Patents
Literature
31results about How to "Avoid bypassing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
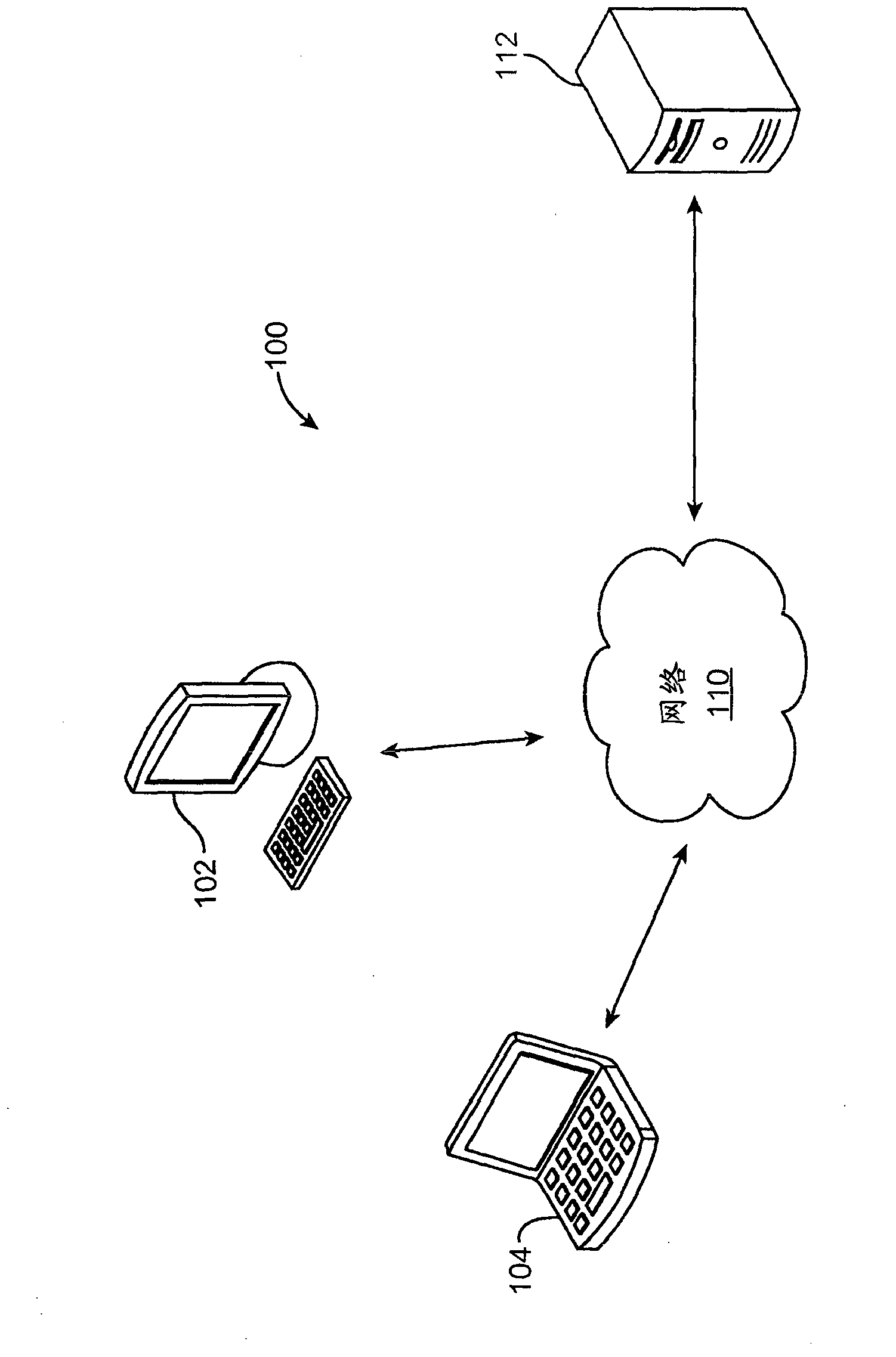
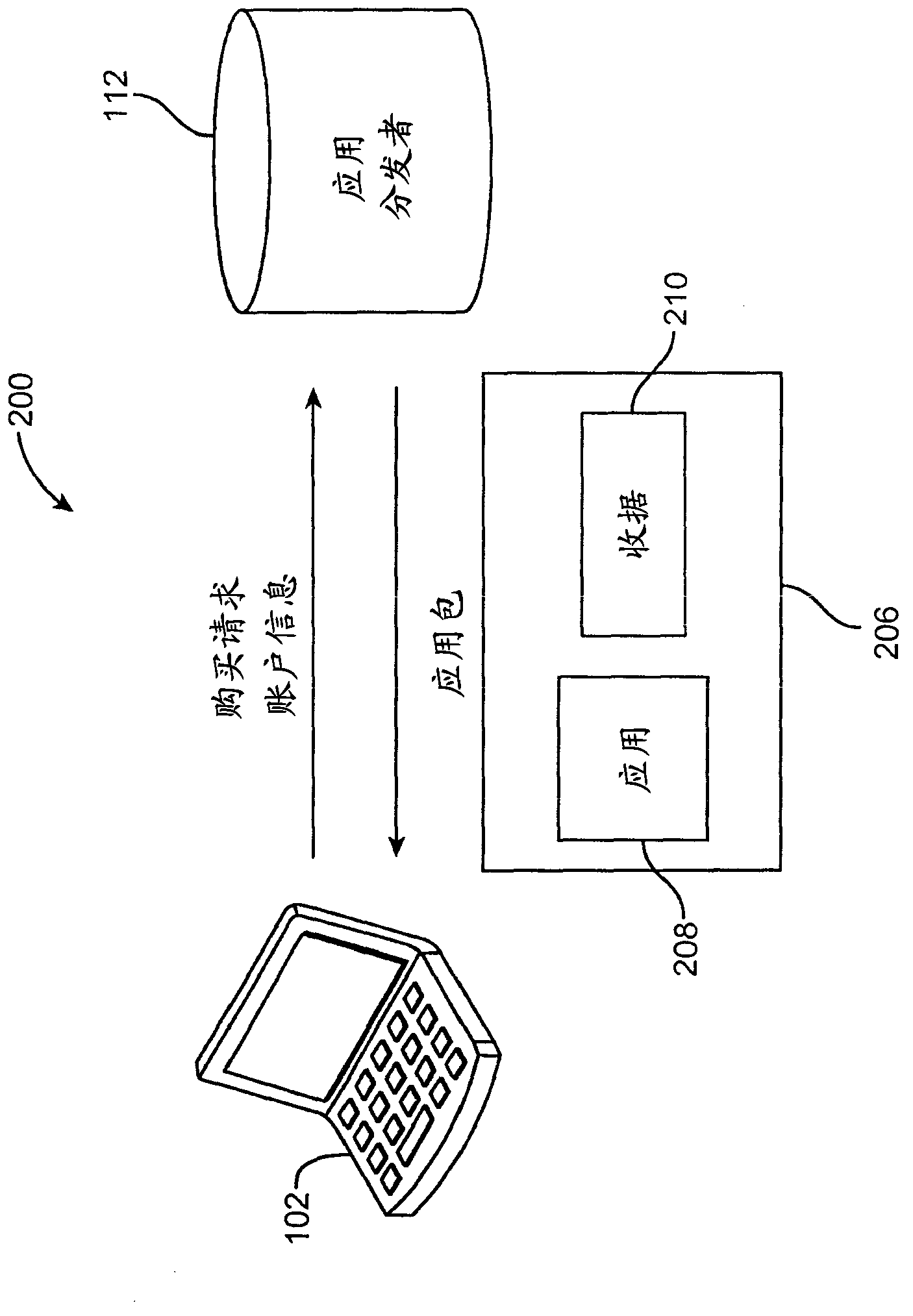
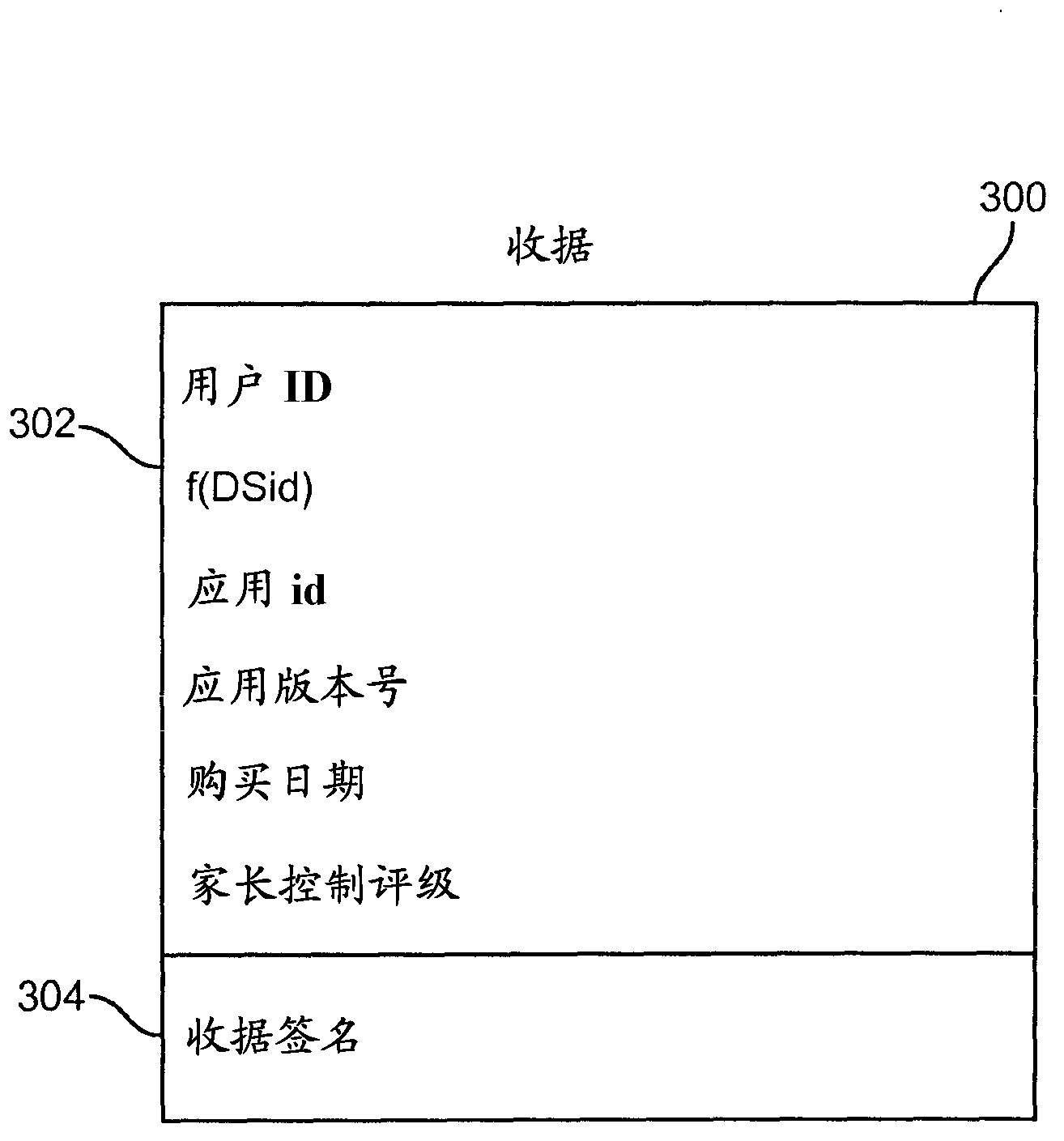
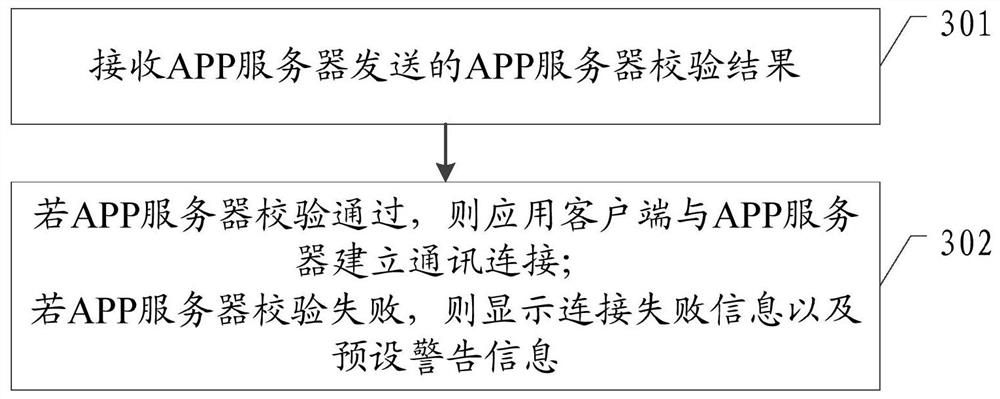
Application usage policy enforcement
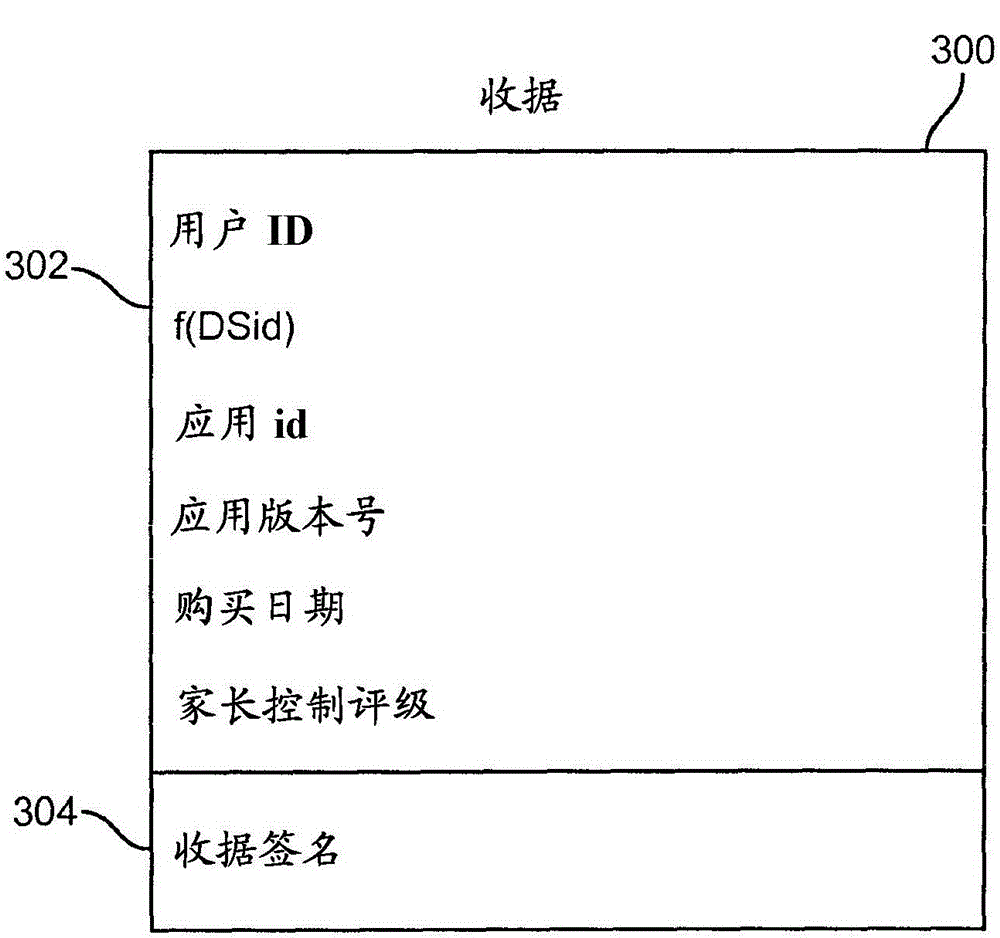
ActiveCN103180859AAvoid bypassingBuying/selling/leasing transactionsProgram/content distribution protectionReceiptAuthorization
Disclosed herein are systems, methods, and non-transitory computer-readable media for enforcing application usage policies. As part of an application purchase transaction, the application distributor creates a unique proof of purchase receipt. This receipt can be bundled with the application and delivered to the purchaser. Each machine can maintain an authorization file that lists the users authorized to use applications on that machine. A system configured to practice the method verifies that a user is authorized to use an application on a machine based on an application proof of purchase receipt and the authorization file. If the application proof of purchase receipt and the authorization file are both valid, the system checks if the user account identifier in the receipt is contained in the authorization file. If so, the user can be considered authorized to use the application on the machine.
Owner:APPLE INC
Application program anti-attack method and system based on code injection and behavior analysis
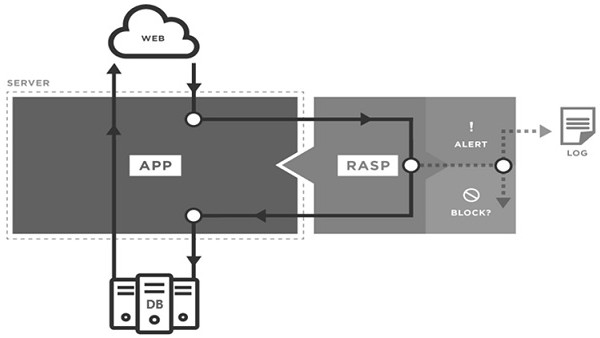
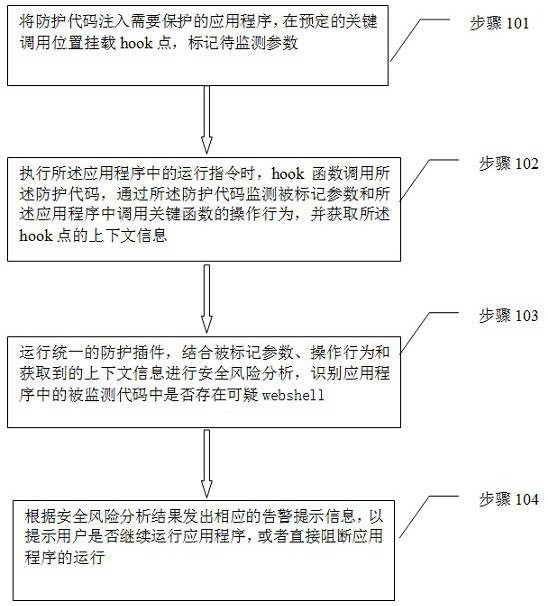
ActiveCN111931166AAvoid bypassingComprehensive hook point coverageHardware monitoringPlatform integrity maintainanceAttackCode injection
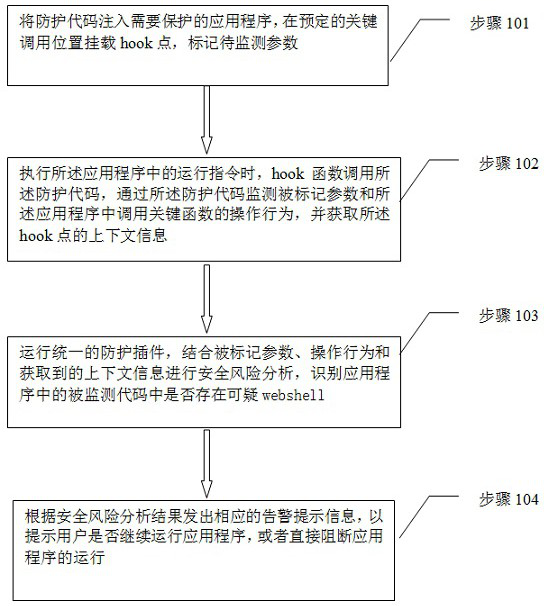
The invention provides an application program anti-attack method and system based on code injection and behavior analysis. The method is characterized in that a protection code is injected into an application program needing to be protected, and attack behaviors in the application program are recognized. The method comprises the steps of injecting the protection code into the application program needing to be protected, and mounting a hook point at a preset key calling position, wherein the protection code monitors marked parameters and operation behaviors of calling a key function in the application program; running a unified protection plug-in, performing security risk analysis based on the operation behavior, the marked parameters and the context information, and identifying whether a suspicious webshell exists in a monitored code in the application or not; and sending out corresponding alarm prompt information according to the security risk analysis result, or directly blocking theoperation of the application program. According to the method, through reasonable deployment of the protection codes, attacks can be detected and self-protection can be carried out during operation,so that less missing report and false report, more comprehensive and accurate protection and faster vulnerability response are realized.
