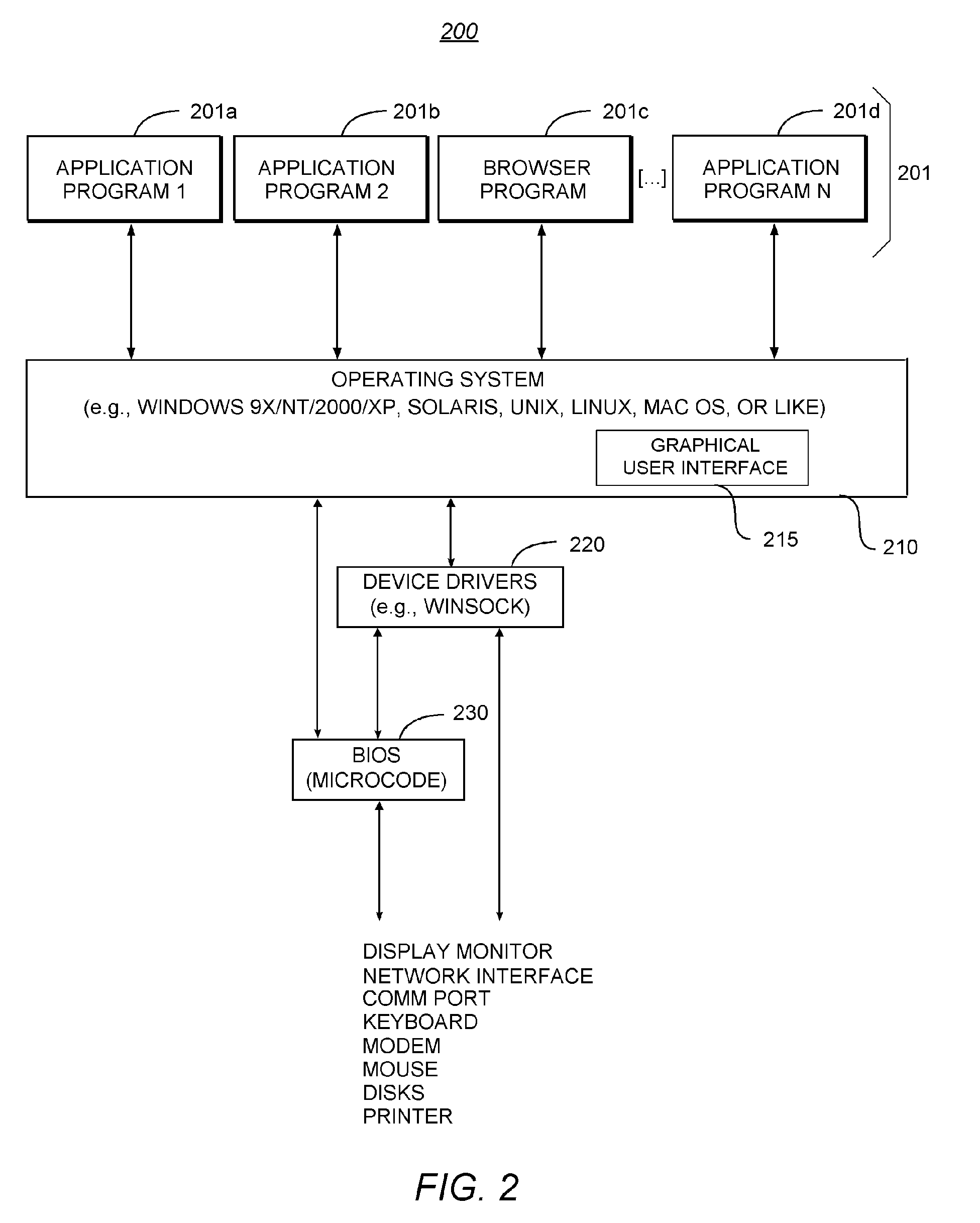
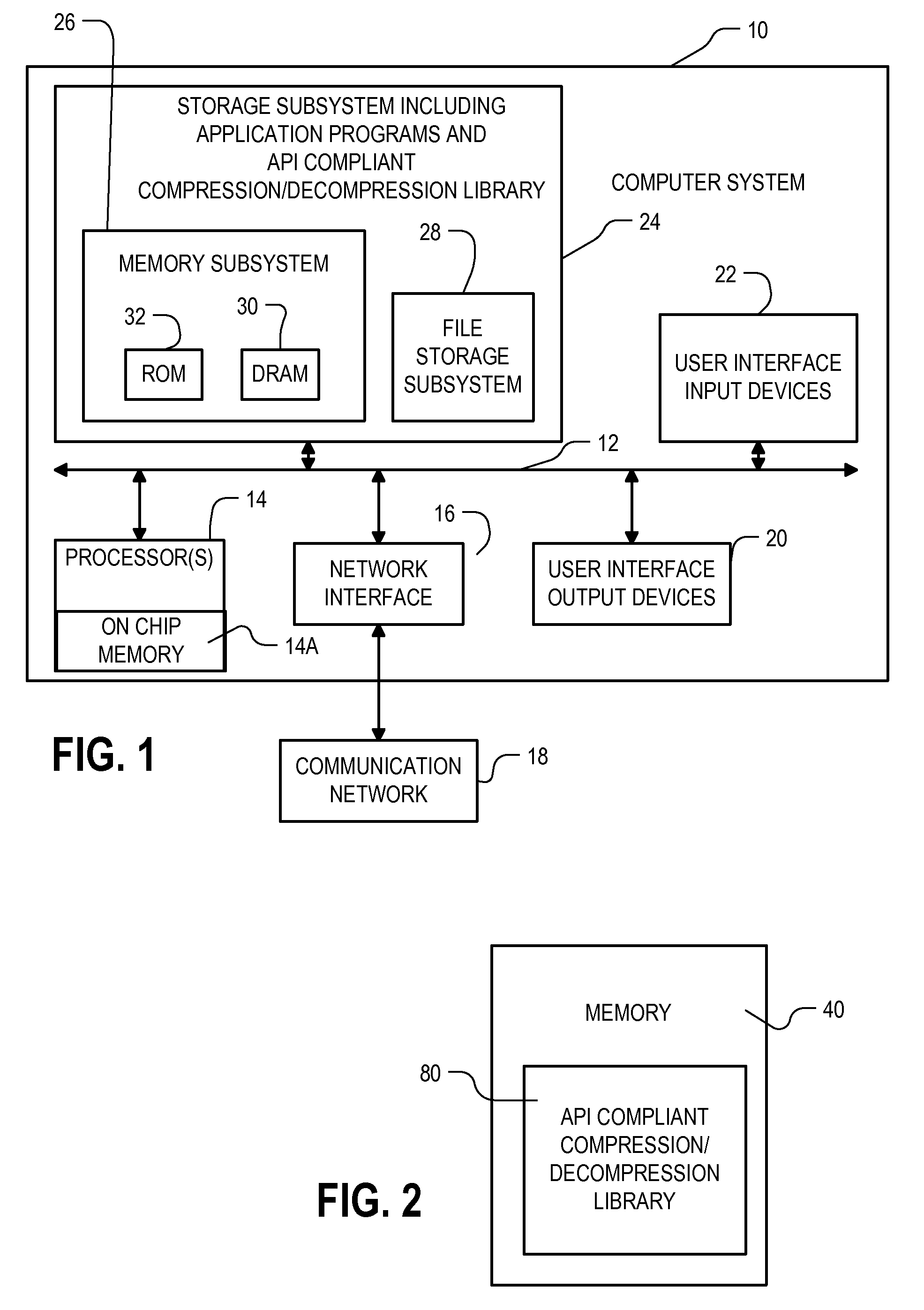
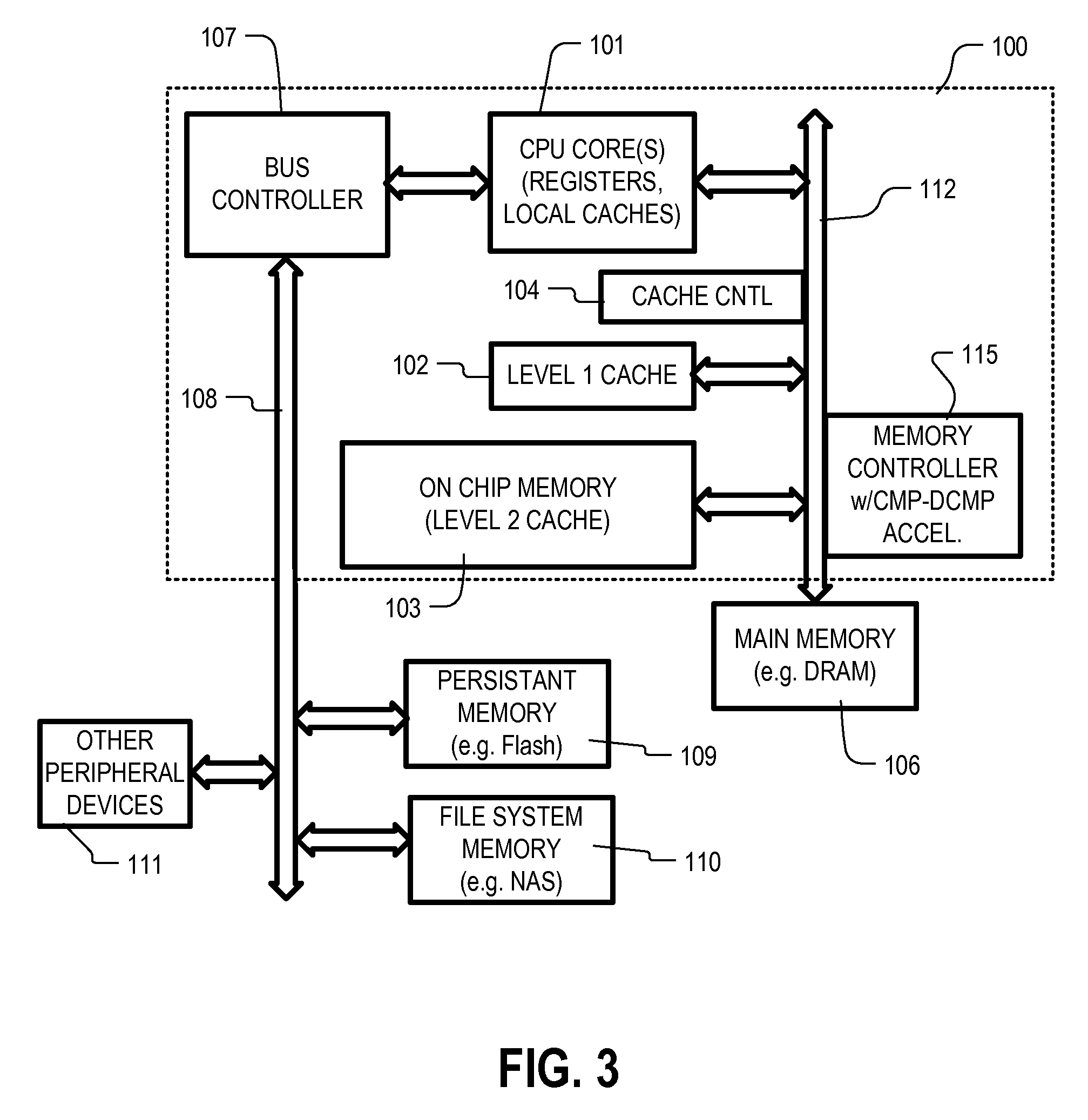
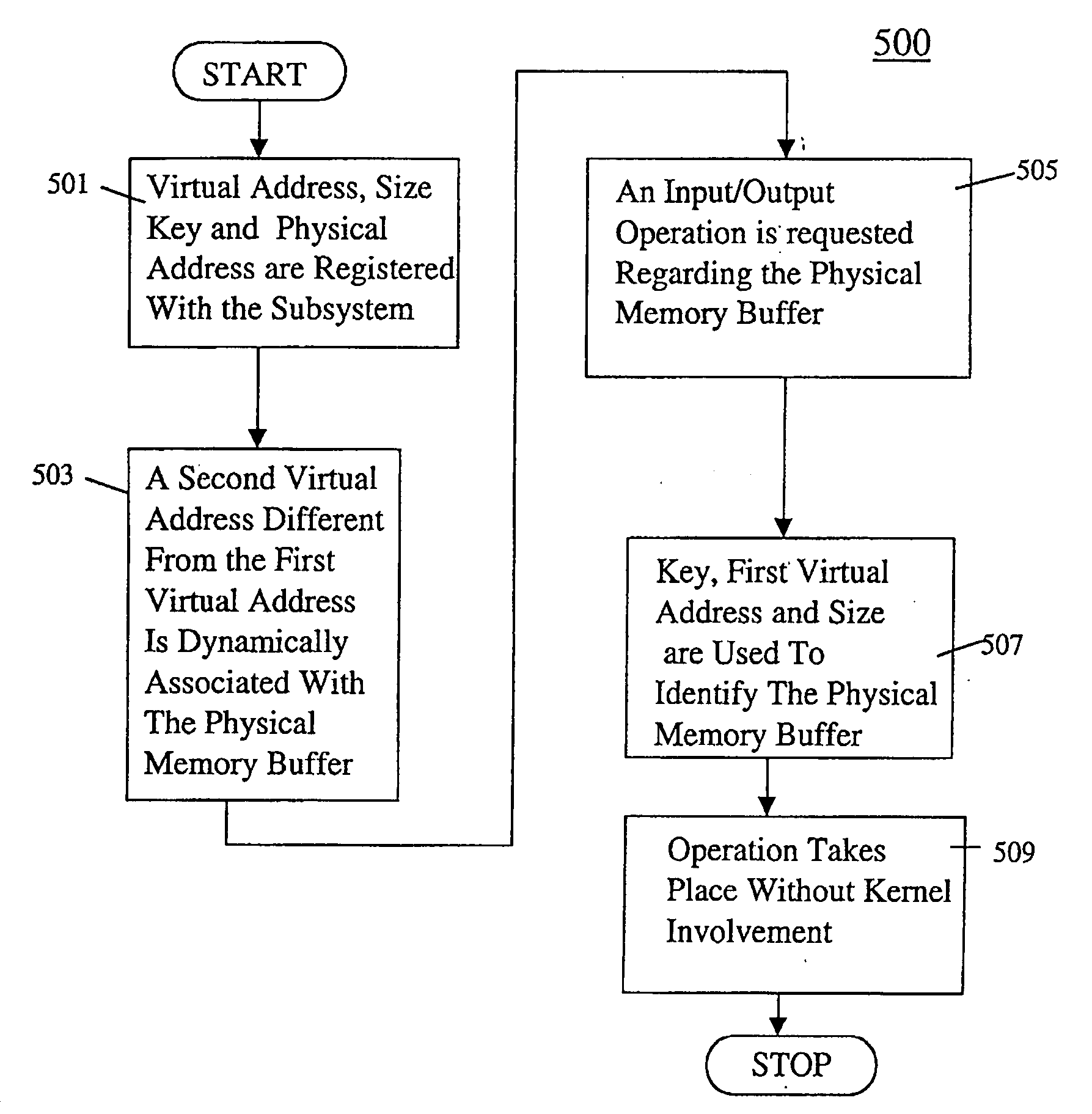
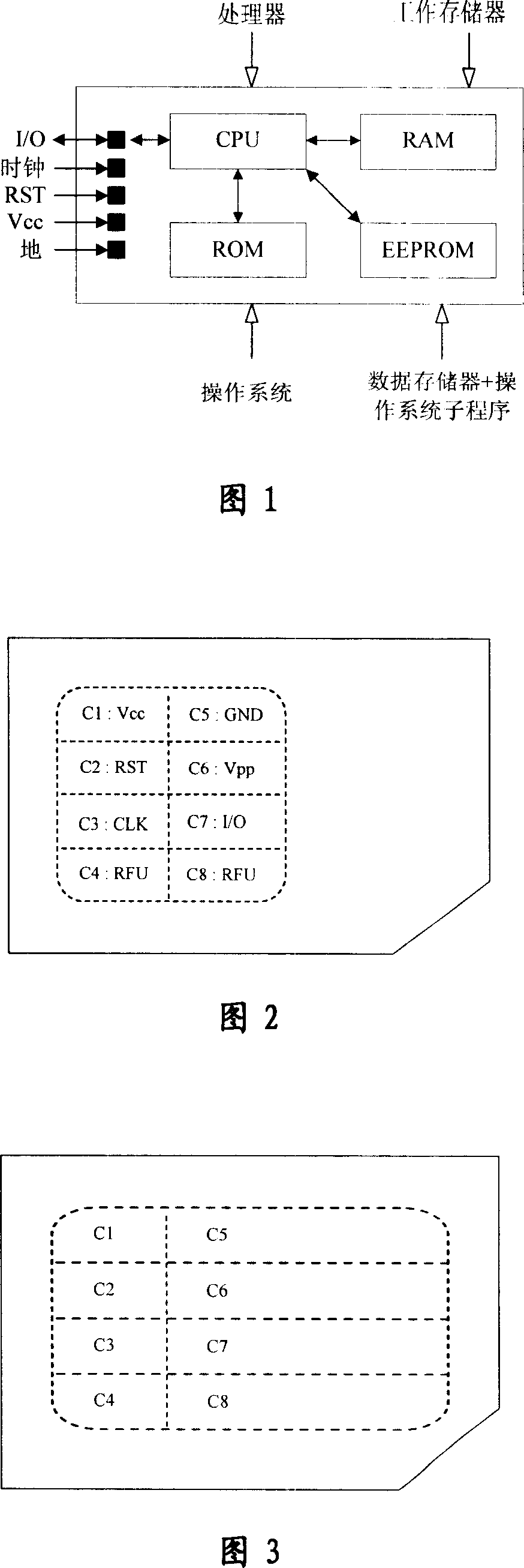
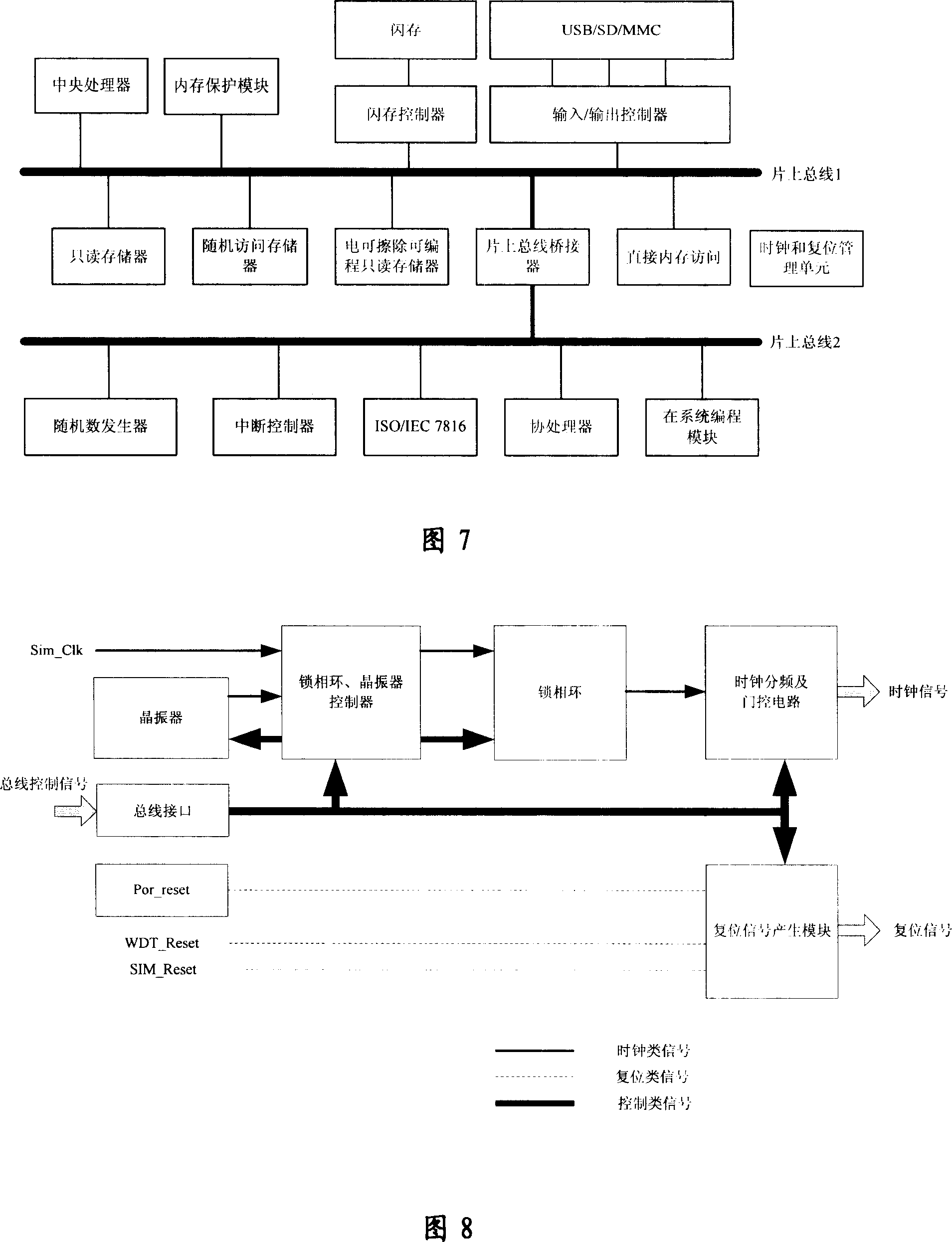
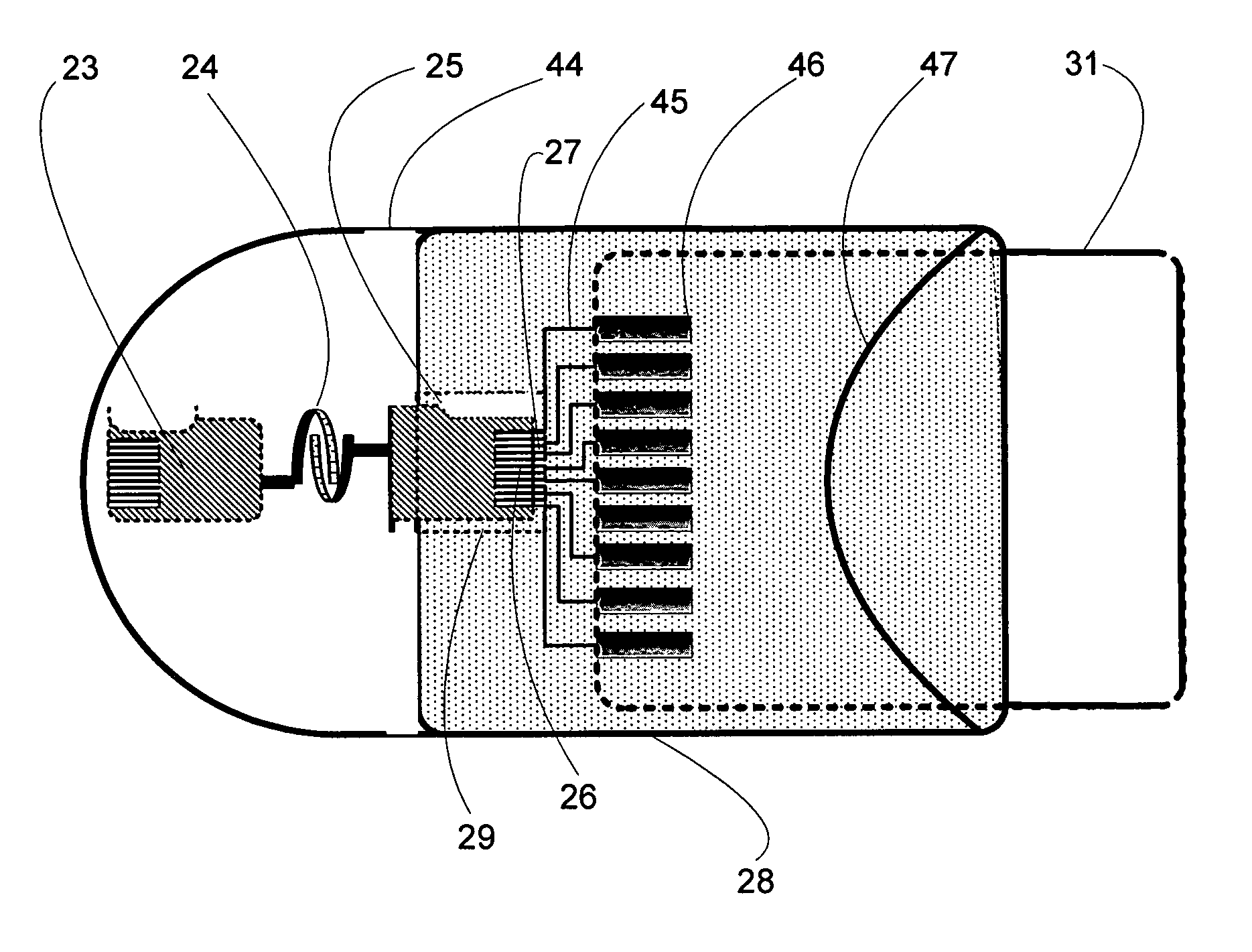
Patents
Literature
265 results about "Expanded memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
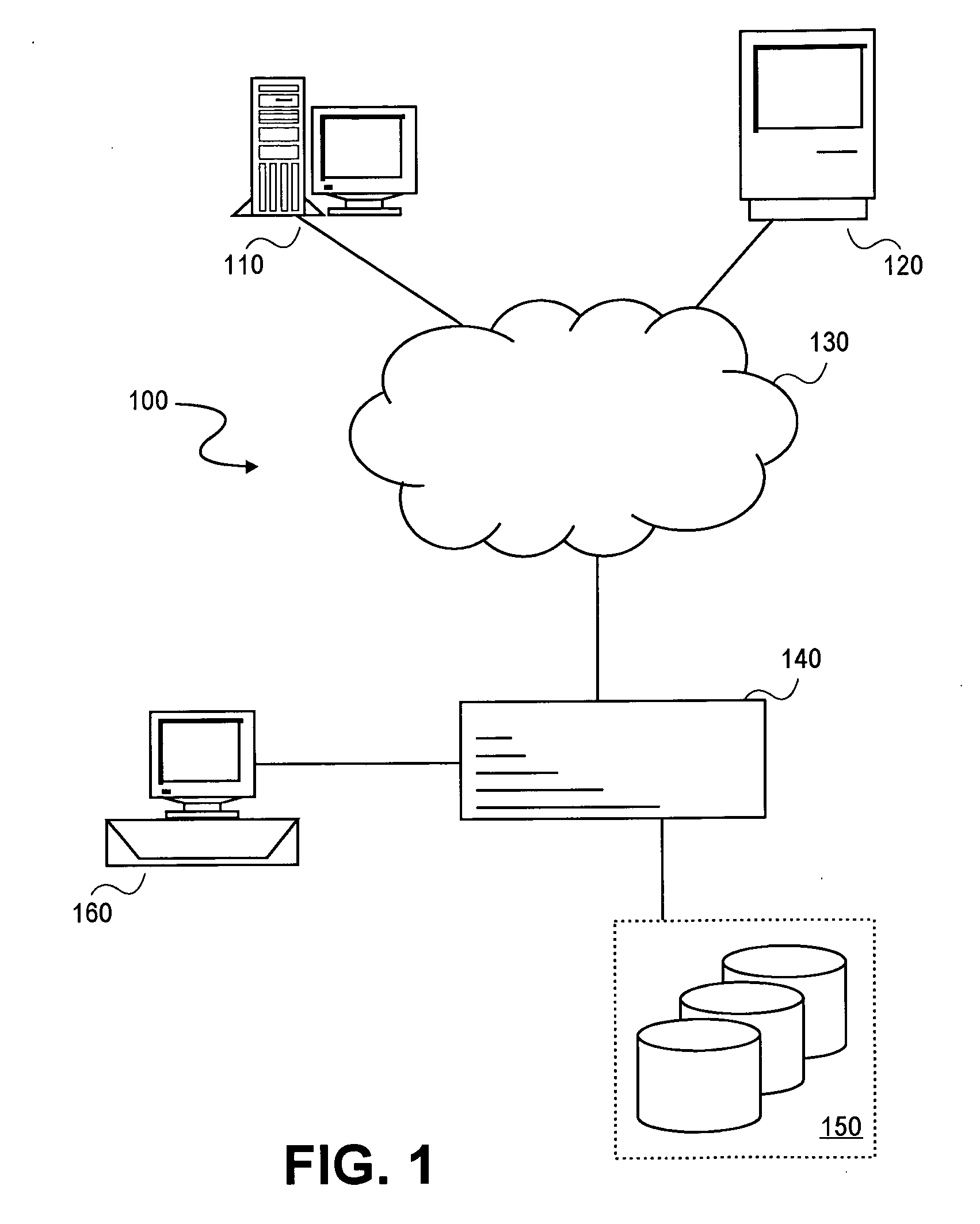
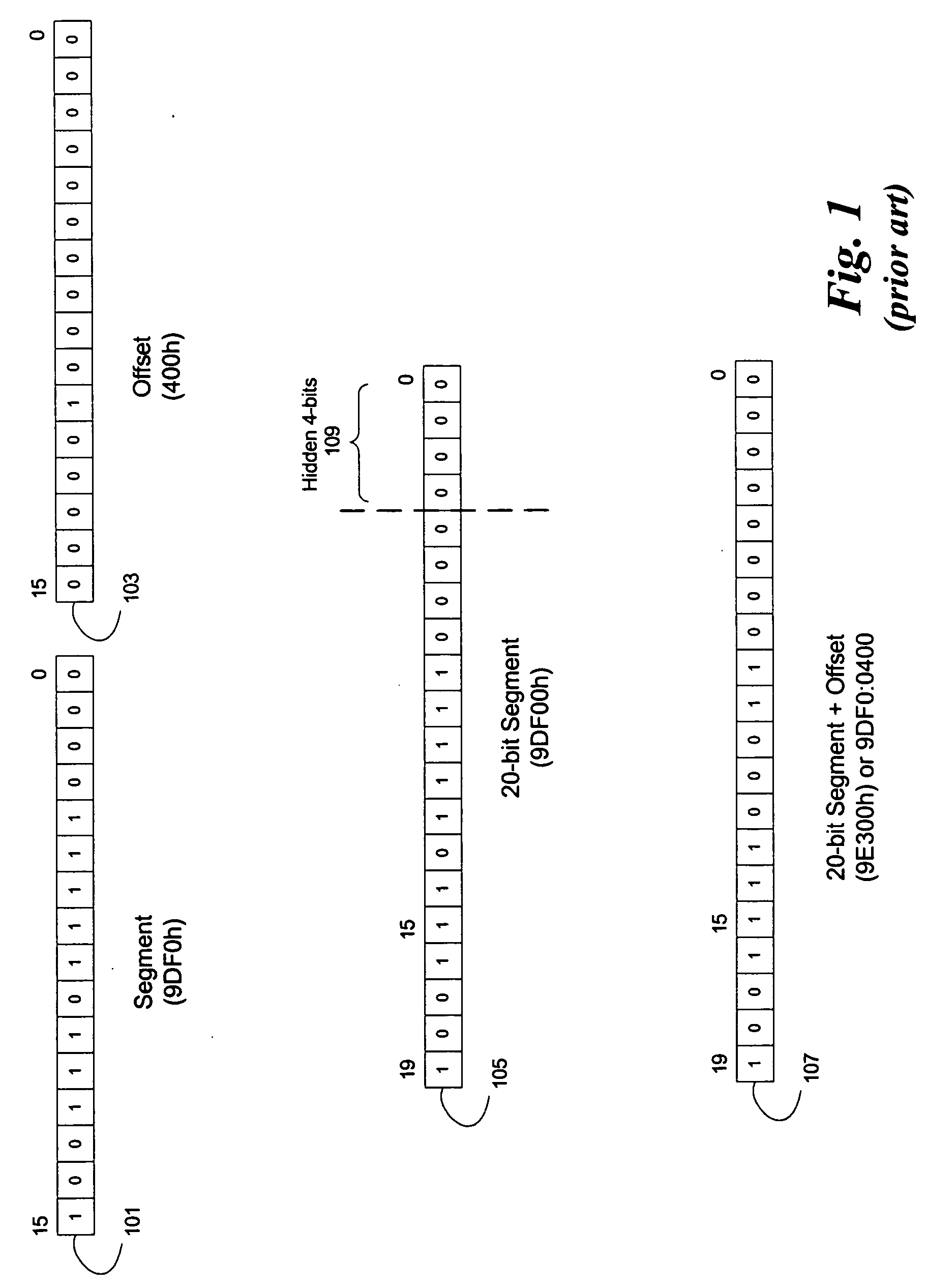
In DOS memory management, expanded memory is a system of bank switching that provided additional memory to DOS programs beyond the limit of conventional memory (640 KB). Expanded memory is an umbrella term for several incompatible technology variants. The most widely used variant was the Expanded Memory Specification (EMS), which was developed jointly by Lotus Software, Intel, and Microsoft, so that this specification was sometimes referred to as "LIM EMS". LIM EMS had several versions. The first widely implemented version was EMS 3.2, which supported up to 8 MB of expanded memory and uses parts of the address space normally dedicated to communication with peripherals (upper memory) to map portions of the expanded memory. EEMS, an expanded-memory management standard competing with LIM EMS 3.x, was developed by AST Research, Quadram and Ashton-Tate ("AQA"); it could map any area of the lower 1 MB. EEMS ultimately was incorporated in LIM EMS 4.0, which supported up to 32 MB of expanded memory and provided some support for DOS multitasking as well. IBM, however, created its own expanded-memory standard called XMA.
