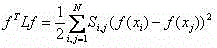Patents
Literature
39 results about "Object domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A domain object is an entity in the domain layer of your application, eg. an Address class. "Model" means the same thing - an entity in the "Domain Model". A POCO (plain old CLR object) is an object that has no behaviour (methods) defined, and only contains data (properties).
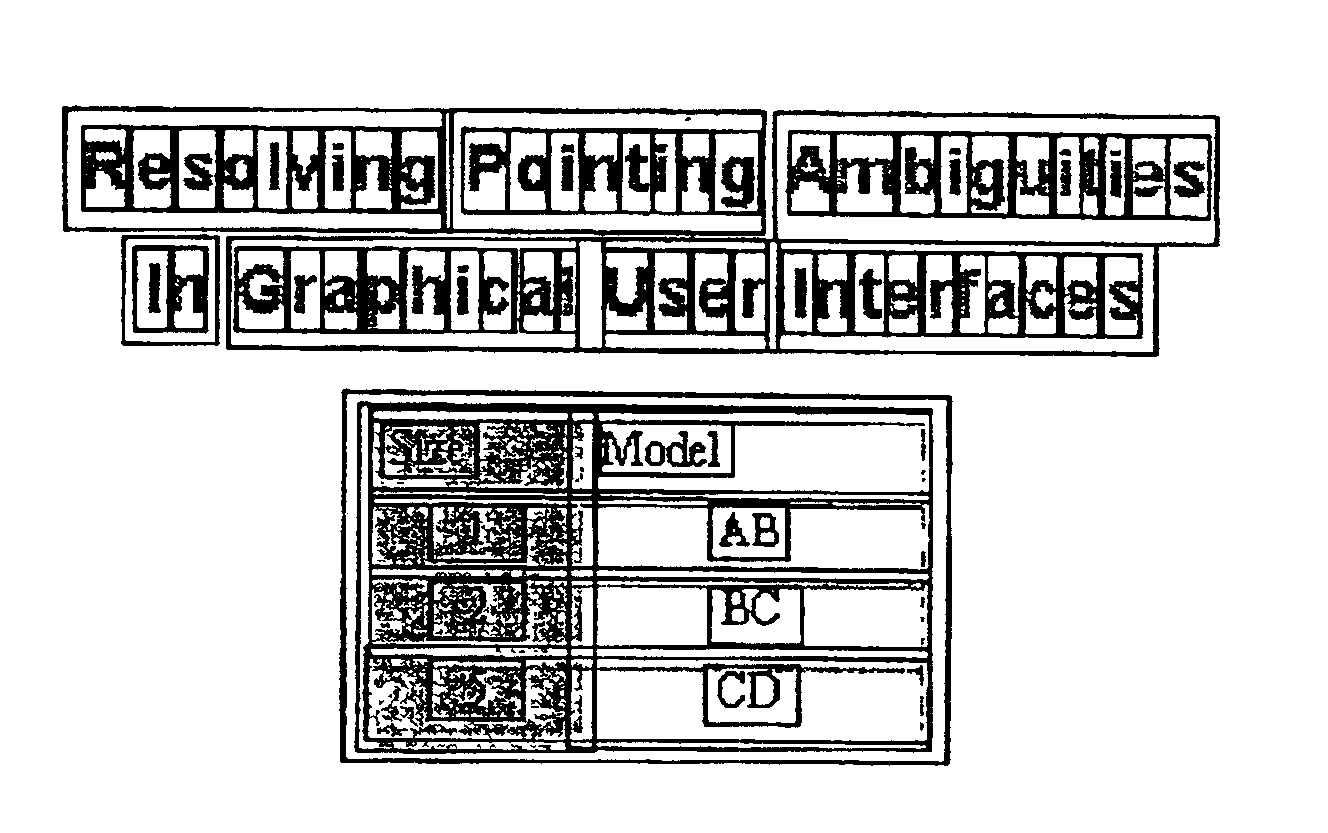
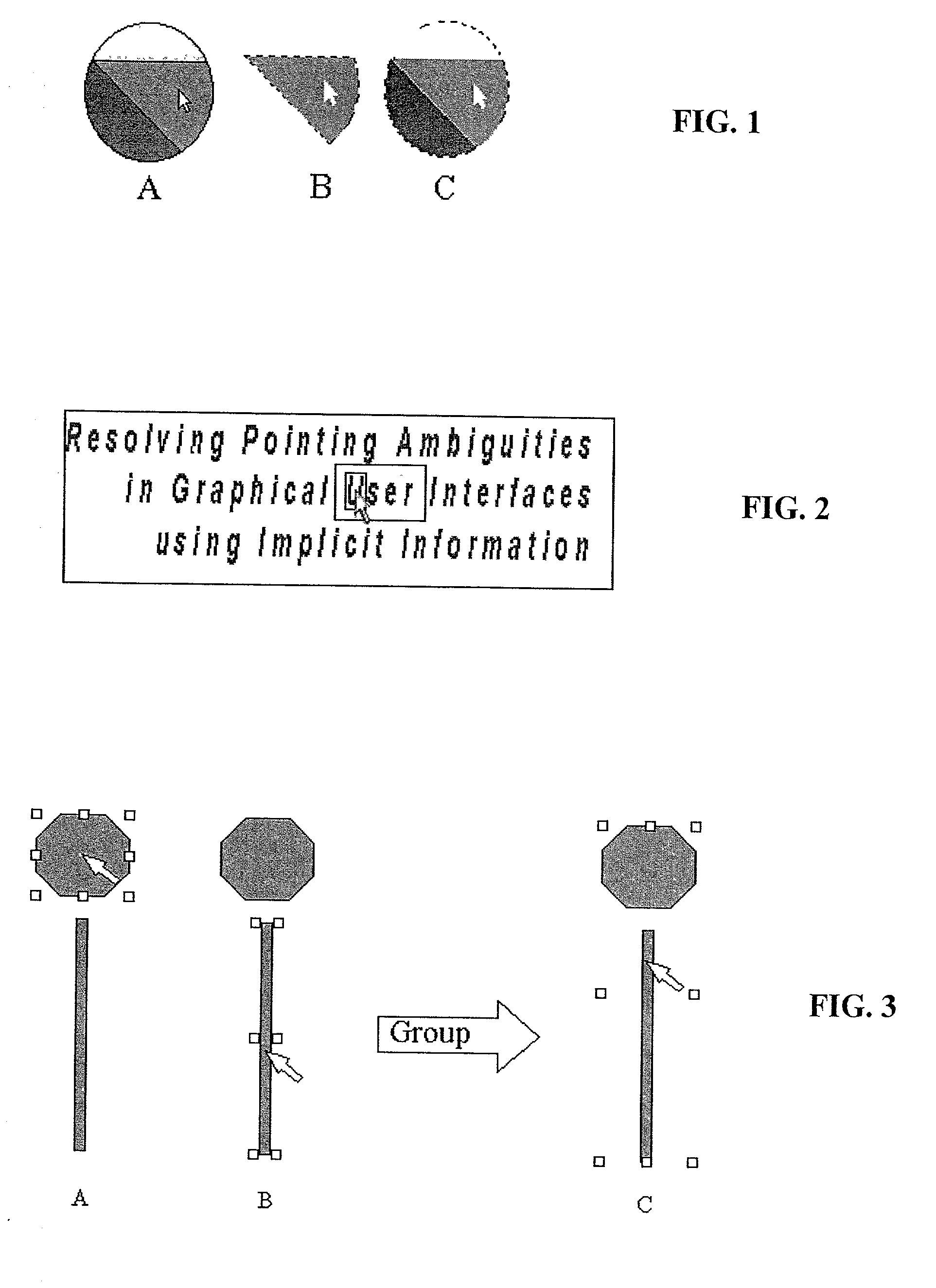
Method and system for implicitly resolving pointing ambiguities in human-computer interaction (HCI)
InactiveUS6907581B2Simple design and implementationEasy accessInput/output processes for data processingObject basedAmbiguity
Owner:RAMOT AT TEL AVIV UNIV LTD
Method and system for implicitly resolving pointing ambiguities in human-computer interaction (HCI)
InactiveUS20030016252A1Accurate understandingStatic indicating devicesInput/output processes for data processingObject basedAmbiguity
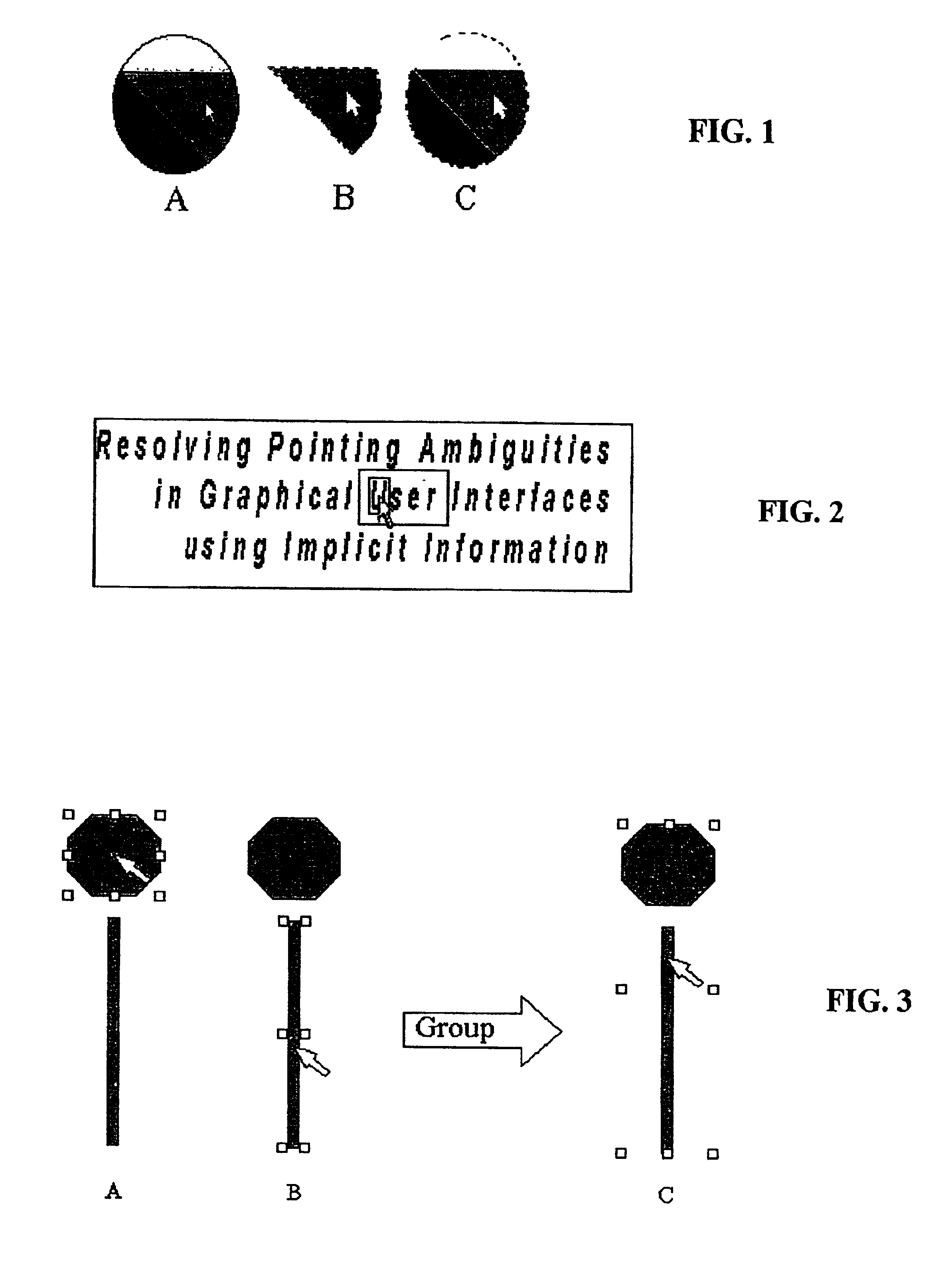
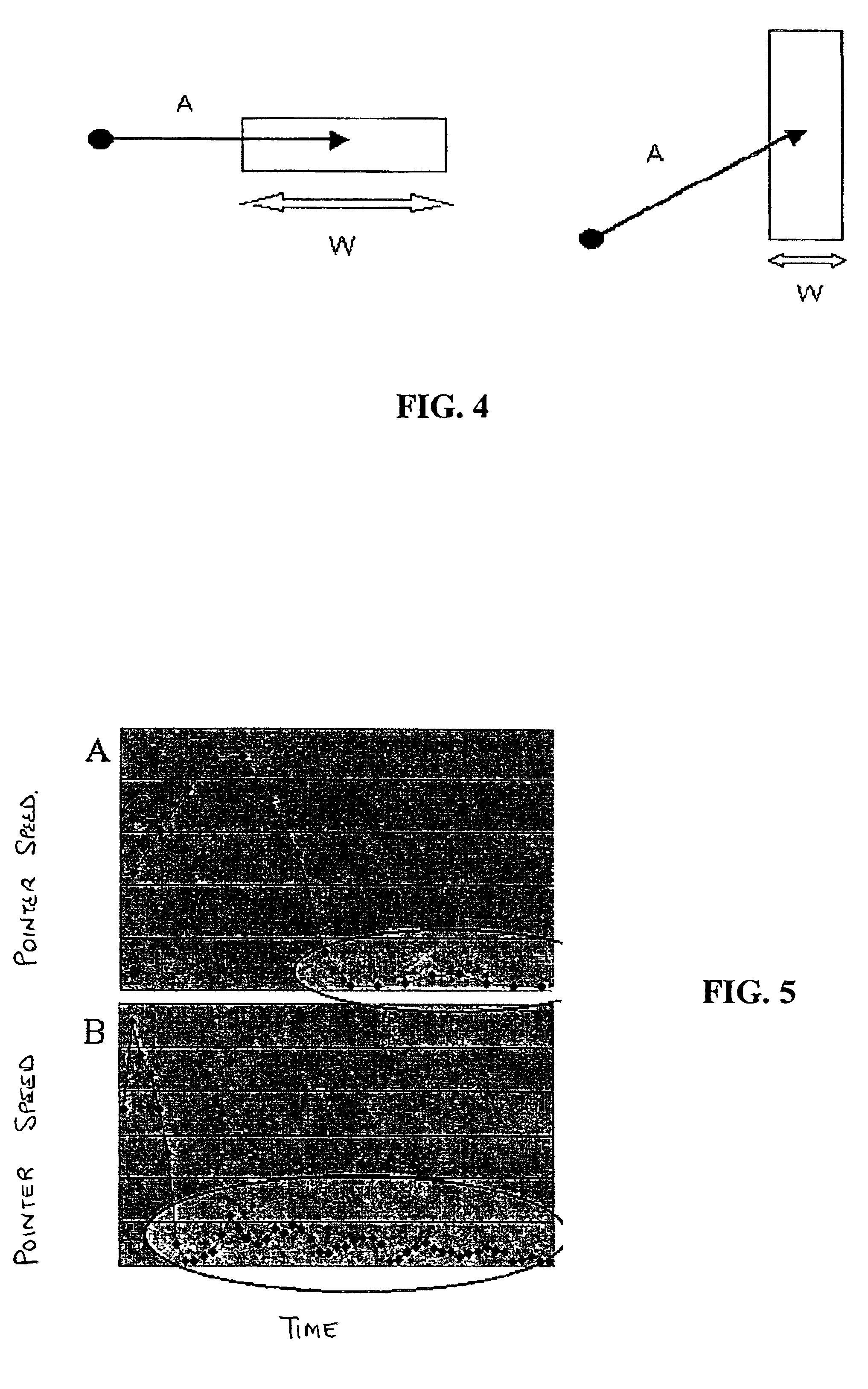
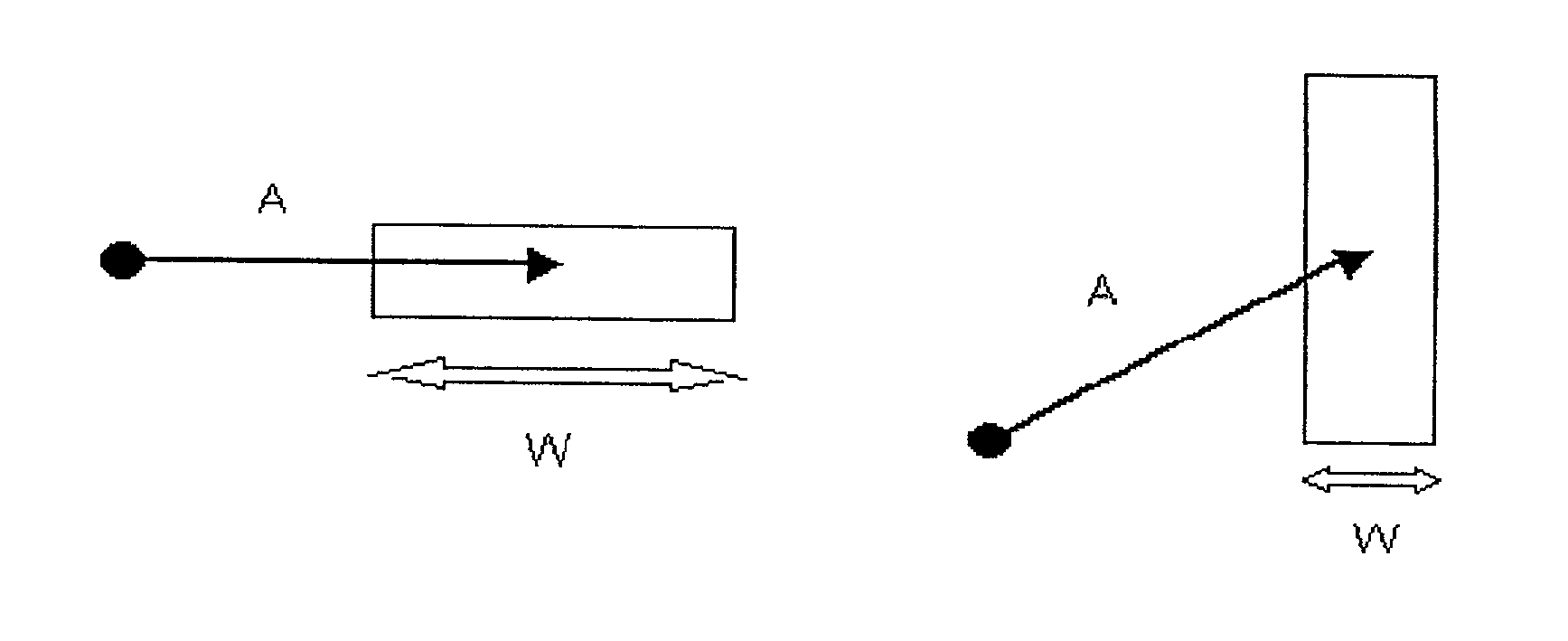
A method and system for implicitly resolving pointing ambiguities in human-computer interaction by implicitly analyzing user movements of a pointer toward a user targeted object located in an ambiguous multiple object domain and predicting the user targeted object, using different categories of heuristic (statically and / or dynamically learned) measures, such as (i) implicit user pointing gesture measures, (ii) application context, and (iii) number of computer suggestions of each predicted user targeted object. Featured are user pointing gesture measures of (1) speed-accuracy tradeoff, referred to as total movement time (TMT), and, amount of fine tuning (AFT) or tail-length (TL), and, (2) exact pointer position. A particular application context heuristic measure used is referred to as containment hierarchy. The invention is widely applicable to resolving a variety of different types of pointing ambiguities such as composite object types of pointing ambiguities, involving different types of pointing devices, and which are widely applicable to essentially any type of software and / or hardware methodology involving using a pointer, such as in computer aided design (CAD), object based graphical editing, and text editing.
