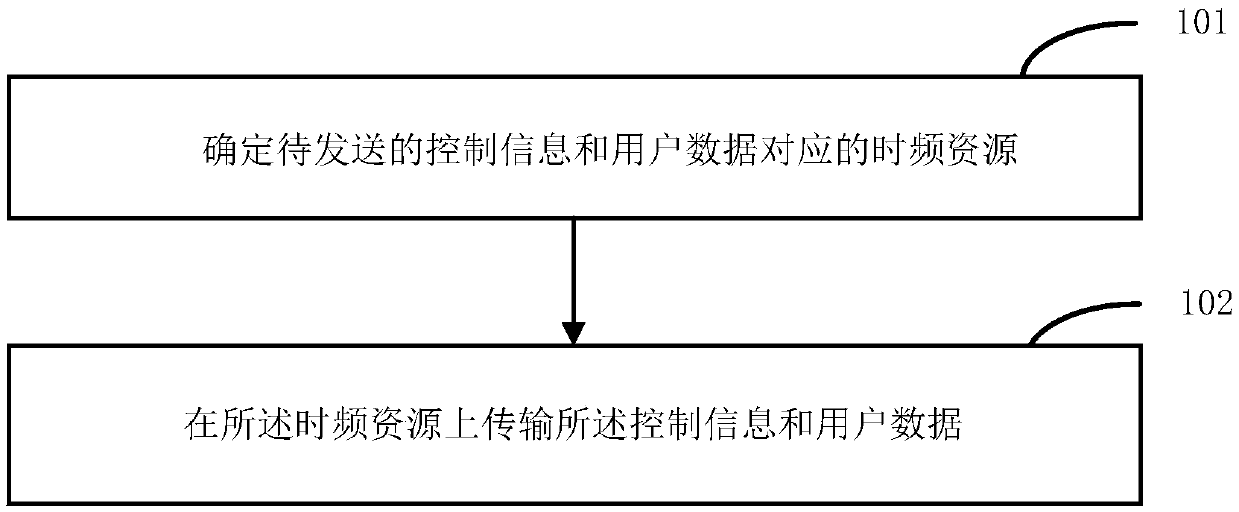
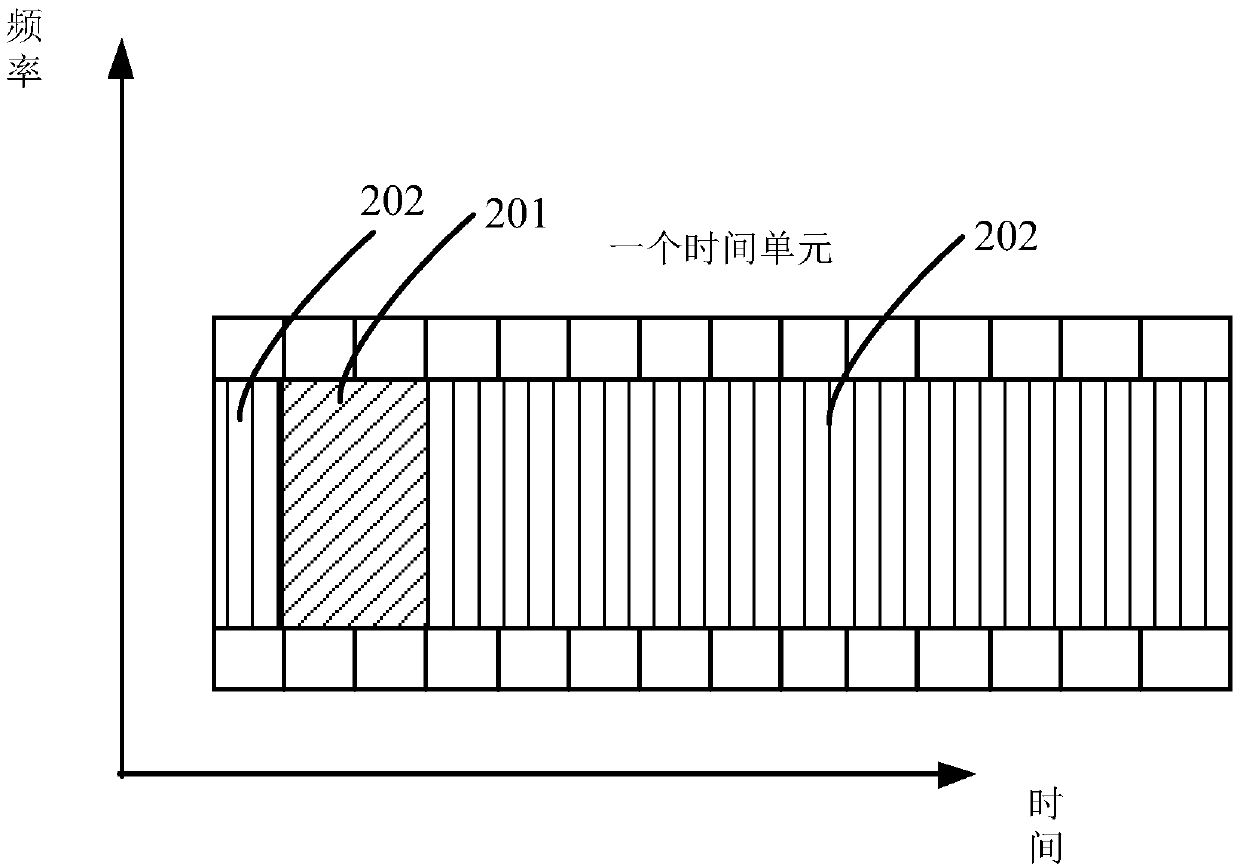
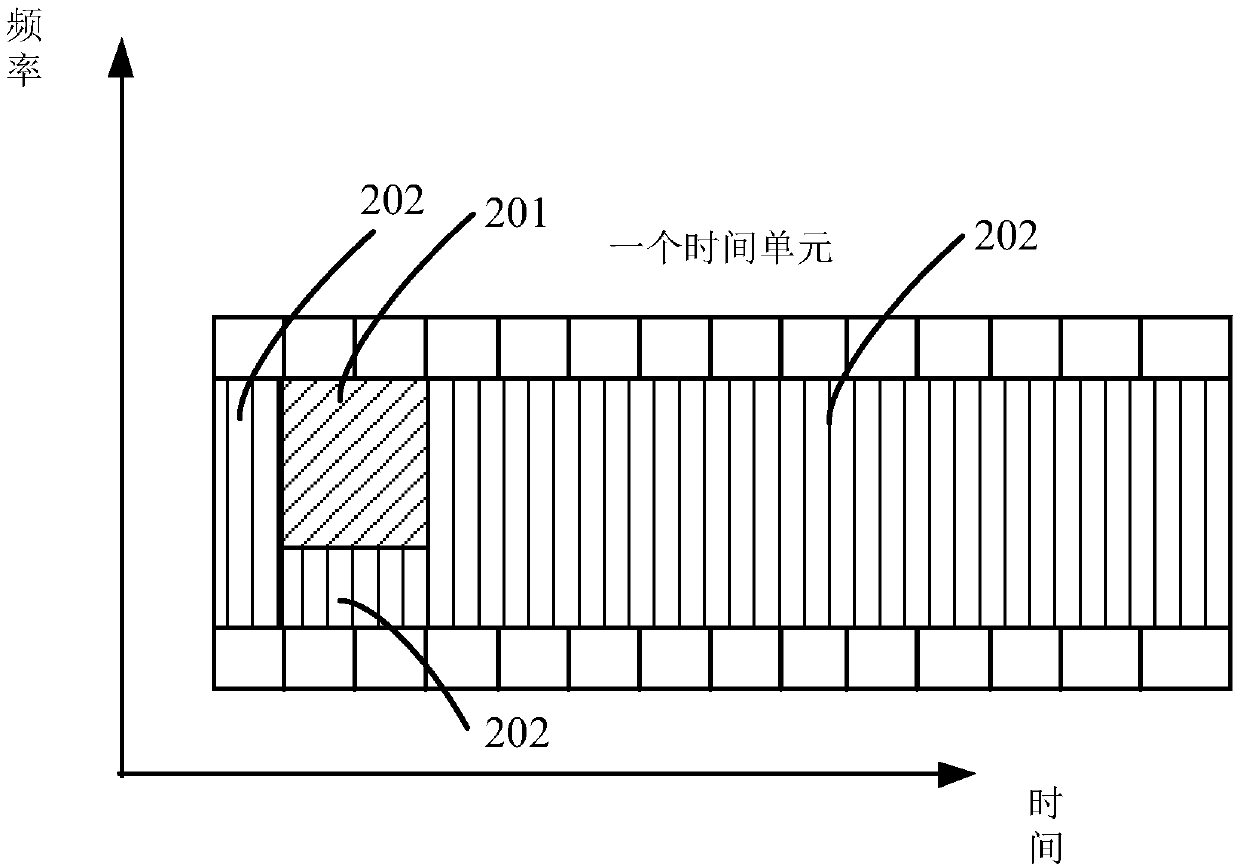
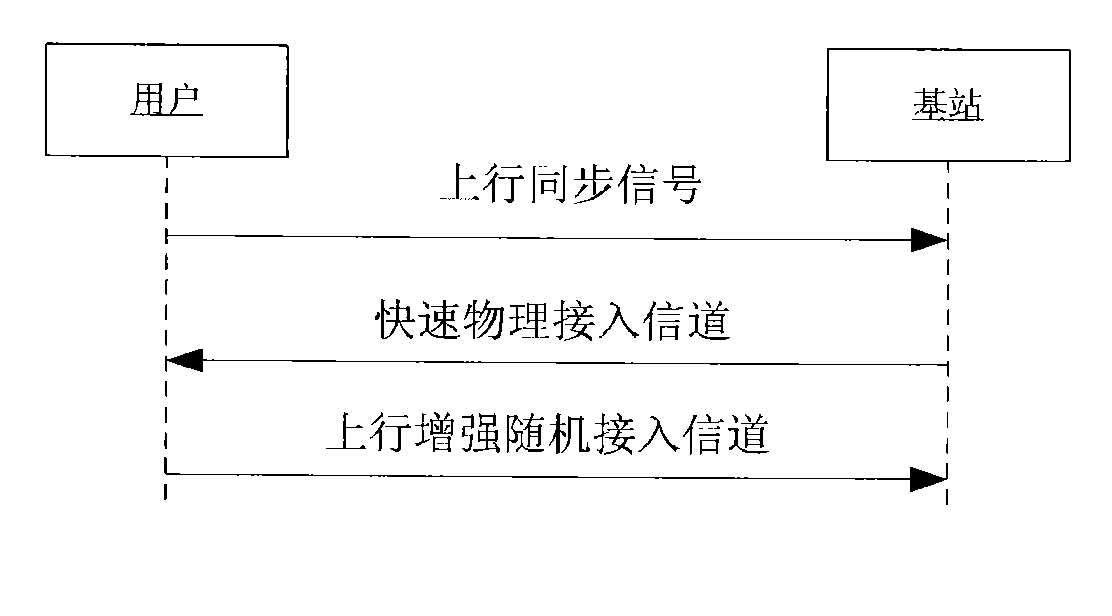
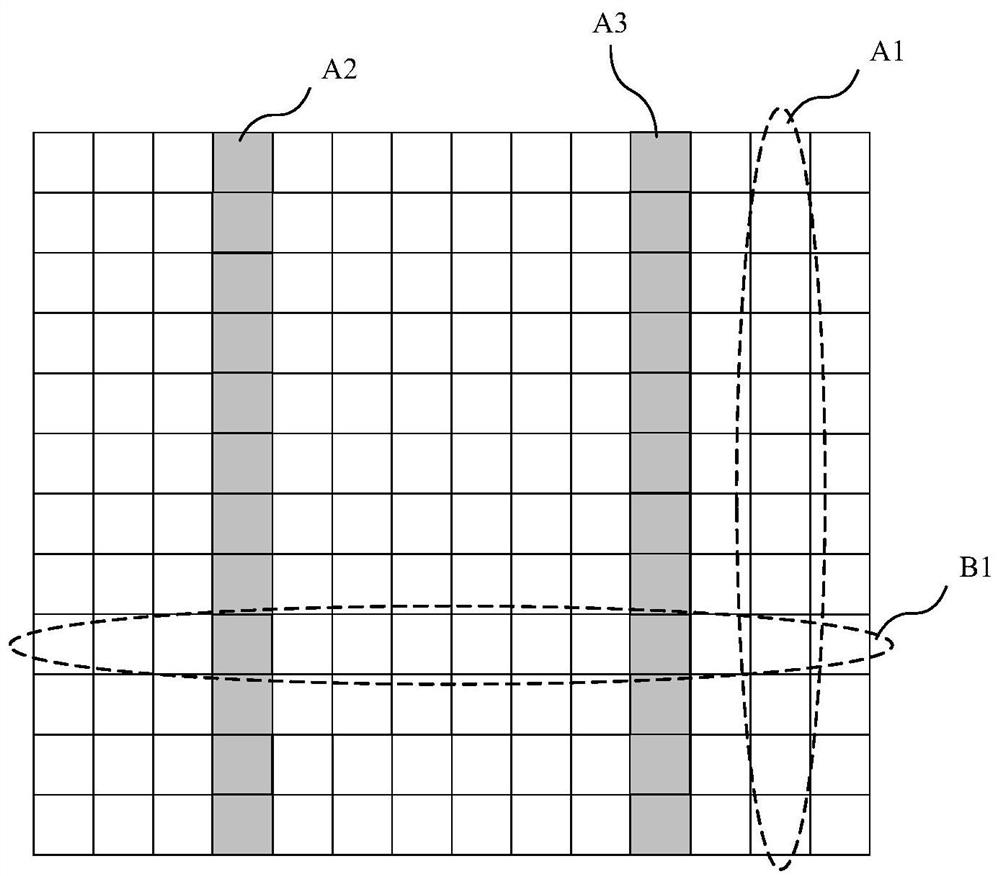
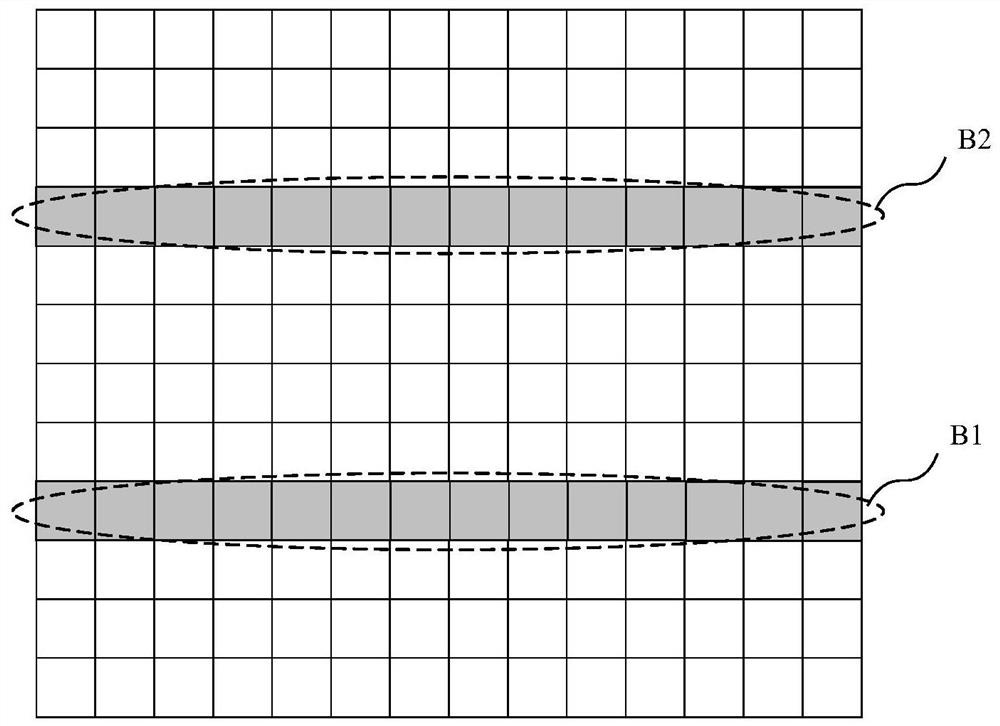
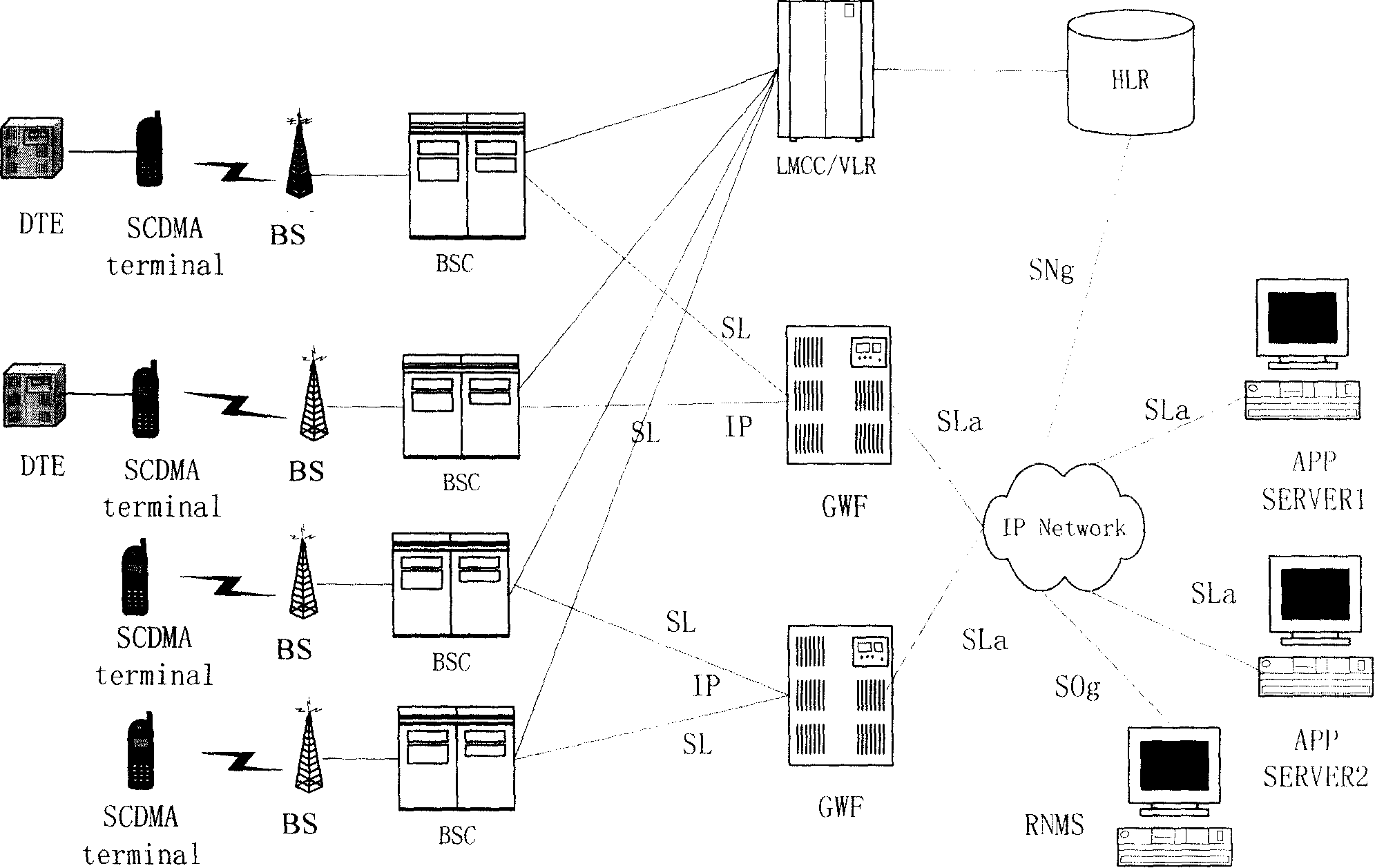
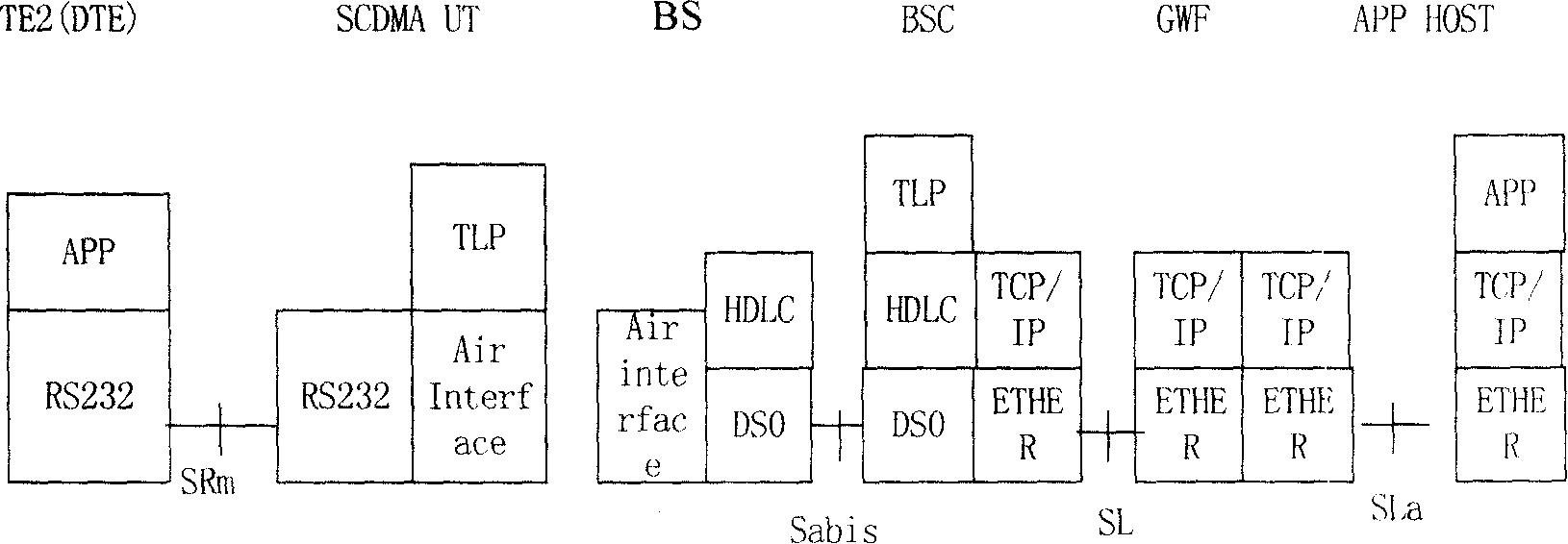
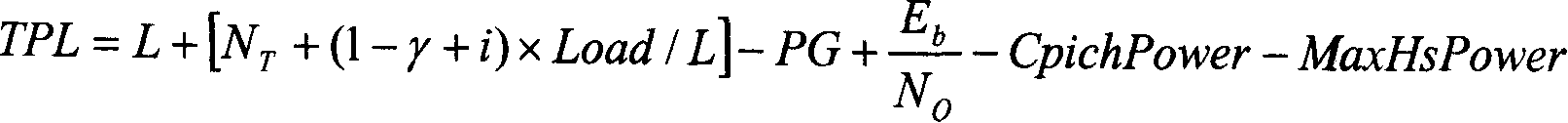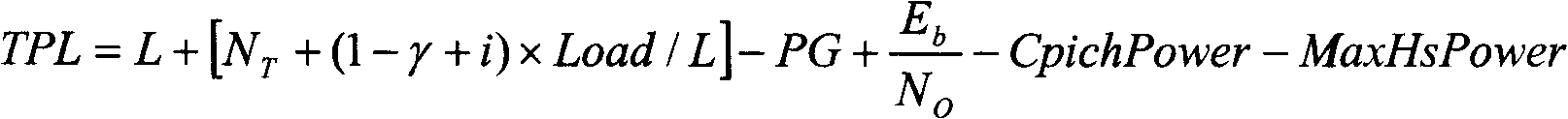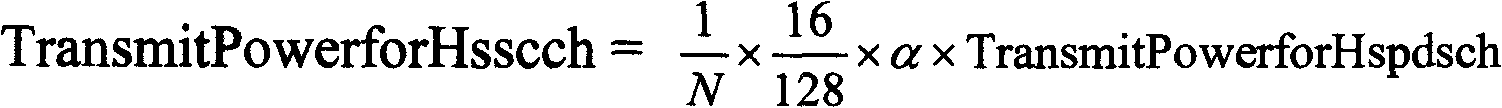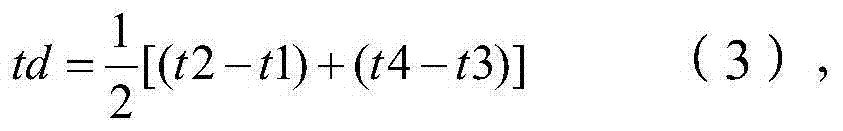Patents
Literature
83results about How to "Guaranteed to receive correctly" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
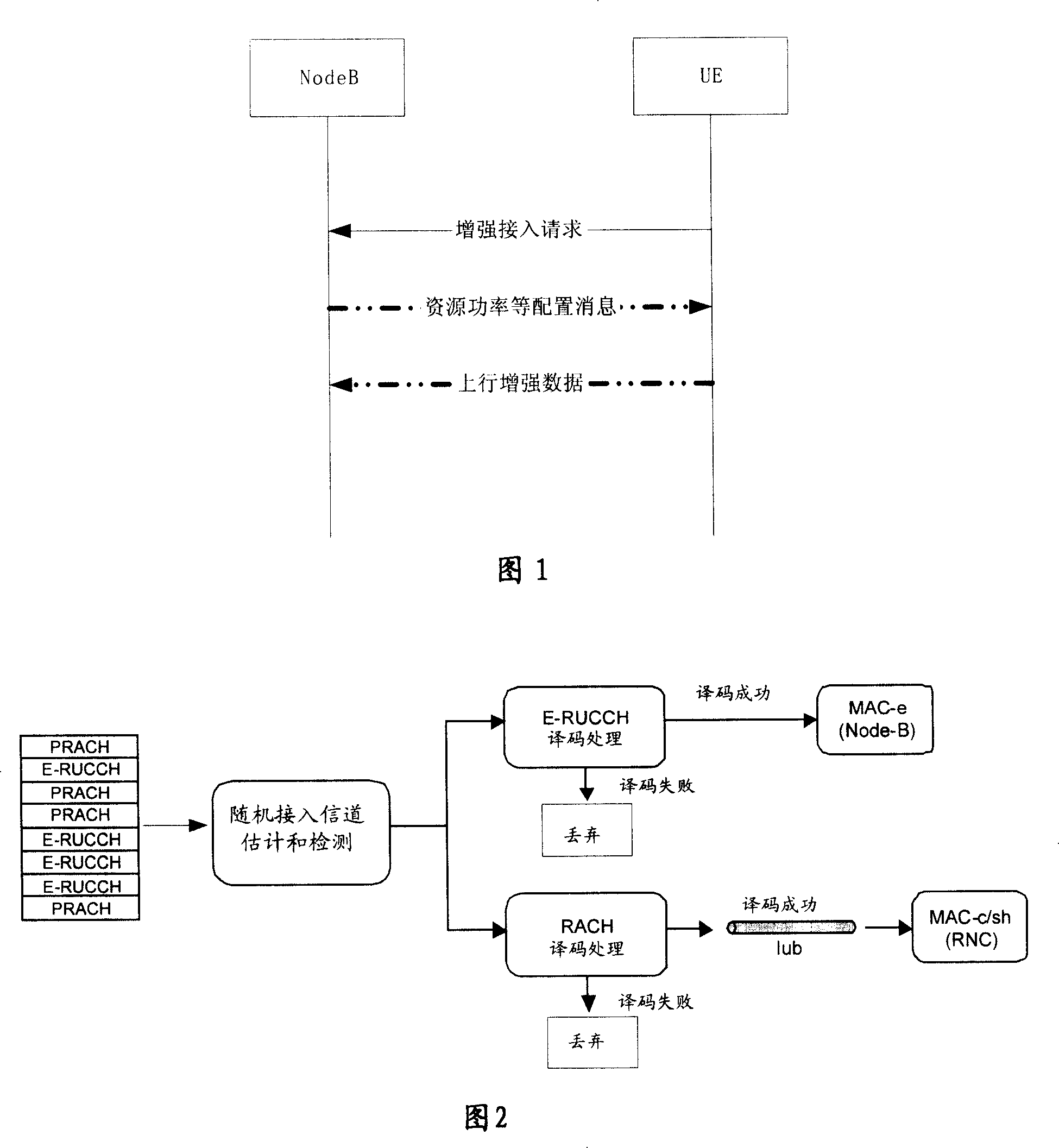
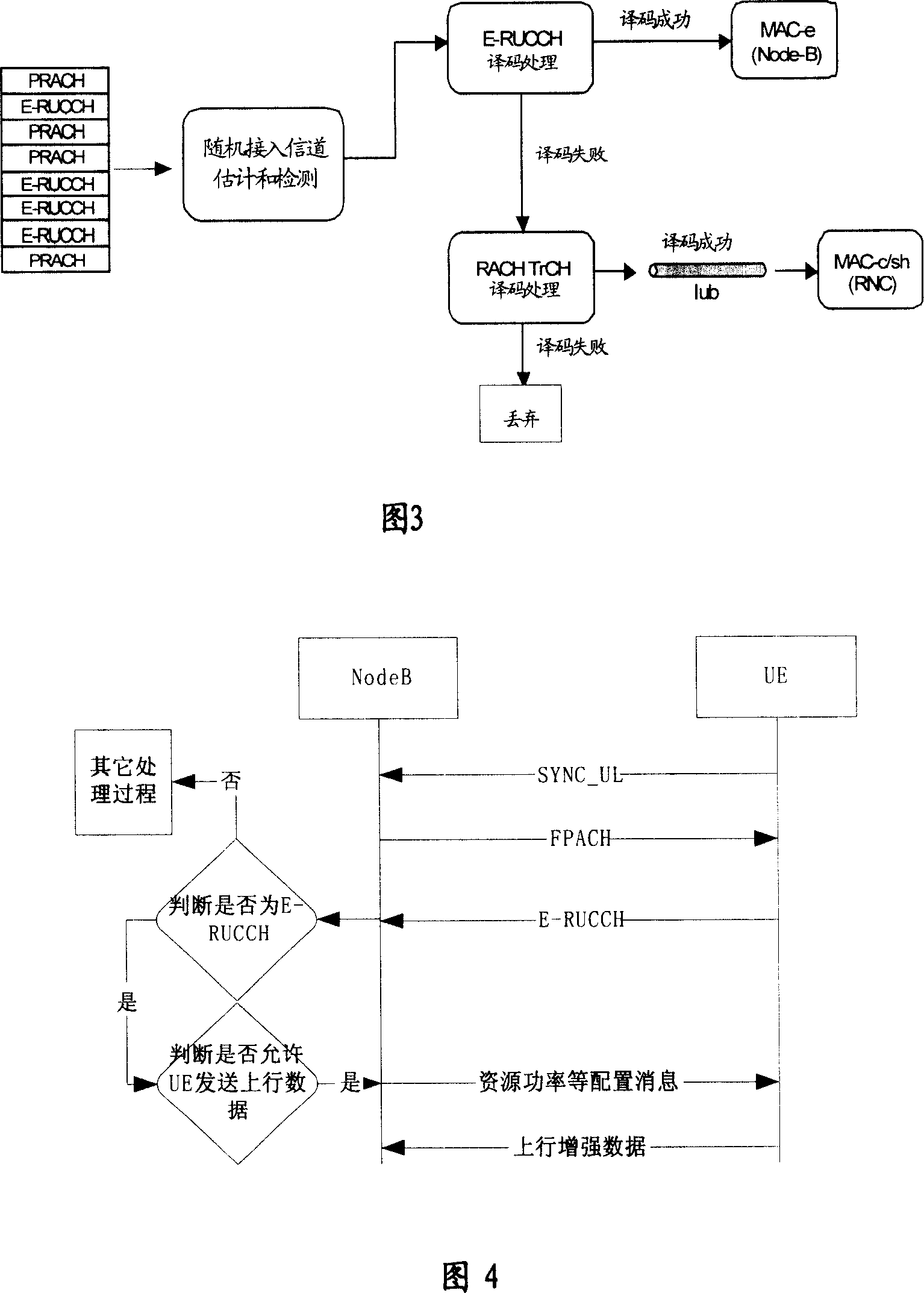
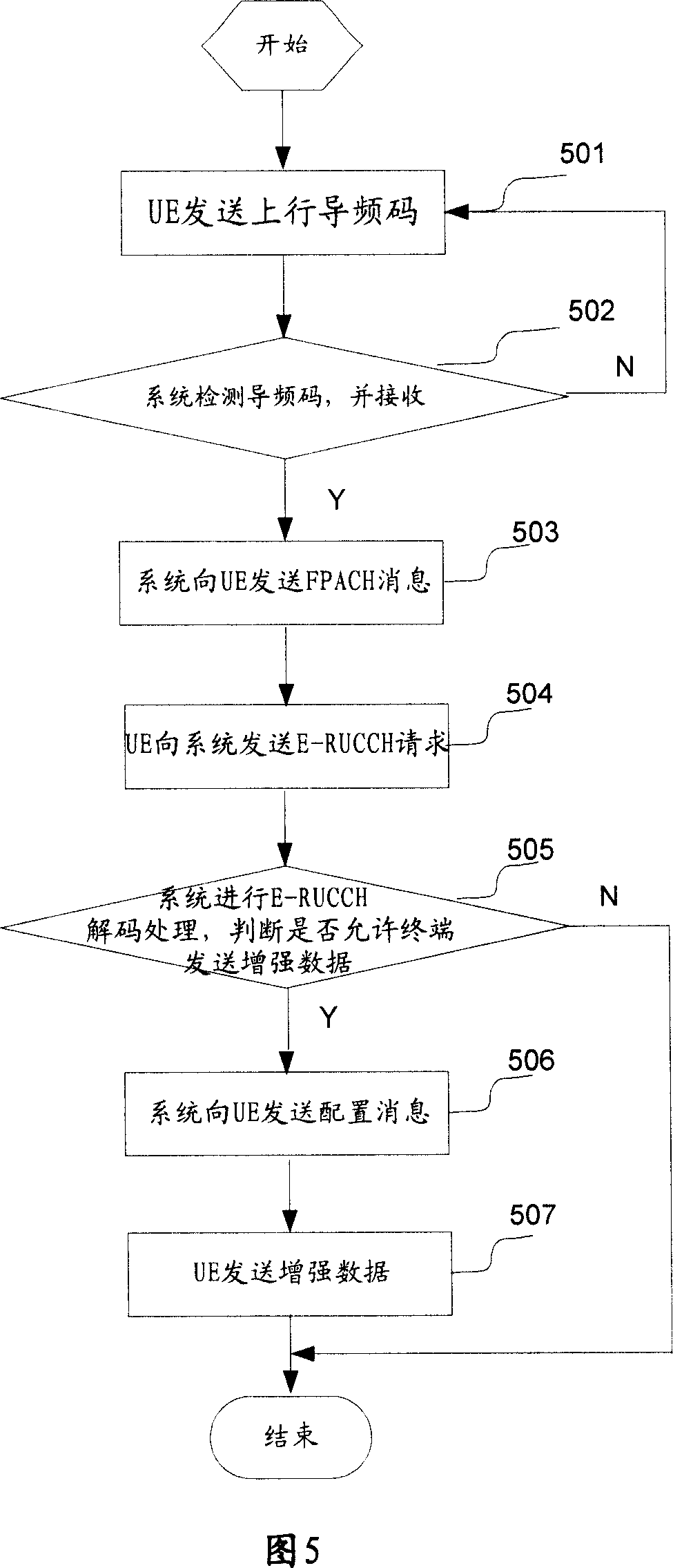
A method and device for enhancing random access
InactiveCN101123467AReduce the probability of collisionFlexible resource allocationTransmission control/equalisingCode division multiplexCollision probabilityFrequency code
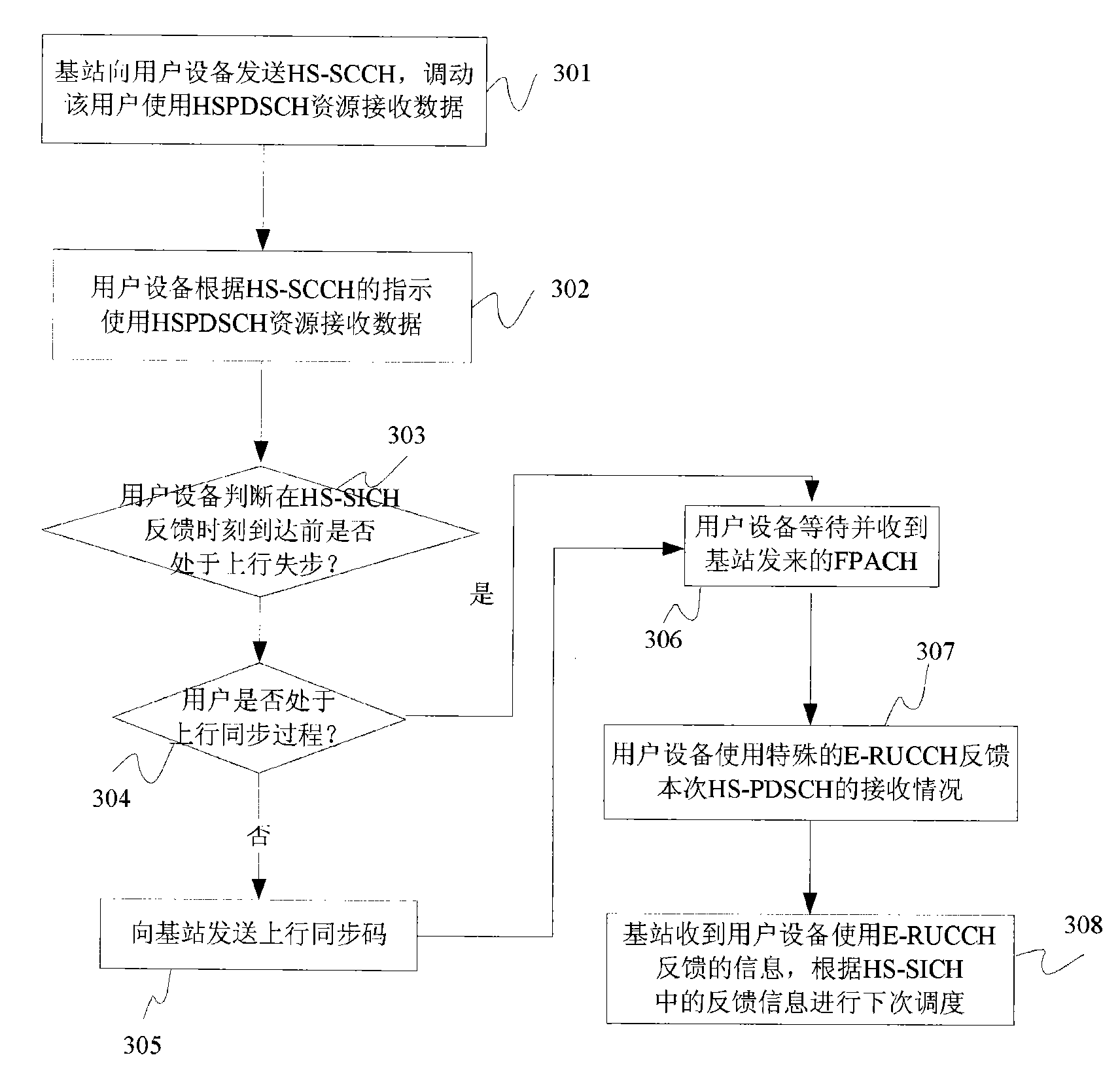
The invention provides a method to randomly access reinforced data, which comprises the following steps. Upstream pilot frequency codes transmitted by a terminal are detected and received; and information is fed back to the terminal. Reinforced data access request is transmitted by a receiving terminal; after that upstream reinforced data are allowed to be transmitted by the terminal is determined, configuration information, such as the information about physical resources and power, is transmitted to the terminal; the upstream reinforced data are received. The invention also provides a device to randomly access reinforced data. The device is detected by a processing unit, and receives upstream pilot frequency code sequence transmitted by a terminal. Reinforced data access request and reinforced data transmitted by the terminal are received. An information