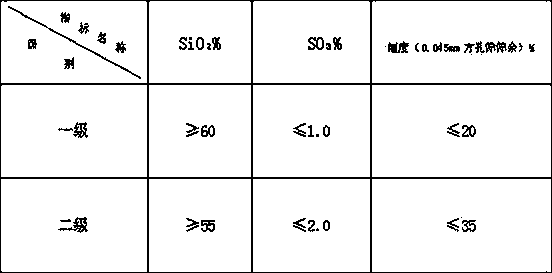
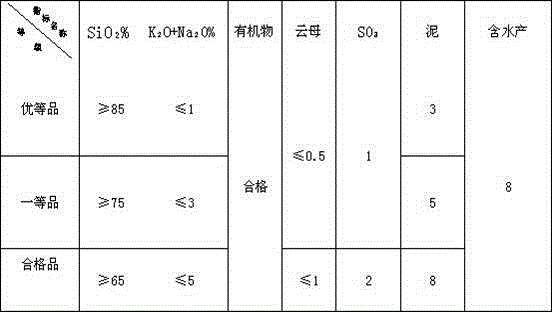
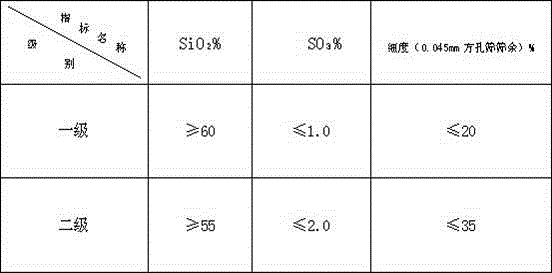
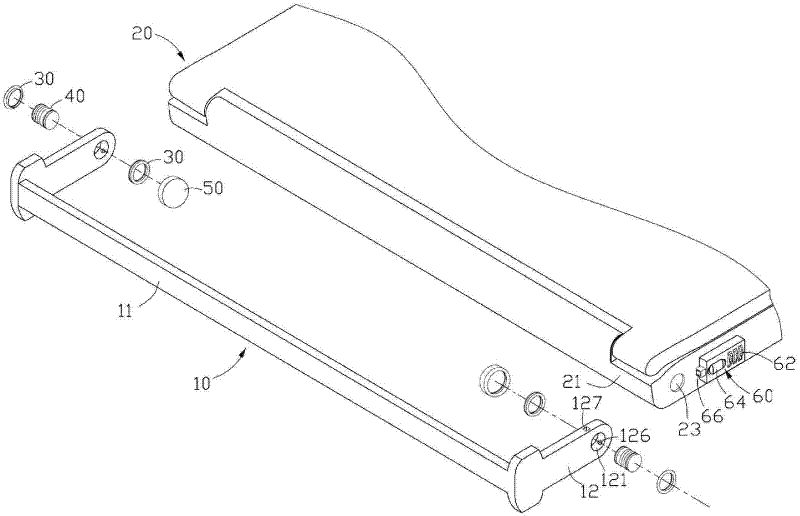
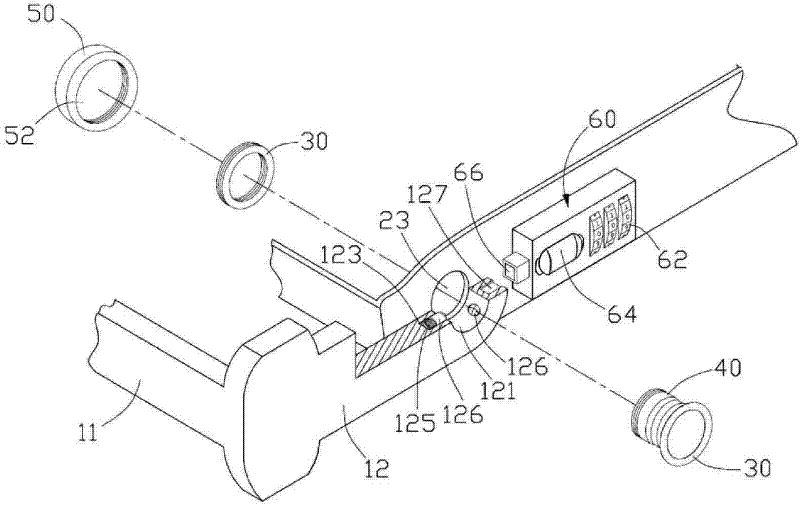
Patents
Literature
36results about How to "Avoid being stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
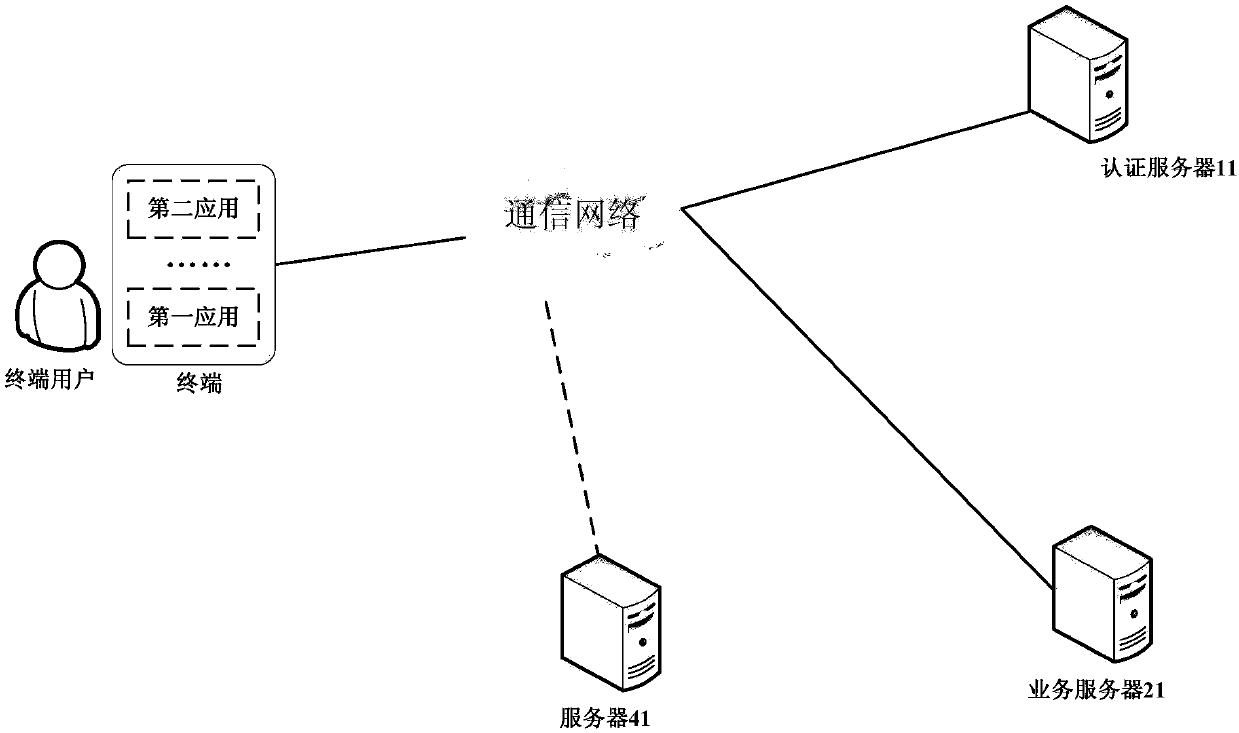
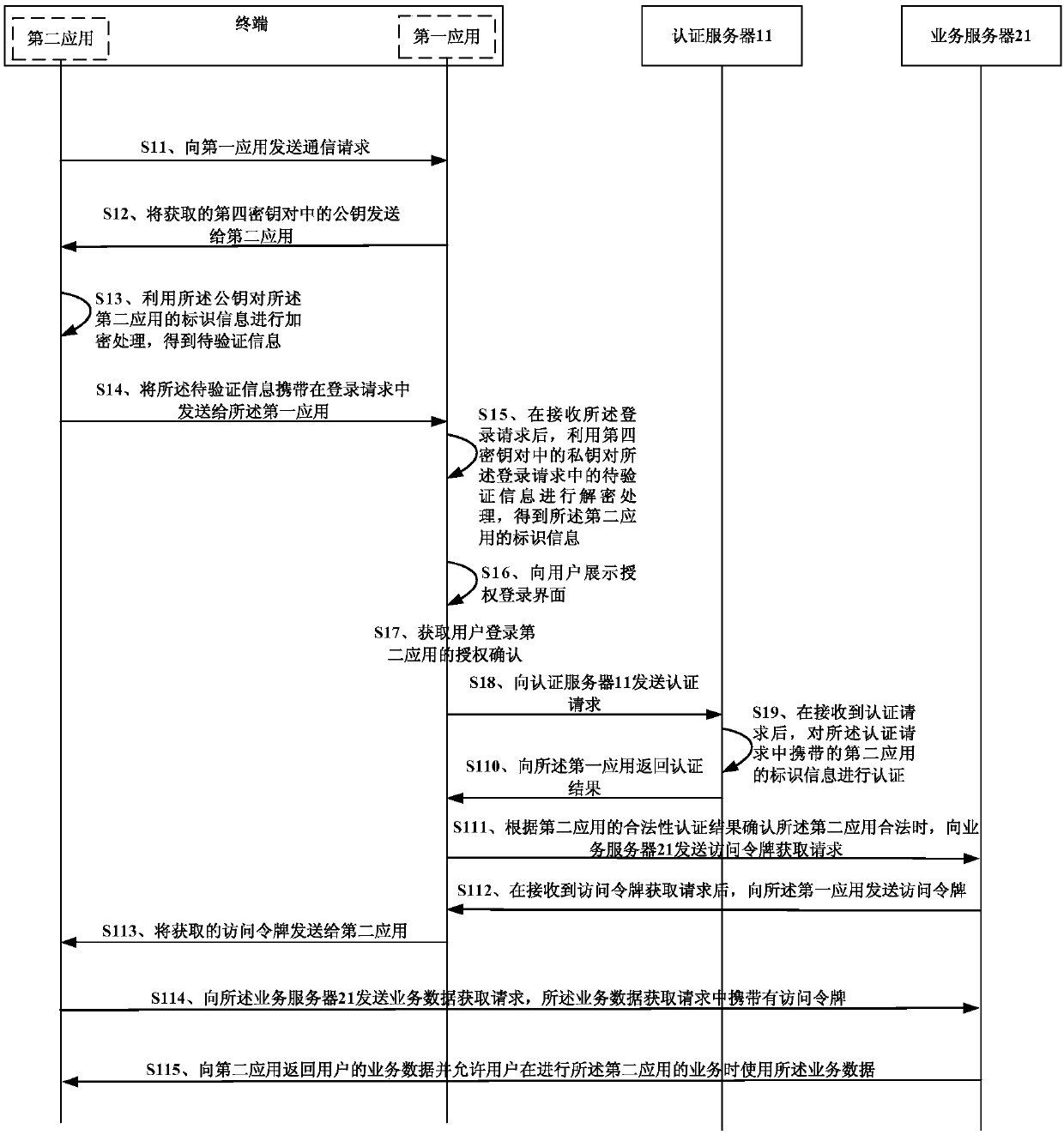
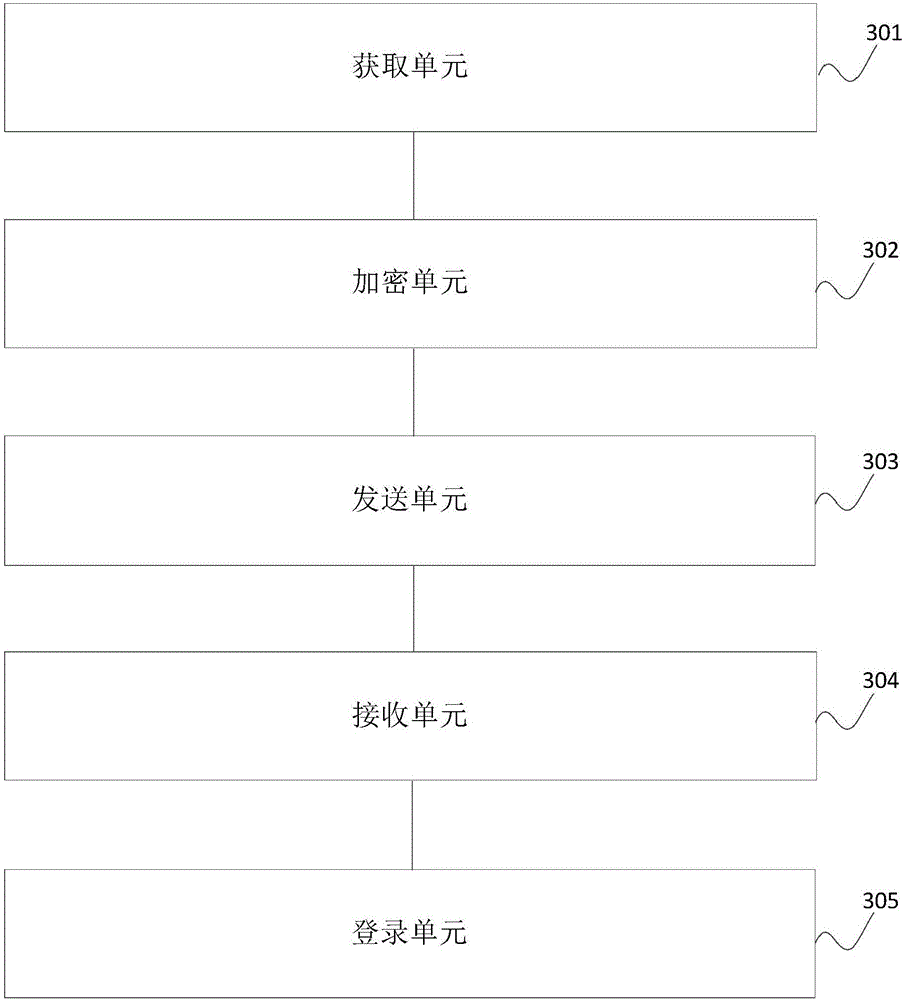
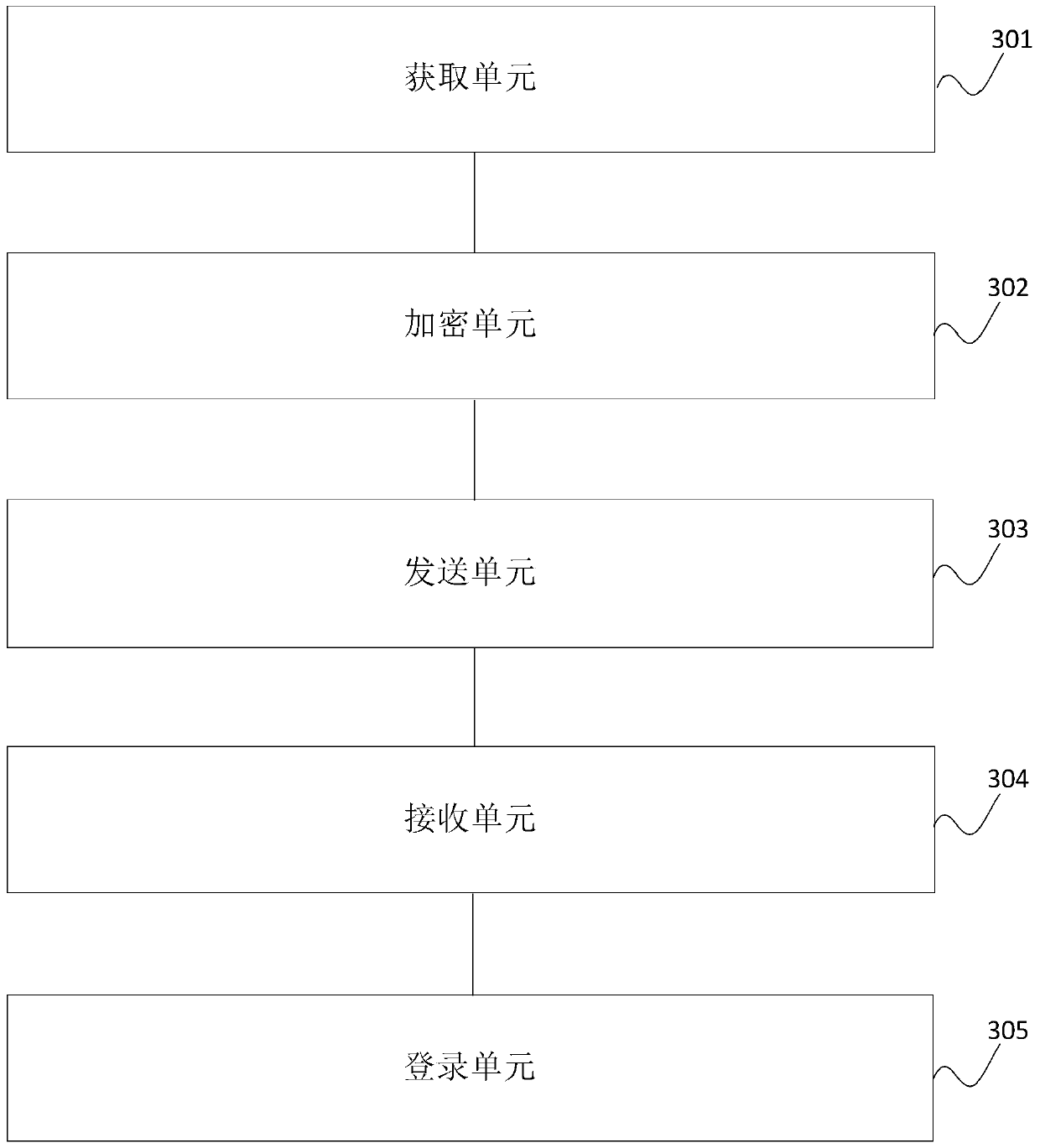
Application login method and system, terminal and electronic equipment
ActiveCN110324276AEnsure safetyPrevent leakageUser identity/authority verificationTransfer procedureBusiness data
The invention discloses an application login method and system, a terminal and electronic equipment, and belongs to the technical field of information security. The method comprises the following steps of: when a first application in a terminal acquires authorization confirmation that a user permits to use user identity information of the first application to log in a second application, sending an authentication request of authentication encryption information carrying the identification information of the second application to an authentication server; when it is determined that the second application is legal according to an authentication result returned by the authentication server, obtaining the access token from the business server of the first application and sending the obtained access token to the second application, so that the second application can obtain the business data of the user from the business server by utilizing the access token, and meanwhile, the user is allowed to use the business data when carrying out the business of the second application. The data is transmitted in an encryption mode, information is prevented from being stolen in the transmission process, and therefore the safety of the data recorded on the service server by a user is guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
