Patents
Literature
101 results about "Scopus" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Scopus is Elsevier’s abstract and citation database launched in 2004. Scopus covers nearly 36,377 titles (22,794 active titles and 13,583 inactive titles) from approximately 11,678 publishers, of which 34,346 are peer-reviewed journals in top-level subject fields: life sciences, social sciences, physical sciences and health sciences. It covers three types of sources: book series, journals, and trade journals. All journals covered in the Scopus database, regardless of who they are published under, are reviewed each year to ensure high quality standards are maintained. The complete list is on the SCImago Journal Rank website. Searches in Scopus also incorporate searches of patent databases. Scopus gives four types of quality measure for each title; those are h-Index, CiteScore, SJR (SCImago Journal Rank) and SNIP (Source Normalized Impact per Paper).
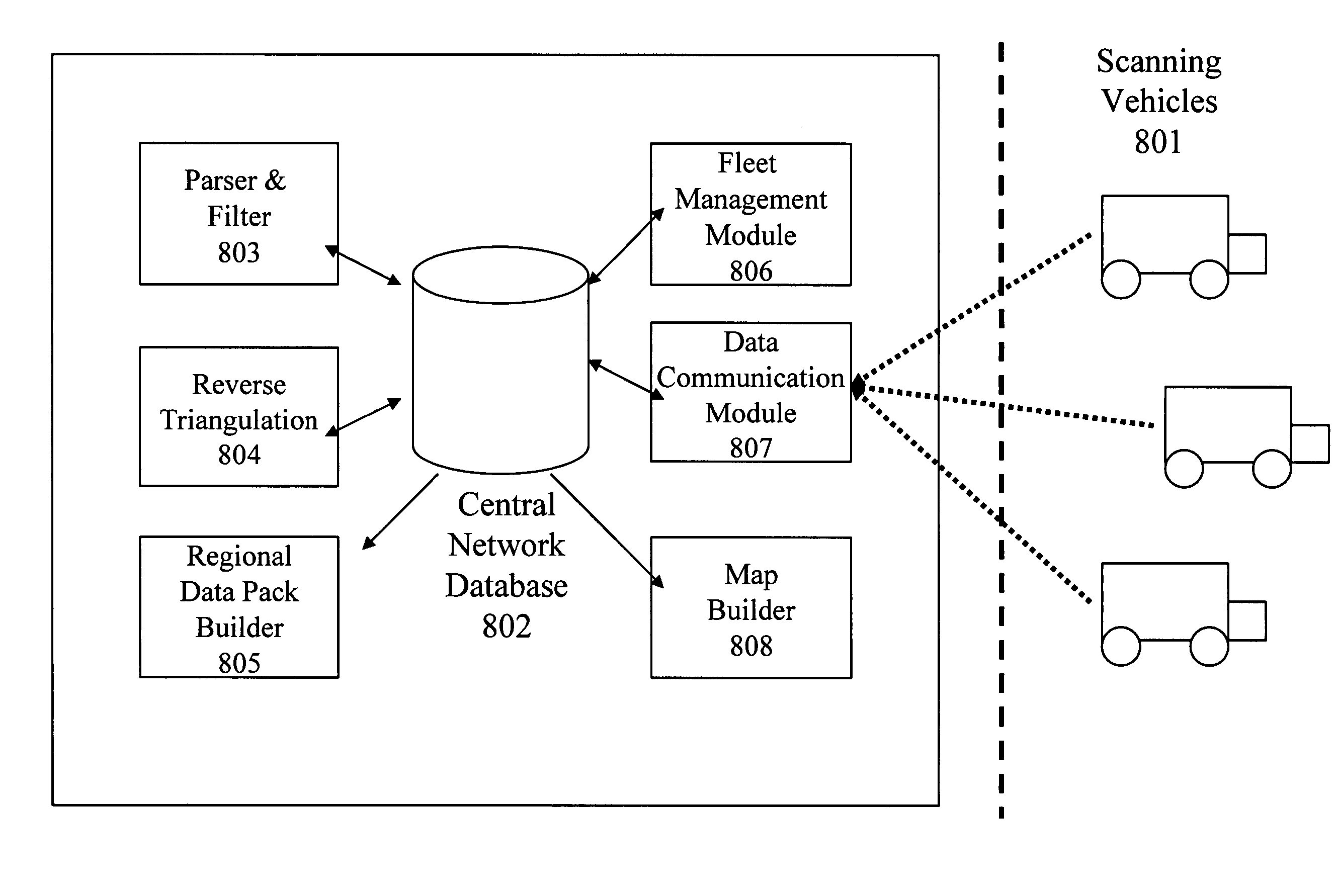
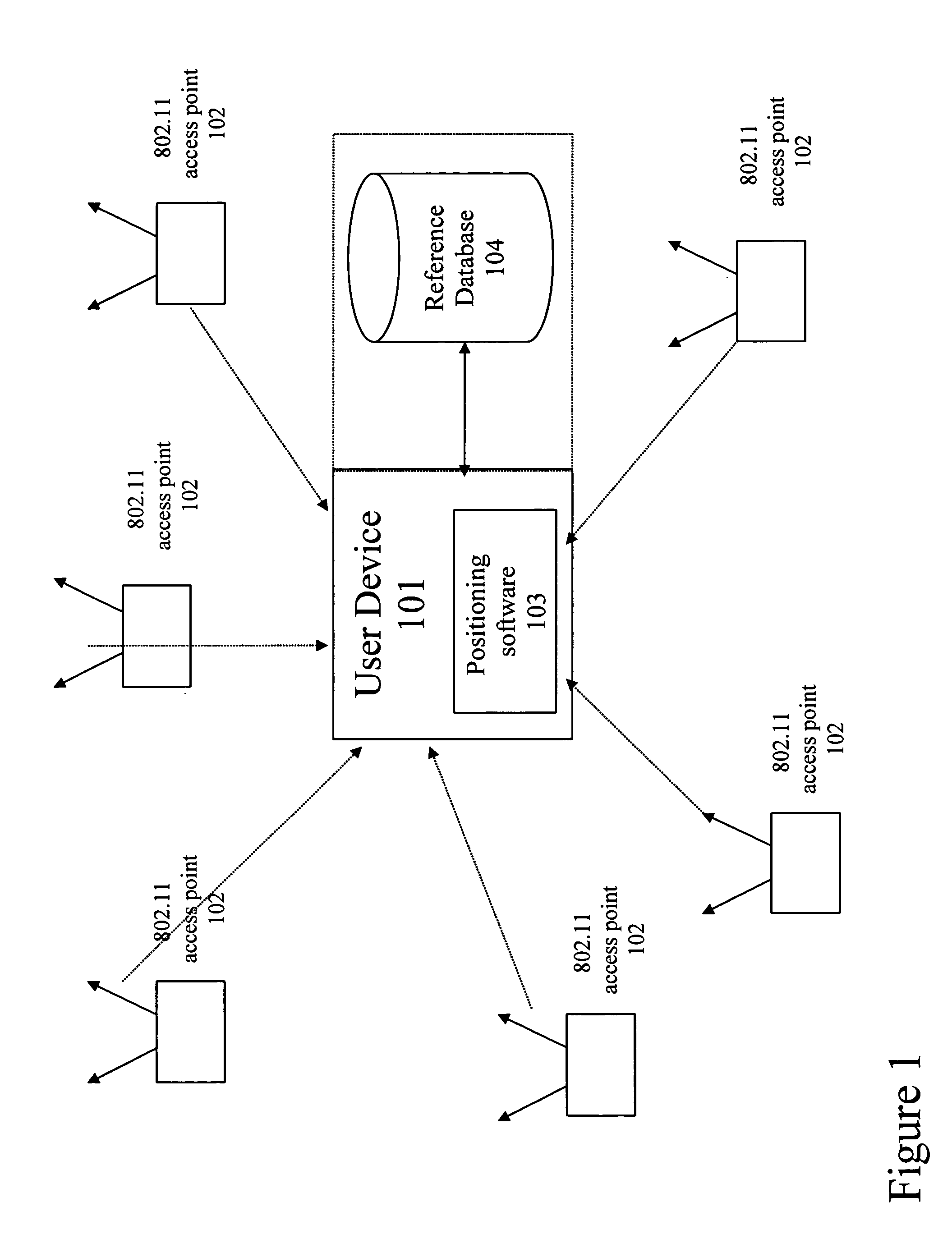
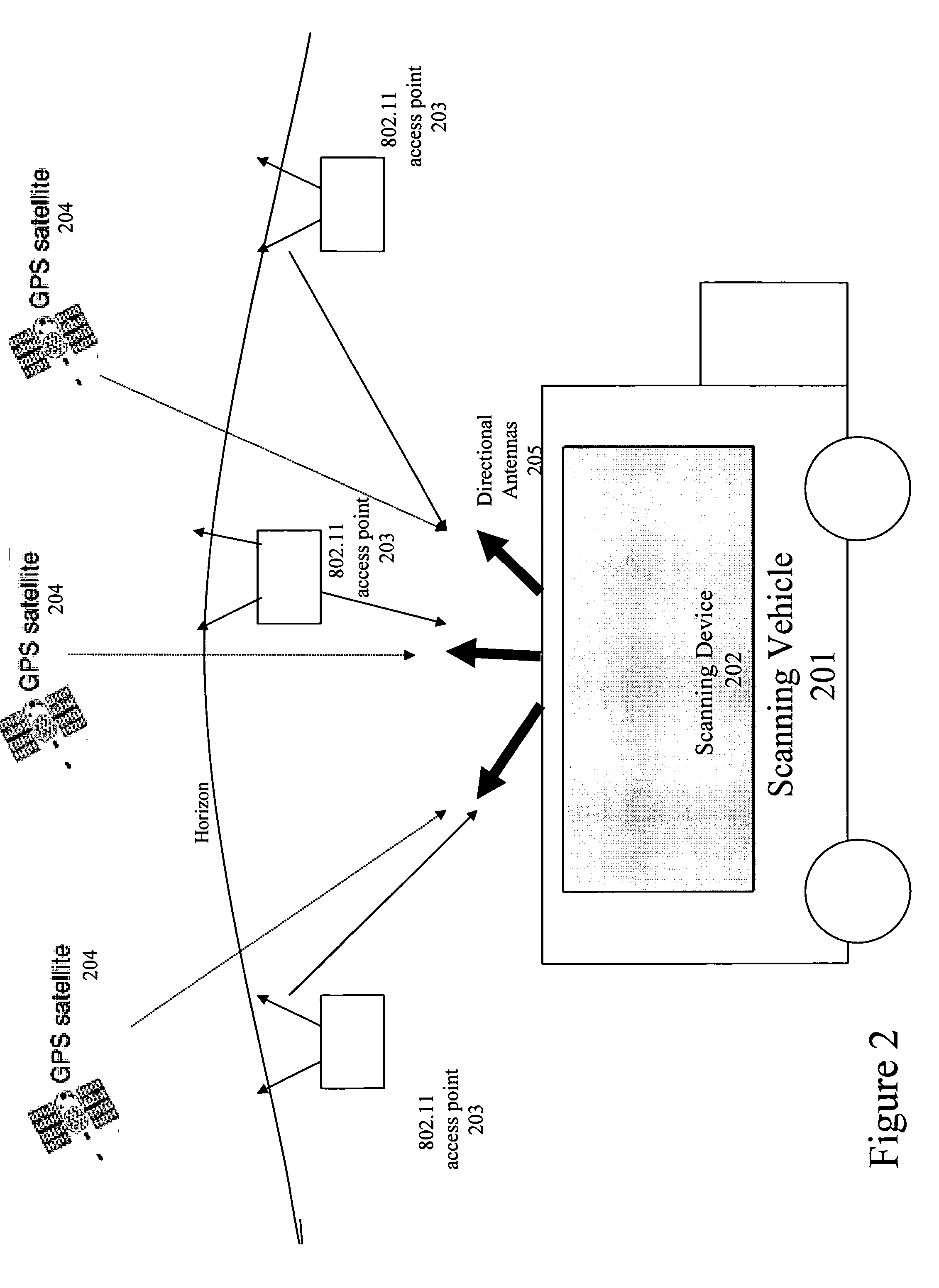
Server for updating location beacon database
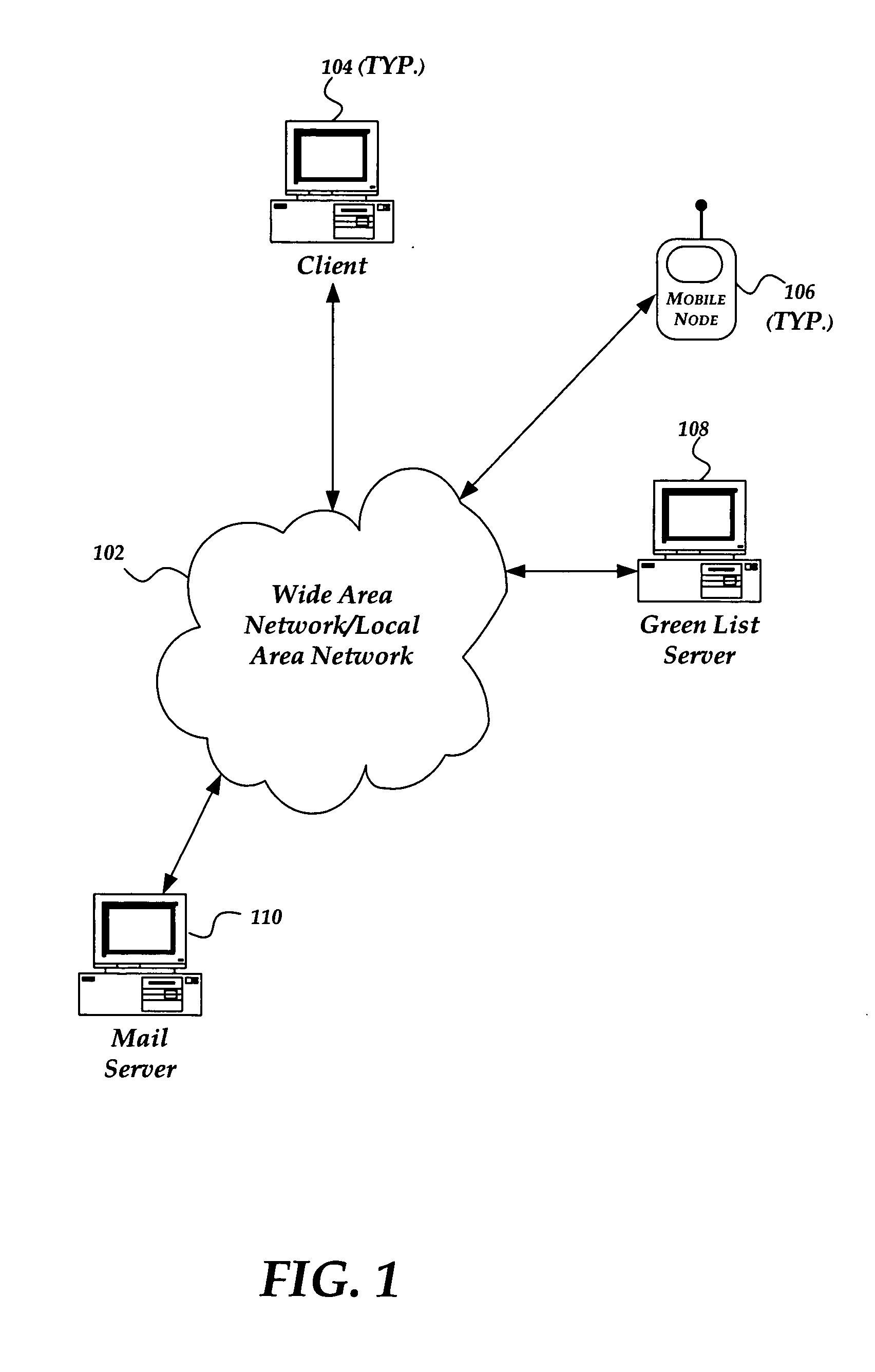
A location beacon database and server, method of building location beacon database, and location based service using same. Wi-Fi access points are located in a target geographical area to build a reference database of locations of Wi-Fi access points. At least one vehicle is deployed including at least one scanning device having a GPS device and a Wi-Fi radio device and including a Wi-Fi antenna system. The target area is traversed in a programmatic route to avoid arterial bias. The programmatic route includes substantially all drivable streets in the target geographical area and solves an Eulerian cycle problem of a graph represented by said drivable streets. While traversing the target area, periodically receive the GPS coordinates of the GPS device. While traversing the target area, detecting Wi-Fi signals from Wi-Fi access points in range of the Wi-Fi device and recording identity information of the detected Wi-Fi access point in conjunction with GPS location information of the vehicle when the detection of the Wi-Fi access point was made. The location information is used to reverse triangulate the position of the detected Wi-Fi access point; and the position of the detected access point is recorded in a reference database. A user-device having a Wi-Fi radio may be located. A reference database of calculated locations of Wi-Fi access points in a target area is provided. In response to a user application request to determine a location of a user-device having a Wi-Fi radio, the Wi-Fi device is triggered to transmit a request to all Wi-Fi access points within range of the Wi-Fi device. Messages are received from the Wi-Fi access points within range of the Wi-Fi device, each message identifying the Wi-Fi access point sending the message. The signal strength of the messages received by the Wi-Fi access points is calculated. The reference database is accessed to obtain the calculated locations for the identified Wi-Fi access points. Based on the number of Wi-Fi access points identified via received messages, choosing a corresponding location-determination algorithm from a plurality of location-determination algorithms, said chosen algorithm being suited for the number of identified Wi-Fi access points. The calculated locations for the identified Wi-Fi access points and the signal strengths of said received messages and the chosen location-determination algorithm are used to determine the location of the user-device. The database may be modified with newly added position information to improve quality of previously determined positions, and error prone information is avoided.
Owner:SKYHOOK WIRELESS
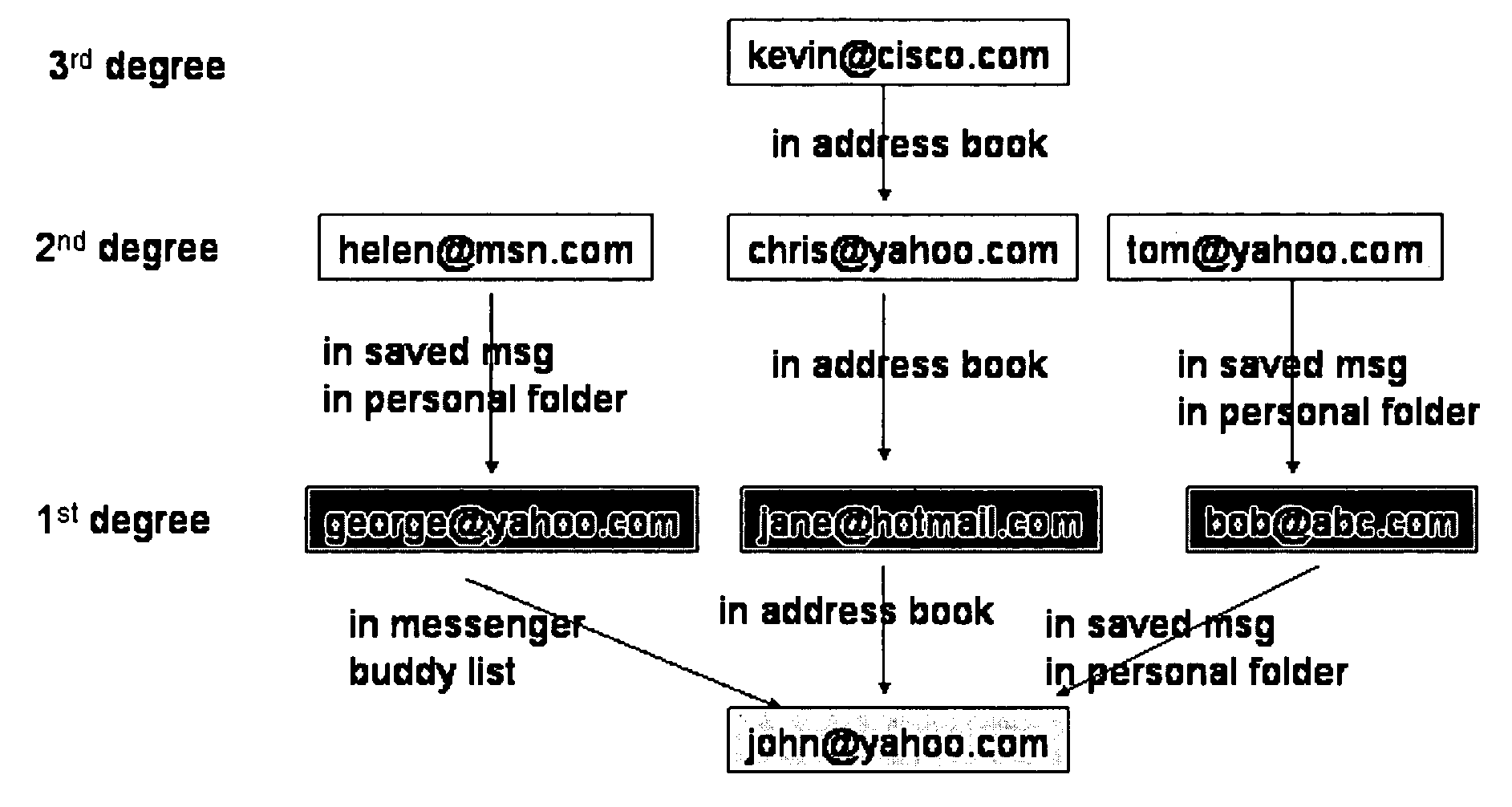
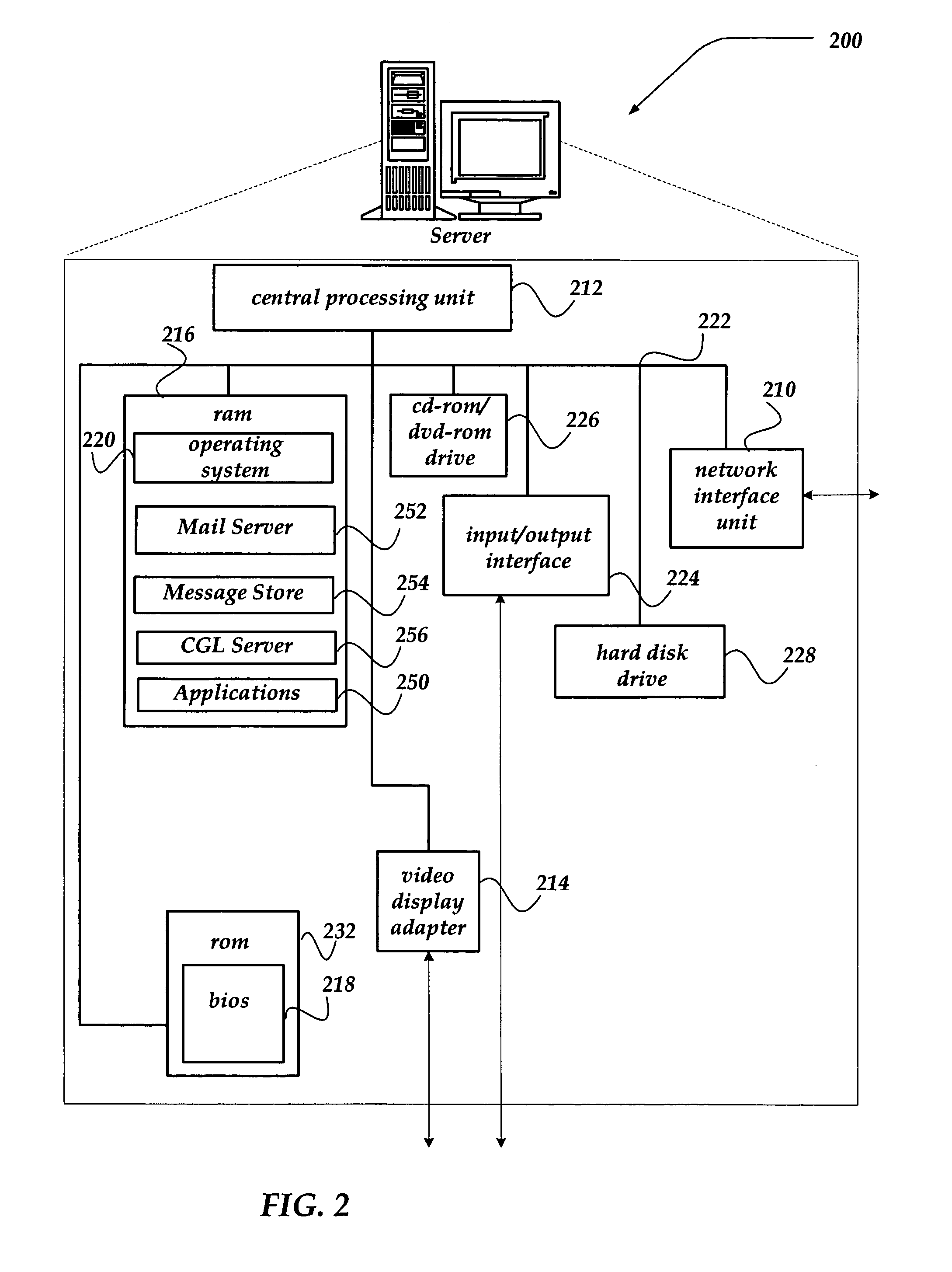
Community-based green list for antispam
ActiveUS20050097170A1Multiple digital computer combinationsData switching networksCommunity basedAddress book
A community-based “green list” (CGL) message filter for mail service providers. The CGL filtering enables trusted messages to be delivered directly into a user's inbox folder and other messages to be delivered to other folders associated with the user. The CGL filtering indicates which messages are sent from those message addresses listed as friends in the user's personal address book. Also, the scope of CGL filtering includes more than those message addresses that the user interacts with directly (one degree of separation). For example, the CGL filtering also evaluates message addresses that are connected more remotely to the user through other nodes (users) in the online community that are located multiple degrees of separation away from the user.
Owner:YAHOO ASSETS LLC
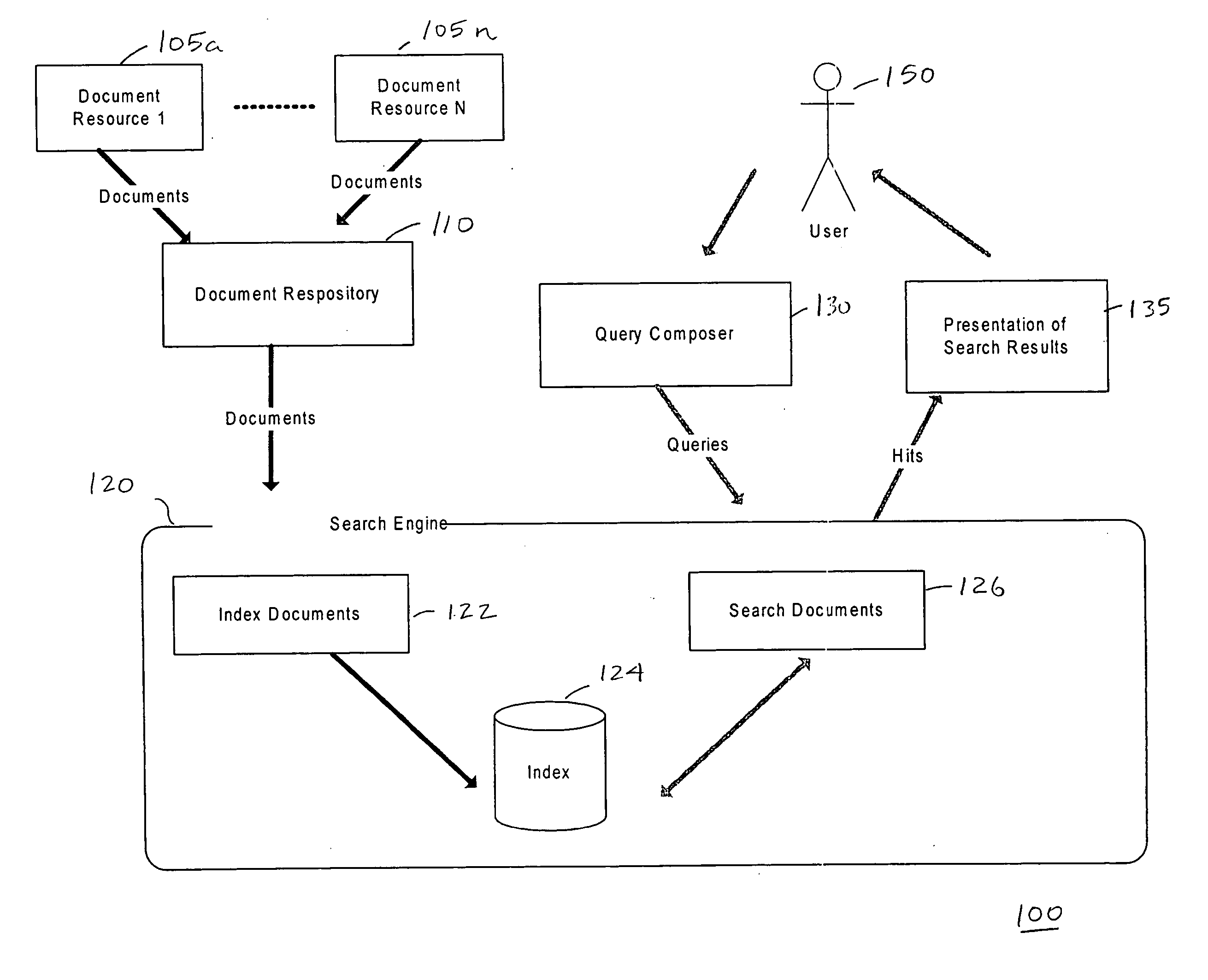
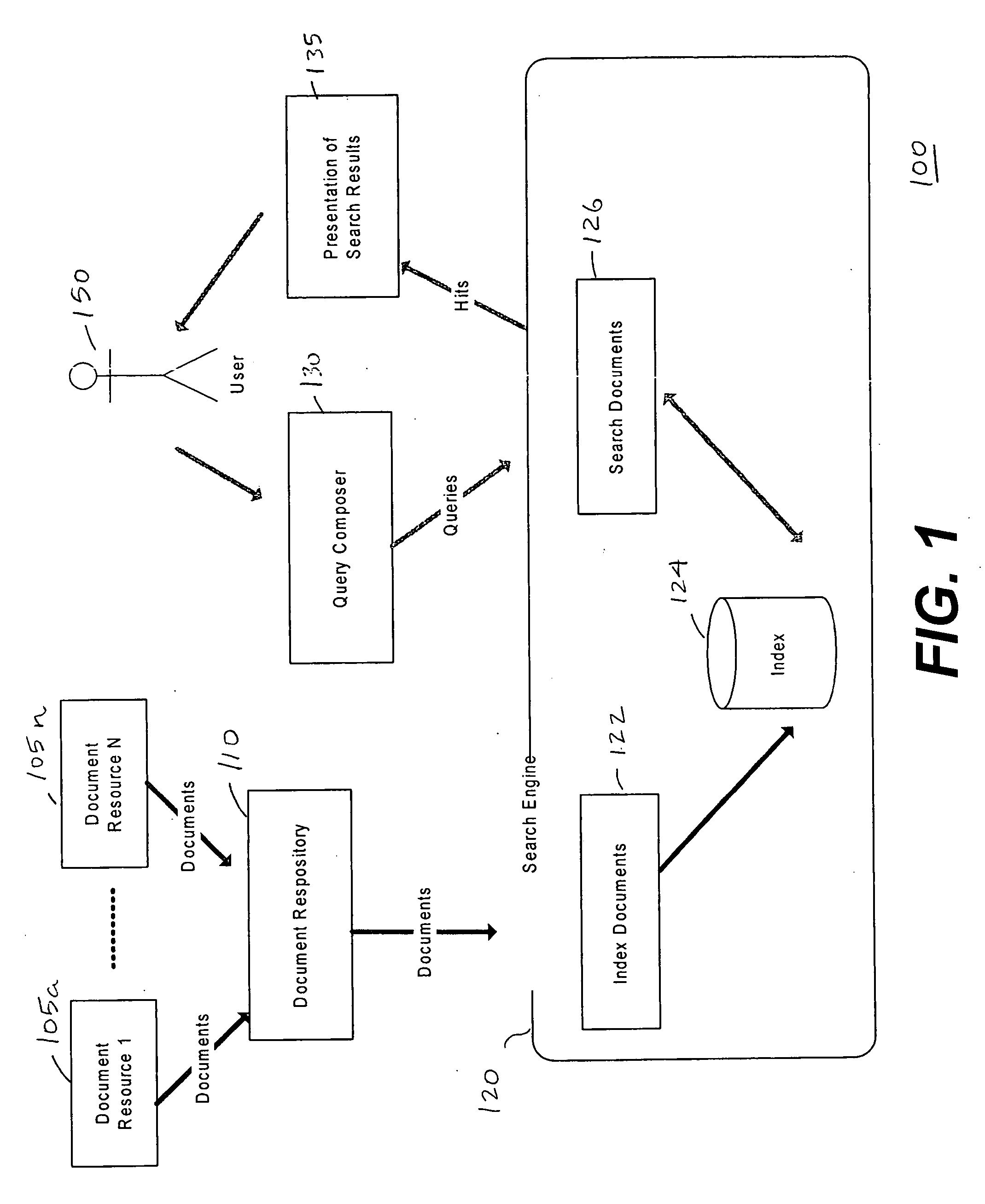
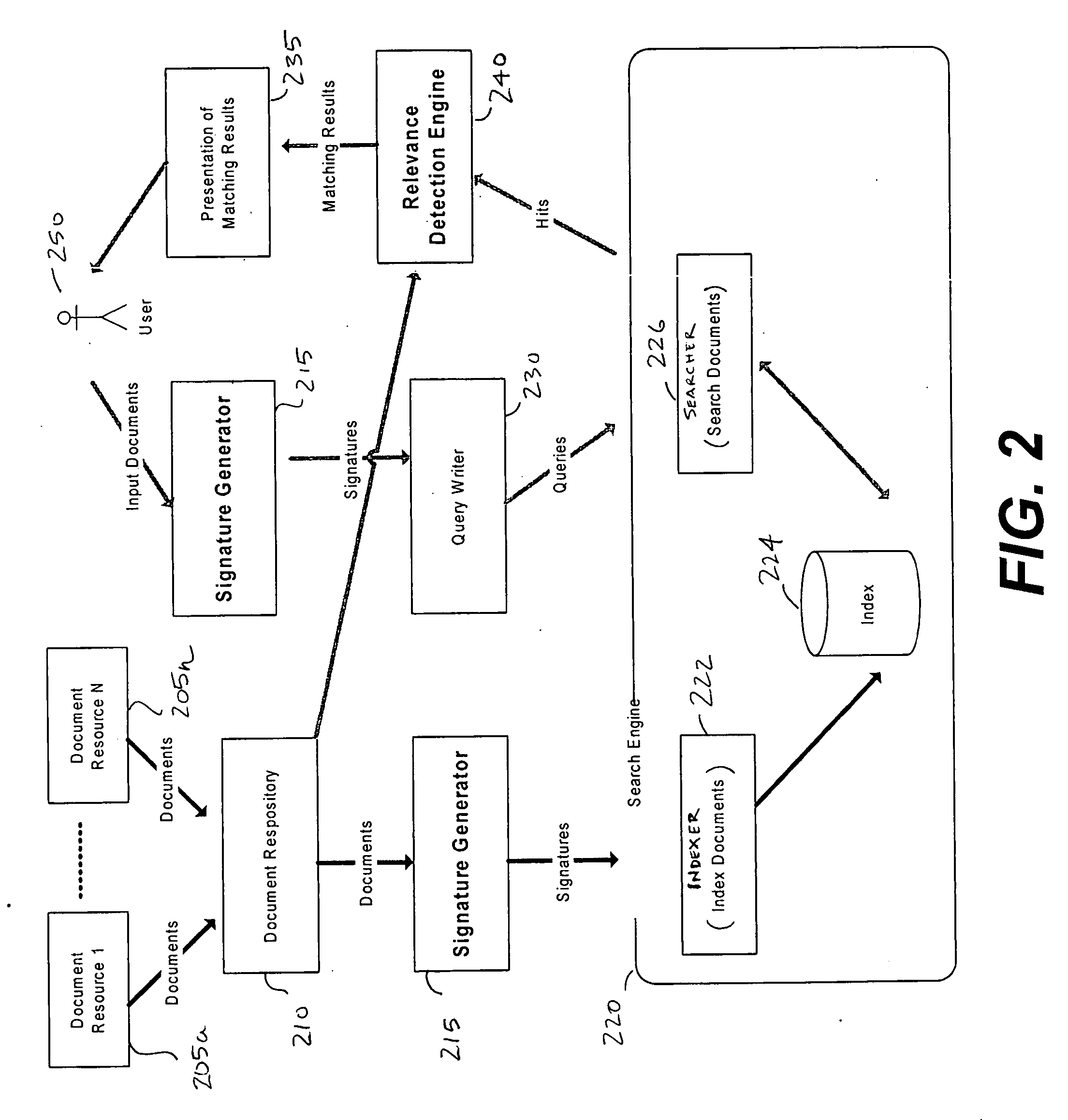
Matching engine for querying relevant documents
ActiveUS20060253439A1Increase search engine utilizationHigh acceptanceDigital data information retrievalDigital data processing detailsPaper documentDocument preparation
A system generates an output of documents having with a particular relevance range. The system receives an initial document comprising text, a list of documents for matching, each document comprising text, and a minimum substring match length. The system normalizes the text of the documents of the list of documents. The system searches common sub-strings between the text of the initial document and the text of each document of the list of documents. The system calculates a match percentage based on the search common sub-strings and outputs documents having a match percentage corresponding to a predetermined value. Also disclosed is a process for generating an output of documents within a particular relevance range.
