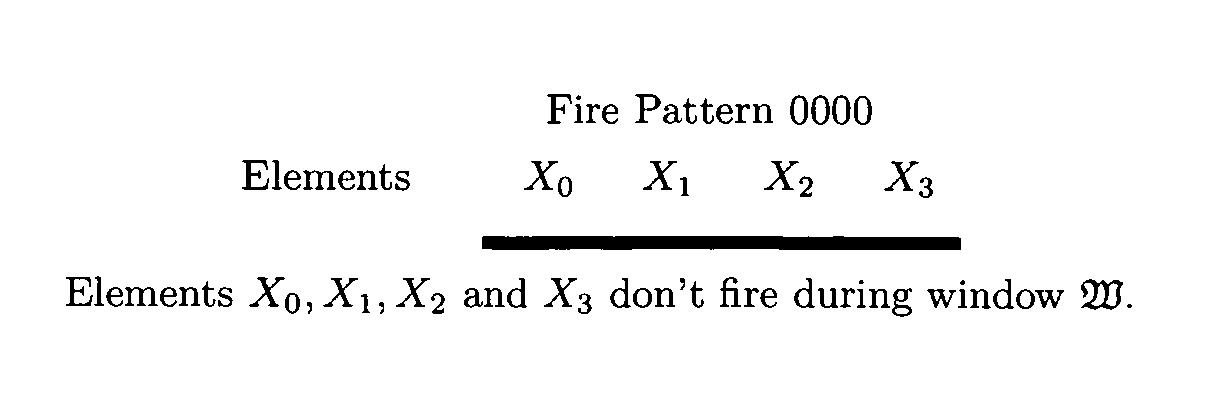Patents
Literature
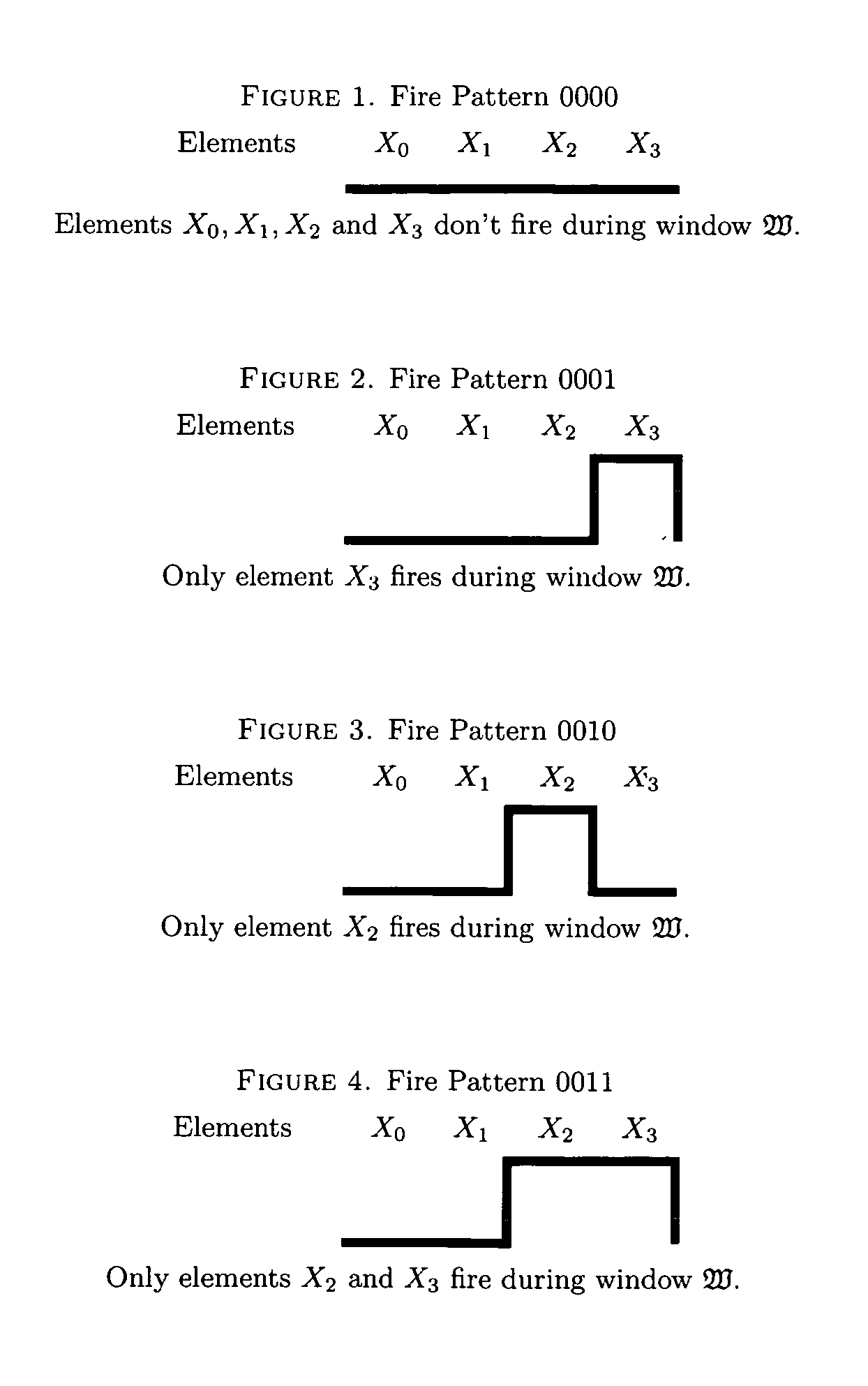
47 results about "Turing machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Turing machine is a mathematical model of computation that defines an abstract machine, which manipulates symbols on a strip of tape according to a table of rules. Despite the model's simplicity, given any computer algorithm, a Turing machine capable of simulating that algorithm's logic can be constructed.
General protocol for proactively secure computation
ActiveUS9449177B1Key distribution for secure communicationDigital data protectionSecret shareSecure multi-party computation
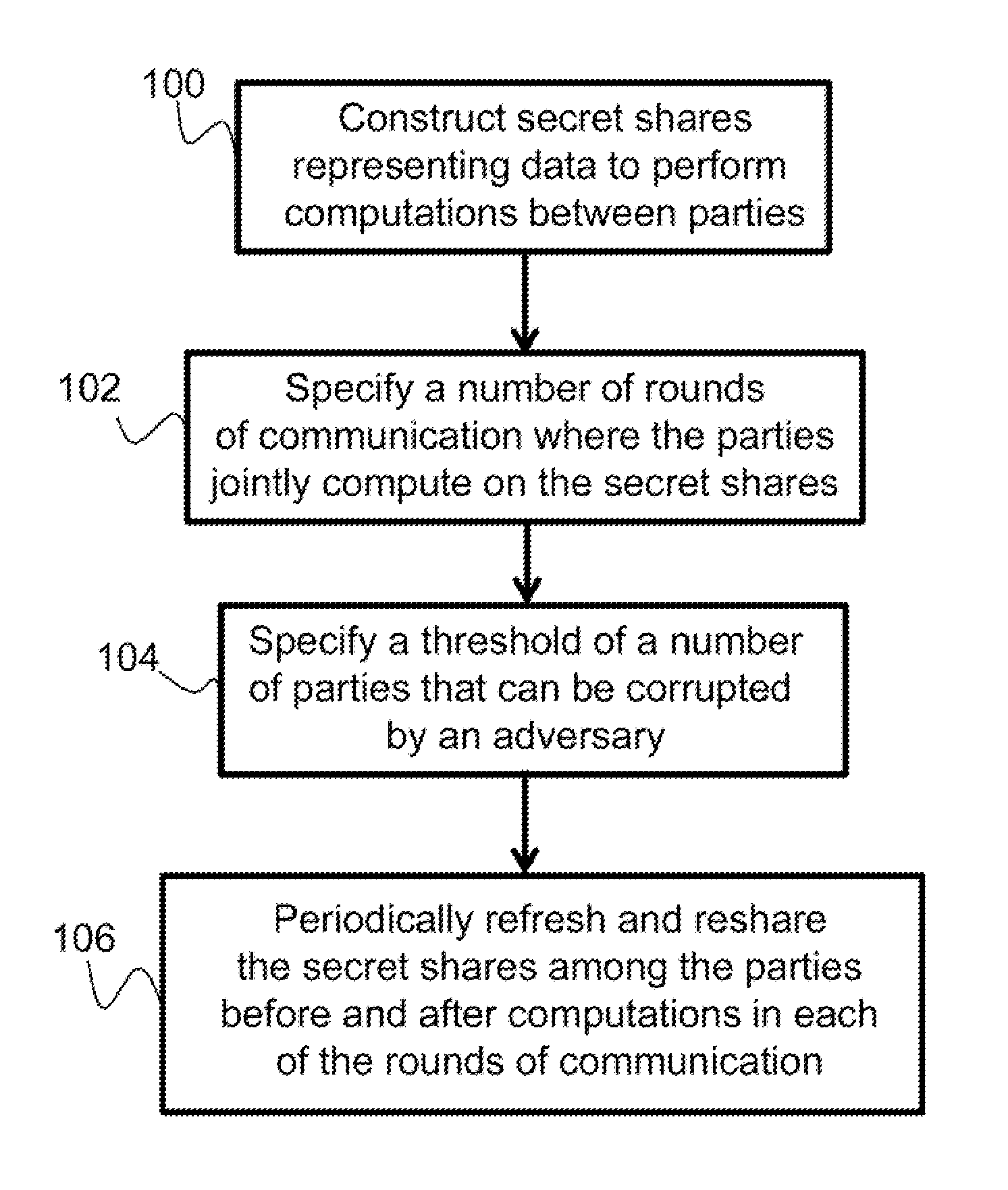
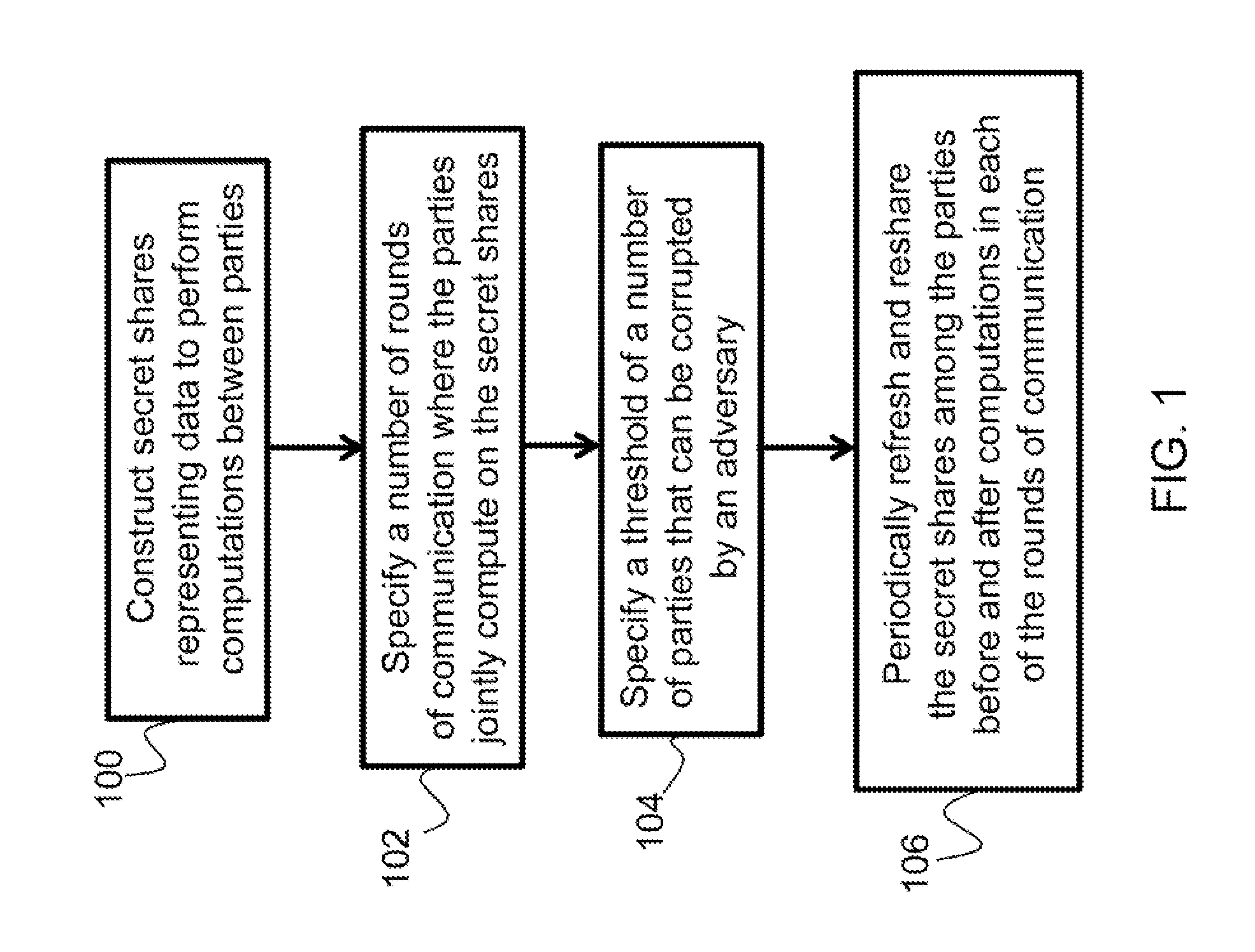
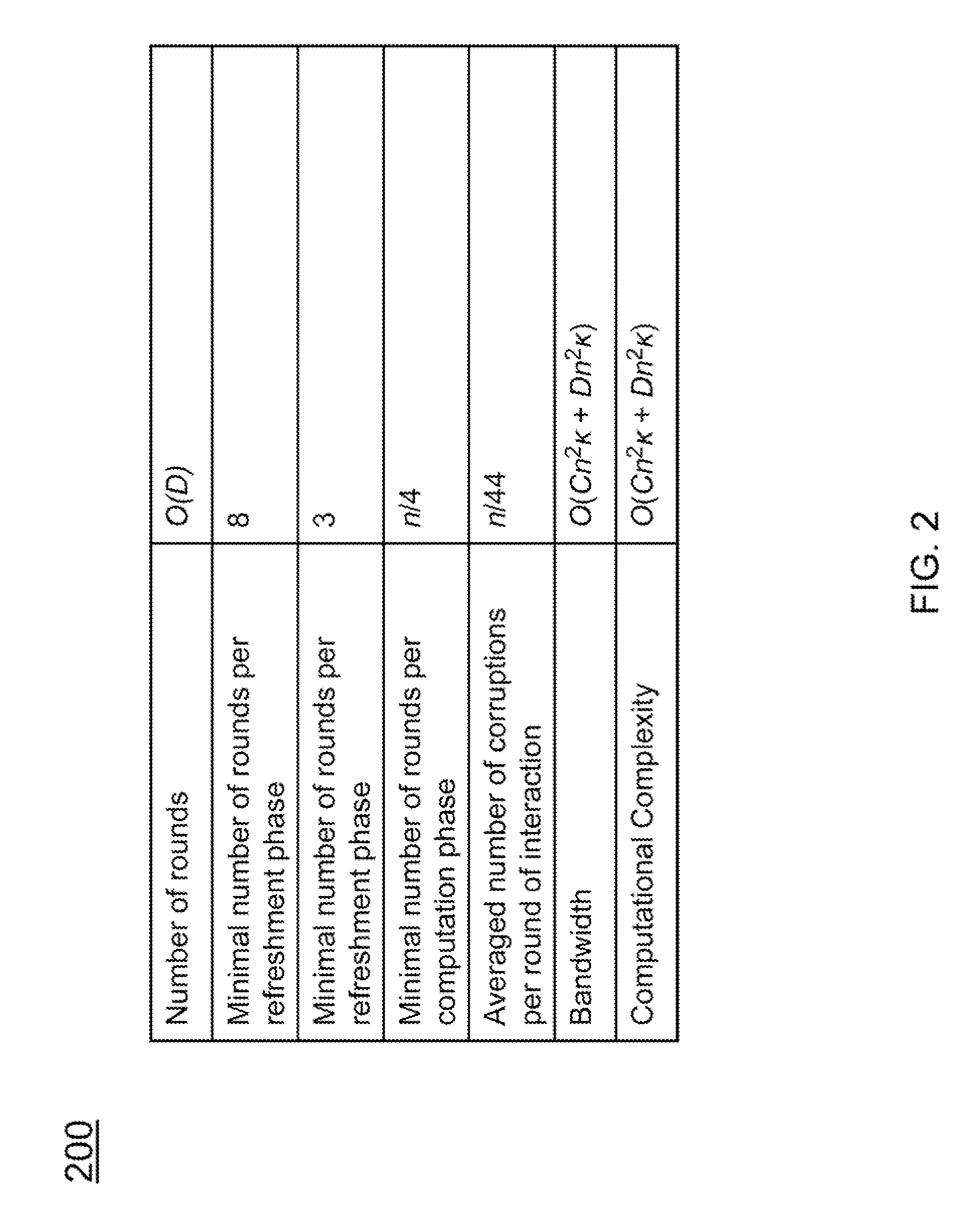
Described is a system for proactively secure multi-party computation (MPC). Secret shares representing data are constructed to perform computations between a plurality of parties modeled as probabilistic polynomial-time interactive turing machines. A number of rounds of communication where the plurality of parties jointly compute on the secret shares is specified. Additionally, a threshold of a number of the plurality of parties that can be corrupted by an adversary is specified. The secret shares are periodicially refreshed and reshared among the plurality of parties before and after computations in each of the rounds of communication. The data the secret shares represent is proactively secured.
Owner:HRL LAB
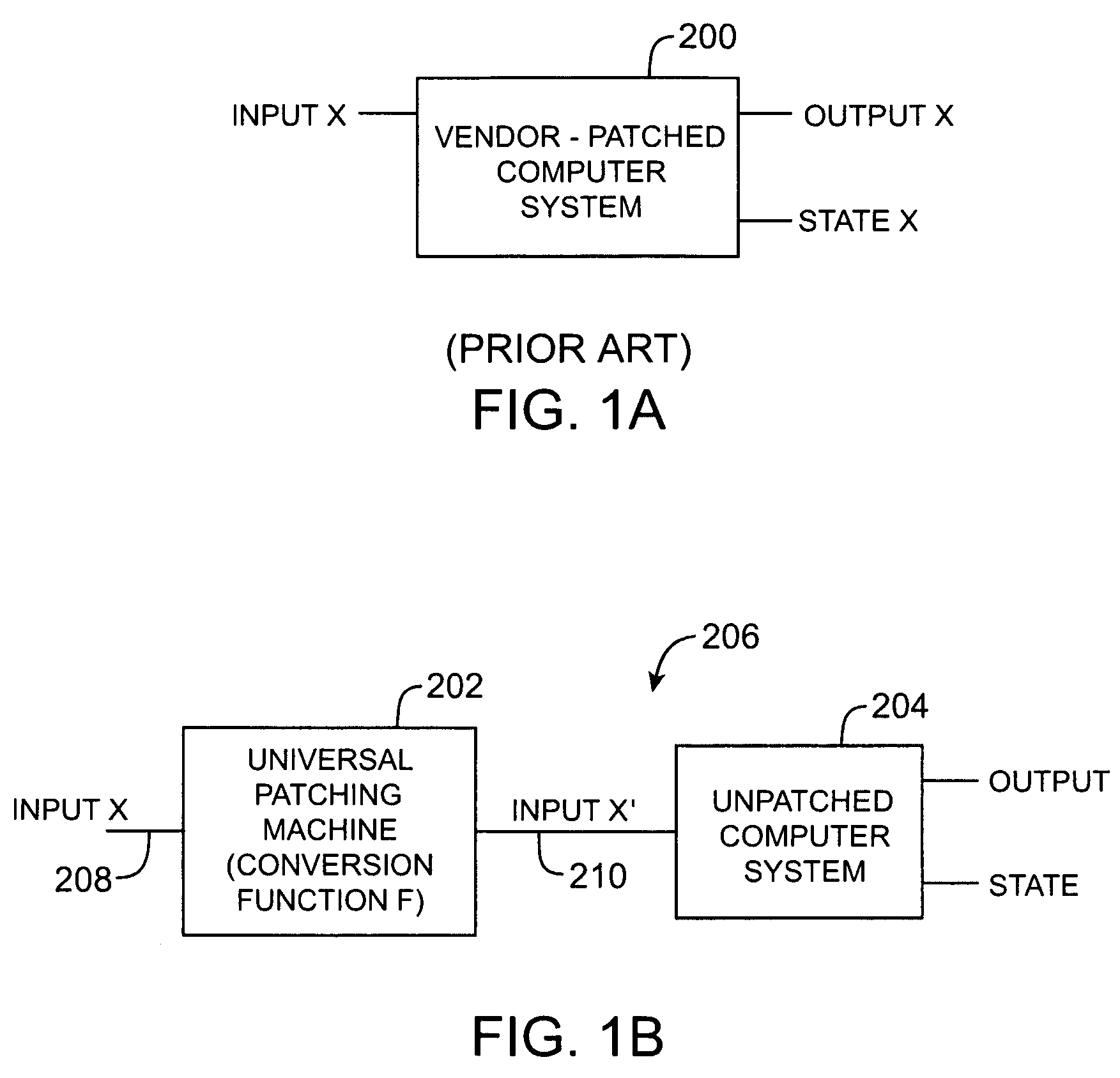
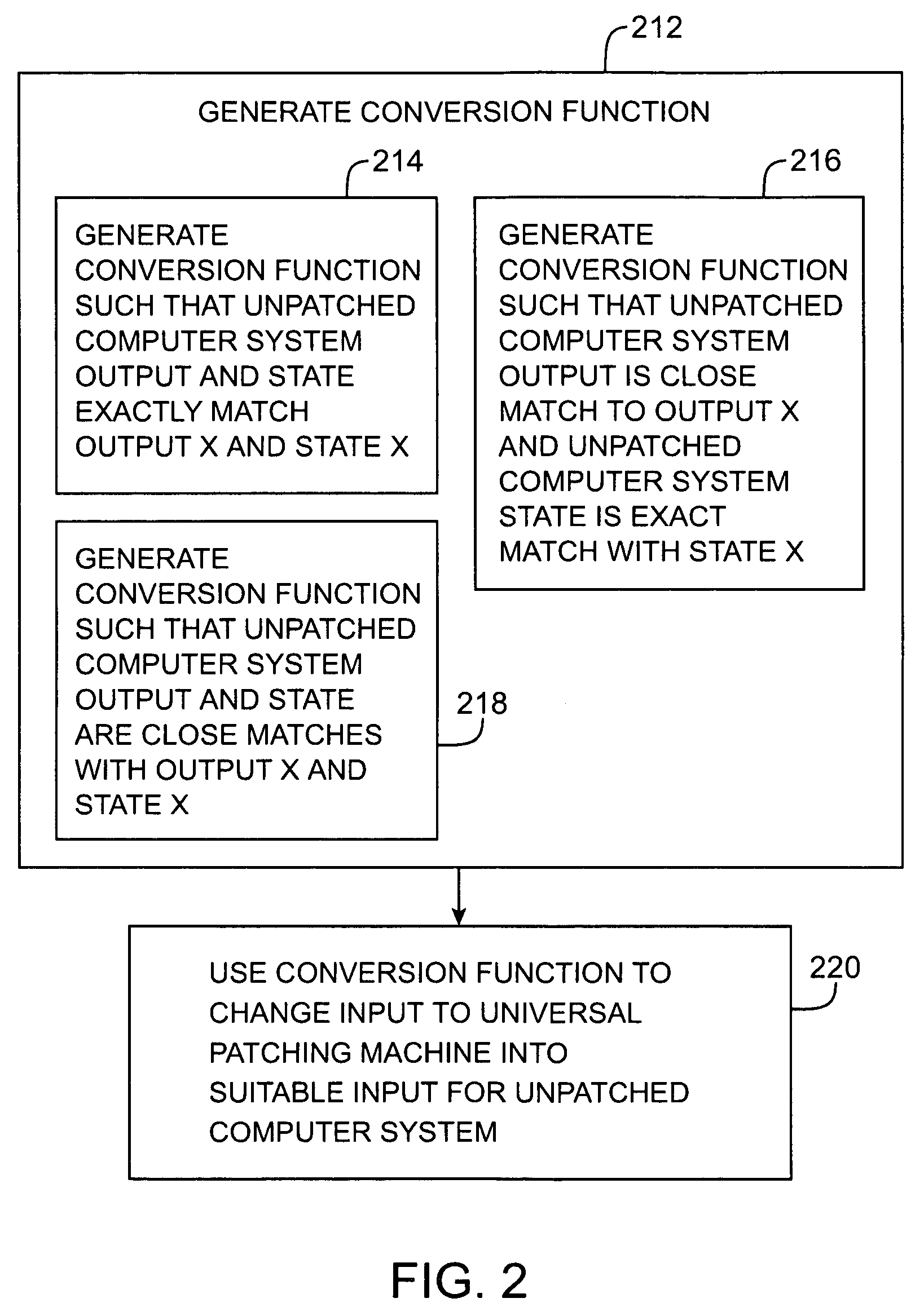
Network-based patching machine
ActiveUS7343599B2Avoid repetitionSmall sizeMemory loss protectionUnauthorized memory use protectionTraffic capacityNetwork packet
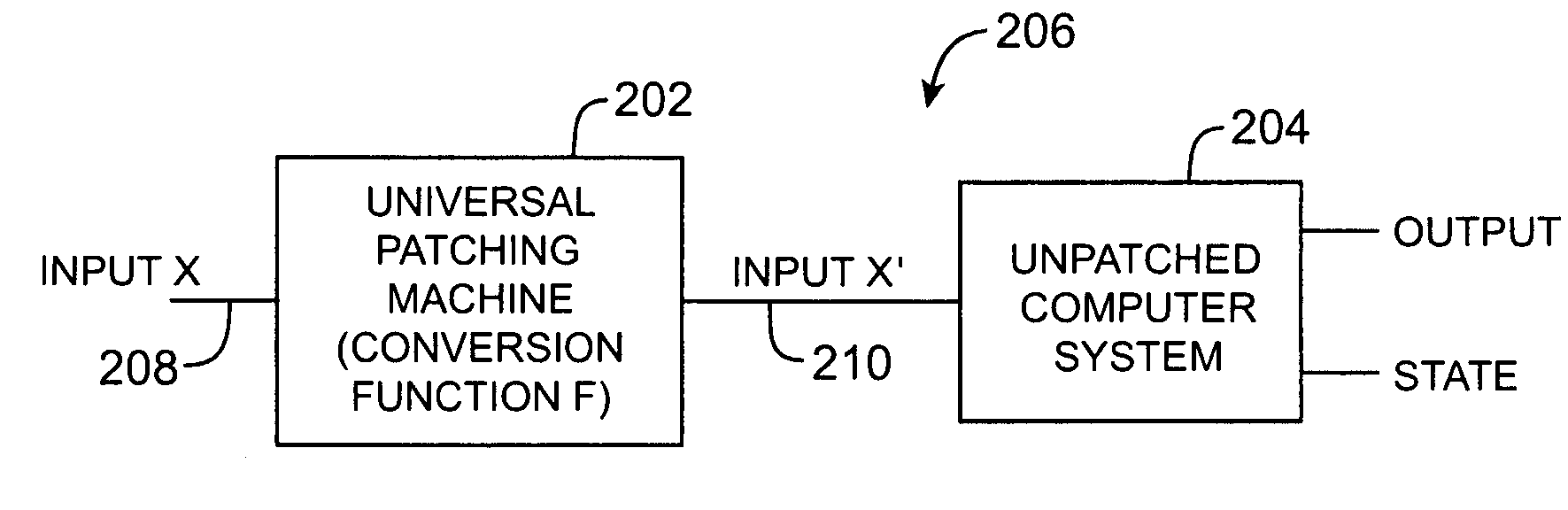
A universal patching machine is used to provide network-based security for a data network. The universal patching machine may be implemented on a network appliance located at the edge of the data network. From this location, the universal patching machine intercepts data traffic between the internet and the data network. The universal patching machine examines the intercepted data traffic to detect security vulnerabilities. If a vulnerability violation is detected, the universal patching machine modifies the data traffic to remove the violation. Fixing the data traffic in this way ensures that the vulnerability cannot be exploited in an attack against the data network. The universal patching machine is formed from patch processors and a packet controller. The patch processors are formed from network patches. In operation, the patch processors detect vulnerabilities and issue modification commands that direct the packet controller to fix the data traffic.
