Patents
Literature
257 results about "System validation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
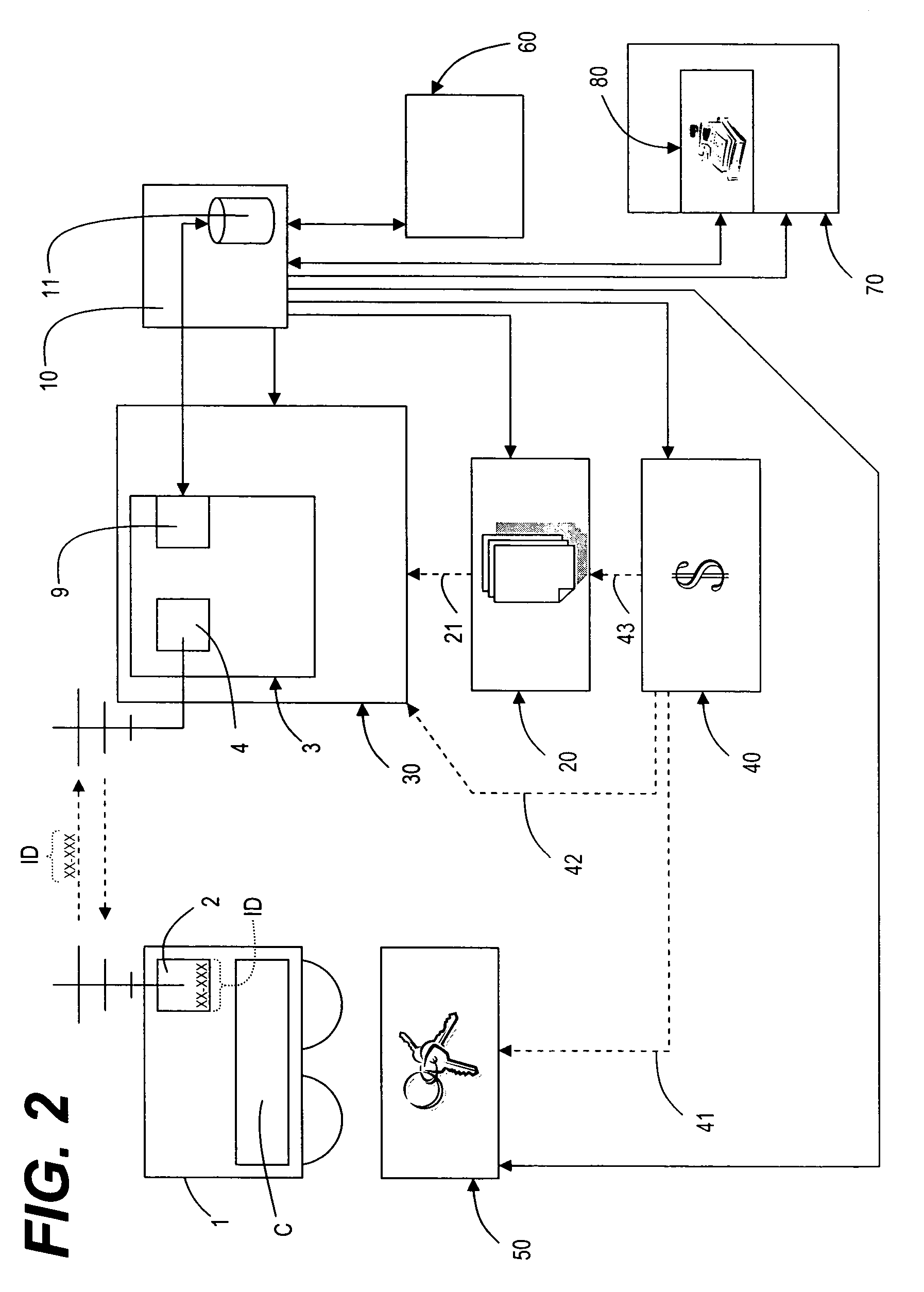
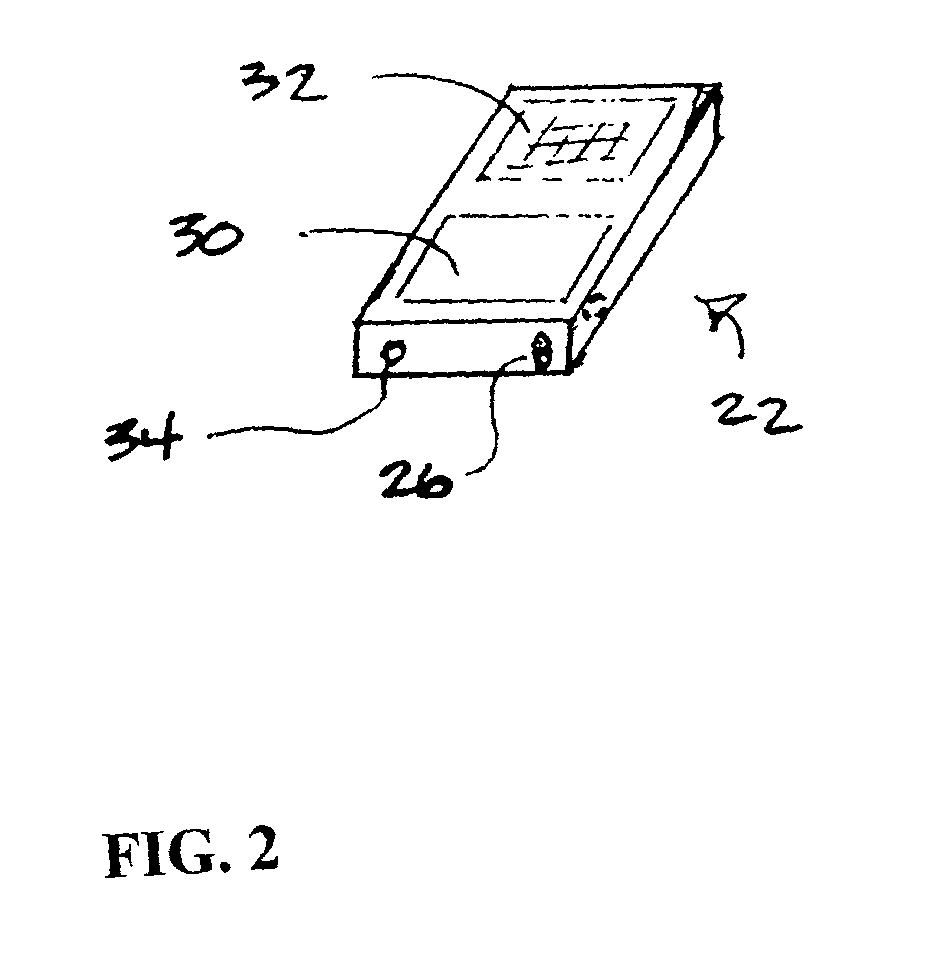
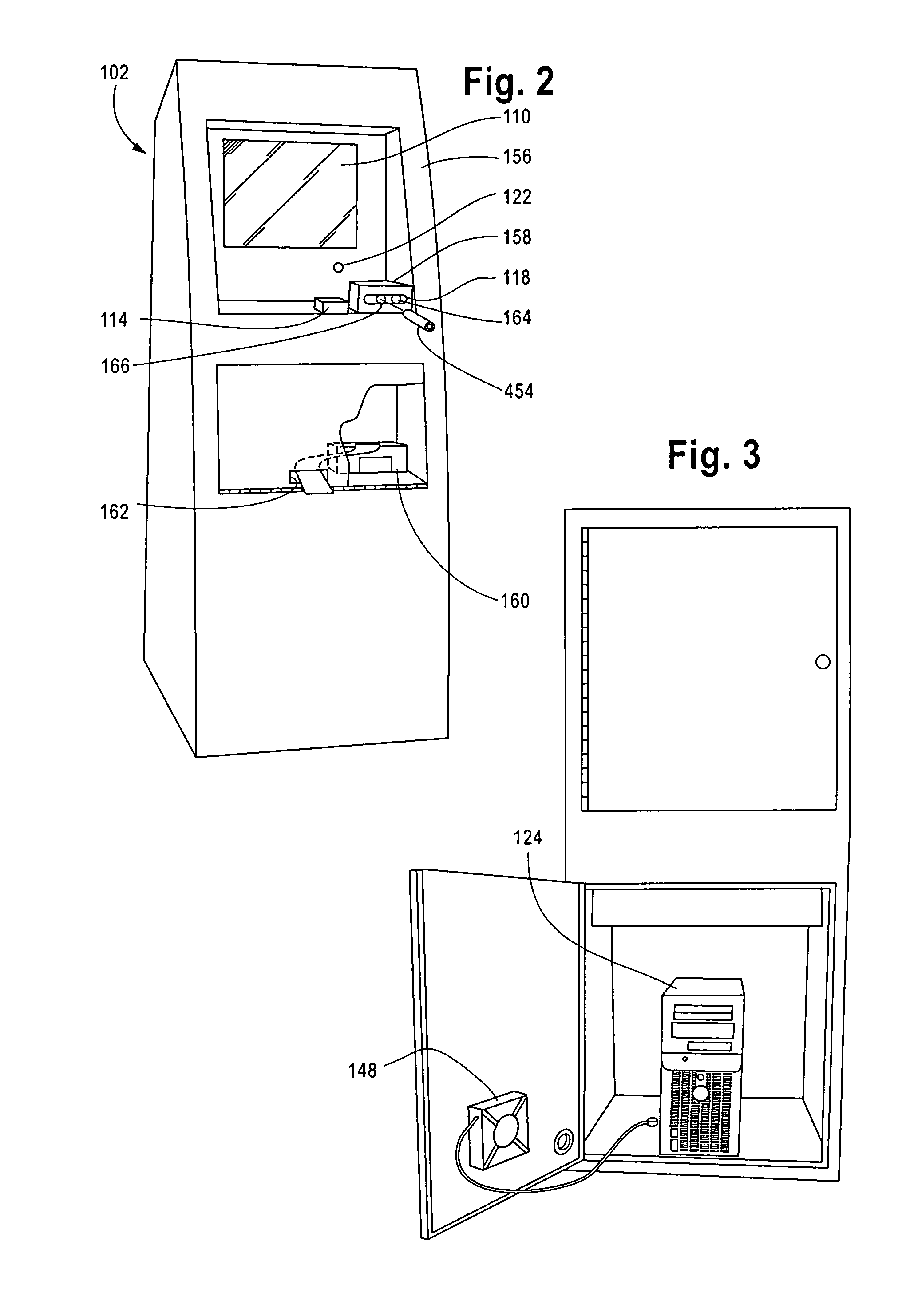
System and method to authenticate users to computer systems
InactiveUS20050091338A1Facilitates rapid secondary logLimited accessDigital data processing detailsDrug and medicationsTelecommunications linkTransceiver
A system utilizing a personal security device to provide access to a computer terminal where the personal security device includes circuitry and transceiver components for transmitting identification information and exchanging other digital information with a computer terminal and other compatible devices and the personal security device establishes a communication link with a computer terminal to allow a user to logon to the terminal so that when a user leaves the computer terminal, the communication link is terminated, causing the computer terminal to lock the keyboard, blank the monitor, and / or logoff the user if the communication link is not restored within a sufficient time period and also allowing the personal security device to facilitate subsequent computer access within a time range by providing time related access codes to the terminal that can be used to reestablish computer terminal access.
Owner:DLH TECH LLC
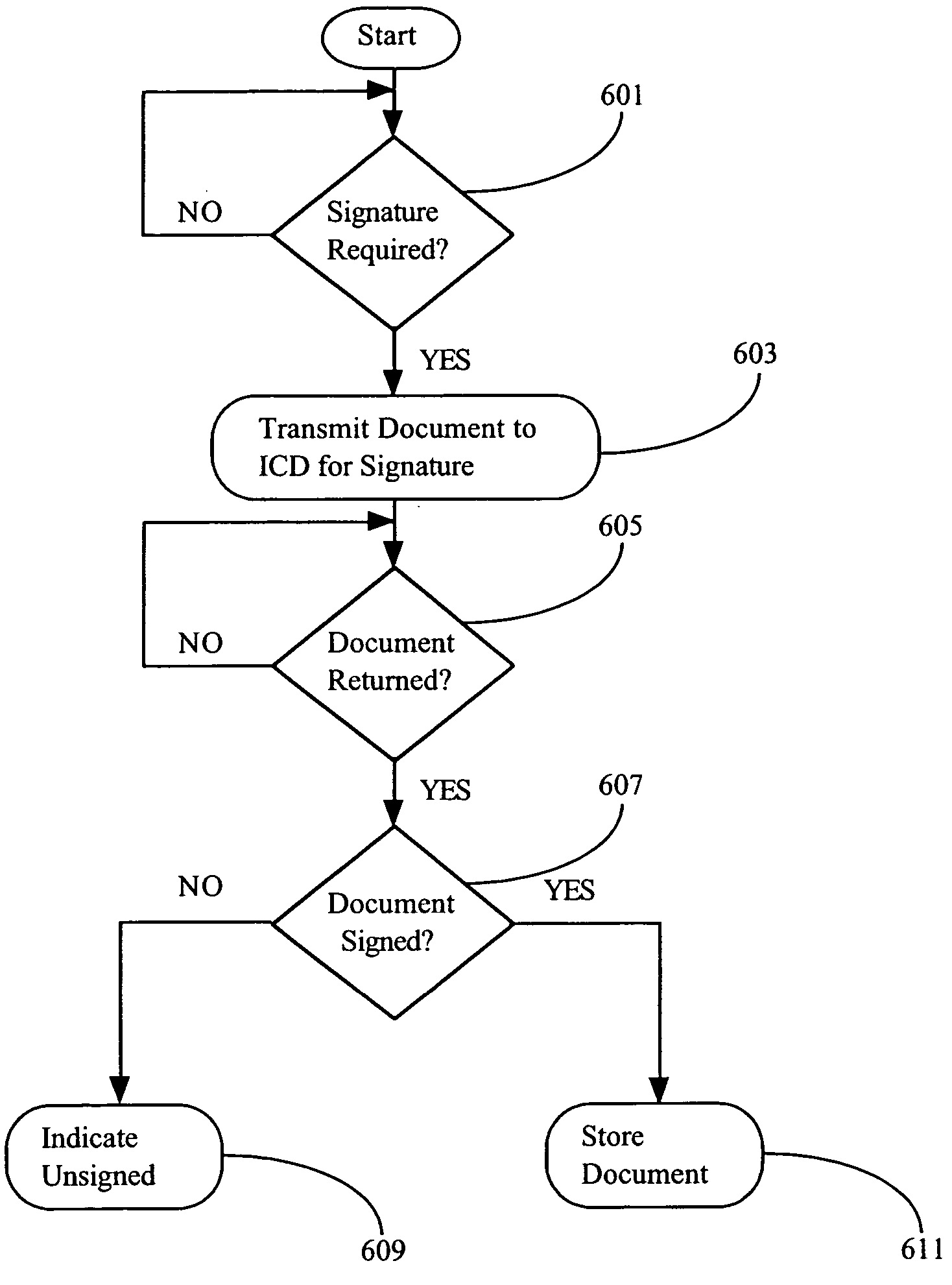
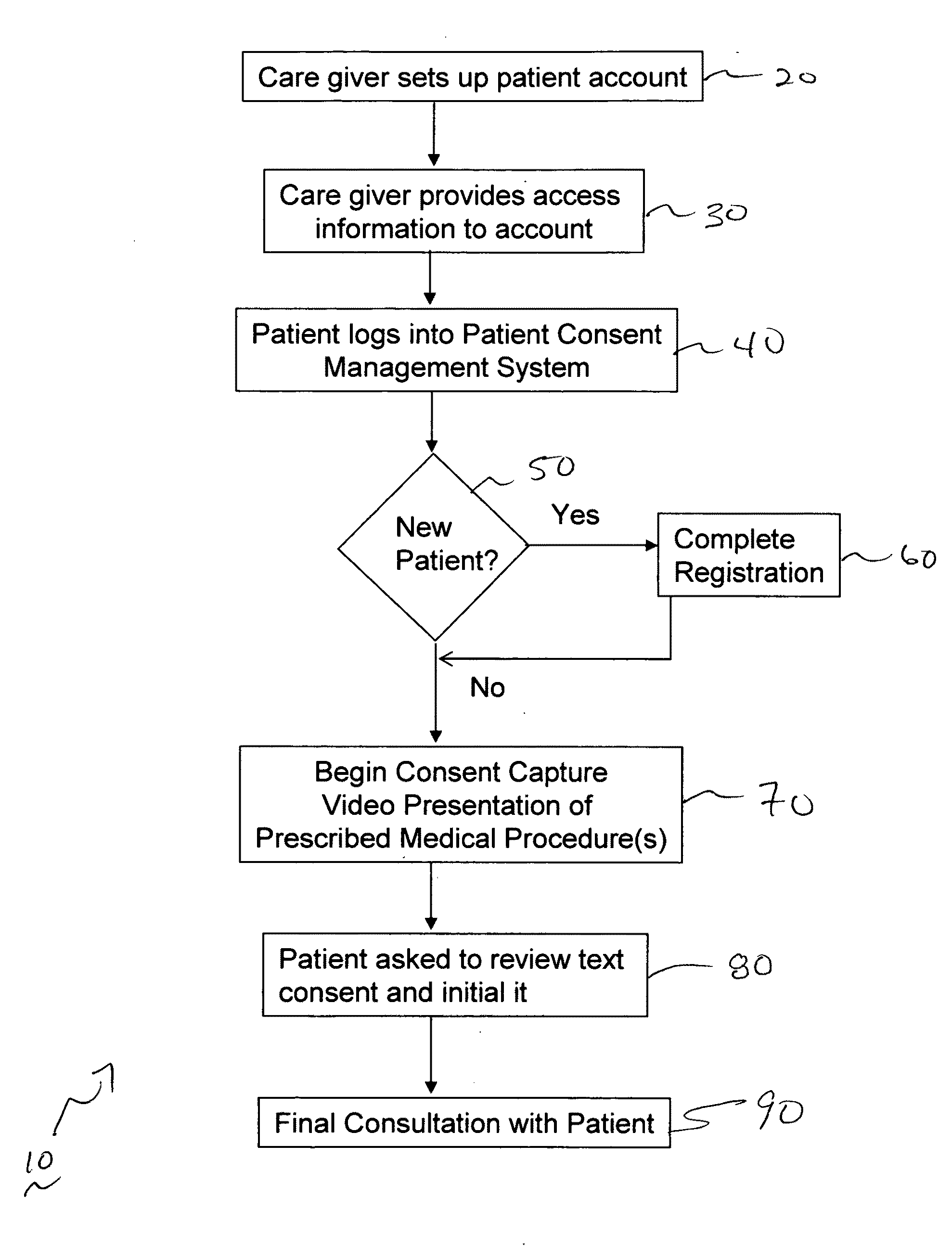
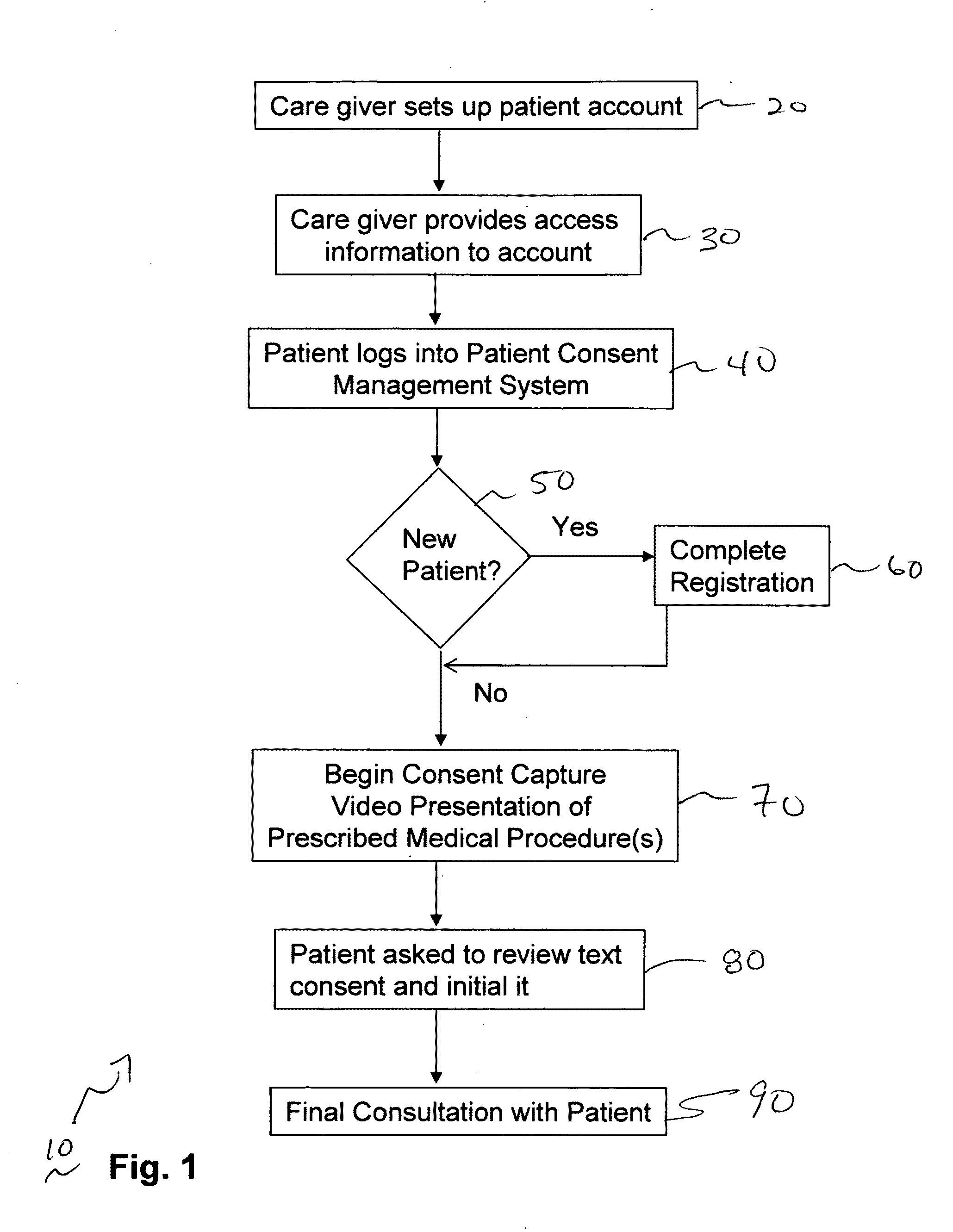
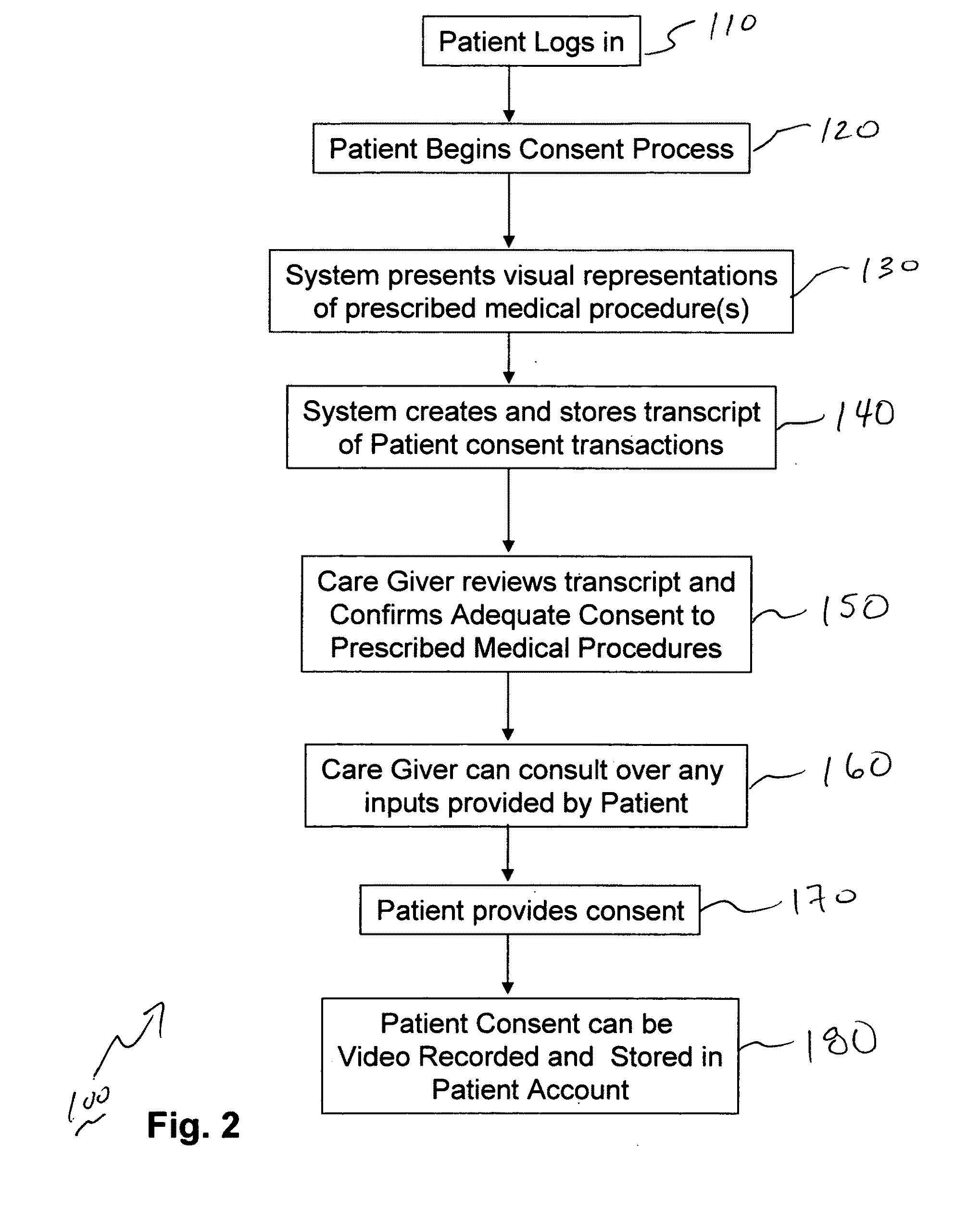
Methods and system for capturing and managing patient consents to prescribed medical procedures
InactiveUS20100094650A1Data processing applicationsComputer-assisted medical data acquisitionCare giverConsent Type
A method of capturing patient consents to a prescribed medical procedures. Patient accounts are created on a computerized patient consent management system. The system authenticates a login attempt by a patient and displays a visual representation of a prescribed medical procedure to the patient. The patient consent management system presents at least one consent request input field for accepting a consent input from the patient and stores the consent input as part of the patient account. The patient consent management system presents the consent input to at least one care giver in order to determine if the patient has given consent to the prescribed medical procedure.
Owner:TRAN SON NAM +2
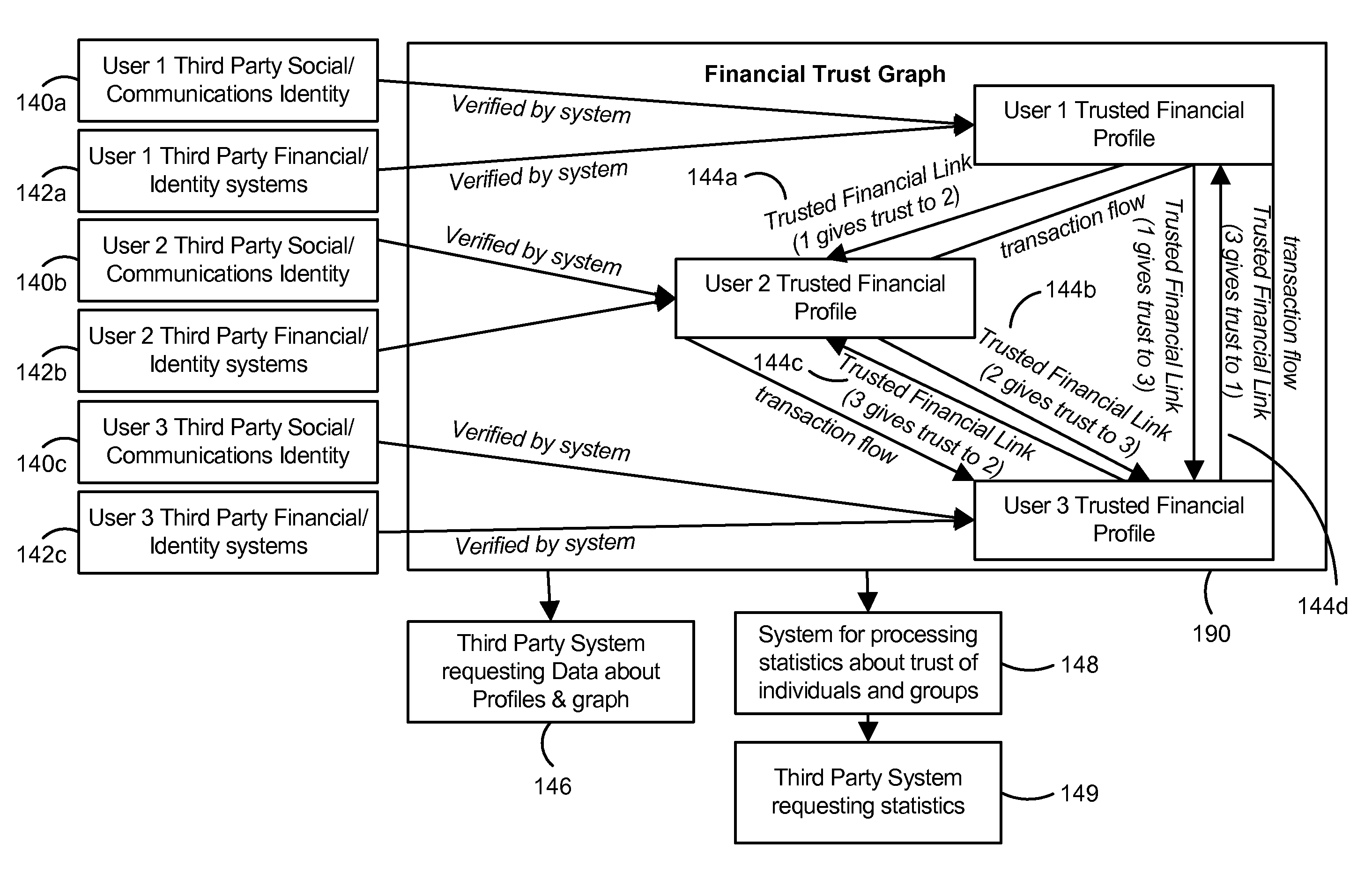
Trust Based Transaction System
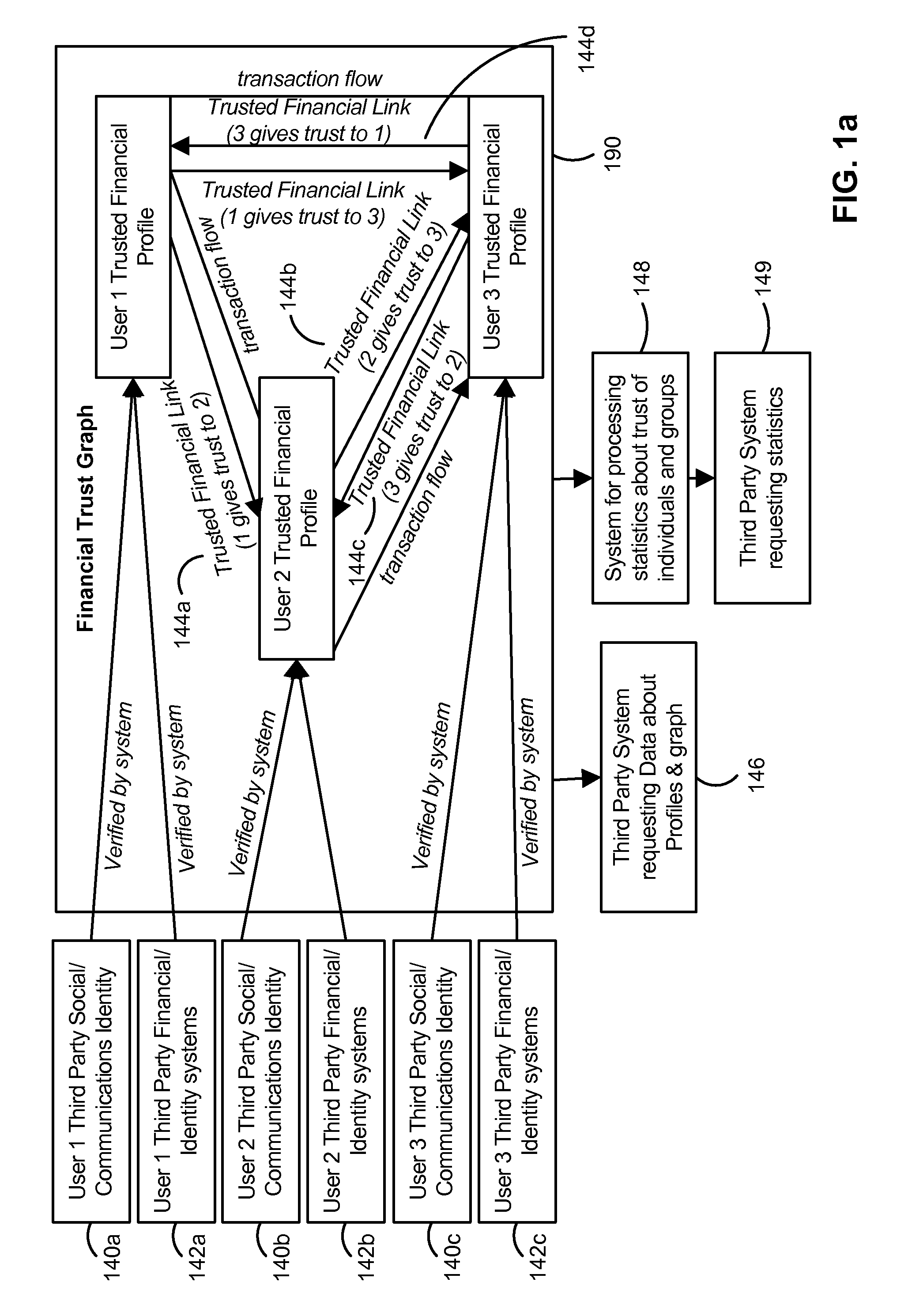
A configuration for more efficient electronic financial transactions is disclosed. Users input personal and financial information into a system that validates the information to generate trusted financial profiles. Each user can establish trusted financial links with other users. The trusted financial link provides a mechanism for the user to allow other users to withdraw money from the link provider account. The data from these relationships and the financial data flowing through the system enable a measure of trustworthiness of users and the trustworthiness of all interactions in the system. The combination of trusted financial profiles, trusted financial links, and financial transactions between users create a measurable financial trust graph which is a true representation of the trusting economic relationships among the users. The financial trust graph enables a more accurate assessment of the creditworthiness and financial risk of transactions by users with little or no credit or transaction history.