Owner:TREND MICRO INC
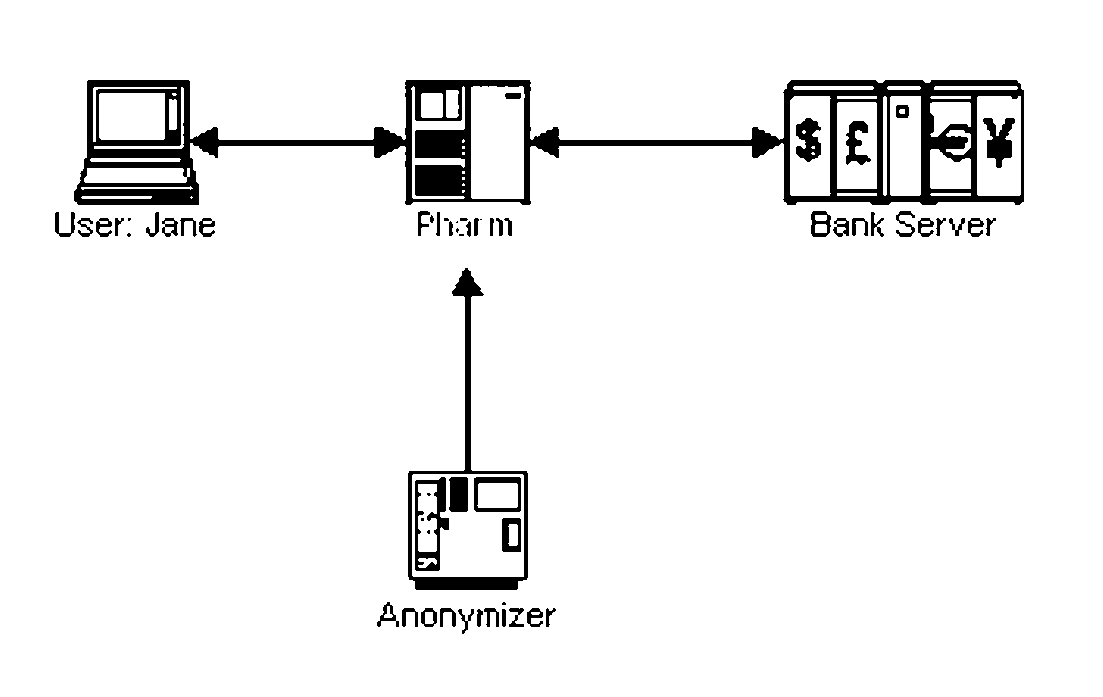
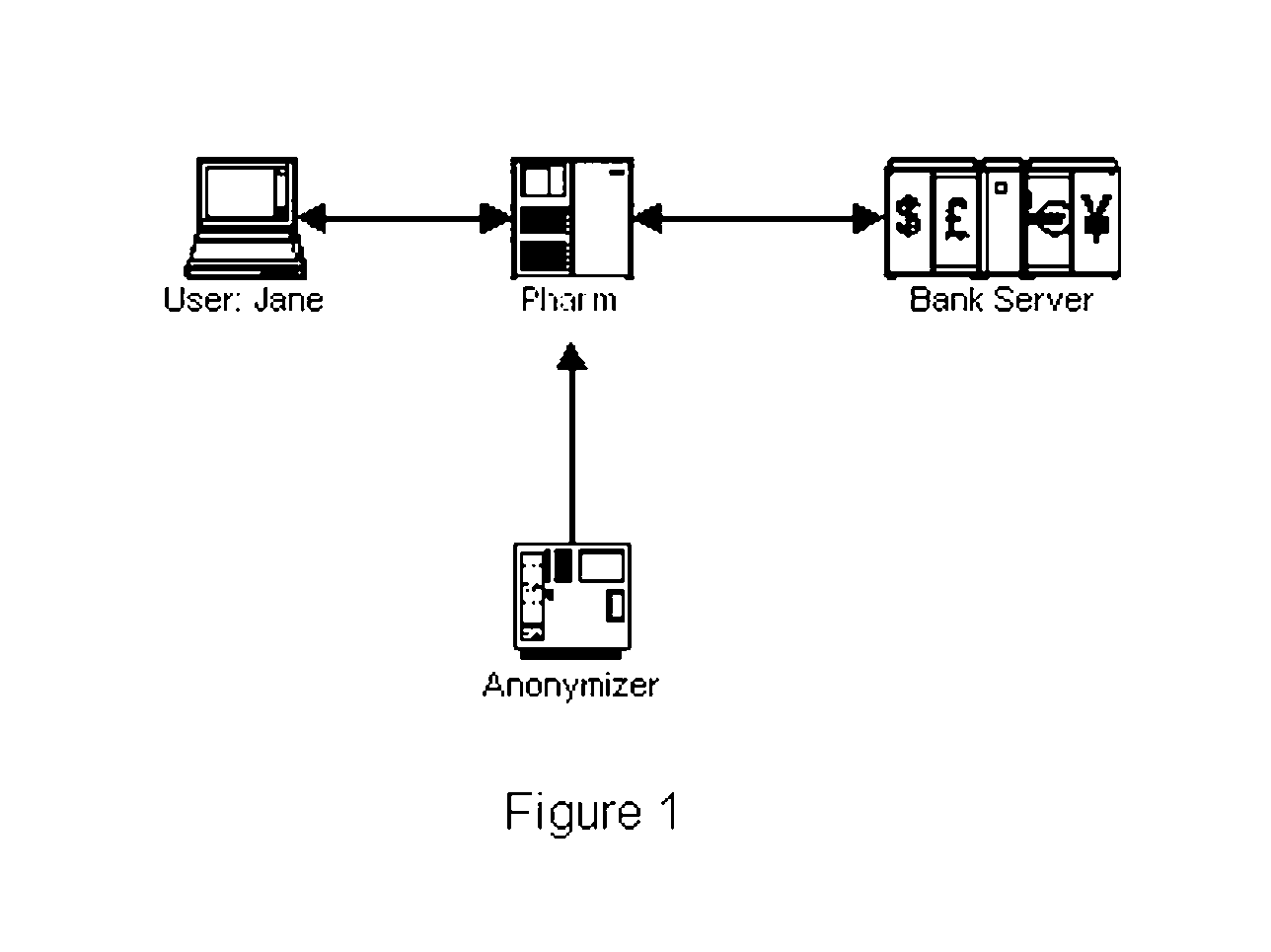
System and Method of Mobile Anti-Pharming and Improving Two Factor Usage
InactiveUS20070174630A1Improve securityLow costRandom number generatorsUser identity/authority verificationPrivate networkSoftware
A variant of phishing involves subverting an Internet access point, often used for mobile computing. Malware can route user requests for bank websites into a phisher's private network, with fake bank websites (pharming). The user can have a “mobile password” at the bank. When she connects from an access point, she sends a hash, found from the password, starting at some position in it. The bank returns a hash, found from the same password, starting at another position in it. Each can verify the other. We protect both from a man in the middle attack. By hashing a web page and the mobile password, and inserting the hash into the page that is sent, the recipient can verify that the page is untampered. We use an anonymizer, external to the access point. A user pre-establishes a password with the anonymizer. At the access point, she and the anonymizer use a zero knowledge protocol to verify each other, based on the password. Then, the password encrypts communication between them. From the anonymizer, she logins elsewhere. The anonymizer is our man in the middle, to defeat a man in the middle attack. W extend earlier antiphishing methods, to attack pharms for non-existent banks, or that are unauthorized websites for actual companies. We show how to use a plug-in to let websites share several two factor implementations. This reduces the cost and inconvenience to consumers, who might otherwise have to carry and use a different two factor gadget, for each of their bank accounts or other corporate websites that mandates the usage of two factor authentication. By expanding the scope of two factor usage, we improve the security of e-commerce, without having to use a public key infrastructure.
Owner:METASWARM INC
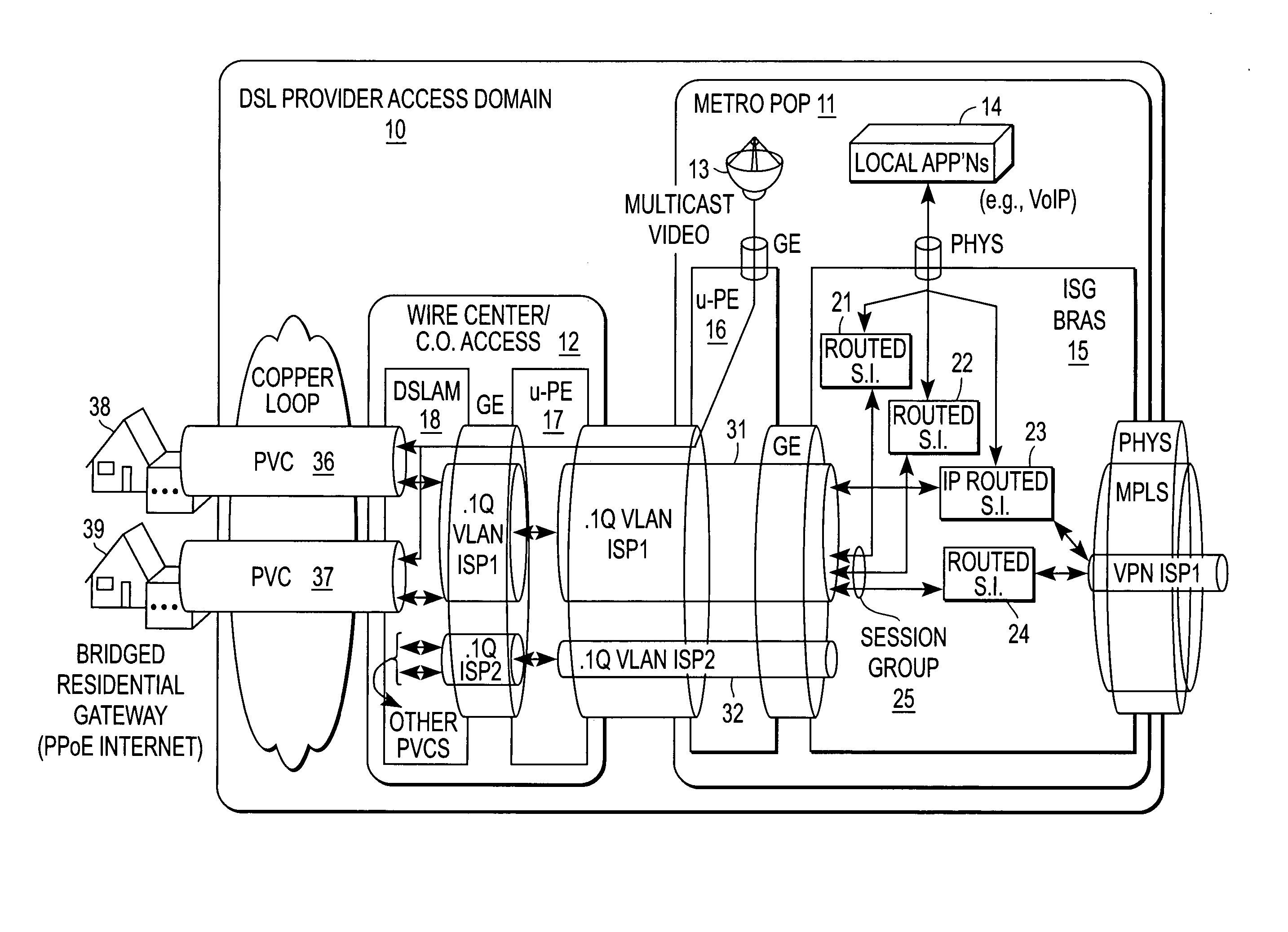
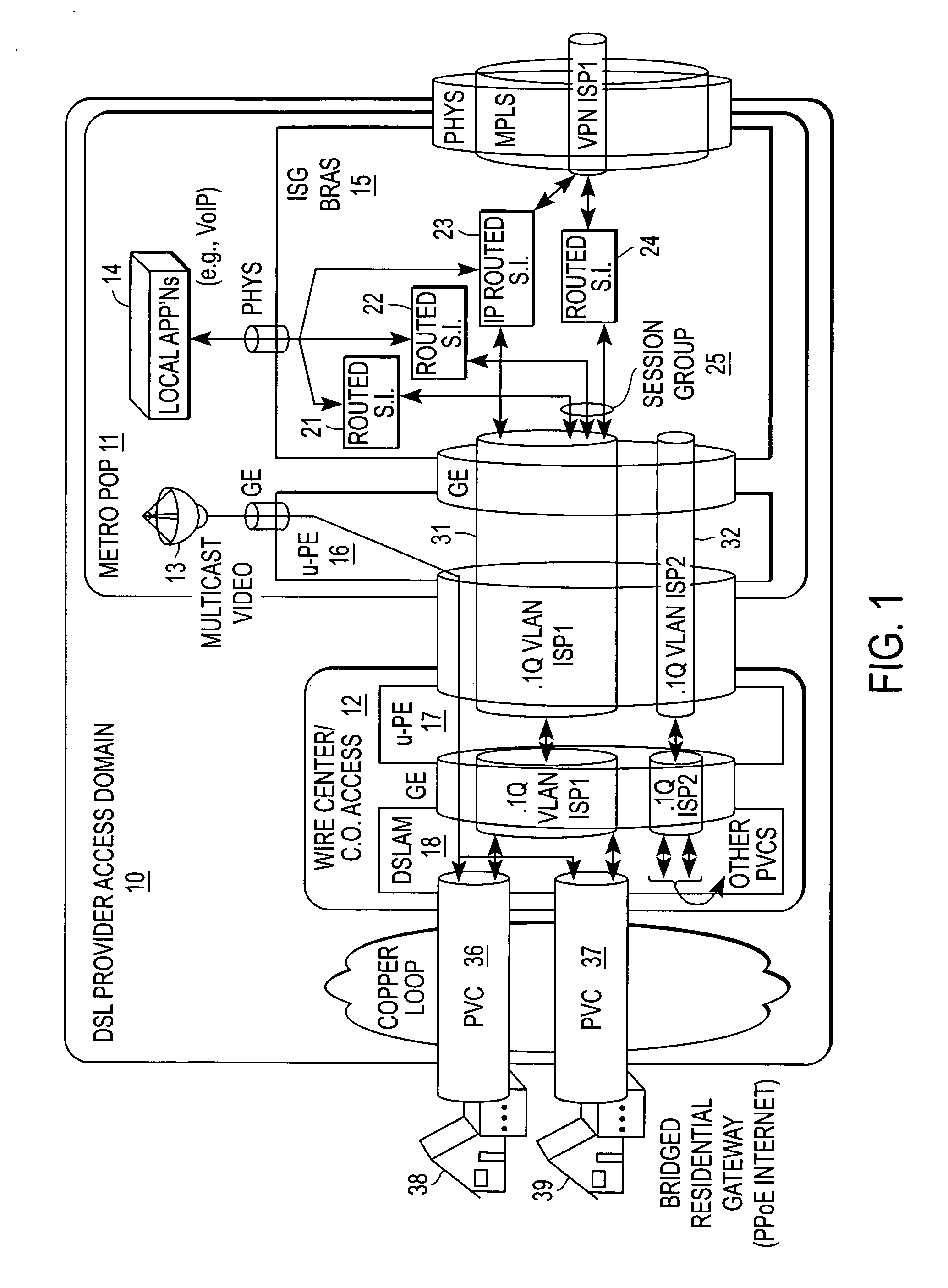
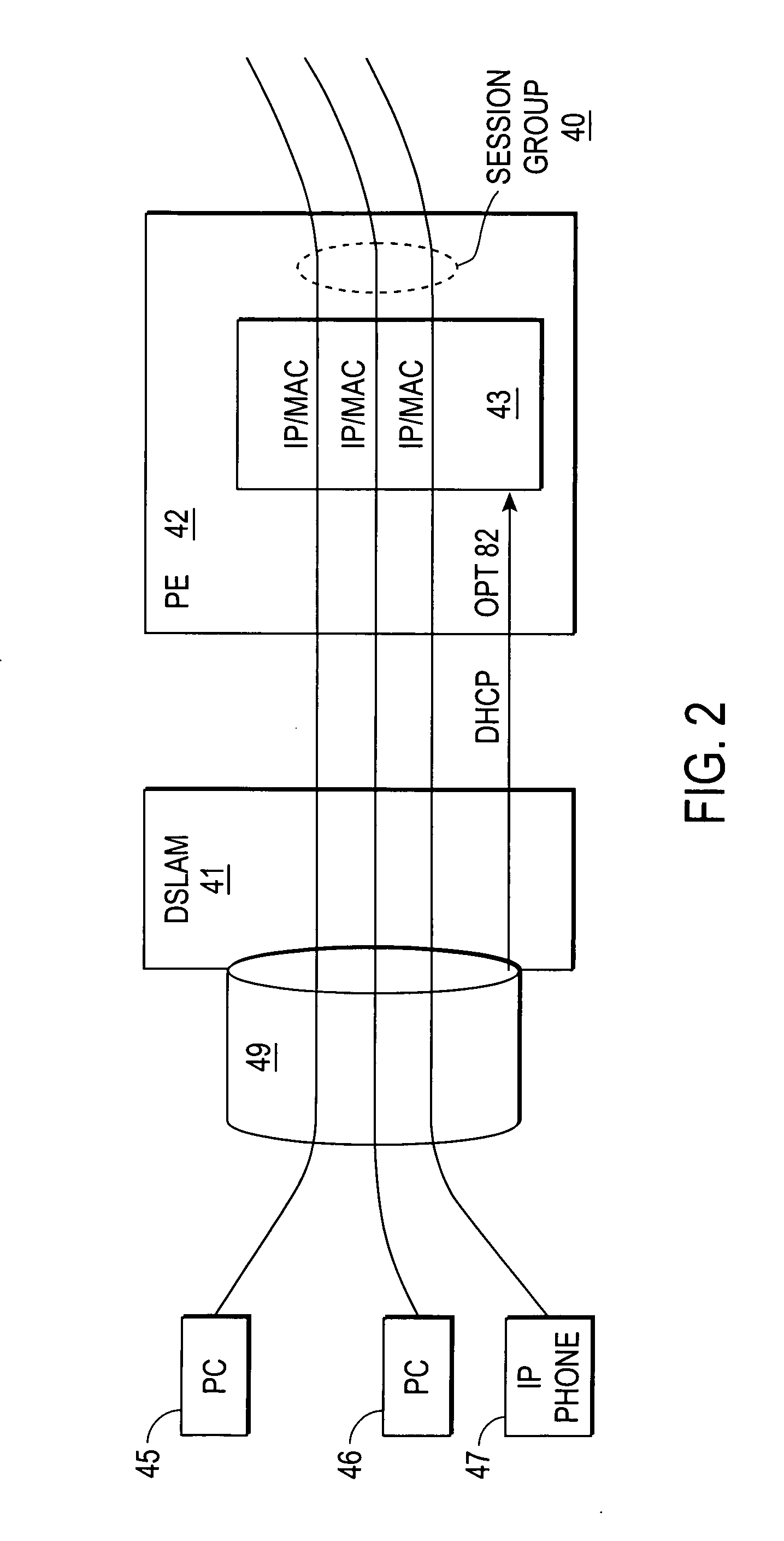
Quality of service based on logical port identifier for broadband aggregation networks
A provider edge (PE) device provides subscribers with access to an Internet Service Provider (ISP) network. The subscribers are connected to the PE device via a broadband aggregation device. The PE device includes a processor operable to snoop control plane traffic for a logical identifier that allows subscriber traffic having varying data plane information to be treated as a session group. The processor is further operable to instantiate the session group based on the logical identifier. A unit of the PE device applies a QOS policy to traffic flow associated with the session group. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
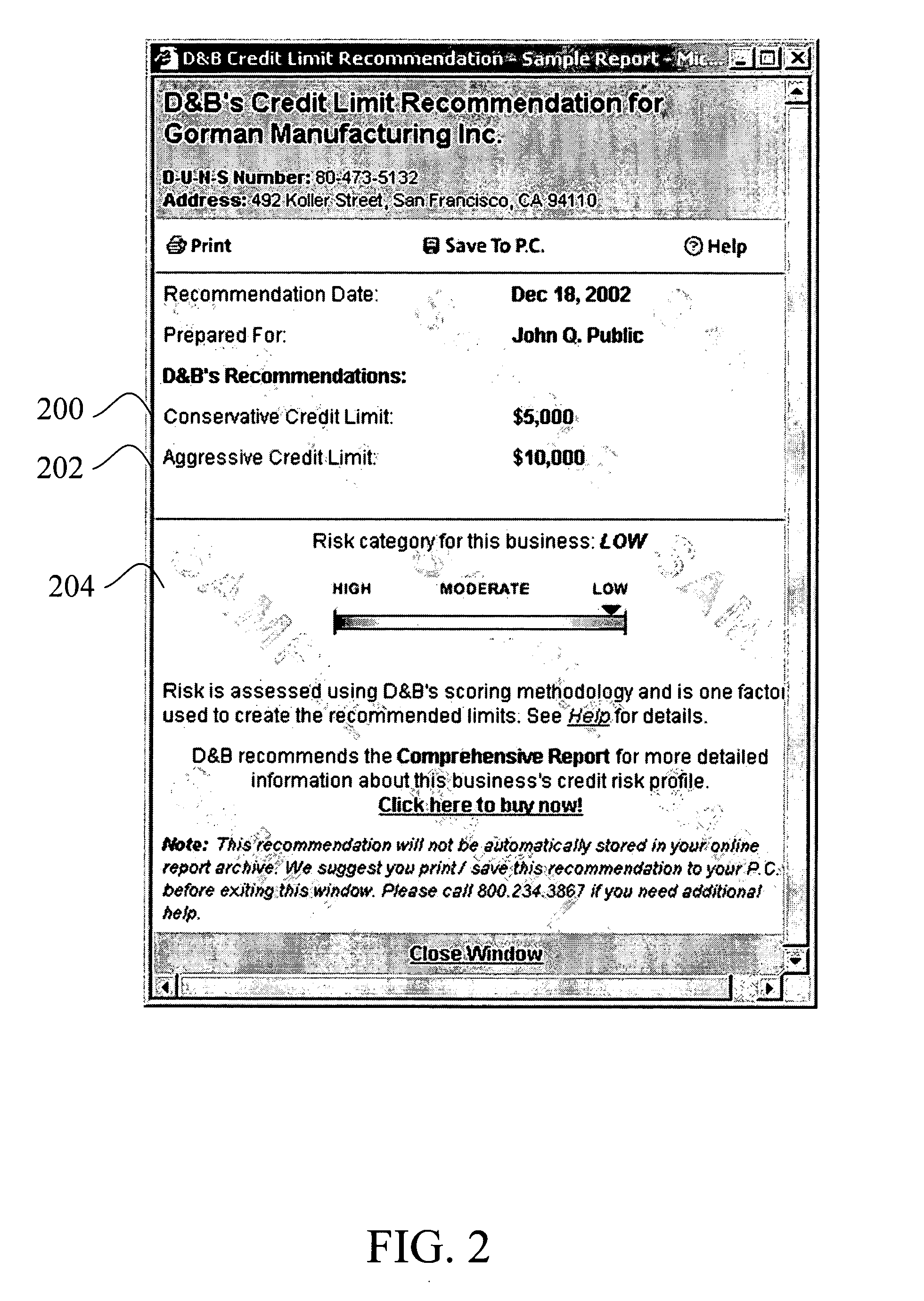
Credit limit recommendation
A credit limit recommendation helps customers more easily manage credit decisions. The credit limit recommendation has two guidelines: an aggressive limit and a conservative limit. The recommendation may be a specific dollar amount or a range or other information. The guidelines are based on an historical analysis of credit demand of customers in a business information database having a similar profile to the business being evaluated with respect to employee size and industry. The feature is available as a clickable link and each recommendation may be billed separately or as part of a subscription service.
