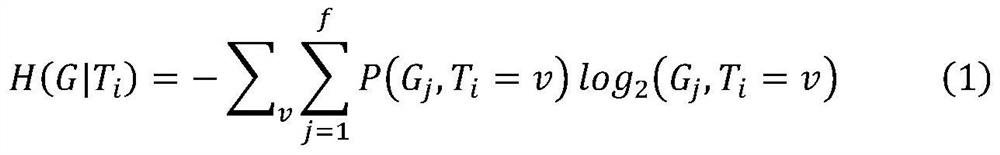Patents
Literature
38results about How to "Reduce computing energy consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
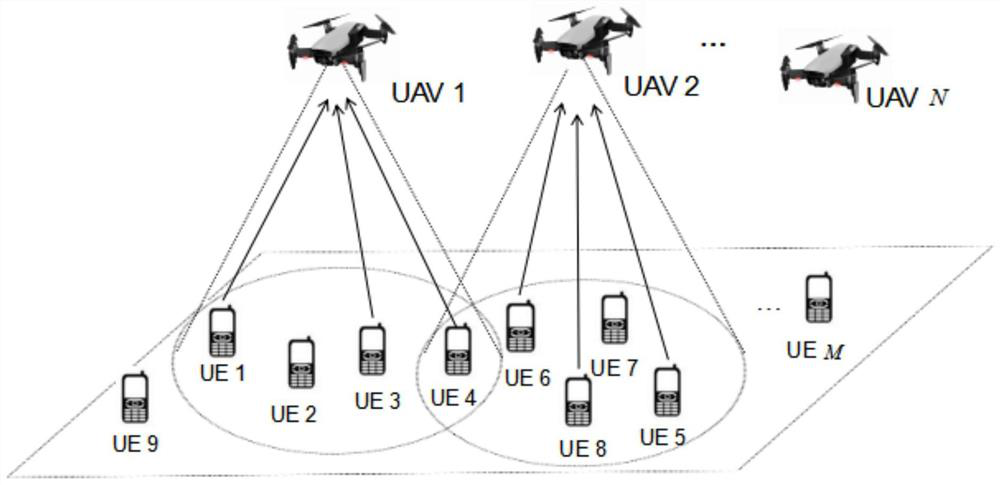
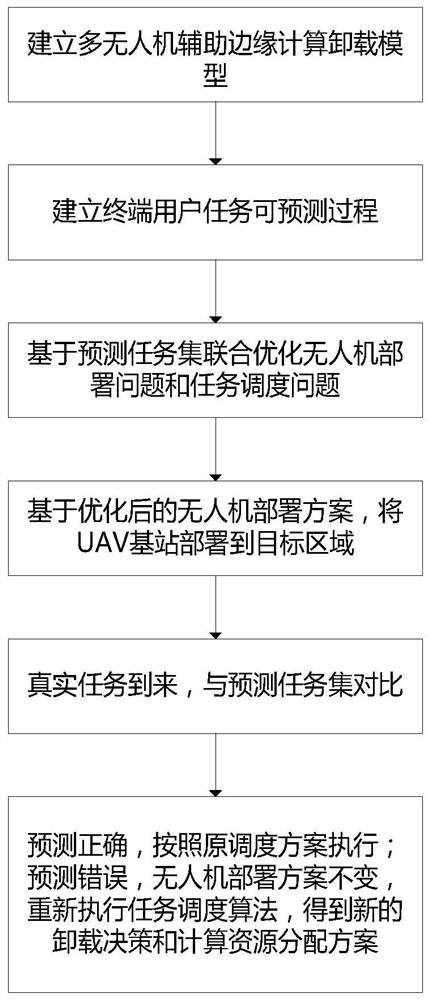
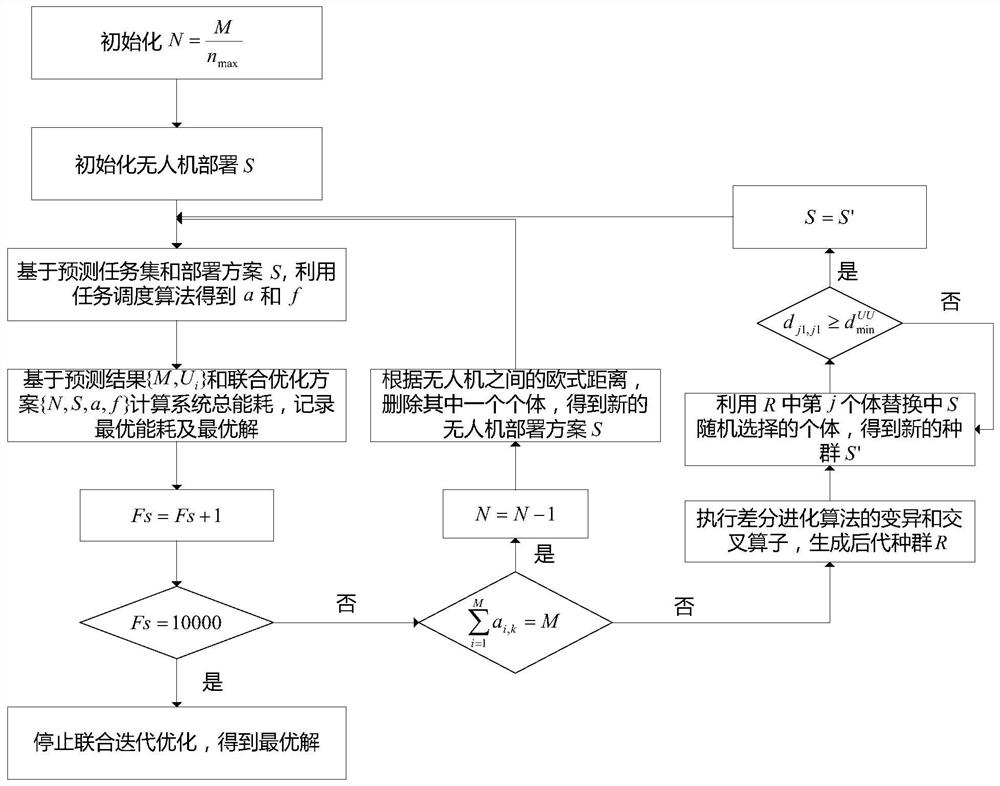
Multi-unmanned aerial vehicle auxiliary edge computing resource allocation method based on task prediction
ActiveCN112351503AReduce response delayReduce energy consumption while hoveringHigh level techniquesWireless communicationEnergy consumption minimizationResource assignment
The invention discloses a multi-unmanned aerial vehicle auxiliary edge computing resource allocation method based on task prediction. The method comprises the following steps of: firstly, modeling a communication model, a computing model and an energy loss model in an unmanned aerial vehicle auxiliary edge computing unloading scene; modeling a system total energy consumption minimization problem of the unmanned aerial vehicle auxiliary edge computing unloading network into task predictable process of terminal devices; obtaining prediction model parameters of different terminal devices by adopting centralized training through accessing historical data of the terminal devices; obtaining a prediction task set of the next time slot by utilizing the prediction model based on the task information of the current access terminal devices; and based on the prediction task set, decomposing an original problem into an unmanned aerial vehicle deployment problem and a task scheduling problem for joint optimization. The response time delay and completion time delay of the task can be effectively reduced through the deep learning algorithm, so that the calculation energy consumption is reduced; anevolutionary algorithm is introduced to solve the problem of joint unmanned aerial vehicle deployment and task scheduling optimization, the hovering energy consumption of the unmanned aerial vehicleis greatly reduced, and the utilization rate of computing resources is increased.
Owner:DALIAN UNIV OF TECH
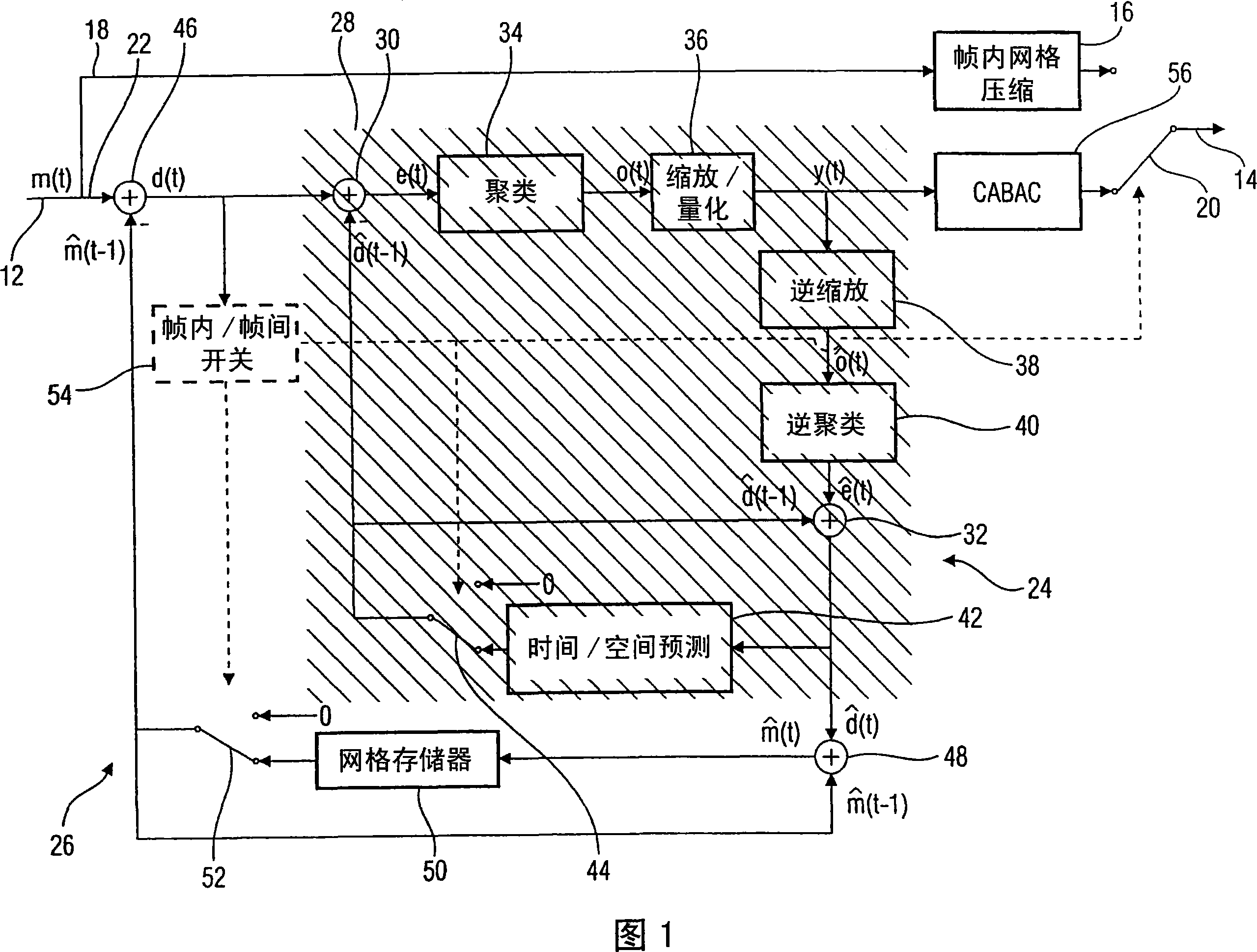
Coding scheme for a data stream representing a temporally varying graphics model
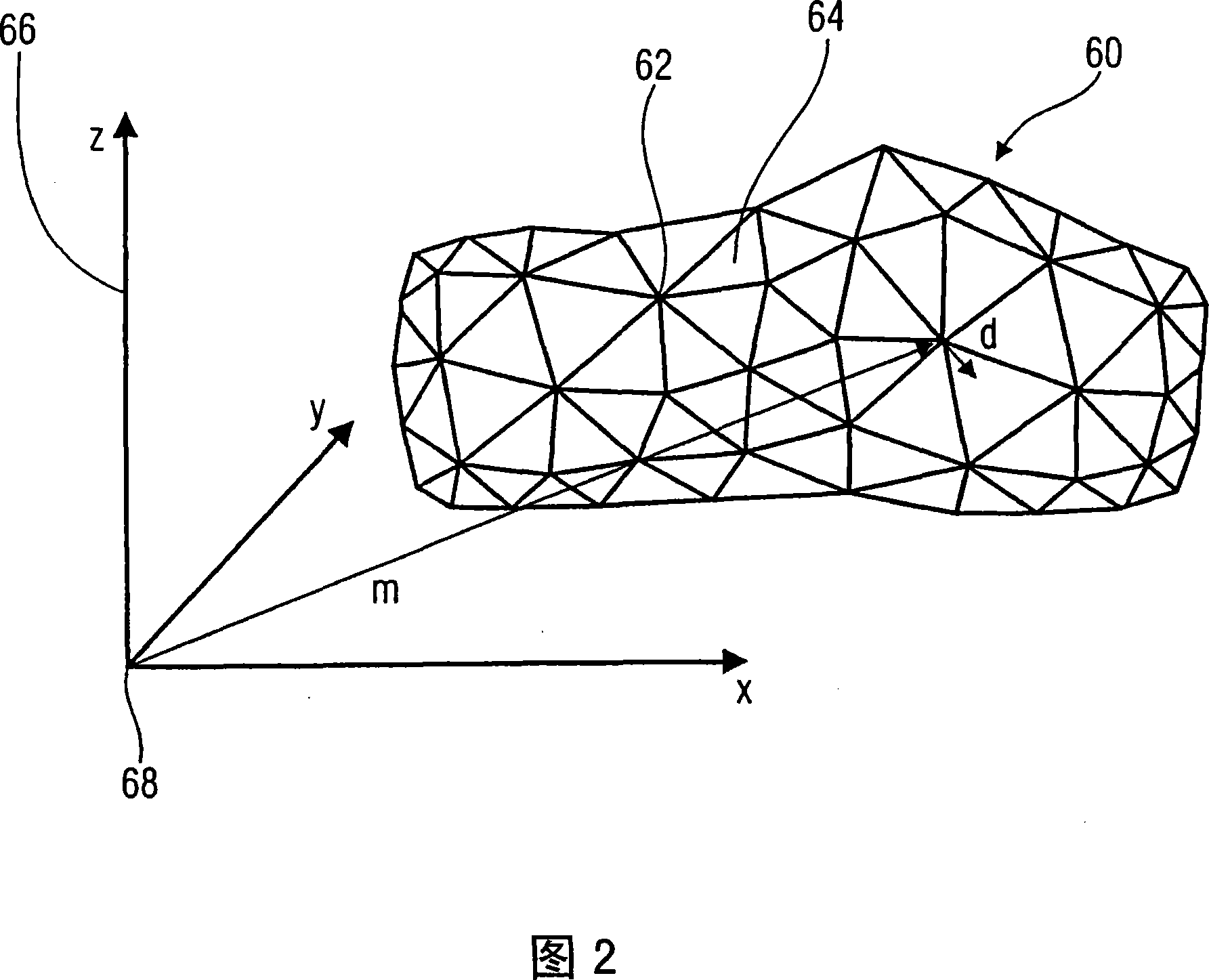
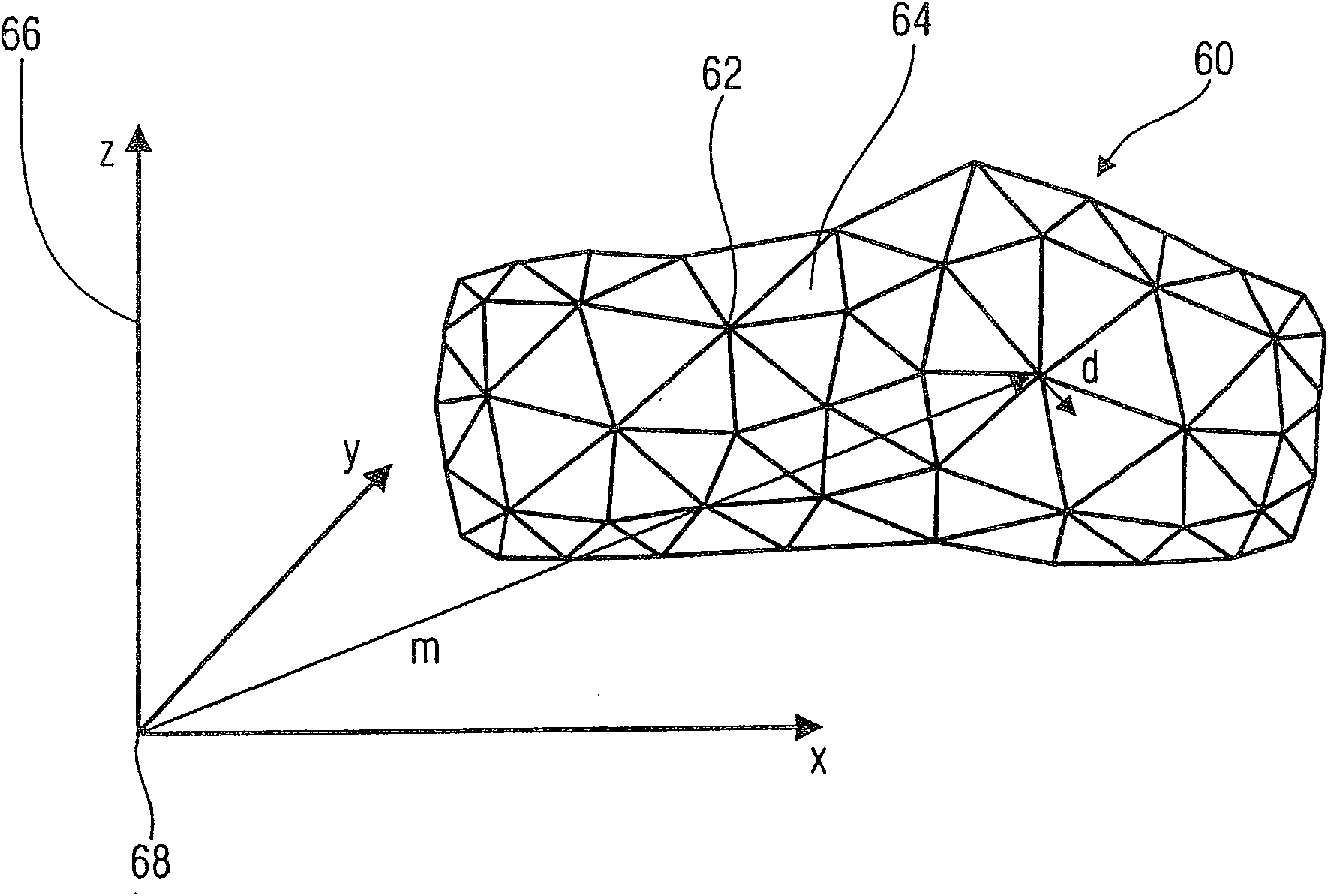
ActiveCN101061515AReduce computing energy consumptionSmall compression lossImage codingTelevision systemsGraphicsData stream
To rapidly retrieve and specify a product including a specific component from data on production results, and to output a retrieval result with priority order set in the case that a plurality of candidates are retrieved. In this product data retrieval system, data of a product configuration are produced from data on work results and are stored so as to rapidly specify the product including the specific component, and the rapid retrieval related to the product is performed by use of it. In the case that the plurality of candidates can be specified and cannot be narrowed down to one candidate, strong / weak data on possibility are imparted by totaling frequency of the possibility to perform the retrieval.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
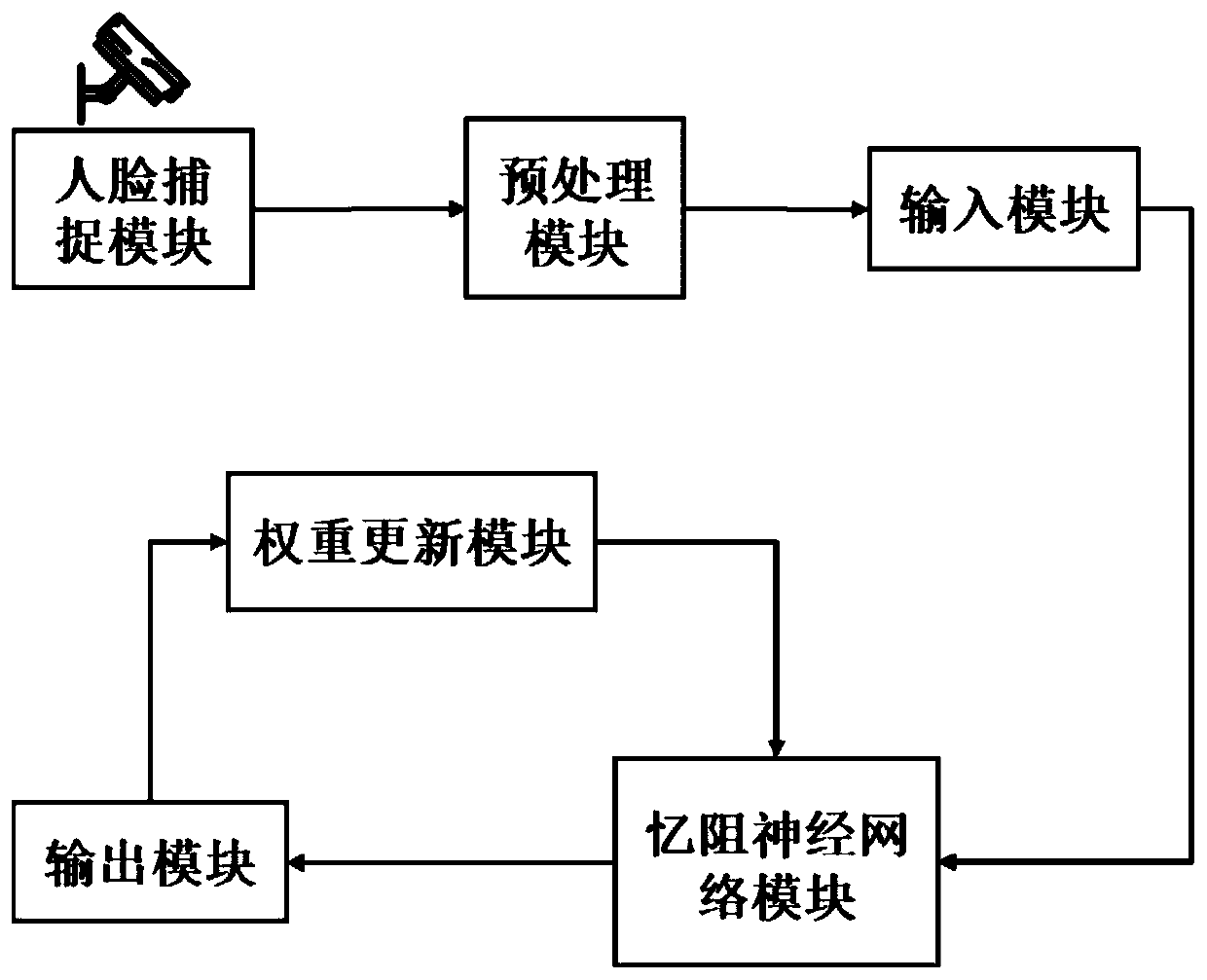
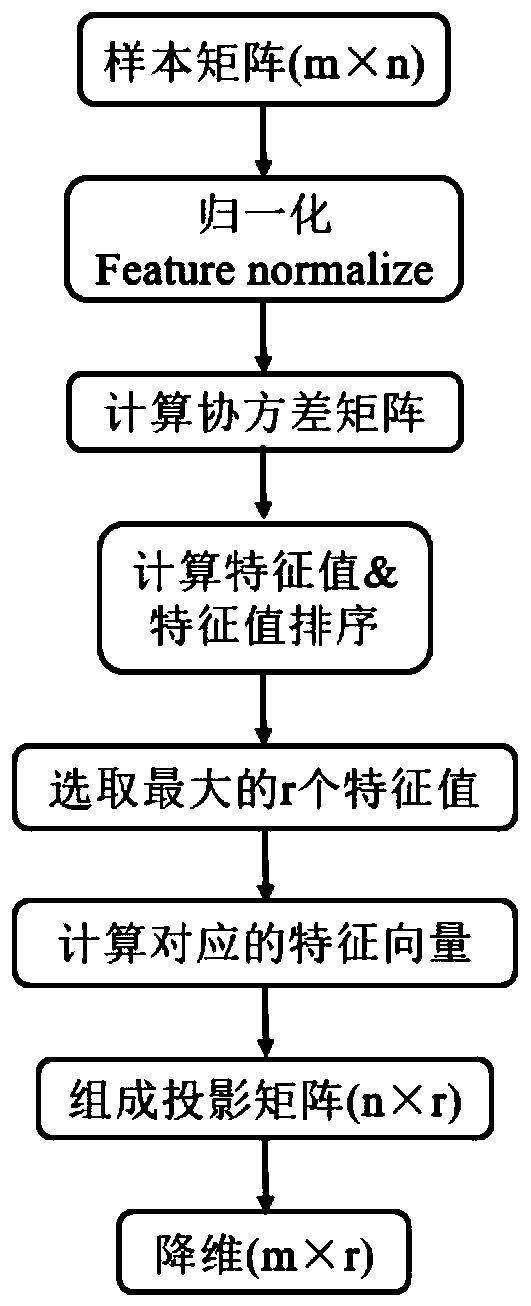
Neural network face recognition system based on memristor
InactiveCN110443168AShorten speedSmall structureCharacter and pattern recognitionNeural architecturesNerve networkMachine learning
The invention discloses a neural network face recognition system based on a memristor. The neural network face recognition system comprises a face capture module, a preprocessing module, an input module, a memristor neural network module, an output module and a weight updating module. The face capture module is used for capturing a face picture in the picture; the preprocessing module is used forcarrying out dimension reduction processing on the face picture; the input module is used for converting the picture subjected to dimension reduction into an electric signal; the memristor neural network module is used for storing network weights, carrying out matrix vector multiplication operation on the electric signals and