Owner:NAT UNIV OF DEFENSE TECH
Message detection method, device, equipment and storage medium
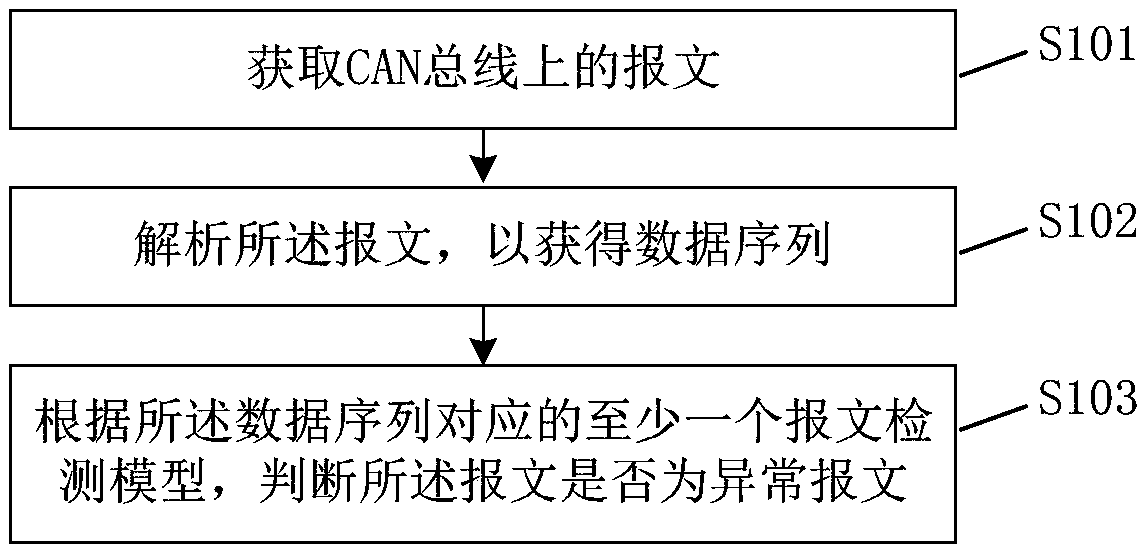
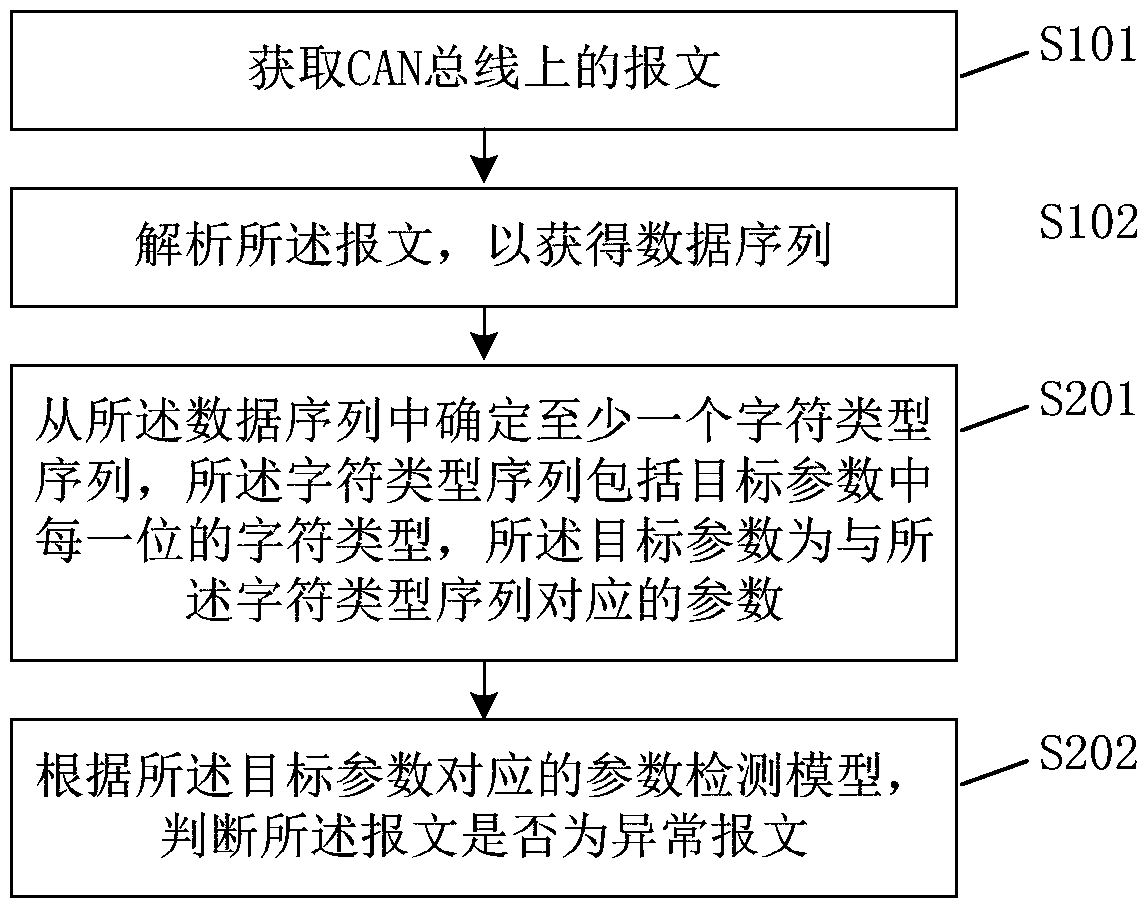
ActiveCN109688030AAvoid bypassingAvoid false positivesBus networksData sequencesComputer engineering
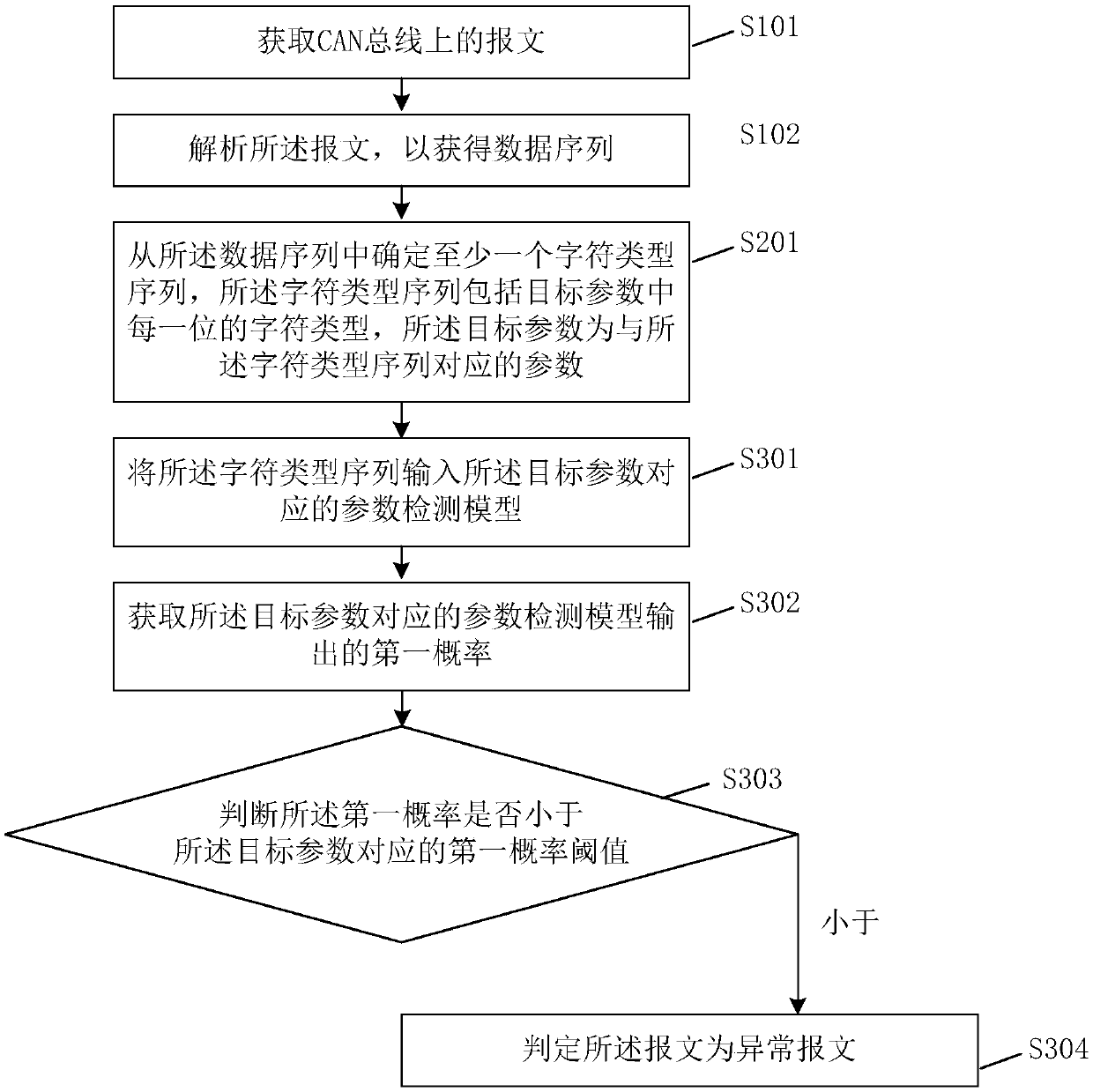
The embodiment of the invention provides a message detection method and device, equipment and a storage medium. The method includes the following steps: acquiring a message on a CAN bus; analyzing themessage to obtain a data sequence; and judging whether the message is an abnormal message according to at least one message detection model corresponding to the data sequence, wherein the message detection model is obtained by training a sample data sequence in a sample message. According to the technical scheme of the embodiment of the invention, abnormal messages at the instruction level and the parameter level can be identified, unknown intrusion behaviors can be found, bypasses and omissions can be avoided, and the cost waste caused by manual maintenance rules can be reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Injection attack detection method and device, server and storage medium
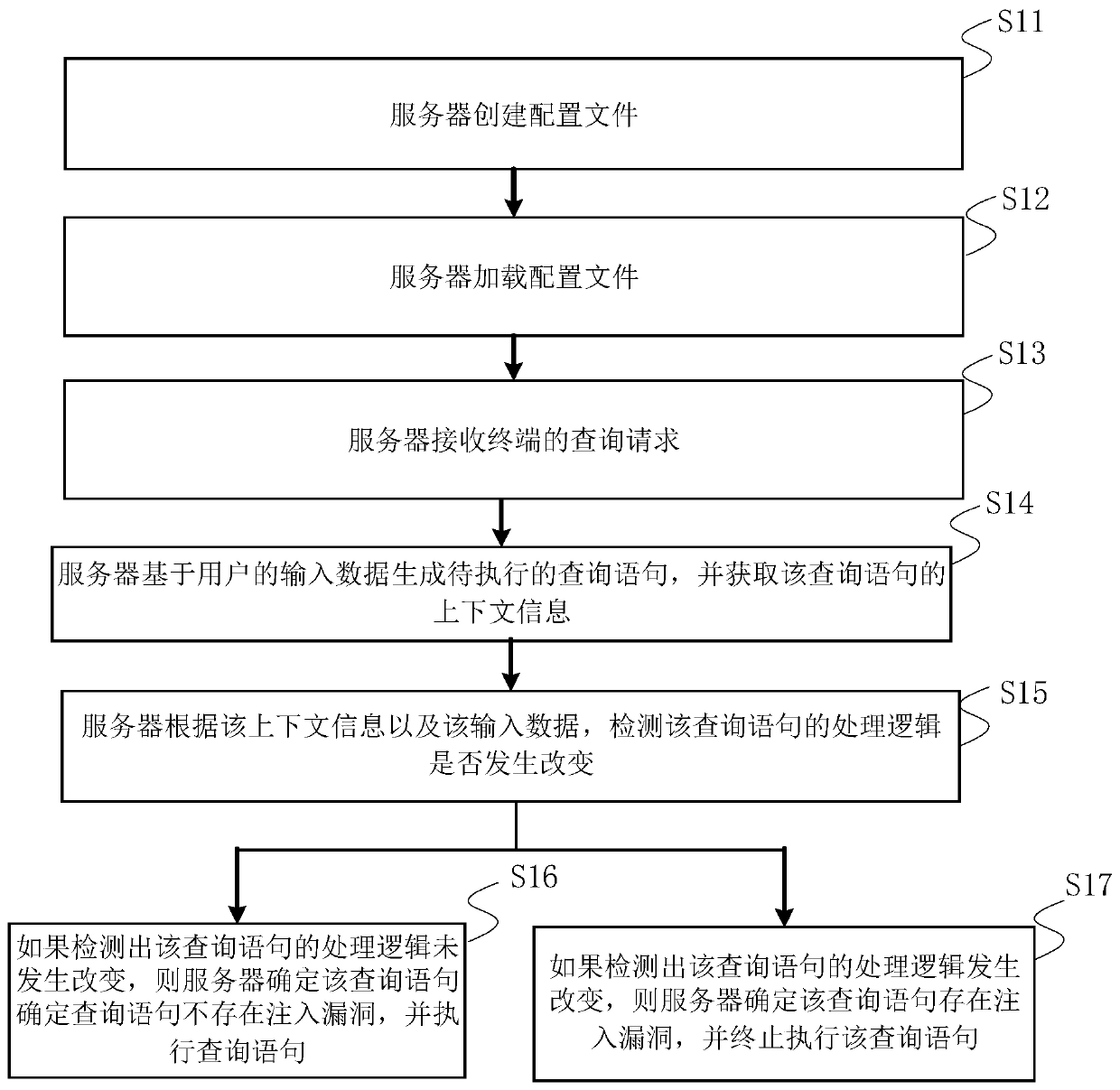
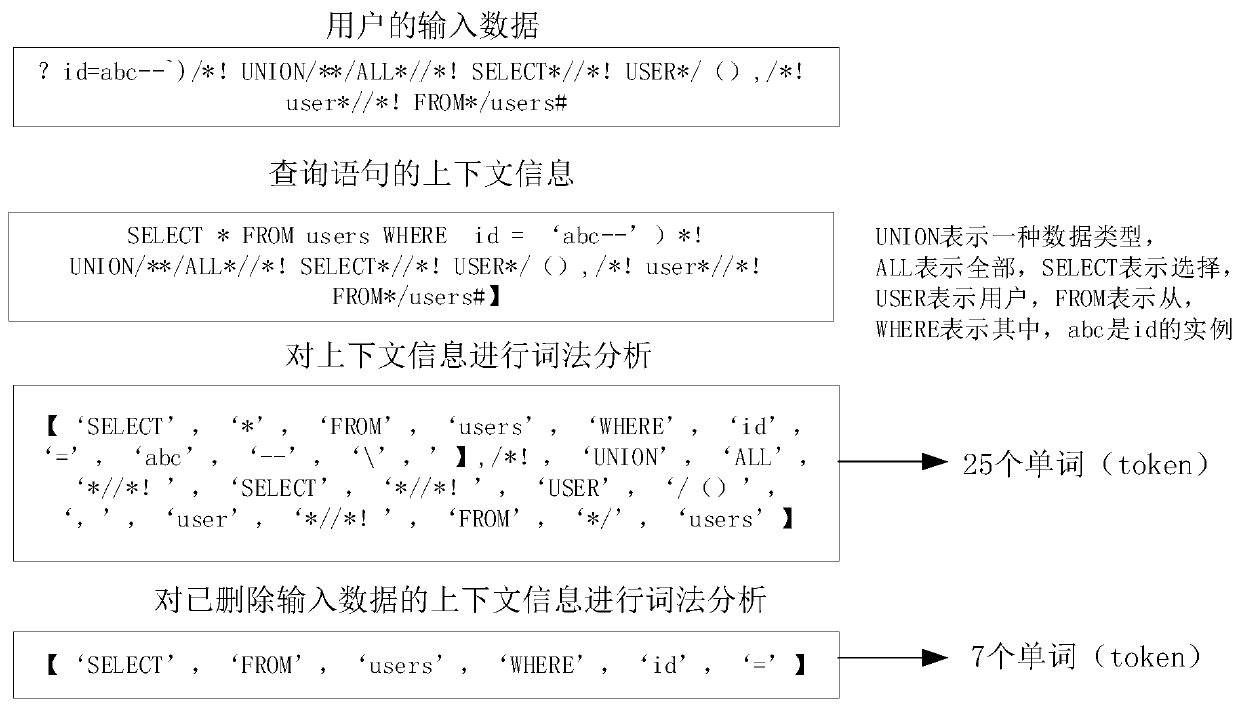
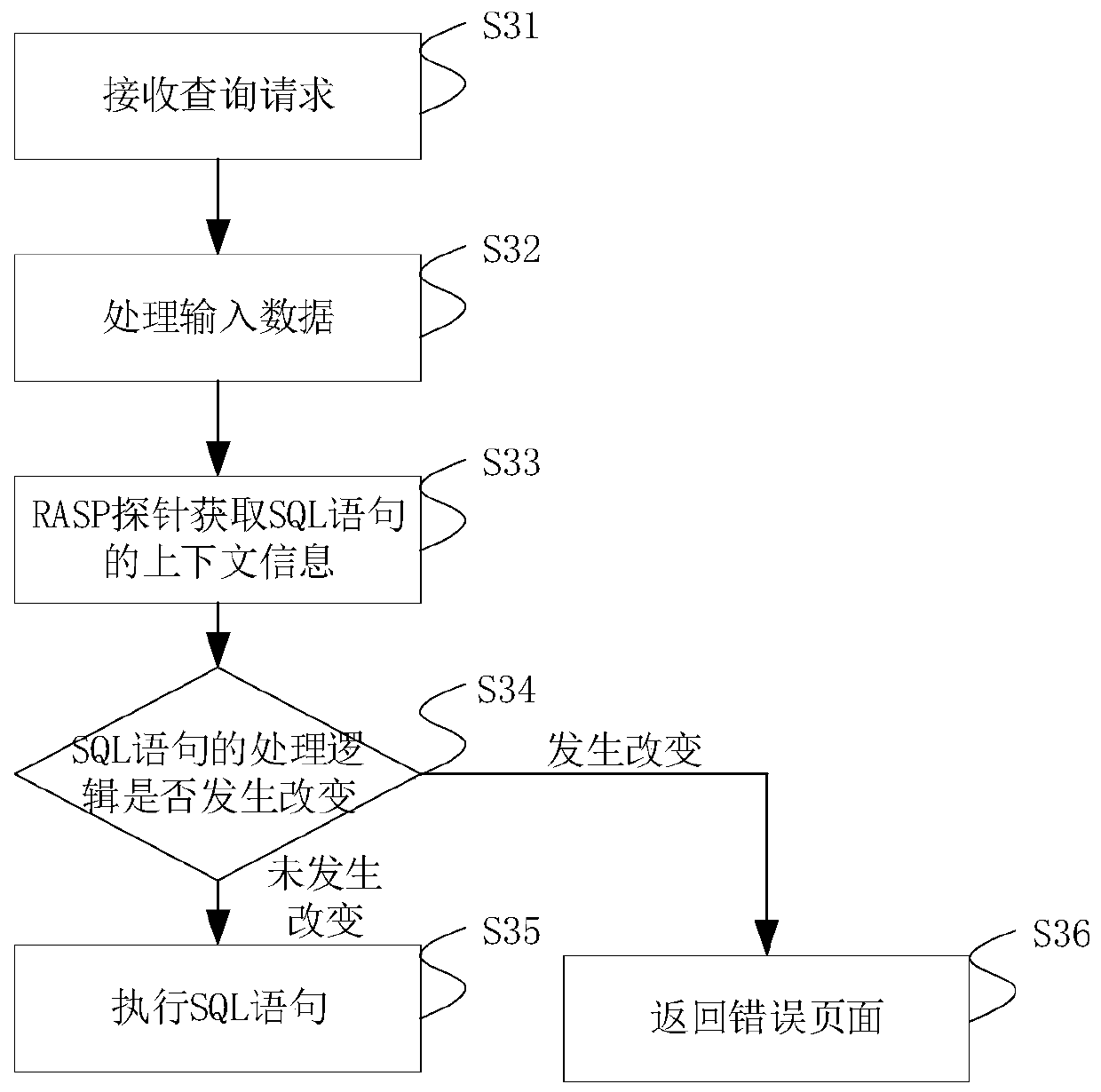
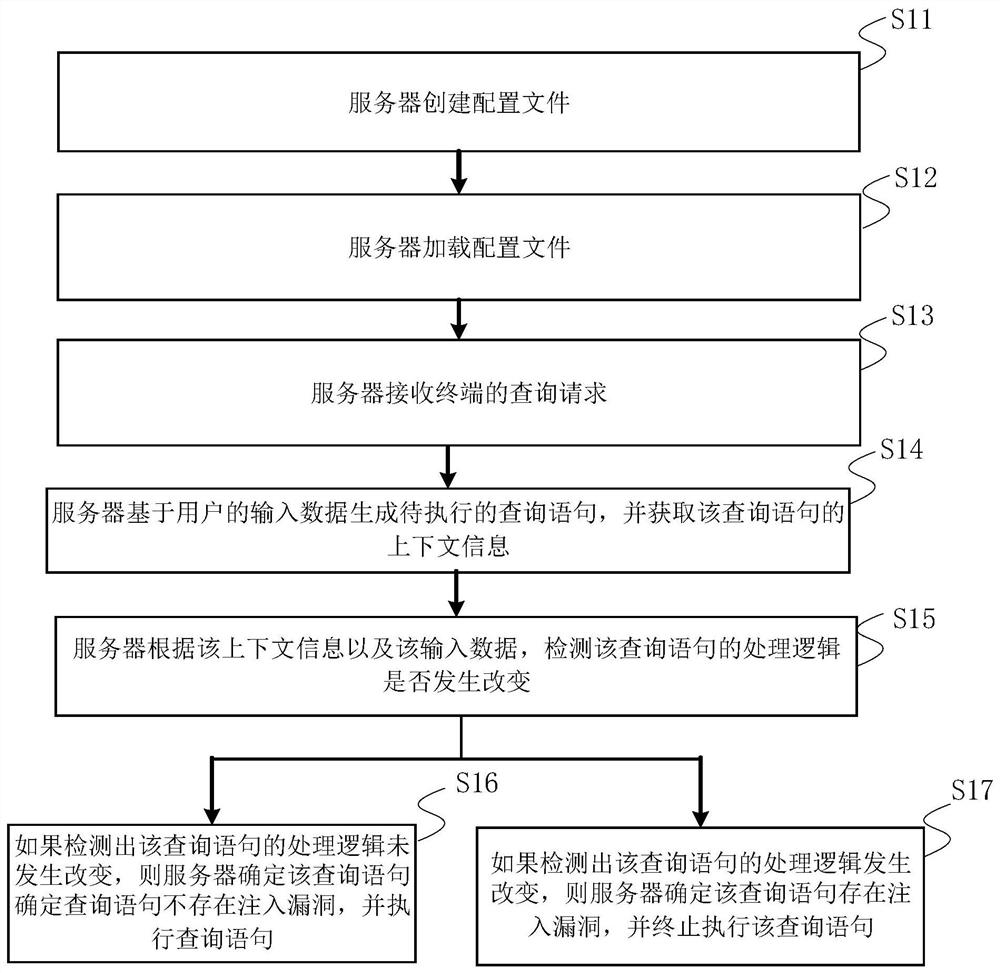
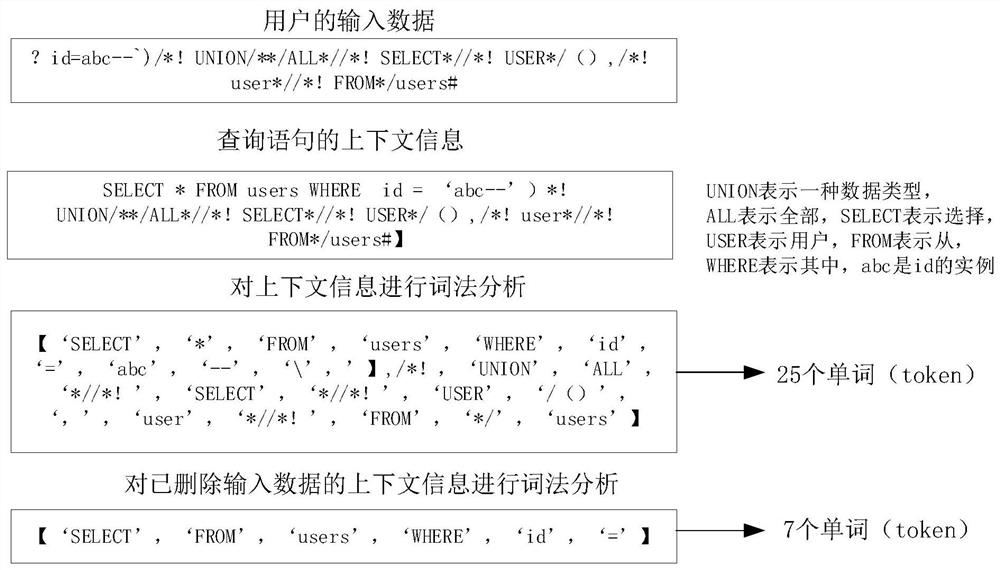
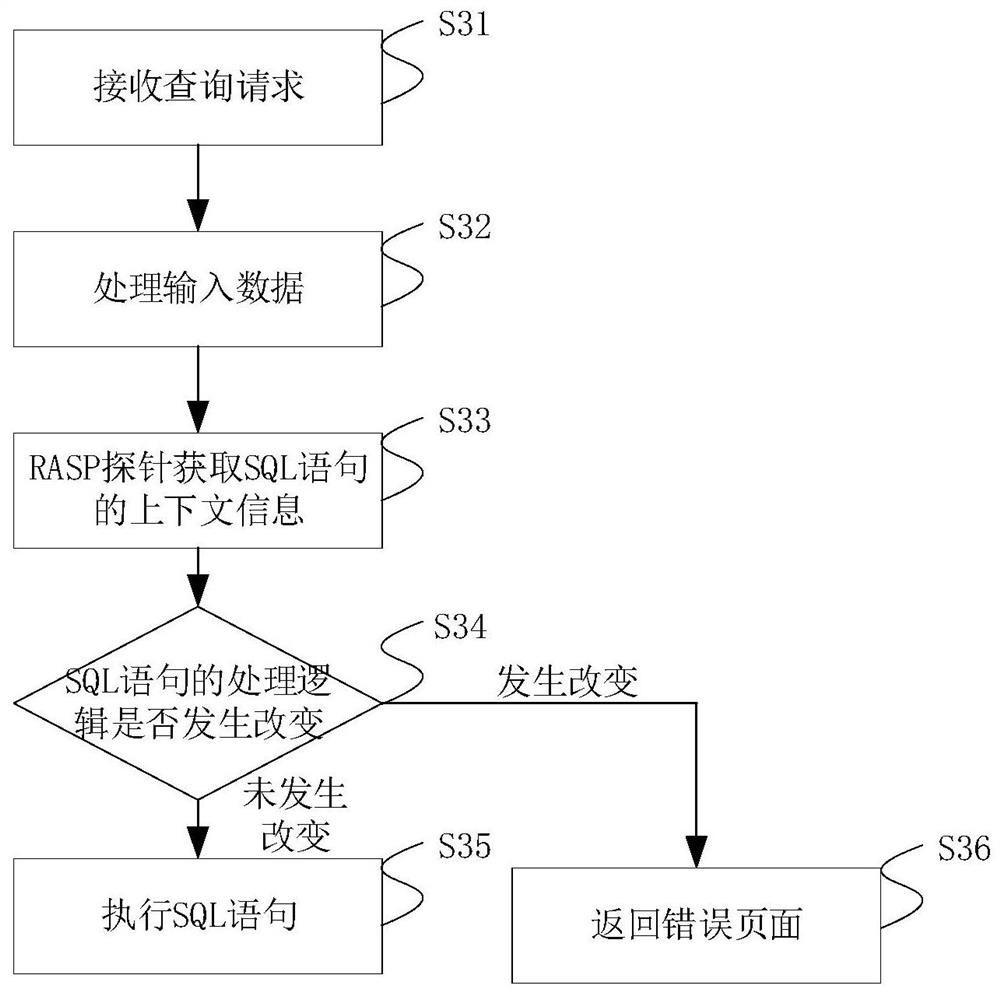
The invention relates to an injection attack detection method and device, a server and a storage medium, and relates to the technical field of computers. The embodiment of the invention provides a method for detecting an injection attack without depending on a regular expression. The method comprises the steps of generating a to-be-executed query statement based on input data of a user; obtaininginput data of a query statement, obtaining context information of the query statement, detecting whether processing logic of the query statement is changed or not according to the context informationand the input data, if it is detected that the processing logic of the query statement is changed, determining that an injection vulnerability exists in the query statement, and terminating executionof the query statement. Through the detection mode, the false alarm rate and the missing alarm rate can be reduced, and the attack detection accuracy is improved.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
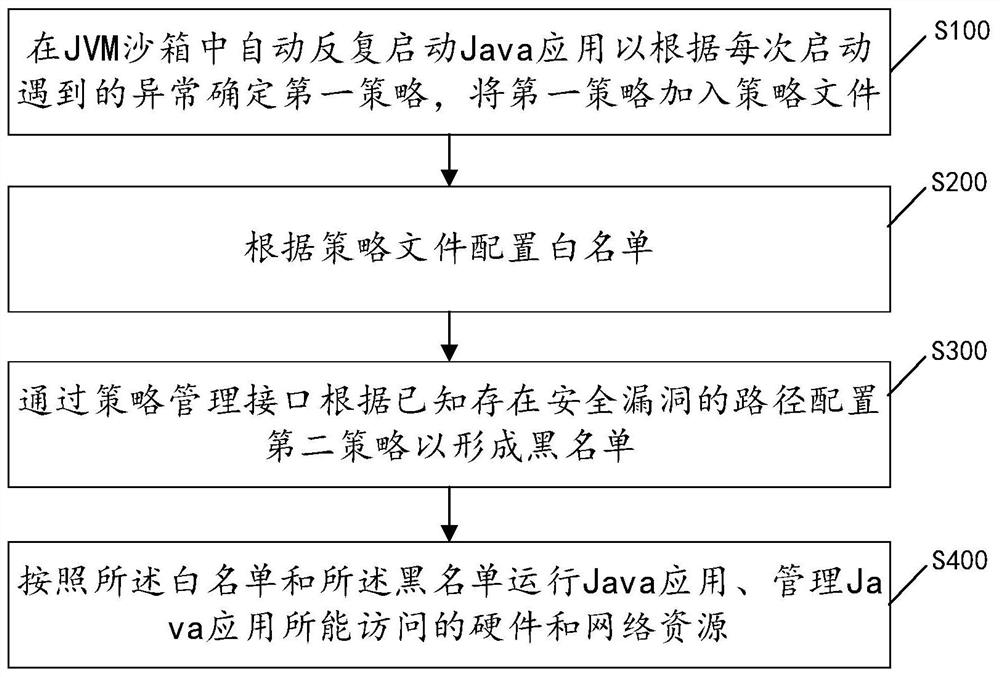
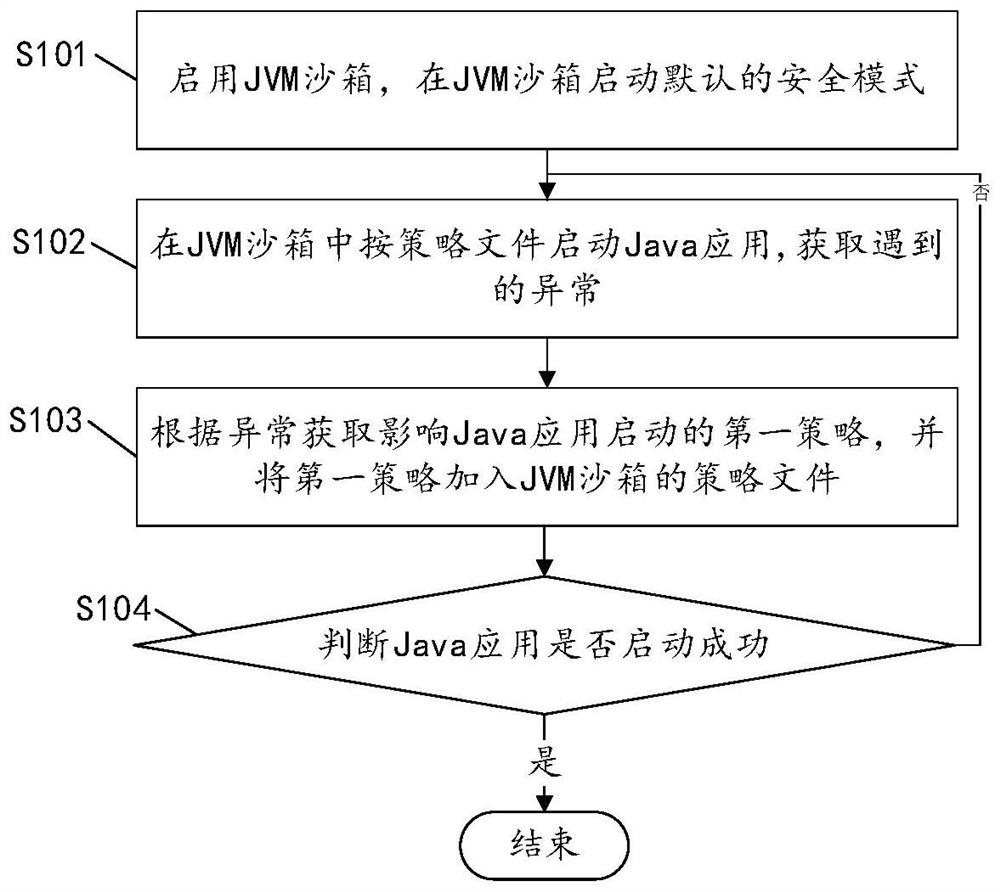
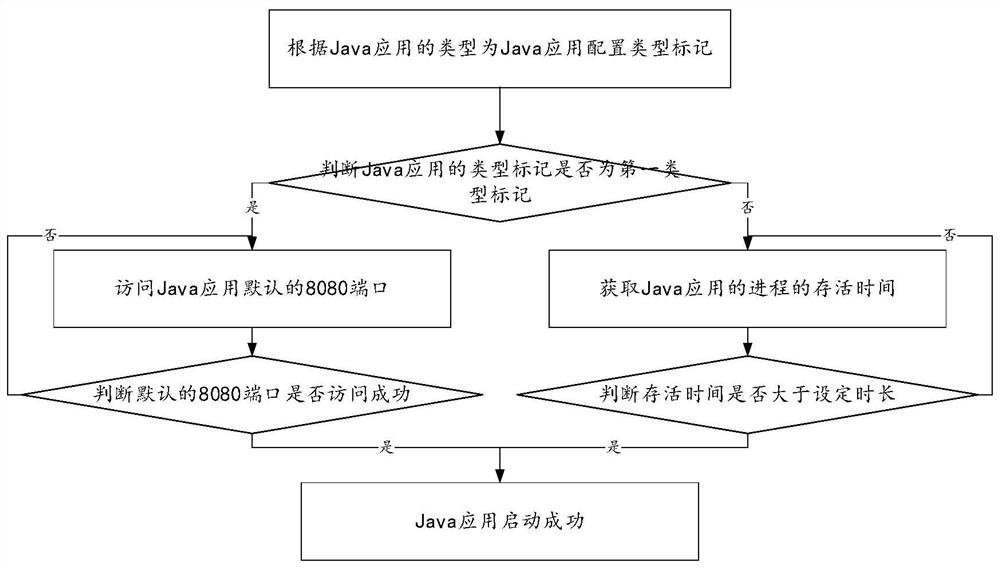
Java security protection method and device based on JVM sandbox and black and white lists and medium
PendingCN113672907ARealize automatic customizationComprehensive Security HardeningPlatform integrity maintainancePathPingJava
The invention relates to a Java security protection method and device based on a JVM sandbox and black and white lists and a medium. The method comprises the following steps: automatically and repeatedly starting a Java application in a JVM sandbox so as to determine a first strategy according to an exception encountered in each starting, and adding the first strategy into a strategy file until the Java application is successfully started; configuring a white list according to the strategy file; configuring a second strategy through the strategy management interface according to the known path with the security hole to form a blacklist, and limiting the API under the path with the security hole to execute Java reflection through the blacklist; and running the Java application according to the white list and the black list, and managing hardware and network resources which can be accessed by the Java application. The operation boundary of the unknown Java application is limited through cooperation of the white list and the blacklist, potential safety hazards caused by the fact that the Java application bypasses the white list through reflection are avoided through the blacklist, the defects in the prior art are overcome, and safety protection of the Java application is enhanced.