Owner:THE DUN & BRADSTREET CORPORATION
Device and method for generating encrypted data, for decrypting encrypted data and for generating re-signed data
InactiveUS20050135613A1High data rate compressionAudio/video qualitySecret communicationProgram/content distribution protectionEncryptionCopying
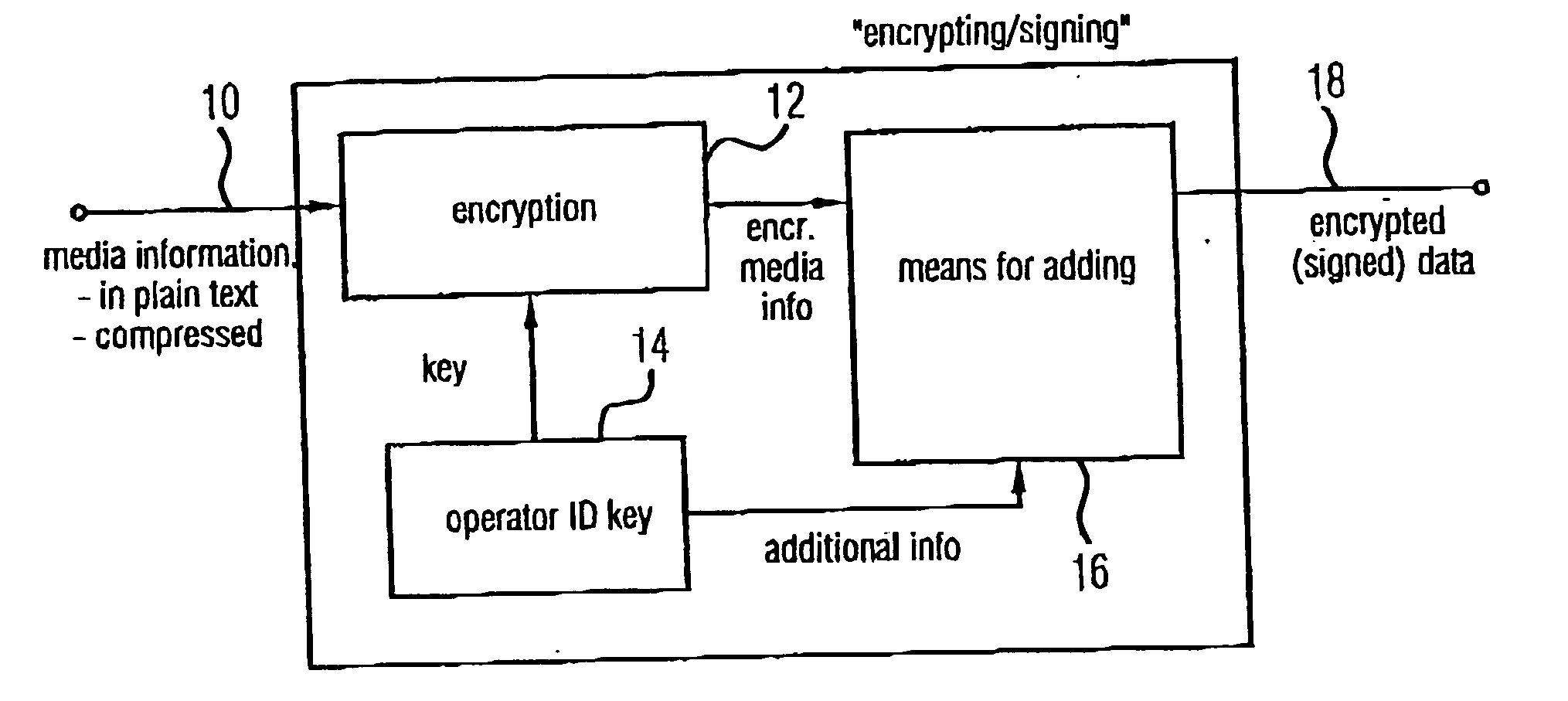
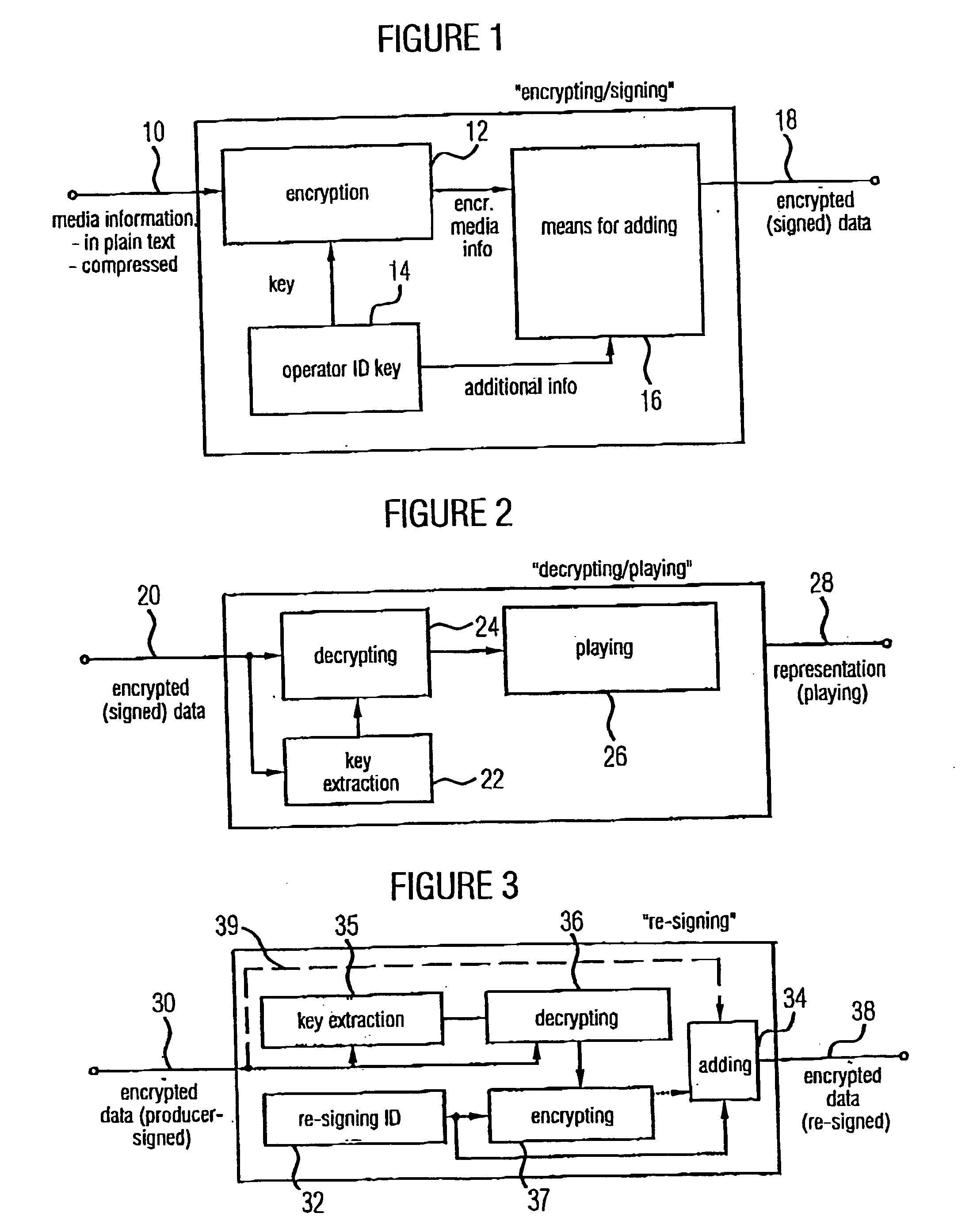
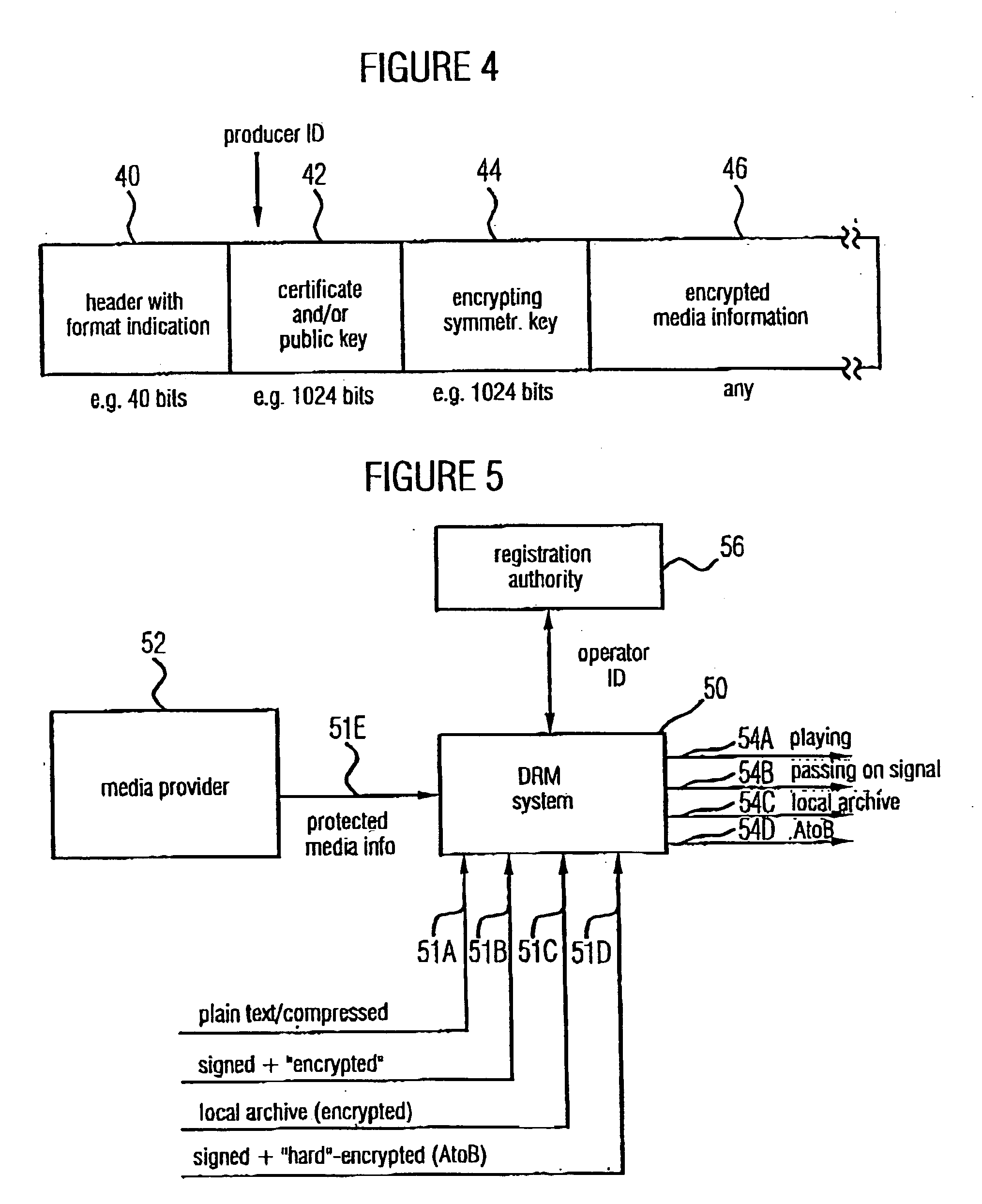
Devices and methods for generating encrypted data, for playing encrypted data and for re-signing originally signed encrypted data are based on the encrypted data, apart from the encrypted media information, to include the information required for decrypting the data and additionally a signature of who has generated the encrypted data. Thus the origin of the encrypted data can be traced back. In particular, passing on the encrypted data to a limited extent by the producer of the *encrypted data, for example to friends or acquaintances, is allowed, while only a mass reproduction of the encrypted data is considered as pirate copying. The pirate copier can, however, be found out with the help of the signature, wherein the signature is optionally protected by an embedded watermark signature. Because this is a concept wherein, when being used legally, only encrypted data occur, the unauthorized removal of the encryption is a statutory offence. The inventive concept makes possible finding the offender and at the same time considers ownerships of the operators with regard to a limited passing-on of media information, and thus has the potential of being accepted on the market.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
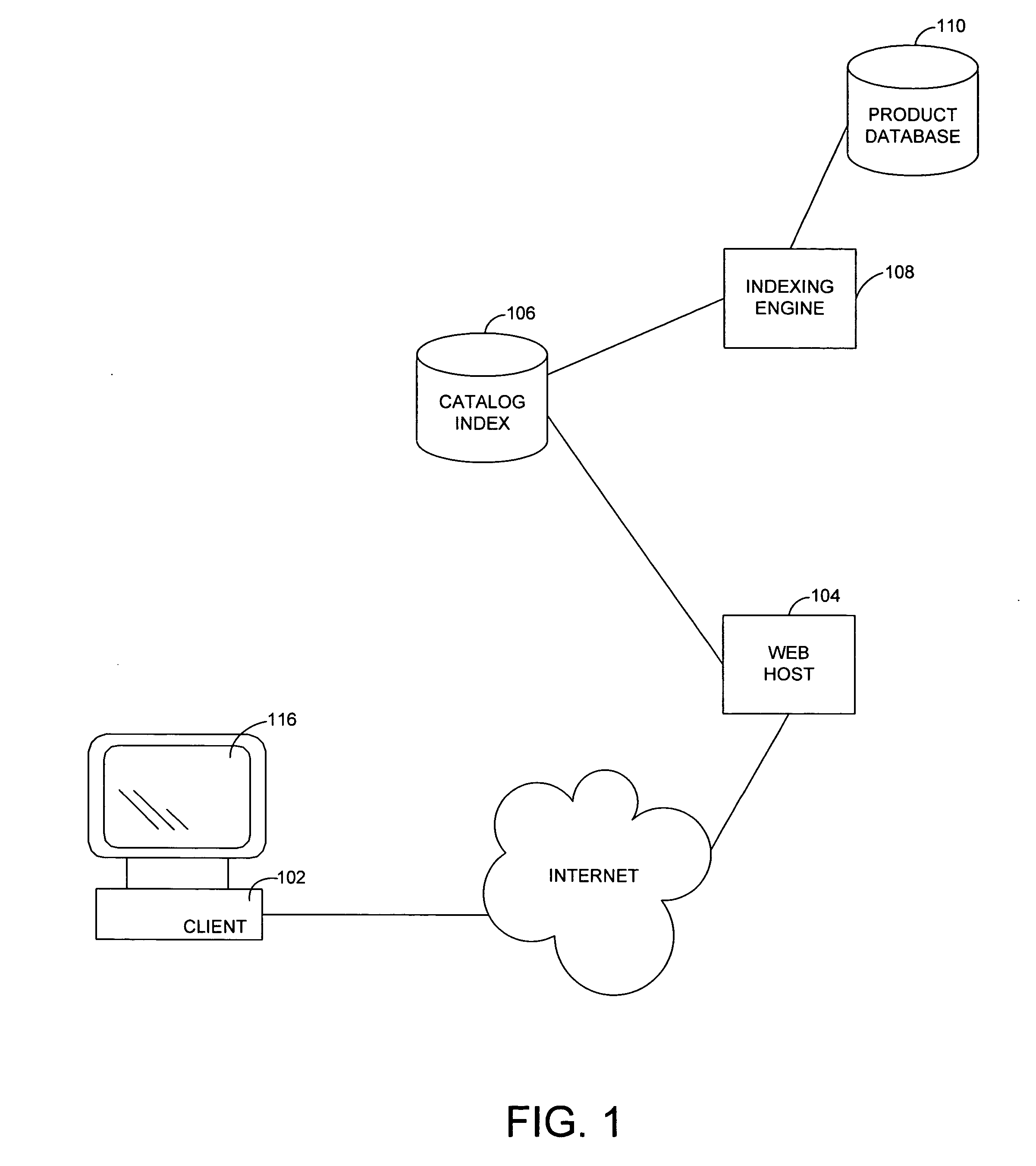
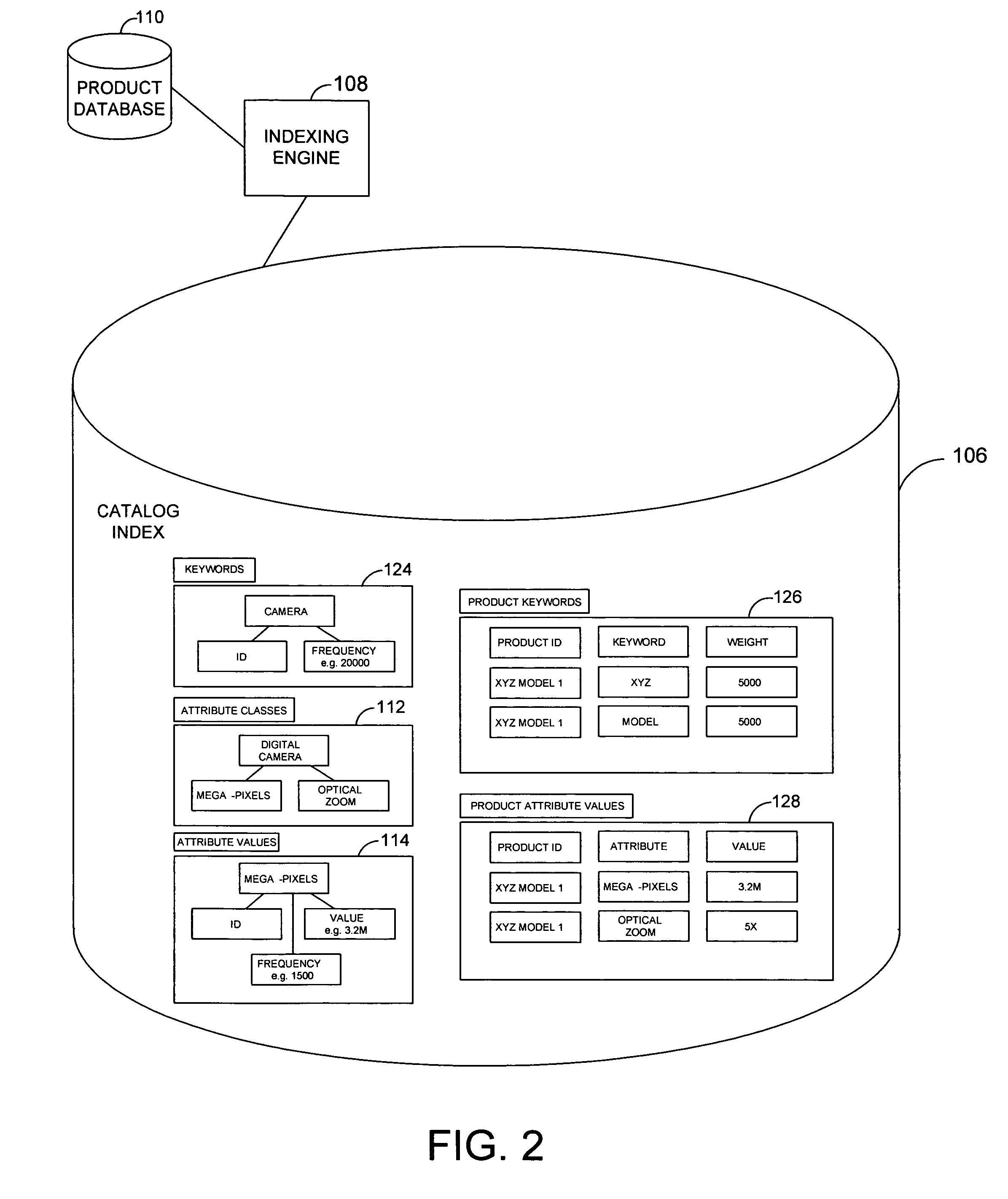
System and method for an online catalog system having integrated search and browse capability
InactiveUS20060095345A1Extend or refine their search or browsing activityCommerceSpecial data processing applicationsLevel of detailSQL
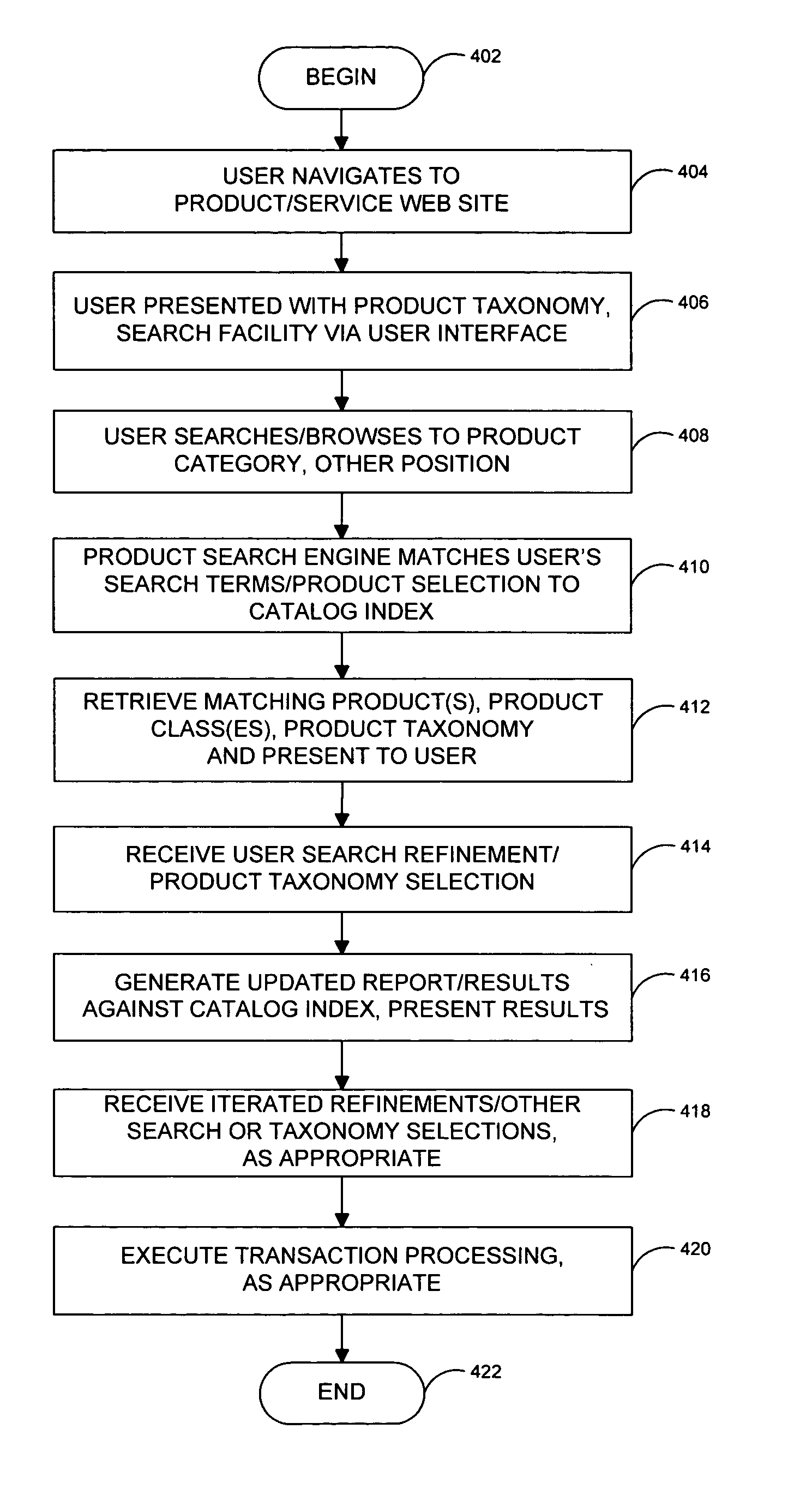
A system and related techniques generate and maintain a unified product index, to perform searching and browsing in an online product, service, content or information catalog. A user investigating, for example, a set of retail offerings of digital cameras may for instance browse through a Web site layout or taxonomy to locate products of interest, such as cameras having resolution in the range of 3-4 megapixels or in the price range of $200-300. Alternatively, the user may input search terms in a search dialogue box to locate those or other features. Unlike conventional e-commerce platforms in which search may be performed against structured databases while browsing may access unstructured HTML or other descriptive material, according to the invention navigation and searching may be integrated and both access a structured index derived from product descriptions as well as traditional SQL or other structured data. A user may thus transparently move between browsing the Web site and searching the Web site, refining their search or browsing activity in a seamless fashion. The HTML or other unstructured data may in one regard be processed by an index engine to identify product attributes such as type (electronics), size, price, weight or other specifications as well as attribute values, which may be sorted or stored in a separate table. A set of results generated by conducting an initial search may thus be continued or refine by further browsing down to a particular product or other level of detail. Conversely a user who has browsed to a given level of detail, such as digital camcorders priced less than $700, may initiate a search through products at that level of the hierarchy without resetting search terms or position in the taxonomy. Greater ease of use, more efficient location of products or services and less dead-end pathways are thus achieved.
Owner:MICROSOFT TECH LICENSING LLC
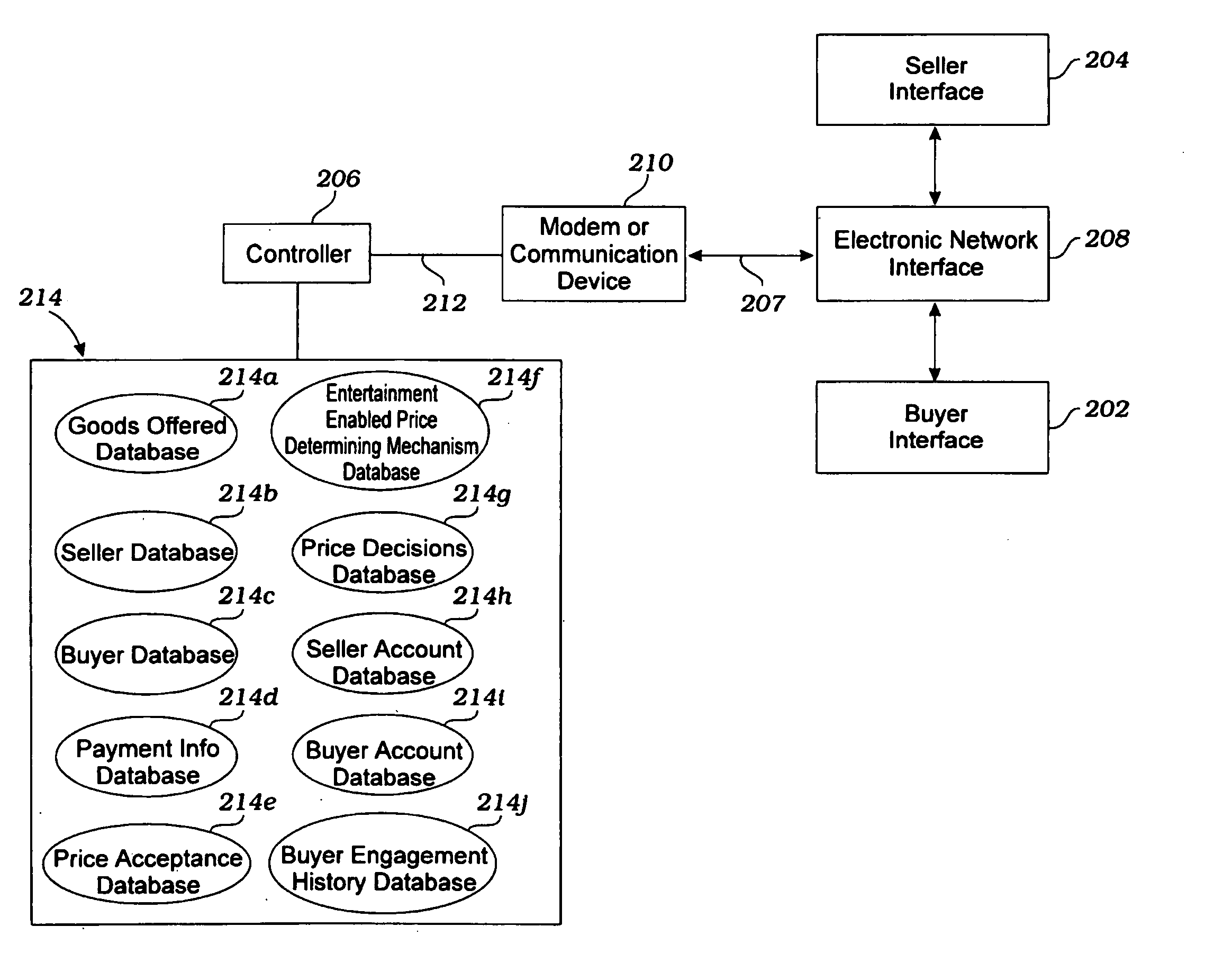
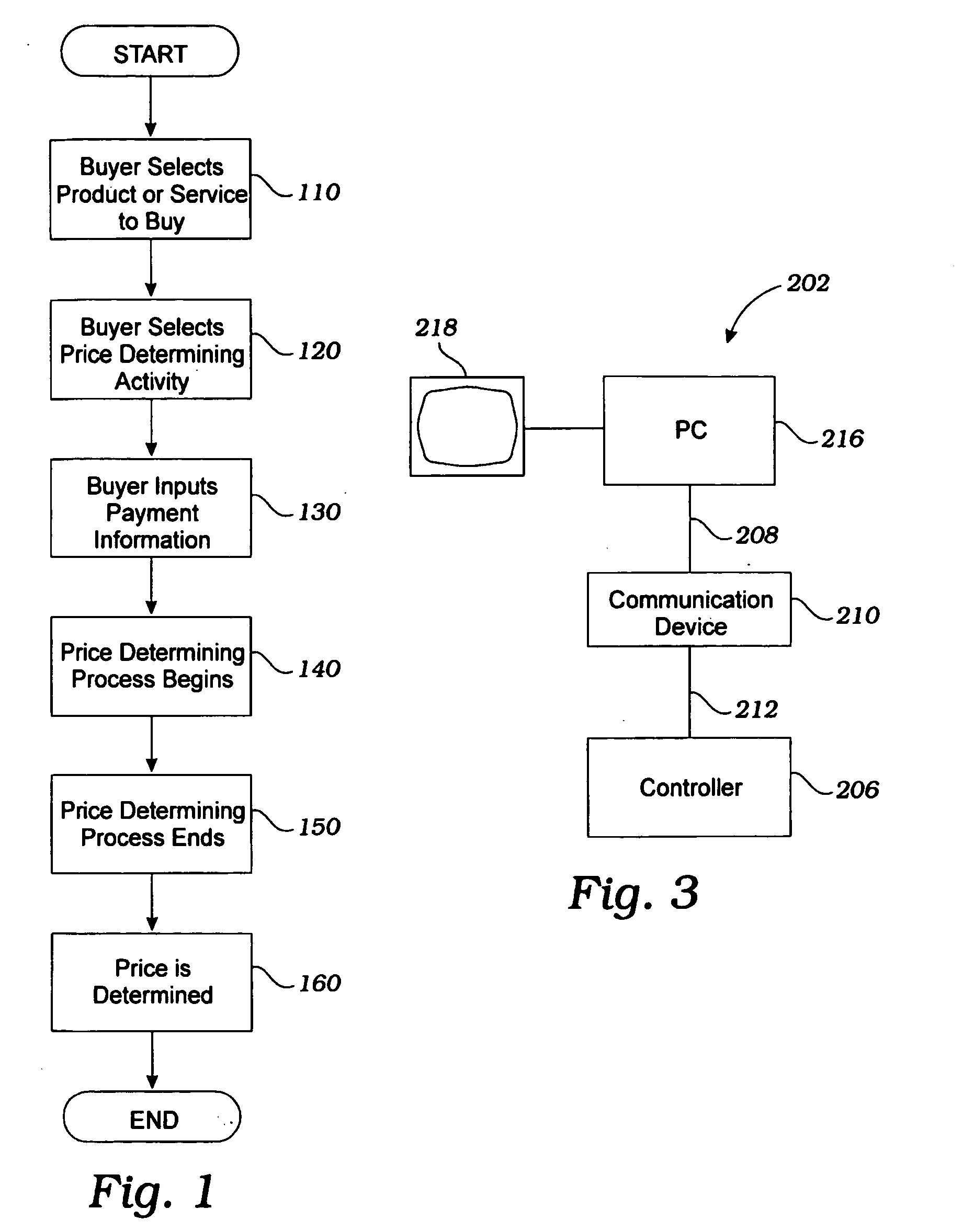
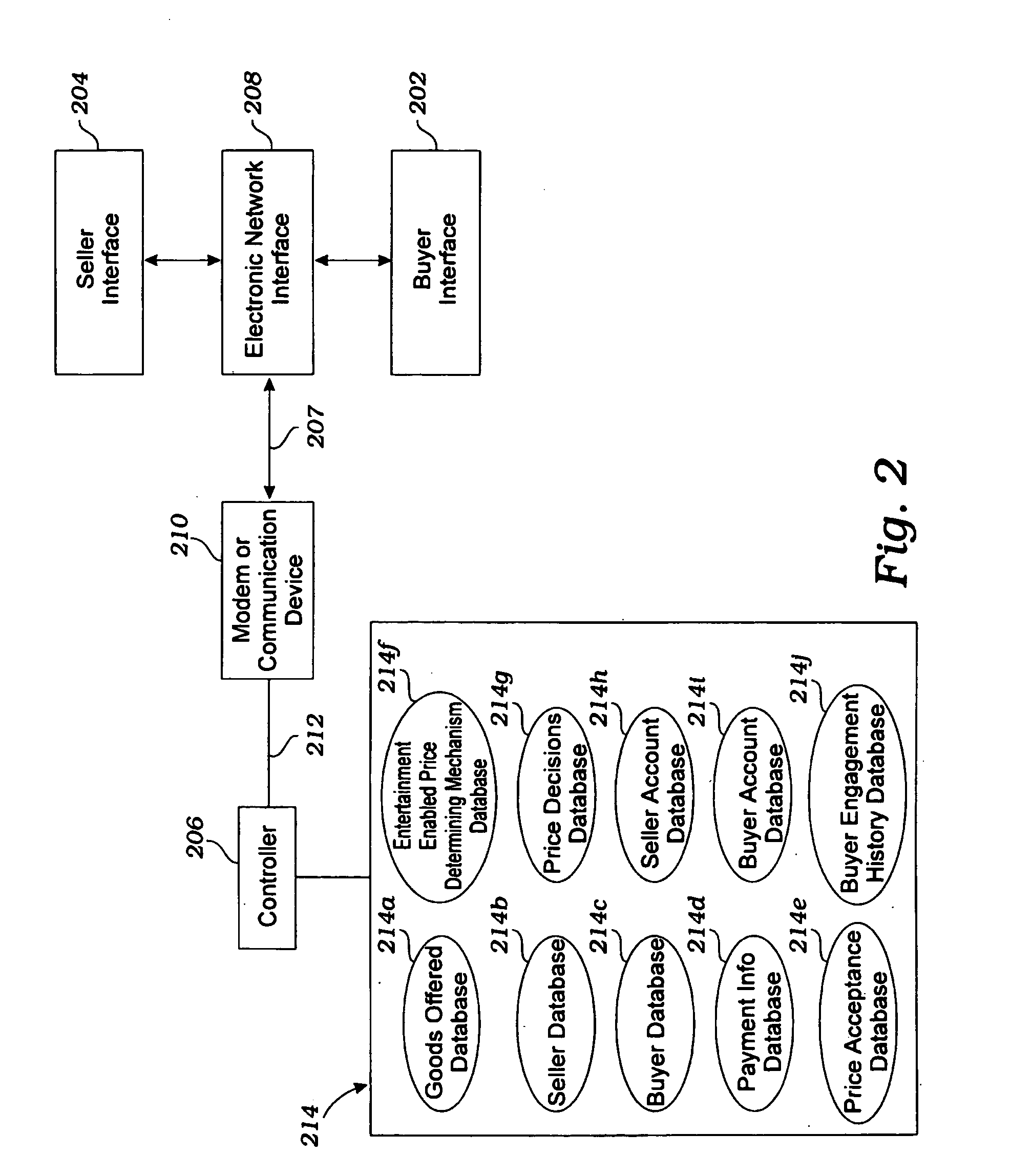
Systems and methods for transacting business over a global communications network such as the internet
InactiveUS20060059055A1Address rising pricesBuying/selling/leasing transactionsVideo gamesPaymentWeb site
A business model / process is described for conducting business transactions over the Internet, allowing buyers to reduce the price of the selected product / service based on the buyer's performance during a collateral activity. Sellers offer the product / service within a specified price range, and buyers accept the offer, in exchange for the opportunity to close the transaction at the lowest price offered by achieving a high score or performance rating during the collateral activity. The ultimate price is within the agreed upon range, but is determined based upon the buyer's performance and scaled to the performance at the collateral activity. The price may change throughout performance of the collateral activity, and the available price at any given time may be displayed or otherwise made available to the buyer. The price change may be continuous, at intervals, in response to certain events, etc. The activity may be a video game, electronic board game, sports bet, card game, or any other activity, and may be performed against the seller, a pre-programmed software opponent, a computer opponent, another buyer competing for the same or a different product, a player participating as a player only and not as a buyer, or anyone or anything else. The seller will receive payment for listing products for sell, and as the products attracts buyers to participate in PDAs and compete for lower prices, revenues will be generated from the time spent by the buyers during the PDAs, the time can turn into advertisement revenues for the host of the web site, and the revenue can be shared accordingly with the sellers.