transmitting an operation result to the output module; the output moduletransmits the operation result to a weight updating module for weight updating, and transitting the updated weight to a memristor neural network module, and the output module reads an identificationresult of the network; the memristor neural network module is composed of a memristor array. The structure scale of the memristor neural network is reduced by utilizing a principal component analysisalgorithm, so that the operation speed is increased, the operation energy consumption is reduced, and the hardware cost is reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
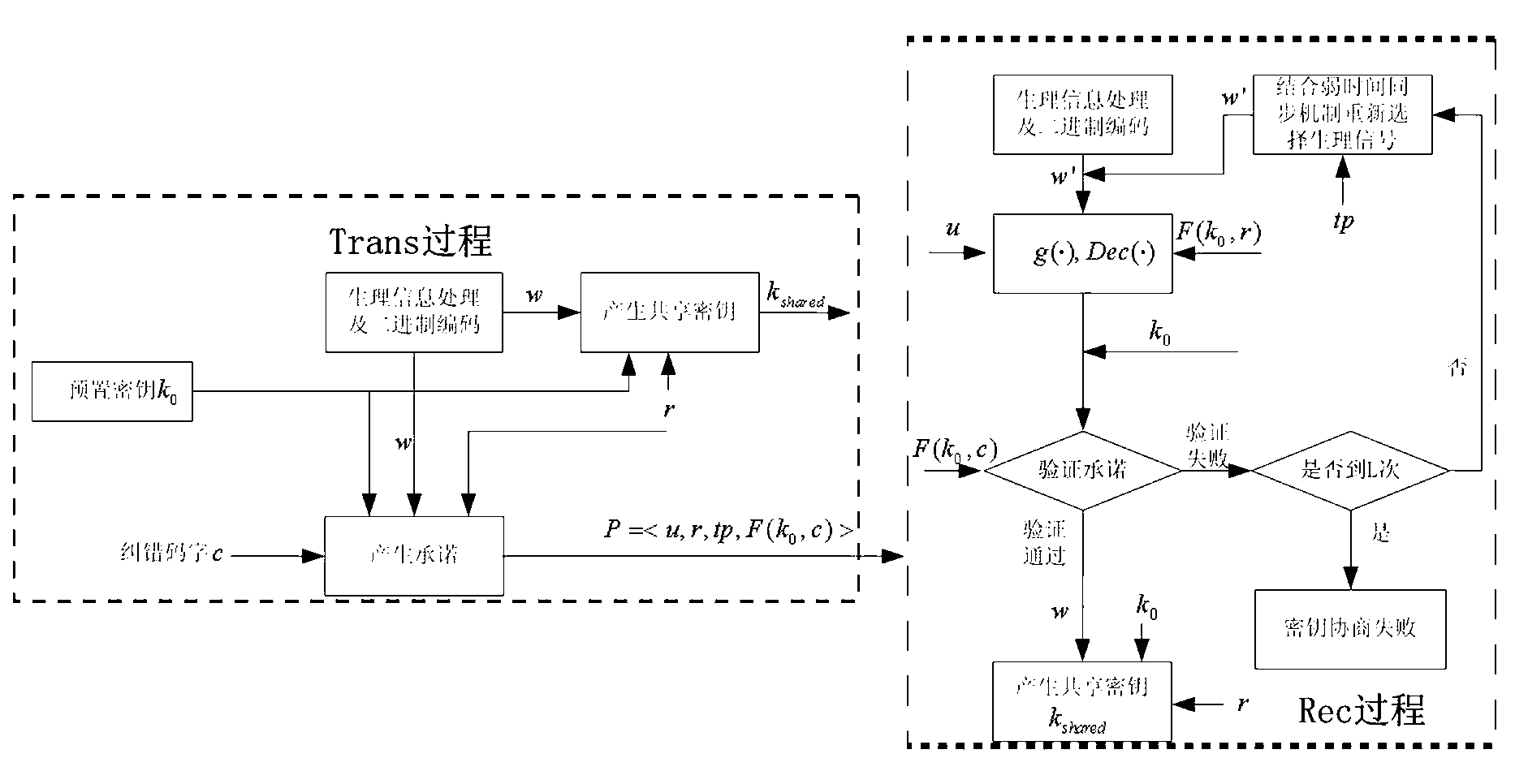
Wireless body area network symmetric key negotiation method
ActiveCN102802151AImprove the odds of successIncrease varietyEnergy efficient ICTSecurity arrangementComputer hardwareBody area network
The invention discloses a wireless body area network symmetric key negotiation method. A promise is initiated to a node B by a node A. The wireless body area network symmetric key negotiation method is characterized by comprising the steps that: the node A acquires a physiological signal at a tp moment, the physiological signal is set as w; then a sharing secret key is generated according to the w, data is transmitted to the node B in a hidden manner; the node B extracts a physiological signal at the same moment, the physiological signal is denoised and the value of the physiological signal is verified whether to be correct; if the value of the physiological signal is correct, a negotiation secret key is solved; and if the value of the physiological signal is wrong, the physiological signal is obtained near the moment w, and the secret key is continuously solved. According to the wireless body area network symmetric key negotiation method, the requirement of accurate synchronization for time is avoided, the problem of high energy consumption of frequent broadcasting of synchronous signals is solved; and in a process of secret key negotiation, most of nodes are used for processing data without transmitting the data, thus the energy consumption in the process of secret key negotiation is effectively reduced. According to the wireless body area network symmetric key negotiation method, the negotiation is unconcerned with the entropy of the signal, a weak time synchronization method and a secret key presetting technology are adopted, and a better attack preventing property is achieved.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
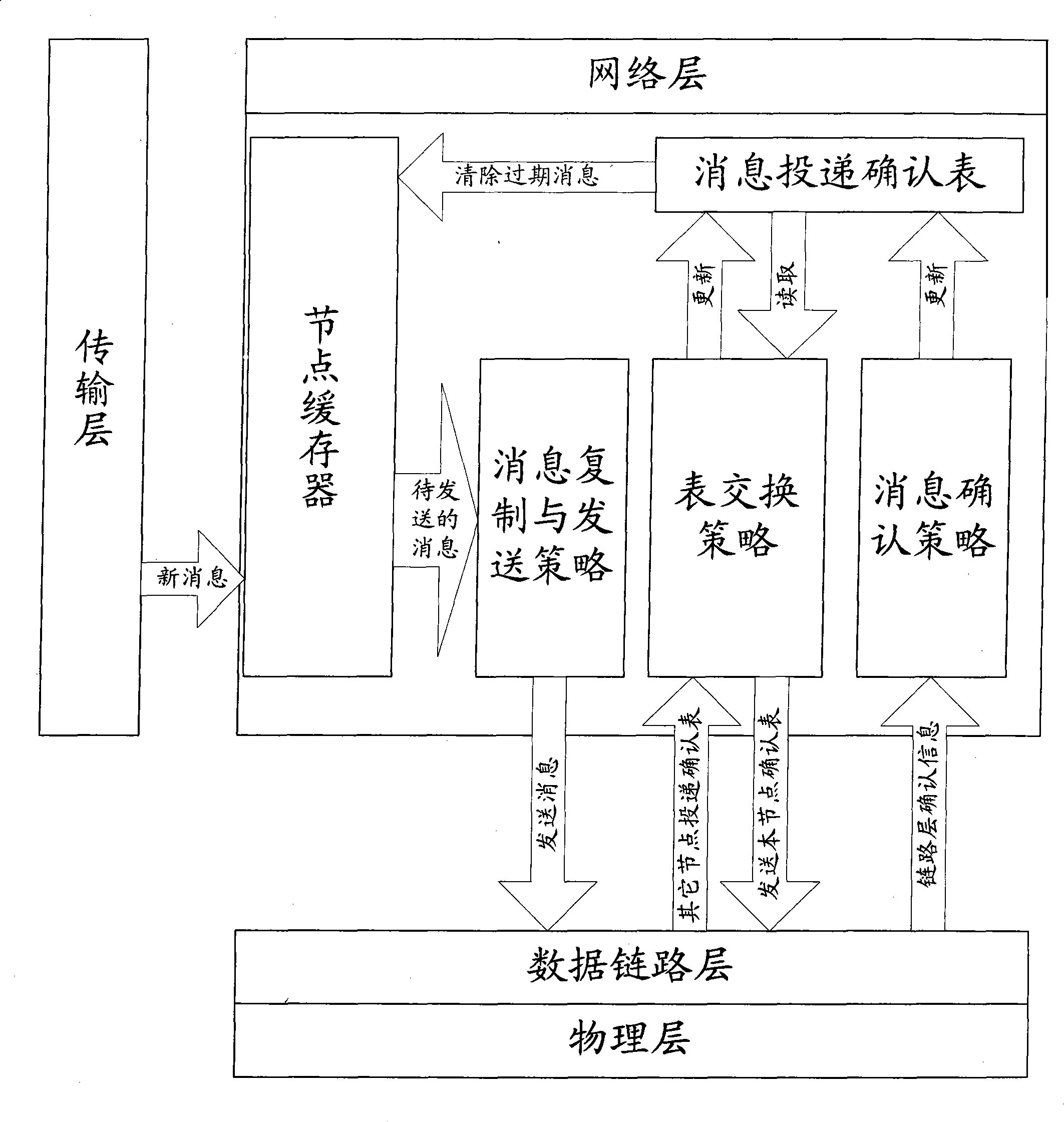
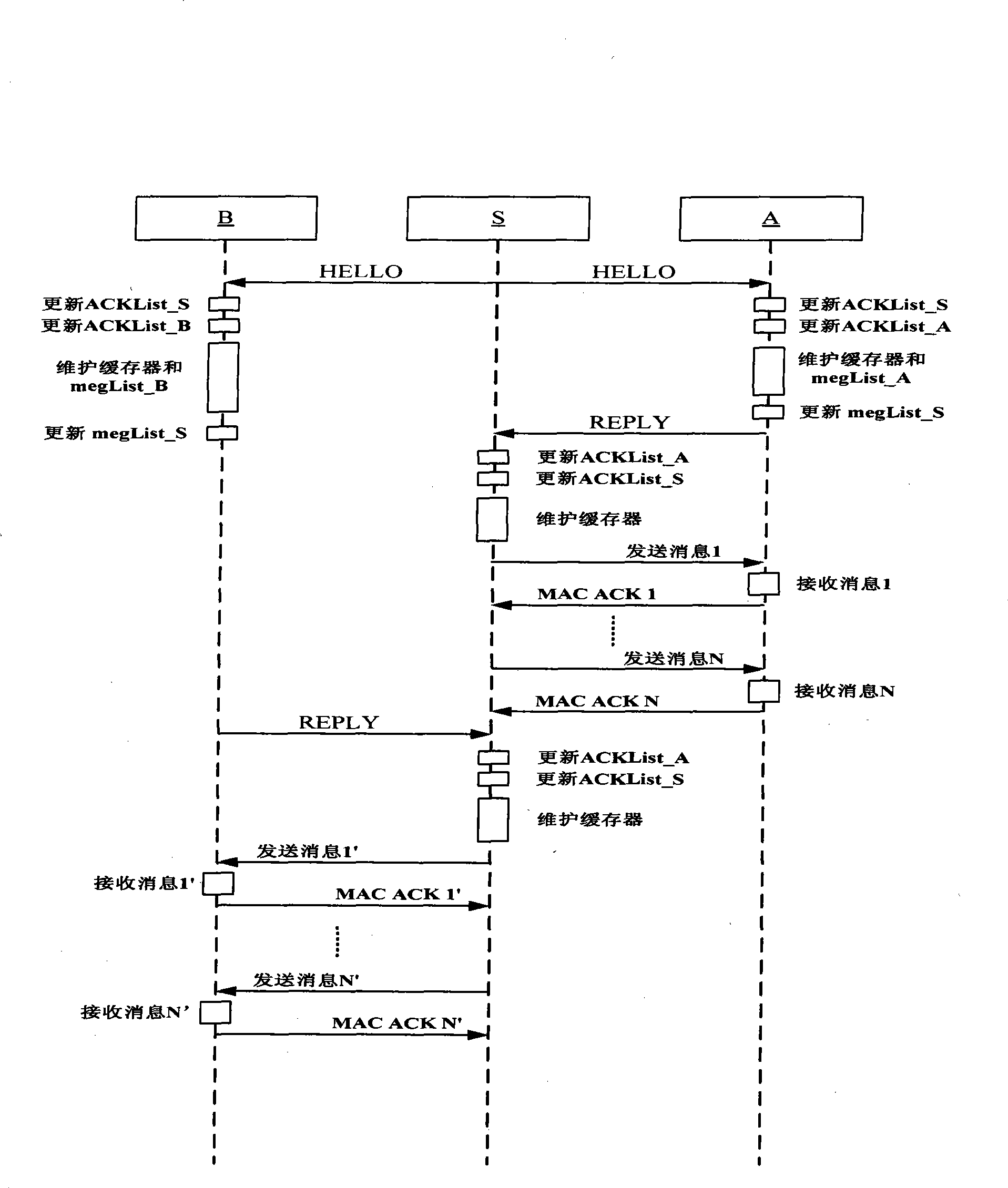
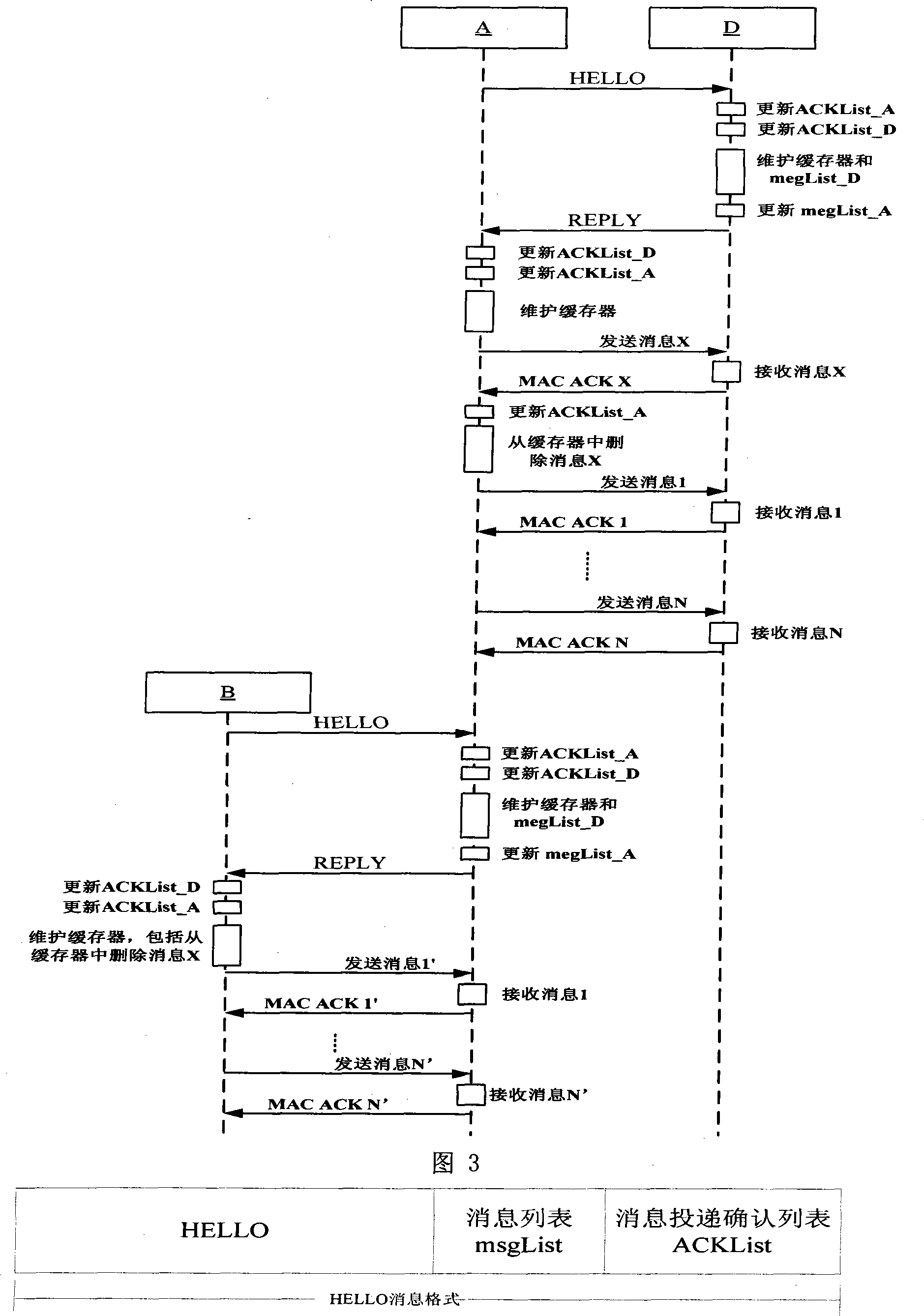
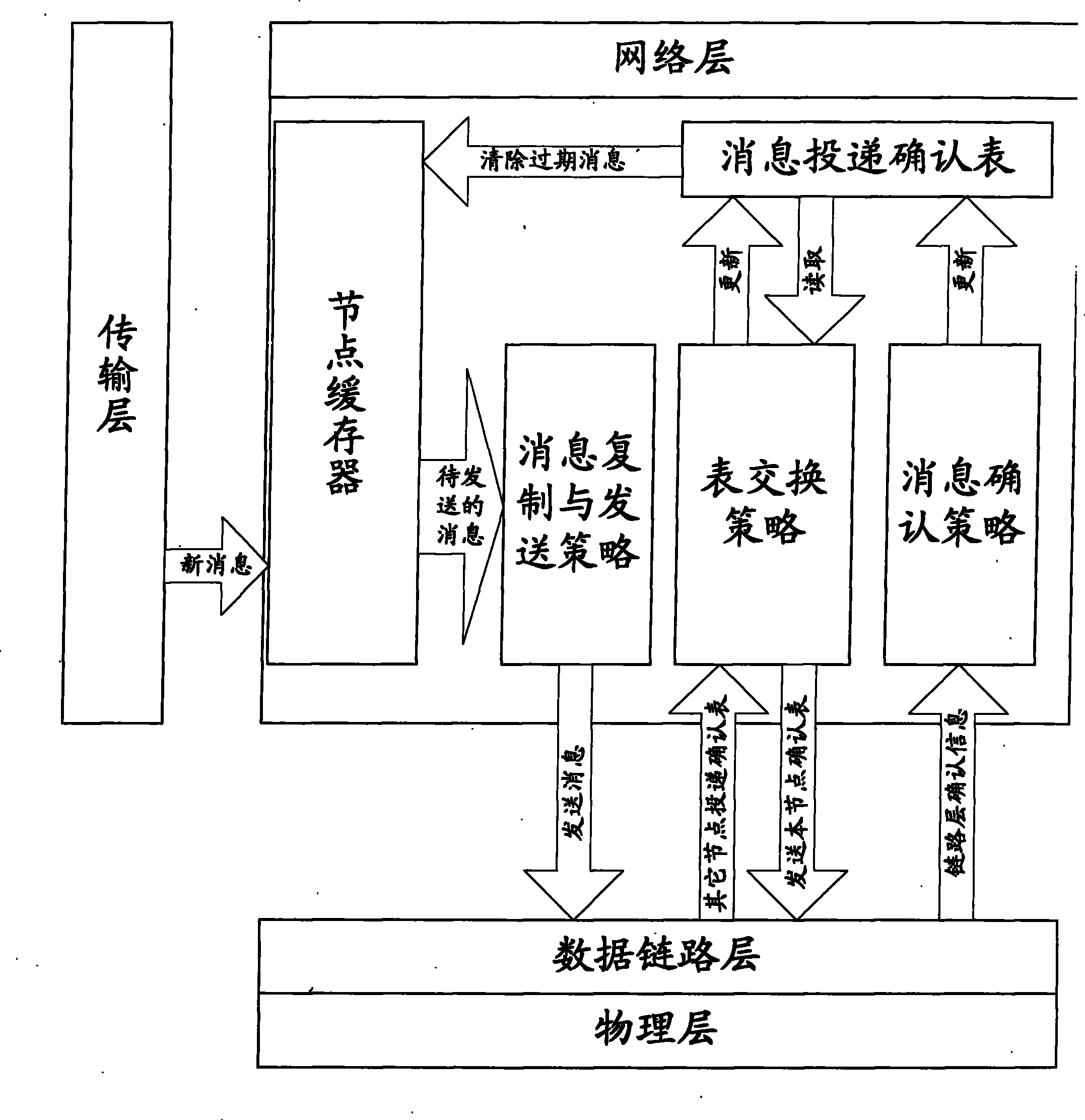
Method for saving node energy of delay-tolerant network and intermittently-connected network
InactiveCN101414965AReduce delivery rateResearch methods to reduce message duplication to reduce delivery rateError prevention/detection by using return channelData switching networksMessage deliveryNetwork communication
The invention relates to a method used for saving node energy in a delay tolerant network and an intermittent connection network, belonging to the field of network communication technique. The method comprises the steps as follows: a source node queries a node neighbor list; if no destination node information exists, the message is temporarily memorized in a node buffer; the non-empty nodes in the buffer periodically send exploration information which is used to exchange a message list and a message delivery acknowledgement list; when the node sending the exploration information receives a return information, the buffer is actively maintained according to the message delivery acknowledgement list carried in the return information and a message is sent by the node; after an intermediate node successfully transmits the message to the destination node, the node adds corresponding records into the message delivery acknowledgement list memorized locally and deletes the message from the buffer. The method can effectively reduce the quantity of the redundant nodes, improves the performance of the whole network and prolongs the life period.
