Patents
Literature
50results about How to "Increased latency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
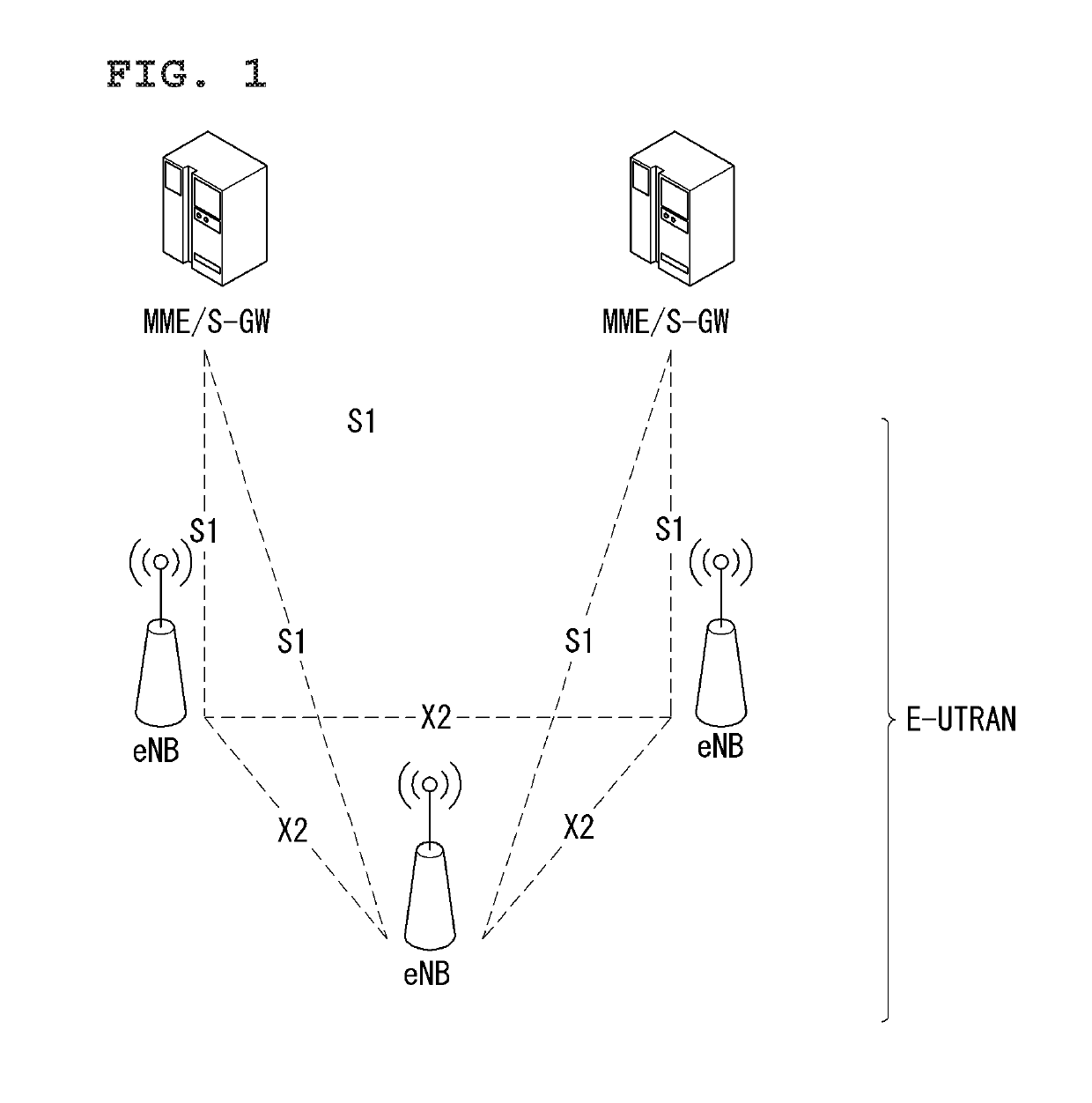
Techniques for beam shaping at a millimeter wave base station and a wireless device and fast antenna subarray selection at a wireless device
ActiveUS20160198474A1Improve latencyQuick selectionSpatial transmit diversityWireless communicationCommunications systemLink margin
Methods, systems, and devices are described for wireless communication at a user equipment (UE). A wireless communications system may improve UE discovery latency by dynamically selecting and switching beam forming codebooks at the millimeter wave base station and the wireless device. Selecting an optimal beam forming codebook may allow the wireless communication system to improve link margins between the base station without compromising resources. In some examples, a wireless device may determine whether the received signals from the millimeter wave base station satisfy established signal to noise (SNR) thresholds, and select an optimal beam codebook to establish communication. Additionally or alternately, the wireless device may further signal the selected beam codebook to the millimeter wave base station and direct the millimeter wave base station to adjust its codebook based on the selection.
Owner:QUALCOMM INC
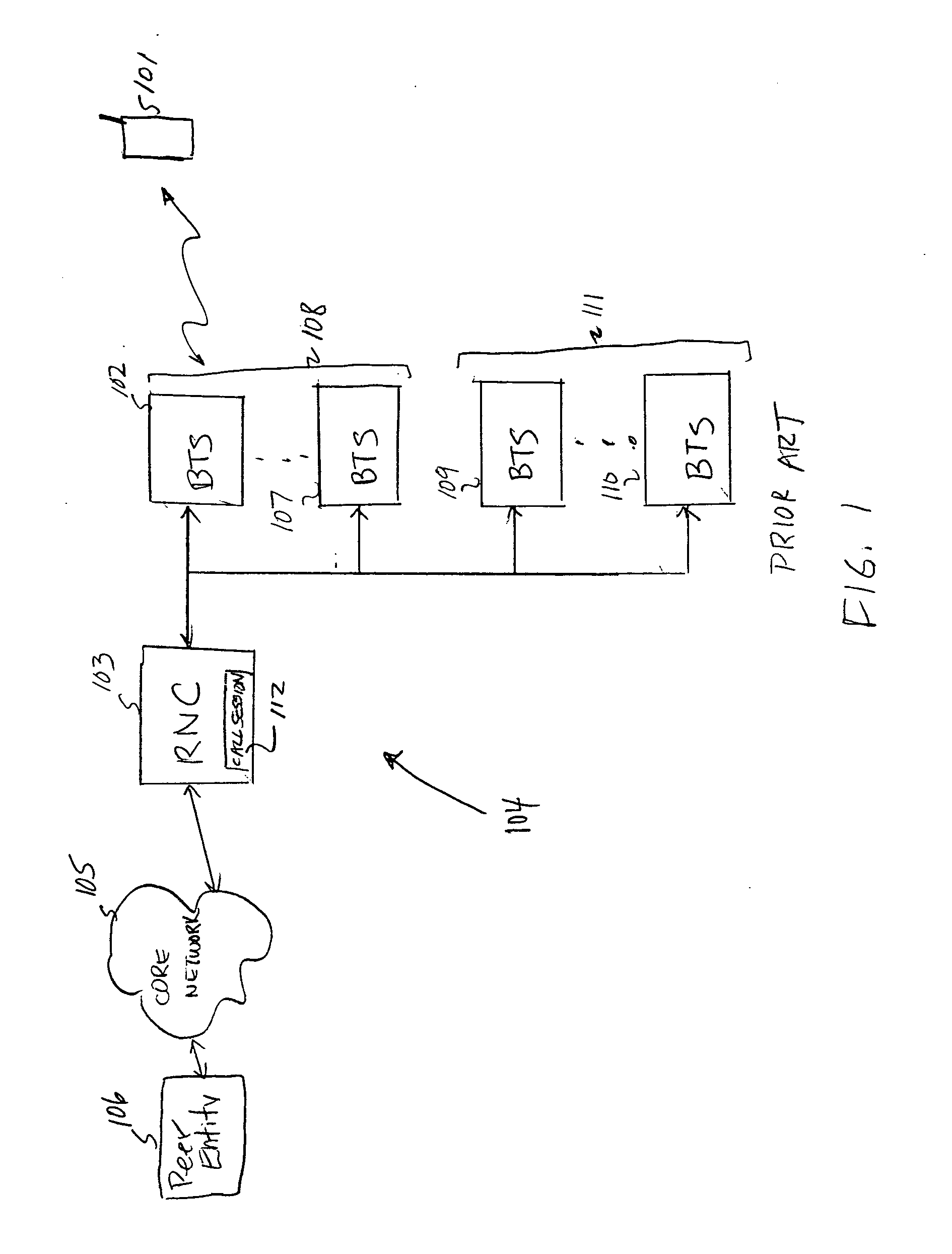
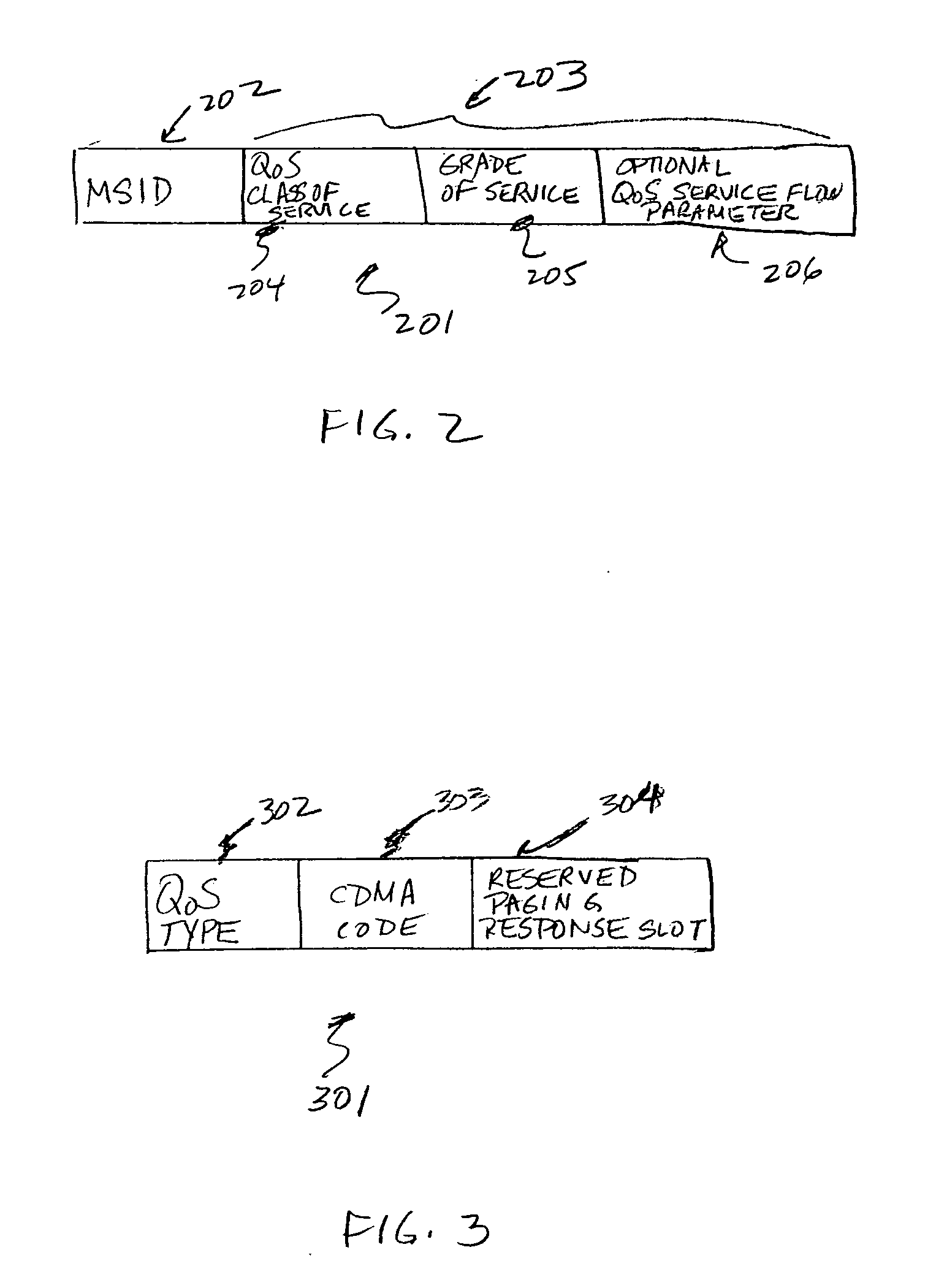
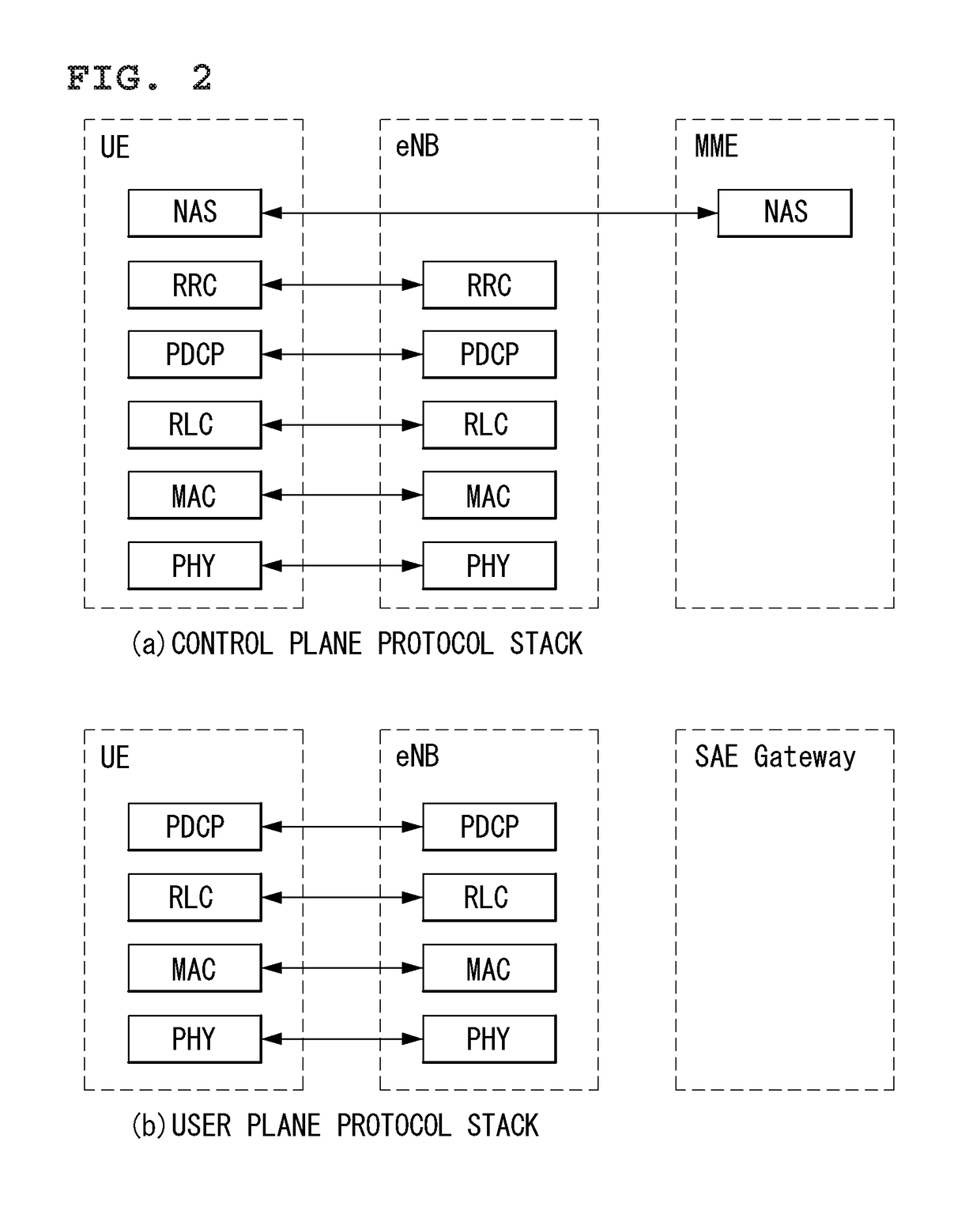
QoS-aware paging in a wireless communication system
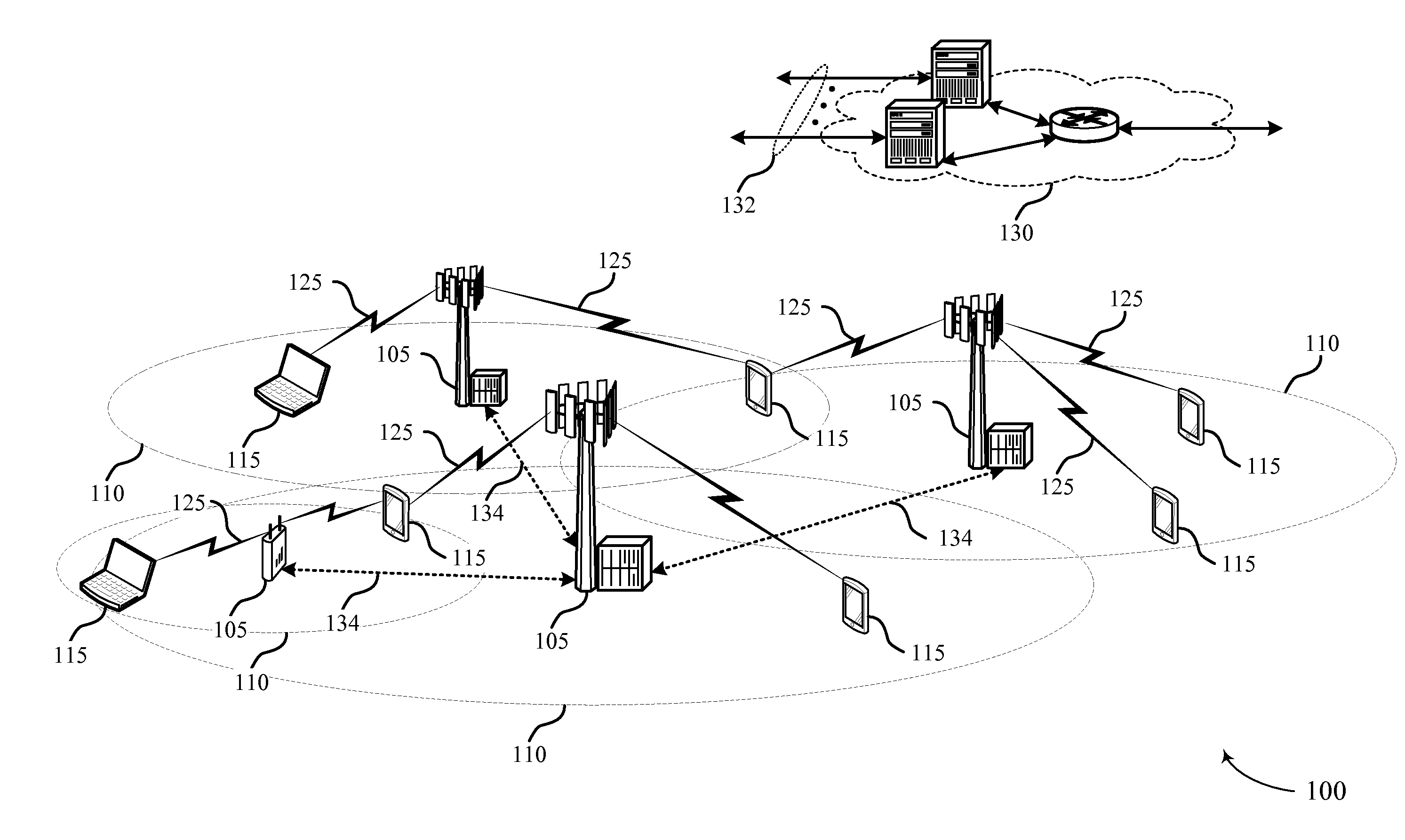
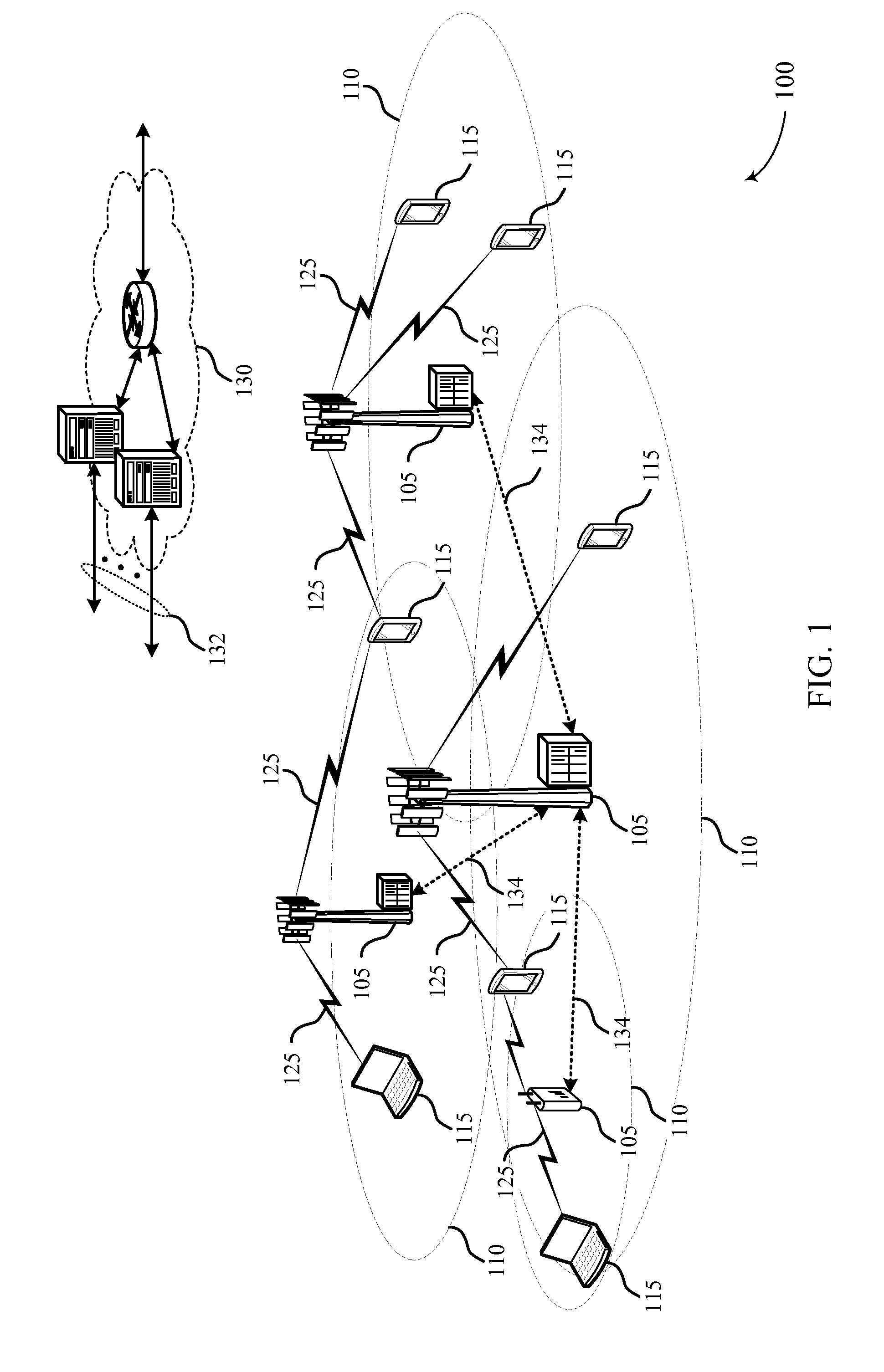
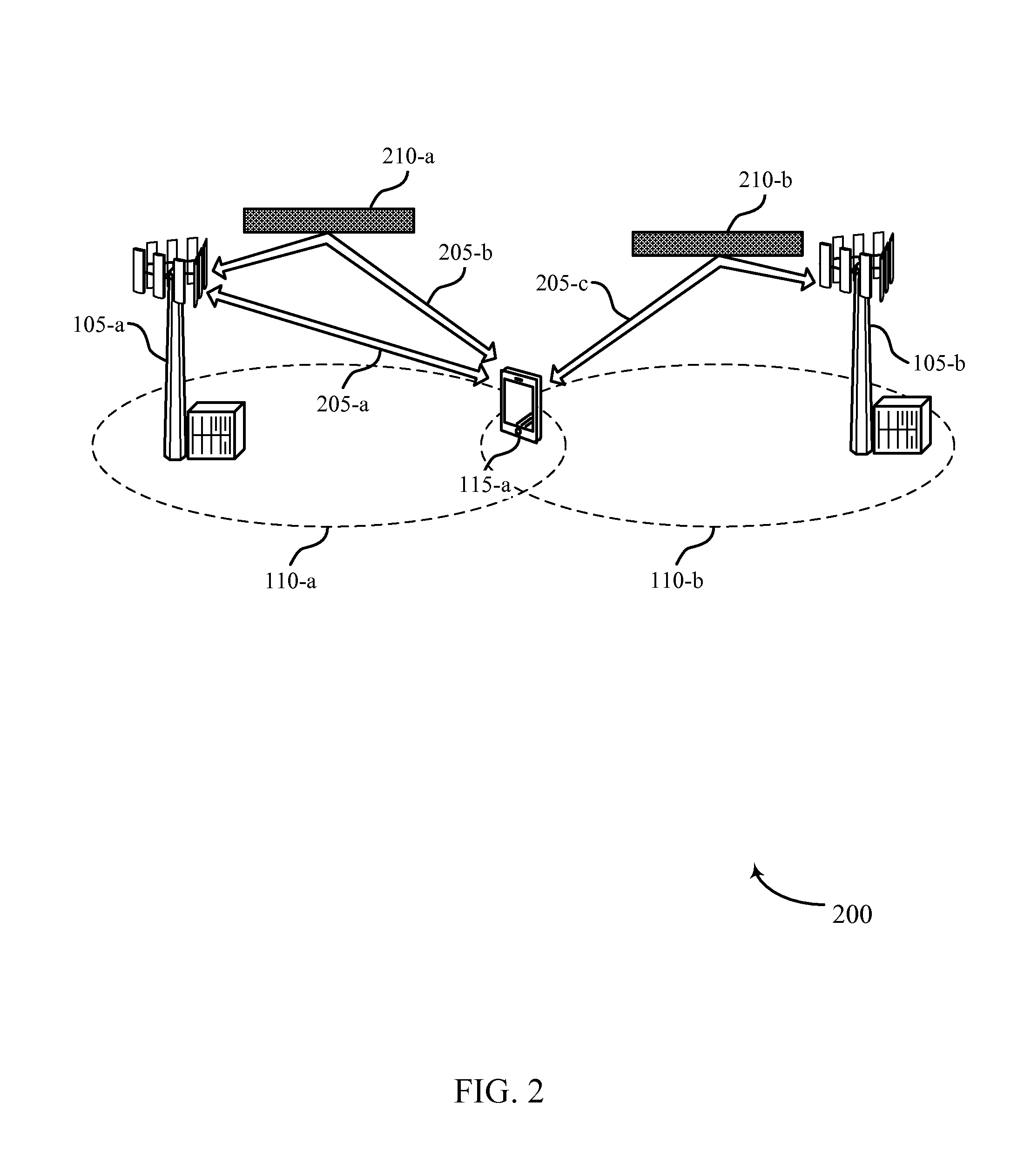
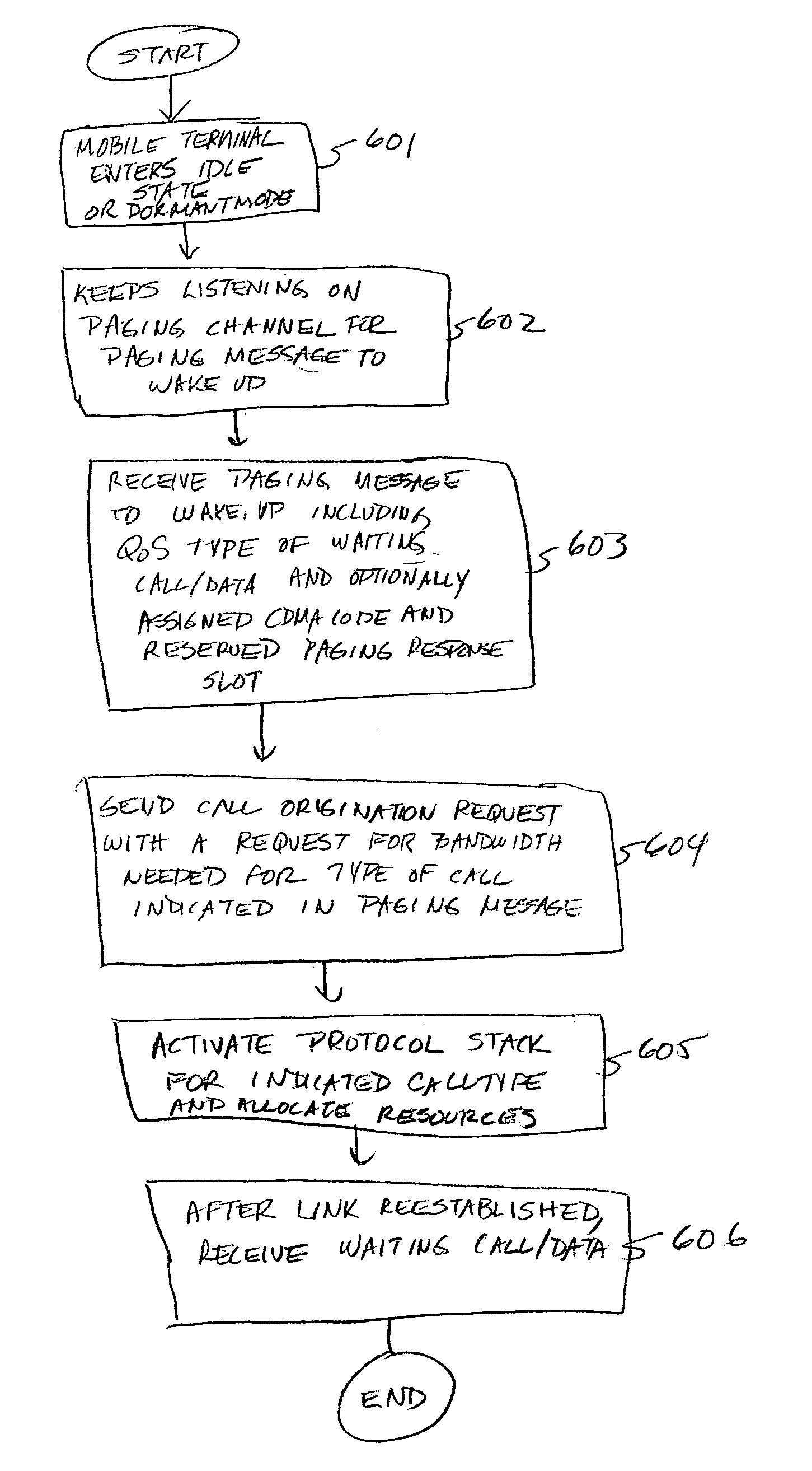
ActiveUS20070171850A1Increased latencyShorten the timeError preventionFrequency-division multiplex detailsService flowCommunications system
Paging messages are transmitted by a wireless communications network to mobile terminals, which have been in an idle state or dormant mode and which have waiting calls / data from their associated peer entities, in accordance with the qualities of service (QoS) associated with the waiting calls / data, where the QoS associated each waiting call / data includes a type of the call / data. To make paging of mobile terminal QoS aware, a QoS field is included in the Paging Announce requests sent from an RNC to another RNC, or from an RNC to a BTS. The QoS field includes: a QoS class of service of the waiting call / data indicating the type of the waiting call; a grade of service of the waiting call / data to which the mobile terminal is subscribed; and, optionally, other QoS service flow parameters whose presence depends on the type of wireless technology being used in the network.
