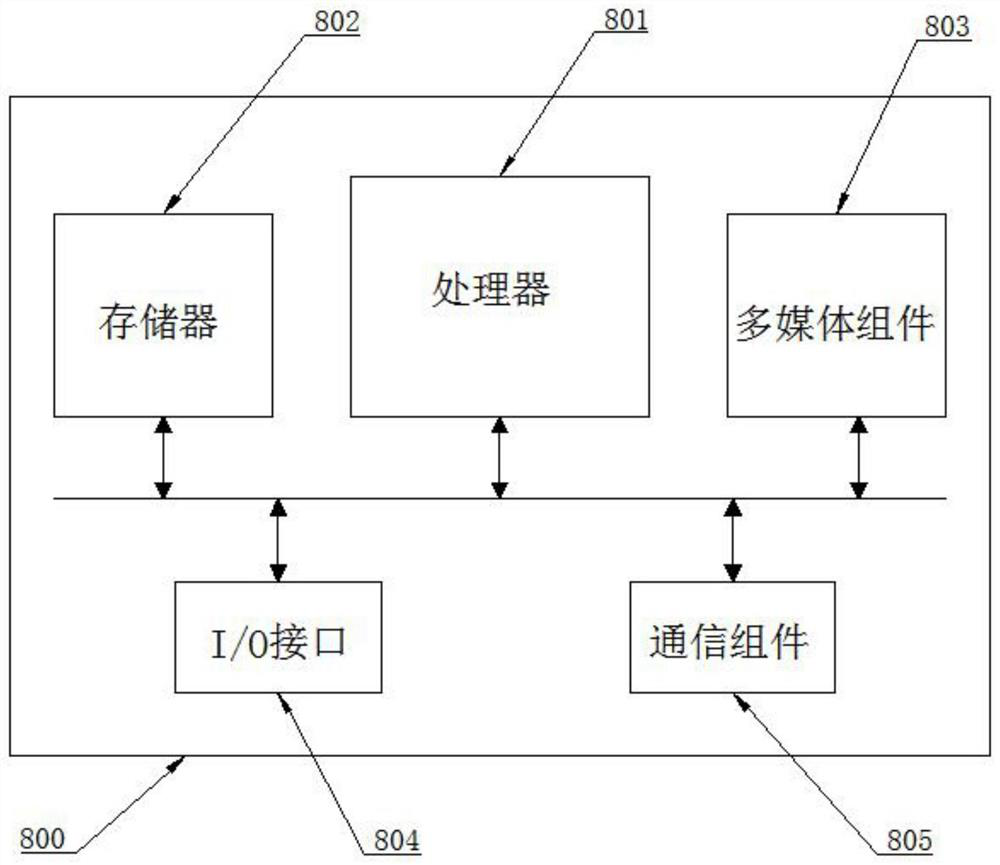
Patents
Literature
31results about How to "Reduce operation and maintenance complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
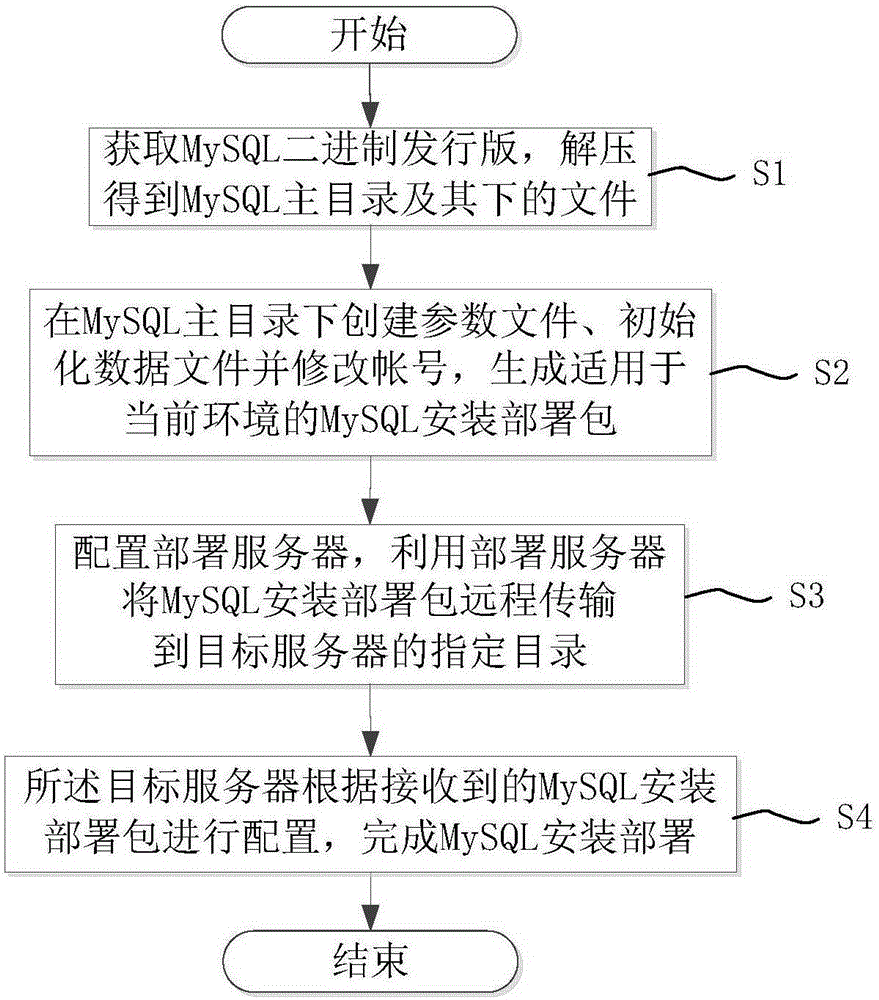
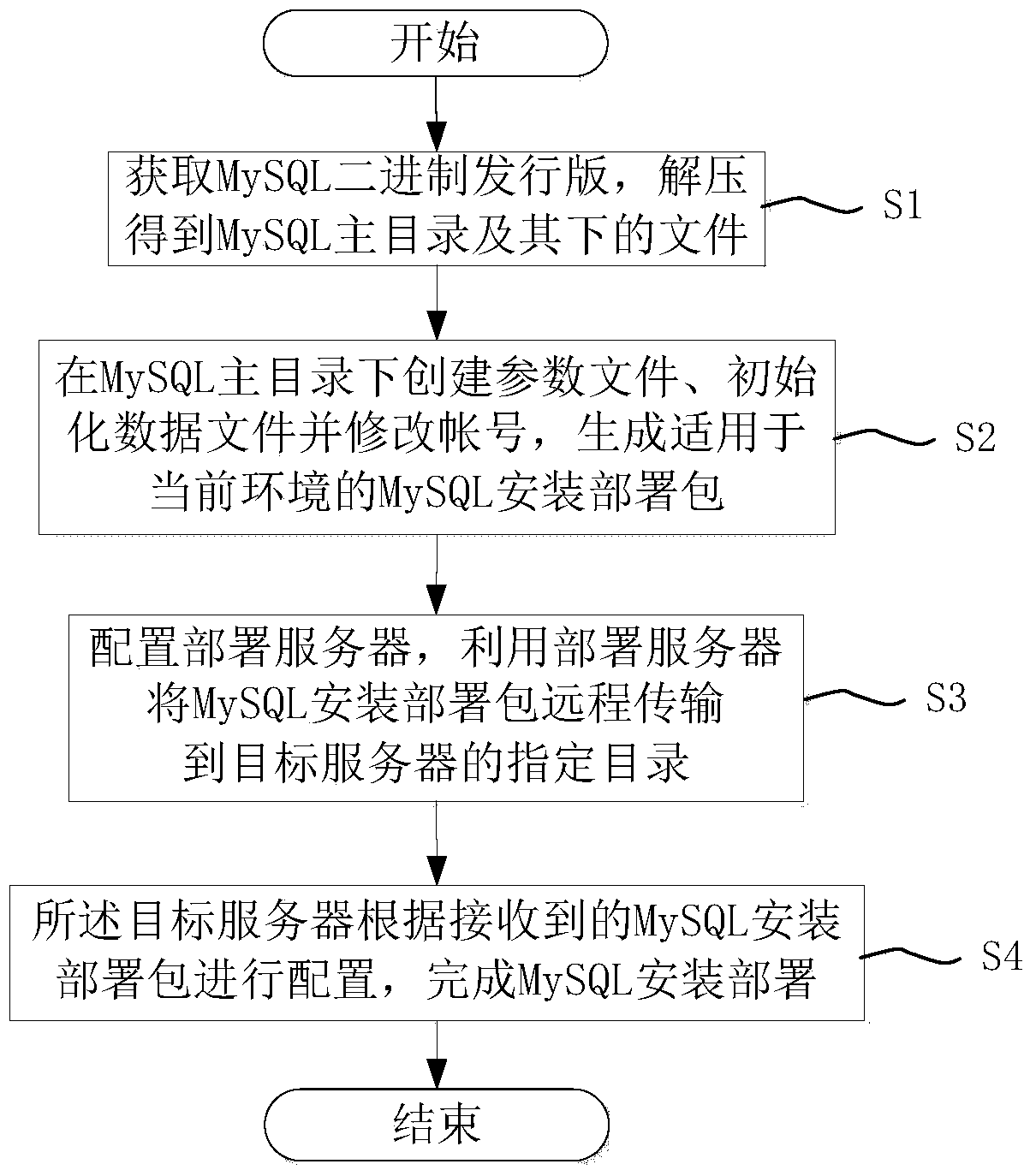
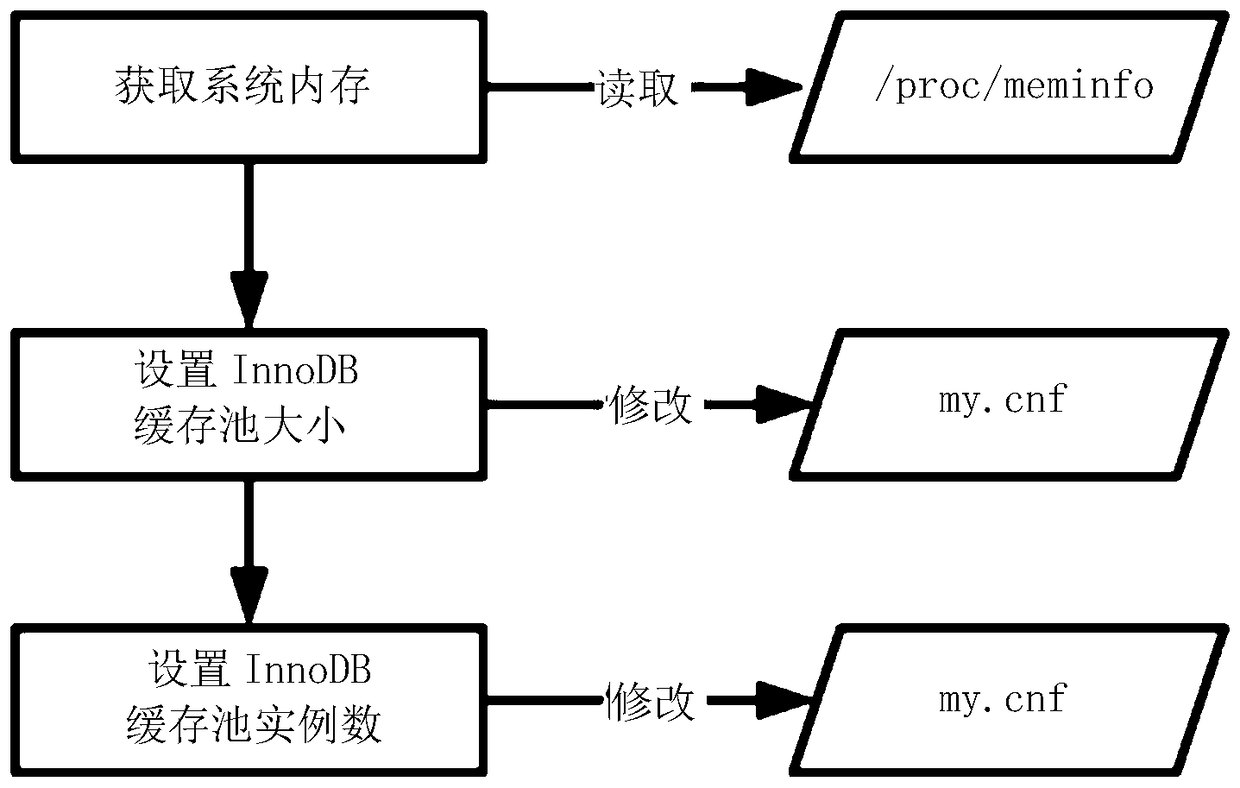
Batched MySQL installation and deployment method
ActiveCN105204897AImprove deployment efficiencyHigh feasibilityProgram loading/initiatingData fileHome directory
The invention discloses a batched MySQL installation and deployment method. The method comprises the following steps: (a) acquiring an MySQL binary release version, and unzipping the MySQL binary release version to obtain an MySQL home directory and files in the MySQL home directory; (b) creating parameter files in the MySQL home directory, initiating data files, correcting an account number, and generating an MySQL installation and deployment packet applicable to a current environment; (c) configuring a deployment server, and remotely transmitting the MySQL installation and deployment packet to an assigned directory of a target server; (d) performing configuration by the target server according to the received MySQL installation and deployment packet to complete MySQL installation and deployment. According to the batched MySQL installation and deployment method, by pre-generating the MySQL installation and deployment packet applicable to the current environment, needed steps and time for actual deployment are reduced; remote transmission is achieved by utilizing the deployment server, MySQL installation and deployment can be completed in batches, the MySQL deployment efficiency is greatly improved, and the feasibility is high.
Owner:SHANGHAI SNC NET INFORMATION TECH CO LTD
Code stream data management method and device and storage medium
PendingCN112632129AImprove perceptionSave resourcesDatabase updatingDatabase management systemsData queryStreaming data
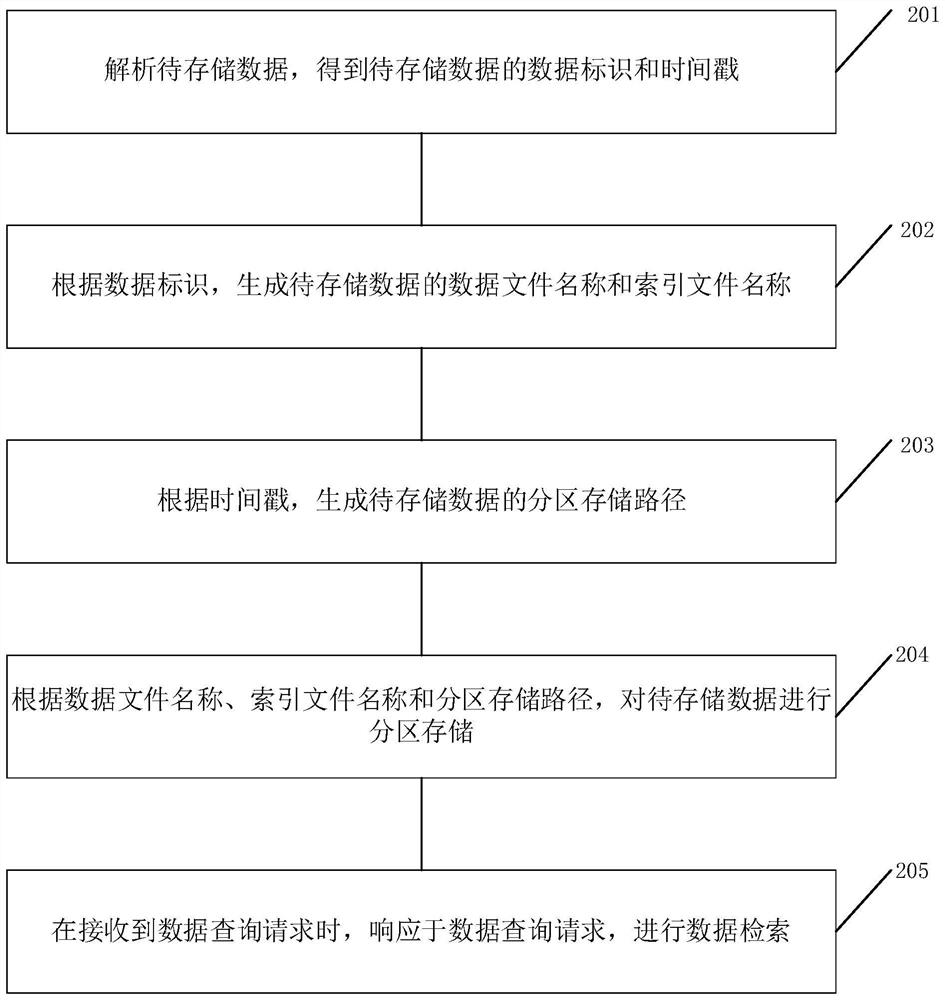
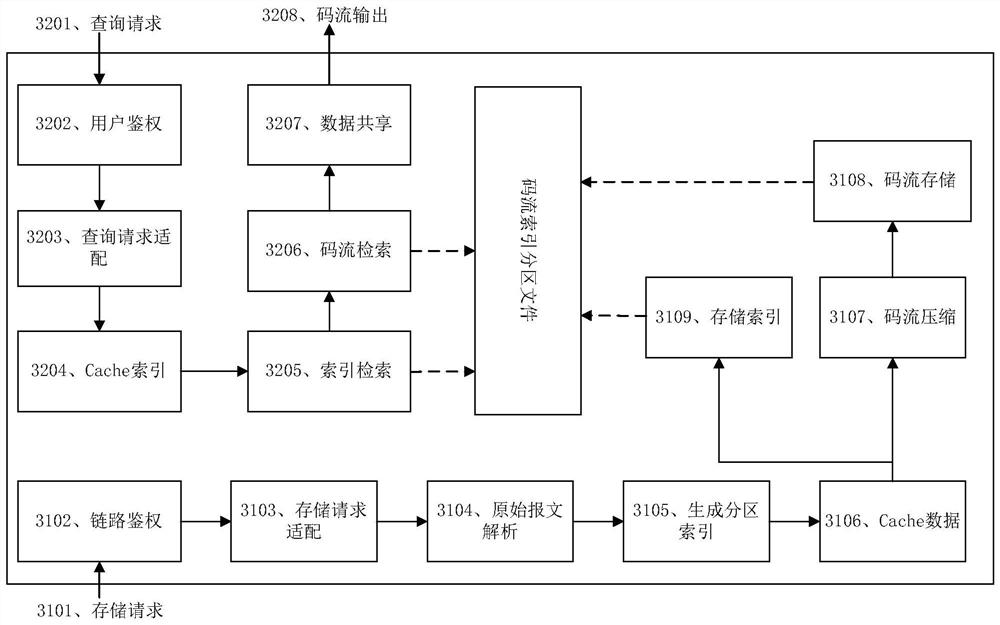
The invention discloses a code stream data management method and device and a storage medium, and the method comprises the steps of analyzing to-be-stored data, and obtaining a data identification and a timestamp of the to-be-stored data; generating a data file name and an index file name of the to-be-stored data according to the data identifier; generating a partition storage path of the to-be-stored data according to the timestamp; performing partition storage on the to-be-stored data according to the data file name, the index file name and the partition storage path; and when a data query request is received, performing data retrieval in response to the data query request. Thus, partition storage is performed according to the analysis result of the code stream data, equipment resources are greatly saved, the operation and maintenance complexity is reduced, the index file is constructed during data storage, and when the code stream data needs to be queried, the required data can be quickly searched from the corresponding storage space according to the characteristics of partition storage in combination with the index file, so that the query response time is effectively accelerated, and the user perception is obviously improved.
Owner:联想未来通信科技(重庆)有限公司
Local mirror image warehouse management method, device and system
PendingCN112433814AReduce operation and maintenance complexityReduce Logical ComplexityInterprogram communicationSoftware simulation/interpretation/emulationMessage queueComputer graphics (images)
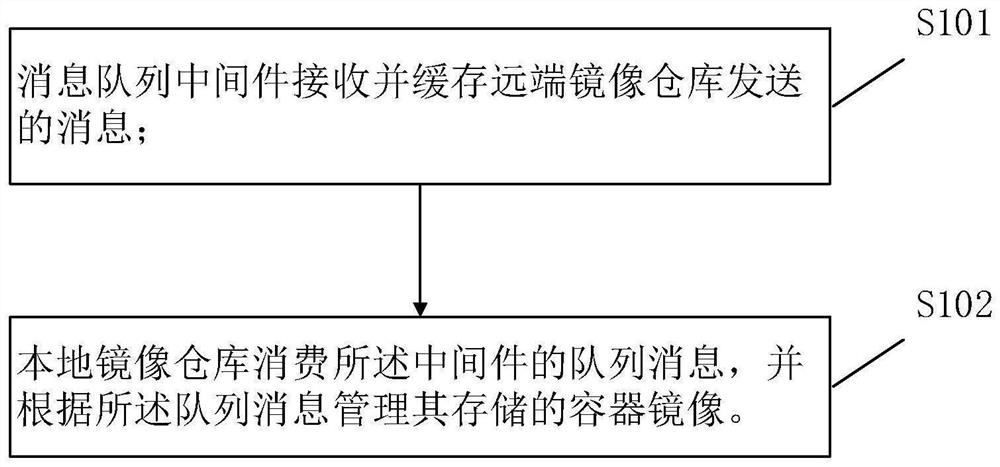
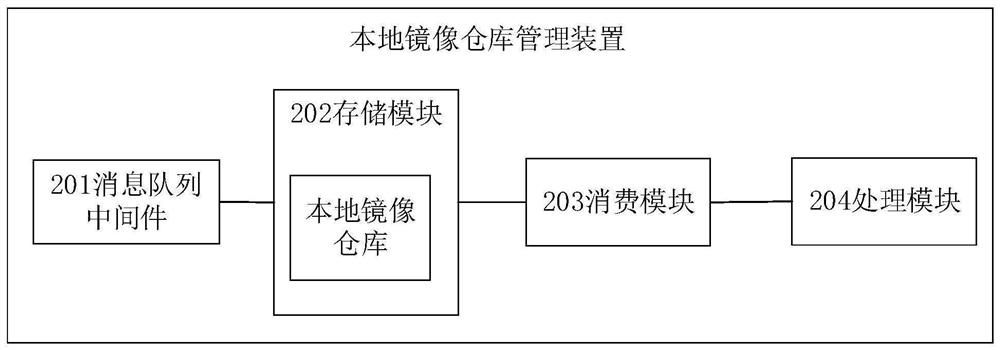
The invention relates to the technical field of cloud containers, in particular to a local mirror image warehouse management method, device and system. The method comprises the steps that message queue middleware receives and caches messages sent by a far-end mirror image warehouse; and the local mirror image warehouse consumes the queue message of the middleware and manages the container mirror images stored in the local mirror image warehouse according to the queue message. According to the local mirror image warehouse management scheme, local mirror image warehouse management is optimized,and it is prompted that the local mirror image storage space can be released to improve the use efficiency of the mirror image warehouse.