transmitting unit transmits feedback information to the terminal. When that the terminal is allowed to transmit reinforced data is determined, configuration information, such as the information about physical resources and power and so on, is transmitted to the terminal. A decoding processing unit decodes the reinforced data access request, and determines whether the terminal is allowed to transmit the reinforced data. The invention can ensure that the information of random access request of reinforced data can be received by a base station correctly; and the collision probability of E-RUCCH or PRACH of different terminals is reduced.
Owner:CHINA ACAD OF TELECOMM TECH
User equipment for wireless communication, and method and device in base station
ActiveCN109245869AInterference coordinationAvoid interferenceError preventionSignal allocationTime domainControl signal
The invention discloses user equipment for wireless communication, and a method and device in a base station. The user equipment receives a first signal at first, and then transmits a first wireless signal, and finally transmits a second signal. A time domain resource occupied by the first signal is used for determining a time domain resource occupied by the second signal. The first wireless signal is used for determining the time domain resource occupied by the second signal, and the first and second signals are respectively transmitted on a cellular link and a secondary link. Through the design of building a correlation between the time domain resources occupied by the first wireless signal and the second signal, the user equipment achieves a purpose that the adjacent base stations monitors a control signal on the secondary link in the D2D transmission, thereby achieving the inter-cell interference coordination, and improving the system performances and transmission efficiency.
