Patents
Literature
119 results about "Recovery management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Zones of Recovery Management. The Recovery management model is based on the recognition that recovery most often occurs through incremental progress within five zones of personal experience. These zones are the physical, psychological, relational, lifestyle and spiritual.
Disaster recovery virtual roll call and recovery management system
InactiveUS7026925B2Data processing applicationsFrequency-division multiplex detailsThe InternetPersonal computer
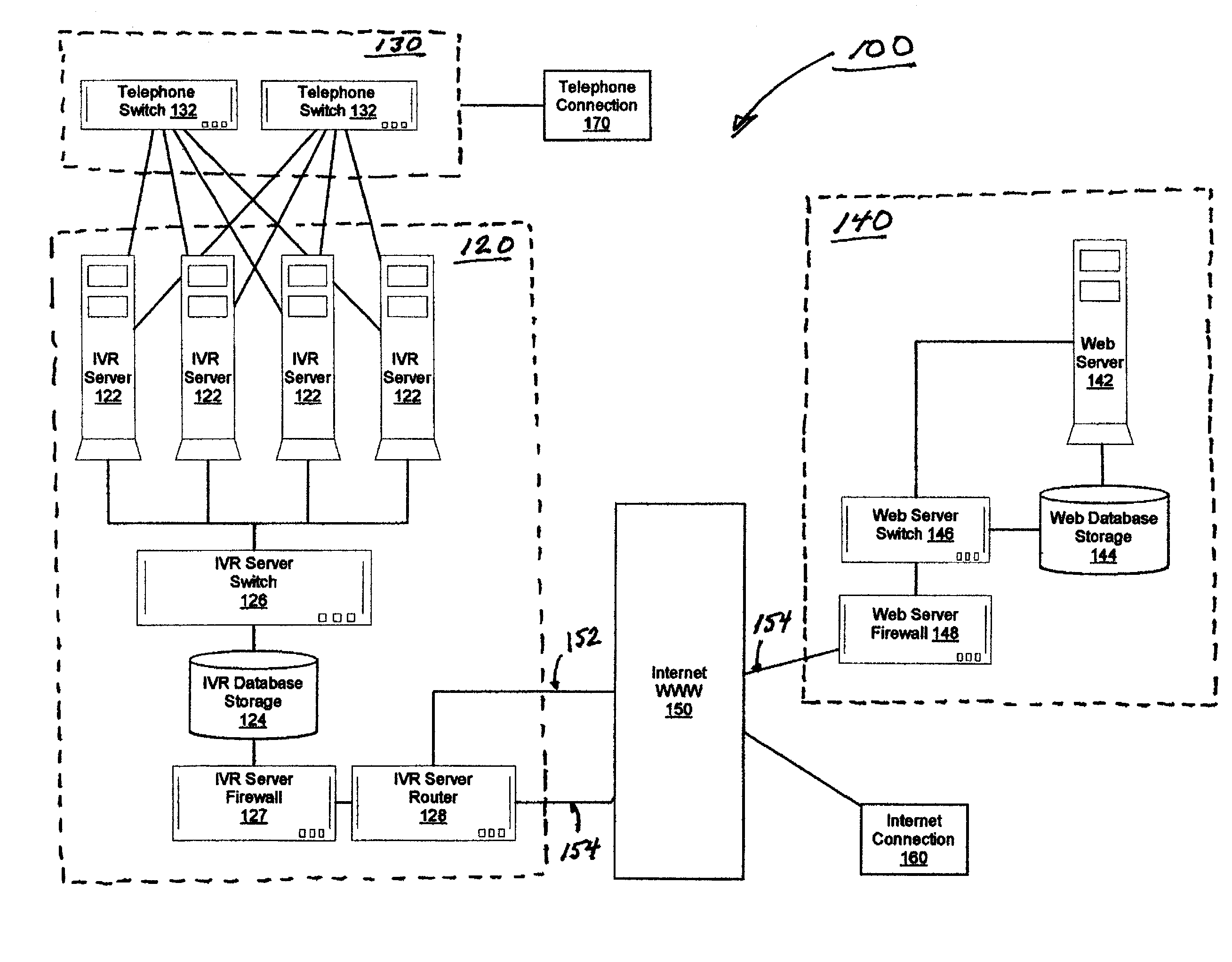
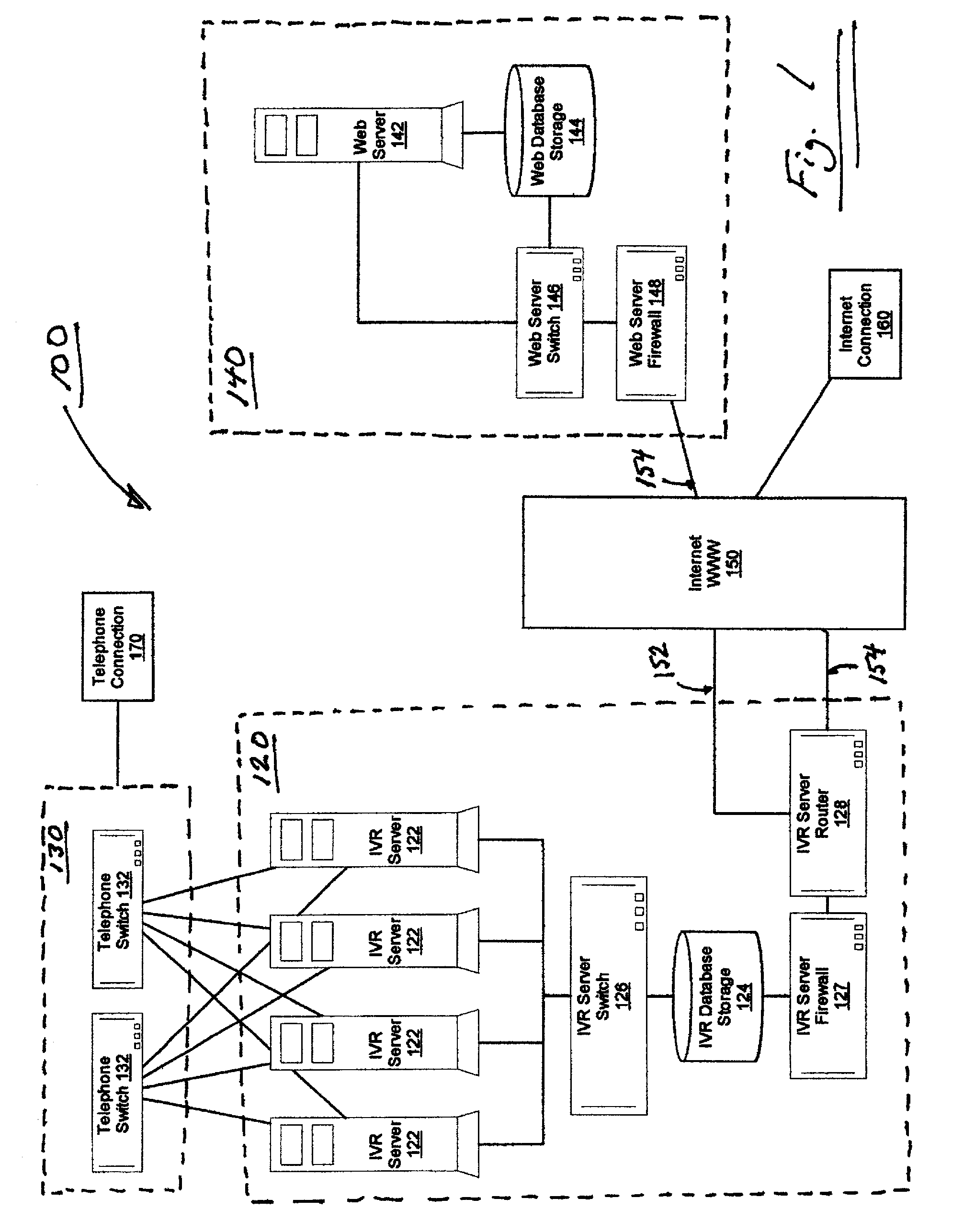
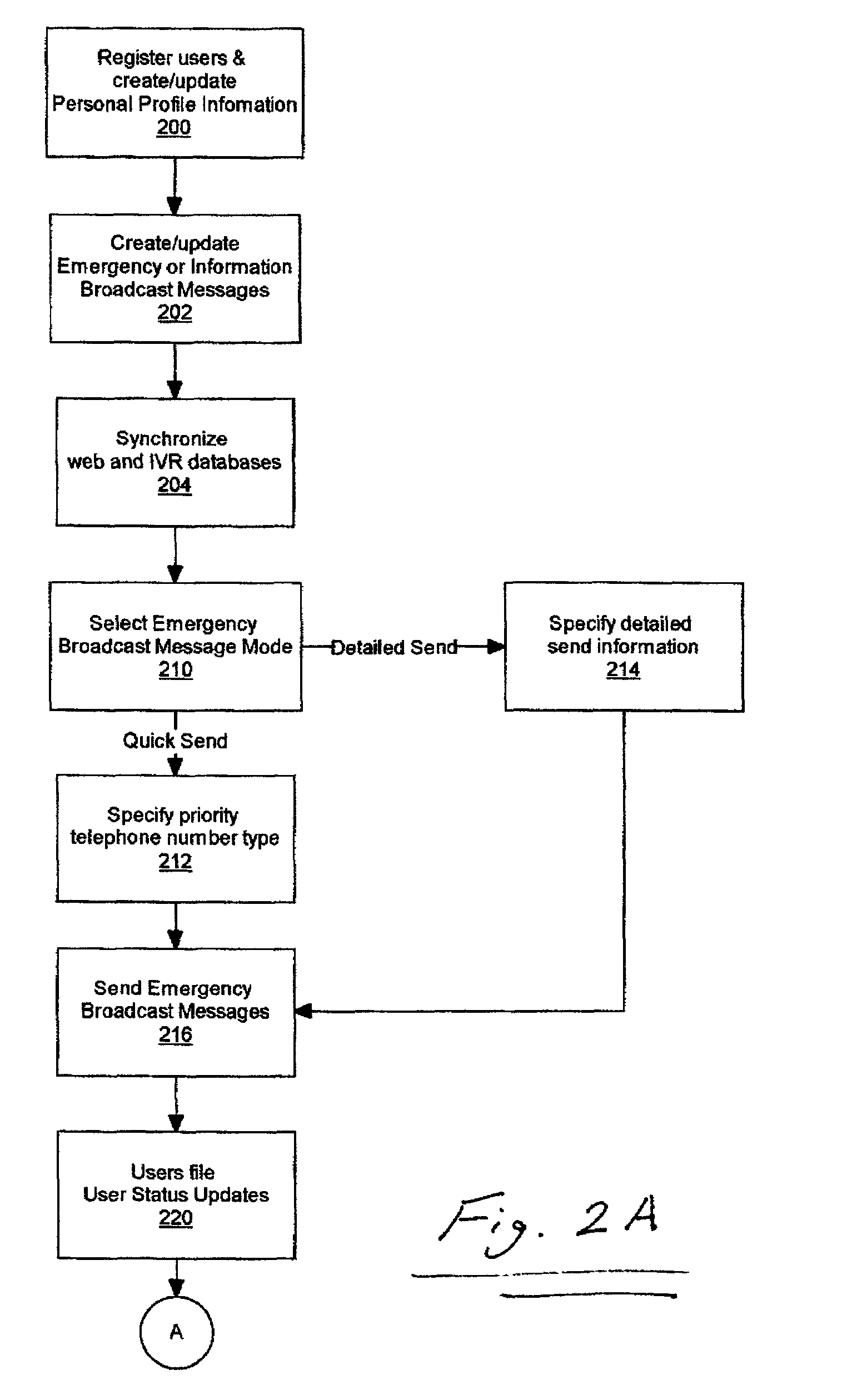
A disaster recovery virtual roll call and recovery management system and method allows any organization to locate their staff and allocate resources to their staff in the event of a disaster. User information can be stored on remote, distributed computer networks to assure that the information is available during a disaster. The computer networks can be web networks and Interactive Voice Response (IVR) networks, to provide different methods of user interaction with the system. In case of disaster, the system can contact the users over one or more communications networks, such as by email or IVR message, and request the user provide their status. The users can send user status updates to the web network using internet enabled devices, such as personal computers, telephones, or handheld portable computers, or to the IVR network using standard or wireless telephones. The system can compile the information, and generate reports on group and individual status.
Owner:OAK LAWN MARKETING
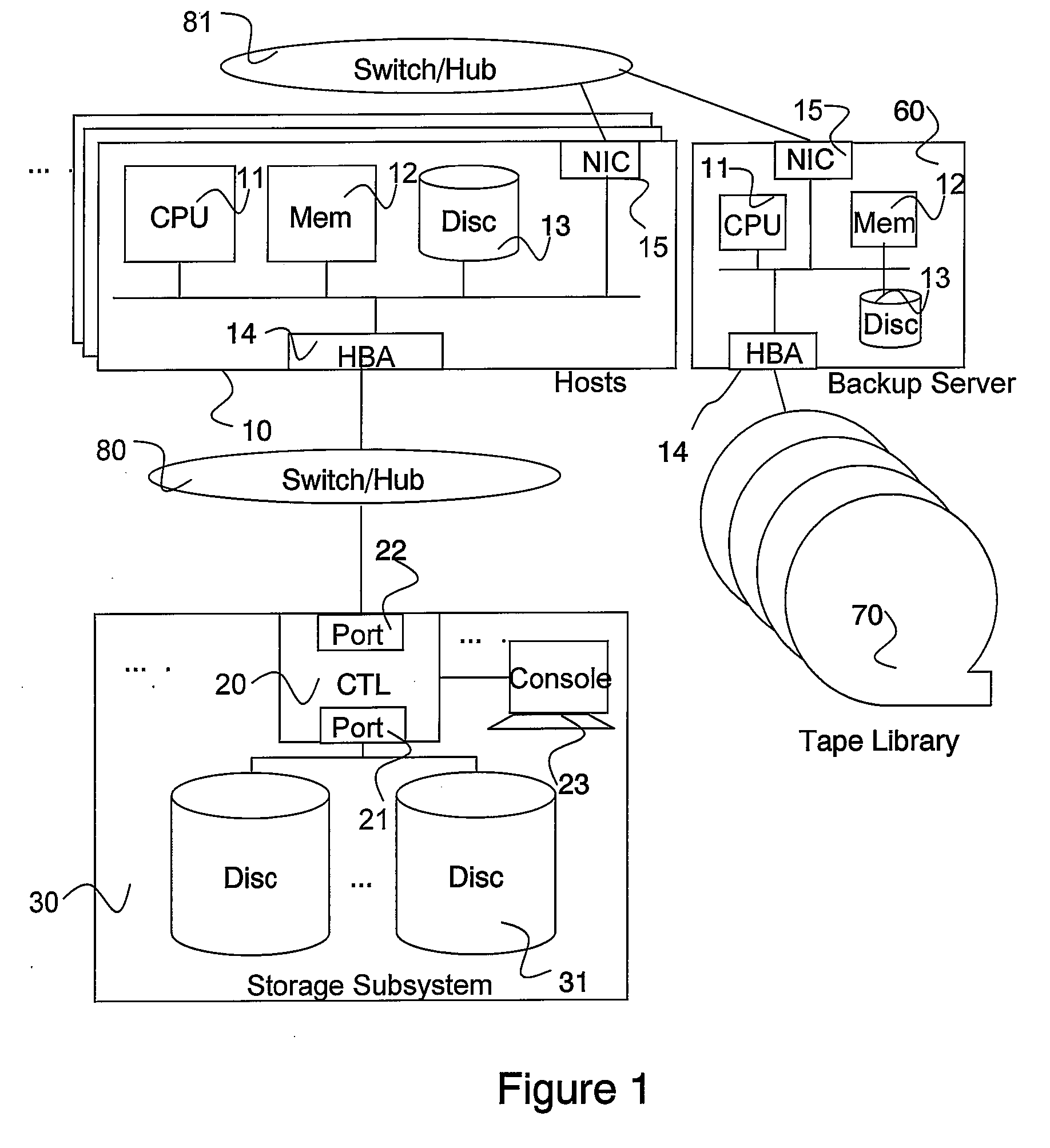
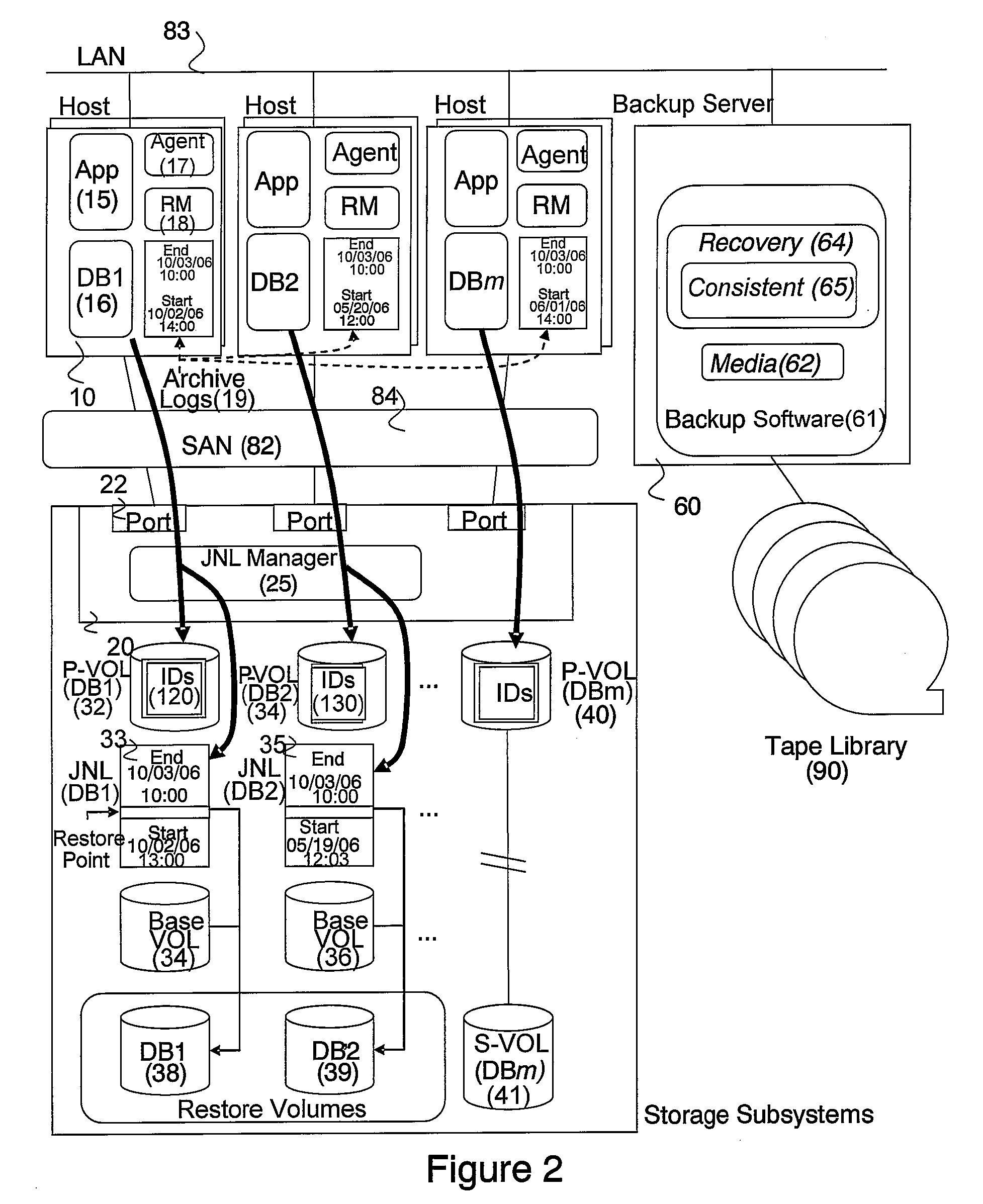
System and method for managing consistency among volumes based on application information
InactiveUS20080228833A1Eliminate the problemData processing applicationsDigital data information retrievalDatabase applicationApplication software
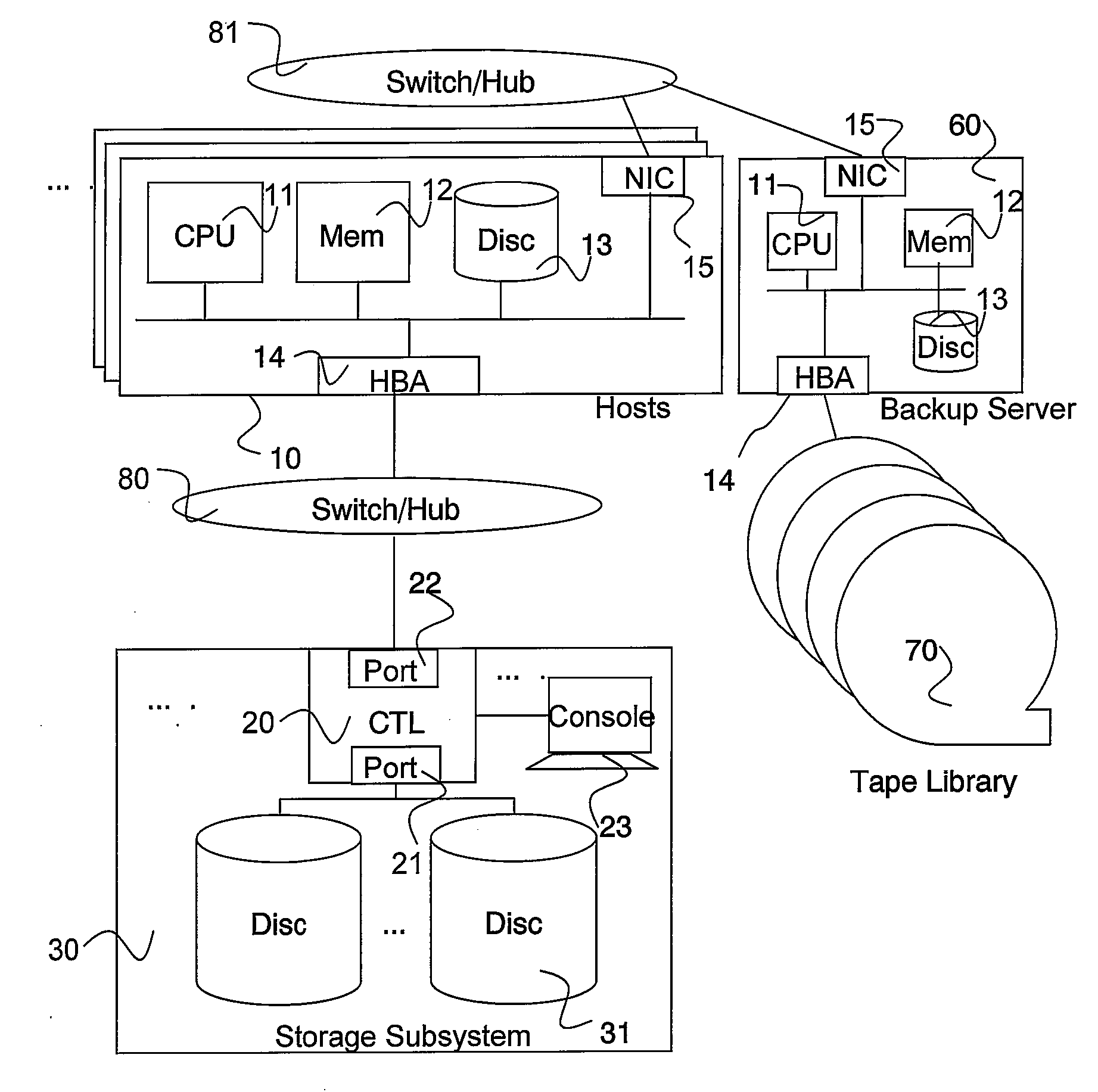
In accordance with new technique, a computerized data recovery system includes a storage subsystem and a backup server operatively coupled to backup storage medium, the storage subsystem including a continuous data protection system. The backup server executes a recovery manager which: collects consistency points from at least two database applications executing on at least one host; collects journal terms of the continuous data protection system for each of the at least two database applications; collects log terms associated with each of the at least two database applications; displays to a user a timeline for a protected term and consistency points for the at least two database applications; receives recovery time selection from a user; receives recovery database application selection from the user; receives baseline database application selection from the user; performs crash recovery for each database application; and performs recovery of data based on transactions associated with the at least two database applications.
Owner:HITACHI LTD
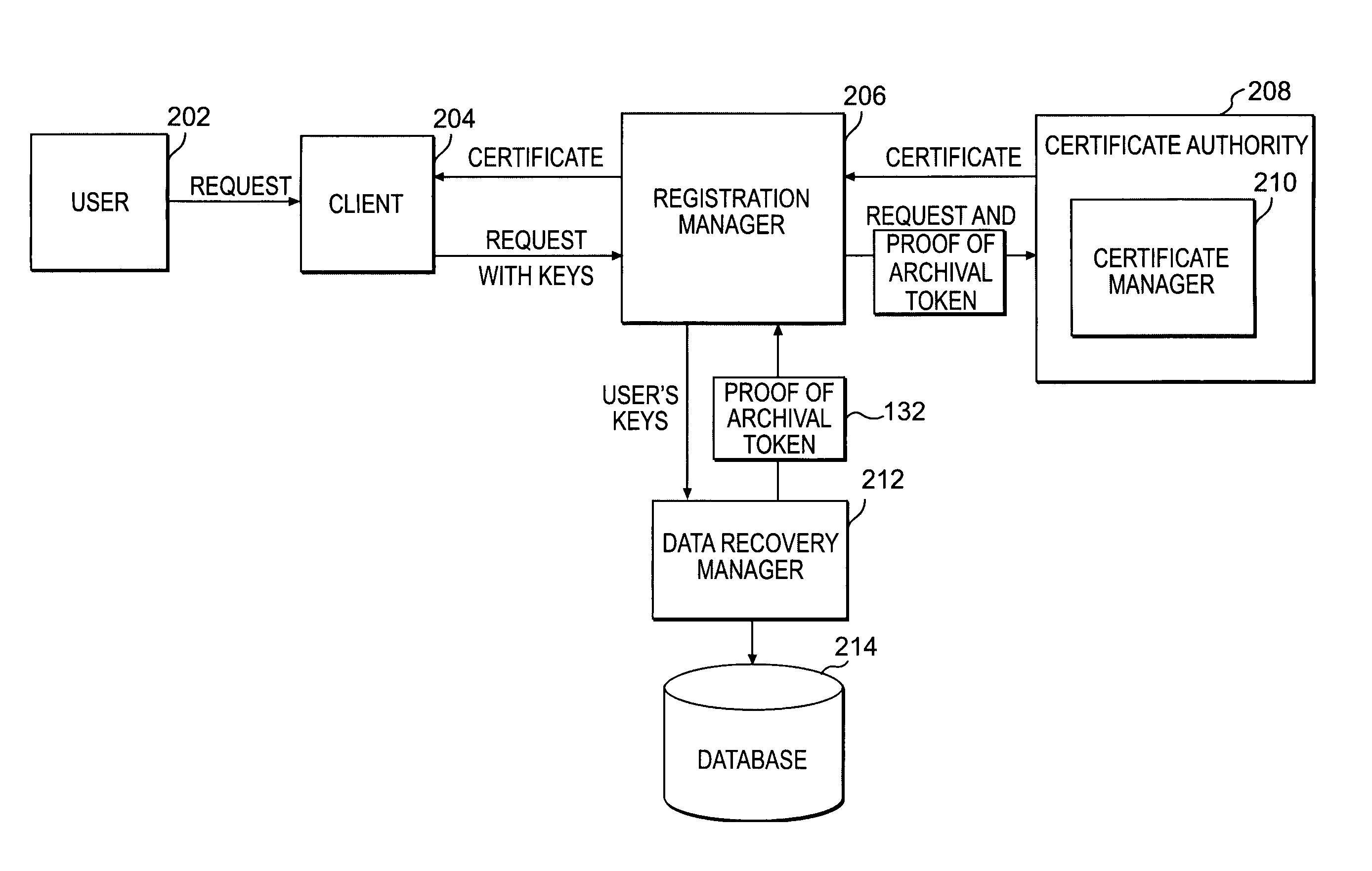
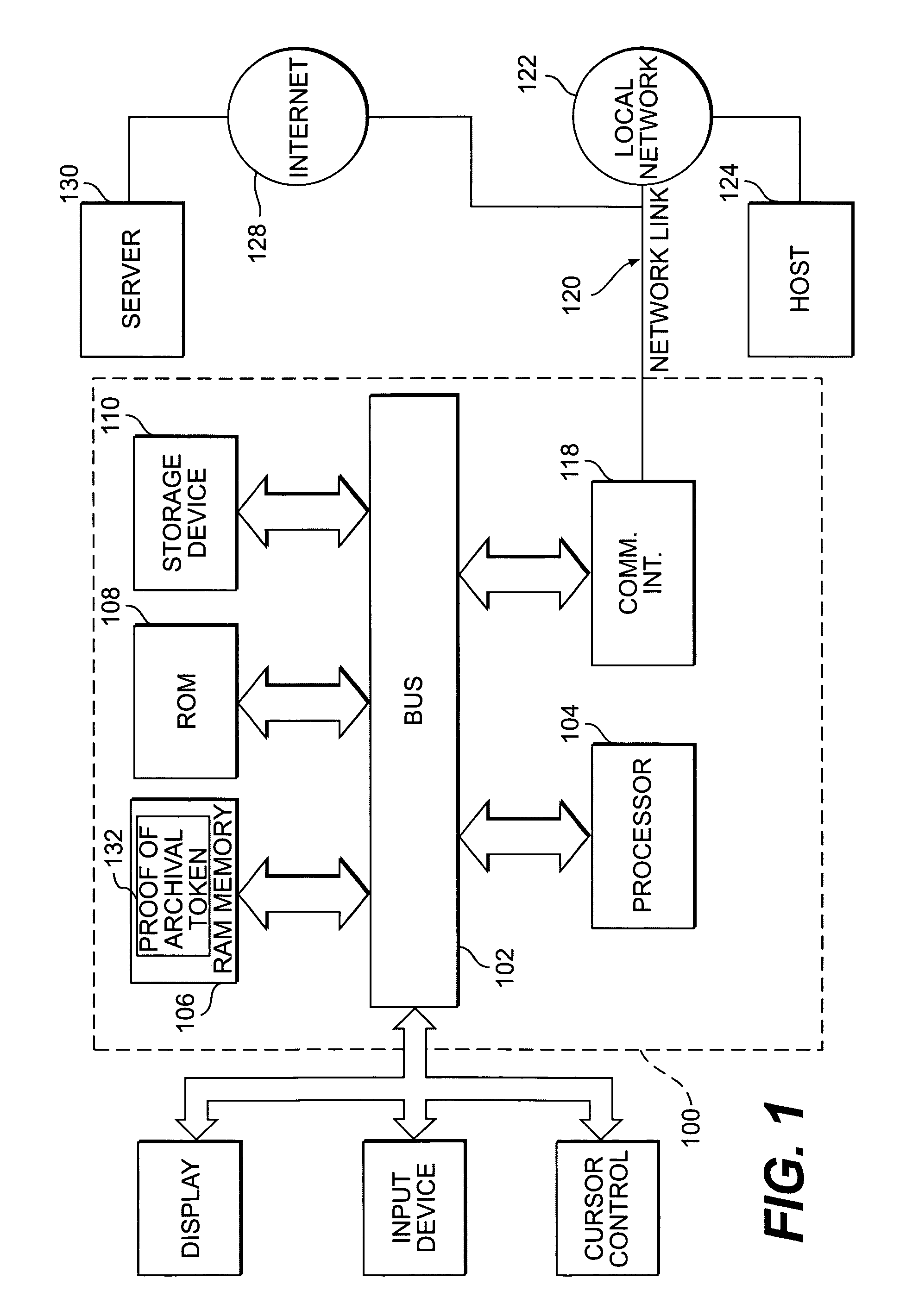
Client controlled data recovery management
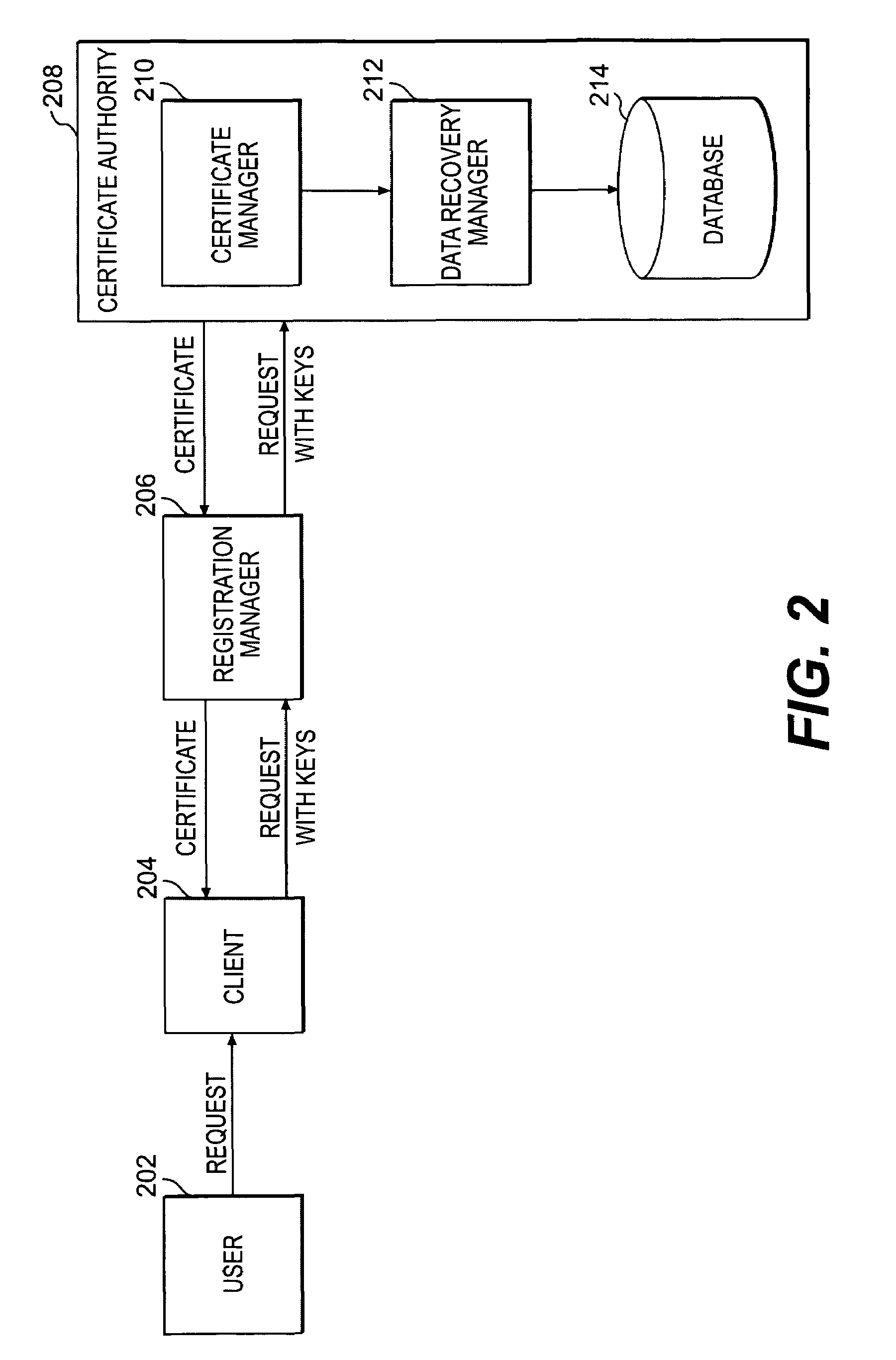
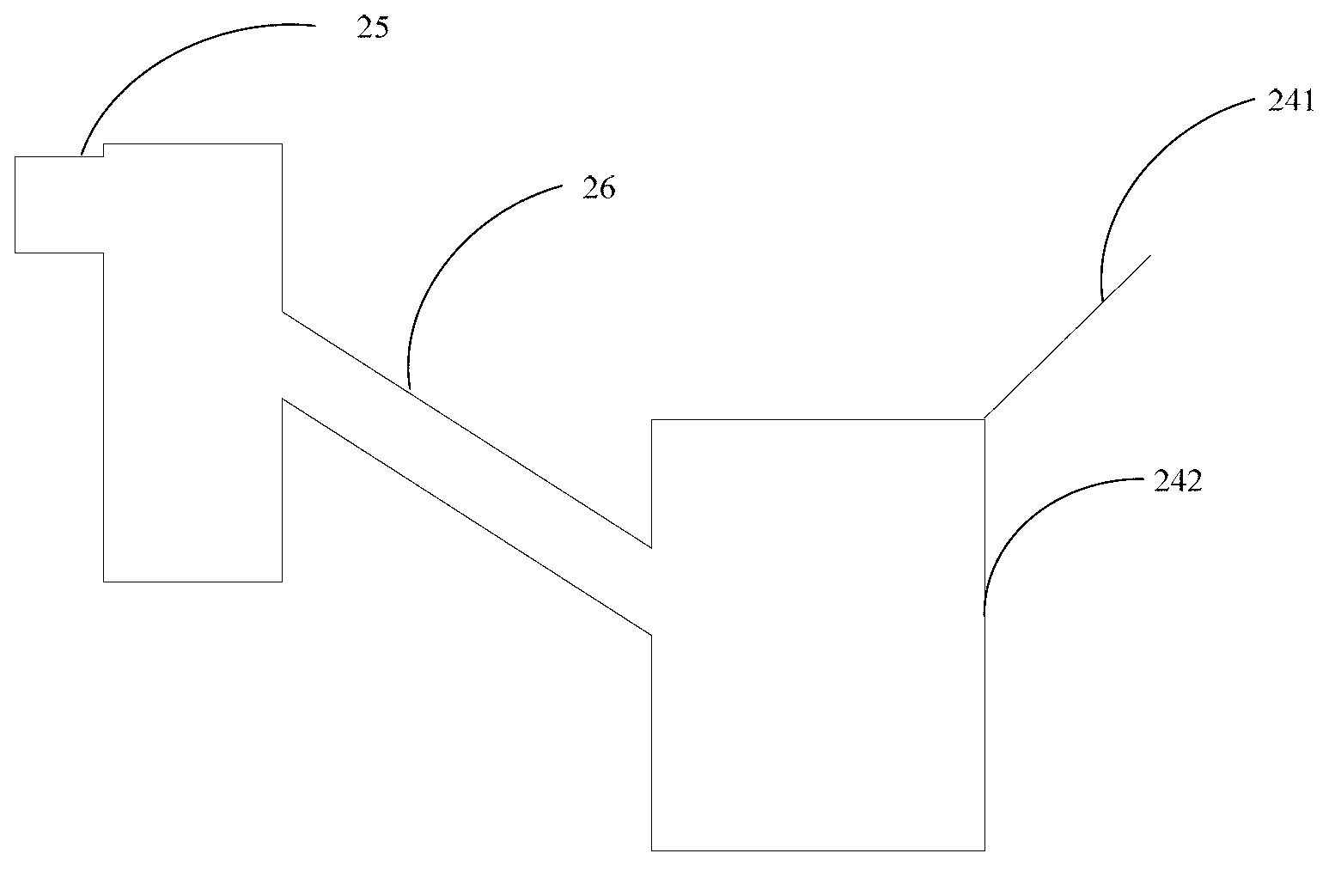
ActiveUS7050589B2Key distribution for secure communicationDigital data processing detailsDigital signatureControl data
Methods and systems in accordance with the present invention allow users' private keys corresponding to their digital certificates to be stored and archived outside of the control of a Certificate Authority (“CA”). A CA may have a policy that a user's private key must be archived in order to receive a digital certificate upon a registration request from the user. Typically, the CA knows that the user's private key is archived because it implements the archival of the key, for example, on a data recovery manager and associated internal database that the CA controls. Methods and systems in accordance with the present invention allow for the enforcement of such a policy while allowing the archival of the private keys to be outside of the control of the CA by having a data recovery manager supply a digitally signed proof of archival token with a digital certificate request to a CA. The CA is assured that the key has been archived. Methods and systems allow for the data recovery manager and a database of archived keys to be controlled by other entities, including the user or client, for example.