Owner:PERFORMANCE PRICING INC +1
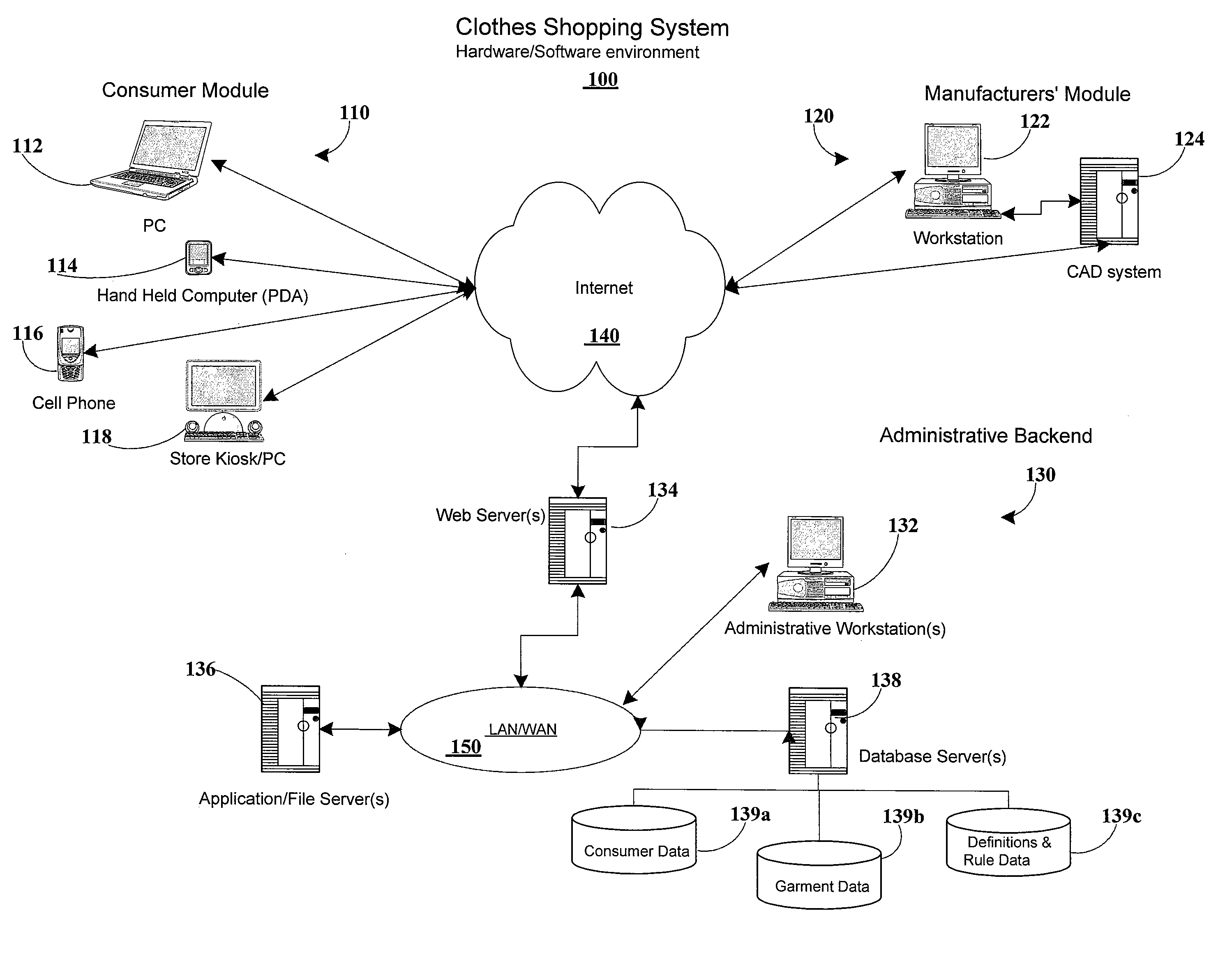
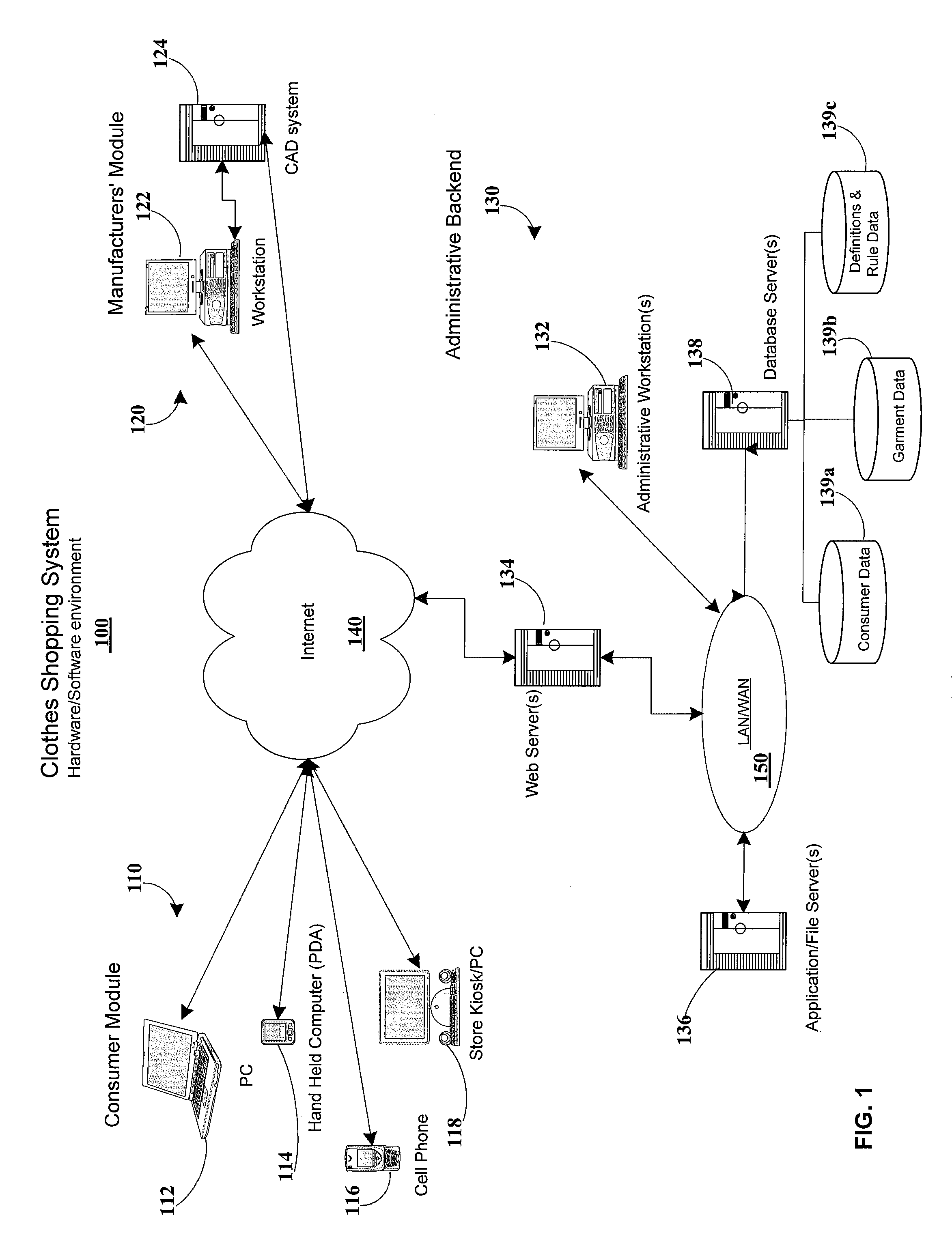
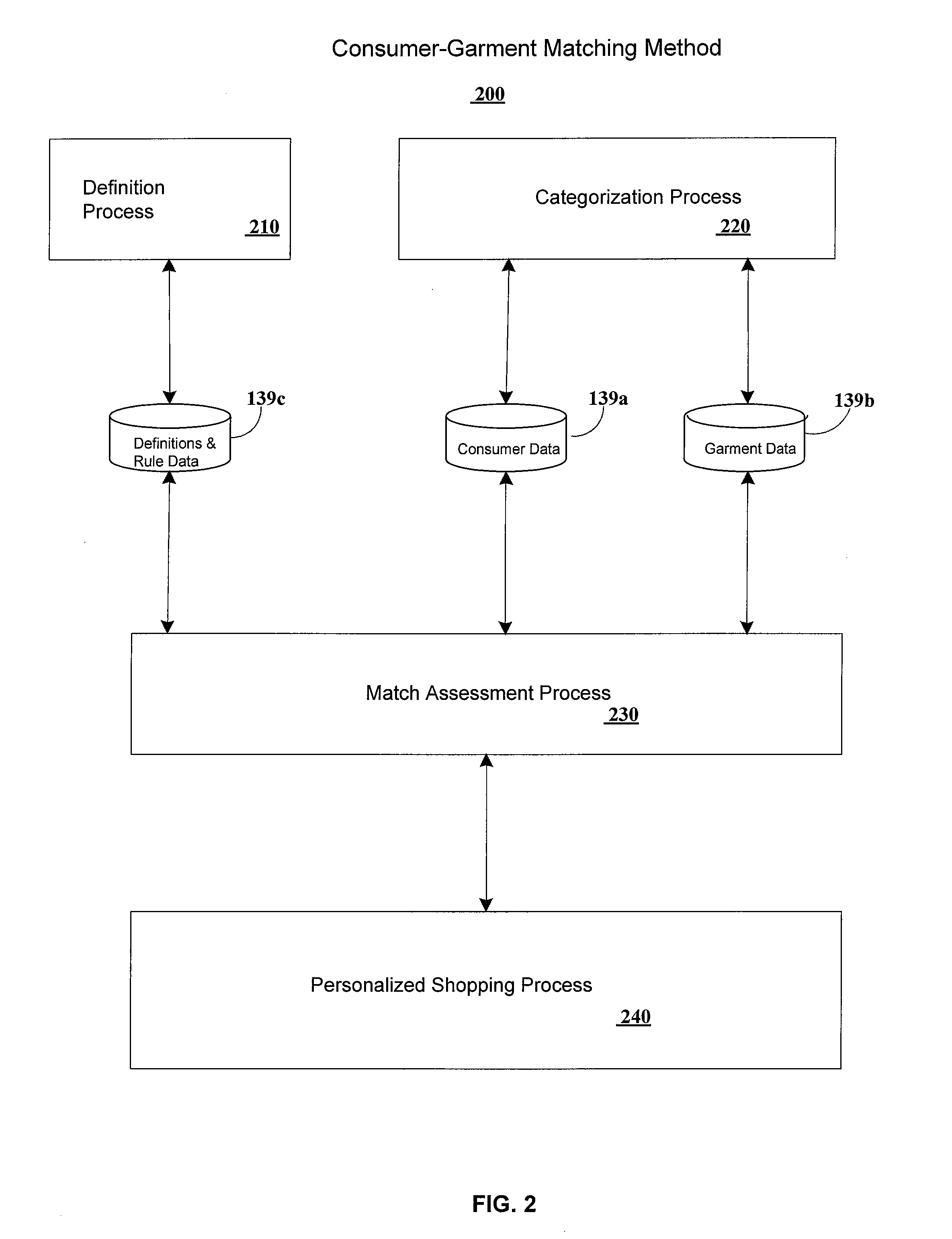
Computer system for rule-based clothing matching and filtering considering fit rules and fashion rules
InactiveUS20070198120A1Increase probabilityBuying/selling/leasing transactionsSpecial data processing applicationsData miningComputer generation
Owner:MIPSO
Method of reducing silicosis caused by inhalation of silica-containing proppant, such as silica sand and resin-coated silica sand, and apparatus therefor
InactiveUS8636832B2Reduce exposureMinimizing chanceCombination devicesAuxillary pretreatmentTrademarkSilicosis
A method of reducing silicosis caused by inhalation of silica-containing proppant, such as silica sand and resin-coated silica sand, and apparatus therefor. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KSW ENVIRONMENTAL LLC D B A AIRIS WELLSITE SERVICES
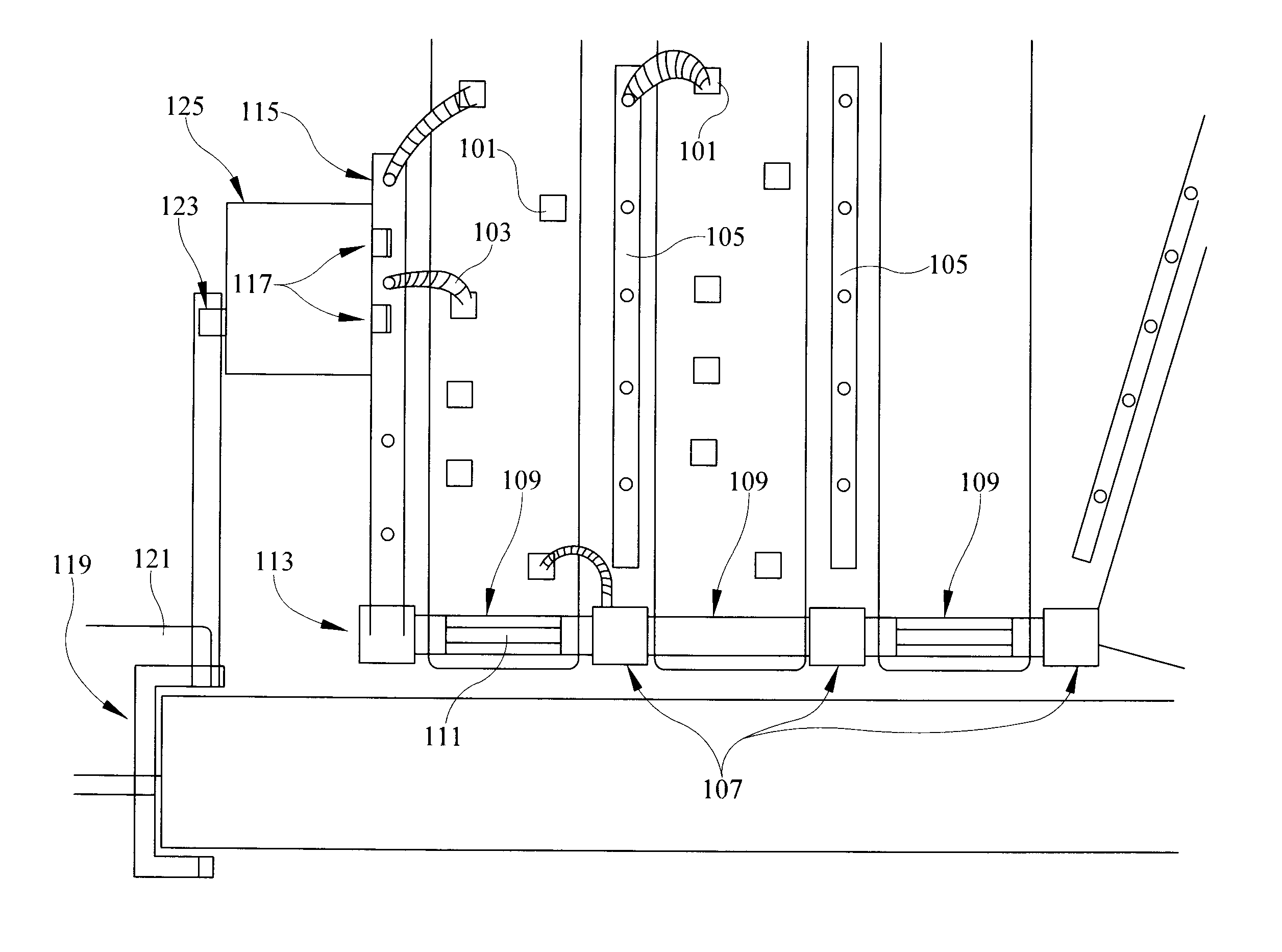
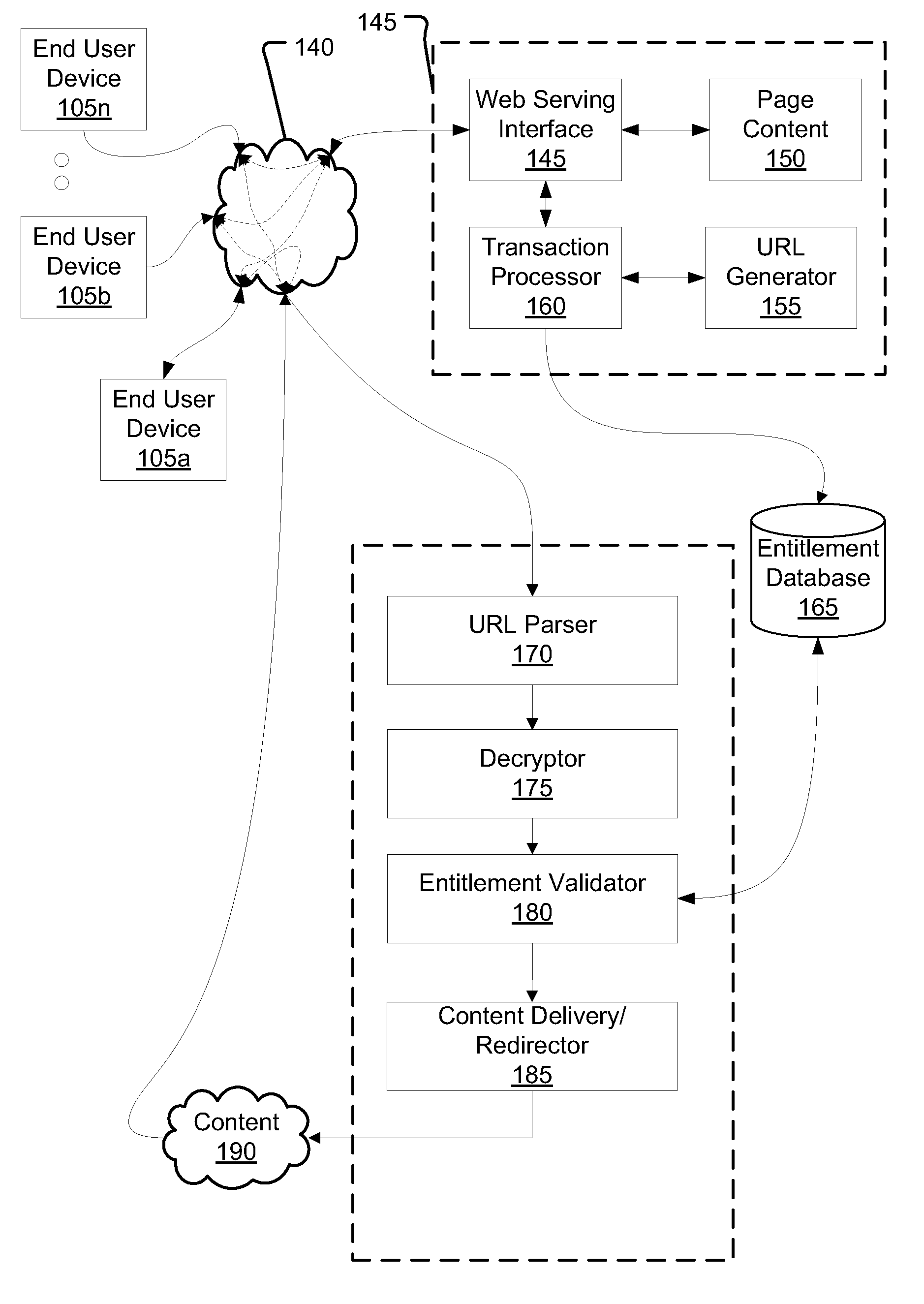
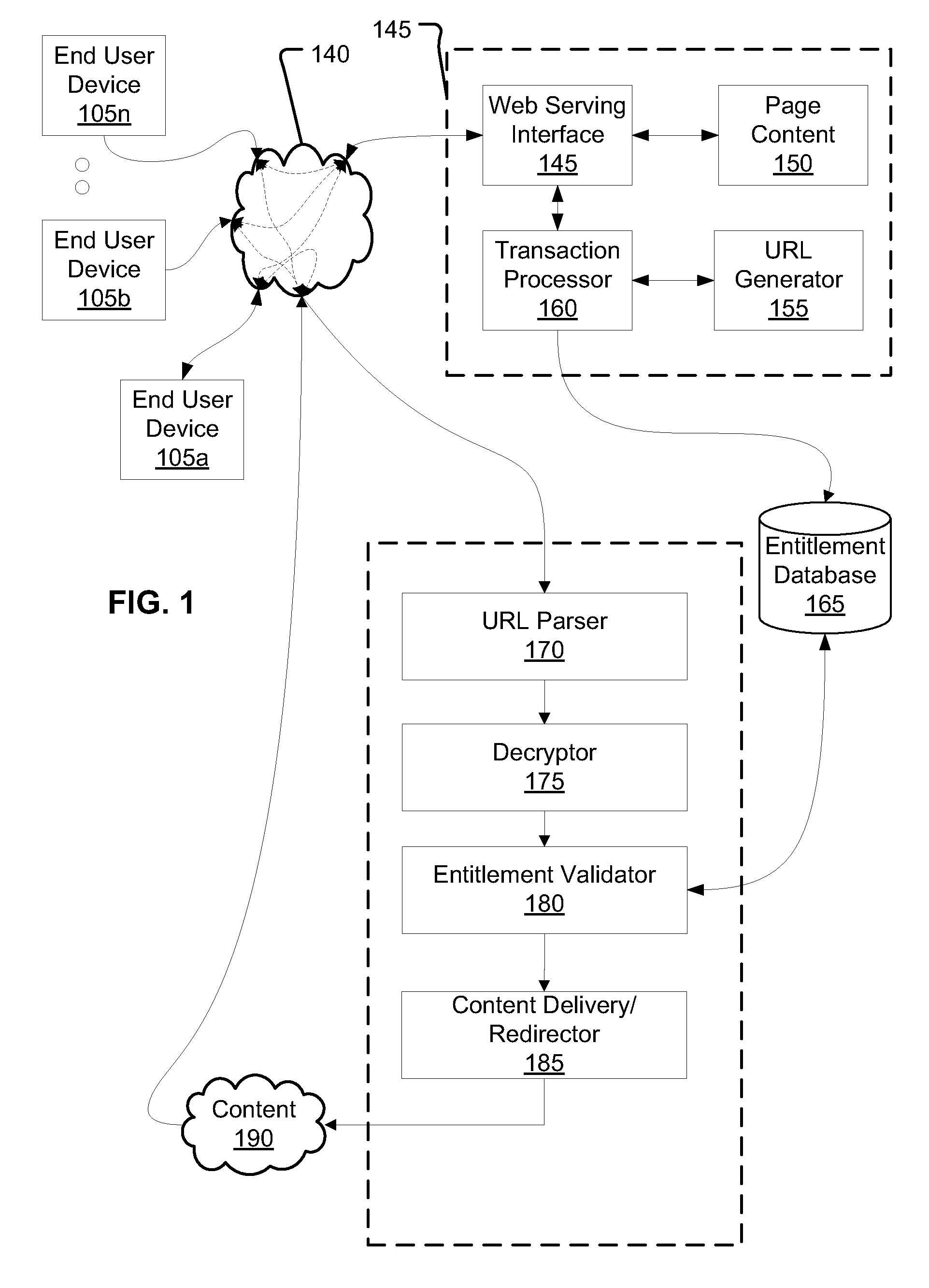
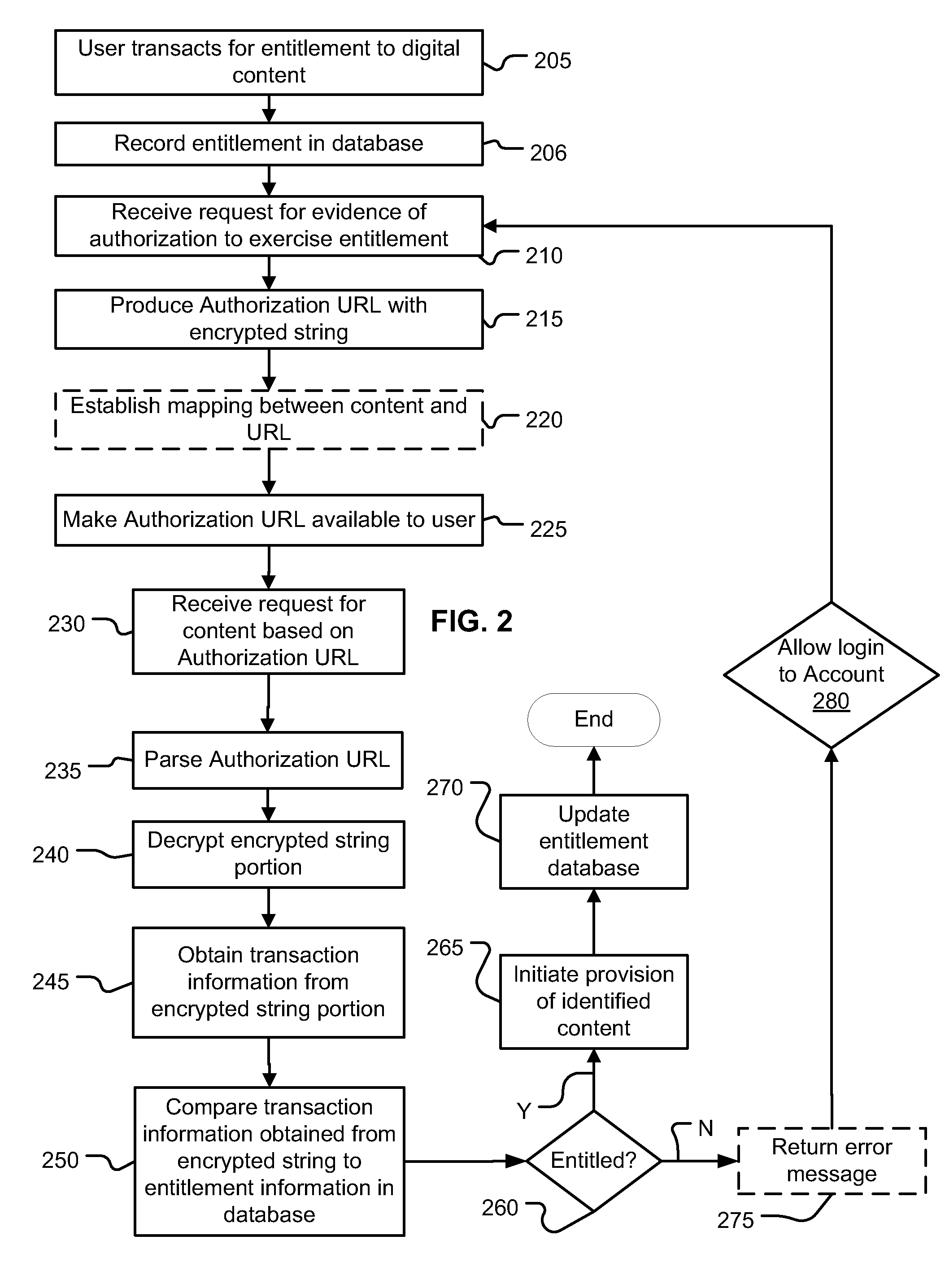
Method and system for verifying entitlement to access content by URL validation
ActiveUS20100192210A1Digital data processing detailsUser identity/authority verificationDigital contentNumber content
Aspects include a mechanism of entitling users to transacted-for digital content access, indicating download authorization with discrete authentication URLs, and validating download attempts using each such URL. The authentication mechanism comprises producing an encrypted string included in a URL provided to a user. The encrypted string comprises transaction identifier information, and information about the transacted-for entitlement. When a user wishes to exercise the transacted-for entitlement, the user activates the URL, which is resolved to a location that has / can obtain access to the key(s) used in producing the encrypted string, decrypt the string, and use the information in it to validate the URL and the entitlement. The validation can use data retrieved from a database, using the transaction identifier as a key. The entitlement information included in the now-decrypted string can be compared with the prior download information. A byte range of requested by a browser using the URL can be used in validation, as well as how a particular authorization / validation should count for entitlement fulfillment.