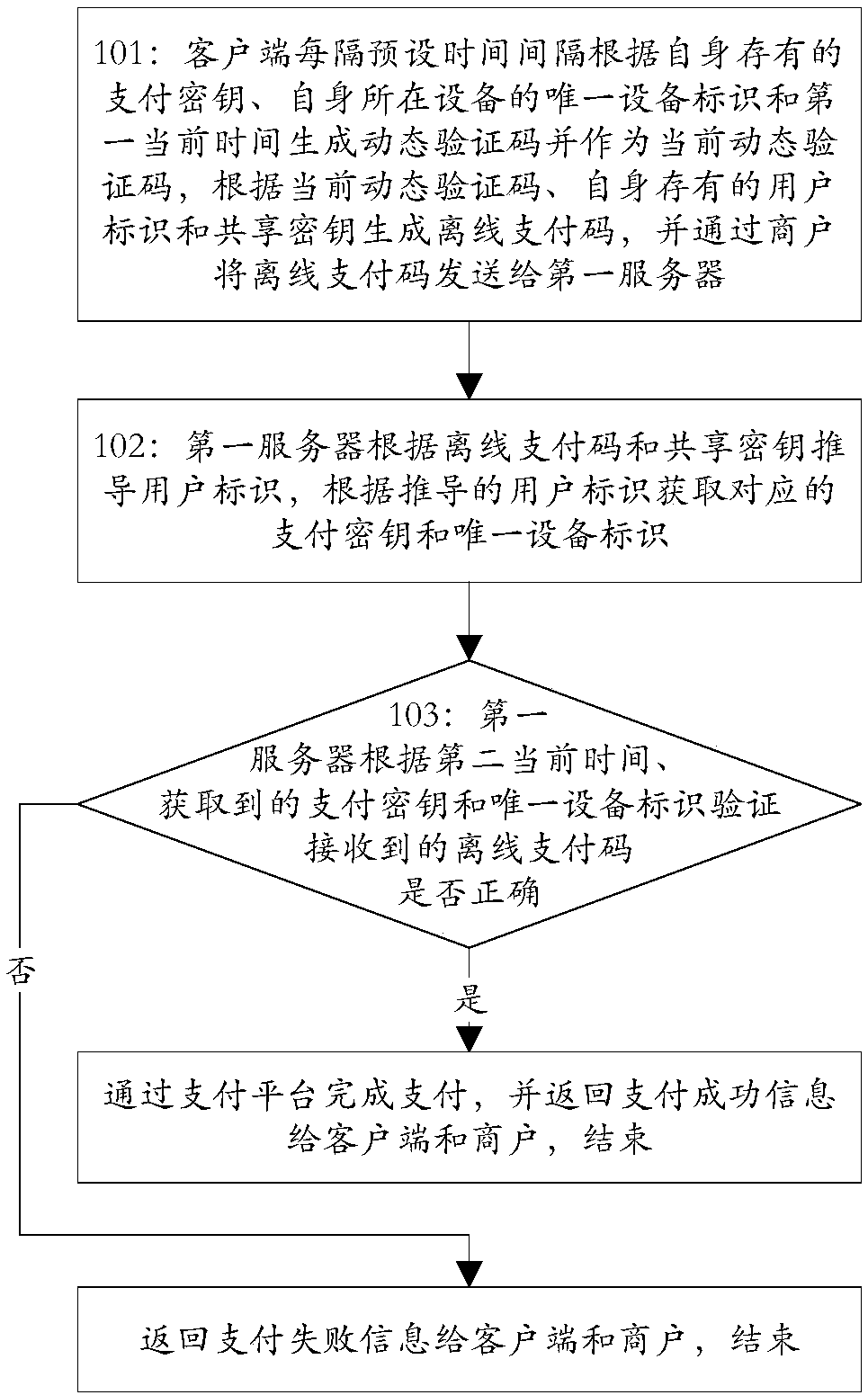
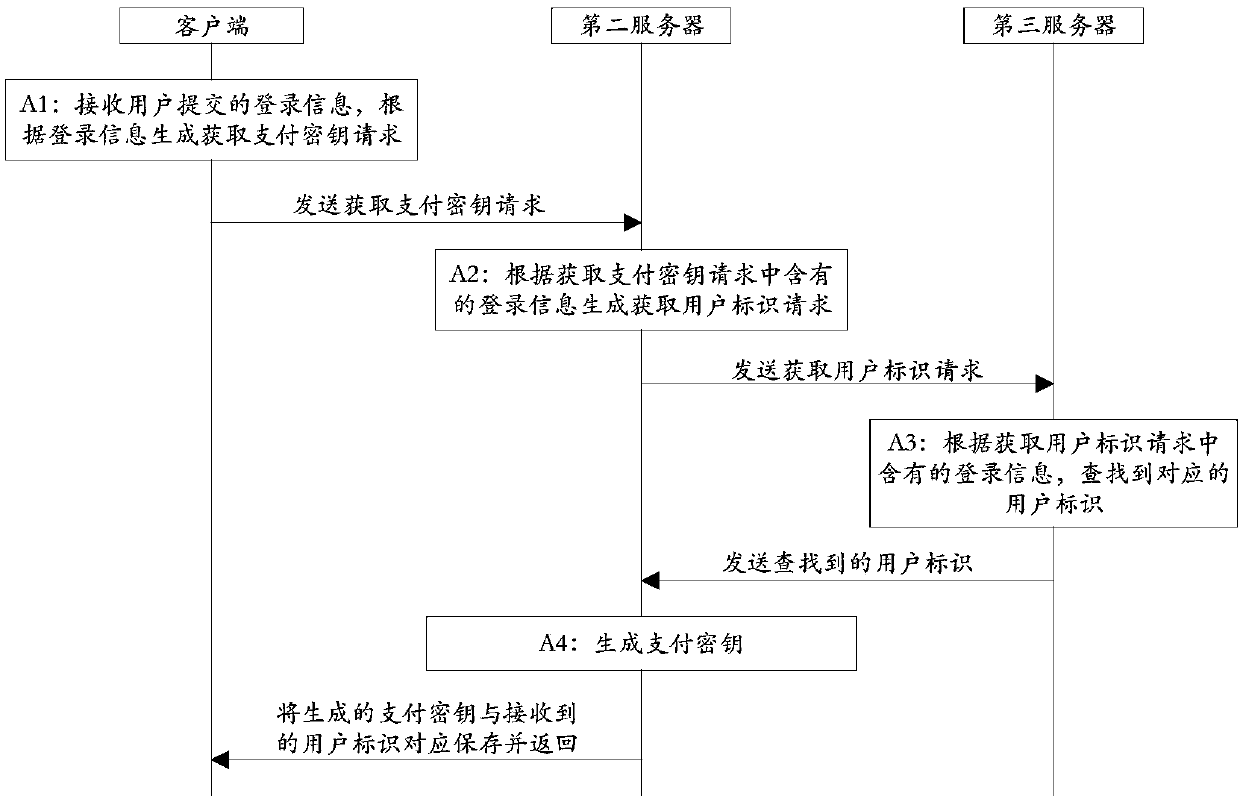
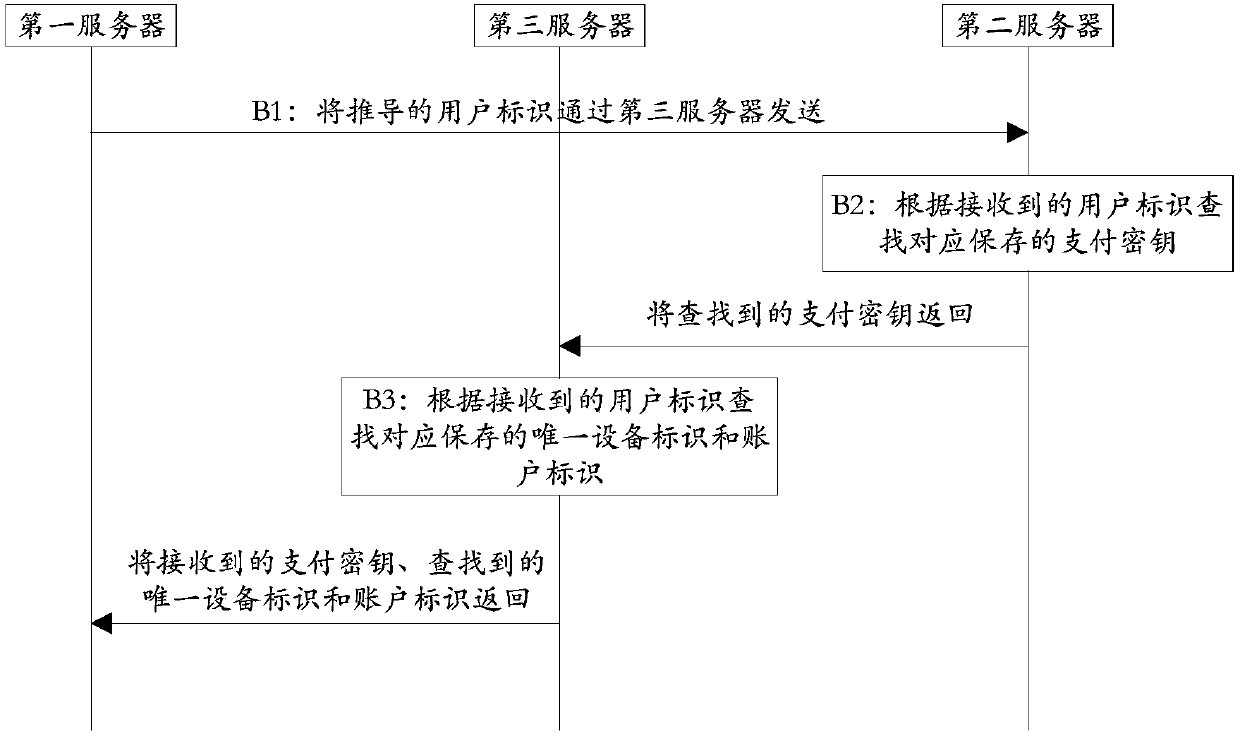
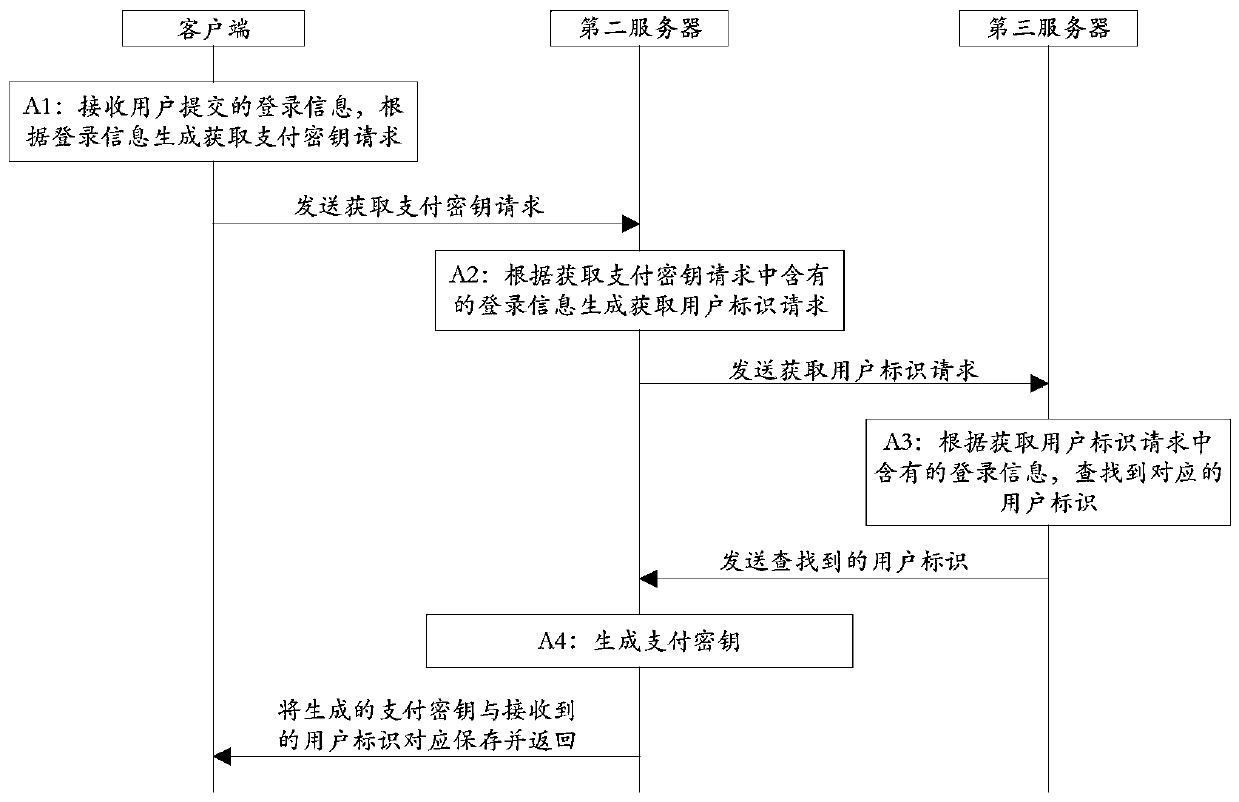
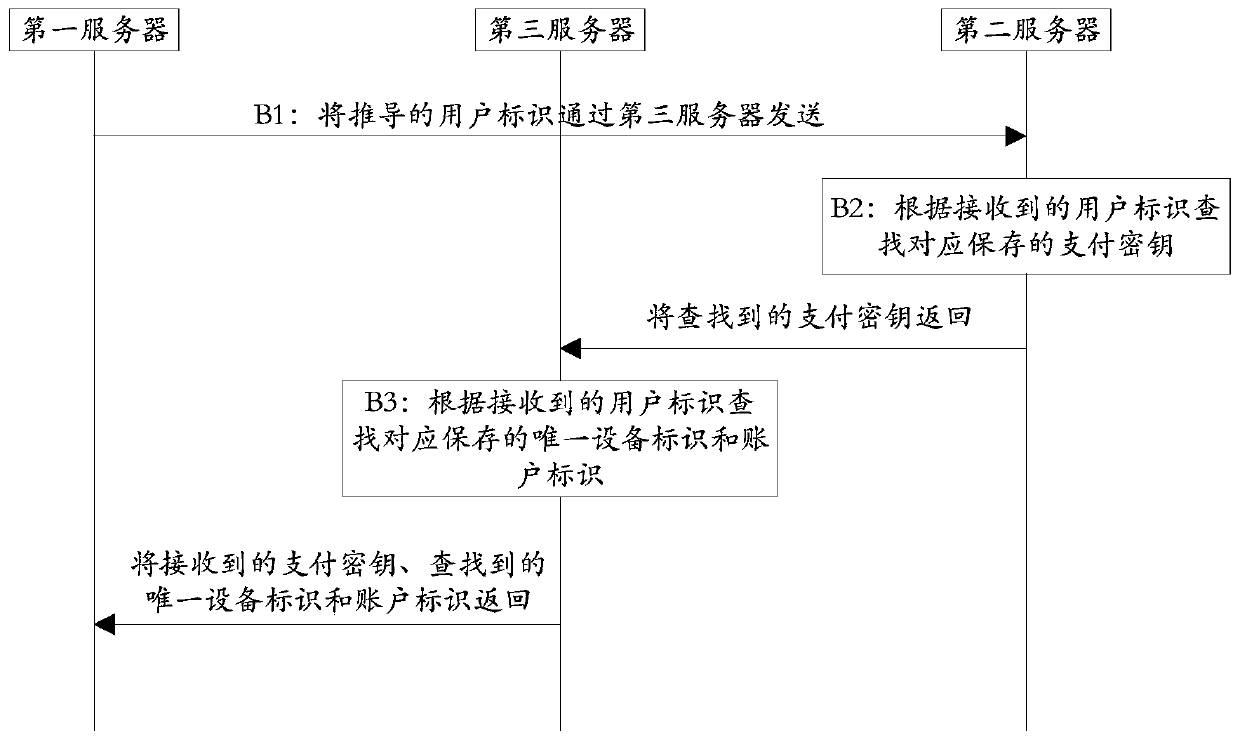
Off-line payment method and system based on TOTP algorithm
ActiveCN107818463AAvoid being stolenGuaranteed payment securityKey distribution for secure communicationPayment schemes/modelsPaymentUnique device identifier
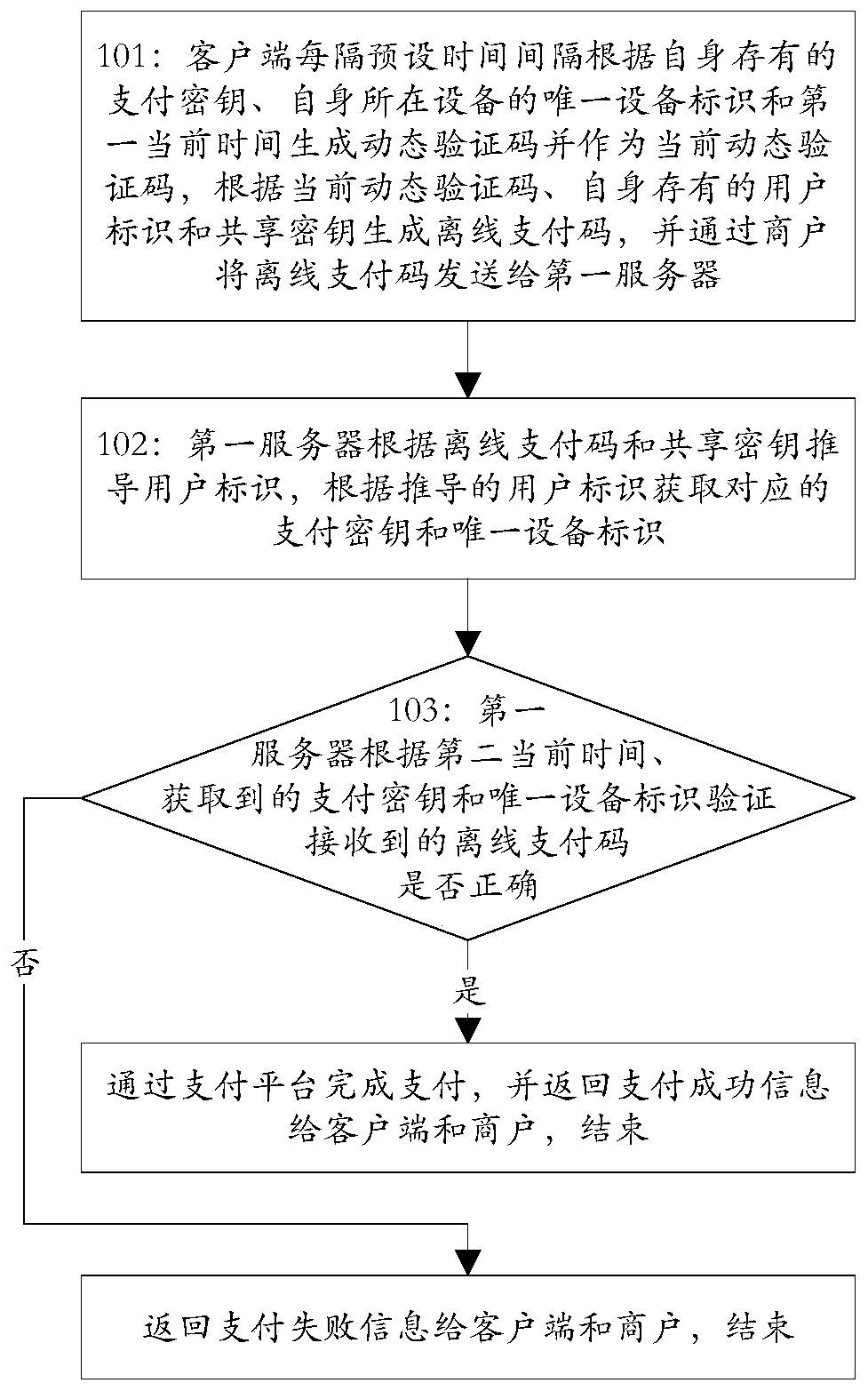
The invention discloses an off-line payment method and system based on a TOTP (Time-based One-time Password) algorithm, and belongs to the technical field of computers. The off-line payment method andsystem based on a TOTP algorithm includes the steps: a client generates a dynamic verification code according to the self-stored payment key, the unique equipment identifier of the equipment and thefirst current time every preset time interval, takes the dynamic verification code as the current dynamic verification code, generates an off-line payment code according to the current dynamic verification code, the user identifier and the shared key, and sends the off-line payment code to a first server through a merchant; the first server derives the user identifier according to the off-line payment code and the shared key, and acquires the corresponding payment key, the unique equipment identifier and the account identifier according to the user identifier, and verifies whether the off-linepayment code is correct according to the second current time, the obtained payment key and the obtained unique equipment identifier; if the off-line payment code is correct, according to the accountidentifier, payment is completed through a payment platform and payment success information is returned to the client and the merchant, and over; and if the off-line payment code is not correct, payment failure information is returned to the client and the merchant, and over.