Owner:TIANJIN UNIV
Wireless sensor network self-adaptation compression method
InactiveCN103957582AEnergy optimizationAchieve energy optimizationPower managementNetwork topologiesSelf adaptiveData compression
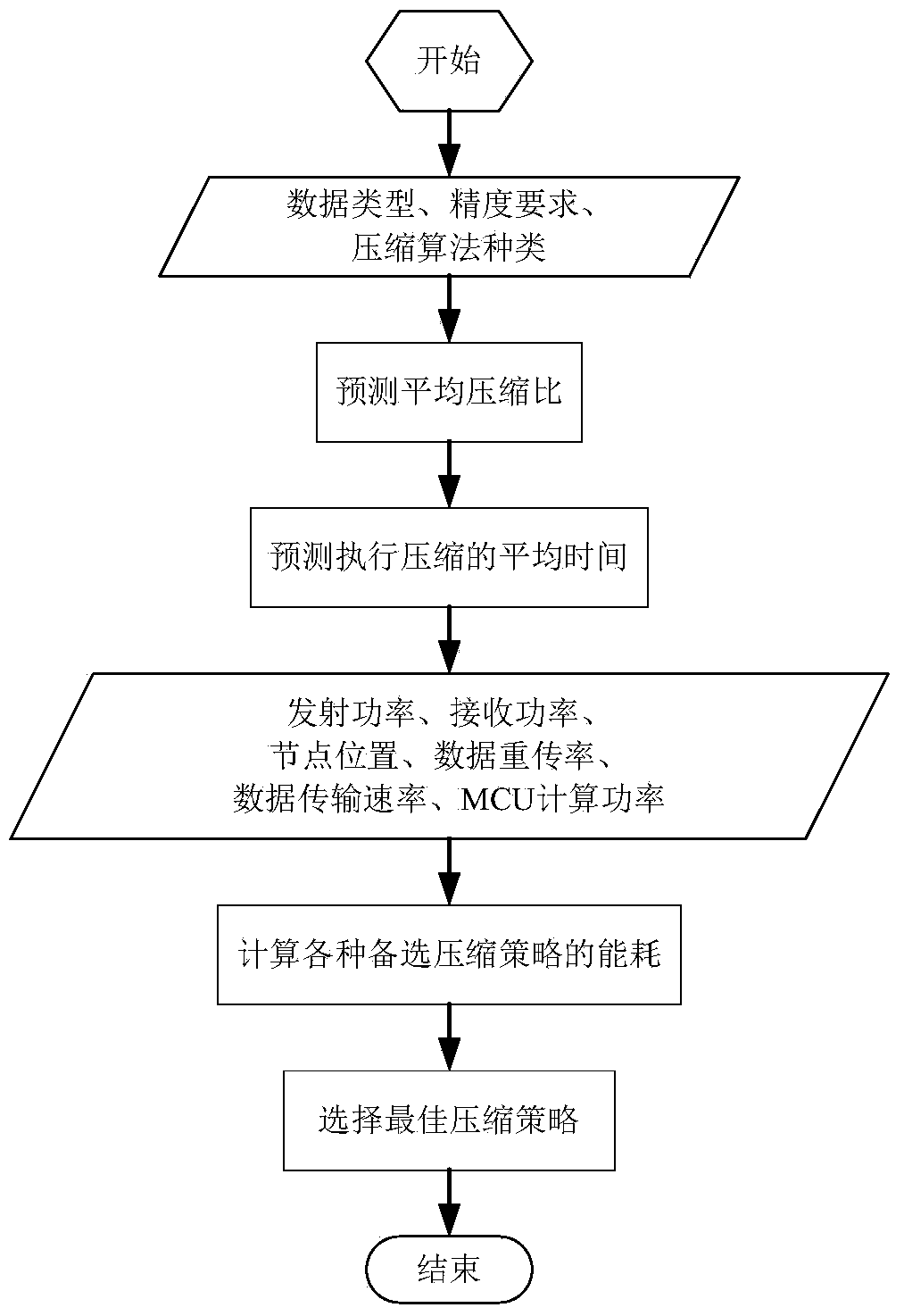
The invention discloses a wireless sensor network self-adaptation compression method which can achieve energy optimization in the whole network. The method comprises the step of a compression judging process. In the compression judging process, the total energy consumption Ecomp caused when compression is executed and the total energy consumption Euncomp caused when compression is not executed are compared, if the total energy consumption Ecomp is larger than the total energy consumption Euncomp, initial data are not compressed and directly sent out, if the total energy consumption Ecomp is smaller than the total energy consumption Euncomp, the data compression process is executed, the initial data are compressed and then sent out, and if the total energy consumption Ecomp is equal to the total energy consumption Euncomp, the initial data are not compressed and directly sent out or the initial data are compressed and then sent out.
Owner:NINGBO INST OF TECH ZHEJIANG UNIV ZHEJIANG
Smart grid wireless communication encryption method based on dynamic key
InactiveCN102438240ARealize dynamic generationEffective cracking in real timeSecurity arrangementData transmissionSmart grid network
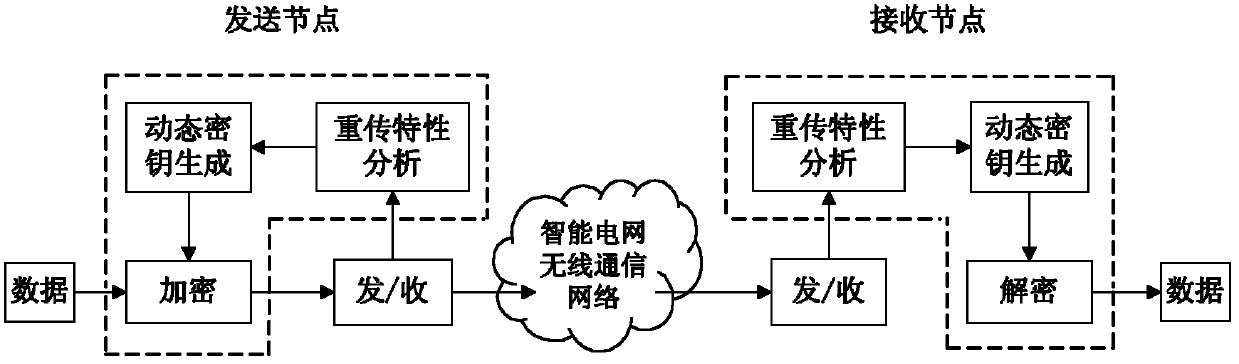
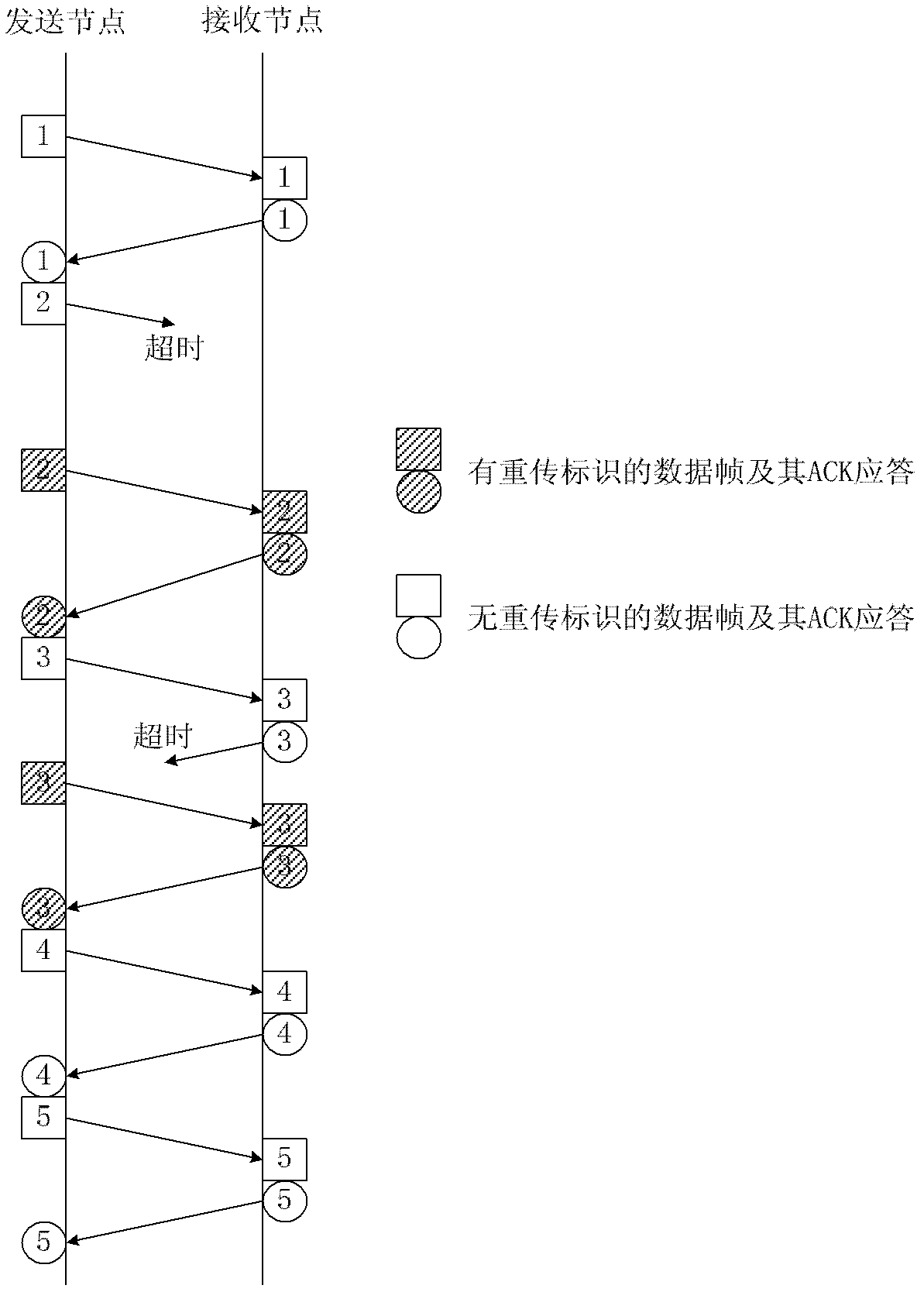
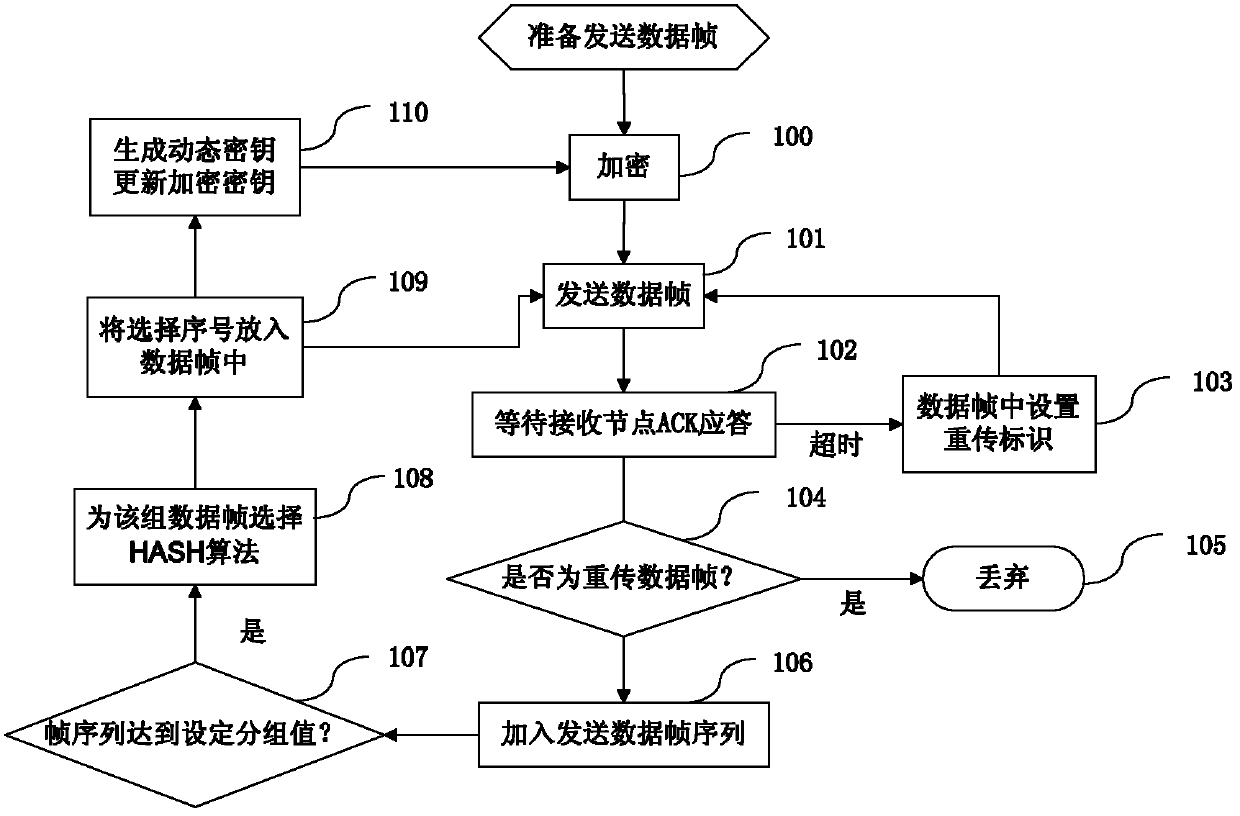
The invention discloses a smart grid wireless communication encryption method based on a dynamic key. A wireless communication node in a smart grid analyzes a data transmission characteristic in the process of wireless communication by observing a communication data frame based on a data retransmission mechanism, and a dynamic key is generated to encrypt and decrypt communication data. By the method, the security of the wireless communication in the smart grid can be effectively improved and computing overhead is reduced.
Owner:XI AN JIAOTONG UNIV
Deep neural network computing system and method
InactiveCN107341545AReduce computing energy consumptionLow running costPhysical realisationUser inputAlgorithm
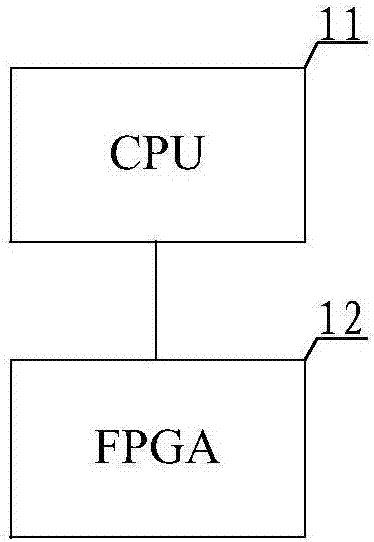
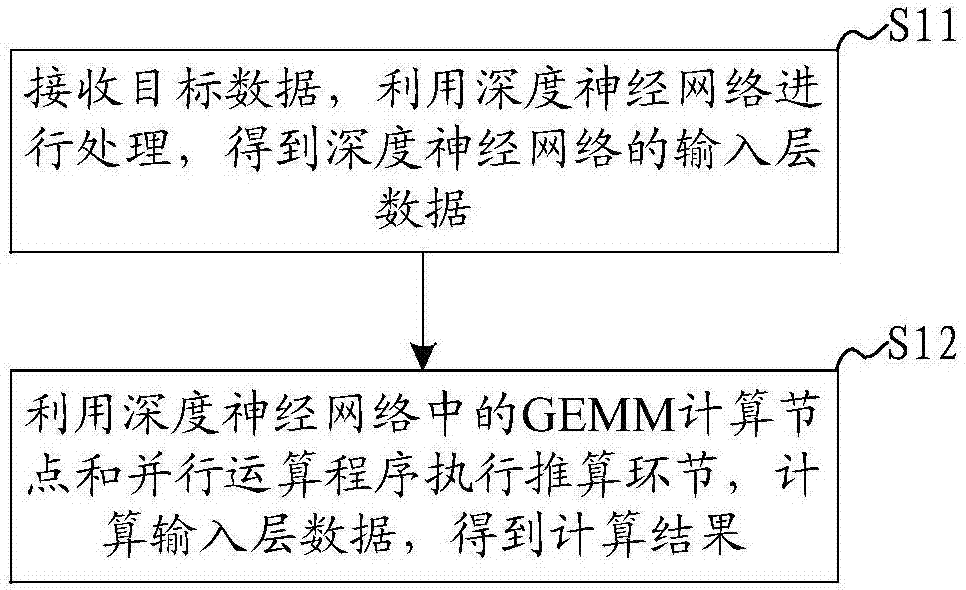
This application discloses a deep neural network computing system and method. The system is composed of a CPU for receiving target data and carrying out processing by using a deep neural network to obtain input layer data of the deep neural network and an FPGA for performing a calculation link by using a GEMM calculation node and a parallel operation program in the deep neural network and calculating the input layer data to obtain a calculation result. According to the invention, the GEMM computing node of the deep neural network is transplanted to FPGA and the CPU receives the target data inputted by a user. On the basis of the deep neural network, the target data are transformed into the input layer data of the deep neural network and the transformed data are sent to the FPGA; and the FPGA performs the calculation link by using the GEMM calculation node and the parallel operation program in the deep neural network and calculates the input layer data to obtain the calculation result, thereby completing the calculation. On the basis of the hardware characteristics of the FPGA, the FPGA completes the calculation link, so that the operation energy consumption is reduced substantially and the operation cost is lowered.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
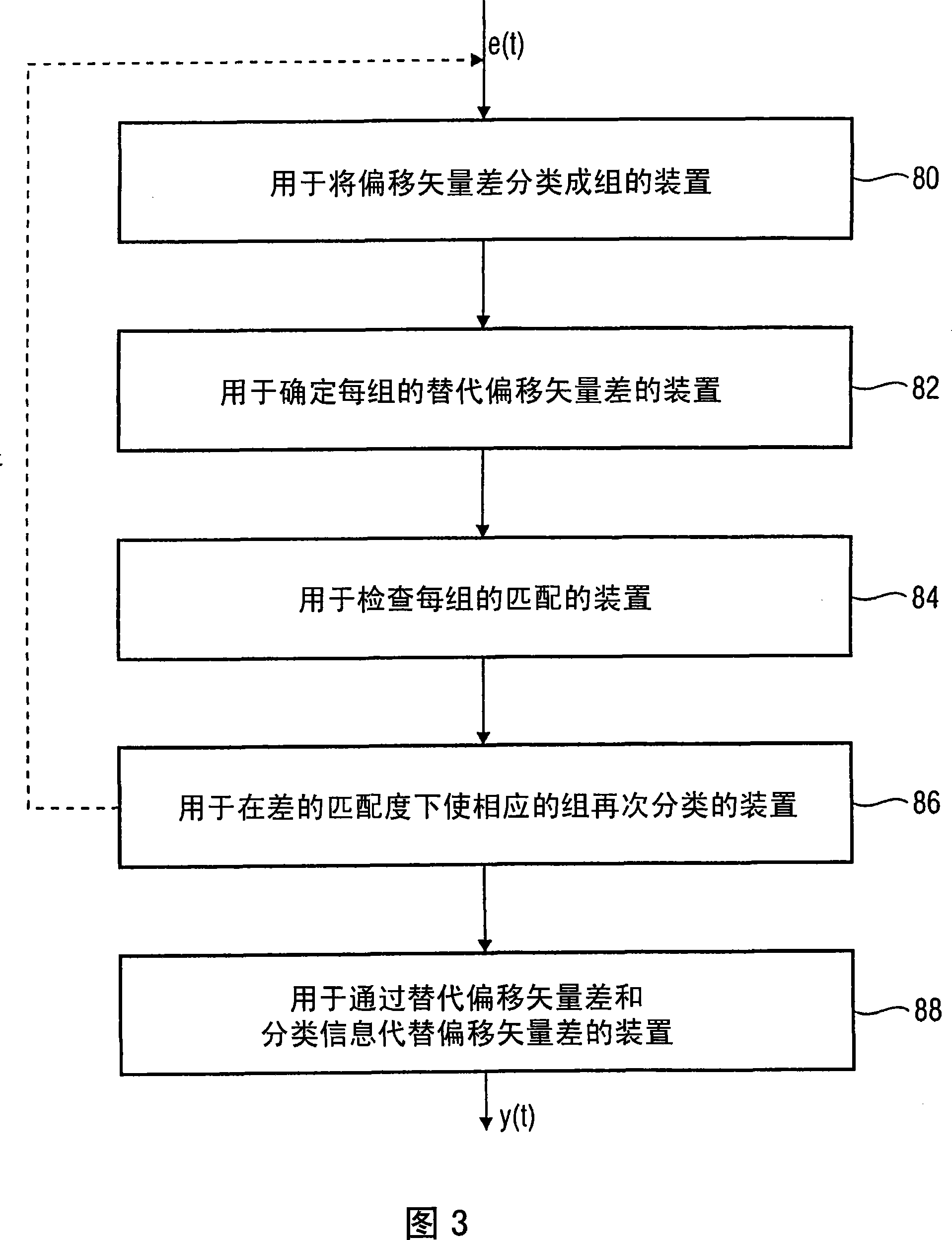
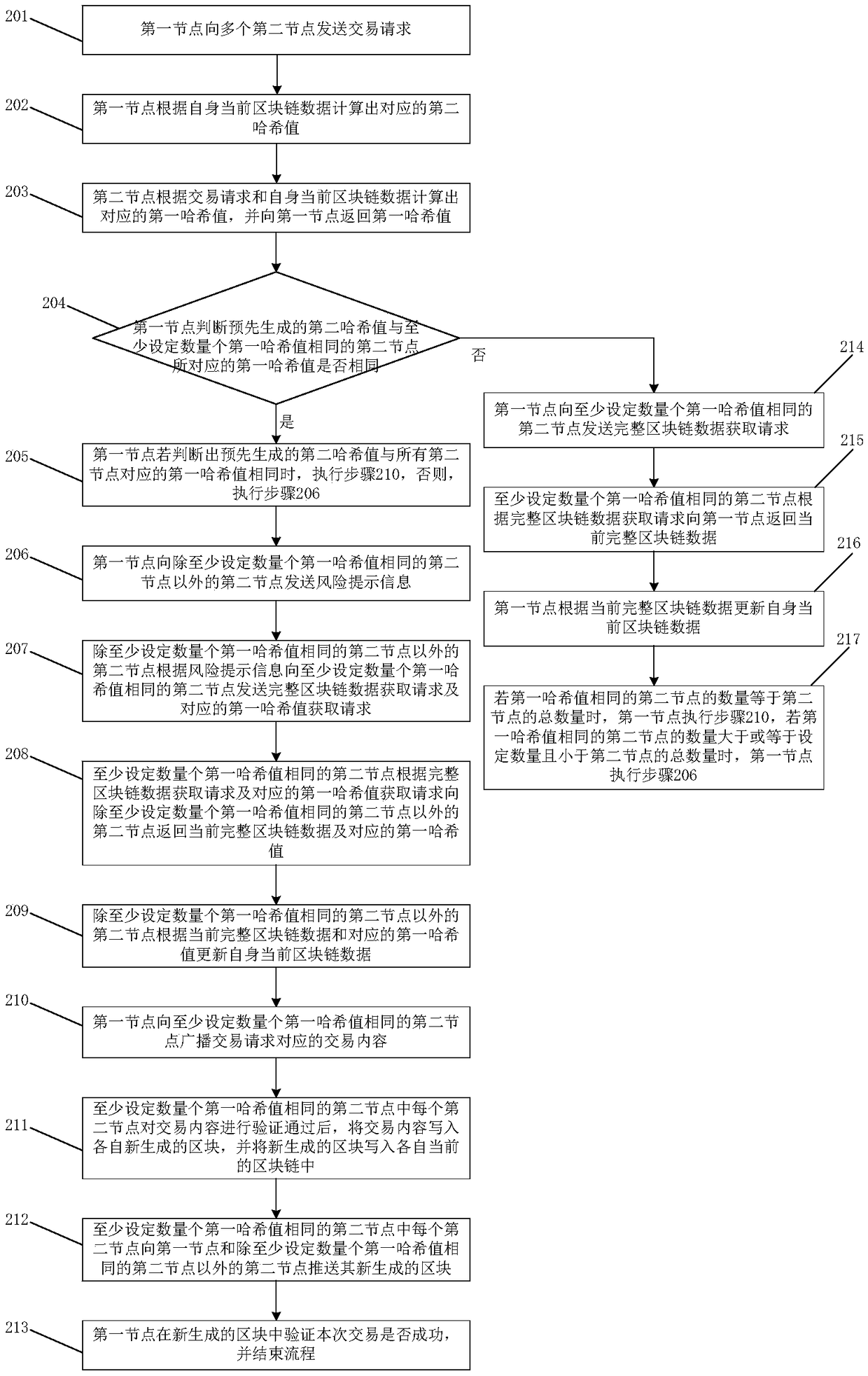
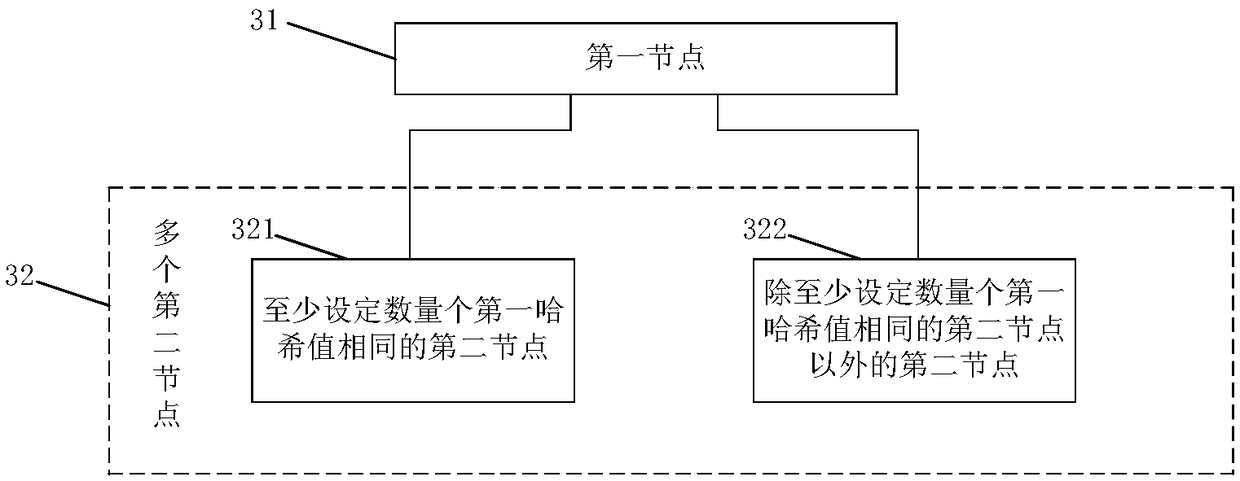
Transaction request processing method and system
ActiveCN108989052AEnsure safetyReduce computing energy consumptionFinanceUser identity/authority verificationFinancial transactionHash table
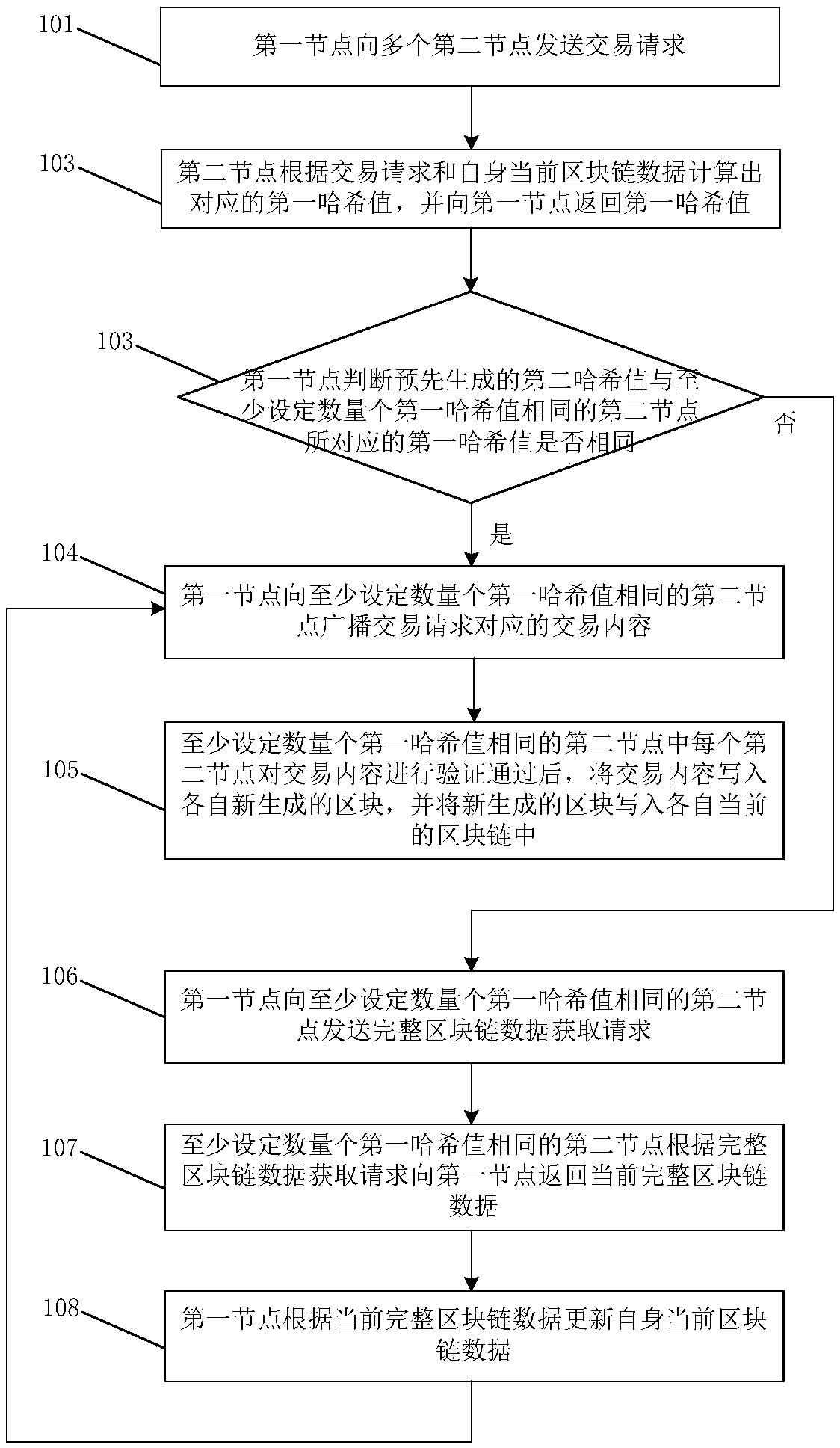
