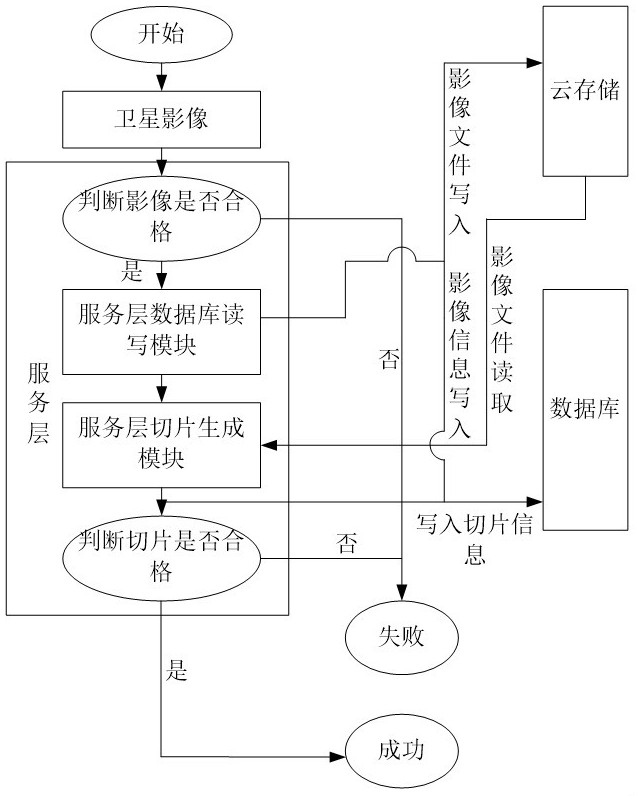
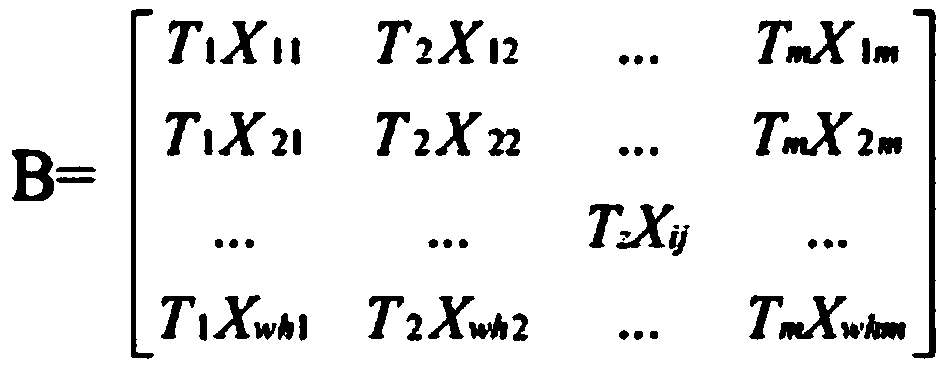Patents
Literature
71results about How to "Reduce memory pressure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
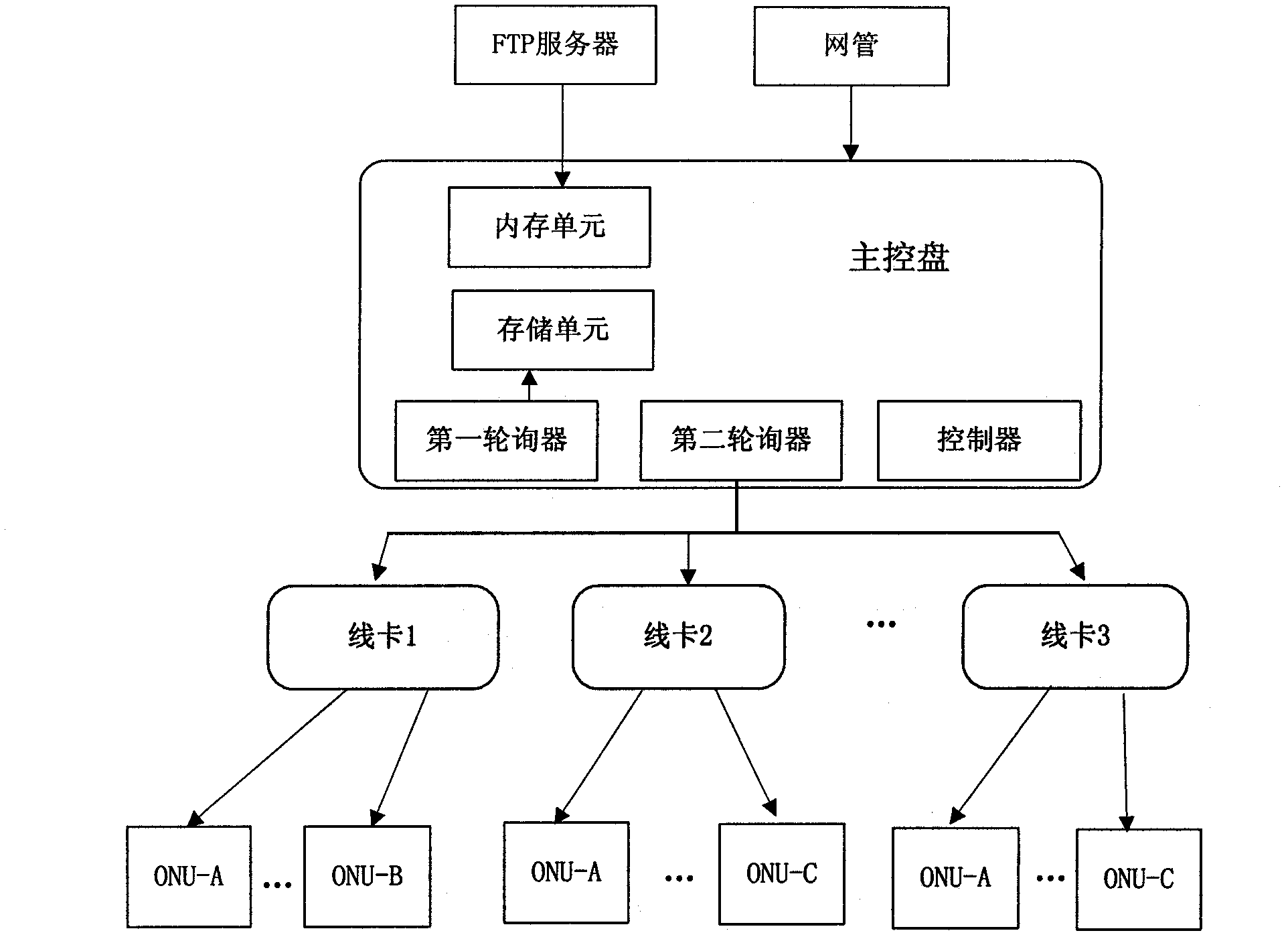
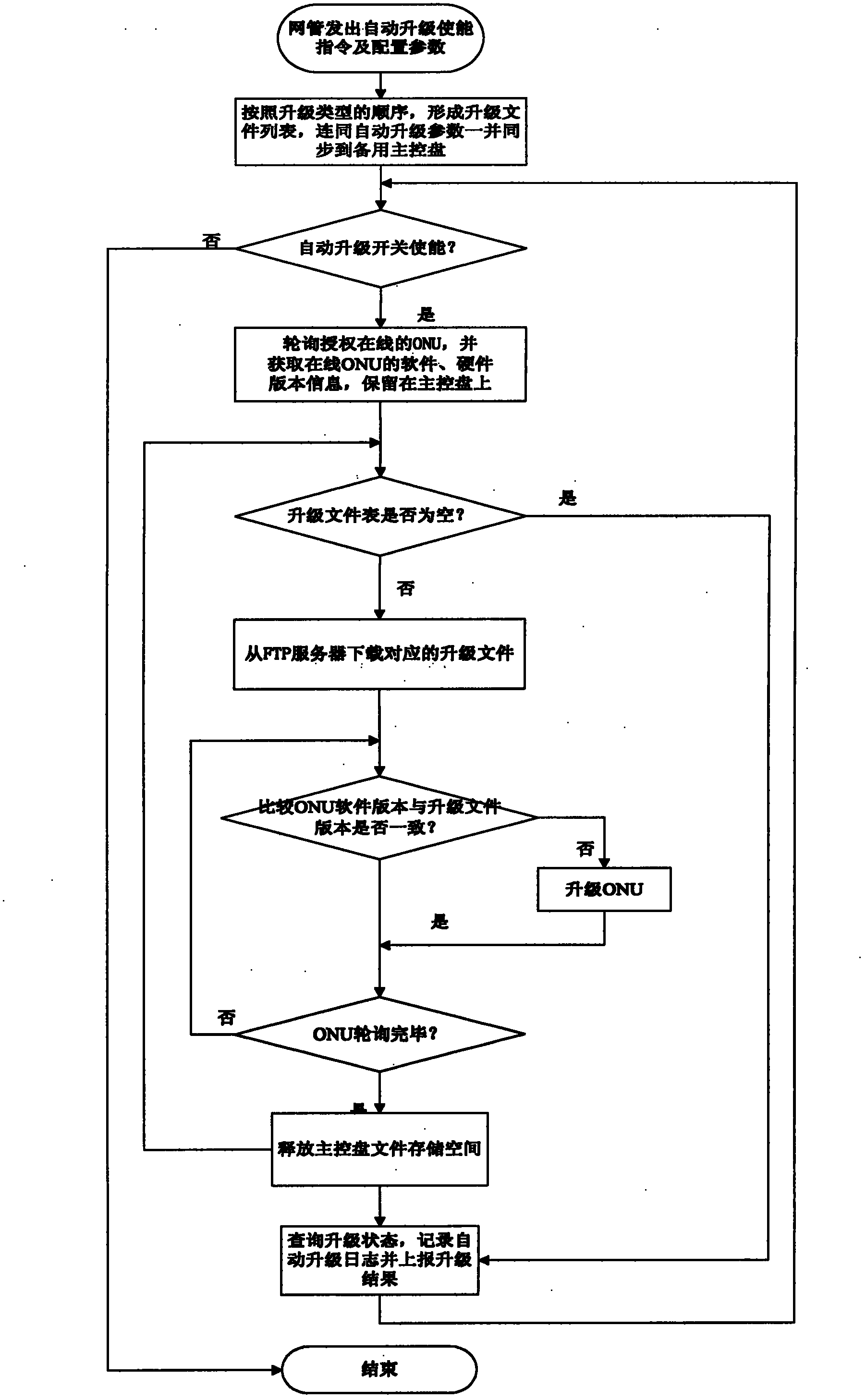
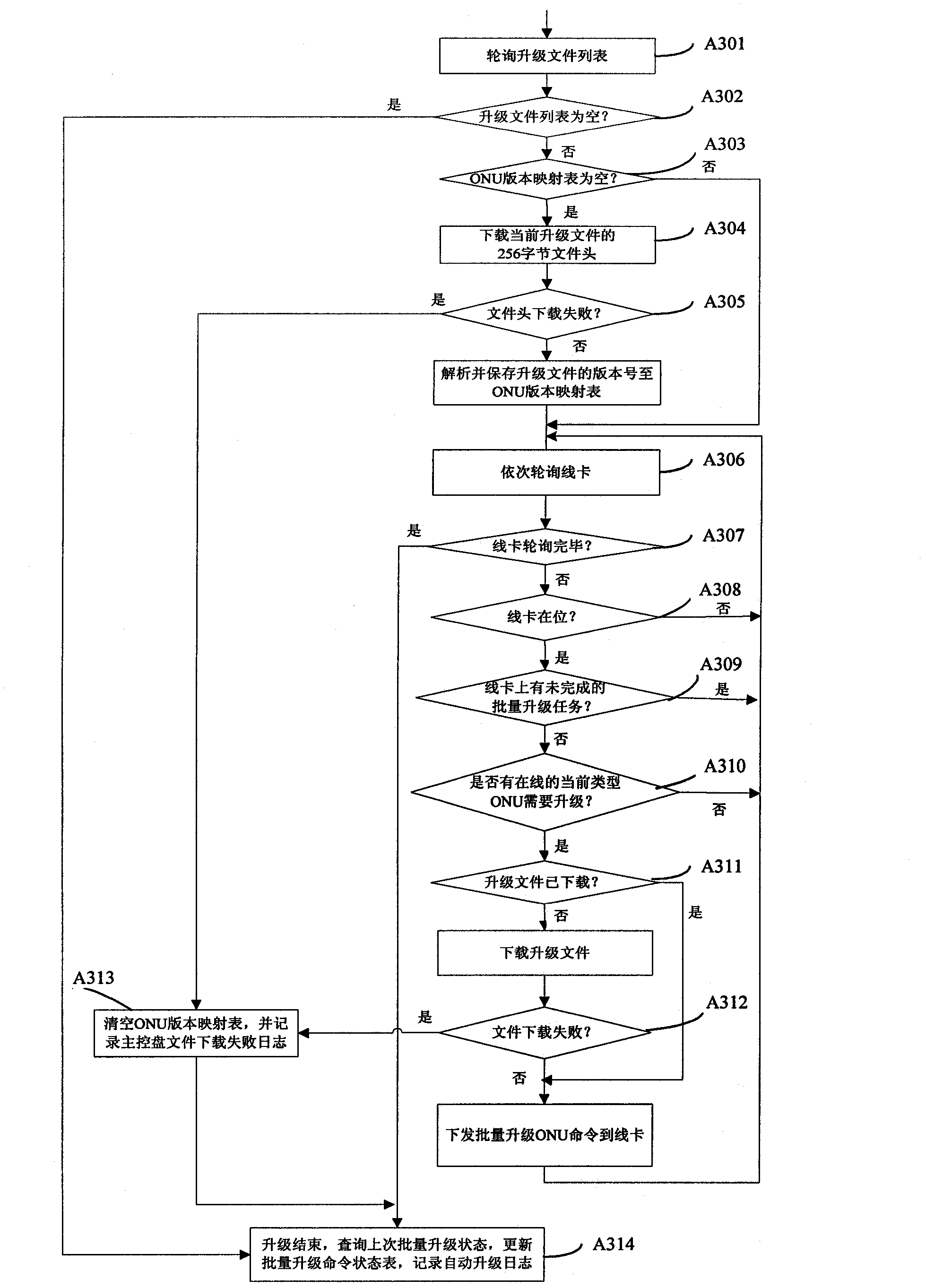
Method and system for multi-ONU (optical network unit) automatic upgrading in GPON (gigabit-capable passive optical network) access system
The invention discloses a method and a system for multi-ONU (optical network unit) automatic upgrading in a GPON (gigabit-capable passive optical network) access system. The method comprises the following steps: A10, a plurality of upgraded files are sorted to form an upgraded file list; A20, after a master control panel receives an automatic upgrade enabling instruction which is sent by a web master, the master control panel inquires in turn authorized and on-line OUN on each line card, and all on-line ONU hardware and software inversions are obtained; A30, the master control panel downloads a corresponding upgraded file into a memory according to the sequence of the upgraded file list, and sends batch upgrading orders and sends the upgraded files to a or a plurality of corresponding line cards according to the type of the ONU corresponding by the upgraded files, and the corresponding line cards control all ONU which take down from the line cards and are corresponding with the upgrading files to realize upgrading; A40, the master control plane releases the space which stores the upgraded files in the memory. According to the invention, the master control plane only downloads one upgraded file into the memory each time, and the pressure of the system memory is relieved greatly.
Owner:FENGHUO COMM SCI & TECH CO LTD
Method and system for displaying web pages on mobile communication terminal
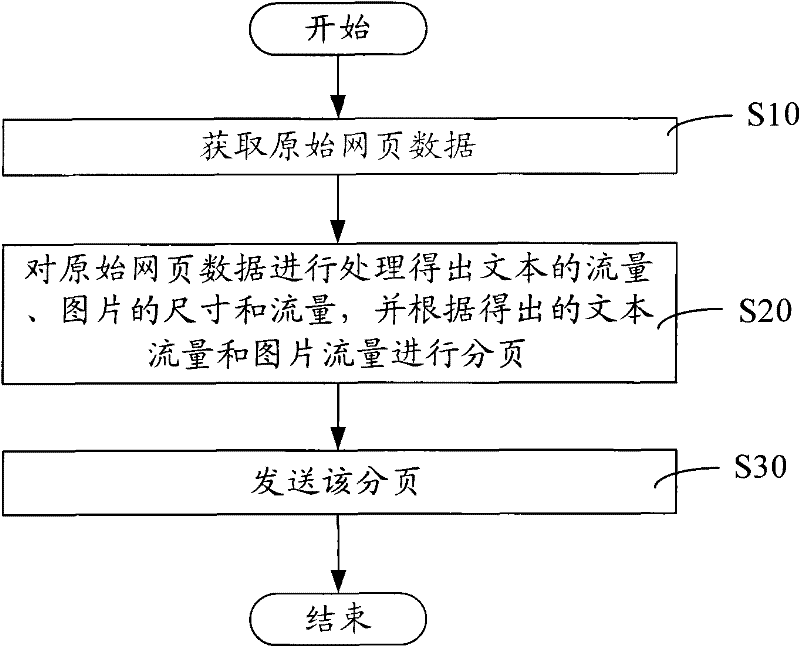
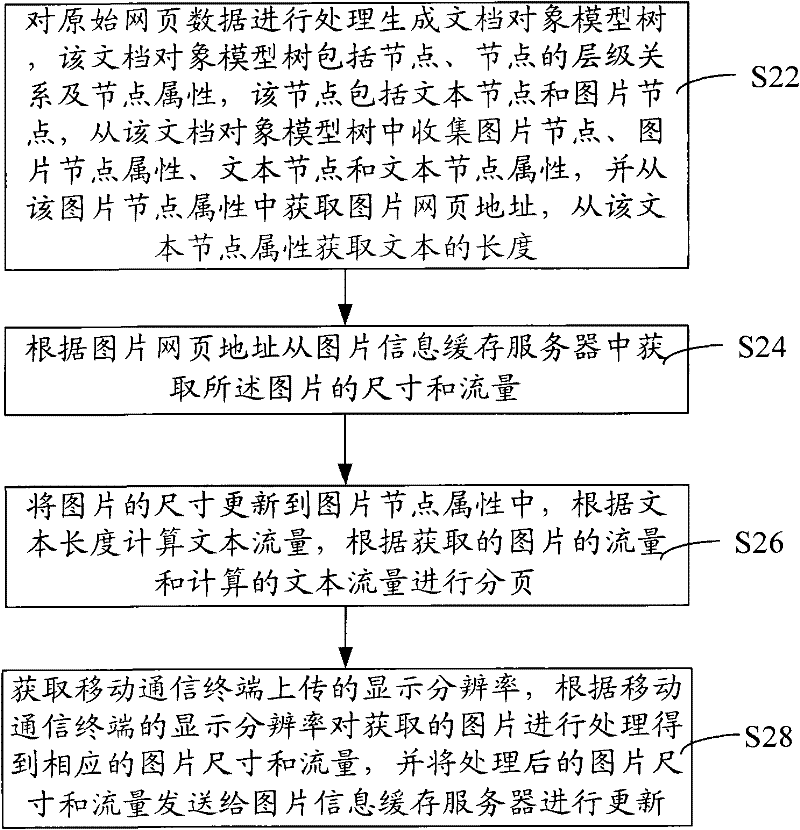
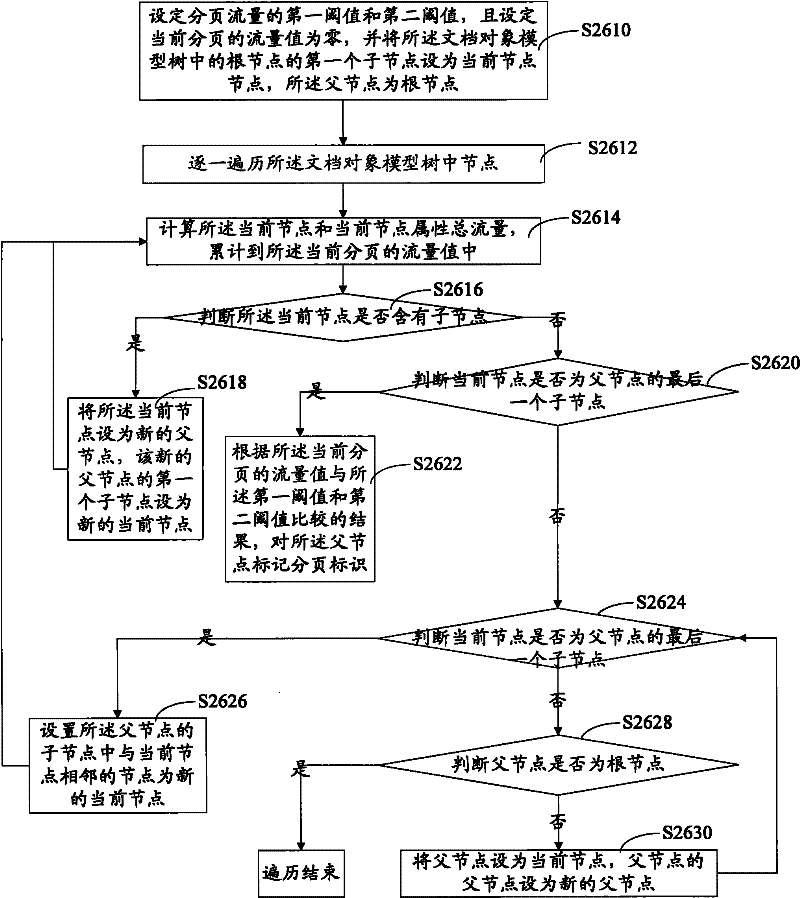
ActiveCN102457613AIncrease pressureRelieve pressureSubstation equipmentTransmissionTraffic volumePaging
The invention relates to a method and a system for displaying web pages on a mobile communication terminal. The method comprises the following steps of: obtaining initial web page data; processing the initial web page data to get text traffic, picture size and picture traffic, and paging according to the gotten text traffic and picture traffic; and transmitting the pages. In the method and the system for displaying the web pages on the mobile communication terminal, size and traffic of the pictures are obtained, paging is executed accurately according to the text traffic and the picture traffic, while displaying the web pages, space is reserved for the pictures, then, the pictures are obtained to fill the reserved space to form a complete page, type resetting for web page display is not needed, web browsing efficiency is improved and paging is accurate, increase of pressure on the memory of the communication terminal caused by oversize paging is avoided, and the pressure on the memory of the mobile communication terminal is reduced.