Owner:APPLE INC
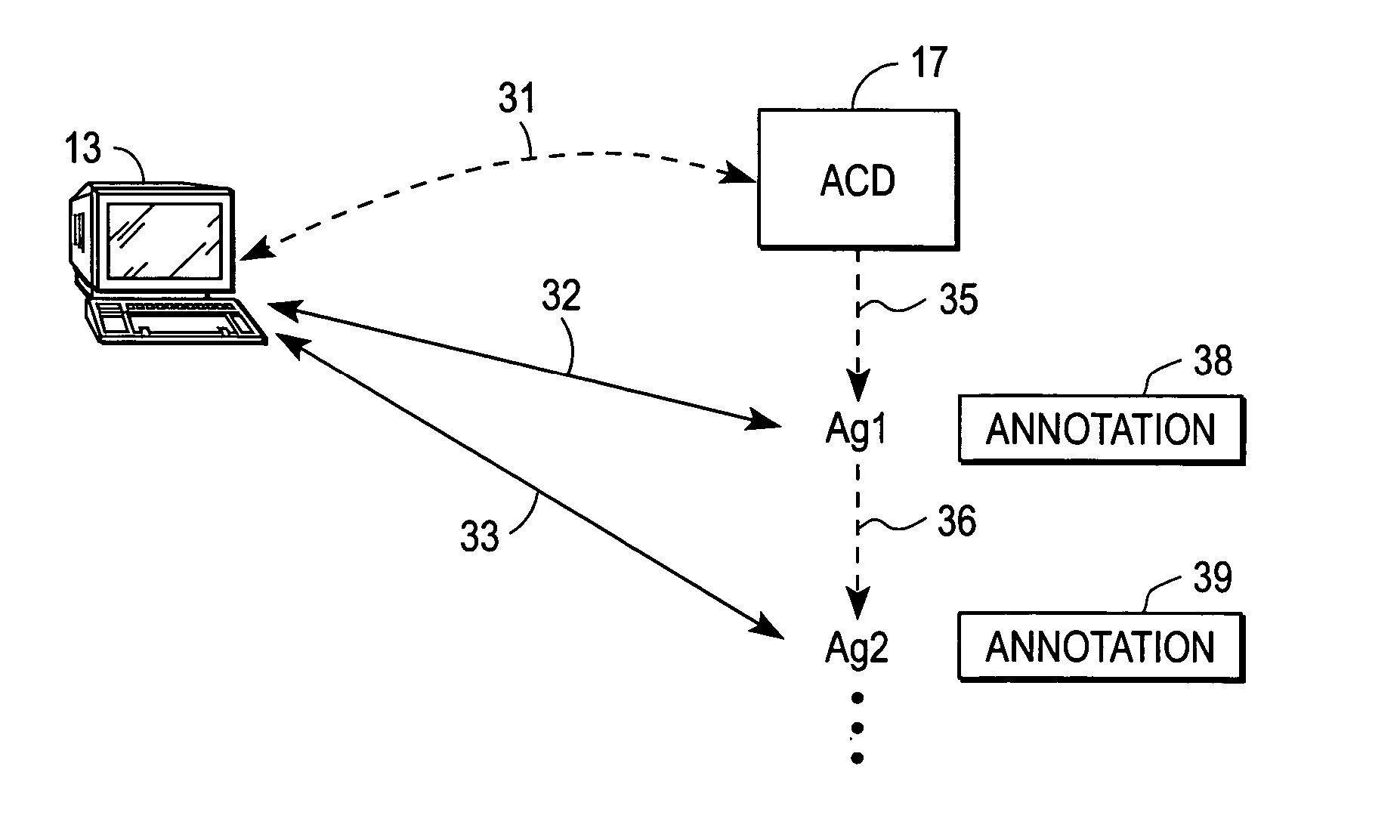
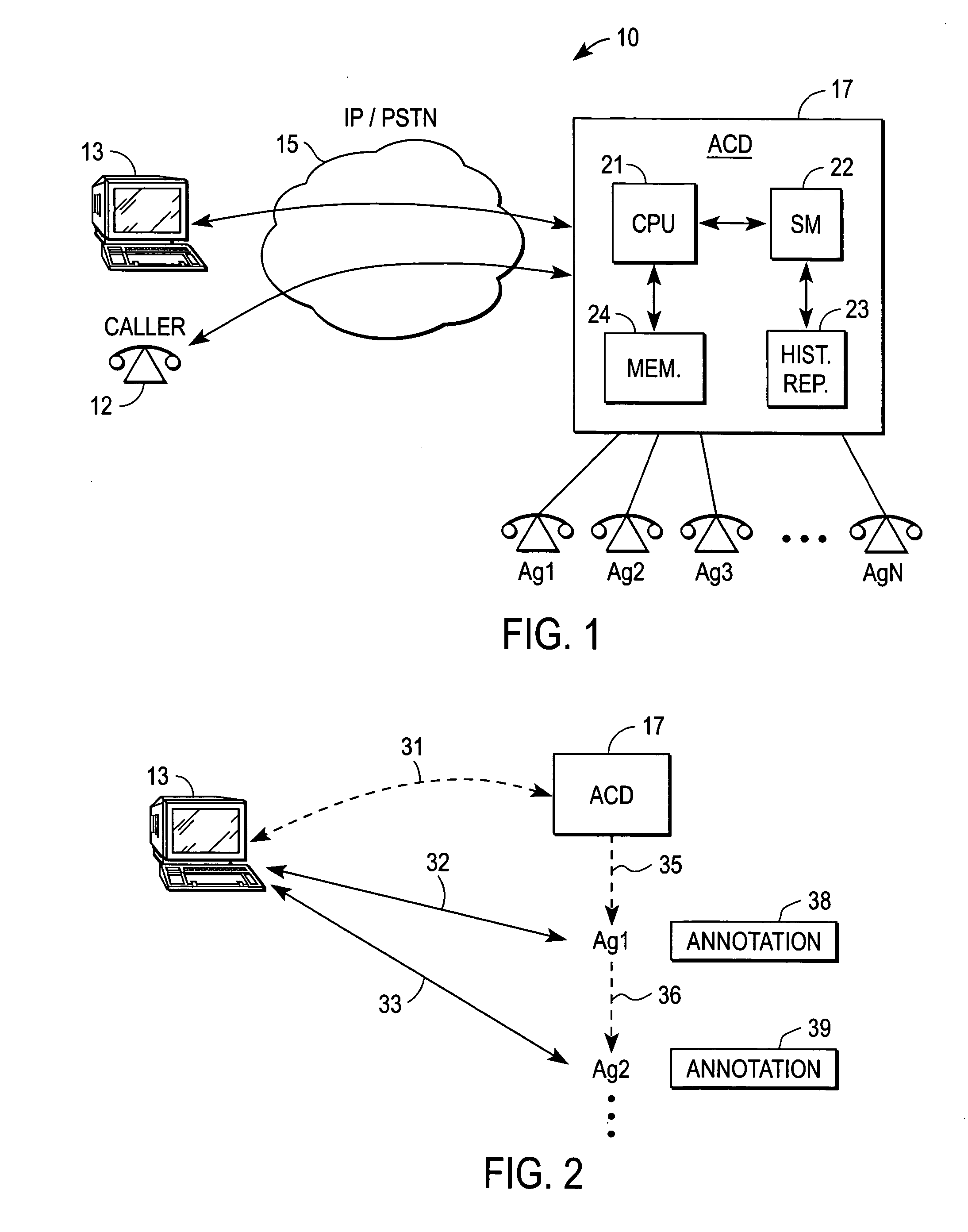
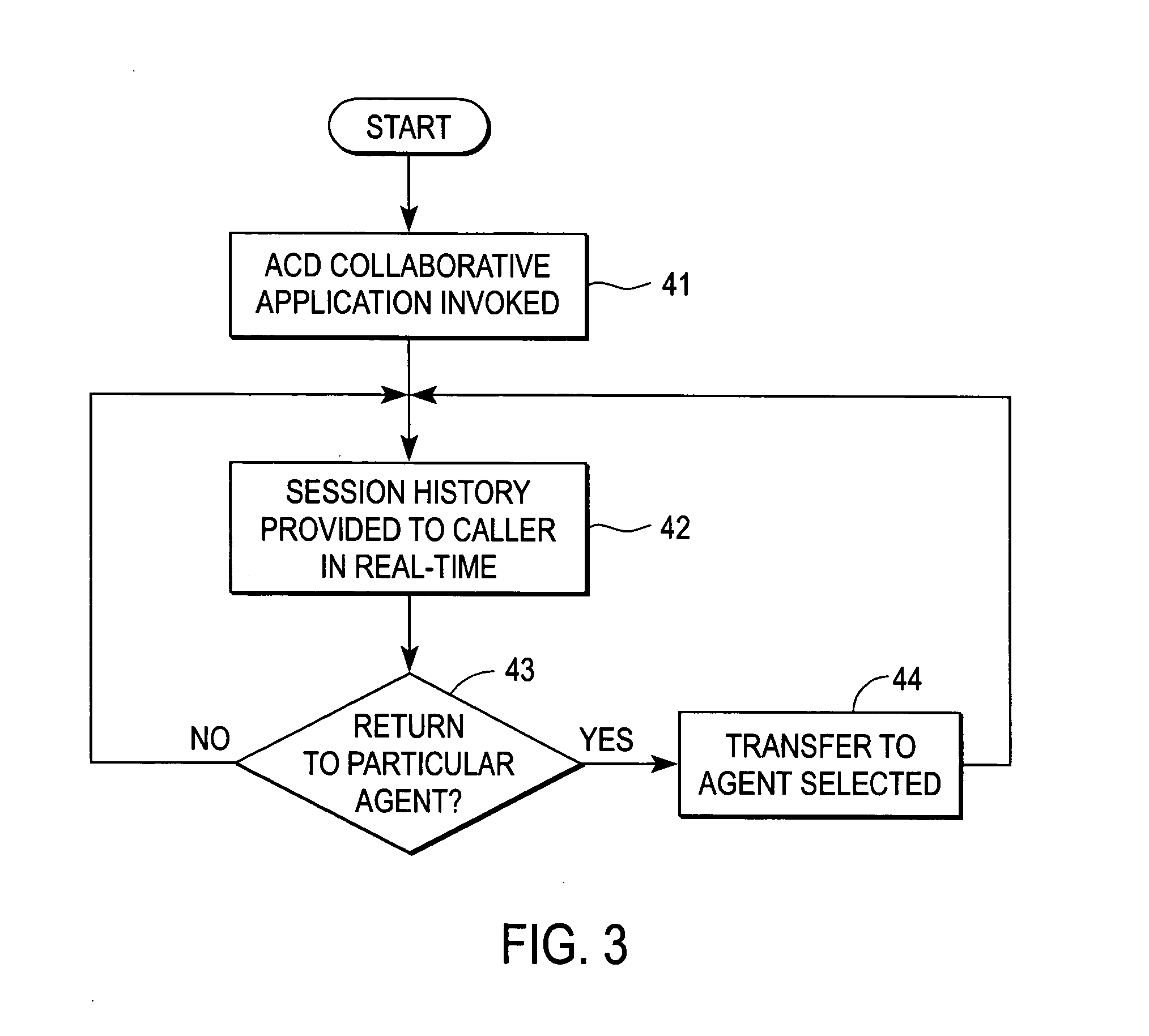
System and method for return to agents during a contact center session
A system and method for servicing a caller at a contact center includes a processor subsystem and one or more modules that include code executable by the processor subsystem. Execution of the code invoking an automatic call distributor (ACD) collaborative application that provides the caller with a visual or aural call session history that lists each agent with whom the caller has interacted. The ACD collaborative application also providing the caller with an option to request return to a previous agent listed in the call session history. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
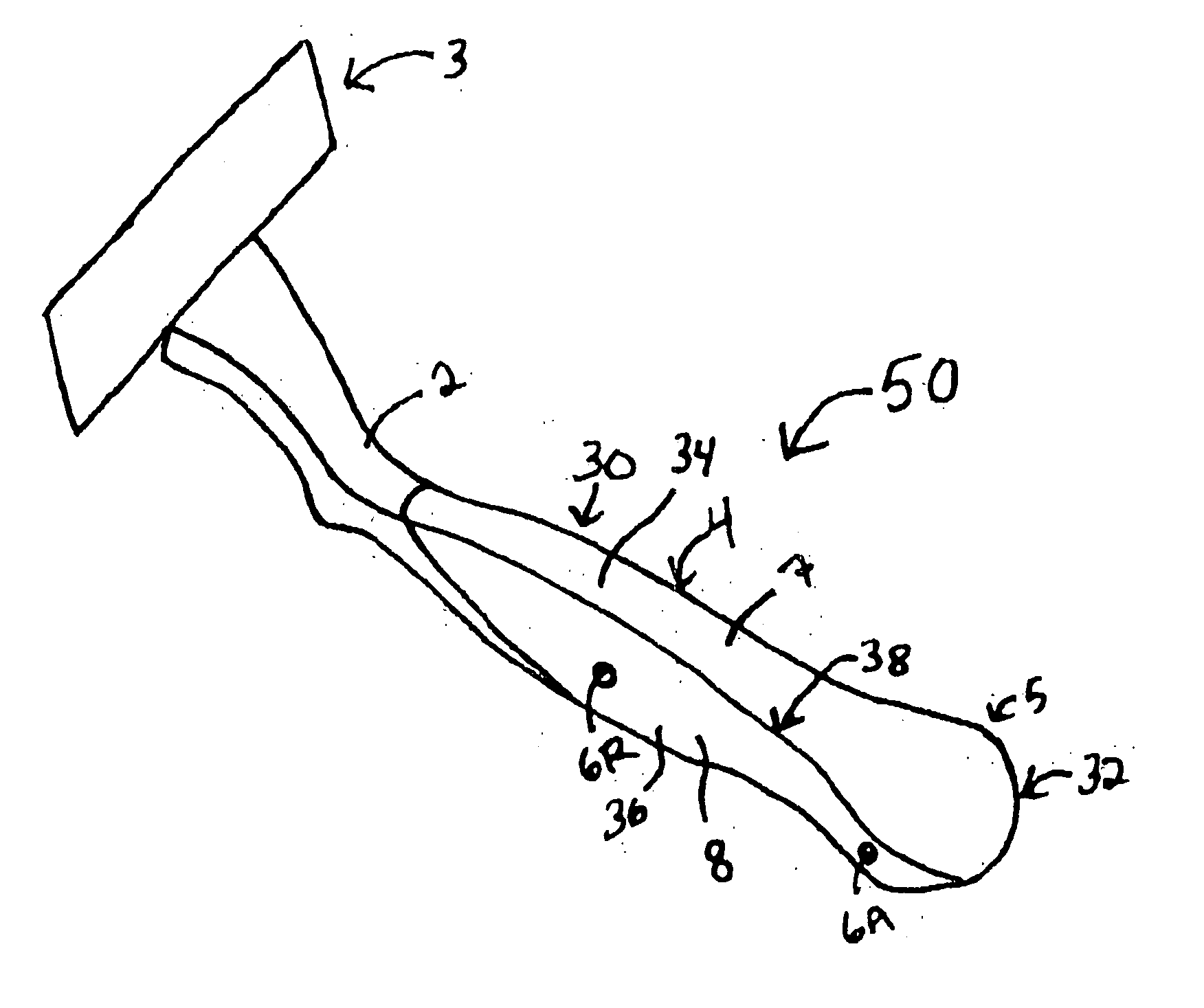
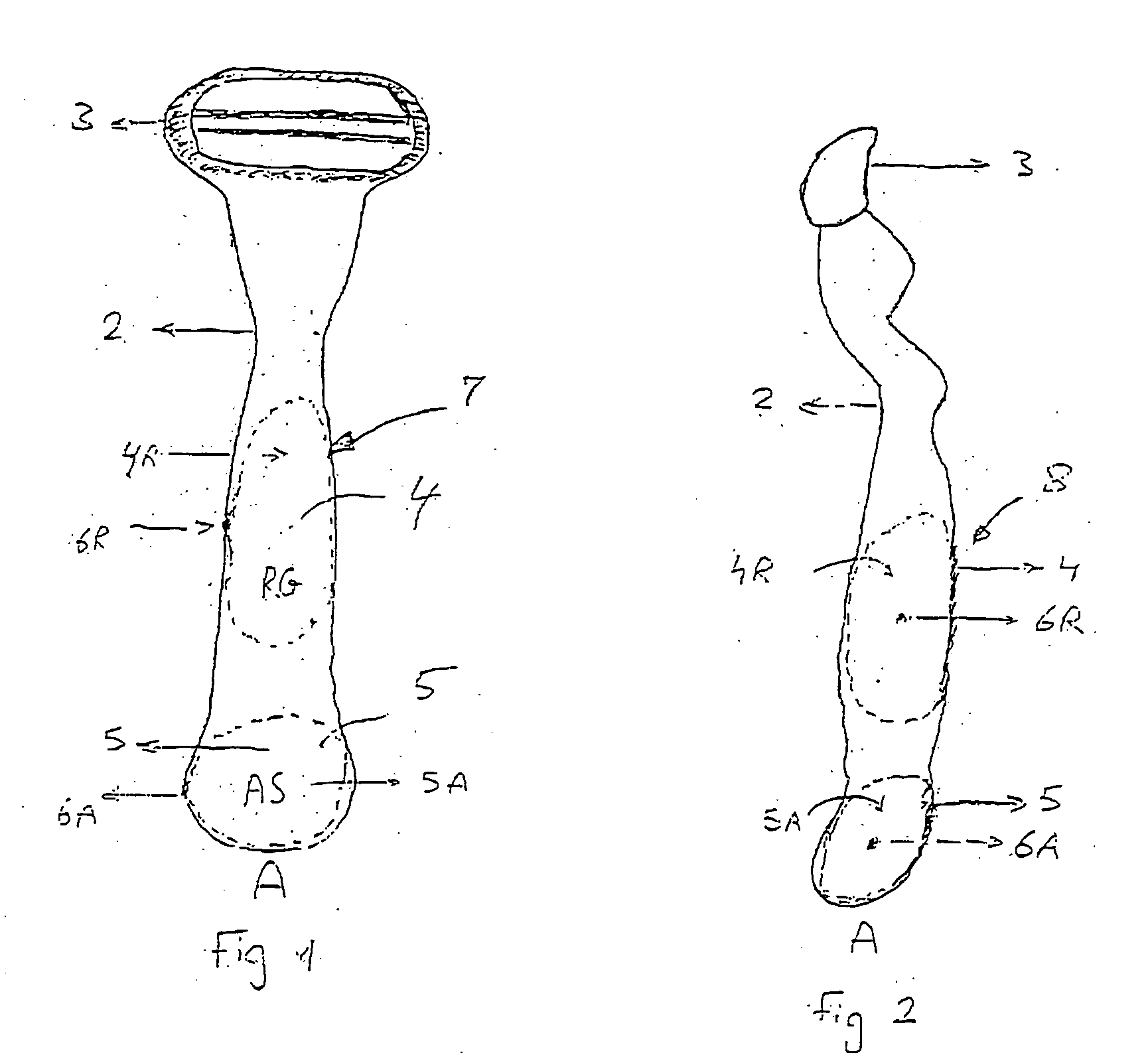
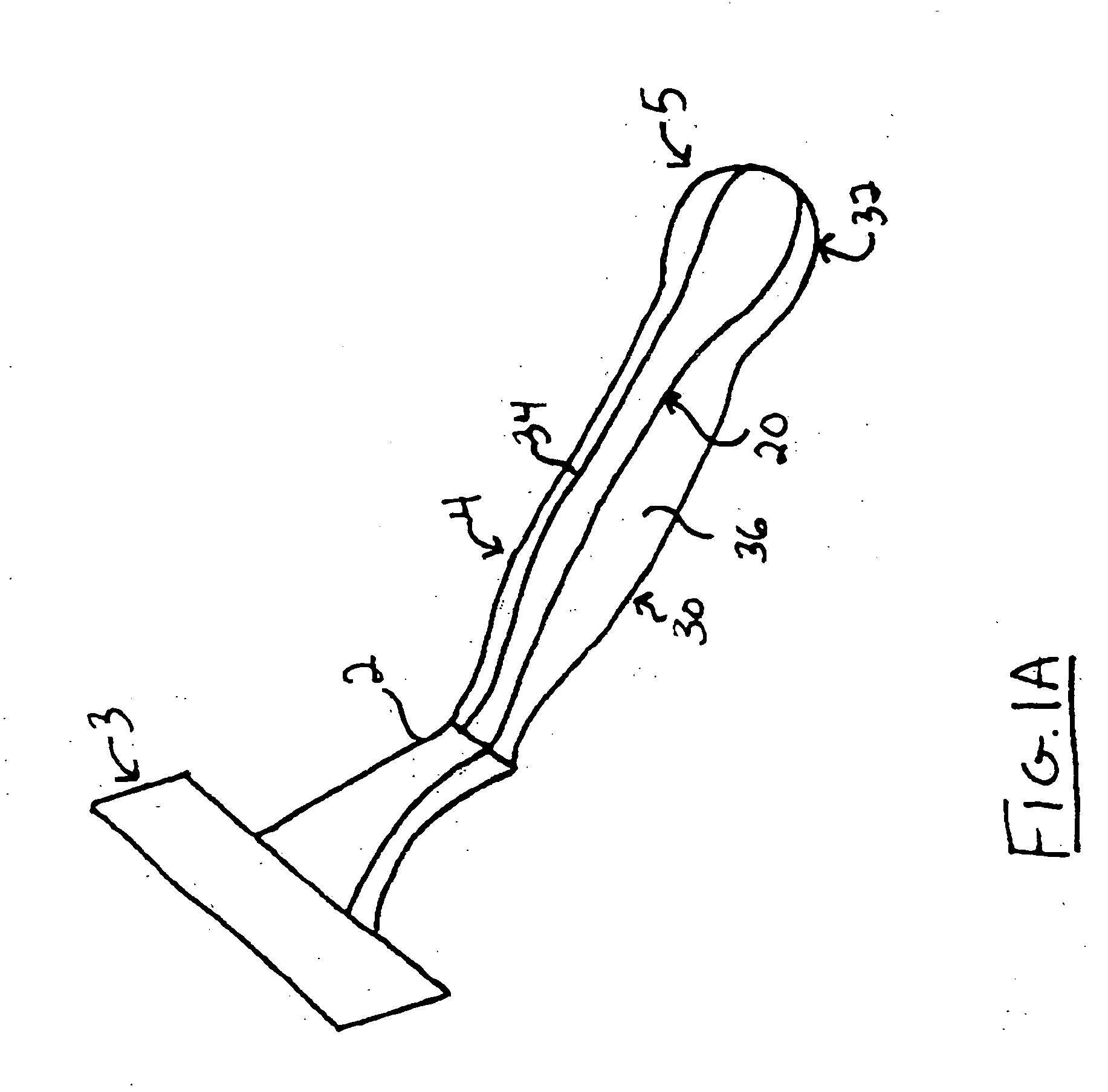
Razor comprising a skeletal body and a bladder for a shaving agent, and a method for the manufacture thereof
A razor comprising a skeletal body and a reservoir for a shaving agent, and a method for the manufacture thereof. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:WANLI MAHRAN +1
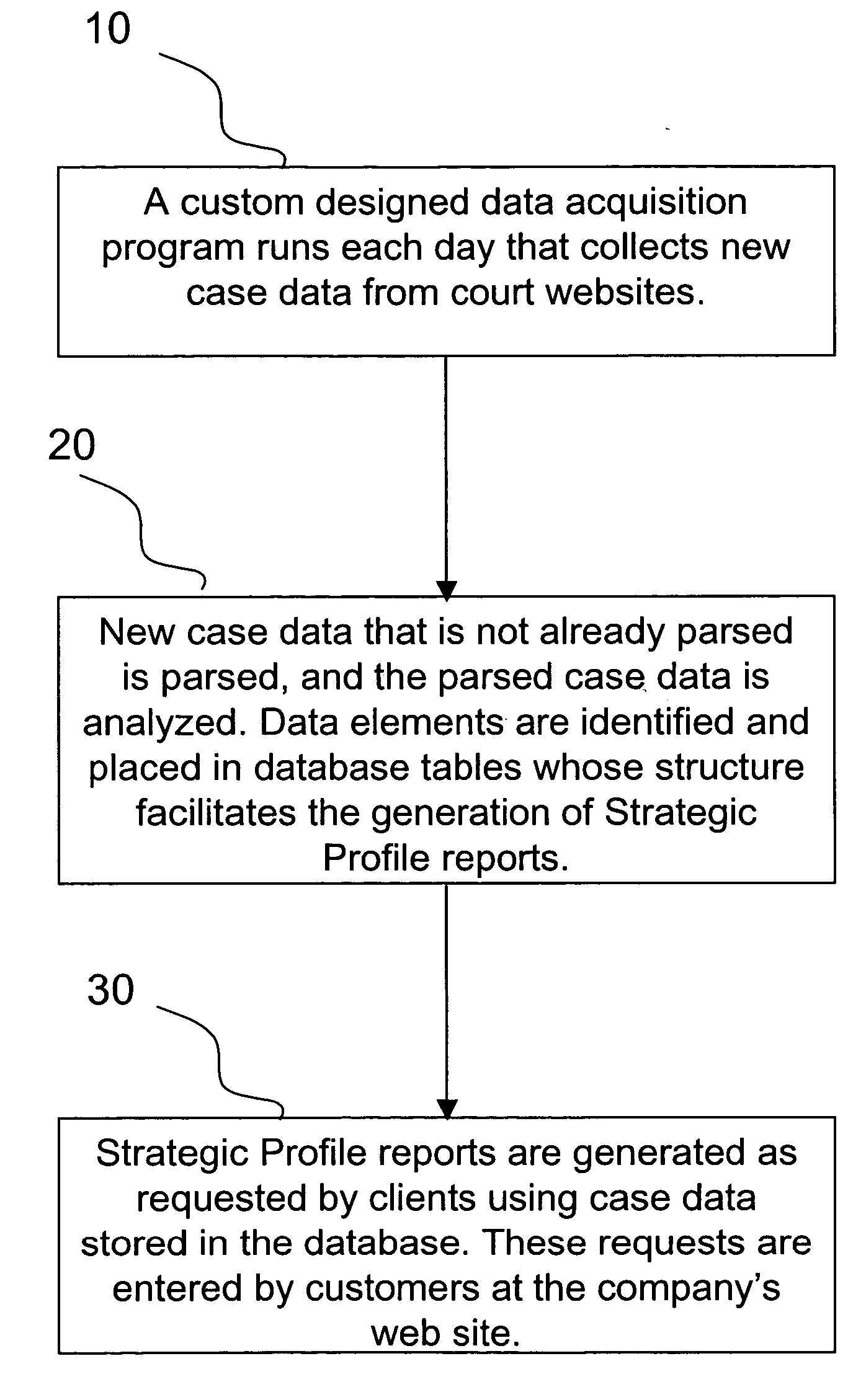
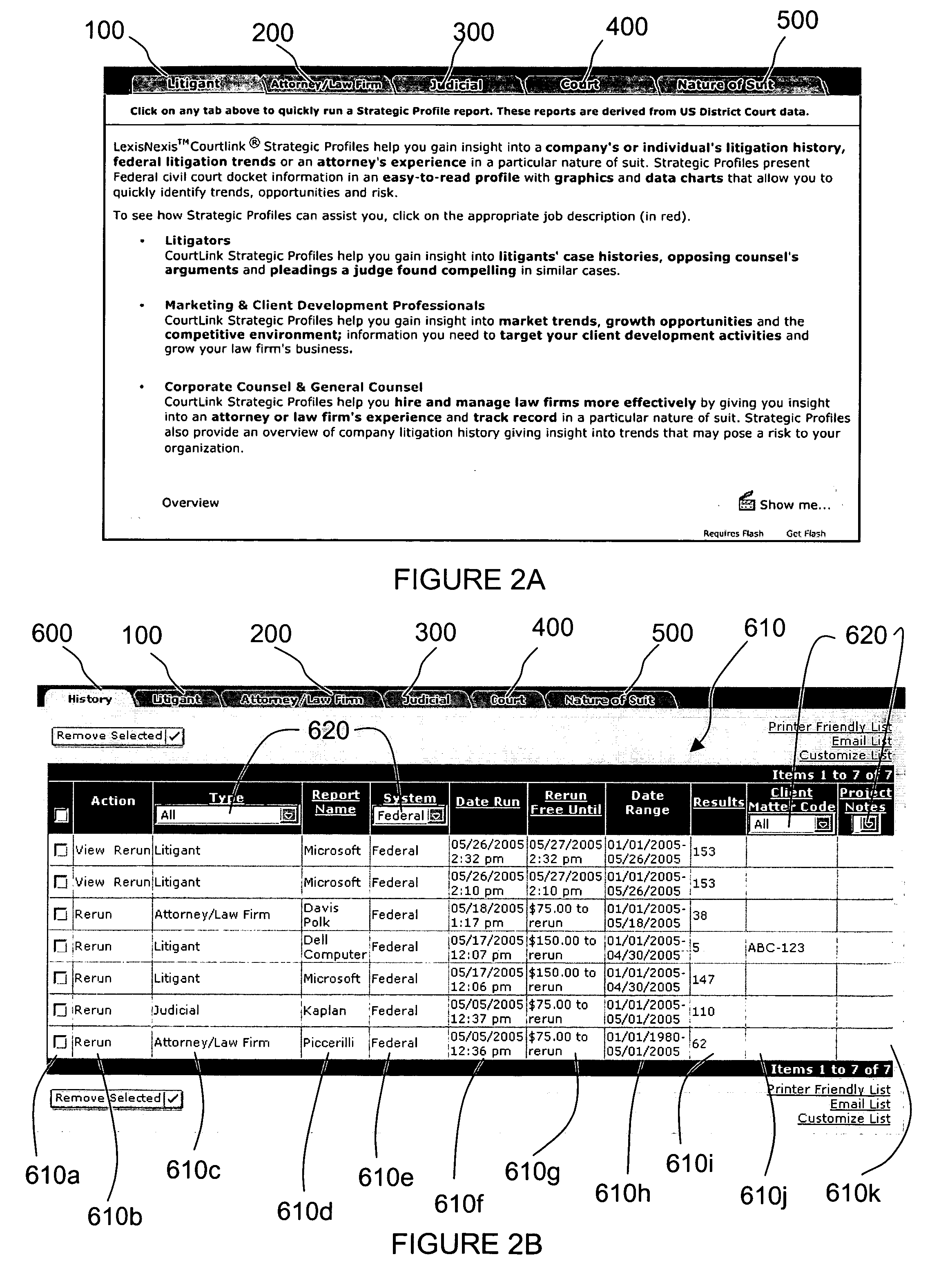
Computerized system and method for creating aggregate profile reports regarding litigants, attorneys, law firms, judges, and cases by type and by court from court docket records
ActiveUS20060129593A1Eliminate the problemEliminates all hyperlinks and header graphicsDigital data information retrievalDigital data processing detailsRelevant informationUser input
Computerized method for aggregating relevant information from court records and presenting such information in electronic reports including tables and charts. There are five types of reports that focus on cases filed by Litigant, Attorney or Law Firm, Judge, Court, and Nature of Suit. A History option also is provided, in which are grouped all reports previously run by the user in one table. The user inputs a time frame and identifies specific reporting entities. The process accepts these inputs and constructs a list of cases that meet the specified criteria. The information in the list is presented to the user as a multi-part report containing tables and charts of aggregate information of particular interest to the user. Most report sections allow for “drilldowns” that bring additional specific focus to the reports. The reports are also configurable in a variety of ways including selecting graph types and section inclusion / exclusion.
Owner:RELX INC
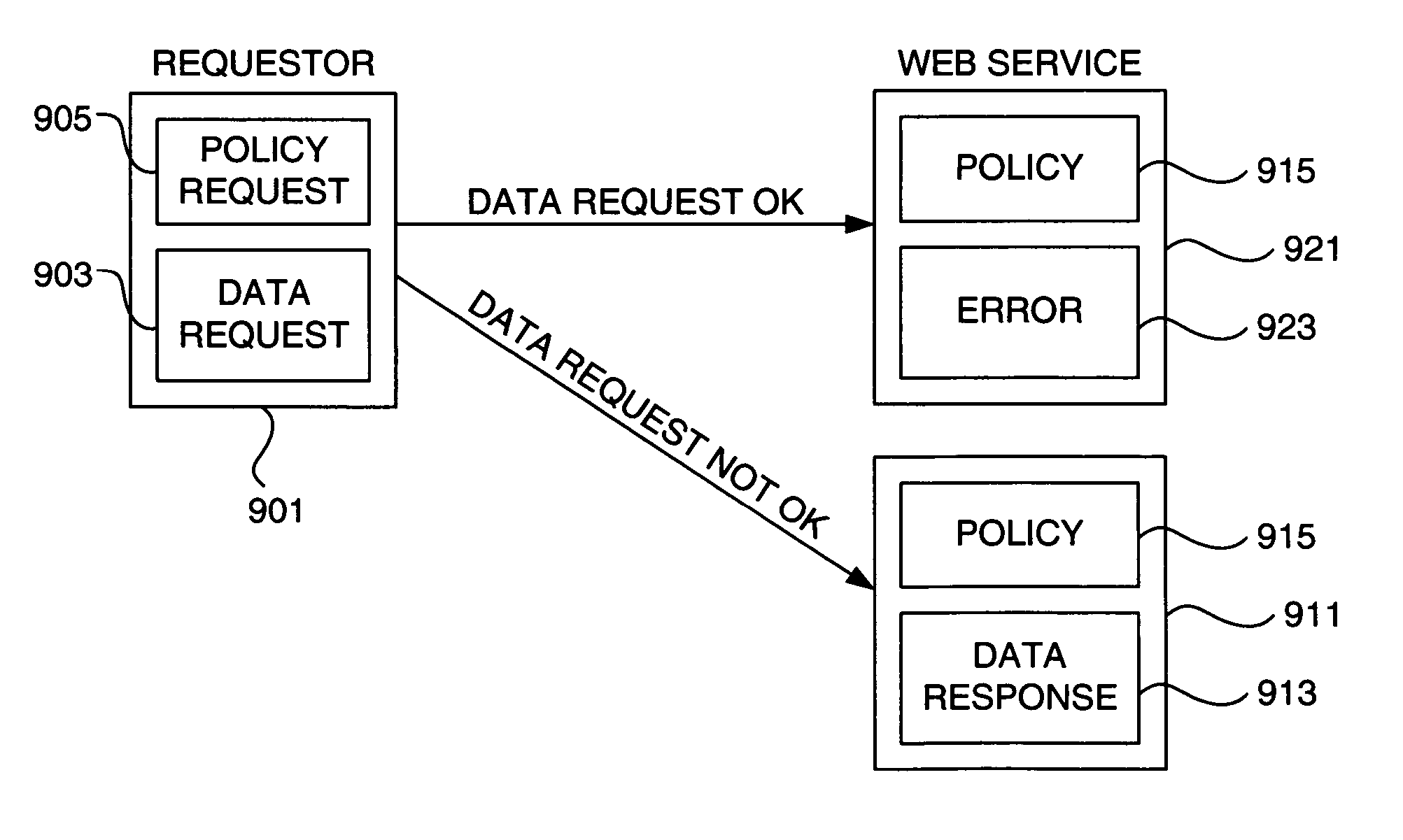
Scoped metadata
Methods, systems, and data structures for communicating object metadata are provided. A generic metadata container is presented that allows object metadata to be described in an extensible manner using protocol-neutral and platform-independent methodologies. A metadata scope refers to a dynamic universe of targets to which the included metadata statements correspond. Metadata properties provide a mechanism to describe the metadata itself, and metadata security can be used to ensure authentic metadata is sent and received. Mechanisms are also provided to allow refinement and replacement of metadata statements. Communication of metadata is expedited using hash digests to confirm metadata versions, and by piggybacking policy metadata requests and responses on other substantive data communication messages, thereby dynamically altering future communications.
