Patents
Literature
106 results about "Action rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
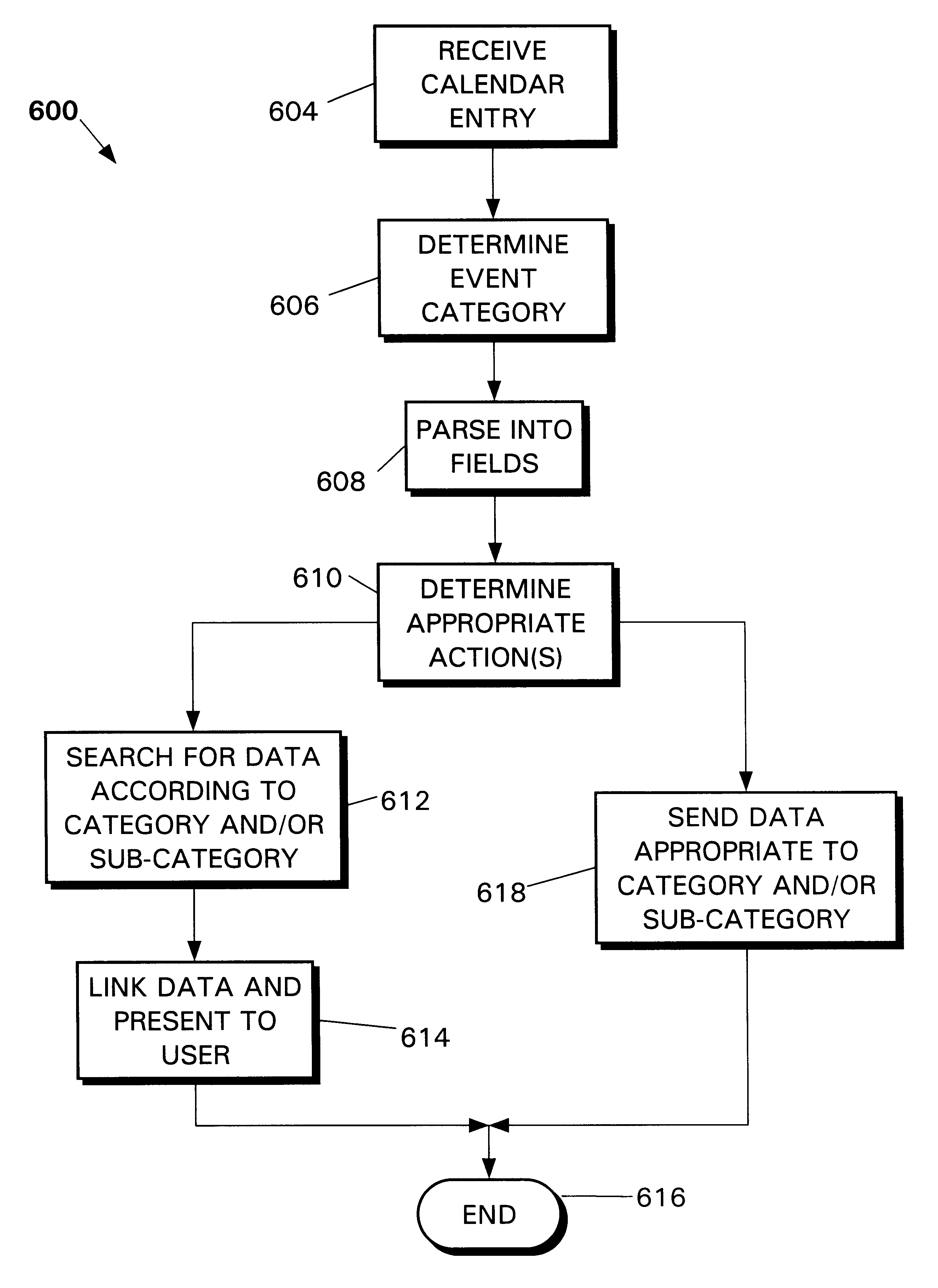
Active calendar system
An "active" calendar automatically analyzes a user's calendar entries and sends machine-readable messages to destinations appropriate to content of the calendar entry. A group of event categories is established, each category specifying one class of anticipated calendar entry. An action rule database pre-associates each event category with one or more message formats each having a content and a destination. The action rule database also contains data identifying sources containing the content and destination for each message format. These sources include records of the action rule database itself, subparts of calendar entries of the pre-associated event category, one or more other databases, or a combination of the foregoing. After the calendar receives a user-submitted computer calendar entry describing a planned event, it identifies one of the event categories of the established group that classifies the planned event. For each message format pre-associated with the identified event category, the calendar determines the content and destination for the message as specified by the action rule database, and transmits the message to the destination.
Owner:IBM CORP
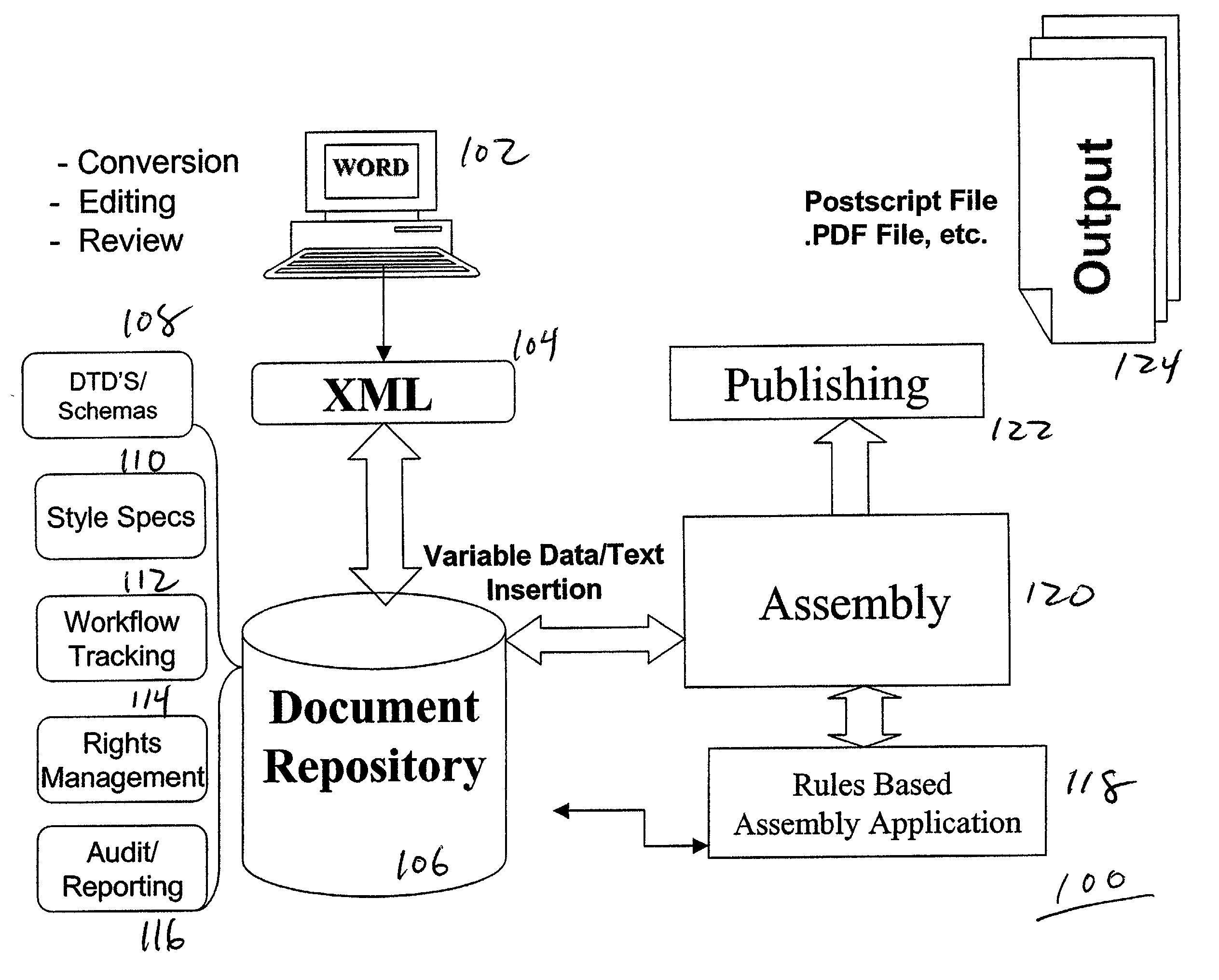
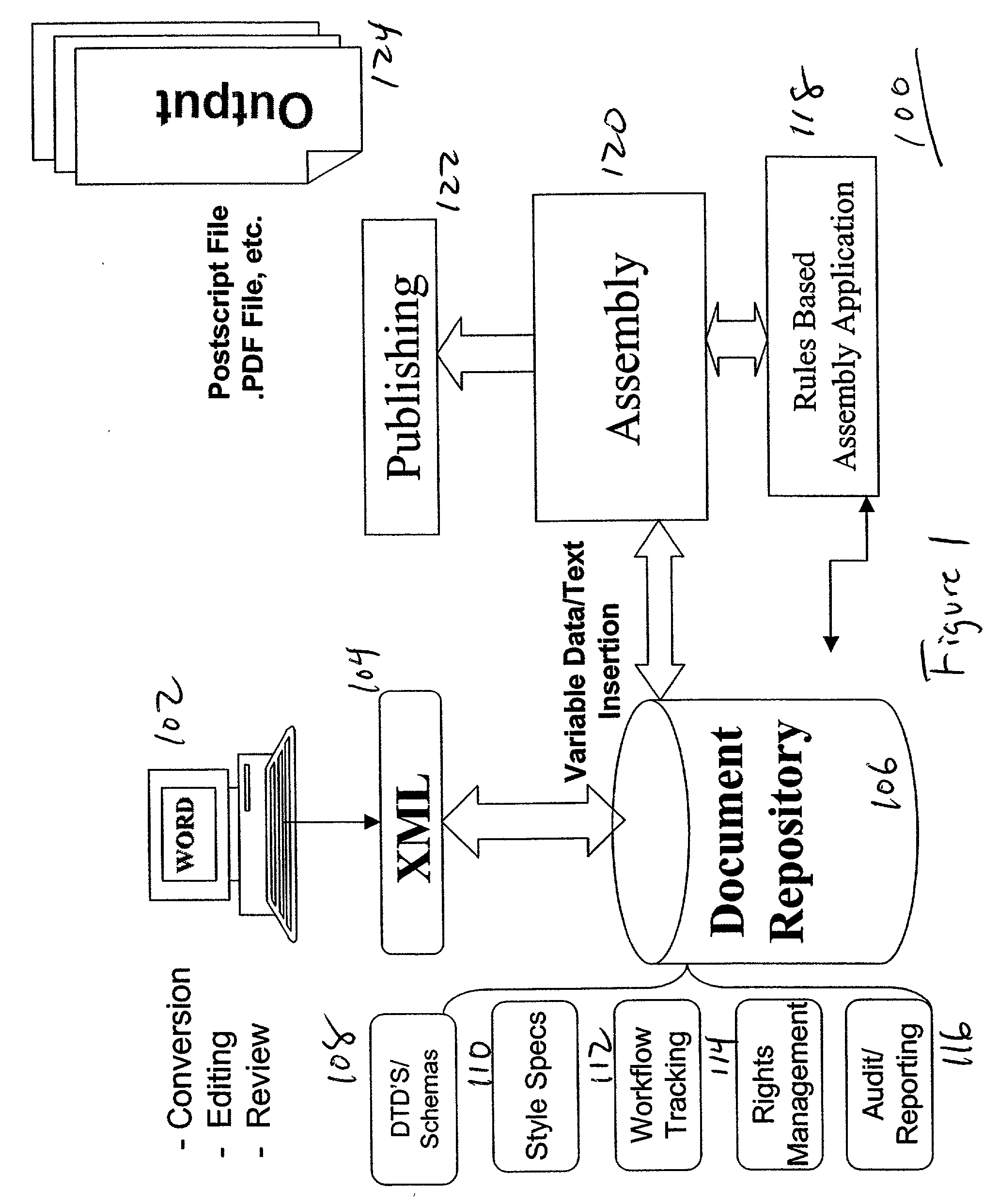
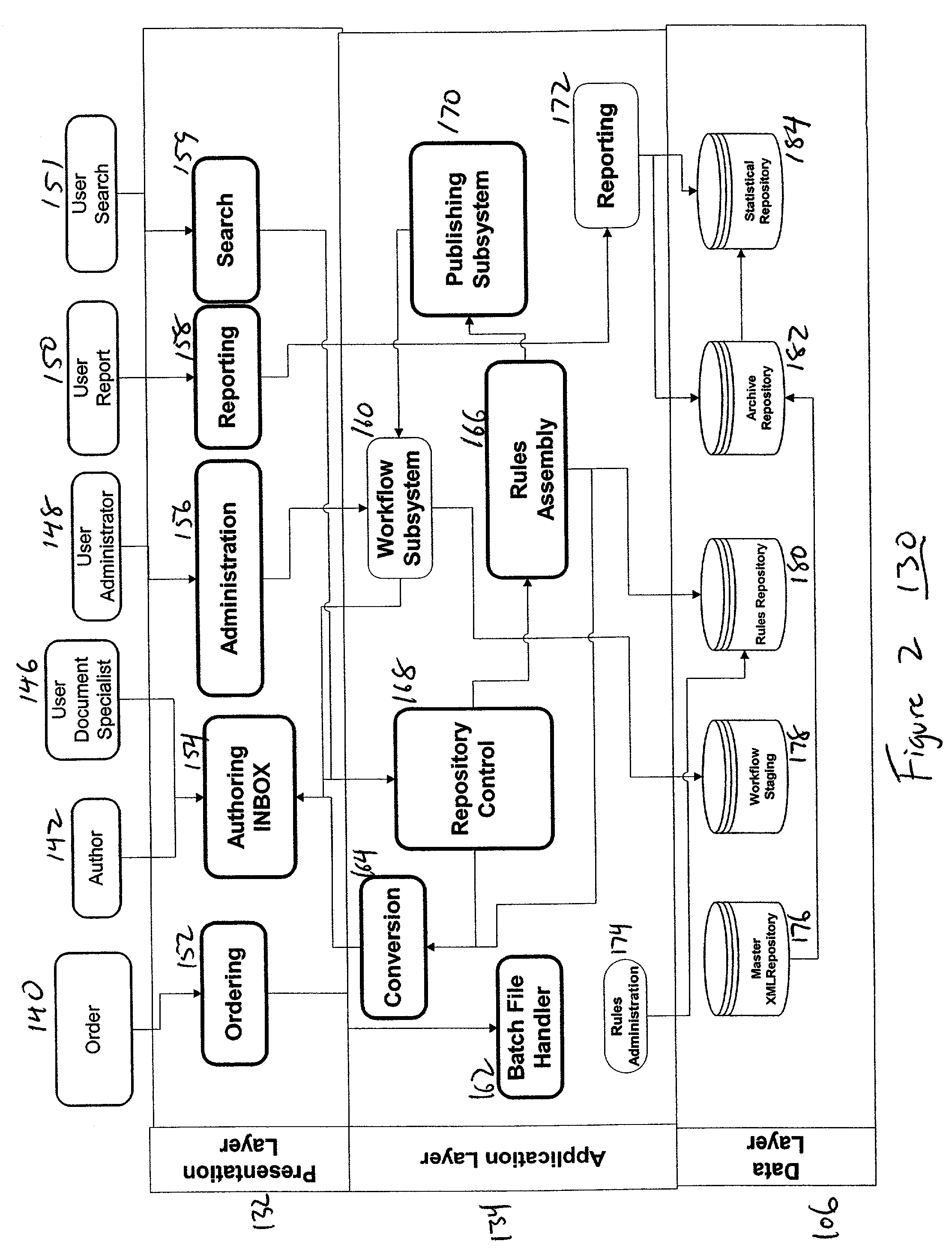
Document rules data structure and method of document publication therefrom
InactiveUS20040205656A1Natural language data processingSpecial data processing applicationsDocumentation procedureAction rule
A data structure and method of automatically creating a plurality of individually customized documents, each for a corresponding one of a plurality of individuals. Document components are created and stored. Document, condition and action rules governing document assembly are created and stored. Document specific data and text specific to individuals is provided with a document request that initiates assembly of a document. Each requested document is assembled automatically in response to the rules and provided data and text.
Owner:BENEFITNATION
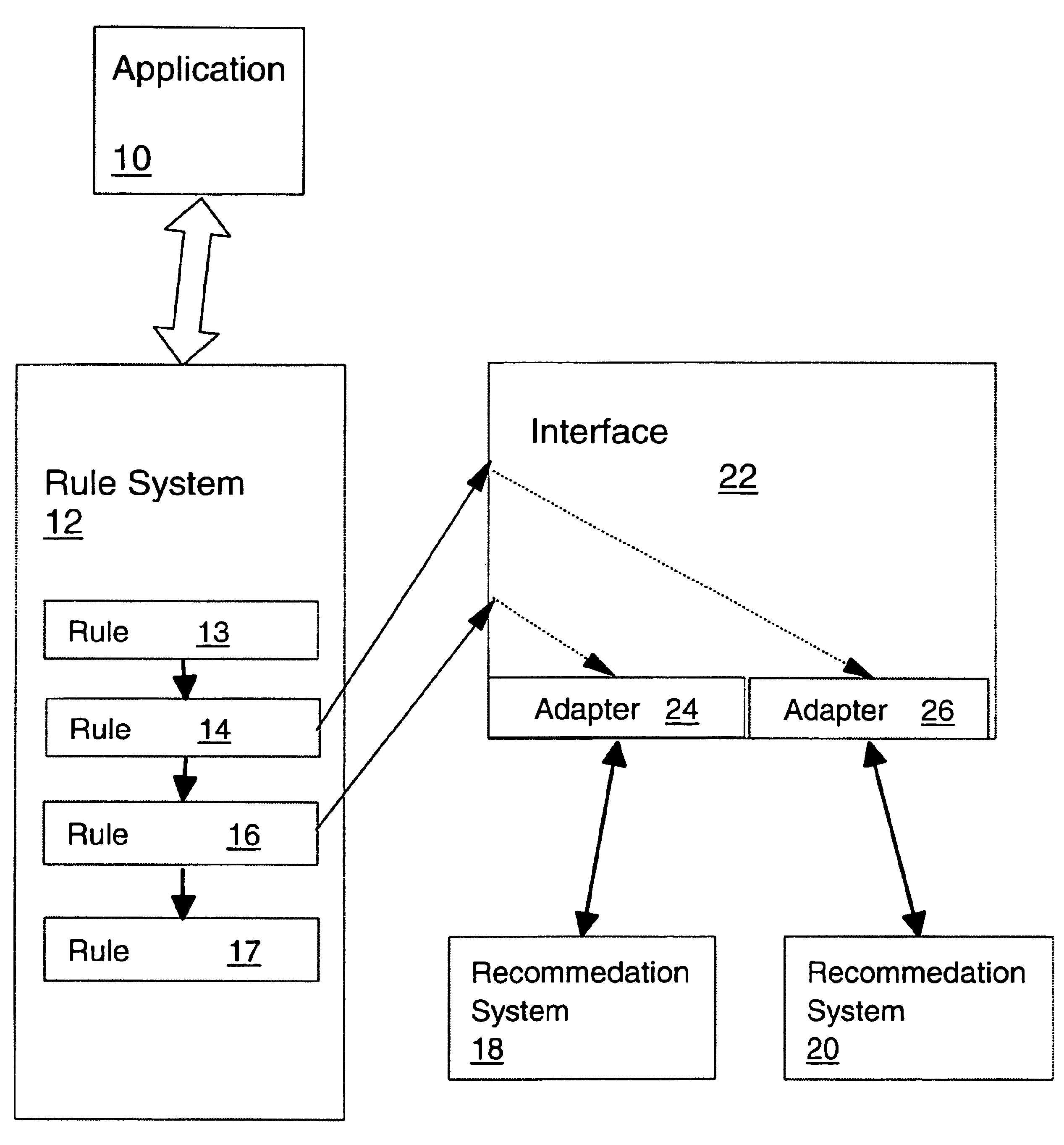
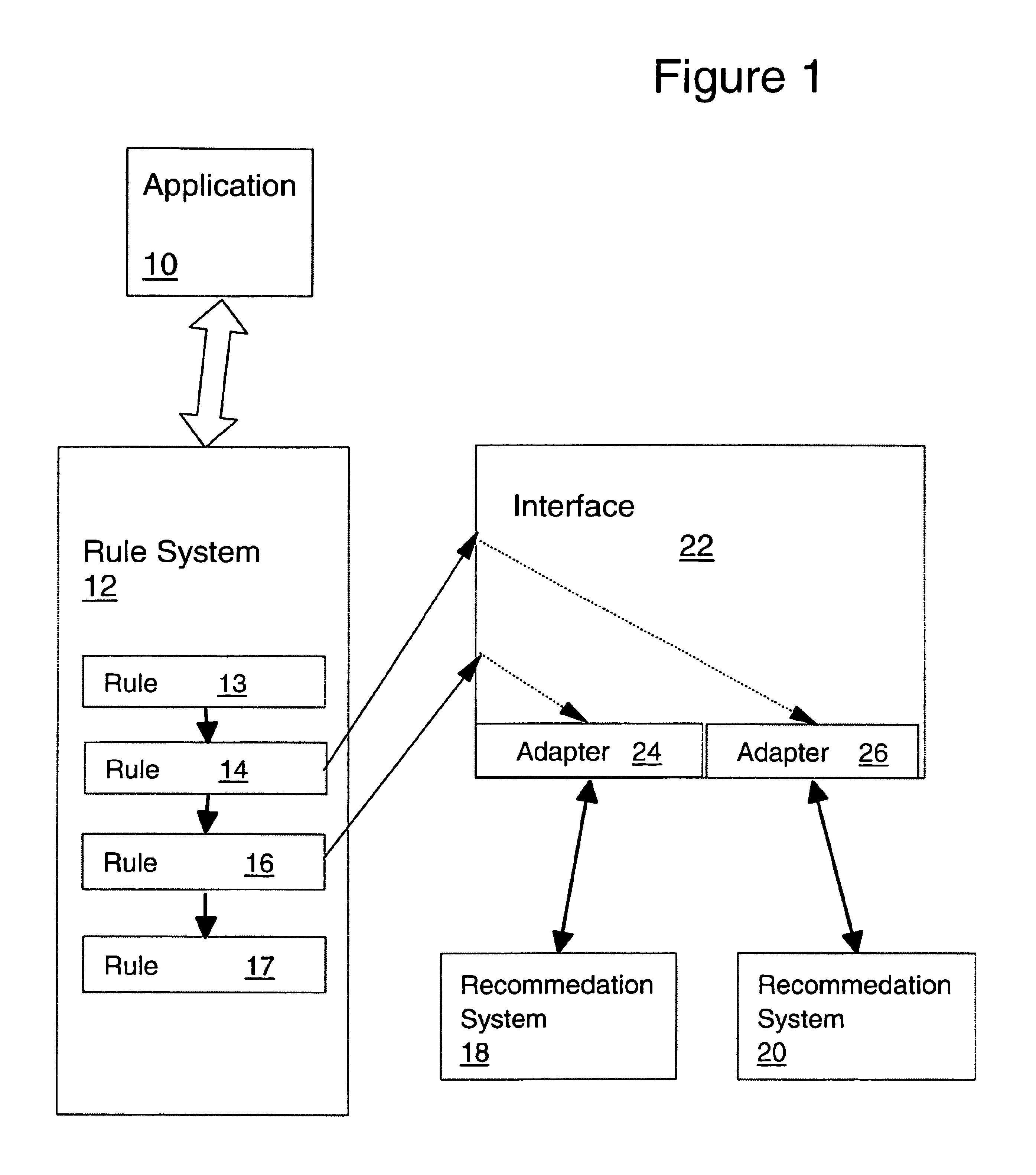
Rule-based personalization framework for integrating recommendation systems
InactiveUS6865565B2Knowledge representationSpecial data processing applicationsData feedPersonalization
A recommendation system includes a rule system for which defined recommendation system interfaces are available. The recommendation system interfaces are used in the action portion of predicate-action rules in the rule system to invoke non-rule-based systems. The non-rule-based systems provide recommendations to the rule system based on information passed to the non-rule-based systems on invocation and based on data made available to the non-rule-based systems. The rule system establishes a event-listener connection with the non-rule-based system to provide a data feed to the non-rule-based system.
Owner:PAYPAL INC
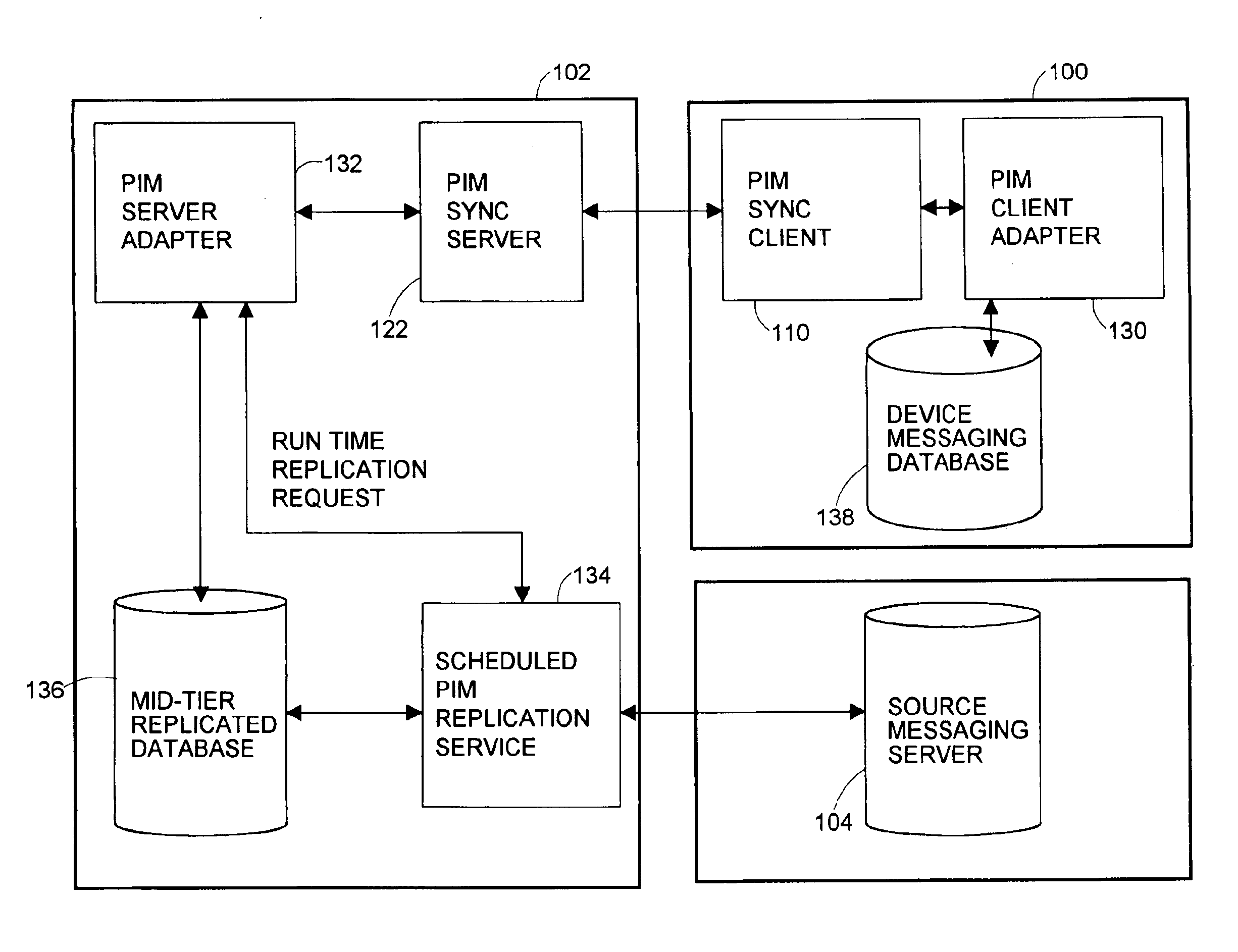
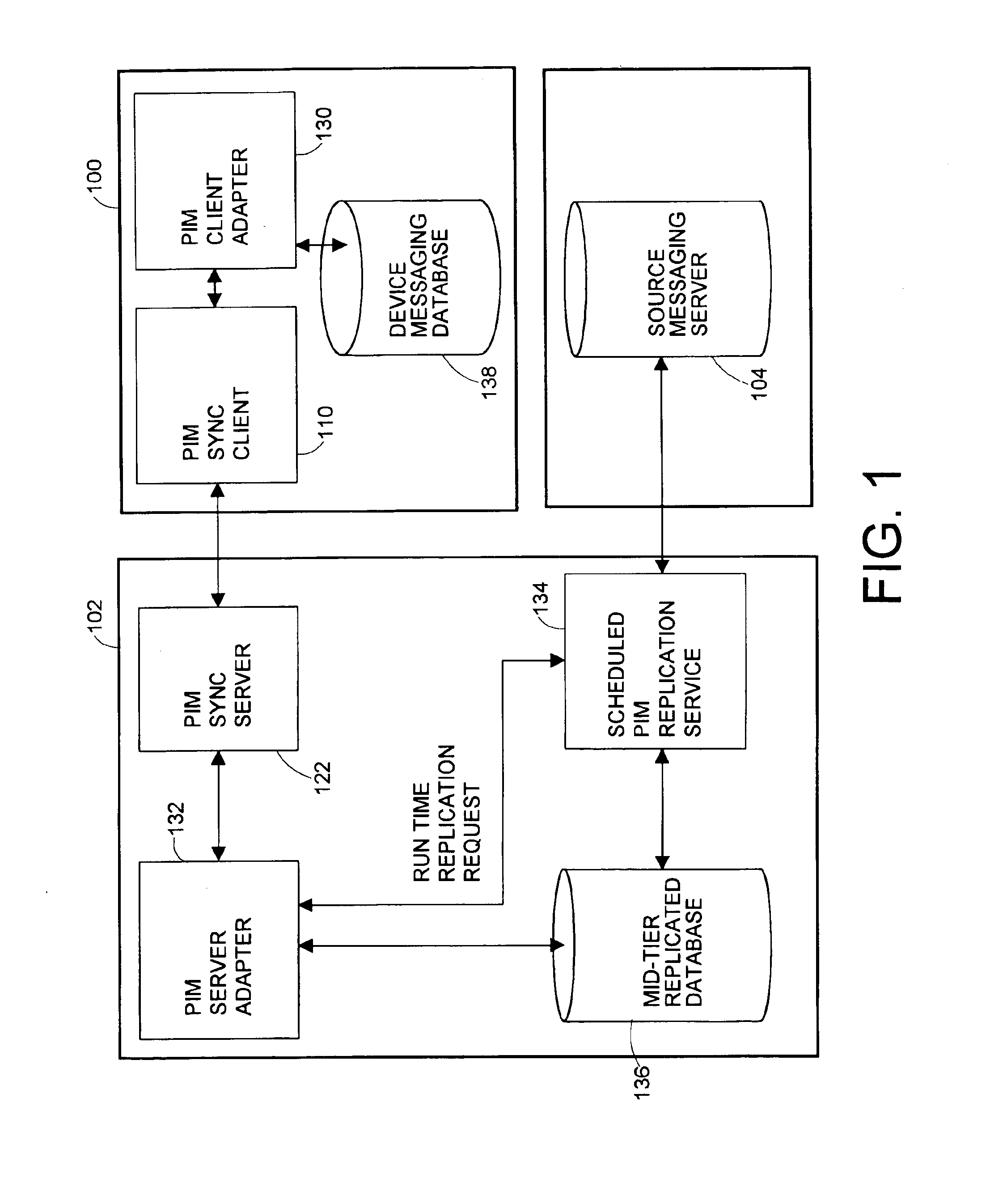
Mid-tier-based conflict resolution method and system usable for message synchronization and replication
ActiveUS6983293B2Data processing applicationsDatabase distribution/replicationCommunications systemClient-side
A system, method and a computer usable medium tangibly embodying a program of instructions executable by the computer to perform a computer-based method for providing a conflict detection and resolution in a mid-tier server of a multi-tier client-server communication system which performs message synchronization in a client / mid-tier environment and replication in a mid-tier / server environment. The method defines a client / mid-tier conflict resolution look-up table listing all possible conflict states in the client / mid-tier environment and corresponding action rules, and a mid-tier / server conflict resolution look-up table listing all possible conflict states in the mid-tier / server environment and corresponding action rules. For any detected conflict state the method finds and executes the corresponding action rule.