Owner:九派天下支付有限公司
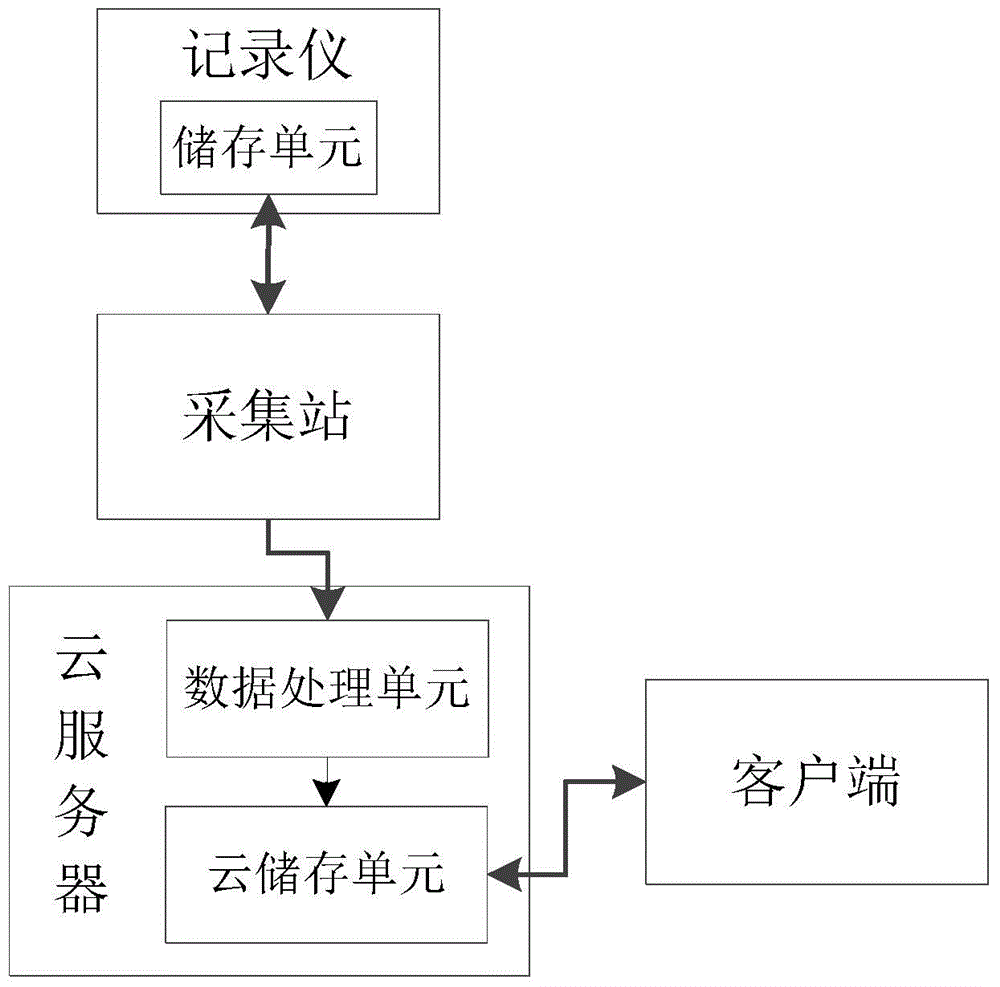
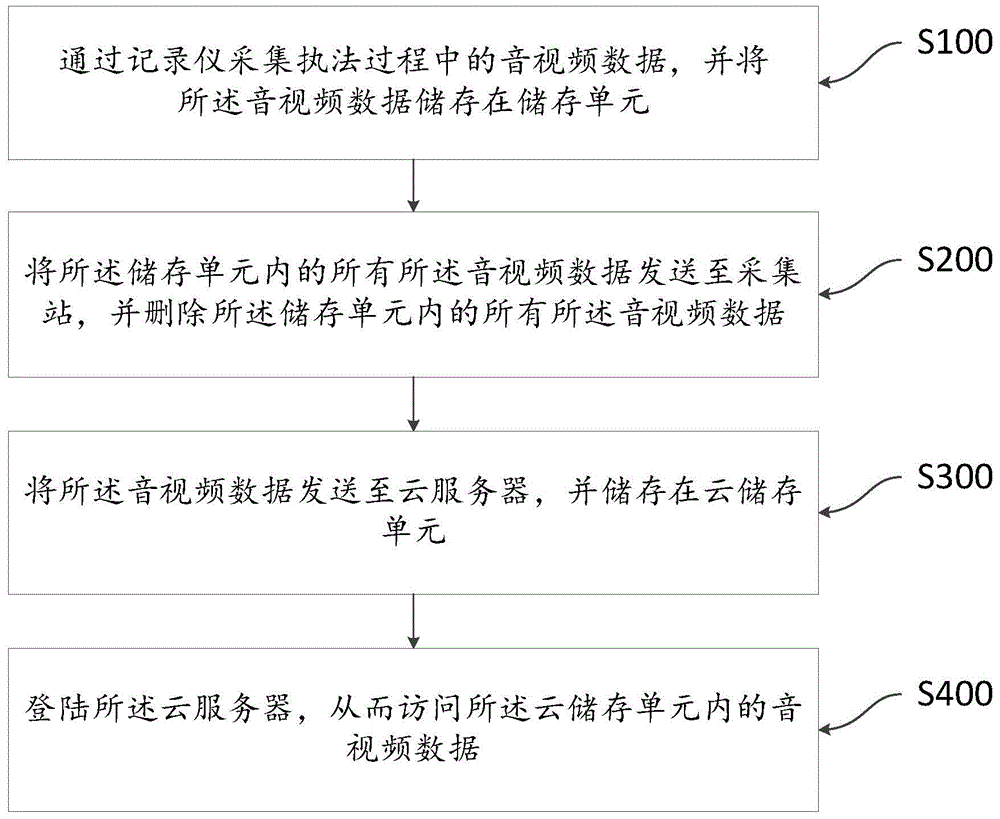
Policeman law enforcement audio and video recording system and recording method
InactiveCN105049798AAlleviate insufficient memoryMitigation of insufficientTelevision system detailsColor television detailsThe InternetVideo recording
The invention relates to a policeman law enforcement audio and video recording system. The policeman law enforcement audio and video recording system includes a recorder, an acquisition station, a cloud server and a client end; the recorder is used for acquiring audio and video data in a law enforcement process and storing the audio and video data in a storage unit in the recorder; the recorder is also used for transmitting the audio and video data in the storage unit to the acquisition station; the acquisition station is used for receiving the audio and video data transmitted by the recorder and transmitting the audio and video data to the cloud server; after receiving all audio and video data in the storage unit, the acquisition station transmits instructions to the recorder so as to control the recorder to delete all the audio and video data in the storage unit; the cloud server is used for receiving the audio and video data transmitted by the acquisition station and storing the audio and video data in a cloud storage unit in the cloud server; and the client end can log in the cloud server through the Internet, so as to visit the audio and video data stored in the cloud storage unit. The policeman law enforcement audio and video recording system has the advantages of convenient management and safe storage.
Owner:HUBEI DI SIGHT SCI & TECH
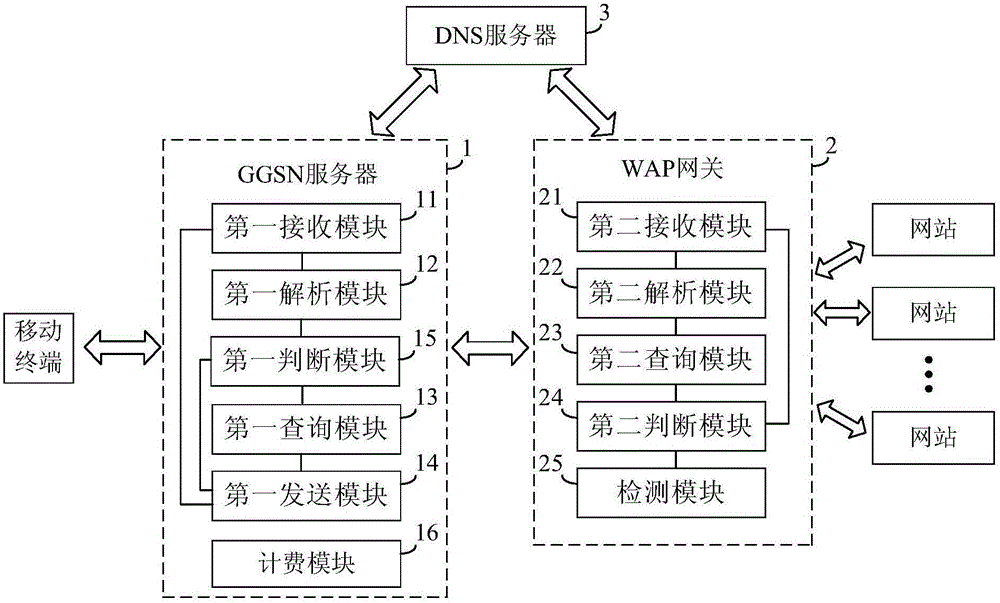
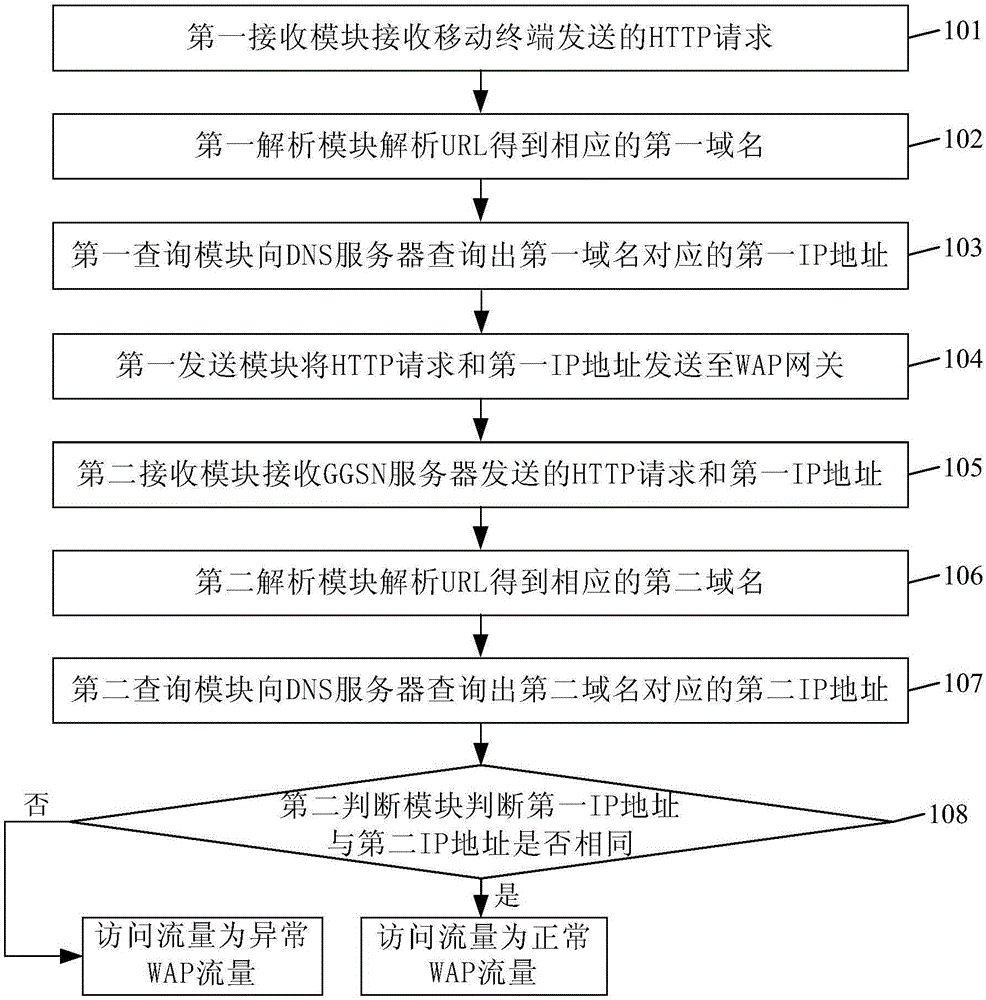
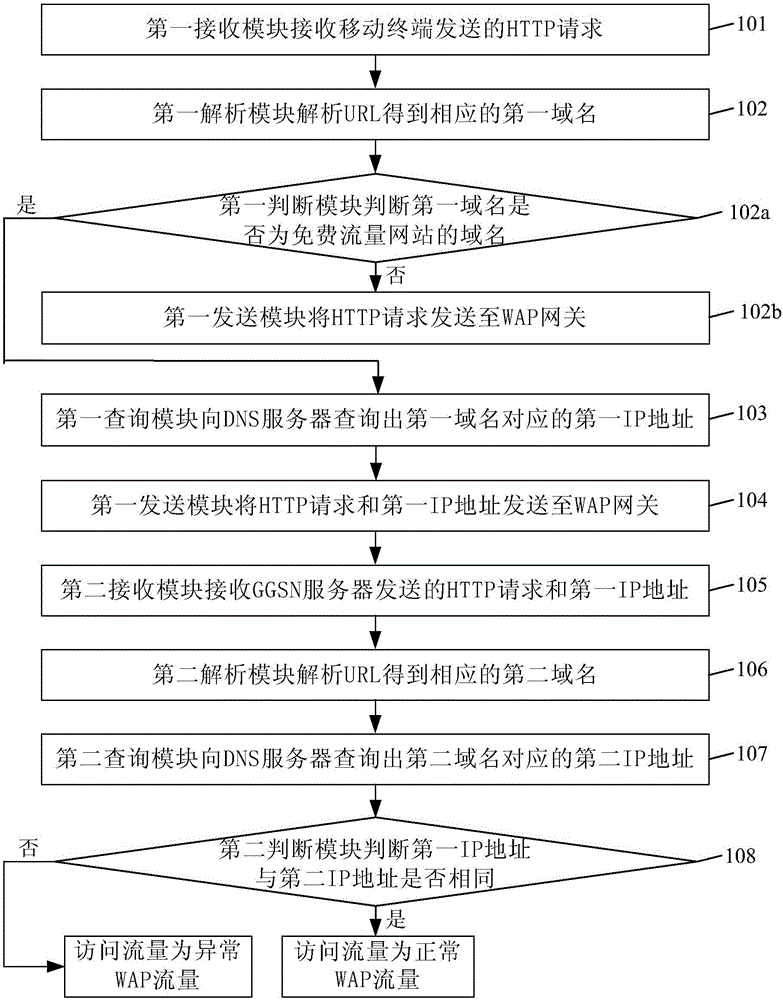
WAP (wireless application protocol) traffic detection method and system, GGSN (gateway GPRS support node) server and WAP gateway
InactiveCN106789124AAvoid being stolenReduce lossesMetering/charging/biilling arrangementsDomain nameTraffic capacity
