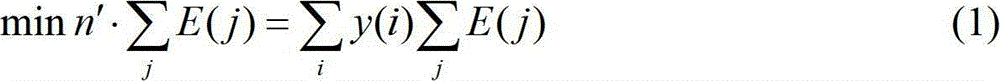Patents
Literature
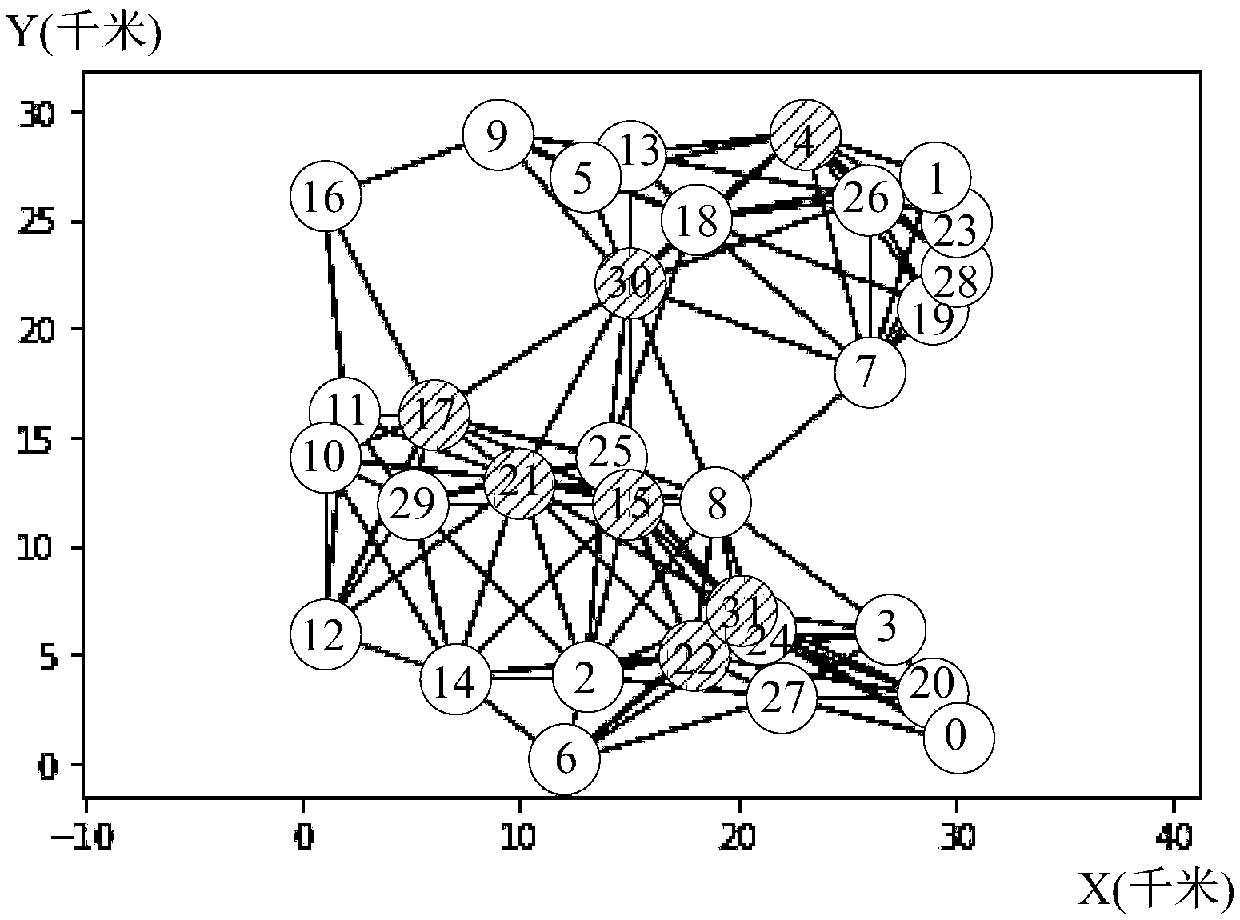
39 results about "Connected dominating set" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
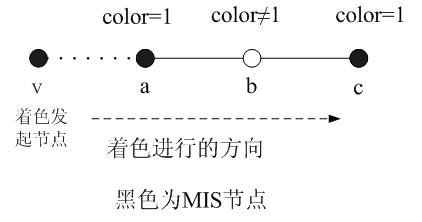
In graph theory, a connected dominating set and a maximum leaf spanning tree are two closely related structures defined on an undirected graph.
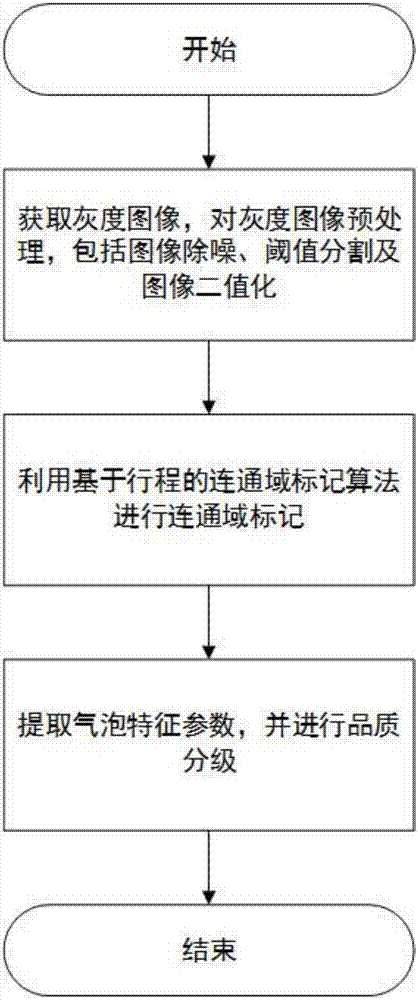
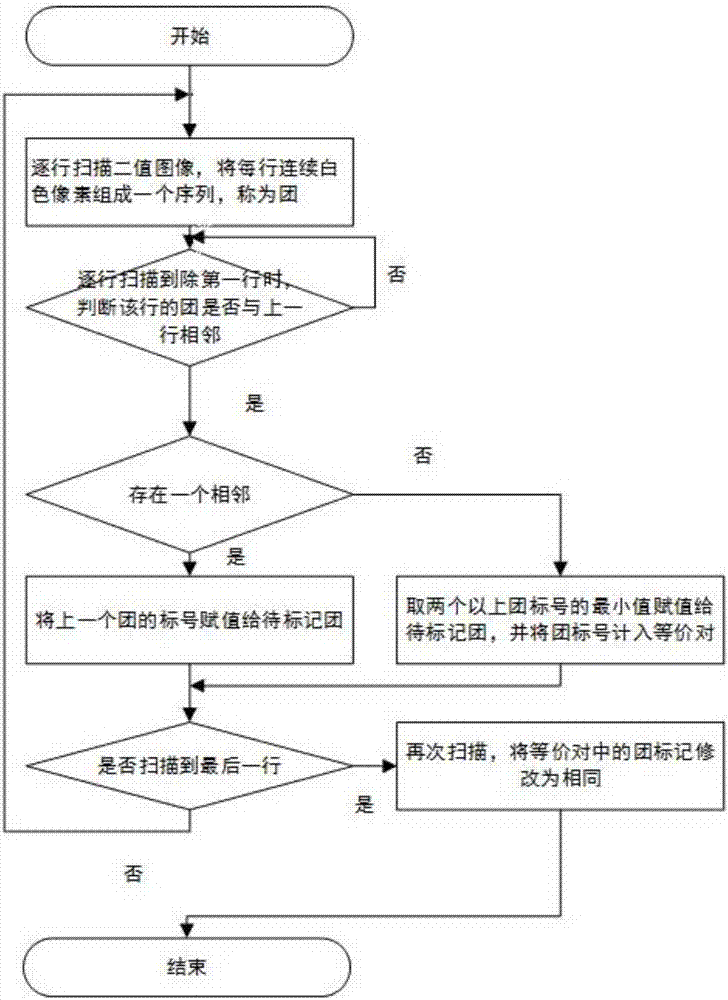
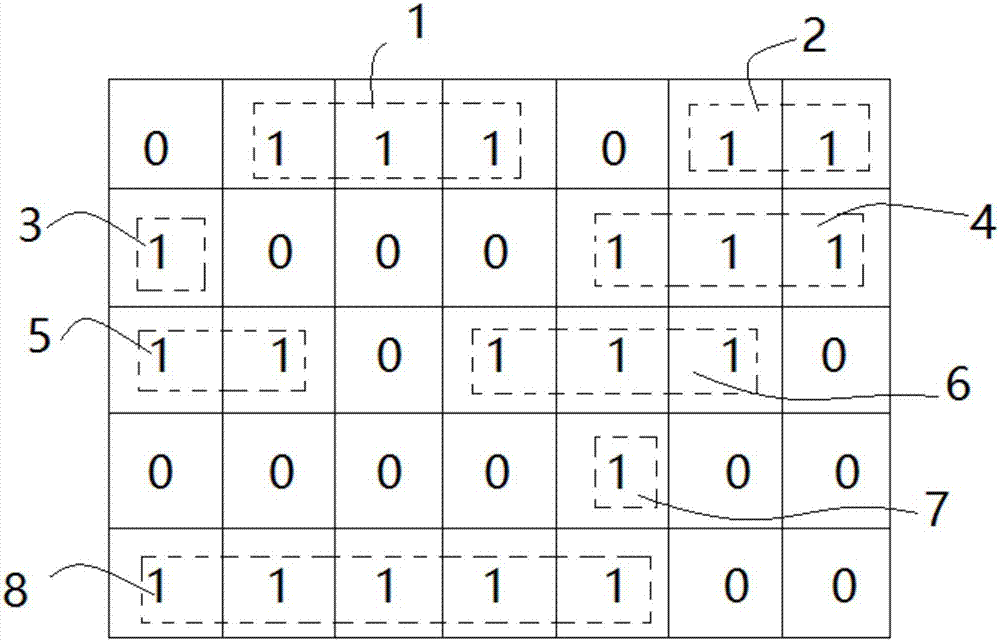
Quartz rod bubble detection and quality grading method based on machine vision
InactiveCN107084991AAccurate detectionUnified testing standardsImage analysisOptically investigating flaws/contaminationMachine visionImaging processing
The invention discloses a quartz rod bubble detection and quality grading method based on machine vision. The method comprises the following steps: S1. a quartz rod is placed in a darkroom, a laser beam is irradiated from one side to the quartz rod, and an industrial camera is used for shooting a grey-scale image of a quartz rod cross section; S2. noise removing, threshold segmentation, and binaryzation of the grey-scale image are carried out in order, and a binary image is obtained; S3. a connected domain of the binary image is labeled by a course-based connected domain labeling method, and the labeled connected domain is a bubble; S4. characteristics of the bubble are extracted from the connected domain, and quality of the quartz rod is graded according to the characteristics of the bubble. Bubbles in the quartz rod can be detected based on image processing techniques, detection standard is unified, capability for resisting interference of ambient light is high, and bubbles in the quartz rod can be rapidly and accurately detected.
Owner:WUHAN UNIV OF TECH
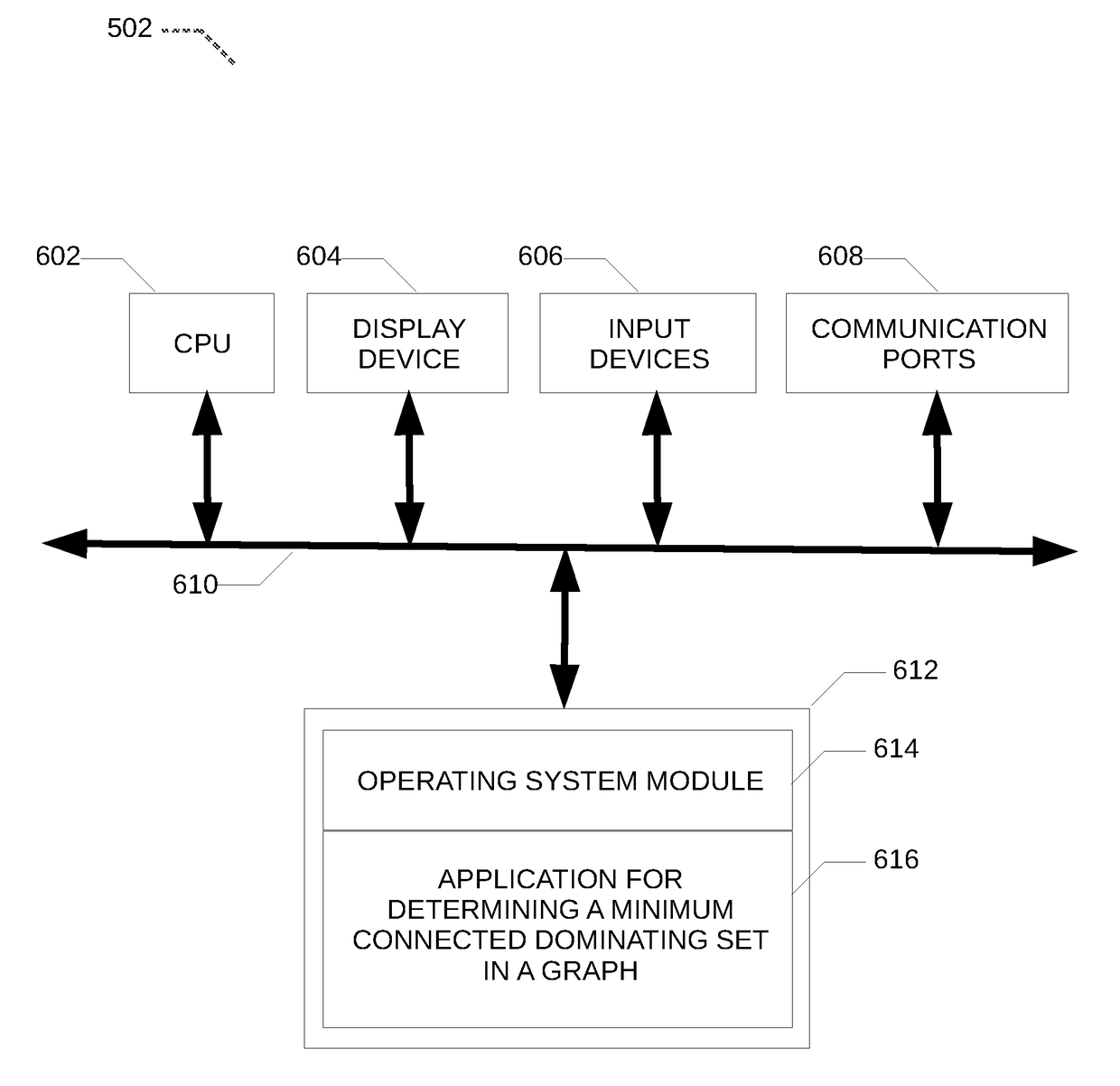
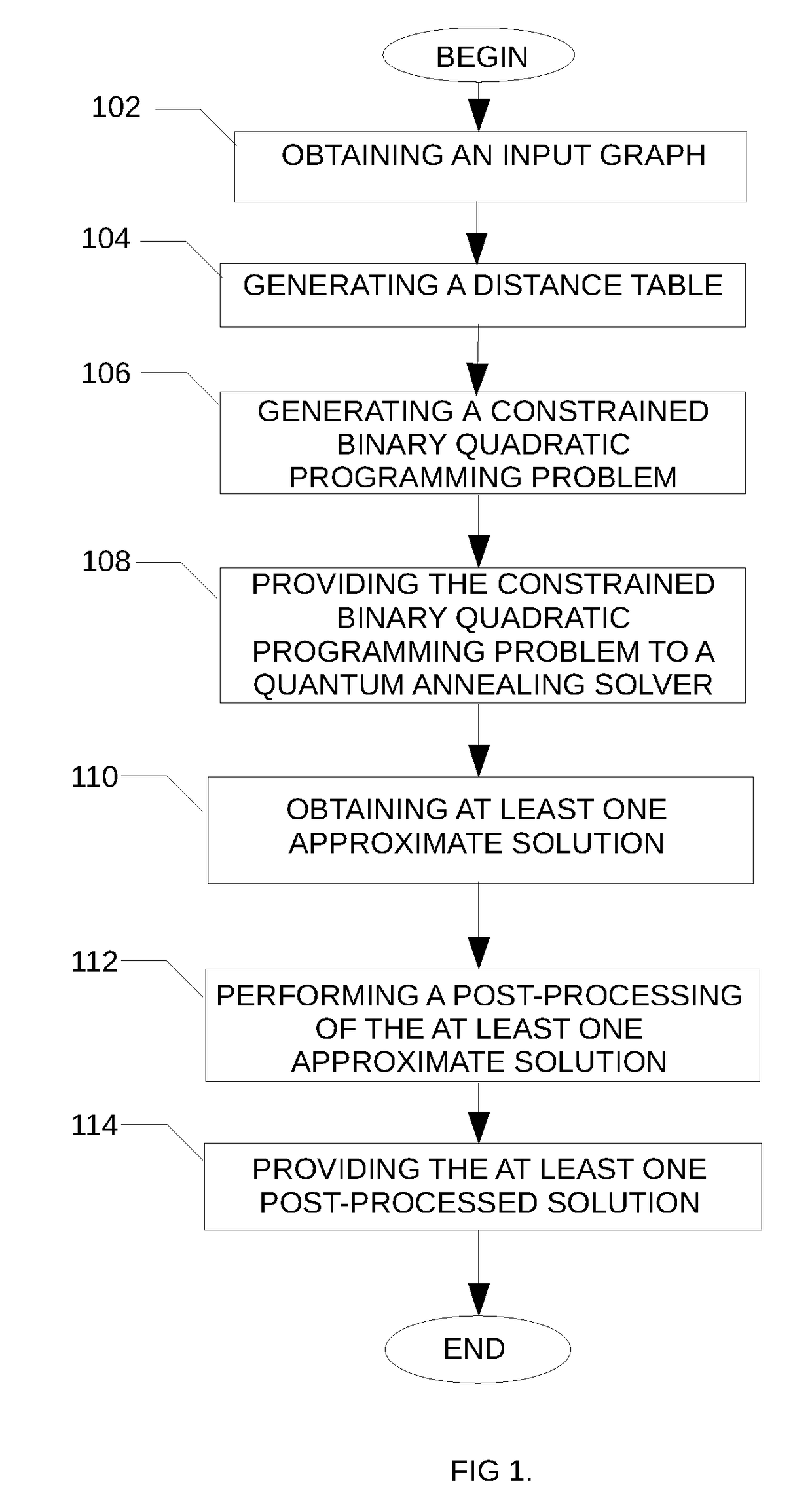
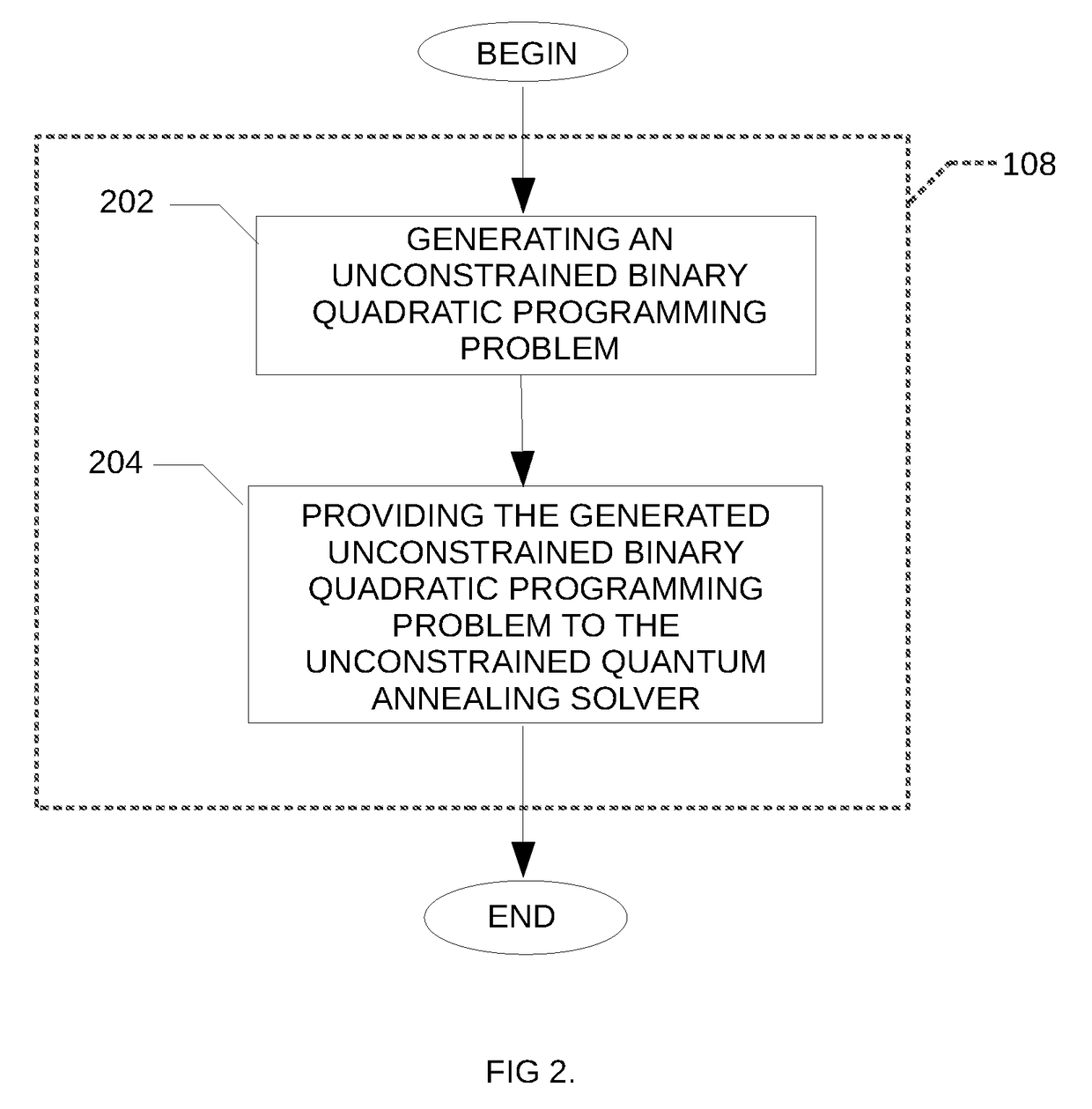
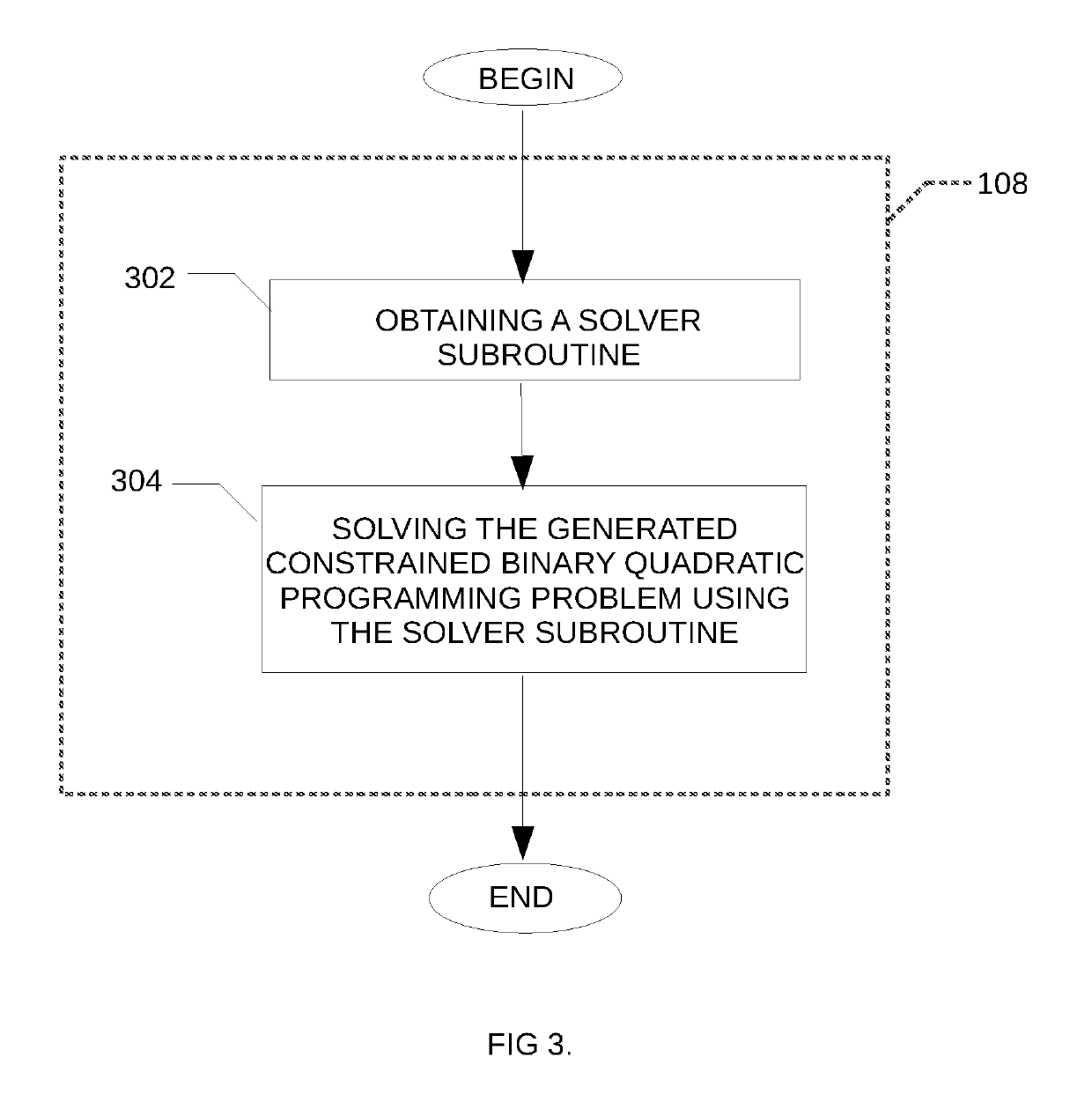
Method and system for solving a minimum connected dominating set problem using quantum annealing for distance optimization
ActiveUS20170286852A1Less timeProcessing problemForecastingMachine learningNODALConnected dominating set
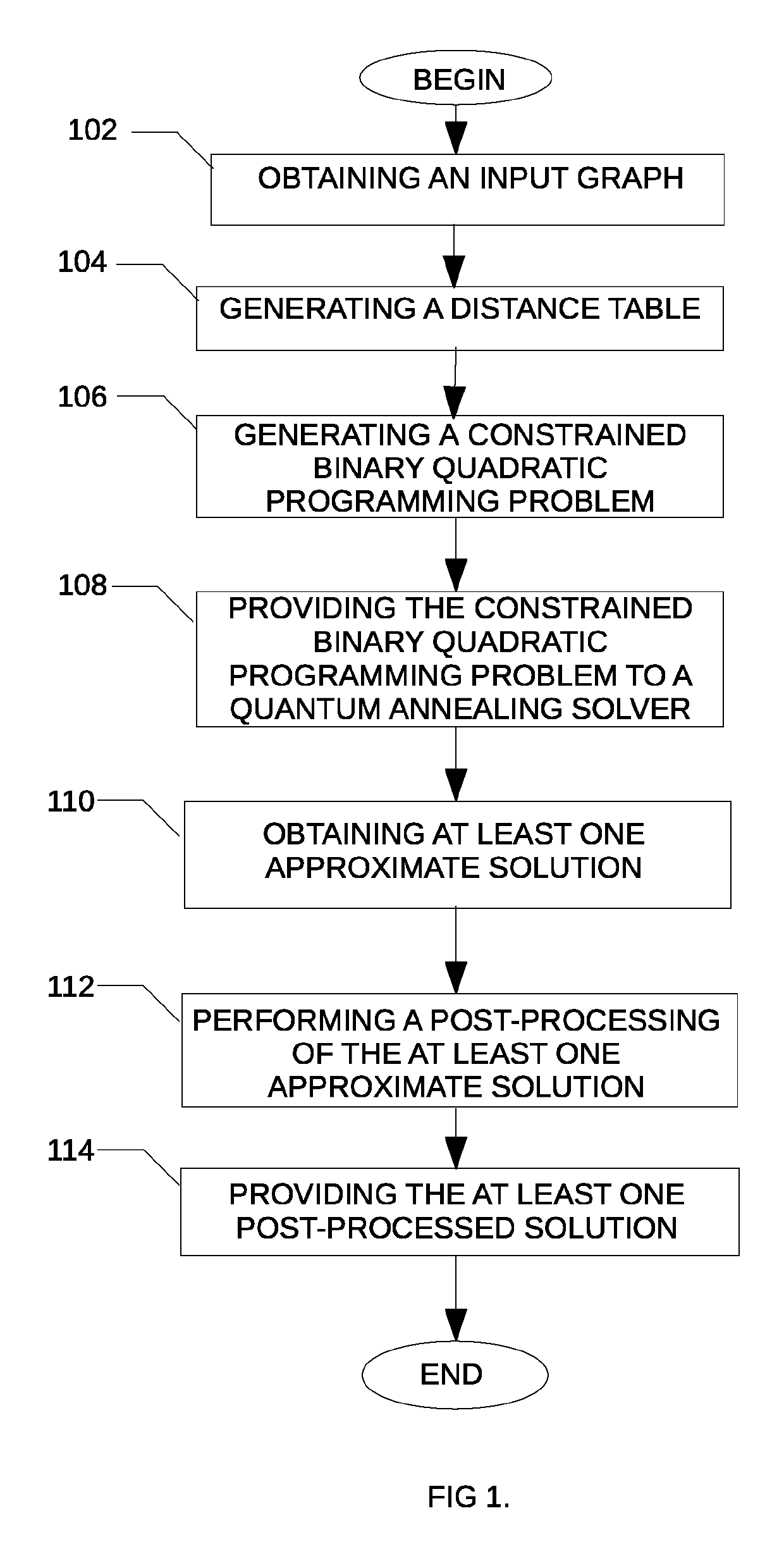
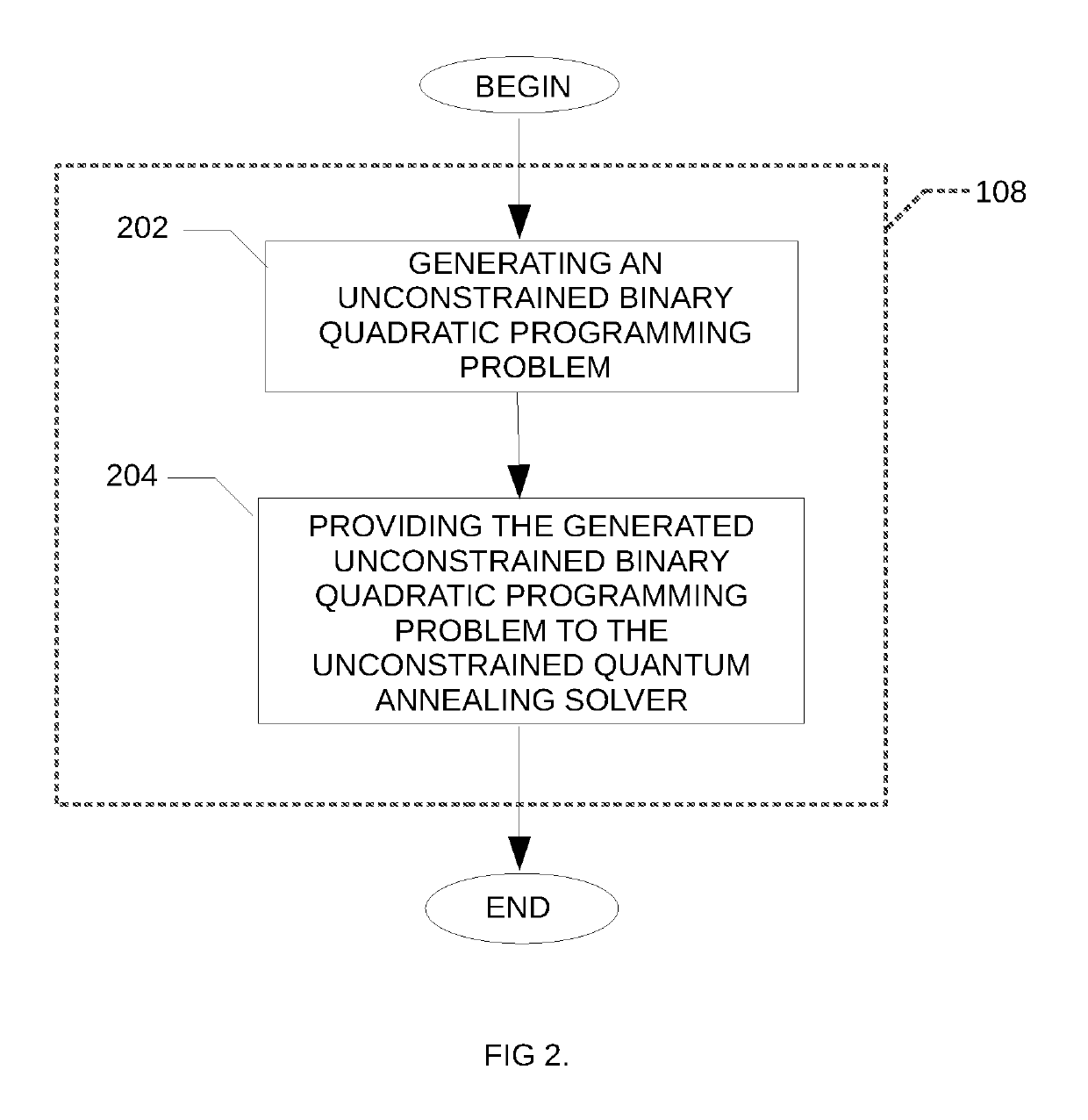