Owner:济南浪潮数据技术有限公司
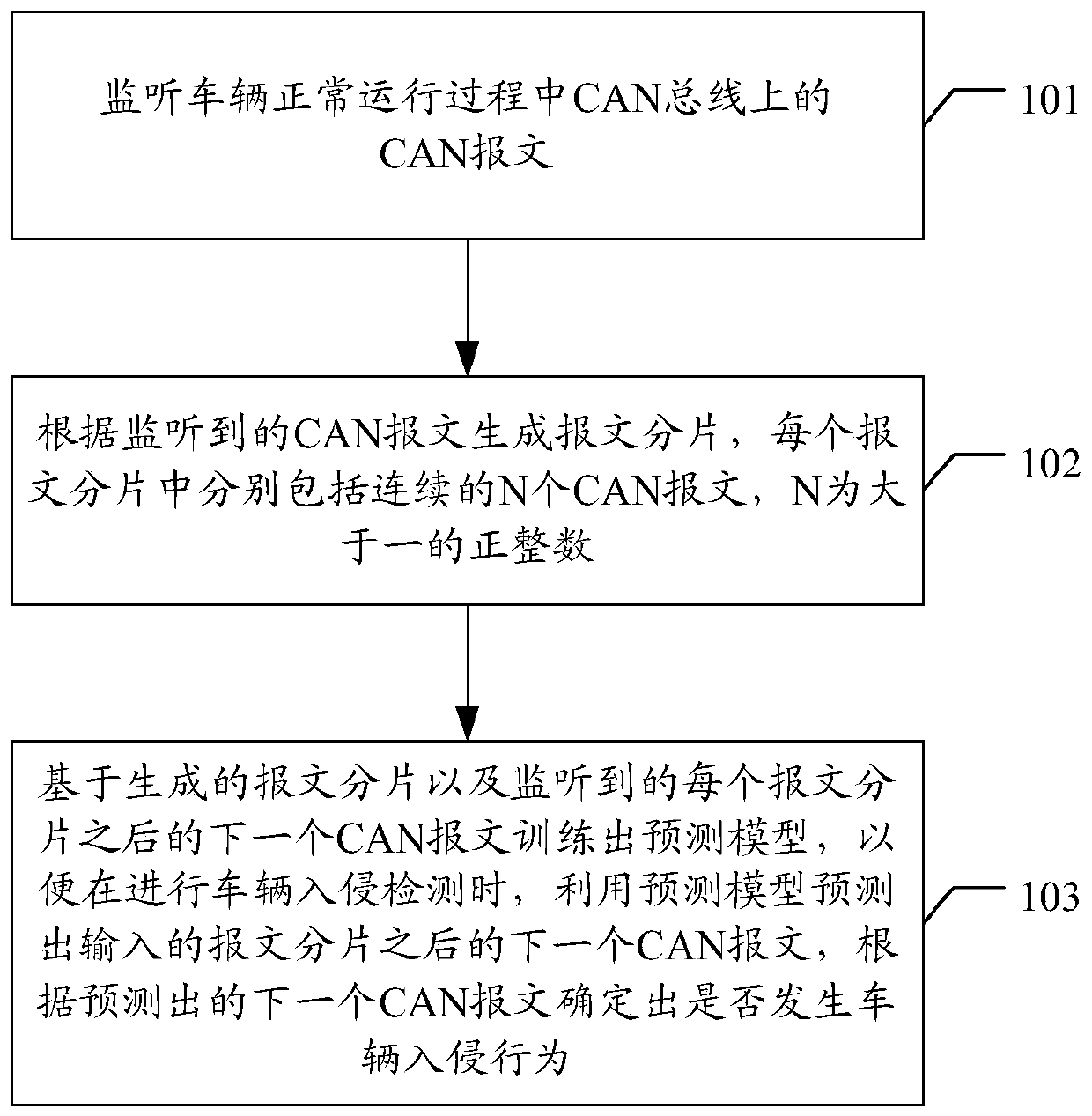
Vehicle intrusion detection and prediction model training methods and devices, and storage medium
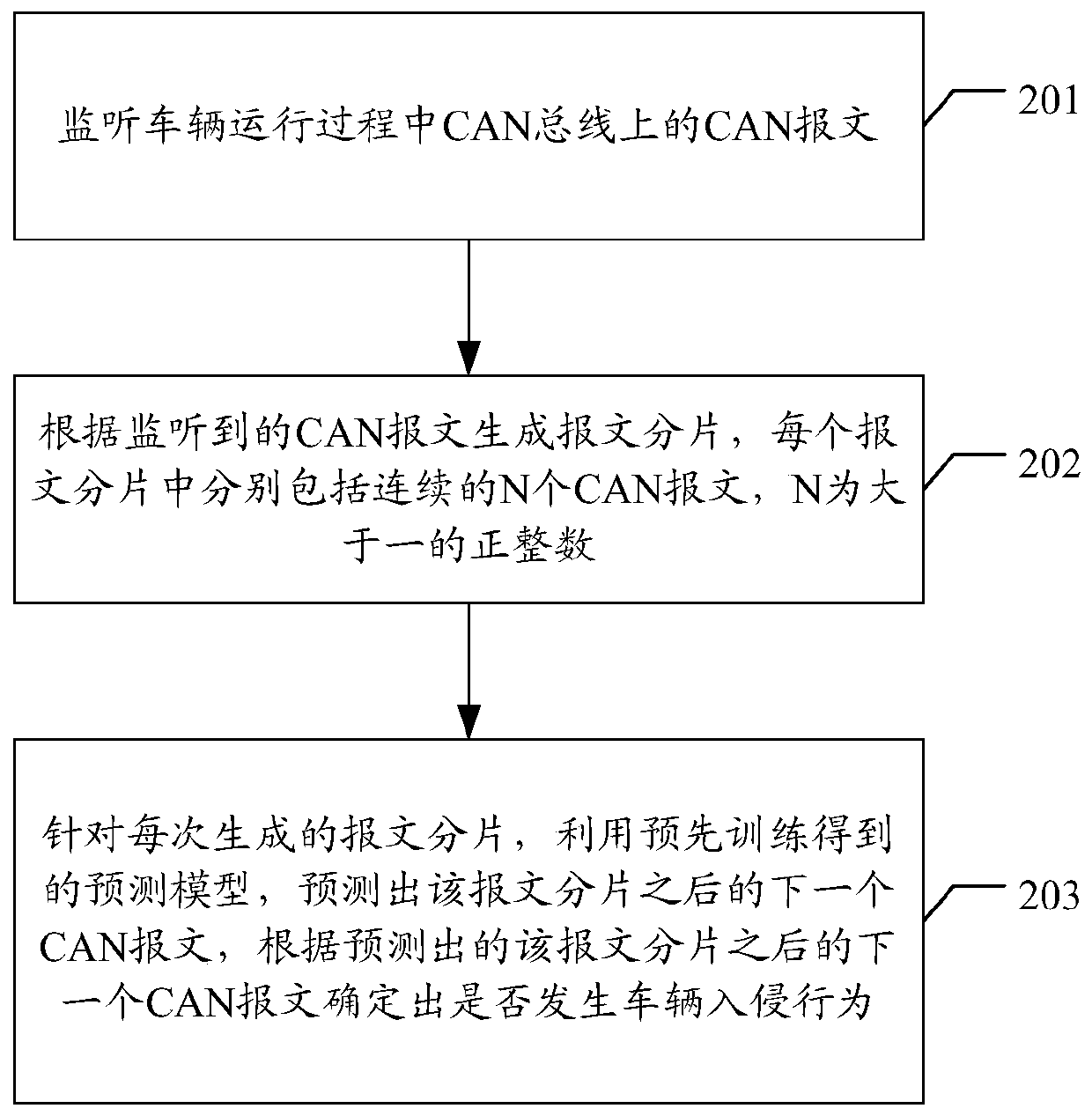
PendingCN110040107AImprove accuracyAvoid bypassingAnti-theft devicesDesign optimisation/simulationArea networkSimulation
The invention discloses vehicle intrusion detection and prediction model training methods and devices, and a storage medium. The vehicle intrusion detection method can comprise the steps: controller area network (CAN) messages on a CAN bus in the vehicle operation process are monitored; message fragments are generated according to the monitored CAN messages, each message fragment comprises the corresponding N continuous CAN messages, and N is a positive integer larger than one; and aiming at the message fragment generated each time, the next CAN message after the message fragment is predictedthrough a prediction model trained in advance, and according to the predicted next CAN message after the message fragment, whether the vehicle intrusion behavior occurs or not is determined. By applying the vehicle intrusion detection and prediction model training methods and devices, and the storage medium, the accuracy of the detection result can be improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
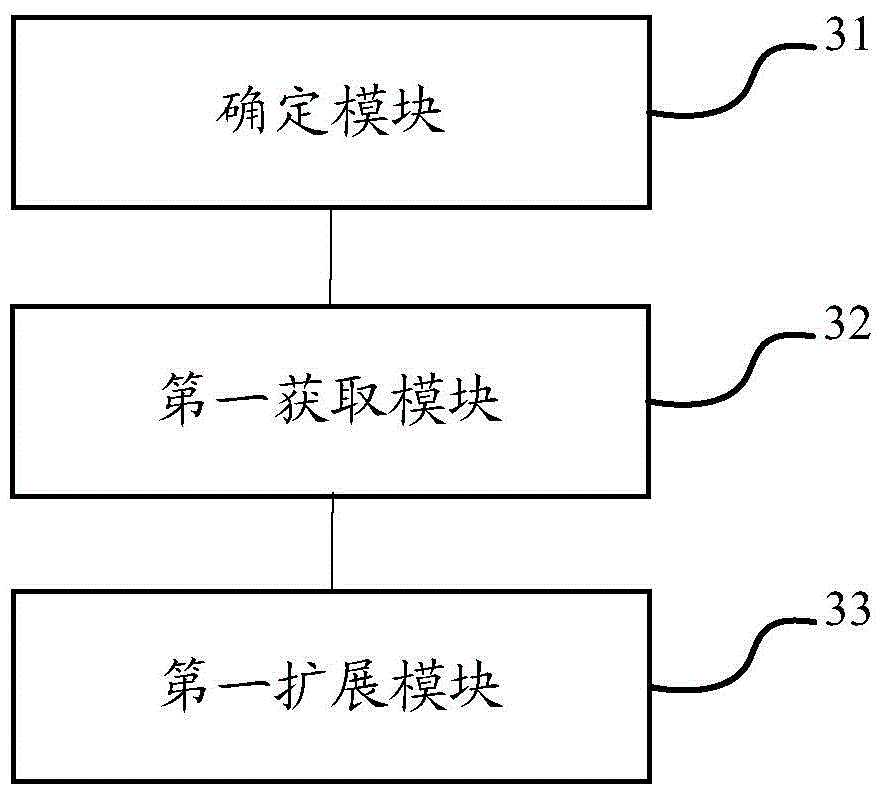
List extending method and list extending equipment
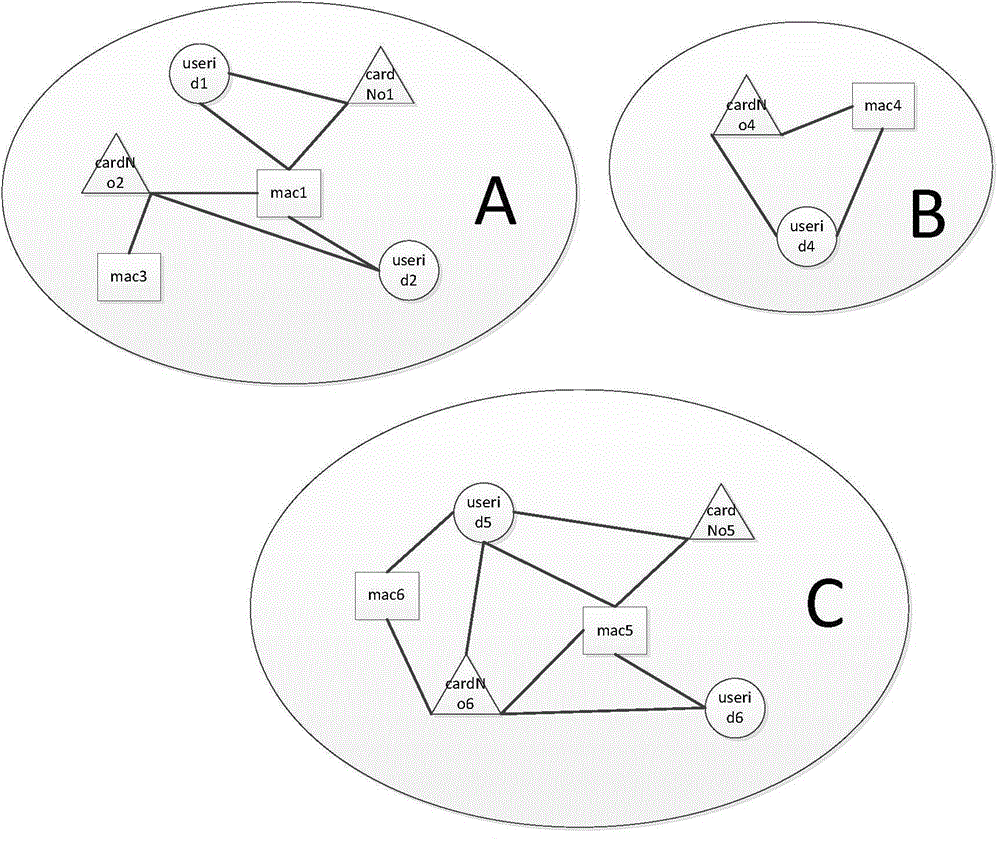
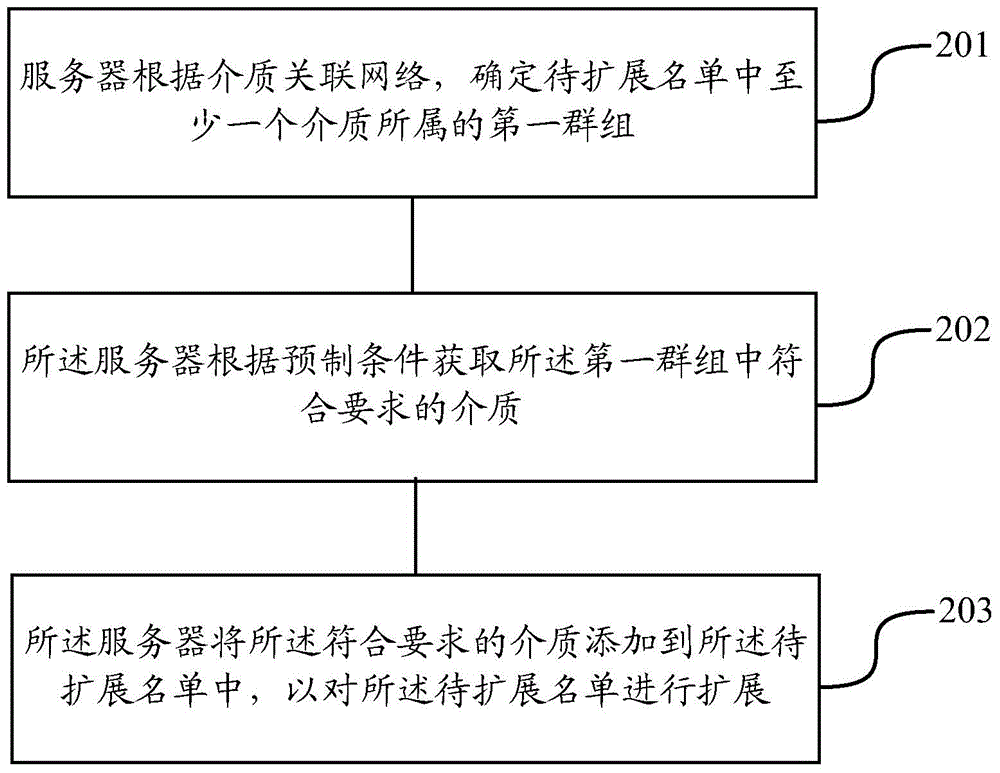
The invention discloses a list extending method. The list extending method comprises steps that a server is used to determine a first group of at least one medium in a to-be-extended list according to a medium association network; the server is used to acquire the medium capable of satisfying requirements in the first group according to a prefabricated condition; the server is used to add the medium capable of satisfying the requirements to the to-be-extended list in order to extend the to-be-extended list. The medium capable of satisfying the requirements in the first group is determined according to the conventional medium association network and a medium type list, and therefore the corresponding conventional medium list is extended, and then a problem of efficacy-losing of a conventional trusted list or a conventional untrusted list is reduced.