Owner:RAMOT AT TEL AVIV UNIV LTD
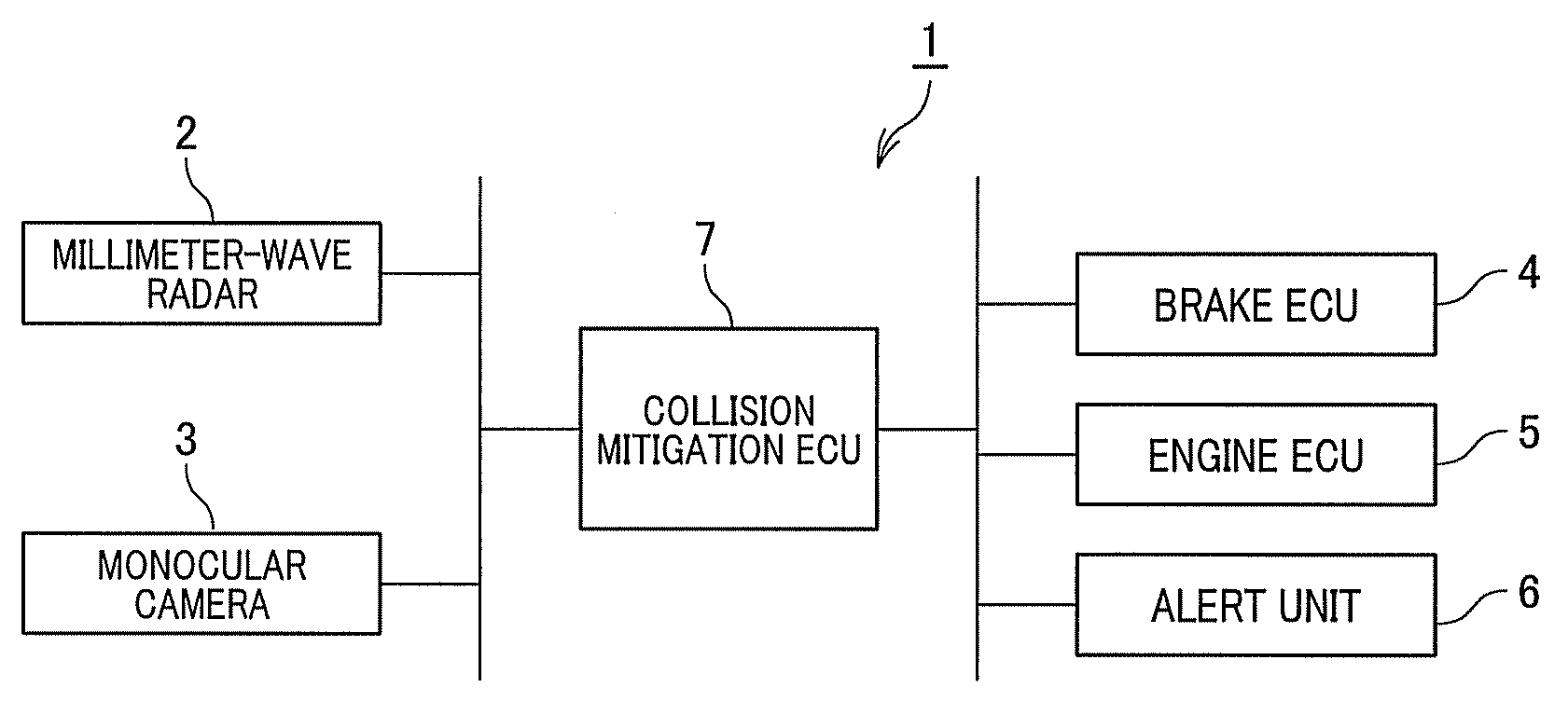
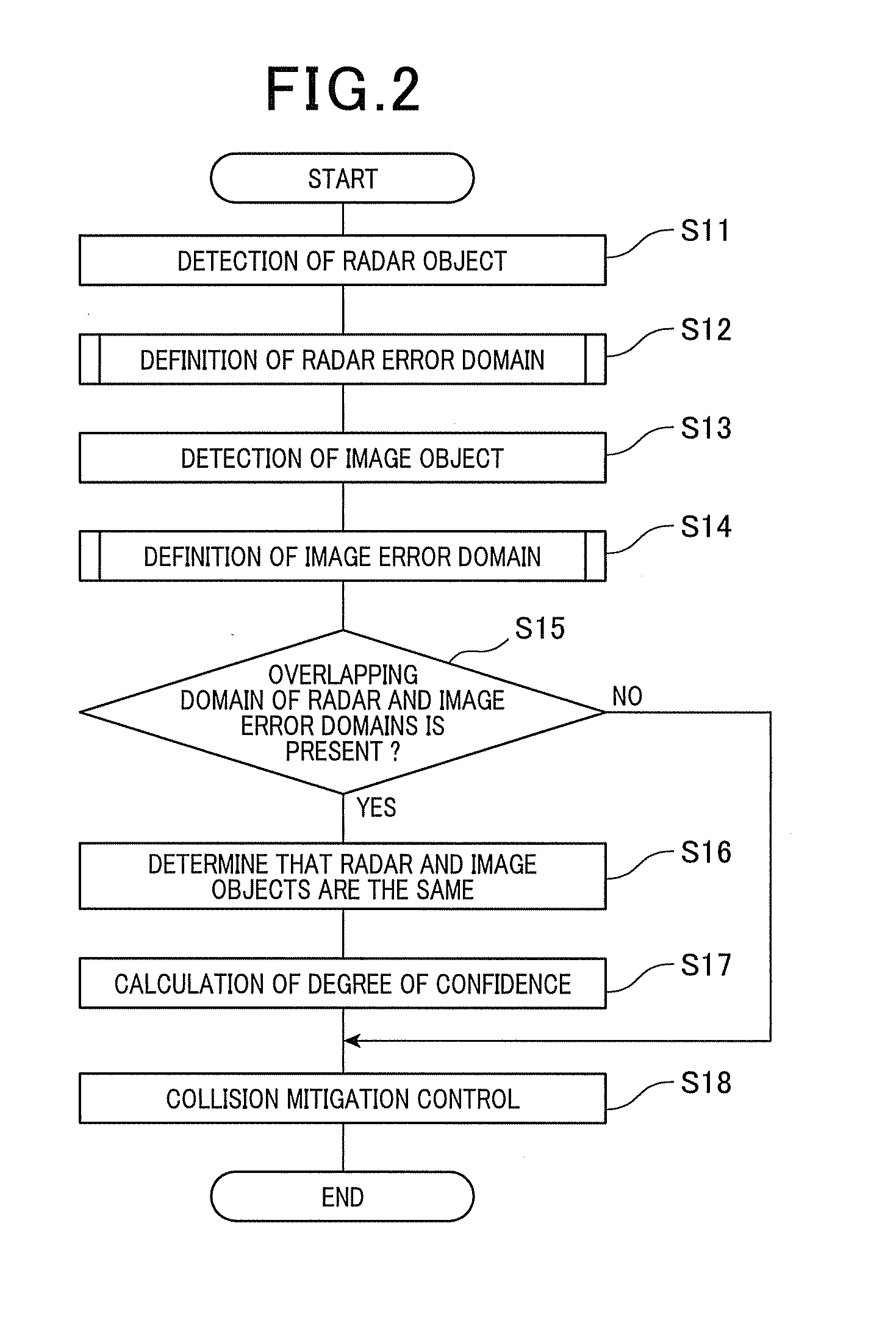
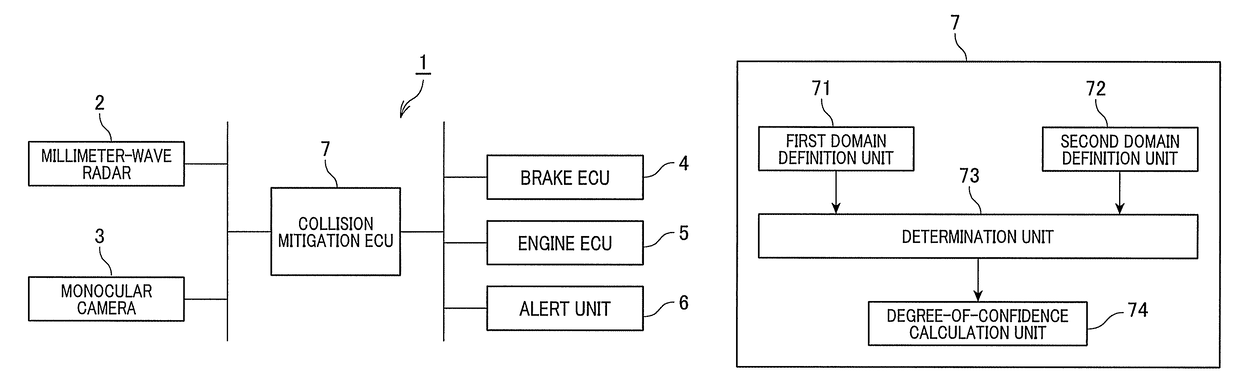
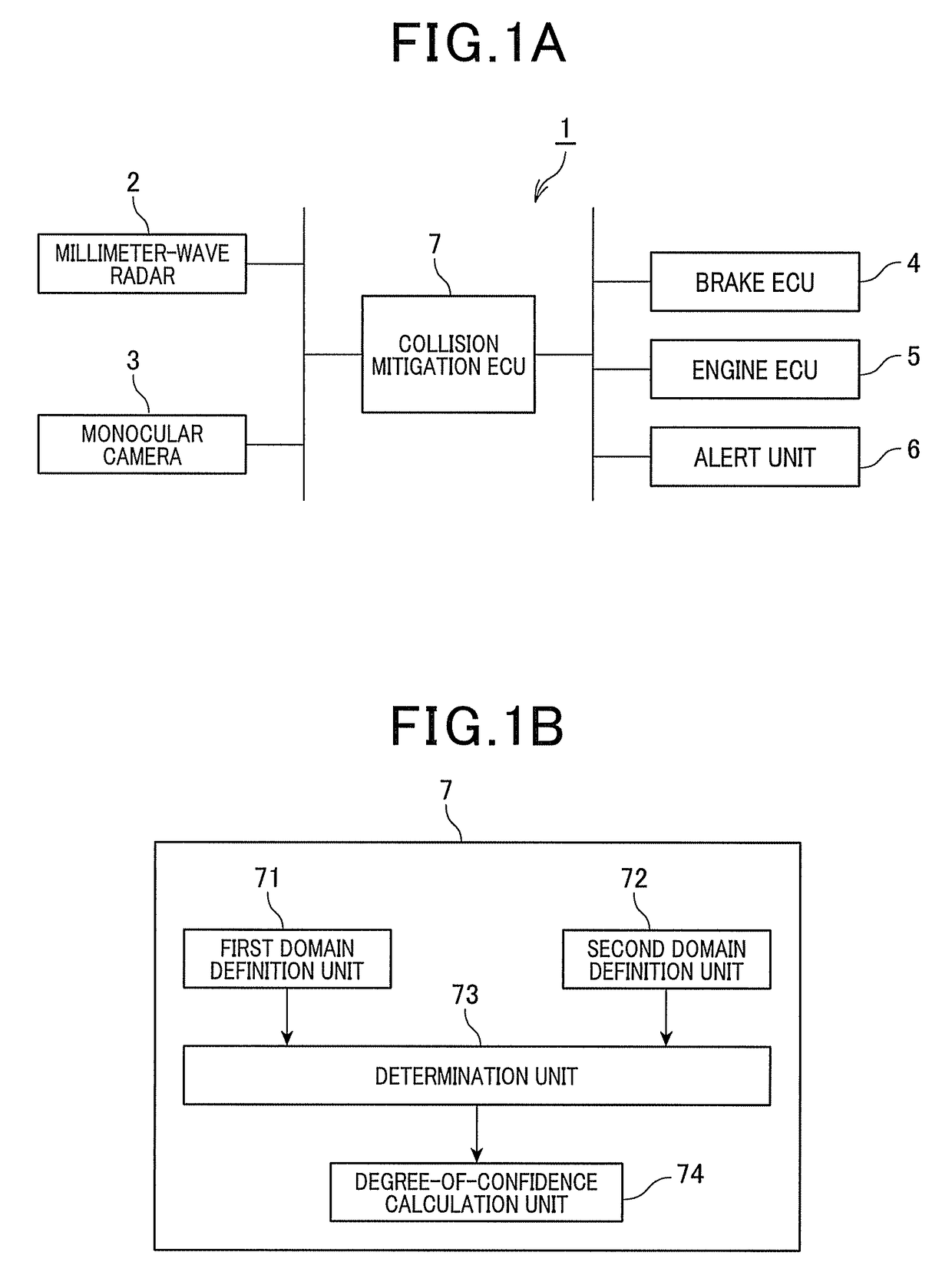
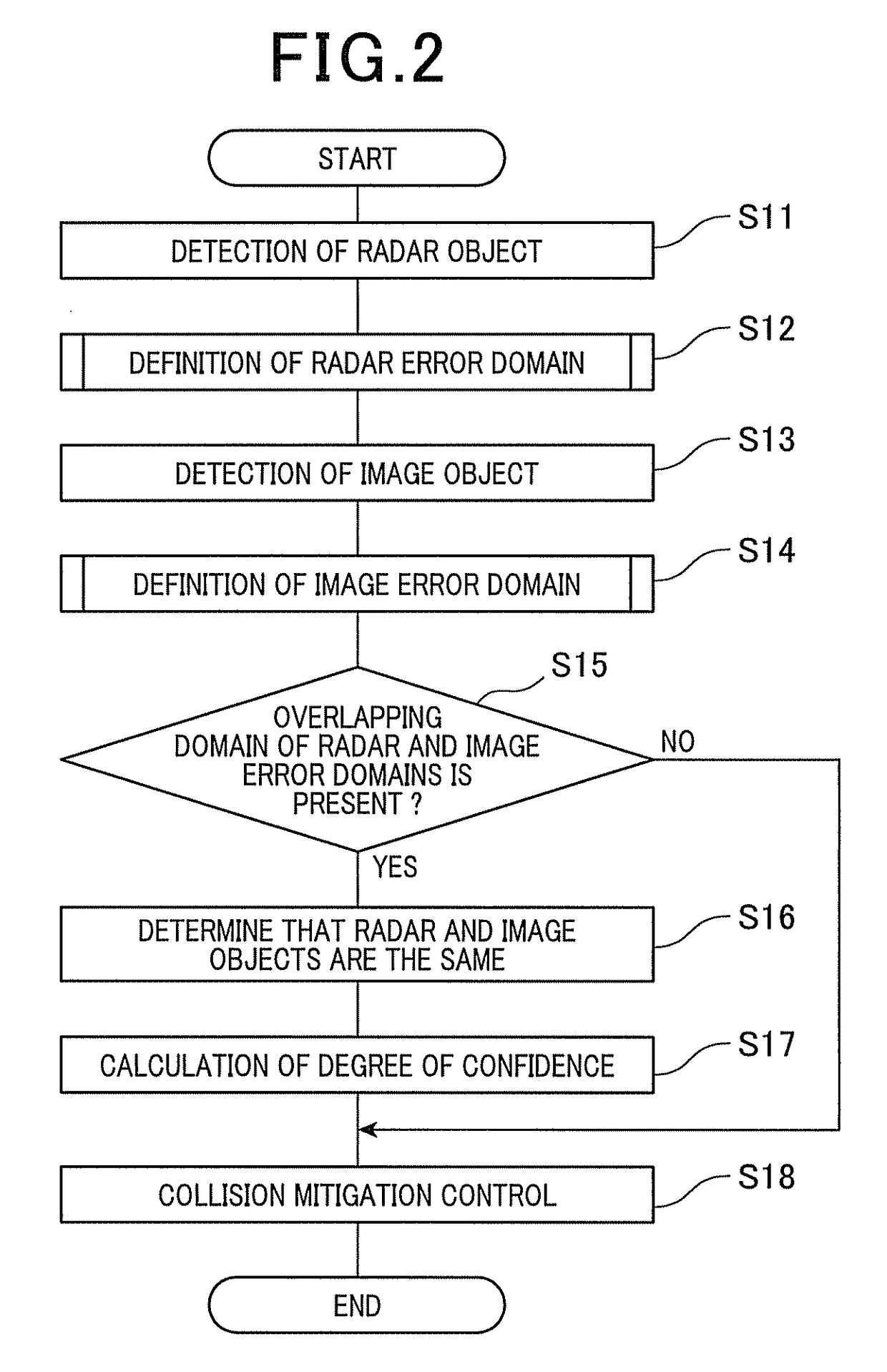
Object detection apparatus
ActiveUS20140139369A1Avoid misjudgmentPedestrian/occupant safety arrangementOptical detectionRadarImage detection
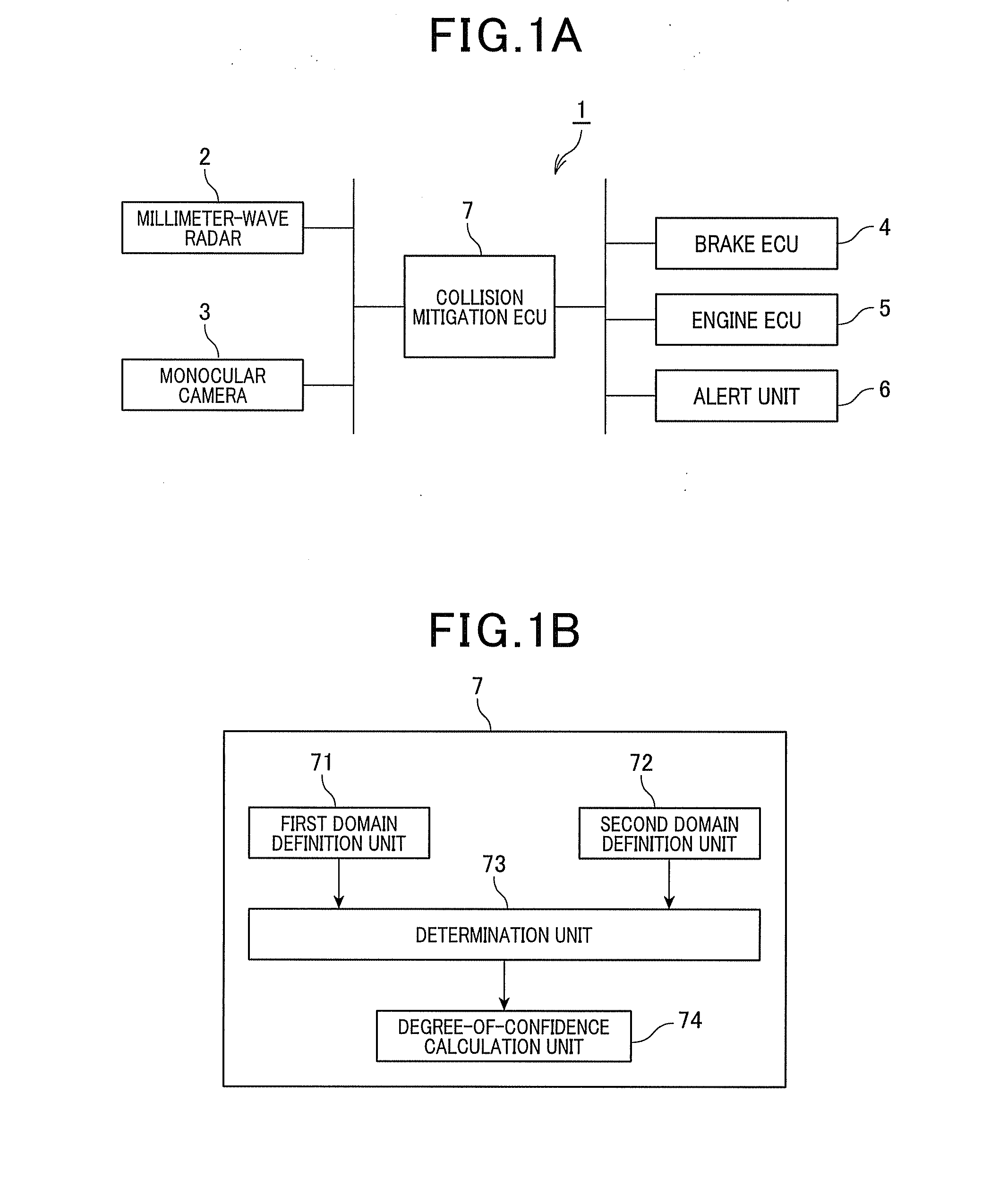
An object detection apparatus mounted in a vehicle, includes a first domain definition unit, a second domain definition unit, and a determination unit. The first domain definition unit defines a first object domain including a first detection point which is indicative of a position of a first object detected by using a vehicle-mounted radar. The second domain definition unit defines a second object domain including a second detection point which is indicative of a position of a second object detected on the basis of an image captured by a vehicle-mounted monocular camera. The determination unit determines whether or not an overlapping domain of the first and second object domains is present, and when it is determined that an overlapping domain of the first and second object domains is present, then determines that the first and second objects are the same.
Owner:DENSO CORP
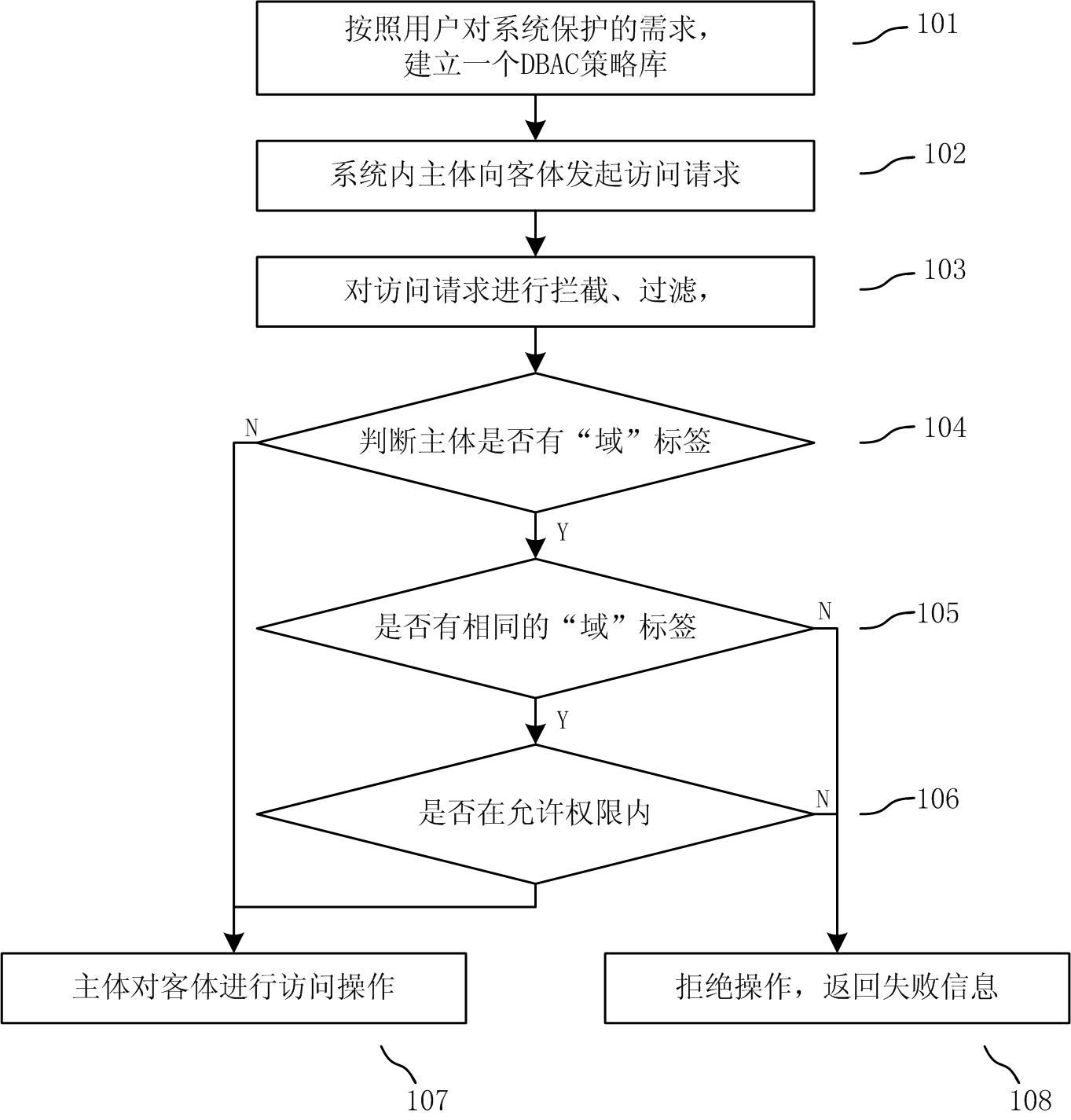
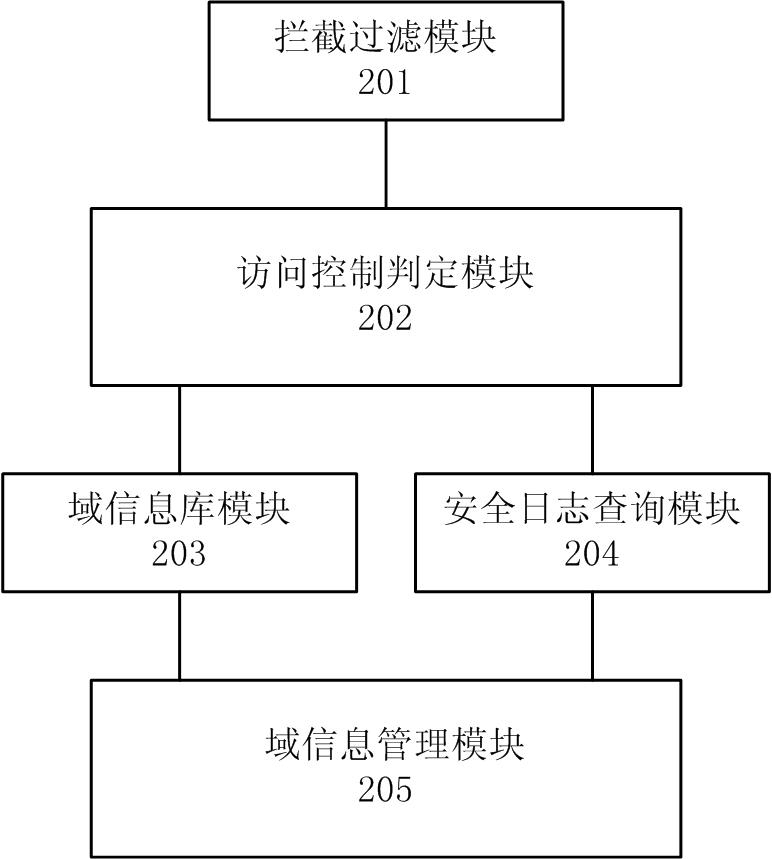
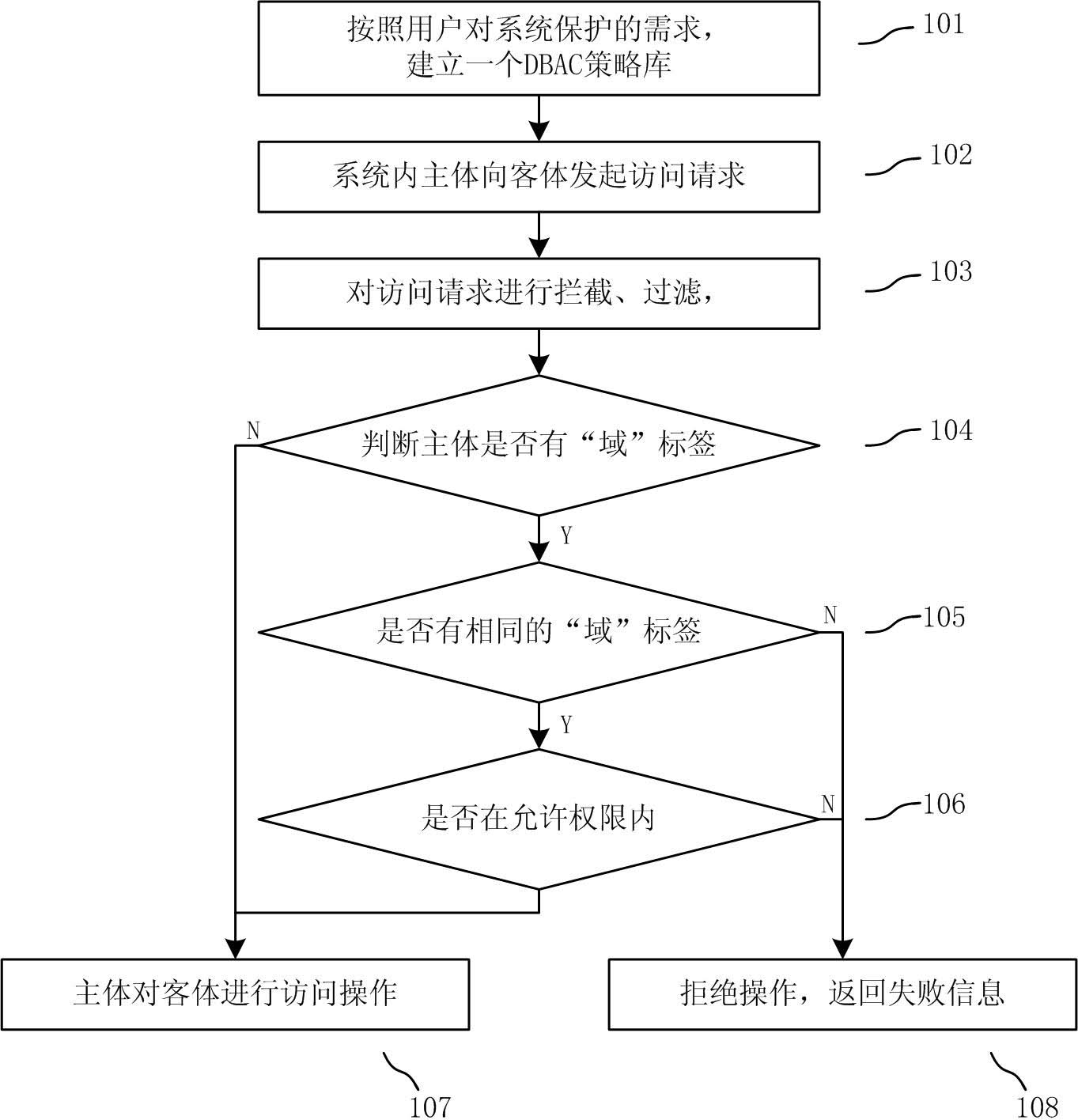
Domain-based access control method and system
InactiveCN102495988AImprove applicabilityEase of usePlatform integrity maintainanceInformation repositoryOperational system
The invention relates to a domain-based access control method and system. The domain-based access control method comprises the following steps of: setting a domain label of each application and establishing a domain-based access control policy library on subject and object of each application in a system through aiming at different application domains according to requirements of a user on protection of the system; capturing an access request of the subject on the object in the system; submitting the access request to the domain-based access control policy library to perform domain label detection; and judging whether a current operation is allowed or not, accepting the current access request if the current operation is allowed, and refusing the current access request if the current operation is not allowed. The domain-based access control system comprises a capturing filtering module, an access control judging module, a domain database module, a domain information managing module and a safety journal querying module, wherein the capturing filtering module is used for capturing and filtering data access requests of application programs in the system, the access control judging module is used for judging whether a subject domain label and an object domain label are same or not and determining whether an access action is allowed or not, the domain database module is used for saving information of the access control policy library, the domain information managing module is used for modifying the information of the access control policy library and querying safety journals, and the safety journal querying module is used for storing dangerous operation information disobeying an access control policy. According to the domain-based access control method and system, disclosed by the invention, the application program can be effectively protected, and the safety of the application program and an operating system can be improved.