Owner:ORACLE INT CORP
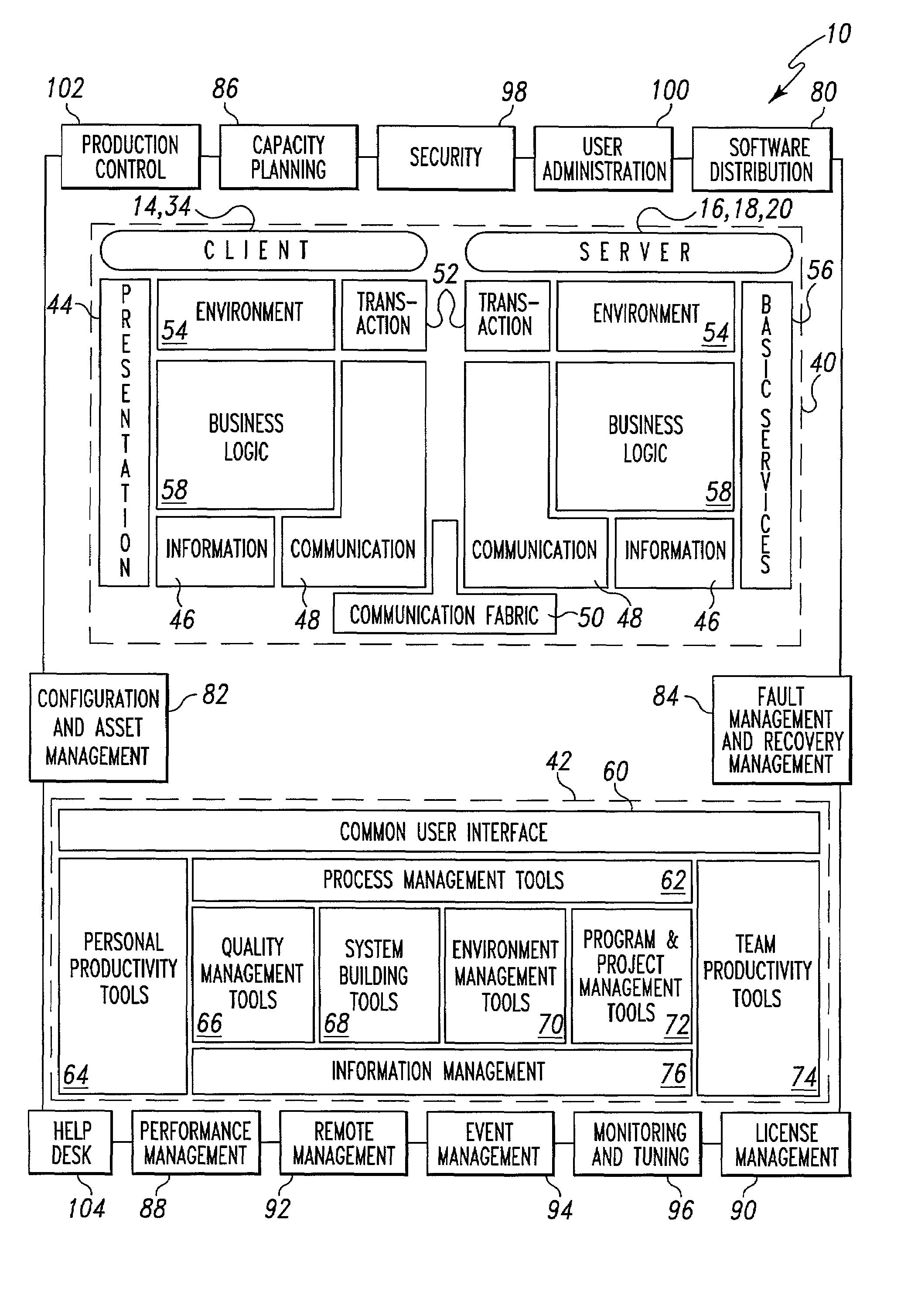
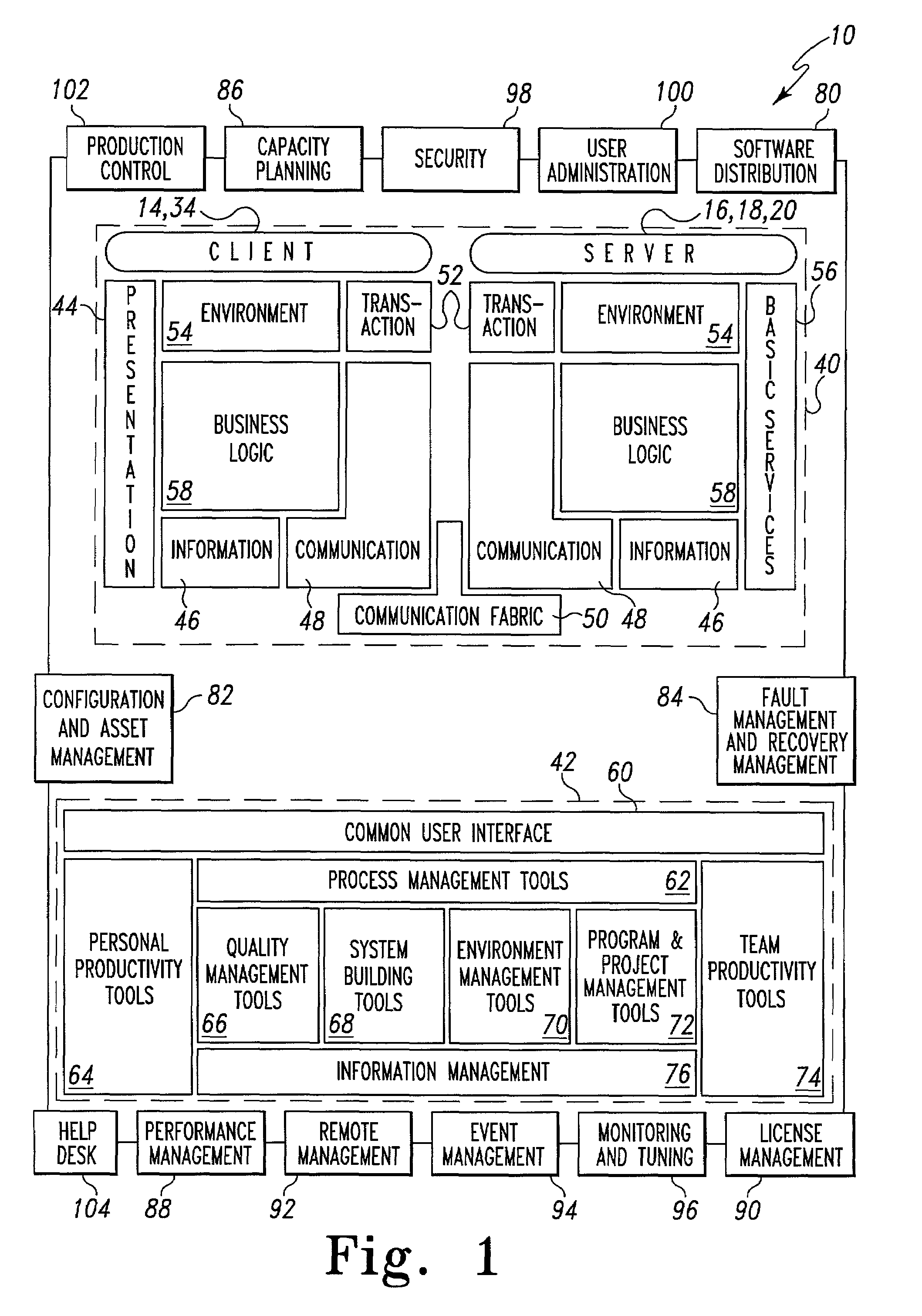
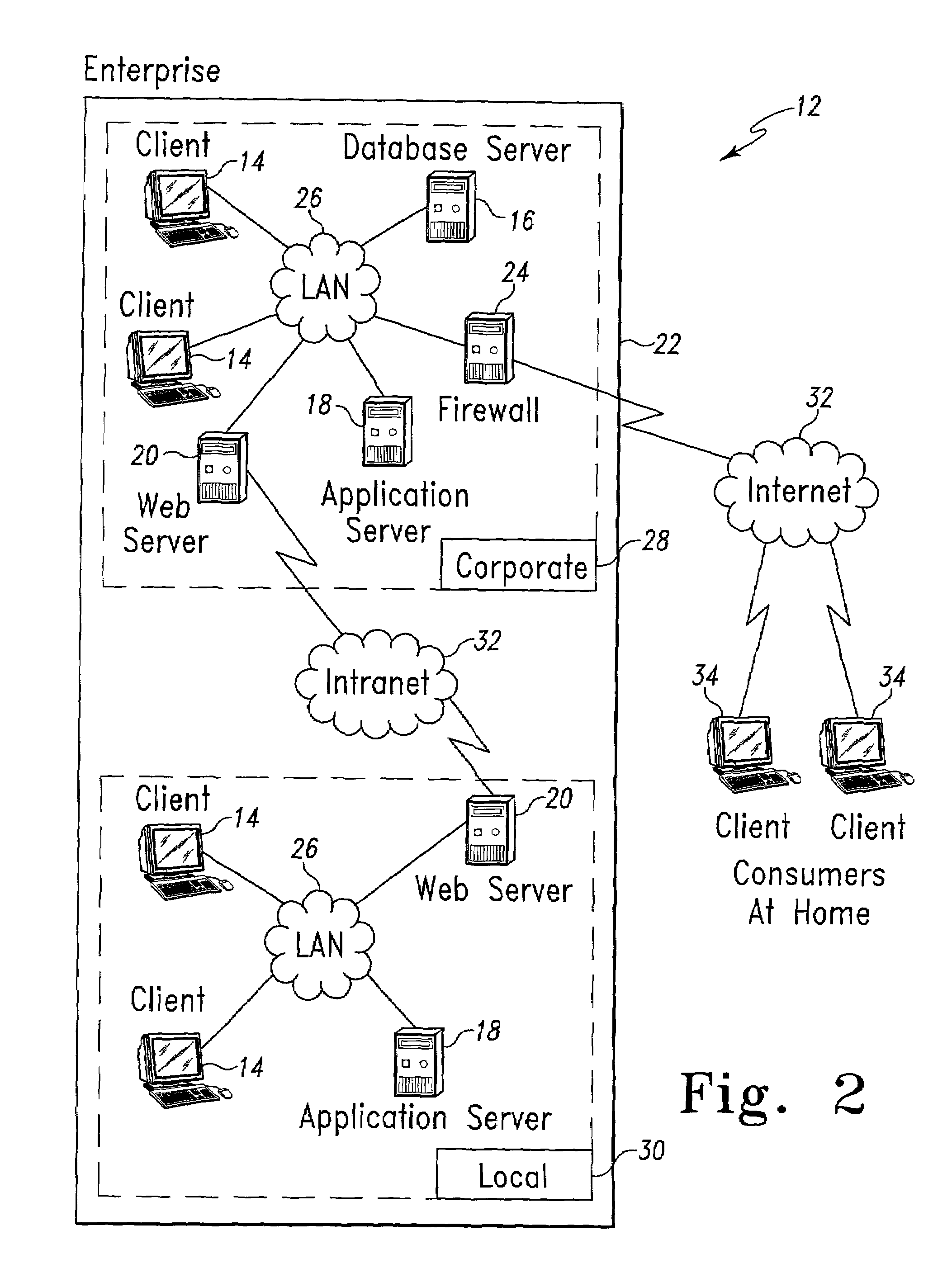
Operations architectures for netcentric computing systems
InactiveUS7415509B1Data processing applicationsWeb data retrievalManagement toolSoftware distribution
An operations architecture for a netcentric computing system including a server connected with a client. The preferred operations architecture includes a software distribution tool, a configuration and asset management tool, a fault management and recovery management tool, a capacity planning tool, a performance management tool, a license management tool, a remote management tool, a event management tool, a systems monitoring and tuning tool, a security tool, a user administration tool, a production control application set and a help desk tool that support the server and the client in the netcentric computing system.
Owner:ACCENTURE GLOBAL SERVICES LTD
Snapshot system and method of use thereof
InactiveCN101183383AFlexible choiceAdd supportRedundant operation error correctionSpecial data processing applicationsManagement toolResource management
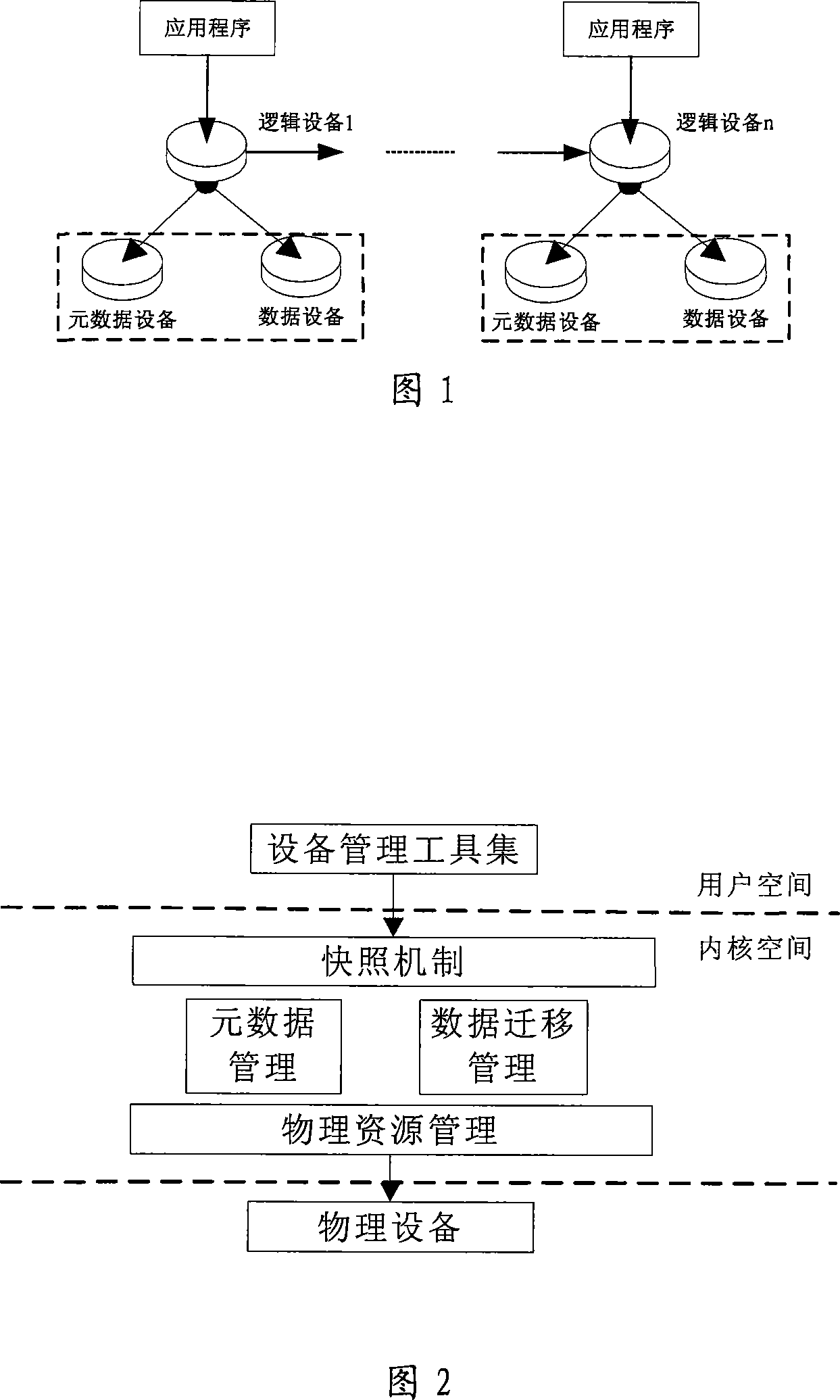
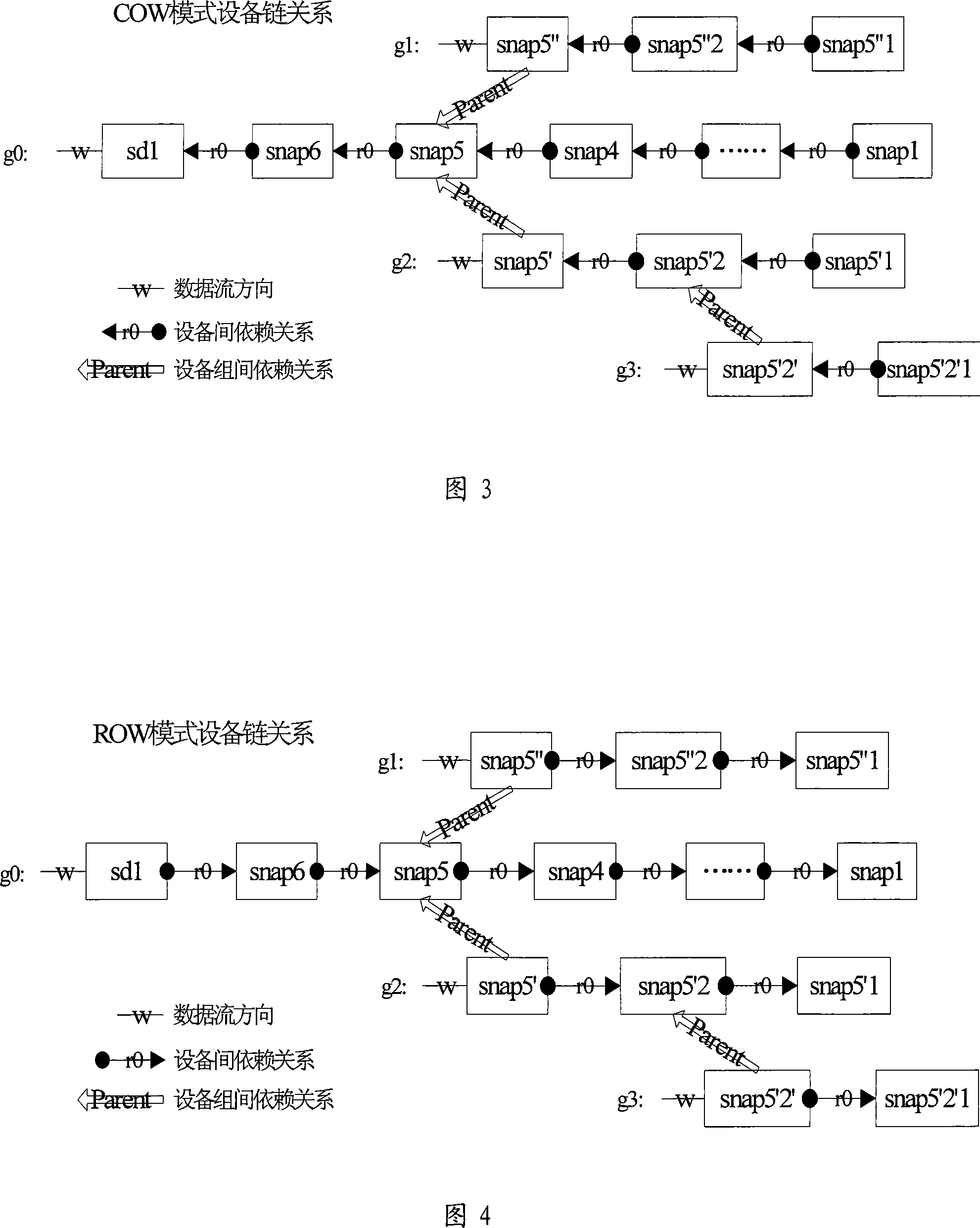
The invention provides a snapshot system, comprising an equipment managing tool set, a snapshot realization module and a physical device. The invention is characterized in that the snapshot realization module comprises a snapshot mechanism layer used for data research and time point management, and a physical resource management layer used for distribution and recovery management of the physical device; the snapshot mechanism layer comprises at least one snapshot group, and different snapshot groups can employ different snapshot technologies; the physical resource management layer comprises a metadata equipment and a data equipment corresponding with the snapshot group. The invention has an advantage that the invention can support two snapshot technologies of COW and ROW, thus users can flexibly select one snapshot technology depending on actual demands.
Owner:TIANJIN ZHONGKE BLUEWHALE INFORMATION TECH +1
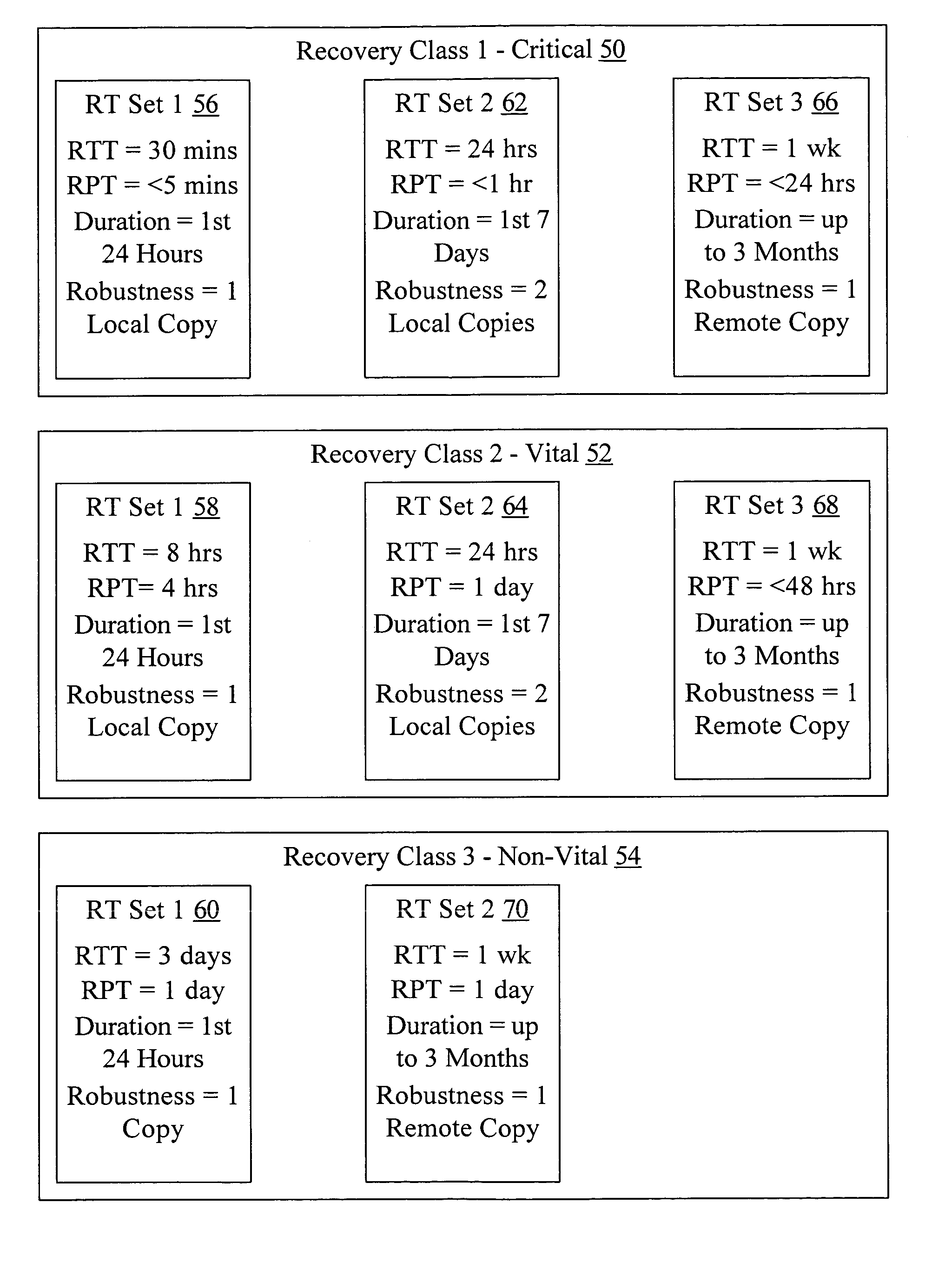
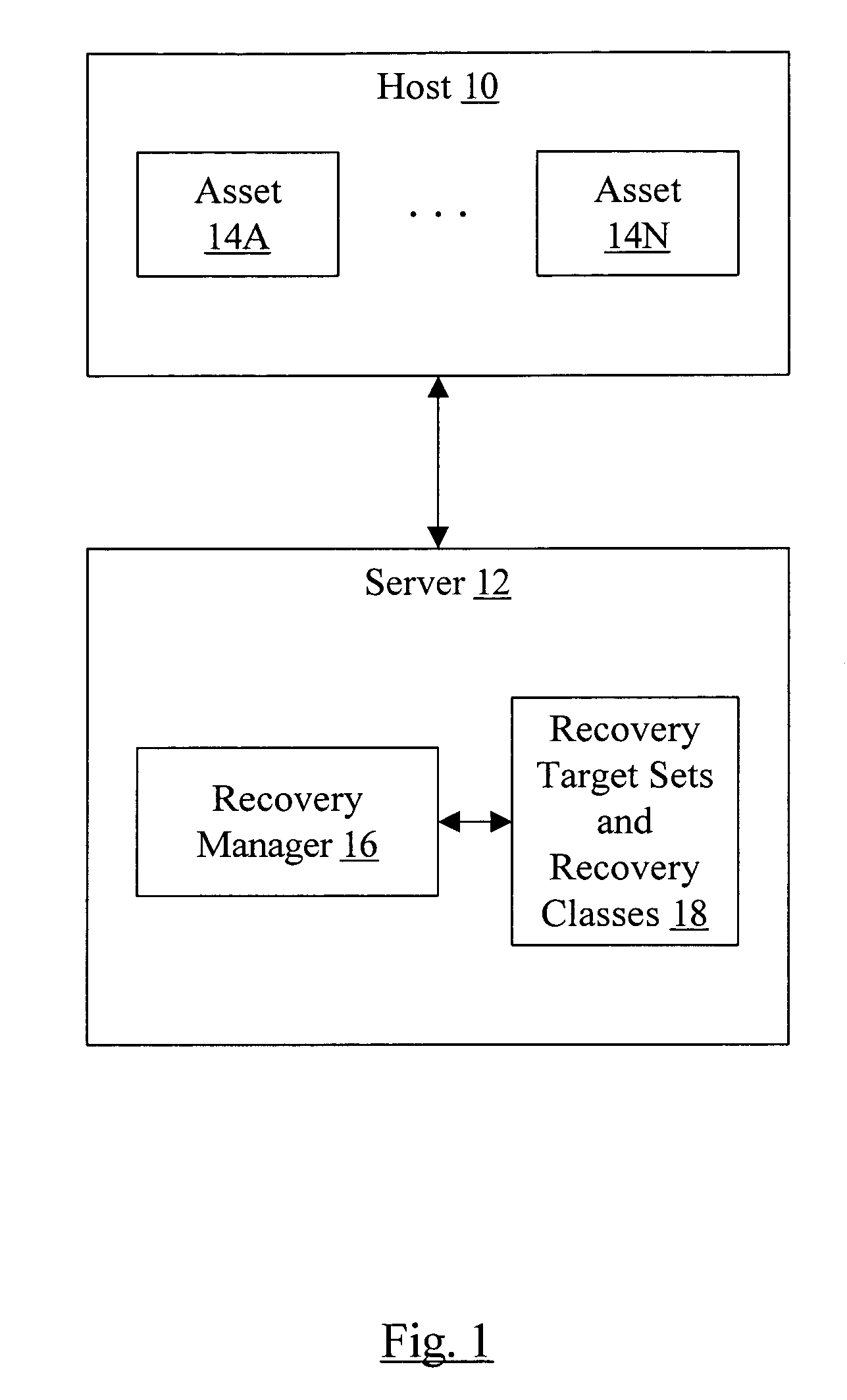
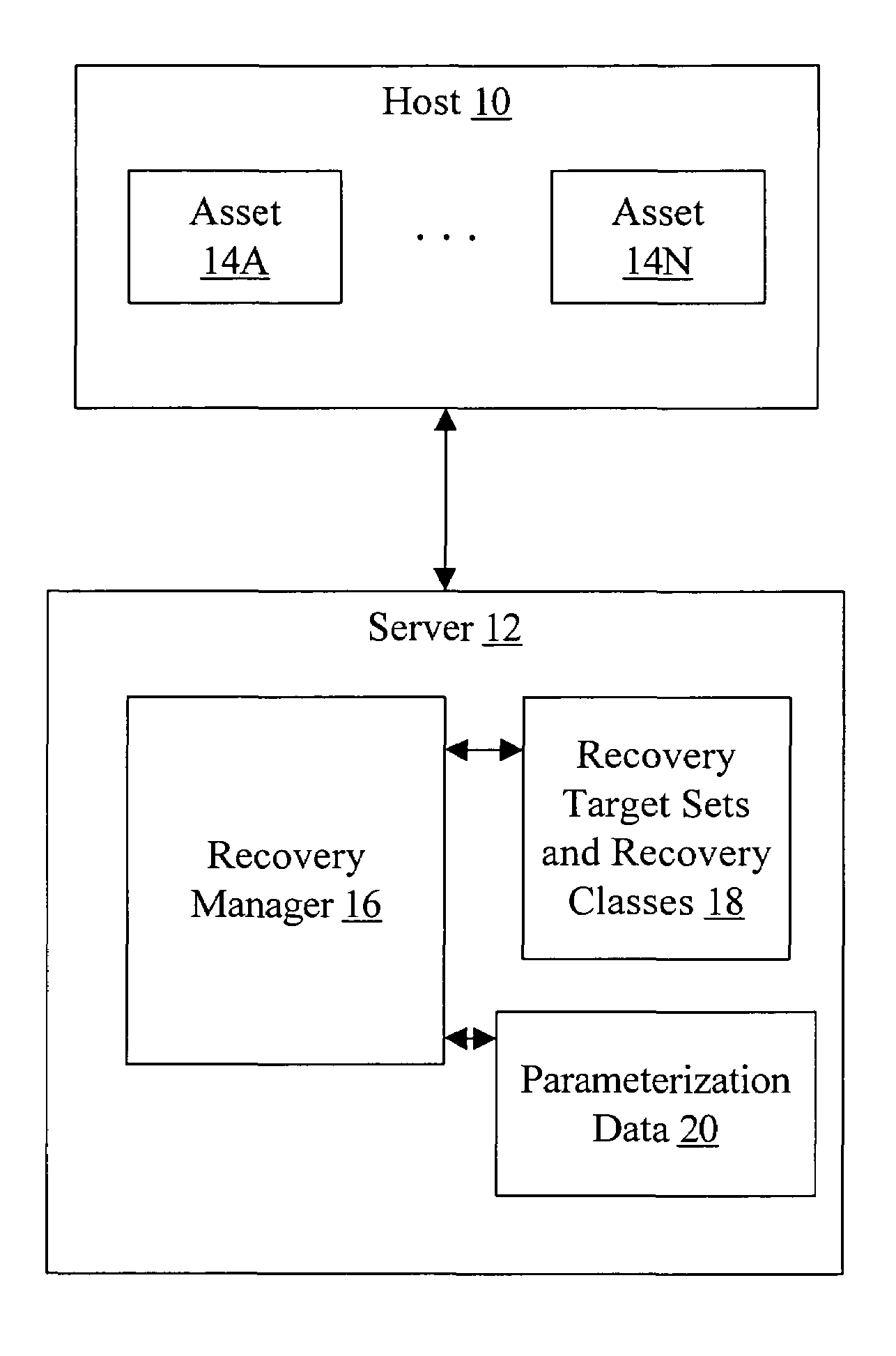
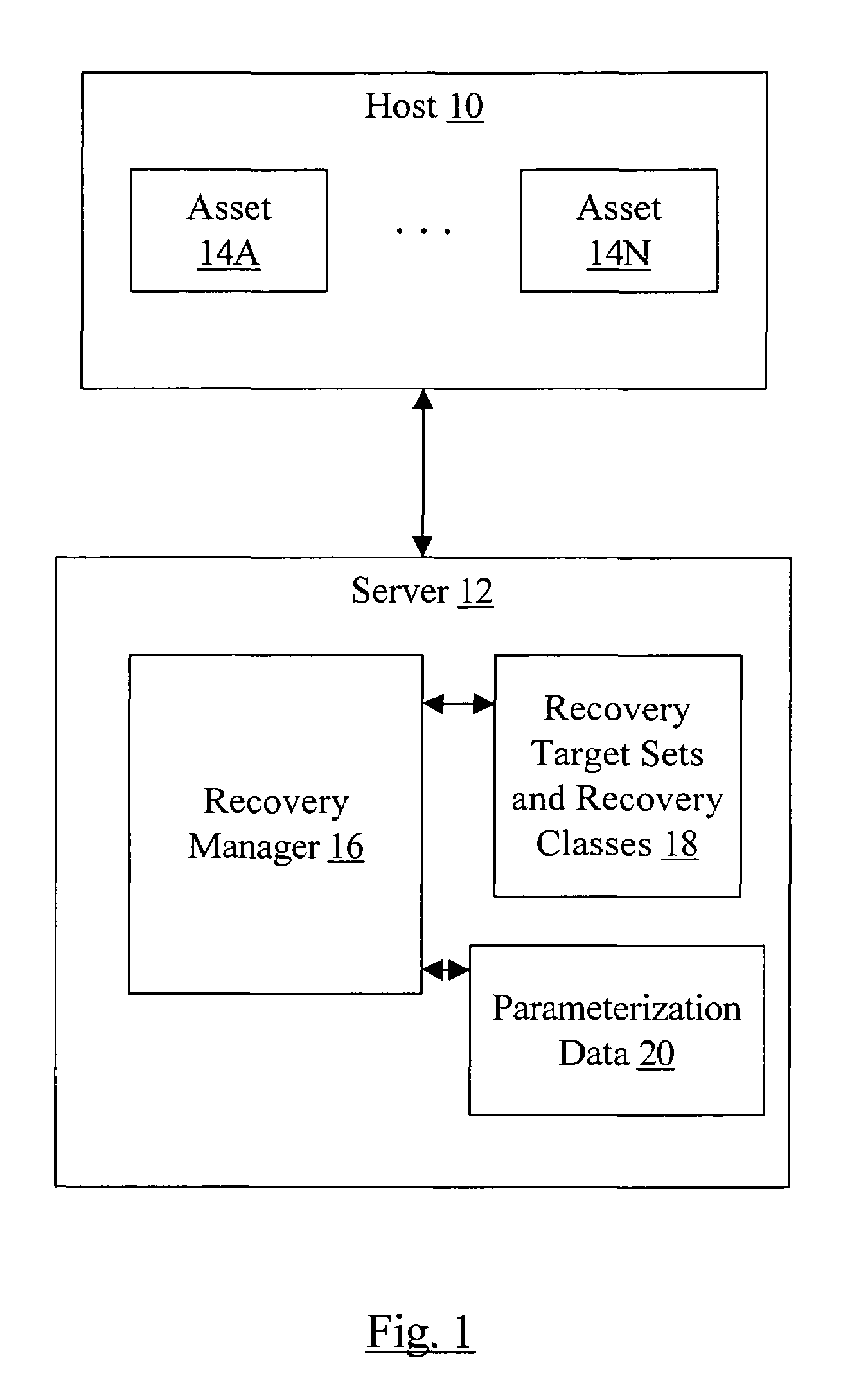
Classification of recovery targets to enable automated protection setup
In one embodiment, a recovery manager may define a plurality of recovery target sets. Each recovery target set comprises a recovery point target, a recovery time target, and at least one other property. The recovery manager also defines a plurality of recovery classes. Each recovery class comprises at least one recovery target set of the plurality of recovery target sets. Each recovery class describes recovery requirements over an asset state life cycle. The recovery manager applies a first recovery class of the plurality of recovery classes to a first asset dependent on an importance of the first asset to an owner of the first asset. In some cases, the first recovery class and / or other recovery classes of the plurality of recovery classes may each be applied to multiple assets. In another embodiment, a recovery manager defines one or more recovery target sets to be applied to one or more assets and saves the one or more recovery target sets. In some embodiments, recovery classes are also saved.