Owner:ALIBABA GRP HLDG LTD
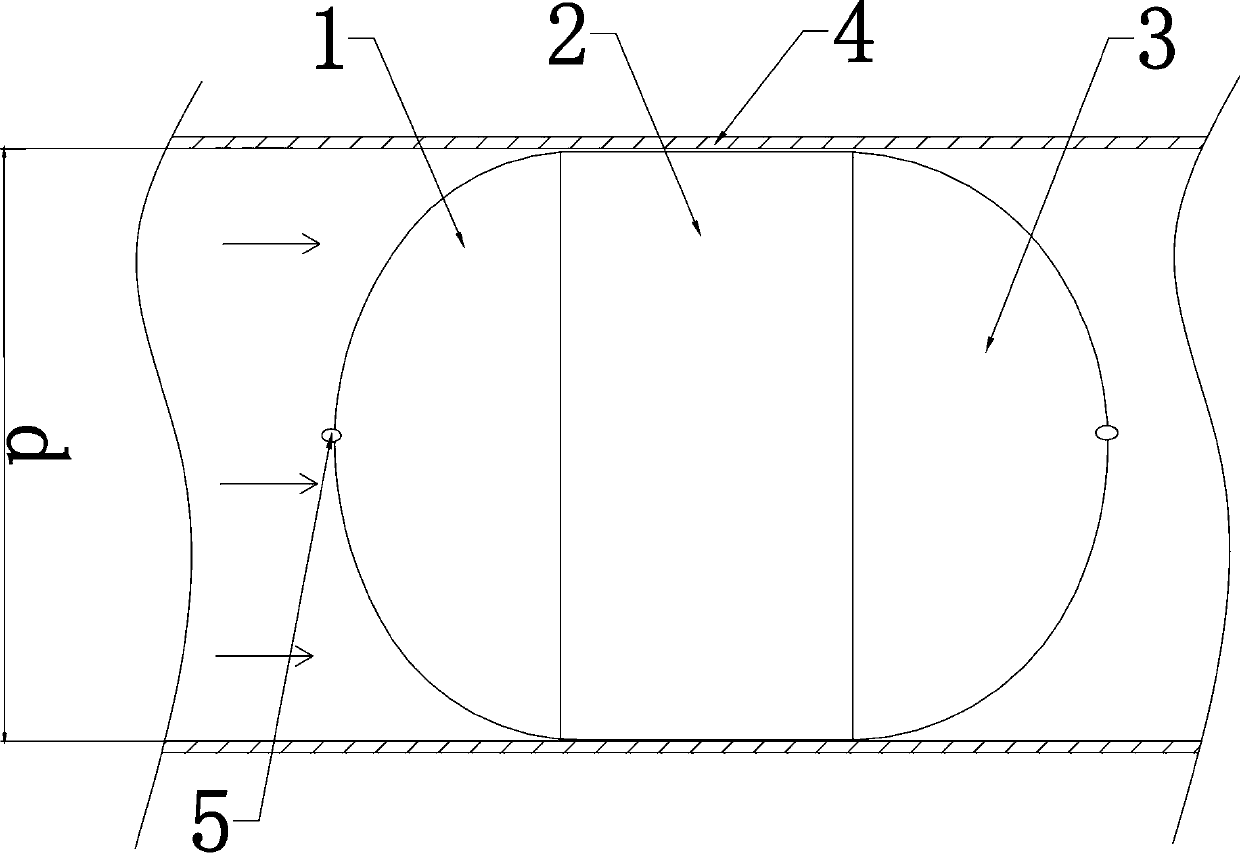
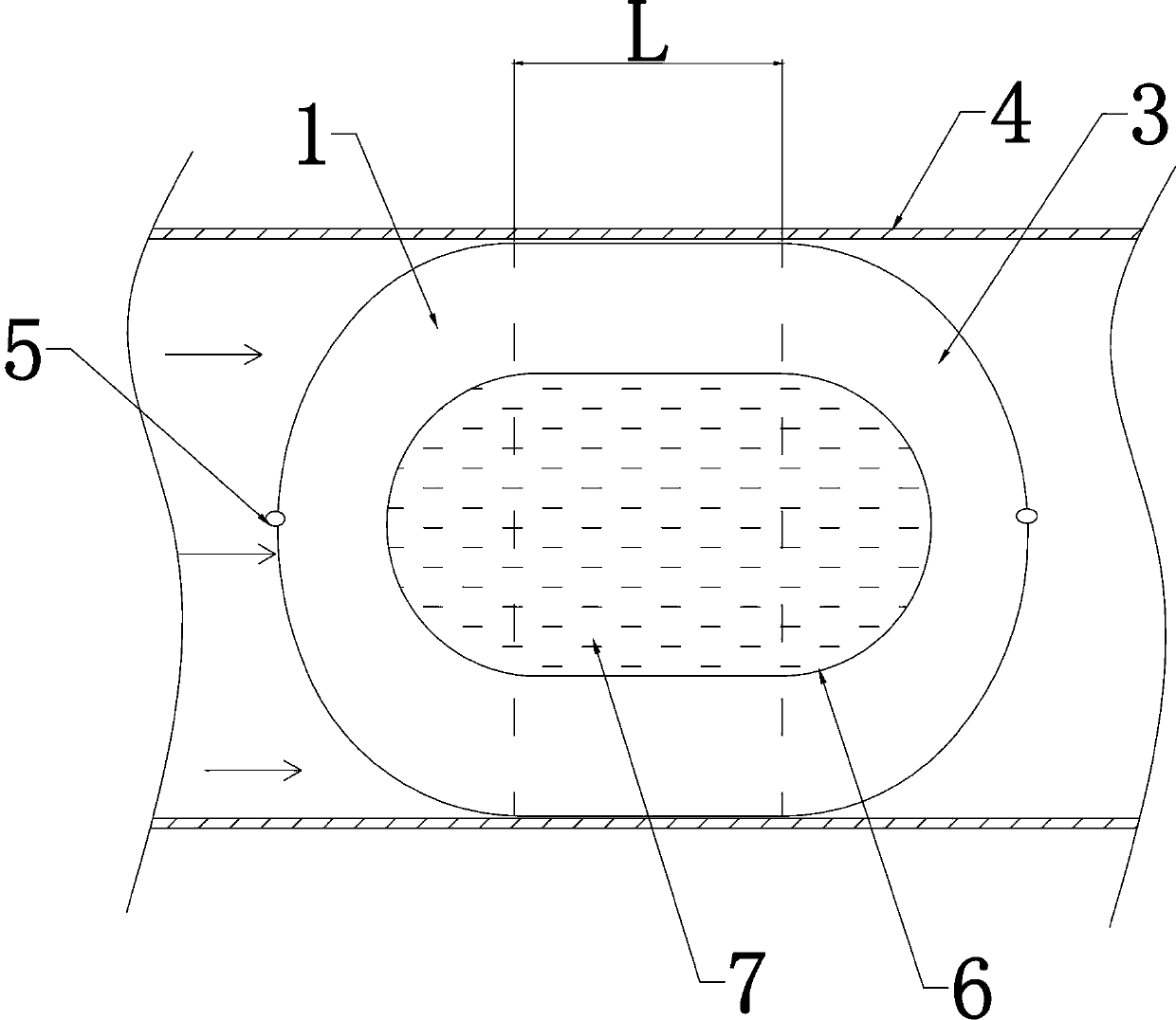
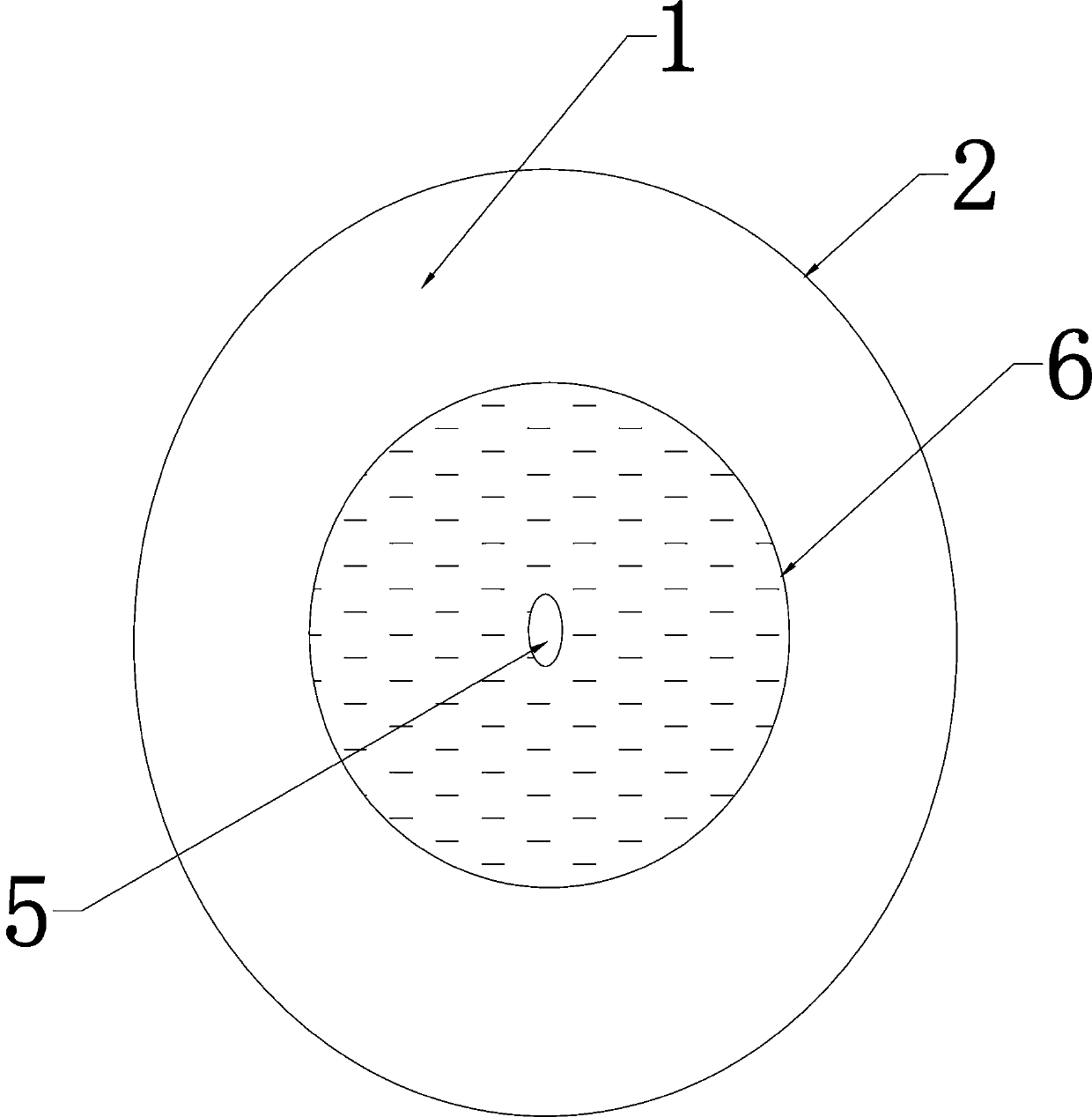
Mechanical tube cleaner
InactiveCN108971152AAvoid BypassingRealize normal pigging operationHollow article cleaningRight hemispherePigging
The invention discloses a mechanical tube cleaner. The mechanical tube cleaner consists of three portions which are a hollow left hemisphere, an annular hollow cylinder and a hollow right hemisphere respectively; and the left hemisphere and the right hemisphere are separately connected to the two ends of the annular hollow cylinder to form an integrated structure. The tube cleaner mainly changes the sealing mode of the original tube cleaning ball and the inner wall of a seabed tube, circumferential linear sealing is designed into annular belt shaped surface sealing, by the belt shaped surfacesealing, a bypass circumstance generated in a running process due to the fact that upstream and downstream circumferential linear sealing of an imported M-brand tube cleaning ball is poor is avoided,the pressure difference between upstream and downstream is maintained, and can also be maintained even if the flow is ultra-low, and thus, the tube cleaning ball can keep moving forwards by driving force generated by the pressure difference; and when the tube cleaner has ultra-low flow, the upstream and the downstream are sealed effectively, and normal tube cleaning operation and gas condensate pushing operation are realized.
Owner:CHINA NAT OFFSHORE OIL CORP +1
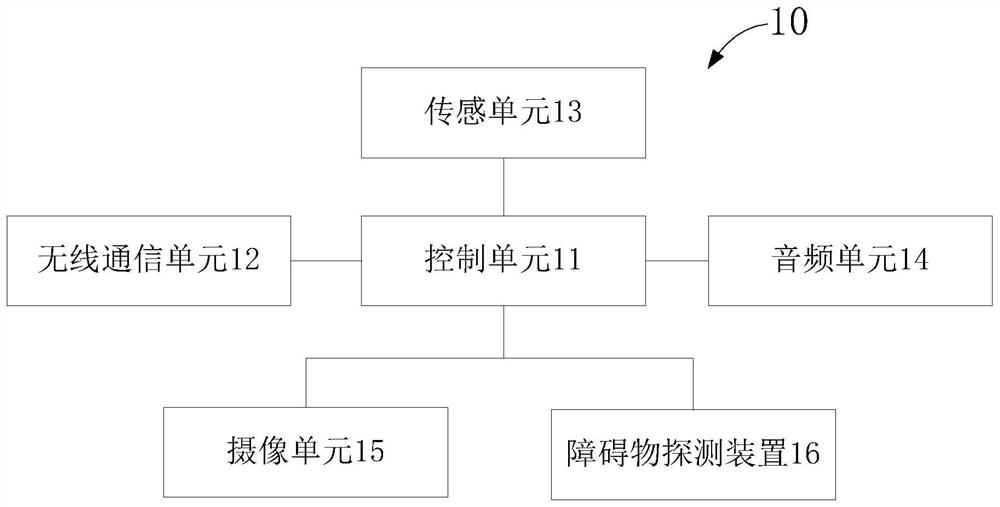
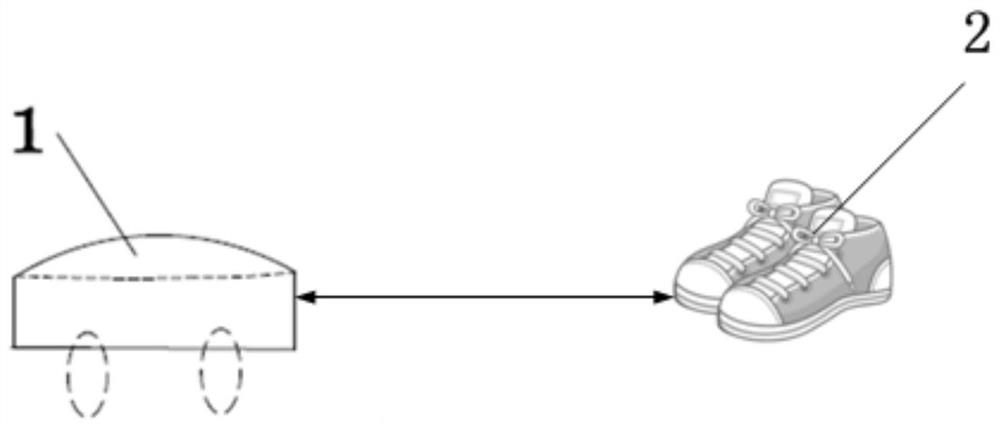
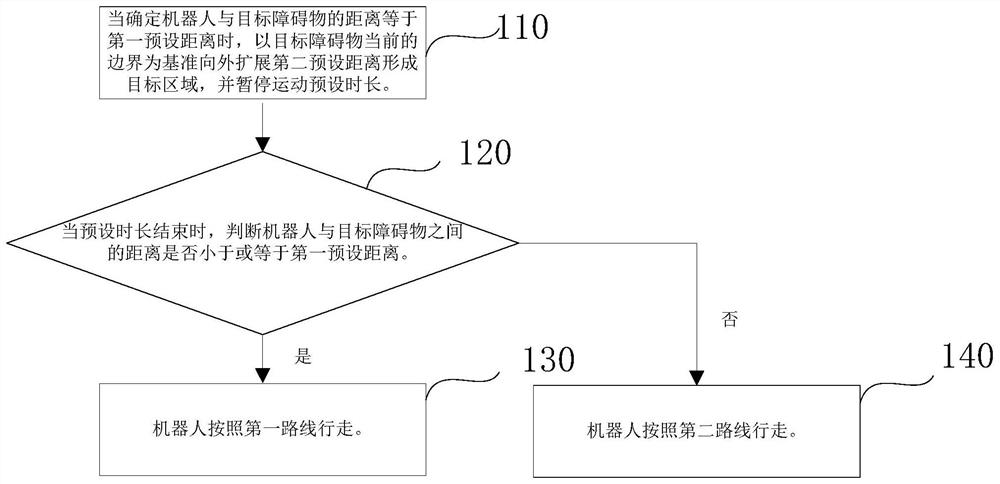
Robot obstacle avoidance method, robot and storage medium
PendingCN112540610AAvoid bypassingAvoid missed scansPosition/course control in two dimensionsSimulationObstacle avoidance
The invention provides a robot obstacle avoidance method, a robot and a storage medium. The method comprises the steps of outwards expanding a current boundary of a target obstacle for a second presetdistance to form a target region when the distance between the robot and the target obstacle is determined to be equal to a first preset distance, and pausing the movement for a preset duration, whenthe preset duration is over, judging whether the distance between the robot and the target obstacle is smaller than or equal to a first preset distance or not, if the preset duration is over and thedistance between the robot and the target obstacle is smaller than or equal to a first preset distance, enabling the robot to walk according to a first route, and if the preset duration is over and the distance between the robot and the target obstacle is larger than the preset distance, enabling the robot to walk according to the second route. The first route is different from the second route. By pausing the motion, the robot can be prevented from bypassing the target obstacle by adopting the same path, and the possibility of collision is reduced.
Owner:SHENZHEN SILVER STAR INTELLIGENT TECH CO LTD
Breeze-type air outlet structure of air conditioner
ActiveCN108759049AReduce the sense of windImprove comfortAir-flow control membersAerospace engineering
Owner:CHINA YANGZI GRP CHUZHOU YANGZI AIR CONDITIONERCO
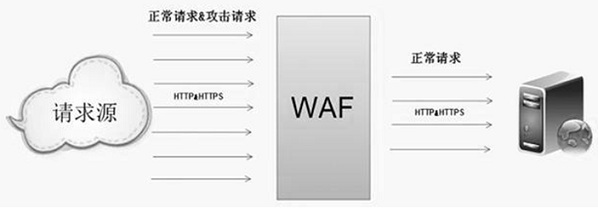
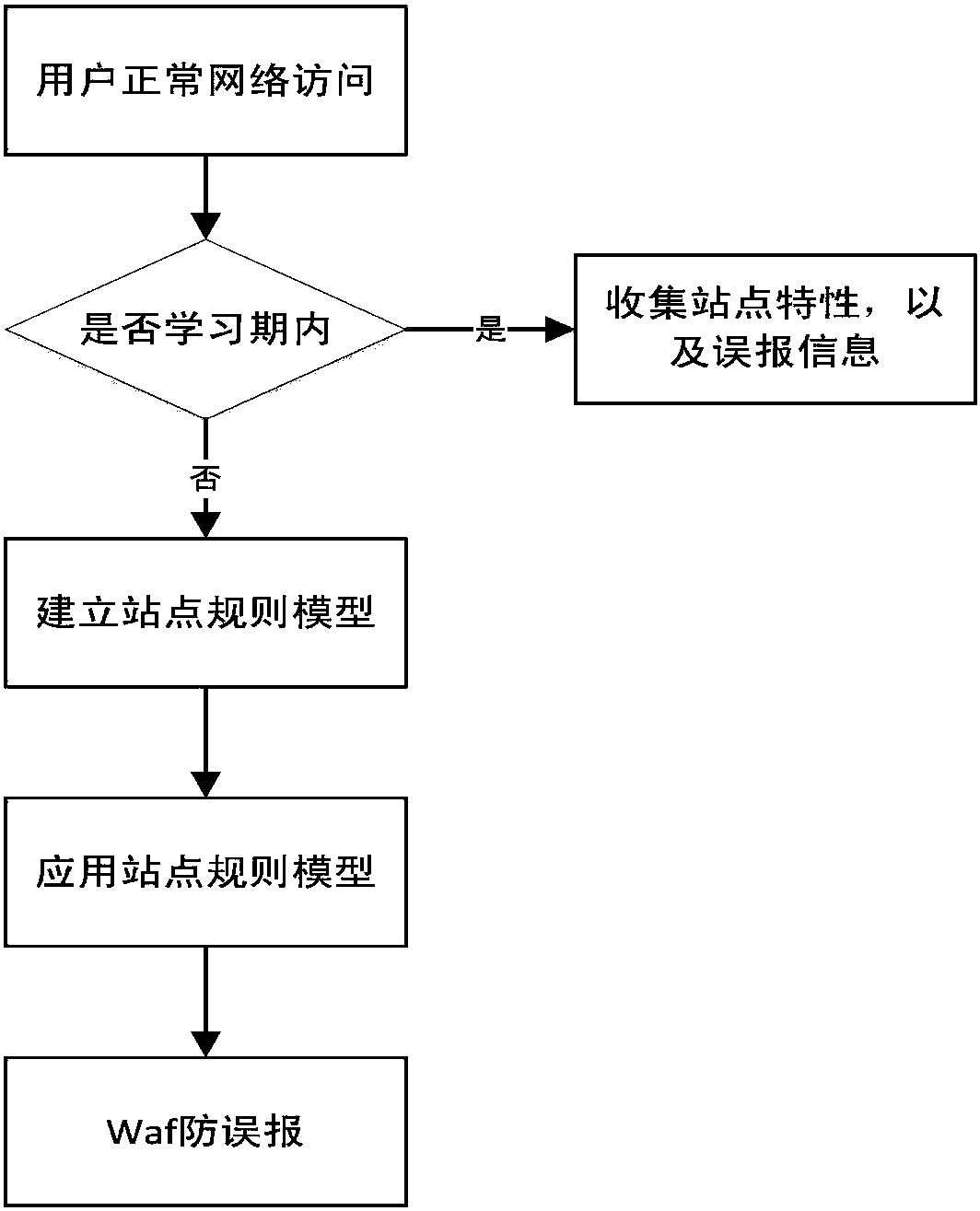
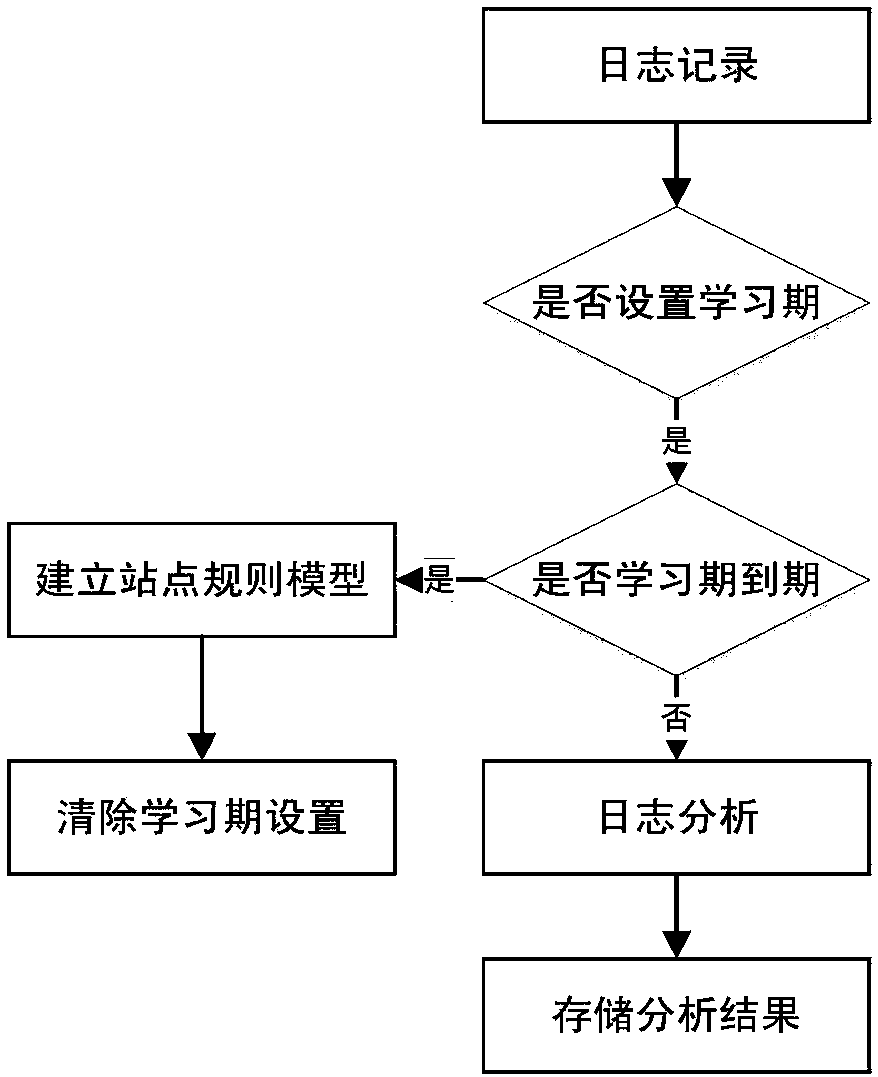
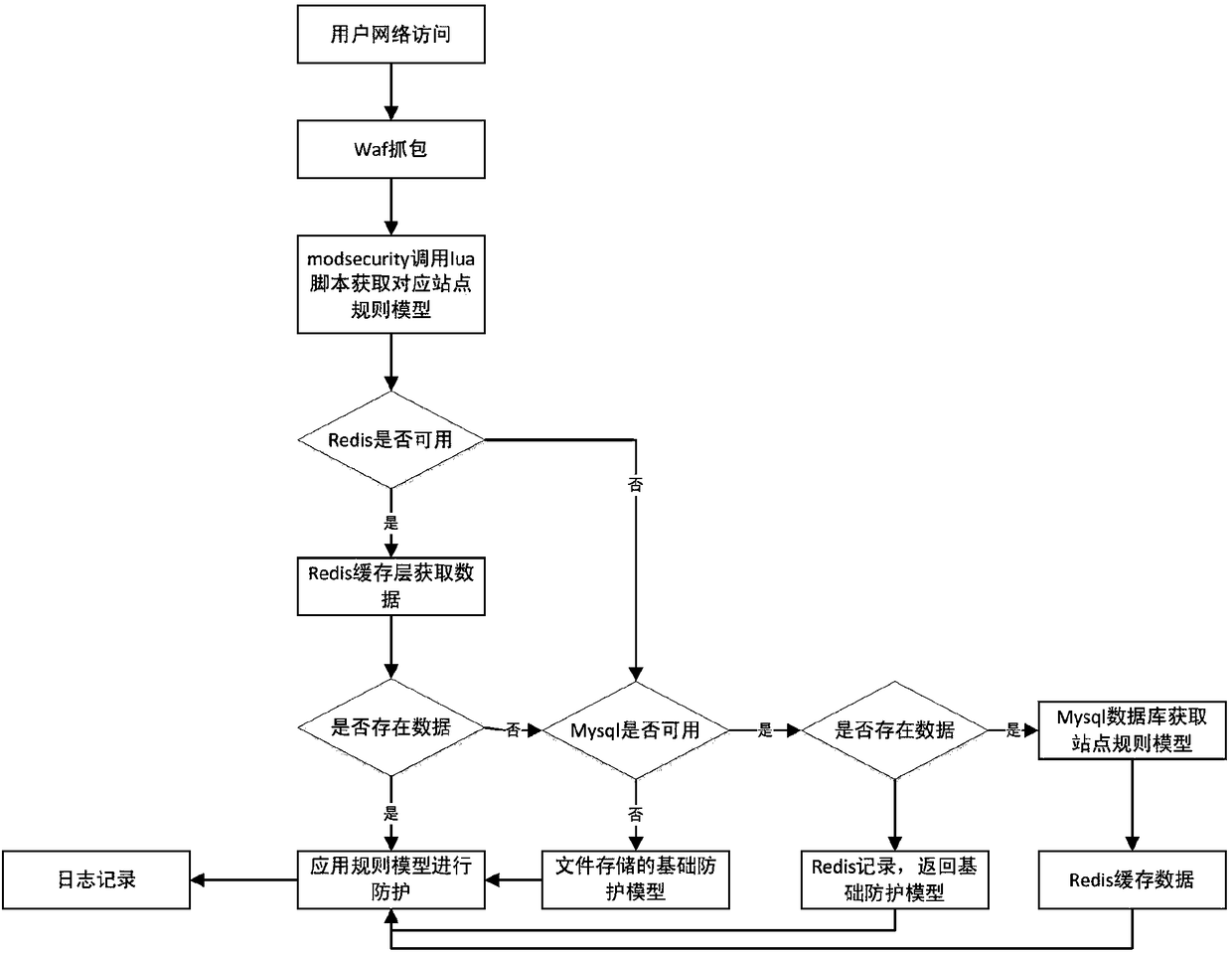
Technology of preventing WAF false alarm based on self learning
InactiveCN108092944AImprove the protective effectAvoid bypassingTransmissionFalse alarmComputer science
The invention discloses a technology of preventing WAF false alarm based on self learning, in the technology provided by the invention, through a self learning technology, a site rule model is established, and an aim of preventing WAF rule false alarm is realized.