Owner:VMWARE LLC
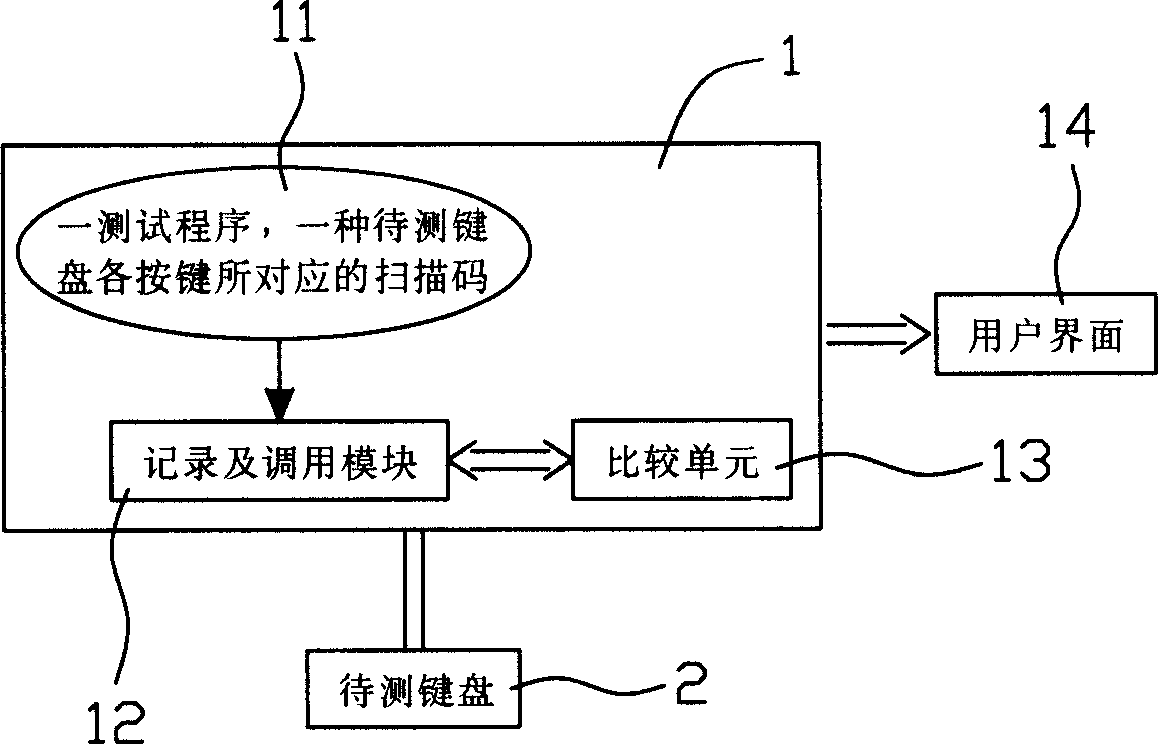
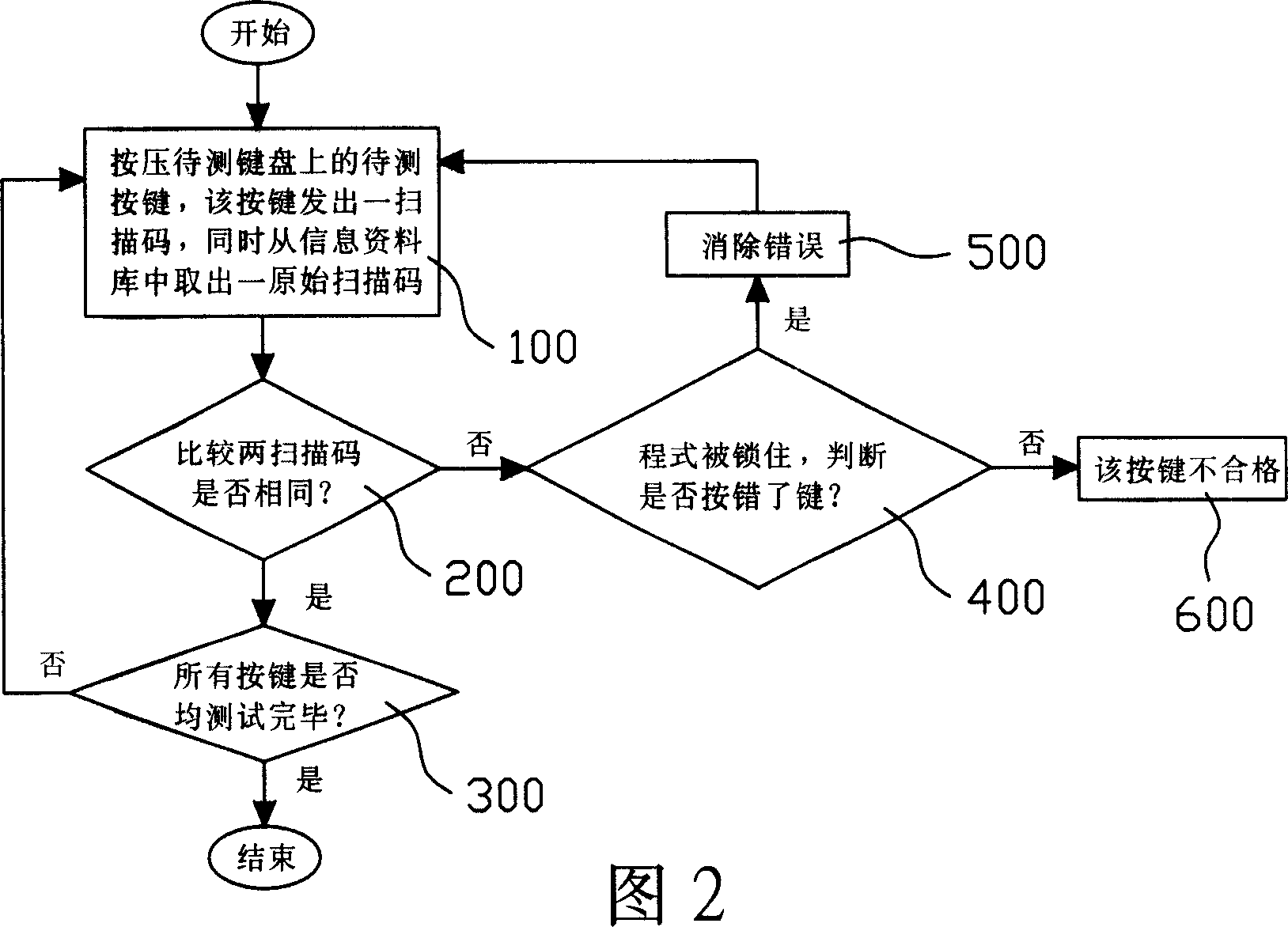
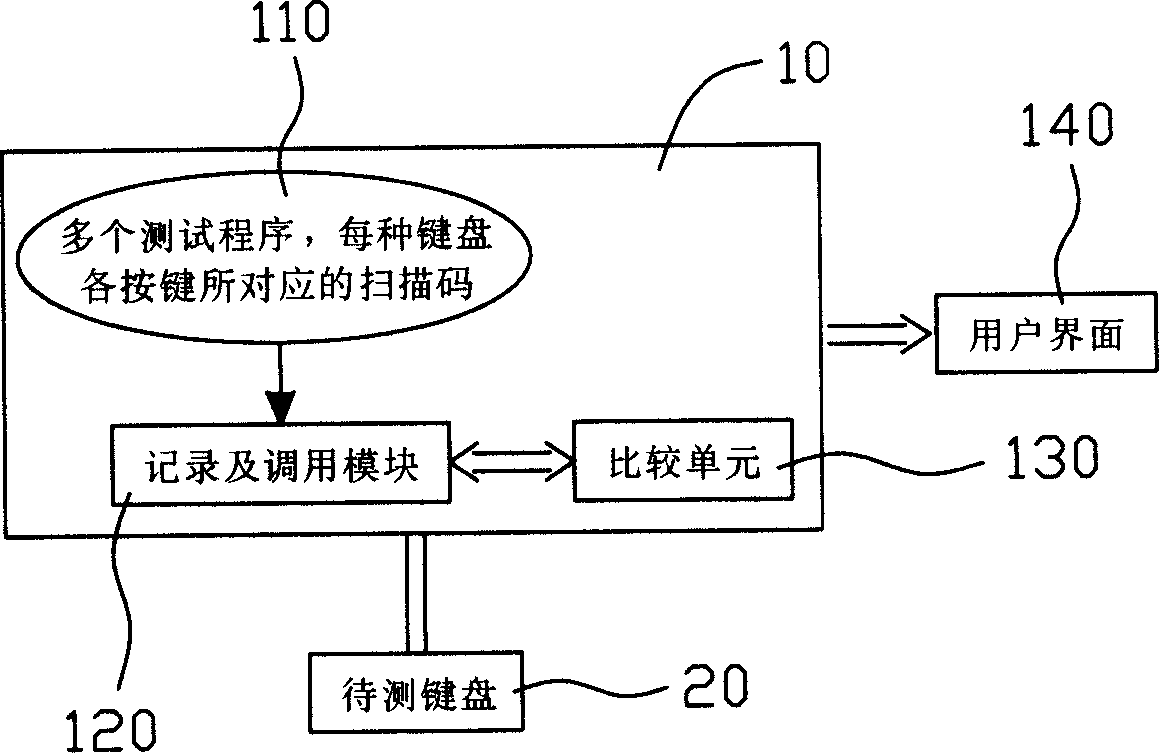
Keyboard measuring method
The invention relates to a keyboard testing method. It tests keyboard by a testing machine. The testing machine comprises a information database, a registering and calling module and a comparing unit. The information database has at least one testing program and original scanning code of the key on keyboard. When testing, the tested key should be pressed to gain a scanning code, and comparing to the original scanning code. If the two codes are same, testing program would continue running and testing the next key; else testing program would stop running and press the same key to check whether it is the same with the original scan code. If same, testing would continue; else the keyboard is unqualified.
Owner:SHUNDA COMP FACTORY SHUNDE CITY
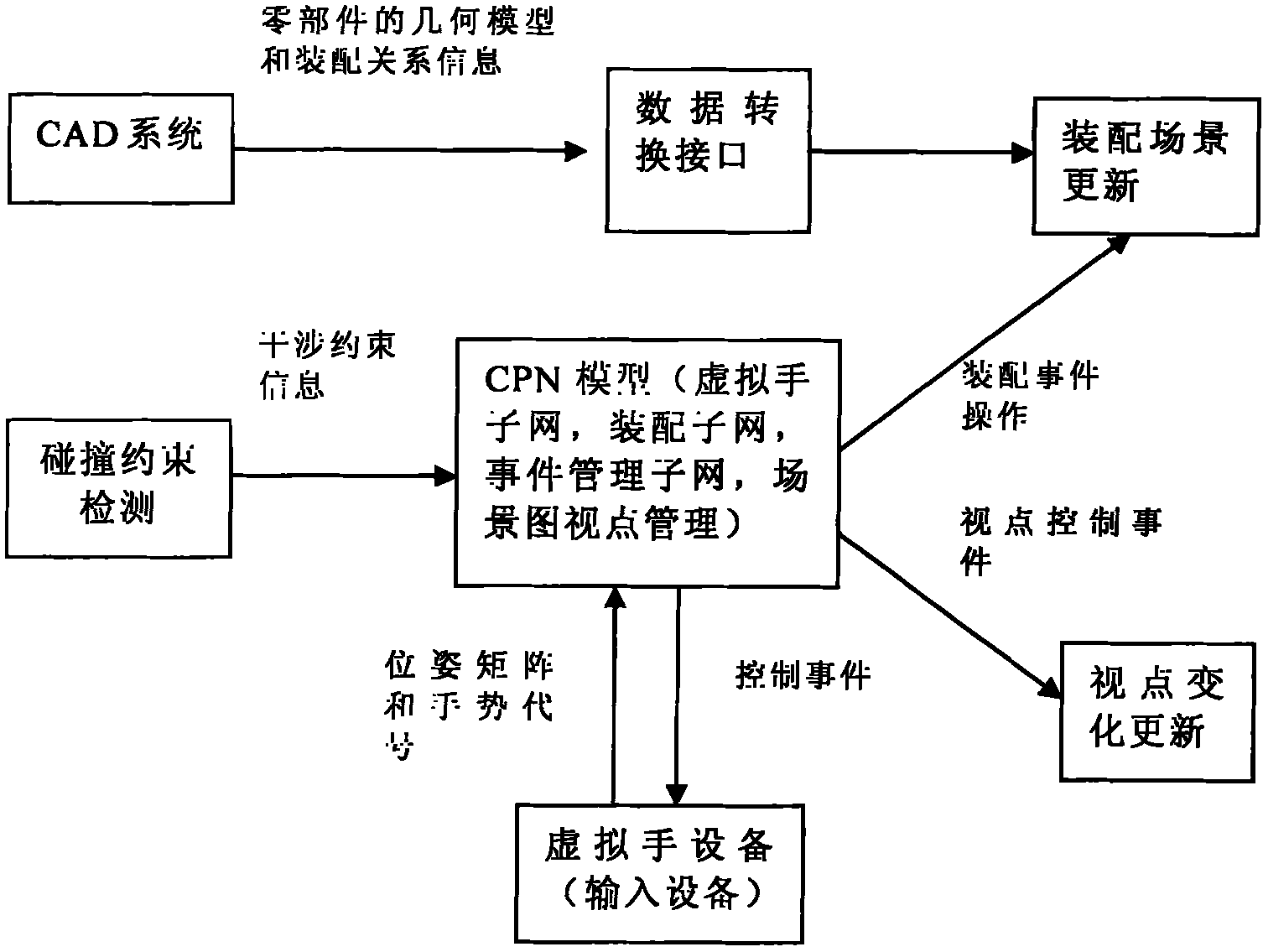
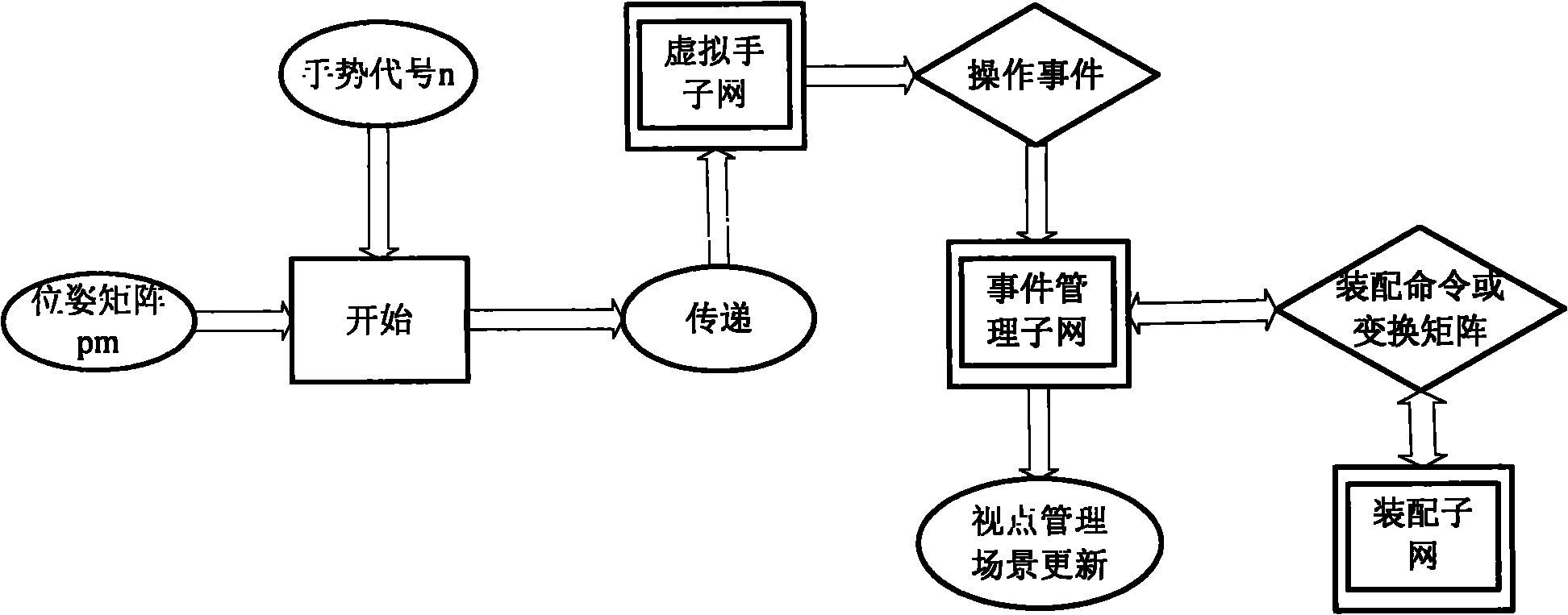
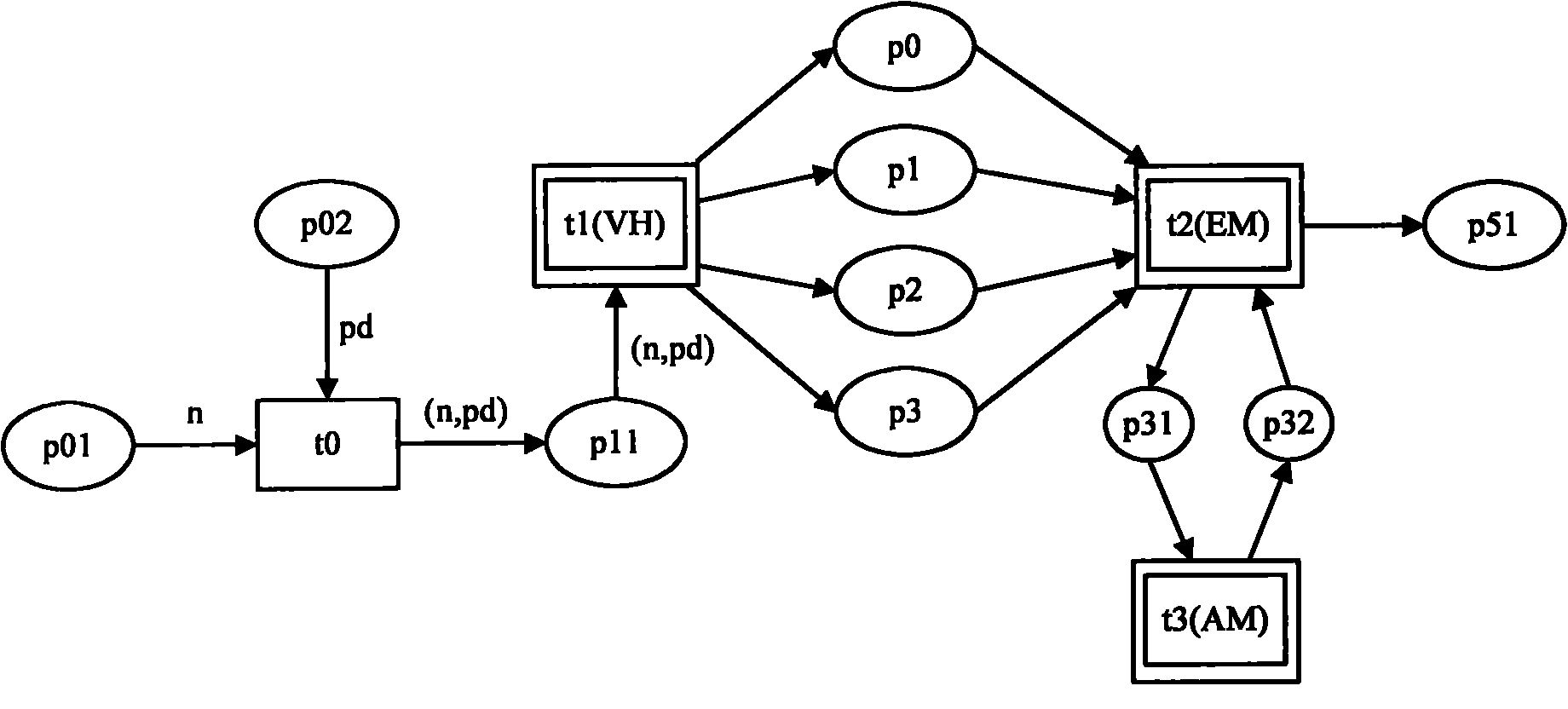
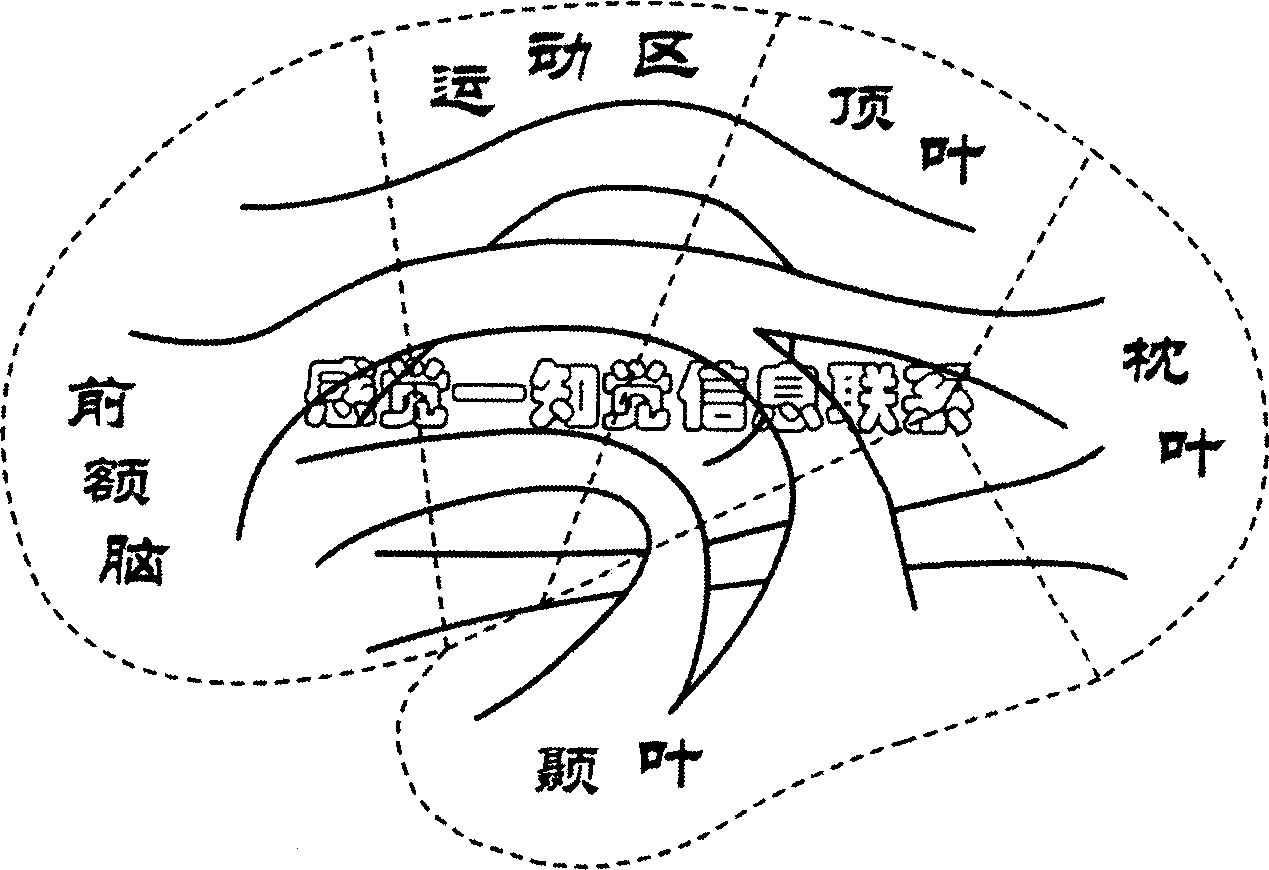
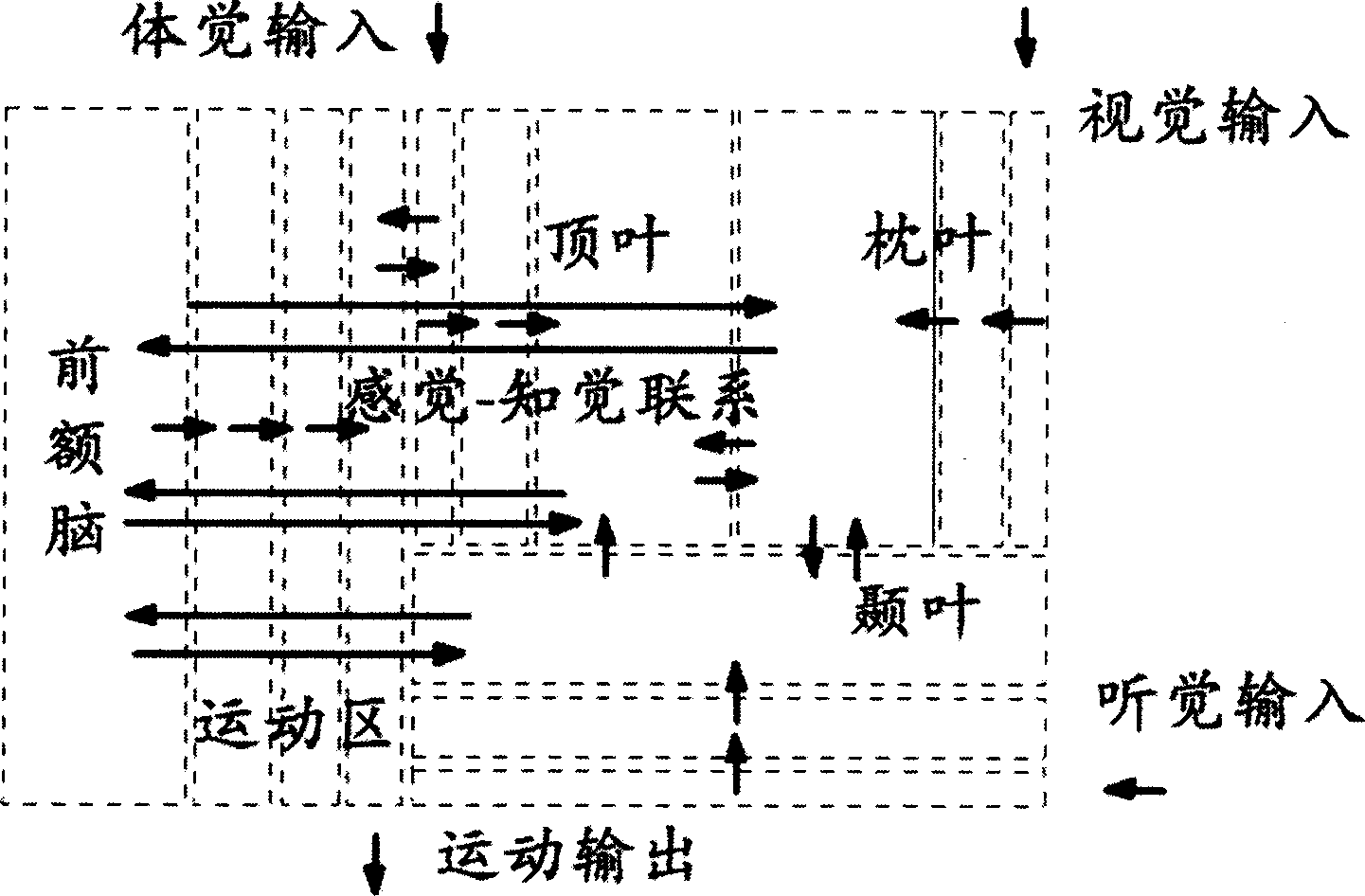
Turing model-based augment reality assembly environment system modeling method
InactiveCN102073758AEasy to express dynamic build processAbility to perceive user intentSpecial data processing applicationsColored petriSimulation
The invention relates to a Turing model-based augment reality assembly environment system hierarchical colored petri nets (HCPN) modeling method. By taking a Turing with a model of calculating 'X+1' for reference, the Turing can record the current state X, acquires an up-to-date command after input is given, provides the up-to-date state output, and applies the state output to establishment of a hierarchical colored Petri net model to ensure that the model can remember the current internal state and combines the input to make correct judgment of the state at the next moment. Colored petri nets (CPN) Tools are adopted to establish a model of the augment reality assembly environment system, wherein a network is layered; and a virtual hand sub-network, an event management sub-network, an assembly sub-network and the like are refined, input and output of each sub-network are utilized to realize event driving, and the relations among various factors in the network are determined, so that the augment reality assembly environment system has logical inference property, can effectively process massive random discrete events, is convenient to express the dynamic establishing process of the assembly model, and has the capability of sensing the user intention.