Owner:RPX CORP
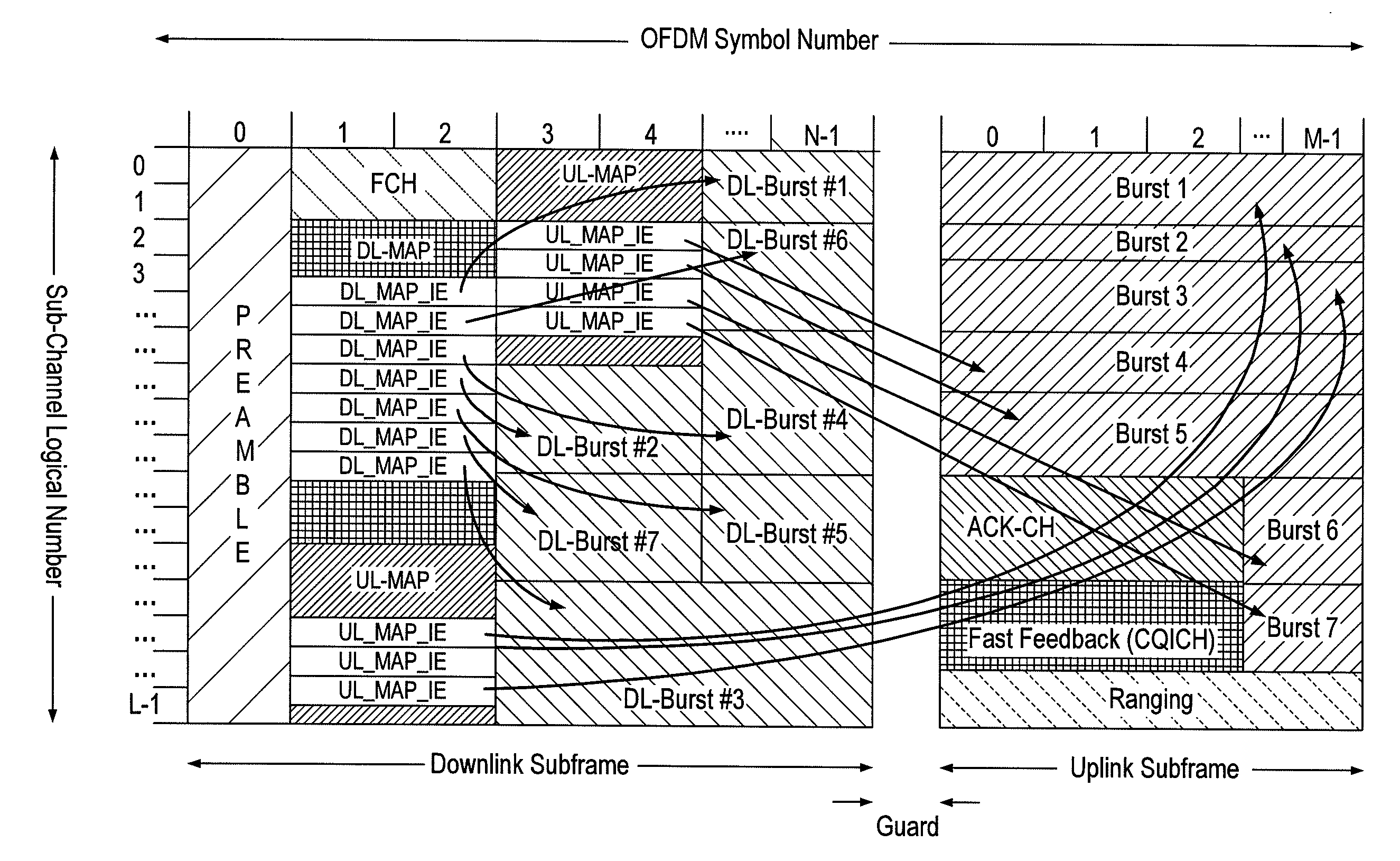
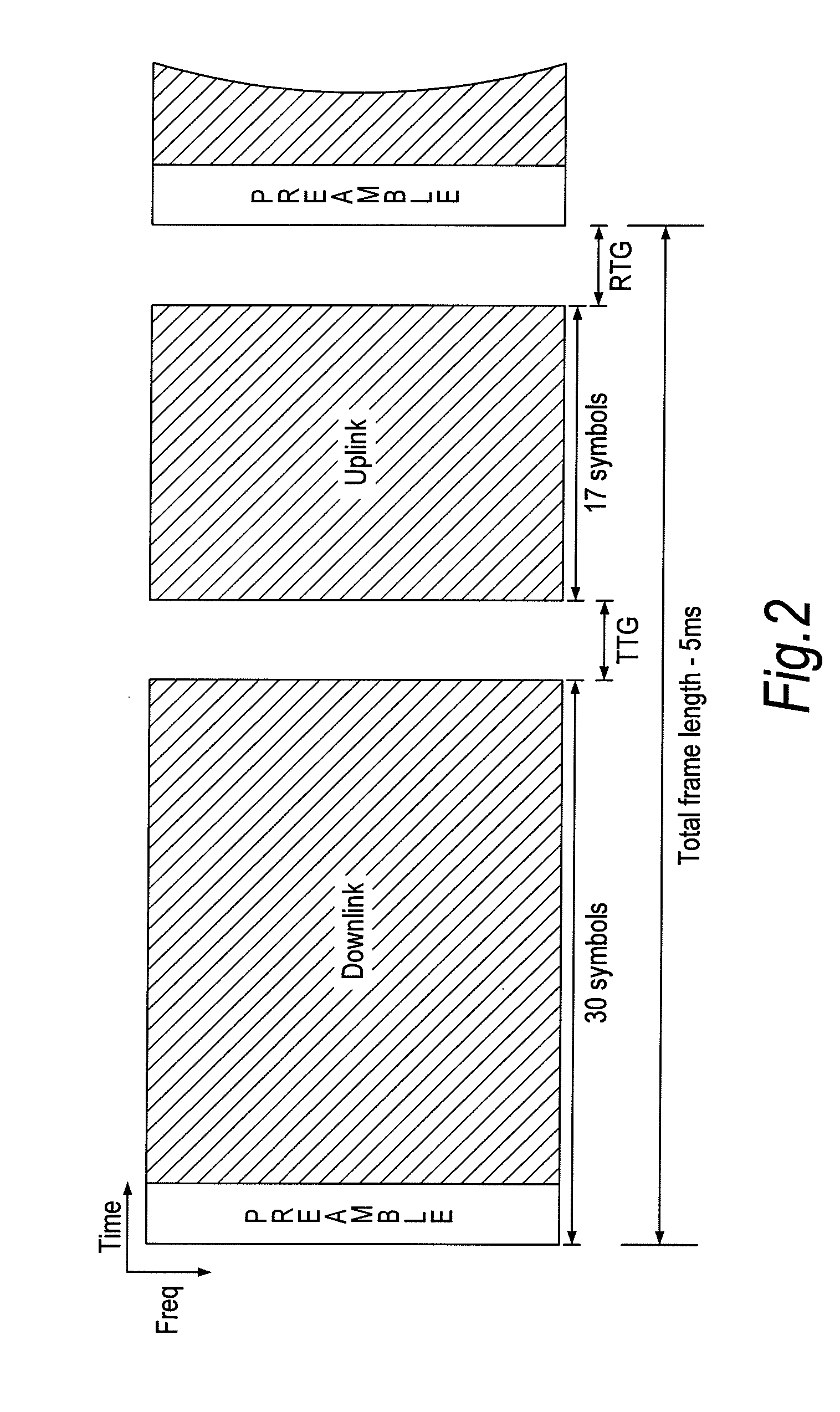
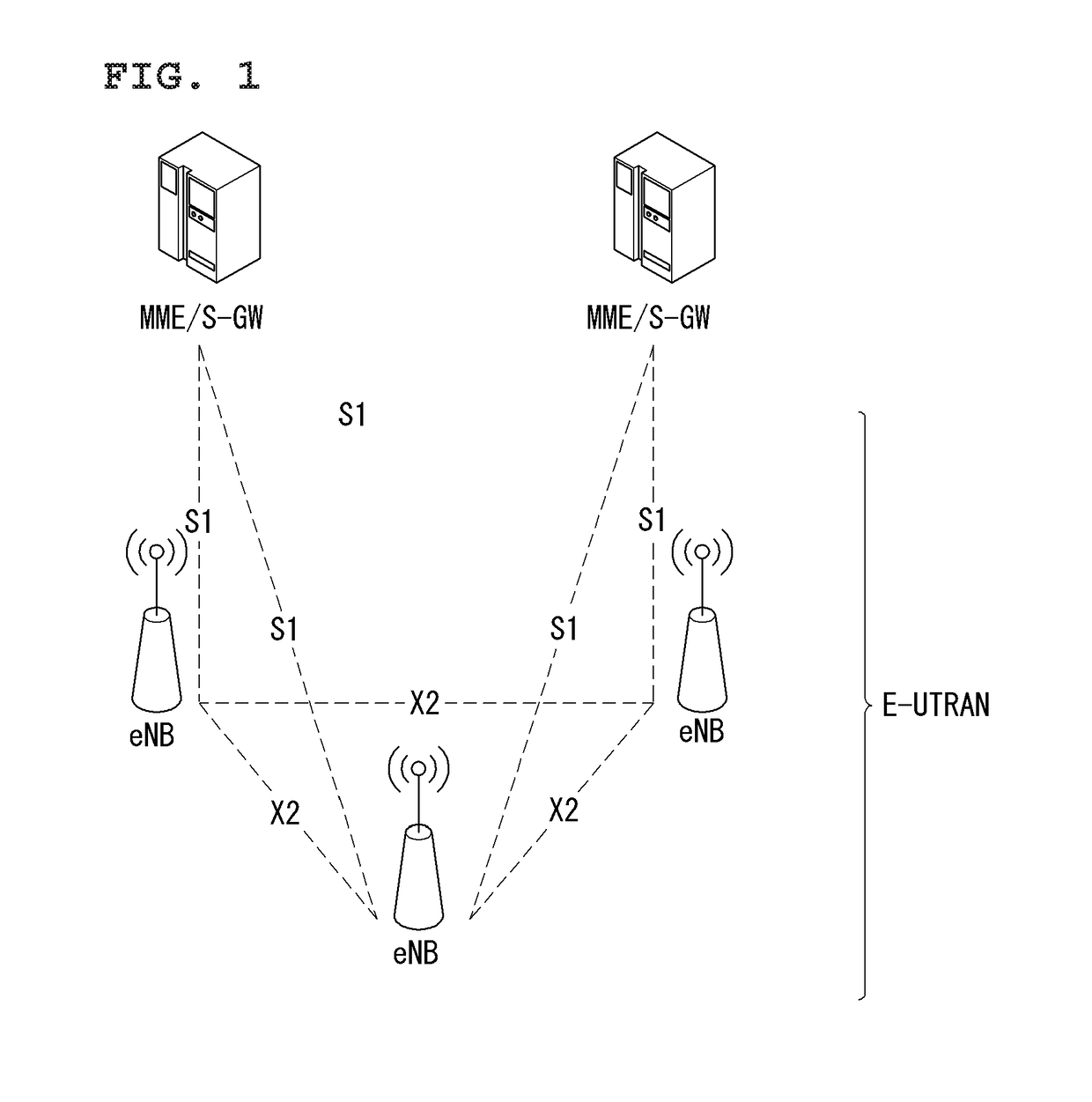
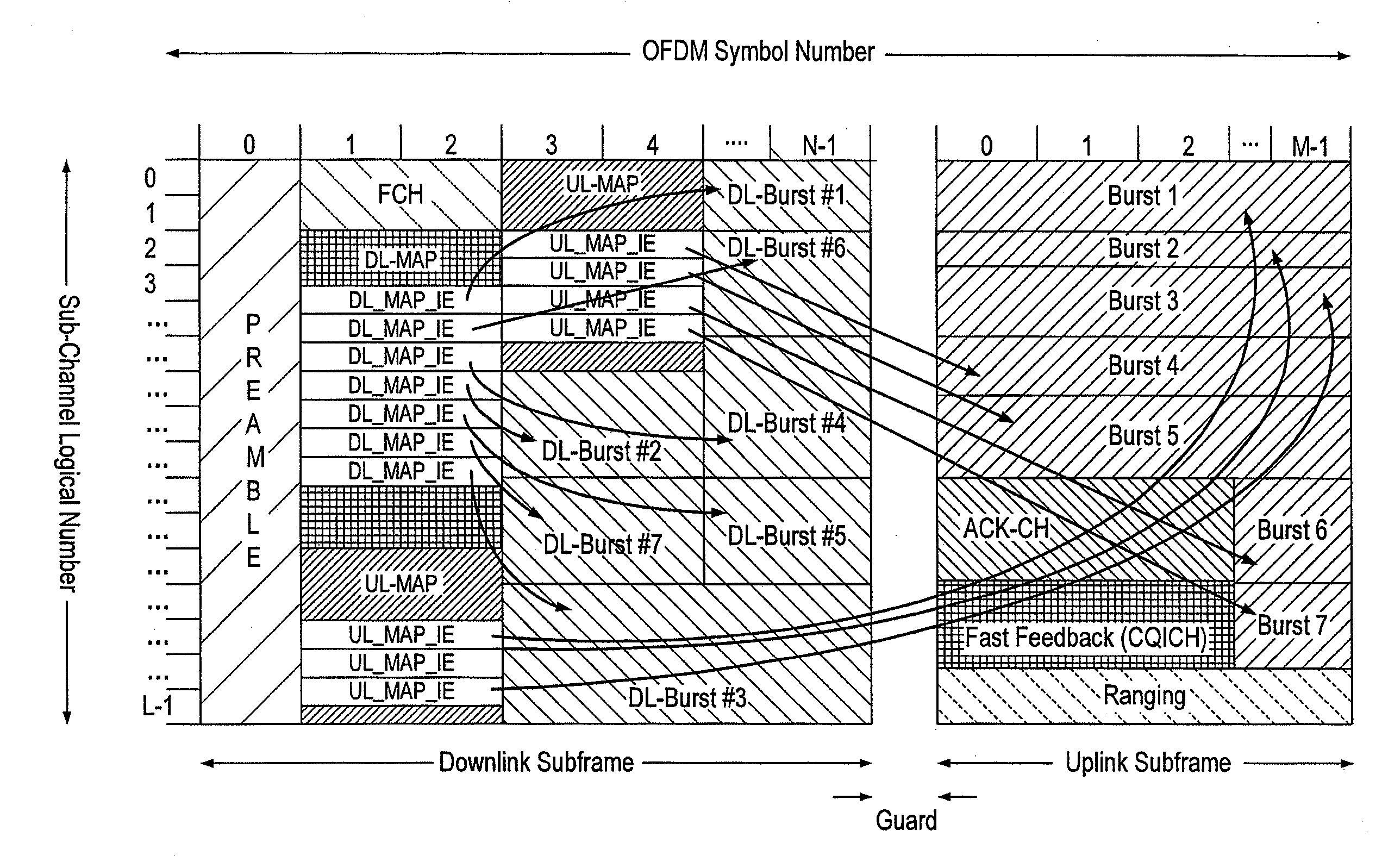
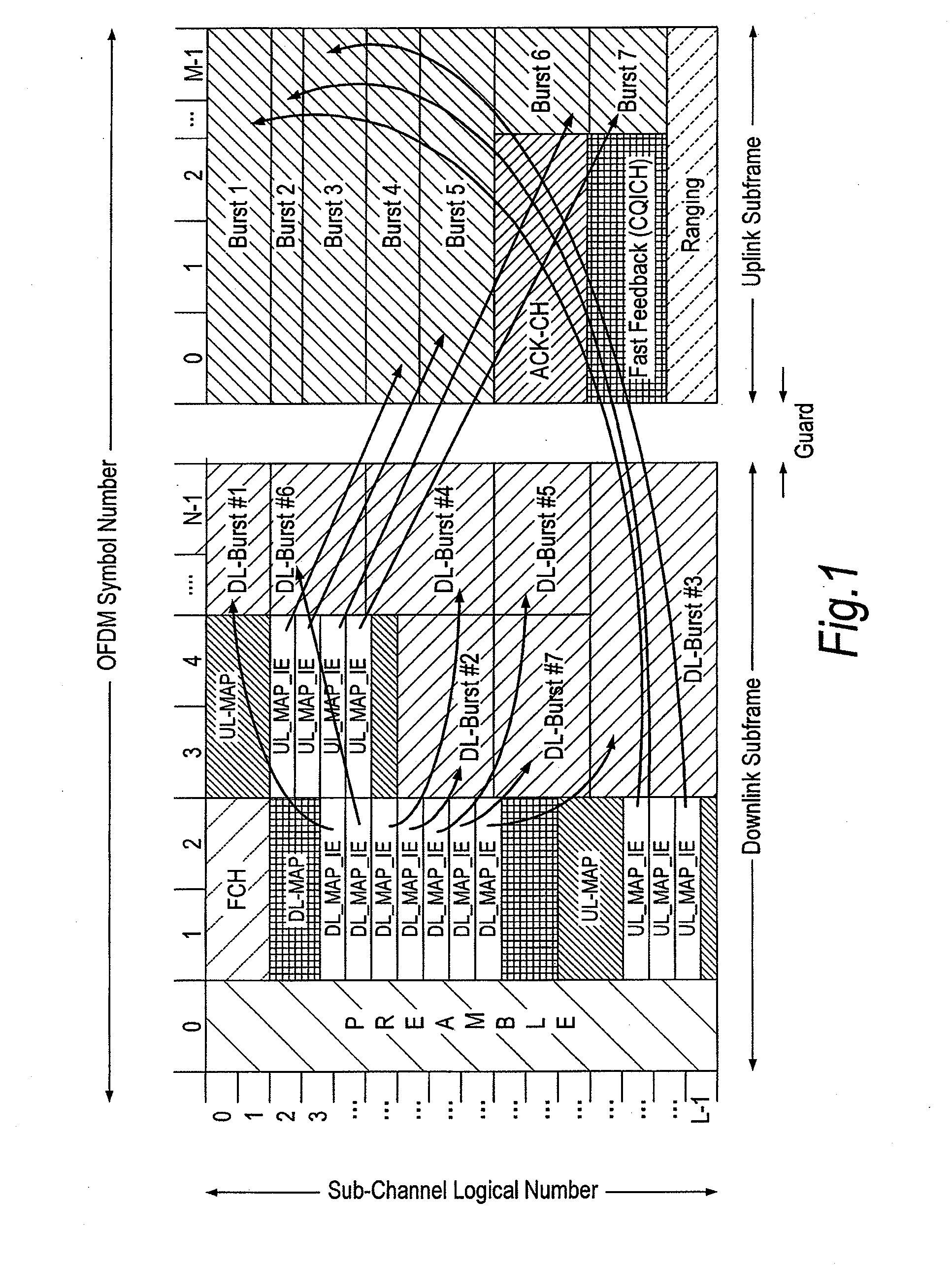
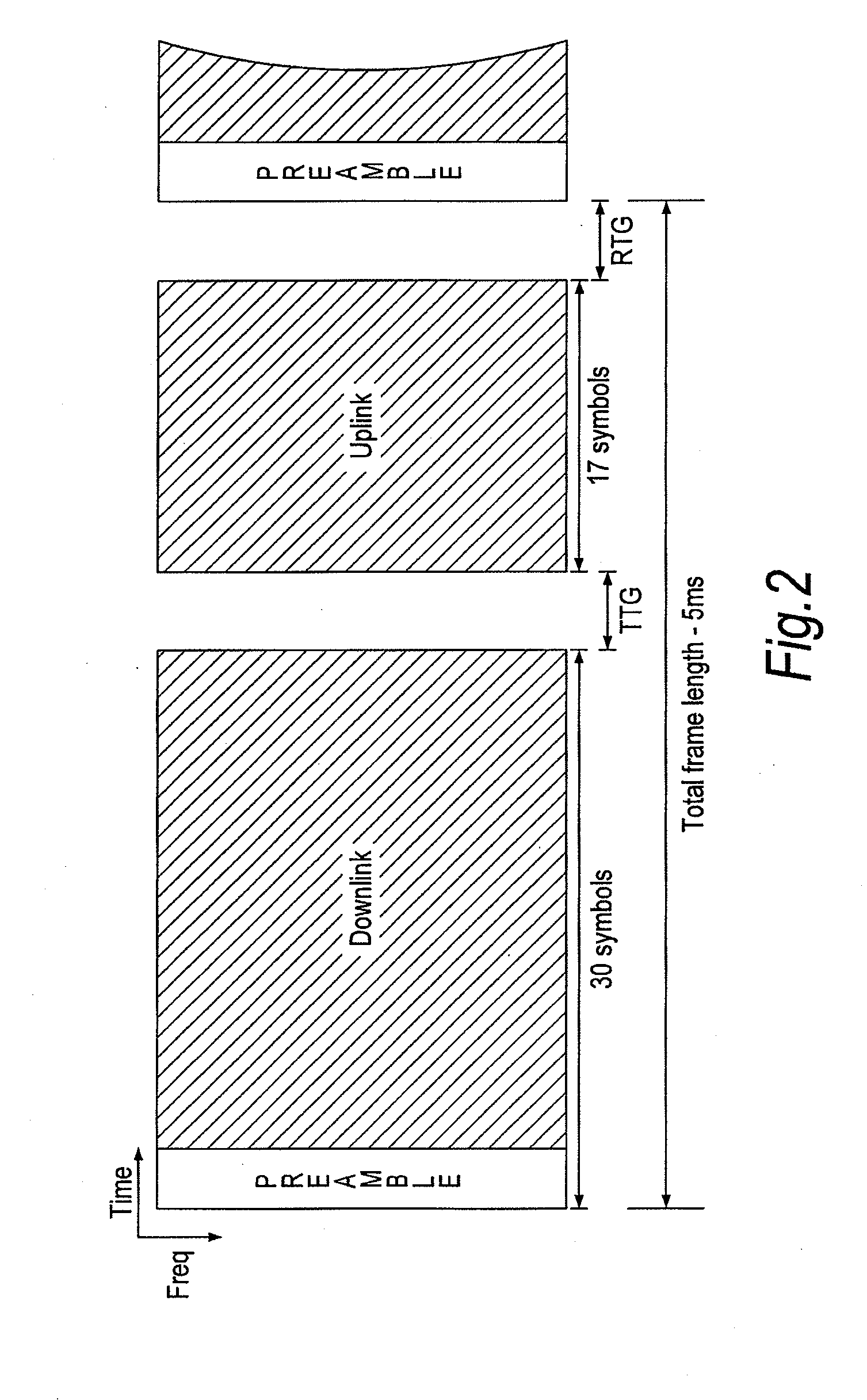
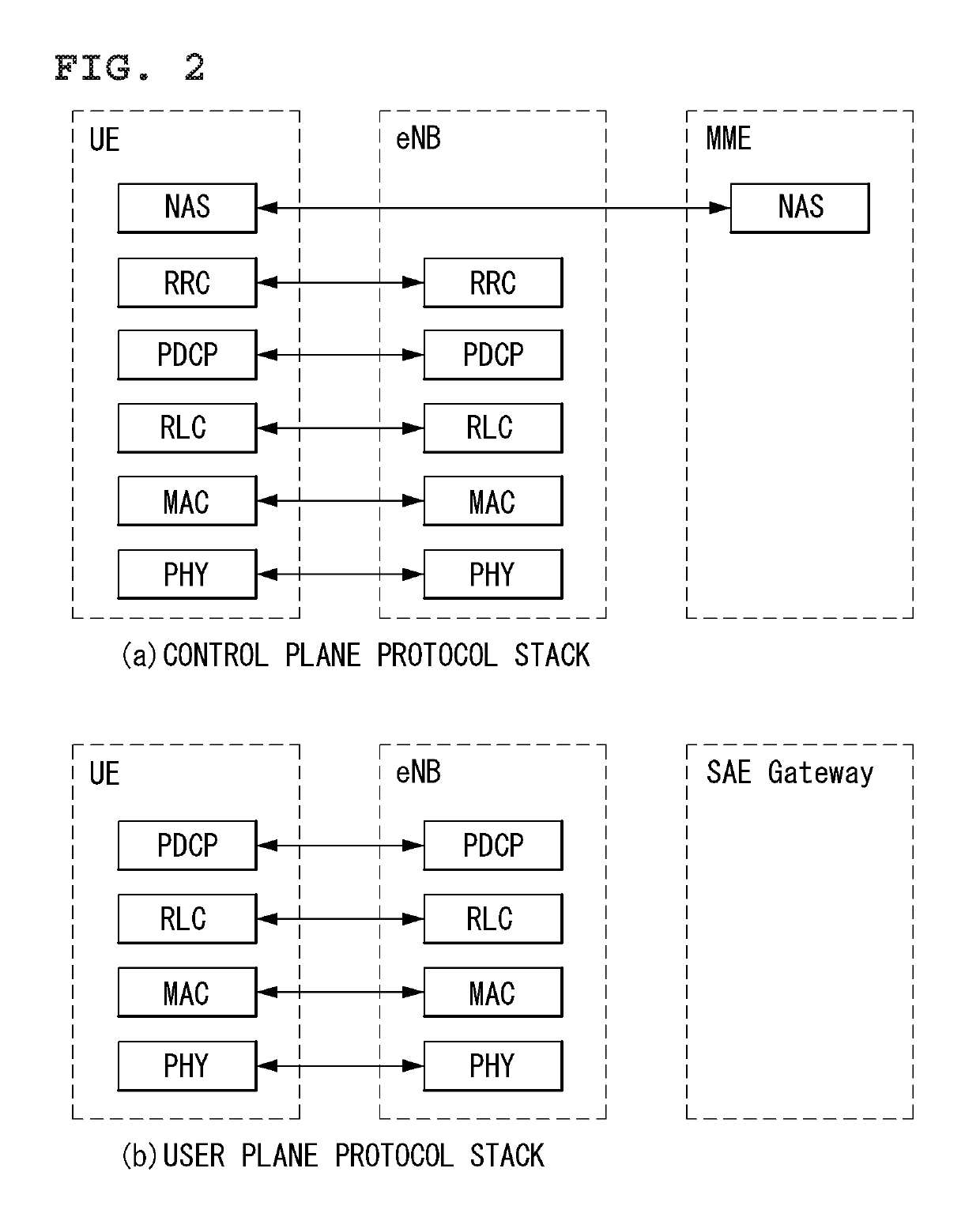
Frame structure for a wireless communication system
ActiveUS20090257366A1Improve latencyFully compatibleTime-division multiplexSecret communicationCommunications systemFeature set
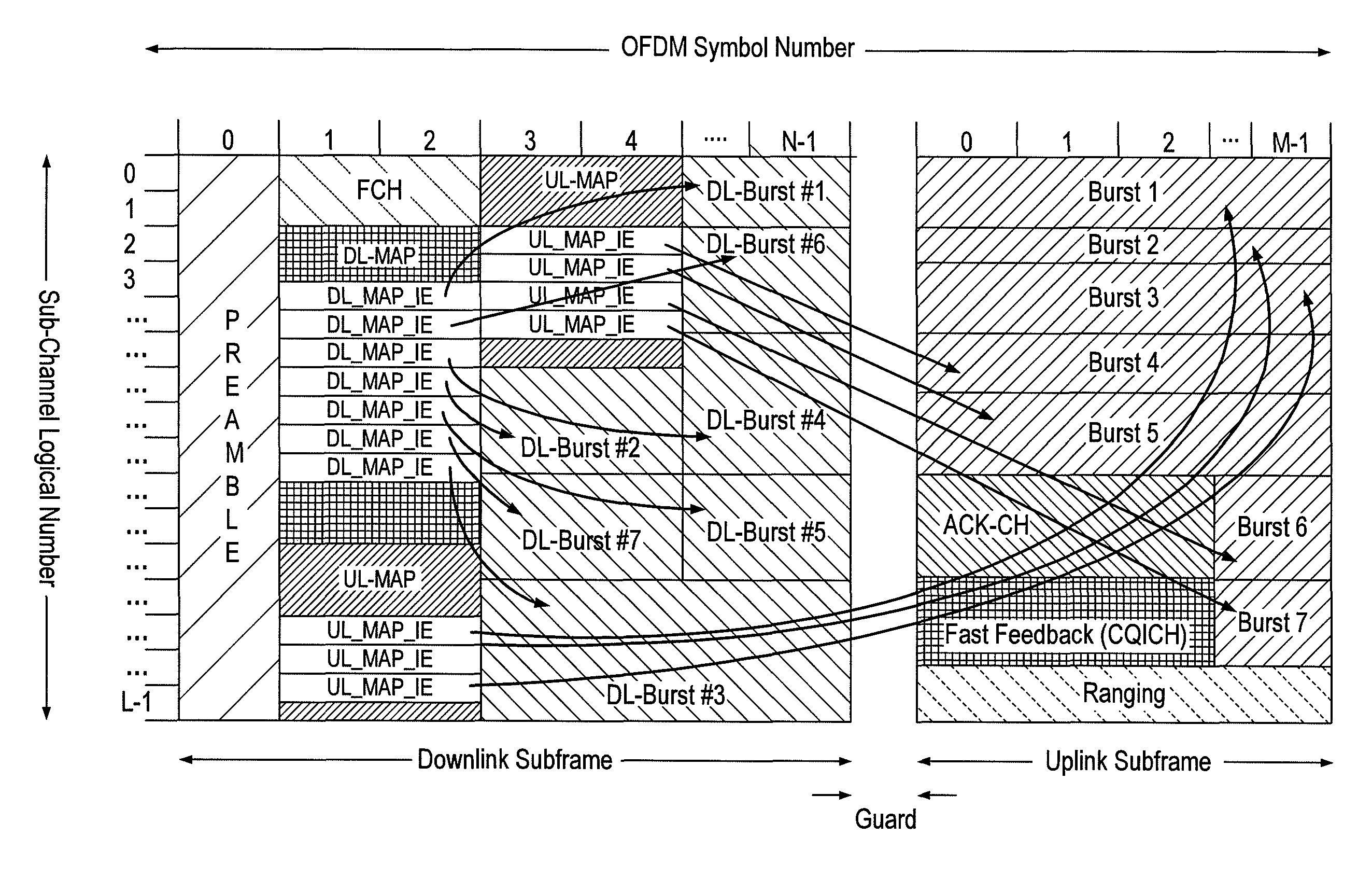
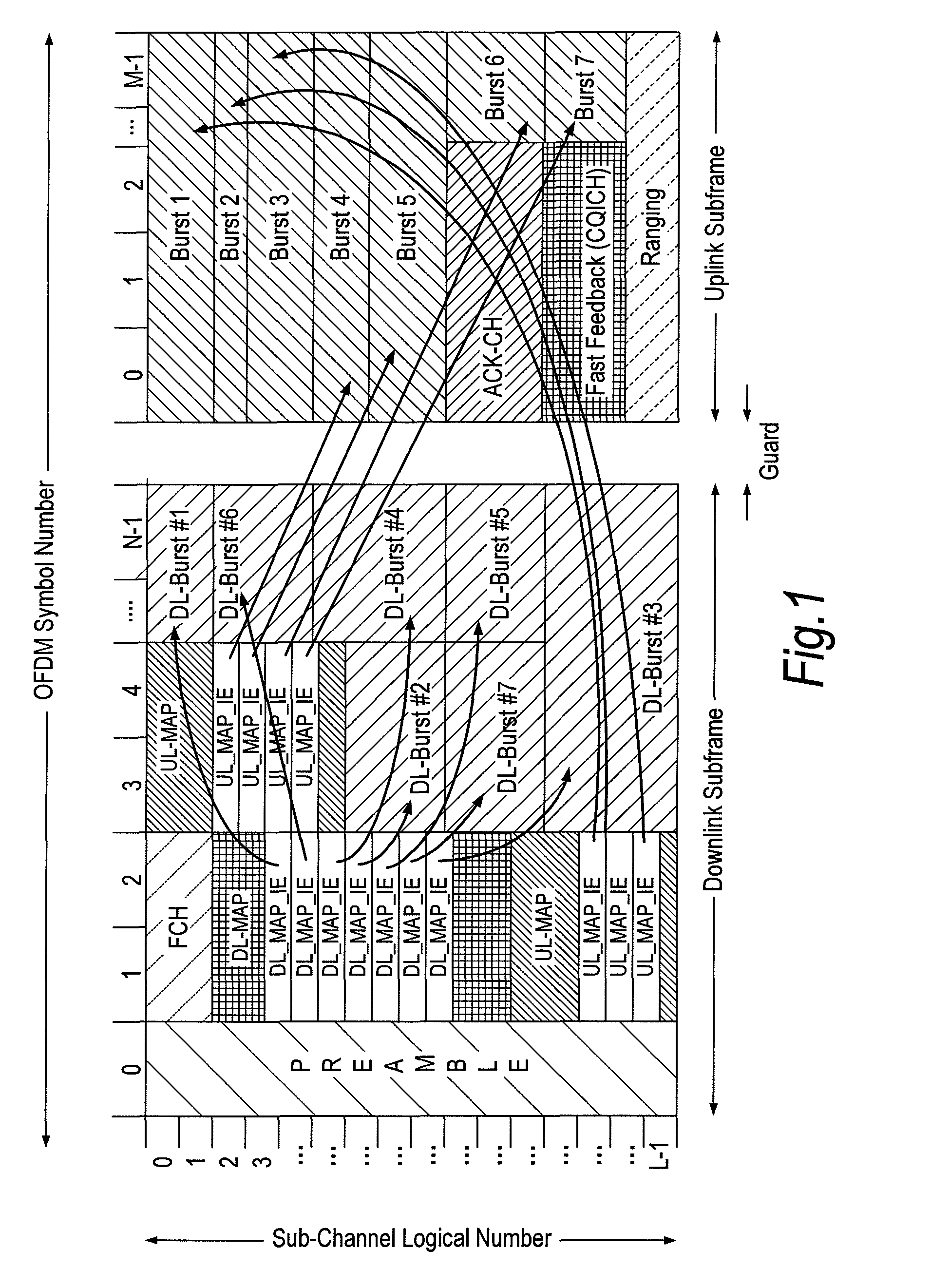
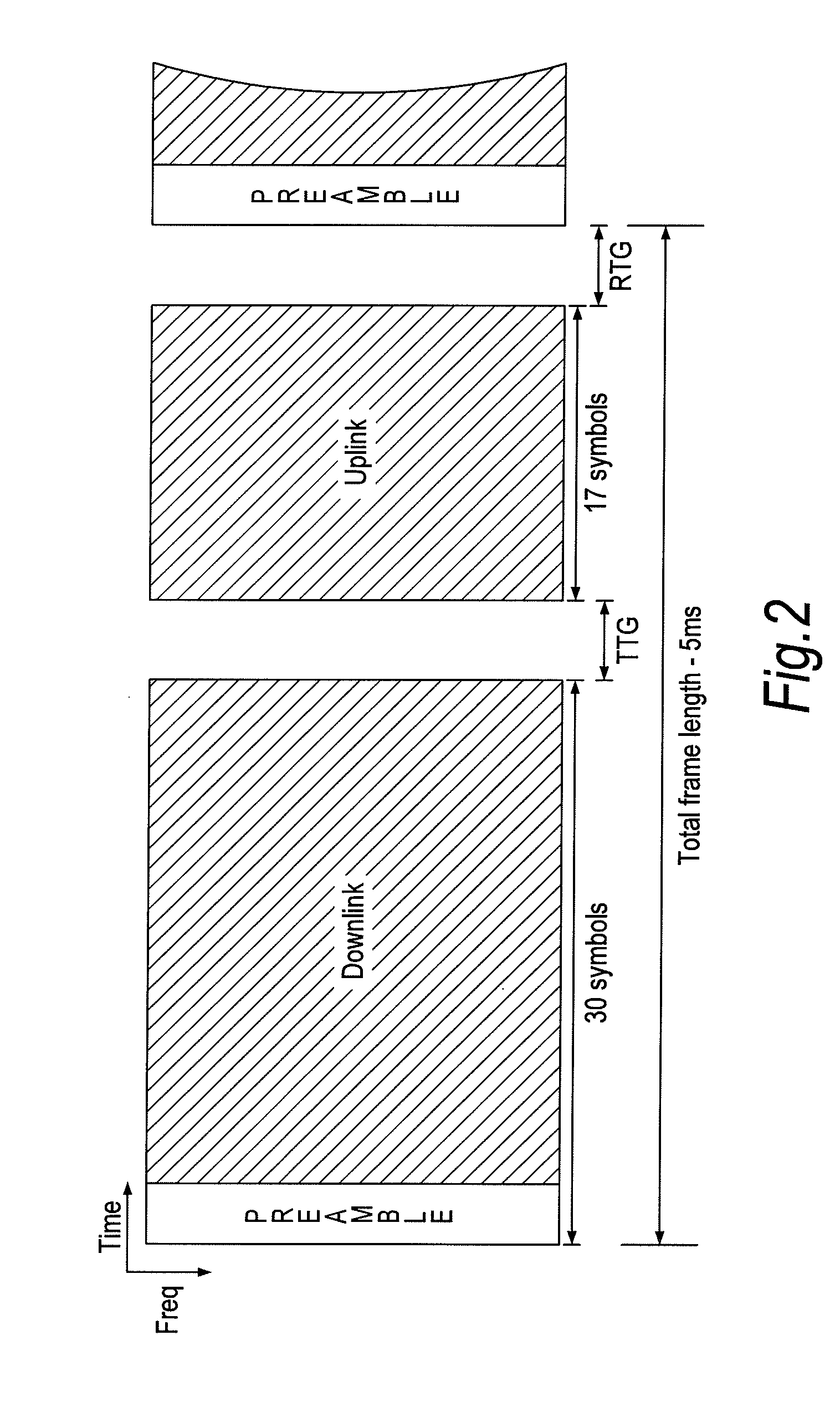
A frame format used in a wireless communication system, more particularly an OFDMA TDD wireless communication system, of the kind comprising a base station and a plurality of fixed or mobile subscriber stations, the base station maintaining connections with each of the subscriber stations by performing wireless communication in units of frames having said frame format, and within each frame, allocating resources for data transmission and signalling.Each frame has a plurality of downlink subframes and a plurality of uplink subframes including, in time order, a first downlink subframe, a first uplink subframe, a final downlink subframe and a final uplink subframe. One or more further downlink subframe / uplink subframe pairs may be interposed between the first and final subframes as desired, and the configuration can be changed dynamically.The frame structure is capable of adapting to a system that is evolving from supporting predominantly legacy terminals to one which will be supporting an increasing number of enhanced terminals. The coexistence of both legacy and enhanced terminals within the proposed frame structure will have minimal impact of the performance of legacy subscriber stations. Depending on the required number of either legacy or enhanced terminals that need to be supported, the base station has the ability to define a frame configuration where the number of subframes per frame is configured based on the feature set of the operational subscriber stations and the mobility requirements of enhanced subscriber stations such that the frame structure at all times retains sufficient features to support the attachment of legacy stations that do not support the enhanced features.
