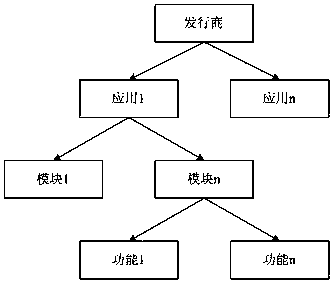
Patents
Literature
31results about How to "Perform avoidance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
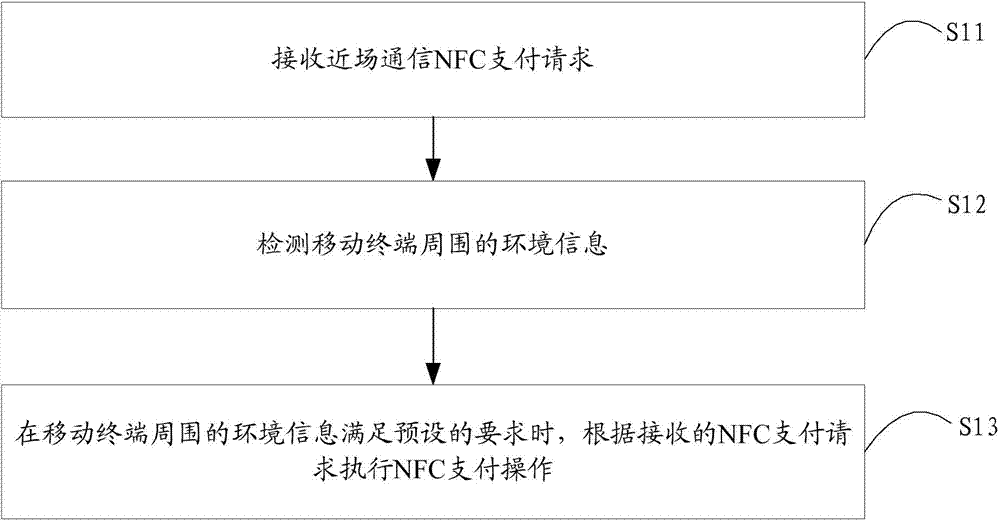
NFC (near field communication) based payment method and device
ActiveCN104732390APerform avoidanceReduce the probability of incorrectly performing NFC payment operationsPayment architecturePaymentComputer terminal
The invention is applicable to the field of mobile terminal payment and provides an NFC (near field communication) based payment method and device. The method includes: receiving a payment request of NFC; detecting environmental information around a mobile terminal; executing NFC payment operations according to the received NFC payment request when the environmental information around the mobile terminal meets preset requirements. With the method, probability that the NFC is brushed by mistake can be lowered.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
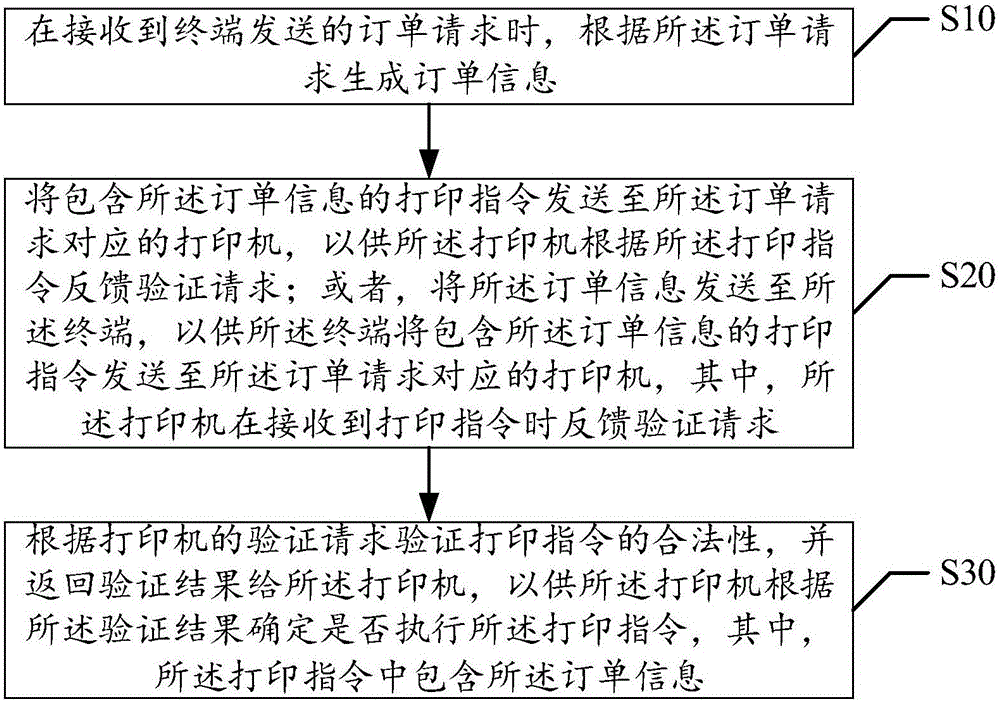
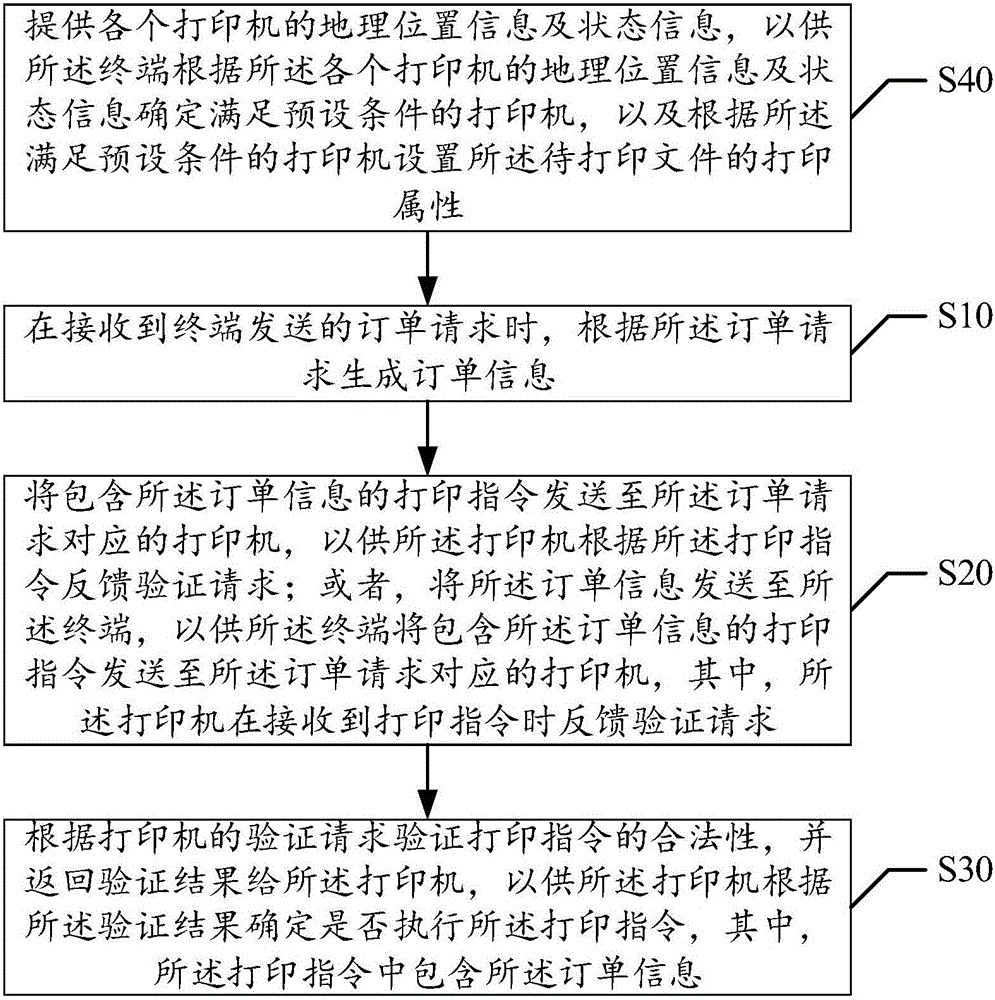
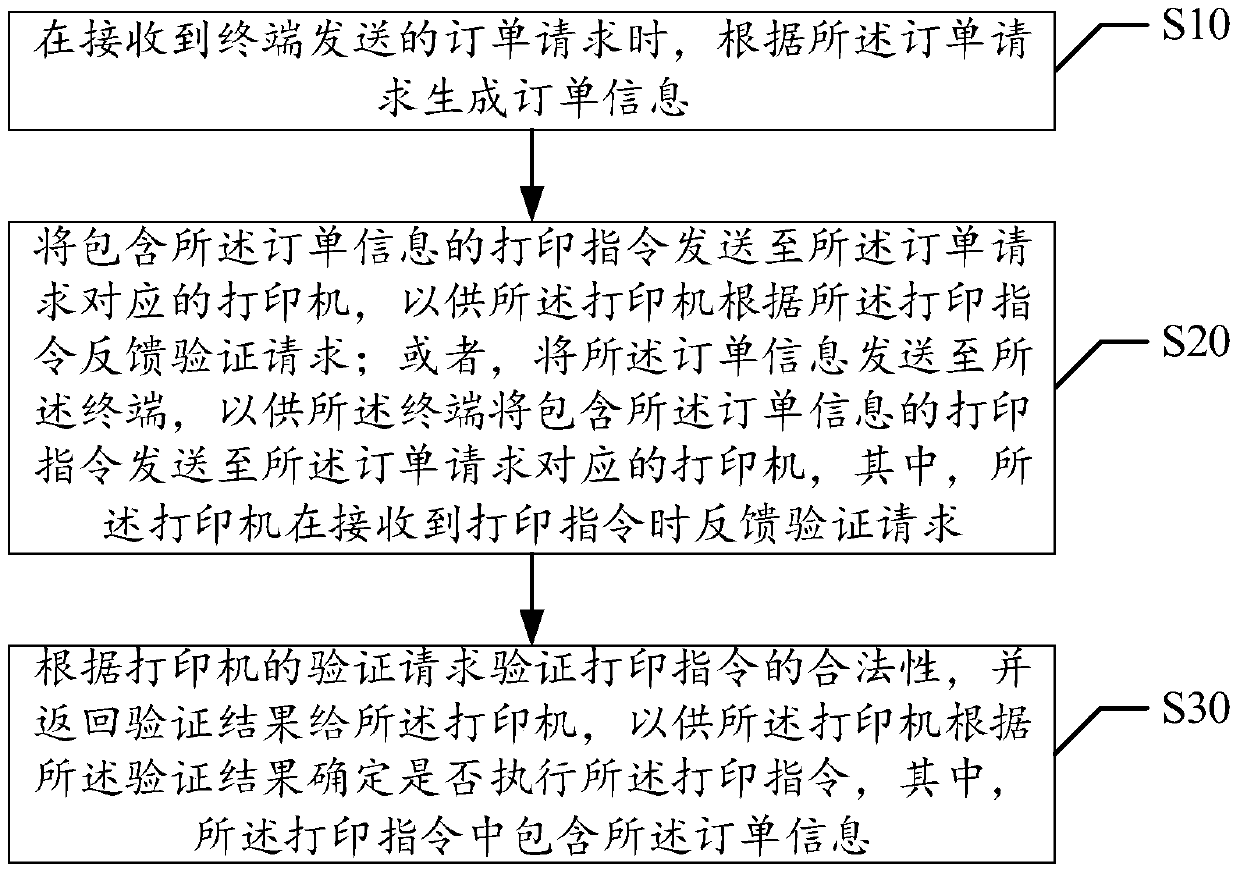
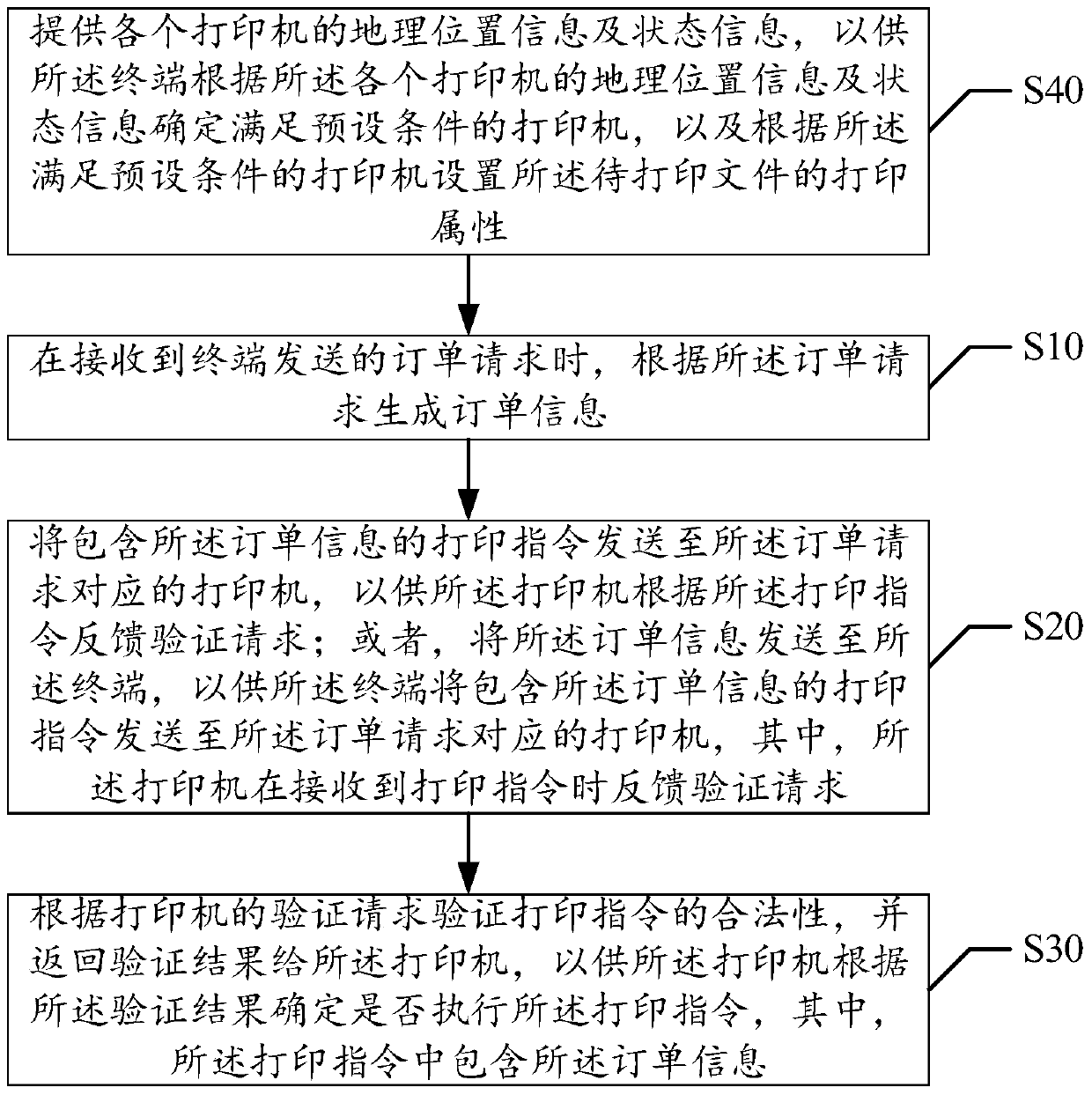
Remote printing control method and device
ActiveCN106227474AImprove securityPerform avoidanceDigital output to print unitsComputer terminalComputer engineering
The invention discloses a remote printing control method. The method includes the steps of generating order information according to an order request when receiving the order request sent by a terminal, sending a printing instruction containing the order information to a printer corresponding to the order request so that the printer can feed back a verification request according to the printing instruction, or sending the order information to the terminal so that the terminal can send the printing instruction containing the order information to the printer corresponding to the order request, verifying the legality of the printing instruction according to the verification request when receiving the verification request fed back by the printer, and returning the verification result to the printer. The invention further discloses a remote printing control device. The problem that an existing printer is poor in safety in the printing process is solved. The safety of the printer in the printing process is improved.
Owner:宜春小马快印科技有限公司
Data object verification method, device and system based on rules, and electric device
InactiveCN106326776AImprove verification speedReduce the number of executionsDigital data protectionSource Data VerificationValidation rule
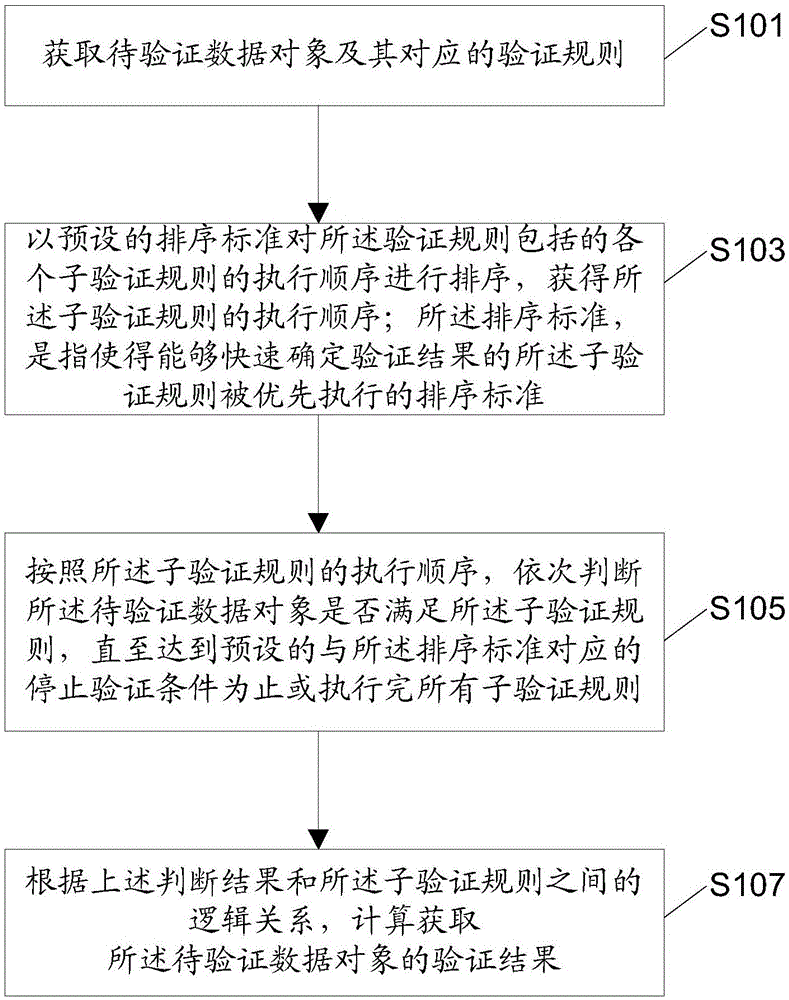
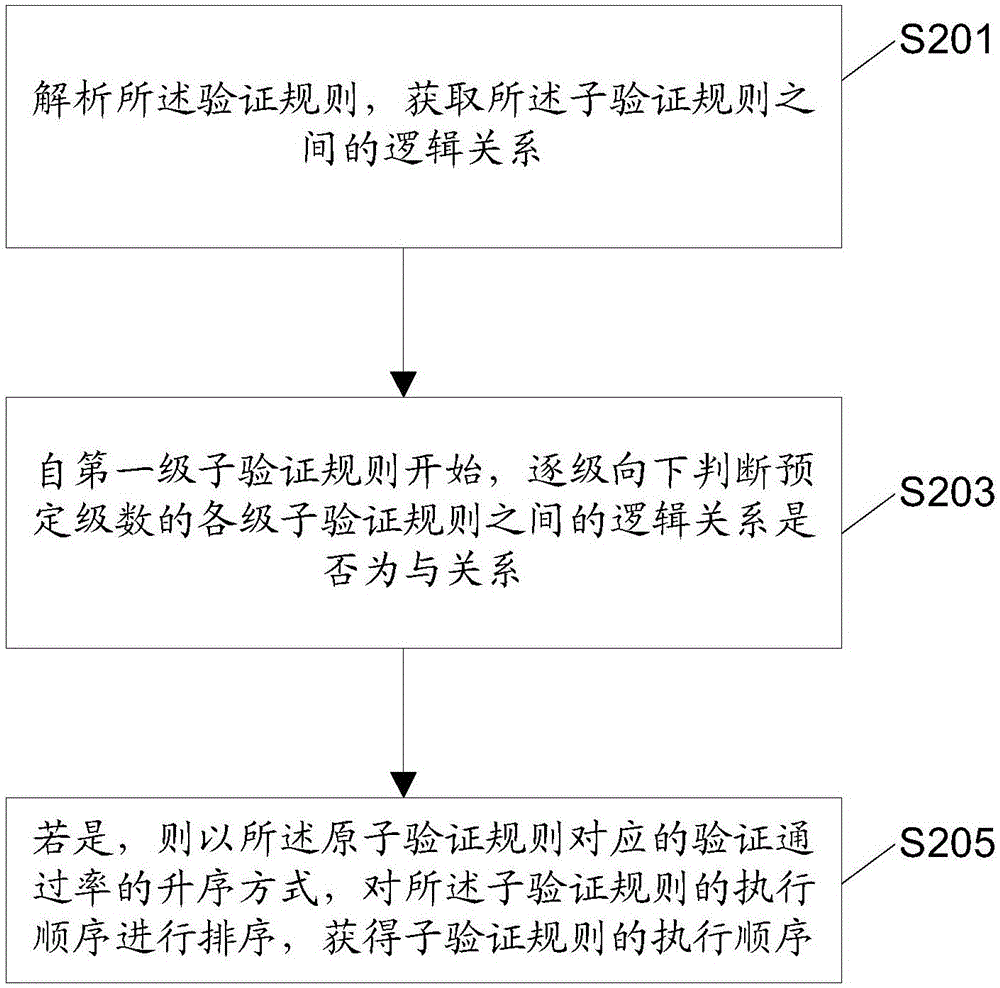
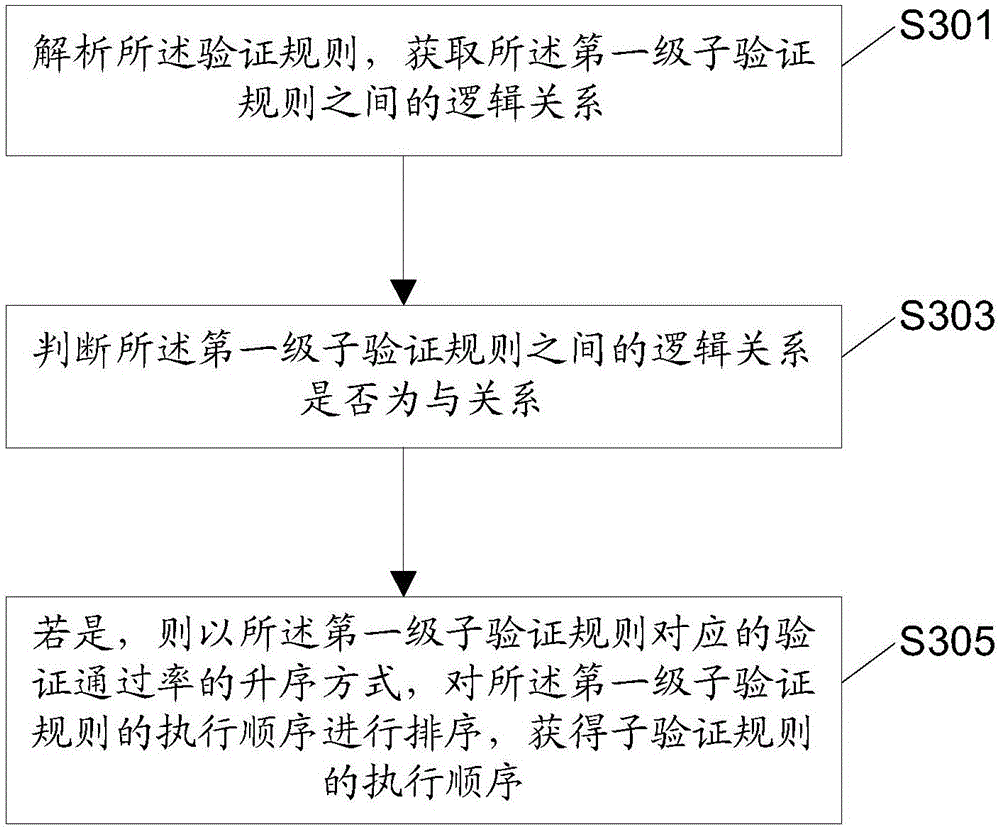
The invention discloses a data object verification method, device and system based on rules, and an electric device. The data object verification method based on the rules comprises the steps of obtaining a to-be-verified data object and a corresponding verification rule; sorting a performing sequence of sub-verification rules contained in the verification rule according to a preset sorting standard, thereby obtaining the performing sequence of the sub-verification rules; judging whether the to-be-verified data object satisfies the sub-verification rules or not in sequence according to the performing sequence of the sub-verification rules, until a preset verification stopping condition corresponding to the sorting stand is realized or all the sub-verification rules are performed completely; and calculating to obtain a verification result of the to-be-verified data object according to logic relationships between judging results and the sub-verification rules. Through adoption of the method provided by the method, the device, the system and the electric device, the sub-verification rules capable of determining the verification result rapidly are performed preferentially, and the sub-verification rules are prevented from being performed completely, thereby achieving an effect of improving a data verification speed.