Owner:BEIJING UNIV OF POSTS & TELECOMM
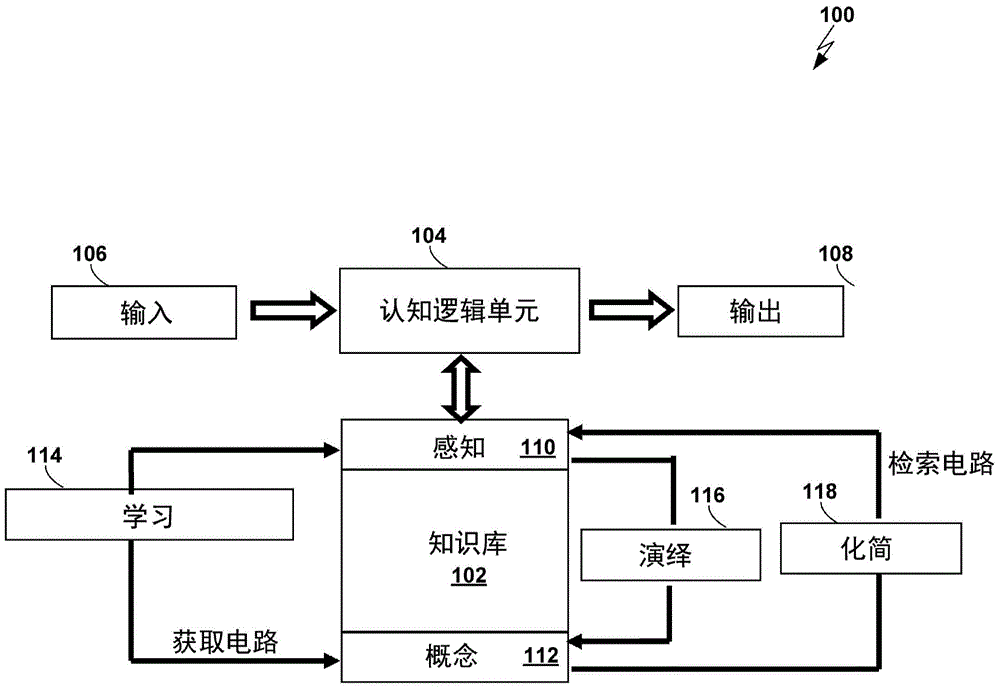
Cognition logic machine and its information processing method
This invention relates to a cognition logic machine and its information processing method. Wherein, on deterministic Turing machine, it simulates hierarchic dual- memory structure of human brain and then generates logic cognition to relevant store and access natural language. The machine comprises: an input device, a logic cognitive process device, a knowledge-memory device, and an output device. Besides, the process of the machine comprises the perception, induction, deduction, and inversion, which realizes learning / forgetting, understand / memory, recognition / image and reasoning in machine. This invention overcomes the problem of exponential growth for the command access algorithm time, and provides storage and inquest method for natural language process.
Owner:BEIJING BOSI BIOINTELLIGENCE TECH +1
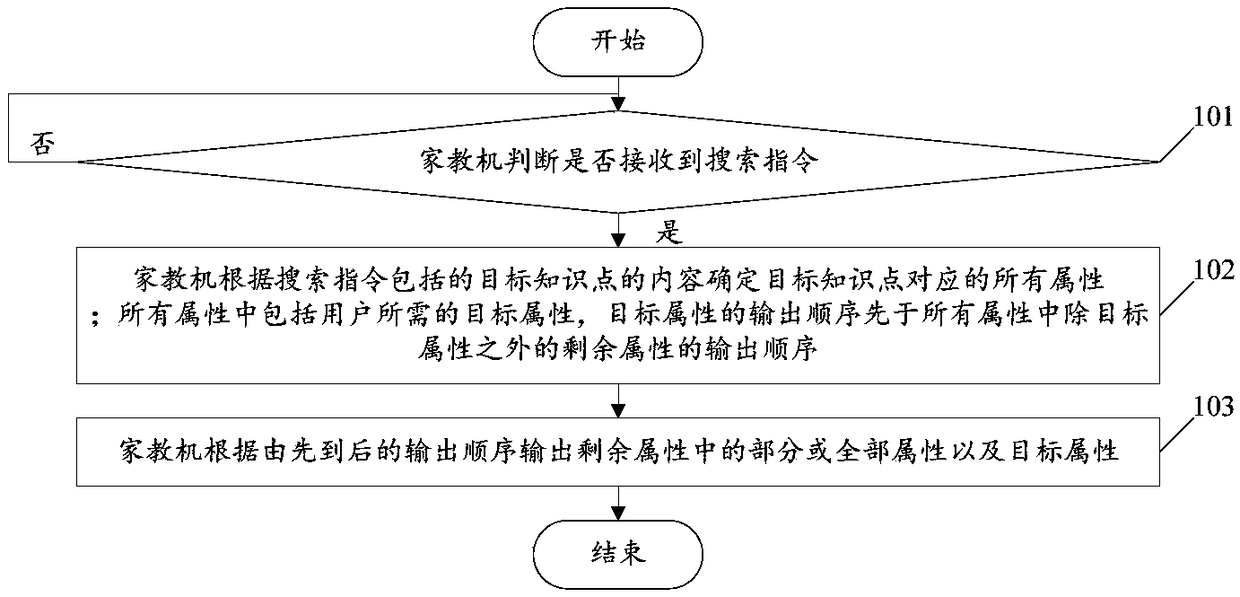
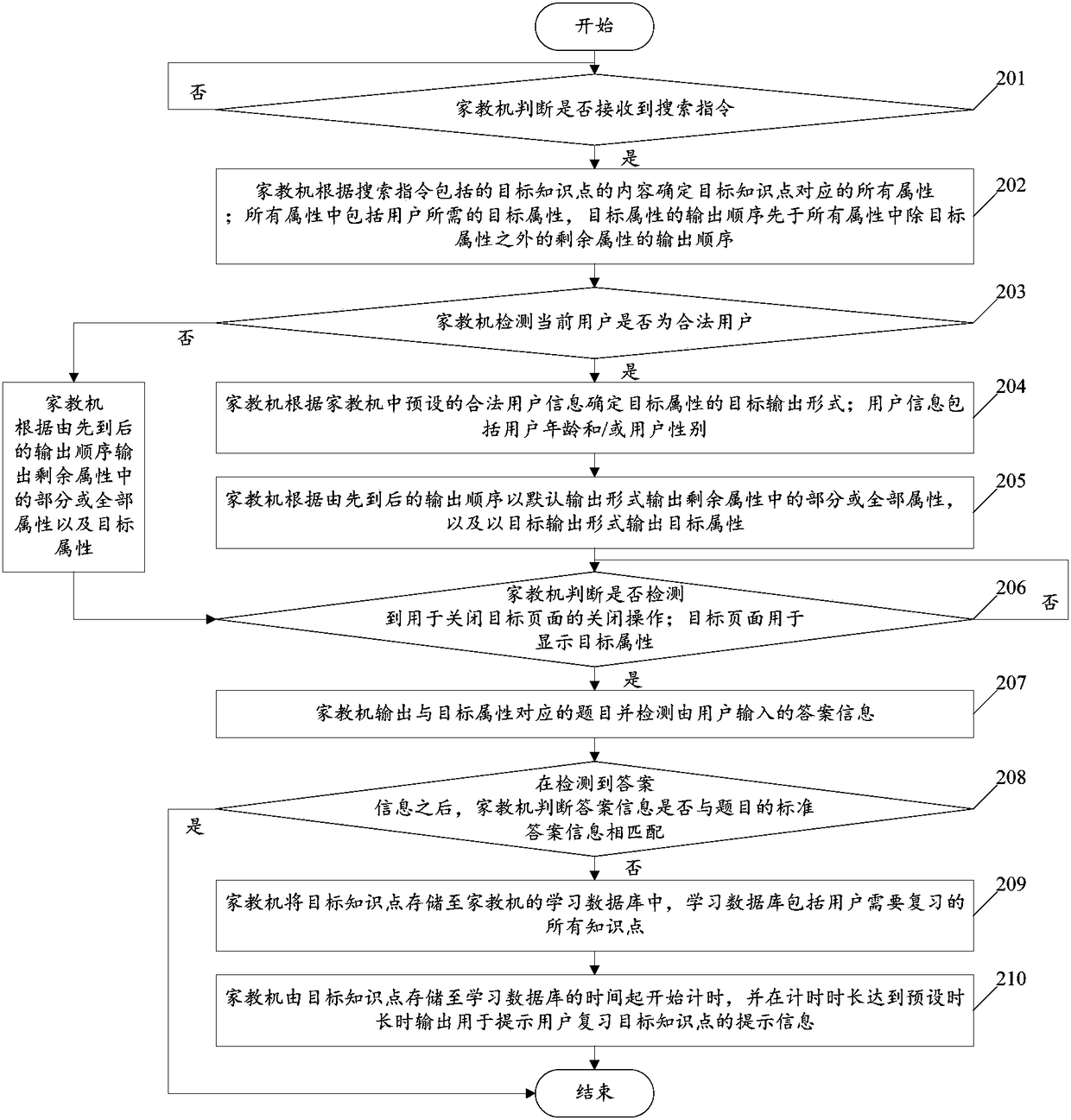
Tutoring machine-based learning method and tutoring machine
ActiveCN108763552AImprove learning effectData processing applicationsElectrical appliancesContent determinationStudy methods
The invention discloses a tutoring machine-based learning method and a tutoring machine. The method comprises the following steps of: judging whether a search instruction is received or not by the tutoring machine, wherein the search instruction comprises a target knowledge point to be learnt by a user; if the search instruction is received, determining all the attributes corresponding to the target knowledge point by the tutoring machine according to content of the target knowledge point in the search instruction, wherein all the attributes comprise a target attribute required by the user, and an output sequence of the target attribute is prior to output sequences of the residual attributes except the target attribute in all the attributes; and outputting a part of or all the attributes in the residual attributes and the target attribute in sequence by the tutoring machine according to the output sequences. By implementing the method, users can be helped to systematically learn targetknowledge points in a targeted manner, so that the learning effect of the users is improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
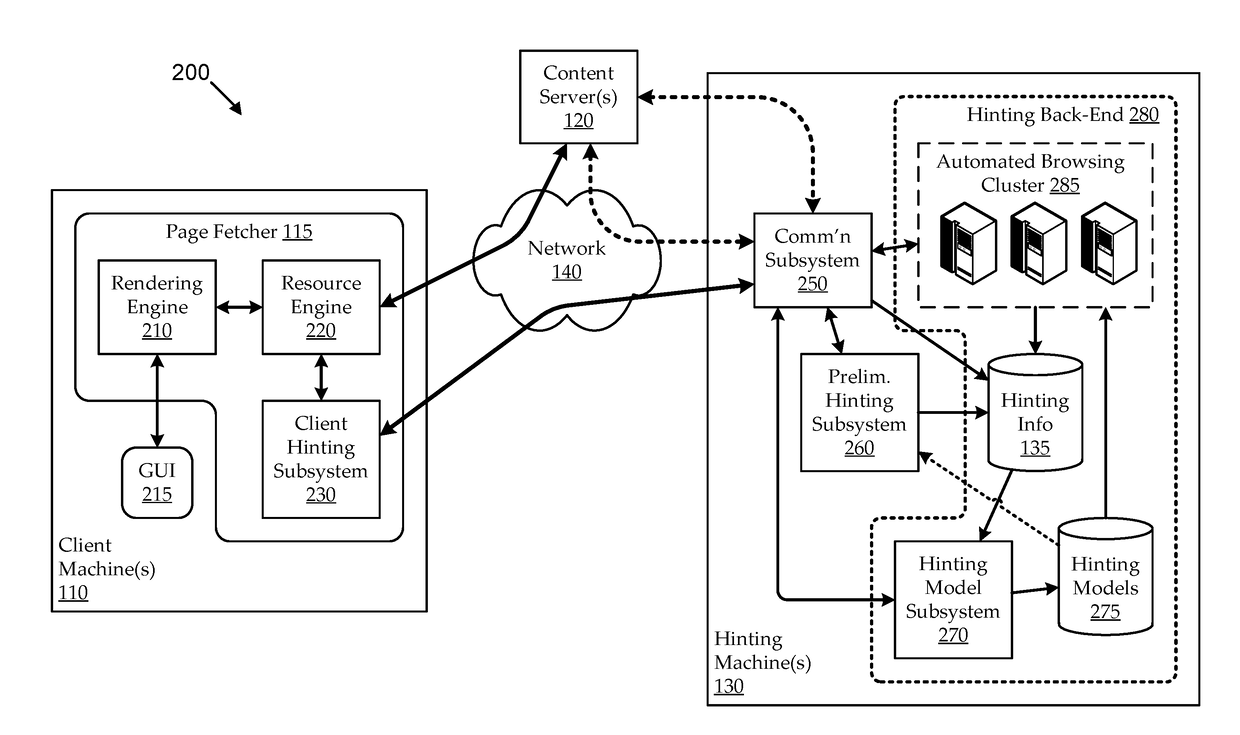
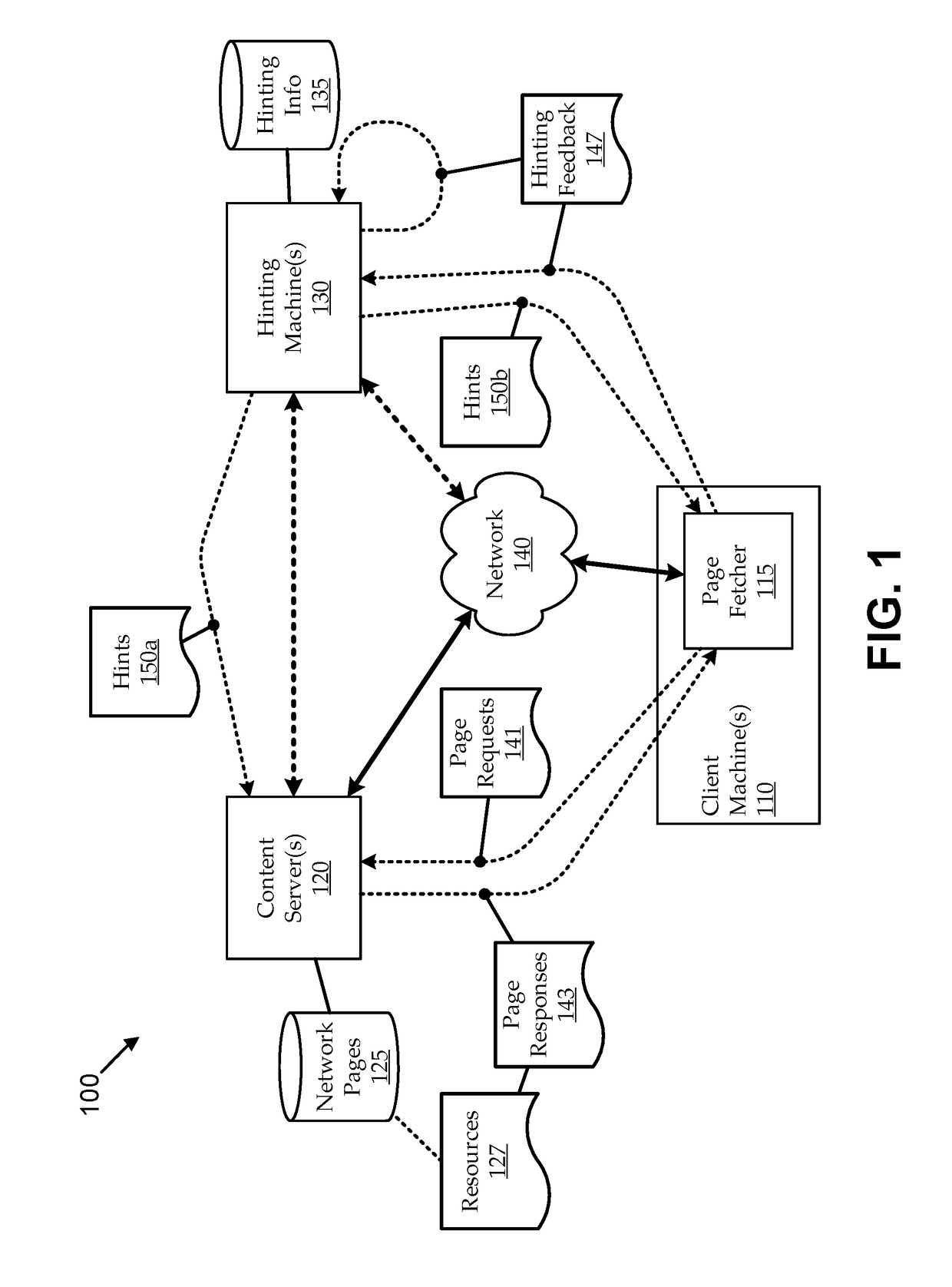
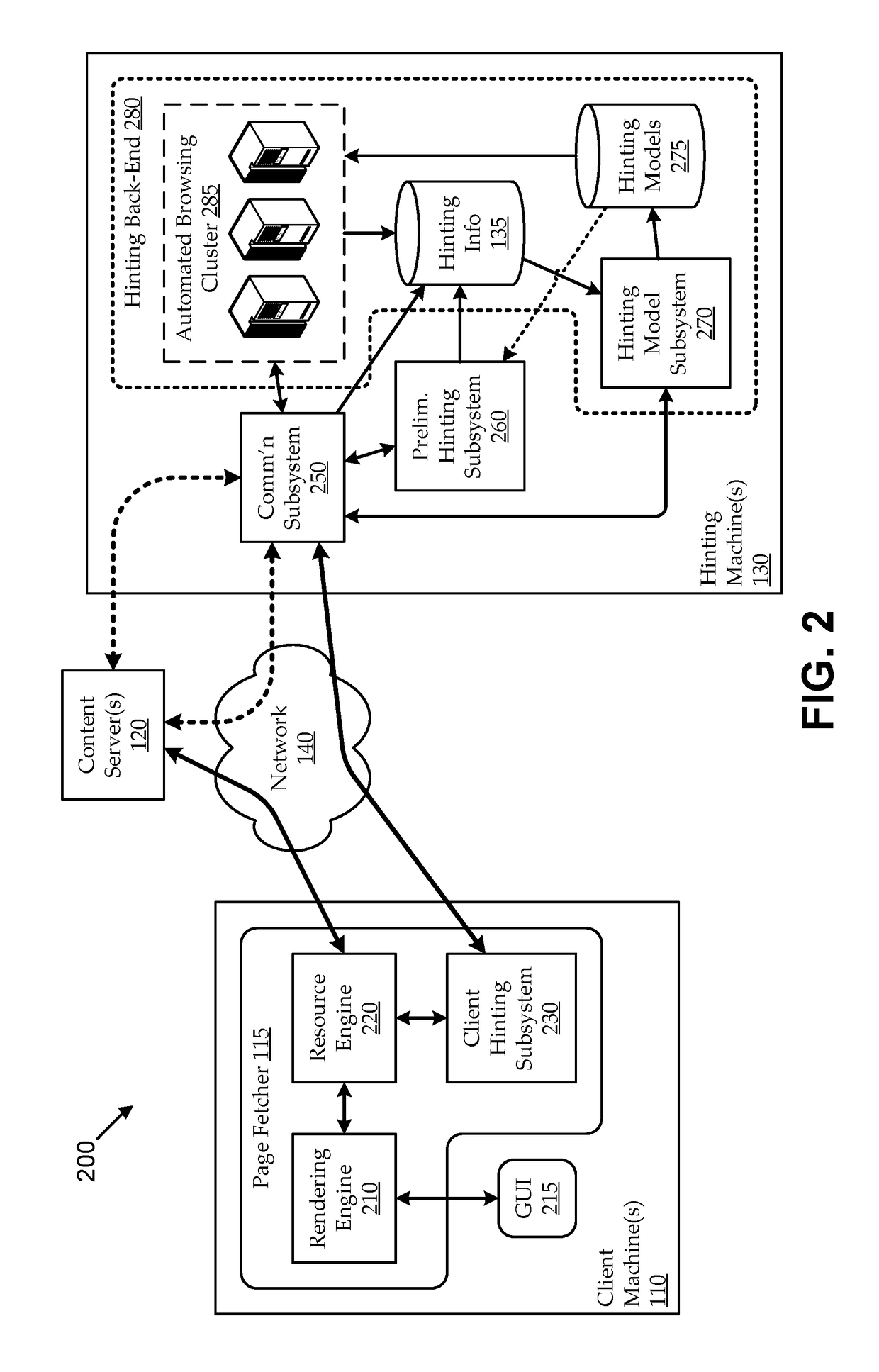
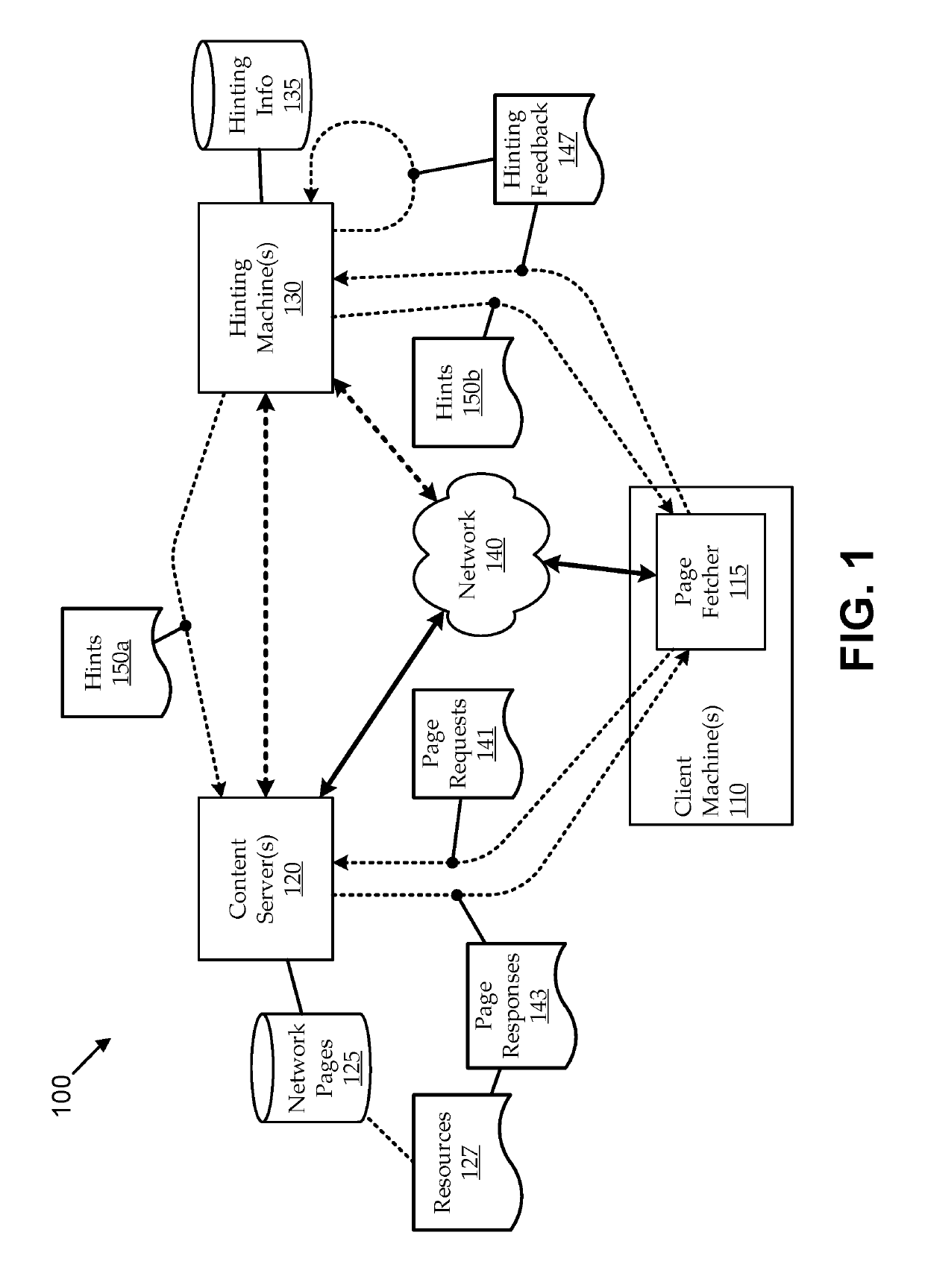
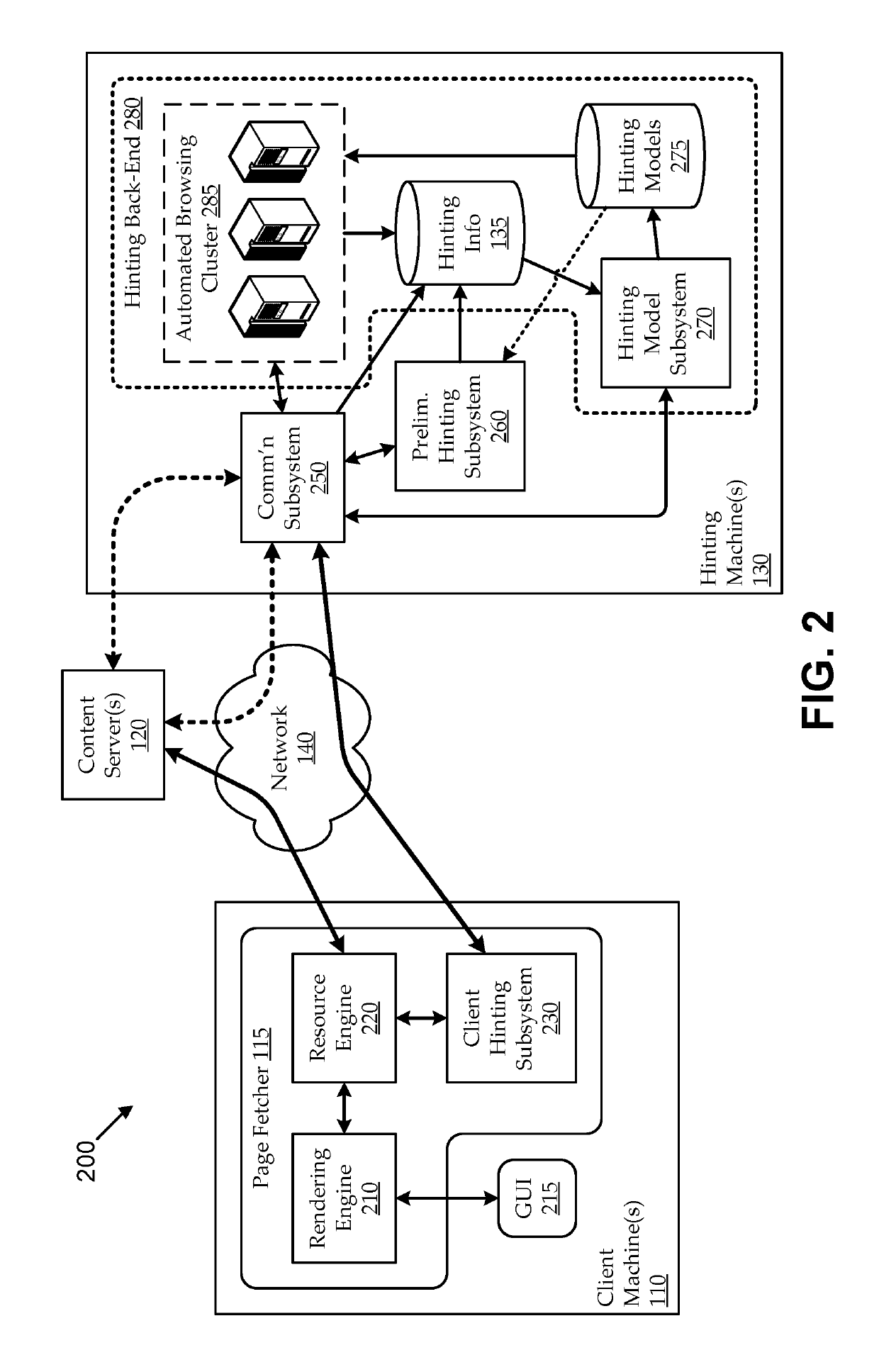
Hint model updating using automated browsing clusters
ActiveUS20180246982A1Improving prefetch hintingImprove page load timingMemory architecture accessing/allocationDatabase updatingClient-sideWeb page
Embodiments seek to improve prefetch hinting by using automated browsing clusters to generate and update hinting models used for machine-generated hints. For example, hinting machines can include browsing clusters that autonomously fetch web pages in response to update triggers (e.g., client web page requests, scheduled web crawling, etc.) and generate timing and / or other hinting-related feedback relating to which resources were used to load the fetched web pages. The hinting machines can use the hinting feedback to generate and / or update hinting models, which can be used for machine-generation of hints. Some embodiments can provide preliminary hinting functionality in response to client hinting requests, for example, when hinting models for a requested page are insufficient (e.g., unavailable, outdated, etc.). For example, without having a sufficient hinting model in place, the hinting machine can fetch the page to generate preliminary hinting feedback, which it can use to machine-generate preliminary hints.