Owner:MICROSOFT TECH LICENSING LLC
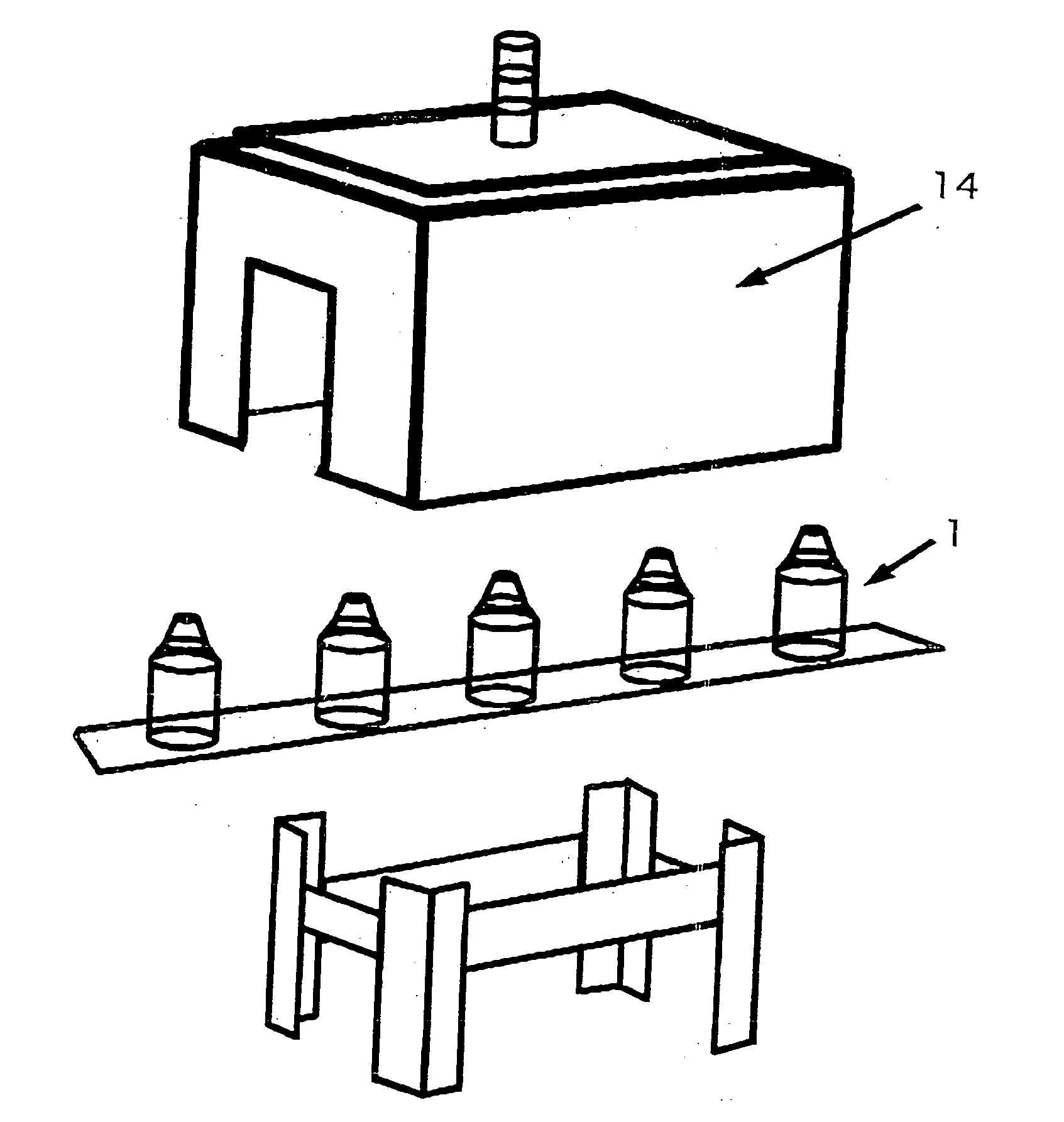
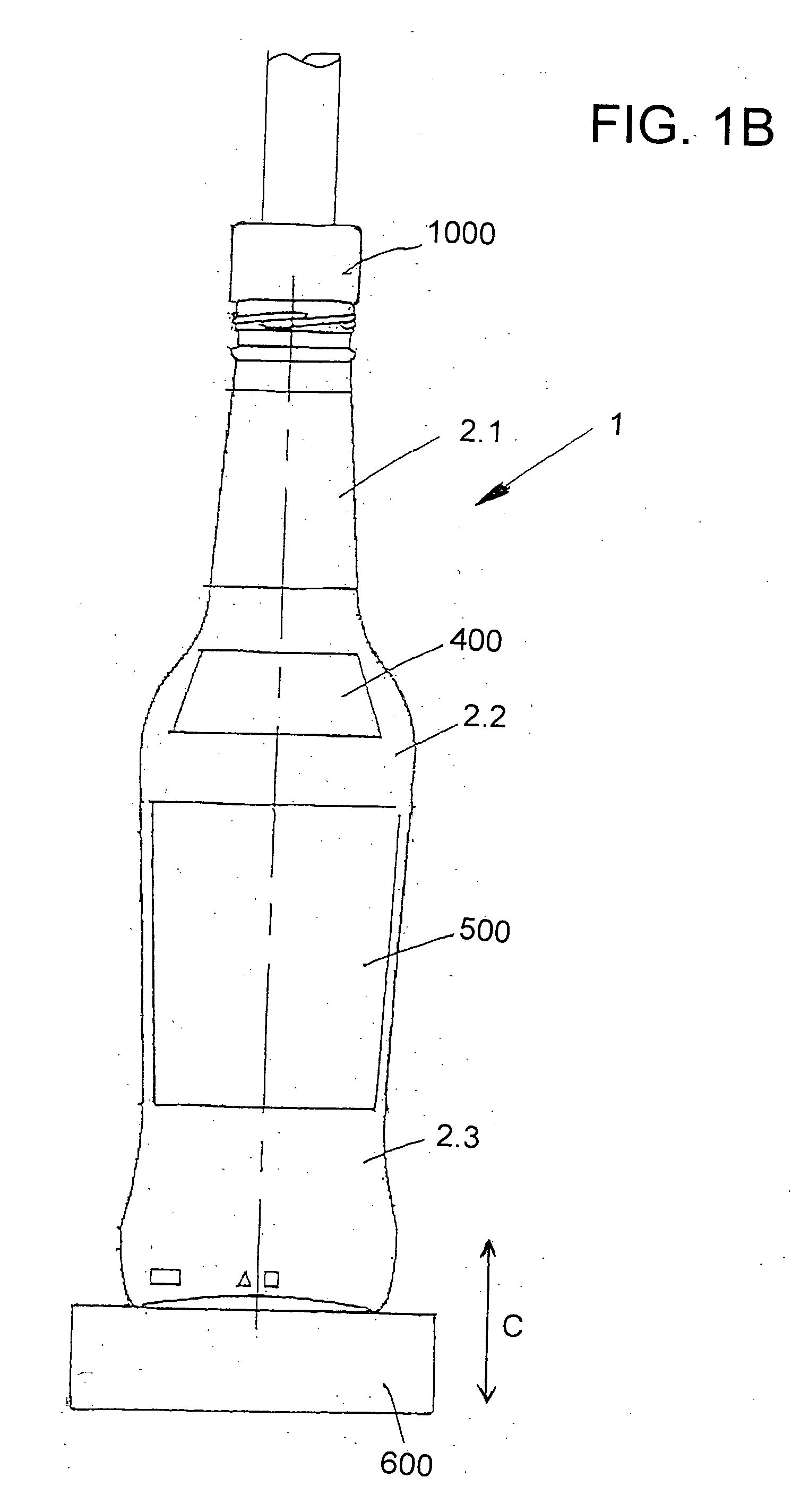
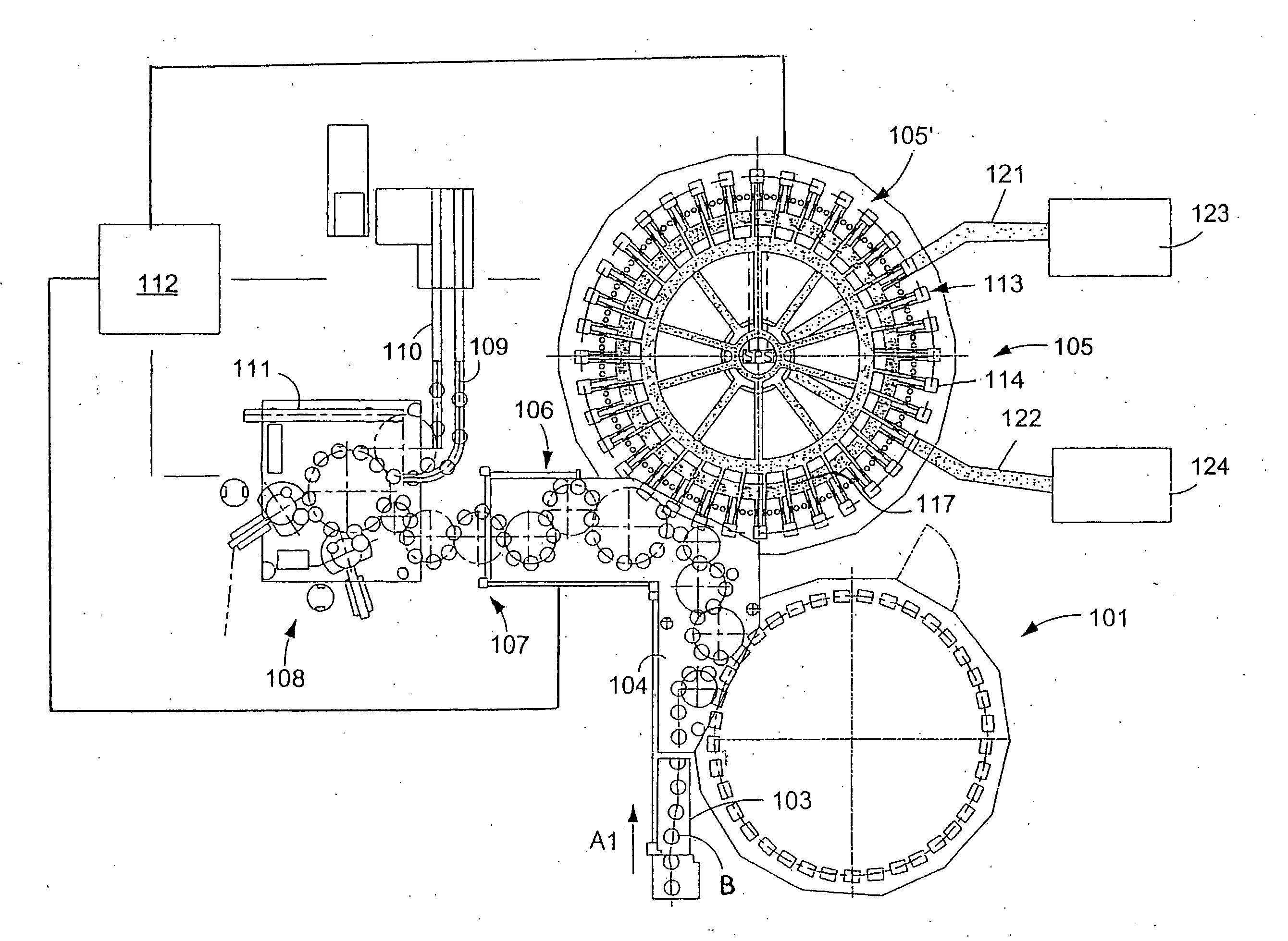
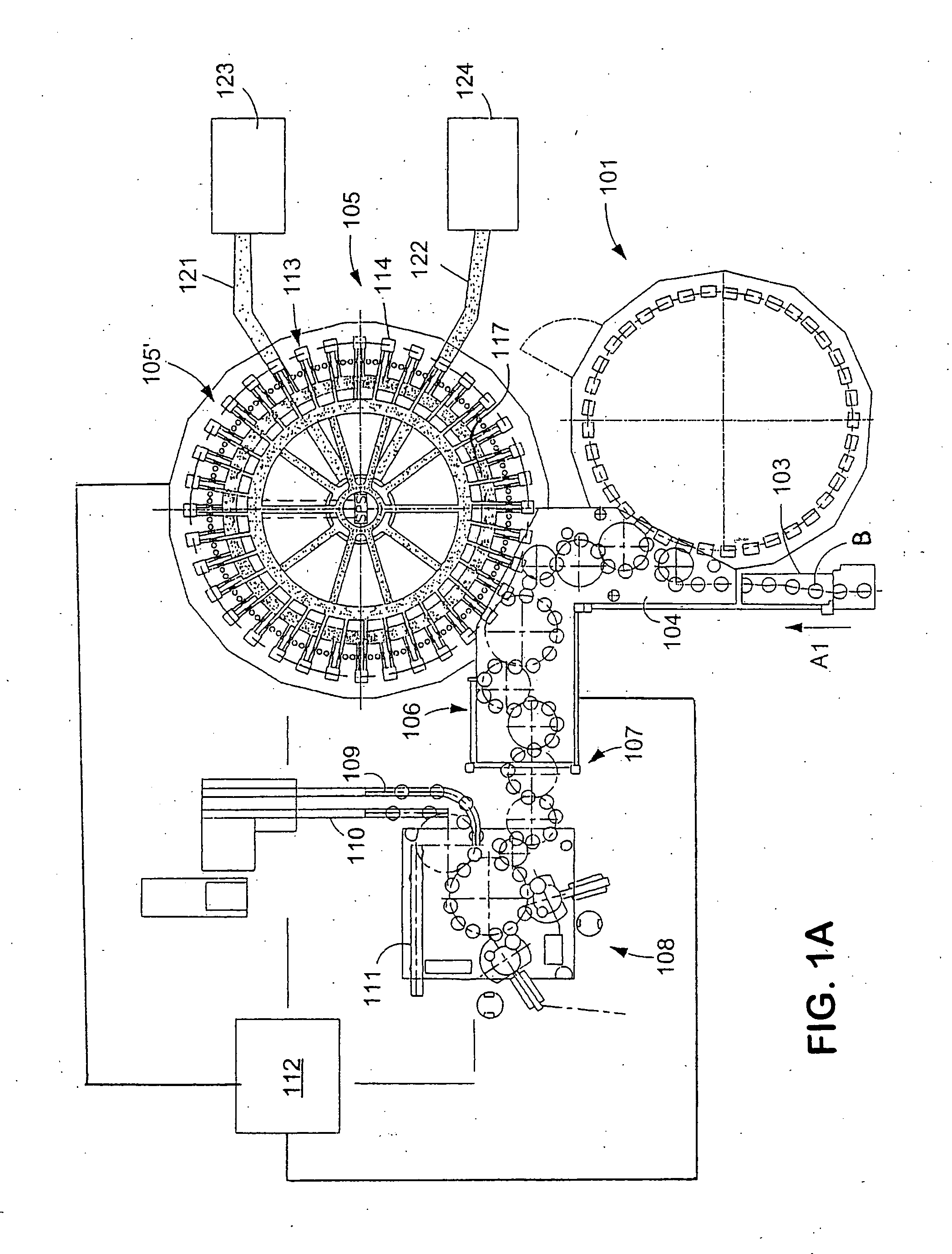
Beverage bottling plant for filling bottles with a liquid beverage material having a machine and method for wrapping filled bottles
InactiveUS20060026926A1Smooth and accurate connectionAccurate connectionMechanical working/deformationWrapping material feeding apparatusTrademarkEngineering
A beverage bottling plant for filling bottles with a liquid beverage material having a machine and method for wrapping filled bottles. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KHS GMBH
Cutting tool, particularly for end-cut and longitudinal turning and for groove cutting
A cutting tool, such as for end-cut and longitudinal turning, and for cutting grooves in a workpiece, has an end or major cutting edge and two side or minor cutting edges, each of which are connected to the end or major cutting edge by two outer corners. An additional corner chip-breaker is formed between each of the outer corners and the ends of a chip-guiding rib. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KENNAMETAL INC
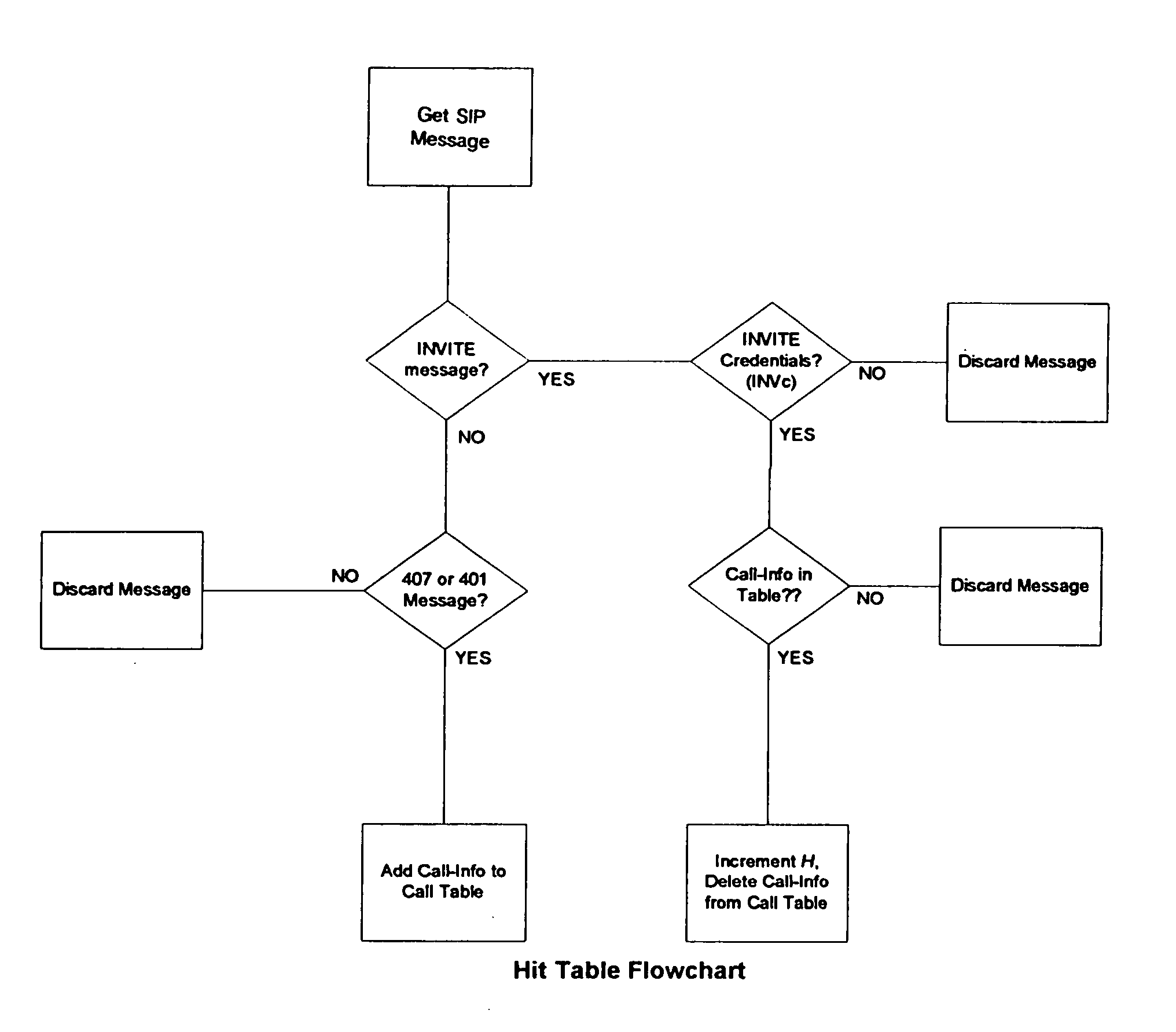
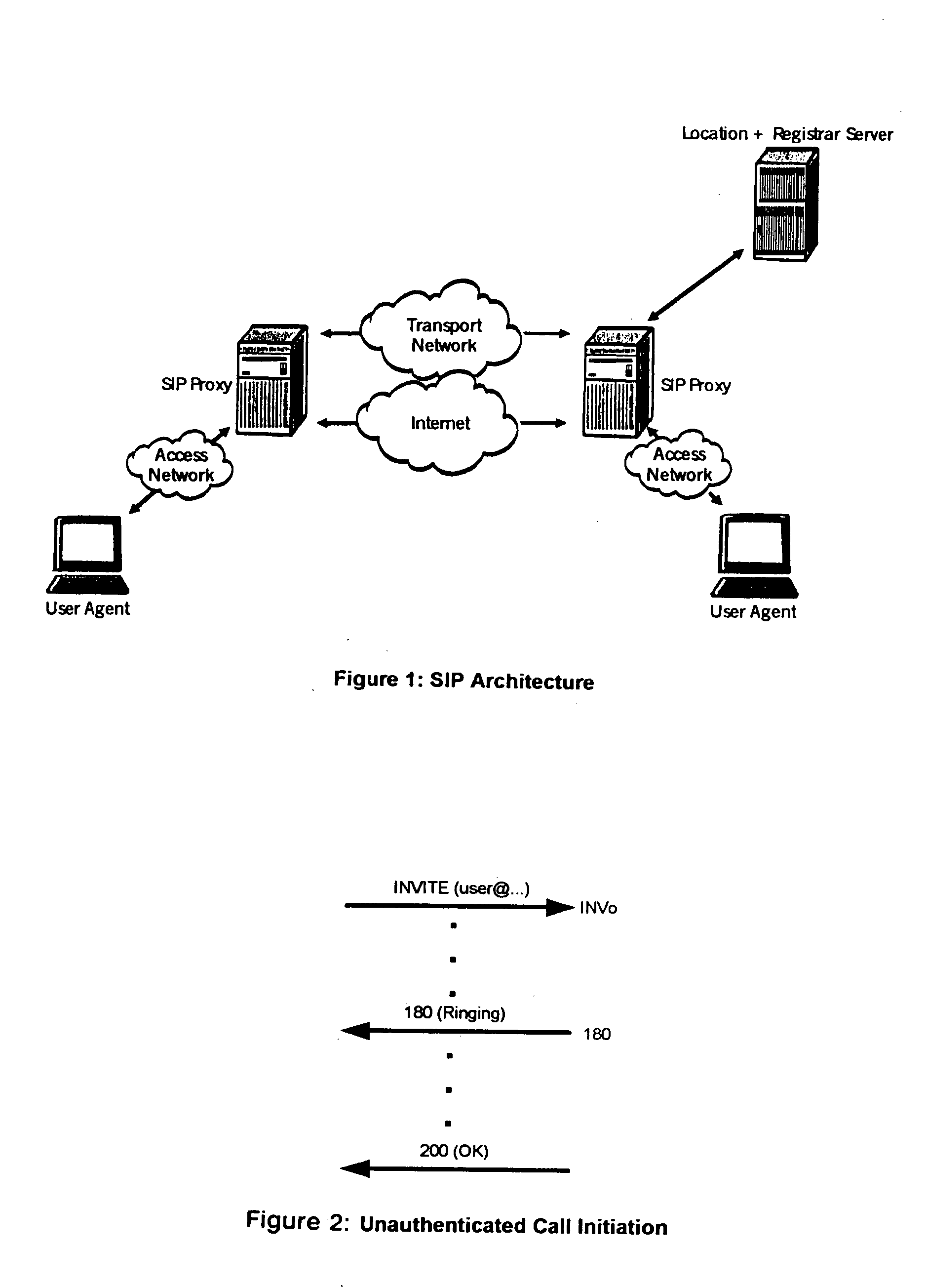
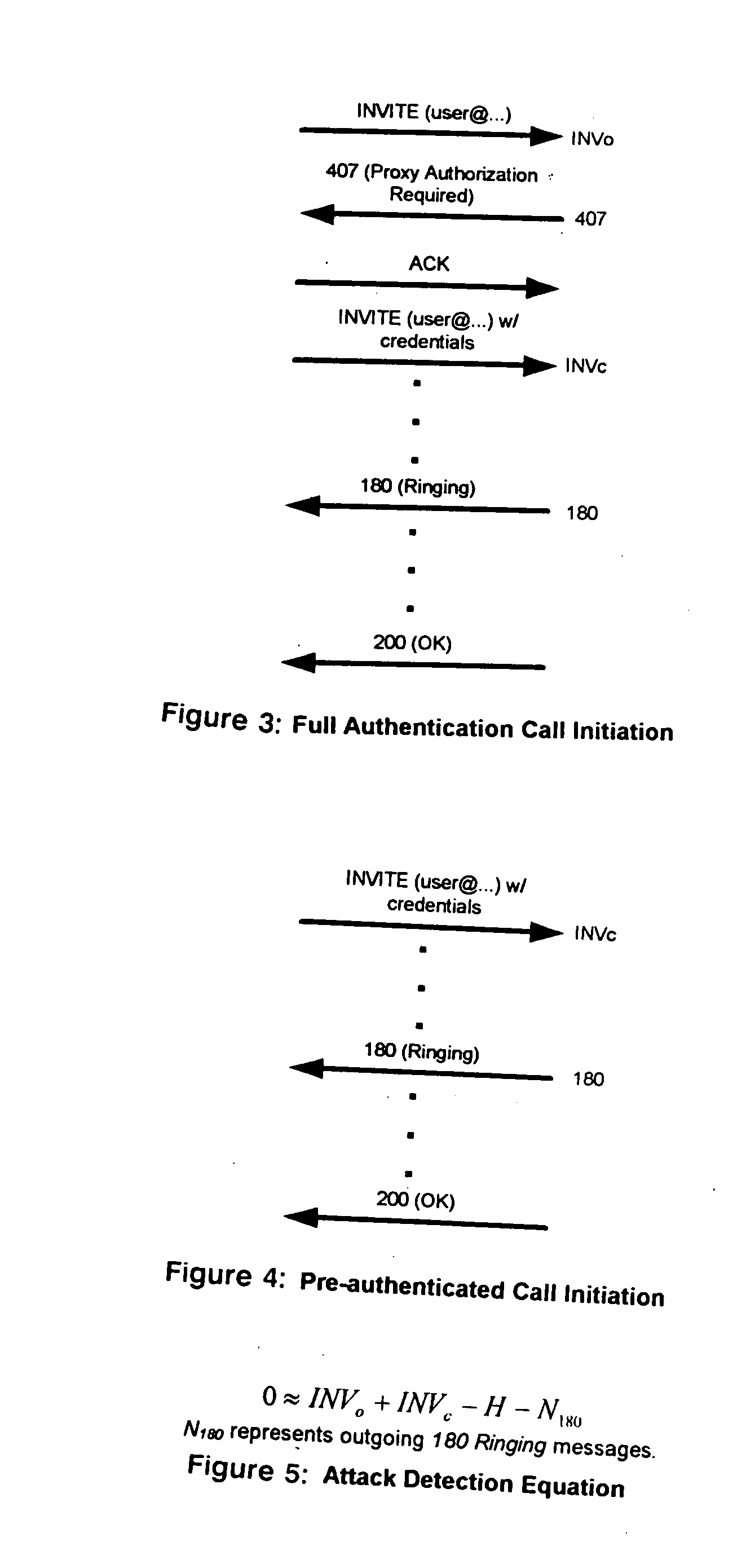
Detection of denial of service attacks against SIP (session initiation protocol) elements
ActiveUS20050108567A1InhibitionError preventionFrequency-division multiplex detailsSession Initiation ProtocolClient-side
A method and apparatus directed to detecting DoS (denial of service) attacks against SIP enabled devices. A substantial imbalance between an accounting of SIP INVITE (INV) and SIP 180 Ringing (N180) messages indicates a DoS attack. Preferably the number (H) of INVITE messages including credentials (INVc) that are sent from a user client in response to a 407 Authentication Required message from a proxy server are removed from the accounting before the balance is tested. If the equation INVo+INVc−H=N180 (where INVo is the number of INVITE messages without credentials) is not true within a small margin of error then the presence of a current DoS attack on the proxy server is indicated by the inequality.
Owner:PIECE FUTURE PTE LTD
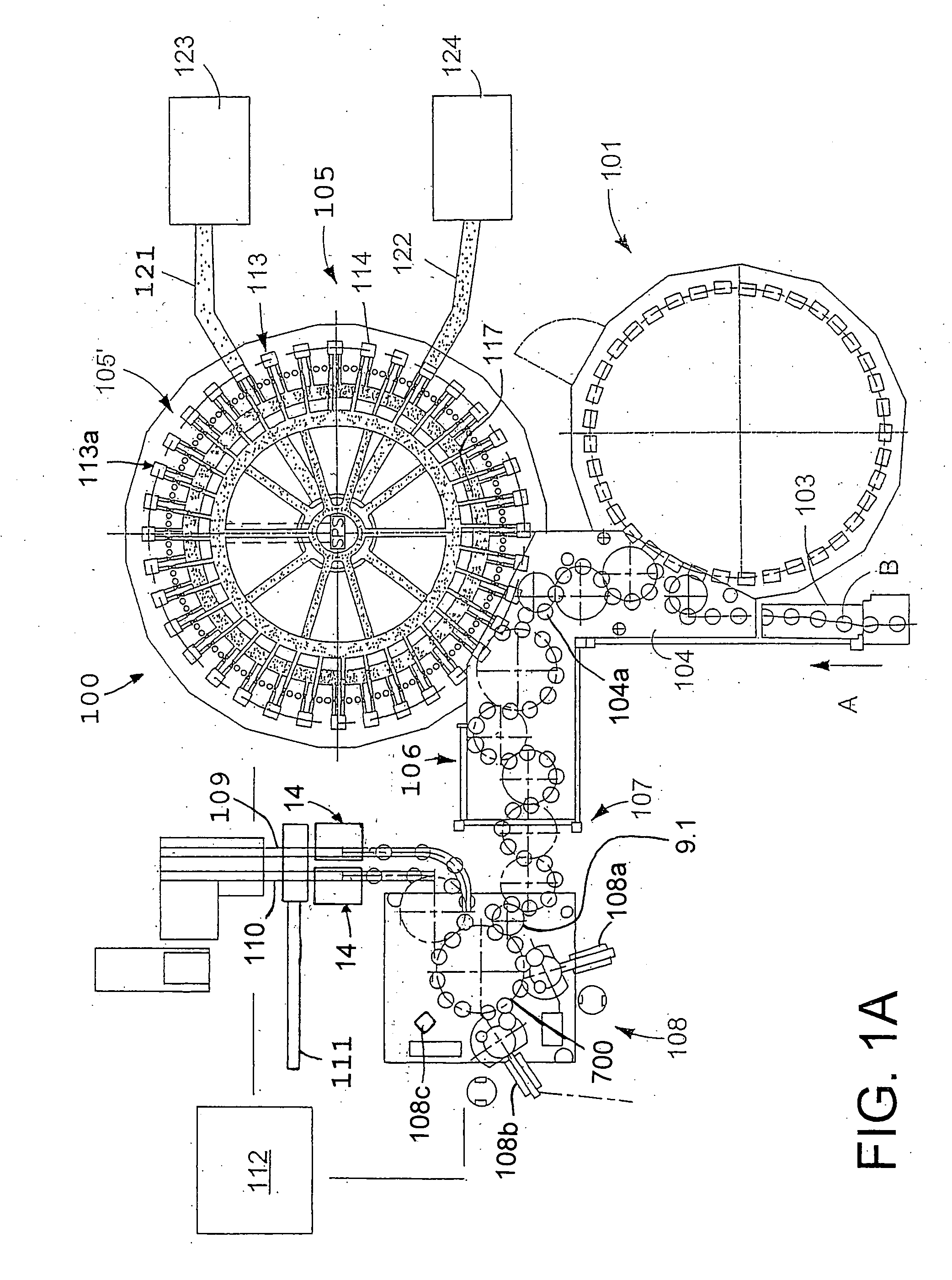
Container filling plant, such as a beverage bottling plant, for filling containers with a liquid beverage and for closing filled containers
Container filling plant, such as a beverage bottling plant, for filling containers with a liquid beverage and for closing filled containers. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): “A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims.” Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KHS GMBH
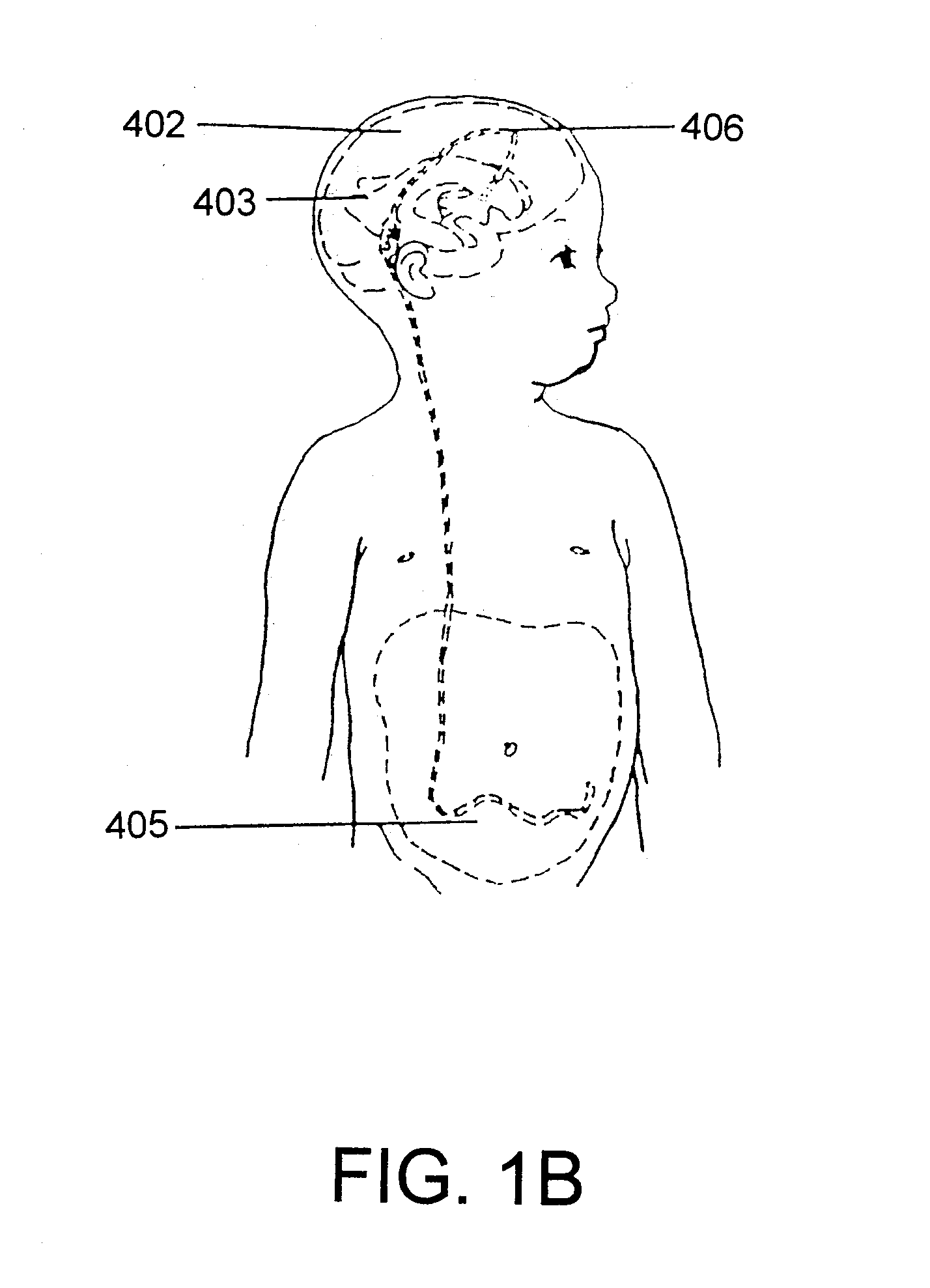
Adjustable hydrocephalus valve
Hydrocephalus valves, the valve pressure of which, when the patient is in the standing position, is determined at least partly by the weight of an additional gravitation part, are provided with an adjustable spring which partly or fully neutralizes the action of the weight. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:CHRISTOPH MIETHKE
Beverage bottling plant for filling bottles with a liquid beverage material having an inspection apparatus for inspecting bottles
InactiveUS20060283145A1Material analysis by optical meansSafety device in filling machineryTrademarkEngineering
A beverage bottling plant for filling bottles with a liquid beverage material having an inspection apparatus for inspecting bottles. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KHS MASCHEN UND ANALAGENBAU AKTIENGES
Postal services method and system
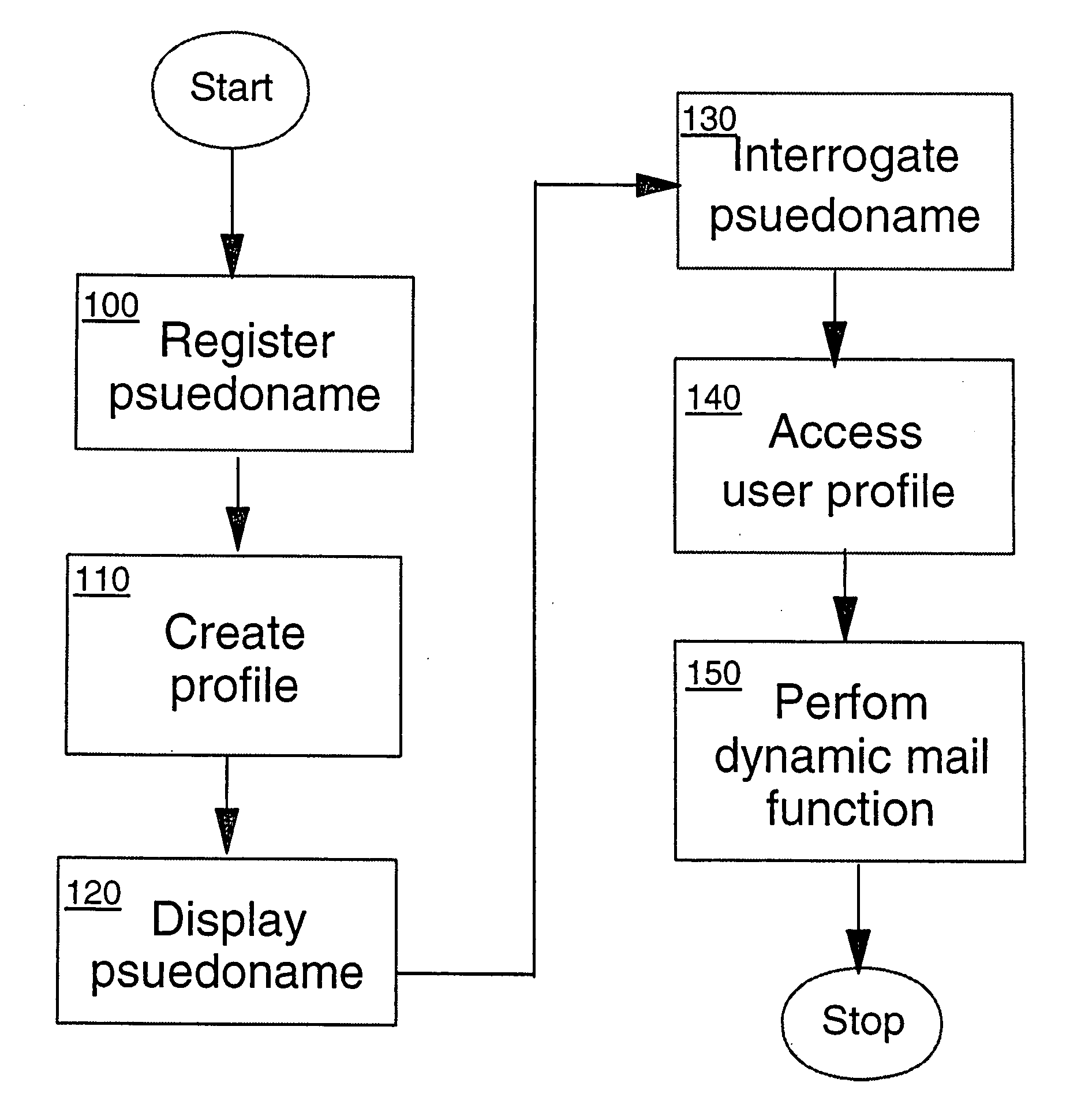
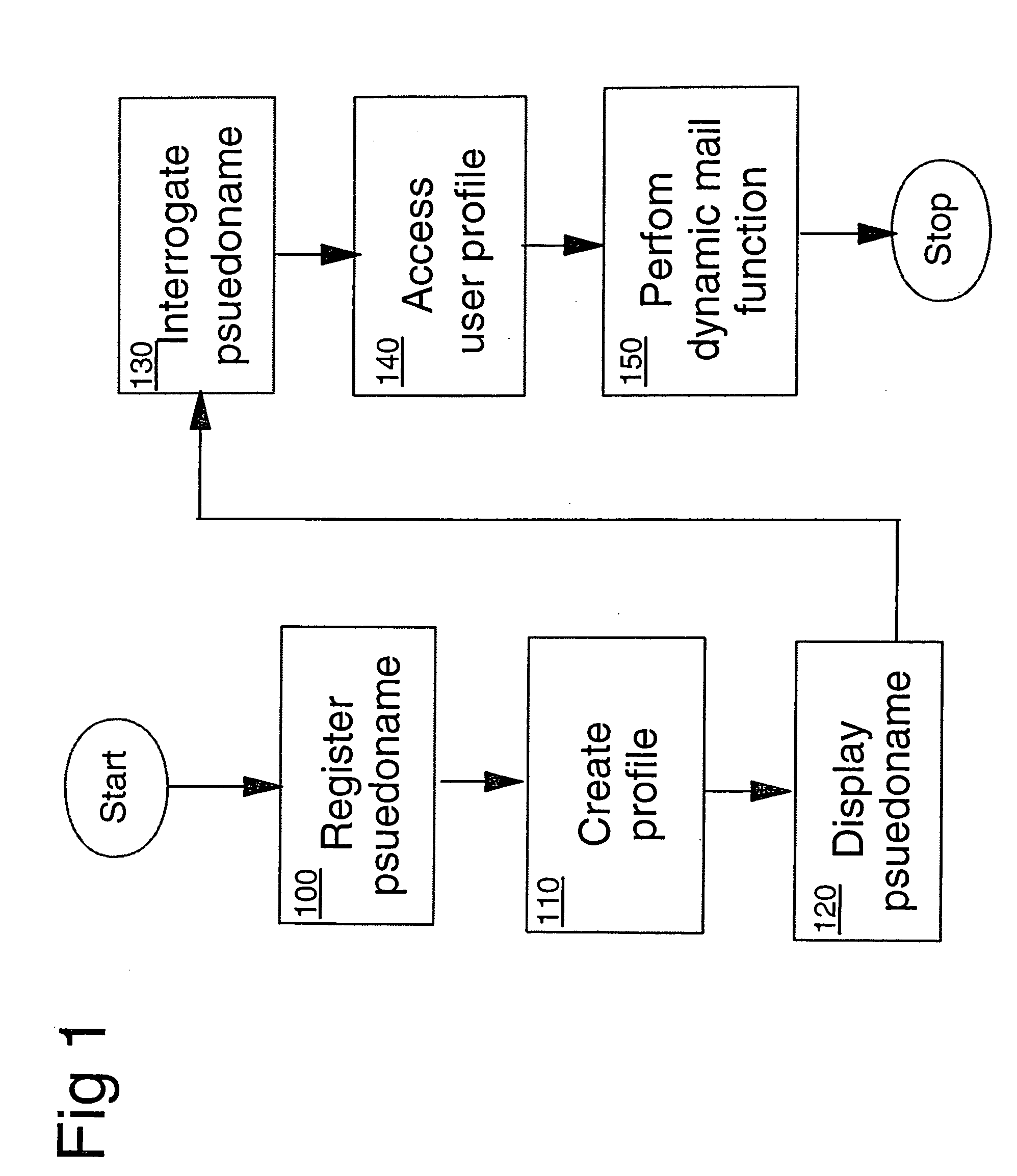
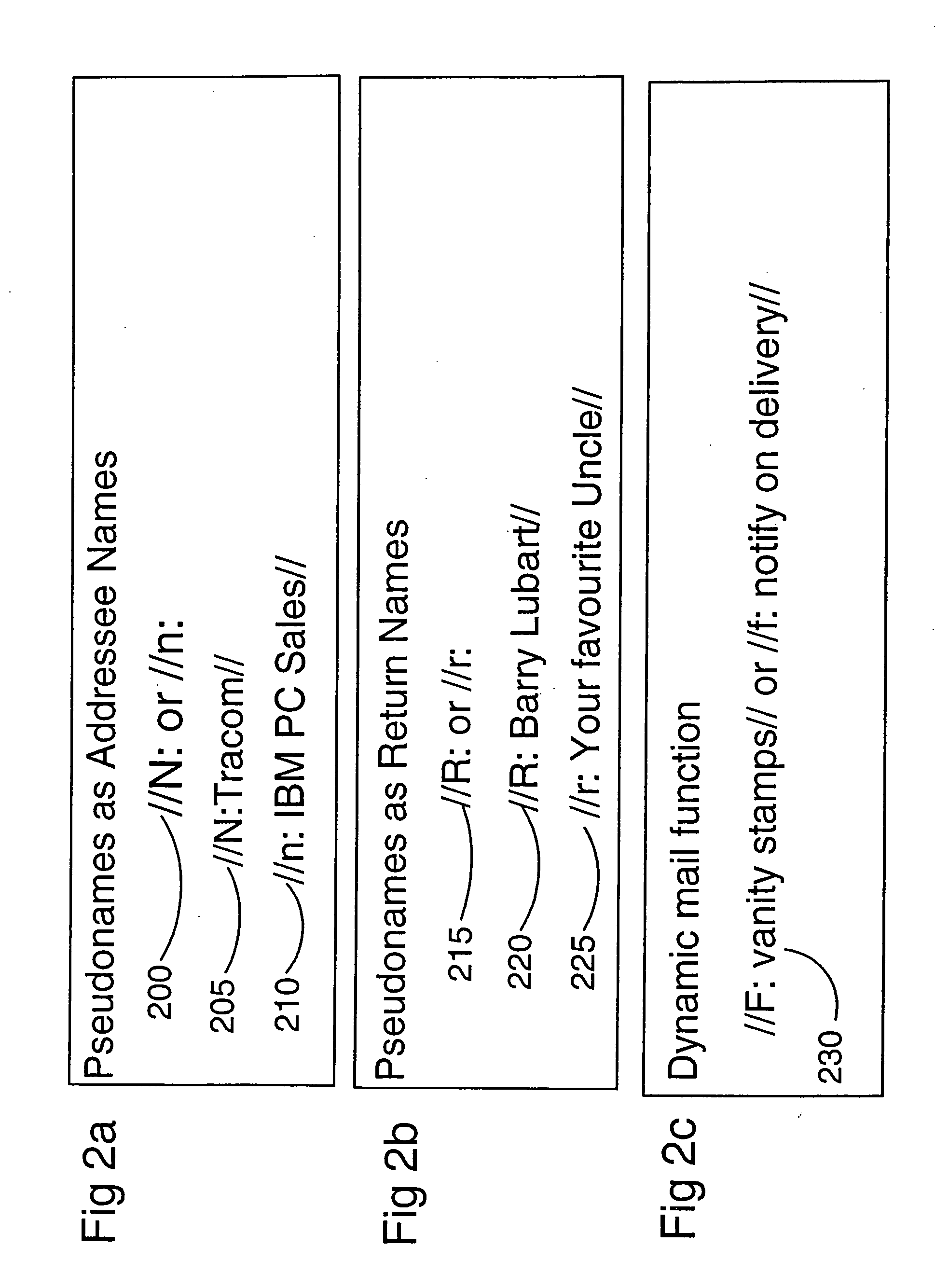
A postal service is provided for routing mail objects such as an envelope or a parcel to a designated person. A user registers a pseudo name which is displayed on the mail object. The user also enters one or more profiles into a system. Various mail services may be set up by the profiles. Mail services include a follow me service allowing a user to specify a different delivery address for a date range, a mail delivery notification service, a vanity stamp service, and a bulk mail service. Changes made in the profiles take immediate effect. A payment method may be designated in a franking profile.