Owner:PAYPAL INC
Intelligent platform management interface validating system and method
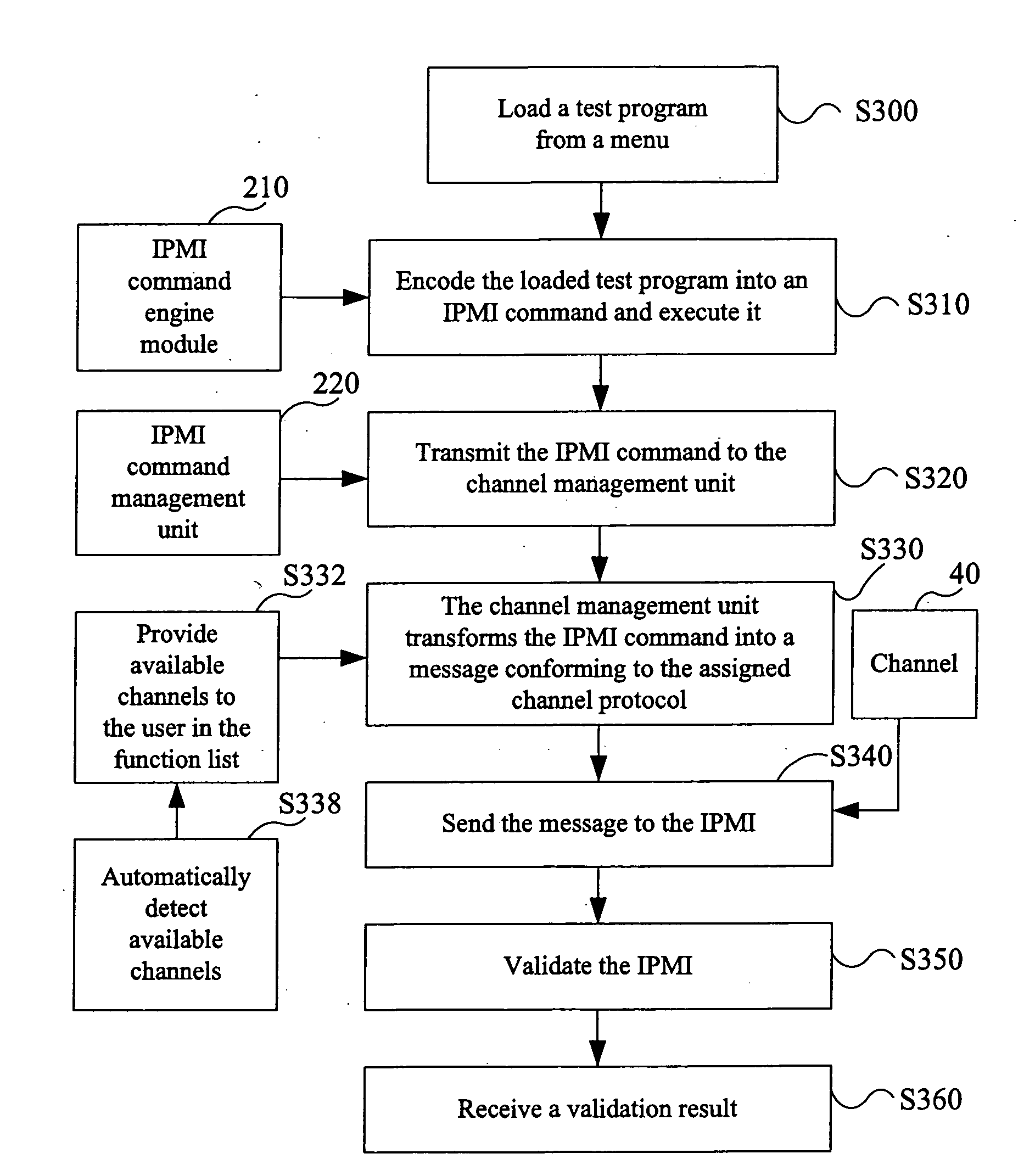
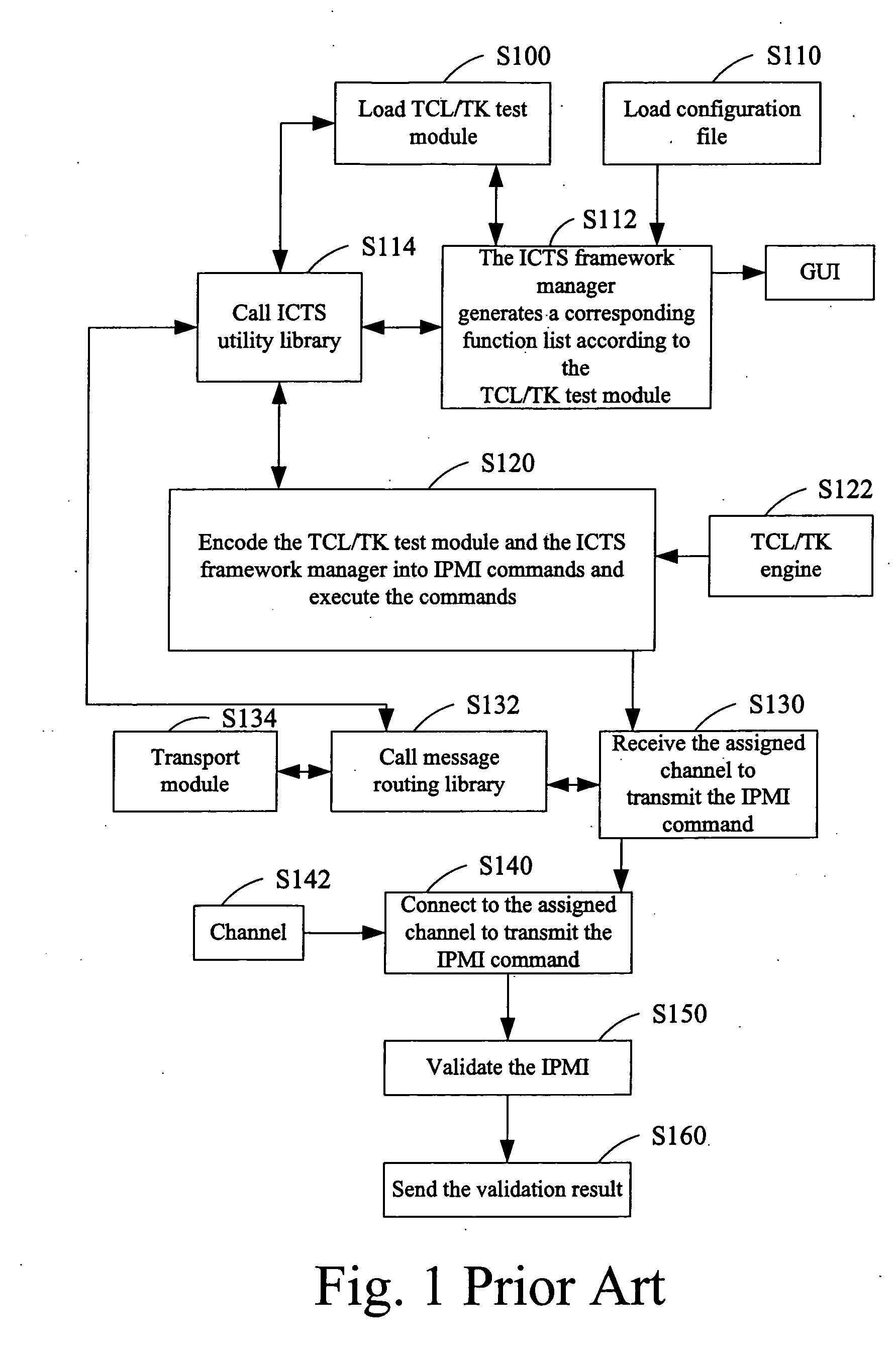
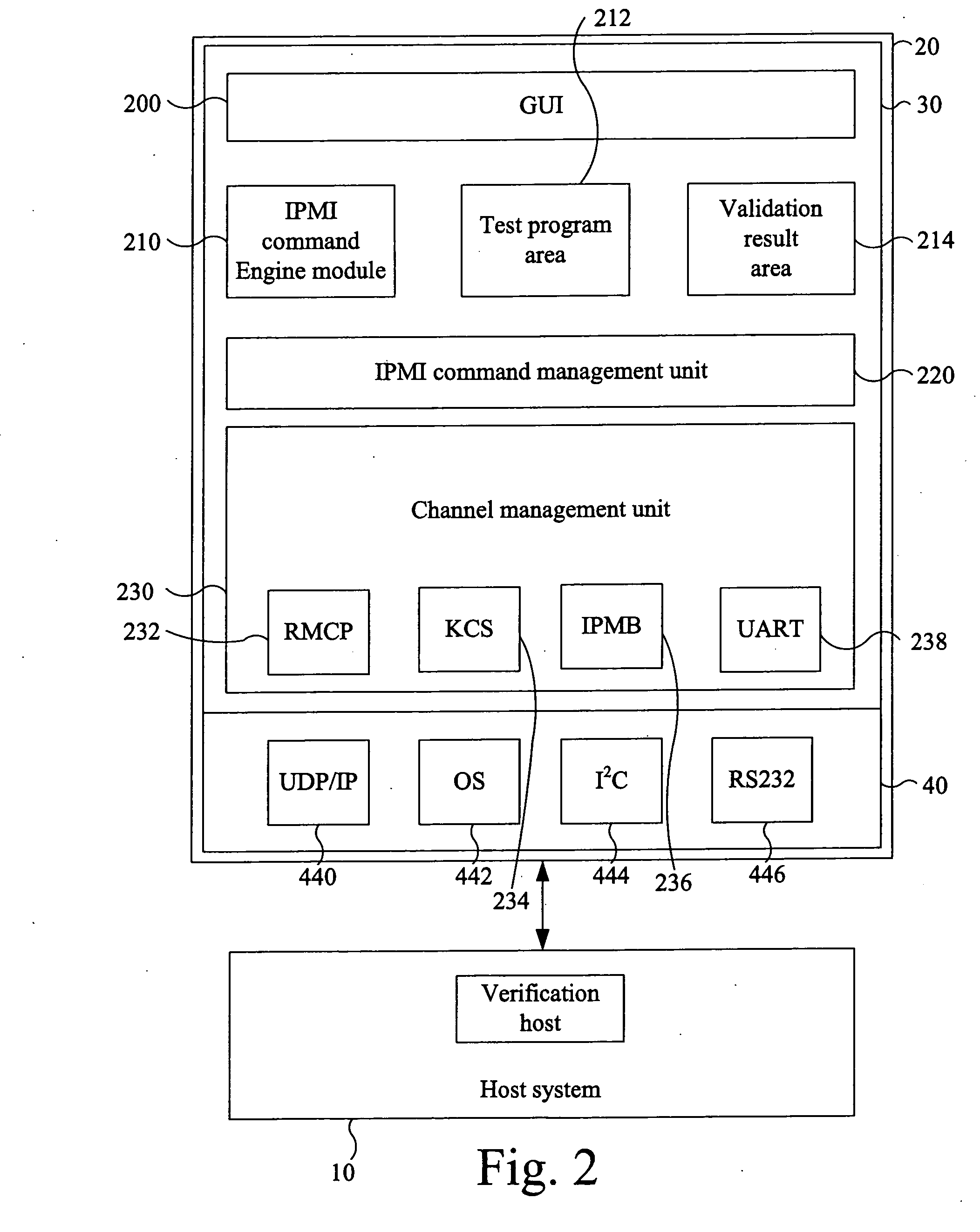
InactiveUS20060167919A1Error detection/correctionDigital data processing detailsIntelligent Platform Management InterfaceVerification system
An Intelligent Platform Management Interface (IPMI) validating system used between a host system and an operation terminal is provided. The IPMI validating system includes a validating program library for storing a plurality of validating programs coded in a programming language, a user interface configured in the operation terminal, for providing a plurality of selectable commands to be assigned wherein each of the selectable commands corresponds to one of the validating programs stored in the validating program library, and a validating module disposed at the host system for executing a health test of the host system according to the validating programs corresponding to the assigned selectable commands.
Owner:ATEN INT CO
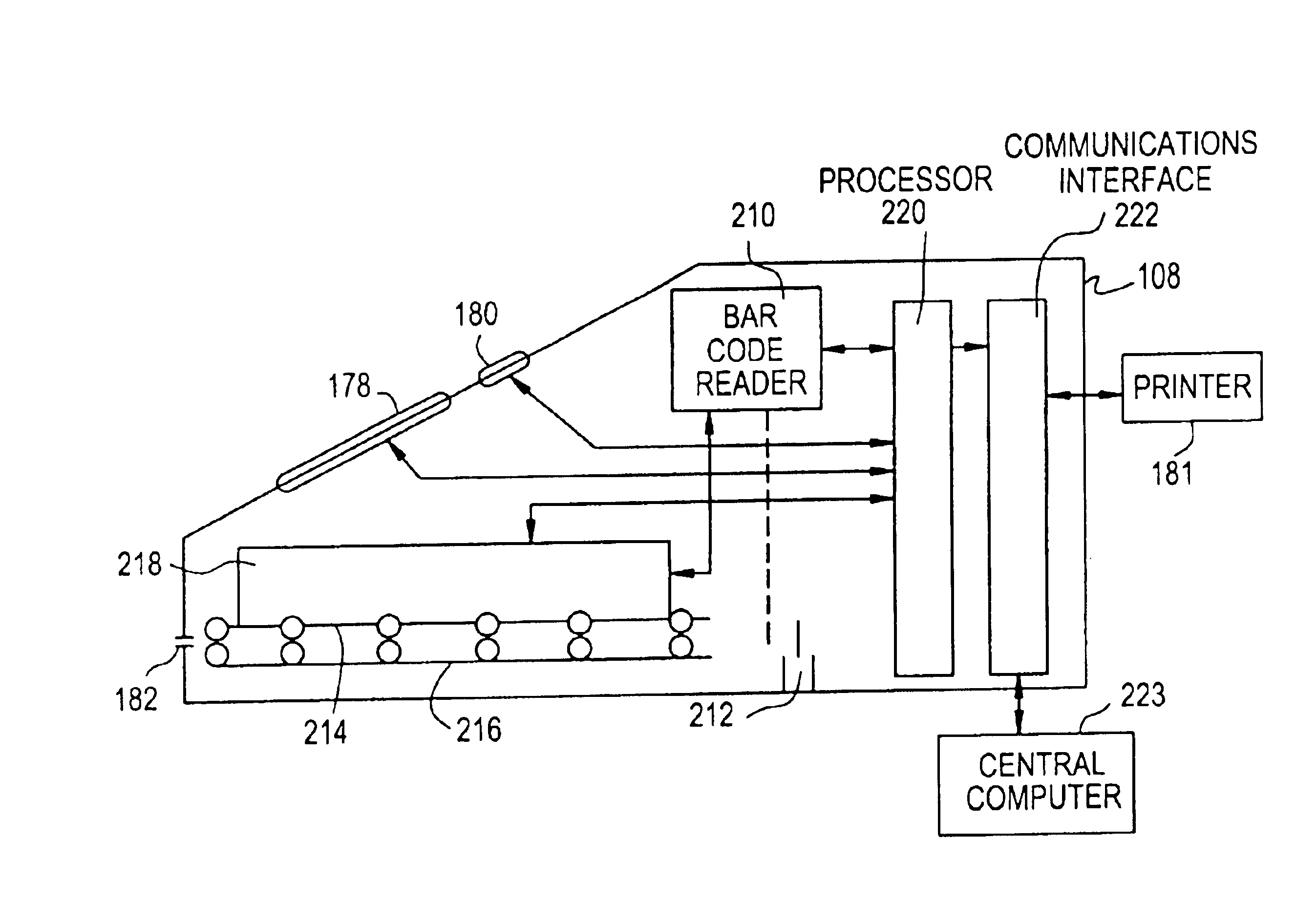
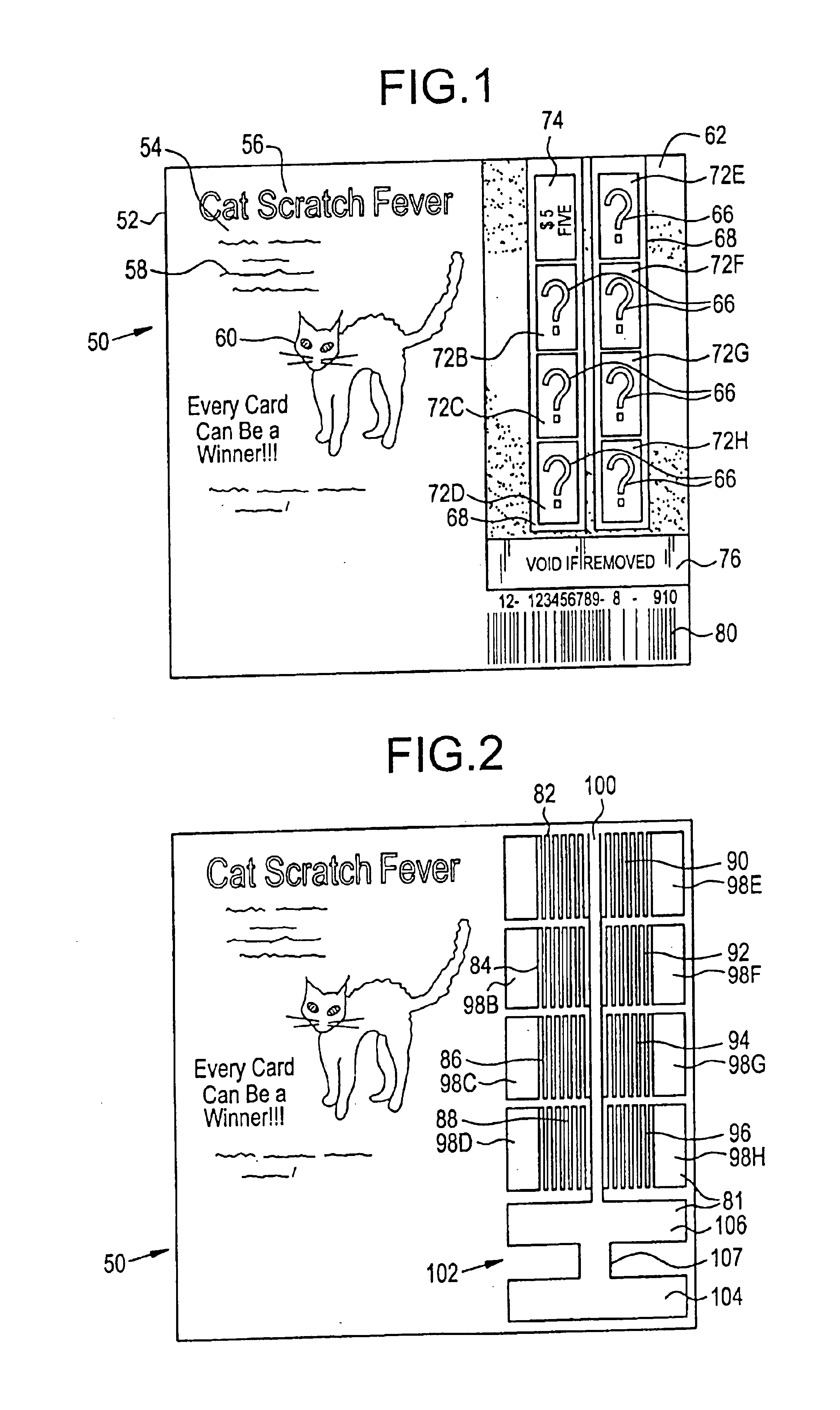
Lottery ticket validation system
InactiveUS6875105B1Electric signal transmission systemsMultiple keys/algorithms usageBarcodeEngineering
A lottery ticket validation system validates a probability lottery ticket that has predetermined play rules and that includes a plurality of player removable material covering play spots that in turn cover play indicia located in predetermined locations on the ticket. In addition, validation data is printed on the ticket in the form of a bar code. The validation system includes a housing, a controller located in the housing, a document channel configured in the housing, a sensor, a data reader, a transport mechanism, a scanning circuit, a memory, a processor, and a stigmatization circuit. The sensor includes an optical detector located in the housing and operatively connected to the controller. The data reader is operatively connected to the controller and is adapted to read the bar code. The transport mechanism is located in the housing and is operatively connected to the controller. The transport mechanism includes at least one roller, a plurality of ticket sensors, and a motor. The roller is effective to transport the probability lottery ticket through the document channel such that at least a portion of the play spots is substantially aligned with the sensor and such that the bar code is substantially aligned with the data reader. The scanning circuit is operatively connected to the sensor and to the controller and scans at least a portion of the probability lottery ticket for the player removable material covering the play spots and generates a validation signal indicating which, if any, of the player removable material covering the play spots has been removed from the probability lottery ticket. The memory is operatively connected to the controller and contains data representing the probability lottery ticket, including at least a portion of the validation data obtained from the data reader, and removed play spot data obtained from the validation signal. The processor is operatively connected to the controller and the memory and relates the portion of the validation data to the removed play spot data to verify the probability lottery ticket and to cause the transport mechanism to exit the probability lottery ticket from the document channel. The stigmatization circuit is operatively connected to the processor and is adapted to change at least a portion of a color of the probability lottery ticket prior to the transport mechanism exiting the probability ticket from the document channel.
Owner:SCI GAMES
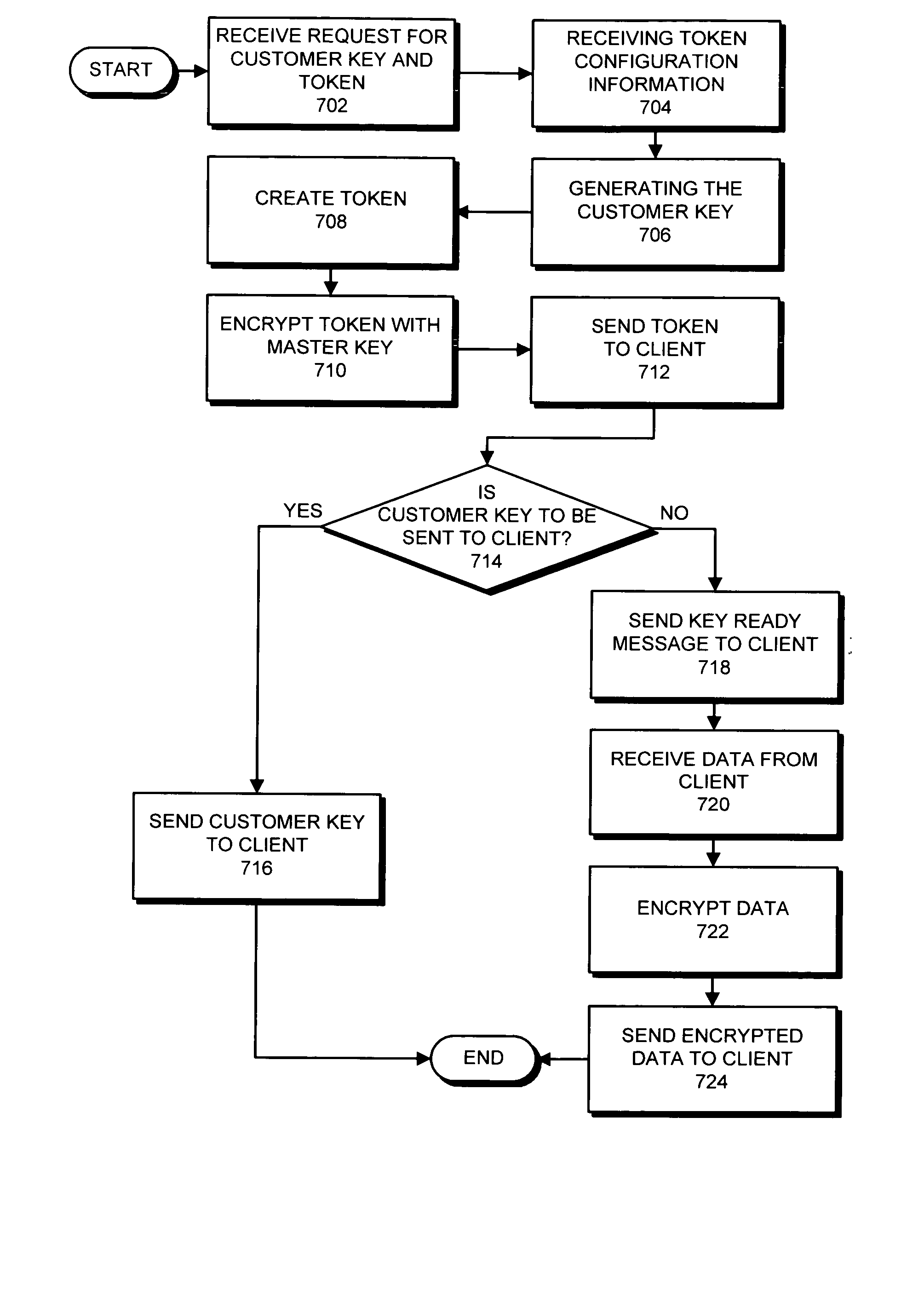
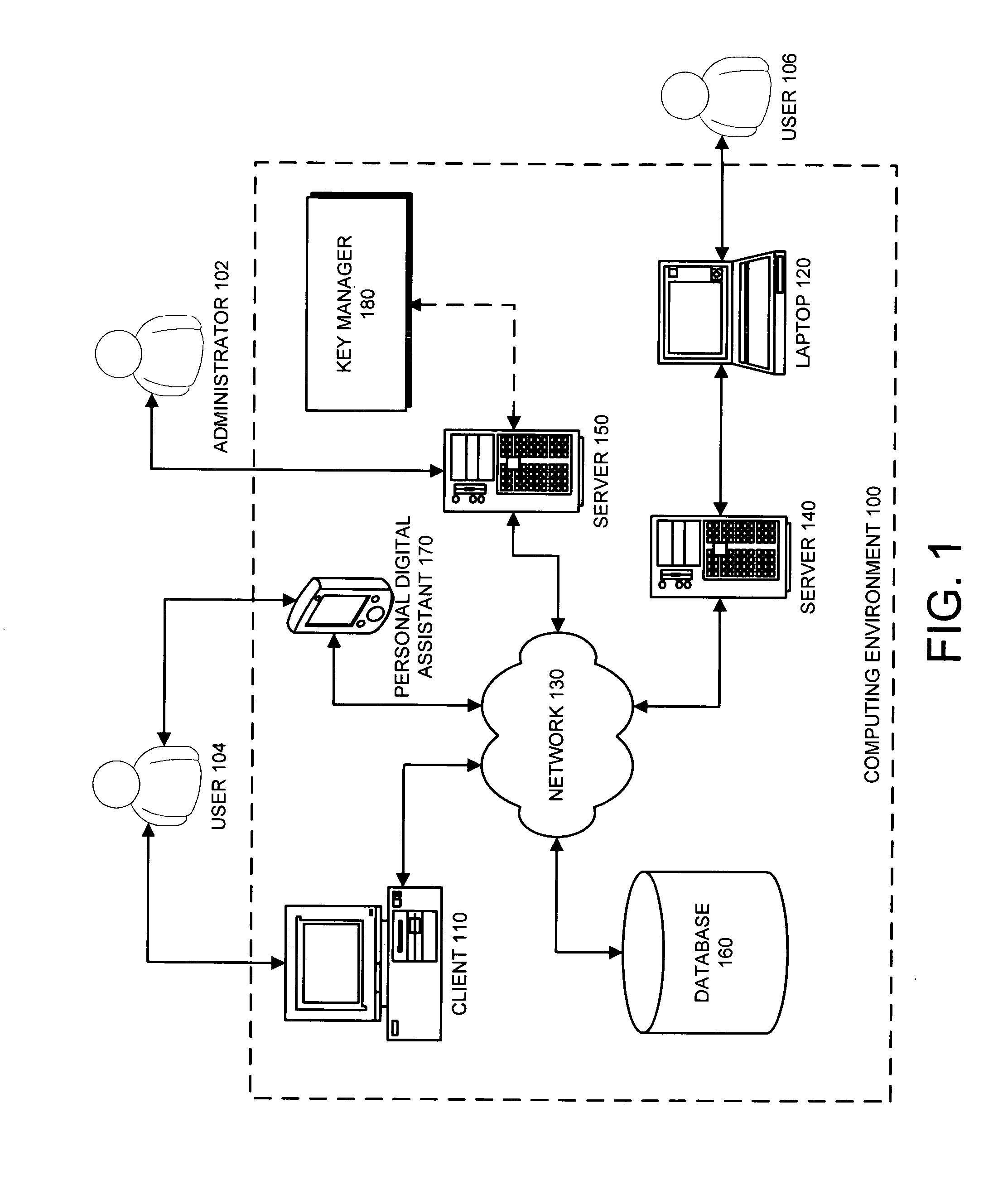
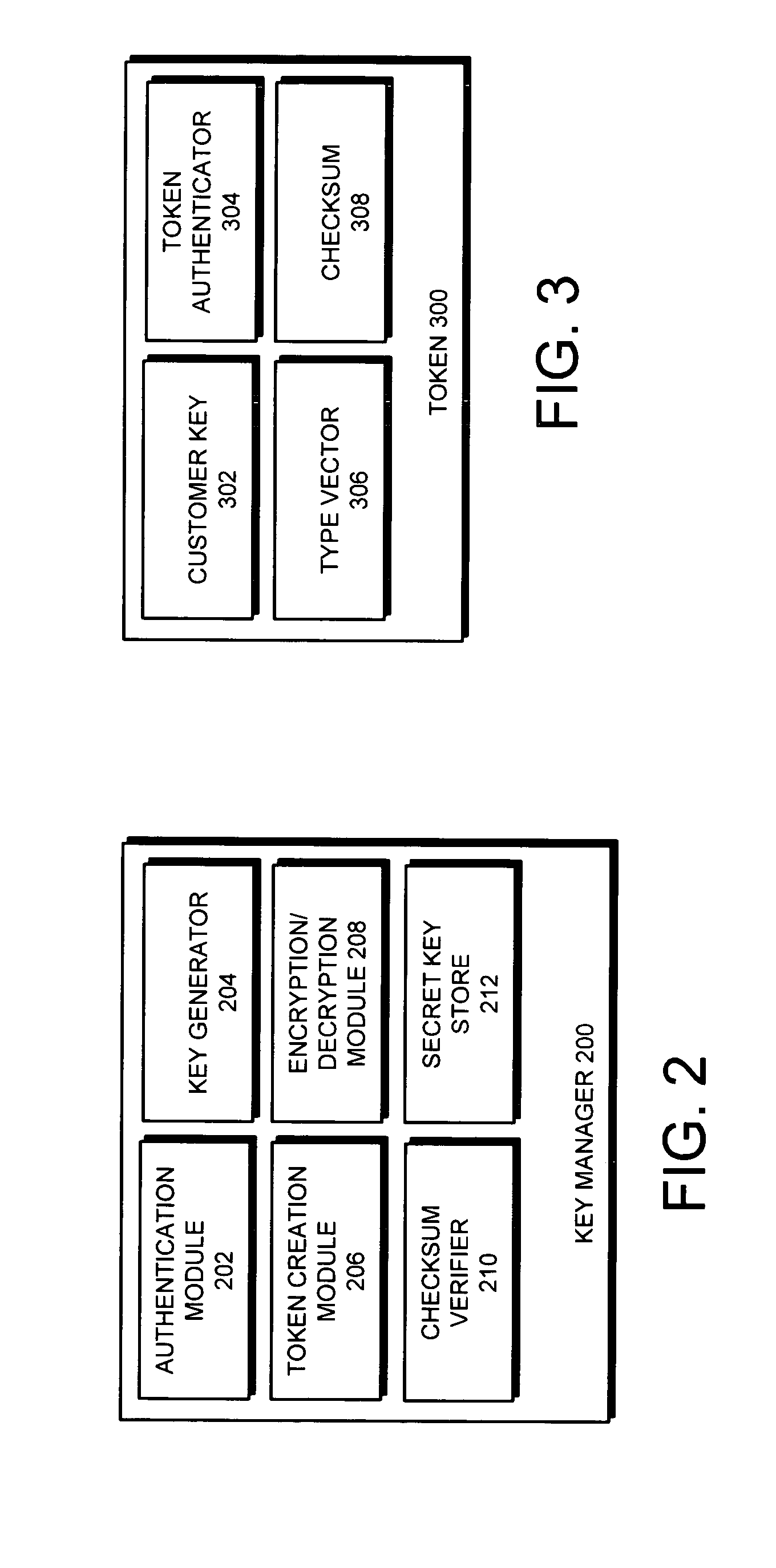
Method and apparatus for managing cryptographic keys
ActiveUS20080019527A1Easy to identifyKey distribution for secure communicationEncryption decryptionMaster key
One embodiment of the present invention provides a system for managing keys. During operation, the system authenticates a client at a key manager. Next, the system receives a token from the client at the key manager, wherein the token is associated with a customer key, and includes a token authenticator. This token authenticator comprises one-half of an authenticator pair which is used to determine if the client is the owner of the customer key. Next, the system decrypts the token using a master key. The system then verifies a client authenticator, which comprises the other half of the authenticator pair which is used to determine if the client is the owner of the customer key. If the client is the owner of the customer key, the system sends the customer key to the client, which enables the client to encrypt / decrypt data. Finally, the client deletes the customer key.
