Patents
Literature
35results about How to "Guaranteed data communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
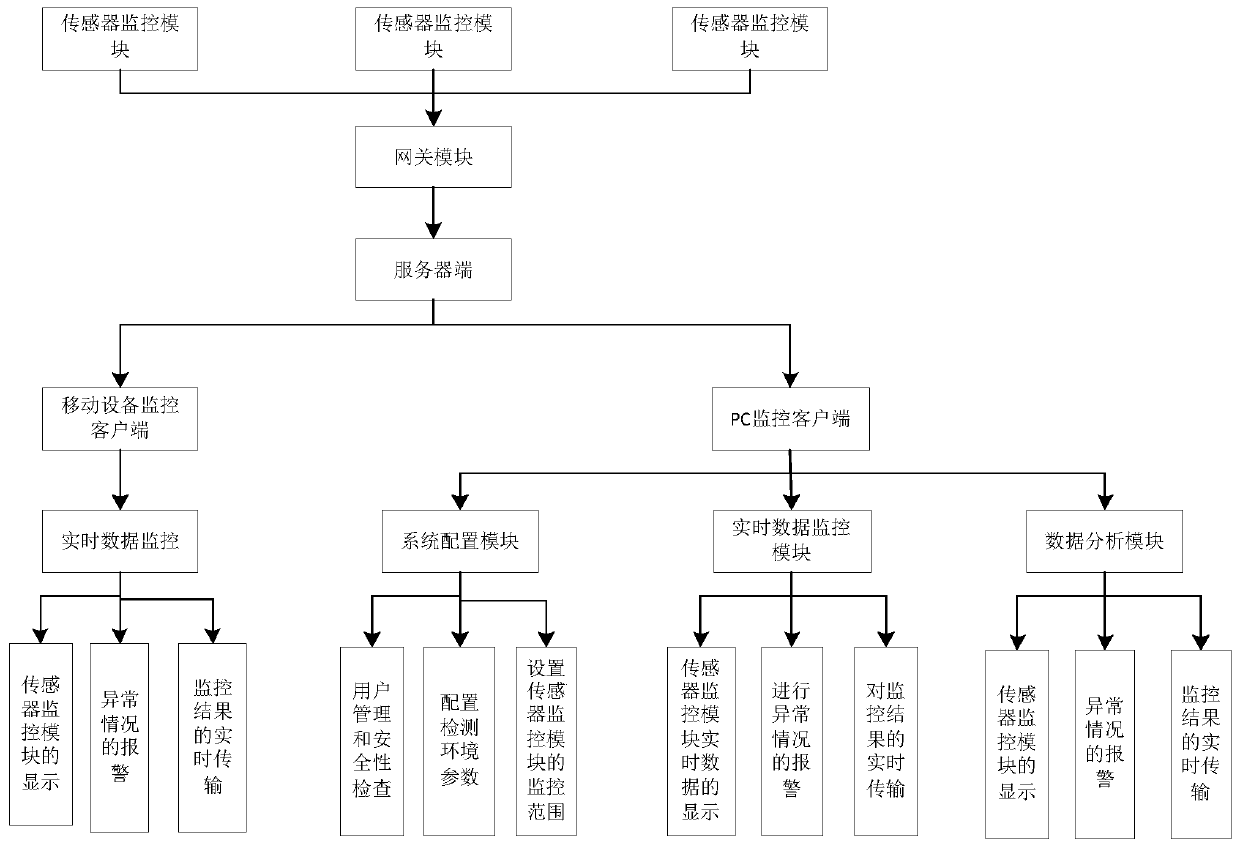
Multi-sensor intelligent monitoring system based on Internet of things
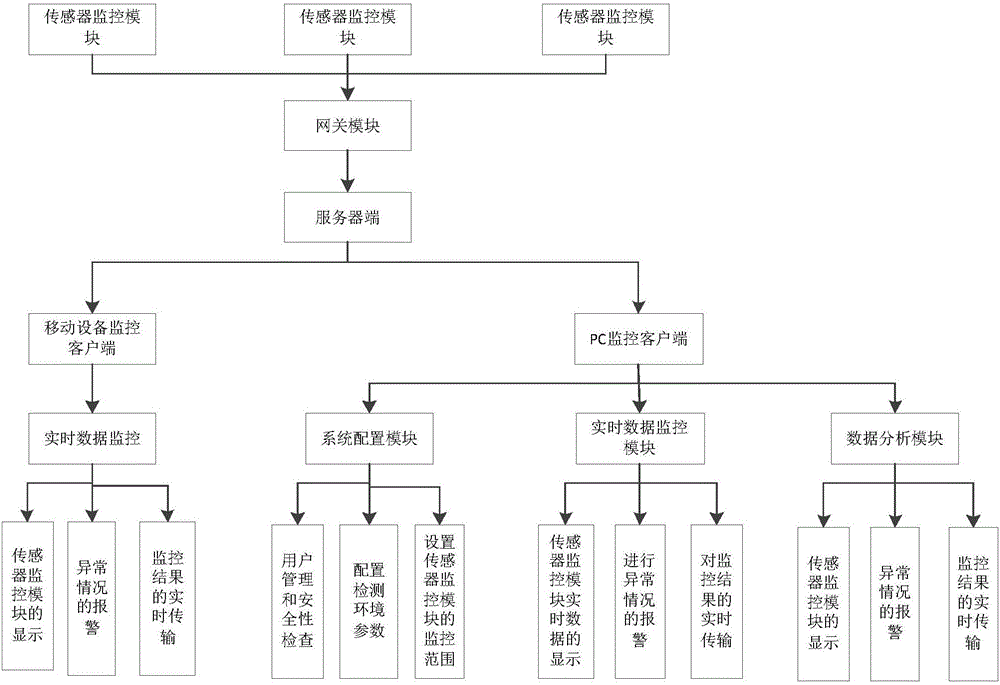
ActiveCN106572189AEasy to install and deployShorten networking timeMeasurement devicesNetwork topologiesTime conditionReal-time data
The invention provides a multi-sensor intelligent monitoring system based on the Internet of things, which comprises a monitoring client, a server and a plurality of sensor monitoring modules, and is characterized in that the sensor monitoring modules and the monitoring client are connected with the server; the monitoring client comprises a mobile equipment monitoring client and a PC monitoring client, and the mobile equipment monitoring client is used for performing real-time data monitoring; and the PC monitoring client comprises a system login module, a real-time data monitoring module and a data analysis module. The multi-sensor intelligent monitoring system further comprises a gateway module, and the sensor monitoring modules are connected with the server through the gateway module. According to the invention, real-time monitoring is performed on target equipment by means of various sensor modules, data is transmitted to the server, and real-time conditions of a monitoring target can be seen by a user visually on an interface of the monitoring client after the data is analyzed and processed, and the multi-sensor intelligent monitoring system is convenient, efficient, more intelligent and low in cost.
Owner:GUANGZHOU UNIVERSITY
Network storage device
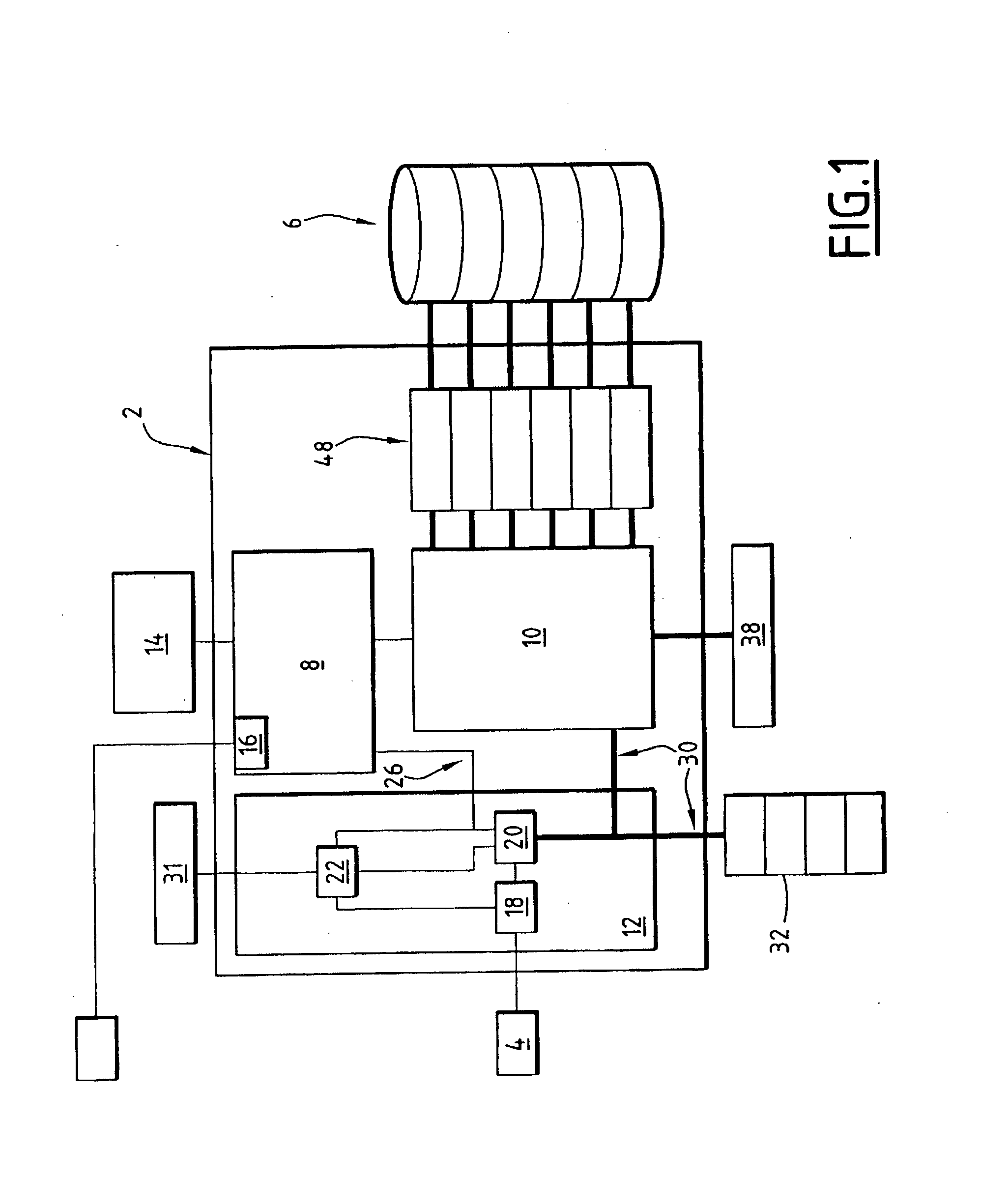
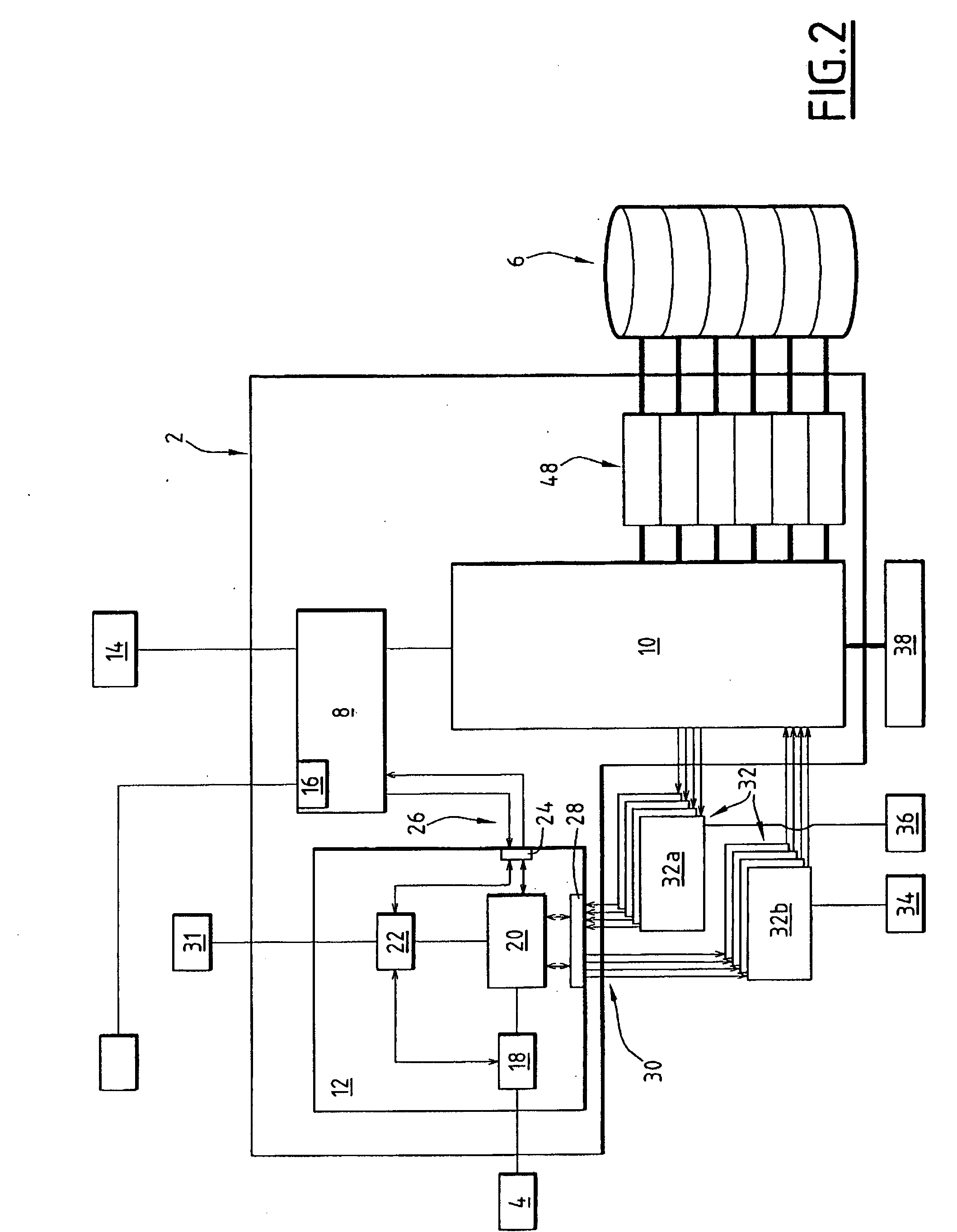
InactiveUS20080010647A1Efficient data processingGuaranteed data communicationTransmissionInput/output processes for data processingControl dataData interface
The invention concerns a network storage device for communicating data between a network and a storage unit. The network storage device comprises an embedded system processor adapted to manage the storage space of the storage unit, an network interface component and a storage unit management processor adapted to organise storage data communication and to communicate storage data. The network storage device is characterised in that the network interface component comprises a hardware processor implemented in dedicated hardware for dedicated hardware processing of data. The network interface component additionally comprises a control data interface and a storage data interface and the storage data interface and the control data interface are completely separated from one another.
Owner:THOMSON LICENSING SA
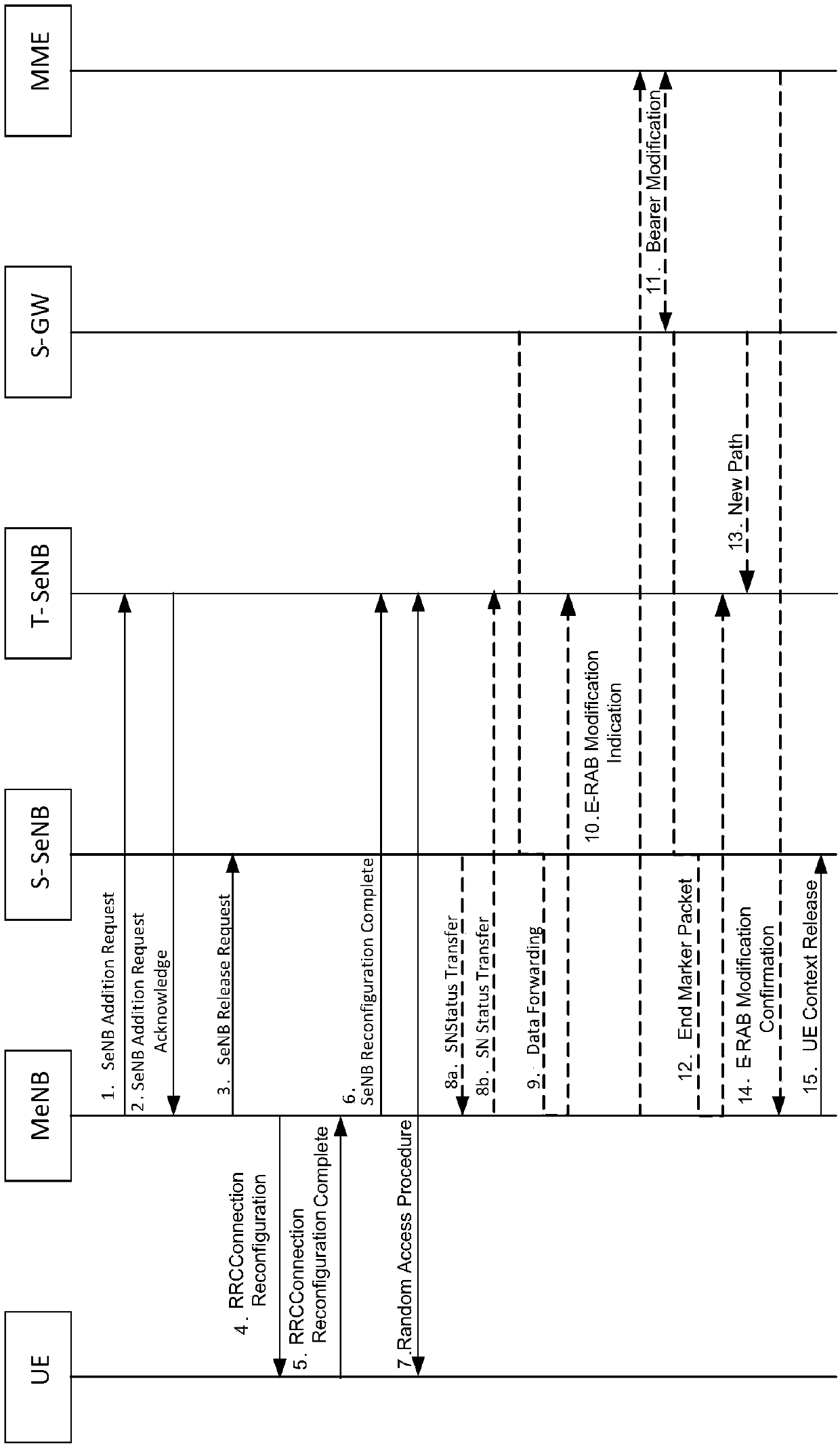
Secondary eNB (SeNB) changing method and device
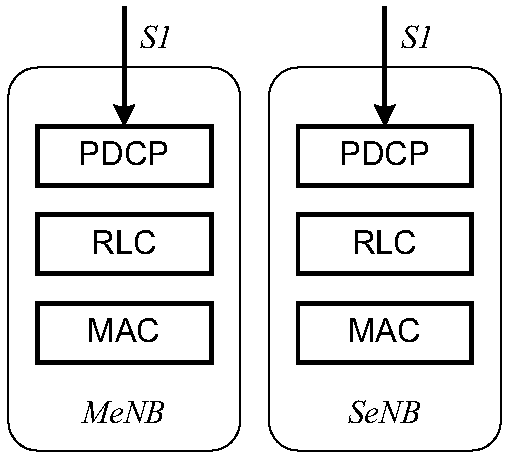
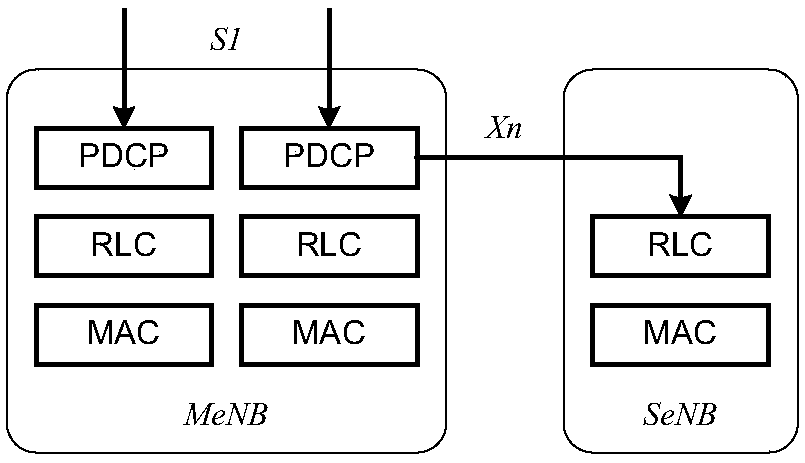
ActiveCN107708104AReduce downtimeGuaranteed data communicationNetwork topologiesConnection managementUser equipmentFronthaul
The invention provides a secondary eNB (SeNB) changing method and device. The SeNB changing method comprises the following steps: informing a target SeNB, a source SeNB and user equipment (UE) that the UE keeps a connection with the source SeNB in an SeNB changing process; receiving an indication message from the target SeNB, wherein the indication message is used for indicating that the UE accesses the target SeNB successfully; and instructing the source SeNB to release the connection with the UE according to the indication message. Through adoption of the method and the device, the problem that data forwarding and releasing of the SeNB cannot be triggered effectively since change of the SeNB under DC (Dual Connectivity) is not supported in the prior art is solved, and the effects of keeping data communication and shortening data interrupt time in an SeNB changing process of the UE are achieved.