Owner:CHINA CITIC BANK
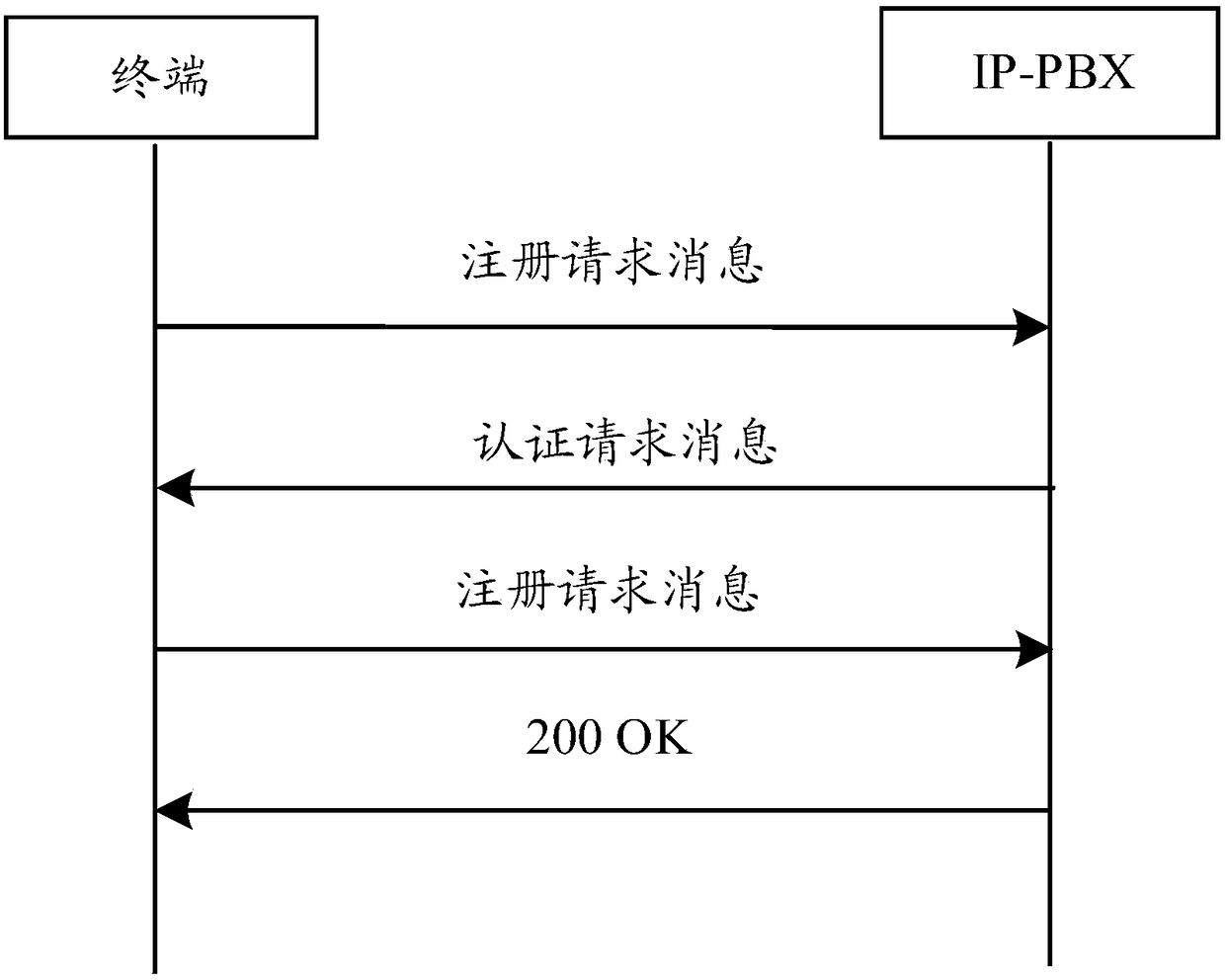
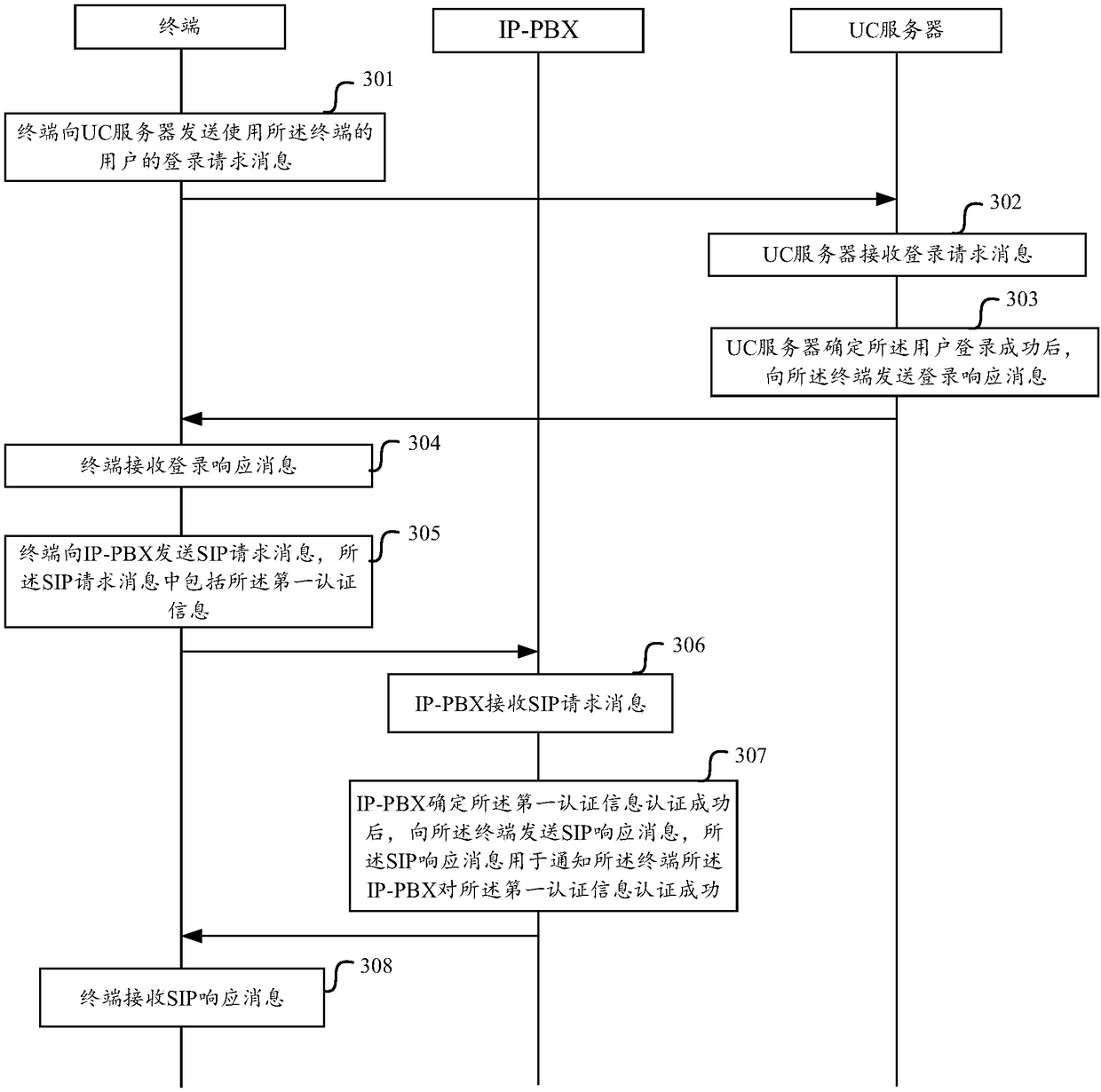
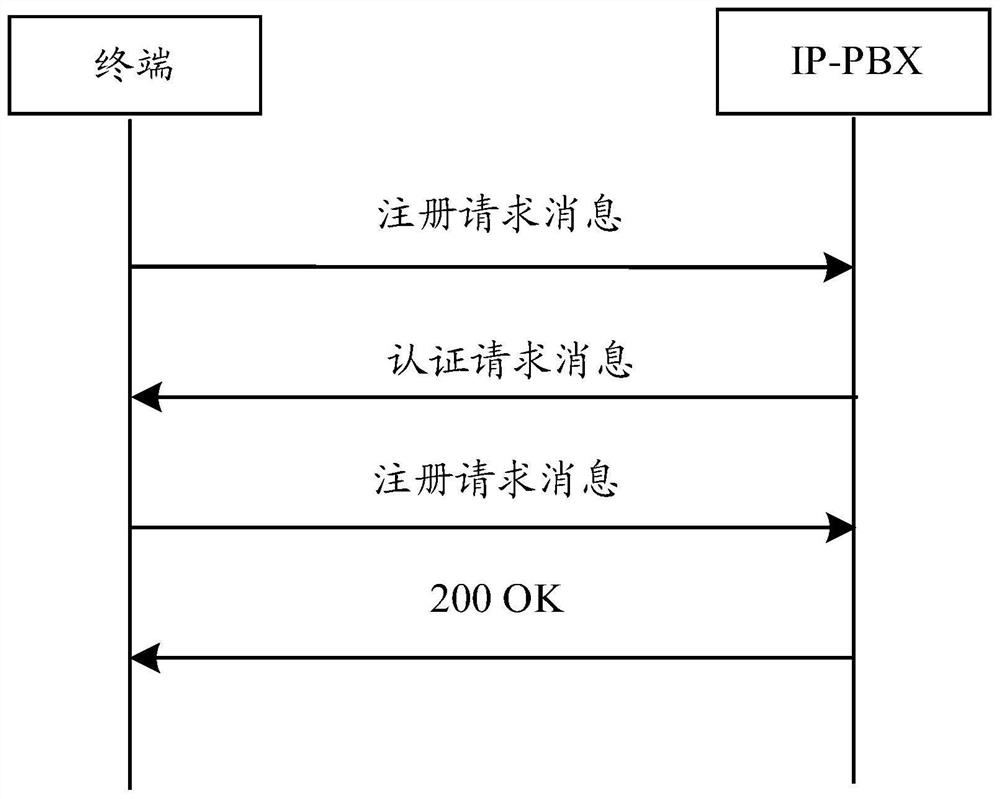
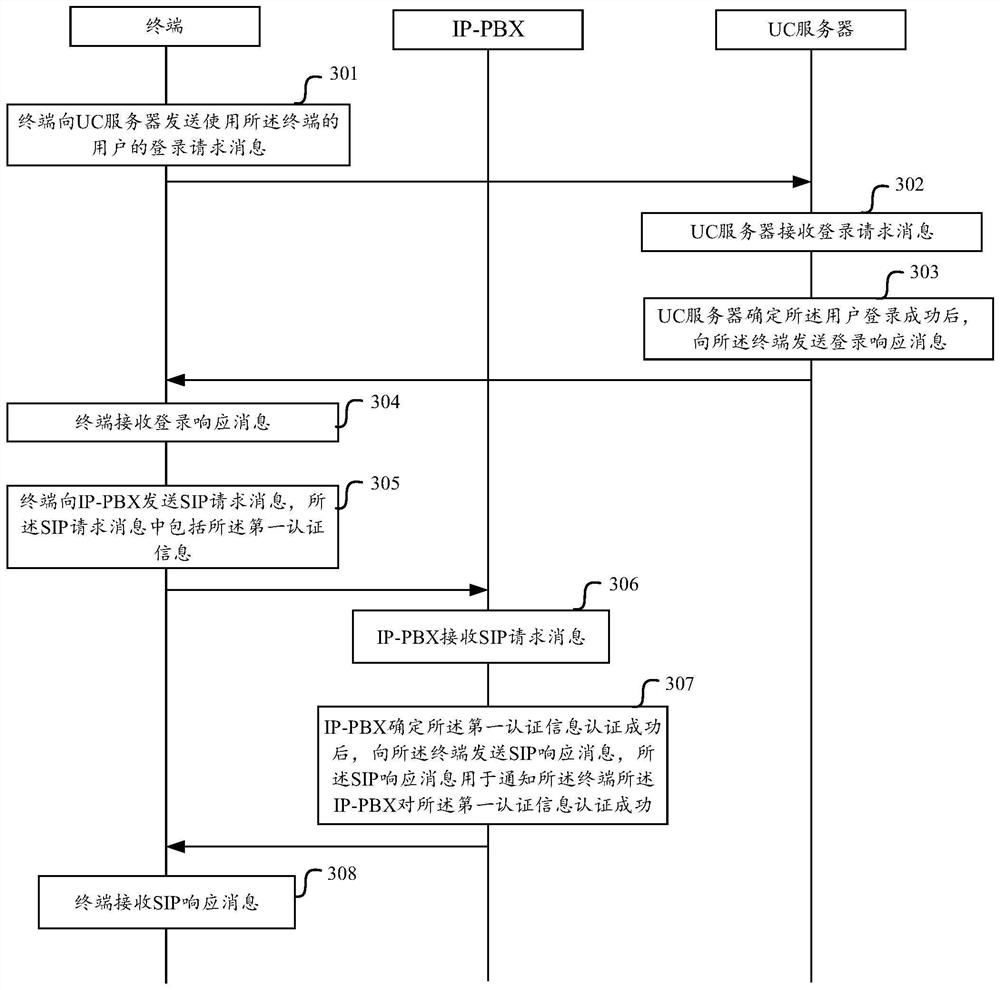
Authentication method and device
ActiveCN108270747AReduce usage complexityIncrease the difficulty of stealingInterconnection arrangementsTransmissionAuthentication schemeAuthentication information
The embodiment of the invention discloses an authentication method and device. In the authentication method, a terminal sends a login request message of a user to a server, and receives an authentication message which is sent by the server after the user is determined to successfully log in; and the terminal sends an SIP (Session Initiation Protocol) including first authentication information to an IP-PBX (IP Private Branch eXchange) and receives an SIP response message sent by the IP-PBX. According to the invention, the server distributes the first authentication information to the user afterthe user logs in the server, the user carries the first authentication information in the subsequent SIP request message, and the IP-PBX performs authentication on the first authentication information. Illegal users cannot successfully log in the server to obtain the first authentication information, so that the IP-PBX refuses an SIP request of the illegal users due to the authentication failureof the first authentication information after receiving an SIP request message of the illegal users, thereby being capable of effectively refusing, relieving and avoiding the embezzlement risk, and protecting expensive long-distance telecommunication resources.
Owner:HANGZHOU HUAWEI ENTERPRISE COMM TECH
Operation and maintenance method, operation and maintenance management platform, equipment and medium
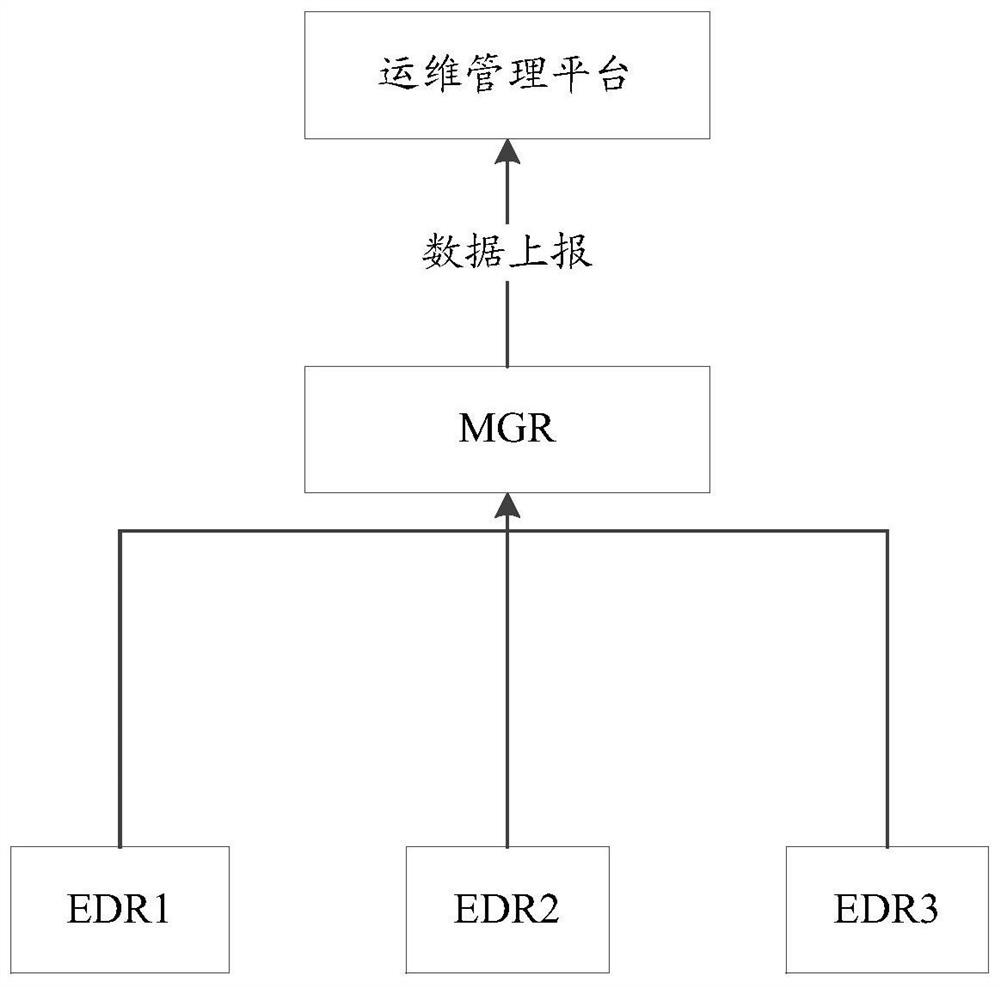
PendingCN112532435ARealize data collectionReduce operation and maintenance complexityData switching networksTerminal equipmentMaintenance management
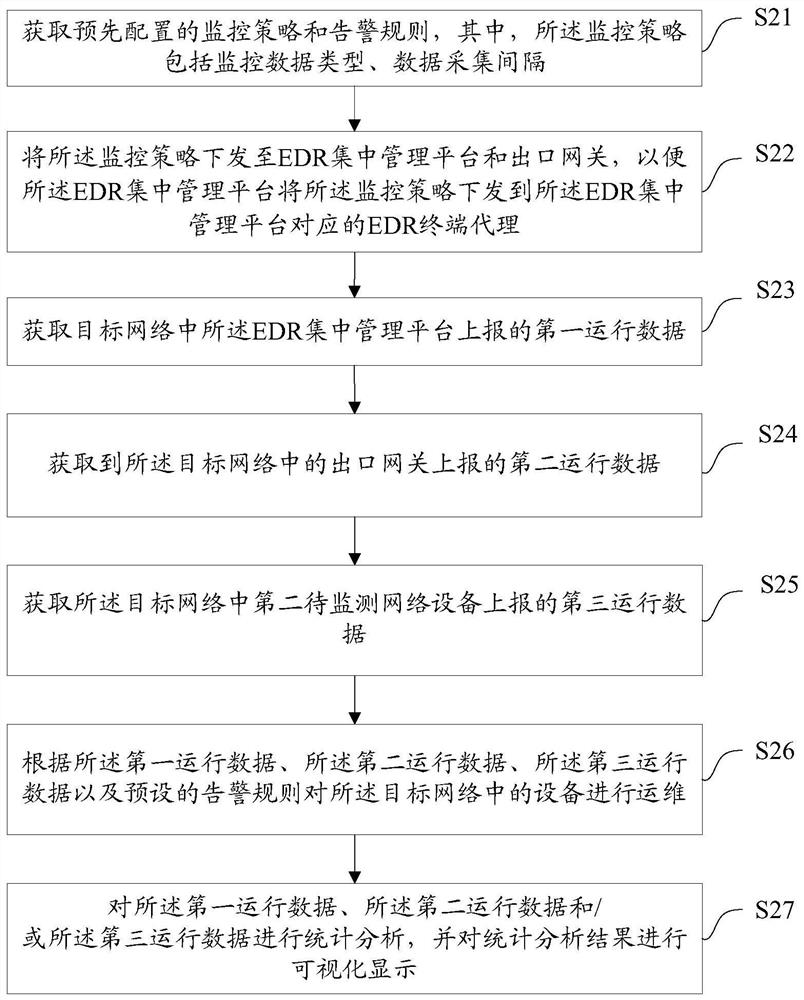
The invention discloses an operation and maintenance method, an operation and maintenance management platform, equipment and a medium, and the method comprises the steps: obtaining first operation data reported by an EDR centralized management platform in a target network, wherein the first operation data is data collected and reported to the EDR centralized management platform by an EDR terminalagent on to-be-monitored terminal equipment deployed in the target network; obtaining second operation data reported by an exit gateway in a target network, wherein the second operation data is data on a first to-be-monitored network device in the target network collected by the exit gateway, and the first to-be-monitored network device is a device in indirect communication with the operation andmaintenance management platform in the target network; and performing operation and maintenance on equipment in the target network according to the first operation data, the second operation data anda preset alarm rule. In this way, centralized operation and maintenance management and control can be performed on the equipment in the enterprise-level data center, the operation and maintenance complexity is reduced, and the operation and maintenance efficiency is improved.