Owner:ORACLE INT CORP
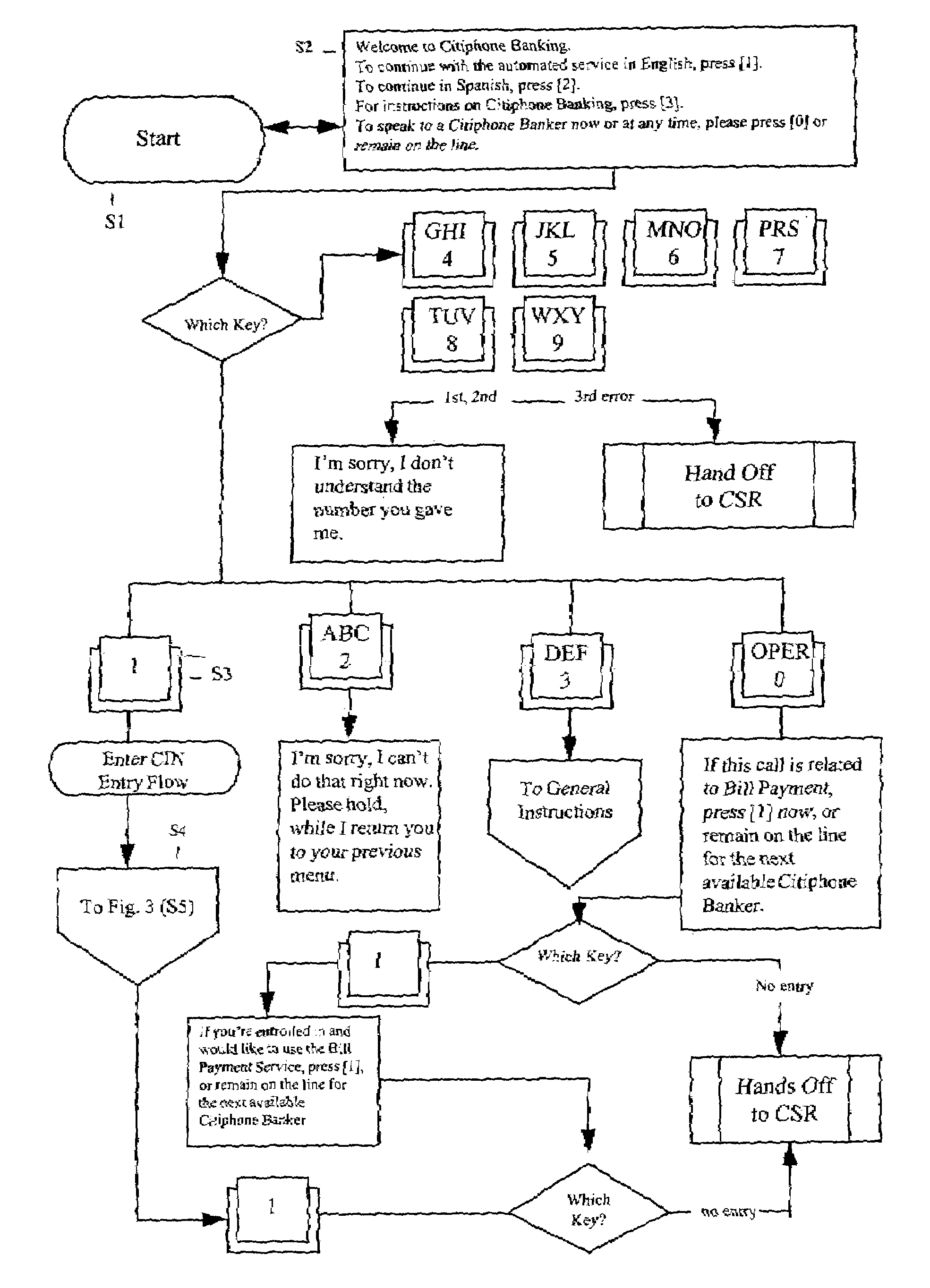
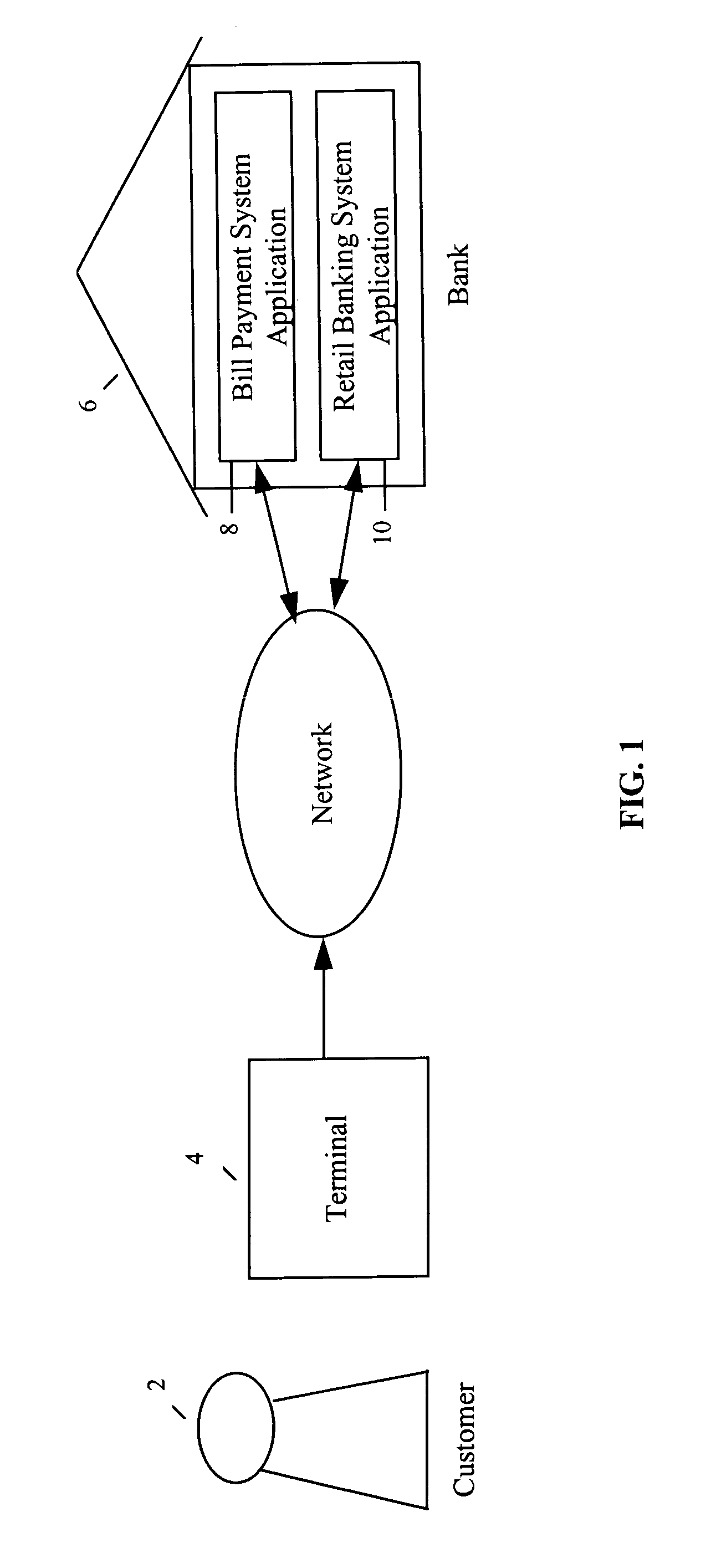
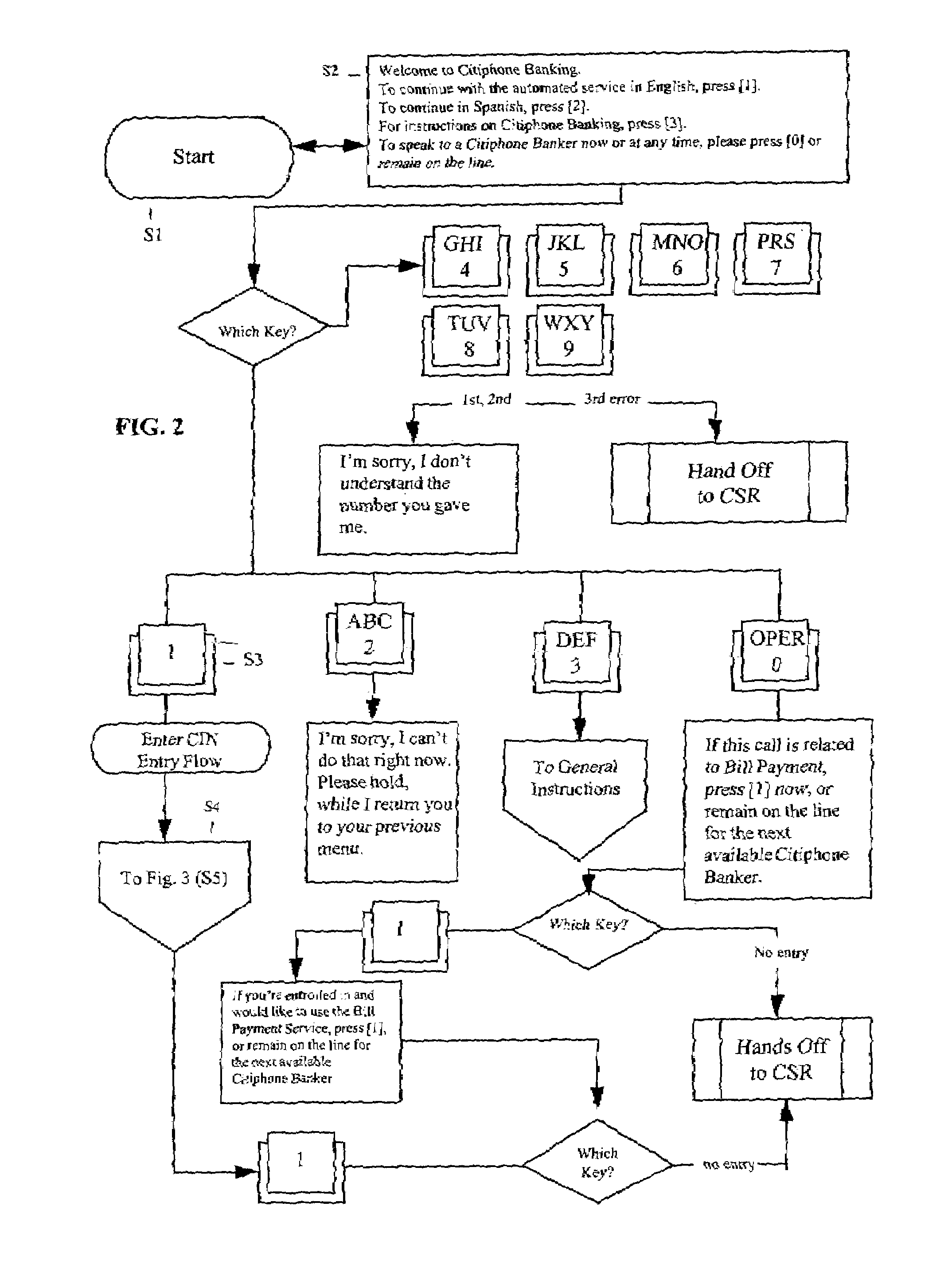
System and method for automated bill payment service
A method and system for automated bill payment service makes use of one or more application programs, such as a bank's retail system application and a bill payment application, running on one or more servers, as well as one or more data storage devices. A customer calls, for example, an 800 number and enters identification information in response to prompts by the system. The system verifies the customer's identification and, in response to selection of a single bill payment option, prompts the customer to enter information about at least one bill payment for a payee. The system provides selection of the payee from a customer-specific bill payee list or a system-spoken payee list and various menu functions. The system automatically schedules the bill payment for the customer according to the entered bill payment information, and renders the scheduled payment to the payee for the customer. The system also provides the customer with the ability to check the status of payments that have already been scheduled, as well as to change or cancel payments.
Owner:CITIBANK
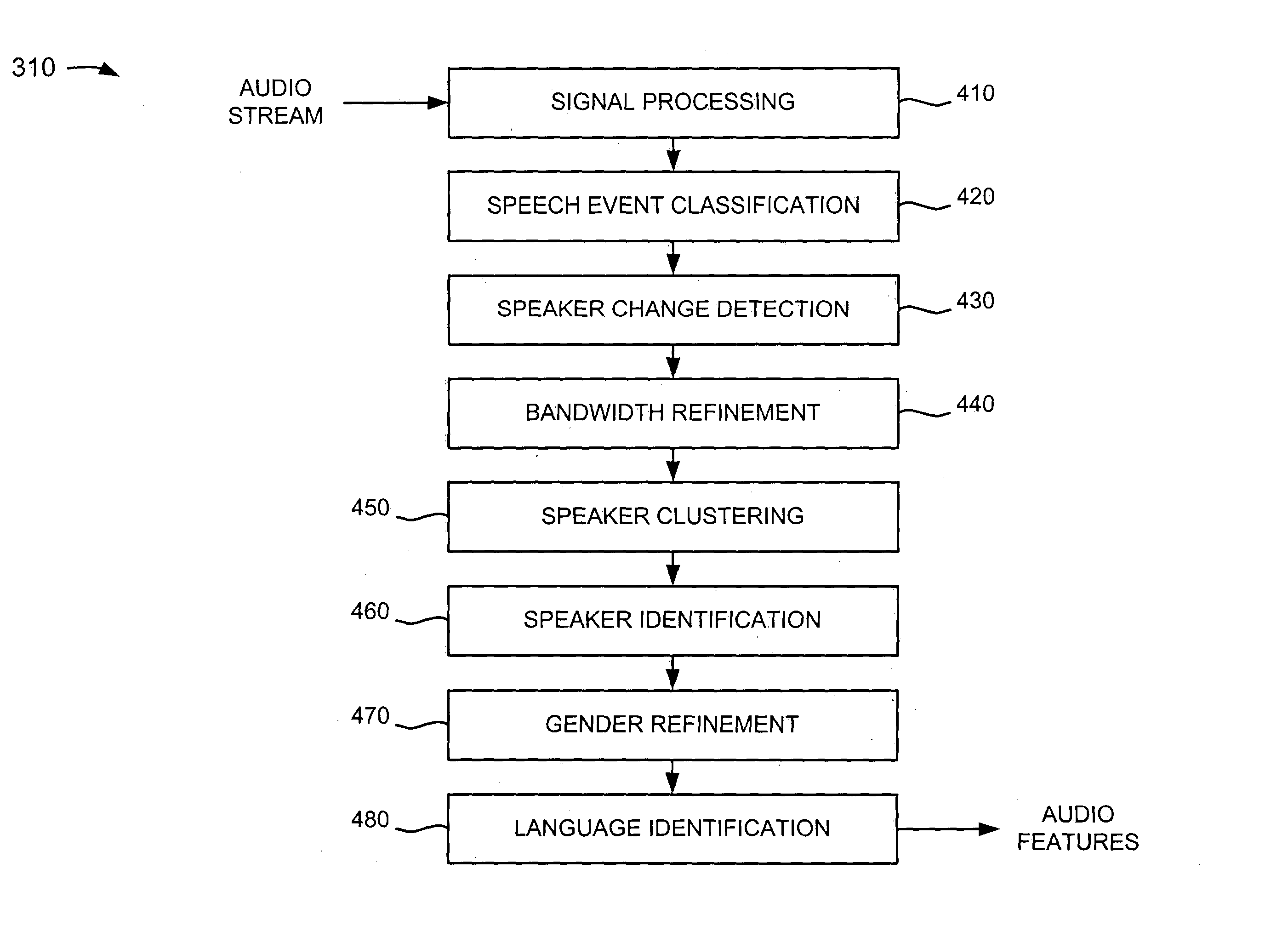
Systems and methods for providing acoustic classification
ActiveUS20040030550A1Data processing applicationsDigital data processing detailsMore languageSpeech identification
A speech recognition system receives an audio signal and detects various features of the audio signal. For example, the system classifies the audio signal into speech and non-speech portions, genders of speakers corresponding to the speech portions, and channel bandwidths used by the speakers. The system detects speaker turns based on changes in the speakers and assigns labels to the speaker turns. The system verifies the genders of the speakers and the channel bandwidths used by the speakers and identifies one or more languages associated with the audio signal. The system recognizes the speech portions of the audio signal based on the various features of the audio signal.
Owner:VERIZON PATENT & LICENSING INC +1
Systems and methods for online identity verification
ActiveUS7308581B1Digital data processing detailsUser identity/authority verificationBiometric dataIncluded study
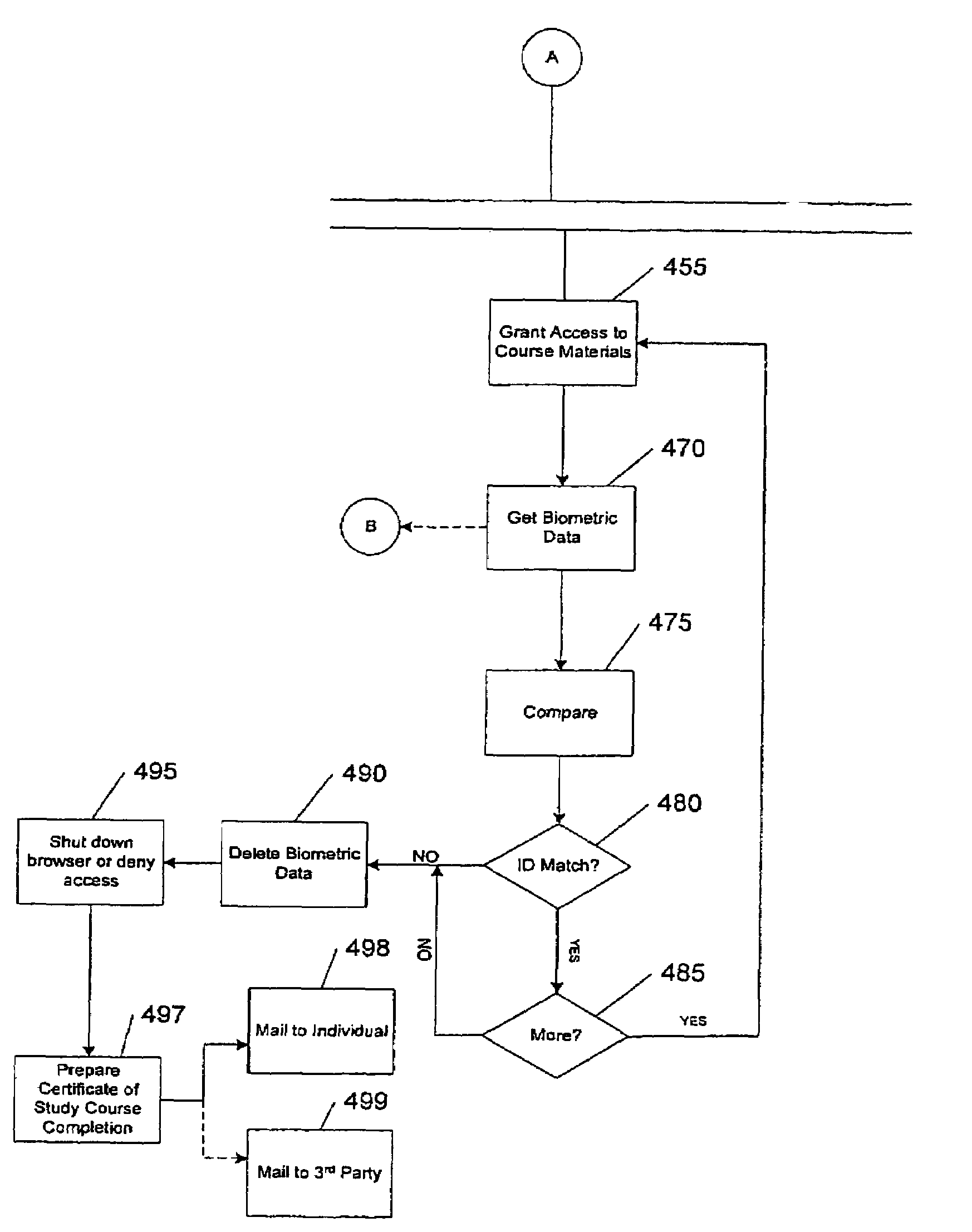
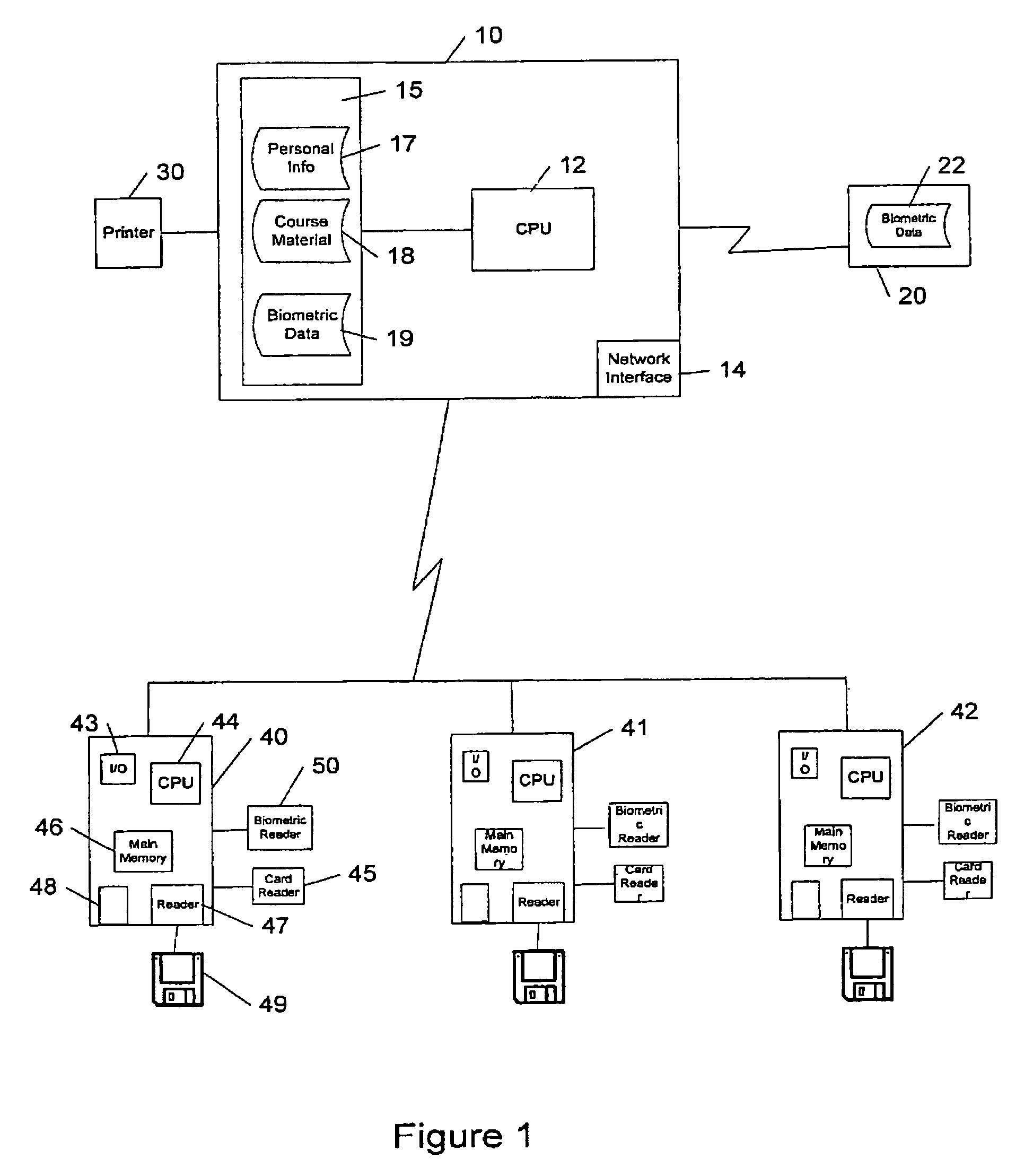
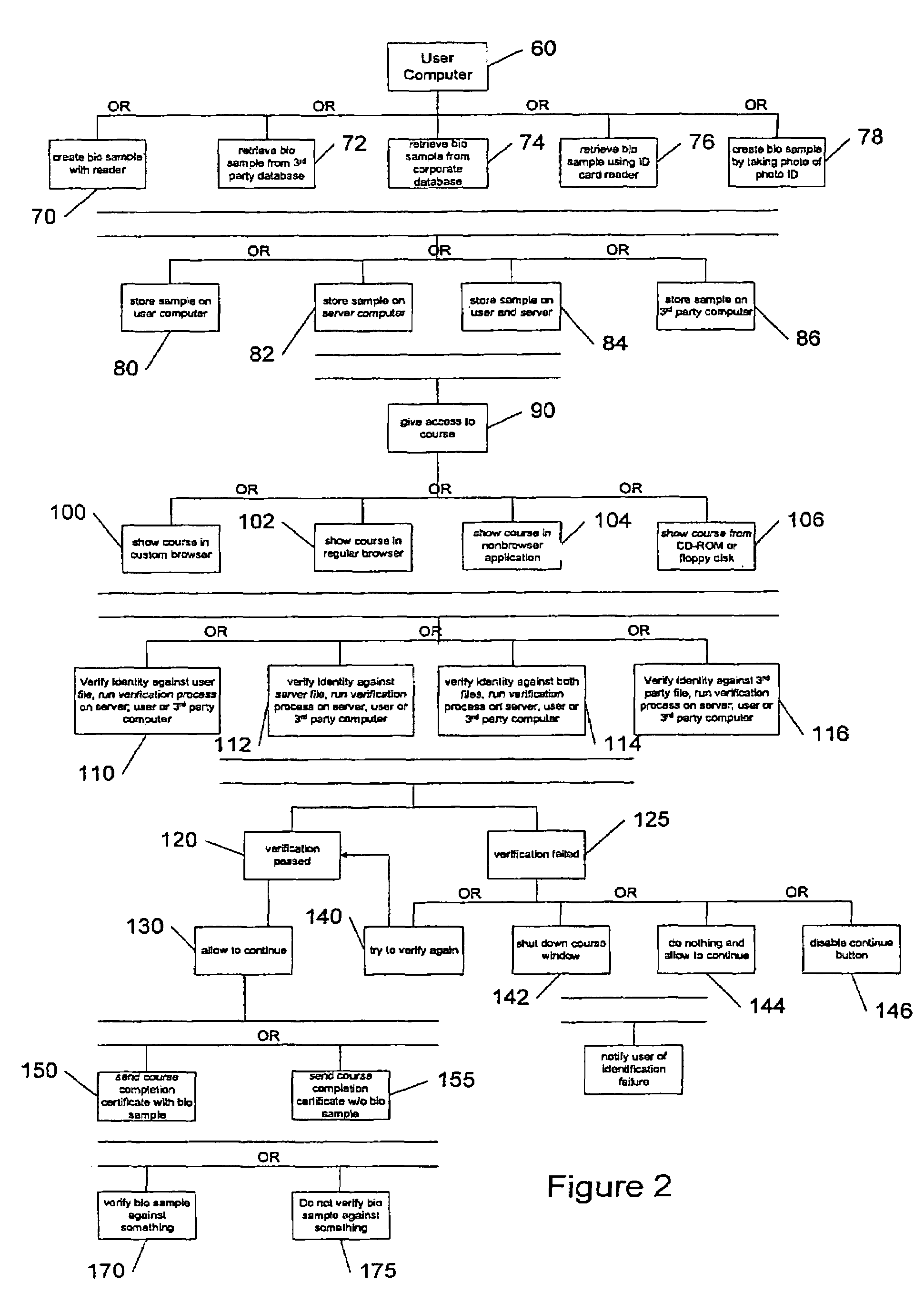
A system controlling online access to a study course verifies the identity of an individual taking a study course over a global computer network from a first computer at a node of the network. The first computer has a biometric identification program and communicates over the network with a second computer that is at a network node other than a node of the first computer. The second computer includes study course material. The first computer operates a biometric reader, which obtains a first set of biometric data from the individual and a second set of biometric data from the individual while access is granted to course material. The biometric identification program compares the first set of data with the second set of data to make a verification of the identity of the individual and communicates the verification to the second computer.
Owner:RAKUTEN GRP INC
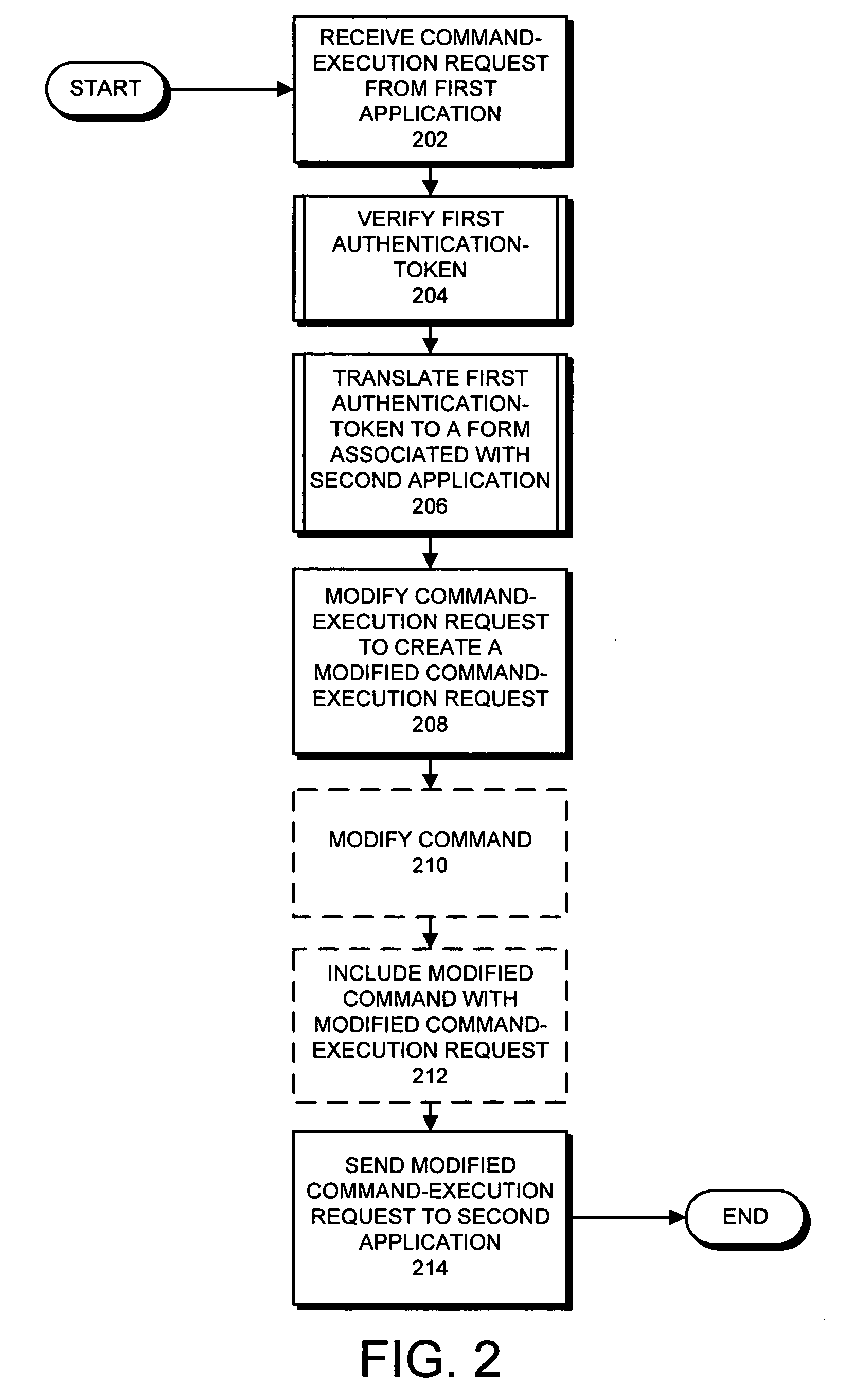
Method and apparatus for converting authentication-tokens to facilitate interactions between applications
ActiveUS20080046715A1Digital data authenticationSecuring communicationComputer scienceAuthentication
One embodiment of the present invention provides a system that converts authentication-tokens to facilitate interactions between applications. During operation, the system receives a command-execution request from a first application, wherein the command-execution request specifies a command to execute on a second application. Subsequently, the system verifies a first authentication-token included with the command-execution request. Next, the system translates the first authentication-token into a form associated with the second application to produce a second authentication-token. The system then modifies the command-execution request by replacing the first authentication-token with the second-authentication-token to create a modified command-execution request. Then, the system sends the modified command-execution request to the second application.