Owner:深圳市雅阅科技有限公司
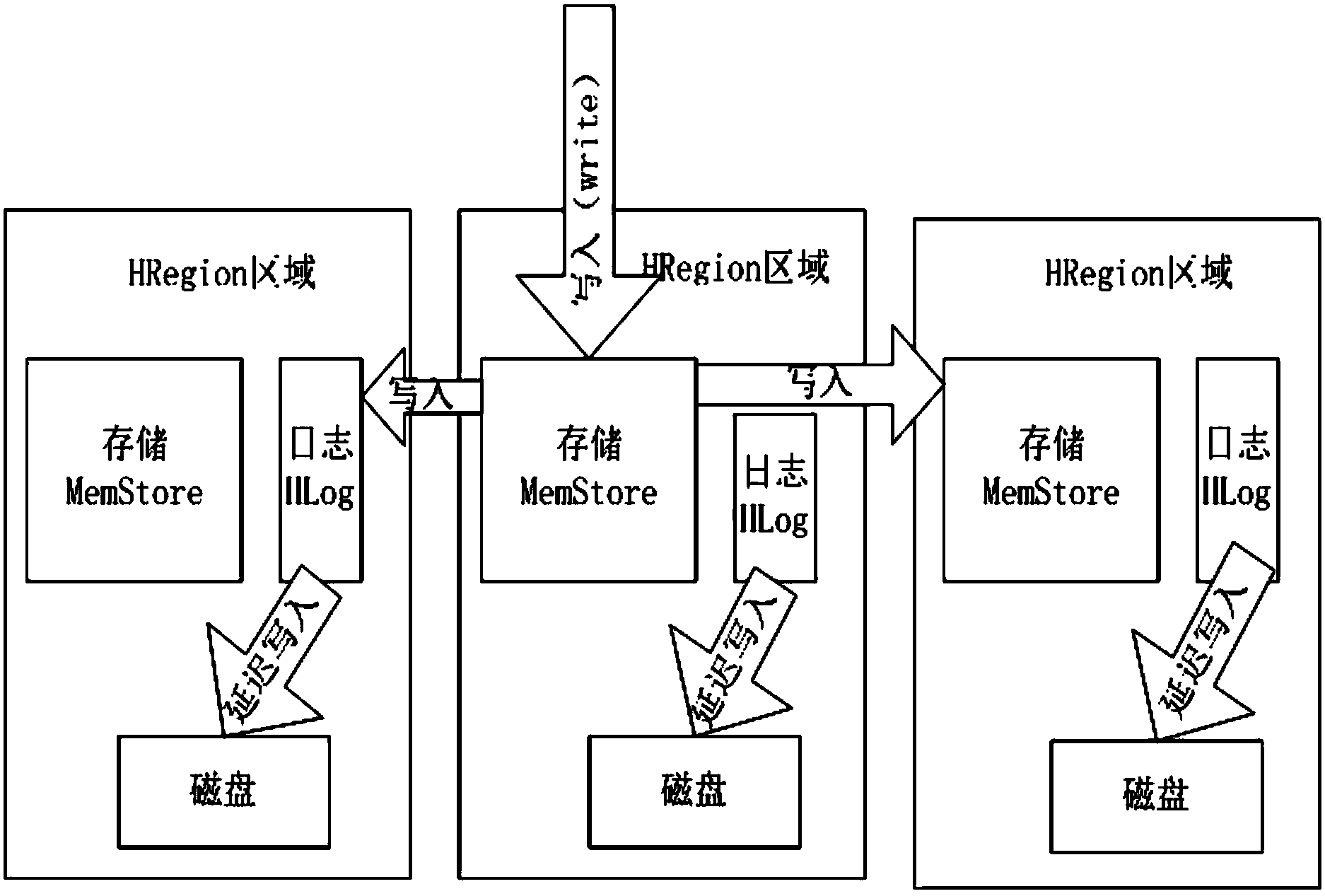
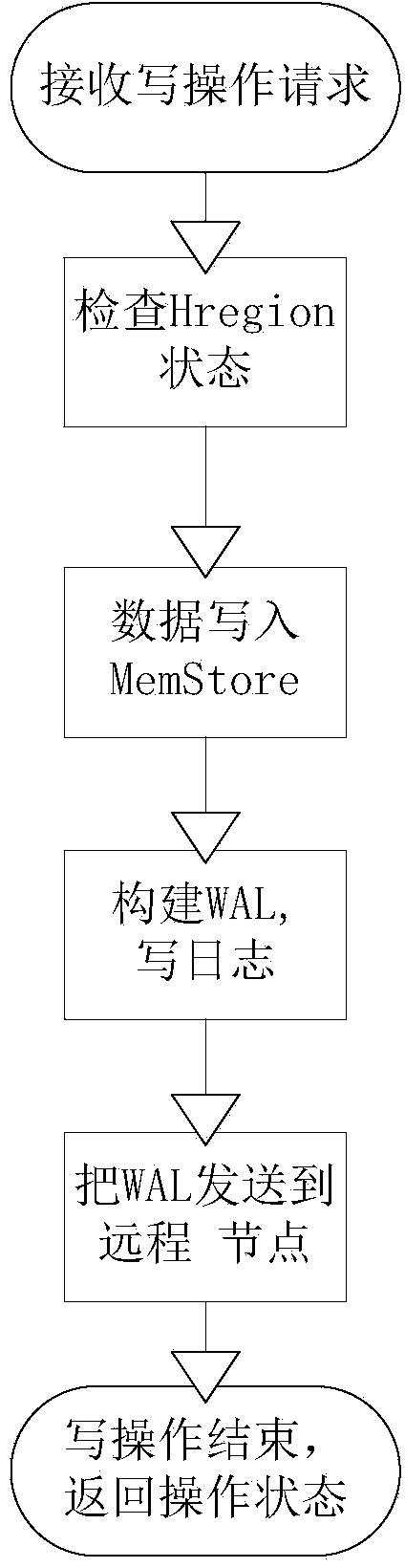
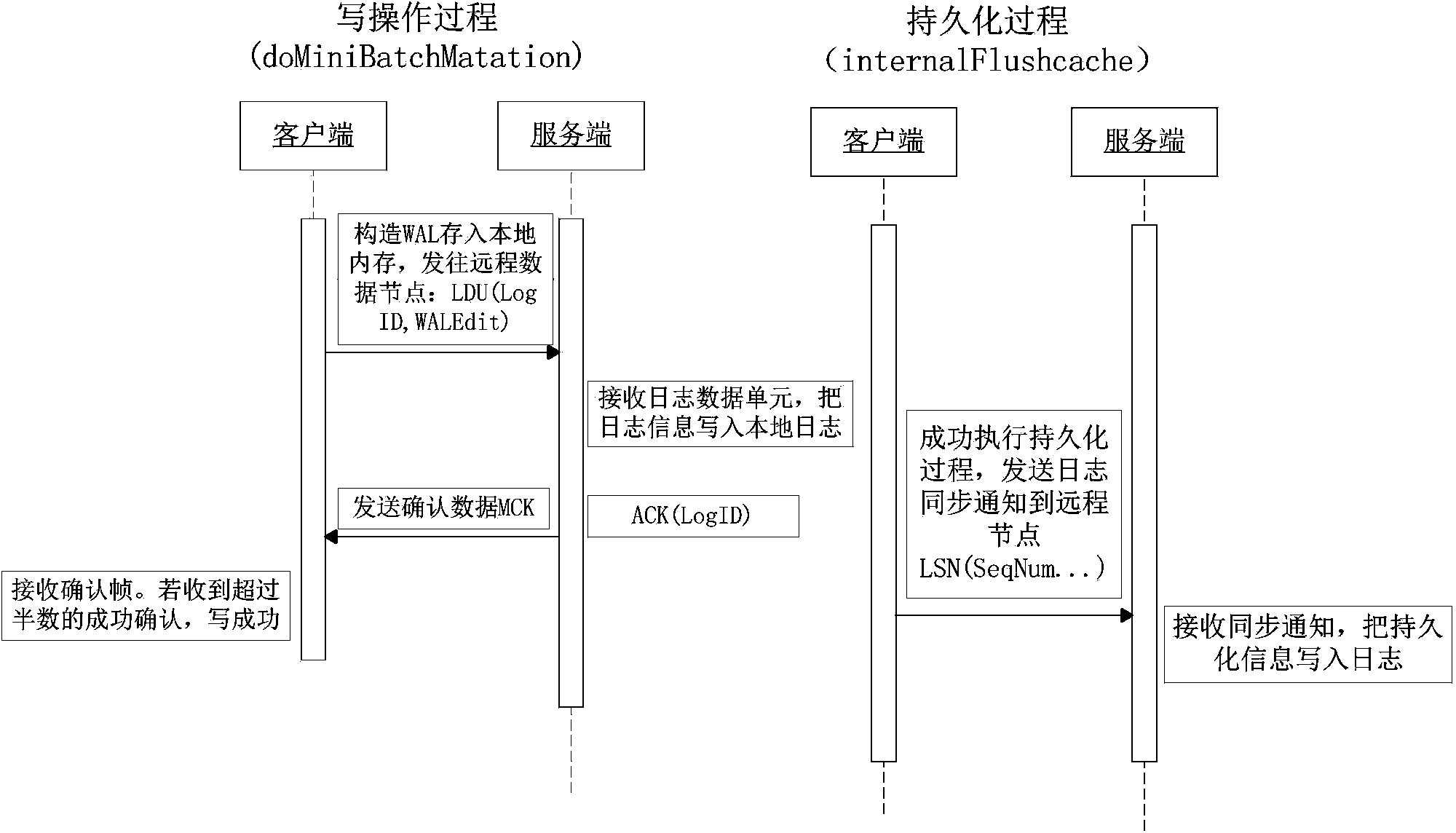
HBase (Hadoop database) data usability and durability method based on remote log backup
ActiveCN103870570AGuaranteed availabilityGuaranteed persistenceHardware monitoringSpecial data processing applicationsFile systemData node
The invention discloses an HBase (hadoop database) data usability and durability method based on remote log backup. The method is characterized in that when a data node of the HBase is written, the log record is first encapsulated through a distributive system, the log is backed up to a preliminarily-designated remote node through a network, the usability and durability of the data can be guaranteed, on the basis of the data, a great amount of user data and log record are temporarily stored in a memory, and the data persisting process in the data processing process is reduced; when the data node of the HBase is idle, the data in the memory is persisted to a file system, the storage pressure of the memory can be alleviated, the frequency of the persistence process in the writing process can be reduced, and the data writing time performance can be improved. By adopting the method, the usability and durability of the data can be guaranteed, the data writing speed can be greatly increased, and the system performance is improved.
Owner:上海艾讯云计算有限公司
Automatic tracking and positioning jet flow extinguishing method
InactiveCN105080023ARealize precise fire extinguishingThe positioning method is accurateFire rescueJet flowSurveillance camera
The invention discloses an automatic tracking and positioning jet flow extinguishing method. A camera is used for collecting on-site video images, the water falling point position is corrected through human assistance, and remote quick positioning of a fire point is achieved on a monitoring platform of an upper computer. The method comprises the steps that a fire source signal is detected through a jet flow extinguishing device, and the center position of a fire source region is determined preliminarily and sent to the upper computer so as to control the extinguishing device to spray water for extinguishing; according to on-site real-time monitoring videos collected by the monitoring camera, whether outflow water falls in an effective range of the center position of the fire source is judged, and if yes, adjustment is not needed; if the outflow water is out of range, human-assisted positioning adjustment is conducted on the water falling point position, and the water falling point is made to be in the effective range of the center position of the fire source. By the adoption of the extinguishing method, the positioning precision of an extinguishing system is improved to a great extent, the possibility of software misjudgment is reduced, and a guarantee is provided for quick, efficient and reliable operation of the fire-fighting extinguishing system.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
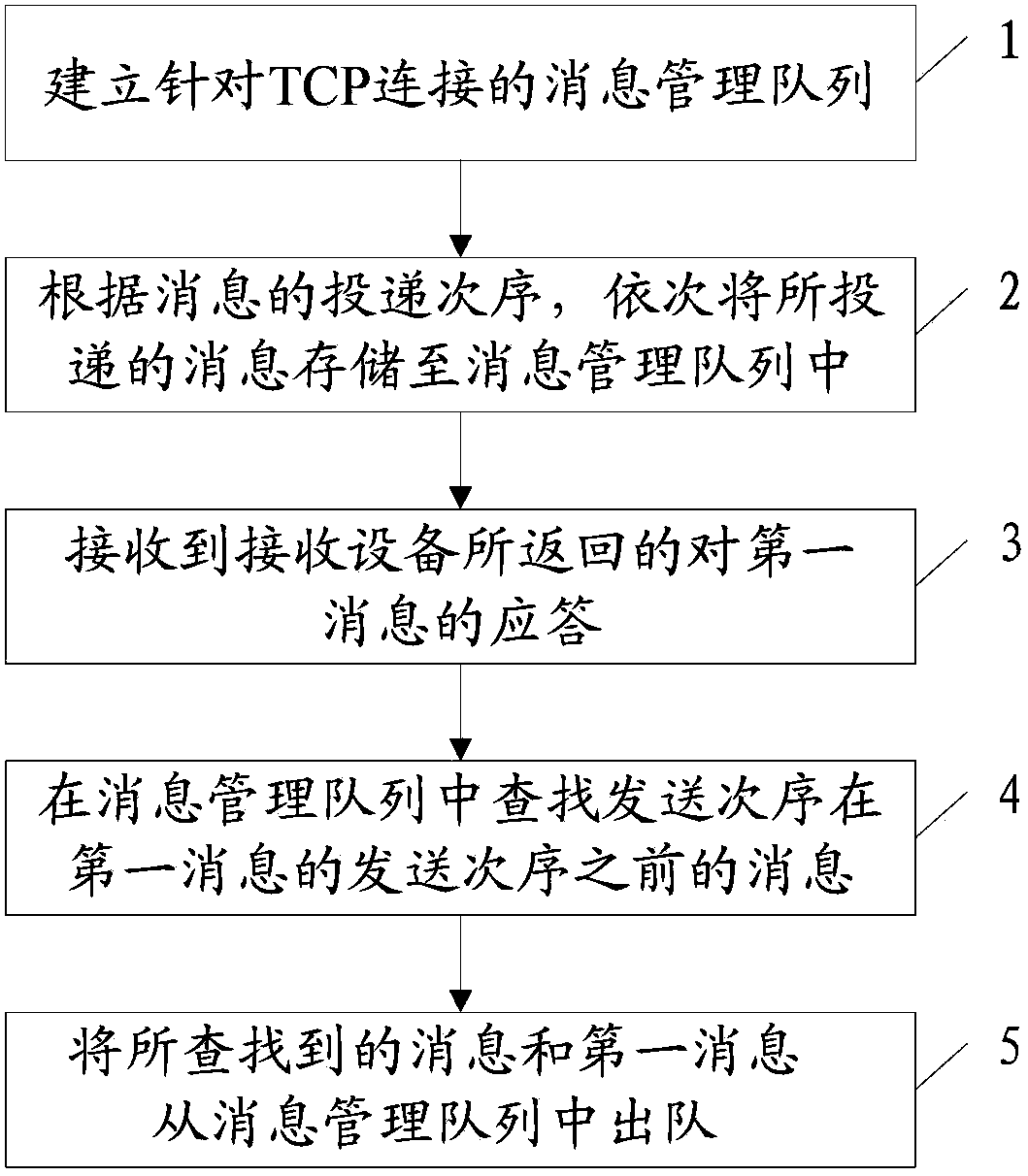
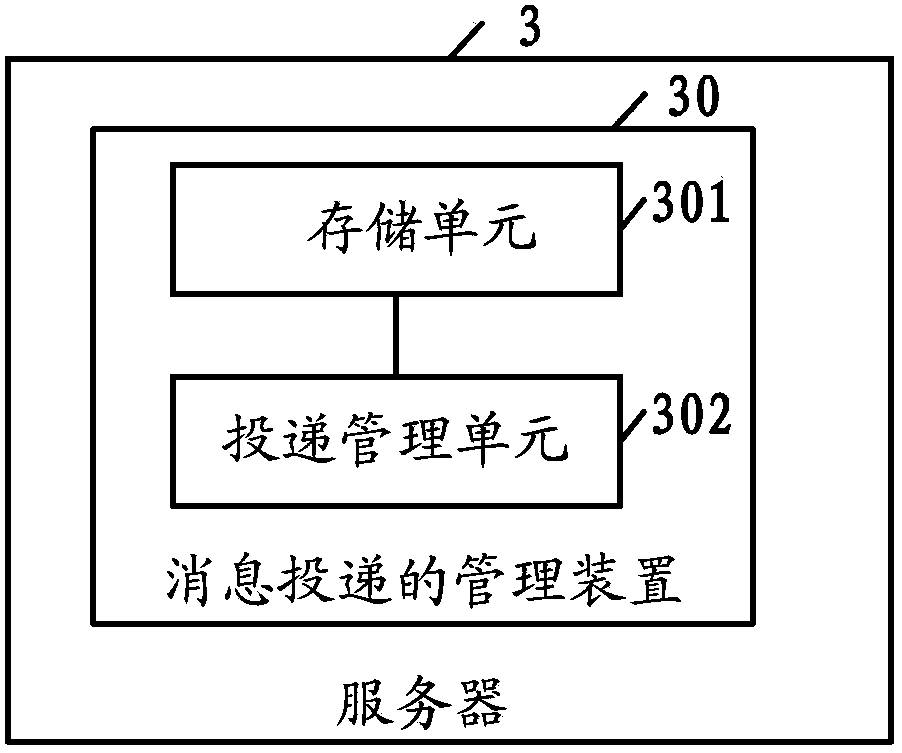
Management method for message delivery, server and system thereof
ActiveCN103532822AQuality improvementReduce memory pressureData switching networksMessage deliveryComputer science
The present invention discloses a management method for message delivery, a server and a system thereof. The management method has the functions of: reducing memory load of a server, accurately determining whether the message is successively transmitted, and improving message quality. The management method for message delivery according to one embodiment of the invention comprises the following steps: according to delivery order of the messages, storing the messages which are delivered by delivery equipment through a TCP connection, wherein the messages comprise first message; and when the response which is returned from receiving equipment for the first message is received, searching the message with delivery order which is before the delivery order of the first message from the stored messages, confirming success delivery of the searched message and the first message, and removing the searched message and the first message from the stored message.
Owner:ULTRAPOWER SOFTWARE
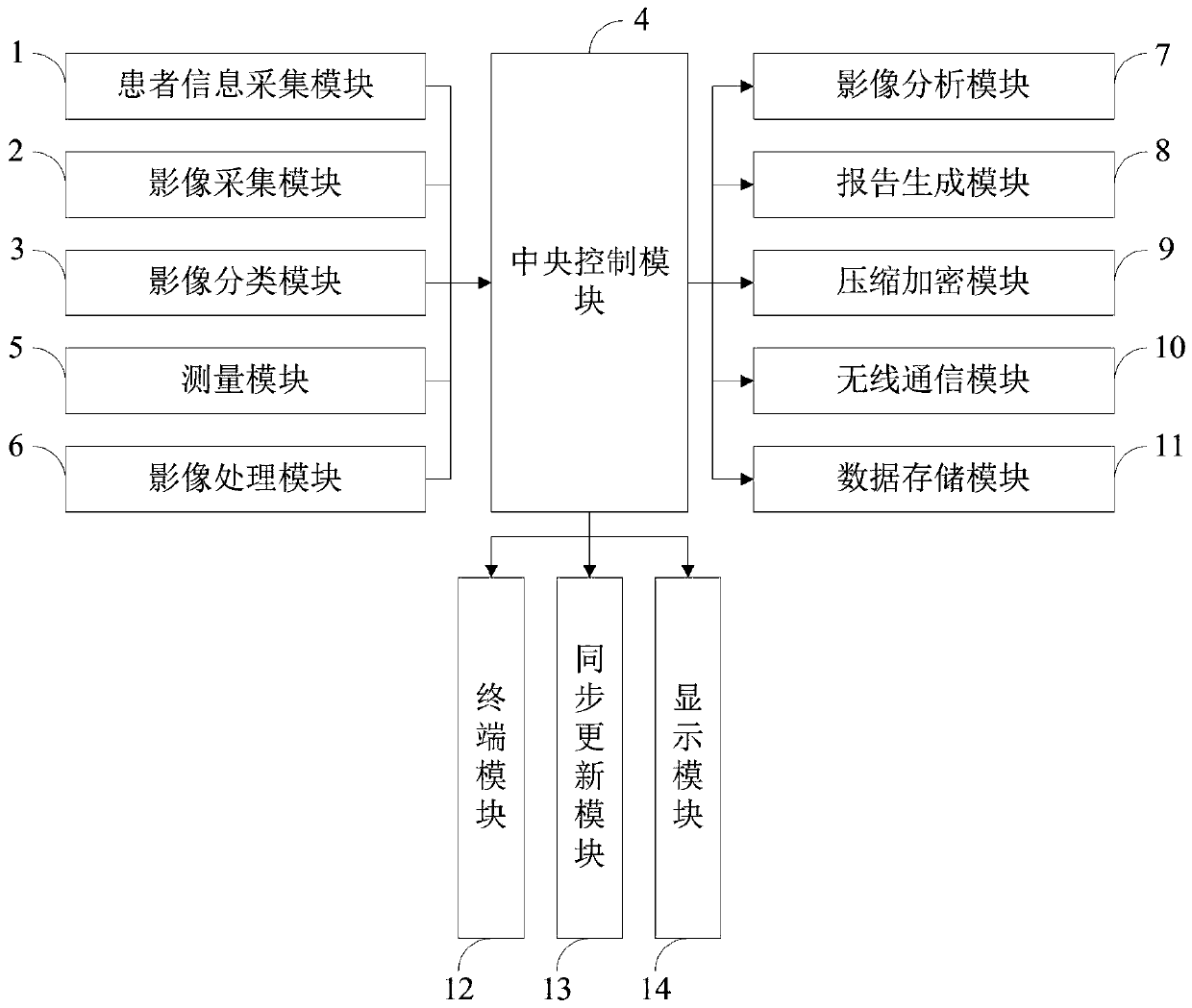
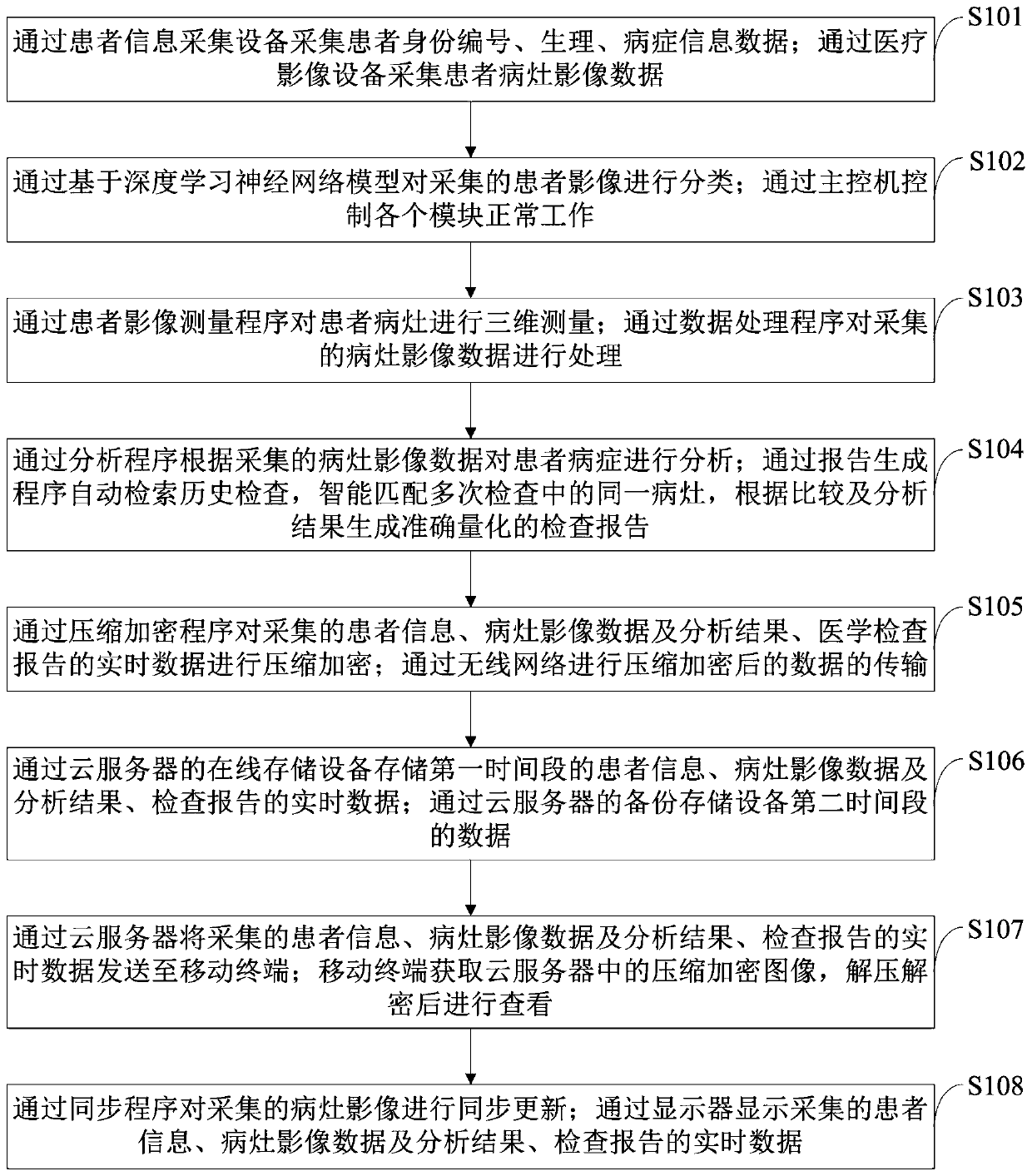
Intelligent AI PACS system and examination report information processing method thereof
PendingCN111223554AReduce loadImplement storageMedical data miningMedical imagesInformation processingVoxel
The invention belongs to the technical field of medical images, and discloses an intelligent AI PACS system and an examination report information processing method thereof. The intelligent AI PACS system comprises a patient information acquisition module, an image acquisition module, an image classification module, a central control module, a measurement module, an image processing module, an image analysis module, a report generation module, a compression encryption module, a wireless communication module, a data storage module, a terminal module, a synchronous updating module and a display module. All voxel data of a focus can be comprehensively collected through the measurement module, the measurement result is closer to the real volume of the focus, and objectivity and accuracy are high; through the synchronization module, image data of all hospital PACS systems can be synchronized with low cost, a convenient mode is provided for patient transfer, storage and management of self-image data by a patient are realized, and complete image data of the patient are provided for diagnosis of clinicians.