Owner:HUAWEI TECH CO LTD
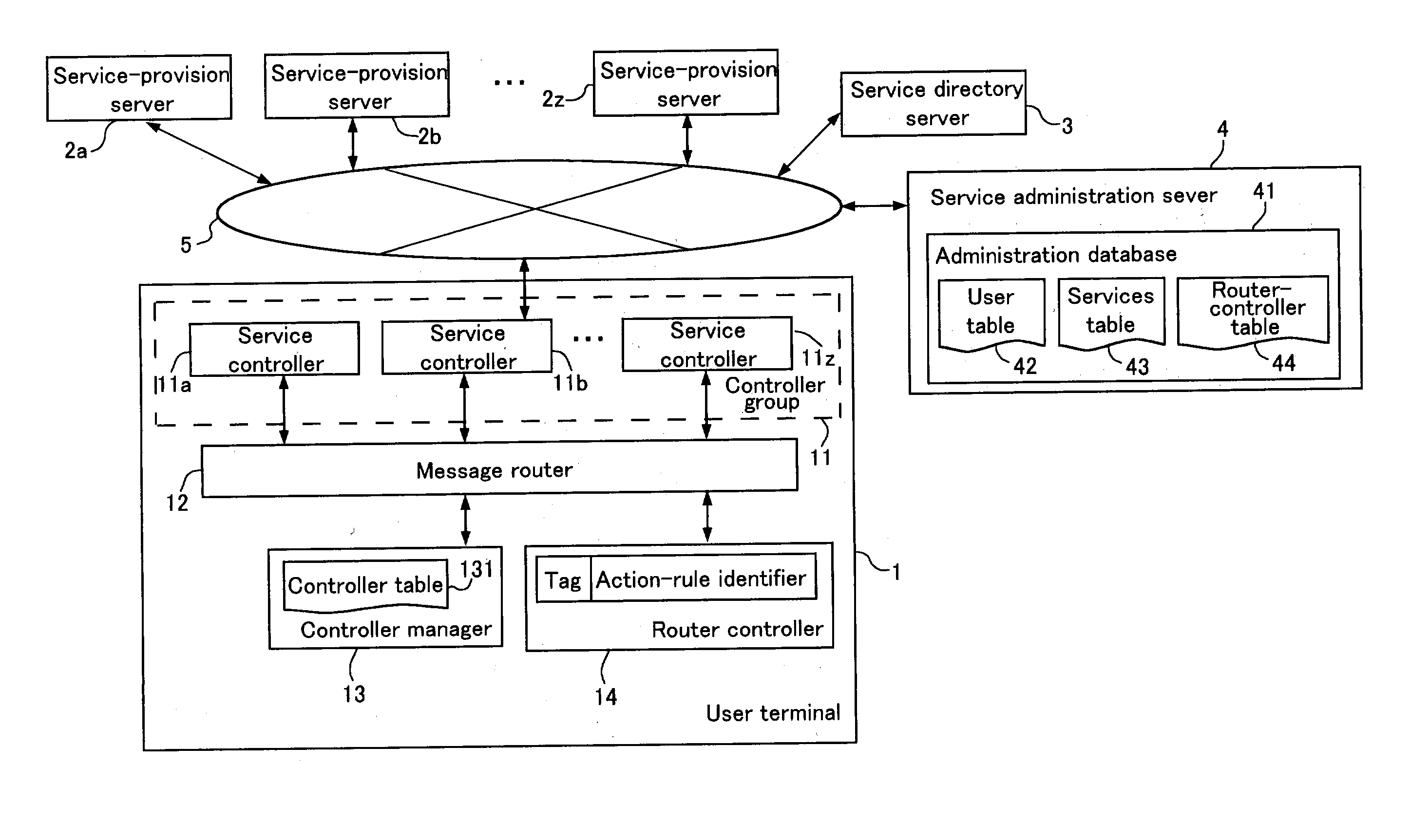
Information sharing method, information sharing device, and information sharing computer product
InactiveUS20040006591A1Reduce processing burdenFlexible sharing of informationMultiple digital computer combinationsElectric digital data processingInformation sharingService provision
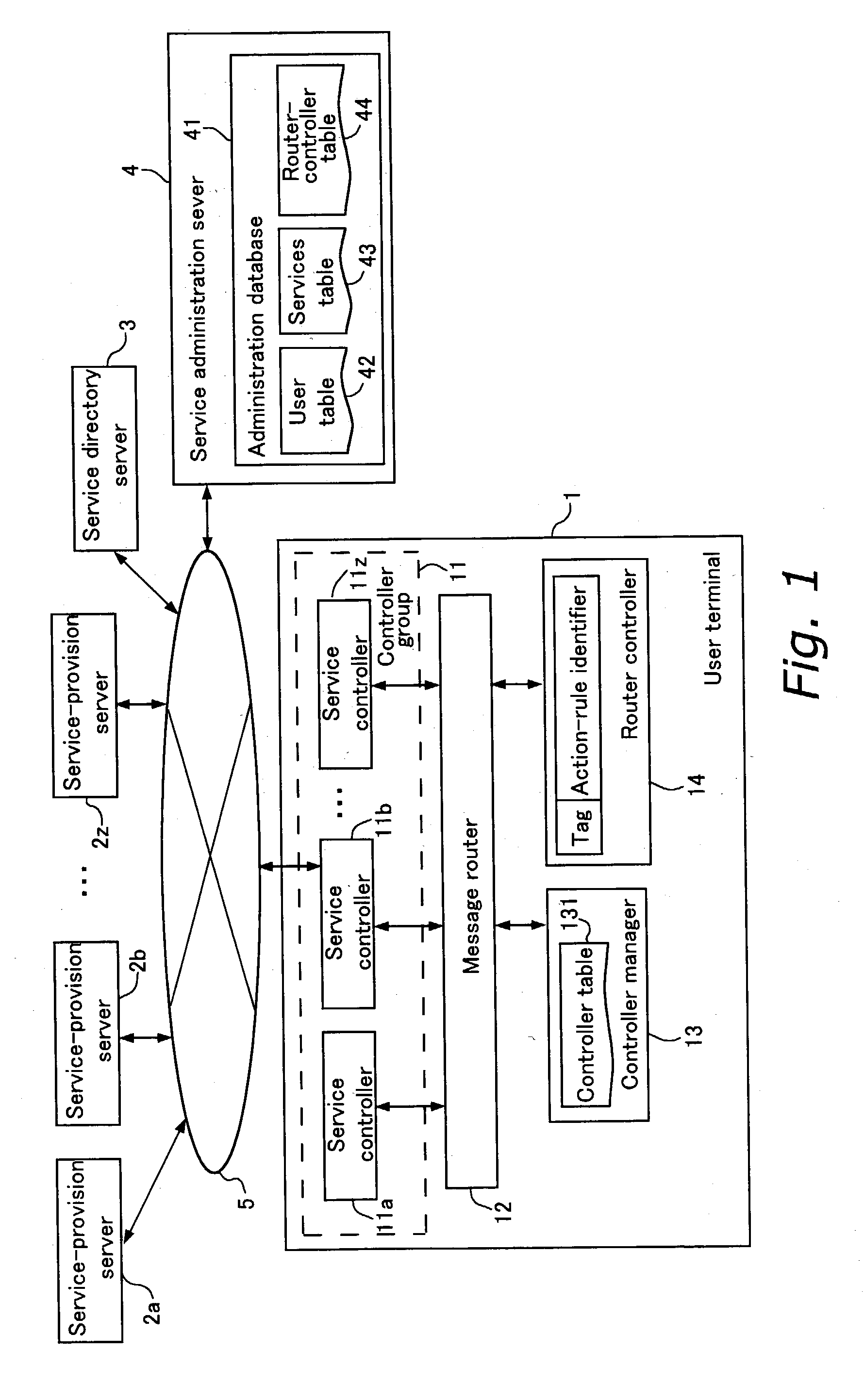
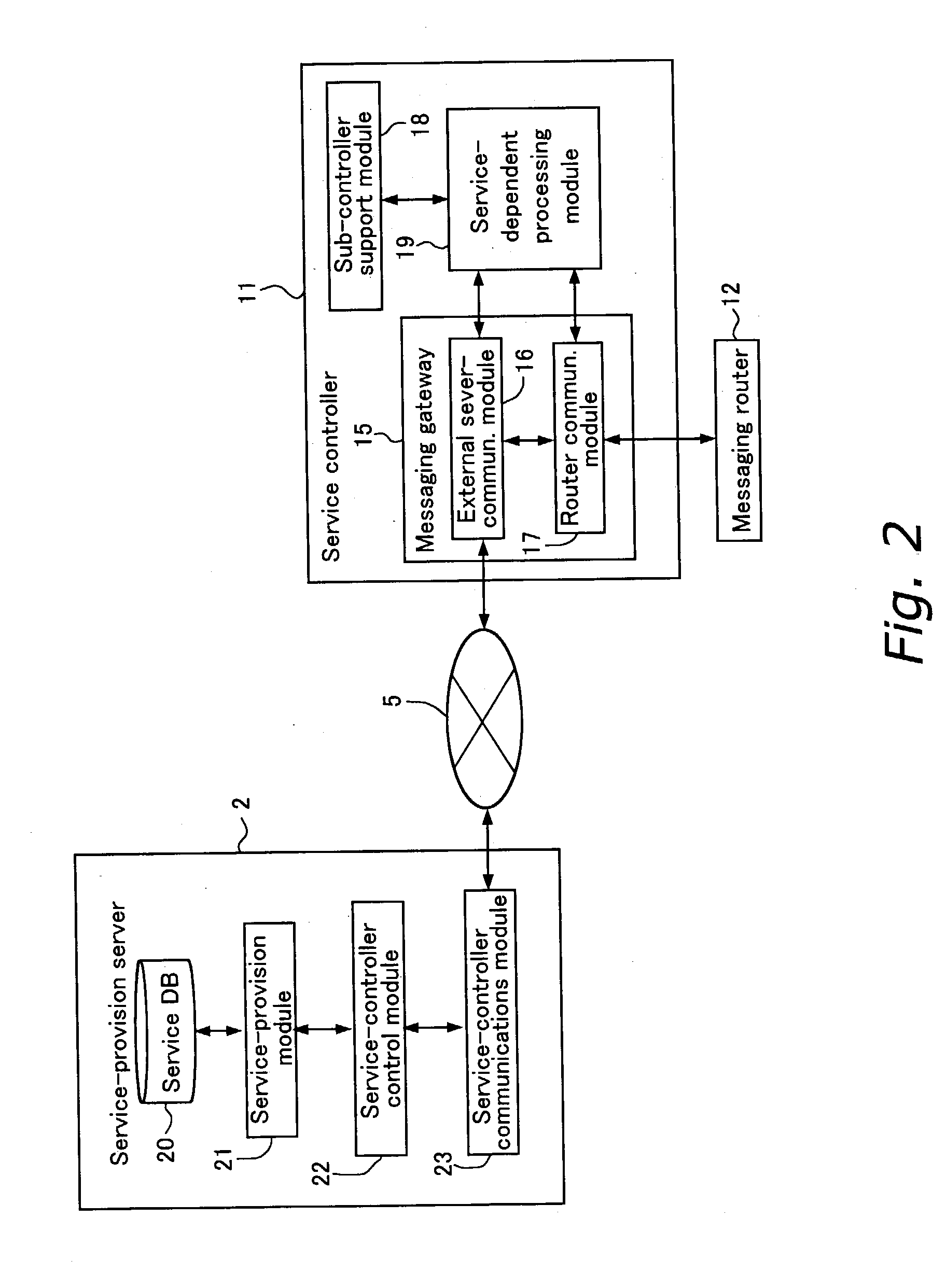
Simplified sharing of information among service-provision systems. A first message (Msg1) containing service information is transmitted from a first service-provision server (2a) to a first service controller (11 a) [#1], wherein it is interpreted, and, for example, a second message (Msg2) is created from the service information contained in the first message (Msg1) and is transmitted to a message router (12) [#2]. The second message (Msg2) is further sent to a router controller (14) and interpreted [#3], and an action rule is determined [#4]. The action rule is executed by the message router (12), whereby the second message (Msg2) is transmitted to a second service controller (11b) [#5]. As a result, a portion of the service information contained in the second message (Mesg2) is extracted, and a third message (Msg3) is created and transmitted to a second service-provision server (2b) [#6]. The second service-provision server (2b) receives the third message (Msg3) and carries out processes corresponding to services that are provided.
Owner:FUJITSU LTD
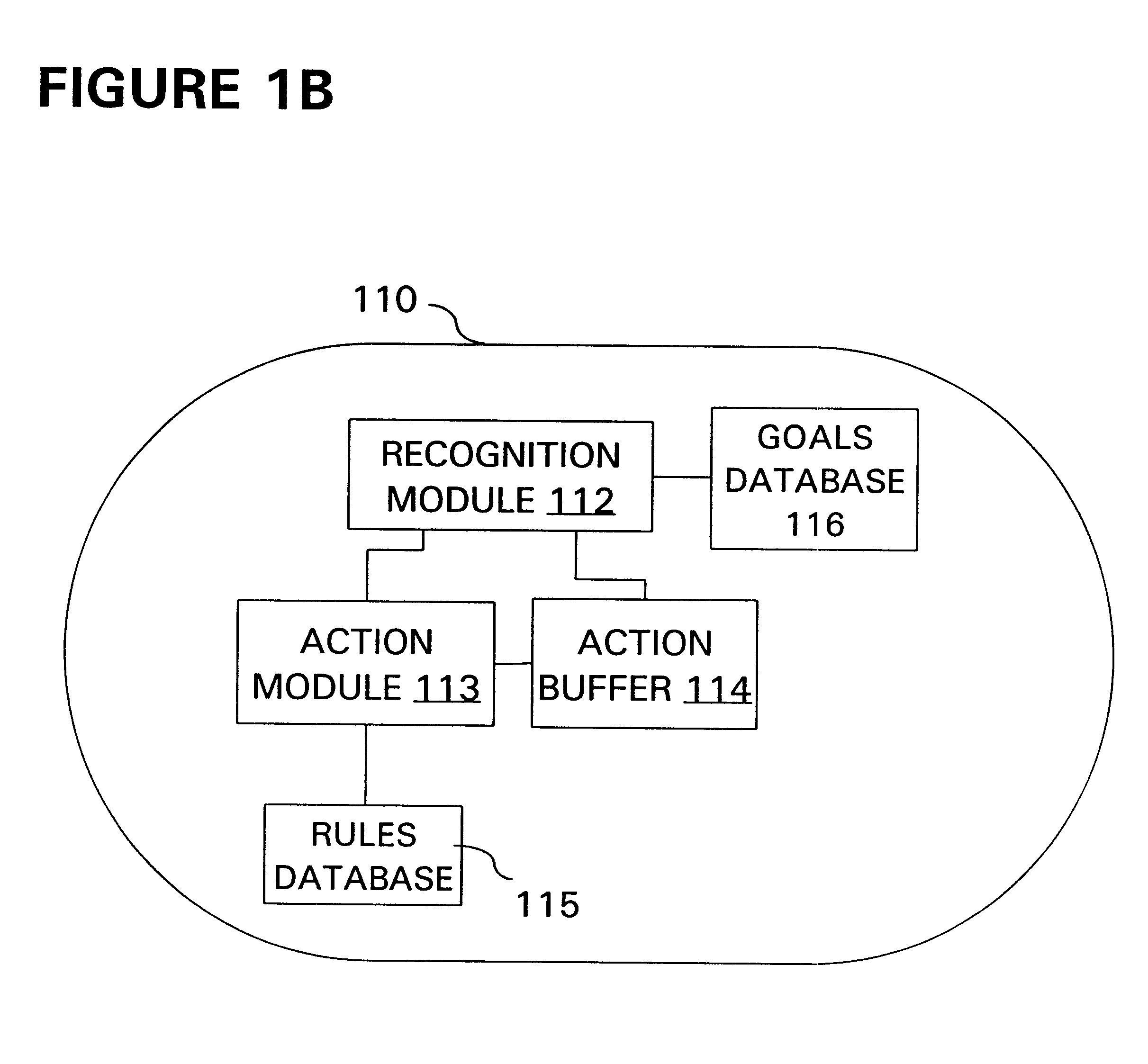
Distributed file system with automated file management achieved by decoupling data analysis and movement operations
InactiveUS6542930B1Easy to set upSpeed implementationMultiple digital computer combinationsSpecial data processing applicationsDistributed File SystemProgram planning
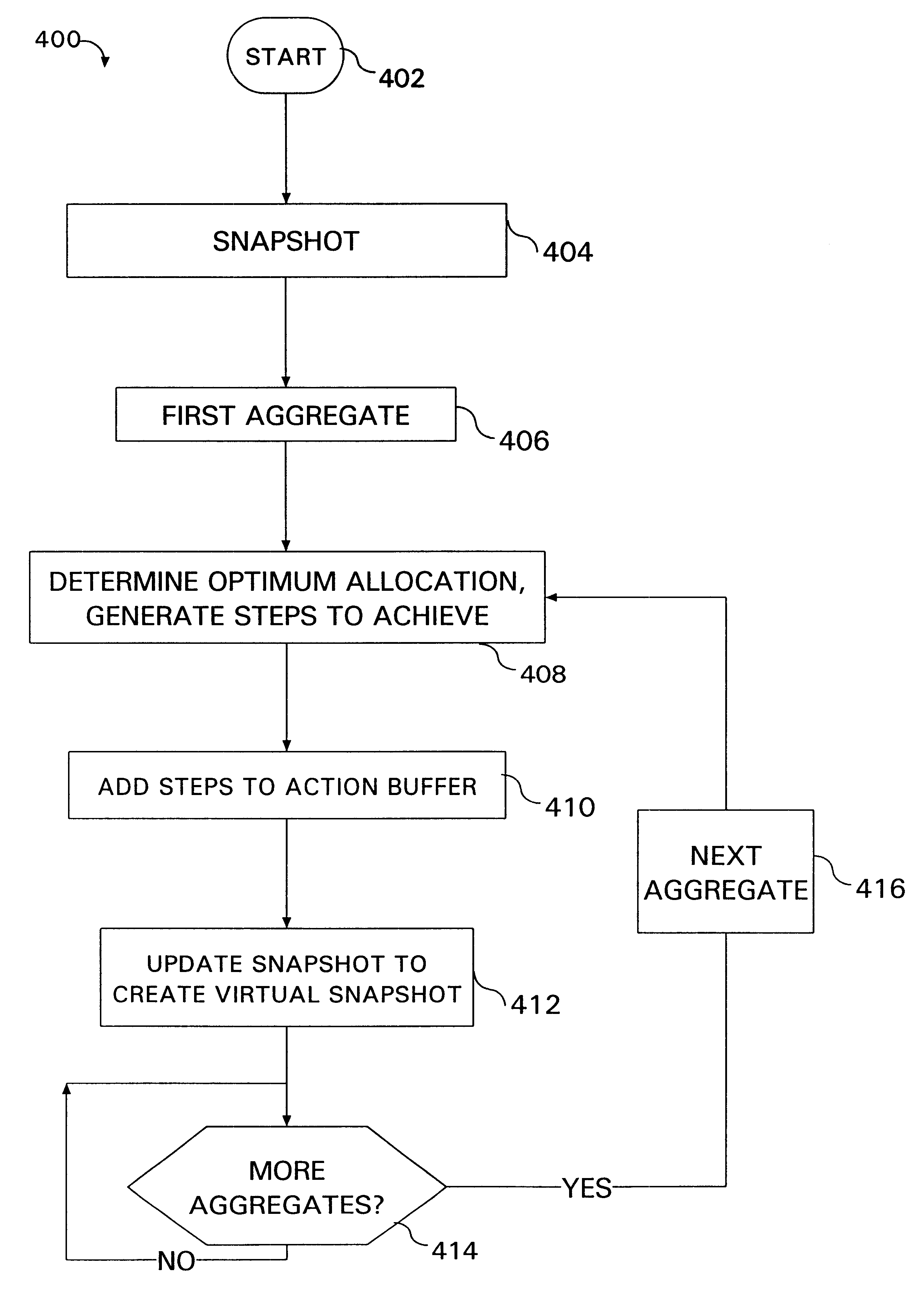
A computer-driven file management technique is applied to a distributed file system with multiple storage "aggregates" to improve file distribution, user access, server workload, and the like. For a first aggregate, a recognition module analyzes file contents of all aggregates, plans a set of physical data movement operations to configure data stored upon a first one of the aggregates according to certain prescribed "goals," and buffers the planned physical data movement operations. The planned set of physical data movement operations constitute a "virtual" data move. The reviewing, planning, and buffering operations are repeated for all remaining aggregates in the distributed file system. However, each repeated reviewing operation considers the file contents of the aggregates as if all previous virtual data moves had actually been performed. Asynchronously with the storage analysis and reconfiguration planning, the system processes the action buffer. Namely, the system reads buffer contents according to a prescribed order, consults predetermined action "rules," and then carries out the physical data moves in accordance with the action rules. The action rules may specify desirable hours to move data or avoid moving data, for example.
Owner:IBM CORP
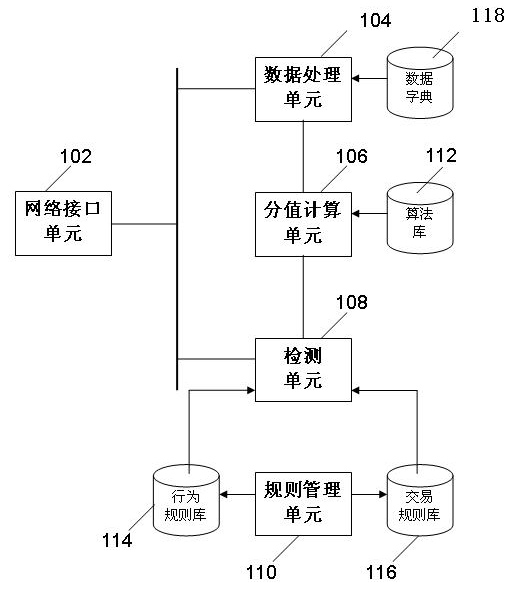
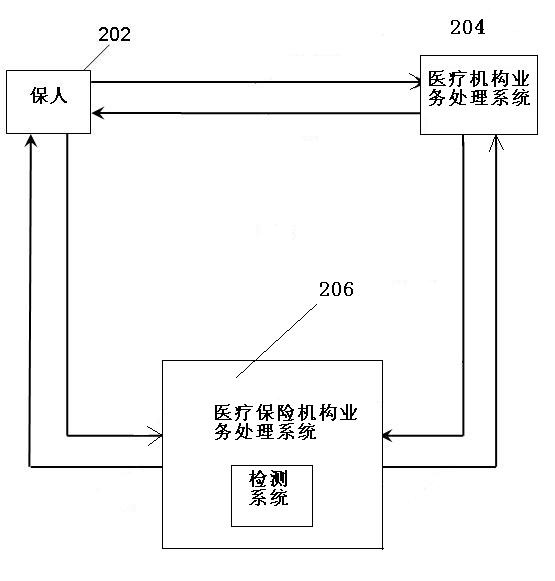
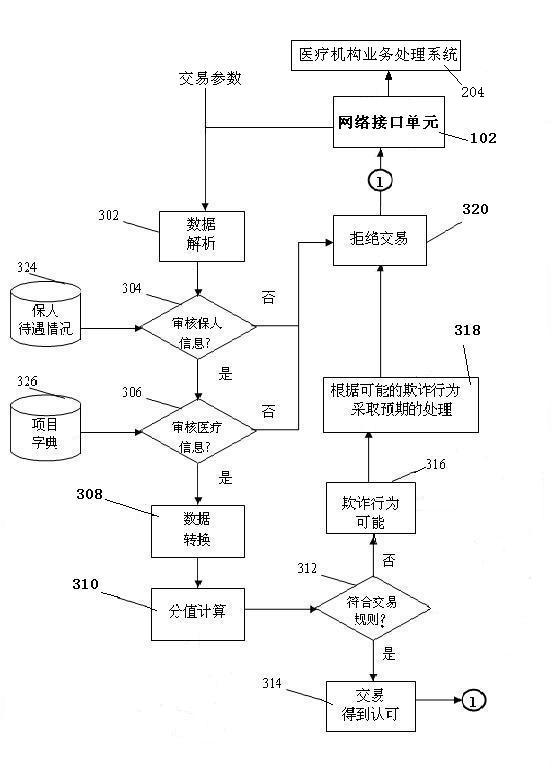
System and method for detecting fraudulent transactions in medical insurance outpatient services
InactiveCN102013084AReduce regulatory costsData processing applicationsFinancial transactionProcessing element
The invention discloses a system and method for detecting fraudulent transactions in medical insurance outpatient services. In the invention, a data processing unit, a score calculating unit and a detecting unit are sequentially connected in series; the detecting unit comprises two modules which conform to transaction rules and probability of the fraudulent transactions; the output of a data dictionary is connected with the data processing unit; the input of an algorithm library is connected with the score calculating unit; the output of an action rule library and the output of a transaction rule library are respectively connected with the detecting unit; a rule management unit is connected between the action rule library and the transaction rule library; and the system is connected inside or outside a business processing system of a medical insurance institution for detecting, when the system is connected on the outside, a transaction information extraction module is arranged in front of the data processing unit for carrying out analysis, inquiry and statistics on the history of actions which are detected to be abnormal. By detecting the medical transaction rules in the outpatient services and evaluating the transaction fraudulence unlawful actions, the quantitative basis can be provided for defining the medical fraudulence unlawful actions, and the supervision cost of medical insurance fraudulence and unlawful phenomena can be reduced.