Owner:ZTE CORP
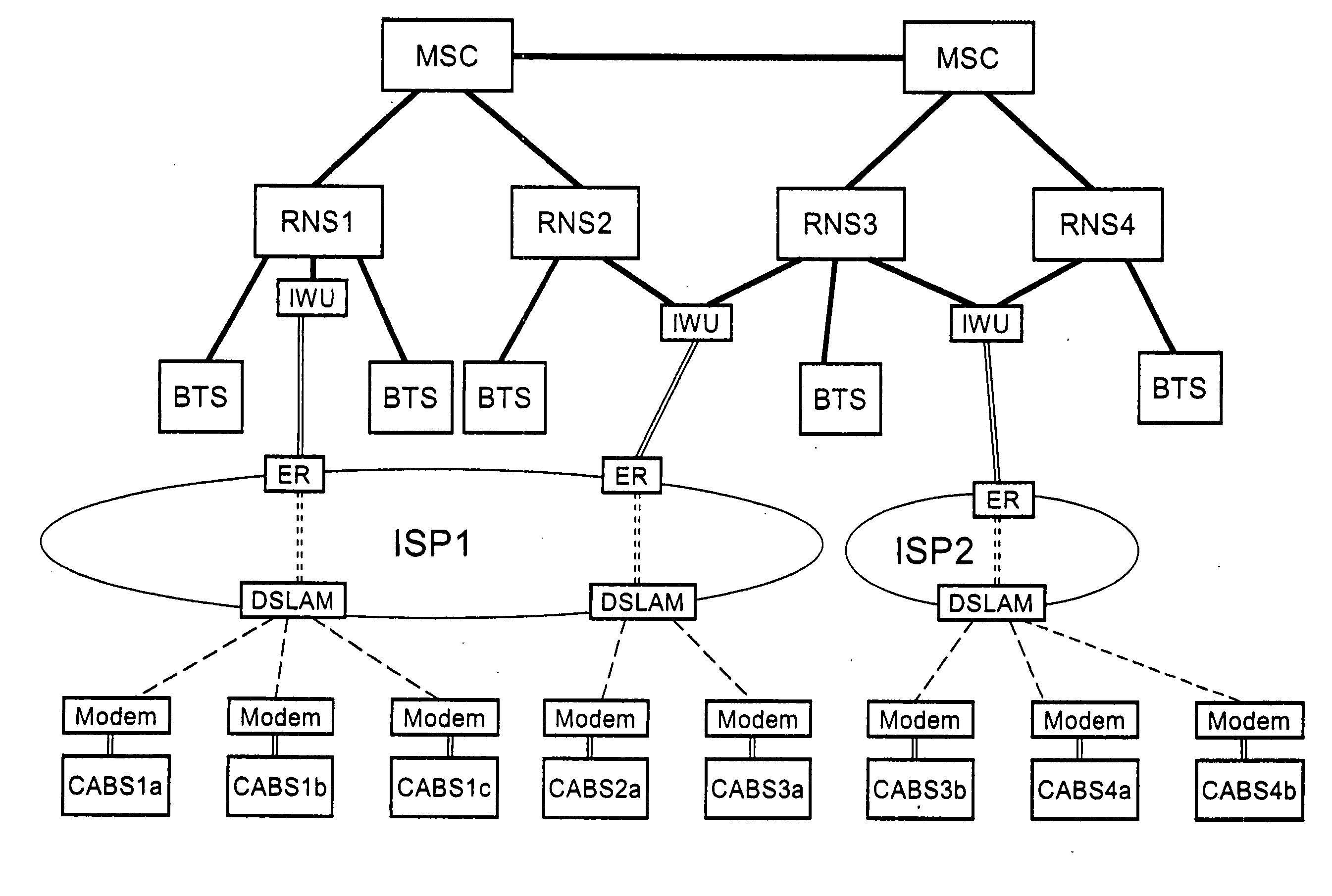
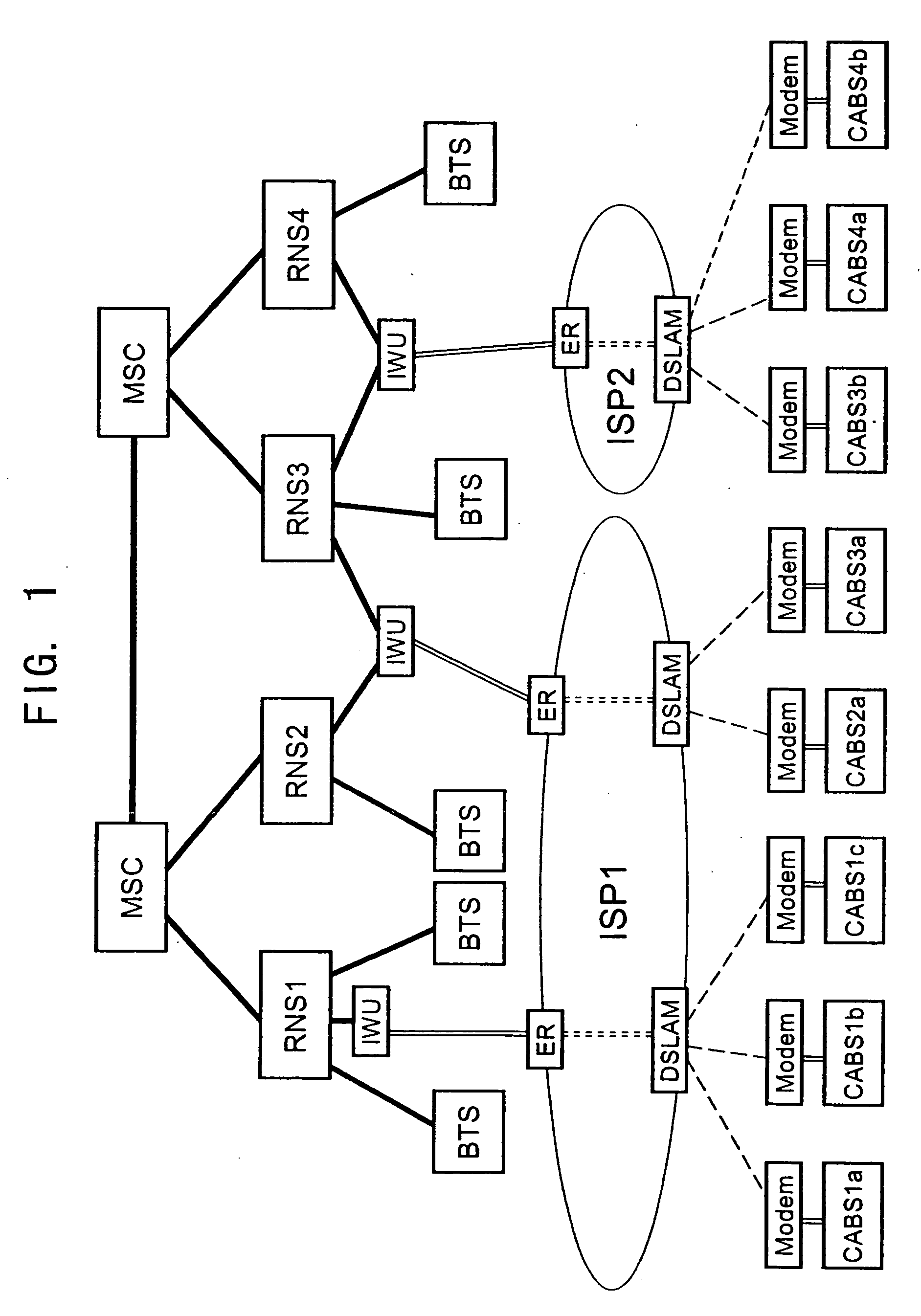
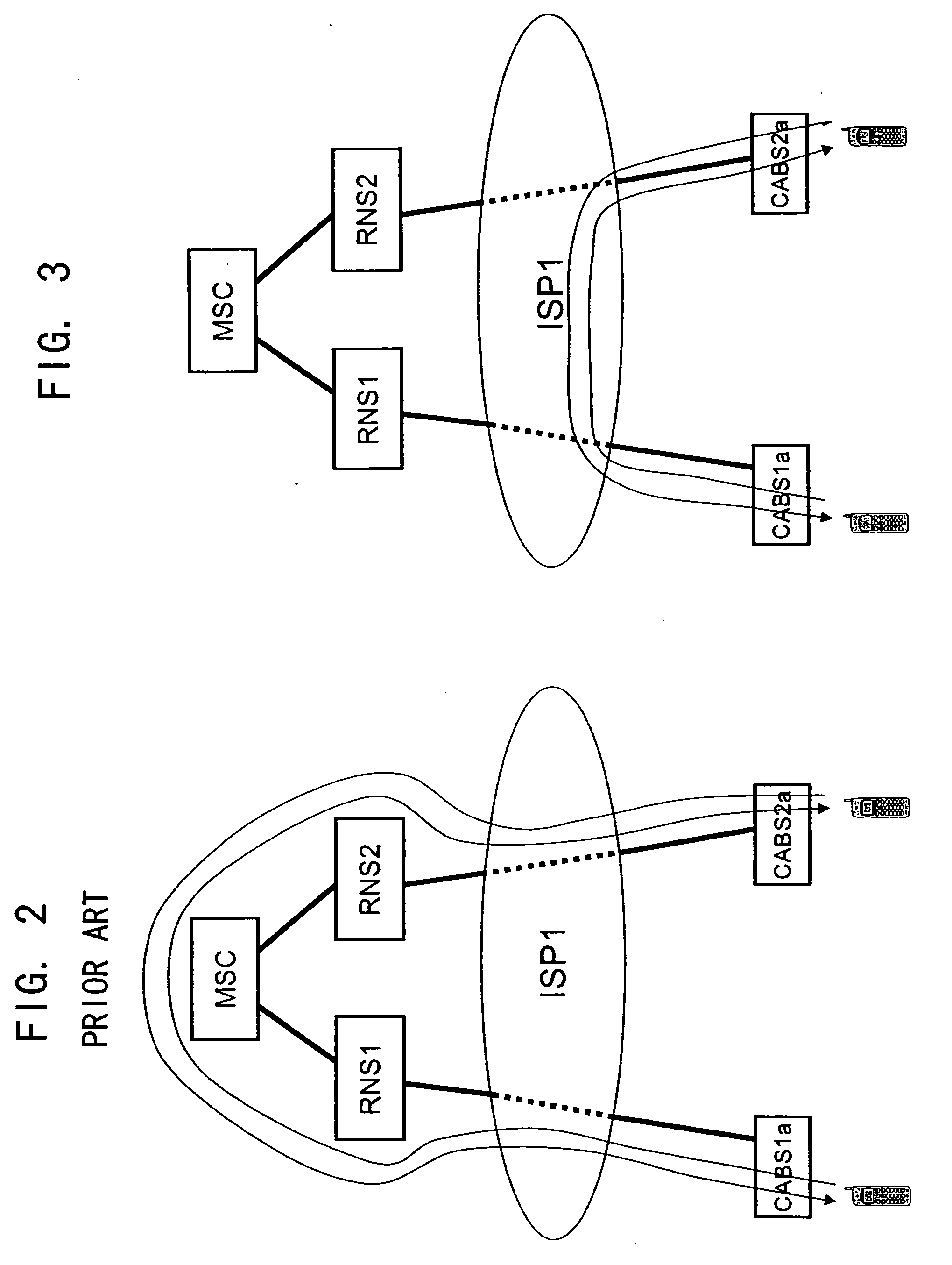
System for establishing data transmission path between mobile phone terminals
InactiveUS20060084470A1Efficient use ofReduce traffic problemsCurling-ironsCurling-tongsNetworked systemMobile phone operator
In a network system including base stations accommodated in a mobile phone network through an IP network, when a mobile phone terminal as a calling terminal makes a calling request and the calling request from the calling terminal is sent through a source base station to the mobile phone network and then from the mobile phone network through a destination base station to a mobile phone terminal as a called terminal, it is judged whether the source base station and the destination base station are both connected to the mobile phone network through the same IP network, and when the source base station and the destination base station are both connected to the mobile phone network through the same IP network, a data transmission path is established between the calling terminal and the called terminal that directly connects the source base station and the destination base station through the same IP network and without via the mobile phone network.
Owner:FUJITSU LTD
Professional meteorological service application platform based on power grid GIS
InactiveCN106844595AIntegrity guaranteedGuaranteed correctnessData processing applicationsIndication of weather conditions using multiple variablesElectric power systemModel selection
The invention relates to the field of meteorological application of electric power systems, in particular to a professional meteorological service application platform based on a power grid GIS. The platform includes a data acquisition and conversion module, a data storage module, a professional service adding module, a professional service module and a page display module; the ideas of modular design and object orientation are adopted, and according to the needs of business expansion, function modules can be flexibly added or modified without affecting original business, so that the system is good in function expansibility; when the current configuration of the system can not meet the function implementation need or the overall performance of the system is reduced, the expansibility can achieve smooth upgrading of the system by adjusting hardware configuration or increasing servers, so that the overall performance of the system is extended. The system can perform equipment model selection and flexible configuration according to the user quantity and the function implementation need and is scientific, rigorous and flexible.
Owner:SHANDONG LUNENG SOFTWARE TECH
Inter-site communication state detection method and device for power line communication network
InactiveCN106533501AReduce the burden onGuaranteed data communicationPower distribution line transmissionLine-transmission monitoring/testingElectric powerDistributed computing
The present invention provides an inter-site communication state detection method for a power line communication network. The method comprises the steps of sending a detection request message to an STA site from a CCO site at a pre-set time interval; on the condition that the CCO site does not receive a detection response message sent from the STA site within a preset period of time, judging that the communication between the CCO site and the STA site is in the abnormal state; sending a whole-network broadcast offline message to all STA sites within the power line communication network from the CCO site, and recovering TEI resources corresponding to STA sites in the communication abnormal state. The whole-network broadcast offline message contains the TEI information of each STA site, and is used for indicating all STA sites within the power line communication network to delete the routing information corresponding to the TEI information. In this way, the communication between STA sites in the communication abnormal state and other sites in the power line communication network is cut off. The invention also provides an inter-site communication state detection device for the power line communication network.
Owner:SANECHIPS TECH CO LTD
System for establishing data transmission path between mobile phone terminals
InactiveUS7751376B2Efficient use ofReduce traffic problemsCurling-ironsCurling-tongsNetworked systemMobile phone operator
In a network system including base stations accommodated in a mobile phone network through an IP network, when a mobile phone terminal as a calling terminal makes a calling request and the calling request from the calling terminal is sent through a source base station to the mobile phone network and then from the mobile phone network through a destination base station to a mobile phone terminal as a called terminal, it is judged whether the source base station and the destination base station are both connected to the mobile phone network through the same IP network, and when the source base station and the destination base station are both connected to the mobile phone network through the same IP network, a data transmission path is established between the calling terminal and the called terminal that directly connects the source base station and the destination base station through the same IP network and without via the mobile phone network.
Owner:FUJITSU LTD
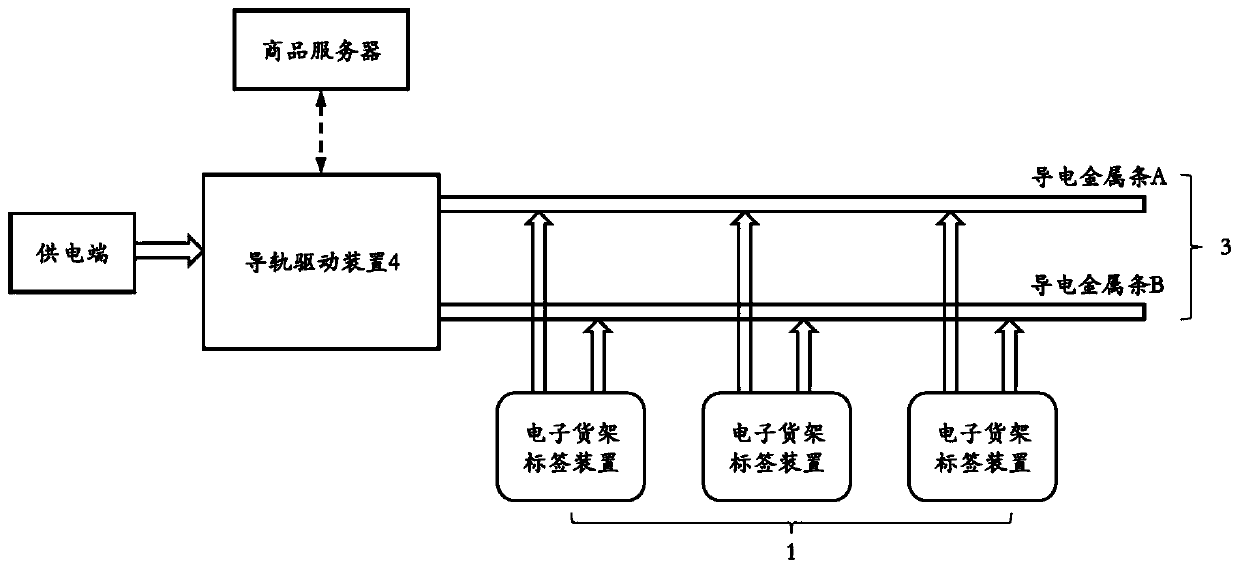
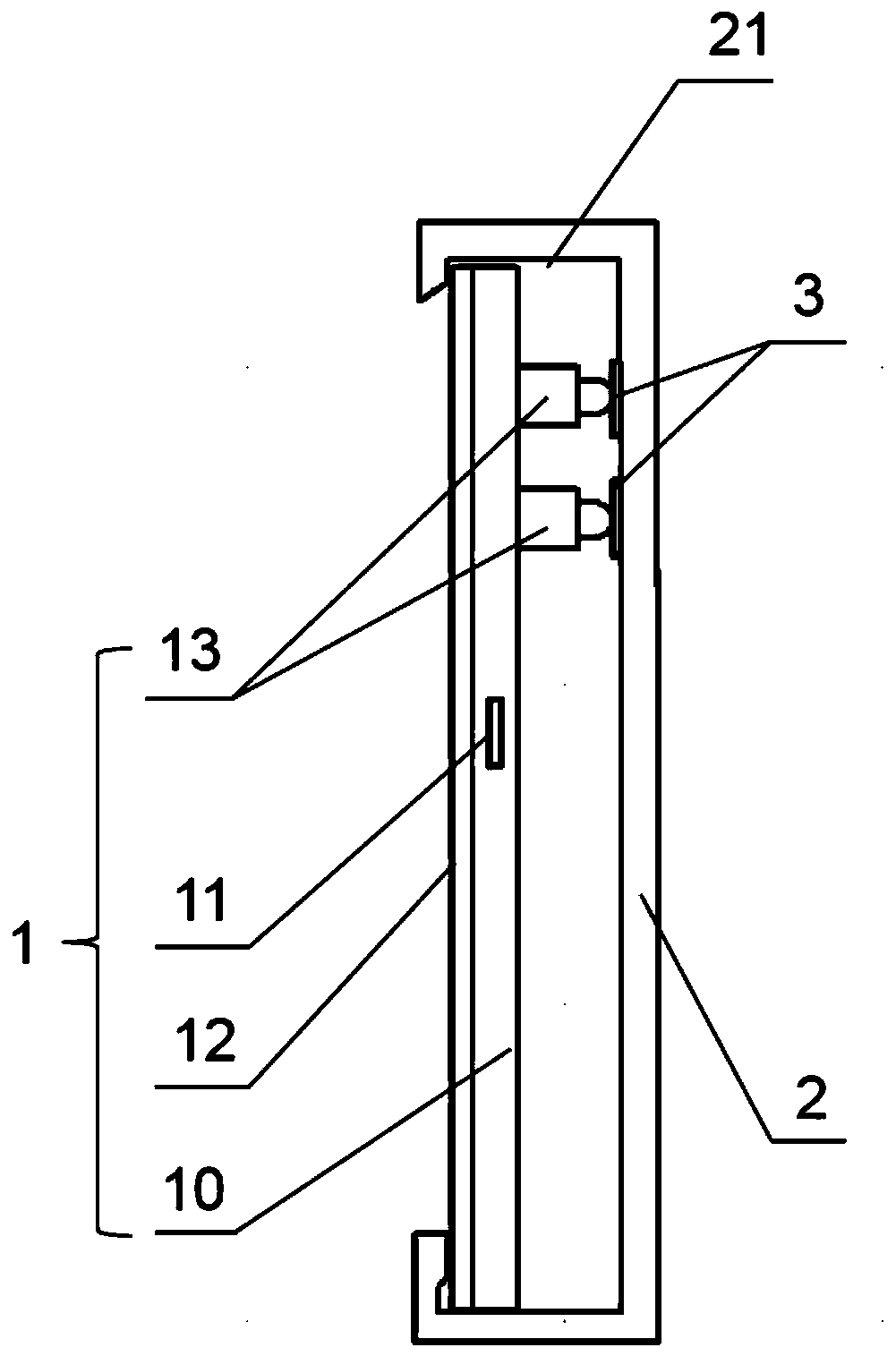
Electronic shelf label system
PendingCN110379297ARealize two-way data communicationImprove satisfactionCo-operative working arrangementsDuplex signal operationElectricityMetal strips
The invention relates to an electronic shelf label system. The system comprises a power supply side, a commodity server, a guide rail arranged on the shelf and multiple electronic shelf label devicesarranged on the guide rail in a sliding manner; two conductive metal strips are paved on the guide rail along the length direction of the guide rail; a guide rail driving device is arranged at one endof the guide rail; one end of each of conductive metal strips is electrically connected with the guide rail driving device; each electronic shelf label device is electrically connected with two conductive metal strips; and the guide rail driving device is electrically connected with the power supply side, and the guide rail driving device communicates and connects with a commodity server througha wireless network. The electronic shelf label system can realized one-to-multiple integrated power supply and one-to-multiple bidirectional data communication, effectively reduce the cost of the whole electronic shelf label system, and is suitable for generalization.