Owner:WEST CHINA HOSPITAL SICHUAN UNIV
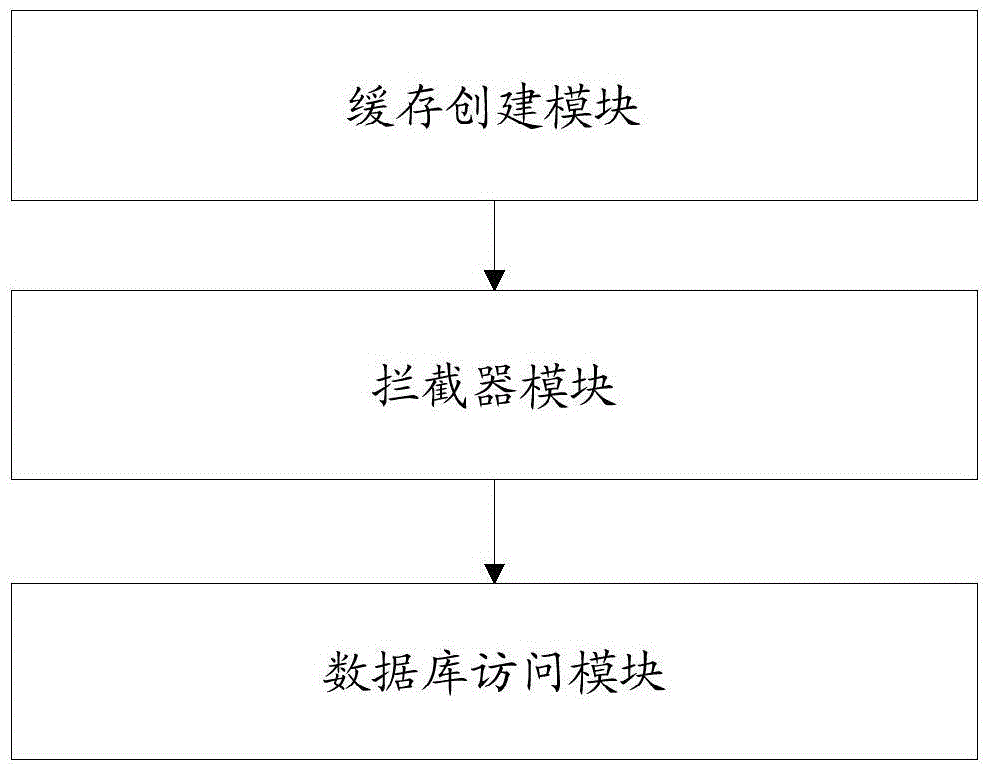
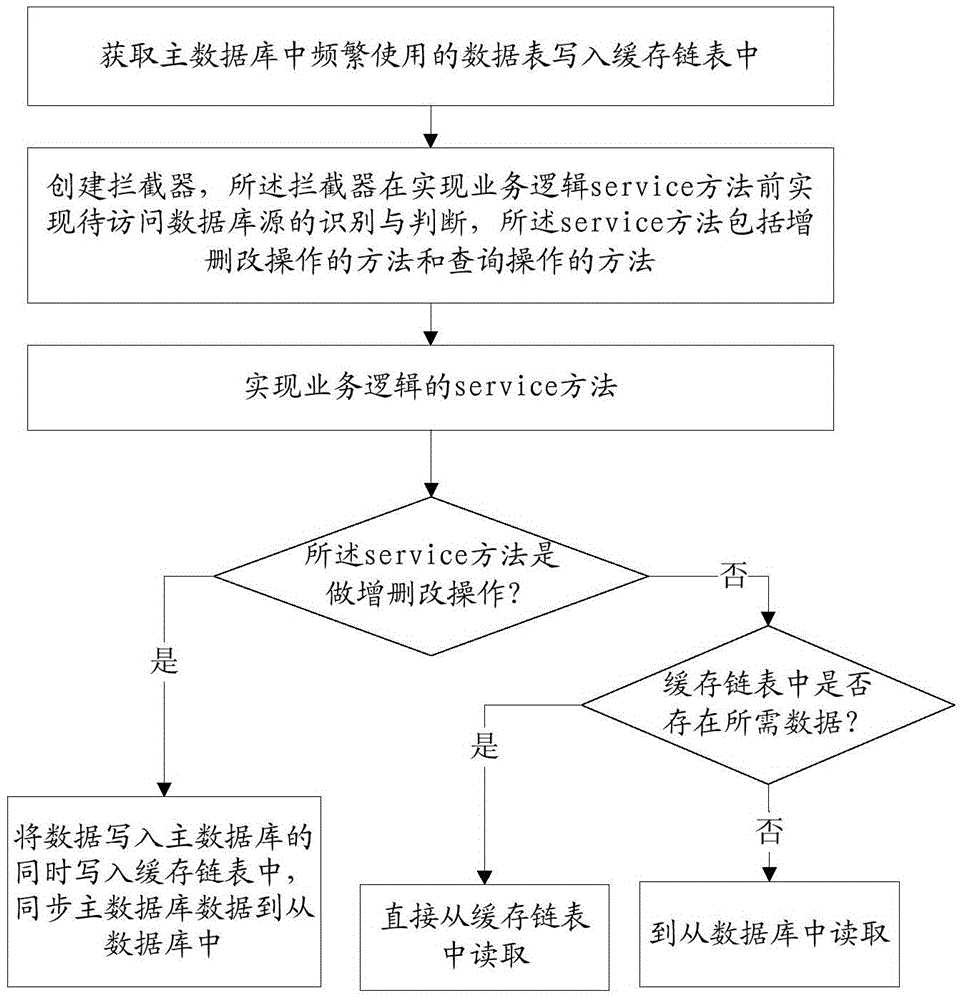
System and method for synchronizing master-slave databases
InactiveCN105608229AReduce accessRelieve pressureDatabase distribution/replicationSpecial data processing applicationsDatabase accessLinked list
The invention provides a system and method for synchronizing master-slave databases. The system comprises a cache creating module, an interceptor module and a database access module. The method comprises the steps: acquiring data sheets frequently used in a master database, and writing the data sheets in a cache chain table; creating an interceptor which is used for achieving identification and judgment on a database source to be accessed before achieving a business logic service method, wherein the service method comprises an adding, deleting and revising method and a querying method; if the service method carries out adding, deleting and revising operations, writing data in the cache chain table while writing the data in the master database, and synchronizing the data of the master database to a slave database; if the service method carries out a querying operation, judging whether data required exist in the cache chain table or not, reading the data directly from the cache chain table if the data required exist in the cache chain table, or reading the data from the slave database if the data required do not exist in the cache chain table. According to the system and the method, the problem that the databases are out of sync is solved, latest data are read in real time, and meanwhile, the access efficiency is increased.
Owner:RETURNSTAR INTERACTIVE TECH GRP
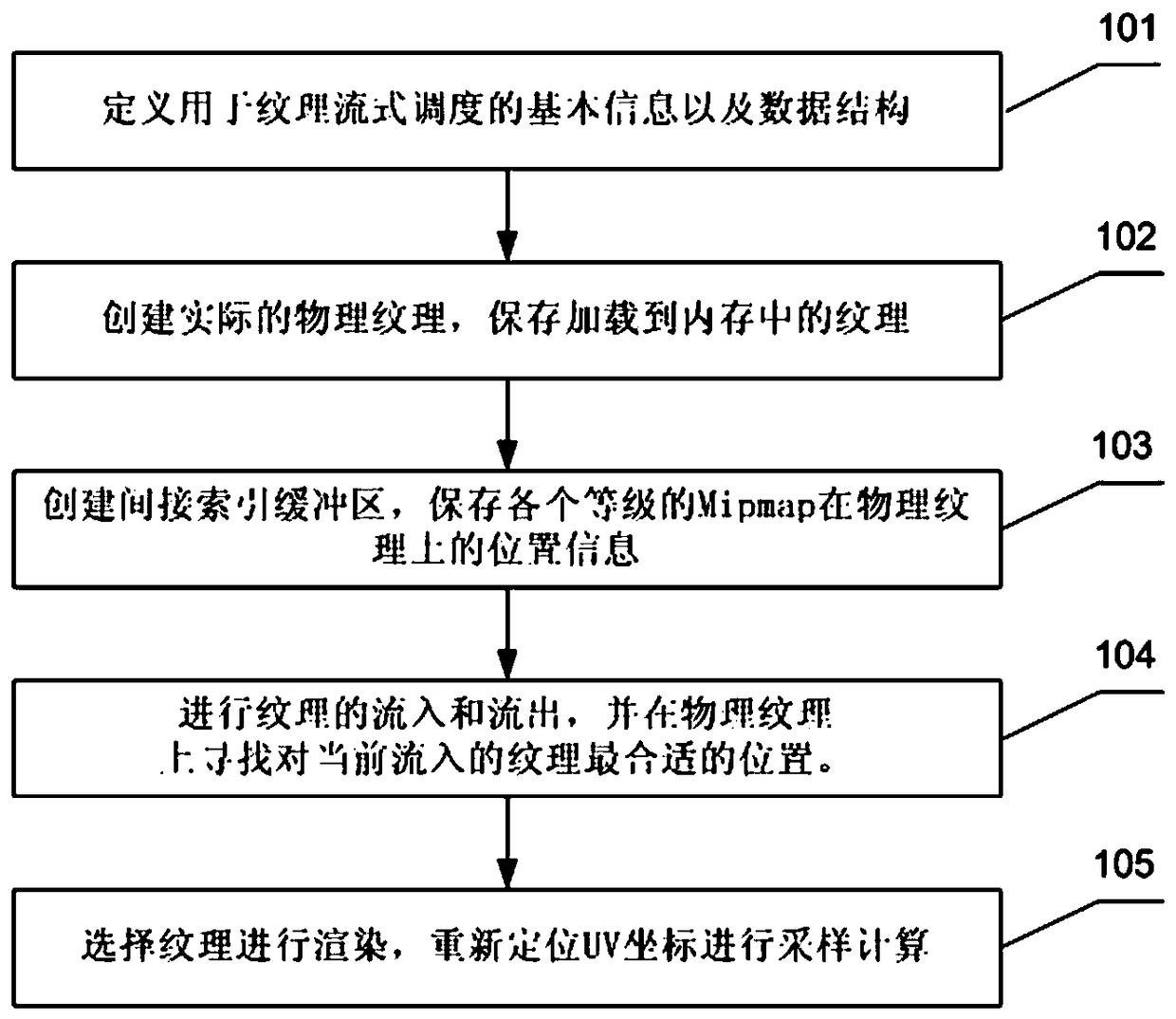
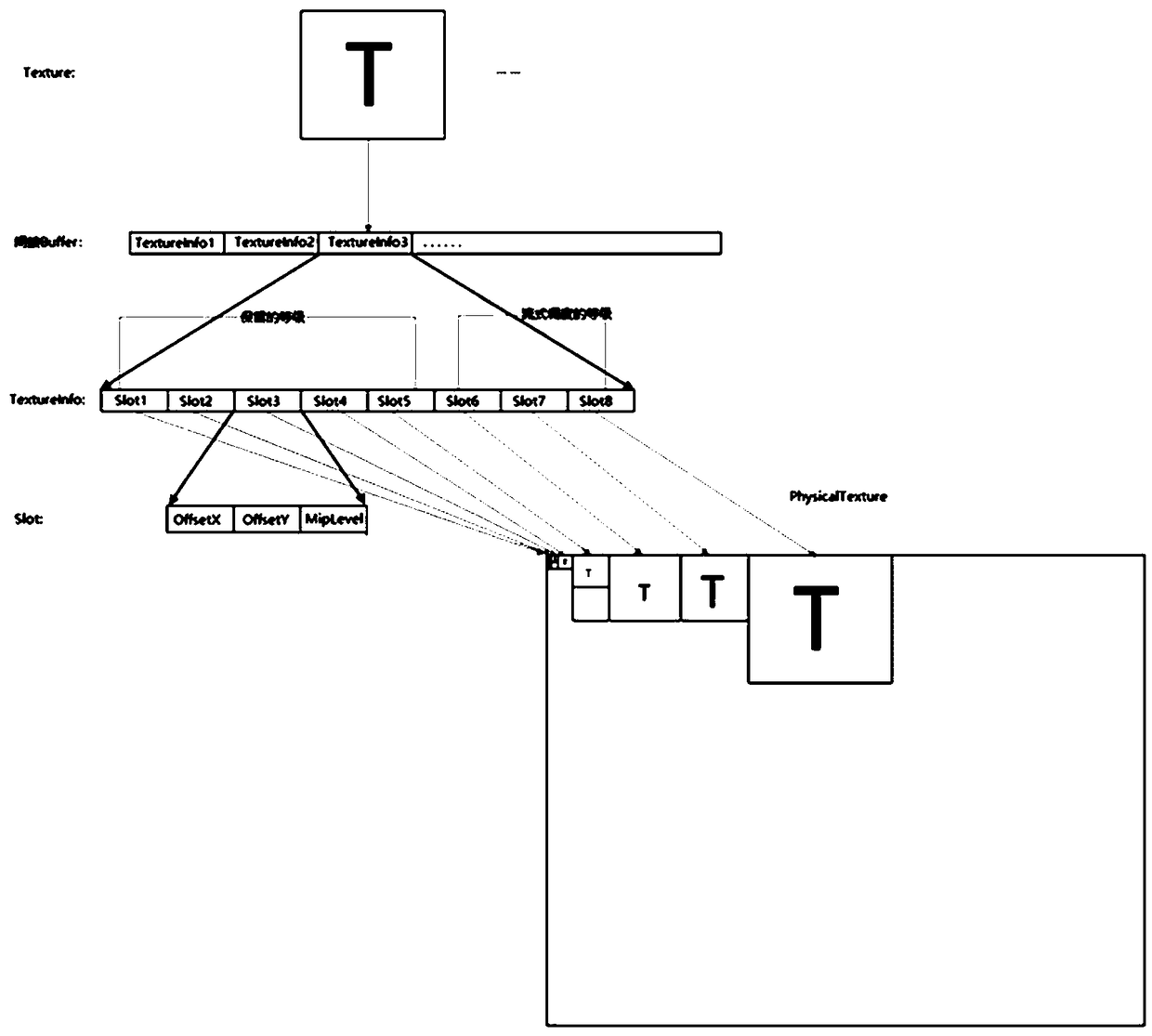
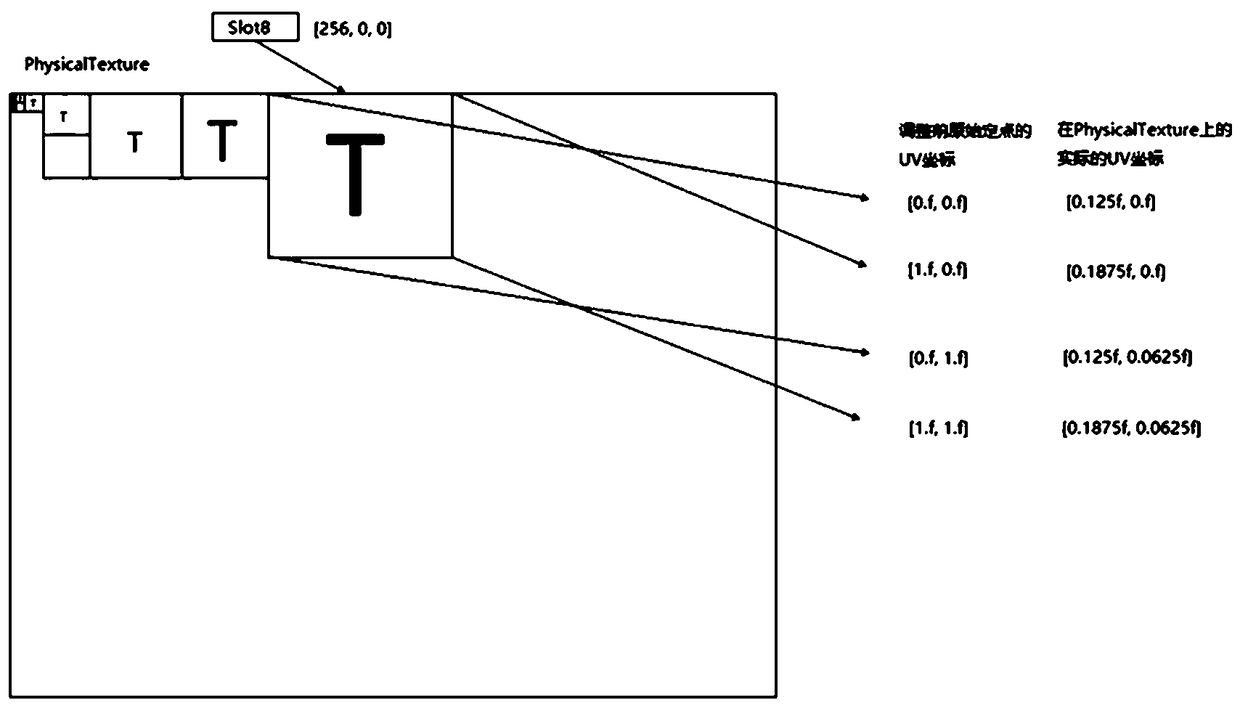
A texture atlas scheduling method
A texture atlas scheduling method comprises the following steps of determining basic information for texture streaming scheduling and a data structure; creating the actual physical texture and save the texture loaded into memory; creating an indirect index buffer to store the location information of Mipmap on the physical texture; according to the level of detail information of texture, carrying out the inflow and outflow of texture, and according to the rectangular texture packing algorithm, finding the position information of the current inflow texture on the physical texture; rendering thetexture and relocating the UV coordinates for sampling calculation. The texture atlas scheduling method of the invention is based on a rectangular texture packing algorithm, and effectively reduces the number of DrawCalls by merging texture maps, so that the rendering efficiency is improved. Through the scheduling of textures, the memory usage can be reduced, the necessary texture resources can beloaded gradually, and the memory pressure can be reduced. The invention can effectively reduce the pressure of the graphics processing unit in the rendering process.
Owner:SNAIL GAMES
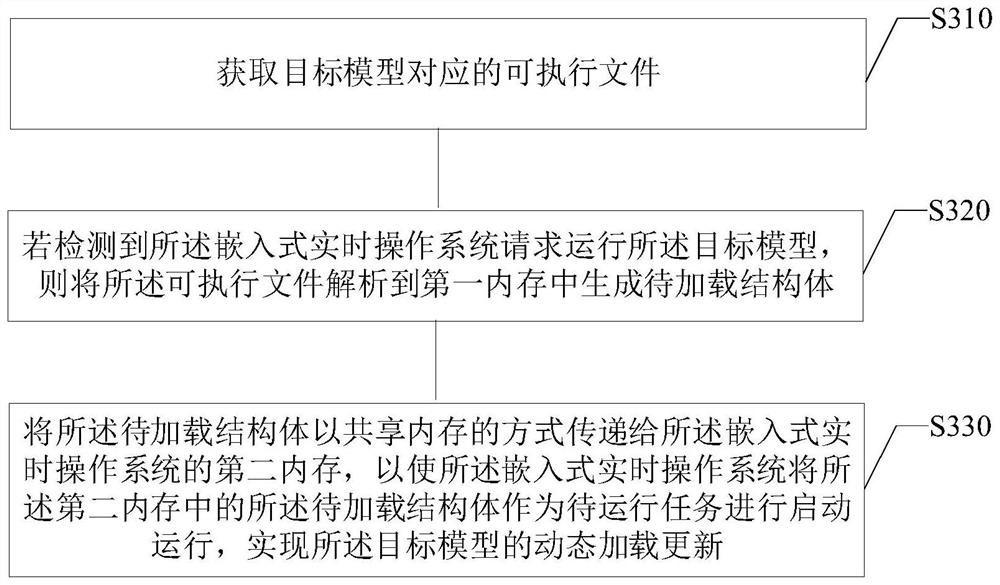
Target model loading and updating method and device, readable medium and electronic equipment
PendingCN113641413AImplement dynamic loadingRealize dynamic loading updateBootstrappingProgram loading/initiatingEngineeringMemory sharing
The invention provides a target model loading and updating method and device, a computer readable medium and electronic equipment, and relates to the technical field of computers. The method comprises the following steps: obtaining an executable file corresponding to a target model; if it is detected that an embedded real-time operating system requests to run the target model, analyzing the executable file to generate a to-be-loaded structure; and transmitting the to-be-loaded structure to a second memory of the embedded real-time operating system in a memory sharing manner, so that the embedded real-time operating system starts and runs the to-be-loaded structure as a to-be-run task, and loading and updating of the target model are realized. According to the invention, dynamic loading or updating of an artificial intelligence model can be realized in a SensorHub environment, the artificial intelligence model and an OS kernel do not need to be compiled into a complete mirror image to run in the SensorHub every time, the updating efficiency of the artificial intelligence model in the SensorHub environment is effectively improved, and the memory space is saved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
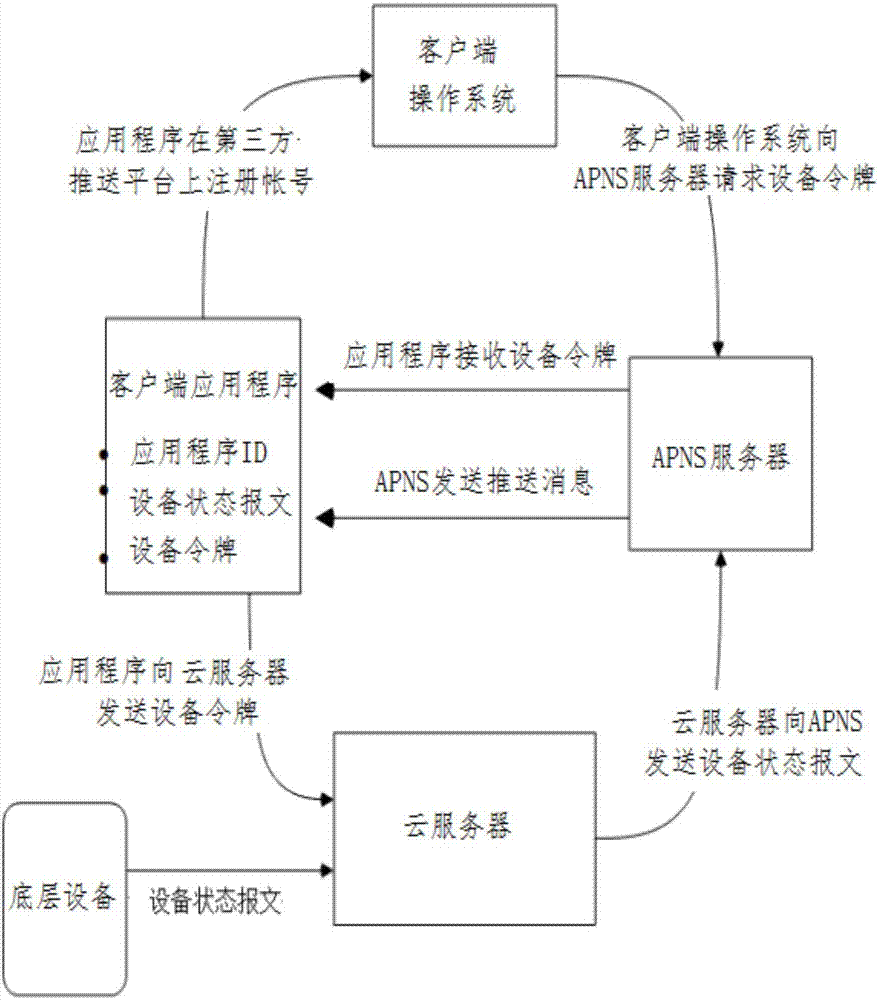
Third party push platform-based client message refresh method
The present invention relates to a third party push platform-based client message refresh method applied to a smart home system. The smart home system includes an underlying device, a smart host, a cloud server and a client, wherein the client is used for communicating with the cloud server and controlling the operation of the underlying device through the cloud server and the smart host. The third party push platform-based client message refresh method comprises the following steps that: the smart home system transmits a device status message to a third party push platform when the status of the underlying device changes; the third party push platform transmits the device status message to a client message push server; and the client message push server pushes the device status message to the client. With the third party push platform-based client message refresh method adopted, the real-time performance of the state refresh of the client device can be improved, and the pressure of the memories of the cloud server and the client can be decreased.