Owner:ALIBABA GRP HLDG LTD
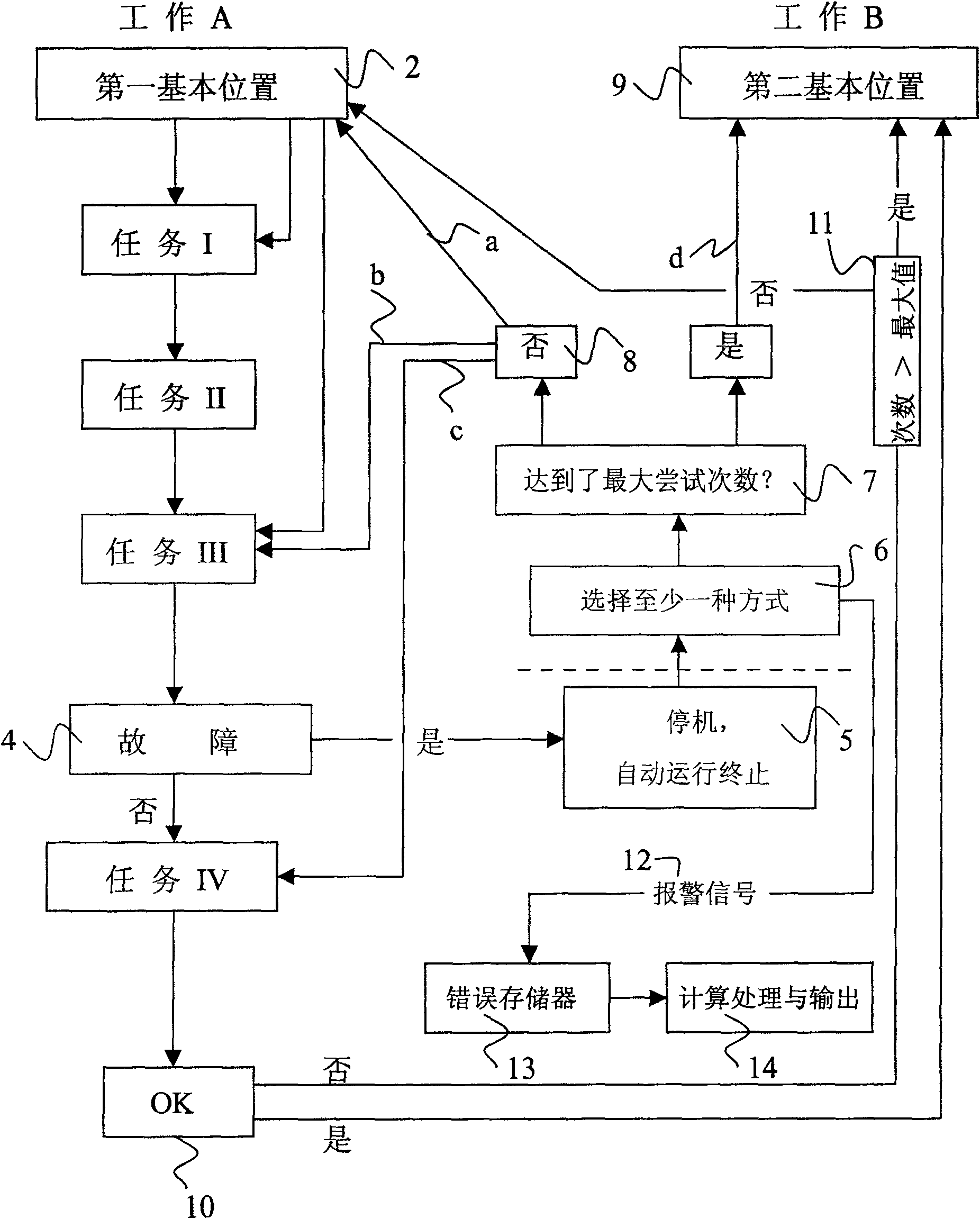
Intelligent type trouble handling device
InactiveCN1609297AShorten the timeTimely maintenanceAnalogue computers for control systemsContinuous wound-up machinesEngineeringAutomation
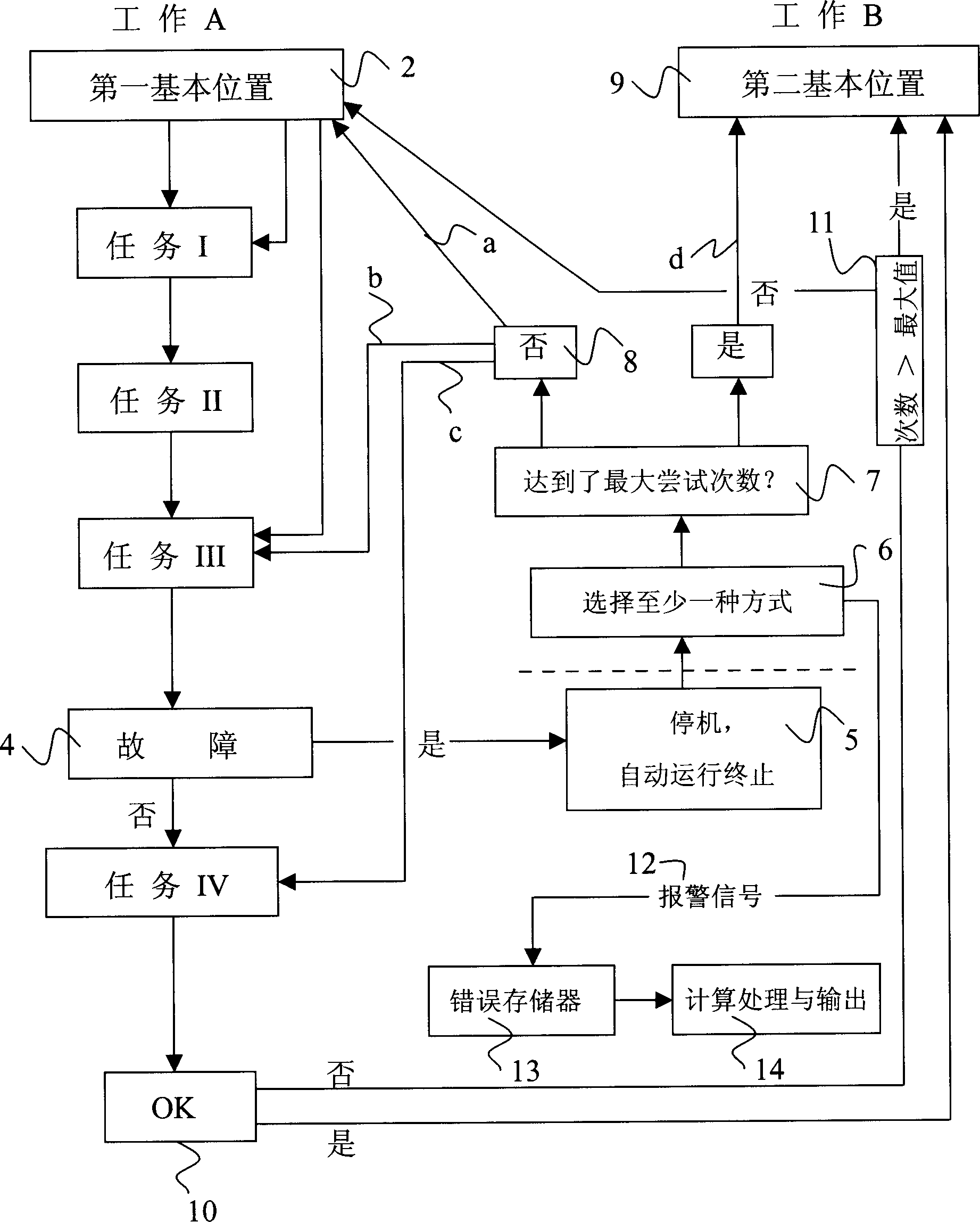
The method for controlling the maintenance device for maintaining the spinning part and a maintenance device for performing the method are provided. The method is performed in a spinning machine capable of performing at least one work (A) on each spinning part and each of the works (A) comprises at least one job (I-IV). When the trouble (4) happens in treating the job (I-IV), the maintenance device is turned over from a working state of automation to the halting state and then at least one counter measure (a, b, c, d) is automatically applied to remove the existing trouble (4) by the maintenance device so as to finish the work (A) to be performed, or to return the maintenance device ready to be reusable.
Owner:利特英格纺织机械制造股份公司
Security protection method for operation system command
InactiveCN106570395AProtection securityImprove securityDigital data protectionPlatform integrity maintainanceOperational systemPower user
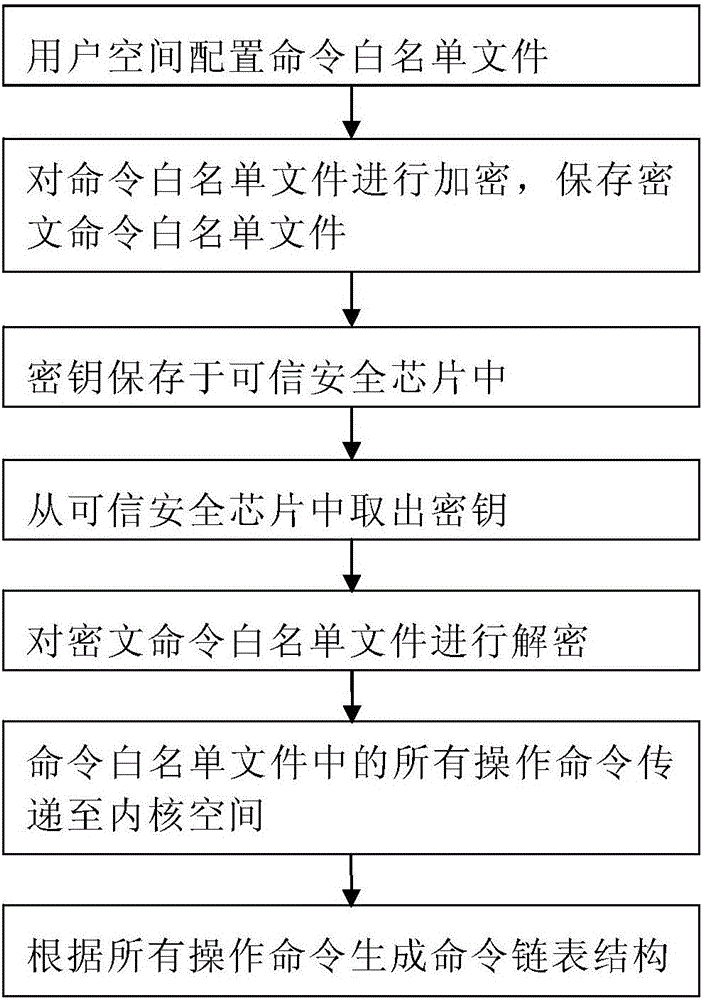
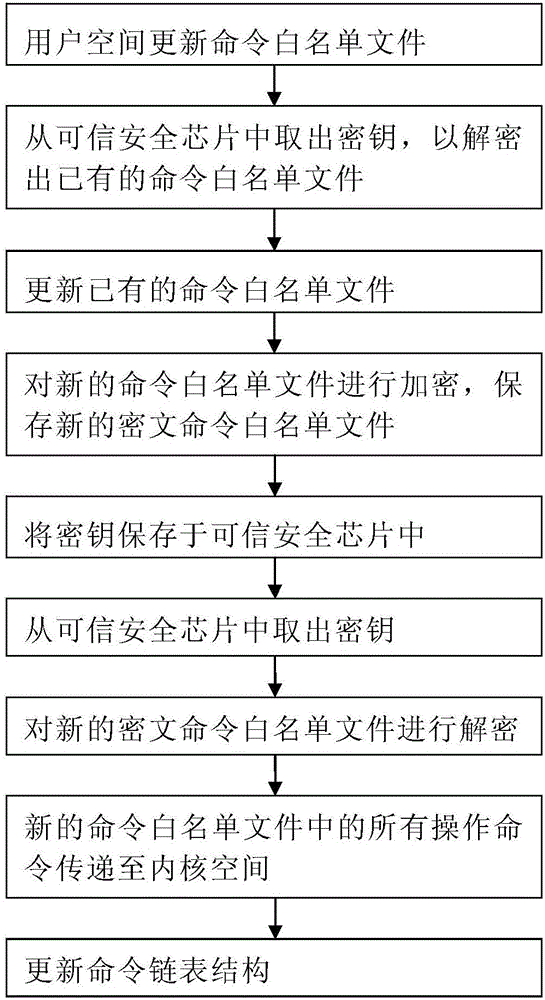
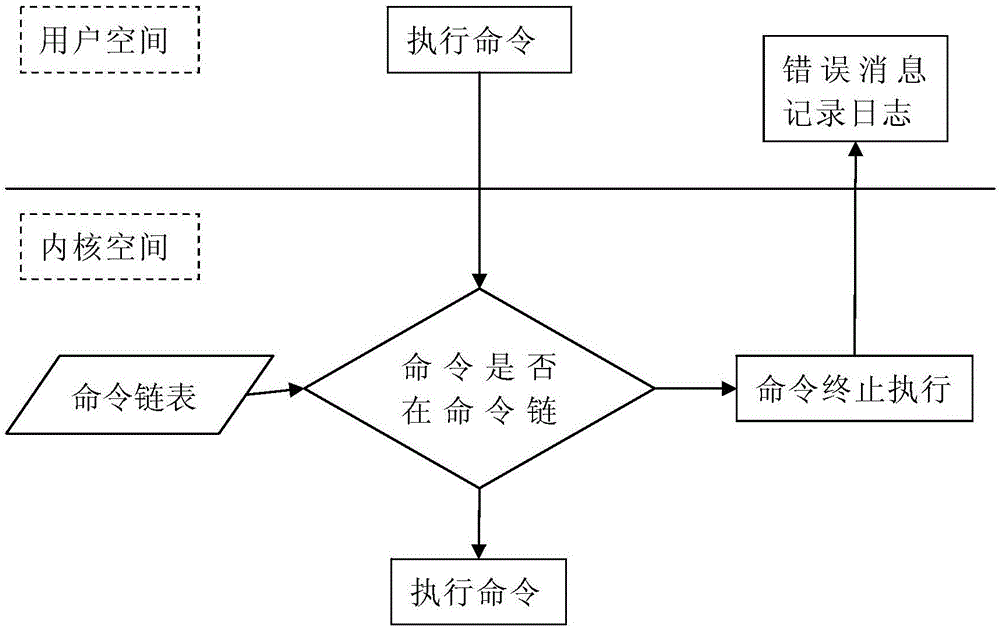
The invention provides a security protection method for an operation system command. A command white list file comprising all operation commands allowed to be executed is configured and encrypted, and an encryption key is stored in a credible security chip, so that the security of the command white list file can be effectively protected and prevented from being stolen or tampered; all the operation commands in the command white list file are stored in a kernel space in the form of a command linked list structure; and when a kernel space execution command executes a processing function, whether the operation command can be executed or not can be judged by judging whether the to-be-executed operation command is in a command white list file list or not. According to the method, the operation commands of an operation system are managed through a method of configuring the command white list file, so that a superuser can be prevented from executing any operation command by utilizing a right of the superuser, the execution of an illegal operation command of a malicious program is avoided, the security of the operation system commands is improved, and the system security is enhanced.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
Dynamic web content request handling method
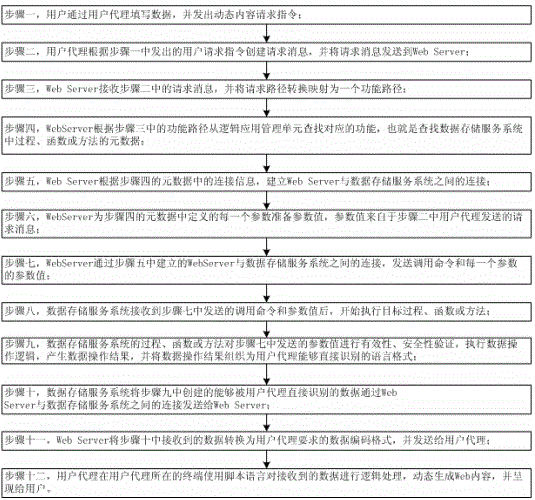
ActiveCN104965909AReduce resource usageImprove operational efficiencyWebsite content managementSpecial data processing applicationsManagement unitData operations
The invention belongs to the technical field of computer software and provides a dynamic web content request handling method. The method comprises the steps of: filling data and sending out a dynamic content request instruction; creating a request message and sending the request message to a Web Server; converting a request path into a functional path by the Web Server, finding a corresponding function from a logic application management unit, establishing a connection with a data storage service system, and preparing parameter values according to metadata; sending a calling command and the parameter values; after receiving the calling command and the parameter values by the data storage service system, executing a corresponding process, function or method, carrying out effectiveness and security verification, executing data operation logic, and generating a data operation result; sending data created according to the data operation result to the Web Server and a user agent in sequence; and dynamically generating the Web content and presenting the Web content to a user by a terminal of the user agent. According to the method, application codes do not need to be executed in the Web Server, few Web Server resources are occupied, and the running efficiency and throughput capacity of the Web Server are high.