Owner:SYMANTEC OPERATING CORP
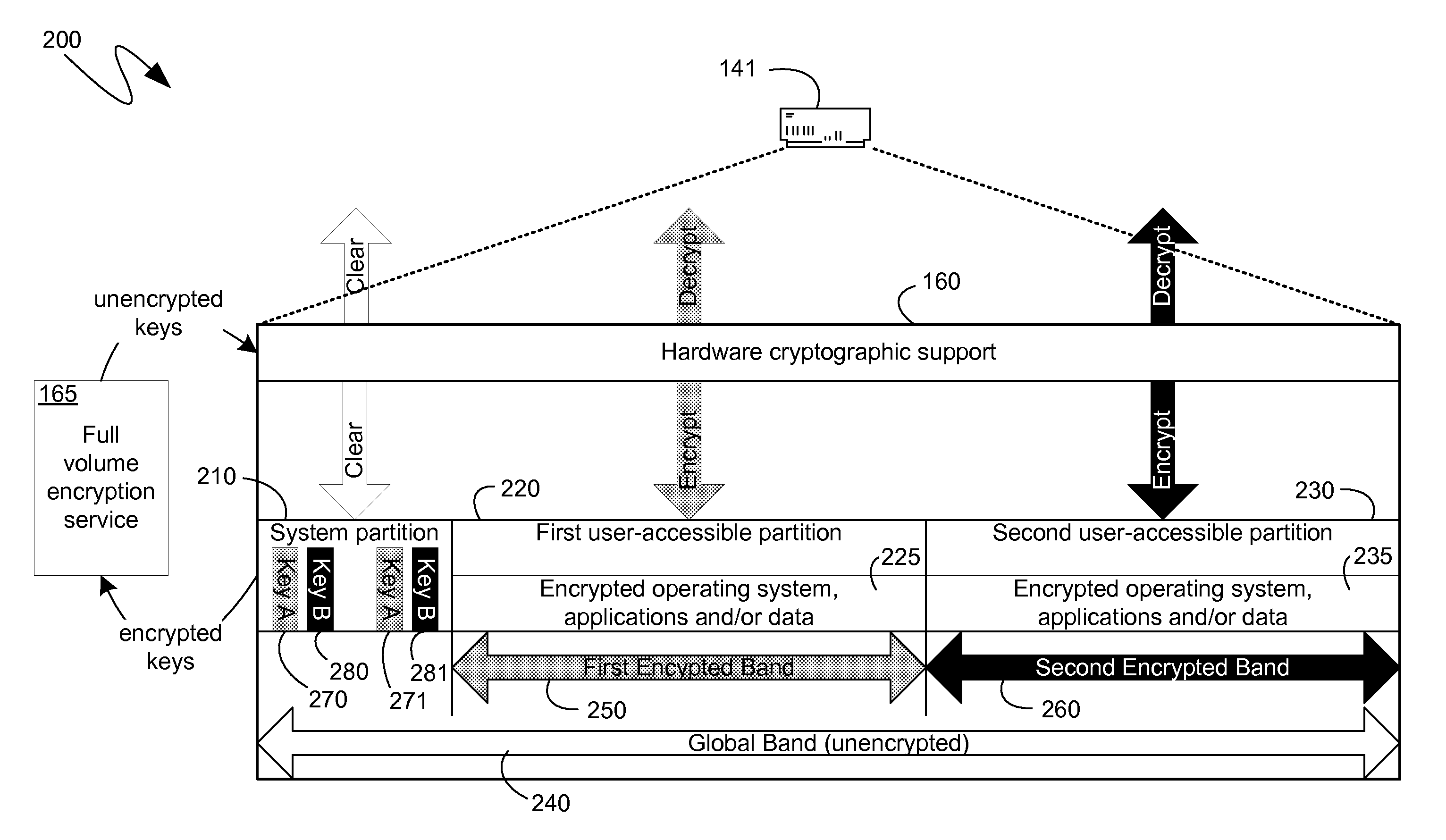
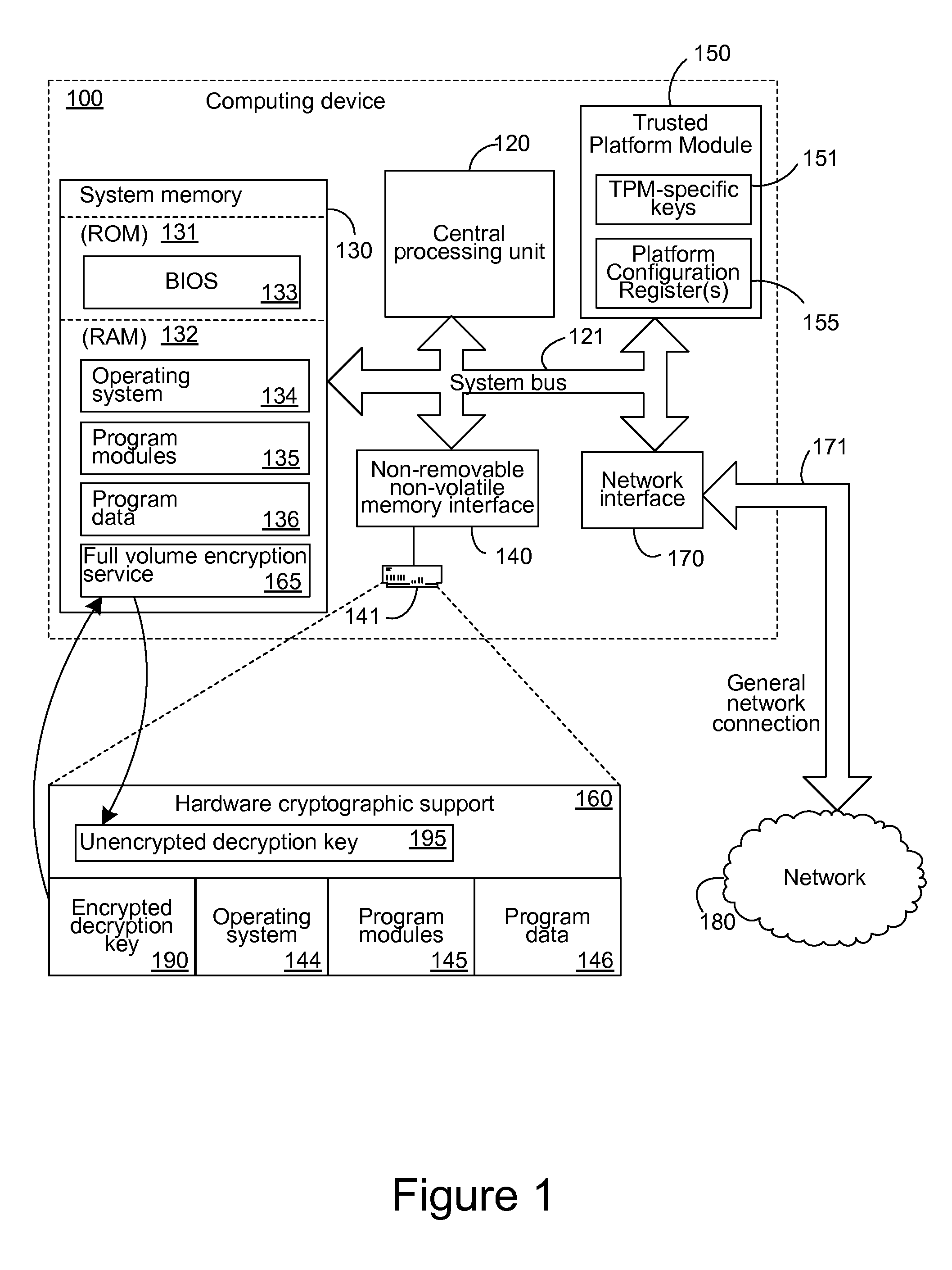
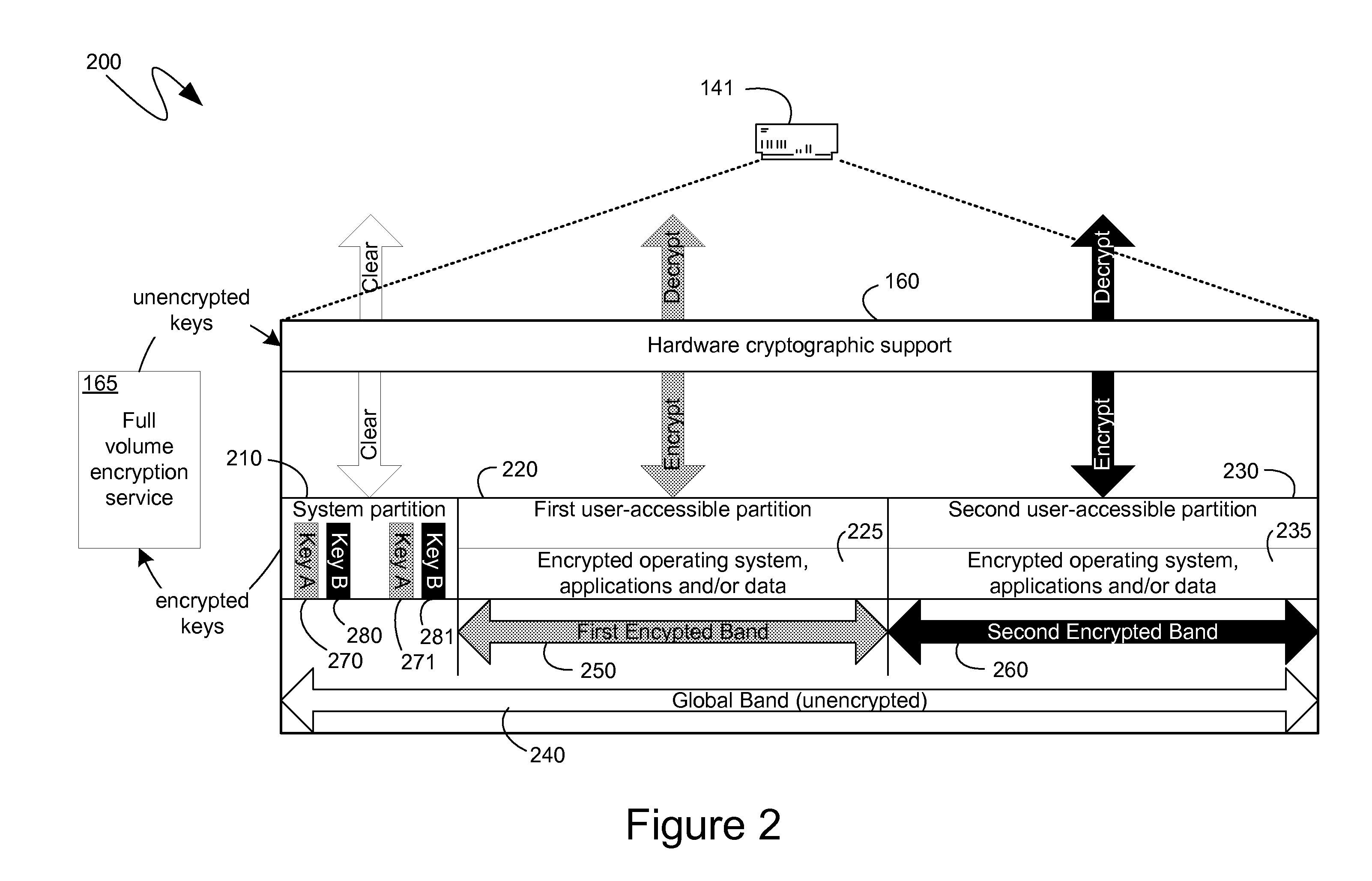
External encryption and recovery management with hardware encrypted storage devices
ActiveUS20100088525A1Efficient executionEasy to operateUnauthorized memory use protectionHardware monitoringComputer hardwareResource protection
Hardware encrypting storage devices can provide for hardware encryption of data being written to the storage media of such storage devices, and hardware decryption of data being read from that storage media. To utilize existing key management resources, which can be more flexible and accommodating, mechanisms for storing keys protected by the existing resources, but not the hardware encryption of the storage device, can be developed. Dedicated partitions that do not have corresponding encryption bands can be utilized to store keys in a non-hardware-encrypted manner. Likewise, partitions can be defined larger than their associated encryption bands, leaving room near the beginning and end for non-hardware encrypted storage. Or a separate bit can be used to individually specify which data should be hardware encrypted. Additionally automated processes can maintain synchronization between a partition table of the computing device and a band table of the hardware encrypting storage device.
Owner:MICROSOFT TECH LICENSING LLC
Processing method for power down and abnormal writing of solid state disc and system
ActiveCN102591807ASolve the damageReduce performance lossMemory loss protectionPower supply for data processingElectricityPhysical address
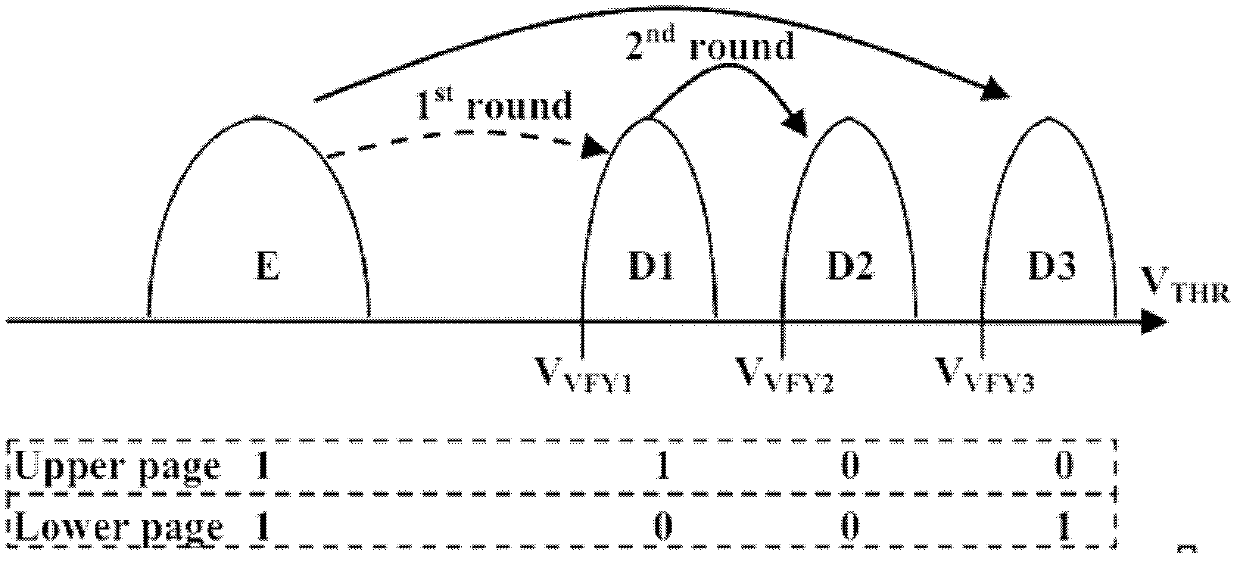
A processing method for power down and abnormal writing of a solid state disc comprises the steps of step 100, scanning a flash array, obtaining stored management information, performing initialization after extracting the management information, generating a plurality of mapping areas, dynamically adjusting the mapping areas, and managing the conversion between a multi level cell (MLC) to a single level cell (SLC); step 200, performing data reading and writing, during reading, finding a corresponding physical address through the two mapping areas, and reading the data on a flash memory; step 300, when the data is written, if finding a first mapping area already has no spare low level page, then starting waste page recovery management and abrasion balance management, after the abrasion balance management preferably recovers the waste page according to information in a mapping list of the first mapping area and then distributes the spare page, writing the data into the first mapping area; and step 400, when the conditions of power down or abnormal writing happen, enabling the plurality of mapping areas to perform corresponding operations to recover the data.
Owner:RAMAXEL TECH SHENZHEN
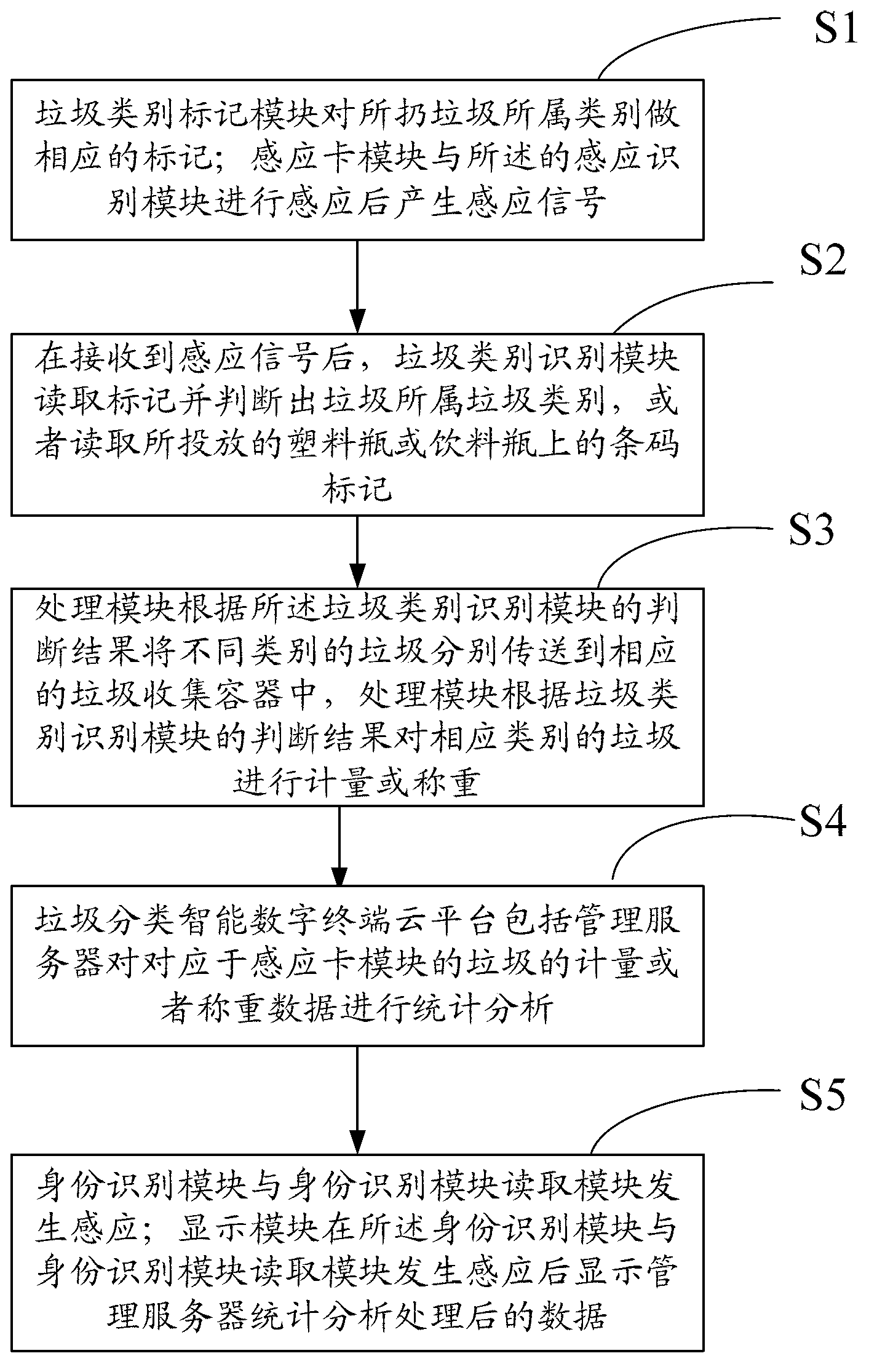
Garbage classification recovery intellectualized system and garbage classification recovery intellectualized method
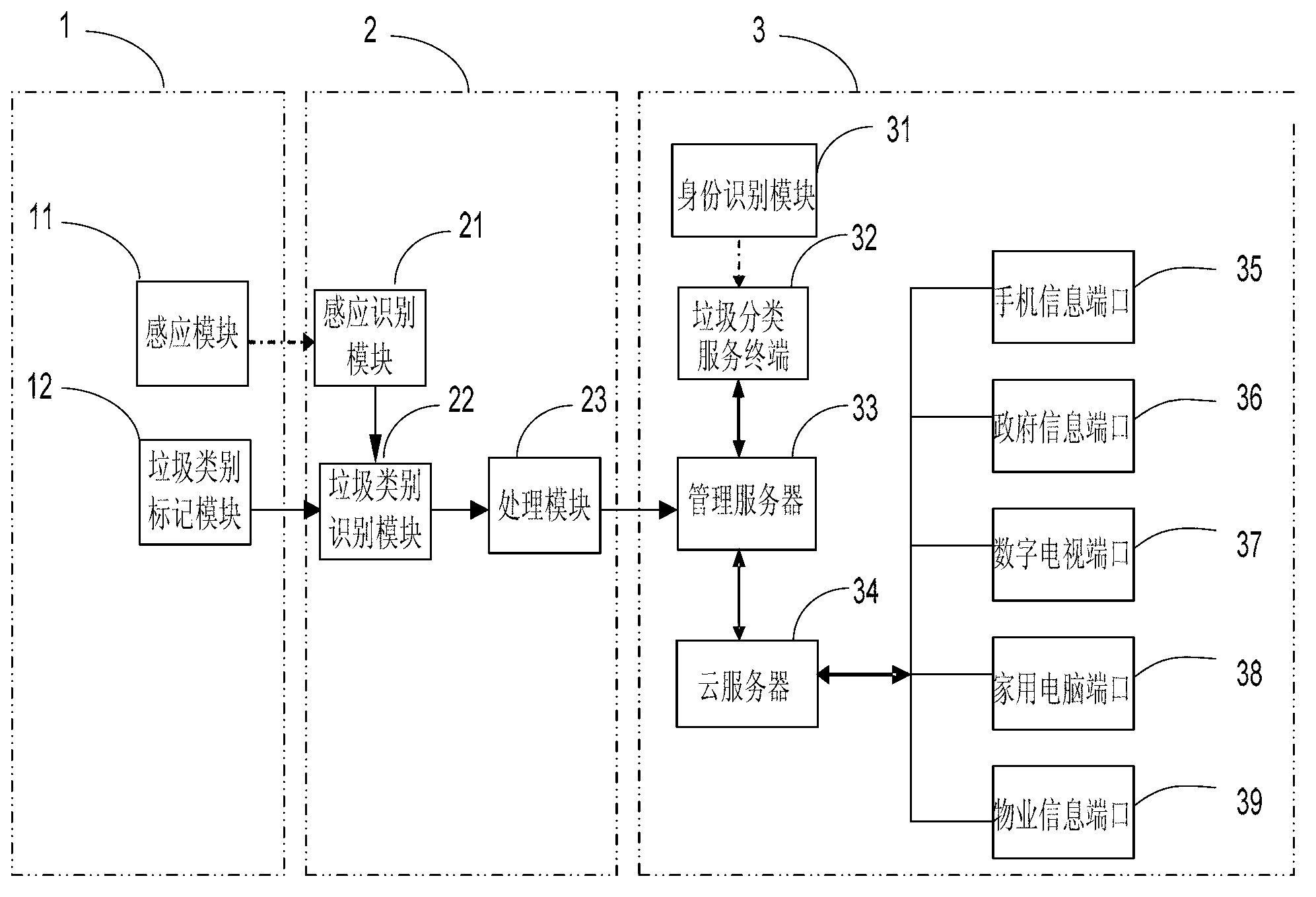
The invention provides a garbage classification recovery intellectualized system and a garbage classification recovery intellectualized method. The garbage classification recovery intellectualized system comprises a garbage identification module, a garbage classification intellectualized recovery device and a garbage classification intellectualized digital terminal cloud platform. The garbage classification recovery intellectualized method identifies classified garbage to determine house owner information and garbage category according to a digital identification technical scheme. The garbage classification intellectualized recovery device comprises an induction identification module, a garbage classification identification module and a processing module. A garbage classification intellectualized classification module respectively takes corresponding treatment measures on garbage of different classification according to garbage classification by using a plurality of methods such as bar code scanning and garbage classification identification, the garbage is ensured to be put into corresponding garbage collection containers, and measurement or weighting is conducted, therefore, garbage classification recovery intellectualization is eventually achieved. The garbage classification recovery intellectualized system and the garbage classification recovery intellectualized method achieve garbage classification recovery intellectualization, besides, garbage classification recovery intellectualized system and the garbage classification recovery intellectualized method can be excellently applied to real garbage classification recovery management, a device is low in manufacturing cost, the garbage classification recovery intellectualized system and the garbage classification recovery intellectualized method are easy to promote among residential quarters in towns and have very important practical significance.