A method is disclosed for determining a minimum connected dominating set in a graph, the method comprising obtaining an indication of an input graph, the input graph comprising a plurality of nodes and a plurality of edges; generating a distance table comprising for each node of the input graph, an indication of a distance between the given node and each of the other node of the plurality of nodes; generating a corresponding constrained binary quadratic programming problem using the generated distance table; providing the corresponding constrained binary quadratic programming problem to a quantum annealing solver; obtaining at least one approximate solution from the quantum annealing solver; post-processing the at least one approximate solution and providing the post-processed at least one approximate solution.
Owner:1QB INFORMATION TECHNOLOGIES INC
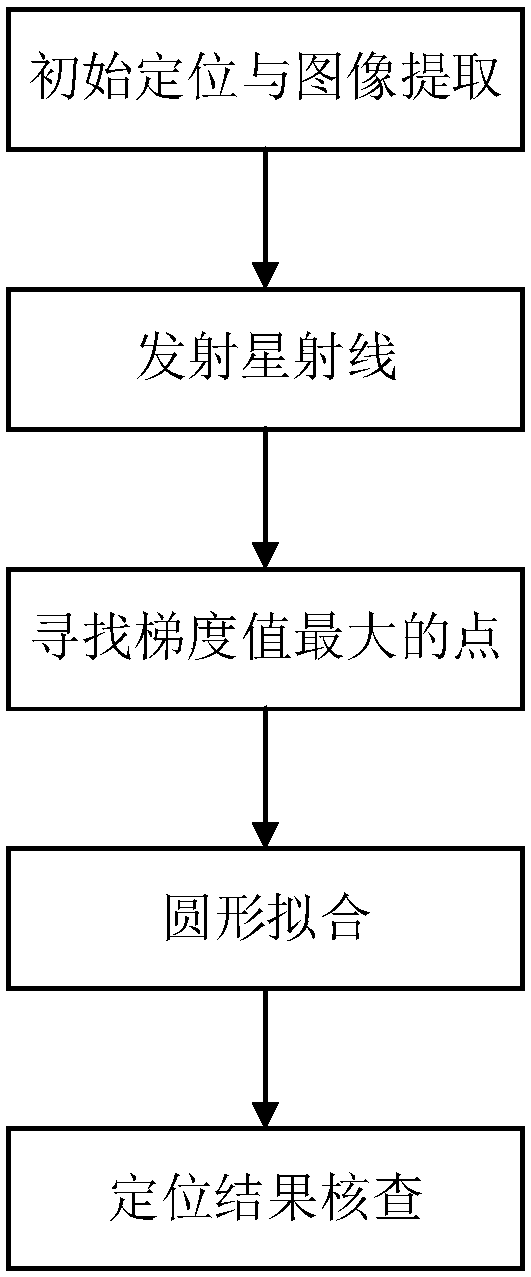
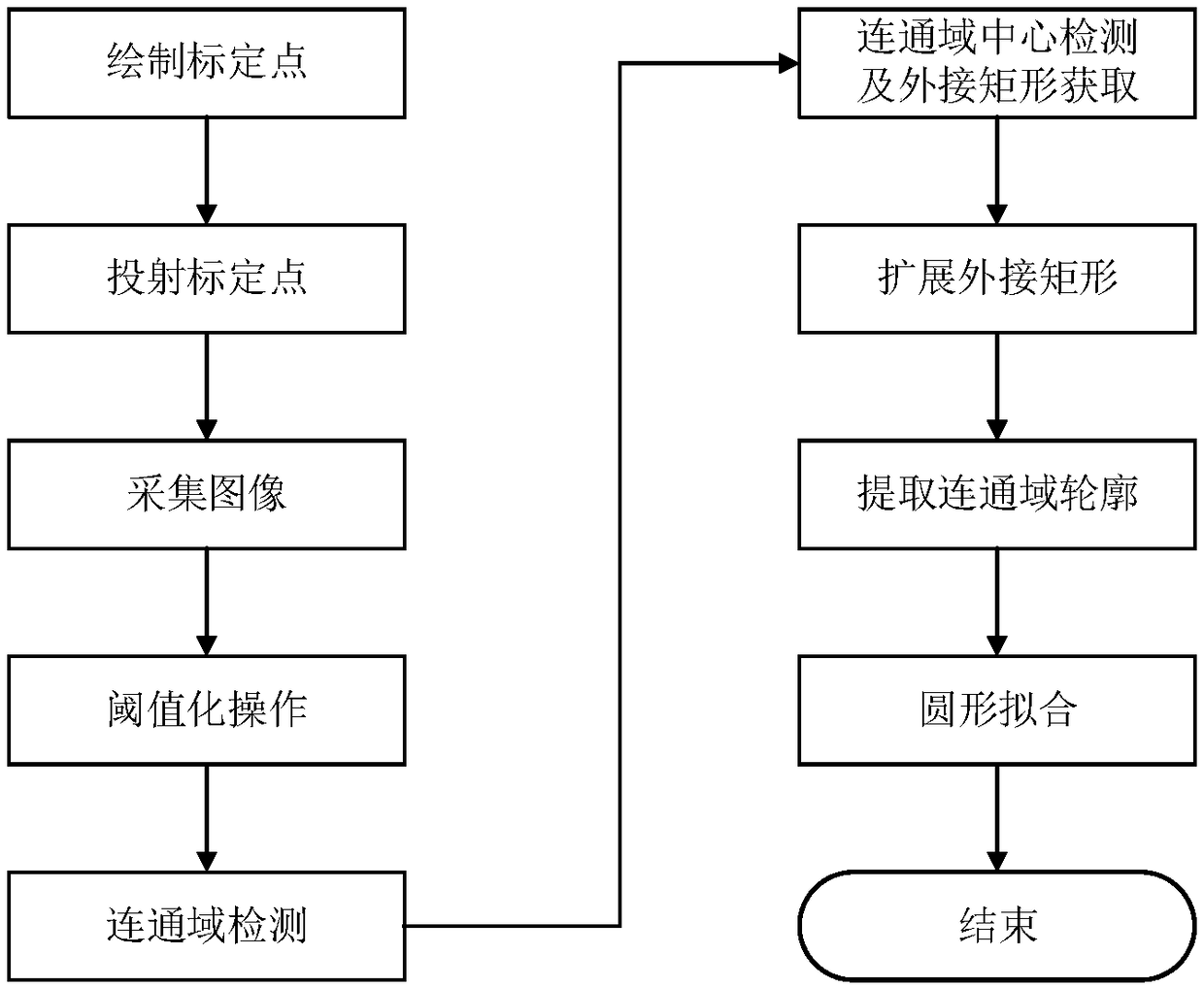
Accurate positioning method for calibration point center coordinate
ActiveCN108205395AHigh precision solutionMeet the problem of positioning accuracyInput/output processes for data processingConnected dominating setComputer science
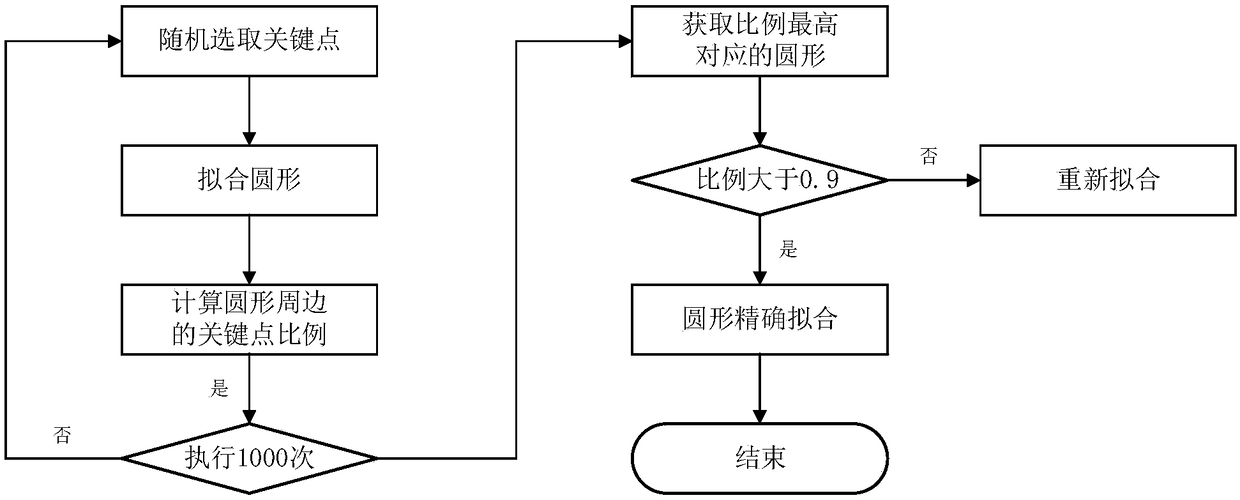
The present invention relates to a precise positioning method for a calibration point center coordinate. The method comprises the steps of: drawing a calibration point and acquiring a grayscale imageof the calibration point; performing a thresholding operation and connected domain detection on the grayscale image to obtain a calibration point region; calculating to obtain the center coordinate ofthe connected domain of the calibration point and the circumscribed rectangle of the connected domain, and expanding the size of the circumscribed rectangle; according to the size of the circumscribed rectangle and the center coordinate, extracting the contour corresponding to the connected domain of the calibration point of the corresponding region in the grayscale image; carrying out circular fitting to obtain the initial center point of the contour; taking the center point as the center, emitting radiation to the surrounding area, and calculating the gradient amplitude; traversing all thestar rays to obtain the maximum point of the gradient value on each star ray, marking the maximum point as a key point, and completing the circular fitting through the key point to obtain a circle; and reviewing the obtained circle and verifying the positioning result. According to the method disclosed by the present invention, the problems of solving the center coordinate of the positioning areawith high precision and satisfying the positioning accuracy to a great degree are implemented.