Owner:EAST CHINA JIAOTONG UNIVERSITY
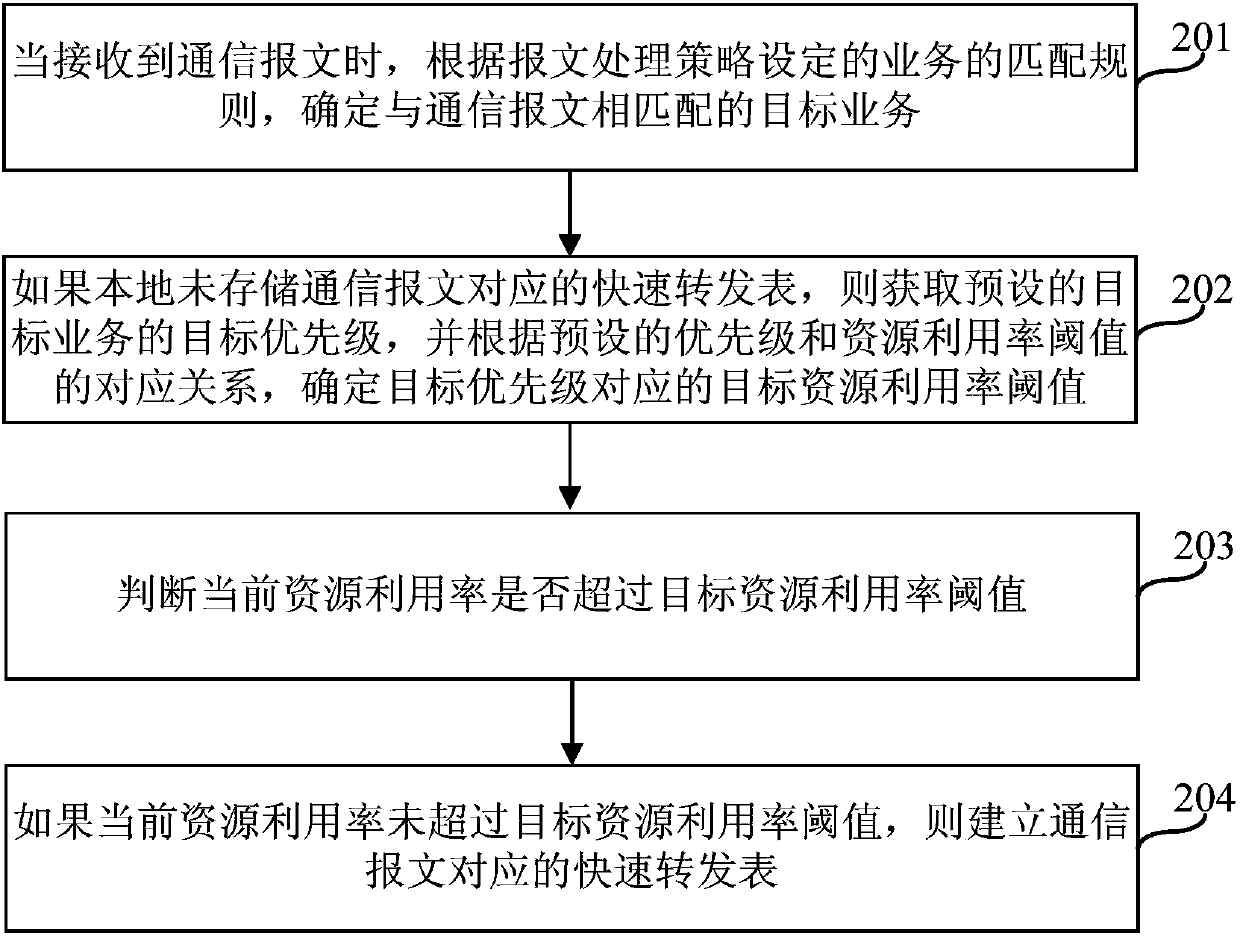
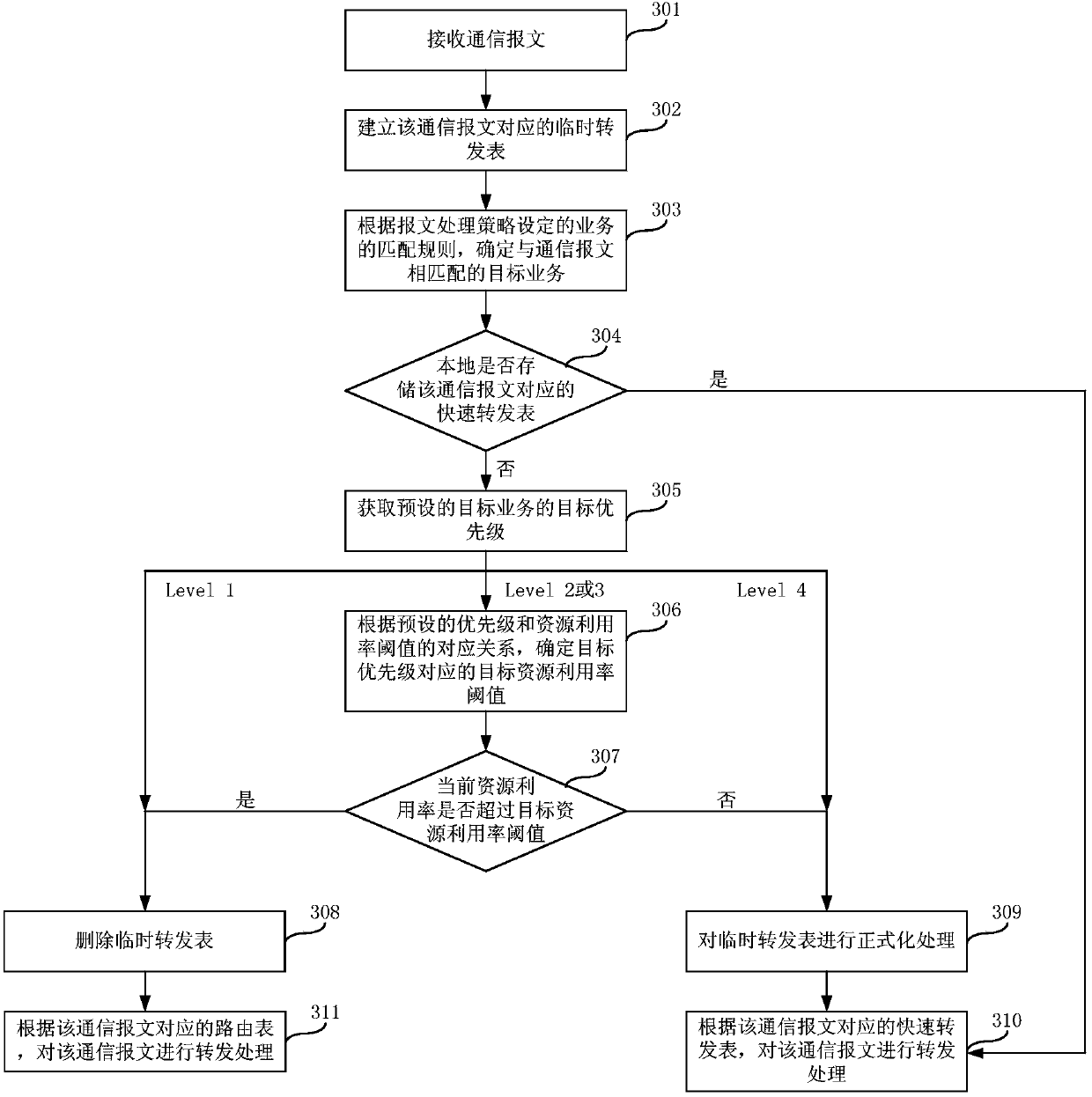
Method and device for establishing fast forwarding table
ActiveCN110278152AReduce memory pressurePrevent hangingData switching networksResource utilizationMessage processing
The embodiment of the invention provides a method and a device for establishing a fast forwarding table, and belongs to the technical field of communication. The method comprises the following steps: when a communication message is received, according to a service matching rule set according to a message processing strategy, determining a target service matched with the communication message, if the fast forwarding table corresponding to the communication message is not stored locally, obtaining a preset target priority of the target service, according to a corresponding relation between a preset priority and a resource utilization rate threshold value, obtaining a resource utilization rate; and determining a target resource utilization rate threshold value corresponding to the target priority, judging whether the current resource utilization rate exceeds the target resource utilization rate threshold value, and if the current resource utilization rate does not exceed the target resource utilization rate threshold value, establishing a fast forwarding table corresponding to the communication message. By adopting the method and the device, the memory pressure of the network equipment can be reduced, and the network equipment is prevented from being suspended or restarted.
Owner:NEW H3C SECURITY TECH CO LTD
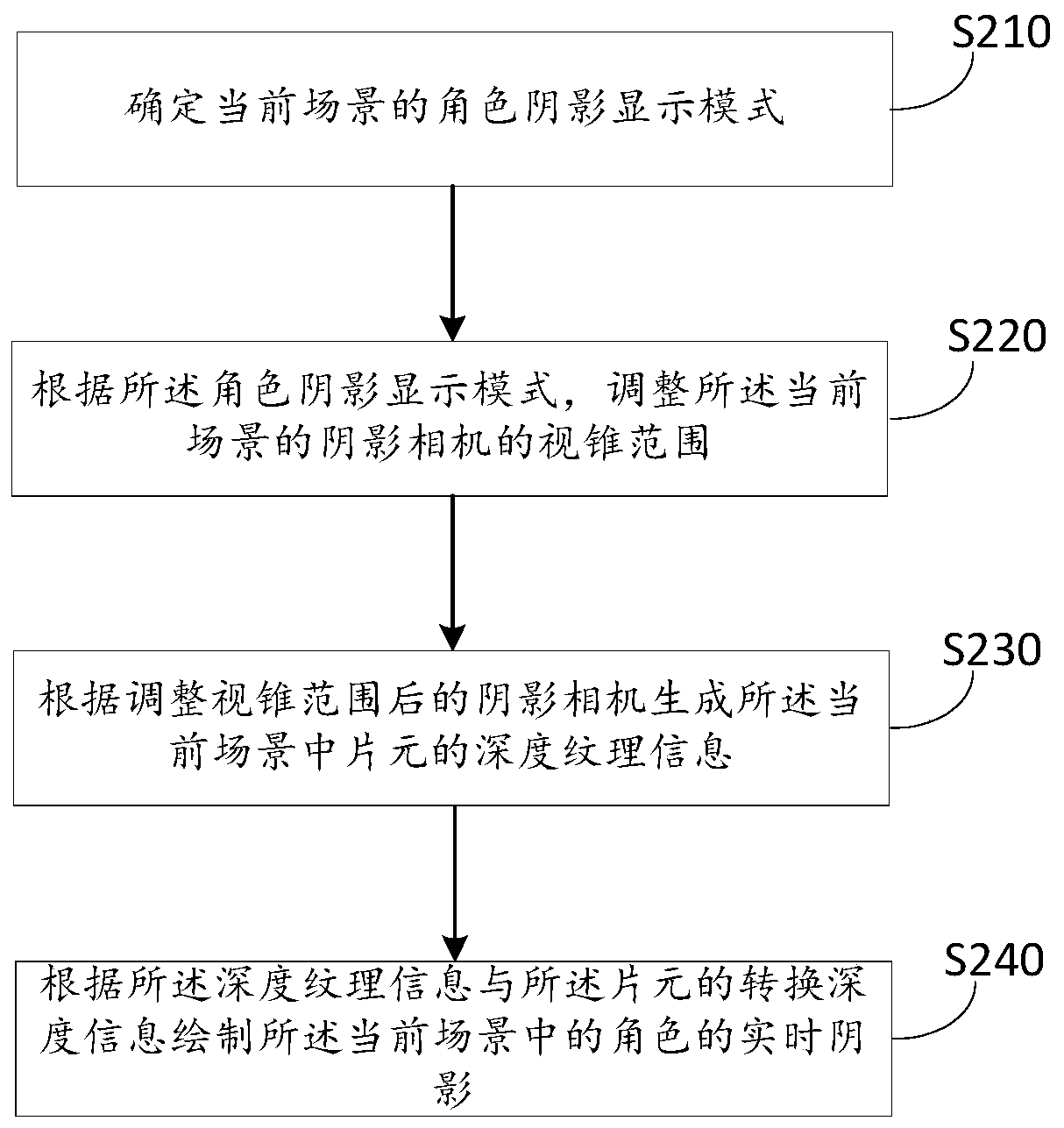
Shadow implementation method and device of game scene, electronic equipment and readable medium
ActiveCN110585713AImprove shadow precisionIncrease speedAnimationVideo gamesOccupancy rateComputer graphics (images)
Embodiments of the invention provide a shadow implementation method and device of a game scene, electronic equipment and a readable medium. The method comprises the following steps of determining a character shadow display mode of a current scene; according to the character shadow display mode, adjusting a view cone range of a shadow camera of the current scene; generating depth texture information of a fragment in the current scene according to the shadow camera subjected to the adjustment of the view cone range; and drawing a real-time shadow of a character in the current scene according tothe depth texture information and conversion depth information of the fragment. According to the shadow implementation method and device of the game scene, the electronic equipment and the readable medium, according to different character shadow display modes, the view cone range of the shadow camera is adjusted, so that a shadow picture can be optimized and the memory occupancy rate of shadow sampling is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
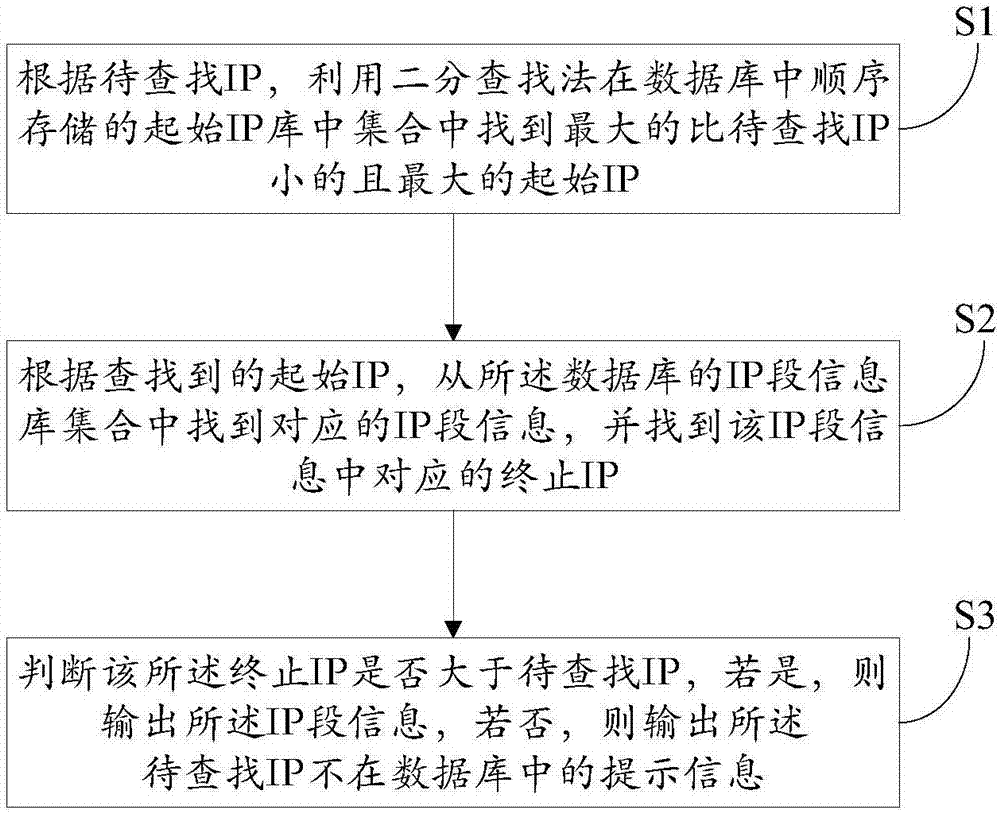
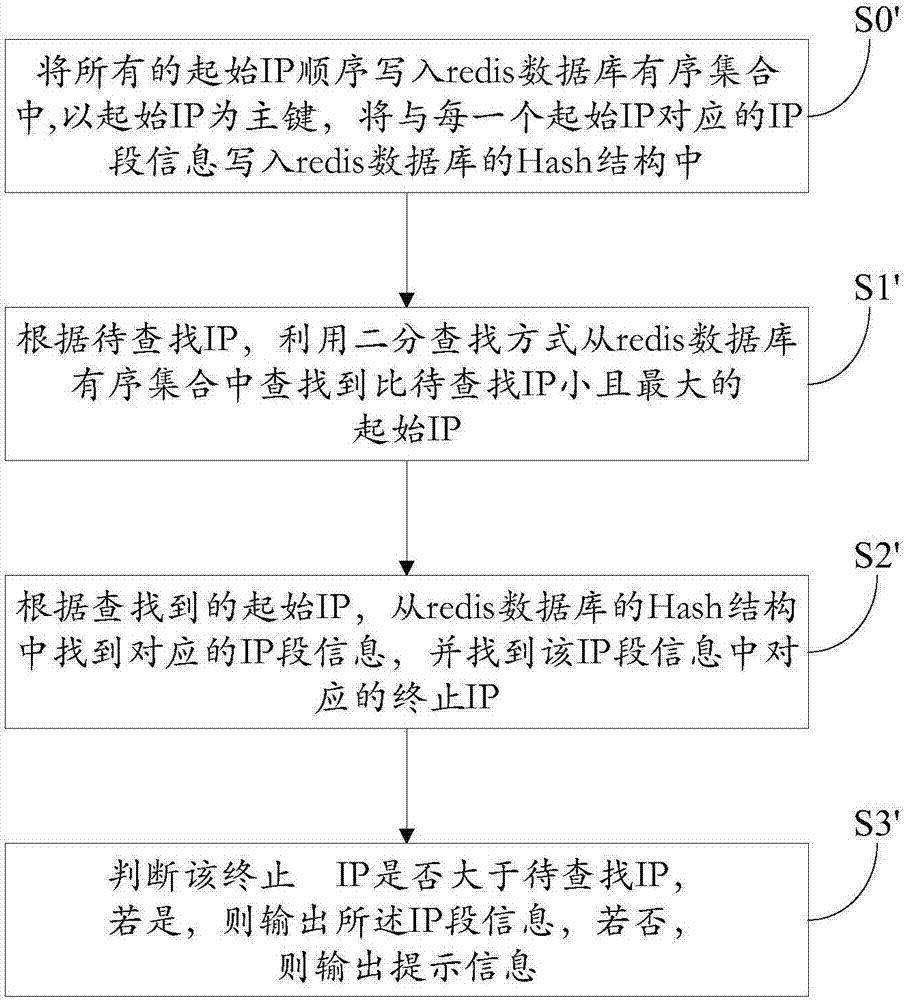
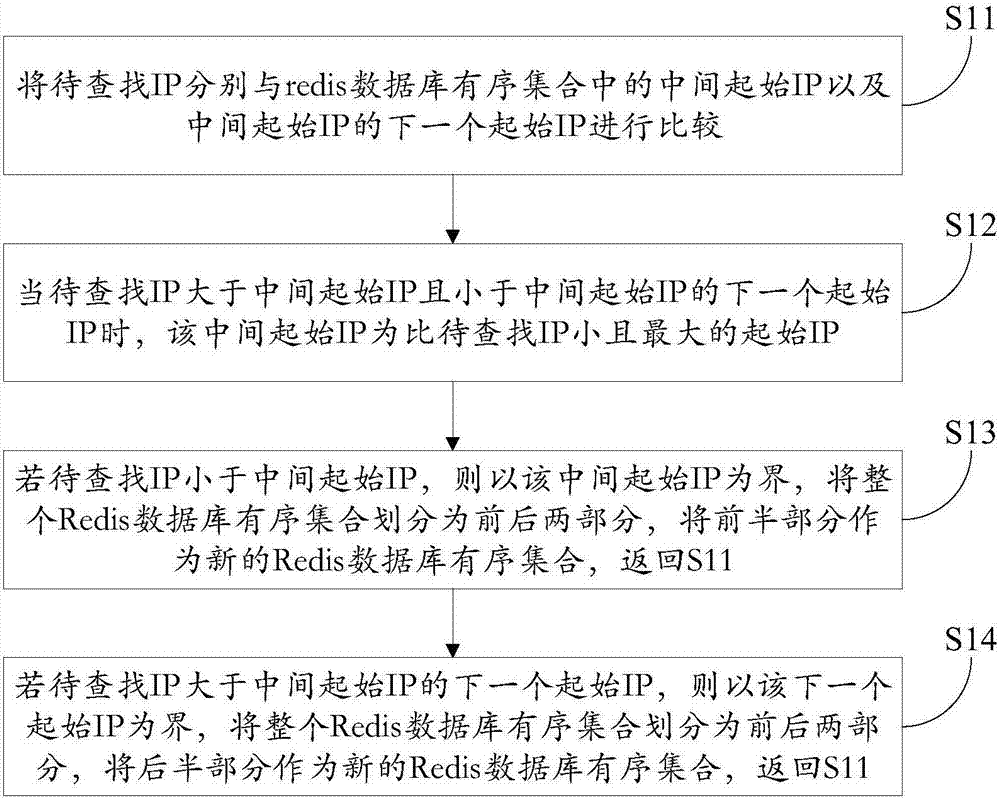
Method and system for positioning within IP (internet protocol) range based on binary finding method
InactiveCN106940708AReduce memory pressureImprove search efficiencySpecial data processing applicationsWorld Wide WebInternet Protocol
The invention relates to a method and a system for positioning within IP (internet protocol) range based on a binary finding method. The method comprises the following steps of S1, according to to-be-found IP, utilizing the binary finding method to find the maximum initial IP which is smaller than the to-be-found IP from an initial IP set which is sequentially stored in a database; S2, according to the found initial IP, finding the IP field information corresponding to an IP field information set of the database, and finding the corresponding final IP of the IP field information; S3, judging whether the final IP is greater than the to-be-found IP or not; when the final IP is greater than the to-be-found IP, outputting the IP field information; when the final IP is not greater than the to-be-found IP, outputting the prompting information that the to-be-found IP does not exist in the database. The method has the advantages that the corresponding IP field information of the to-be-positioned IP is positioned from massive IP bases by the binary finding method; compared with the traditional finding method, the finding efficiency is improved, and the memory stress on the database in which the IP is stored is reduced.