Owner:BEIJING NASE HENGXIN TECH
Smart city system
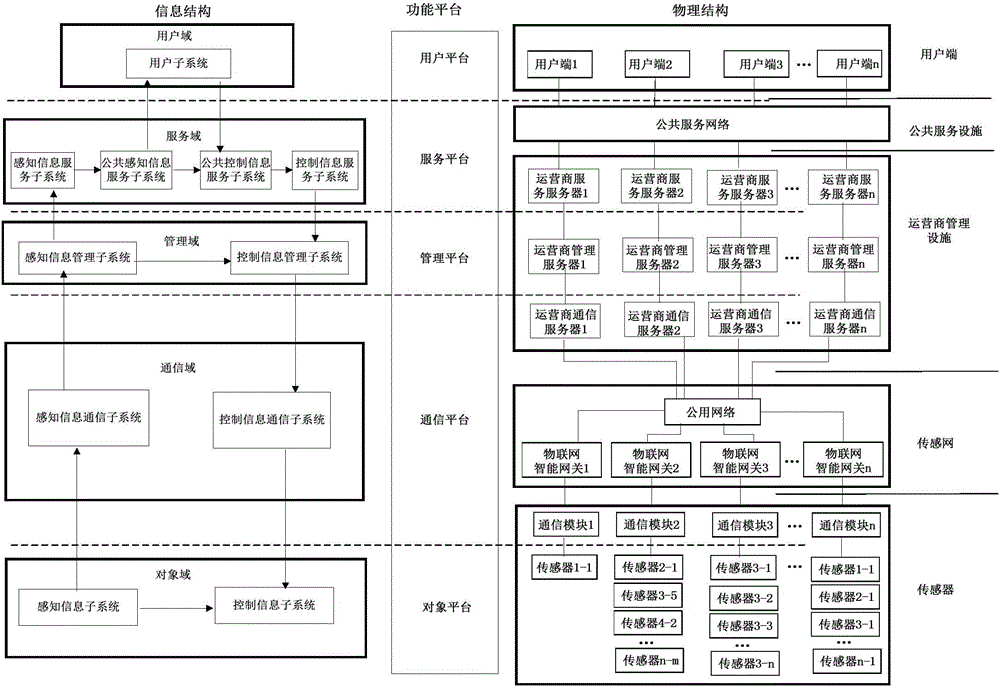
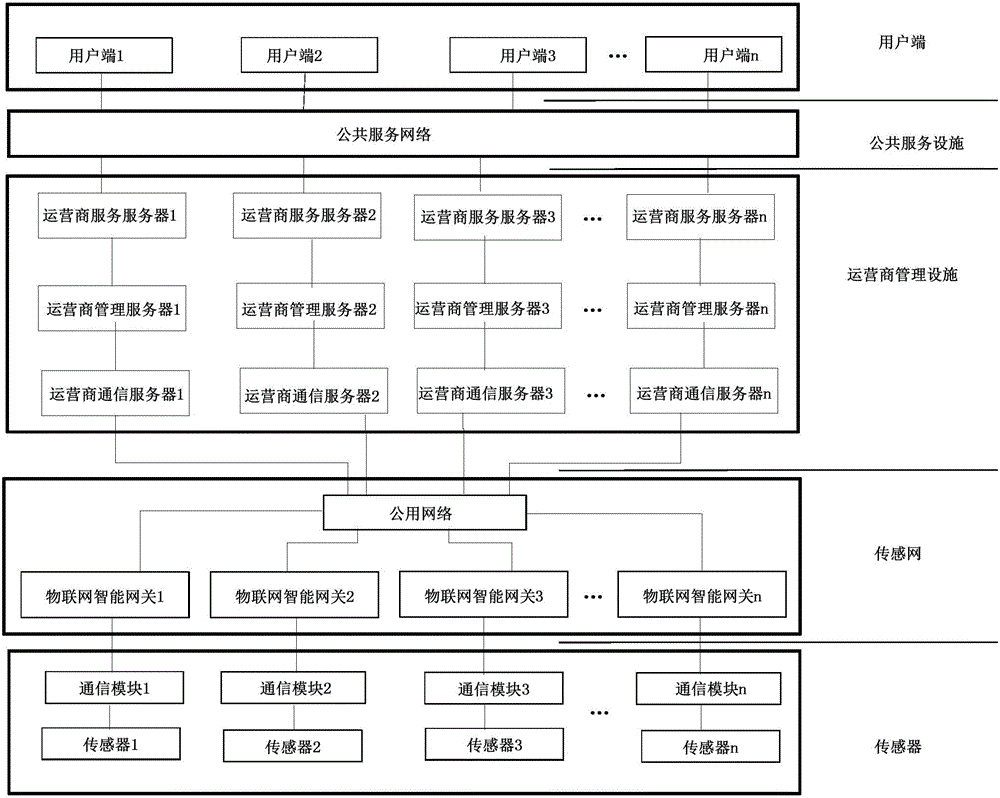
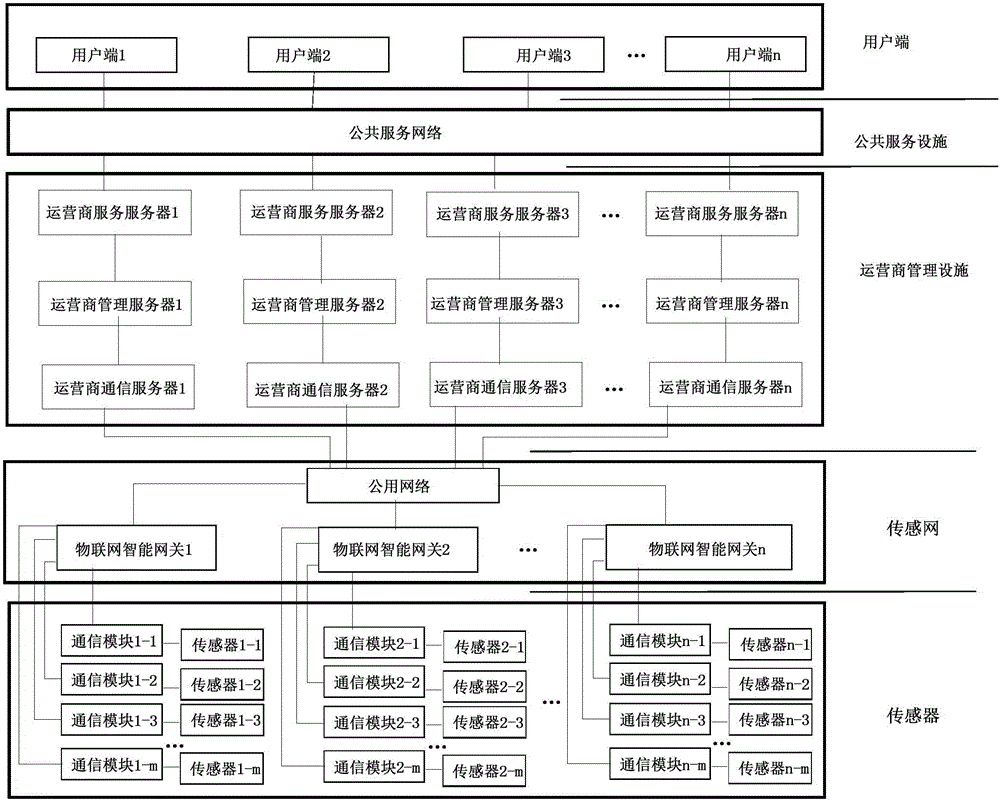
The invention discloses a smart city system, and belongs to an Internet of things system. The system comprises a smart city information system, a smart city physical system and a smart city function system. The smart city information system comprises an object domain, a communication domain, a management domain, a service domain and a user domain; the smart city physical system comprises multiple Internet of things units, wherein each Internet of things unit comprises a sensor, an Internet of things intelligent gateway, a service provider management server and a user end; and the smart city function system comprises an object platform, a communication platform, a management platform, a service platform and a user platform. The integral smart city system provided by the invention is simple in structure and diversified in transmission modes, has great reference significance for arrangement of various modes in construction of a smart city, can be used as a system with different functions in a smart city design system, and is wide in application scope.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
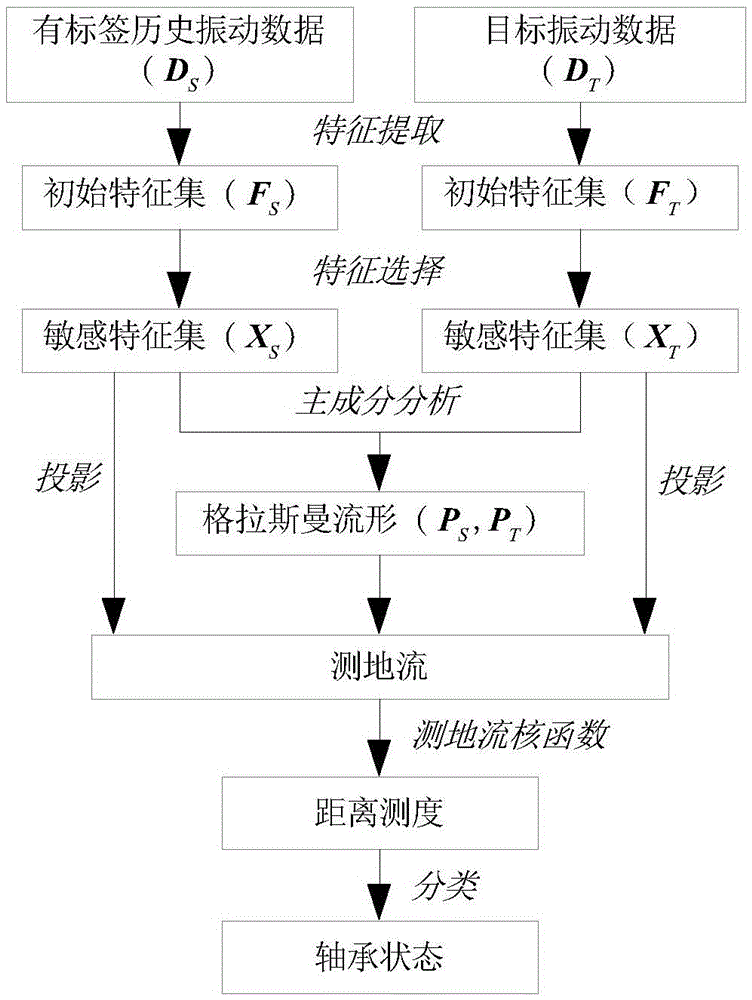
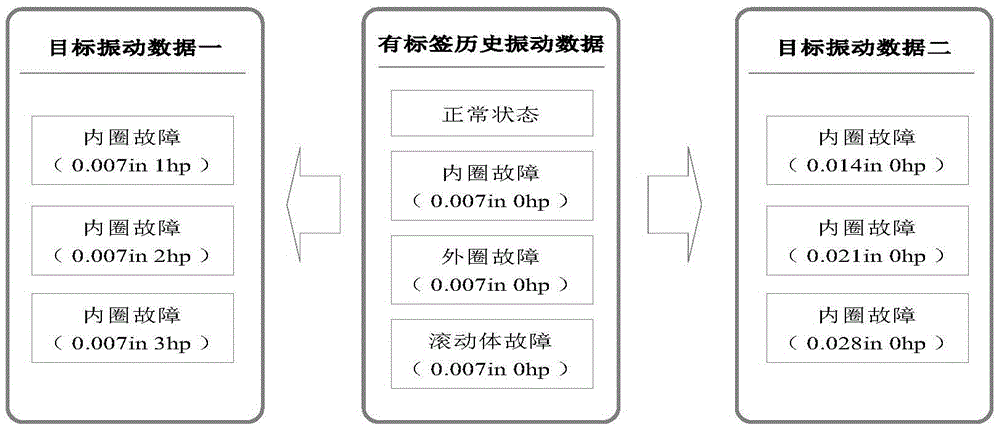
Bearing fault diagnosis method based on domain adaptation
The invention relates to a bearing fault diagnosis method based on domain adaptation. The method comprises the following steps: respectively performing feature extraction on label historical vibration data and object vibration data, based on distance indexes, selecting sensitive feature sets, Grassman manifolds are constructed through principle component analysis, geodesic flows are constructed based on this, by taking the sensitive feature set of vibration of the label historical vibration data as a source domain and the sensitive feature set of the object vibration data as an object domain, the two domains are projected on the geodesic flows for the domain adaptation, and based on distance measurement of projection, bearing state identification of the object vibration data is realized. A result obtained by applying the method to a bearing fault diagnosis indicates that the method can effectively overcome vibration data deviations caused by such factors as working conditions, bearing individual differences and the like and displays a quite high engineering application value.
Owner:UNIV OF JINAN
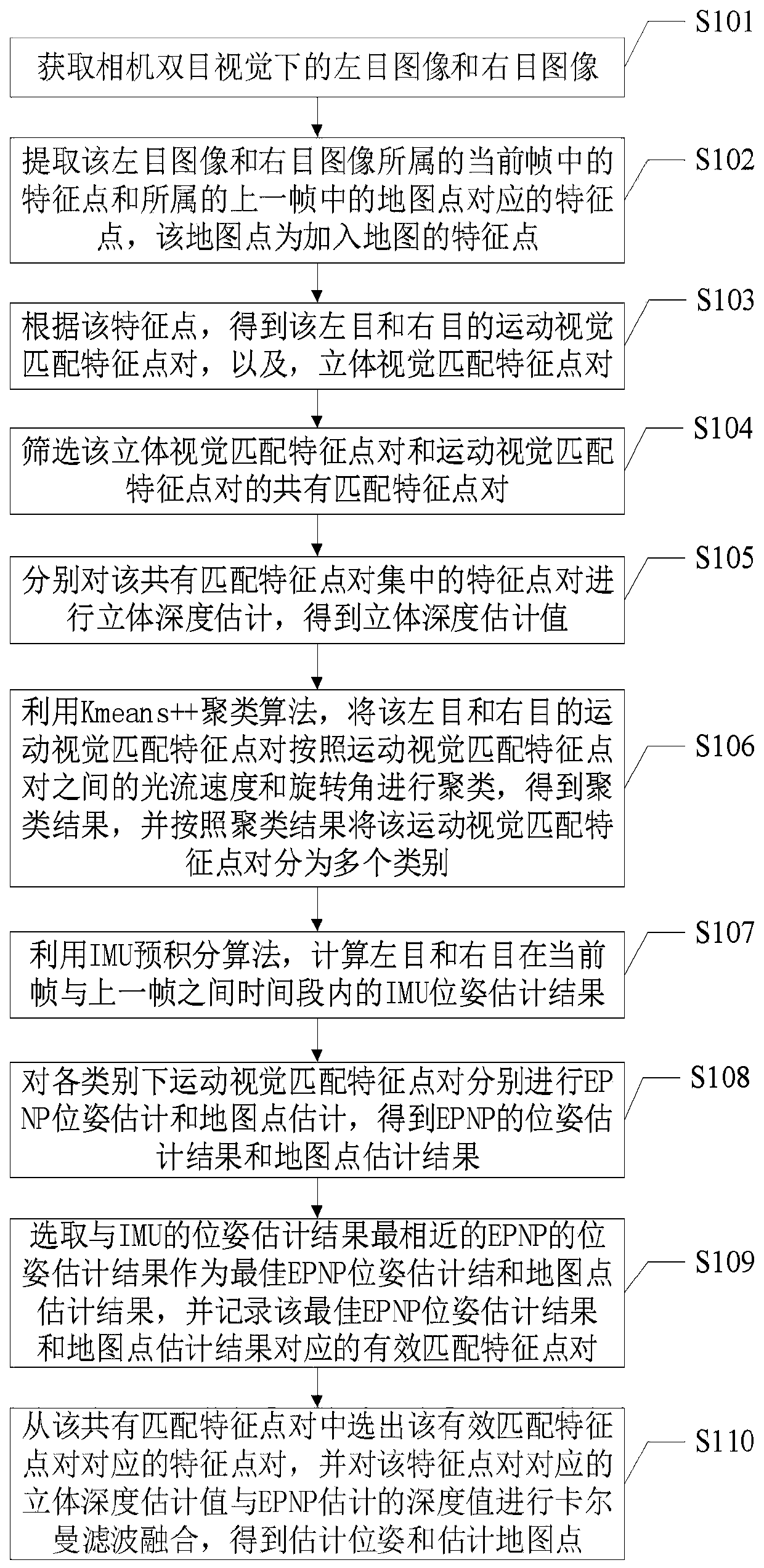
Binocular vision positioning method and system in dynamic environment
ActiveCN110490900AAccurate removalAvoid cullingImage enhancementImage analysisObject pointVisual perception
The invention discloses a binocular vision positioning method and system in a dynamic environment applied to the technical field of robot positioning. The method comprises the following steps of extracting image feature points, distinguishing the feature points on the moving object points and the feature points on the non-moving object points in a mode of clustering the feature points. The featurepoints on the moving object can be effectively eliminated so that elimination of feature points on a static dynamic attribute object is avoided, more available feature points are reserved, and poseswhich are closest to IMU data and are estimated based on different feature point sets are screened through an inter-frame pose transformation matrix obtained through an IMU pre-integration algorithm,so that some external points such as feature points belonging to a moving object are effectively eliminated. According to the poses and depth estimation method integrating monocular motion vision andbinocular stereoscopic vision, the estimation precision can be effectively improved.
Owner:UNIV OF SCI & TECH OF CHINA
Multi-spectral reconstruction method based on adaptive finite element
ActiveUS20080259074A1Less discomfortQuality improvementCharacter and pattern recognitionDiagnostics using tomographyRegion selectionPrior information
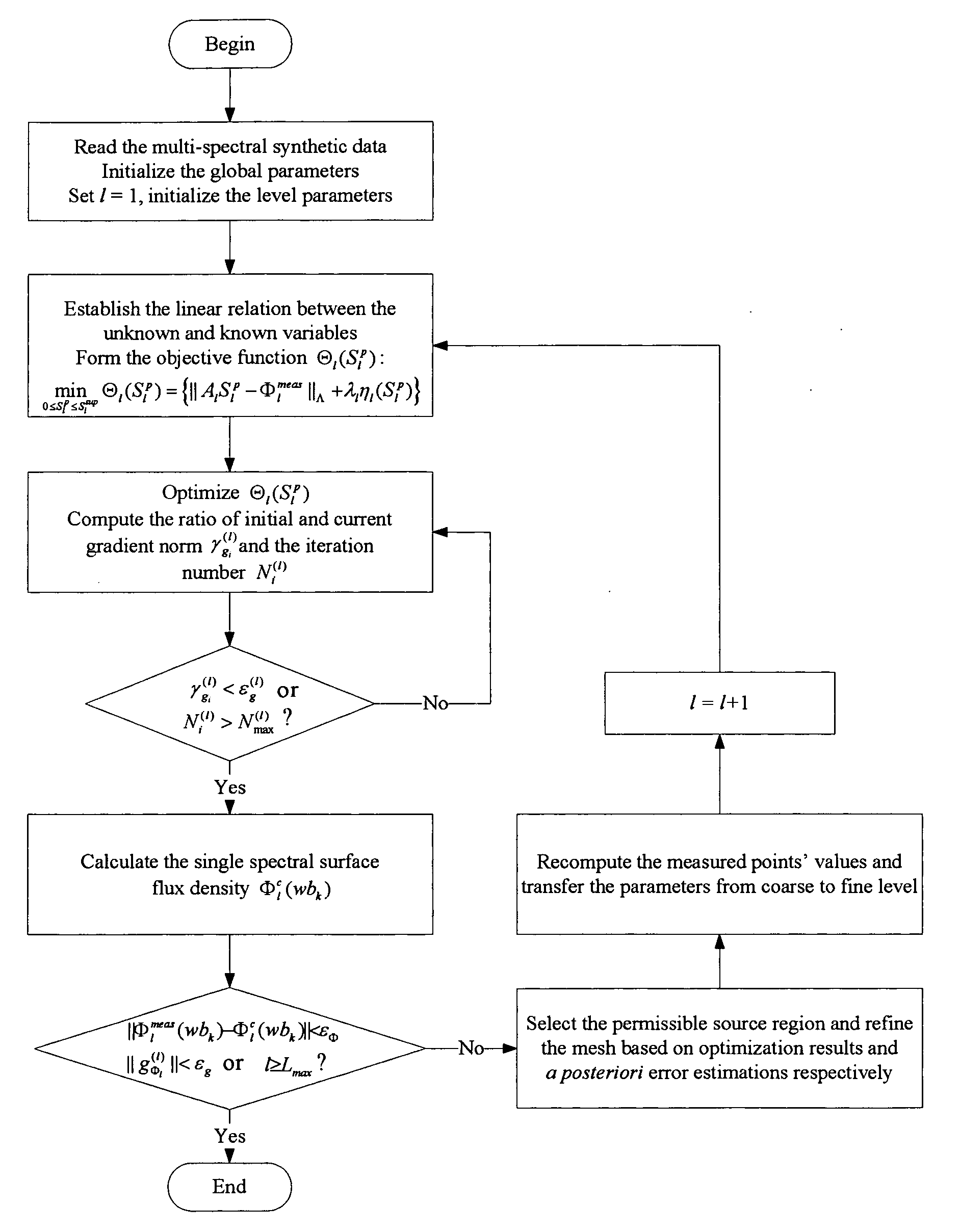
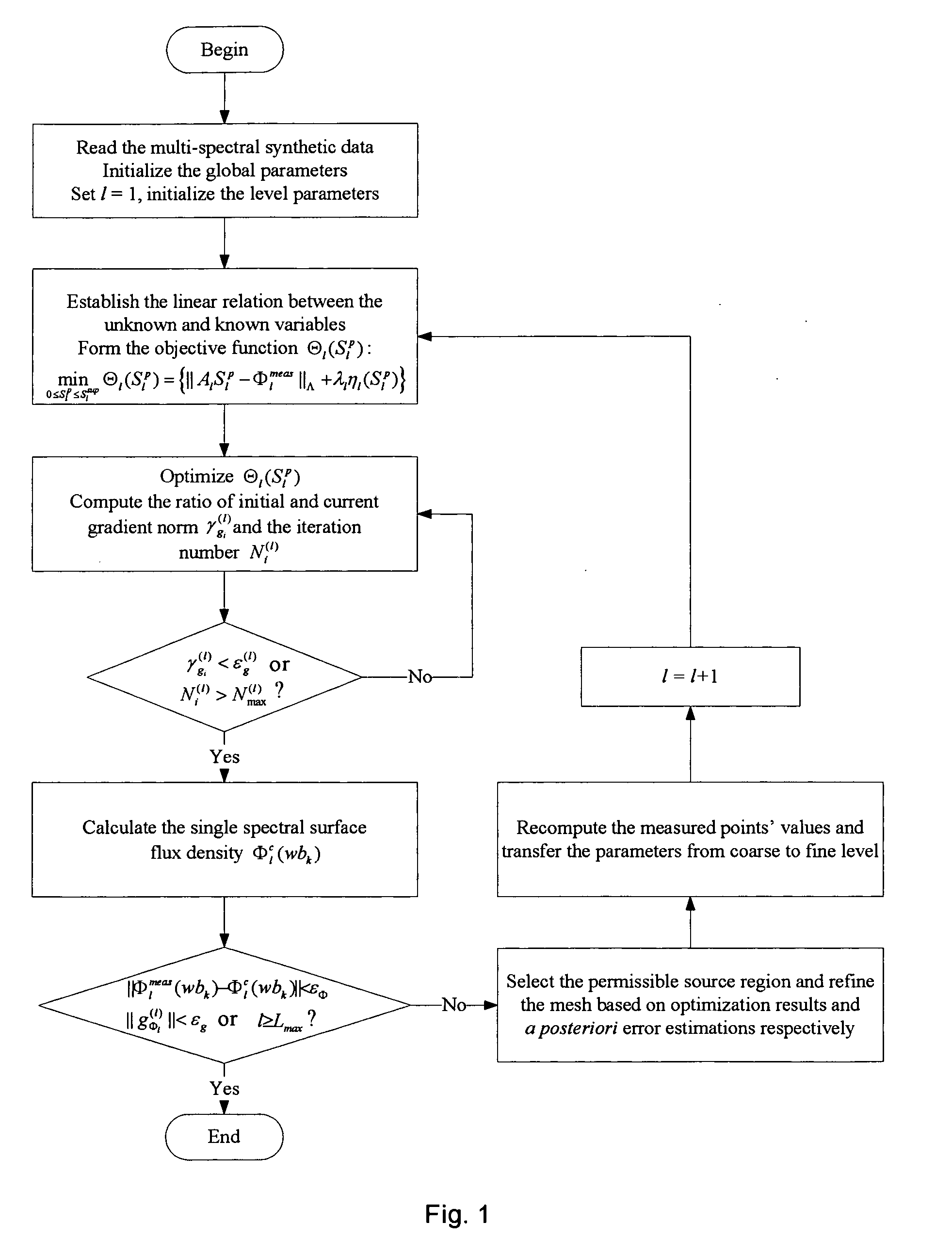
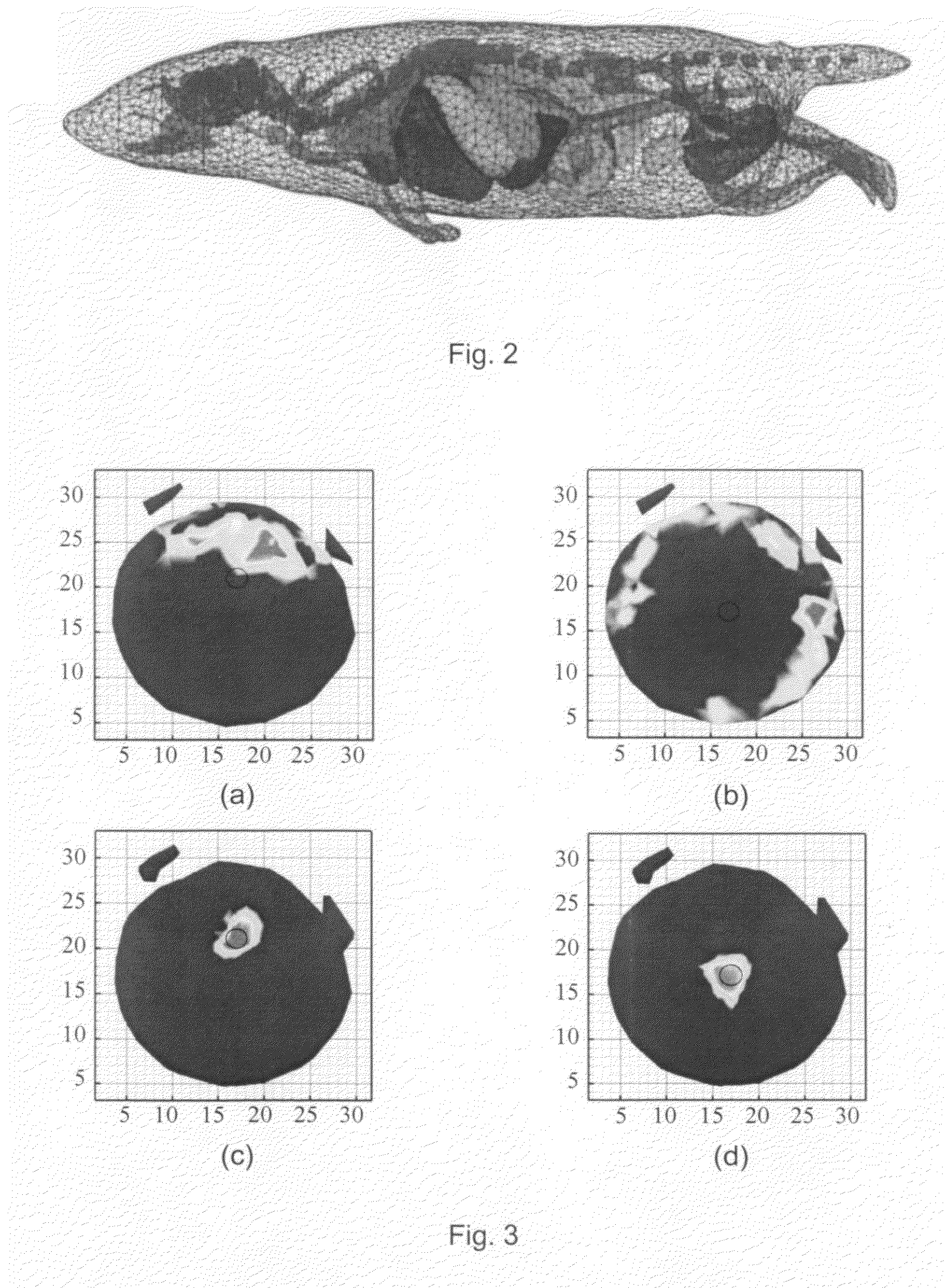
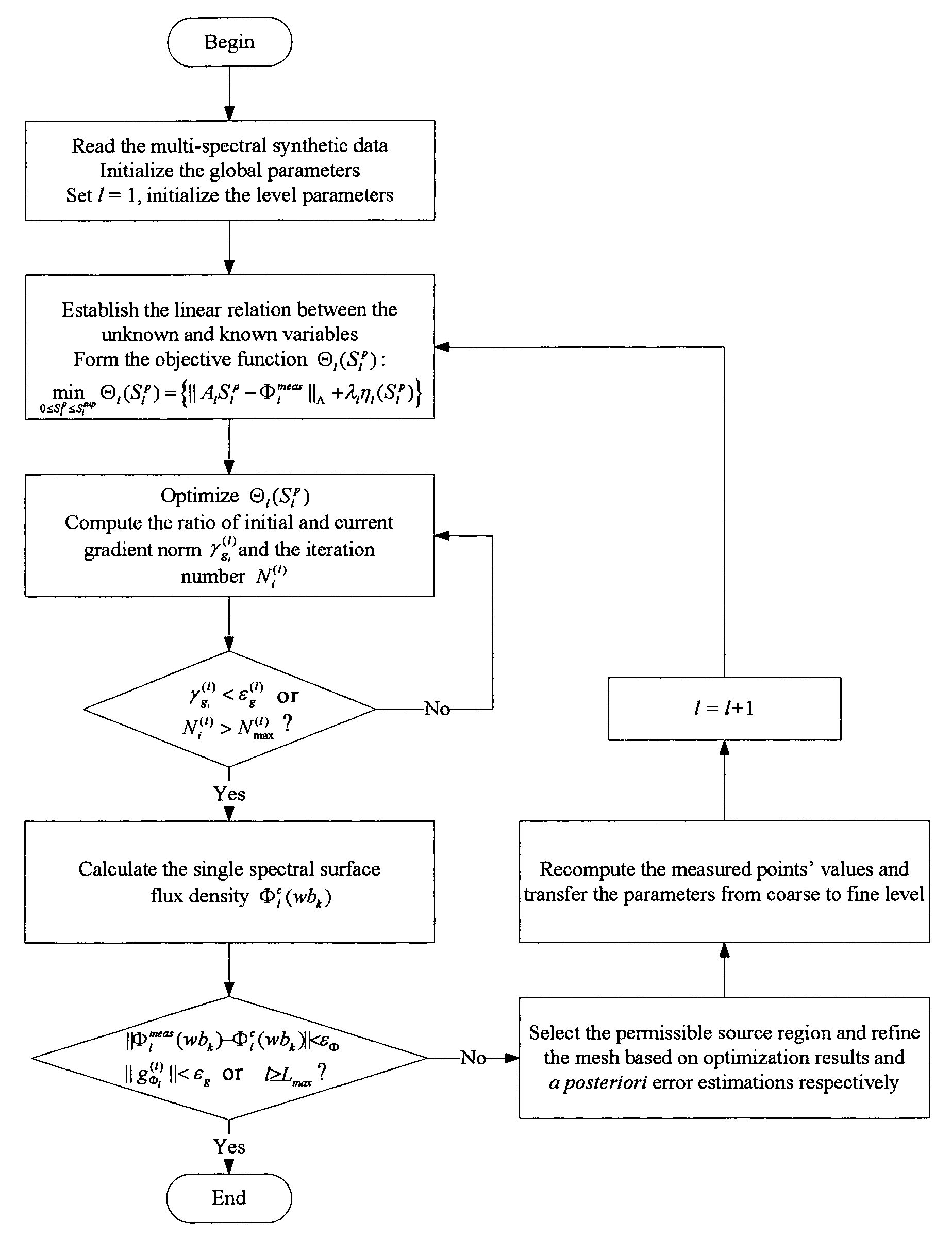
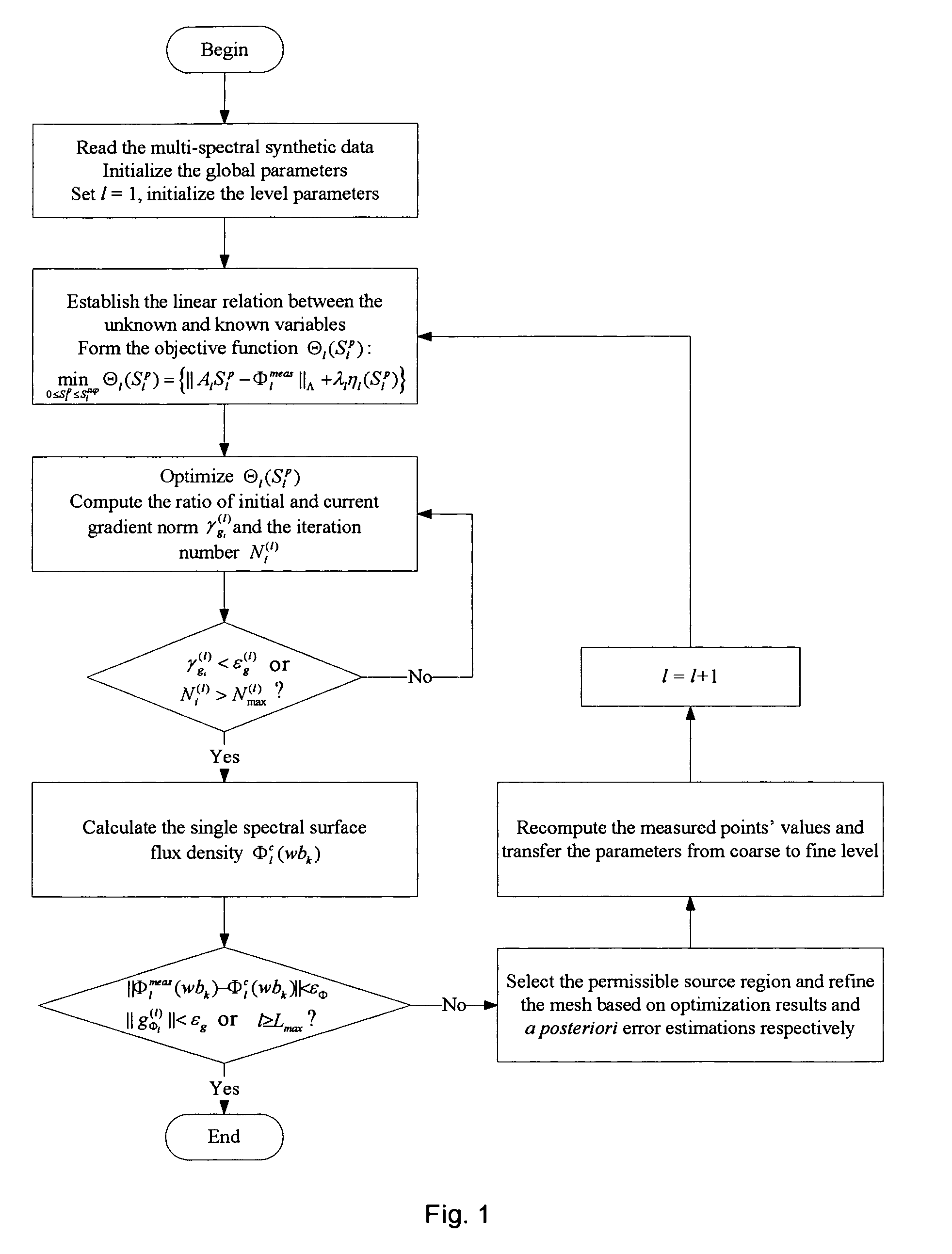
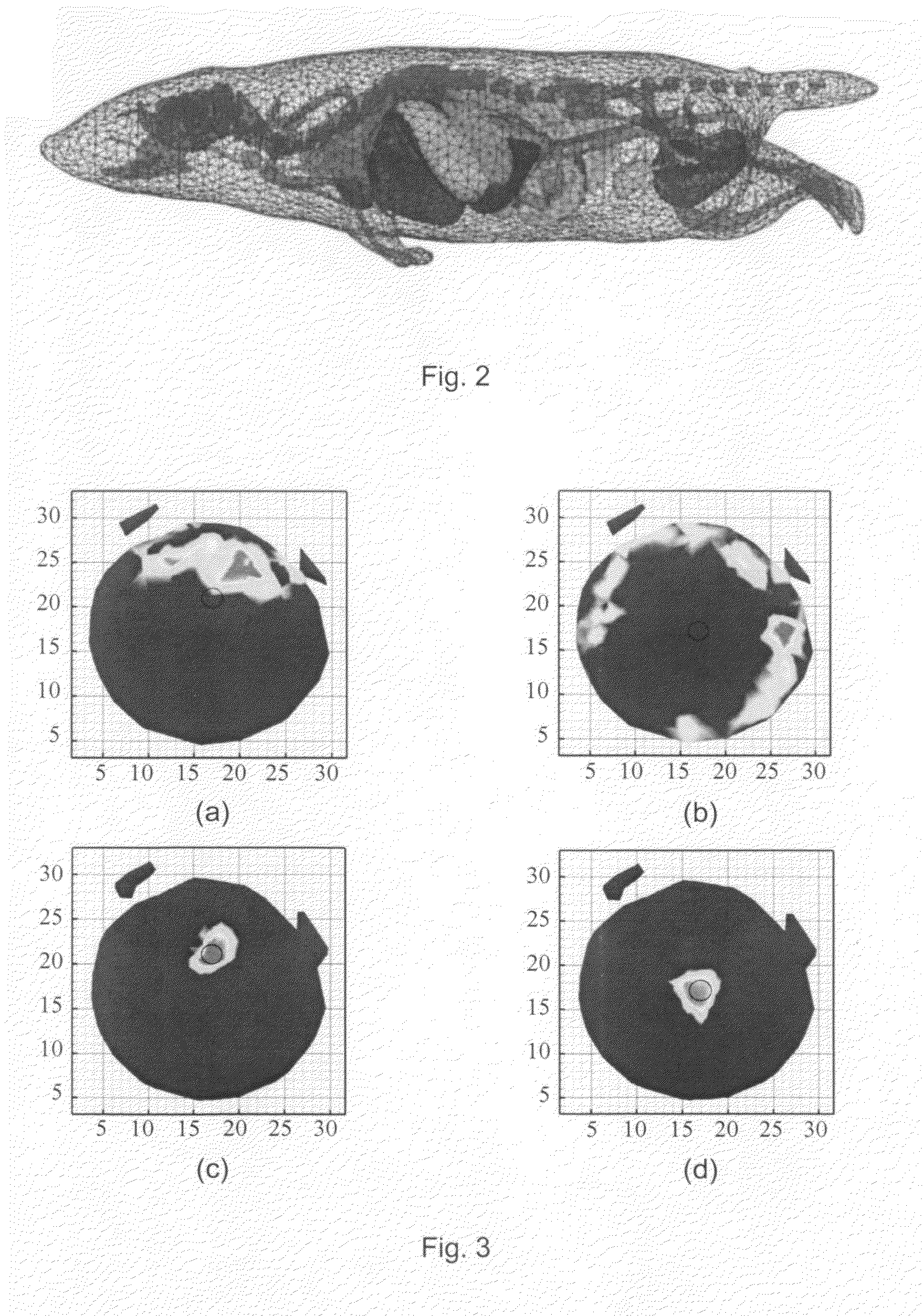
A multi-spectral reconstruction method based on adaptive finite element comprising the following steps: discretizing the diffusion equation in the object domain on the single spectral; establishing the relationship between the boundary measurement data and the unknown source variables on single spectral based on a posteriori permissible source region selection method, and forming the objective function based on the multi-spectral characteristics and the regularization method; optimizing the objective function and determining if the reconstruction shall be stopped or not; and if the reconstruction shall not be stopped, refining the mesh adaptively by using a posteriori measure method, and then returning to the first step to continue the reconstruction process. This method uses kinds of a priori information and the multi-spectral information, combined with the adaptive finite element method, proposes a posteriori permissible source region strategy, improves the reconstruction quality and speed of BLT availably, and reduces the ill-posedness of this imaging modality.