Owner:上海沃恩信息科技有限公司
Method, device and system for triggering service
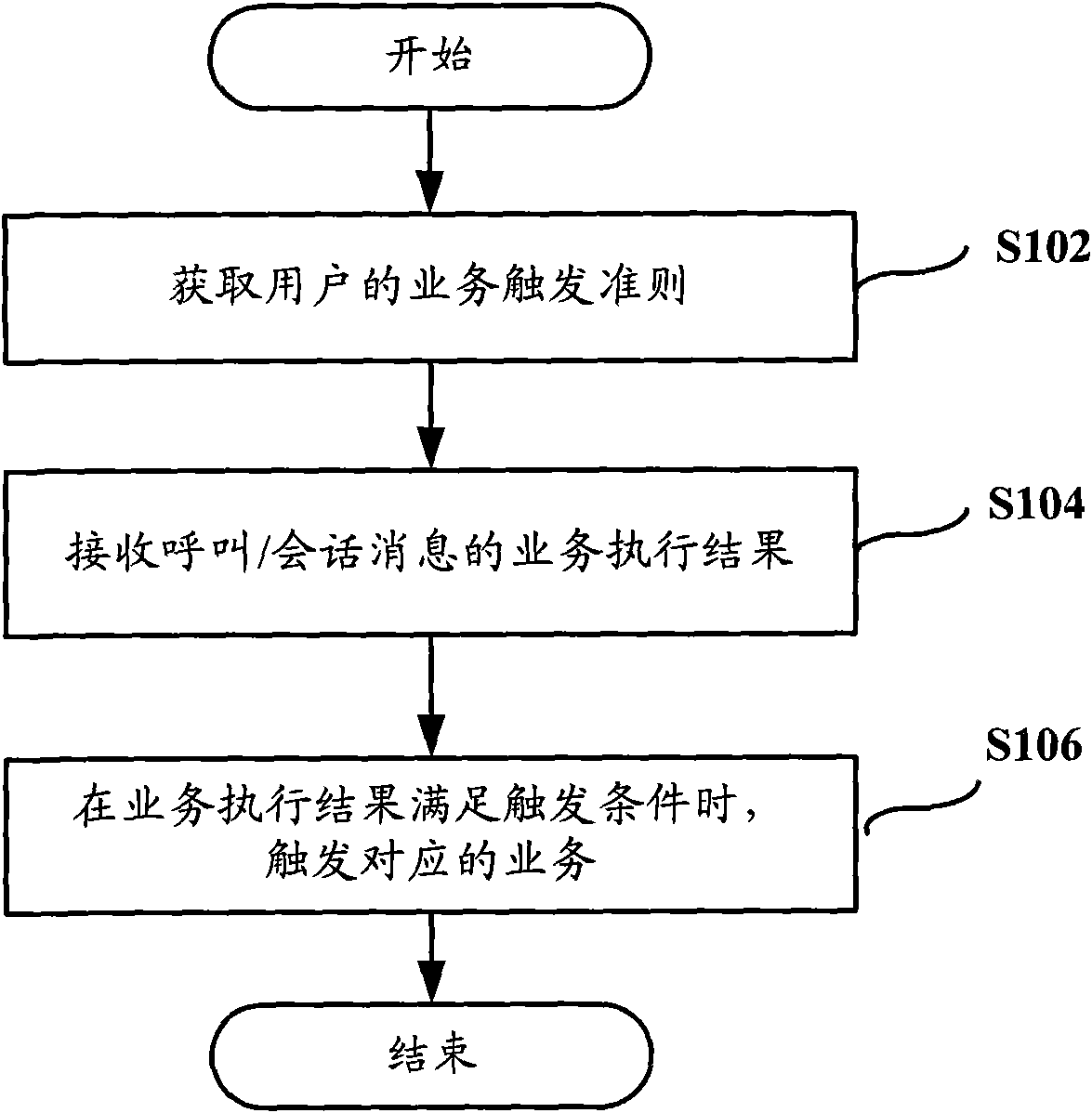
InactiveCN101667994AAvoid meaningless executionRich business trigger mechanismSpecial service for subscribersTransmissionReal-time computingComputer science
The invention discloses a method, a device and a system for triggering a service. The method comprises the following steps: acquiring a service triggering criteria of a user; receiving a service execution result of a calling / session message; and when the service execution result satisfies triggering conditions in the service triggering criteria, triggering a corresponding service, wherein the service triggering criteria comprises the triggering conditions corresponding to each service of the user. Each embodiment of the invention can effectively overcome the defects that the service triggeringmode in the prior art cannot process complex triggering conditions and can trigger the services which are not executed, the session time is long and the like; besides, each embodiment can provide abundant service triggers, avoid triggering the services which are not executed, and improve the overall performance of the system.
Owner:CHINA MOBILE COMM GRP CO LTD
APP test method, APP test script generation device and APP test script execution device
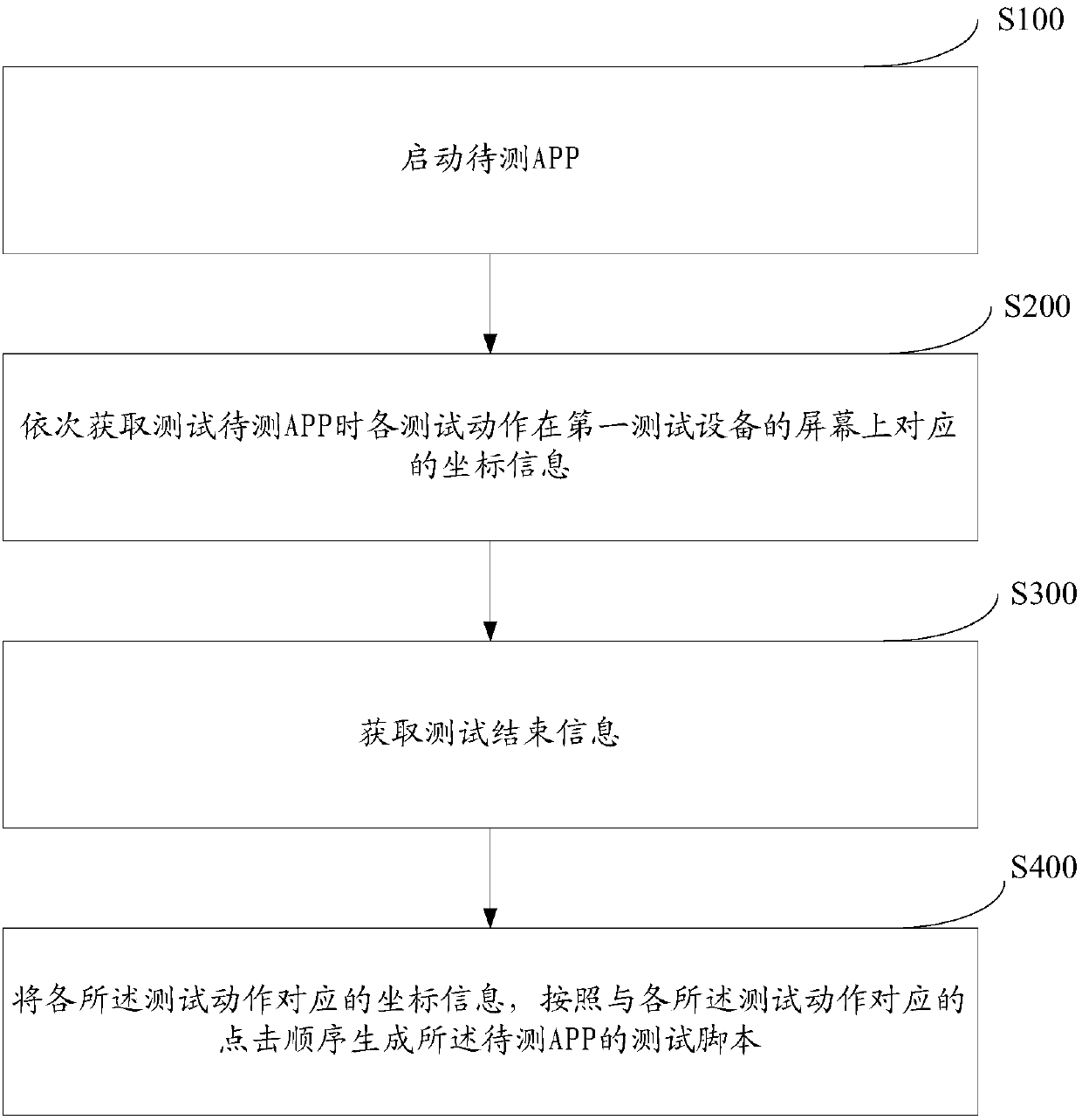
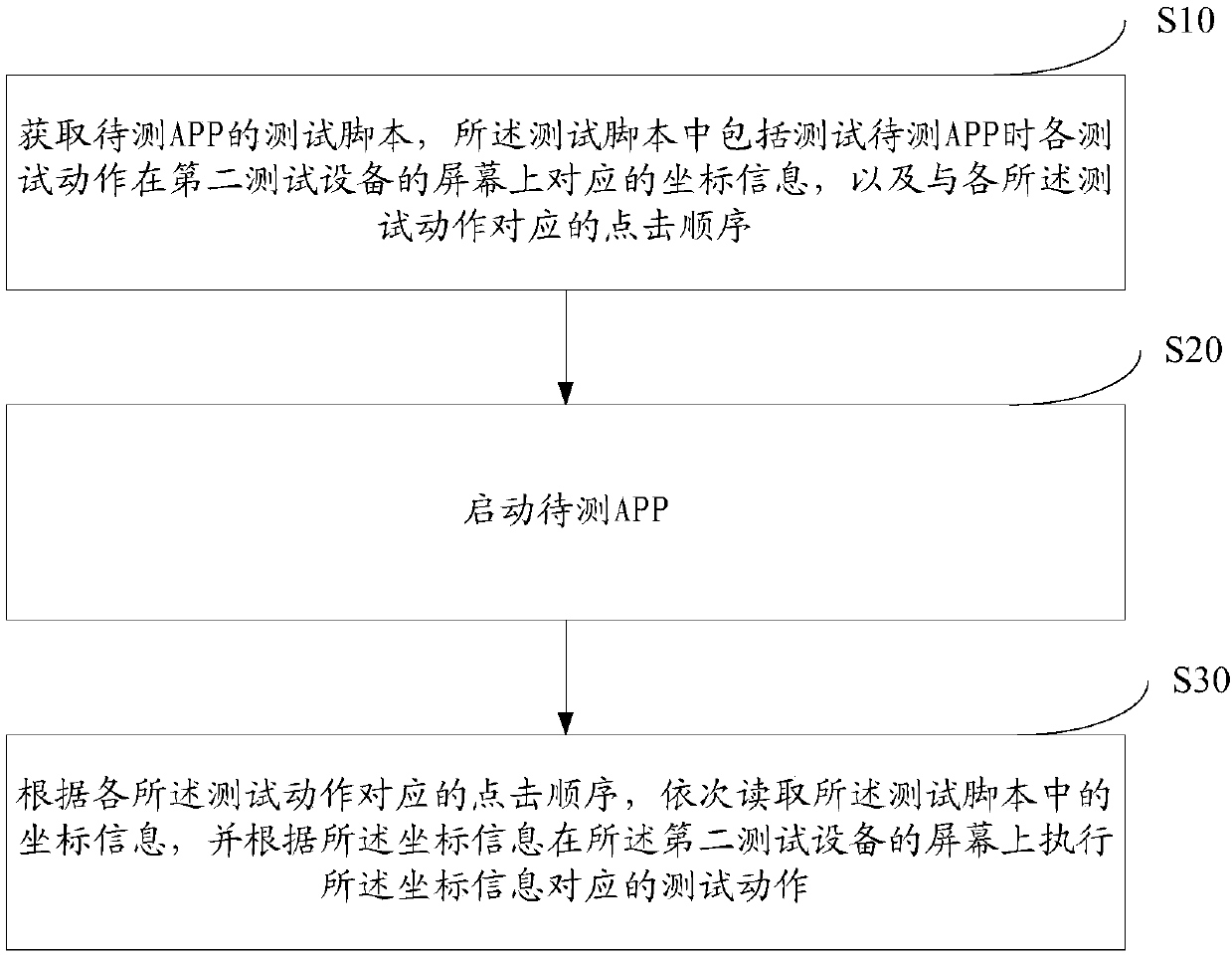
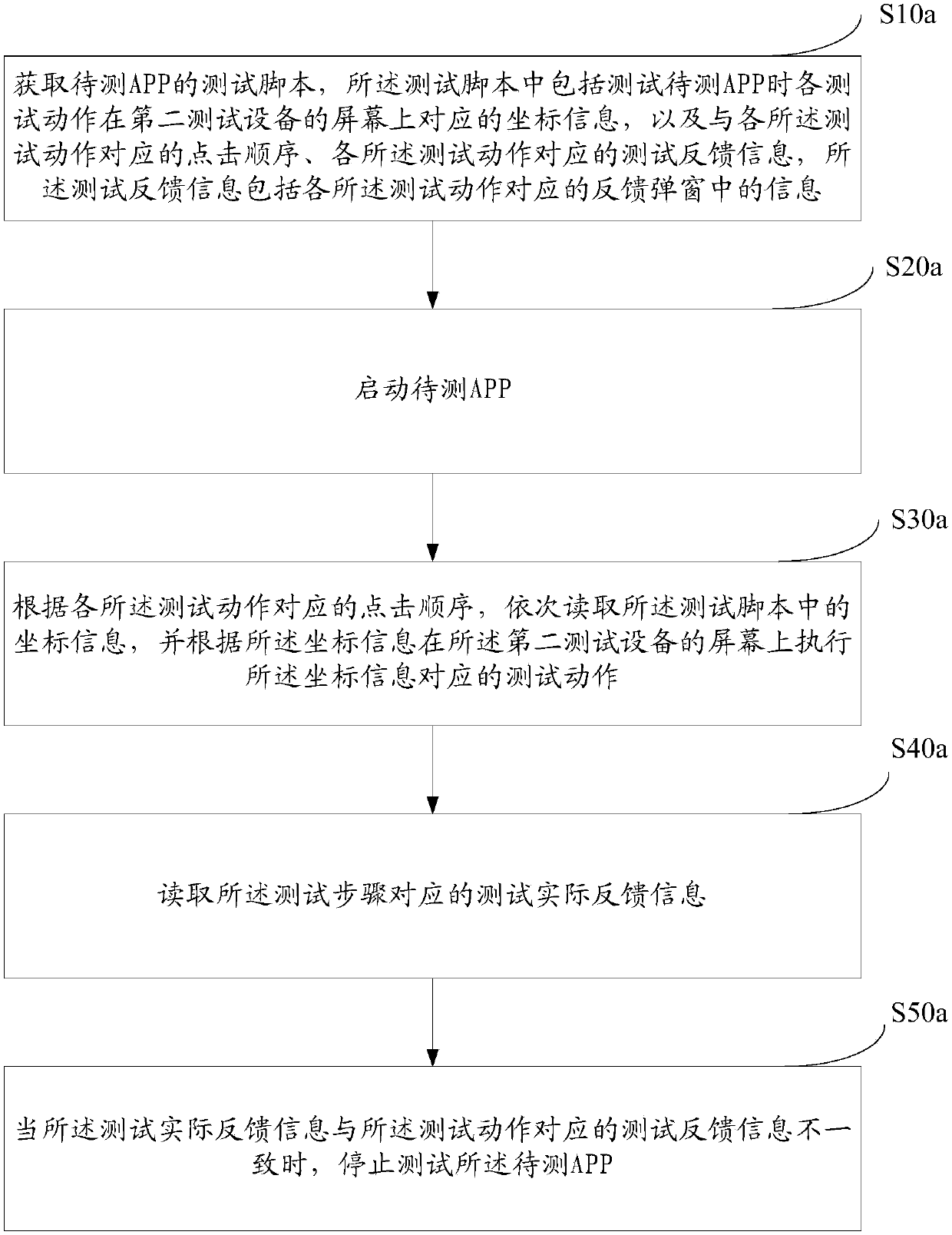
InactiveCN106933738AIncrease generation speedImprove update speedSoftware testing/debuggingTest efficiencyComputer hardware
The invention relates to an APP test method, an APP test script generation device and APP test script execution device. The method comprises the following steps of: starting a to-be-tested APP; obtaining corresponding coordinate information, on a screen of first test equipment, of each test action in sequence when the to-be-tested APP is tested; obtaining test end information; and generating a test script of the to-be-tested APP through the coordinate information corresponding to each test action according to a clicking sequence corresponding to each test action. According to the method, the generation of the APP test script can be finished by common testers without script software edition ability, so that the generation and updating speeds of the test script are improved and the test efficiency of the whole APP test is improved.
Owner:GREE ELECTRIC APPLIANCES INC
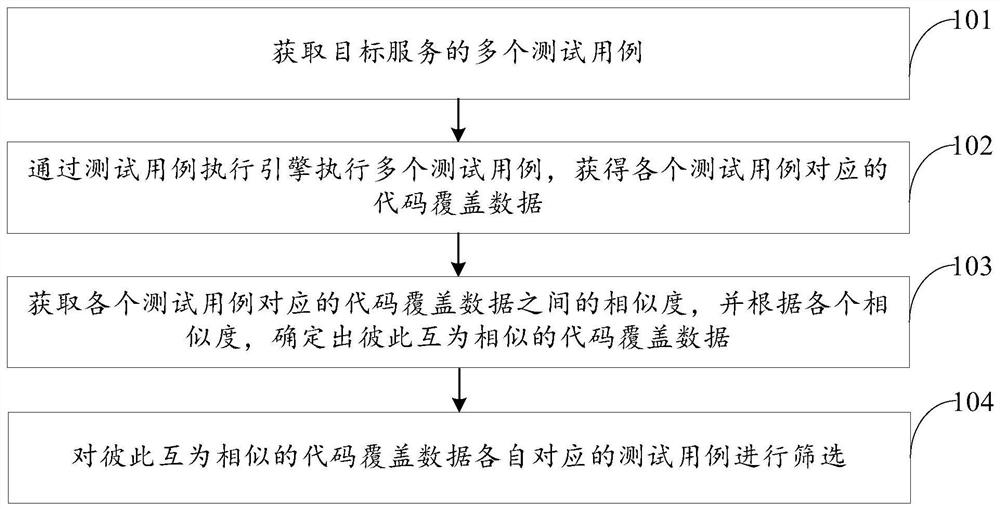
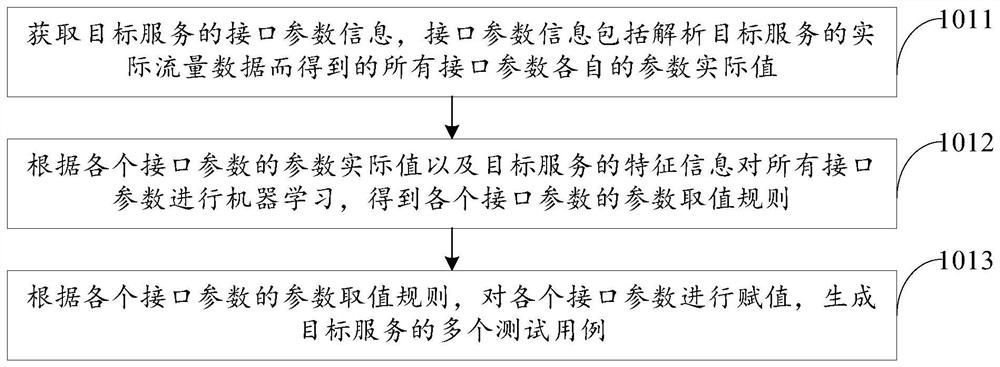
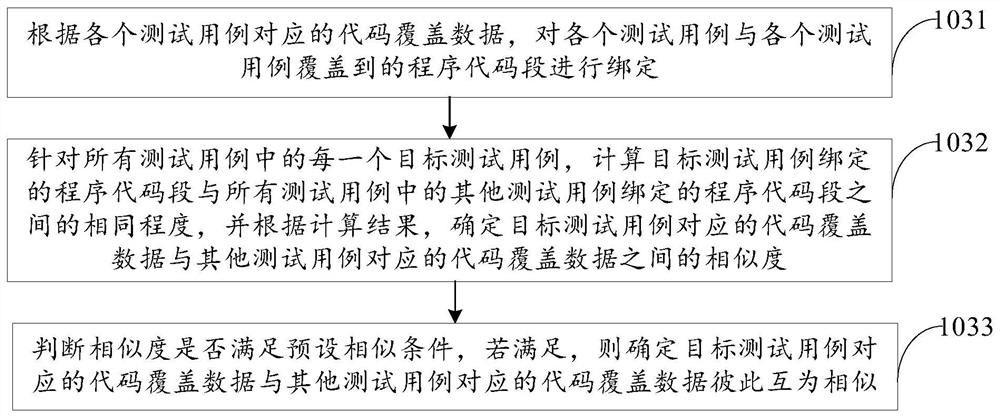
Test case screening method and device, computer equipment and storage medium
PendingCN112559365AReduce in quantityPerform avoidanceSoftware testing/debuggingTested timeCode coverage
The invention relates to a test case screening method and device, computer equipment and a storage medium, and belongs to the technical field of software testing. The method comprises the steps of obtaining a plurality of test cases of a target service; executing the plurality of test cases through a test case execution engine to obtain code coverage data corresponding to each test case; obtainingthe similarity between the code coverage data corresponding to each test case, and determining the code coverage data similar to each other according to each similarity; according to the software test case screening method and device, selecting the test cases corresponding to the code coverage data similar to each other, so that the screened test cases are high in pertinence, the number of the test cases of software can be effectively reduced, execution of a large number of redundant test cases is avoided, the test time is saved, and the test efficiency of a software system is improved.