Owner:深圳市英尔科技有限公司
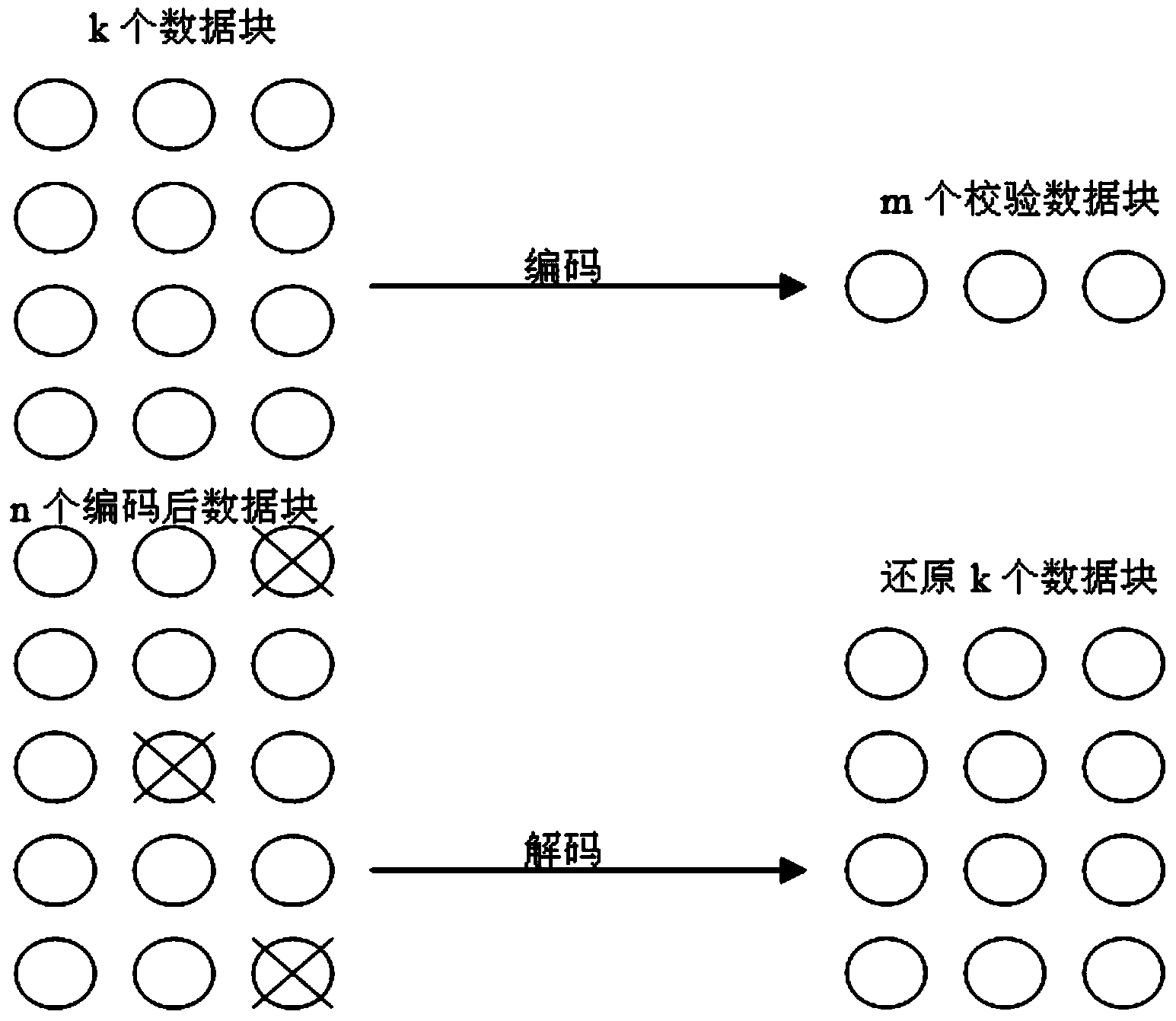
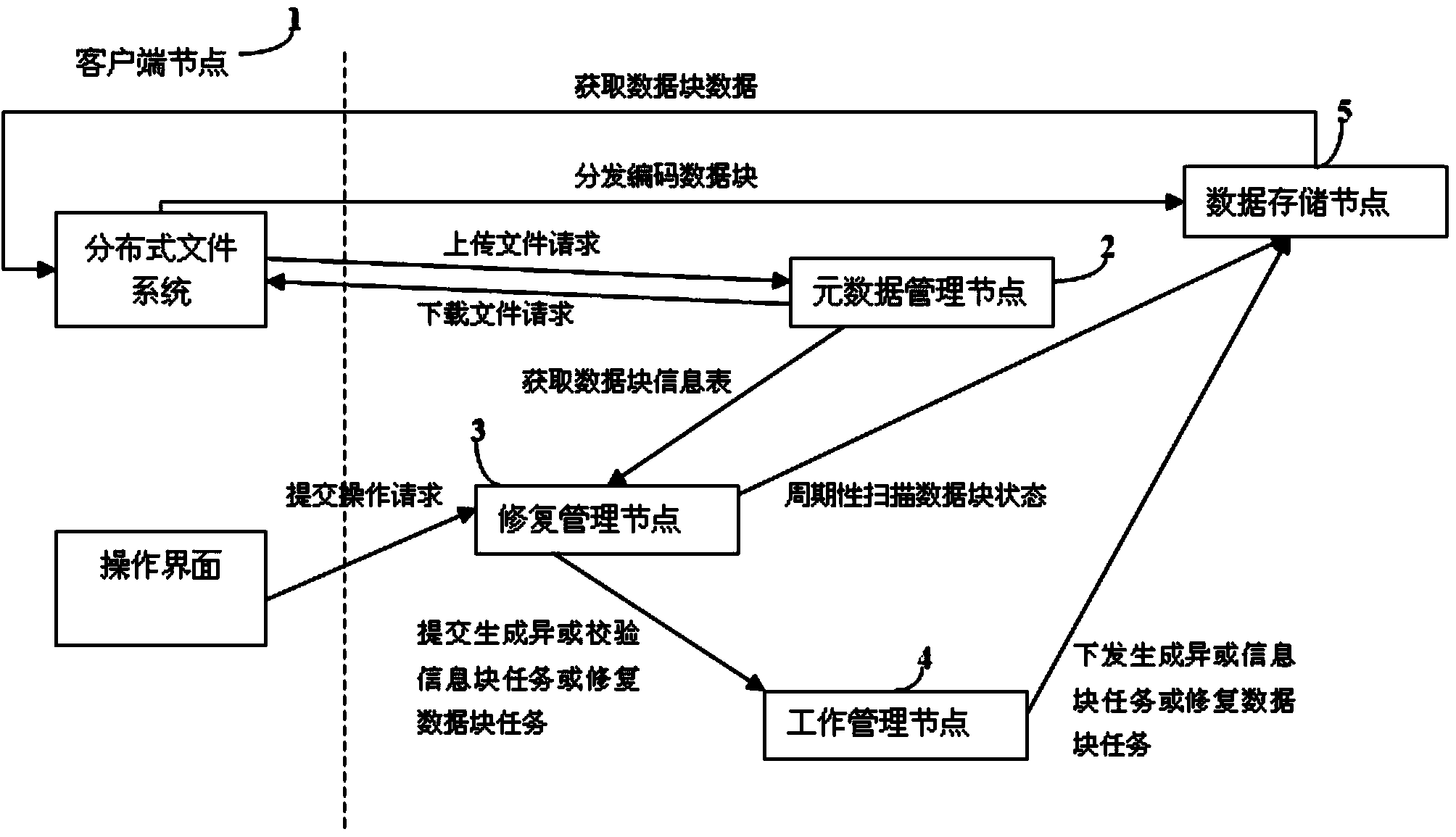
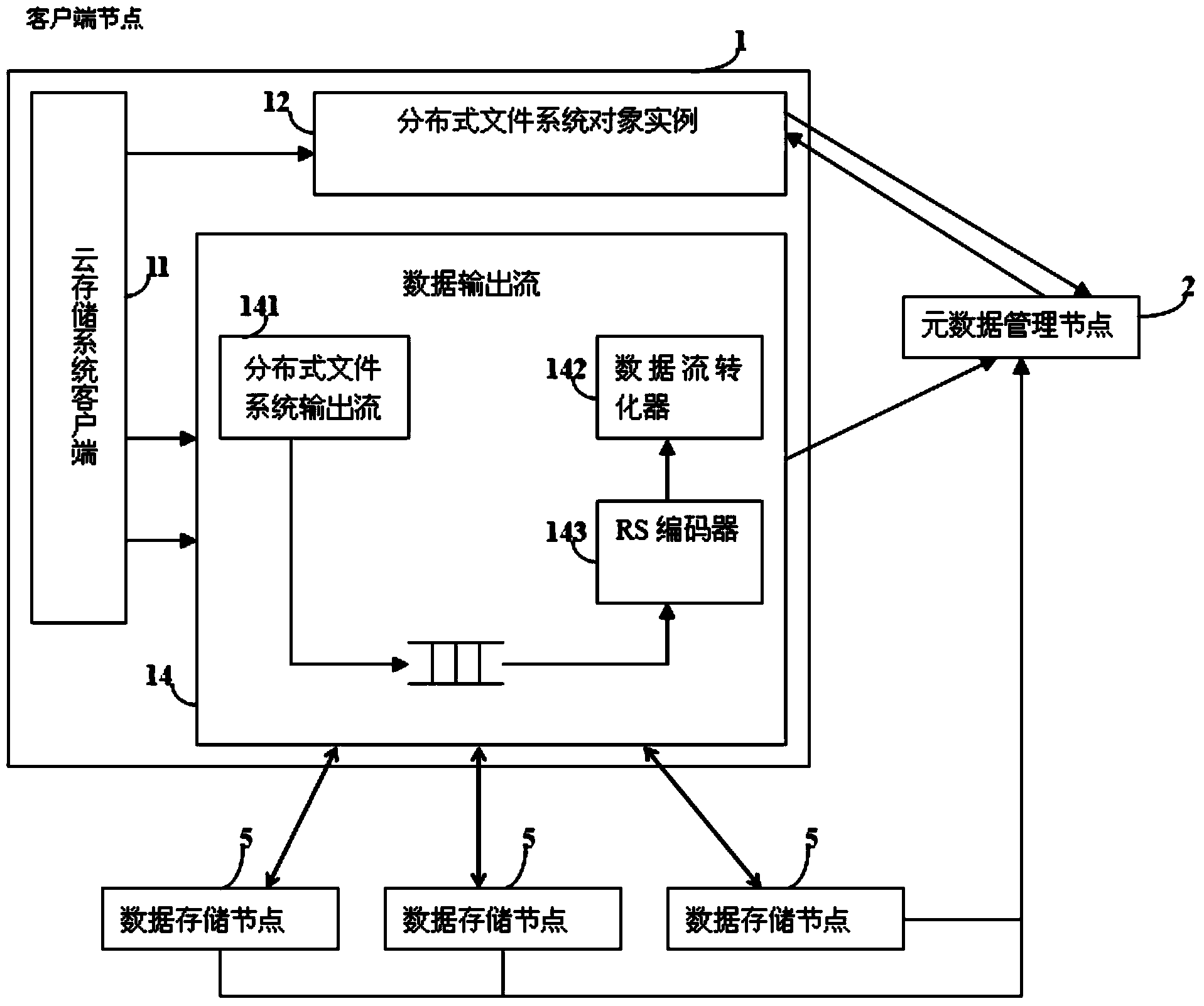
Cloud storage system and implement method based on erasure code technological improvement
ActiveCN103944981APromote recoveryReduce loadTransmissionSpecial data processing applicationsDistributed File SystemMetadata management
The invention discloses a cloud storage system and implement method based on erasure code technological improvement and relates to a distributed file system. The method includes the steps of building a metadata management node, a data storage node, a recovery management node, a work management node and a client node, storing and reading data through the metadata management node, the data storage node and the client node according to the erasure code technology, and recovering lost or damaged data blocks after the erasure code technology is adopted through the recovery management node and the work management node. The recovery process of erasure codes is separated from a file management node of the cloud storage system, burdens of the metadata management node in the recovery process are relieved, and the stability, high reliability and high availability of the system in the recovery process are ensured.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
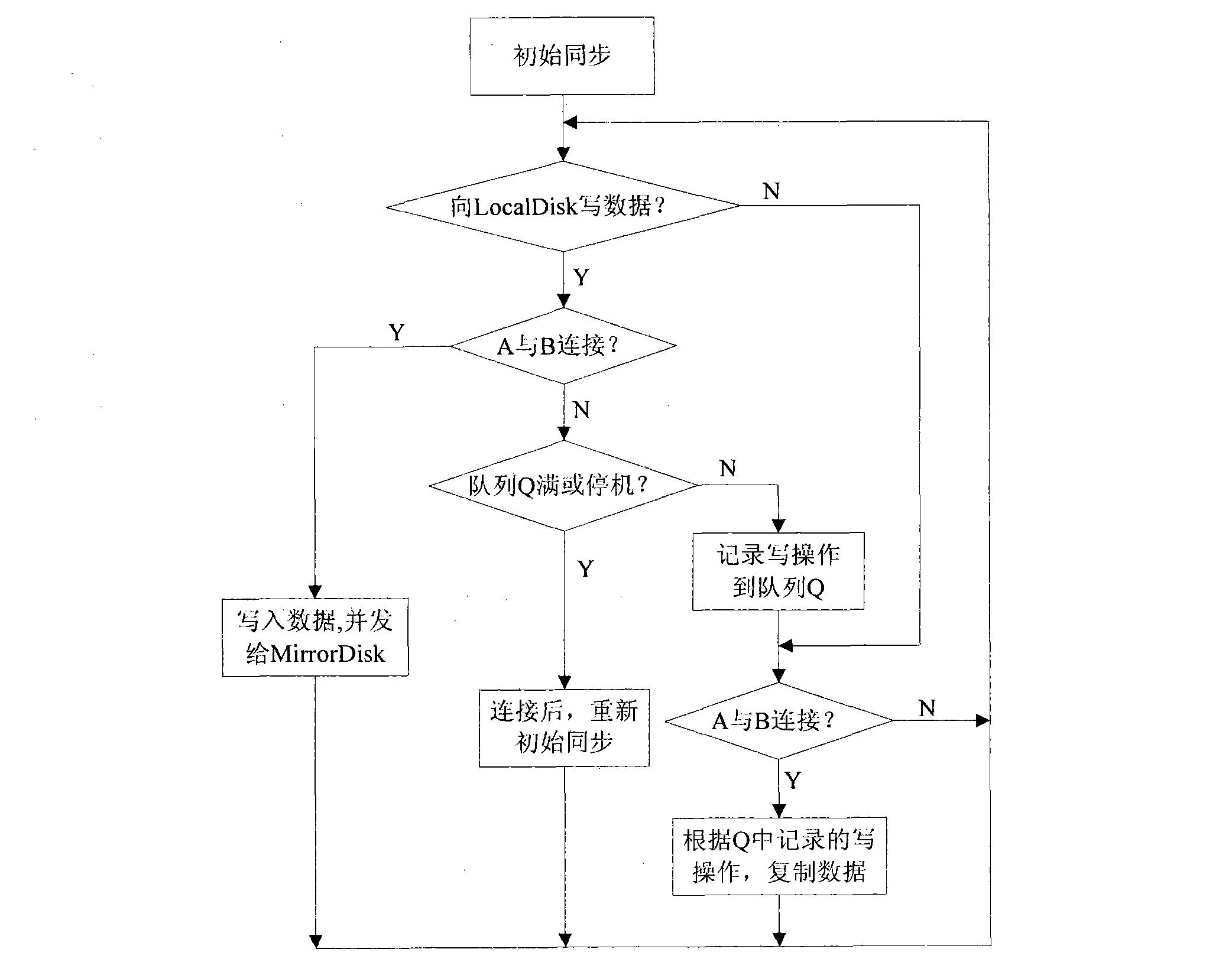
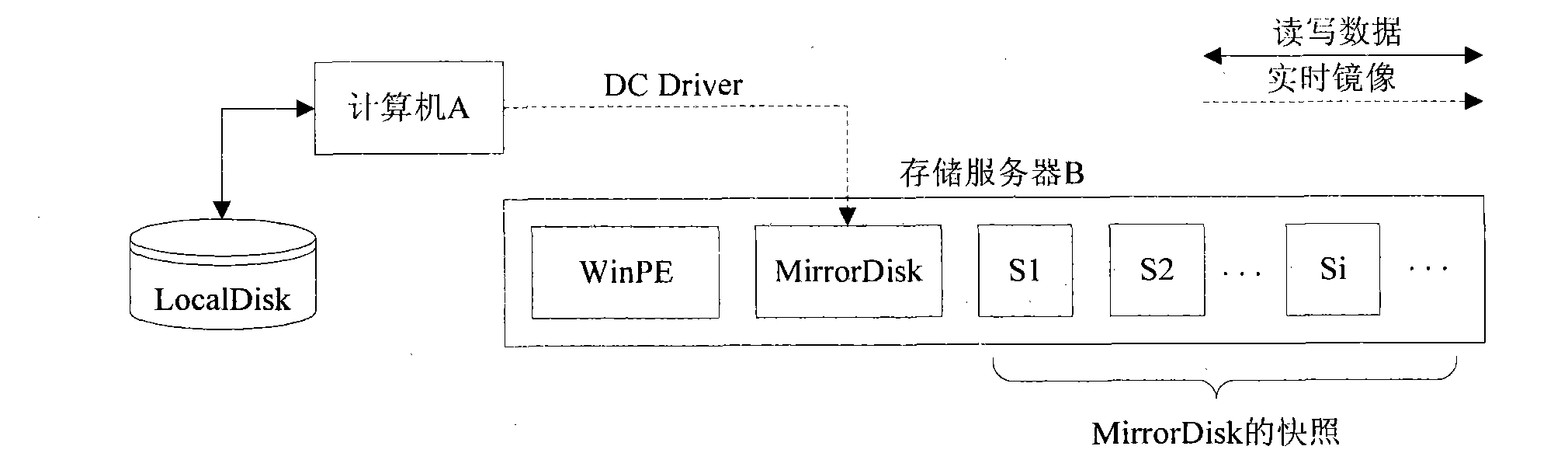
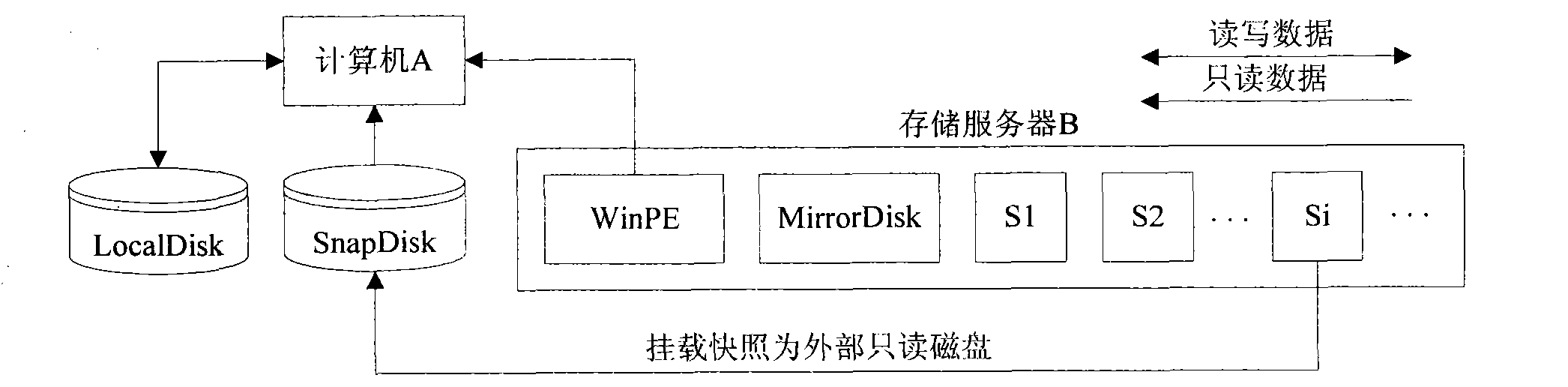
Copying and snapshot combined Windows system protection method
ActiveCN101777018ADigital data protectionRedundant operation error correctionSystem protectionWindows Registry
The invention discloses a copying and snapshot combined Windows system protection method. A driver is run in a Windows system, the change of a local disk block of a computer is mirrored to a storage server on line in real time, and a snapshot of the mirror is generated on the storage server. The storage server is provided with a WinPE system with a recovery management program. When the system is recovered, the computer starts the WinPE system with the recovery management program on the storage server remotely, and the snapshot is mounted as a remote read-only disk which can execute disk grade recovery; the recovery management program is run, the files and registries of the remote disk and a local disk are compared, and according to the comparison result, the recovery of the file grade and the registry items can be executed. By adopting the method, multi-grade recovery and fine-grain comparison and recovery can be realized without the need of a recovery optical disc or a U disk.
Owner:TOYOU FEIJI ELECTRONICS
Multistage system recovery framework
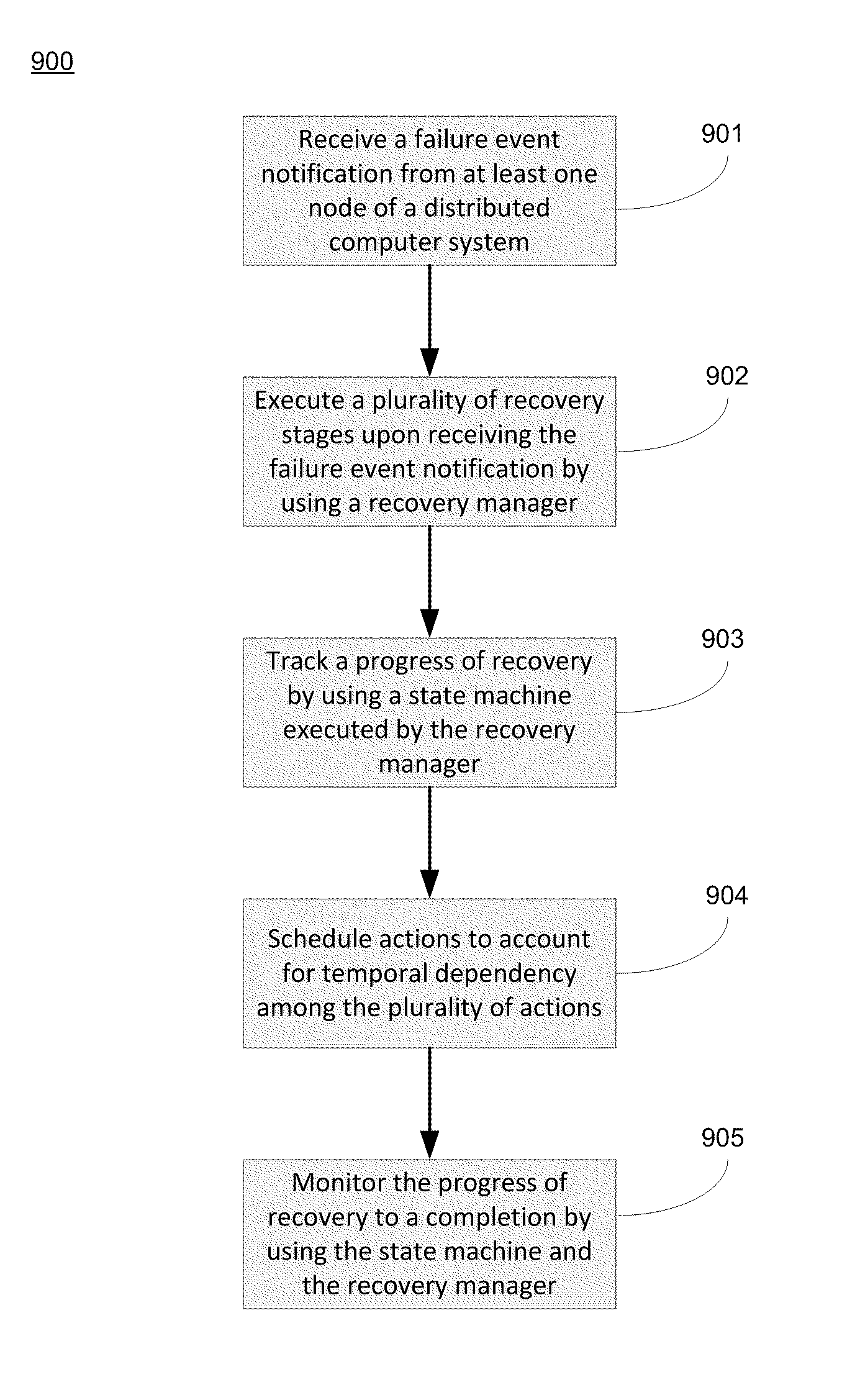
A method and system for multi-staged recovery of a distributed computer system. The method includes receiving a failure event notification from at least one node of the distributed computer system and executing a plurality of recovery stages upon receiving the failure event notification by using a recovery manager, wherein each of the plurality of recovery stages performs a defined recovery task. The progress of recovery is tracked by using at least one state machine executed by the recovery manager, wherein the state machine reflects progress of each of the recovery stages. The progress of recovery is monitored to a completion by using the state machine and the recovery manager.
Owner:VERITAS TECH
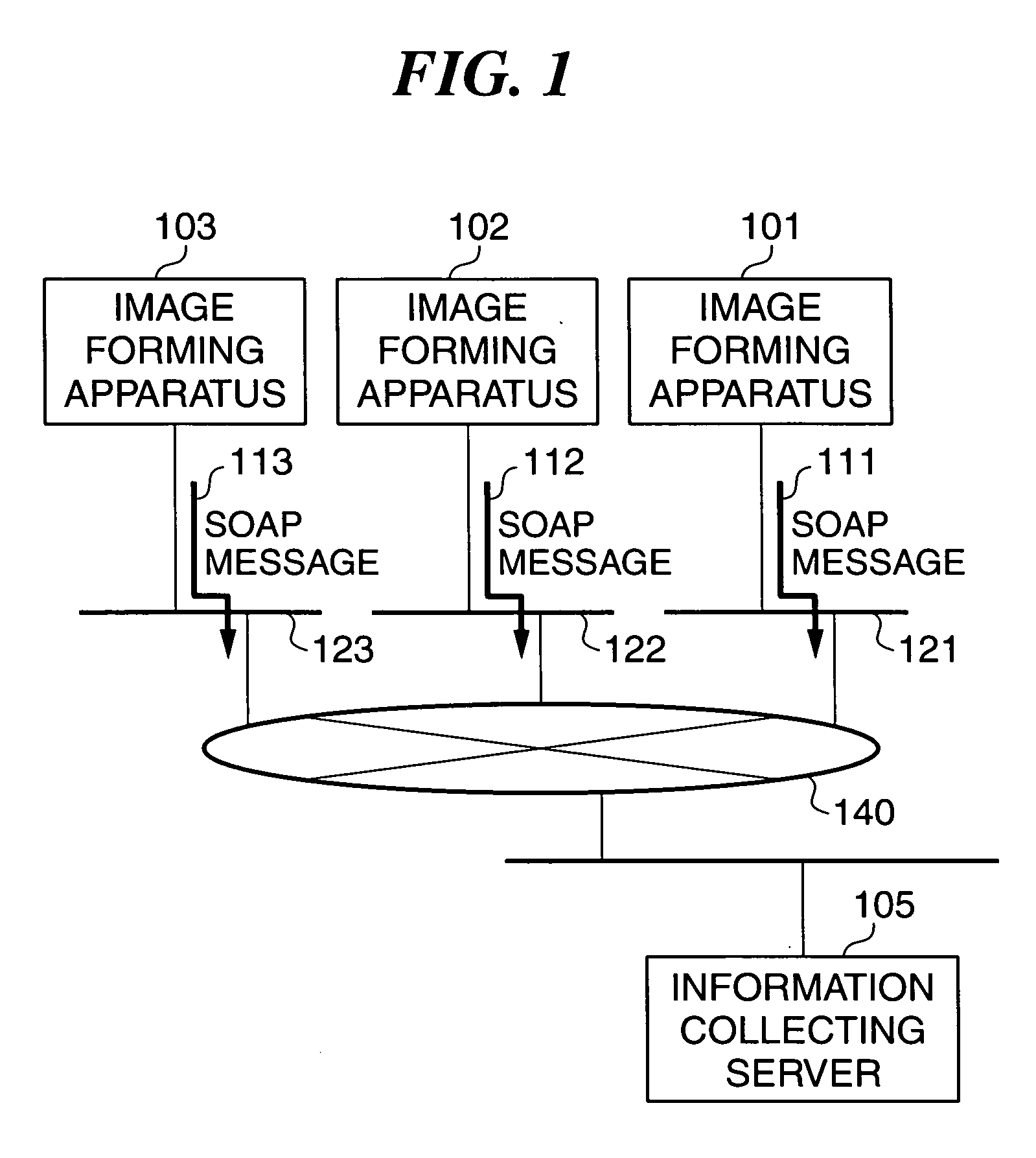
Information processing apparatus and notification method therefor, program for implementing the method, and storage medium storing the program
ActiveUS20060031906A1Error prevention/detection by using return channelTransmission systemsComputer hardwareInformation processing
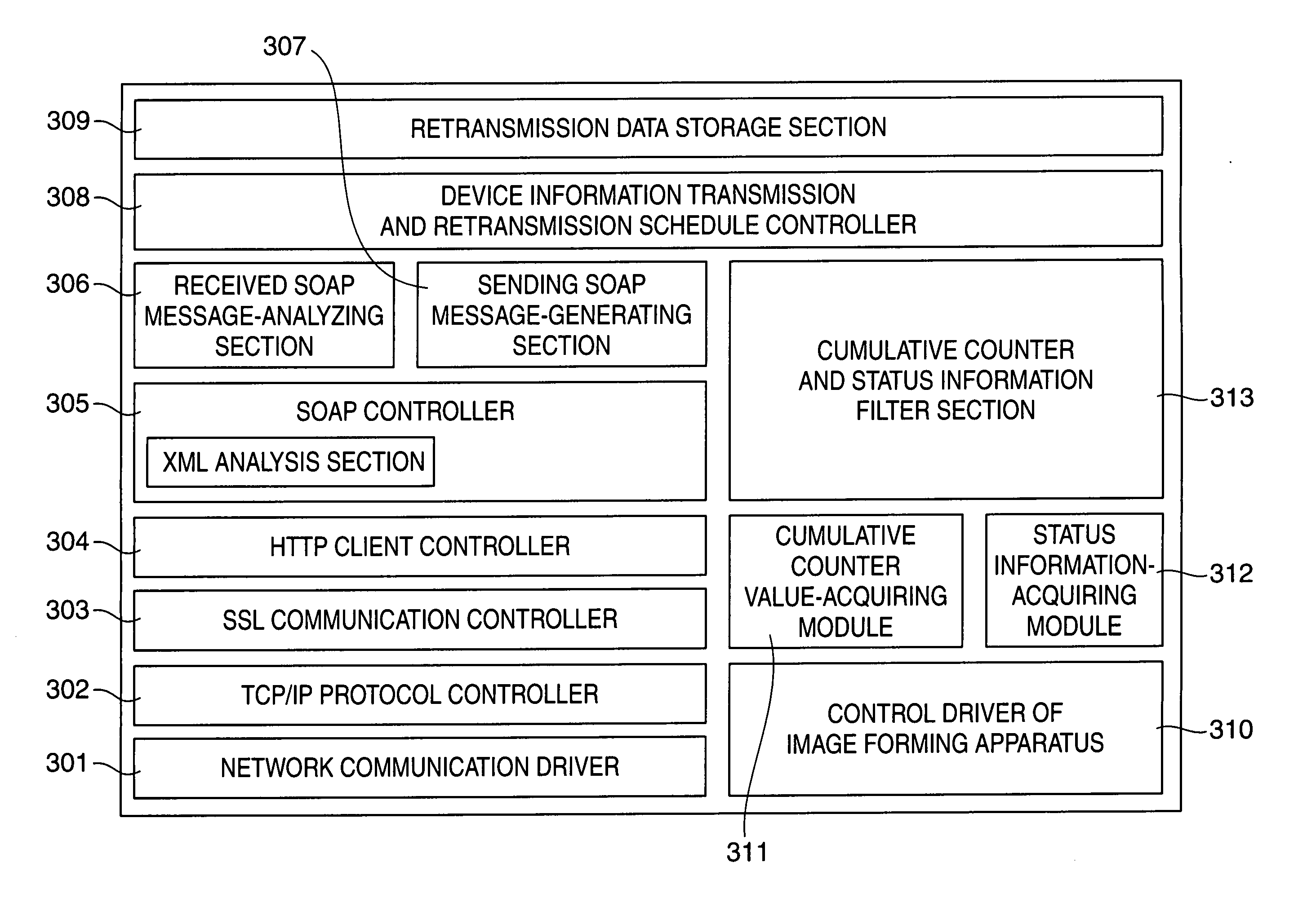
An information processing apparatus which is capable of notifying a management server of only necessary information for the management server to perform its proper maintenance function, as information on the maintenance of an image forming apparatus after recovery of the management server, to thereby avoid the management server from performing processing more than necessary. A device information transmission and retransmission schedule controller transmits maintenance information including status information and cumulative counter information on an image forming apparatus to an information collecting server. A retransmission data storage section stores the status information and the cumulative counter information. Upon recovery from failure in communication with the server, the schedule controller transmits the status information collected in a plurality of timings and part of the cumulative counter information collected in a plurality of timings to the server.