Owner:VIASAT INC
Mongolian-Chinese machine translation method based on neural network Turing machine
ActiveCN110619127AHigh precisionHigh speedNeural architecturesSpecial data processing applicationsInternal memoryNerve network
A Mongolian-Chinese machine translation method based on a neural network Turing machine comprises the following steps: firstly, preprocessing Mongolian-Chinese bilingual corpus, vectorizing the Mongolian-Chinese bilingual corpus, and constructing a bilingual dictionary on the basis of the Mongolian-Chinese bilingual corpus; secondly, further expanding storage through a neural network totem machine(NTM), expanding from an internal memory unit of the LSTM to an external memory, introducing a memory mechanism, realizing semantic relation extraction, and giving a semantic relation between two entity words; and finally, searching an optimal solution through decoder model training. Compared with the prior art, according to the invention, semantic analysis is carried out by means of a neural totem machine; related semantic knowledge is found out and extracted, the accuracy of natural language processing is greatly improved by means of the semantic knowledge, corpora are preprocessed by meansof parallel work of a CPU and a GPU, the speed is increased by nearly one time, and the overall translation quality is further improved.
Owner:INNER MONGOLIA UNIV OF TECH
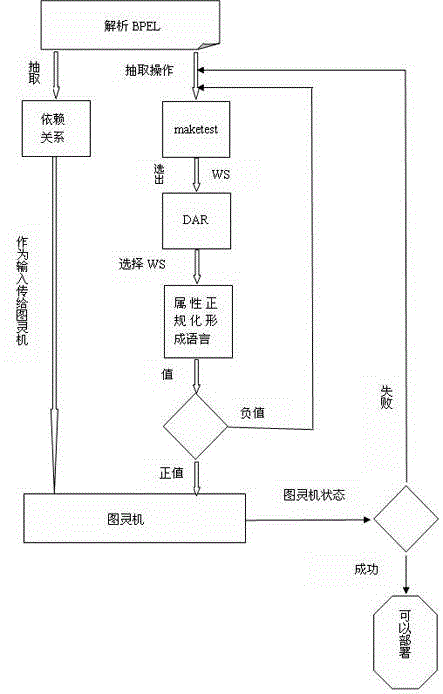
Method for deploying network service in cloud
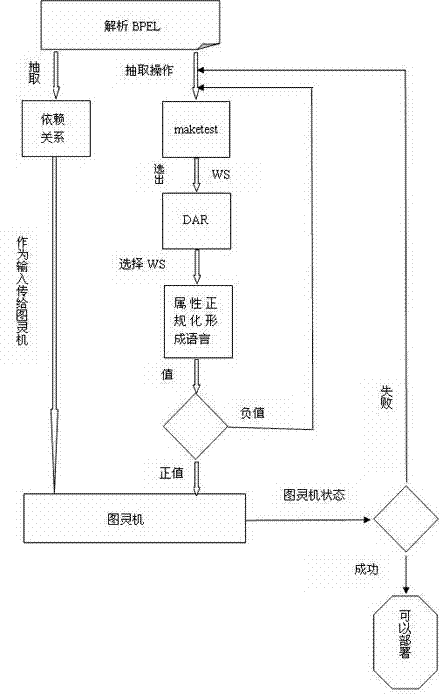
The invention provides a method for deploying a Web service in a cloud based on a Turing machine technology and a DAR (display aspect ratio) algorithm, which combines the abstraction and the wide range of languages capable of being accepted by a Turing machine with the dynamism and the reliability of the DAR algorithm to select the Web service under an easily-failed environment to further establish a model of deploying the Web service in the cloud. With adoption of the method disclosed by the invention, the challenges of rapidly and reliably deploying the Web service in the cloud can be solved. The system is formed by four modules; the uppermost layer is responsible for analyzing a BPEL (business process execution language) Web service; and the middle layer is responsible for selecting a reliable atom Web service, obtaining an attribute value and constructing the normalized Turing machine. The method is mainly is used for two parts of the construction of the turning machine and the Web service selection algorithm DAR. The verification shows that the technology of the invention has the advantages that: 1, the reliable Web service can be selected; and 2, the method has more advantages than the previous technology on the aspect of deploying Web service time and real time.
Owner:广东中南元建网络工程有限公司
Hint model updating using automated browsing clusters
ActiveUS10387522B2Improving prefetch hintingIncrease loadMemory architecture accessing/allocationDatabase updatingWeb pageData mining
Embodiments seek to improve prefetch hinting by using automated browsing clusters to generate and update hinting models used for machine-generated hints. For example, hinting machines can include browsing clusters that autonomously fetch web pages in response to update triggers (e.g., client web page requests, scheduled web crawling, etc.) and generate timing and / or other hinting-related feedback relating to which resources were used to load the fetched web pages. The hinting machines can use the hinting feedback to generate and / or update hinting models, which can be used for machine-generation of hints. Some embodiments can provide preliminary hinting functionality in response to client hinting requests, for example, when hinting models for a requested page are insufficient (e.g., unavailable, outdated, etc.). For example, without having a sufficient hinting model in place, the hinting machine can fetch the page to generate preliminary hinting feedback, which it can use to machine-generate preliminary hints.
Owner:VIASAT INC
Secure active element machine
ActiveUS20120198560A1Simple and safe processComputing performance that isDigital data processing detailsAnalogue secracy/subscription systemsComputational problemComputation process
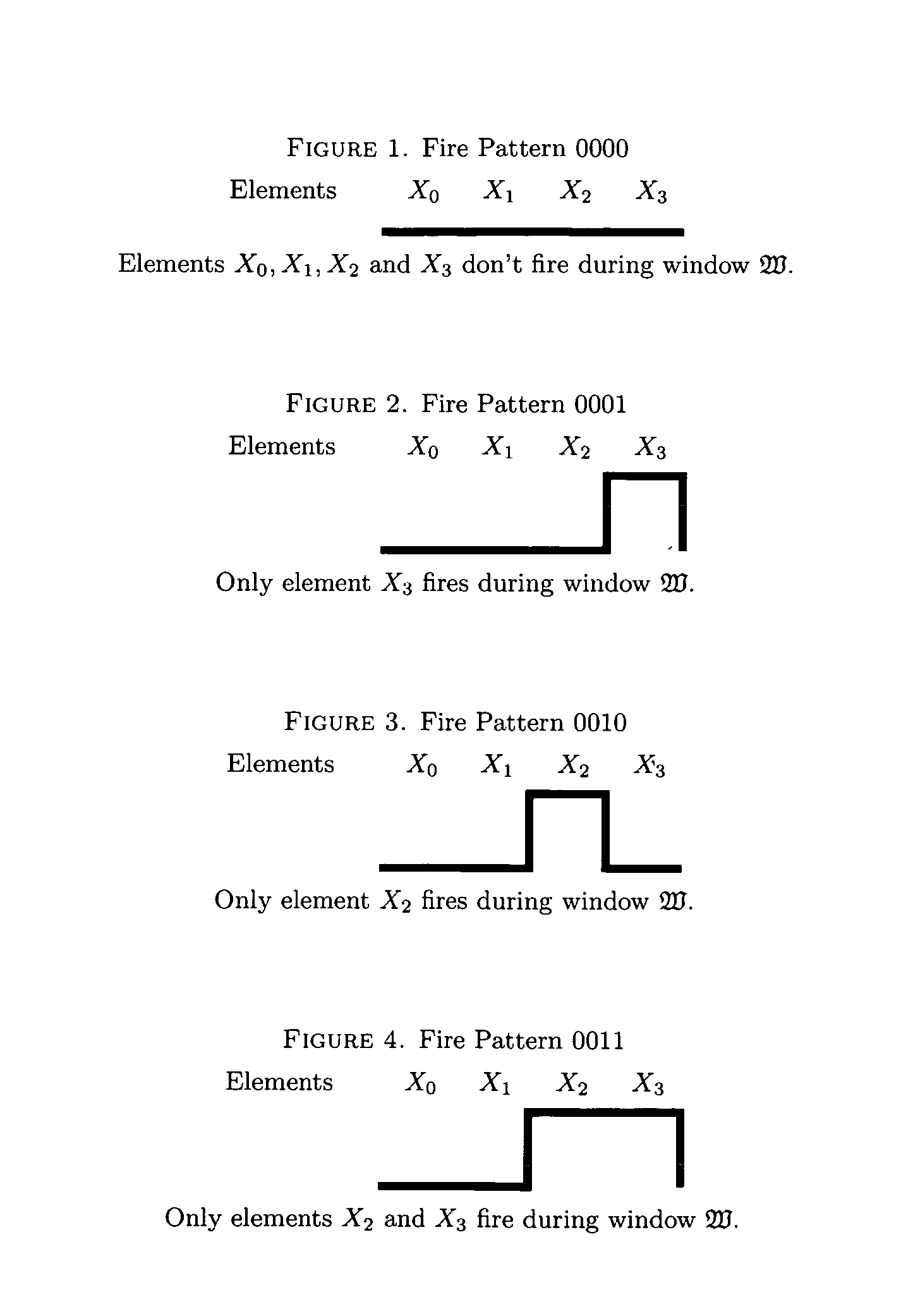
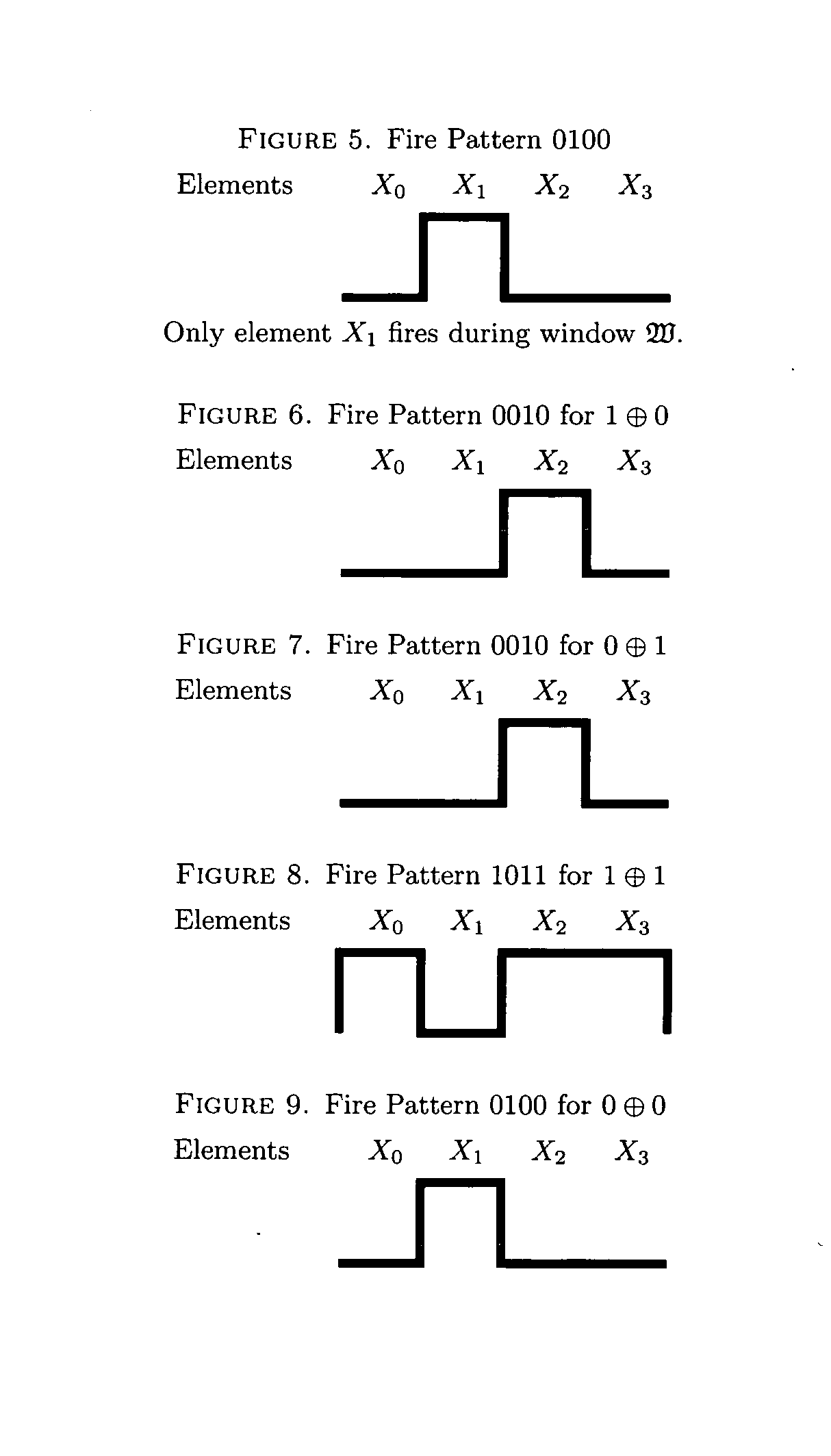
Based upon the principle of Turing incomputability, and novel properties of the Active Element Machine, a malware-resistant computing machine is constructed. This new computing machine is a non-Turing, non-register machine (non von-Neumann), called an Active Element Machine (AEM). AEM programs are designed so that the purpose of the computation is difficult to apprehend by an adversary and hijack with malware. These methods can help hinder reverse engineering of proprietary algorithms and hardware design.Using quantum randomness, the AEM can deterministically execute a universal digital computer program with active element firing patterns that are Turing incomputable. In some embodiments, a more powerful computational procedure is demonstrated than Turing's computational procedure (digital computer procedure). Current digital computer algorithms can be derived or designed with a Turing machine computational procedure. A novel class of computing machines is built where the purpose of the program's execution is difficult to apprehend (Turing incomputable).
Owner:AEMEA
Hardware reboot testing method and system based on MOC board card
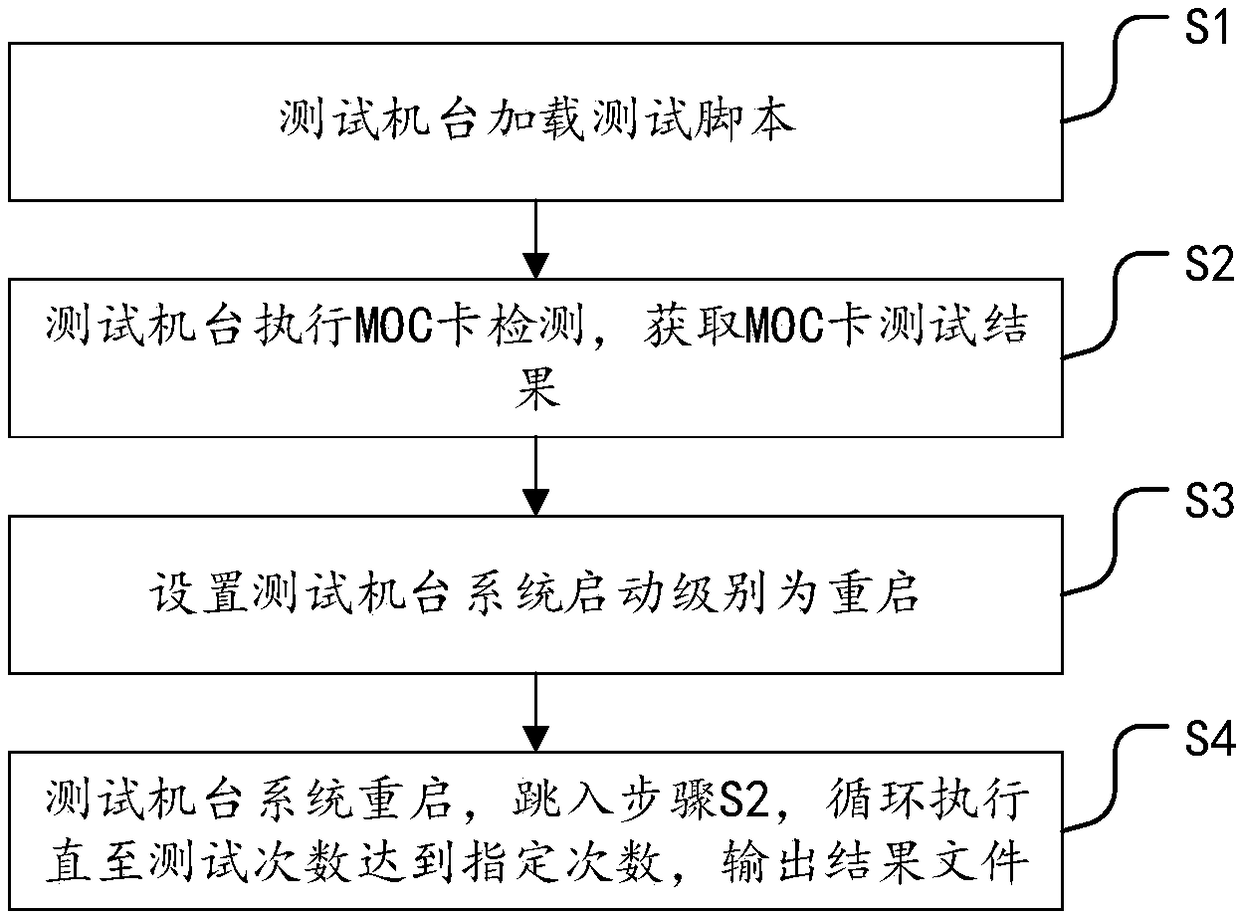
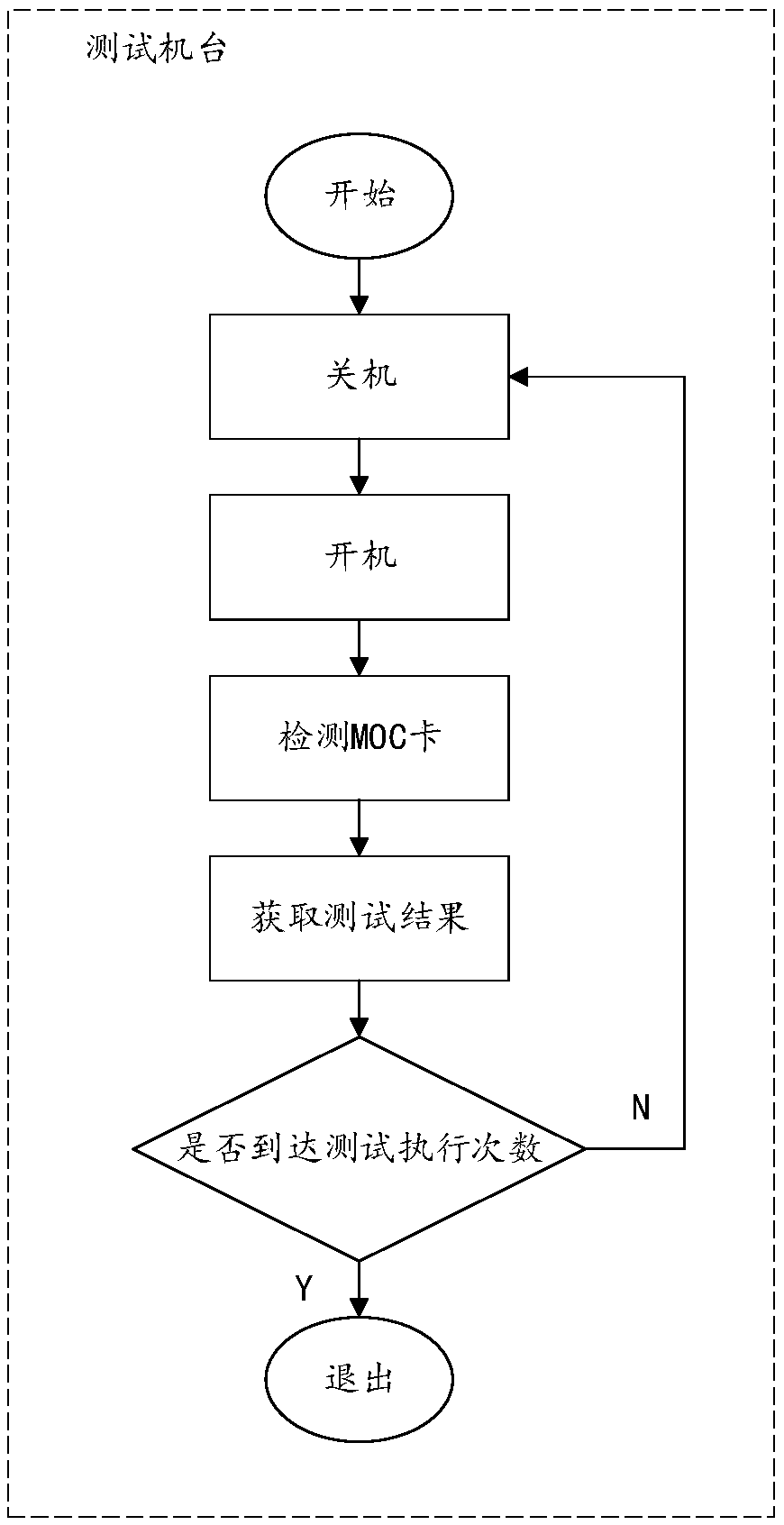
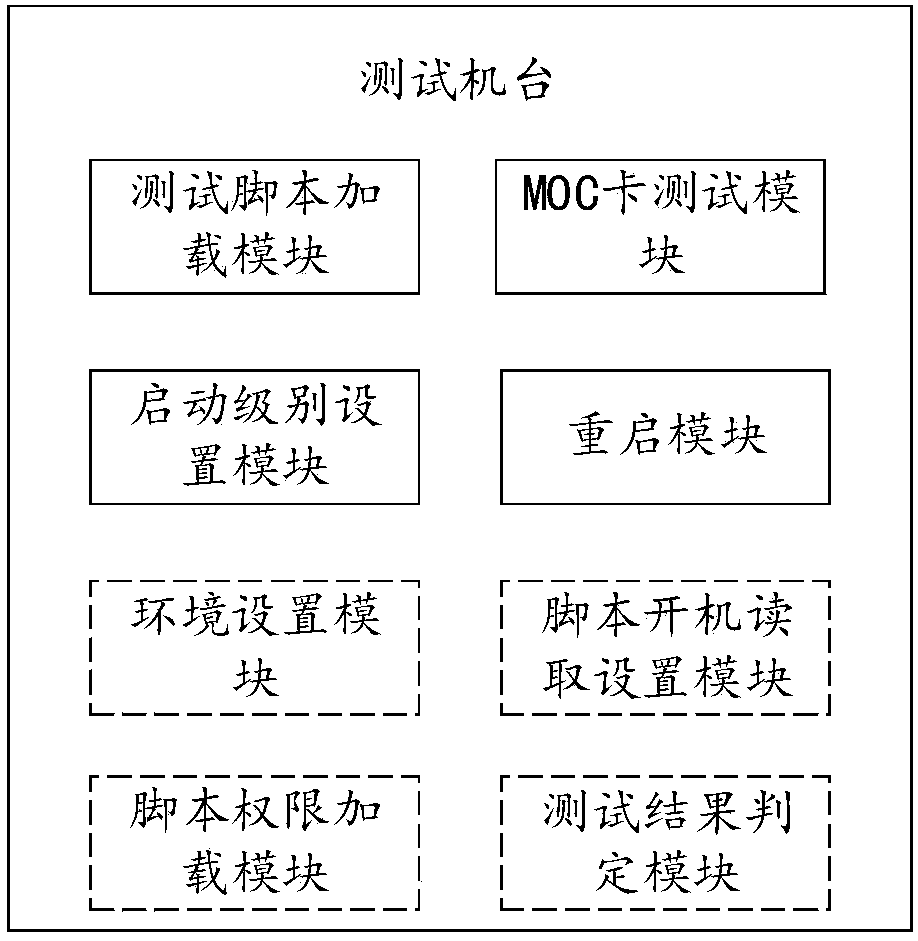
InactiveCN108089961ASolve artificial ginsengSolve the real problemFaulty hardware testing methodsComputer hardwareTest script
The invention provides a hardware reboot testing method and system based on an MOC board card. The method comprises the steps that S1, a testing machine loads a testing script; S2, the testing machineexecutes MOC card detection, and an MOC card testing result is acquired; S3, the starting level of a testing machine system is set to be reboot; and S4, the testing machine system is rebooted, the step S2 is skipped to, the steps are executed cyclically till the number of tests reaches a designated number, and a result file is output. Through the testing method and system, a system reboot instruction, a logic relation for checking MOC board card information, a logic relation for judging whether MOC board card state information is correct and other logic relations are integrated in one script,therefore, as long as the script is run, the system can cyclically execute MOC card tests, that is, one-key starting detection is realized. In this way, the problem that manual participation is needed in traditional hardware tests is solved, repeated startup and shutdown operation is avoided, manpower and material resources are saved, and detection efficiency and testing accuracy are improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
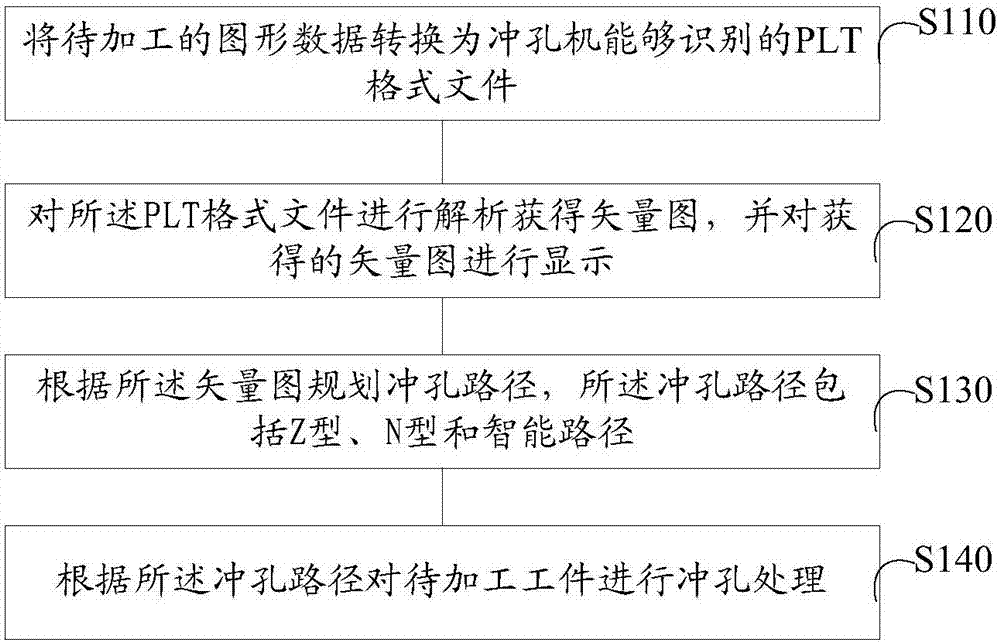
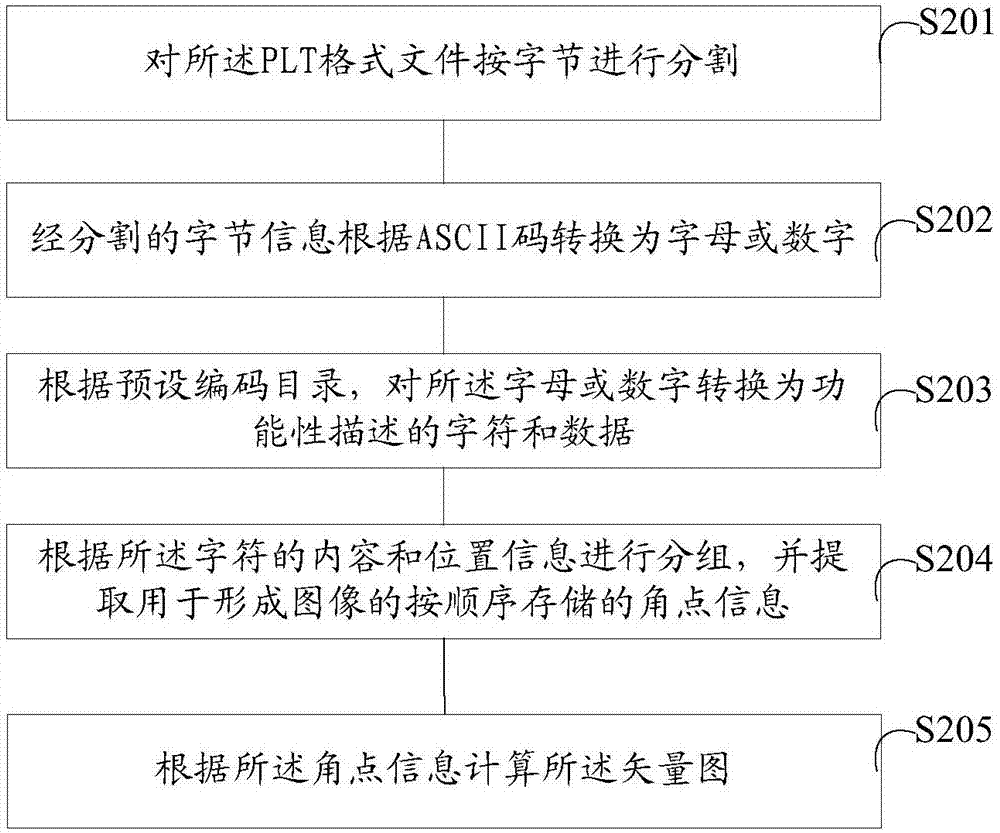
Numerical control punching control method and system
The invention relates to a numerical control punching control method. The control method comprises a step of converting graphic data to be processed into a PLT format file which can be identified by a punching machine, a step of analyzing the PLT format file to obtain a vector graph, and displaying the obtained vector graph, a step of planning punching paths according to the vector graph, wherein the punching paths comprise Z type, N type and intelligent paths, and a step of carrying put punching processing on a work piece to be processed according to the punching paths. Through the above control method, the control of the whole process of machine tool operation is completed, the running time of punching is reduced, the time is saved, and thus the operation efficiency of the numerical control punching machine is greatly improved.