Owner:上海品顺信息科技有限公司
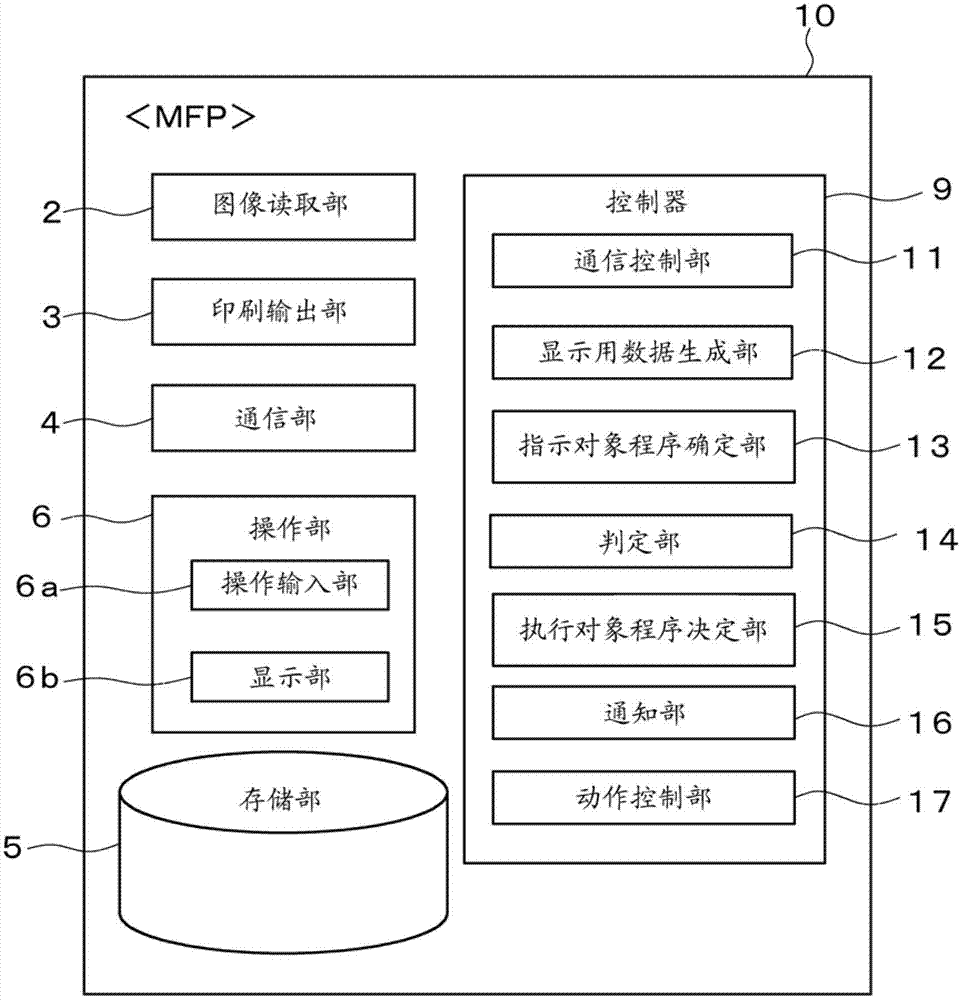
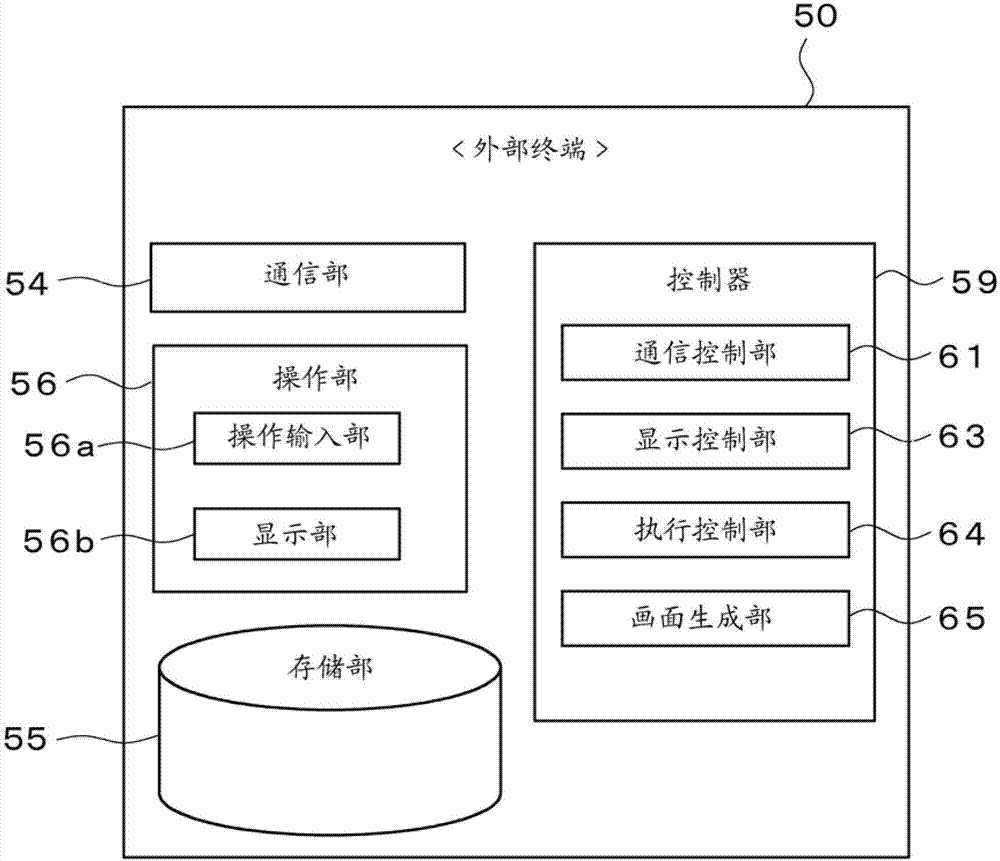
Image forming system, image forming apparatus and external terminal
ActiveCN103369174AReduce communication trafficPerform avoidancePictoral communicationImage formationExecution control
Owner:KONICA MINOLTA BUSINESS TECH INC
Sewing machine
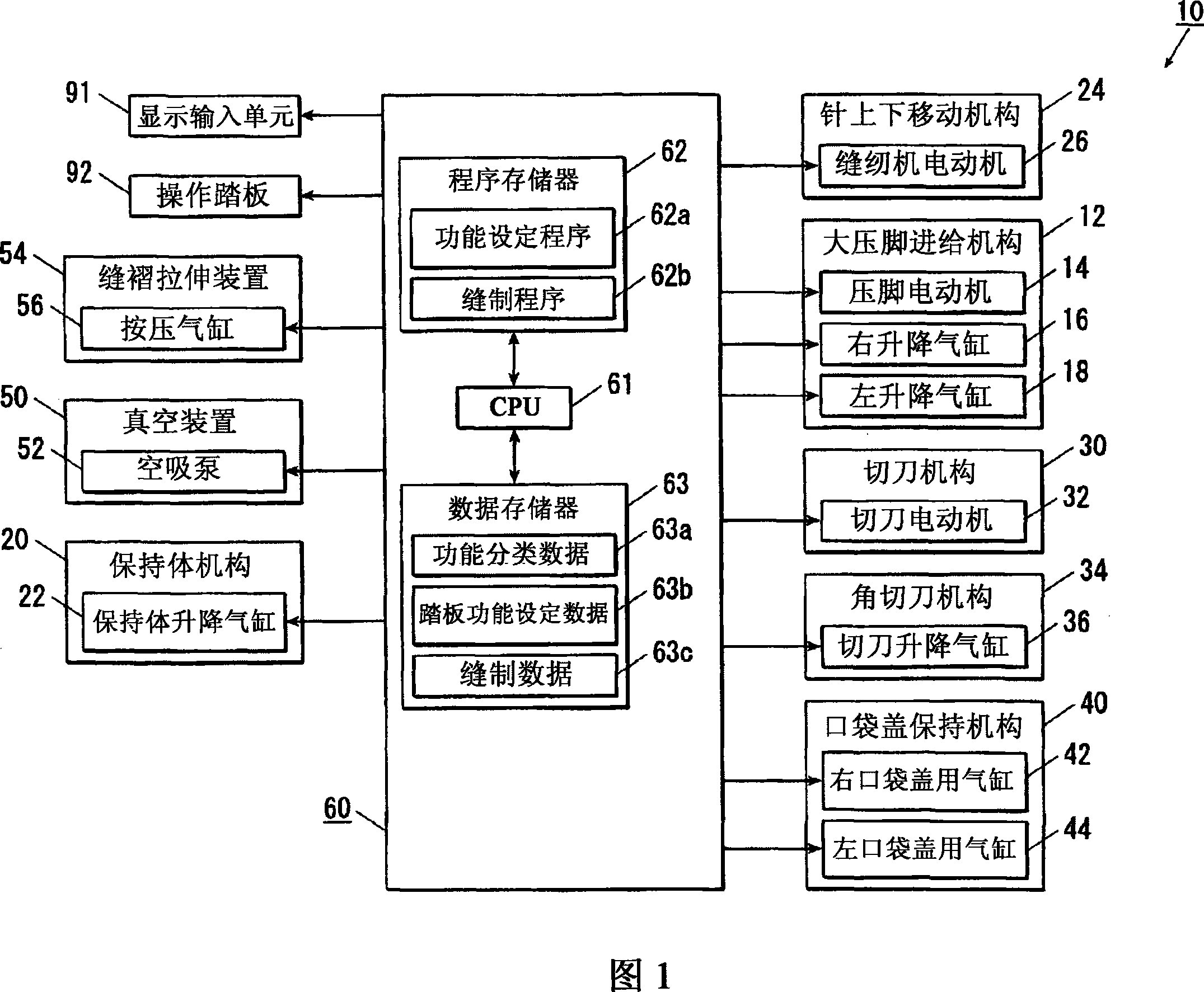
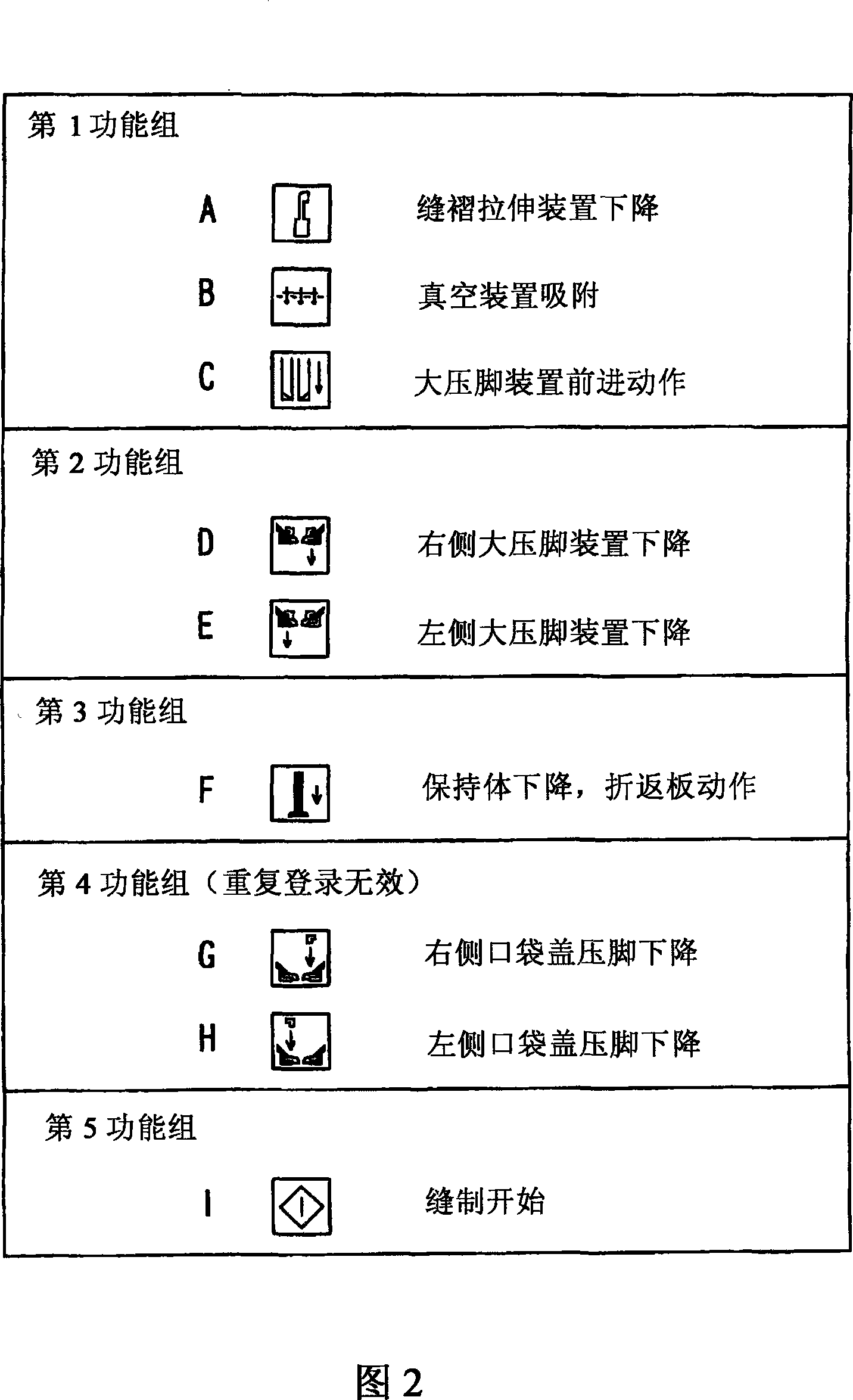
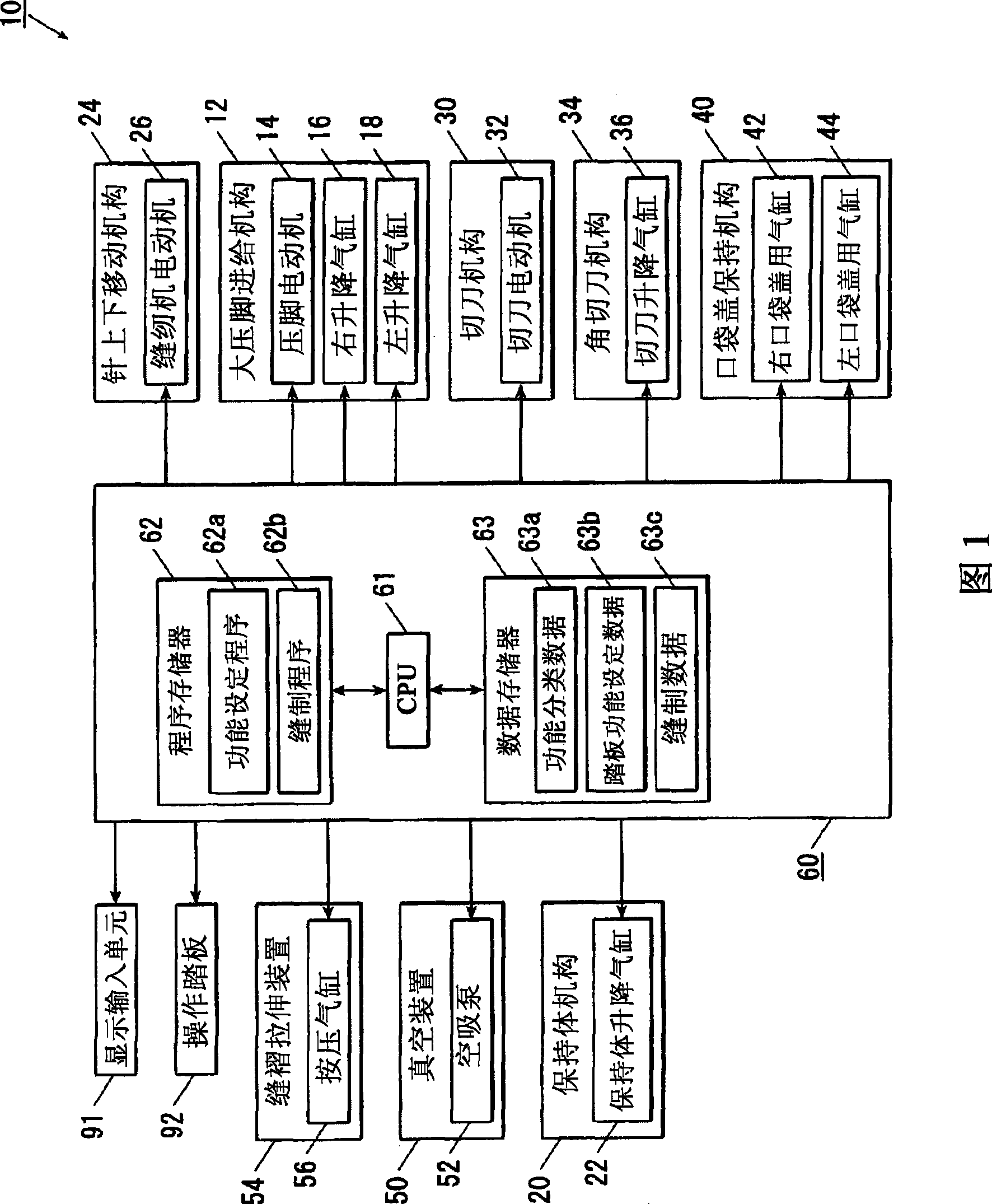
ActiveCN101070666AImplementation orderTo further rationalizeProgramme-controlled sewing machinesSewing machineControl unit
The invention can freely and easily choose order of all sorts of operations required by tailoring. A sewing machine has a number of action devices (14,16,18,22,26,32,36,42,44,52,56) for all sorts of operations required by tailoring. The operations are sub-divided into steps, each conducted in sequence. The sewing machine has an operating unit (92) for generating command signals to direct to execute each process in sequence through input operation; setting unit (91) for distributing all sorts of operations in each process; and action control unit (60) to control the action of each action device, in order to execute the assigned process of each operation in sequence, based on the command signals generated by the operating unit in sequence.
Owner:JUKI CORP
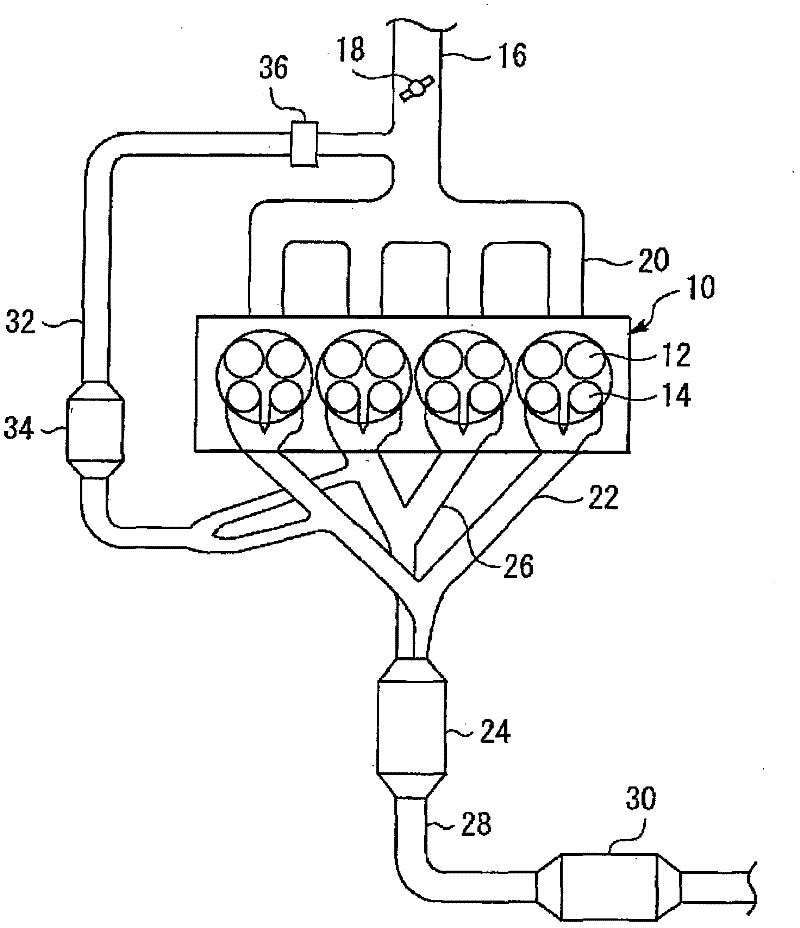
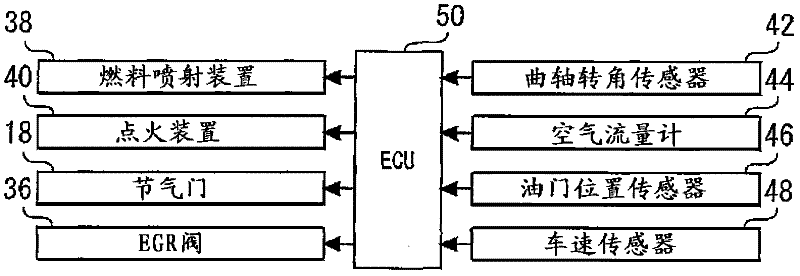
Exhaust purification device for internal combustion engines
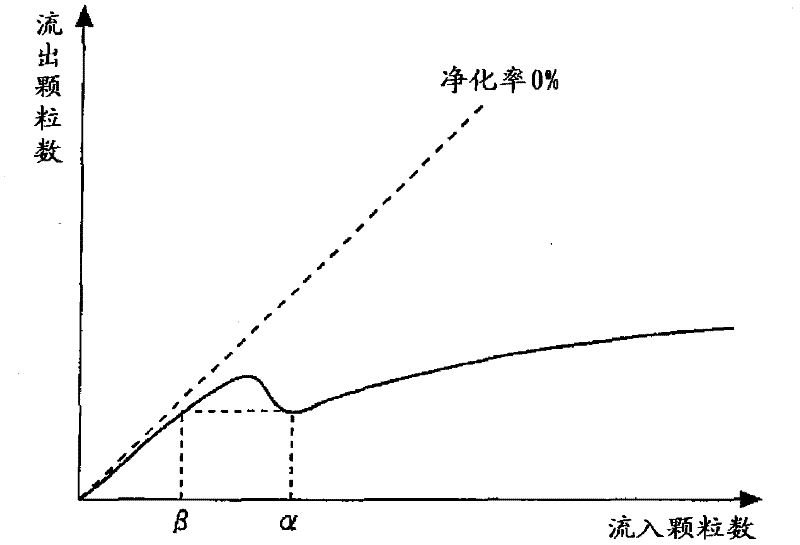
InactiveCN102265009AIncrease inflowInflow Increase ControlElectrical controlInternal combustion piston enginesParticulatesExternal combustion engine
The present invention relates to an exhaust gas purifying apparatus for an internal combustion engine. An object of the invention is to reduce the amount of particulate matter that flows out from a catalytic converter that continuously burns particulate matter contained in an exhaust gas. The exhaust gas purifying apparatus for an internal combustion engine of the present invention includes a catalytic converter that continuously burns particulate matter contained in an exhaust gas; particle amount acquisition means that acquires an inflow amount of particulate matter to the catalytic converter; and particle amount increase means that, when an acquired inflow amount of particulate matter is less than a predetermined threshold value ±, changes a value of a control parameter of the internal combustion engine in a direction such that the inflow amount of particulate matter to the catalytic converter increases. The threshold value ± corresponds to a value of a particulate matter inflow amount to the catalytic converter at a time when a particulate matter outflow amount from the catalytic converter is a local minimum in a graph showing a relation between a particulate matter inflow amount to the catalytic converter and a particulate matter outflow amount from the catalytic converter.