The invention discloses a WAP (wireless application protocol) traffic detection method and system, a GGSN (gateway GPRS support node) server and a WAP gateway. The WAP traffic detection method includes: receiving, by a second receiving module, an HTTP (hypertext transport protocol) request and a first IP (internet protocol) address sent by the GGSN server; analyzing, by a second analysis module, a corresponding second domain name according to a uniform resource locator included in the HTTP request received; querying, by a second query module, a DNS (domain name server) to obtain a second IP address corresponding to the second domain name; judging, by a second judging module, whether the first IP address is identical with the second IP address or not; if not, detecting, by a detection module, corresponding access traffic of a mobile terminal is anomalous WAP traffic. The WAP traffic detection method and system, the GGSN server and the WAP gateway allow anomalous WAP traffic to be detected effectively when a mobile terminal undergoes WAP surfing, the traffic quantity can be avoided being stolen, and operators' loss can be reduced effectively.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
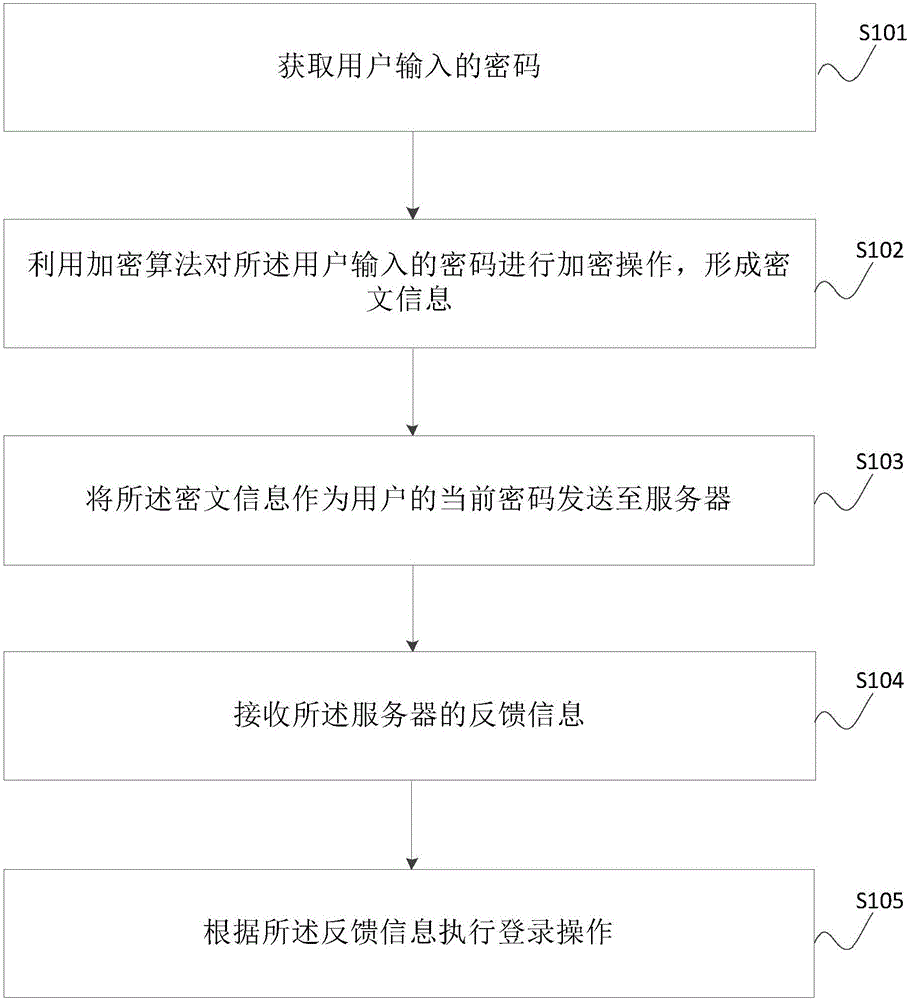
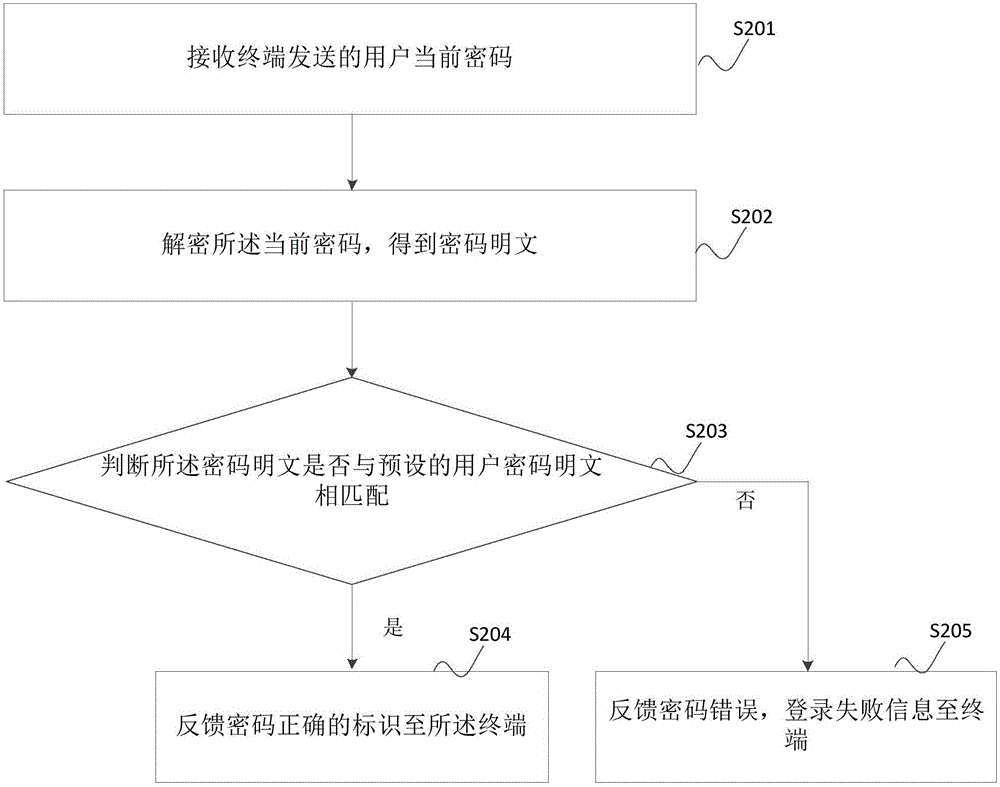
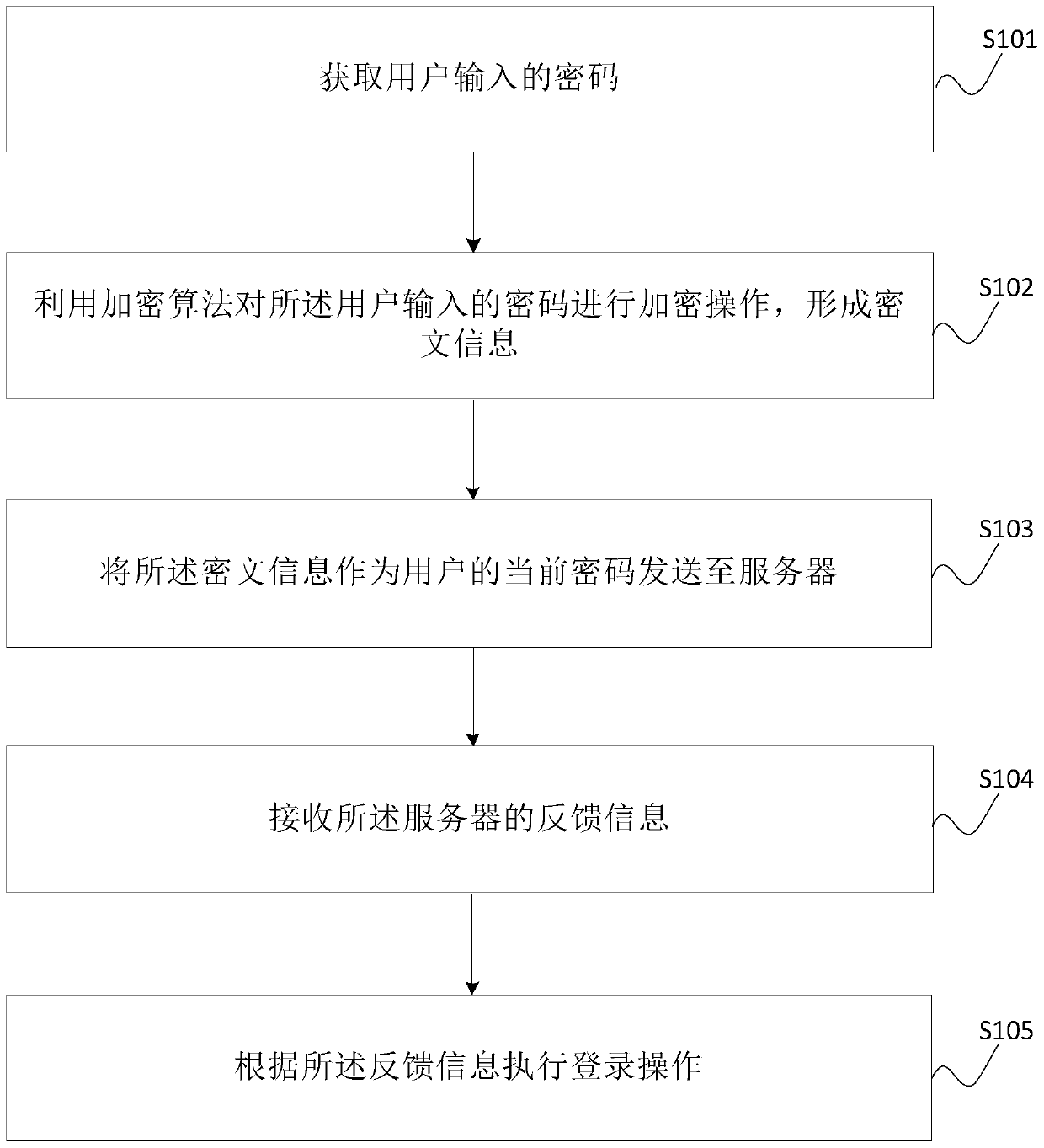
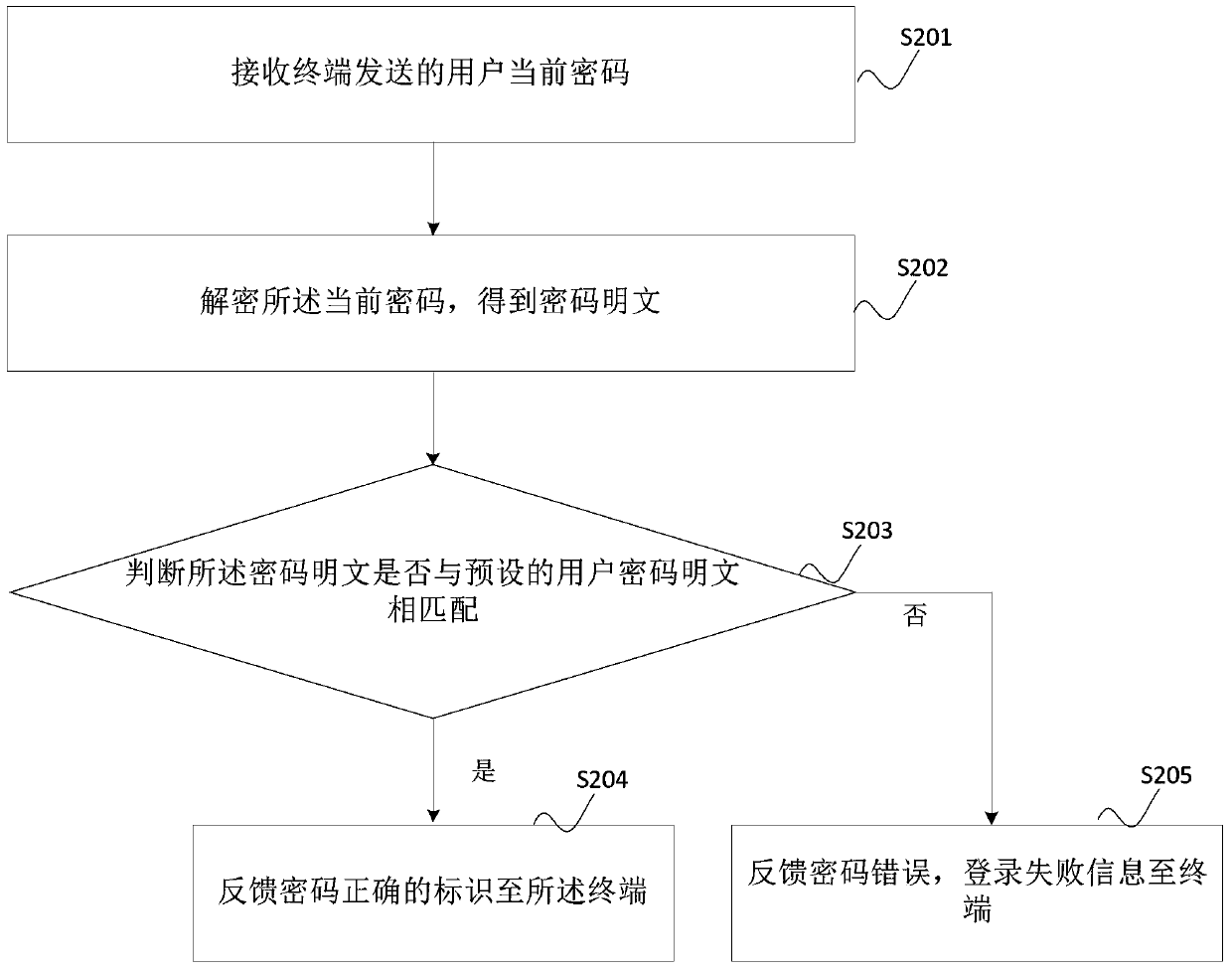
Terminal, server and account security login method, device and system
The application provides an account security login method. The method comprises the steps of obtaining a cipher inputted by a user; utilizing an encryption algorithm to encrypt the cipher inputted by the user to form the ciphertext information; taking the ciphertext information as the current cipher of the user to send to a server; receiving the feedback information of the server; according to the feedback information, executing a login operation. During the sending process, when other users capture a weblog to obtain the account and the cipher of the user with the help of tools, the obtained cipher is just the encrypted cipher, and the cipher inputted by the user is not obtained, thereby effectively avoiding a phenomenon that the user information is stolen, and guaranteeing the security of the user information.