Owner:SANGFOR TECH INC
Service management method and device for ensuring service continuity and storage medium
PendingCN111698301AImprove usabilityIncrease the level of automationData switching networksHigh availabilityMonitoring features
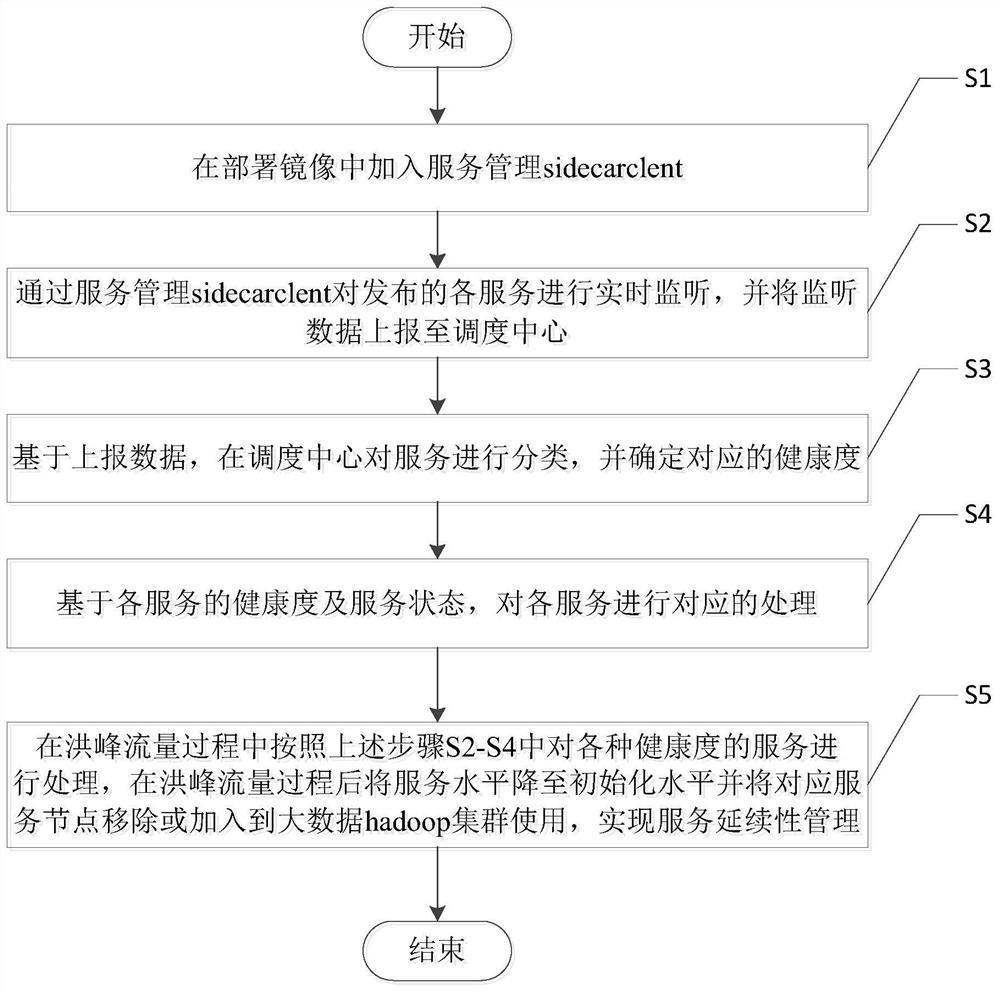
The invention discloses a service management method and device for ensuring service continuity and a storage medium. The method comprises the following steps: S1, adding a service management side intoa deployment mirror image; S2, performing real-time monitoring on each published service through a service management side, and reporting monitoring data to a scheduling center; S3, based on the reported data, classifying the services in a scheduling center, and determining a corresponding health degree; S4, based on the health degree and the service state of each service, carrying out corresponding processing on each service; and S5, processing services of various health degrees in the flood peak flow process according to the steps S2-S4. According to the invention, automatic processing canbe realized during service operation, a basic monitoring function is provided, the availability is improved, and the service operation and maintenance cost is reduced.
Owner:成都新希望金融信息有限公司
Method for controlling electronic lock, electronic lock, key terminal and lock cylinder terminal
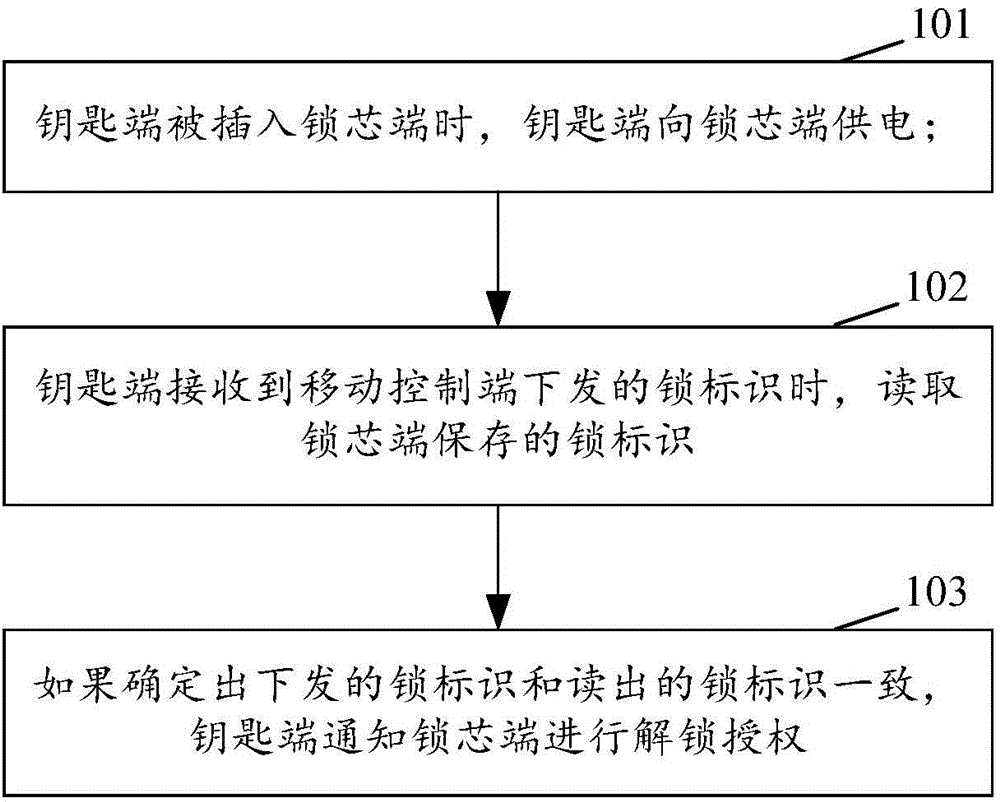
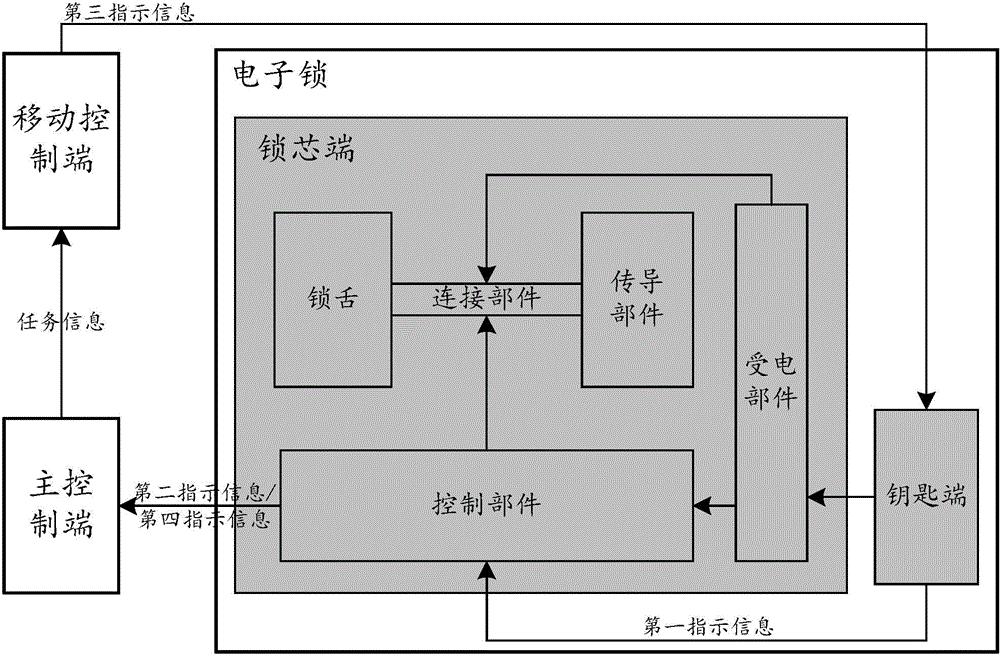
InactiveCN105989648AReduce operation and maintenance complexityReduce operation and maintenance costsNon-mechanical controlsElectric permutation locksAuthorizationManagement system
The invention discloses a method for controlling an electronic lock, the electronic lock, a key terminal and a lock cylinder terminal. The method comprises the following steps that when the key terminal is inserted into the lock cylinder terminal, the key terminal supplies power to the lock cylinder terminal; when the key terminal receives a lock mark transmitted by a mobile control terminal, the key terminal reads a lock mark stored by the lock cylinder terminal; and if it is determined that the transmitted lock mark is identical to the read lock mark, the key terminal informs the lock cylinder terminal of unlocking and authorization. According to the invention, an internal power supply in a case is prevented from supplying power to the electronic lock, so considerable regular maintenance of the internal power supply in the case is avoided, and complexity in operation and maintenance of a lock management system is reduced; and thus, operation and maintenance cost for a communication network is decreased.
Owner:ZTE CORP +1
Method for managing multiple sets of big data clusters through Ambari
InactiveCN106445519AReduce investmentLow costSoftware designSpecific program execution arrangementsNODALMulti cluster
The invention discloses a method for managing multiple sets of big data clusters through Ambari. According to the method, four file corresponding code source codes, namely, leftNavbar.htm, mail.html, main.js and app.js in Ambari are modified, codes in html and js files are closely interconnected, the need of managing the multiple sets of big data clusters is met, and at least one management node can be reduced during assembly deploying. Aiming at the scene of multi-cluster management, investment of physical nodes can be reduced, cost is effectively reduced, the operation and maintenance complexity is reduced, and high application and popularization value is achieved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
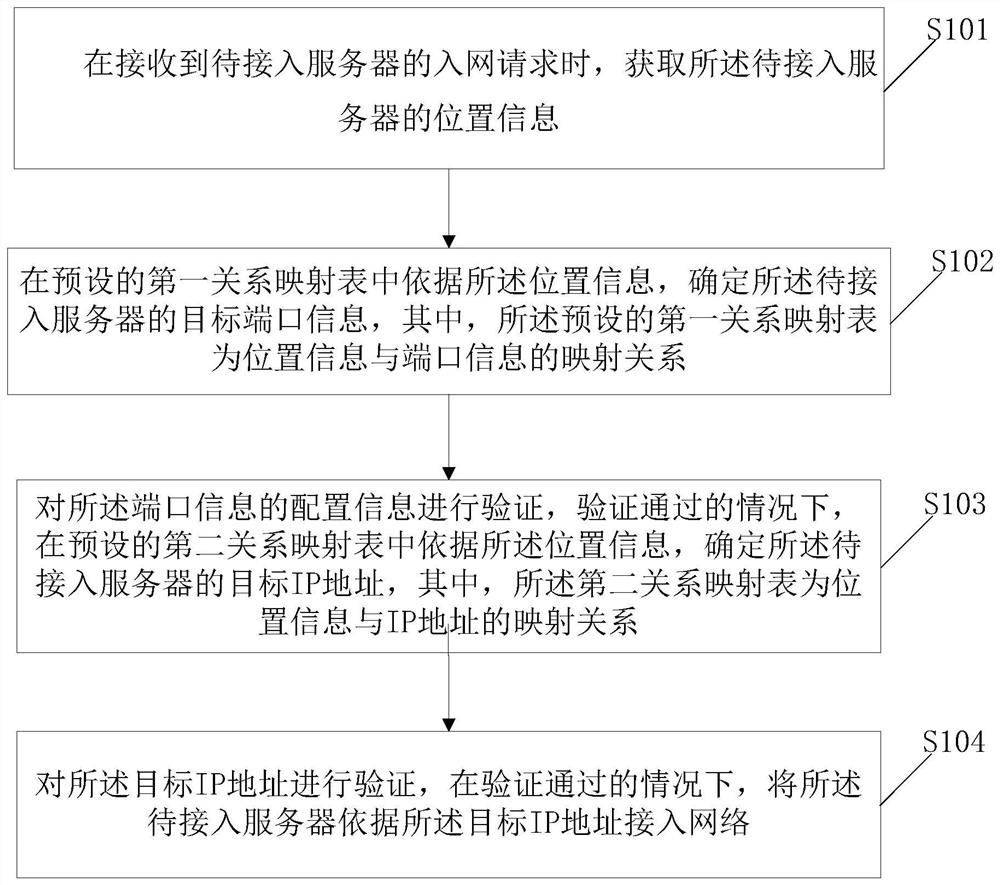
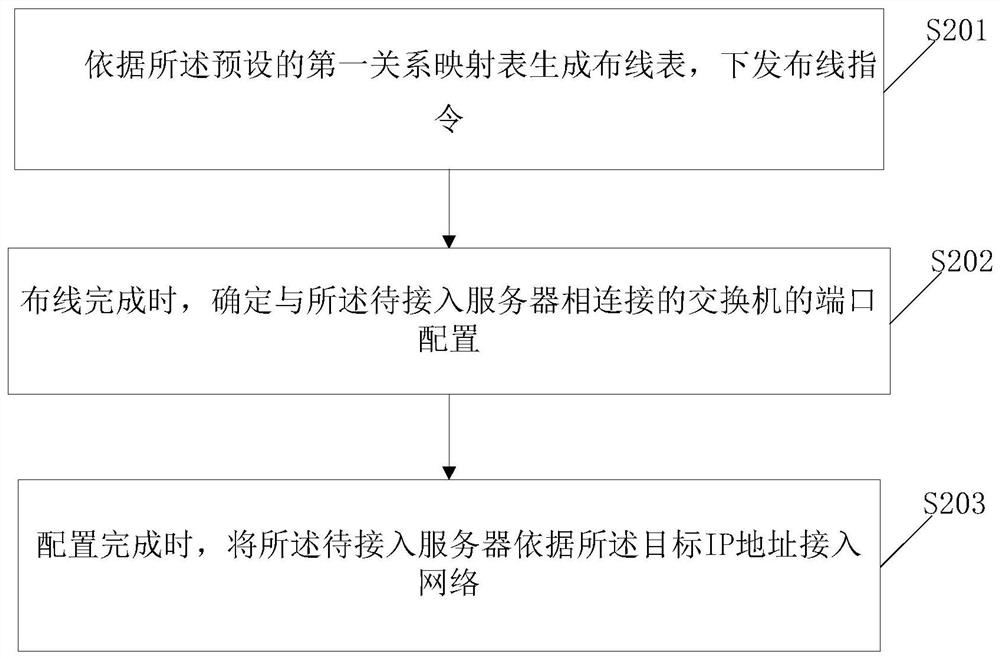
Method and device for accessing server to network
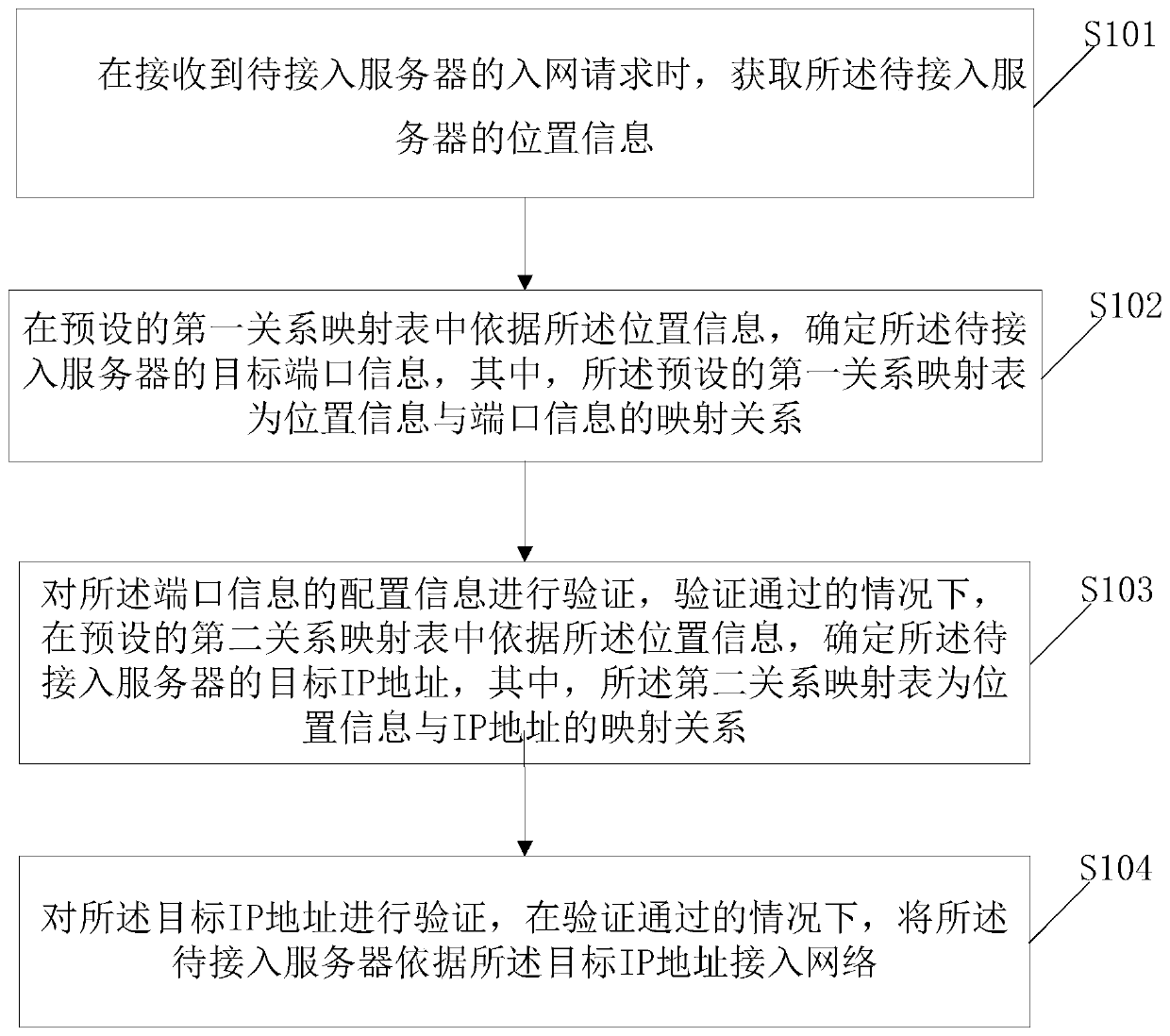
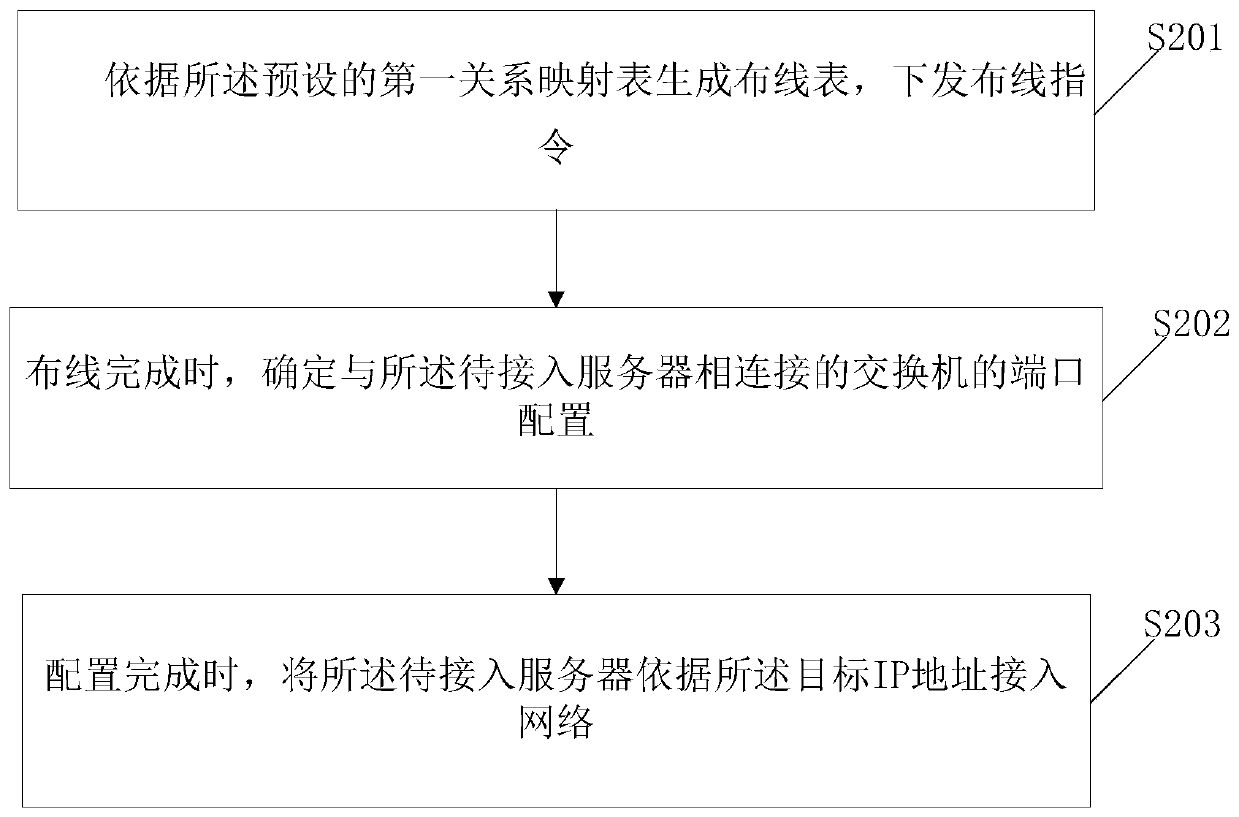
ActiveCN111130963AImprove access speedReduce error rateData switching by path configurationAccess networkIp address
The invention discloses a method for accessing a server to a network. The method comprises the steps of acquiring position information of a to-be-accessed server; determining target port information of the to-be-accessed server in a preset first relationship mapping table according to the position information, wherein the preset first relationship mapping table is a mapping relationship between position information and port information; verifying the configuration information of the port information, and determining a target IP address of the to-be-accessed server according to the position information in a preset second relationship mapping table under the condition that the verification is passed, wherein the second relationship mapping table is a mapping relationship between the positioninformation and the IP address; and verifying the target IP address, and accessing the to-be-accessed server to the network according to the target IP address under the condition that the verification is passed. According to the method, the target IP address is determined according to the position information of the to-be-accessed server, the preset first relationship mapping table and the presetsecond relationship mapping table, and the to-be-accessed server is accessed to the network according to the target IP address.