Owner:SHANGHAI LANGBO COMM TECH CO LTD
Information reporting method and device
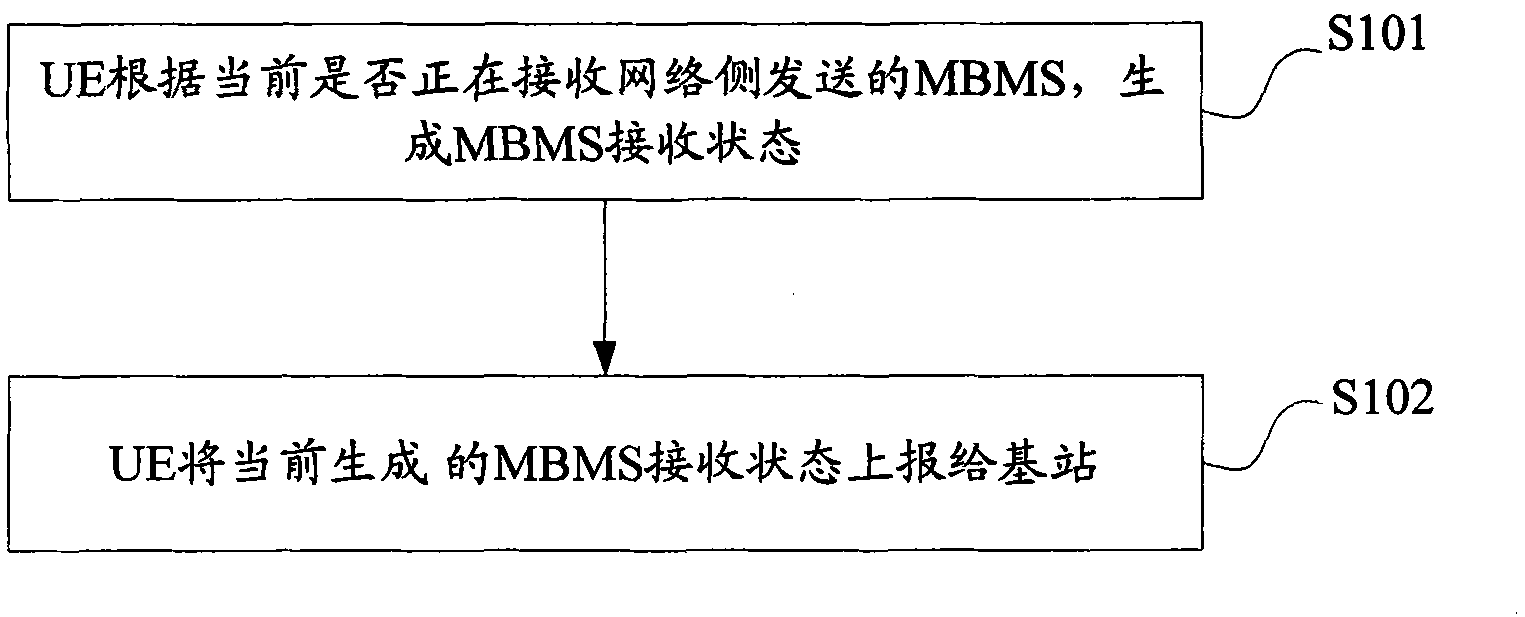
ActiveCN101931870AGuaranteed to receive correctlyConnection managementBroadcast service distributionMultimedia Broadcast Multicast ServiceComputer science
The invention discloses an information reporting method and an information reporting device, which are used for enabling a network to instantly acquire a multimedia broadcast multicast service (MBMS) receiving state reported by user equipment (UE) in a connected state, so that the network can configure rational parameter information such as time for measuring Gap and DRX in the UE and guarantee that the UE receives the MBMS normally. The information reporting method provided by the invention comprises the steps that: the UE generates the MBMS receiving state according to the receiving condition of the MBMS sent by the network; and the UE reports the currently generated MBMS receiving state to a base station.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Data distribution method and device in wireless heterogeneous network and wireless network controller
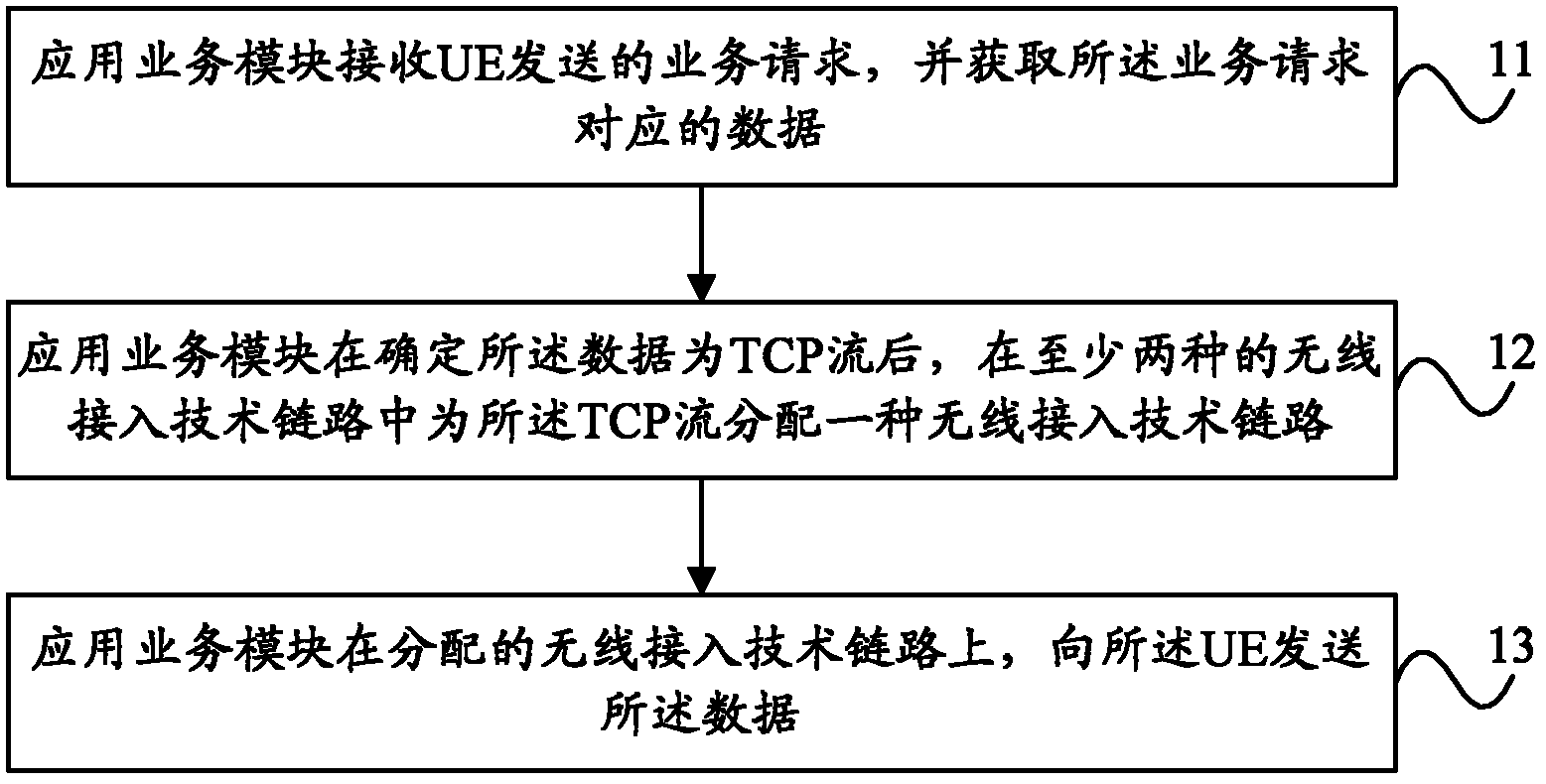
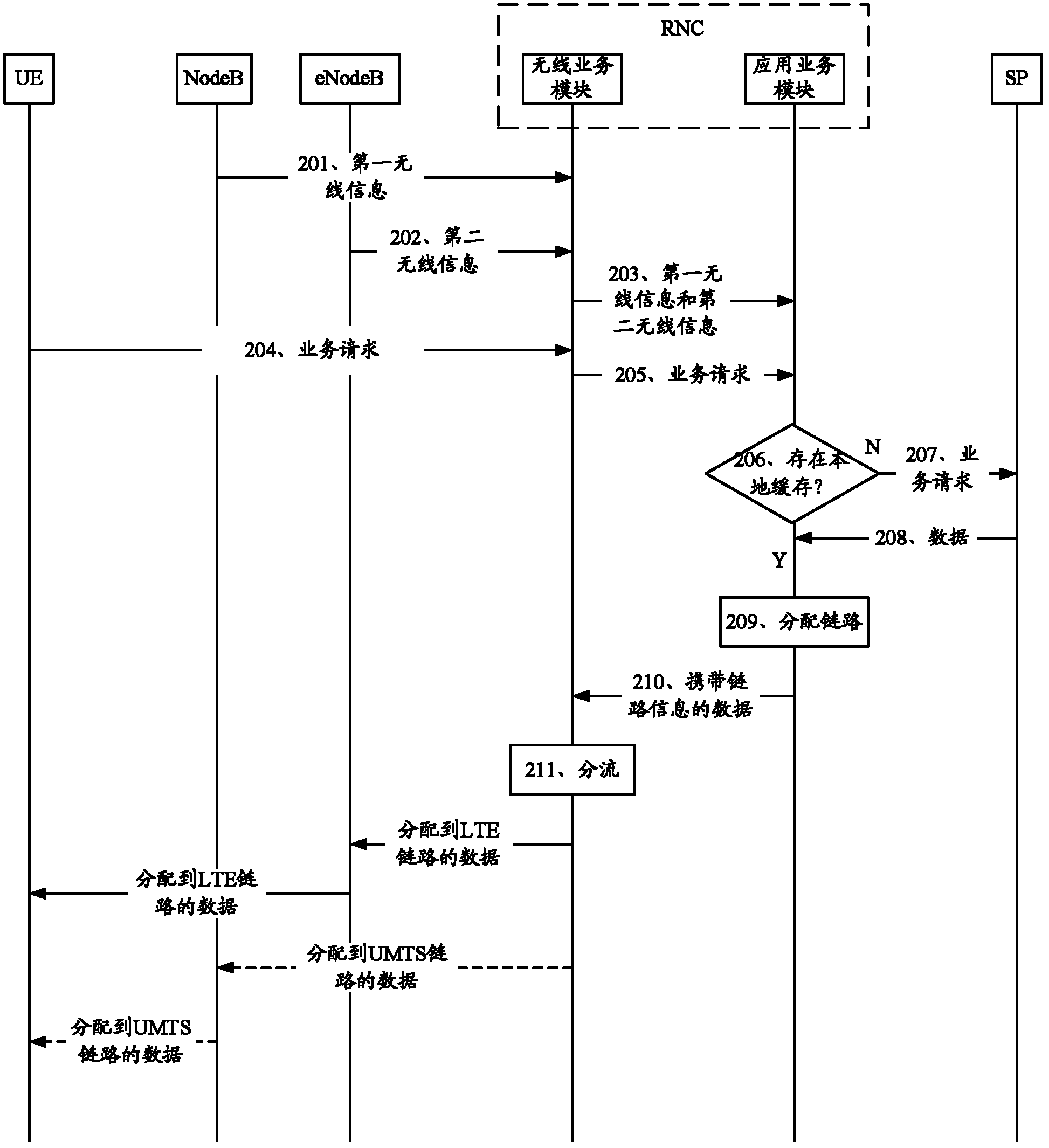
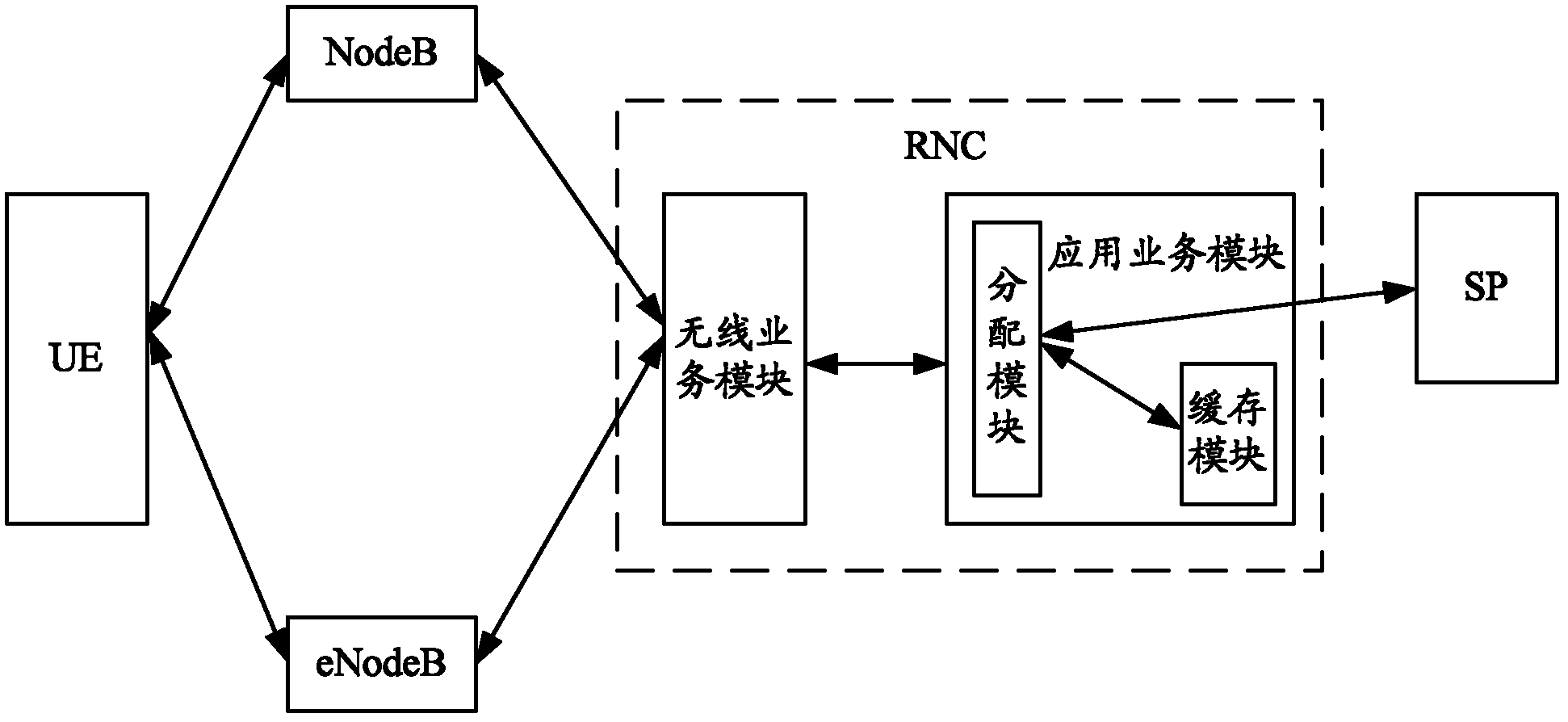
InactiveCN102355694AGuaranteed in-order deliveryGuaranteed to receive correctlyNetwork traffic/resource managementAssess restrictionDistribution methodWireless network coding
The invention provides a data distribution method and device in a wireless heterogeneous network and a wireless network controller. The method comprises receiving a service request sent by UE (user equipment), and acquiring data corresponding to the service request; distributing a wireless access technology link circuit for a TCP (Transmission Control Protocol) stream in at least two wireless access technology link circuits after determining that the data is a TCP stream; and transmitting the data on the distributed wireless access technology link circuit. The embodiment of the invention can ensure the sequential transmission of data of the same TCP connection.
Owner:HUAWEI TECH CO LTD
Method for controlling upline control channel power in soft switching of high speed data packet insertion system
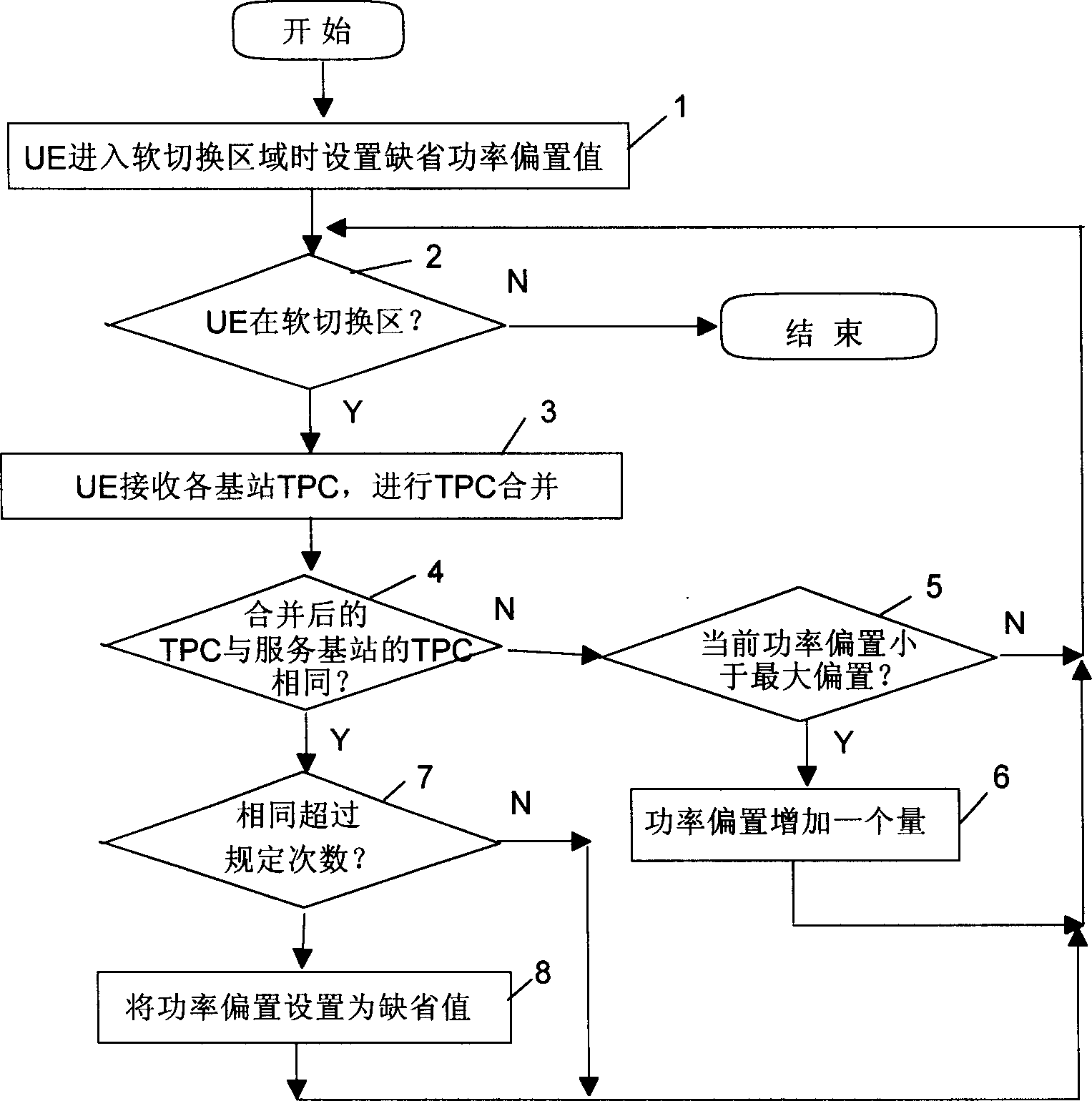
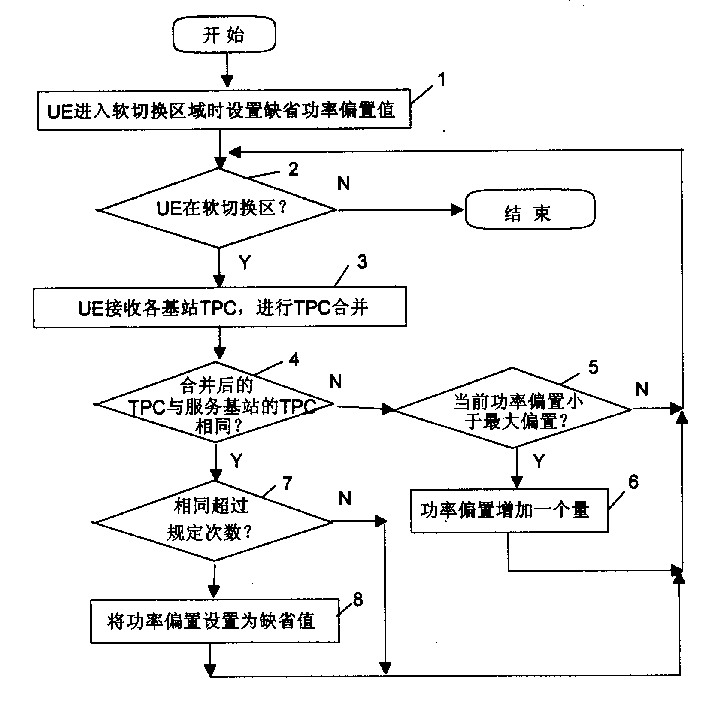
InactiveCN1450743AReduce transmit powerGuaranteed BERPower managementTransmission control/equalisingSoft switchingNetwork packet
The method sets powr offset of HS-DPCCH and RPP DPCCH as system default offst when UE is entering soft-switching area. It receives TPC of each base station and carries on TPC combination as well as sets power offset of HS-DPCCH and R 99 uplink DPCCH as system default offset if frequency of the combined TPC being the same with TPC received from service base station is over the appointed figure, and increases power offset tobe one more capacity if the combined TPC note being the same with TPC received from service base station at it being in range of the maximum allowable power offset when UE is on the period of soft-switching. By applying the method, HS-DPCCH emission power can be controlled in real-time when UE is at soft-switching area.