Owner:CANON KK
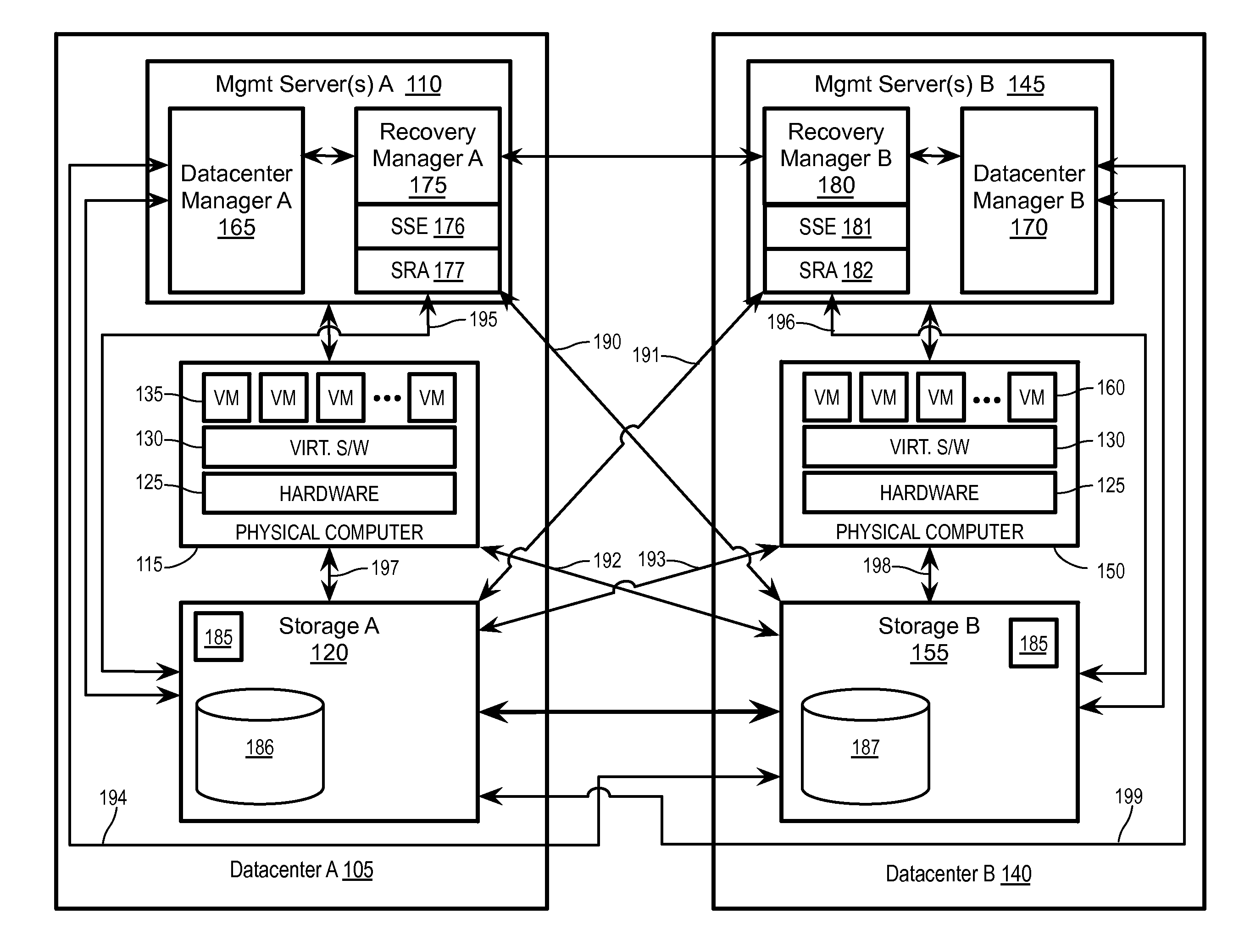
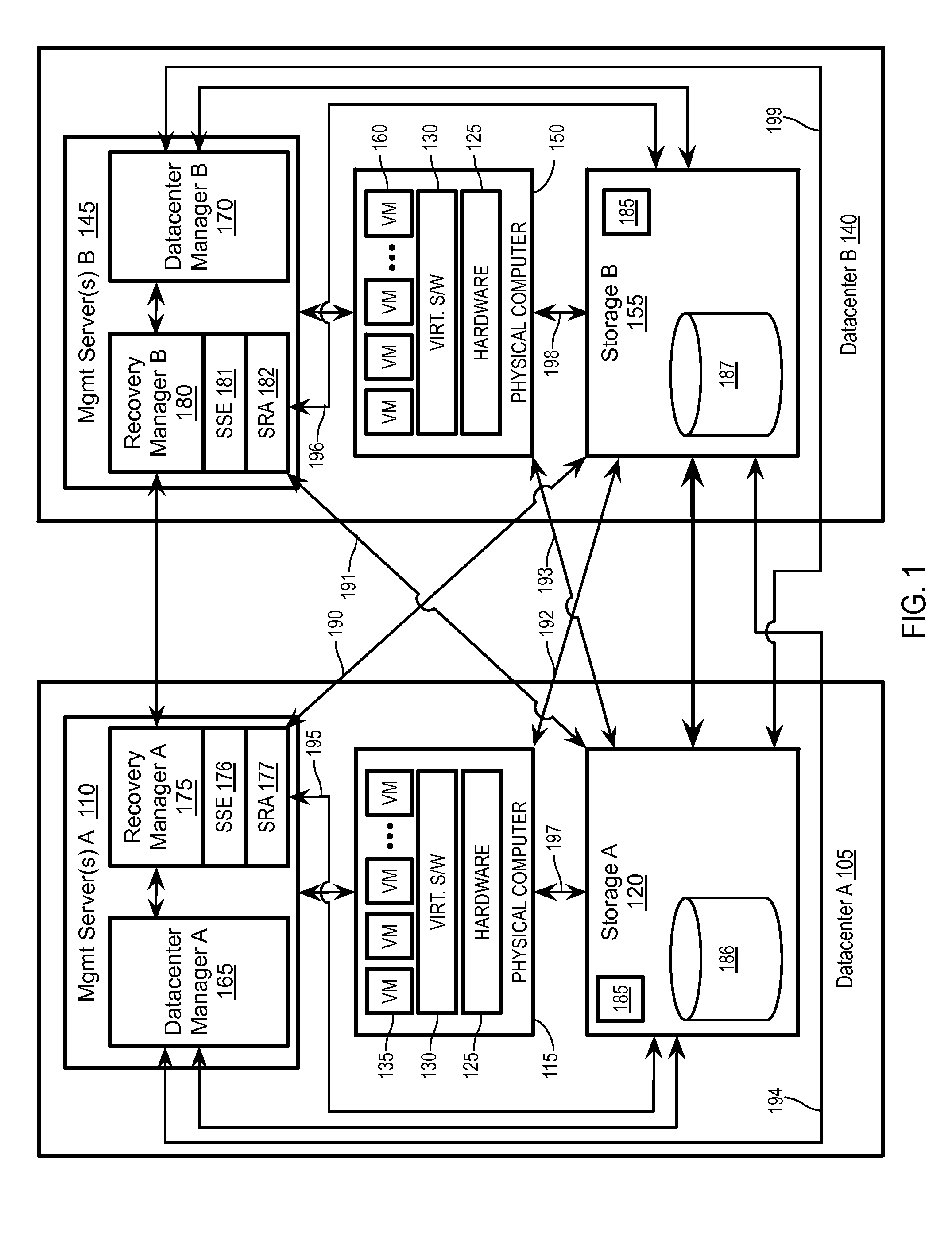
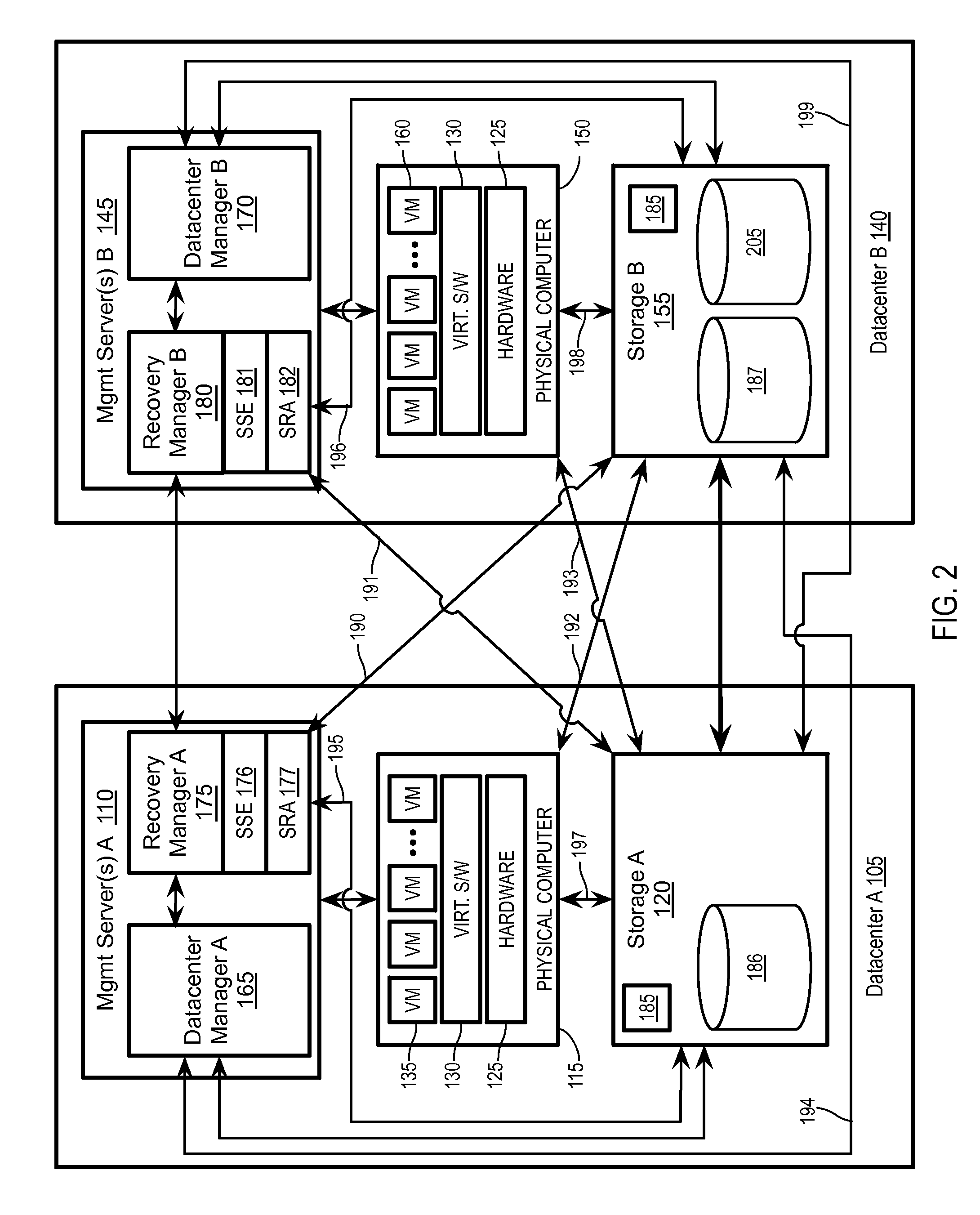
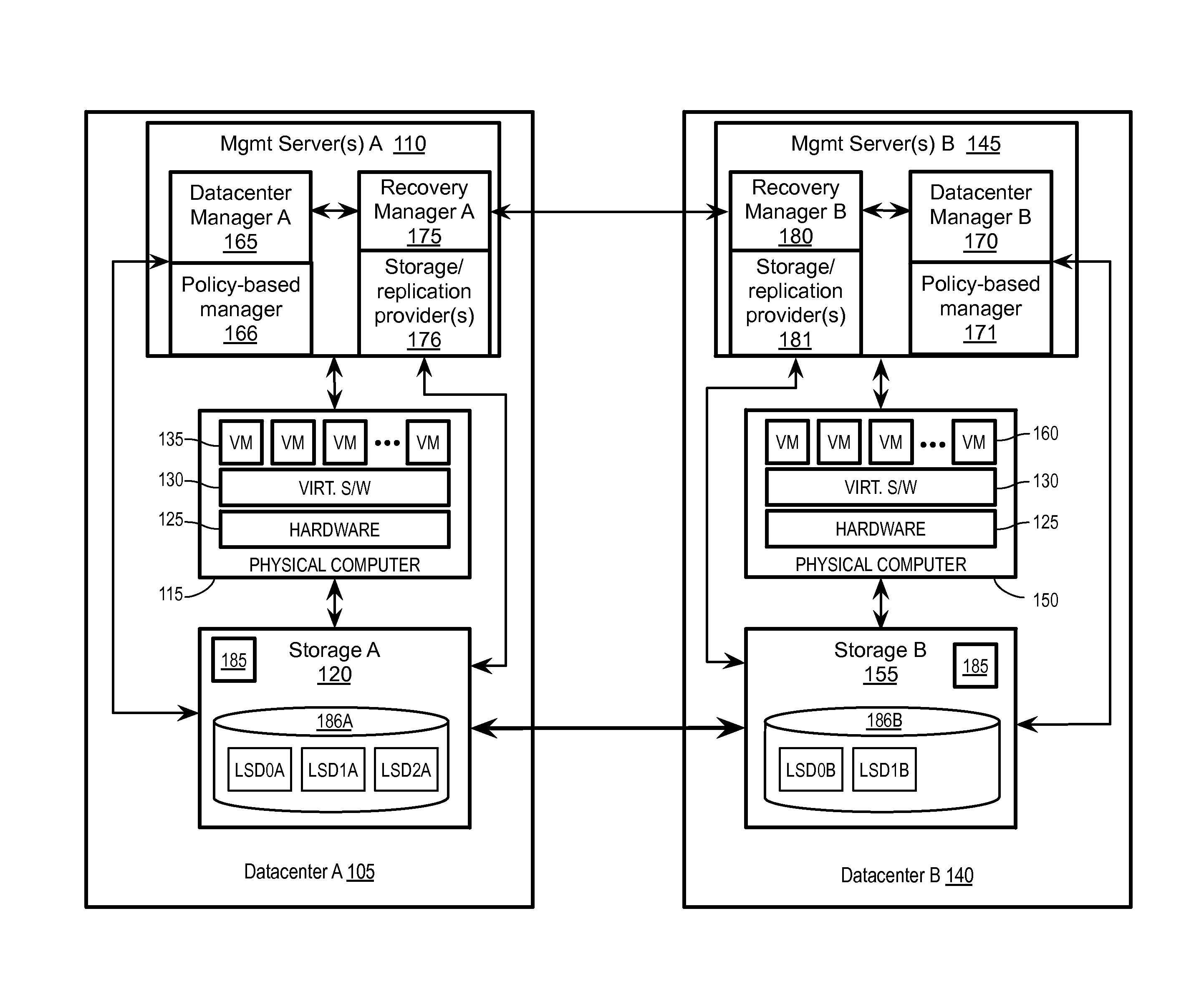
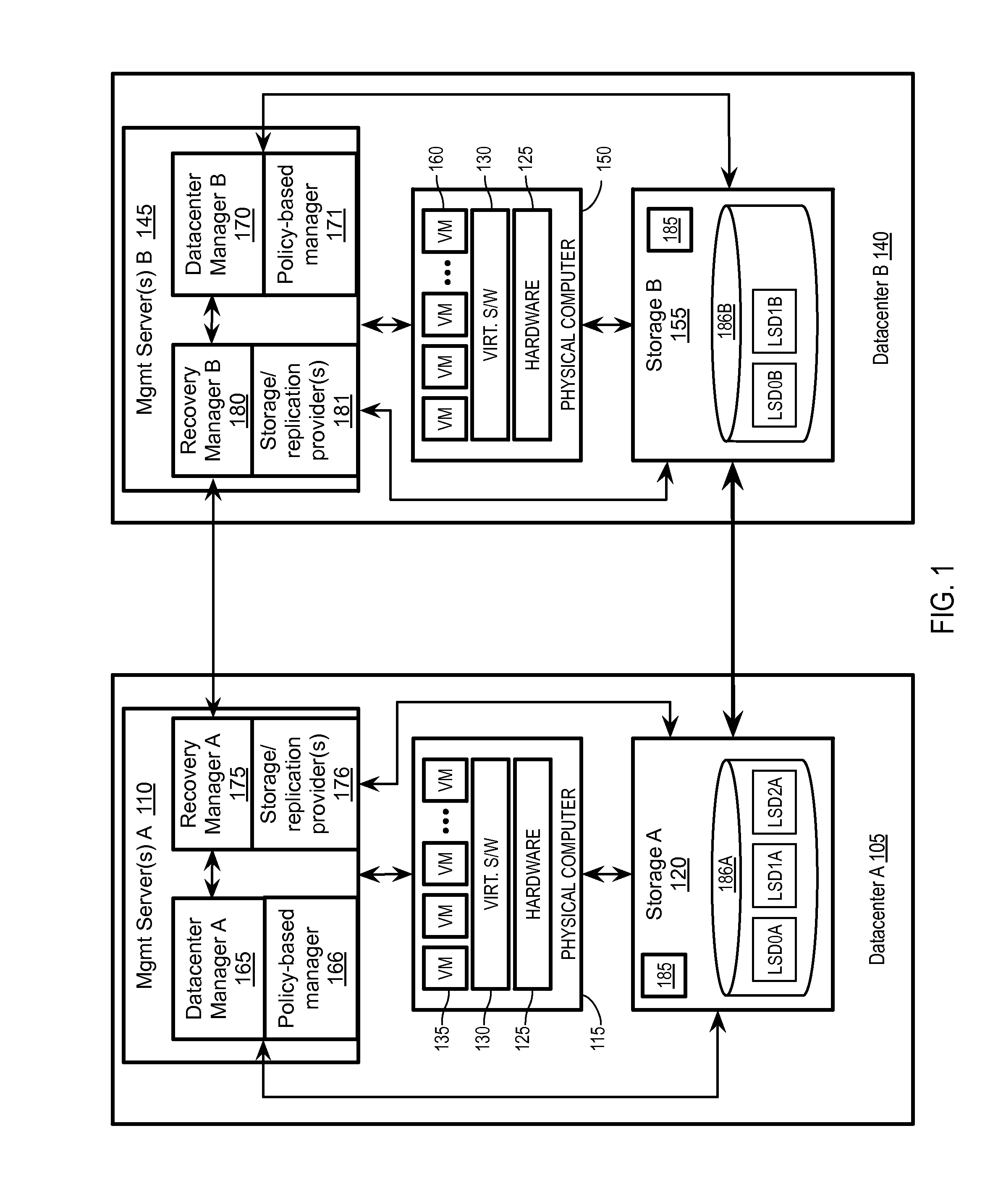
Emulating a stretched storage device using a shared storage device
Exemplary methods, apparatuses, and systems include receiving a device discovery command from a recovery manager running on a management server within a first or second datacenter. In response to the device discovery command, device identifiers for one or more logical storage devices within the first datacenter are requested. In response to the request, a device discovery response including a first identifier is received. The received device discovery response is modified to include the first device identifier as the identifier for both an underlying logical storage device and as an identifier for a peer logical storage device. The modified response is returned to the recovery manager in response to the device discovery command.
Owner:VMWARE INC
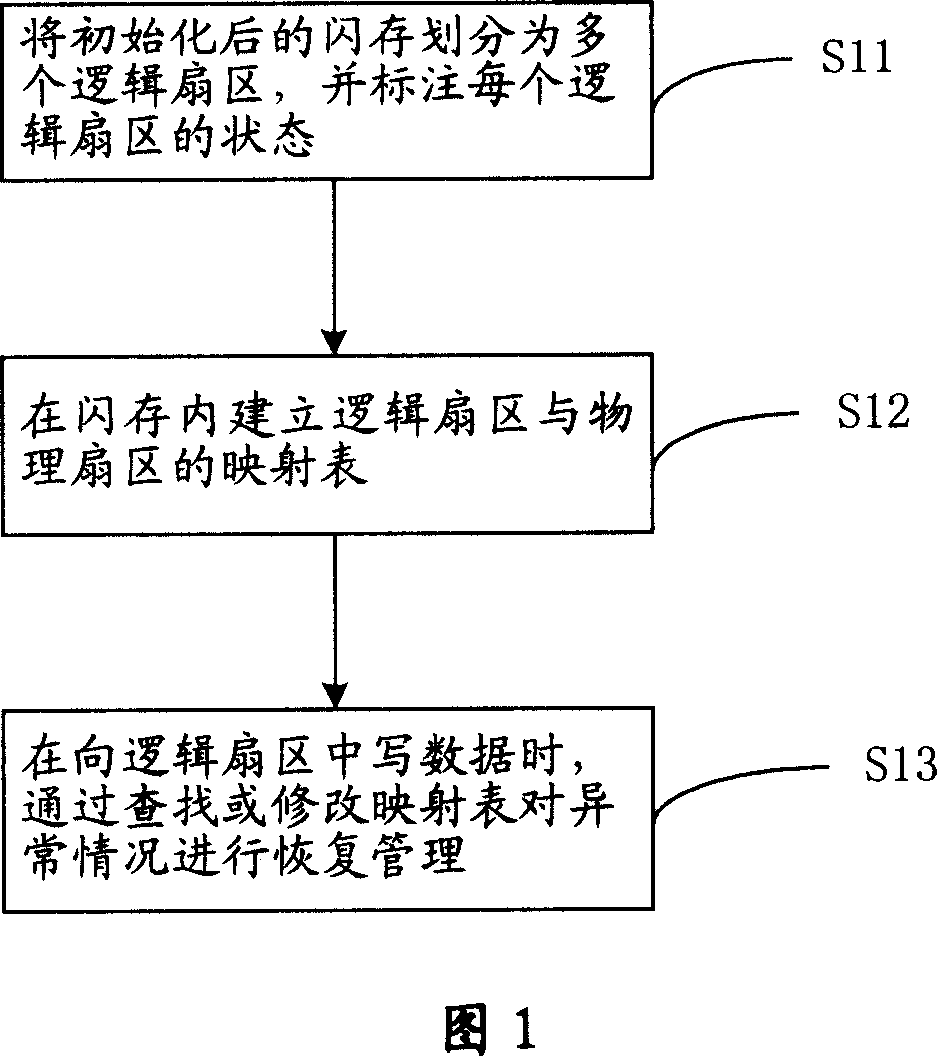
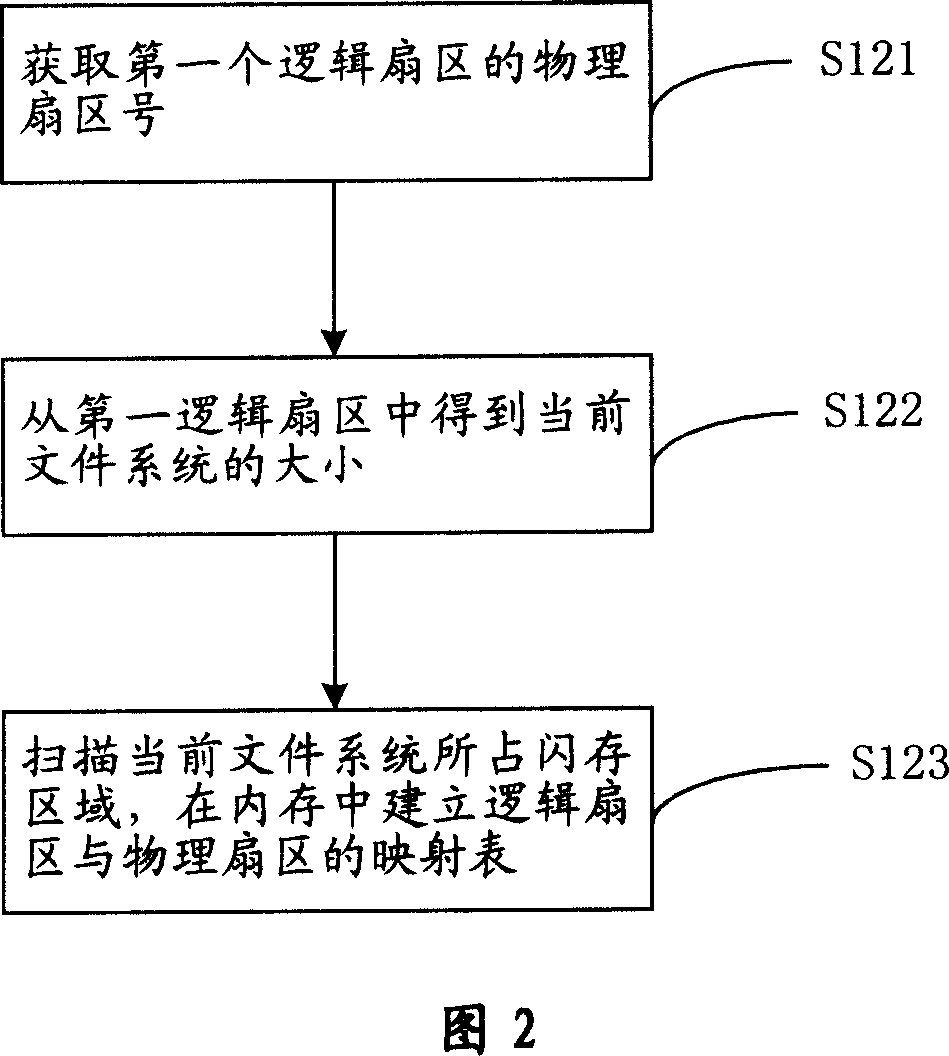
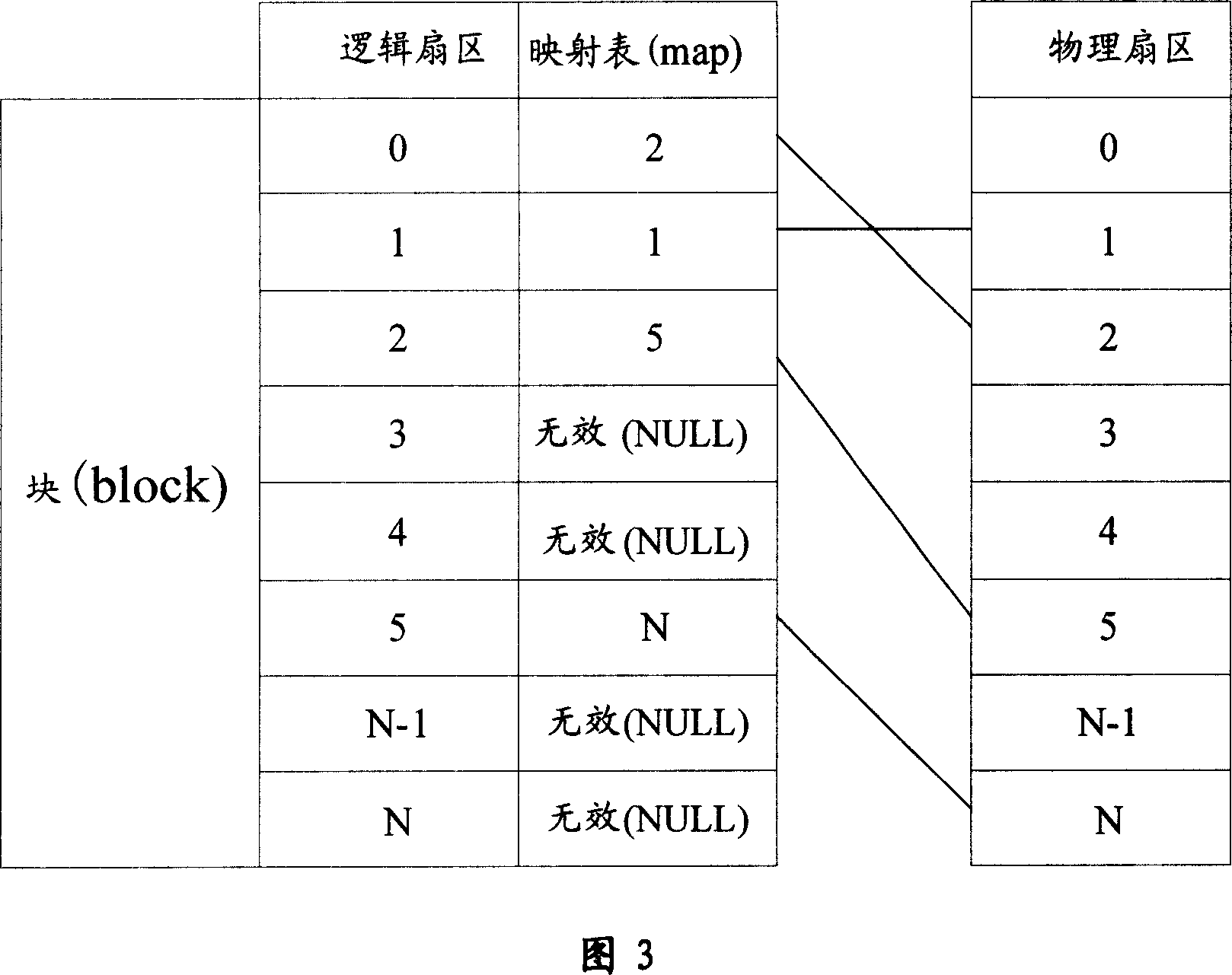
Safety management method and device of file system
ActiveCN101046803APlay a power-down protectionProtectSpecial data processing applicationsMemory systemsFile systemSecurity management
The present invention relates to a safety management method of file system and its device. The described method includes the following steps: A, dividing initialized flash memory into several logical sectors, and noting state of every logical sector; B, in the flash memory interior creating mapping table of logic sector and physical sector; and C, when the data are written into logic sector, searching or modifying mapping table and making recovery management of abnormal condition. The described device includes the following several portions: division unit, creation unit and recovery management unit.
Owner:LEADCORE TECH
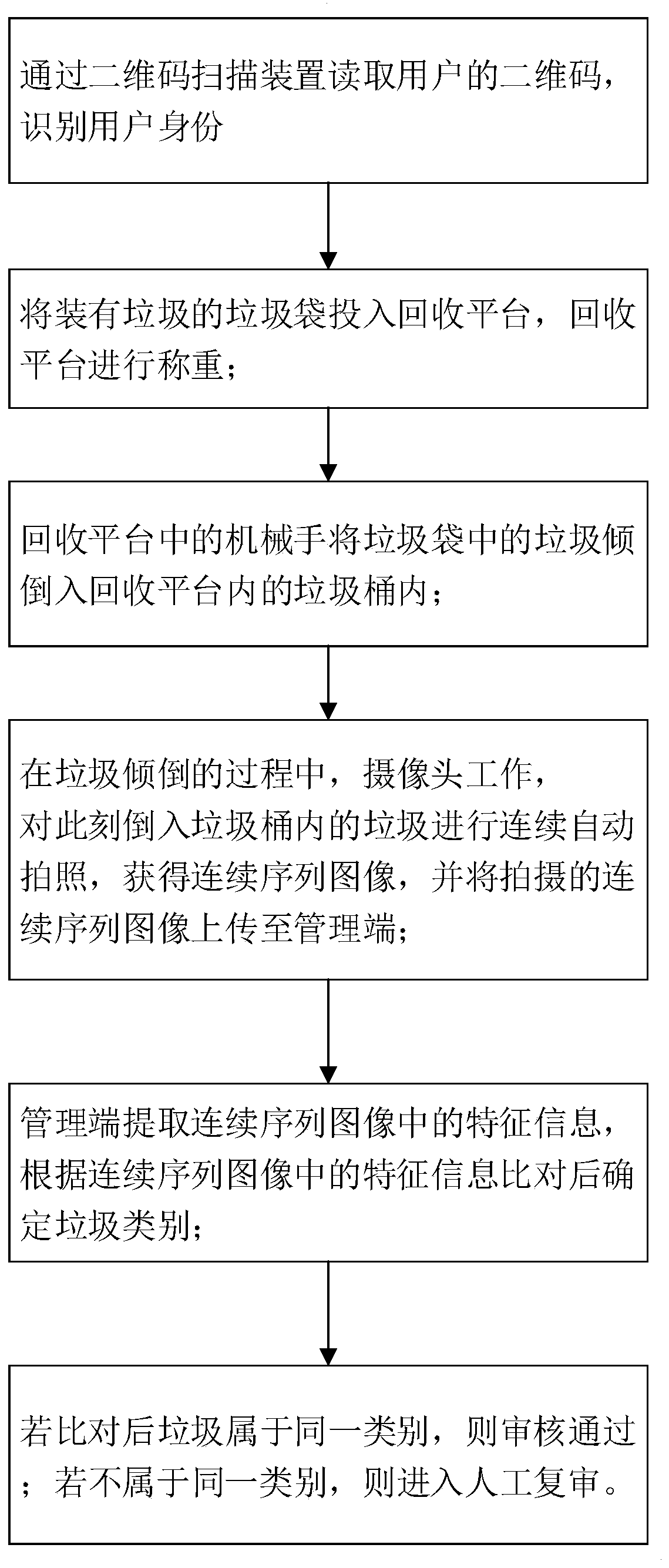
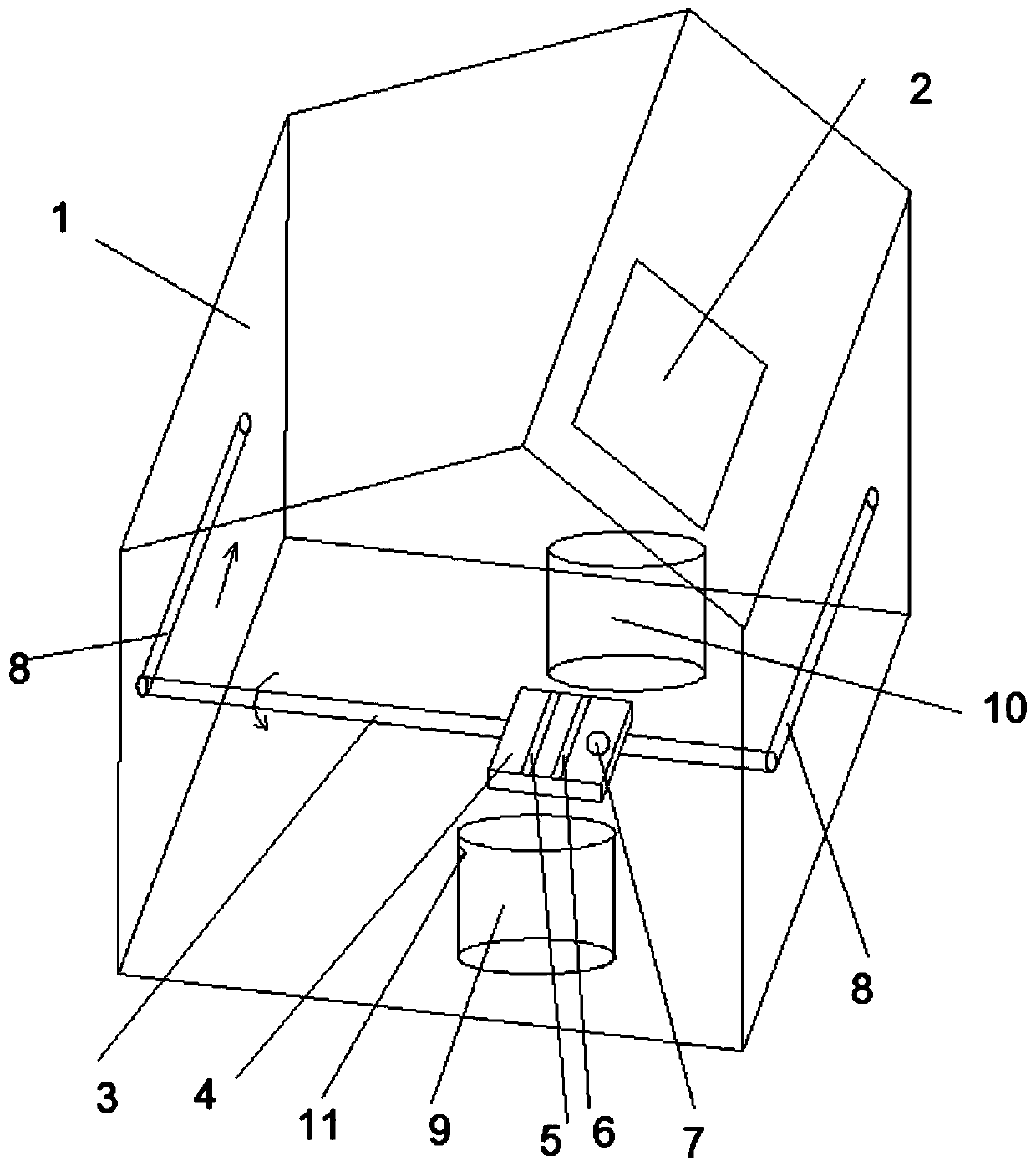
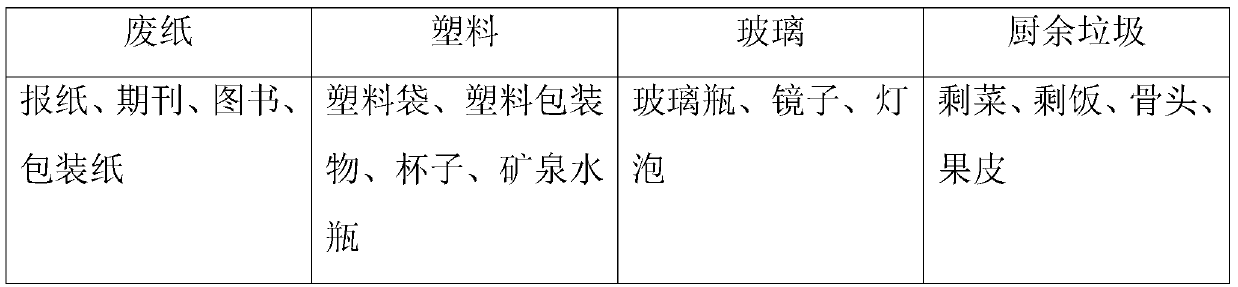
Household waste classification and recovery management system and method
ActiveCN110053903AReduce direct contact timeData processing applicationsCo-operative working arrangementsClosed loop feedbackWaste management
The invention provides a household waste classification and recovery management system and method. The household waste classification and recovery management system comprises a recovery platform and amanagement terminal. The recovery platform comprises a two-dimensional code scanning device, a weighing unit, a sorting unit and a camera unit, wherein the two-dimensional code scanning device is used for reading two-dimensional codes of users; the weighing unit is used for weighing waste in waste bags; the sorting unit is used for separating the waste from the waste bags, so that the waste is poured into a dustbin on the recovery platform; and the camera unit is used for continuously photographing the waste currently poured into the dustbin so as to acquire a continuous sequential image. Themanagement terminal receives the continuous sequential image and conducts characteristic comparison to judge whether the waste currently poured into the dustbin meets the classification requirement of the dustbin or not. According to the household waste classification and recovery management system and method, the camera unit is arranged to automatically check whether the waste thrown by the users is effectively classified or not, so that the time of direct contact of sorting workers with the waste is shortened. In this way, a closed-loop feedback process is formed, and the waste classification standardability of the users is continuously improved.