Owner:TOYOTA JIDOSHA KK
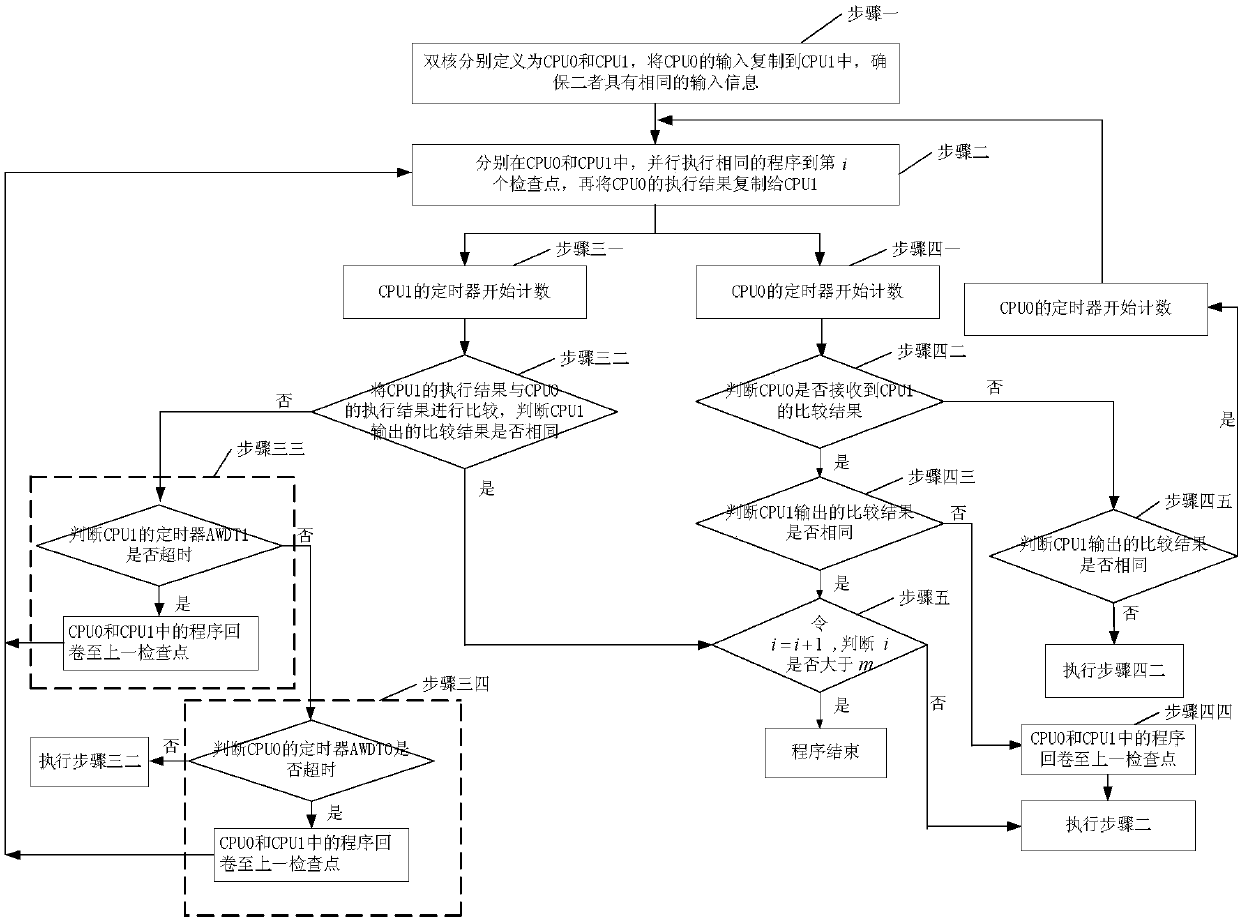
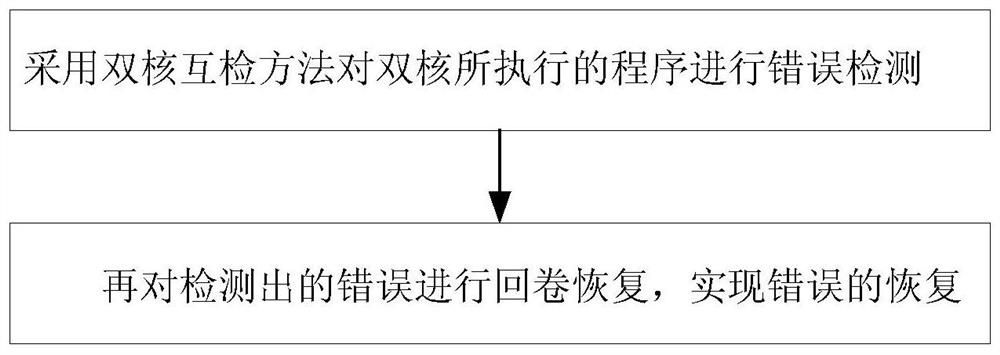
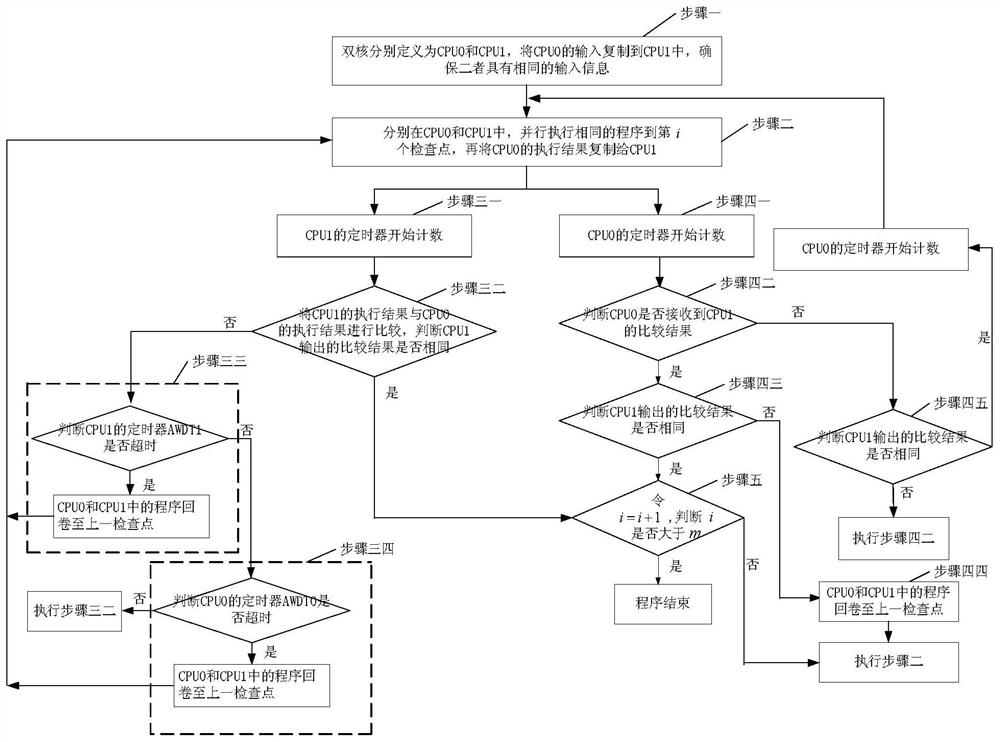
Zynq-7000-based dual-core ARM processor anti-single-event-upset protection method
ActiveCN108052420AGuaranteed uptimeMutual inspection process is simpleRedundant operation error correctionRedundant hardware error correctionDual coreDual mode
The invention discloses a Zynq-7000-based dual-core ARM processor anti-single-event-upset protection method, belongs to the field of processor antiradiation reinforcing and solves the problems that dual-mode redundancy methods can only realize fault detection and cannot realize fault restoration and existing fault detection is complex. The method includes following steps: adopting a dual-core mutual-detection method to perform error detection on programs executed by dual cores; performing rollback restoration on detected errors to realize error restoration. The method is mainly used for errordetection and restoration of the programs executed by the dual cores.
Owner:HARBIN INST OF TECH
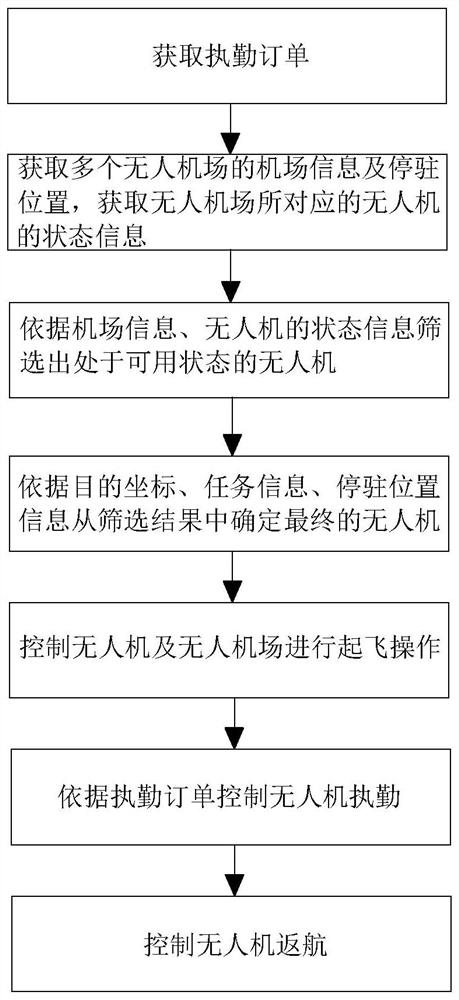
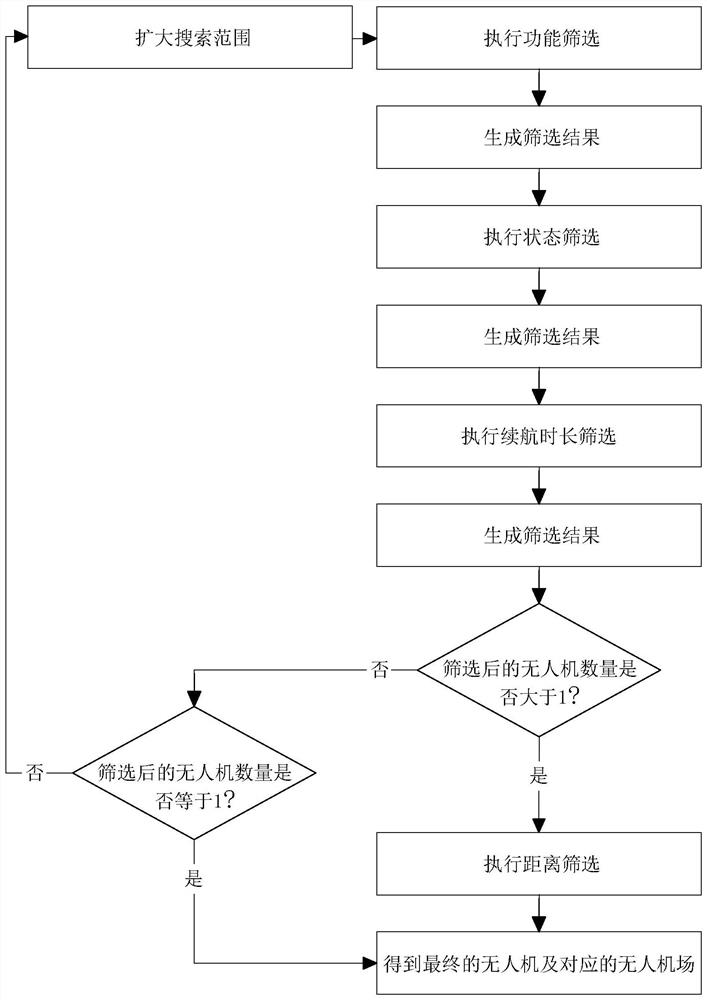
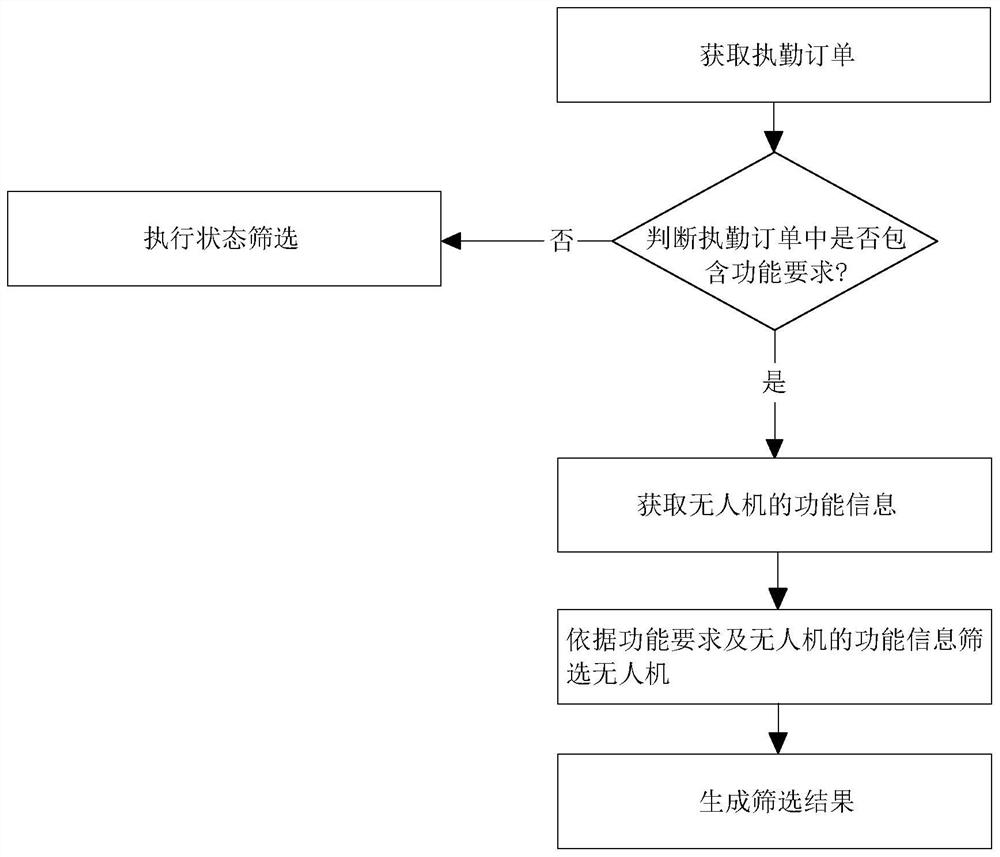
Operation management method and system based on unmanned aerial vehicle field, terminal and medium
ActiveCN114462853AImprove operational management efficiencyPerform avoidanceBuying/selling/leasing transactionsResourcesControl engineeringUncrewed vehicle
The invention relates to an operation management method and system based on an unmanned aerial vehicle farm, a terminal and a medium, and the method comprises the steps: obtaining an on-duty order which comprises a target coordinate and task information; monitoring information of multiple groups of preset unmanned aerial vehicle fields is obtained, and the monitoring information comprises airport information and parking positions of the unmanned aerial vehicle fields and further comprises state information of unmanned aerial vehicles corresponding to the unmanned aerial vehicle fields; screening out available unmanned aerial vehicles according to the airport information and the state information of the unmanned aerial vehicles; determining a final unmanned aerial vehicle from the screening result according to the target coordinate, the task information and the parking position information; the unmanned aerial vehicle and the unmanned aerial vehicle field are controlled to take off; and controlling the unmanned aerial vehicle to be on duty according to the on-duty order. The method has the effects of reducing the workload of manual management of the unmanned aerial vehicle and the unmanned aerial vehicle field and improving the operation management efficiency.
Owner:浙江极客桥智能装备股份有限公司
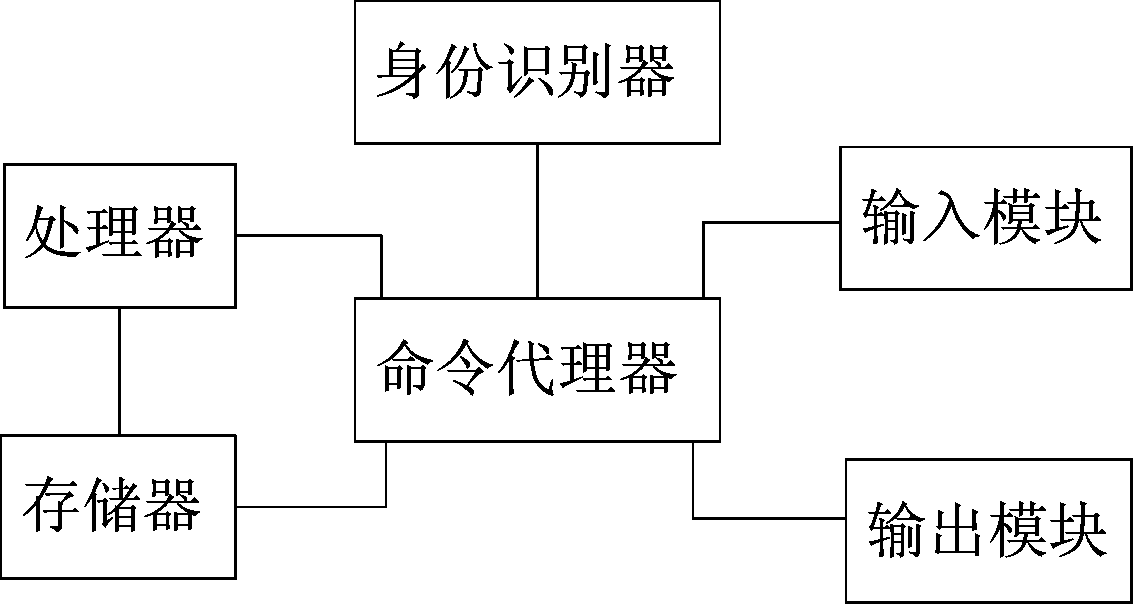
Wearable device self-safety protection system
ActiveCN106095077BEnsure safetyPerform avoidanceInput/output for user-computer interactionGraph readingComputer moduleInformation security
The invention discloses a self-security protection system of wearable equipment. The self-security protection system comprises an input module, an output module, a processor and a storage module, wherein the input module, the output module, the processor and the storage module are arranged in the wearable equipment. The self-security protection system also comprises a command proxy arranged in the wearable equipment, wherein the command proxy is independently connected with the input module, the output module, the processor and the storage module; and the command proxy is also connected with an identity recognizer. The self-security protection system has the following beneficial effects that the wearable equipment is provided with the command proxy, the operation of a user can be identified and analyzed and is converted into an internal instruction to be executed, the execution of a direct external instruction is avoided, and information security in the equipment is improved.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
A remote printing control method and device
ActiveCN106227474BImprove securityPerform avoidanceDigital output to print unitsComputer engineering
The invention discloses a remote printing control method. The method includes the steps of generating order information according to an order request when receiving the order request sent by a terminal, sending a printing instruction containing the order information to a printer corresponding to the order request so that the printer can feed back a verification request according to the printing instruction, or sending the order information to the terminal so that the terminal can send the printing instruction containing the order information to the printer corresponding to the order request, verifying the legality of the printing instruction according to the verification request when receiving the verification request fed back by the printer, and returning the verification result to the printer. The invention further discloses a remote printing control device. The problem that an existing printer is poor in safety in the printing process is solved. The safety of the printer in the printing process is improved.