Owner:シェンジェンインムーテクノロジーシーオーエルティーディー
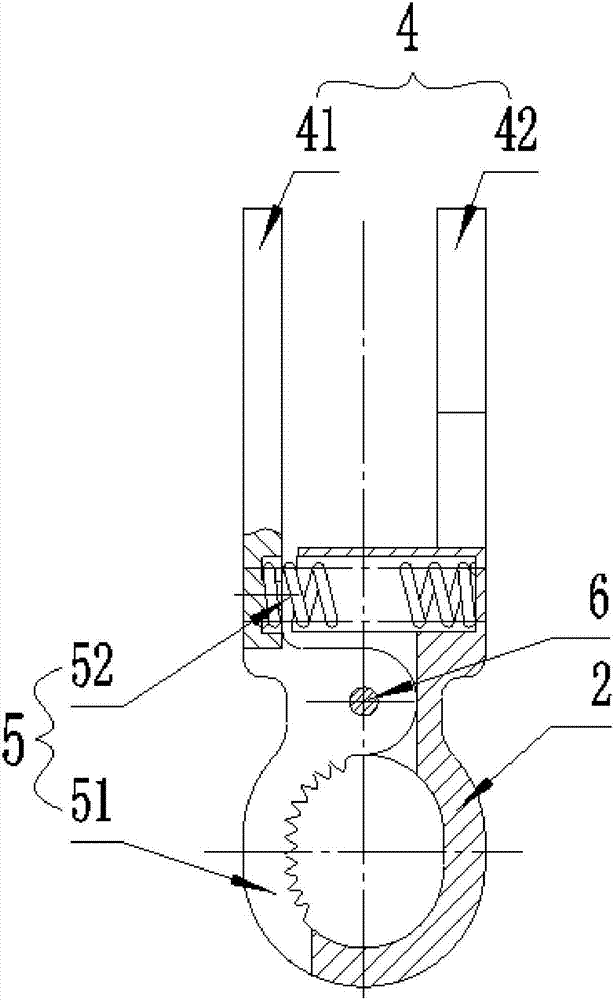
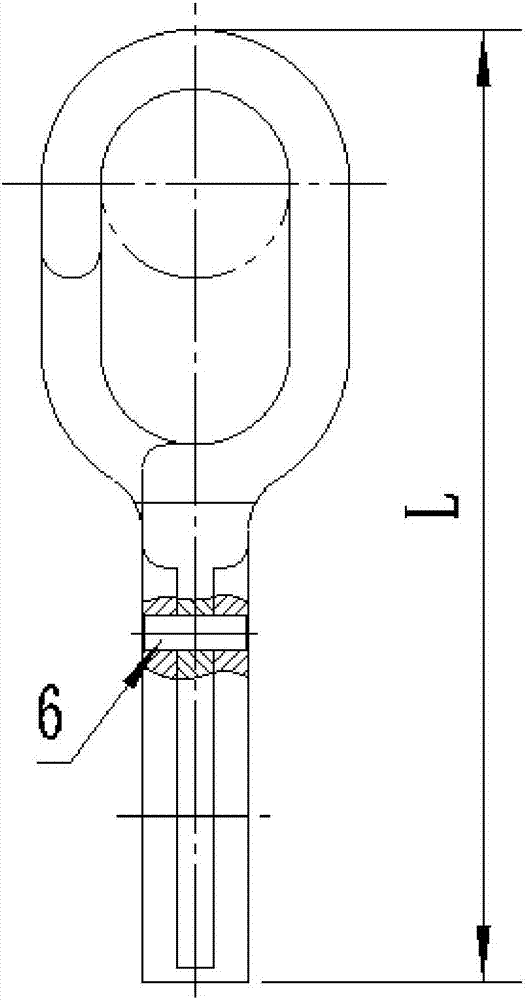
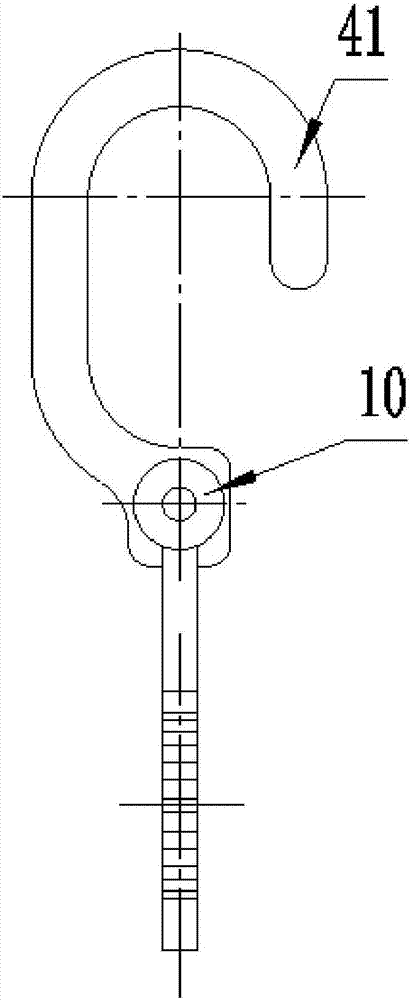
Movable type foot nail hook
ActiveCN107998624AImprove securityReduce manufacturing costSafety beltsClimbingMovable typeWorking environment
The invention provides a movable type foot nail hook, including a hitching body. One end of the hitching body is provided with a casing pipe cooperated with the foot nail, and the other end of the hitching body is provided with an open hook cooperated with a rope. The casing pipe is provided with a clamping mechanism used to clamp the foot nail. The movable type foot nail hook can be sleeved on afoot nail of an iron tower through the casing pipe. The foot nail is clamped by the clamping mechanism, and the casing pipe is ensured to be firmly sleeved on the foot nail. An anti-falling rope passes through the open hook on end of the hitching body, and a plurality of movable type foot nail hooks are hitched on the foot nail of an iron tower main body from top to bottom, and safety coefficientof operation personnel in an iron tower climbing process is improved. The movable type foot nail hook is advantaged by low manufacturing cost, fast and convenient installation, and detachable and cycling use, and prevents corrosion and theft phenomenon caused by being in outdoor working environment for long time.
Owner:STATE GRID CORP OF CHINA +1
New energy charging gun convenient to carry
InactiveCN112467485AAvoid being stolenEasy access and storageVehicle connectorsCharging stationsElectric machineNew energy
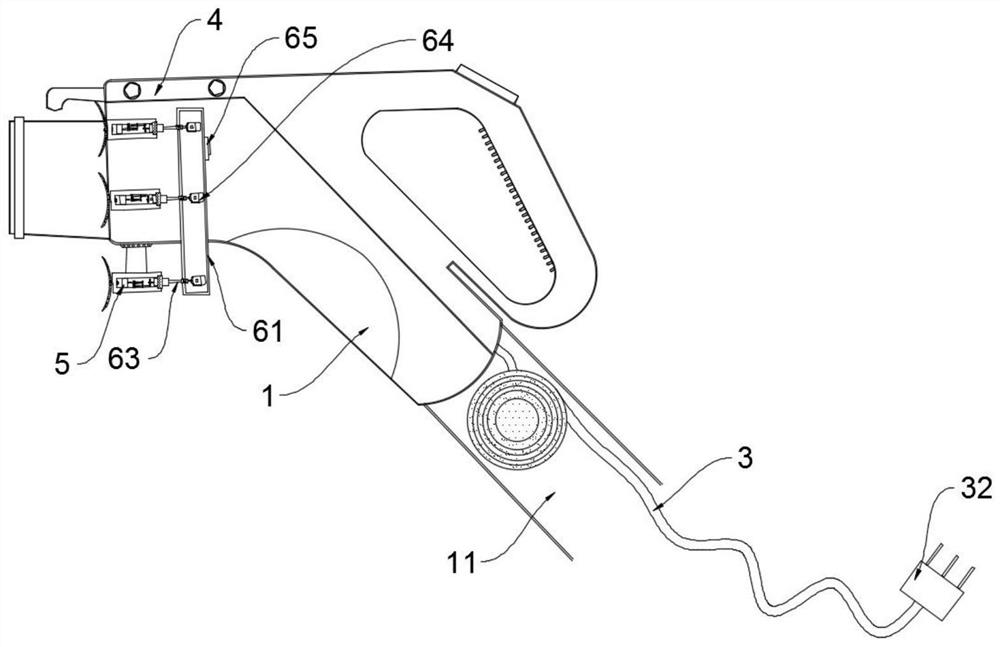
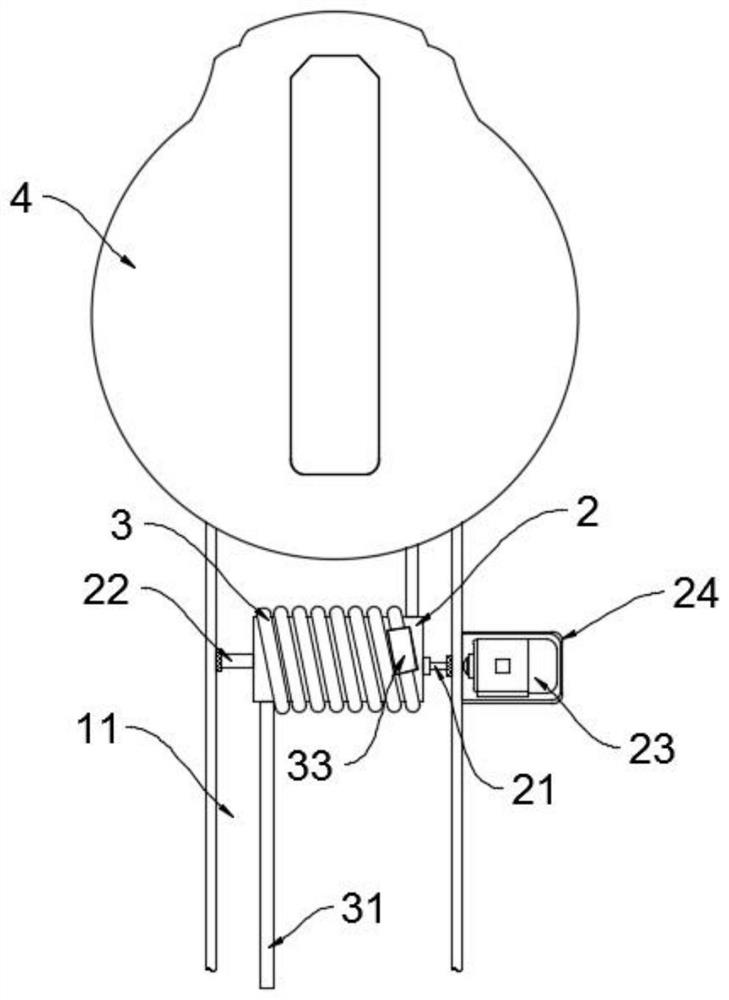
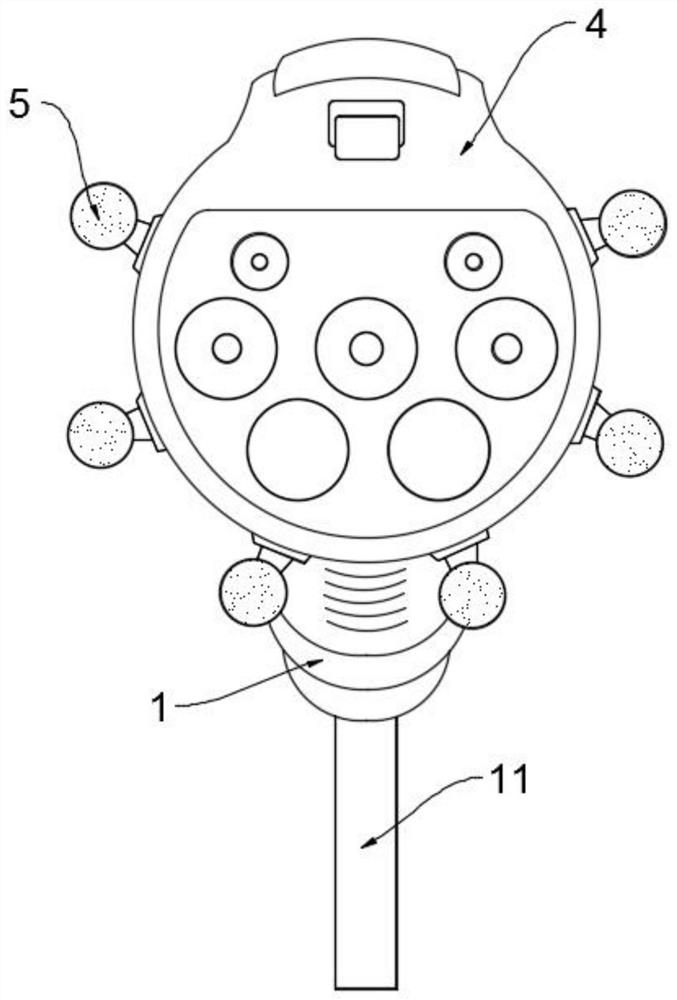
The invention discloses a new energy charging gun convenient to carry. When the new energy charging gun convenient to carry by hand is used, a charging socket is connected with a charging pile, then awinding motor is driven, the winding motor adopts a positive and negative rotation gear motor, and the winding motor drives a winding wheel to rotate, so that the movable end of an electric wire extends, and a user can use the charging gun conveniently; the household charging pile is generally installed in an underground parking lot of a community, a charging gun placed in the parking lot has therisk of being stolen and lost, when the charging gun is not used, a user can separate a charging socket in the charging gun from a charging pile body, then a winding motor drives a winding wheel to rotate, and an electric wire is contracted, wound and stored, so that the user can take and store the charging gun conveniently, and the charging gun is effectively prevented from being stolen and lost; the multiple suction cups can be adsorbed to the surface of an automobile in a negative pressure mode, large adsorption force is generated on the surface, the charging gun is stabilized on a charging interface of the automobile, the charging gun is not prone to being touched by other people to loosen or fall off, and the anti-theft performance is improved.
Owner:杨益
Electronic credit card transaction method based on block chain
PendingCN111652707ACost of protectionGuaranteed incomeFinanceDigital data protectionCredit cardComputer network
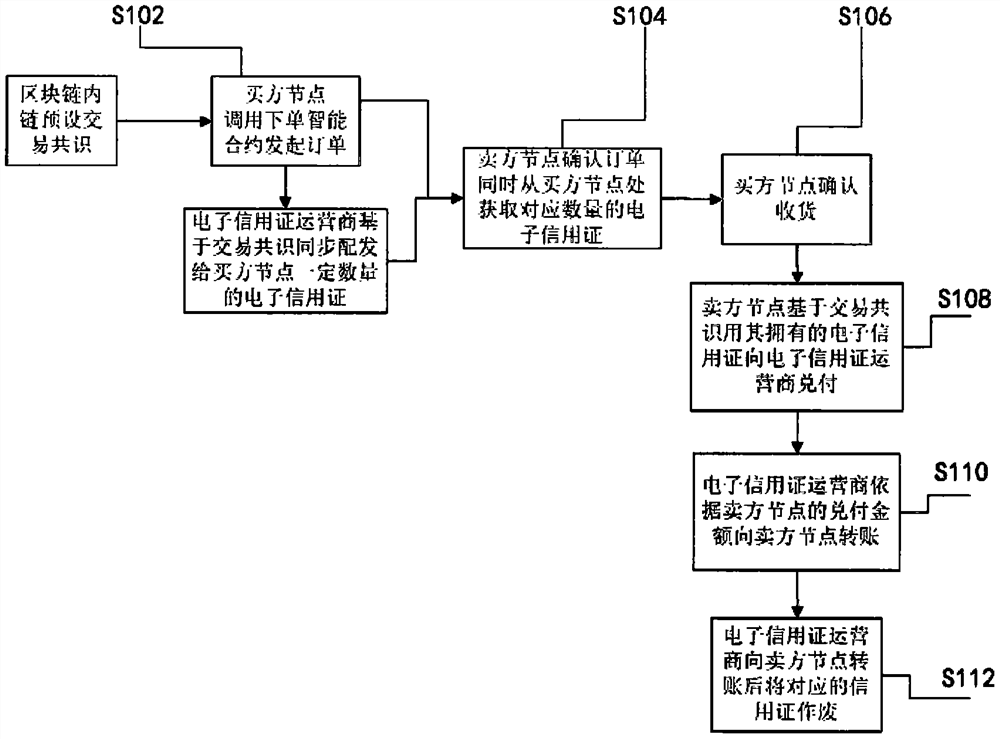
The invention discloses a credit card transaction method based on a block chain, which comprises a seller node, a buyer node and an electronic credit card operator node, and develops a transaction method capable of accurately tracing the state of each credit card so as to obtain the credit condition of the node by combining a block chain technology and an existing credit card technology. Further,when the buyer node or the seller node is learned to be dishonest, the electronic credit card operator node broadcasts the dishonest node information in the blockchain system; after three times of default, the electronic credit card operator node clears the node out of the blockchain internal chain, cancels the nodes in the blockchain and records the real names of the nodes in a dishonest list; according to the method, the transparency of the integrity of each node of the blockchain internal chain is improved, and the health and cleanness of the blockchain system environment are maintained, sothat the transaction security in the system is ensured, a guarantee is provided for credit card cashing, and the benefits of electronic credit card operator nodes are maintained.
Owner:链农(深圳)信息科技有限公司
RFID (Radio Frequency Identification) key ring capable of tracing and locating children
InactiveCN106073047AAvoid being stolenAvoid being abductedCo-operative working arrangementsKey-ringsEngineeringAluminum foil
The invention discloses an RFID (Radio Frequency Identification Device) key ring capable of tracing and locating children. The RFID key ring comprises a key ring body and is characterized in that the key ring body is of an annular hollow structure which is internally provided with an RFID antenna and chip tabling body assembly, wherein the RFID antenna and chip tabling body assembly comprises a PET hard base membrane arranged on the inner wall of a shell of the hollow structure, the PET hard base membrane is provided with an aluminum foil antenna, and the aluminum foil antenna is provided with a radio frequency chip. According to the key ring provided by the invention, by using the FRID antenna and chip tabling body assembly arranged in the hollow structure of the key ring, the function of remote identification is realized, information written in the key ring in advance can be read in a non-contact manner by virtue of readers at different positions, and information also can be written in the chip of the key ring, so that the phenomena that a child is stolen or abduct and traffic can be avoided before crime, and important tracks of the children can be provided in time after crime.
Owner:田艺儿
Safe well cover
InactiveCN102041817AAvoid being stolenPut an end to municipal traffic safety hazardsArtificial islandsUnderwater structuresBilgeEngineering
The invention discloses a safe well cover which comprises a well cover main body, a derailing switch, a locking device and the like, and is used for an underground bilge well cover, a subterranean cable well cover, underground tap water well cover, a gas conduit well cover and the like, and belongs to the technical field of municipal construction appliances. The well cover and a well mouth are locked and fastened by the locking device, therefore, the well cover is avoided from being stolen and losing, and the municipal traffic safety hazard is precluded.