Owner:HUAWEI TECH CO LTD
Method and system for dynamically raising upper limit of PDCCH capacity and mobile terminal
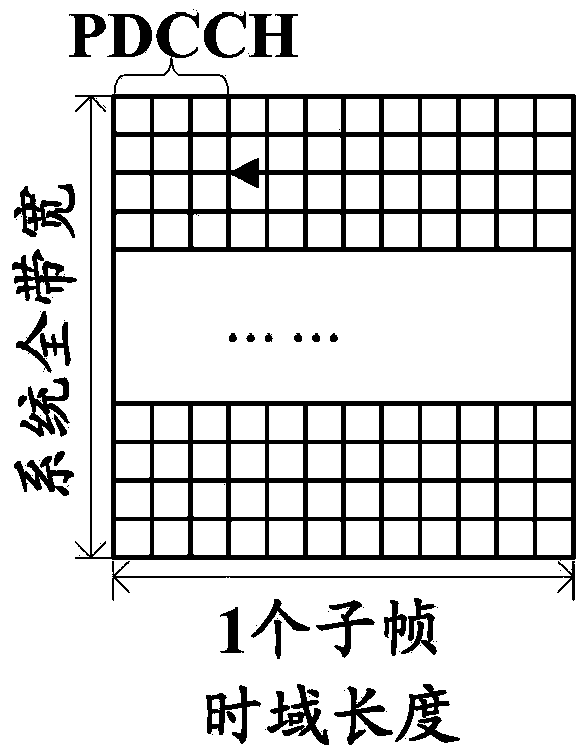
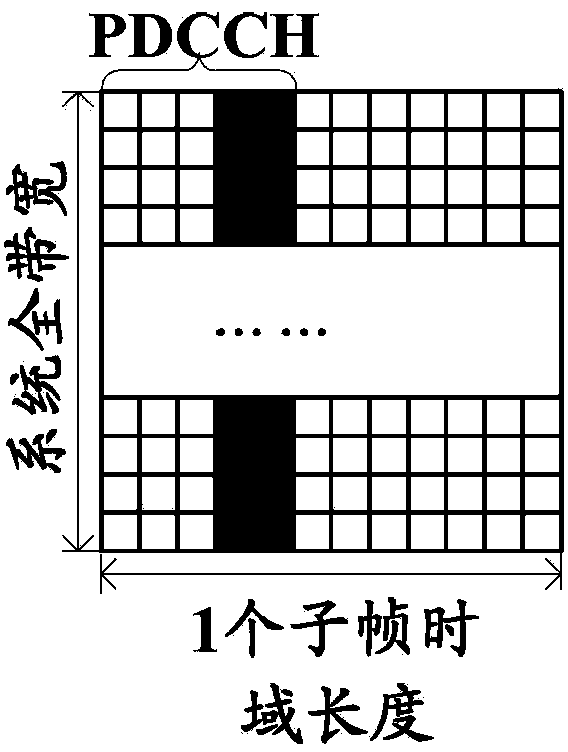
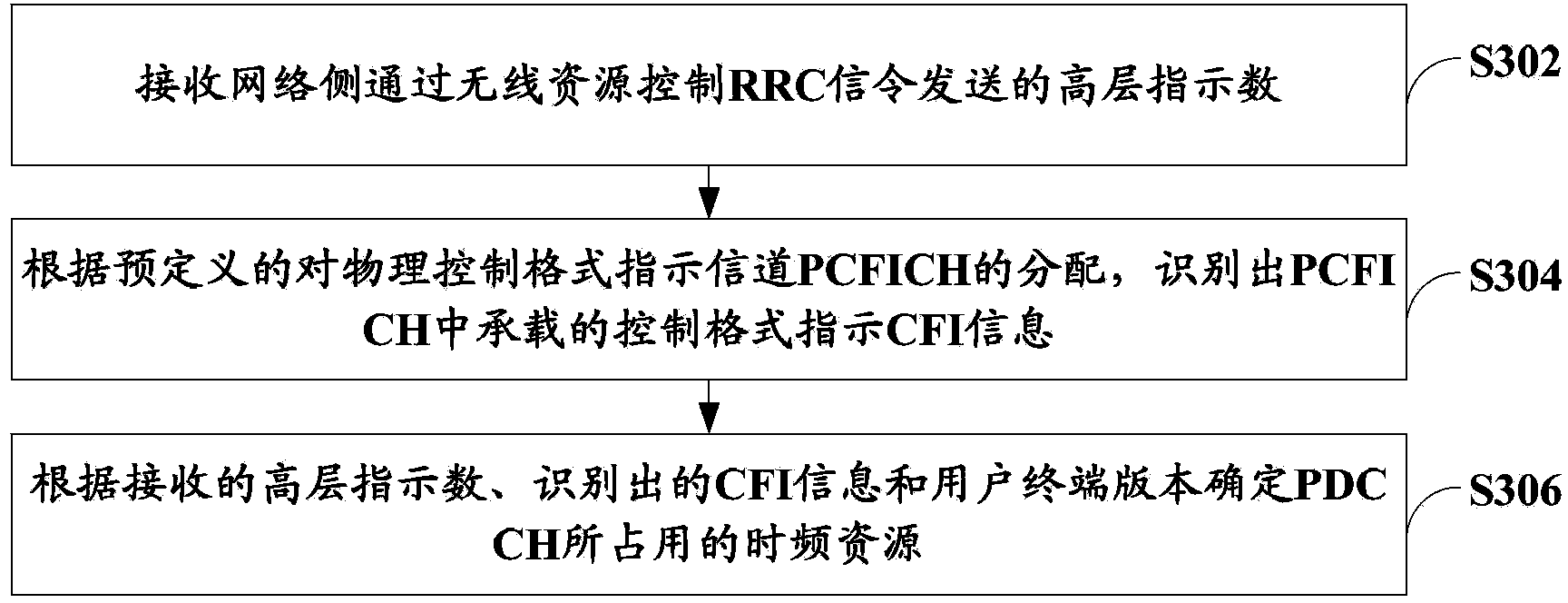
ActiveCN104144503AGuaranteed to receive correctlyMulti-frequency code systemsWireless communicationTelecommunicationsActive state
The invention relates to a method and system for dynamically raising the upper limit of the PDCCH capacity and a mobile terminal. The method comprises a high-level indication number sent by a receiving network side through RRC signaling is received, wherein the high-level indication number is determined on the basis of channel quality fed back by uplink data and / or the number of current users in the active state in a cell; according to predefined assignment of a PCFICH, CFI information carried in the PCFICH is recognized; time-frequency resources occupied by a PDCCH are determined according to the received high-level indication number, the recognized CFI information and a user terminal version. According to the method and system for dynamically raising the upper limit of the PDCCH capacity and the mobile terminal, on the premise that backward compatibility is guaranteed, dynamic configuration can be achieved, and the PDCCH capacity can be recognized.
Owner:CHINA TELECOM CORP LTD
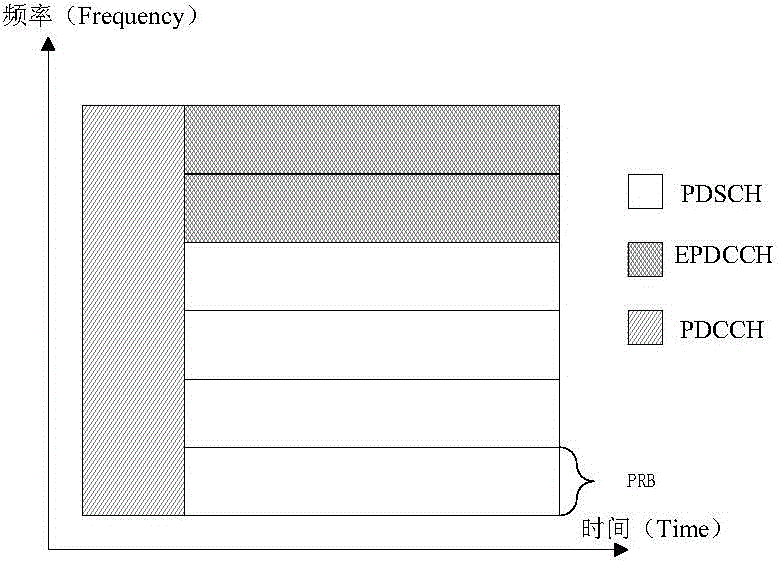
Downlink information sending method, downlink information receiving method, downlink information sending device and downlink information receiving device
ActiveCN105610556AGuaranteed to receive correctlySolve the problem that the downlink information cannot be receivedTransmission path multiple useWireless communicationTelecommunicationsNarrow band
Owner:ZTE CORP
Signal transmission method of a wireless earphone and a wireless earphone system
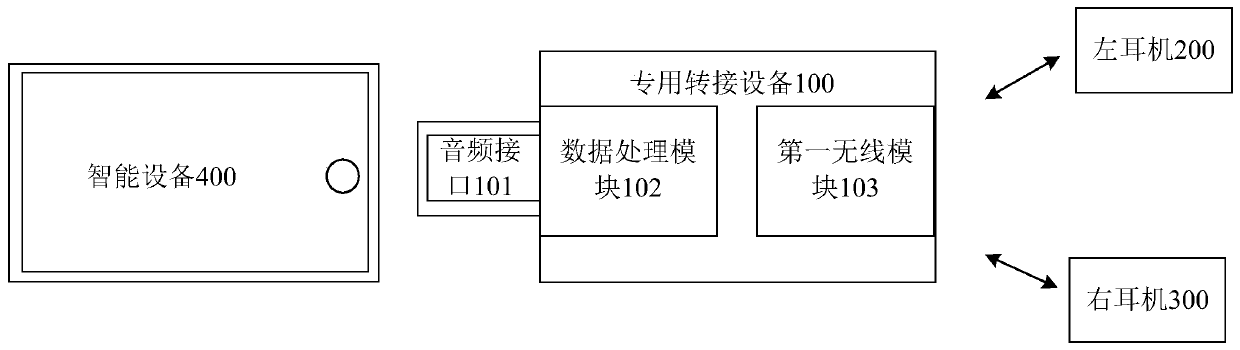
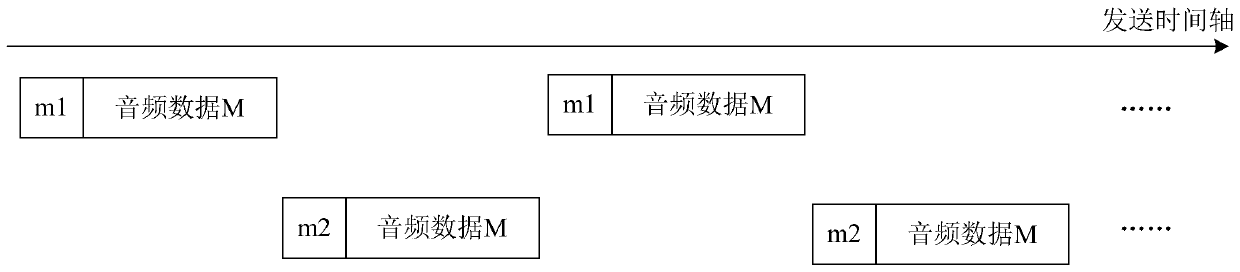
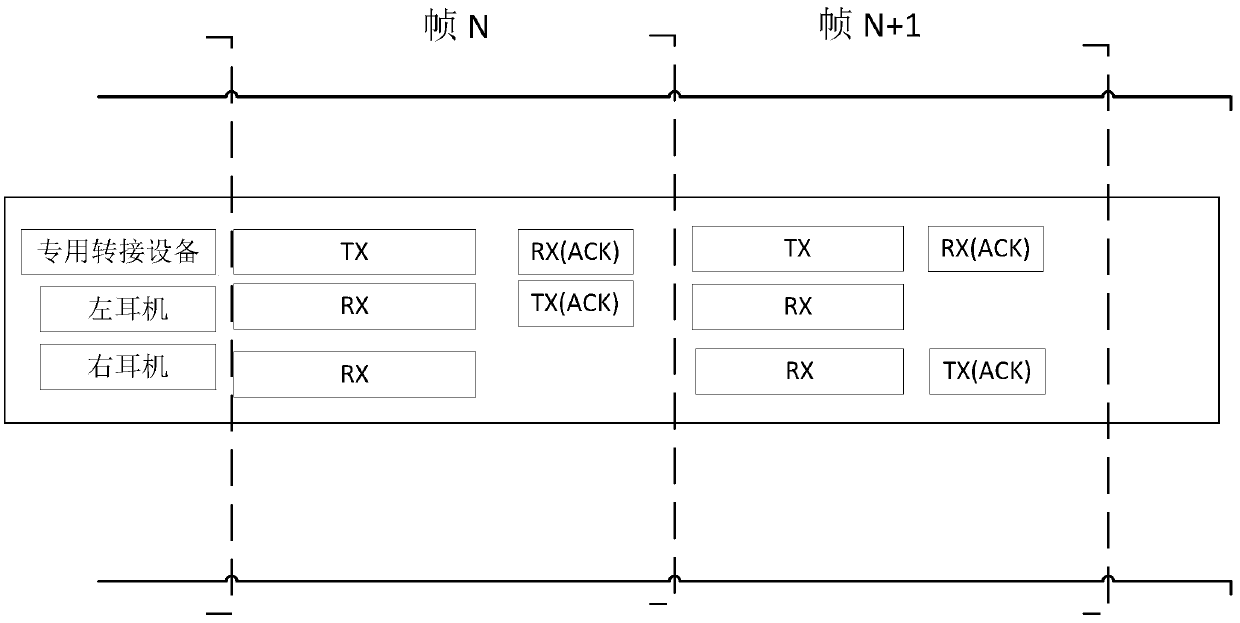
ActiveCN109819377AMeet the requirements of low-latency scenariosGuaranteed to receive correctlyConnection managementLoudspeaker signals distributionNetwork packetHeadphones
The invention provides a signal transmission method of a wireless earphone. The signal transmission method comprises the following steps that: a special switching device respectively marks a first identifier and a second identifier for certain audio data, and repeatedly sends the audio data with the first identifier and the audio data with the second identifier to a left earphone and a right earphone in turn; when the left earphone receives the audio data with the first identifier, an ACK data packet is returned to the special switching equipment; and when the right earphone receives the audiodata with the second identifier, an ACK data packet is returned to the special switching equipment. According to the signal transmission method of the wireless earphone, the delay of the wireless earphone can be effectively reduced aiming at a specific use scene, and low-delay communication between the intelligent equipment and the wireless earphone is realized.
Owner:BESTECHNIC SHANGHAI CO LTD
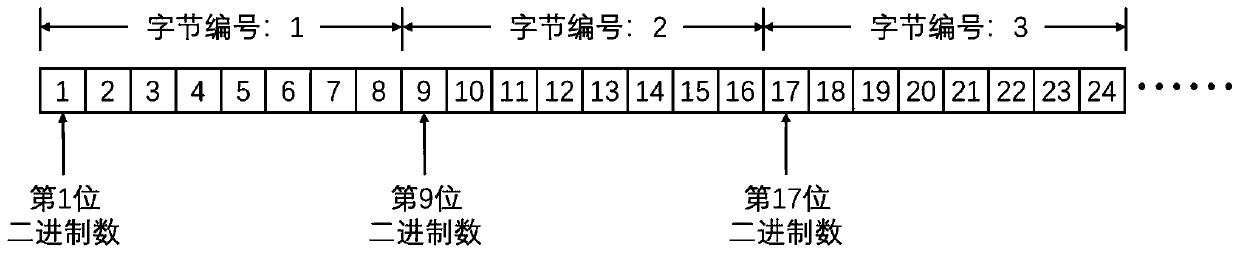
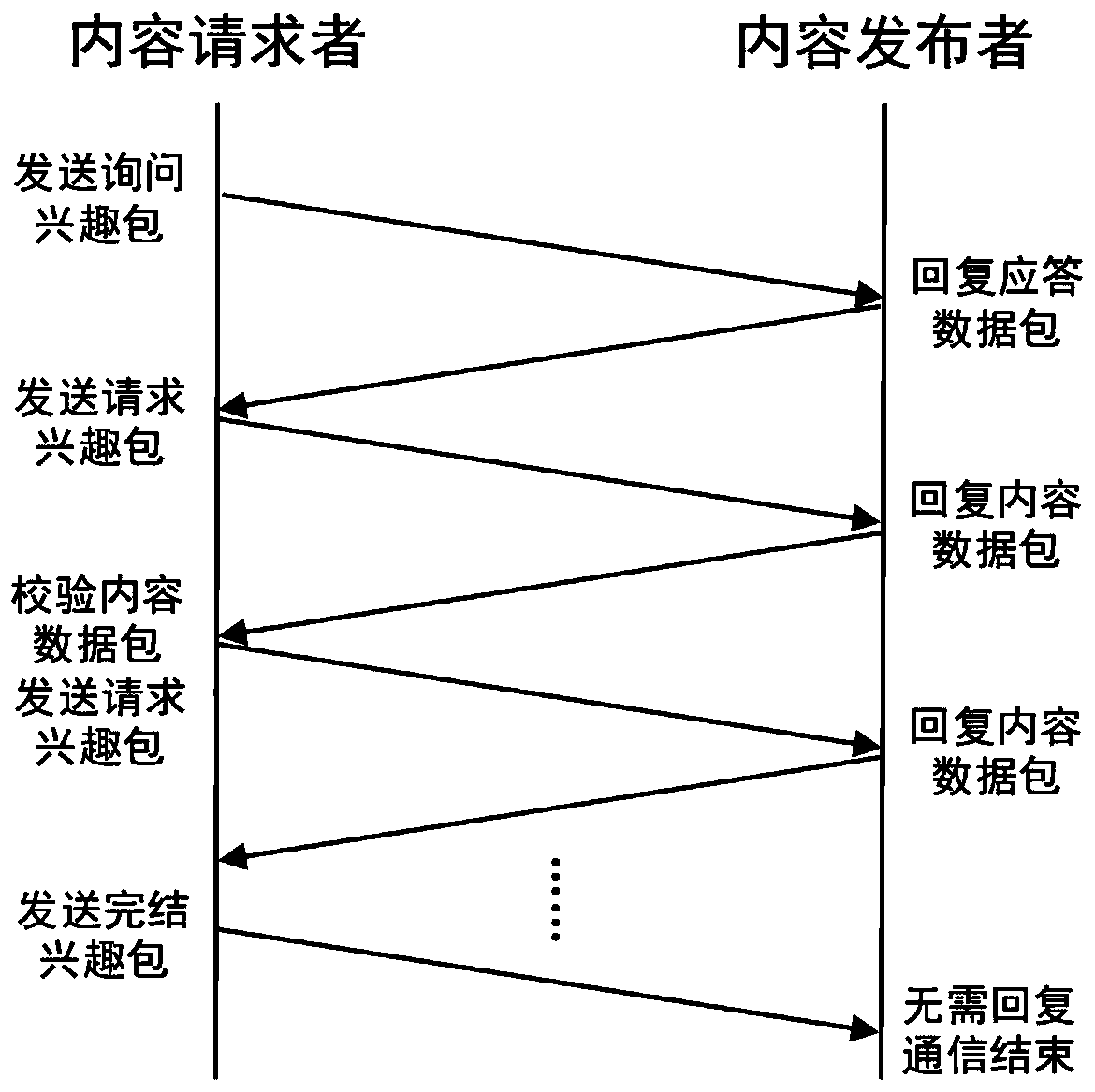
Reliable transmission method for named data network data fragments based on byte numbers
ActiveCN110753003AGuaranteed to receive correctlyReliable transmissionError prevention/detection by using return channelData switching networksComplete dataData pack
The invention relates to a reliable transmission method for named data network data fragments based on byte numbers, and belongs to the technical field of computer network data transmission. The method comprises the following steps: a publisher numbers each item of data content according to bytes; a requester sends an inquiry interest packet and compares the maximum transmission unit MTU record minimum values of the forwarding nodes; the publisher replies the response data packet to inform the byte length, the starting byte number and the maximum transmission unit, wherein the request interestpacket sent by the requester comprises the name and byte number range of the data content to be acquired; the publisher encapsulates the data content of the corresponding byte into a content data packet and replies the content data packet to the requester; the requester waits for receiving the content data packet and prepares to retransmit the request interest packet; the requester receives and verifies the content data packet, and determines to retransmit the request interest packet or continuously request the subsequent content data packet according to the verification result; and the requester correctly receives the complete data content and then finishes data transmission. According to the method, reliable data transmission and link congestion avoidance are realized.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Multicast method for distributing mass file applied to satellite data broadcasting system
InactiveCN1481132AGuaranteed correctnessGuaranteed stabilityTransmissionComputer hardwareSatellite data
The invention guarantees that in transferring large type of file, data transmission is correct and reliable as well as transmitting speed and redundancy are adjustable so as to raise stability and quality of satellite system of operation. UDP / IP protocol is adopted in the invention, and forward error correction (FEC), asynchronous layered code (ALC) and receive layered control (RLC) is utilized in code transmission layer. Recovery volumes are adopted in file process layer of application layer. Thus, large file is divided into hundreds or thousands of small files. Recovery volume is generated for each small file. When error occurs, receiver through redundant volume recovers and corrects errors. The invention is mainly applied to transmission of large file on monodirectional unreliable link of satellite.
Owner:TSINGHUA TONGFANG CO LTD
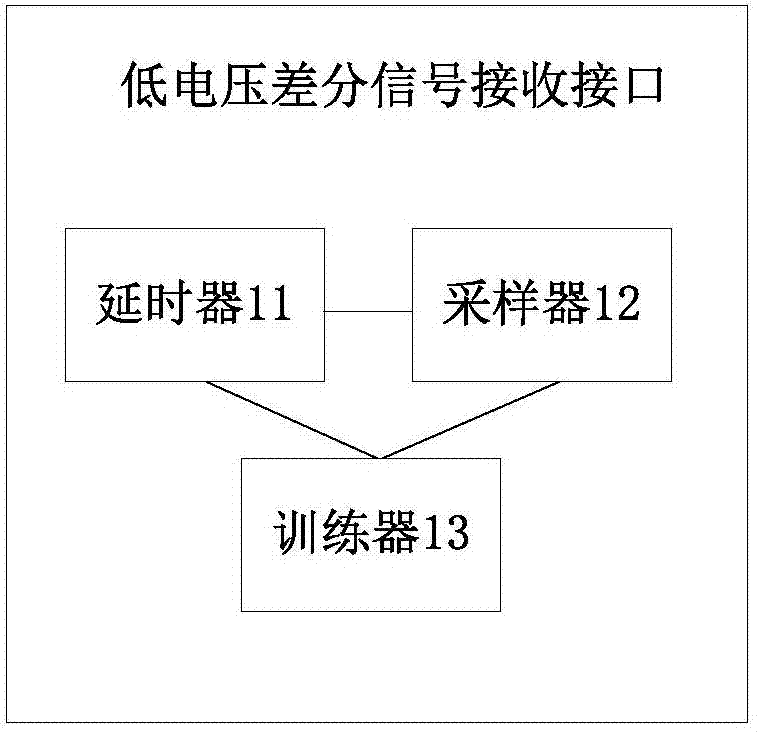
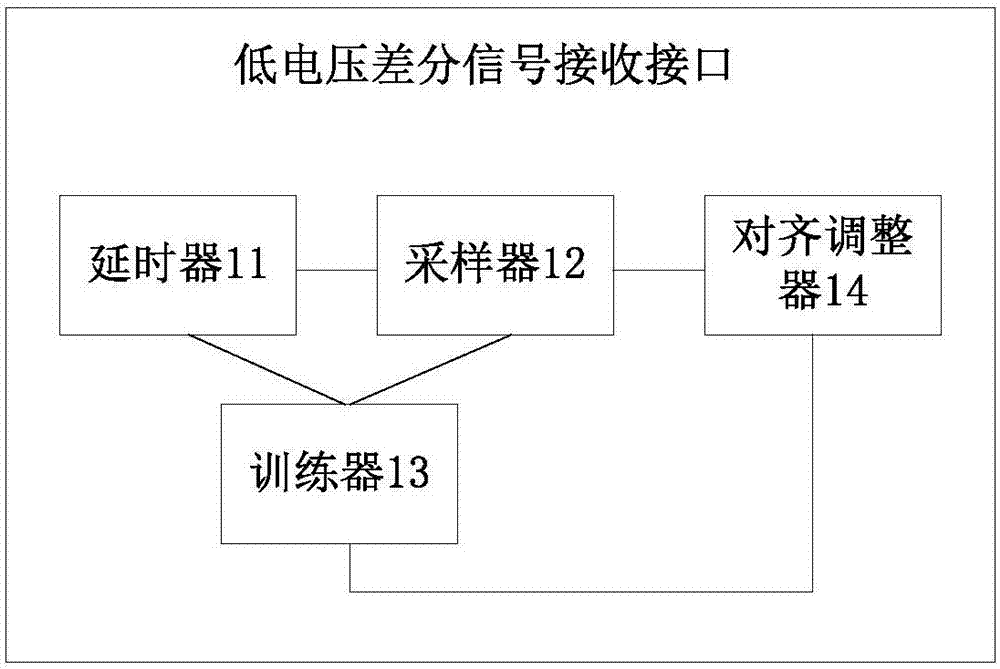
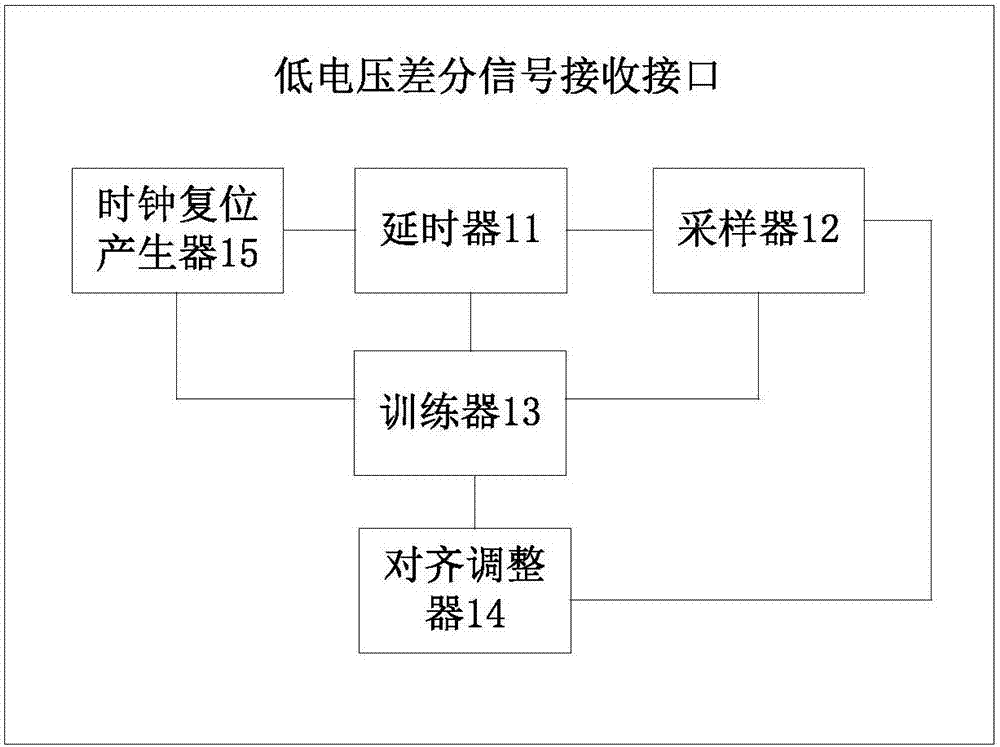
Low-voltage differential signaling receiving interface and low-voltage differential signaling receiving method
ActiveCN106959934AGuaranteed to receive correctlyElectric digital data processingStep countingData subject
The invention discloses a low-voltage differential signaling receiving interface and a low-voltage differential signaling receiving method. The method comprises the following steps of carrying out delay processing on serial sample data sent by a sender according to a preset delay step, carrying out sampling on the serial sample data subjected to delay processing within the delay step and converting the serial sample data into parallel sample data; analyzing the collected parallel sample data, determining a steady state of the corresponding delay step and determining a data boundary; and if the data boundary is not determined when the delay step reaches a preset maximum delay step N and each delay step is in the steady state, directly obtaining delay time corresponding to an N / 2th delay step as sampling delay time to carry out delay setting. When a data sampling window exceeds an adjustable range of a delay unit, if each delay step is in the steady state, the delay time corresponding to the N / 2th delay step is taken as the sampling delay time, so that a best sampling point of the data is determined, and thus the correct reception of transmission data is guaranteed.