Owner:IBM CORP
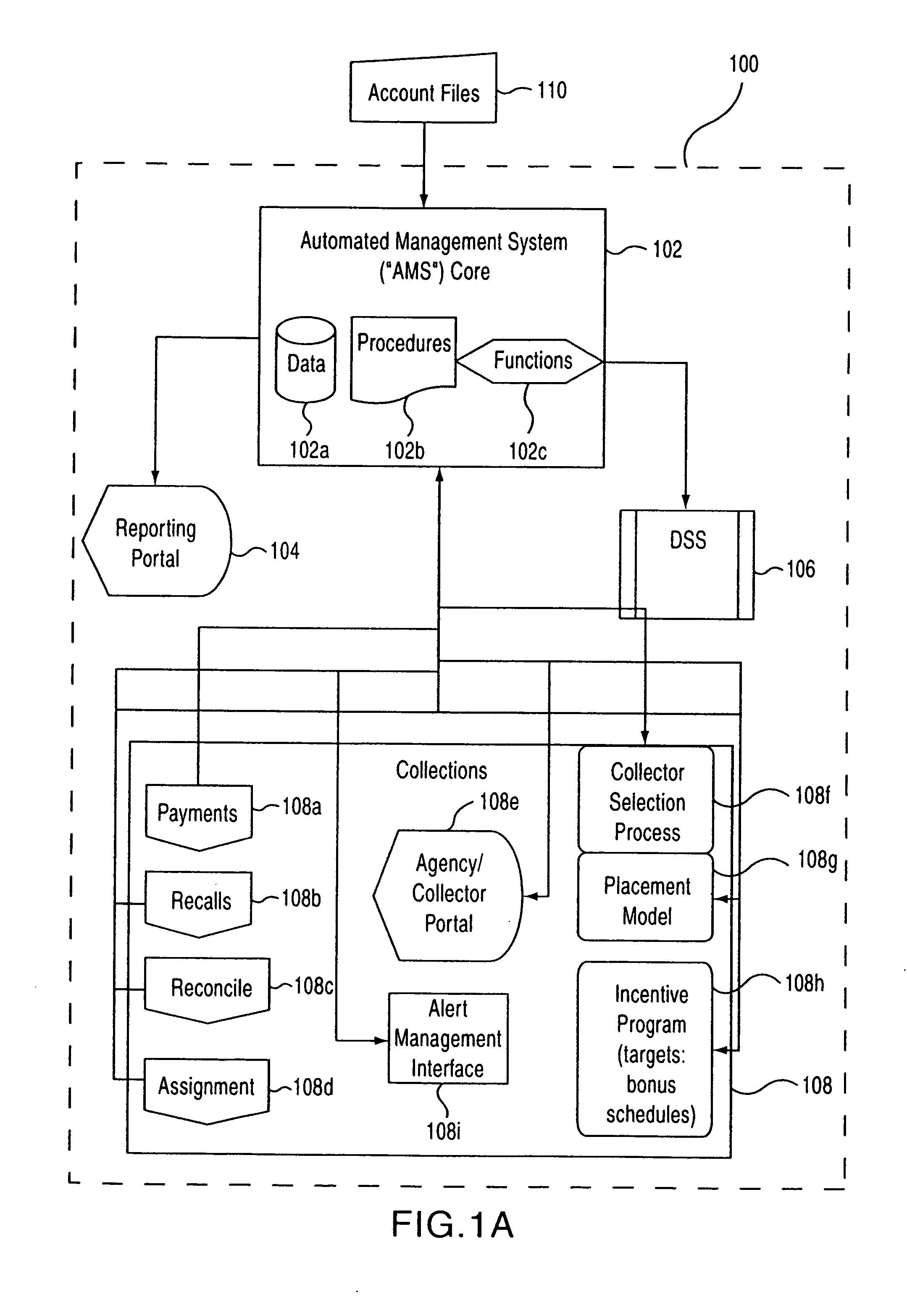
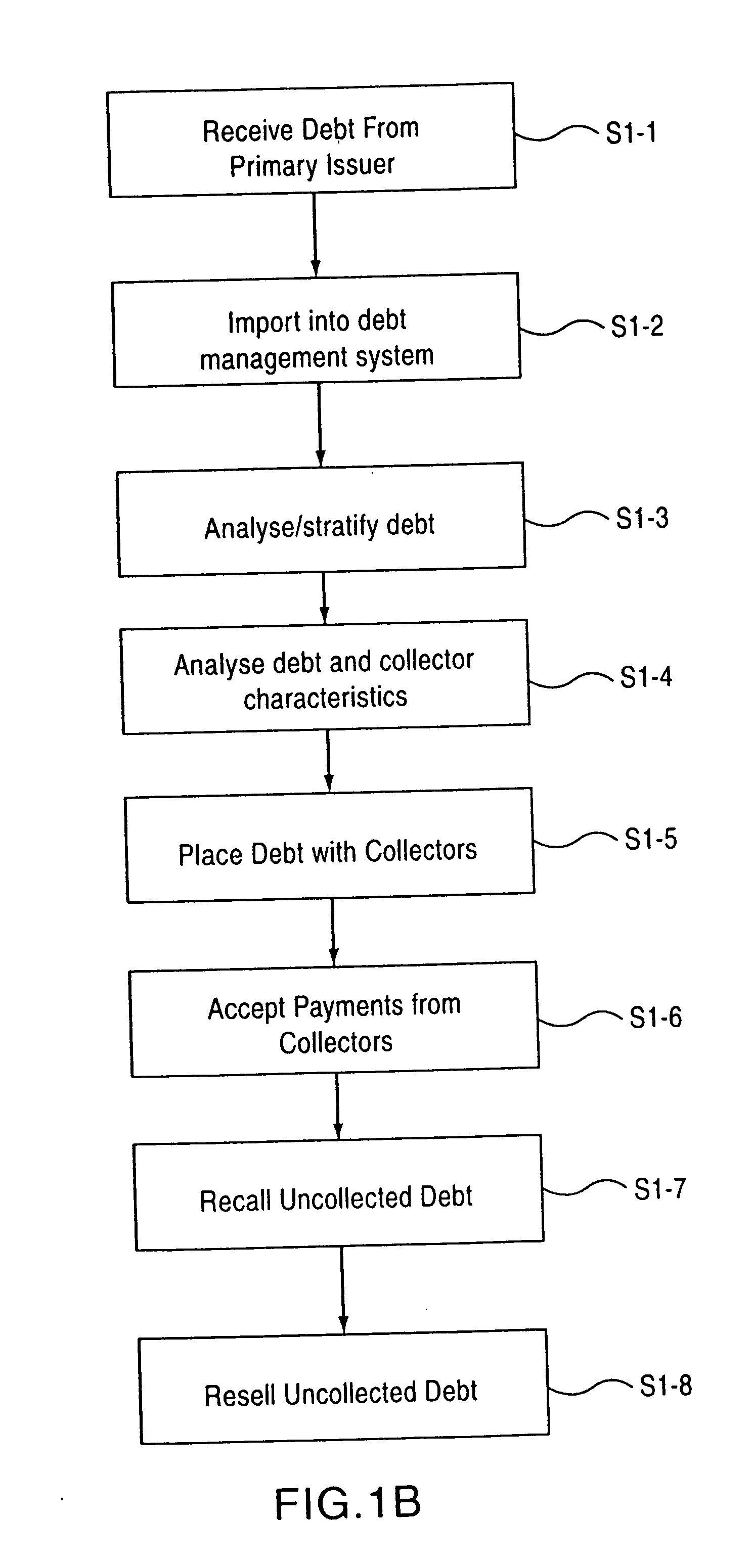
Systems and methods for acquiring, managing, placing, collecting and reselling debt
InactiveUS20070043659A1Improve efficiencyComprehensive managementFinanceMarketingCredit cardComputer science
A system is provided for comprehensive debt management. Debt is typically acquired in the form of portfolios from the issuers of debit (e.g., creditors, such as credit card banks), which are referenced herein as “primary issuers” of debt. The custodian of the present invention is the acquiring party and is referenced as the “secondary issuer” of debt. Such portfolios are normally expansive and may cover a very large geographically region, such as the state of Texas. The system can parse the debt and assign any portion thereof to collection agencies or even directly to individual collectors.
Owner:CREDITMAX
System and method for authentication of SP Ethernet aggregation networks
ActiveUS20060268856A1Digital data processing detailsUnauthorized memory use protectionSubject matterCustomer-premises equipment
A Service Provider (SP) authentication method includes receiving a message from a subscriber-premises device, the message being compatible with an authentication protocol and being transported from the subscriber-premises device to a u-PE device operating in compliance with an IEEE 802.1x compatible protocol. Access to the SP network is either allowed or denied access based on a logical identifier contained in the message. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims. 37 CFR 1.72(b).
Owner:CISCO TECH INC
Validation of call-out services transmitted over a public switched telephone network
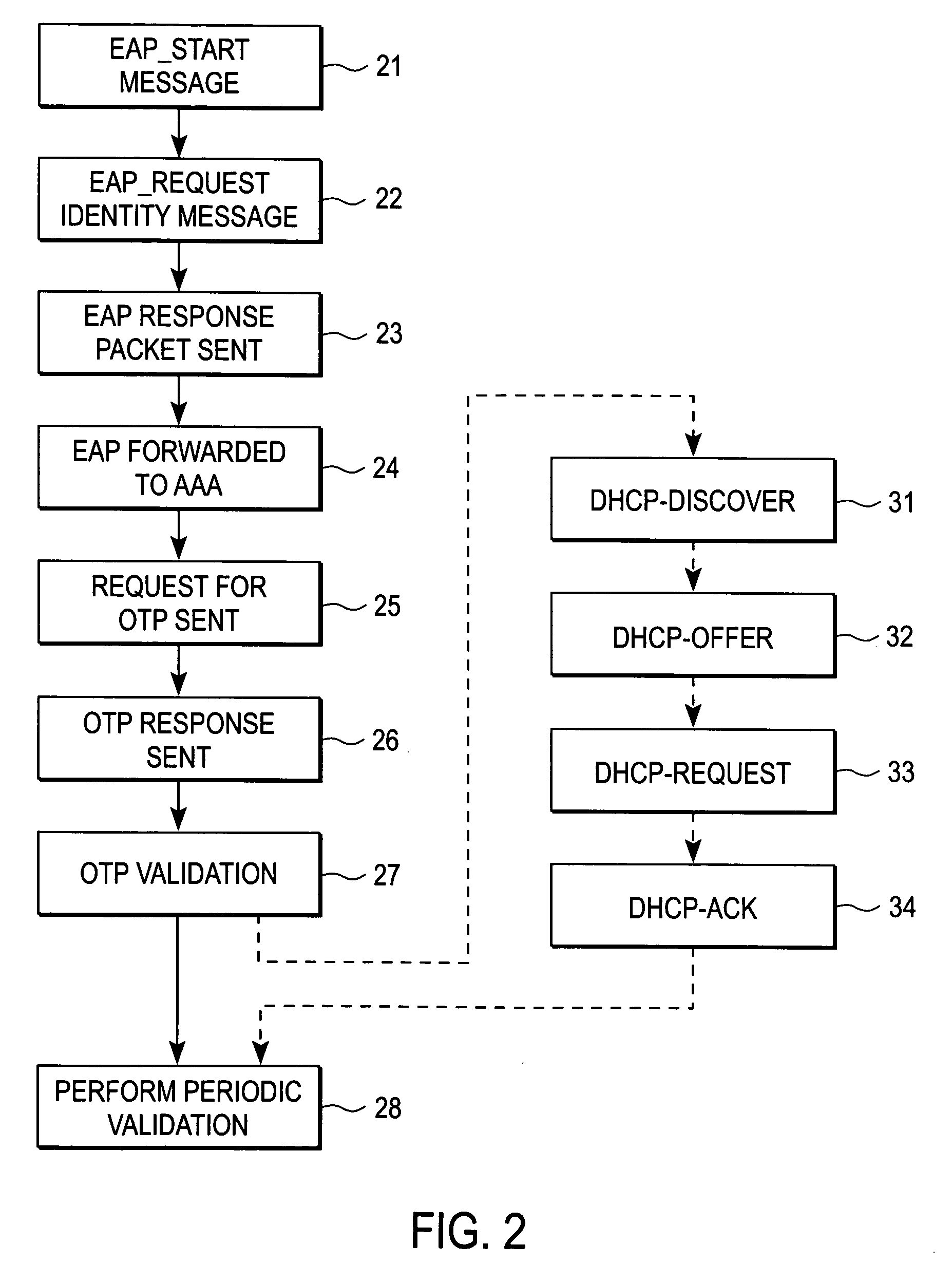
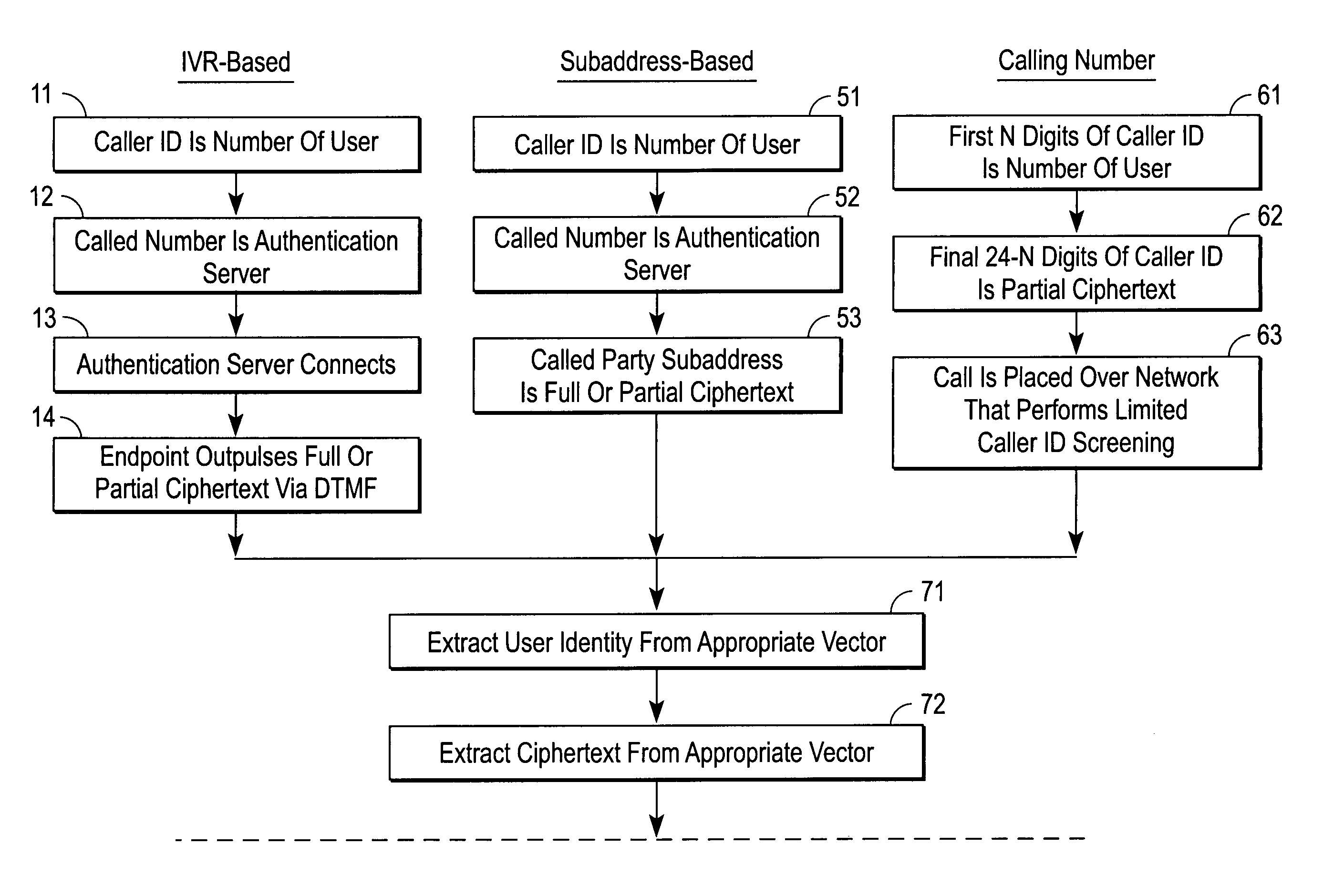
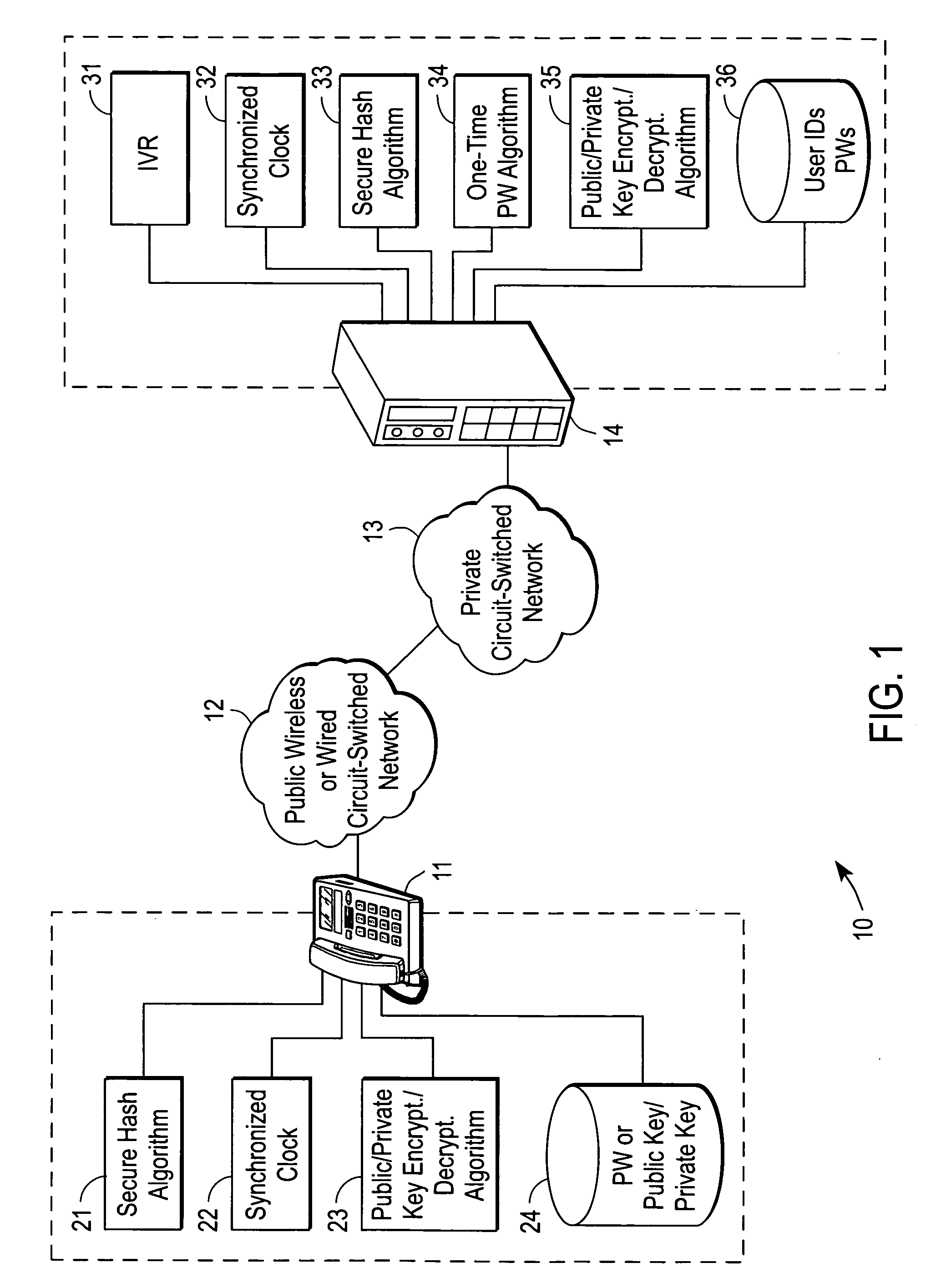
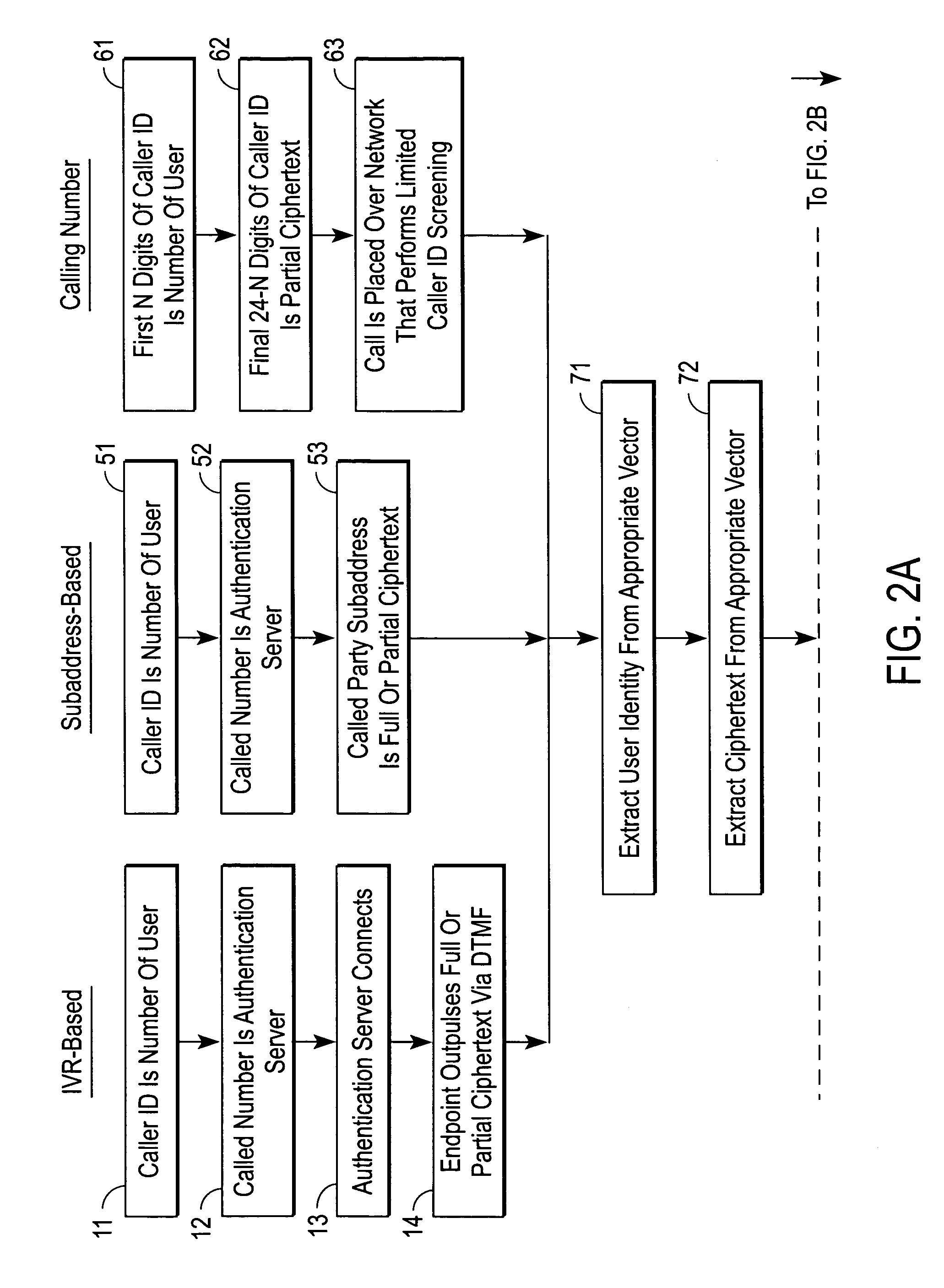
InactiveUS20070083918A1Digital data processing detailsUser identity/authority verificationCiphertextSubject matter
A server for authenticating call-out services over a public switched telephone network (PSTN) includes a memory, a port to receive information provided by a caller over the PSTN, the information including ciphertext, and a processor operable to use the information to look-up a value in the memory and to perform a calculation that produces a result utilizing an algorithm. The processor authenticates the caller if the ciphertext matches a set of initial bytes of the result. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
Method of operating a beverage bottling plant with a beverage filling machine for filling beverage bottles, and a method and apparatus for monitoring beverage bottle or container handing machines in the beverage bottling plant
Method of operating a beverage bottling plant with a beverage filling machine for filling beverage bottles, and a method and apparatus for monitoring beverage bottle or container handling machines in the beverage bottling plant. The abstract of the disclosure is submitted herewith as required by 37 C.F.R. §1.72(b). As stated in 37 C.F.R. §1.72(b): A brief abstract of the technical disclosure in the specification must commence on a separate sheet, preferably following the claims, under the heading “Abstract of the Disclosure.” The purpose of the abstract is to enable the Patent and Trademark Office and the public generally to determine quickly from a cursory inspection the nature and gist of the technical disclosure. The abstract shall not be used for interpreting the scope of the claims. Therefore, any statements made relating to the abstract are not intended to limit the claims in any manner and should not be interpreted as limiting the claims in any manner.