Intelligent home automation
InactiveUS20100332235A1Electric signal transmission systemsMultiple keys/algorithms usageSpoken languageThe Internet
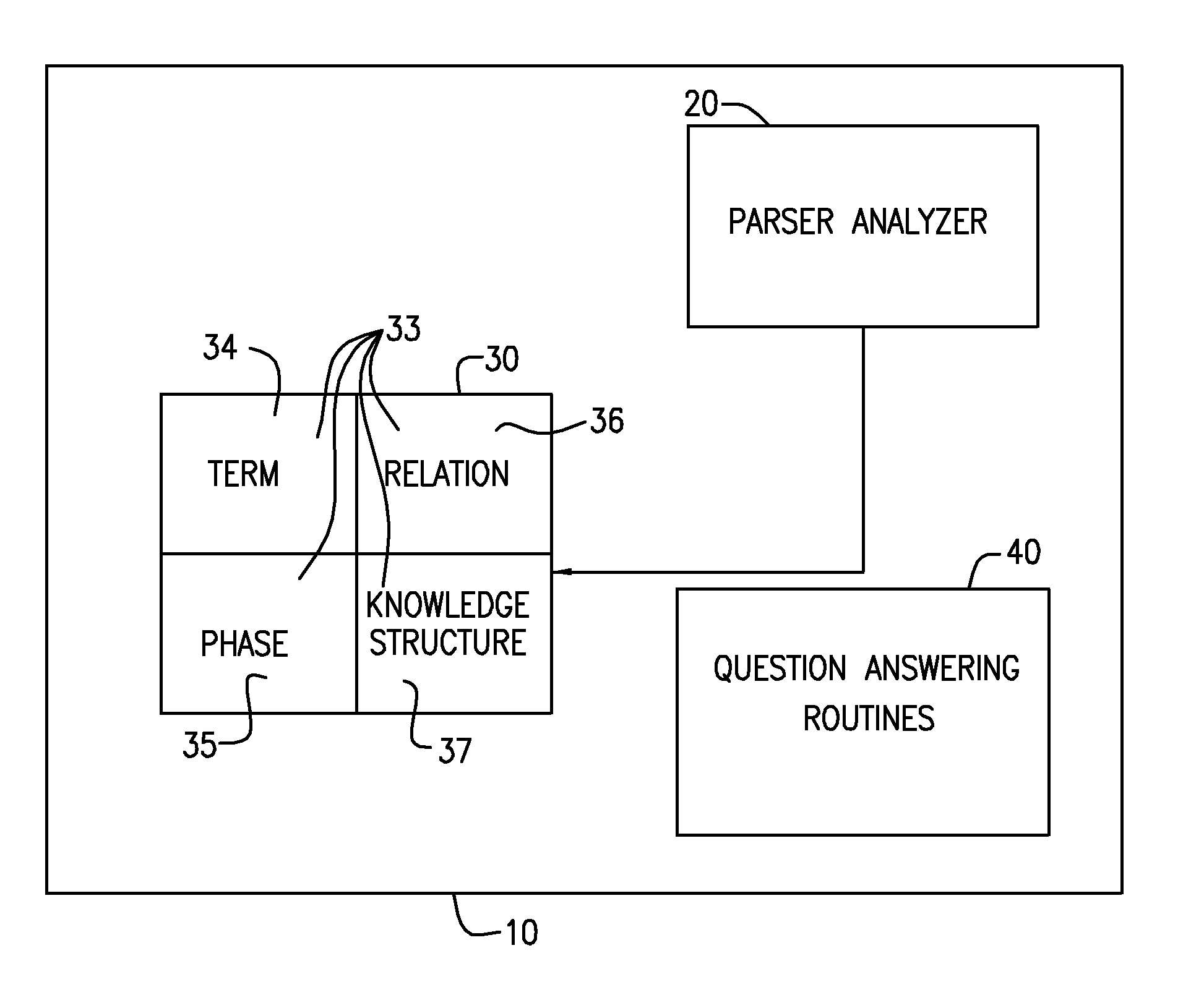
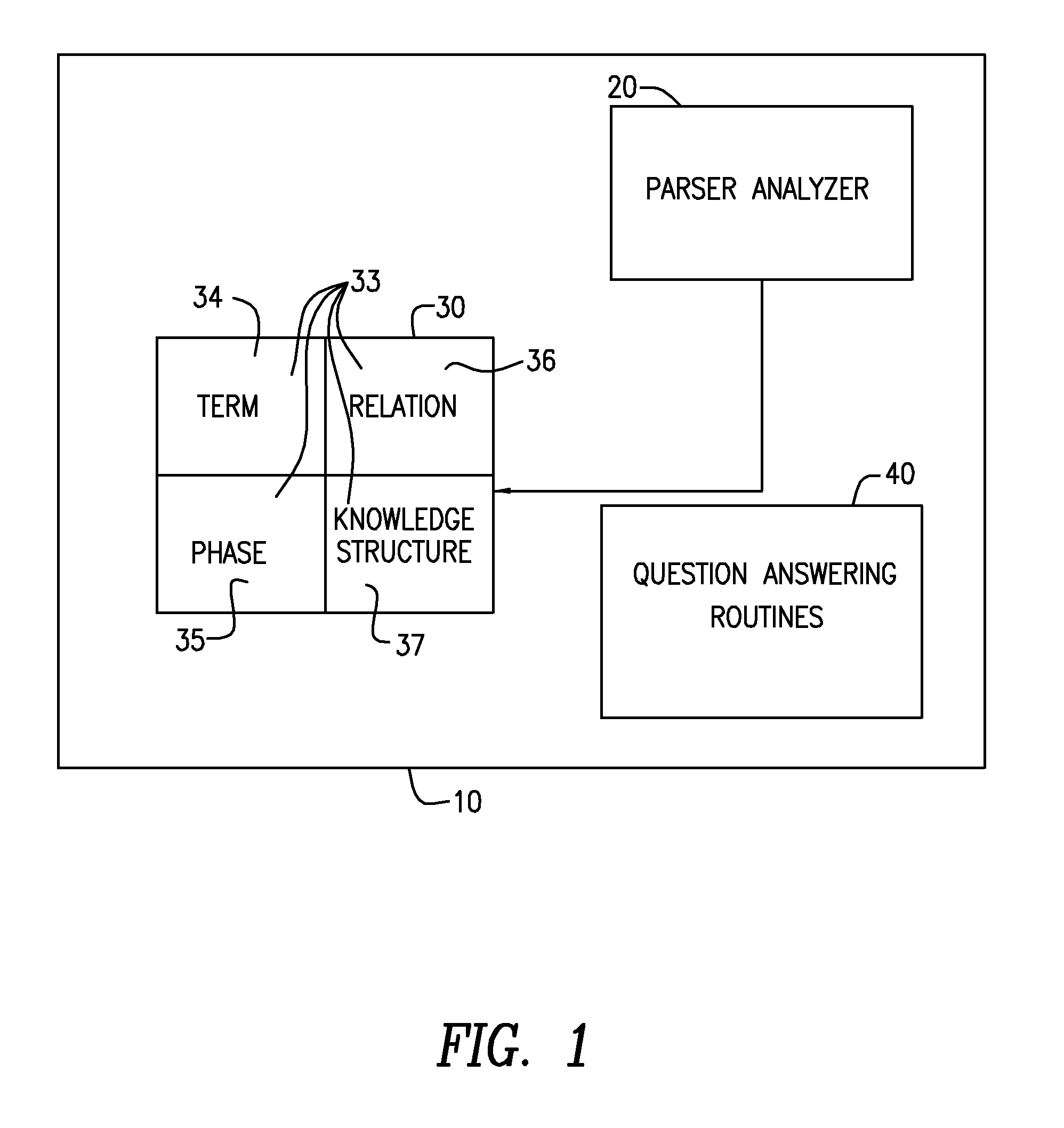
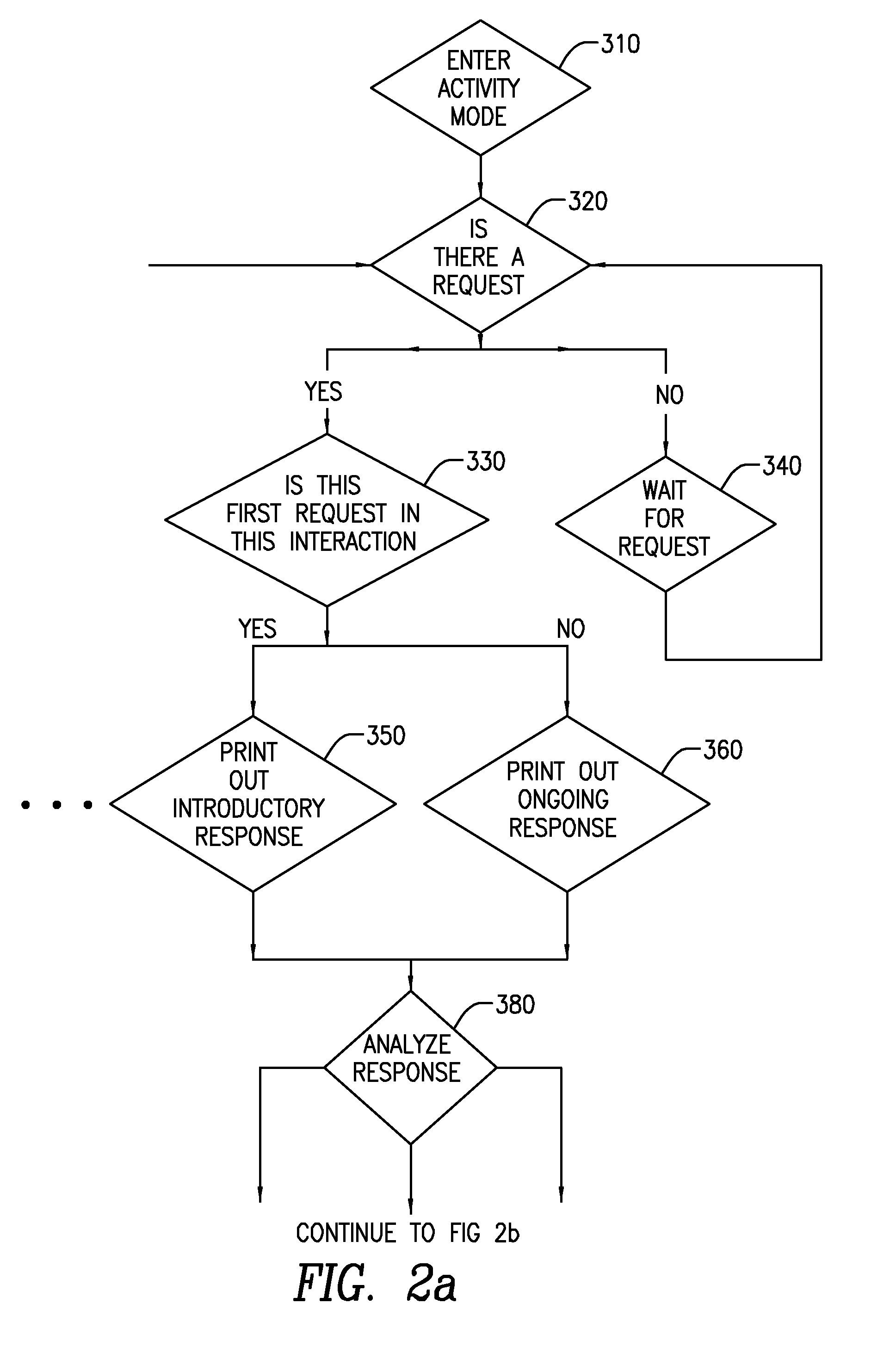
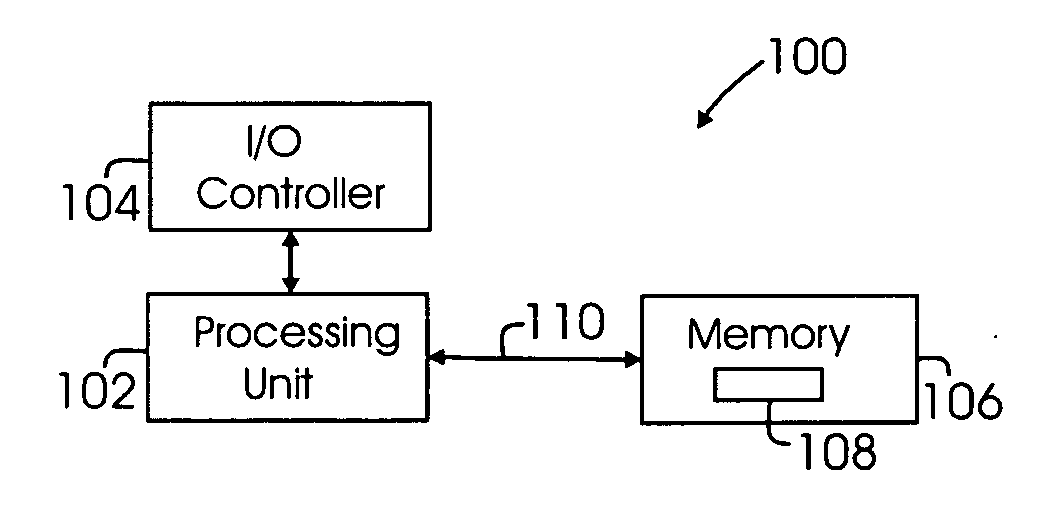
An intelligent home automation system answers questions of a user speaking “natural language” located in a home. The system is connected to, and may carry out the user's commands to control, any circuit, object, or system in the home. The system can answer questions by accessing the Internet. Using a transducer that “hears” human pulses, the system may be able to identify, announce and keep track of anyone entering or staying in the home or participating in a conversation, including announcing their identity in advance. The system may interrupt a conversation to implement specific commands and resume the conversation after implementation. The system may have extensible memory structures for term, phrase, relation and knowledge, question answering routines and a parser analyzer that uses transformational grammar and a modified three hypothesis analysis. The parser analyzer can be dormant unless spoken to. The system has emergency modes for prioritization of commands.