Owner:SHENZHEN PANGO MICROSYST CO LTD
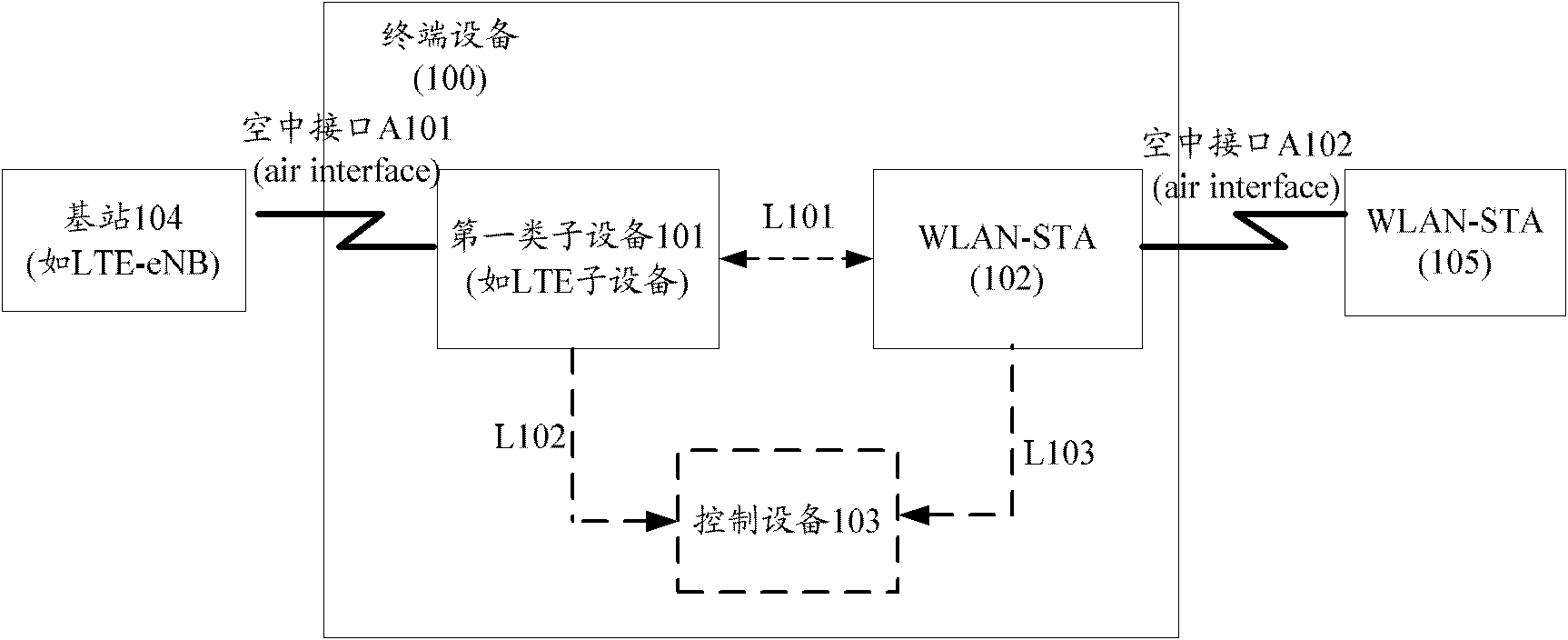
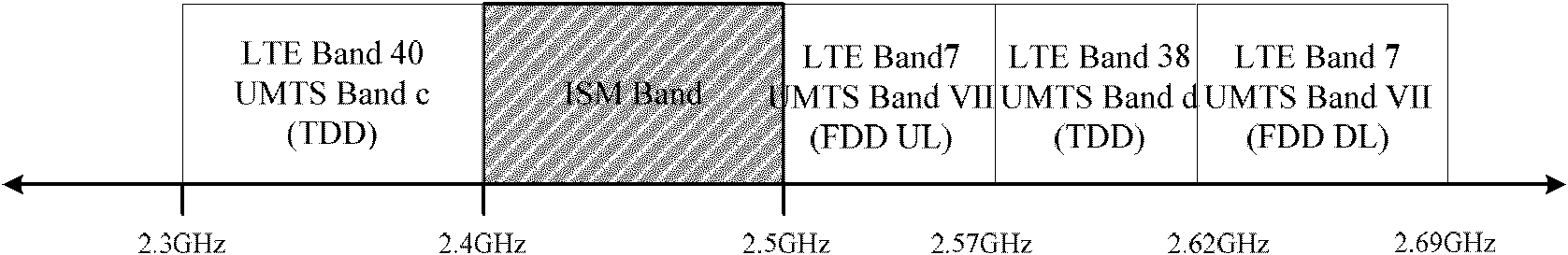
Processing method and terminal device for avoiding WLAN beacon
InactiveCN102595424AGuaranteed to receive correctlyGuaranteed communication qualityNetwork traffic/resource managementNetwork planningCommunication qualityTerminal equipment
The invention discloses a processing method and a terminal device for avoiding a WLAN (wireless local area network) beacon, which are used for solving the problem of interference between a WLAN beacon signal and a signal of a first type sub-device when the frequency interval between the working frequencies used by the first type sub-device and a WLAN sub-device is very small in the terminal device simultaneously supporting a first type technology (LTE (long term evolution) and / or UMTS (universal mobile telecommunications system) technology) and the WLAN technology. In the processing method of the invention, after the first type sub-device obtains a beacon processing timing sequence information of the WLAN sub-device, a base station configures the beacon processing time for the first type sub-device or the first type sub-device sets the beacon processing time by itself, and the first type sub-device stops transmitting and / or receiving data within the beacon processing time. The processing method and the terminal device can effectively ensure the correct receiving of the WLAN beacon in the terminal device supporting both the LTE technology and the WLAN technology, or guarantee that the first type sub-device cannot be affected when transmitting the WLAN beacon, thereby ensuring the communication quality of the LTE and the WLAN.
Owner:ZTE CORP
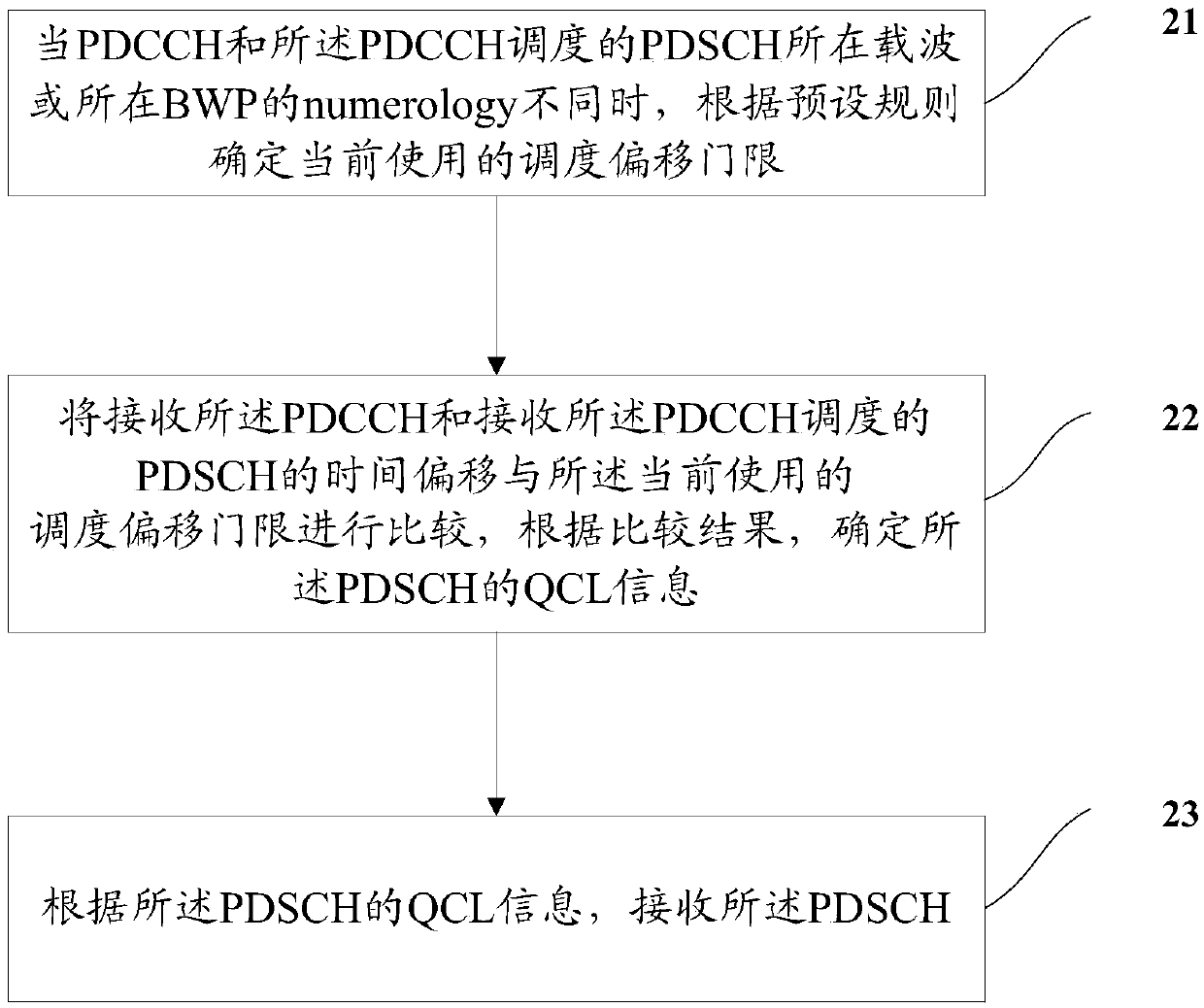
Determination method and configuration method of scheduling parameters, terminal and network side equipment
ActiveCN110719631AGuaranteed to receive correctlyModulated-carrier systemsTransmission path divisionComputer networkCarrier signal
Owner:VIVO MOBILE COMM CO LTD
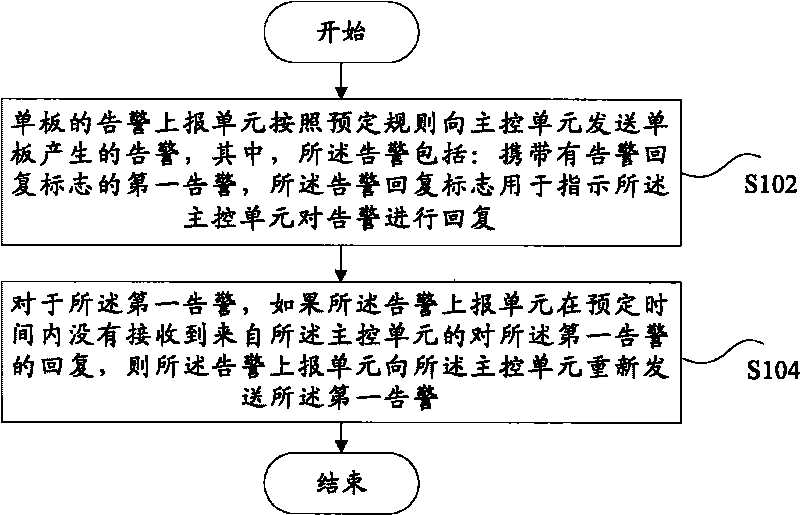
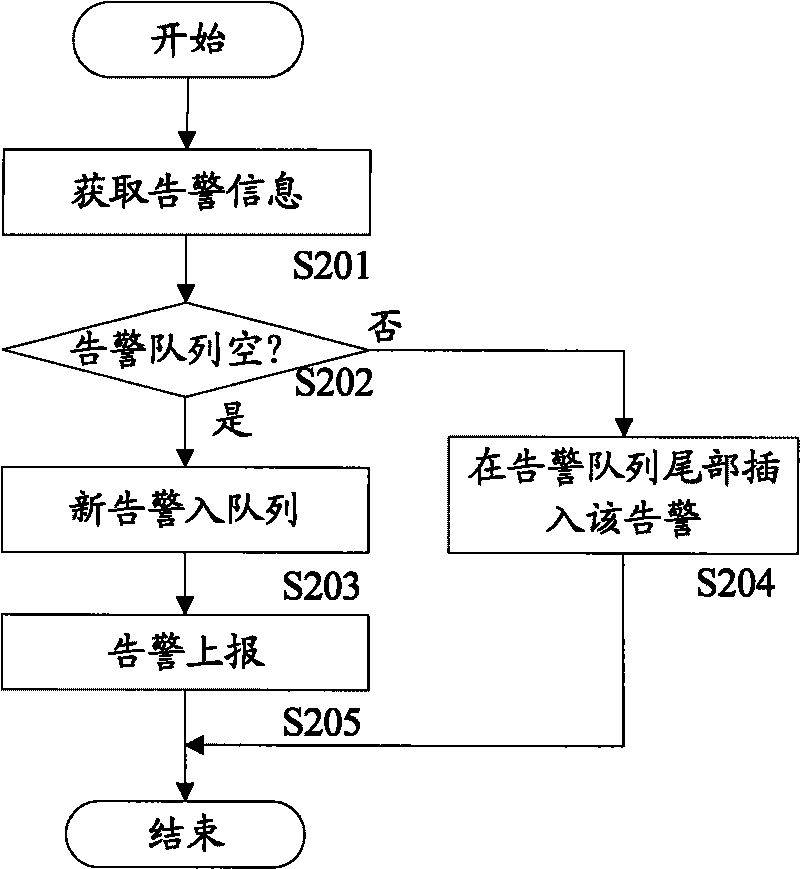
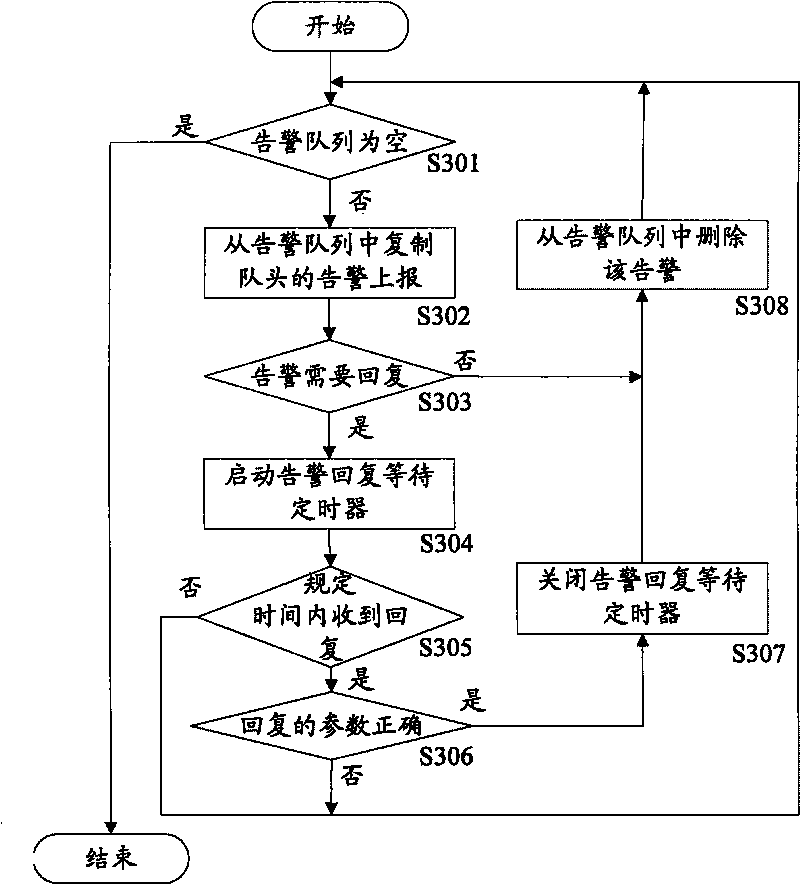
Alarming reporting method and device
InactiveCN101765204AGuaranteed to receive correctlySolve problems receivedWireless communicationSingle plateComputer science
The invention discloses an alarming reporting method and a device; wherein the method comprises the following steps: an alarming reporting unit of a single plate transmits alarming generated by the single plate to a main control unit according to the presetting rule, wherein the alarming comprises a first alarming which carries over an alarming reply sign, and the alarming reply sign is used for indicating the reply of the main control unit to the alarming; for the first alarming, if an alarming reporting unit can not receive the reply of the first alarming, from the main control unit within presetting time, the alarming reporting unit transmits the first alarming to the main control unit again; by adopting the technical proposal, the alarming reporting unit indicates the main control unit to reply to the first alarming, so as to ensure the first alarming to be accurately received by the main control unit and solve the problem that the important alarming can not be ensured to be received by the main control unit in the related technology.