Owner:安徽慧视金瞳科技有限公司
Satellite network multicast routing method and system based on minimum connected dominating set
InactiveCN107370536ALow costReduce complexityRadio transmissionData switching networksBroadcast radiationPerformance index
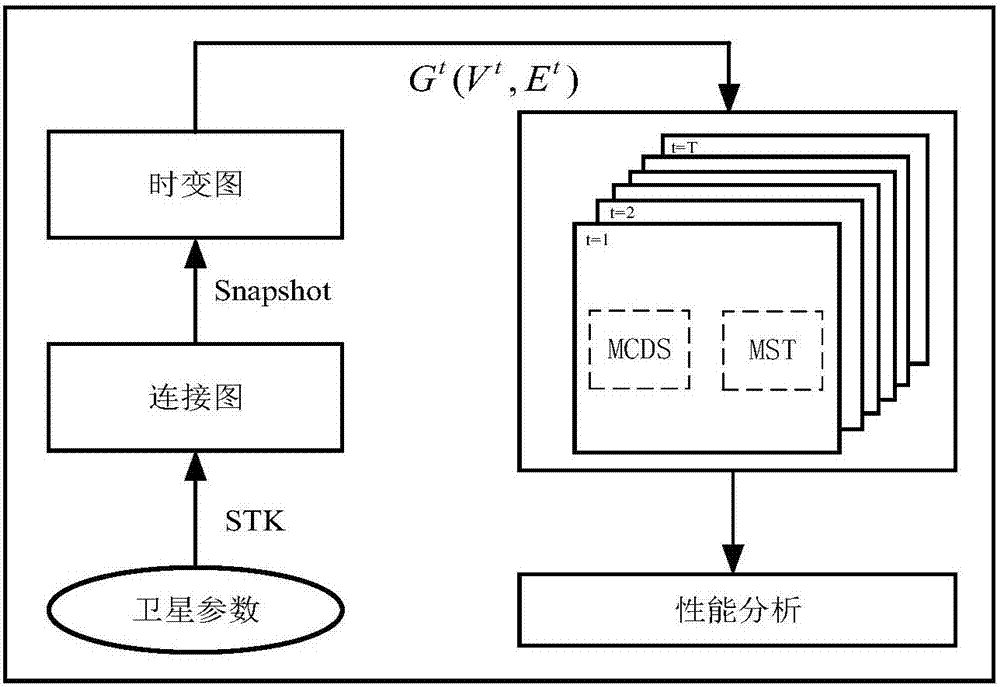
The invention discloses a satellite network multicast routing method and system based on a minimum connected dominating set. The method comprises the following steps: obtaining specific parameters of a three-layer satellite network, and simulating the operation condition of a satellite in the STK software to obtain an on-off condition table of a satellite node within a whole period; constructing a space-time diagram model by time slot division based on the on-off condition table to obtain time link information and space link information of the satellite network; and performing multicast routing service by using a preset MCDS routing algorithm based on the minimum connected dominating set according to the obtained time link information and the space link information of the satellite network. By adoption of the satellite network multicast routing method and system, the waste of resources is reduced, the broadcast storm is avoided, the routing cost caused by the increase of node number under the condition of a single time slot is reduced, and in the case that the number of the time slots is increased, the routing cost is also effectively reduced, and a balance is obtained between two performance index, that is the routing cost and the end-to-end hop number, and in addition, the implementation complexity of the algorithm is low.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
MCDS approximation algorithm-based multicast route method with minimized resource consumption
ActiveCN101562780AReduce consumptionReduce the number of nodesEnergy efficient ICTNetwork topologiesNetwork communicationMulticast communication
The invention belongs to a route optimization technique in wireless network communication, relates to the problem of saving energy and bandwidth resource consumption of the wireless broadcast transmission in a wireless network, and provides a construction method for a distributive multicast tree with minimized network communication resource consumption based on the problem of MCDS (minimum connected dominating set) in a graph theory. Based on the established multicast tree, the MCDS approximation algorithm-based multicast route method with minimized resource consumption finds a maximum independent set MIS, and then finds all MIS nodes connected with of a dominating node set so as to obtain a dominating multicast tree. The method optimizes the resource consumption of the multicast communication in the communication network. Due to the broadcasting nature of a wireless medium, the bandwidth and energy consumption in the multicast communication mainly depends on the message relay times in the multicast tree. Therefore, the method achieves the aim of reducing the network resource consumption through the reduction of the number of the nodes undertaking the relay mission in the multicast tree.
Owner:WESTERN MINING CO LTD
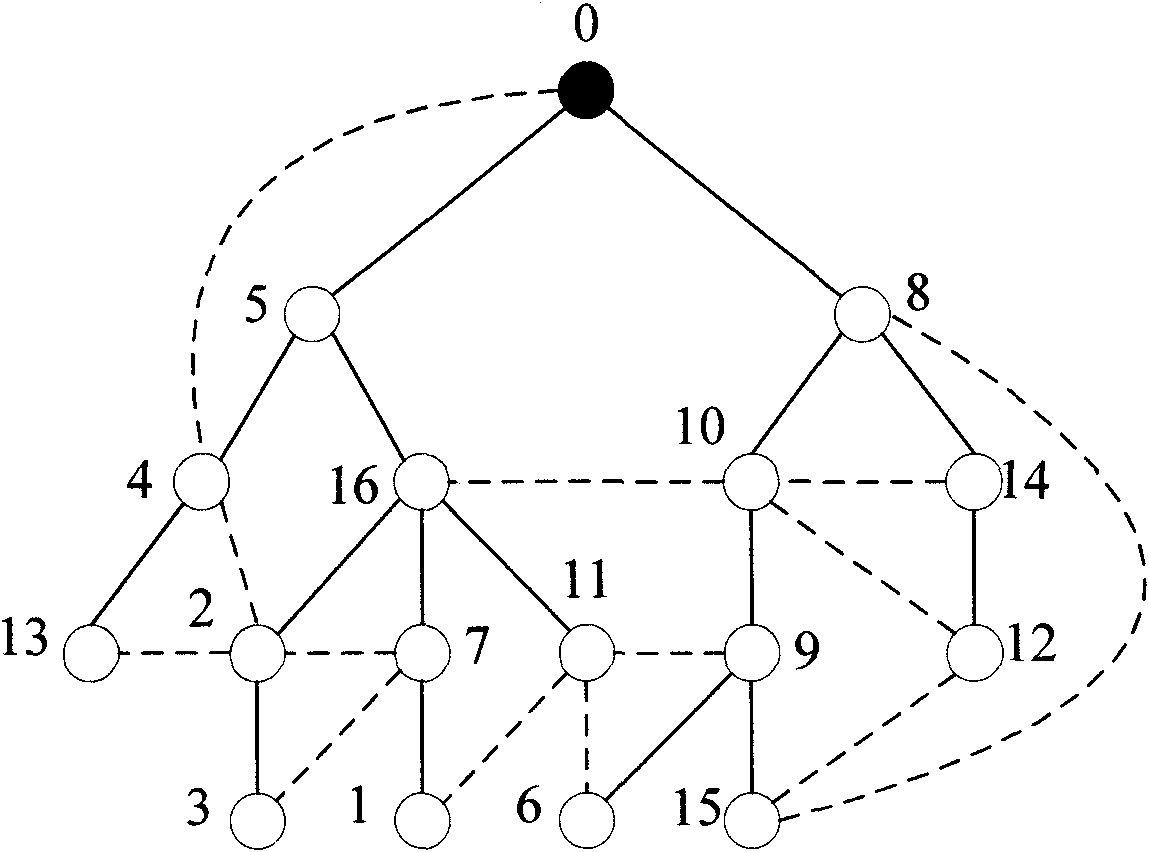
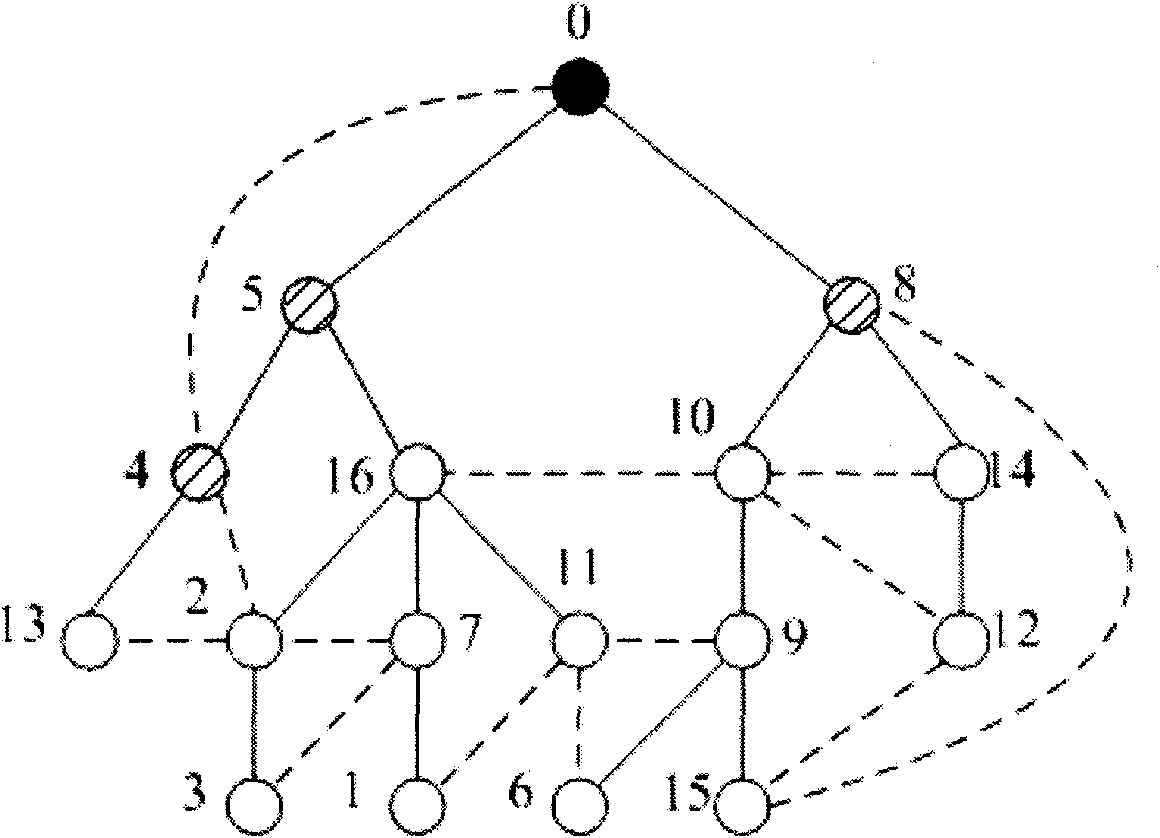
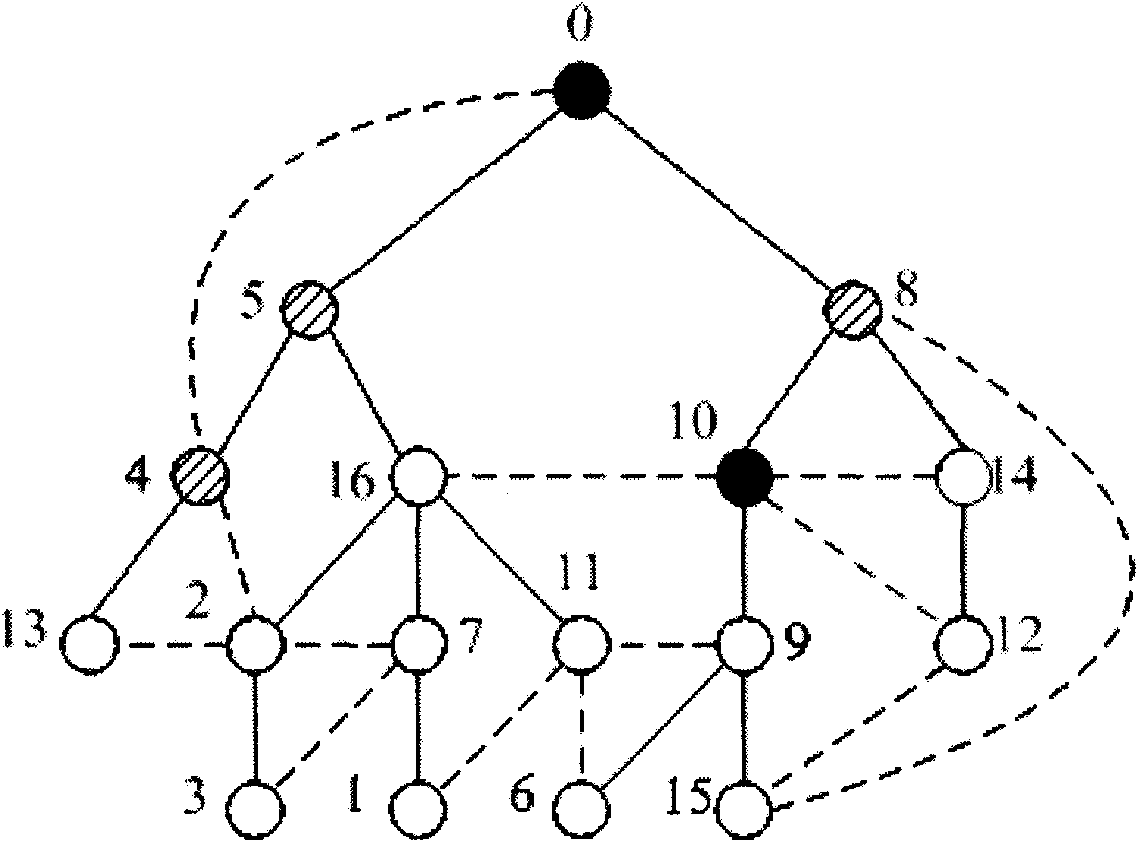
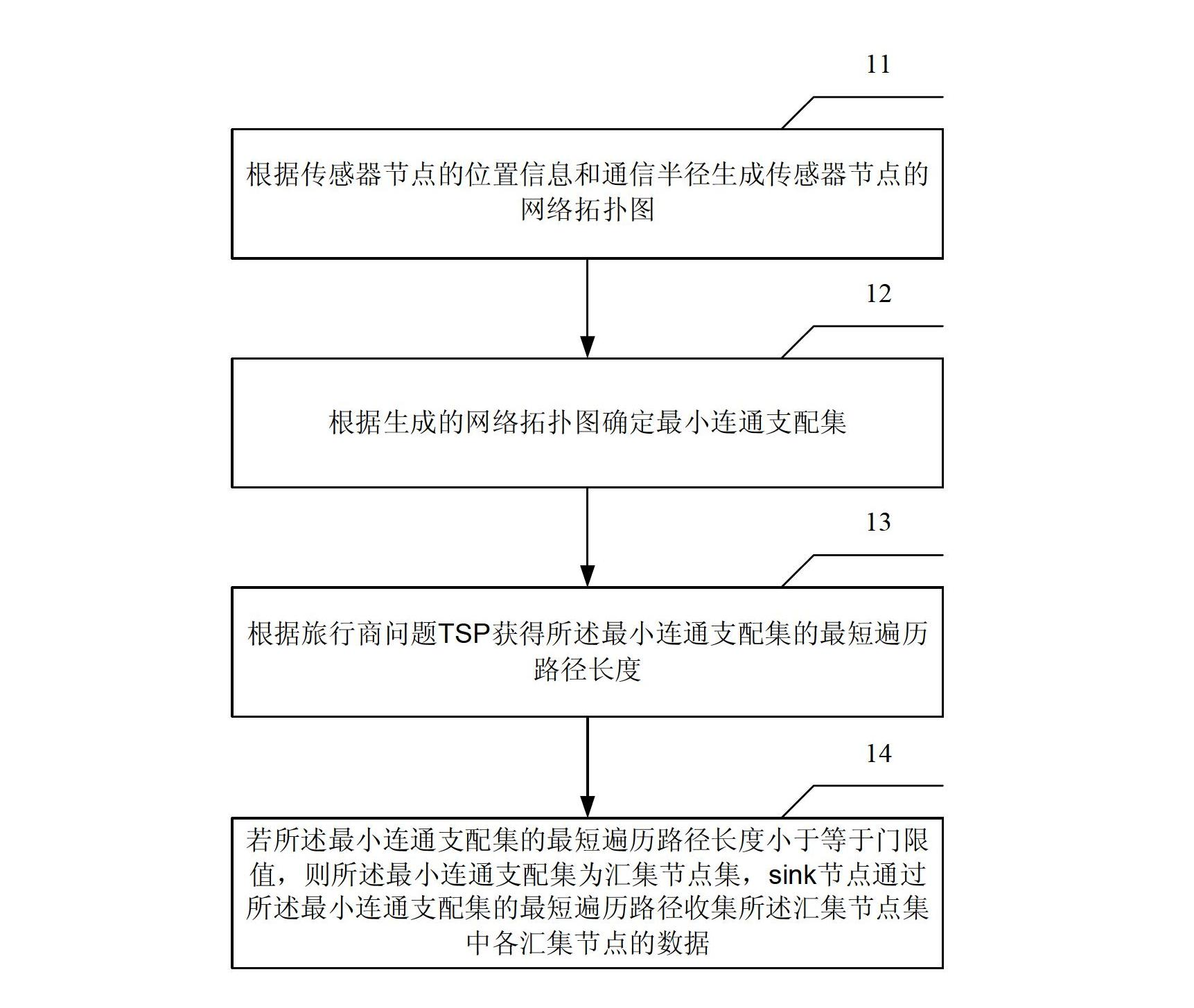
Method and device for collecting data by sink nodes of wireless sensor network
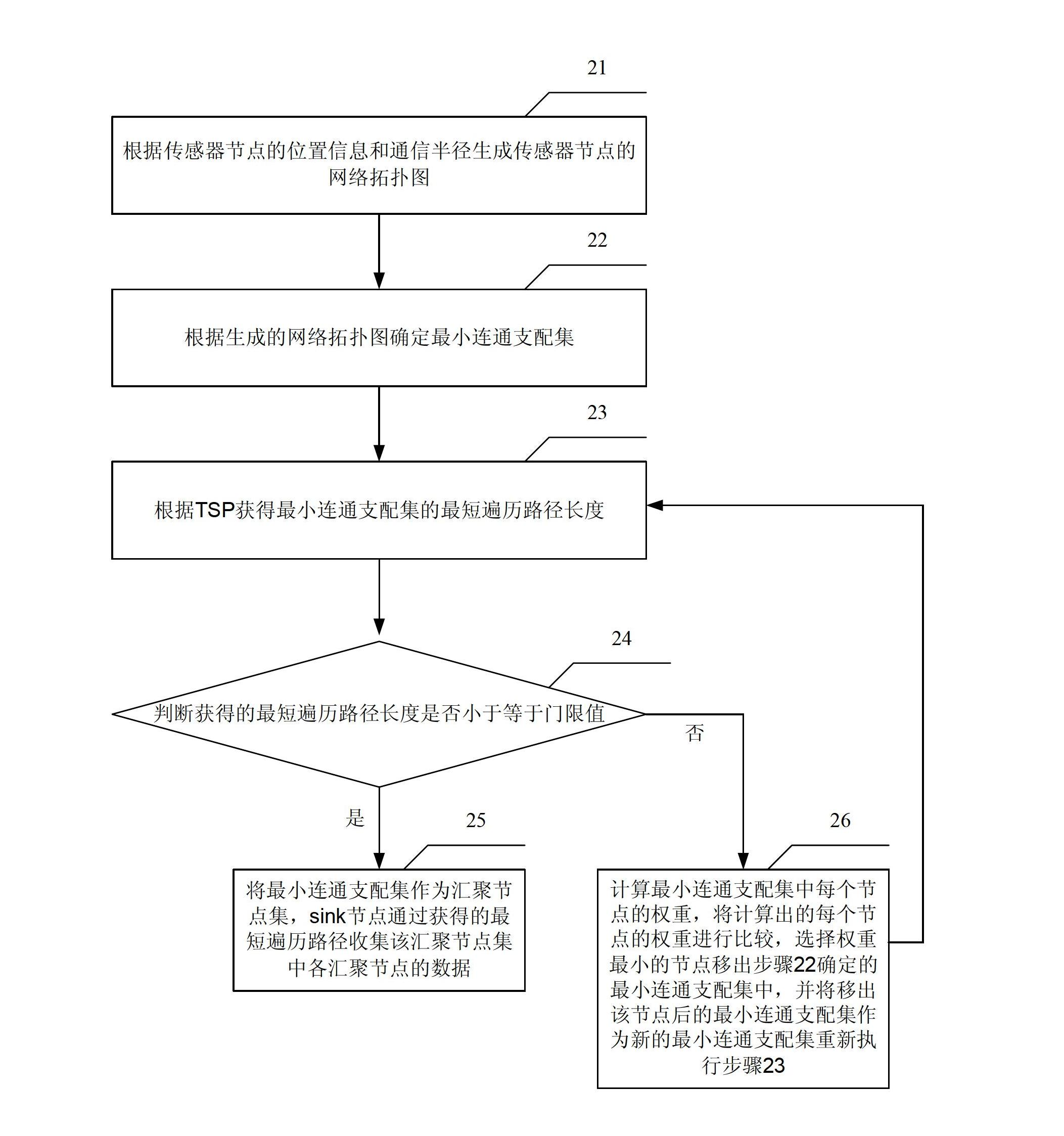
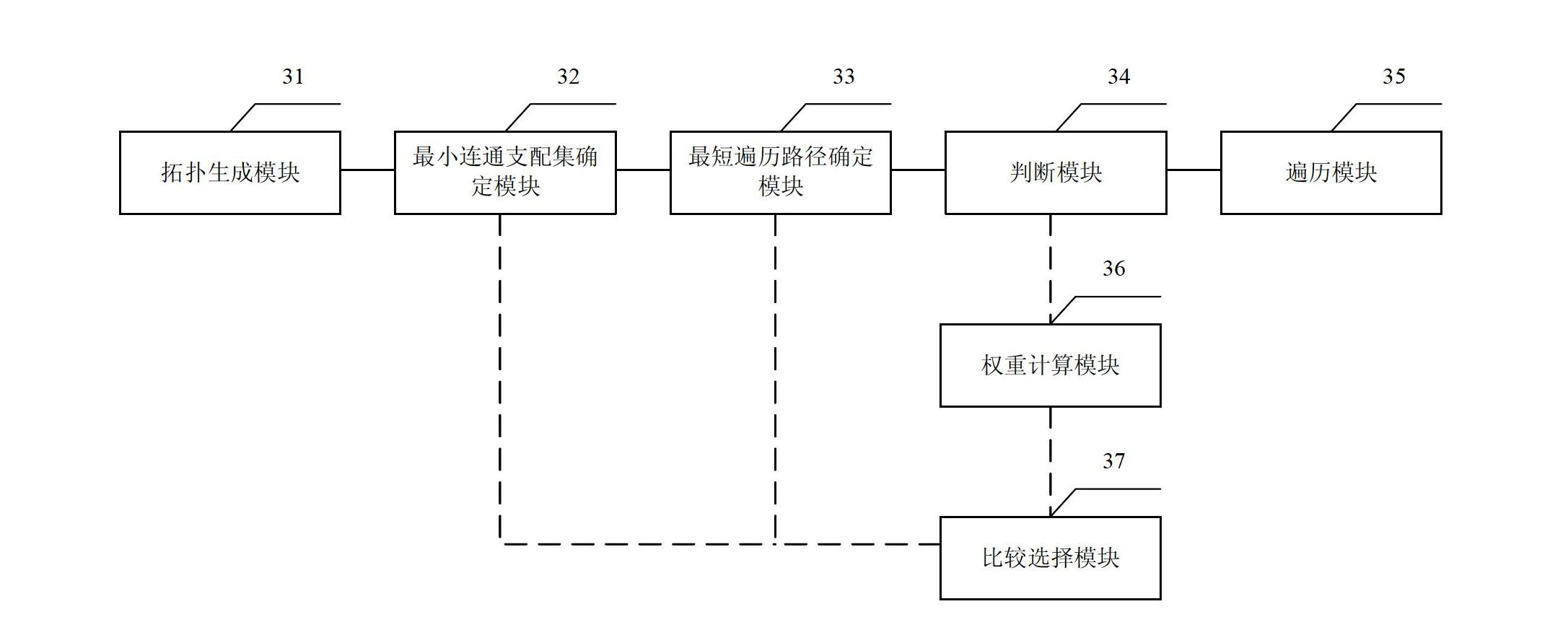
InactiveCN102685861AGuaranteed accuracyReduce multi-hop transmissionEnergy efficient ICTPower managementLine sensorPath length
The invention relates to a method and device for collecting data by sink nodes of a wireless sensor network, belonging to the technical field of network communication. The method comprises the following steps of: firstly, generating a network topology of sensor nodes according to position information and communication radiuses of the sensor nodes and determining a minimum connected dominating set according to the generated network topology; then acquiring the shortest traversal path length of the minimum connected dominating set according to a TSP (Travelling Salesman Problem); and finally, if the shortest traversal path length of the minimum connected dominating set is smaller than or equal to a threshold value, considering the minimum connected dominating set as a sink node set, and collecting data of all sink nodes in the sink node set through the shortest traversal path of the minimum connected dominating set. According to the embodiment of the invention, multi-hop transmission of a wireless sensor is effectively reduced under the condition of ensuring the data delay requirement in the sensor network, the data transmission accuracy is ensured and the energy consumption is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
MCDS (minimum connected dominating set)-based method for constructing delay limit multicast forwarding structure
The invention relates to a problem of minimizing the cost of a multicast routing forwarding structure in an AdHoc network, and construction of a delay limit multicast forwarding structure in a wireless network based on an MCDS (minimum connected dominating set) algorithm in a graph theory. According to particularity of a wireless signal transmission method, the cost and delay function in the wireless multicast routing are redefined. In the method for constructing the delay limit multicast forwarding structure based on the vertex coloring ideas in the graph theory, which is proposed based on the MCDS theory in the graph theory, by solving the MCDS, the purpose of constructing a multicast routing structure with the minimum cost is achieved, the concept of multicast routing delay limit is proposed, and the MCDS is constructed under the constraint. The algorithm is proved to be correct by the theoretical derivation, and the algorithm is proved to be effective by a lower approximate ratio compared with the similar algorithm. At the same time, the algorithm has a time complexity of O(n) and a message complexity of O(n), thus the high efficiency of the algorithm is proved further; and the algorithm has the advantage of adapting to flexible Adhoc networks.