Owner:DAVID ABRAHAM BEN
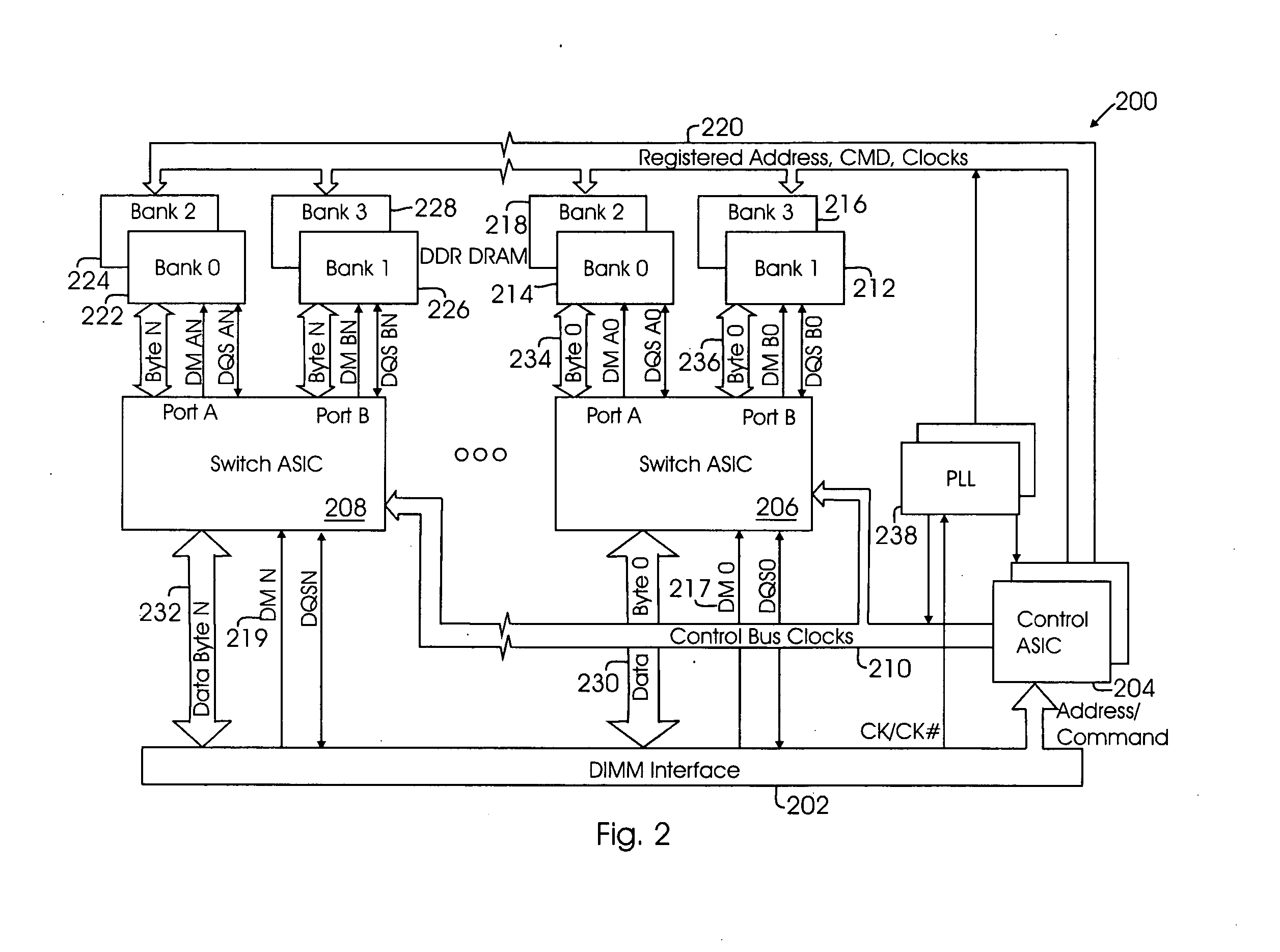
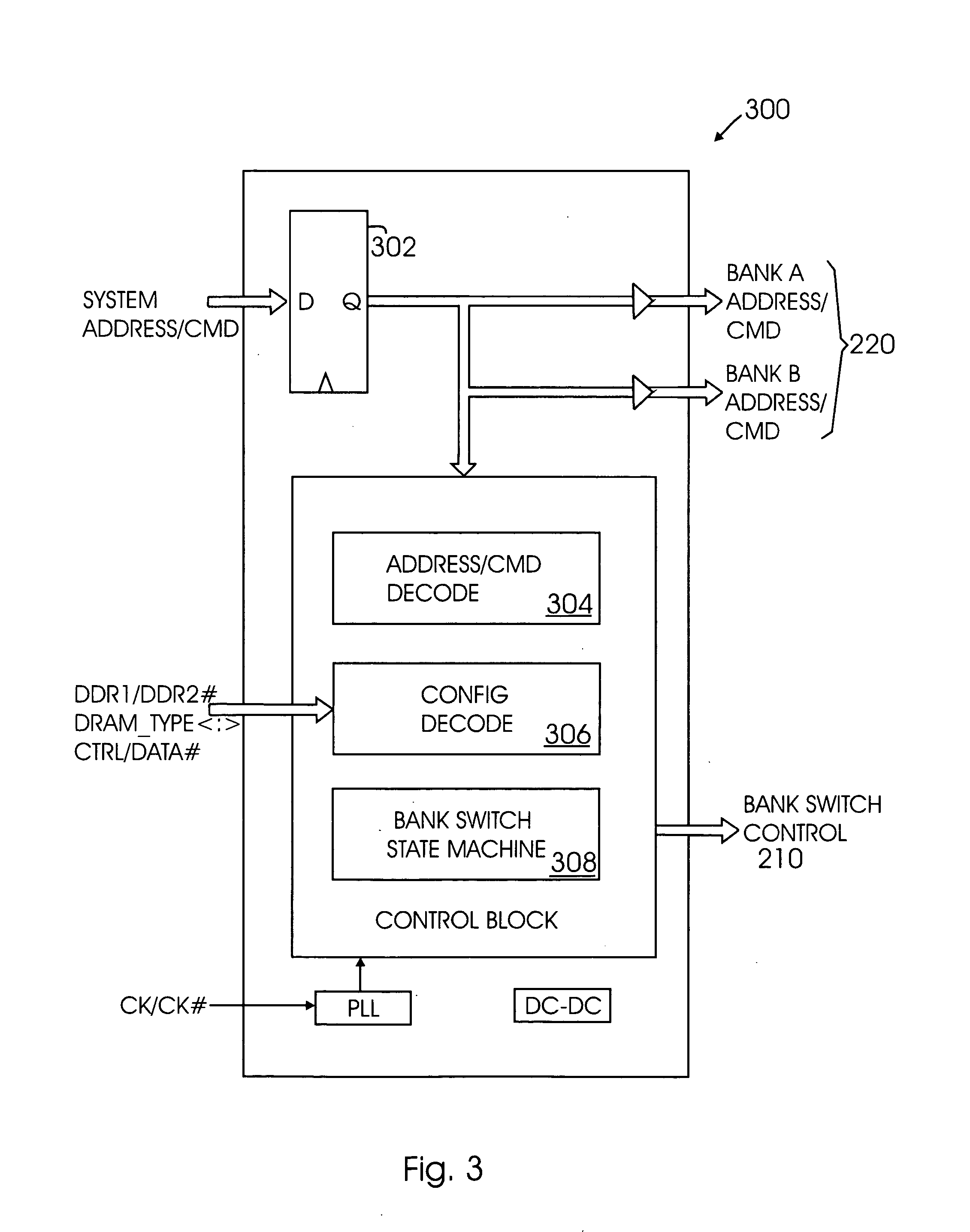
Capacity-expanding memory device
InactiveUS20060277355A1Increase memory capacityReduce loadMemory adressing/allocation/relocationMemory bankMemory module
Owner:SANMINA-SCI CORPORATION
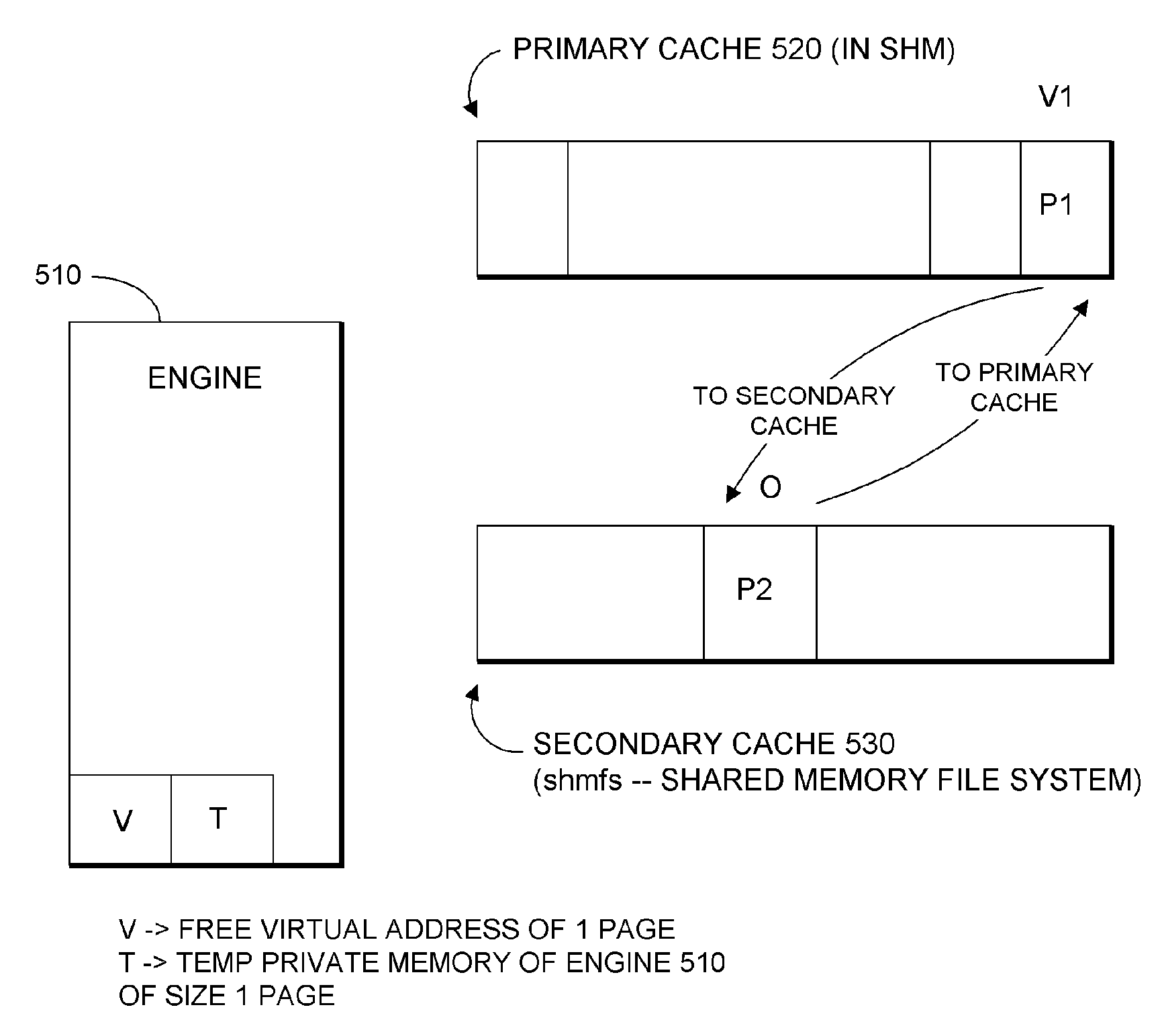
Database System Providing Methodology for Extended Memory Support
ActiveUS20050193160A1Memory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingVirtual address space
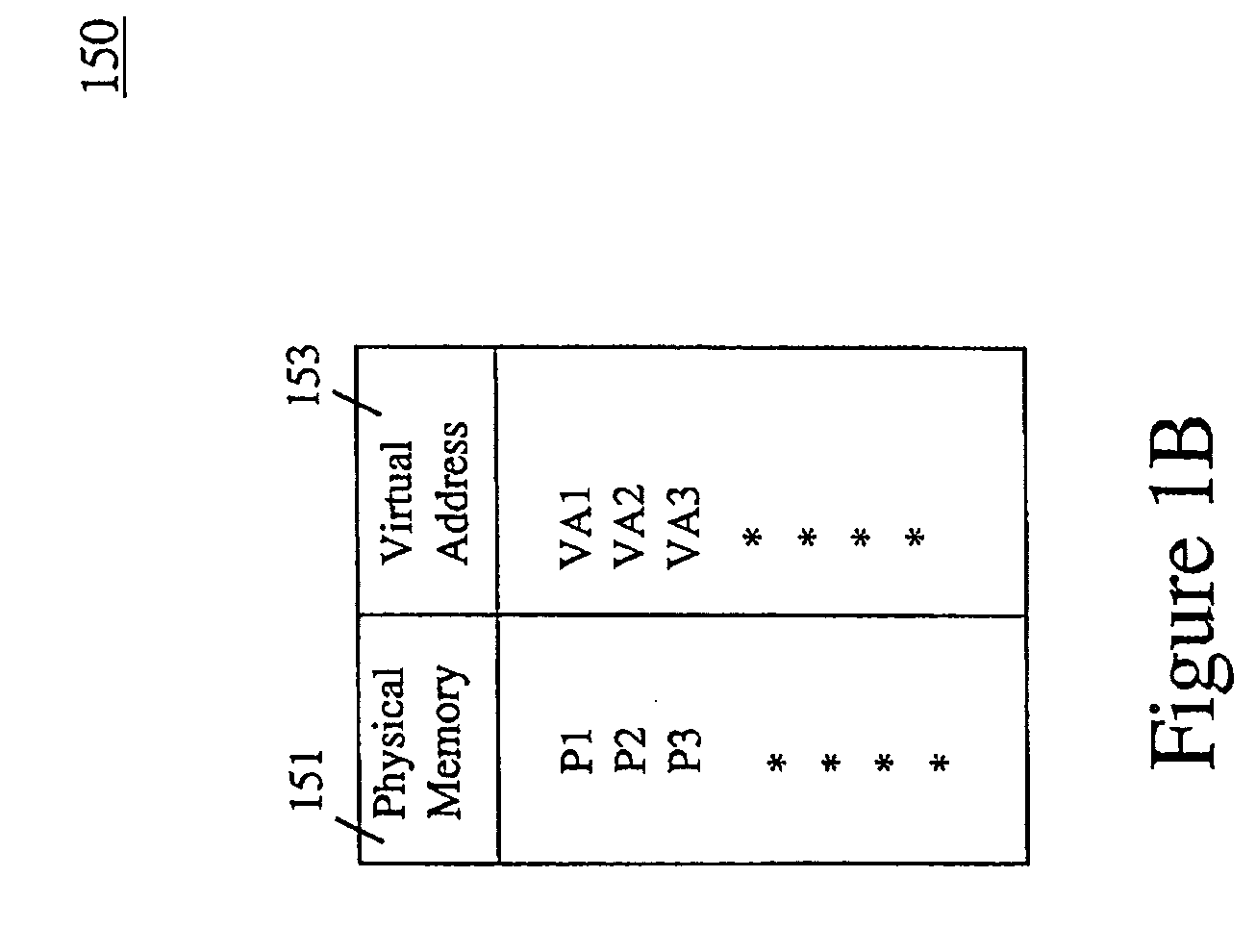
A database system providing methodology for extended memory support is described. In one embodiment, for example, a method is described for extended memory support in a database system having a primary cache, the method comprises steps of: creating a secondary cache in memory available to the database system; mapping a virtual address range to at least a portion of the secondary cache; when the primary cache is full, replacing pages from the primary cache using the secondary cache; in response to a request for a particular page, searching for the particular page in the secondary cache if the particular page is not found in the primary cache; if the particular page is found in the secondary cache, determining a virtual address in the secondary cache where the particular page resides based on the mapping; and swapping the particular page found in the secondary cache with a page in the primary cache, so as to replace a page in the primary cache with the particular page from the secondary cache.
Owner:SYBASE INC
Systems and methods for supporting document centered discussion across heterogeneous devices and displays
InactiveUS20020073163A1Special service for subscribersDigital computer detailsElectronic documentDevice type
The decreasing cost of communication has led to a focus on including workgroup participants based on their abilities rather than their physical location. However, collaboration workgroup participants are still dependent on electronic documents which are difficult or impossible to view on smaller web-enabled devices such as web-enabled phones, web-enabled personal digital assistants and the like. If the documents can be viewed at all, they must be pre-encoded for a single format supported across all devices, or the range of participating devices must be limited to a single display type. Furthermore, some document types may require hardware upgrades including expanded memory to load the additional code necessary to view the document. This excludes impromptu workgroup formation since the device types of the collaborating users and / or the set of required documents for a meeting cannot always be predicted. Moreover, even when a document has been previously encoded, collaboration is difficult due to the inability to view the overall structure of the page. Accordingly the techniques presented allow for impromptu access to documents in the native application format. The collaboration of users within a document is facilitated by allowing the users to indicate context within the document for collaboration based on the display capabilities of each user's device.
Owner:FUJIFILM BUSINESS INNOVATION CORP
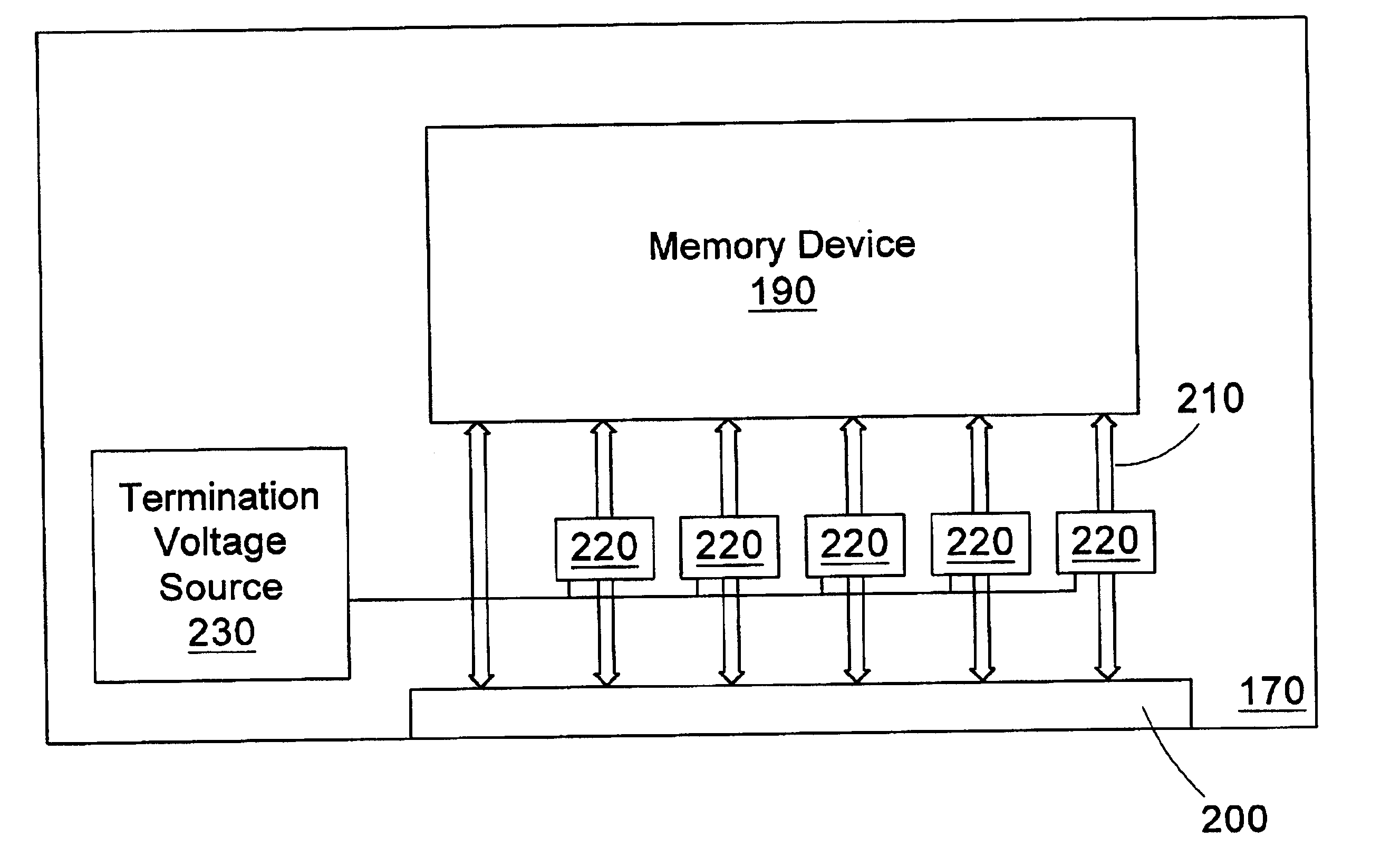
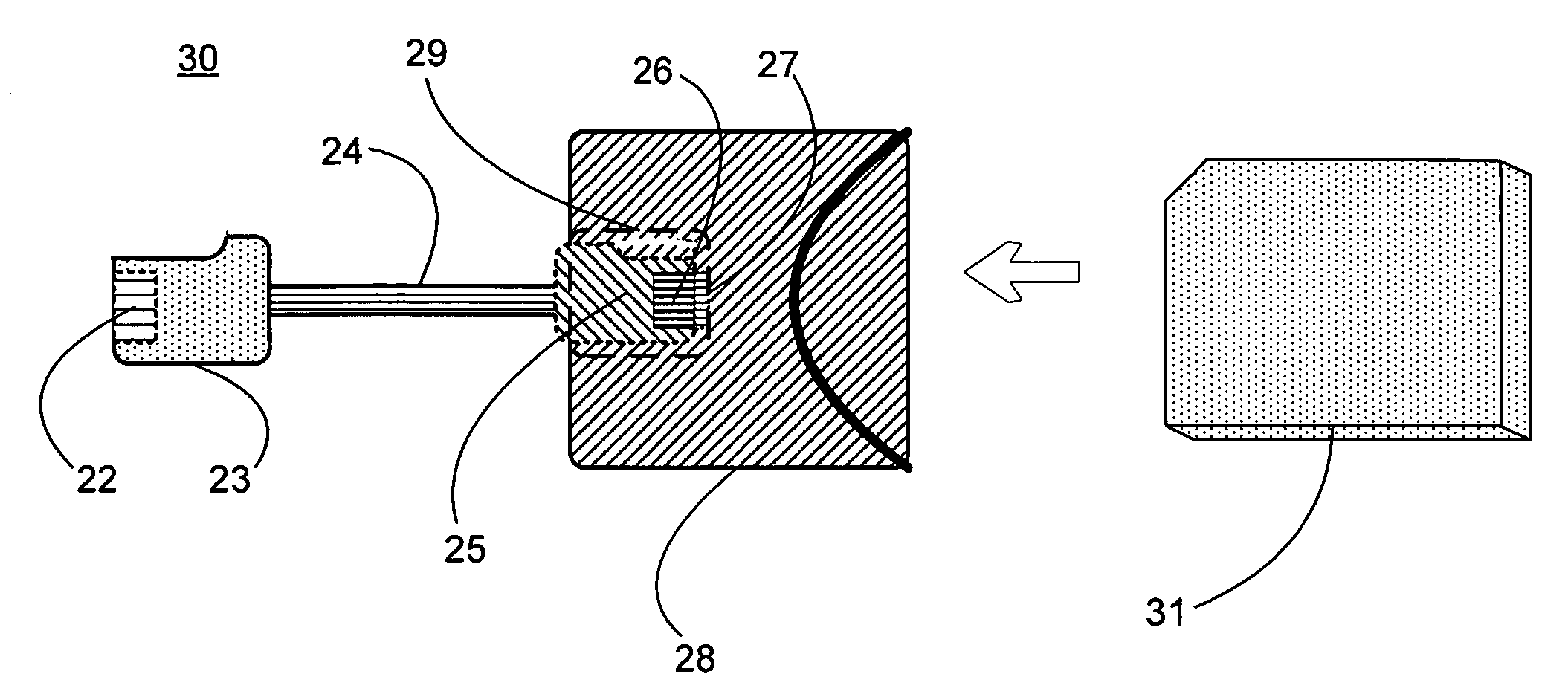
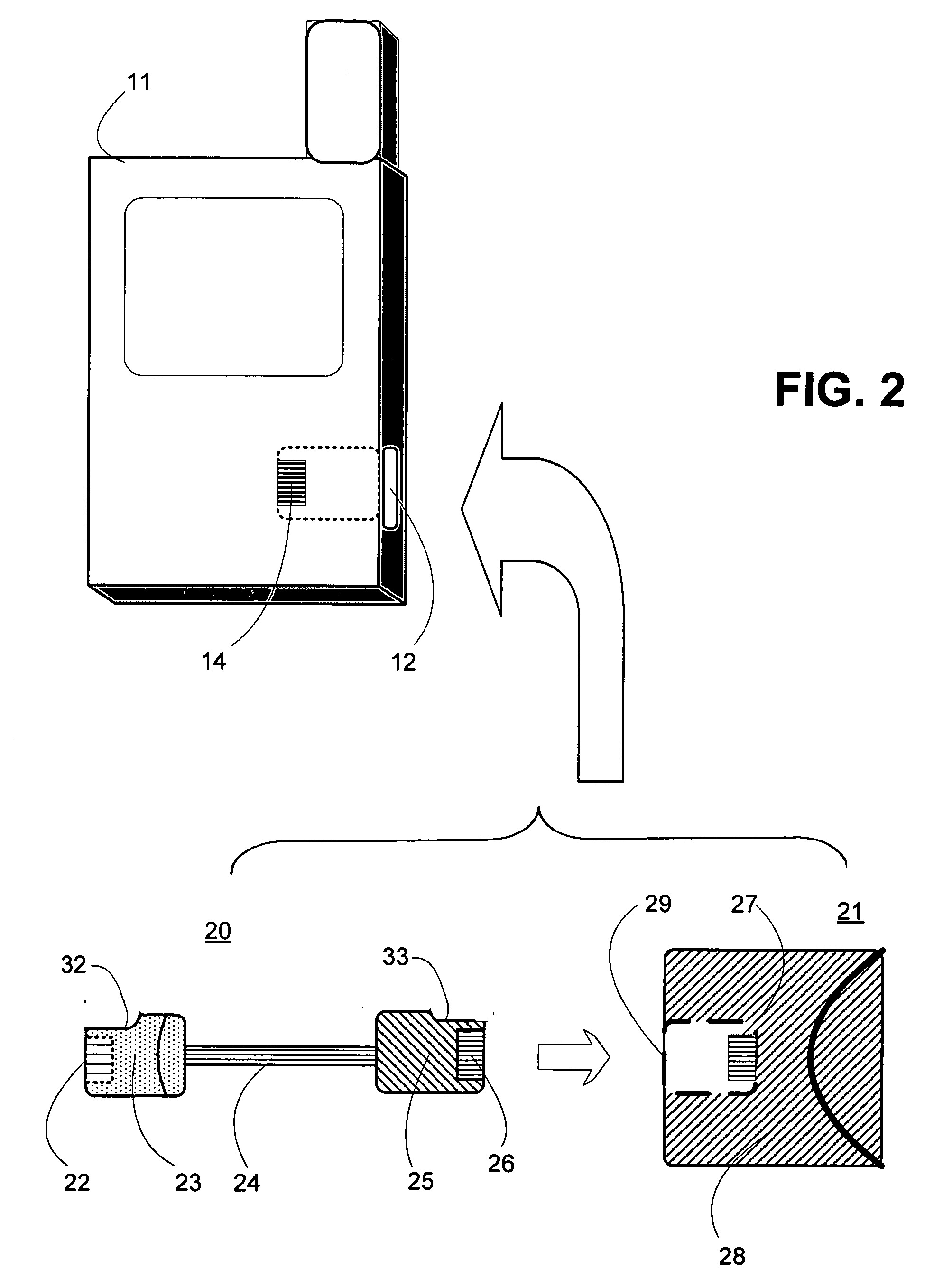
Memory module with integrated bus termination
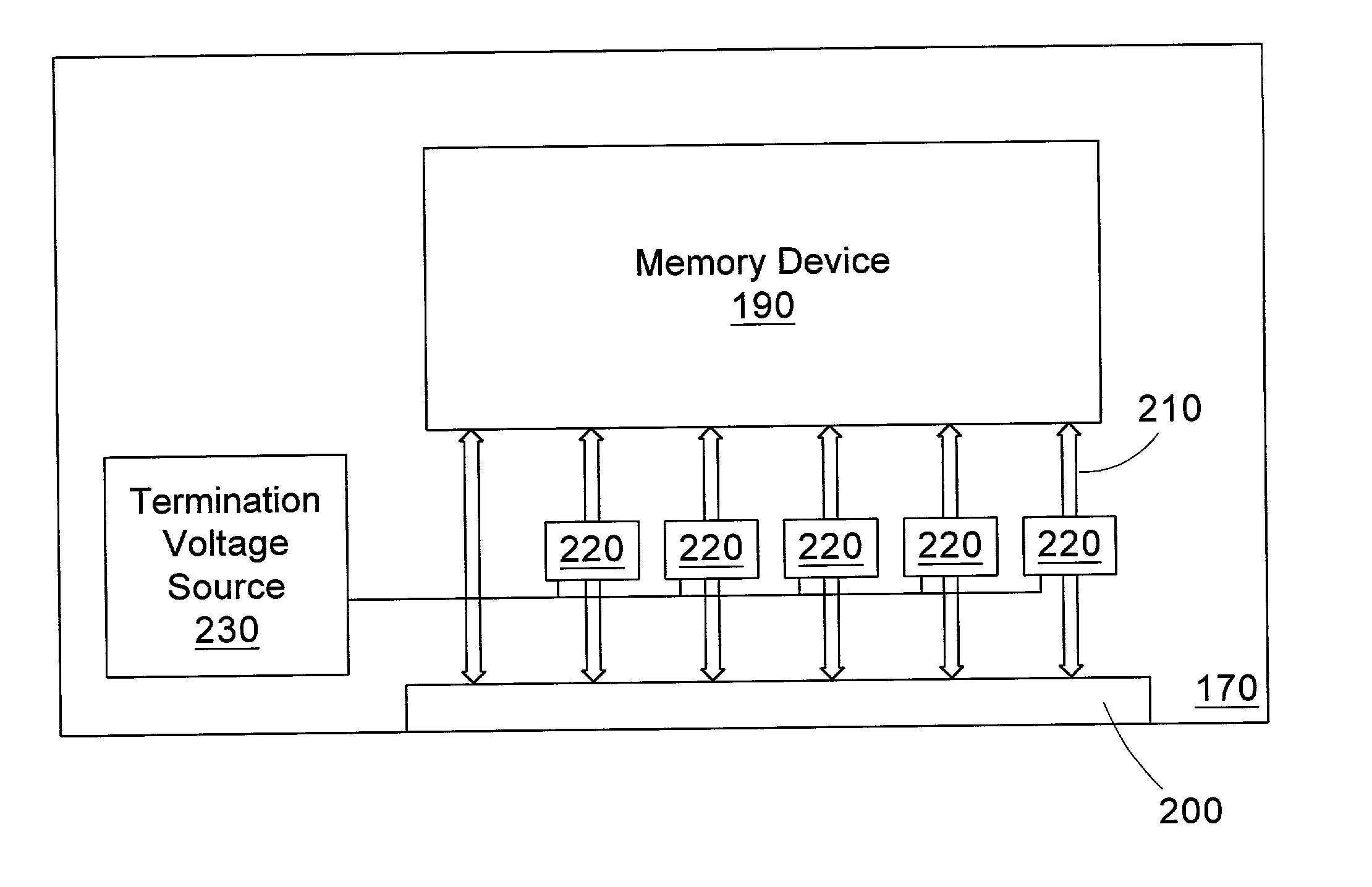
A memory module includes a memory device, a connector, a plurality of lines coupling the memory device and the connector, and termination circuitry coupled to at least a subset of the lines. A method for terminating a memory bus includes providing at least two expansion sockets coupled to the memory bus; interfacing two expansion memory modules including termination circuitry with the expansion sockets; and disabling the termination circuitry for one of the expansion memory modules.
Owner:ROUND ROCK RES LLC
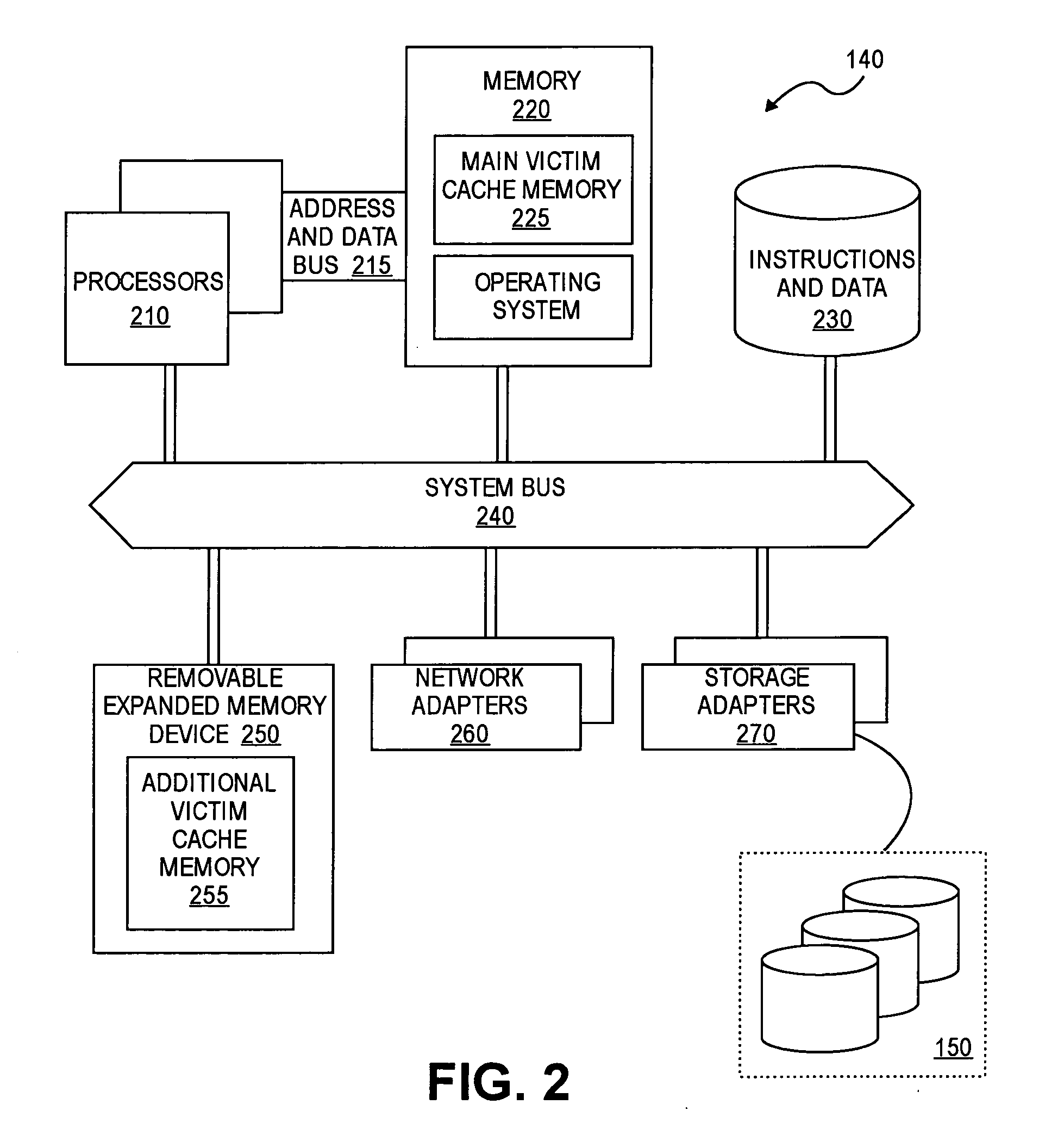