Owner:王涛
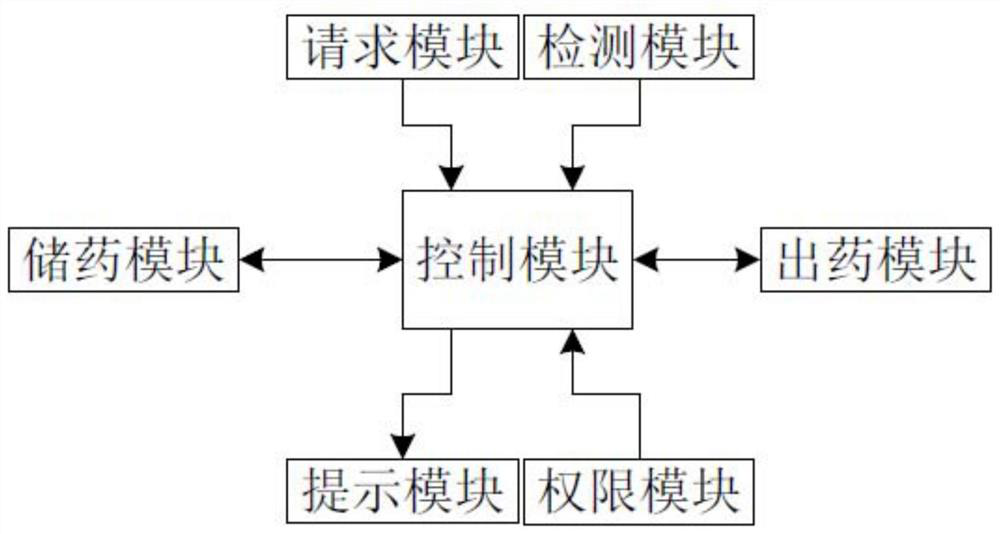
Intelligent medicine taking control system and method
InactiveCN112863055AAvoid taking and selling at willImprove accuracyDrug and medicationsApparatus for meter-controlled dispensingControl systemEngineering
The invention relates to the field of intelligent medicine box equipment, in particular to an intelligent medicine taking control system and method. The system comprises a medicine storage module, a medicine outlet module, an authority module and a control module, the medicine storage module is used for storing various medicines, the medicine storage module conveys the medicines to the medicine outlet module, and the medicine outlet module is used for providing medicines for user; the authority module is used for inputting and verifying identity information of the users, and the authority module sends an authority signal to the control module after verifying the identity information; the control module is used for opening the medicine storage module or the medicine outlet module according to the permission signal. According to the invention, the related authority of medicine placing or medicine taking is developed according to the authority signal, the medicine is prevented from being randomly taken out and sold by non-patient groups, the accuracy of medicine distribution objects is improved, and the effectiveness of later user data acquisition is ensured.
Owner:重庆未来健康管理有限公司 +1
Office table capable of achieving safe use of computer
InactiveCN105962637ASimple structureEasy to useOffice tablesWriting tablesOpen structureComputer engineering
The invention discloses a computer desk for safe use, which includes a computer desk body and a computer arranged on the computer desk body, a storage box is arranged on the computer desk body, and a storage box is arranged on one side of the storage box. Opening structure, the computer table body is also provided with a slot, one end of the slot extends into the storage box, and a horizontal conveying track is arranged below the slot, and the transporting track and the storage box The opening structure is arranged vertically, and the computer is arranged above the conveying track. The invention is simple in structure, easy to use, can effectively protect the safety of the computer, avoid being stolen, and guarantee property safety.
Owner:苏州盛开信息科技有限公司
Anti-theft vehicle-mounted ETC machine convenient to disassemble
InactiveCN112550178AProtect property safetyChange signal propagation range and strengthAnti-theft devicesIn vehicleEngineering
The invention discloses an anti-theft type vehicle-mounted ETC machine convenient to disassemble. The ETC machine comprises a convenient-to-disassemble main body, a convenient-to-disassemble device isarranged in the inner upper side of the convenient-to-disassemble main body, the convenient-to-disassemble device comprises a stabilizing cavity which is formed in the convenient-to-disassemble mainbody in a left-right penetrating mode and provided with a forward opening, and an anti-theft sliding groove with a forward opening is formed in a communicating mode. An anti-theft block is arranged inthe anti-theft sliding groove in a front-back sliding mode, an ETC machine body arranged in the stabilizing cavity in a front-back sliding mode is fixedly arranged in the center of the lower end faceof the anti-theft block, conveniently-disassembled sliding grooves with forward openings are formed in the left side and the right side of the upper portion of the anti-theft sliding groove in a communicating mode, and conveniently-disassembled sliding blocks provided with through holes and arranged in the upper sides of the left and right end surfaces of the anti-theft block are arranged in theconveniently-disassembled sliding grooves in a front-back sliding mode. According to the anti-theft device for the vehicle-mounted ETC, the sliding plate is controlled to slide up and down to drive aninserting rod to enter and exit from the through hole in the conveniently-disassembled sliding blocks so as to control the degree of freedom of the conveniently-disassembled sliding blocks, and then disassembly and assembly of the vehicle-mounted ETC are controlled.
Owner:石家庄纳逐贸易有限公司
Road well lid produced by utilizing waste residue and production method thereof
InactiveCN103951336AAvoid being stolenHigh compressive strengthSolid waste managementCompression moldingEnvironmental engineering
The invention relates to a road well lid produced by utilizing waste residue and a production method thereof. The road well lid is characterized by being prepared from the following raw materials in percentage by weight: 50%-60% of waste residue, 20%-30% of quartz sand and 20%-30% of 500# cement. Production steps are as follows: (1), stirring raw materials and 0.12% of water into a material mixture; (2), digesting the material mixture; (3), carrying out compression molding to obtain a well lid blank; (4), carrying out autoclaved curing at a high temperature of 200 DEG C under high pressure of 1.3 MPa; (5), detecting outline and quality, grading and piling up; (6), recycling after clearing. According to the invention, beneficial effects are as follows: the road well lid is produced by utilizing the waste residue, and the road well lid is prevented from being stolen as no recycling utilization value exists; compressive strength and rupture strength are good; the road well lid is durable in use, and the preparation is simple and practical.
Owner:黄俞霖
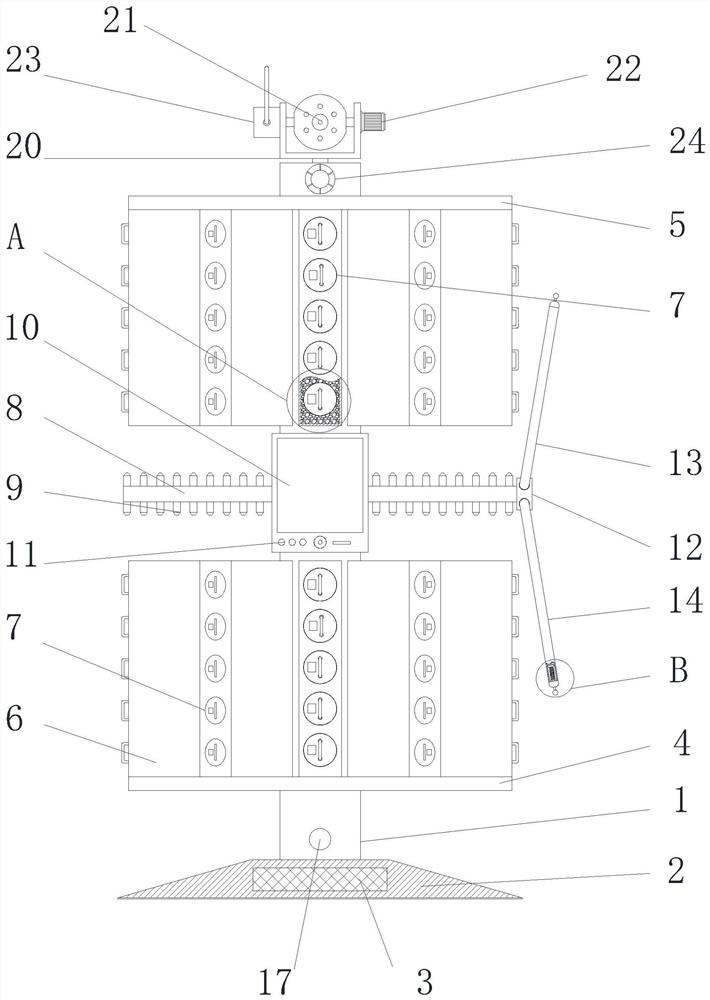
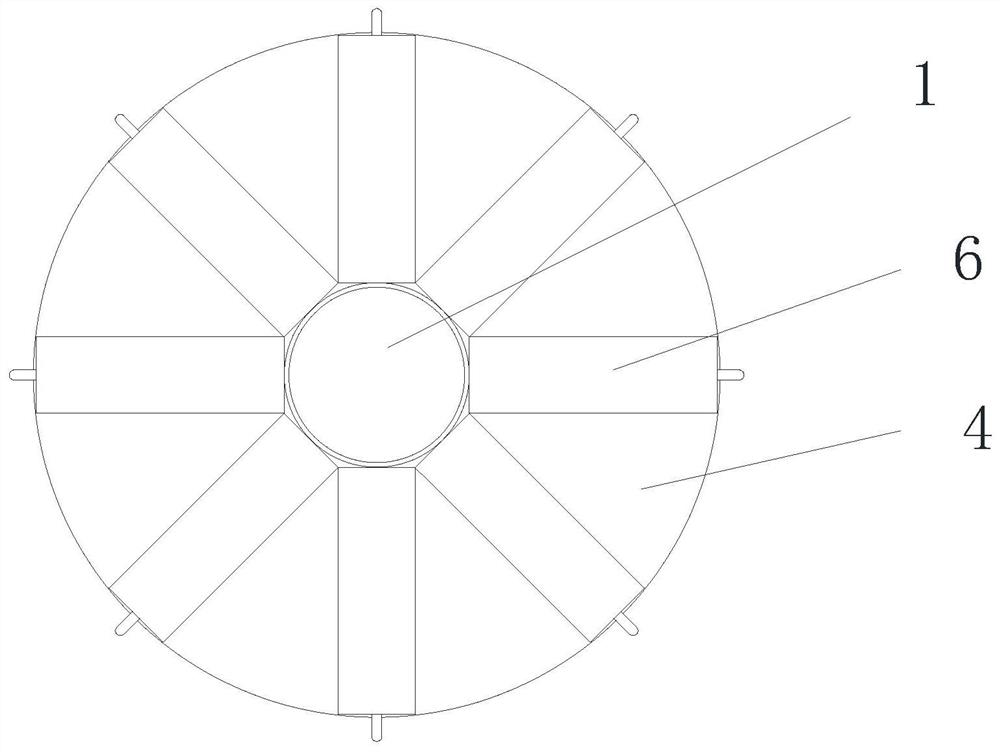
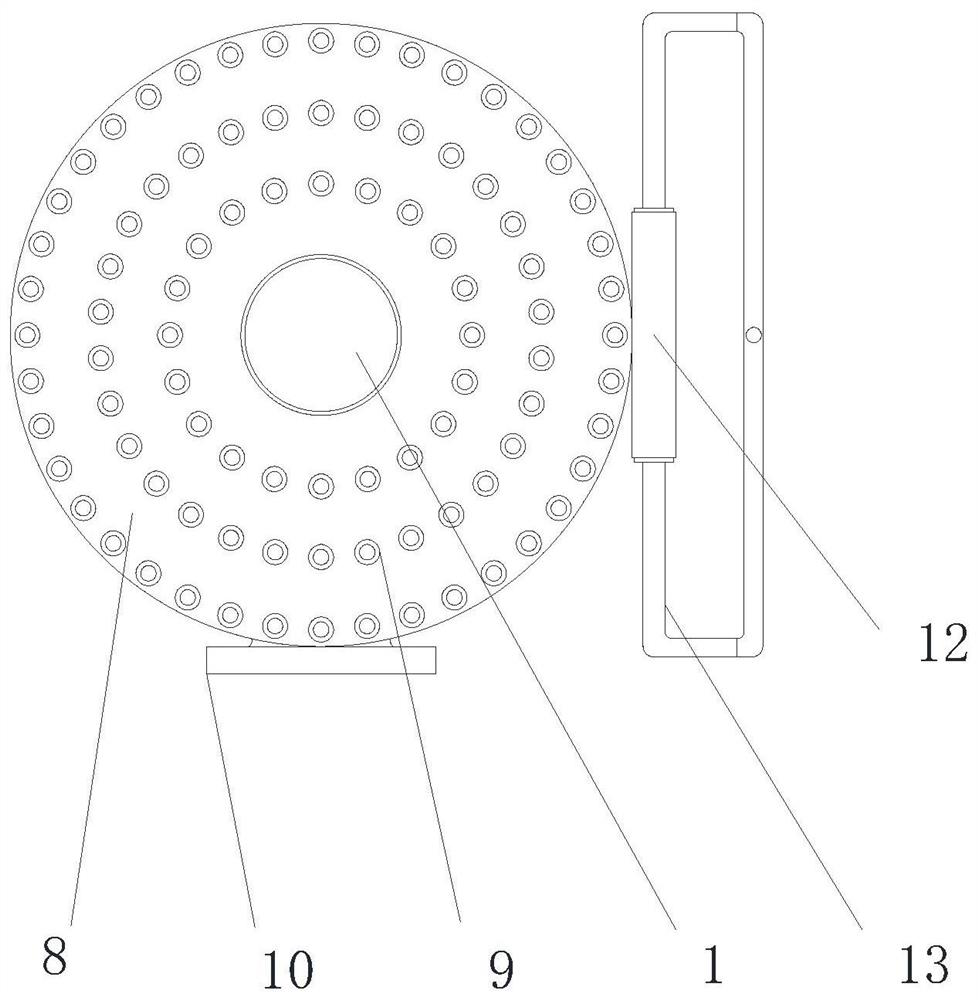
A security device for classified management of intellectual property rights
ActiveCN112046167BIncrease ground areaAvoid being stolenData processing applicationsFiling appliancesComputer hardwareIntellectual property
A safety device for classified management of intellectual property rights, including a column, a folder holder module and a monitoring anti-theft warning module. A bottom round platform is arranged in the middle of the lower end of the column, and the first class A classification disk is connected to the lower part of the column through bearing rotation, and the upper part of the column is connected to it through bearing rotation. There is a second A-level sorting tray, a number of rectangular B-level sorting boxes are provided at the opposite ends of the first A-level sorting tray and the second A-level sorting tray, and a number of C-level sorting boxes are slidingly connected to the end of the rectangular B-level sorting box away from the column. Cylinder; the structure of the present invention is stable, and can be quickly previewed through the display, avoiding time-consuming and laborious search for closely guarded physical documents, clear and clear classification management and storage of documents, easy to retrieve, view and organize, and has good fireproof insulation High temperature performance, good fire extinguishing effect, false triggering of the alarm will not damage the file, excellent security, it is convenient to hold and watch the data file, and it is safe and convenient to carry, and can be flexibly monitored for anti-theft.
Owner:合肥皖臻科技有限公司
Remote monitoring device for municipal drainage pipelines
InactiveCN107366309AAvoid lostAvoid being stolenArtificial islandsUnderwater structuresRemote controlEngineering
The invention discloses a remote monitoring device for municipal drainage pipelines. The remote monitoring device comprises a base, a pipeline opening and a pipeline opening cover, wherein the base is fixedly arranged at the end part of the pipeline opening and is fixedly sheathed with the pipeline opening; the pipeline opening is arranged at the center of the base and is internally provided with a limiting seat by the base; the pipeline opening cover is fixed with the inner part of the pipeline opening by a limiting seat; the inner part of the base, corresponding to the top part of the pipeline opening cover, is provided with an installing groove; the installing groove, corresponding to the installing groove, is provided with an electronic lock; the inner wall of the base, corresponding to the electronic lock, is provided with a touch alarm; the input end of the electronic lock is connected with a remote control device; the input end of the remote control device is electrically connected with a storage battery; and the storage battery and the remote control device are fixedly arranged in the base. The remote monitoring device disclosed by the invention has the advantages that the structure is simple, and the anti-theft function is strong, so that the phenomenon that the pipeline opening cover is stolen can be effectively avoided and the road-driving safety can be improved.