Owner:JIANGSU UNIV
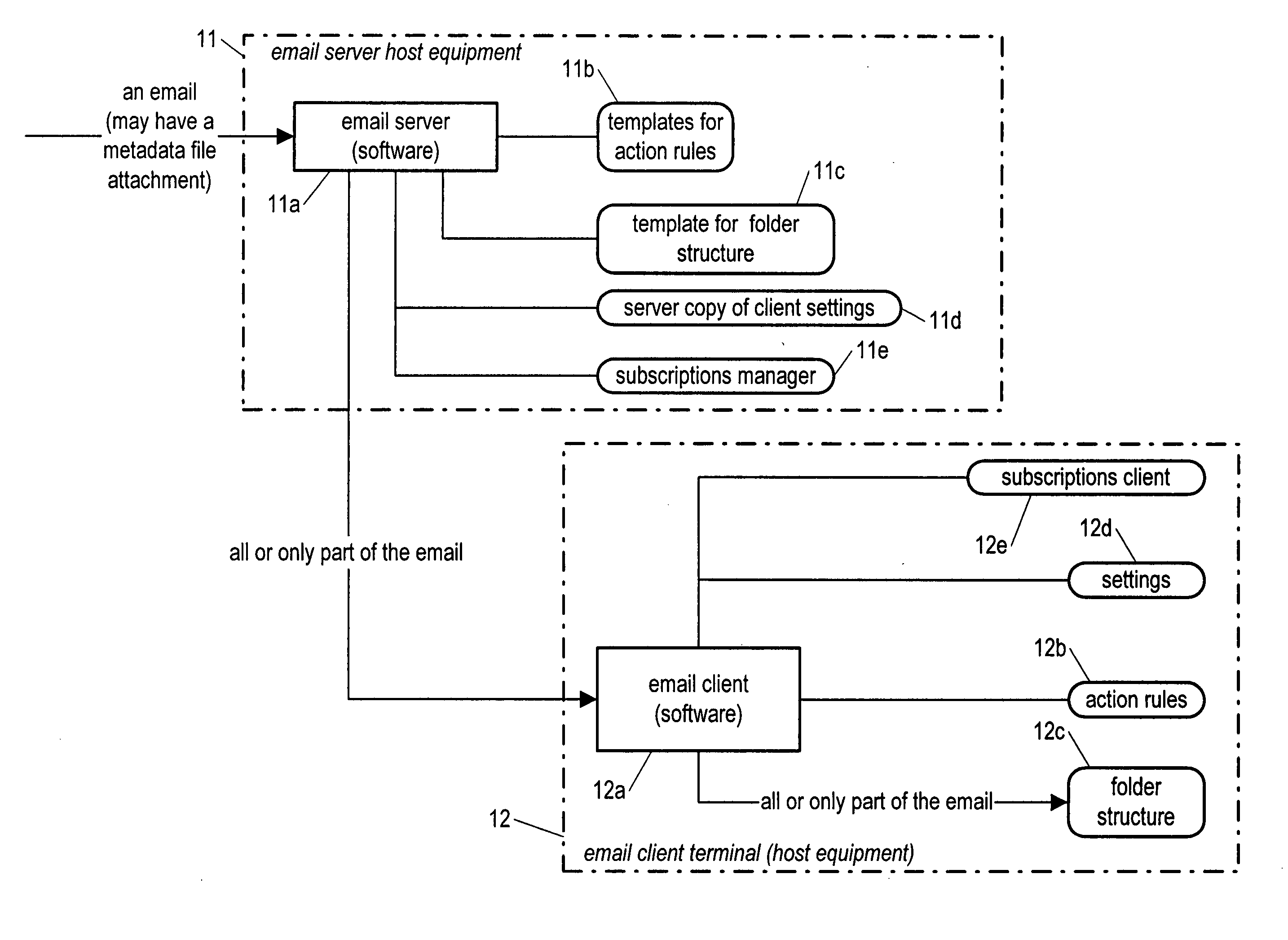
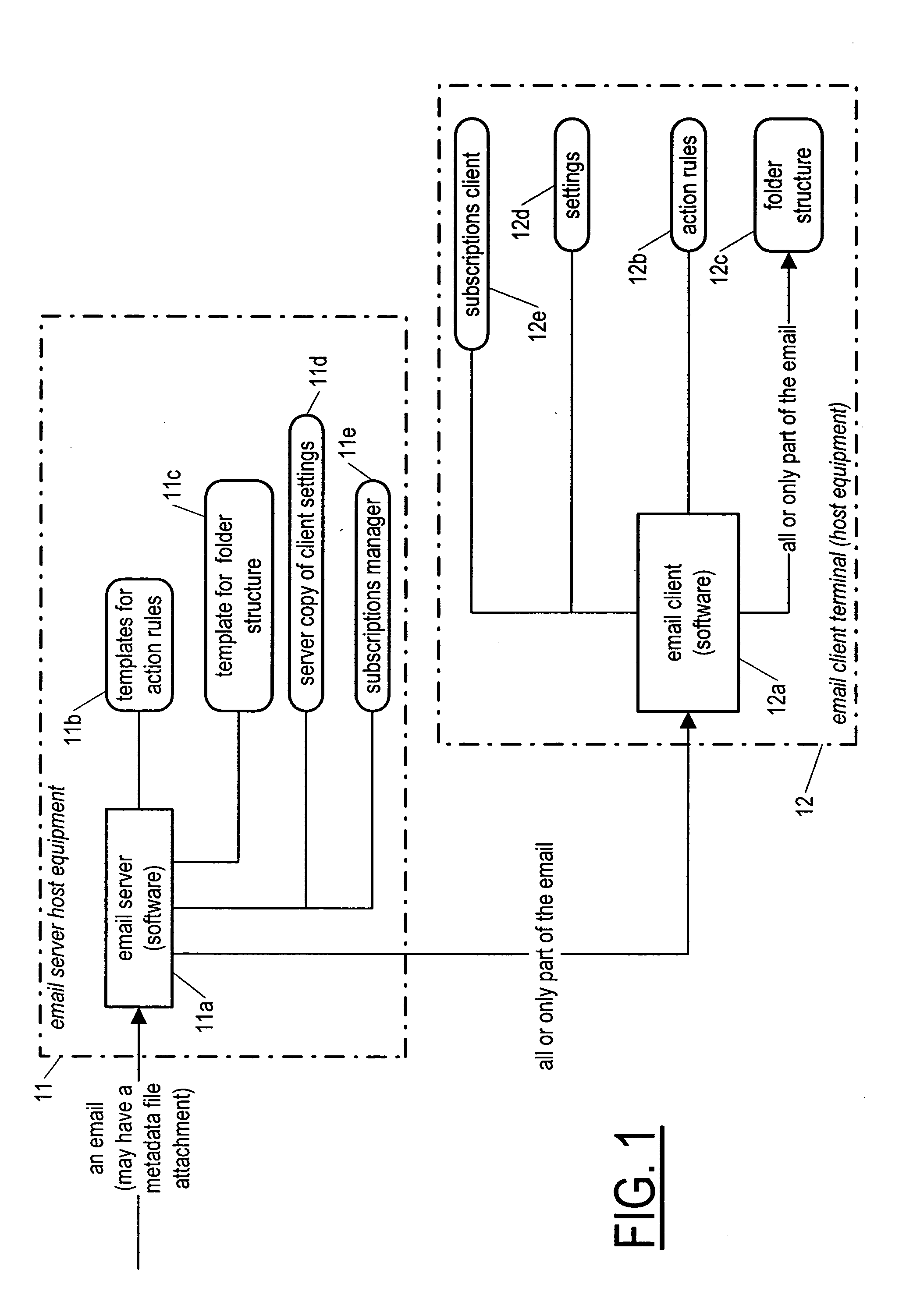
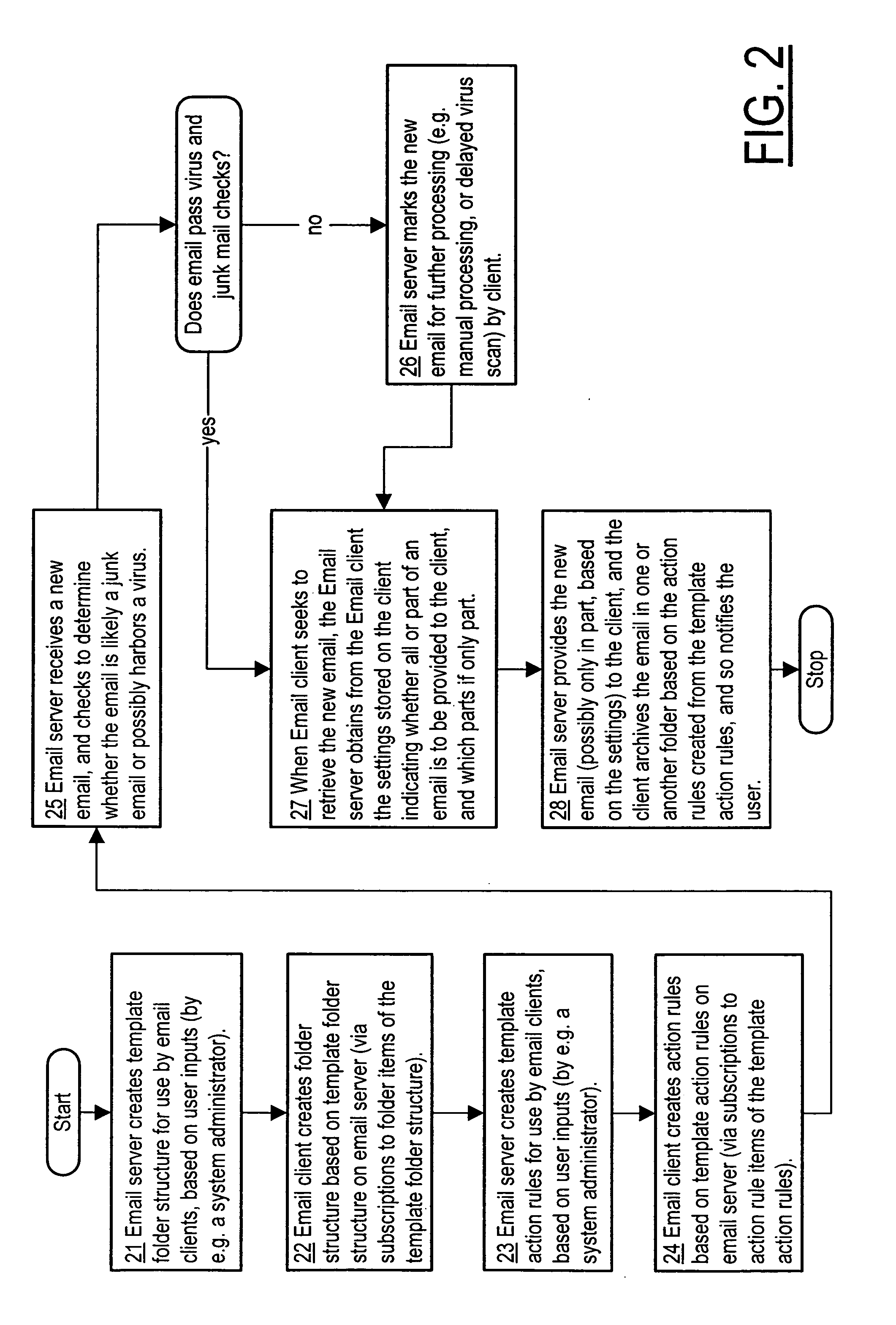
Corporate email system
InactiveUS20060031347A1Multiple digital computer combinationsData switching networksAction ruleElectronic mail
Owner:NOKIA CORP
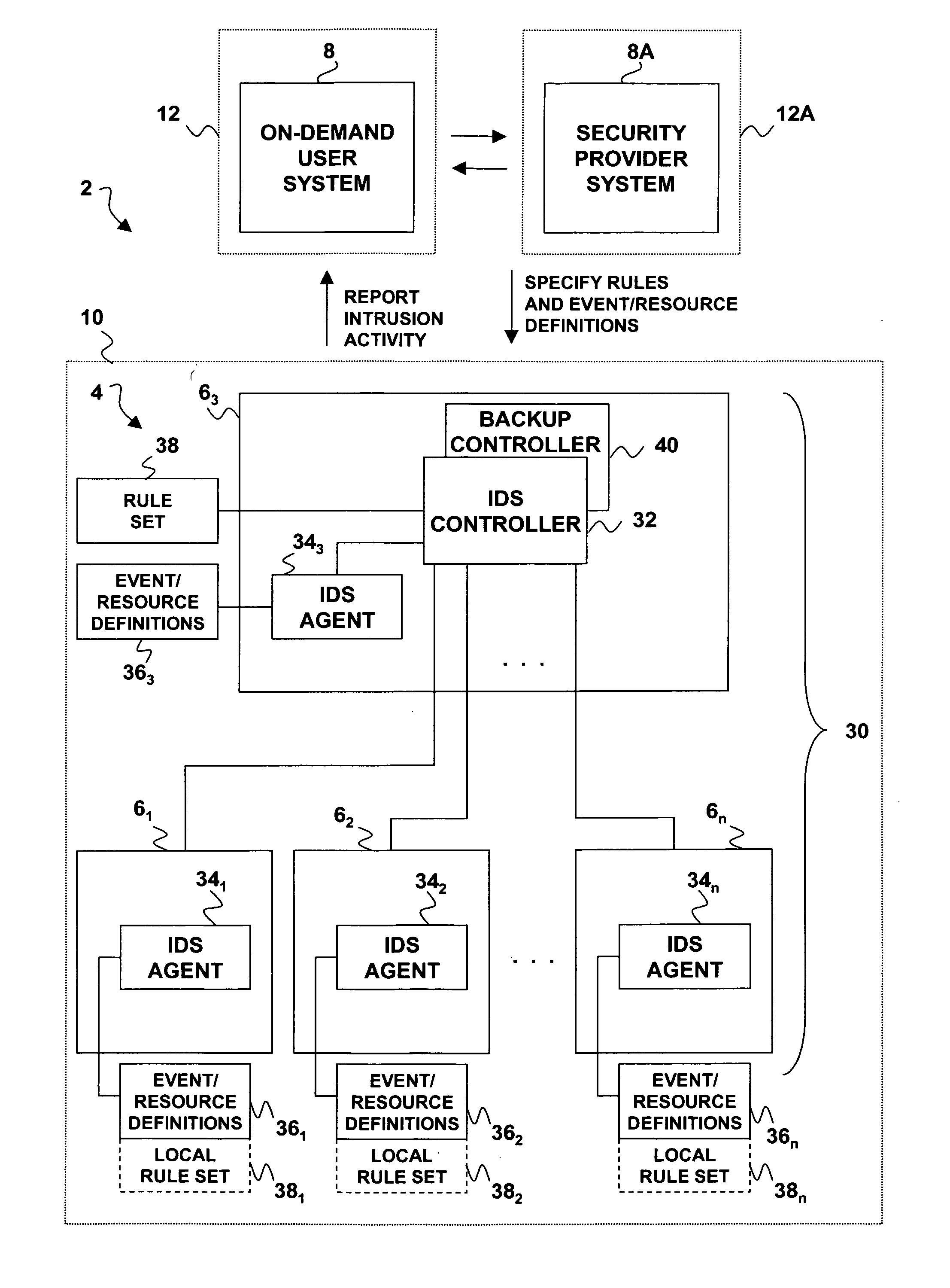
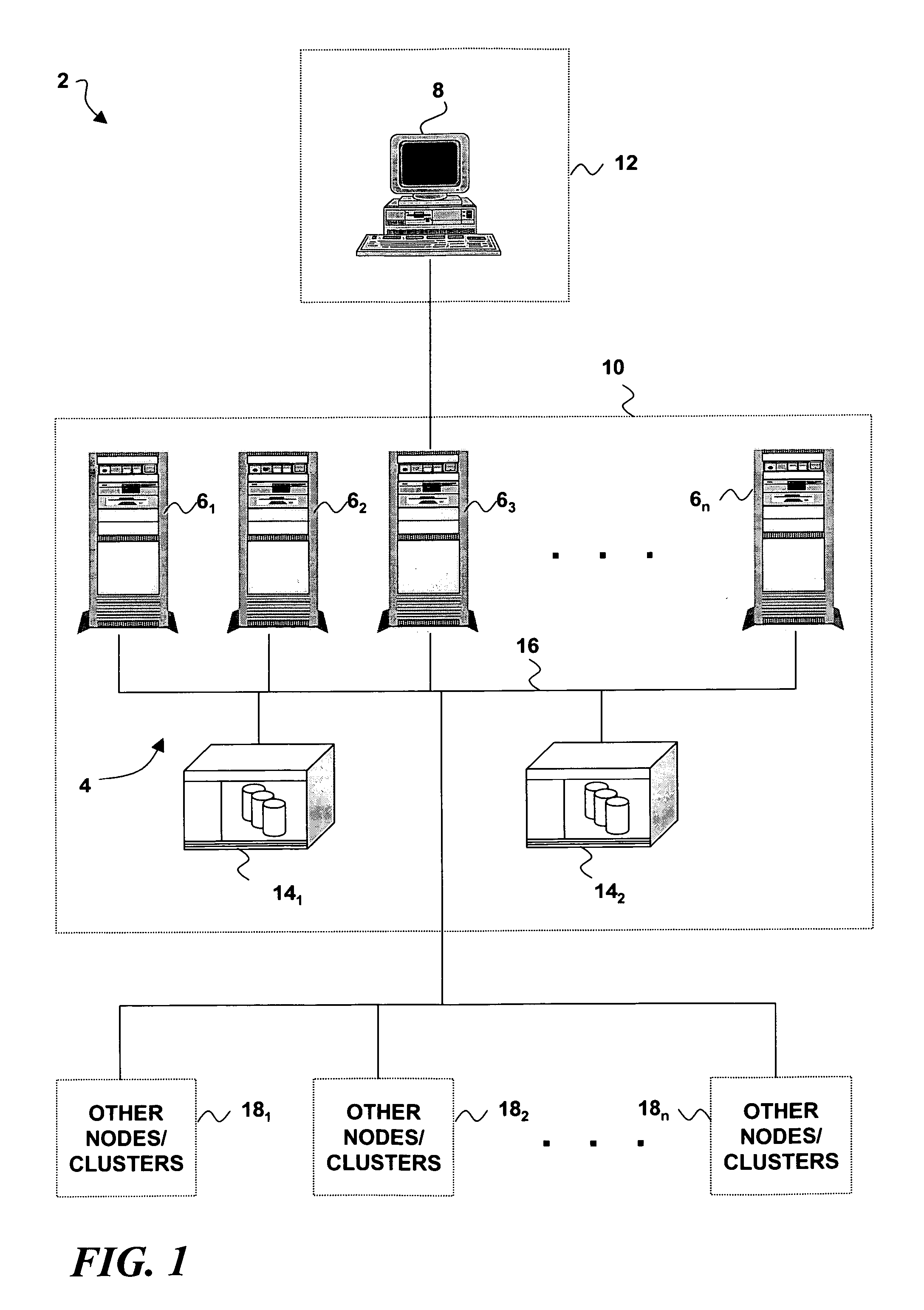
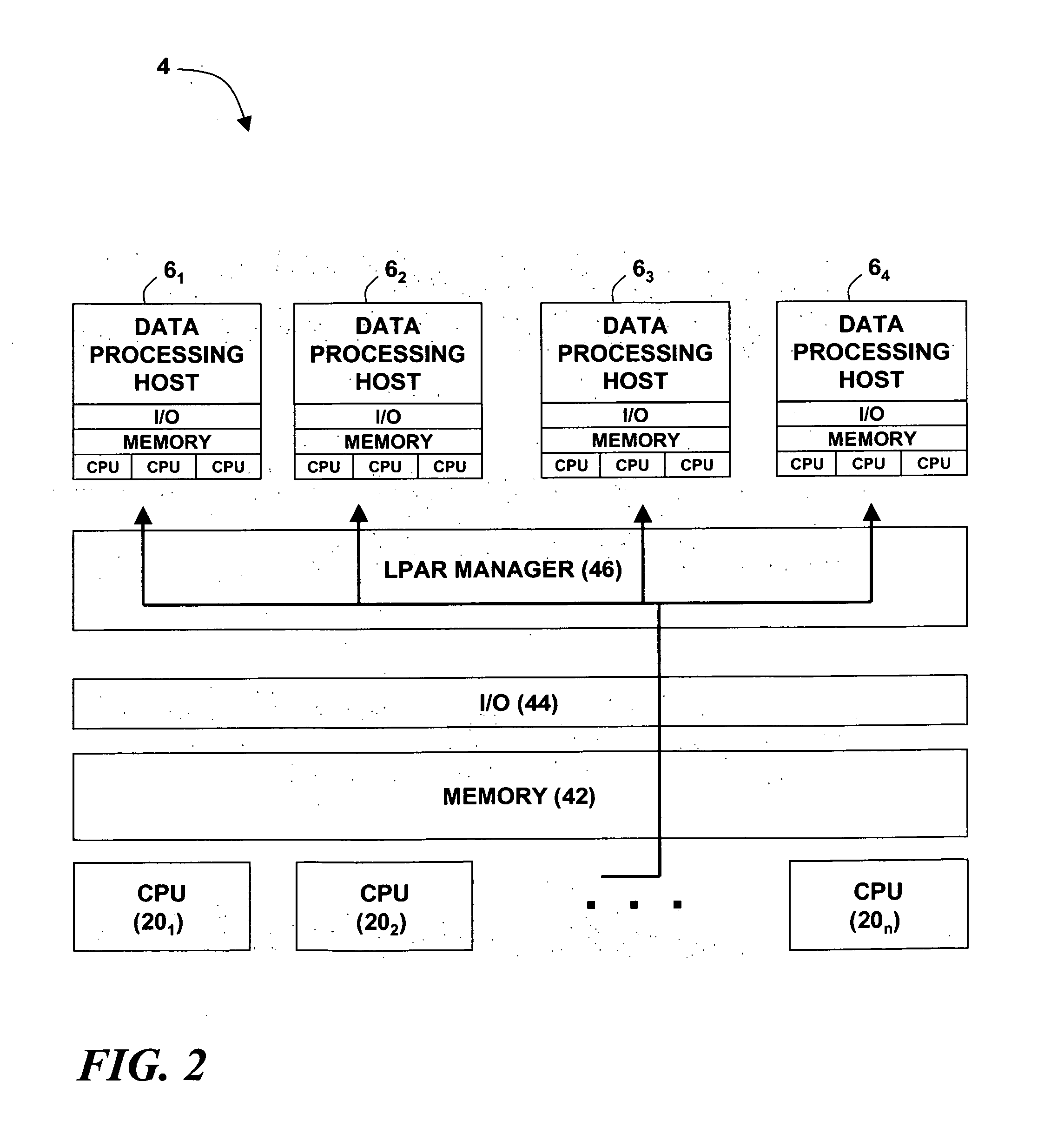
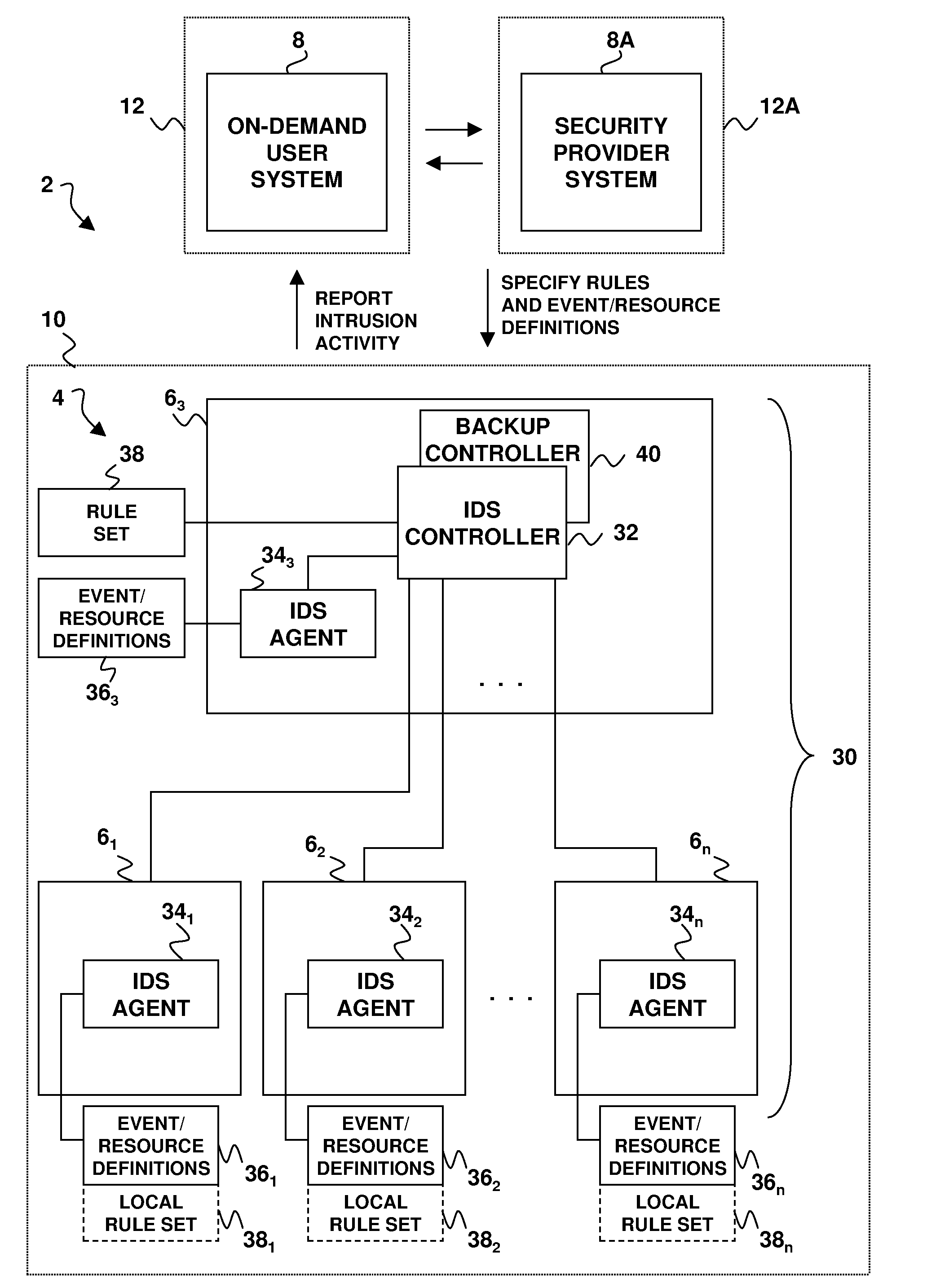
Computer security intrusion detection system for remote, on-demand users
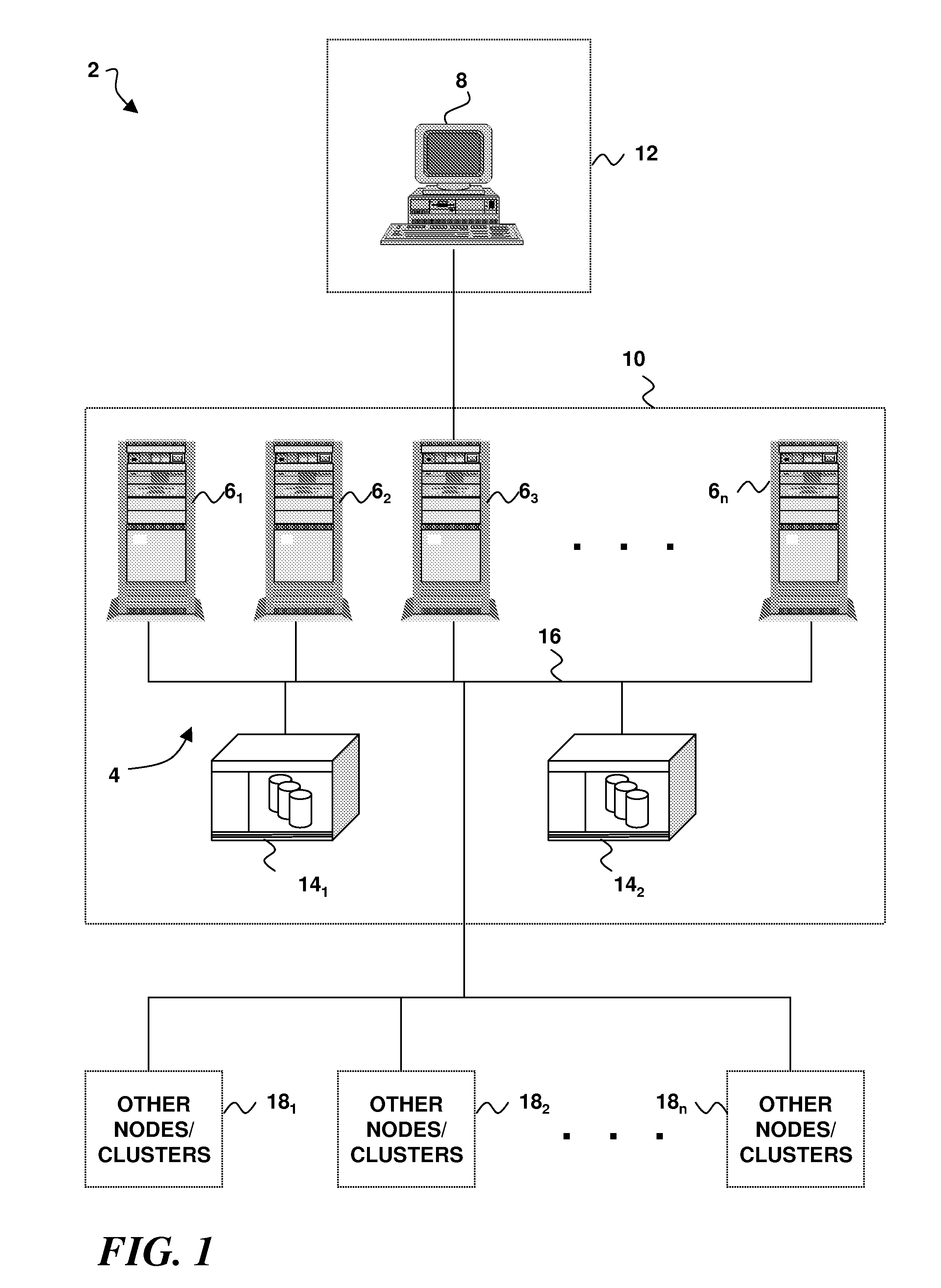
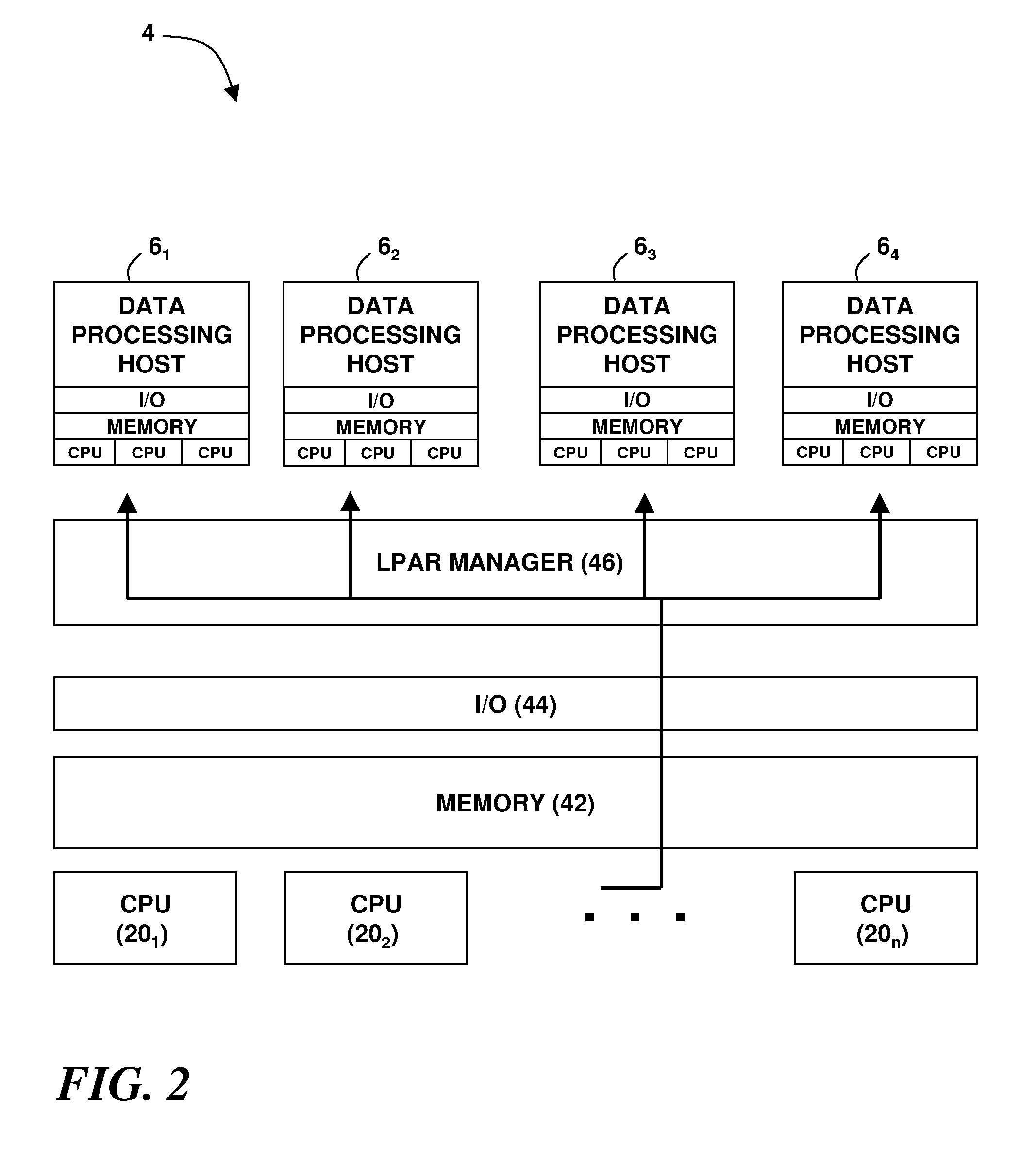
An intrusion detection system, and a related method and computer program product, for implementing intrusion detection in a remote, on-demand computing service environment in which one or more data processing hosts are made available to a remote on-demand user that does not have physical custody and control over the host(s). Intrusion detection entails monitoring resources defined by the on-demand user (or a third party security provider) for intrusion events that are also defined by the on-demand user (or security provider), and implementing responses according to event-action rules that are further defined by the on-demand user (or security provider). An intrusion detection system agent is associated with each of the data processing hosts, and is adapted to monitor the intrusion events and report intrusion activity. If there are plural intrusion detection system agents, they can be individually programmed to monitor and report on agent-specific sets of the intrusion events. An intrusion detection system controller is associated with one of the data processing hosts. It is adapted to manage and monitor the intrusion detection system agent(s), process agent reports of intrusion activity, and communicate intrusion-related information to the on-demand user (or security provider). The responses to intrusion events can be implemented by the intrusion detection system controller in combination with the intrusion detection system agents, or by any such entity alone.