Owner:青海西部矿业科技有限公司
Simulating device of leakage-stopping training of damaged pipes on ship
ActiveCN102063814ASimple structureSwing realisticCosmonautic condition simulationsSimulatorsLocking mechanismHydraulic pump
The invention relates to a simulating device of leakage-stopping training of damaged pipes on a ship, belonging to the technical field of simulation. The simulating device is characterized by comprising two parts, namely a mechanical platform body and a hydraulic driving mechanism, wherein the mechanical platform body consists of a simulating cabin, a shaft system and a locking mechanism; the simulating cabin consists of a cabin body and a leakage-stopping pipe group; the shaft system consists of a driving bracket, a locking bracket, a half shaft and a bearing seat; the driving bracket, the locking bracket and the half shaft are assembled on the bearing seat; the hydraulic driving mechanism consists of a servo hydraulic pump station, a control integrated block and a servo cylinder; the servo hydraulic pump station is communicated with the control integrated block so as to drive the servo cylinder; and the servo cylinder drives the mechanical platform body by the driving bracket. The simulating device has the advantages of simpleness in structure, economy, practicability, vivid swinging, safety, reliability, excellent performance, good simulating effect and the like.
Owner:TIANJIN ENG MACHINERY INST
Pressure vessel air tightness detection method based on connected domain determination
ActiveCN109115417AAccurately judge the air leakageDetection of fluid at leakage pointImage analysisConnected dominating setEngineering
The invention discloses a pressure vessel air tightness detection method based on connected domain determination. The method comprises the following steps of step1, setting the original pressure valueof a pressure vessel to be P0, setting the pressure value after T time to be P1, and when P0-P1< / =delta, setting the delta as a pressure difference threshold, which expresses a unpressurized state; when P0-P1>delta, expressing that the pressure is being applied and an air tightness test begins; step2, taking the N frames of the images of a video after the air tightness test is started, wherein the n equals to t*f, the t is test time and the f is a video frame rate; and taking the N frames of the images as I1, I2,..., In, graying Ii and acquiring a corresponding grey-scale map Gi, wherein thei equals to 1, 2,...,n; and step3, considering the continuity of bubbles, calculating the number Q of connected images Fj in which the number of connected domains wj is greater than k in the n framesof the connected images Fj, if the Q is greater than a threshold T, considering that there is an air leakage condition. The method has an advantage that based on the connected domain determination, through combining the sizes and the number of the bubbles, and a dynamic characteristic, whether a pressure vessel has the air leakage condition can be accurately determined.
Owner:ZHEJIANG UNIV OF TECH
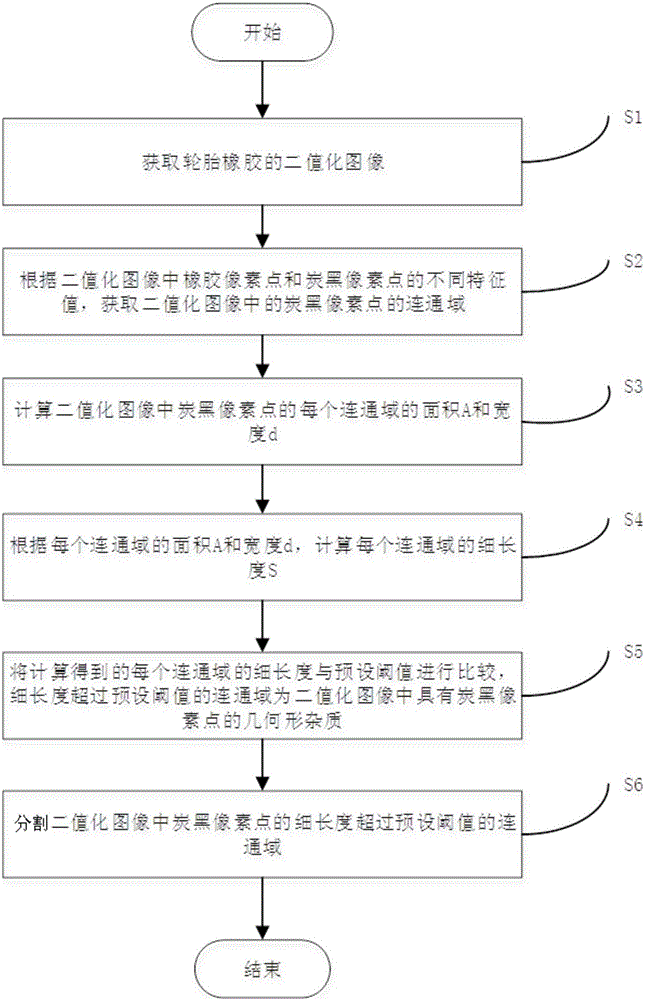
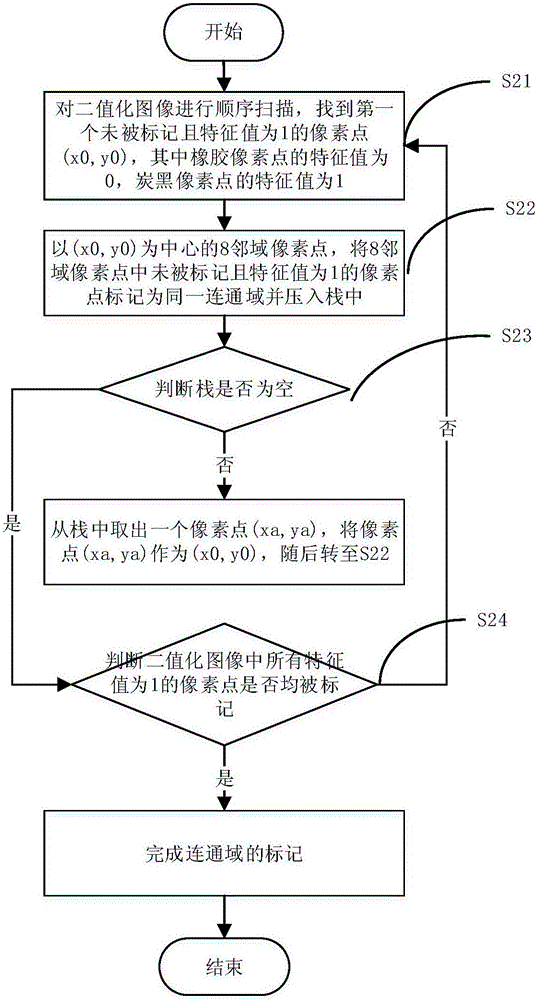
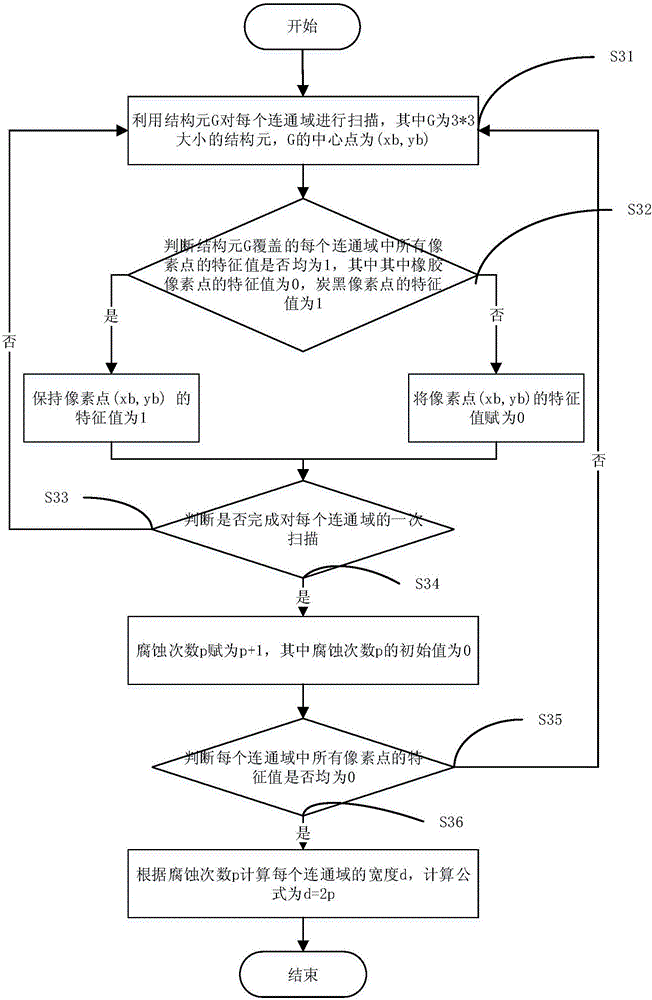
Image processing method and system of detecting tyre rubber geometric impurities
InactiveCN106097344AReflect the distributionImage enhancementImage analysisImaging processingImage segmentation
The invention discloses an image processing method and system for detecting geometric impurities in tire rubber. The method includes: step 1, obtaining a binarized image of the tire rubber; step 2, according to different characteristics of rubber pixel points and carbon black pixel points value, obtain the connected domain of carbon black pixels in the binarized image; step 3, calculate the area A and width d of each connected domain; step 4, calculate each connected domain according to the area A and width d of each connected domain The slender length S of the connected domain; Step 5, compare the calculated slender length of each connected domain with a preset threshold, and the connected domain whose slender length exceeds the preset threshold is a geometry with carbon black pixels in the binarized image shape impurities. The beneficial effects of the present invention are: processing the binarized image by using the slender length of the connected domain, the geometric impurities such as straight lines, circles and curves in the binarized image can be identified and image-segmented, and the obtained binarized image is more accurate. It can reflect the distribution of carbon black in rubber.
Owner:WUHAN UNIV OF TECH
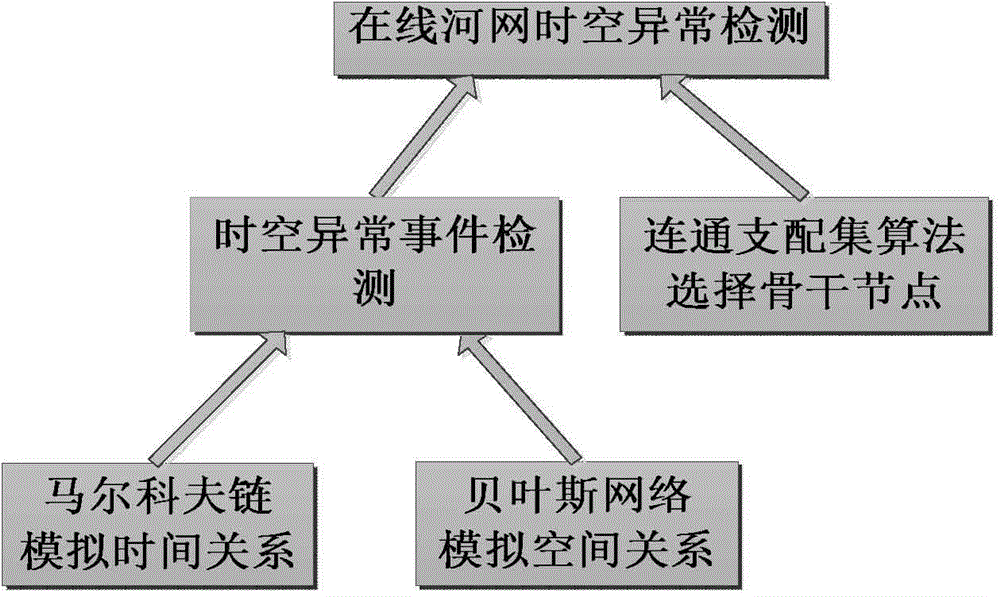
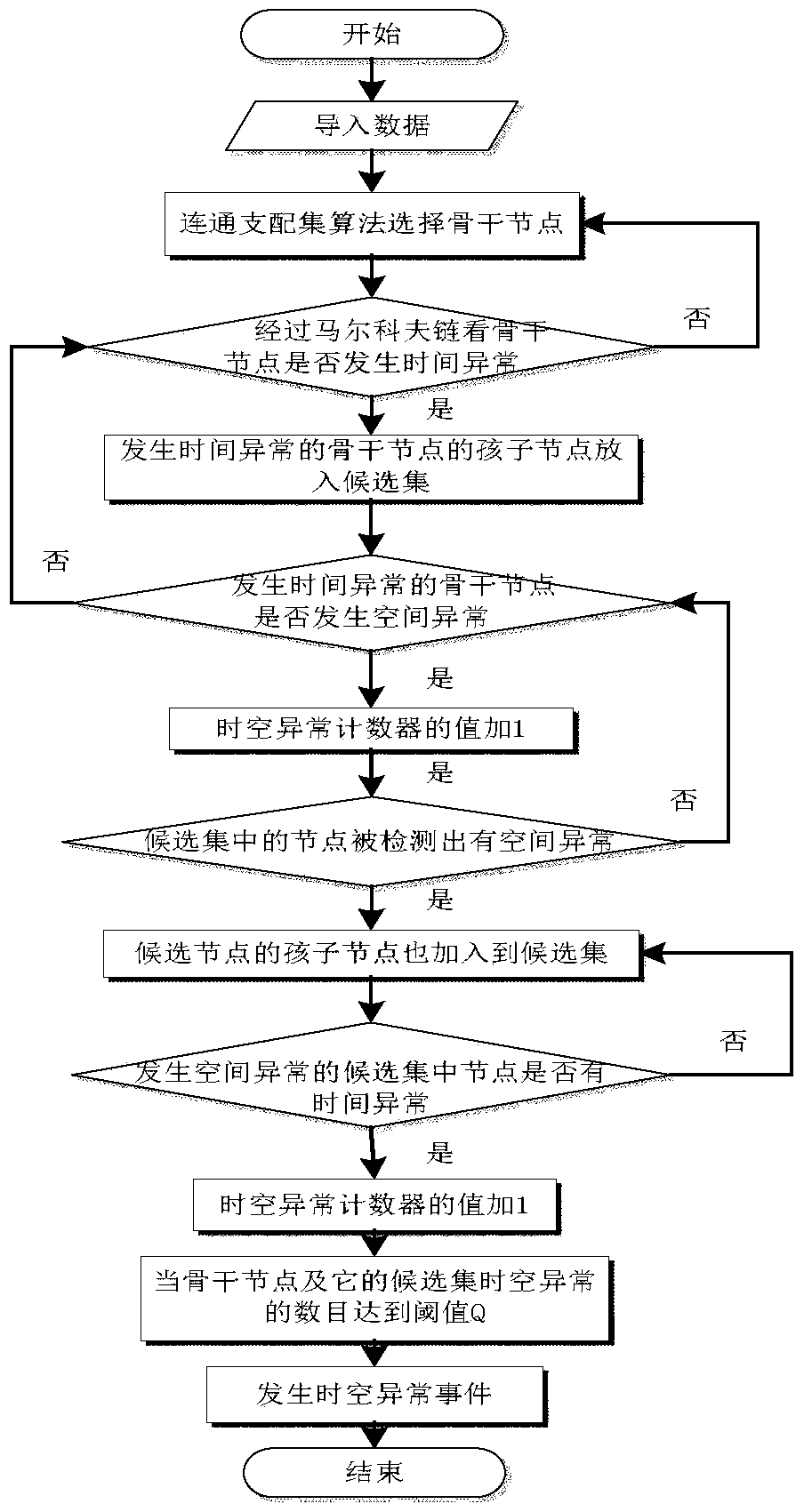
Online detection method for time and space abnormal events by river network
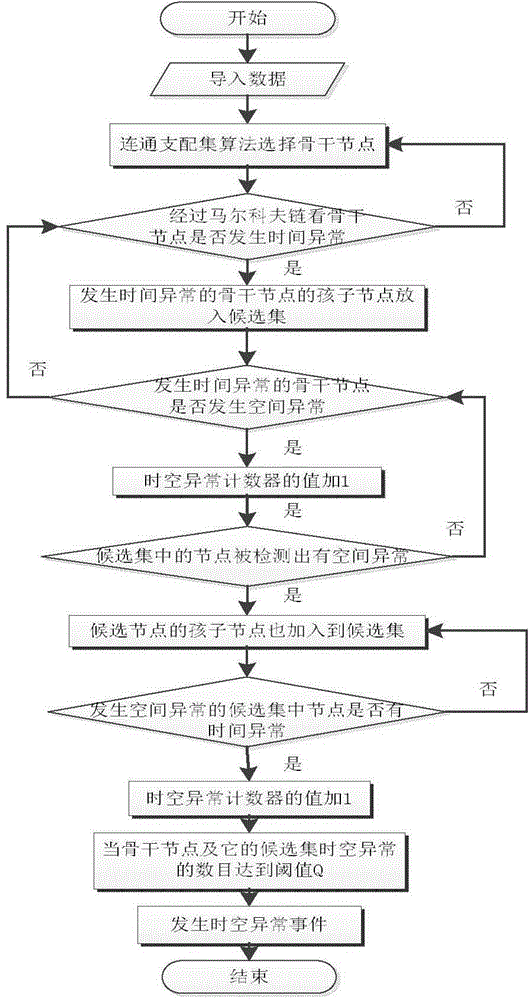
ActiveCN104809205AImprove detection efficiencyShort response timeNetwork topologiesSpecial data processing applicationsRiver networkAlgorithm
The invention discloses an online detection method for time and space abnormal events by a river network. The online detection method comprises the following steps of firstly, selecting backbone nodes by using a connected dominating set algorithm, and only detecting the states of the backbone nodes in each time stamp sensor network; secondly, detecting whether the time and space abnormal events occur in the backbone nodes or not; if the backbone nodes have time abnormality, adding child nodes of the backbone nodes in a detected candidate set; detecting whether the backbone nodes having the time abnormality are deviated from the spatial relation obtained by learning or not by comparing the expected state obtained by Bayesian network learning with the observation state; if the spatial abnormality occurs, adding one to a time and space abnormality counter; at next time stamp, widening the detection range including the backbone nodes and nodes in the candidate set, and continuously detecting whether the space abnormality or the time abnormality occurs or not; finally, when the number of the backbone nodes and the nodes of the candidate set of the backbone nodes with the time and space abnormalities reaches a threshold Q, considering that the time and space abnormal events occur.