Owner:JIANGSU DONGHENG DADI ENG TECH
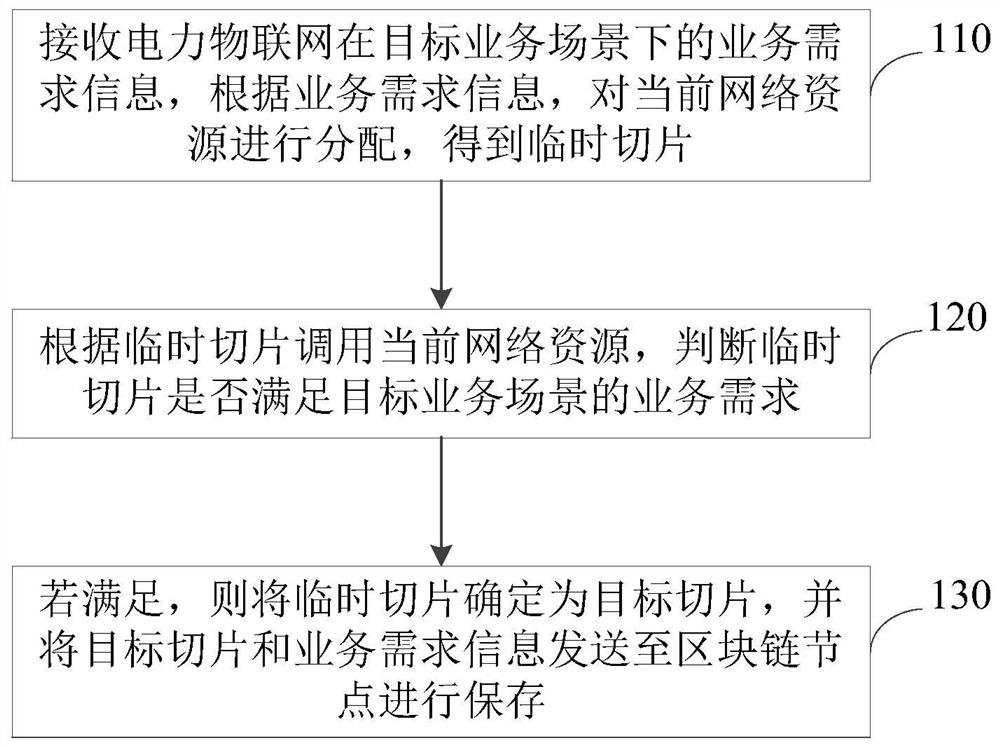
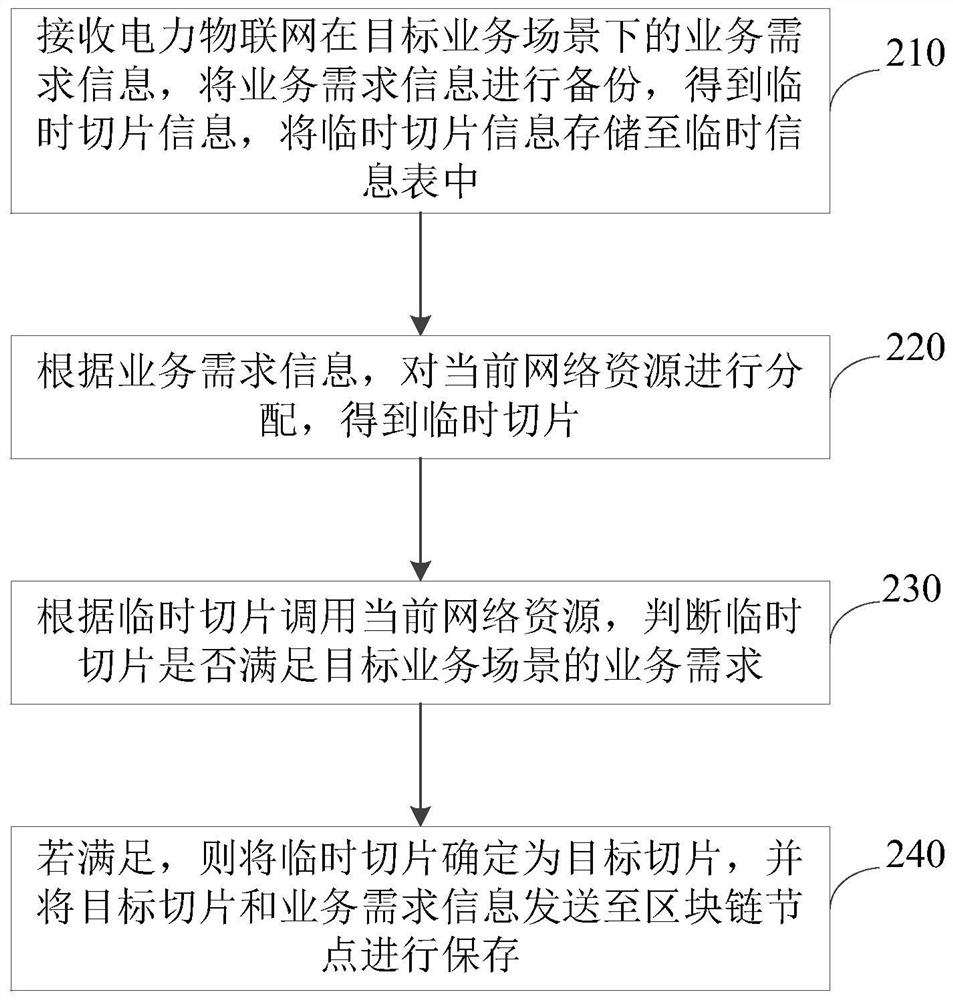
Network slice determination method and device, electronic equipment and storage medium
PendingCN113381889AImprove determination efficiencyImprove the determination accuracyService provisioningData switching networksComputer hardwareEngineering
The embodiment of the invention discloses a network slice determination method and device, electronic equipment and a storage medium. The method comprises the following steps: receiving service demand information of the power Internet of Things in a target service scene, and allocating current network resources according to the service demand information to obtain a temporary slice; calling a current network resource according to the temporary slice, and determining whether the temporary slice meets a service requirement of the target service scene or not; and if so, determining the temporary slice as a target slice, and sending the target slice and the service demand information to a blockchain node for storage. The temporary slice is generated, and after the temporary slice is detected, the temporary slice is stored in the blockchain as the target slice, so that it is ensured that the network slice in the blockchain is correct and is prevented from being tampered, and thus, the slice determination precision and the slice security are improved.
Owner:QINGYUAN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD
Method, device and system for terminal, server and account security login
The application provides an account security login method. The method comprises the steps of obtaining a cipher inputted by a user; utilizing an encryption algorithm to encrypt the cipher inputted by the user to form the ciphertext information; taking the ciphertext information as the current cipher of the user to send to a server; receiving the feedback information of the server; according to the feedback information, executing a login operation. During the sending process, when other users capture a weblog to obtain the account and the cipher of the user with the help of tools, the obtained cipher is just the encrypted cipher, and the cipher inputted by the user is not obtained, thereby effectively avoiding a phenomenon that the user information is stolen, and guaranteeing the security of the user information.
Owner:シェンジェンインムーテクノロジーシーオーエルティーディー
Automotive label assembly and automobile
InactiveCN109353290AAchieve fixationRealize anti-theftVehicle componentsControl systemPulp and paper industry
The invention relates to an automobile, in particular to an automotive label assembly and an automobile. The automotive label assembly comprises: a label body mounted on a housing and a mounting postfixed coaxially to the label body; the housing is provided with a mounting hole in rotational fit with the mounting post; the mounting post is also provided with two positioning protrusions mutually fastened to the housing; part of the mounting hole is extended out to form two hollowed-out portions; the two positioning protrusions are mutually separated from the housing via the two hollowed-out portions. The automotive label assembly also includes: two electronic locks arranged on the housing; a master control system of the automobile is used for locking or unlocking the two electronic locks at the same time; when unlocked, the two electronic locks allow inner cylinders to be popped out respectively; the cylinder of any electronic lock is used for holding one positioning protrusion in therotational direction of the mounting post. Compared with the prior art, the automotive label assembly and the automobile have the advantages that the cylinders of the two electronic can be popped outto ensure that the two positioning protrusions never separate from the housing, and antitheft of the automotive label is implemented.
Owner:SHENZHEN POLYTECHNIC
Automobile logo assembly and automobile
InactiveCN109353290BAvoid being stolenAnti-theftVehicle componentsControl systemMechanical engineering
The invention relates to an automobile, in particular to an automotive label assembly and an automobile. The automotive label assembly comprises: a label body mounted on a housing and a mounting postfixed coaxially to the label body; the housing is provided with a mounting hole in rotational fit with the mounting post; the mounting post is also provided with two positioning protrusions mutually fastened to the housing; part of the mounting hole is extended out to form two hollowed-out portions; the two positioning protrusions are mutually separated from the housing via the two hollowed-out portions. The automotive label assembly also includes: two electronic locks arranged on the housing; a master control system of the automobile is used for locking or unlocking the two electronic locks at the same time; when unlocked, the two electronic locks allow inner cylinders to be popped out respectively; the cylinder of any electronic lock is used for holding one positioning protrusion in therotational direction of the mounting post. Compared with the prior art, the automotive label assembly and the automobile have the advantages that the cylinders of the two electronic can be popped outto ensure that the two positioning protrusions never separate from the housing, and antitheft of the automotive label is implemented.
Owner:SHENZHEN POLYTECHNIC
A road manhole cover made of waste residue and its preparation method
InactiveCN103951336BAvoid being stolenHigh compressive strengthSolid waste managementEnvironmental engineeringUltimate tensile strength
The invention relates to a road manhole cover made of waste residue and a preparation method thereof. Its characteristics are: calculated by weight percentage, it is composed of the following raw materials: 50%-60% of waste residue, 20%-30% of quartz sand, and 20%-30% of 500-grade cement. The preparation steps are: (1) mixing raw materials and 0.12% water to form a mixture; (2) digesting the mixture; (3) pressing and forming the manhole cover blank; (5) Carry out appearance and quality inspection, and stack them in grades; (6) Reuse after cleaning. The beneficial effects of the present invention are: the present invention uses the waste residue to make the road manhole cover, which not only avoids theft and loss because of no recycling value; but also has good compressive and flexural strength; it is also durable, and its preparation method is simple and easy OK.
Owner:黄俞霖
Computer handle device
InactiveCN101241385BTo achieve the purpose of anti-theftAvoid being stolenWing handlesConstruction fastening devicesEngineeringElectrical and Electronics engineering
A computer handle device comprises a handle and a pair of fixation assemblies for fixing the handle rotating set on the two side walls of the computer base. The handle comprises a beam and a pair of folding slices disposed at the two ends of the beam. A lock pore is disposed at one end of the pair of folding slices of the handle. The computer handle device also comprises a coded lock which is disposed on one side wall of the base corresponding to the folding slice with the lock pore. The coded lock comprises a movable tenon which extends into the lock pore of the handle to lock the handle when the handle rotates to a position that the beam of the handle is above the upper cover of the computer. The handle of the computer handle device can adjust rotating angle according to requirement. The tenon of the coded lock can extend into lock pores at different position of the terminal of the handle selectively to lock the handle. When the handle rotates to and is locked at a position above the upper cover of the computer, the upper cover of the computer is blocked by the beam and can not be opened, so that computer data and important images are prevented to be stolen, so as to implement an antitheft objective.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Application authentication system and authentication method
ActiveCN109255207BEnsure controllabilityEnsure safetyProgram/content distribution protectionApplication procedureEngineering
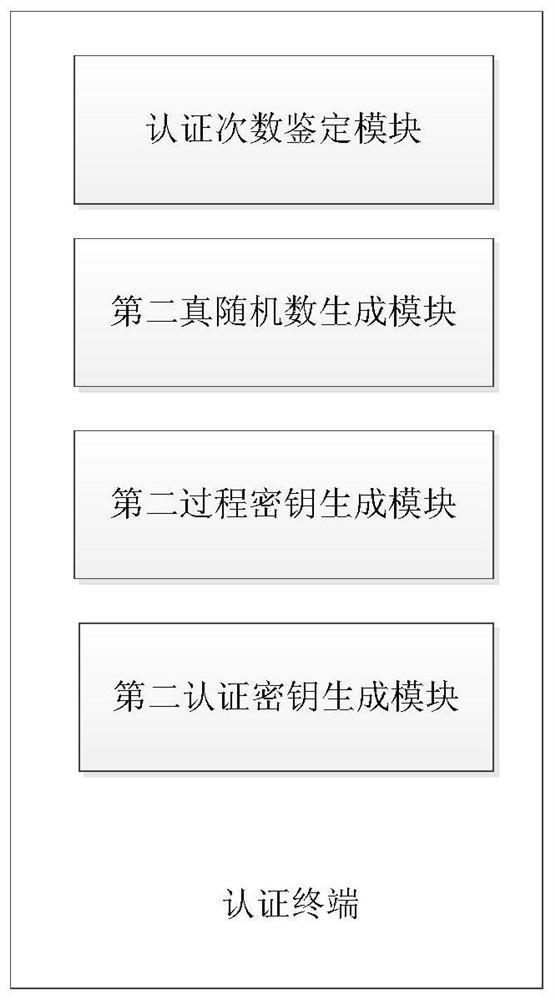
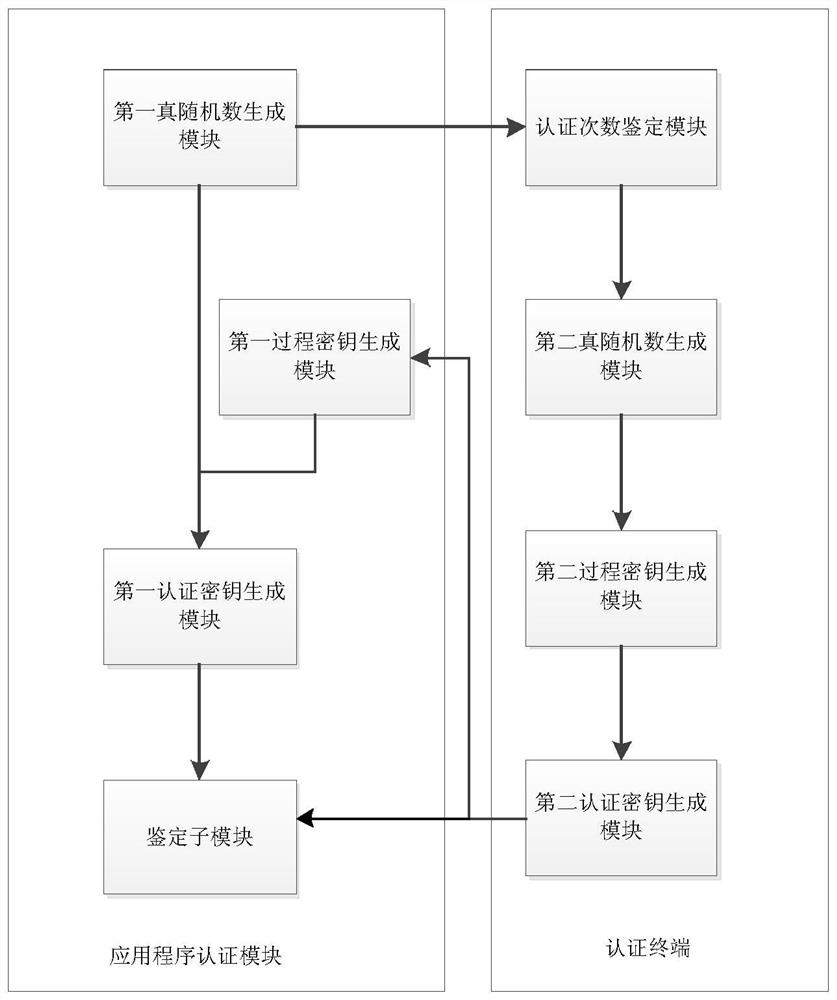
The invention provides an application program authentication system and an authentication method. The authentication system includes an authentication terminal and an application program authentication module. The application program authentication module includes a first true random number generating module for generating a first true random number; according to the first true random number A first authentication key generation module that generates a first authentication key with the second true random number obtained from the authentication terminal; an authentication submodule that compares whether the first authentication key is consistent with the second authentication key obtained from the authentication terminal . The authentication terminal includes: a second true random number generation module for generating a second true random number; an authentication times identification module for comparing the number of times the application is used with a preset upper limit; A second authentication key generation module that generates a second authentication key. The technical solution provided by the present invention ensures the security of the application scope provided by the application developer and the controllability of the usage times.
Owner:STATE GRID SHANGHAI ENERGY INTERCONNECTION RES INST CO LTD
Gas concentration and temperature state monitoring device and method
PendingCN113701806AAvoid exposureAvoid being stolenMeasurement devicesNetwork topologiesComputer monitoringEngineering
The invention provides a gas concentration and temperature state monitoring device and method. The method comprises the following steps of enabling part of sample flue gas in a flue to pass through a mixed gas flow cell and then enter a constant flow device for constant flow; then using a gas concentration sensor which is arranged in the constant current device and adopts the Wheatstone bridge principle to sample the concentration information of the gas in the sample flue gas and transmit the concentration information to a processor, and using a general temperature sensor arranged in the constant current device to sample the temperature information of the gas in the sample flue gas and transmit the temperature information to the processor; using the processor to respond the gas concentration state information in the flue gas transmitted by the processor to a single chip microcomputer or a computer monitoring system through a WIFI module; configuring the tasks of a WIFI router serving as a network element, storing the information in a differentiated manner, so that the application efficiency of the software and hardware of the WIFI router is better, the integrity of the concentration state information of the gas in the smoke stored by the single WIFI router is reduced, and the confidentiality is improved.
Owner:南京三鸣智自动化工程有限公司
A kind of offline payment method and system based on TOTP algorithm
ActiveCN107818463BAvoid being stolenGuaranteed payment securityKey distribution for secure communicationPayment schemes/modelsPaymentUser identifier
Owner:九派天下支付有限公司
Control circuit board integrated with face recognition function
PendingCN111867251AAvoid being stolenAchieve the advantages of face recognitionCasings/cabinets/drawers detailsDigital data authenticationDisplay deviceControl theory
The invention discloses a control circuit board integrated with a face recognition function. The control circuit board comprises a control circuit board body, and the top of the left side of the control circuit board body is fixedly connected with a power line. The top of the left side of the front surface of the control circuit board body is fixedly connected with a display screen, the top of theright side of the front surface of the control circuit board body is fixedly connected with a camera, the left side of the center of the front surface of the control circuit board body is fixedly connected with an operation panel, and the top of the front surface of the operation panel is fixedly connected with a micro-display. According to the invention, the display screen, the camera, the operation panel, the micro-display, operation buttons, a protection box, a data storage card, the processor, a protection shell, a comparison module, a heat dissipation groove and a dustproof net cooperatewith one another, the advantage of face recognition of the control circuit board is achieved, when the control circuit board is used, face recognition unlocking can be conducted on the control circuit board, and data are prevented from being stolen and lost.
Owner:深圳市骏威实创电子有限公司
Quick integration method of electronic certificate exchange platform based on block chain
PendingCN114398674ATransparent and reliable interactionEnsure safetyDatabase distribution/replicationDigital data protectionIdentity recognitionData retrieval
The invention discloses a quick integration method of an electronic certificate exchange platform based on a block chain, and relates to the technical field of electronic certificate exchange platforms, comprising the following steps: S1, storing an electronic certificate; s2, authenticating the identity; s3, generating an electronic certificate request; s4, voucher data retrieval; s5, generating an electronic certificate; and S6, evaluating user credit. According to the rapid synthesis method of the electronic certificate exchange platform based on the block chain, consistency, integrity and security of electronic certificate data can be ensured, complete trustworthiness of the data can be ensured, cross-bank efficient traceability query can be performed on the data, and a very safe user identity verification system is provided; the biological information of the user is used as replacement information of a digital password in traditional identity verification, the characteristics that the biological information is not repeated and similar information cannot be changed are achieved, the system randomly generates a section of identity identification code for each user to serve as a unique certificate for subsequent user identity verification in the system, and the situation that the identification codes are similar is avoided.