Owner:ZHUHAI DI PU MEDICAL TECH CO LTD
Object detection apparatus
ActiveUS9798002B2Avoid misjudgmentPedestrian/occupant safety arrangementOptical detectionRadarImage detection
An object detection apparatus mounted in a vehicle, includes a first domain definition unit, a second domain definition unit, and a determination unit. The first domain definition unit defines a first object domain including a first detection point which is indicative of a position of a first object detected by using a vehicle-mounted radar. The second domain definition unit defines a second object domain including a second detection point which is indicative of a position of a second object detected on the basis of an image captured by a vehicle-mounted monocular camera. The determination unit determines whether or not an overlapping domain of the first and second object domains is present, and when it is determined that an overlapping domain of the first and second object domains is present, then determines that the first and second objects are the same.
Owner:DENSO CORP
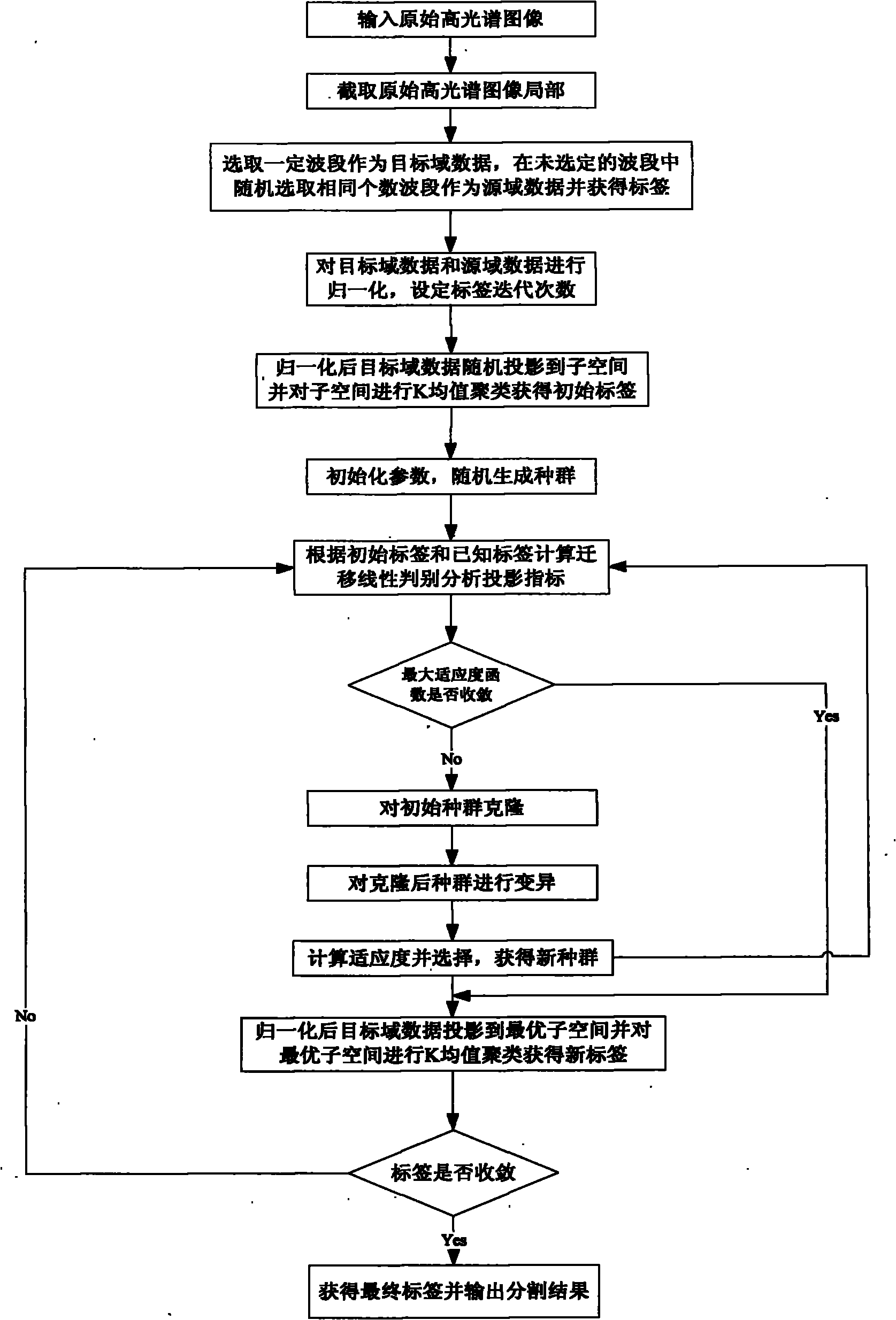
Projection pursuit hyperspectral image segmentation method based on transfer learning
InactiveCN101840569AOptimal Projection DirectionImprove Segmentation AccuracyImage enhancementImage segmentationImaging data
The invention discloses a projection pursuit hyperspectral image segmentation method based on transfer learning, belonging to the technical field of image processing. The technical key points are as follows: the multiband characteristic of the hyperspectral image data is utilized to regard each wave band as a gray level image, each image is analyzed and researched; the characteristic that the images of different wave bands are similar but not the same to introduce transfer learning in the projection pursuit clustering algorithm; and a ground object marked graph is used to obtain the label of the source domain image data, and the known label knowledge is utilized to guide the image data without label in the object domain and obtain the optimal projection direction and the optimal subspace, thus increasing the segmenting precision. The method has the advantage that the priori knowledge is utilized to increase the segmenting precision, and can be used for military reconnaissance and in the civil and industrial fields.
Owner:XIDIAN UNIV
Domain-self-adaptive facial expression analysis method
InactiveCN104616005AIncrease the scope of applicationSolve the training dataCharacter and pattern recognitionApplicability domainObject based
The invention relates to a domain-self-adaptive facial expression analysis method and belongs to the field of computer vision and emotion computing research. The method aims to solve the problem that the prediction precision is hindered by training and test data domain differences in automatic expression analysis, and is more aligned with the actual needs. The invention provides the domain-adaptive expression analysis method based on an object domain. The method comprises the following steps: defining a data domain for each tested object; defining the distance between object domains in a way of establishing an auxiliary prediction problem; selecting a group of objects similar to the data character of the tested object from a source data set to form a training set; on the training set, directly using part of tested object data in model training in a way of weighted cooperative training, and thus enabling a prediction model to be closer to the tested object domain. The method has the advantages that the isolation problem of training and testing data is solved, and the prediction model is adaptive to the testing data domain; the method has robustness for the domain differences and is wide in range of application.
Owner:南京宜开数据分析技术有限公司
System and Method for Determining Heat and Fluid Flow in or Around Objects
InactiveUS20150347651A1Computation using non-denominational number representationDesign optimisation/simulationFinite difference equationsData file
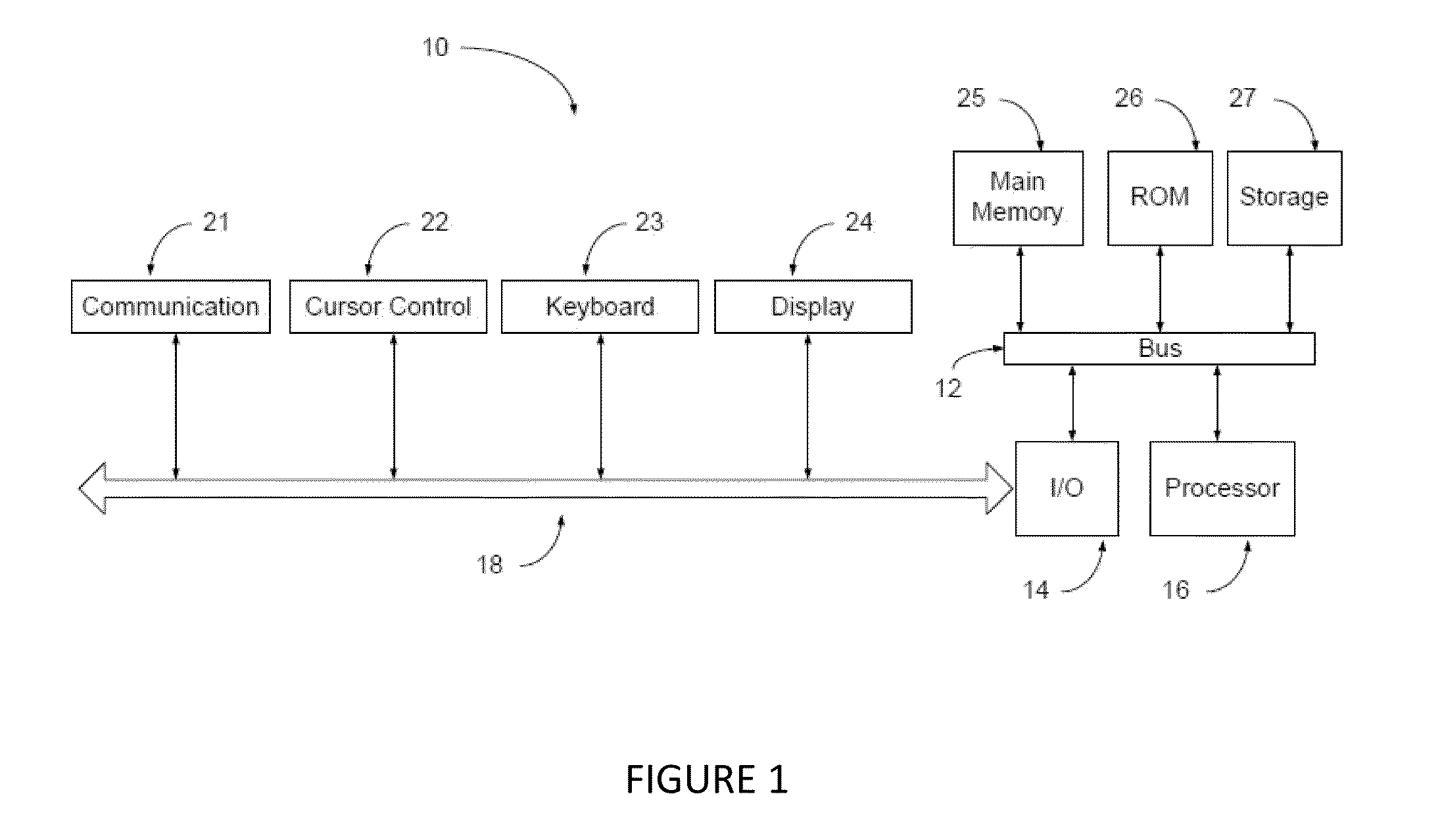
A system includes a processor with stored instructions for generating a Cartesian mesh model of a bounded or unbounded object domain. The model includes active, inactive and boundary nodes which encompass the domain. The processor effects of discretizing a partial differential equation based on a stencil associated with each active node in the mesh by (i) selecting an active node, (ii) identifying the stencil associated with the selected node, (iii) mapping the stencil from the physical domain to a generic uniform computational stencil, (iv) applying finite difference formulas on the computational stencil to approximate the partial differential equation by a finite difference equation, (v) solving the finite difference equation to obtain an approximate value for the solution, and thereafter (vi) checking the iteration process for convergence. If the solution has not converged, the system repeats the aforementioned steps, or terminates the iteration process if the solution has converged, and outputs to a user the calculated data file.