Owner:INTUIT INC
Moveable object accountability system
InactiveUS7080778B1Readily apparentHand manipulated computer devicesPayment architectureData processing systemElectronic identification
An accountability system for monitoring the status of a certain condition of a moveable object having an electronic identification device with a transmittable unique identification code is disclosed. A verification station with an electronic signal transmission and reception device remotely initiates communication with the electronic identification device on the moveable object and receives the unique identification code. A database at the verification station retrieves information related to the unique identification code, and a camera captures a digital image of the moveable object, while displaying the image and querying a user to input verification data to an input device. A data processing sub-system at the verification station verifies the user's input and compiles a data record of the unique identification code, the digital image, and data input from the user into a data record and stores the compiled record in memory for later communication with a remote storage device.
Owner:TEETEE COMM
Methods and Systems for Distributing Cryptographic Data to Authenticated Recipients
ActiveUS20120179905A1Digital data authenticationSelective content distributionIdentity providerClient-side
A method for distributing cryptographic data to authenticated recipients includes receiving, by an access control management system, from a first client device, information associated with an encrypted data object. The method includes receiving, by the access control management system, from a second client device, a request for the information associated with the encrypted data object. The method includes verifying, by the access control management system, that a user of the second client device is identified in the received information associated with the encrypted data object. The method includes authenticating, by the access control management system, with an identity provider, the user of the second client device. The method includes sending, by the access control management system, to the second client device, the received information associated with the encrypted data object.
Owner:VIRTRU
System for preventing fraudulent purchases and identity theft
InactiveUS20080217400A1Prevent theftPreventing fraudulent purchasesPayment circuitsVerifying markings correctnessIdentity theftSecurity Measure
An anti-fraud / anti-identity theft system verifies the authenticity of genuine identification devices, including credit cards, cellular telephones, and the like. Likewise the system detects counterfeit credit cards or lines of credit. The system comprises a modified retailer machine that verifies the cards and / or person at the time of buying or selling with a wide variety of security measures. The system further utilizes cellular telephones or electronic devices as a credit card-holding device, which device has a microprocessor computer embedded within the cellular telephone or device, which microprocessor computer can be operated to selectively turn on or turn off availability of credit card funds without closing the credit card account itself.
Owner:PORTANO MICHAEL D
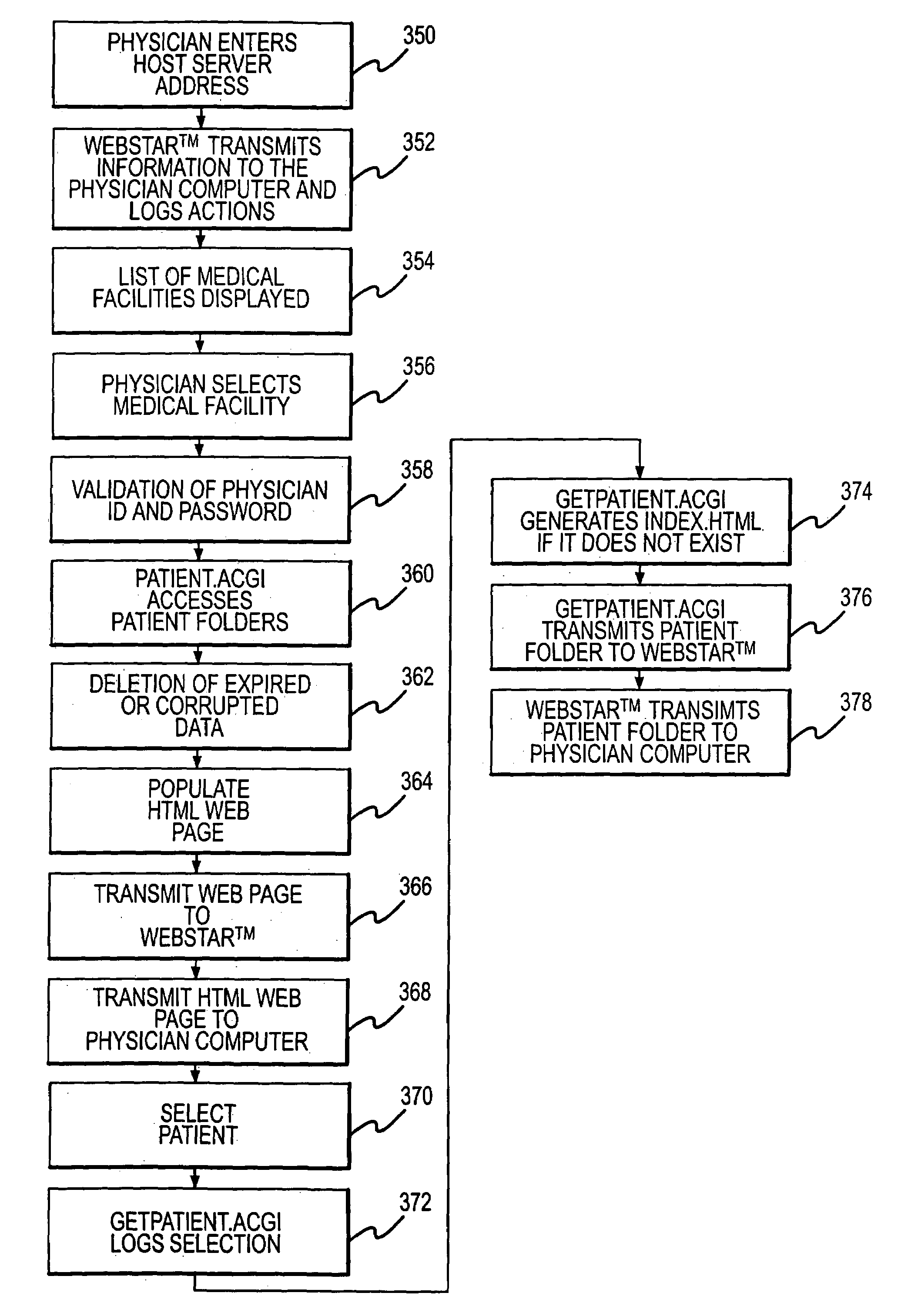
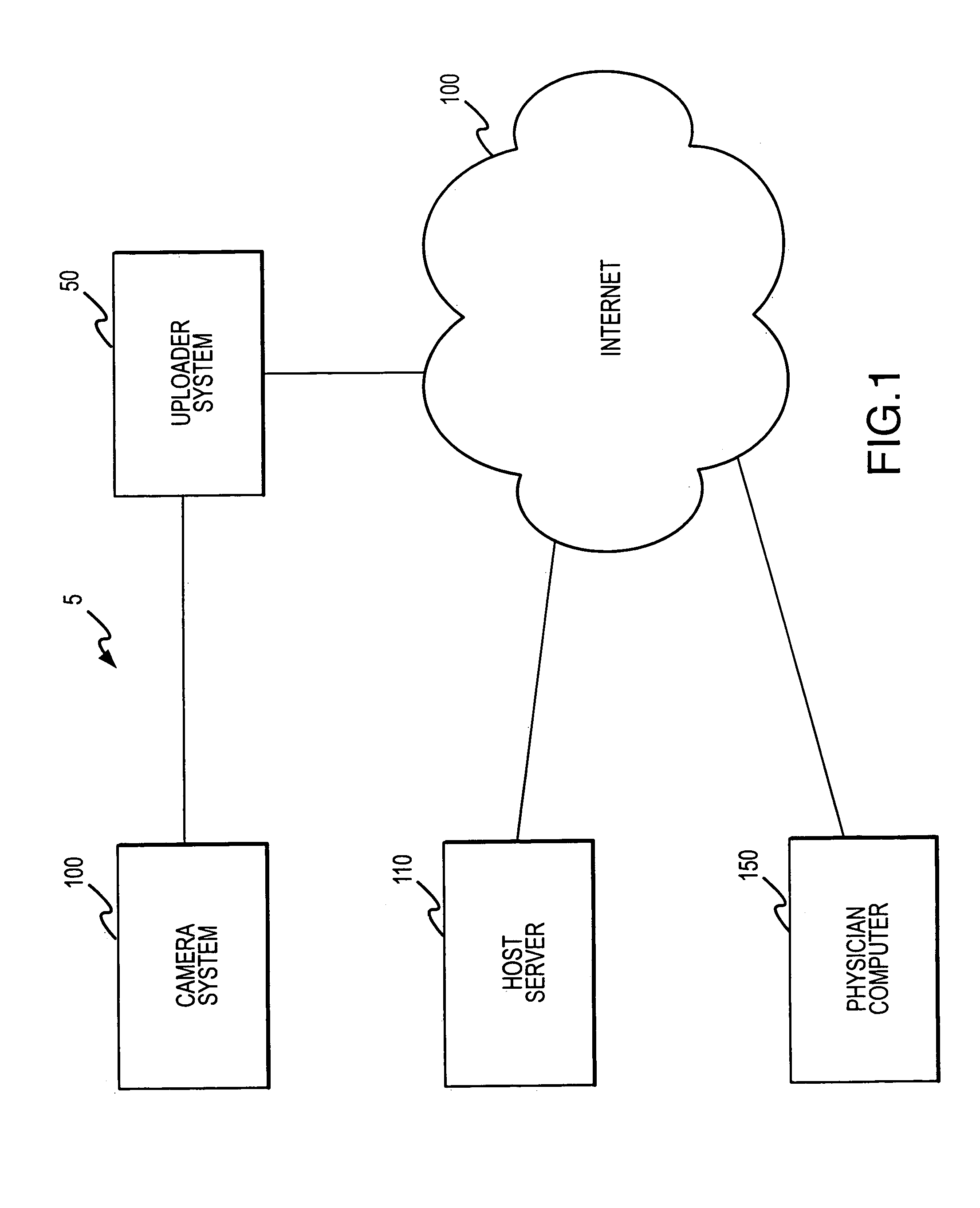
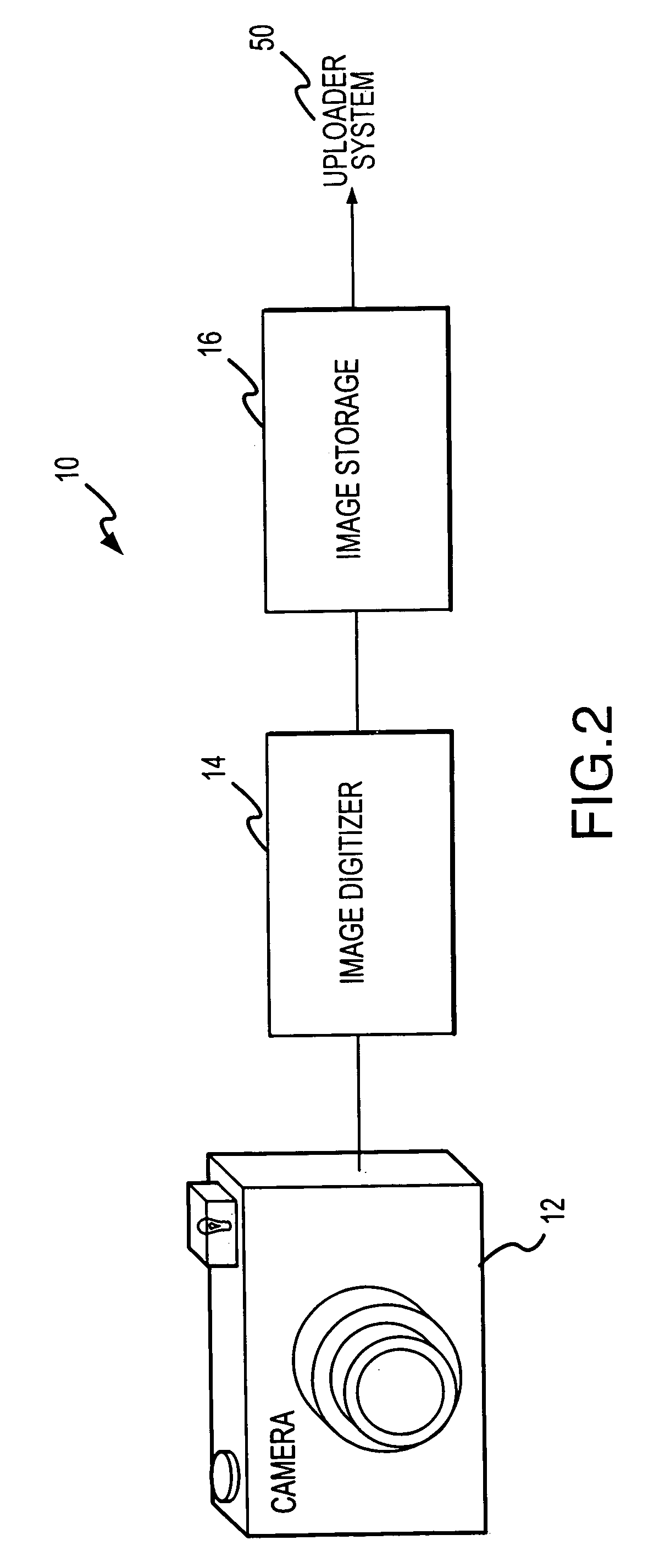
Systems and methods for remote viewing of patient images
InactiveUS7180624B2Down Internet connectionComputer security arrangementsMultiple digital computer combinationsPasswordComputer science
A digital camera containing patient images is connected to an uploader computer and the patient's name or history is entered into the uploader computer. The uploader computer then connects to the Internet, connects to the secure host server, uploads the images to the host server and shuts down the Internet connection. After the physician selects a medical facility and the system verifies the physician's user I.D. and password, the host server constructs an HTML web page which includes a list of patients whose images were previously uploaded by the medical facility and are available for viewing The physician simply selects the name of a patient and the host server displays the patient information and images on the physician's computer. The system is password-protected at all levels and the operator for each medical facility determines who may have access to the medical facility images.
Owner:IBM CORP +1
Method and system of contactless interfacing for smart card banking
InactiveUS8346663B2Eliminate needImprove usabilityComplete banking machinesElectric signal transmission systemsCommunication interfaceTransceiver
A method and system of smart card banking utilizes a contactless communication interface, such as infrared or a wireless or radio frequency interface, including, for example, a proximity interface. A contactless communication is initiated for a smart card user between a smart card application and the on-line system of a financial institution, such as a bank, the system verifies authorization for the communication, the information is communicated for the user to the on-line system. The contactless communication is initiated, and the information is communicated, for example, between a contactless interface transceiver of a personal data assistant, into which the smart card is inserted, and the contactless interface transceiver of an on-line terminal. Alternatively, the contactless communication is initiated, and the information is communicated between a contactless interface transceiver of the smart card and the contactless interface transceiver of the terminal.
Owner:CITICORP CREDIT SERVICES INC (USA)
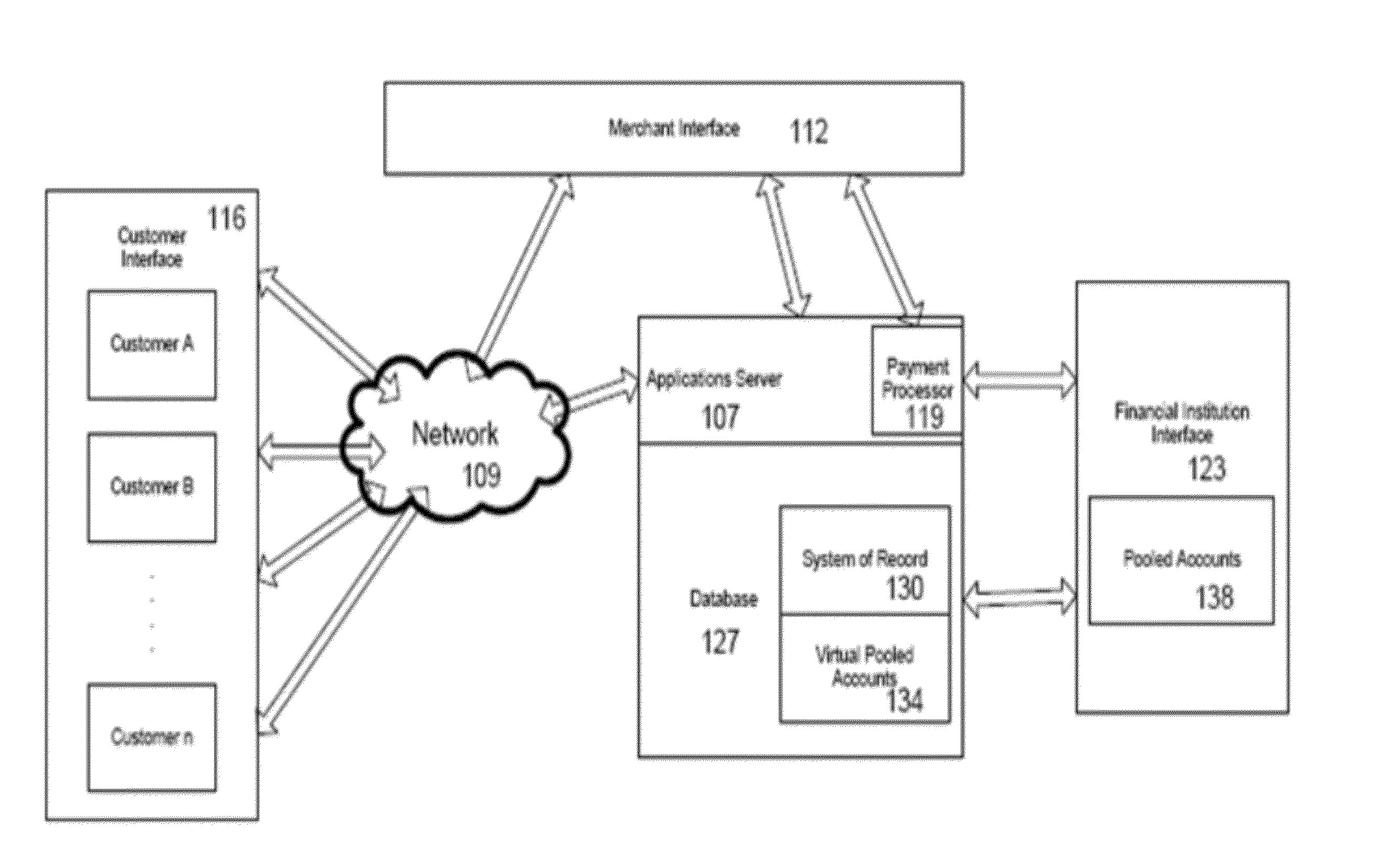
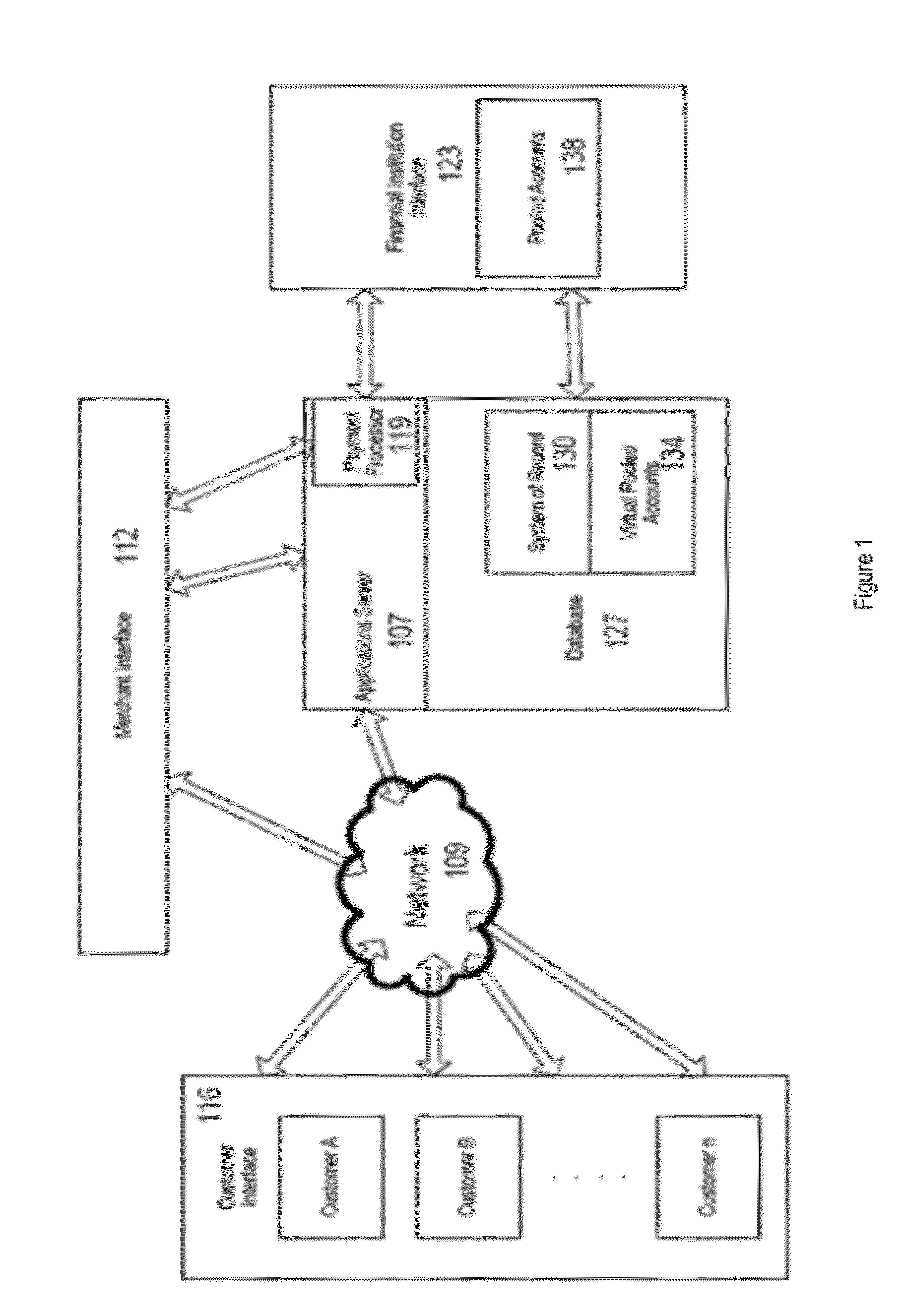
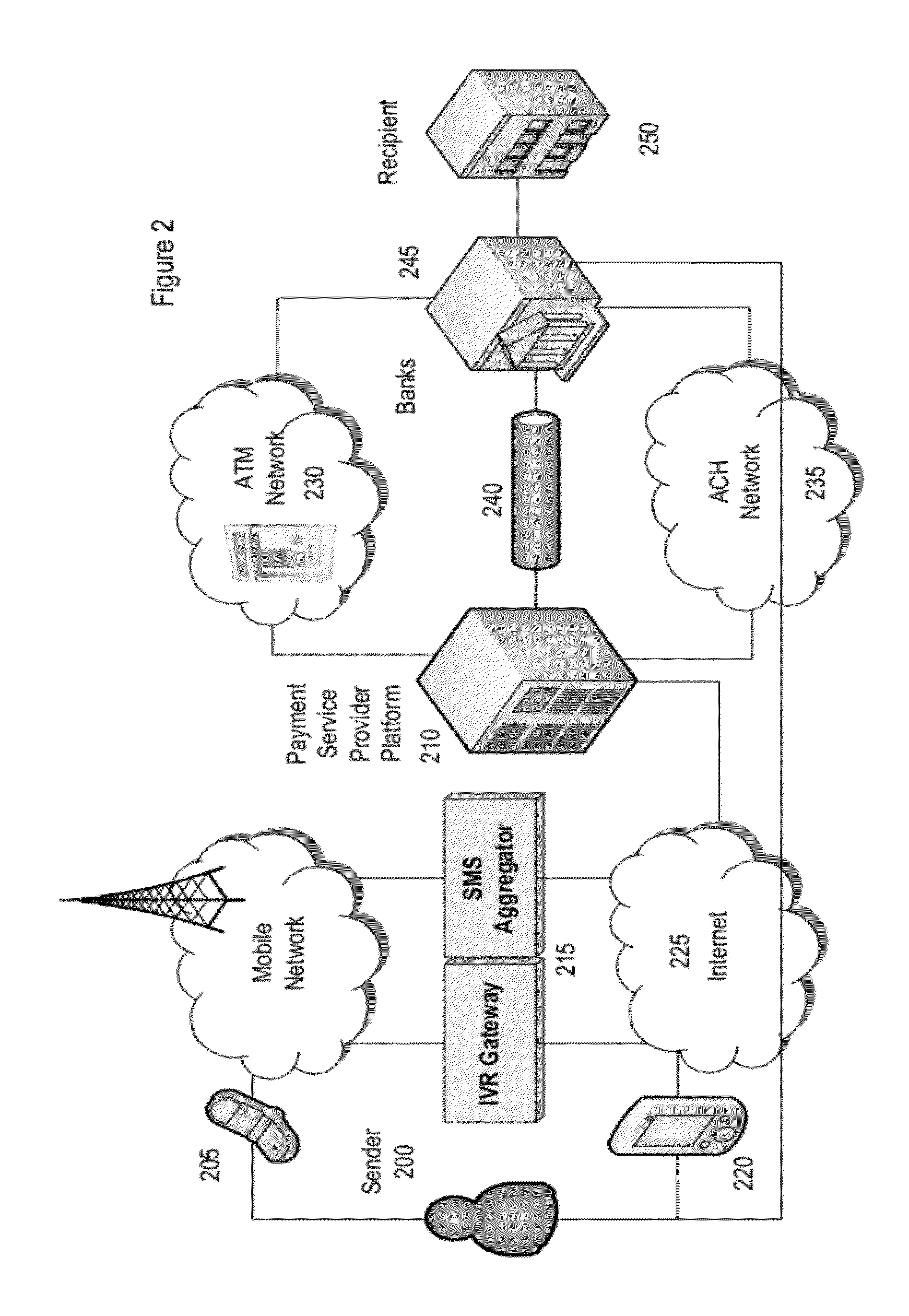
Method & System for Providing Payments Over A Wireless Connection
The present invention relates to a method and system for providing payments over a wireless connection. Instant messaging services—such as mobile text messaging—addressed to a command interpretation and processing system are utilized in conjunction with a checkout procedure on a mobile device to enable a user making a payment to simply define and confirm the amount of his or her payment, and the recipient. The checkout procedure can be completed with SMS, Mobile Web, Mobile App or IVR implementation. Previously Registered as well as new unregistered users are supported. The payer, through his or her mobile device, interacts with a system for managing mobile payment transactions that validates the sender and recipient of the funds, the presence of funds in a transacting account and other fraud management and authentication checks, and effects a settlement. The Sender may chose a variety of funding sources to fund the transaction, while the recipient can receive the funds on a debit or credit account, or immediately in a demand deposit account of their choice. In one embodiment of the present invention the system is used to pay for purchases of goods and services. In another embodiment of the present invention, the system is use to provide donations to charities.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
Transaction processing system and method
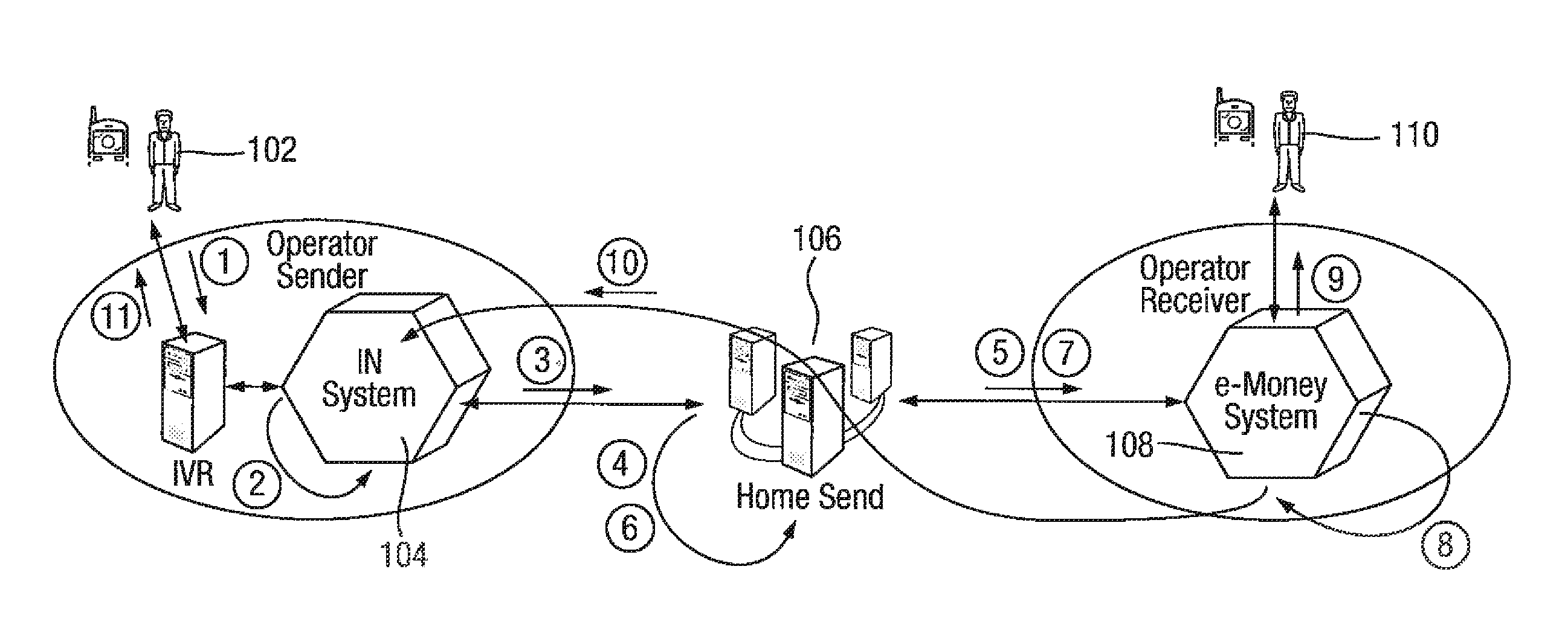
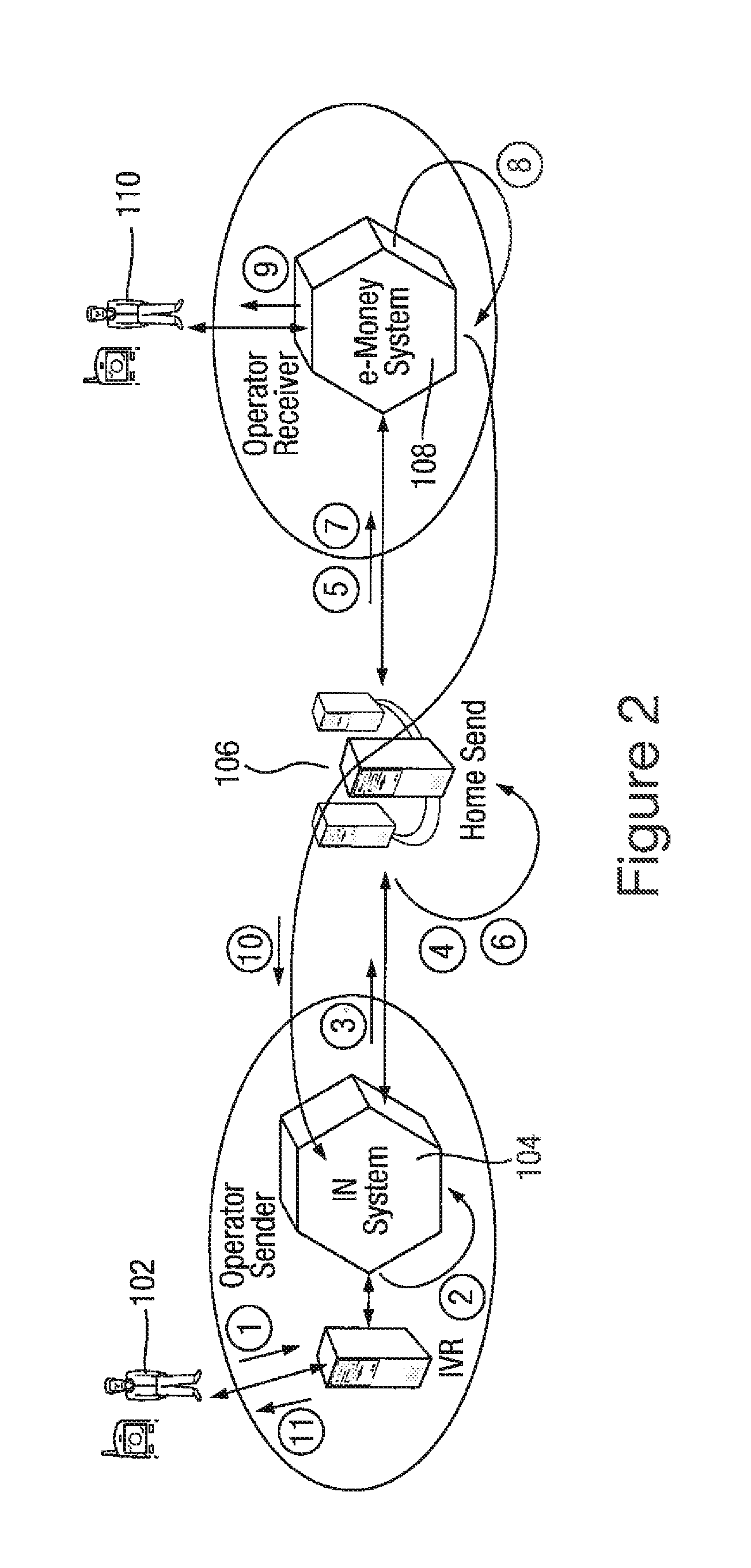
InactiveUS20120209762A1Reduce decreaseCarefully controlledAccounting/billing servicesFinanceThird partyTelecommunications network
A method of processing a transaction between a first user in a first telecommunications network and a second user in a second telecommunications network is disclosed. The first and second telecommunications networks comprise respective first and second transaction processing systems which are not required to have a direct interface between them. A transaction request is received from a first user in the first telecommunications network to effect a transfer of credit to a second user in the second telecommunications network. The transaction request includes an identifier of the second user. A credit value for the transaction is determined. The system verifies that the first user has access to credit sufficient to effect the transfer, and credit associated with the first user is reserved in the first network for the transaction. A transaction instruction message (including the determined value for the transaction) is generated to instruct transfer of credit to the second user, and is forwarded to a trusted third party intermediary server, which interfaces to a plurality of telecommunications networks to arrange transactions between the telecommunications networks. After a confirmation message is received confirming delivery of the credit to the second user, the reserved credit is then debited from an account associated with the first user in the first telecommunications network. An accounting packet associated with at least one transaction and the accounting packet or an aggregated accounting packet for a plurality of transactions is forwarded to an accounting server associated with the intermediary server. This effects transfer of monetary value between an account associated with the first telecommunications network and an account associated with the trusted third party intermediary server.