Owner:HOHAI UNIV
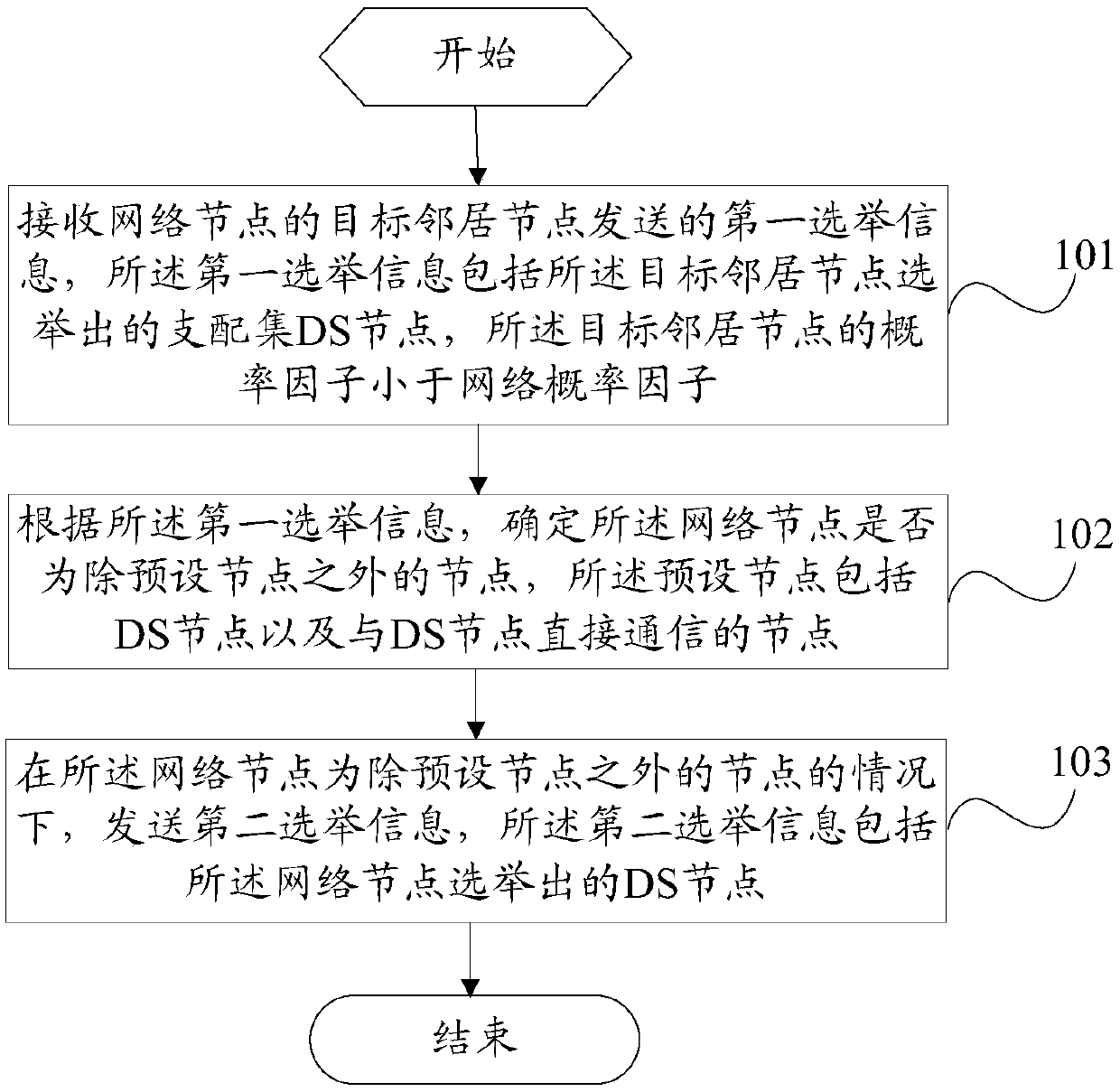
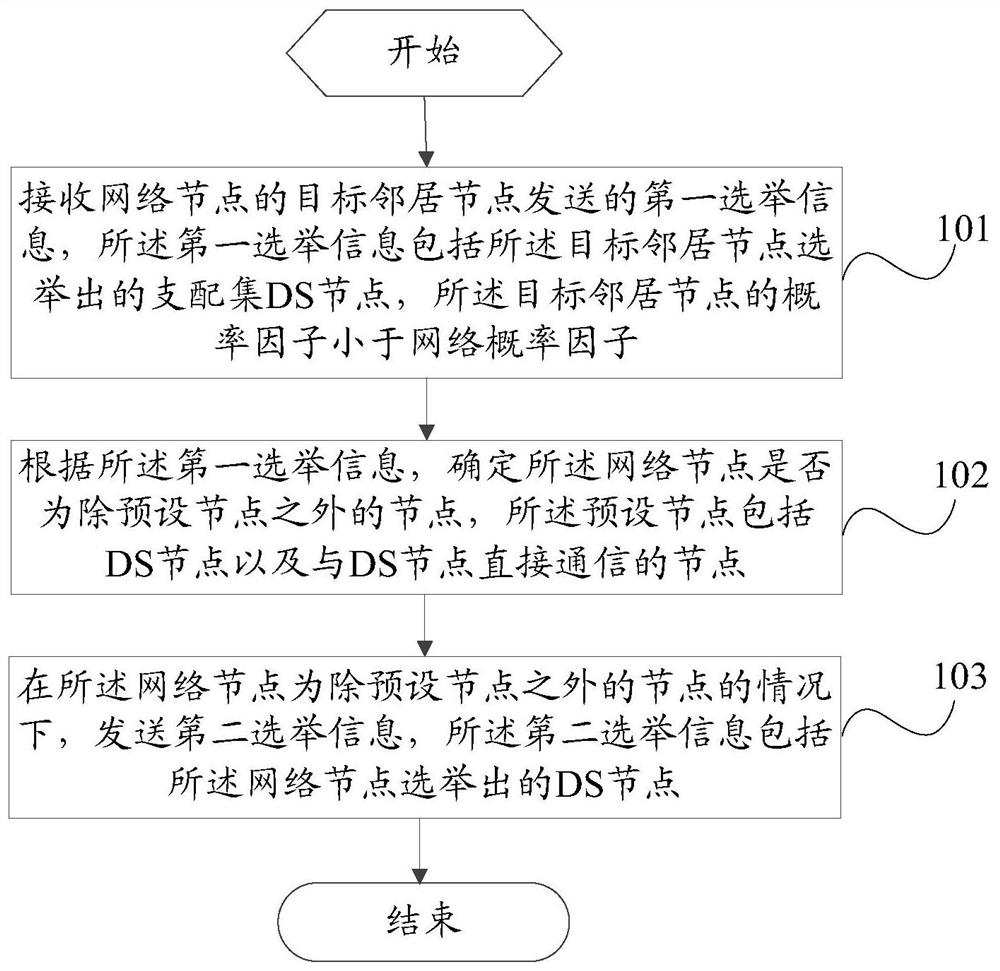
Network node election method and node equipment
ActiveCN111371572ATake advantage ofFull deliveryData switching networksWireless communicationComputer networkEngineering
The invention provides a network node election method and node equipment, and solves the problem that when an existing distributed clustering or connected dominating set algorithm is adopted for election, more redundant nodes and a large amount of redundant system message overhead can be generated. The method comprises the steps of receiving first election information sent by a target neighbor node of a network node, wherein a probability factor of the target neighbor node is smaller than a network probability factor; according to the first election information, whether the network node is a node except a preset node is determined, and the preset node comprises a DS node and a node directly communicating with the DS node; and under the condition that the network node is a node except the preset node, sending second election information, the second election information comprising the DS node elected by the network node. In the embodiment of the invention, the election process is executed step by step, the information generated in the election process is fully utilized and transmitted, and the number of redundant DS nodes generated by election and the system overhead generated by DSelection are reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
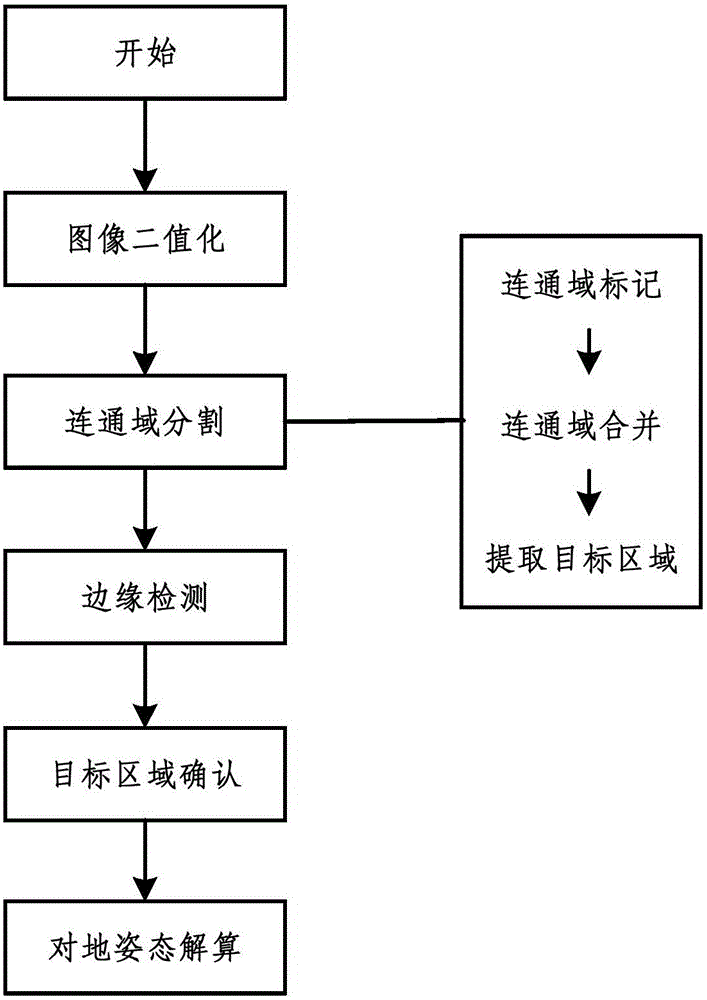
Area method-based to-ground attitude calculation method
ActiveCN106056574AEliminate distractionsImprove calculation accuracyImage enhancementImage analysisSimulationConnected dominating set
The present invention discloses an area method-based to-ground attitude calculation method, and belongs to the spacecraft navigation, guidance and control field. The method comprises the following steps of 1 carrying out the image binaryzation operation; 2 marking and merging the connected domains, and extracting a maximum connected domain; 3 extracting edges and utilizing the target characteristics to further confirm a target connected domain; 4 calculating the to-ground attitudes. The area method-based to-ground attitude calculation method provided by the present invention has a good effect on the conditions that the noise points are more, other interference target areas are less than a to-be-extracted target, and a to-be-extracted target area is more normative.
Owner:SHANGHAI AEROSPACE CONTROL TECH INST
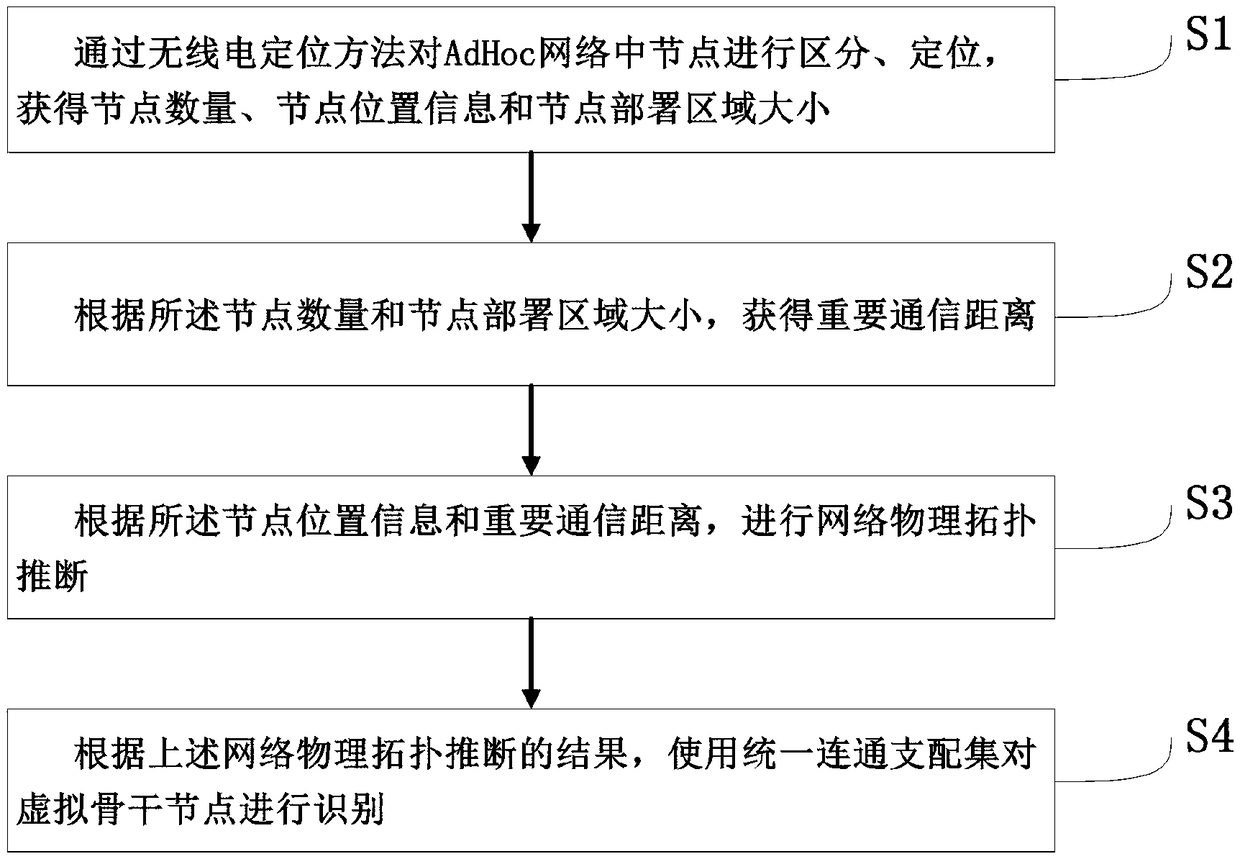
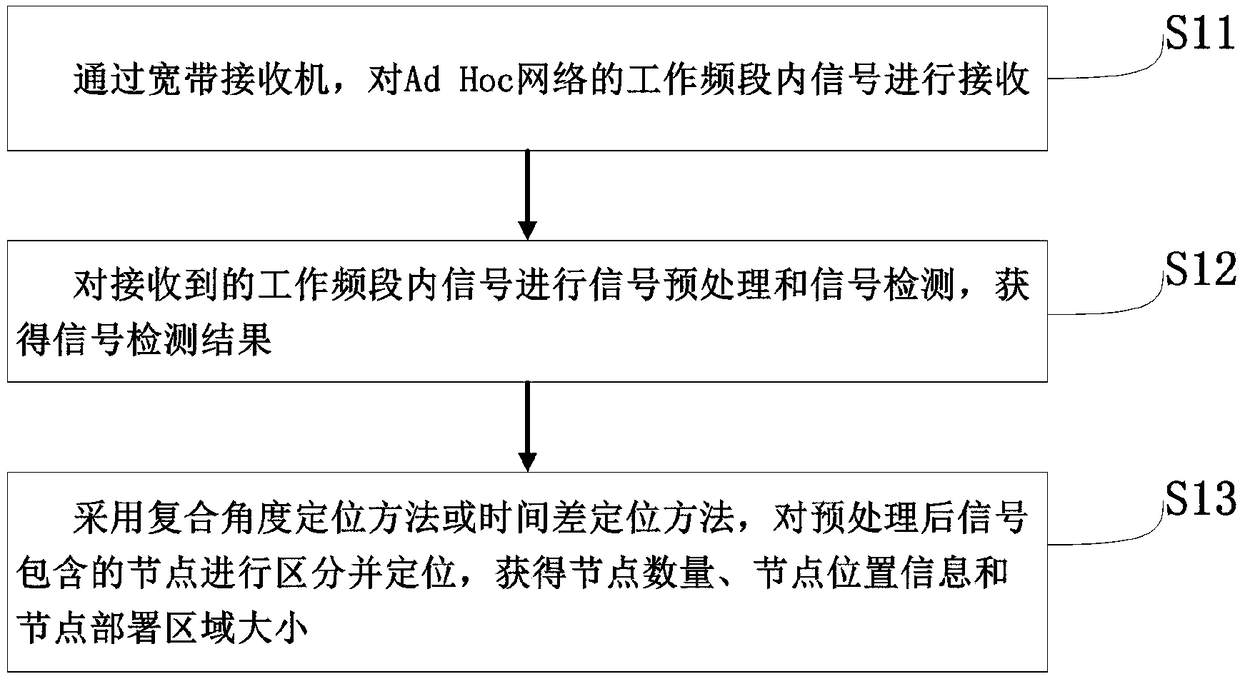
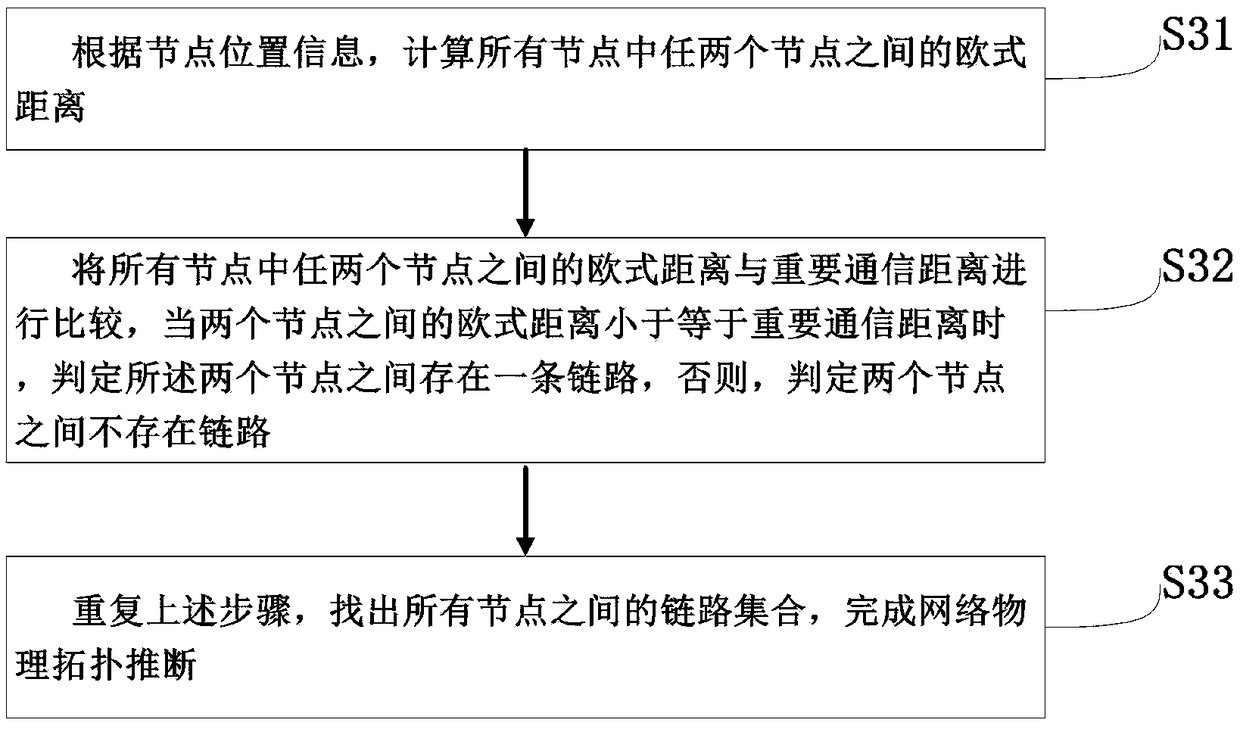
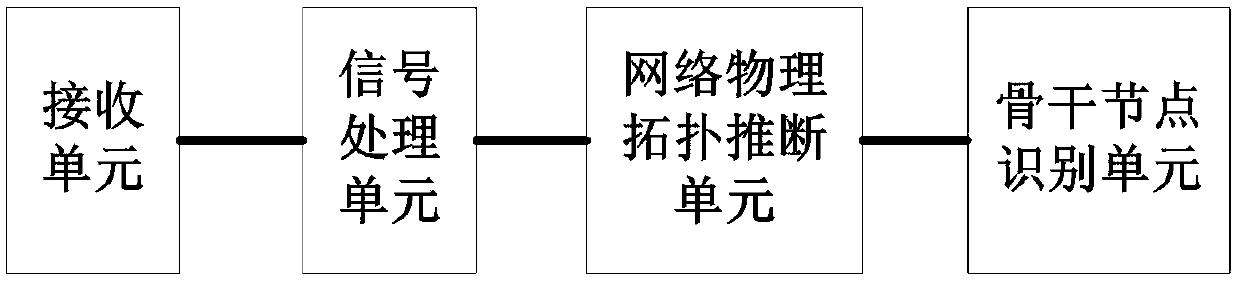
Ad Hoc network virtual backbone node identification method
ActiveCN109451429AImprove performanceImprove protectionTransmission monitoringLocation information based serviceInformation processingNode deployment
The invention relates to an Ad Hoc network virtual backbone node identification method, which belongs to the technical field of communication and solves the problem that the Ad Hoc network backbone nodes cannot be effectively identified in the prior art. The Ad Hoc network virtual backbone node identification method comprises the following steps: distinguishing and locating the nodes in the Ad Hocnetwork through a radio locating method, so as to obtain the number of the nodes, the location information of the nodes, and the size of the node deployment area; obtaining an important communicationdistance according to the number of the nodes and the size of the node deployment area; performing network physical topology inference according to the location information of the nodes and the important communication distance; and performing identification on the virtual backbone nodes using a unified connected dominating set according to the result of the network physical topology inference. The Ad Hoc network virtual backbone node identification method realizes automatic identification of the virtual backbone nodes in the Ad Hoc network. The result obtained by the Ad Hoc network virtual backbone node identification method is beneficial to the protection of the backbone nodes in the network, and improves the overall performance of the Ad Hoc network by improving the operational capability and information processing capability of the backbone nodes.