Owner:HANS LASER TECH IND GRP CO LTD +1
Voting method
ActiveUS20190325684A1Voting apparatusEncryption apparatus with shift registers/memoriesTuring machineComputer engineering
A voting method, comprising the steps: a person casting a vote at a voting machine, wherein the voting machine includes a voter list that includes a first record in which the person is registered, wherein the voting machine includes a vote list that is separate from the voter list and a reference list that is separate from the voter list and from the vote list; the voting machine generating a second record in the vote list and recording the vote in the second record; the voting machine computing a hash value of the second record with the vote in the vote list to form a reference; and the voting machine generating a third record in the reference list and recording the reference into the record in the reference list.
Owner:REGIO IT GES FUR INFORMATIONSTECH MBH
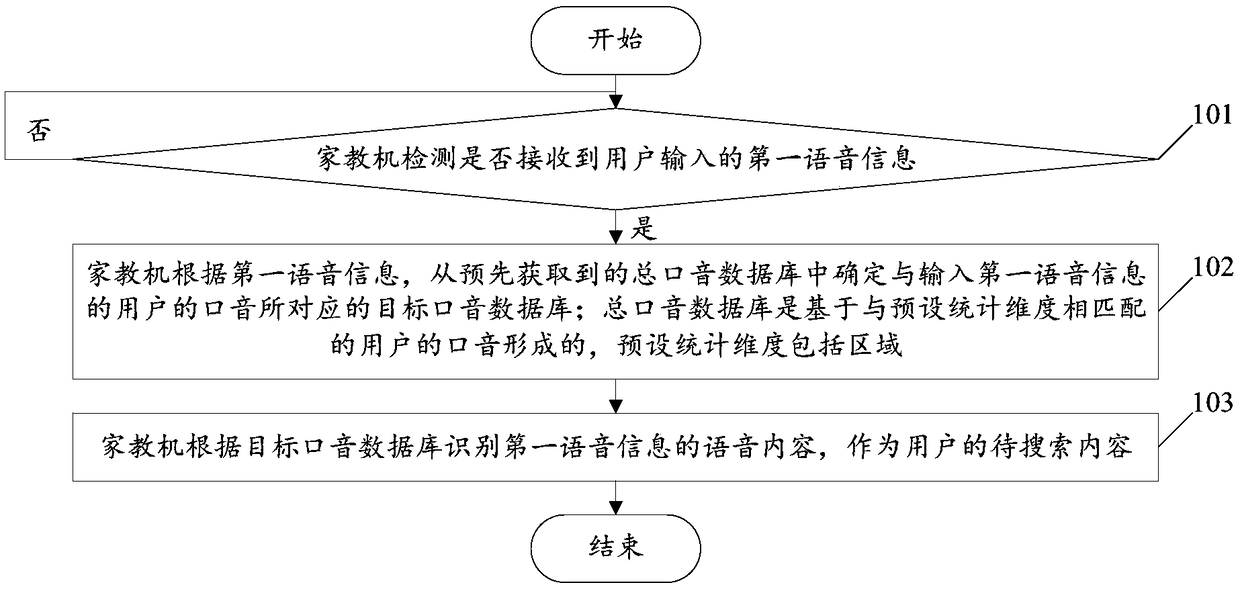
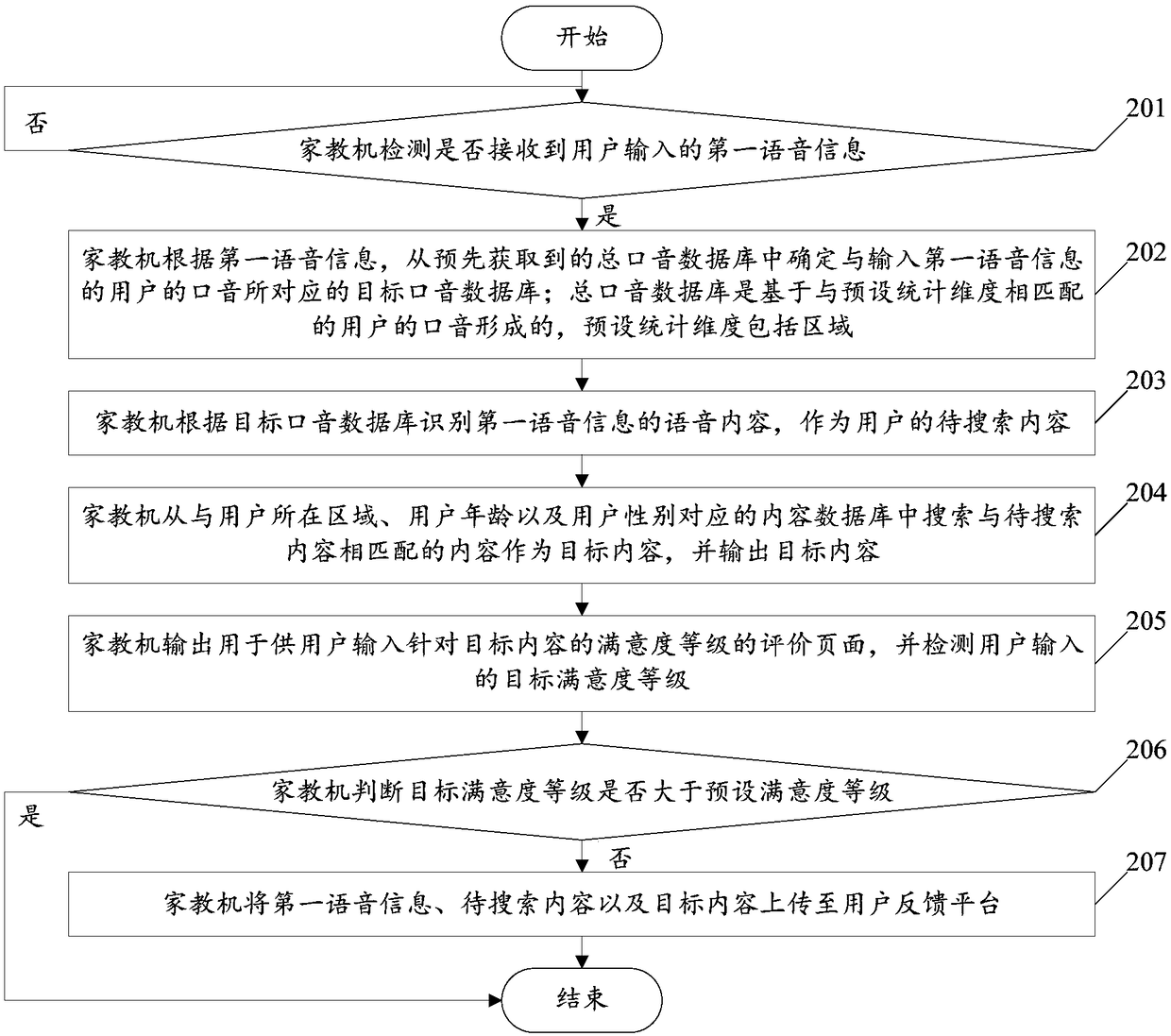
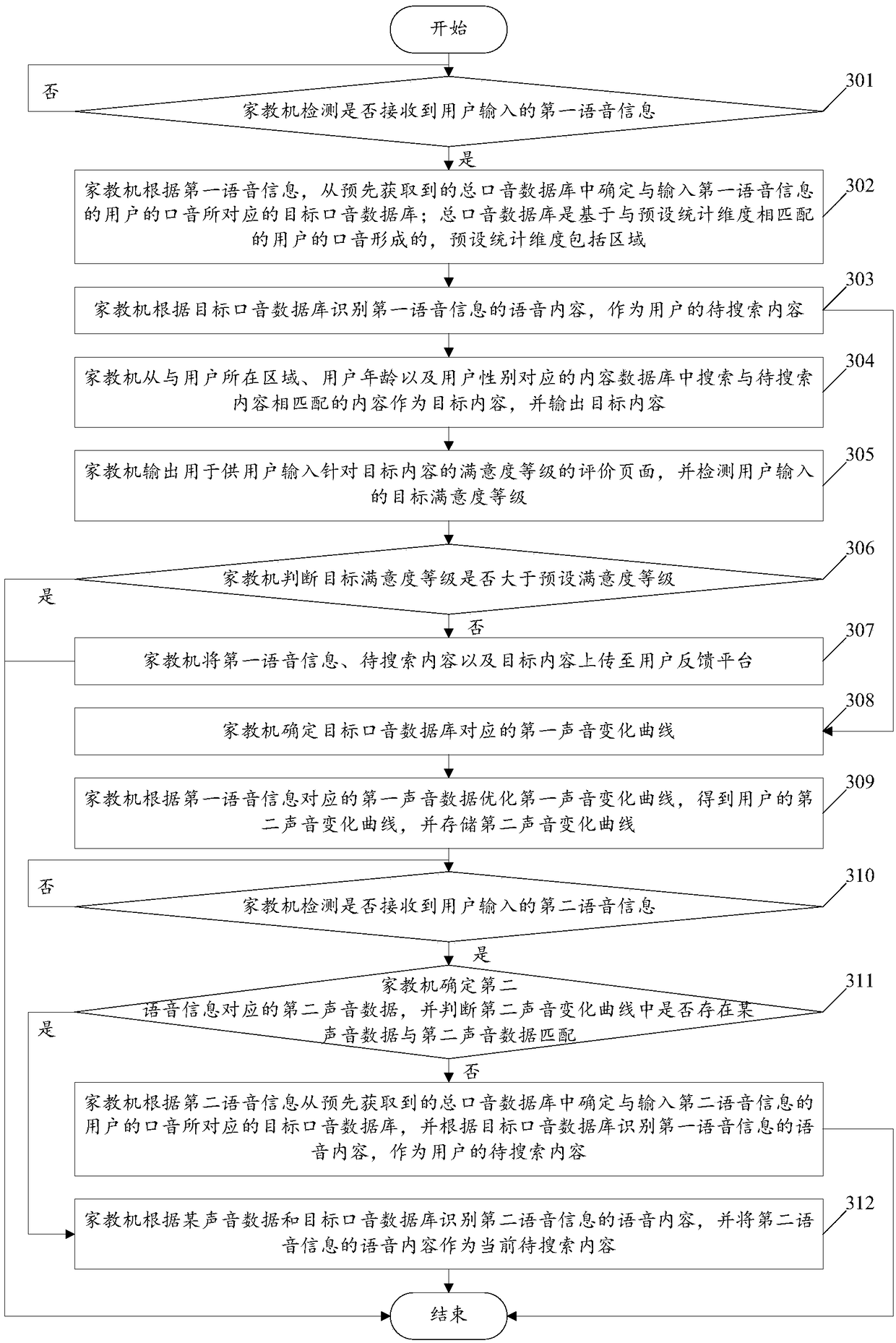
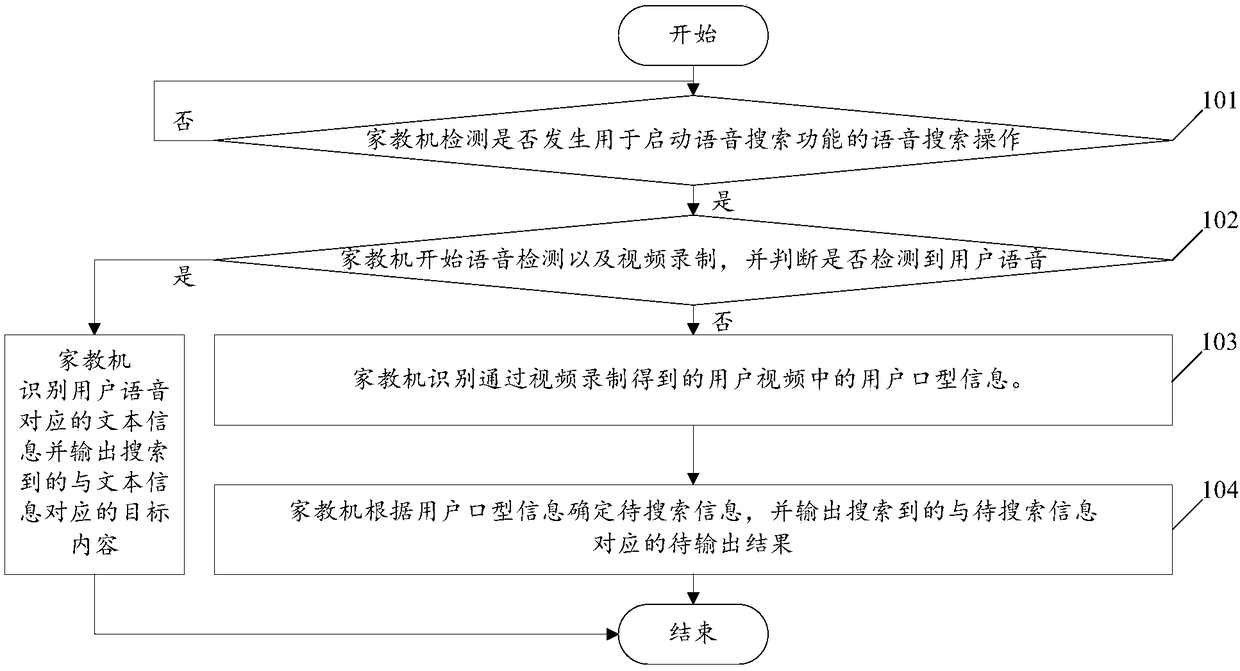
Identification method based on voice search and tutoring machine
InactiveCN108920541AImprove recognition accuracyImprove accuracySpecial data processing applicationsUser inputVoice search
The invention relates to and identification method based on voice search and a tutoring machine. The method includes: the tutoring machine detects whether a first voice message input by a user is received or not; if so, the tutoring machine determines a target accent database corresponding to the accent of the user inputting the first voice message from a total accent database acquired in advance,wherein the total accent database is formed by user accents matched with preset statistics dimensionality, and the preset statistics dimensionality comprises areas; the tutoring machine uses the voice content, identified according to the target accent database, of the first voice message as the to-be-searched content of the user. By the method, the voice problem identification accuracy of the tutoring machine can be increased, and the accuracy of the voice problem search results of the tutoring machine is increased.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
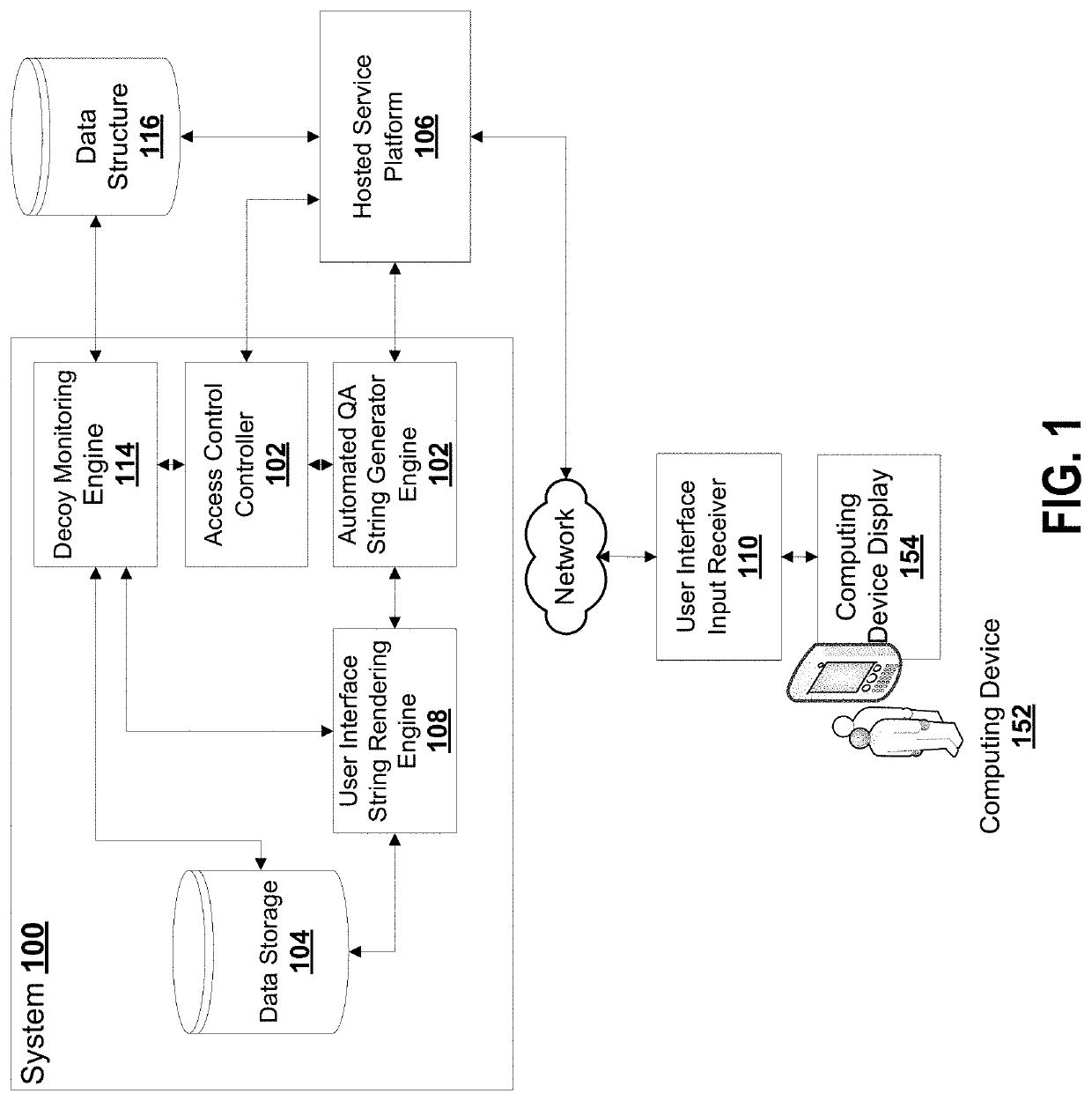
System and method for reverse-turing bot detection
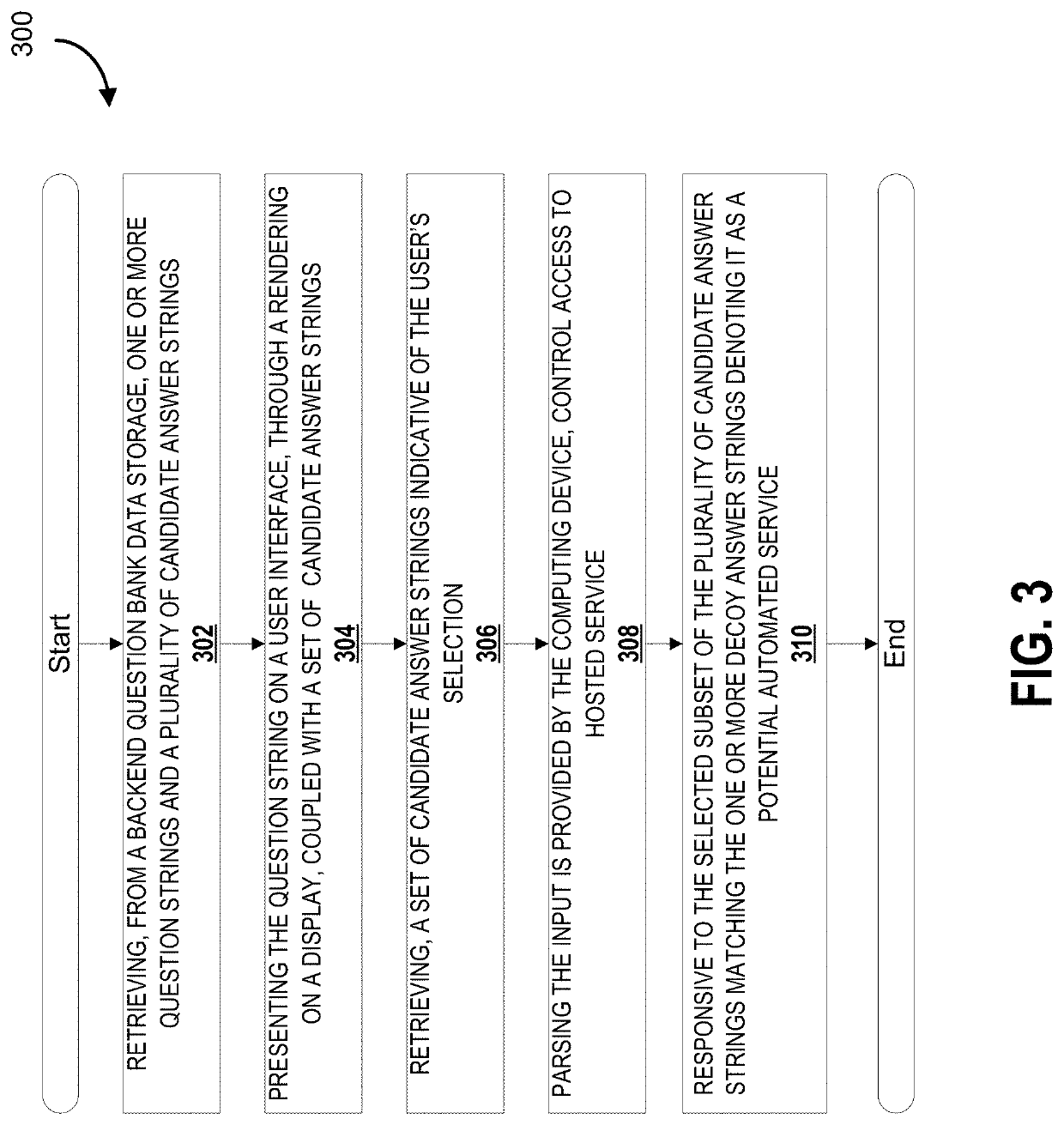
ActiveUS20200151347A1Improve vulnerabilitySimple calculationSemantic analysisDigital data protectionPerson detectionEngineering
A system for controlling access to hosted services using computer generated question answer sets is described. The question answer sets are generated and include relationships which are designed to distinguish between human and automated system interpretation through the inclusion of a dynamically established transformation of characteristics in relation to objects described in the question answer sets. The dynamically established transformation provides an additional defense against malicious neural networks used to overcome mechanisms for distinguishing between humans and automated systems. Corresponding methods and devices are contemplated. In an additional embodiment, a decoy set of answer sets are also established to maintain a blacklisted set of suspected automated systems.