The invention discloses a transaction request processing method and a system. The method includes a first node sends a transaction request to a plurality of second nodes; the second node calculates acorresponding first hash value according to the transaction request and the current block chain data of the second node, and returns the first hash value to the first node; the first node judges whether the second hash value generated in advance is the same as the first hash value corresponding to the second node with at least a set number of the same first hash values; if the first node judges that the pre-generated second hash value is the same as the first hash value corresponding to at least a set number of second nodes with the same first hash value, the first node broadcasts the transaction content corresponding to the transaction request to at least a set number of second nodes with the same first hash value; at least a numb of second nodes with that same first hash value are set, and after each second node verifies the transaction content, the transaction content is written into respective newly generate blocks, and the newly generated blocks are written into respective currentblock chains.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
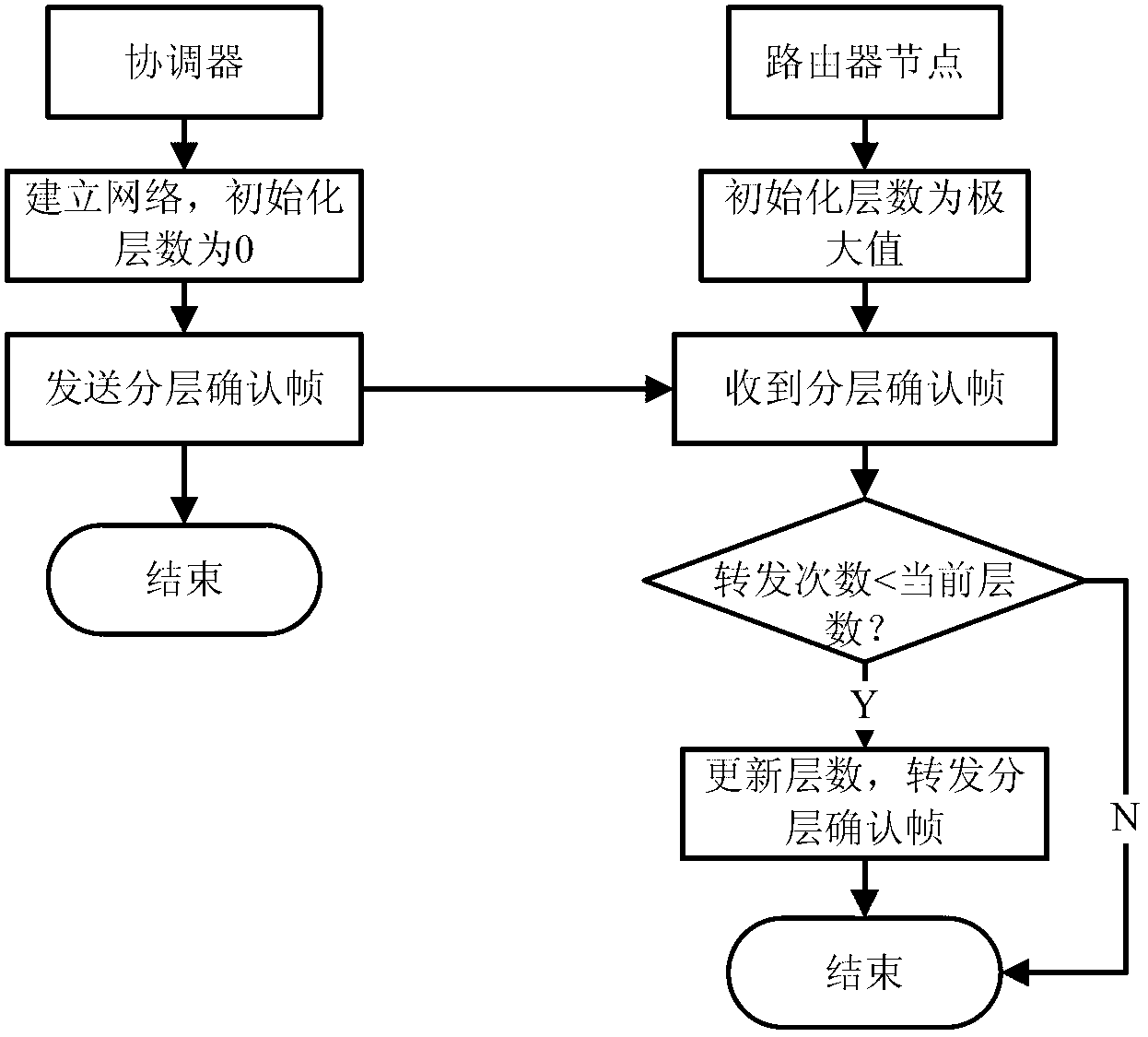
Improved Zigbee network lamination method
InactiveCN102802166AReduce computing energy consumptionReduce waste of resourcesNetwork topologiesData switching networksLevel numberDistributed computing
The invention discloses an improved Zigbee network lamination method. The invention discloses the improved Zigbee network lamination method which specifically comprises the following steps of: a Zigbee network is built, wherein the initialization level number of a coordinator is 0, the number of initialization levels of the other nodes is a maximum value (greater than the maximal estimation level number of the network), and the coordinator begins to broadcast lamination affirming frame; the node updated a mechanism and self level number according to the level number after receiving the lamination affirming frame, namely, the level number is updated to be the smaller value between the current level number and forwarding times of the lamination affirming frame; and meanwhile, the lamination affirming frame is forwarded until the lamination affirming frame is to distributed to the whole network. A node possibly receives the lamination affirming frame for multiple times, a frame forwarding control mechanism is introduced in order to prevent resources wasting, namely, not all of the lamination affirming frame are forwarded and only the lamination affirming frame which enables the updated level number to be smaller is forwarded. The Zigbee network lamination method provided by the invention solves the problem that the node level number can not reflect the distance of node and a network coordinator in certain cases.
Owner:NANKAI UNIV
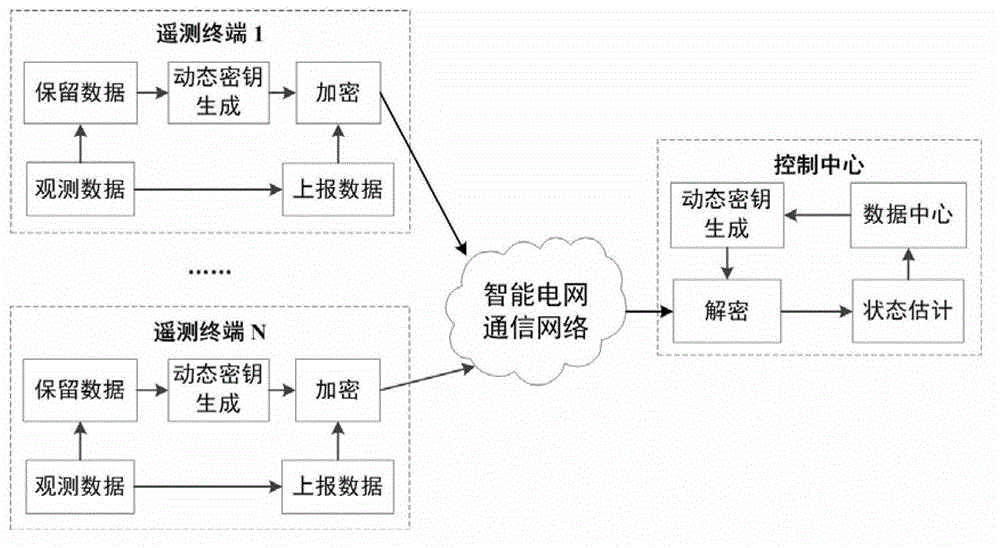
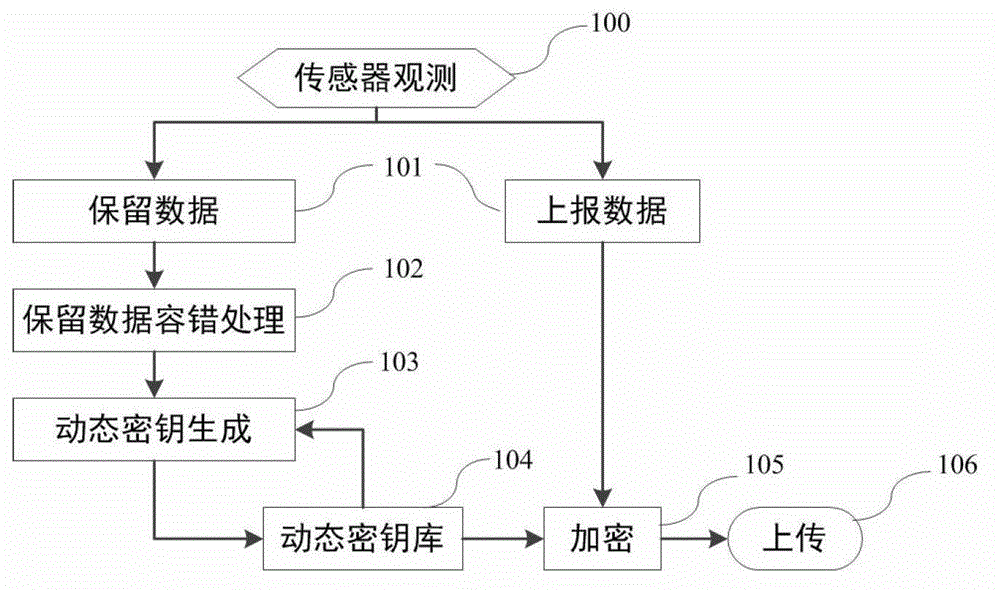
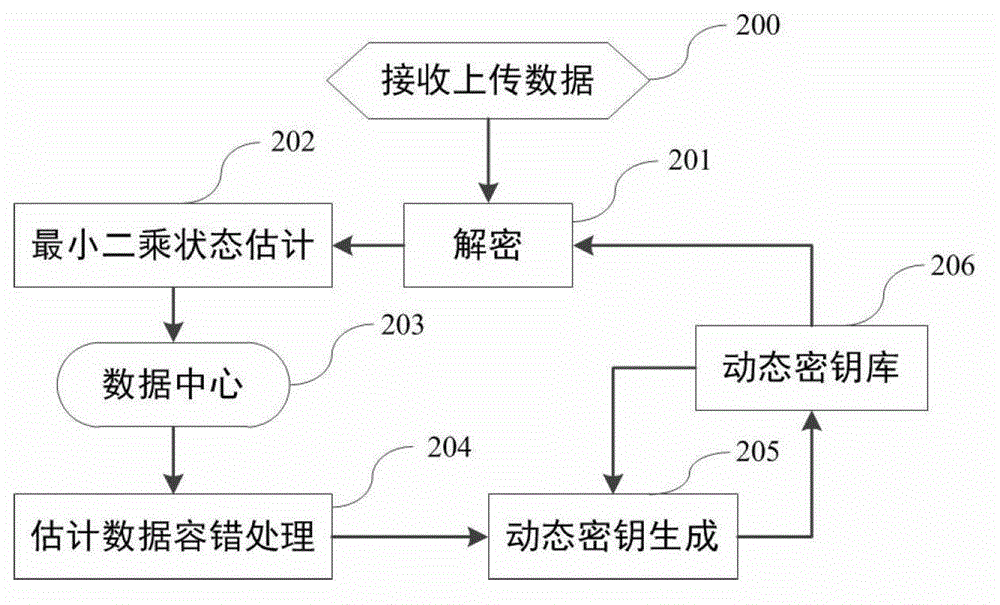
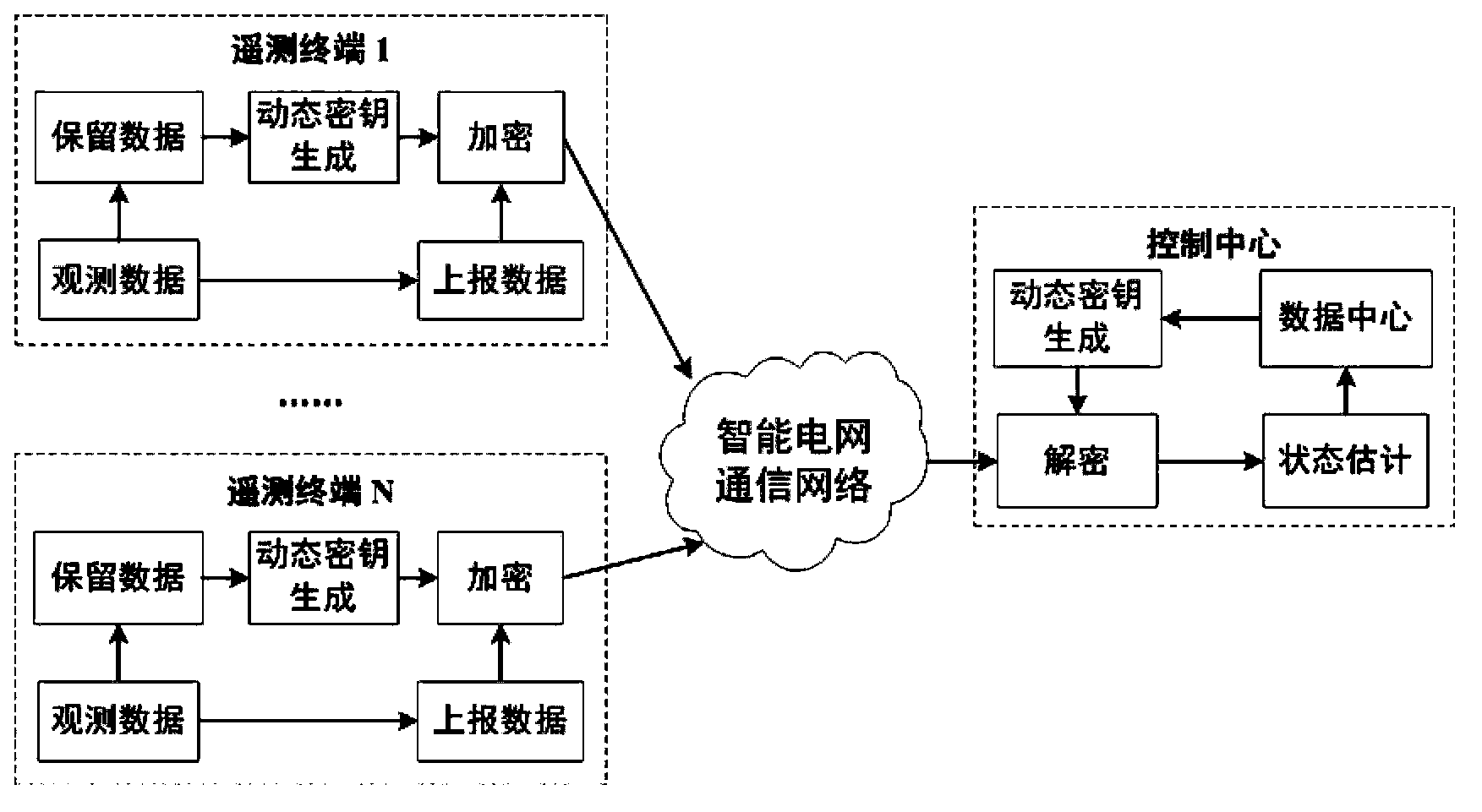
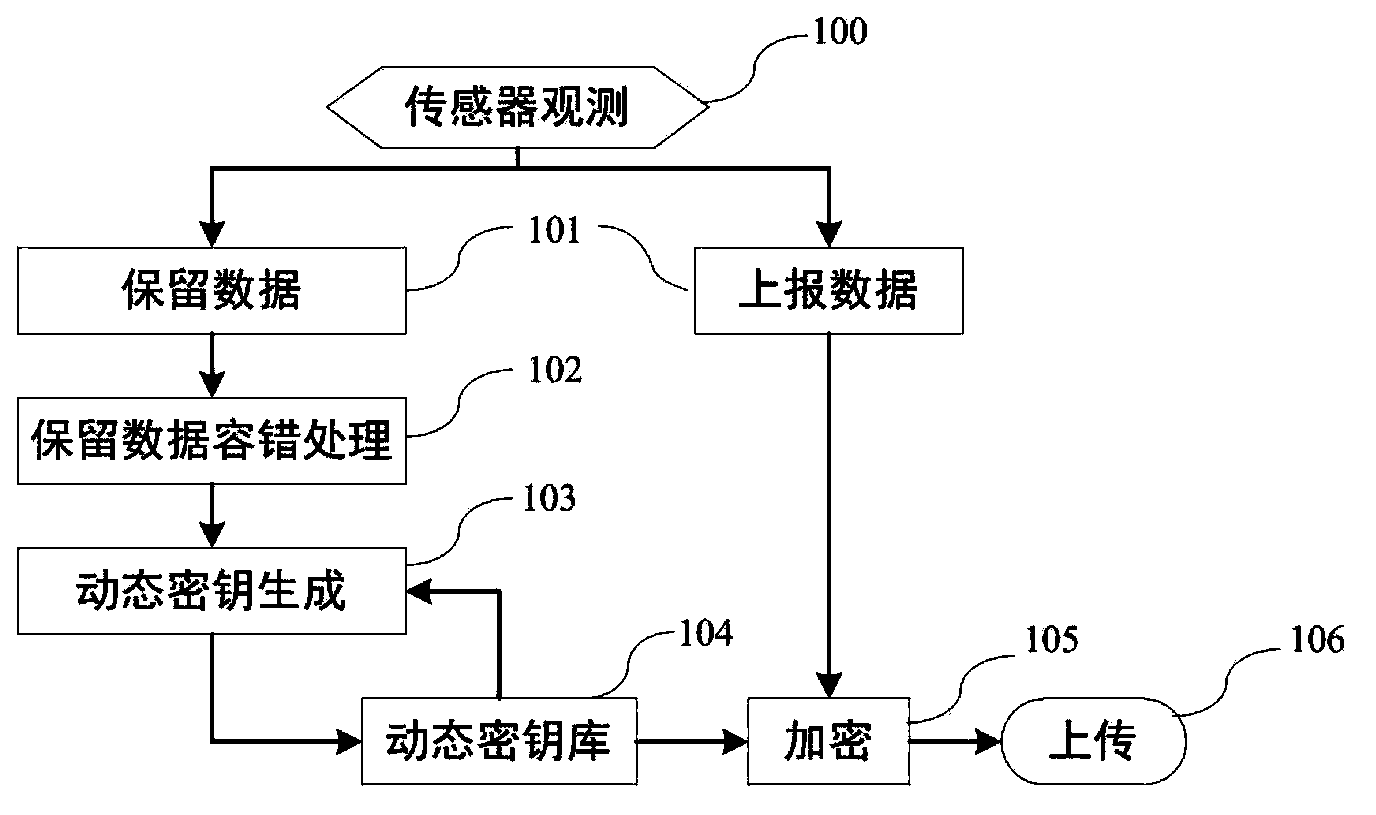
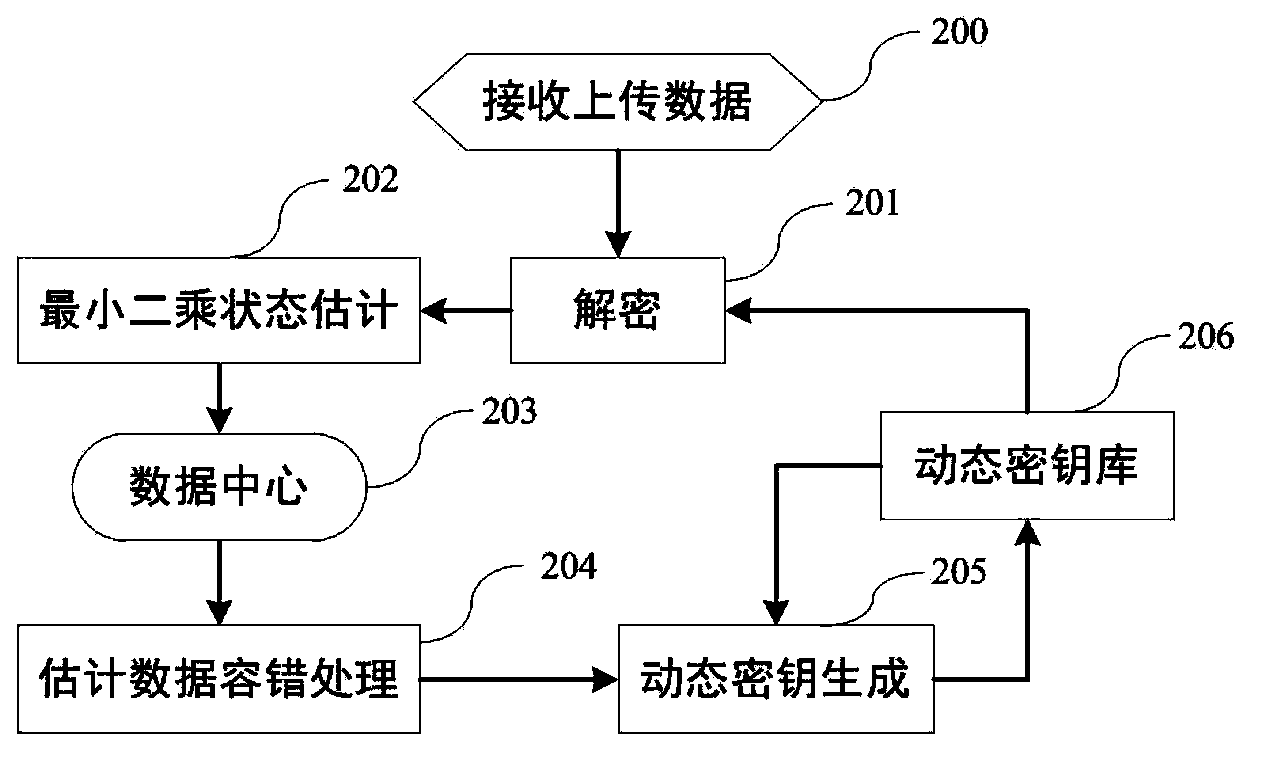
State estimation based intelligent power grid dynamic data encryption method
ActiveCN102916813AAvoid synchronous dynamic generationRealize synchronous dynamic generationKey distribution for secure communicationUser identity/authority verificationCommunications securityComputation complexity
The invention discloses a state estimation based intelligent power grid dynamic data encryption method. The method includes: each telemetering terminal divides observation data into reporting data and retention data, uses the retention data to generate a dynamic key to encrypt the reporting data, generates a ciphertext and transmits the ciphertext to a control center; and the control center computes the retention data of each telemetering terminal based on a state estimation method to generate a dynamic key and decrypts the ciphertext transmitted by each telemetering terminal, so that the reporting data of each telemetering terminal are obtained. Synchronous dynamic key generation can be realized between the intelligent power grid control center and each remote terminal without key distribution, and communication safety in an intelligent power grid is effectively improved while computing complexity, energy consumption and hardware cost of terminal equipment are lowered effectively.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Privacy protection oriented continuous data gathering method in sensor network
ActiveCN106714088AGuaranteed accuracyReduce data trafficPower managementParticular environment based servicesTime correlationPrivacy protection
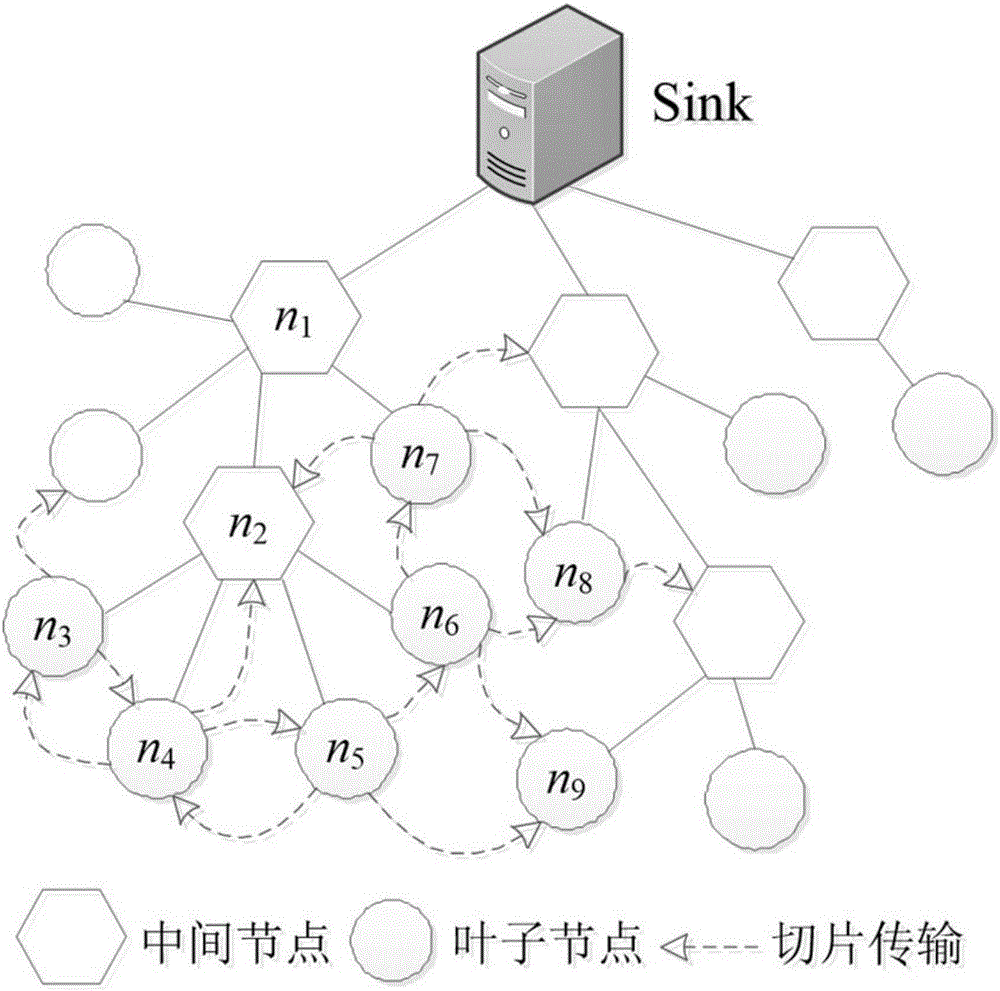
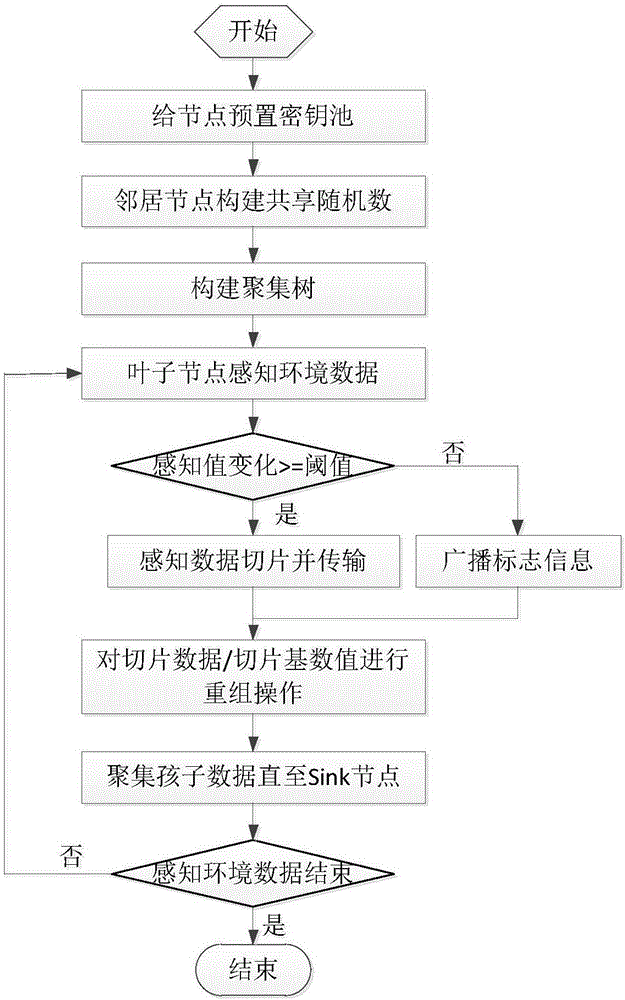
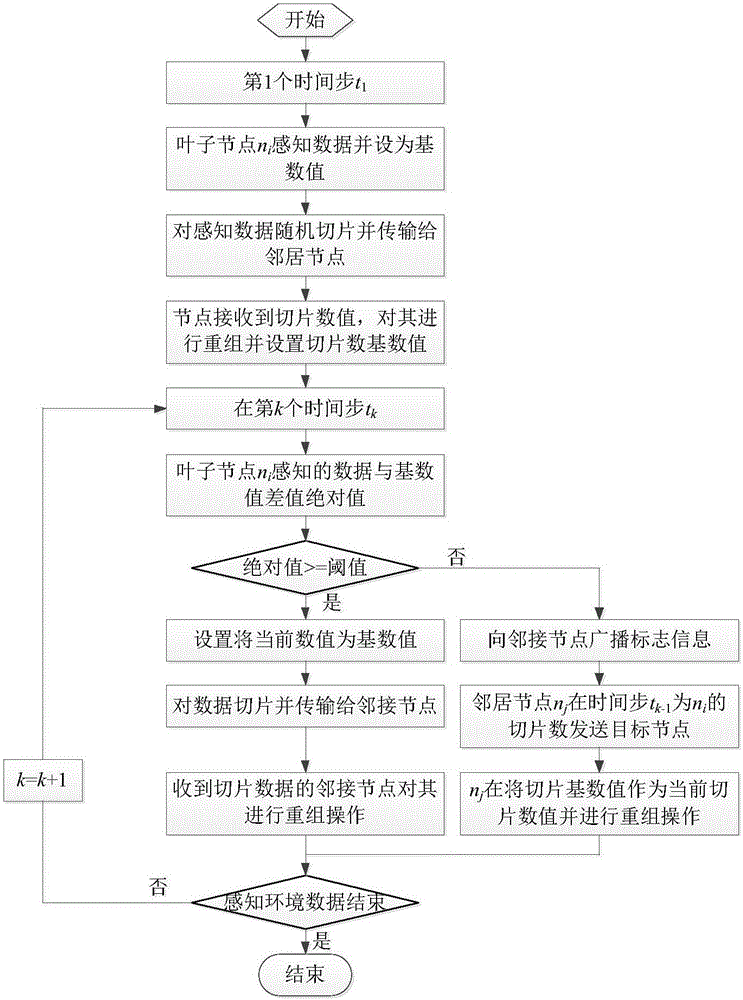