Owner:UNIVERSITY OF WINDSOR
Apparatus and method for sensory-type learning
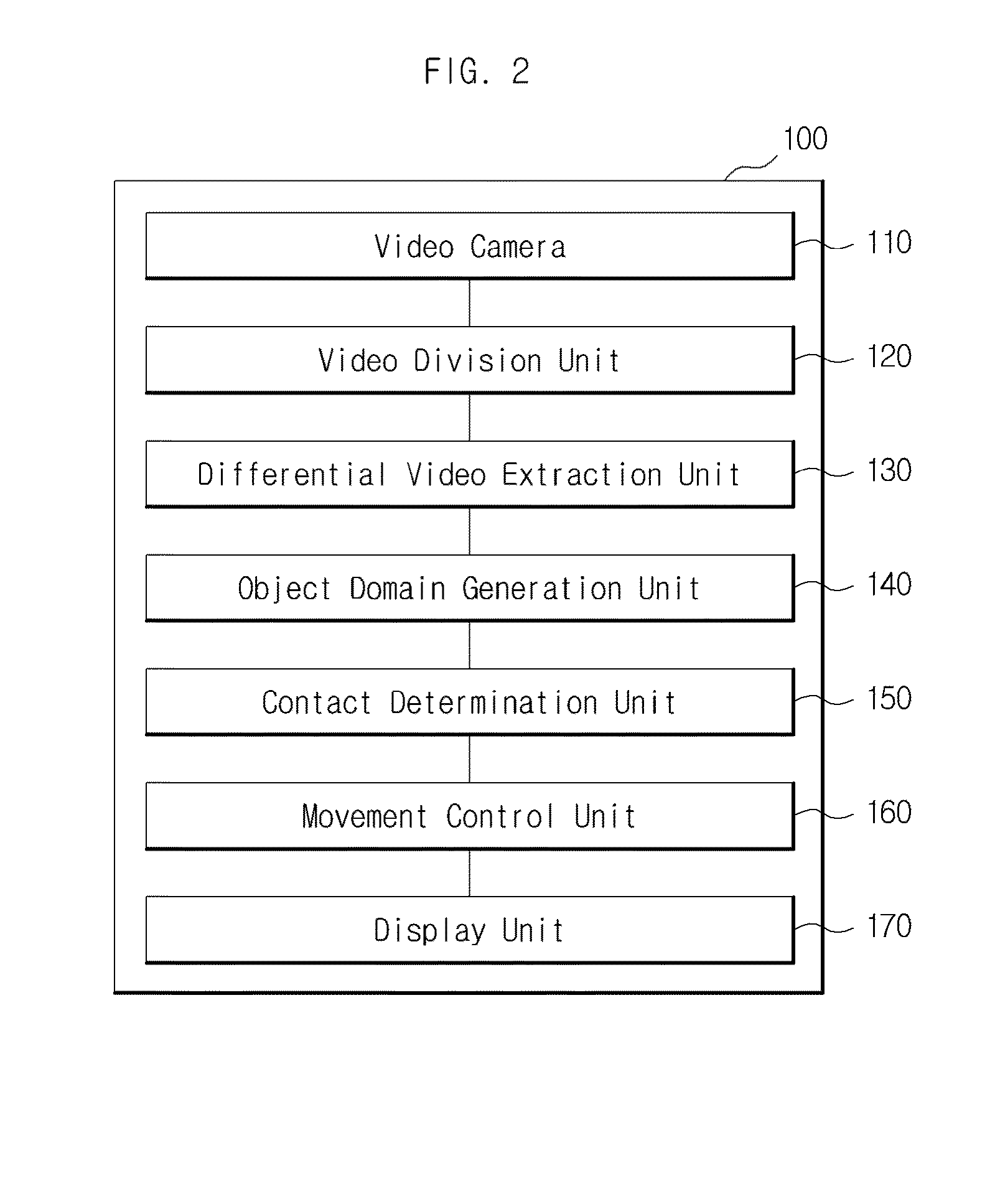
InactiveUS20140342344A1Add featureImprove learning effectInput/output for user-computer interactionComputerized toysPattern recognitionAnimation
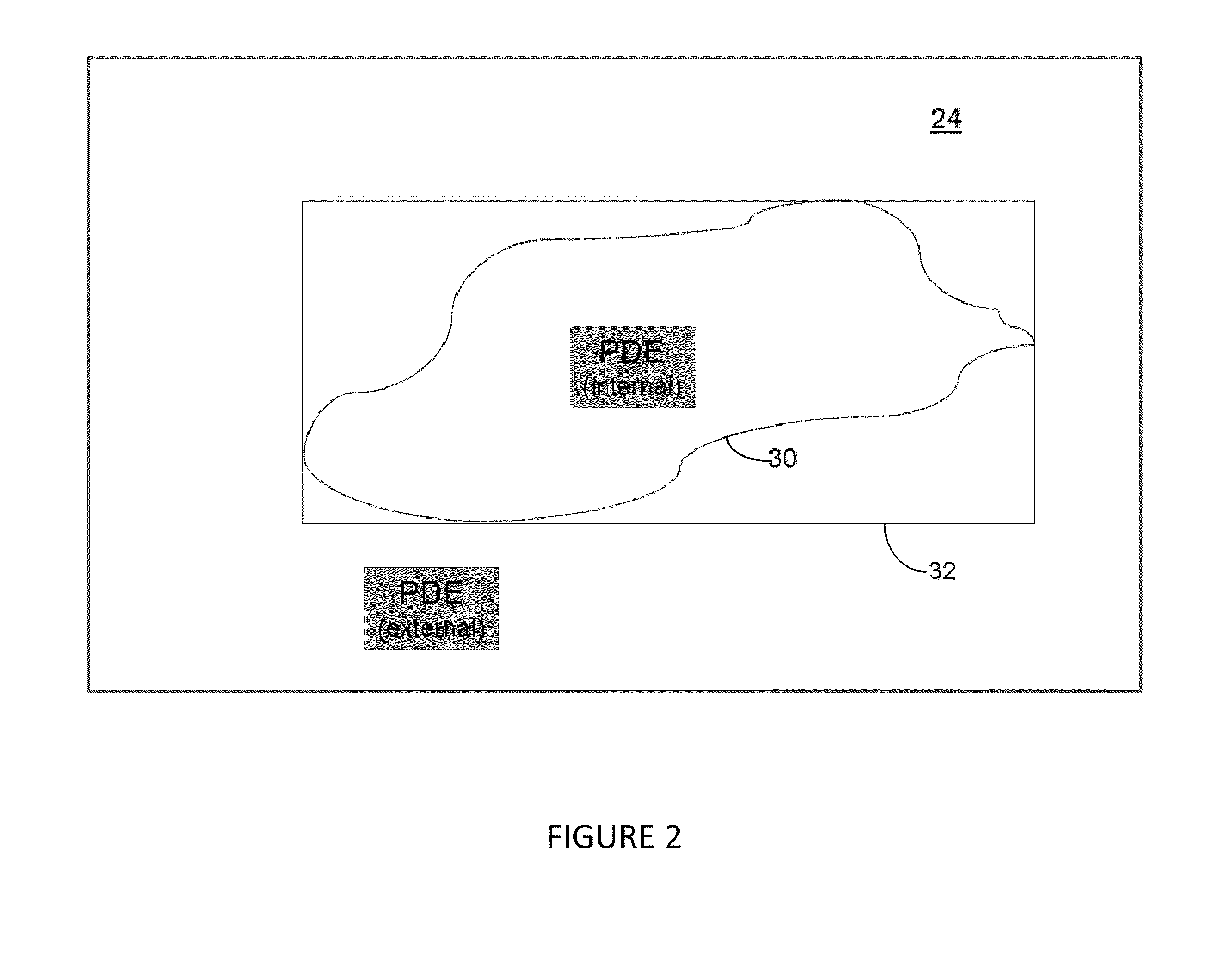
An apparatus and a method for sensory-type learning are disclosed. An apparatus for sensory-type learning comprises: a video divider configured to divide a video of a recorded learner into a plurality of blocks, and divide the video which has been divided into a plurality of blocks into previously set time intervals; a differential video extractor configured to extract a differential video; an object domain generator configured to generate a first object domain, which is a single object domain; a contact determiner configured to determine whether the first object domain came into contact with a second object domain pertaining to a background object appearing on a screen; and a movement controller configured to apply the change in animation to the background object and control the apparatus for sensory-type learning to execute a previously set movement.
Owner:KT CORP
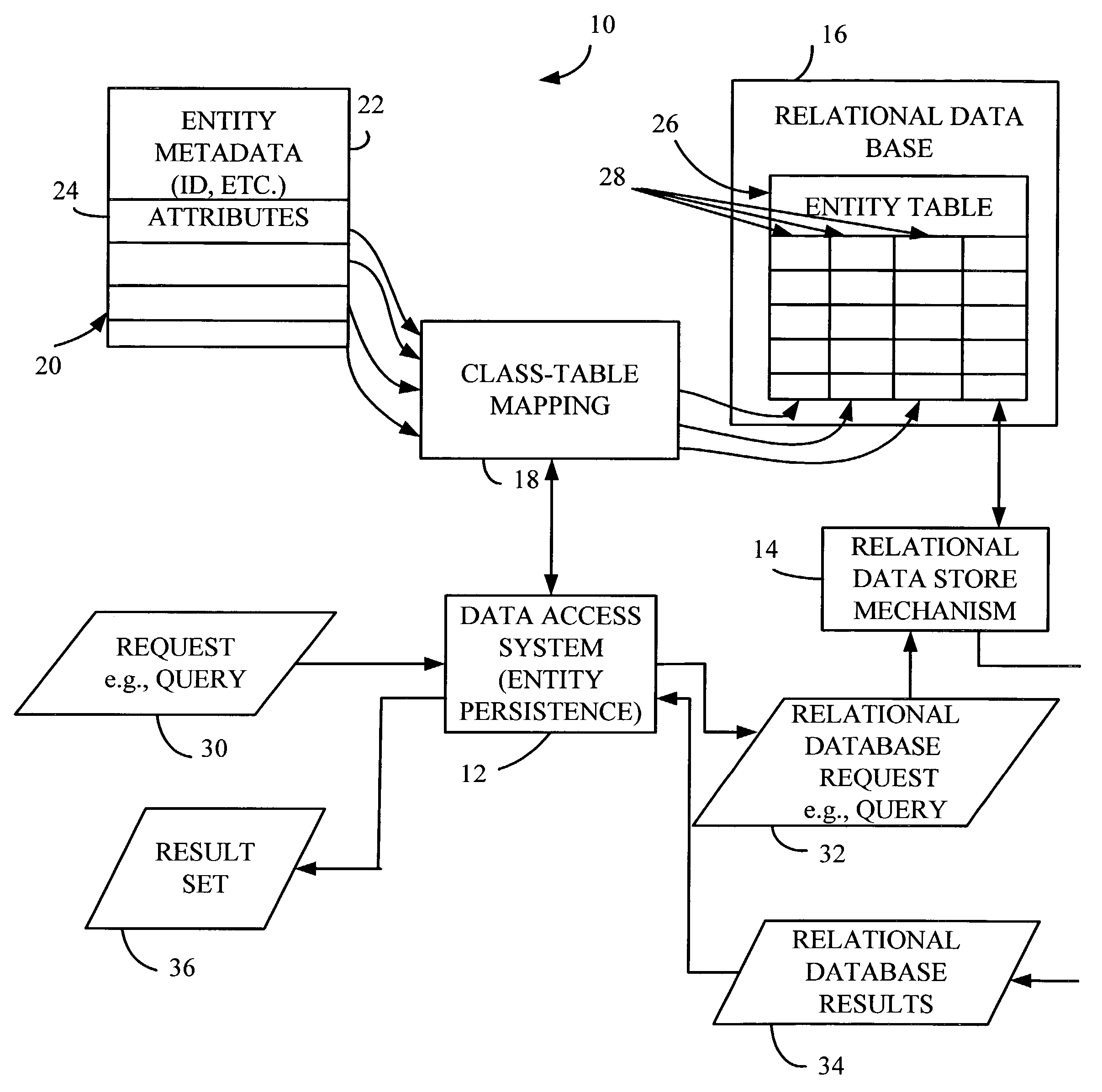
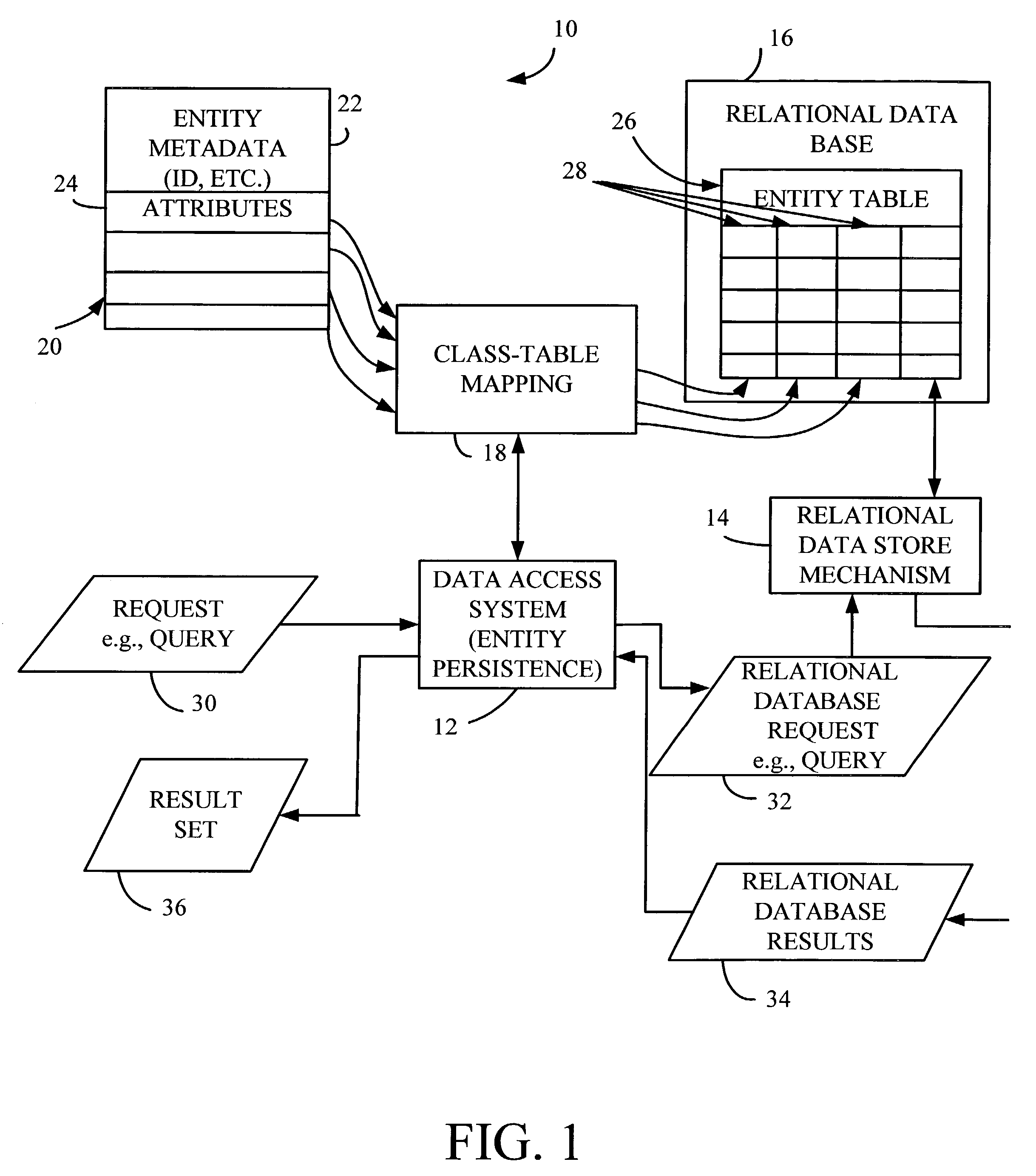
Database simulation of data types
The present invention is a method for comparing object data in an object domain with database data in a database domain. The method includes applying a first transfer function to the object data so as to generate a first transformed data. The method also includes applying a second transfer function to the database data so as to generate a second transformed data. Finally, the method includes comparing the first transformed data with the second transformed data.
Owner:MICROSOFT TECH LICENSING LLC
Multi-spectral reconstruction method based on adaptive finite element
ActiveUS8094149B2Less discomfortQuality improvementCharacter and pattern recognitionDiagnostics using tomographyRegion selectionPrior information
A multi-spectral reconstruction method based on adaptive finite element comprising the following steps: discretizing the diffusion equation in the object domain on the single spectral; establishing the relationship between the boundary measurement data and the unknown source variables on single spectral based on a posteriori permissible source region selection method, and forming the objective function based on the multi-spectral characteristics and the regularization method; optimizing the objective function and determining if the reconstruction shall be stopped or not; and if the reconstruction shall not be stopped, refining the mesh adaptively by using a posteriori measure method, and then returning to the first step to continue the reconstruction process. This method uses kinds of a priori information and the multi-spectral information, combined with the adaptive finite element method, proposes a posteriori permissible source region strategy, improves the reconstruction quality and speed of BLT availably, and reduces the ill-posedness of this imaging modality.
Owner:ZHUHAI DI PU MEDICAL TECH CO LTD
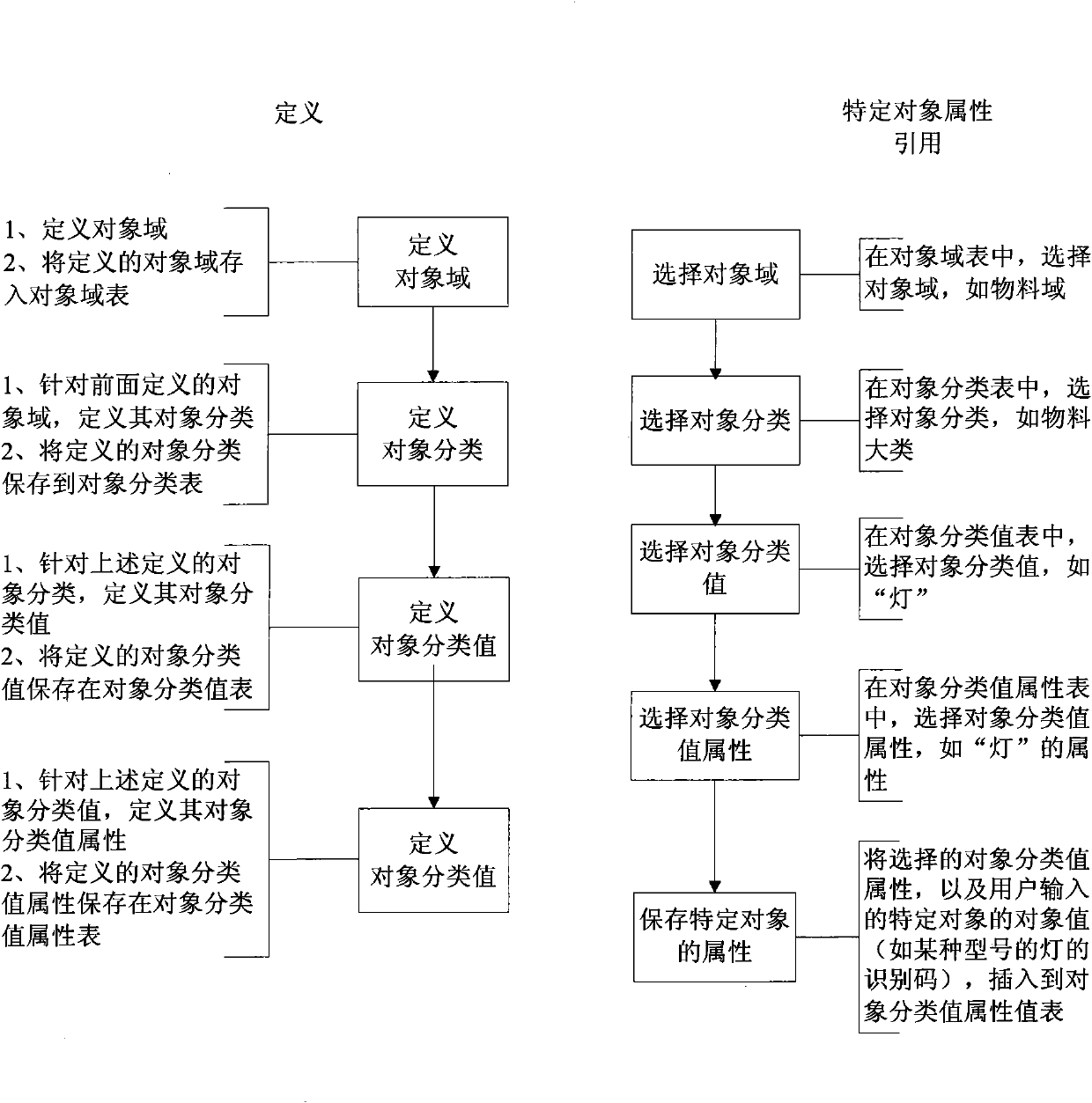
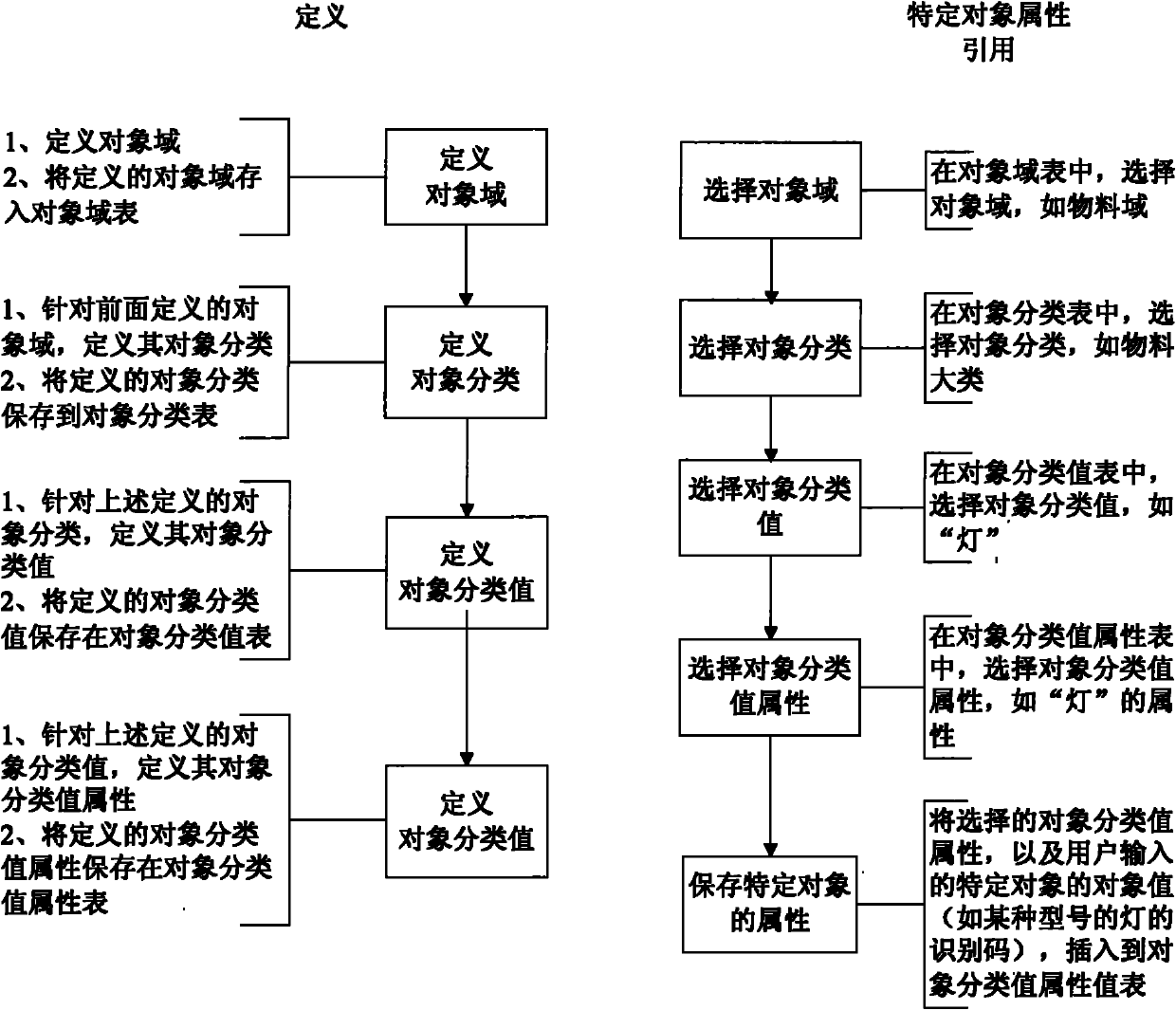
Enterprise information management system
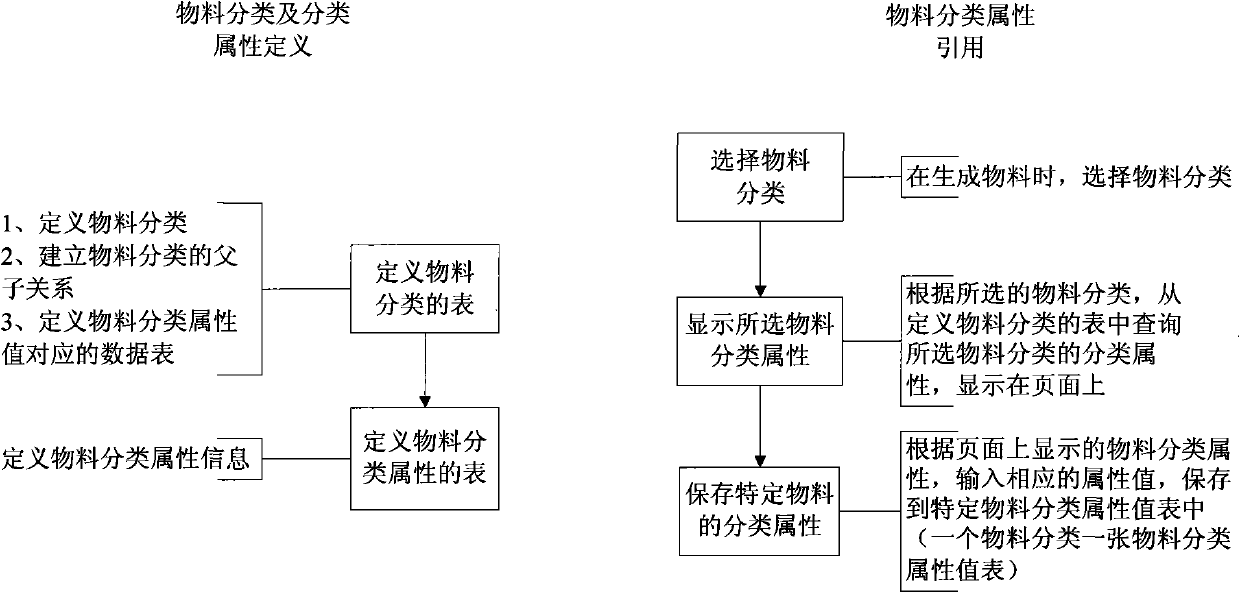
InactiveCN102024183AEasy to manageSpecial data processing applicationsObject domainEnterprise information management
The invention discloses an enterprise information management system, which comprises a user interface, an application program and a database. The database comprises an object domain table, an object classification table, an object classification value table, an object classification value attribute table and an object classification value attribute value table; a user can add or delete the attribute of a specific object, and the newly added / deleted attribute of the specific object is only retained in the object classification value attribute value table. The enterprise information management system defines the attribute of each specific object, does not relate to the changes of an attribute defining data table structure and the application program in the process of adding the attribute, and is convenient to manage enterprise information.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
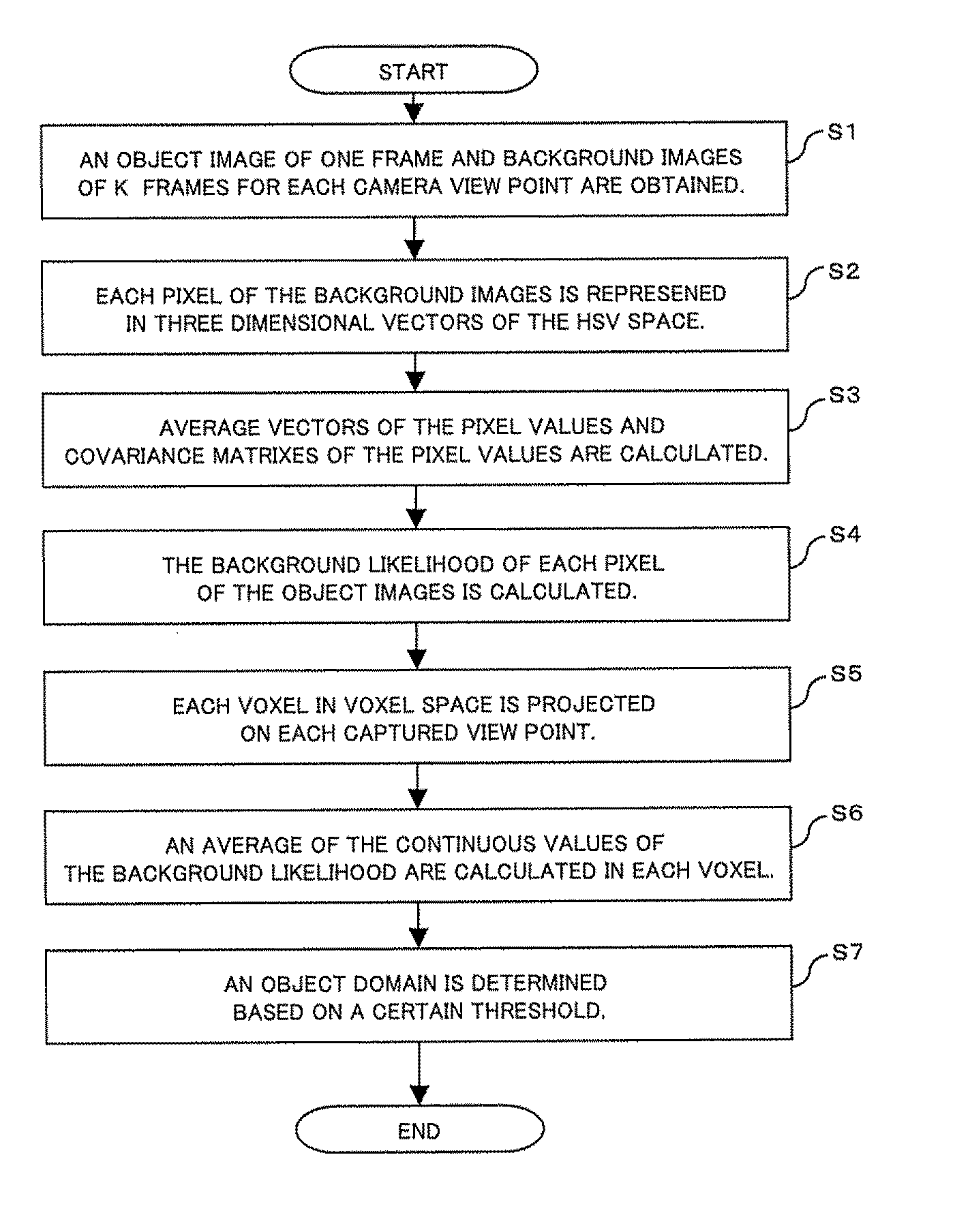
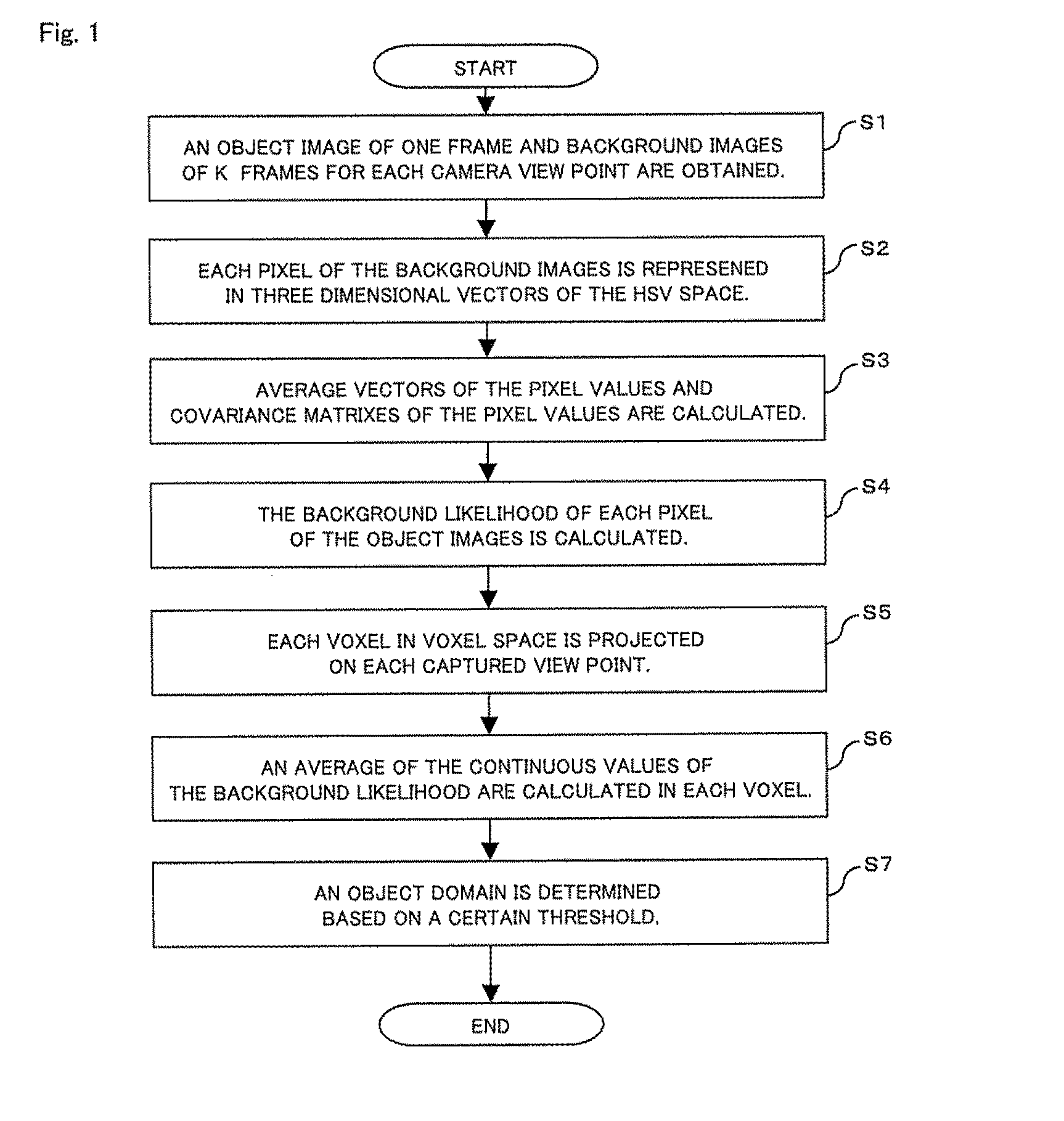
Method and program for constructing three dimensional object model
InactiveUS20110122133A1High accurate visual hullHigher accurate visual hullImage enhancementImage analysisVoxelVisual hull
A present invention provides a method for constructing a highly accurate visual hull from multi view point images without highly accurate silhouettes. A method of the present invention comprises calculating continuous values to represent background likelihood of each pixel for every object image based on pixel values of said object images and those of said background images, calculating the projection pixels for each voxel at every captured view point by projecting each voxel in voxel space on each captured view point of said object images, and determining an object domain with judging whether said voxel belongs to the object domain or not based on the continuous value of said pixel at every captured view point.