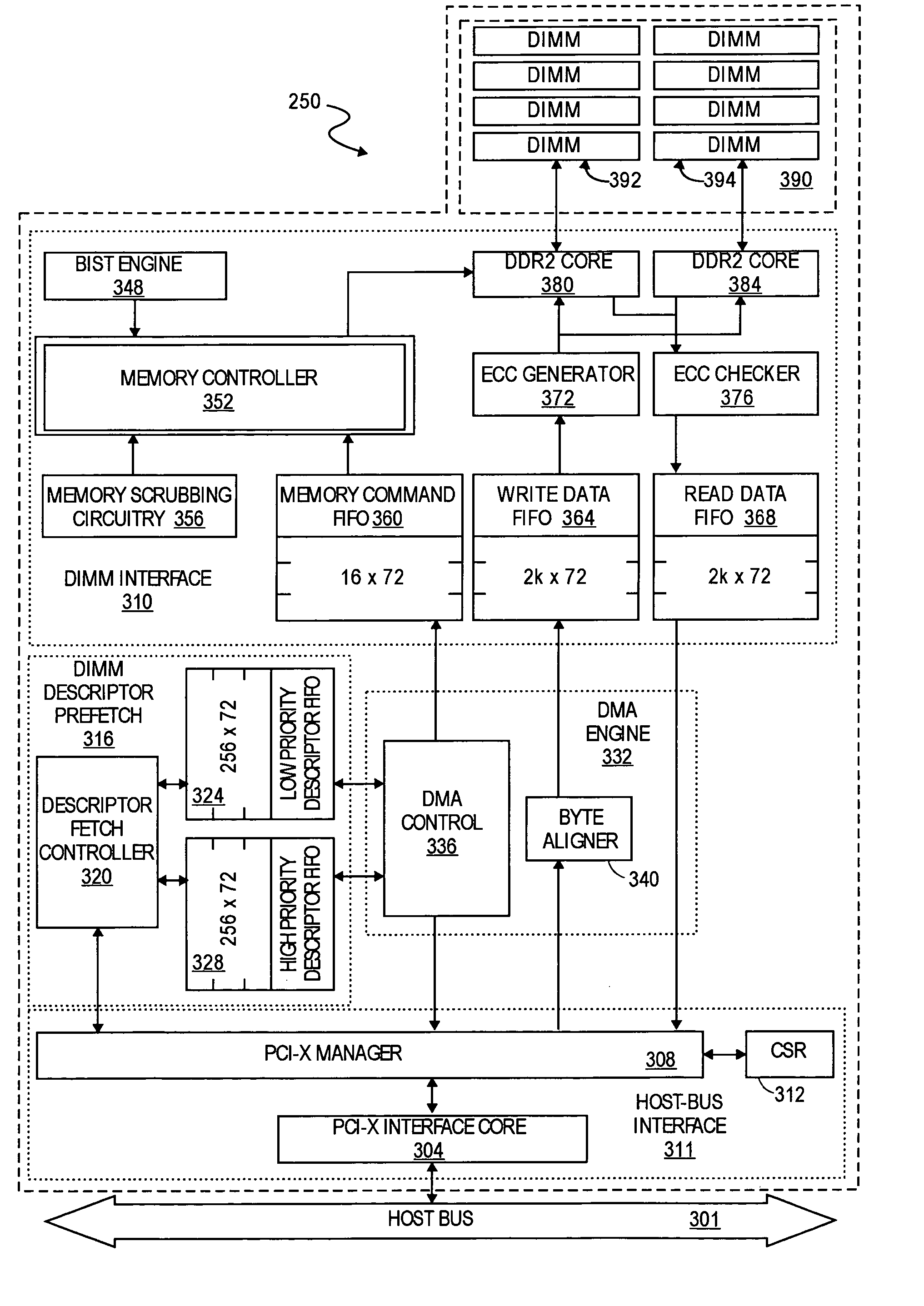
Memory scrubbing of expanded memory
Embodiments of the invention include a memory device, such as a removable expanded memory card, having a host bus interface that allows a host to access a memory of the device. The memory device also includes memory scrubbing circuitry to read data stored at addresses in the memory and to identify single-bit errors and multiple-bit errors in the data read from the memory.
Owner:NETWORK APPLIANCE INC
Code and thread differential addressing via multiplex page maps
InactiveUS7073173B1Provide securityOvercome problemsSpecific access rightsMemory adressing/allocation/relocationSingle processParallel computing
Described is a system and method whereby processes may have multiple memory maps associated therewith to provide curtained memory and overcome other memory-related problems. Multiple maps are used to restrict memory access of existing code such as drivers, without changing that code, and without changing existing microprocessors. A thread of a process is associated with one memory map at a time, which by mapping to different memory locations, provides memory isolation without requiring a process switch. Memory isolation may be combined with controlled, closed memory map switching performed only by trusted code, to ensure that some protected memory is inaccessible to all but the trusted code (curtained memory). Map switching among multiple maps eliminates the need to change a process in order to access different memory, thereby allowing expanded memory addressing in a single process and isolating untrusted code run in process from certain memory of that process.
Owner:MICROSOFT TECH LICENSING LLC
Data compression for direct memory access transfers
ActiveUS20130262538A1Avoid excessive impactDigital data processing detailsCode conversionData compressionDirect memory access
Memory system operations are extended for a data processor by DMA, cache, or memory controller to include a DMA descriptor, including a set of operations and parameters for the operations, which provides for data compression and decompression during or in conjunction with processes for moving data between memory elements of the memory system. The set of operations can be configured to use the parameters and perform the operations of the DMA, cache, or memory controller. The DMA, cache, or memory controller can support moves between memory having a first access latency, such as memory integrated on the same chip as a processor core, and memory having a second access latency that is longer than the first access latency, such as memory on a different integrated circuit than the processor core.
Owner:ALTERA CORP
File transfer protocol for mobile computer
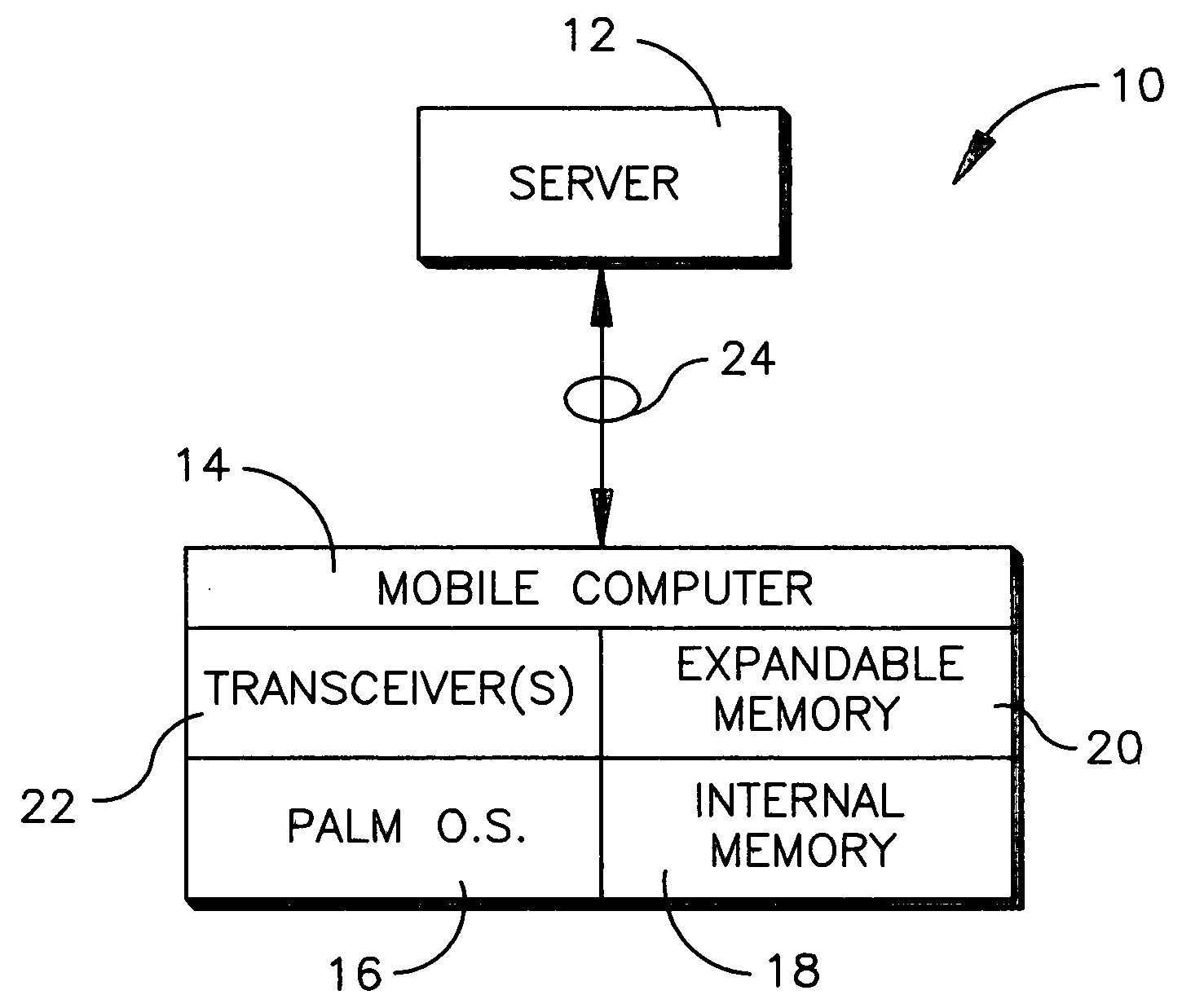
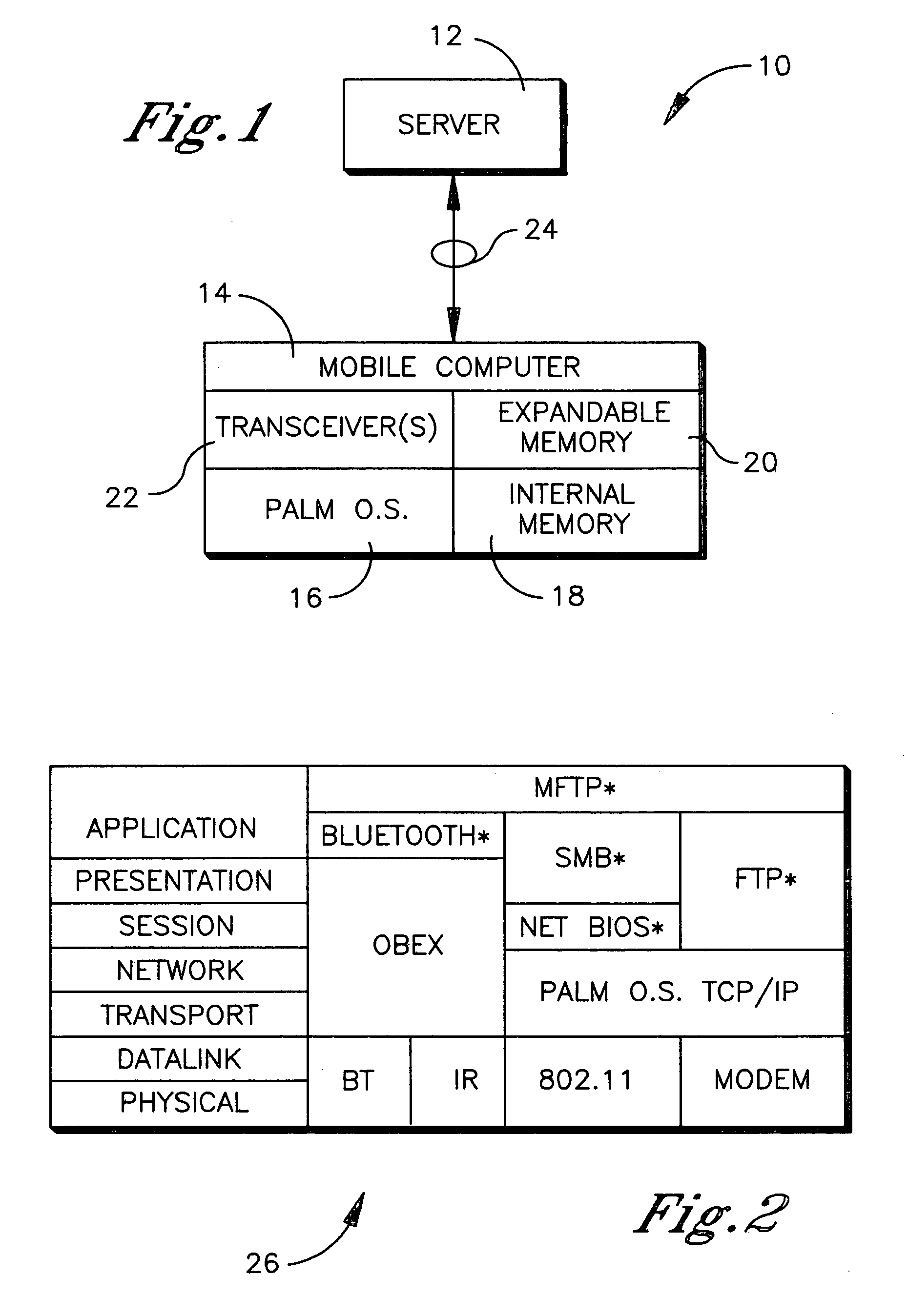
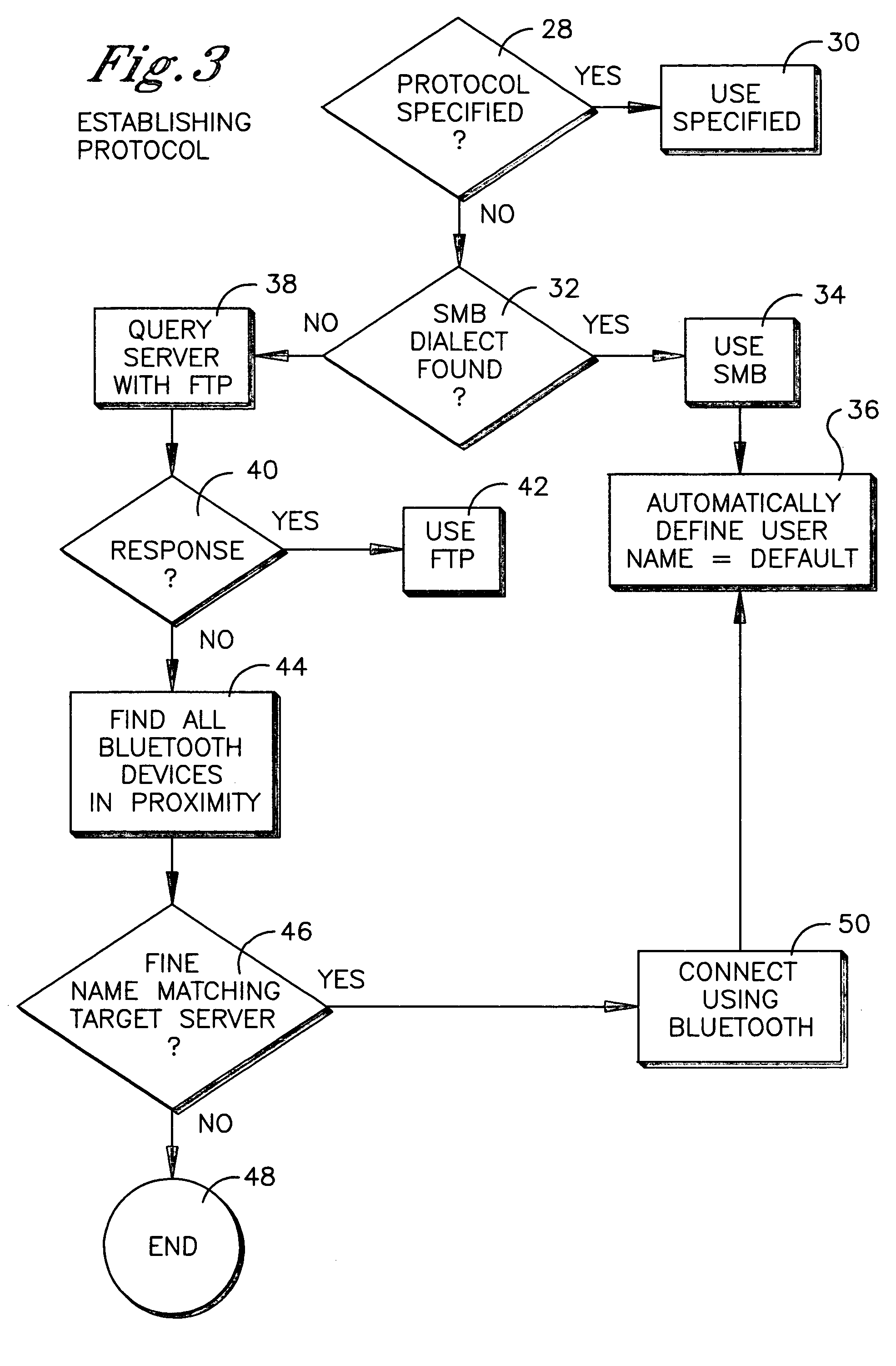
InactiveUS20050102537A1Digital data processing detailsPicture reproducers using cathode ray tubesInternal memoryBluetooth
A method is disclosed for communicating using a device having a Palm OS. SMB is preferentially used to communicate with a node, and if use of SMB is not possible, FTP is used, and if use of FTP is not possible, Bluetooth is used. If FTP or Bluetooth is selected as the protocol, file sharing between the device and node that entails a read or write is executed by temporarily copying a file to an internal Palm OS memory of the device, performing the read or write on the file, and then copying the file back to the node to overwrite a previous version of the file at the node. For non-Palm OS file transfer to the internal memory, the file is wrapped in a Palm OS stream in the internal memory for executing reads or writes. For file transfer to an expansion Palm OS memory card, byte-to-byte copying of the file is executed using the FAT of the expansion memory, with the file being transferred through an internal Palm OS memory of the device.