The invention discloses a privacy protection oriented continuous data gathering method in a sensor network. An existing privacy protection oriented data gathering algorithm mainly is focused on snapshot gathering, while the traffic and energy consumption of the snapshot gathering algorithm are unsuitable for being directly applied to continuous data gathering. According to the method, through utilization of time correlation of sensing data, whether nodes transmit current sensing data or not is determined by setting a threshold value, thereby effectively reducing the data traffic. According to the method, for the problem that excessive encryption / decryption calculation results in the fact that the calculation energy consumption of the nodes is relatively high, the privacy of the data is ensured by adding random numbers to the transmitted sensing data, the sensing data is prevented from being encrypted / decrypted among the nodes in the data transmission process, the calculation energy consumption of the nodes is saved, and the network service life is prolonged well. According to the method, under the condition that the privacy of the sensing data is ensured, the traffic and calculation energy consumption are effectively reduced, and the good network expansibility is achieved.
Owner:ANHUI NORMAL UNIV
Multi-AUV underwater target identification method based on super-resolution selectable network
ActiveCN114266977AAchieving Color RestorationImplement data reconstructionImage enhancementGeometric image transformationImaging qualityEngineering
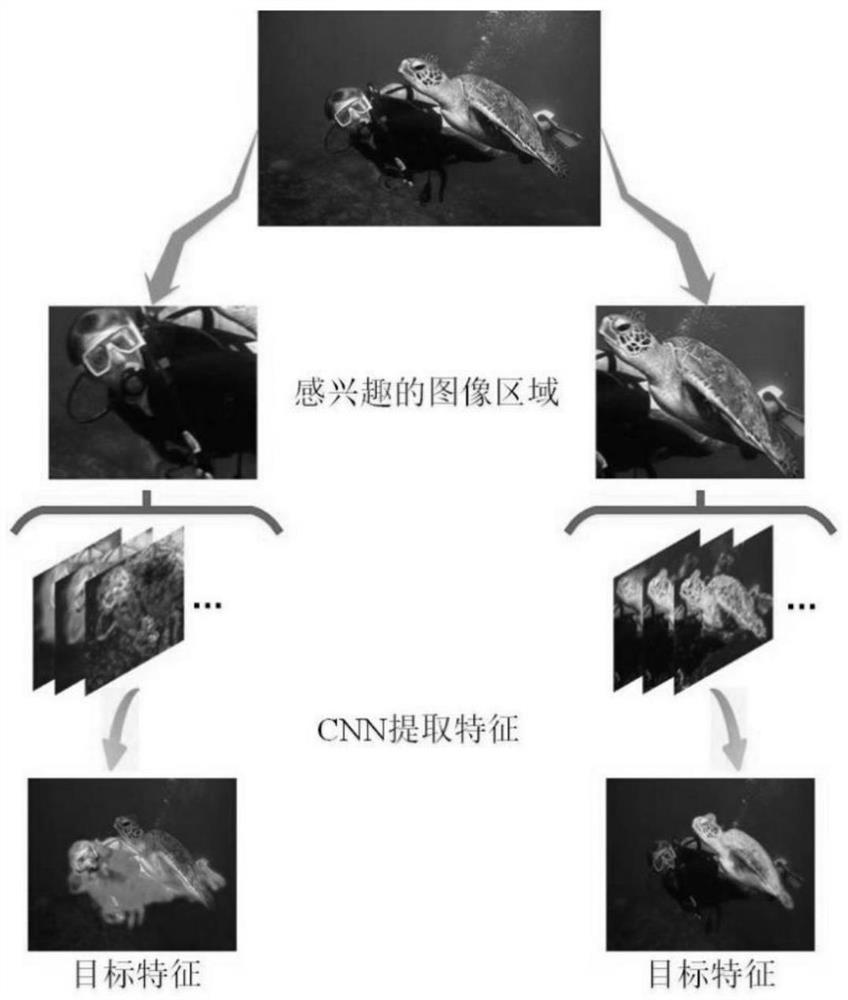
The invention discloses a multi-AUV underwater target identification method based on a super-resolution selectable network, and the method comprises the steps: collecting acoustic image and optical image information, carrying out the color recovery and data reconstruction, improving the image quality through image super-resolution, and achieving the super-resolution of an underwater image; target feature extraction and target feature similarity measurement: based on a lightweight convolutional neural network, fusing the features of the target information collected by the multiple AUVs, and calculating the similarity between the features by adopting a mahalanobis distance; a threshold value is set, a learning model is designed according to the relation between the threshold value and the similarity, and target recognition under different conditions is carried out; and when the similarity is higher than a threshold value, the improved transfer learning is adopted for identification, so that the calculation energy consumption of the AUV is reduced, and the real-time performance of the algorithm is ensured. And when the similarity is lower than a threshold value, identifying the target by adopting few-sample learning, carrying out centralized training on target information with unobvious features caused by a complex background, extracting effective features, reducing interference of environmental factors, and realizing efficient underwater target identification of multiple AUVs (Autonomous Underwater Vehicles).
Owner:青岛澎湃海洋探索技术有限公司
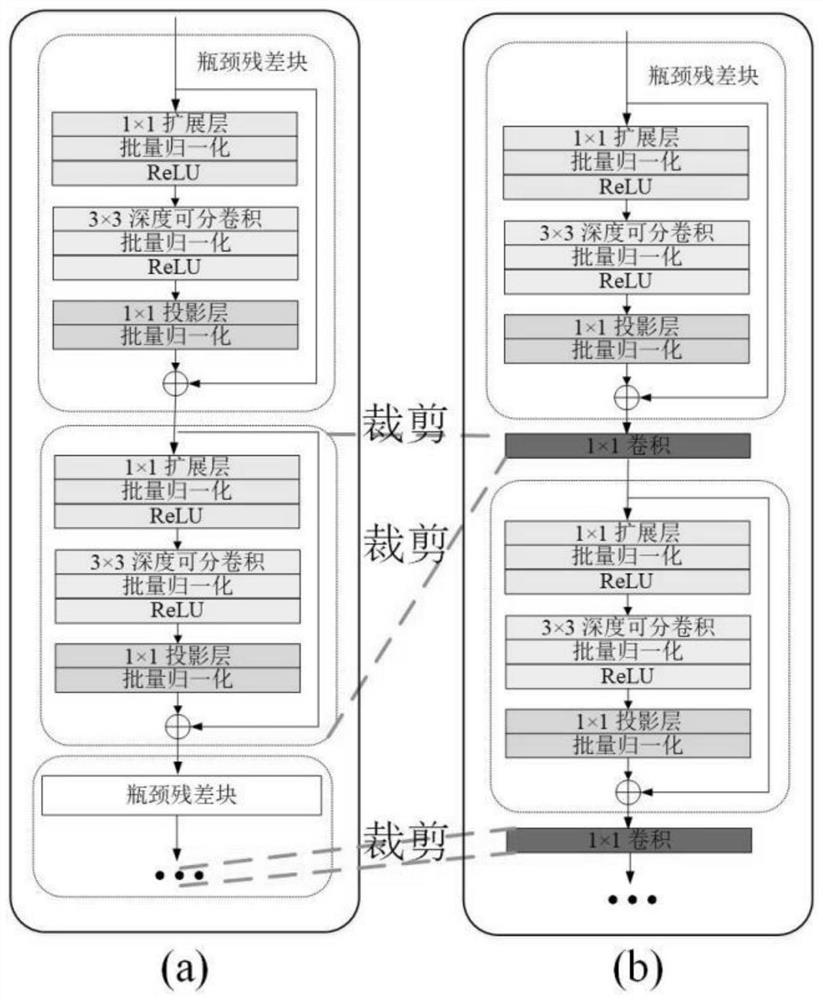
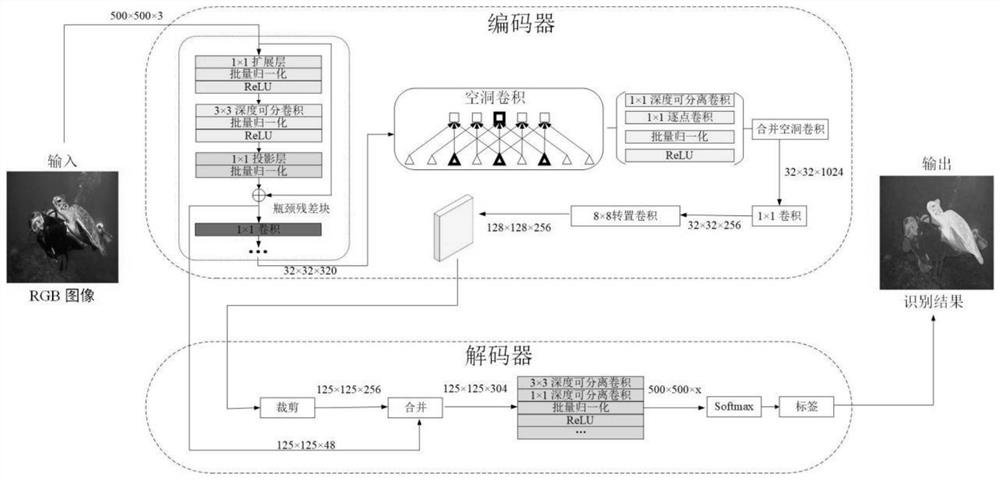
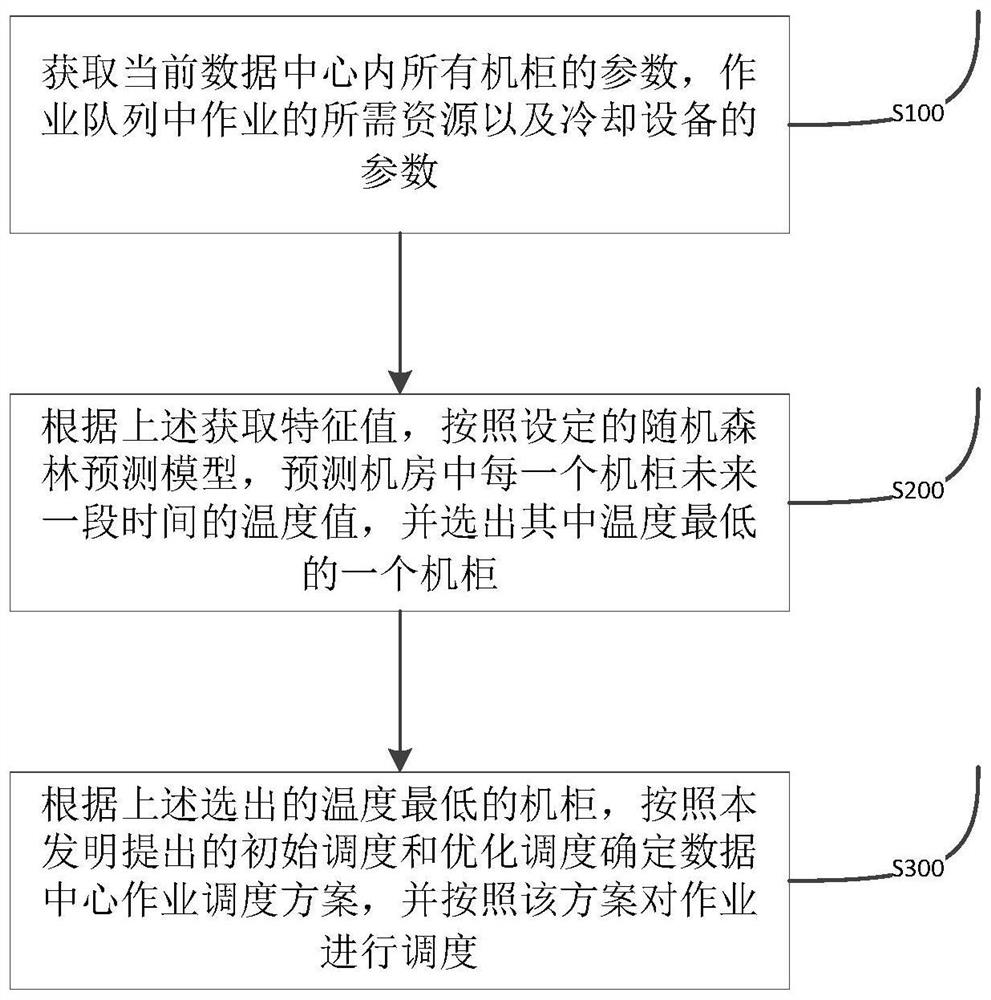
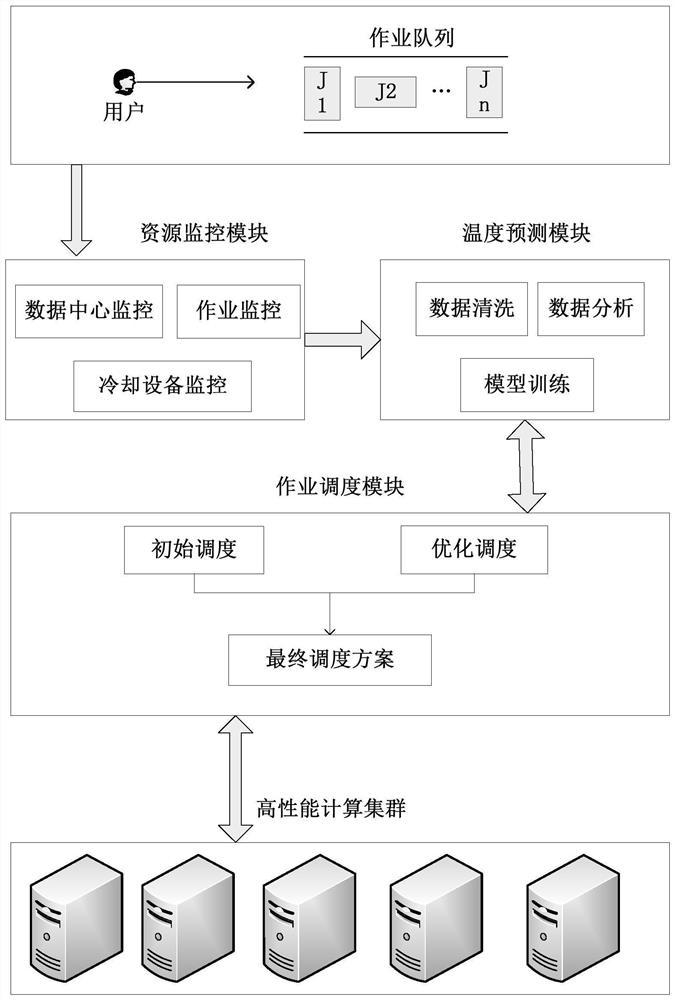
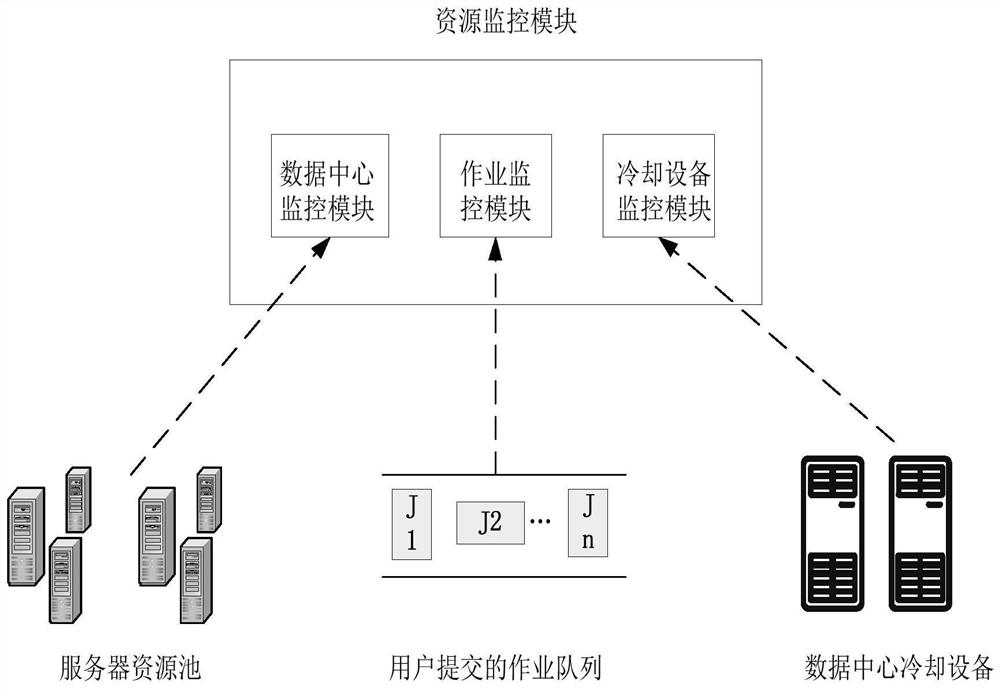
Data center job scheduling method and system based on temperature prediction
PendingCN114816699AReduce air conditioning energy consumptionReduce energy consumptionProgram initiation/switchingDigital data processing detailsData centerOptimal scheduling
The invention discloses a data center job scheduling method and system based on temperature prediction. The method comprises the following steps: acquiring related parameters of a data center cabinet, related parameters of a server in the cabinet, the size of resources required by a job to be scheduled in a job queue and related parameters of cooling equipment; preprocessing the acquired data, and performing feature screening on the preprocessed data; based on the trained machine learning model and the screened features, predicting the temperatures of the cabinets in a future set time period, and selecting the cabinet with the lowest temperature; initial scheduling and optimal scheduling are carried out on to-be-scheduled jobs in a plurality of servers of the cabinet with the lowest temperature, and an optimal mapping scheme between the servers and the to-be-scheduled jobs is selected through multiple iterations; and scheduling the to-be-scheduled job according to the optimal mapping scheme.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN +1