Owner:北京思特奇信息技术股份有限公司
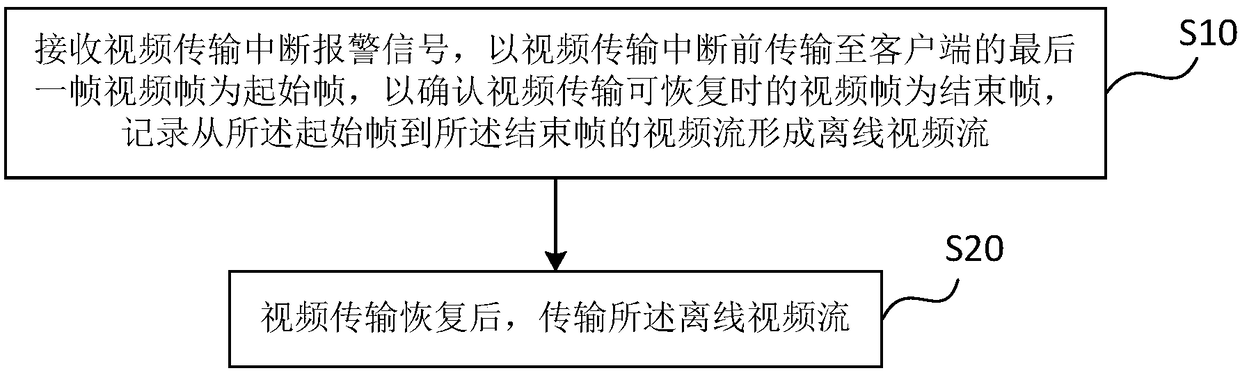
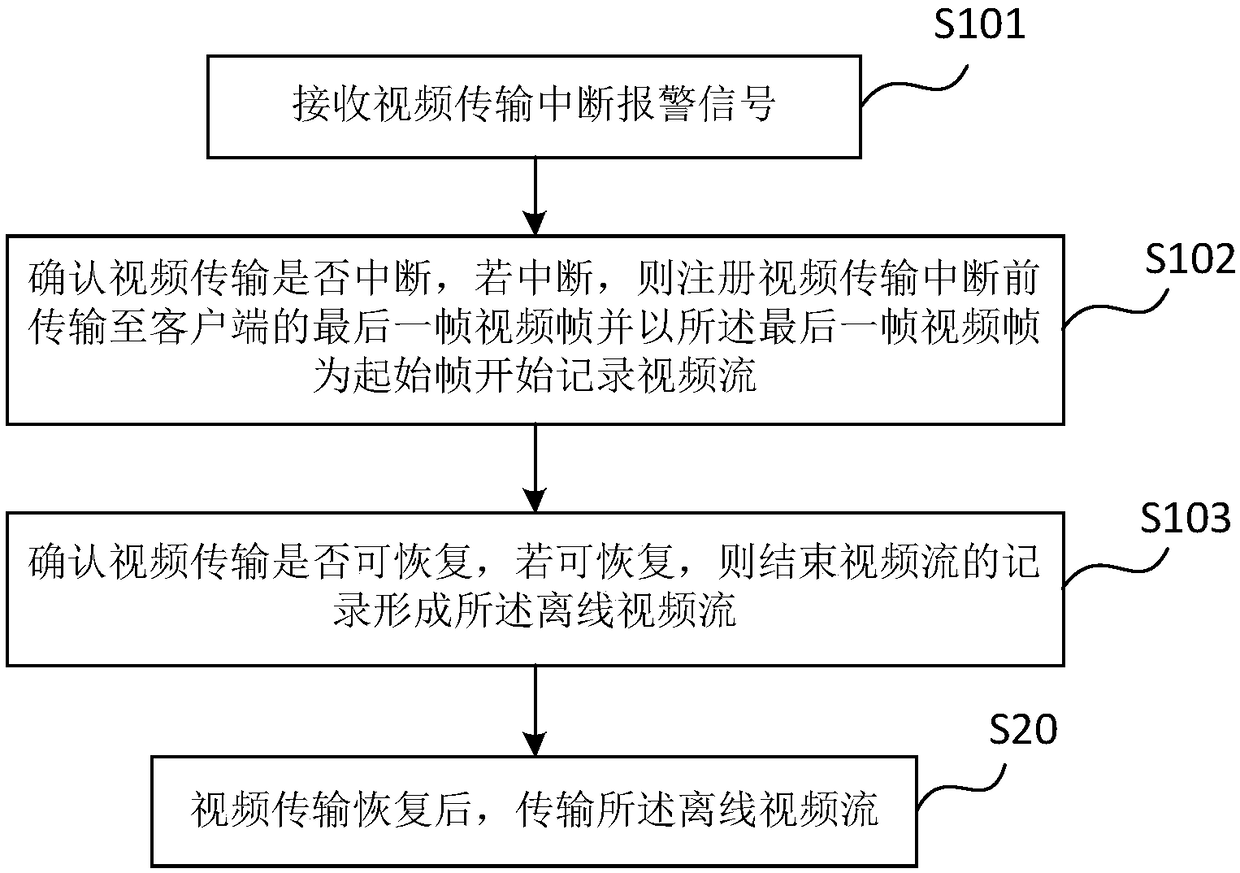
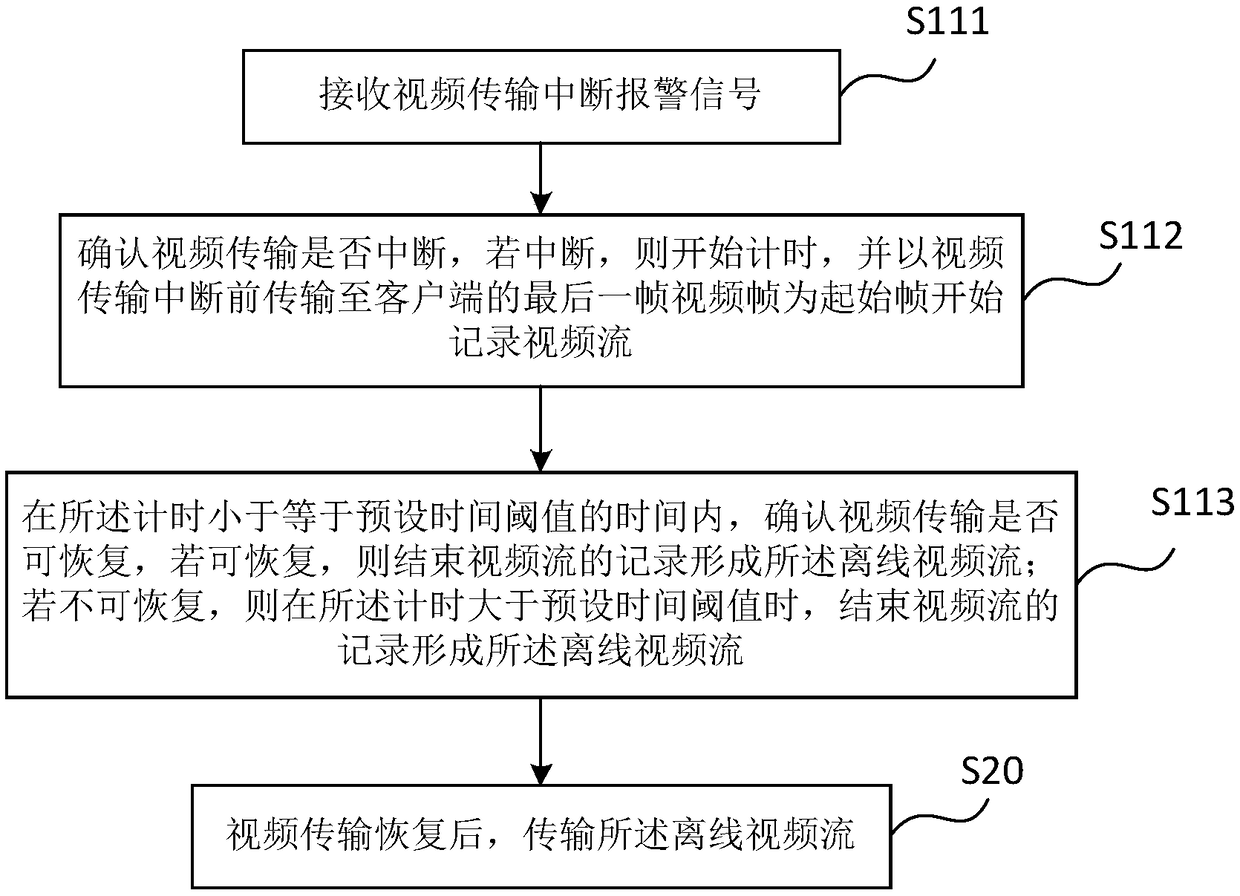
Real-time video stream interruption processing method and system for client, and monitoring system
ActiveCN108924485AReduce data lossReduce memory storage pressure and computationClosed circuit television systemsTransmissionCost savingsVideo transmission
The invention relates to the field of video monitoring, and discloses a real-time video stream interruption processing method and system for a client, and a monitoring system. The method comprises thefollowing steps: S10: receiving a video transmission interruption alarm signal, and by taking the last video frame transmitted to the client before the video transmission interruption as a start frame and taking a video frame when the video transmission is confirmed to be recovered as an end frame, recording a video stream from the start frame to the end frame to form an offline video stream; andS20: after the video transmission is recovered, transmitting the offline video stream. The method disclosed by the invention can help reduce data loss in a video stream interruption recovery processto reduce memory pressure in an interruption processing process, decrease the computing volume and improve the video stream retransmission efficiency after the video transmission is recovered, and isfavorable for realizing hardware configuration increase-free and cost-saving interruption processing.
Owner:HUANENG JILIN POWER GENERATION JIUTAI ELECTRIC FACTORY
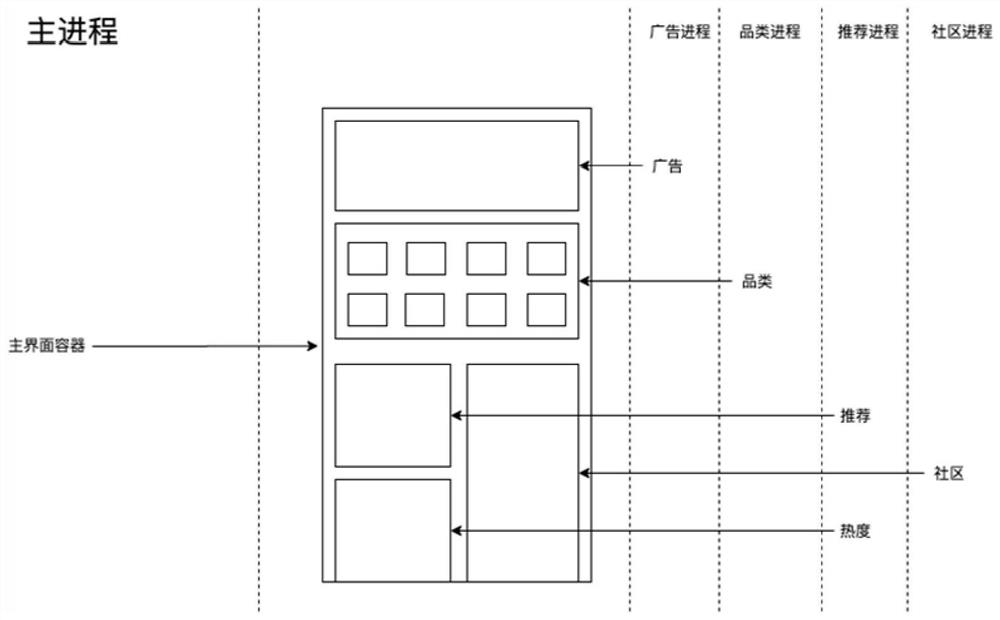
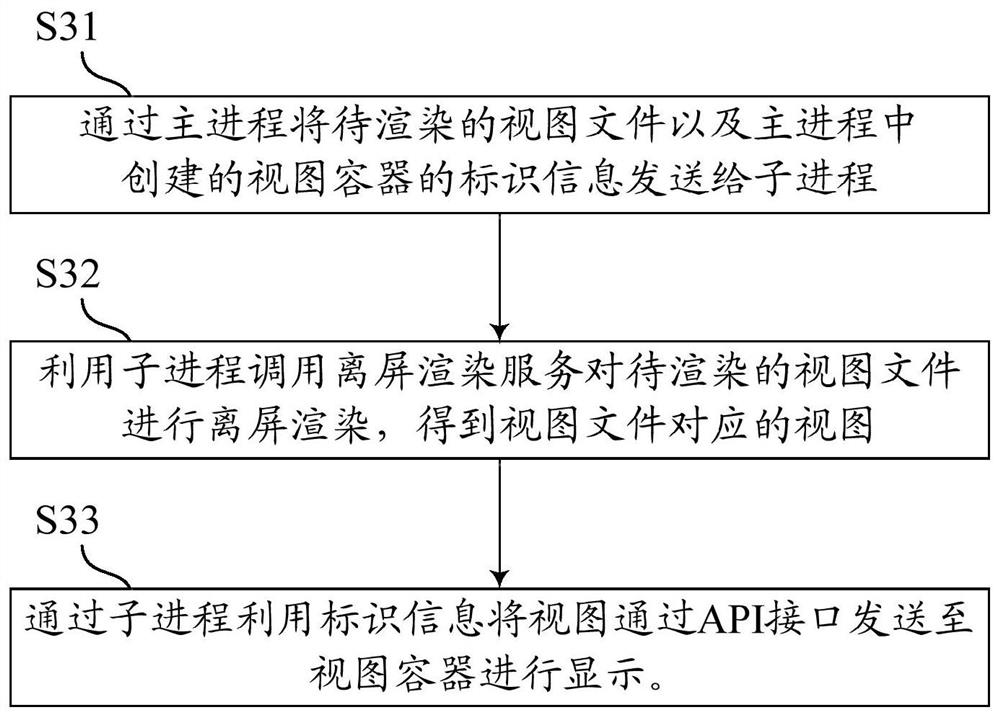
Cross-process off-screen rendering method and device, electronic equipment and storage medium
PendingCN112486620AReduce the frequency of OOM problemsImprove stabilityResource allocationExecution for user interfacesComputer hardwareApplication procedure
The invention discloses a cross-process off-screen rendering method and device, electronic equipment and a storage medium, and the cross-process off-screen rendering method comprises the steps: transmitting a to-be-rendered view file and the identification information of a view container created in a main process to a sub-process through the main process, and calling an off-screen rendering service to perform off-screen rendering on a to-be-rendered view file by utilizing the sub-process to obtain a view corresponding to the view file, and sending the view to the view container for display through the sub-process by utilizing the identification information and the API interface. Off-screen rendering is carried out in the sub-process, and the view obtained by rendering in the sub-process isdisplayed in the main process, so that the memory pressure of the main process is reduced, the memory pressure and the crash risk are shared, the frequency of OOM problems occurring in a complex pagein an Android system application program is reduced, and the stability of the complex page is improved.
Owner:GUANGZHOU HUYA TECH CO LTD
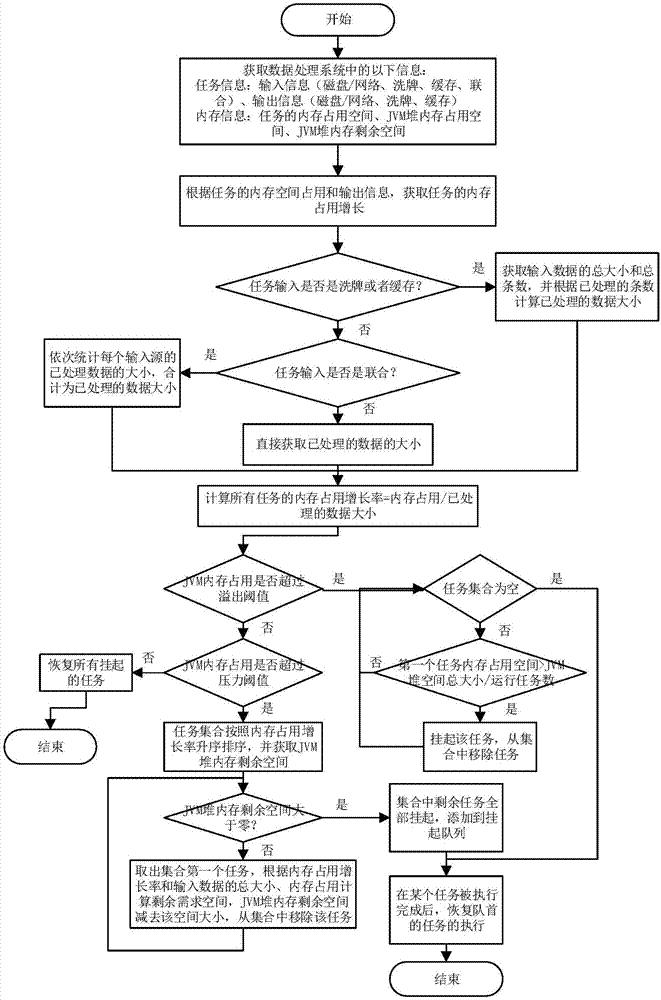
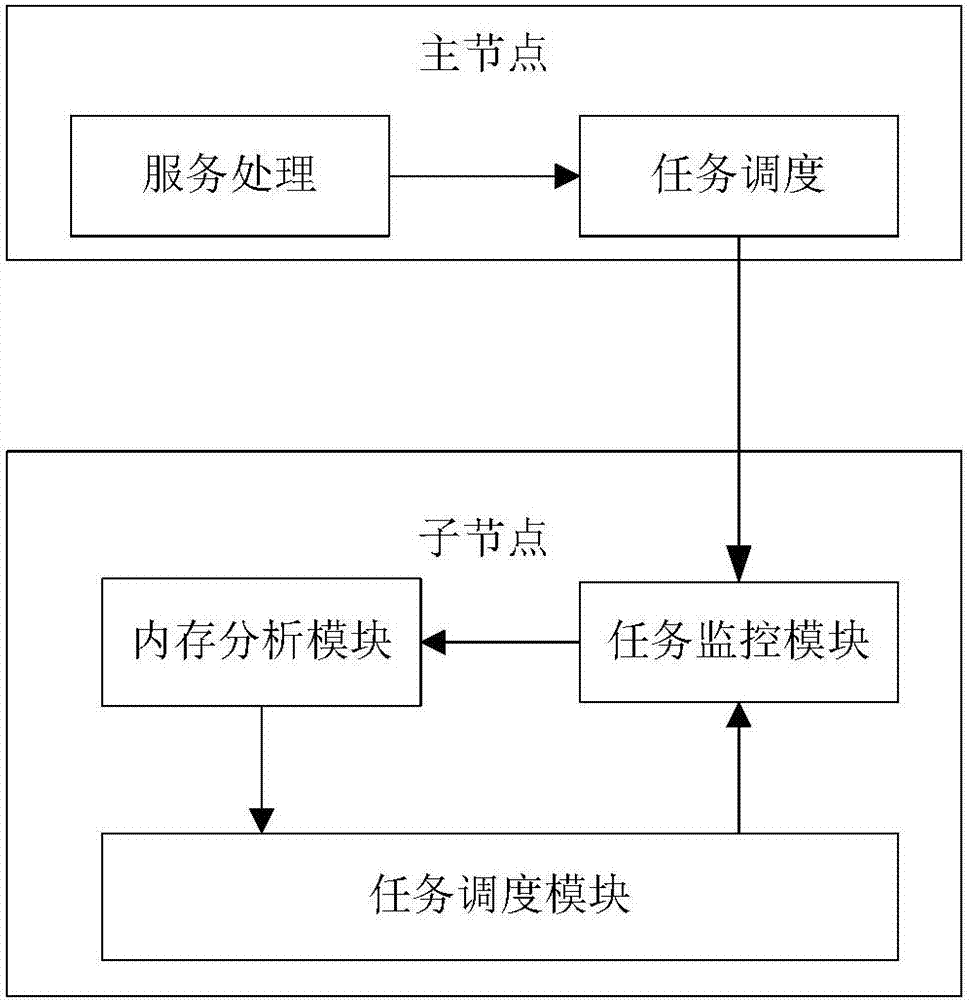
Scheduling method and system for relieving memory pressure in distributed data processing systems
InactiveCN107066316AReduce memory pressureAvoid waitingResource allocationDistributed object oriented systemsService systemDistributive data processing
The invention discloses a scheduling method for relieving memory pressure in distributed data processing systems. The scheduling method comprises the following steps of: analyzing a memory using law according to characteristics of an operation carried out on a key value pair by a user programming interface, and establishing a memory using model of the user programming interface in a data processing system; speculating memory using models of tasks according to a sequence of calling the programming interface by the tasks; distinguishing different models by utilizing a memory occupation growth rate; and estimating the influence, on memory pressure, of each task according to the memory using model and processing data size of the currently operated task, and hanging up the tasks with high influences until the tasks with low influences are completely executed or the memory pressure is relieved. According to the method, the influences, on the memory pressure, of all the tasks during the operation are monitored and analyzed in rea time in the data processing systems, so that the expandability of service systems is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
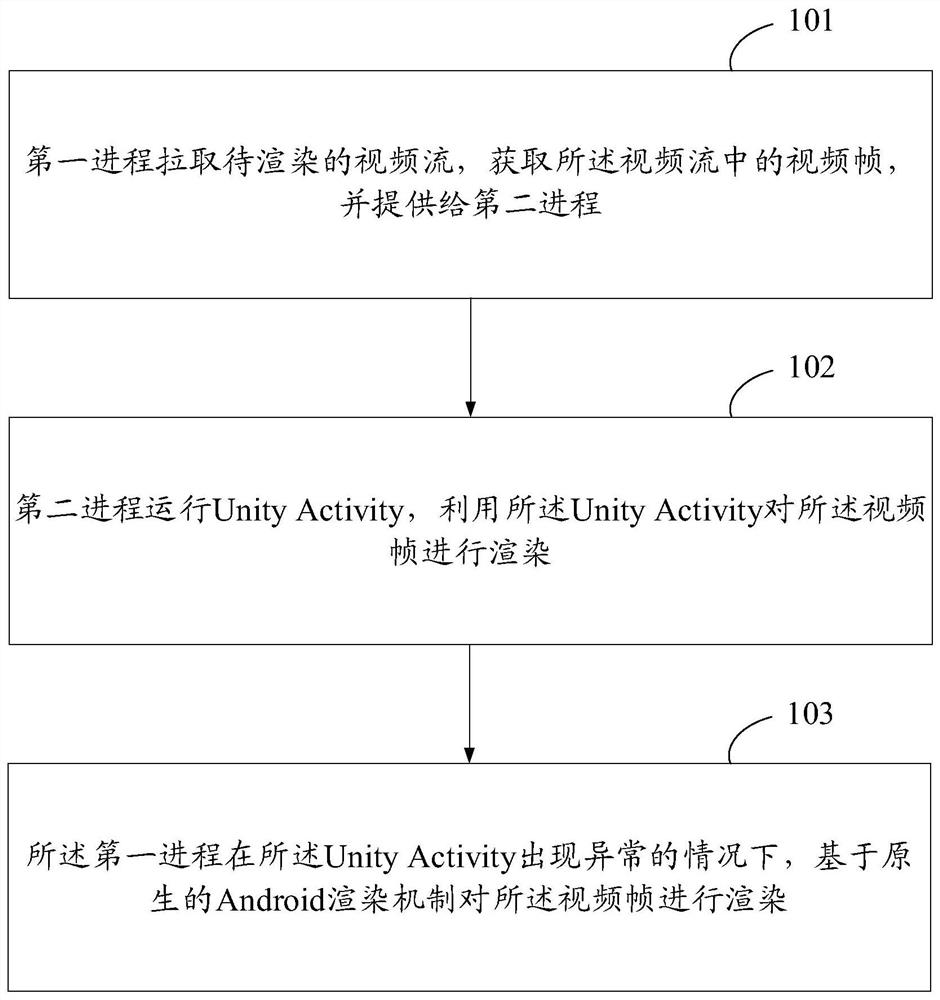
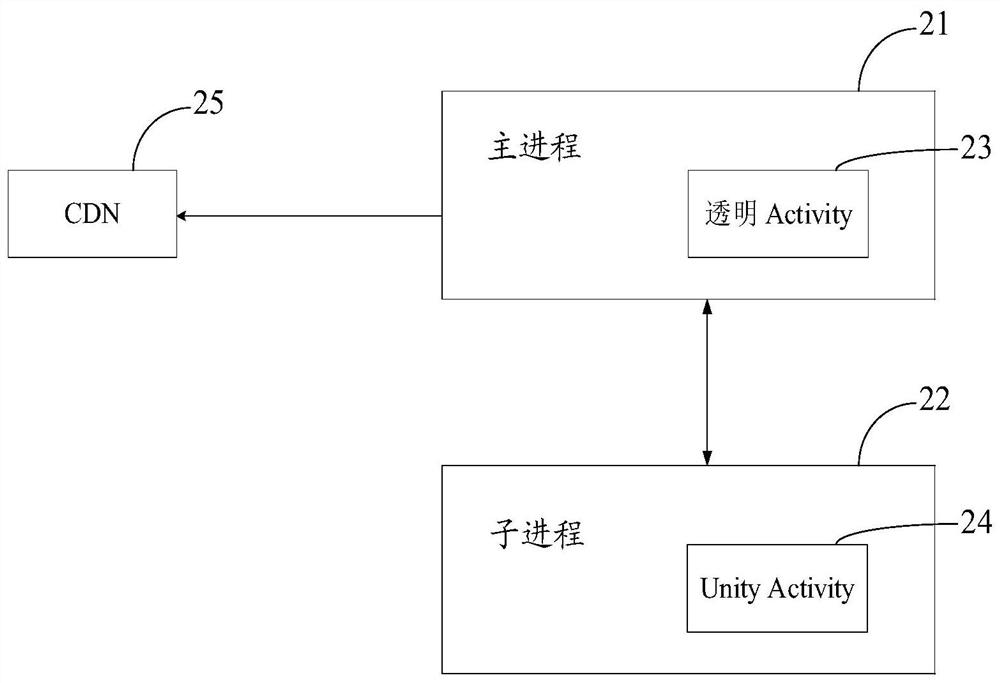
Method and device for rendering video stream, storage medium and equipment
ActiveCN112929740AReduce memory pressureGuaranteed uptimeSelective content distributionEnergy efficient computingComputer hardwareComputer graphics (images)
The invention provides a video stream rendering method and device, a storage medium and equipment. The method comprises the following steps: embedding Unity into an application program, pulling a stream by a first process and acquiring a video frame in a video stream, and operating Unity Activity by a second process and rendering the video frame by utilizing the Unity, so that the memory pressure of the first process is reduced, and if the Unity is abnormal, rendering the first process based on a native Android rendering mechanism, so that normal operation of rendering work is ensured, and the viewing experience of a user is improved.