Owner:NAT UNIV OF DEFENSE TECH
Vehicle video analysis method and system thereof
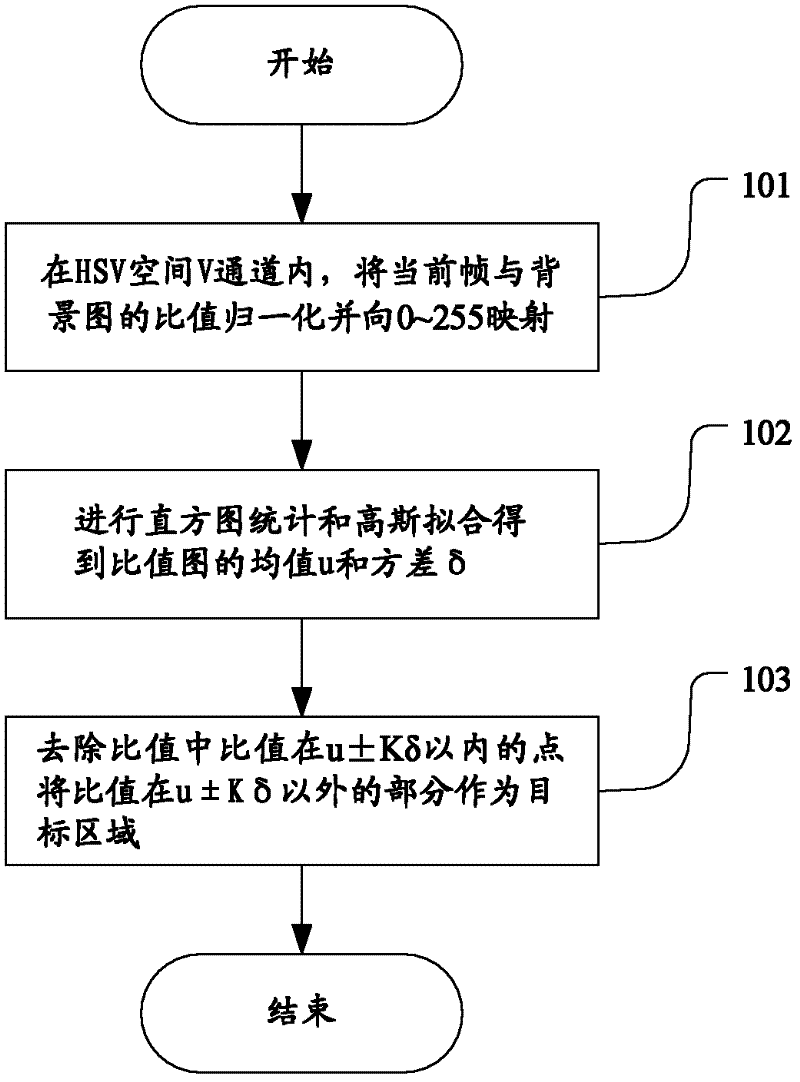
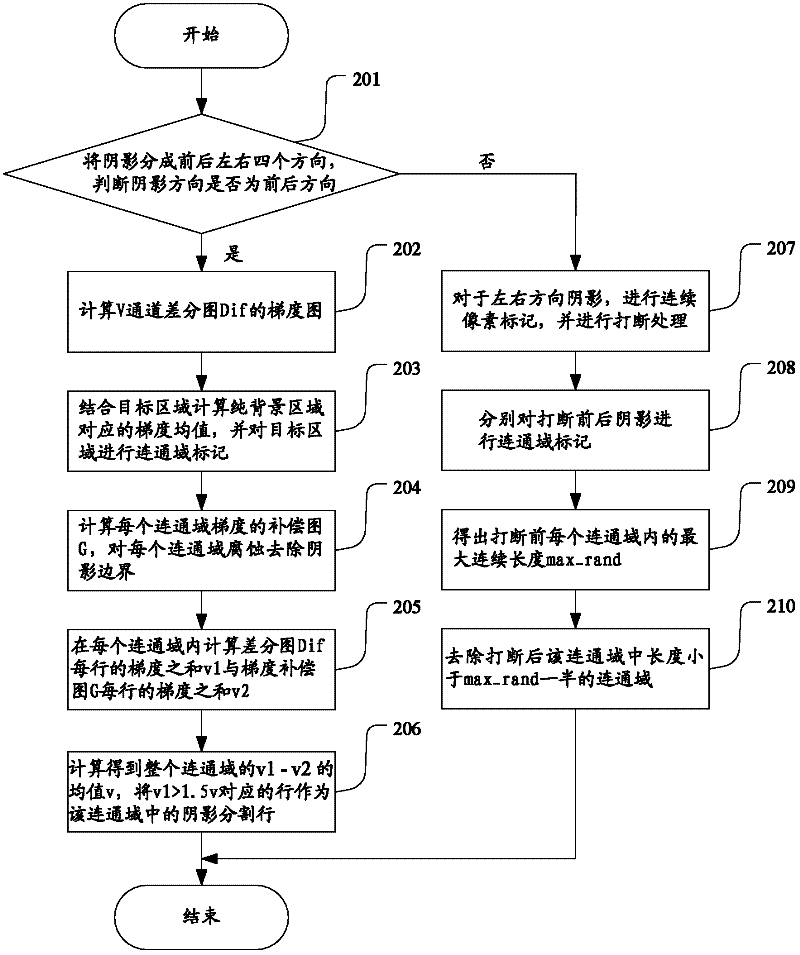
InactiveCN102411714ARemove obstaclesAvoid misjudgmentDetection of traffic movementCharacter and pattern recognitionConnected dominating setAnalysis method
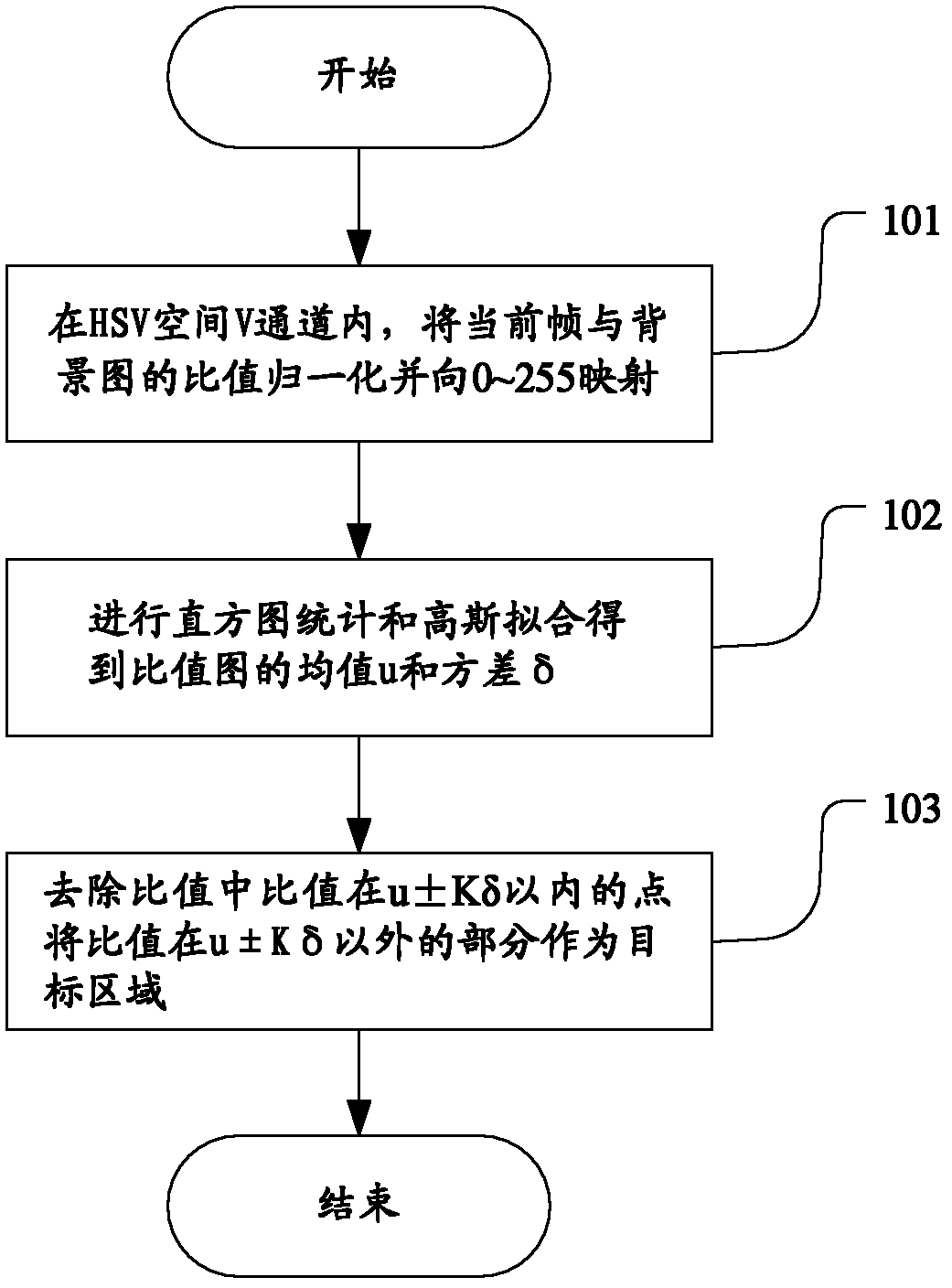
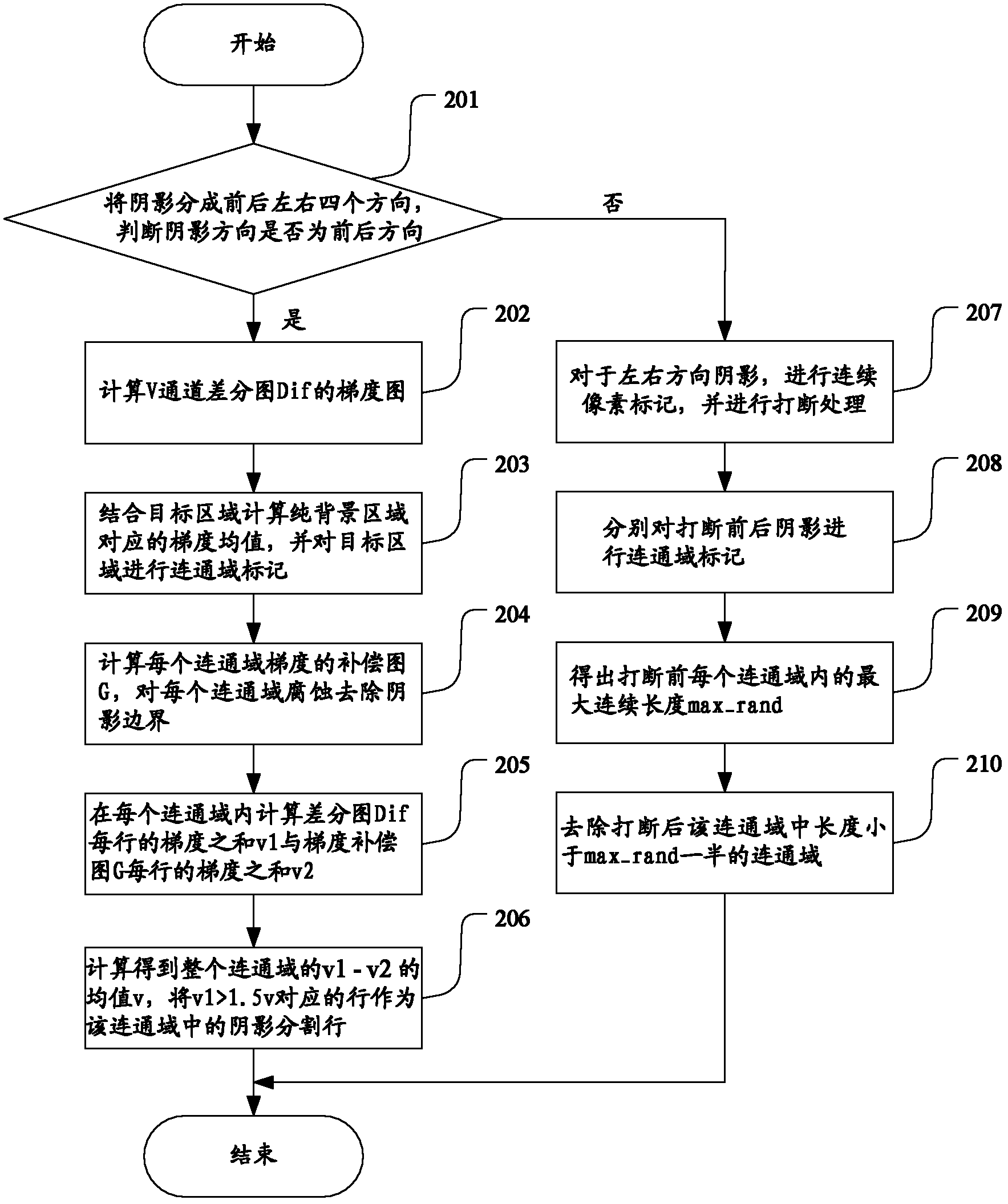
The invention provides a vehicle video analysis method and a system thereof. The method comprises the following steps: (1) extraction of a target area: in a V channel of HSV space, carrying out normalization on a ratio graph of a present frame and a background graph and mapping the ratio graph to a 0-255 range, obtaining an average value u and a variance delta of the ratio graph through histogramstatistics and Gaussian fitting, and taking a part except for u+ / - Kdelta in the ratio graph as the target area, wherein, K is a coefficient related to image noise; (2) removal of a shadow: dividing directions of the shadow into four directions; with regards to removal of the shadow at left and right directions, carrying out breaking and segmentation according to width of the shadow and a vehiclebody in a same connected domain, and with regards to removal of the shadow at front and back directions, comparing gradient sum of each row and a gradient row average value of the whole connected domain in a same connected domain and carrying out segmentation. According to the video analysis method, a complete body area can be extracted, obstruction of realizing subsequent video analysis functions of analyzing behaviors of pressing a line, changing a lane, running a red light and the like of a vehicle is eliminated, and misjudgement of the functions is avoided.
Owner:ANHUI CHAOYUAN INFORMATION TECH
Method and system for solving a minimum connected dominating set problem using quantum annealing for distance optimization
ActiveUS10268964B2Less timeProcessing problemForecastingMachine learningConnected dominating setDominating set
A method is disclosed for determining a minimum connected dominating set in a graph, the method comprising obtaining an indication of an input graph, the input graph comprising a plurality of nodes and a plurality of edges; generating a distance table comprising for each node of the input graph, an indication of a distance between the given node and each of the other node of the plurality of nodes; generating a corresponding constrained binary quadratic programming problem using the generated distance table; providing the corresponding constrained binary quadratic programming problem to a quantum annealing solver; obtaining at least one approximate solution from the quantum annealing solver; post-processing the at least one approximate solution and providing the post-processed at least one approximate solution.
Owner:1QB INFORMATION TECHNOLOGIES INC
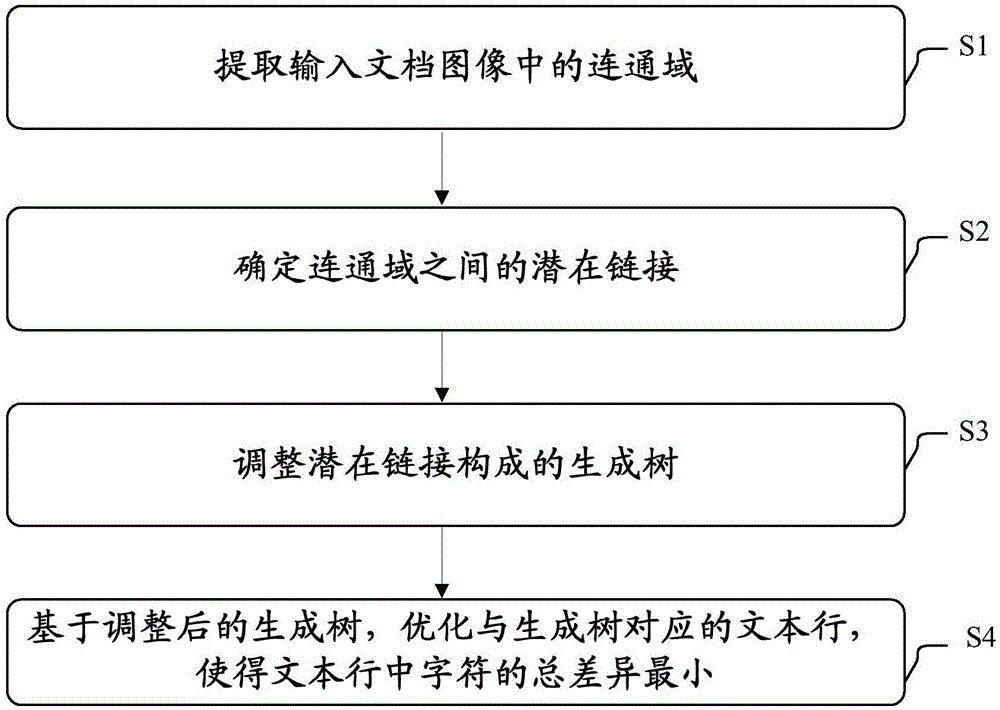
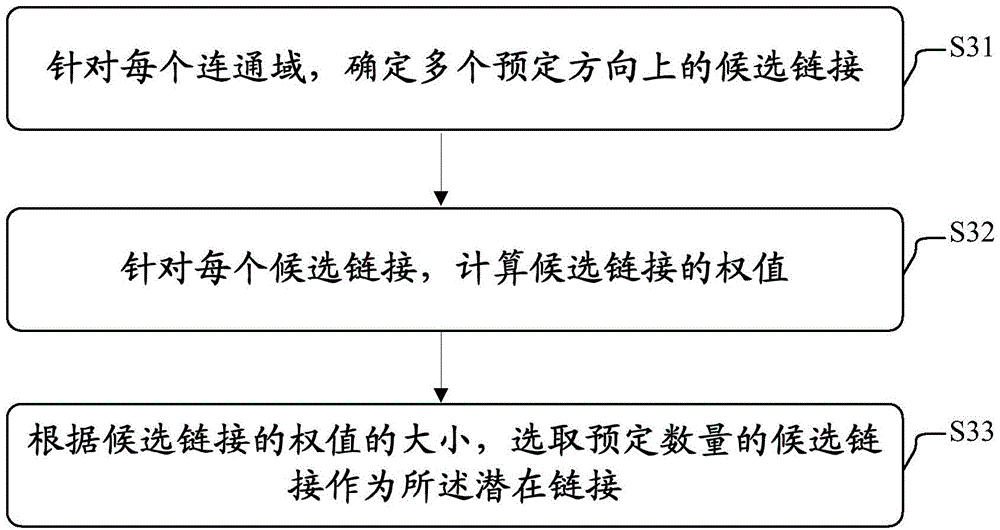
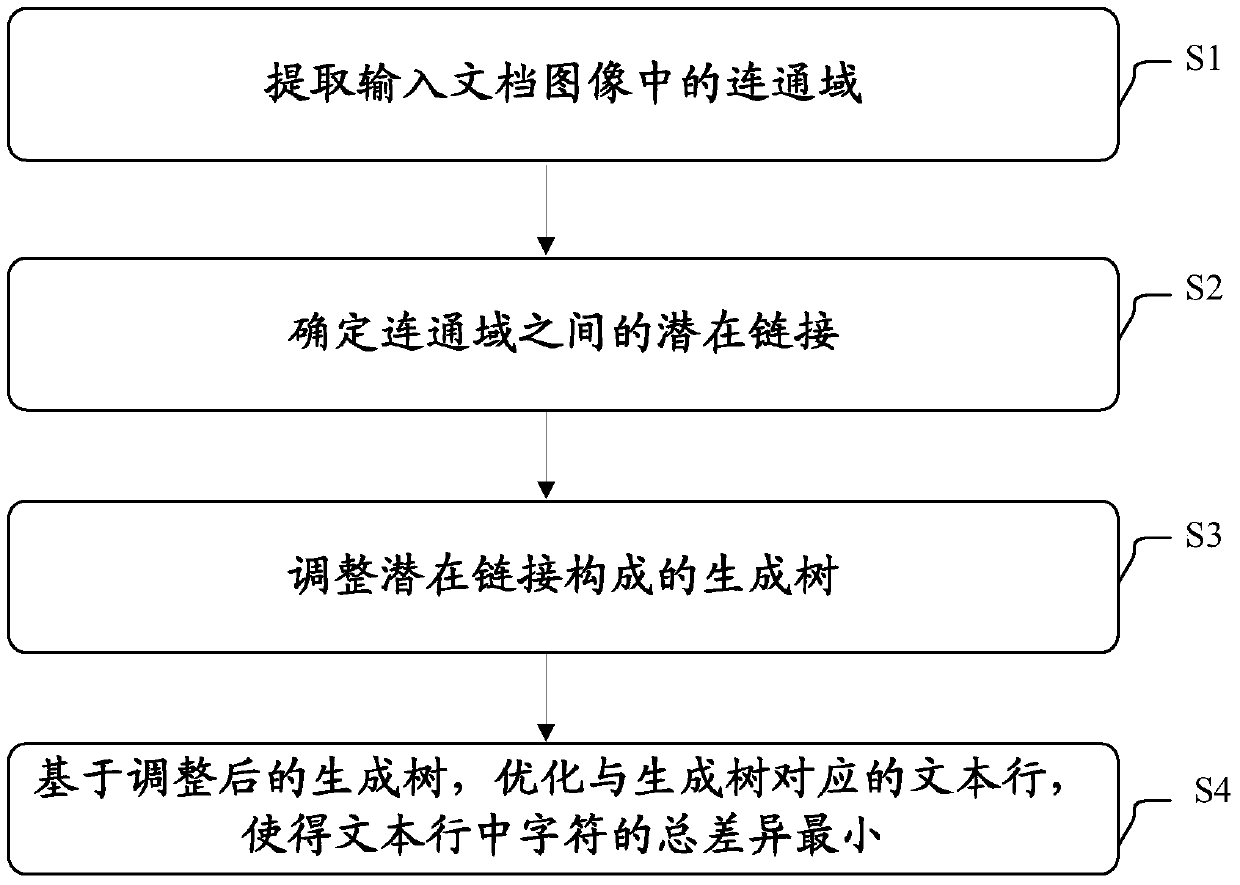
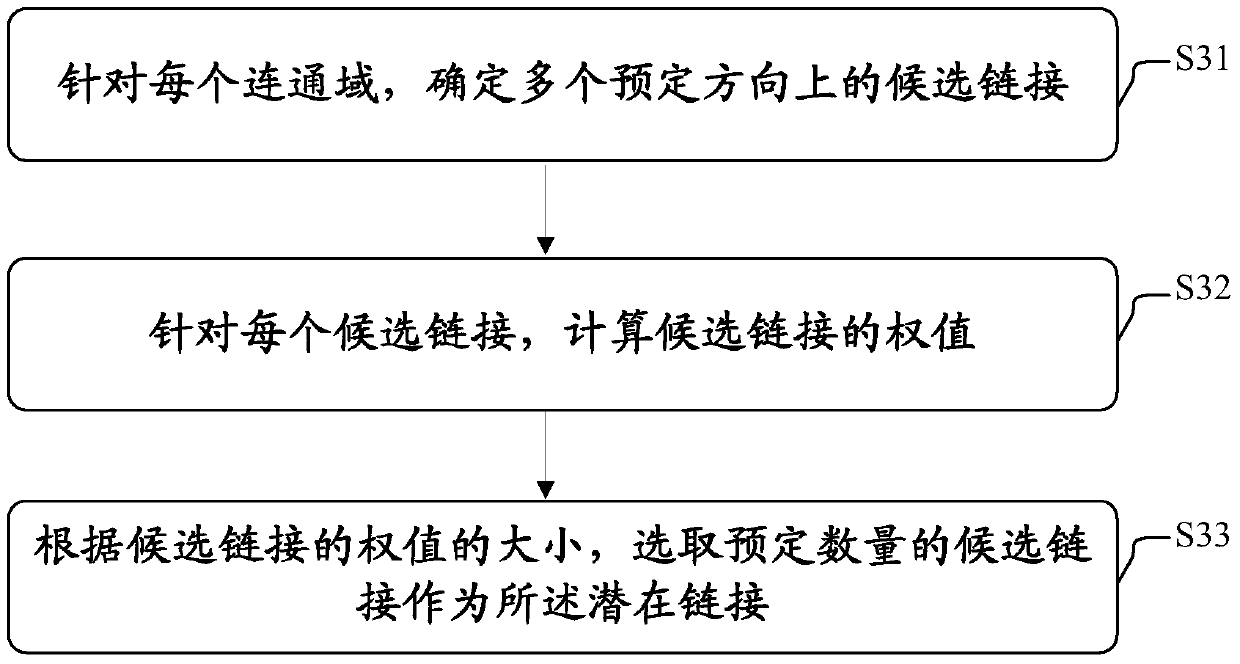
Text line extraction method and text line extraction equipment
ActiveCN105844207ACharacter and pattern recognitionSpecial data processing applicationsNatural language processingConnected dominating set
The invention discloses a text line extraction method and a piece of text line extraction equipment. The text line extraction method of the invention comprises the following steps: extracting connected domains in an input document image; determining the potential link between the connected domains; adjusting a spanning tree constituted by the potential link; and optimizing a text line corresponding to the spanning tree based on the adjusted spanning tree to minimize the total difference between the characters in the text line. Through the text line extraction method and the text line extraction equipment of the invention, a text line in a document image can be extracted accurately and robustly.