Owner:ROYAL BANK OF CANADA
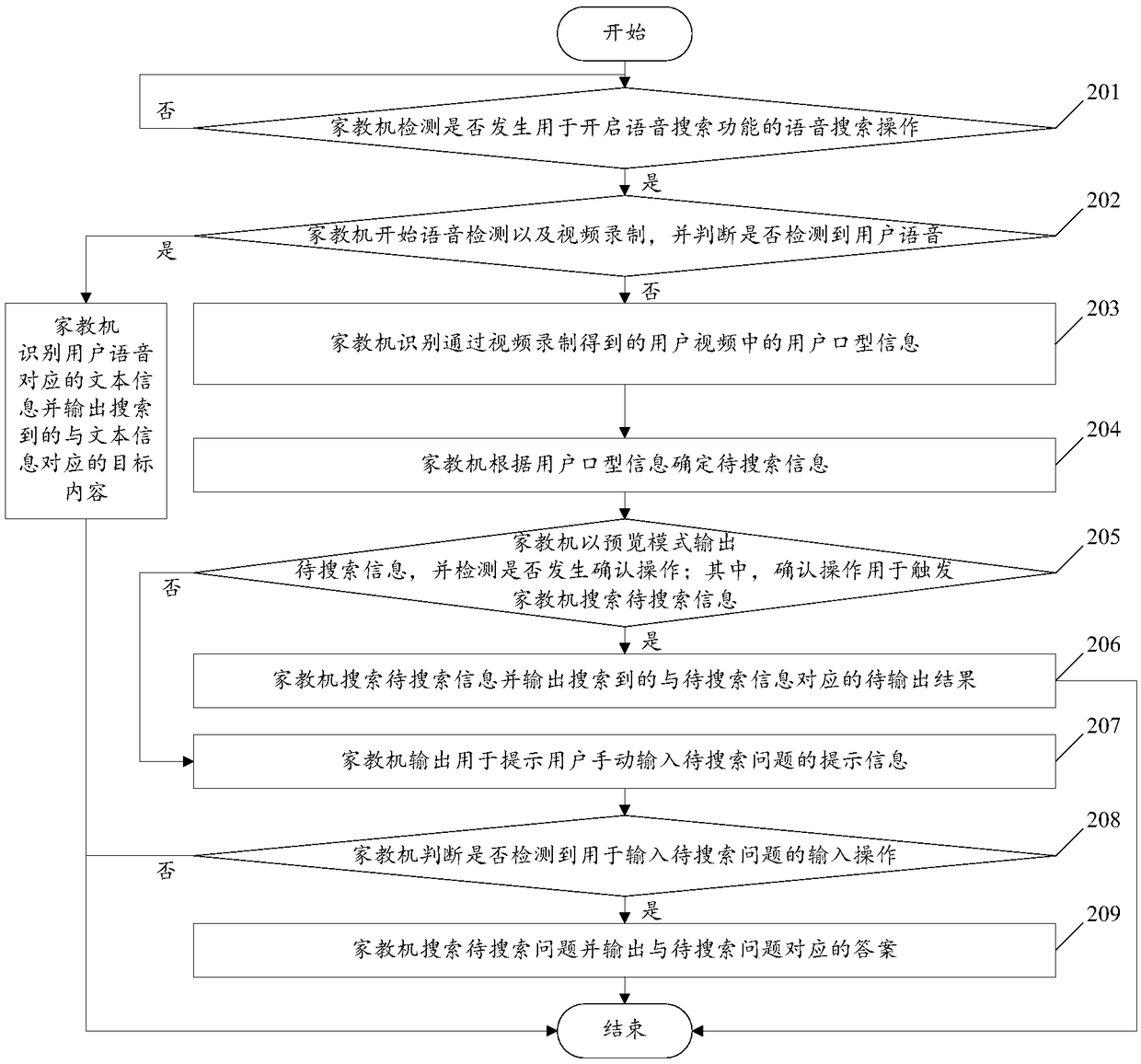
A search method based on a tutor machine and a tutor machine
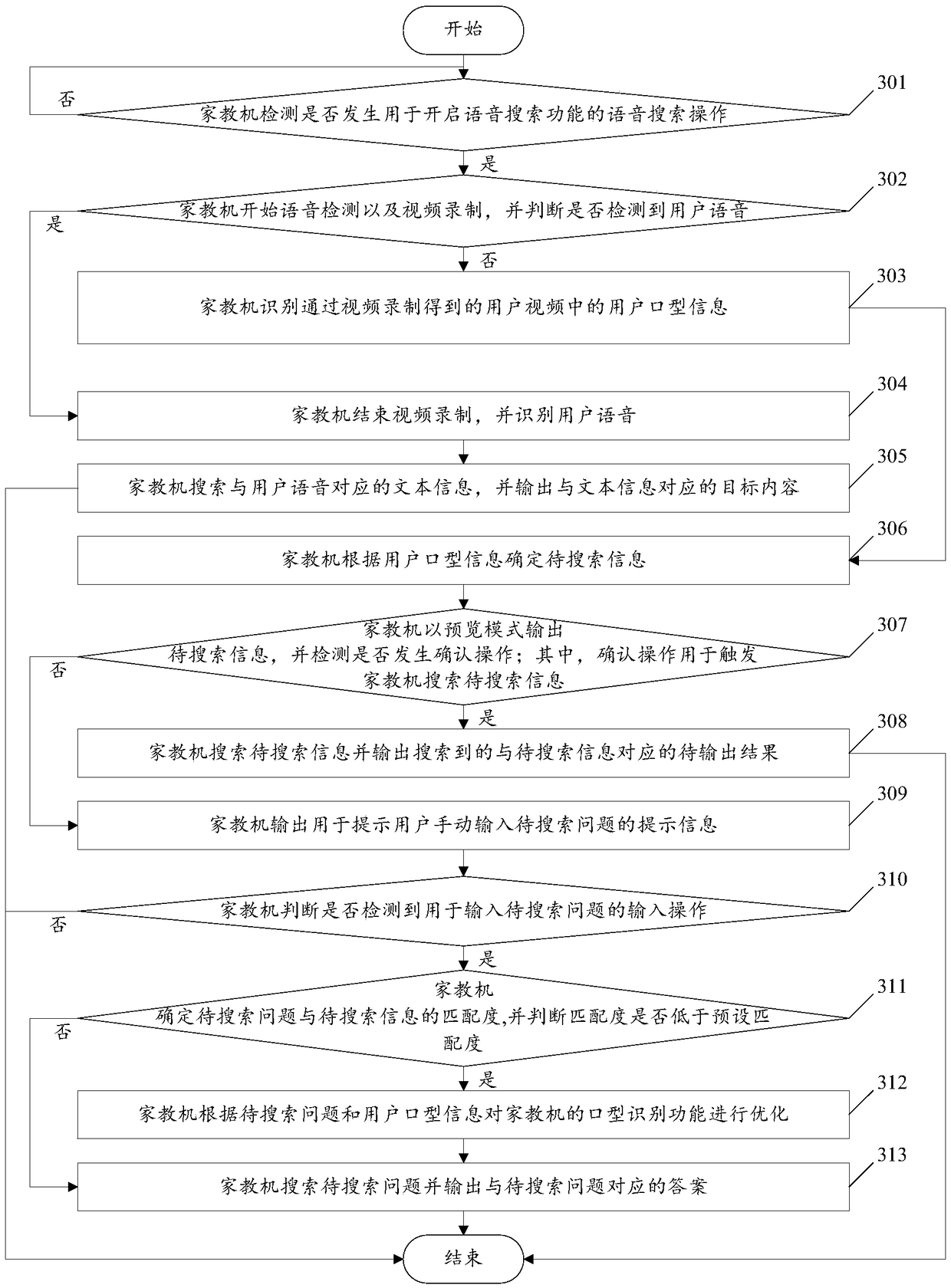
InactiveCN109145088AImprove use viscosityRich interactionCharacter and pattern recognitionSpeech recognitionVideo recordingMouth shape
The invention relates to a search method based on a tutor machine and a tutor machine, comprising the following steps: detecting whether a voice search operation for starting a voice search function occurs; if a speech search operation is detected, speech detection and video recording being started; if no user voice is detected, identifying user mouth shape information in the user video obtained by video recording; the information to be searched being determined according to the user's mouth shape information, and the searched result corresponding to the information to be searched being outputted. By implementing the embodiment of the invention, the students with speech barriers can search for problems through the tutor machine, and the interaction mode between the tutor machine and the students can be enriched, so as to improve the viscosity of the user of the tutor machine.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Parallel hardware searching system for building artifical intelligent computer
InactiveCN104516939AFix search problemsWith artificial intelligence functionDigital data information retrievalMachine learningProgram instructionParallel computing
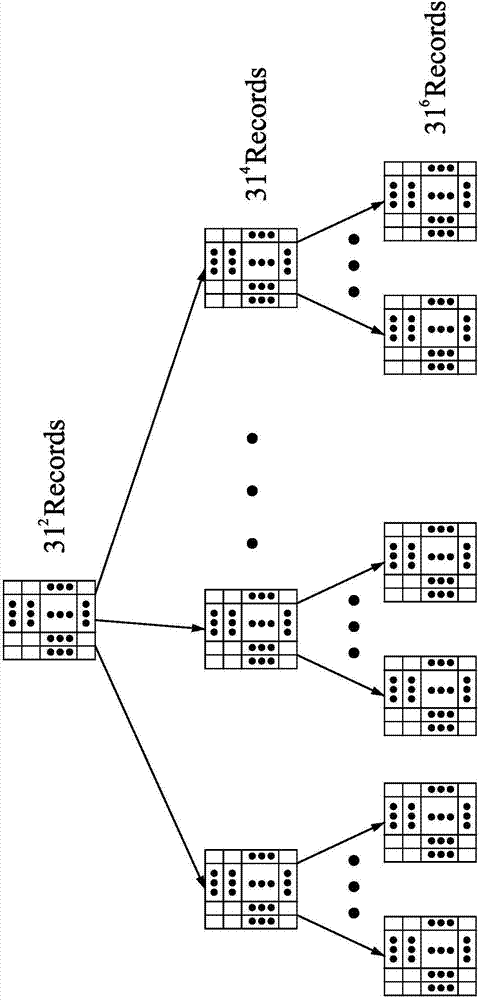
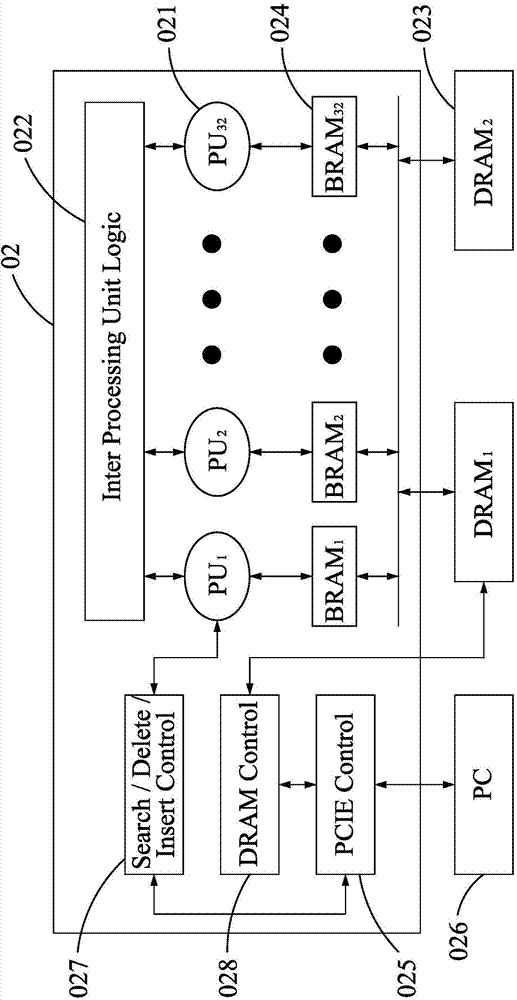
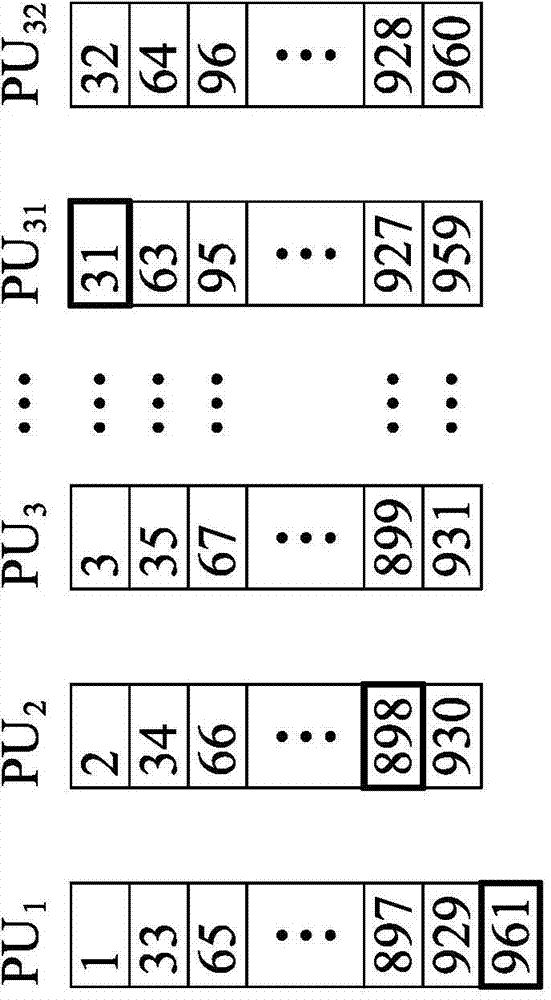
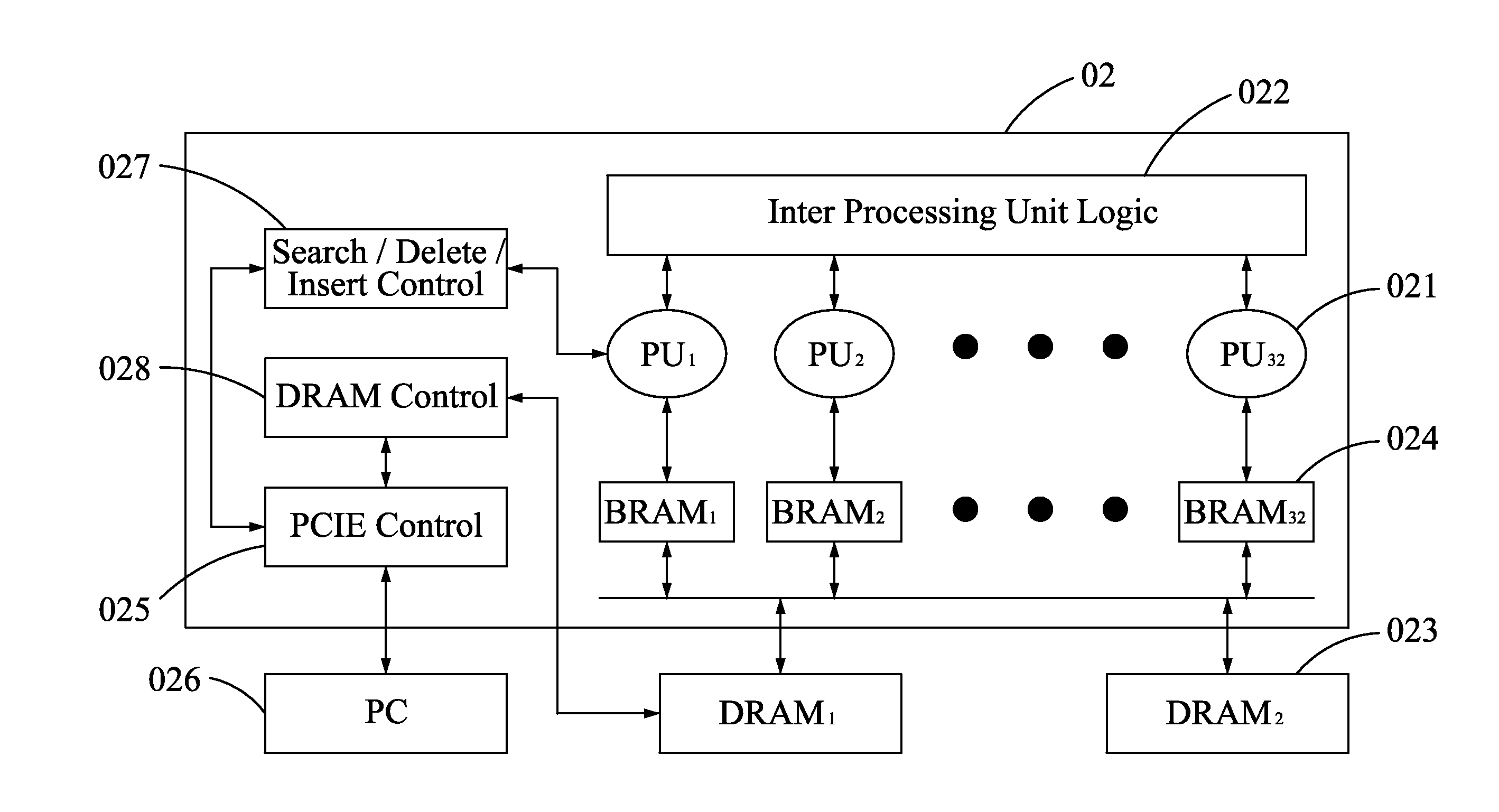
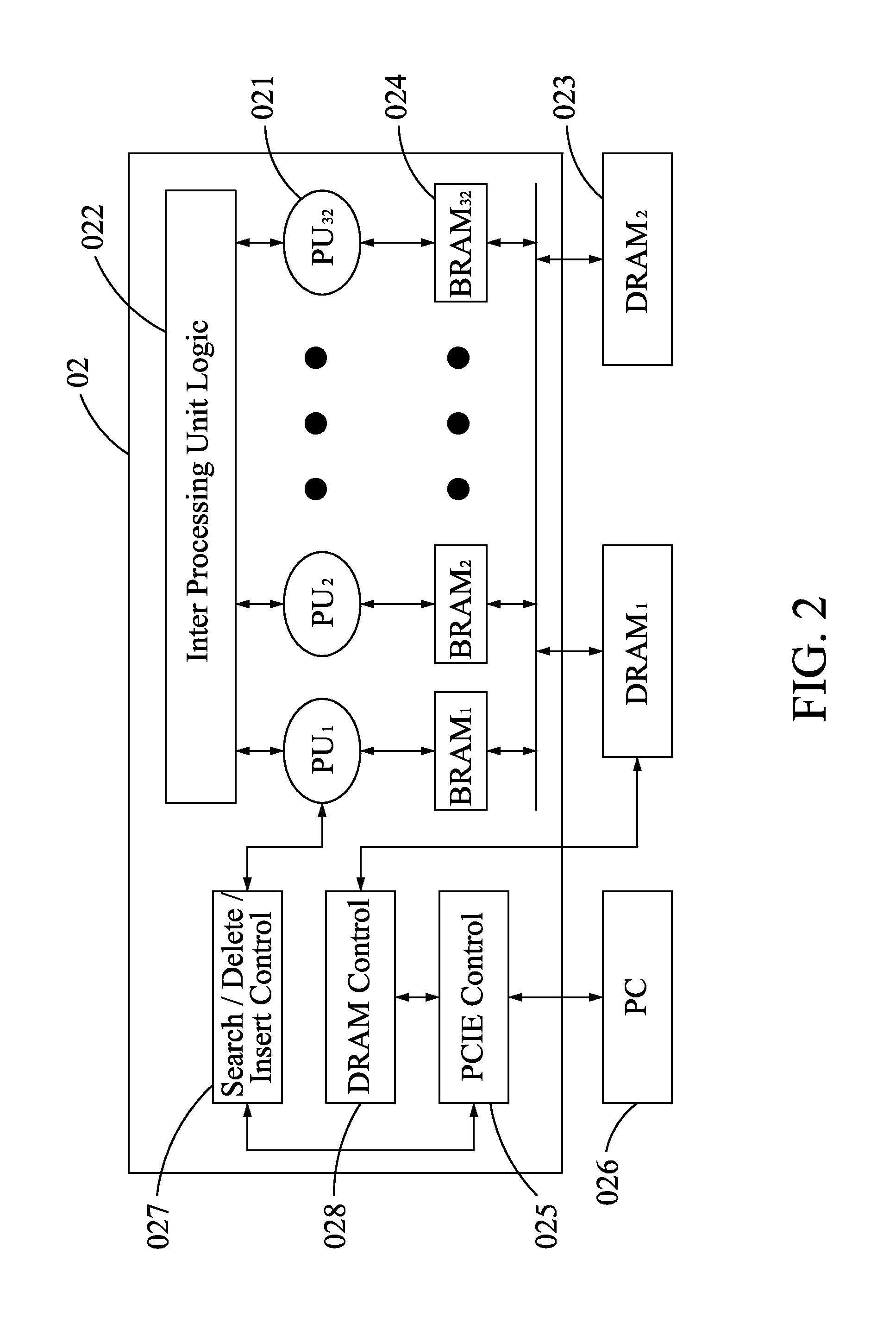
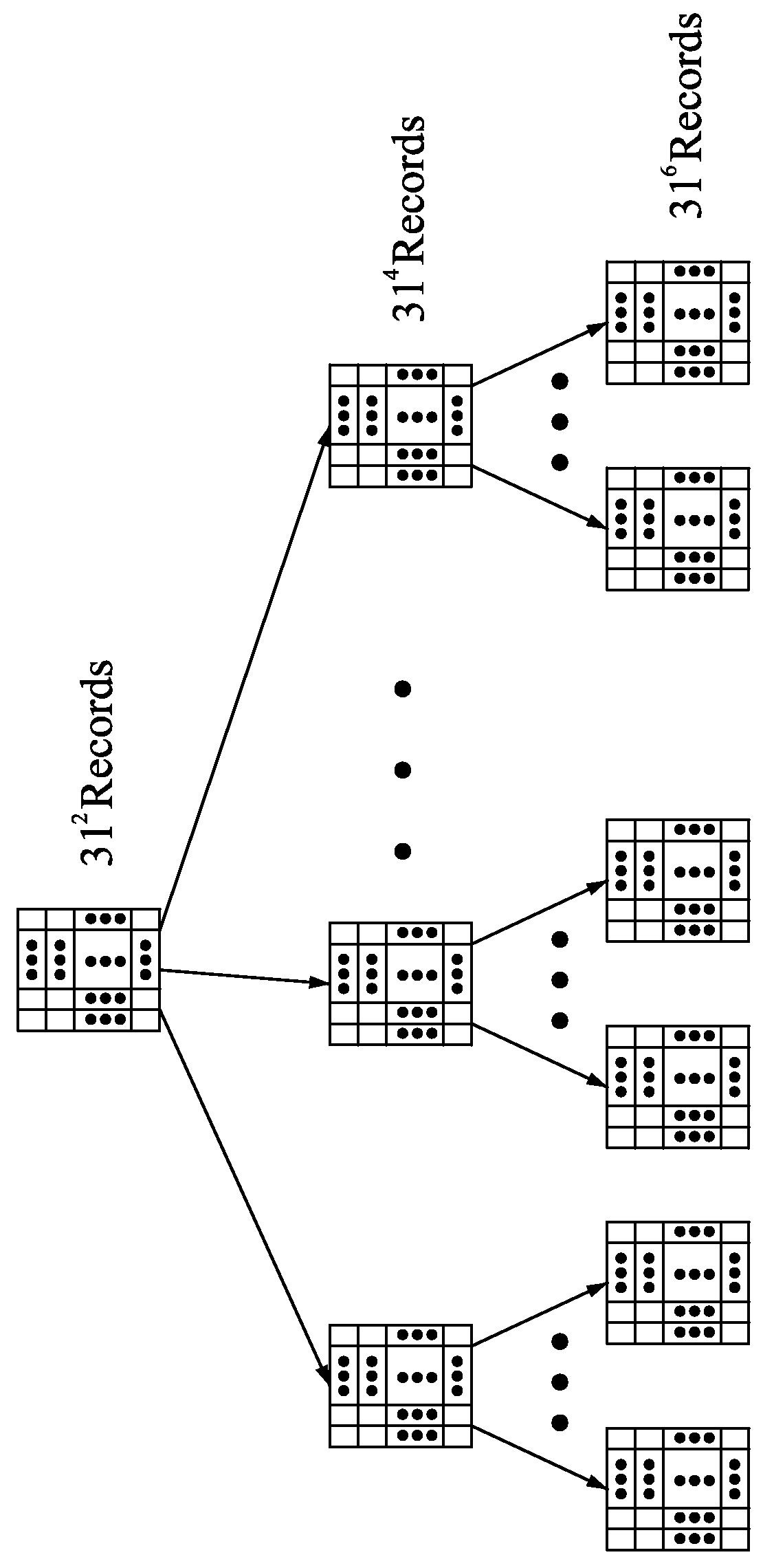
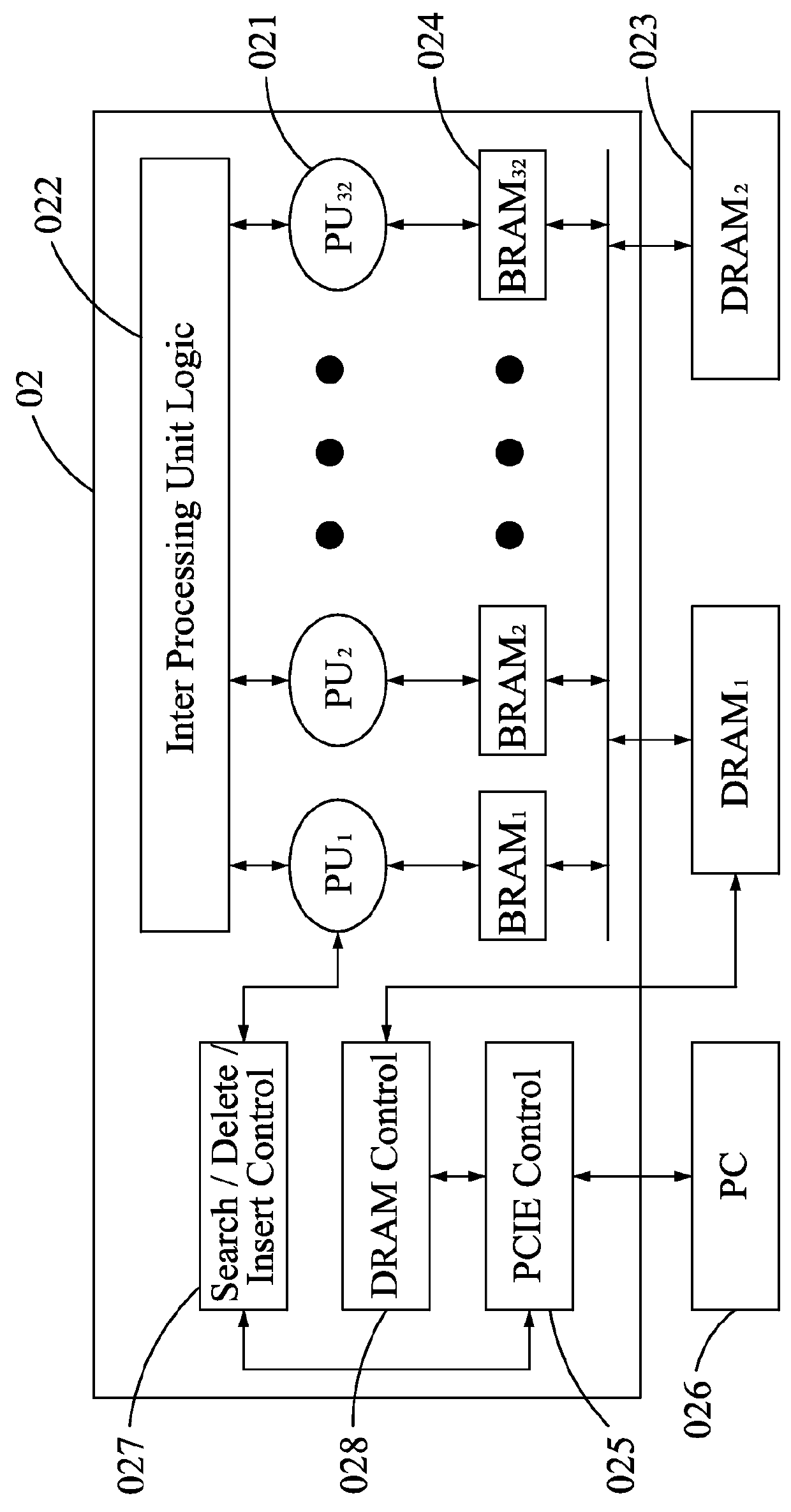
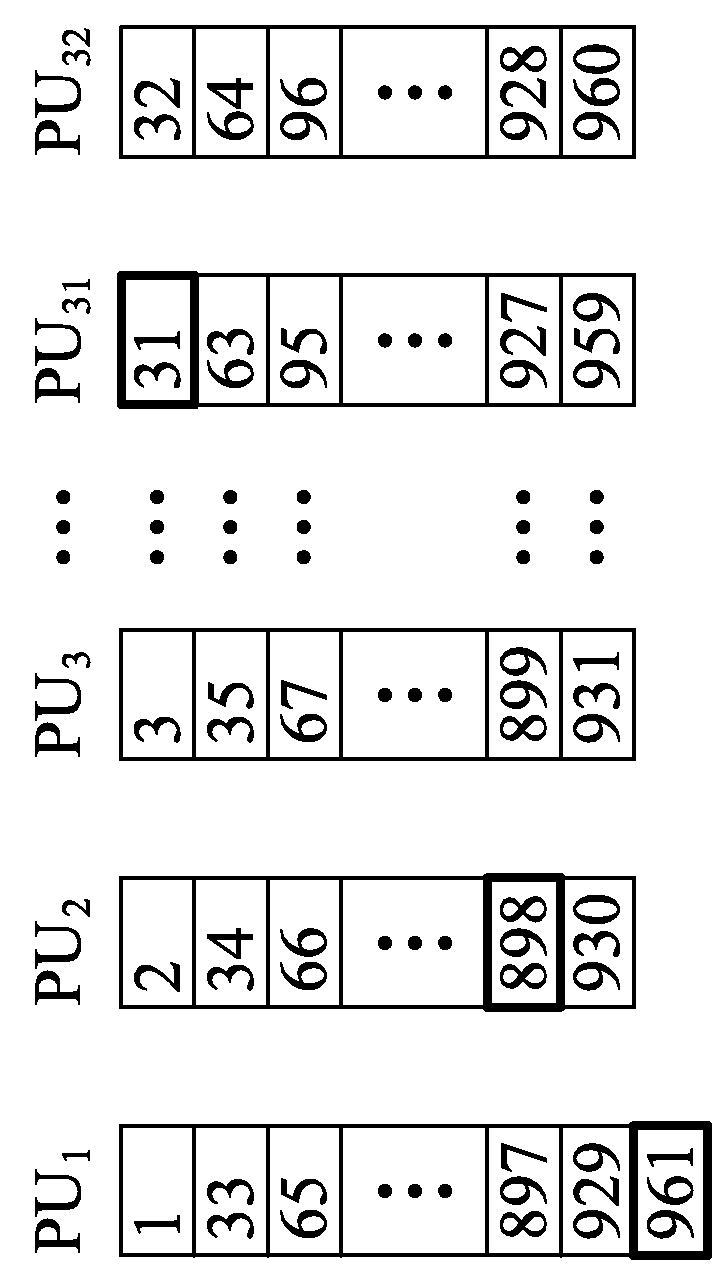
An affordable artificial intelligent (AI) computer is invented by combining present computer with a parallel hardware search system. Such a computer can be treated as a Turing Machine. Instead of sequentially processing computer instructions, this computer executes AI logic reasoning The parallel hardware search system use pure parallel hardware to execute virtual B-tree search. Hierarchical page table and hash techniques are also used for very large data volume. The prototype of this invented system is successfully built into a PCIE card which mainly contains a Xilinx's Kintex7 FPGA chip and two DDR3 memory modules. FPGA chip includes: 32 32-bit processing units (PUs), one PCIE controller, one search / delete / insert controller and two DDR3 controllers.