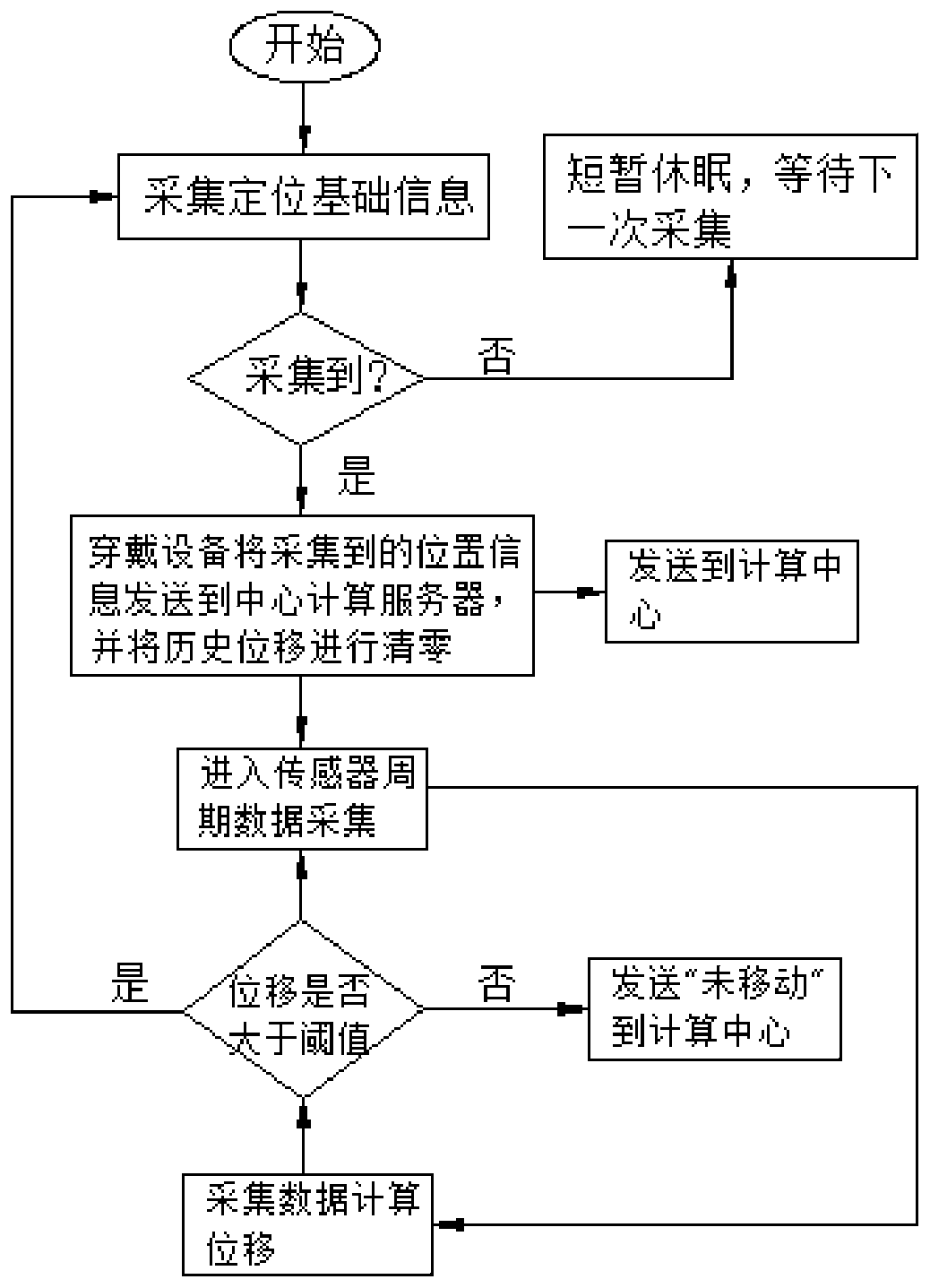
Method for reducing positioning power consumption of wearable equipment and guaranteeing positioning precision
InactiveCN109814138AReduce power consumptionReduce acquisition power consumptionPower managementSatellite radio beaconingComputer scienceEmbedded system
The embodiment of the invention discloses a method for reducing the positioning power consumption of wearable equipment and guaranteeing the positioning precision. The method comprises the following steps that position information is acquired by the wearable equipment; the wearable equipment sends the acquired position information to a center calculation server and carries out zero clearing on historical displacement; the wearable equipment acquires relevant data through a sensing device, and displacement data of the wearable equipment is calculated through the relevant data; the displacementdata calculated by the wearable equipment is compared with a preset displacement threshold, and if the displacement data exceeds the preset displacement threshold, the position information is collected again; if the displacement data does not exceed the preset displacement threshold, the wearable equipment does not need to carry out further data calculation after the center calculation server receives an event indicating that the wearable equipment is not moved, and then the position point closest to the equipment can be used.
Owner:成都众云微科技有限公司
Hierarchical pruning method based on layer recovery sensitivity
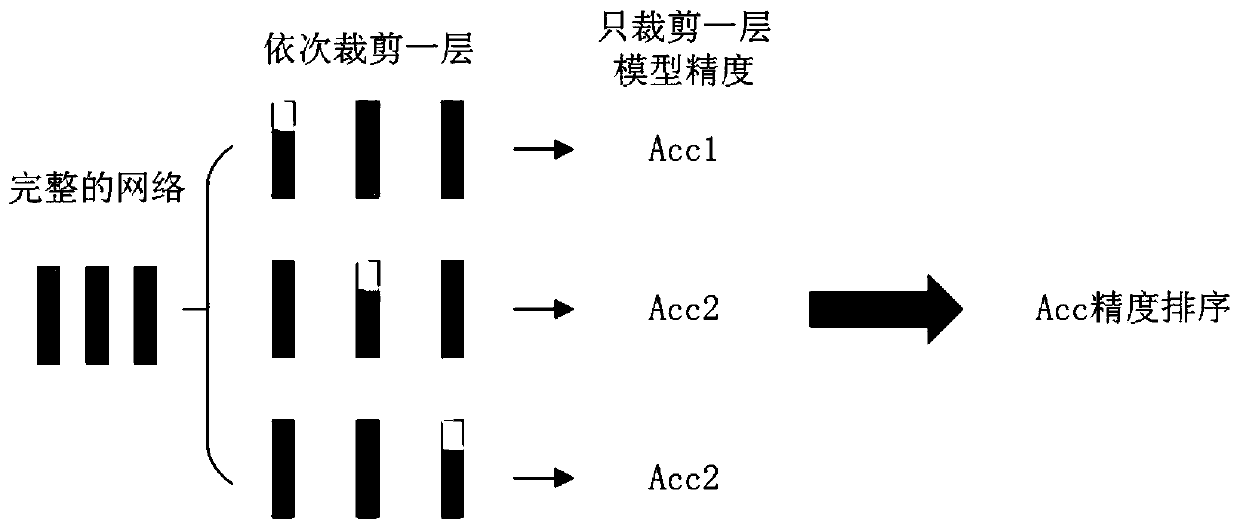
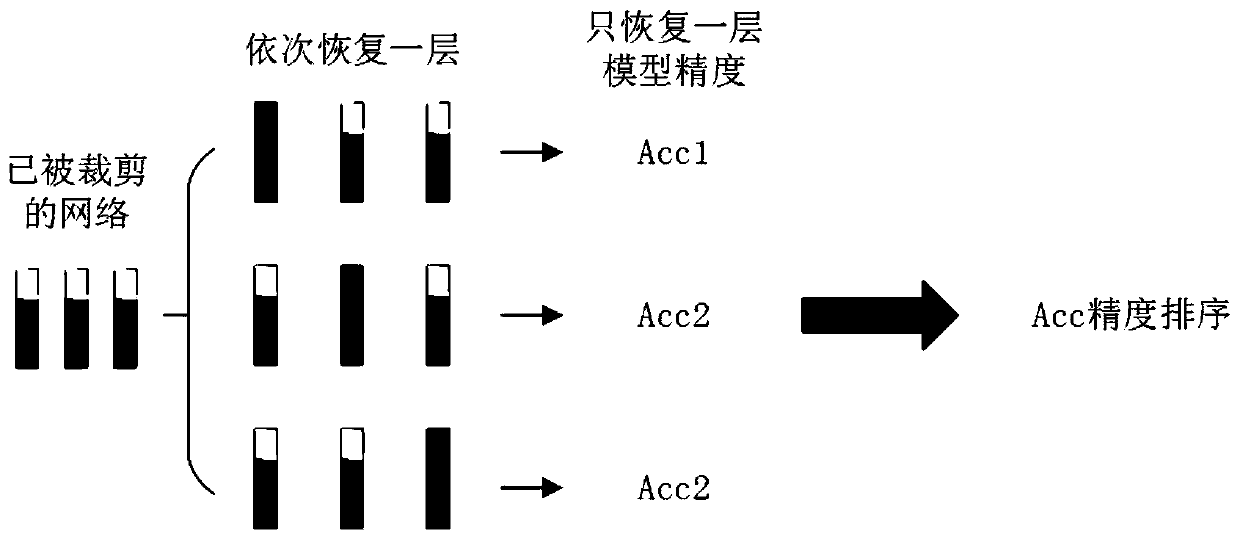
PendingCN111461324AContribution is intuitive, efficient and simpleReducing randomness brings shock problemsNeural architecturesNeural learning methodsAlgorithmEngineering
The invention provides a hierarchical pruning method based on layer recovery sensitivity. The method comprises the steps of S1, performing uniform pruning on each layer of a target neural network model; S2, performing layer recovery on the target neural network model after uniform pruning to obtain the performance contribution degree of each layer to the model; S3, grading each layer in the targetneural network model according to contribution degrees, and setting a pruning proportion for each stage; and S4, pruning the original target neural network model according to the set pruning proportion. The contribution degree of each layer to the model performance is judged more visually, efficiently and simply. Moreover, the oscillation problem caused by randomness during model parameter initialization can be greatly reduced, the model calculation amount is greatly reduced, the hardware requirement is reduced, the calculation speed is increased, the calculation energy consumption is reduced, and the equipment real-time performance is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
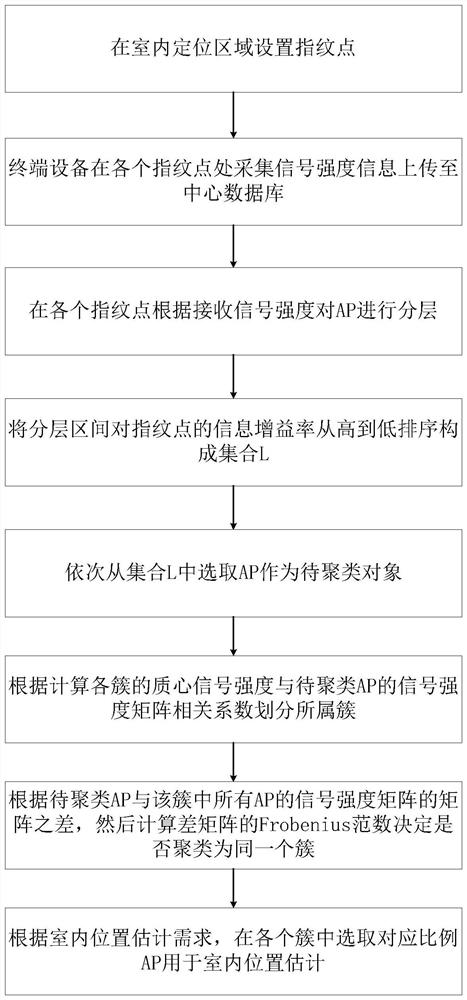
Indoor AP clustering selection method and equipment based on information gain rate
ActiveCN114269006AEfficient removalReduce multipath effectsAssess restrictionParticular environment based servicesPattern recognitionCorrelation coefficient
The invention discloses an indoor AP (Access Point) clustering selection method and equipment based on an information gain rate. The method comprises the following steps: acquiring signal intensity information at fingerprint points in a preset indoor positioning area, and constructing a fingerprint database; layering the APs according to the signal intensity information, calculating the information gain rate of each interval layer for the fingerprint points, and sorting each layered interval according to the information gain rate; for the APs in the sorted hierarchical intervals, clustering is carried out according to correlation coefficients of signal intensity matrixes of the APs; and according to a clustering result, selecting the APs with corresponding proportions from the corresponding categories as the indoor positioning AP access points. According to the method, the AP observed by each fingerprint point is layered and then clustered to distinguish the correlation of each AP, redundant APs and APs with poor observation quality can be effectively removed, the calculated amount of a system in an online position estimation stage is reduced, and the positioning speed and precision are improved.