Owner:GUANGZHOU HUYA TECH CO LTD
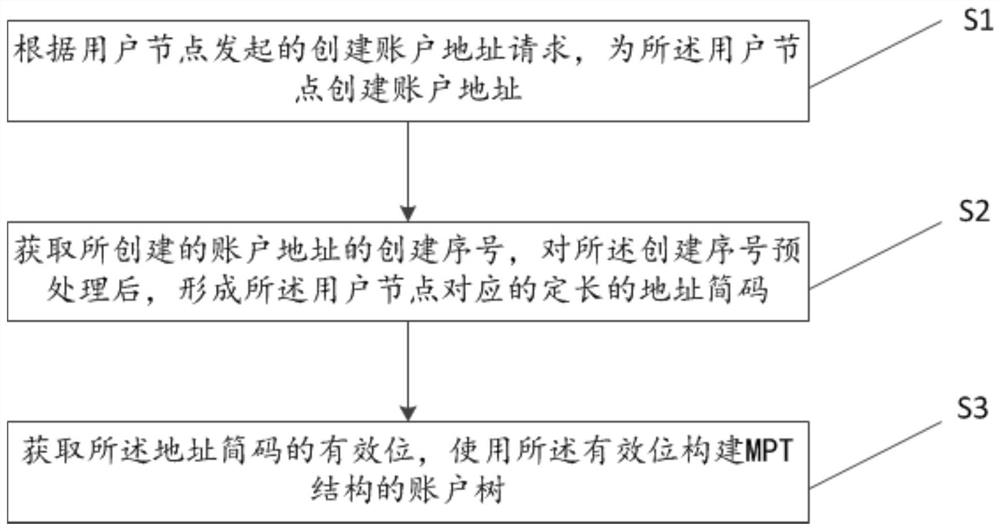
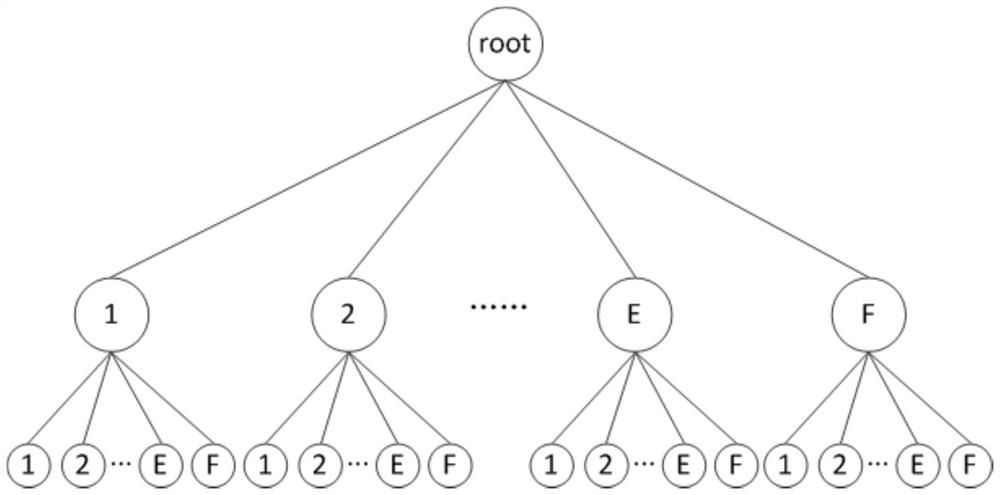
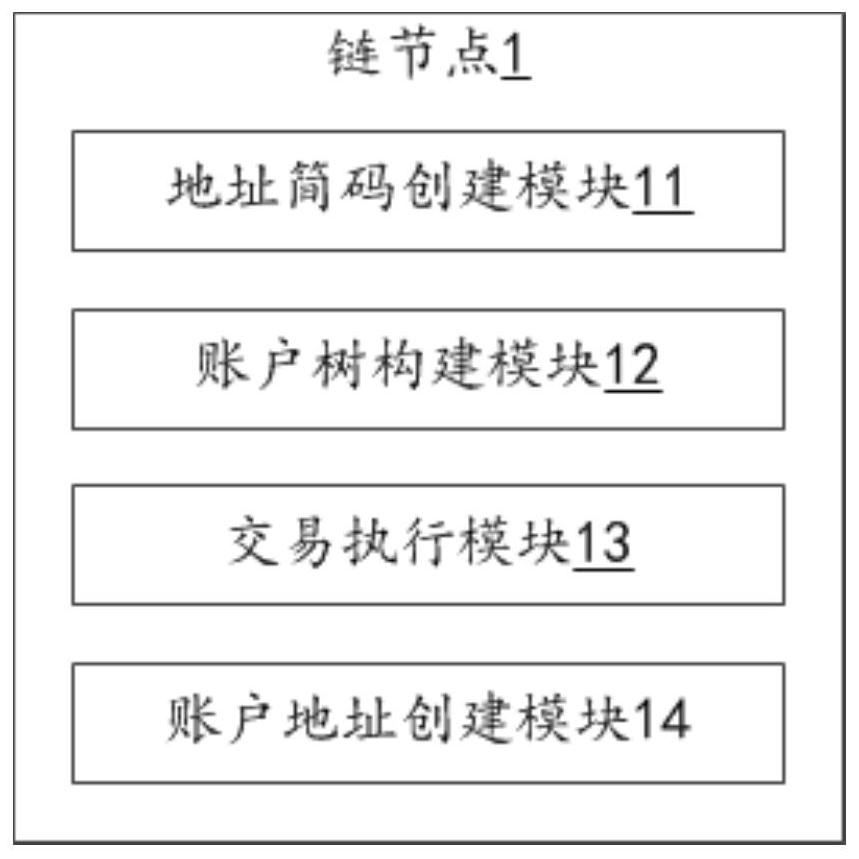
Data compression method and system for account tree of MPT structure
ActiveCN112511629AAvoid wastingTake advantage ofFinanceSecuring communicationData compressionTheoretical computer science
The invention relates to the technical field of block chains, and provides a data compression method and system for an account tree of an MPT structure, and the method comprises the steps: building anaccount address for a user node according to an account address building request initiated by the user node; obtaining a creation serial number of the created account address, and forming a fixed-length address brief code corresponding to the user node after preprocessing the creation serial number; and obtaining a significant bit of the address brief code, and constructing an account tree of anMPT structure by using the significant bit. According to the method, the account tree of the MPT structure is compressed, and the intermediate node of the account tree is fully utilized, so that the account is also stored on the intermediate node, the waste of resources is avoided, and the storage space of the account tree is reduced. And meanwhile, the storage space of the account tree is reduced, so that the account tree can reside in the memory, repeated migration and replacement of the account data in the memory and the hard disk are avoided, and the calculation pressure and time cost of the blockchain during transaction execution are reduced.
Owner:上海简苏网络科技有限公司
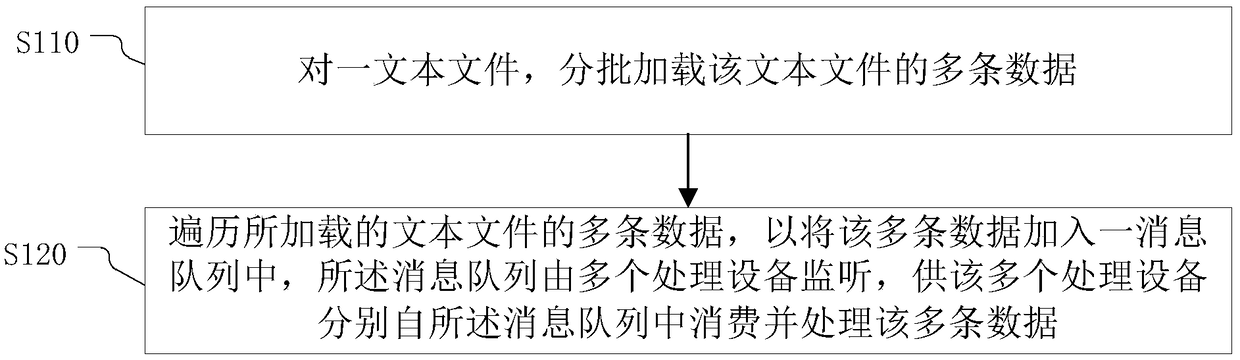
Text file processing method, device and system, electronic device, and storage medium
ActiveCN109325002AReduce machine memory pressureImprove processing efficiencyInterprogram communicationNatural language data processingText fileMessage queue
The invention provides a text file processing method, device and system, an electronic device and a storage medium. The text file processing method comprises the steps of: loading a plurality of pieces of data of a text file in batches; traversing the loaded plurality of pieces of data of the text file to add the plurality of pieces of data in a message queue, monitoring the message queue by a plurality of processing devices for the plurality of processing devices, and using the plurality of processing devices to consume and process the plurality of pieces of data from the message queue, respectively. The method and the device provided by the invention can reduce the pressure of the machine memory and improve the processing efficiency.
Owner:JINGDONG TECH HLDG CO LTD
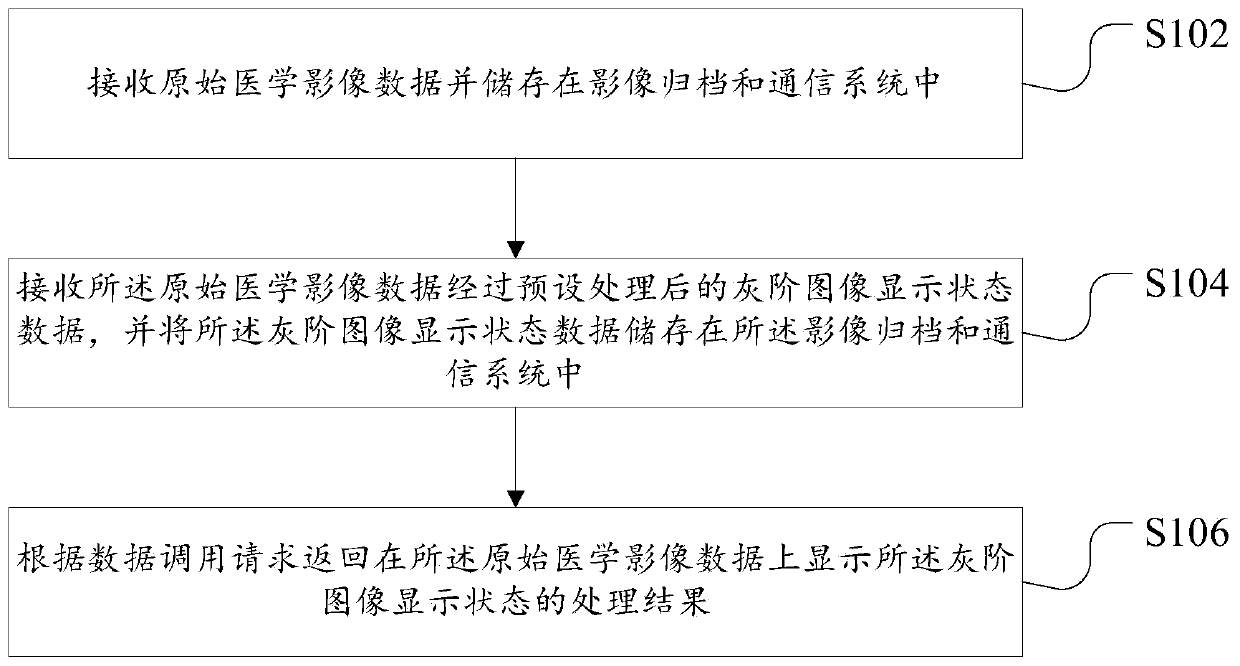
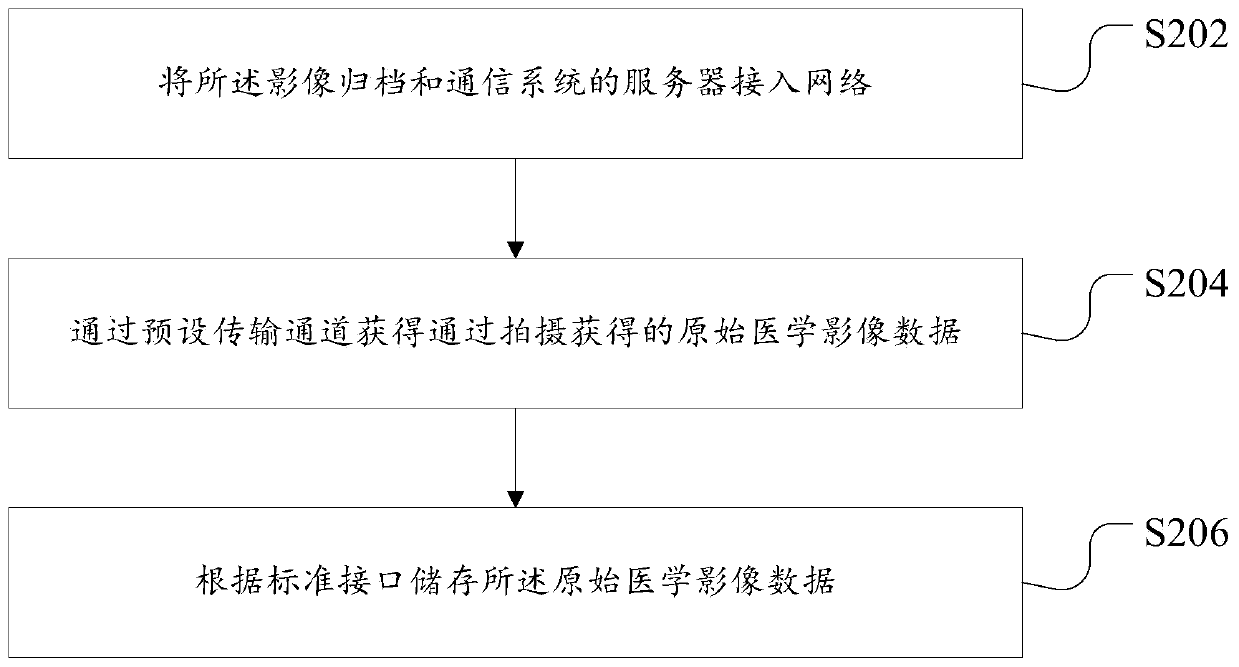
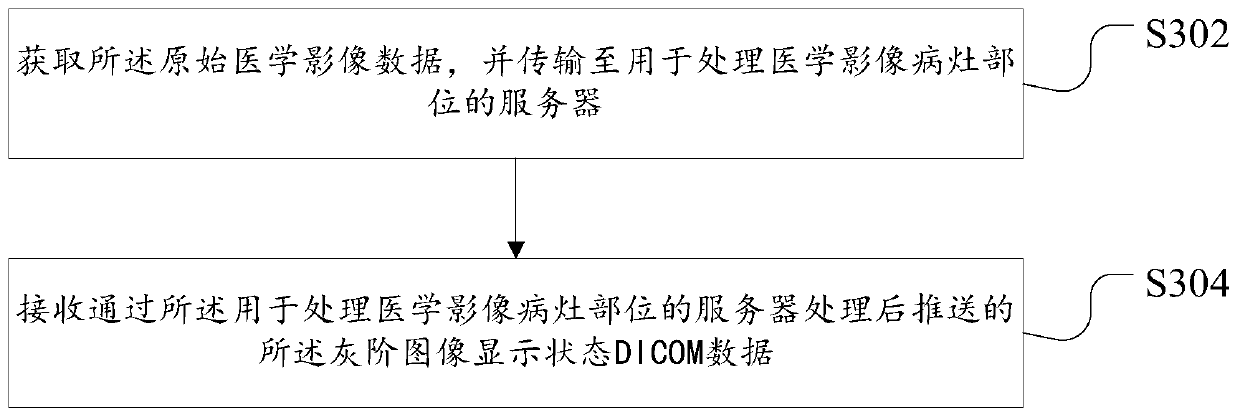
Data processing method for medical image and device thereof
InactiveCN109754868AReduce memory pressureReduce maintenance costsMedical imagesInstrumentsComputer hardwareCommunications system
The invention discloses a data processing method for a medical image and a device thereof. The method comprises the steps of receiving original medical image data and storing in an image filing and communication system; receiving gray-scale image display state data which are obtained after performing preset processing on the original medical image data, and storing the gray-scale image display state data into the image filing and communication system; and returning a processing result for displaying the gray-scale image display state on the original medical image data according to a data calling request. The data processing method and the device thereof settle technical problems of relatively low response speed and relatively high equipment memory occupancy factor in medical image readingcaused by oldness or relatively low performance of hardware equipment. Communication of different systems is realized through the data processing method and the device thereof, thereby reducing hardware equipment memory pressure and hardware equipment maintenance cost.
Owner:HANGZHOU SHENRUI BOLIAN TECH CO LTD +1
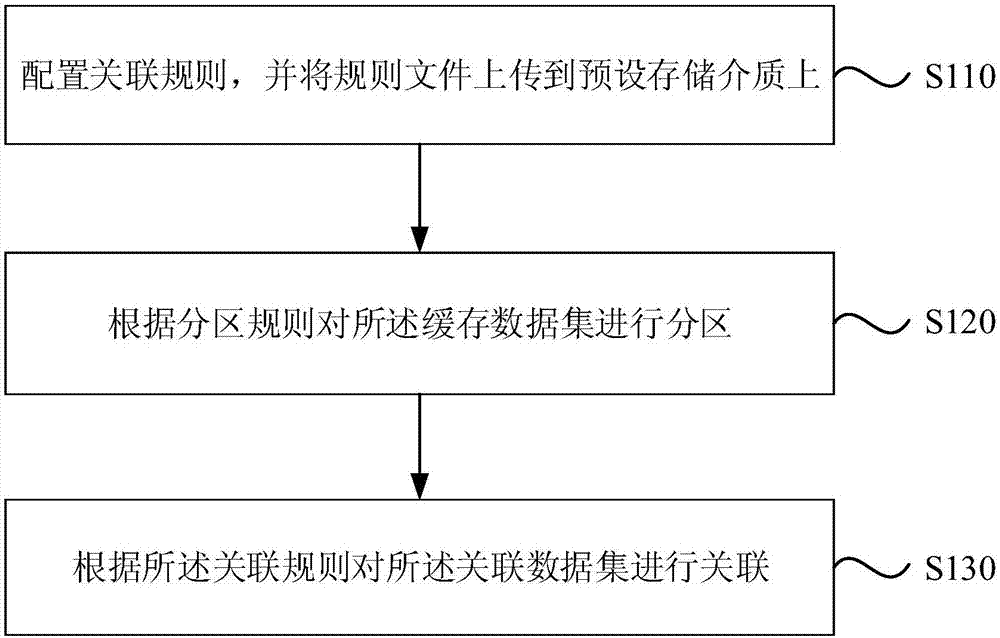
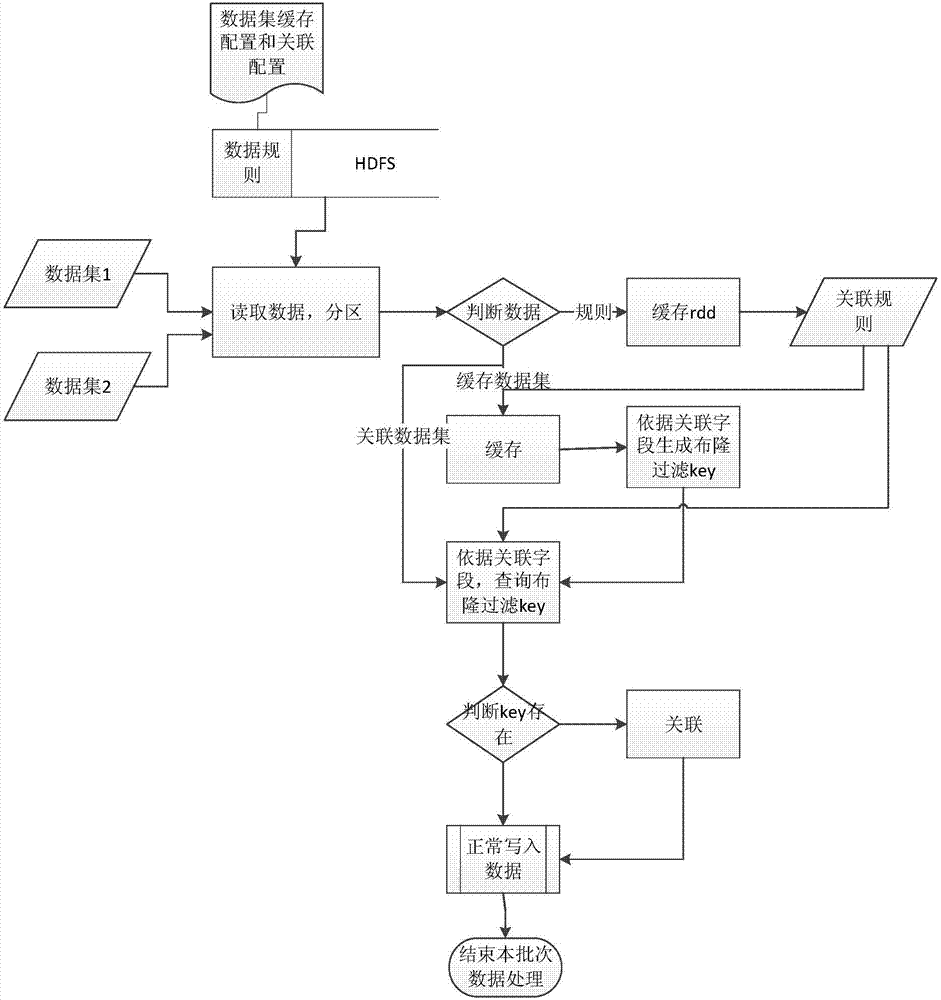
Data processing method and device, equipment and storage medium
ActiveCN107391770AReduce memory pressureReduce network transfer timeDatabase updatingDatabase distribution/replicationData processingData set
An embodiment of the invention discloses a data processing method and device, equipment and a storage medium. Association rules are configured, and a rule file is uploaded to a preset storage medium; a buffered dataset is acquired and is partitioned according to partitioning rules; an association dataset is acquired and is associated according to the association rules. Therefore, stream-type real-time associational computing power is achieved.