Owner:IBM CORP
All-directional mobile monitoring system
InactiveCN103795983AInnovative ideasImprove practicalityTelevision system detailsColor television detailsMonitoring systemGeolocation
The invention discloses an all-directional mobile monitoring system which comprises a camera array, a movement positioning device, a monitoring terminal and a server. The camera array is composed of a plurality of camera modules distributed in a monitoring area, a storage module and a server processor are arranged in the server, and the camera modules and the movement positioning device are connected with the server. The all-directional mobile monitoring system is novel in thought and good in practicability, position information during movement is reported through the movement positioning device fixed to the body of a monitored object, the corresponding camera module is triggered to carry out shooting in real time, the defects that the known positioning technology at present is prone to losing positioning signals and insufficient in accuracy are overcome, and particularly inside a room, the server sets comprehensive strategy calling and combines different monitoring data through pre-stored geographic positions of the camera modules, a pre-stored building internal structural chart and a pre-stored monitored object action rule to achieve the aims of monitoring dead angles and carrying out all-directional monitoring.
Owner:彭世藩
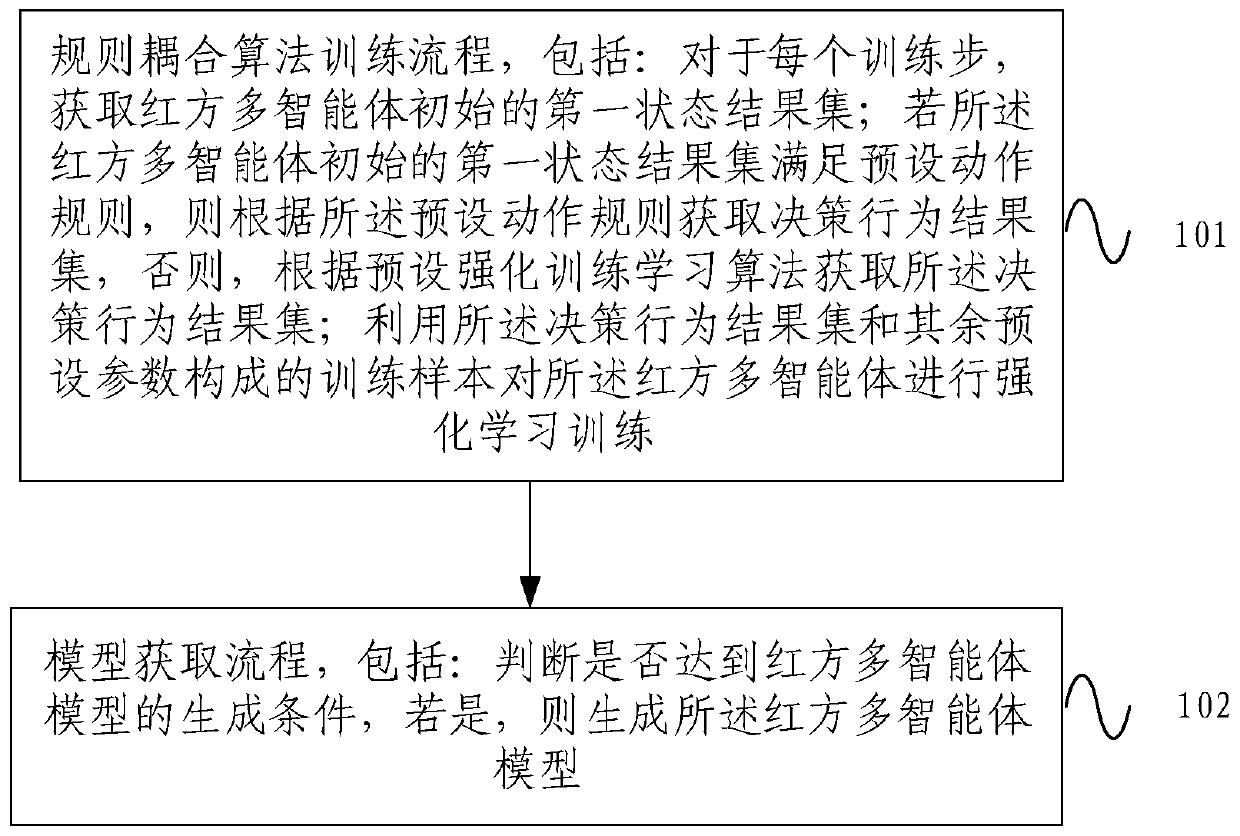
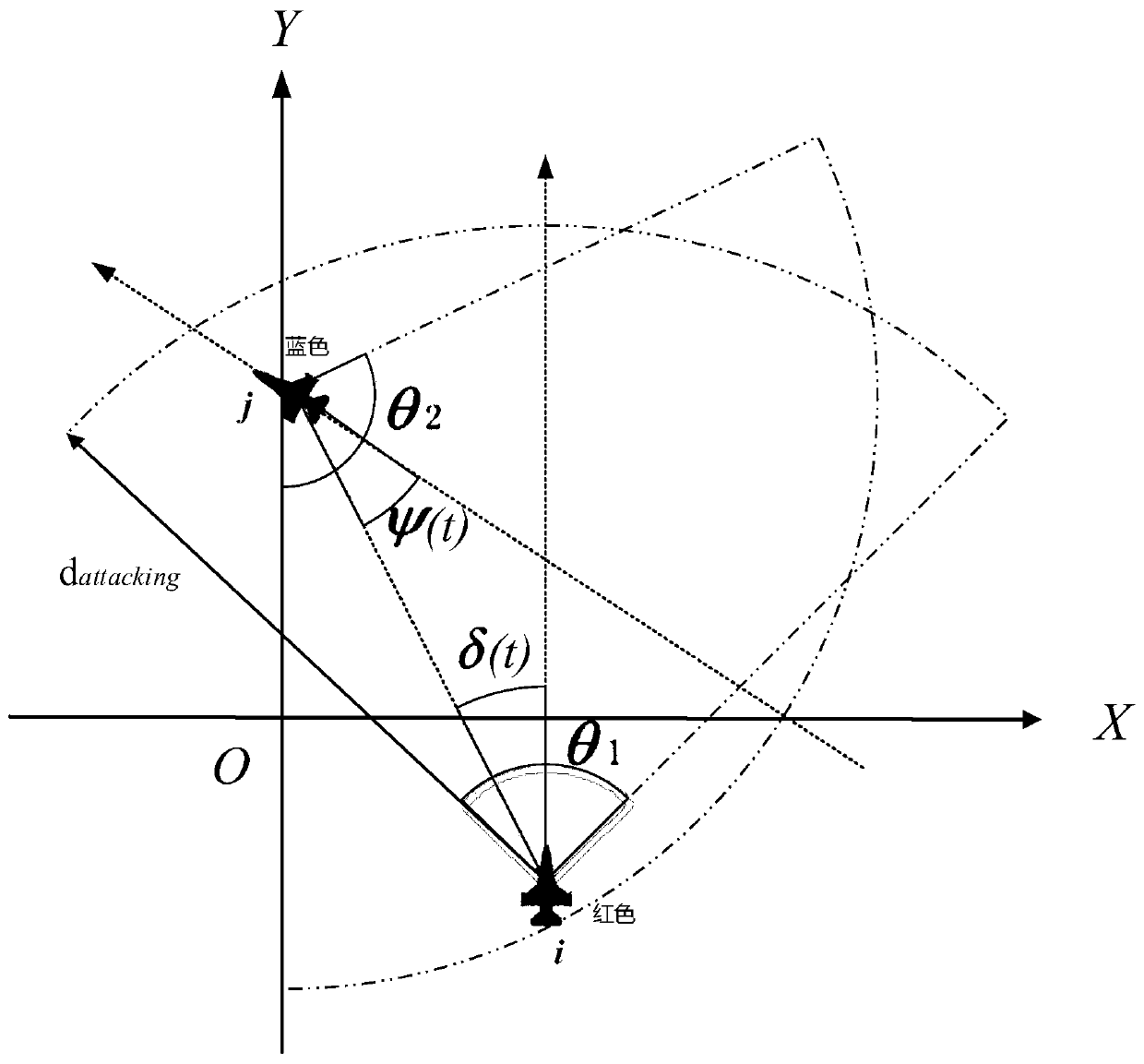
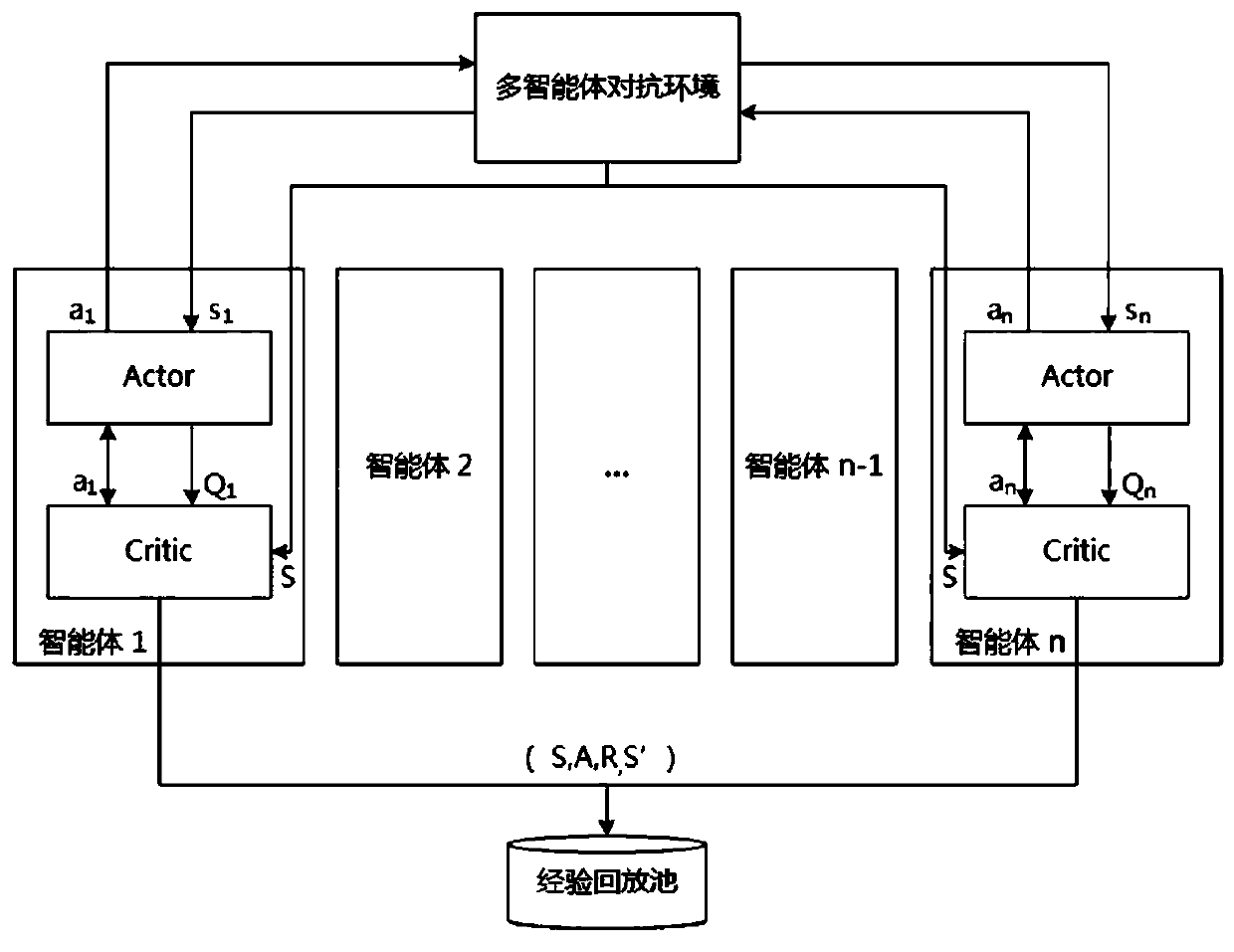
Reinforcement learning training optimization method and device for multi-agent confrontation
ActiveCN110991545AImprove training efficiencyFast trainingCharacter and pattern recognitionArtificial lifeAlgorithmEngineering
The embodiment of the invention provides a reinforcement learning training optimization method and device for multi-agent confrontation. The method comprises the following steps of a rule coupling algorithm training process including the steps of acquiring an initial first state result set of a red party multi-agent for each training step, if the initial first state result set of the red party multi-agent meets a preset action rule, obtaining a decision-making behavior result set according to the preset action rule, and otherwise, acquiring the decision-making behavior result set according toa preset reinforcement training learning algorithm; and performing reinforcement learning training on the red-party multi-agent by utilizing a training sample formed by the decision-making behavior result set and other preset parameters. The embodiment of the invention provides the reinforcement learning training optimization method and device for multi-agent confrontation. In the whole training process, the preset action rule can guide the multiple agents to act, invalid actions are avoided, the problems that in the training process in the prior art, invalid exploration is much, and the training speed is low are solved, and the training efficiency is remarkably improved.
Owner:NAT INNOVATION INST OF DEFENSE TECH PLA ACAD OF MILITARY SCI
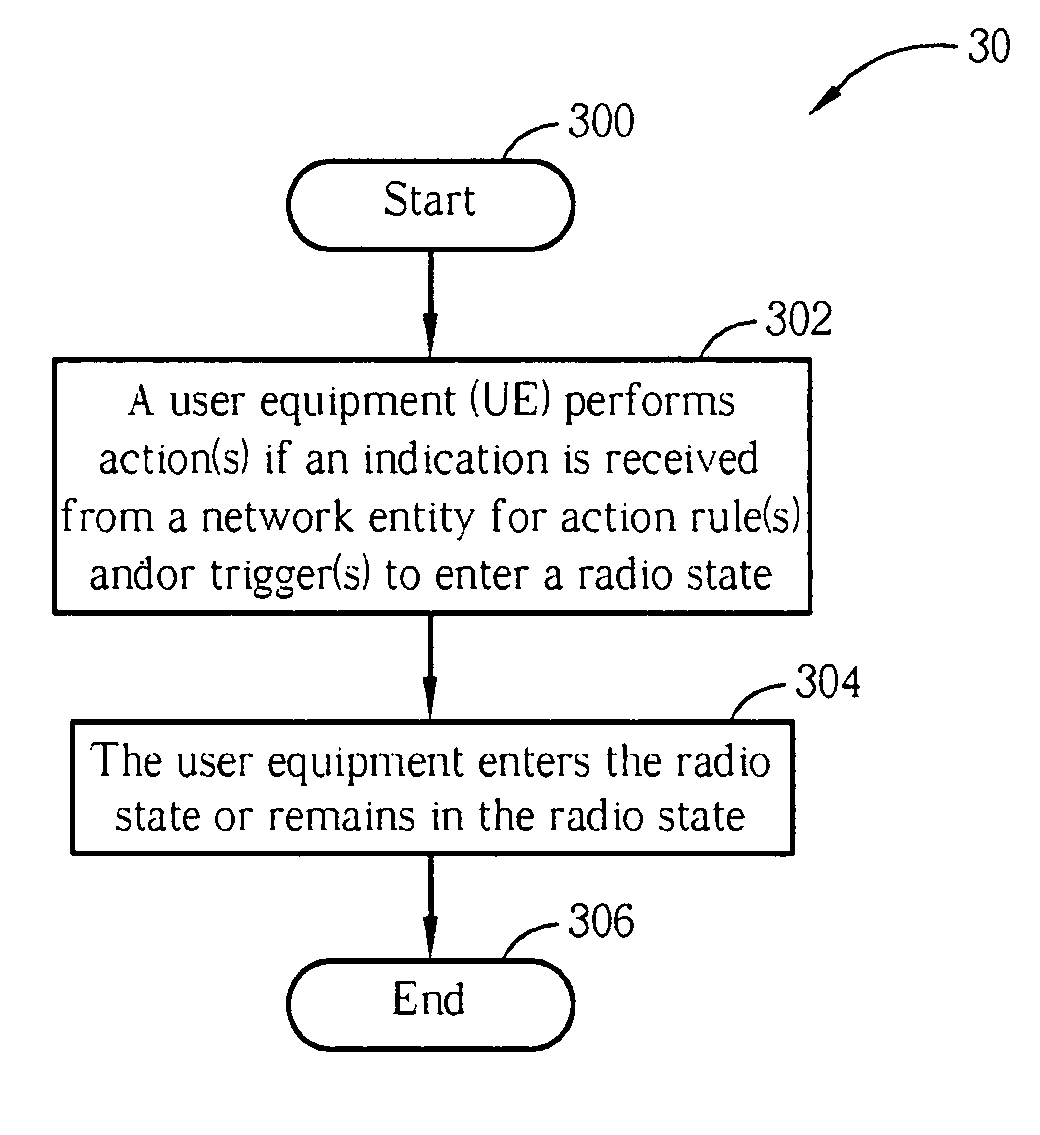
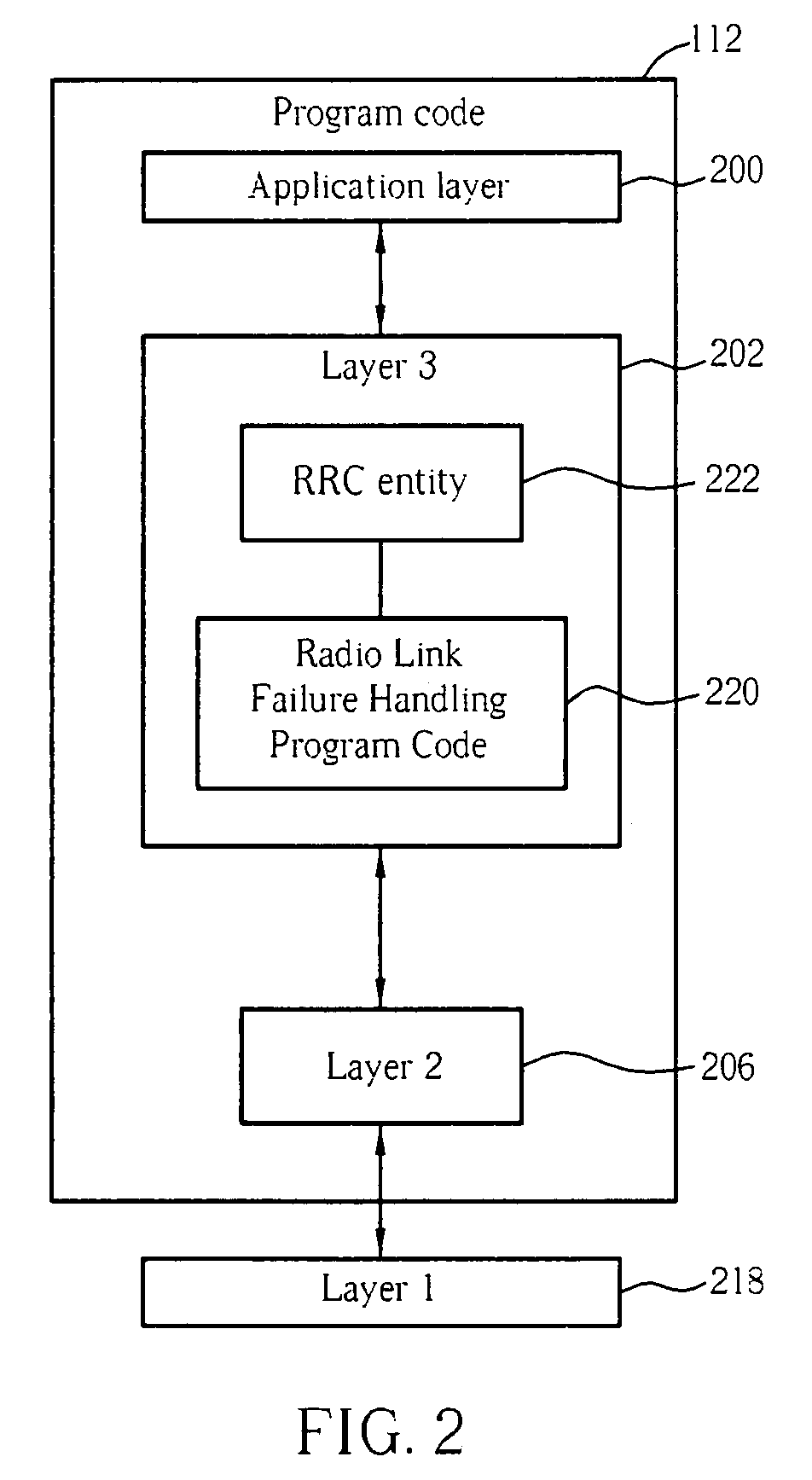
Method of handling radio link failure in wireless communications system and related device
InactiveUS20080076405A1Limited efficiencyOptimizationError preventionTransmission systemsCommunications systemRadio link failures
Handling radio link failure efficiently in a packet switching domain of a wireless communications system includes a user equipment performing an action when an indication is received from a network entity for an action rule or action rules and a trigger or triggers to enter a radio state, and the user equipment entering the radio state.