Owner:CHINA CONSTRUCTION BANK
Multi-path equipment shielding system, method and equipment and readable storage medium
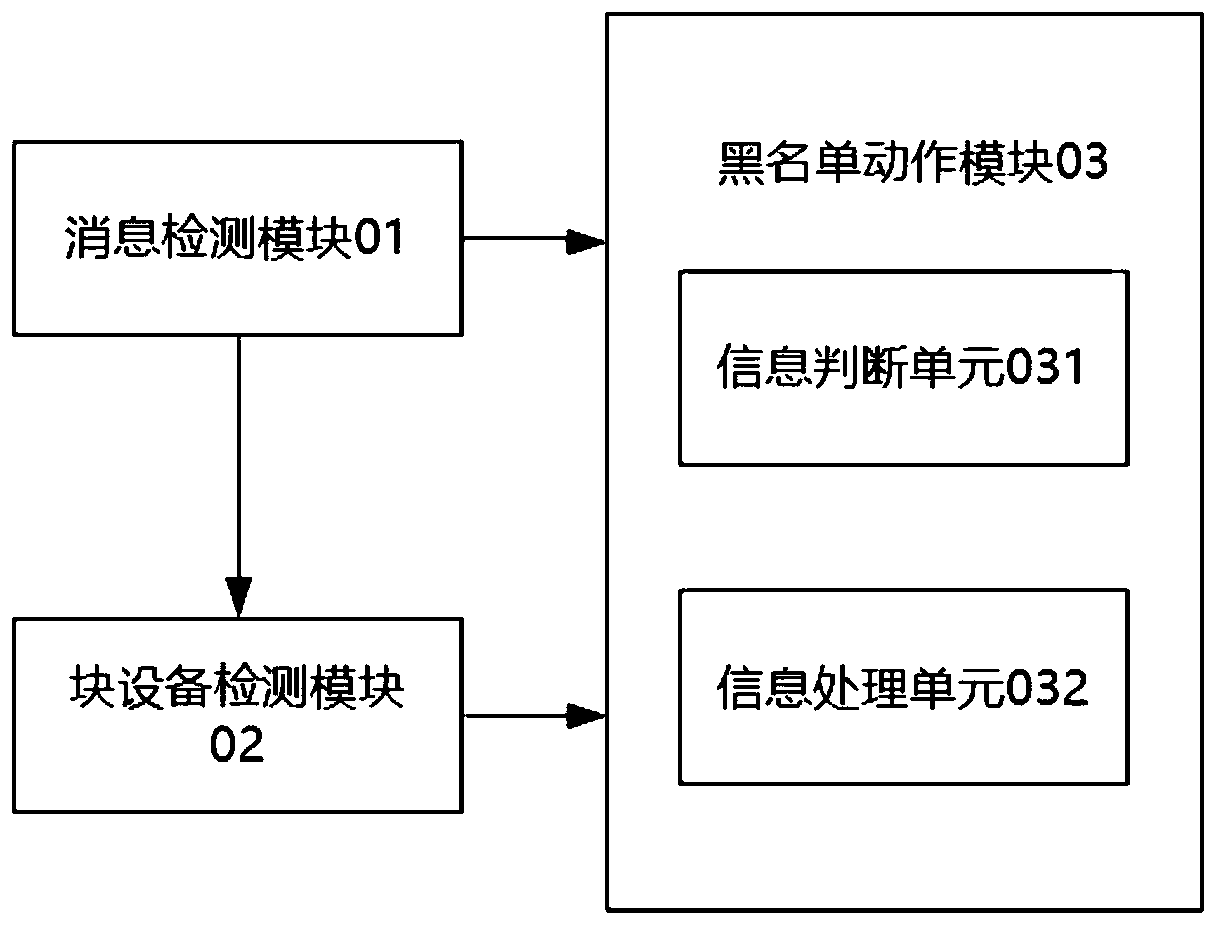
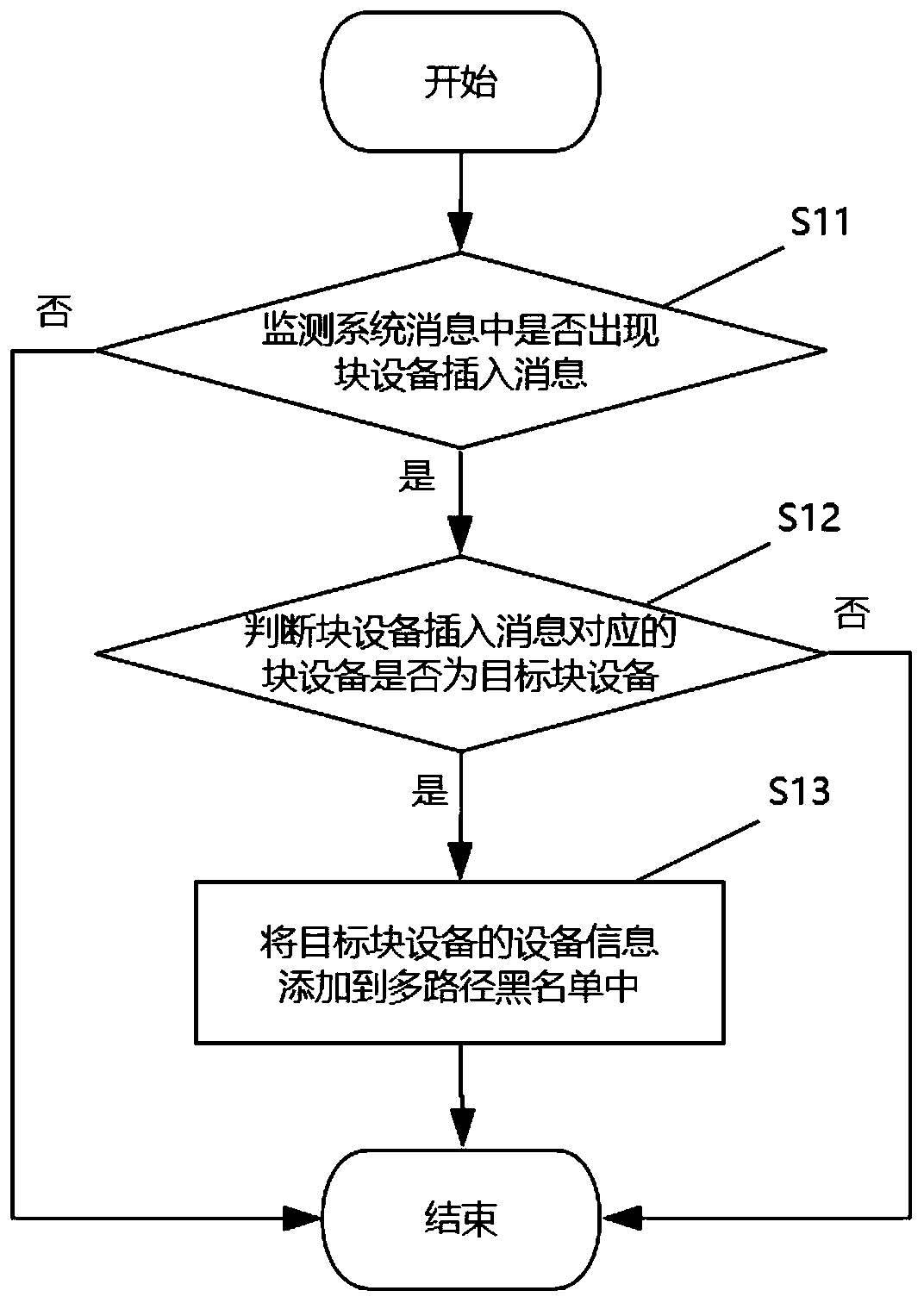
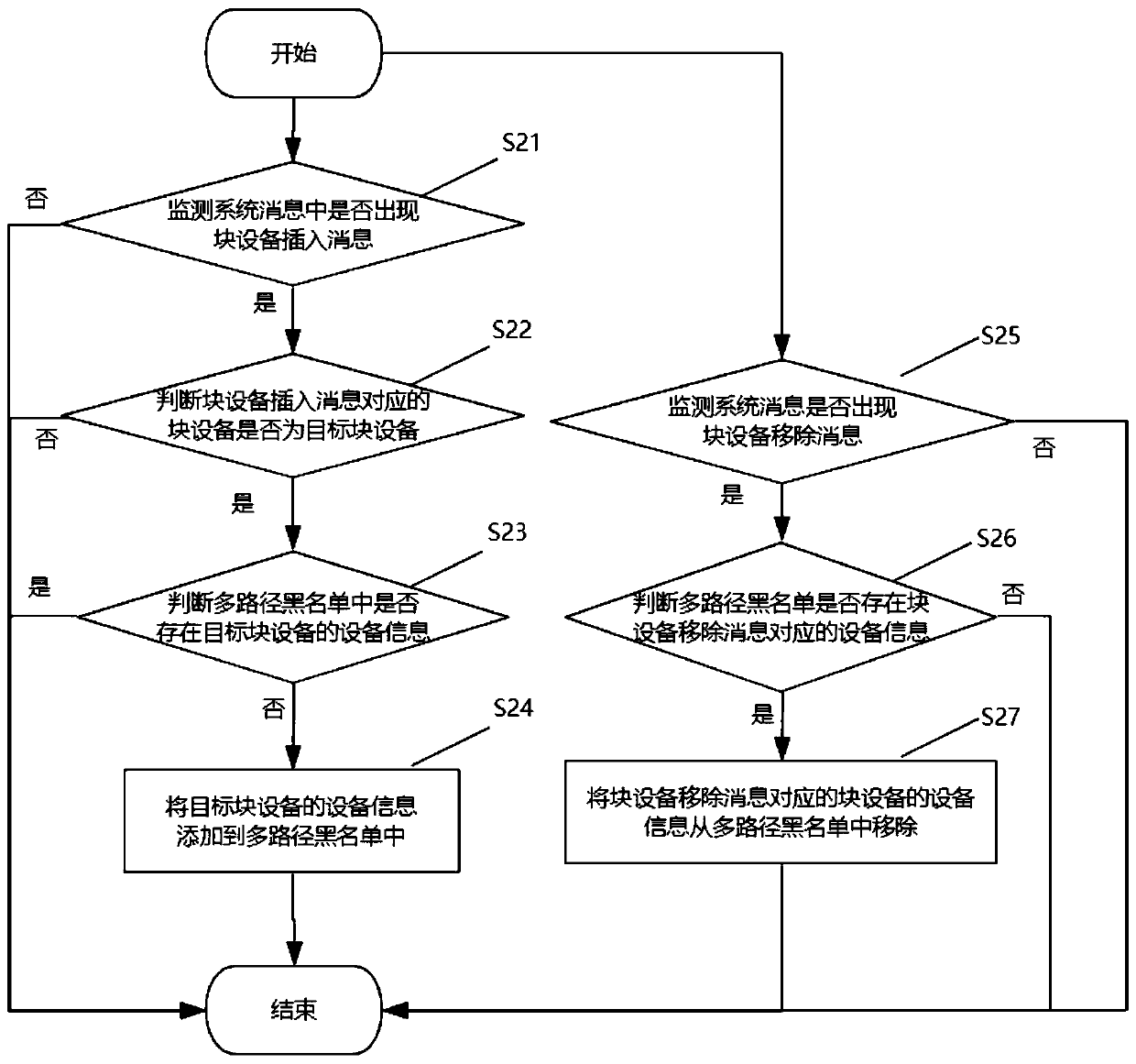
InactiveCN111290915ASimple stepsReduce operation and maintenance complexityHardware monitoringMulti pathEmbedded system
The invention discloses a multipath equipment shielding system, method and equipment and a readable storage medium, and the system comprises a message monitoring module which is used for detecting whether a block equipment insertion message appears in a system message or not; if yes, triggering a block equipment monitoring module; a block equipment detection module which is used for judging whether block equipment corresponding to the block equipment insertion message is target block equipment or not, and if so, triggering the blacklist action module, wherein the target block equipment is specifically random plugging block equipment or a block equipment whose physical link protocol is a to-be-shielded protocol; and a blacklist action module which is used for adding the equipment information of the target block equipment into a multi-path blacklist. According to the application, the targets of automatically monitoring information, judging whether the target block equipment is the targetblock equipment and adding the equipment name of the target block equipment into the multi-path blacklist are realized, the steps are simple and efficient, the operation and maintenance complexity isreduced, and the possibility of misoperation and the security risk of the system are reduced.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Sensitive data detection cloud service method and cloud service platform
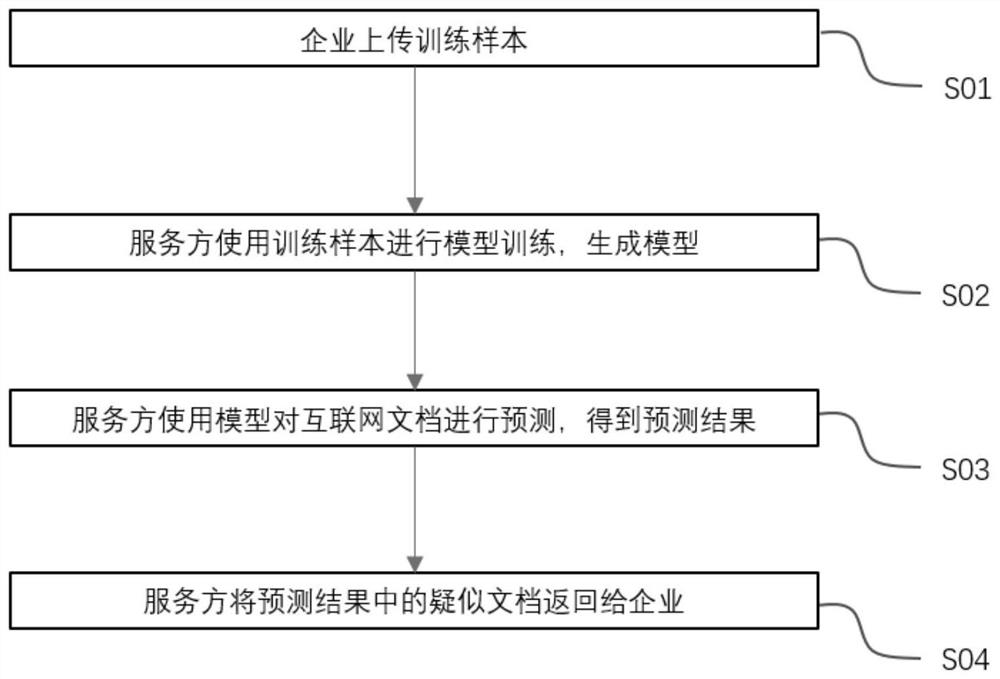
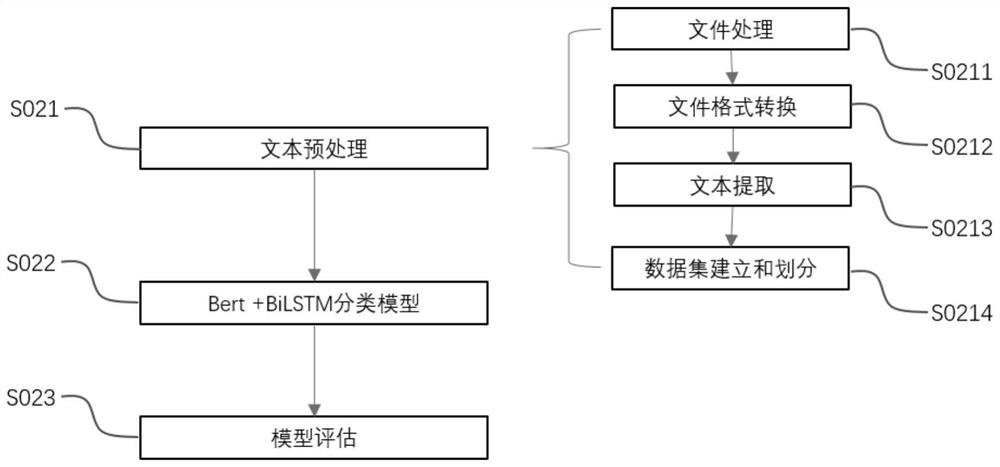
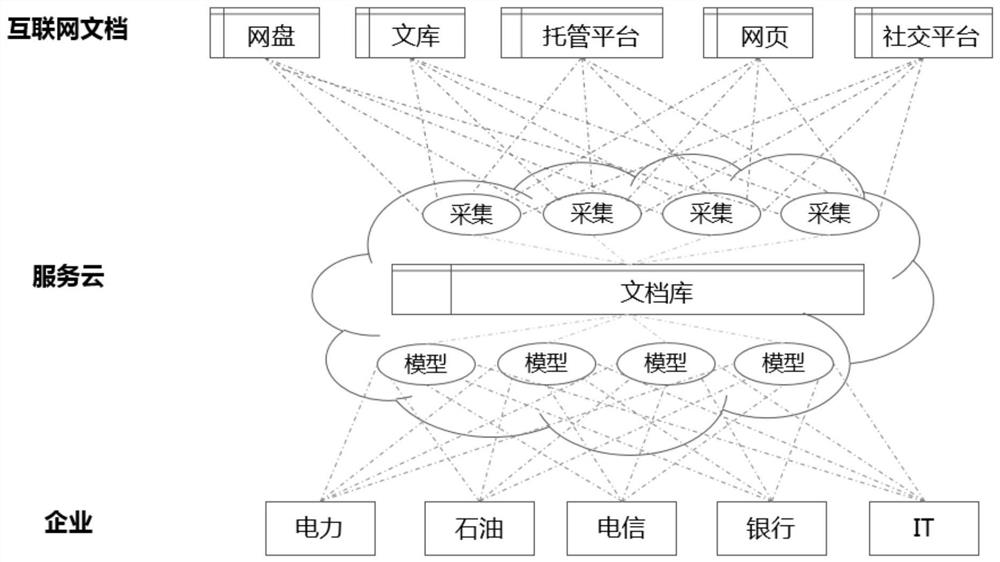
PendingCN111666414ALow costLower the thresholdCharacter and pattern recognitionNatural language data processingBusiness enterpriseSmall to medium enterprises
The invention discloses a sensitive data detection cloud service method and a cloud service platform, and the method comprises the following steps: S01, an enterprise uploads a training sample, and the enterprise uploads the training sample to a service side through a data interface opened by the service side; S02, the service side performs model training by using the training sample to obtain a Bert+BiLSTM classification model; s03, the server predicts the internet document by using the Bert+BiLSTM classification model to obtain a prediction result; and S04, the service party returns the suspected document in the prediction result to the enterprise. Sensitive data detection service is provided for an enterprise in a cloud service mode, the cost and threshold for the enterprise to obtain service are reduced, and repeated investment is avoided; large, medium and small enterprises can obtain detection services with the same standard through the service, the safety of network data is integrally improved, and great social significance is achieved.
Owner:SHANGHAI GUAN AN INFORMATION TECH
Method for constructing multi-task computer vision application service based on deep learning
PendingCN112508769AEasy dockingImprove good performanceResource allocationProcessor architectures/configurationData sourceEngineering
The invention discloses a method for constructing a multi-task computer vision application service based on deep learning, and belongs to the technical field of artificial intelligence. The method forconstructing the multi-task computer vision application service based on deep learning comprises the following steps: S1, defining a data input data source format of the application service; s2, defining GPU resource scheduling rules are defined so that GPU resources are automatically allocated as required; s3, defining a service internal bus; s4, defining a model arrangement pipeline; and S5, containerized deployment and operation and maintenance of the application service. According to the method for constructing the multi-task computer vision application service based on deep learning, theimplementation difficulty of deep learning can be reduced, the development efficiency is improved, meanwhile, the development cost is reduced, and good application and popularization value is achieved.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
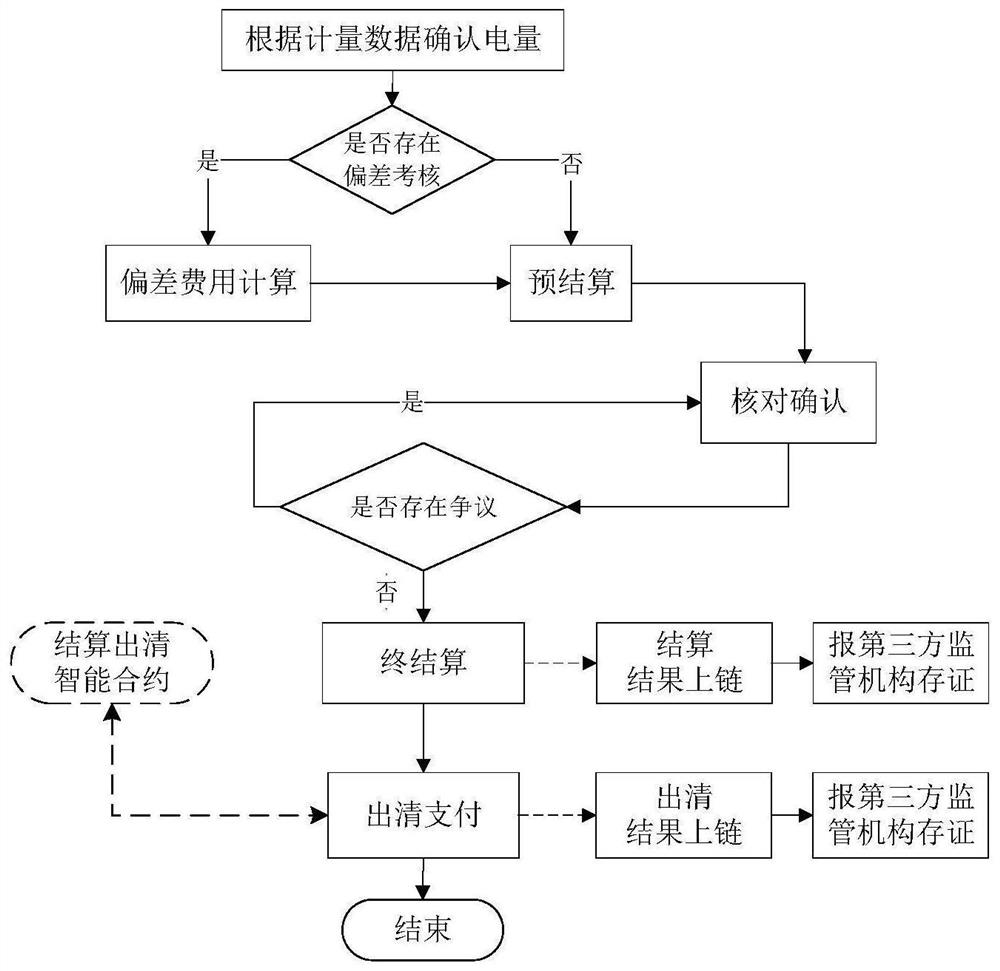
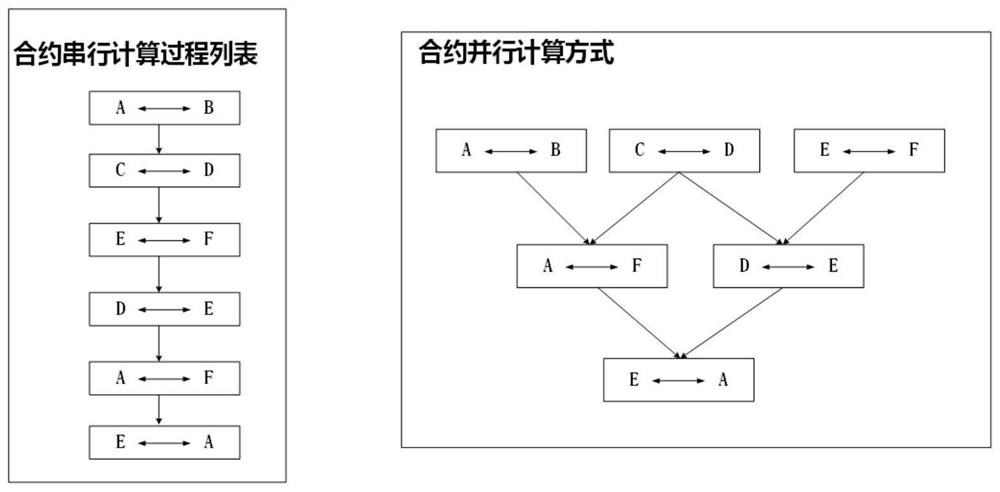
Distributed power supply settlement clearing method and system
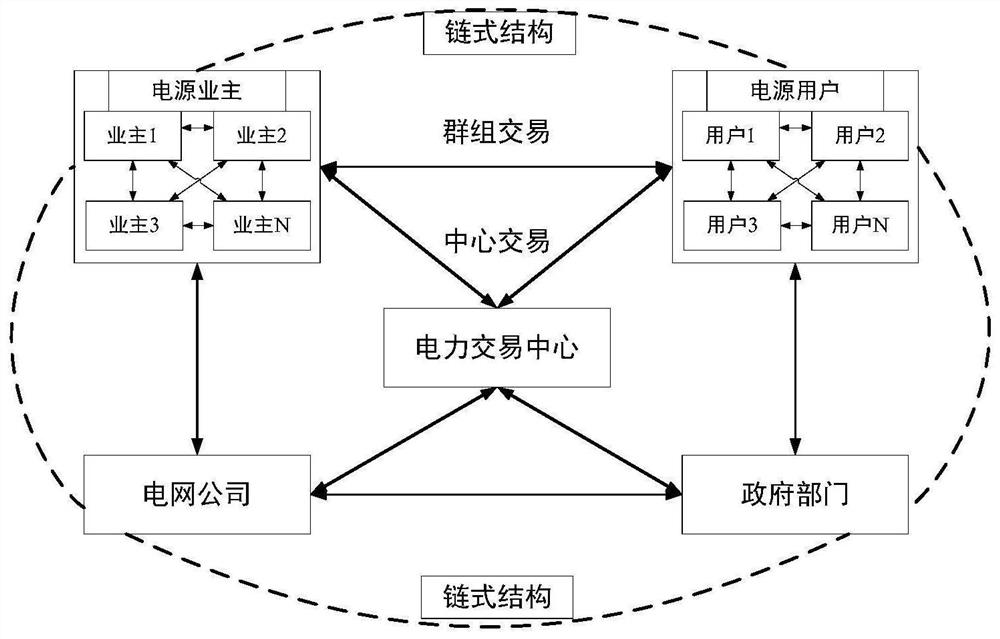
PendingCN113935808AReduce operation and maintenance complexitySimplify operation and maintenance complexityDigital data protectionBuying/selling/leasing transactionsConcurrent computationEngineering
The invention discloses a distributed power supply settlement clearing method and system, and the method comprises the steps that the power supply transaction settlement is carried out on a block chain network, a clearing contract stored on a block chain is automatically triggered, and the clearing between distributed power supply settlement clearing objects is completed; if the objects of the two groups of clearing transactions comprise the same object, the clearing contract is executed in a serial calculation mode, and otherwise parallel calculation is adopted; the block chain network takes a distributed power supply settlement object as a node, and a node consensus adopts a group architecture; and finally, settlement and clearing results are stored on the chain, and perfect man-machine interaction functions of querying historical transactions, displaying user information on the chain and the like can be provided through a client of the block chain network. According to the method, the block chain network with low operation and maintenance complexity and high node consensus speed is constructed, the contract execution efficiency is improved by adopting a parallel computing mode based on the dependency relationship, the fairness and reliability of settlement and clearing are ensured, and the settlement and clearing cost is reduced.