Owner:蓝盾信息安全技术有限公司
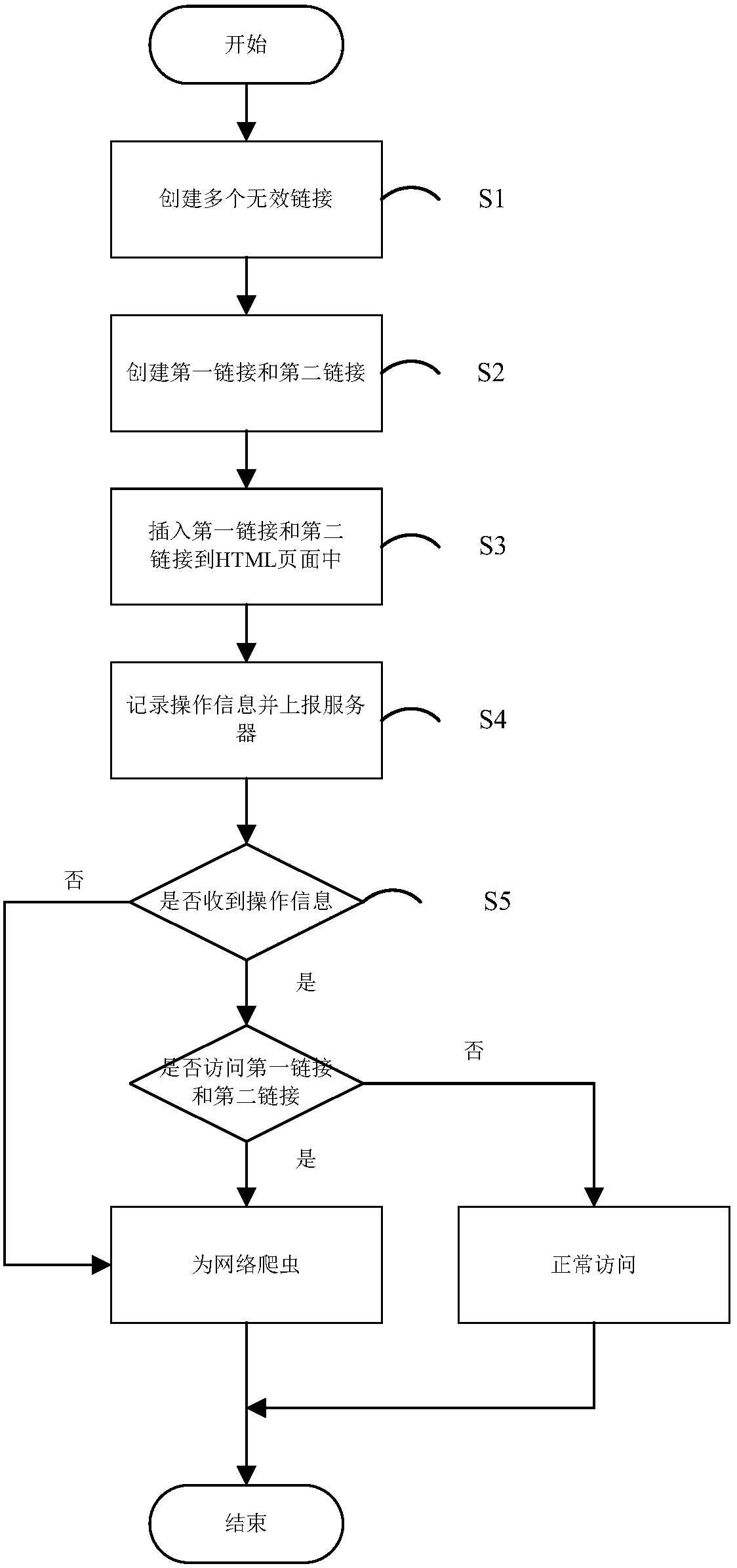
Method and system for identifying web crawler, storage medium and electronic apparatus
InactiveCN109214181AIdentify wellRealize identificationPlatform integrity maintainanceWebsite content managementElectric equipmentHTML
The invention discloses a method and a system for identifying a web crawler, a storage medium and an electronic apparatus, which relate to the information processing field. The method for identifyingthe web crawler comprises the following steps: creating a plurality of invalid links for detecting the web crawler behavior; using the link address provided by the invalid link to create a first linkthat hides link attribute information, and creating a second link that is invisible to the naked eye with the same background color as the HTML page. The first link and the second link are inserted into the HTML page. The operation information recorded on the HTML page is reported to the server. The server judges whether the operation information is received, and if not, the web crawler is determined; if yes, the server further judges whether there is access to the first link and the second link, and if yes, the web crawler is determined; if not, it is determined that the access is normal access. The invention can better avoid the crawler from bypassing the crawler detection strategy and more effectively identify the web crawler.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
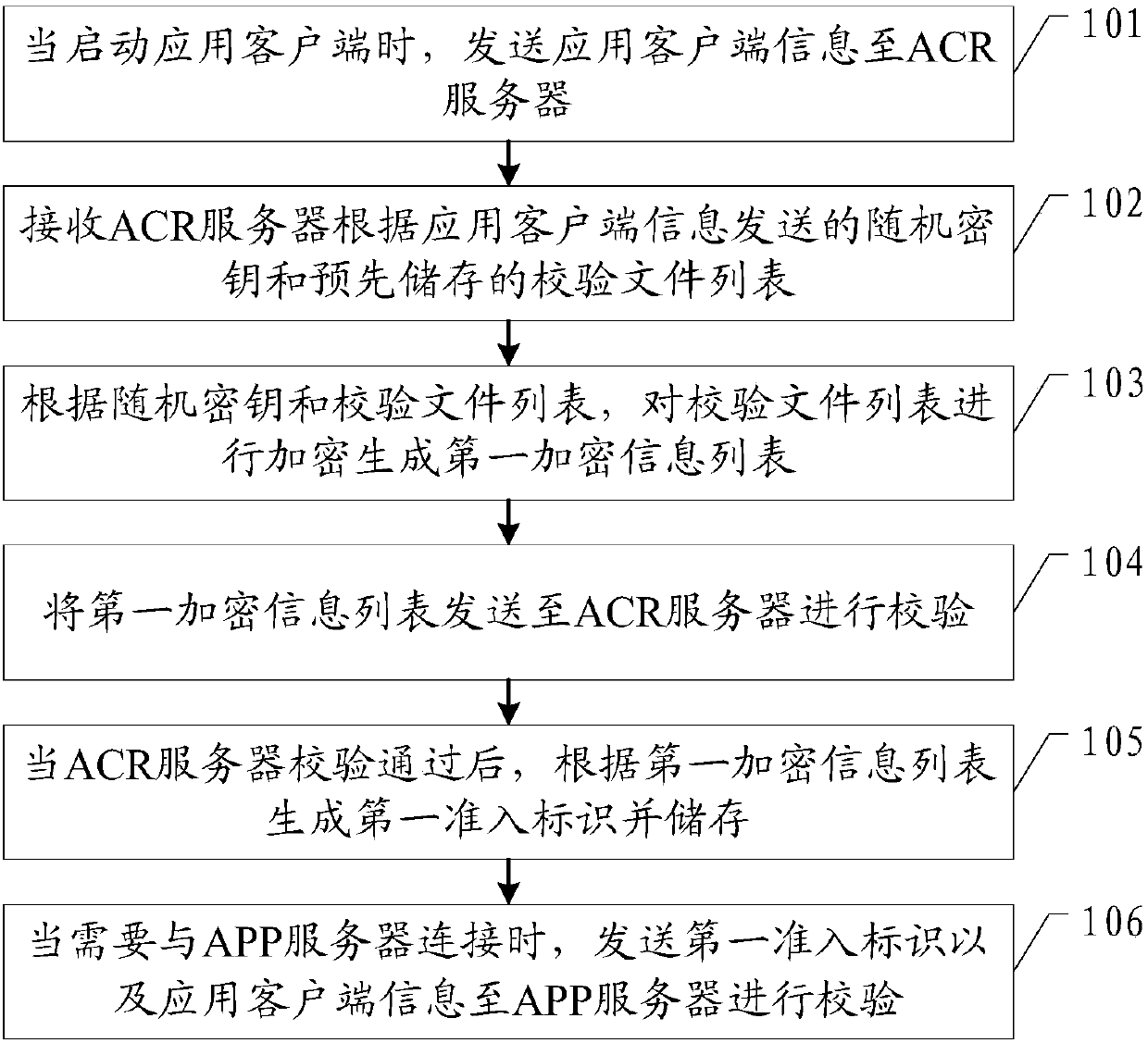
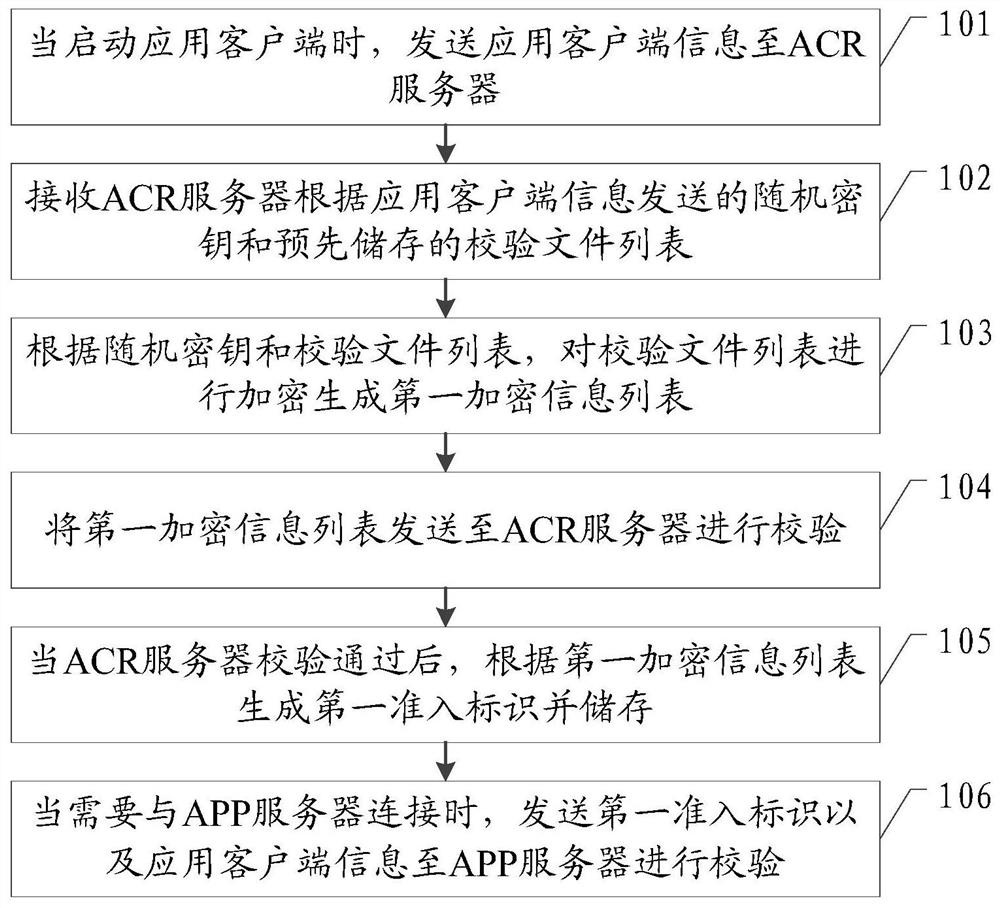
Safety protection method of application program, application client and ACR server
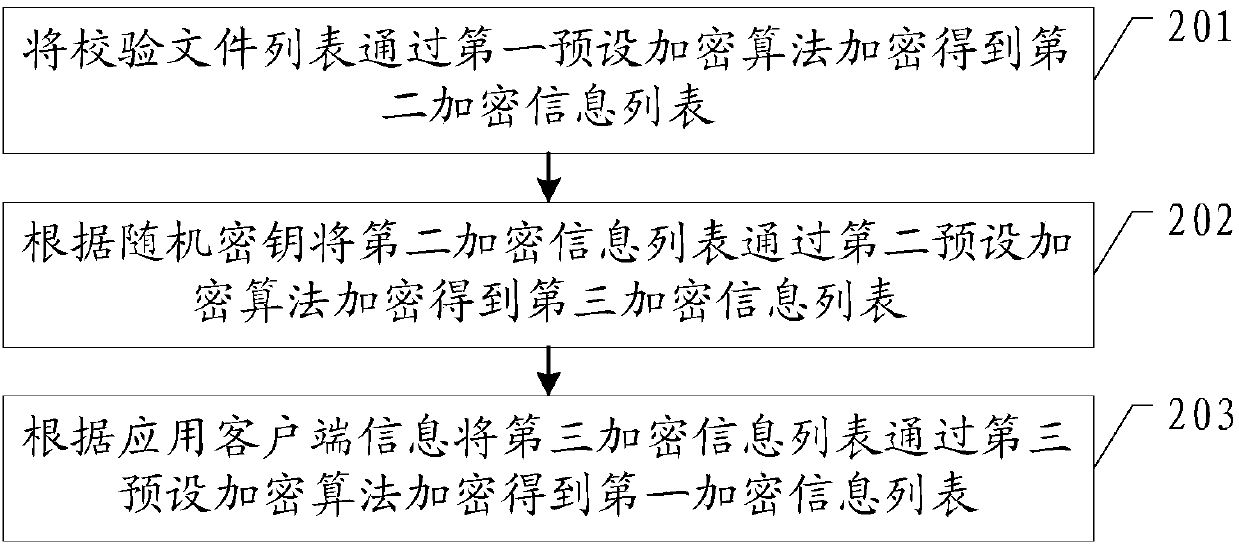
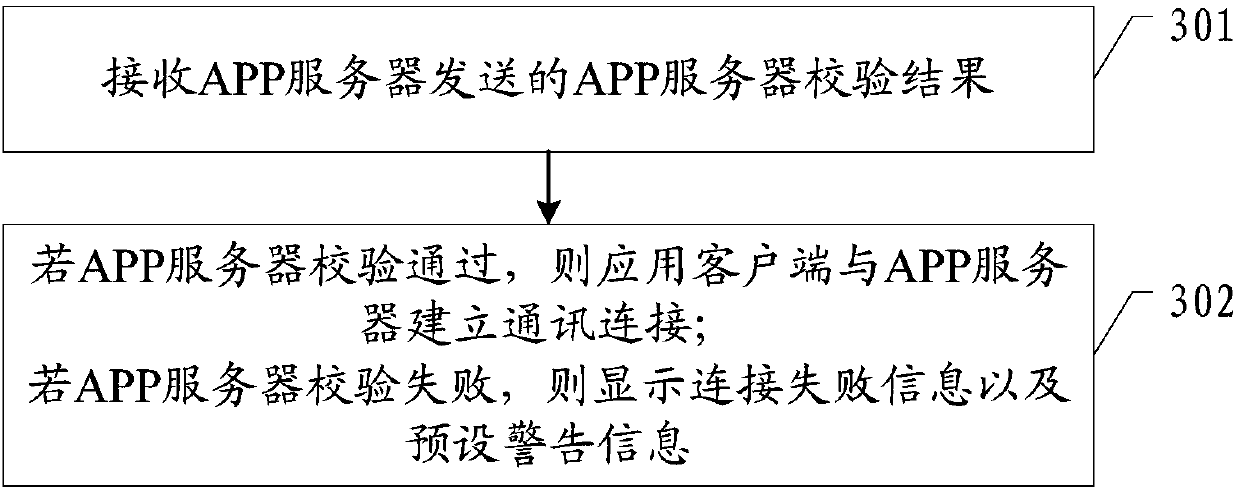
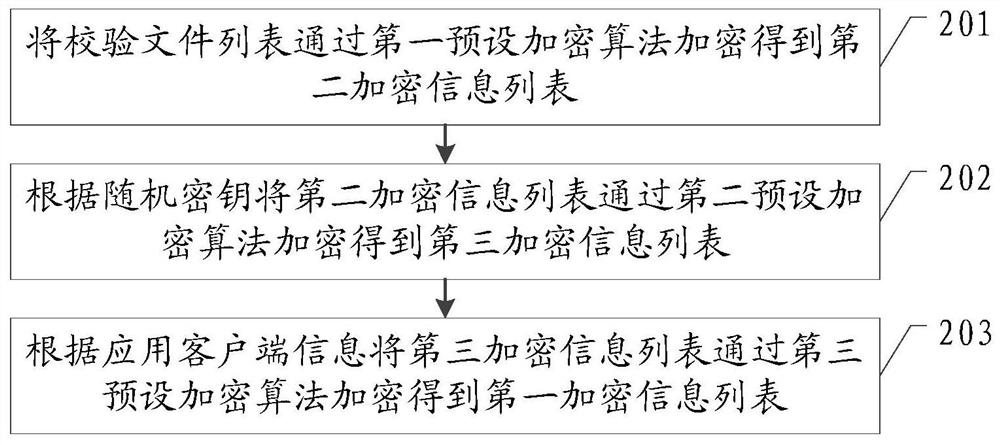
ActiveCN109995700AAvoid parityPrevent intrusionComputer security arrangementsTransmissionFirst admissionApplication software
The invention provides an application security protection method, an application client and an ACR server, and the application security protection method comprises the steps: sending application client information to the ACR server; receiving a random key sent by the ACR server and a pre-stored check file list; according to the random key and the check file list, encrypting the check file list togenerate a first encrypted information list; sending the first encrypted information list to an ACR server for verification; after the ACR server passes the verification, generating a first admissionidentifier according to the first encryption information list and storing the first admission identifier; and when needing to be connected with the APP server, sending the first admission identifier and the application client information to the APP server for verification. According to the embodiment of the invention, through a dual-verification mode, a hacker is prevented from obtaining sensitiveinformation of a user or disseminating illegal information by cracking an application client, so that the information security of the user is protected.
Owner:北京易安睿龙科技有限公司
Air-conditioning system, method and device for controlling the air-conditioning system
ActiveCN112050292BImprove heat transfer effectEnsure the amount of circulationMechanical apparatusSpace heating and ventilation safety systemsLiquid stateAir conditioning
The invention discloses an air-conditioning system, a control method and a device for the air-conditioning system. The air conditioning system includes an outdoor heat exchanger, a first throttling device, and a refrigerant tank. All branches in the outdoor heat exchanger are divided into the first group of circuits and the second group of circuits; the refrigerant tank is located between the first throttling device and the outdoor Between the heat exchangers; the refrigerant tank includes: the first port is connected to the first throttling device for allowing the throttled refrigerant to enter the refrigerant tank for gas-liquid separation; the second port is connected to the first group of circuits for The separated gaseous refrigerant is transmitted to the first group of circuits; the third port is connected to the second group of circuits through a flow distribution component, and is used to transmit the separated liquid refrigerant to the second group of circuits. The present invention is provided with a refrigerant tank, and the throttled refrigerant in the heating mode enters the refrigerant tank to realize gas-liquid separation, and the separated gas refrigerant and liquid refrigerant are respectively transported to different branches of the outdoor heat exchanger to ensure that the outdoor heat exchanger The amount of refrigerant circulation in the medium ensures uniform liquid separation and improves heat exchange capacity.