Owner:KDDI CORP
Input verification method
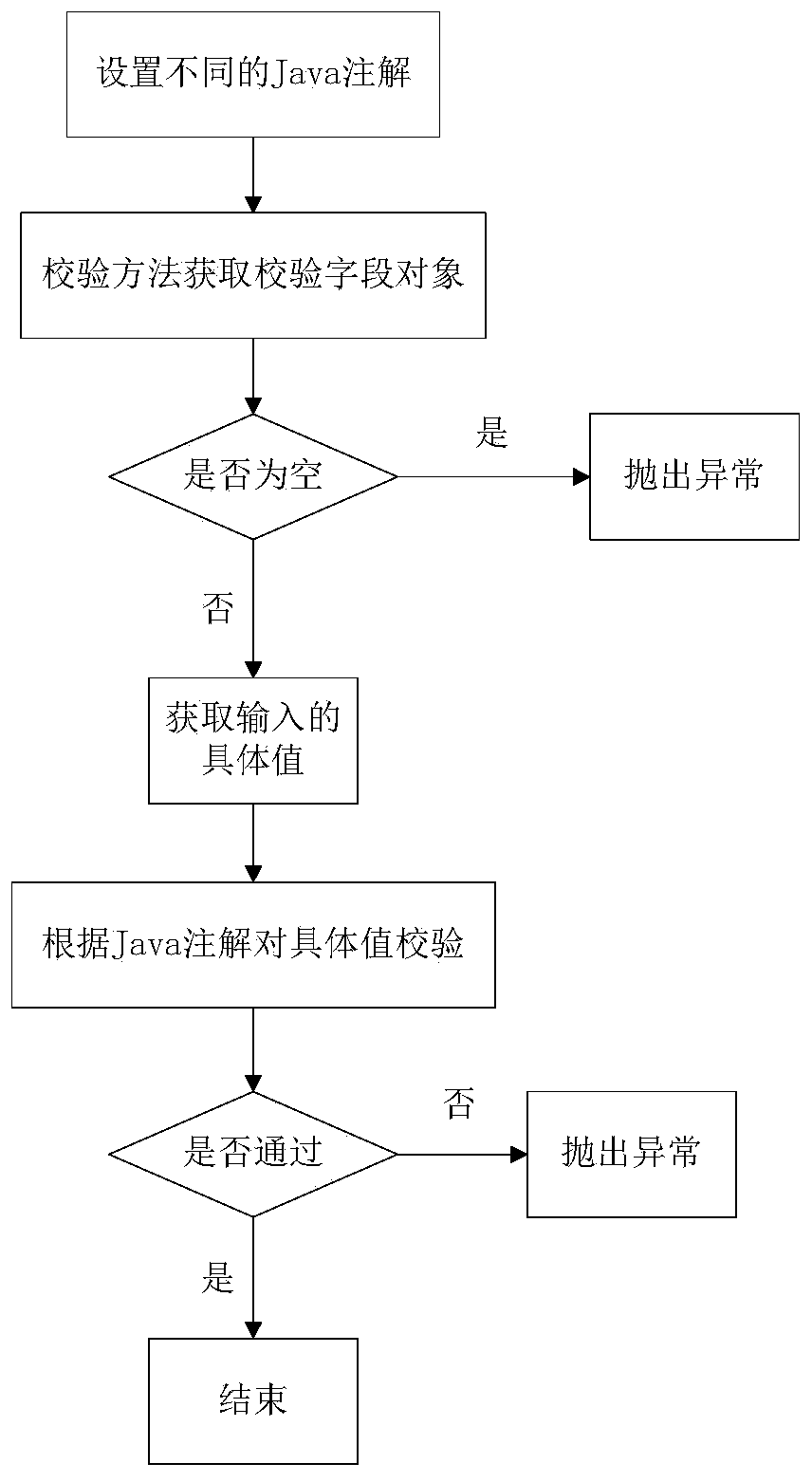
PendingCN110673838AAchieve decouplingRealize friendly interactionProgram documentationCreation/generation of source codeSoftware engineeringJava annotation
The invention relates to an input verification method, which comprises the following steps: A, respectively setting corresponding Java annotations according to different verification types of verification fields in a Java system, and enabling the Java annotations to comprise field attributes and error information corresponding to the verification types; and B, creating a verification method, wherein the verification method comprises the following steps: acquiring a specific value input to a verification field by a user and a Java annotation of the verification field through a Java object domain mechanism; and verifying the specific value according to the Java annotation of the verification field, and if the specific value does not pass the verification, throwing out an exception, wherein corresponding error information in the Java annotation is contained in the exception. According to the input verification method, the development cost and the operation and maintenance cost are greatlyreduced; developers do not need to repeatedly compile tedious verification logic codes; the developers and the operation and maintenance personnel do not need to learn complex specifications; a unified verification mode for various verification fields is achieved; and unified specifications of the codes are guaranteed.
Owner:SICHUAN XW BANK CO LTD
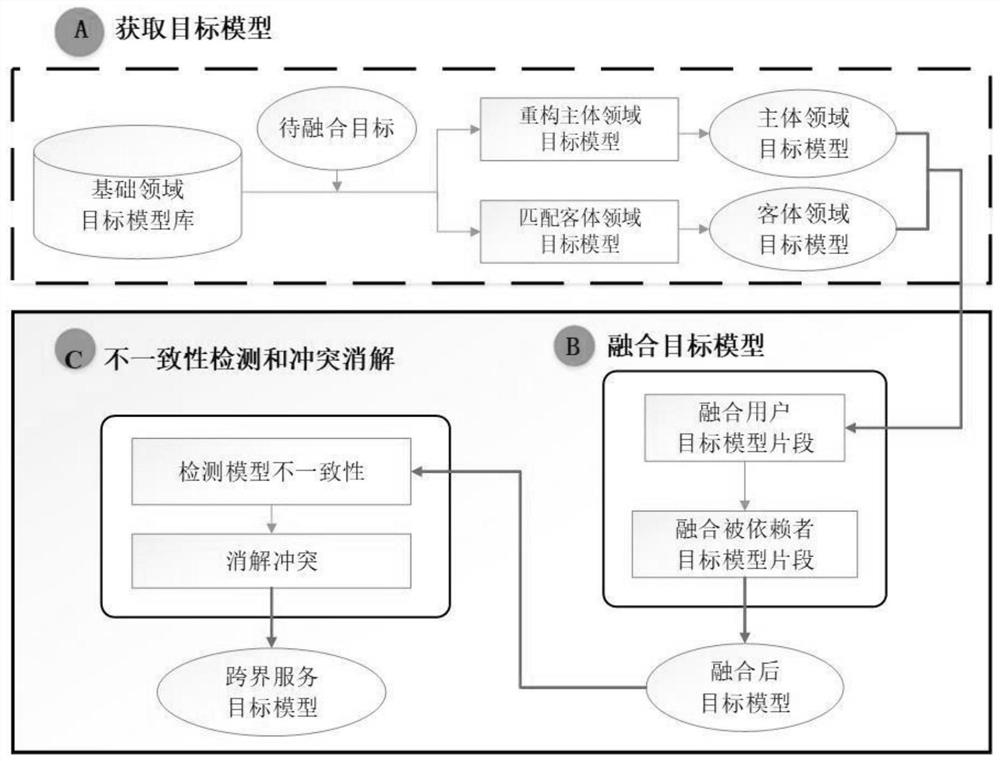
Cross-boundary service target fusion method
PendingCN112183066AEasy to integrateDetect non-functional target inconsistenciesSemantic analysisCharacter and pattern recognitionEngineeringOperability
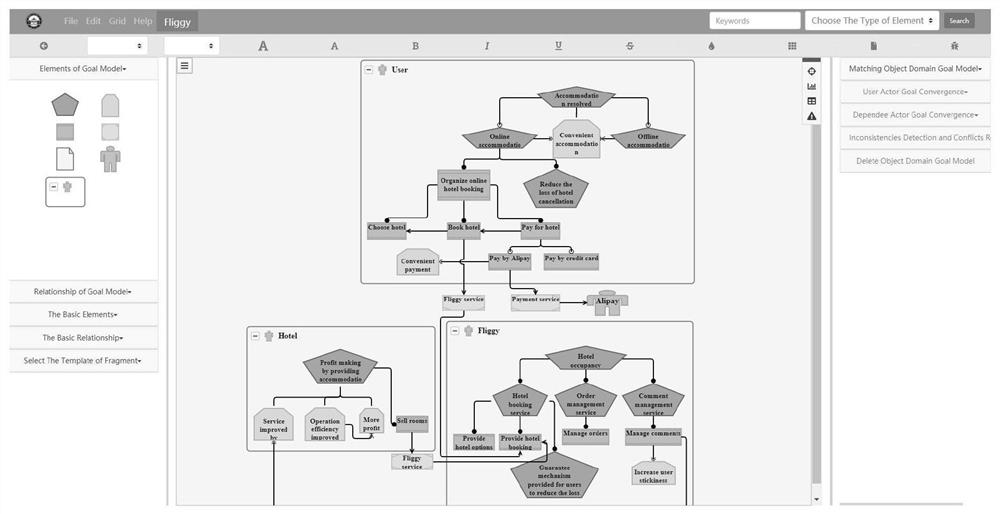
The invention discloses a cross-boundary service target fusion method, and the method comprises the following steps: 1, obtaining a target model which comprises a reconstruction subject field target model and a matching object field target model; 2, fusing the obtained subject domain target model and the object domain target model; and 3, carrying out target inconsistency detection on the fused target model to obtain a finally fused cross-boundary service target model. The beneficial effects of the method are that: 1) the method can guide the fusion process of the cross-boundary service very well, solves a problem of the cross-boundary service deeply, achieves the engineering solving of a complex problem of the cross-boundary service, meets the requirements of a complex target of a user which is difficult to meet in a single field, and creates a value which is difficult to create in a service of the single field; and 2) an inconsistency detection and conflict resolution method is provided, so that the inconsistency of non-functional targets, the inconsistency of functional targets and the inconsistency of operable targets can be effectively detected, and conflicts can be resolved.
Owner:WUHAN UNIV
Software tool for automation technology
InactiveCN102779036ASoftware designSpecific program execution arrangementsSoftware engineeringApplication software
Owner:SIEMENS AG
Trans-boundary service target fusion conflict detection method and device
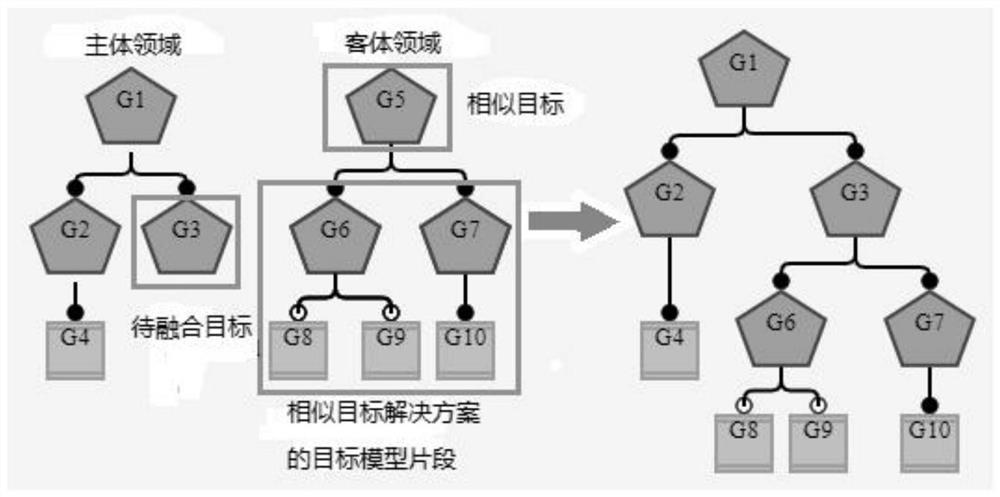
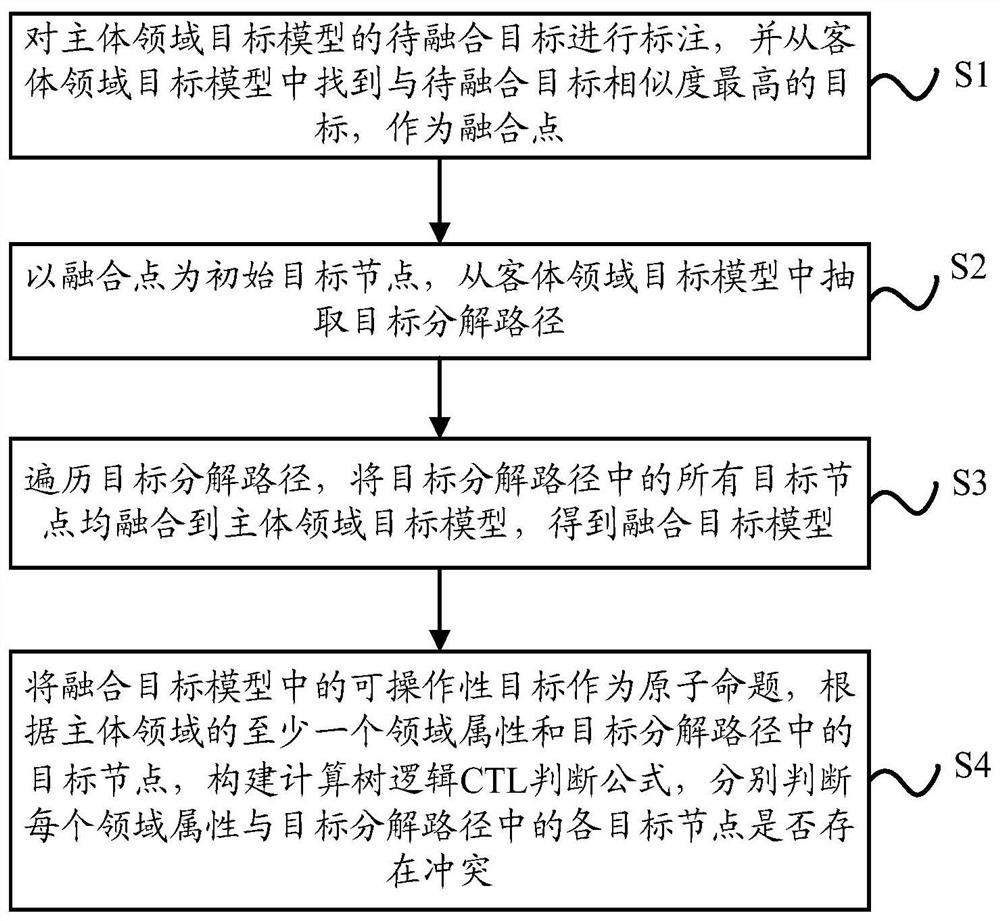
PendingCN113361232AImprove practicalityFinanceSemantic analysisServices computingComputational physics
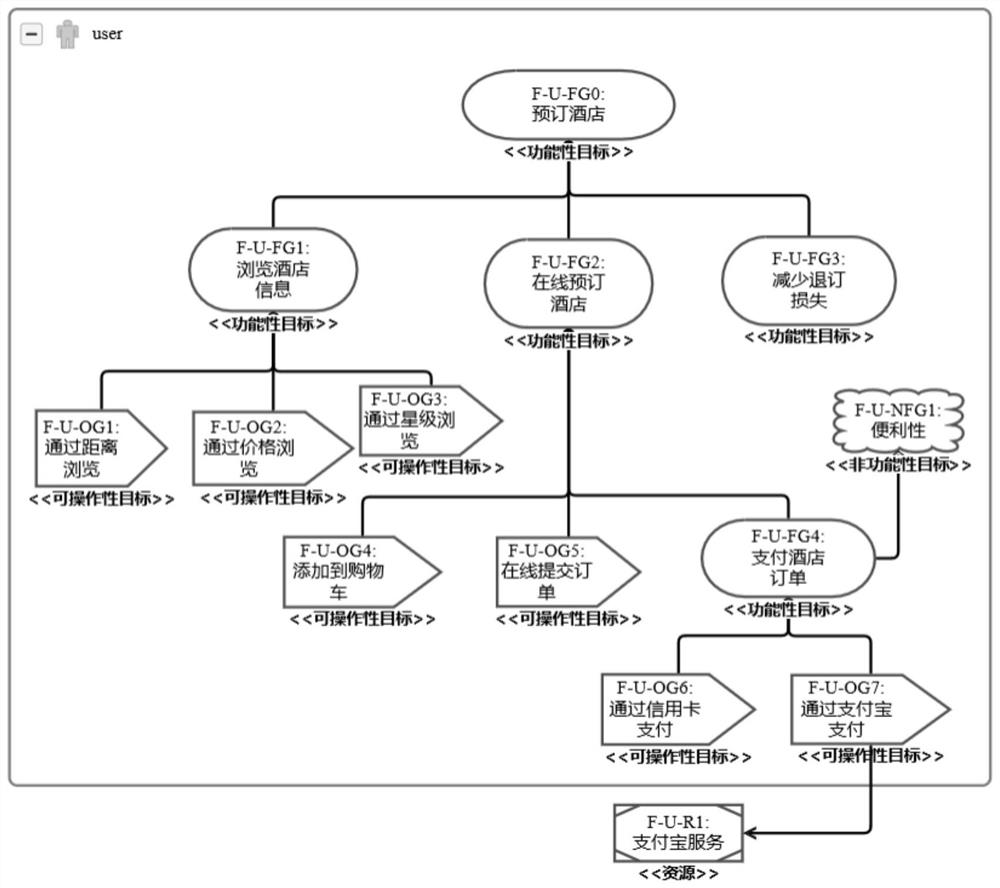
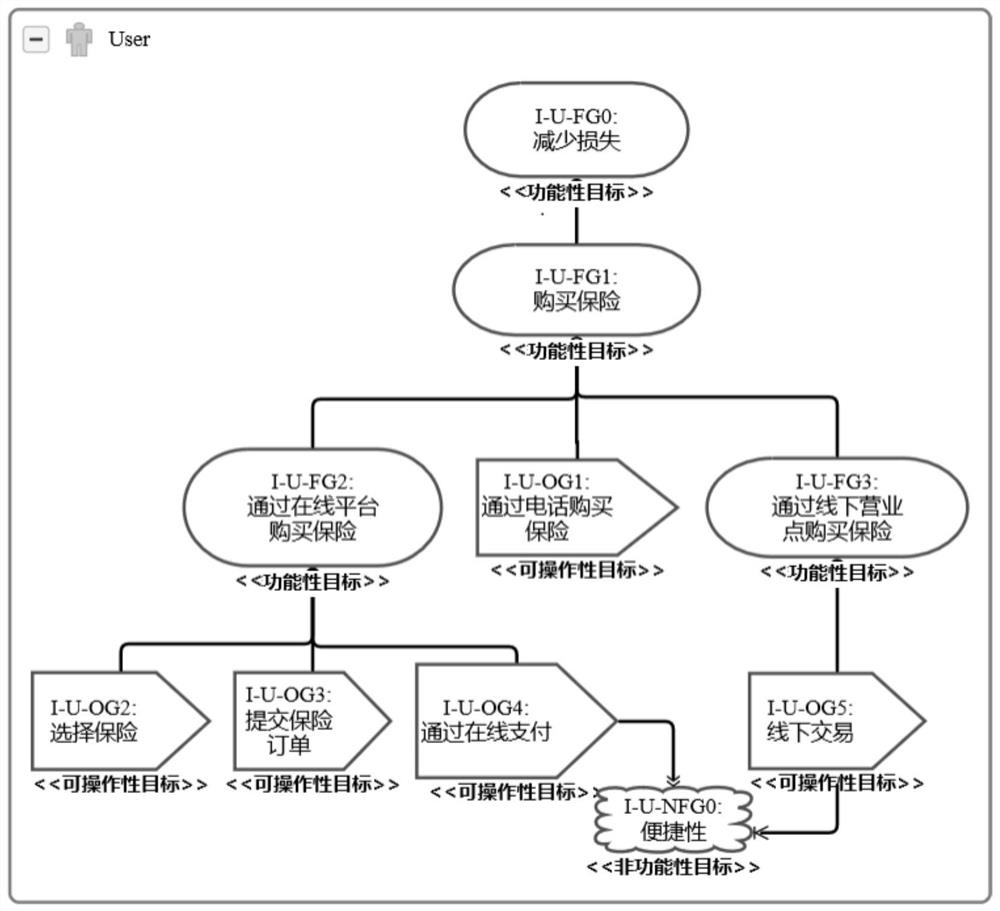
The invention discloses a trans-boundary service target fusion conflict detection method and device, and relates to the technical field of service computing, and the method comprises the steps: marking a to-be-fused target of a subject domain target model, finding a target having the highest similarity with the to-be-fused target from an object domain target model, and taking the target as a fusion point; taking the fusion point as an initial target node, and extracting a target decomposition path from the object domain target model; fusing all target nodes in the target decomposition path into the subject domain target model to obtain a fused target model; and taking an operability target in the fusion target model as an atomic proposition, constructing a CTL judgment formula according to at least one domain attribute of the subject domain and a target node in the target decomposition path, and respectively judging whether each domain attribute conflicts with each target node in the target decomposition path. According to the invention, deep fusion of target models in different fields can be supported, and conflicts occurring after fusion of targets in different fields can be accurately detected.