Owner:HOHAI UNIV
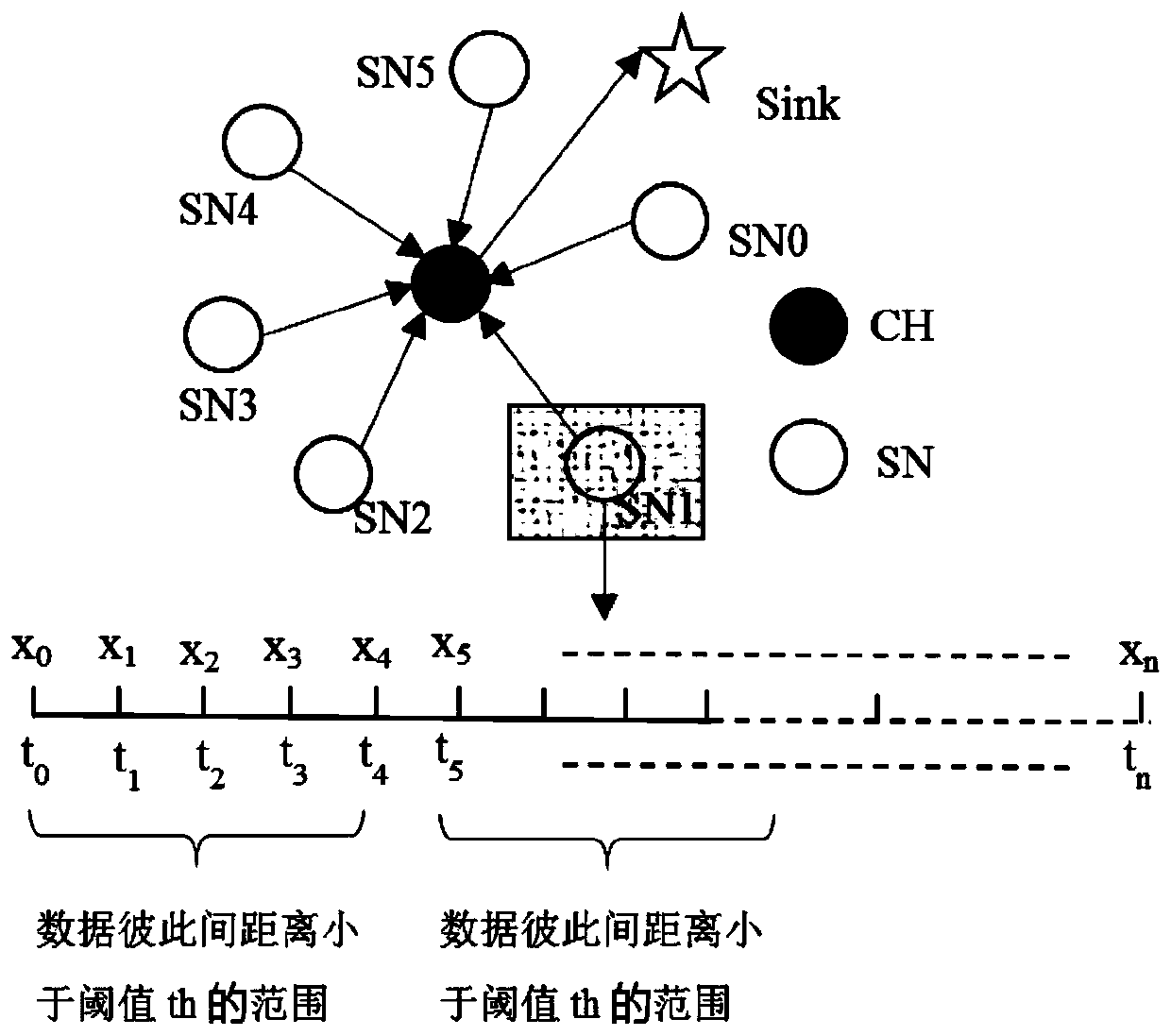
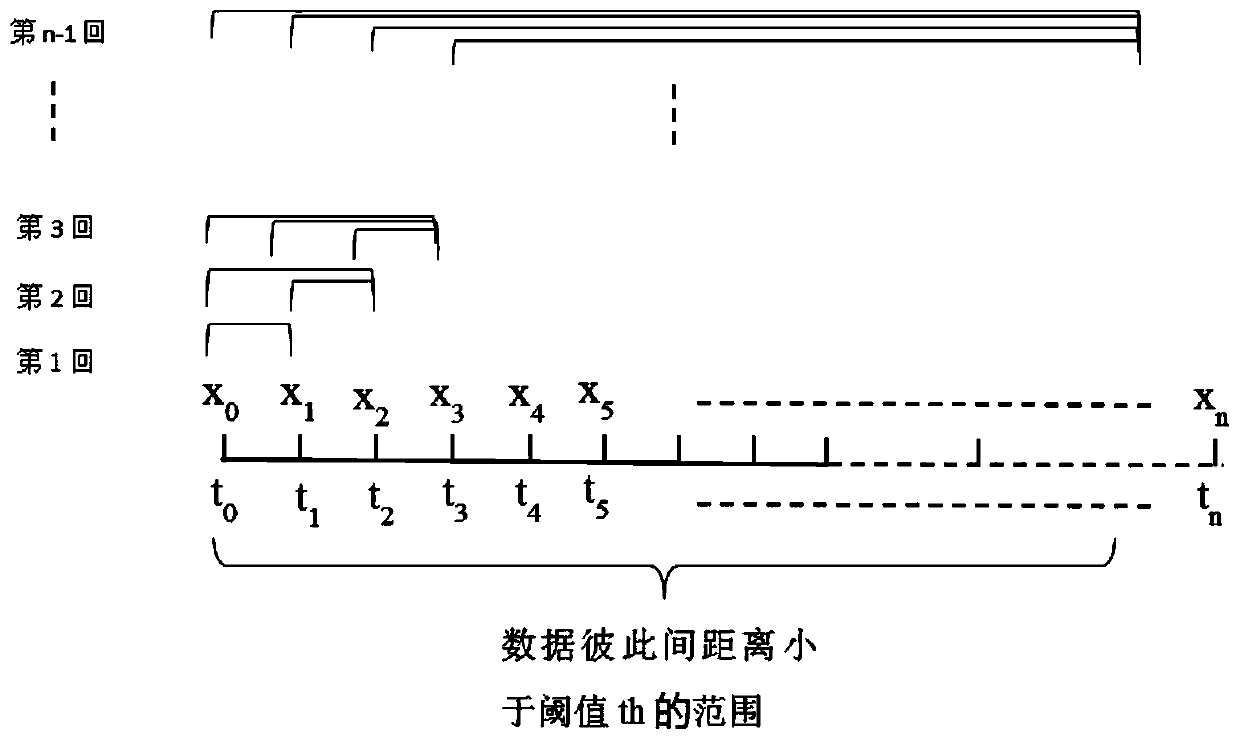
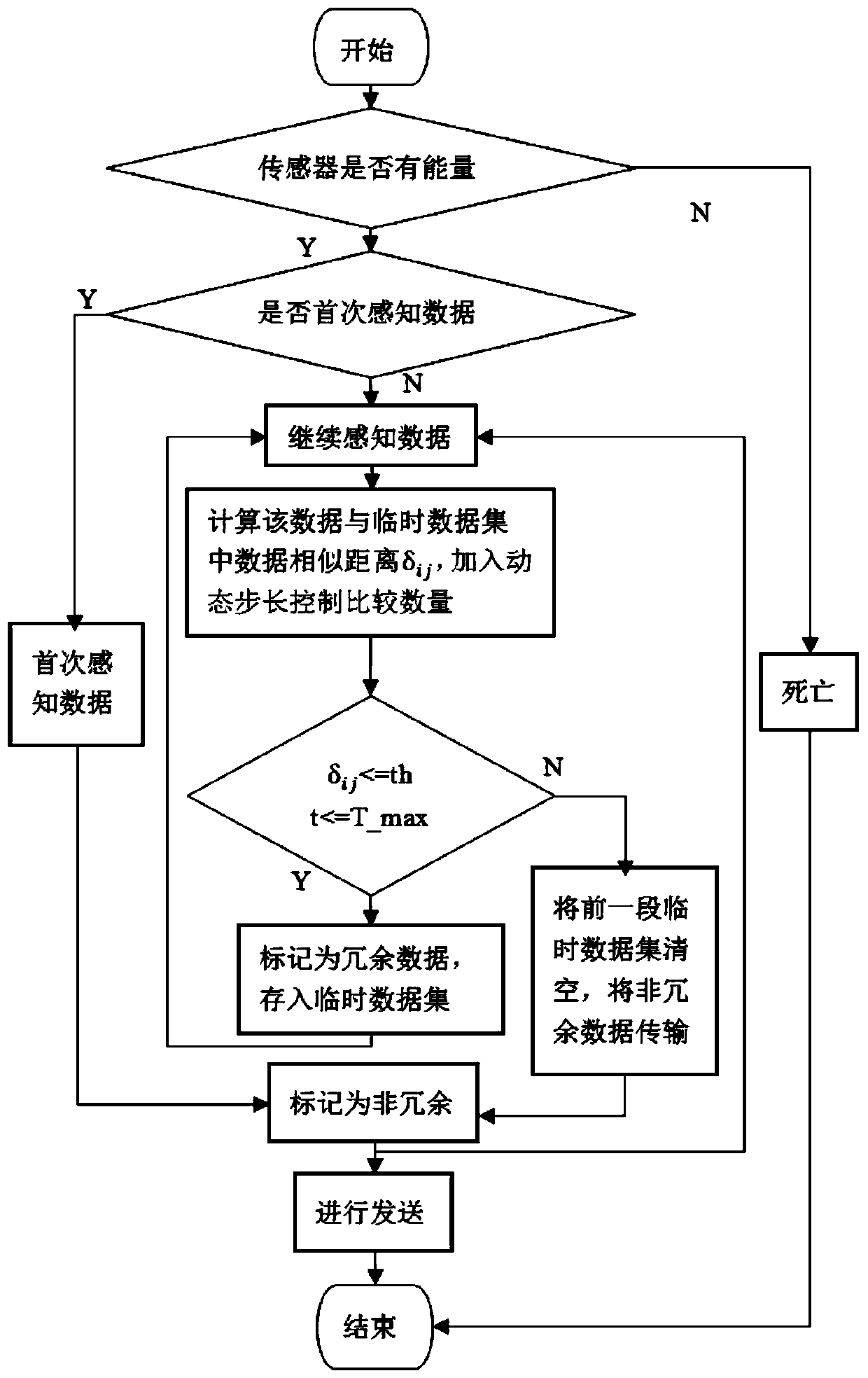
Time correlation redundancy removal method for temperature sensing data
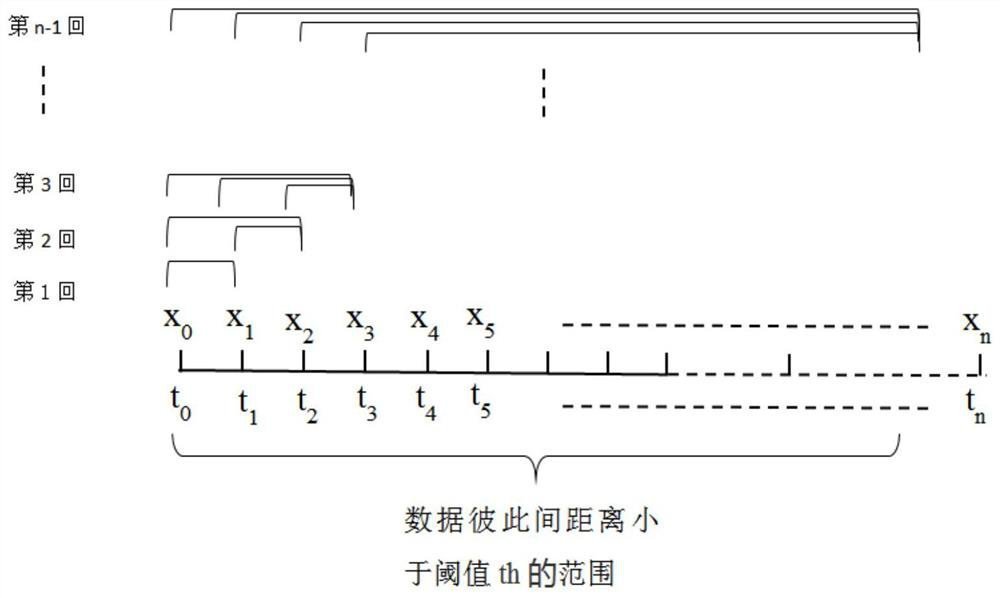
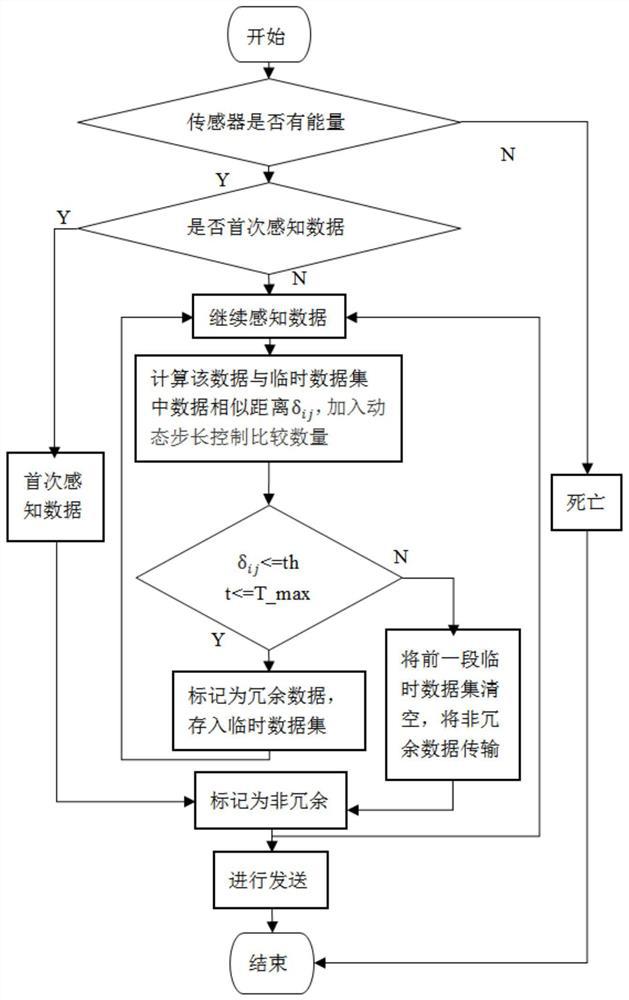
ActiveCN110674356ADoes not affect analysisReduce transmission energy consumptionOther databases retrievalSpecial data processing applicationsData setTime control
The invention discloses a time correlation redundancy removal method for temperature sensing data, and the method comprises the steps of 1, obtaining the temperature sensing data collected by a plurality of temperature sensors, and carrying out the preliminary processing on the temperature sensing data; 2, calculating the similar distance between the currently acquired temperature sensing data andthe data in a temporary data set; 3, calculating the farthest time difference of the continuous redundant temperature sensing data in each period, setting a threshold value of the similar distance and a numerical value of maximum time control, comparing the similar distance with the threshold value of the similar distance, and comparing the farthest time difference with the numerical value of themaximum time control to serve as a redundant condition for judging redundancy; adding a dynamic step length to control the comparison quantity during calculation; and 4, outputting the temperature sensing data after time correlation redundancy removal. According to the method, the special data can be reserved, the problem of the excessive data loss caused by the excessive redundancy elimination is solved, and the temperature sensing data is more reasonable during the redundancy elimination process and more conforms to the acceptance form of a user.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
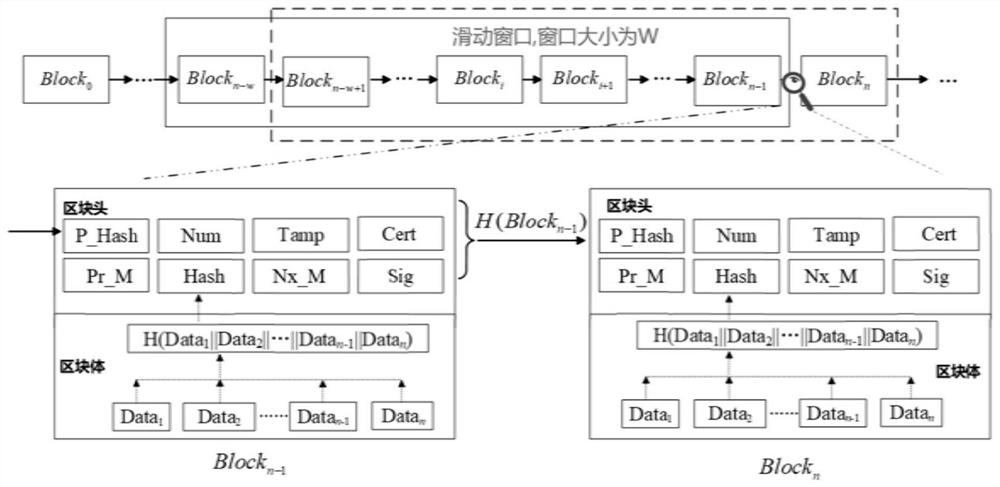
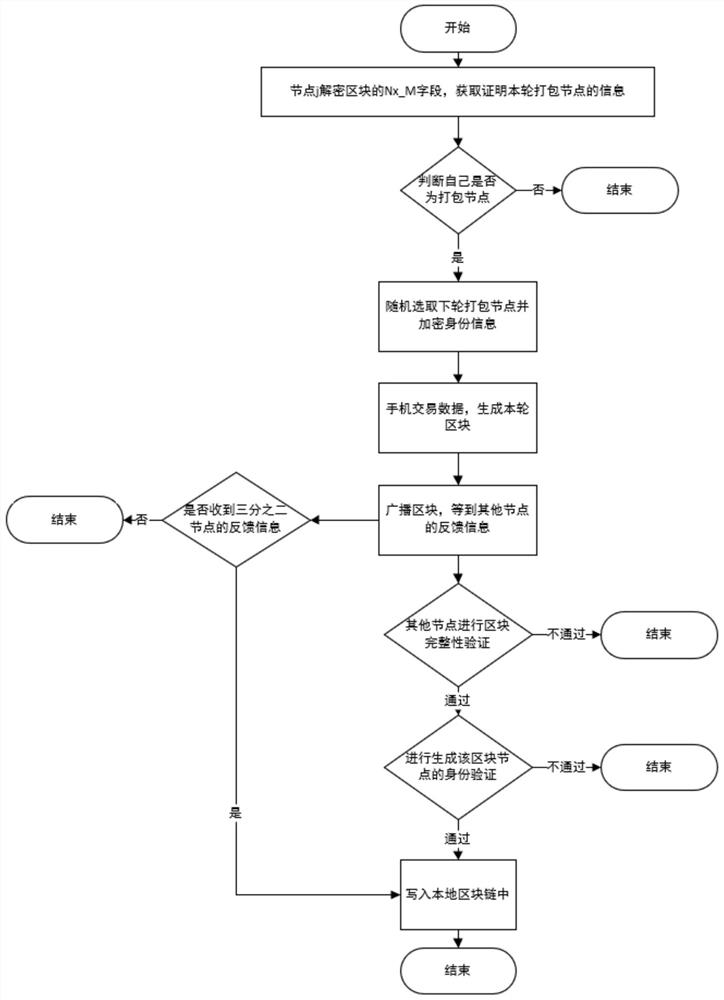
Satellite cluster distributed data security storage method based on block chain
PendingCN114116899ASolve problems such as single point failures that are prone to occurSolve problems such as single point of failureDatabase distribution/replicationSpecial data processing applicationsParallel computingEngineering
The invention discloses a block chain-based satellite cluster distributed data security storage method, which adopts a block chain technology to store sensitive data in a satellite cluster in a distributed manner, and solves the problem that a traditional centralized storage service is easy to generate single-point failure and the like. An efficient consensus algorithm and a double-layer storage architecture are adopted, and the problems that a traditional block chain is large in storage overhead, low in consensus efficiency, slow in data retrieval and the like are solved; the block chain system and the client platform are adaptively deployed in the cloud computing platform, so that the problems of complex deployment, difficult compatibility and the like in traditional block chain system development are solved; a client platform based on a front-end interface is adopted, a visual interface is provided for the storage and query process of a block chain database, and a user can conveniently use a satellite cluster-oriented block chain-based distributed data storage system.
Owner:XIAN MICROELECTRONICS TECH INST
Method for saving node energy of delay-tolerant network and intermittently-connected network
InactiveCN101414965BReduce delivery rateResearch methods to reduce message duplication to reduce delivery rateError prevention/detection by using return channelData switching networksMessage deliveryNetwork communication
The invention relates to a method used for saving node energy in a delay tolerant network and an intermittent connection network, belonging to the field of network communication technique. The method comprises the steps as follows: a source node queries a node neighbor list; if no destination node information exists, the message is temporarily memorized in a node buffer; the non-empty nodes in the buffer periodically send exploration information which is used to exchange a message list and a message delivery acknowledgement list; when the node sending the exploration information receives a return information, the buffer is actively maintained according to the message delivery acknowledgement list carried in the return information and a message is sent by the node; after an intermediate node successfully transmits the message to the destination node, the node adds corresponding records into the message delivery acknowledgement list memorized locally and deletes the message from the buffer. The method can effectively reduce the quantity of the redundant nodes, improves the performance of the whole network and prolongs the life period.
Owner:TIANJIN UNIV
Coding scheme for a data stream representing a temporally varying graphics model
ActiveCN100547615CReduce computing energy consumptionSmall compression lossImage codingTelevision systemsGraphicsData stream
Introducing a further prediction stage, namely a prediction of the motion vectors or the prediction error of the first prediction stage, does indeed at first increase the encoding or compression effort and, correspondingly, also the decoding or decompression effort, but the prediction proposed here leads to a significant improvement of the compression gain in relation to the effort in most graphics model sequences due to the uniformity of the motion.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
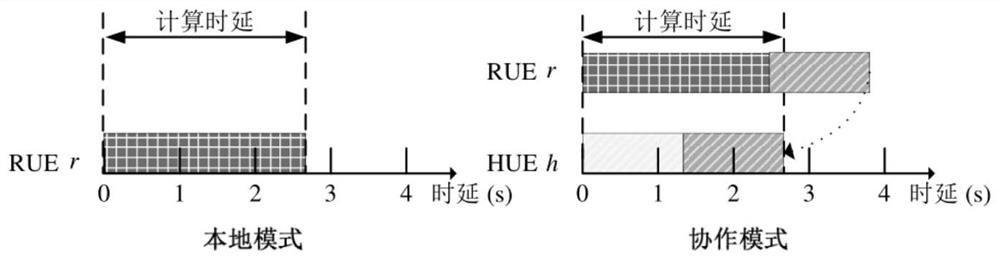
D2D distributed cooperative computing method for minimizing system computing energy consumption
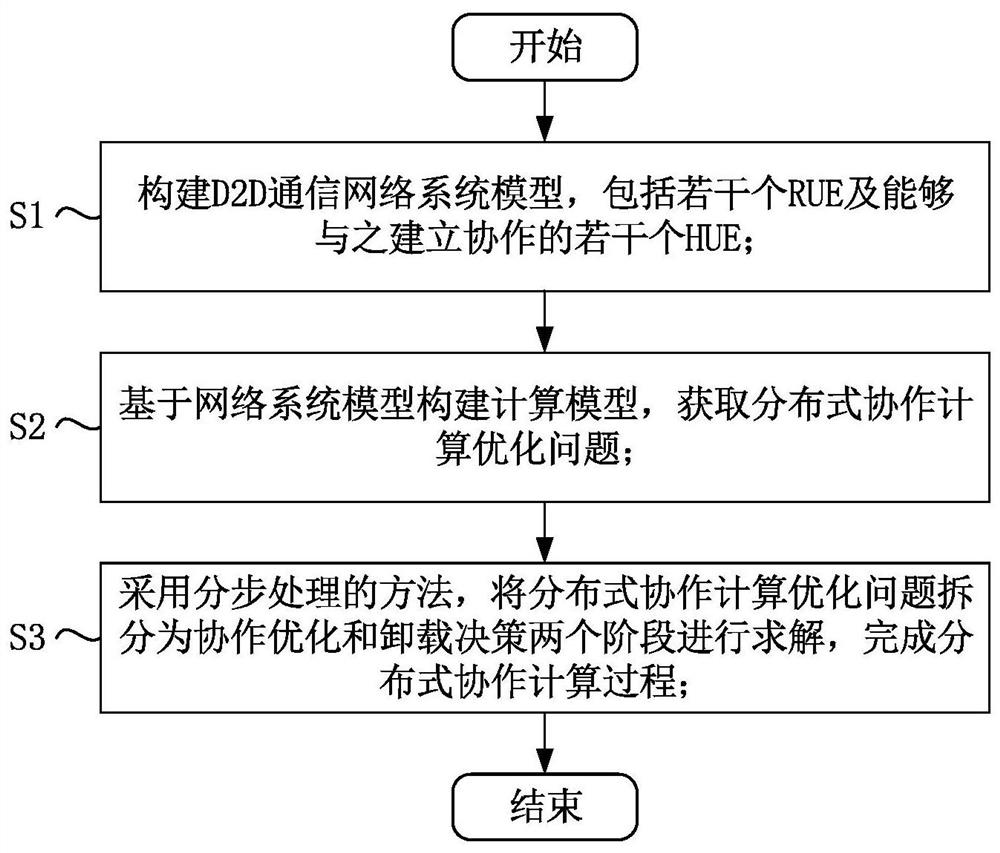
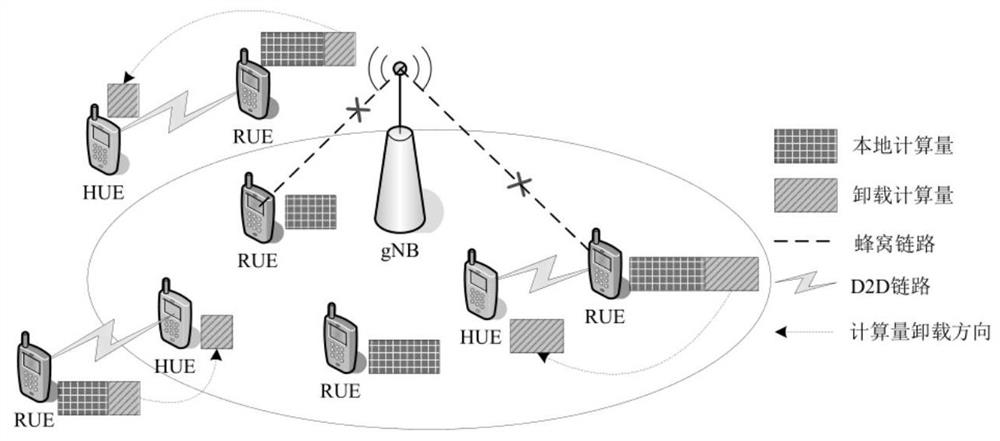
ActiveCN113411786AIncrease the number of tasksReduce computing energy consumptionPower managementNetwork traffic/resource managementNetworked systemComputational model
The invention provides a D2D distributed cooperative computing method for minimizing system computing energy consumption, which comprises the following steps: constructing a D2D communication network system model which comprises a plurality of pieces of RUE and a plurality of pieces of HUE capable of establishing cooperation with the RUE; constructing a calculation model based on the network system model, and obtaining a distributed cooperative calculation optimization problem; adopting a step-by-step processing method, splitting a distributed cooperative computing optimization problem into two stages of cooperative optimization and unloading decision making to be solved, and completing a distributed cooperative computing process. The invention provides the D2D distributed cooperative computing method for minimizing system computing energy consumption, so as to solve the problems of shortage of user computing resources and lack of concentrated nodes in an off-network scene. Compared with an existing scheme, the method can give full play to the advantages of D2D cooperative calculation, improves the number of tasks successfully completed on time in the system, and saves the calculation energy consumption of the system.