Owner:INNOVATIVE SONIC
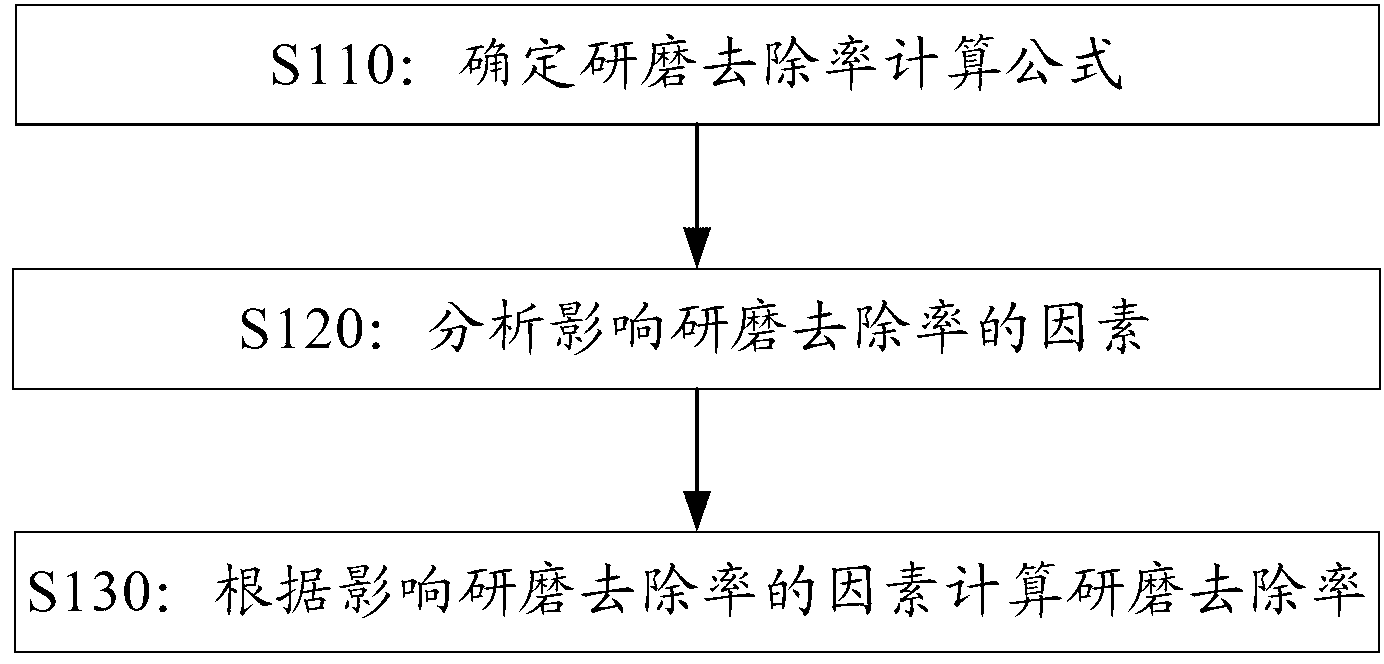
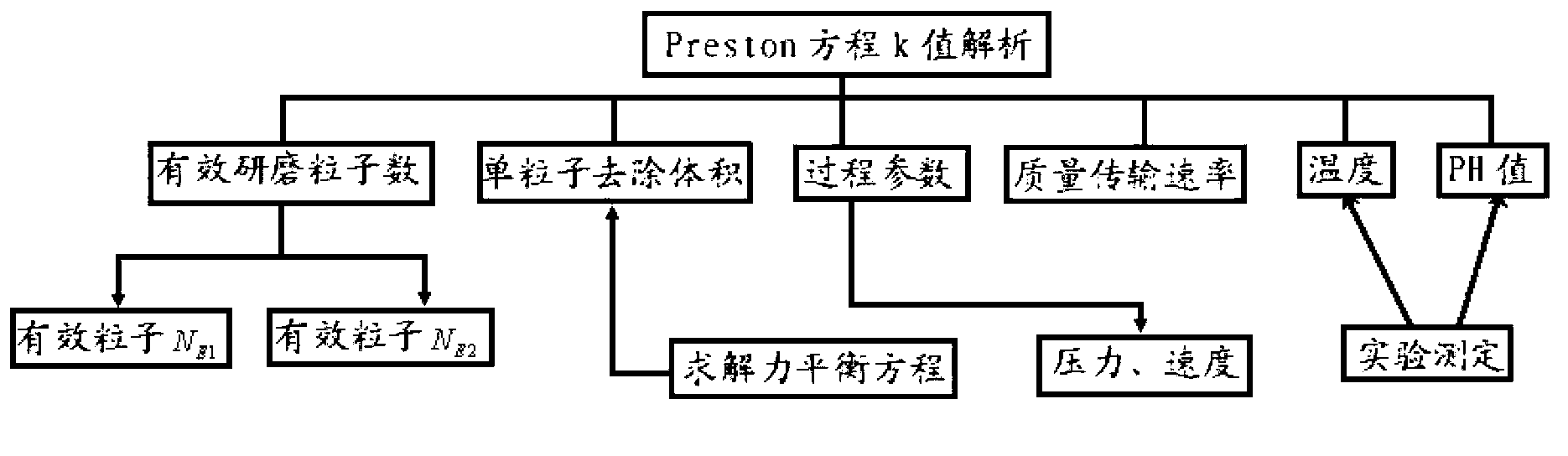
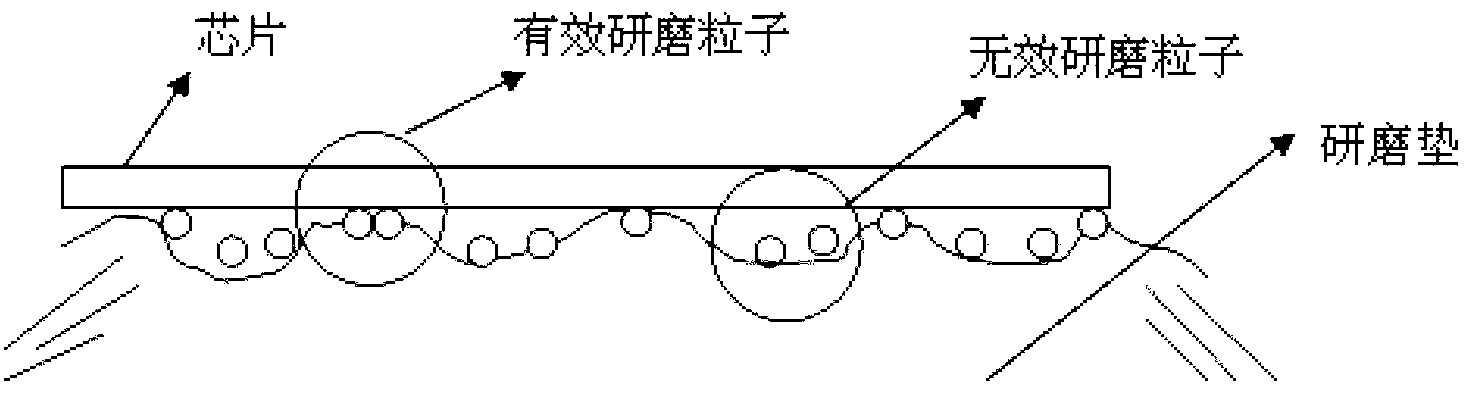
Method and device for calculating chemical mechanical polishing material removal rate
ActiveCN102799793AObjective true descriptionSpecial data processing applicationsProduction lineMaterial removal
The invention provides a method for calculating chemical mechanical polishing material removal rate. The method comprises the following steps: determining a calculation formula MRR=kPV of the material removal rate; analyzing a factor which affects the material removal rate, and obtaining a function equation of the factor which affects the material removal rate; and substituting the function equation of the factor into the MRR=kPV, obtaining a specific calculation formula of the material removal rate, and calculating the material removal rate MRR according to the specific calculation formula. Besides, the invention further provides a device for calculating the chemical mechanical polishing material removal rate. According to the schemes provided by the invention, the action rule among multiple bodies is deeply revealed by the analyzing of the factor which affects the material removal rate and the comprehensive considering of an interaction relationship among four bodies including wafers, particles, polishing pads and polishing fluids, the actual process of chemical mechanical polishing can be relatively objectively and truly described, and the method for calculating the chemical mechanical polishing material removal rate has active guiding functions on the mechanism analysis and the layout design of the CMP (Chemical Mechanical Polishing), as well as the research and the development of a large production line process.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
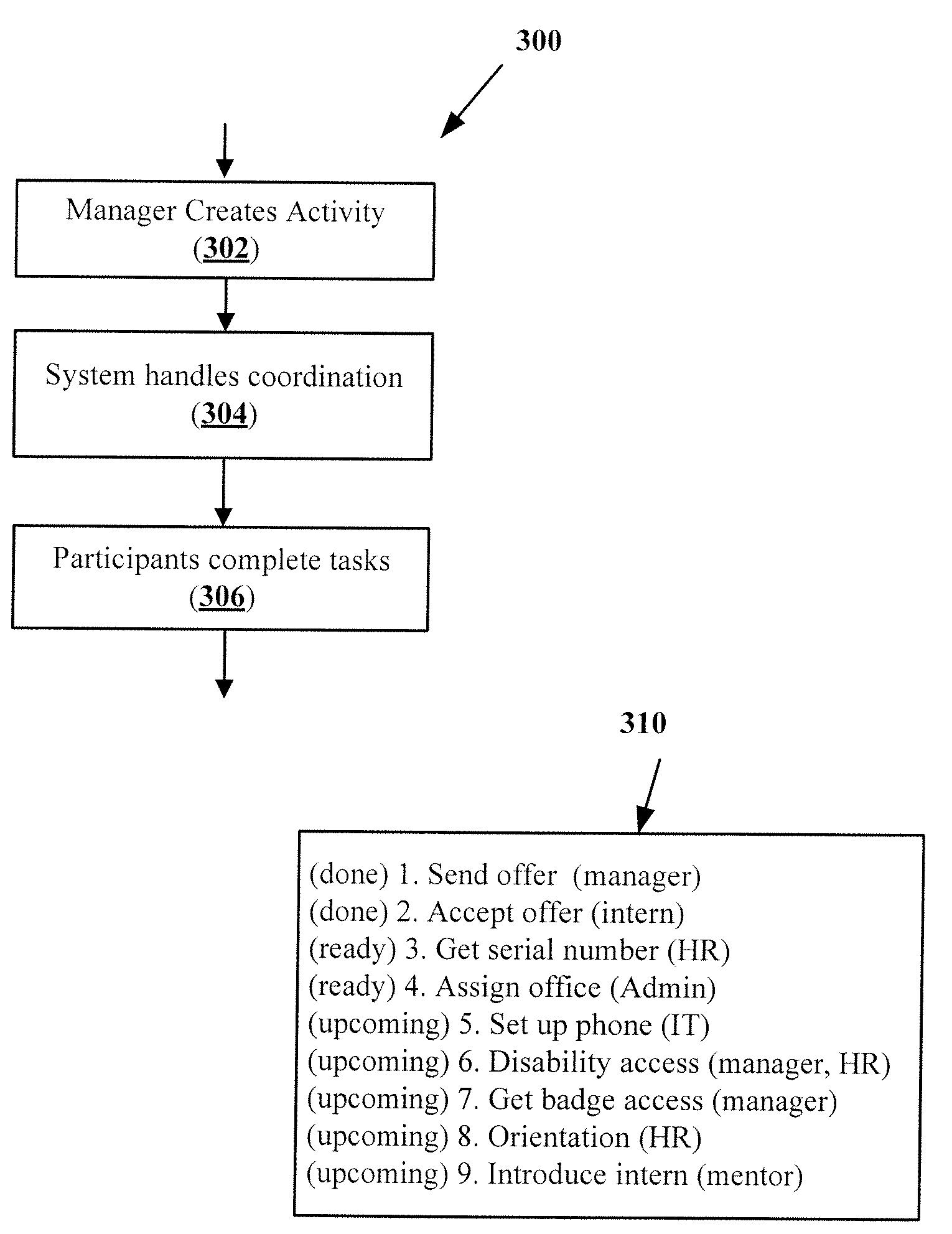
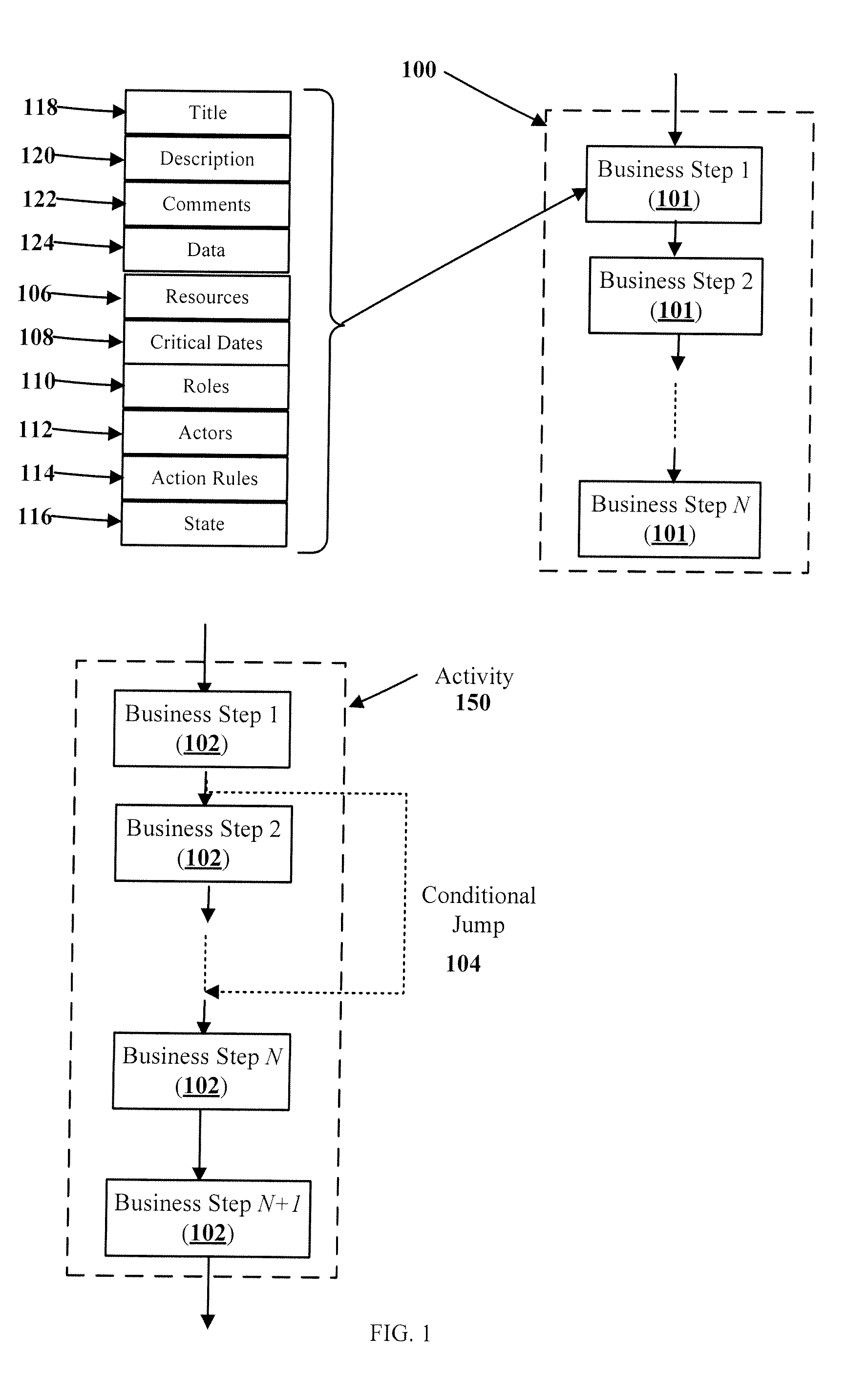
Method for evolving shared to-do lists into business processes
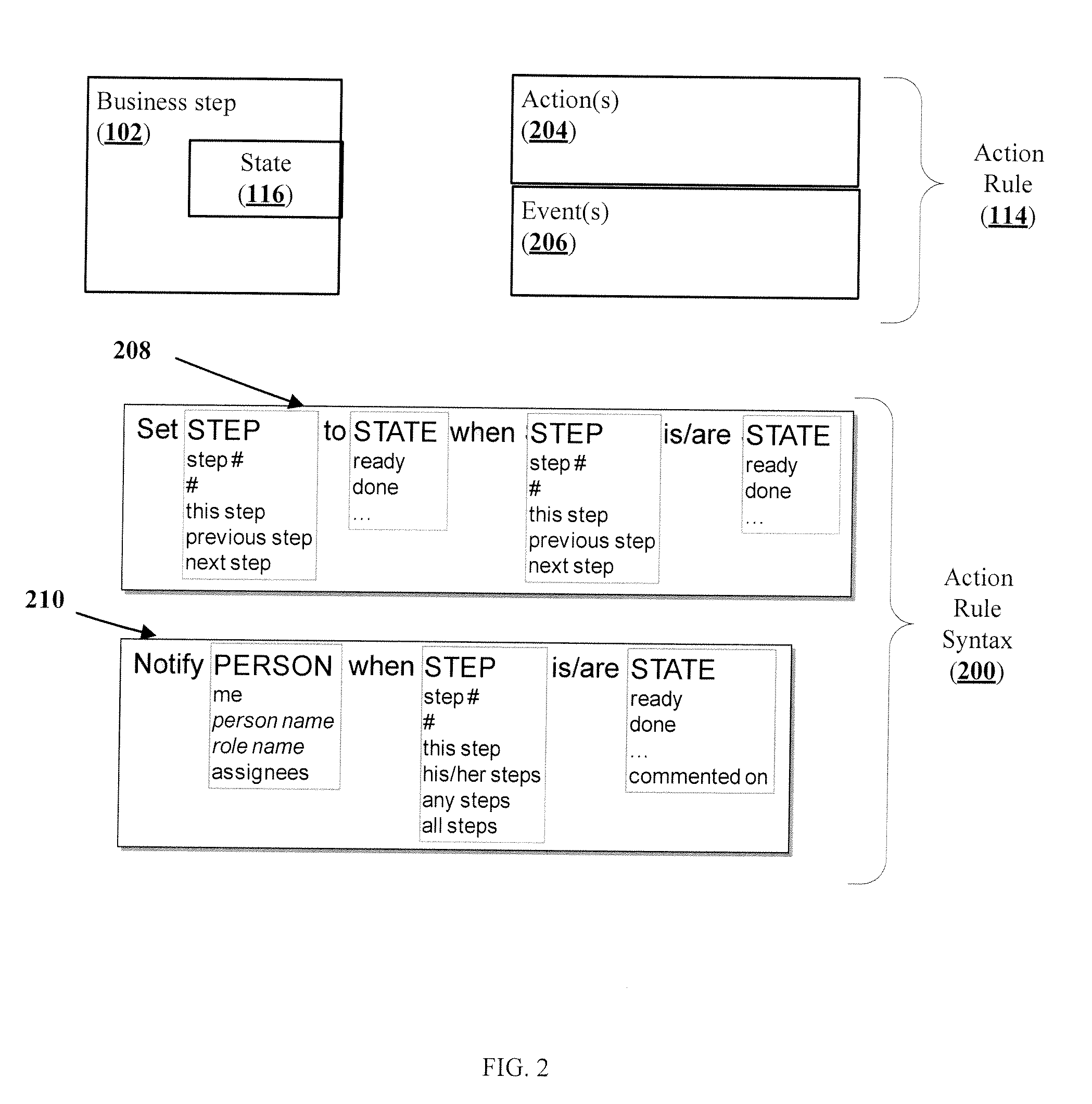
A method and apparatus for evolving a shared to-do list into a business process is disclosed. A business process includes one or more business steps and zeroor more action rules related to the business steps. Members of a workgroup participate in the business process and are able to view, modify, add and delete business steps and action rules as needed. An action rule is comprised of one or more business actions and one or more events that trigger the actions to be executed. A computer program keeps track of the business steps, interprets the set of rules, and updates states of the business process, notifies the members and validates and accepts modifications by the members to the action rules of a business steps.
Owner:IBM CORP
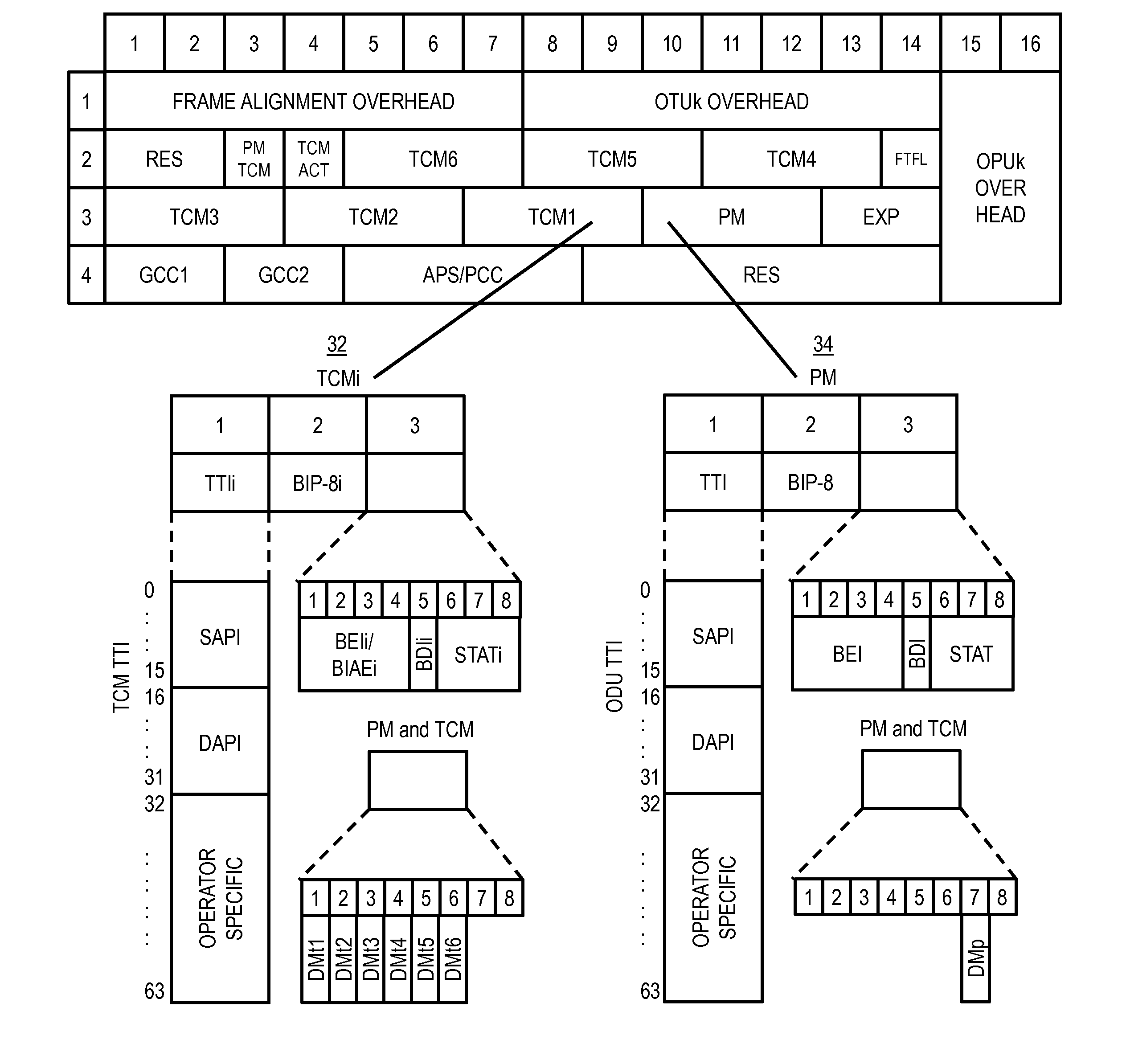
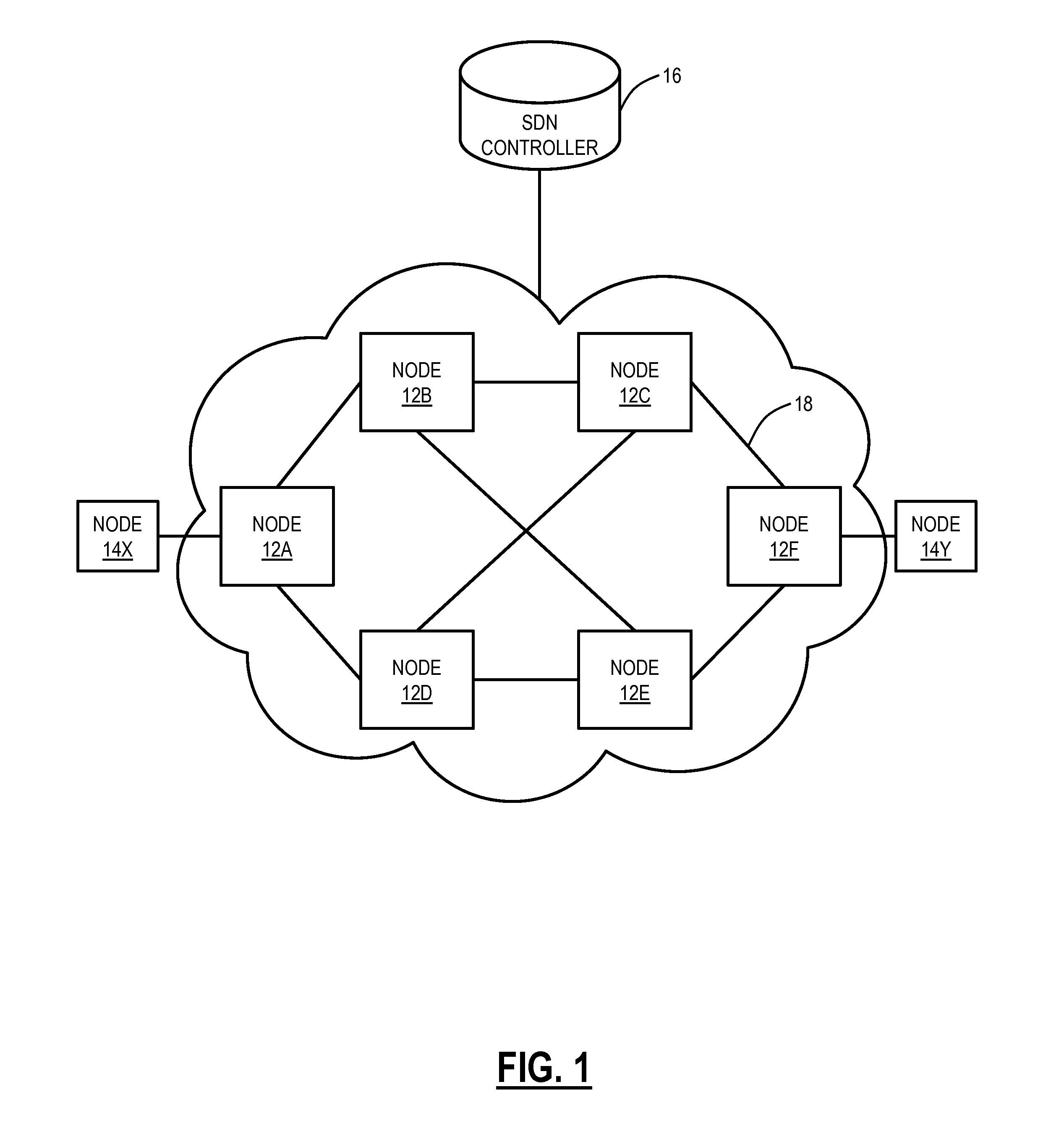
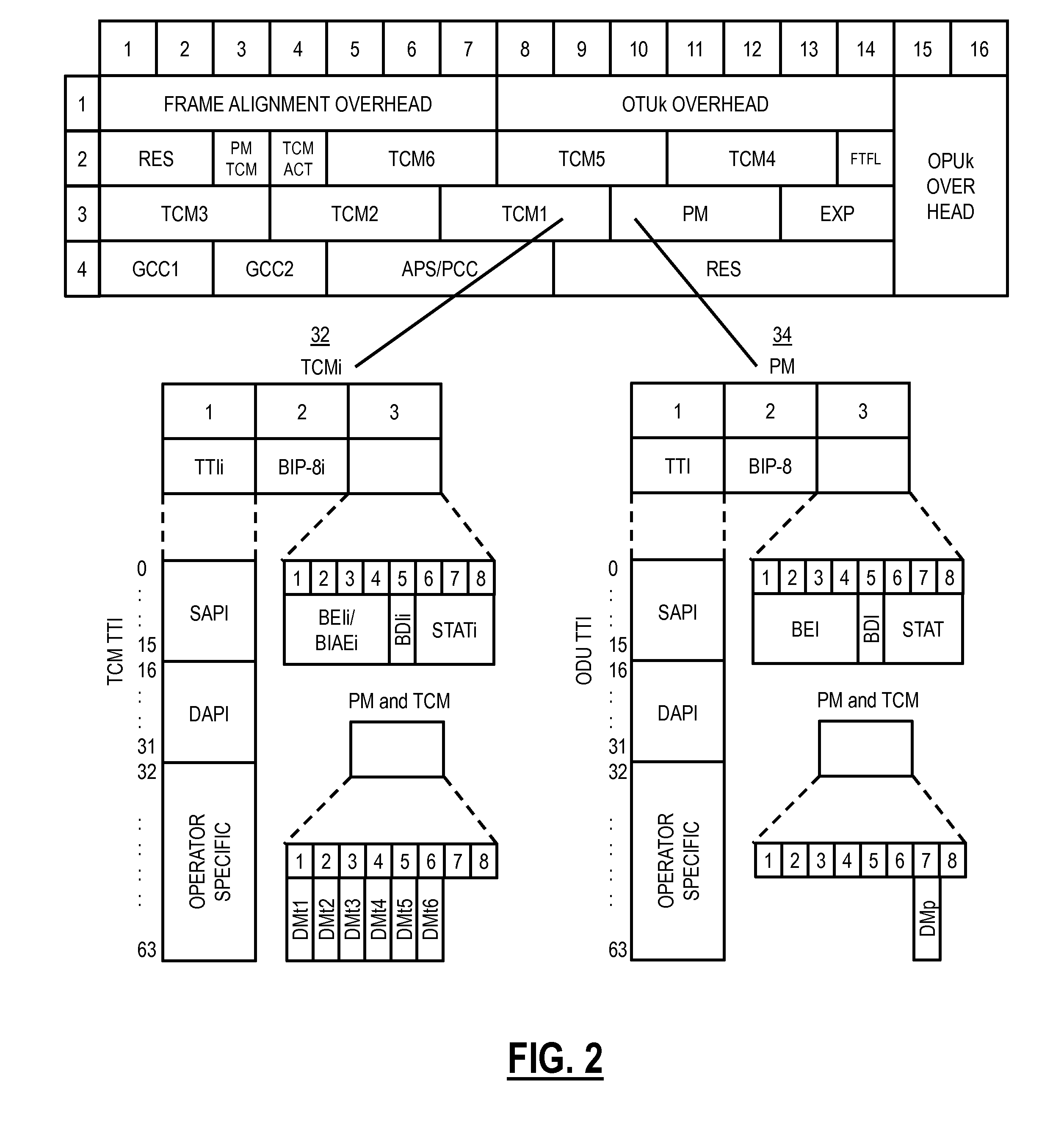
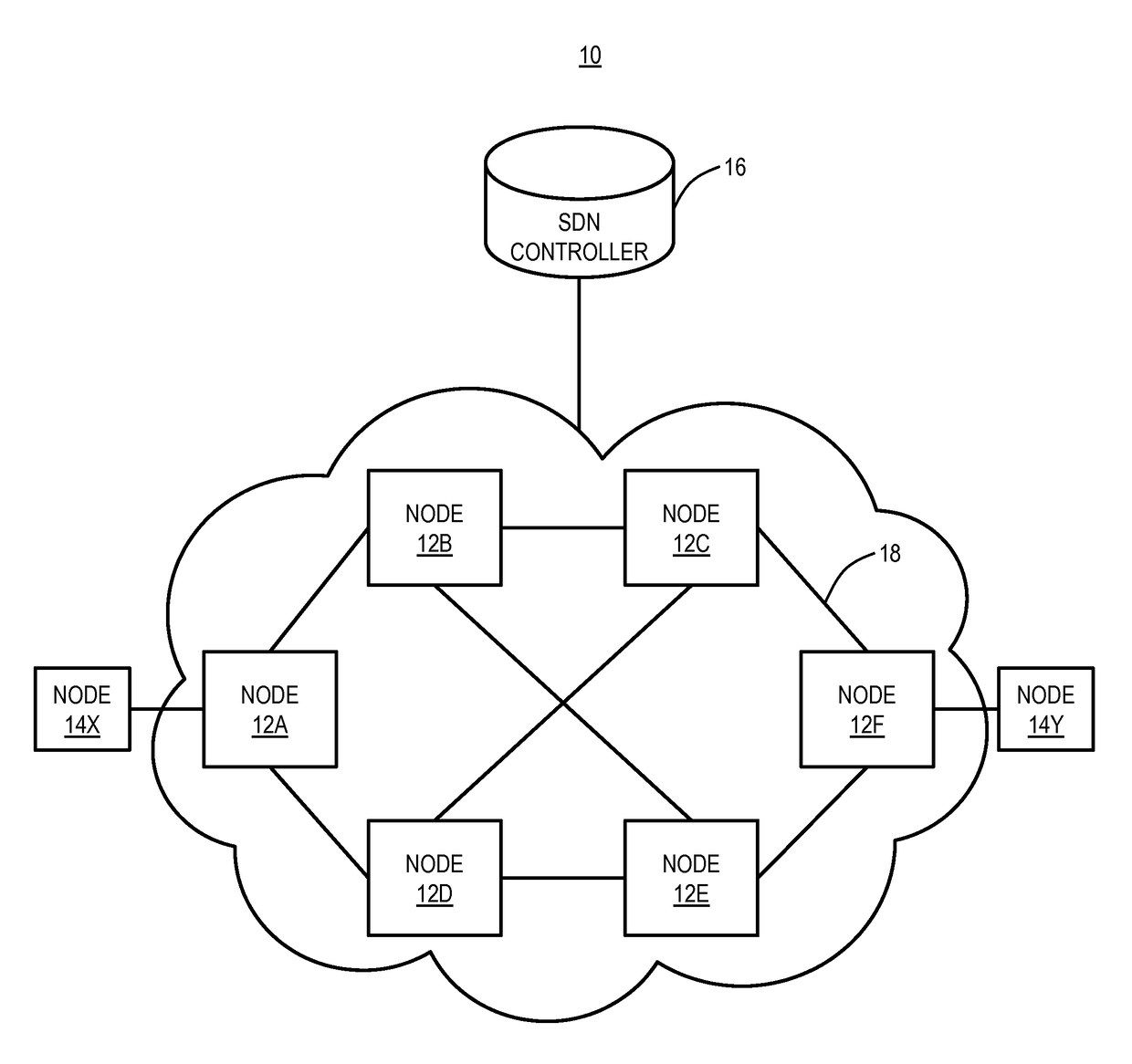
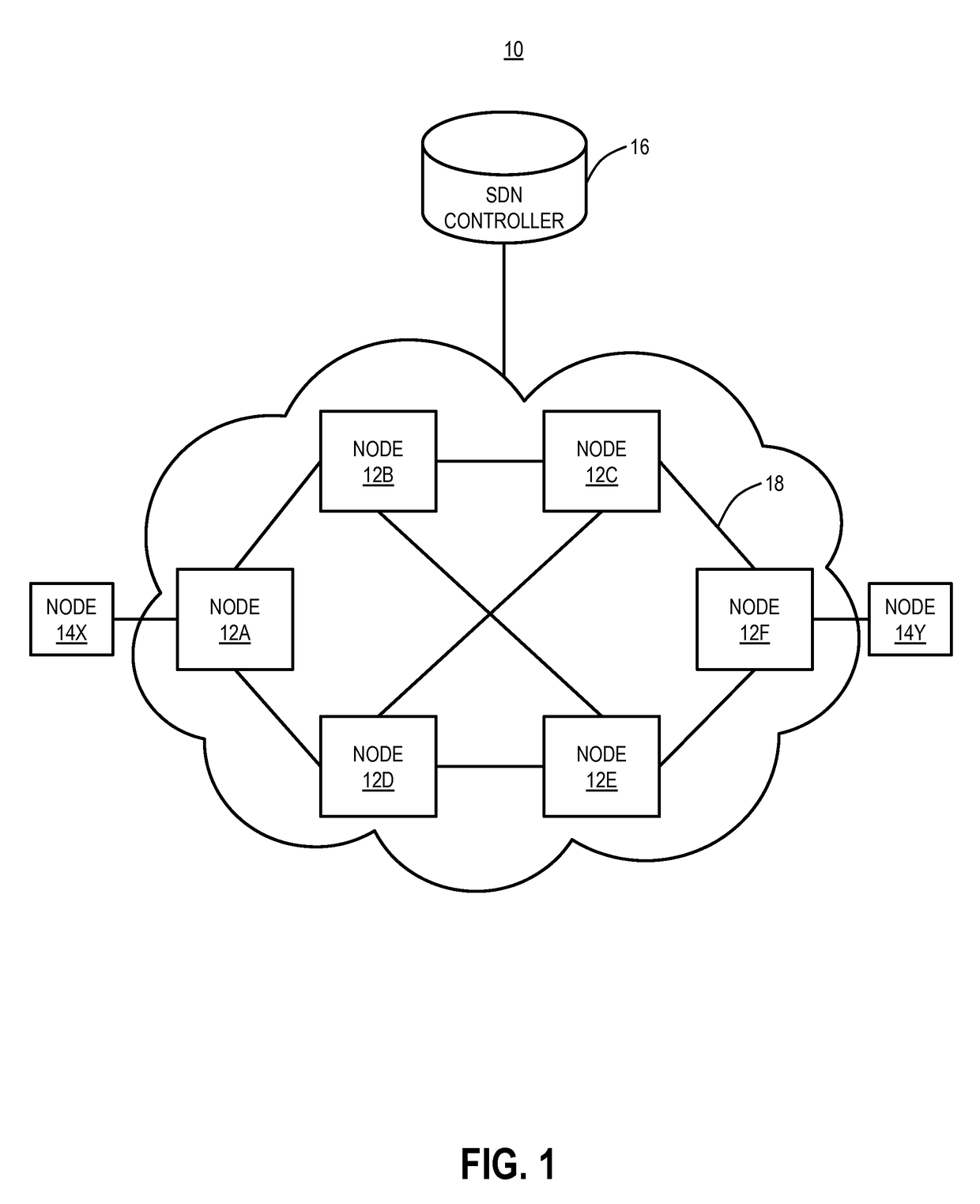
Otn switching systems and methods using an SDN controller and match/action rules
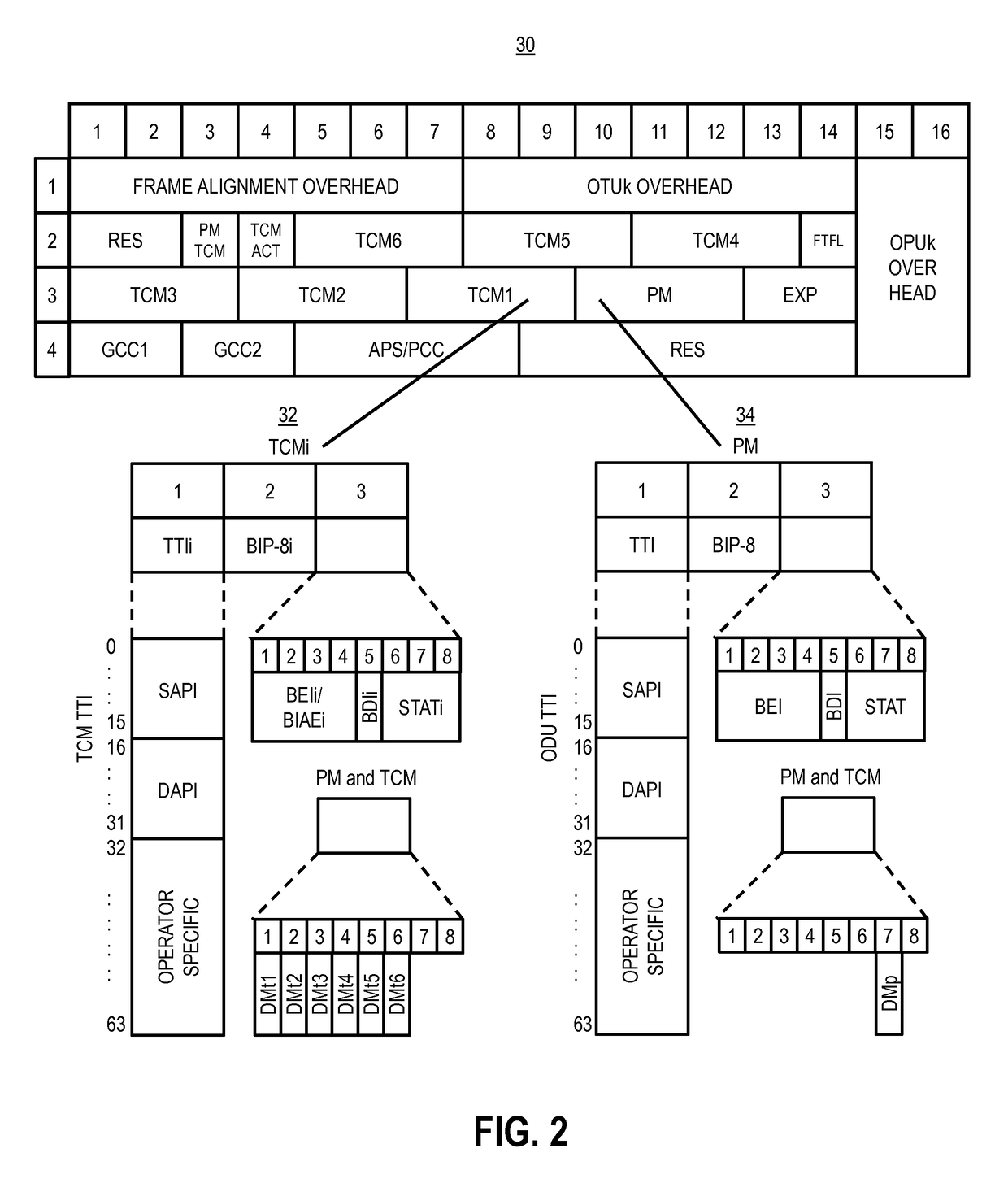
ActiveUS20150365193A1Multiplex system selection arrangementsTime-division optical multiplex systemsTime-division multiplexingAction rule
A method and network include receiving a Time Division Multiplexing (TDM) connection; determining information in overhead of the TDM connection; and if match / action rules defined by controller exist for the TDM connection, establishing the TDM connection based on matching an associated rule in the match / action rules. A Software Defined Networking (SDN) controller is configured to receive a request from a node related to a new TDM connection in the network; determine one or more routes in the network for the new TDM connection; determine match / action rules for the one or more routes at associated nodes of the one or more nodes; if the one or more routes include at least two routes, determine a group table at associated nodes of the one or more nodes to distinguish between the at least two routes; and provide the match / action rules and the group table to the associated nodes.