Owner:HOMESEND SCRL
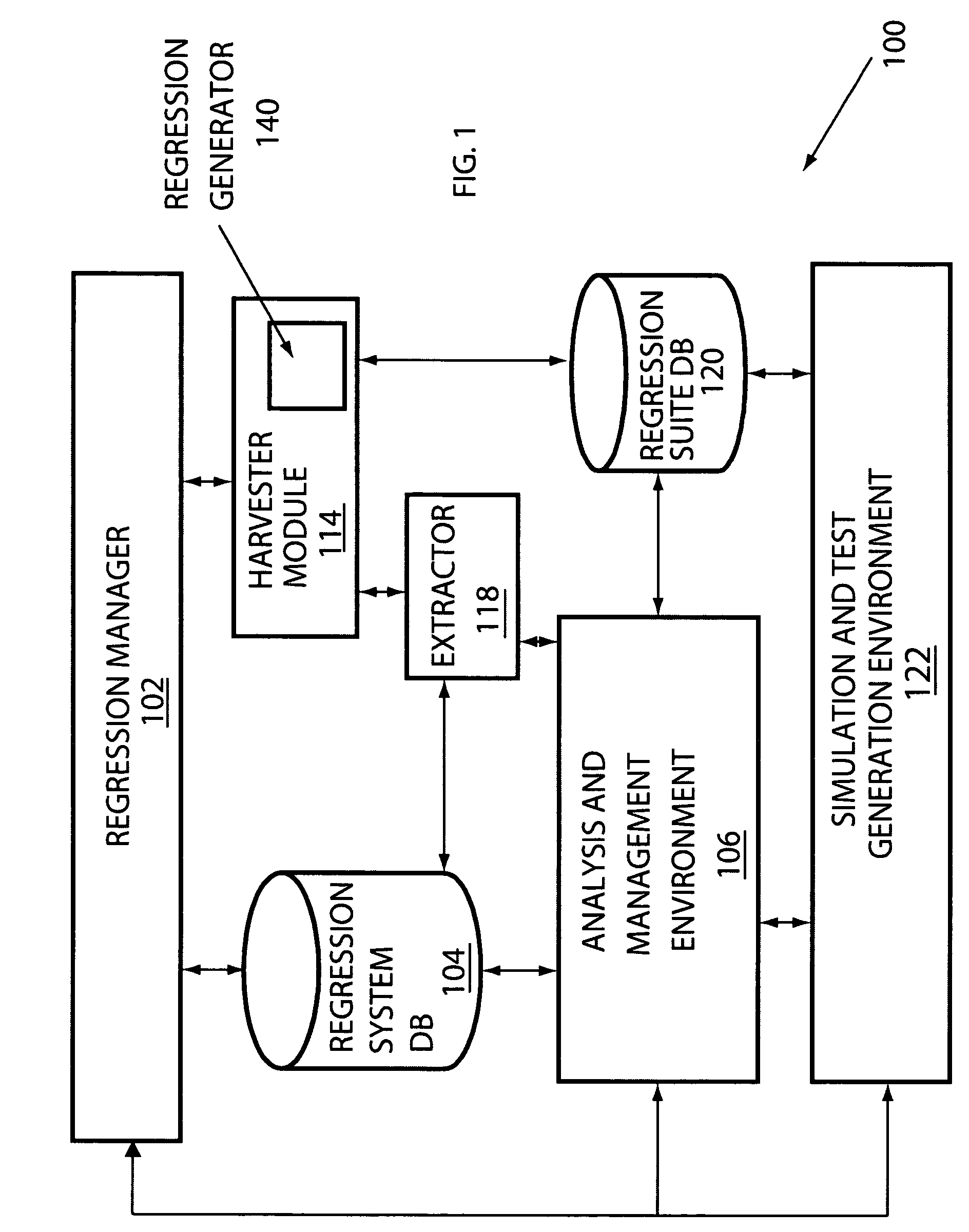
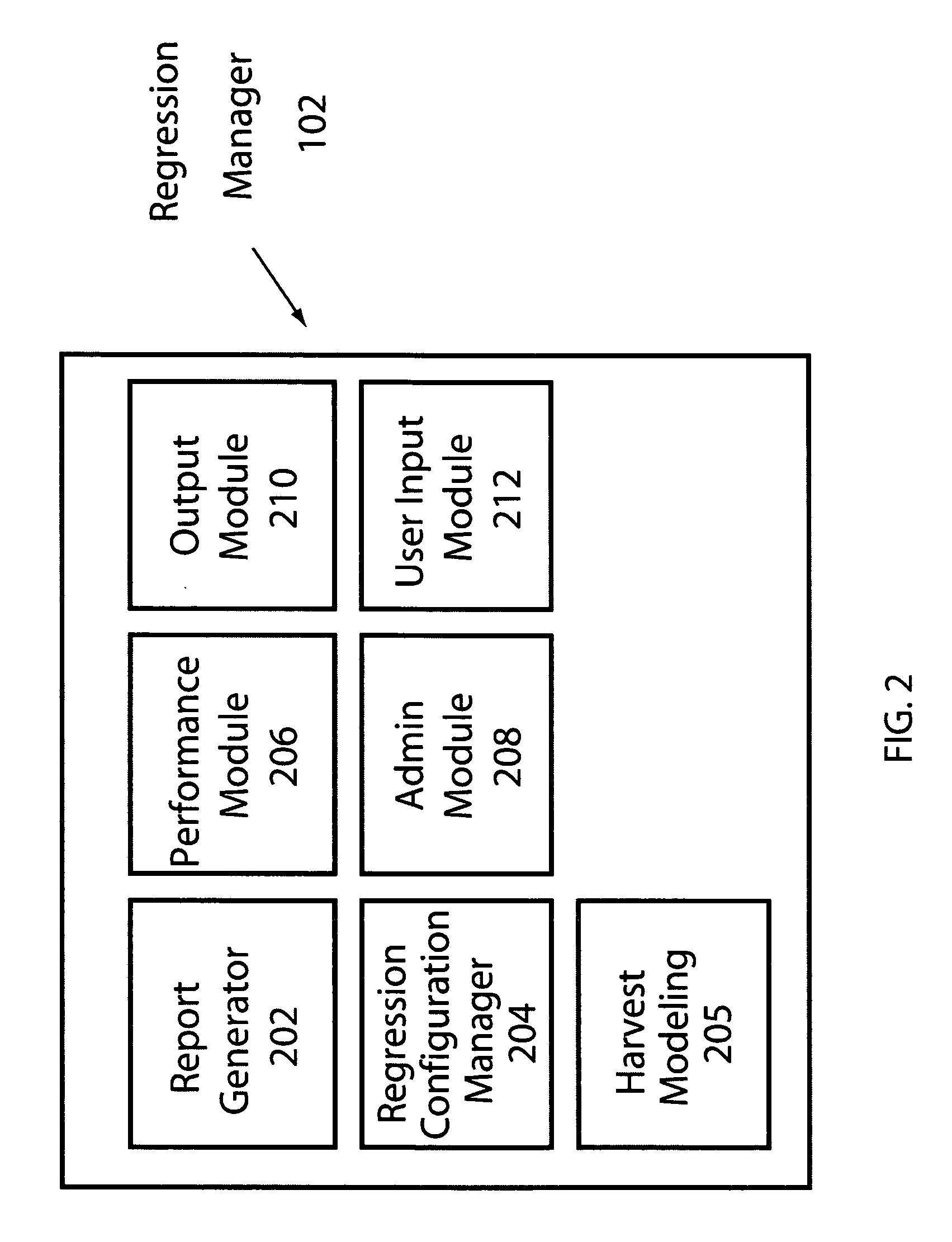
Methods, systems, and media for generating a regression suite database
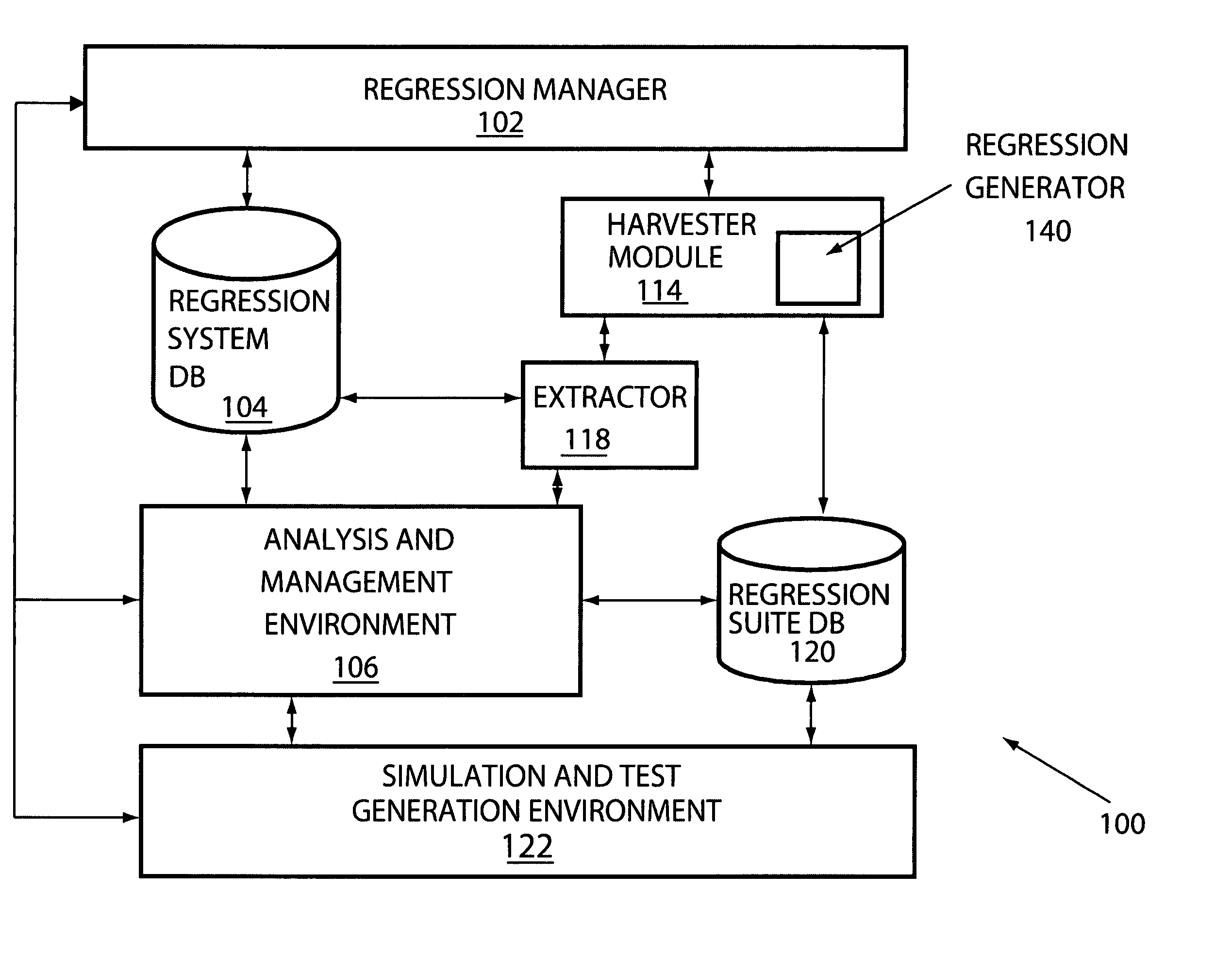
ActiveUS20050283664A1Functional testingSoftware simulation/interpretation/emulationUser inputModeling language
Methods, systems and media for generating an improved regression suite by applying harvesting models and / or regression algorithms to tests utilized in verification of a system are disclosed. In one embodiment, a regression manager responsive to user input may be coupled to a harvester module, an analysis module, and a management module. In one embodiment, the harvester module is responsive to harvesting models defined in a modeling language, where the harvester module is coupled to a regression suite database. In another embodiment, a regression methodology may be defined from a collection of regression strategies and each regression strategy may be defined from a combination of harvesting models and / or regression algorithms. A regression generator to receive tests, to apply one or more regression strategies to the tests, to provide reports, and to allow user control may also be provided.
Owner:META PLATFORMS INC
Apparatus and method for passive testing of alcohol and drug abuse
InactiveUS20100204600A1Digital data processing detailsPerson identificationCompound organicAlcohol and drug
An automated system and method for passive testing of alcohol and drug abuse. The system enters a participant or subject into the system who is to be monitored during a probationary or other program for alcohol or drug abuse offenders. The system provides a drug testing home device or a drug testing kiosk device for use by the participant. The system enrolls the biometrics information of the participant into the computer system (e.g., finger print, voice, image, volatile compound organic gas level, and pH level). When the participant is to be tested in accordance with a testing schedule, the system validates these same biometrics of the participant, conducts the test, and then analyzes the test information for determining if the participant has been using alcohol or other drugs and should be subjected to a confirming urinalysis exam.
Owner:JUSTICE EZ TRAC
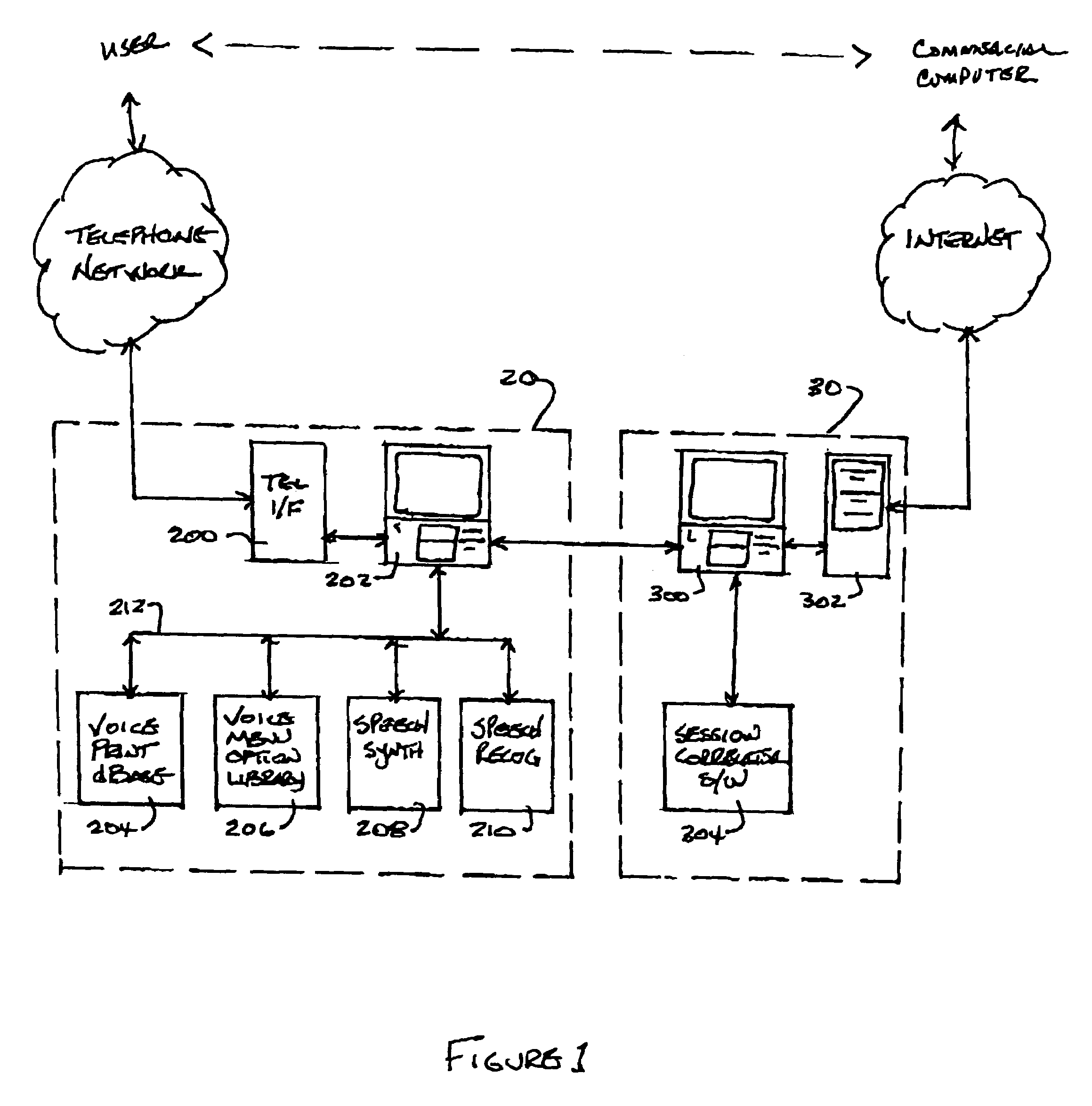
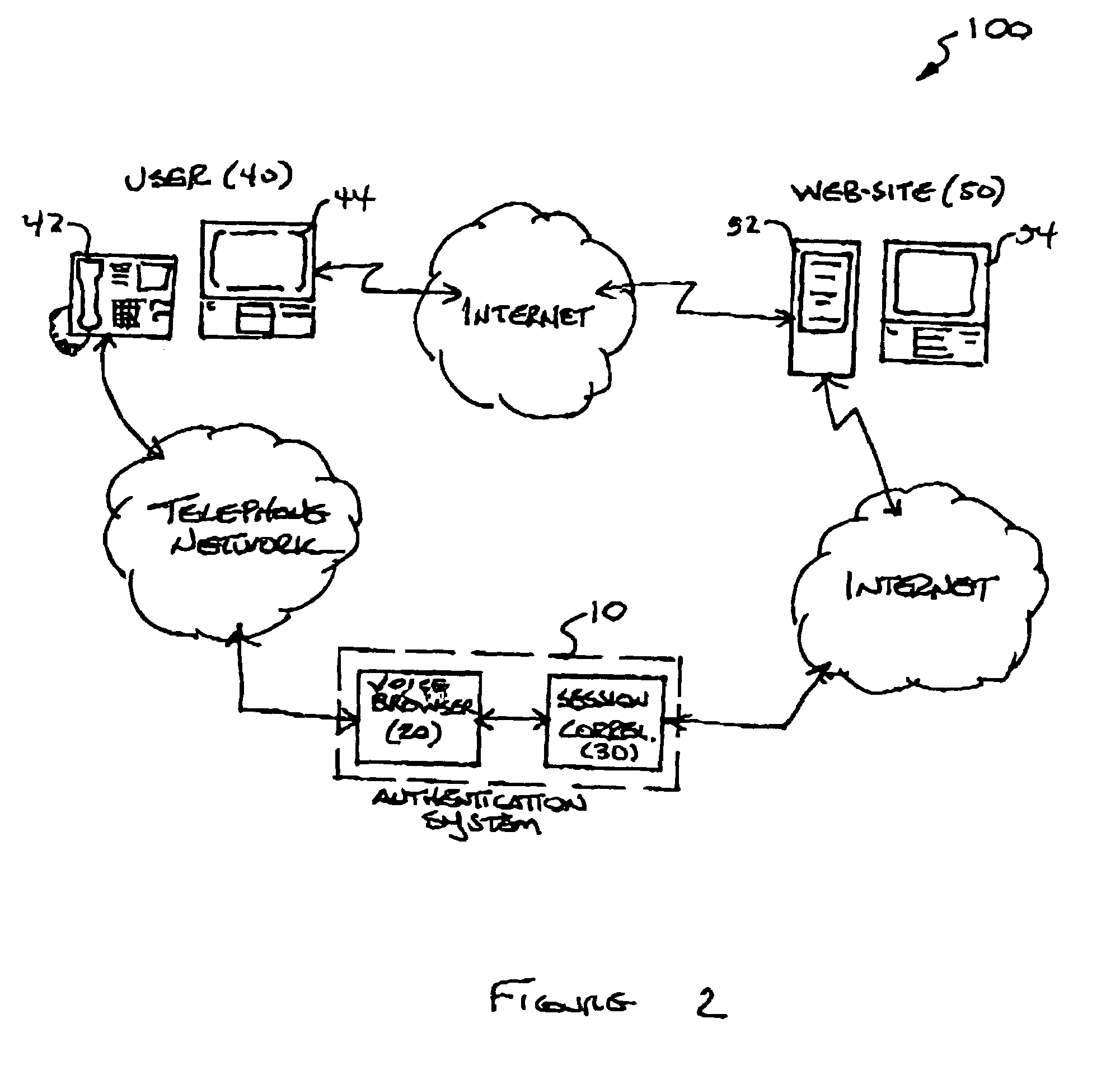
System and method for multi-modal authentication using speaker verification
ActiveUS7174323B1User identity/authority verificationDigital computer detailsSpeaker verificationComputer science
A system authenticates an electronic transaction between a first user-operated device and a computer. The computer is configured to conduct electronic transactions. The system includes a voice browser and a session correlator. The voice browser is configured to receive and process user-spoken information from a second user-operated device, where the voice browser is programmed to compare a user-spoken transaction identifier to a computer generated transaction identifier, and to compare a user-spoken verification identifier to a voice print of the user. The session correlator is coupled to the voice browser and is configured to transmit an authentication message to the computer if the user-spoken transaction identifier matches the computer transaction identifier, and if the user-spoken verification identifier matches the voice print.
Owner:RAKUTEN GRP INC
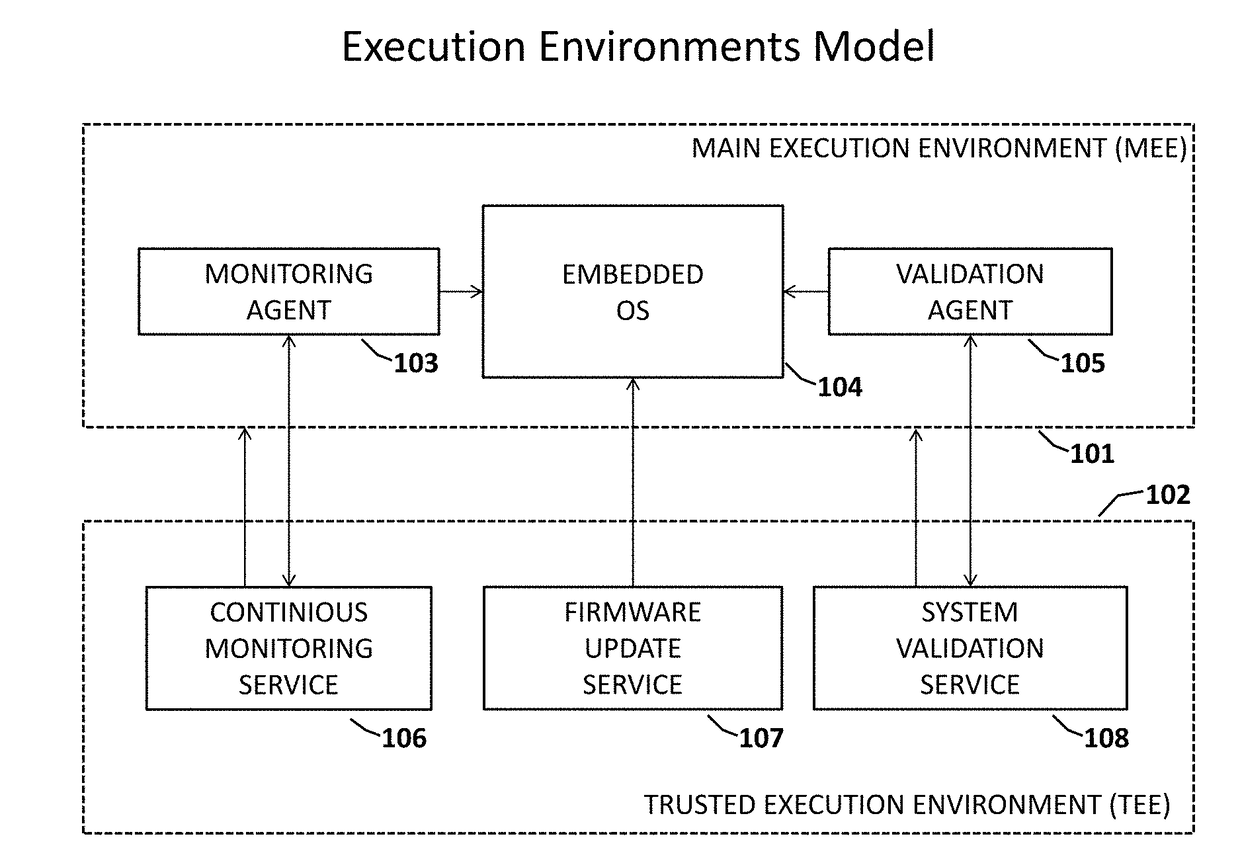
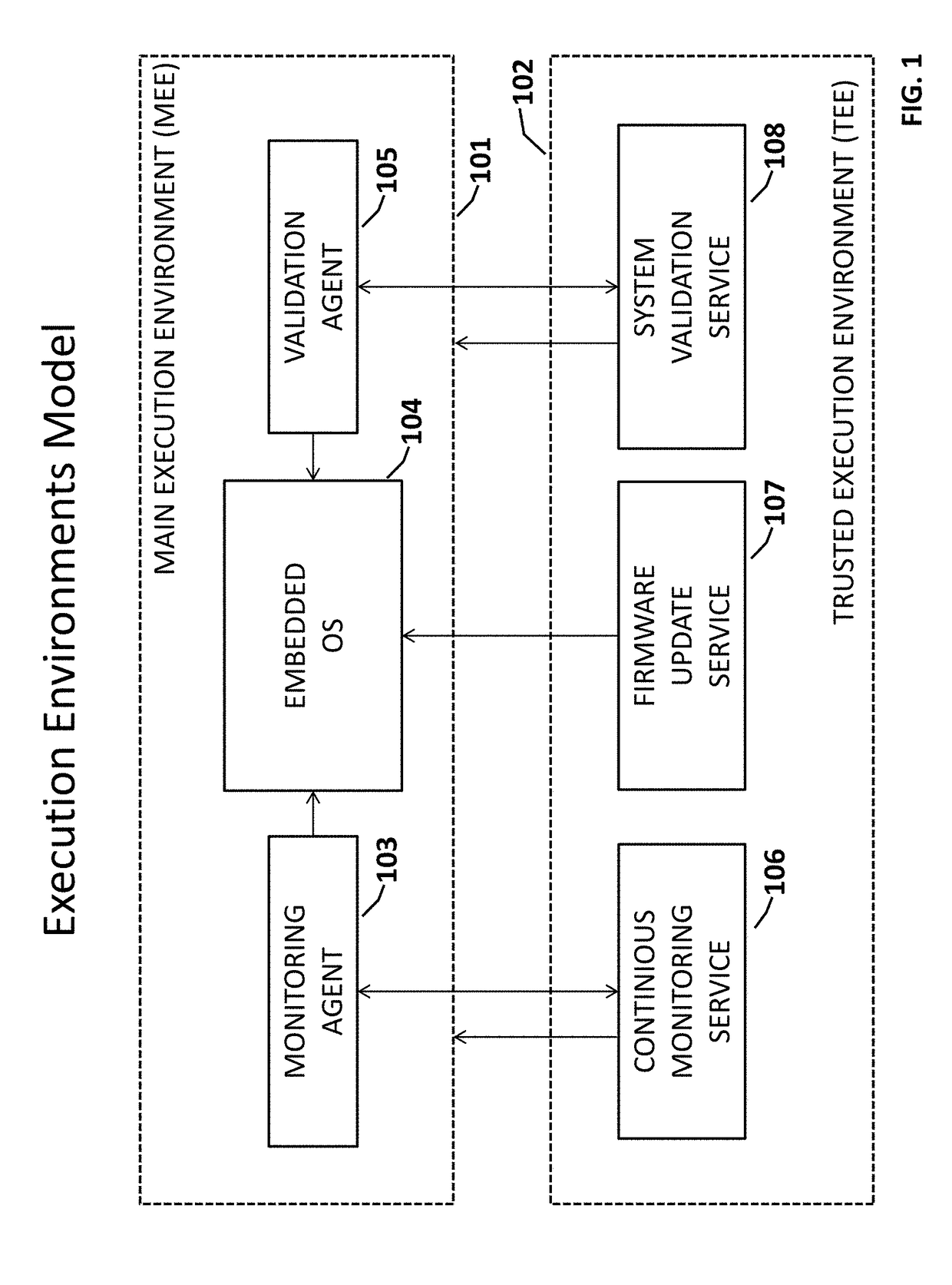
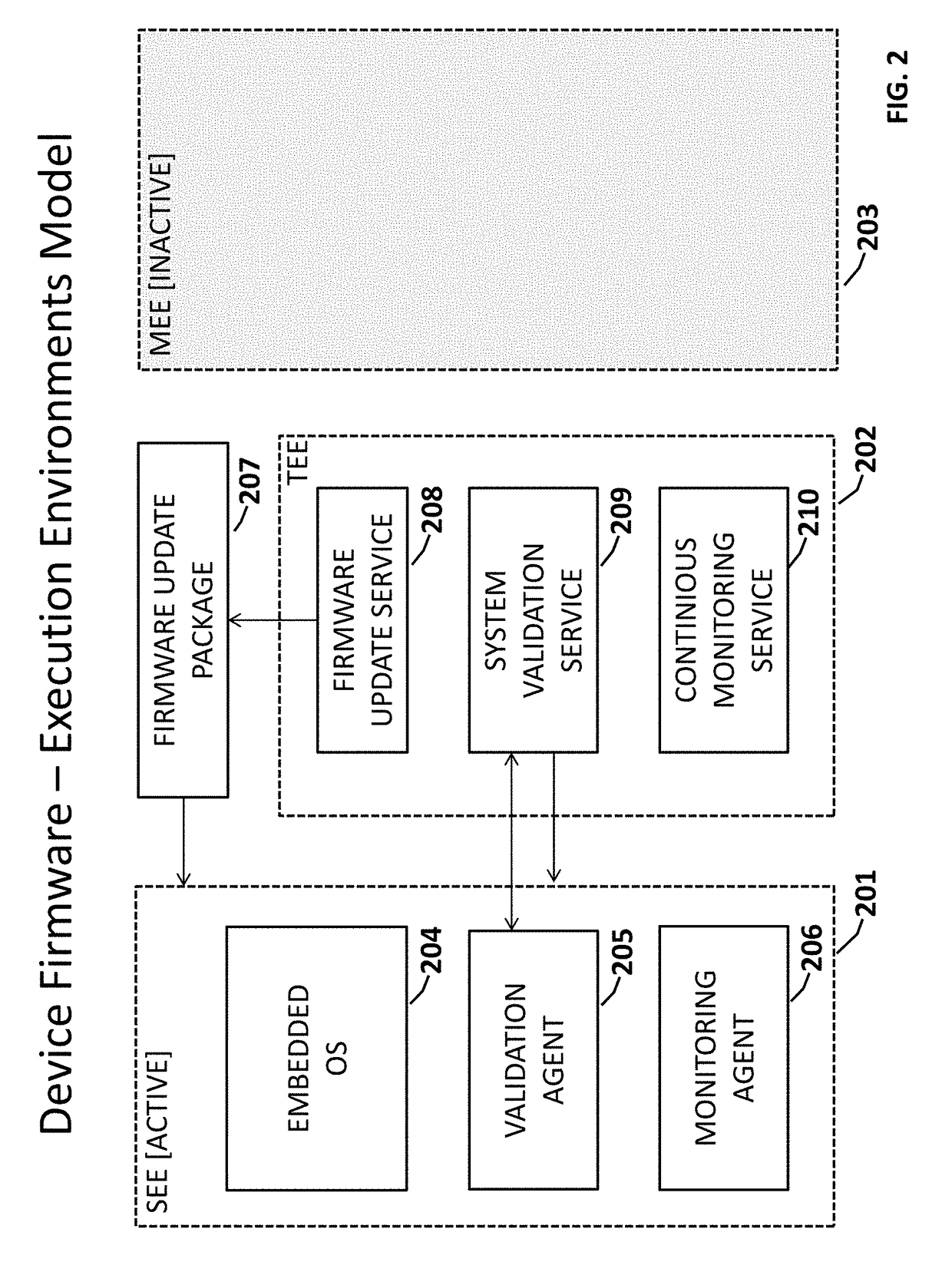
Reliable and Secure Firmware Update with a Dynamic Validation for Internet of Things (IoT) Devices
ActiveUS20170322790A1Fast and efficientReduce downtimeVersion controlDigital data protectionUse of servicesOperability
A computing system for a secure and reliable firmware update through a verification process, dynamic validation and continuous monitoring for error or failure and speedy correction of Internet of Things (IoT) device operability. The invention uses a Trusted Execution Environment (TEE) for hardware-based isolation of the firmware update, validation and continuous monitoring services. The isolation is performed by hardware System on a Chip (SoC) Security Extensions such as ARM TrustZone or similar technologies on other hardware platforms. The invention therefore comprises Firmware Update Service (FUS), System Validation Service (SMS) and Continuous Monitoring Service (CMS) running in the TEE with dedicated memory and storage, thus providing a trusted configuration management functionality for the operating system (OS) code and applications on IoT devices.Services running in the TEE use both direct (hardware level) and indirect (software agents inside main execution environment (MEE)) methods of control of the MEE. Embodiments of the invention apply all updates to a staging (new) execution environment (SEE) without changing of the MEE.