Owner:FUJITSU LTD
Ad Hoc network virtual backbone node identification system
ActiveCN109526016AImprove performanceQuick filterNetwork topologiesData switching networksInformation processingNode deployment
The invention relates to an Ad Hoc network virtual backbone node identification system, belongs to the technical field of communication, and solves the problem that an Ad Hoc network backbone node cannot be effectively identified in the prior art. The system comprises a receiving unit, a signal processing unit, a network physical topology inference unit and a backbone node identification unit. A signal in a working frequency band of an Ad Hoc network is received through the receiving unit; the number of nodes, node position information and the size of a node deployment area are obtained through the signal processing unit; the network physical topology inference unit is used for conducting network physical topology inference; and through the backbone node identification unit, a unified connected dominating set is used for identifying virtual backbone nodes according to a network physical topology inference result. The method can realize automatic identification of the virtual backbone nodes in the Ad Hoc network; the obtained result is beneficial to special protection for the backbone nodes; and the operation capability and the information processing capability of the backbone nodesare improved, so that the overall performance of the Ad Hoc network is improved.
Owner:NAT UNIV OF DEFENSE TECH
Topology control method for underground flight ad hoc network for post-disaster emergency communication
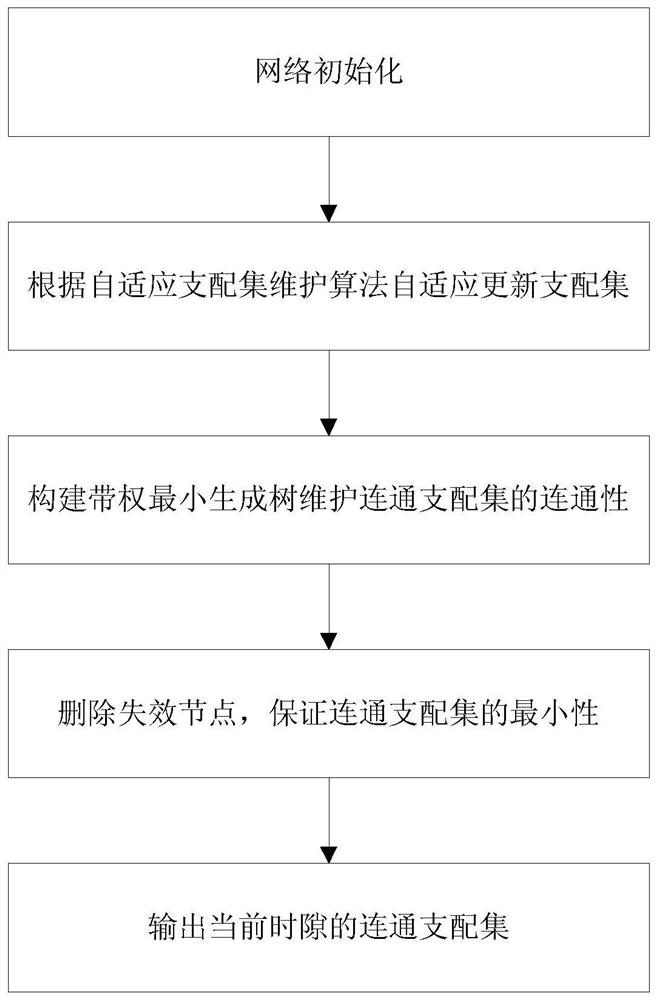
ActiveCN112838887AGuaranteed minimumImprove universalityMining devicesNetwork topologiesEngineeringConnected dominating set
The invention discloses a topology control method for an underground flight ad hoc network for post-disaster emergency communication, which comprises the following steps of: firstly, providing a hierarchical method to adaptively maintain a dominating set, then repairing the connectivity of the dominating set by maintaining a weighted minimum spanning tree, and finally, dynamically detecting failure joint nodes to ensure the minimum of the connected dominating set. In order to ensure that the time complexity of maintaining the minimum connected dominating set after each update is smaller than the time complexity of recalculation, only the topology change part is processed, all types of topology changes, including entry, exit and movement of nodes, in the flight ad hoc network can be processed, and good universality and expandability are achieved.
Owner:CHINA UNIV OF MINING & TECH
Gateway node selection method, node and device and medium
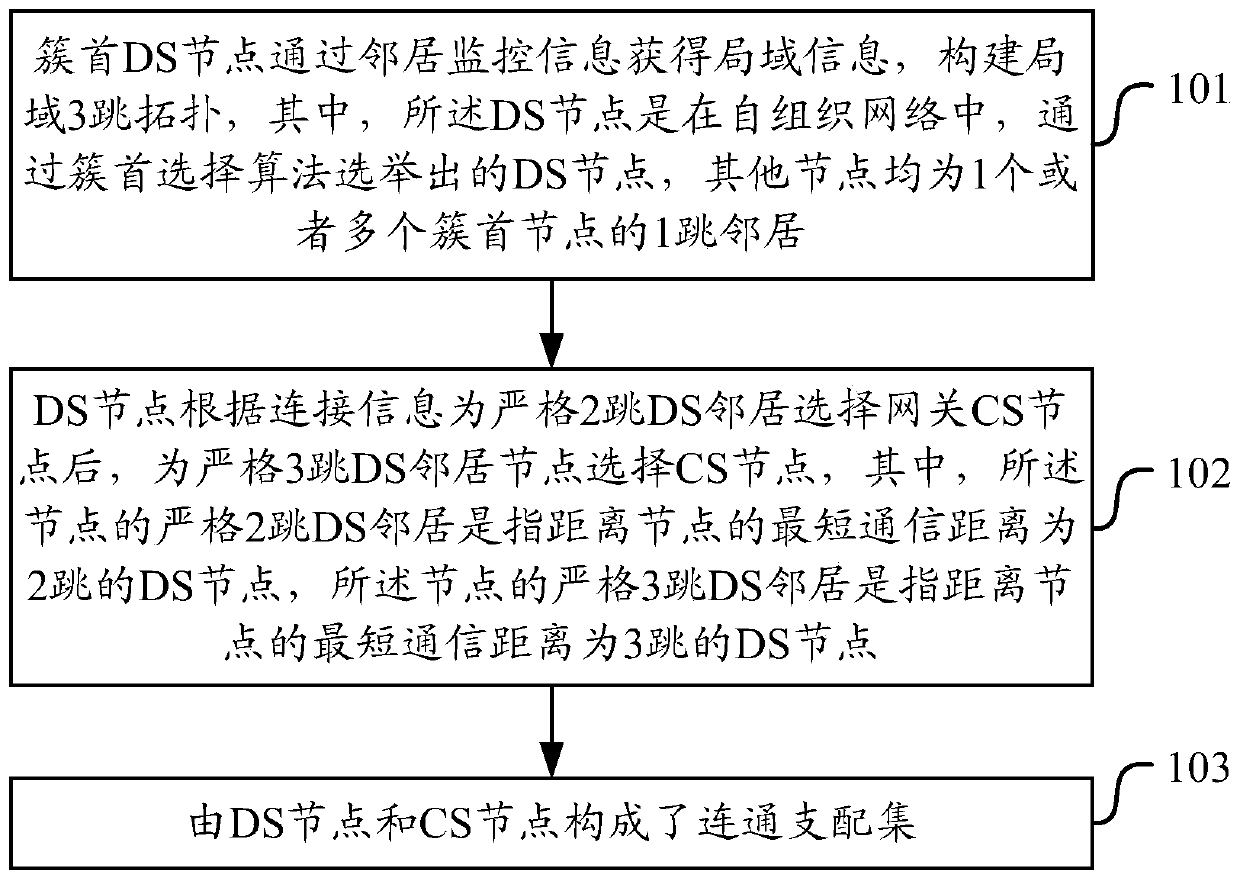
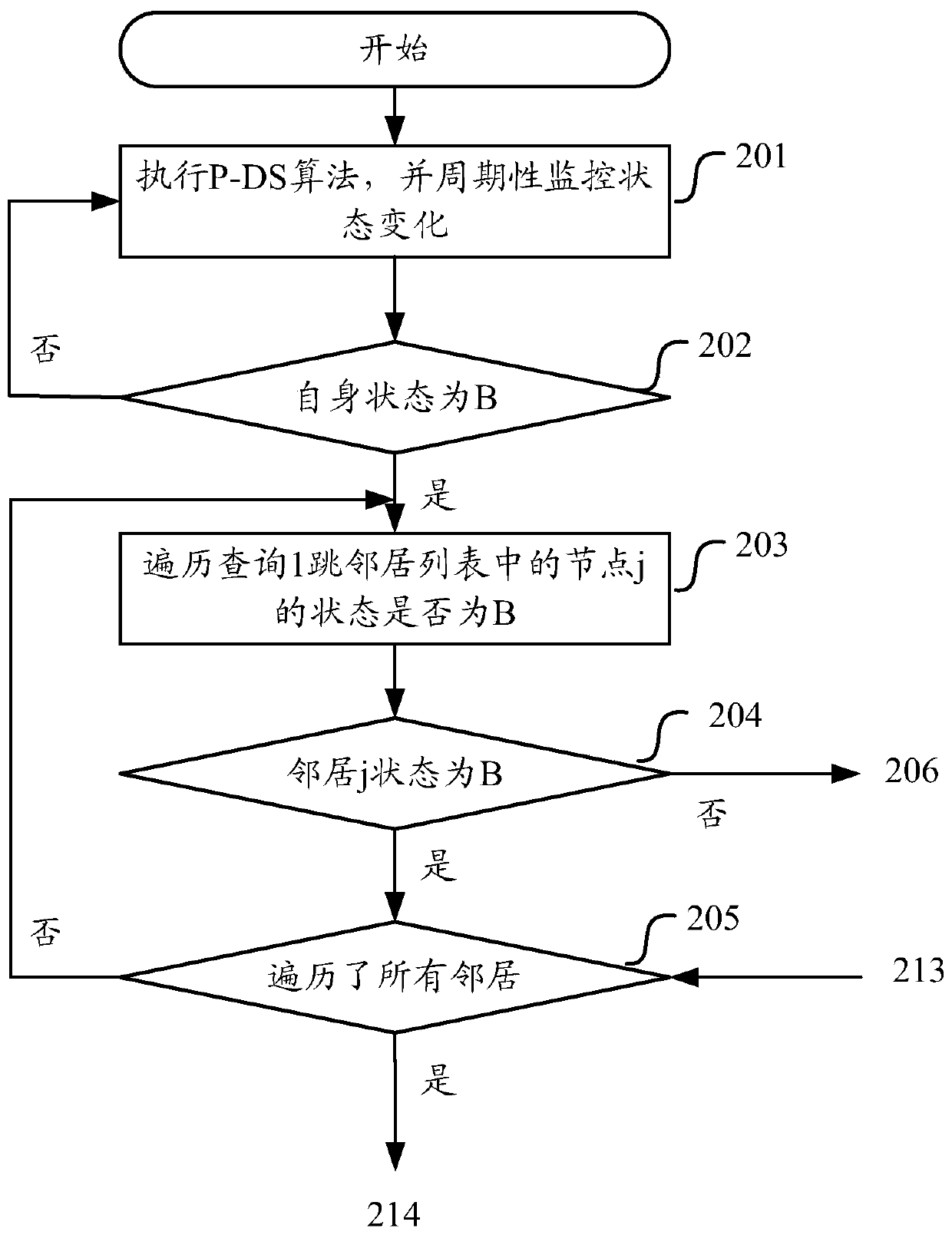
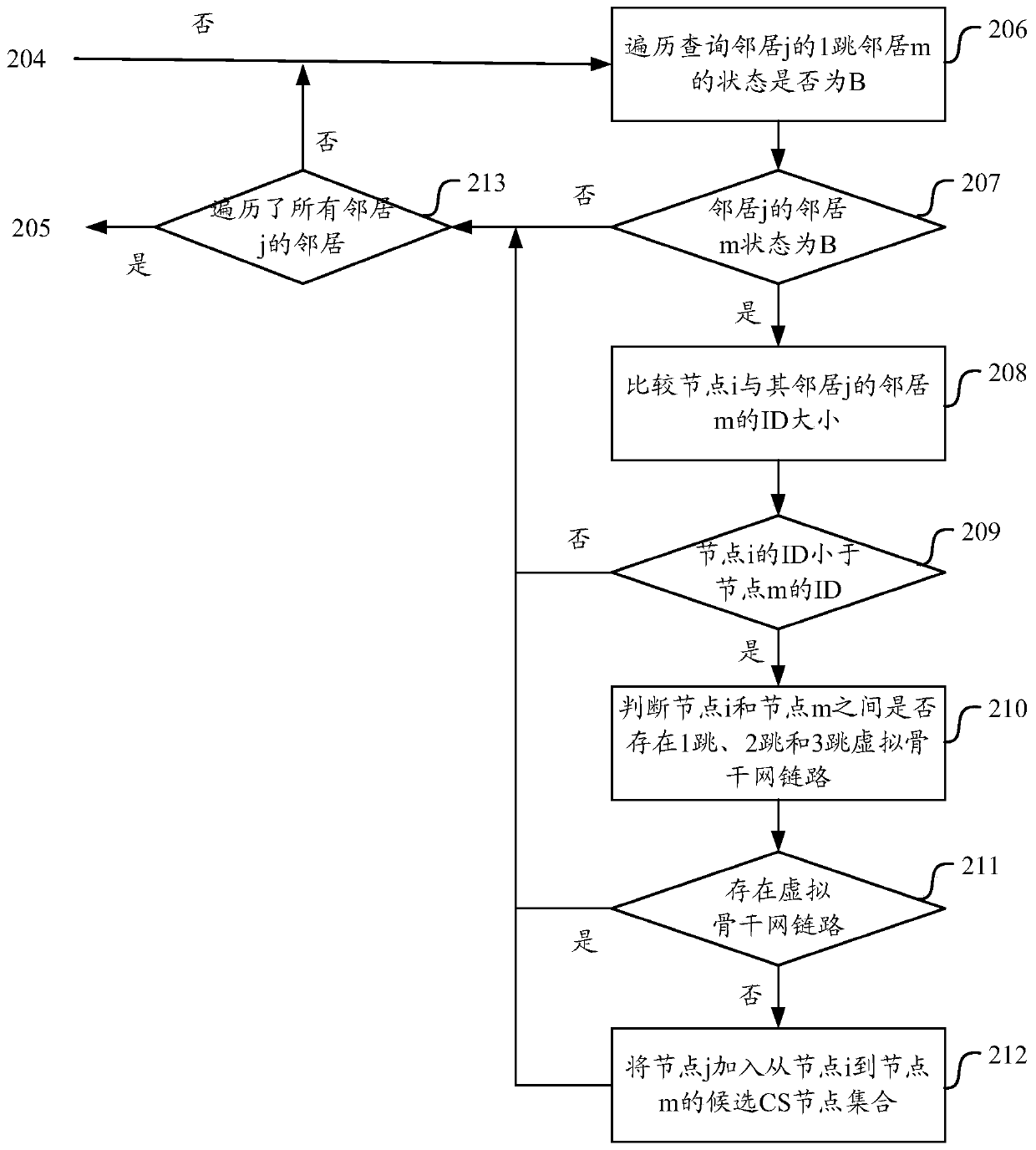
ActiveCN111601351AReduce in quantityReduce the number of nodesNetwork topologiesEngineeringConnected dominating set
The invention discloses a gateway node selection method, a node, a device and a medium. The method comprises: cluster head DS nodes obtaining local area information through neighbor monitoring information and constructing a local area three-hop topology, the DS nodes being DS nodes elected through a cluster head selection algorithm in a self-organizing network, and other nodes being all one-hop neighbors of one or more cluster head nodes; the DS node selecting a gateway CS node for a strict two-hop DS neighbor according to the connection information; selecting CS nodes for strict three-hop DSneighbor nodes, strict two-hop DS neighbors of the nodes refering to DS nodes with the shortest communication distance of two hops away from the nodes, and strict three-hop DS neighbors of the nodes referring to DS nodes with the shortest communication distance of three hops away from the nodes; a DS node and a CS node forming a connected dominating set. According to the invention, the number of redundant gateway nodes can be reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Text line extraction method and text line extraction device
ActiveCN105844207BCharacter and pattern recognitionSpecial data processing applicationsNatural language processingConnected dominating set
The invention discloses a text line extraction method and a piece of text line extraction equipment. The text line extraction method of the invention comprises the following steps: extracting connected domains in an input document image; determining the potential link between the connected domains; adjusting a spanning tree constituted by the potential link; and optimizing a text line corresponding to the spanning tree based on the adjusted spanning tree to minimize the total difference between the characters in the text line. Through the text line extraction method and the text line extraction equipment of the invention, a text line in a document image can be extracted accurately and robustly.