Owner:重庆左岸环境服务股份有限公司
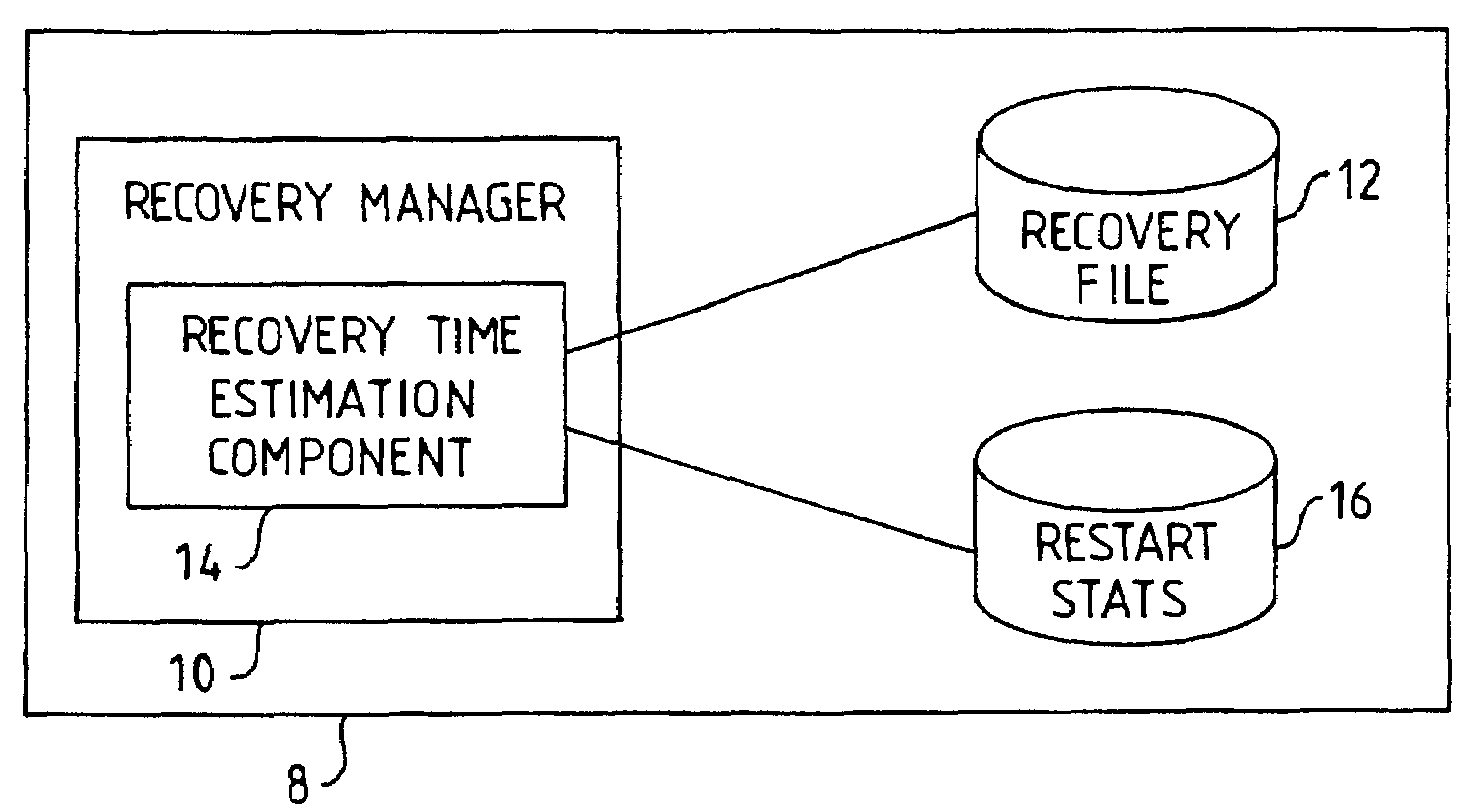
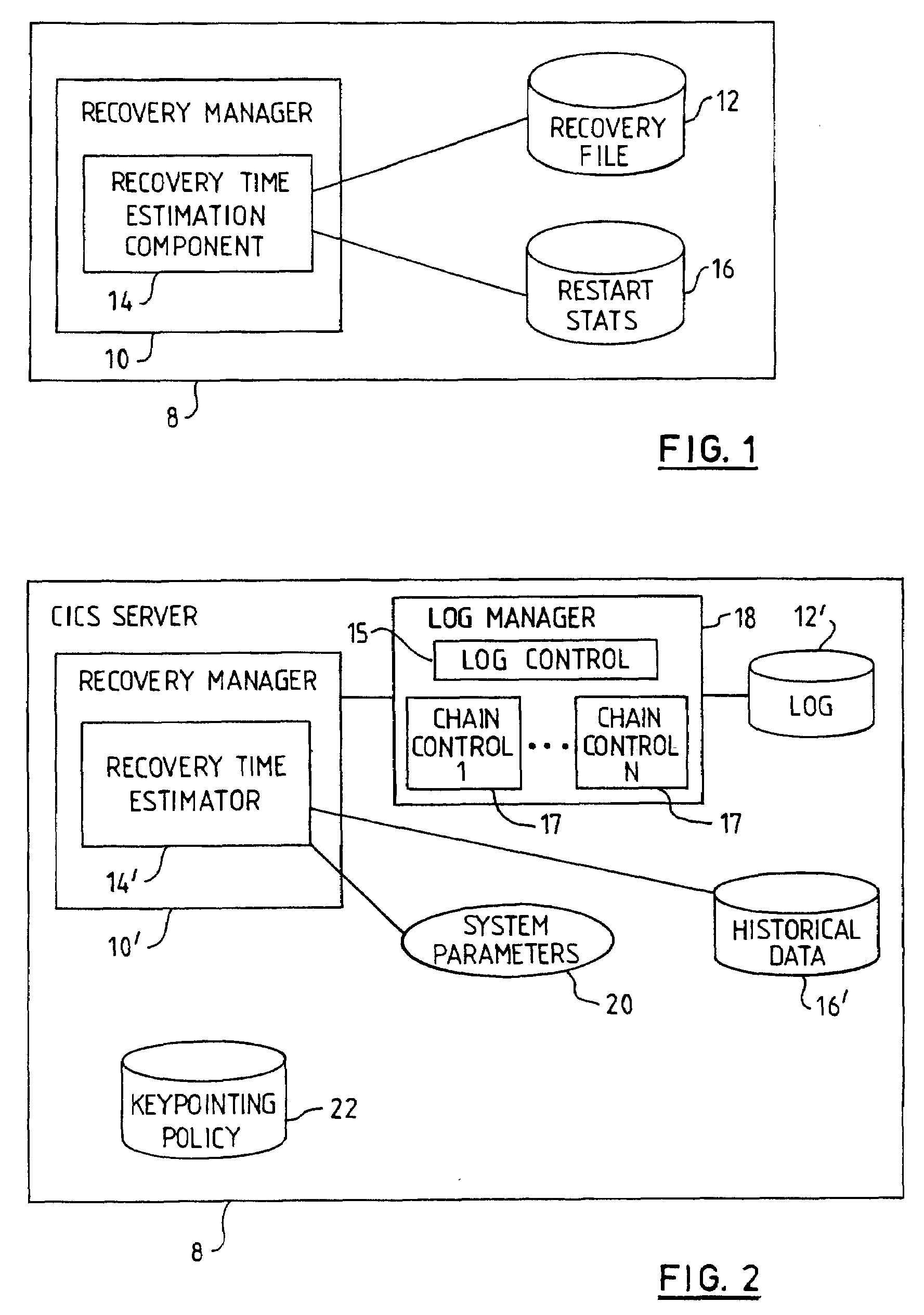
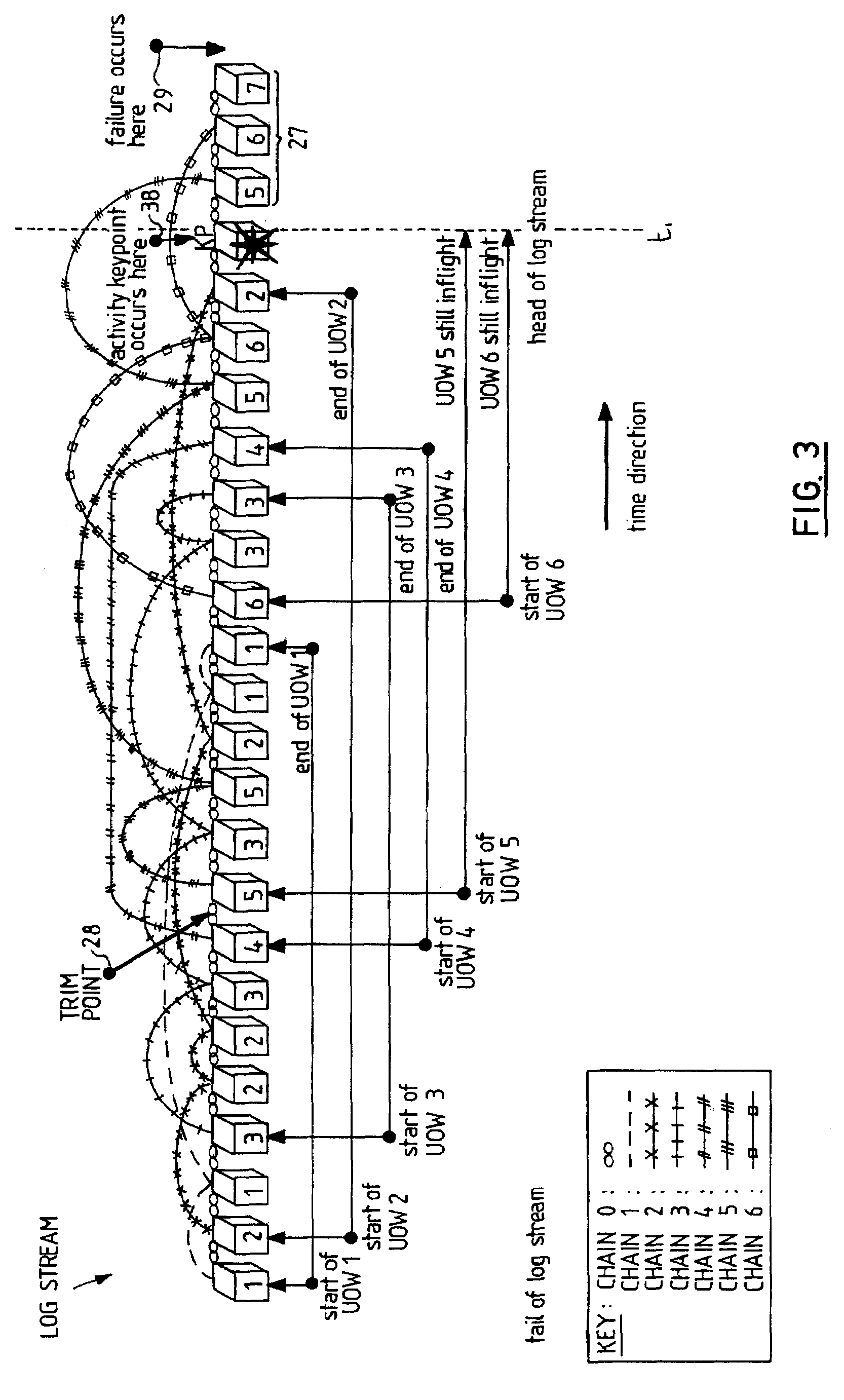
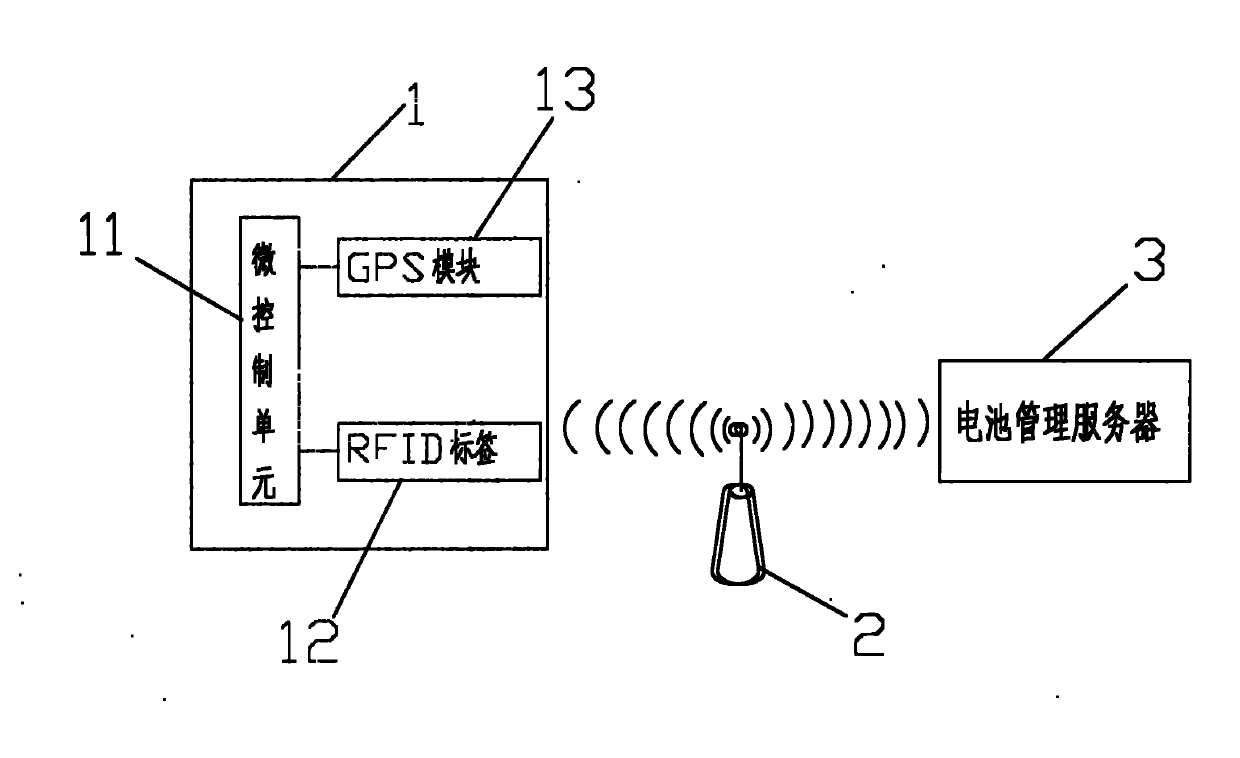
Method and System for Transaction Recovery Time Estimation
InactiveUS20070260908A1Direct monitoringImprove manageabilityError detection/correctionComputer scienceTime estimation
To generate a recovery time estimate in a transaction environment, a system includes a recovery manager, a recovery file containing recovery data, a store of historical restart data, and a recovery time estimation component. The recovery manager includes a component which is operable to measure the volume of active data on the recovery file, and to generate a recovery time estimate based on the measured volume and the historical restart data. This recovery time estimate can then be used as a characteristic of the system's keypointing policy to provide a more flexible and efficient keypointing procedure.
Owner:IBM CORP
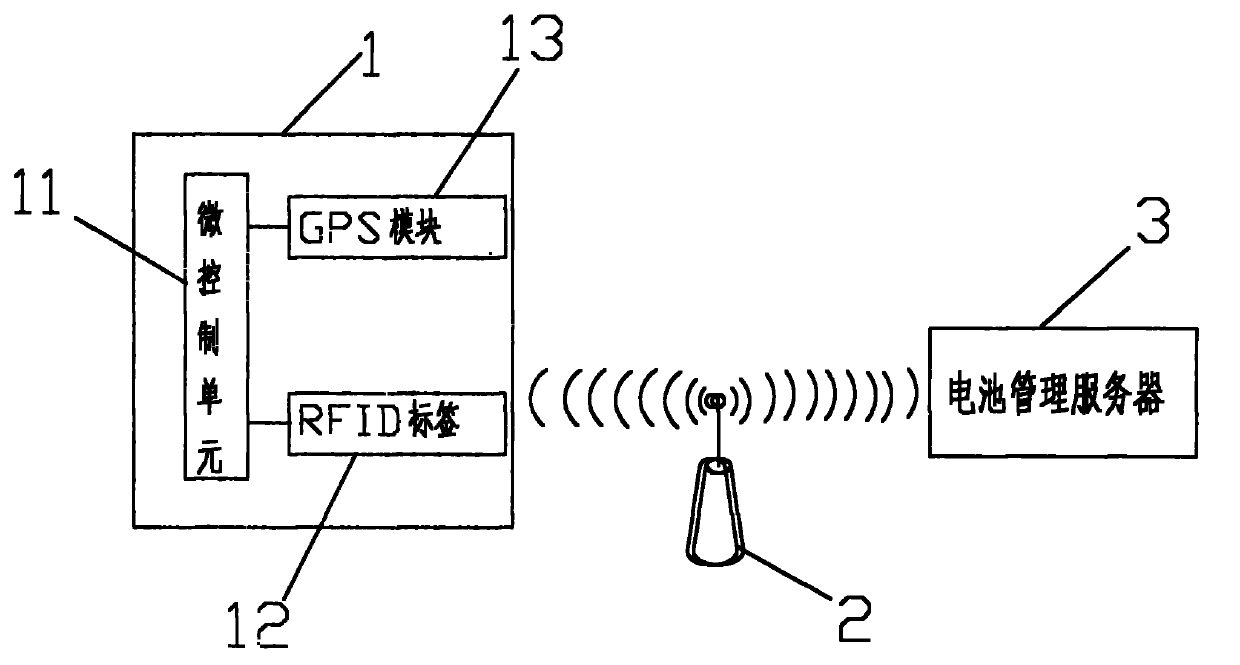
Power battery total life cycle monitoring system based on internet of thing
InactiveCN102169548ATimely recycling managementStandardized recycling managementCo-operative working arrangementsSecondary cells servicing/maintenancePower batteryElectrical battery
The invention discloses a power battery total life cycle monitoring system based on an internet of thing. The monitoring system comprises a power battery and an RFID (Radio Frequency Identification Device) reader, wherein the power battery is provided with a micro control unit, a GPS (Global Position System) module and an RFID label inside, the GPS module and the RFID label are connected with the micro control unit, the RFID label is connected with the RFID reader in a wireless communication manner, and the RFID reader is further connected with a battery management server in a communication manner. The system provides a brand-new power battery management strategy to realize the full-process traceability of power battery information and ensure the information transparence in life cycle of the power battery, and can offer timely use suggestions and recovery guide for consumers and decision support for functional departments, standardizes the recovery management of the power battery and reduces the pollution of wastes to the environment, and further plays the role of antitheft.
Owner:GEOBY ELECTRIC VEHICLE +1
Multistage system recovery framework
A method and system for multi-staged recovery of a distributed computer system. The method includes receiving a failure event notification from at least one node of the distributed computer system and executing a plurality of recovery stages upon receiving the failure event notification by using a recovery manager, wherein each of the plurality of recovery stages performs a defined recovery task. The progress of recovery is tracked by using at least one state machine executed by the recovery manager, wherein the state machine reflects progress of each of the recovery stages. The progress of recovery is monitored to a completion by using the state machine and the recovery manager.
Owner:VERITAS TECH
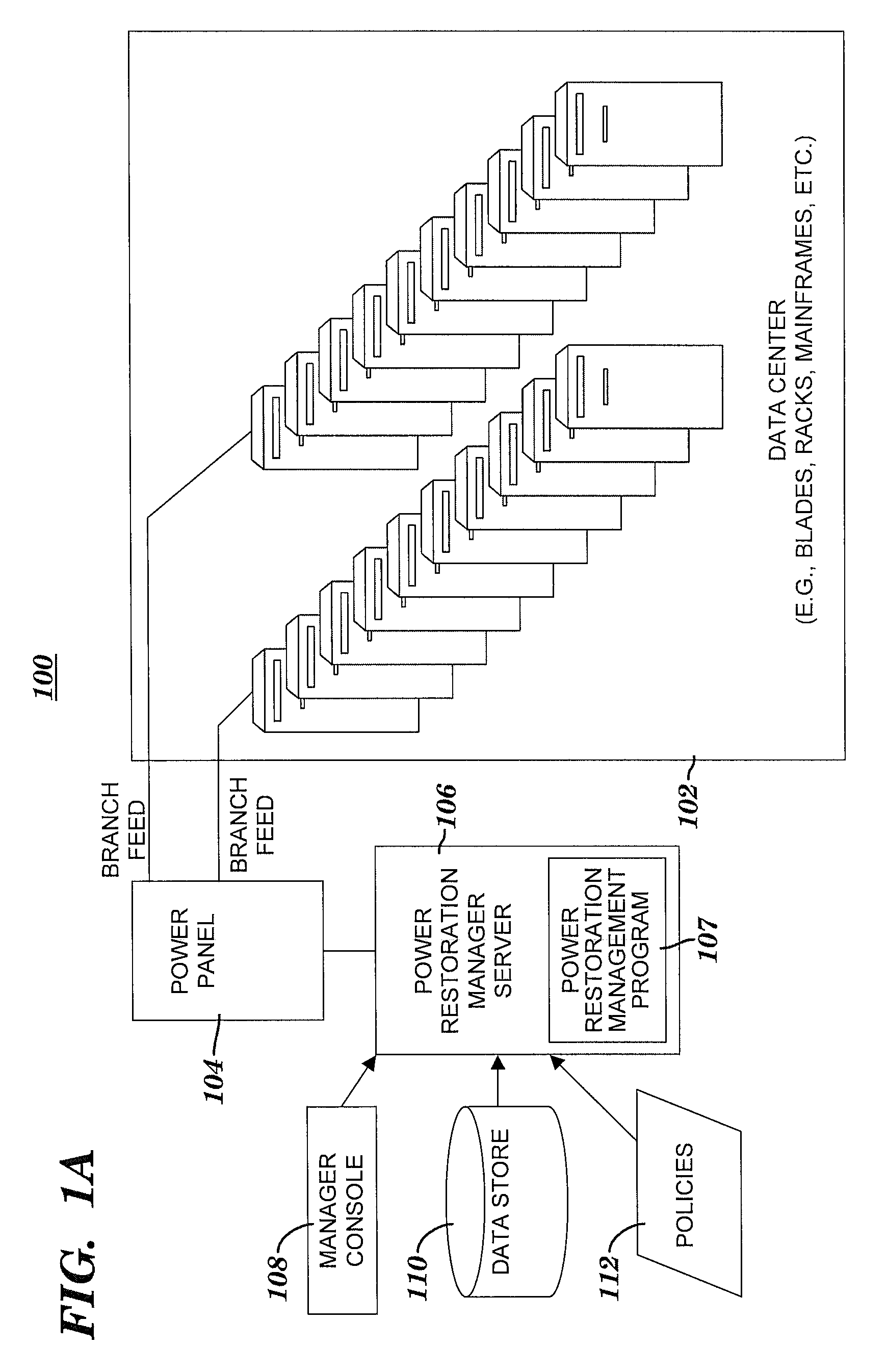
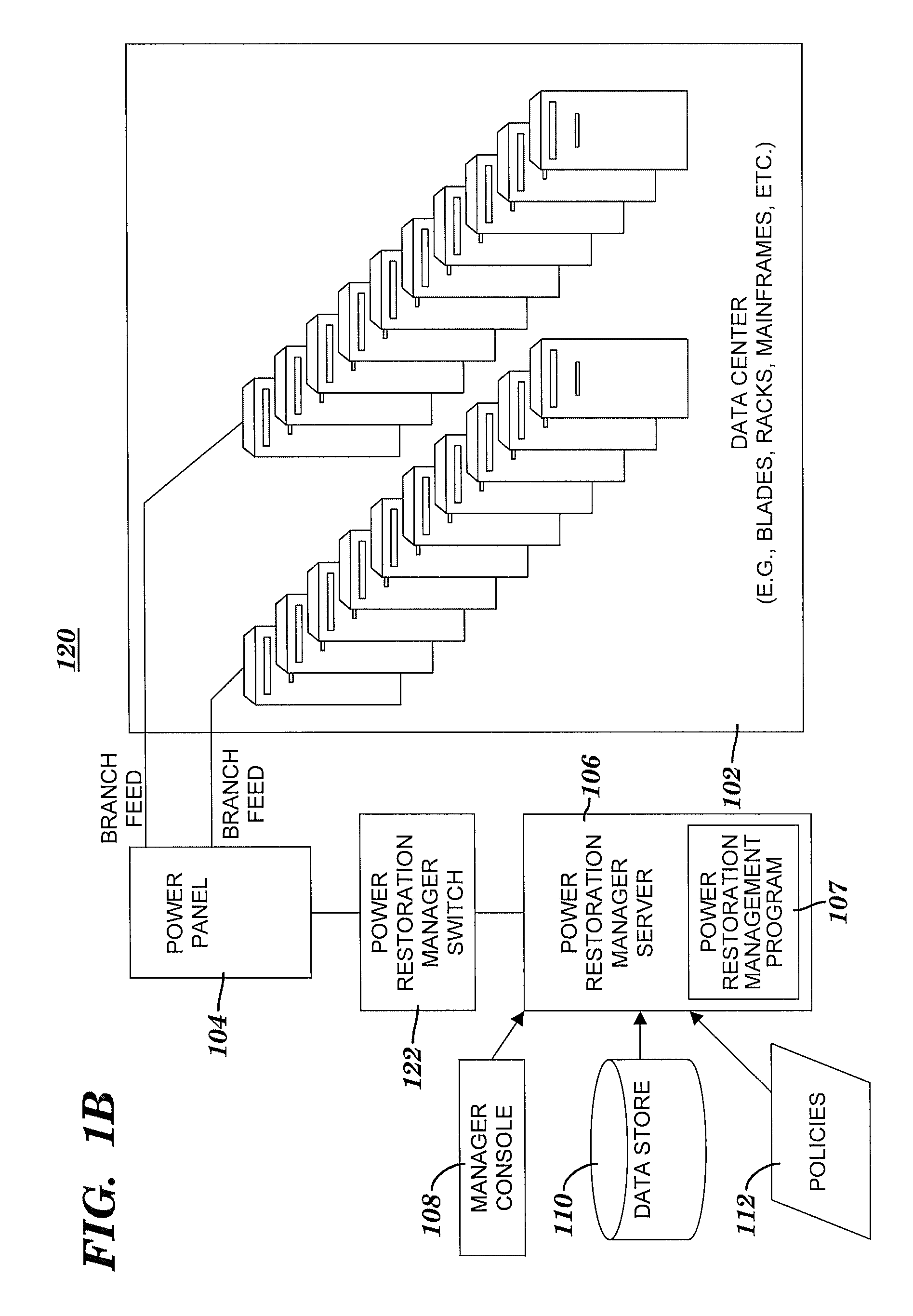
Data center boot order control
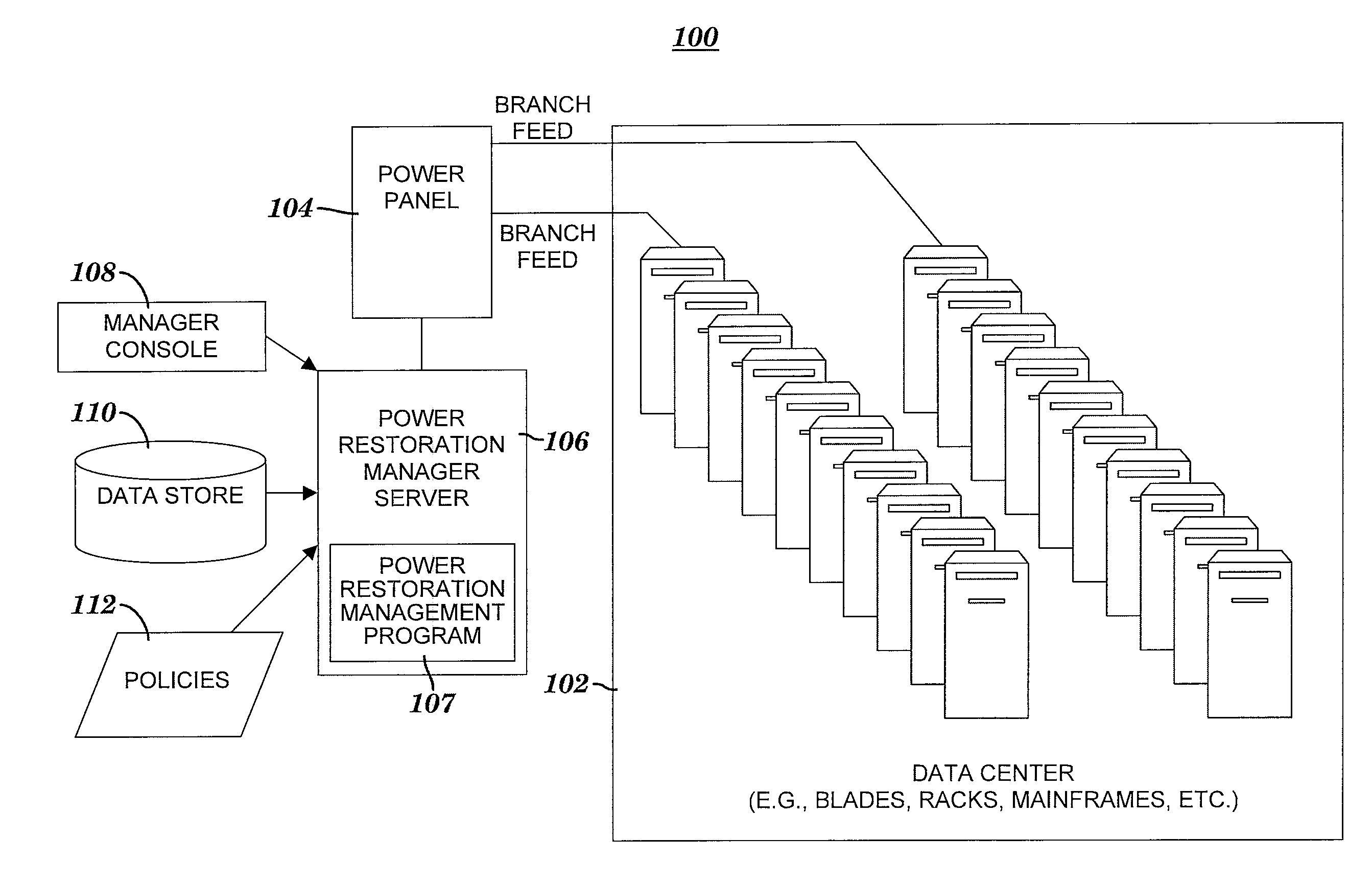
InactiveUS20080172553A1Precise positioningIncreasing a financial profit or decreasing a financial loss of the entityError detection/correctionDigital computer detailsOrder controlData center
A method and system for determining an optimal order for rebooting servers in a data center. After an abnormal shutdown event in a data center, a power restoration management (PRM) server detects a restoration of power capable of being available for a rebooting of servers in the data center. A power restoration management program automatically and dynamically determines an optimal order for rebooting the servers, where the order is a result of applying policies based on weighted factors. The PRM server or a manual process reboots the servers in the determined order. The rebooting includes an enhancement of a financial position of an organizational entity associated with the data center. The enhancement of the financial position includes increasing a financial profit of the organizational entity or decreasing a financial loss of the organization entity.
Owner:IBM CORP
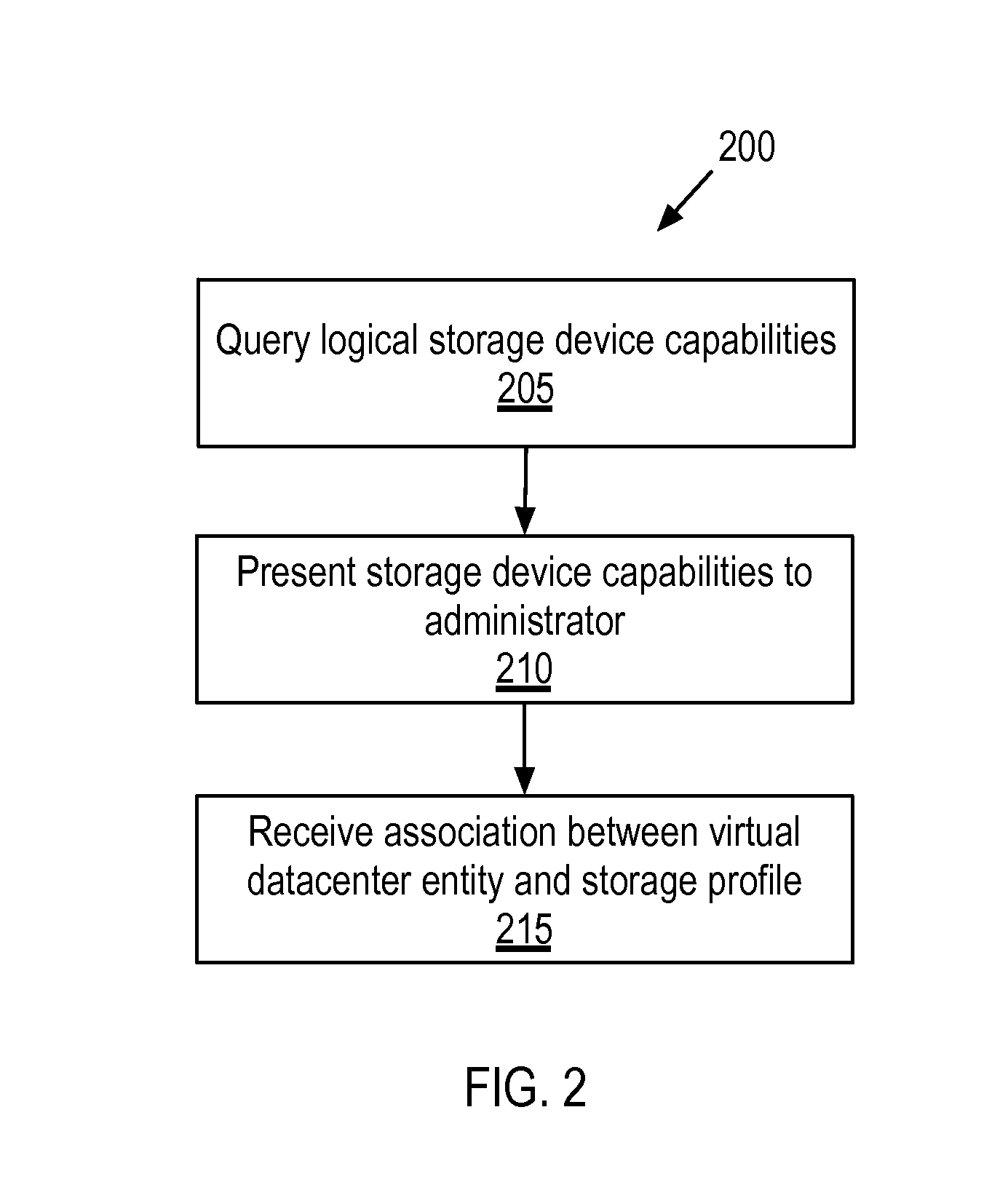
Storage policy-based automation of protection for disaster recovery
ActiveUS20160062858A1Redundant operation error correctionRedundant hardware error correctionFailoverData center
Exemplary methods, apparatuses, and systems include a recovery manager receiving selection of a storage profile to be protected. The storage profile is an abstraction of a set of one or more logical storage devices that are treated as a single entity based upon common storage capabilities. In response to the selection of the storage profile to be protected, a set of virtual datacenter entities associated with the storage profile is added to a disaster recovery plan to automate a failover of the set of virtual datacenter entities from a protection site to a recovery site. The set of one or more virtual datacenter entities includes one or more virtual machines, one or more logical storage devices, or a combination of virtual machines and logical storage devices. The set of virtual datacenter entities is expandable and interchangeable with other virtual datacenter entities.
Owner:VMWARE INC
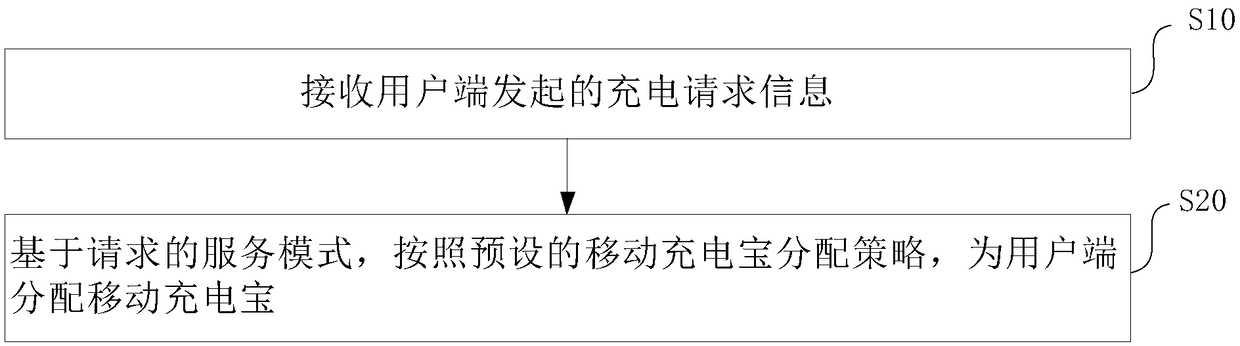
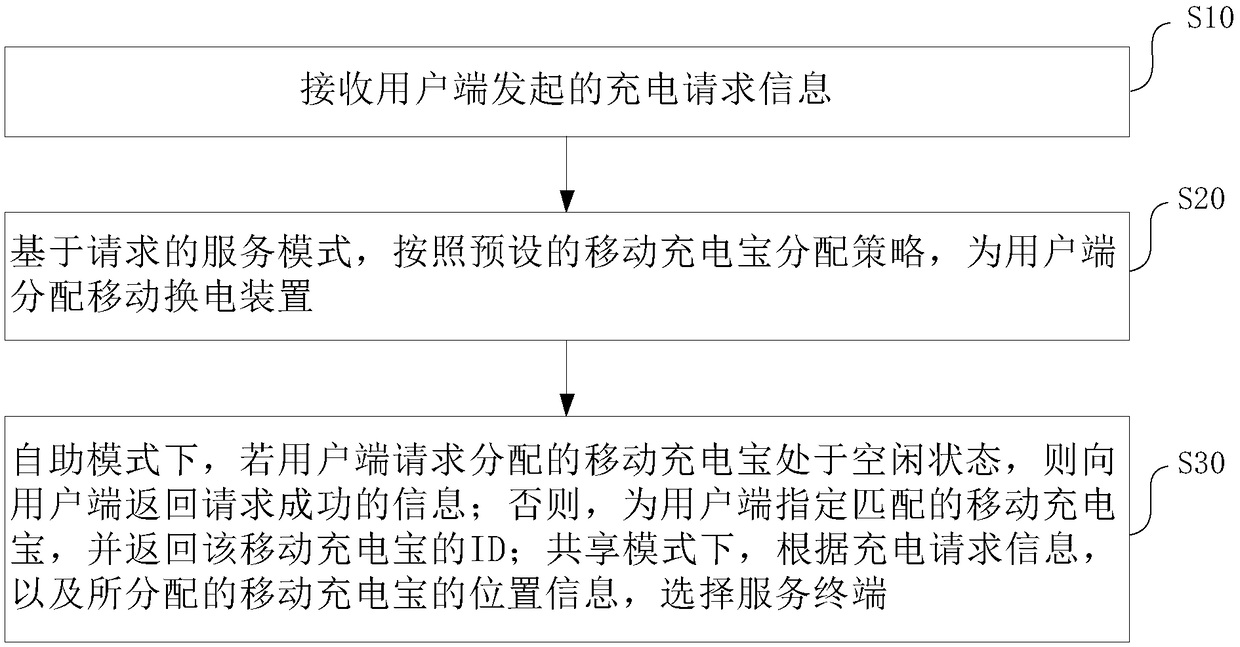
Mobile charging treasure scheduling method, system, scheduling server and device
InactiveCN109146255ASolve the problem of finding charging pilesRelieve travel anxietyCharging stationsReservationsElectricityComplete resolution
The invention relates to the electric vehicle charging and exchanging field, in particular to a mobile charging treasure dispatching method, a system, a dispatching server and a device, aiming at solving the problem that the number and distribution of charging piles and charging stations can not meet the demand. The mobile charging treasure scheduling method of the invention supports a sharing mode and a self-help mode. In the sharing mode, the user terminal initiates a charging request after parking at any position, and the server broadcasts a charging order for the service terminal to obtainor selects the service terminal by assigning an order, so that the vehicle to be charged is charged. In the self-service mode, the user terminal selects the mobile charging treasure and initiates thecharging request. After the server confirms, the user completes the charging by himself or requests the service executor to assist in completing the charging. The invention also provides a recovery management method, which constitutes a complete solution, solves the problem of difficulty in finding a charging pile and a charging station, and further relieves the travel anxiety of a user.