Owner:宜春小马快印科技有限公司
Spinning machine maintenance control equipment and control method
InactiveCN100545333CImproves chances of troubleshootingEasy to troubleshootAnalogue computers for control systemsContinuous wound-up machinesProcess equipmentMachine maintenance
Owner:利特英格纺织机械制造股份公司
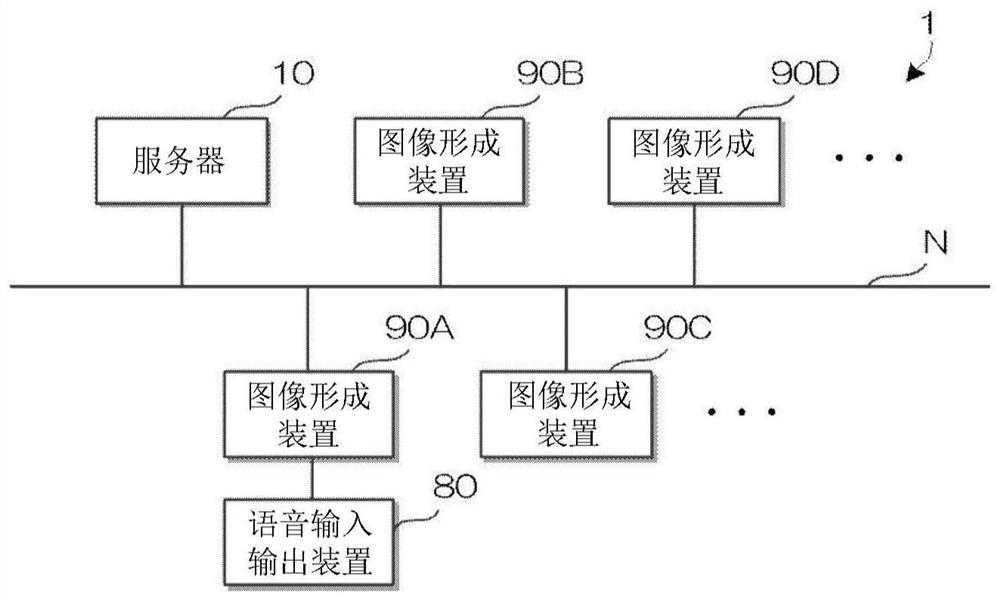
Information processing apparatus, information processing method, and computer readable medium
PendingCN113364924AShorten the timeAccept changeSpeech recognitionInput/output processes for data processingComputer hardwareInformation processing
Owner:FUJIFILM BUSINESS INNOVATION CORP
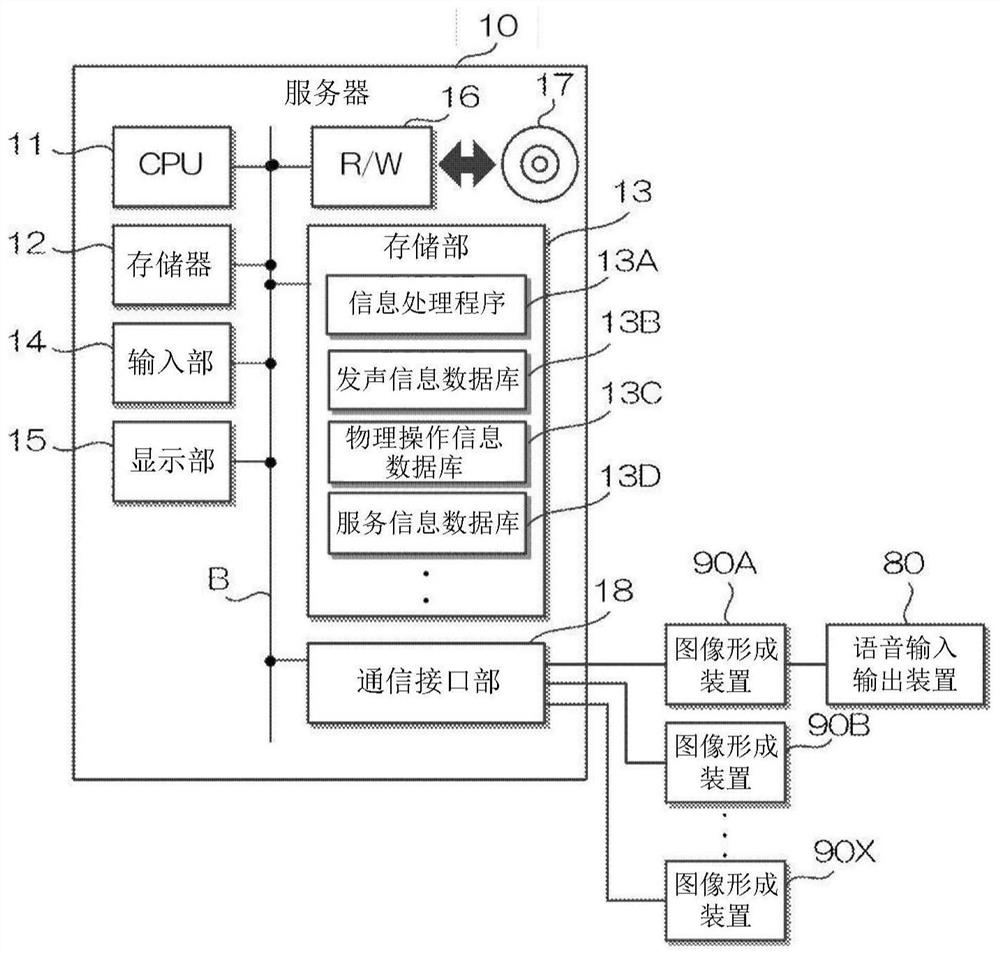
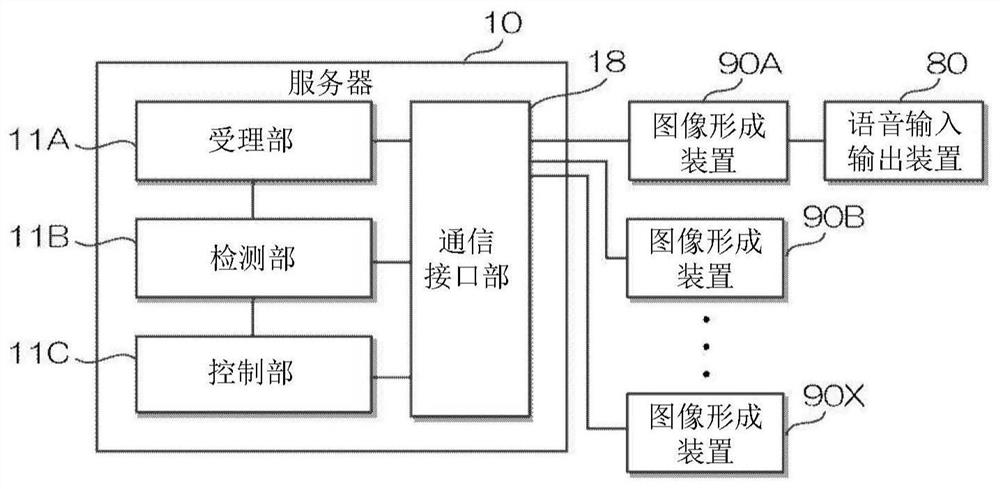
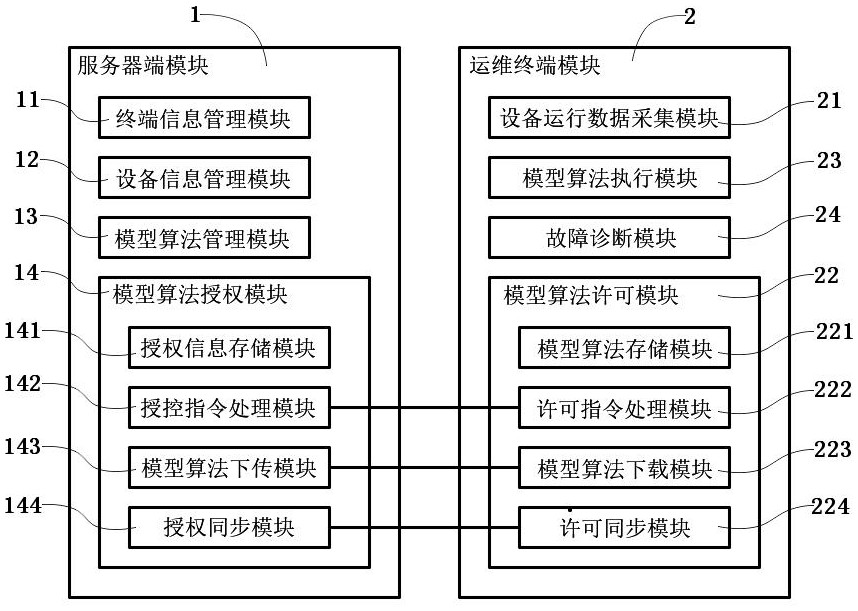
Authorization system and method of model algorithm
PendingCN112287304AGuarantee copyright rights and interestsReduce the burden onProgram/content distribution protectionData switching networksEngineeringAnalysis of algorithms
The invention discloses an authorization system and method of a model algorithm. According to the system, authorization information is synchronized to operation and maintenance terminals through a server via a control instruction, and then the operation and maintenance terminals download corresponding model algorithms according to model algorithm identification codes in the authorization information to achieve release of the model algorithms in the corresponding operation and maintenance terminals. Therefore, the operation and maintenance terminal is controlled by the server when executing themodel algorithm according to the operation data of the equipment to analyze the operation state of the equipment, and therefore, the operation and maintenance terminal is prevented from executing unnecessary model algorithms while the copyright rights and interests of manufacturers for executing the model algorithms on the model algorithms are ensured, and the burden of executing the model algorithm by the operation and maintenance terminal is reduced. Moreover, the authorization information and the model algorithm are respectively transmitted, so that the transmission rate of the model algorithm can be reduced under the condition that the data communication load of the server is relatively large, the data communication burden of the server is reduced, and the robustness of the whole system is improved.
Owner:南京燚麒智能科技有限公司
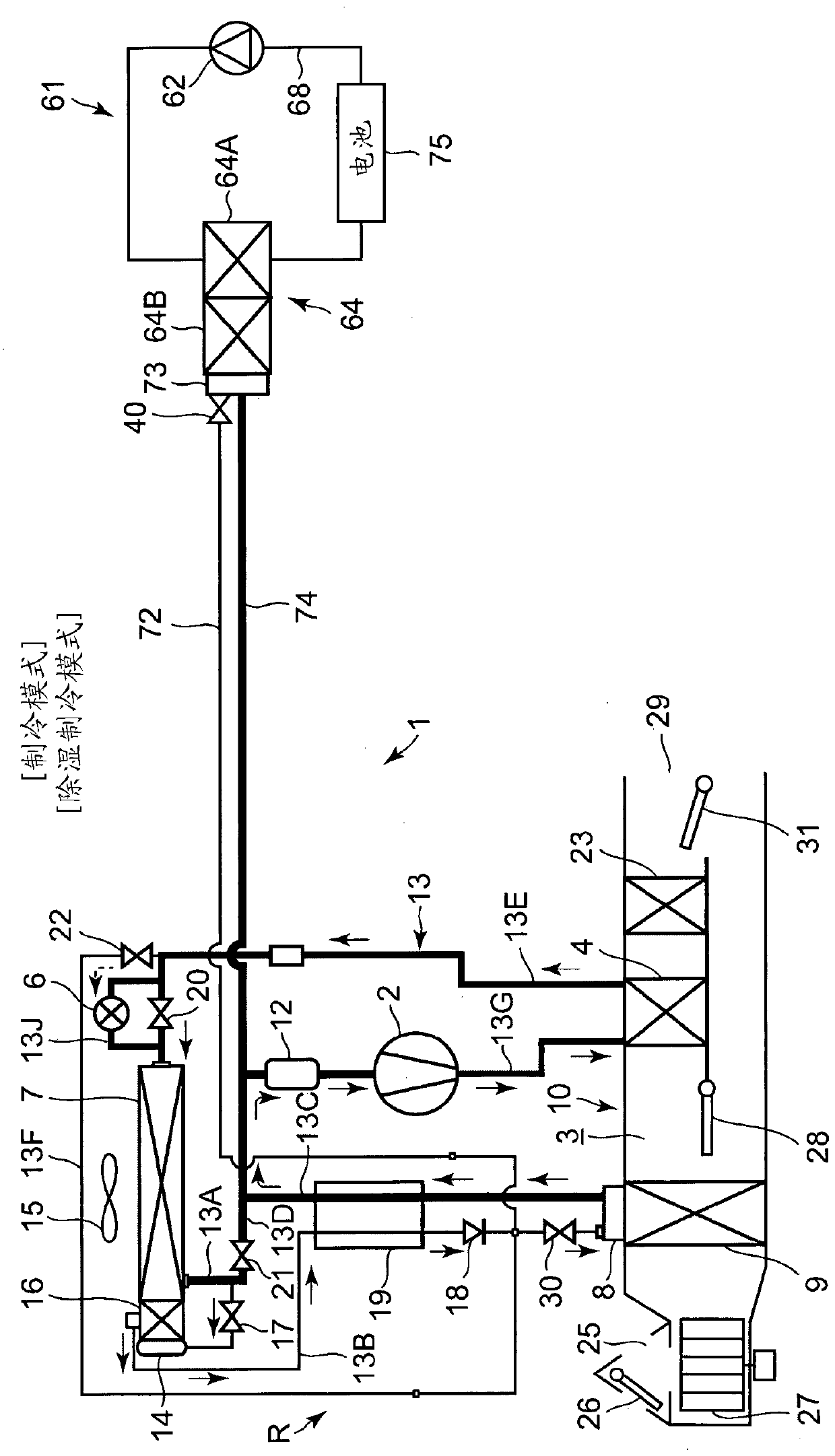
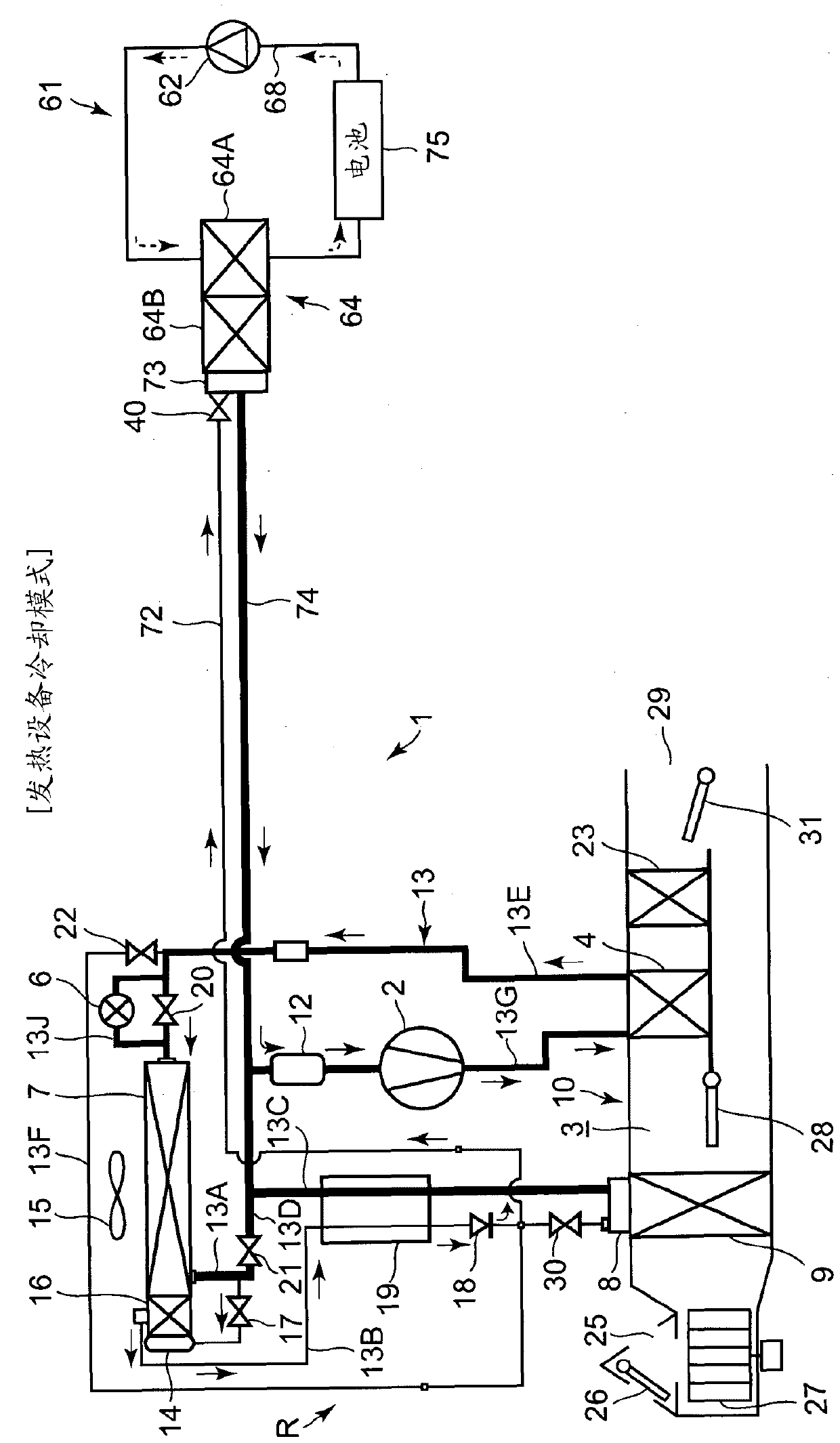
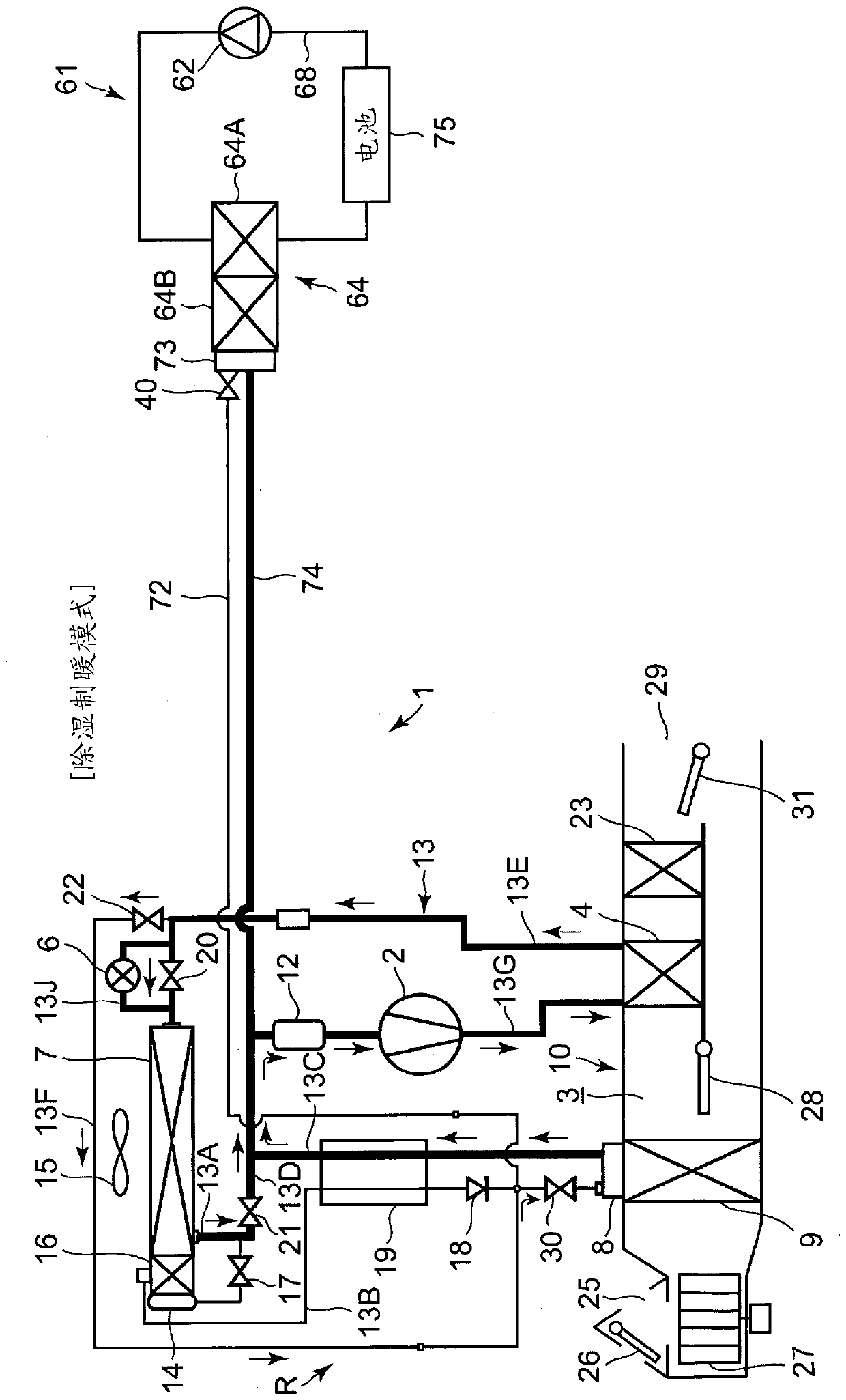
Vehicle air conditioner
ActiveCN111051096ADecreased accommodationTo prevent the reduction of the amount of refrigerantAir-treating devicesVehicle heating/cooling devicesHeat carrierSolenoid valve
Provided is a vehicle air conditioner by which it is possible to prevent or mitigate a decrease in reliability resulting from oil remaining in a refrigerant supply pipe which is for cooling a heater.In the present invention, the following are executed: a cooling mode in which a solenoid valve (17) is opened and a refrigerant is sent to a heat absorber (9); and a heating mode in which the solenoidvalve (17) is closed. A heater cooling device (61) includes: a refrigerant / heat carrier heat exchanger (64) for exchanging heat between the refrigerant and a heat carrier; a refrigerant supply pipe (72) that branches off from the refrigerant downstream side of the solenoid valve (17) and that supplies the refrigerant to the refrigerant / heat carrier heat exchanger; and a solenoid valve (40) provided in the refrigerant intake opening of the refrigerant / heat carrier heat exchanger. The heater cooling device closes the solenoid valve (40) during the cooling mode and opens the solenoid valve (40)during the heating mode.