Owner:SONY CORP +1
Processing system and method including data compression api
ActiveUS20130262809A1Avoid excessive impactMemory architecture accessing/allocationMemory adressing/allocation/relocationData compressionApplication programming interface
Memory system operations are extended for a data processor by an application programming interface API, including a set of operations and parameters for the operations, which provides for data compression and decompression during or in conjunction with processes for moving data between memory elements of the memory system. The set of operations can be configured to use the parameters and perform the operations of the API. The API can support moves between memory having a first access latency, such as memory integrated on the same chip as a processor core, and memory having a second access latency that is longer than the first access latency, such as memory on a different integrated circuit than the processor core.
Owner:ALTERA CORP
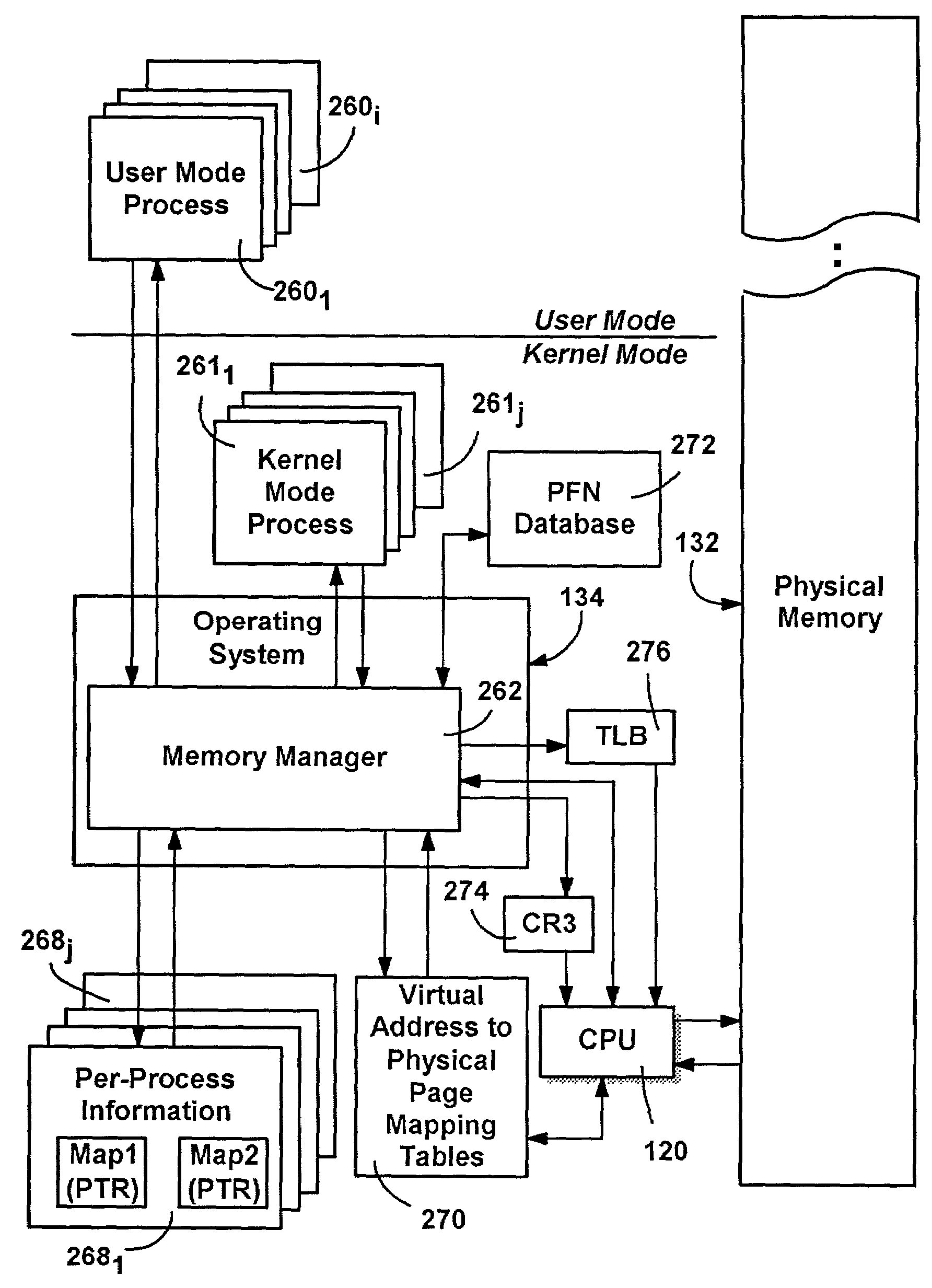
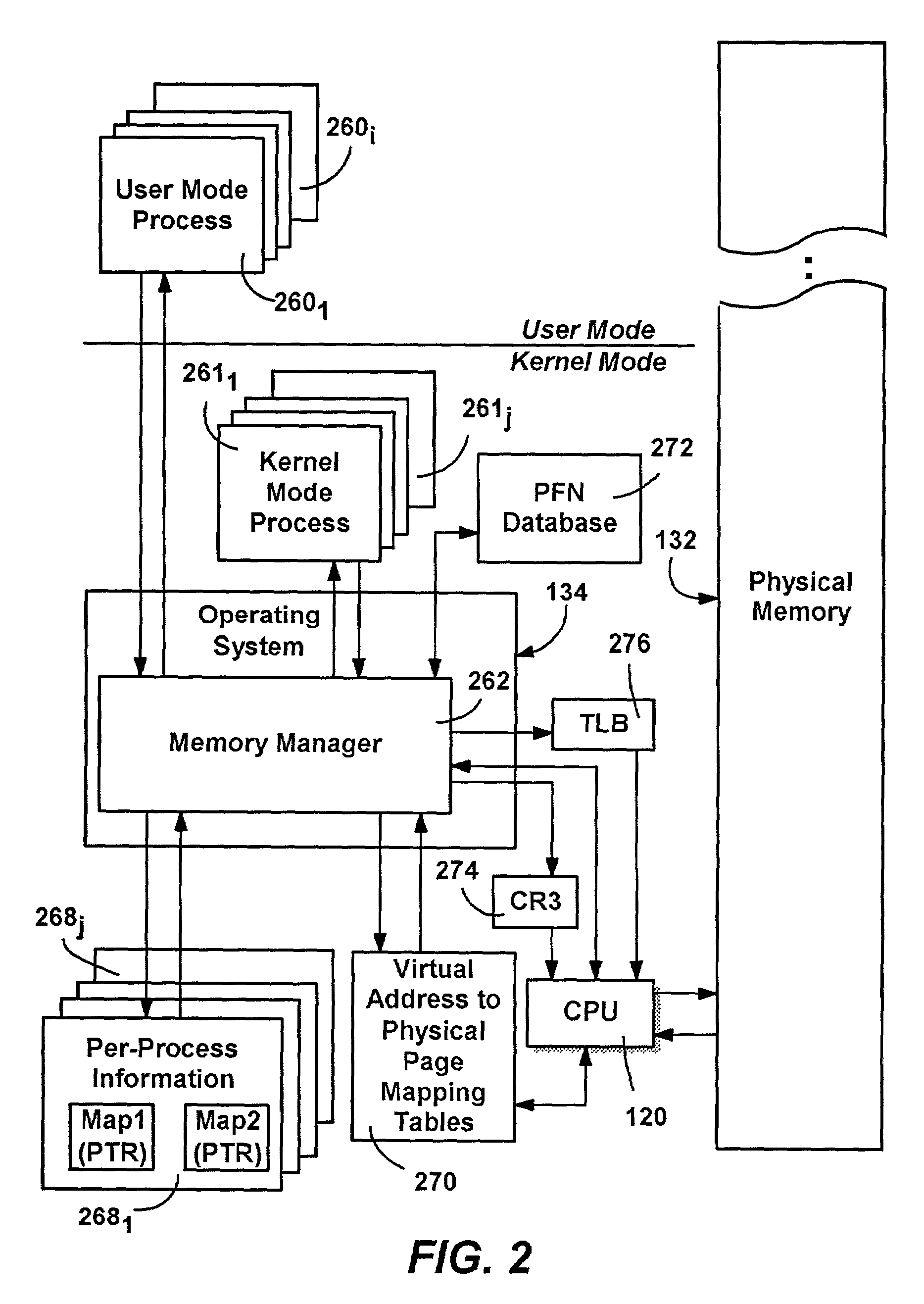
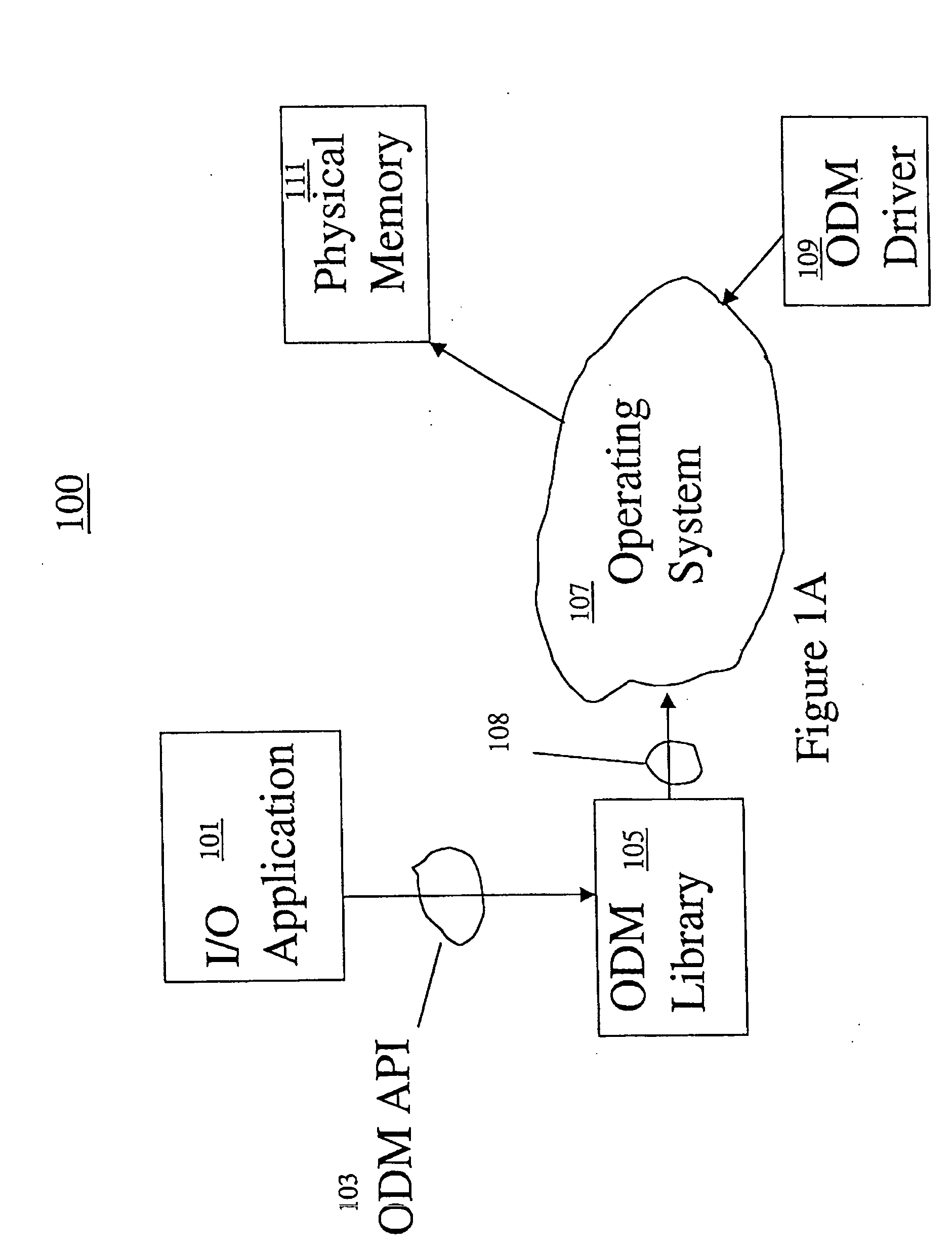
Method and system for extended memory with user mode input/output operations
ActiveUS20050256976A1Easy to operateEliminate needMemory adressing/allocation/relocationComputer security arrangementsMemory addressVirtual memory
A computer system having a kernel for mapping virtual memory address space to physical memory address space. The computer system uses a method for performing an input / output operation. A physical memory buffer is registered with a subsystem, and the physical memory buffer is associated with a first virtual address, a size and a key. The physical memory buffer is dynamically associated with a second virtual address which is different from the first virtual address. As part of an application program an input / output operation is requested regarding the second virtual address. An application table is used to obtain the first virtual address, the key and the size. The first virtual address, the key and the size are supplied to the subsystem. The subsystem uses the first virtual address, the key and the size, to determine the physical memory buffer and performs an input / output operation using the physical memory buffer without intervention of the kernel.
Owner:ORACLE INT CORP
Memory module with integrated bus termination
A memory module includes a memory device, a connector, a plurality of lines coupling the memory device and the connector, and termination circuitry coupled to at least a subset of the lines. A method for terminating a memory bus includes providing at least two expansion sockets coupled to the memory bus; interfacing two expansion memory modules including termination circuitry with the expansion sockets; and disabling the termination circuitry for one of the expansion memory modules.
Owner:ROUND ROCK RES LLC
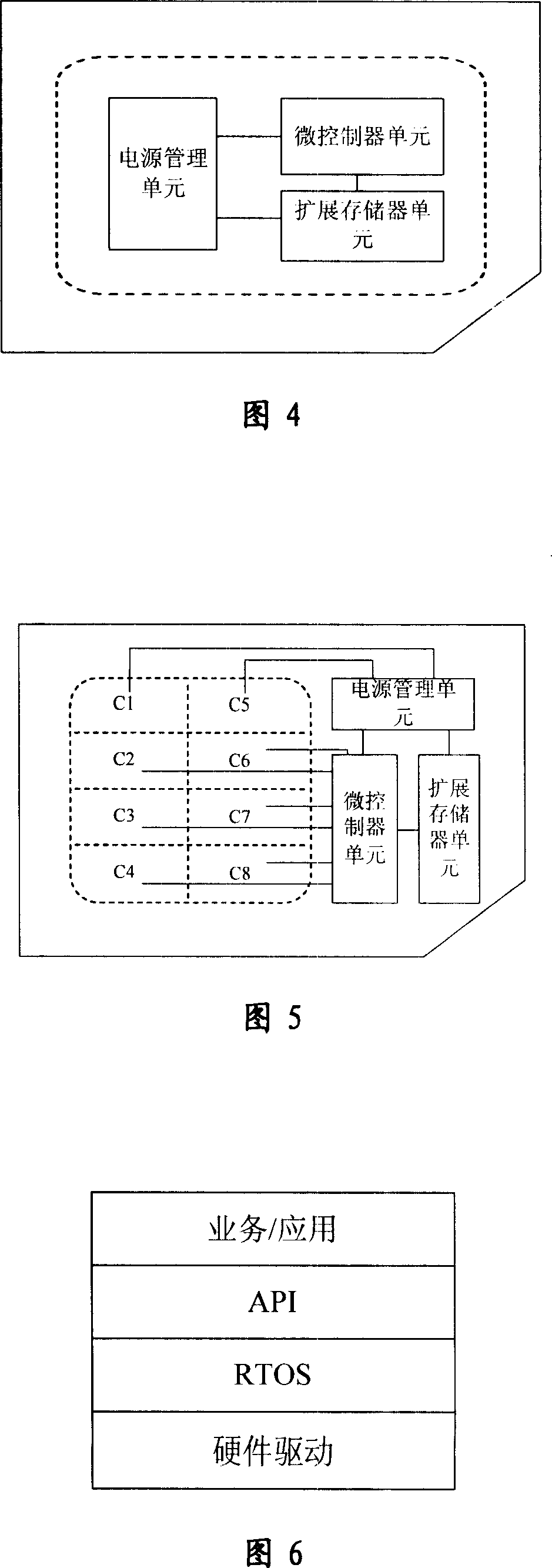
Smart card of supporting high performance computing, large capacity storage, high-speed transmission, and new type application
ActiveCN101004798AImprove securityQuick exchangeMemory record carrier reading problemsRecord carriers used with machinesMicrocontrollerMass storage
An intelligent card supporting high performance calculation and large-capacity storage as well as high speed transmission is prepared for connecting power supply management unit with two base pins and connecting microcontroller unit to the other six base pins according to base pin code defined by ISO / IEC 7816-3 protocol, connecting expansion storage unit separately to power supply management unit and microcontroller unit.
Owner:RDA MICROELECTRONICS SHANGHAICO LTD
Flash memory card expander
ActiveUS7832645B2Reduced cost per memory capacityCoupling device connectionsElectric discharge tubesMemory cardsHost machine
Method and system for expanding the memory capacity of devices that use flash memory cards. In one aspect, a memory card expander assembly includes an adaptor shaped to be connected to a memory card slot of a host device, and a receptacle assembly in communication with the adaptor and operative to be attached to the host device. The receptacle assembly includes an expanded memory card slot operative to connect to a memory card such that the host device can communicate with the connected memory card when the adaptor is connected to the memory card slot.