Owner:CIENA
Method for handling radio link failure in wireless communications system and related apparatus
Handling radio link failure efficiently in a packet switching domain of a wireless communications system includes a user equipment performing an action when an indication is received from a network entity for an action rule or action rules and a trigger or triggers to enter a radio state, and the user equipment entering the radio state.
Owner:INNOVATIVE SONIC
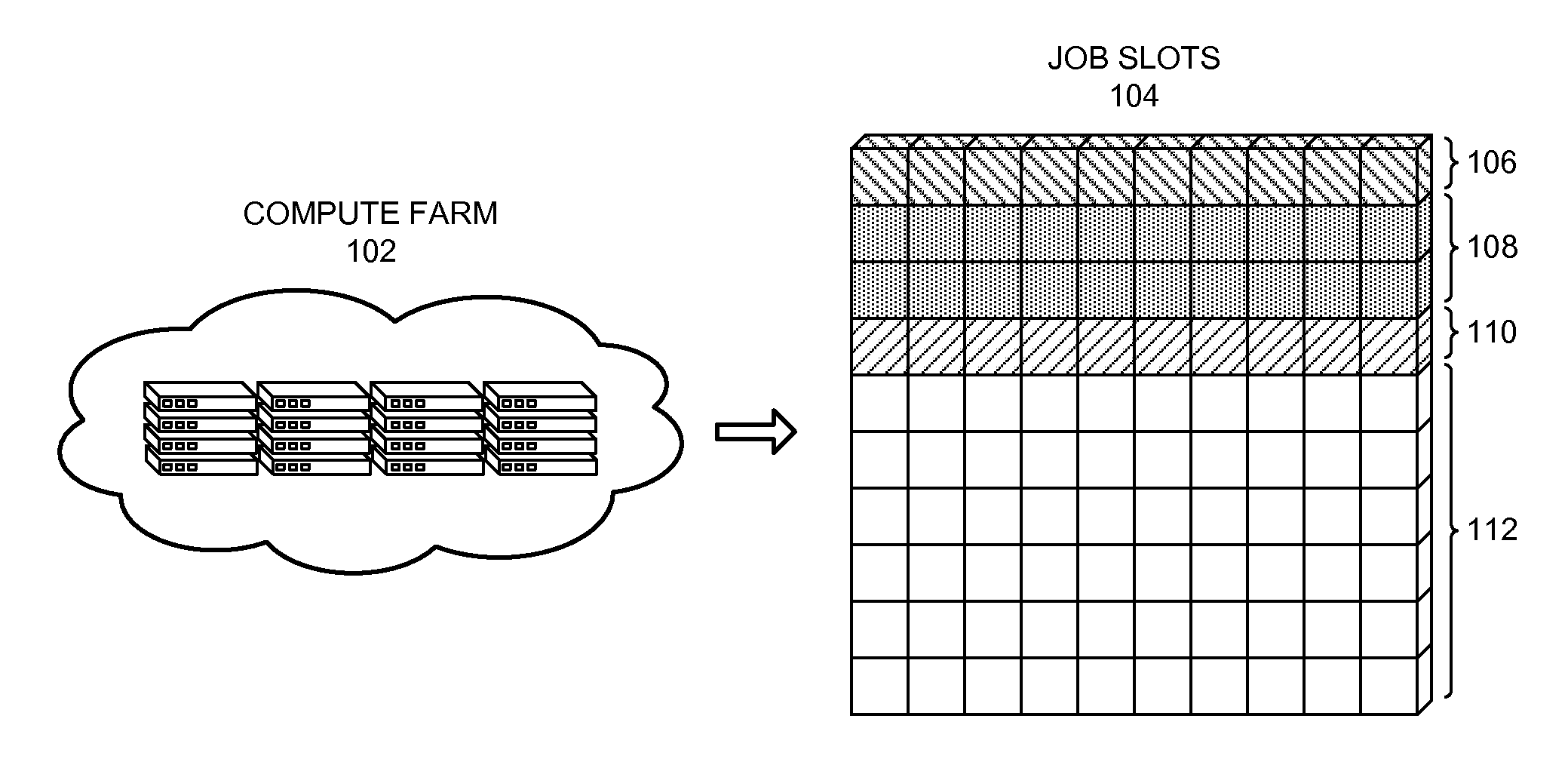
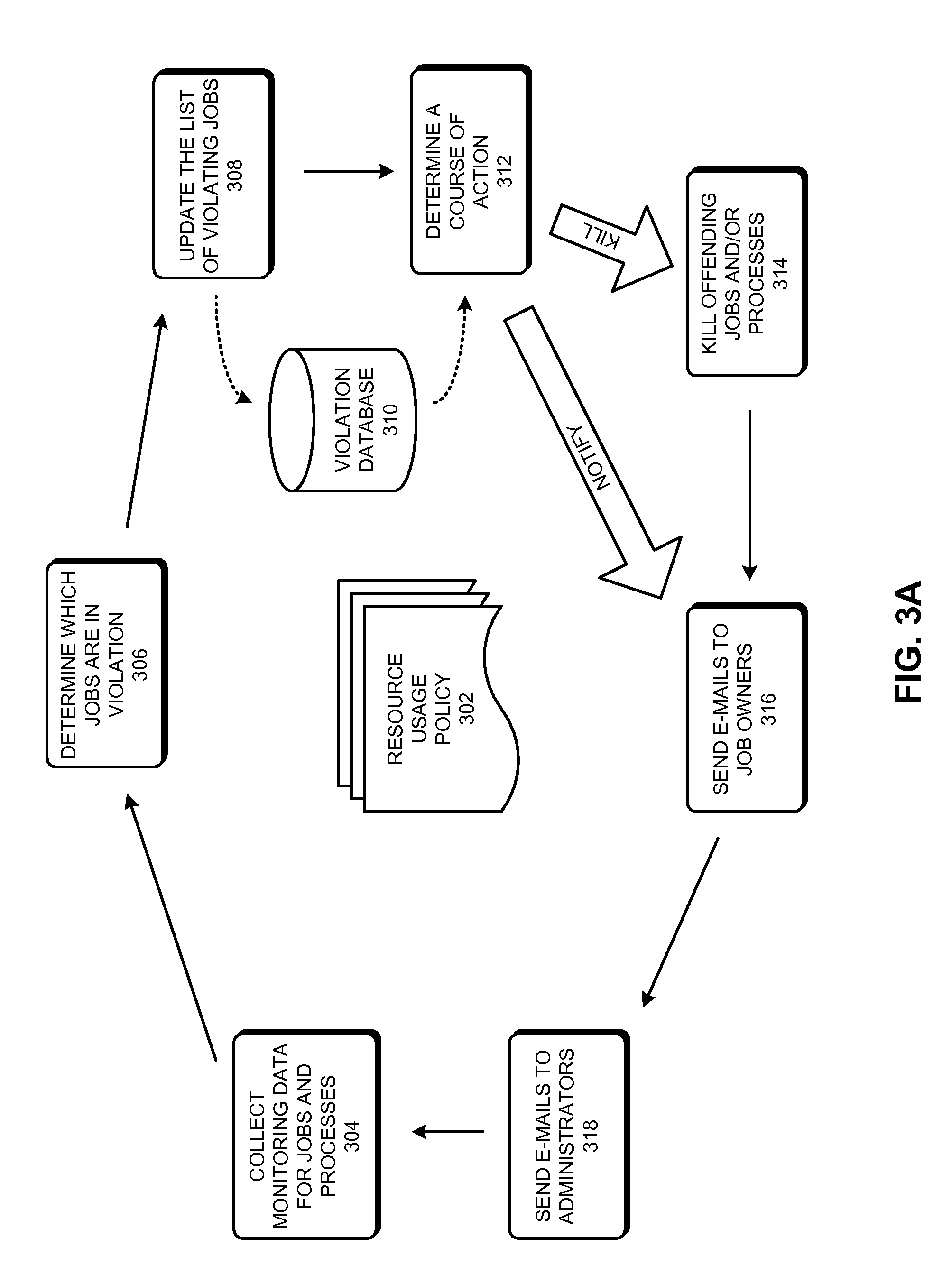
Method and apparatus for enforcing a resource-usage policy in a compute farm
One embodiment of the present invention provides a system that enforces a resource-usage policy in a compute farm. During operation, the system can receive etiquette rules which include resource-usage rules and corrective-action rules. Resource-usage rules can specify situations in which the resource-usage policy is violated, and corrective-action rules can specify situations in which a corrective action needs to be performed. Next, the system can receive resource-usage information which includes job monitoring data and process monitoring data. The system can then determine a resource-usage violation by applying the resource-usage rules to the resource-usage information. Next, the system can store the resource-usage violation in a violation database. The system can then determine a corrective action by applying corrective-action rules to a series of violations stored in the violation database. Next, the system can perform the corrective action, thereby enforcing the resource-usage policy in the compute farm.
Owner:SYNOPSYS INC
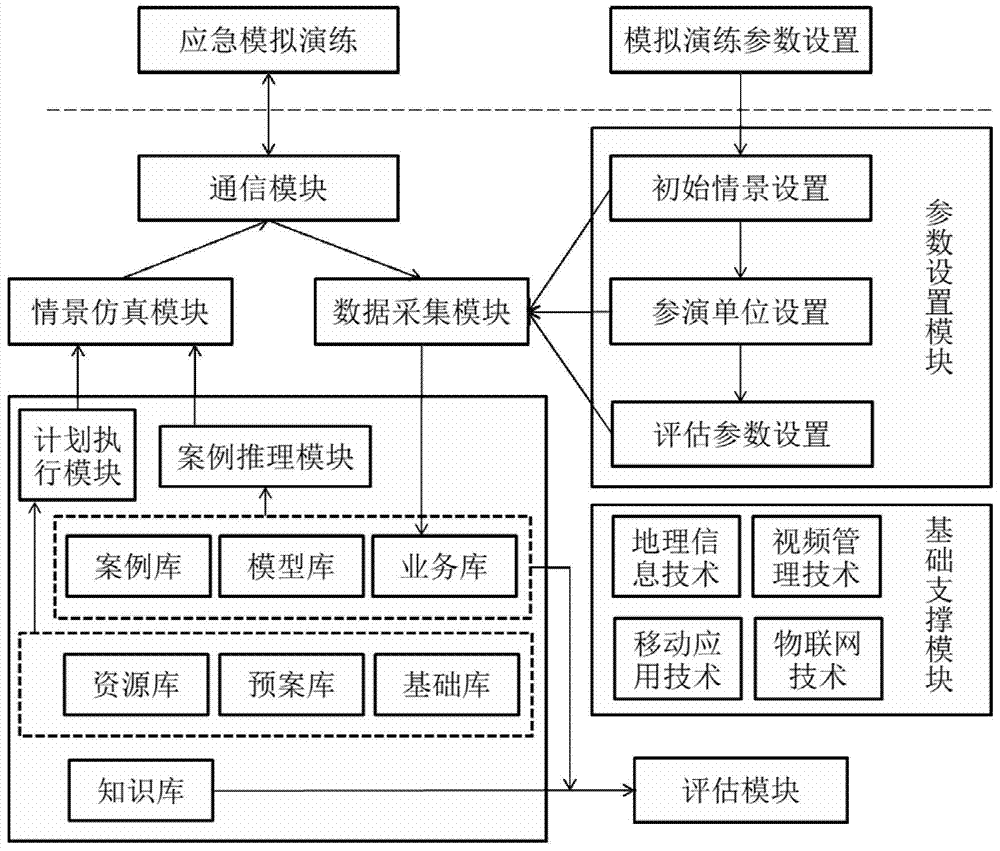
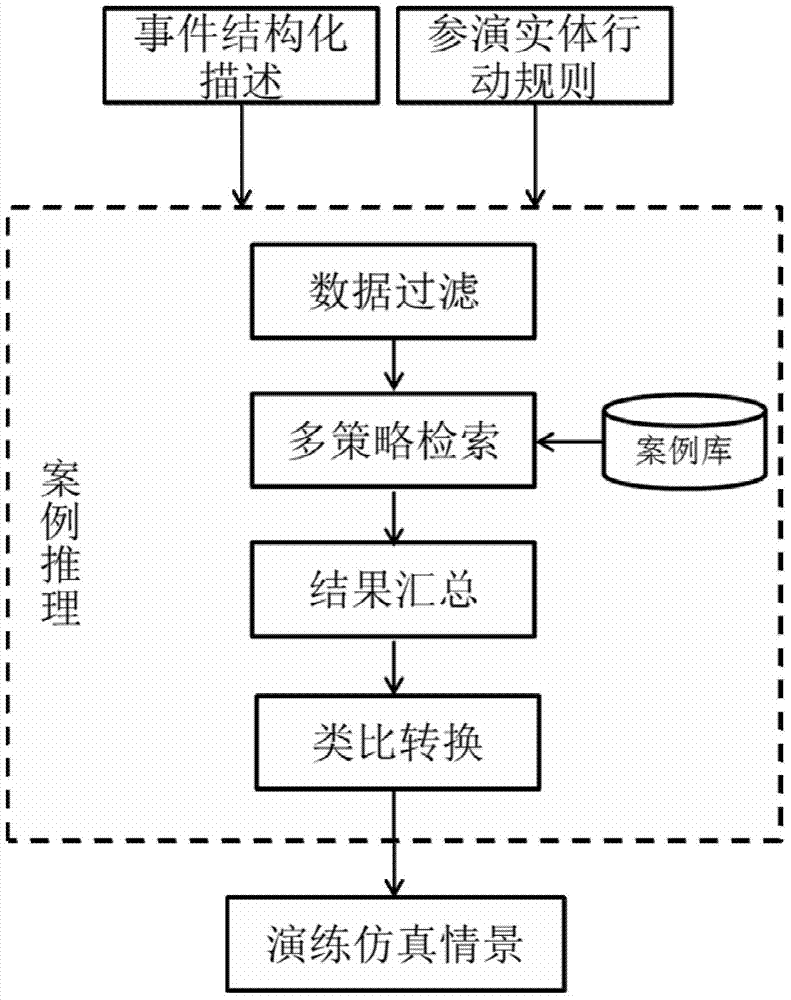
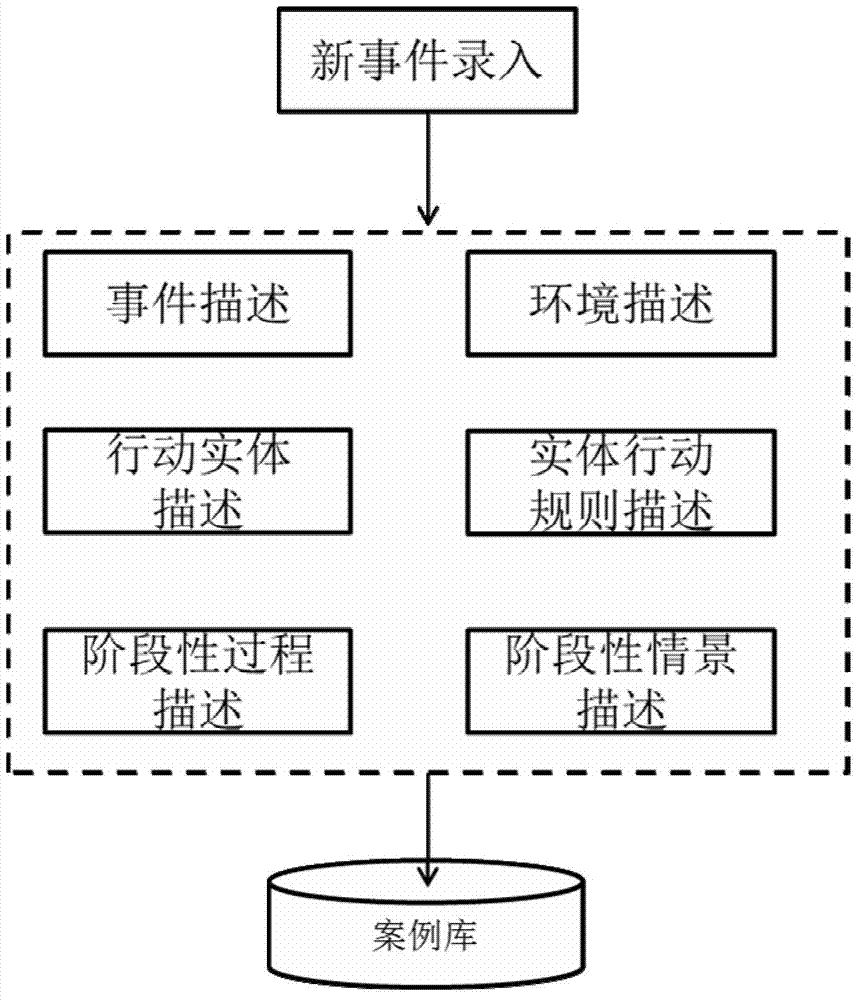
City comprehensive emergency intelligent simulation system based on case-based reasoning and operation method thereof
InactiveCN103679611ASolve intelligent generationSolve the problem of dynamic evolutionData processing applicationsInference methodsSimulation basedAction rule
The invention relates to the technical field of comprehensive emergency management, in particular to a city comprehensive emergency intelligent simulation system based on case-based reasoning and an operation method of the city comprehensive emergency intelligent simulation system. According to the method, with structured event information as conditions, a case base is searched for similar cases, effective reasoning is carried out based on action rules of all participating entities according to a model, and scenes in the cases are modified to form new simulation exercise scenes to be used by participating units for participation. When city comprehensive emergency simulation exercises are finished, by carrying out evaluation, modification and summarization on the simulation exercises and saving the cases as new cases finally, self-increasing of the case base and self-learning capacity of a simulation exercise system are achieved, and solid foundations are laid for further simulation exercise scene generation. The method solves the problem that simulation exercise scenes are lack of scene exercise analog simulation based on behavior rules of all current participating entities, and can be applied to the city comprehensive emergency intelligent simulation system.