Owner:WUHAN INSTITUTE OF TECHNOLOGY +1
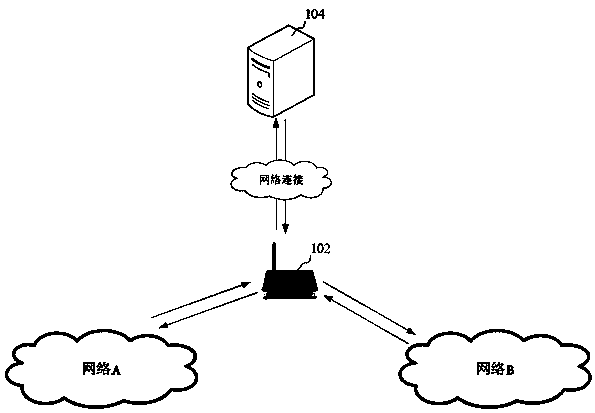
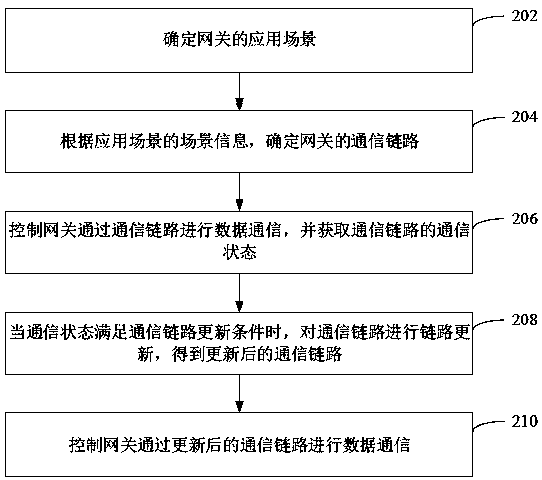
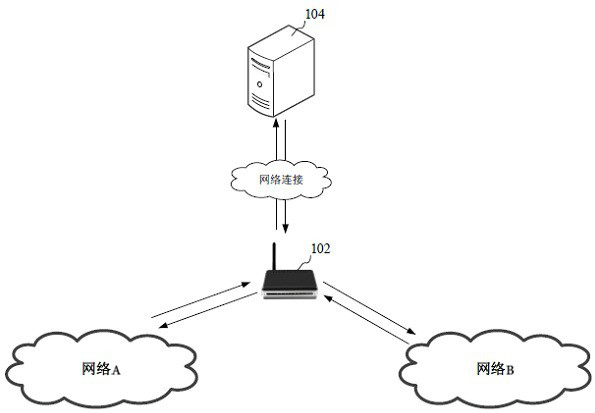
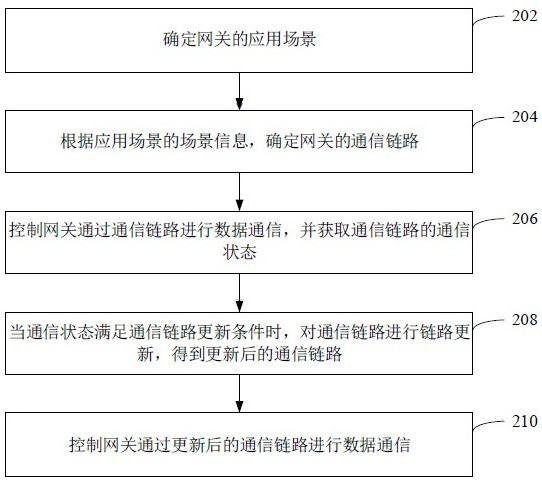
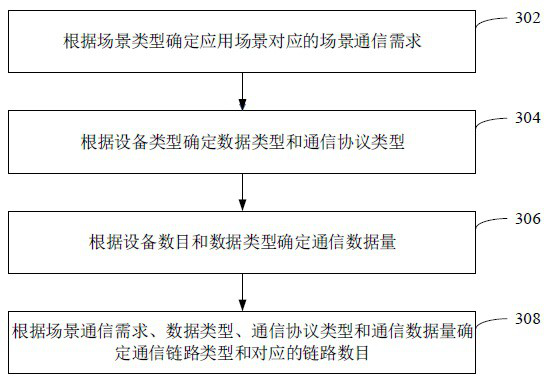
Industrial gateway control method and device, computer equipment and storage medium
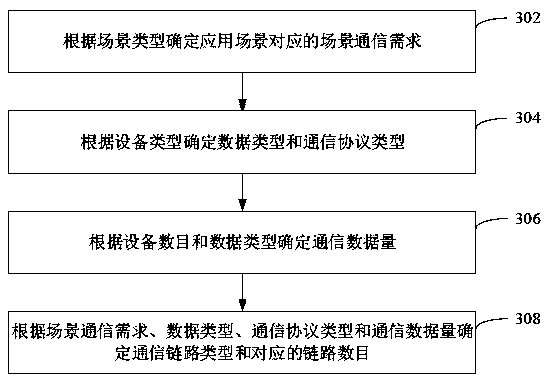
ActiveCN111541579AGuaranteed uptimeGuaranteed data communicationNetwork connectionsTelecommunications linkEngineering
The invention relates to an industrial gateway control method and device, computer equipment and a storage medium. The method comprises the following steps: determining an application scene of a gateway; determining a communication link of the gateway according to the scene information of the application scene; instructing the gateway to perform data communication through the communication link and acquire the communication state of the communication link; when the communication state meets a communication link updating condition, performing link updating on the communication link to obtain anupdated communication link; and instructing the gateway to perform data communication through the updated communication link. By adopting the method, the gateway stability can be improved, and the data communication efficiency is ensured.
Owner:深圳市乙辰科技股份有限公司
Data processing method and system, device testing system and node testing system
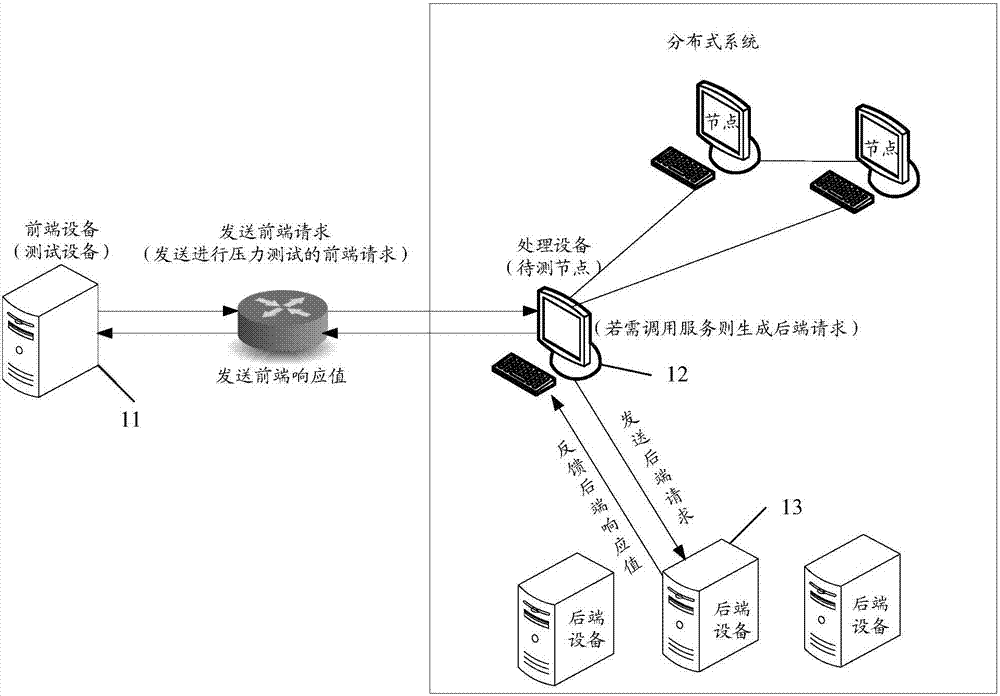
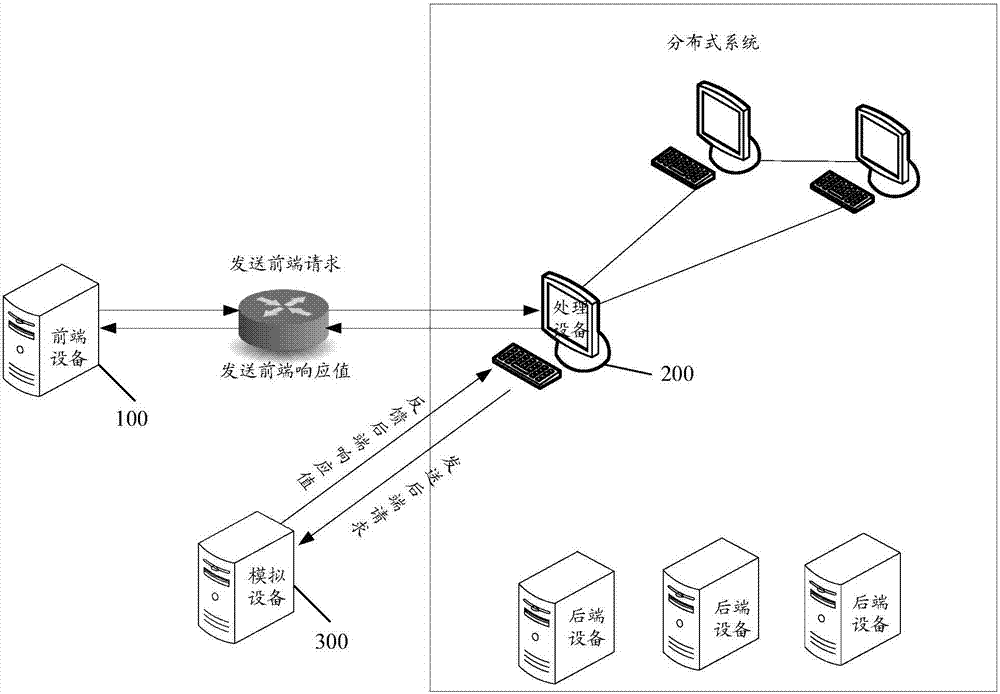
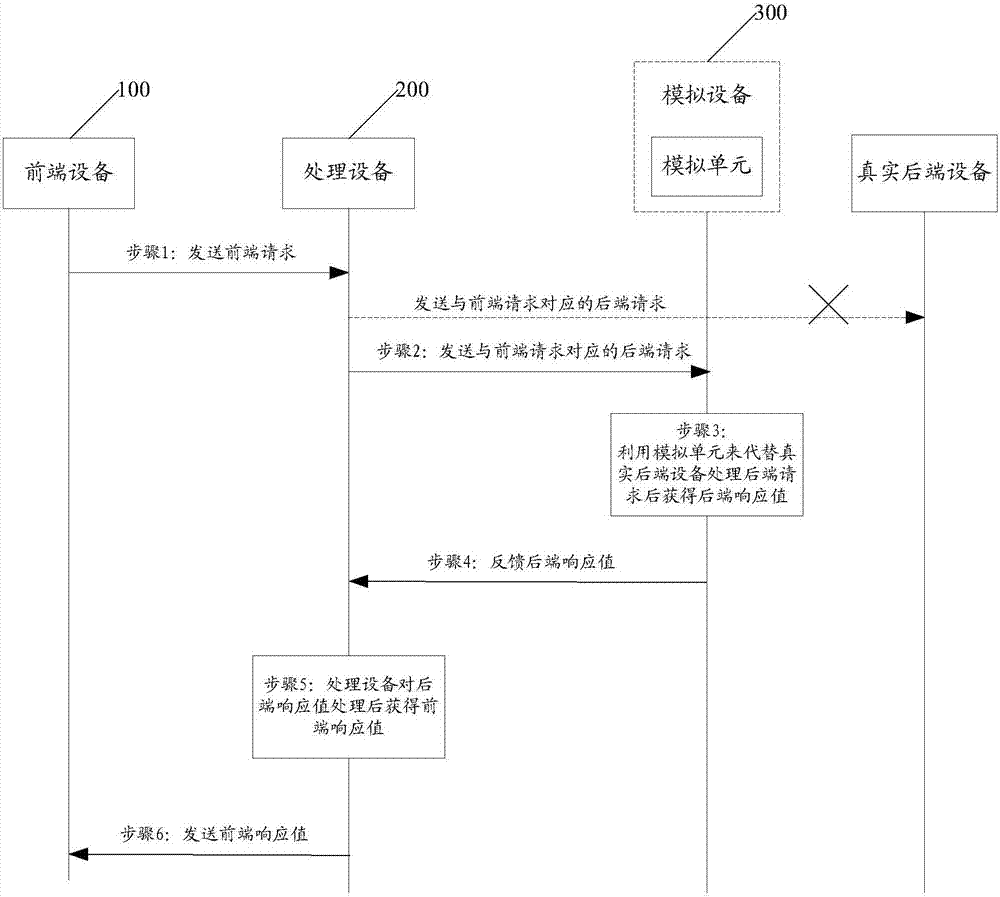
InactiveCN107517139ARealize data interactionGuaranteed data communicationData switching networksTraffic volumeEmbedded system
The invention provides a data processing method and system, a device testing system and a node testing system. The data processing system comprises a front-end device and a processing device, wherein the front-end device is used for sending a front-end request to the processing device, and is further used for receiving a back-end request that is sent by the processing device and is corresponding to the front-end request, replacing a real back-end device by using an analog unit constructed in advance to process the back-end request and to obtain a back-end response value, and sending the back-end response value to the processing device; and the processing device is used for receiving the front-end request, and under a condition in which a service provided by the real back-end device needs to be invoked in the process of determining to process the front-end request, redirecting the back-end request corresponding to the front-end request to the front-end device by using a traffic hijack service set in advance, and is further used for receiving the back-end response value, and feeding a front-end response value obtained after the back-end response value is processed back to the front-end device. According to the data processing method and system, the device testing system and the node testing system, the data interaction between the front-end device and the processing device can be implemented on the premise of not affecting the real back-end device.
Owner:ALIBABA GRP HLDG LTD
Communication interface for network security protection and communication method
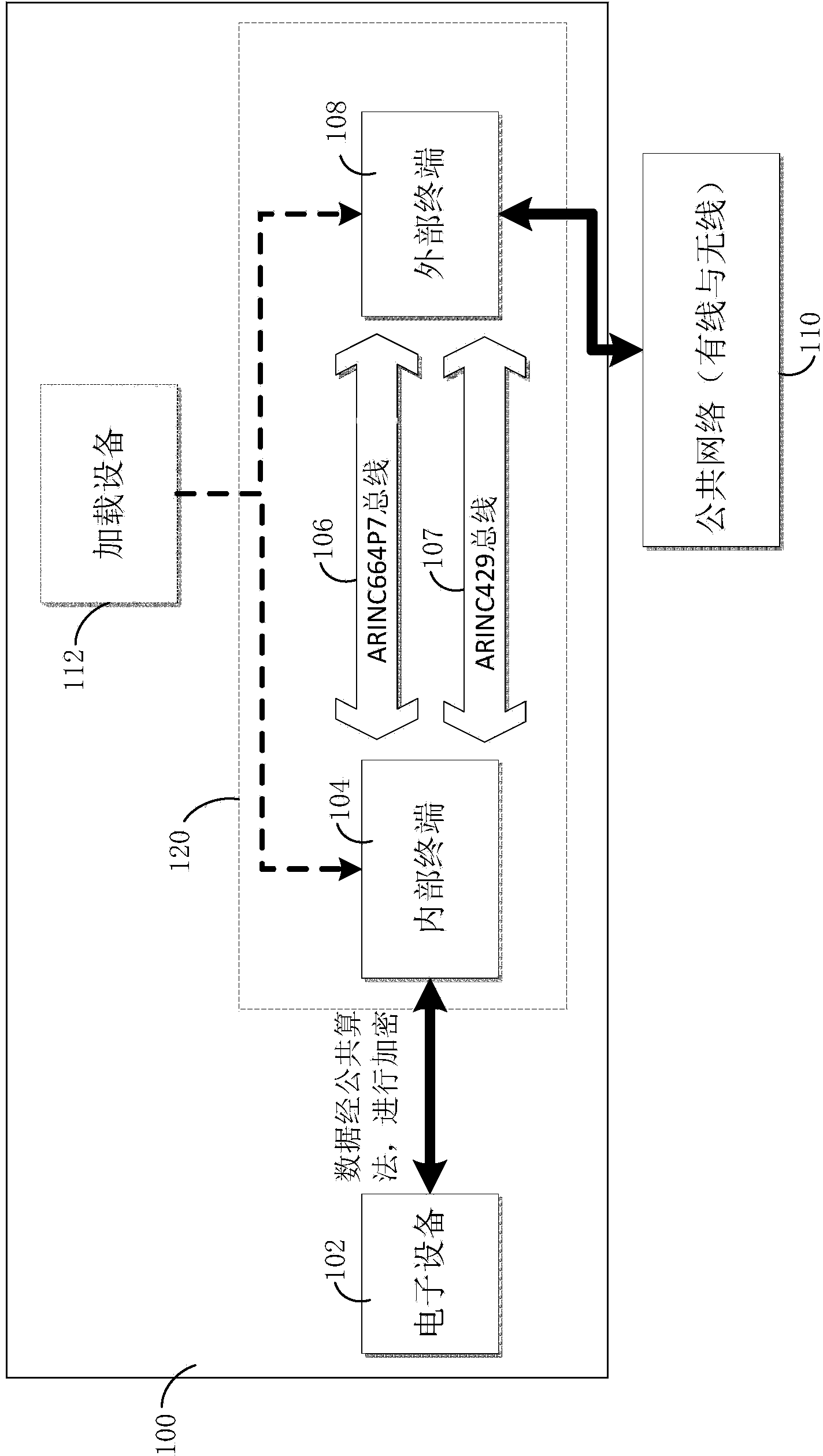
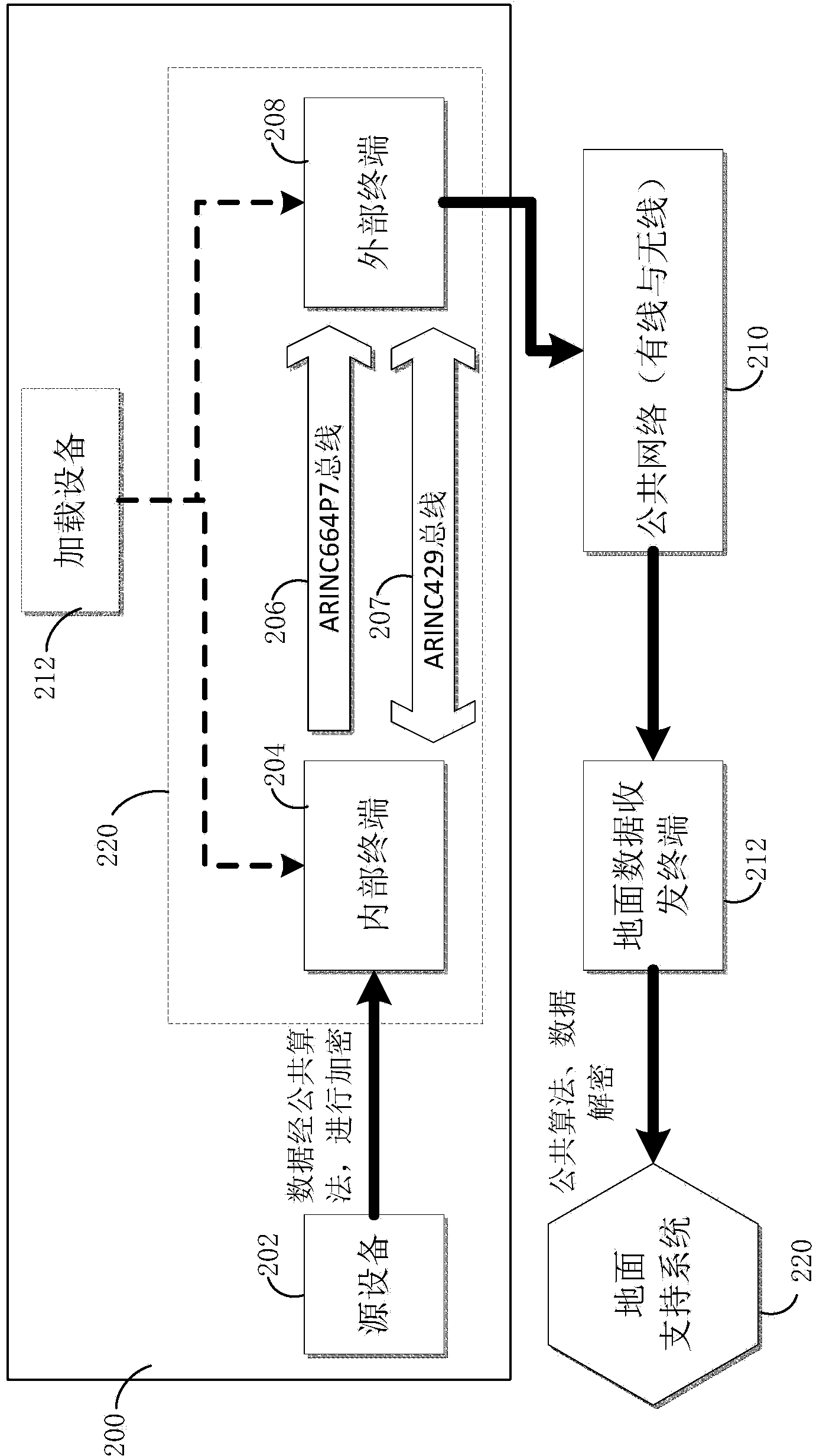
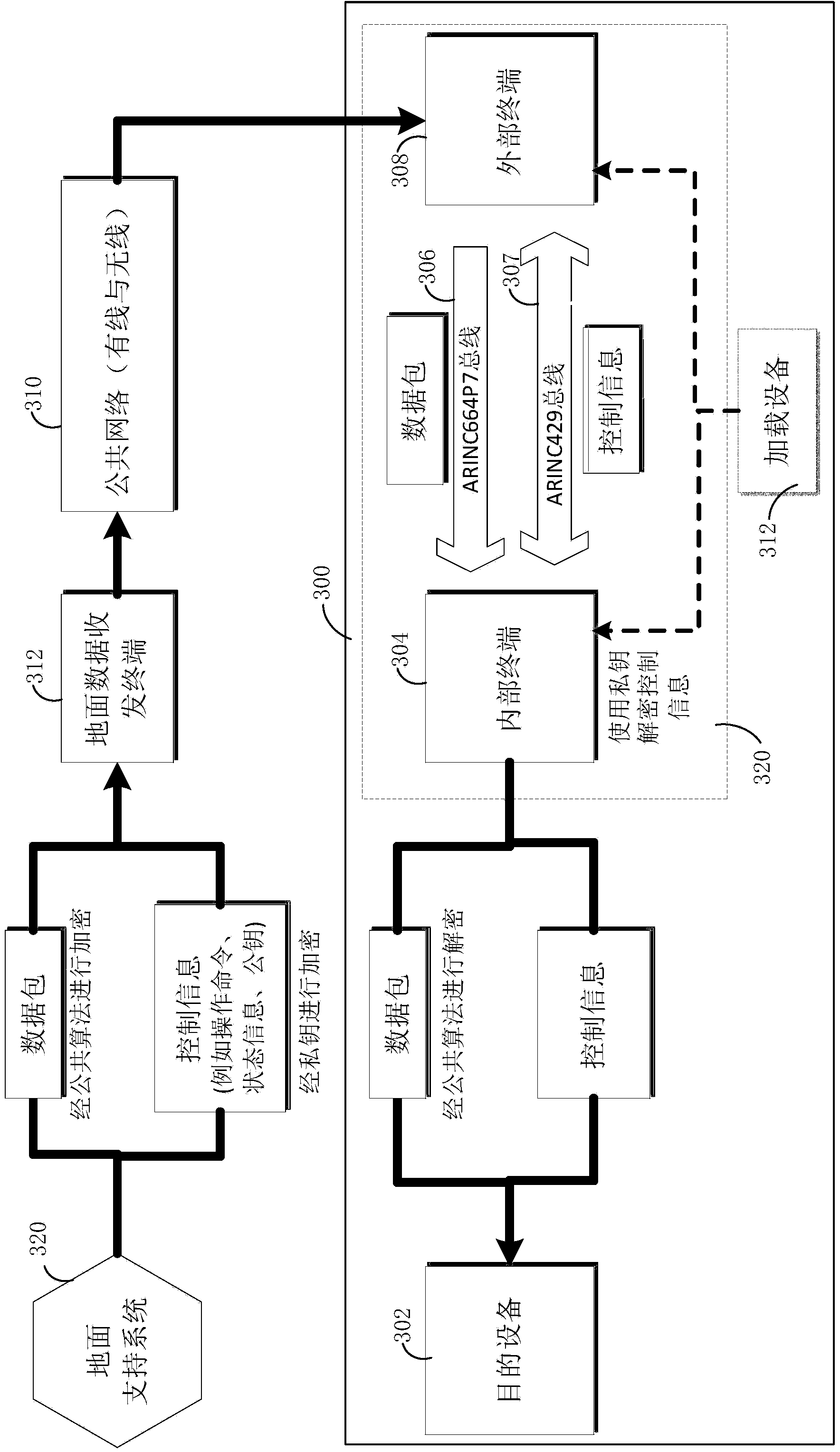
ActiveCN103986736AEffective isolationGuaranteed data communicationTransmissionCommunication interfaceComputer terminal
The invention discloses a communication interface for network security protection and a communication method. The communication interface is used for connecting electronic equipment to a network and comprises an internal terminal connected to the electronic equipment, an external terminal connected to the network in a wired or wireless manner, an ARINC664P7 bus which is connected with the internal terminal and the external terminal to transmit data, and an ARINC429 bus which is connected with the internal terminal and the external terminal to transmit control information related to the data.