Owner:NARI TECH CO LTD +1
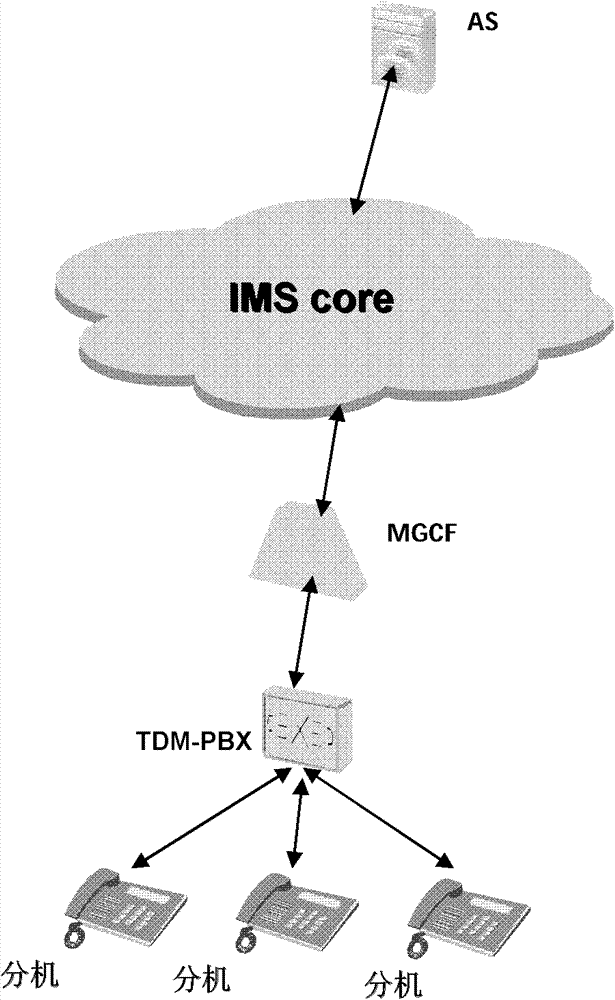
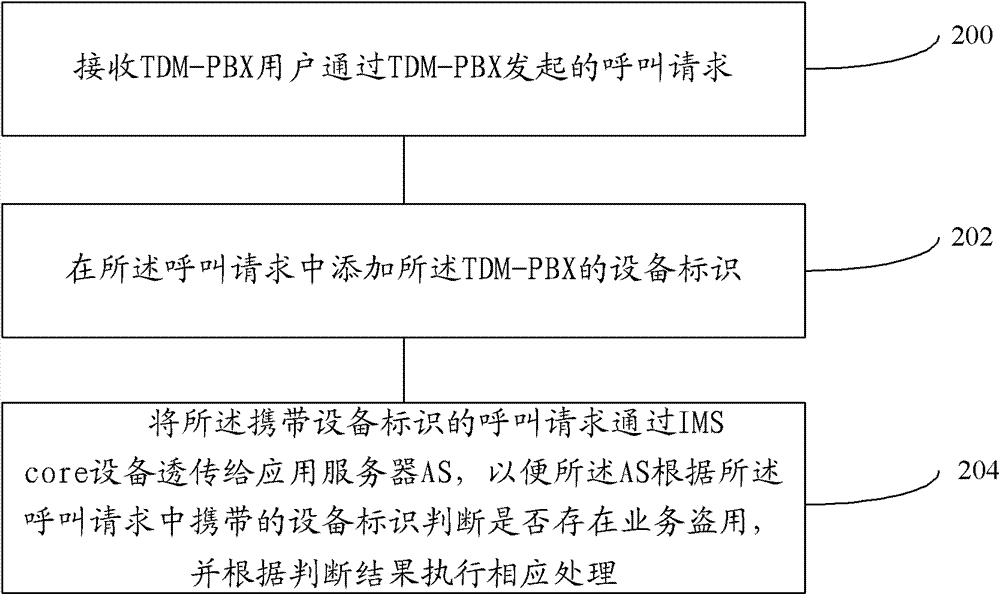
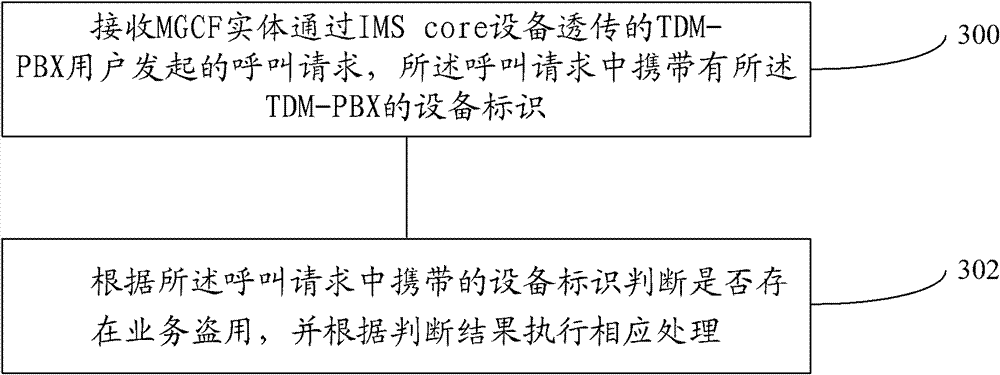
Method, equipment and system for preventing service embezzlement
ActiveCN102075939BReduced operating requirementsRealize automatic service provisioningTransmissionSecurity arrangementApplication serverBranch exchange
The embodiment of the invention provides a method for preventing service embezzlement. The method comprises the following steps of: receiving a call request sent by a telemetric data monitor private branch exchange (TDM-PBX) user through a TDM-PBX; adding an equipment identifier of the TDM-PBX into the call request; and transmitting the call request with the equipment identifier to an applicationserver (AS) through information management system (IMS) core equipment so that the AS can judge whether service embezzlement exists according to the equipment identifier in the call request, and executes corresponding process according to a judged result. Correspondingly, the invention provides a media gateway control functional entity, the application server and a system. On the premise of access of the TDM-PBX to the IMS network, the risk of sending an illegal call caused by error configuration of a user or intentional embezzlement of other numbers by the user is avoided.
Owner:HUAWEI TECH CO LTD
Method and device for server access to network
ActiveCN111130963BImprove access speedReduce error rateData switching by path configurationAccess networkIp address
The invention discloses a method for a server to access a network, comprising: obtaining the location information of the server to be accessed; and determining the target port information of the server to be accessed according to the location information in a preset first relational mapping table, wherein, The preset first relationship mapping table is the mapping relationship between location information and port information; verify the configuration information of the port information, and if the verification is passed, determine the pending connection according to the location information in the preset second relationship mapping table Enter the target IP address of the server, wherein, the second relationship mapping table is the mapping relationship between location information and IP address; verify the target IP address, and if the verification is passed, the server to be accessed will be connected to the network according to the target IP address . In the above method, the target IP address is determined according to the location information of the server to be accessed, the preset first relationship mapping table and the preset second relationship mapping table, and the server to be accessed is connected to the network according to the target IP address.
Owner:CHINA CONSTRUCTION BANK
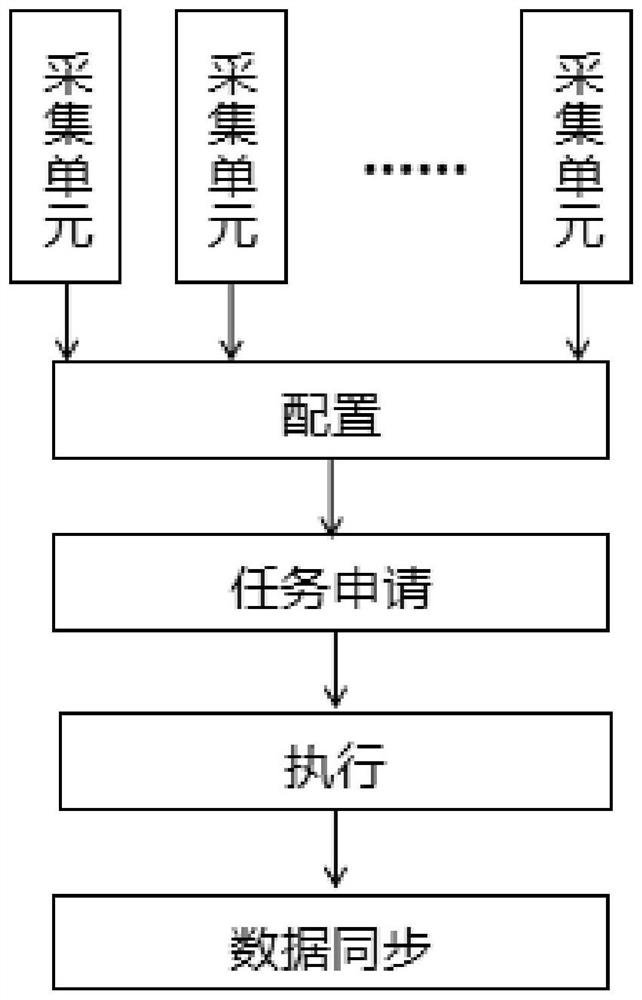
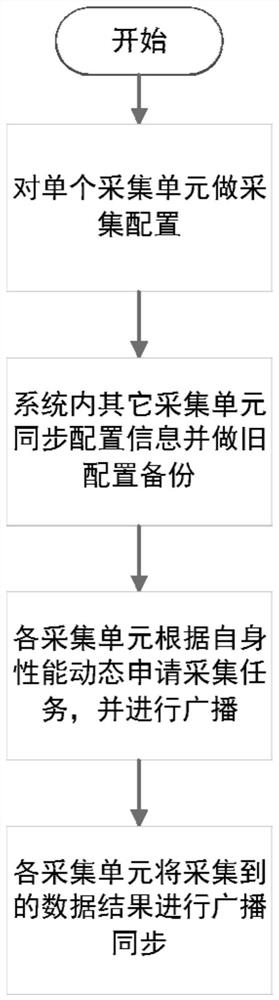
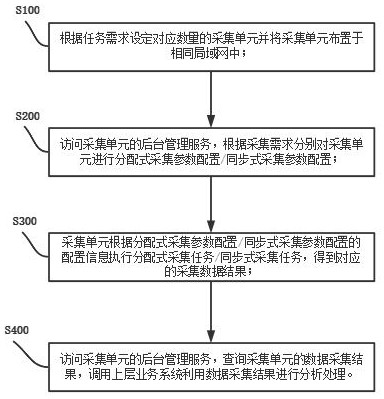
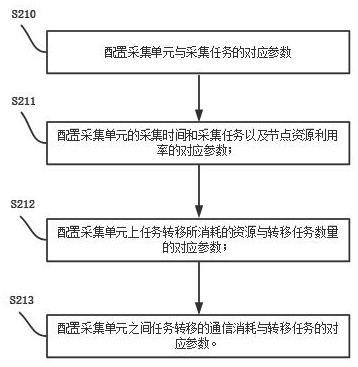
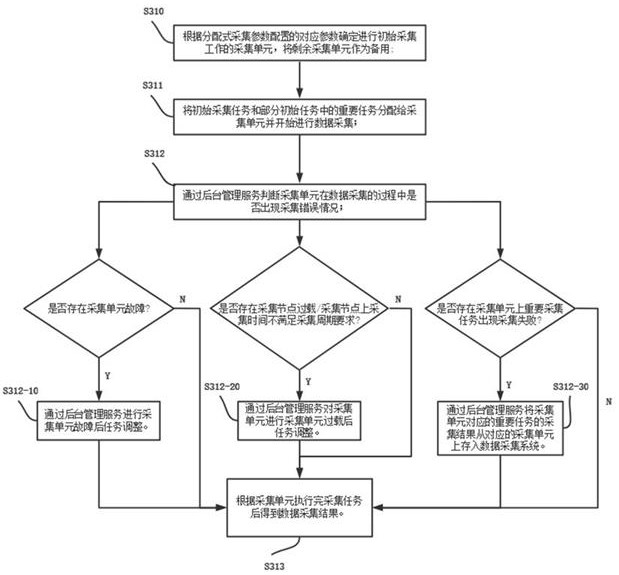
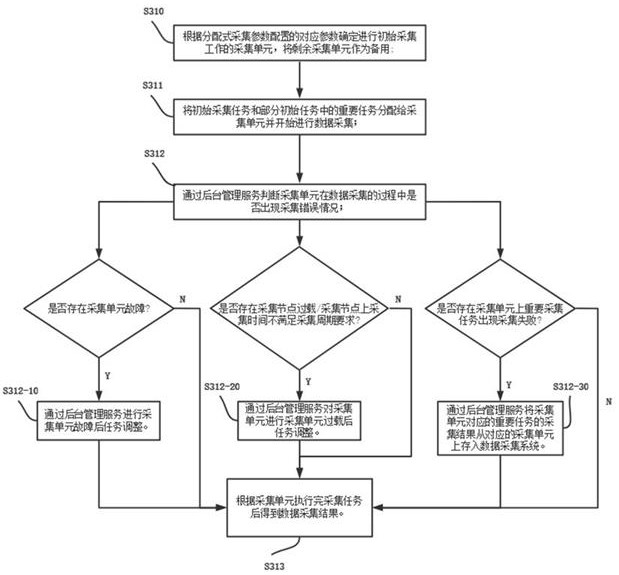
Distributed data acquisition system operation method
InactiveCN114124958ANot easy to cause configuration lossReduce operation and maintenance complexityTelemetry/telecontrol selection arrangementsDatabase distribution/replicationData acquisitionDatacasting
The invention relates to an operation method of a distributed data acquisition system. The operation method comprises the following steps: arranging acquisition units in the same local area network; performing acquisition configuration on a single acquisition unit, and synchronizing configuration information and performing antique configuration backup on other acquisition units; each acquisition unit dynamically and circularly applies for a task according to own hardware configuration and residual acquisition performance, and executes a response acquisition task; each acquisition unit broadcasts the acquired data to a local area network, and other acquisition units synchronously update the data result of the acquisition task. According to the method, a decentralized chained technology is adopted, data acquisition task configuration information is broadcasted in real time and synchronously stored in multiple units, configuration loss is not prone to being caused, and the operation and maintenance complexity is reduced; the data acquisition unit dynamically applies for and executes an acquisition task according to the performance configuration and the operation condition of the data acquisition unit, so that autonomous load balancing is achieved; in addition, capacity reduction and capacity expansion can be flexibly carried out, operation of the rest of the whole system is not affected, and the system stability is improved.
Owner:智昌科技集团股份有限公司
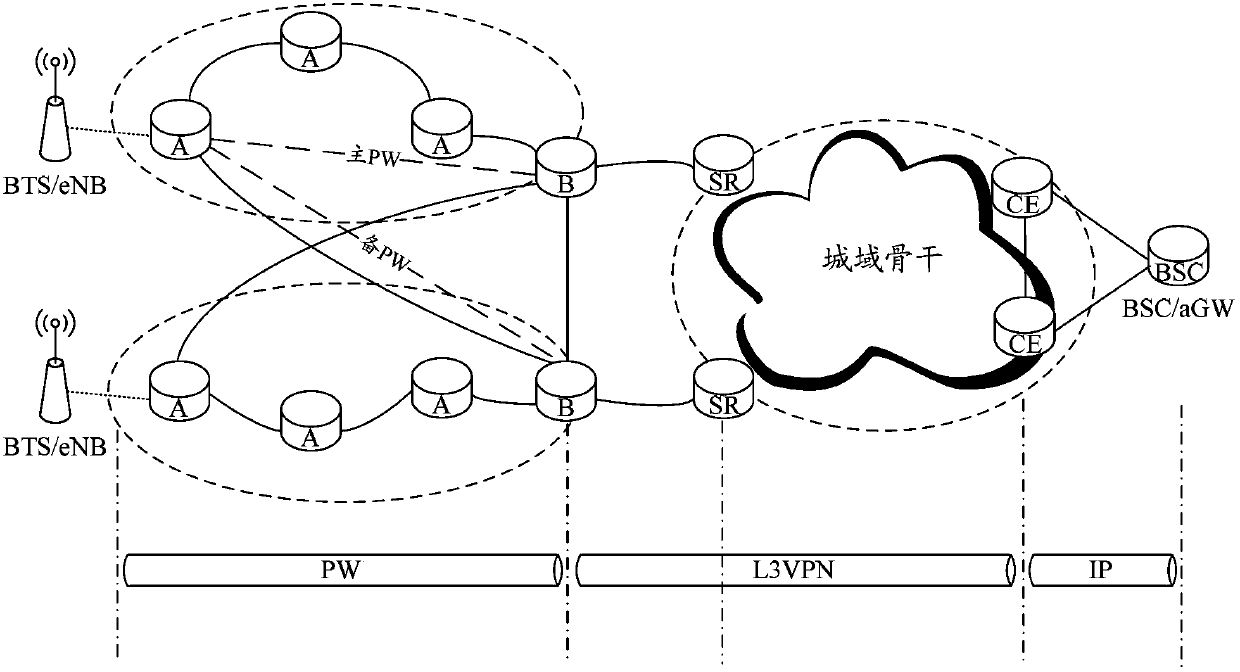
A pw+l3vpn protection method and system
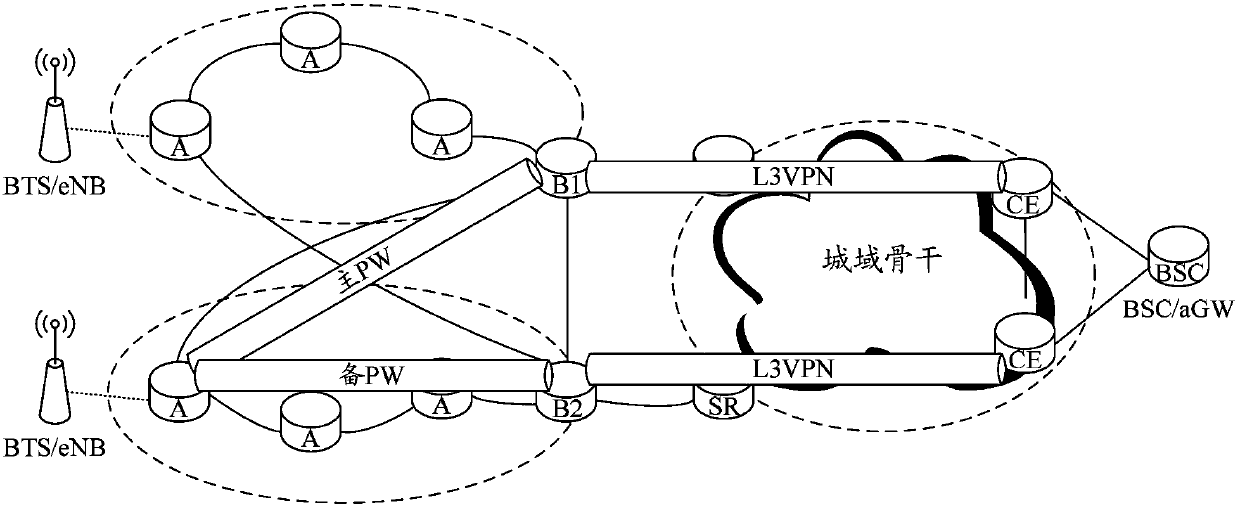
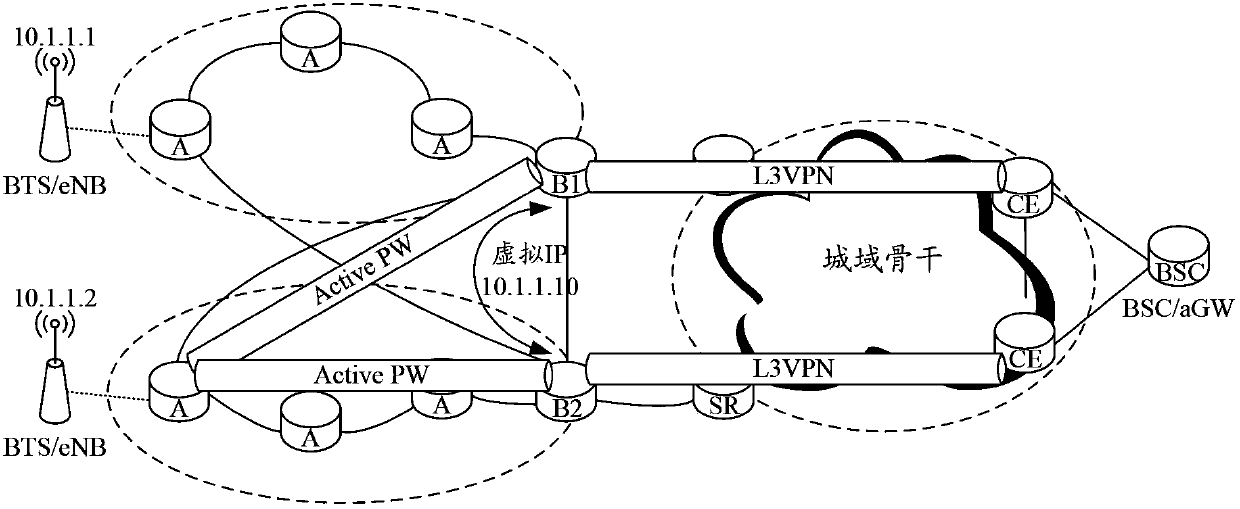
InactiveCN103457817BAchieve loose couplingImprove robustnessNetworks interconnectionTraffic capacityAddress Resolution Protocol
The invention discloses a PW+L3VPN protection method and system. The method includes: configuring a primary and a standby pseudowire (PW) with a single-transmit and double-receive attribute on an access node, and the primary and standby PWs are terminated to two layer-3 gateways Node; the access node sends Address Resolution Protocol (ARP) information and routing information to two layer-3 gateway nodes through the active and standby PWs, and the ARP information and routing information are transmitted in the layer-3 virtual private network (L3VPN) via the layer-3 gateway node Intra-domain notification; each node configures its own forwarding state according to ARP information and routing information, and forwards uplink and downlink traffic respectively according to the forwarding state; when the network fails, the forwarding state of the node affected by the failure changes, and The subsequent forwarding state forwards the upstream and downstream traffic respectively. Through the present invention, the switching speed is fast, which is conducive to improving the robustness of the network and reducing the complexity of operation and maintenance; it is not necessary to configure VRRP on the three-layer gateway node, and the problem of VRRP dual masters will not occur.