Owner:CLOUD COMPUTING CENT CHINESE ACADEMY OF SCI
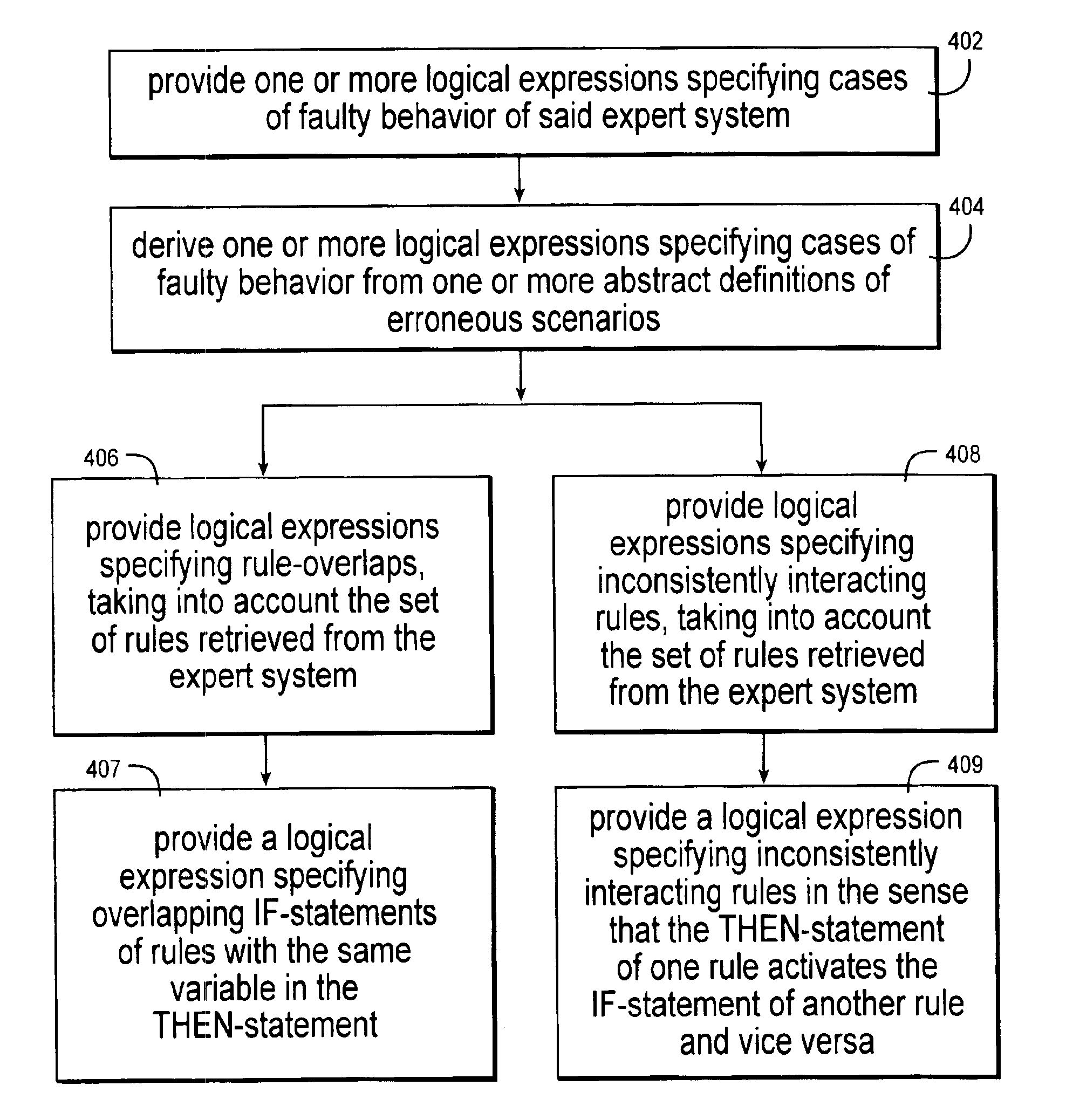
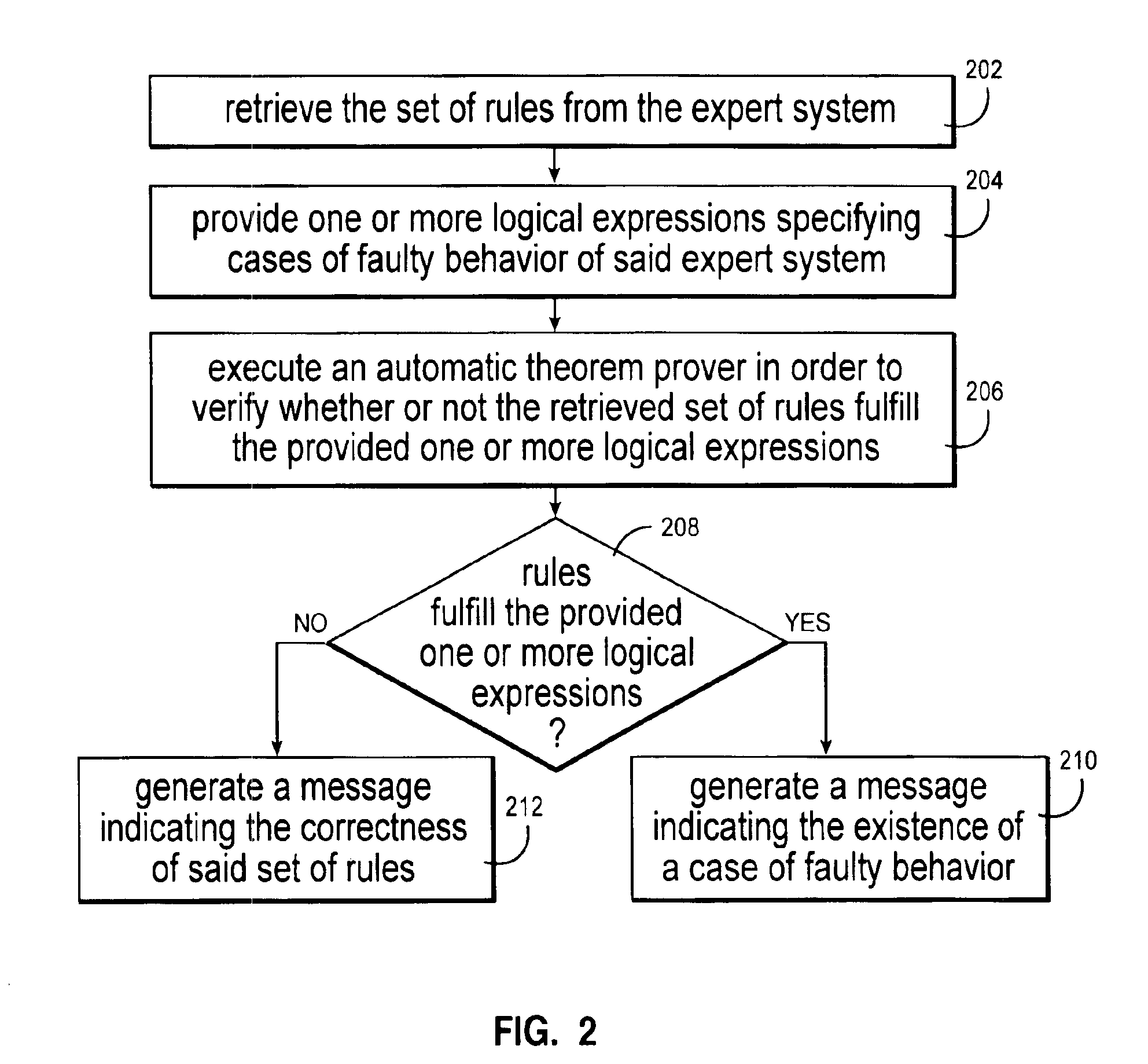
Loop detection in rule-based expert systems
InactiveUS6952690B2Easy to understandKnowledge representationSpecial data processing applicationsRule based expert systemAlgorithm
This invention describes a method to verify non-looping properties of programs implemented as rule-based expert systems. Our method detects conditions under which the expert system enters erroneous infinite program loops, which lead to non-terminating or oscillating computations, or otherwise proves the absence of such conditions. Our automatic procedure also gives advice on how to correct these errors. The expert systems considered consist of condition-action rules (IF-THEN-statements), where the conditions are logical expressions (formulas of a propositional finite domain logic), and the actions modify the value of a single variable which in turn can be part of other logical expressions. There may be additional (external) variables not controlled by the expert system, and each rule may have an associated evaluation priority.
Owner:IBM CORP +1
Remote diagnosis and decision method for running state of hydroelectric generating set
ActiveCN104331631AGuaranteed uptimeImprove troubleshooting efficiencyEngine testingSpecial data processing applicationsFunctional indicesCollision analysis
The invention discloses a remote diagnosis and decision method for the running state of a hydroelectric generating set. The method comprises the following steps: building a remote diagnosis and decision basic repository and fault database of the running state of the hydroelectric generating set; remotely monitoring and acquiring the important parameters such as the running vibration, amplitude and pressure pulsation of the hydroelectric generating set, a collision signal of an underwater portion of a top cover, the static feature, dynamic feature, functional index, switch-on / off time and rule of a speed regulating control system, and the starting-stopping time of an oil pump of an oil pressing groove; remotely diagnosing and deciding the running stability of the set by adopting the methods of trend analysis, specific frequency band collision analysis, specific index comparison, switch-on / off time and action rule analysis, the starting-stopping time analysis of the oil pump of the oil pressing groove and the like.
Owner:STATE GRID CORP OF CHINA +2
OTN switching systems and methods using an SDN controller and match/action rules
ActiveUS9680588B2Multiplex system selection arrangementsTime-division multiplexTime-division multiplexingAction rule
A method and network include receiving a Time Division Multiplexing (TDM) connection; determining information in overhead of the TDM connection; and if match / action rules defined by controller exist for the TDM connection, establishing the TDM connection based on matching an associated rule in the match / action rules. A Software Defined Networking (SDN) controller is configured to receive a request from a node related to a new TDM connection in the network; determine one or more routes in the network for the new TDM connection; determine match / action rules for the one or more routes at associated nodes of the one or more nodes; if the one or more routes include at least two routes, determine a group table at associated nodes of the one or more nodes to distinguish between the at least two routes; and provide the match / action rules and the group table to the associated nodes.
Owner:CIENA
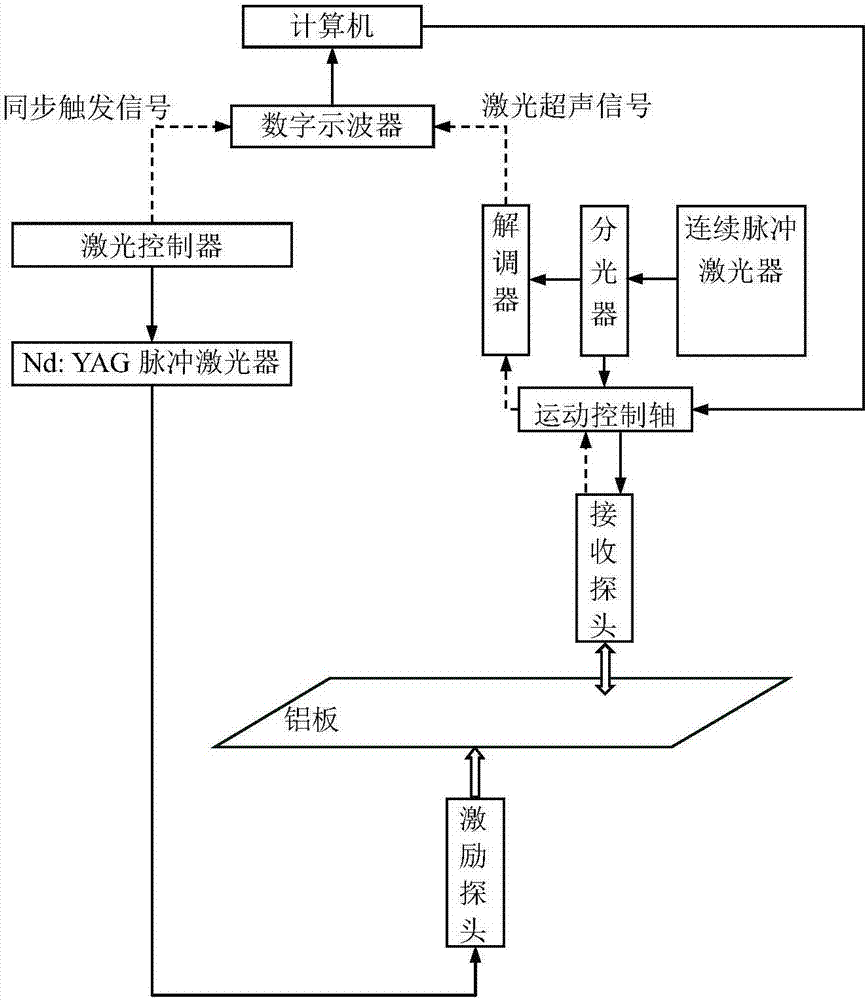
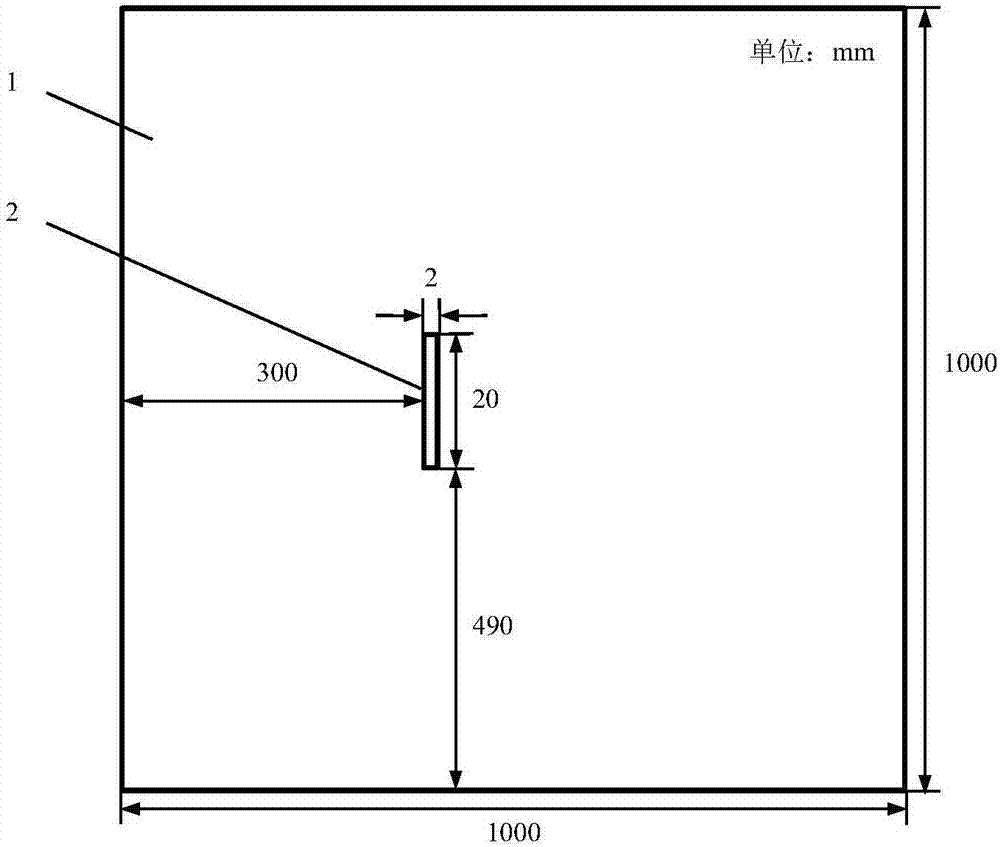
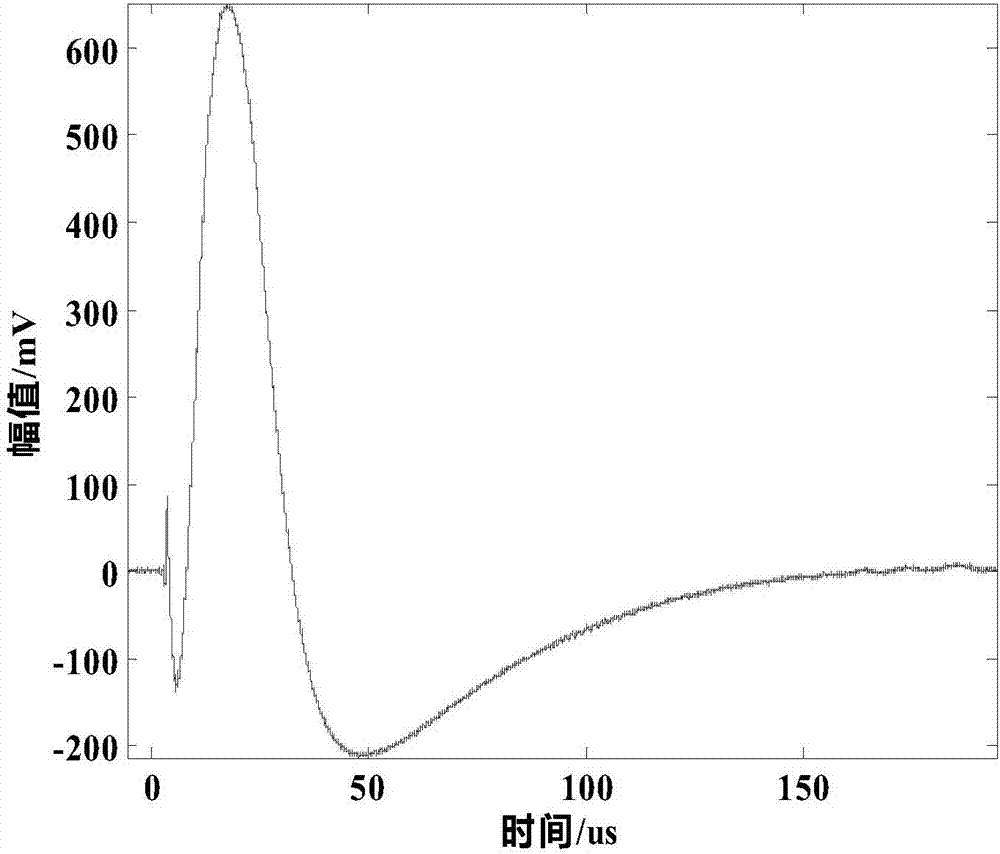
Metal plate defect location method based on laser Lamb wave frequency-wave number analysis
The invention discloses a metal plate defect location method based on laser Lamb wave frequency-wave number analysis and belongs to the field of laser ultrasonic non-destructive testing. The method comprises the following steps: firstly, excitation is performed by a laser excitation probe in a fixed position on a metal plate, a laser receiving probe scans defect lines to receive N groups of Lamb wave data, and a time-space wave field on a scanning path is obtained; secondly, signals under specific center frequency are extracted from the acquired N groups of Lamb wave data with a continuous wavelet transform method, and analyzability of a defect location result is guaranteed; finally, the extracted wave field signals are subjected to space-frequency-wave number imaging with short-space two-dimensional Fourier transform algorithm, and defect location is realized according to characteristics of a wave number spectrum on the scanning path. One completely non-contact type detection method is provided, and action rules between Lamb waves and defects in the wave number field are disclosed.
Owner:BEIJING UNIV OF TECH
Fault diagnosis method for power grid based on improved Bayesian Petri net
ActiveCN107656176AReduce uncertaintyImprove accuracyFault location by conductor typesPetri netAction rule
The invention discloses a fault diagnosis method for a power grid based on an improved Bayesian Petri net, and the method comprises the steps: firstly introducing a time sequence correlation rule, andstarting from the quantification angle to describe the time sequence relation between all places and a logic rule; secondly carrying out the reasoning of the time sequence constraint correlation of alarm information through a protection action rule under the condition that fault information is not complete, and giving an algorithm for recognizing the loss of alarm information, a breaking point and false alarm; finally achieving the positioning of a fault element quickly and accurately through combining with a Bayesian network. According to the invention, the method makes the most of the information in an alarm signal, and a fault diagnosis model which is based on the improved Bayesian Petri net and gives consideration to the time sequence correlation rule is proposed on the basis of the deep analysis of the time sequence attribute in the alarm information. The method reduces the uncertainty of an alarm result, is strong in resistance to interference, and can greatly improve the accuracy of a diagnosis result.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Computer Security Intrusion Detection System For Remote, On-Demand Users
An intrusion detection system, and a related method and computer program product, for implementing intrusion detection in a remote, on-demand computing service environment in which one or more data processing hosts are made available to a remote on-demand user that does not have physical custody and control over the host(s). Intrusion detection entails monitoring resources defined by the on-demand user (or a third party security provider) for intrusion events that are also defined by the on-demand user (or security provider), and implementing responses according to event-action rules that are further defined by the on-demand user (or security provider). An intrusion detection system agent is associated with each of the data processing hosts, and is adapted to monitor the intrusion events and report intrusion activity. If there are plural intrusion detection system agents, they can be individually programmed to monitor and report on agent-specific sets of the intrusion events. An intrusion detection system controller is associated with one of the data processing hosts. It is adapted to manage and monitor the intrusion detection system agent(s), process agent reports of intrusion activity, and communicate intrusion-related information to the on-demand user (or security provider). The responses to intrusion events can be implemented by the intrusion detection system controller in combination with the intrusion detection system agents, or by any such entity alone.
Owner:INT BUSINESS MASCH CORP
A Network Fault Reconfiguration Method Applicable to Aircraft Distributed Power Distribution System
InactiveCN102270837ASolve conflictsFlexible control methodEmergency protective circuit arrangementsInformation technology support systemJet aeroplaneControl layer
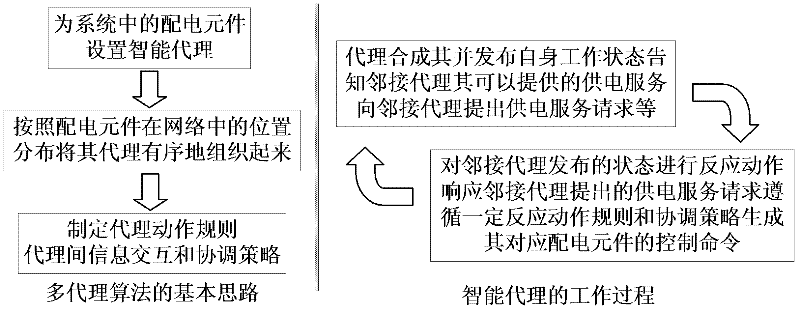
The invention discloses a network failure reconstruction method suitable for an airplane distributed distribution system. The method comprises the following steps of: setting a corresponding intelligent agent for each distribution element of a power distribution network in a control layer; making an agent action rule and an information interactive coordination strategy according to position distribution of distribution elements in the network; synthesizing and releasing a working condition of the distribution element corresponding to each intelligent agent by using each intelligent agent, informing an adjacent agent of power supply service which can be provided by the intelligent agent, and making a power supply service request by using the adjacent agent; and perceiving a state which is released by the adjacent agent and responding by using each agent, and responding to the power supply service request which is made by the adjacent agent, and generating a control command corresponding to the distribution element according to the certain response action rule and the coordination strategy. The method has the advantages of better solving the problem of the conventional failure reconstruction algorithm, automatically tracking and monitoring the topology and the working condition of a network, and restoring power supply for a loading point in the network as far as possible on the premise that a failure in the network is ensured to be isolated.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
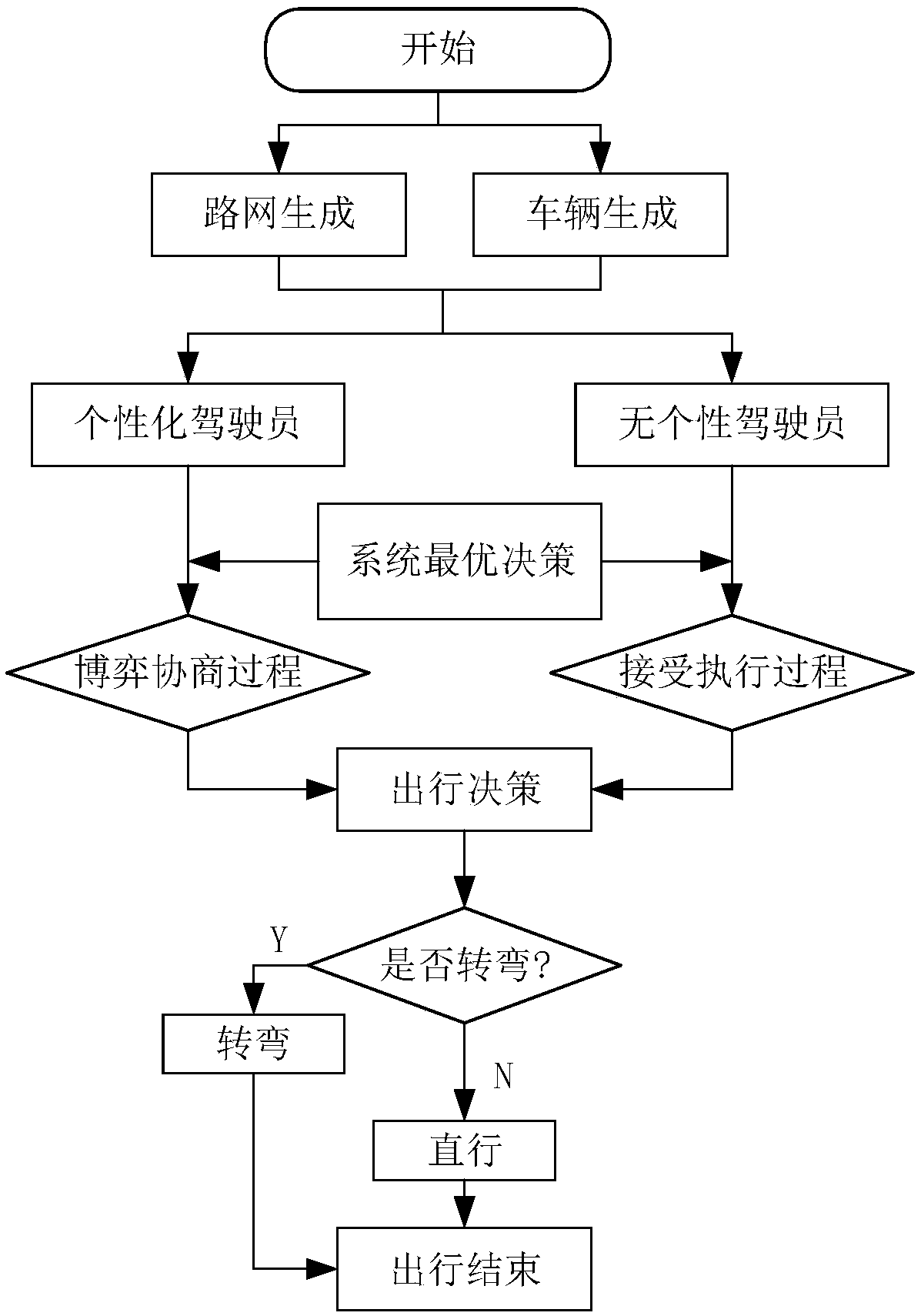
Multi-agent based route selection simulation system in vehicle online environment
InactiveCN106529064APersuasiveImprove effectivenessDesign optimisation/simulationSpecial data processing applicationsTransfer modelIn vehicle
The present invention discloses a multi-agent based route selection simulation system in a vehicle online environment. The system consists of two parts: foreground and background. A foreground interface is a human-computer interaction module, and a background program is responsible for implementing a function of the simulation system. The system comprises a route network generation and initialization model, a vehicle generation and initialization model, a simulation kernel model and an information acquisition and transfer model. A simulation kernel is core rules for driving a vehicle to run in a route network and comprises two layers of rules: micro rules and macro rules. The present invention studies overall design of the multi-agent simulation system for a route selection behavior of a traveler in the vehicle online environment, two layers of action rules of the vehicle-online multi-agent and information acquisition and transfer in the simulation system and the like; and starting from each vehicle action rule, the macro state of the system is reflected, so that simulation of the complicated dynamic system is feasible and effective.