Owner:FUJITSU LTD
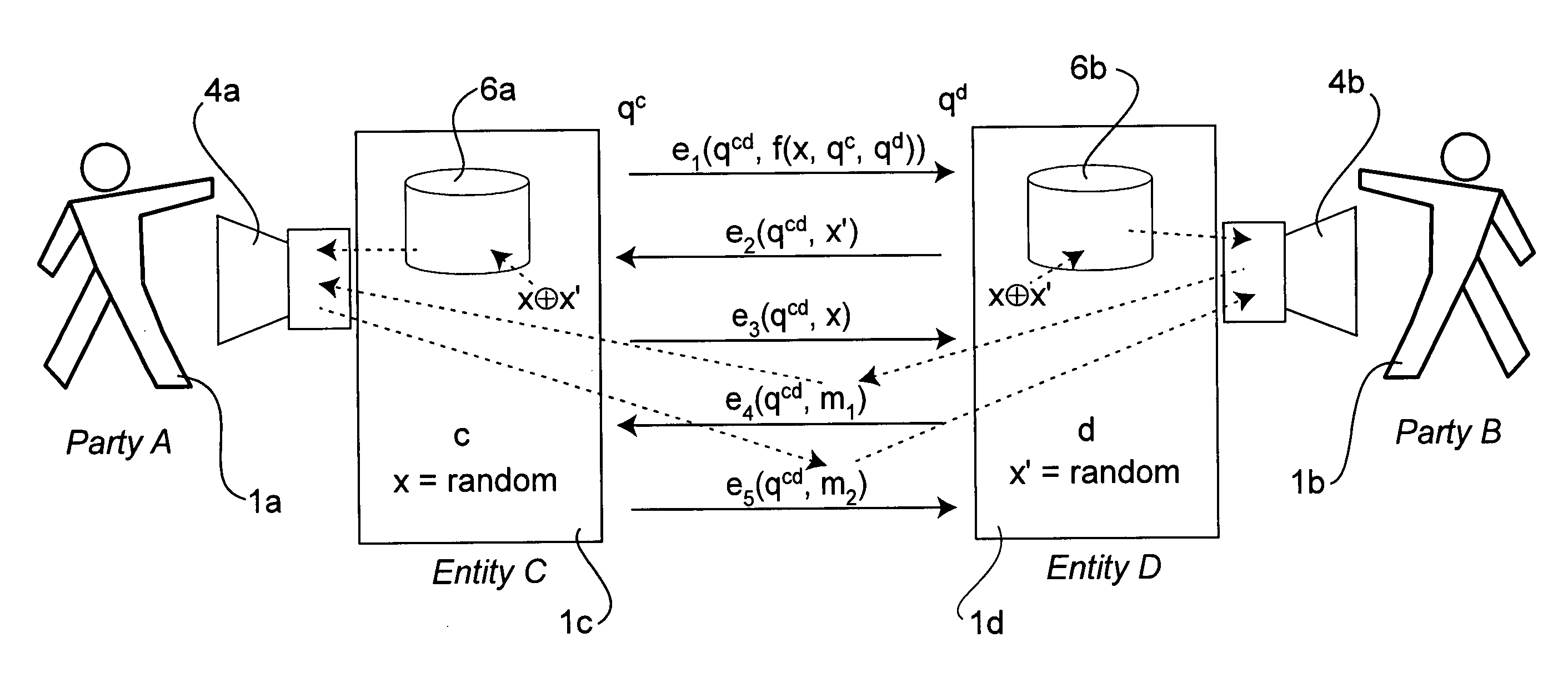
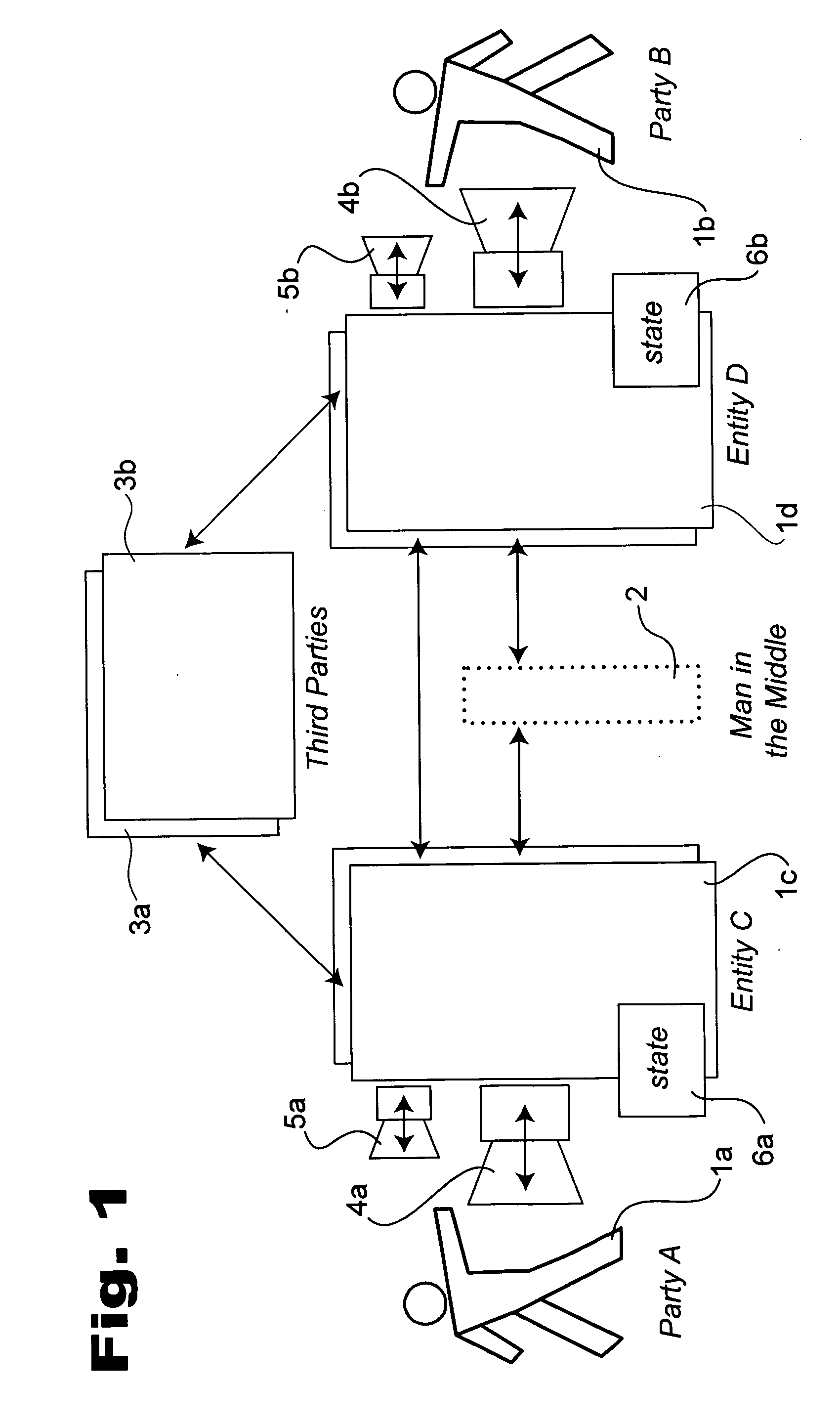
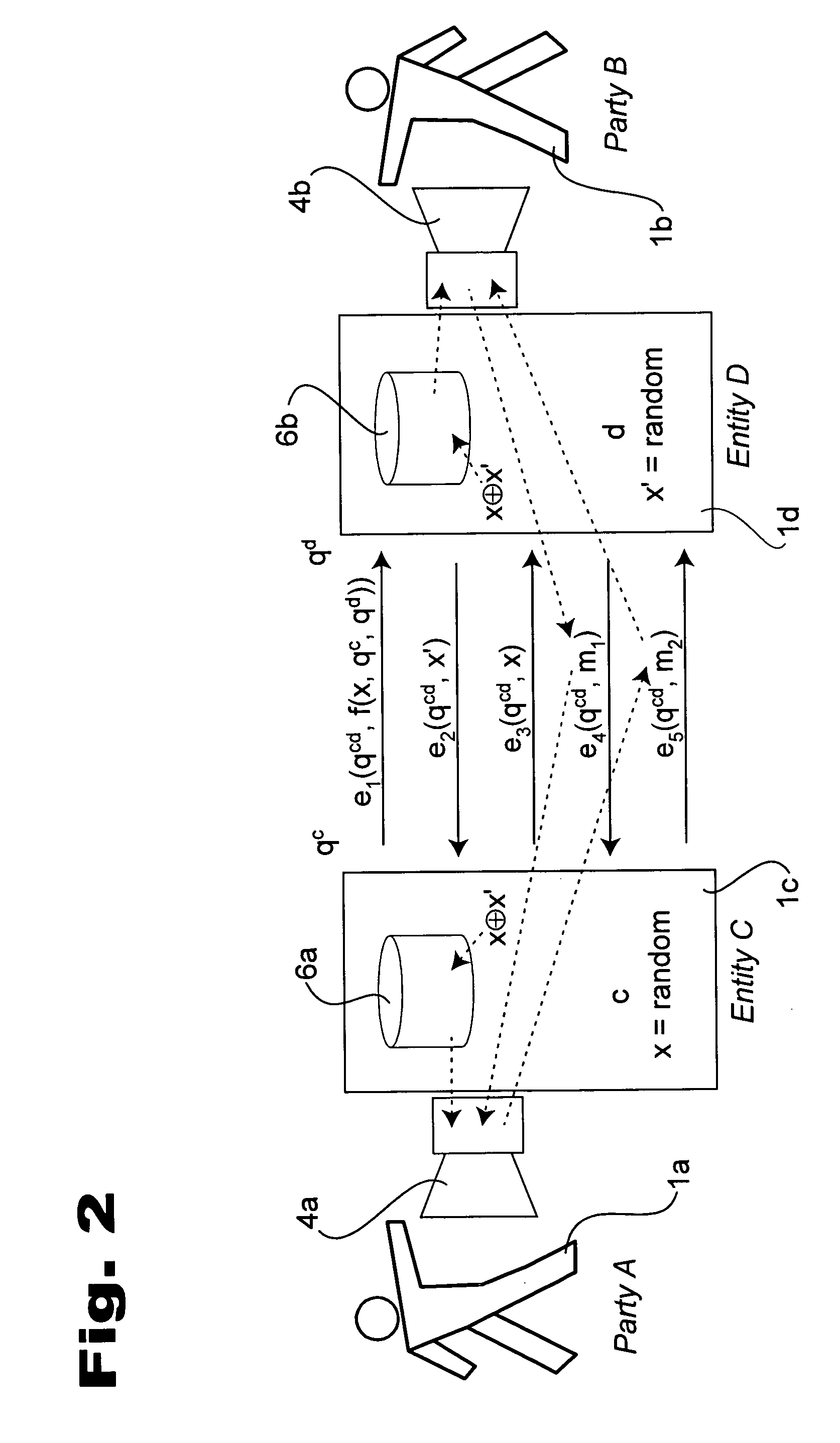
Distributed communication security systems
InactiveUS20060218636A1Increased latencyImprove completenessMemory loss protectionError detection/correctionRandom oracleCommunications security
Solutions to the so-called “man in the middle” problem are disclosed. One example uses a mutually-random value that is the same for each of two communicants absent a man in the middle, but differs between the communicants in case a man-in-the-middle is present. Communicants become aware if their random values differ, for example, through stock content inserted into the communication stream, interactive games, or derived limitations on the channel. In other examples, opening of encrypted parts of the communication is delayed until certain other communication takes place and / or is imminent. In still further examples, a man in the middle becomes apparent because of increased latency of communication between the participants and the effect is optionally accentuated through mutually-random values that shift latency. Further aspects allow parties to apply authentication related to participants they have communicated with when they were convinced that no man in the middle was present. In some examples such communication between common participants is also applied and / or information about the origin of authentication information is hidden.
Owner:CHAUM DAVID
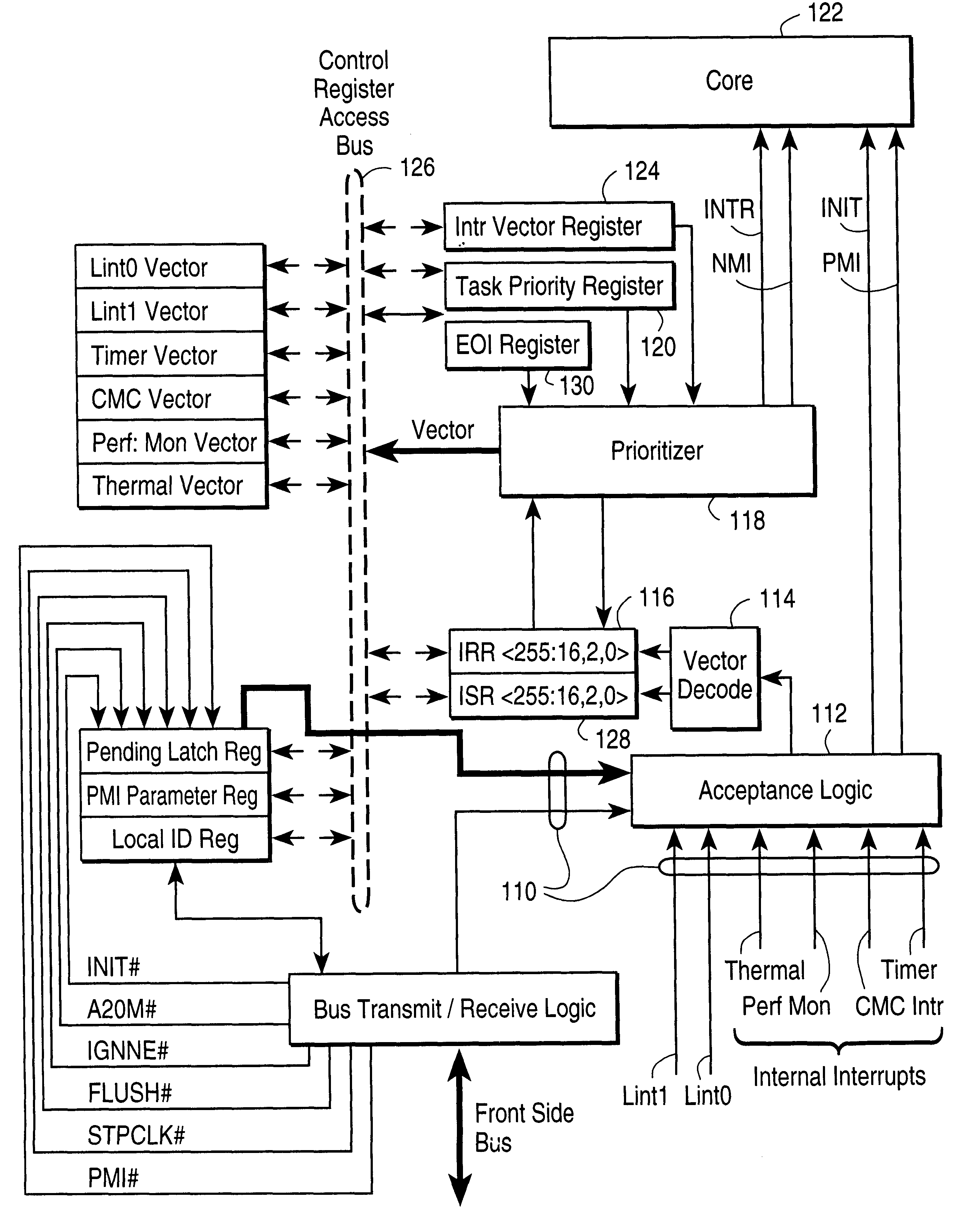
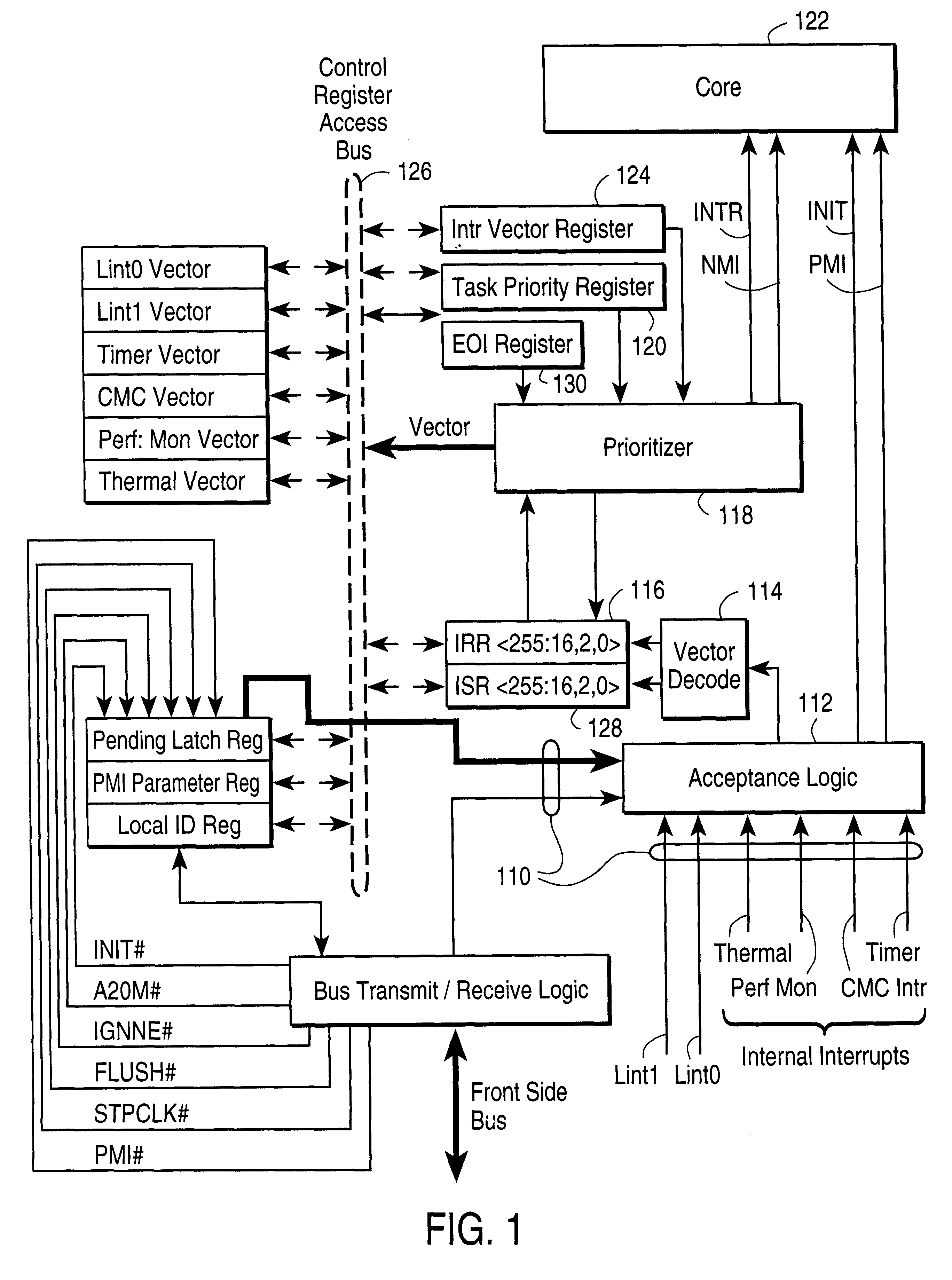
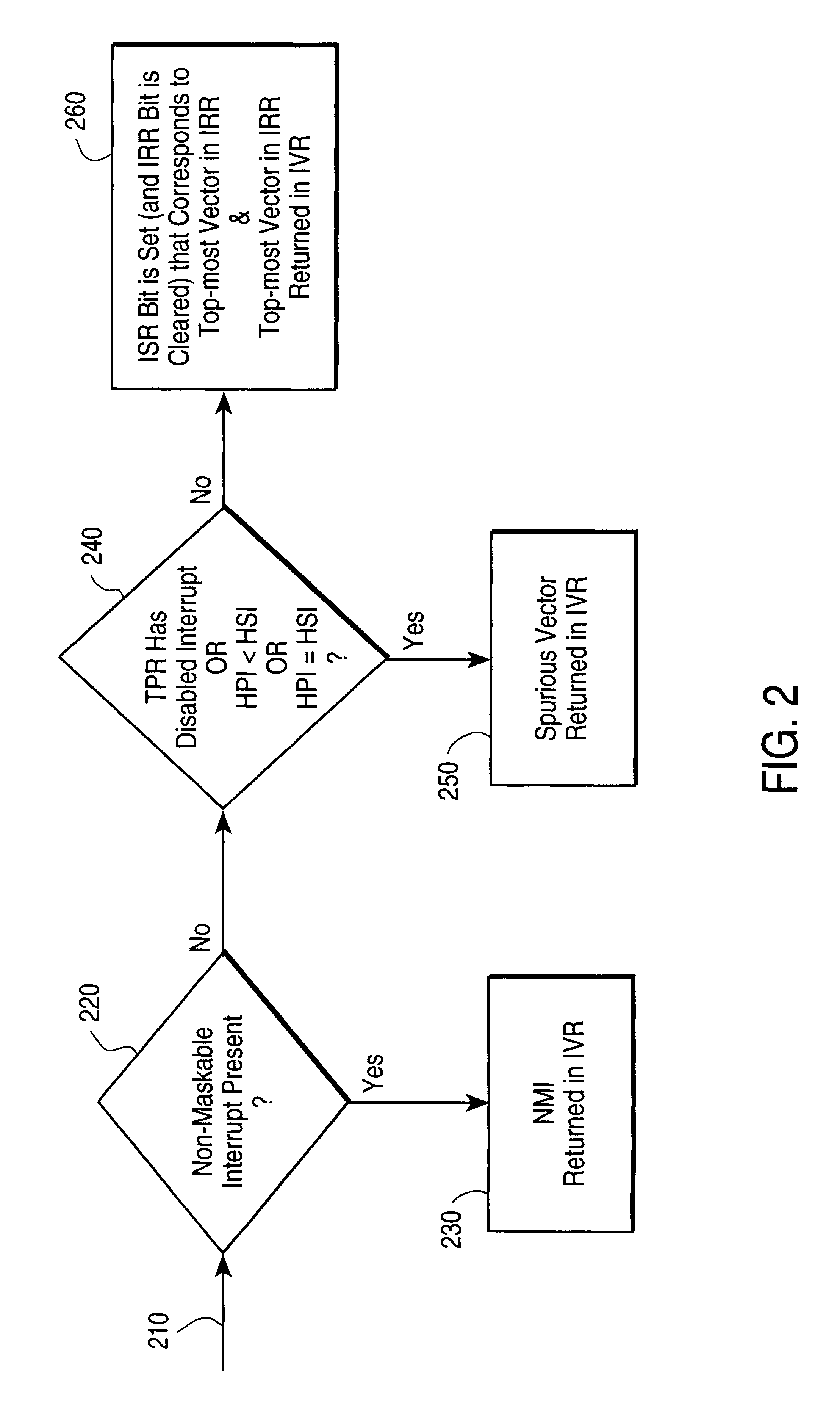
Apparatus and method for initiating hardware priority management by software controlled register access
InactiveUS6298410B1Increased latencyEasy to changeGeneral purpose stored program computerElectric digital data processingProcessor registerControl register
An apparatus and method for controlling interrupts in a computer are disclosed, in which programmable software operates to control when data concerning the interrupt having highest priority is to be provided, and hardware logic operates to control how that data is provided. An interrupt vector register is included in the computer CPU. The interrupt vector register does not act like the typical register. It is not a physical register, and cannot be written to. A read to this register by the programmable software, triggers the hardware logic. Once triggered, this logic performs certain control tasks, the end result of which is returning to the programmable software, a vector corresponding to the interrupt having highest priority. The programmable software can implement various software policies, in addition to the hardware policy implemented by the hardware logic.
Owner:INTEL CORP
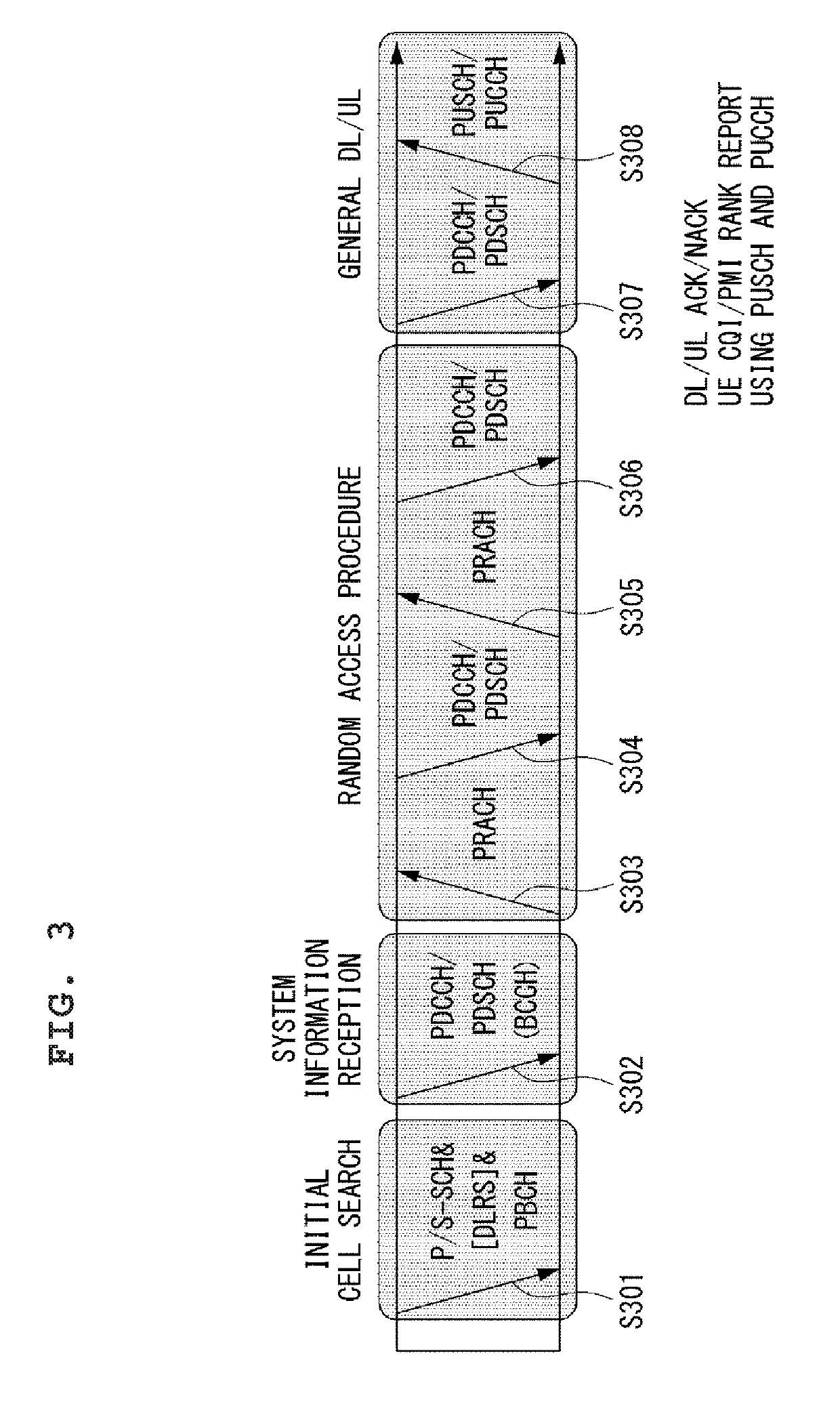
Method and apparatus for scheduling request in a wireless communication system
ActiveUS20180227938A1Increased latencyMaximize resource utilizationSignal allocationConnection managementData transmissionResource information
Provided are a method and apparatus for requesting scheduling for an uplink data transmission in a wireless communication system. The method may include receiving, by a user equipment, an additional scheduling request (SR) resource configuration information including additional SR resource information and buffer size information configured to the additional SR resource in addition to a default SR resource from a base station, transmitting, by the user equipment, an SR through the default SR resource or the additional SR resource to the base station, receiving, by the user equipment, an uplink resource allocation information which is determined according to the resource in which the SR is transmitted from the base station, and transmitting, by the user equipment, the uplink data to the base station through a physical uplink shared channel (PUSCH) resource which is allocated by the uplink resource allocation information.