Owner:COMAC +1
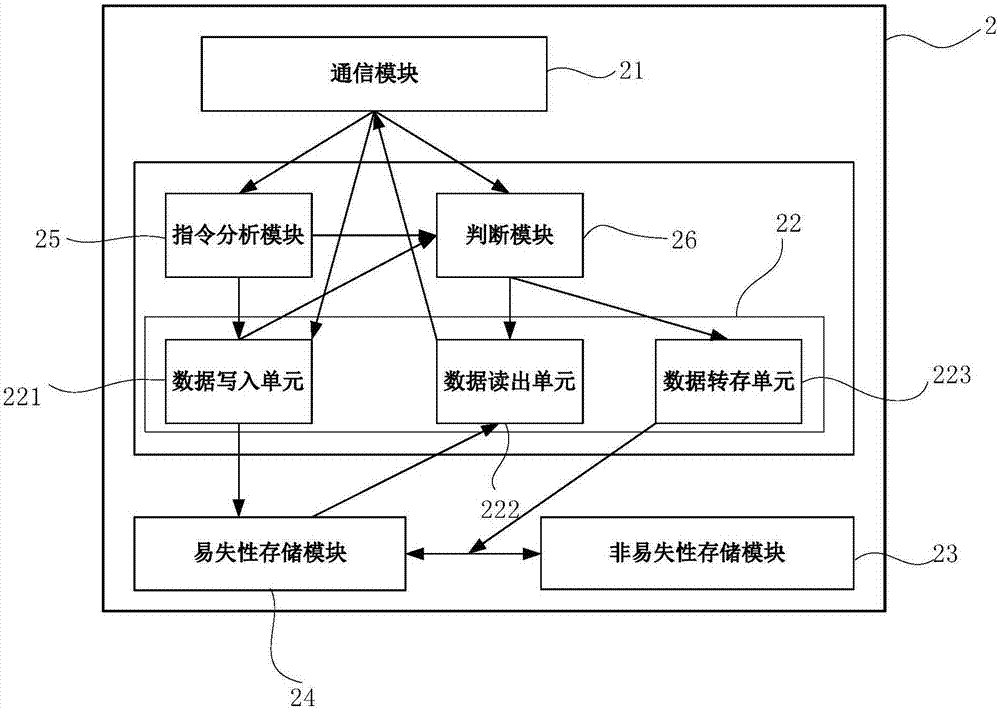
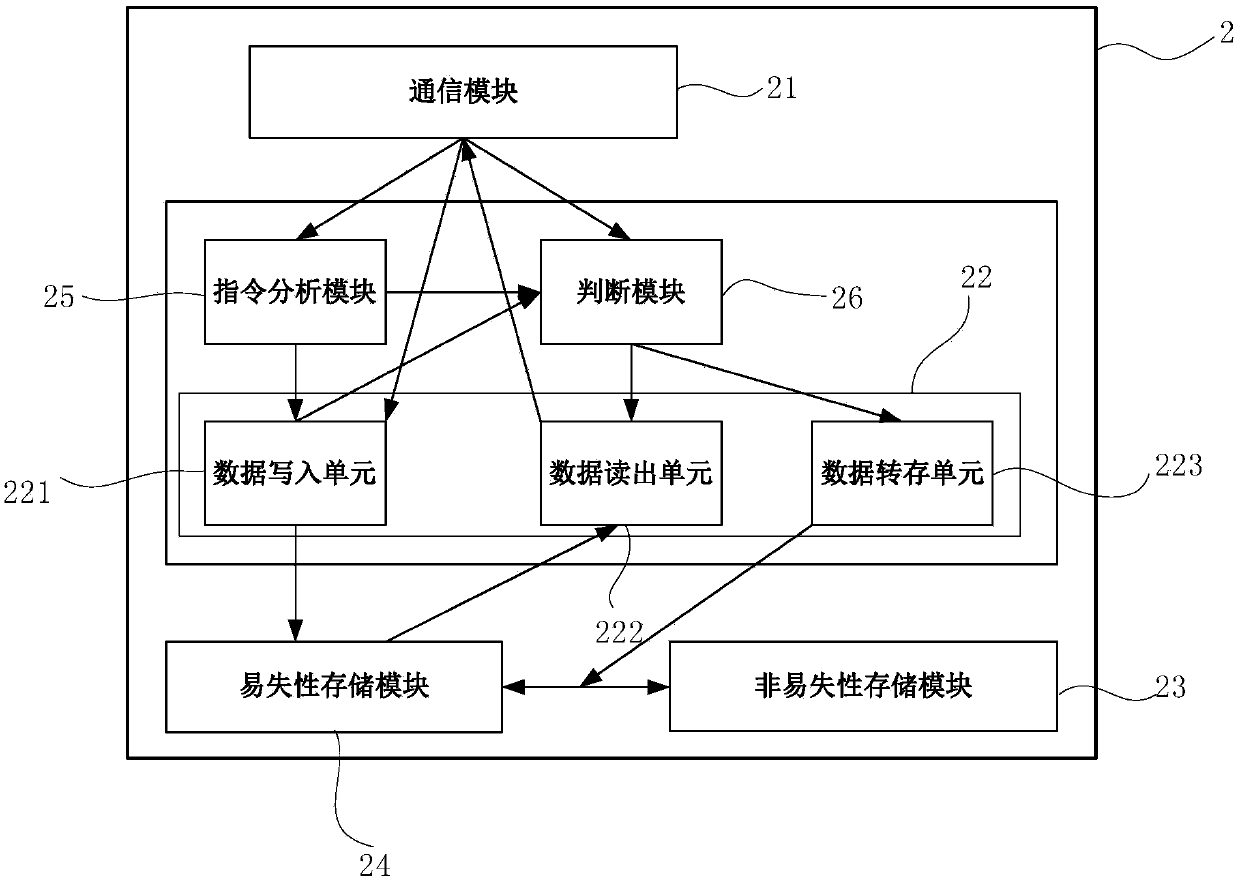
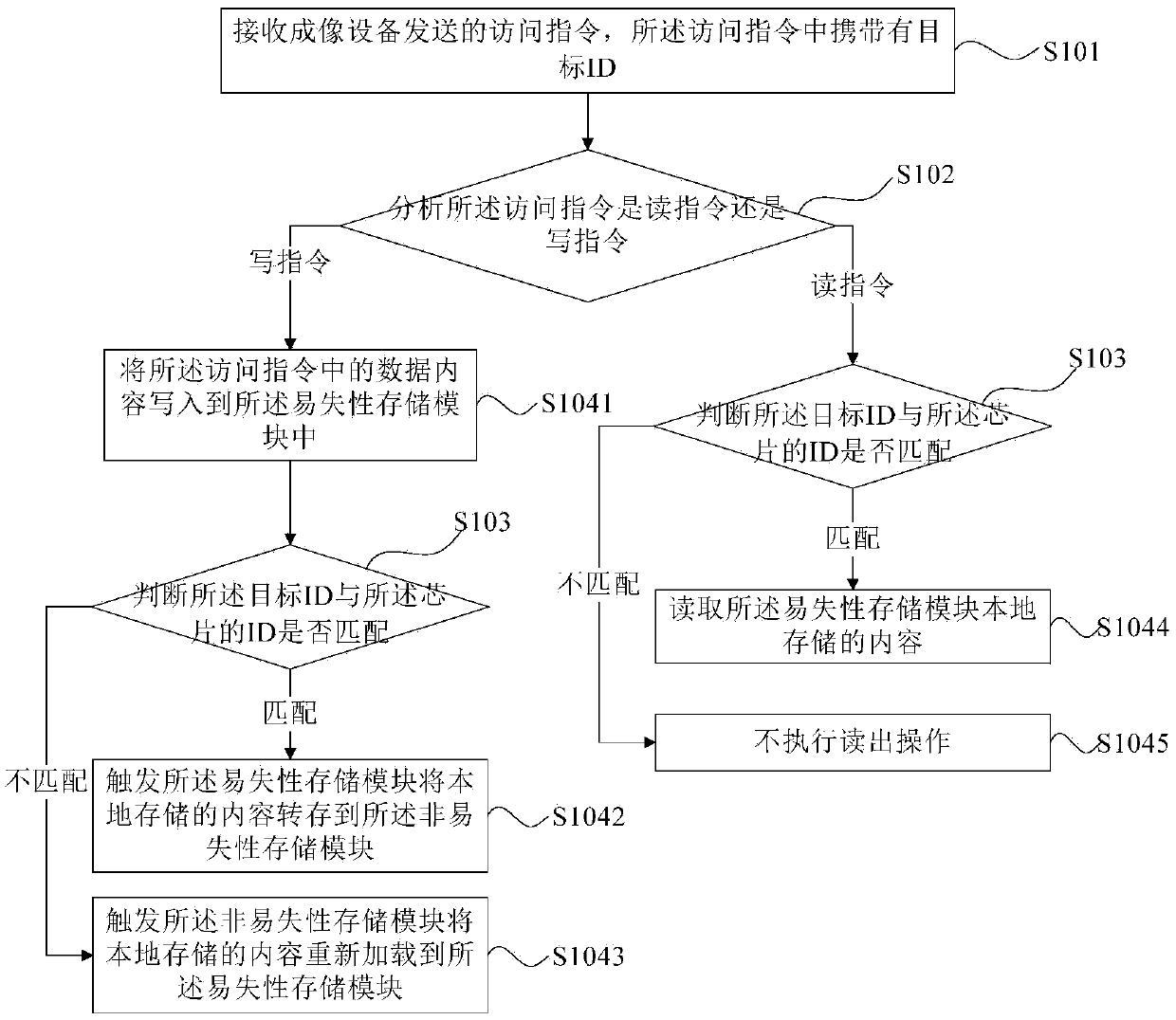
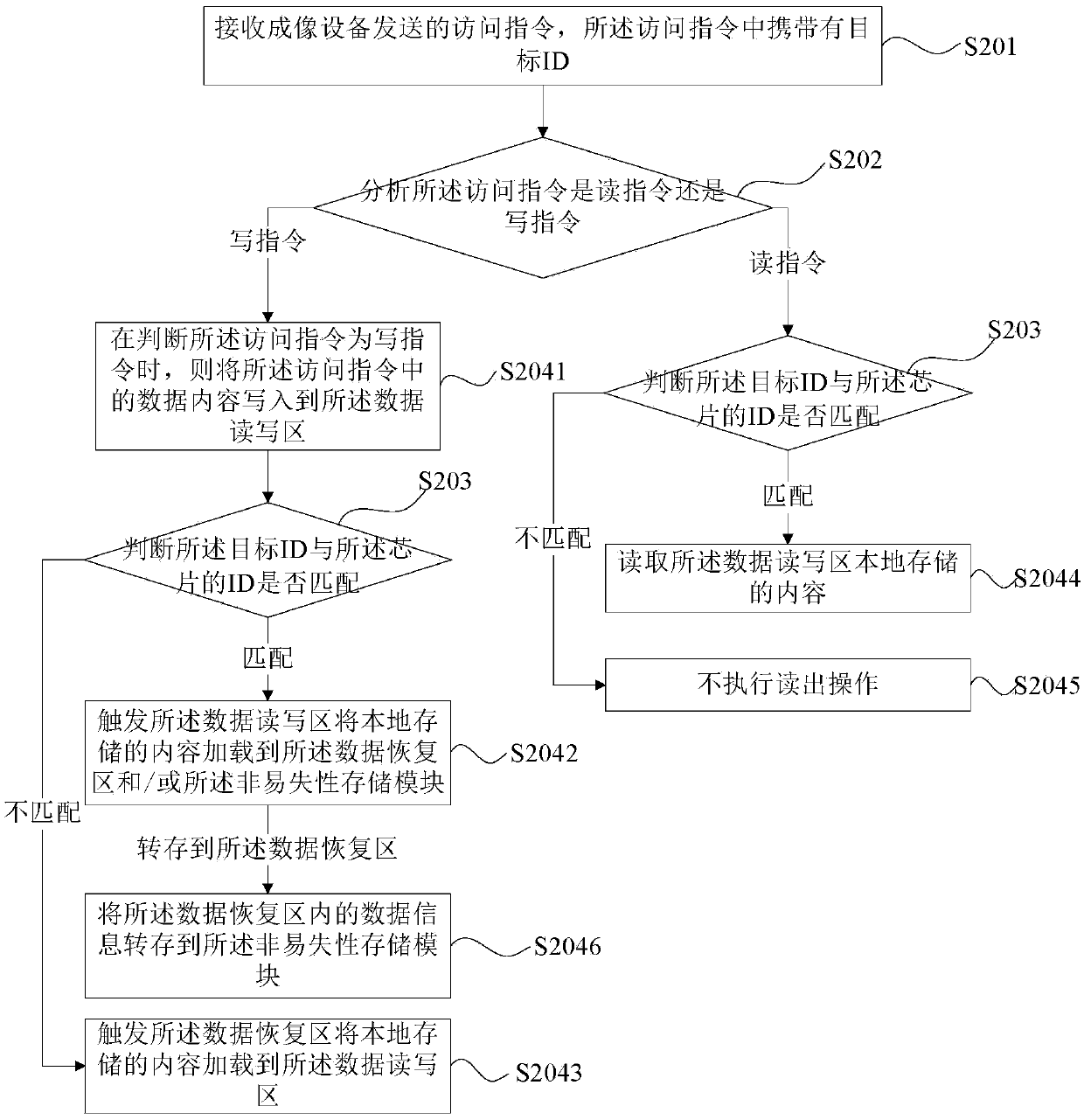
Data processing device and method based on imaging box chip, chip and imaging box
ActiveCN107310274AImprove practicalityGuaranteed data communicationPrintingComputer architectureImaging equipment
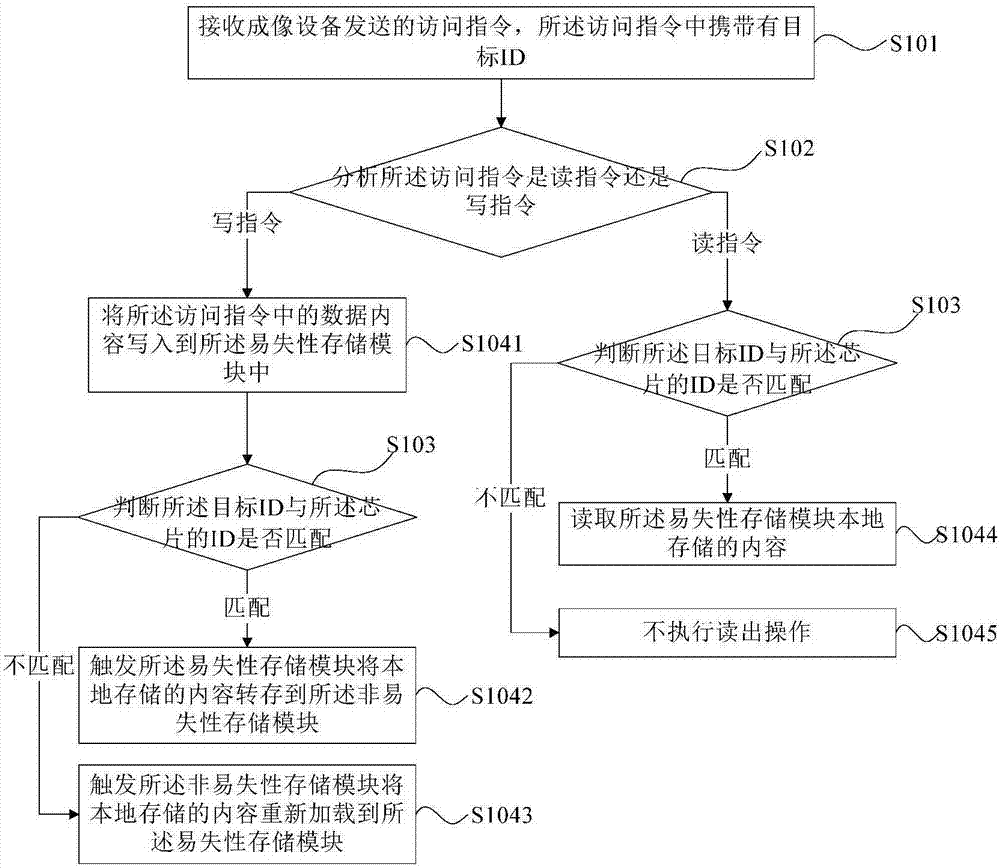
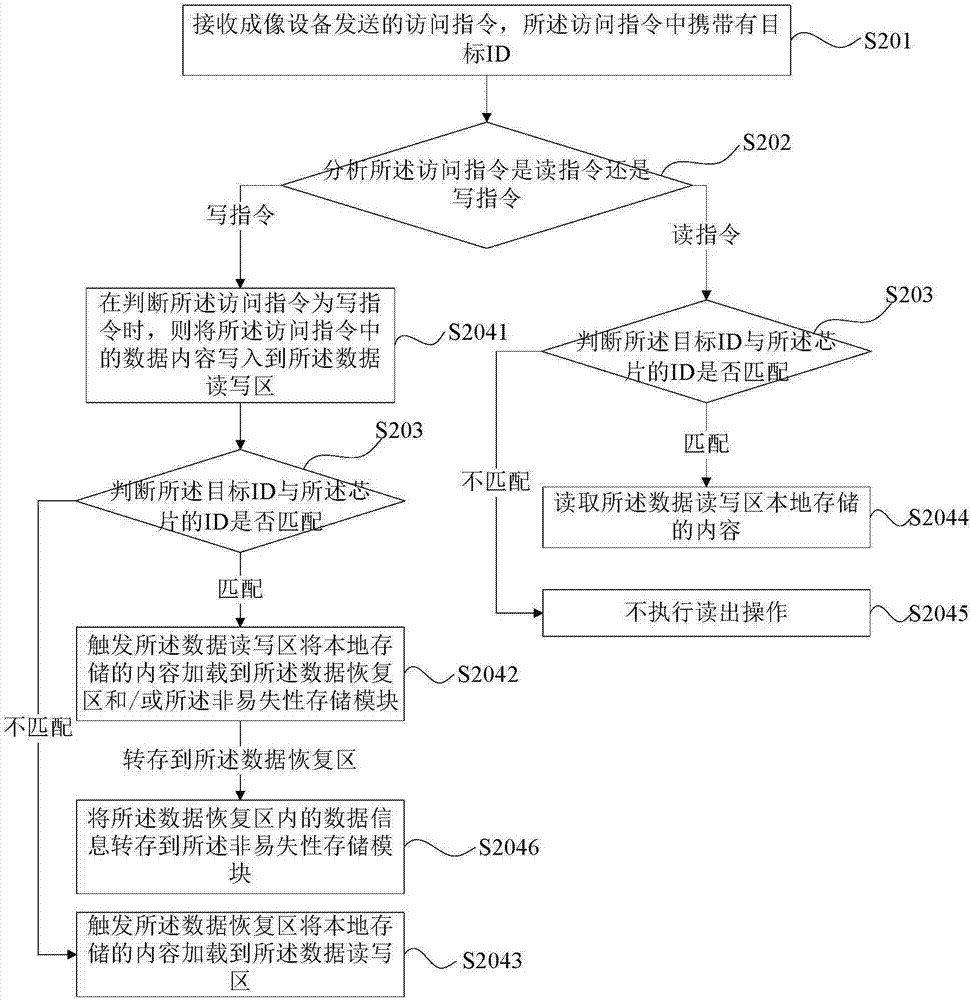
The invention provides a data processing device and method based on an imaging box chip, the chip and an imaging box. The chip comprises a volatile storage module and a nonvolatile storage module connected with the volatile storage module. ID of the chip is stored in the nonvolatile storage module. The data processing device comprises a communication module, an instruction analysis module, a judgement module and a data writing unit, wherein the communication module is used for being connected to a bus of imaging equipment and receiving an access instruction sent by the imaging equipment, and the access instruction carries a target ID; the instruction analysis module is connected with the communication module and used for analyzing whether the access instruction is a reading instruction or a writing instruction; the judgement module is connected with the communication module and used for judging whether the target ID is matched with the ID of the chip; and the data writing unit is connected with the instruction analysis module, the judgement module and the volatile storage module and used for writing data contents in the access instruction into the volatile storage module if the access instruction is the writing instruction before whether the target ID and the ID of the chip is matched or not is judged.