Owner:NIO ANHUI HLDG CO LTD
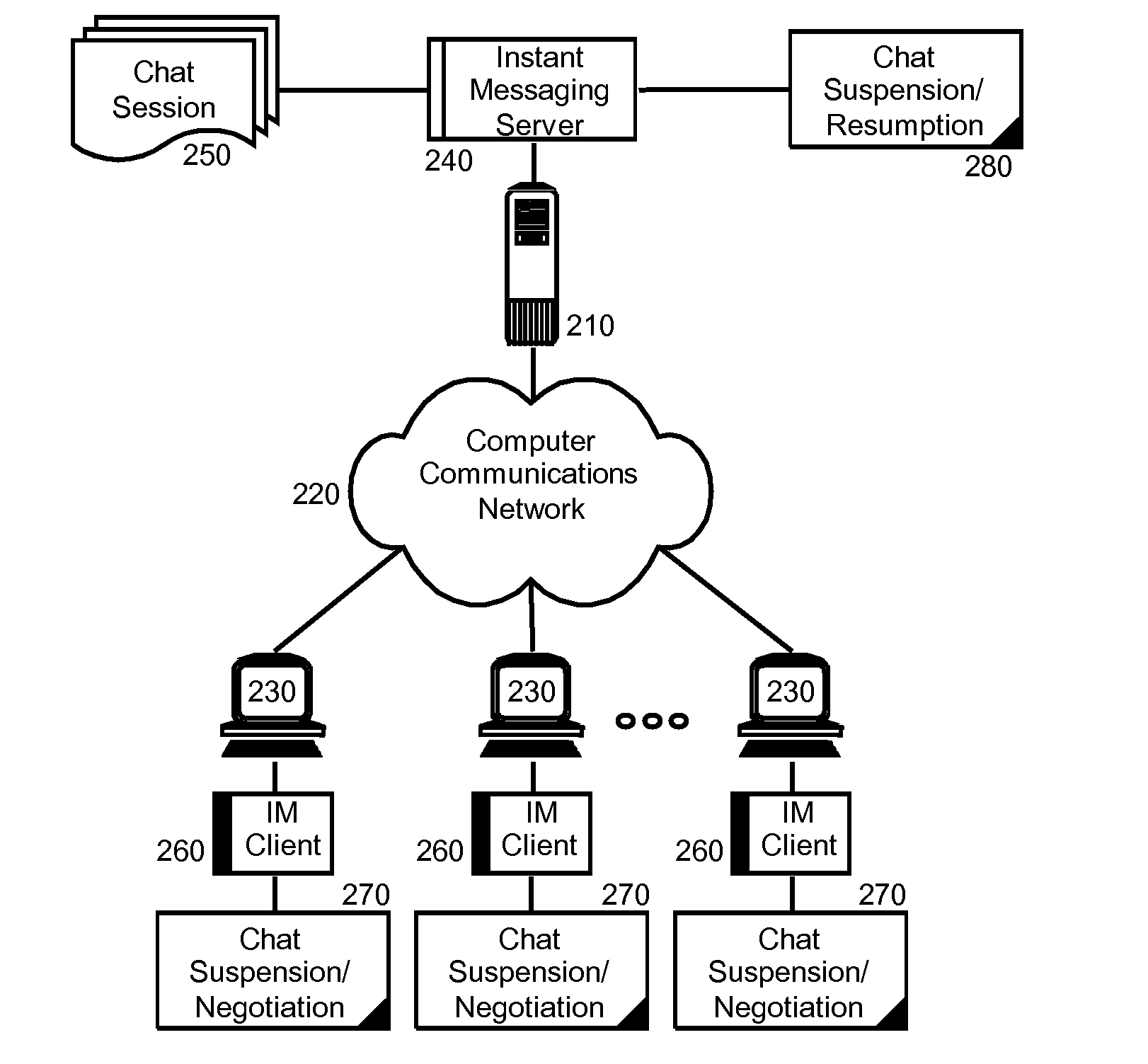
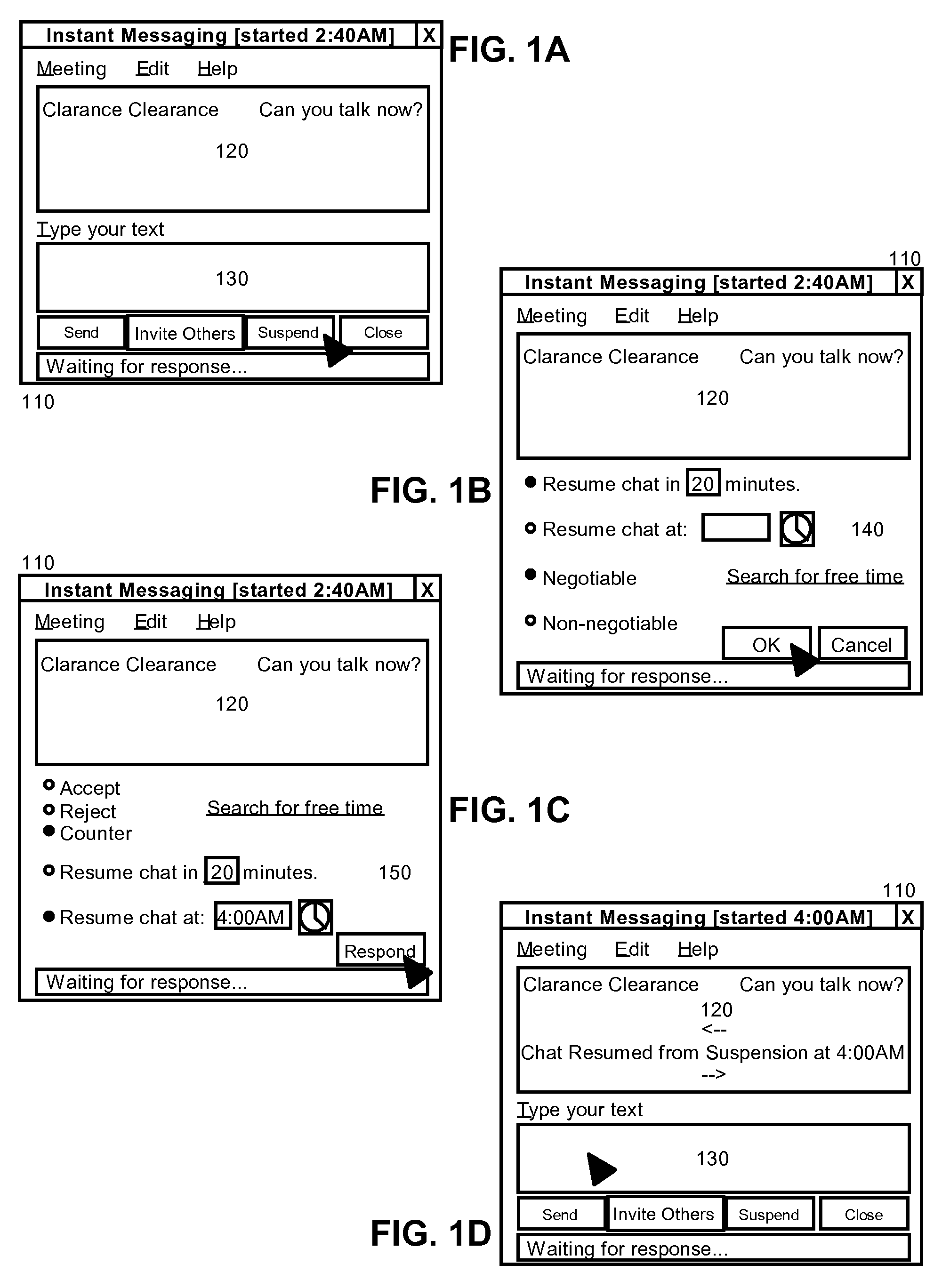
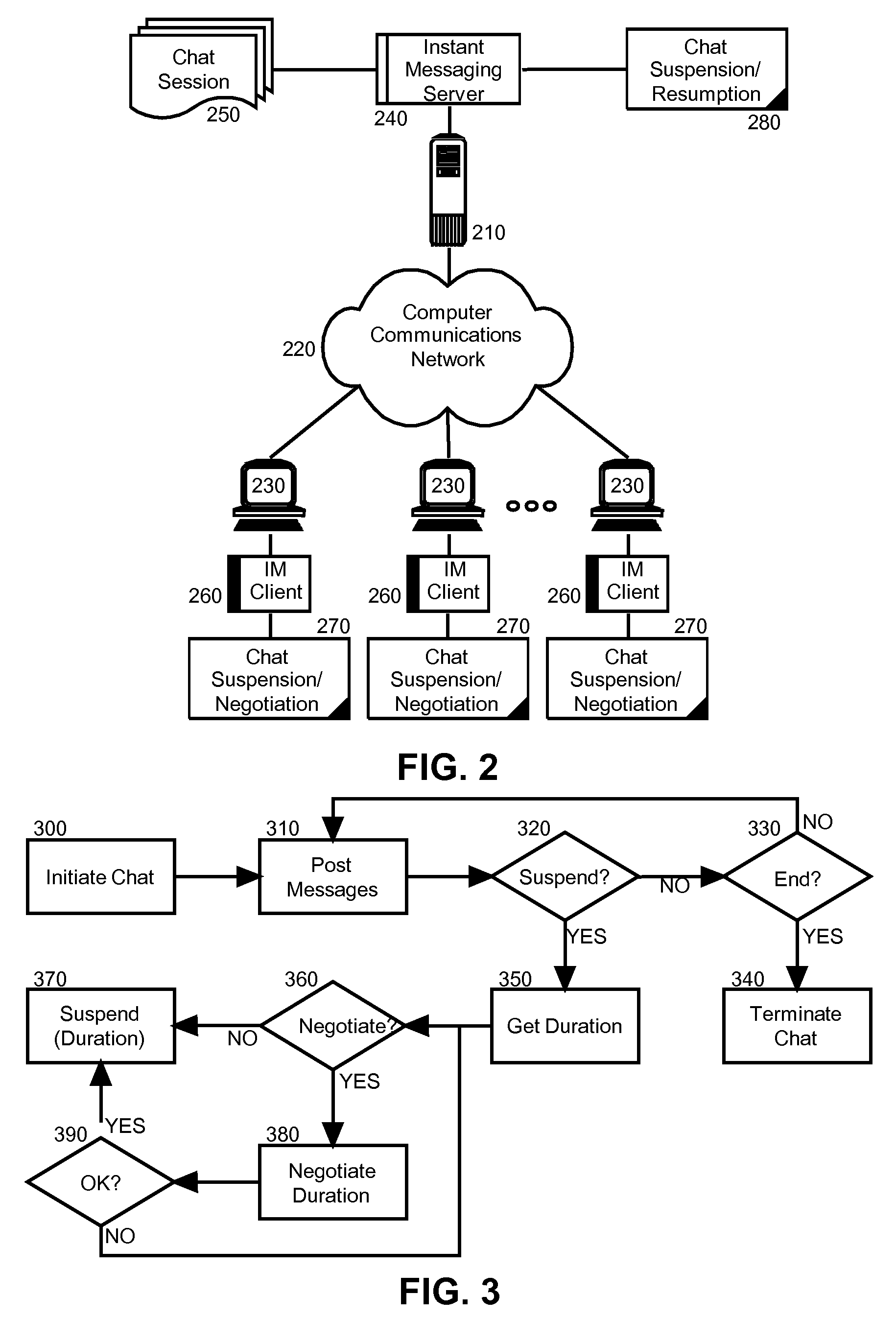
Automated instant messaging chat suspension and resumption
InactiveUS20080162633A1Multiple digital computer combinationsData switching networksMessage passingInstant messaging
Embodiments of the present invention address deficiencies of the art in respect to instant messaging and provide a method, system and computer program product for. In one embodiment of the invention, a chat session suspension and resumption management method can include establishing a chat session among at least two conversants, receiving a request by one of the conversants to suspend the established chat session for a specified duration of time, and suspending the chat session for the specified duration of time and automatically resuming the chat session subsequent to the specified duration of time without further instruction by the conversants. The method further can include determining whether the request to suspend the established chat session for the specified duration of time permits negotiation of the specified duration of time, and exchanging negotiated durations of time between the conversants until arriving at an agreed upon duration only if permitted by the request.
Owner:IBM CORP
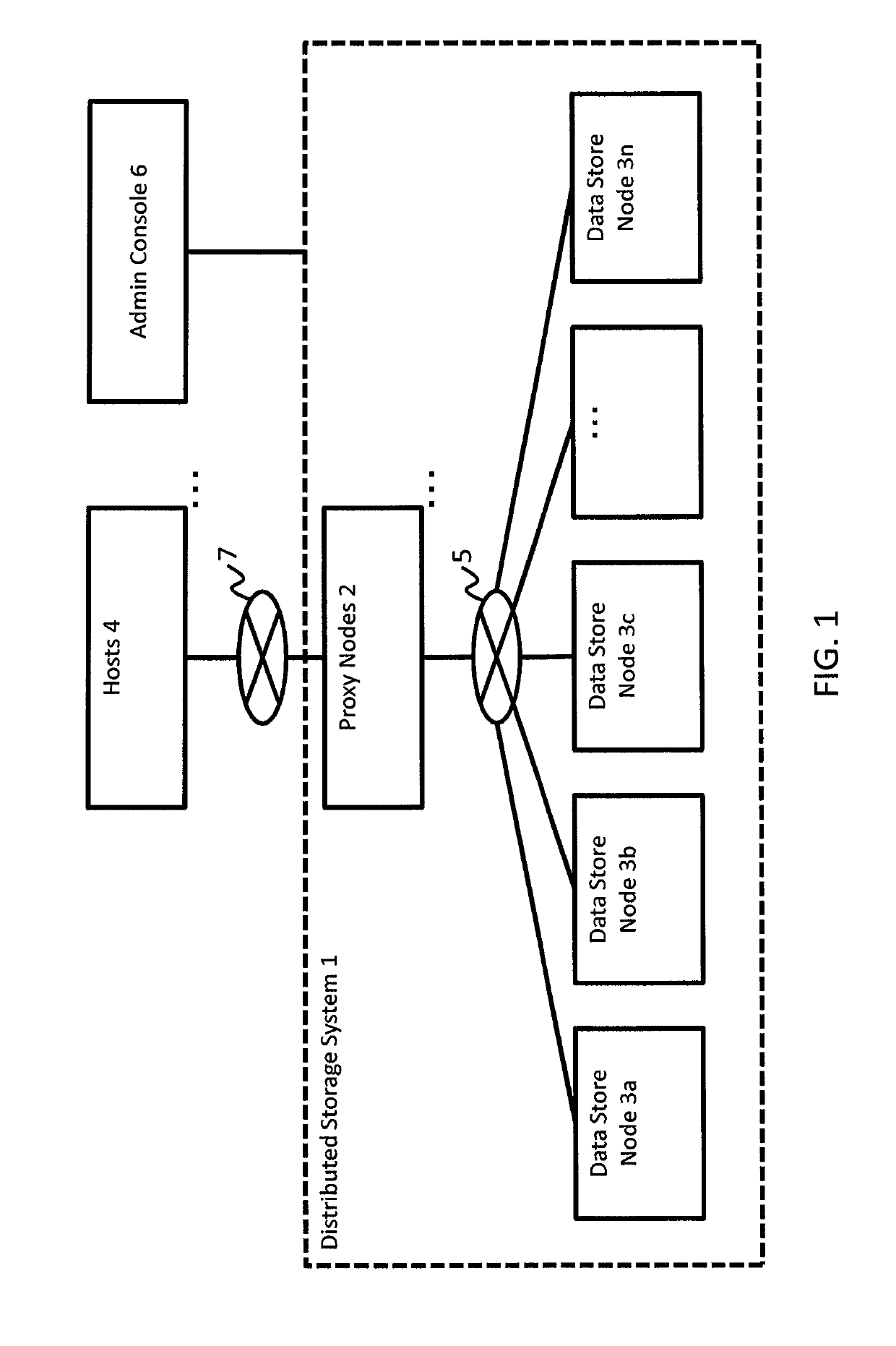
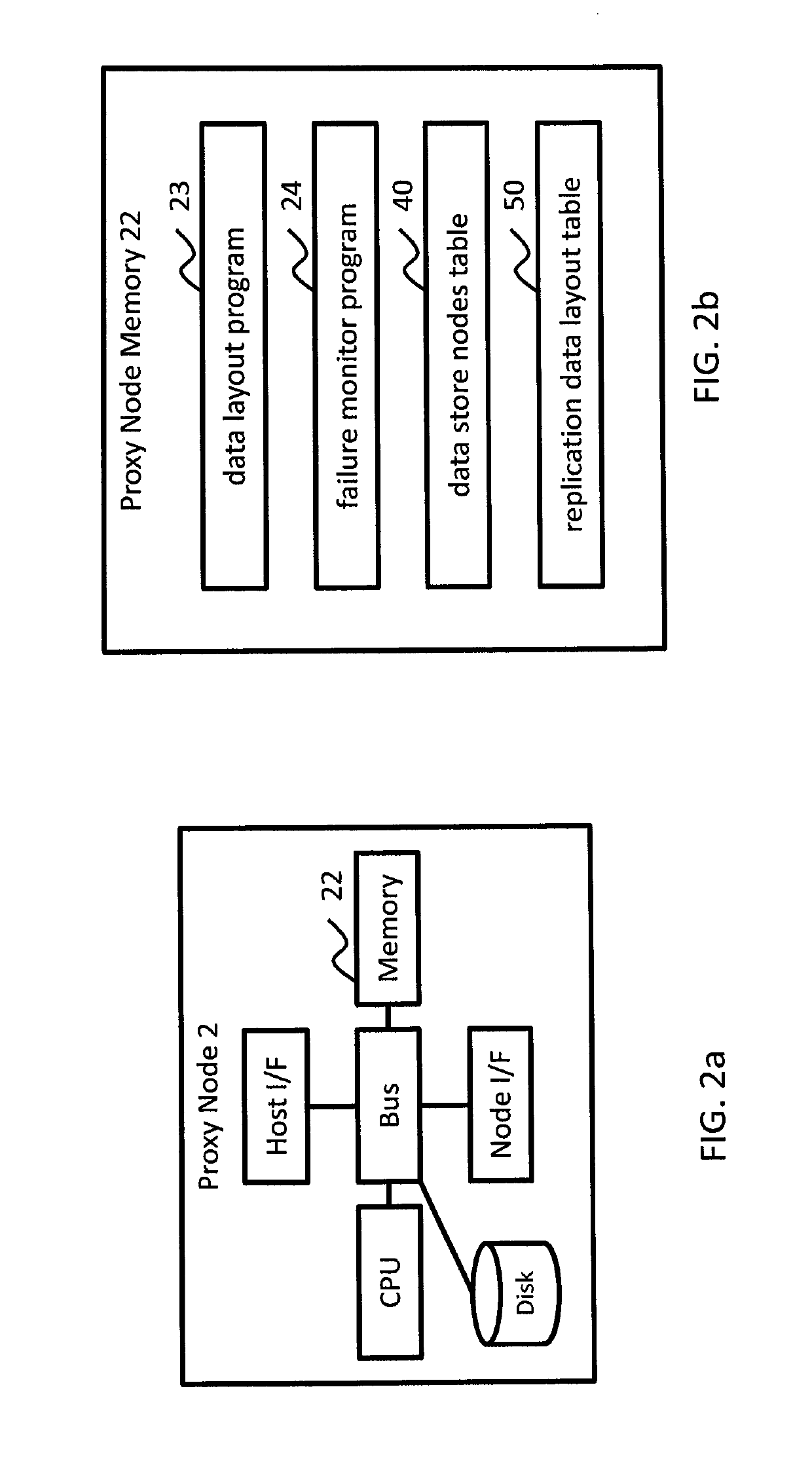
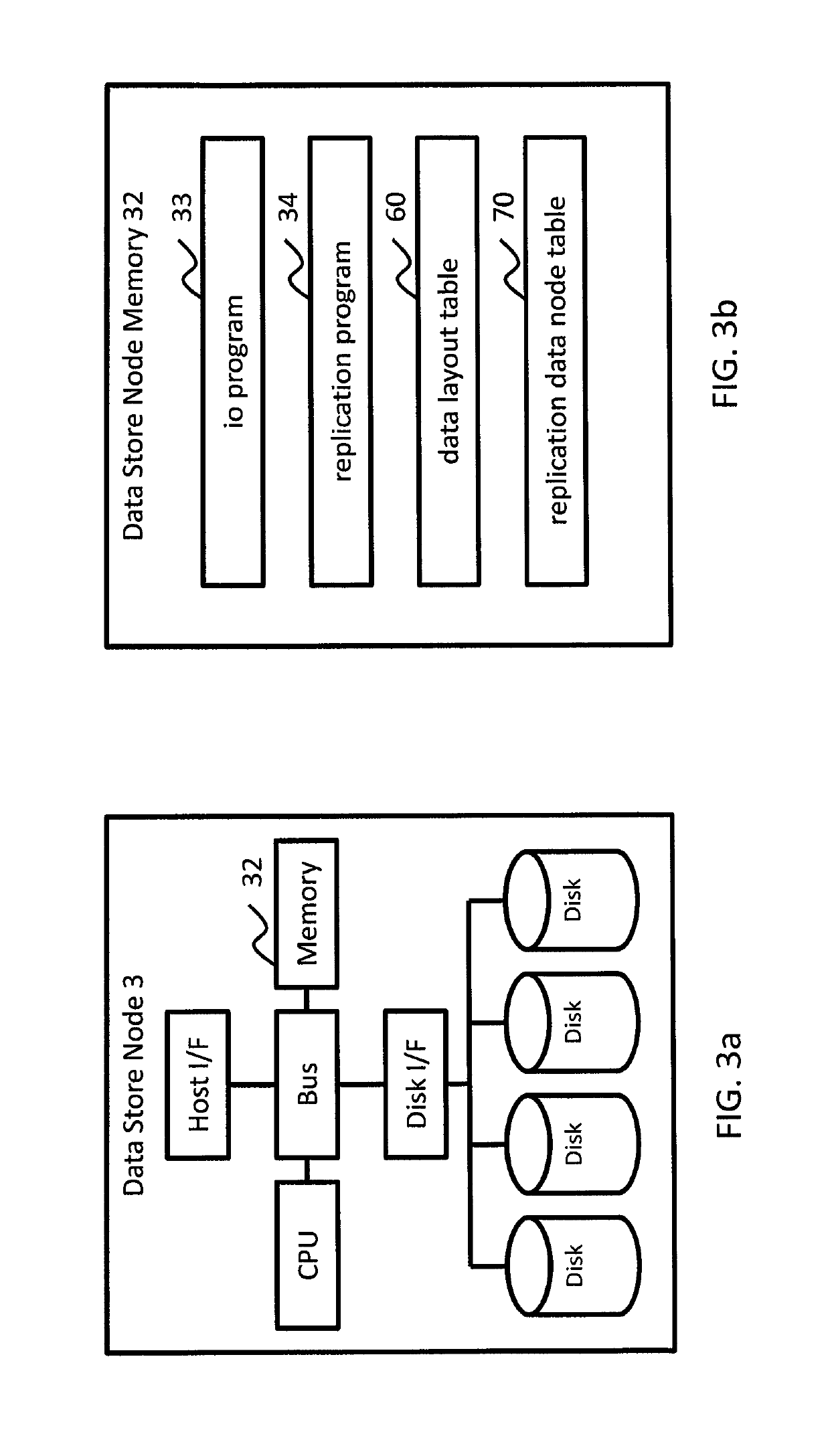
Method and apparatus for managing data recovery of distributed storage system
Exemplary embodiments provide a way to manage data recovery in a distributed system having multiple data store nodes. A storage system comprises: a first node including a first processor; and a plurality of second nodes coupled to the first node, each of the plurality of second nodes including a second processor and one or more second storage devices. The first processor is configured to control to store data and replication of the data in the second storage devices of two or more second nodes. If at least one of the second nodes has failed and a storage capacity of the plurality of second nodes is below a given threshold, one of the second nodes is configured to receive a first data, which is replication of data stored in a failed second node, from another of the second nodes, and create parity data based on the received first data.
Owner:HITACHI LTD
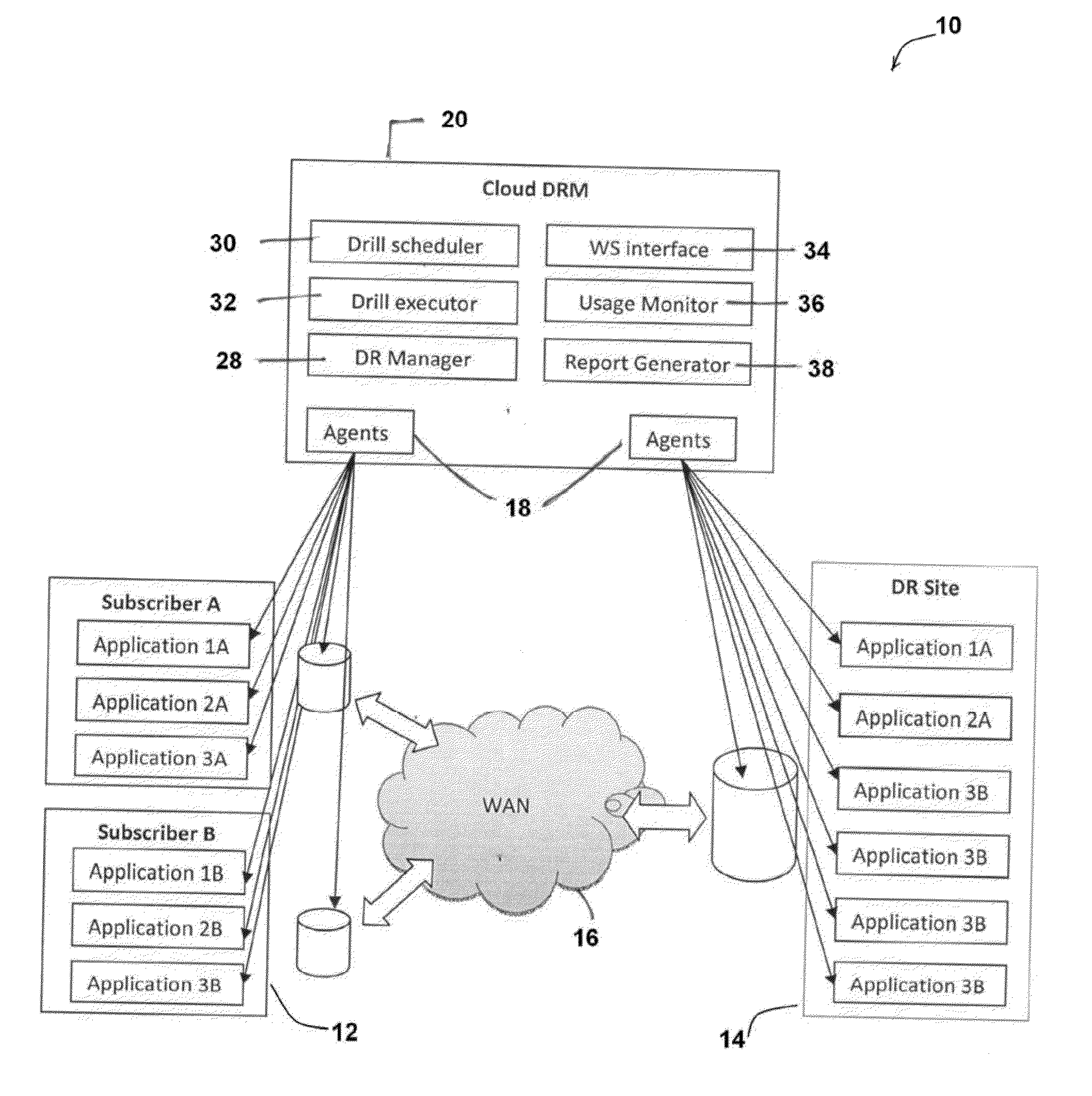
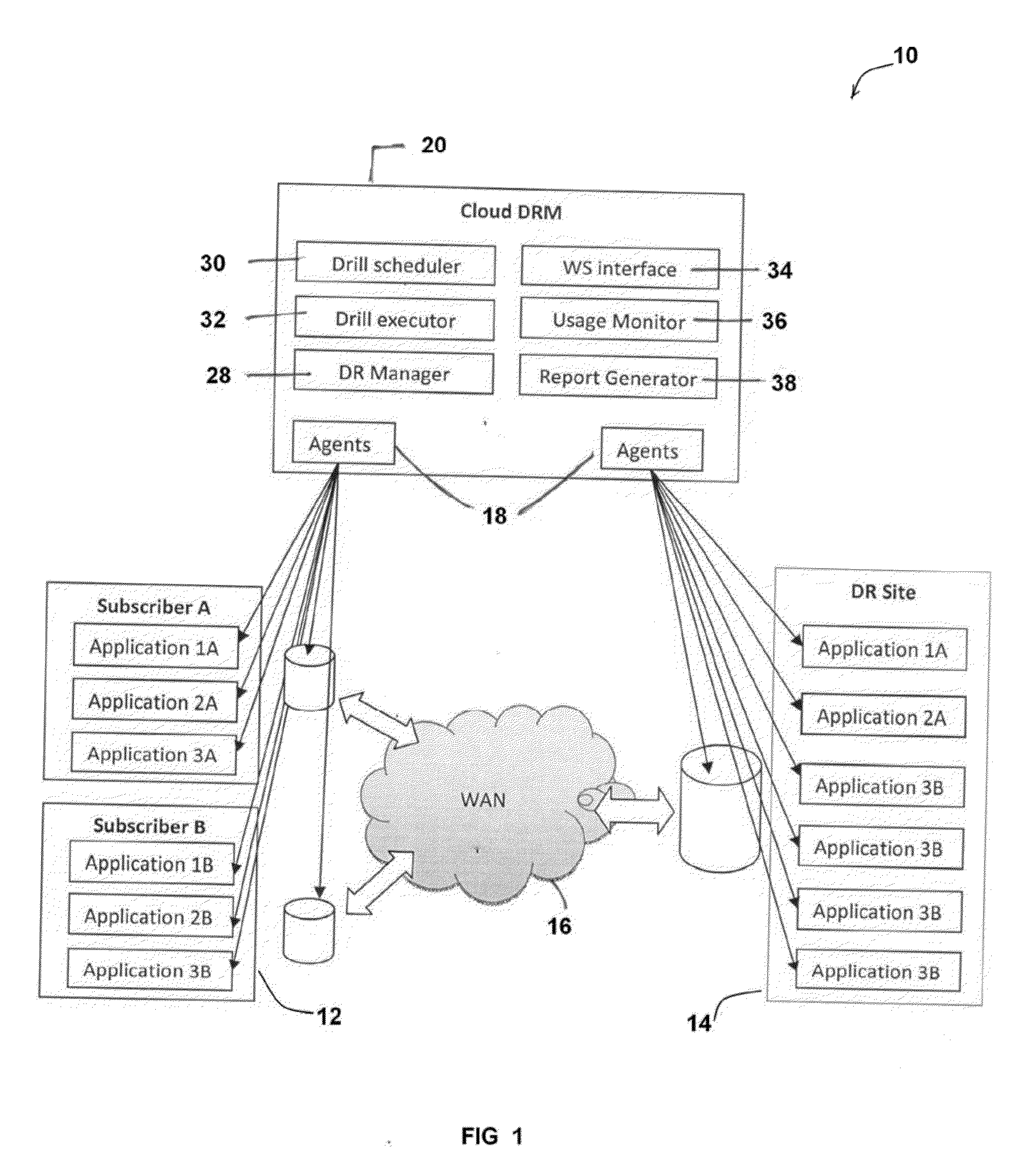
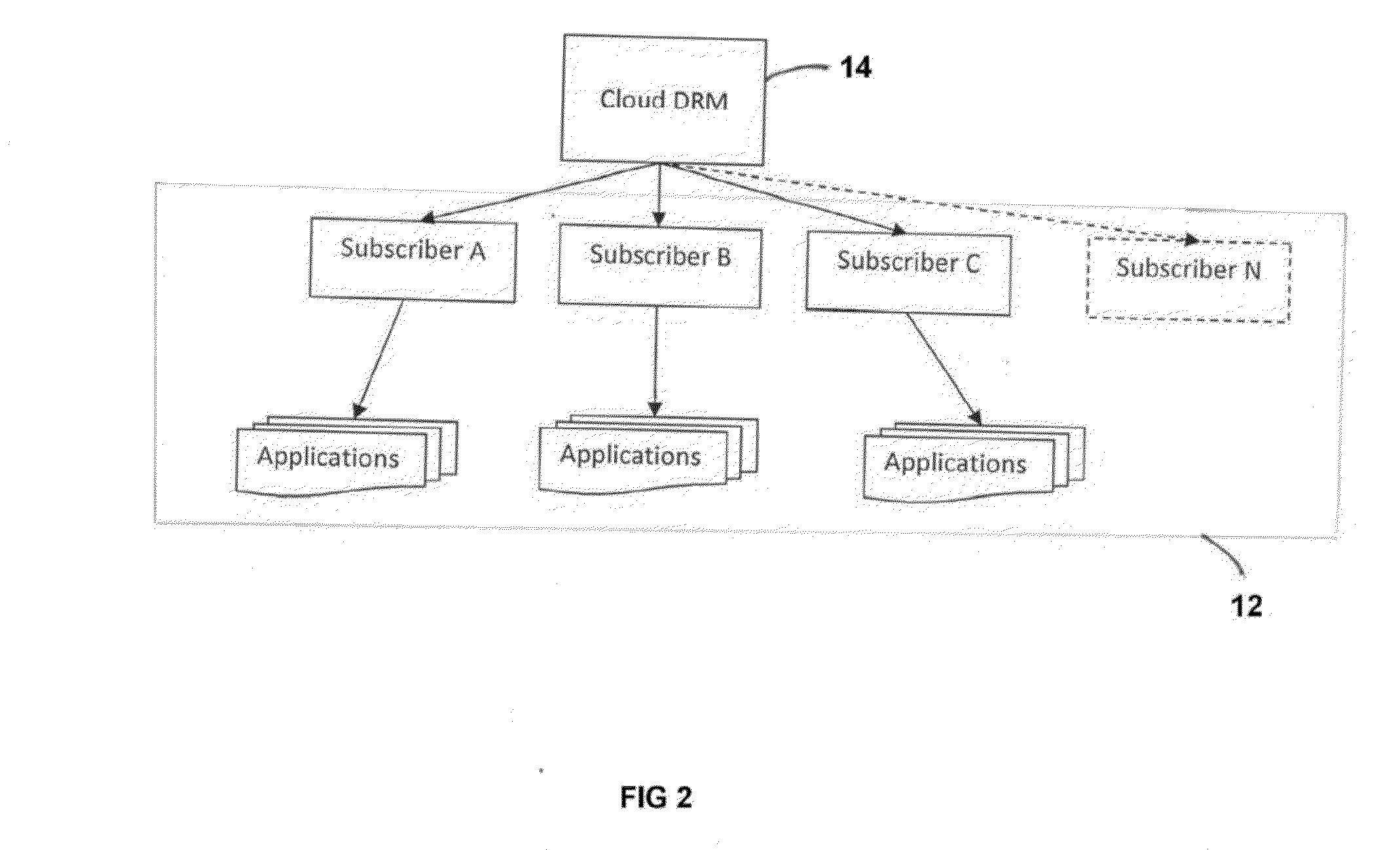
Multi-tenant disaster recovery management system and method for intelligently and optimally allocating computing resources between multiple subscribers
ActiveUS20150039930A1Effective and efficient solutionLow costFunctional testingData switching networksCloud baseDistributed computing
A Multi-Tenant Disaster Recovery Management System and method for intelligently and optimally allocating computing resources between multiple subscribers, the system comprising: one or more Multi-Tenant Disaster Recovery Management Server logically connected to one or more Production Site and one or more cloud based Disaster Recovery Site; a Network connecting said Multi-Tenant Disaster Recovery Management Server with said Production Site and said cloud based Disaster Recovery Site, wherein said Multi-Tenant Disaster Recovery Management Server is provided with at least one Disaster Recovery (DR) Manager Module, at least one Drill Scheduler Module, at least one Drill Executor Module, at least one WS Interface Module, at least one Usage Monitor Module and at least one Report Manager Module.