Owner:GREE ELECTRIC APPLIANCES INC
System and method for air handling and air conditioning
InactiveCN105612392AGuaranteed heat transferStable deliveryEnergy recovery in ventilation and heatingMechanical apparatusCold airComputer module
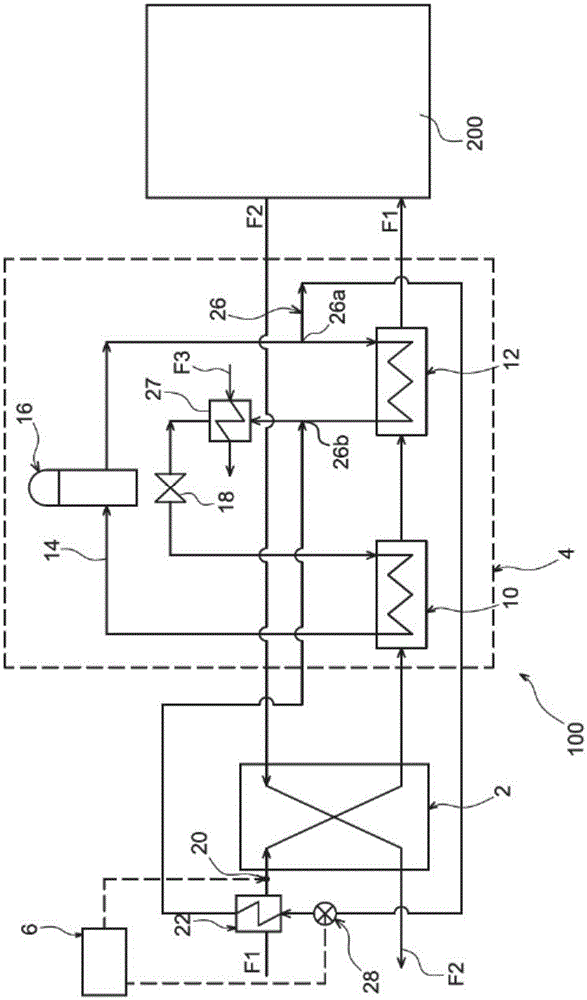
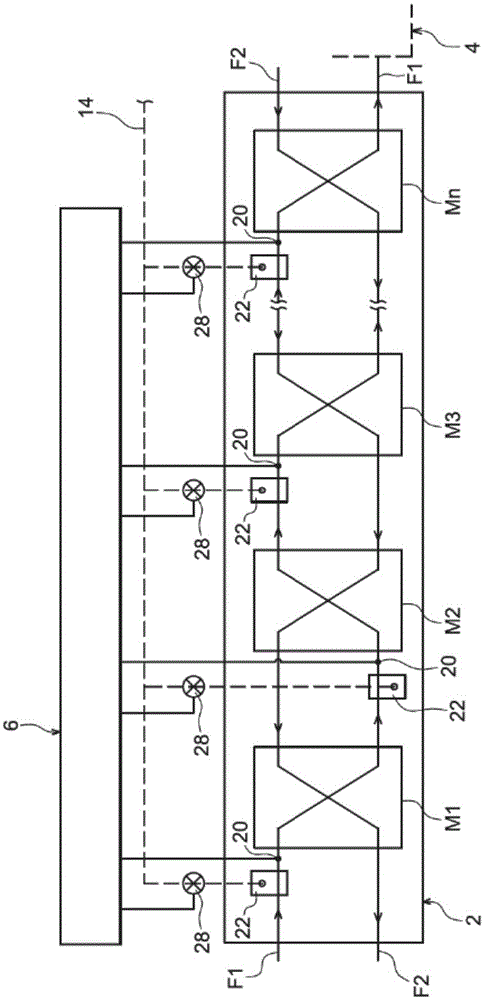
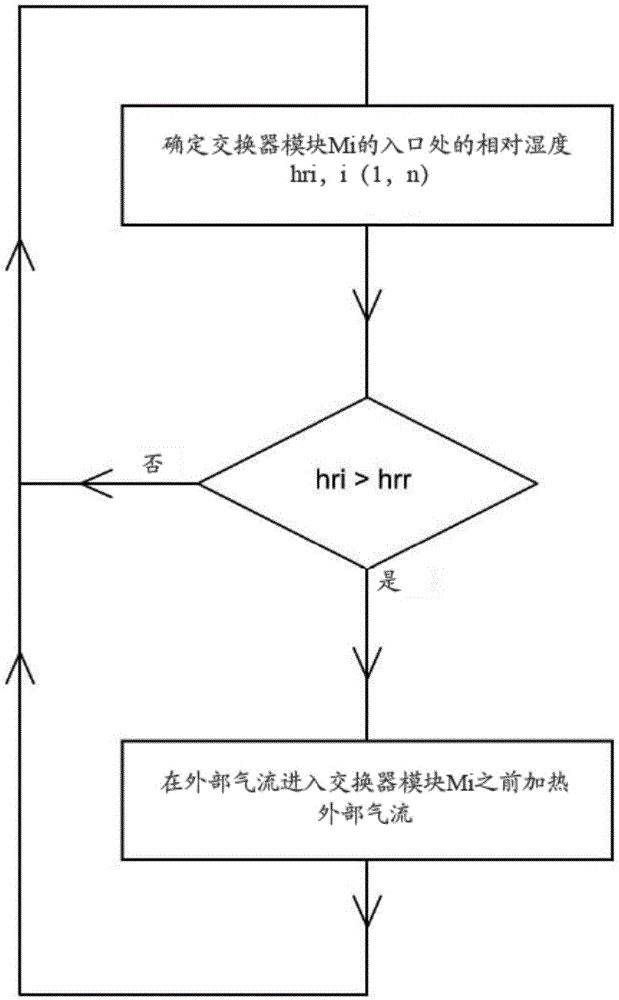
The invention relates to an air handling and air conditioning system (100) intended to provide fresh air to the interior of a volume (200), preferably a building, the system comprising at least one heat exchanger module with dual air flow allowing heat transfer and transfer of water vapour between the two air flows, the system being designed to be able to function in a mode for cooling the building, in which the two air flows are respectively comprised of an exterior air flow (F1) intended to be introduced into the building (200), and a cooler and drier stale air flow (F2) coming from the interior of the building. According to the invention, the system also comprises: means (20) for determining the relative humidity of the exterior air flow (F1) at the inlet to said heat exchanger module; and control means (6) configured to order a contribution of heat to the exterior air flow (F1) before its entry into the module if its relative humidity exceeds a predetermined value.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Injection attack detection method, device, server and storage medium
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
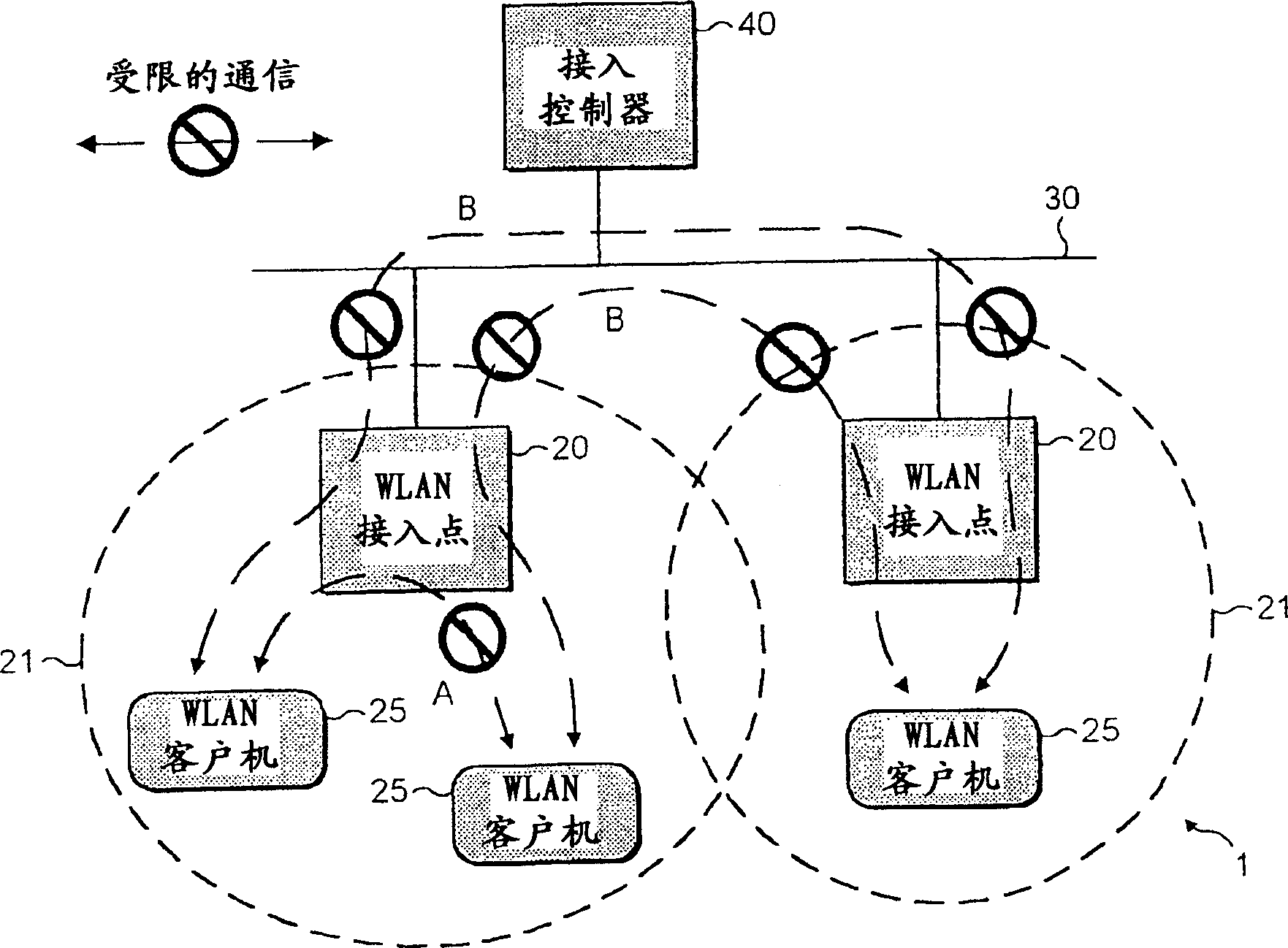
Security in area networks
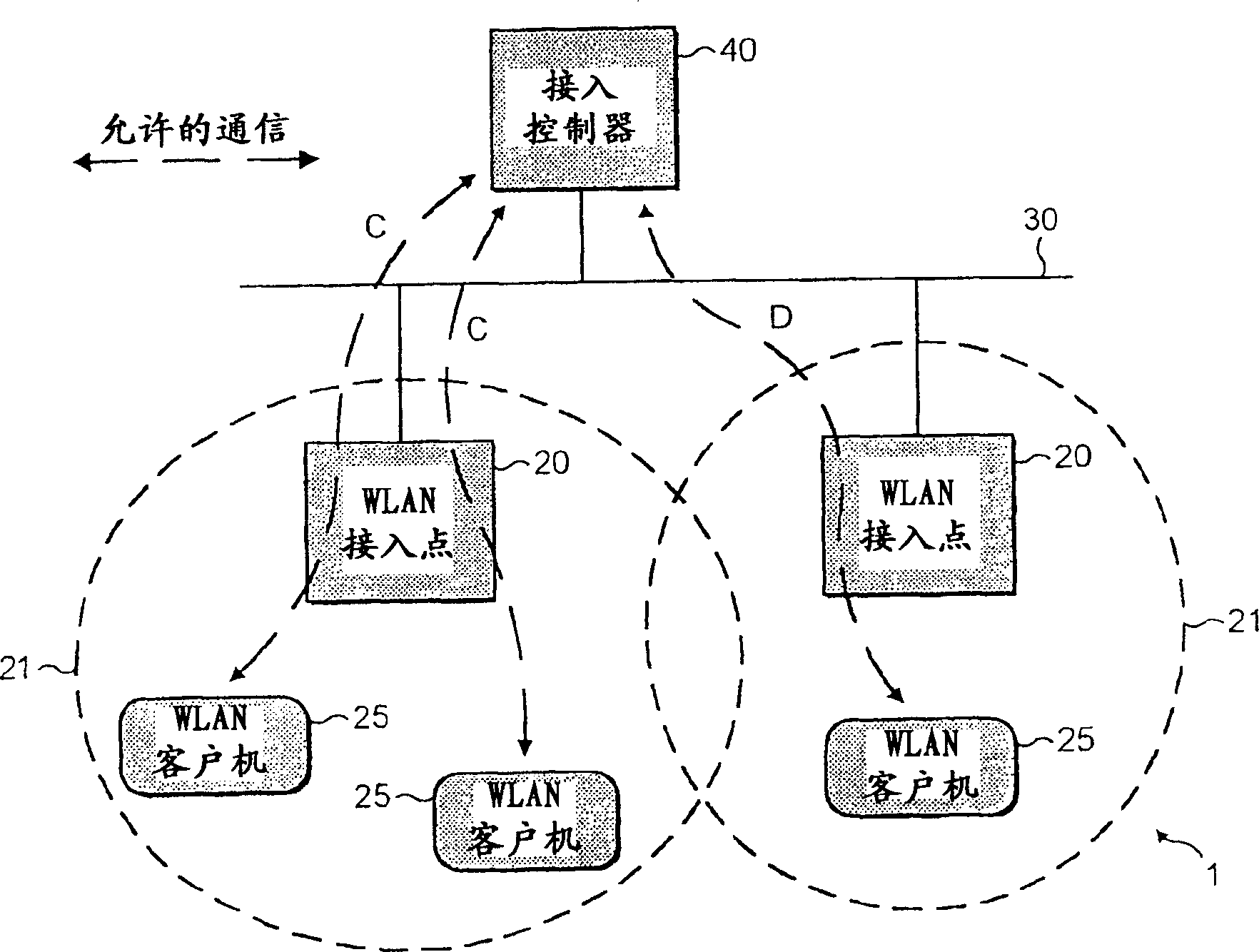
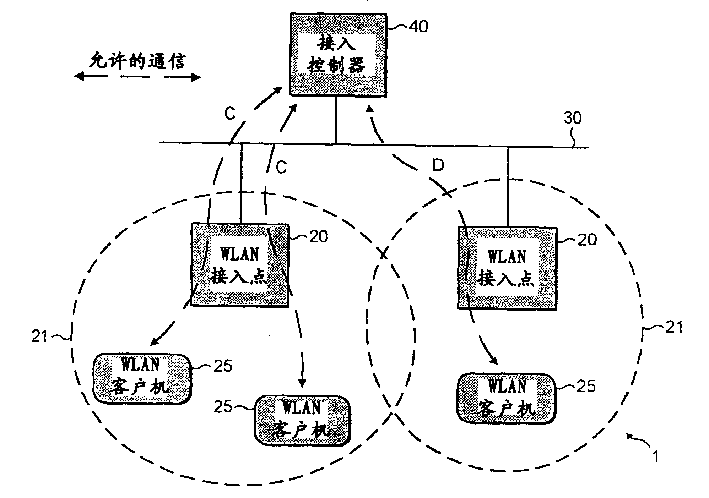
InactiveCN1545789AEasy to controlEasy to monitorSpecial service provision for substationError preventionArea networkClient data
The present invention provides an access point device arranged to receive data packets from one or more client devices and transmit them along an area network characterised wherein the access point device comprises security means arranged to configure the client data packets such that they are directed only to one or more permitted area network device(s).
Owner:NOKIA CORP
Artificial intelligence-based black production account detection method and related device
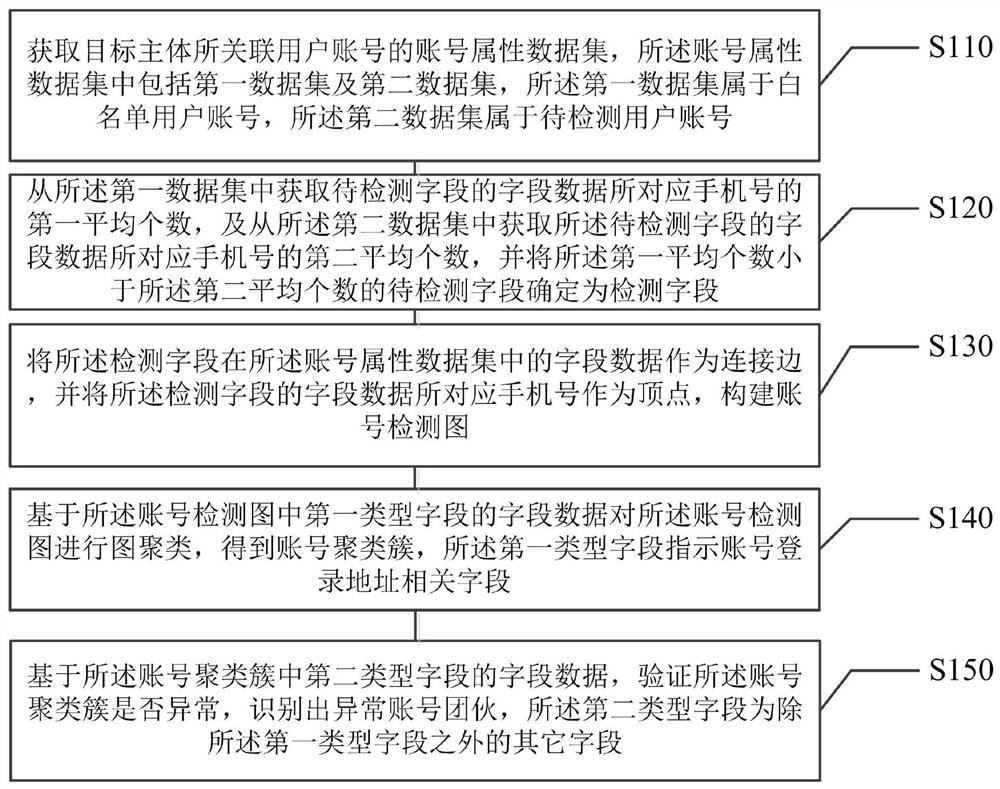
ActiveCN111931047BPrevent overfittingImprove accuracyDigital data information retrievalCharacter and pattern recognitionData setEngineering
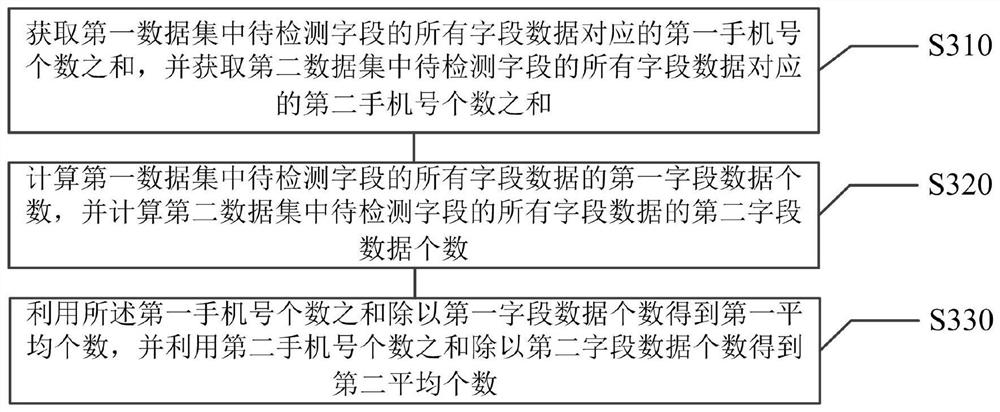
This application relates to an artificial intelligence-based method for detecting illegal accounts and related devices, belonging to the field of artificial intelligence technology. The method includes: obtaining the account attribute data set of the user account associated with the target subject; from the first data set and the second Obtain the first average number and the second average number of the mobile phone number corresponding to the field data of the field to be detected in the data set, and determine the field to be detected with the first average number less than the second average number as the detection field; The field data of the detection field is used as a connection edge, and the mobile phone number is used as a vertex to construct an account detection graph; based on the field data of the first type of field in the account detection graph, the account detection graph is graph-clustered to obtain account clusters, said The first type of field indicates the field related to the account login address; based on the field data of the second type of field, it is verified whether the account cluster is abnormal. This application effectively improves the detection accuracy and reliability of illegal accounts.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Application program attack defense method and system based on code injection and behavior analysis
ActiveCN111931166BAvoid bypassingComprehensive hook point coverageHardware monitoringPlatform integrity maintainanceBehavioral analyticsAttack
The present invention proposes an application program attack defense method and system based on code injection and behavior analysis. By injecting protection codes into applications that need protection, identifying attack behaviors in applications includes: injecting protection codes into applications that need protection Program, mount the hook point at the predetermined key call position, and the protection code monitors the marked parameters and the operation behavior of calling key functions in the application; run a unified protection plug-in, and conduct security risk analysis in combination with the operation behavior, marked parameters and context information , identify whether there is a suspicious webshell in the monitored code in the application program; send a corresponding alarm message according to the security risk analysis result, or directly block the operation of the application program. The above method can detect attacks and protect itself at runtime through reasonable deployment of protection codes, achieving fewer false negatives and false negatives, more comprehensive and accurate protection, and faster vulnerability response.
Owner:NAT UNIV OF DEFENSE TECH
Firewall
InactiveCN111870840AImprove structural strengthPrevent deformation or damageFire rescueWall plateEnvironmental geology
The invention belongs to the technical field of fire-fighting equipment, and particularly discloses a firewall. The firewall comprises a wallboard, an elastic piece and a flow guide plate. The wallboard is vertically arranged between an oil-gas cabin and a living cabin of an oil tanker and is connected to a deck of the oil tanker in a sliding manner; one end of the elastic piece is fixedly arranged, and the other end of the elastic piece is connected to the upper middle part of the firewall; and the flow guide plate is connected to the end, in the width direction, of the wallboard in an included-angle manner and extends in the direction away from the oil-gas cabin. The wallboard is vertically arranged and slidably connected to the deck, and the elastic piece is connected to the upper middle portion of the firewall, so that the wallboard is prevented from forming a cantilever structure on the deck, and the structural strength of the wallboard is improved. The elastic piece can absorb part of energy of shock waves, and the protection capacity of the firewall is improved. The end part of the wallboard is connected with the flow guide plate, so that flames and / or the shock waves are prevented from bypassing the firewall to enter the living cabin, and the protection capability of the firewall is further improved.
Owner:GUANGZHOU SHIPYARD INTERNATIONAL LTD
App usage policy enforcement
ActiveCN103180859BAvoid bypassingBuying/selling/leasing transactionsProgram/content distribution protectionInternet privacyEngineering
Disclosed herein are systems, methods, and non-transitory computer-readable media for enforcing application usage policies. As part of an application purchase transaction, the application distributor creates a unique proof of purchase receipt. This receipt can be bundled with the application and delivered to the purchaser. Each machine can maintain an authorization file that lists the users authorized to use applications on that machine. A system configured to practice the method verifies that a user is authorized to use an application on a machine based on an application proof of purchase receipt and the authorization file. If the application proof of purchase receipt and the authorization file are both valid, the system checks if the user account identifier in the receipt is contained in the authorization file. If so, the user can be considered authorized to use the application on the machine.
Owner:APPLE INC
Electronic equipment, authentication method, storage medium, and program product
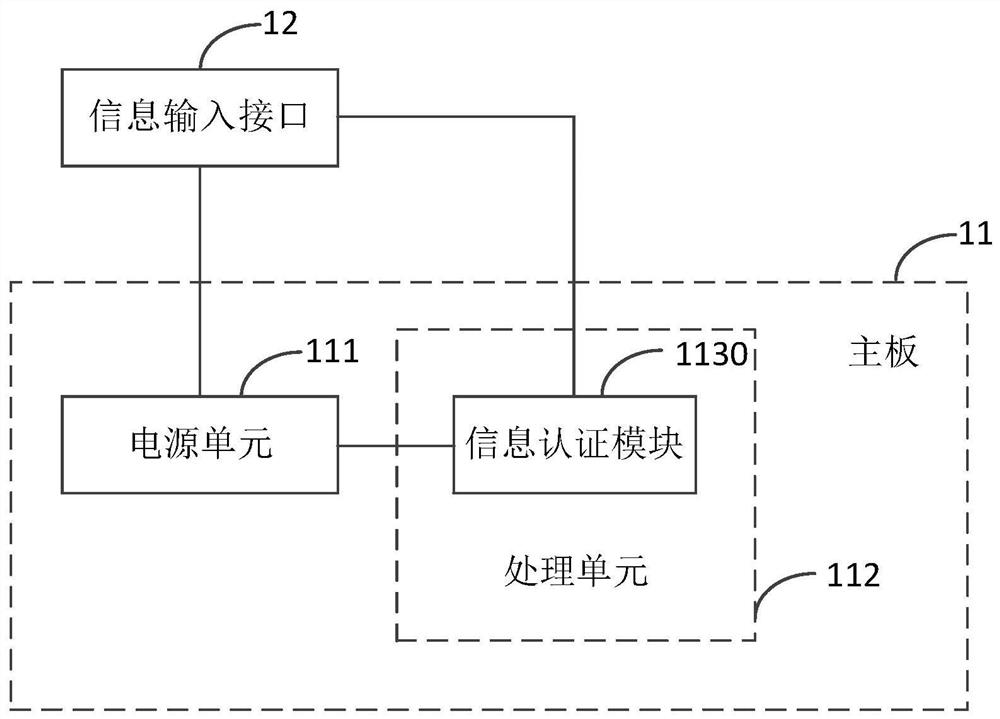
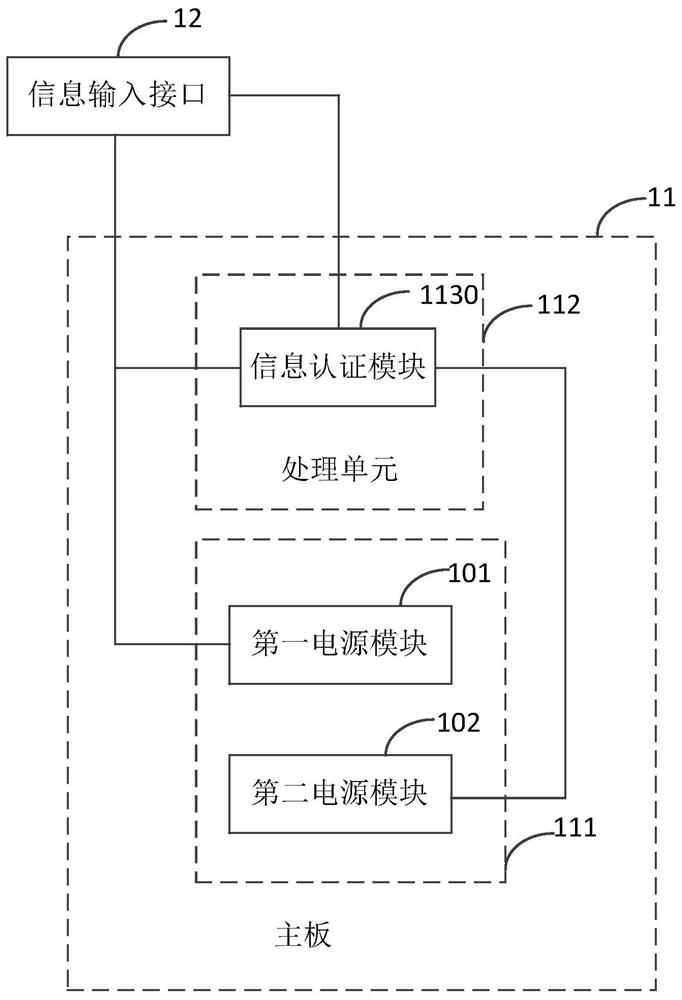
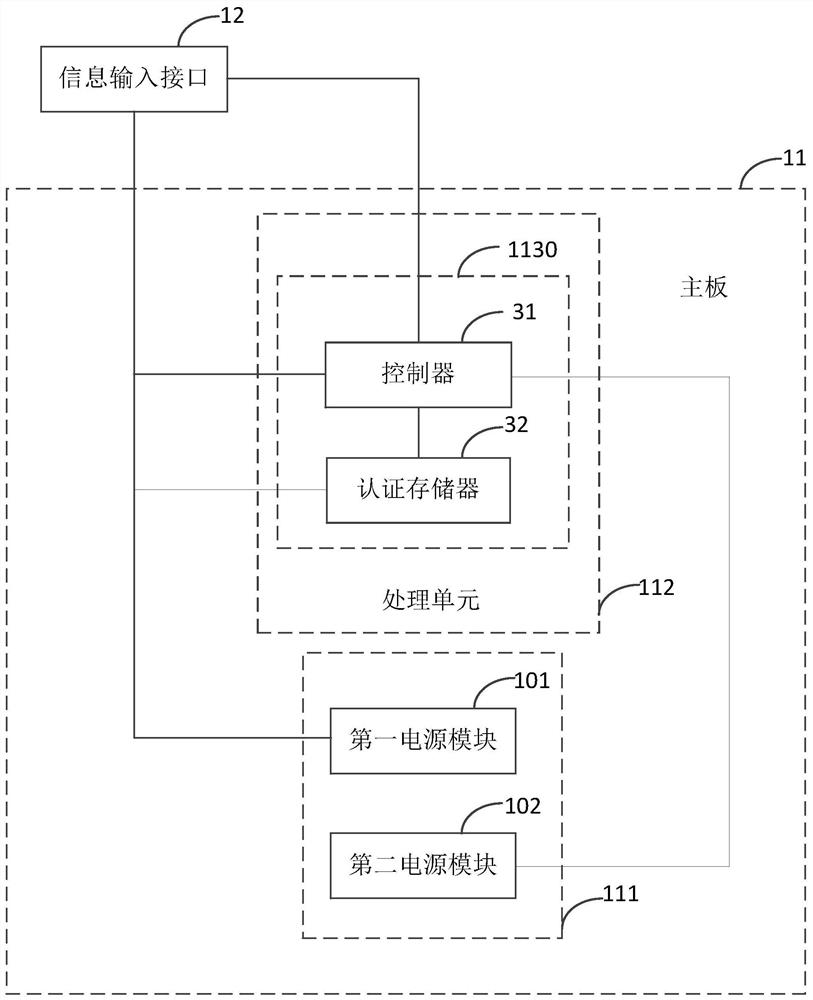
PendingCN113792281AImprove securityNot easy to loseDigital data protectionDigital data authenticationProcessing elementEmbedded system
The embodiment of the invention provides electronic equipment, an authentication method, a storage medium and a program product. The electronic equipment comprises a mainboard and an information input interface; the mainboard comprises a power supply unit and a processing unit; the processing unit comprises an information authentication module; the information authentication module is respectively connected with the information input interface and the power supply end and the control end of the power supply unit; the information input interface is also connected with the power supply end of the power supply unit; and the information authentication module is used for acquiring to-be-authenticated information through the information input interface, and sending a power-on enable signal to the power supply unit after determining that the to-be-authenticated information passes authentication, so that the power supply unit is started to supply power to at least a part, which is related to startup operation, of the mainboard. The security of the electronic equipment is improved.