Owner:SANDEN CORP
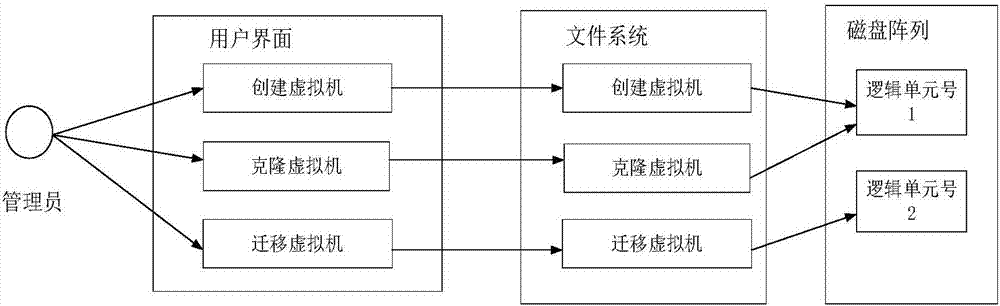
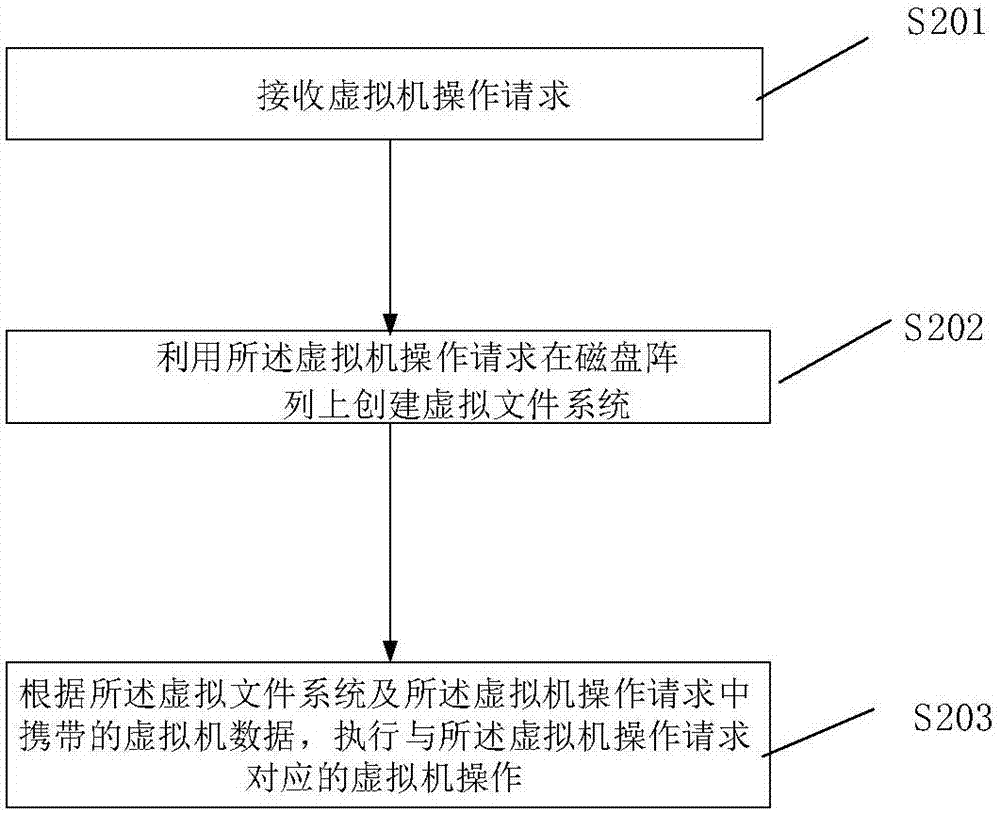
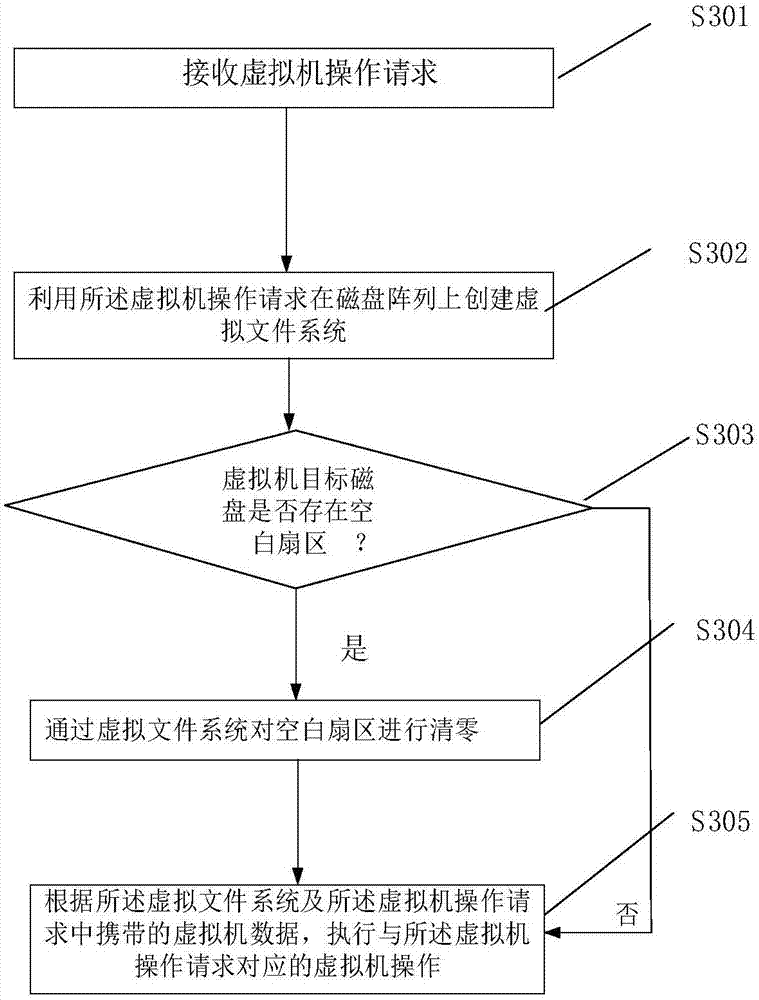
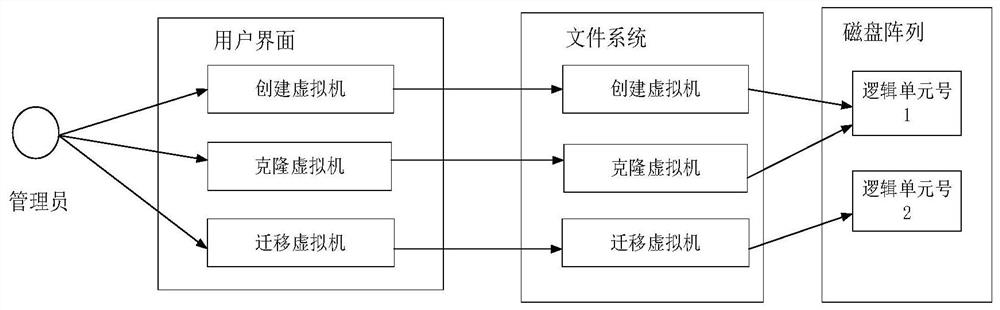
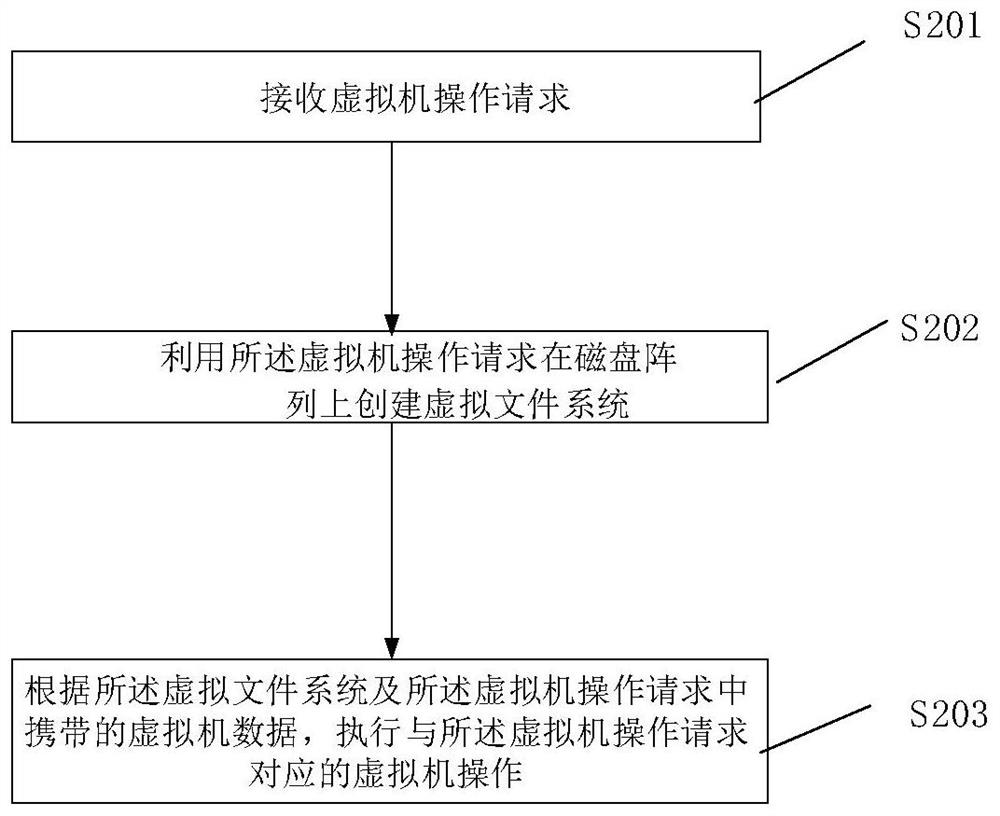
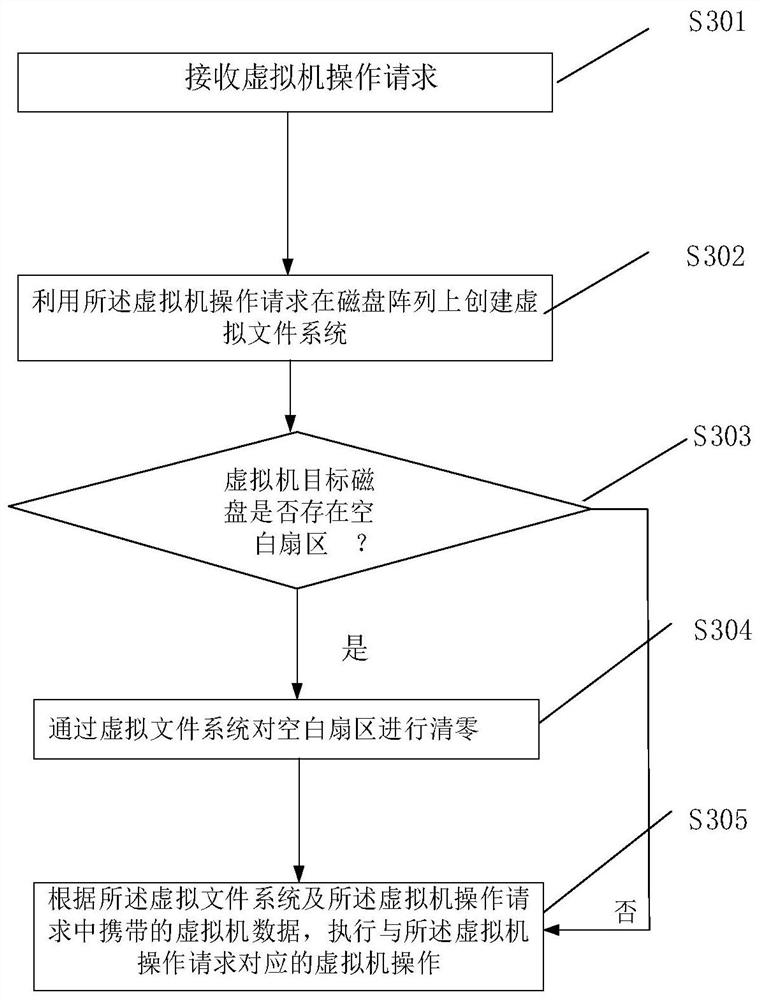
Virtual-machine operation method, device and system based on disc array
ActiveCN107357531AAvoid occupyingPerform avoidanceInput/output to record carriersSoftware simulation/interpretation/emulationVirtual file systemFile system
The invention discloses a virtual-machine operation method based on a disc array. The virtual-machine operation method includes the steps that a virtual-machine operation request is received; a virtual file system is established on the disc array through the virtual-machine operation request; according to the virtual file system and virtual machine data carried in the virtual-machine operation request, virtual-machine operation corresponding to the virtual-machine operation request is carried out. Therefore, in the technical scheme, virtual-machine operation is carried out on the disc array, it is avoided that as excessive data storage units are established on the disc array, an internal storage resource and a CPU resource are occupied; meanwhile, it is avoided that virtual-machine operation corresponding to the virtual-machine operation request is carried out through the file system on the disc array, system response time is shortened accordingly, and the system response rate is increased. The invention also discloses a device and system for virtual-machine operation, and the technical effect can also be achieved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Sewing machine
ActiveCN101070666BRationalizeSimplifyProgramme-controlled sewing machinesReliability engineeringControl unit
A sewing machine has a number of controls for a range of operations. The operations are sub-divided into steps, each conducted in sequence. The sewing machine has a control unit that triggers each step, dependent upon completion of the previous step, and settings that allocate individual processes to the respective step. The controls also regulate the operations in correct sequence and check that the commands have been executed in accordance with the original operation selected. The sewing machine is equipped with an electronic central processing unit.
Owner:JUKI CORP
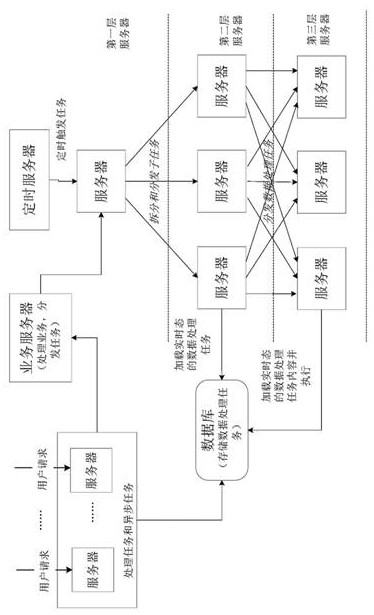
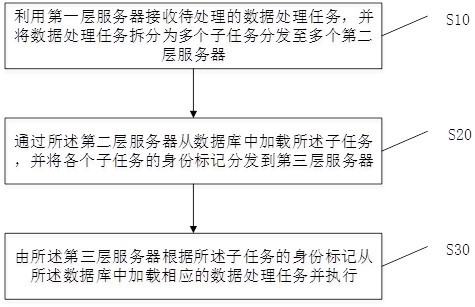
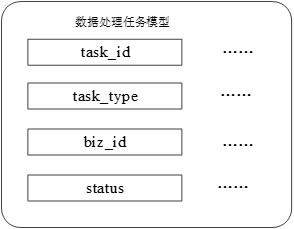
Data processing method and device, computer equipment and storage medium
InactiveCN113254506ARelieve pressureImprove processing efficiencyDatabase management systemsSpecial data processing applicationsRapid processingServer
The embodiment of the invention provides a data processing method and a device, computer equipment and a storage medium, and the method comprises the steps: receiving a to-be-processed data processing task through a first-layer server, splitting the data processing task into a plurality of sub-tasks, and distributing the sub-tasks to a plurality of second-layer servers; loading the sub-tasks from a database through the second-layer servers, and distributing the identity marks of the sub-tasks to a third-layer server; and adopting the third-layer server to load the corresponding data processing task from the database according to the identity marks of the sub-tasks and execute the data processing task. According to the technical scheme, a three-layer distribution asynchronous task processing architecture is constructed, the processing resources of the server cluster can be fully utilized, the time-consuming and resource-consuming data processing tasks are decomposed into the sub-tasks to be rapidly processed, the processing efficiency of a large number of data processing tasks high in time consumption is improved, a large number of blocking is avoided, and the server pressure is reduced.
Owner:ZHEJIANG KOUBEI NETWORK TECH CO LTD
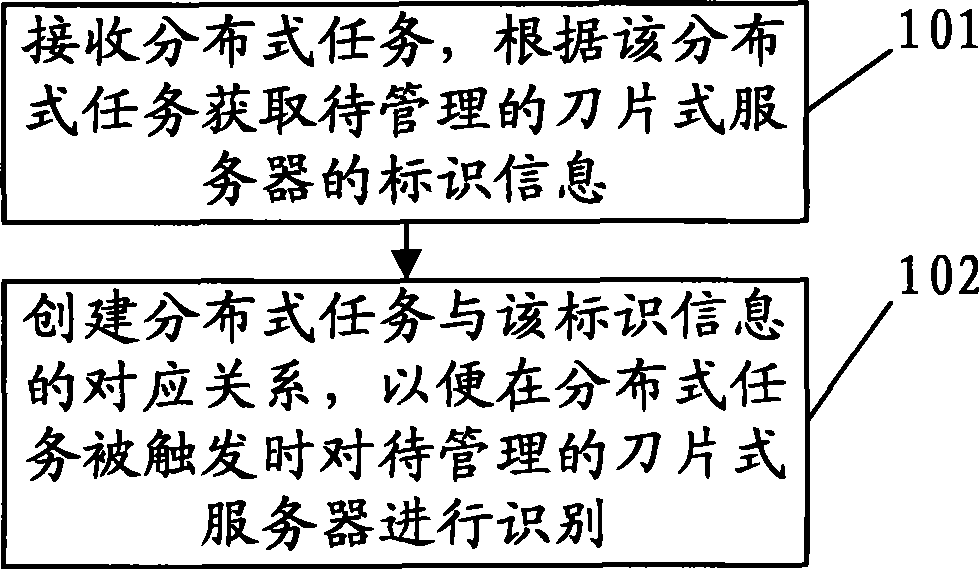
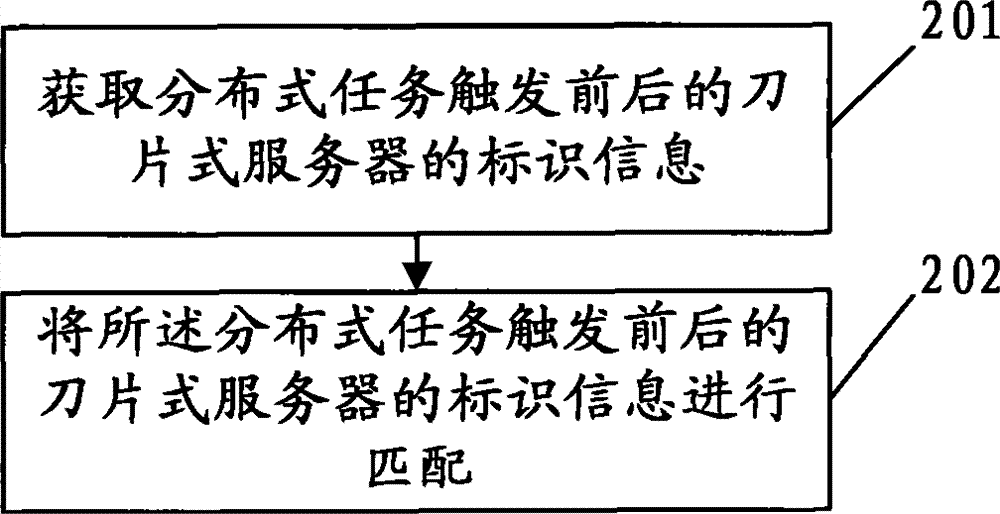
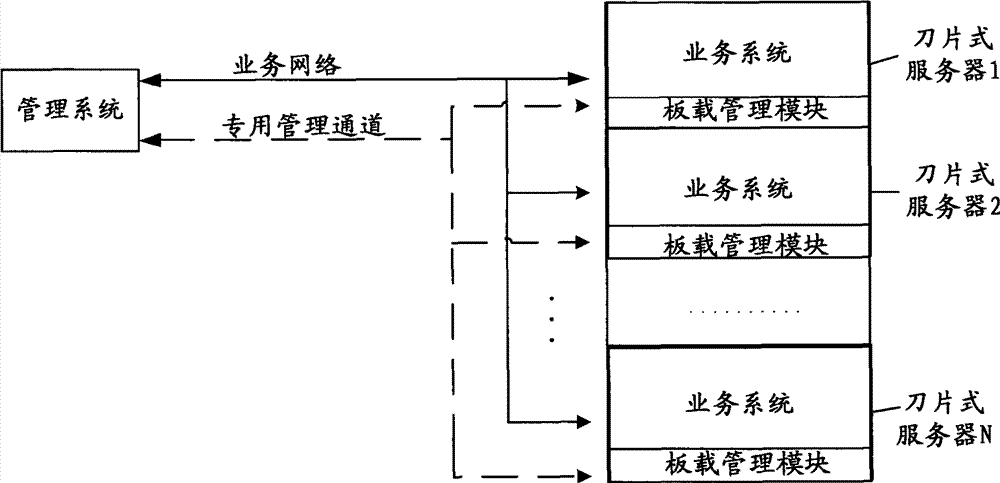
Method, device and system for marking and identifying blade server
ActiveCN101686148BGuaranteed uptimePerform avoidanceData switching networksInformation layerEmbedded system
The invention discloses a method, a device and a system for marking and identifying blade server, relating to the network technical field and aiming at solving the problem of unexpected distributed task implementation caused by that in the prior art the distributed task implementation executed by the blade server uses host IP as task blade server identification. The embodiment of the invention provides a blade server identifying method, comprising the following steps: acquiring identification information of the blade server before and after the distributed task is triggered; matching the identification information of the blade server before and after the task is triggered; and controlling the blade server to continuously implement the distributed task if matching is successful. By adopting the method and the device of the invention, the blade server used for implementing the distributed disk can have a unique identification, thus avoiding unexpected distributed task implementation. The embodiment of the invention also discloses a method and a device for establishing an identification information layered identification relationship table for the blade server.