Owner:RUN TECH CO LTD BEIJING
Webpage browser memory optimization method and system, equipment and storage medium
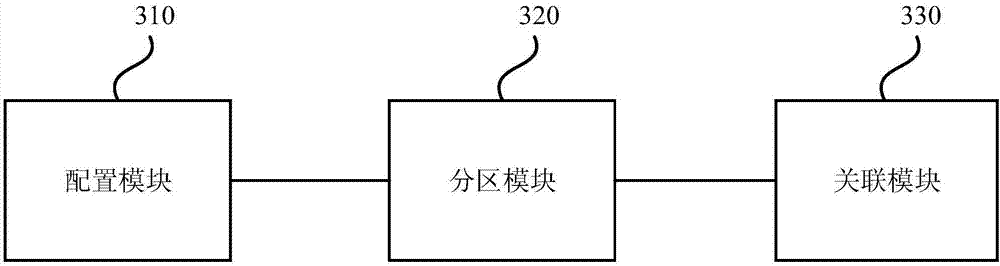
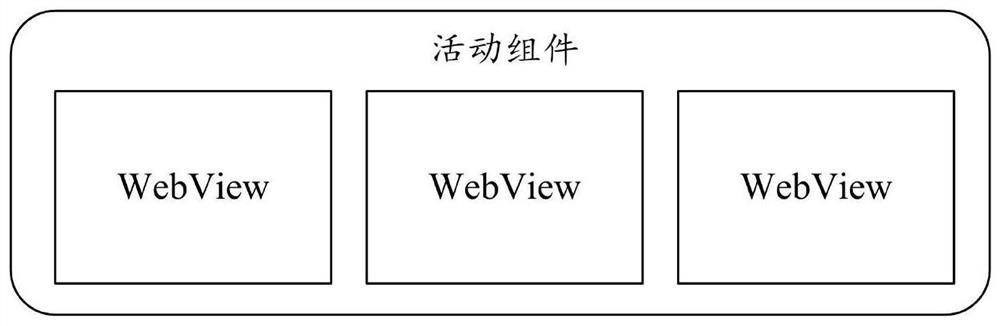
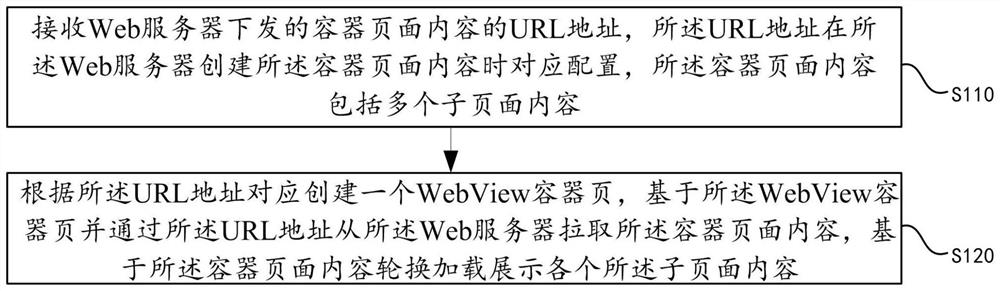
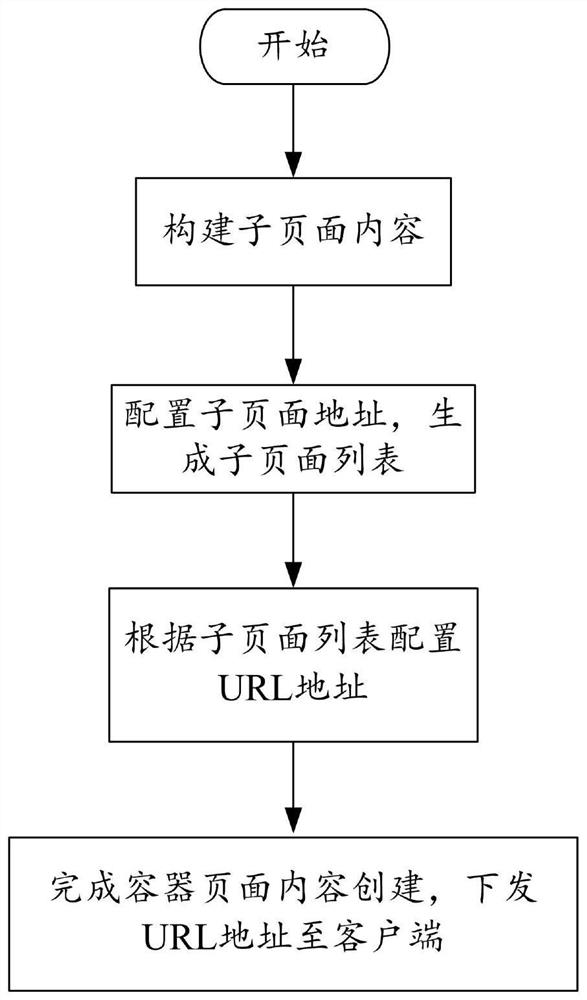
PendingCN112559172AReduce creationReduce memory pressureResource allocationSpecial data processing applicationsWeb browserEngineering
The embodiment of the invention discloses a web browser memory optimization method and system. equipment and a storage medium. According to the technical scheme provided by the embodiment of the invention, the URL address correspondingly configured when the Web server creates the container page content is received, the WebView container page is correspondingly created according to the URL address,the container page content is pulled from the Web server through the URL address on the basis of the WebView container page, and the content of each sub-page in the container page content is loaded and displayed in turn on the basis of the container page content. By adopting the technical means, the content of the container page is pulled and the content of each sub-page is alternately loaded anddisplayed, so that the creation of a WebView control can be reduced, and the content of a plurality of web pages is displayed through one WebView container page, thereby reducing the memory pressureof the system, avoiding system memory shortage caused by excessive creation of the WebView control and excessive creation of a rendering process. And the running stability of the application is improved under the condition that the application is forcibly closed.
Owner:BIGO TECH PTE LTD
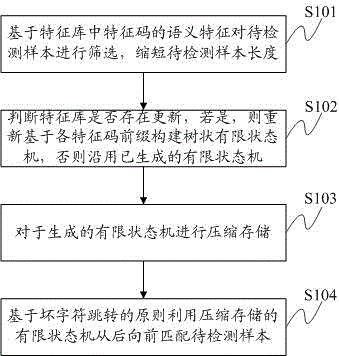
Malicious code matching method and apparatus based on multi-mode
InactiveCN105653950AReduce in quantityReduce matching timePlatform integrity maintainanceFinite-state machineTheoretical computer science
The invention discloses a malicious code matching method based on multi-mode. The method comprises steps of screening a to-be-detected sample based on semantic features of feature codes in a feature base, shortening the length of the to-be-detected sample, determining whether update is required for the feature base, building a tree-like finite-state machine based on each feature code prefix if update is required, following an existing finite code prefix if update is not required, compressing and storing the generated finite code prefix, and matching the to-be-detected sample from back to front via the compressed and stored finite state machine based on a bad character skip principle. Meanwhile, the invention discloses a malicious code matching apparatus based on the multi-mode. By the use of the technical scheme, even with more feature codes in the feature base, feature codes can be matched in quick matching speed and system resource occupation can be reduced.
Owner:HARBIN ANTIY TECH
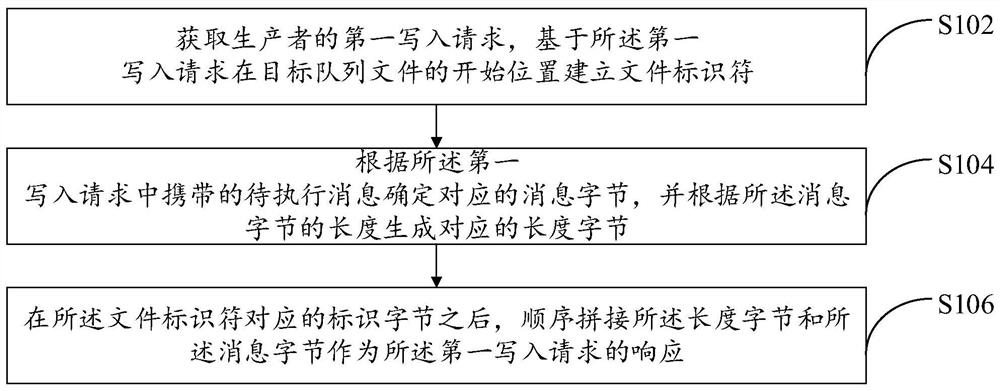
Message processing method and device
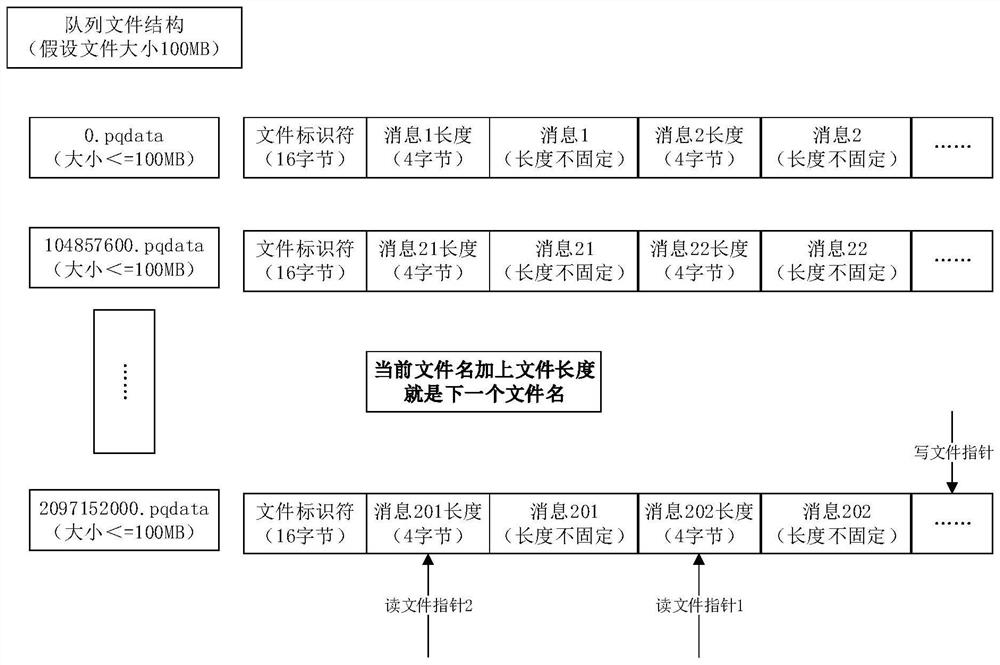
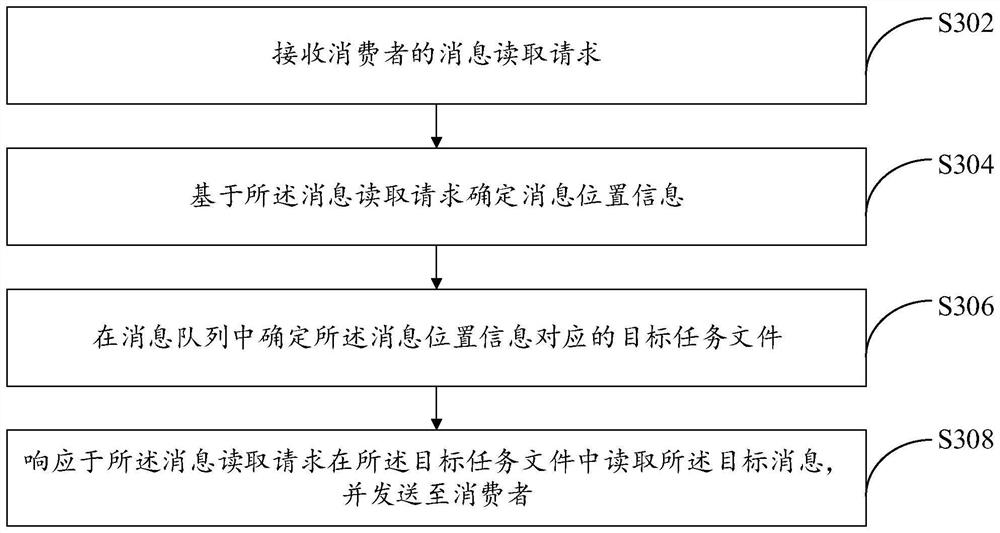
PendingCN113986576AReduce memory pressureSimple and fast processInterprogram communicationIndexed fileDatabase
The invention provides a message processing method and device, and the message processing method comprises the steps: obtaining a first write-in request of a producer, and building a file identifier at a starting position of a target queue file based on the first write-in request; determining a corresponding message byte according to a to-be-executed message carried in the first write-in request, and generating a corresponding length byte according to the length of the message byte; and after the identification byte corresponding to the file identifier, splicing the length byte and the message byte in sequence to serve as the response of the first write-in request, so that an index file is omitted in the process of storing a message to be stored, and the memory pressure of a system is relieved. In the process of reading the message, the process of quoting an index file can also be omitted, so that the message reading process is simpler and quicker, and a good environment is provided for reading and querying the message.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD +1
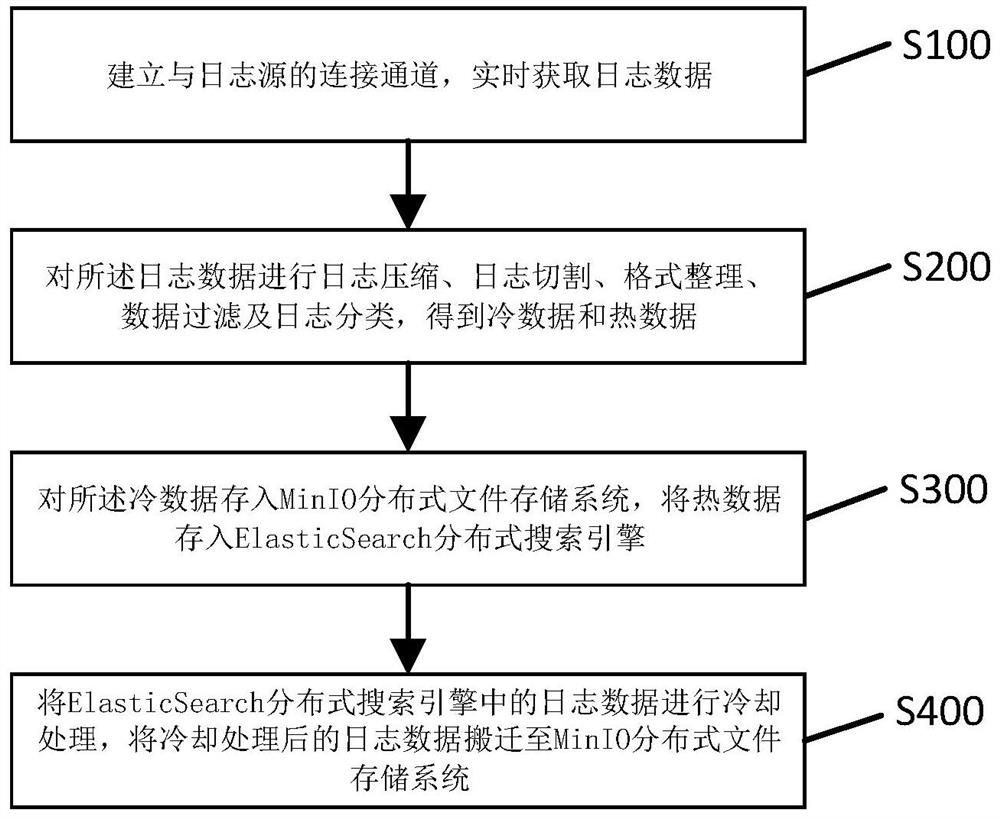
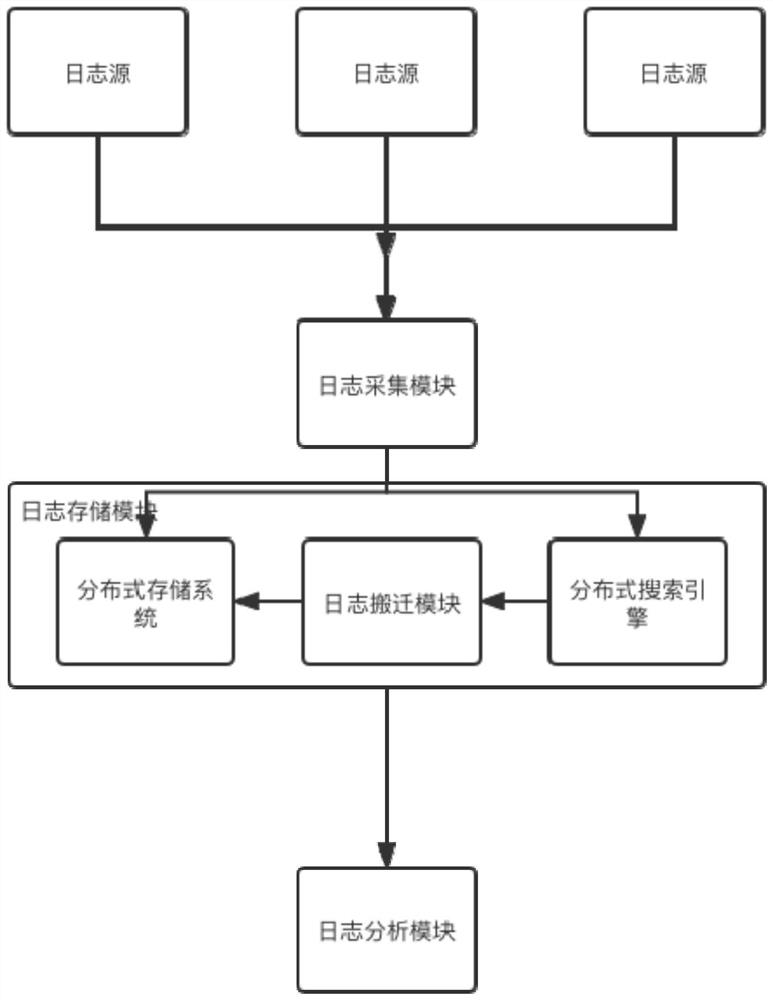
Log information acquiring and monitoring method
PendingCN114860932AEfficient collectionTimely processingText database indexingEnergy efficient computingEngineeringTerm memory
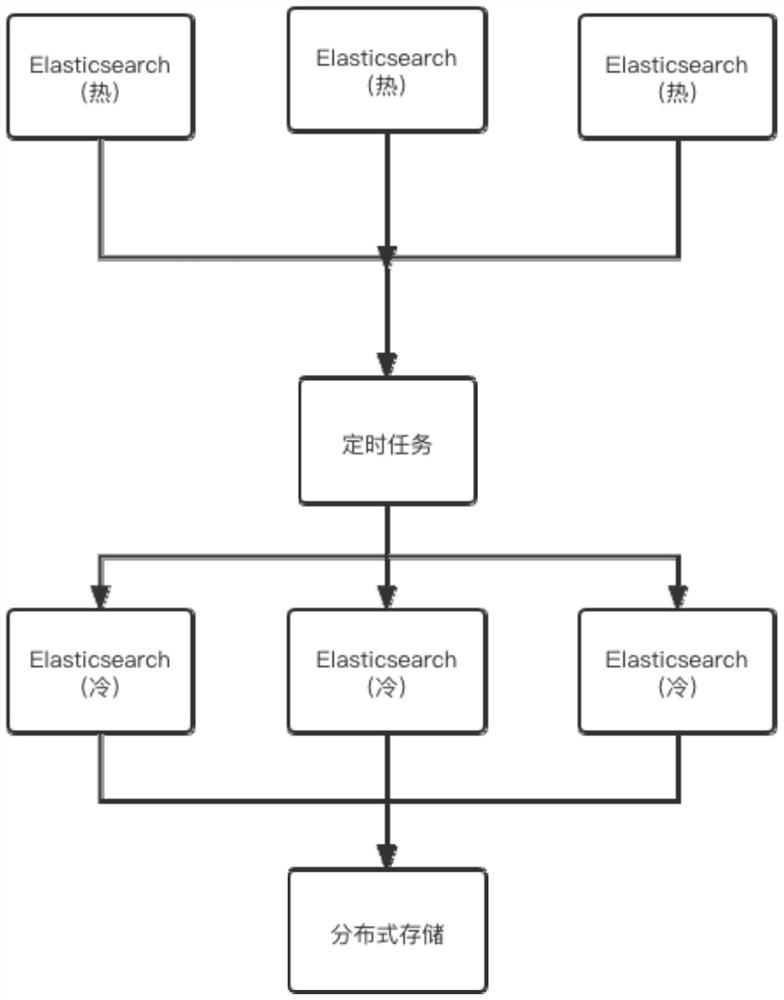
The invention relates to the technical field of data monitoring and processing, and particularly discloses a log information acquisition and monitoring method, which comprises the following steps: establishing a connection channel with a log source, and acquiring log data in real time; performing log compression, log cutting, format arrangement, data filtering and log classification on the log data to obtain cold data and hot data; the cold data is stored in a MinIO distributed file storage system, and the hot data is stored in an ElasticSearch distributed search engine; the log data in the ElasticSearch distributed search engine is cooled, and the cooled log data is moved to the MinIO distributed file storage system. According to the method, multiple log sources can be efficiently collected, data are not lost, and the log retrieval efficiency is improved; massive data can be stored through distributed storage, so that the memory pressure is reduced; cold and hot data can be processed in time, data of log data on a retrieval system is reduced, and log retrieval analysis efficiency is better improved.