Owner:APEX MICROELECTRONICS CO LTD
Tramcar network monitoring system
InactiveCN109466332AGuaranteed data communicationMeet needsSpeed controllerElectric devicesElectric power transmissionEeg data
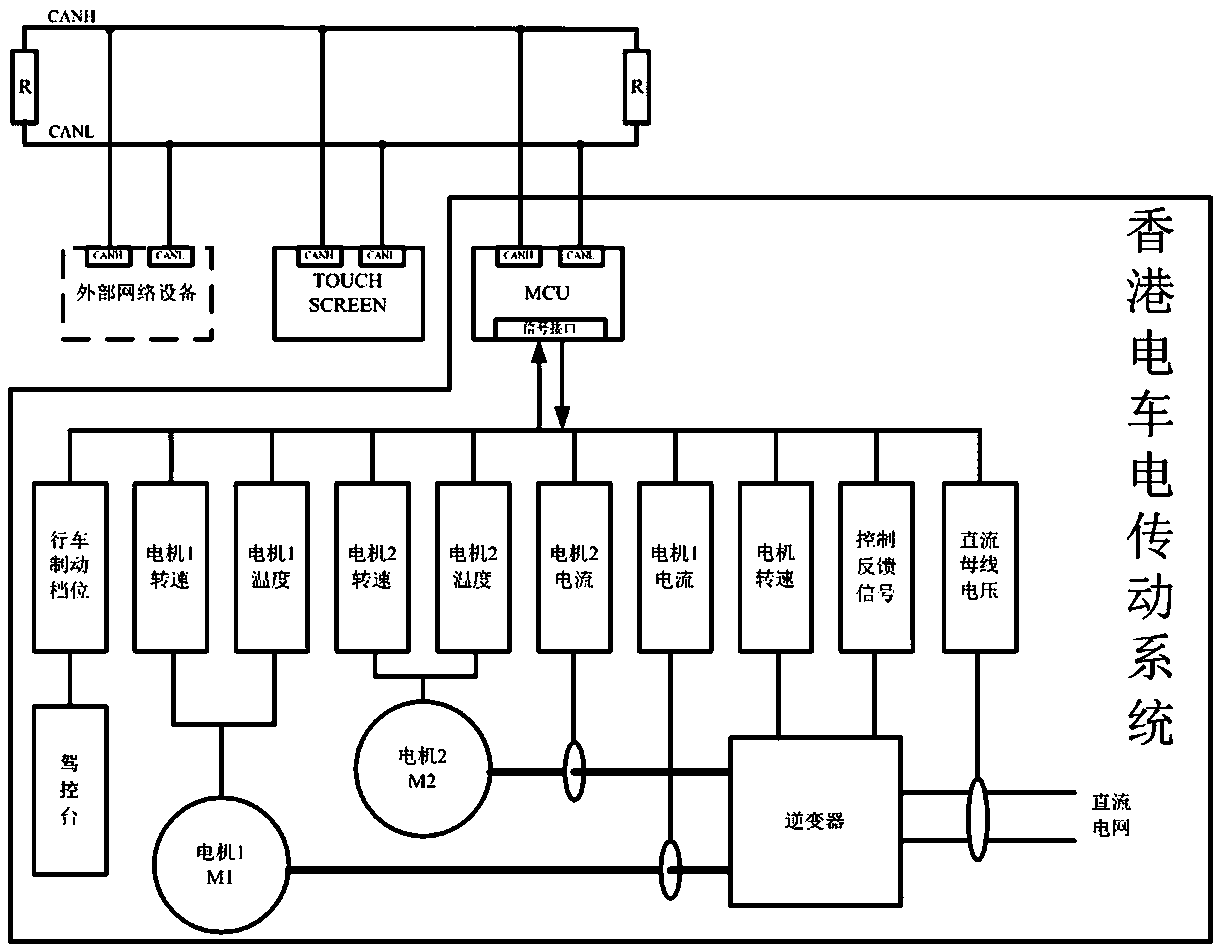
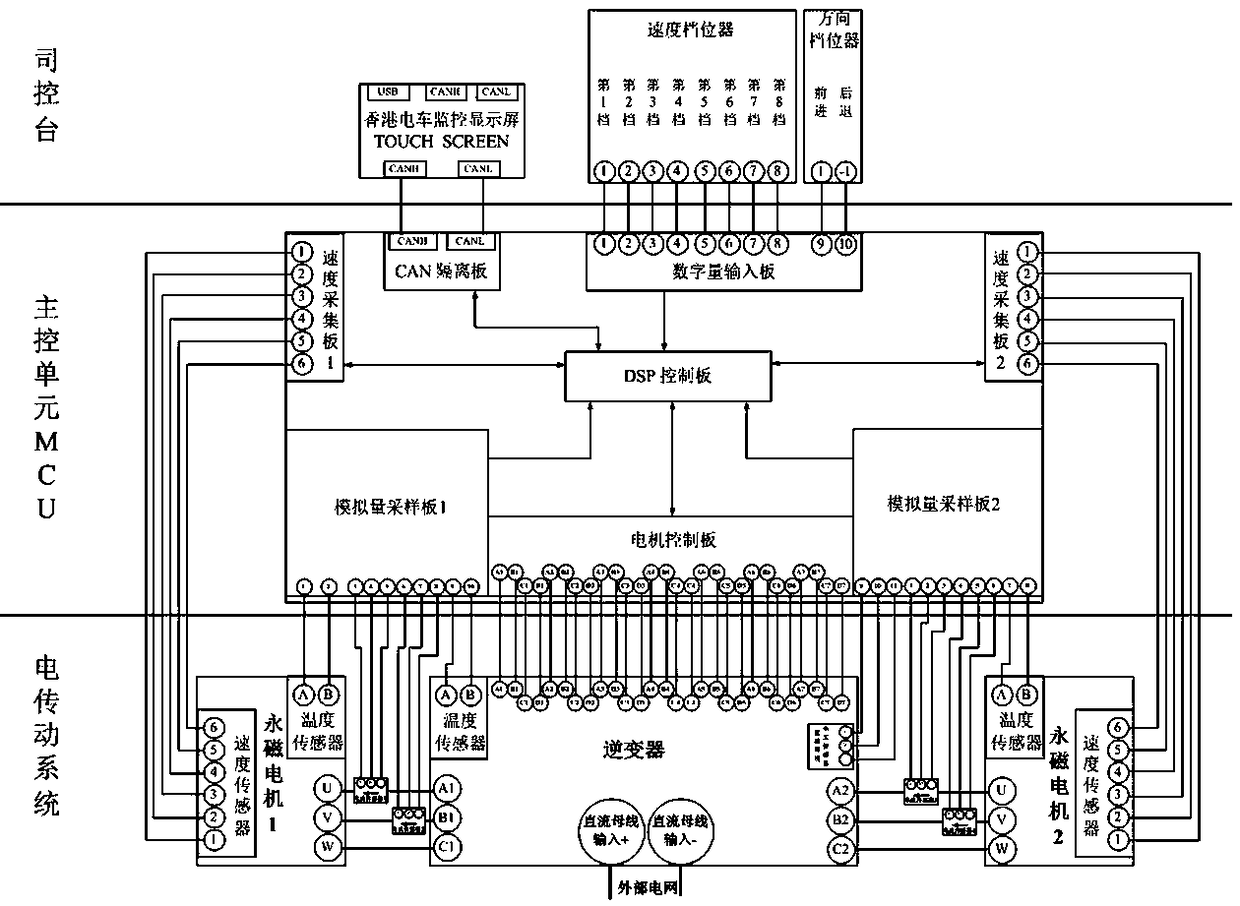
The invention relates to monitoring of permanent magnet electric transmission of tramcars in Hong Kong, in particular to a tramcar network monitoring system. The network monitoring system is designedand arranged on a driver console of a tramcar in Hong Kong, the monitoring system is connected with an electric transmission system of the tramcar in Hong Kong through a network interface, data information collected by the electric transmission system and fault information analyzed by the electric transmission system are transmitted to the monitoring system through a network to be displayed and stored, and a control instruction can be sent to the electric transmission system through the monitoring system. The monitoring system is a human-computer interaction interface between a driver, field debugging personnel and the electric transmission system, which provides convenience for viewing the data information, and network control on the electric transmission system can also be achieved. Thetramcar network monitoring system is arranged on a driving console to ensure data communication of the electric transmission system, so that the electric transmission system runs safely and reliably,the actual needs of users are met, the affirmation of the users is obtained, and the good economic and social benefits are obtained.
Owner:CRRC YONGJI ELECTRIC CO LTD
Power data processing method and device, computer equipment and storage medium
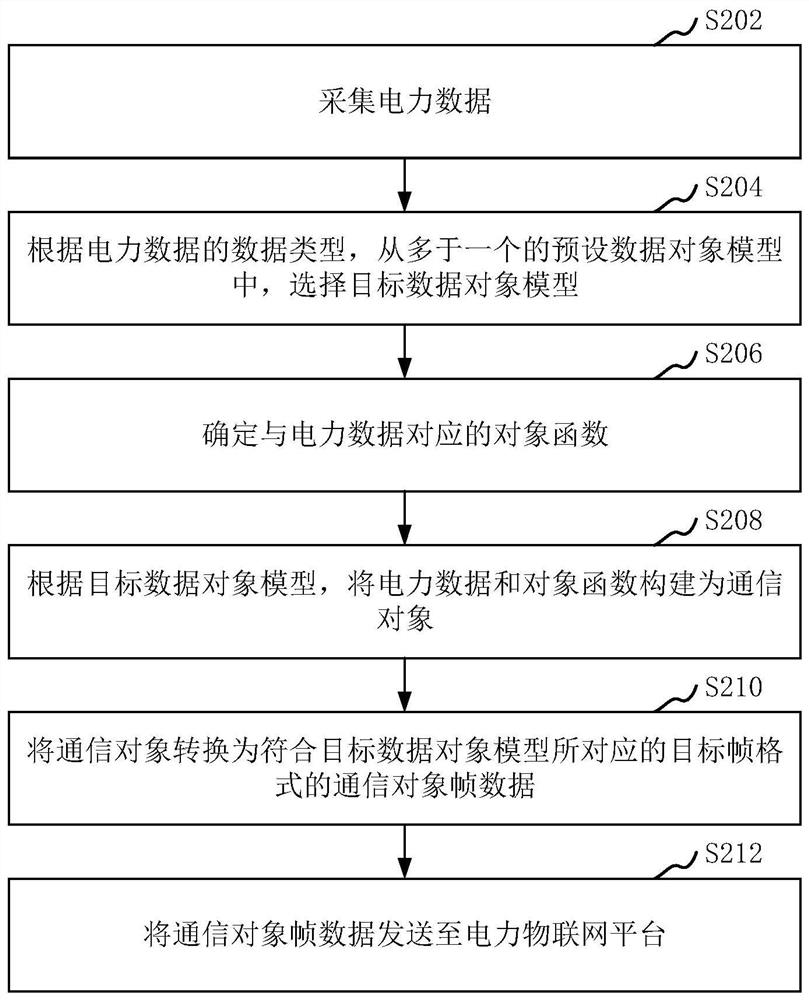
PendingCN112256774AImprove collection efficiencyGuaranteed data communicationData processing applicationsDatabase management systemsComputer hardwareData class
The invention relates to an electric power data processing method and device, computer equipment and a storage medium. The method comprises the following steps: acquiring electric power data; selecting a target data object model from more than one preset data object model according to the data type of the power data; determining an object function corresponding to the power data; constructing thepower data and the object function into a communication object according to the target data object model; converting the communication object into communication object frame data conforming to a target frame format corresponding to the target data object model; and sending the communication object frame data to an electric power Internet of Things platform. The method can improve the power data collection efficiency.
Owner:SHENZHEN POWER SUPPLY BUREAU
Situation awareness virtual link defense method, device and system
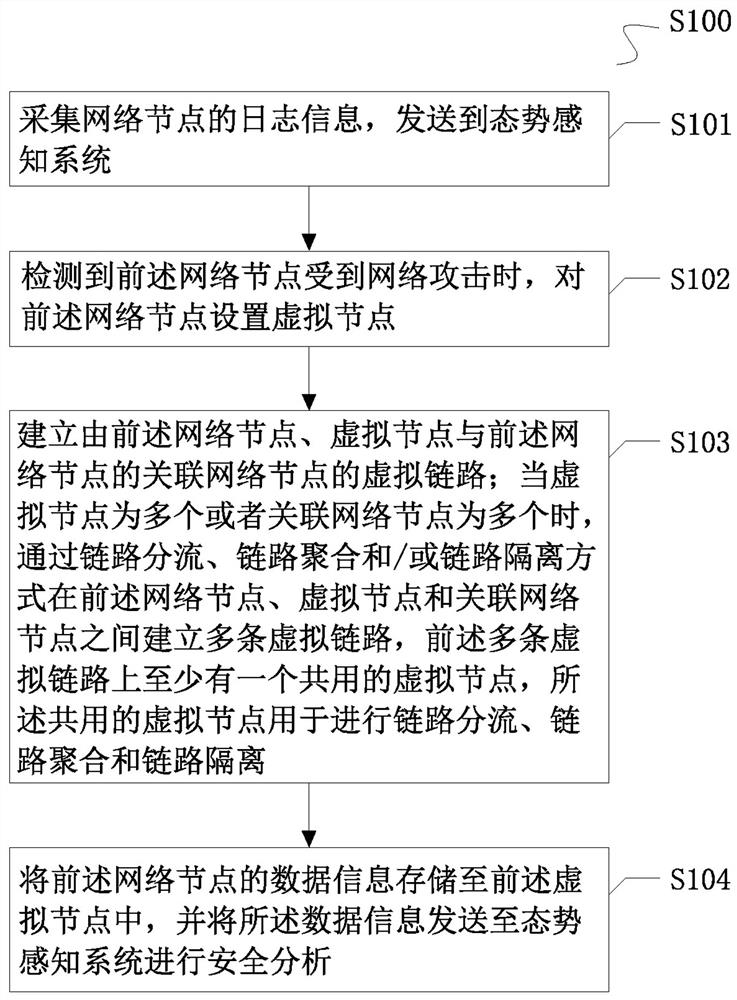
ActiveCN113411296AChange the transmission pathRealize security dynamic defenseTransmissionHigh level techniquesEngineeringLink aggregation
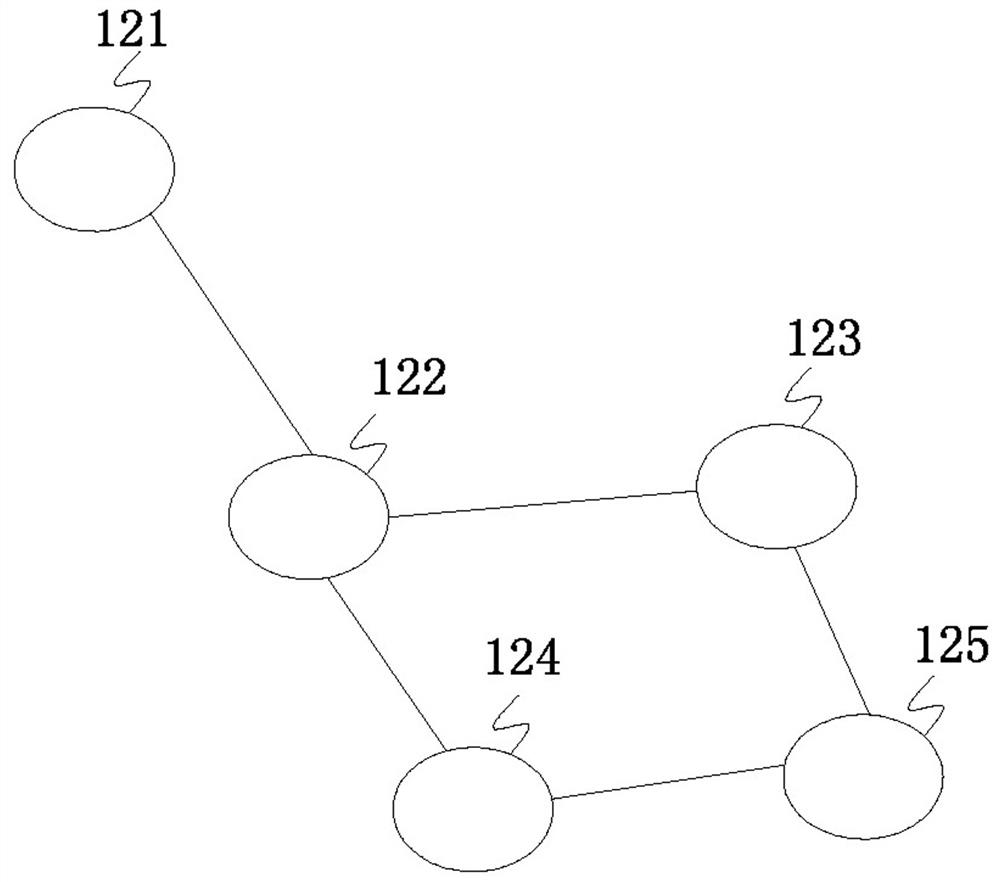
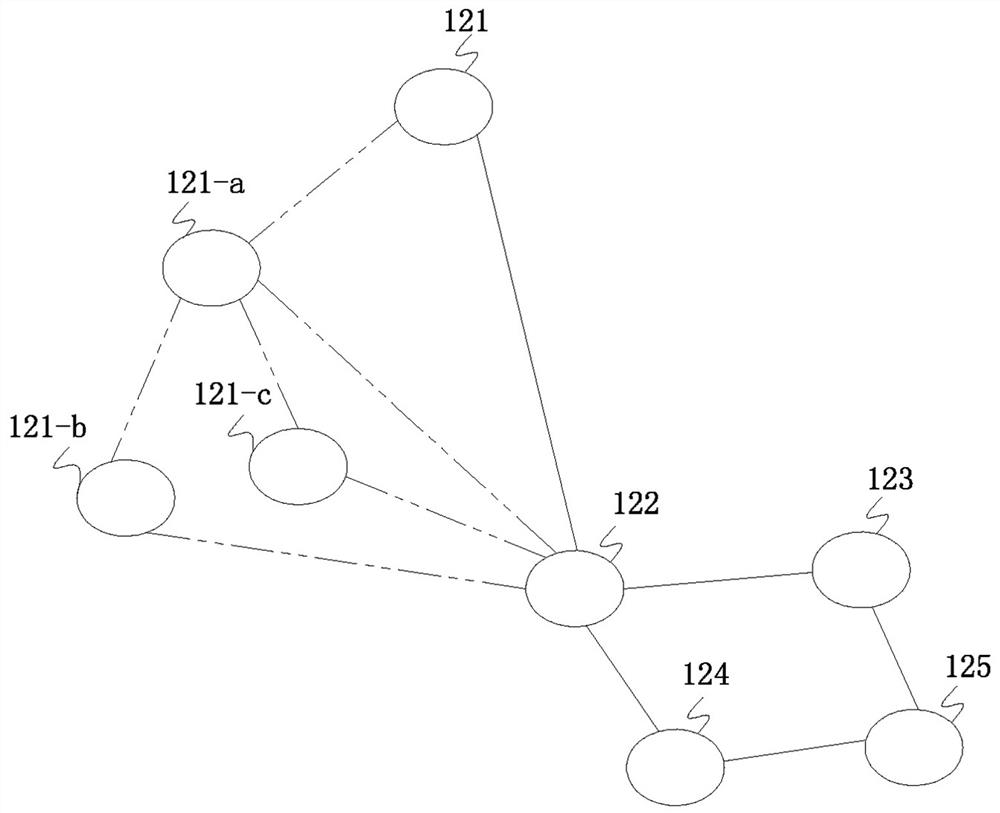
The invention provides a situation awareness virtual link defense method, device and system, and relates to the technical field of network security. The defense method comprises the following steps of: collecting log information of a network node, and sending the log information to a situation awareness system; when the network node is detected to be subjected to network attack, setting a virtual node for the network node; establishing a virtual link consisting of the network node, the virtual node and an associated network node of the network node; when the number of the virtual nodes or the associated network nodes is multiple, establishing a plurality of virtual links among the network node, the virtual nodes and the associated network nodes in a link shunting, link aggregation and / or link isolation mode; and storing the data information of the network node into the virtual node, and sending the data information to the situation awareness system for security analysis. According to the situation awareness virtual link defense method, device and system, the virtual links are established by using the virtual nodes, the communication path of the data information is changed, an attacker is prevented from stealing private data, and the data security is guaranteed.
Owner:SHANGHAI NEWDON TECH CO LTD
Mobile payment network architecture
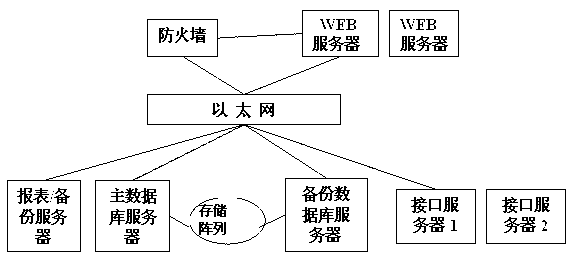
InactiveCN103001949AEnsure safetyEasy accessPayment architectureTransmissionDatabase serverNetwork architecture
A mobile payment network architecture mainly comprises a database server, an interface server, a backup server and a WEB server, and is characterized in that a service platform utilizes a double-network mode, important data devices including the database server, the interface server and the backup server are disposed in an enterprises inner network environment, the WEB server is disposed in an internet environment. The mobile pavement network architecture can effectively guarantee safety of network data, and safety grade of payment service is improved while guaranteeing data communication.