Owner:LG ELECTRONICS INC
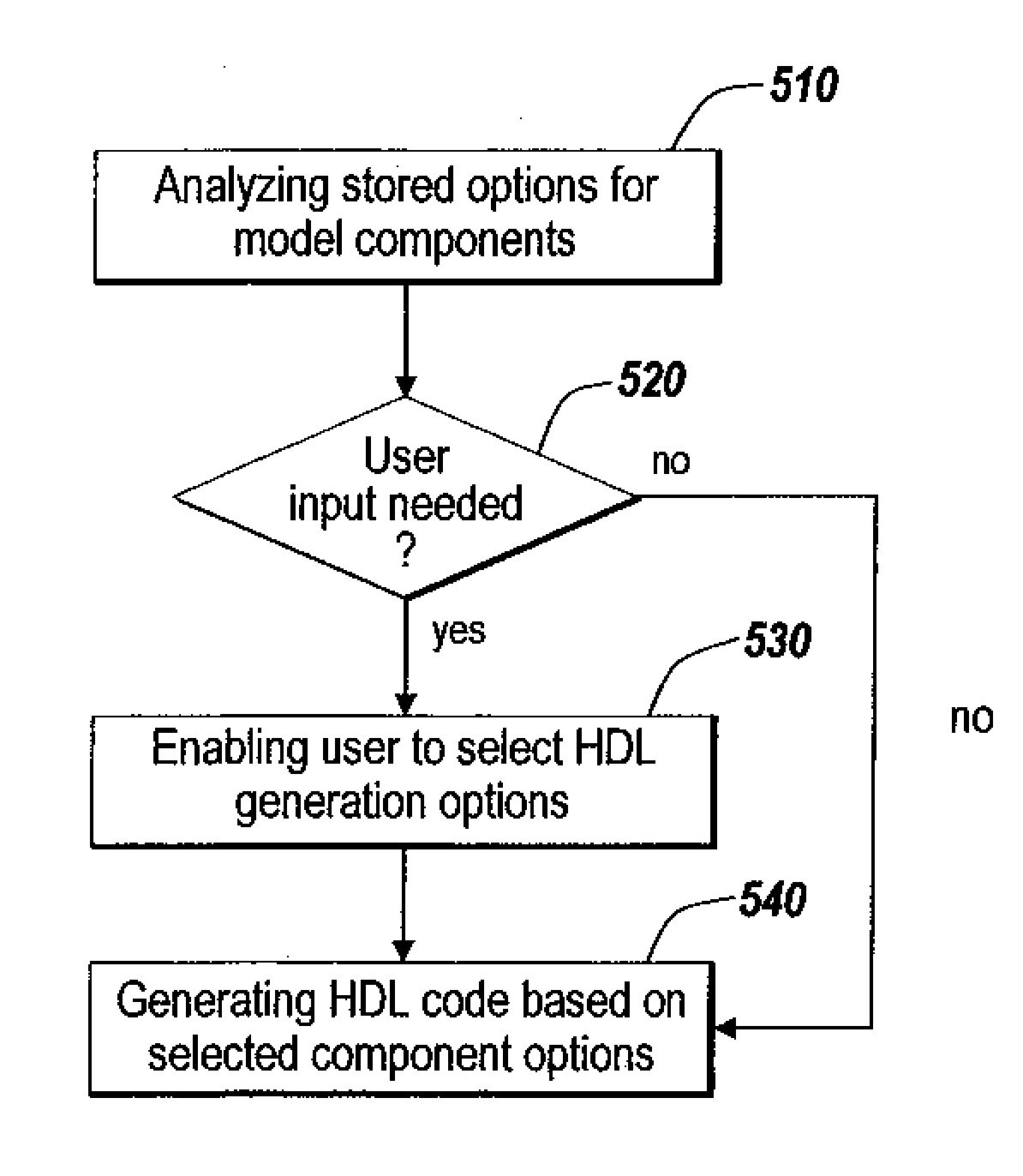
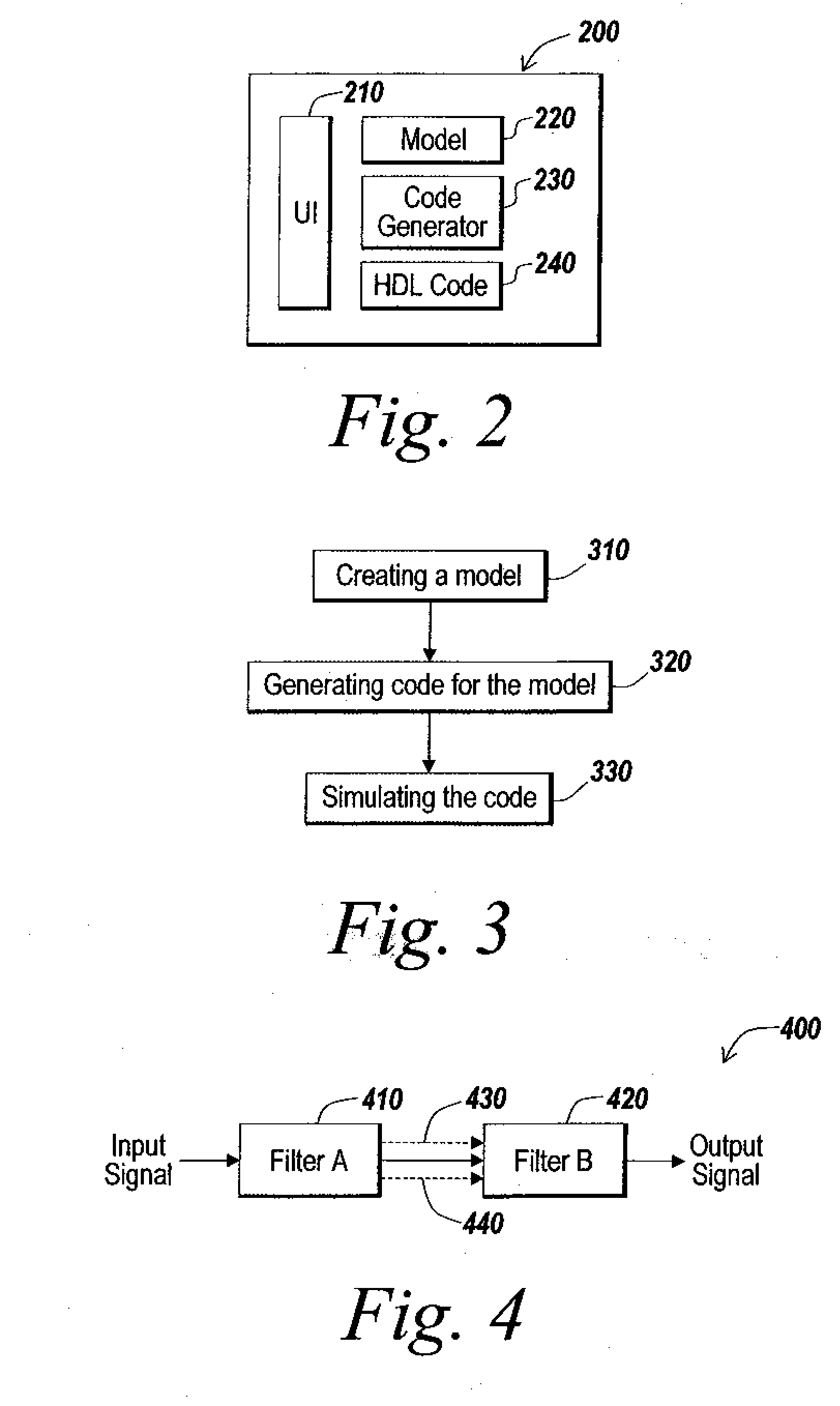
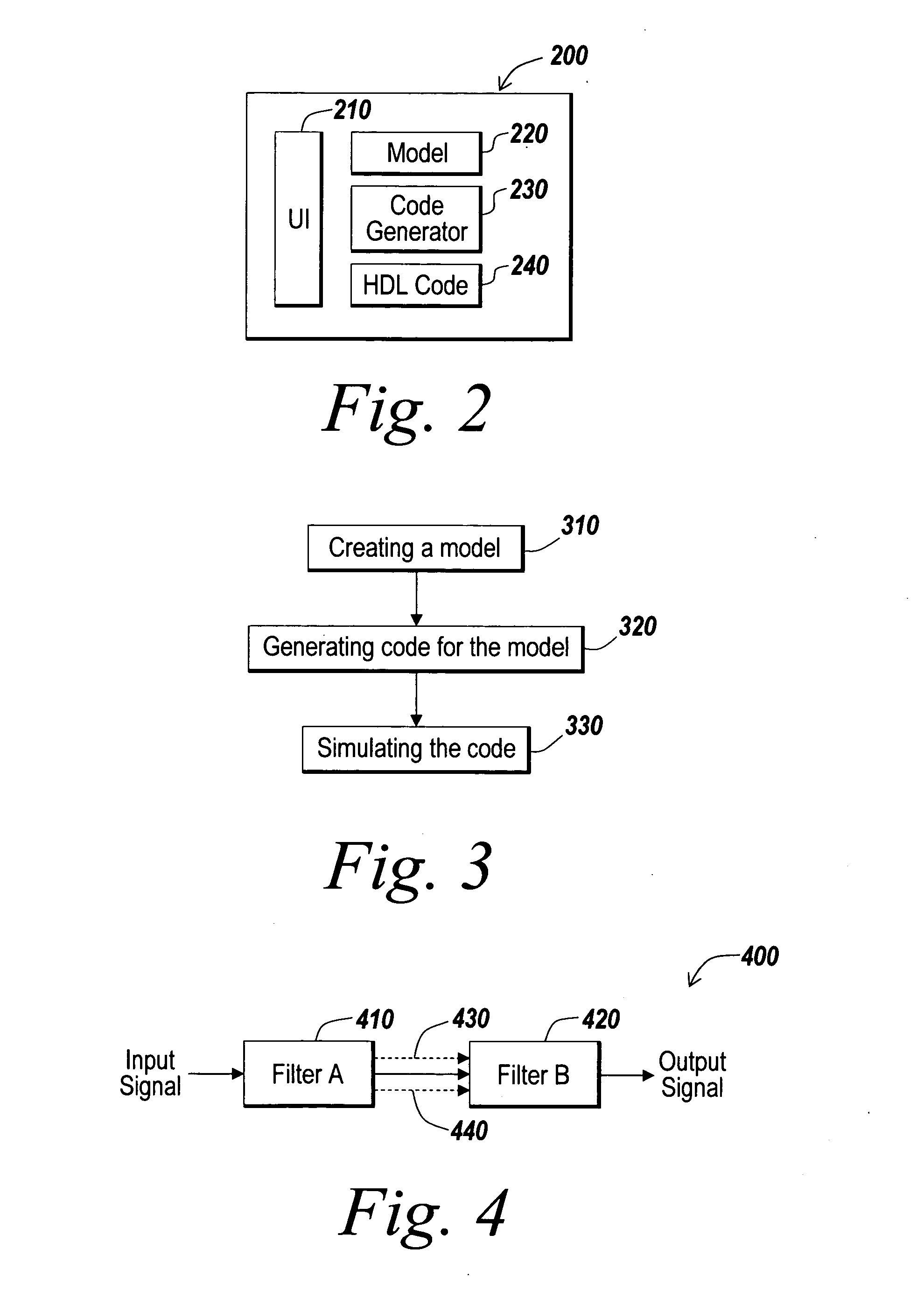
Hardware definition language generation for frame-based processing
ActiveUS20090013301A1Increased latencyMinimized in sizeCAD circuit designSoftware simulation/interpretation/emulationProgramming languageFrame based
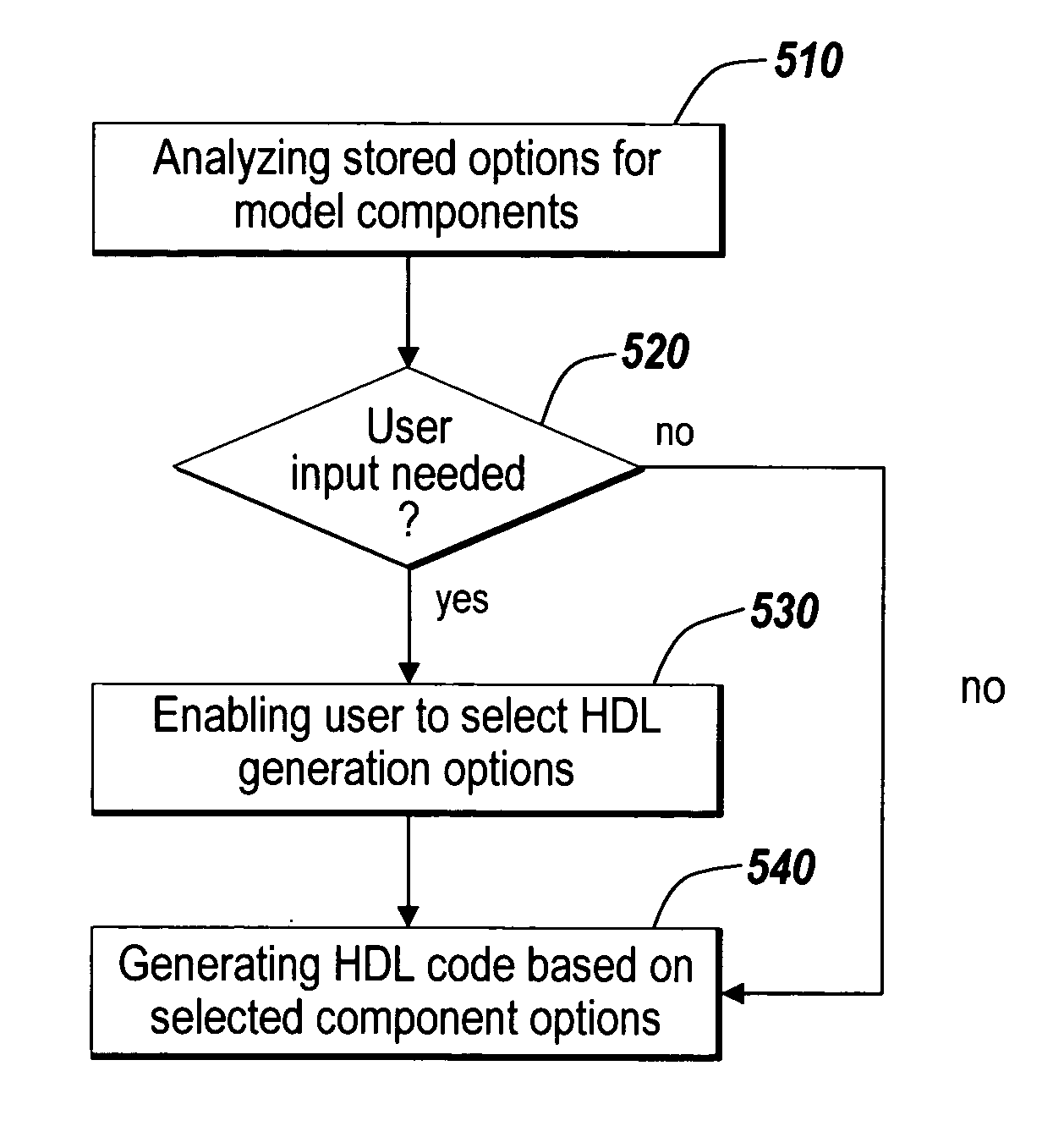
A method generates hardware description language (HDL) code from a model having a plurality of components, including at least one component that processes frame-based input data. A selected preference is received for implementing the frame-based component. The generated HDL code includes a hardware implementation of the frame-based component that satisfies the selected preference.
Owner:THE MATHWORKS INC
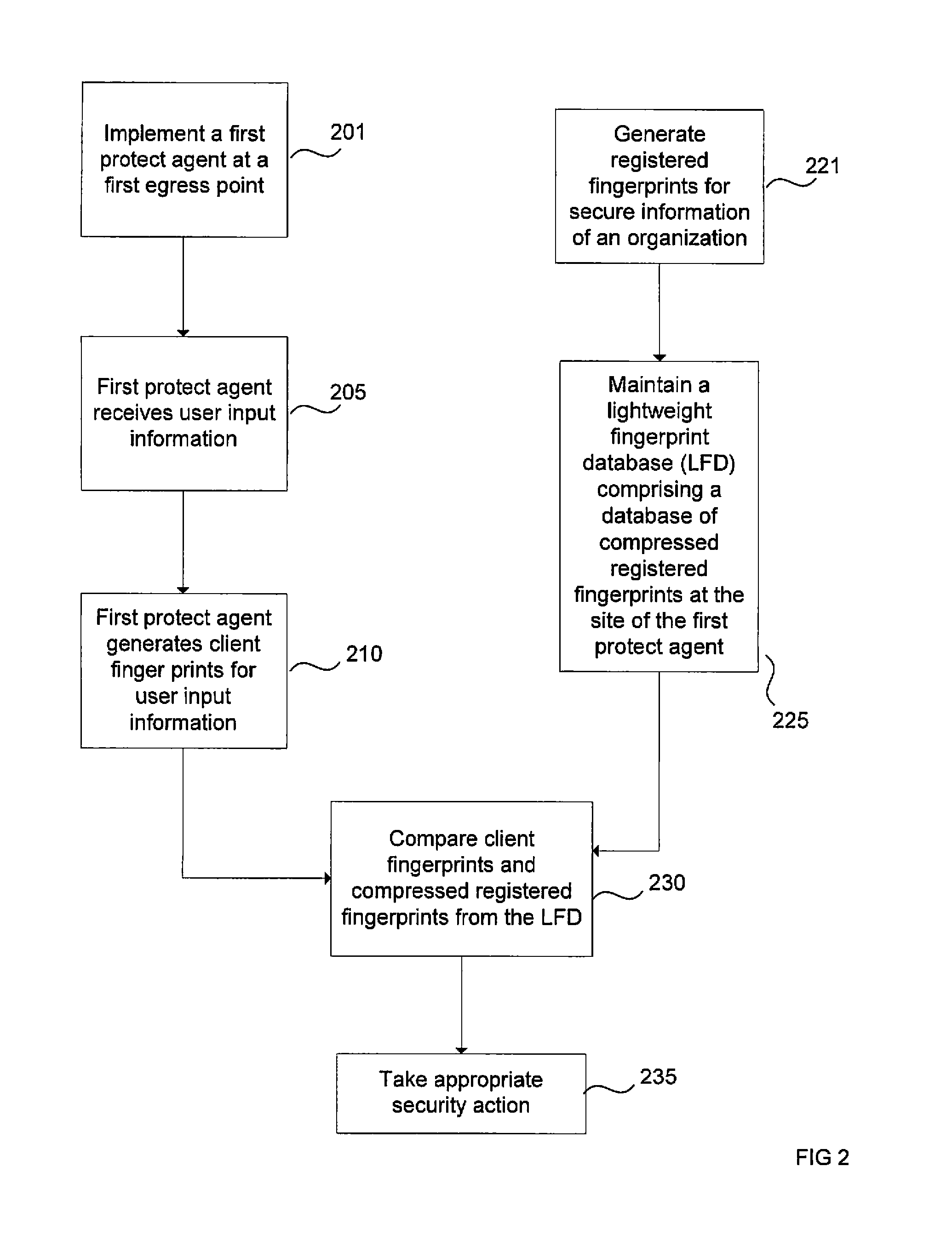
Methods and systems for protect agents using distributed lightweight fingerprints
ActiveUS20100064347A1Increased latencyReduce storage sizeRandom number generatorsUnauthorized memory use protectionCombined methodSystem usage
The present invention provides methods and systems to protect an organization's secure information from unauthorized disclosure. The present system uses protect agents installed across various egress points (e.g., email server, user's computer, etc.) to monitor information disclosed by a user. The present system also provides the use of lightweight fingerprint databases (LFD) to maintain a database of fingerprints associated with the organization's secure data. In one embodiment, the LFD is stored locally at the site of each protect agent such that the organization's secure information can be protected even when a protect agent is disconnected from the network. Methods and systems to compress fingerprints to achieve the lightweight fingerprint databases are also provided. In one embodiment, a combined approach, utilizing both the local lightweight fingerprint database and a remote fingerprint server comprising registered fingerprints is used to achieve overall protection of the organization's secure information.
Owner:FREEDOM SOLUTIONS GROUP
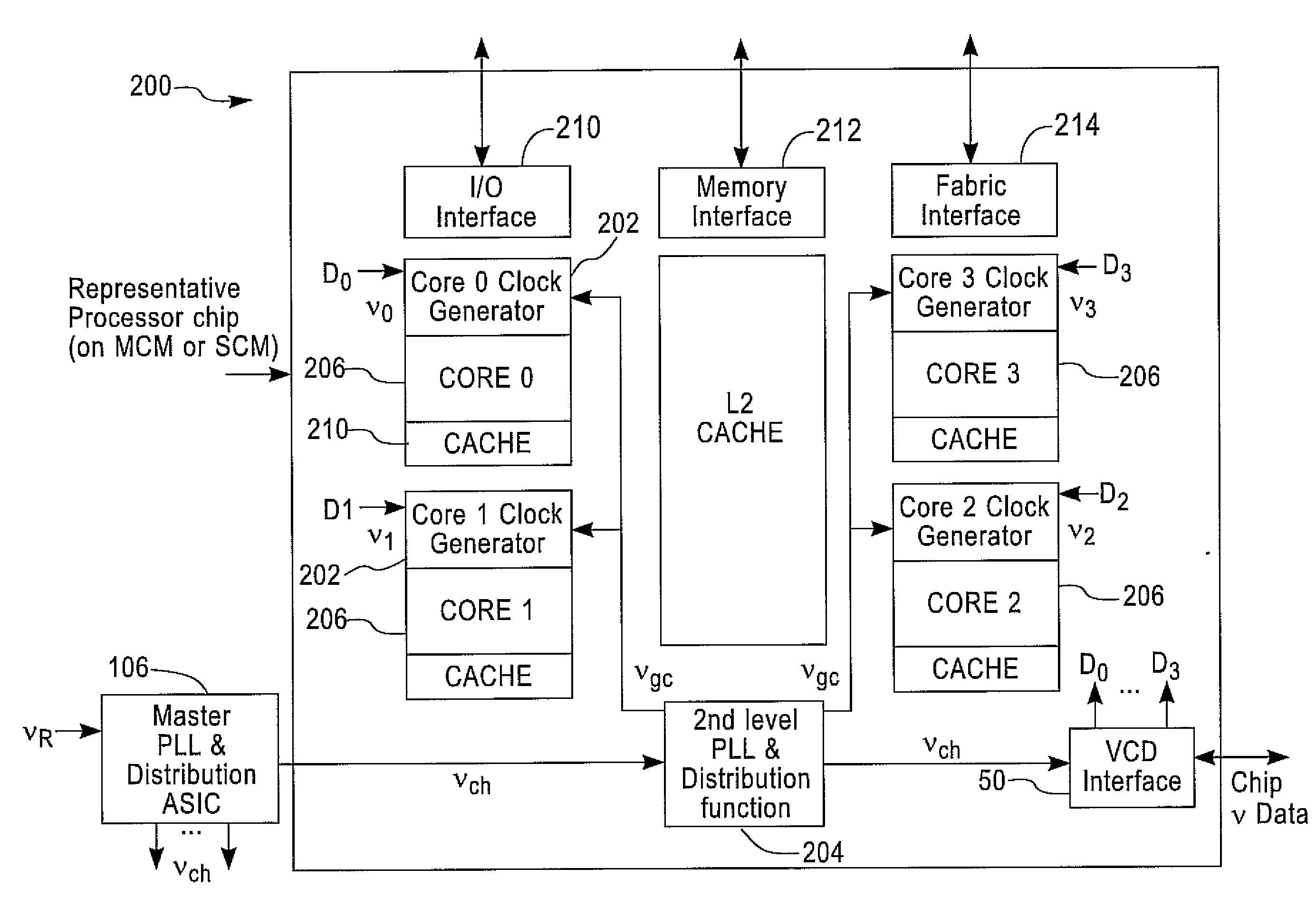
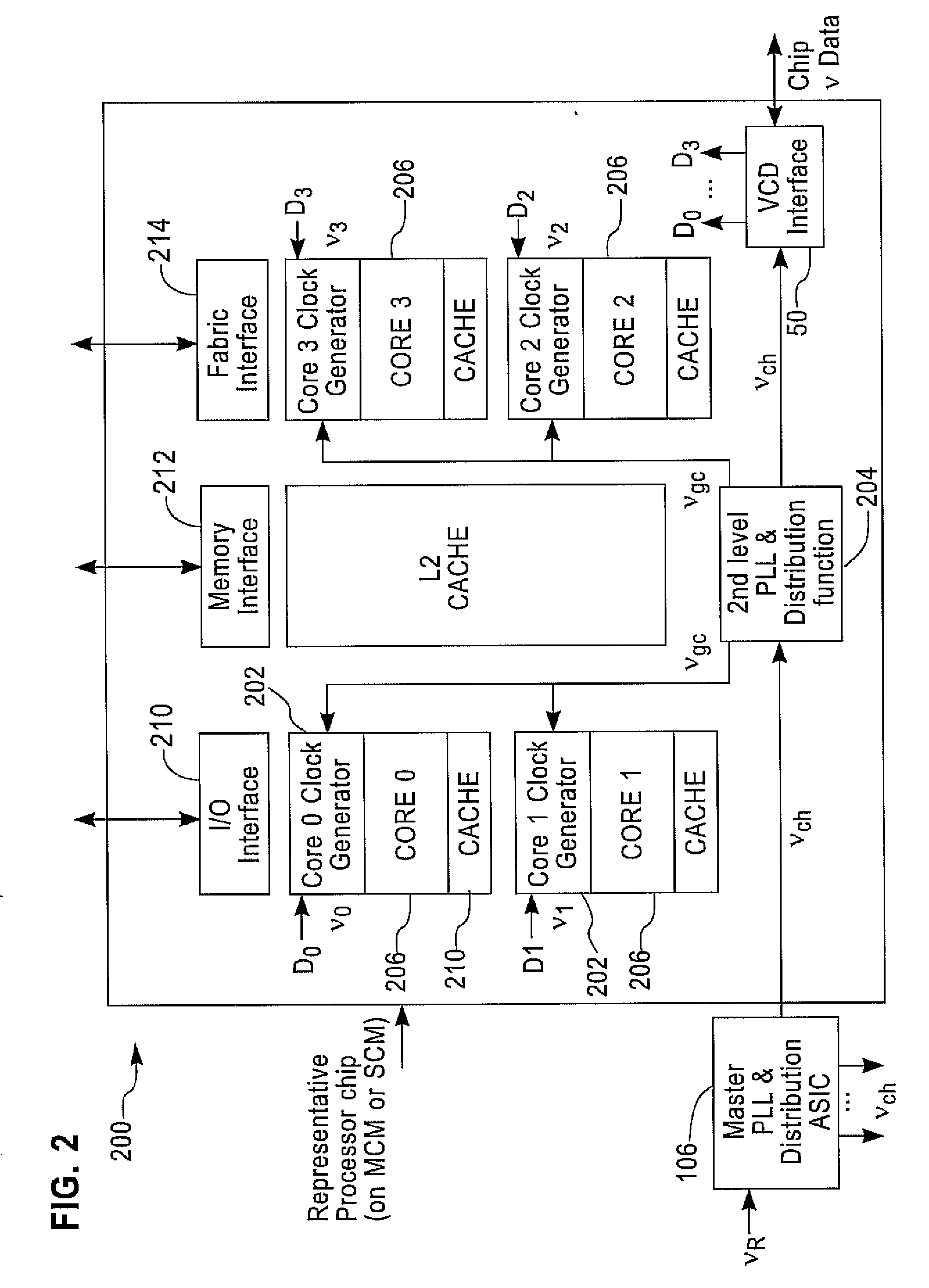
Method and system for analog frequency clocking in processor cores
ActiveUS20080256381A1Minimize latencyIncreased latencyPulse automatic controlGenerating/distributing signalsClock signalControl data
A method of and system for frequency clocking in a processor core are disclosed. In this system, at least one processor core is provided, and that at least one processor core has a clocking subsystem for generating an analog output clock signal at a variable frequency. Digital frequency control data and an analog signal are both transmitted to that at least one processor core; and that processor core uses the received analog signal and digital frequency control data to set the frequency of the output clock signal of the clocking subsystem. In a preferred implementation, multiple cores are asynchronously clocked and the core frequencies are independently set.