Owner:ZTE CORP
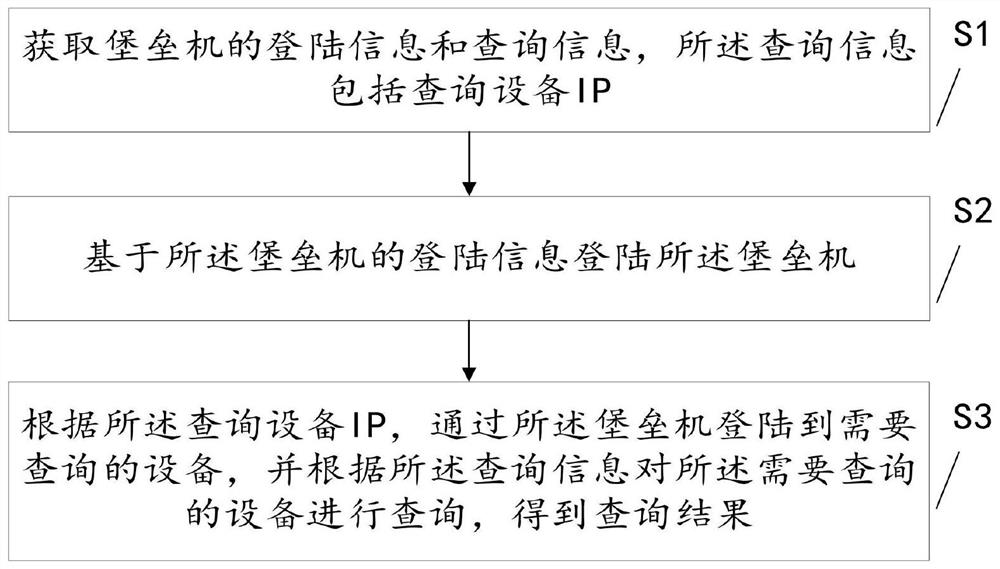
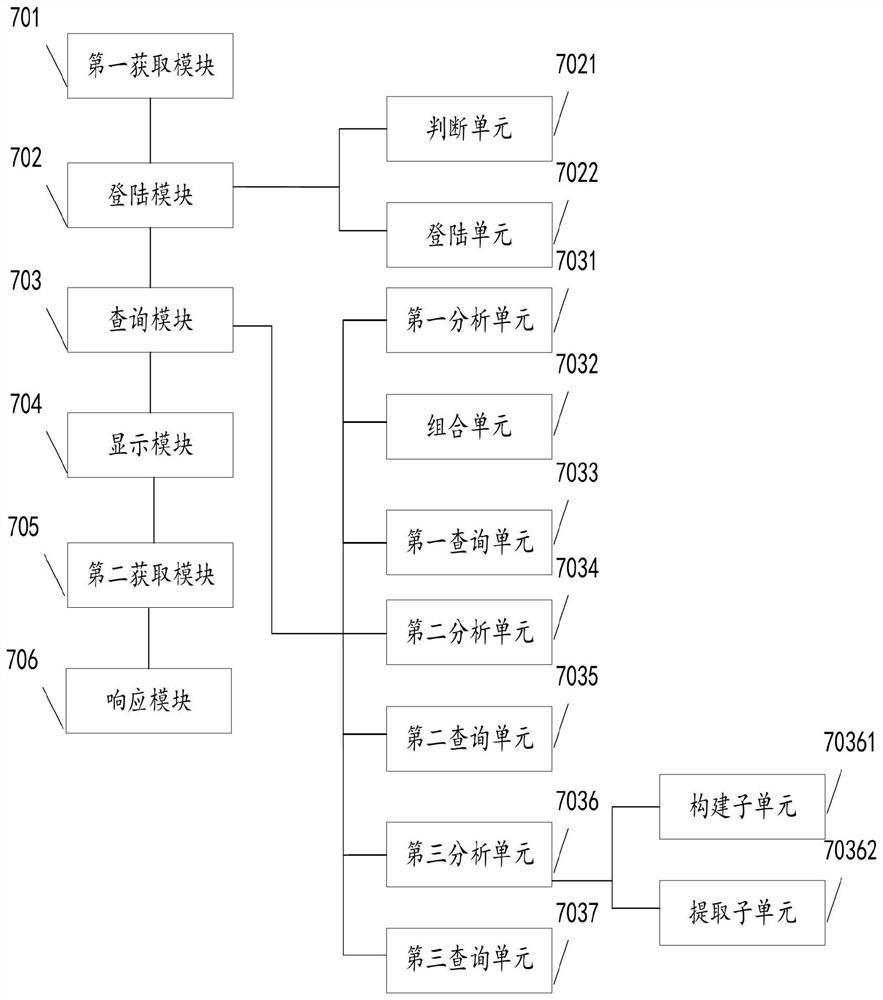
Automatic query method, device and equipment and readable storage medium
PendingCN114238800AReduce query complexityRealize automated querySpecial data processing applicationsWeb data retrieval using information identifiersDaily operationEngineering
The invention provides an automatic query method, device and equipment and a readable storage medium, and the method comprises the steps: obtaining login information and query information of a bastion host, and the query information comprises a query equipment IP; logging in the bastion host based on the login information of the bastion host; and according to the query device IP, logging in a device needing to be queried through the bastion host, and querying the device needing to be queried according to the query information to obtain a query result. The bastion host access device can be automatically operated, automatic query of different scenes is realized, daily operation and maintenance command query complexity is reduced, operation and maintenance efficiency is improved, operation and maintenance efficiency is improved by about three times compared with traditional manual login bastion host query, operation and maintenance personnel do not need to memorize query commands, and operation and maintenance cost is reduced. And the operation and maintenance complexity is reduced.
Owner:CHINA CITIC BANK
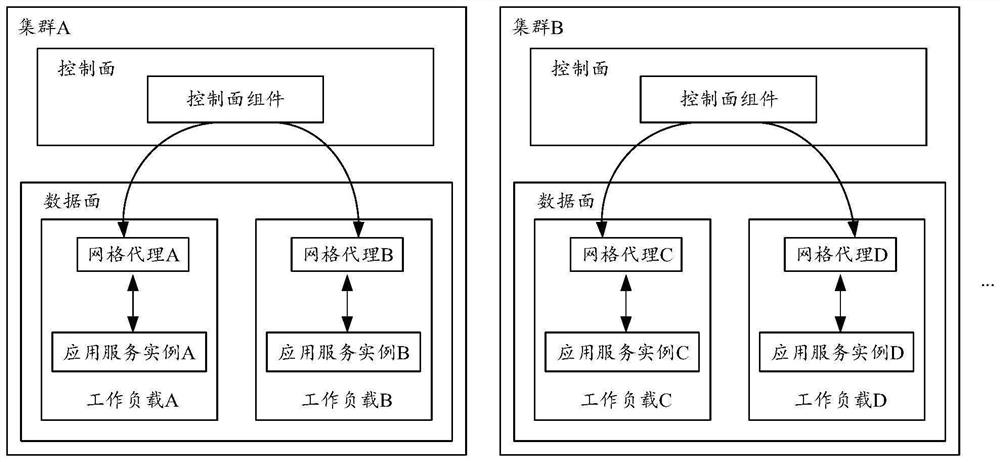
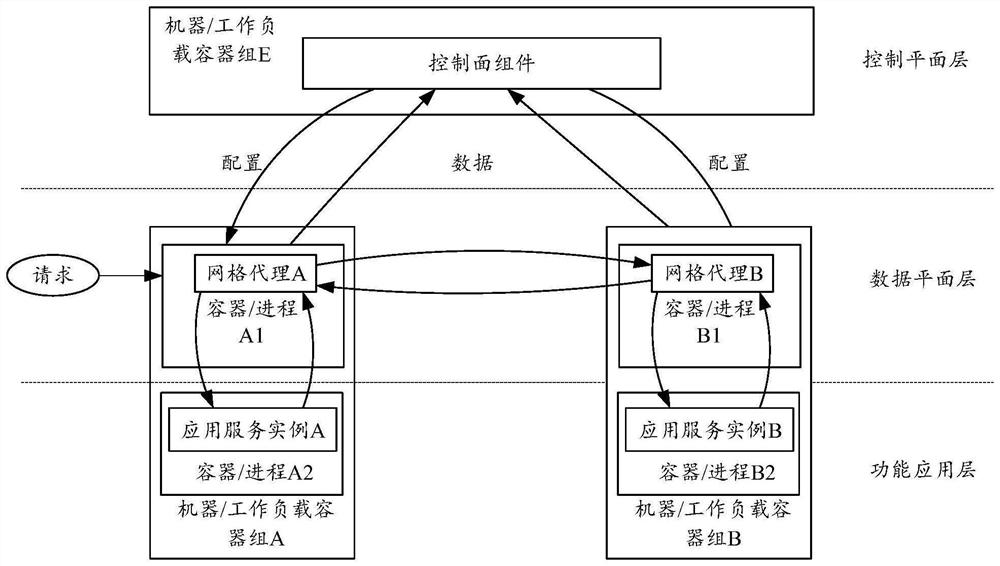
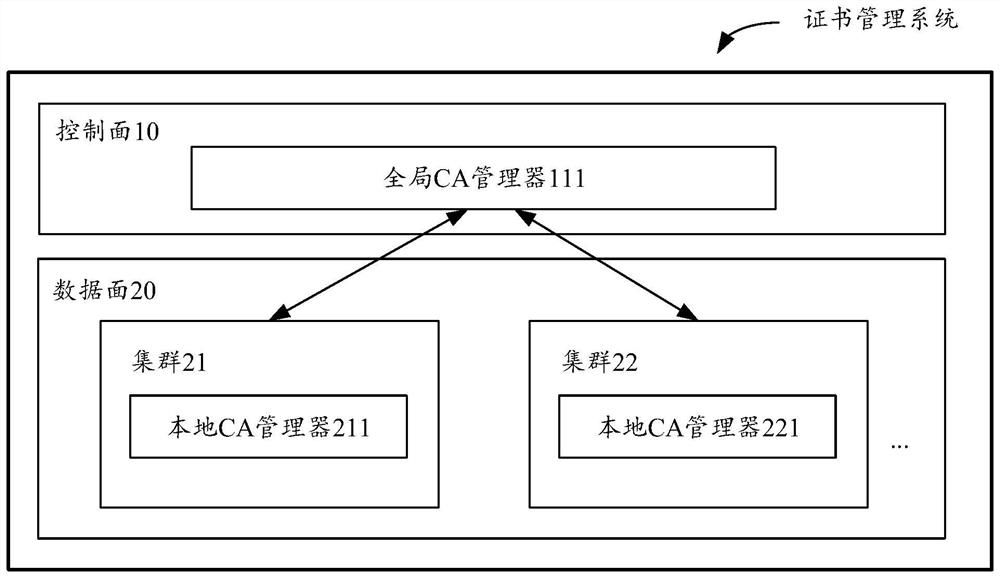
Certificate management system, certificate management method and construction method of certificate management system
PendingCN114666131AReduce workloadReduce operation and maintenance complexityUser identity/authority verificationSystems managementDistributed computing
The embodiment of the invention provides a certificate management system, a management method and a construction method of the certificate management system. The system comprises a global CA manager deployed on a control plane of a service grid, at least one cluster deployed on a data plane of the service grid, and a local CA manager included in each of the at least one cluster, wherein the local CA manager in each cluster is used for managing the CA certificate of each component in the corresponding cluster; and the global CA manager is used for managing CA certificates of the components in each cluster in the at least one cluster. Through the cooperation of the global CA manager and the local CA manager, the hierarchical management of the multi-cluster certificates in the multi-cluster environment is realized, and the operation and maintenance complexity and the operation and maintenance cost are reduced.
Owner:ALIBABA (CHINA) CO LTD
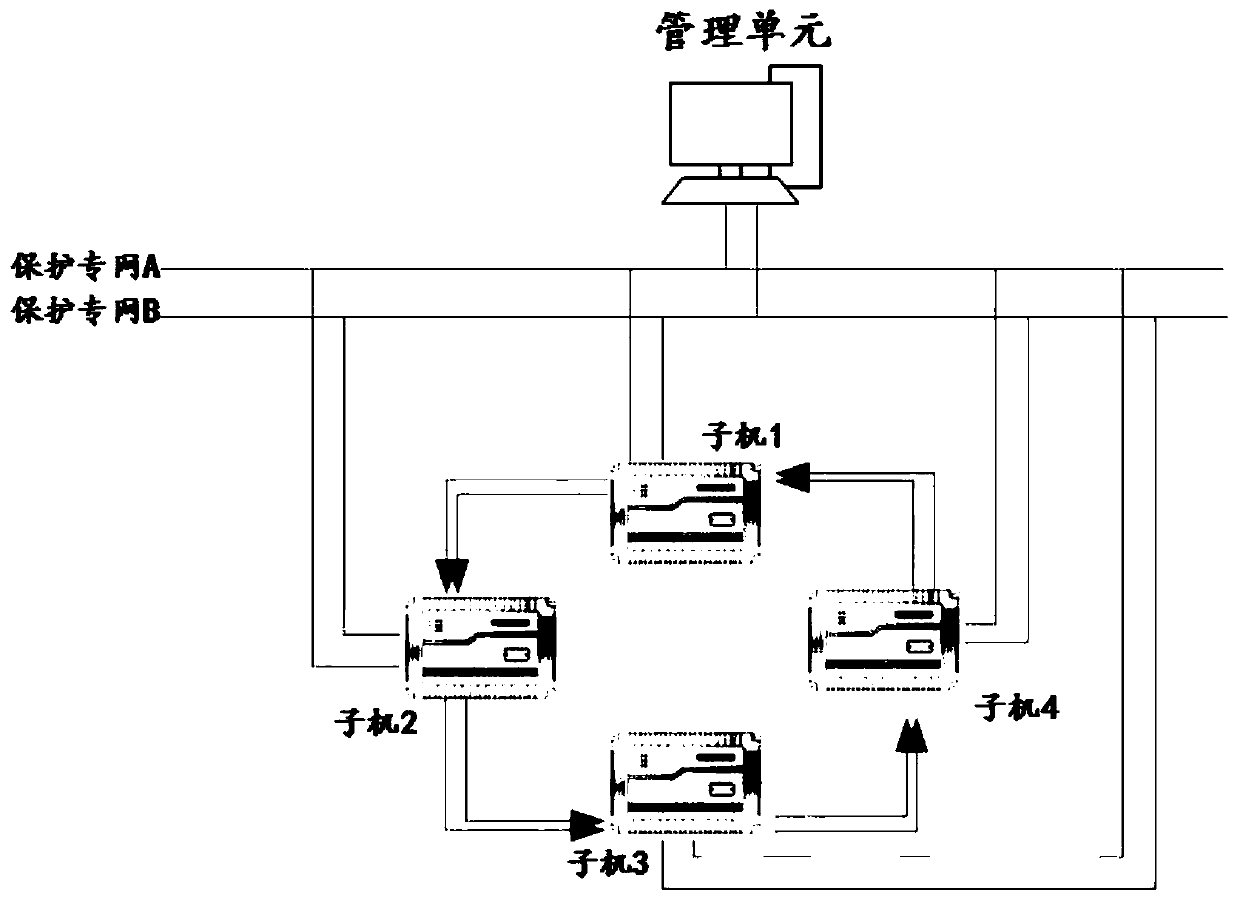
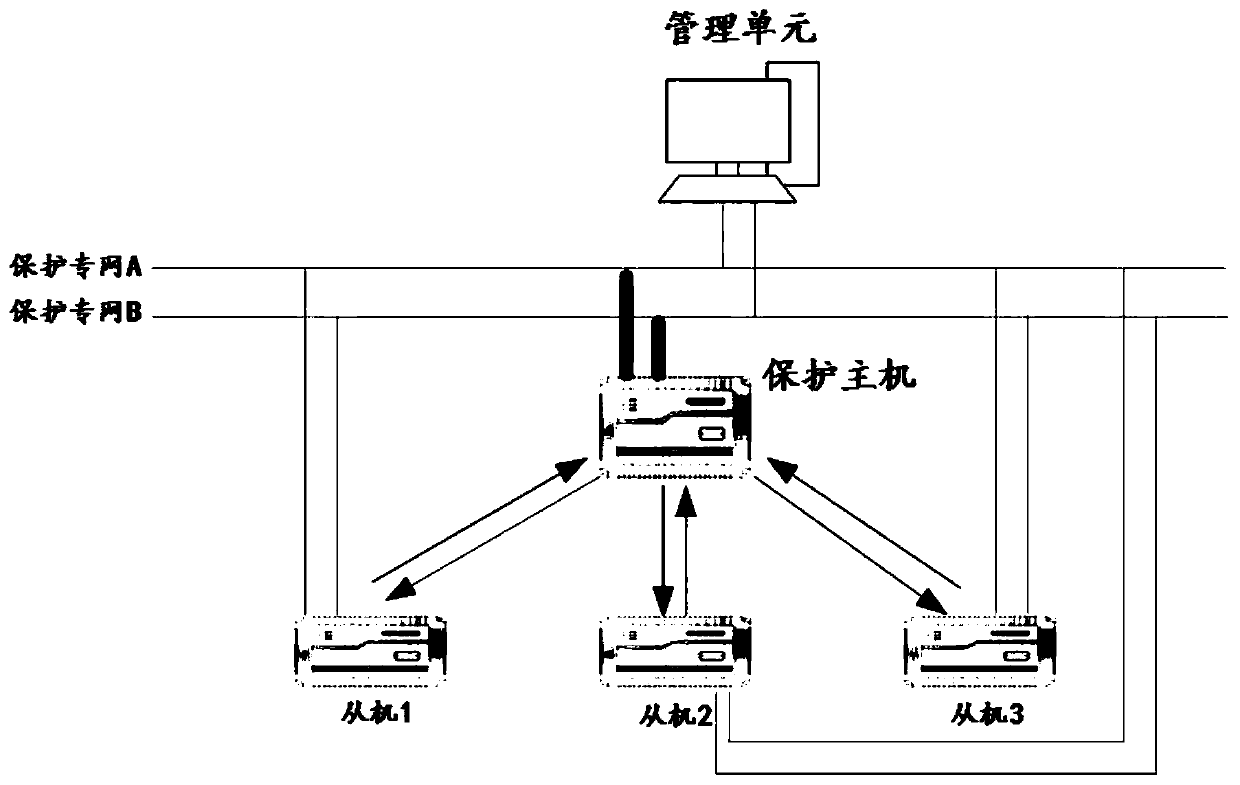
In-situ bus protection method and system based on star network topology
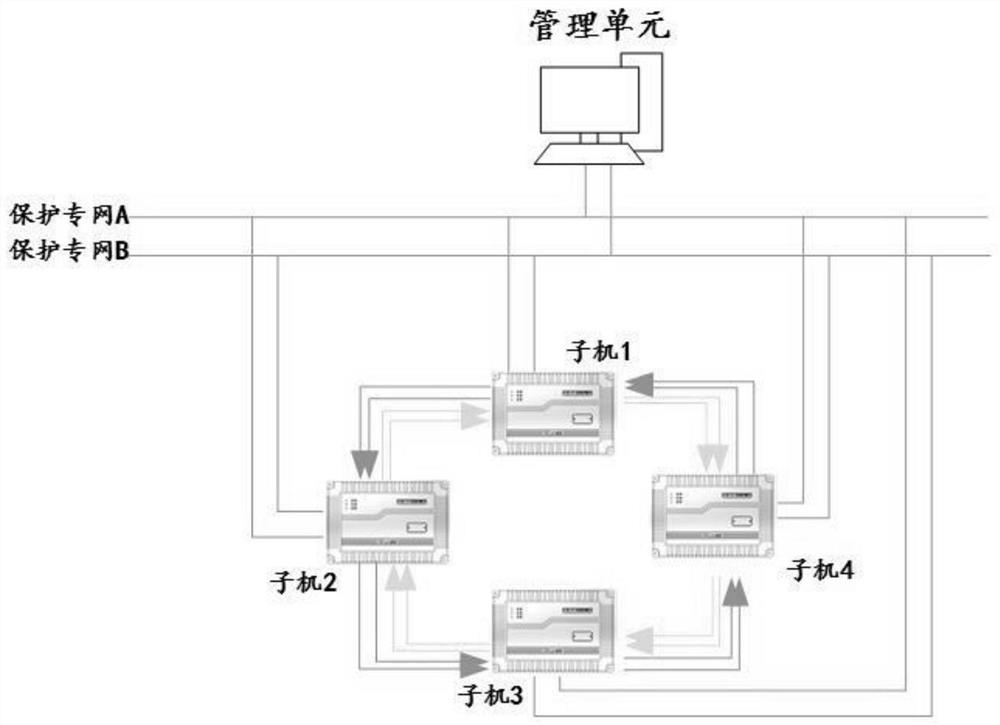
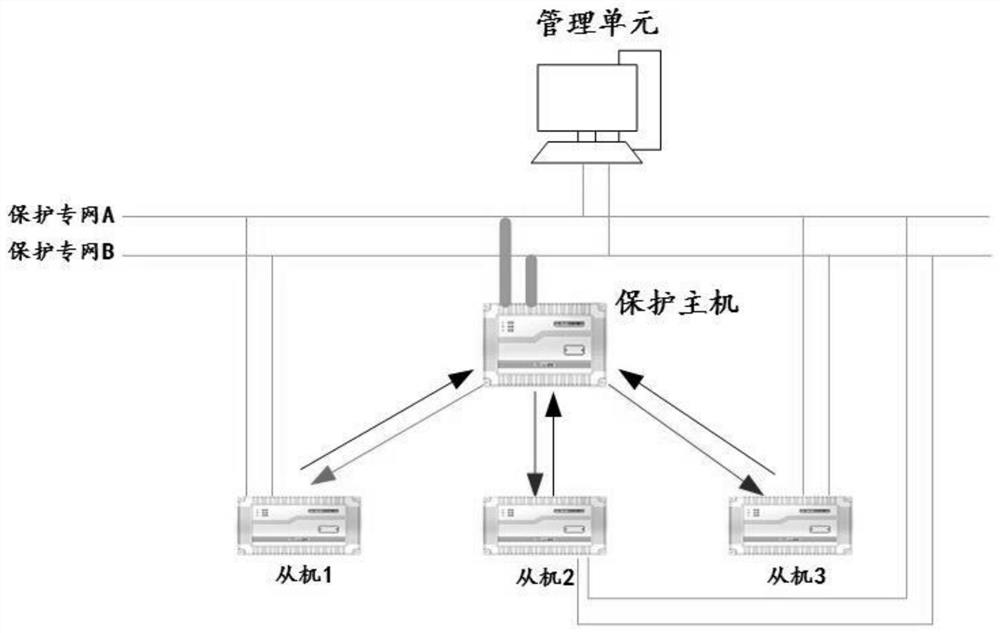
ActiveCN110676818AReduce operation and maintenance complexityReduce the complexity of networkingEmergency protective circuit arrangementsManagement unitEngineering
The invention provides an in-situ bus protection method and system based on a star network topology. A networking mode of an in-situ distributed bus protection device is constructed through the star network topology mode. Any in-situ distributed bus protection device is used as a protection host. Other devices are taken as slave machines. The host is connected with the slave machines through optical fibers. The host and the slave machines are connected with a management unit so as to form a star network. When a protection action is generated, the host judges a fault position according to analog quantity sampling data transmitted by the slave machines and switching value disconnecting link position data, and issues a slave machine tripping command through the star network so as to greatly reduce direct networking complexity of each sub-machine under a condition that a protection function and performance are not affected, and improve overall reliability of a protection device.