Owner:ZTE CORP
Uplink control information sending and receiving method and device
ActiveCN110224796AGuaranteed to receive correctlyError prevention/detection by using return channelTransmission path divisionTerminal equipmentComputer terminal
Owner:HUAWEI TECH CO LTD
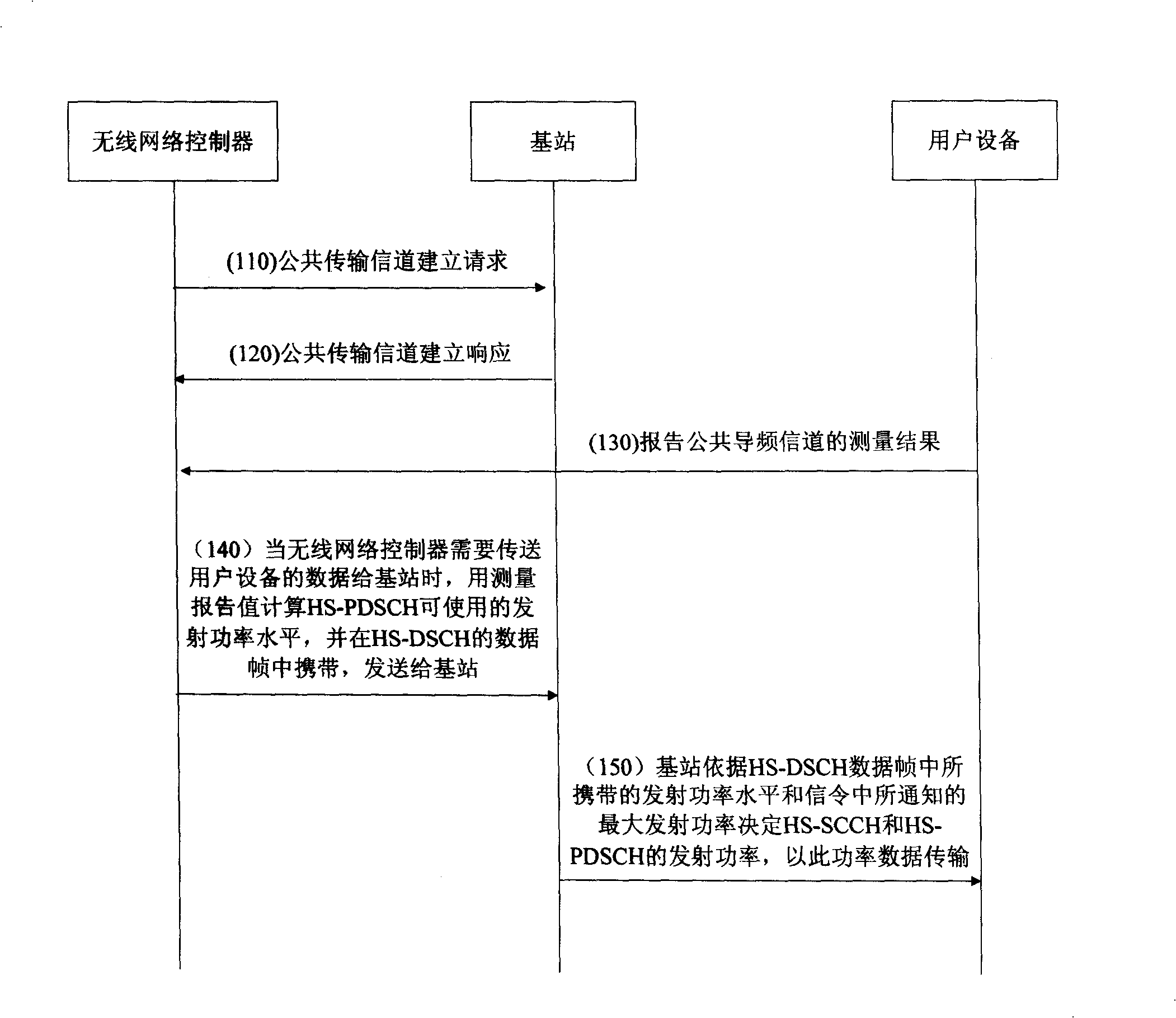
Power control method of physical channel mapped by high speed descending sharing channel
InactiveCN101247146AGuaranteed to receive correctlyIncrease capacityTransmission control/equalisingRadio/inductive link selection arrangementsPower controlPower level
The present invention discloses a method for controlling the power of the physical channel mapped by the high-speed descending sharing channel, and the method comprises the following steps: (a) informing the maximum emitting power of the physical channel mapped by the high-speed descending sharing channel by the wireless network controller, and the maximum emitting power is the deviation value between the emitting power which is needed when the subscriber facility correctly receives the data with the high-speed descending sharing channel at the edge of the subdistrict and the emitting power of the common pilot channel; (b) when the wireless network controller transmits the data which needs to be transmitted to the subscriber facility to the base station, carrying the emitting power level used in transmitting the data in the data frame of the high-speed descending sharing channel; and (c) when the base station transmits data to the subscriber facility, confirming the emitting power which is actually used by the physical channel according to the pre-obtained maximum emitting power, the emitting power level and the emitting power of the common pilot channel, and transmitting signaling and / or data to the subscriber terminal.
Owner:ZTE CORP
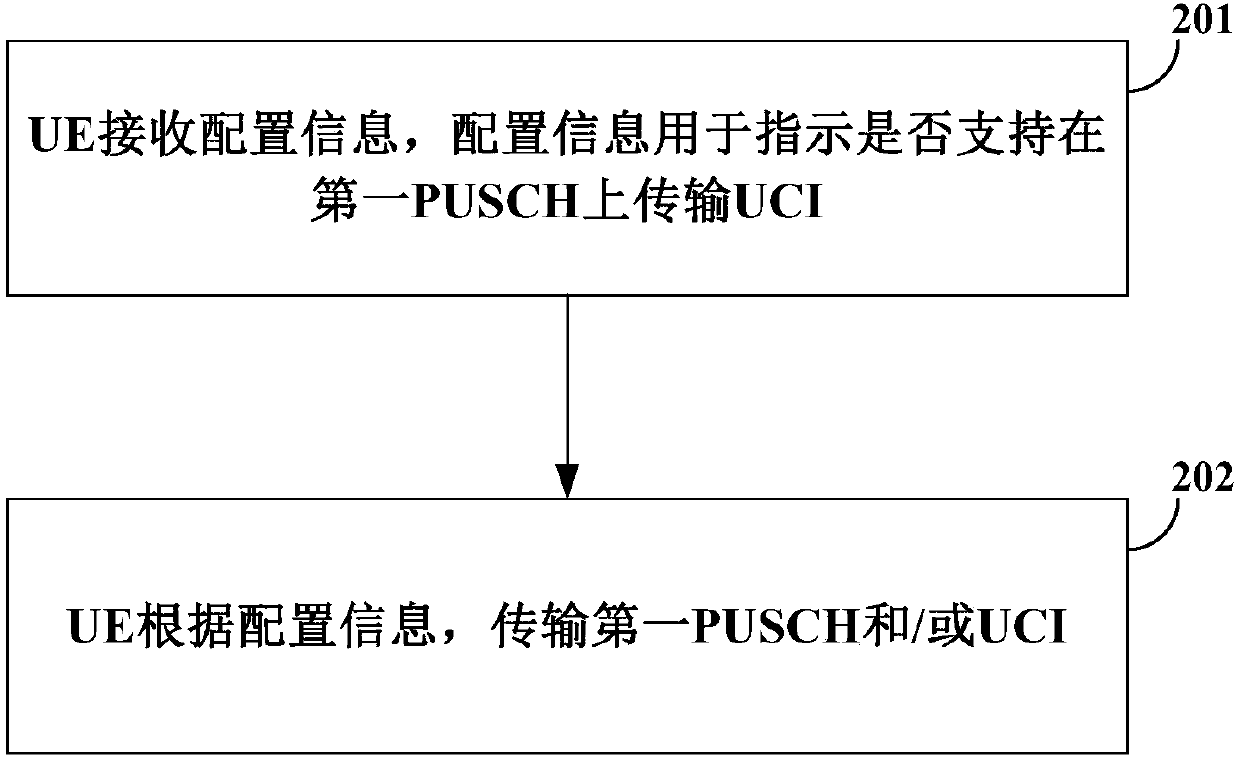
Transmission method and device
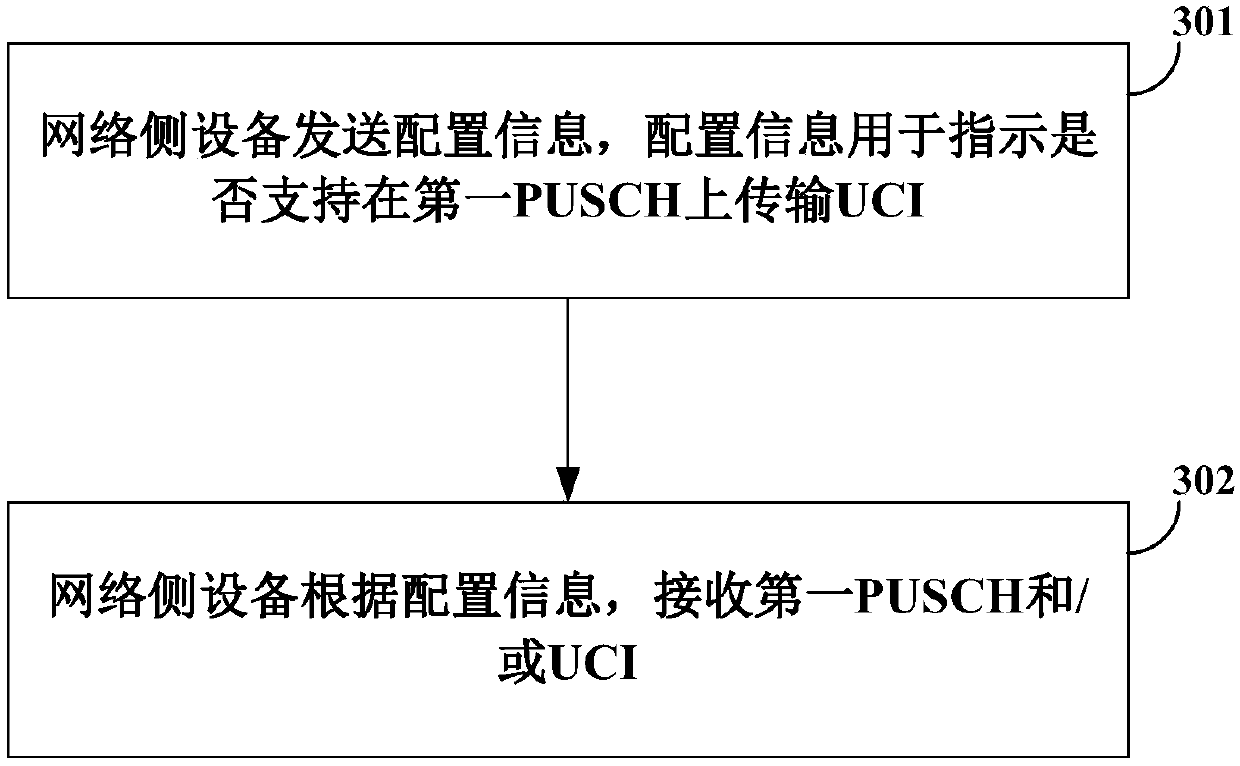
ActiveCN109905215AGuaranteed to receive correctlyAvoid inconsistenciesError prevention/detection by using return channelSignal allocationData transmissionTransmission performance
The embodiment of the invention provides a transmission method and equipment, and the method comprises the steps that UE receives configuration information which is used for indicating whether to support the transmission of uplink control information UCI on a first physical shared channel PUSCH; and the UE transmits the first PUSCH and / or the UCI according to the configuration information. Thus, whether the UCI is transmitted on the first PUSCH or not is determined through the configuration information, inconsistent understanding of resources occupied by data transmission on the PUSCH by the UE and the network side equipment due to the fact whether the UCI exists or not is avoided, it is guaranteed that the network side equipment correctly receives the PUSCH, and the transmission performance is improved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Method and apparatus for indicating DC subcarrier, and electronic device
ActiveCN108024265AGuaranteed to receive correctlyReduce overheadTransmission path multiple useWireless communicationCarrier signalSubcarrier
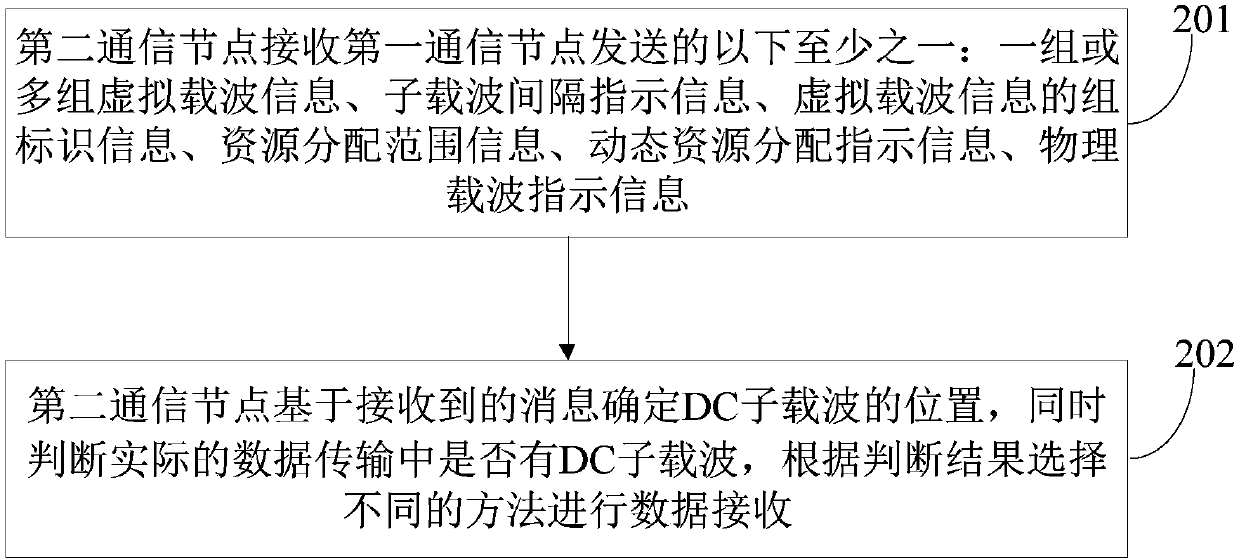
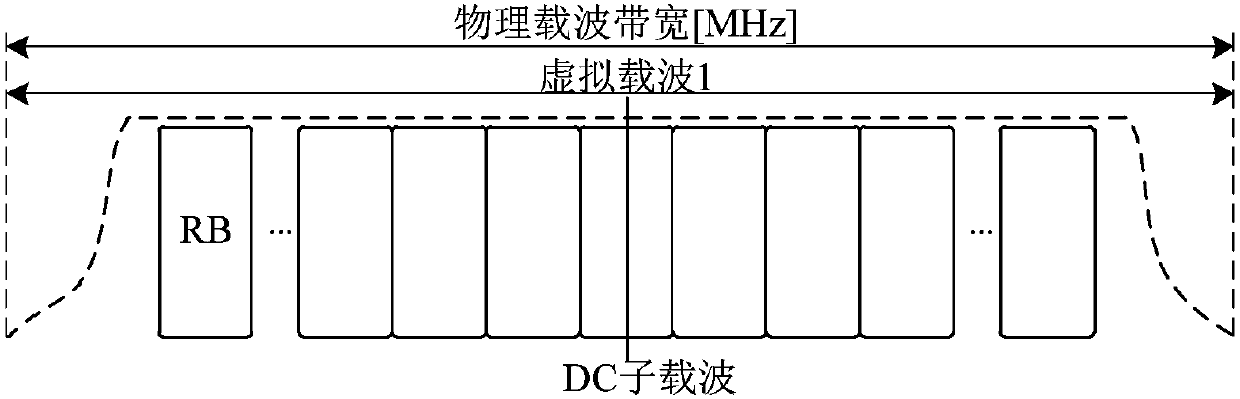
The invention discloses a method and apparatus for indicating a DC subcarrier, and an electronic device. The method comprises the following steps: a first communication node sends one or multiple groups of virtual carrier information to a second communication node, wherein the virtual carrier information at least comprises one of the following: the number of virtual carriers, the bandwidths of thevirtual carriers, virtual carrier index information, a subcarrier spacing used by the virtual carriers, and the number of Fast Fourier Transform FFT points used by the virtual carriers.
Owner:ZTE CORP
Data retransmission method and data retransmission device
ActiveCN110784289AReduce bandwidth pressureGuaranteed to receive correctlyError prevention/detection by using return channelSignal allocationNAKReal-time computing
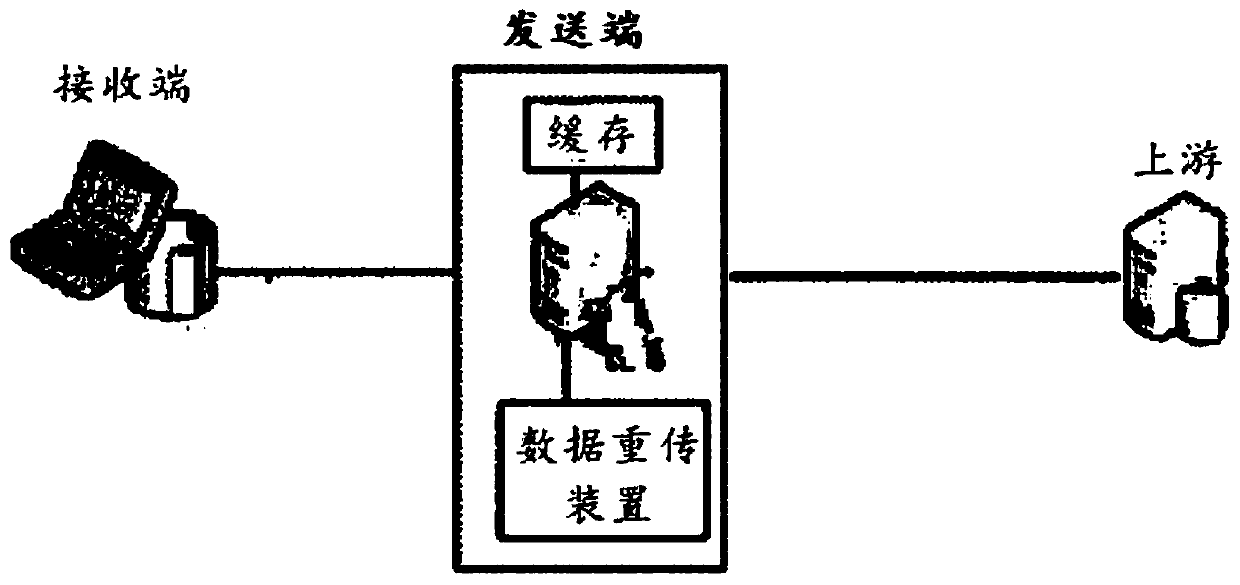
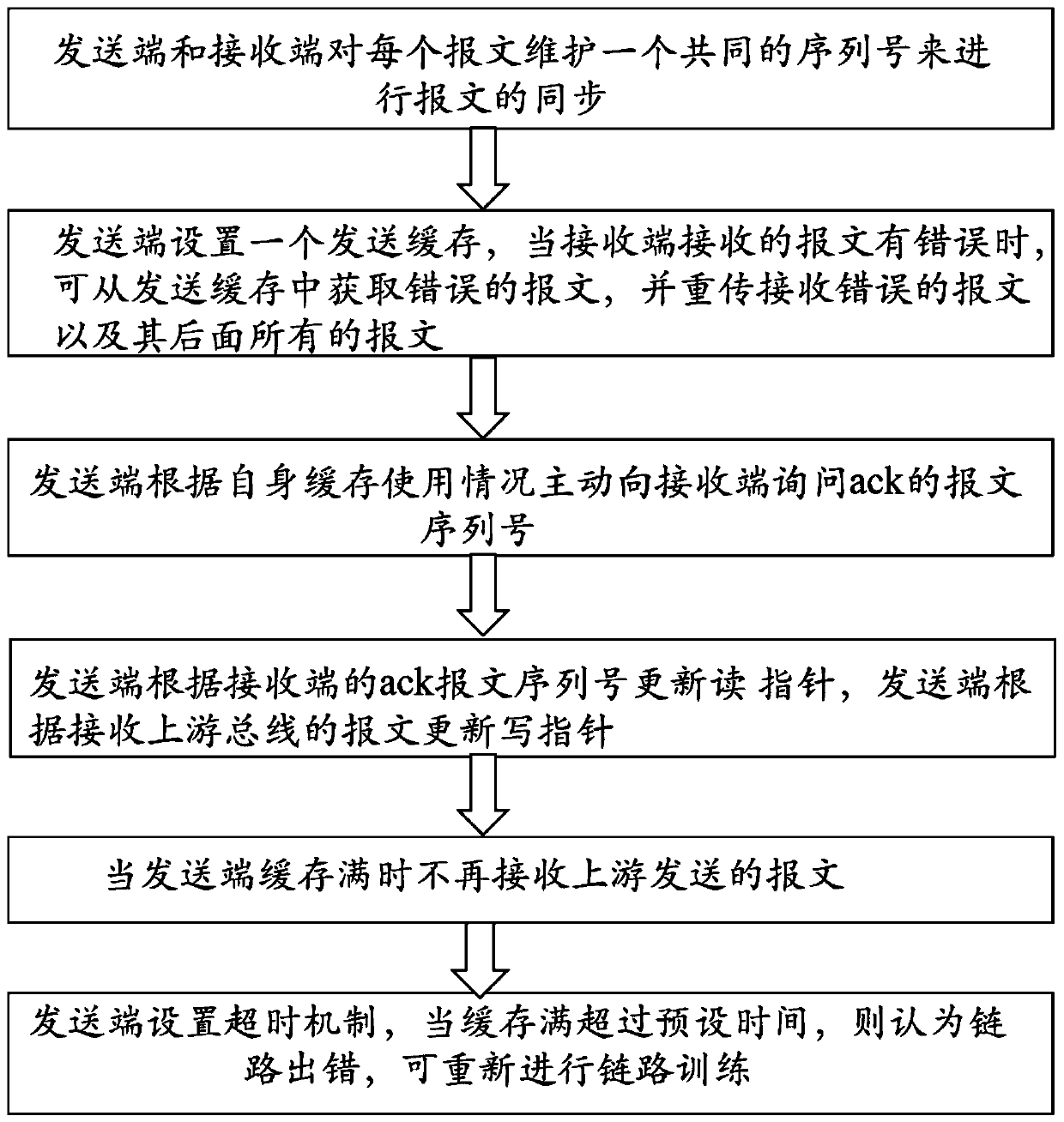
The invention relates to a mechanism for performing data retransmission by using an ACK / NAK protocol when an error occurs in bus interconnection, which comprises the following steps that: 1) a sendingend and a receiving end maintain a common serial number for each message to perform message synchronization; (2) the sending end is provided with a sending cache, when the messages received by the receiving end have errors, the wrong messages can be obtained from the cache, and the wrong messages and all messages behind the wrong messages are retransmitted and received; 3) the sending end actively inquires the message serial number of the ack to the receiving end according to the cache use condition of the sending end; 4) the sending end updates the read pointer according to the ack message serial number of the receiving end and updates the write pointer according to the received message of the upstream bus, 5) the message sent by the upstream is not received when the sending end is fullof the cache, and 6) the link is considered to have an error and link training is carried out again when the cache is full of the cache for more than a preset time.