Owner:KOUTIN TECH INC
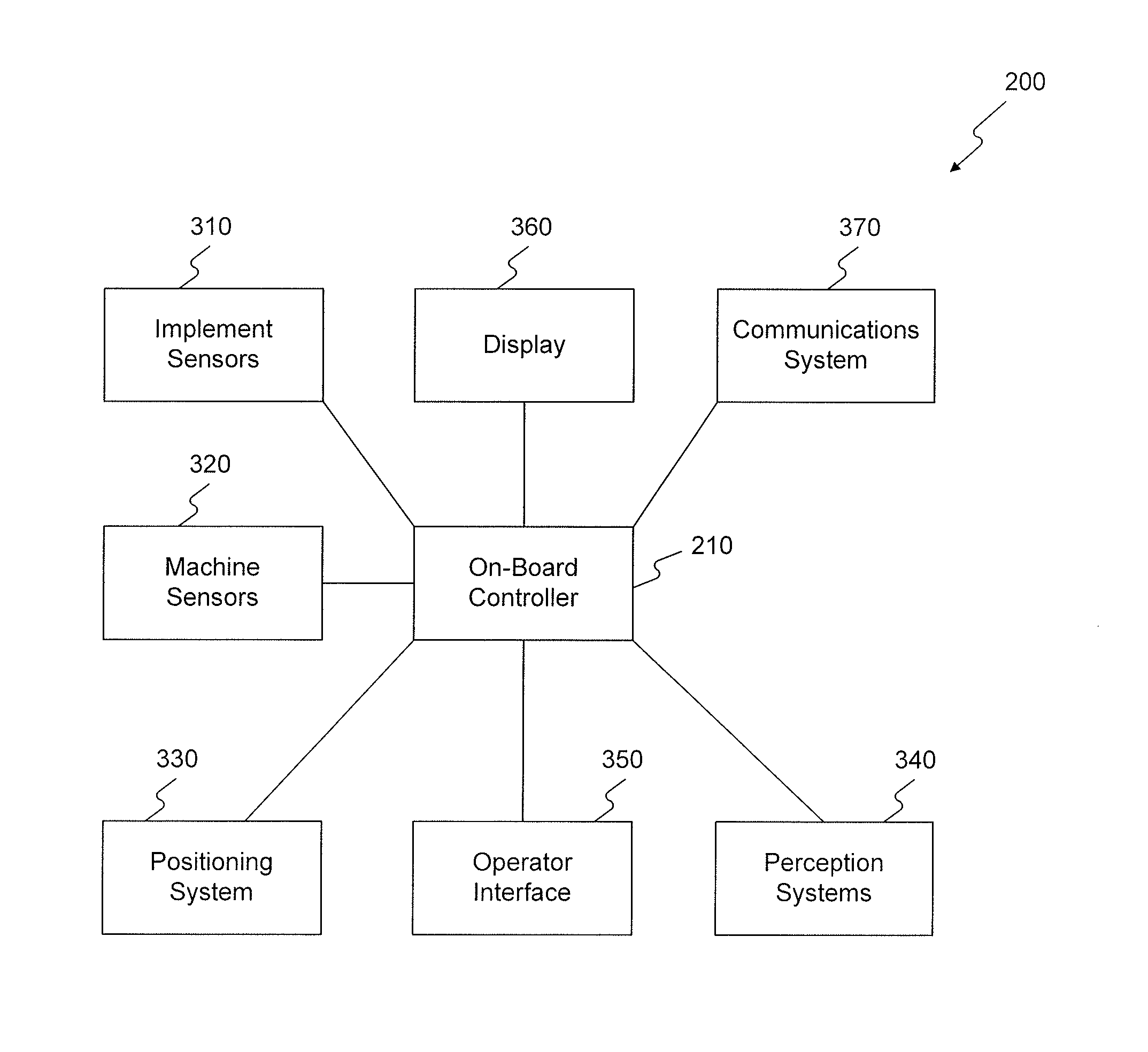
Systems and methods for machine-to-machine coaching
Systems and methods are disclosed for machine-to-machine coaching. According to certain embodiments, first operation data associated with a trainee machine is received. Second operation data associated with a trainer machine is also received. An operator of the trainee machine may be trained using the second operation data. Training the operator of the trainee machine may include demonstrating an operation of the trainer machine on the trainee machine using the second operation data.
Owner:CATERPILLAR INC
Secure active element machine
ActiveUS9032537B2Simple and safe processComputing performance that isDigital data processing detailsAnalogue secracy/subscription systemsComputational problemComputation process
Based upon the principle of Turing incomputability, and novel properties of the Active Element Machine, a malware-resistant computing machine is constructed. This new computing machine is a non-Turing, non-register machine (non von-Neumann), called an Active Element Machine (AEM). AEM programs are designed so that the purpose of the computation is difficult to apprehend by an adversary and hijack with malware. These methods can help hinder reverse engineering of proprietary algorithms and hardware design.Using quantum randomness, the AEM can deterministically execute a universal digital computer program with active element firing patterns that are Turing incomputable. In some embodiments, a more powerful computational procedure is demonstrated than Turing's computational procedure (digital computer procedure). Current digital computer algorithms can be derived or designed with a Turing machine computational procedure. A novel class of computing machines is built where the purpose of the program's execution is difficult to apprehend (Turing incomputable).
Owner:AEMEA
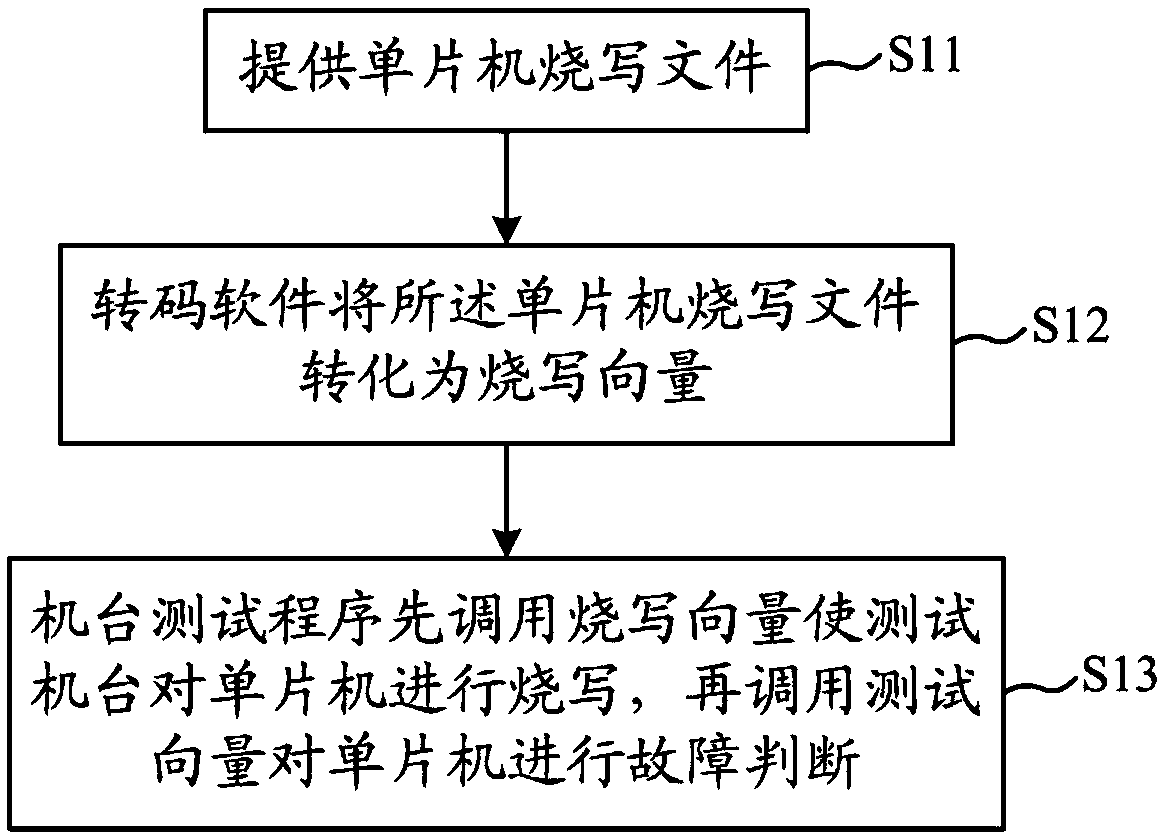
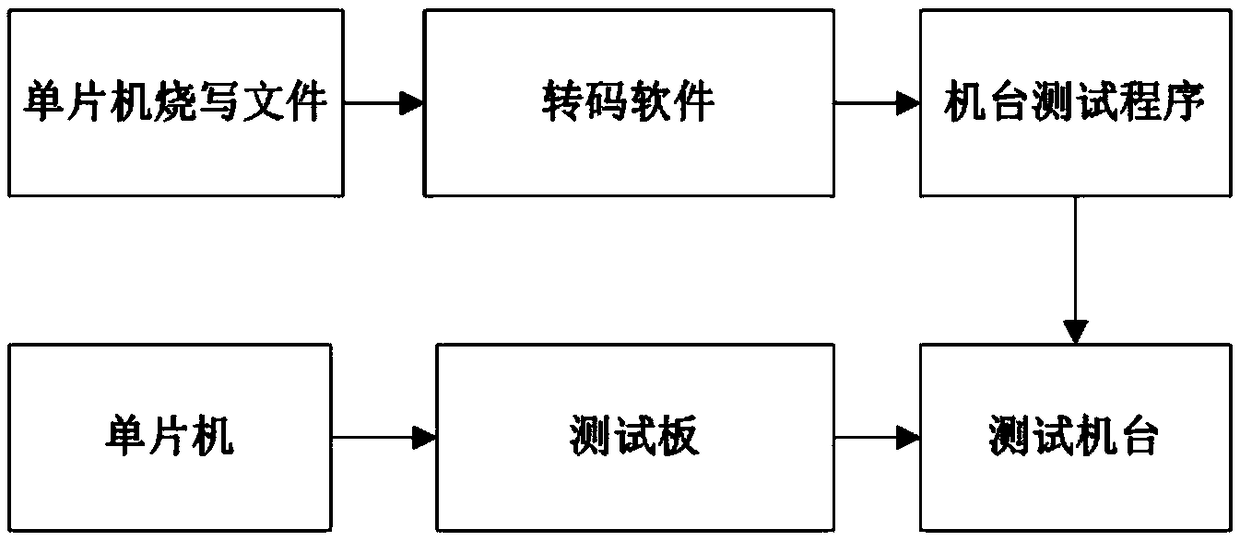
An on-line programming test method of single chip microcomputer
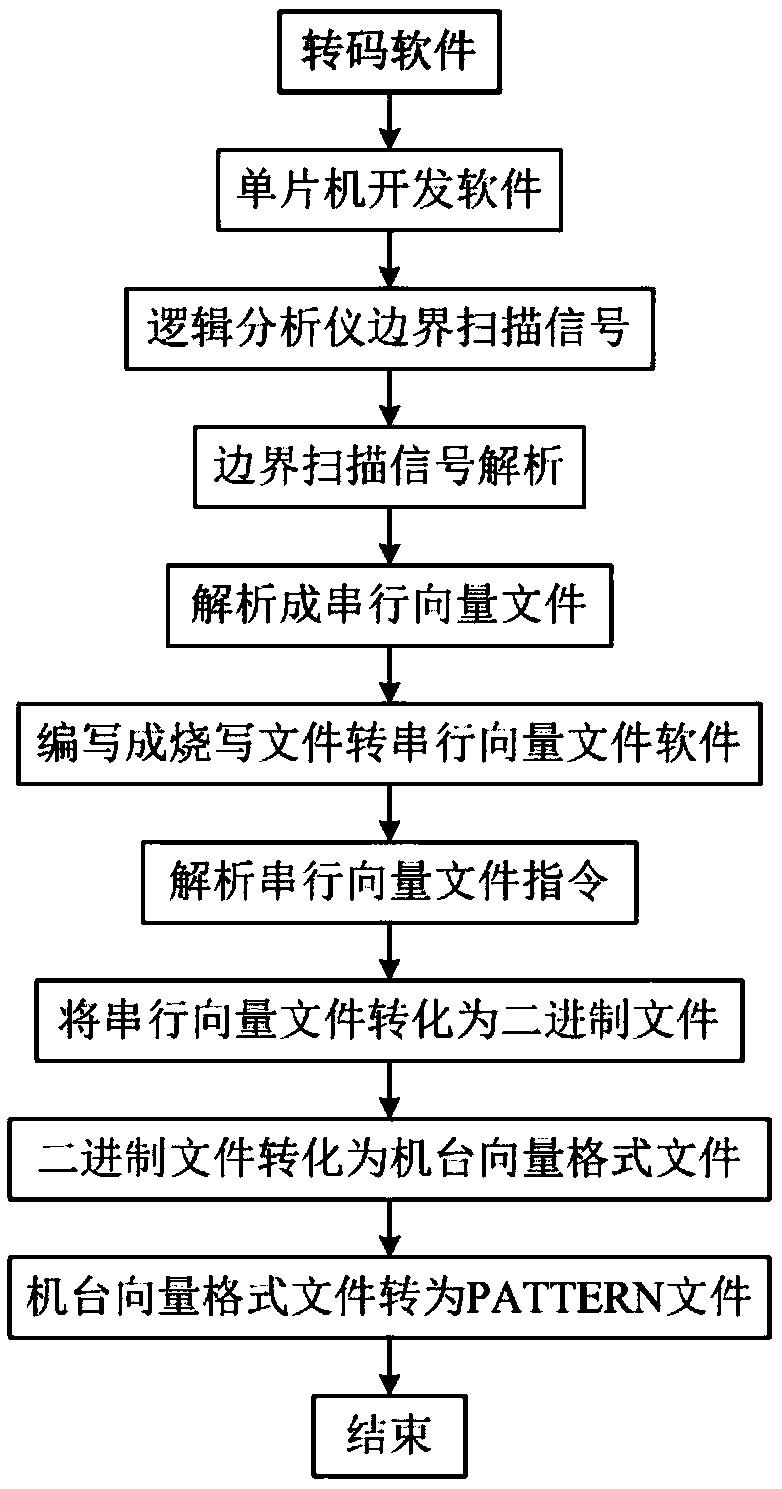
InactiveCN109165030ASolve the limitation of programmingLow costSoftware deploymentSingle chipTuring machine
The invention discloses an on-line programming test method of a single chip microcomputer, belonging to the technical field of the single chip microcomputer. At first, that burn-write file of the single chip microcomputer is provides; then the transcoding software converts the singlechip burning and writing files into burning and writing vectors; finally, the testing program of the machine first calls the burning and writing vector to make the testing machine burn and write the MCU on-line, and then calls the testing vector to judge the fault of the MCU. The conventional method of burning andwriting and testing of single chip microcomputer is classified as online burning and writing test, which solves the limitation of burning and writing of downloader, and is simple and easy to operate.Compared with the conventional downloader programming test method, the method has the advantages that the hardware cost is reduced, the manual operation in the test process is reduced, and the production efficiency is improved.
Owner:58TH RES INST OF CETC
Parallel hardware searching system for building artifical intelligent computer
ActiveUS20150100536A1Big amount of dataEfficient managementDigital data information retrievalKnowledge representationParallel computingPage table
An affordable artificial intelligent (AI) computer is invented by combining present computer with a parallel hardware search system. Such a computer can be treated as a Turing Machine. Instead of sequentially processing computer instructions, this computer executes AI logic reasoning The parallel hardware search system use pure parallel hardware to execute virtual B-tree search. Hierarchical page table and hash techniques are also used for very large data volume. The prototype of this invented system is successfully built into a PCIE card which mainly contains a Xilinx's Kintex7 FPGA chip and two DDR3 memory modules. FPGA chip includes: 32 32-bit processing units (PUs), one PCIE controller, one search / delete / insert controller and two DDR3 controllers.
Owner:KOUTIN TECH INC
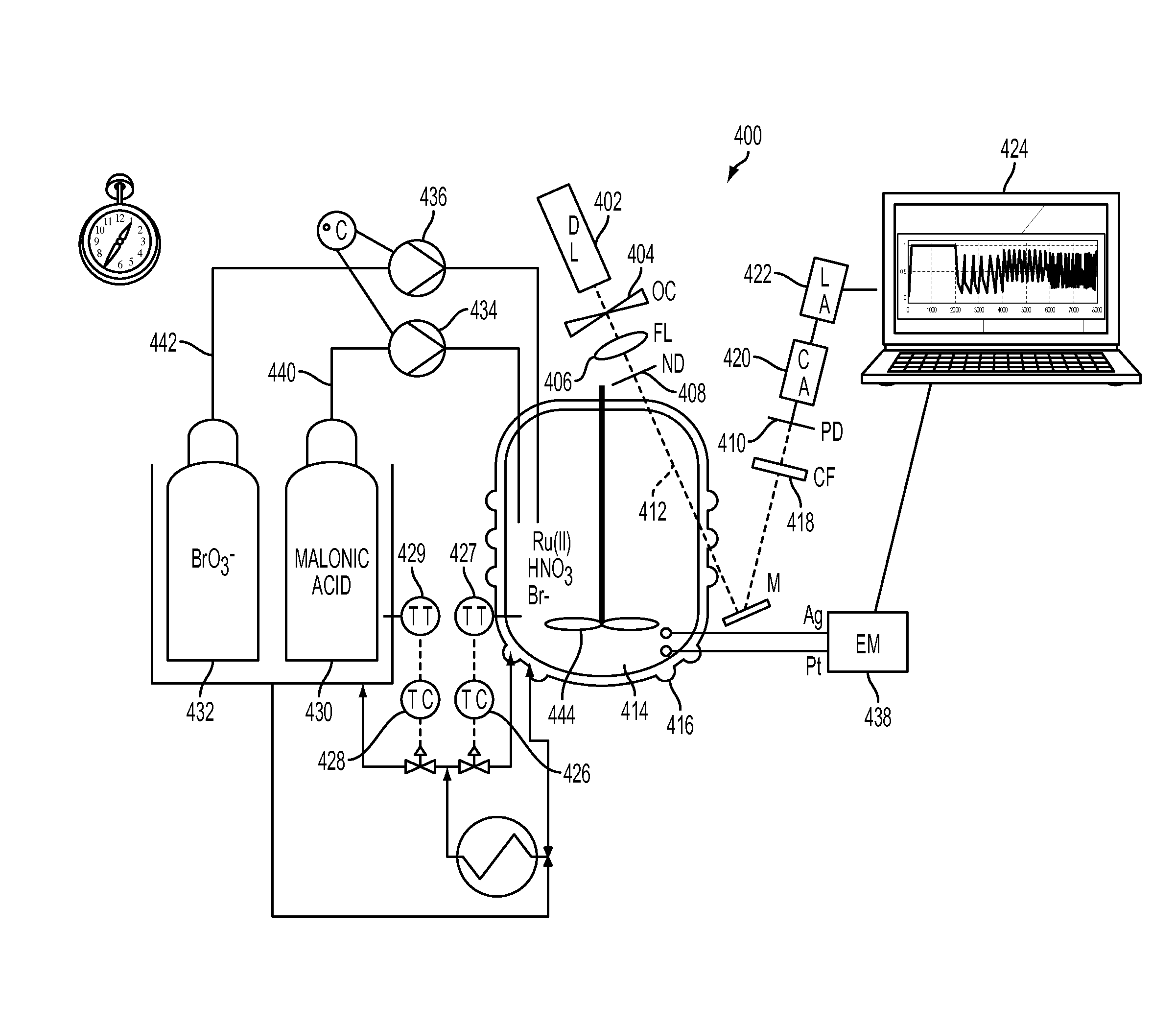
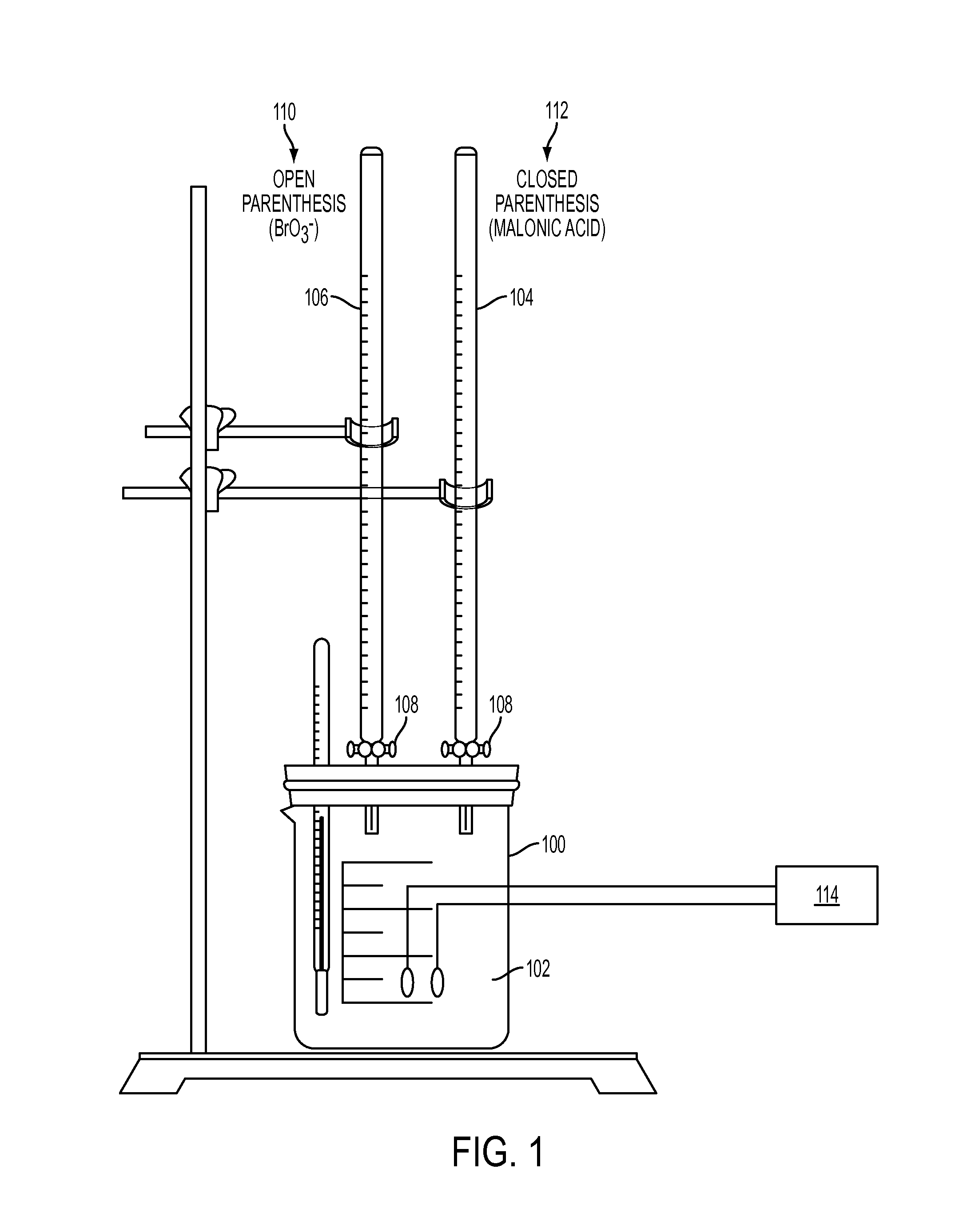
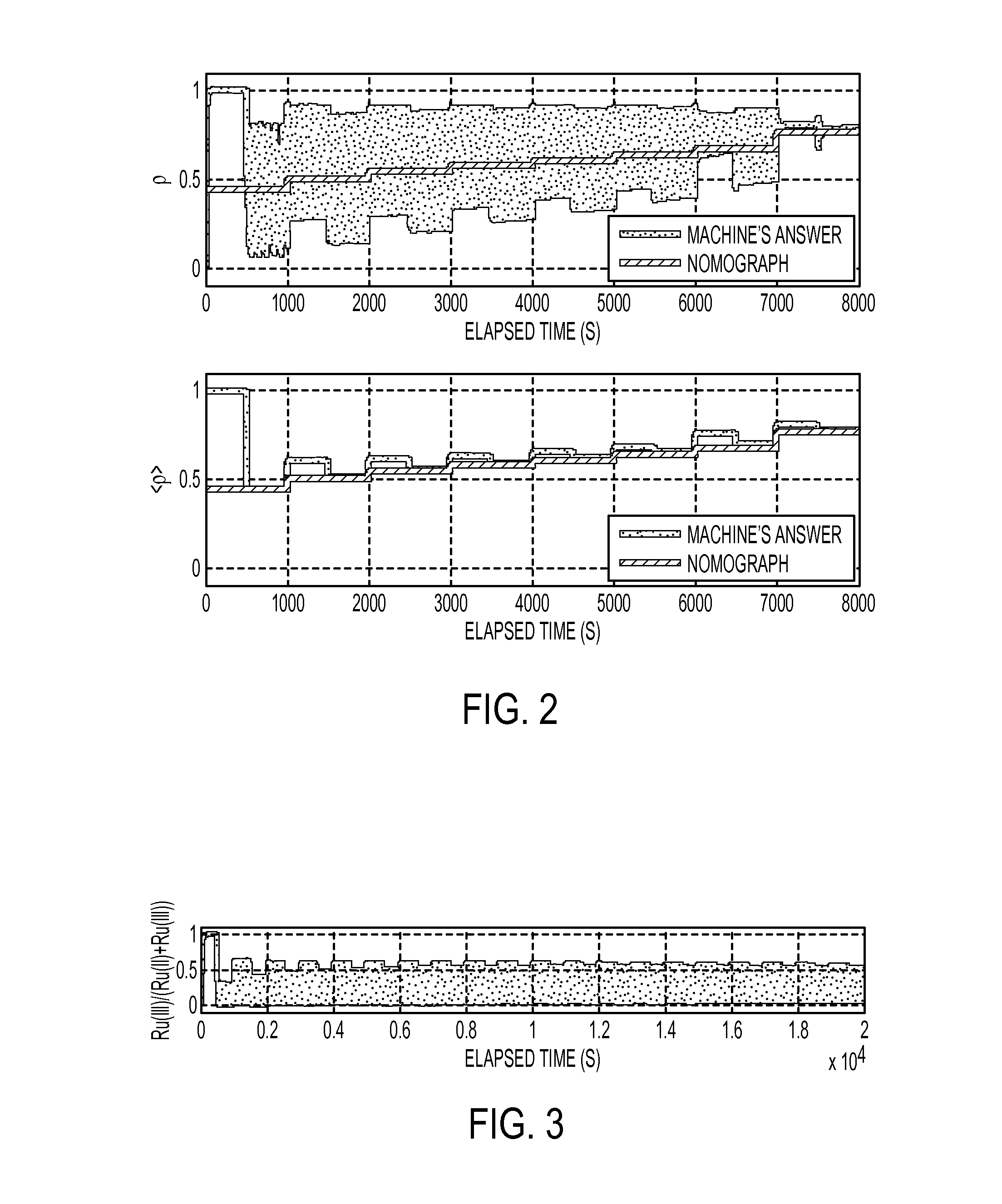
Chemically-operated turing machine
The present disclosure relates to a Turing machine having a reactor comprising a reactant solution comprising a reactant; a first chemical species source to provide a selected amount of a first chemical species; a second chemical species source to provide a selected amount of a second chemical species; one or more controllers coupled to control the addition of the first and second chemical species from the first and second chemical species sources responsive to an input; and a sensor positioned to sense changes in the reactant as the controller controls the first and second chemical species sources to add selected amounts of the respective first and second chemical species to the reactor. The controller receives signals corresponding to the state of the reactant and correlates the states of the reactant to a result that is computed as a function of the input.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE +1
A polynomial method of constructing a non-deterministic (NP) turing machine
ActiveCN105190632AObvious featuresObvious advantagesKnowledge representationInference methodsPolynomial methodNon-deterministic Turing machine
A nondeterministic Turning machine (NTM) performs computations using a spatial binary enumeration system, a three-dimensional relation system, a simulated-human logic system, and a bijective-set memory system. The NTM may be used to perform a variety of computational tasks, such as multiple sequence alignment, factorization, and other nondeterministic polynomial algorithms in polynomial time. The NTM may be constructed by a deterministic Turing machine (DTM) using the four systems listed above.