Owner:BEIHANG UNIV
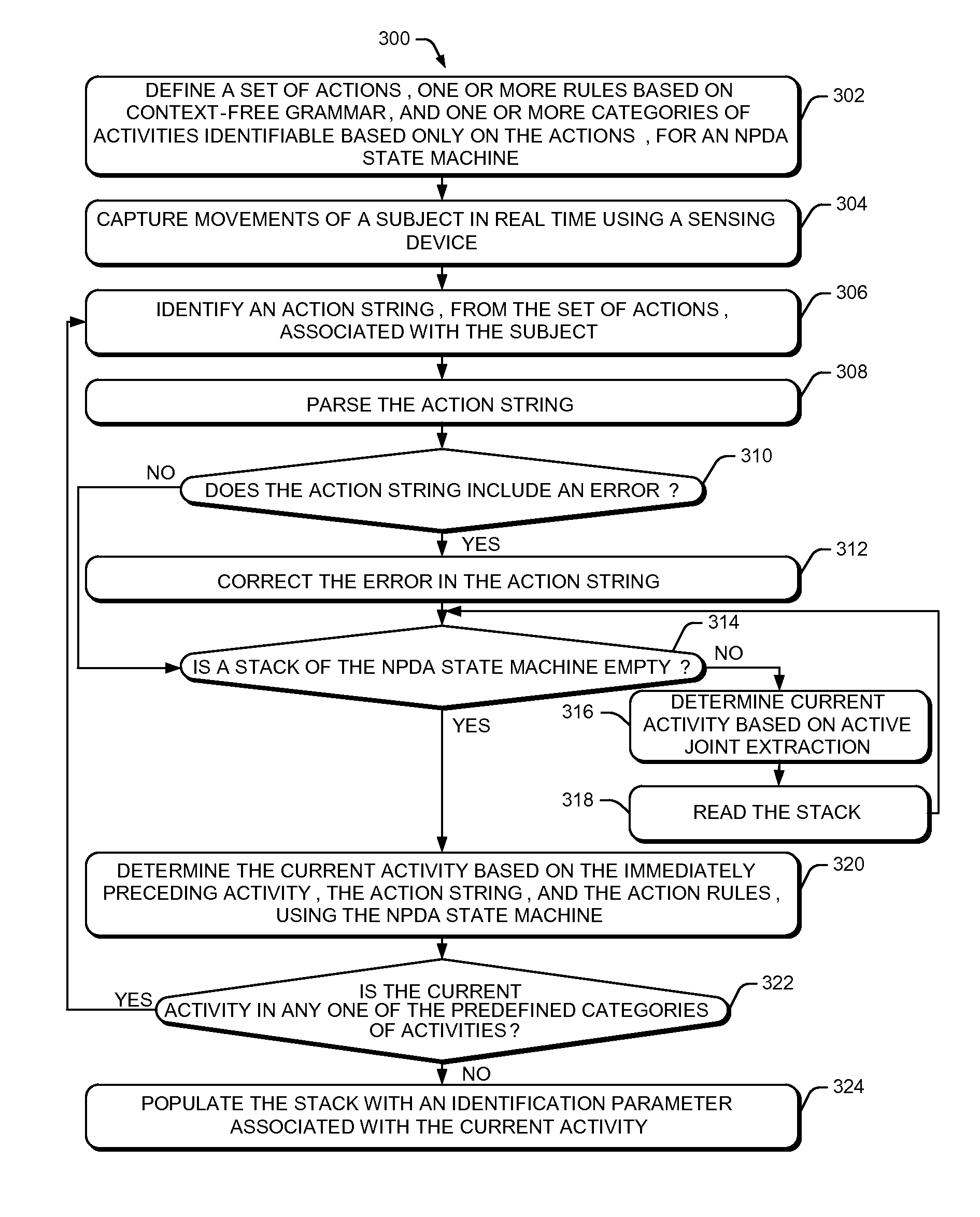
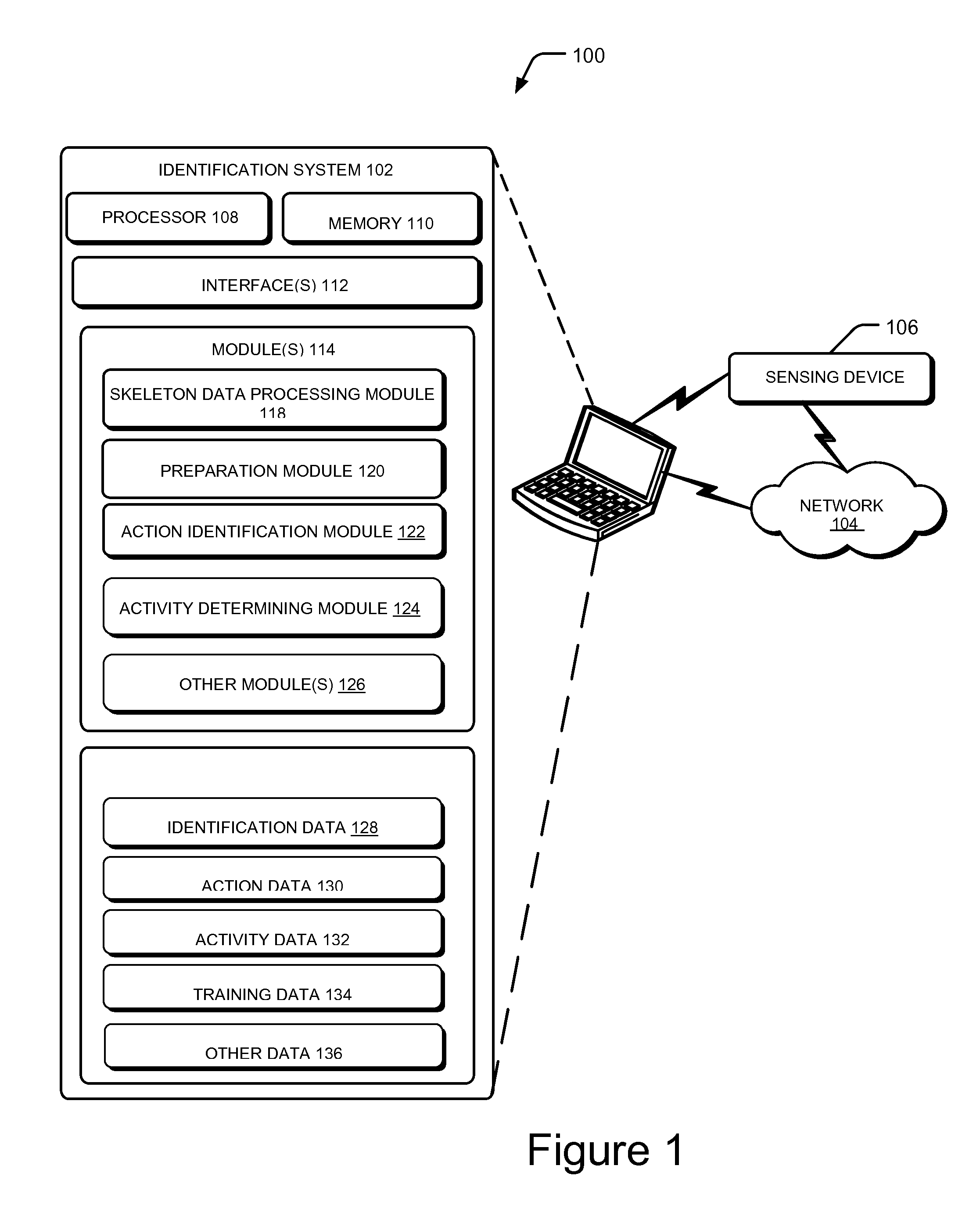
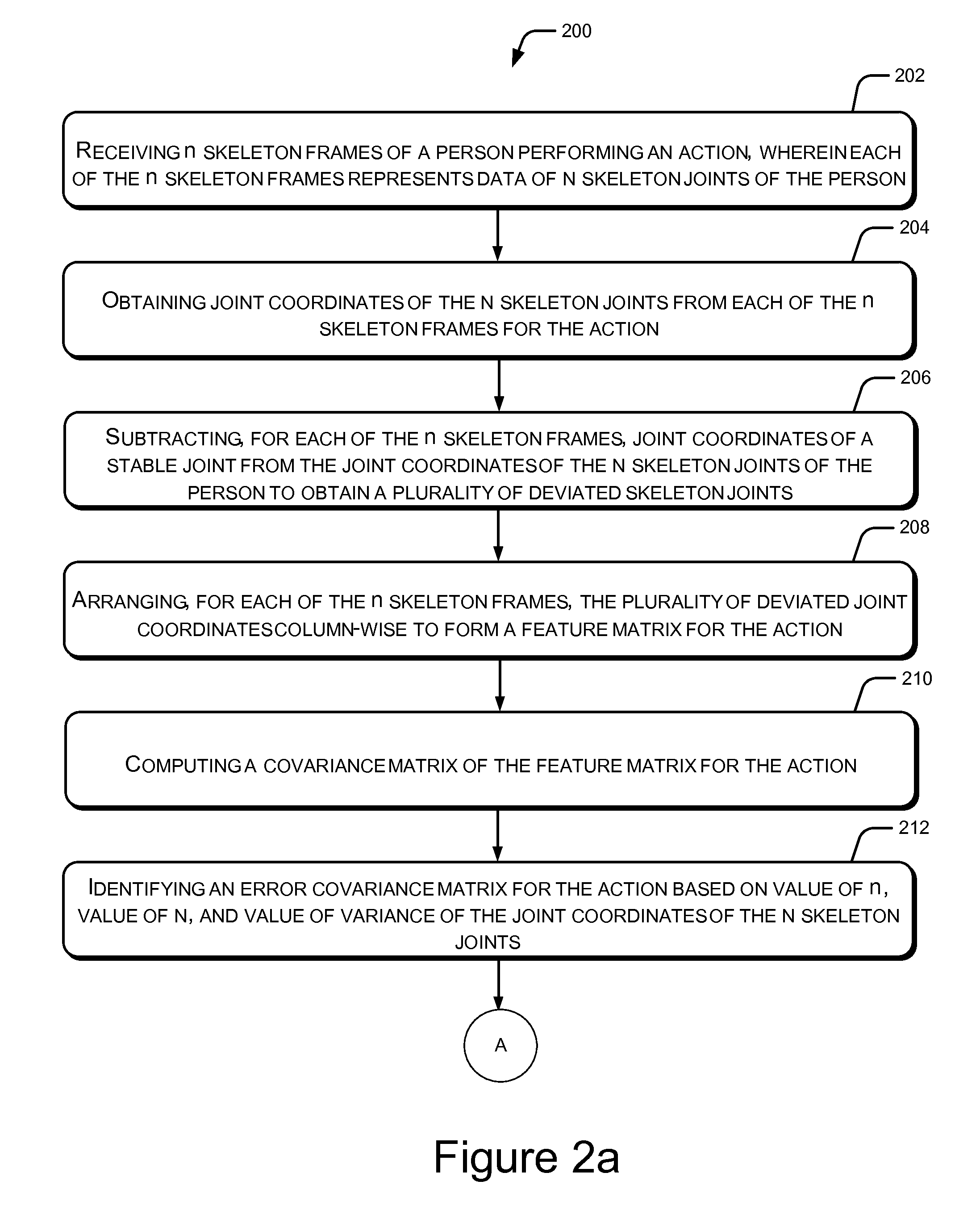
Action based activity determination system and method
A processor implemented system and method for identification of an activity performed by a subject based on sensor data analysis is described herein. In an implementation, the method includes capturing movements of the subject in real-time using a sensing device. At least one action associated with the subject is ascertained from a predefined set of actions. From the predefined set of actions, a plurality of actions can collectively form at least one activity. The ascertaining is based on captured movements of the subject and at least one predefined action rule. The at least one action rule is based on context-free grammar (CFG) and is indicative of a sequence of actions for occurrence of the at least one activity. Further, a current activity performed by the subject is dynamically determined, based on the at least one action and an immediately preceding activity, using a non-deterministic push-down automata (NPDA) state machine.
Owner:TATA CONSULTANCY SERVICES LTD
UUV multi-layer hybrid type immune agent structure modeling method
InactiveCN107133416ADegree of realizationFulfillment requirementsDesign optimisation/simulationKnowledge representationHybrid typeModularity
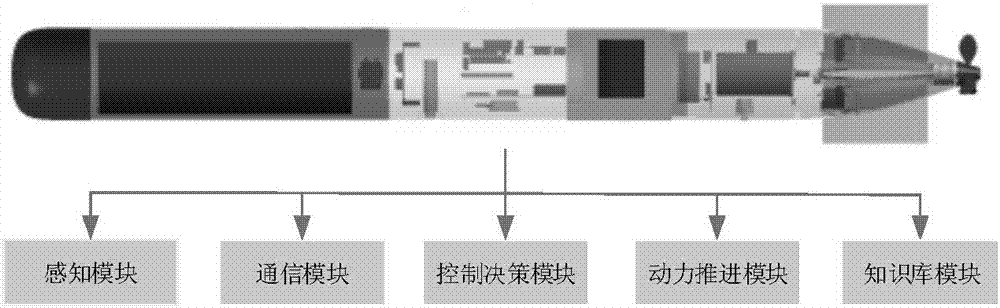
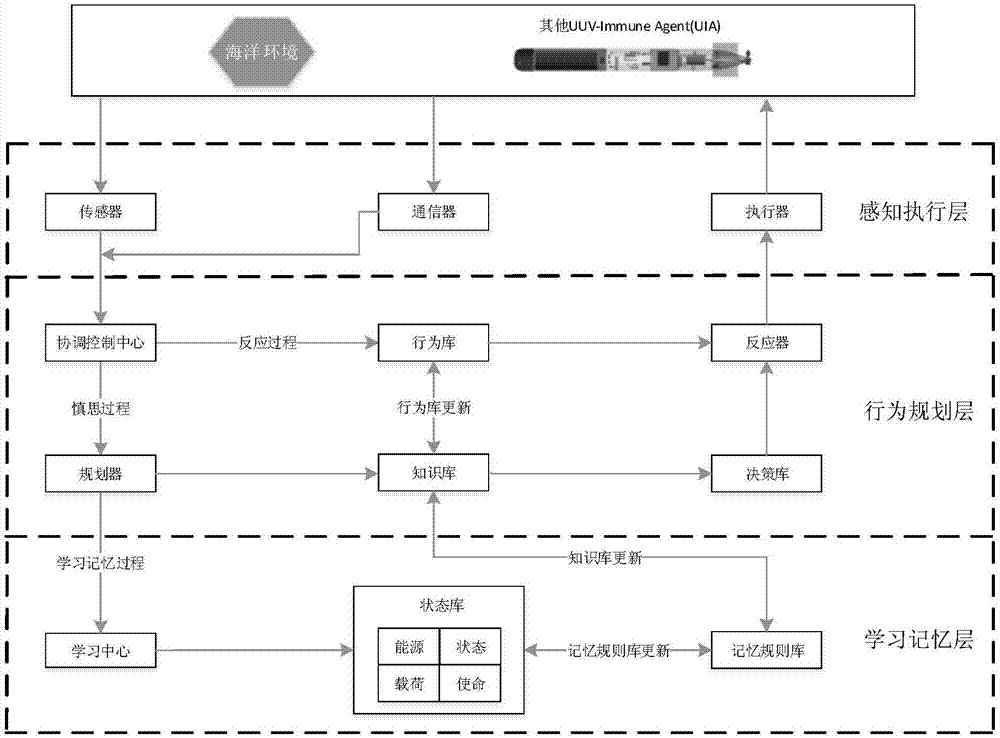
The invention provides an UUV multi-layer hybrid type immune agent structure modeling method. The method comprises the following steps: comparing a biological immune response mechanism and an Agent theory, and proposing an immune agent IA model; abstractly dividing the UUV model into a sensing module, a power propulsion module, a communication module, a control strategy module and a knowledge base module through a building block type modular abstracting method; designing a multi-layer hybrid structural UIA including a sensing performing layer, an action planning layer and a learning and memorizing layer; analyzing the function of each layer; designing formal description for an object; designing an UIA action rule library and a state library in detail; comprehensively describing the properties of an UIA model. According to the method, the UIA structure model built through the method packs a plurality of functions and properties, moreover, the structure layers are clear; the logic is clear; the module division is clear; the UIA structure model is clear to the UUV actual system; the modeling requirement of underwater UAV battle on UUV self-control degree and intelligence level can be achieved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
A travel information service strategy and simulation verification system in an Internet of Vehicles environment
PendingCN109670620AImprove effectivenessForecastingTransmissionAmbulatory systemComplex dynamic systems
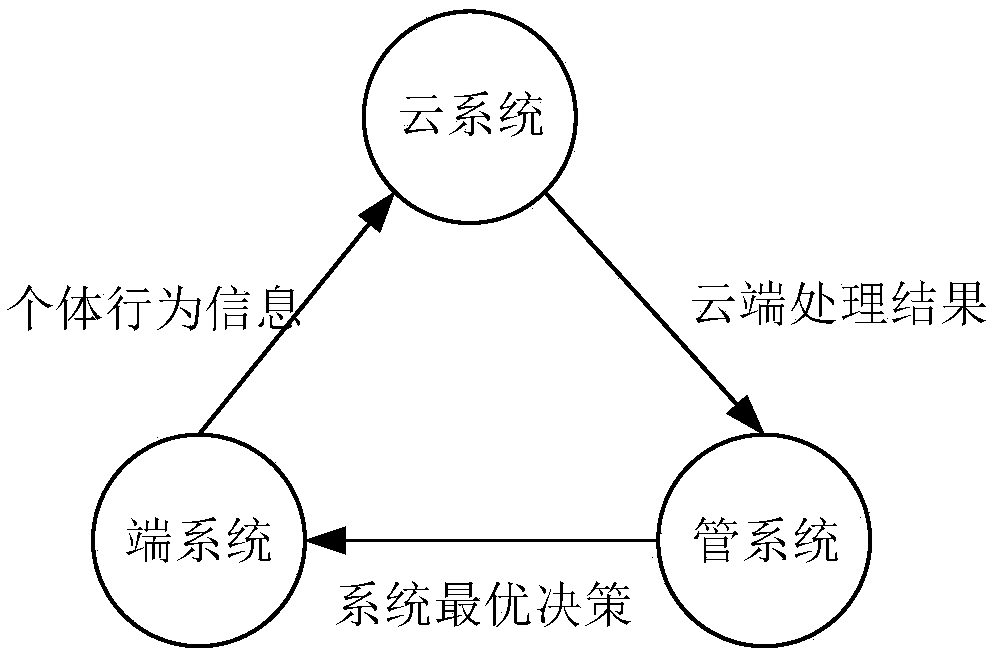
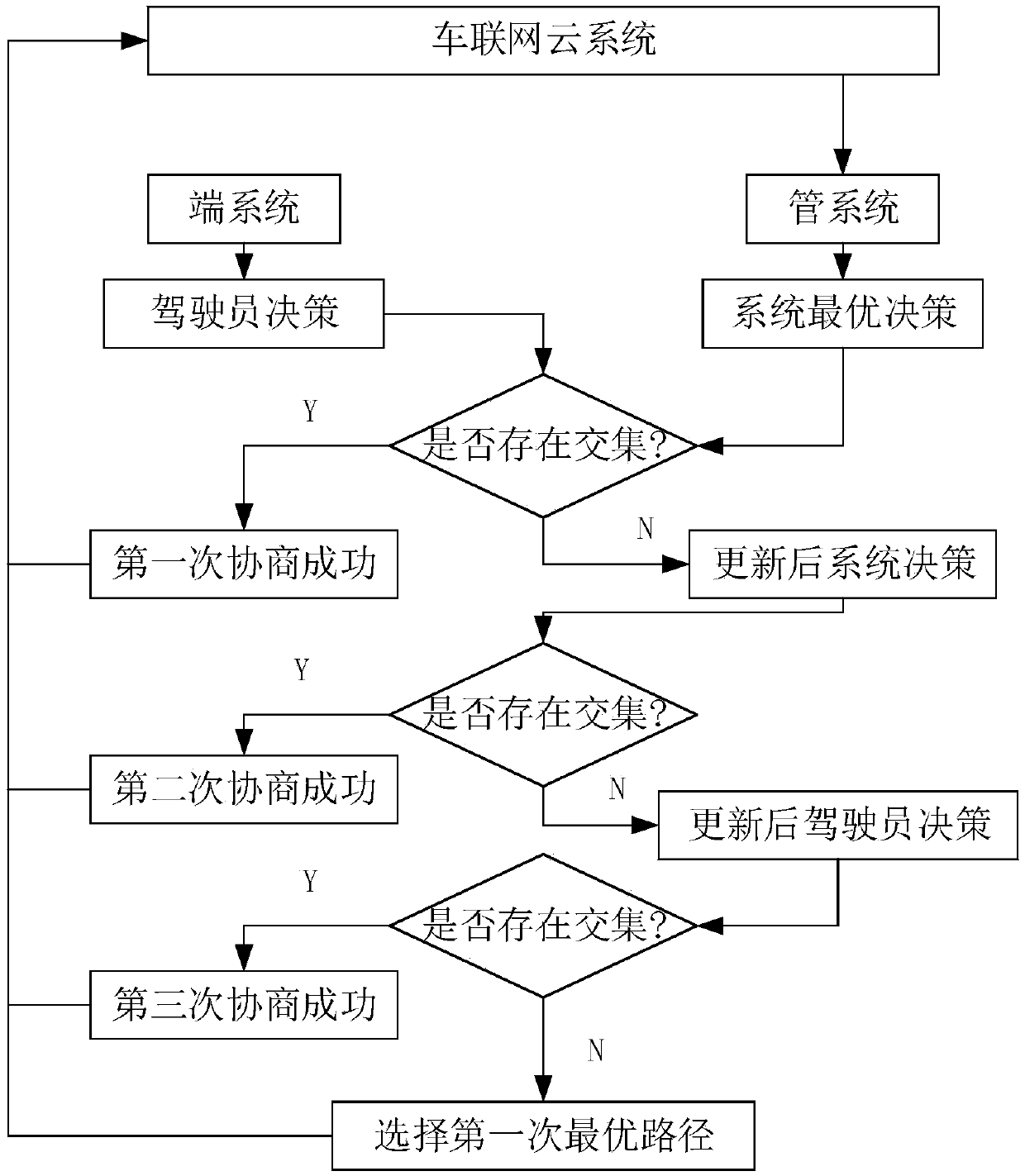
The invention discloses a travel information service strategy and simulation verification system in an Internet of Vehicles environment, wherein the travel information service strategy research designs a game negotiation mechanism for solving the contradiction conflict between a system optimal travel service strategy proposed by a road network manager and a personalized travel decision of a vehicle driver in an Internet of Vehicles environment. According to the mechanism, a cloud system, a management system and a terminal system in an Internet of Vehicles environment are fully considered, three game negotiation processes are designed, the optimal system and the personality of a driver are fully communicated, and a multi-agent simulation software NetLogo is utilized to establish an Internetof Vehicles travel service strategy simulation system for simulation verification. The simulation verification system is composed of a foreground part and a background part, a foreground interface isa man-machine interaction module, and a background program is responsible for achieving the function of the simulation system, including simulation scene setting, vehicle generation and division, simulation content and simulation data information acquisition of several models, and the simulation content is a core strategy rule for driving a vehicle to run in a road network and comprises a microscopic layer and a macroscopic layer. According to the invention, the optimal path selection provided by the system to drivers with different accepting personalities in the Internet of Vehicles environment, the game negotiation mechanism for path selection by a driver and a road network effect which can be achieved under the action of the mechanism are designed and studied, so that the reflection ofa macroscopic state of the system from each vehicle action rule is realized, and the feasibility and effectiveness are provided for realizing simulation of a complex dynamic system.
Owner:BEIHANG UNIV
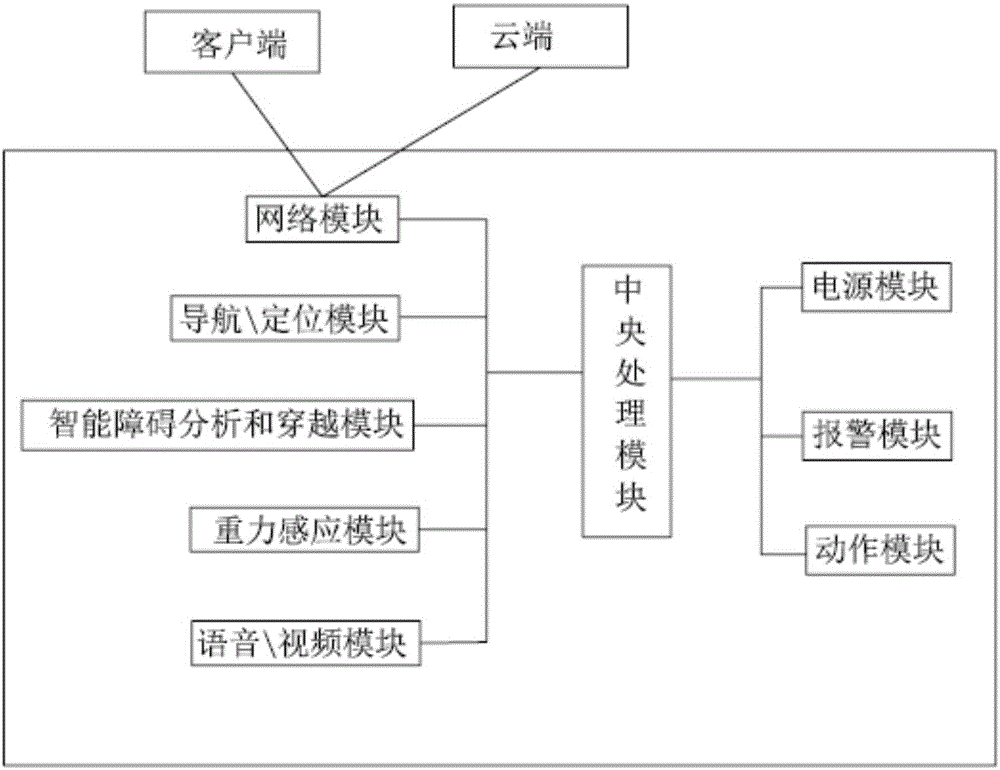
Intelligent garbage can and method for door-to-door service of intelligent garbage can
The invention provides an intelligent garbage can which comprises a box body, a power module, a central processing module, a navigating and positioning module, a network module, an action module, an intelligent obstacle analyzing and crossing module and a gravity induction module. A cover body is arranged on the top of the box body. The central processing module is used for transmitting, processing and analyzing data, and alarm action rules are loaded in the central processing module. The network module is used for connecting a client end with a network center and used for transmitting data to the client end and obtaining resource orders on the network center. The action module is used for receiving instructions sent by the central processing module so that the position of the intelligent garbage can can be changed. The intelligent obstacle analyzing and crossing module is connected to the central processing module. Thus, the automatic door-to-door service can be achieved to change the life style of people; and in addition, the invention provides a method for the door-to-door service of the intelligent garbage can, the traditional design concept, the traditional thinking mode and the traditional working mode are broken through due to the service manner of changing the roles of a guest and a host, and the time of people is saved.
Owner:杨小东
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com