Owner:IBM CORP
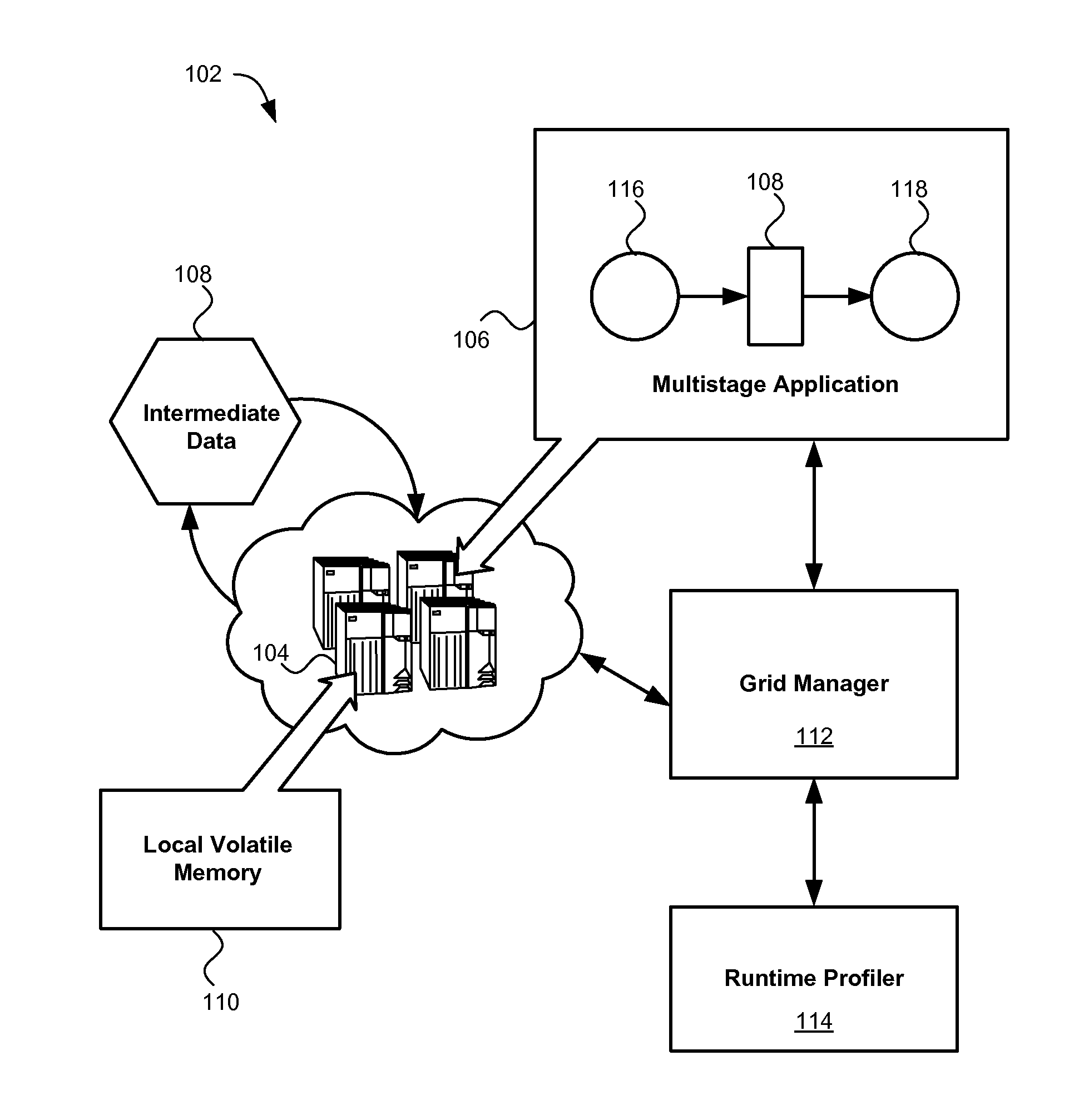
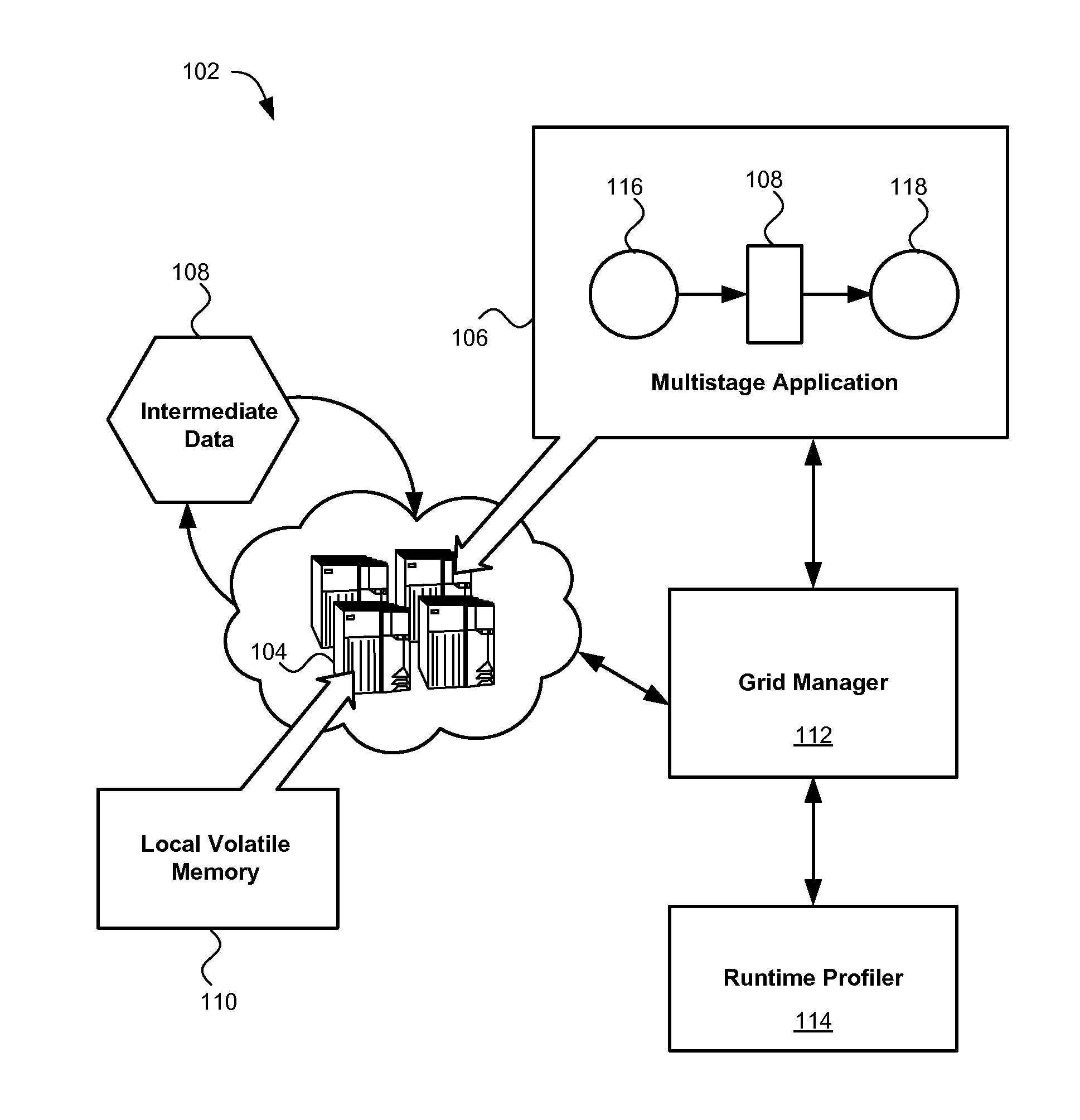
Execution of dataflow jobs
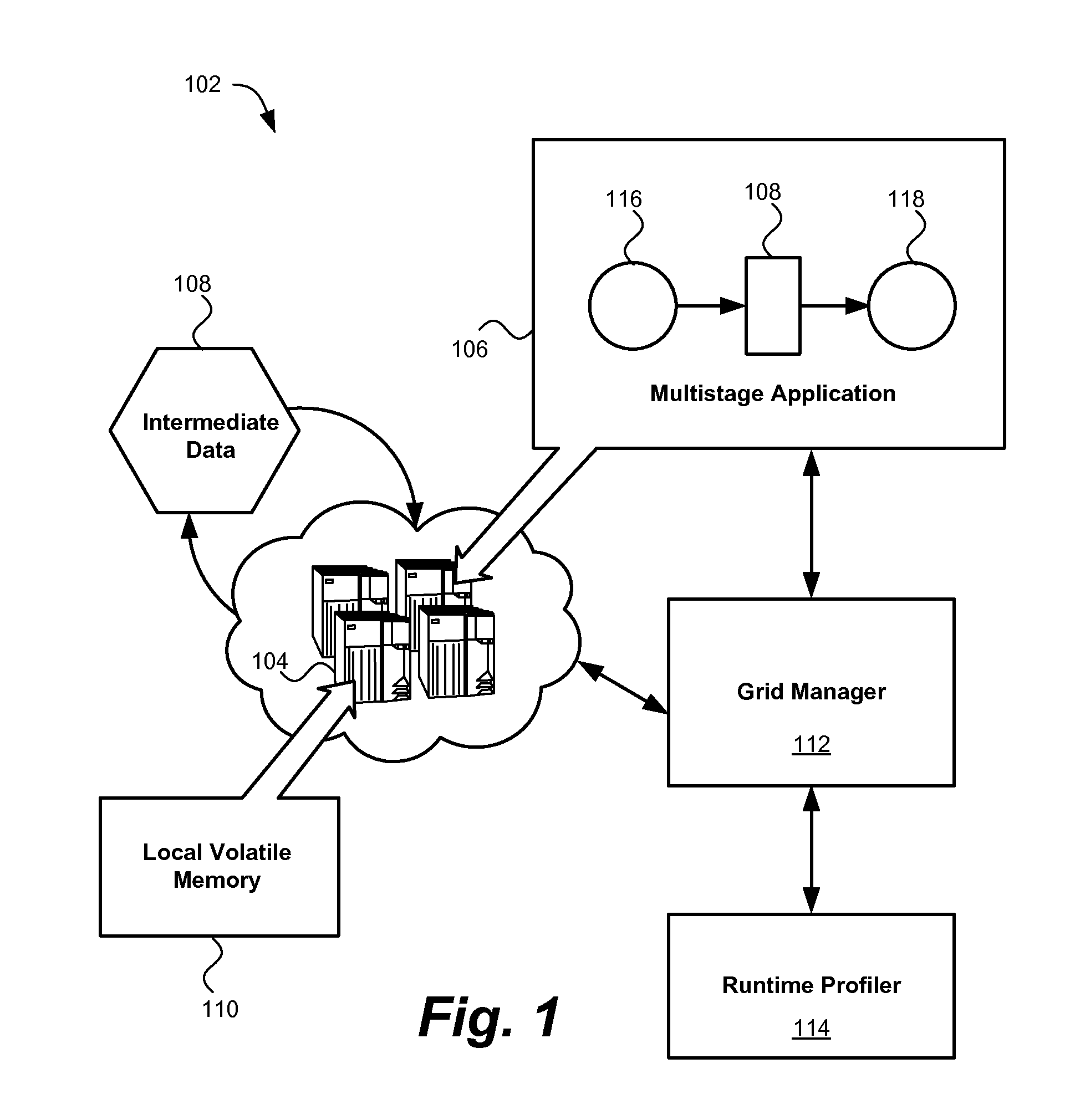
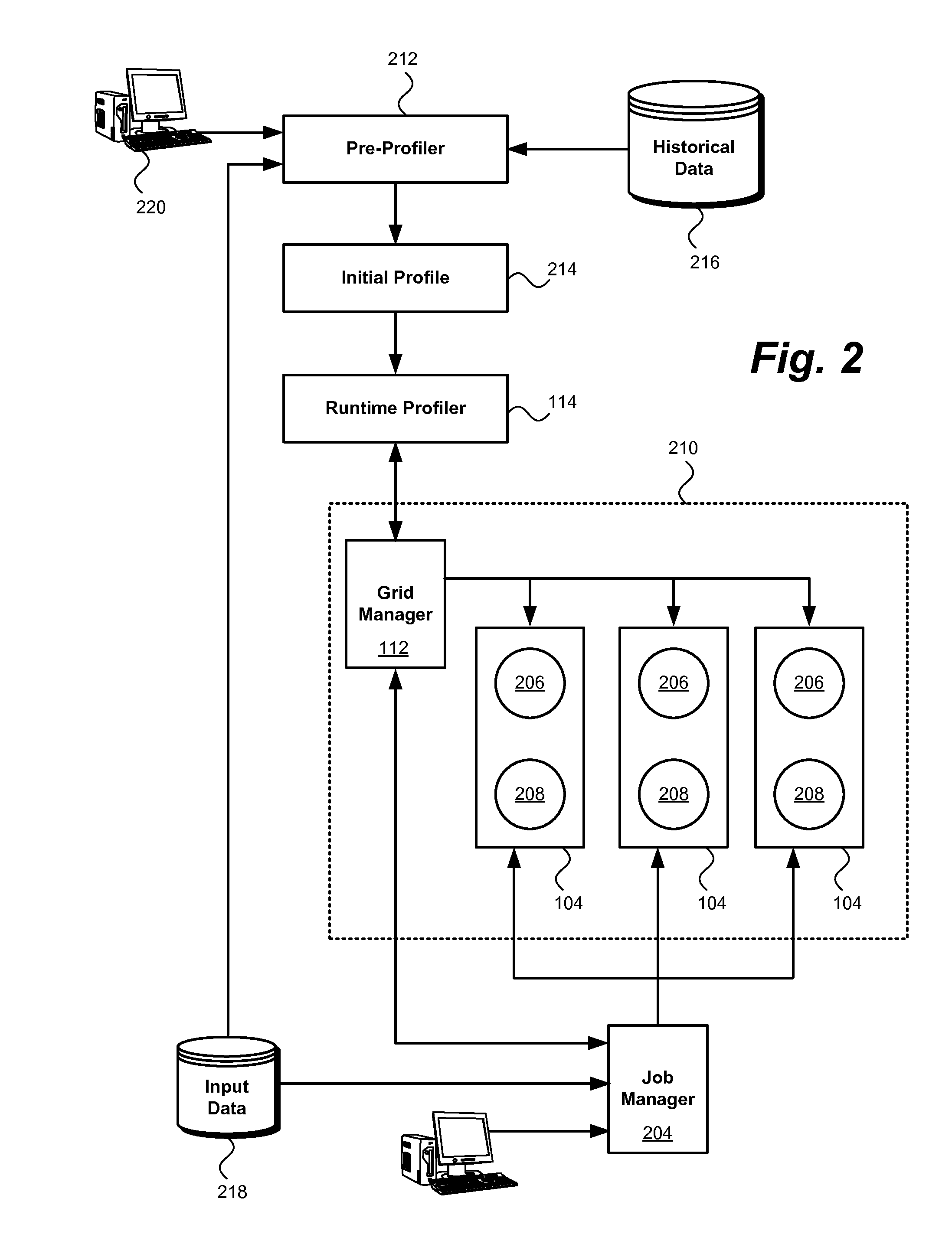
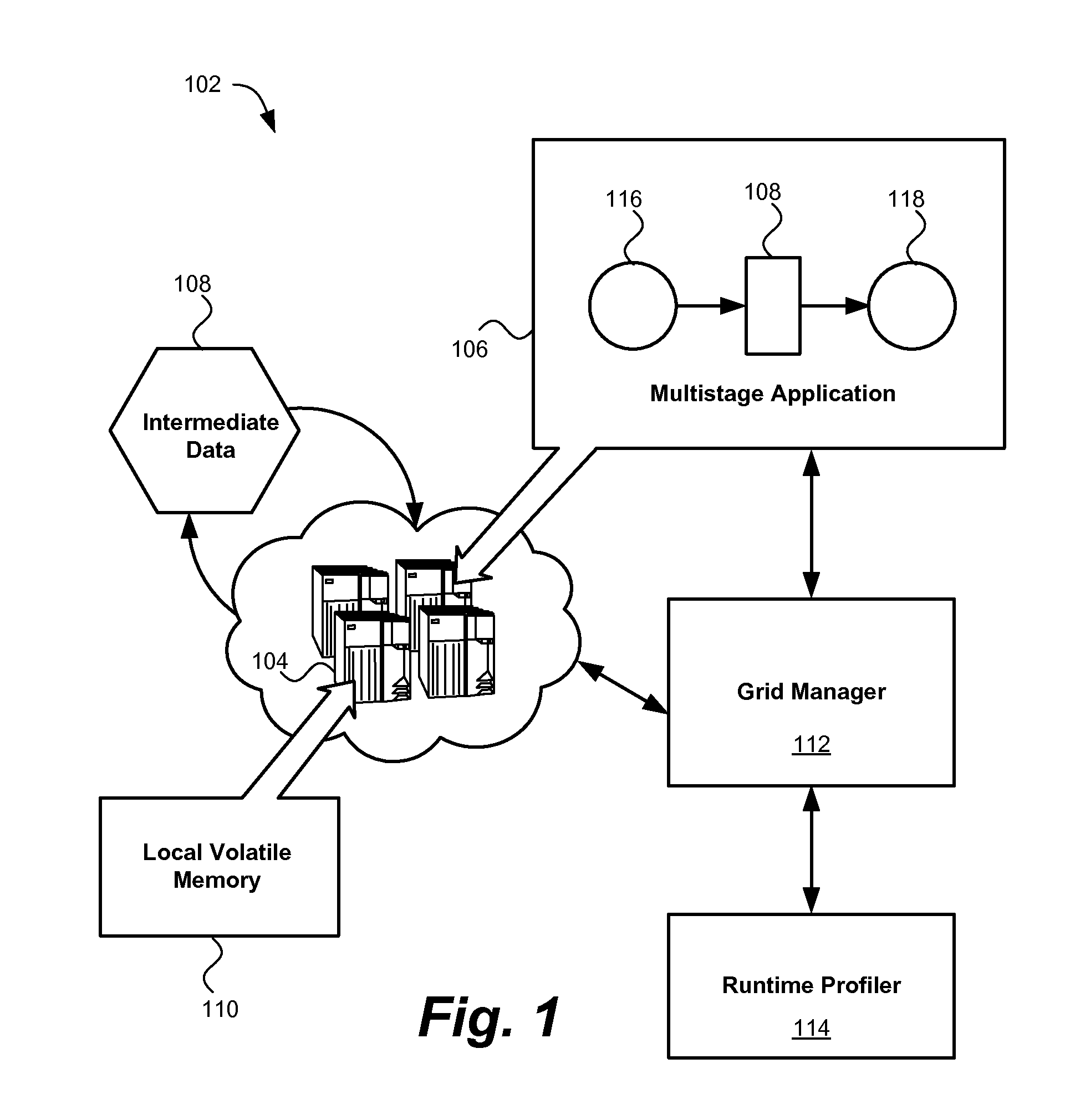
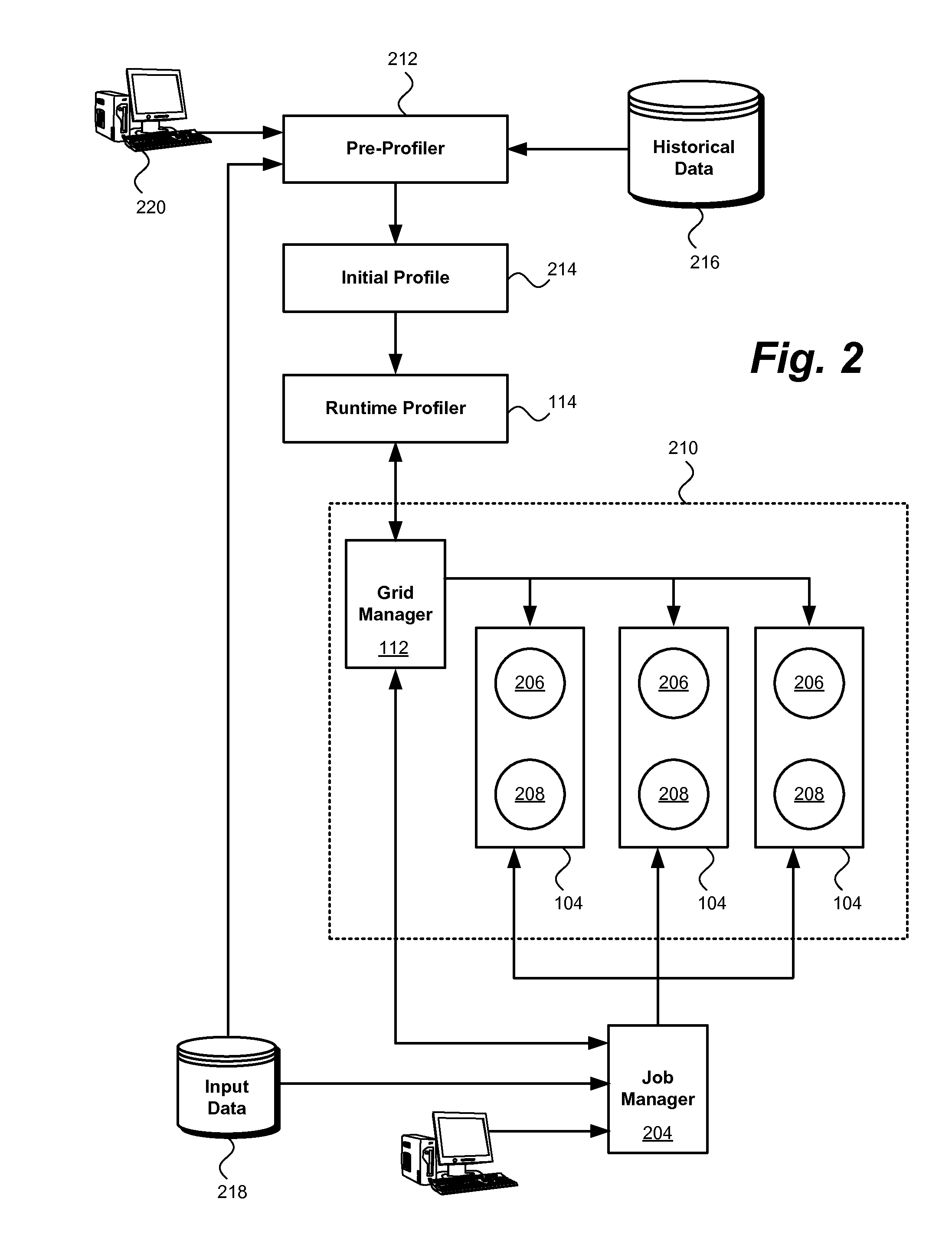
InactiveUS20110173410A1Reducing data storage latencyImprove latencyError detection/correctionMemory adressing/allocation/relocationApplication softwareMesh grid
A method, system and computer program product for storing data in memory. An example system includes at least one multistage application configured to generate intermediate data in a generating stage of the application and consume the intermediate data in a subsequent consuming stage of the application. A runtime profiler is configured to monitor the application's execution and dynamically allocate memory to the application from an in-memory data grid.
Owner:IBM CORP
Hardware definition language generation for frame-based processing
ActiveUS20080066046A1Increased latencyMinimized in sizeCAD circuit designSoftware simulation/interpretation/emulationProgramming languageGraphics
An automatic code generation application is used to automatically generate code and build programs from a textual model or graphical model for implementation on the computational platform based on the design. One or more model elements may be capable of frame-based data processing. Various options and optimizations are used to generate Hardware Description Language (HDL) code for the frame-based model elements.
Owner:THE MATHWORKS INC
Techniques for beam shaping at a millimeter wave base station
ActiveUS20170347358A1Increased latencyImprove link marginSpatial transmit diversityWireless communicationSignal-to-noise ratio (imaging)Communications system
Owner:QUALCOMM INC
Frame structure for a wireless communication system
InactiveUS20110158196A1Increased latencyIncrease the stationModulated-carrier systemsInter user/terminal allocationCommunications systemData transmission
Owner:FUJITSU LTD
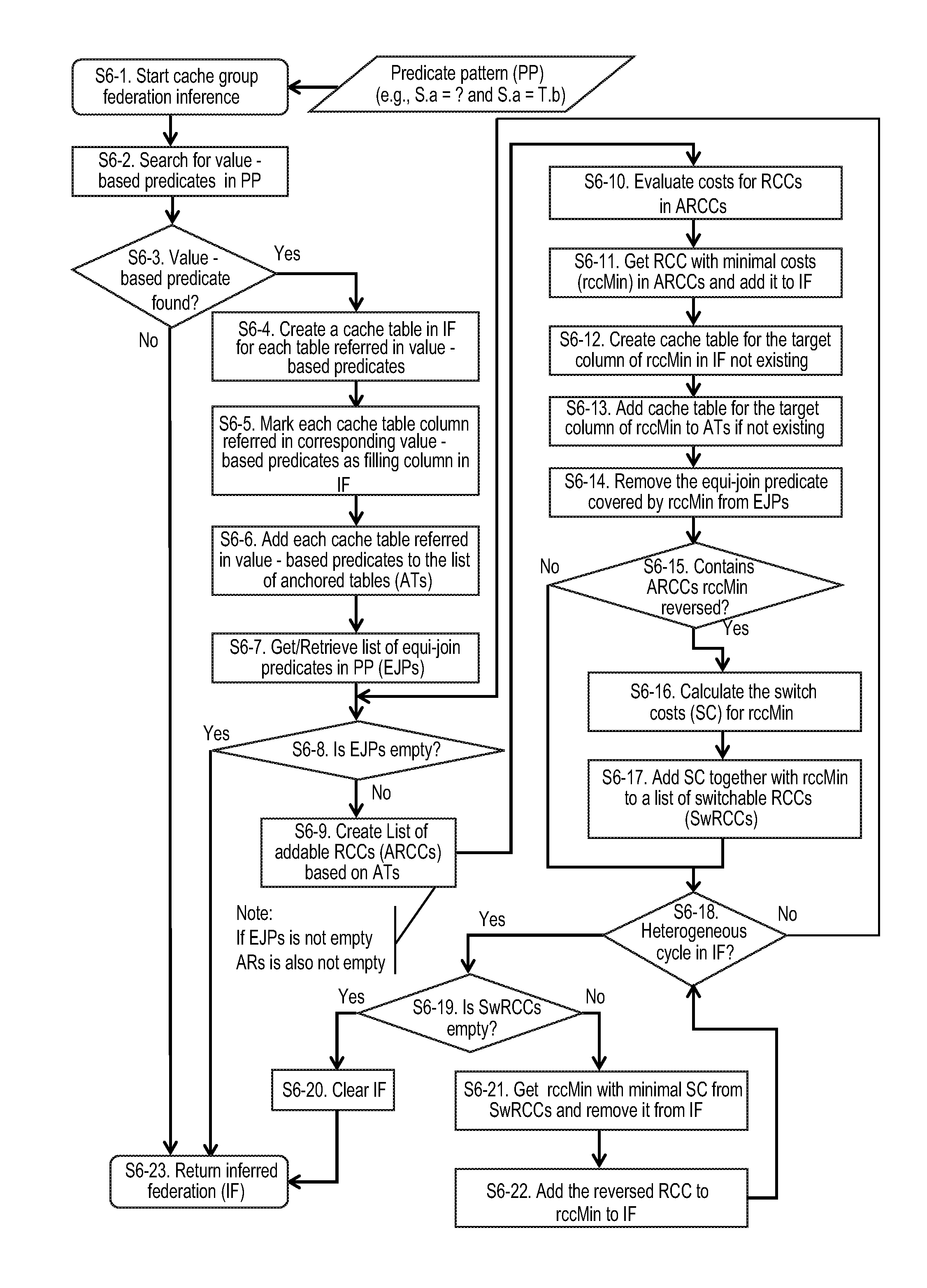
Automatic and dynamic design of cache groups
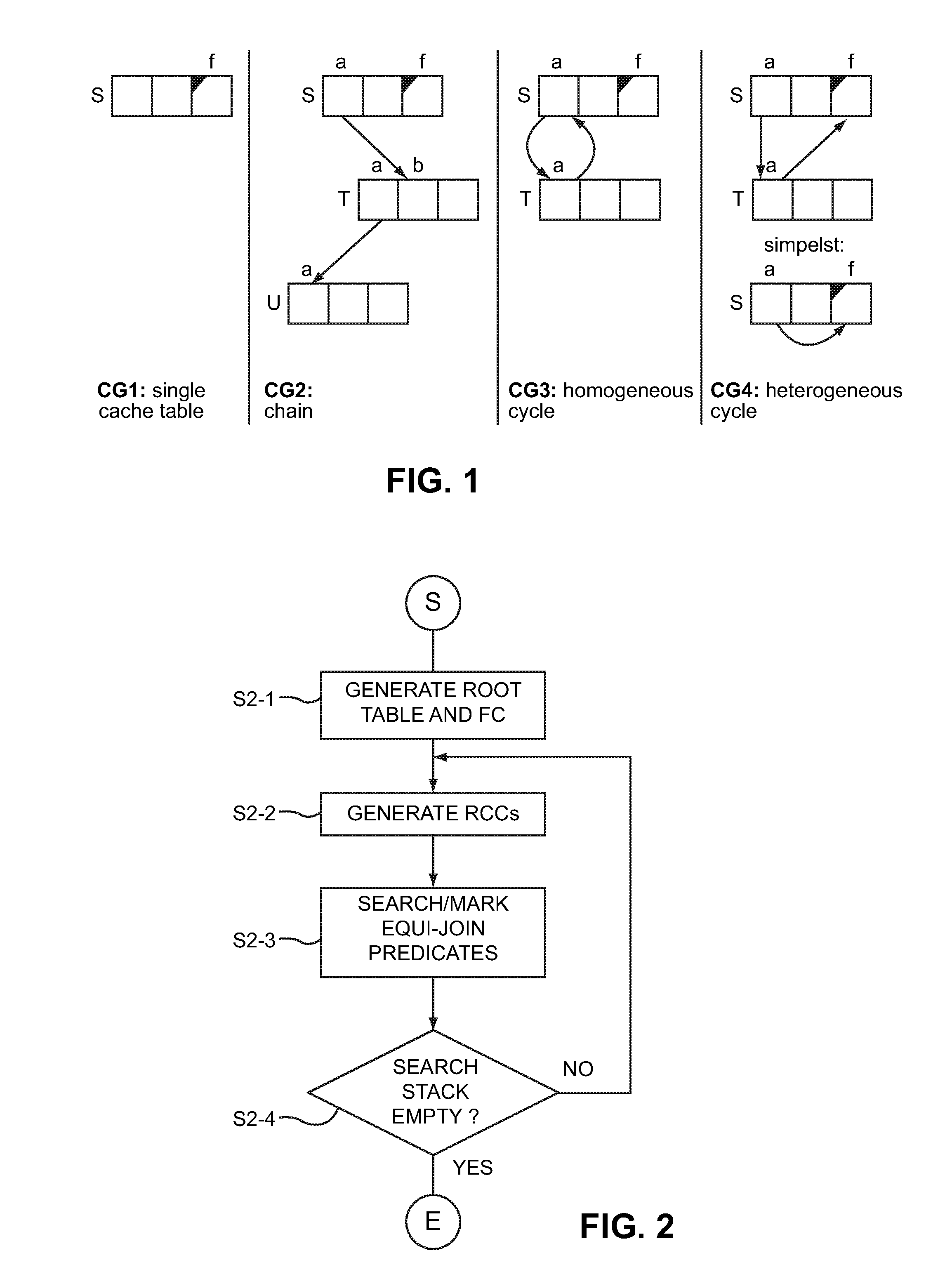
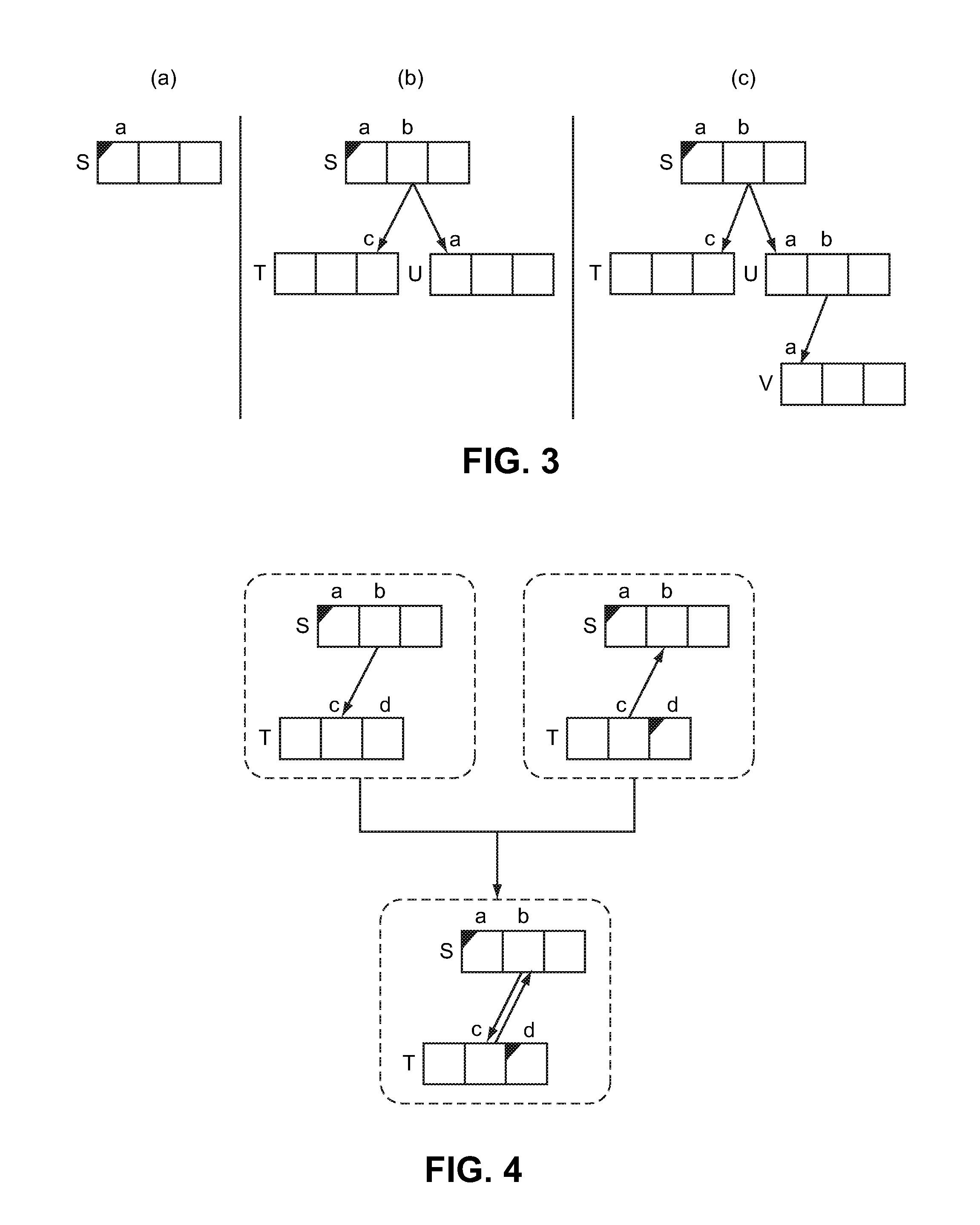
ActiveUS20130159347A1Improve latencyIncreases memory access timeDigital data information retrievalDigital data processing detailsAnalysis dataParallel computing
A system and method is provided for automatic and dynamic adaptation of cache groups in a database system having one or more processors. The method includes analyzing a database query and determining if a set of predicates in a predicate pattern are suitable for inclusion in one or more cache groups, with the one or more cache groups having one or more cache tables; mapping value-based predicates in the predicate pattern to a filling column in the one or more cache tables; and mapping equi-join predicates in the predicate pattern to a referential cache constraint in the one or more cache tables. New cache groups can be created for predicate patterns occurring more frequently and existing cache groups can be deleted if the frequency of the predicate pattern falls below a predetermined threshold value.
Owner:SOFTWARE AG
Dynamically adjusting the transmission mode in a satellite communication system
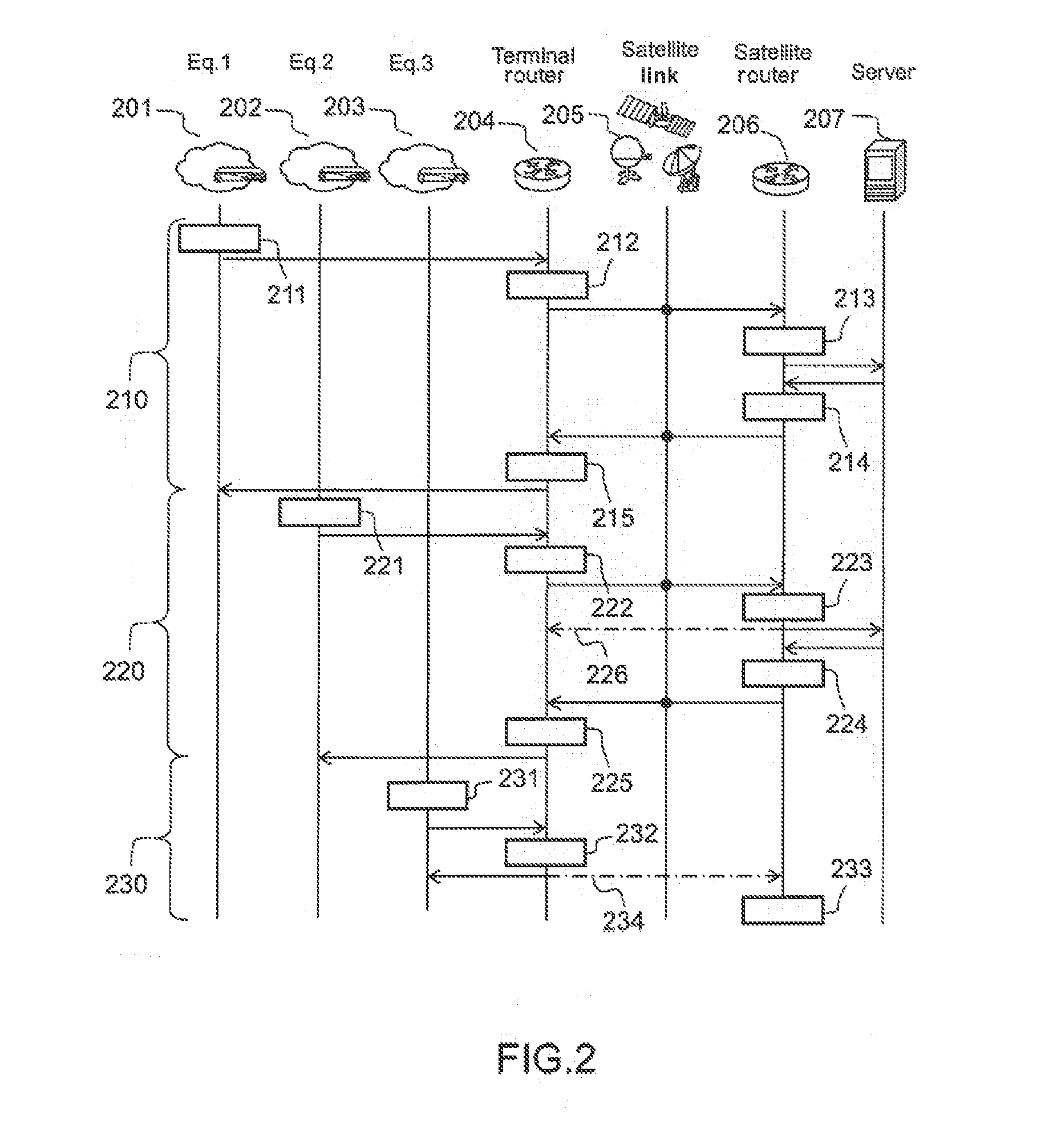
ActiveUS20160233950A1Reduce bandwidth usageImprove latencyBroadcast service distributionRadio transmissionData streamSatellite router
A system and method for transmitting a data stream between a server and a user terminal, comprises at least one satellite gateway associated with a satellite router communicating with at least one satellite terminal associated with a terminal router, wherein the terminal router is configured, when it receives a stream request from a user terminal, to search for it in its memory resources and, if appropriate, transmit it to the user terminal, the satellite router is configured to transmit the request to the server, estimate a popularity of the stream and transmit a message of correspondence between the stream and broadcasting parameters then convert the stream into a point-to-multipoint stream adapted to the broadcasting parameters, the terminal router is configured to convert point-to-multipoint streams into point-to-point streams and transmit them to the user terminals.