Owner:WUHAN UNIV
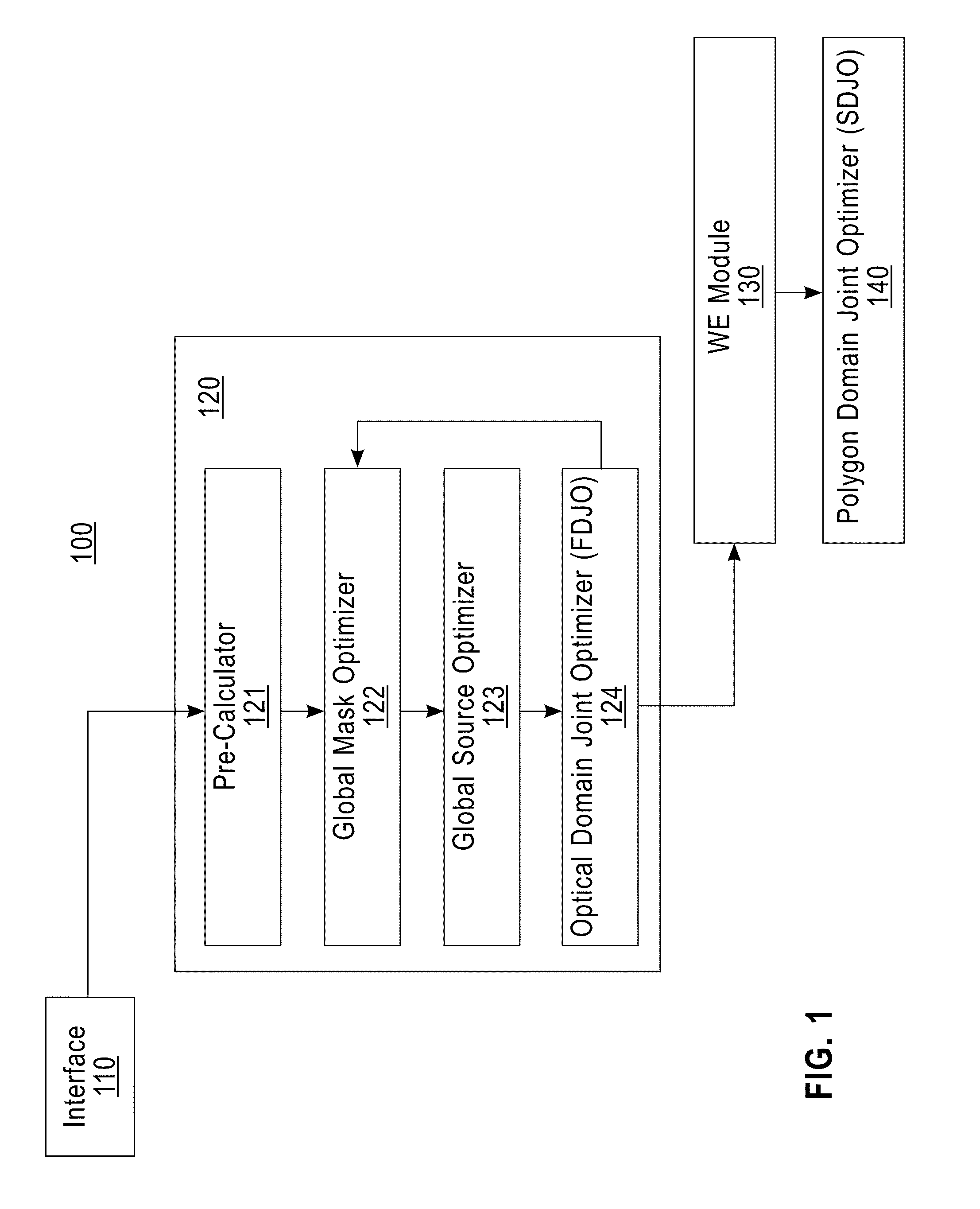
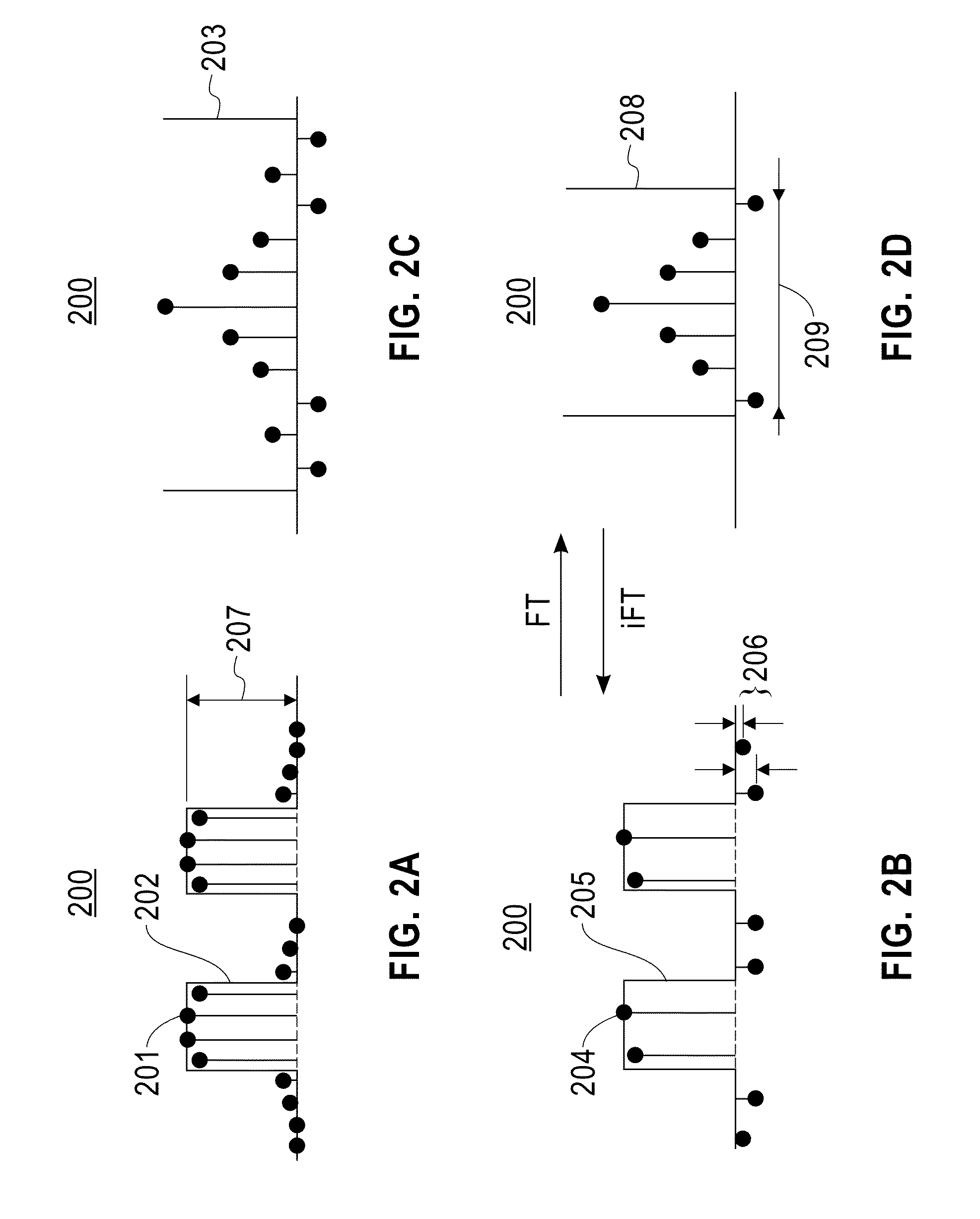
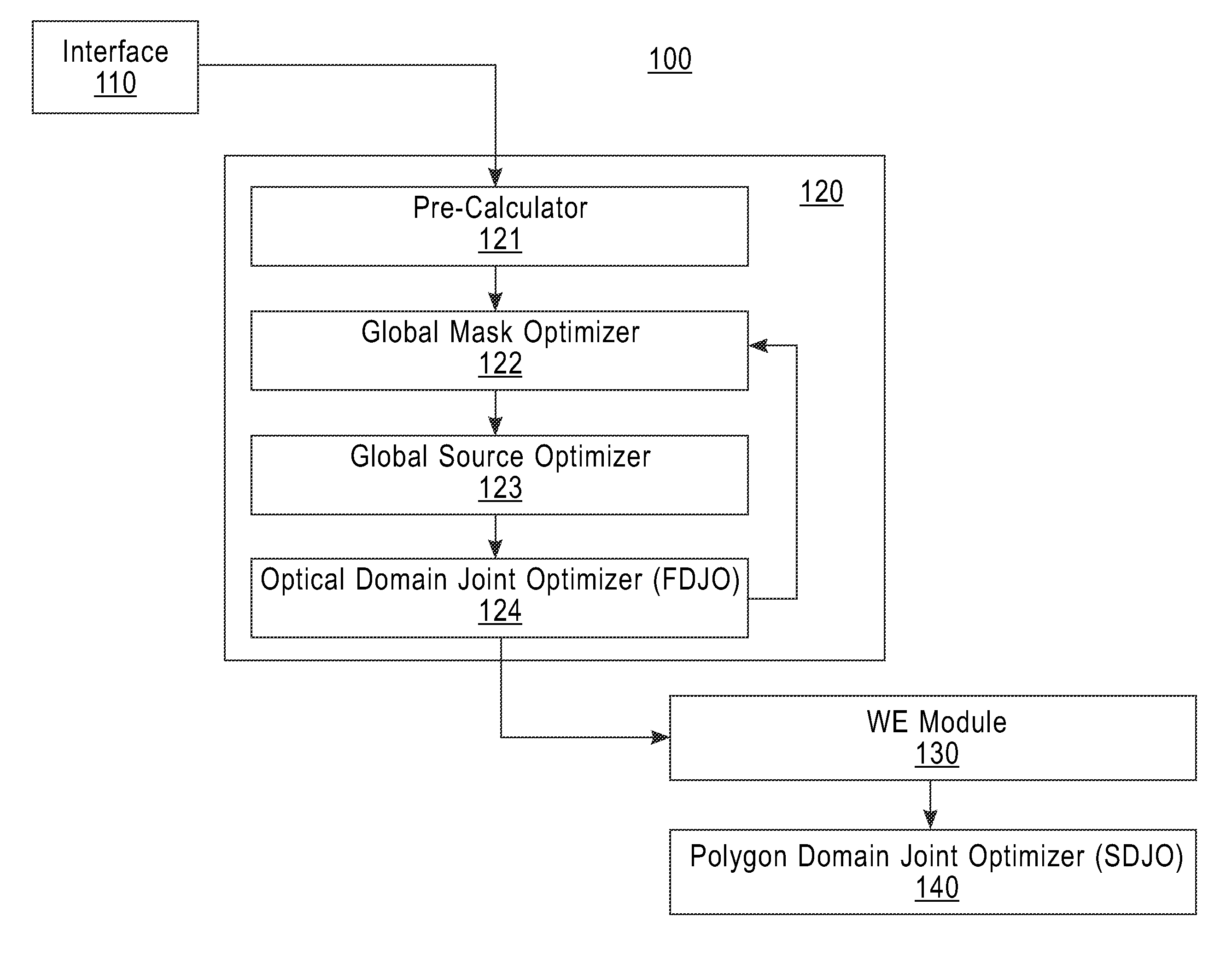
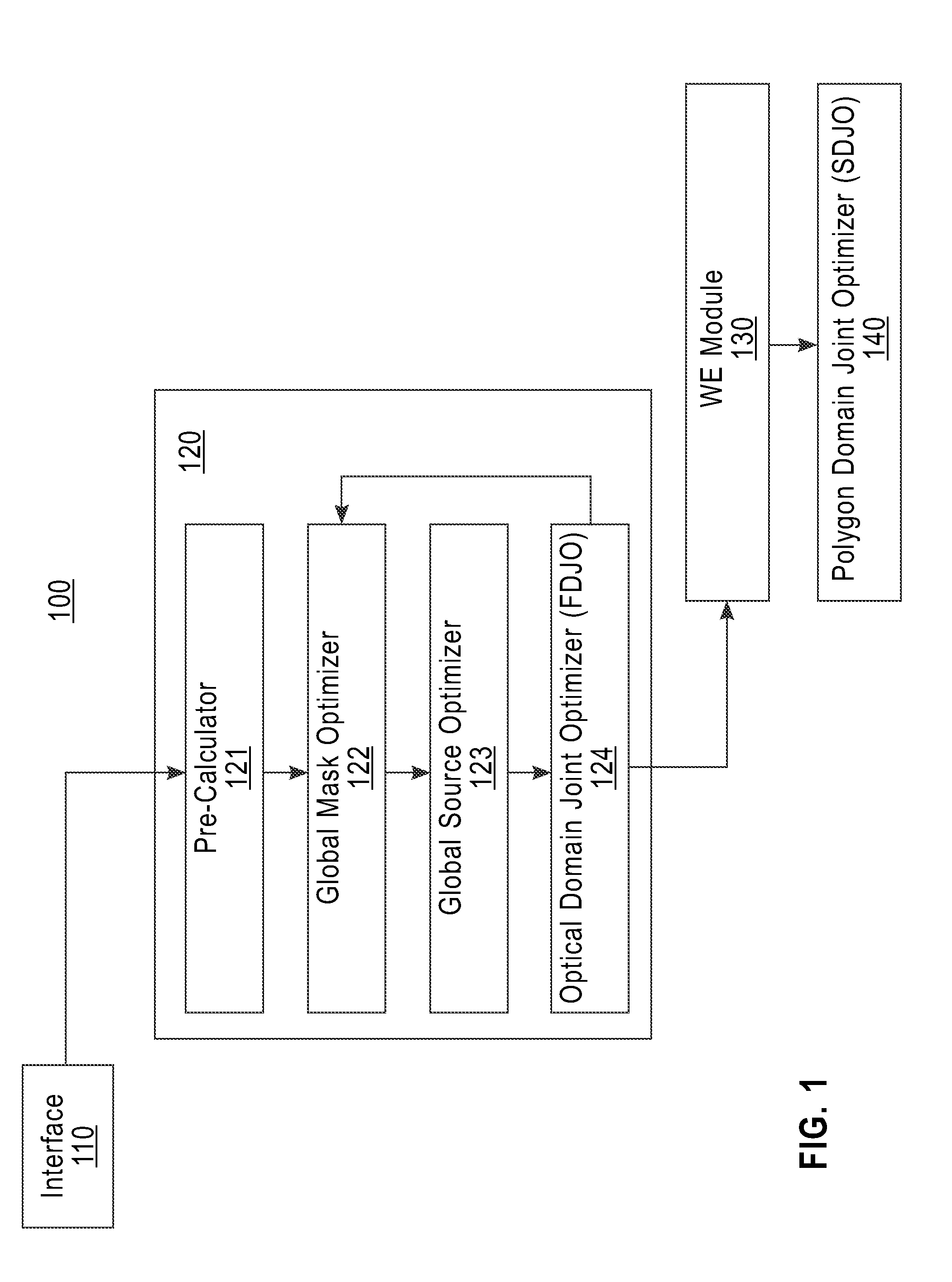
Mask design method, program, and mask design system
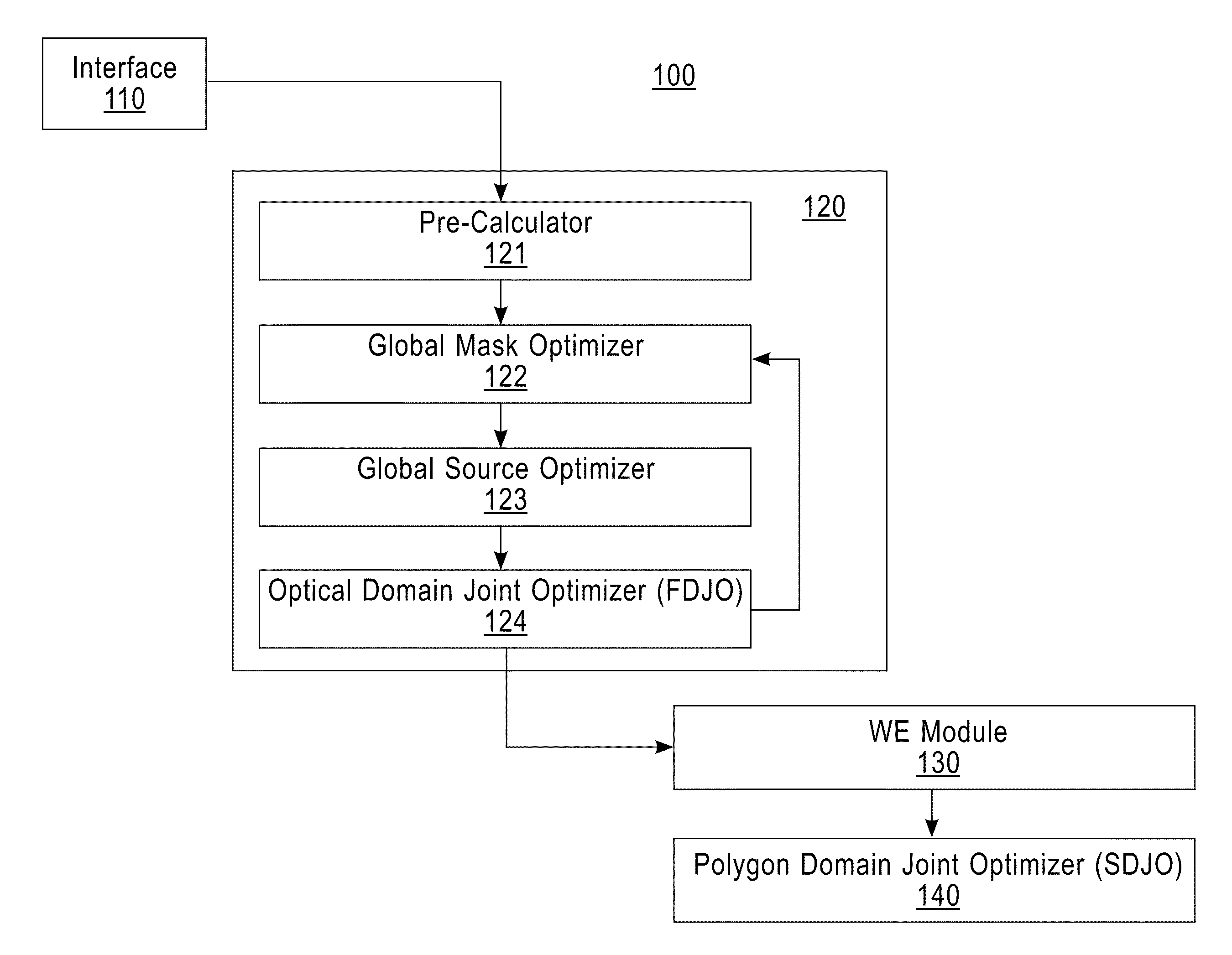
InactiveUS8959462B2Originals for photomechanical treatmentSpecial data processing applicationsWavefrontComputer module
A method, an article of manufacture, and a system for designing a mask. The method for designing a mask is implemented by a computer device having a memory, a processor device communicatively coupled to the memory, and a module configured to carry out the method including the steps of: generating an optical domain representation from a design pattern and an imaging light; and optimizing the optical domain representation under a constraint that values of negative excursions at predetermined evaluation points must be greater than or equal to predetermined negative threshold values assigned to the predetermined evaluation points; where: the optical domain representation is a variable representation of a wavefront; the imaging light is light that is transmitted through the mask; the negative excursions are in an object domain representation of the optical domain representation; and the predetermined evaluation points are in the object domain representation.
Owner:GLOBALFOUNDRIES INC
Mask design method, program, and mask design system
InactiveUS20130263063A1Originals for photomechanical treatmentSpecial data processing applicationsWavefrontComputer science
A method, an article of manufacture, and a system for designing a mask. The method for designing a mask is implemented by a computer device having a memory, a processor device communicatively coupled to the memory, and a module configured to carry out the method including the steps of: generating an optical domain representation from a design pattern and an imaging light; and optimizing the optical domain representation under a constraint that values of negative excursions at predetermined evaluation points must be greater than or equal to predetermined negative threshold values assigned to the predetermined evaluation points; where: the optical domain representation is a variable representation of a wavefront; the imaging light is light that is transmitted through the mask; the negative excursions are in an object domain representation of the optical domain representation; and the predetermined evaluation points are in the object domain representation.
Owner:GLOBALFOUNDRIES INC
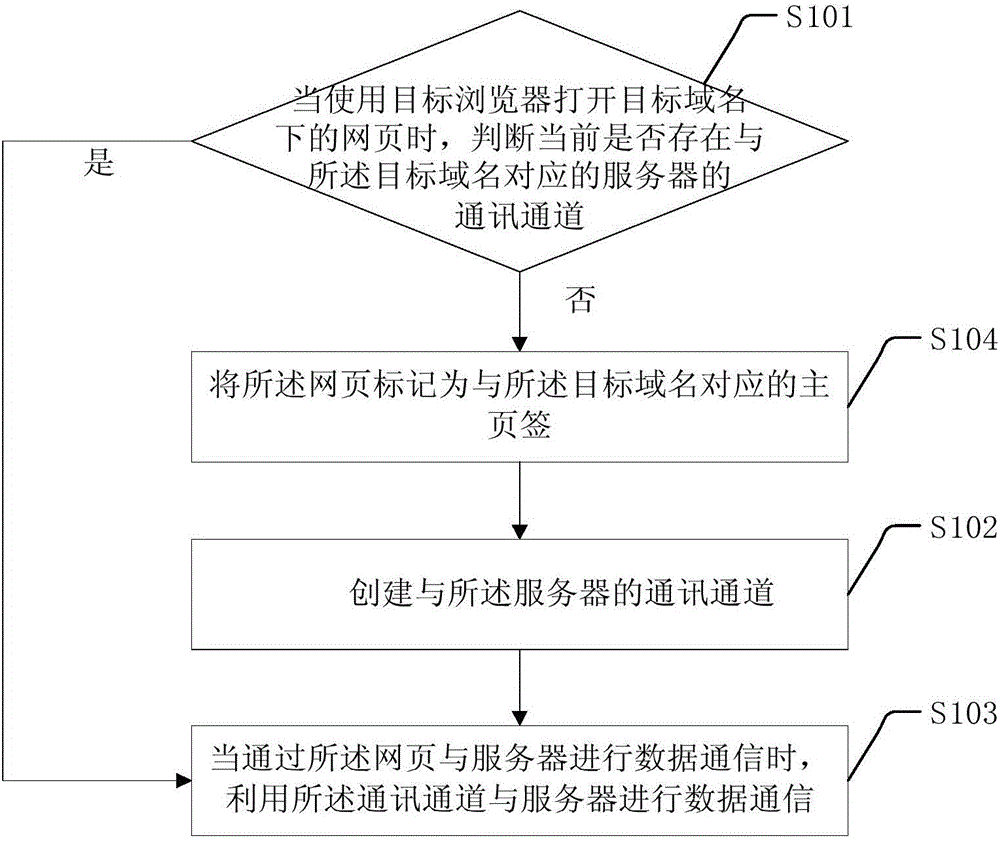
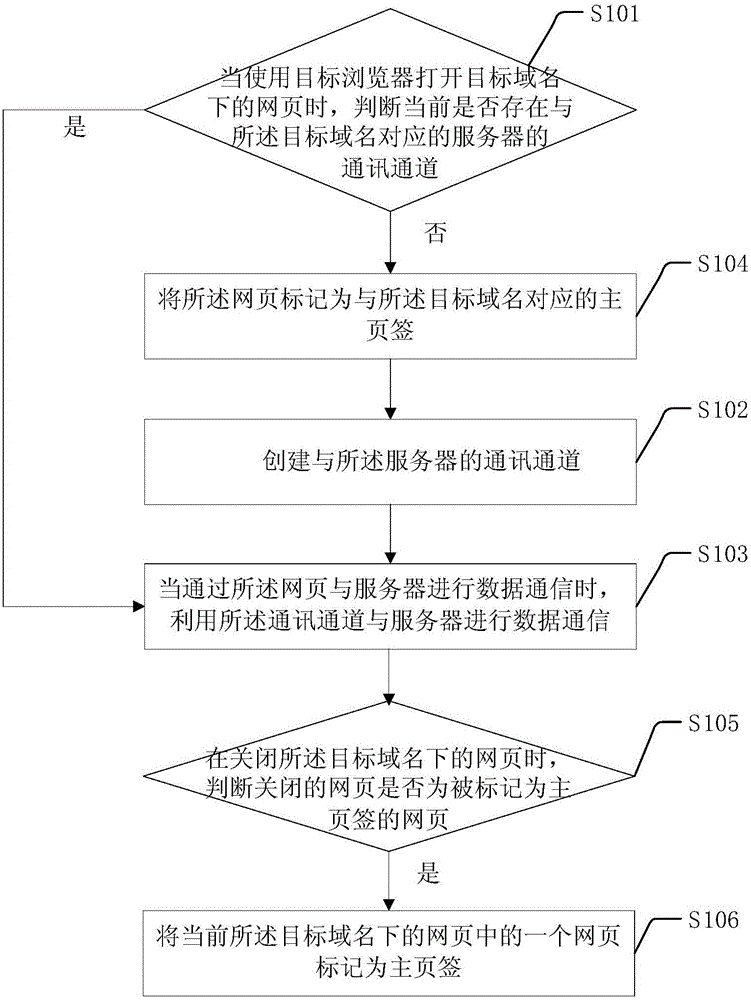
Communication channel sharing method and device
The invention discloses a communication channel sharing method and device applied to the field of Internet technology. The method comprises when an object browser is used to open a webpage in an object domain name, whether a communication channel, corresponding to the object domain name, exists for a server at present is determined; if NO, the communication channel for the server is created; when data communication with the server is carried out via the webpage, the communication channel is used for implementing data communication with the server; and if the communication channel exists at present, the existing communication channel is used for implementing data communication with the server when data communication with the server is carried out via the webpage. According to the communication channel sharing method and device, the communication efficiency can be improved, and the bandwidth and IO load of the server are reduced.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
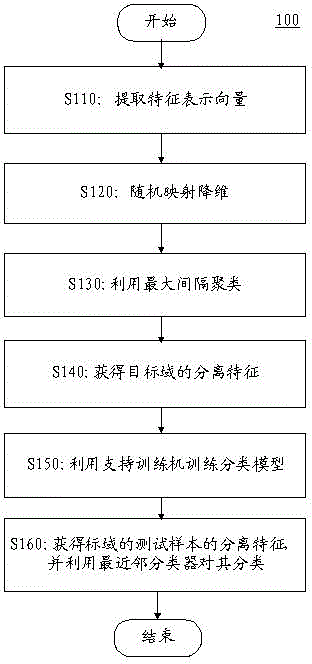
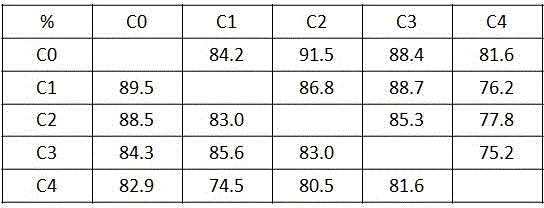
Multi-view behavior identification method based on largest-interval meaning clustering
Each embodiment mode of the invention provides a multi-view behavior identification method based on largest-interval meaning clustering. The method comprises steps that: global profile flow characteristics of each frame of each motion video sample are firstly extracted, a words-bag model is utilized to acquire characteristic expression vectors of the corresponding motion video sample frames; dimensionality reduction for the characteristic expression vectors is carried out by utilizing multi-time random mapping; the characteristic expression vectors which are acquired through dimensionality reduction at each random mapping are clustered through a largest-interval meaning clustering method; source object samples of all the samples are determined by utilizing a trained model, and separation characteristics of the source samples are directly taken as separation characteristics of an object domain; the separation characteristics of an object domain are taken as input, and a classification model is trained by utilizing a support vector machine; separation characteristics of a test sample of the object domain are acquired by utilizing the classification model of the support vector machine, and classification is carried out by utilizing a nearest neighbor classifier.