Owner:KYNDRYL INC
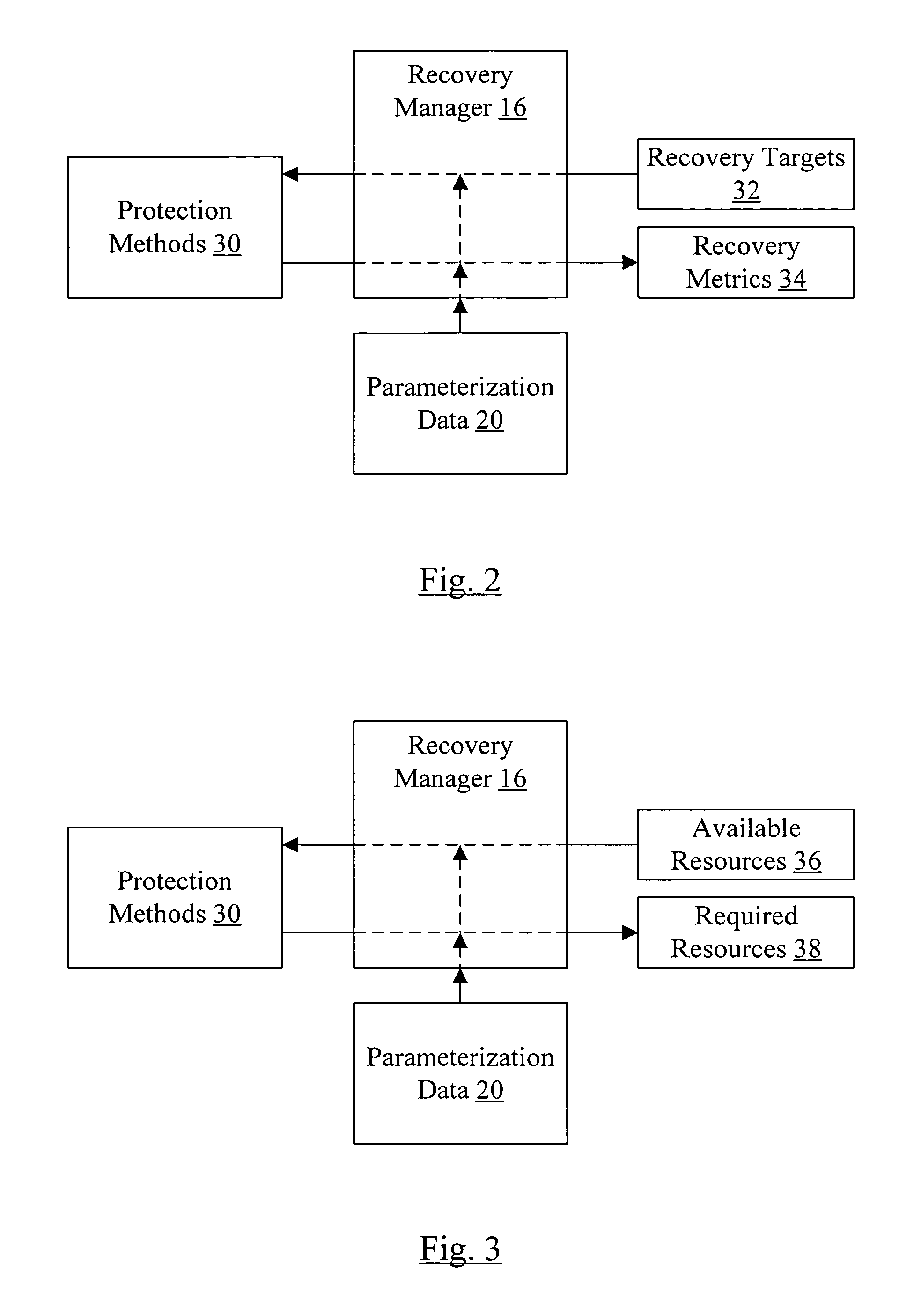
Conveying causal relationships between at least three dimensions of recovery management
In one embodiment, a method is contemplated. The method includes exposing at least three dimensions of a protection system to a user. The three dimensions are interrelated. The method further includes receiving user input indicating a modification in a first dimension of the at least three dimensions; and determining an effect of the modification in each other dimension of the at least three dimensions. A computer accessible medium comprising a plurality of instructions which, when executed, implement the method and a system implementing the method are also contemplated.
Owner:SYMANTEC OPERATING CORP
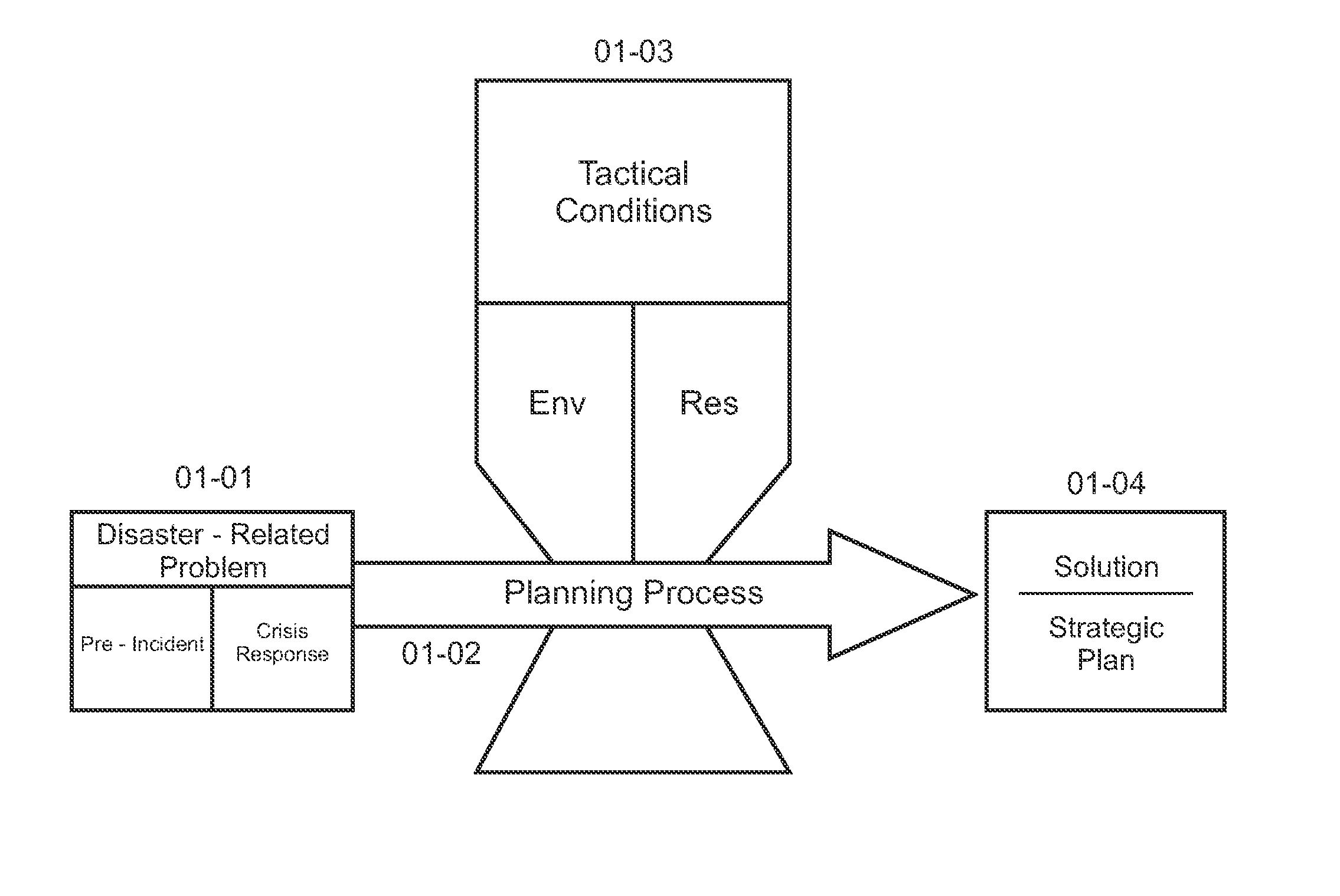
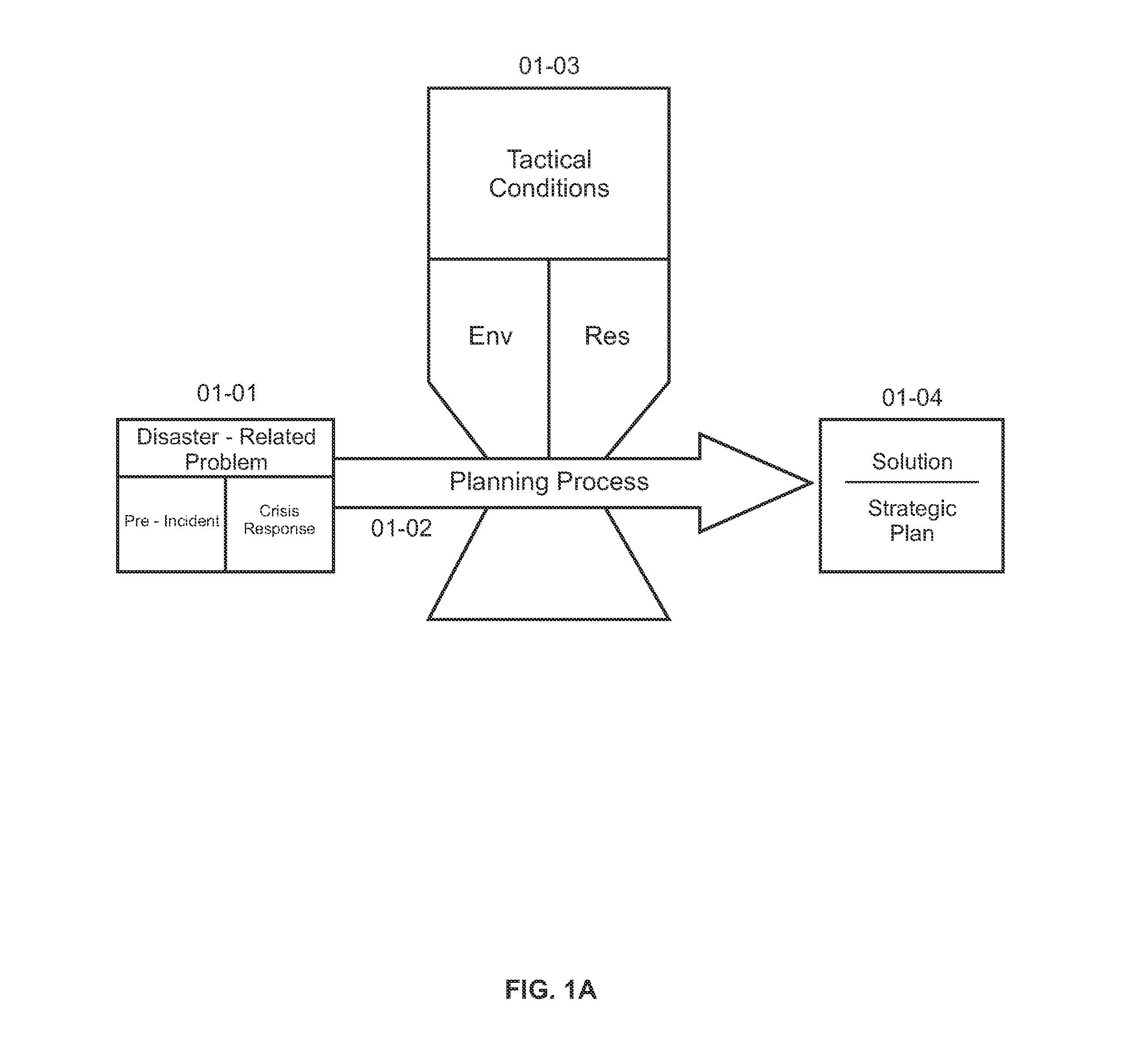
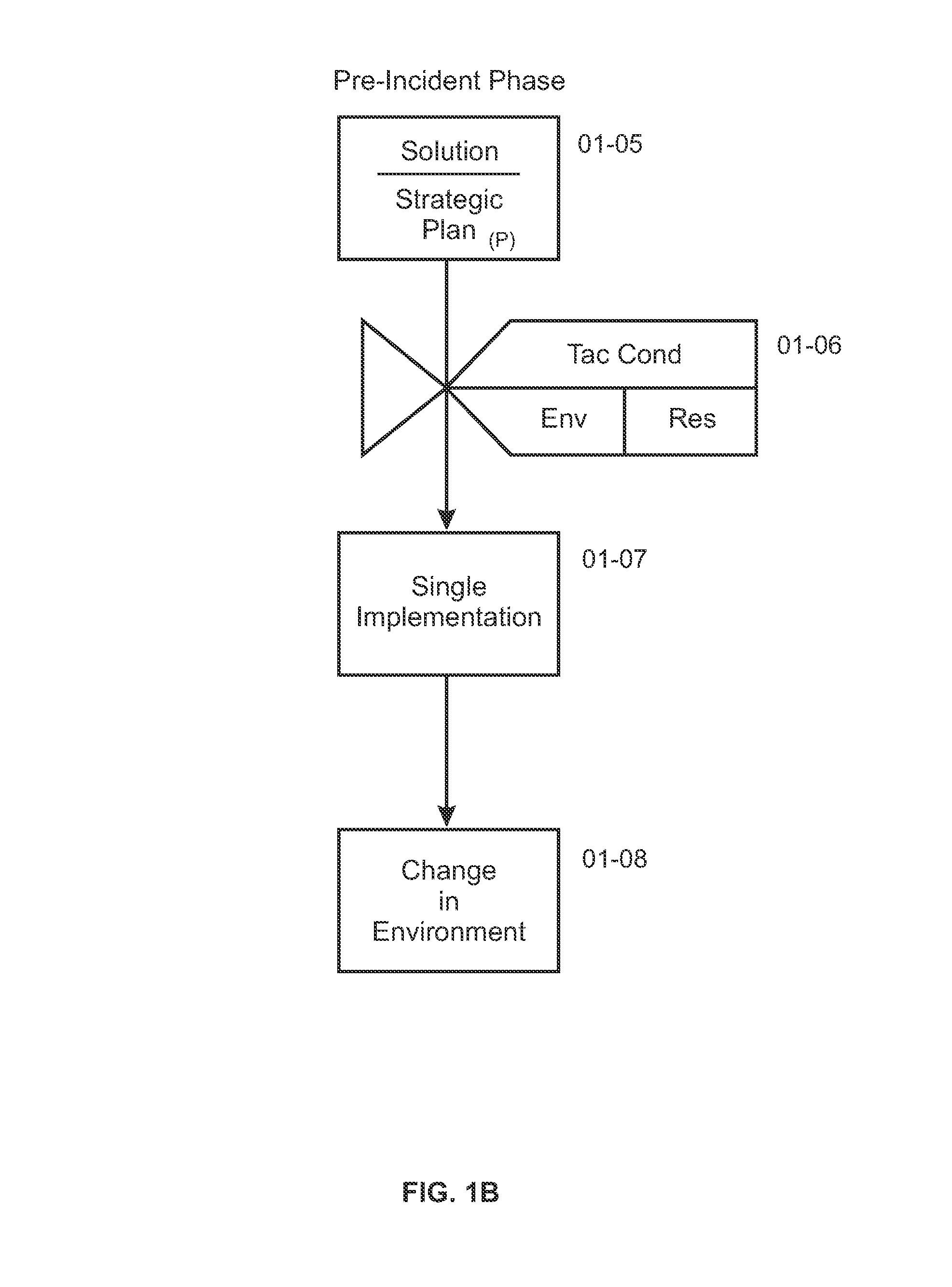
System for multi-phase management of a natural disaster incident
InactiveUS20120047187A1Digital data processing detailsGeographical information databasesNatural resourceNatural disaster
A computerized system for multi-phase management of a natural disaster incident is disclosed. In one embodiment of the invention, the computerized system incorporates a pre-incident risk reduction management module, a crisis response management module, and a restoration and rehabilitation management module to correspond to these three distinct phases of managing a natural disaster incident. This multi-phase natural disaster management system can be utilized by private entities, community groups, state, national, and / or international agencies to assist prevention or reduction of damage to human and natural resources in a particular disaster incident. Furthermore, the multi-phase natural disaster management system can assist or enable protection of lives, health, and safety of community members and disaster incident response personnel. A prioritization model in the pre-incident risk management module can take an empirical or subjective weighting factor in evaluating a particular geographic section to optimize disaster prevention and management.
Owner:DAUS STEVEN J
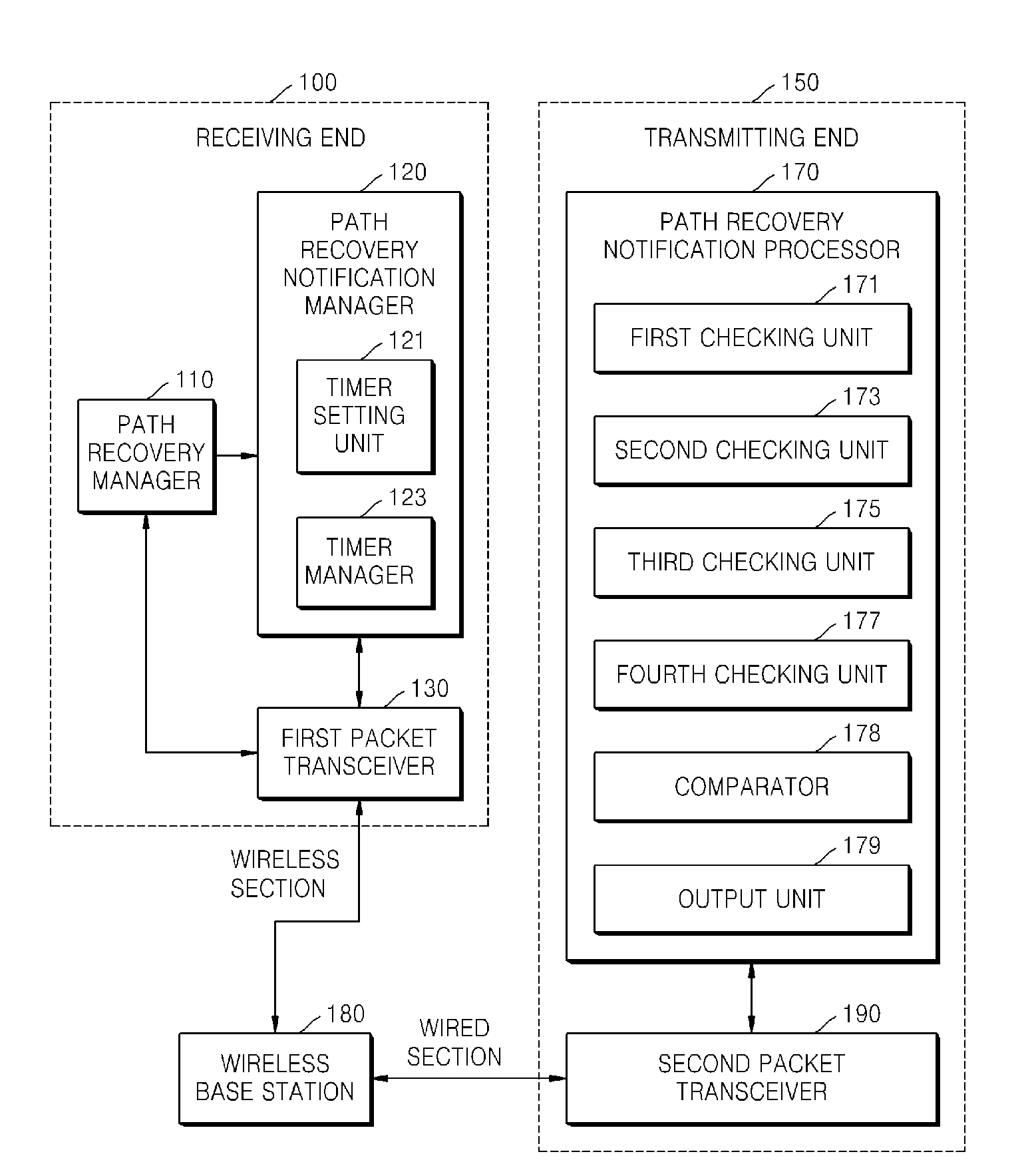
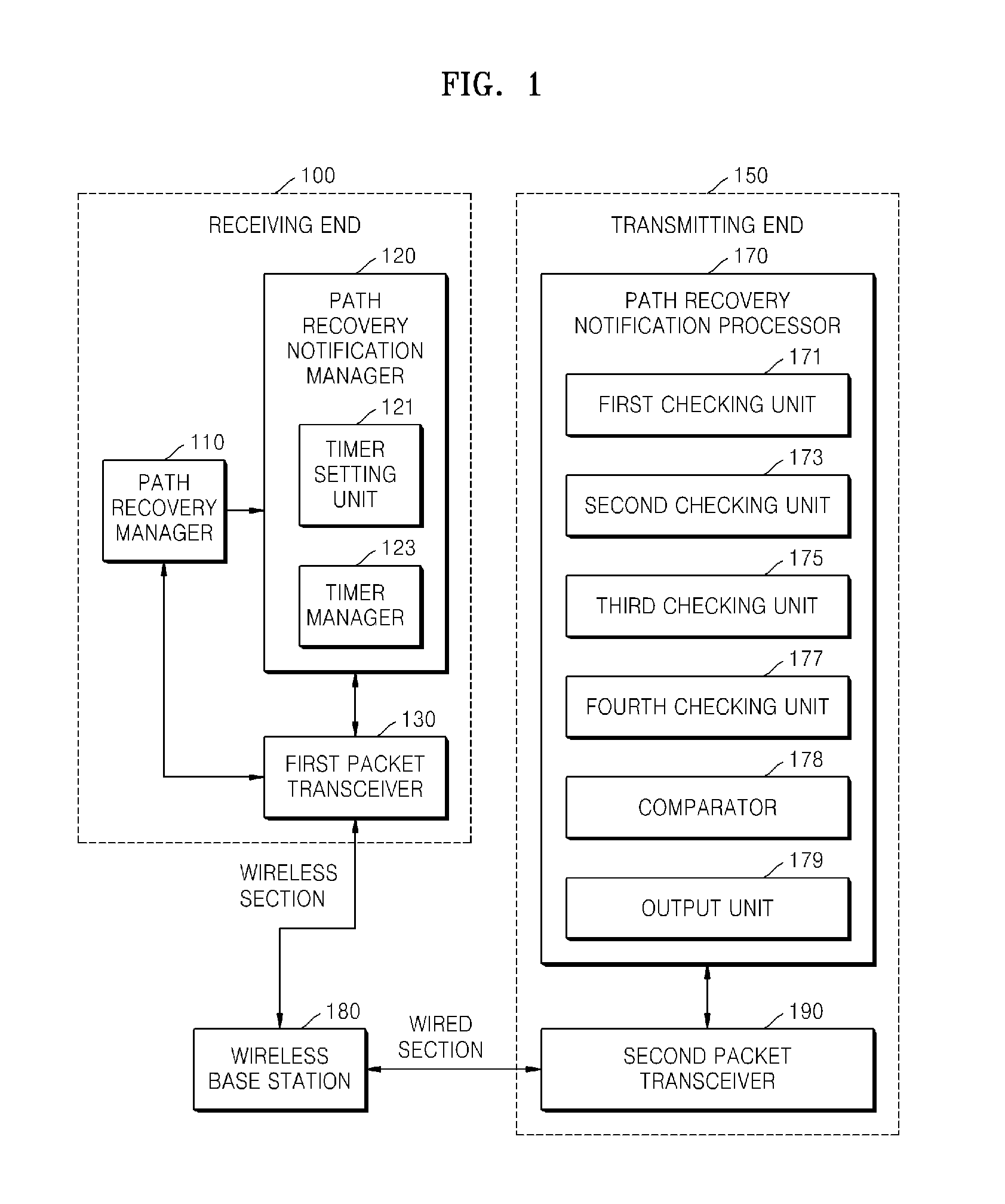
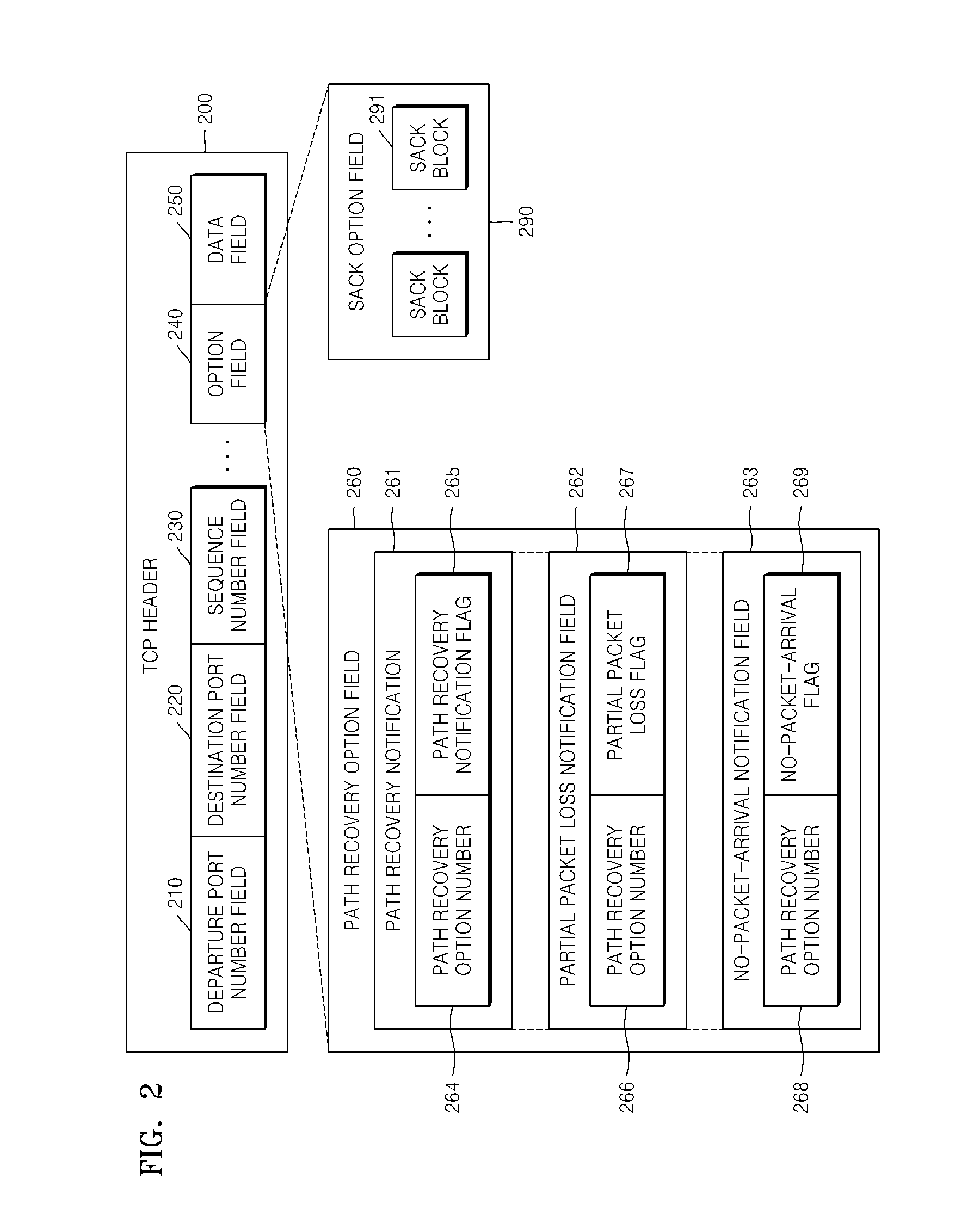
Apparatus and method for improving transport control protocol performance using path recovery notification over wireless network
InactiveUS20100014419A1Improving transport control protocol (TCP) performanceImproving TCP performanceError preventionFrequency-division multiplex detailsTransport control protocolTransceiver
Provided are an apparatus and method for improving transmission control protocol (TCP) performance using path recovery notification over a wireless network. The apparatus includes: a path recovery manager which detects a mobile host recovered from a temporary disconnection state and then outputs a detection signal to notify the detection result; a path recovery notification manager which receives the detection signal and generates an ACK (acknowledgement) packet to inform a transmitting end that the mobile host is recovered; and a first packet transceiver which transmits / receives the generated ACK packet and a data packet. Accordingly, a temporary disconnection state of a wireless network is explicitly informed to a transmitting end so as to transmit only lost packets without performing unnecessary congestion control, thereby improving TCP performance.
Owner:ELECTRONICS & TELECOMM RES INST
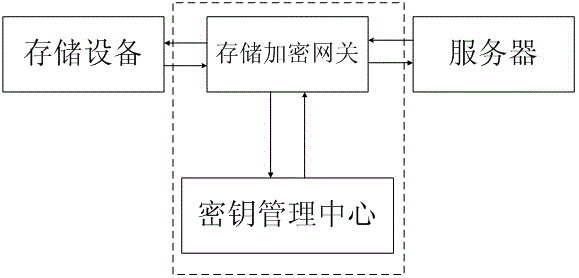
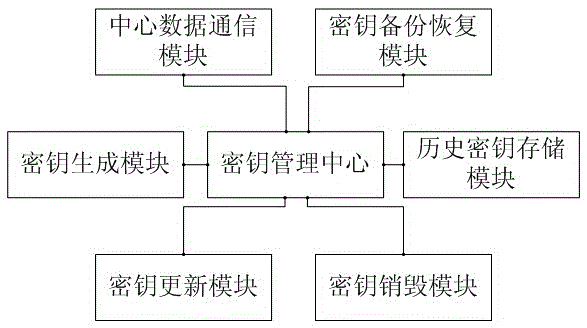
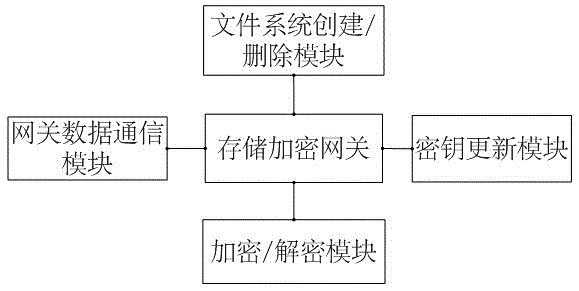
Storage encryption gateway key management system and method
ActiveCN105681031AGuaranteed recoverabilityPrevent undecryptedKey distribution for secure communicationManagement systemKey management
The invention discloses a storage encryption gateway key management system and method, and relates to the technical field of network securities. The system comprises a key management center and a storage encryption gateway; the key management center is used for managing a whole life cycle of keys in a whole system, including generation, allocation, updating, destruction and recovery management of the keys; and the storage encryption gateway is used for encrypting and decrypting data, and connecting data communication between a front-end server and a storage device. Aiming at the disadvantages in the current storage encryption gateway management system that the life cycle management of the keys is incomplete and encrypted data are easily cracked and the security is low and so on, the invention provides an improved system and method, which can effectively enhance the function and security of the storage encryption gateway management system.
Owner:成都卫士通信息产业股份有限公司
Beverage enterprise production and marketing integrated management system
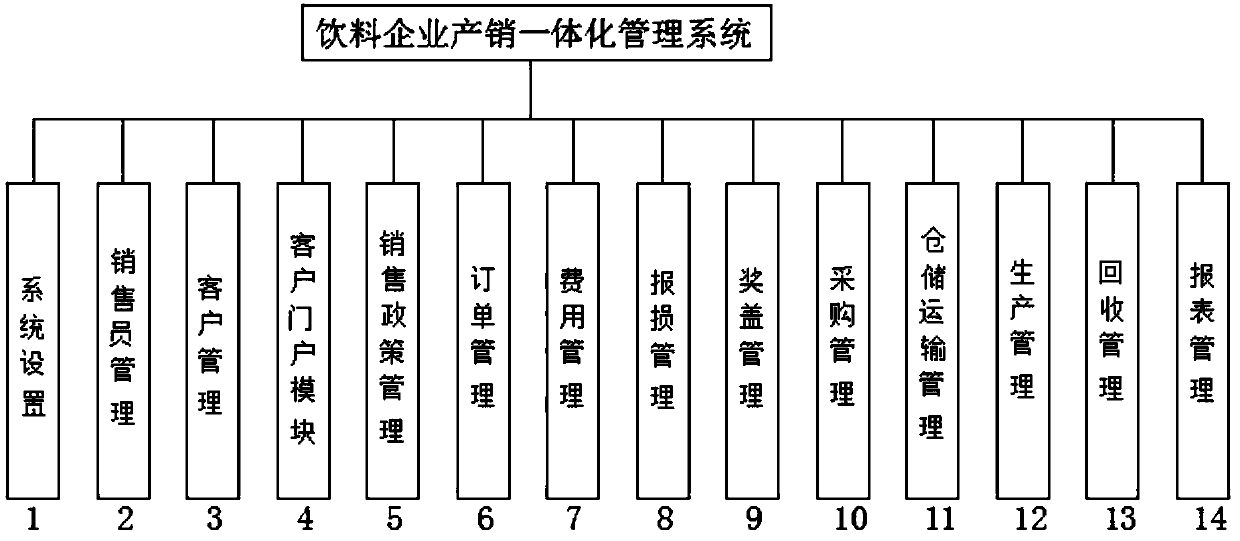
InactiveCN107748962AAddress flexibilityRealize integrated managementResourcesPurchasing managementEngineering
The invention discloses a beverage enterprise production and marketing integrated management system comprising a system setting module, a salesman management module, a customer management module, a customer portal module, a sales policy management module, an order management module, an expense management module, a loss report management module, an award cover management module, a purchasing management module, a warehousing and transportation management module, a production management module, a recovery management module and a report management module. Integrated management of commodities, customers, orders, sales polices, expenses, loss report, purchasing, warehousing, transportation, production and daily work can be realized so that various information including the commodity stock, the order delivery state and the daily purchase-sale-stock report can be conveniently inquired, different personnel have different operation authority in the system, order creating and other inputting workcan be performed, order checking and other checking work can also be performed and inputting and checking are separated and thus cooperative work is facilitated, the data preciseness can be guaranteed and the work efficiency and quality can be enhanced.
Owner:杭州立越网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com