Owner:JIANGSU LEMAIDAO NETWORK TECH
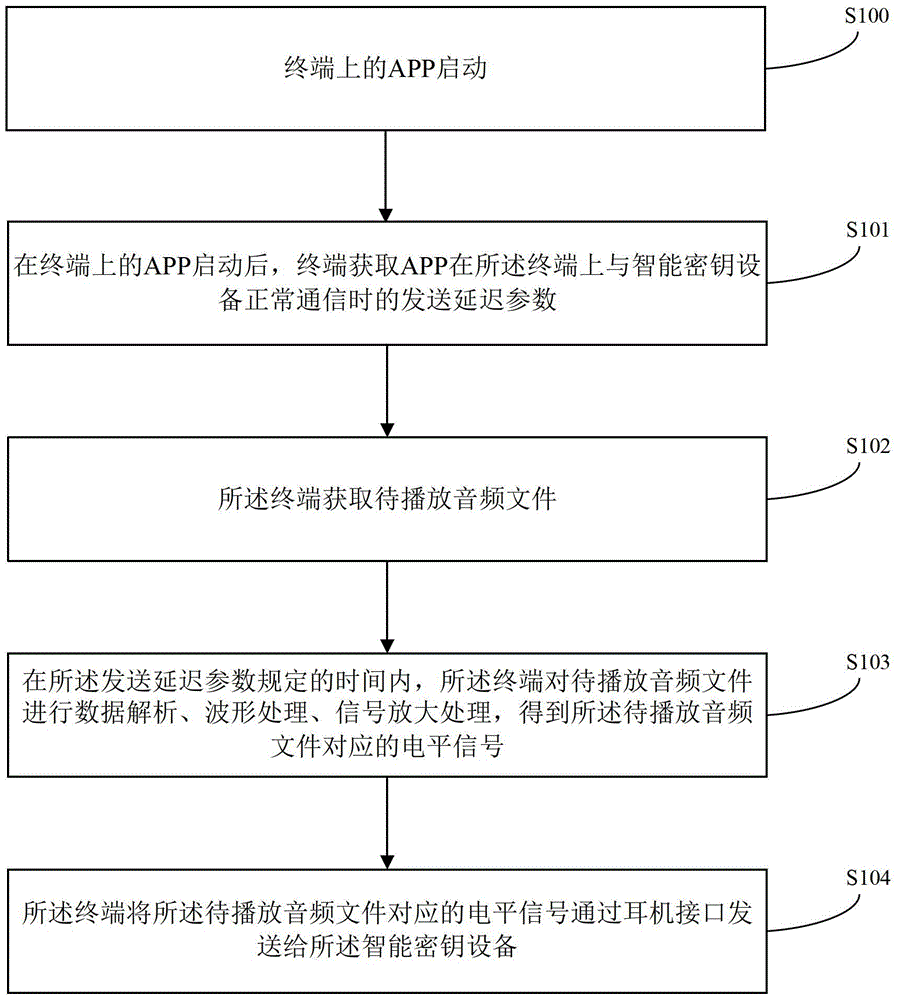
Data processing method and terminal
ActiveCN103532703AGuaranteed to receiveGuaranteed data communicationKey distribution for secure communicationComputer hardwareHeadphones
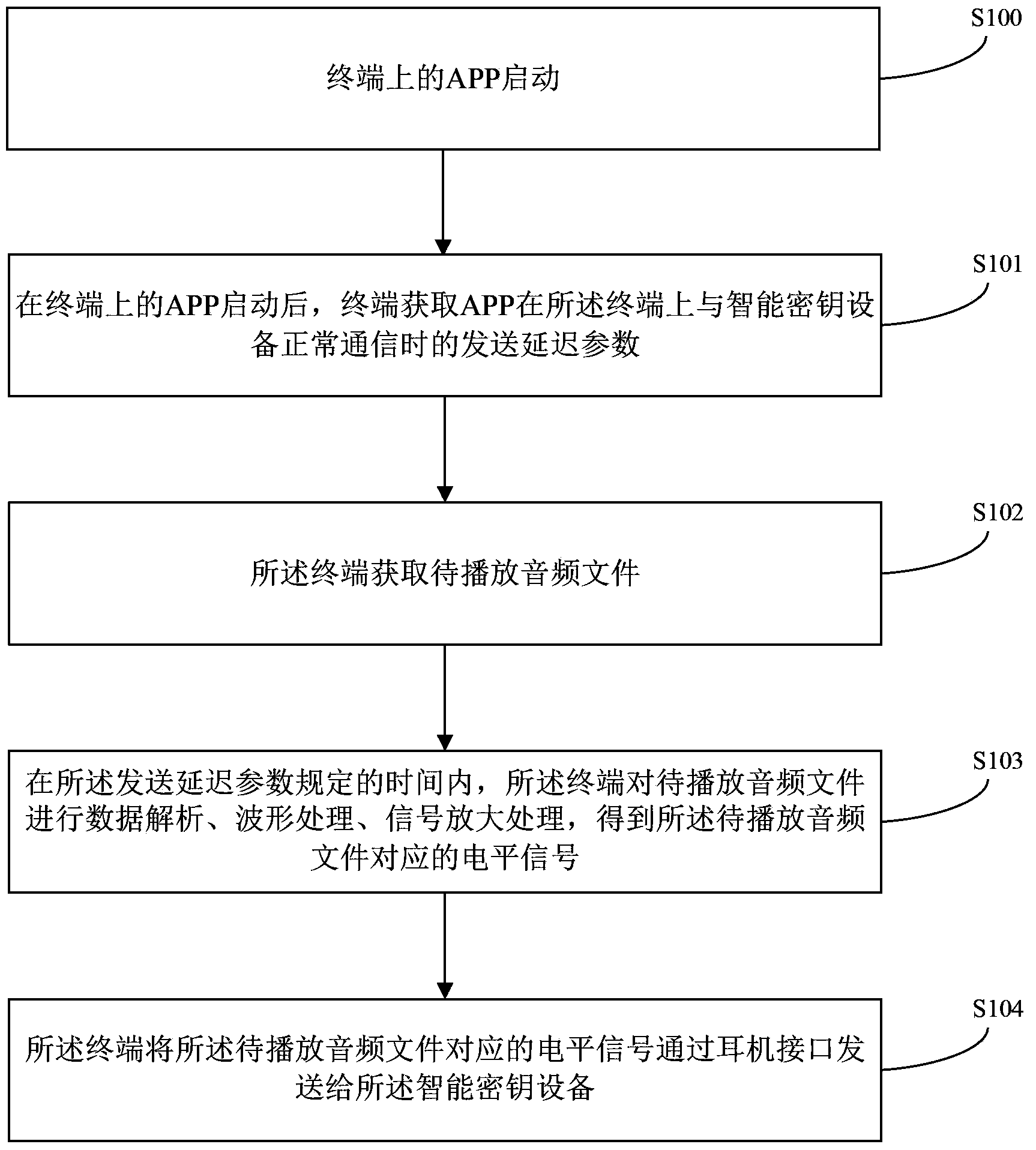
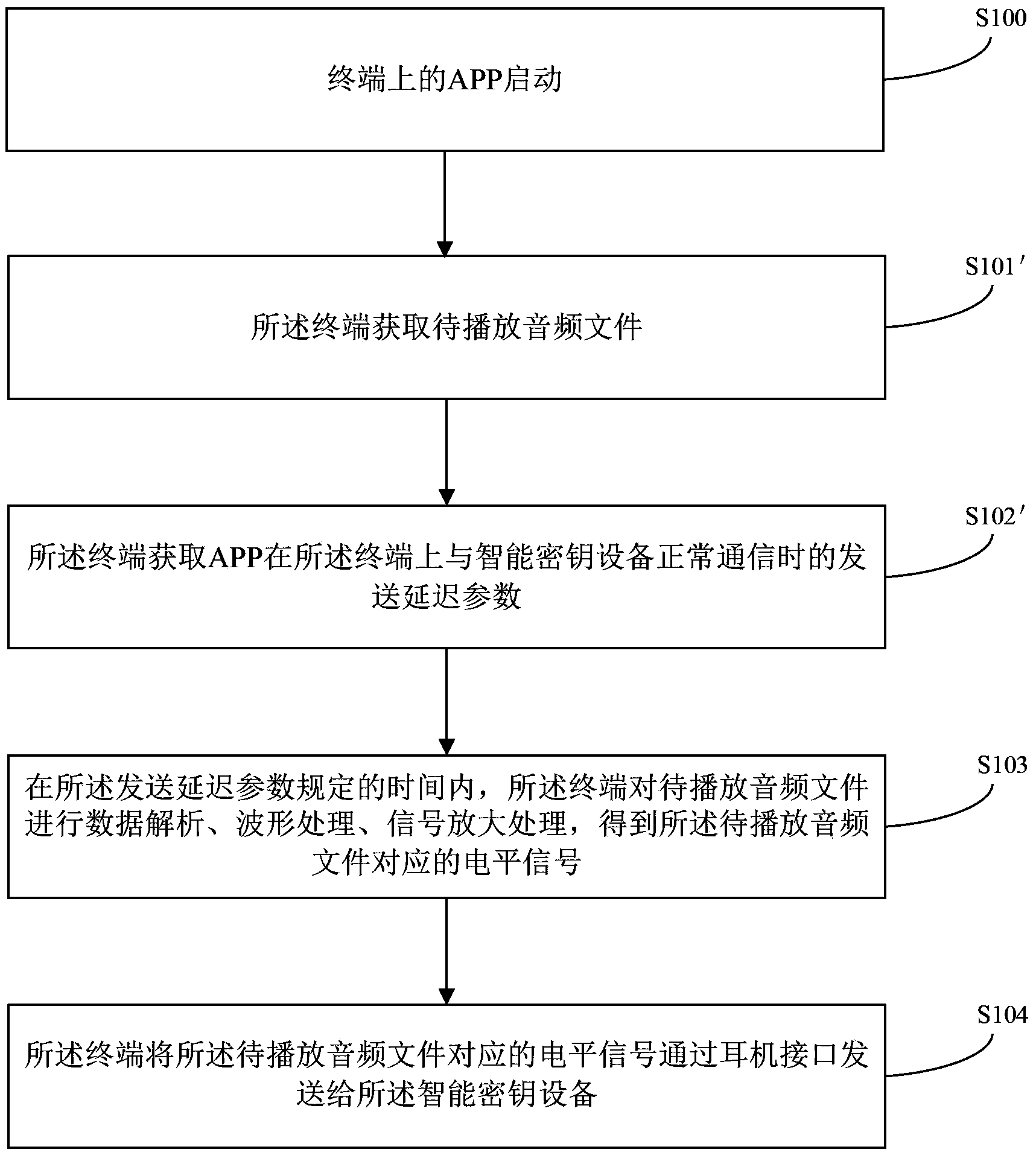
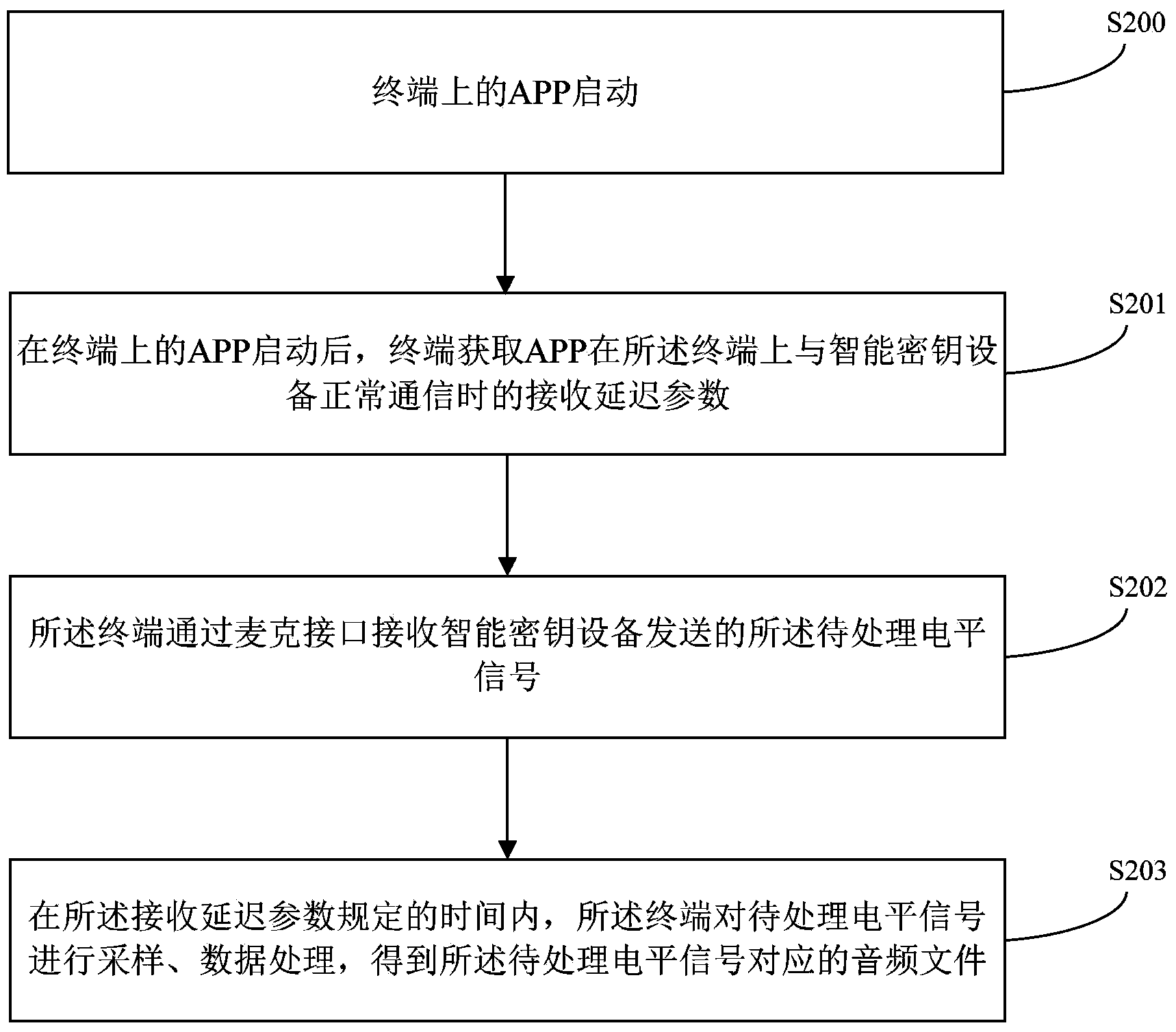
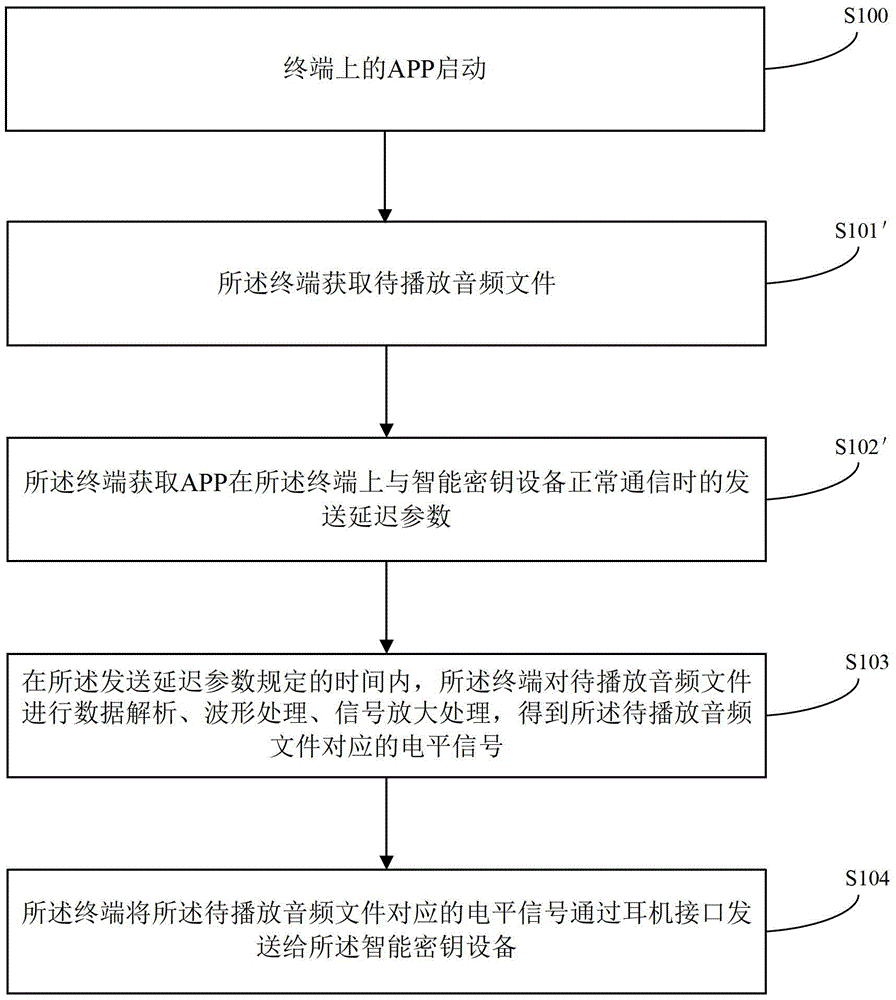
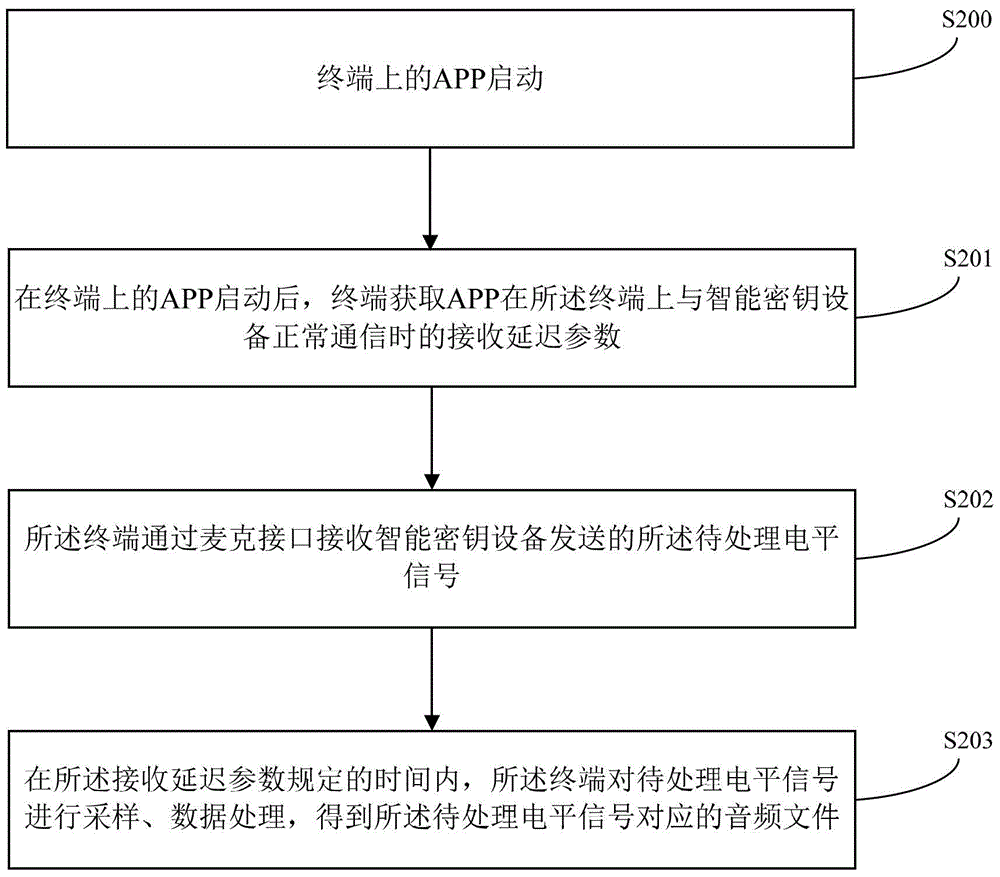
The invention provides a data processing method and a terminal, and relates to the technical field of electronics. Normal communication between the terminal and intelligent key equipment can be ensured. The method comprises the following steps that the terminal acquires a transmission delay parameter when an APP (application) normally communicates with the intelligent key equipment on the terminal; the terminal performs data analysis, waveform processing and signal amplification processing on an audio file to be played within a time specified by the transmission delay parameter to obtain a level signal corresponding to the audio file to be played; the terminal transmits the level signal corresponding to the audio file to be played to the intelligent key equipment through an earphone interface. The data processing method is mainly applied to a process of data communication between the terminal and the intelligent key equipment.
Owner:TENDYRON CORP
Bridge detection device and method and bridge analysis system
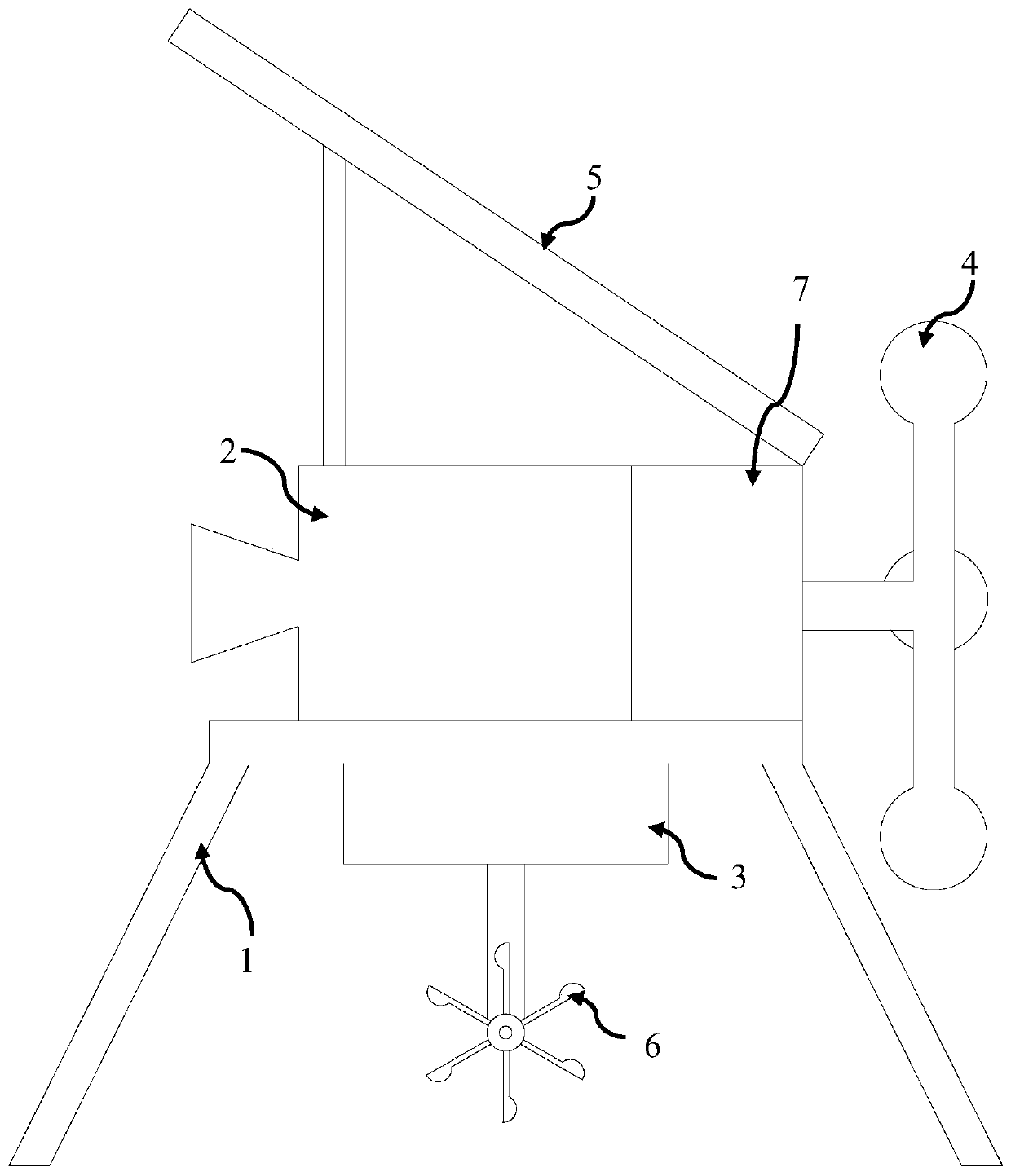
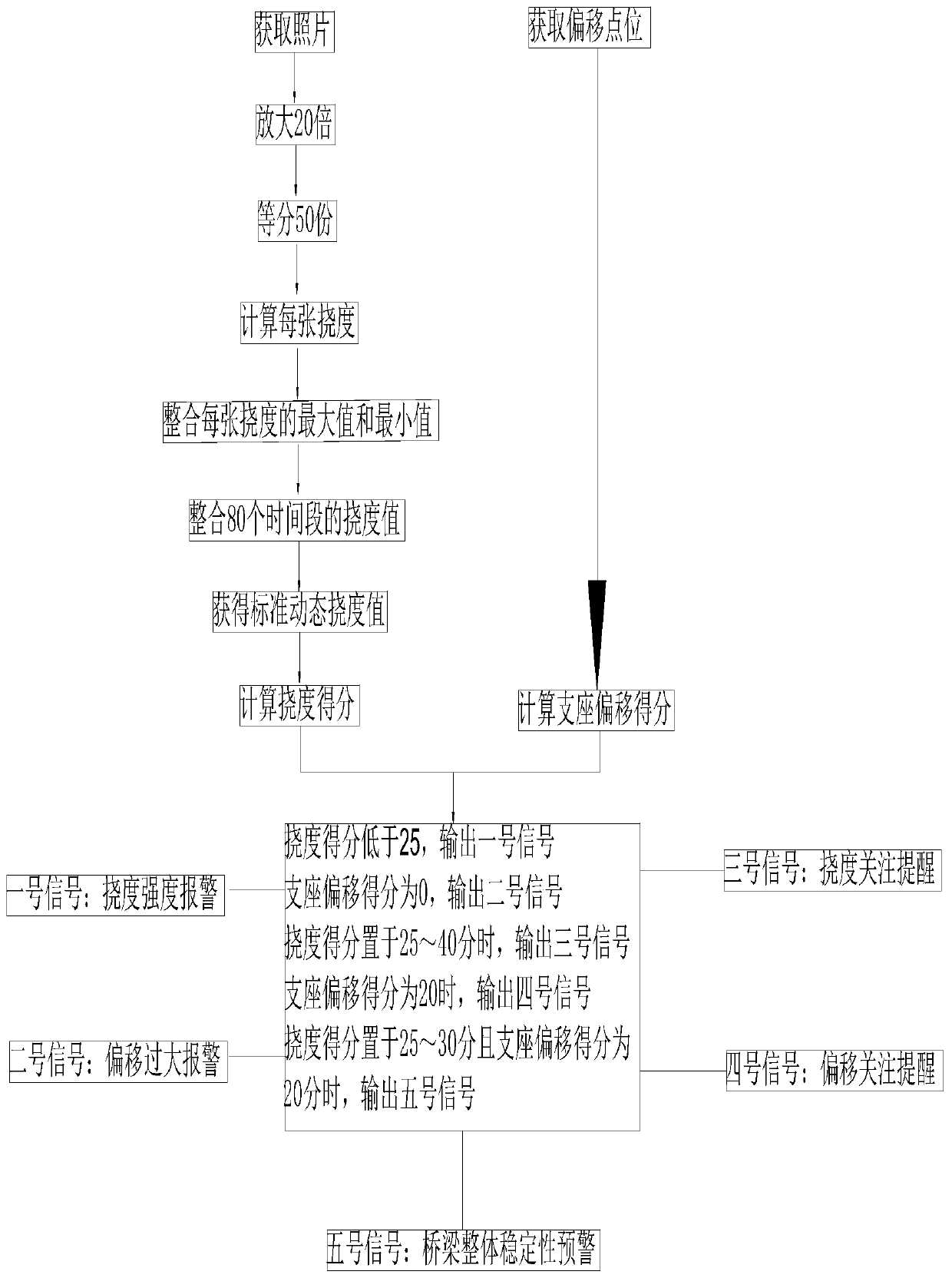
InactiveCN110146240AEasy to installLong-term job stabilityBatteries circuit arrangementsMachines/enginesEngineeringSolar power
The invention discloses a bridge detection device relating to the technical field of bridge measurement. The bridge detection device comprises a flexibility detection device, a bridge bearer offset detection device and a communication module, the flexibility detection device comprises a flexibility detection camera, an infrared range finder and a support, the flexibility detection camera is placedon the support, the viewing side of the flexibility detection camera just faces the intermediate section of a bridge, the infrared range finder is mounted on the support and just faces the bridge, the support supports the flexibility detection camera so that the camera is stabilized over the water surface, a first lithium battery is arranged under the support, a first wind power generator is arranged in the side surface of the lithium battery, a hydroelectric power generator is arranged in the position where the support is sank to the water, and a first solar power generator is arranged in the top of the flexibility detection camera.