Owner:HYGON INFORMATION TECH CO LTD
Serial communication method and device, computer equipment and storage medium
ActiveCN110098897AGuaranteed accuracyExtended durationReceiver specific arrangementsTransmitter specific arrangementsComputer scienceSerial communication
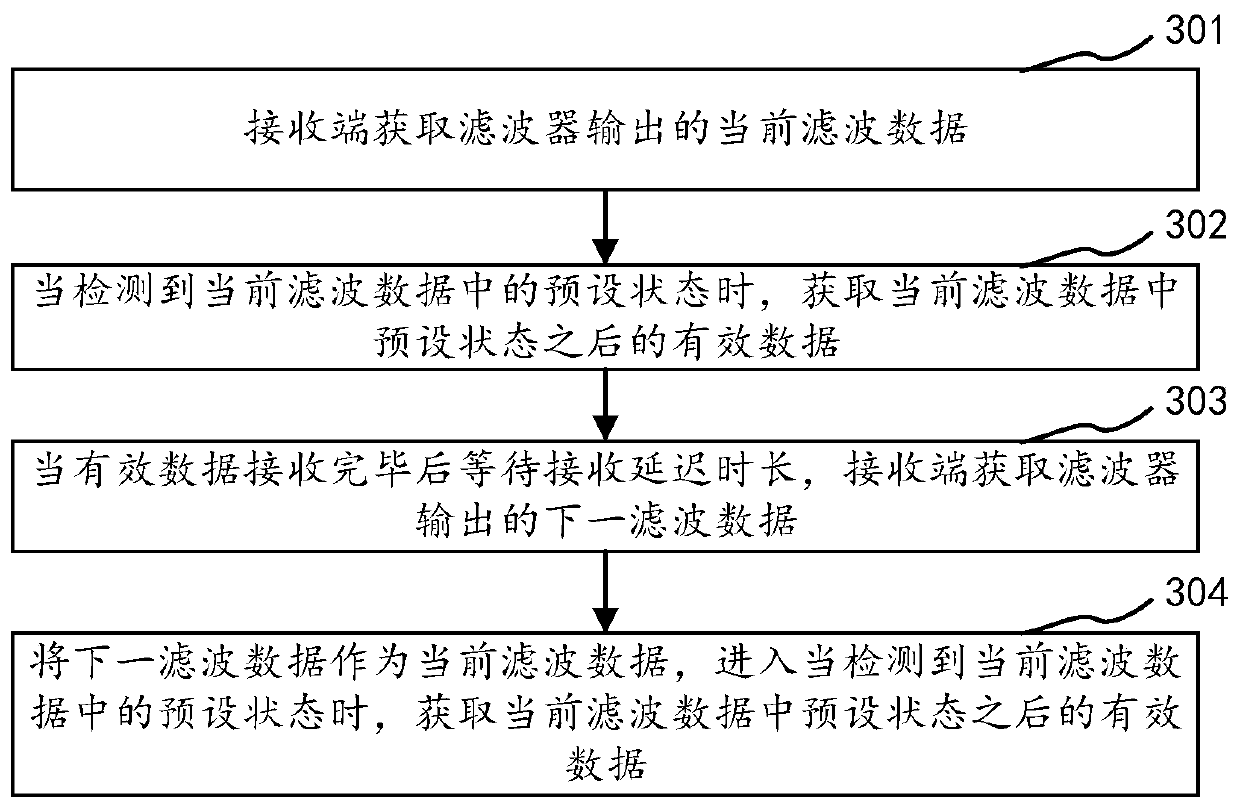
The invention relates to a serial communication method and device, computer equipment and a storage medium. The method comprises: enabling a receiving end to obtain current filtering data output by afilter; when a preset state in the current filtering data is detected, obtaining valid data after the preset state in the current filtering data; after the effective data is received, waiting for a receiving delay time length, and acquiring next filtering data output by the filter by a receiving end; and taking the next filtering data as the current filtering data, and when a preset state in the current filtering data is detected, obtaining effective data after the preset state in the current filtering data. Data is filtered through a filter, the receiving end only needs to capture the currentfiltering data output by the filter, when the preset state in the current filtering data is detected, effective data in the current filtering data can be obtained, the data receiving duration of thereceiving end is prolonged, namely, delayed receiving is achieved, and therefore the accuracy of the data received by the receiving end can be guaranteed.
Owner:GREE ELECTRIC APPLIANCES INC
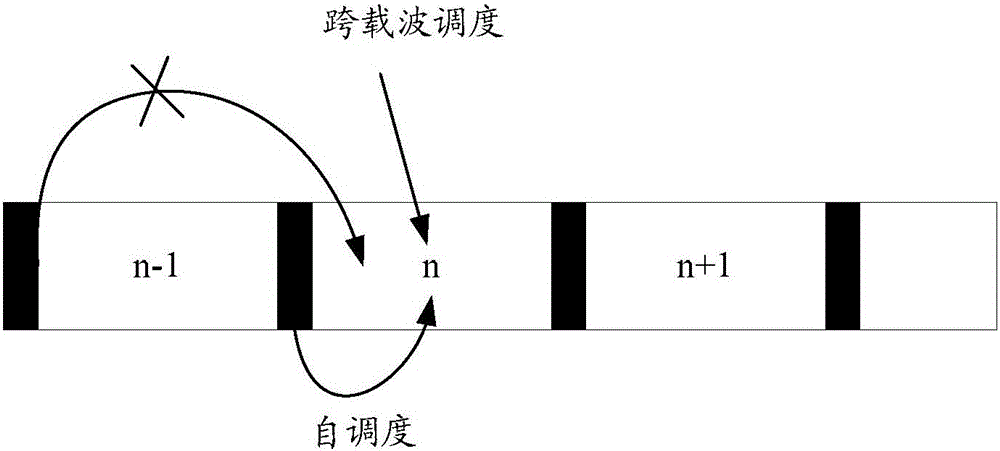
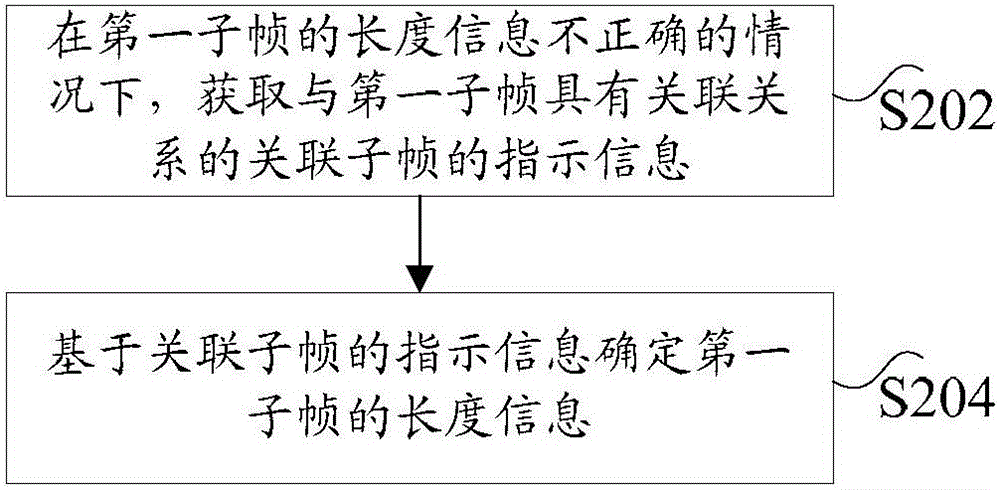
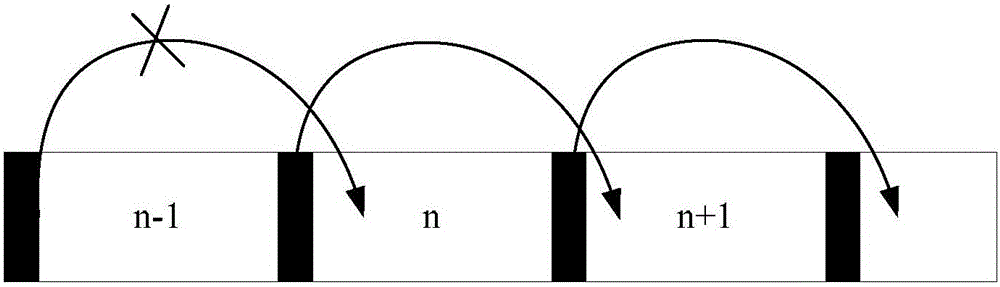
Subframe length information acquisition method and terminal
ActiveCN105764147AAvoid situations where you cannot receive correctlyThe situation that cannot be received correctly is resolvedSignal allocationWireless communicationAlgorithmComputer terminal
The invention discloses a subframe length information acquisition method and a terminal. The method comprises the steps that indication information of an association subframe having the association relation with a first subframe is acquired under the condition that length information of the first subframe is incorrect, and the indication information is used for indicating length of the association subframe; and the length information of the first subframe is determined based on the indication information of the association subframe. The technical problems in the prior art that the data on the current subframe cannot be correctly received due to loss or error of common information indicating the length information of the current subframe can be solved.
Owner:BAICELLS TECH CO LTD
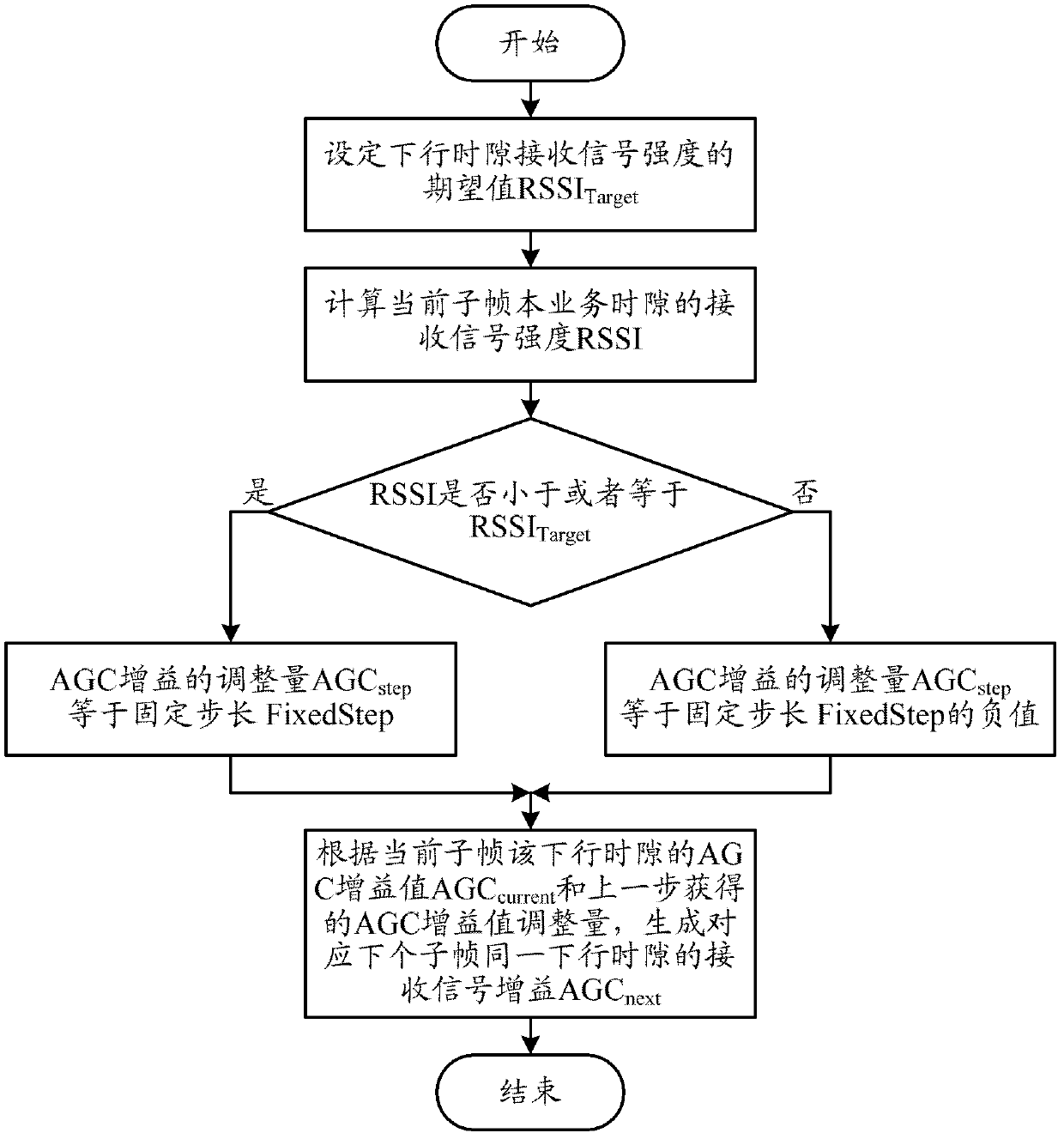
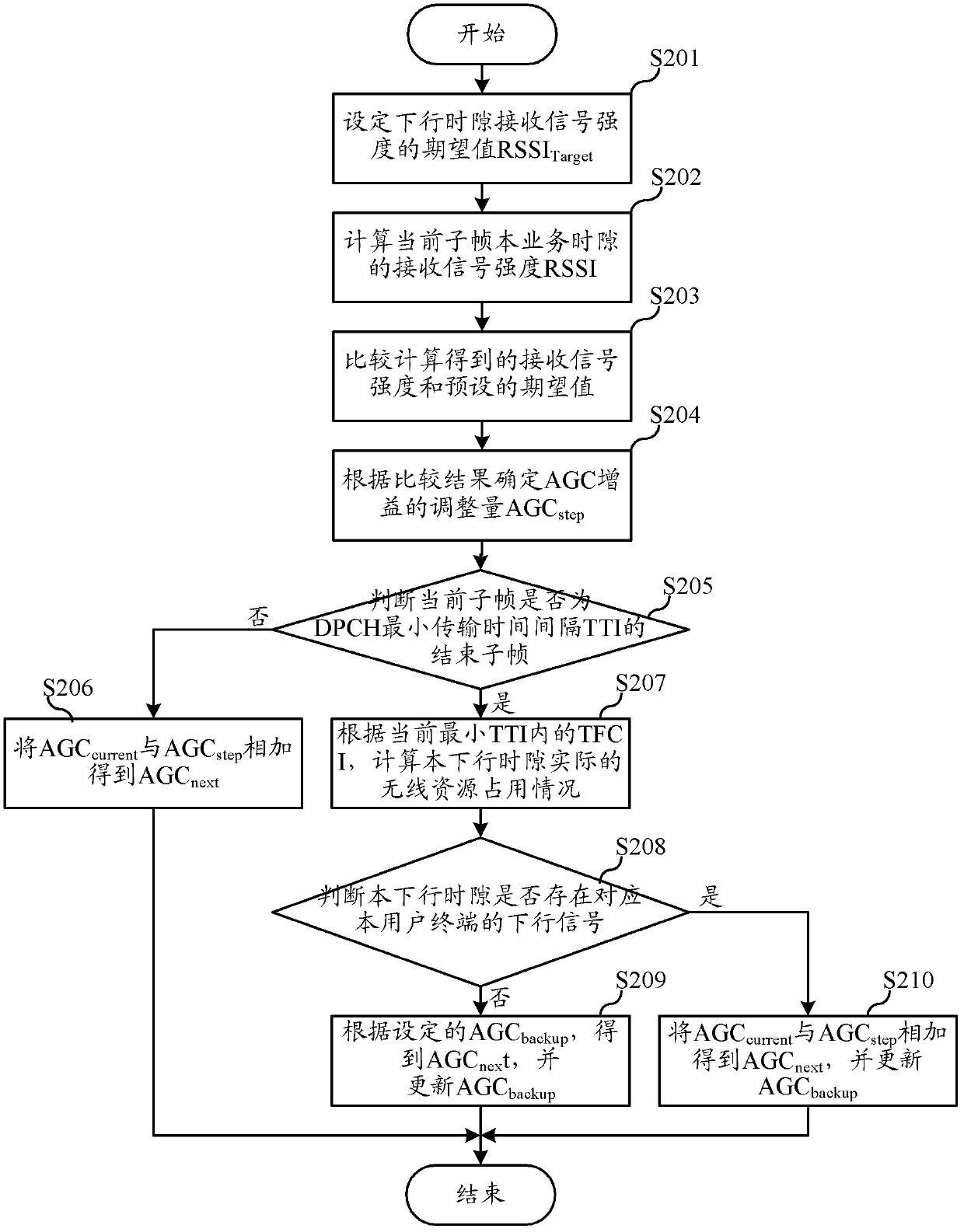
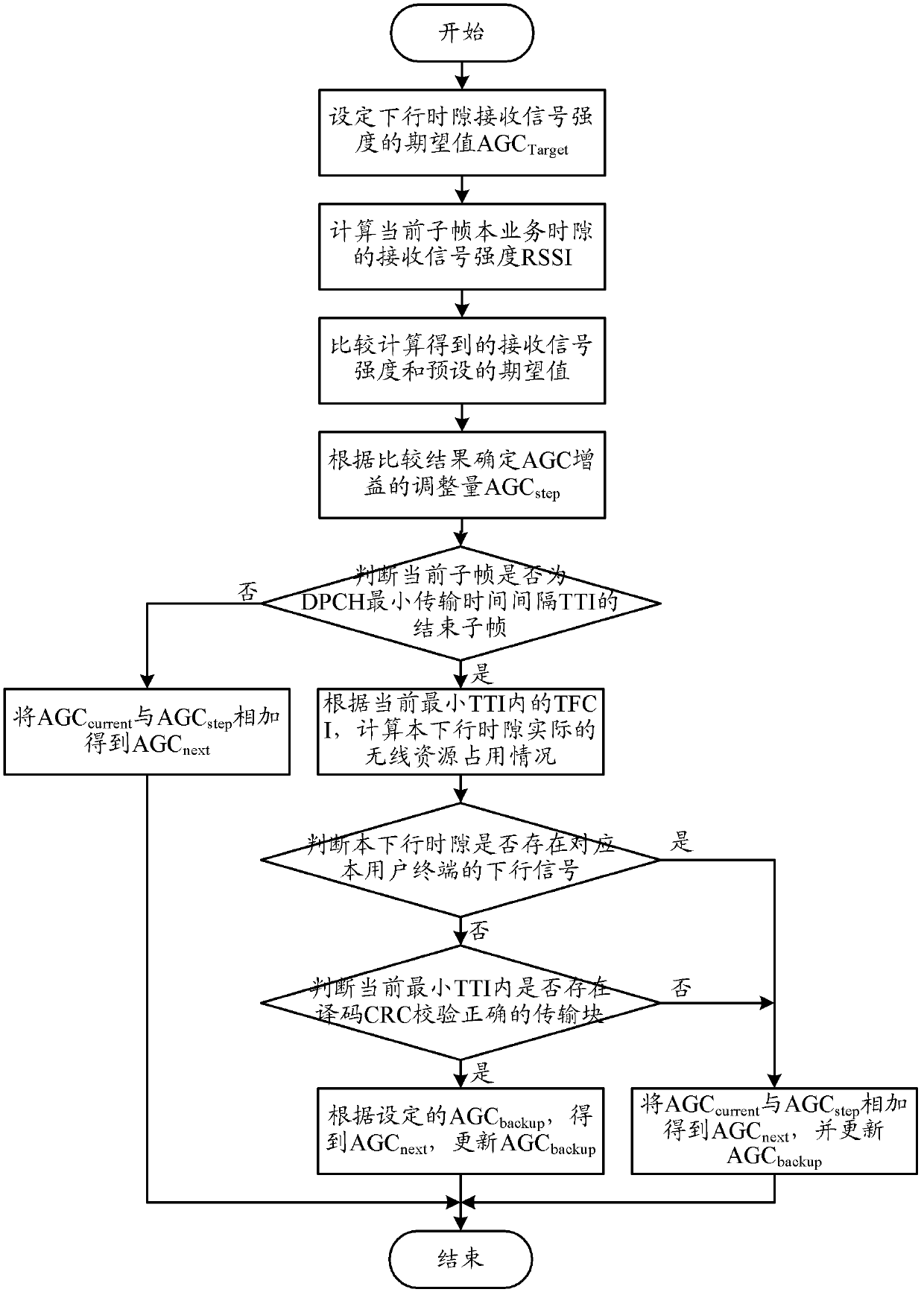
Terminal automatic gain control method and terminal for down link multi-slot business
ActiveCN103379602AGuaranteed to receive correctlySolve the real problemPower managementEngineeringAutomatic gain control
The invention relates to the wireless communication field and discloses a terminal automatic gain control (AGC) method and terminal for down link multi-slot business. In the invention, according to each down time slot of a current subframe, the terminal determines whether the down time slot exists a down signal corresponding with the terminal according to a transport format combination indicator (TFCI) carried by the subframe; if the down time slot does not exist the down signal, the terminal obtains AGC gain value AGC next of a next subframe corresponding with the down time slot according to a set AGC gain value backup value AGC backup; if the down time slot exists the down signal, the terminal obtains the AGC next according to a current AGC gain value and AGC adjustment amount of the down time slot. The terminal automatic gain control method and terminal for down link multi-slot business can handle receiving backup saturation caused by non-first time slot discontinuous transmission under down multi-slot configuration and ensure correct receiving of down signals by the terminal.
Owner:LEADCORE TECH
Power control method of physical channel mapped by high speed descending sharing channel
InactiveCN101247546AGuaranteed to receive correctlyIncrease capacityTransmission control/equalisingRadio/inductive link selection arrangementsControl channelCommon pilot channel
The invention relates to a method for controlling power of a physics channel mapped by a high speed downstream sharing channel, comprising: (a) a wireless network controller informs a base station via signaling that a protocol data unit of a media accession controlling entity of the high speed downstream sharing channel can use a maximum transmitting power MaxHspdschPower or a maximum transmitting power which can be used by the MaxHspdschPower and a sharing controlling channel HS-SCCH for the high speed downstream sharing channel in a transmission time interval; (b) when the wireless network controller sends data which needs to be transmitted to a user device to the base station, an emission power level used for transmitting the data is carried in data frame of the high speed downstream sharing channel; (c) when sending the data to the user device, the base station determines an actually used emission power of HS-PDSCH and HS-SCCH according to the MaxHspdschPower, the emission power level and an emission power of a public pilot channel which are gained in advance, and uses the actually used emission power of HS-PDSCH and HS-SCCH to send the signaling and / or data.