Owner:KHS GMBH
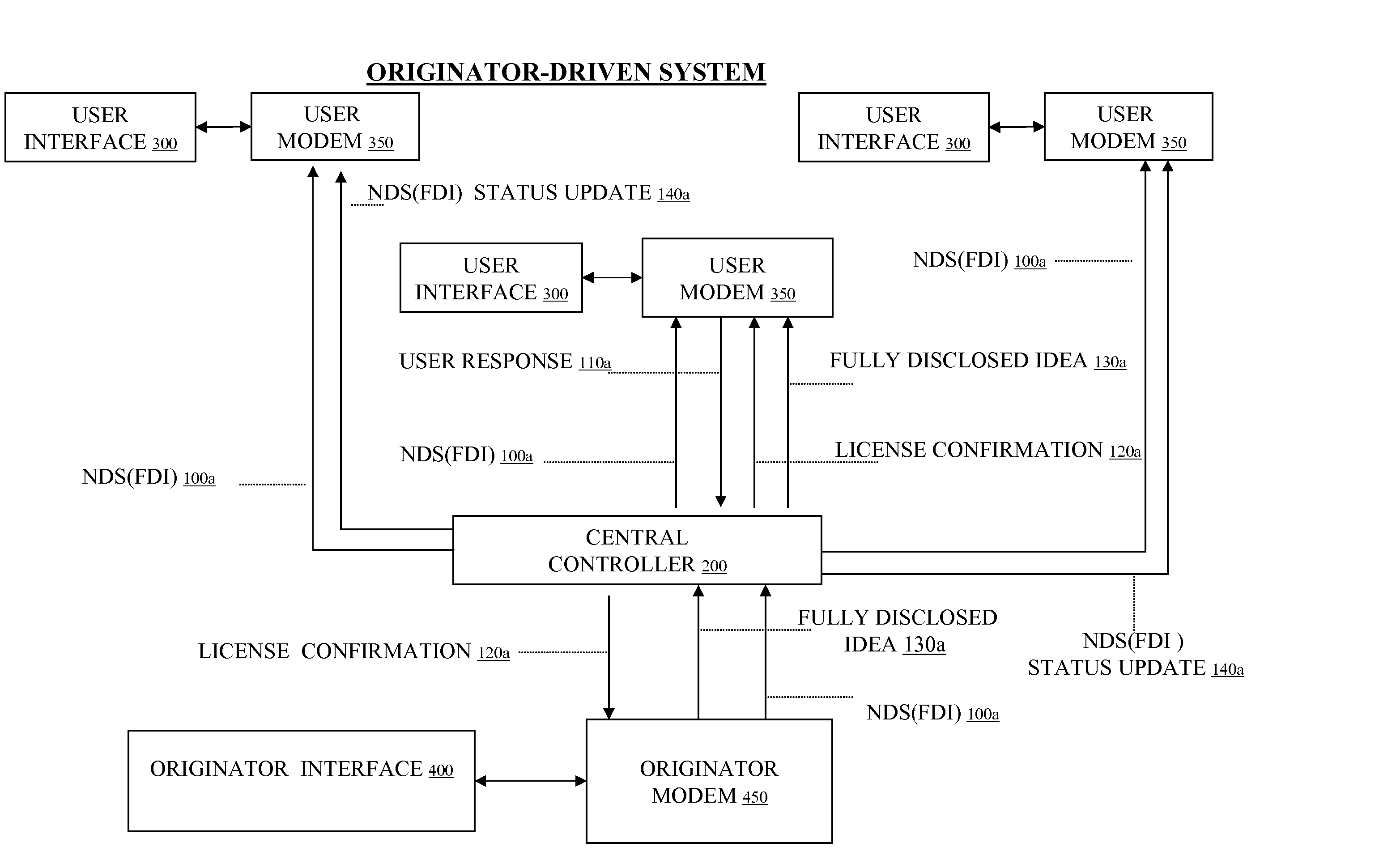
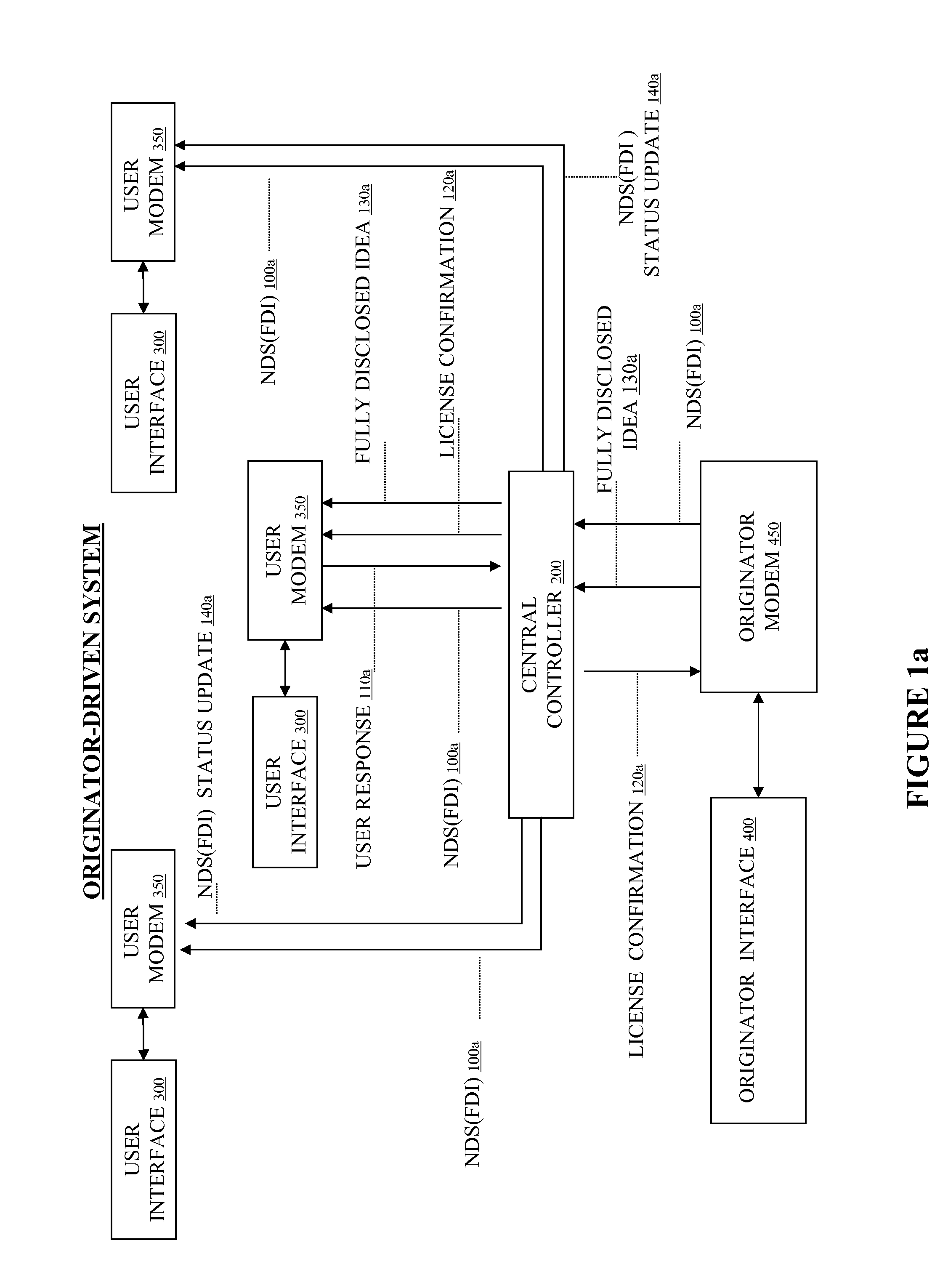
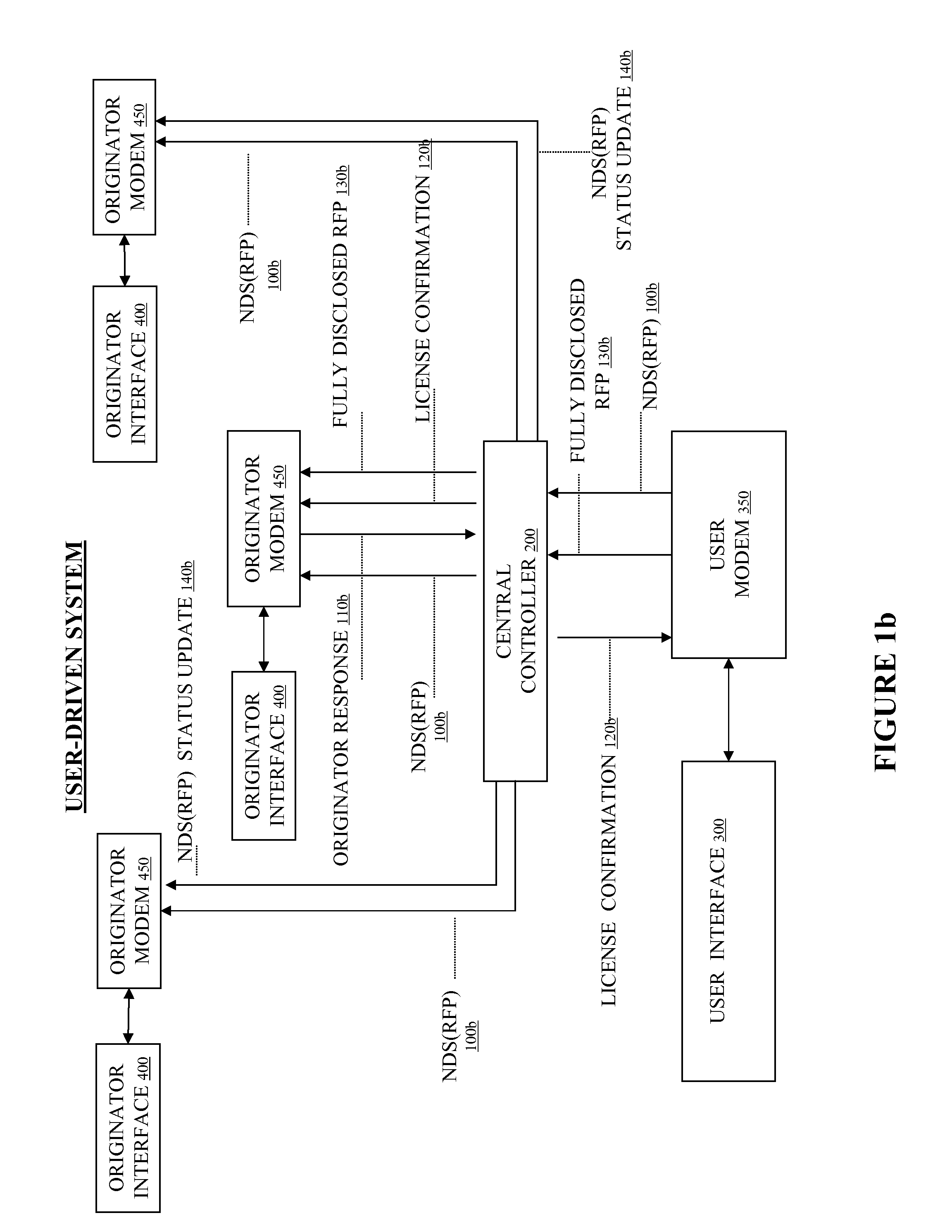
System and Method to Facilitate and Support Exchange of Proprietary Information
InactiveUS20060200423A1Facilitates submissionEasy to adaptFinanceComputer security arrangementsBusiness-to-businessUnresolved Issue
A method and apparatus effectuates bilateral commerce in ideas. An originator and user-driven on-line commercial network system is designed to facilitate idea submission, purchase, and licensing, and is easily adapted to business-to-business transfers of innovation as well as consumer-to-business transfers of innovation. The invention allows originators of ideas to communicate nondisclosing synopses of ideas globally to potential users, for users conveniently to search for relevant ideas and for users potentially to bind an originator to a limited duration license granting user the exclusive right to access and consider confidentially the originator's fully disclosed idea. The invention also allows users to communicate confidentially or nonconfidentially unsolved problems or needs globally to potential originators, for originators conveniently to search for relevant unsolved problems or needs, and for originators to submit and communicate confidentially proposed solutions to the soliciting user.
Owner:PITCHWARE
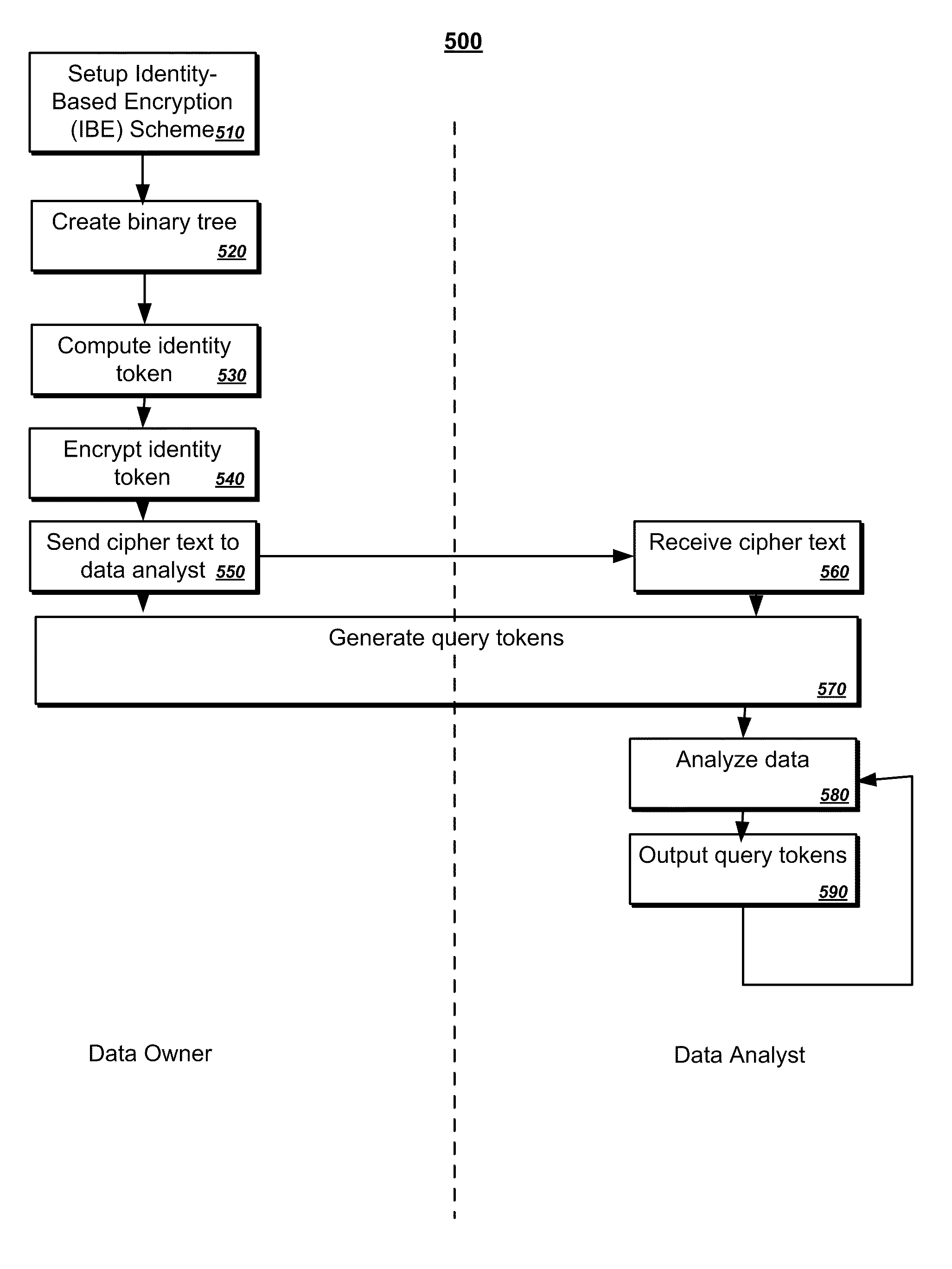
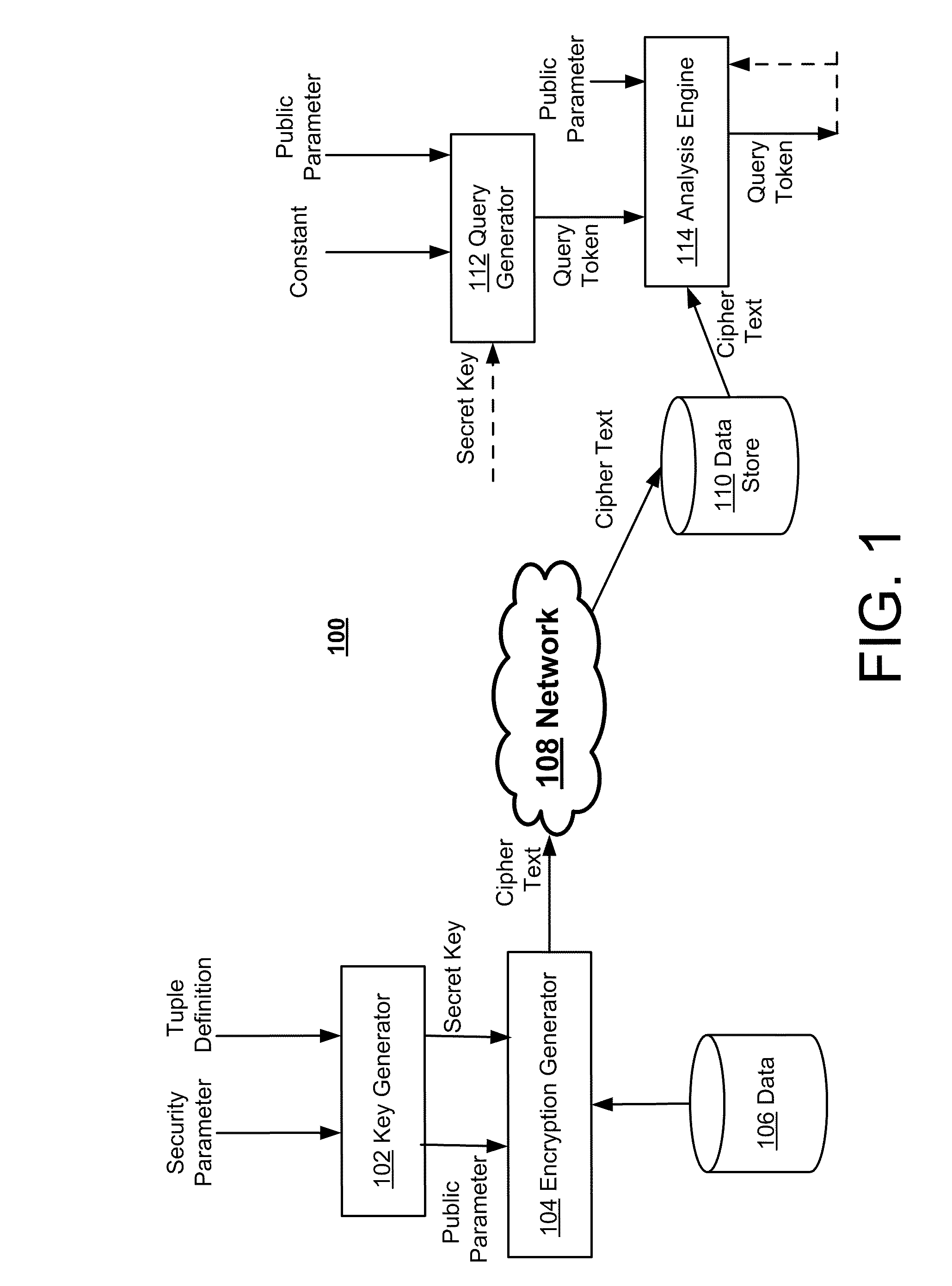
Searchable encryption for outsourcing data analytics
ActiveUS8291509B2Digital data information retrievalDigital data processing detailsAnalysis dataData profiling
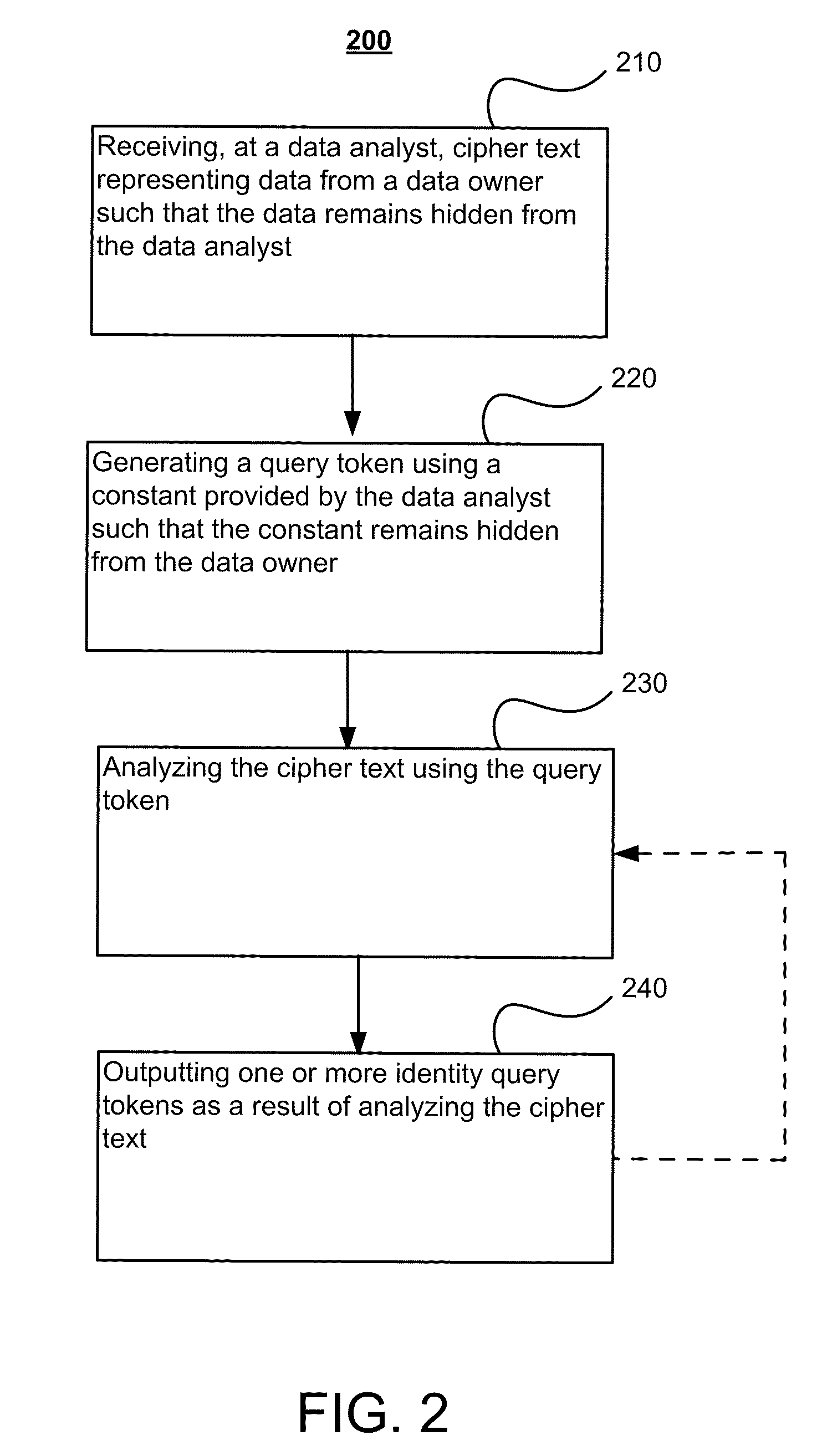
A method for performing data analytics on outsourced data may include generating, by a data owner, a binary tree representing data from the data owner, where each node of the binary tree is associated with an identity that represents a data element or an interval of data elements, computing, by the data owner, an identity token and encrypting the identity token for each of the identities in the binary tree, generating a range query token using an identity selected by a data analyst and a secret key input by the data owner and computing a decryption key for the selected identity, and analyzing the data, by the data analyst, by comparing the computed decryption key for the selected identity with each of the encrypted identities.
Owner:SAP AG
Electronic information item selection for trade and traded item control delivery system
InactiveUS20070088614A1Secure deliveryTelevision system detailsNon-circular curve drawing instrumentsTime rangeTransaction data
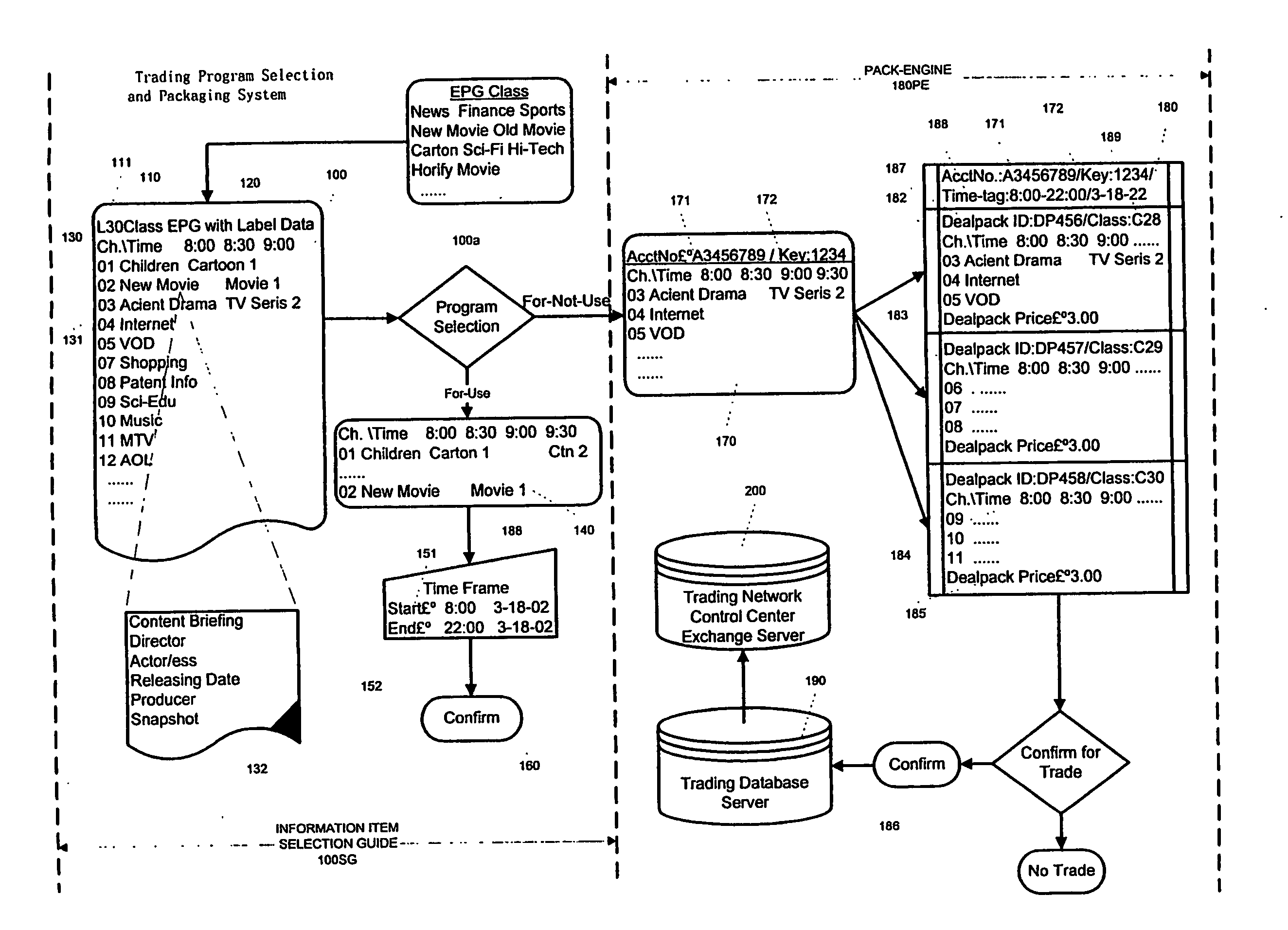
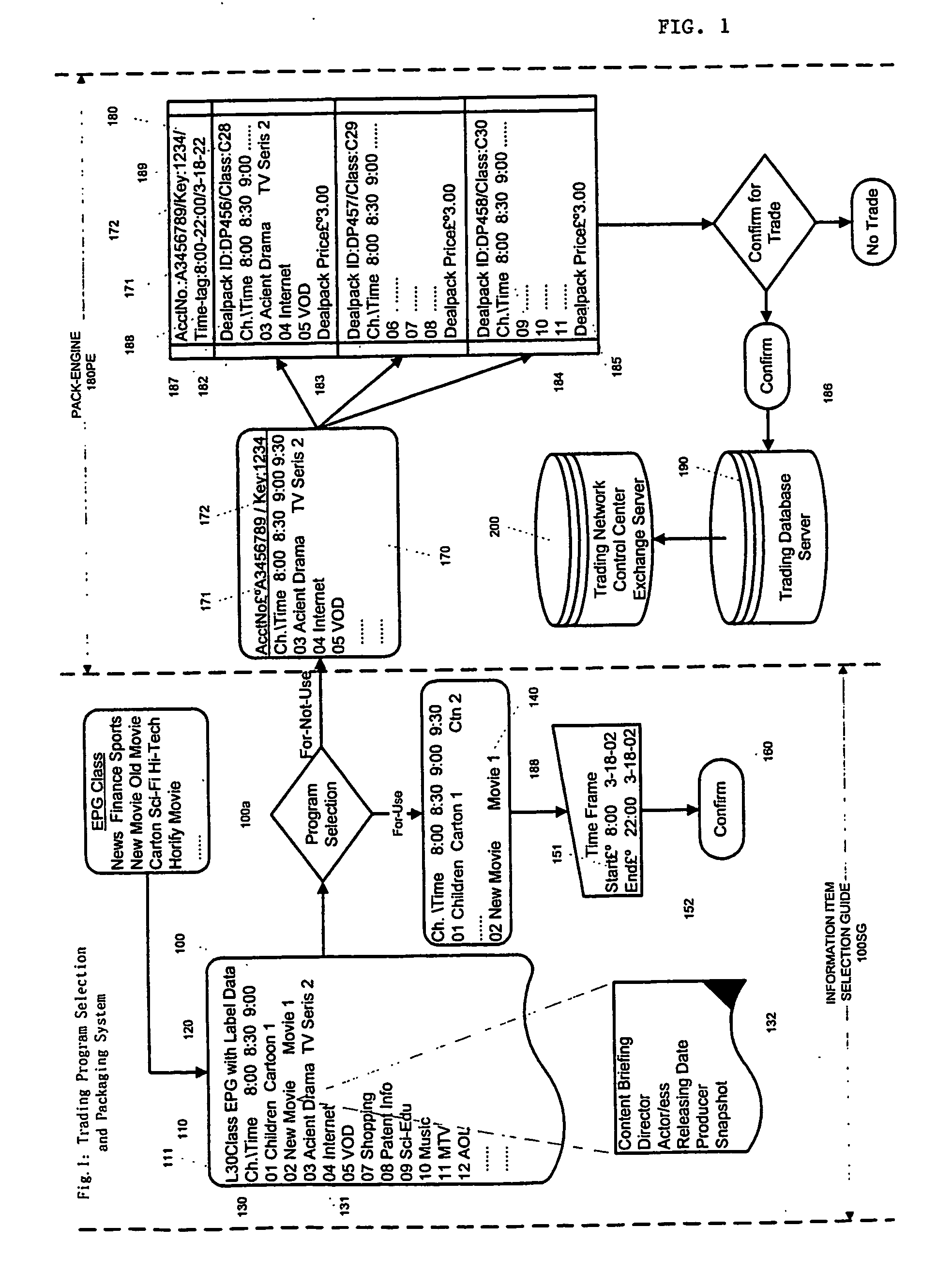
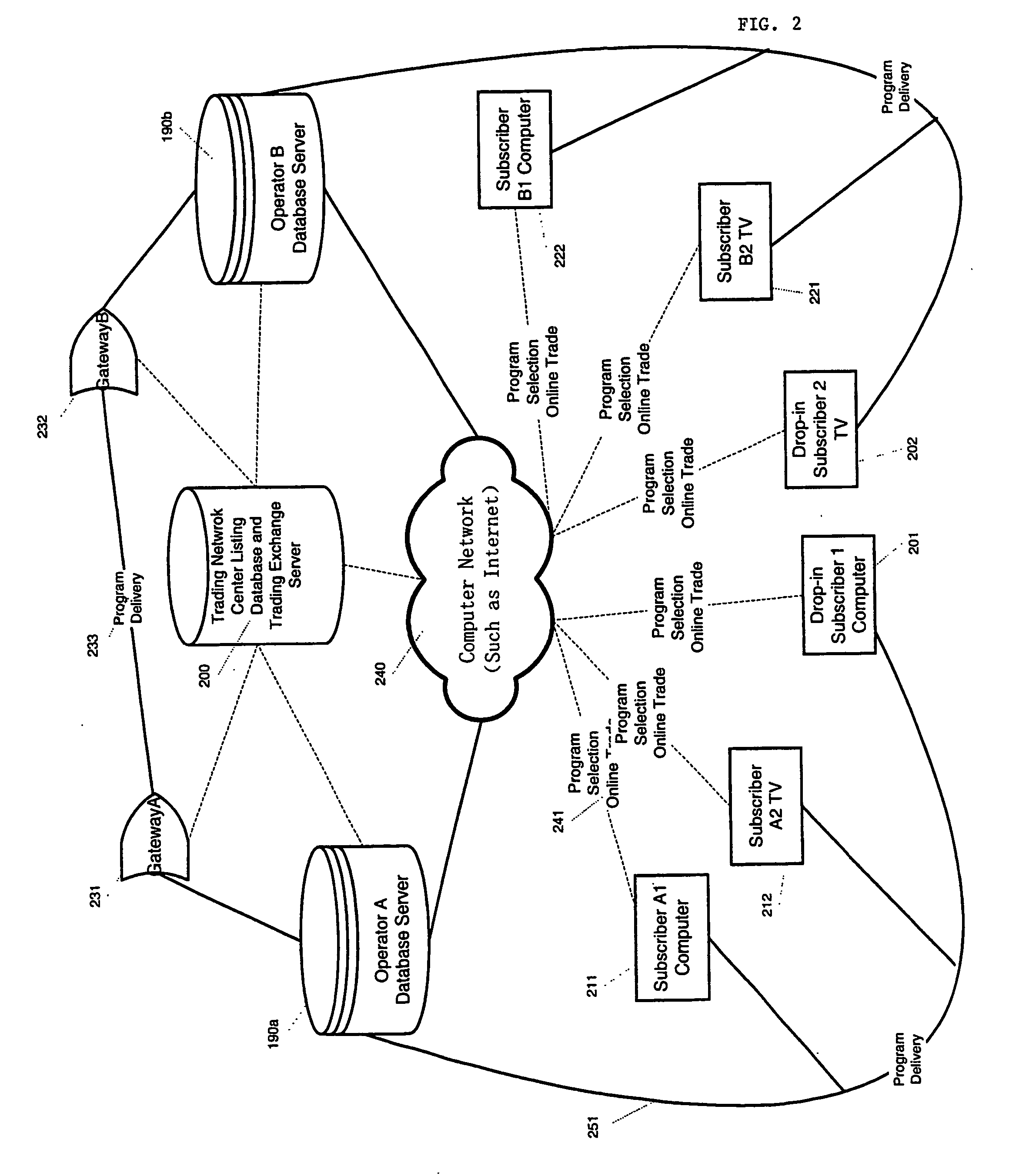
The objective of this invention is to provide a solution that enable real, delayed or relayed time trade and delivery of time-tagged electronic information items from / among same or different regions' information content providers (190a, 190b) and / or their subscribers (201, 202, 211, 212, 221, 222) , or via their corresponding region's information content network operators and their subscribers (201, 202, 211, 212, 221, 222). In order to realize the objective, this invention provide a system to select wanted information items and package the unselected or for-not-use information items in specified time frame by mapping and grouping via a grid / matrics to packaging, labeling and pricing the items into for-trade-items or dealpacks and register them into trading database (200); a system for dealpack listing, online searching and purchasing; and dealpack's secret key submitting, verifying, encrypting transmission and decrypting delivery.
Owner:HUO SHUYA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com