Owner:INZERO TECH LLC
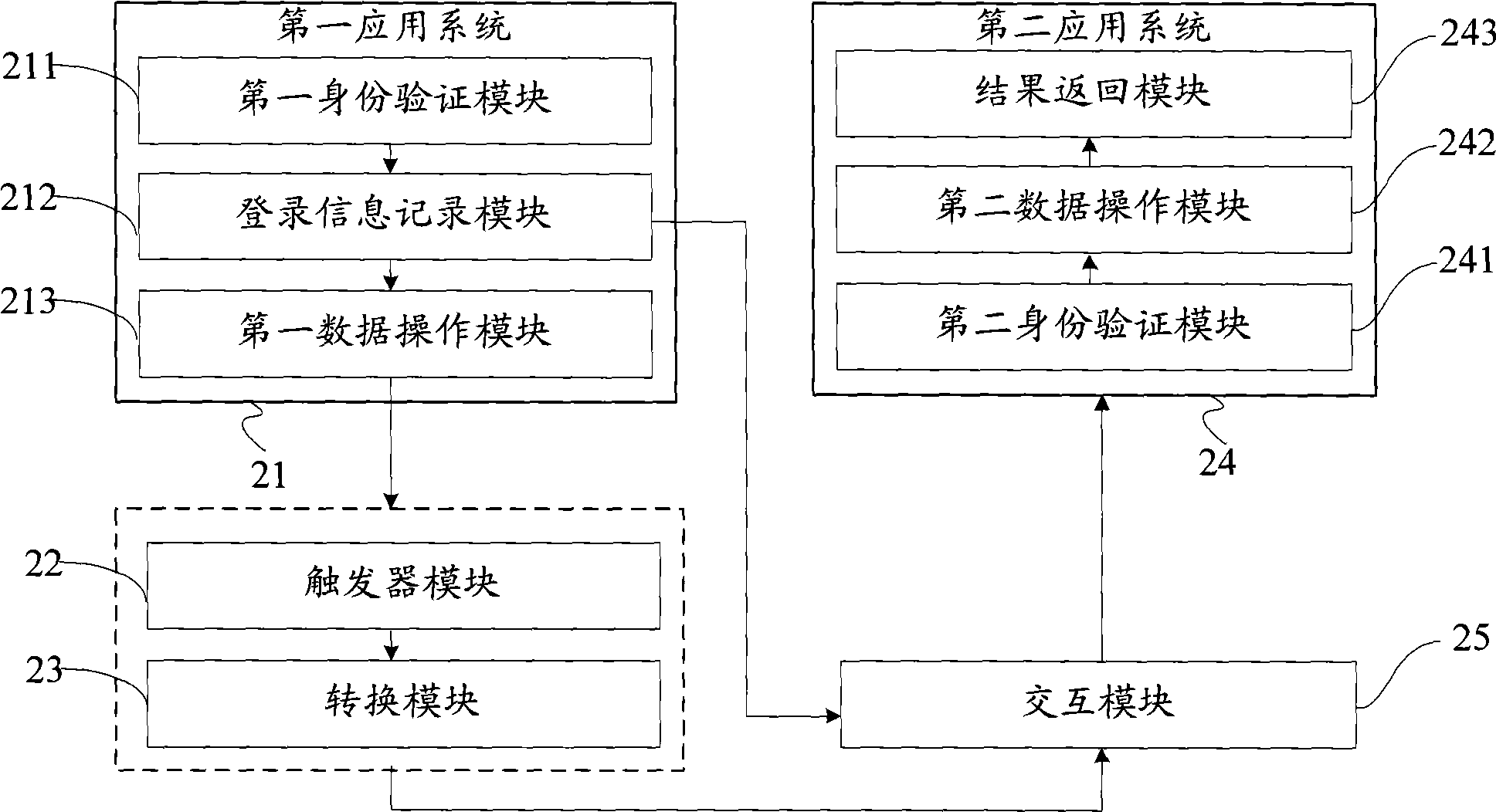
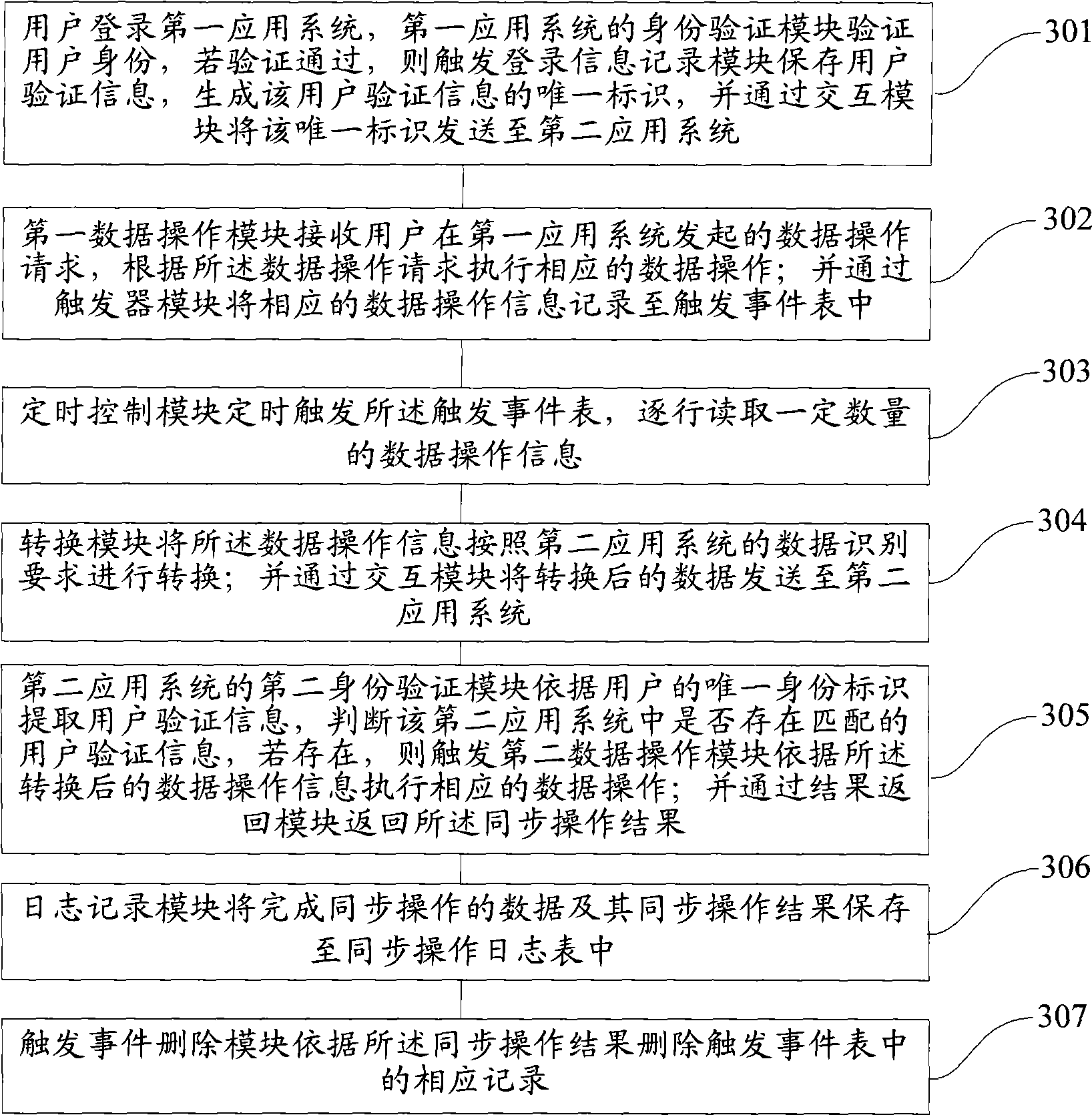
Method and device for data synchronization of multi-application systems for unifying user authentication
InactiveCN101547092AEnsure safetyUser identity/authority verificationDigital data authenticationUser verificationData synchronization
The invention provides a method for data synchronization of multi-application systems for unifying user authentication, which comprises that: a first application system verifies identification of a user, if the authentication is passed, the first application system stores user authentication information to generate unique identification of the user authentication information; a data operation request initiated by the first application system is received, corresponding data operation is executed according to the data operation request, and corresponding data operation information is recorded into a trigger event table; the data operation information in the trigger event table is converted according to the data identification requirement of a second application system, and is sent to the second application system; and the second application system extracts the user authentication information for the user authentication according to the unique user identification of the user, and the corresponding data operation is executed according to the converted data operation information and a synchronous operation result is returned if the user is lawful. The method can simply and flexibly realize the user synchronous logon and data synchronous operation between a plurality of application systems, and improves the efficiency and the safety.
Owner:吴霞
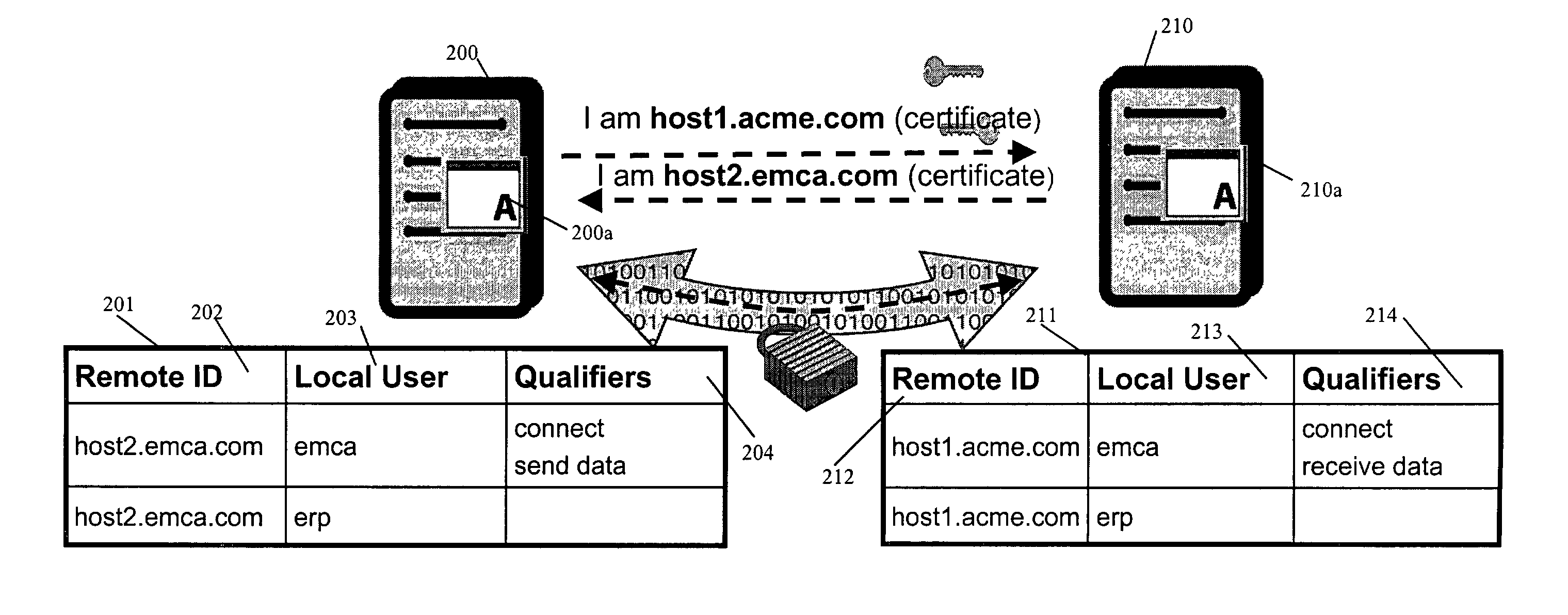
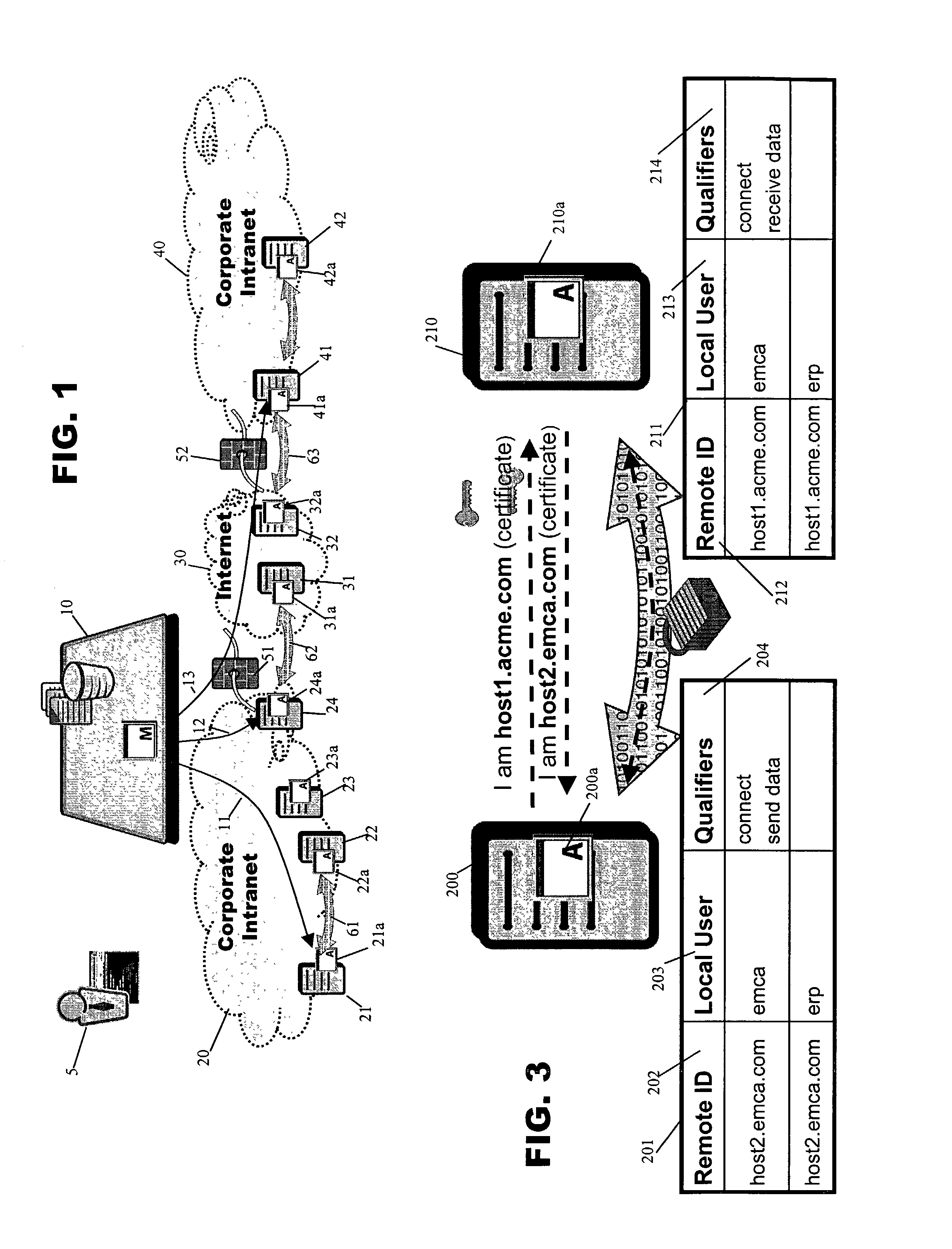
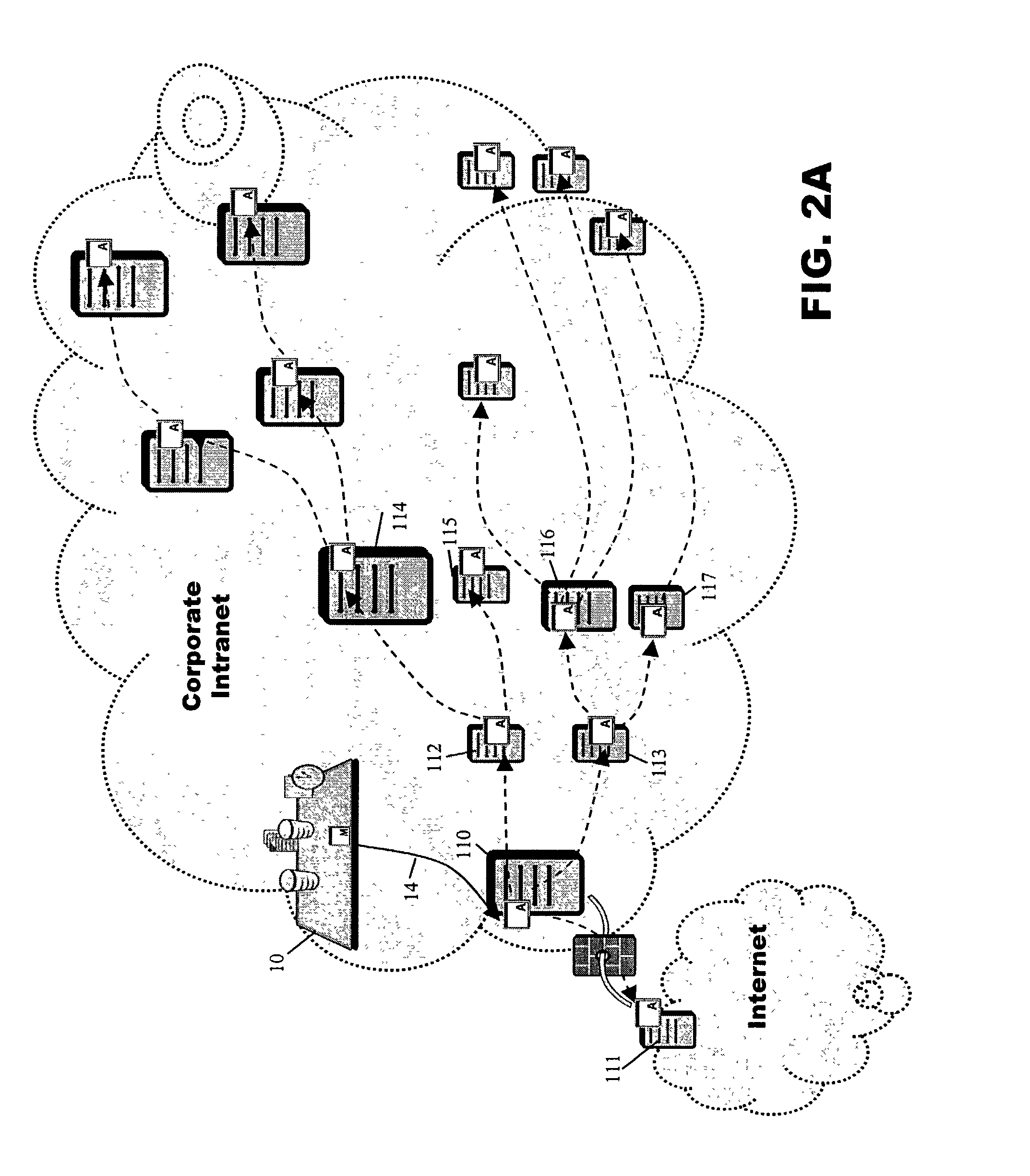
Data transfer system and method with secure mapping of local system access rights to global identities
ActiveUS7152108B1Provide securityDigital data protectionMultiple digital computer combinationsInternet privacyTransfer system
The present invention relates to a method and apparatus for providing security using an authorization process in connection with data transfers. Keyed certificates are used to authenticate remote computers. An authorization table maps remote computers to allowable local users and corresponding qualifiers. In order to complete a data transfer process, the system of the present invention authenticates the remote computer, determines its authority to act as a designated local user, and determines whether the remote computer, acting as the designated local user, can perform the actions required for the data transfer.
Owner:SIGNIANT
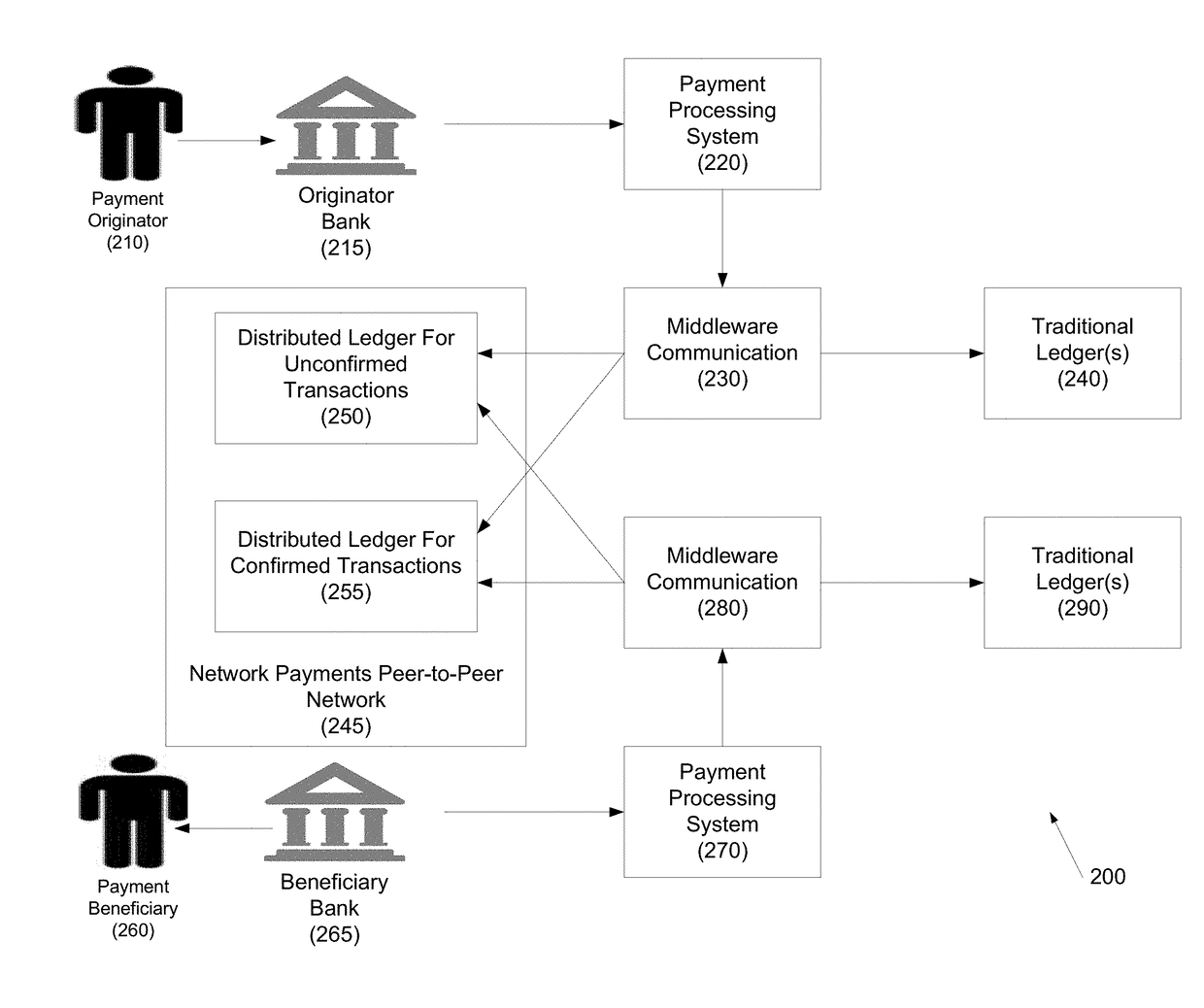
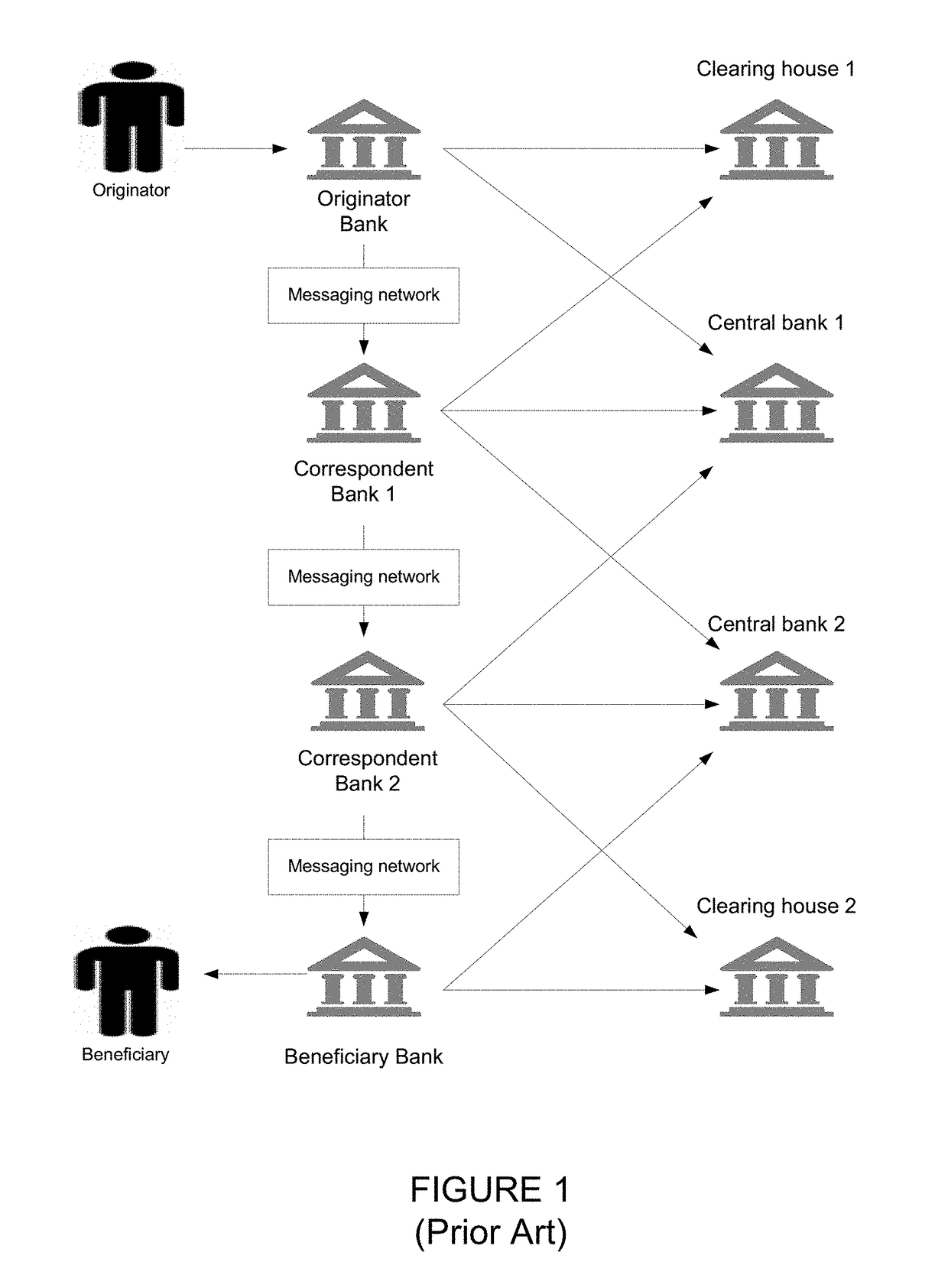
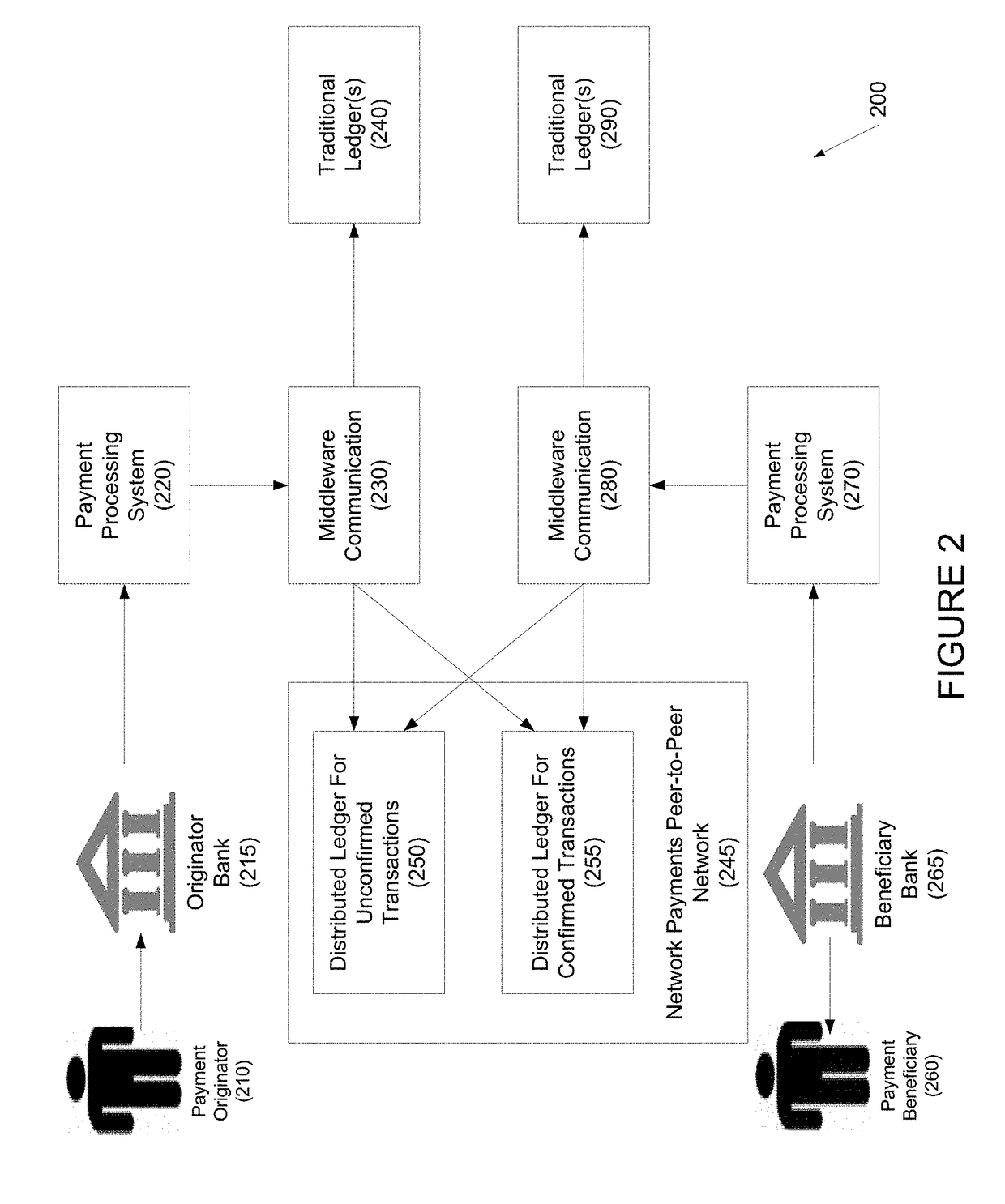
Systems and methods for the application of distributed ledgers for network payments as financial exchange settlement and reconciliation
ActiveUS20180121911A1Cryptography processingDatabase distribution/replicationPaymentFinancial trading
Systems and methods for the application of distributed ledgers for network payments as financial exchange settlement and reconciliation are disclosed. In one embodiment, a method for processing network payments using a distributed ledger may include: (1) a payment originator initiating a payment instruction to a payment beneficiary; (2) a payment originator bank posting and committing the payment instruction to a distributed ledger on a peer-to-peer network; (3) the payment beneficiary bank posting and committing the payment instruction to the distributed ledger on a peer-to-peer network; and (4) the payment originator bank validating and processing the payment through a payment originator bank internal system and debiting an originator account.