Owner:无锡市高桥检测科技有限公司
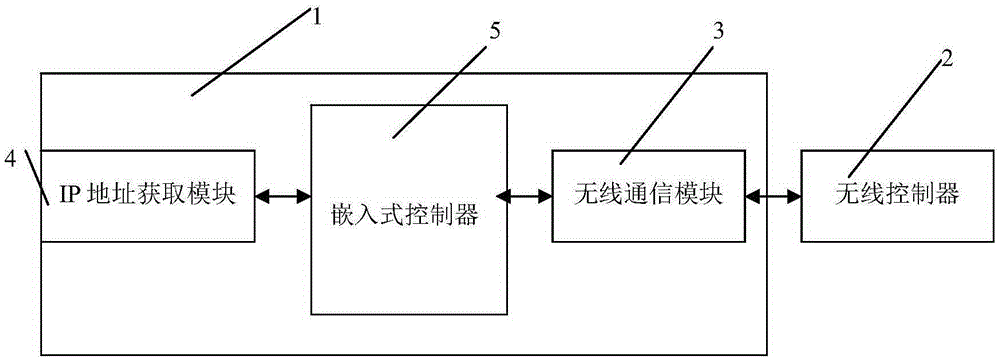
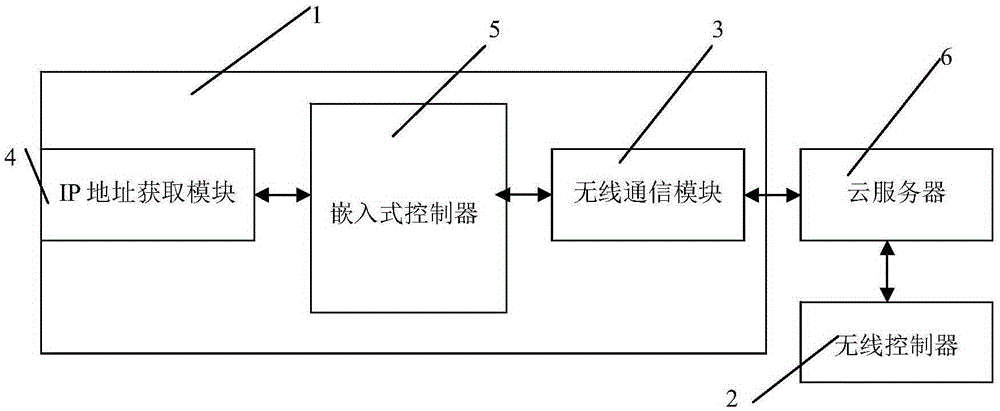
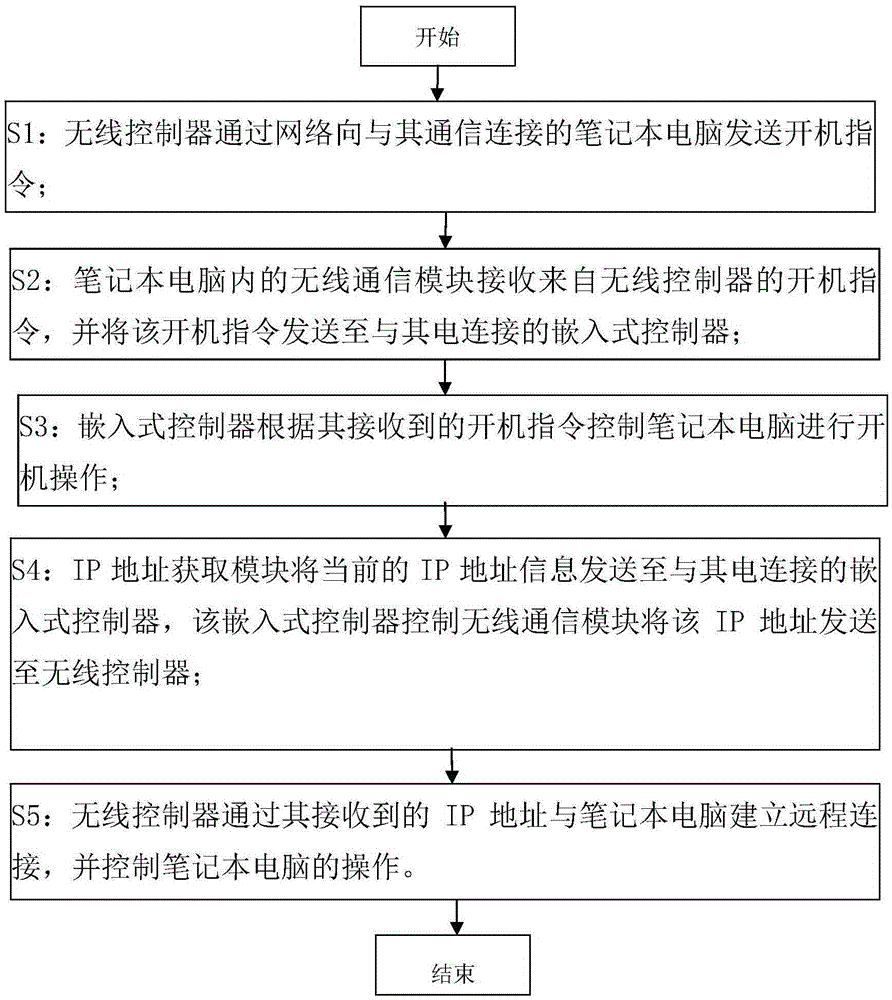
Remote control system used for notebook computer and control method thereof
InactiveCN105425623AGuaranteed data communicationRealize remote controlProgramme control in sequence/logic controllersIp addressData information
The invention provides a remote control system used for a notebook computer. The remote control system comprises a wireless controller and the following components arranged in the notebook computer: a wireless communication module which is connected with the wireless controller in a communication way and receives a control instruction from the wireless controller and transmits data information to the wireless controller; an IP address acquisition module which acquires the current IP address of the notebook computer after the notebook computer is turned on; and an embedded controller which is electrically connected with the wireless communication module and the IP address acquisition module and controls turn-on operation of the notebook computer according to the control instruction received by the wireless communication module and controls the wireless communication module to transmit IP address information acquired by the IP address acquisition module to the wireless controller, wherein the wireless controller is configured in a way that the wireless controller establishes remote connection with the notebook computer via the received IP address and controls operation of the notebook computer. The notebook computer in the turn-off state can be controlled to perform turn-on operation so that remote control can be realized.
Owner:HEFEI LCFC INFORMATION TECH
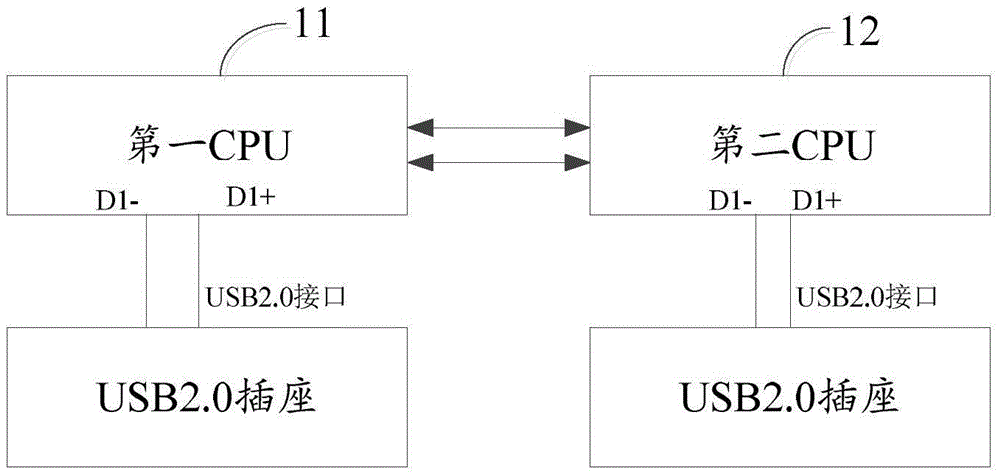
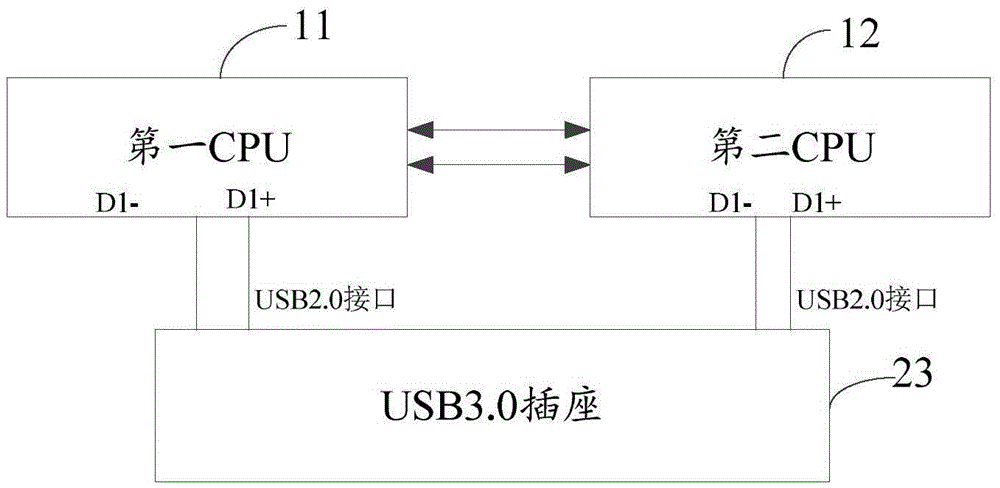
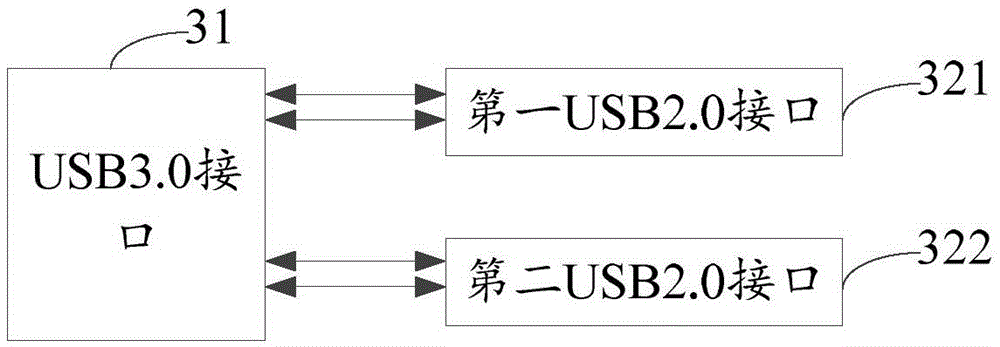
Conversion method for USB socket, USB socket and USB data line
The invention discloses a conversion method for a USB socket, a USB socket and a USB data line, and belongs to the technical field of communication. The method comprises the steps as follows: a USB3.0 interface of the USB data line is inserted into a USB3.0 socket; and a first USB2.0 interface and / or a second USB2.0 interface of the USB data line are / is inserted into USB2.0 sockets / a USB2.0 socket of first external equipment and / or second external equipment. By the conversion method, the quantity of the USB sockets in an actual project can be reduced; and the functions of a pin of the USB3.0 socket can also be fully utilized.
Owner:NUBIA TECHNOLOGY CO LTD
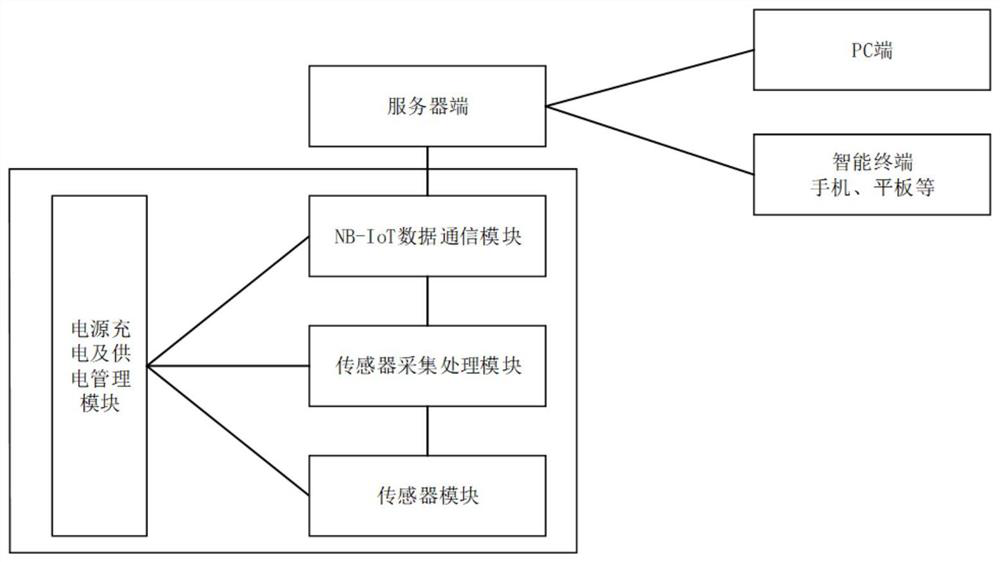
Structure online monitoring system based on NB-IoT protocol
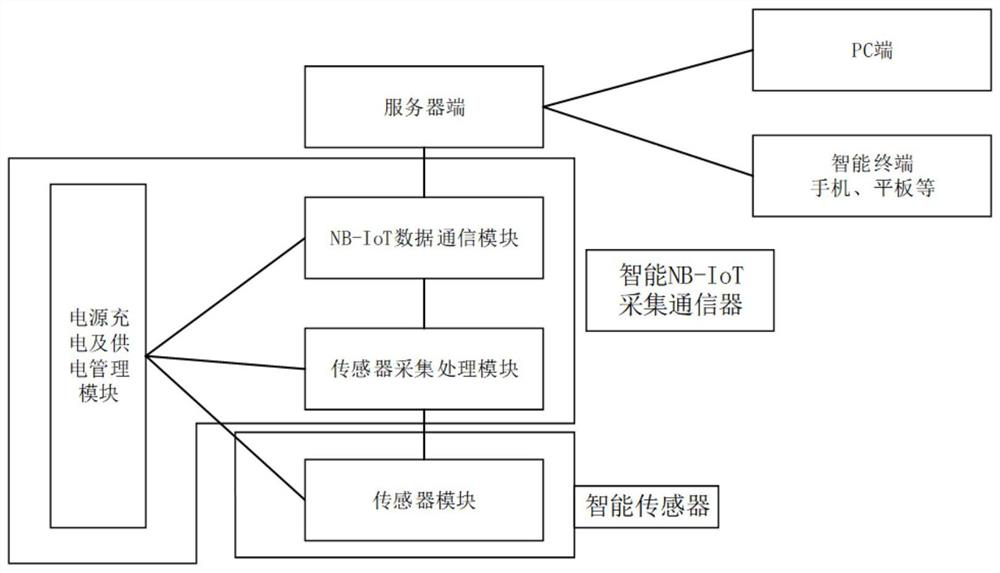
PendingCN113055840AReduce restrictionsLow costSub-station arrangementsMeasurement devicesQuality of serviceStructural monitoring
The invention discloses an NB-IoT protocol-based structure online monitoring system, which comprises a sensor module, a sensor collection and processing module, an NB-IoT data communication module, a power supply charging and power supply management module, a server side and a client terminal, and is characterized in that the sensor module obtains data through measurement, the sensor collection and processing module receives the data and sends the data to the NB-IoT data communication module; the NB-IoT data communication module is arranged at the front end, the server side is arranged at the rear end, the sensor collection processing module remotely transmits data to the server side through the NB-IoT data communication module, the power supply charging and power supply management module provides power supply, and online monitoring data display, storage and analysis management software is arranged at the server side. the monitoring data are displayed in a classified manner and stored as required, and online analysis is performed in real time, and early warning information is given. According to the invention, wiring is not needed, the cost is reduced, the power consumption is smaller, the telecom operator-level service quality can be provided, and the method can be conveniently applied to a complex structure monitoring environment.
Owner:杭州浙程科技有限公司
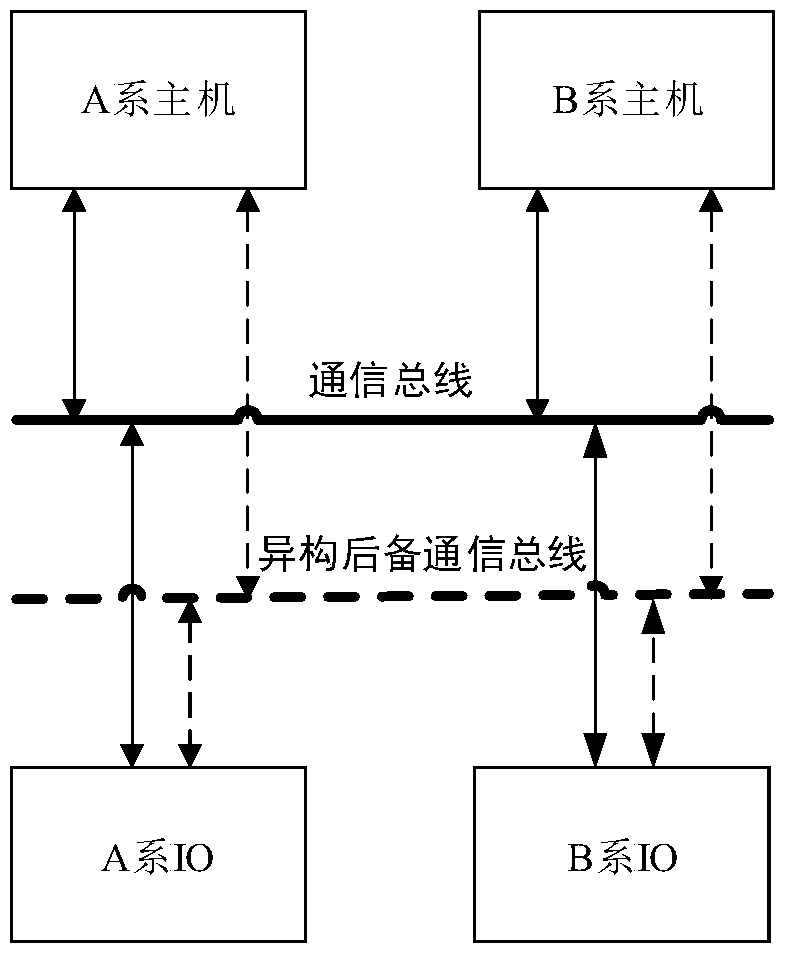
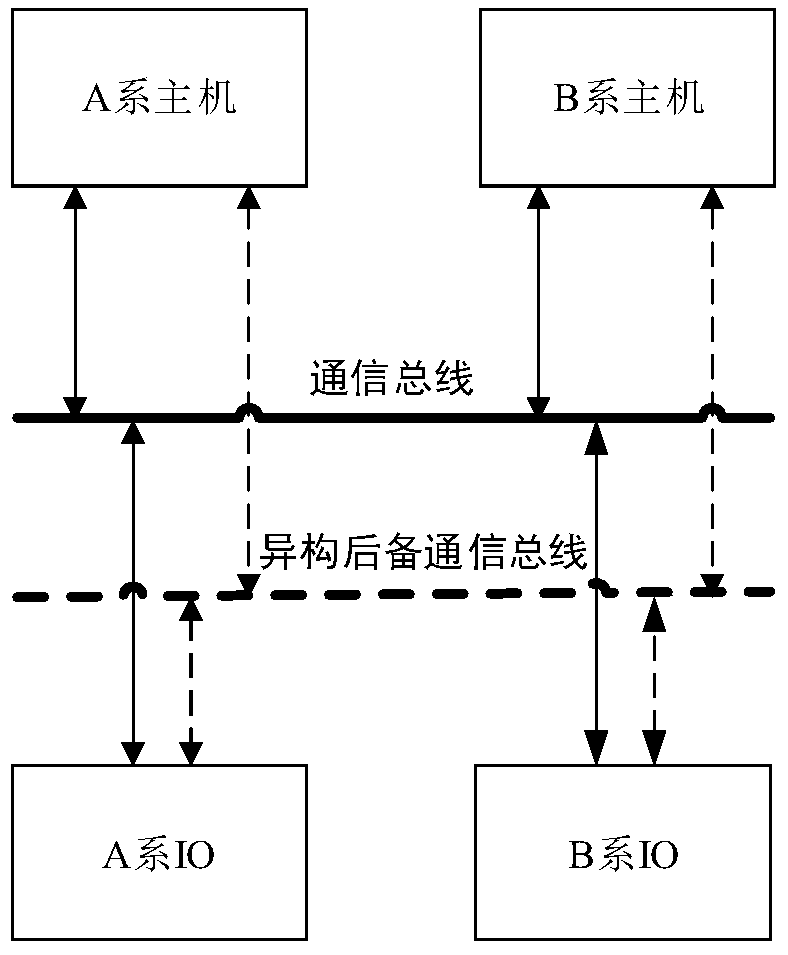
Active/Standby State Management Method for Dual-machine Hot Standby System
ActiveCN105915375BImprove work performanceGuaranteed data communicationData switching networksState managementEmbedded system
The invention provides a main / standby state management method of a hot / standby system. The method mainly comprises a step of arranging an A-series host computer, a B-series hot computer, an A-series host computer IO and a B-series IO which are connected through a communication bus in the hot / standby system, and when the communication bus is available, the A-series hot computer performs data communication with the B-series hot computer, the A-series and the B-series IO through the communication bus. The B-series host computer performs data communication with the A-series host computer, the A-series IO and the B-series IO through the communication bus. According to the main / standby state management method, through dividing the hot / standby system into a host machine part and an input / output (IO) part, the communication bus and a standby communication line are arranged. Based on a specific processing strategy, adverse influences of double main states at the host machine part to outward input output of the input / output (IO) part and the whole hot / standby system can be eliminated. The main / standby state management method can effectively ensure data communication among the A-series host computer, the B-series host computer, the A-series IO and the B-series IO.