Owner:ZTE CORP
Method and device for transmitting control information and data
ActiveCN109565427AAvoid occupyingGuaranteed to receive correctlyPower managementModulated-carrier systemsTime domainStart time
The invention relates to a method and device for transmitting control information and data. The method comprises the following steps: determining to-be-sent control information and time-frequency resources corresponding to user data; transmitting the control information and the user data on the time-frequency resource, wherein when a first time-frequency resource corresponding to the control information and a second time-frequency resource corresponding to the user data belong to the same time unit, part of the second time-frequency resource occupies a starting time domain symbol of the time unit; and / or, when the first time-frequency resource corresponding to the control information and the second time-frequency resource corresponding to the user data belong to different time units, the first time-frequency resource at least occupies half of the time domain symbol of the first time unit.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Feedback method of resources of high-speed physical downlink shared channel
InactiveCN101594680AAvoid wasting resourcesGuaranteed to receive correctlyRadio transmission for post communicationWireless communicationTelecommunicationsRandom-access channel
The invention provides a feedback method of the resources of a high-speed physical downlink shared channel, comprising the following steps: after user equipment receives the resources of the high-speed physical downlink shared channel, which are sent by a base station and before the feedback time of a high-speed shared information channel, if the user equipment is in an uplink step-out state, the user equipment gives up the use of the high-speed shared information channel to carry out feedback, and after the uplink synchronization is carried out, the user equipment uses an enhanced uplink random access channel to feed back the receiving conditions of the resources of the high-speed physical downlink shared channel to the base station. The technical scheme of the invention avoids the resource waste caused by that the base station can not receive the feedback information to carry out blind retransmission and can also ensure that the base station can correctly receive the feedback information.
Owner:ZTE CORP
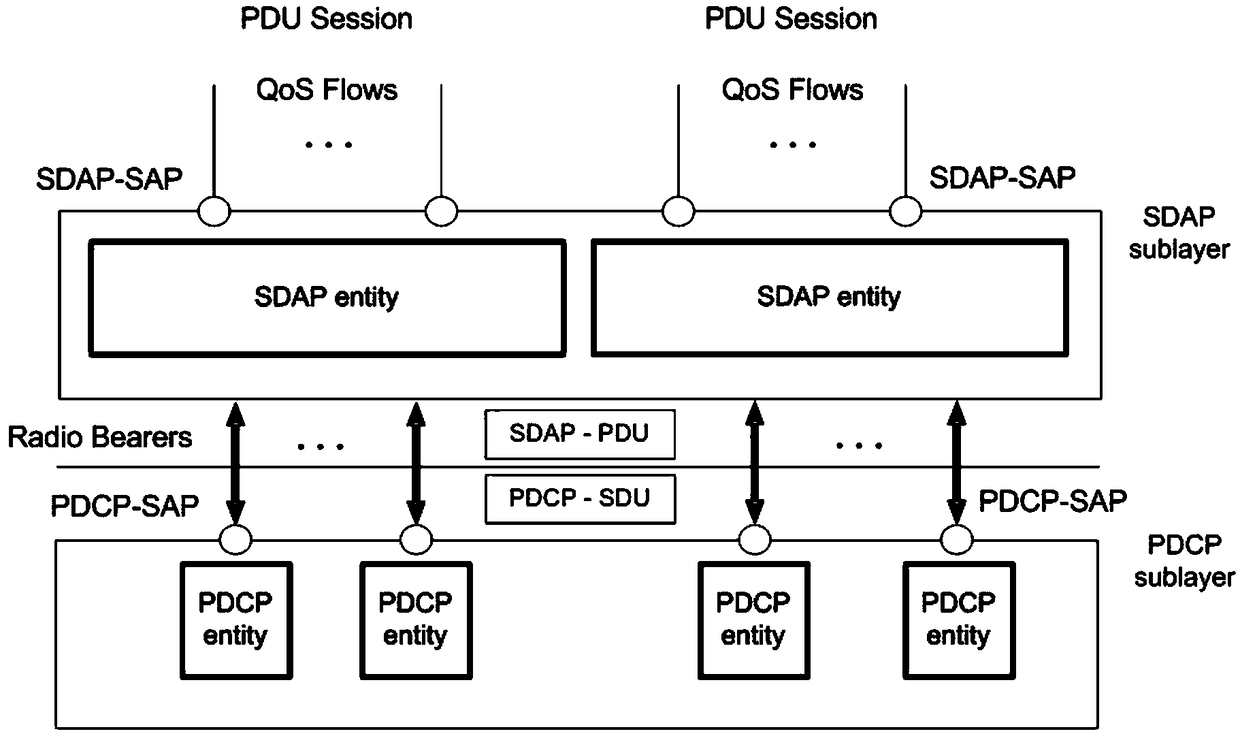
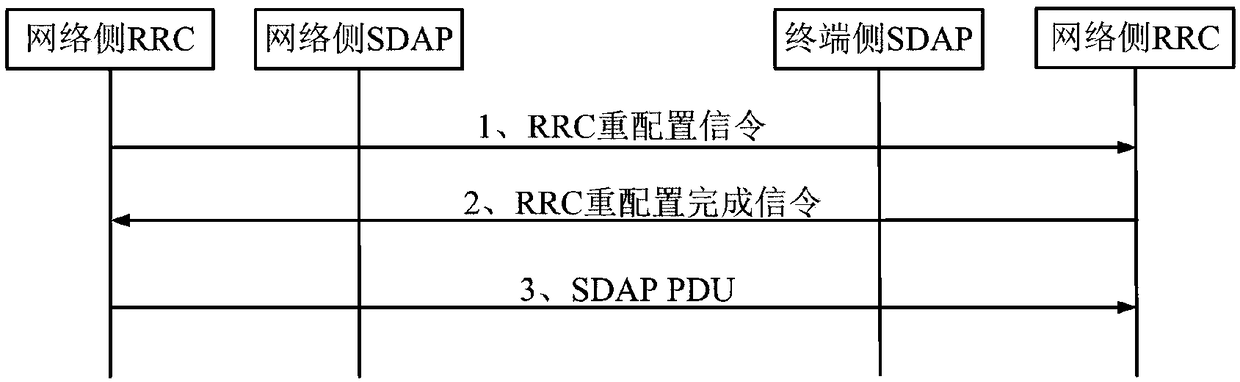
SDAP (Service Discovery Application Profile) layer remapping method based on SDAP PDU (Protocol Data Unit) length
ActiveCN109121163AHigh reliability transceiverGuaranteed to receive correctlyNetwork traffic/resource managementAir interfaceDependability
The invention relates to an SDAP (Service Discovery Application Profile) layer remapping method based on the SDAP PDU (Protocol Data Unit) length, which belongs to the technical field of communicationand solves a problem that uplink data cannot be ensured to be correctly received by a receiving terminal in the prior art. The method is applied to the network side, and comprises the steps that network-side RRC (Radio Resource Control) sends RRC reconfiguration signaling to terminal-side RRC so as to enable the terminal side to perform reconfiguration according to the RRC reconfiguration signaling and generates reconfiguration completion signaling; the network-side RRC receives the reconfiguration completion signaling fed back by the terminal-side RRC, wherein the content of the reconfiguration completion signaling at least includes an SDAP PDU length field and a time point StartPoint at which the RRC reconfiguration signaling is successfully received in an air interface; and the network-side RRC starts the remapping and transmits an SDAP PDU to the terminal-side RRC so as to enable the terminal side to confirm whether the correct SDAP PDU is received or not according to the time point StartPoint and the stored SDAP PDU length field. According to the method, the terminal-side RRC can be ensured to correctly receive the SDAP PDU, high-reliability transmitting and receiving of remapping information are realized, the development cost is reduced, and the perfection of the remapping process is ensured at the same time.
Owner:36TH RES INST OF CETC
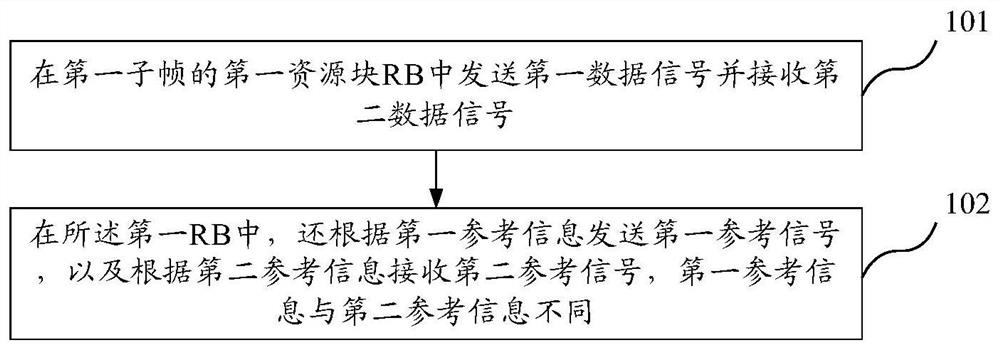
Signal processing method and device
ActiveCN109547187BNo mutual interferenceGuaranteed to receive correctlyModulated-carrier systemsTransmission path divisionTelecommunicationsData signal
The present invention provides a signal processing method and device, wherein the method includes: sending a first data signal and receiving a second data signal in a first RB in a first subframe; in the first RB, further according to the first reference sending a first reference signal with information, and receiving a second reference signal according to second reference information, where the first reference information is different from the second reference information; the first reference information includes: the time occupied by the first reference signal A frequency resource location, and sequence information of the first reference signal; the second reference information includes: a time-frequency resource location occupied by the second reference signal, and sequence information of the second reference signal. The invention ensures the correct reception of the reference signal.
Owner:HUAWEI TECH CO LTD
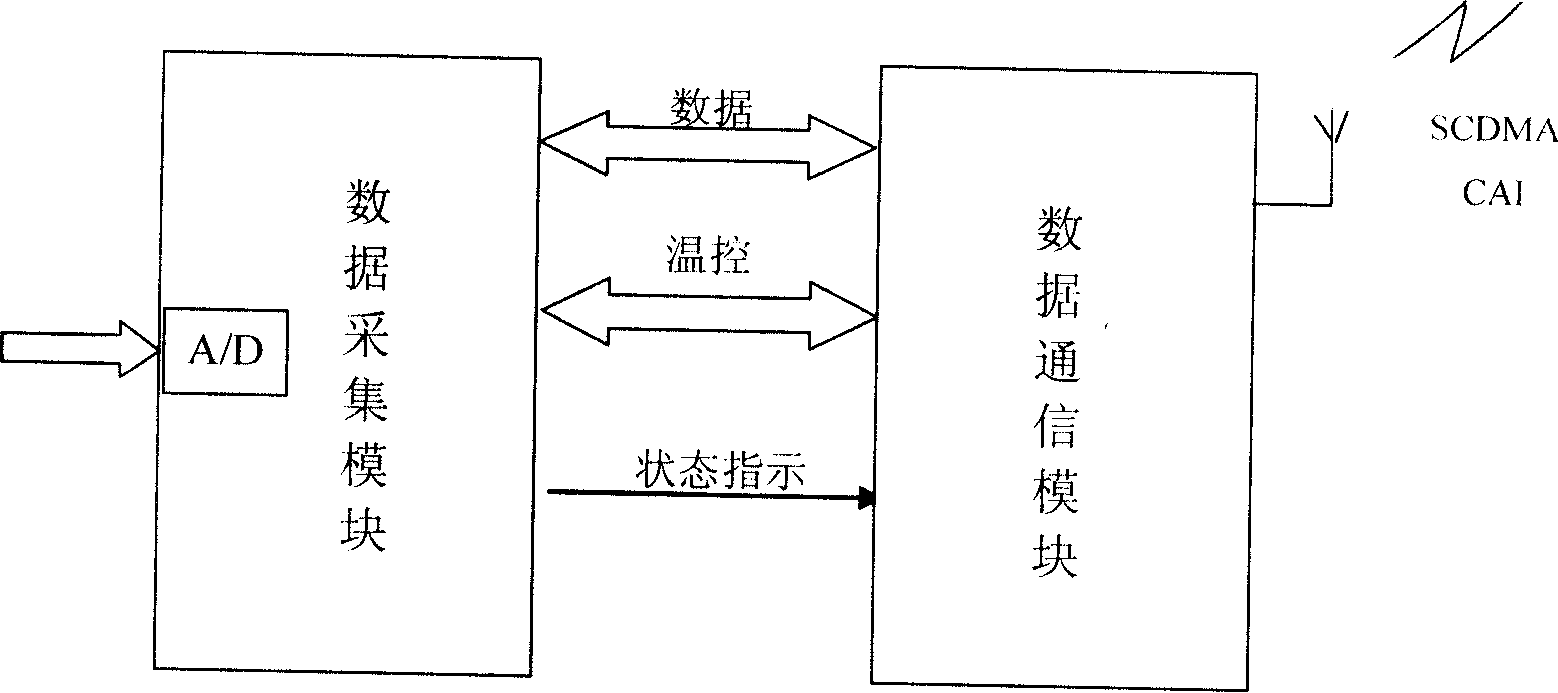
Data acquisition method and system for implementing data acquisition in SCDMA system
InactiveCN101179828AOvercoming Multipath InterferenceGuaranteed to receive correctlyTransmission control/equalisingRadio/inductive link selection arrangementsSystem capacityData acquisition
The invention provides a method and system for collecting data in an SCDMA system. The system at least contains BSes, a BSC, an HLR, a data collection device, a GWF and an APP Server; the method contains the following: a plurality of BSes on an ACCO generate a paging request toward a DCE which launches a distribution establishment process of a wireless link on an ACCI; after signaling interaction with other devices, the BSes transmit allowed information of data transmission to the DCE; then data transmission is conducted between the DCE and a DTE; upon receipt of data transmitted by the BSC, the GWH transmits the data to the APP Server through an SLa interface. By adopting the invention, transmission interference of multi-paths is avoided; accurate receiving and realizing in-phase CDMA is ensured; interference among multiple accesses is reduced; system capacity is increased; the problem of aero link blockage caused by large capacity of data collection and short time of burst communication in a single time is prevented.
Owner:BEIJING XINWEI TELECOM TECH
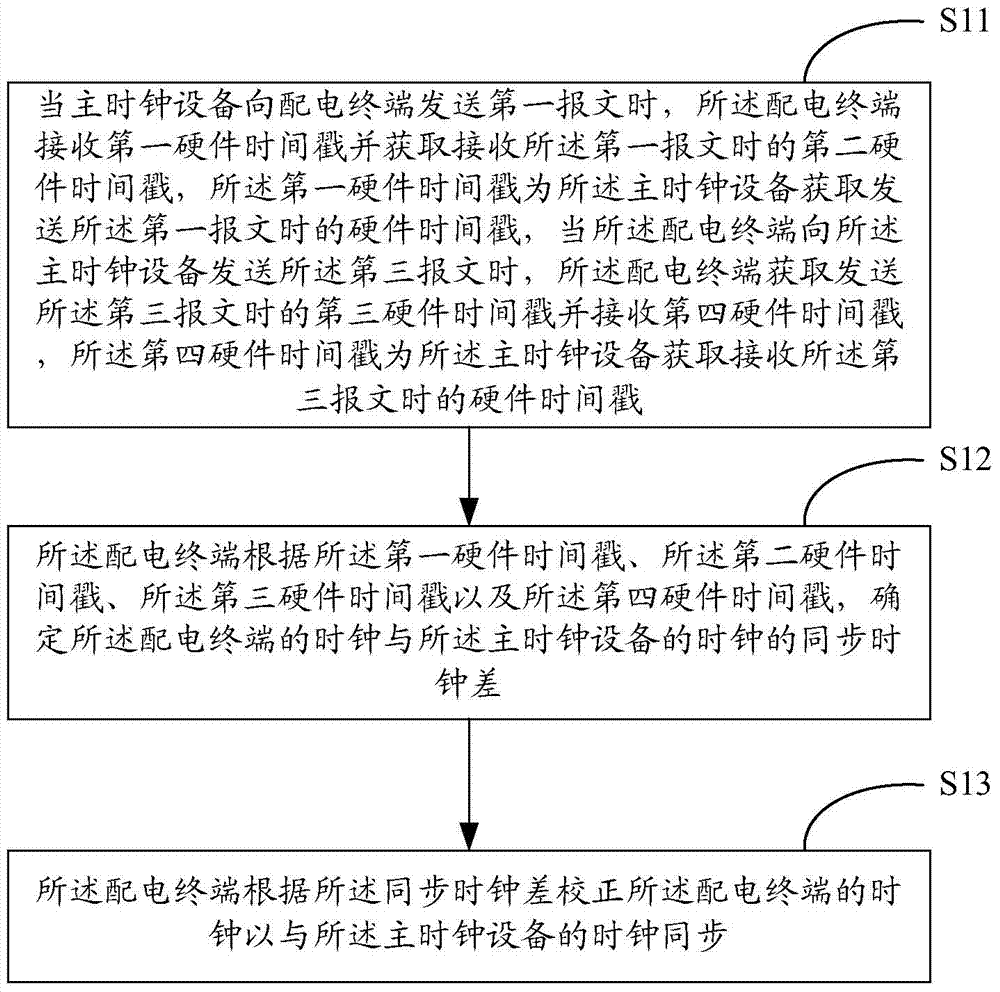
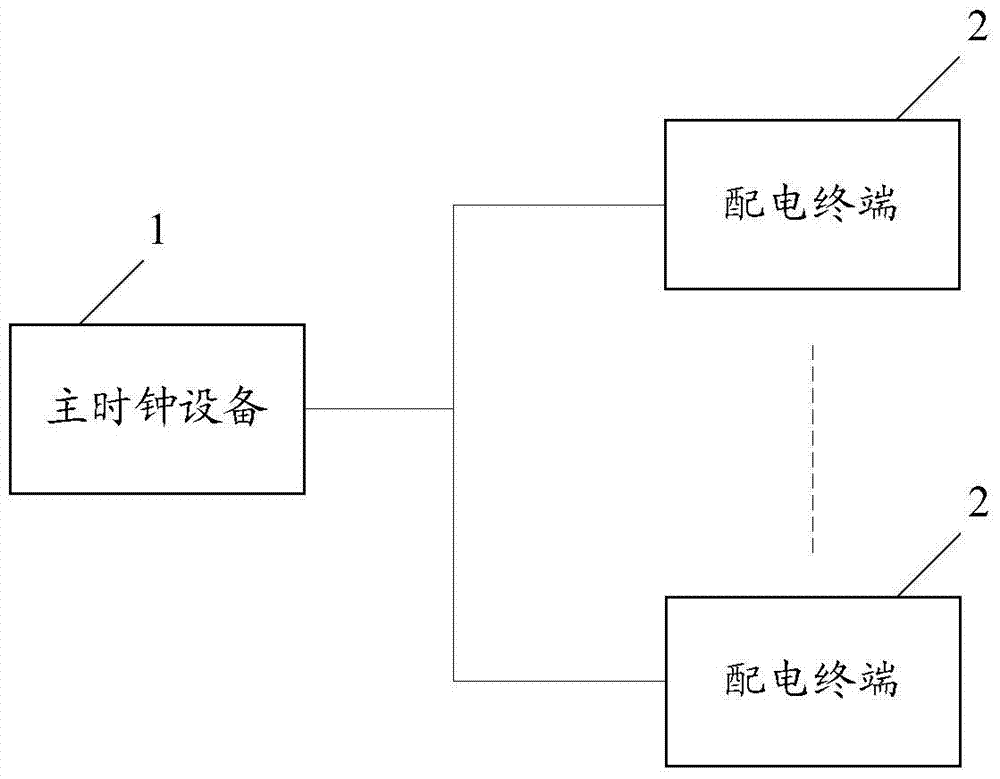
Clock synchronization method and system of power distribution terminal
InactiveCN103546270AAchieve normal operationGuaranteed to receive correctlySynchronising arrangementTimestampComputer terminal
The invention belongs to the field of electric power, and provides a clock synchronization method and system of a power distribution terminal. The clock synchronization method of the power distribution terminal comprises the steps that when main clock equipment sends a first message to the power distribution terminal, the power distribution terminal receives a first hardware timestamp and obtains a second hardware timestamp while receiving the first message, and when sending a third message to the main clock equipment, the power distribution terminal obtains a third hardware timestamp while sending the third message and receives a fourth hardware timestamp; the power distribution terminal determines synchronous clock difference between the clock of the power distribution terminal and the clock of the main clock equipment, and the clock of the power distribution terminal is corrected according to the synchronous clock difference; correct receiving of interactive data between the main clock equipment and the power distribution terminal or among the power distribution terminals is guaranteed.
Owner:AEROSPACE SCI & IND SHENZHEN GROUP
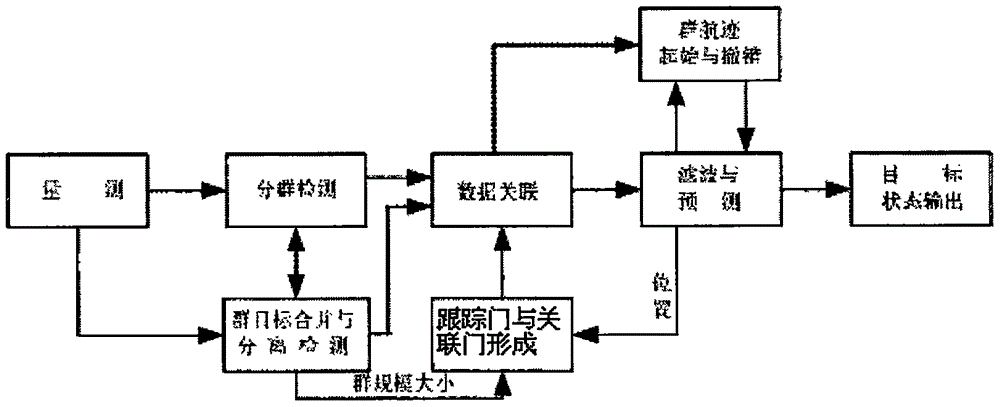
Restricted group target associated door formation method
ActiveCN106291532AAssociation ability unchangedGuarantee ConfirmationRadio wave reradiation/reflectionRadarEngineering
The invention provides a restricted group target associated door formation method comprising the following steps that S1. a geometric area of the group target scale is acquired; S2. the geometric center of the group target is solved; and S3. a restricted group target associated door threshold value is determined. The restricted group target associated door threshold value is the same with a group target associated door threshold value so that group target member determination can be guaranteed; and the restricted group target associated door threshold value is far greater than a group target tracking door so that correct receiving of equivalent measurement can be guaranteed. According to the restricted group target associated door method, double thresholds of the conventional associated door and the tracking door are changed into the single threshold so that the efficiency can be enhanced, the computational burden can be reduced and realization of the project is facilitated. The restricted tracking door is suitable for target tracking of narrowband radar and broadband radar and also applied to target tracking of visible light, infrared and multispectral sensors; single targets, multiple targets, dense multiple targets and sparse multiple targets can be tracked; and the method is suitable for group target tracking of the physical domain and also suitable for generalized group target tracking.
Owner:耿文东
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com