Owner:THALES SA
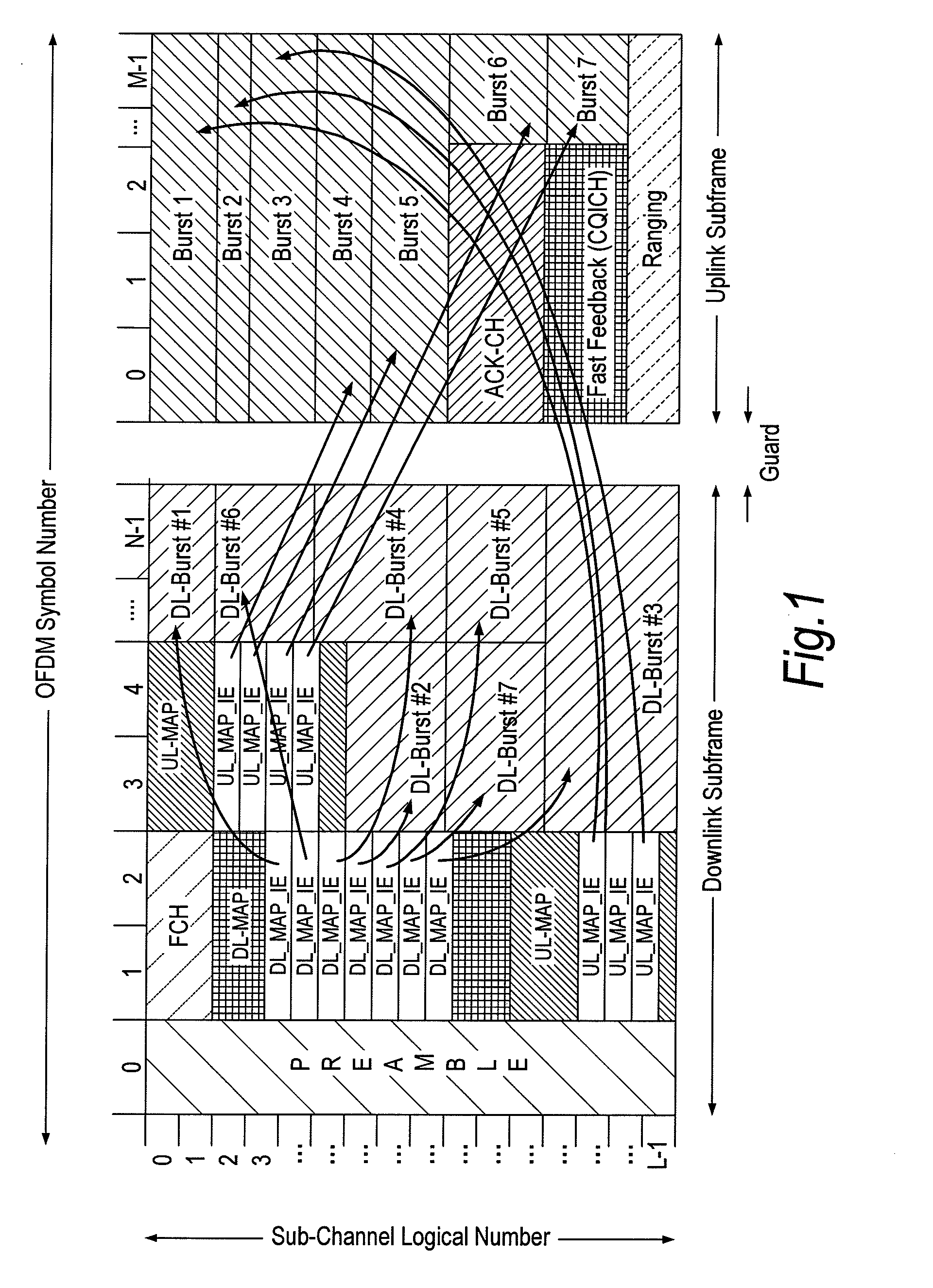
Frame structure for a wireless communication system
InactiveUS8036145B2Increased latencyIncrease the stationTime-division multiplexInter user/terminal allocationCommunications systemData transmission
A frame format used in a wireless communication system, more particularly an OFDMA TDD wireless communication system, of the kind that includes a base station and a plurality of fixed or mobile subscriber stations, the base station maintaining connections with each of the subscriber stations by performing wireless communication in units of frames having the frame format, and within each frame, allocating resources for data transmission and signalling. Each frame has a plurality of downlink subframes and a plurality of uplink subframes including, in time order, a first downlink subframe, a first uplink subframe, a final downlink subframe and a final uplink subframe. One or more further downlink subframe / uplink subframe pairs may be interposed between the first and final subframes as desired, and the configuration can be changed dynamically.
Owner:FUJITSU LTD
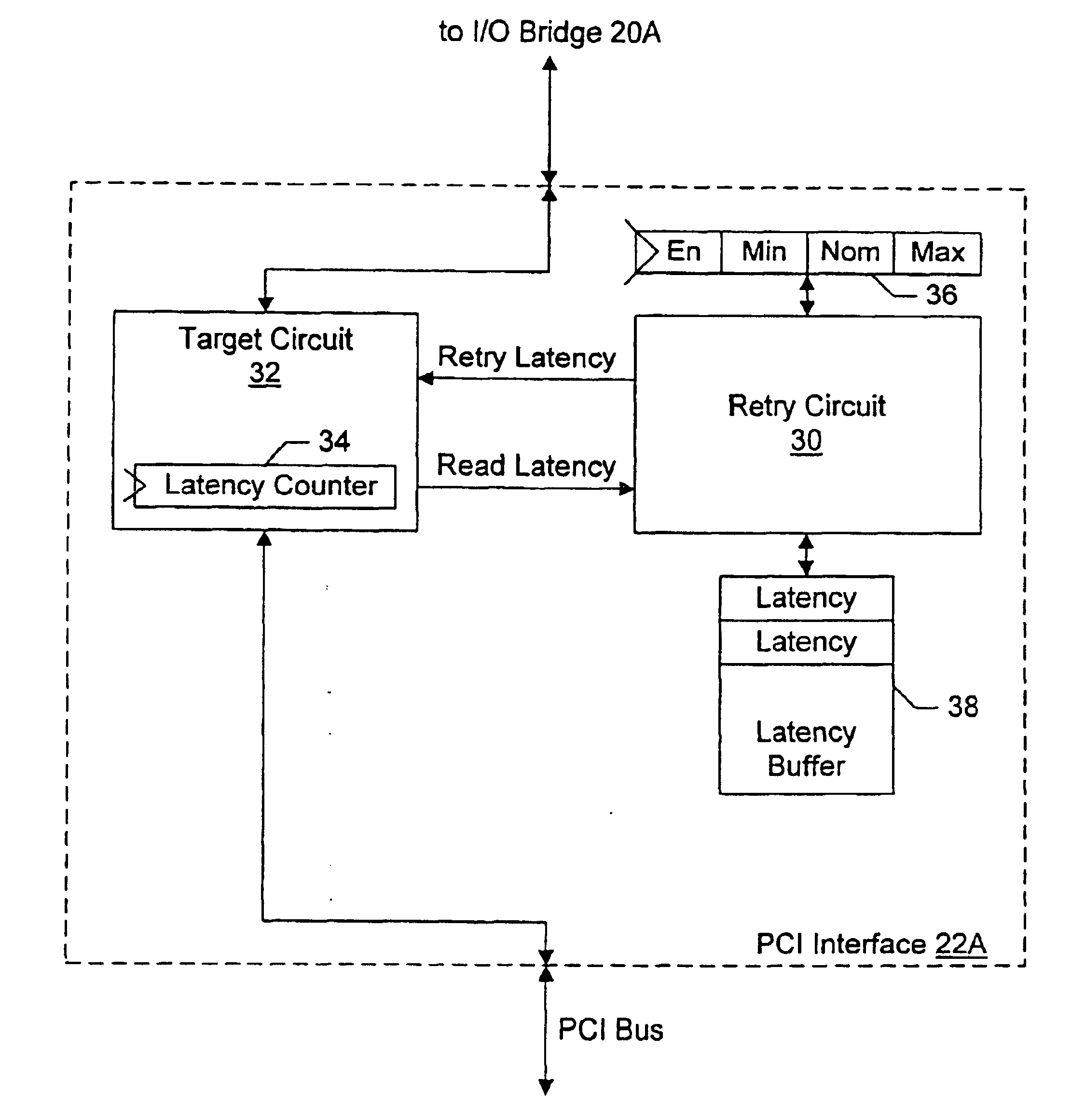
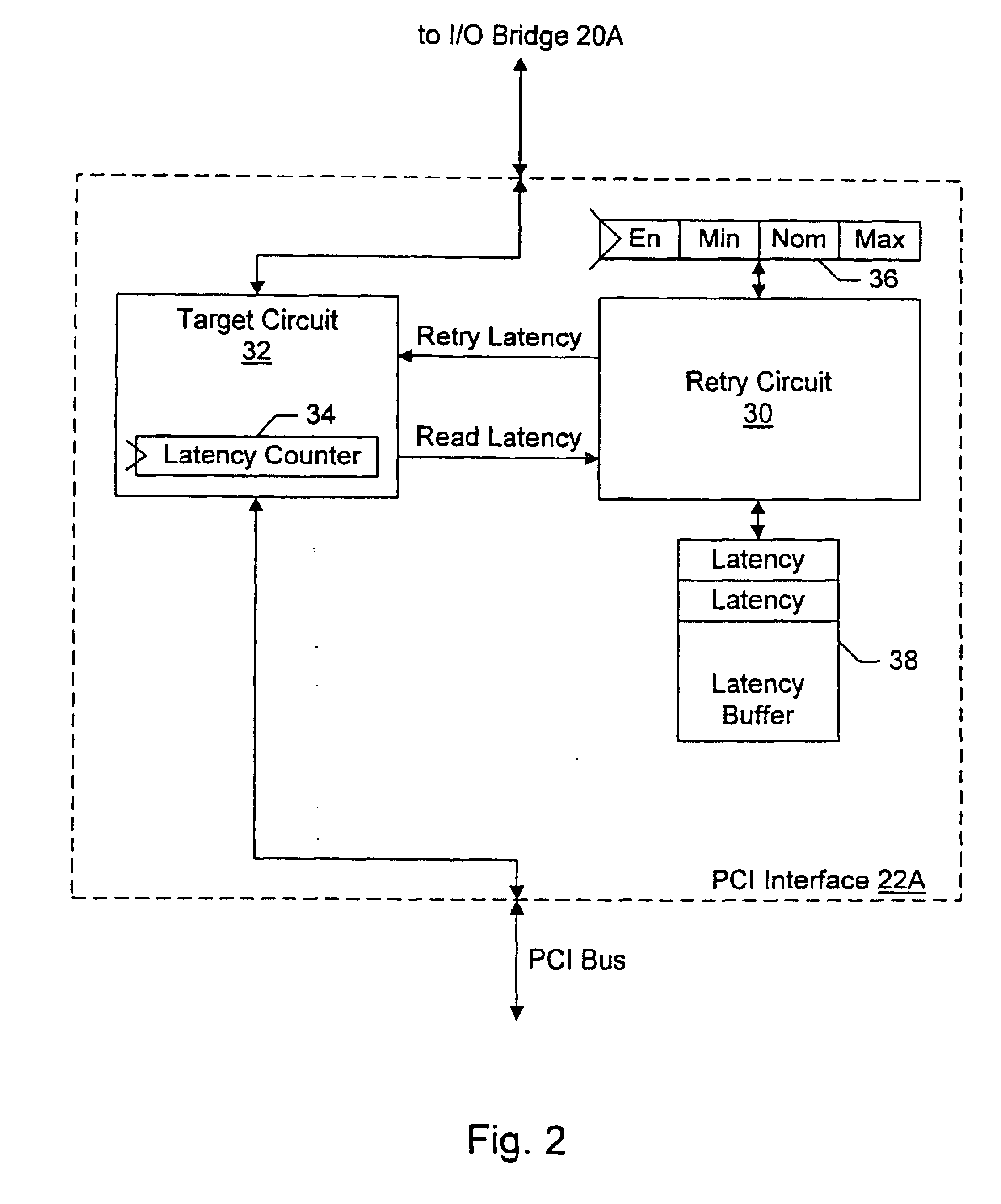
Adaptive retry mechanism
InactiveUS6851004B2Easy to useIncreased latencyElectric digital data processingSelf adaptiveData transmission
An adaptive retry mechanism may record latencies of recent transactions (e.g. the first data transfer latency), and may select a retry latency from two or more retry latencies. The retry latency may be used for a transaction, and may specify a point in time during the transaction at which the transaction is retried if the first data transfer has not yet occurred. In one implementation, the set of retry latencies includes a minimum retry latency, a nominal retry latency, and a maximum retry latency. The nominal retry latency may be set slightly greater than the expected latency of transactions in the system. The minimum retry latency may be less than the nominal retry latency and the maximum retry latency may be greater than the nominal retry latency. If latencies greater than the nominal retry latency but less than the maximum retry latency are being experienced, the maximum retry latency may be selected. On the other hand, if latencies greater than the maximum retry latency are being experienced, the minimum retry latency may be selected.
Owner:AVAGO TECH INT SALES PTE LTD
Execution of dataflow jobs
InactiveUS8539192B2Reducing data storage latencyIncreased latencyError detection/correctionMemory systemsApplication softwareMesh grid
A method, system and computer program product for storing data in memory. An example system includes at least one multistage application configured to generate intermediate data in a generating stage of the application and consume the intermediate data in a subsequent consuming stage of the application. A runtime profiler is configured to monitor the application's execution and dynamically allocate memory to the application from an in-memory data grid.
Owner:INT BUSINESS MASCH CORP
Electronic device and method of communication resource allocation
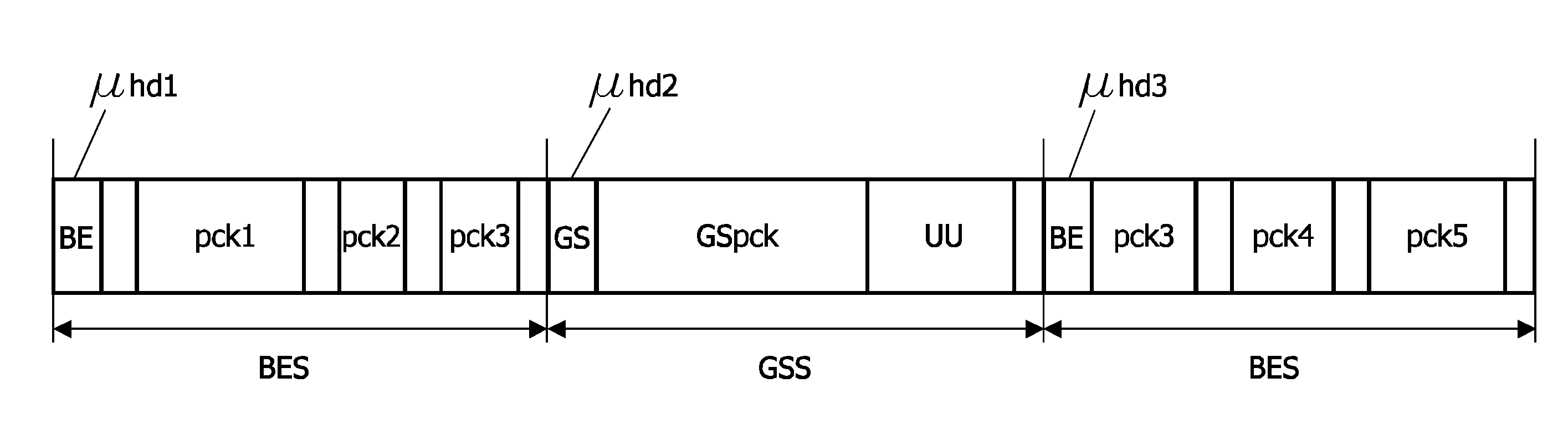
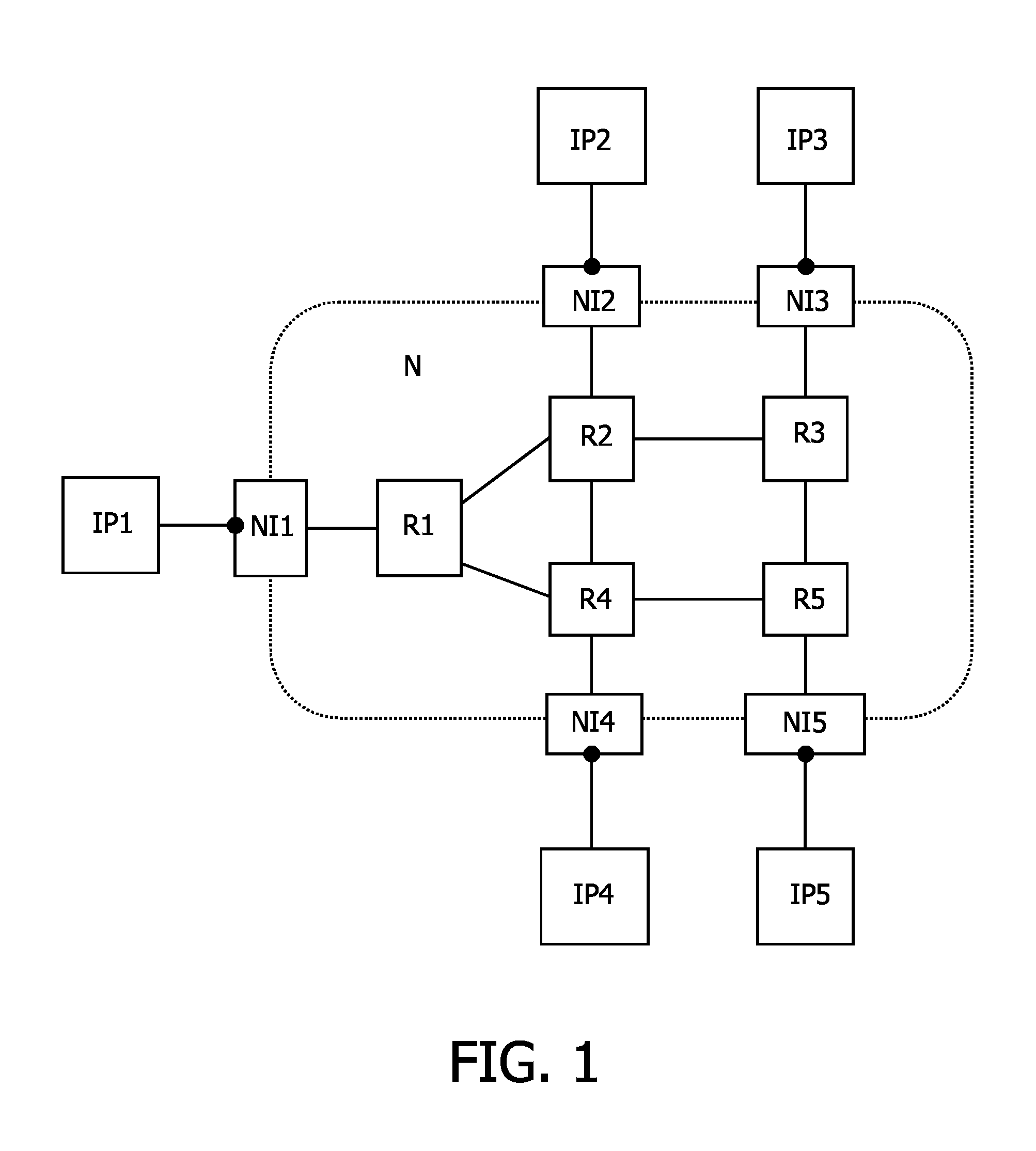
InactiveUS8014401B2Configuration highIncreased latencyError preventionTransmission systemsData trafficResource allocation
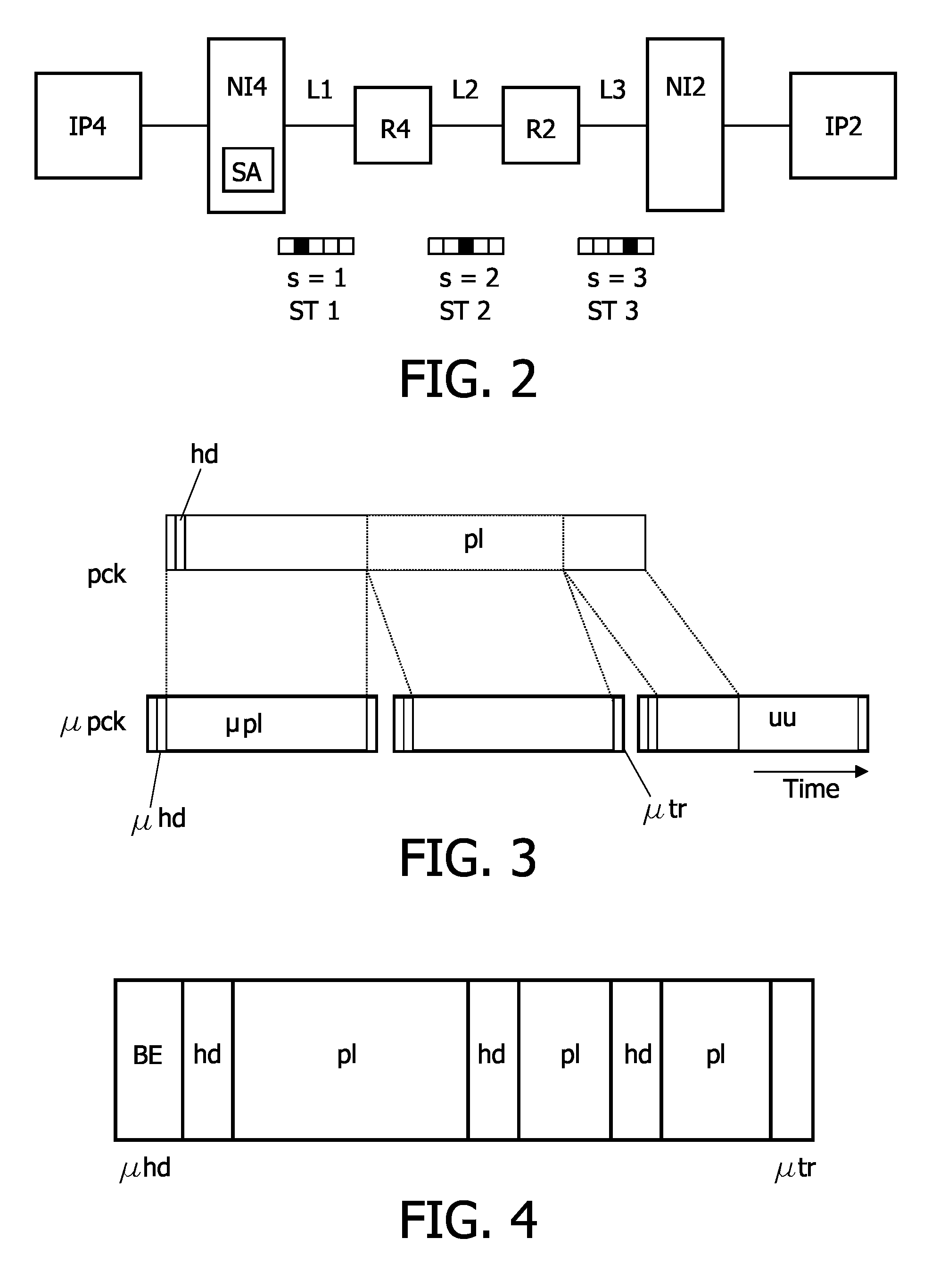
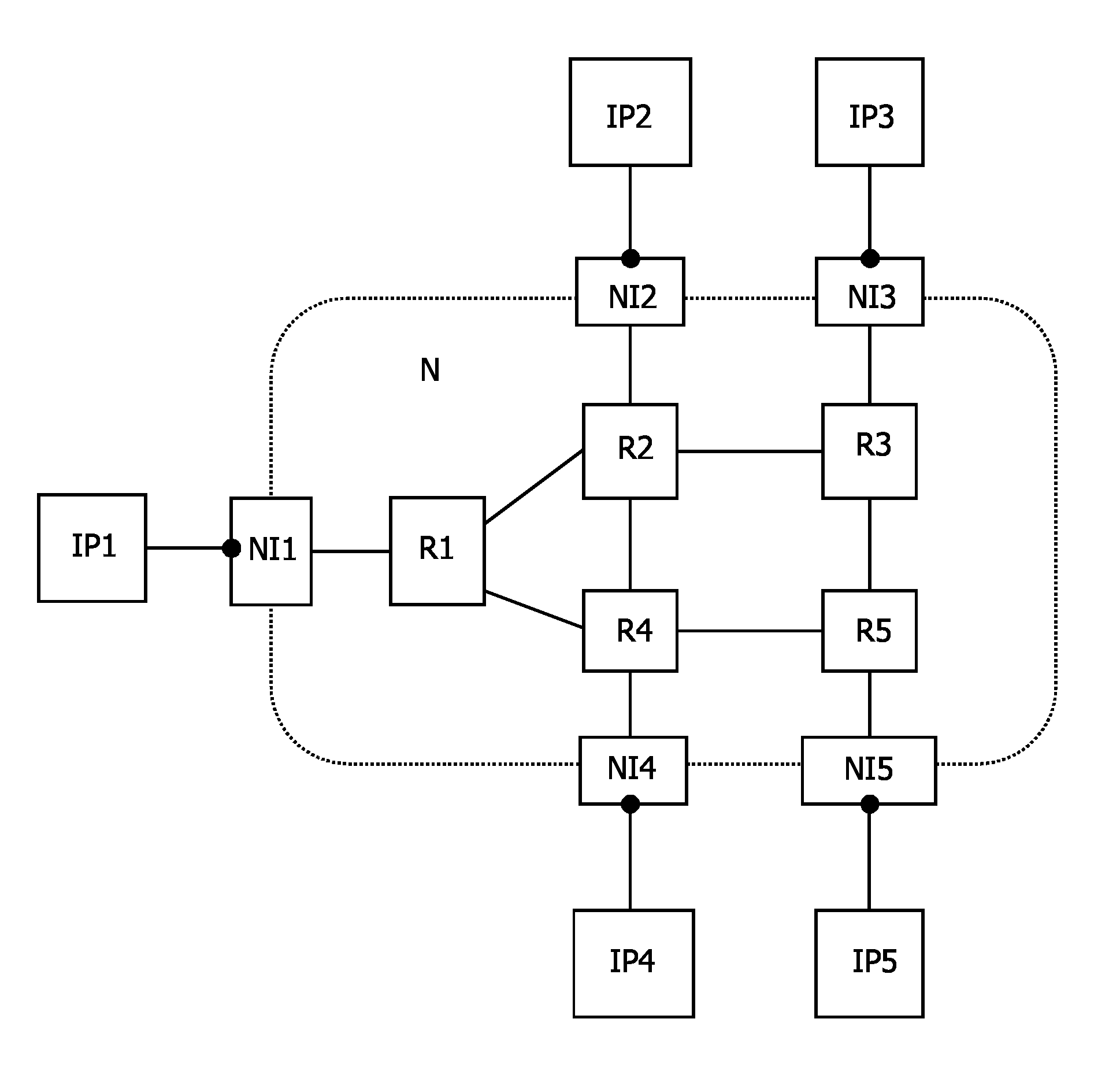
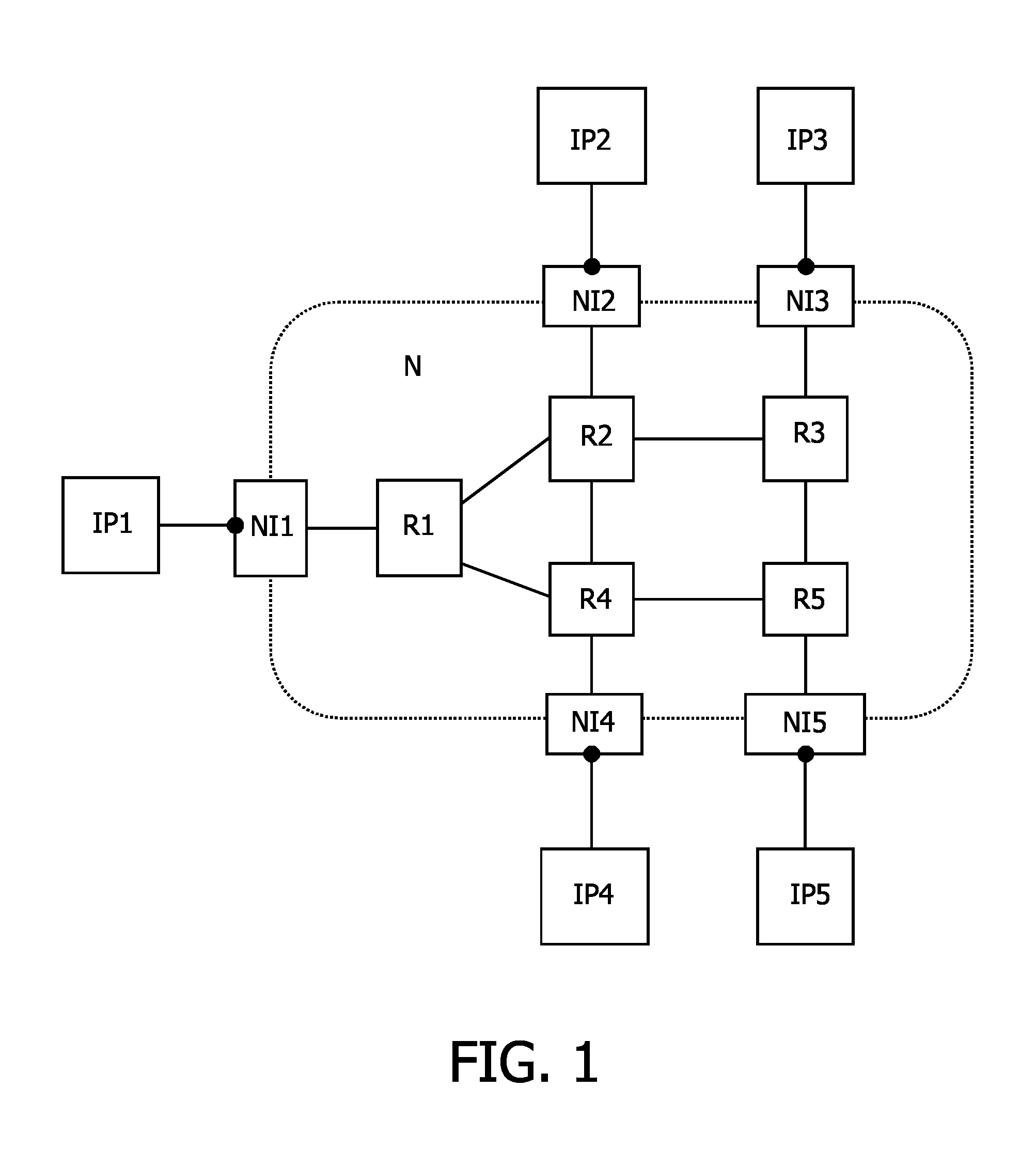
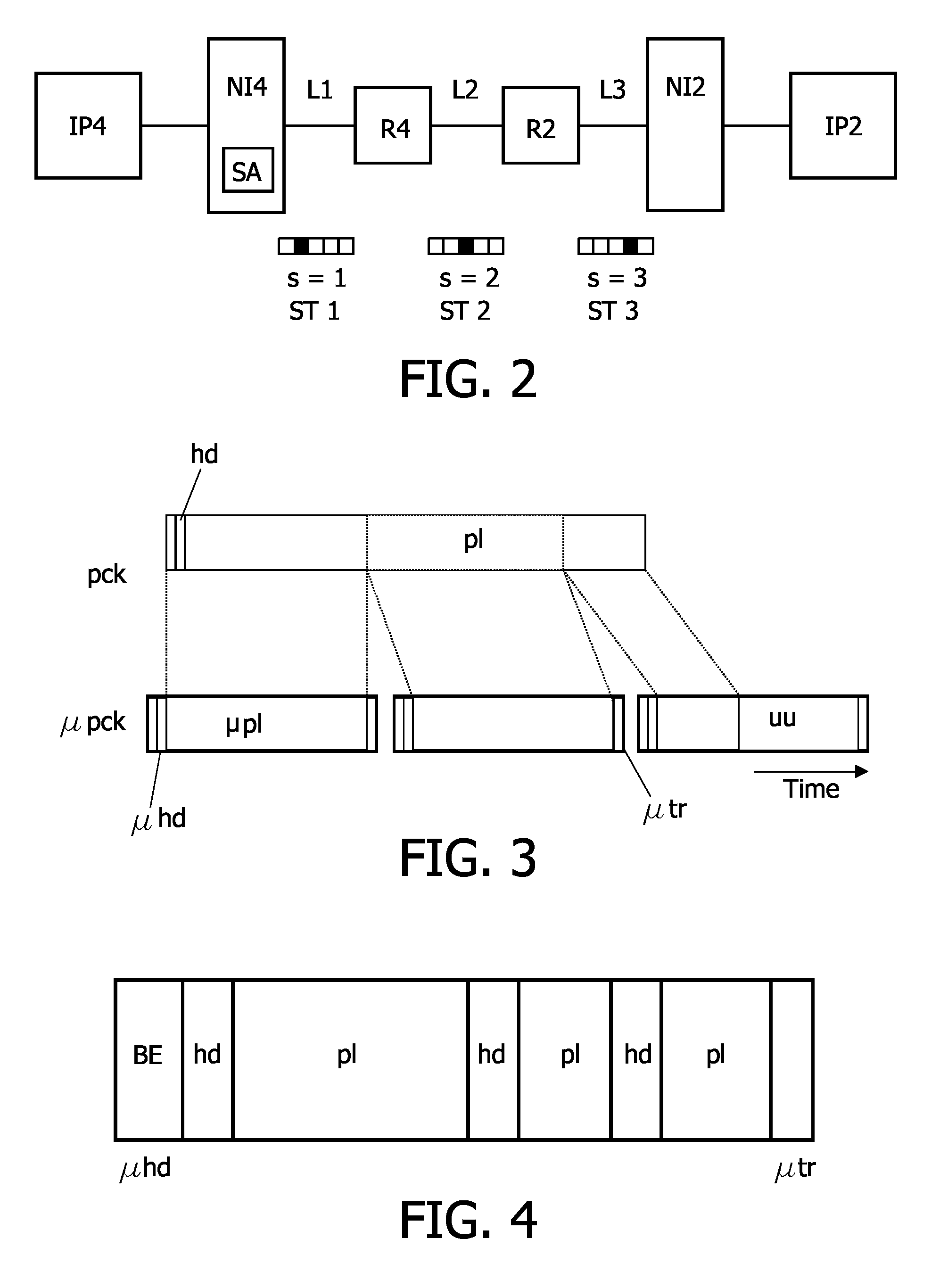
An electronic device is provided comprising an interconnect means (N, sw0-sw2) for connecting a plurality of modules (IP); and at least one network interface (NI) for coupling at least one of the plurality of modules (IP) to the interconnect means (N; sw0-sw2) and for packetizing data from the modules (IP) into first packets (pck). The communication over the interconnect (N; sw0-sw2) is based on time slots, wherein a second packet (μpck) is transferred during one time slot. A data traffic over the interconnect means (N; sw0-sw2) comprises at least one guaranteed service traffic class (GS) and / or at least one best-effort service traffic class (BE). First packets (GSpck) relating to the at least one guaranteed service traffic class (GS) are transferred in second packets (μpck) within time slots reserved for the guaranteed service traffic class (GS). First packets (pck1-pck6) relating to the at least one best-effort service traffic class (BE) are transferred within unreserved second packets (μpck) and / or within unused portions (uu) of the second packets (μpck).