Owner:龙芯中科(南京)技术有限公司
Card making equipment
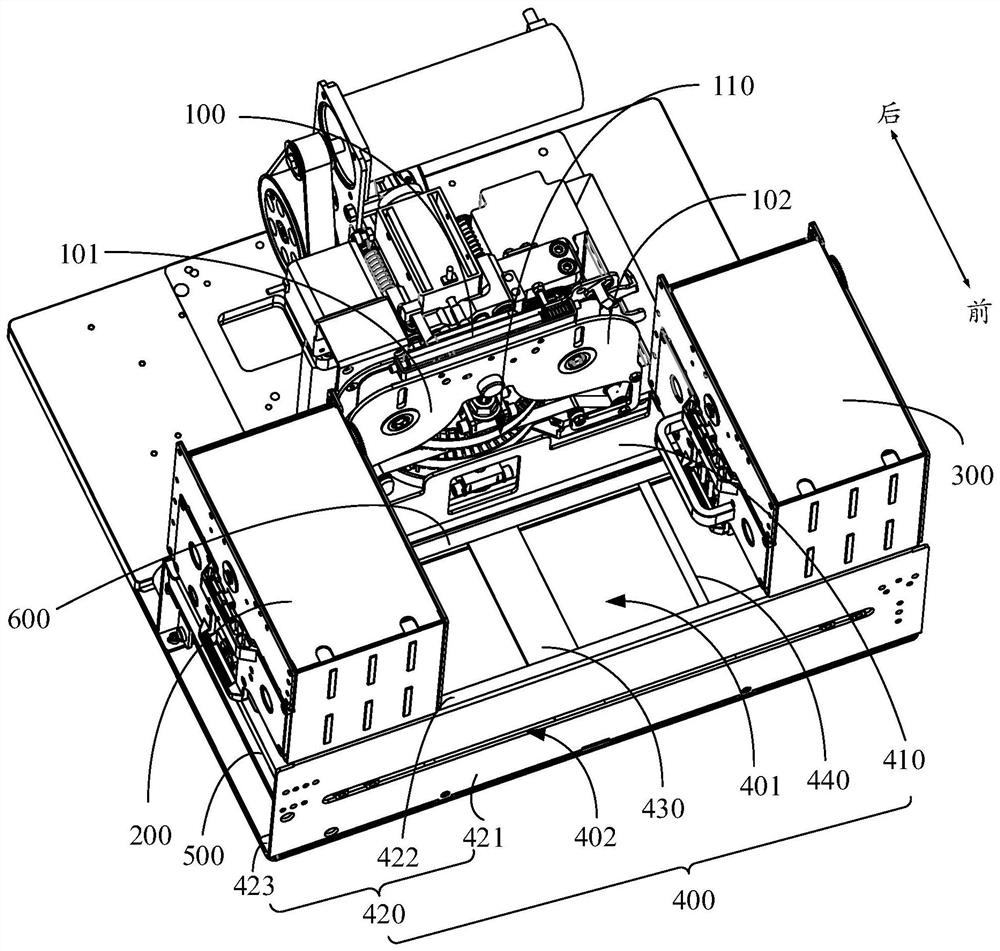
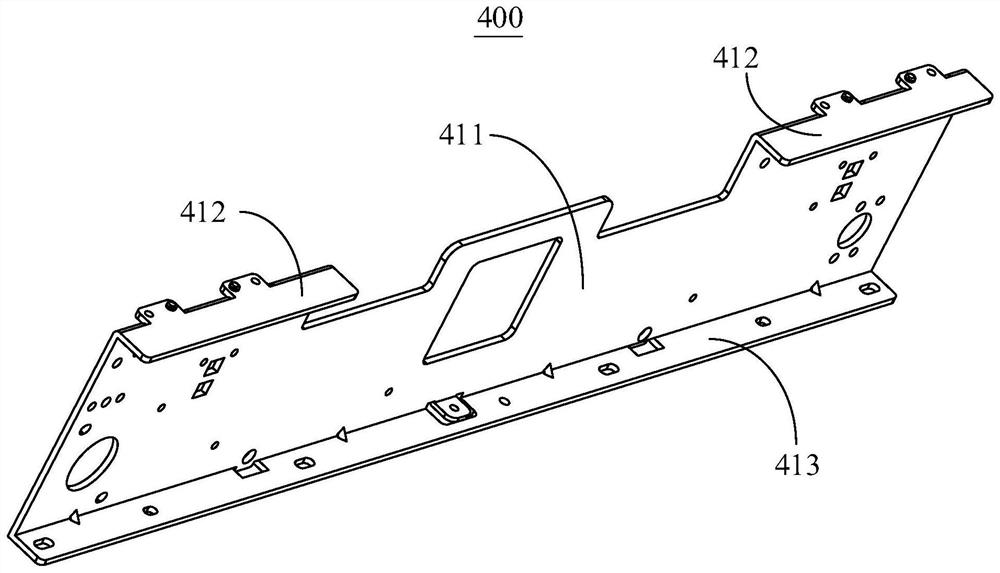
InactiveCN113183619AImprove transmission efficiencyIncrease productivityRotary pressesCode moduleHot stamping
The invention discloses card making equipment which comprises a concave-convex character coding module, a first hot stamping module and a second hot stamping module, wherein the concave-convex character coding module comprises a first area and a second area which are opposite, the concave-convex character coding module is provided with a card inlet and outlet opening located between the first area and the second area, and the direction from the first area to the second area is perpendicular to the card inlet and outlet direction of the card inlet and outlet opening; the first hot stamping module is arranged in front of the concave-convex character coding module and corresponds to the first area or corresponds to the side, away from the second area, of the first area; the second hot stamping module is arranged in front of the concave-convex character coding module and corresponds to the second area or corresponds to the side, away from the first area, of the second area. According to the technical scheme, after the card is sent out from the card inlet and outlet, one of the two opposite directions can be selected to move so as to enter the first hot stamping module or the second hot stamping module, and thus, the movement path is simplified, and the occupied space of the card making equipment is saved.
Owner:CREATOR CHINA TCH CO
Engine lubrication system and engine
The invention belongs to the field of engines, and discloses an engine lubrication system and an engine. According to a method, a crankcase, a side cover and a bridge connection mechanism are included, a crankshaft is arranged in the crankcase, and a main oil passage of the crankshaft is arranged in the crankshaft; the side cover is arranged on one side of the crankcase, and a dark oil passage isarranged in the side cover; the bridge connection mechanism includes a casing and a sealing portion, the sealing portion is fixedly arranged on the outer side wall of the casing, one end of the casingis inserted into an outlet of the dark oil passage, and the sealing portion is located on the outer side of the outlet of the dark oil passage; and when the engine works, the casing moves towards aninlet of the main oil passage of the crankshaft under the pressure effect of the high pressure oil in the dark oil passage, so that the sealing portion is pressed against the inlet end face of the main oil passage of the crankshaft, the outlet of the dark oil passage and the inlet of the main oil passage of the crankshaft are connected in a sealed manner, and the high-pressure oil in the dark oilpassage enters the main oil passage of the crankshaft through the casing. The lubricating system can shorten the lubricating oil passage line, it is not necessary to increase the oil pump flow rate and oil pressure, and the probability of tube burst is reduced.
Owner:JIANGSU CHANGFA AGRI EQUIP
An application security protection method, application client and acr server
ActiveCN109995700BAvoid parityPrevent intrusionComputer security arrangementsTransmissionEngineeringApplication security
The present invention provides an application security protection method, an application client and an ACR server, wherein the application security protection method includes: sending application client information to the ACR server; receiving a random key sent by the ACR server and pre-stored The verification file list; according to the random key and the verification file list, encrypt the verification file list to generate the first encrypted information list; send the first encrypted information list to the ACR server for verification; when the ACR server verification passes Finally, generate and store the first access ID according to the first encrypted information list; when it is necessary to connect to the APP server, send the first access ID and the application client information to the APP server for verification. The embodiment of the present invention prevents hackers from obtaining sensitive information of the user or disseminating illegal information by cracking the application client by means of double verification, thereby protecting the information security of the user.
Owner:北京易安睿龙科技有限公司
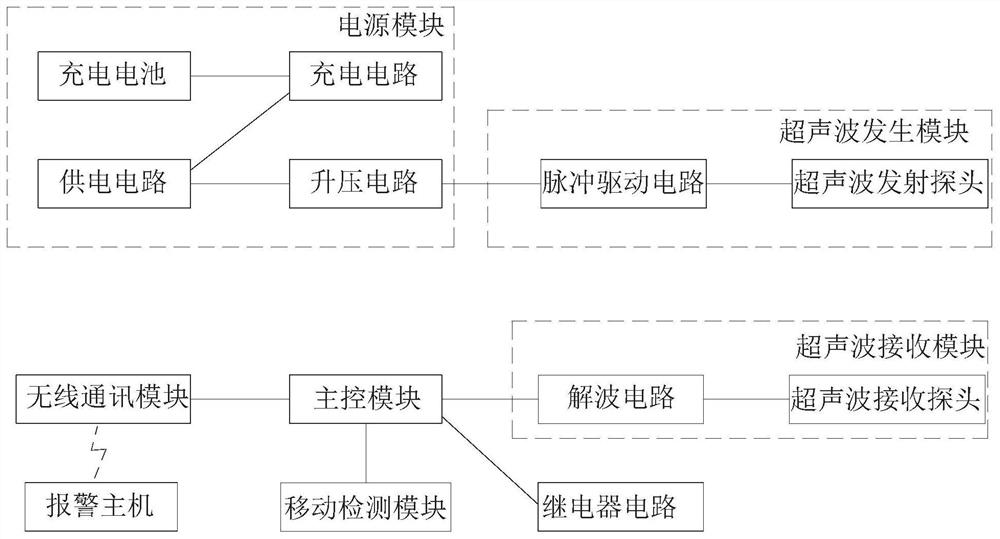
Composite alarm detector and anti-theft alarm method for museum showcase
ActiveCN113611063AMonitor movement statusRealize monitoringElectric transmission signalling systemsBurglar alarm by hand-portable articles removalWirelessReal-time computing
The invention relates to a composite alarm detector for a museum showcase. The composite alarm detector comprises a power supply module, an ultrasonic generation module, an ultrasonic receiving module, a mobile detection module, a main control module, a wireless communication module and an alarm host, wherein the power supply module is used for supplying power to each component and is internally provided with a rechargeable battery. The invention further provides an anti-theft alarm method for the museum showcase. The anti-theft alarm method comprises the steps of periodically transmitting ultrasonic waves into a closed space of the showcase; collecting reflected ultrasonic waves in real time; detecting the spatial change of the showcase, specifically, demodulating the ultrasonic wave collected each time, and if the attribute of the demodulated ultrasonic wave is inconsistent with the attribute of the initial ultrasonic wave, triggering an alarm; and detecting the movement change of the showcase and triggering an alarm. According to the invention, any change of the showcase cavity and the cavity space form is monitored by using ultrasonic waves to generate an alarm, the acceleration is synchronously detected, the moving state of the showcase is monitored, the situation that the showcase is directly moved away under the condition that the space in the showcase is not touched is prevented, the functions are practical, and the comprehensive monitoring of the showcase condition is realized.