Owner:康江科技(北京)有限责任公司
Adaptive extension method and device of data object, and storage medium
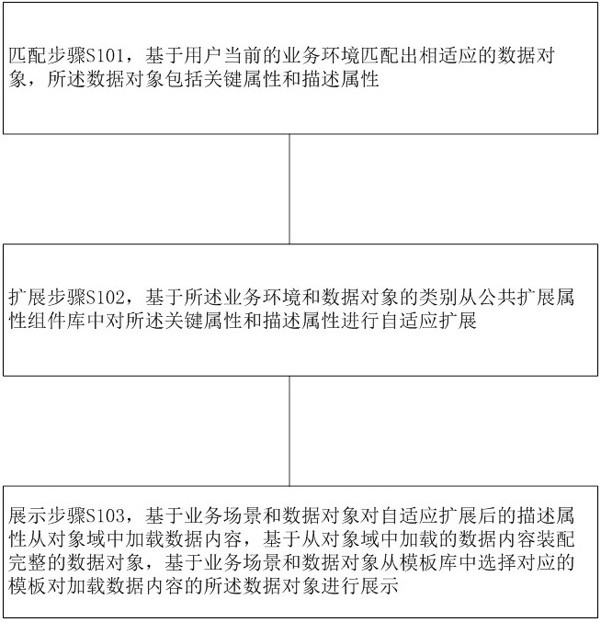
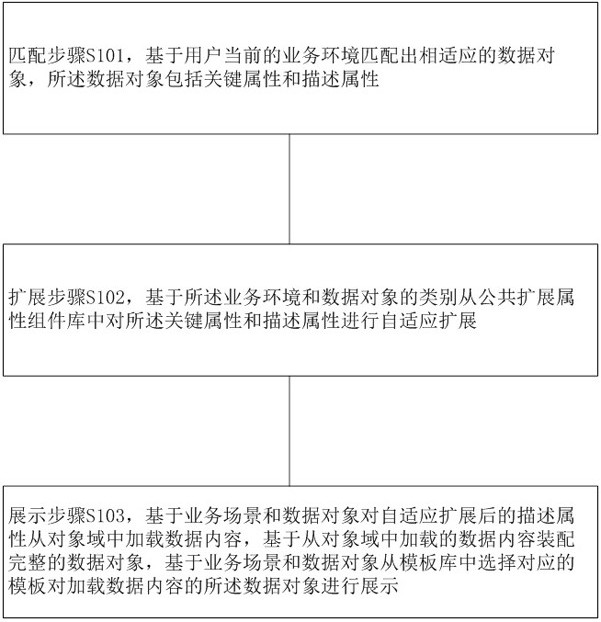
ActiveCN112257401AImprove scalabilityImprove utilization efficiencyText processingProgram loading/initiatingComplete dataScene matching
The invention provides an adaptive extension method and device of a data object, and a storage medium, and the method comprises the steps: a matching step: obtaining an adaptive data object through matching based on a current business scene of a user, and the data object comprises a key attribute and a description attribute; an extension step of performing adaptive extension on the key attributesand the description attributes from a public extension attribute component library based on the business scene and the category of the data object; and a display step: loading data contents from the object domain based on the description attributes after the adaptive expansion of the business scene and the data object pair, and assembling the complete data object based on the data contents loadedfrom the object domain, and selecting a corresponding template from a template library based on the business scene and the data object to display the data object loaded with the data content. According to the method, the expansibility of the data object is improved, the programming development difficulty is reduced, the utilization efficiency of the template is improved, the visibility of documentor report display is enhanced, and the user experience is improved.
Owner:CHANJET INFORMATION TECH CO LTD
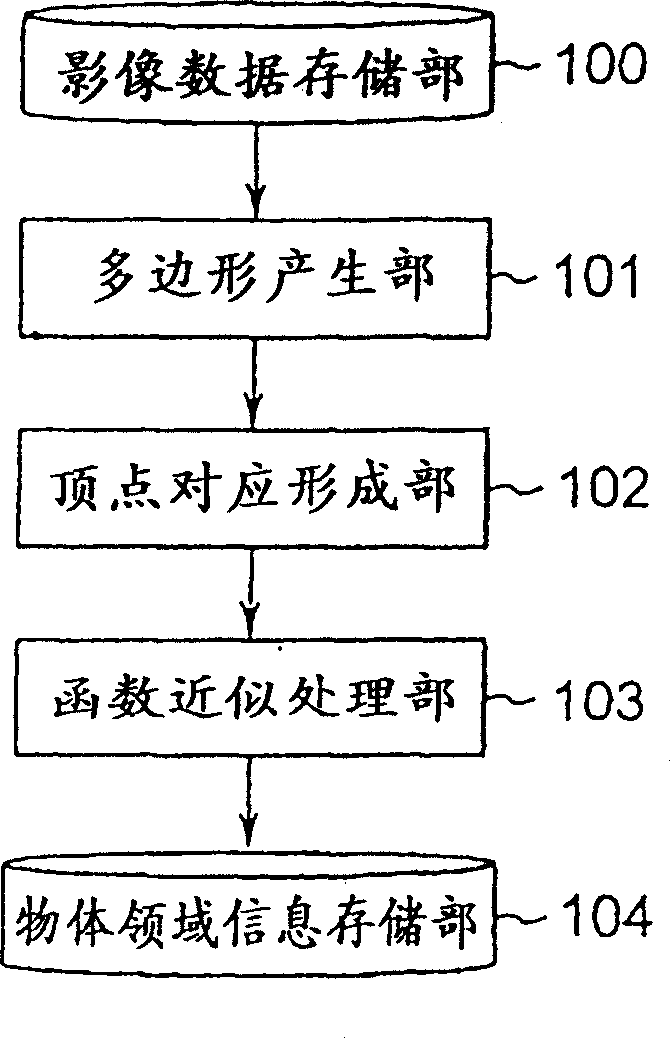
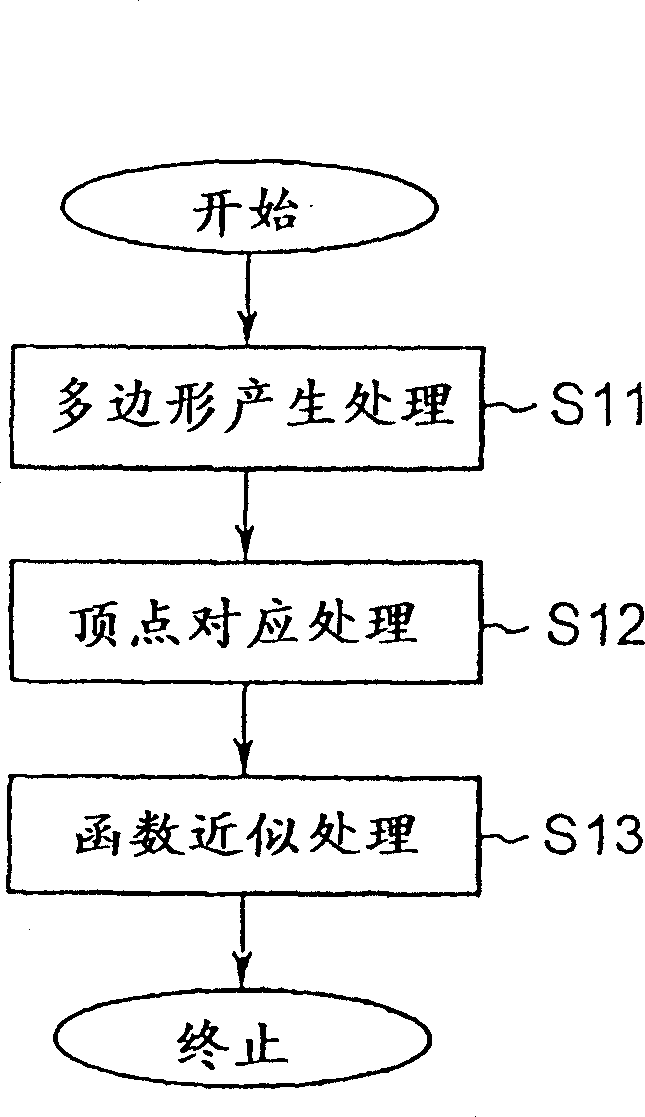
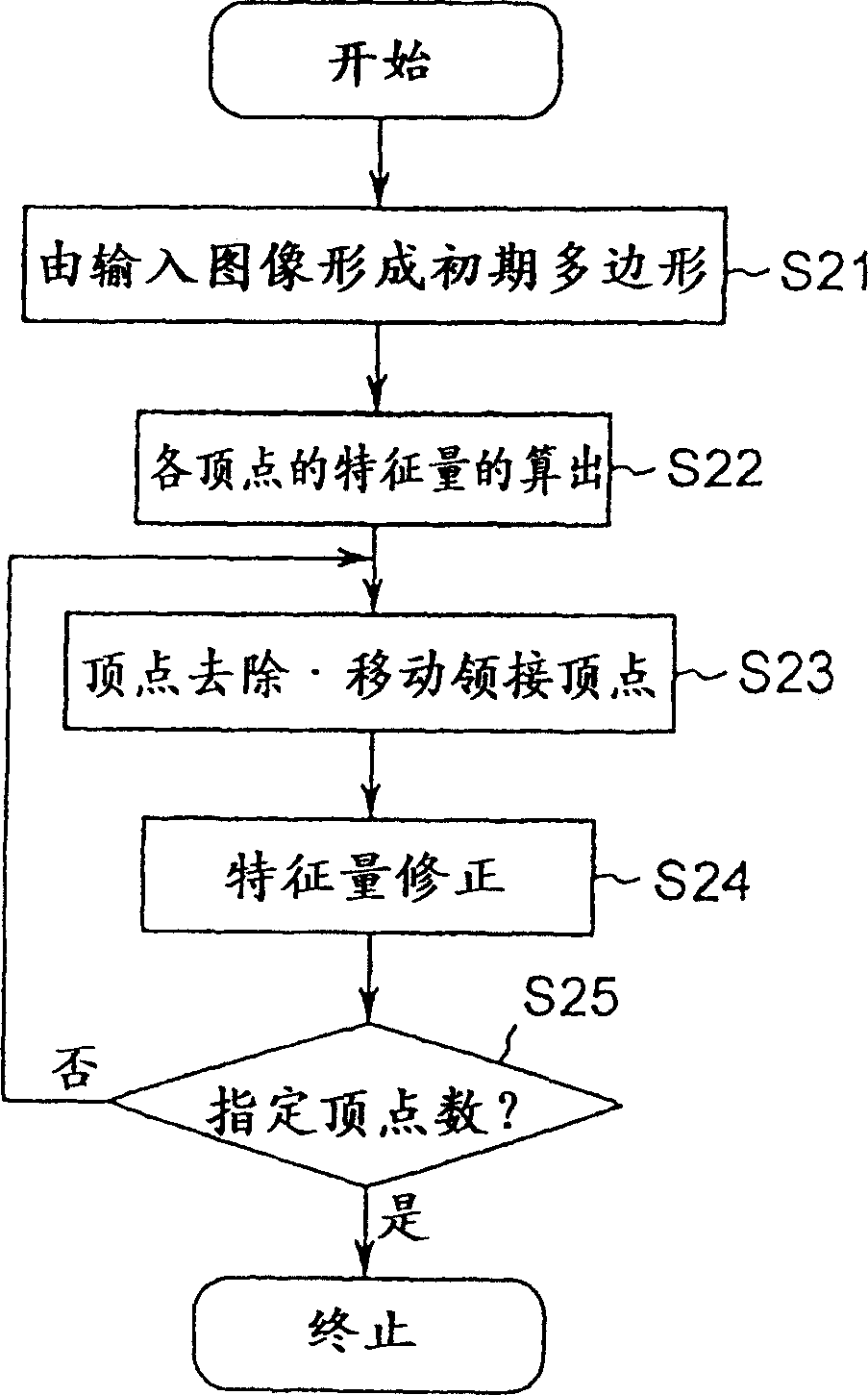
Object realm information producing method and device, and approximate polygon producing method and device
InactiveCN1227624CMove quicklyValid confirmationImage enhancementImage analysisComputer graphics (images)Small data
The present invention provided an object domain information generating device capable of performing polygonal approximation to the domain of a desired object in video precisely and speedily and describing the desired object in the video with a small data quantity. In an object domain information describing method for performing domain information, which generates information describing the domain of the optional matter in the video extending consecutive plural frames, a polygon generation part 101 generates an approximate polygon showing the domain of the objective object in the video, a vertex coordinating generation part 102 specifies the correspondence of the vertex in an adjacent frame at the vertex of the approximate polygon and a function approximating processing part 103 approximates the locus of the vertex in the case of arranging positional data on the vertex of the approximate polygon along the advance of a frame with a prescribed function to make information on the area of the object by using the parameter of the function.
Owner:KK TOSHIBA
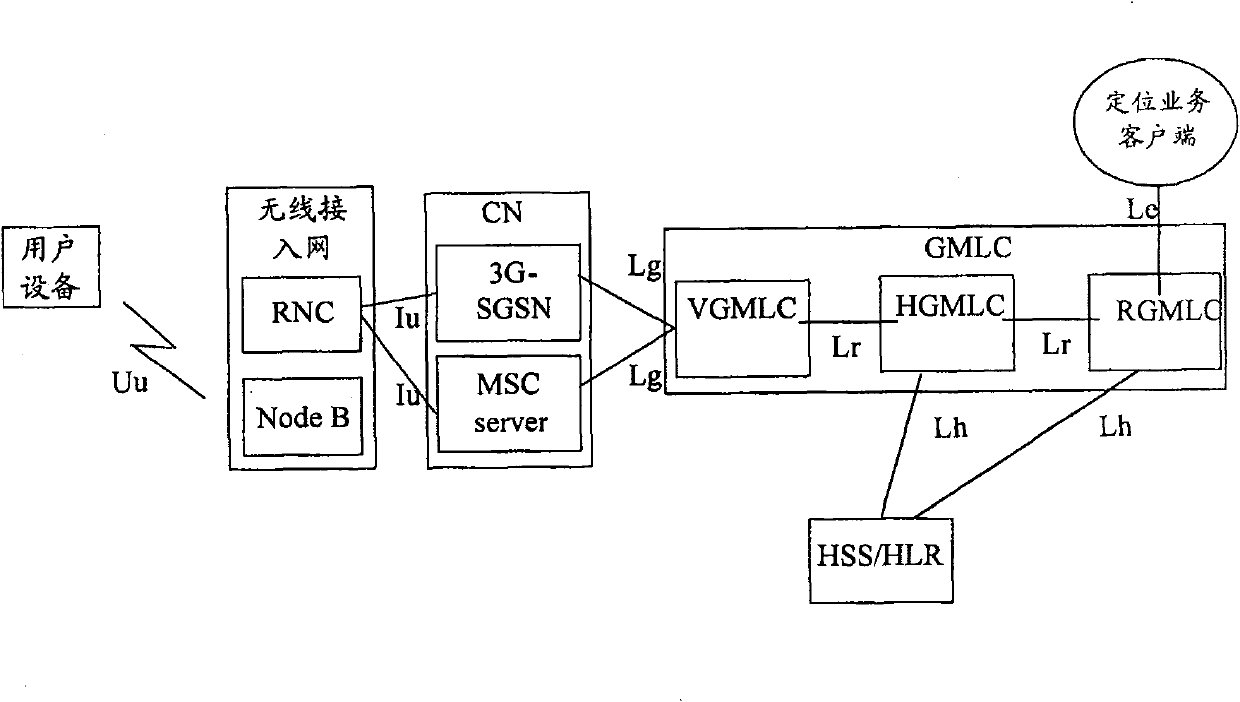
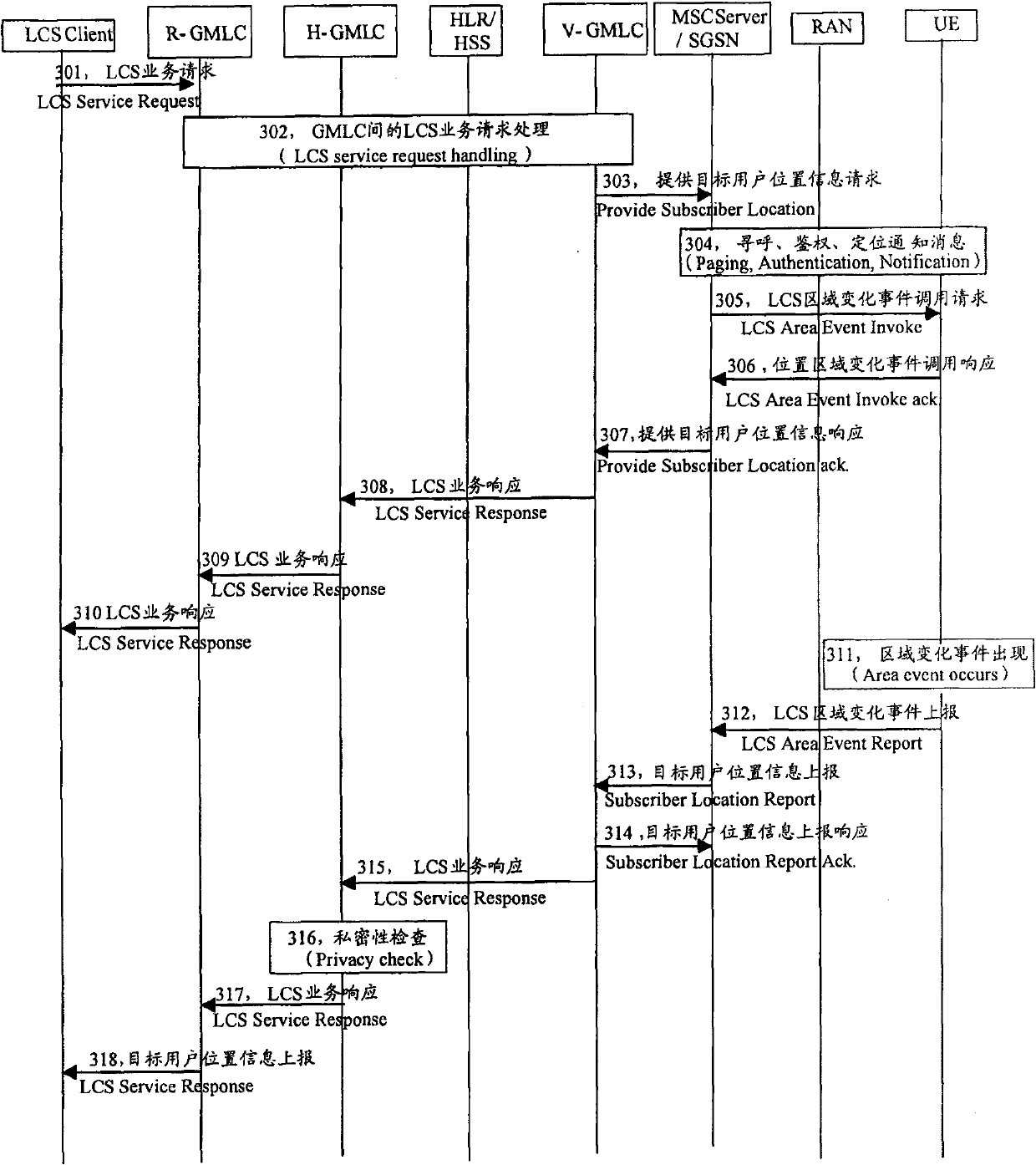
Method of locating intraregion user of mobile communication system
InactiveCN100589605CGet detailed location informationPracticalRadio/inductive link selection arrangementsWireless communicationMobile communication systemsA domain
Owner:ZTE CORP
A method and device for controlling mandatory access
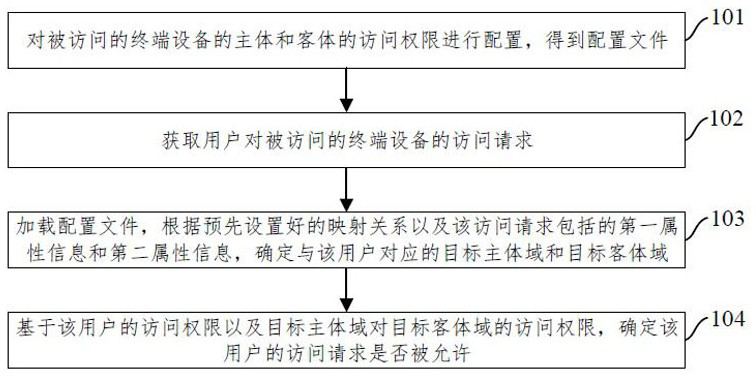
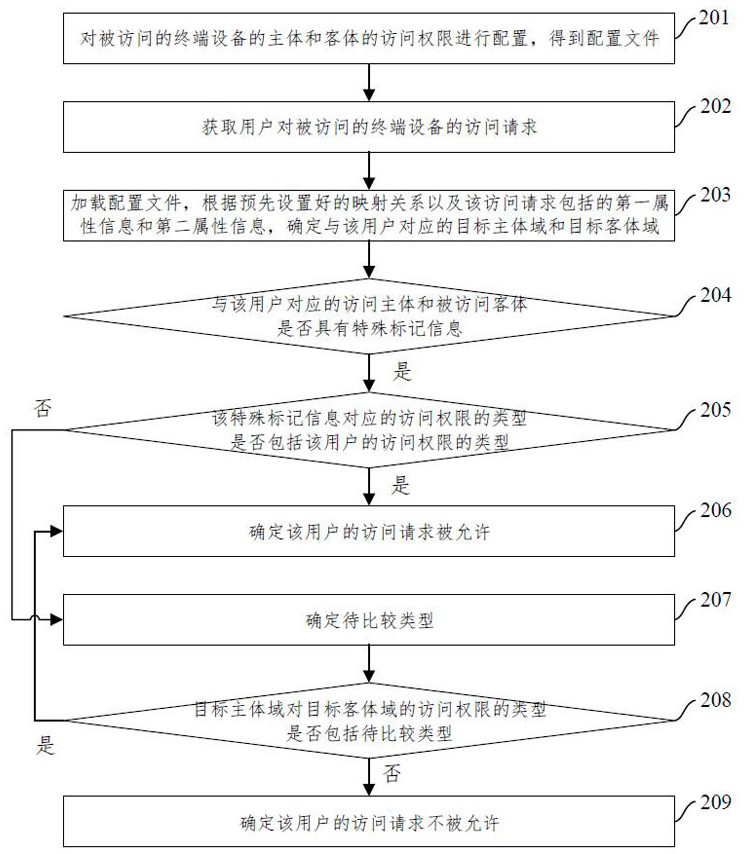
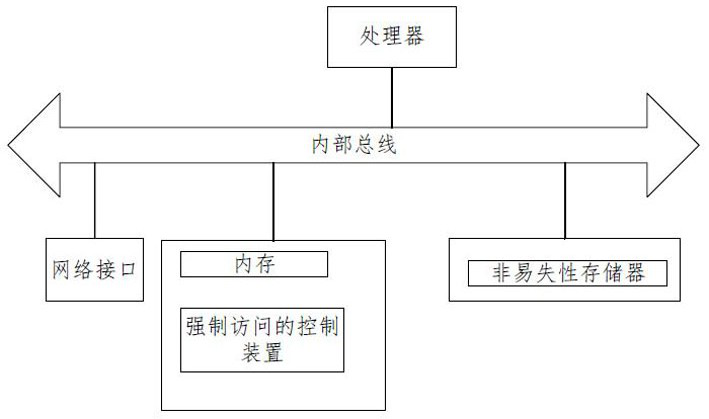
ActiveCN112989429BMeet a variety of application scenariosDigital data protectionSoftware engineeringTerminal equipment
The present invention relates to a method and device for controlling mandatory access. The method includes: configuring the access authority of the subject and object of the terminal equipment being accessed to obtain a configuration file; the configuration file includes a subject field and an object field, and the subject field corresponds to a There is at least one subject, and the object field corresponds to at least one object; obtain the user's access request to the accessed terminal device; the access request carries the user's access right, the first attribute information used to characterize the access subject, and the first attribute information used to characterize the accessed terminal device. The second attribute information of the object; load the configuration file, and determine the target subject domain and target object domain corresponding to the user according to the preset mapping relationship and the first attribute information and second attribute information included in the access request; based on the The user's access rights and the target subject domain's access rights to the target object domain determine whether the user's access request is allowed. The solution of the present invention can satisfy various application scenarios of users.
Owner:BEIJING CHANGYANG TECH CO LTD
A method, device and storage medium for self-adaptive expansion of data objects
ActiveCN112257401BImprove scalabilityImprove utilization efficiencyText processingProgram loading/initiatingComplete dataEngineering
The present invention provides a data object self-adaptive expansion method, device and storage medium. The method includes: a matching step, matching a suitable data object based on the user's current business scene, and the data object includes key attributes and description attributes ; Extending step, based on the business scenario and the category of the data object, the key attribute and the description attribute are adaptively extended from the public extended attribute component library; the display step is based on the description of the business scenario and the data object after the adaptive extension The attribute loads data content from the object domain, assembles a complete data object based on the data content loaded from the object domain, and selects a corresponding template from the template library based on the business scenario and data object to display the data object loaded with data content. The invention improves the expansibility of data objects, reduces the difficulty of programming and development, improves the utilization efficiency of templates, enhances the visibility of documents or reports, and improves user experience.
Owner:CHANJET INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com