Owner:SUN YAT SEN UNIV
State estimation based intelligent power grid dynamic data encryption method
ActiveCN102916813BAvoid synchronous dynamic generationRealize synchronous dynamic generationKey distribution for secure communicationUser identity/authority verificationCommunications securityComputation complexity
The invention discloses a state estimation based intelligent power grid dynamic data encryption method. The method includes: each telemetering terminal divides observation data into reporting data and retention data, uses the retention data to generate a dynamic key to encrypt the reporting data, generates a ciphertext and transmits the ciphertext to a control center; and the control center computes the retention data of each telemetering terminal based on a state estimation method to generate a dynamic key and decrypts the ciphertext transmitted by each telemetering terminal, so that the reporting data of each telemetering terminal are obtained. Synchronous dynamic key generation can be realized between the intelligent power grid control center and each remote terminal without key distribution, and communication safety in an intelligent power grid is effectively improved while computing complexity, energy consumption and hardware cost of terminal equipment are lowered effectively.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
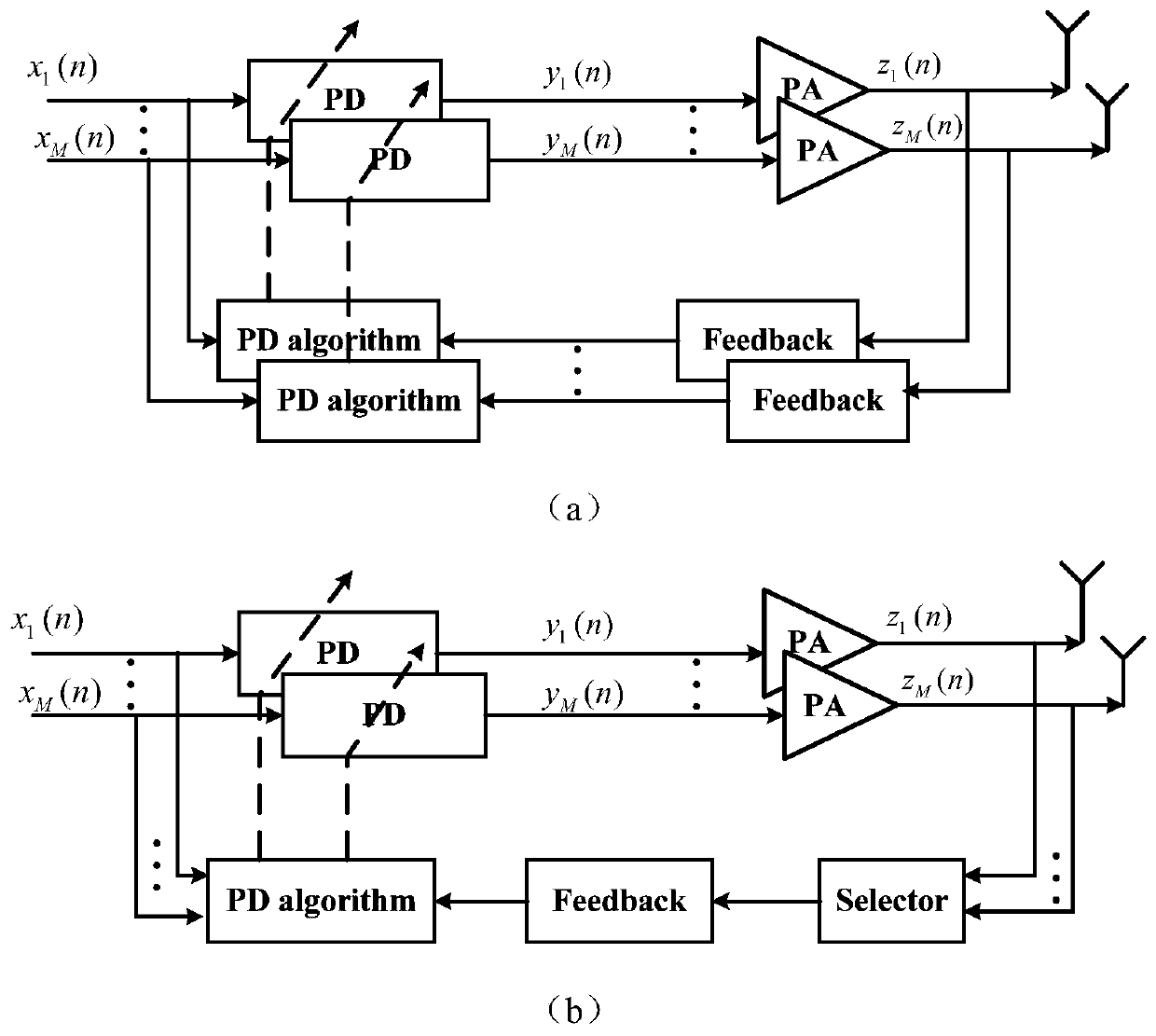
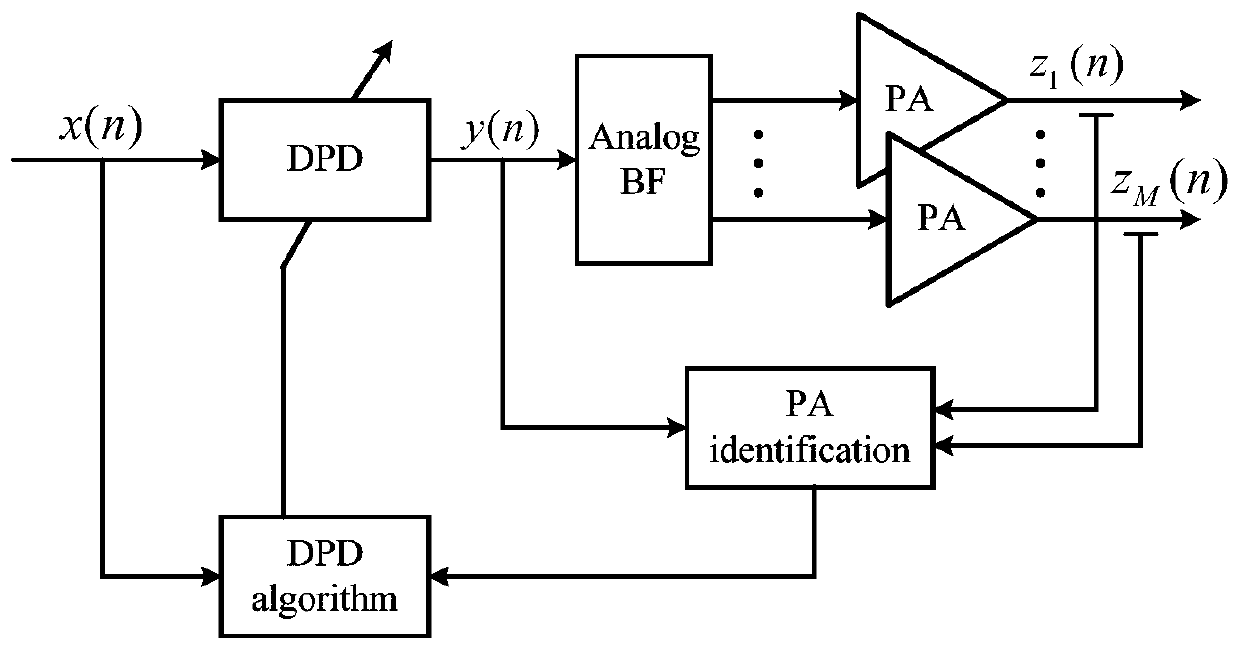
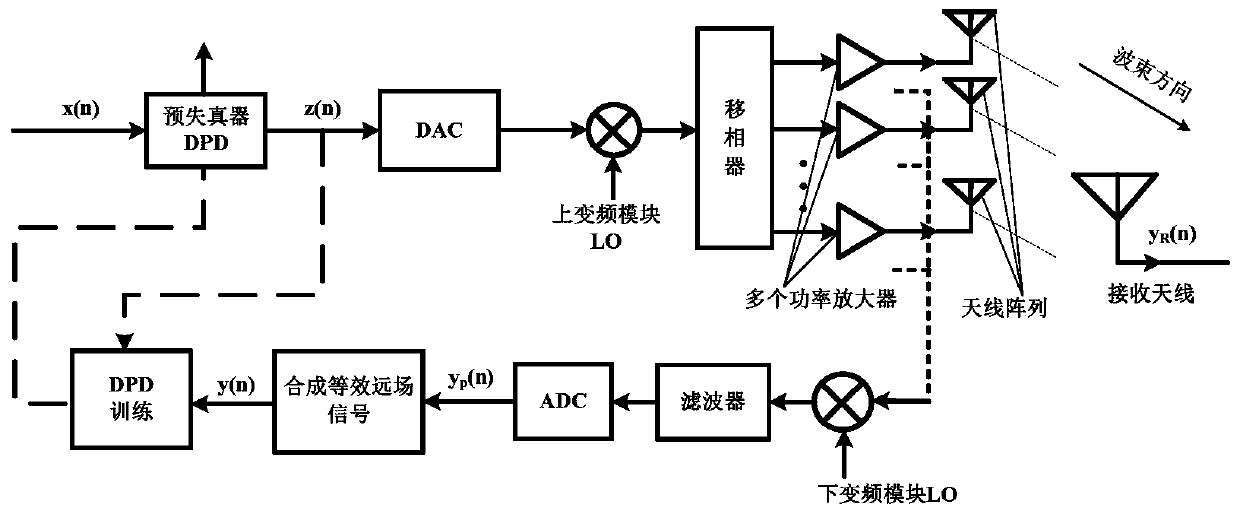
Digital Predistortion Structure and Control Method for Beamforming System
ActiveCN107566306BAchieve linearizationSimple structureSpatial transmit diversityTransmitter/receiver shaping networksBeam directionTime-sharing
The invention provides a digital pre-distortion structure for a beam forming system, and a control method thereof. The control method comprises the following steps: transmitting an input original signal x(n) via an antenna array after processing the original signal via a predistorter, a DAC, an up-conversion module, a phase shifter and a power amplifier; collecting an output signal yp(n) of each power amplifier by a feedback channel in a time sharing manner; synthesizing an equivalent far field signal y(n) of a main beam direction by using a beam forming algorithm according to yp(n); performing DPD training by using an indirect learning structure or a direct learning structure depending on the y(n) and the x(n), and updating the coefficients of the predistorter; and inputting the generatedDPD signal in the system, transmitting the signal via a transmitting channel, and using the transmitted signal as a linear signal of the main beam direction. The digital pre-distortion structure provided by the invention can greatly simplify the transmitter structure, reduce the computing energy consumption, achieves the linearization of the signal of the main beam direction, and can achieve verygood nonlinear performance when the difference of the nonlinear characteristics of each power amplifier is relatively large.
Owner:TSINGHUA UNIV
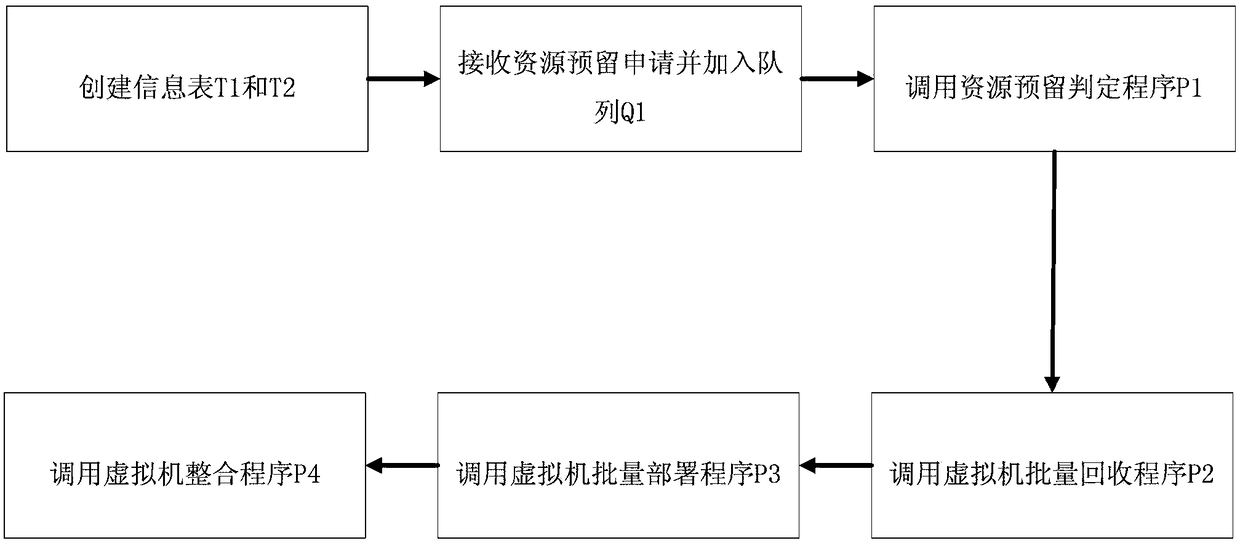
A cloud platform virtual cluster deployment integration method
ActiveCN105843670BOptimize the batch deployment processReduce in quantityResource allocationSoftware simulation/interpretation/emulationVirtual machine consolidationResource utilization
The invention discloses a cloud platform based virtual cluster deployment and integration method. The method, based on the user resource reservation application based cloud service platform, roughly comprises four parts of resource reservation application judgment, virtual machine batch recycling, virtual machine batch deployment and virtual machine integration. In the virtual machine batch deployment, an optimal solution or a quasi-optimal solution is calculated by applying a genetic algorithm, and optimization targets include a comprehensive average resource utilization rate and a comprehensive resource utilization balance rate of clusters. When the comprehensive average utilization rate of the clusters is lower than a critical value, a virtual machine integration program is called and a feasible solution of a virtual machine integration optimization problem is searched for by using a greedy algorithm. According to the method, a virtual cluster resource reservation application function is added, the platform can automatically assist a user in virtual machine life cycle management, the resource utilization rate of a cloud data center can be increased, and the service quality of an application running in a virtual machine can be ensured.
Owner:ZHEJIANG UNIV
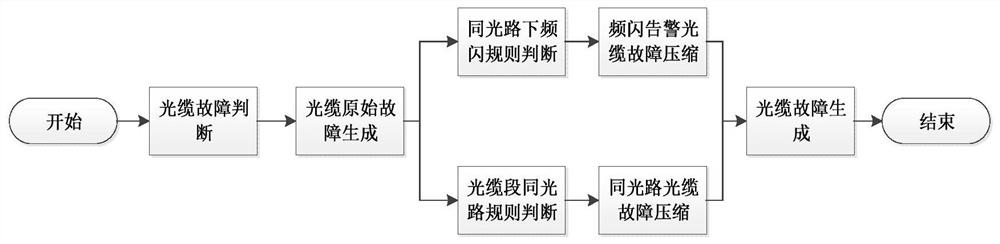
Compression mechanism implementation method applied to optical cable outdoor faults in communication industry
InactiveCN112564784AGuaranteed validityUniqueness guaranteedDigital data information retrievalElectromagnetic transmissionInformation processingTelecommunications
A compression mechanism implementation method applied to optical cable outdoor faults in the communication industry is beneficial to improving stability of optical cable fault processing and providingguarantee for effectiveness and uniqueness of optical cable fault information through an alarm information processing model, a resource information model association model and an optical cable faultcompression processing model. Meanwhile, overall calculation energy consumption of the system is reduced, and overall processing efficiency is improved. According to the invention, the problems that the stroboscopic alarm generates the optical cable fault event and the optical path dimension generates the optical cable fault event to generate excessive invalid optical cable fault events can be solved.
Owner:北京直真科技股份有限公司
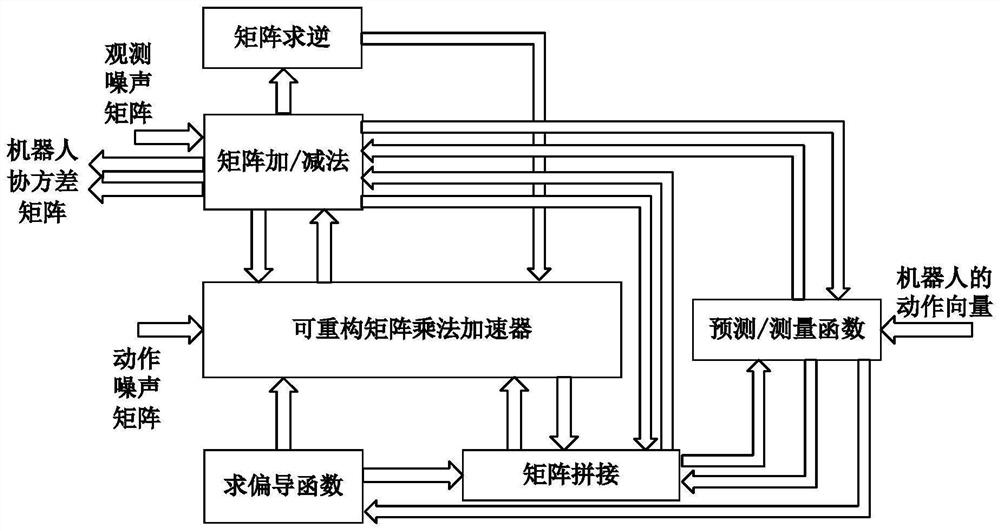
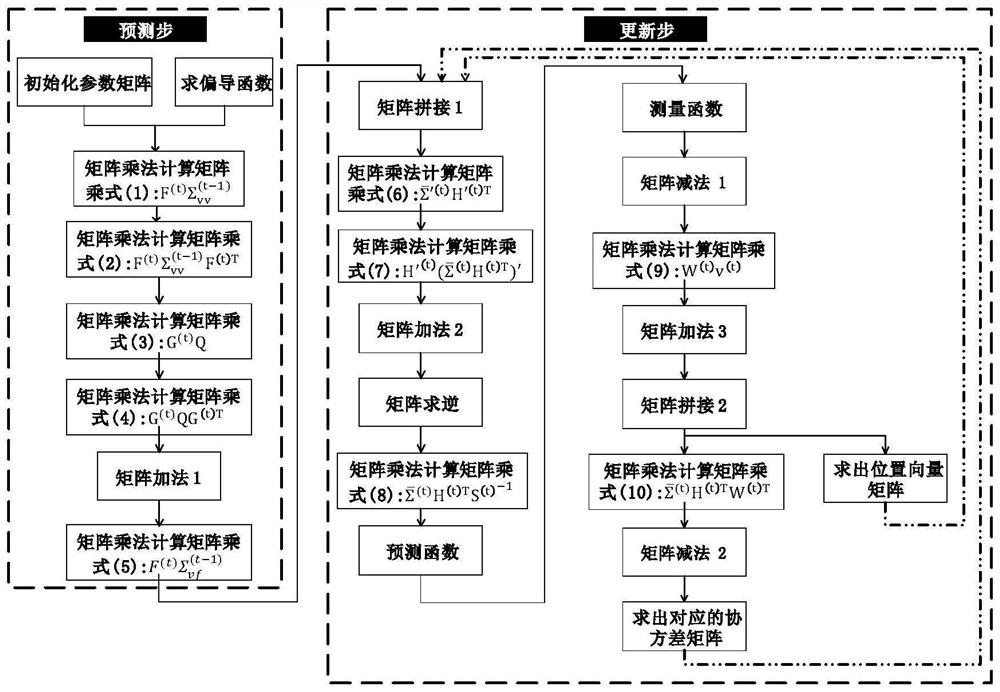
Reconfigurable hardware acceleration system for extended Kalman filtering
PendingCN114860649AAccelerate computingReduce movementCAD circuit designArchitecture with single central processing unitMatrix multiplicationHardware acceleration
The invention discloses a reconfigurable hardware acceleration system for extended Kalman filtering, and belongs to the field of hardware acceleration design of algorithms. According to the method, the matrix data buffer is designed on the basis of analyzing the data equivalence between matrix multiplication in the EKF algorithm, and when the reconfigurable PE array performs current matrix multiplication calculation, the matrix data buffer provides matrix data calculated by previous matrix multiplication for the reconfigurable PE array, so that the reusability of the matrix data is fully realized, and the reusability of the reconfigurable PE array is improved. According to the method, data migration between off-chip and on-chip is reduced, operation acceleration of all matrix multiplication in the EKF algorithm is realized, and energy consumption is reduced at the same time. The data symmetry and the data sparsity in the EKF algorithm are fully utilized, trigonometric function and root extraction calculation are rapidly achieved, the reconfigurable PE array is provided with FIFO, data interaction between modules is achieved on a chip, and other optimization means are adopted, so that the calculation speed is further increased.
Owner:HUAZHONG UNIV OF SCI & TECH
Adaptive Compression Method for Wireless Sensor Networks
InactiveCN103957582BAchieve energy optimizationGood energy saving effectPower managementNetwork topologiesAdaptive compressionWireless sensor networking
The invention discloses a wireless sensor network self-adaptation compression method which can achieve energy optimization in the whole network. The method comprises the step of a compression judging process. In the compression judging process, the total energy consumption Ecomp caused when compression is executed and the total energy consumption Euncomp caused when compression is not executed are compared, if the total energy consumption Ecomp is larger than the total energy consumption Euncomp, initial data are not compressed and directly sent out, if the total energy consumption Ecomp is smaller than the total energy consumption Euncomp, the data compression process is executed, the initial data are compressed and then sent out, and if the total energy consumption Ecomp is equal to the total energy consumption Euncomp, the initial data are not compressed and directly sent out or the initial data are compressed and then sent out.
Owner:NINGBO INST OF TECH ZHEJIANG UNIV ZHEJIANG
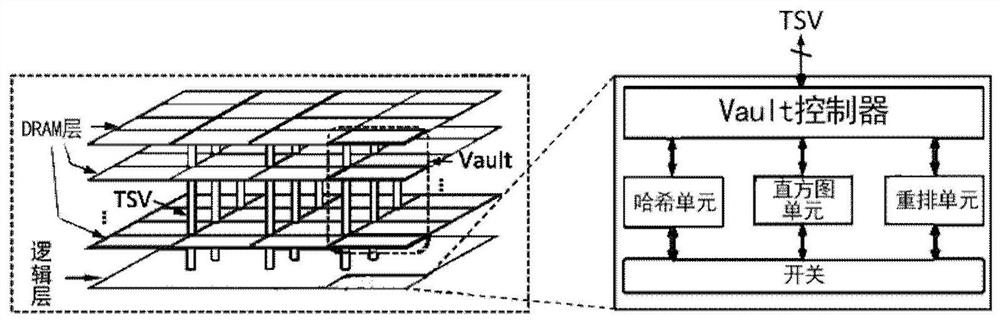
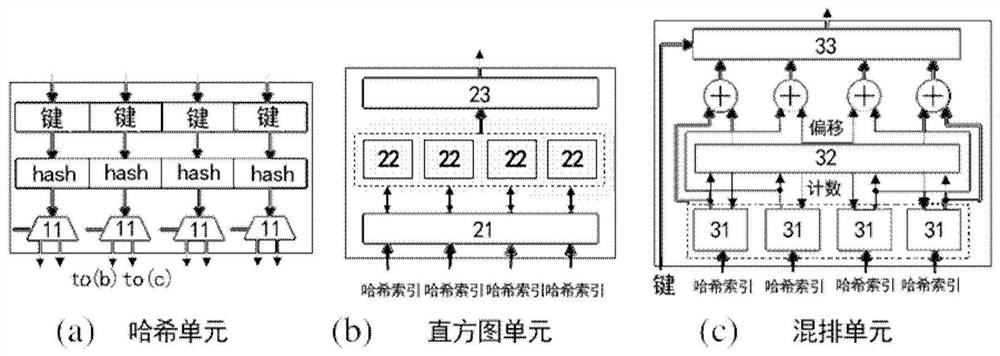
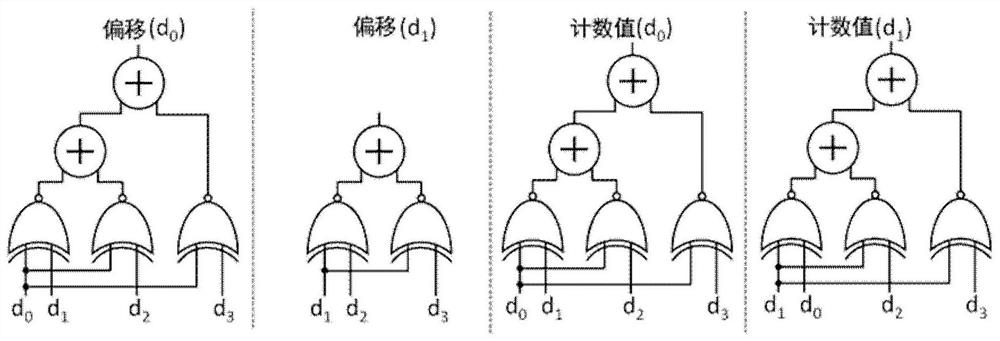
Hash Partition Accelerator
ActiveCN108196662BReduce energy consumptionAvoid round-trip data transfersResource allocationDigital data processing detailsTarget arrayAlgorithm
The invention discloses a Hash partitioning accelerator configured to be integrated on a memory and used for acceleration processing of a Hash connection partitioning stage. The Hash partitioning accelerator comprises a Hash unit, a histogram unit and a shuffle unit, wherein the Hash unit is used for reading multiple tuples in partitioned relation tables from a memory and then parallelly processing keys of the tuples to generate multiple Hash indexes; the histogram unit is used for parallelly updating multiple copies of histogram data stored in the histogram unit according to the Hash indexesand integrating all the updated copies into a histogram data form with data consistency; and the shuffle unit is used for determining positions of all the tuples stored in a target array according tothe Hash indexes, copying the tuples in the relation tables into the target array and realizing division of the relation tables. Through the accelerator, total energy consumption at the partitioning stage is remarkably lowered through acceleration at the memory end.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
A time-dependent de-redundancy method for temperature-aware data
ActiveCN110674356BLoss of analyzabilityAvoid missingOther databases retrievalSpecial data processing applicationsSensing dataData set
The invention discloses a time correlation redundancy removal method for temperature sensing data, and the method comprises the steps of 1, obtaining the temperature sensing data collected by a plurality of temperature sensors, and carrying out the preliminary processing on the temperature sensing data; 2, calculating the similar distance between the currently acquired temperature sensing data andthe data in a temporary data set; 3, calculating the farthest time difference of the continuous redundant temperature sensing data in each period, setting a threshold value of the similar distance and a numerical value of maximum time control, comparing the similar distance with the threshold value of the similar distance, and comparing the farthest time difference with the numerical value of themaximum time control to serve as a redundant condition for judging redundancy; adding a dynamic step length to control the comparison quantity during calculation; and 4, outputting the temperature sensing data after time correlation redundancy removal. According to the method, the special data can be reserved, the problem of the excessive data loss caused by the excessive redundancy elimination is solved, and the temperature sensing data is more reasonable during the redundancy elimination process and more conforms to the acceptance form of a user.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com