Owner:KINGSTON DIGITAL CO LTD
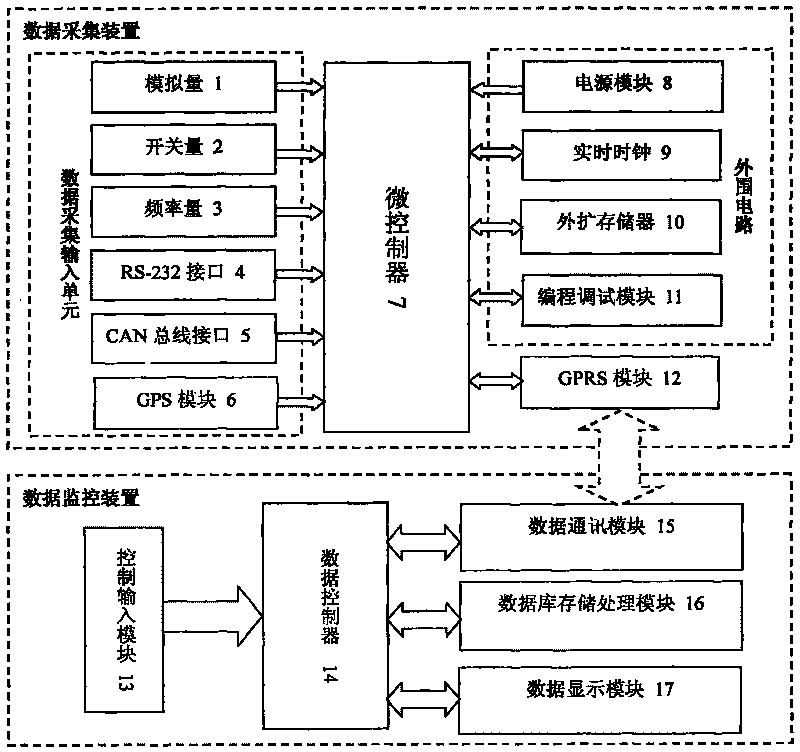
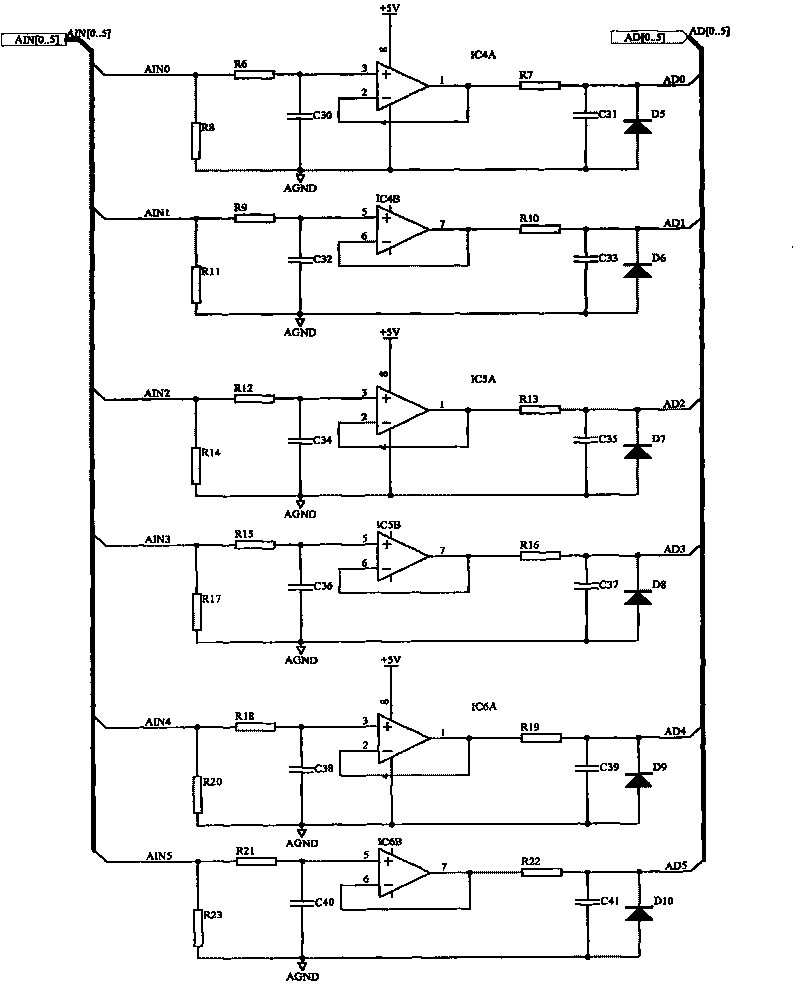
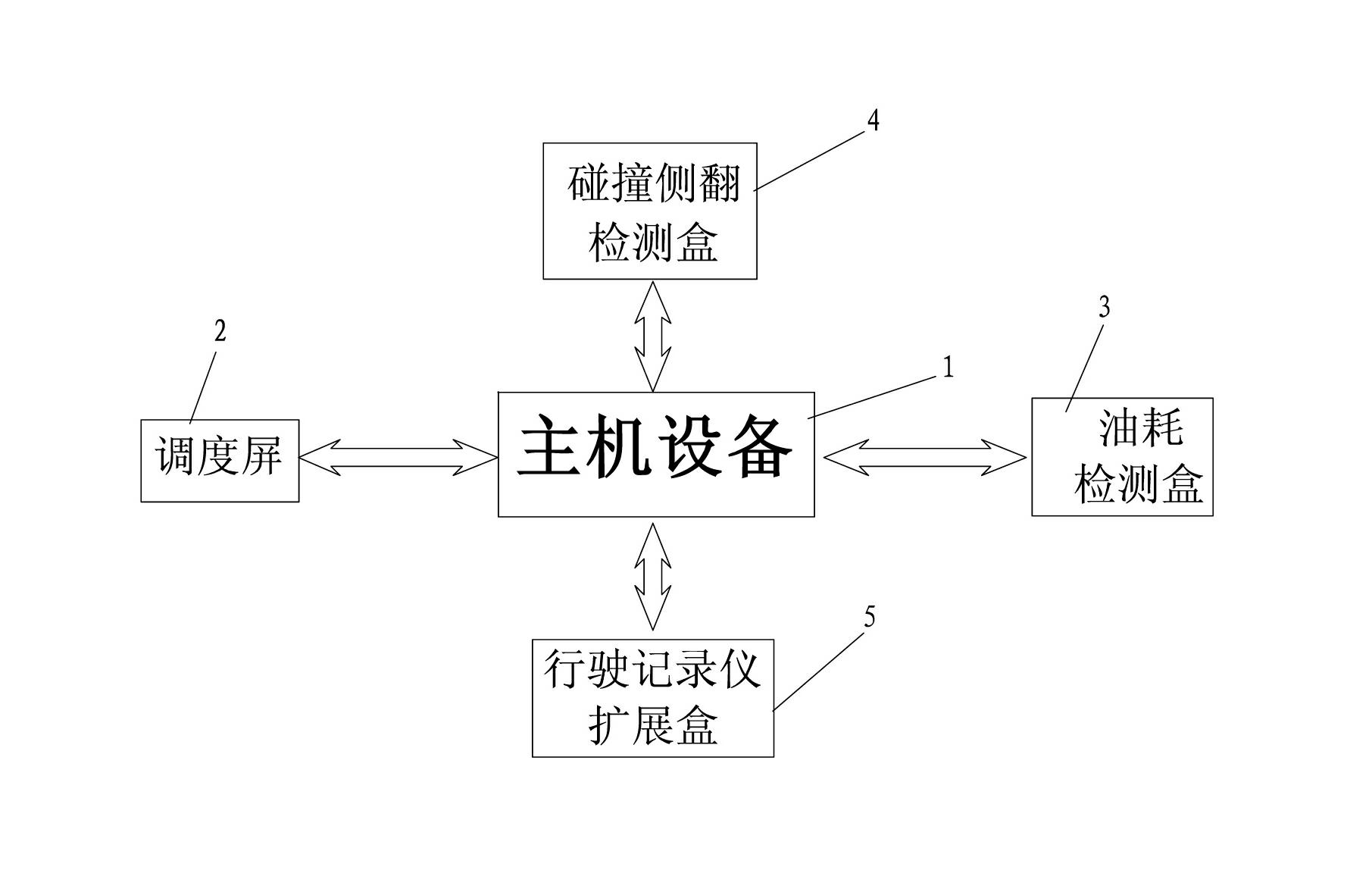
Vehicle-mounted engineering machinery remote wireless data collection and monitoring system and method
InactiveCN101738963ARich data collection channelsMeet the collection requirementsProgramme controlComputer controlGeneral Packet Radio ServiceData display
The invention discloses vehicle-mounted engineering machinery remote wireless data collection and monitoring system and a method. An analogue value, a switching value, a frequency value, a RS-232 interface, a CAN bus interface, a global positioning system (GPS) module, a power module, a real-time clock, an external expanding memory, a programming and debugging module and a general packet radio service (GPRS) communication module in a data collection device are respectively connected with a microcontroller; a control input module, a data communication module, a database storage processing module and a data display module are respectively connected with a data controller in a data monitoring device; and a GPRS communication module of the data collection device is connected with the data communication module of the data monitoring device in a wireless mode through transmission control protocol (TCP) data communication protocol. The system has rich and varied data collection channels, data collection storage, data collection transmission and the period can be remotely configured, local storage data of the data collection device can be remotely extracted, the collected data can be ensured not to lose when a wireless communication network is unawailable. The invention is suitable for vehicle-mounted engineering machinery remoter wireless data collection and monitoring.
Owner:ZHEJIANG UNIV +1
Digital remote store
Expanded storage is provided to portable electronic devices of the type that typically incorporate compact flash memory cards or a similar local replaceable memory device. A transceiver assembly is provided within the form factor of the local replaceable memory normally used in the local storage device. The transceiver assembly communicates with the portable electronic device over the connections and using the same communication protocol as the portable electronic device conventionally uses to communicate with the local replaceable memory device. Data are written to the transceiver assembly as if the transceiver were the conventional memory device. The data are buffered and transmitted over a wireless link to a corresponding wireless link associated with a remote mass storage device. Data transferred across the wireless link are stored in the remote mass storage device as if the mass storage were provided within the portable electronic device, thereby providing greatly expanded storage to the portable electronic device.
Owner:INTEL CORP
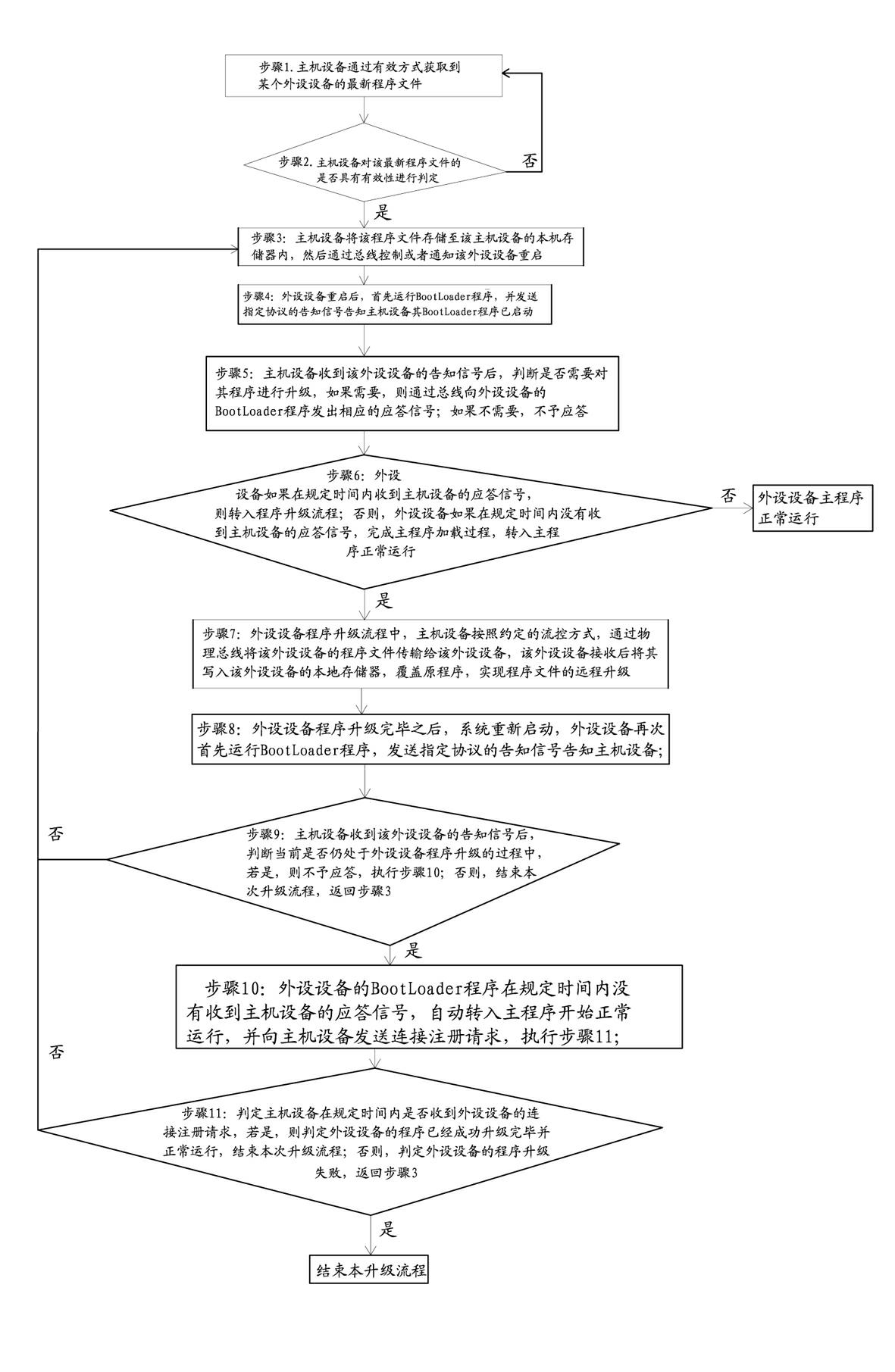
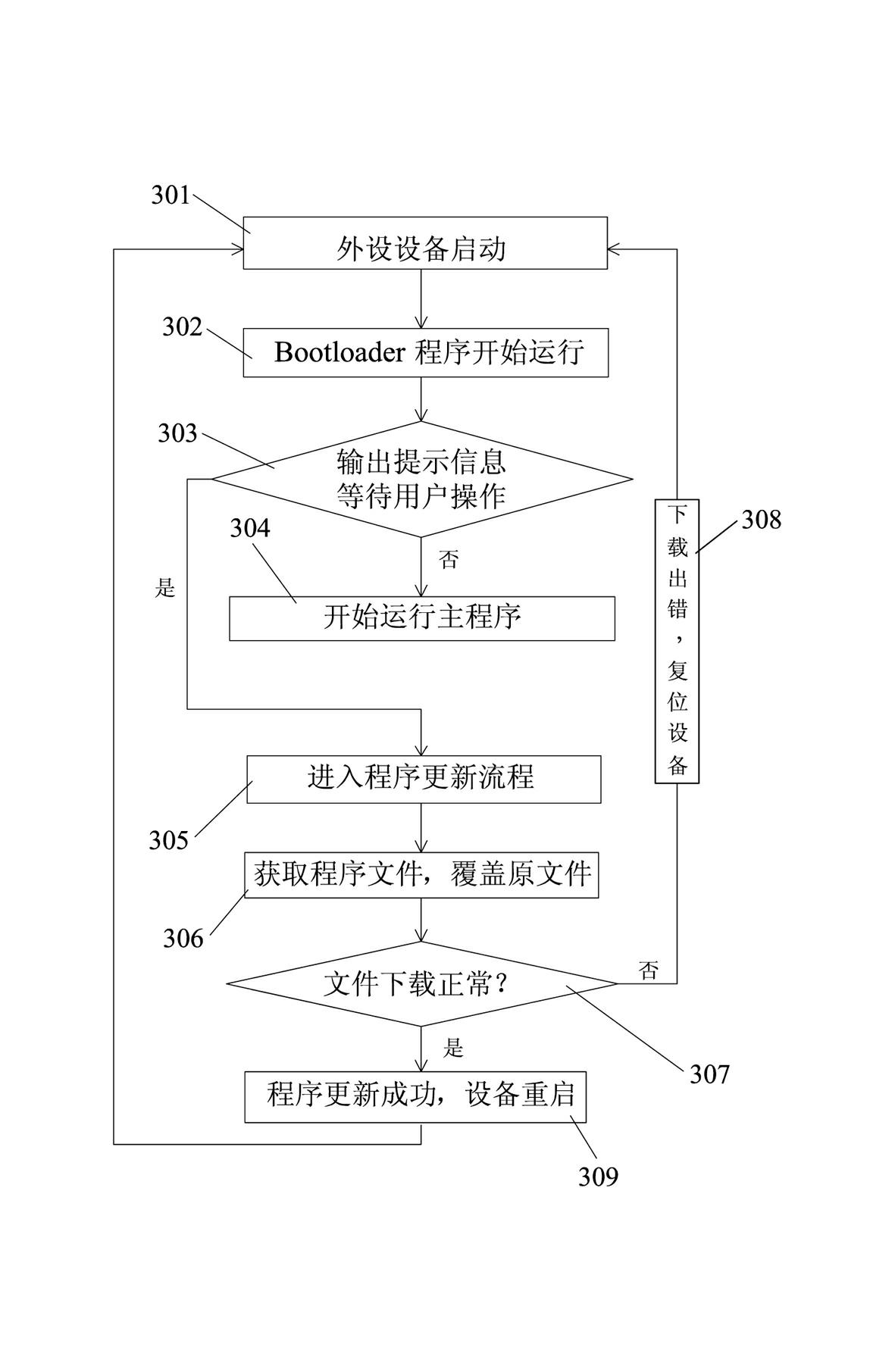
A Program Upgrading Mechanism for Peripheral Devices Based on Microcontroller Without External Memory
ActiveCN102298526ARealize remote upgradeImprove versatilityProgram loading/initiatingMicrocontrollerCommunications system
The invention provides a method for remotely upgrading the program of the peripheral equipment of a single-chip microcomputer without an externally expanded memory. A master-slave device communication system, including a host device and multiple peripheral devices, in which a stable communication is established between the host device and each peripheral device through physical means (such as RS-232 / RS-485 / CAN bus, etc.) Connection, and the program design of the peripheral device adopts the BootLoader program to guide the main program to start. With the help of the storage space of the host, the communication channel between the peripheral device and the host is used. The two parties communicate according to the agreement agreed in advance, and the host recognizes it. And be controlled to realize the remote upgrade of the peripheral device program. The advantage of adopting the present invention is that there is no need to make any changes to the host hardware and peripheral hardware, and the whole mechanism is completed through the interaction of software and protocols, which has good versatility and strong expandability.
Owner:XIAMEN YAXON NETWORKS CO LTD
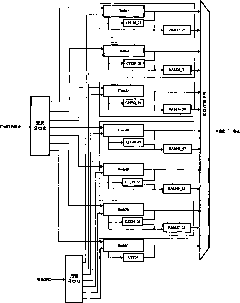
Hash table-based and extended memory-based high-performance IPv6 address searching method
InactiveCN101827137AImprove search efficiencyAdd depthMemory adressing/allocation/relocationData switching networksExtensibilityProcess module
The invention discloses a hash table searching-based and extended memory searching-based IPv6 address searching scheme. A system comprises one searching classifier, one updating classifier, seven parallel hash processing units, six extended memory processing units, seven hash collision processing units and one priority comparing unit. The first six hash processing units are correlated with the corresponding extended memories in two stages and combined with the corresponding hash collision processing units to form six paths of processing modules; the seventh hash processing unit and the corresponding hash collision processing unit form one path of processing module; and the seven paths of modules searches the IPv6 address in parallel so as to determine the next hop of information. Due to the adoption of the method, the searching operation of the IPv6 address is finished in one to two storage periods in combination with the principle of hash searching and extended memory searching according to the distribution rule of the prefix of the IPv6 address. The method has high searching and updating performance and high extensibility, so that the method is a searching scheme suitable for the high-performance IPv6 router.
Owner:XIAN UNIV OF POSTS & TELECOMM
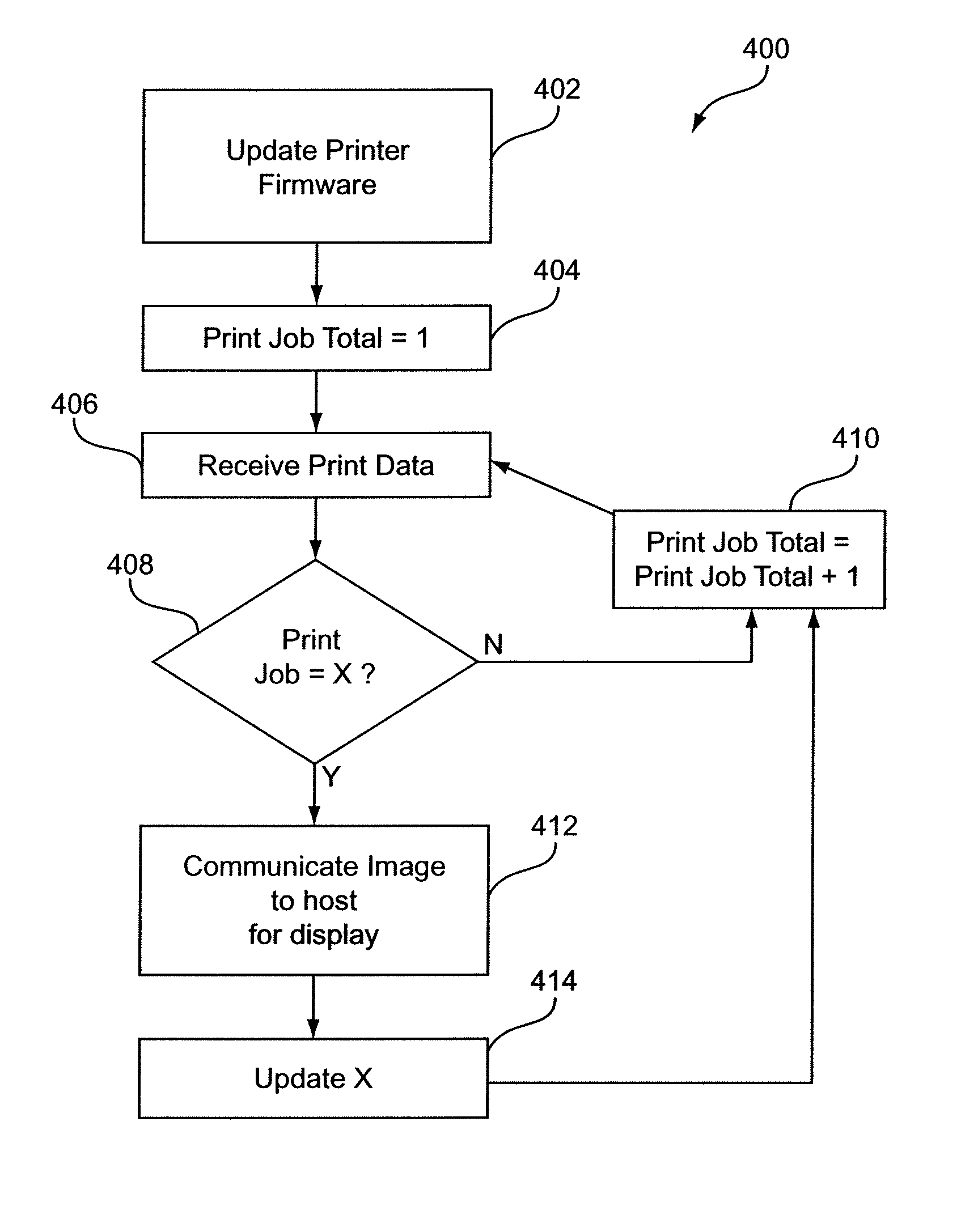
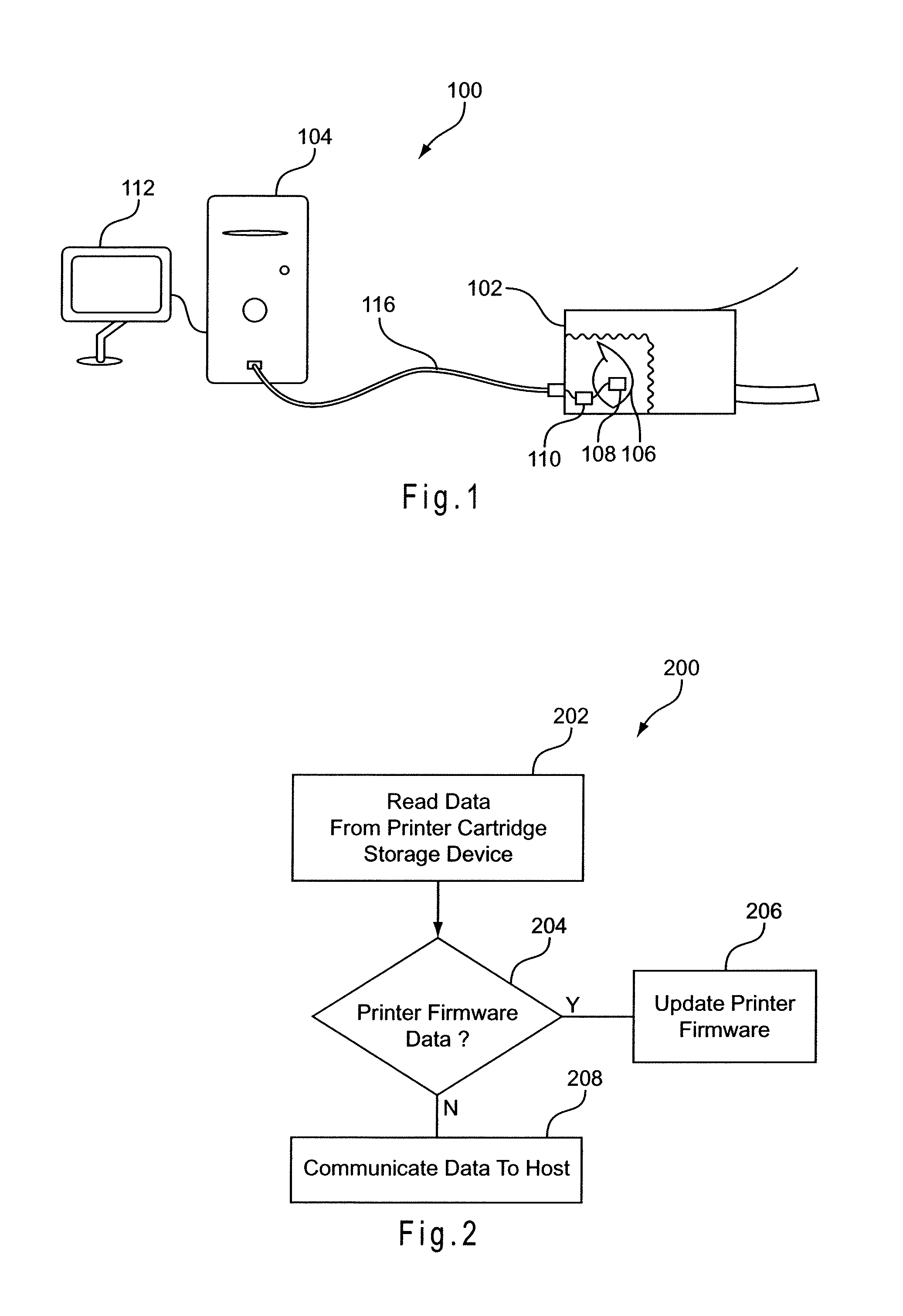
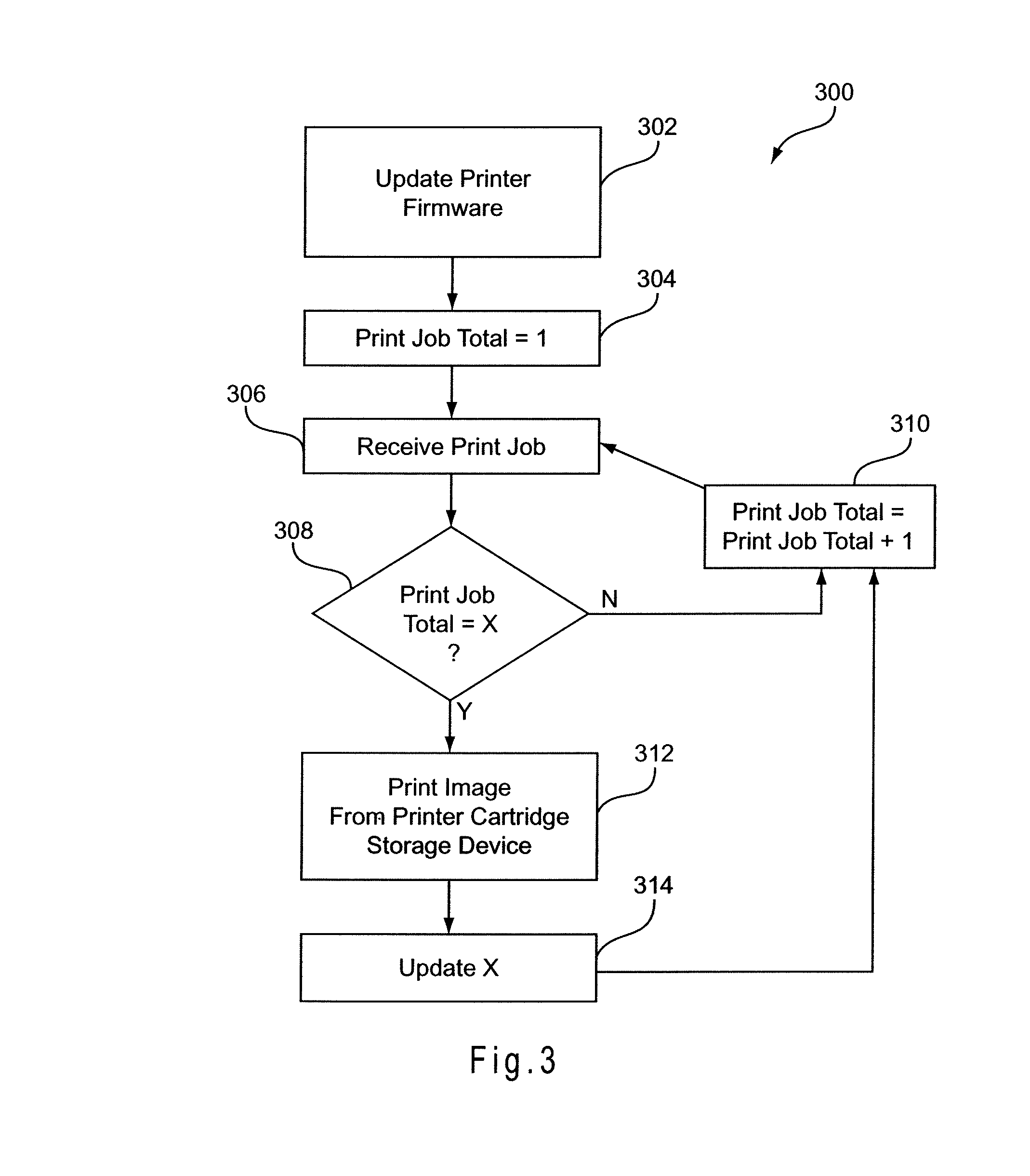
Smart printer cartridge
InactiveUS8161199B1Increasing printer resolutionIncrease printer resolutionElectrographic process apparatusPrintingControl circuitEmbedded system
A system and method are disclosed for modifying the capabilities and functions of a printer after it is manufactured. A consumable / replaceable printer cartridge includes a storage device having updated and / or additional printer function data and other data for use by the printer control circuitry to execute printer functions and other types of functions. In addition, when the printer cartridge is installed in the printer the storage device may be utilized by the printer control circuitry as expanded memory for use in executing the updated and / or additional printer functions and other types of functions.