Owner:深圳市博源电子商务有限公司
A protective isolation net structure to prevent theft of building materials
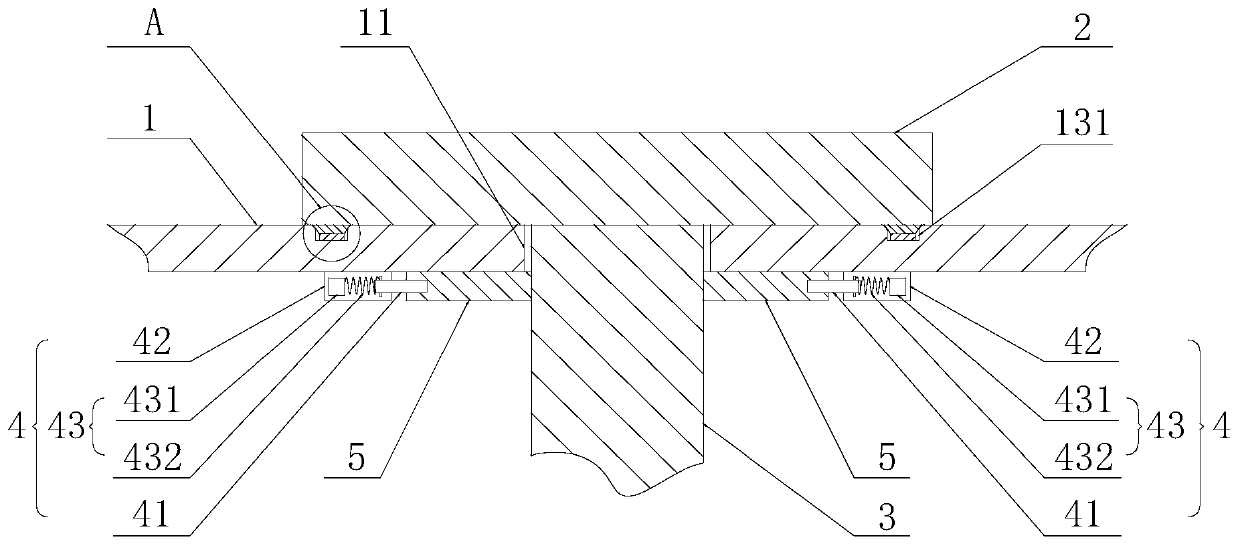
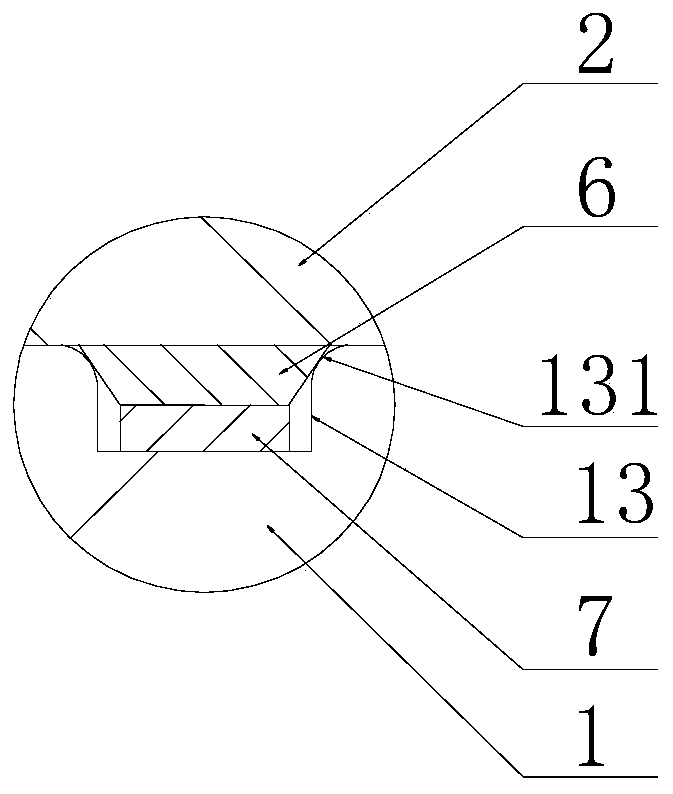
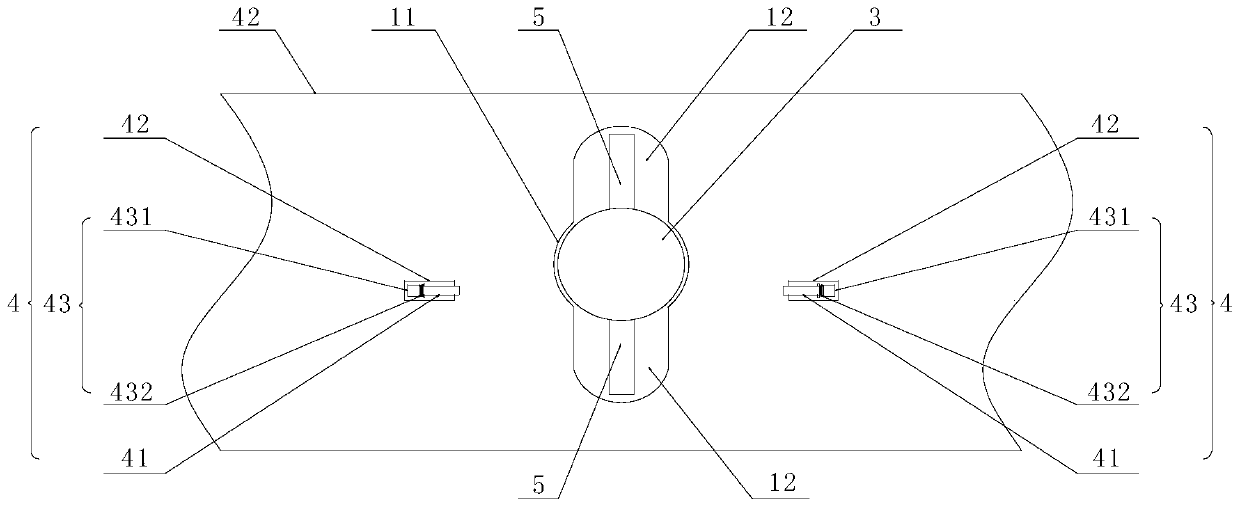
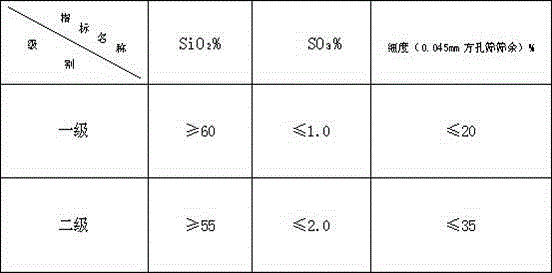
ActiveCN112681748BEasy to storeEasy accessTelevision system detailsColor television detailsFixed frameLocking mechanism
Owner:天长市市政建筑有限责任公司
Intelligent control system based on intelligent home local cloud housekeeper technology
PendingCN113110077AImplement backup storageImplement encryptionComputer controlTotal factory controlWired communicationEmbedded system
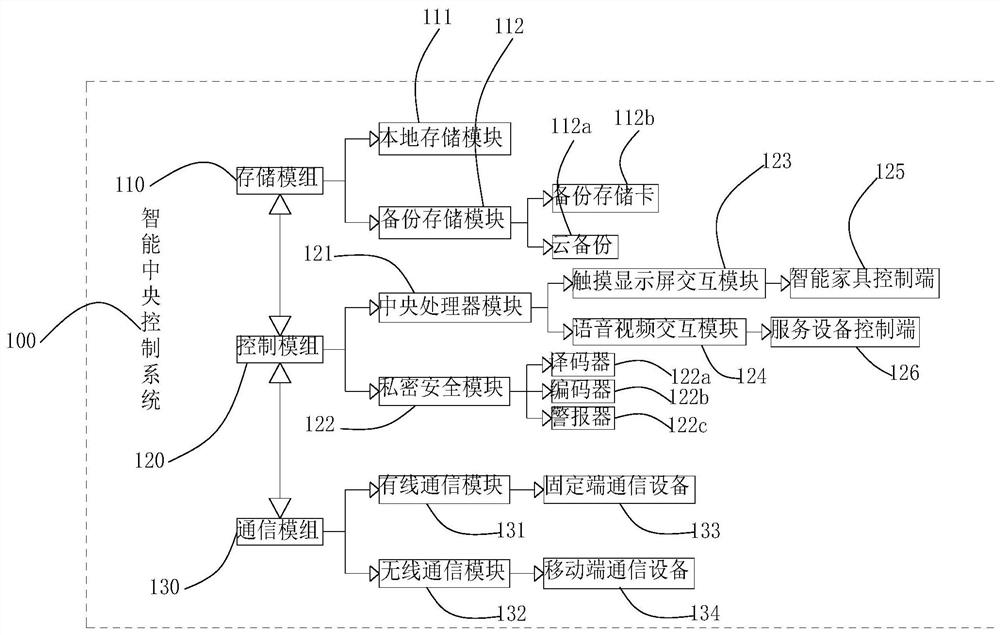
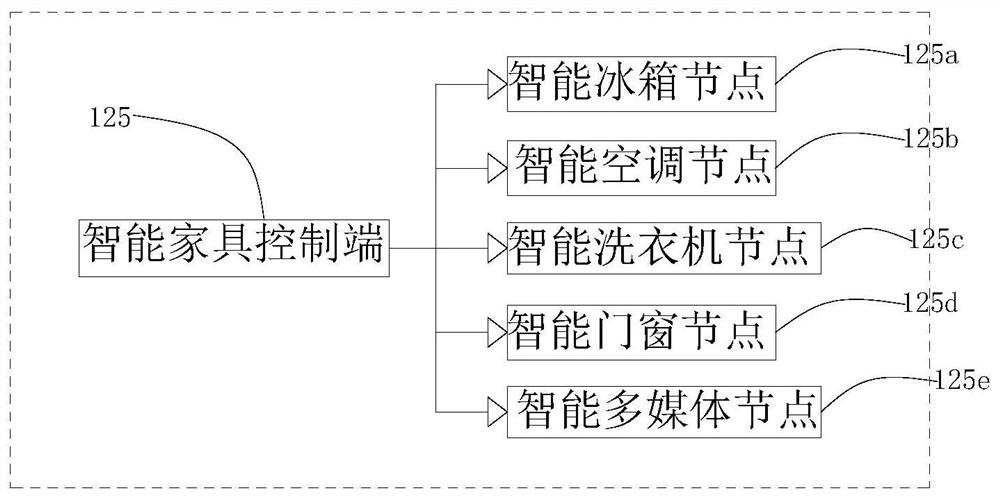
The invention provides an intelligent control system based on an intelligent home local cloud housekeeper technology, which comprises an intelligent central control system and is characterized in that the intelligent central control system comprises a storage module, the storage module comprises a local storage module and a backup storage module, the storage module is in telecommunication connection with a control module, the control module comprises a central processing unit module and a private security module, the central processing unit module is electrically connected with a communication module, the communication module comprises a wired communication module and a wireless communication module, and data interaction is implemented between every two of the storage module, the control module and the communication module. According to the invention, the intelligent home service system realizes more perfect and intelligent home service, not only relates to home service, but also can cover community service, and has the advantages of safety, privacy, health, convenience, warmth, inheritability and the like for users.
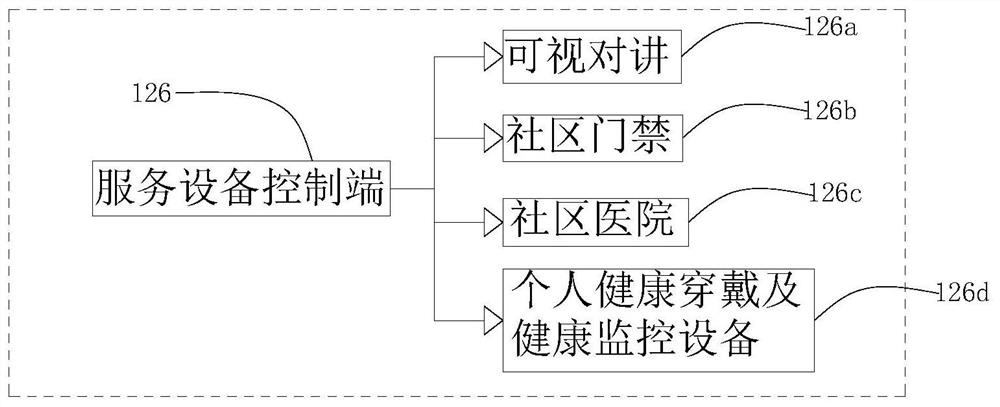
Owner:NANJING IOT SENSOR TECH
Classified storage equipment for financial archives on expressway
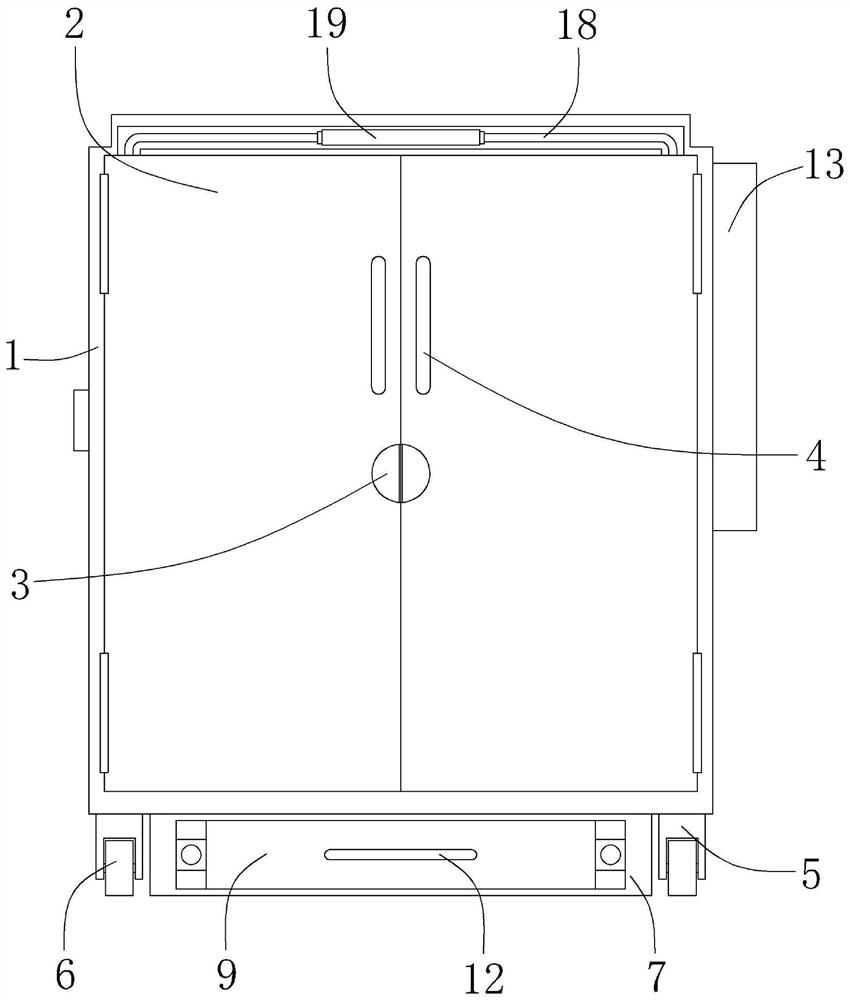
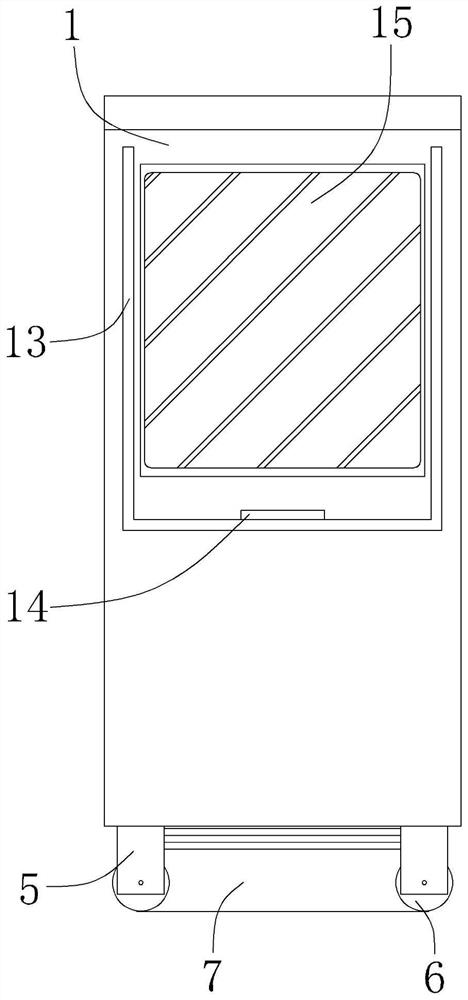
PendingCN114847664AWill not shiftRaise your heightBook cabinetsBurglar alarmElectric machineryStructural engineering
The highway financial archive classified storage equipment comprises a cabinet body, a cabinet door connected to the front end surface of the cabinet body through a hinge and a base connected to the lower surface of the cabinet body, a door lock is installed in the middle of the front end surface of the cabinet door, and a first notch is formed in the base; a heightening plate is arranged in the first notch, a protective rod is connected to the upper surface of the connecting block, an infrared distance meter is installed in the middle of the outer surface of the protective rod, an inner plate is connected to the interior of the cabinet body, a placement box is arranged on the inner side of the inner plate, and a motor embedded into the inner plate is connected to the outer surface of the placement box. And inner cavities are formed in the placement box at equal angles. According to the device, by arranging a series of structures, files can be orderly classified and stored through the device so as to be conveniently taken out subsequently, meanwhile, the files can be taken and placed more safely, the situation that the files are stolen can be avoided, and the safety is high.
Owner:白涛
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com