Owner:JPMORGAN CHASE BANK NA
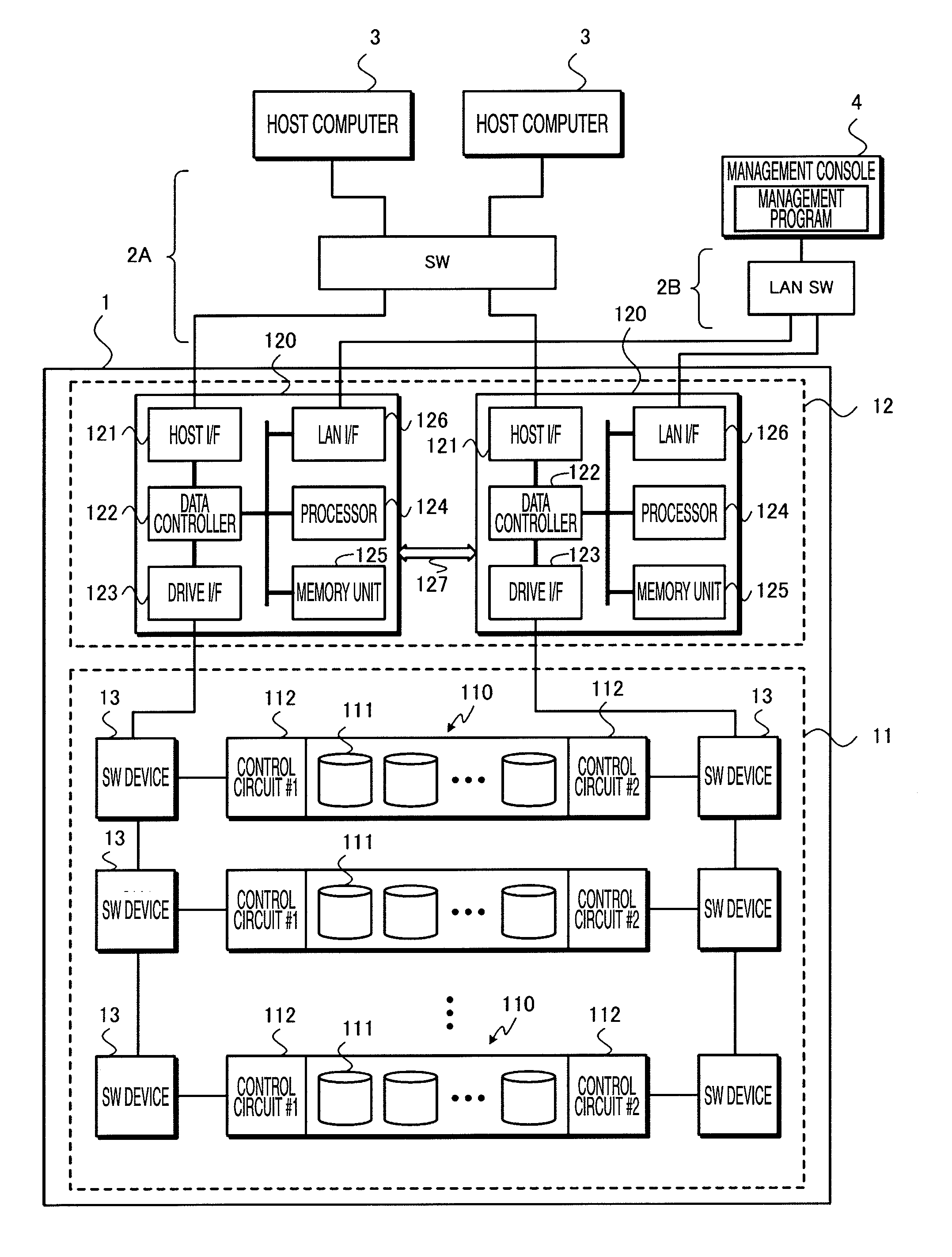
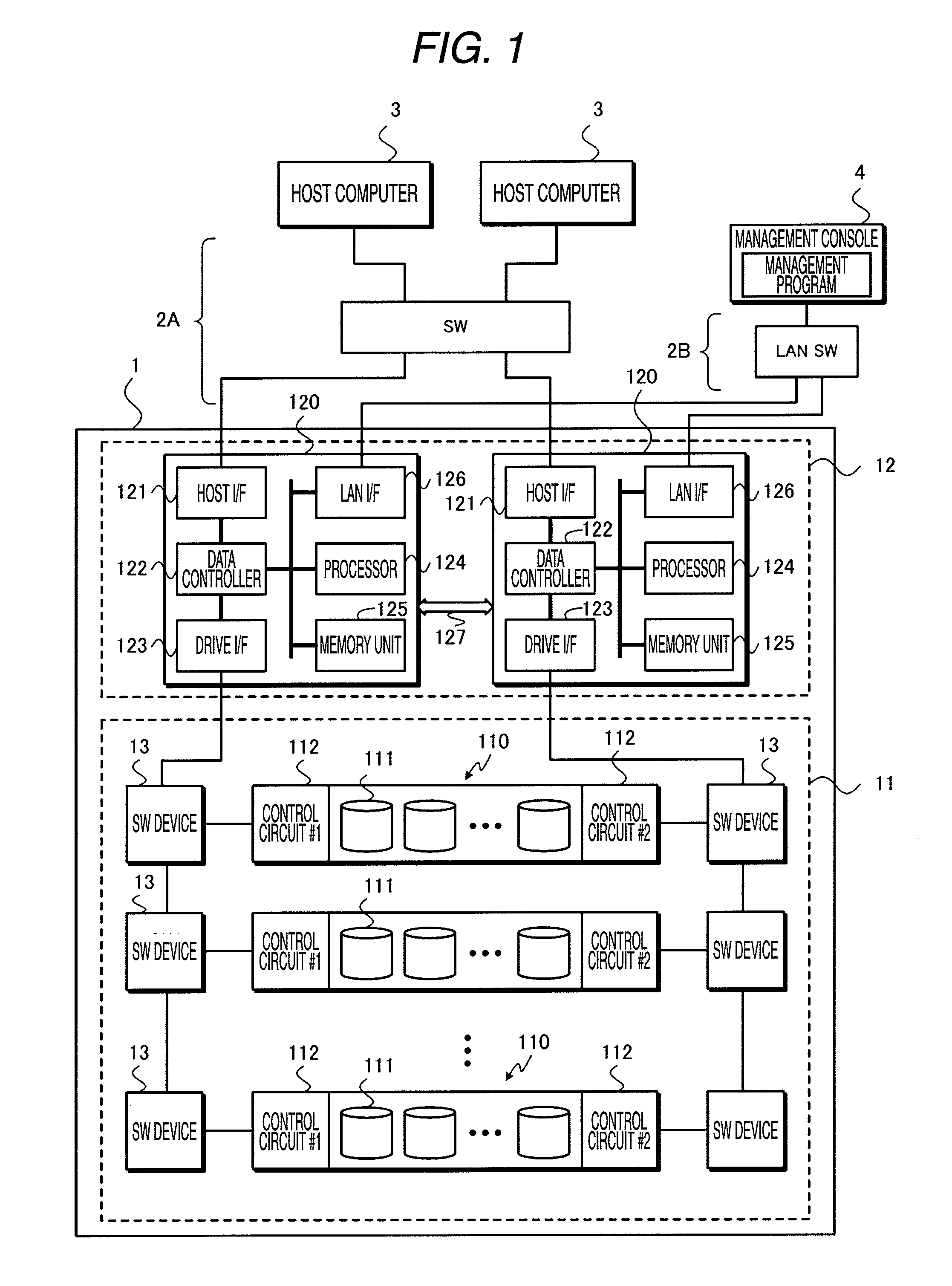
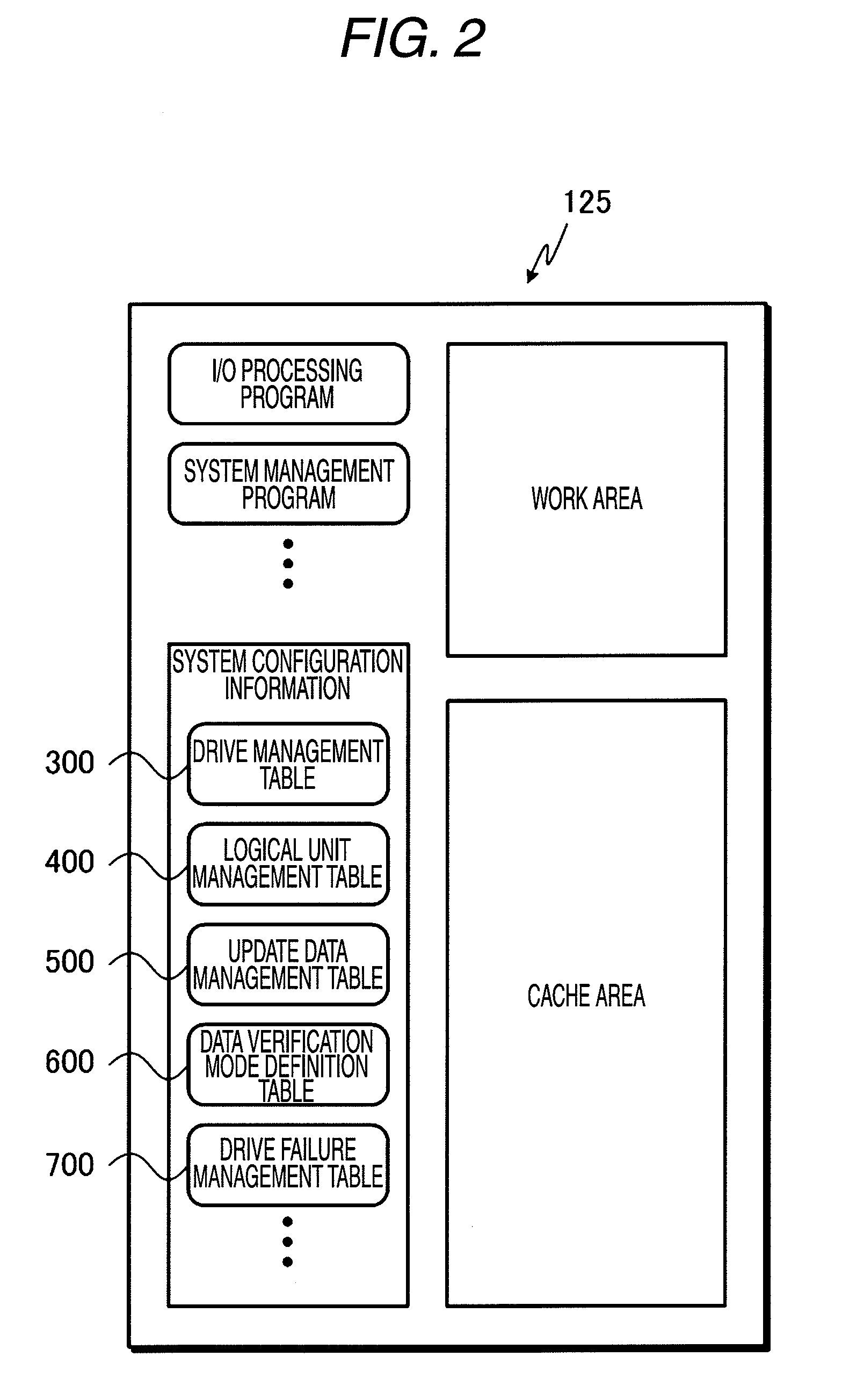
Storage Subsystem and Method for Verifying Data Using the Same
InactiveUS20100023847A1Improve reliabilityLow priceFault responseRedundant array of inexpensive disk systemsHard disc driveDependability
A subject of the invention is to propose a storage subsystem assuring high reliability and not impairing processing performance. The invention is a storage subsystem which includes a storage device including a hard disk drive and a controller for controlling an access to the storage device in response to a predetermined access command transmitted from a host computer. The storage subsystem stores, in response to a write request transmitted from the host computer, data associated with the write request together with its parity in the storage device as well as verifies the validity of the data stored in the storage device independently of a response to the write request and, when there is an abnormality in the data, repairs the abnormal data.
Owner:HITACHI LTD
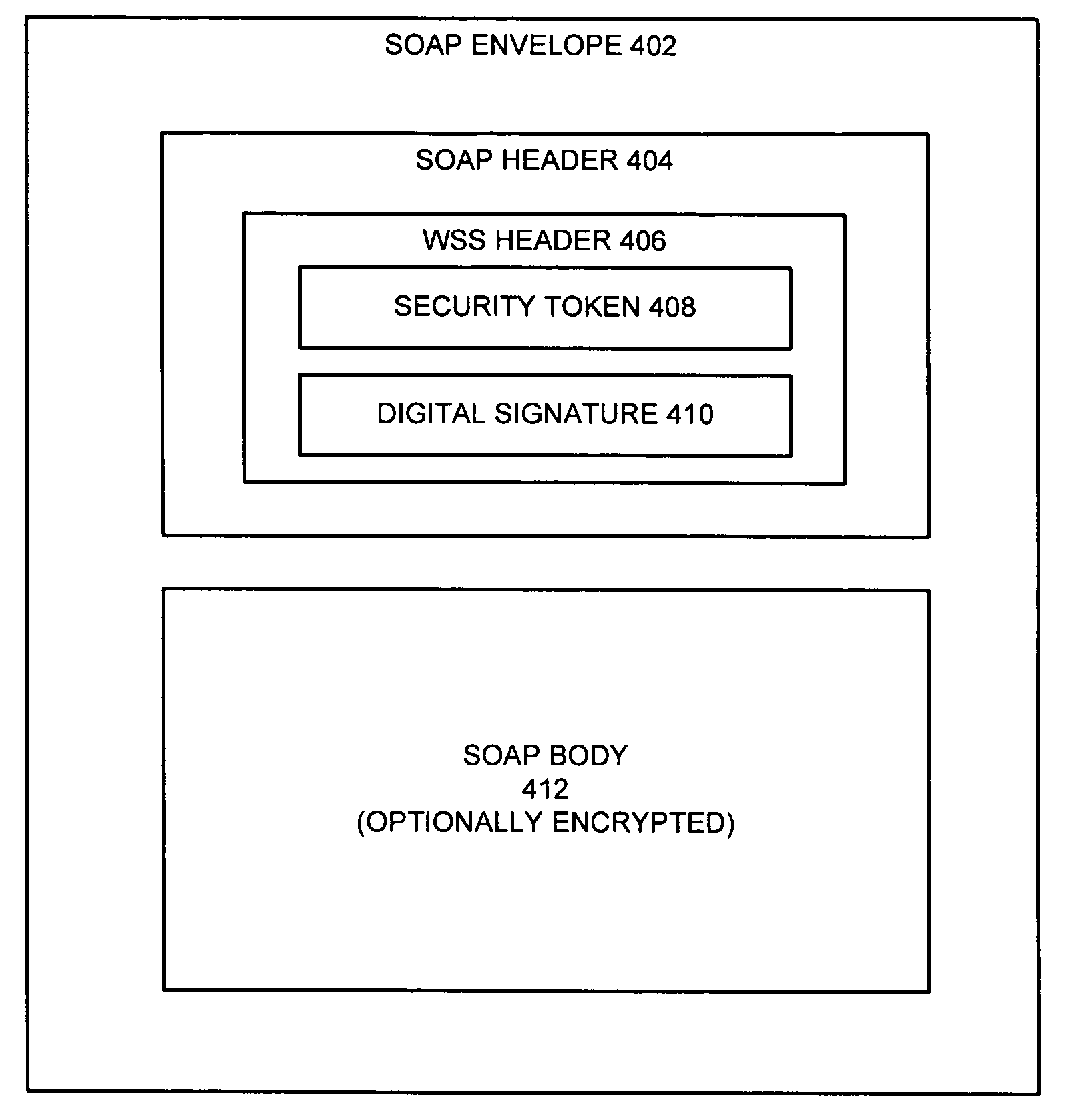
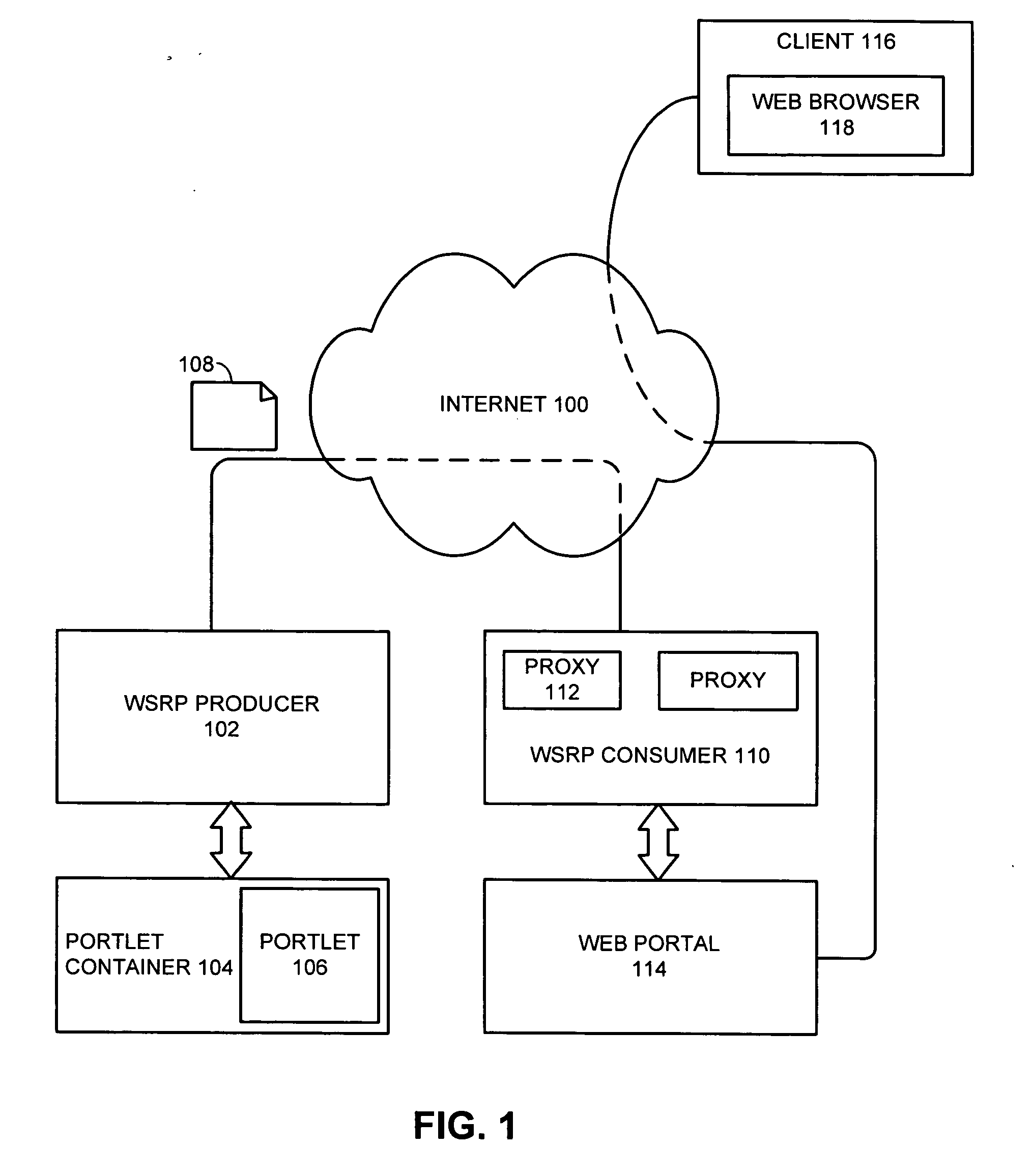
Secure single sign-on authentication between WSRP consumers and producers
ActiveUS20080141028A1Authentication is convenientEasy accessPublic key for secure communicationDigital data processing detailsPasswordDigital signature
One embodiment of the present invention provides a system that facilitates secure single sign-on (SSO) authentication for web-services communications. During operation, the system receives a Web Services for Remote Portlet (WSRP) request from a WSRP consumer and also receives a digital signature associated with the WSRP request. The system then validates the digital signature and authenticates a user based on the validation, thereby allowing the user to sign on without providing a password.
Owner:ORACLE INT CORP
Methods, data structures, and systems for authenticating media stream recipients
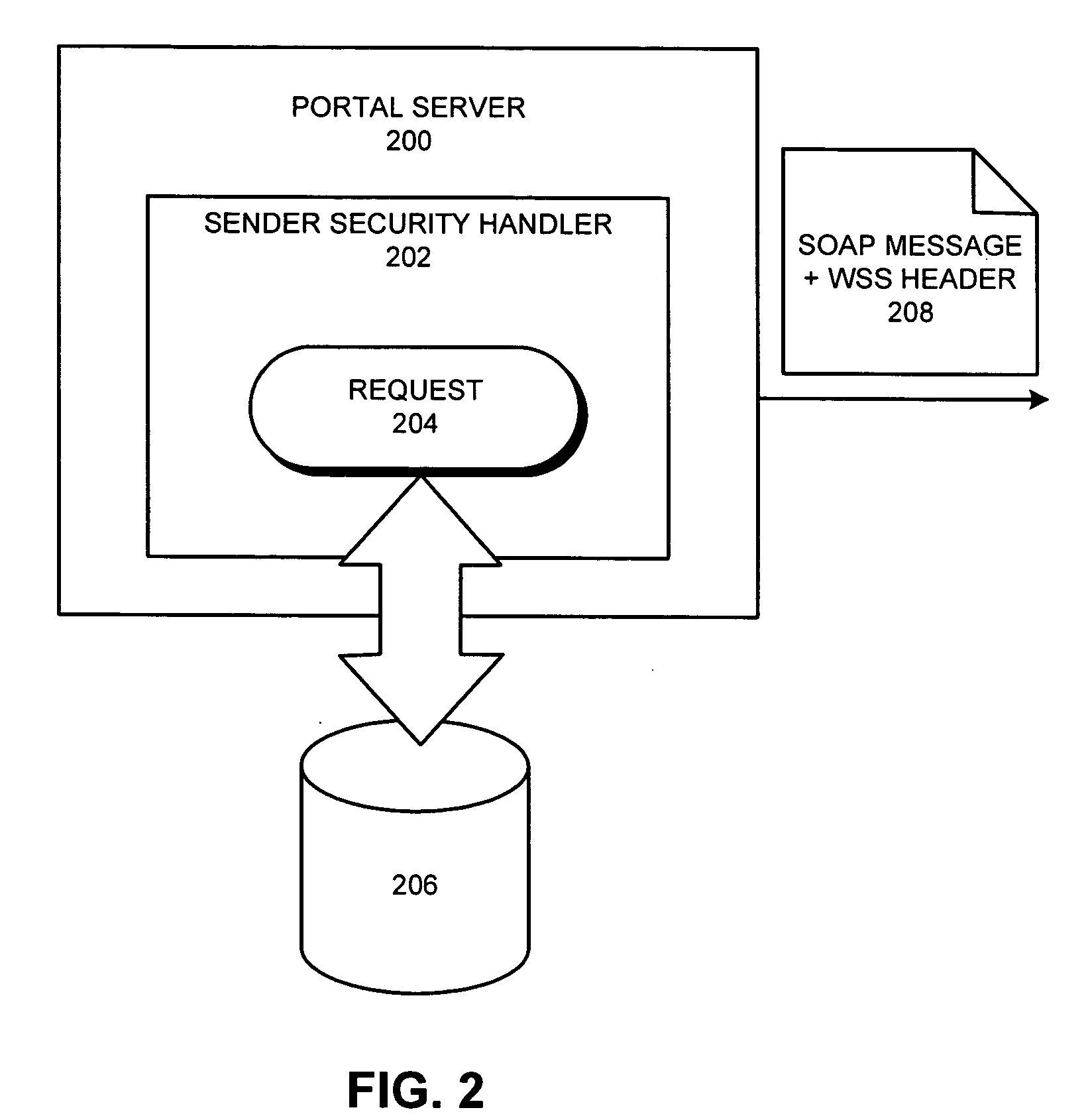
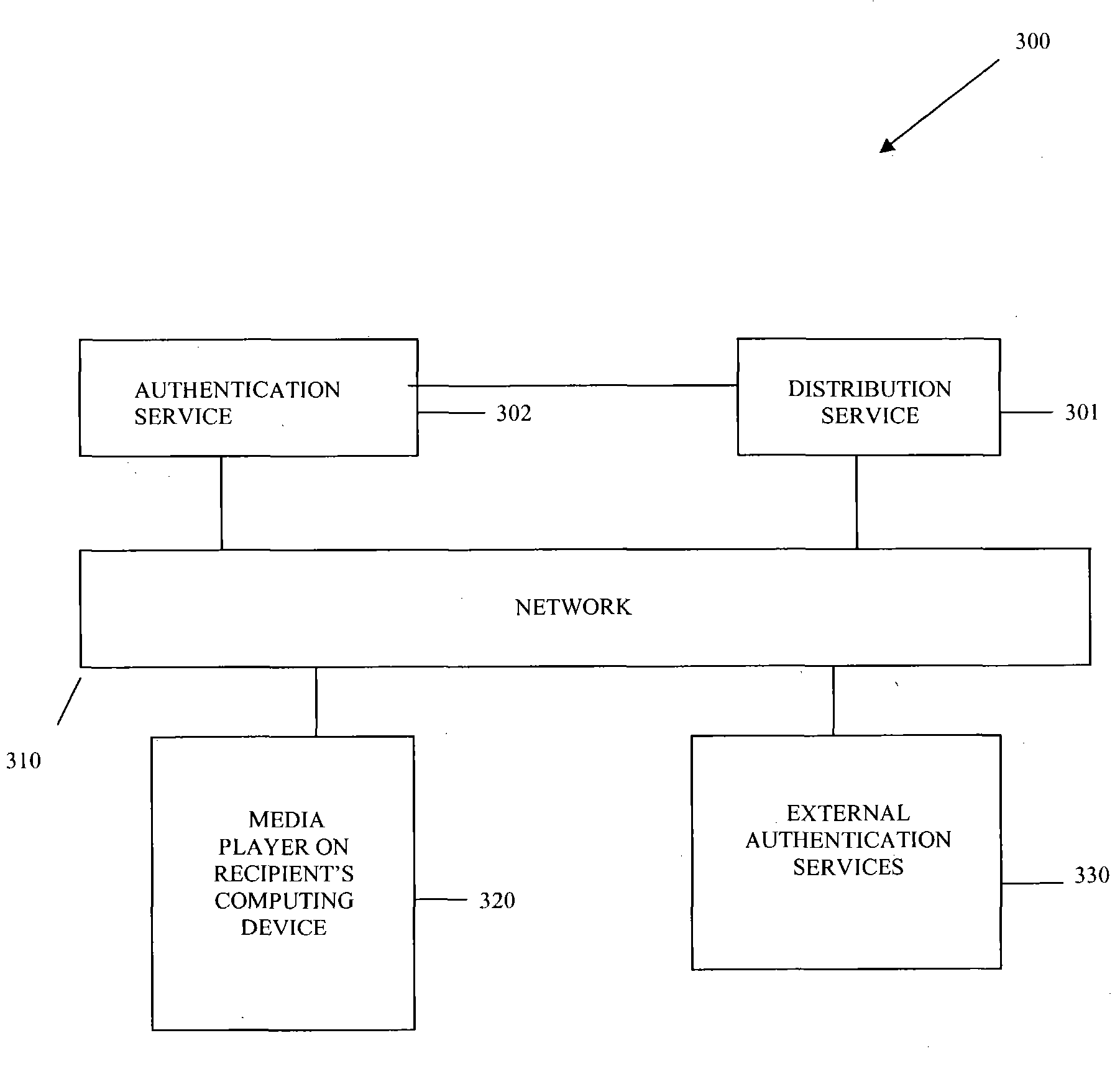
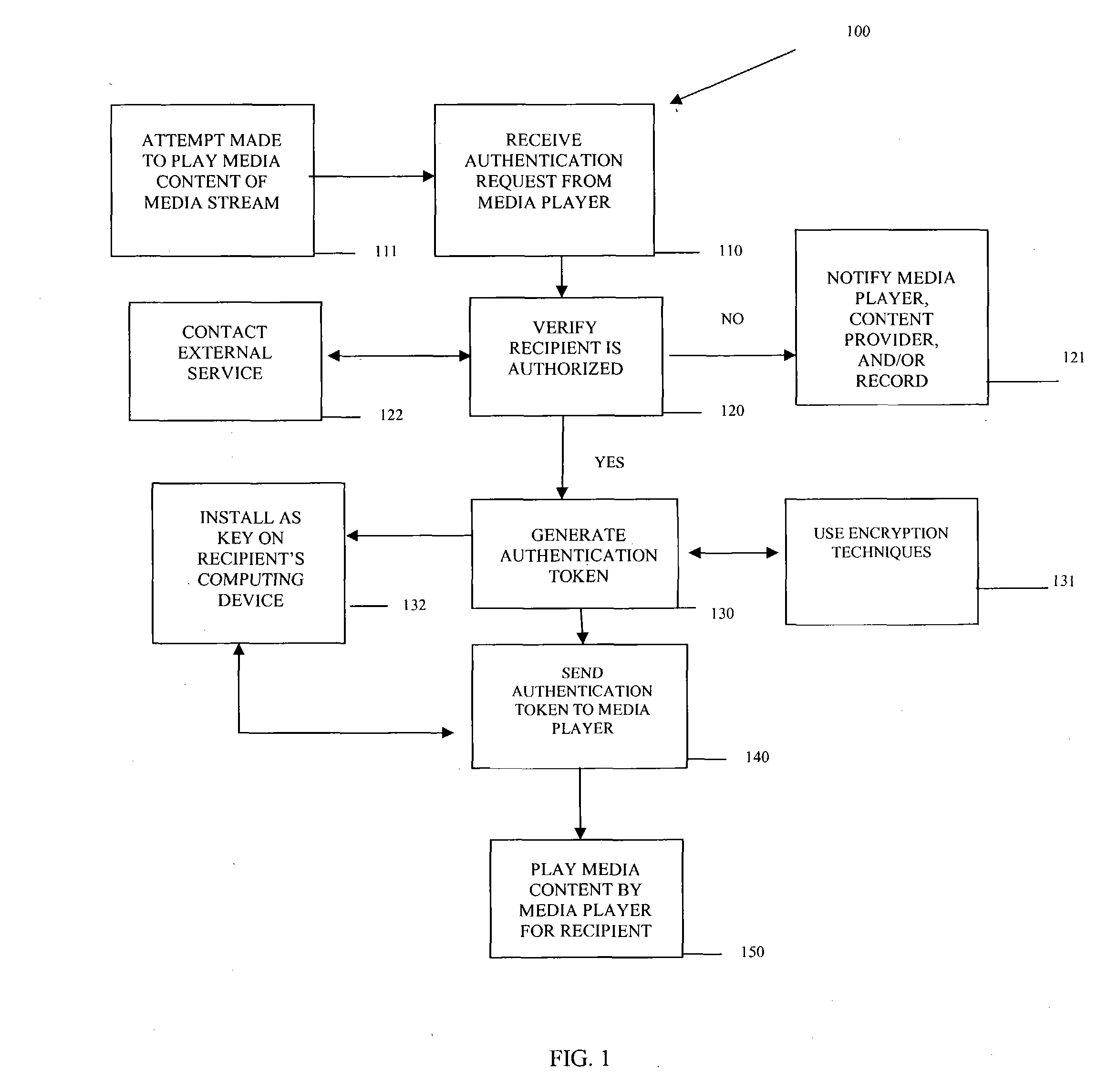
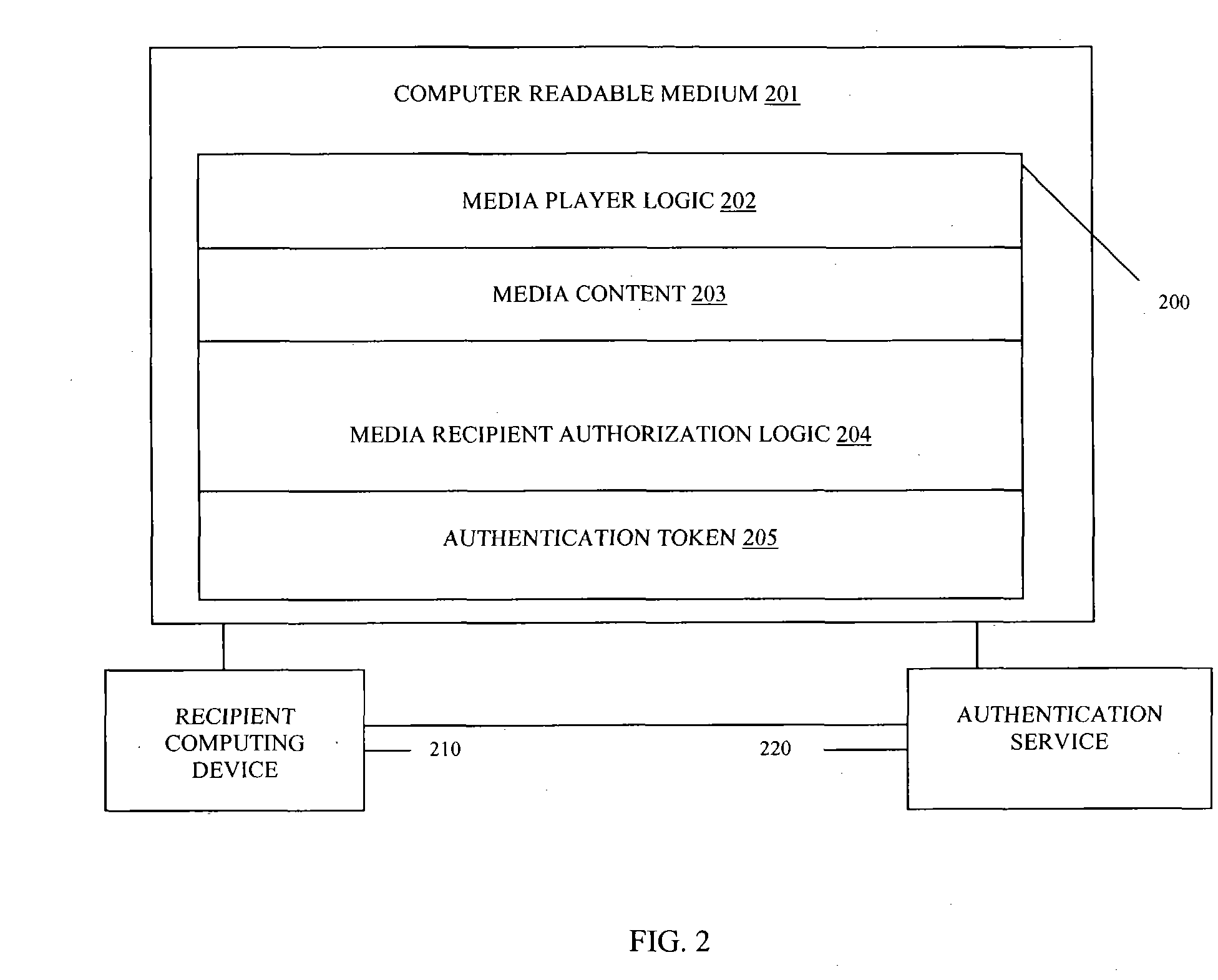
InactiveUS20050005146A1User identity/authority verificationUnauthorized memory use protectionService useData structure
Methods, data structures, and systems authenticate recipients of media streams. A media stream includes a self-installing and self-executing media player and media content. The media player communicates with an authentication service after it self-installs and self-executes. The media player provides authenticating information about a media stream recipient. The authentication service uses the information for authenticating the recipient for access to the media content. The authentication service provides an authentication token for an authorized recipient. Once a valid authentication token is received by the media player, the media player plays the media content for the authorized recipient.