Owner:BEIJING BOSI BIOINTELLIGENCE TECH
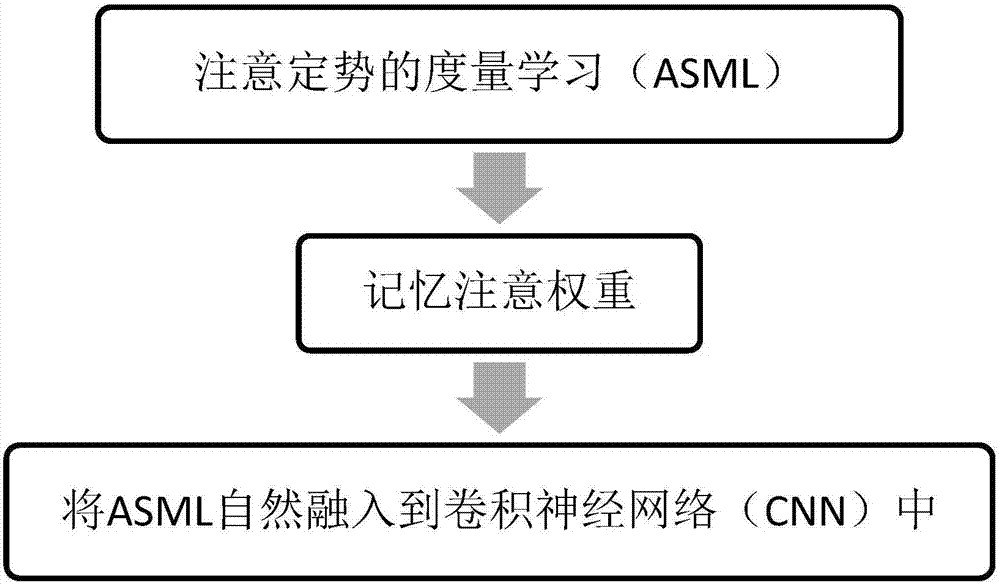
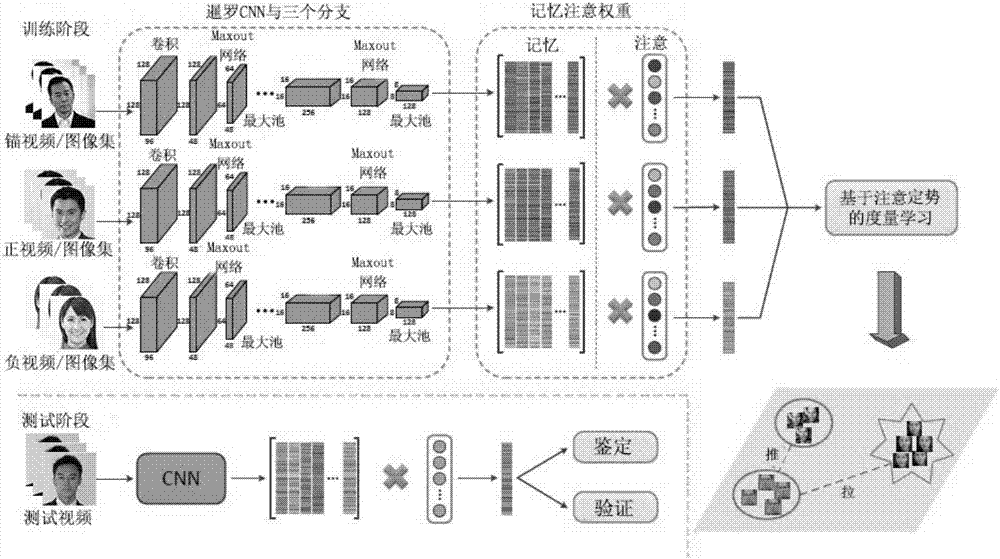
Video face recognition method based on attention set metric learning (ASML)
The invention provides a video face recognition method based on attention set metric learning (ASML), which mainly comprises steps of ASML, memory attention weight and natural integration of the ASML to a convolutional neural network (CNN). The process is that an effective distance metric on an image set is defined firstly, the distance within a set is minimized significantly, the concentration distance is maximized at the same time, the weight is used as a nerve Turing machine, a face feature set is used as a memory, the weight is used as an address read-write memory, the ASML is finally naturally integrated to the convolutional neural network, and an end-to-end learning scheme is thus formed. The gap between probability distributions of the same set is narrowed, and the gap between different sets is expanded at the same time; sample offset and noise in the video or image set is reduced, the information in the video or image set is used effectively, and the recognition performance is thus improved.
Owner:SHENZHEN WEITESHI TECH
Parallel hardware searching system for building artificial intelligent computer
ActiveUS9384449B2Big amount of dataEfficient managementDigital data information retrievalMachine learningParallel computingPage table
An affordable artificial intelligent (AI) computer is invented by combining present computer with a parallel hardware search system. Such a computer can be treated as a Turing Machine. Instead of sequentially processing computer instructions, this computer executes AI logic reasoning. The parallel hardware search system use pure parallel hardware to execute virtual B-tree search. Hierarchical page table and hash techniques are also used for very large data volume. The prototype of this invented system is successfully built into a PCIE card which mainly contains a Xilinx's Kintex7 FPGA chip and two DDR3 memory modules. FPGA chip includes: 32 32-bit processing units (PUs), one PCIE controller, one search / delete / insert controller and two DDR3 controllers.
Owner:KOUTIN TECH INC
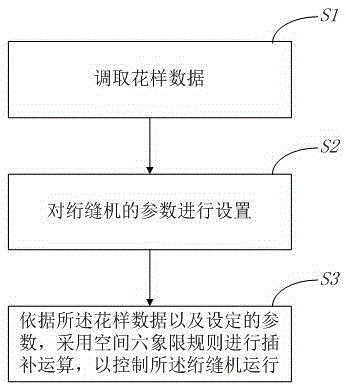
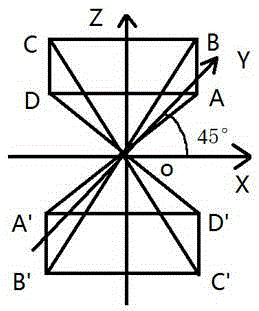
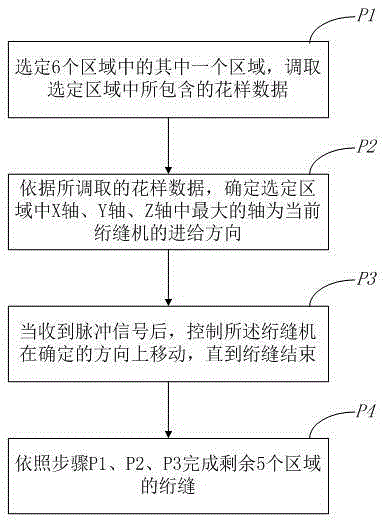
Control method and system for computerized quilting machine
ActiveCN104131419BPracticalImprove efficiencyProgramme-controlled sewing machinesComputer scienceTuring machine
The invention provides a control method and system of a computer quilter. The method comprises the following steps that pattern data are taken; parameters of the quilter are set; and according to the pattern data and the set parameters, a space six-quadrant rule is used for carrying out interpolation operation, and accordingly operation of the quilter is controlled. Compared with the prior art, the space six-quadrant rule is used for controller the quilter to carry out quilting according to the control method and system, space quadrant judging of a program is shortened, accordingly, the length and the executing efficiency of the program are reduced, then the using efficiency of the quilter is improved, using cost is saved, and meanwhile the computer quilter is high in practicability and can be used widely.
Owner:苏州市正步机器制造有限公司
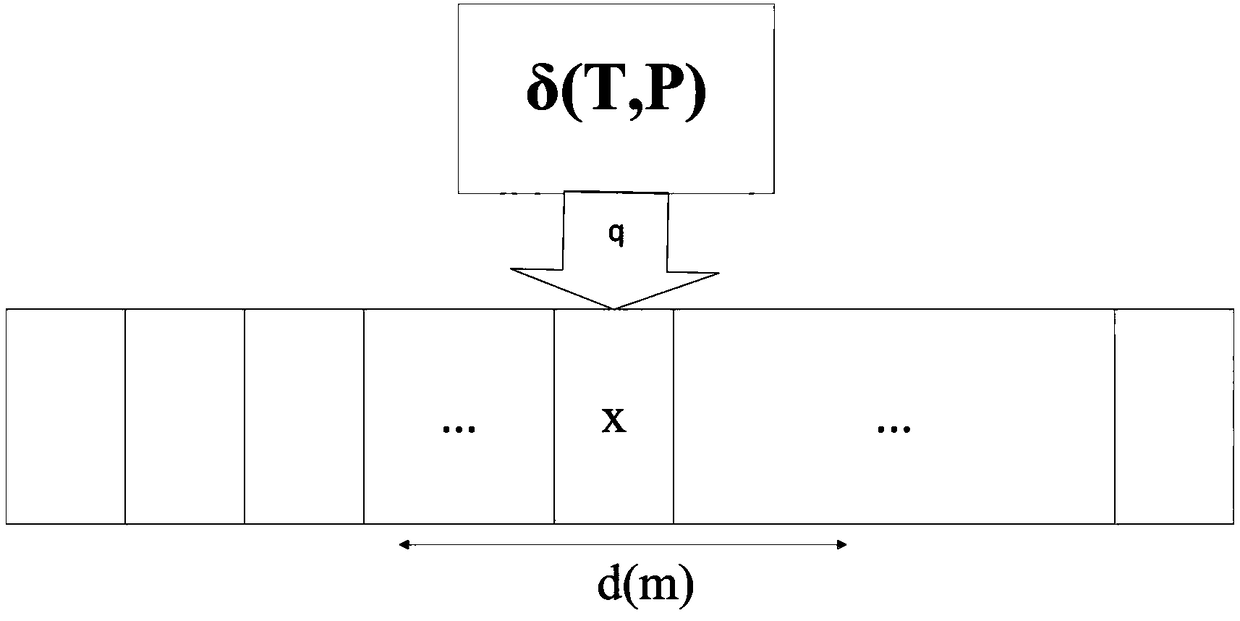
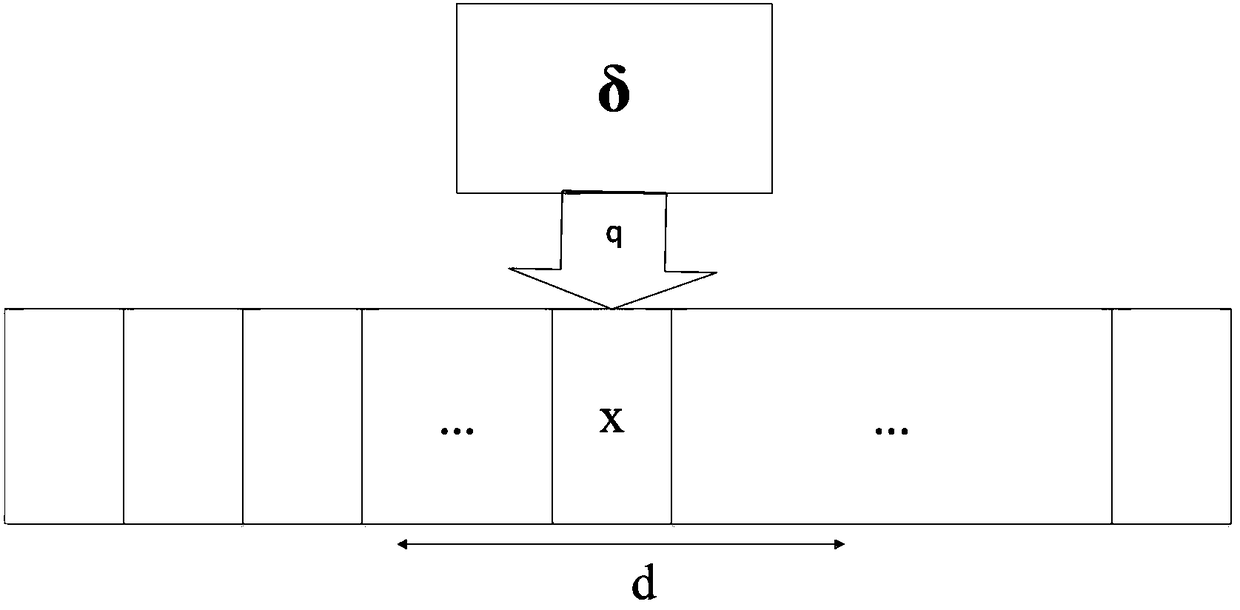
Turing machine insolubility discrimination method and system for big data
The invention discloses a Turing machine insolubility discrimination method and system for big data. According to the Turing machine insolubility distinction method for the big data, a Turing machineM=(Q,sigma,gamma,delta,q0,qaccept,qreject,m,P0,T0,P,T) is defined, and an operating time limit is acquired, wherein an input box is popped up to prompt a user to input the operating time limit as T; aframe threshold of continuous movement of a read-write head is acquired, wherein an input box is popped up to prompt the user to input the frame threshold of continuous movement of the read-write head as m; and a minimum value density threshold and preset operating duration T0 and required value density P of the minimum value density threshold are acquired, wherein an input box is popped up to prompt the user to input the minimum value density threshold, the corresponding preset operating duration and the required value density as P0, T0 and P respectively. According to the discrimination method and system, by adding time, space and output limitations to insolubility judgment of the Turing machine, the demand of big data application is better met.
Owner:SHENZHEN GUOHUA OPTOELECTRONICS +1
Method for deploying network service in cloud
The invention provides a method for deploying a Web service in a cloud based on a Turing machine technology and a DAR (display aspect ratio) algorithm, which combines the abstraction and the wide range of languages capable of being accepted by a Turing machine with the dynamism and the reliability of the DAR algorithm to select the Web service under an easily-failed environment to further establish a model of deploying the Web service in the cloud. With adoption of the method disclosed by the invention, the challenges of rapidly and reliably deploying the Web service in the cloud can be solved. The system is formed by four modules; the uppermost layer is responsible for analyzing a BPEL (business process execution language) Web service; and the middle layer is responsible for selecting a reliable atom Web service, obtaining an attribute value and constructing the normalized Turing machine. The method is mainly is used for two parts of the construction of the turning machine and the Web service selection algorithm DAR. The verification shows that the technology of the invention has the advantages that: 1, the reliable Web service can be selected; and 2, the method has more advantages than the previous technology on the aspect of deploying Web service time and real time.
Owner:广东中南元建网络工程有限公司
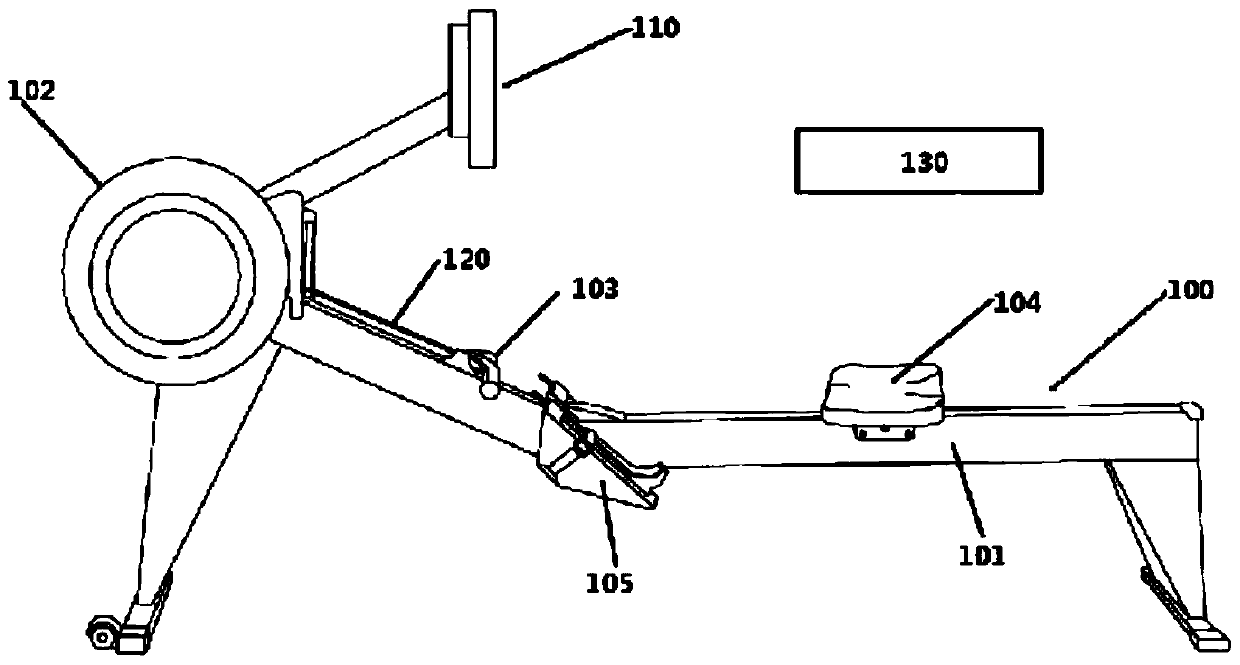
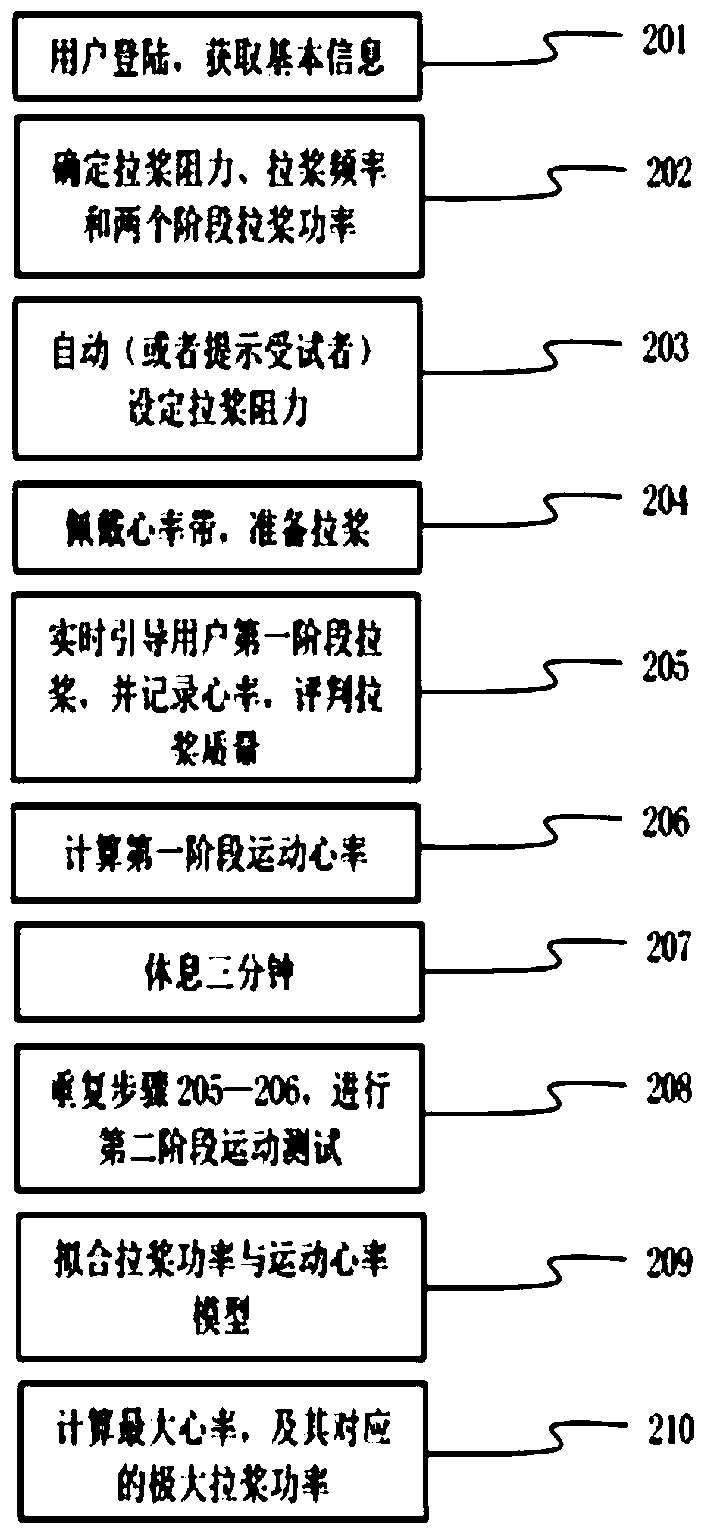
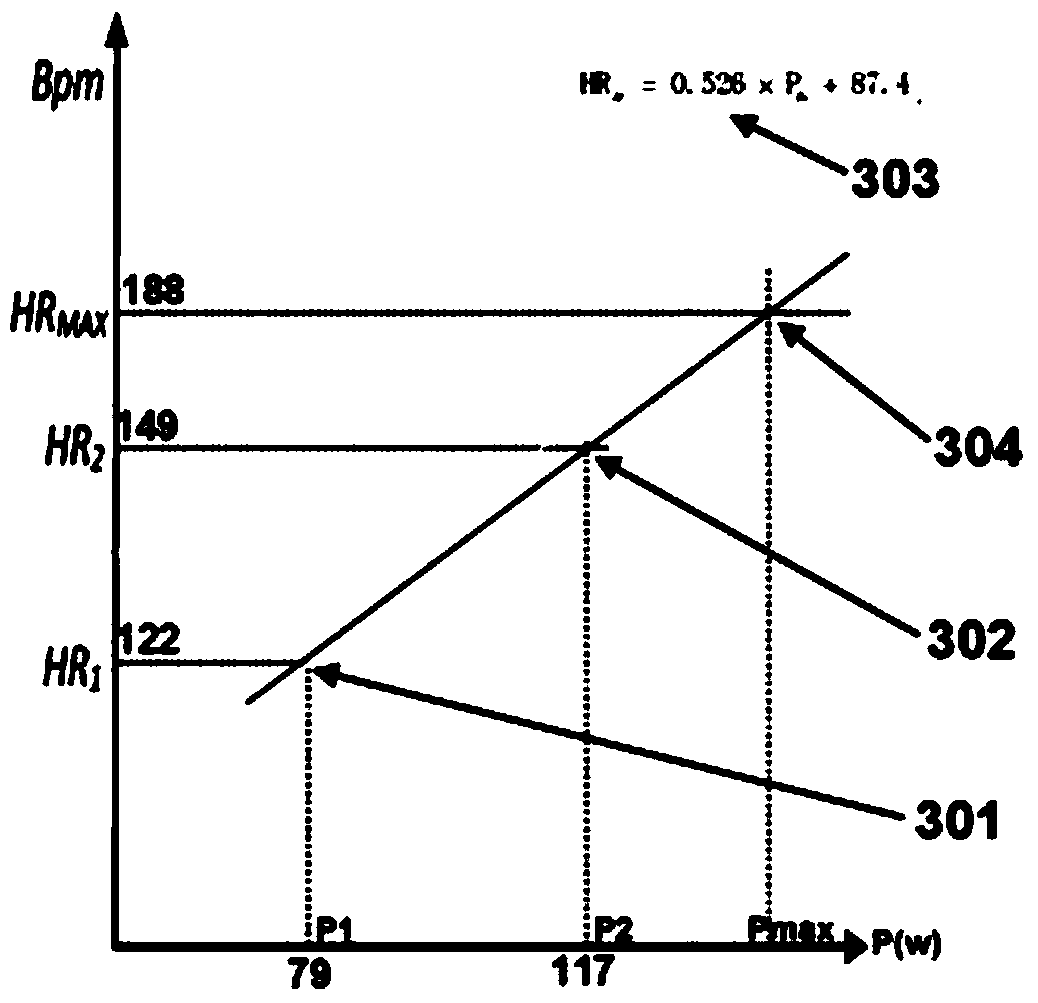
A cardiopulmonary endurance test method based on a rowing machine
InactiveCN104305986BEasy to master the test methodHighly corporatedSensorsMeasuring/recording heart/pulse ratePersonalizationHigh heart rate
The invention discloses a rowing machine-based cardiorespiratory endurance testing method, and is applicable to cardiorespiratory exercise capacity testing in nationwide fitness programs. More specifically, a testing system consisting of a rowing machine body, a testing analysis platform, a pull data acqusition module and a heart rate acqusition module is utilized to guide a subject to finish two groups of stable continuous pull actions with same pull resistance and pull frequency and different pull powers in a set time so as to monitor heart rate response of the subject in real time, establish a linear model between the stage movement heart rate and the pull power and calculate the pull power corresponding to the highest heart rate of the subject to serve as an evaluation index of the cardiorespiratory endurance. Whole-course real-time guide is realized by using sound, light and video signals, the exercise limit is not required to be reached, the method is suitable for a broader crowd of people and is safer, the testing result can objectively reflect the weakness of the cardiorespiratory endurance, a personalized and differentiated fitness plan can be made for the subjects, the exercise effect is improved and scientific guidance is provided.
Owner:HEFEI NORMAL UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com