Owner:KONINK PHILIPS ELECTRONICS NV
Electronic device and method of communication resource allocation
InactiveUS20090016338A1Configuration highIncreased latencyError preventionFrequency-division multiplex detailsData trafficResource allocation
An electronic device is provided comprising an interconnect means (N, sw0-sw2) for connecting a plurality of modules (IP); and at least one network interface (NI) for coupling at least one of the plurality of modules (IP) to the interconnect means (N; sw0-sw2) and for packetizing data from the modules (IP) into first packets (μpck). The communication over the interconnect (N; sw0-sw2) is based on time slots, wherein a second packet (μpck) is transferred during one time slot. A data traffic over the interconnect means (N; sw0-sw2) comprises at least one guaranteed service traffic class (GS) and / or at least one best-effort service traffic class (BE). First packets (GSpck) relating to the at least one guaranteed service traffic class (GS) are transferred in second packets (μpck) within time slots reserved for the guaranteed service traffic class (GS). First packets (pck1-pck6) relating to the at least one best-effort service traffic class (BE) are transferred within unreserved second packets (μpck) and / or within unused portions (uu) of the second packets (μpck).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Memory device having different burst order addressing for read and write operations
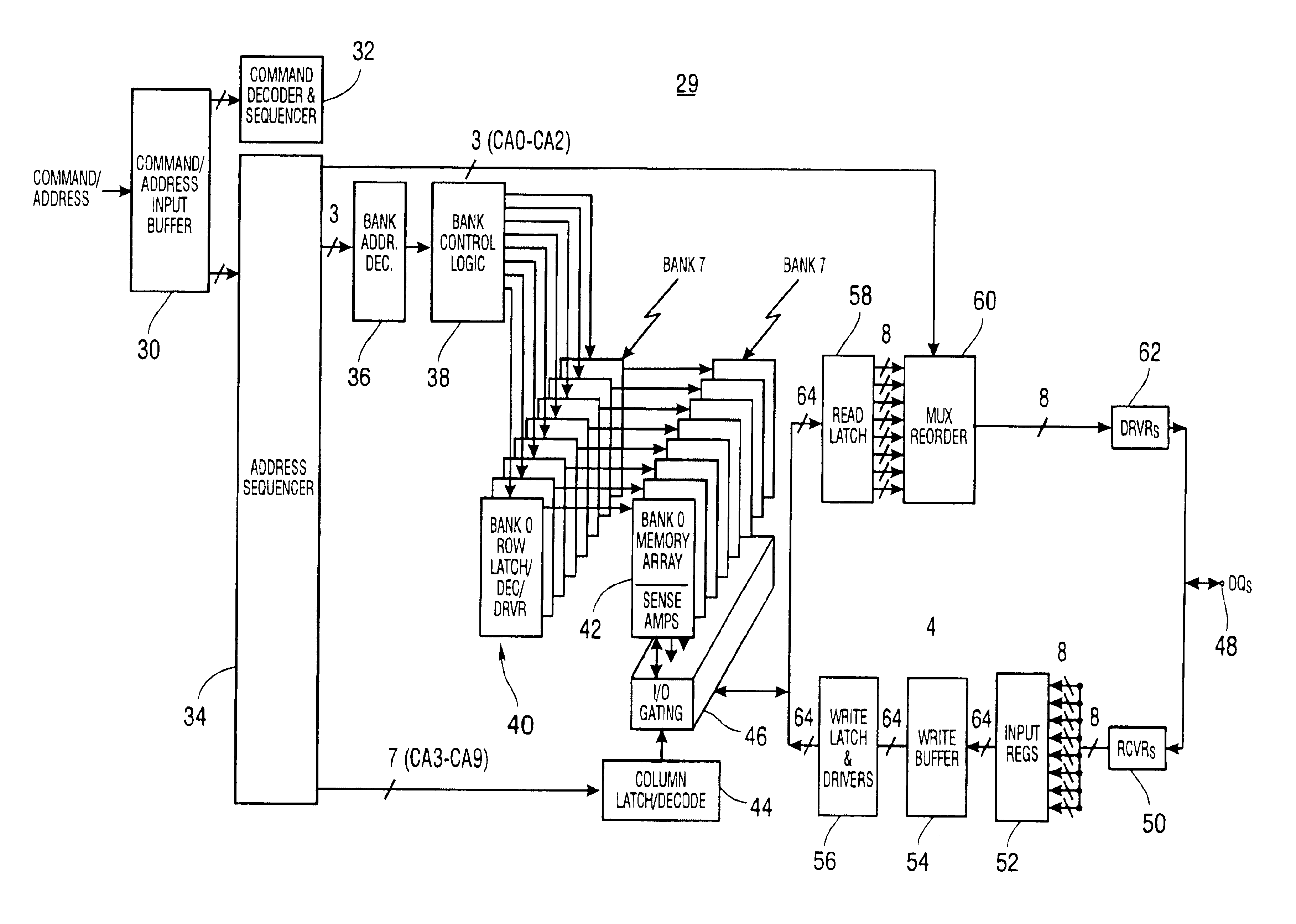
InactiveUS6931483B2Increased latencyDigital storageMemory systemsArray data structureLeast significant bit
A method comprising reordering a block of n-bit words output from a memory array according to information in certain address bits before outputting at least one n-bit word from a memory device and ignoring said certain address bits before inputting at least one n-bit word into said memory array. The method may additionally comprise examining at least two of the least significant bits of a column address and wherein said reordering is responsive to said examining step. Thus, for reads a specific 8 bit burst is identified by the most significant column address bits while the least significant bits CA0-CA2 identify the most critical word and the read wrap sequence after the critical word. For writes, the burst is identified by the most significant column addresses with CA0-CA2 being “don't care” bits assumed to be 000.
Owner:ROUND ROCK RES LLC
Random gap insertion in an optical ring network
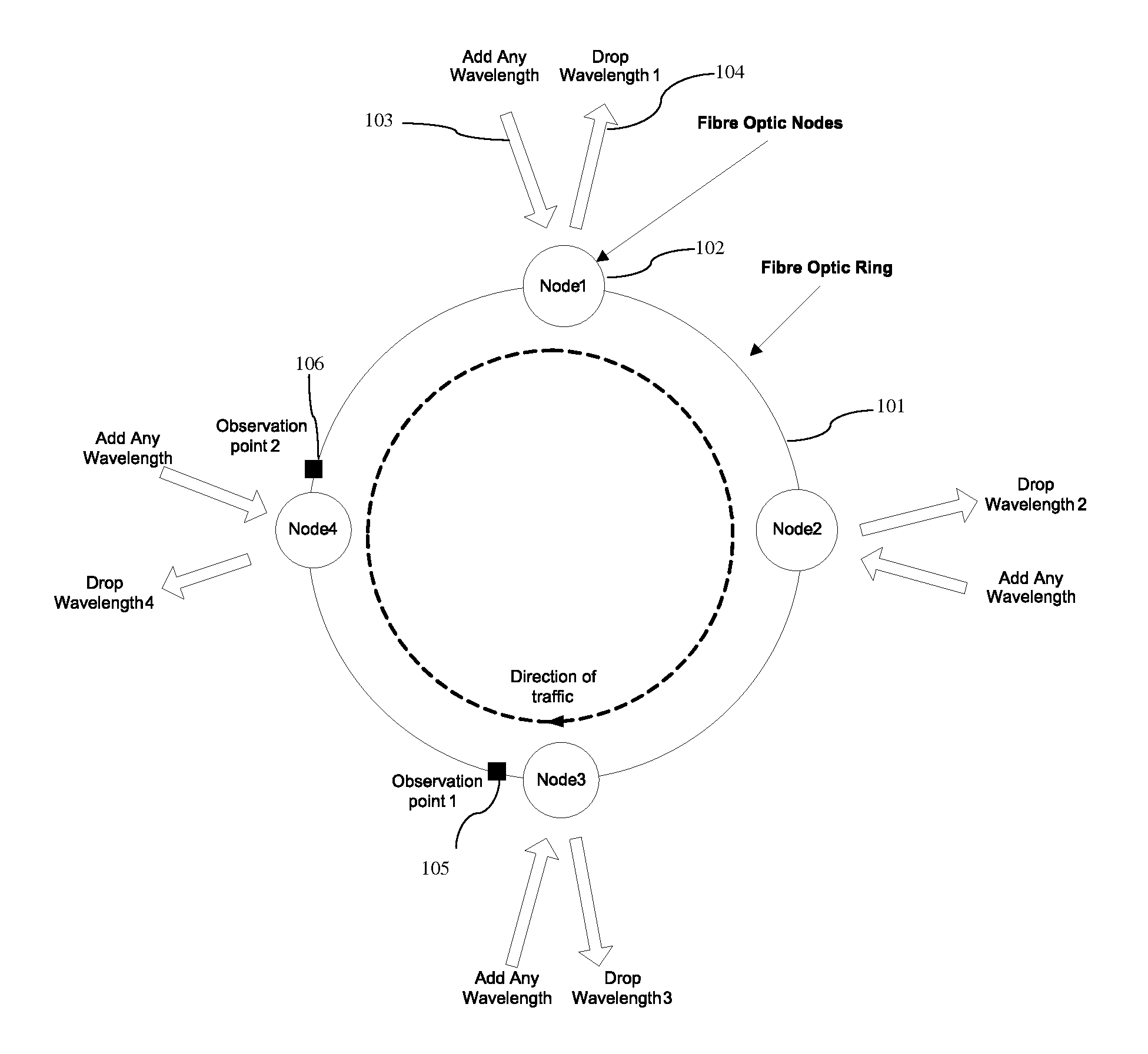
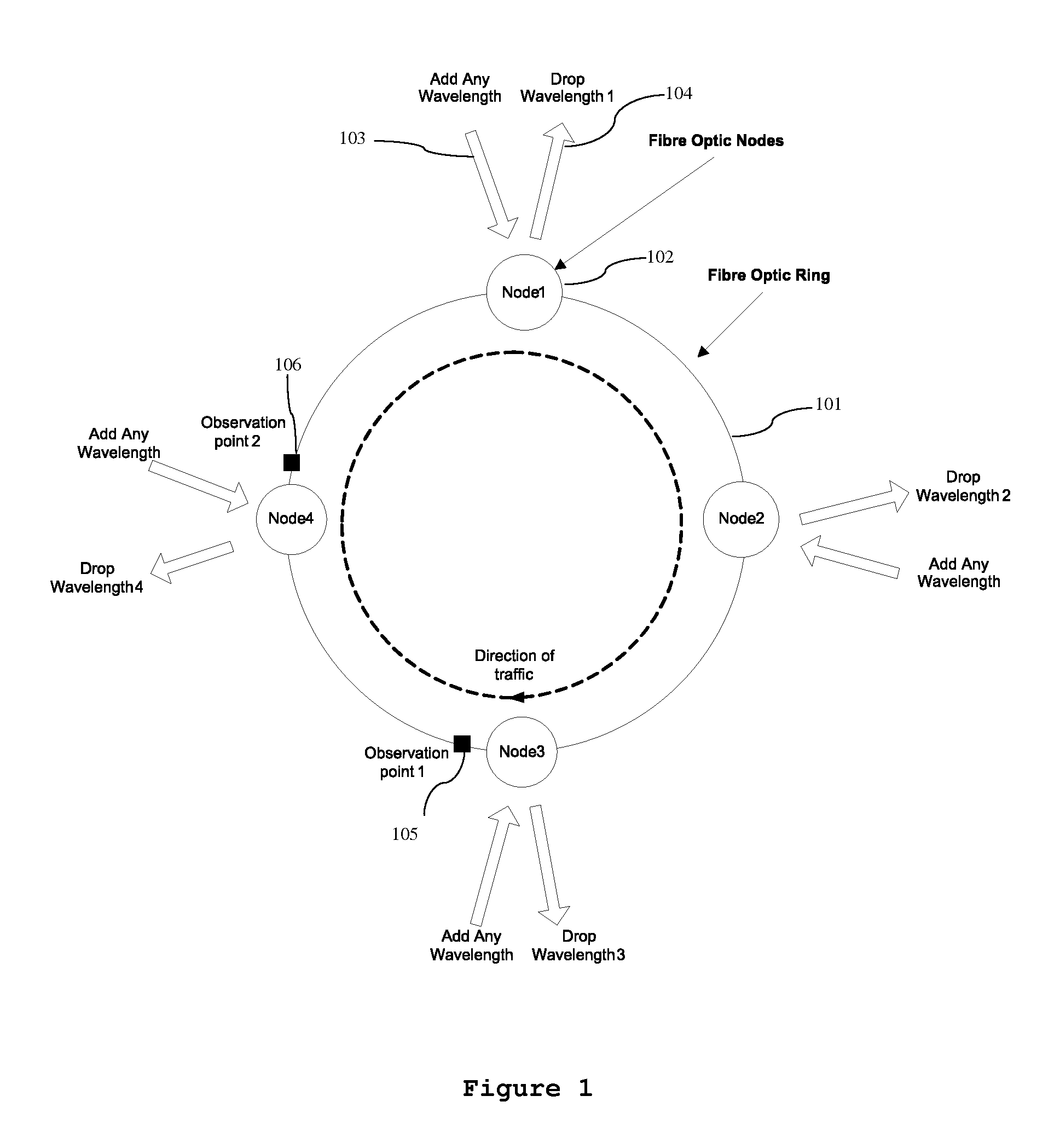
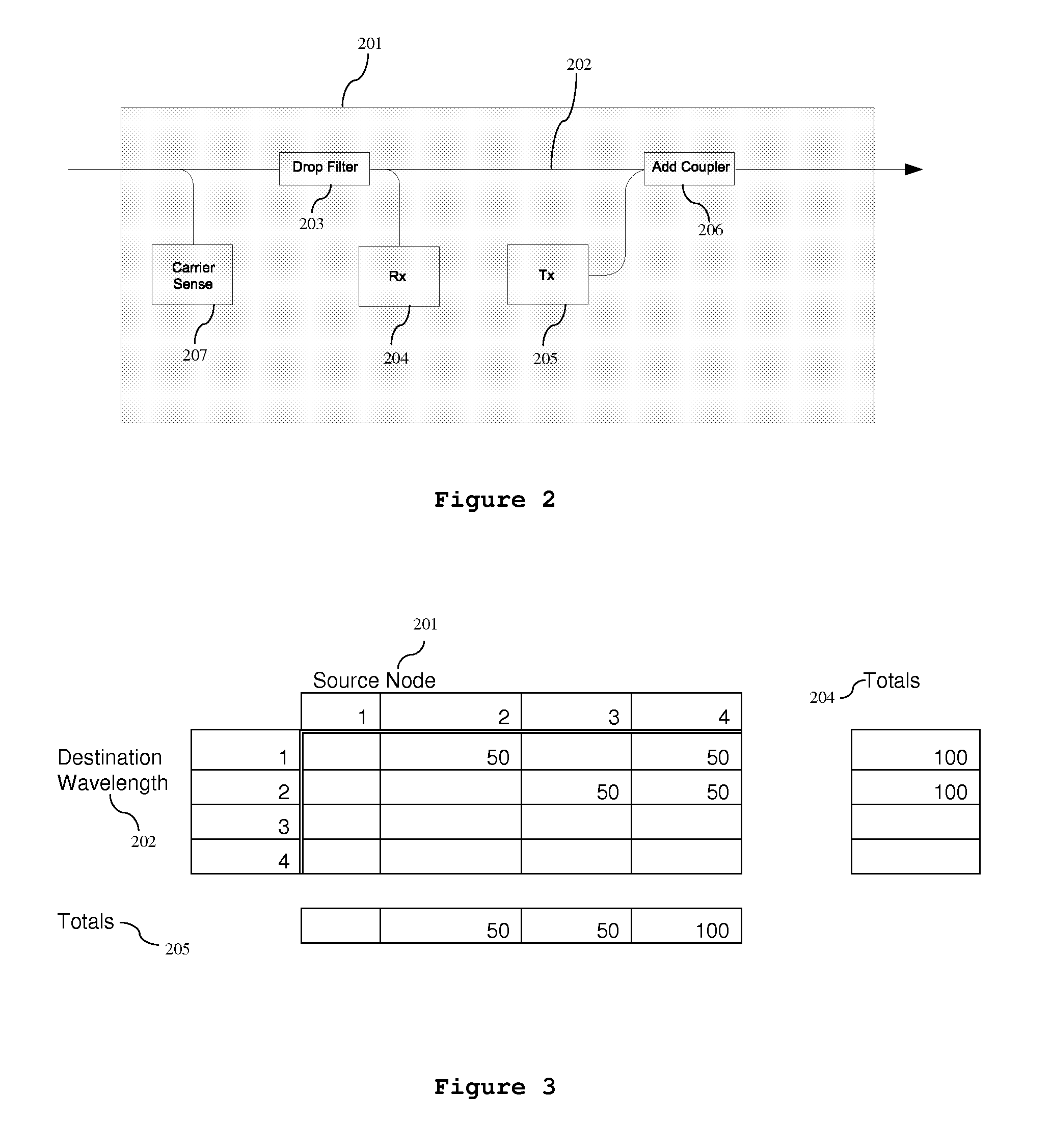
InactiveUS20130114958A1Avoid spreadingFairness in latencyRing-type electromagnetic networksWavelength-division multiplex systemsBurst transmissionRing network
The invention provides a burst transmission optical fibre wavelength routed ring network and method comprising a plurality of nodes on a network ring where each node can drop and add a wavelength. The network has a control means to control the wavelength to be transmitted on the network ring in a burst transmit mode from each node over a scheduling interval. The invention provides a random generator for generating a plurality of gap intervals over the scheduling interval, such that the gap intervals allow for wavelengths from different nodes to transmit wavelengths in said gaps to achieve a fair access to bandwidth and fair latency in the ring network.
Owner:INTUNE TECH
Method and apparatus for transmitting high bandwidth signals with low bandwidth transponders
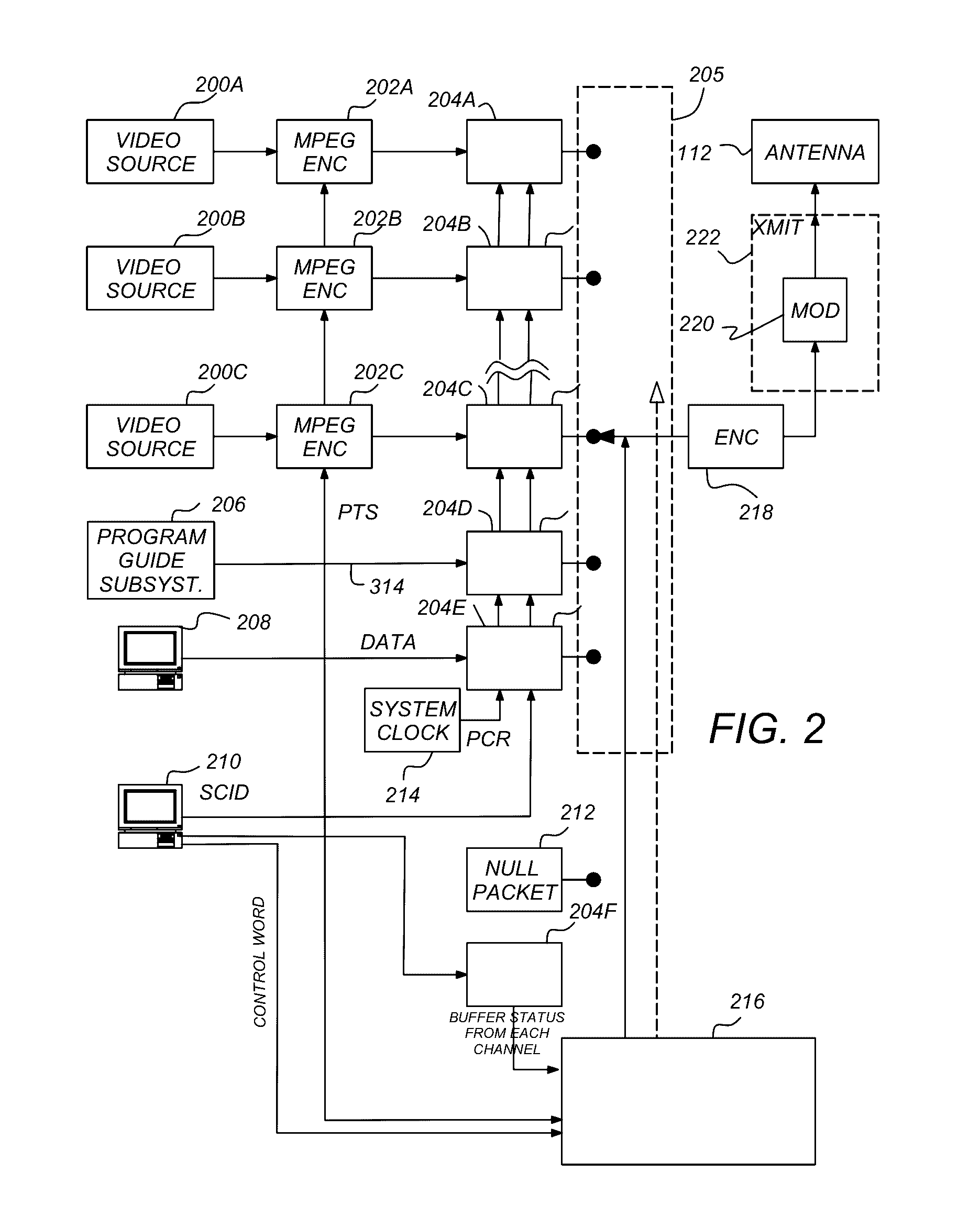
ActiveUS9525978B2Increased latencyBroadcast service distributionSelective content distributionMultiplexingHigh bandwidth
A method and apparatus for transmitting a plurality of elementary data streams to a plurality of receivers is disclosed. In one embodiment, the method comprises the steps of generating M data streams comprising K multiplexed elementary data streams in a first entity, transmitting the M data streams to a second entity, generating N transmitter streams from the M data streams in the second entity; and transmitting each of the N transmitter streams to the plurality of receivers using an associated one of N broadcast sub-transmitters.
Owner:DIRECTV LLC
Polar Coding for Beam Sweeping Broadcast Channel
ActiveUS20210176739A1Good distance propertyEasy to combineAssess restrictionCode conversionWireless transmissionWireless transmitter
Owner:TELEFON AB LM ERICSSON (PUBL)
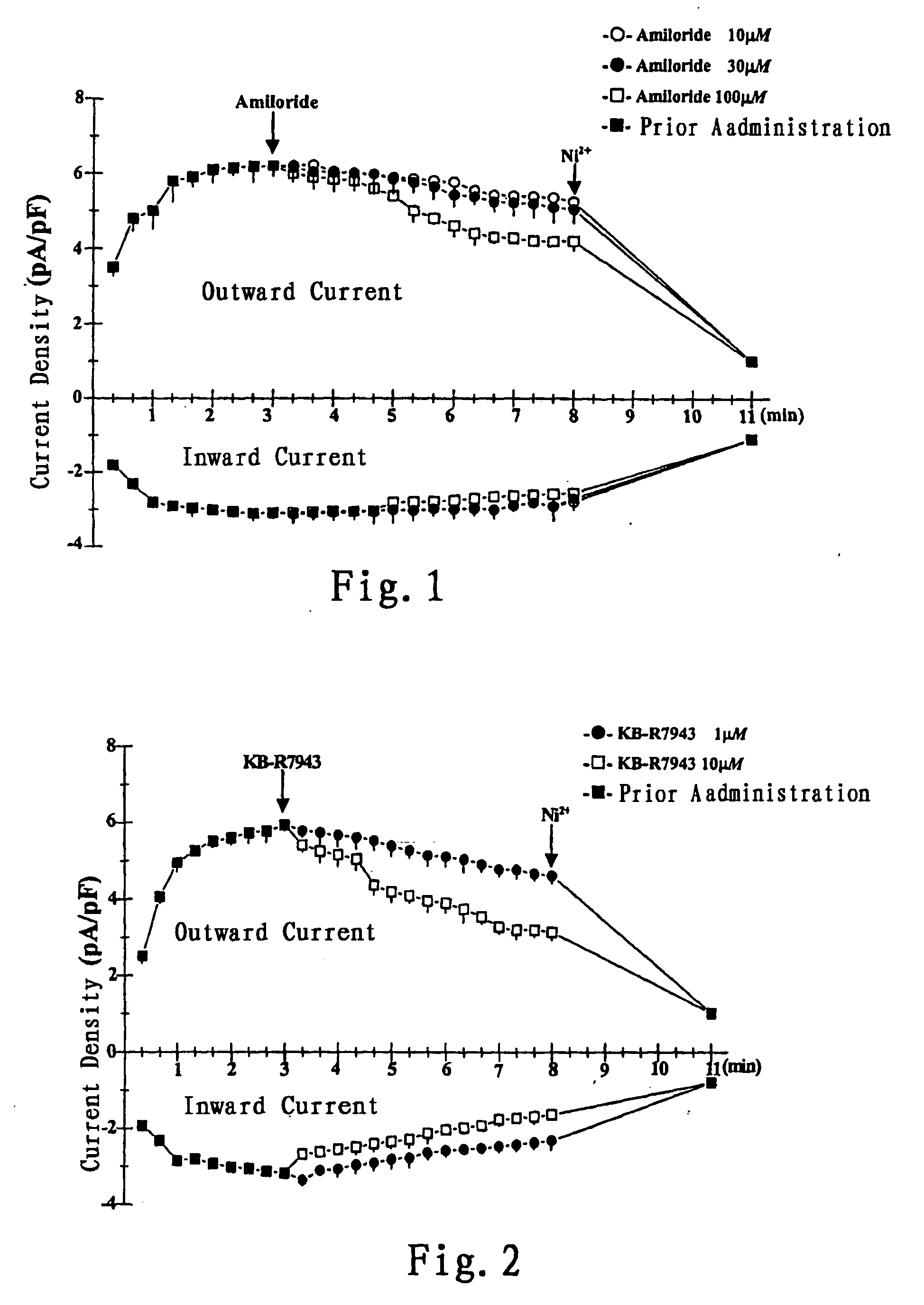
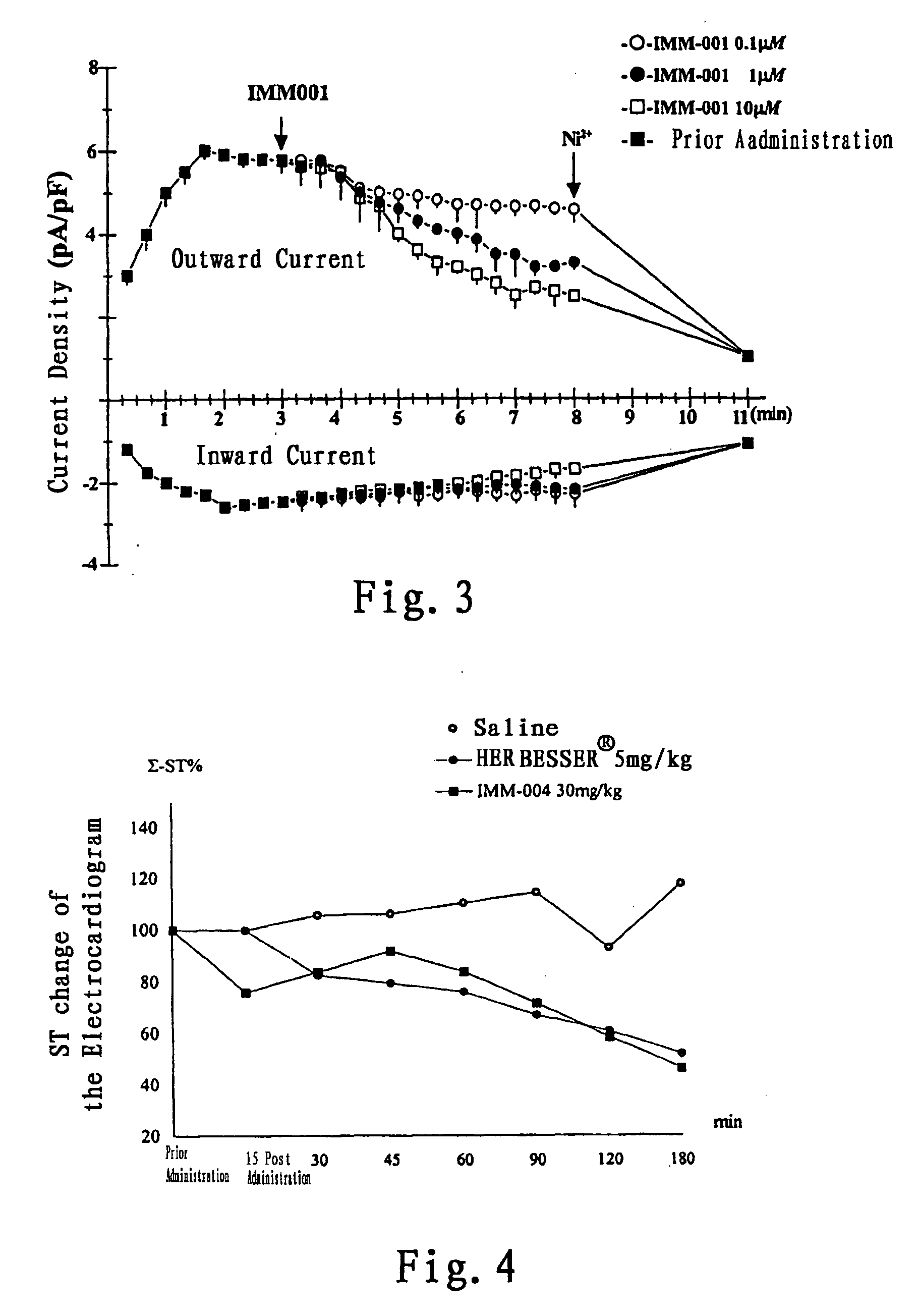
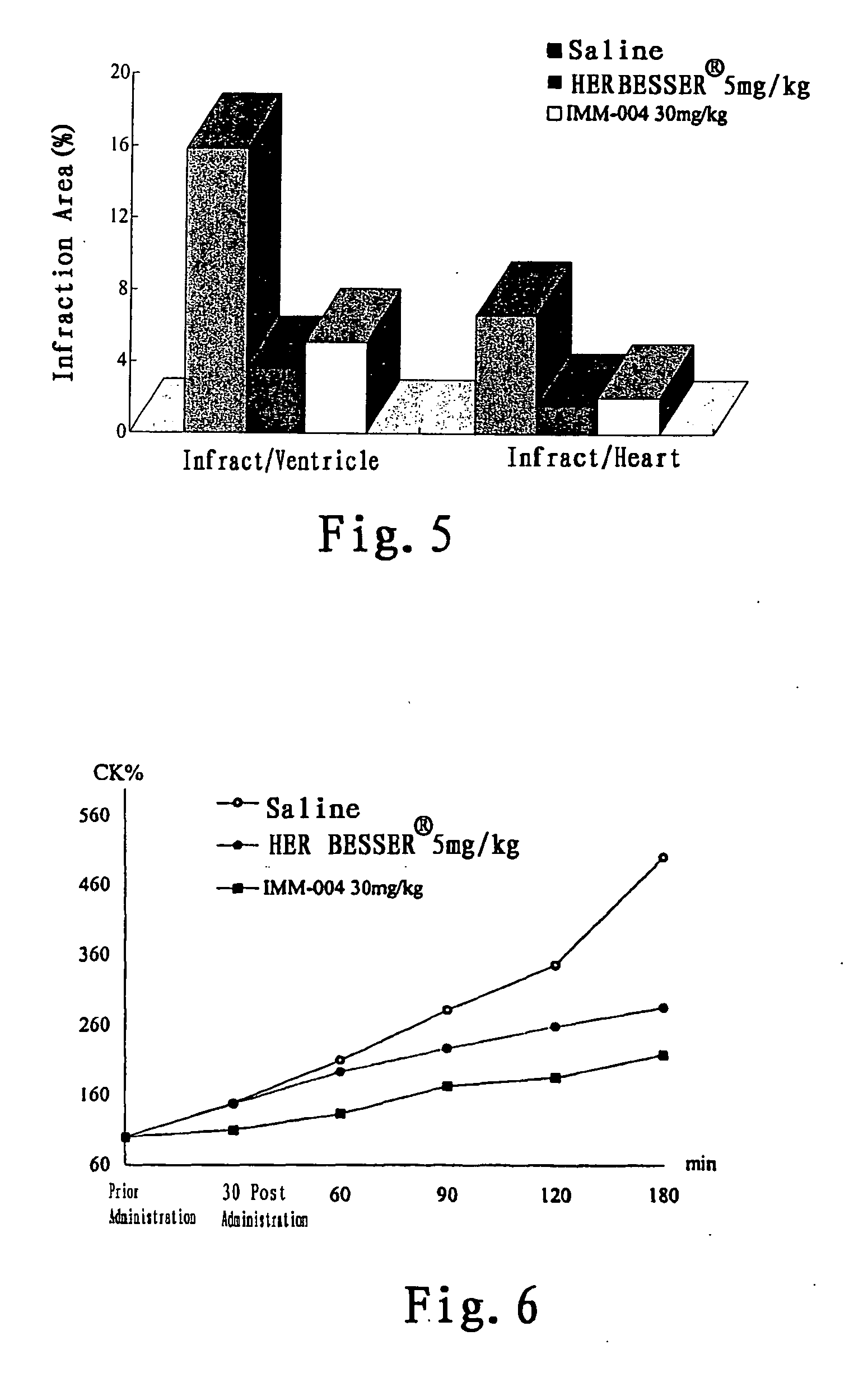
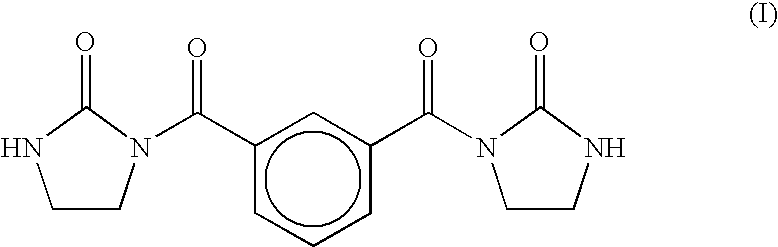
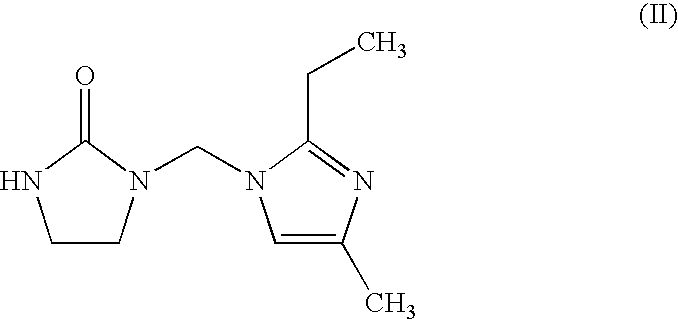
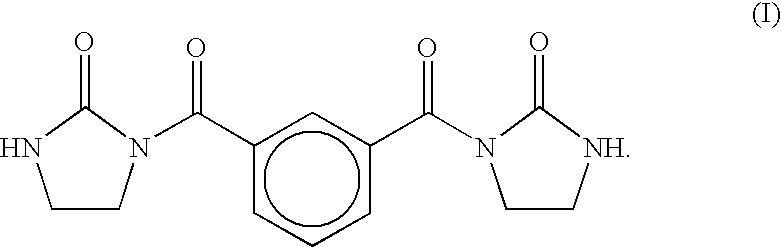
Use of benzisoselenazolone compounds against ischemic myocardial damage
InactiveUS20060135569A1Improve the protective effectImprove latencyBiocideOrganic chemistryCoronary arteriesMedicine
The invention discloses use of benzisoselenazolones, particularly compounds represented by the general formula (I) against ischemic myocardial injury. The compounds are characterized by selectively inhibiting Na+ / Ca2+ exchange, dilating coronary artery and decreasing myocardial oxygen consumption, which possess the advantages of high activity, potent specificity and low toxicity.