Owner:MARVELL ASIA PTE LTD
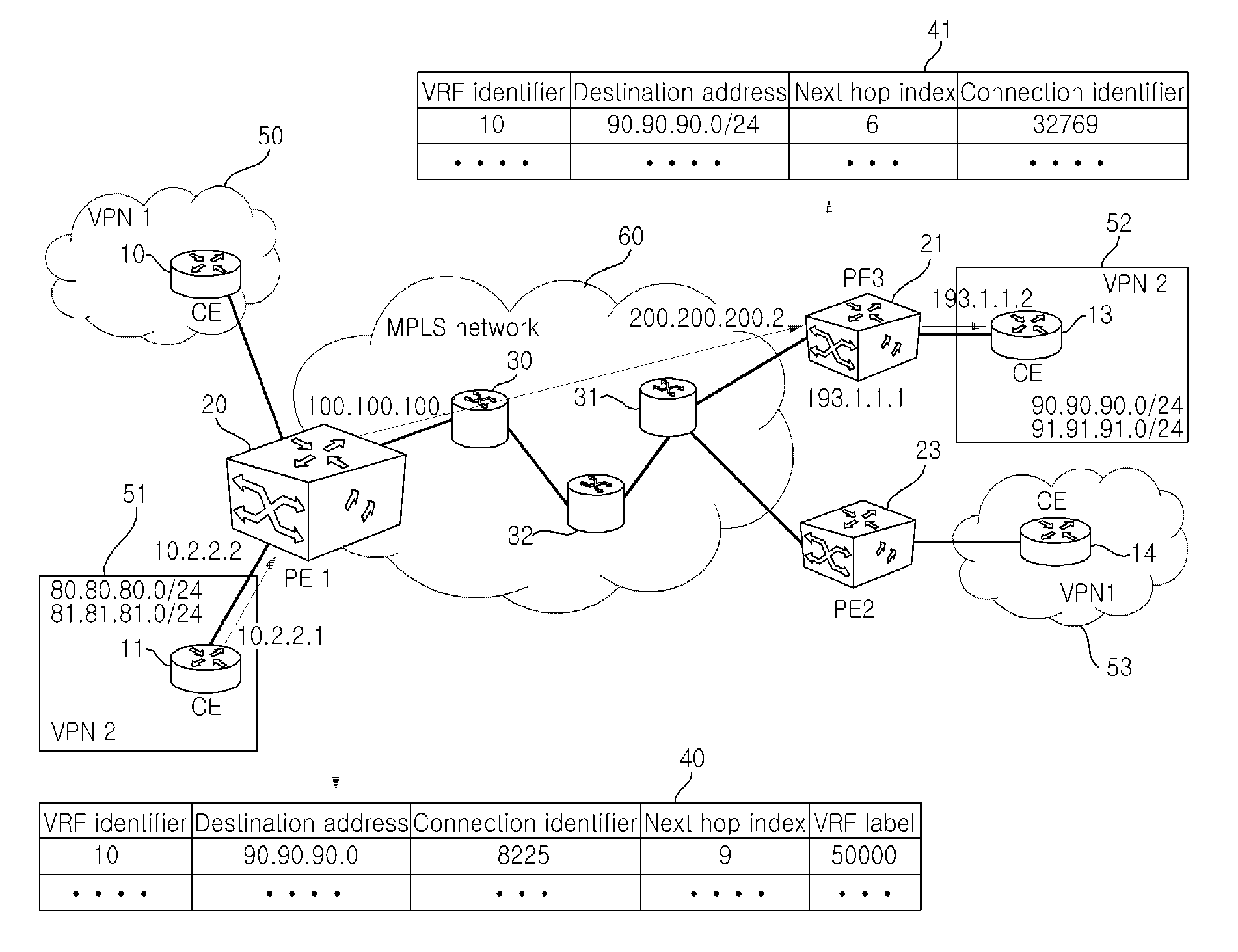
Method for forwarding packet in mpls l3vpn
The present invention relates to a method for forwarding a packet which is to provide a VPN service using an IPv4 address in an MPLS network. The method for forwarding the packet according to the present invention extracts routing information including a VRF identifier from a packet, when the packet is received at one or more CE routers in the MPLS network, searches for next hop information in a forwarding table by using the VRF identifier and a prefix, substitutes the searched next hop information by destination information of the received packet, and transmits the packet to an output port. According to the present invention, since the plurality of forwarding tables for providing the VPN are provided without extending a memory, the packet forwarding can be stably performed.
Owner:ELECTRONICS & TELECOMM RES INST
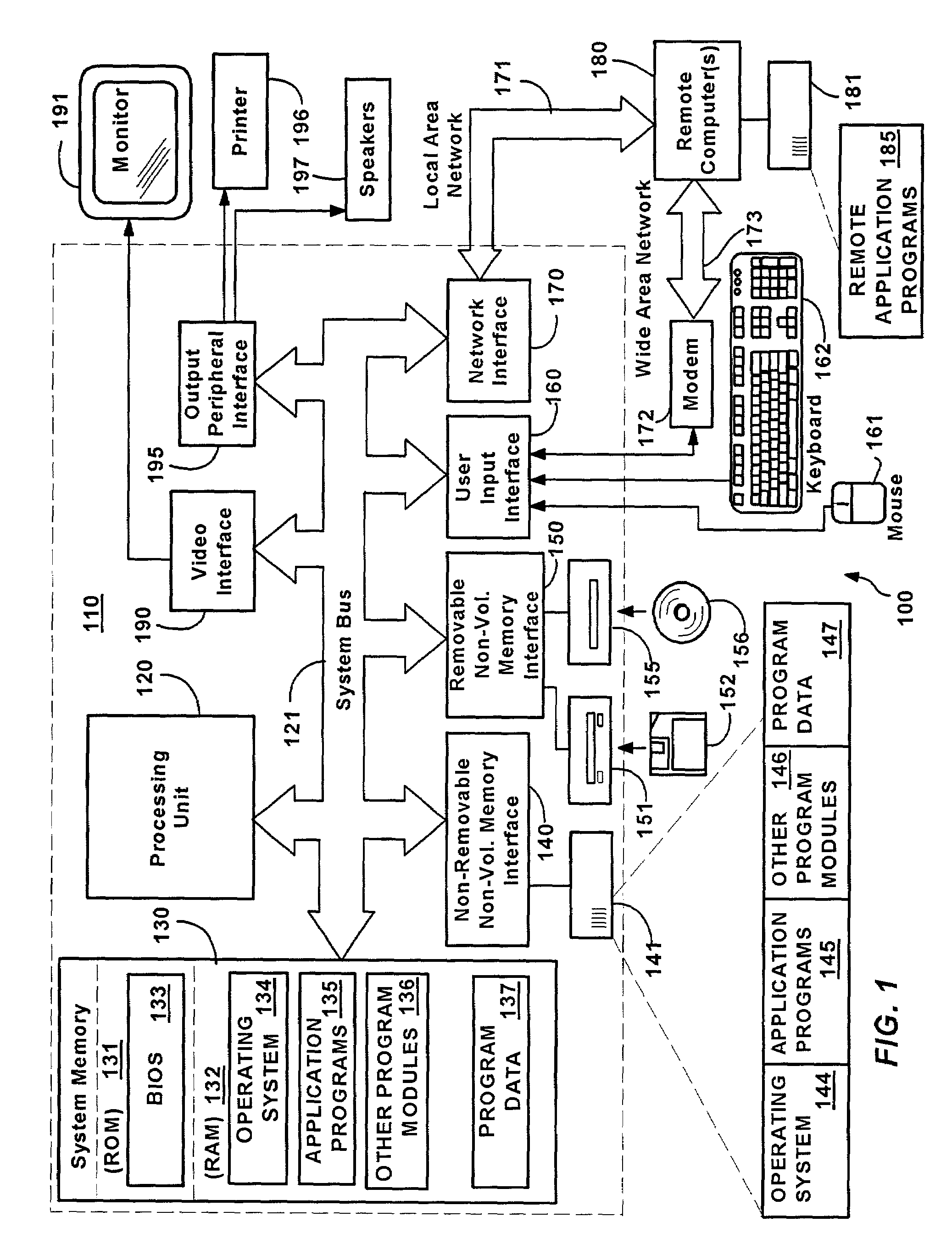
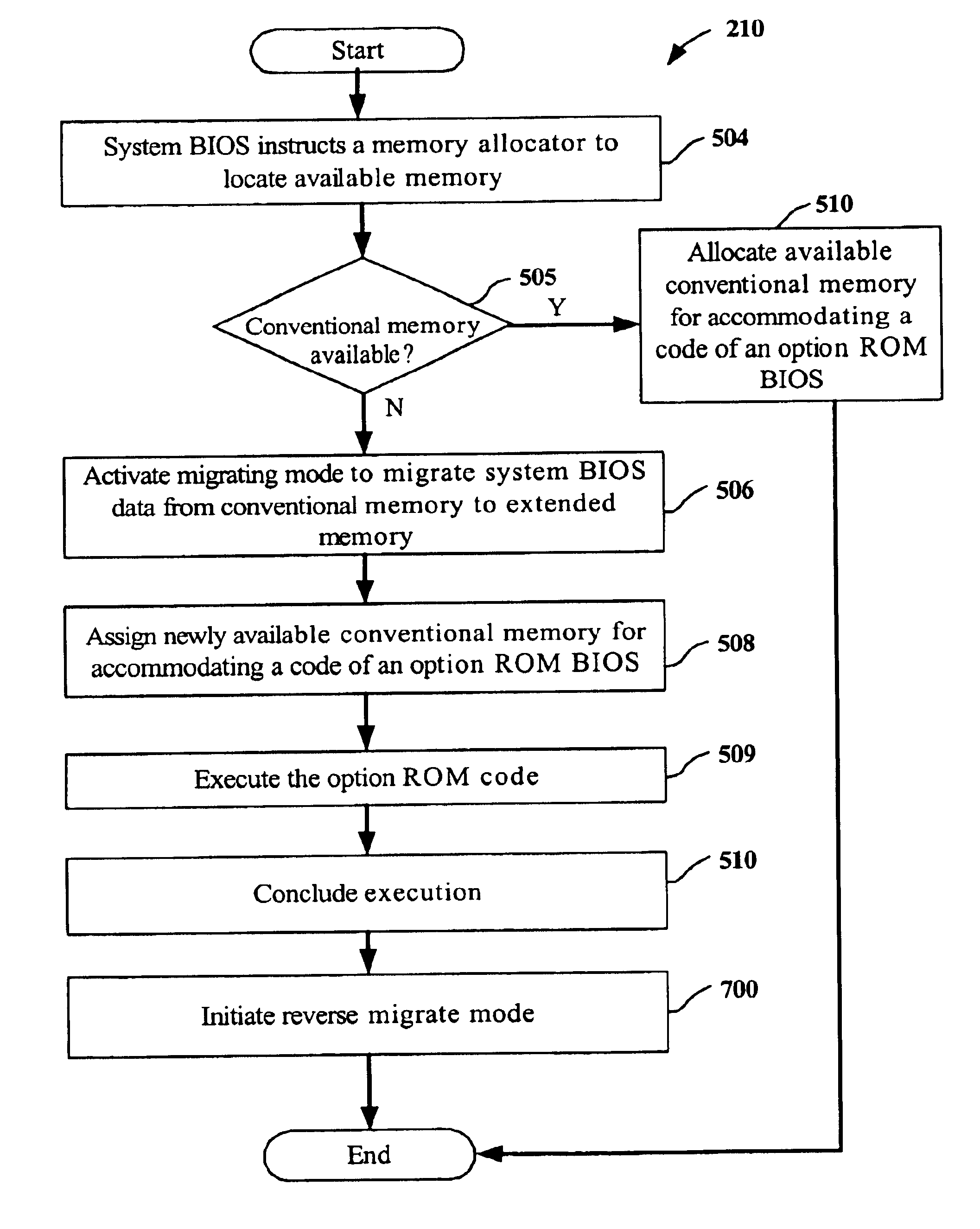
Methods for optimizing memory resources during initialization routines of a computer system
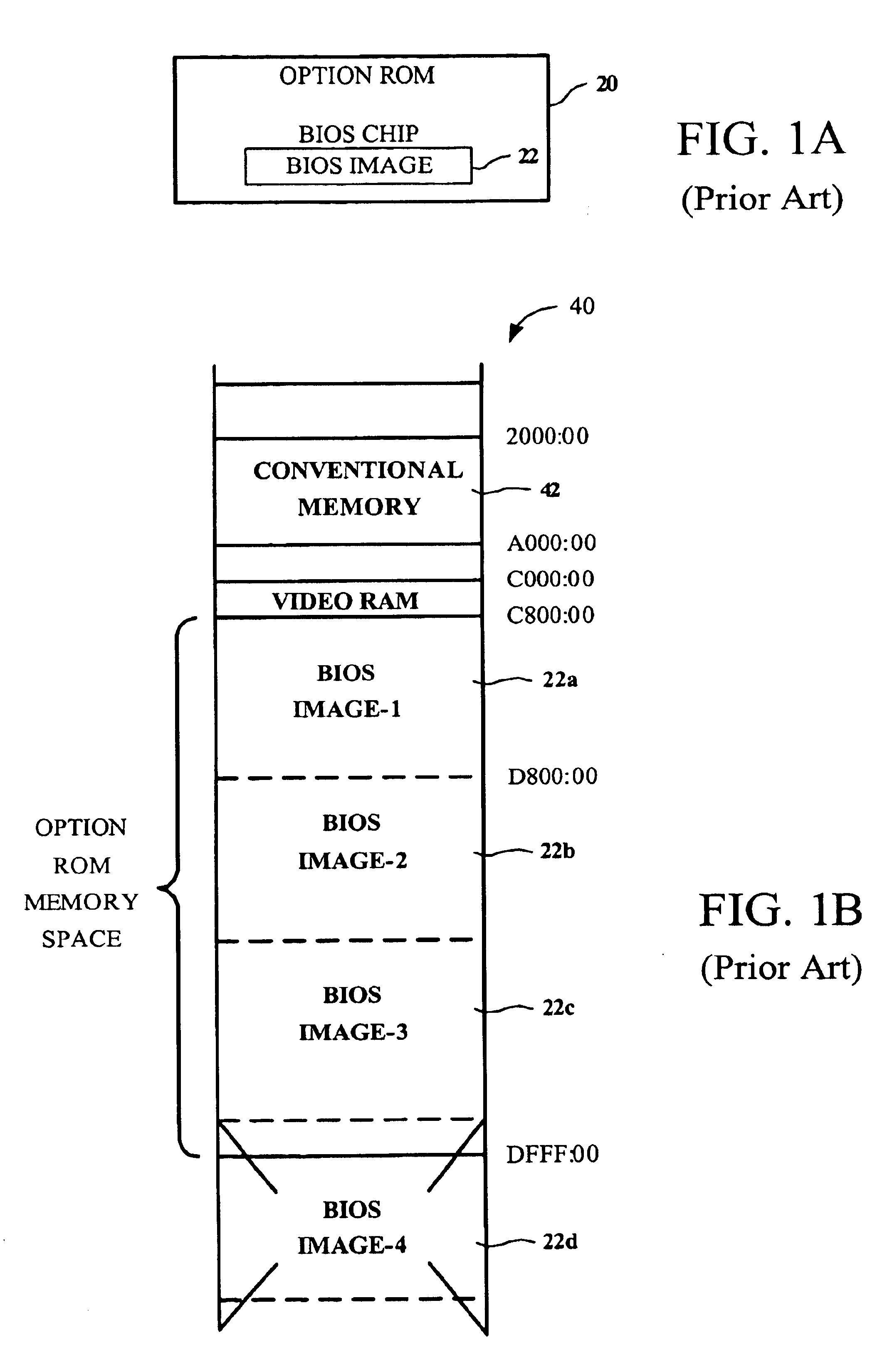
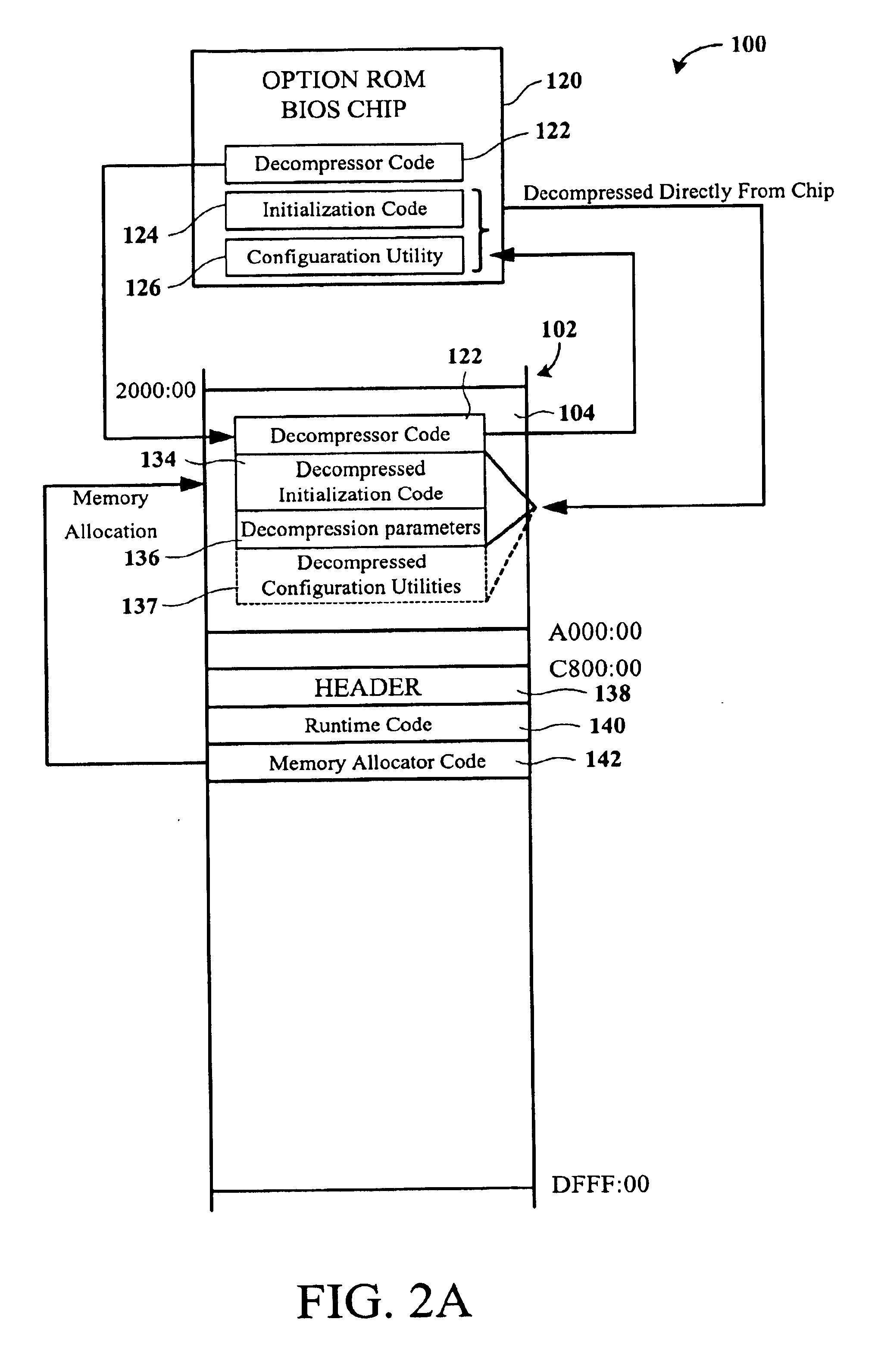
InactiveUS6865669B1Improve abilitiesIncrease capacityData resettingMultiple digital computer combinationsConventional memoryOperational system
Methods for optimizing of memory resources during an initialization routine of a computer system which prepares the computer system for loading of an operating system is disclosed. One exemplary method includes receiving a request from a system BIOS to locate an amount of conventional memory where the amount of conventional memory accommodates at least a decompressed version of data located in an option ROM BIOS. Then the amount of conventional memory requested by the system BIOS is determined. If the amount of conventional memory requested by the system BIOS is not available, the method continues and system BIOS data located within the conventional memory is read where the system BIOS data occupies at least the amount of conventional memory requested by the system BIOS. After the system BIOS data is read, the system BIOS data is written from the conventional memory to an extended memory, and the system BIOS data located in the conventional memory that has been written into the extended memory is deleted.