Owner:BEIJING JIAOTONG UNIV
Data processing device, method, chip and imaging box based on imaging box chip
ActiveCN107310274BImprove practicalityGuaranteed data communicationPrintingData contentImaging equipment
Owner:APEX MICROELECTRONICS CO LTD
A data processing method and terminal
ActiveCN103532703BGuaranteed to receiveGuaranteed data communicationKey distribution for secure communicationComputer hardwareHeadphones
The invention provides a data processing method and a terminal, and relates to the technical field of electronics. Normal communication between the terminal and intelligent key equipment can be ensured. The method comprises the following steps that the terminal acquires a transmission delay parameter when an APP (application) normally communicates with the intelligent key equipment on the terminal; the terminal performs data analysis, waveform processing and signal amplification processing on an audio file to be played within a time specified by the transmission delay parameter to obtain a level signal corresponding to the audio file to be played; the terminal transmits the level signal corresponding to the audio file to be played to the intelligent key equipment through an earphone interface. The data processing method is mainly applied to a process of data communication between the terminal and the intelligent key equipment.
Owner:TENDYRON CORP
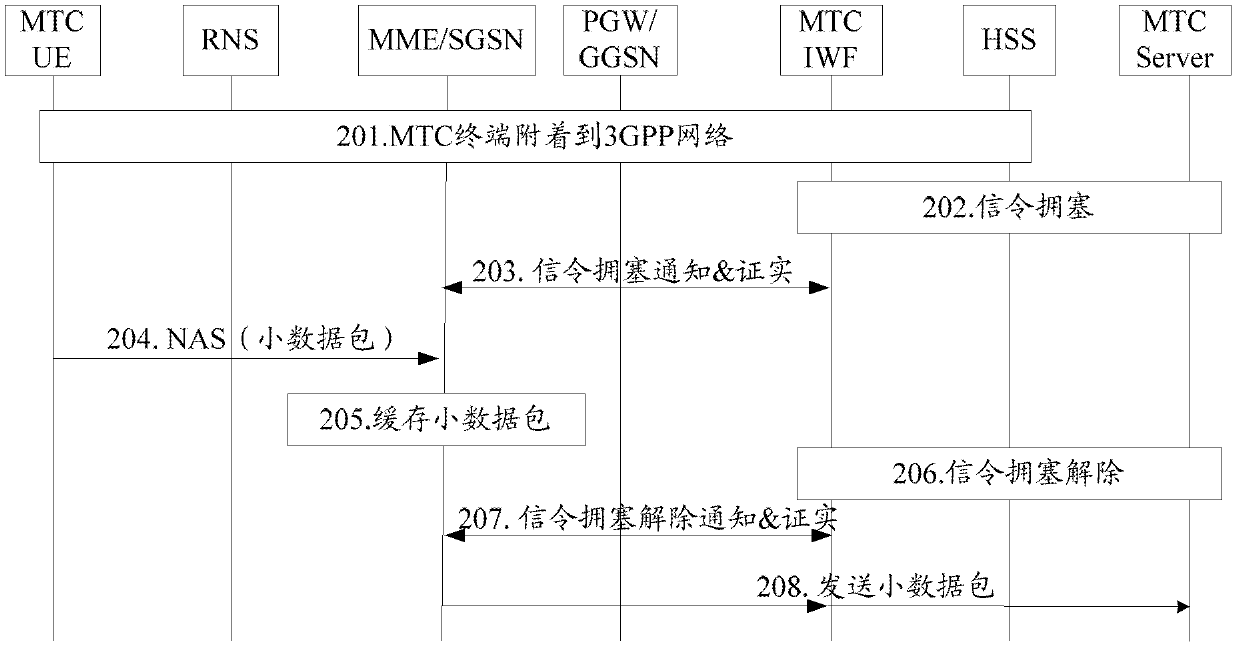
A small data transmission method, device, and system
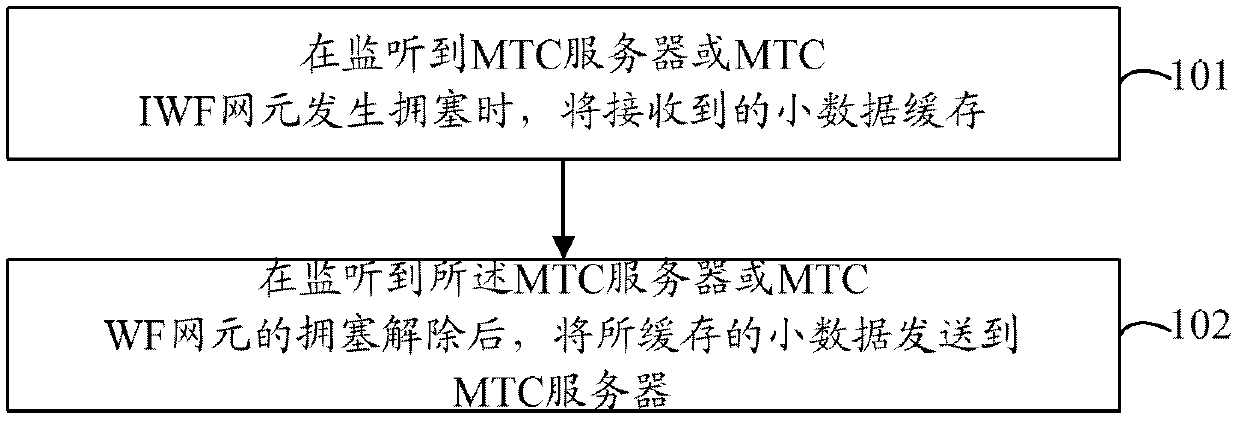
InactiveCN103108358BAvoid lossGuaranteed data communicationError preventionNetwork traffic/resource managementComputer terminalData transmission
The invention discloses a small data transmission method. The method includes: when the MTC server or the MTC IWF network element is detected to be congested, the received small data is cached; when the MTC server or the MTC IWF network element is detected After the congestion is relieved, the cached small data is sent to the MTC server. Correspondingly, the present invention also discloses a small data transmission device and system, which avoids increased congestion during MTC IWF network element or MTC Server congestion, ensures timely data communication between MTC terminals and MTC servers, and meets business requirements of the Internet of Things. Moreover, data loss during congestion of the MTC IWF network element or the MTCServer can be avoided, the normal operation of the small data transmission service can be ensured, and the M2M user experience can be effectively improved.
Owner:ZTE CORP
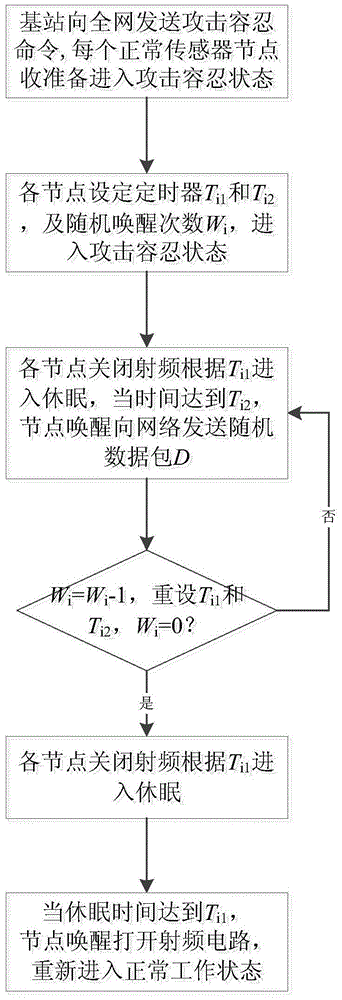
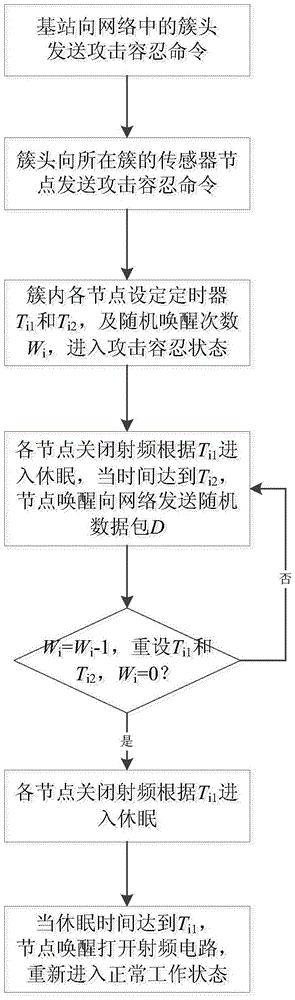
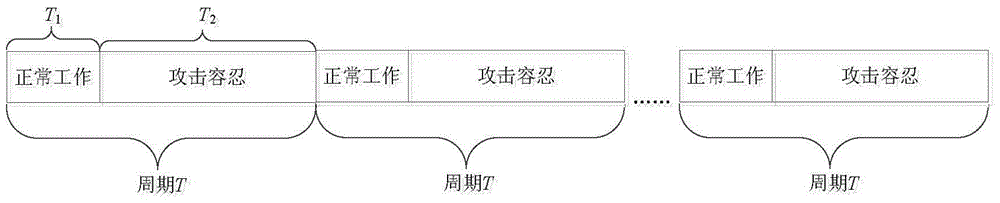
A Malicious Node Tolerance Method in Wireless Sensor Networks
InactiveCN103619011BGuaranteed data communicationEffective protectionNetwork topologiesSecurity arrangementEnergy transferAttack tolerance
The invention discloses a malicious node tolerance method in a wireless sensor network, which changes the traditional security protection method based on encryption, authentication and trust model, and actively protects by actively destroying malicious nodes to achieve the purpose of attack tolerance. The energy of malicious nodes is consumed by transmitting meaningless data in the network. In the state of attack tolerance, normal nodes only generate energy consumption when sending data, while malicious nodes are always in the radio frequency working state. With the small energy consumption of all normal nodes In exchange for the large energy consumption of malicious nodes so that they cannot work. On the premise of ensuring the normal data communication of the sensor network, the effective protection of malicious nodes is completed, which provides a new idea for the secure communication of the wireless sensor network.
Owner:SOUTHEAST UNIV
Method, device and readable storage medium for detecting false data injection attack
ActiveCN110995761BEnsure safetyInjection attacks are efficientTransmissionAc network circuit arrangementsCommunications securityData information
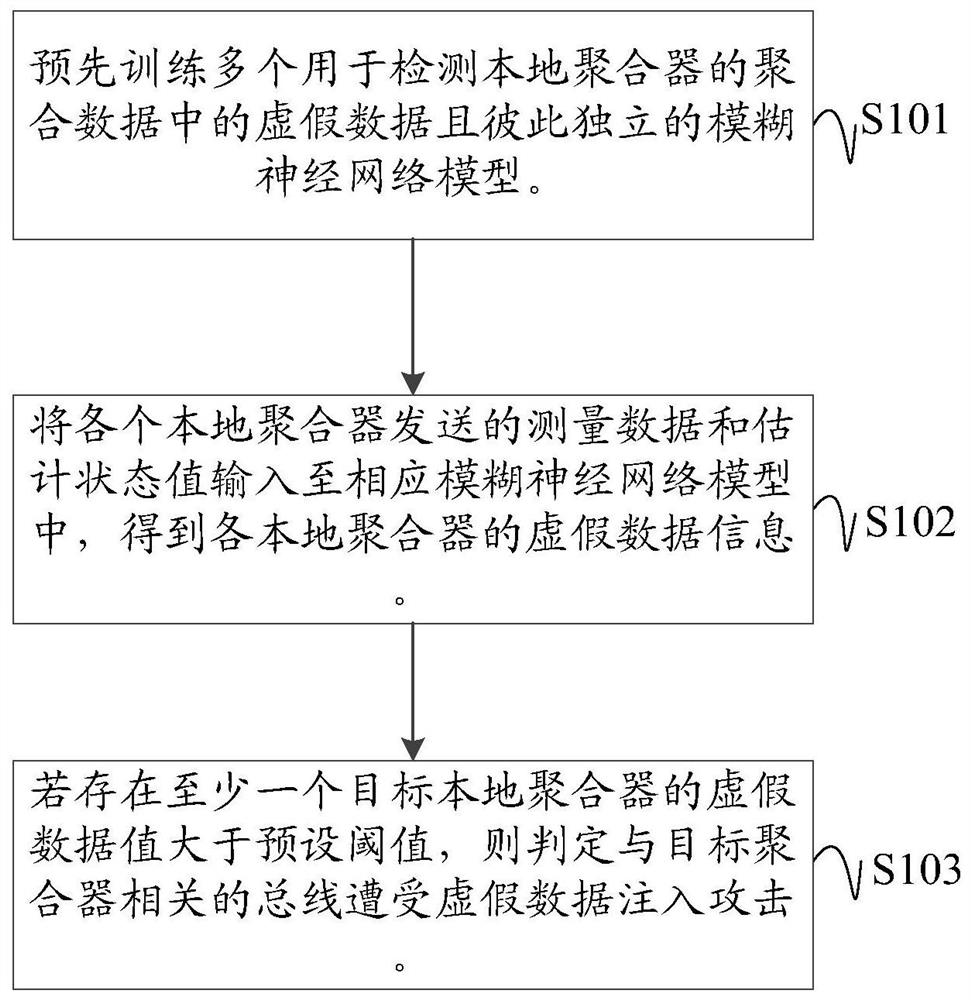
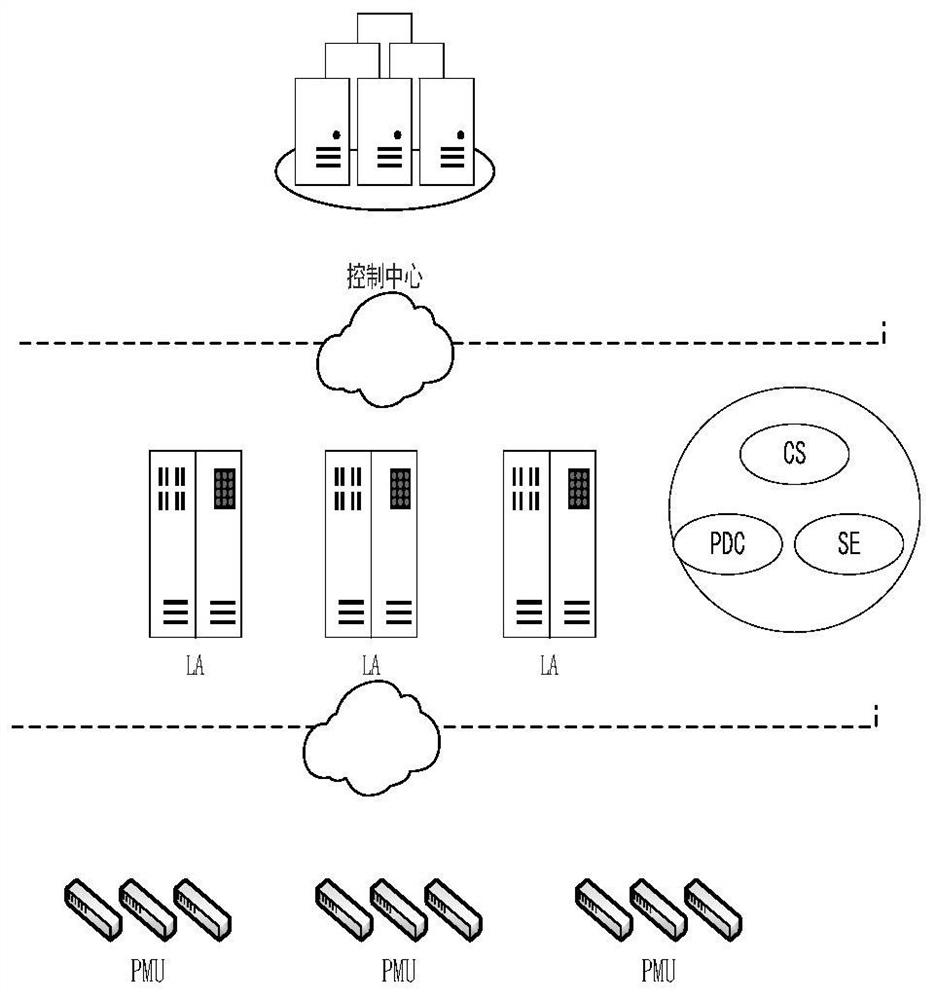
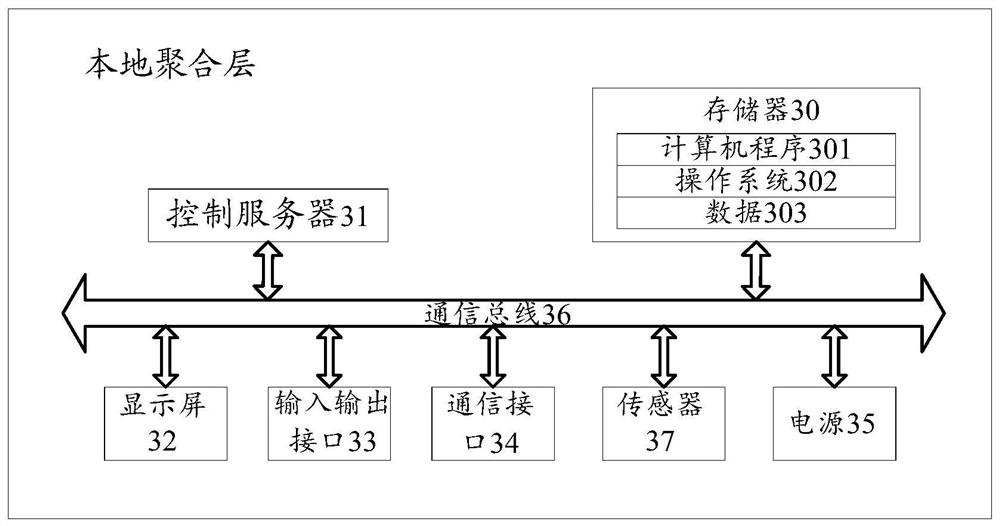
The present application discloses a method, device and computer-readable storage medium for detecting false data injection attacks. Applied to a three-layer smart grid framework consisting of PMU layer, local aggregation layer, and control layer, the local aggregation layer pre-trains multiple fuzzy neural network models that are independent of each other and are used to detect false data in the aggregated data of the local aggregator; Receive the measurement data and estimated state values sent by each local aggregator and input them into the corresponding fuzzy neural network model to obtain the false data information of each local aggregator; if there is at least one target local aggregator whose false data value is greater than the threshold, then determine the bus Suffering from false data injection attacks; the local aggregator aggregates the measurement data collected by the PMUs in the corresponding area and performs state estimation to obtain the estimated state value, and sends the data to the control layer after the identity legality verification request is passed. This application can effectively resist false data injection to attack the grid and ensure the security of grid communication.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
A wireless networking method for explosion effect testing based on wifi
ActiveCN104581768BIncrease transfer rateGuaranteed data communicationNetwork planningLarge rangeWireless network
Owner:THE THIRD ENG CORPS RES INST OF THE HEADQUARTERS OF GENERAL STAFF PLA
Industrial gateway control method, device, computer equipment and storage medium
ActiveCN111541579BGuaranteed uptimeGuaranteed data communicationNetwork connectionsTelecommunications linkCommunication link
The application relates to an industrial gateway control method, device, computer equipment and storage medium. The method includes: determining the application scenario of the gateway; determining the communication link of the gateway according to the scenario information of the application scenario; controlling the gateway to perform data communication through the communication link, and obtaining the communication status of the communication link; when the communication status meets the requirements of the communication link When the path update condition is met, link update is performed on the communication link to obtain an updated communication link; the control gateway performs data communication through the updated communication link. The method can improve the stability of the gateway and ensure the efficiency of data communication.
Owner:深圳市乙辰科技股份有限公司
A multi-sensor intelligent monitoring system based on the Internet of Things
ActiveCN106572189BEasy to install and deployShorten networking timeMeasurement devicesNetwork topologiesThe InternetServer-side
The invention provides a multi-sensor intelligent monitoring system based on the Internet of things, which comprises a monitoring client, a server and a plurality of sensor monitoring modules, and is characterized in that the sensor monitoring modules and the monitoring client are connected with the server; the monitoring client comprises a mobile equipment monitoring client and a PC monitoring client, and the mobile equipment monitoring client is used for performing real-time data monitoring; and the PC monitoring client comprises a system login module, a real-time data monitoring module and a data analysis module. The multi-sensor intelligent monitoring system further comprises a gateway module, and the sensor monitoring modules are connected with the server through the gateway module. According to the invention, real-time monitoring is performed on target equipment by means of various sensor modules, data is transmitted to the server, and real-time conditions of a monitoring target can be seen by a user visually on an interface of the monitoring client after the data is analyzed and processed, and the multi-sensor intelligent monitoring system is convenient, efficient, more intelligent and low in cost.
Owner:GUANGZHOU UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com