Owner:HUAWEI TECH CO LTD
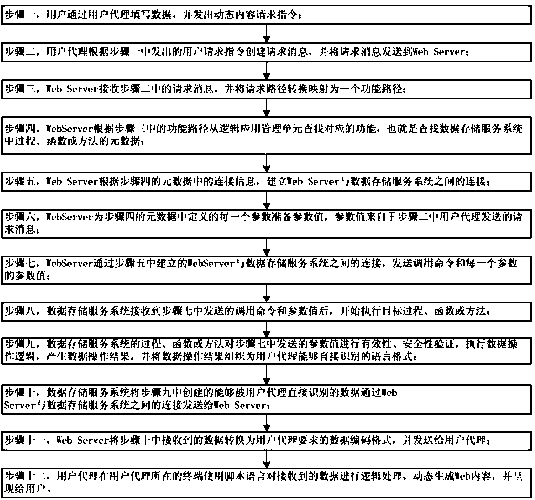
A request processing method for dynamic web content
ActiveCN104965909BReduce resource usageImprove operational efficiencyWebsite content managementSpecial data processing applicationsManagement unitData operations
The invention belongs to the technical field of computer software and provides a dynamic web content request handling method. The method comprises the steps of: filling data and sending out a dynamic content request instruction; creating a request message and sending the request message to a Web Server; converting a request path into a functional path by the Web Server, finding a corresponding function from a logic application management unit, establishing a connection with a data storage service system, and preparing parameter values according to metadata; sending a calling command and the parameter values; after receiving the calling command and the parameter values by the data storage service system, executing a corresponding process, function or method, carrying out effectiveness and security verification, executing data operation logic, and generating a data operation result; sending data created according to the data operation result to the Web Server and a user agent in sequence; and dynamically generating the Web content and presenting the Web content to a user by a terminal of the user agent. According to the method, application codes do not need to be executed in the Web Server, few Web Server resources are occupied, and the running efficiency and throughput capacity of the Web Server are high.
Owner:上海沃恩信息科技有限公司
Method for actuating standard interface devices perform non-standard events
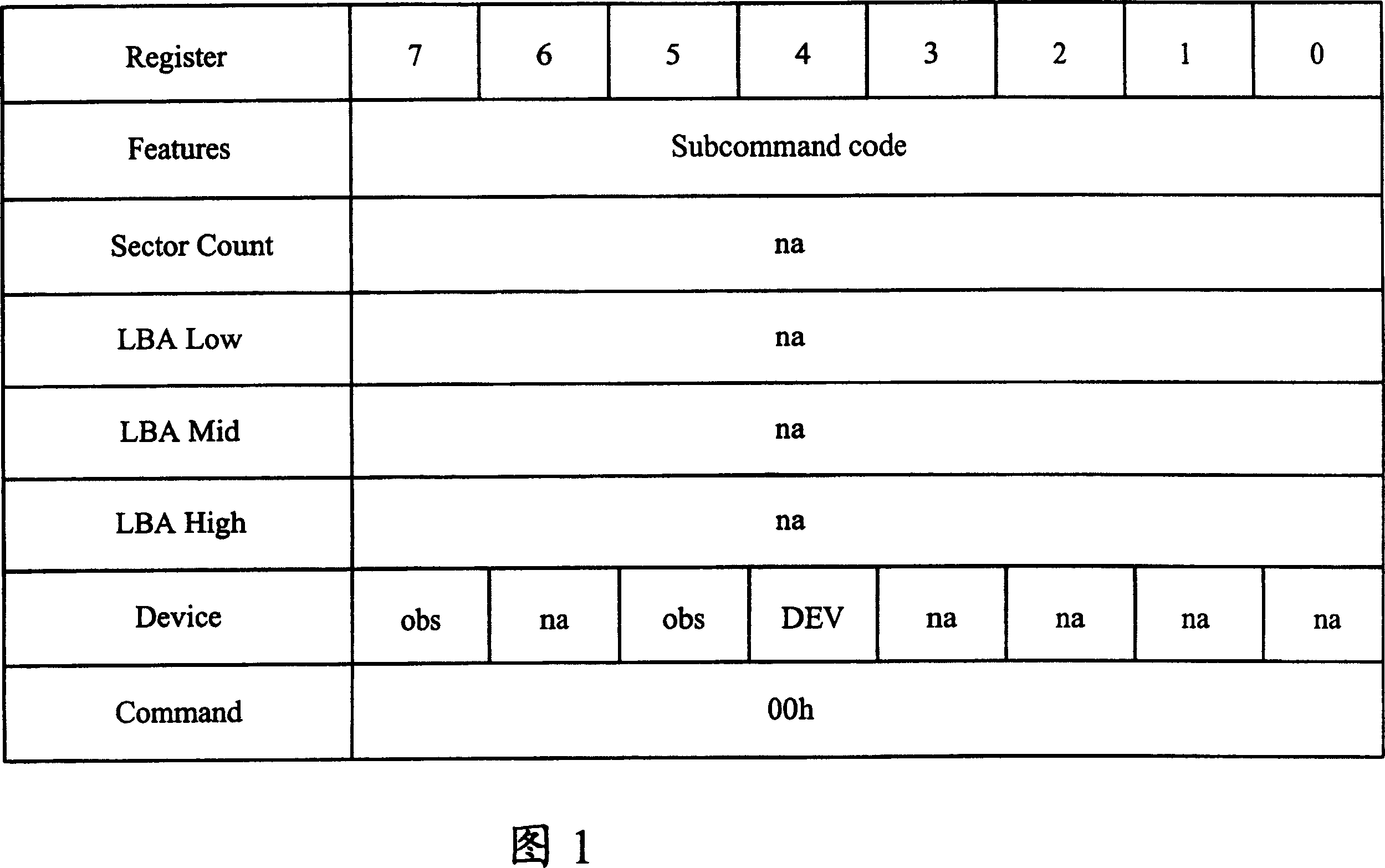
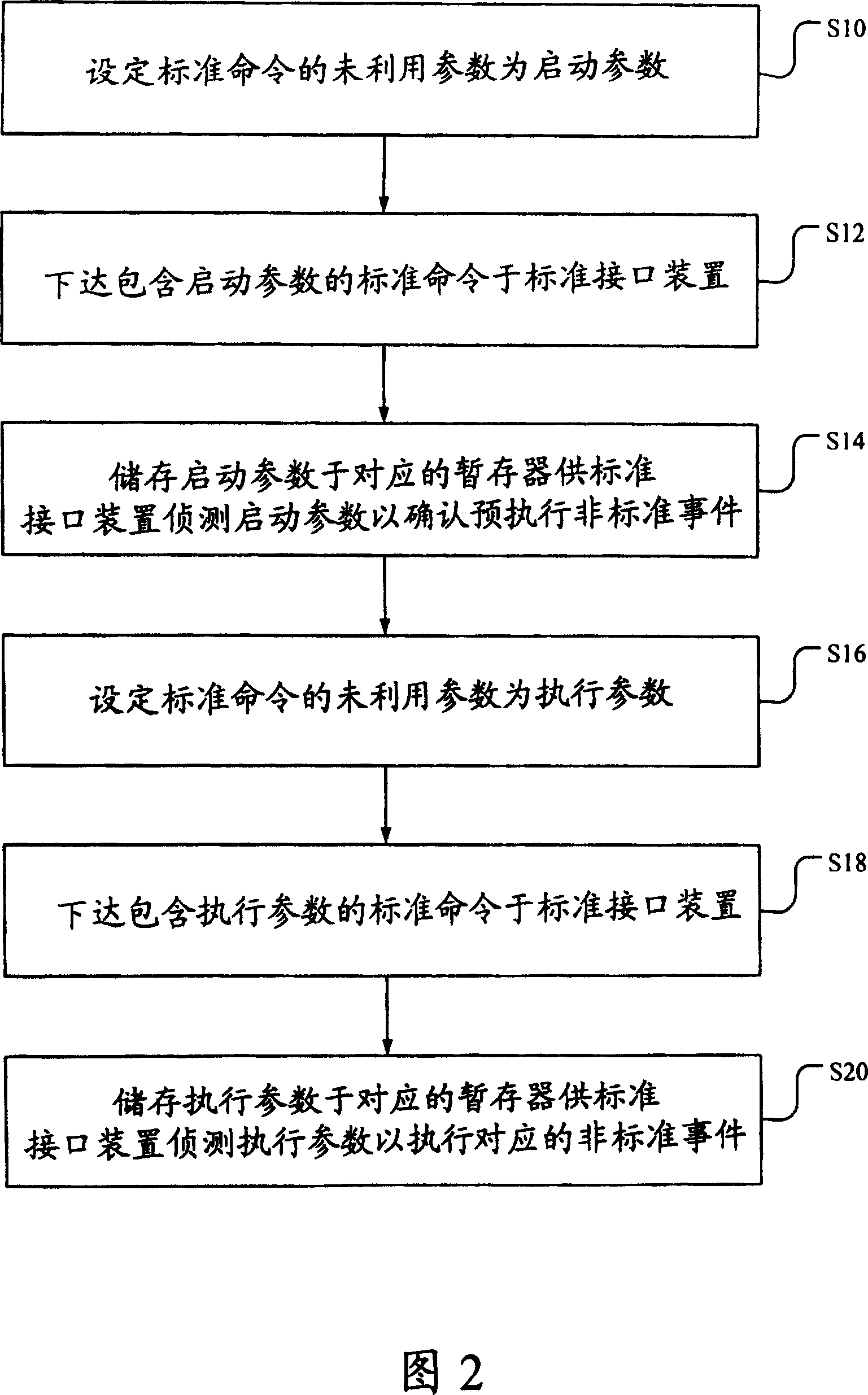
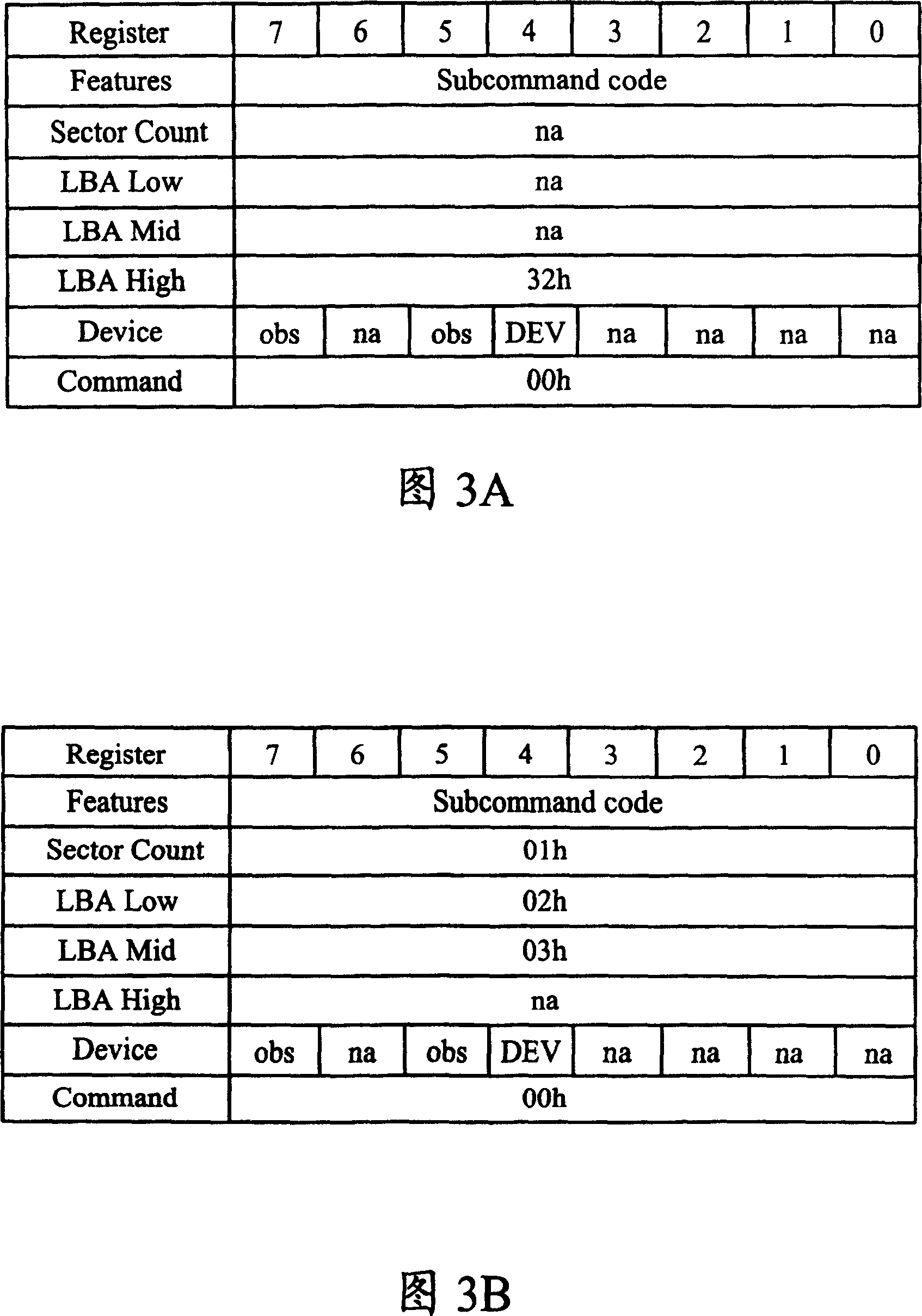
ActiveCN100349146CIncrease elasticityPerform avoidanceInput/output to record carriersComputer hardwareComputer science
Owner:VIA TECH INC
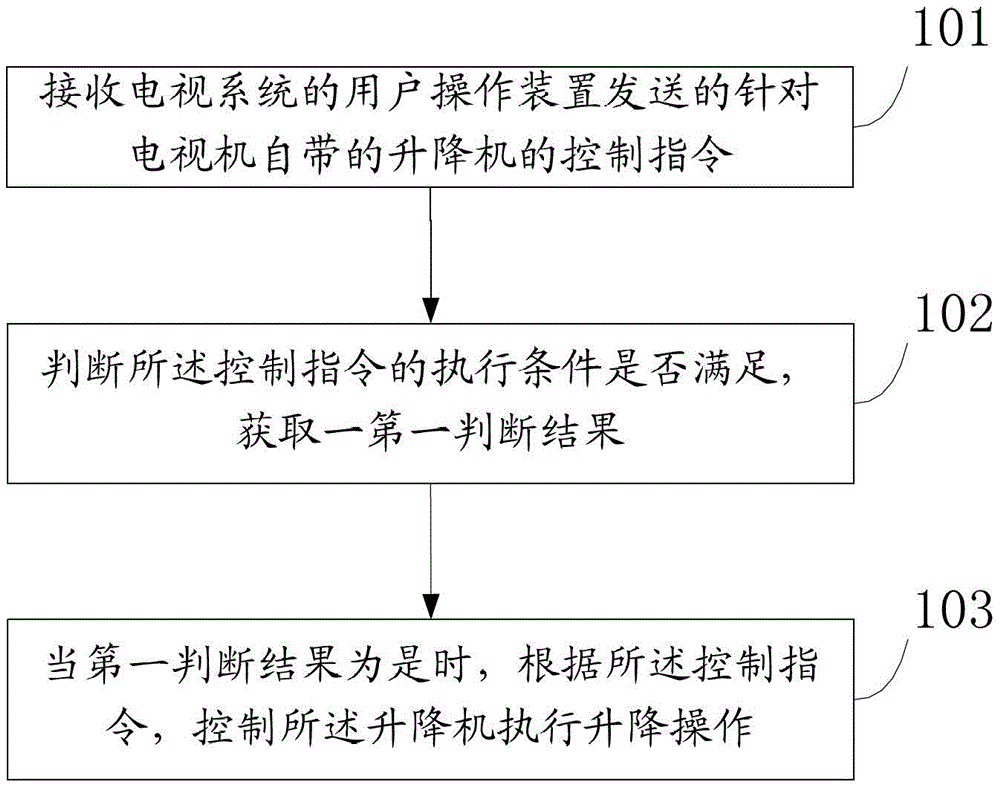
Control method, control device and television system
ActiveCN103442284BPerform avoidanceTransmission systemsSelective content distributionComputer hardwareTelevision system
Provided are a control method, a control device and a television system. The method is used for a television system, and comprises: receiving a control command for a built-in lift of a television set sent by a user operation device of the television system; judging whether an execution condition of the control command is met or not, and acquiring a first judgement result; and when the first judgement result is yes, controlling the lift to execute a lifting operation according to the control command. The embodiments of the present invention avoid unnecessary executions of a lift control command.
Owner:BOE TECH GRP CO LTD +1
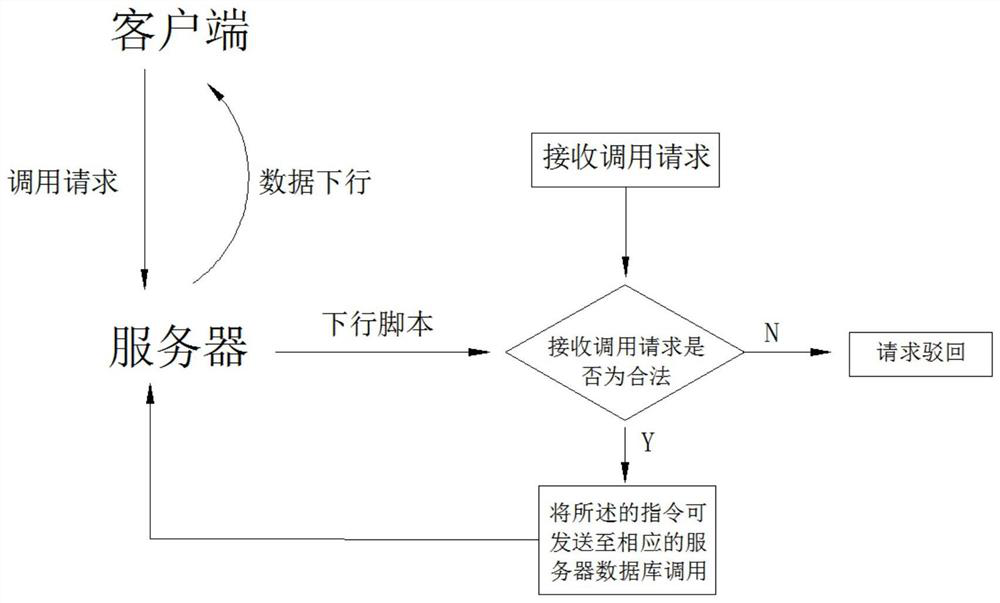
Large-data-volume downlink instruction calling method
PendingCN114157449AImprove securityPerform avoidanceSecuring communicationData packData transmission
The invention discloses a large-data-volume downlink instruction calling method, which comprises the following steps that S1, a client transmits data to a server, the data is encrypted and then packaged to form a data packet, then a downlink script in the server is requested to be called, and the downlink script judges whether a received calling instruction is a legal instruction or not; according to the method, the legality of the calling instruction is judged before the calling instruction is sent to the server, only the legal calling instruction is sent to the server to be executed, illegal operation can be prevented from being sent to the server to be executed, and therefore the safety of the server is improved.
Owner:STATE GRID INFO TELECOM GREAT POWER SCI & TECH
Disk array-based virtual machine operating method, device and system
ActiveCN107357531BAvoid occupyingPerform avoidanceInput/output to record carriersSoftware simulation/interpretation/emulationVirtual file systemFile system
The invention discloses a virtual-machine operation method based on a disc array. The virtual-machine operation method includes the steps that a virtual-machine operation request is received; a virtual file system is established on the disc array through the virtual-machine operation request; according to the virtual file system and virtual machine data carried in the virtual-machine operation request, virtual-machine operation corresponding to the virtual-machine operation request is carried out. Therefore, in the technical scheme, virtual-machine operation is carried out on the disc array, it is avoided that as excessive data storage units are established on the disc array, an internal storage resource and a CPU resource are occupied; meanwhile, it is avoided that virtual-machine operation corresponding to the virtual-machine operation request is carried out through the file system on the disc array, system response time is shortened accordingly, and the system response rate is increased. The invention also discloses a device and system for virtual-machine operation, and the technical effect can also be achieved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Anti-single event flip protection method for dual-core arm processor based on zynq-7000
ActiveCN108052420BGuaranteed uptimeRealize the detection functionRedundant operation error correctionRedundant hardware error correctionDual coreSingle event upset
A Zynq-7000-based dual-core ARM processor anti-single event flip protection method belongs to the field of processor anti-radiation hardening. It solves the problems that the dual-mode redundancy method can only realize fault detection, but cannot realize fault recovery, and the existing fault detection is complicated. The method of the present invention includes the following steps: using the dual-core mutual inspection method to perform error detection on the programs executed by the dual-core, and then rewinding and recovering the detected errors to realize error recovery. It is mainly used for error detection and recovery of programs executed by dual cores.
Owner:HARBIN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com