Owner:郑州丰嘉科技有限公司
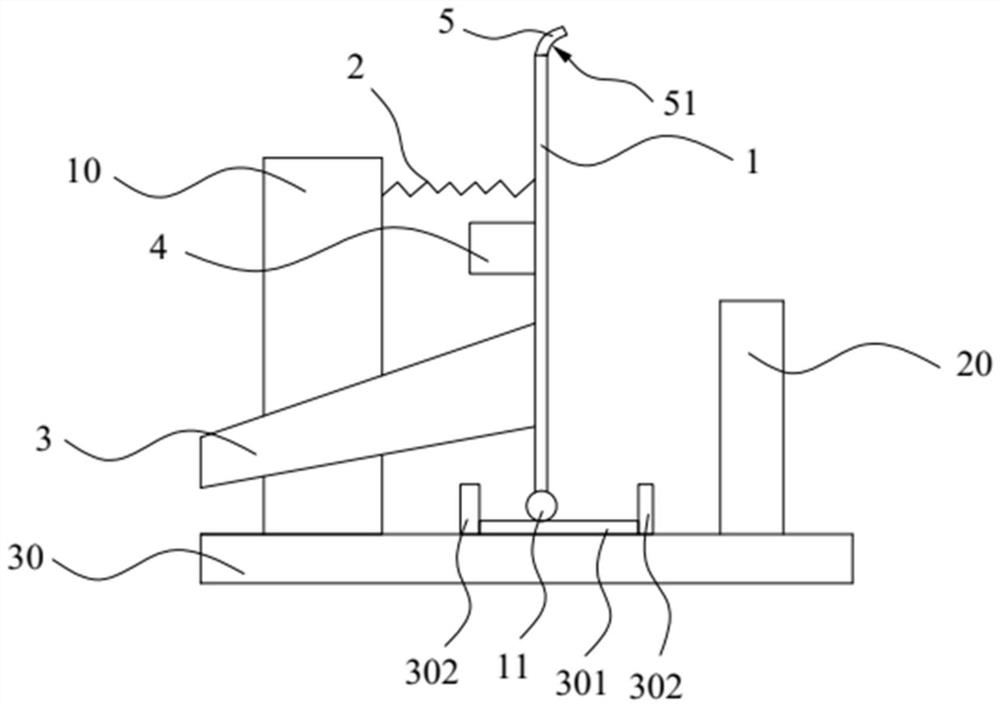
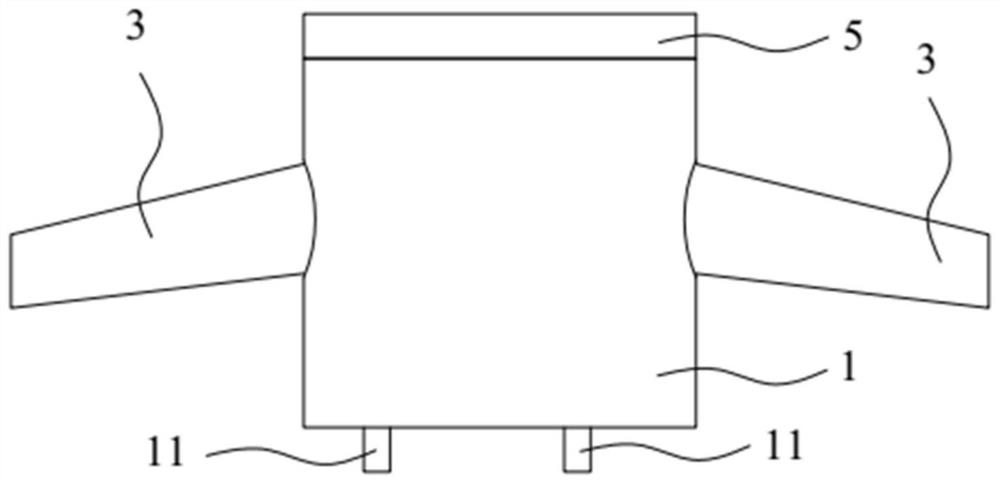
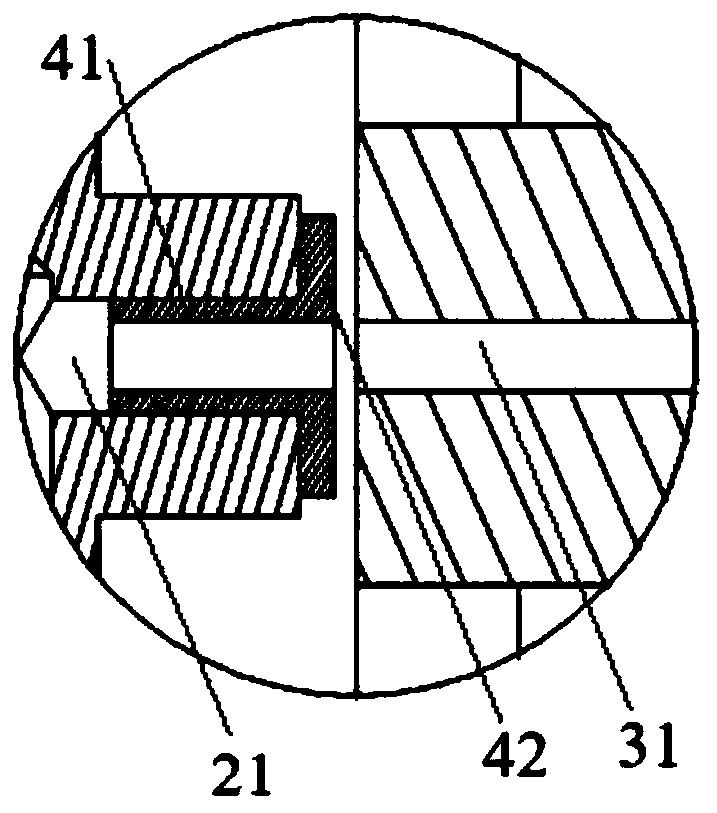
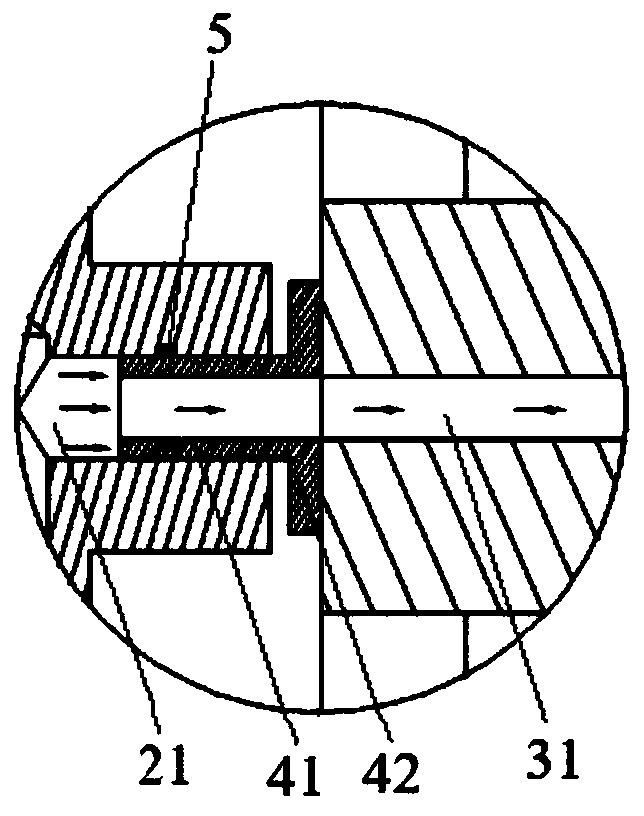
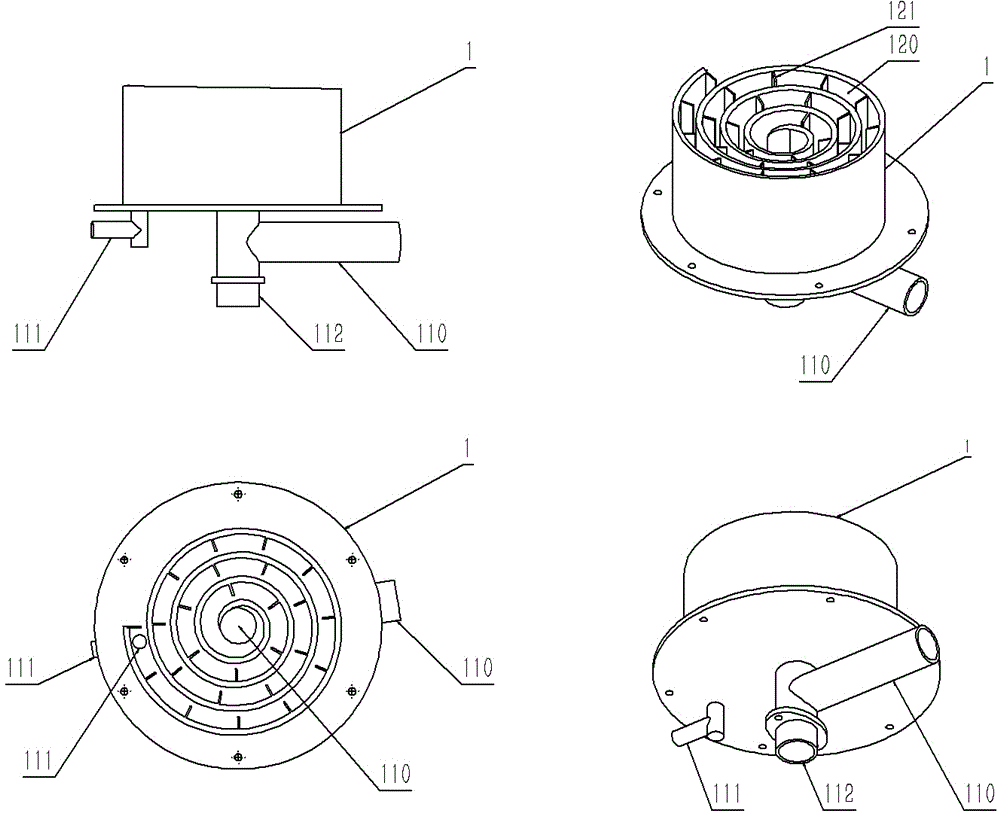
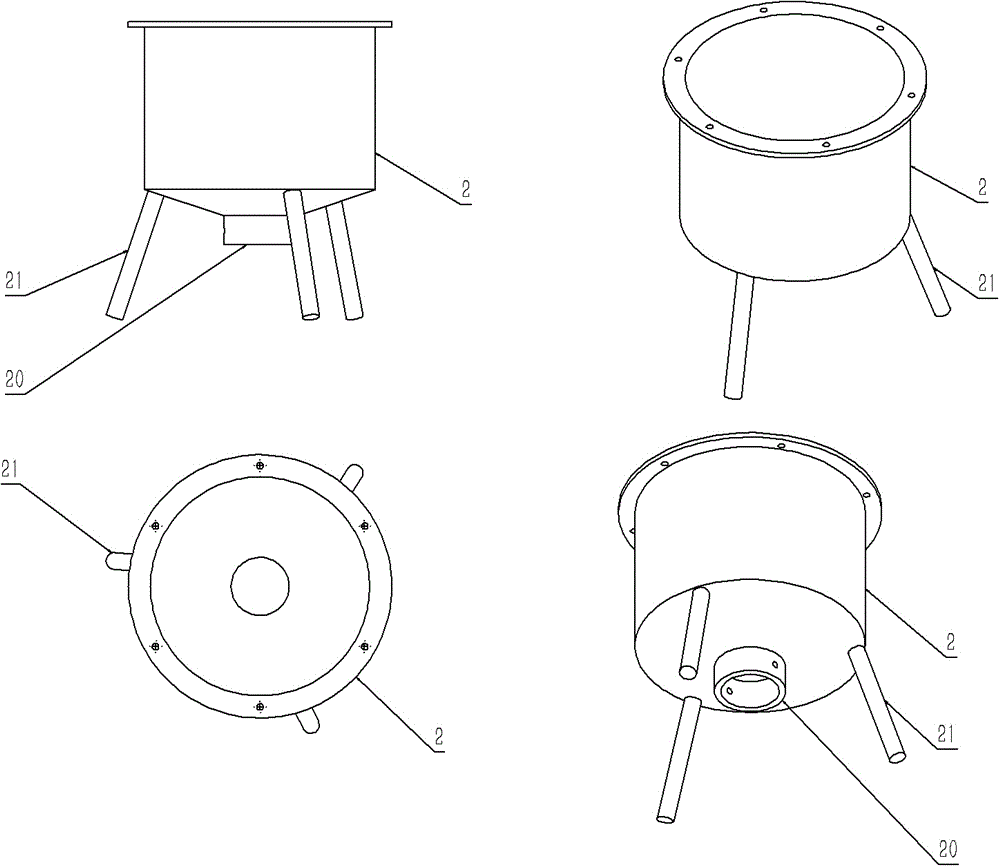
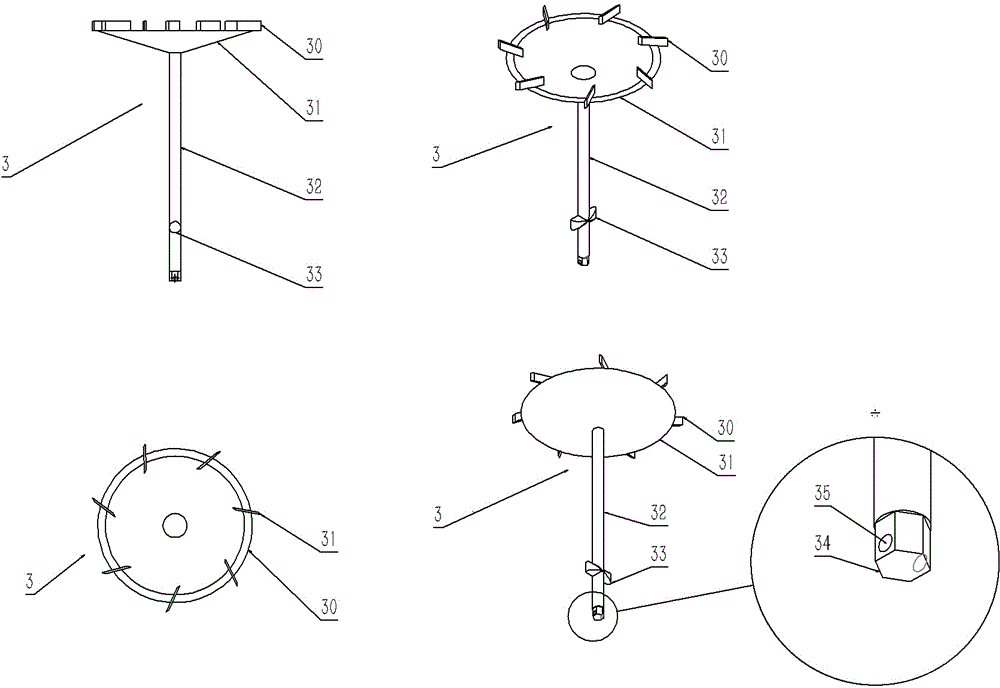
A small sewage sedimentation device
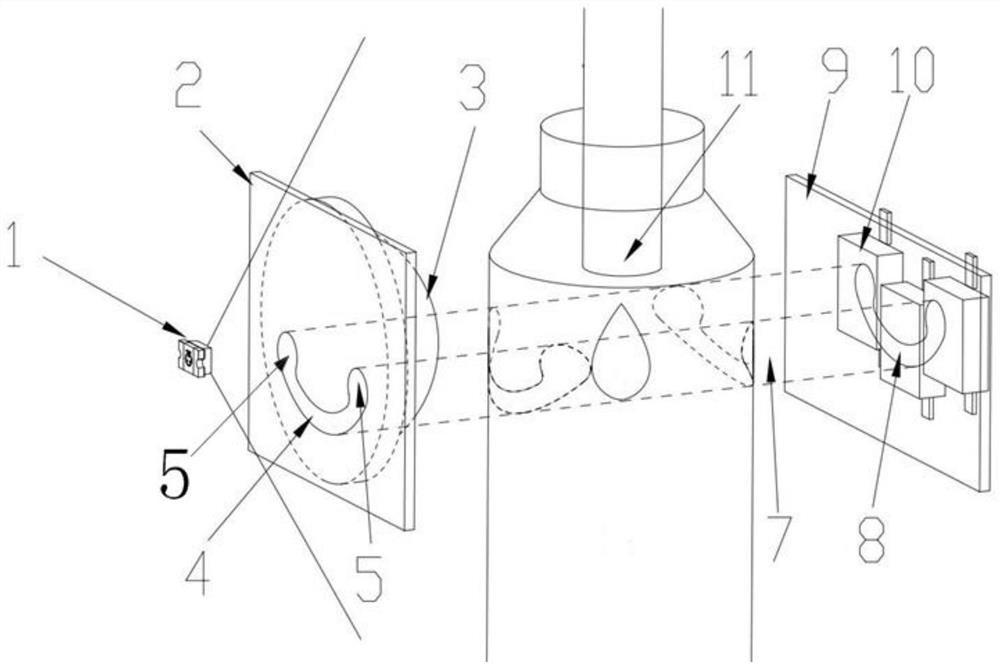
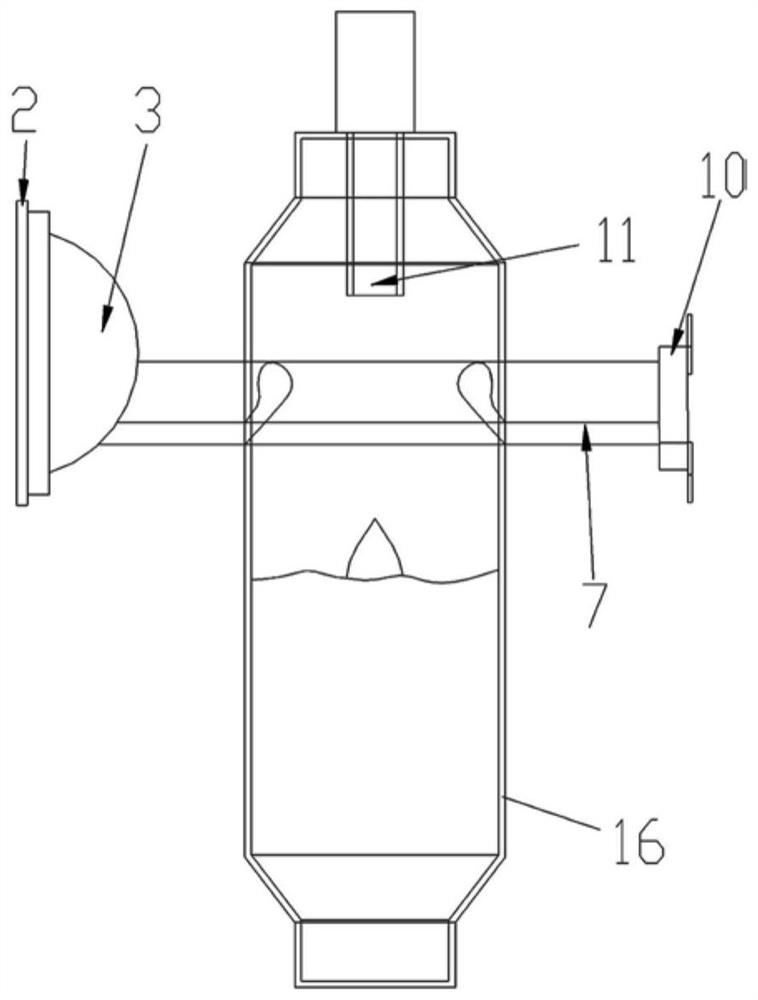
ActiveCN104225972BAvoid bypassingImprove sedimentation efficiencySedimentation settling tanksWater channelSludge
Disclosed is a small sewage precipitation device. The small sewage precipitation device is characterized by mainly comprising a vortex-shaped water channel upper cover (1), a container (2), a vortex-shaped water channel lower cover (3), a position adjusting barrel (5), handles (4 and 6) and sludge valves (7 and 8). The small sewage precipitation device is a miniaturized sewage treatment device, high in precipitation efficiency and low in costs.
Owner:NANJING RONGZHONG ENVIRONMENTAL ENG RES INST CO LTD
Infrared light liquid drop detection device and method
ActiveCN114191653AImprove detection accuracyAvoid drippingMedical devicesFlow monitorsEngineeringMaterials science
The invention discloses an infrared light liquid drop detection device and method.The infrared transmitting device comprises an infrared transmitting tube (1), a light shading piece (2) and a lens (3) which are sequentially arranged from left to right, the convex face of the lens (3) extends into a through groove (19) and is located below a dripping nozzle (11), and an arc-shaped gap (4) used for light passing is formed in the end face of the light shading piece (2); the arc-shaped gap (4) is overlapped with the lower half part of the plane of the lens (3), the length of the arc-shaped gap (4) is smaller than the diameter of the convex surface of the lens (3), and the convex surfaces of the infrared transmitting tube (1) and the lens (3) are located on the same water surface line; the infrared receiving device comprises an infrared light-transmitting piece (9) fixedly arranged in the machine shell (17), and an infrared receiving array (10) is fixedly arranged on the left end face of the infrared light-transmitting piece (9). The liquid drop detection device has the beneficial effects that the structure is compact, the detection reliability is high, false detection and missing detection are avoided, and the liquid drop detection precision is improved.
Owner:广东德澳智慧医疗科技有限公司
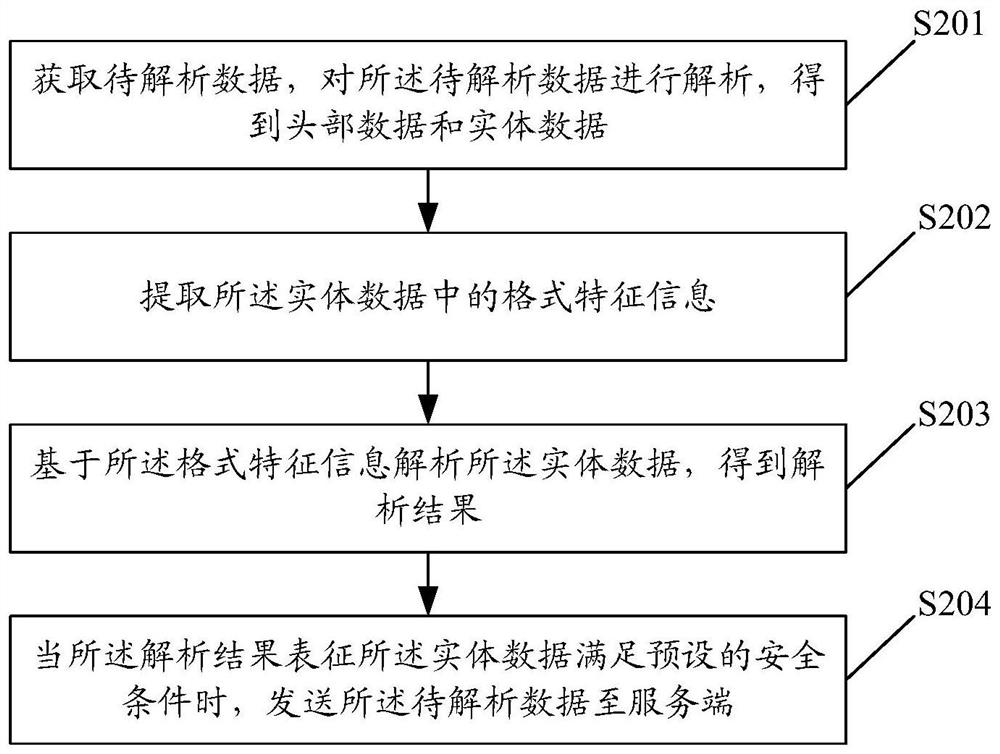
Data analysis method, device and equipment and computer readable storage medium
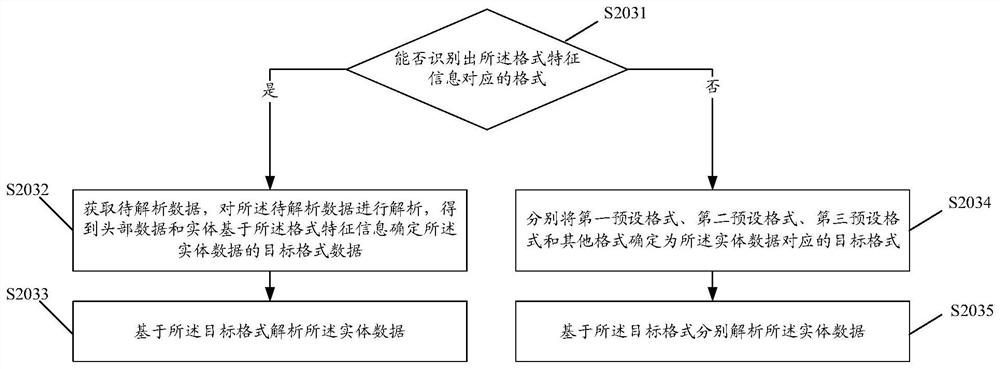
PendingCN112560038AAvoid bypassingImprove security detection accuracyPlatform integrity maintainanceTransmissionEngineeringDatabase
The embodiment of the invention discloses a data analysis method, device and equipment and a computer readable storage medium, and the method comprises the steps: obtaining to-be-analyzed data, analyzing the to-be-analyzed data, and obtaining head data and entity data; extracting format feature information in the entity data; analyzing the entity data based on the format feature information to obtain an analysis result; and when the analysis result represents that the entity data satisfies a preset security condition, sending the to-be-analyzed data to a server.
Owner:SANGFOR TECH INC
Adjustable cable rapid laying device
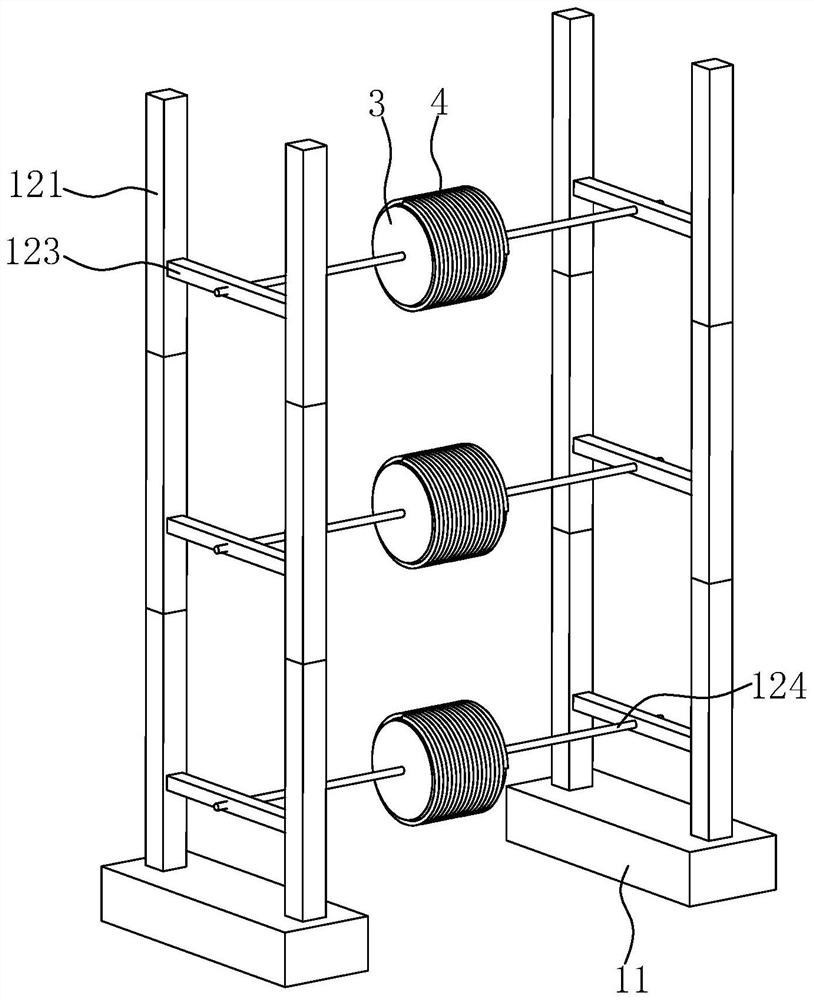
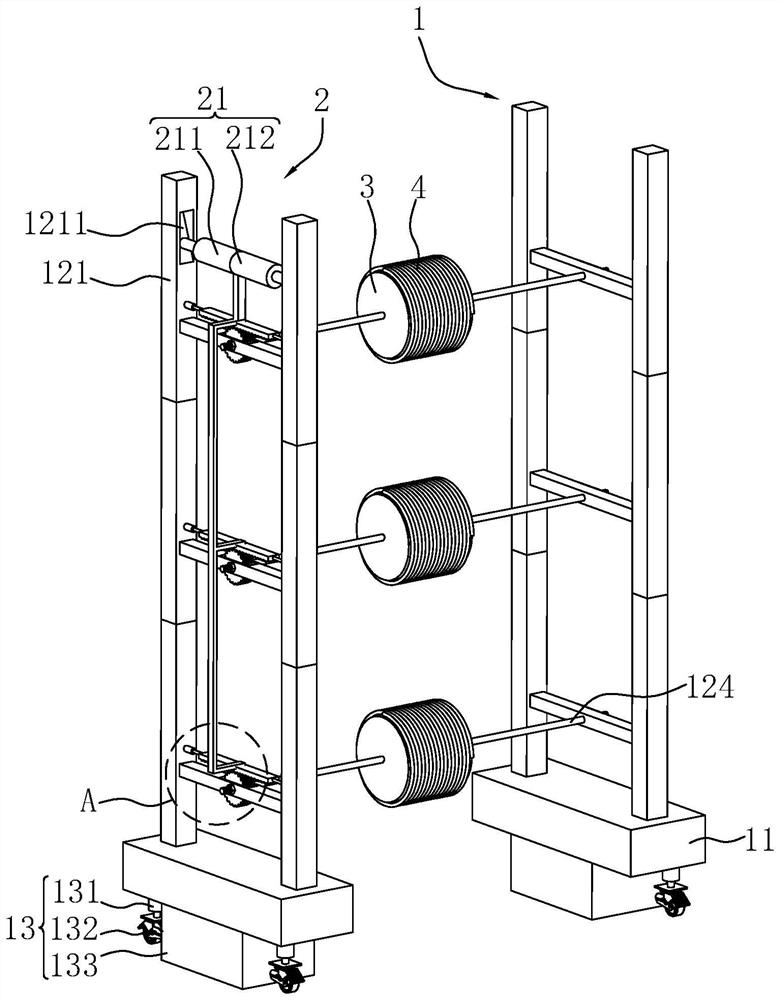
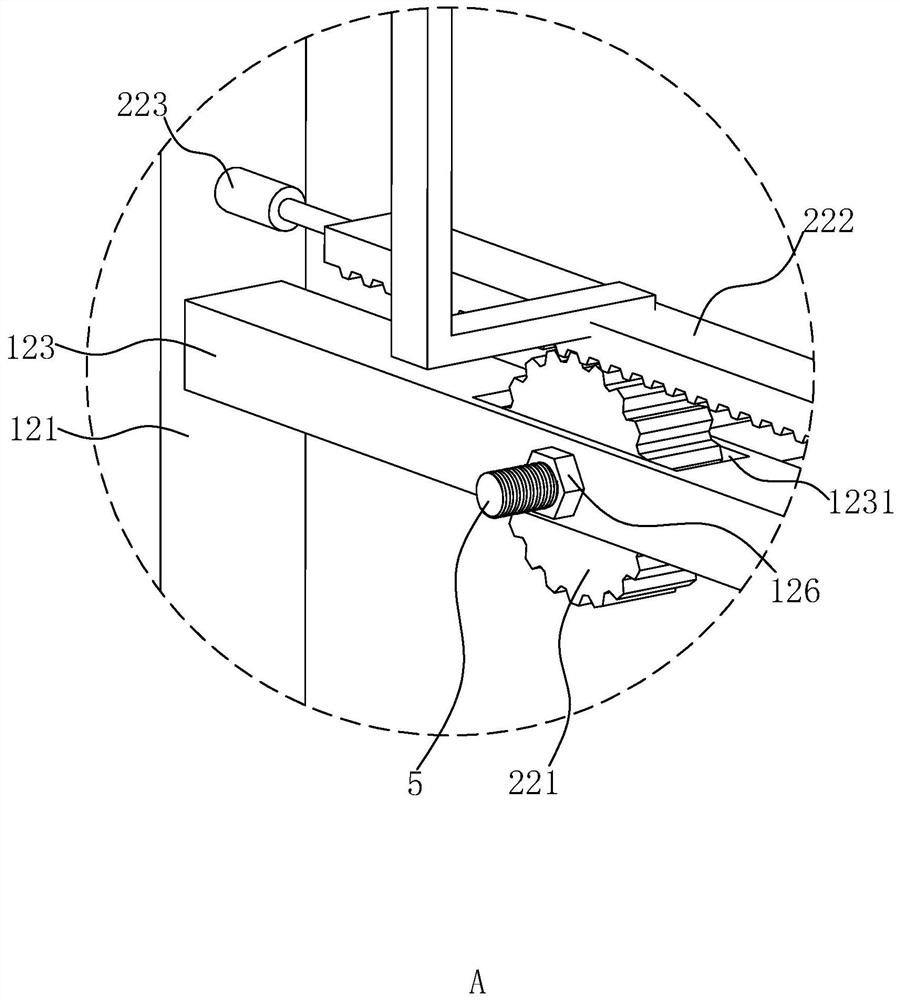
PendingCN114865538AAvoid bypassingAvoid manual windingArrangements using take-up reel/drumApparatus for laying cablesEngineeringStructural engineering
The invention relates to an adjustable cable rapid laying device, and relates to the technical field of cable laying, the adjustable cable rapid laying device comprises a mounting mechanism, the mounting mechanism comprises a base and a supporting assembly, and the base is horizontally arranged; the supporting assembly is located above the base and comprises supports, the supports are vertically arranged, the two supports are arranged in the length direction of the base, the lowermost support is fixedly connected with the base, and the adjacent supports in the vertical direction are fixedly connected; a mounting rod is fixedly arranged between every two adjacent supports, and the length direction of each mounting rod is the same as that of the base. A rotating rod is horizontally arranged on the mounting rod, the length direction of the rotating rod is perpendicular to that of the mounting rod, and the rotating rod is rotationally connected with the mounting rod around the axis of the rotating rod; the rotating rod is coaxially sleeved with a mounting box, and the mounting box is connected with the rotating rod; an electric wire is wound on the mounting box; a transmission mechanism is arranged on the base and used for enabling the rotating rod to rotate around the axis of the rotating rod. The working efficiency of cable laying can be improved.
Owner:力景(北京)系统技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com