Owner:INST OF MATERIA MEDICA AN INST OF THE CHINESE ACAD OF MEDICAL SCI
Method and apparatus for scheduling request in a wireless communication system
ActiveUS10251191B2Increased latencyMaximize resource utilizationSignal allocationConnection managementCommunications systemResource information
Provided are a method and apparatus for requesting scheduling for an uplink data transmission in a wireless communication system. The method may include receiving, by a user equipment, an additional scheduling request (SR) resource configuration information including additional SR resource information and buffer size information configured to the additional SR resource in addition to a default SR resource from a base station, transmitting, by the user equipment, an SR through the default SR resource or the additional SR resource to the base station, receiving, by the user equipment, an uplink resource allocation information which is determined according to the resource in which the SR is transmitted from the base station, and transmitting, by the user equipment, the uplink data to the base station through a physical uplink shared channel (PUSCH) resource which is allocated by the uplink resource allocation information.
Owner:LG ELECTRONICS INC
Epoxy resin with dibasic acid (methyl ester)/ethyleneurea modifier
Owner:ARDES ENTERPRISES
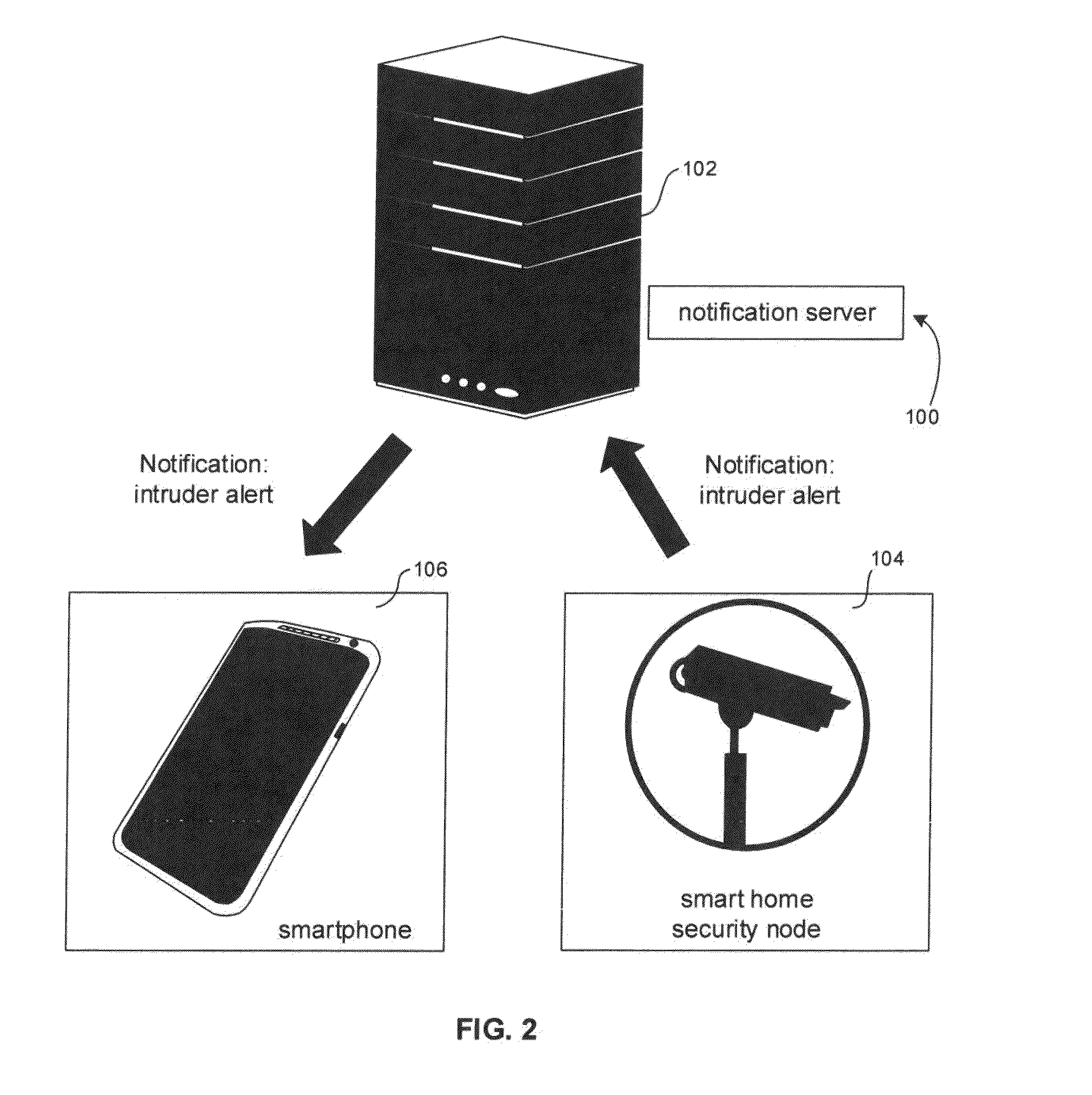
Unified notification and response system
ActiveUS20160255480A1Facilitates unified notificationImprove responseSpeech analysisMessaging/mailboxes/announcementsSocial webNotification system
A unified notification system in which notifications for all of a user's devices and services appear in windows of all of the user's devices. Notifications related to the user's social network friends and public users that the user subscribes to may also appear in the windows of all devices. Events from the user's devices and accounts are sent to a server for aggregation and provisioning back to the user's devices. To this end, a HTTP API may query the server to receive the user's notifications. Notifications that include content can also include metadata. The user can respond to any notification from any device.
Owner:SONY CORP
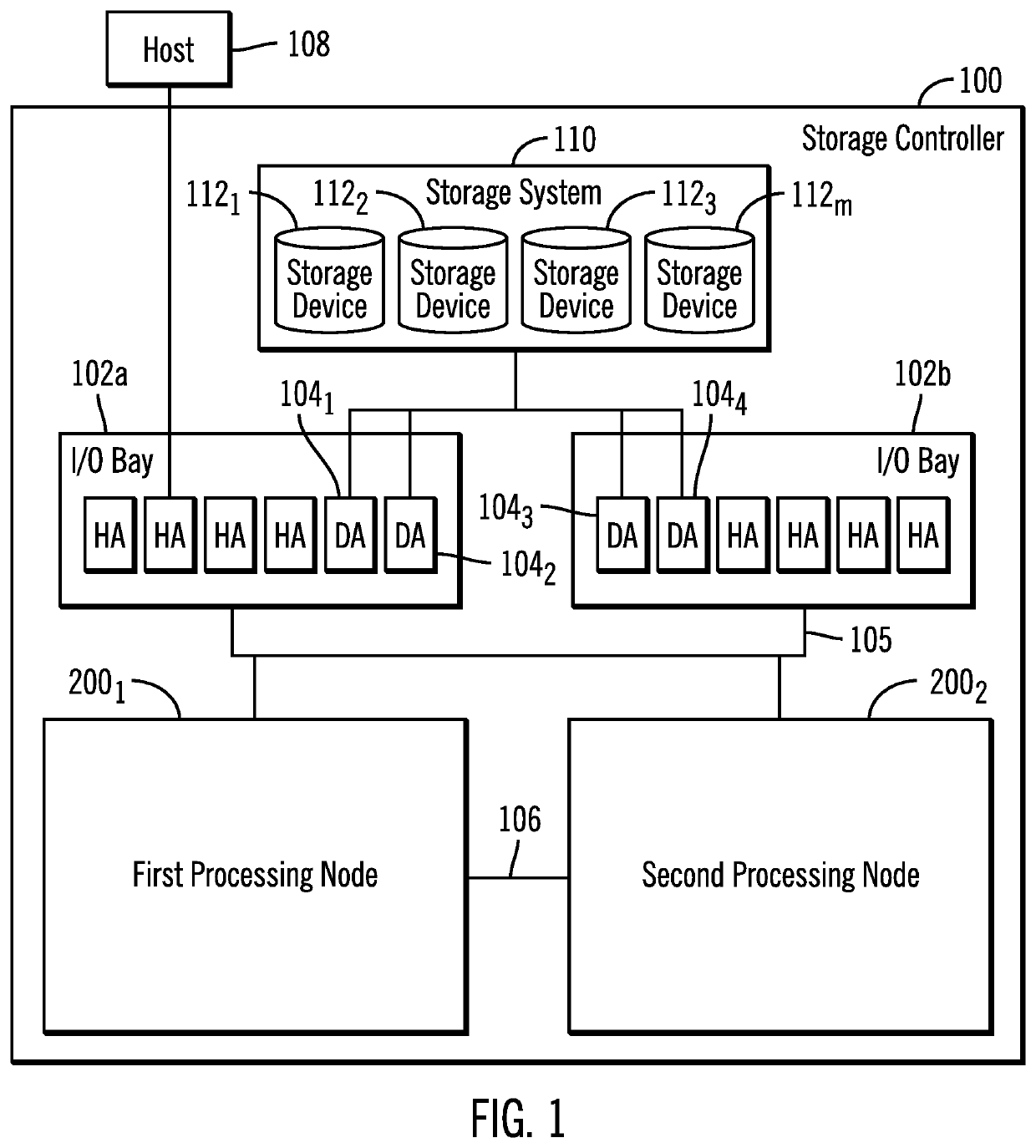
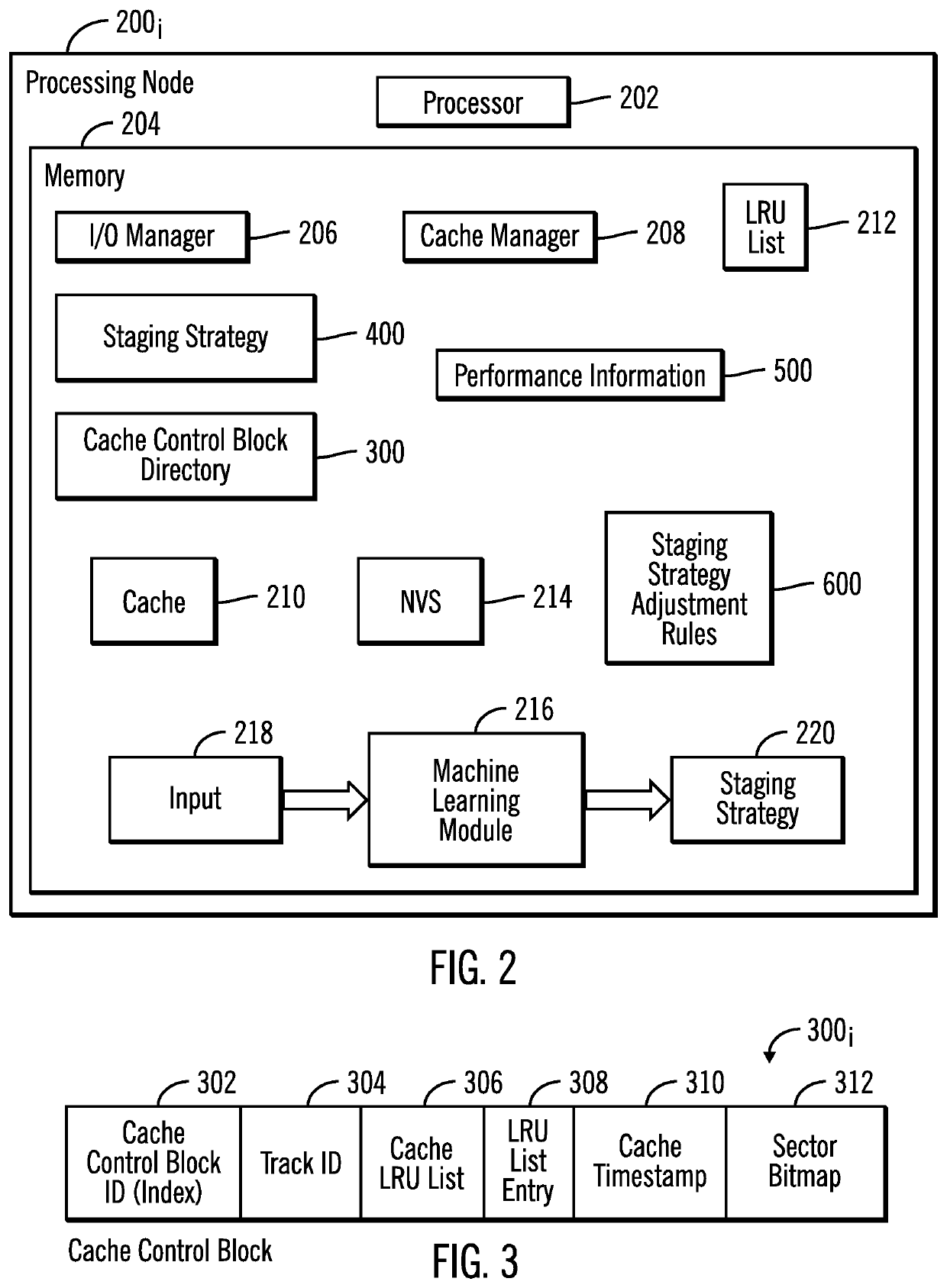
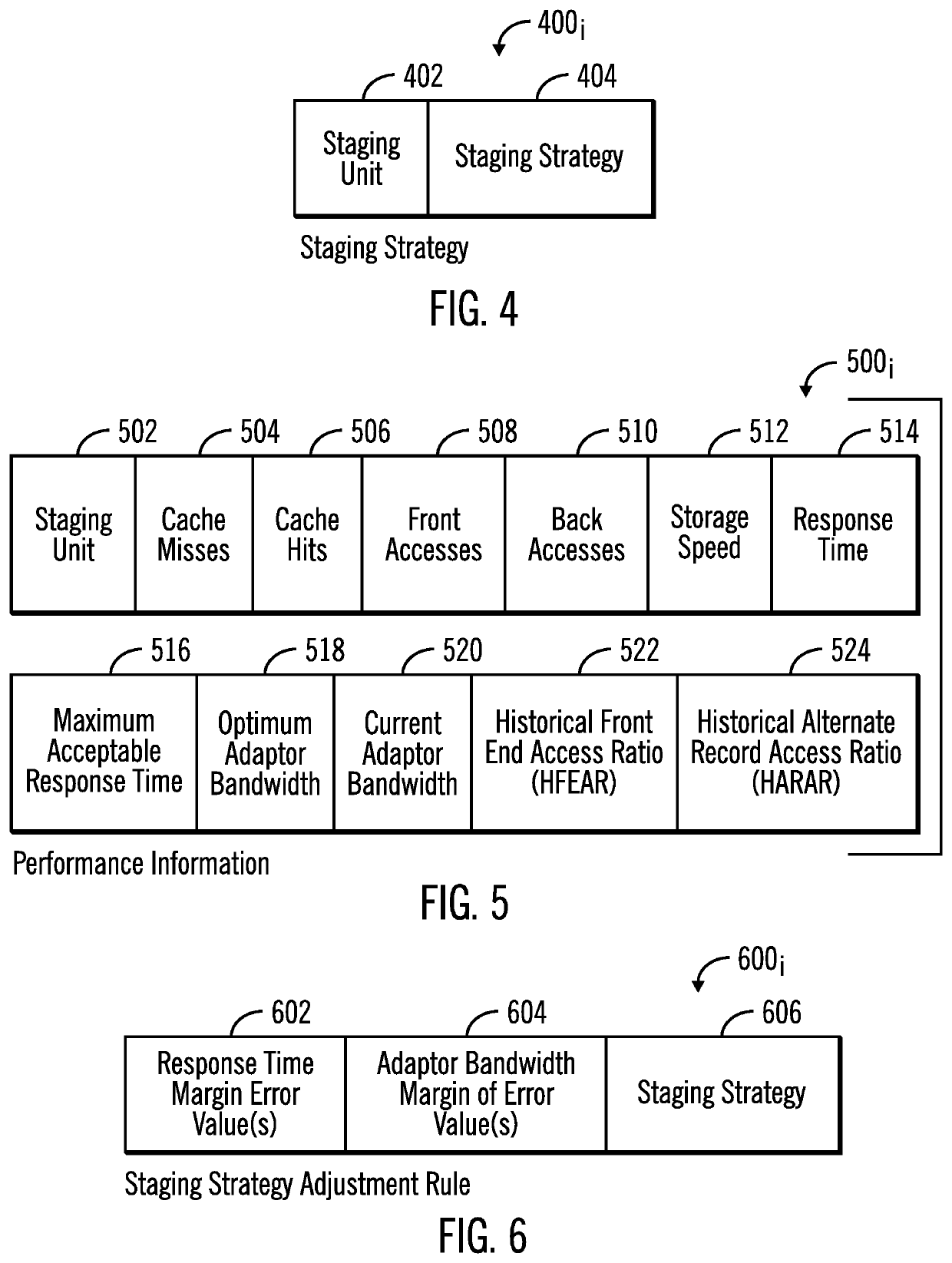
Determining sectors of a track to stage into cache by training a machine learning module
ActiveUS20200042905A1Negatively impacting performanceIncreased latencyMachine learningNeural learning methodsReal-time computingComputer program
Provided are a computer program product, system, and method for determining sectors of a track to stage into cache by training a machine learning module. A machine learning module that receives as input performance attributes of system components affected by staging tracks from the storage to the cache and outputs a staging strategy comprising one of a plurality of staging strategy indicating at least one of a plurality of sectors of a track to stage into the cache. A margin of error is determined based on a current value of a performance attribute and a threshold of the performance attribute. An adjusted staging strategy is determined based on the margin of error. The machine learning module is retrained with current performance attributes to output the adjusted staging strategy.
Owner:IBM CORP
Thin front channel photopolymer drop ejector
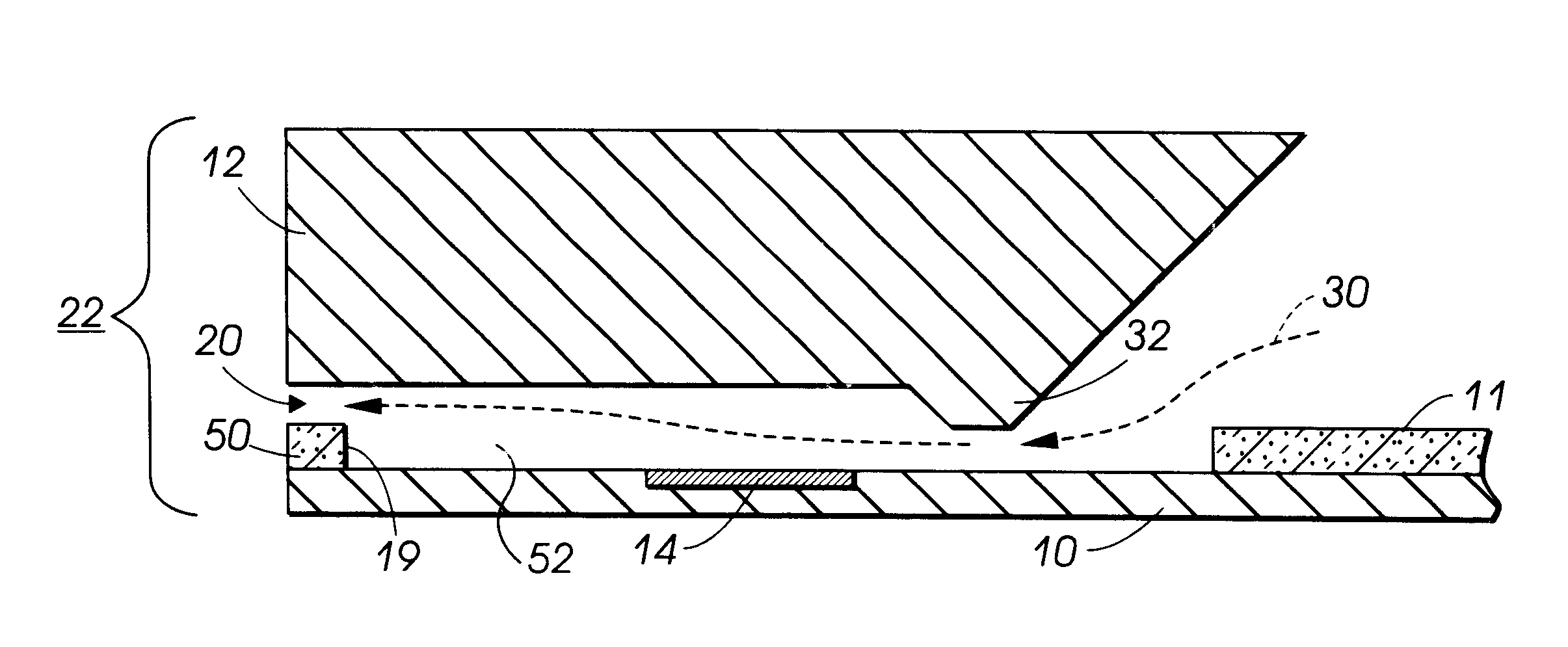
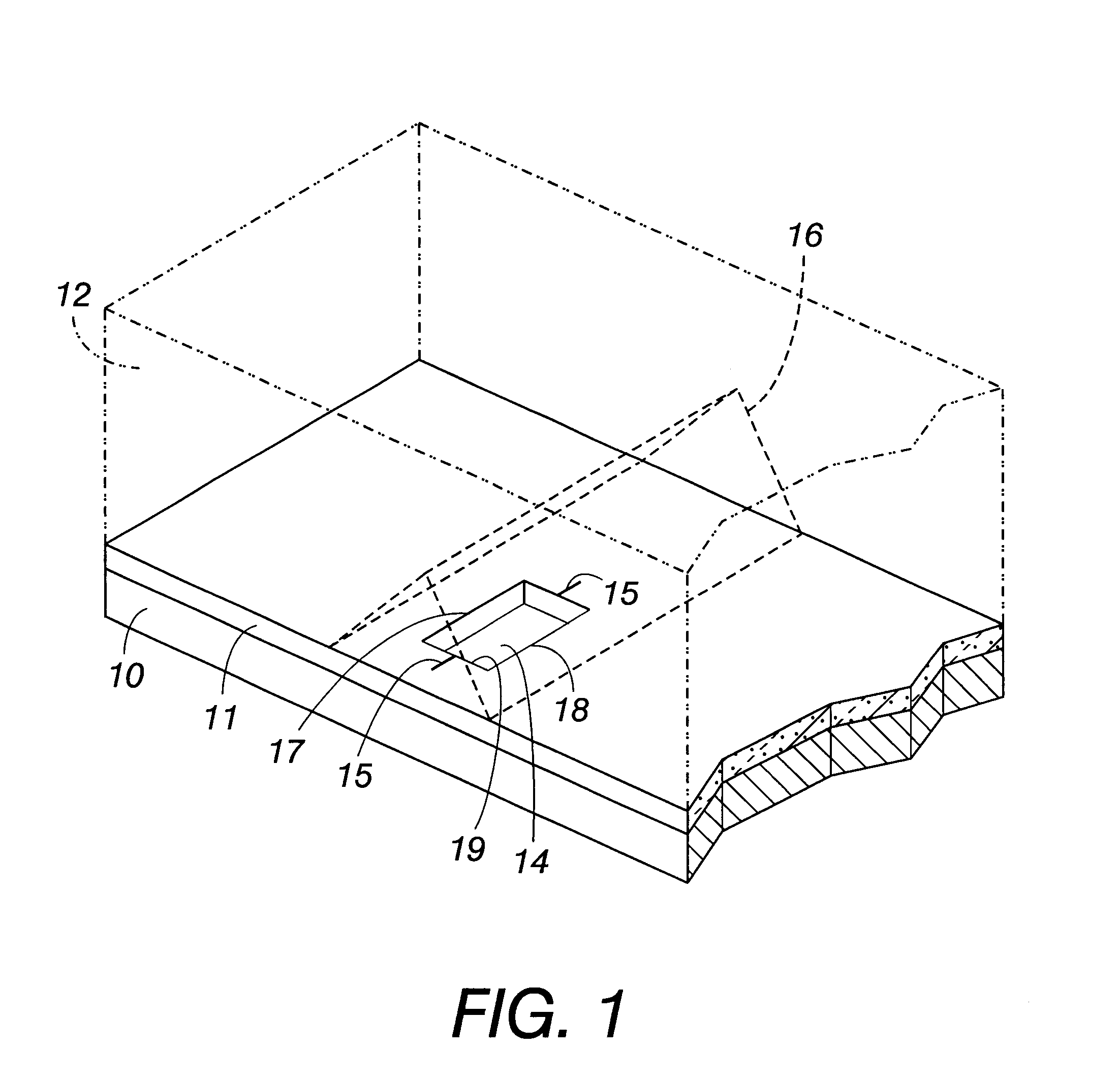
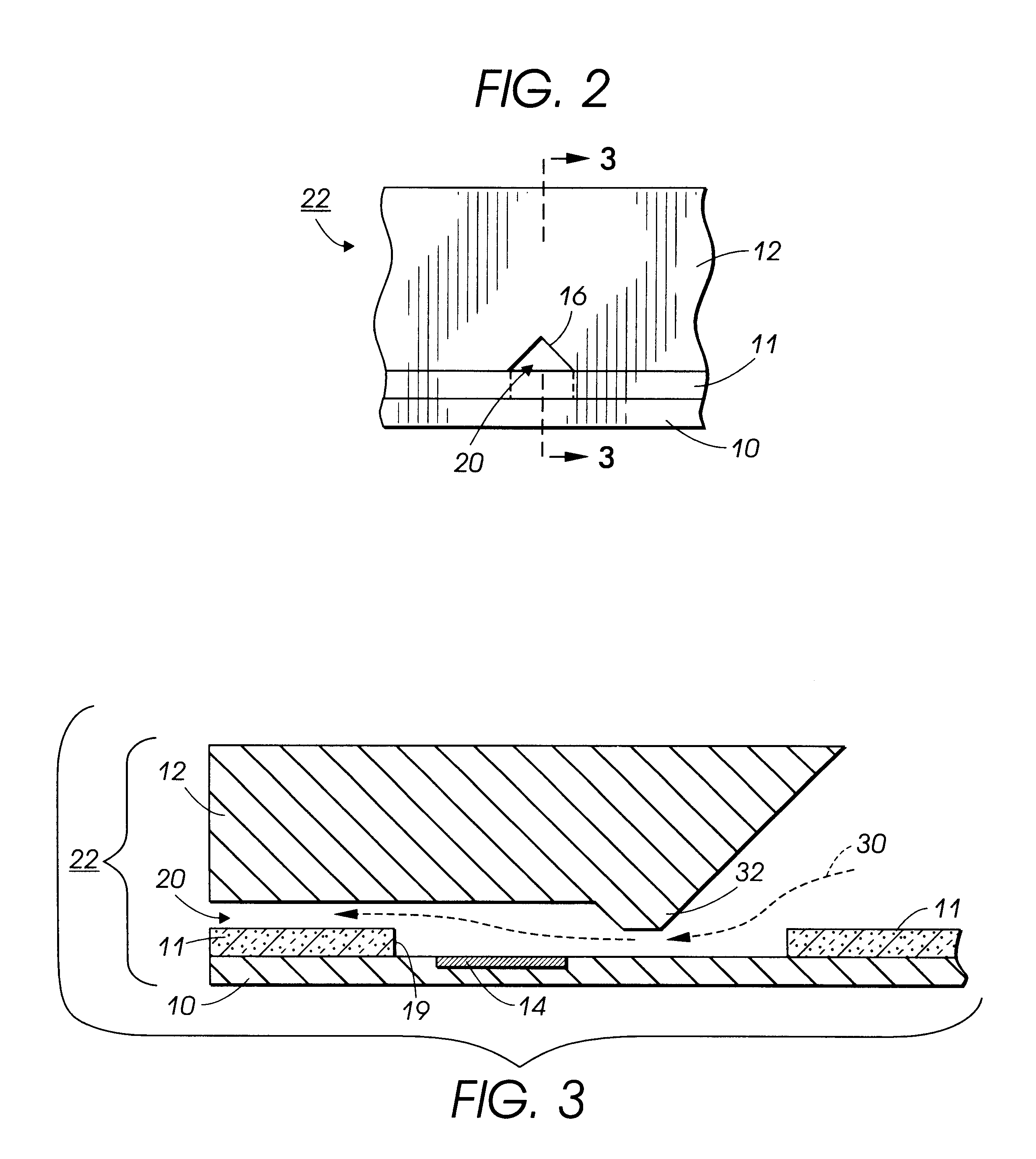
An improved ink jet head wherein an ink reservoir is provided in the ink jet channel. Such a arrangement improves the printhead latency and broadens the range of inks which may be suitably utilized. In one alternative, this ink reservoir is provided between the heater and the face of the printhead and is actually an expansion of the heater pit. In another alternative, this is accomplished by shifting the forward edge of the heater pit as provided in the thick polyimide (or other photopolymer) layer found sandwiched between a heater chip and a ODE channel chip.
Owner:XEROX CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com