Owner:福建财通信息科技有限公司
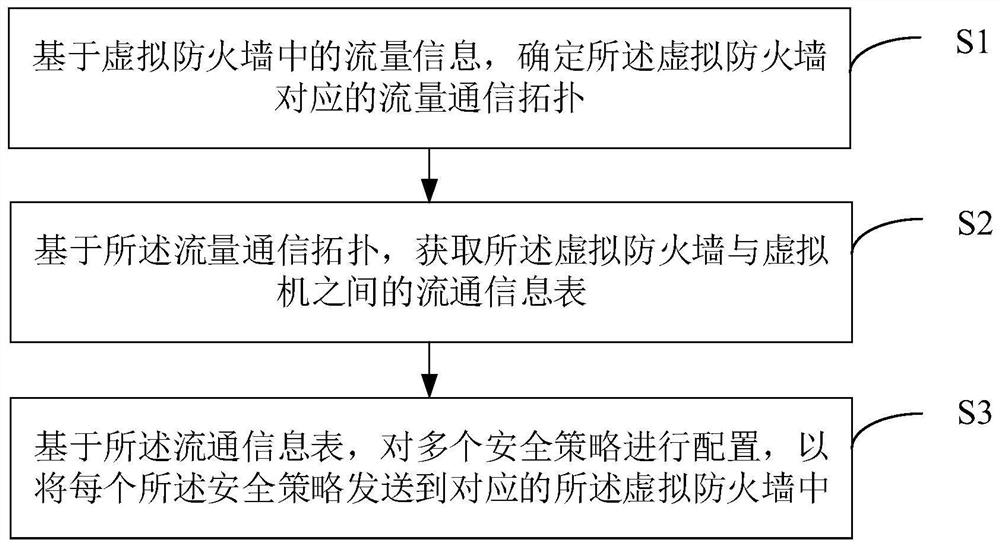
Security policy configuration method and device, electronic equipment and storage medium
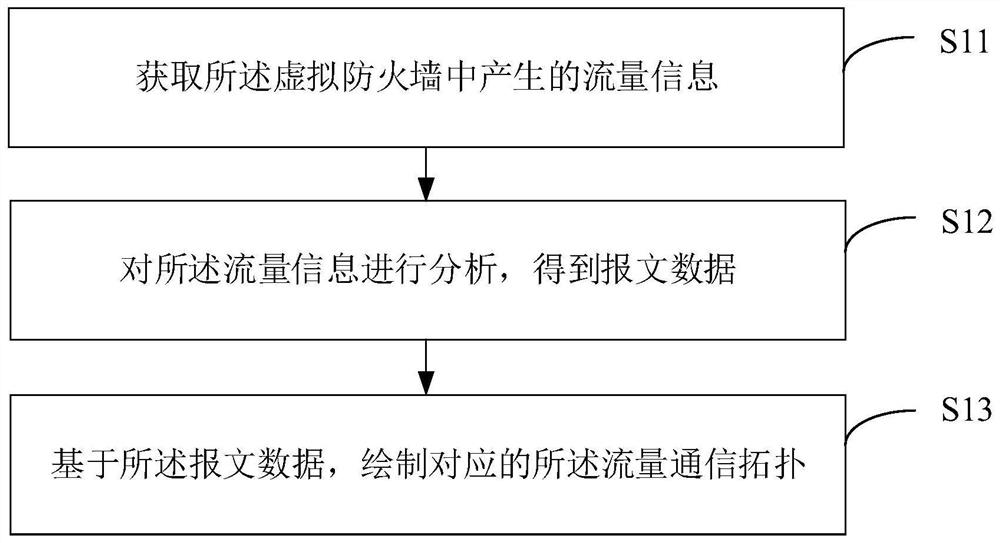
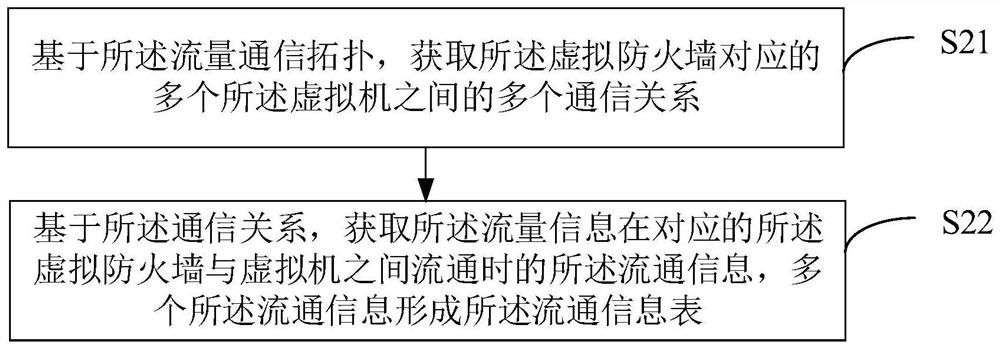
PendingCN114172718ARealize targeted configurationImprove configuration efficiencySecuring communicationVirtual firewallEngineering
The invention provides a security policy configuration method and device, electronic equipment and a storage medium, and relates to the technical field of network security. The method comprises the steps of determining a flow communication topology corresponding to a virtual firewall based on flow information in the virtual firewall; based on the traffic communication topology, a circulation information table between the virtual firewall and the virtual machine is obtained, and the circulation information table comprises circulation information of the multiple pieces of traffic information when the multiple pieces of traffic information circulate between the virtual firewall and the virtual machine; and configuring the plurality of security policies based on the circulation information table so as to send each security policy to the corresponding virtual firewall. According to the method and the device, the flow communication topology of the virtual firewall is drawn, and the circulation information table between the virtual firewall and the virtual machine is obtained on the basis of the flow communication topology, so that a plurality of security policies can be configured according to the circulation information table, and each security policy can be sent to the corresponding virtual firewall; and the configuration efficiency and execution efficiency of the security policy are effectively improved.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
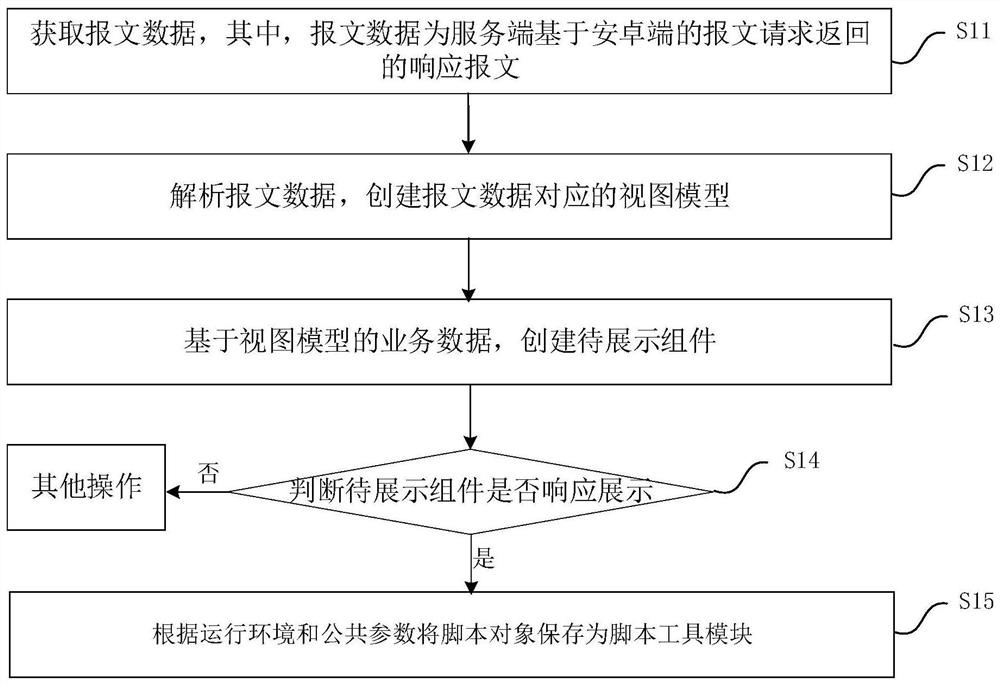
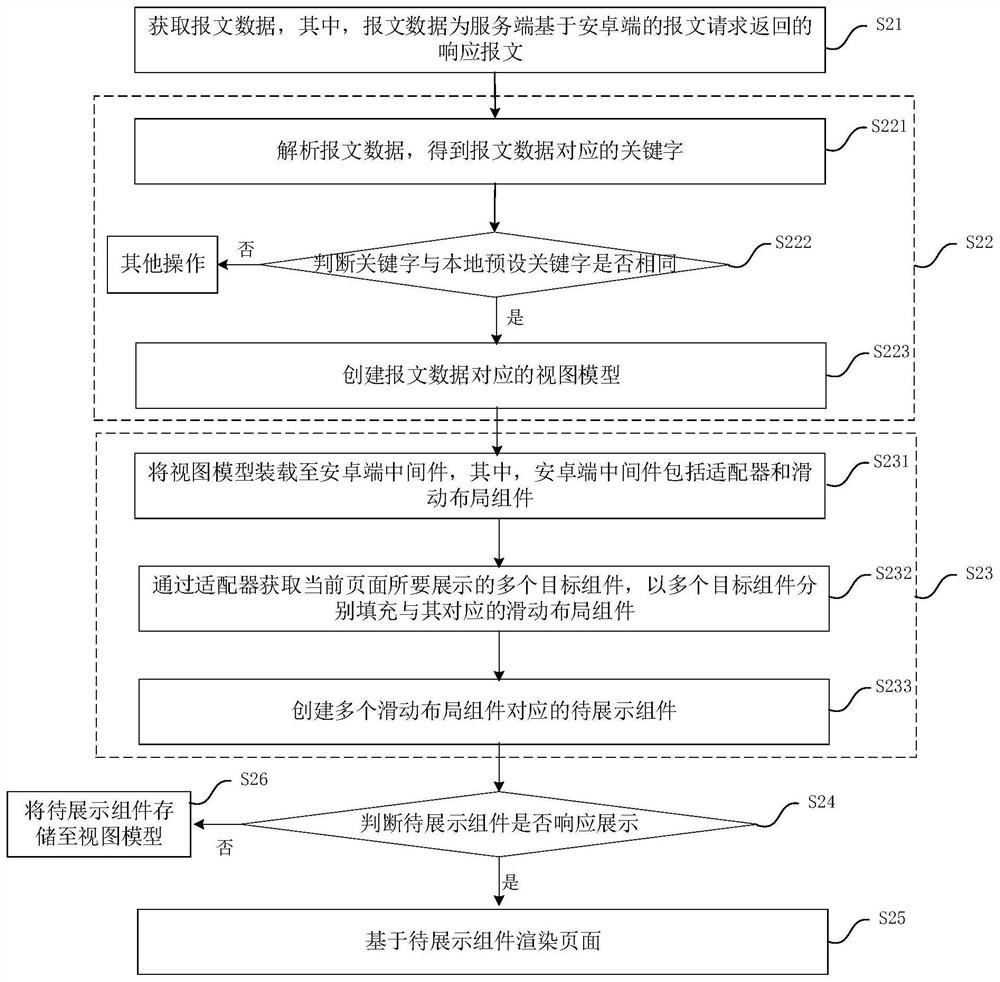
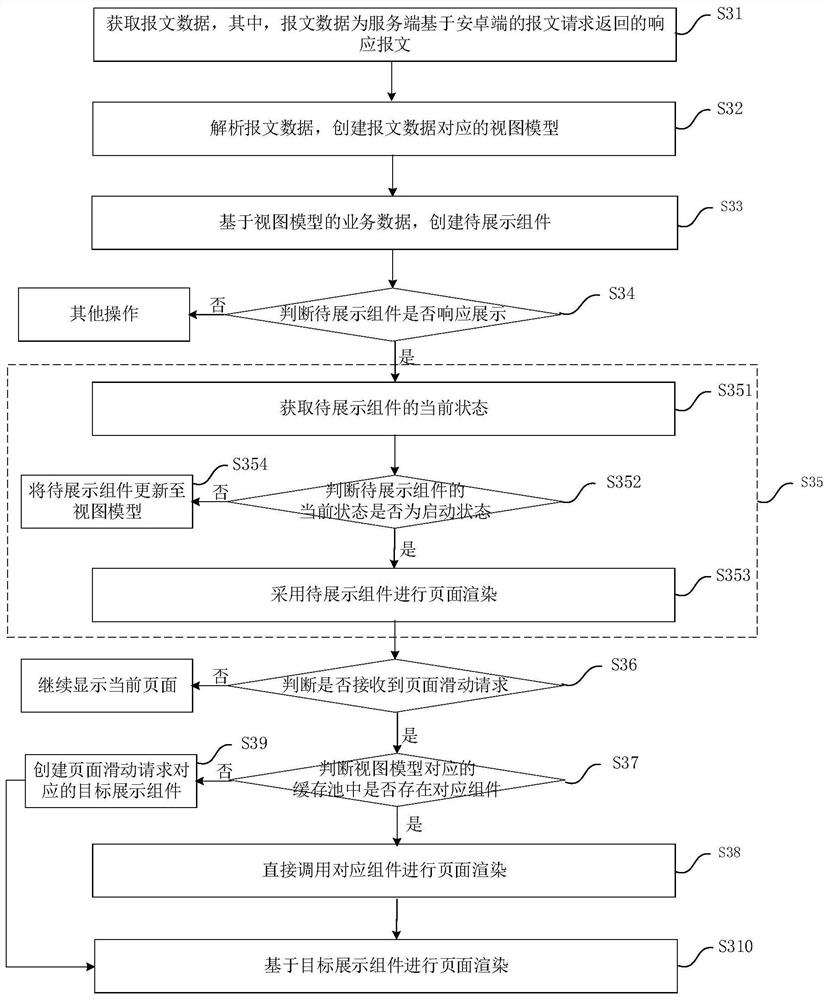
Android end page construction method, device and equipment, and readable storage medium
PendingCN113779463AReduce computing pressureReduce memory pressureExecution for user interfacesSpecial data processing applicationsAndroid appBusiness data
The invention relates to the technical field of Android application development, and discloses an Android end page construction method and device, equipment and a readable storage medium. The method comprises the following steps: acquiring message data, the message data being a response message returned by a server based on a message request of an Android end; analyzing the message data, and creating a view model corresponding to the message data; creating a to-be-displayed component based on the business data of the view model; judging whether the to-be-displayed component responds to display or not; and when the to-be-displayed component responds to display, rendering the page based on the to-be-displayed component. By means of the invention, loading of redundant data is avoided, all data does not need to be loaded at a time, CPU pressure and memory pressure are greatly relieved, and page rendering efficiency is improved.
Owner:北京自如信息科技有限公司
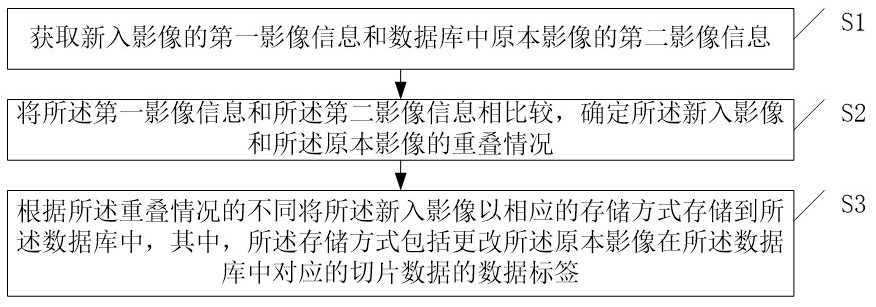
Remote sensing image automatic updating and historical backtracking method and device based on single service
ActiveCN113505139AReduce overheadReduce memory pressureDatabase updatingStill image data indexingComputer graphics (images)Computer vision
The embodiment of the invention provides a remote sensing image automatic updating and historical backtracking method and device based on single service. The method comprises the following steps: acquiring first image information of a new image and second image information of an original image in a database; comparing the first image information with the second image information, and determining the overlapping condition of the new image and the original image; and storing the new image in the database in a corresponding storage mode according to the difference of the overlapping conditions, wherein the storage mode comprises the step of changing a data label of corresponding slice data of the original image in the database. Through the scheme of the embodiment, the development efficiency of the WebGIS is improved, and the development cost and the maintenance cost are reduced.
Owner:成都国星宇航科技股份有限公司
Training sample generation method and device, storage medium and electronic equipment
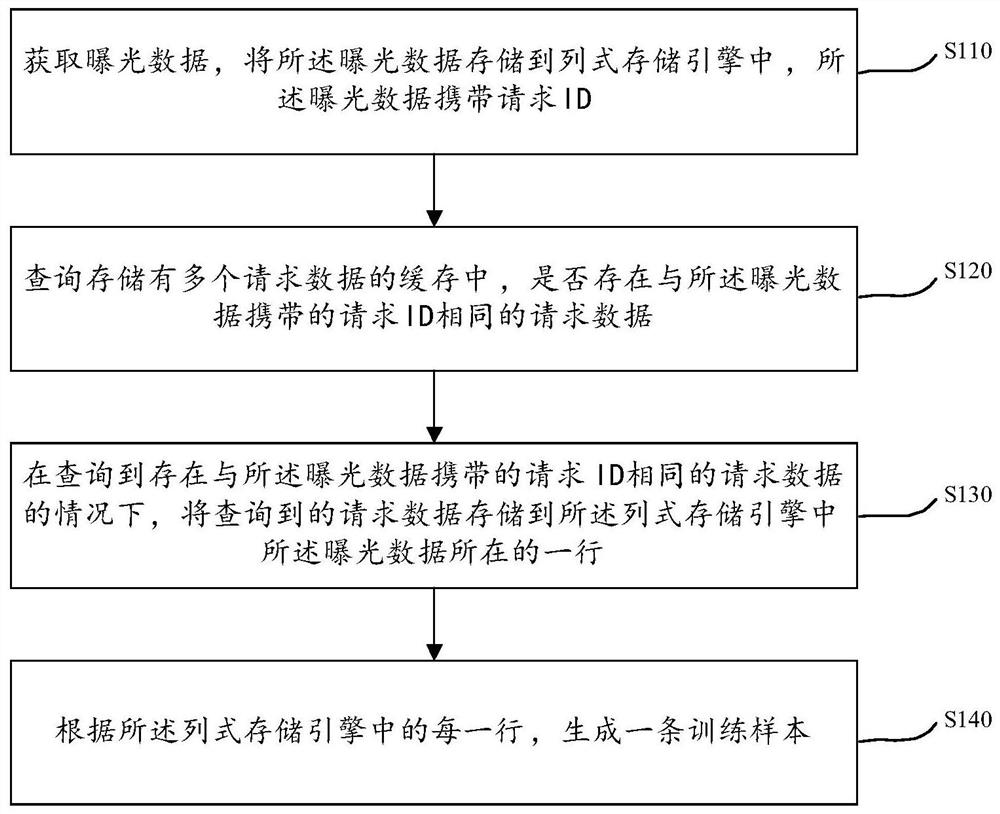
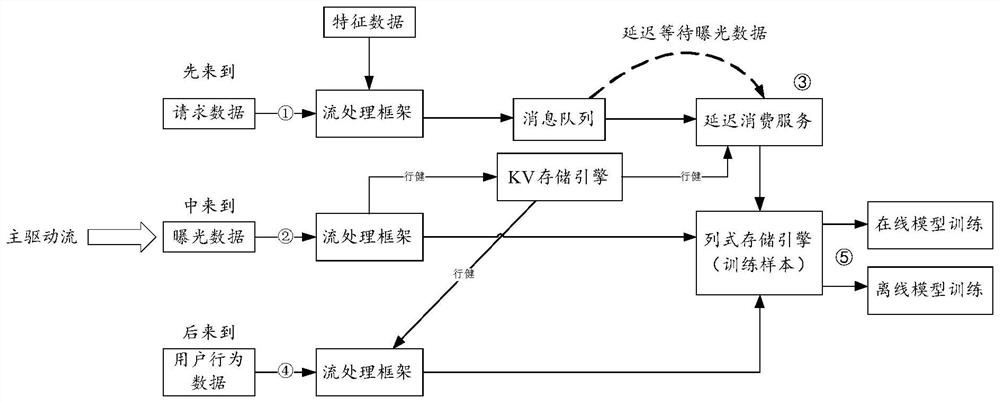
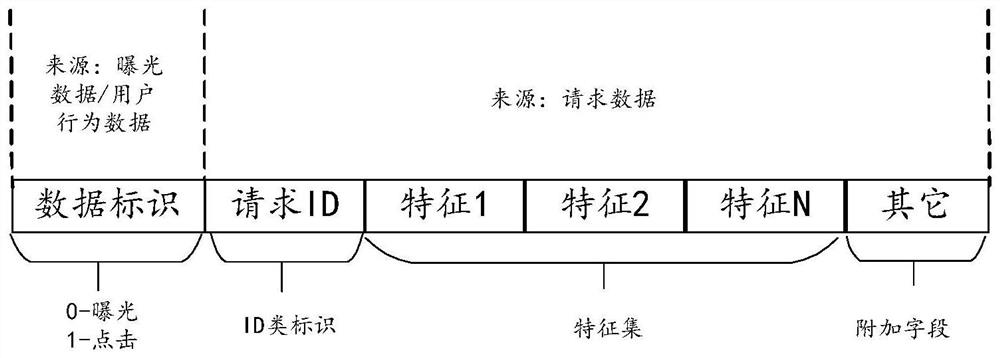
ActiveCN113705629ASave storage spaceAvoid redundancyCharacter and pattern recognitionNeural architecturesData storeReliability engineering
The embodiment of the invention provides a training sample generation method and device, a storage medium and electronic equipment, relates to the technical field of data processing, and aims to provide a high-quality training sample generation method. The method comprises the following steps: obtaining exposure data, storing the exposure data in a column type storage engine, and enabling the exposure data to carry a request ID (Identity); querying whether request data which is the same as the request ID carried by the exposure data exists in a cache in which a plurality of pieces of request data are stored; when it is queried that the request data which is the same as the request ID carried by the exposure data exist, storing the queried request data in a row where the exposure data is located in the column storage engine; and generating a training sample according to each row in the column storage engine.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
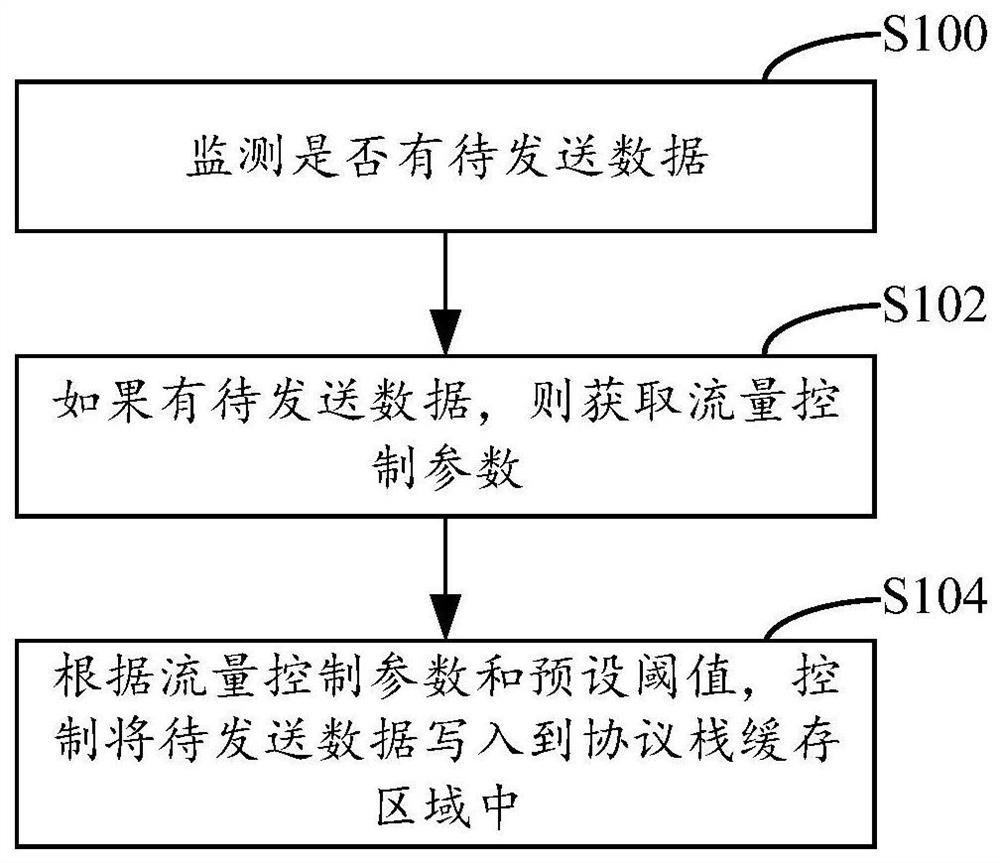
Data writing method, system and device and computer readable storage medium
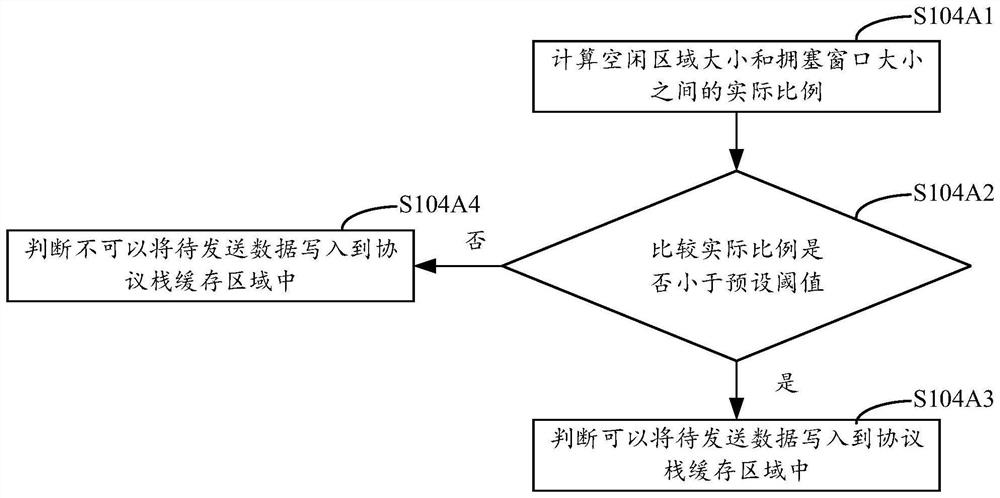
ActiveCN111835651AReduce the burden onReduce memory pressureData switching networksDatabaseProtocol stack
The embodiment of the invention provides a data writing method. The data writing method comprises the steps of monitoring whether to-be-sent data exist or not; if the to-be-sent data exist, obtaininga flow control parameter; and according to the flow control parameter and a preset threshold, controlling to write the to-be-sent data into a protocol stack cache region, the preset threshold being apreset ratio between the size of an idle region in the protocol stack cache region and the flow control parameter. According to the technical scheme provided by the embodiment of the invention, whether the to-be-sent data are written into the protocol stack cache region or not can be determined.
Owner:SHANGHAI BILIBILI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com