Owner:MAUI X STREAM
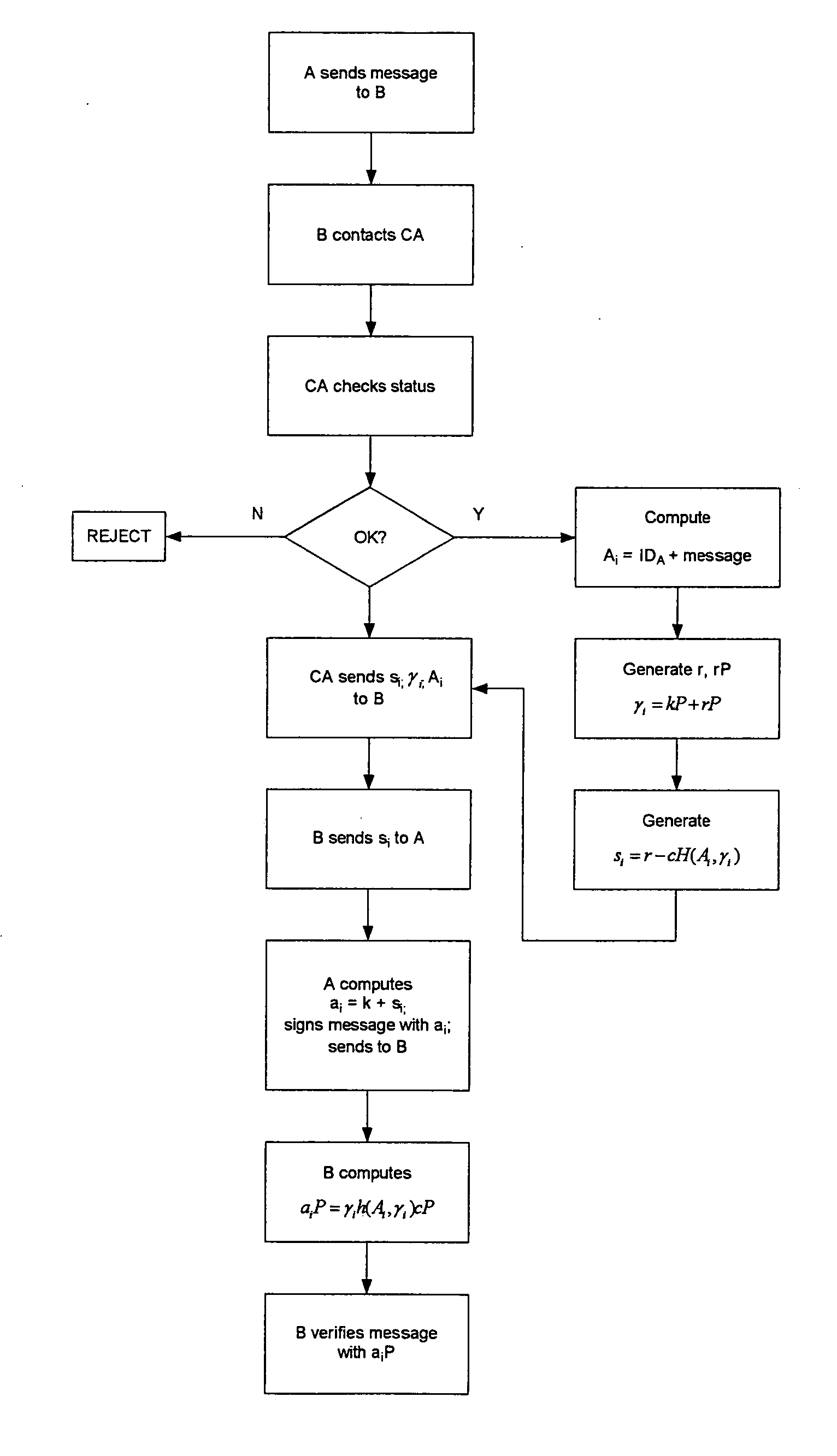
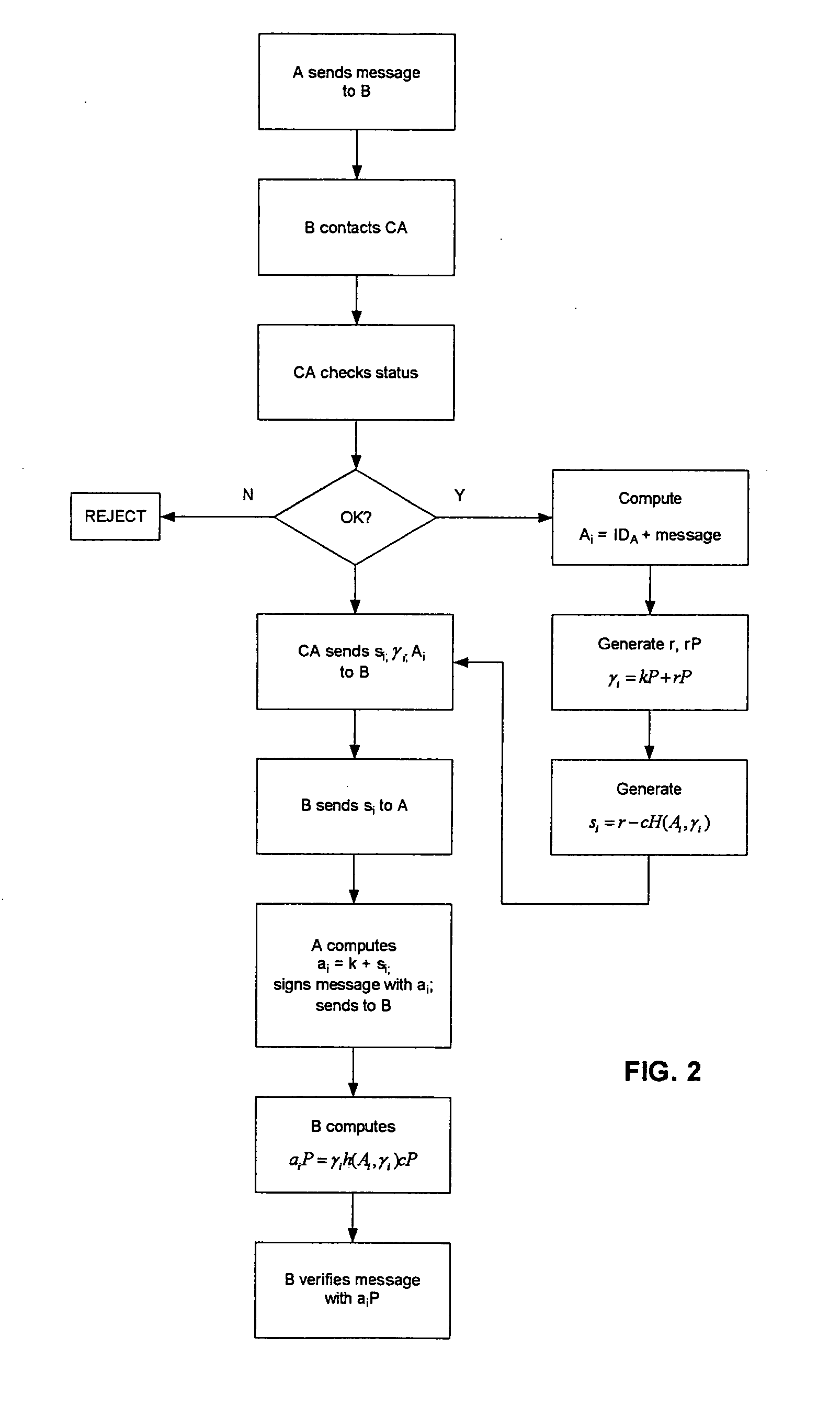
Method for the application of implicit signature schemes
InactiveUS20050193219A1Key distribution for secure communicationDigital data processing detailsCommunications systemAuthorization
A method of verifying a transaction over a data communication system between a first and second correspondent through the use of a certifying authority. The certifying authority has control of a certificate's validity, which is used by at least the first correspondent. The method comprises the following steps. One of the first and second correspondents advising the certifying authority that the certificate is to be validated. The certifying authority verifies the validity of the certificate attributed to the first correspondent. The certifying authority generates implicit signature components including specific authorization information. At least one of the implicit signature components is forwarded to the first correspondent for permitting the first correspondent to generate an ephemeral private key. At least one of the implicit signature components is forwarded to the second correspondent for permitting recovery of an ephemeral public key corresponding to the ephemeral private key. The first correspondent signs a message with the ephemeral private key and forwards the message to the second correspondent. The second correspondent attempts to verify the signature using the ephemeral public key and proceeds with the transaction upon verification.
Owner:MALIKIE INNOVATIONS LTD
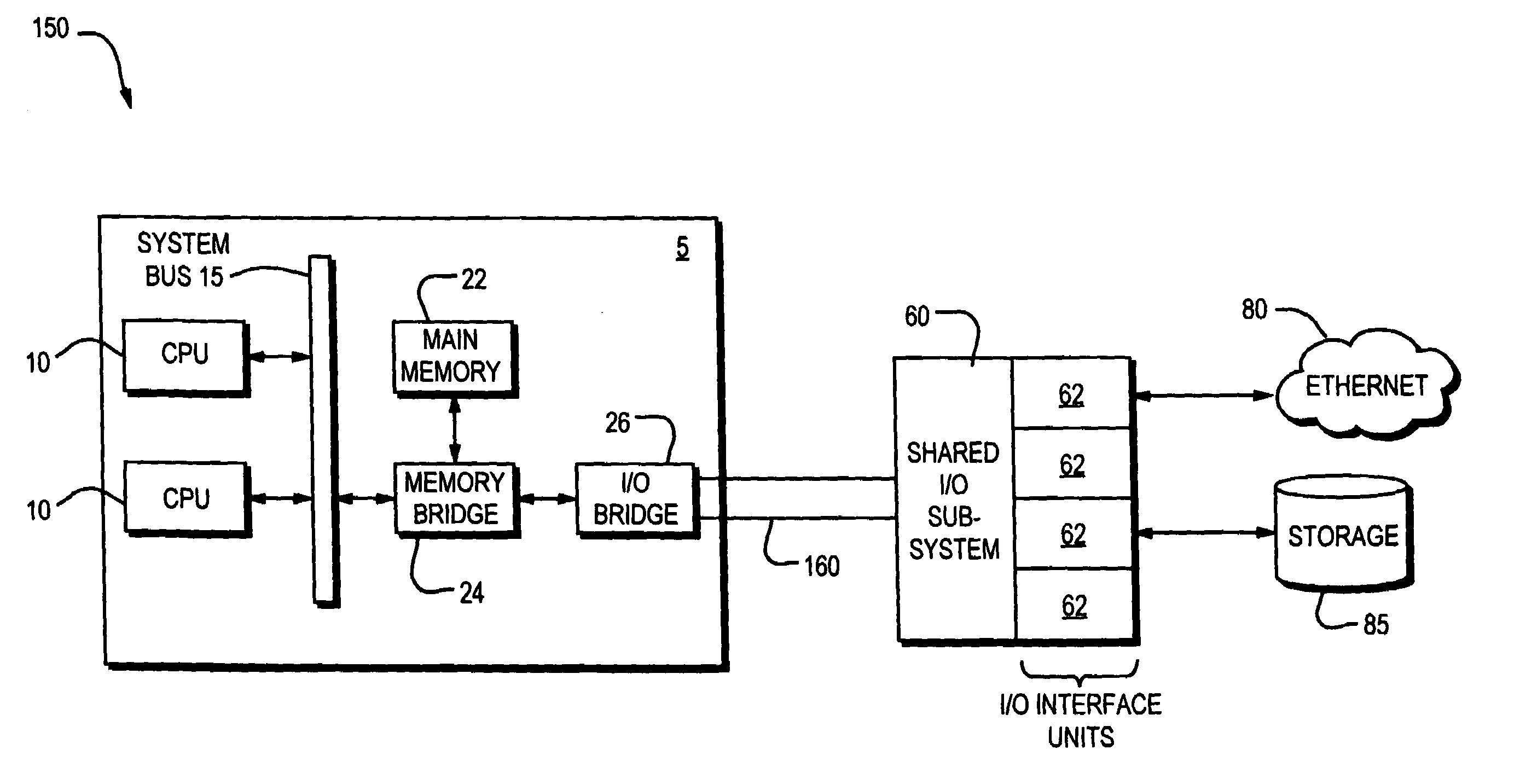
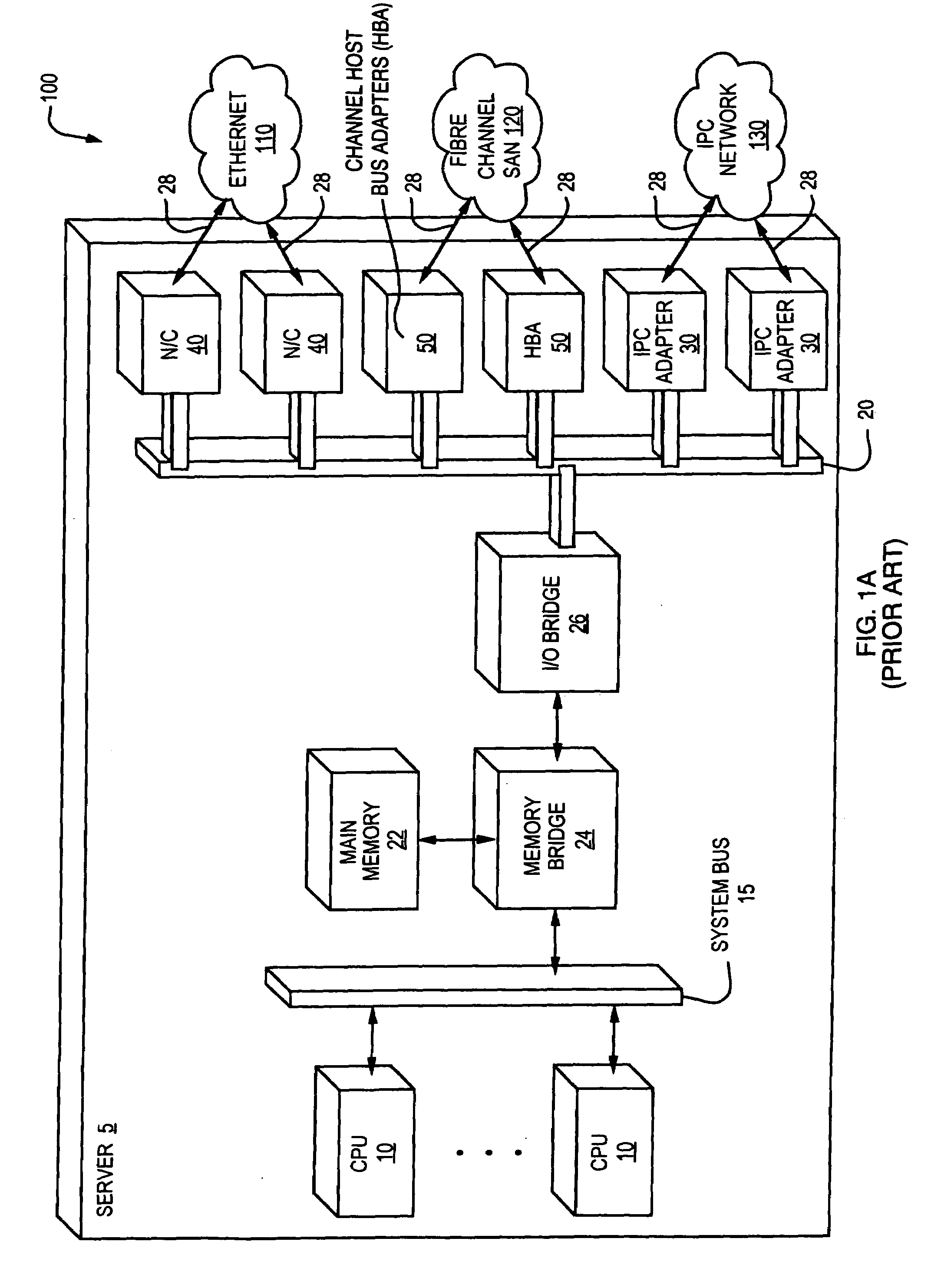
System and method for eventless detection of newly delivered variable length messages from a system area network
InactiveUS6988150B2Multiple digital computer combinationsProgram controlStorage area networkComputerized system
A shared I / O subsystem that includes a plurality of I / O interfaces for coupling a plurality of computer systems where each of I / O interfaces communicatively couples one of the computer systems to the shared I / O subsystem. The shared I / O subsystem receives, at a first one of the I / O interfaces, a data packet from one of the computer systems coupled to the first one of the I / O interfaces where the data packet has a variable length, arranges, at the first one of the I / O interfaces, the data packet into an internal format where the internal format has a first portion that includes data bits and a second portion that includes control bits, receives the data packet in a buffer in the shared I / O subsystem where the second portion is received after the first portion, verifies, with the shared I / O subsystem, that the data packet has been completely received by the buffer by monitoring a memory bit aligned with a final bit in the second portion of the data packet, and transmits, in response to the verifying, the data packet to another one of the computer systems coupled to a second one of the I / O interfaces.
Owner:MARVELL ASIA PTE LTD
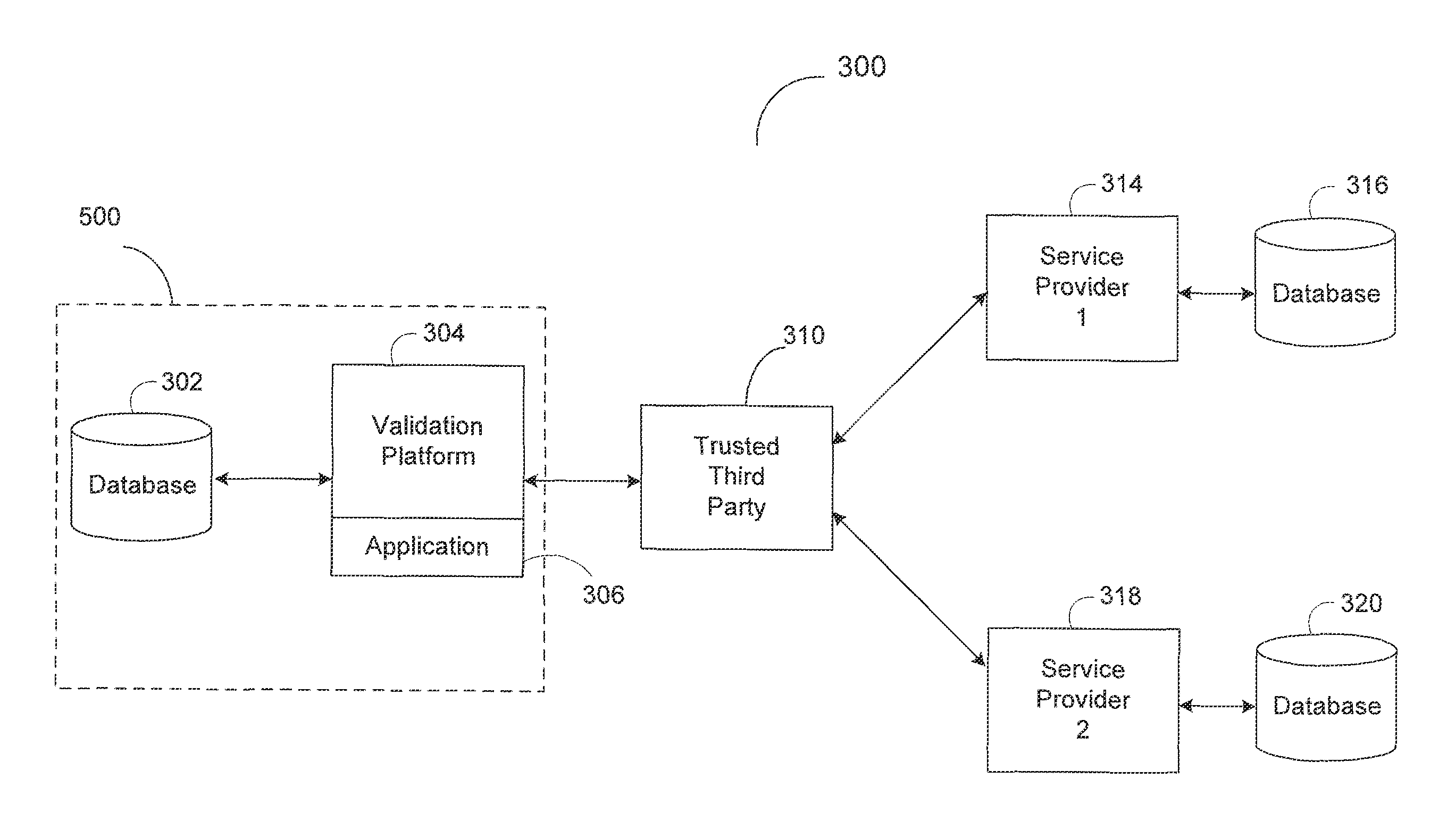
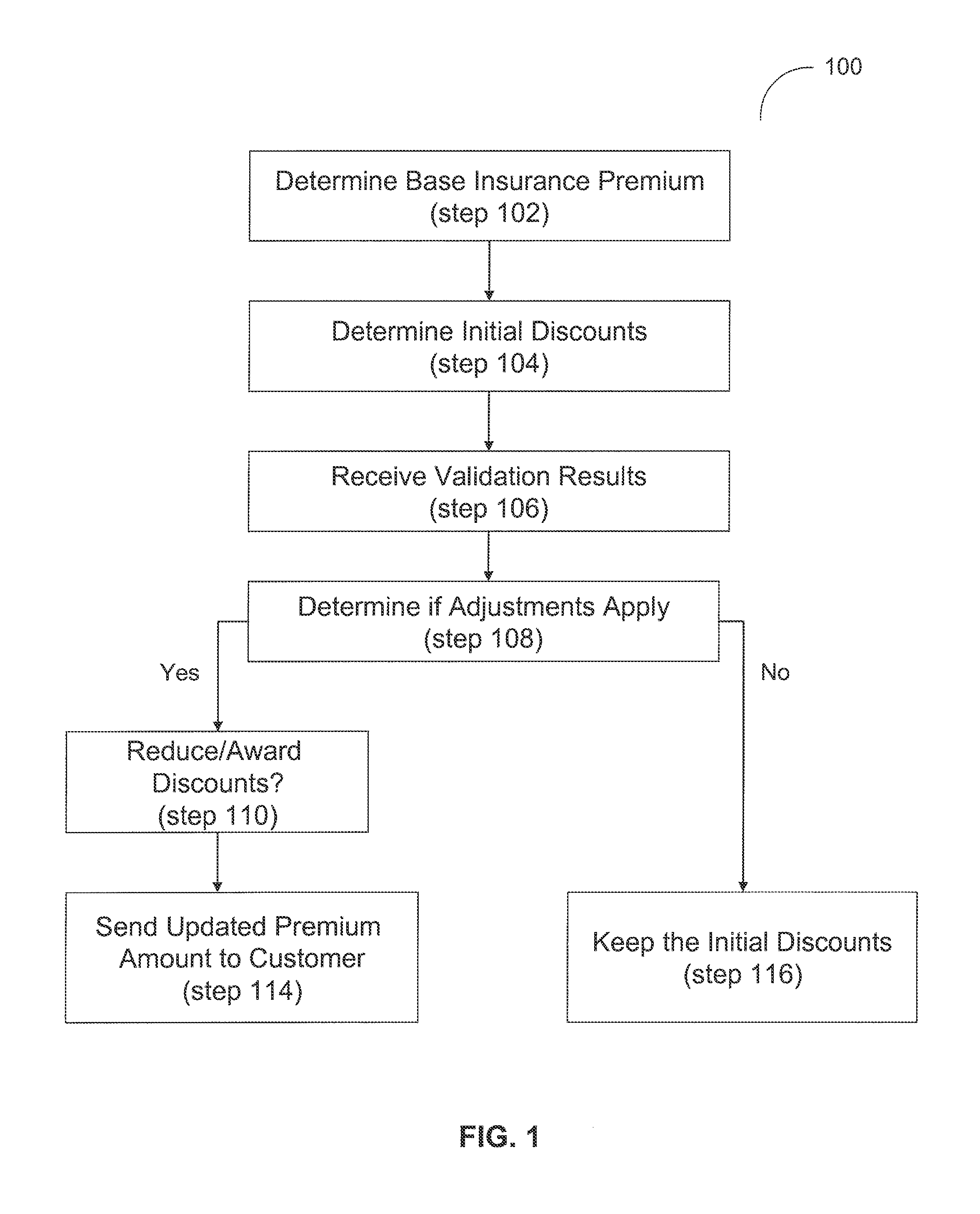
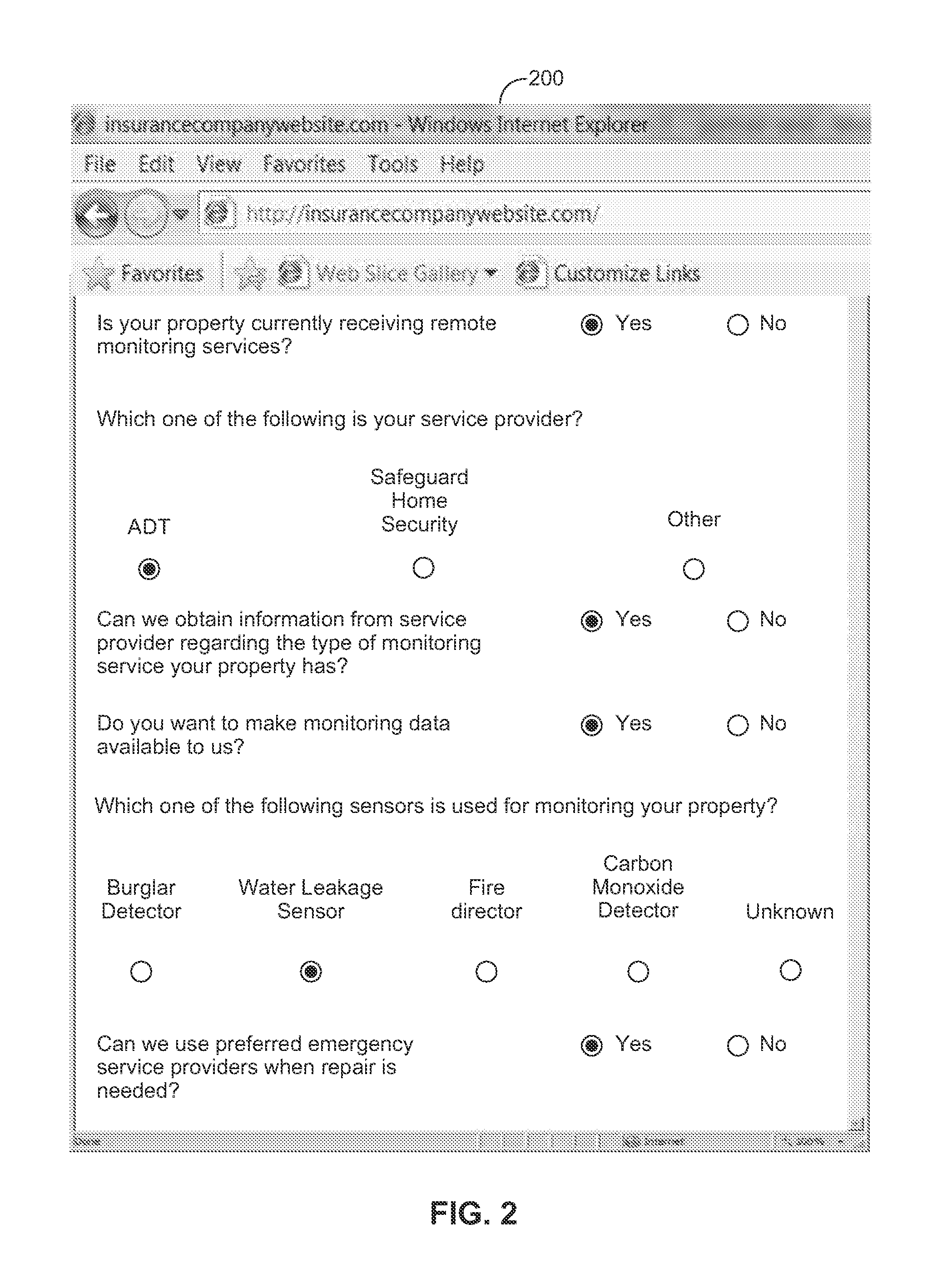
System and method for an automated validation system
An automated validation system validates whether a property of a policyholder receiving at least one insurance benefit is currently receiving remote monitoring services, as represented by the policyholder. The system includes an application server, a trusted third party server, and a business logic computer. The application server requests the trusted third party server to validate whether the property of the policyholder is presently receiving remote monitoring services from a service provider. A business logic computer can adjust the policyholder's insurance policy based on the received validation results.
Owner:HARTFORD FIRE INSURANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com