Owner:FUJITSU LTD
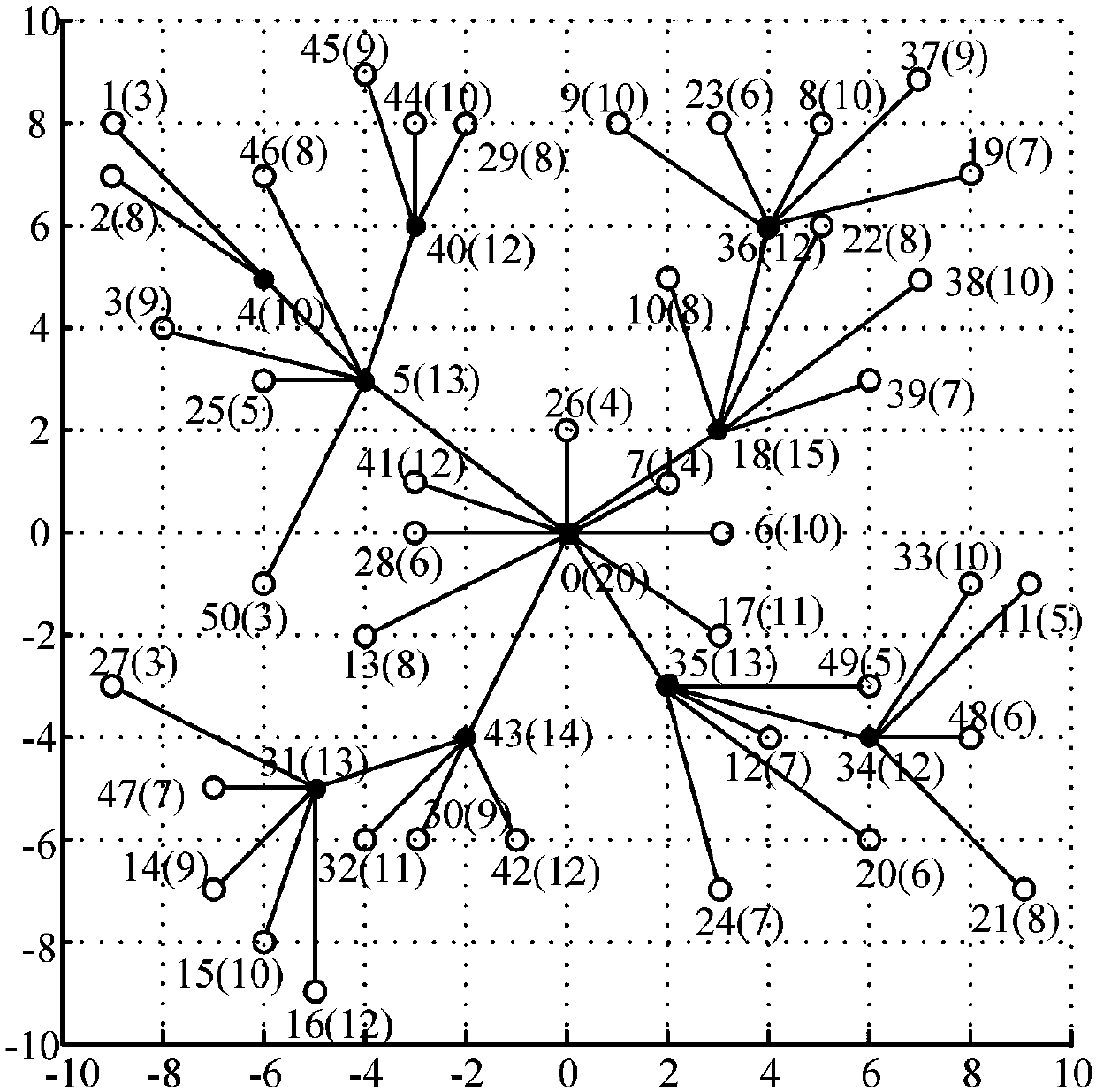
Topology self-healing algorithm for wireless sensor networks based on node neighbor relationship
The present invention provides a wireless sensor network topology self-healing algorithm based on the neighbor relationship of nodes, finds the control set DS of the network by analyzing the neighbor relationship of the nodes, connects the nodes in the DS, and obtains the connected control set CDS; through heuristic clipping rules Cut out the CDS obtained above to complete the entire construction of the minimum connected control set MCDS; query the failed nodes on the entire network, repeat the MCDS construction in the local range of the failed nodes, and finally obtain the current network minimum connected control set MCDS after partial repair '. Simulation experiments show that in most cases, the invention can quickly generate a near-optimal MCDS of the network. The invention only relies on the neighbor information of the node to quickly construct a new MCDS', which solves the problem of network topology change caused by node failure, not only restores the connectivity of the network topology, but also effectively solves the problem of prolonging the life of WSN issue of period.
Owner:NANJING UNIV OF POSTS & TELECOMM
MCDS approximation algorithm-based multicast route method with minimized resource consumption
ActiveCN101562780BReduce consumptionReduce the number of nodesEnergy efficient ICTNetwork topologiesResource consumptionWireless broadcast
Owner:WESTERN MINING CO LTD
A wireless ad hoc network backbone network optimization generation method
ActiveCN111770514BReduce the cost of signal transmissionReduce computing timeNetwork topologiesHigh level techniquesUndirected graphEngineering
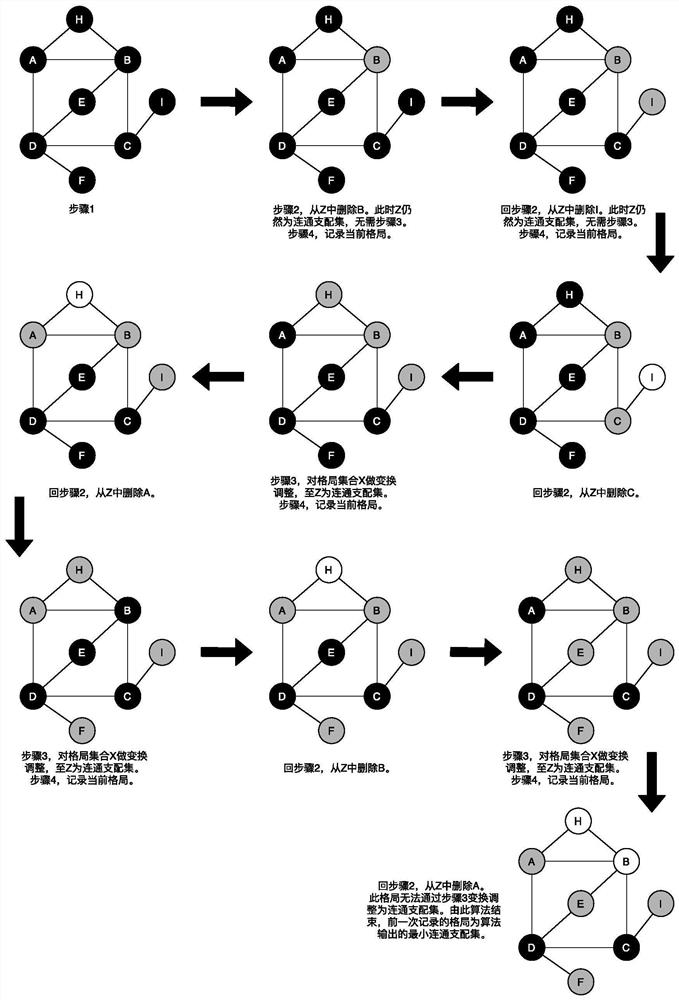
The invention discloses a method for optimizing and generating a backbone network of a wireless ad hoc network. Non-critical nodes, and delete the non-critical nodes from the set Z, and update the pattern set X; Step 3, do transformation and adjustment to the pattern set X; Step 4, if the set in the pattern set X after the transformation and adjustment is an empty set, then Record the set Z of the transformed and adjusted pattern set X as a connected dominating set, and go back to step 2; otherwise, the last recorded connected dominating set is the output. The invention finds a minimum connected dominating set in the undirected graph as the backbone network of the wireless ad hoc network, with less computation time and smaller target value.
Owner:HUBEI UNIV OF TECH
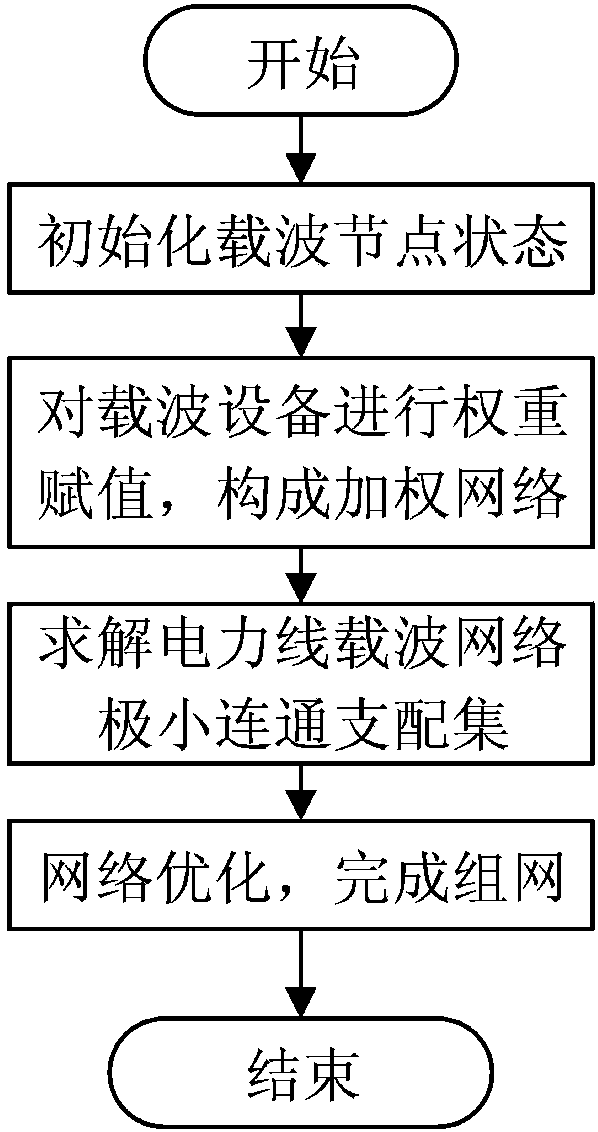
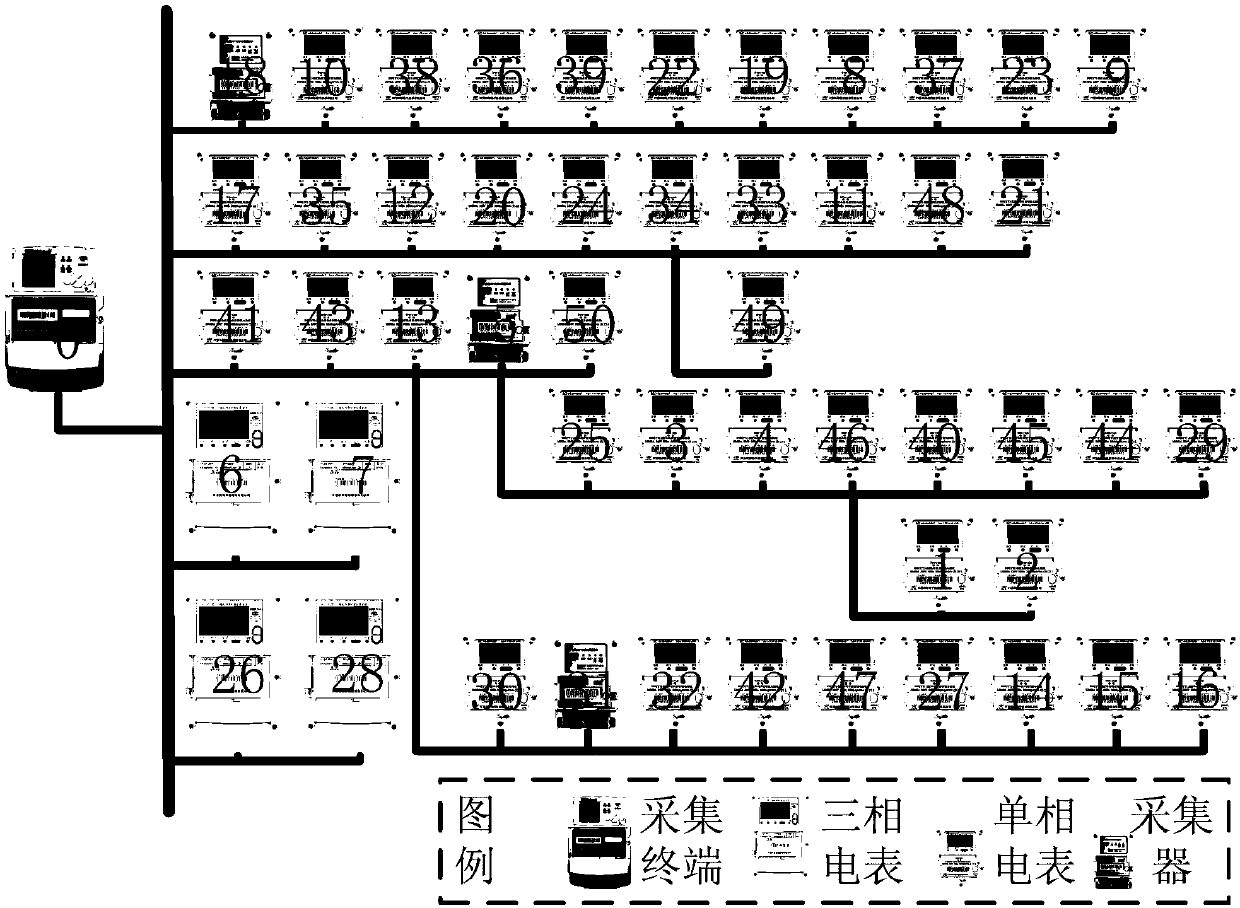
Low-voltage power line carrier communication reliable networking method considering equipment communication performance
ActiveCN107592224AImprove resource utilizationCommunication bit error rate is reliablePower distribution line transmissionData switching networksLow voltageCarrier signal
The present invention relates to a low-voltage power line carrier communication reliable networking method considering equipment communication performance. The method includes the following specific steps that: (1) a network analysis model is constructed; (2) initialization is performed; (3), weights are assigned to carrier equipment, so that a weighted network can be formed; (4) the minimum connected dominating set of a power line carrier network is solved; and (5) network optimization is performed, and the method terminates. According to the method of the present invention, a bi-directionalcommunication low-voltage power line carrier communication network is modeled as an undirected connected graph; with an inverse proportion relationship between the signal to noise ratios of the equipment and the bit error rates of carrier communication considered, a weighted network reliability analysis model with the signal to noise ratios of the equipment adopted as the weights is established; on the basis of the minimum connected dominating set in the graph theory, a minimum connected dominating set method for solving a maximal weight is adopted; and therefore, the reliable networking of the low-voltage power line carrier network of an electric power information acquisition system can be realized, a communication error rate can be low, and the utilization rate of network resources can be improved.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
A Topology Construction Method for Wireless Sensor Networks Based on Mixed Integer Programming
InactiveCN102802163BSmall structureLoad balancingNetwork topologiesNetwork planningWireless mesh networkStructure of Management Information
The invention provides a wireless sensing network topological construction method based on mixed integer programming. The wireless sensing network topological construction method comprises the following steps of: 1) firstly, abstractly converting a problem of searching an optimal virtual backbone network of a wireless sensing network in a random network environment into a problem of a minimum connected dominating set of the wireless sensing network; 2) defining a sign stream, and determining an optimizing function using a product of a sign distribution number and node energy consumption as a target, so as to obtain a minimum generation tree for assigning all the other nodes in a current wireless sensing network; 3) constructing an assignment constraint set: ruling that each node has at least one assignment component as a neighbor node; and 4) constructing a generation tree constraint set: defining the generation tree constraint set, so that the connectivity of a final topological structure can be ensured, and constructing the generation tree constraint set by means of meeting all rules of the sign stream. The wireless sensing network topological construction method provided by the invention does not need any random pre-treatment process and has the advantages of relatively small structural scale, relatively small energy consumption and relatively long network service life.
Owner:ZHEJIANG SCI-TECH UNIV
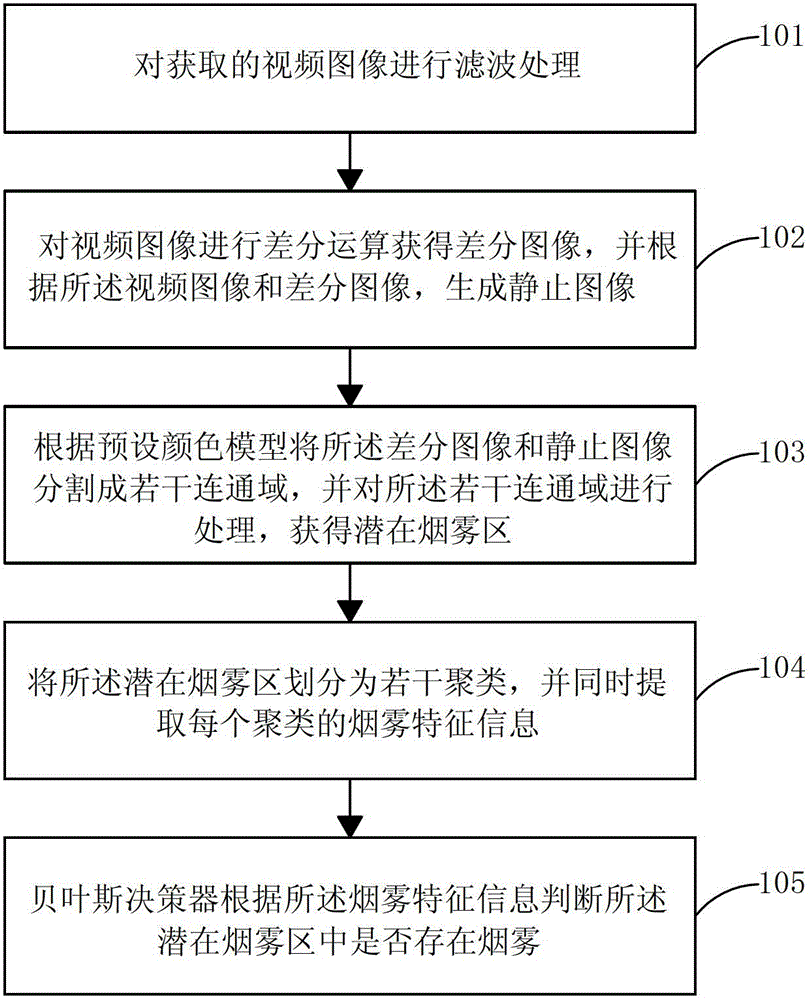
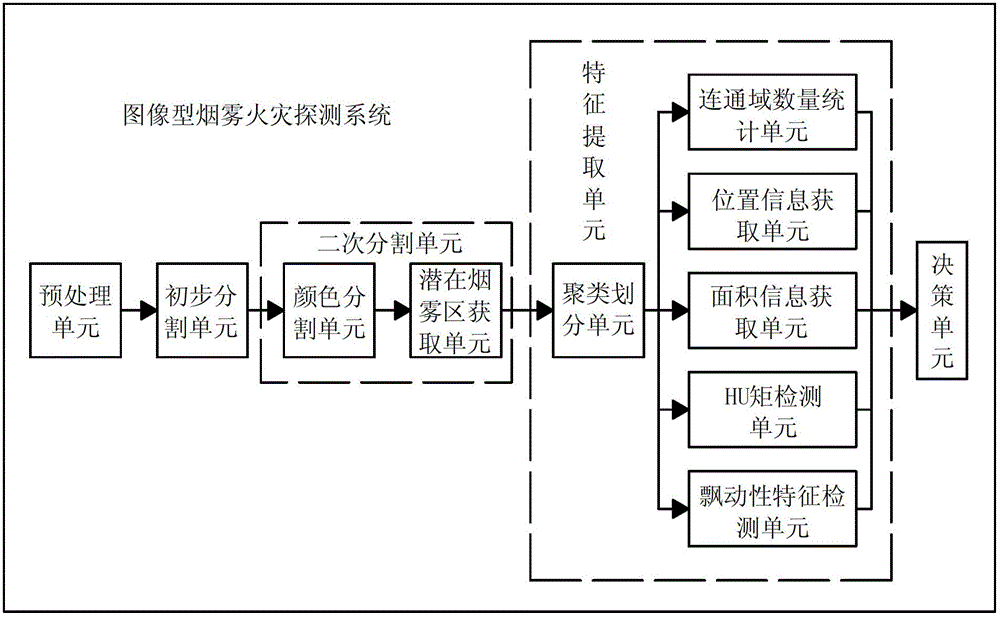
An image-type smoke fire detection method and system
ActiveCN102708651BImprove accuracyIncrease distanceFire alarm smoke/gas actuationFire - disastersImage segmentation
Owner:WUXI BRIGHTSKY ELECTRONICS
A method for detecting spatio-temporal anomalies in online river networks
ActiveCN104809205BImprove detection efficiencyShort response timeNetwork topologiesSpecial data processing applicationsNODALAlgorithm
The invention discloses a method for detecting an online river network spatio-temporal abnormal event, which comprises the following steps: firstly, using a connected dominating set algorithm to select a backbone node, and only detecting the state of the backbone node in each time stamp sensor network; then, detecting Whether the backbone node has a spatio-temporal anomaly event; if the backbone node has a time anomaly, add the child node of the backbone node to the candidate set for detection; learn the expected state and observed state of the backbone node with the time anomaly through Bayesian network learning Make a comparison to see if it deviates from the spatial relationship obtained by learning. If a spatial anomaly occurs, the space-time anomaly counter is incremented by 1. At the next timestamp, expand the detection range to include the backbone nodes and nodes in the candidate set, and continue to detect whether spatial anomalies or temporal anomalies occur. Finally, when the number of spatiotemporal anomalies of the backbone node and its candidate set nodes reaches the threshold Q, it is considered that a spatiotemporal anomaly event occurs.
Owner:HOHAI UNIV
A network node election method and node equipment
ActiveCN111371572BTake advantage ofFull deliveryData switching networksWireless communicationComputer networkEngineering
The present invention provides a network node election method and node equipment, which solves the problem that more redundant nodes and a large amount of redundant system message overhead will be generated when the existing distributed clustering or connected dominance set algorithm is used for election. . The method of the present invention includes: receiving the first election information sent by the target neighbor node of the network node, the probability factor of the target neighbor node is smaller than the network probability factor; according to the first election information, determining whether the network node is a node other than the preset node , the preset node includes a DS node and a node directly communicating with the DS node; when the network node is a node other than the preset node, the second election information is sent, and the second election information includes the DS node elected by the network node . In the embodiment of the present invention, the election process is executed step by step, the information generated in the election process is fully utilized and transmitted, and the number of redundant DS nodes elected and the system overhead generated by the DS election are reduced.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Vehicle video analysis method and system thereof
InactiveCN102411714BRemove obstaclesAvoid misjudgmentDetection of traffic movementCharacter and pattern recognitionConnected dominating setAnalysis method
The invention provides a vehicle video analysis method and a system thereof. The method comprises the following steps: (1) extraction of a target area: in a V channel of HSV space, carrying out normalization on a ratio graph of a present frame and a background graph and mapping the ratio graph to a 0-255 range, obtaining an average value u and a variance delta of the ratio graph through histogramstatistics and Gaussian fitting, and taking a part except for u+ / - Kdelta in the ratio graph as the target area, wherein, K is a coefficient related to image noise; (2) removal of a shadow: dividing directions of the shadow into four directions; with regards to removal of the shadow at left and right directions, carrying out breaking and segmentation according to width of the shadow and a vehiclebody in a same connected domain, and with regards to removal of the shadow at front and back directions, comparing gradient sum of each row and a gradient row average value of the whole connected domain in a same connected domain and carrying out segmentation. According to the video analysis method, a complete body area can be extracted, obstruction of realizing subsequent video analysis functions of analyzing behaviors of pressing a line, changing a lane, running a red light and the like of a vehicle is eliminated, and misjudgement of the functions is avoided.
Owner:ANHUI CHAOYUAN INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com