Owner:INTEGRATED ELECTRONICS SYST LAB
A batch installation and deployment method of mysql
ActiveCN105204897BImprove deployment efficiencyHigh feasibilityProgram loading/initiatingData fileHome directory
The invention discloses a batched MySQL installation and deployment method. The method comprises the following steps: (a) acquiring an MySQL binary release version, and unzipping the MySQL binary release version to obtain an MySQL home directory and files in the MySQL home directory; (b) creating parameter files in the MySQL home directory, initiating data files, correcting an account number, and generating an MySQL installation and deployment packet applicable to a current environment; (c) configuring a deployment server, and remotely transmitting the MySQL installation and deployment packet to an assigned directory of a target server; (d) performing configuration by the target server according to the received MySQL installation and deployment packet to complete MySQL installation and deployment. According to the batched MySQL installation and deployment method, by pre-generating the MySQL installation and deployment packet applicable to the current environment, needed steps and time for actual deployment are reduced; remote transmission is achieved by utilizing the deployment server, MySQL installation and deployment can be completed in batches, the MySQL deployment efficiency is greatly improved, and the feasibility is high.
Owner:SHANGHAI SNC NET INFORMATION TECH CO LTD
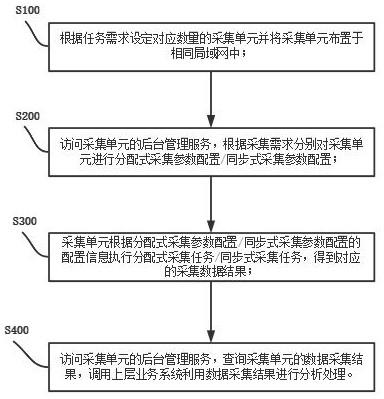
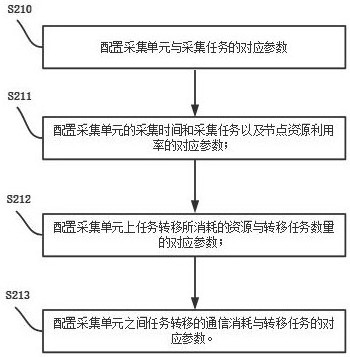
Operation method and system of a distributed data acquisition system
ActiveCN114374695BLoad balancingNot easy to cause configuration lossTelemetry/telecontrol selection arrangementsDatabase distribution/replicationComputer hardwareData acquisition
The invention discloses an operation method and system of a distributed data acquisition system, including setting a corresponding number of acquisition units according to task requirements and arranging the acquisition units in the same local area network; The acquisition unit performs distributed acquisition parameter configuration / synchronous acquisition parameter configuration; the acquisition unit executes the distributed acquisition task / synchronous acquisition task according to the configuration information of the distributed acquisition parameter configuration / synchronous acquisition parameter configuration, and obtains the corresponding acquisition data result; Access the background management service of the collection unit, query the data collection results of the collection unit, and call the upper-level business system to analyze and process the data collection results. The invention satisfies the real-time performance, reliability and effective utilization of resources of the distributed data collection system. requirements, improving system stability.
Owner:ZHEJIANG EMERGEN ROBOT TECH CO LTD
Distributed data acquisition system operation method and system
ActiveCN114374695ALoad balancingNot easy to cause configuration lossTelemetry/telecontrol selection arrangementsDatabase distribution/replicationData acquisitionDistributed computing
Owner:智昌科技集团股份有限公司
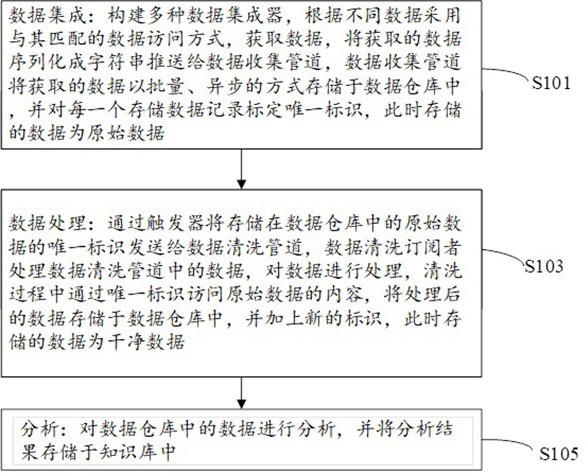
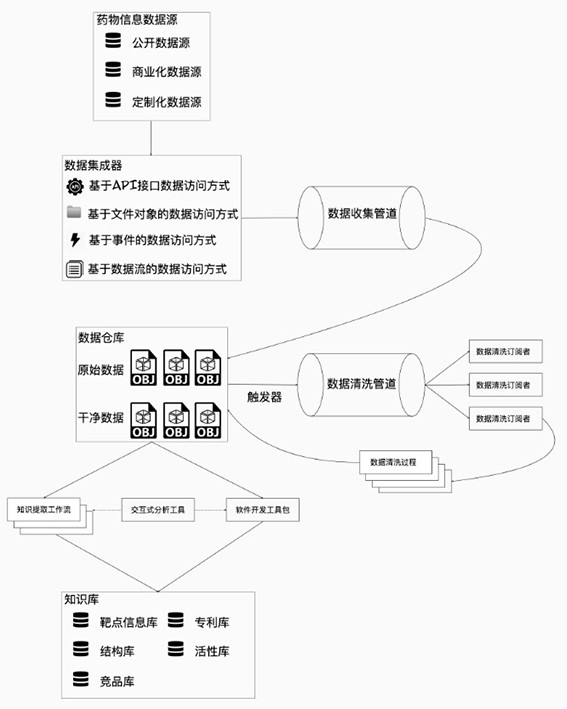
Data processing method and system for drug research and development
PendingCN112164430AReduce operation and maintenance complexityImprove fault tolerance and stabilityChemical machine learningChemometricsData cleansingUnique identifier
The invention discloses a data processing method and system for drug research and development, and the method comprises the steps of building a plurality of data integrators, obtaining data in a matched data access mode according to different data, pushing the data to a data collection pipeline in a serialization mode, enabling the data collection pipeline to store the obtained data in a data warehouse in a batch and asynchronous mode, and storing the data in a database; calibrating a unique identifier for each data record; enablinig the trigger to send the unique identifier of the data storedin the data warehouse to the data cleaning pipeline; allowing the data cleaning subscriber to process the data in the data cleaning pipeline, process the data, store the processed data in the data warehouse, add a new identifier, analyze the data in the data warehouse, and store an analysis result in a knowledge base; according to the data processing method and system for drug research and development, data information of different data sources is connected, original data is stored, cleaned and recalculated through batch data processing and persistence technologies, and then a knowledge baseoriented to domain problems is constructed according to needs.
Owner:SHENZHEN JINGTAI TECH CO LTD
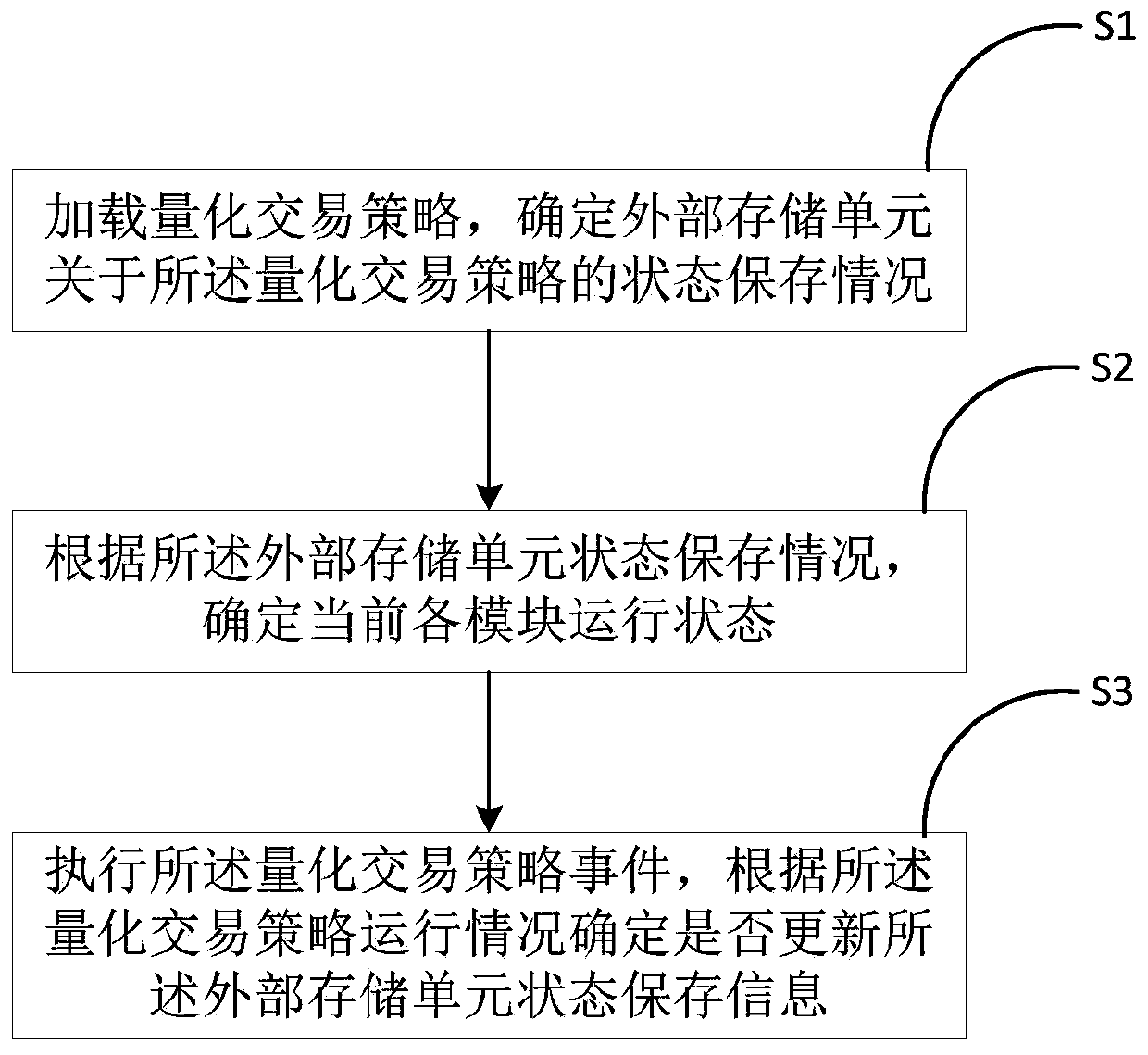
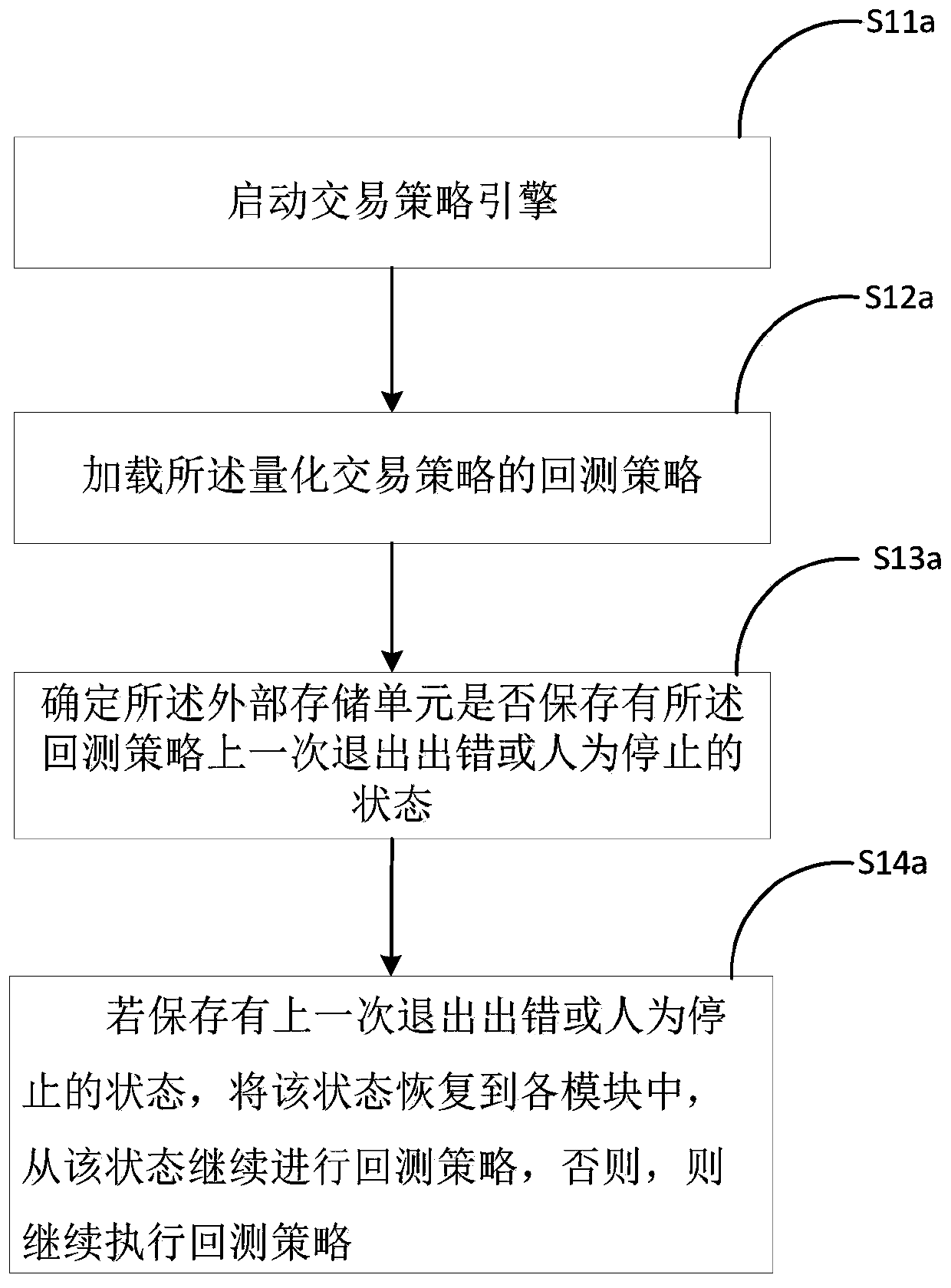
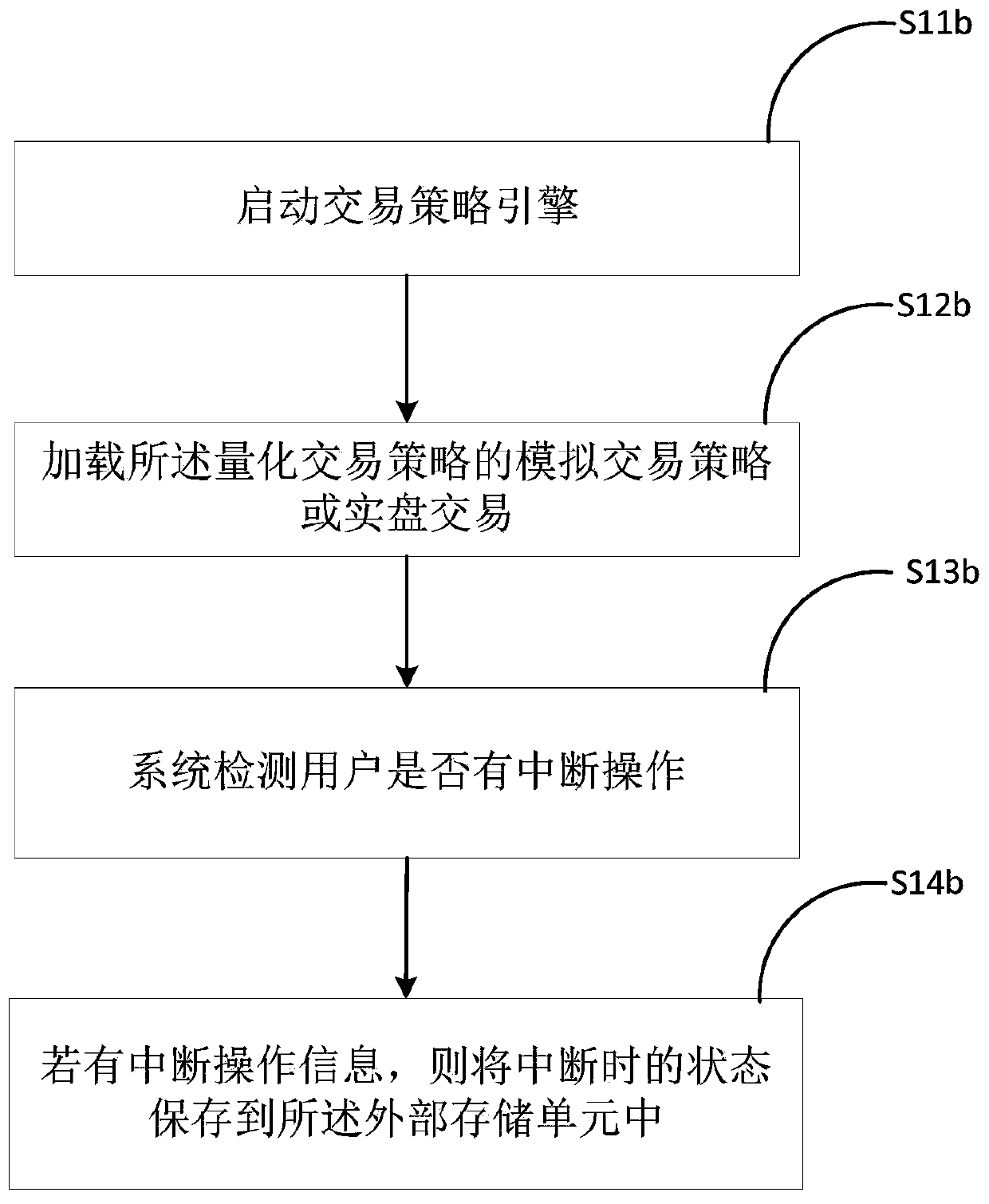
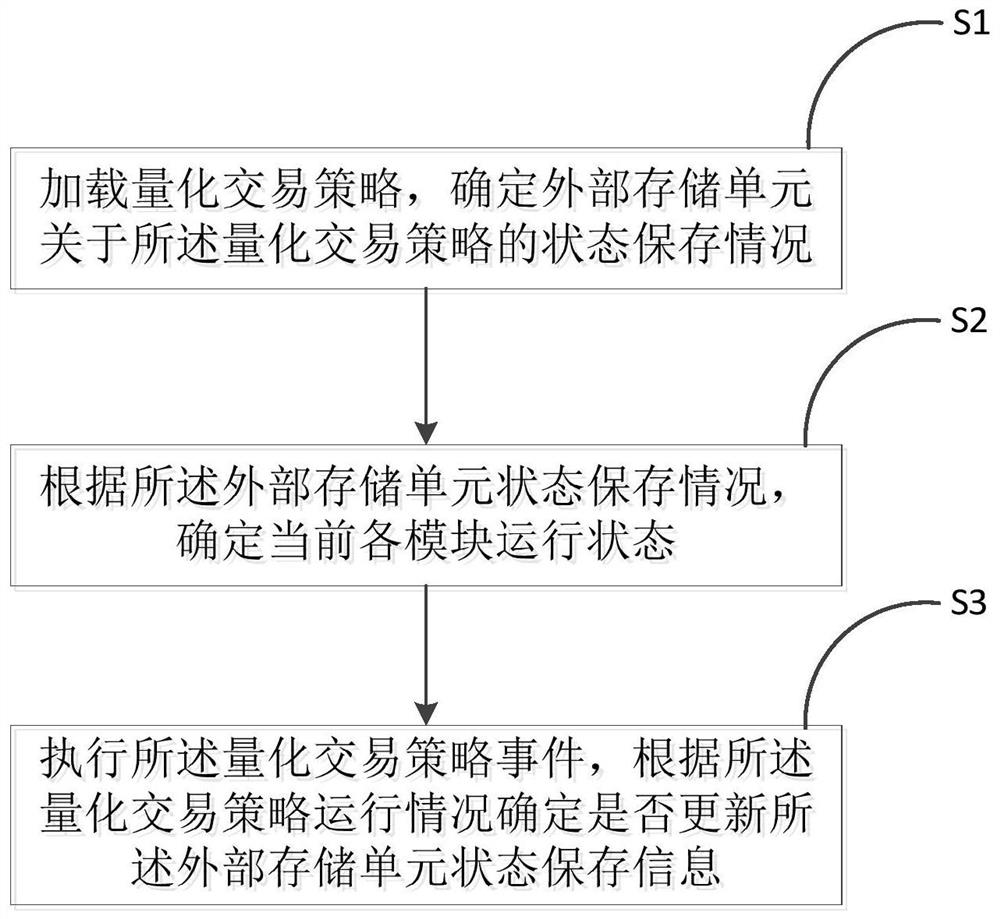
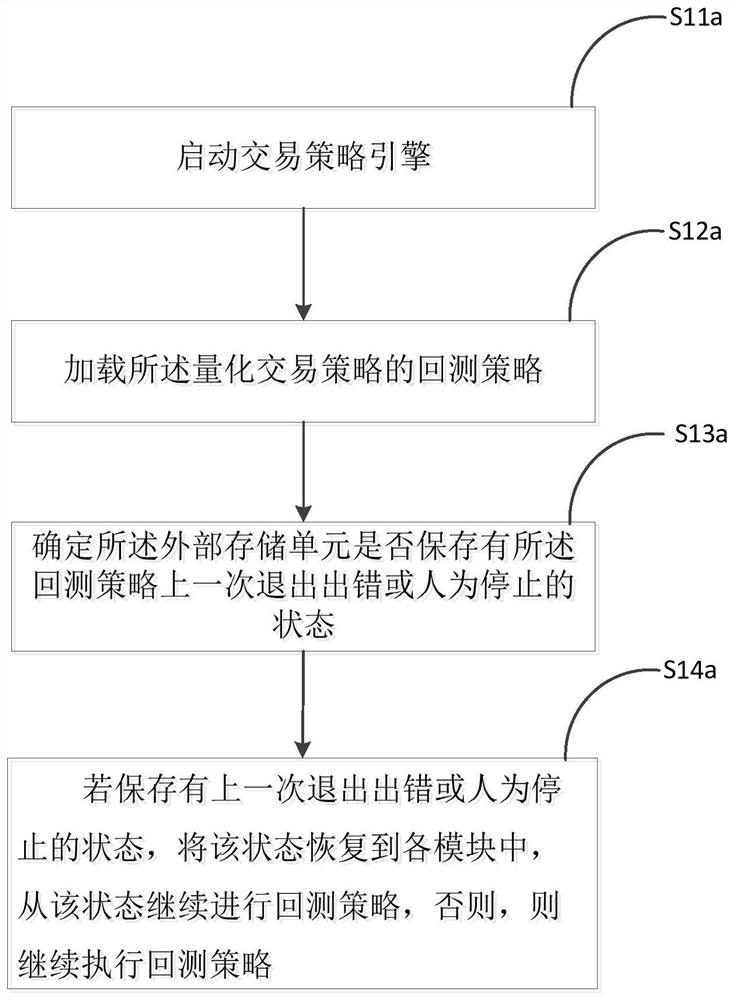
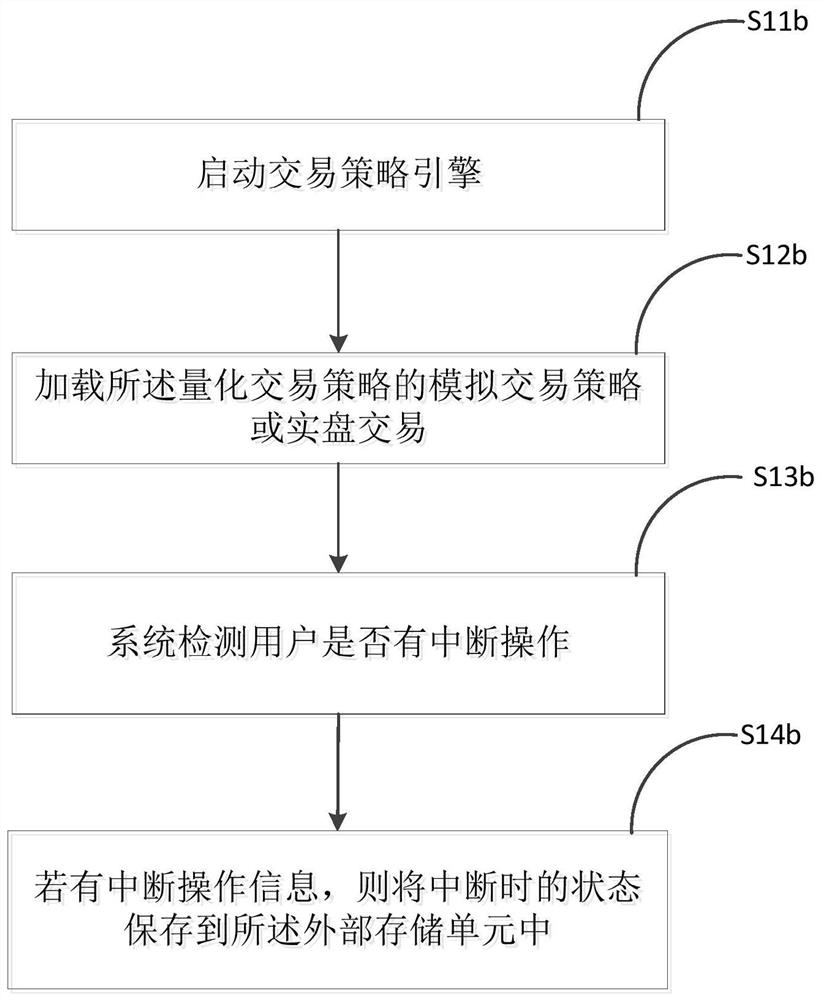
Quantitative transaction state recovery method
ActiveCN111488234AAvoid churnImprove backtesting efficiencyFinanceNon-redundant fault processingExternal storageFinancial transaction
The invention discloses a quantitative transaction state recovery method, and the method comprises the steps: loading a quantitative transaction strategy, and determining a state storage condition ofan external storage unit about the quantitative transaction strategy; determining the current running state of each module according to the state storage condition of the external storage unit; executing the quantitative transaction strategy event, and determining whether to update the state storage information of the external storage unit or not according to the quantitative transaction strategyoperation condition. By implementing the method, the back test efficiency is improved, the system operation and maintenance complexity is reduced, the information loss is avoided, and by using the method, only when the state of each module is changed, the state can be stored in the external storage unit for storage and updating operation, so the external storage pressure is reduced.
Owner:深圳米筐科技有限公司
An authentication method and device
ActiveCN108270747BReduce usage complexityIncrease the difficulty of stealingInterconnection arrangementsTransmissionInternet privacyEngineering
The embodiment of the invention discloses an authentication method and device. In this method, the terminal sends a user's login request message to the server, and receives an authentication information sent by the server after determining that the user has successfully logged in; the terminal sends a SIP request message including the first authentication information to the IP-PBX, and receives the IP-PBX sending It can be seen that after the user logs in to the server, the server assigns the first authentication information to the user, and the user carries the first authentication information in the subsequent SIP request message, and the IP-PBX authenticates the first authentication information. Since the illegal user cannot successfully log in to the server to obtain the first authentication information, after receiving the SIP request message sent by the illegal user, the IP‑PBX will reject the SIP request of the illegal user due to the failure of the first authentication information authentication, thus effectively rejecting the SIP request. Mitigate and avoid the risk of piracy, and protect expensive long-distance telecommunications resources.
Owner:HANGZHOU HUAWEI ENTERPRISE COMM TECH
A method and system for in-situ busbar protection based on star network topology
ActiveCN110676818BReduce operation and maintenance complexityReduce the complexity of networkingEmergency protective circuit arrangementsBusbarEngineering
The present invention provides an on-site busbar protection method and system based on a star network topology. A network of on-site distributed busbar protection devices is constructed through a star network topology, and any one of the on-site distributed busbar protection devices The busbar protection device acts as the protection master, and other devices act as slaves. The master is connected to each slave through optical fibers. The master and slaves are also connected to the management unit respectively to form a star network. When a protection action occurs, the master Judging the fault location according to the analog sampling data transmitted by the slave and the switch position data of the switch, and sending the trip command of the slave through the star network, so as to greatly reduce the protection function and performance of each slave without affecting the protection function and performance. Direct networking complexity, thereby improving the overall reliability of the protection device.
Owner:INTEGRATED ELECTRONICS SYST LAB
A Quantitative Transaction State Restoration Method
ActiveCN111488234BAvoid churnRelieve pressureFinanceNon-redundant fault processingExternal storageMemory cell
The invention discloses a quantitative transaction state recovery method, comprising the steps of: loading a quantitative transaction strategy, determining the state preservation status of an external storage unit with respect to the quantitative transaction strategy; determining the current operating state of each module according to the state preservation situation of the external storage unit; For trading strategy events, determine whether to update the state preservation information of the external storage unit according to the operation of the quantitative trading strategy. The implementation of the present invention improves the efficiency of backtesting, reduces the complexity of system operation and maintenance, and avoids information loss. Using the method of the present invention, only when the state of each module changes, will the state be stored in an external storage unit for storage and update operation, reducing external storage pressure.
Owner:深圳米筐科技有限公司
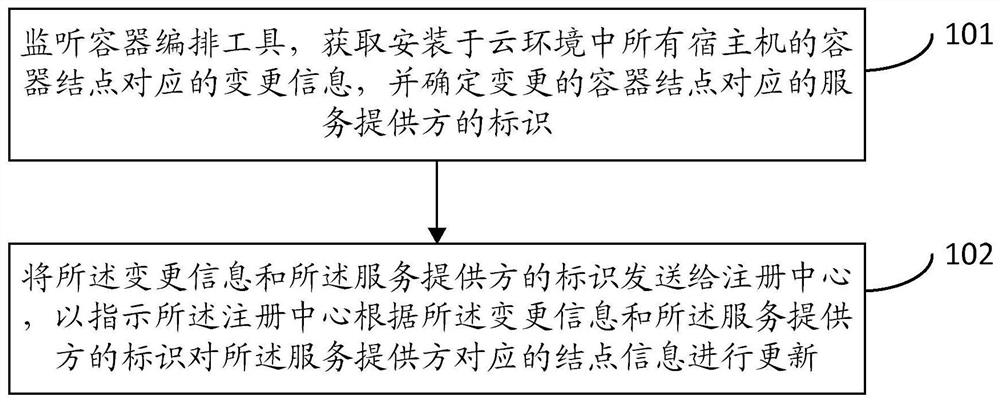
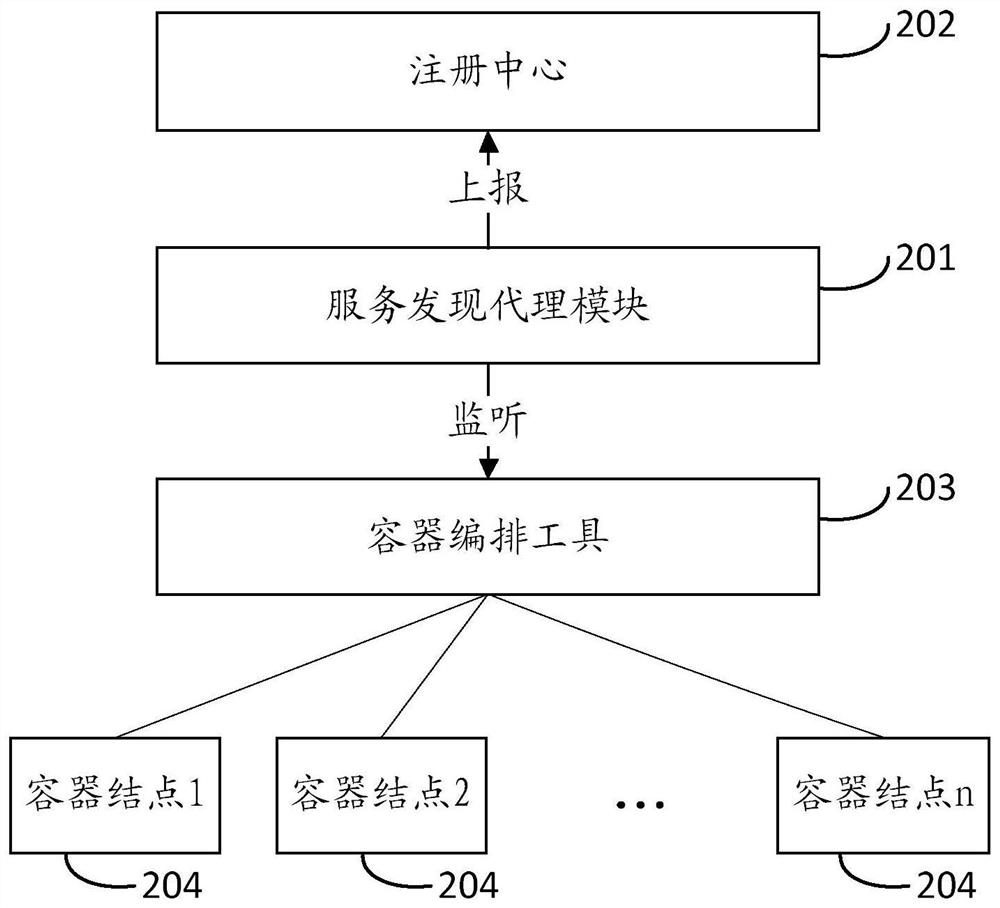
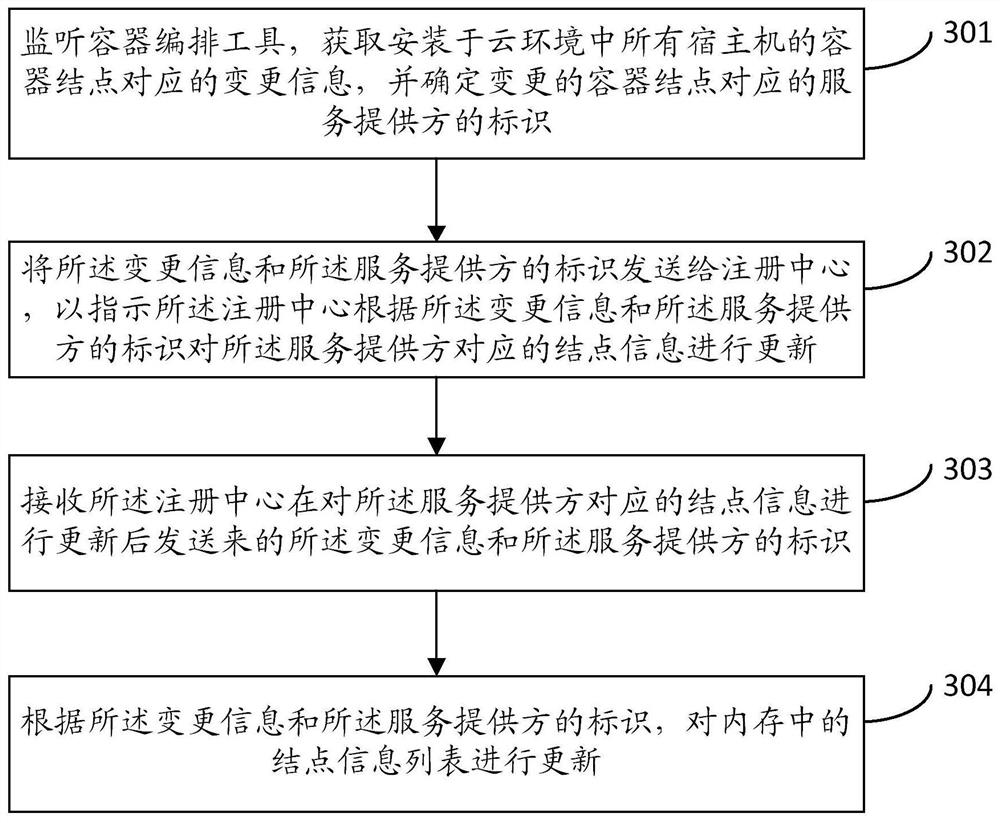
Service discovery method, device, server and storage medium in a cloud environment
ActiveCN109639818BReduce connection stressEasy maintenanceData switching networksEngineeringDatabase
The present invention provides a service discovery method, device, server, and storage medium in a cloud environment. The method includes: monitoring container orchestration tools, obtaining change information corresponding to container nodes installed in all host machines in the cloud environment, and determining The identity of the service provider corresponding to the changed container node; sending the change information and the identity of the service provider to the registration center to instruct the registration center to The node information corresponding to the service provider is updated. The present invention does not need to install an agent in the host computer where each service provider is located, greatly reduces the connection pressure of the registration center, is easier to maintain, and reduces the complexity of operation and maintenance.
Owner:BEIJING CHENGSHI WANGLIN INFORMATION TECH CO LTD
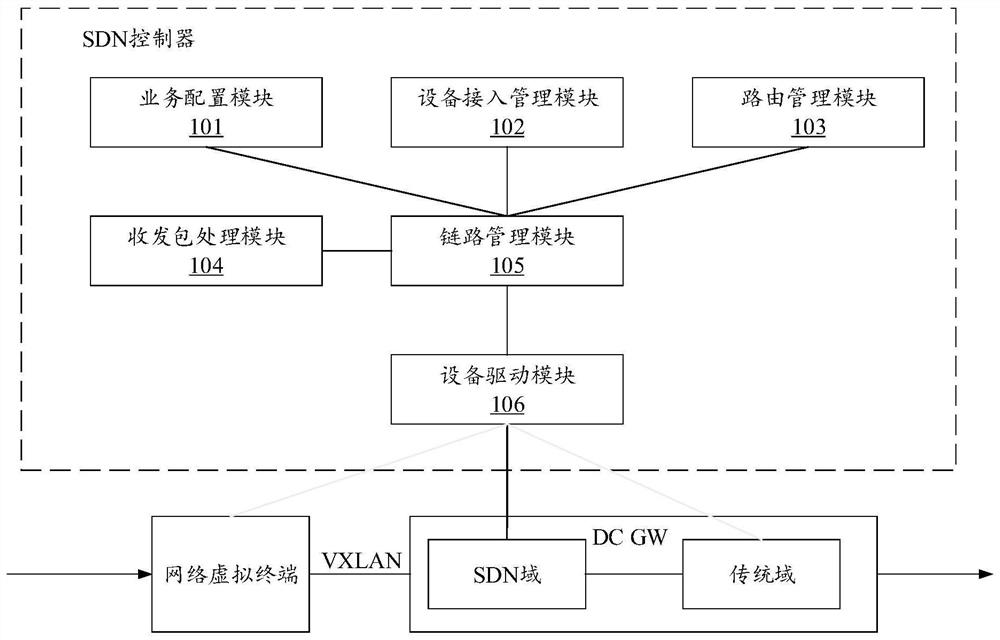
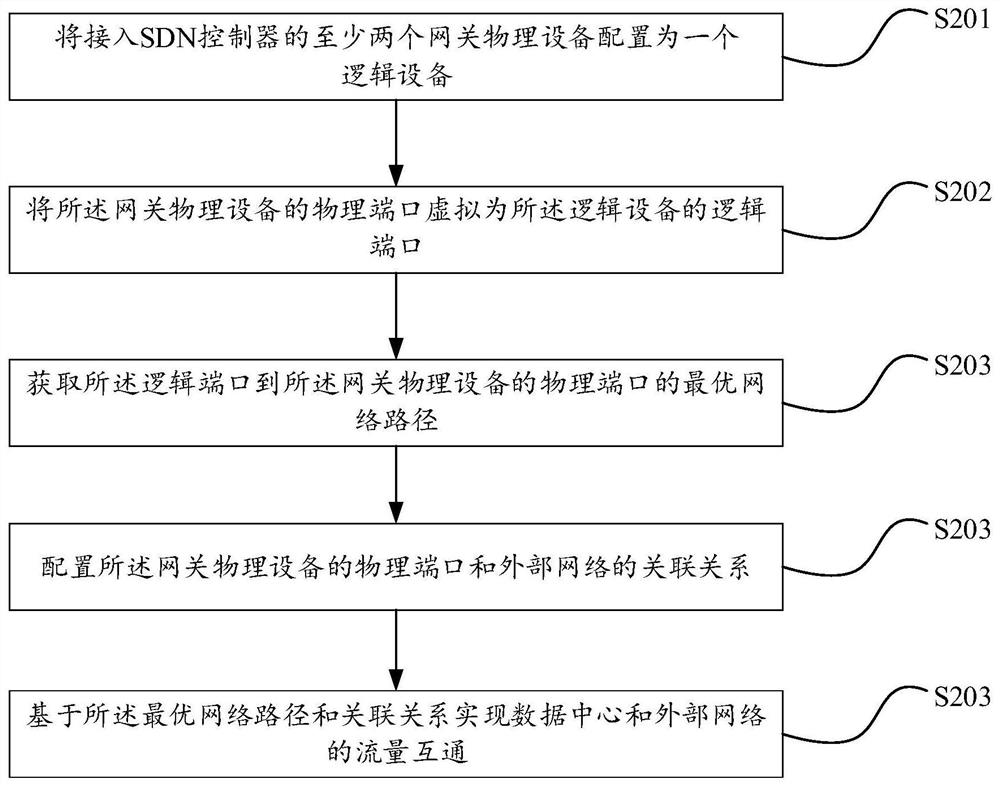
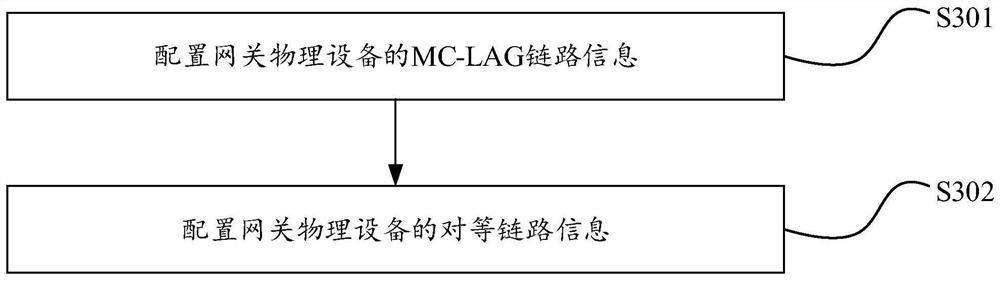
Data center traffic interworking method, device, equipment and storage medium
ActiveCN111277423BReduce operation and maintenance complexityImprove reliabilityNetworks interconnectionHigh level techniquesComputer networkInternet traffic
The invention discloses a data center traffic intercommunication method, device, equipment and storage medium. Among them, the data center traffic intercommunication method is characterized in that an SDN controller is set, and the method includes: configuring at least two gateway physical devices connected to the SDN controller as a logical device, wherein the gateway physical devices The physical port is a logical port of the logical device; traffic intercommunication between the data center and the external network is realized based on an optimal network path and an association relationship, wherein the optimal network path is a physical link from the logical port to the gateway physical device The optimal path of the port, the association relationship is the relationship between the physical port of the gateway physical device and the external network. By setting up the SDN controller, the logical devices configured under the control of the SDN controller can globally manage the traffic of the data center, so as to uniformly schedule the network traffic and achieve the effect of reducing the complexity of operation and maintenance.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com