Owner:PMC-SIERRA
Memory scrubbing of expanded memory
Embodiments of the invention include a memory device, such as a removable expanded memory card, having a host bus interface that allows a host to access a memory of the device. The memory device also includes memory scrubbing circuitry to read data stored at addresses in the memory and to identify single-bit errors and multiple-bit errors in the data read from the memory.
Owner:NETWORK APPLIANCE INC
Database system providing methodology for extended memory support
ActiveUS7421562B2Memory architecture accessing/allocationOperational speed enhancementParallel computingVirtual address space
A database system providing methodology for extended memory support is described. In one embodiment, for example, a method is described for extended memory support in a database system having a primary cache, the method comprises steps of: creating a secondary cache in memory available to the database system; mapping a virtual address range to at least a portion of the secondary cache; when the primary cache is full, replacing pages from the primary cache using the secondary cache; in response to a request for a particular page, searching for the particular page in the secondary cache if the particular page is not found in the primary cache; if the particular page is found in the secondary cache, determining a virtual address in the secondary cache where the particular page resides based on the mapping; and swapping the particular page found in the secondary cache with a page in the primary cache, so as to replace a page in the primary cache with the particular page from the secondary cache.
Owner:SYBASE INC
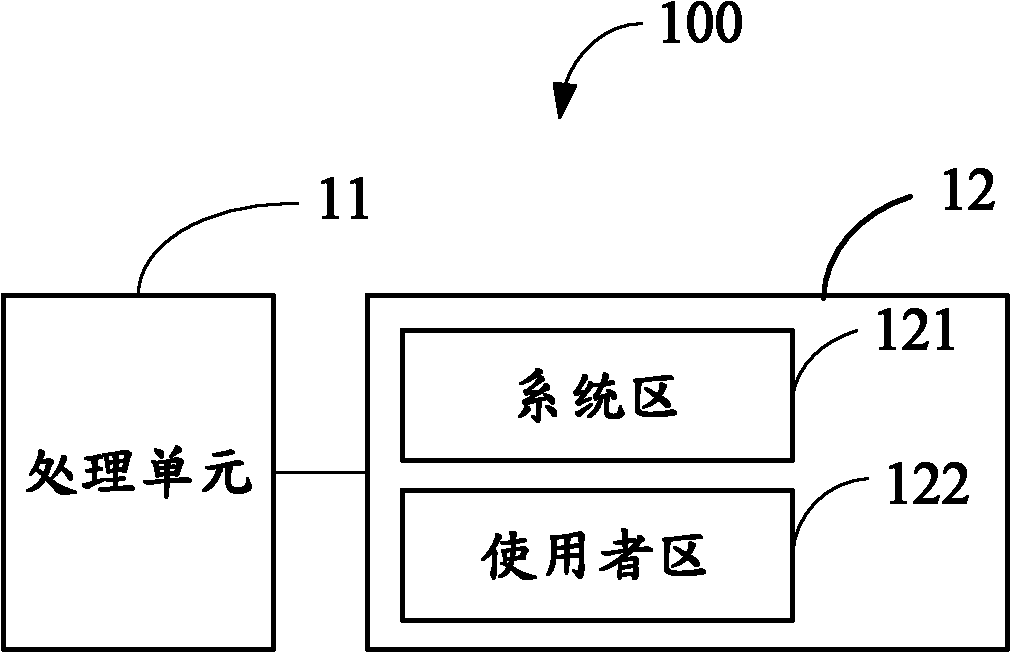
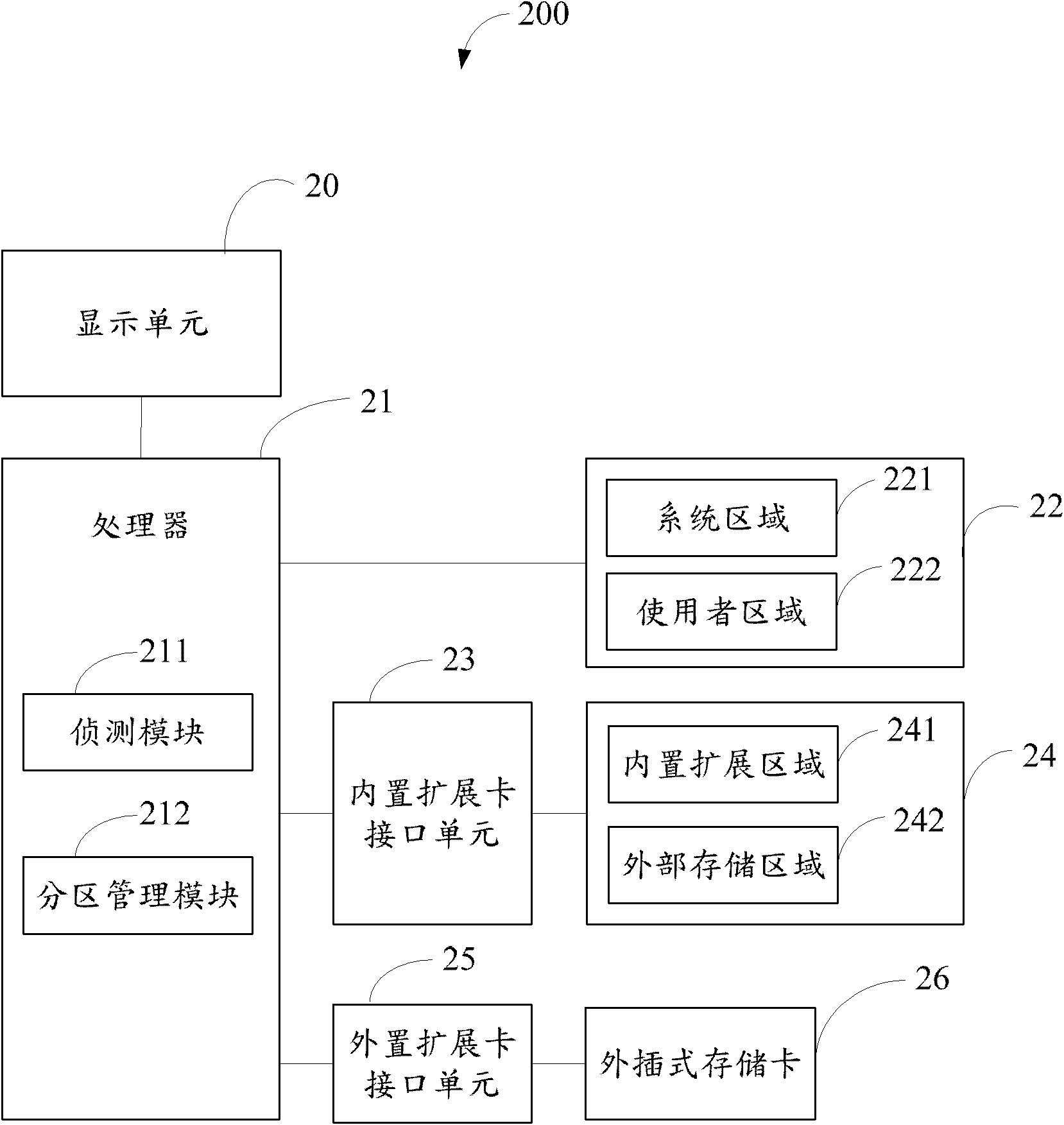
Memory-expandable electronic equipment and memory expanding method
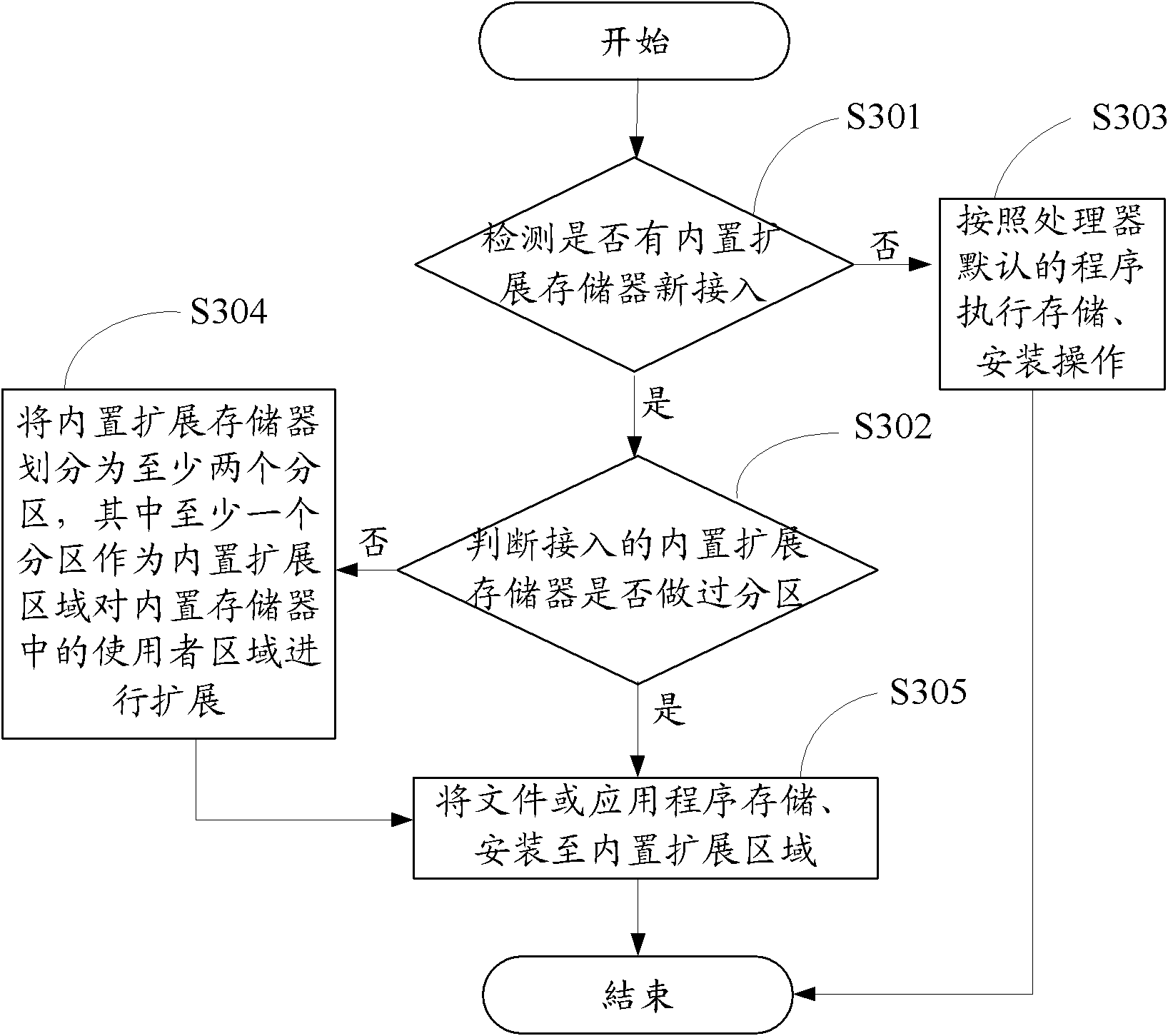
InactiveCN102103470AStorage moreDon't worry about running out of memoryInput/output to record carriersMemory systemsComputer scienceElectronic equipment
The invention discloses a memory expanding method. The method comprises the following steps of: detecting whether a built-in expandable memory is newly inserted; if the built-in expandable memory is not newly inserted, performing storage and installation operation according to a default program of a processor; if the built-in expandable memory is newly inserted, judging whether the inserted built-in expandable memory is partitioned or not; if the built-in expandable memory is not partitioned, partitioning the built-in expandable memory into at least two subareas, wherein at least one subarea is used as a built-in expandable area for expanding a user area in the memory; and storing and installing files or application programs to the built-in expandable area. The invention also provides memory-expandable electronic equipment.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
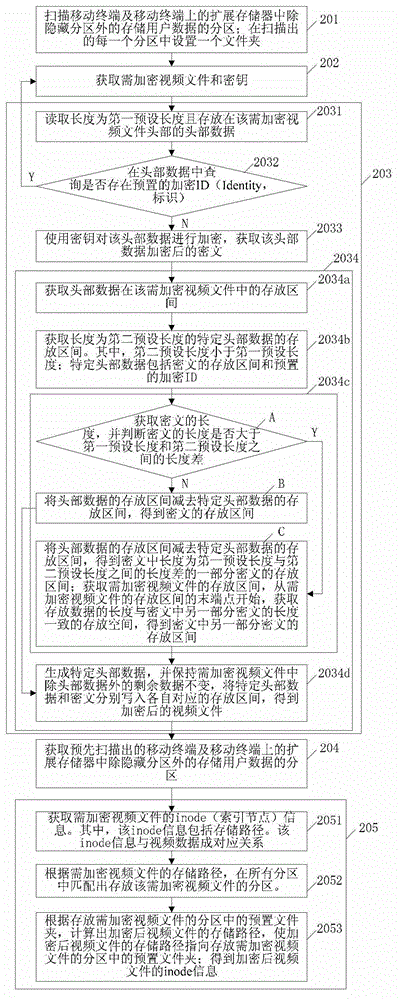
Methods and devices for encrypting and decrypting video file and mobile terminal
ActiveCN102867153AImprove securityImprove encryption efficiencyTelevision system detailsData processing applicationsComputer terminalEncryption
The invention discloses a method for encrypting a video file, a method for decrypting the video file, a device for encrypting the video file, a device for decrypting the video file, and a mobile terminal, and belongs to the field of mobile terminals. The method for encrypting the video file comprises the following steps of: acquiring the video file to be encrypted and a key; encrypting the video file to be encrypted by using the key to obtain an encrypted video file; acquiring a pre-scanned mobile terminal and partitions storing user data except hidden partitions in an extended memory on the mobile terminal; and determining a partition storing the video file to be encrypted in all the partitions, and moving the encrypted video file into a preset folder in the partition storing the video file to be encrypted. The method for decrypting the video file comprises the following steps of: acquiring a video file to be decrypted and the key; decrypting the video file to be decrypted by using the key to obtain a decrypted video file; and determining the storage position of the video file to be decrypted before encryption, and moving the decrypted video file to the storage position before encryption. The video file can be quickly encrypted.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Flash memory card expander
ActiveUS20070235544A1Reduced cost per memory capacityCoupling device connectionsElectric discharge tubesComputer scienceMemory cards
Method and system for expanding the memory capacity of devices that use flash memory cards. In one aspect, a memory card expander assembly includes an adaptor shaped to be connected to a memory card slot of a host device, and a receptacle assembly in communication with the adaptor and operative to be attached to the host device. The receptacle assembly includes an expanded memory card slot operative to connect to a memory card such that the host device can communicate with the connected memory card when the adaptor is connected to the memory card slot.
Owner:KINGSTON DIGITAL CO LTD
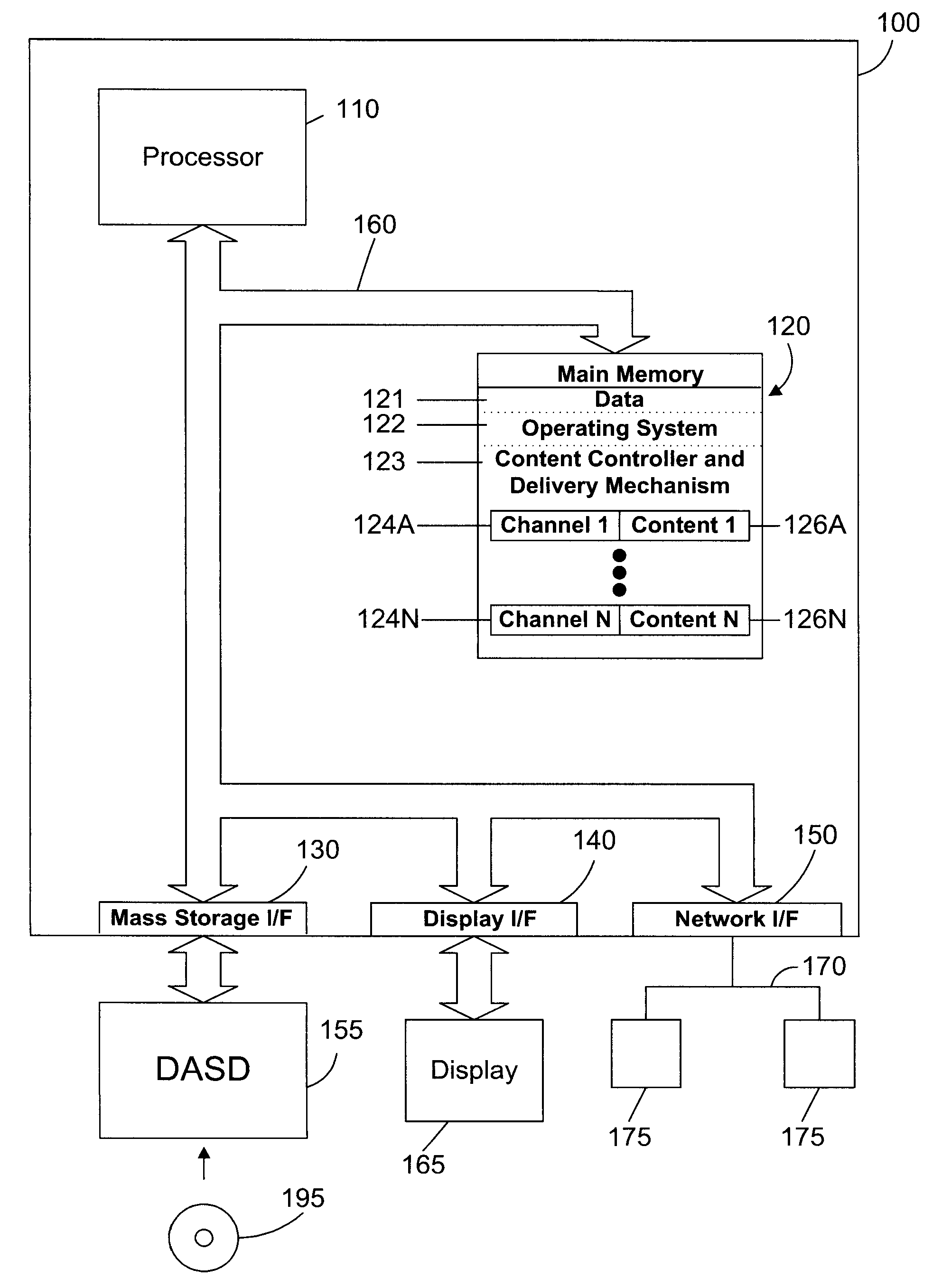
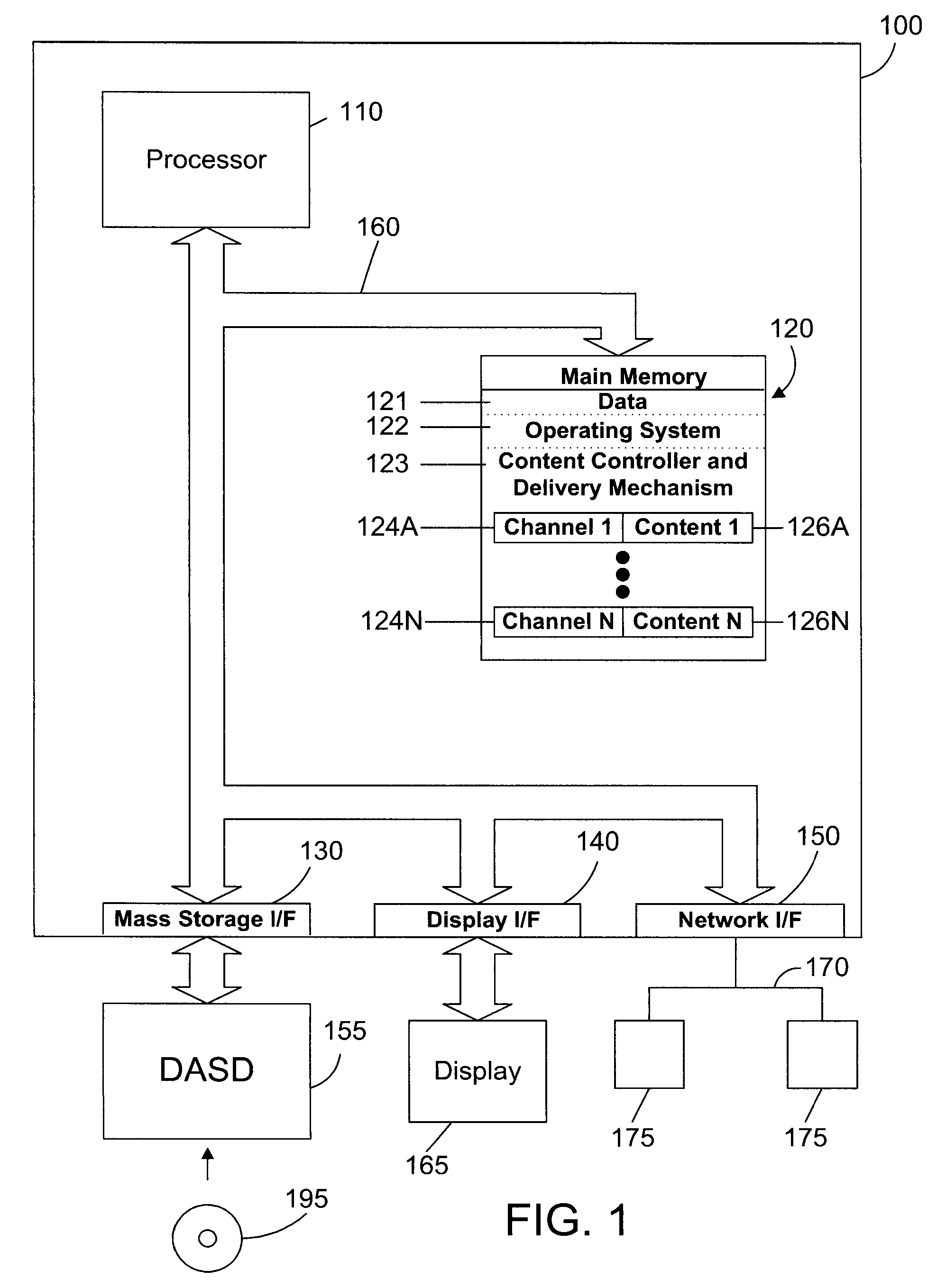
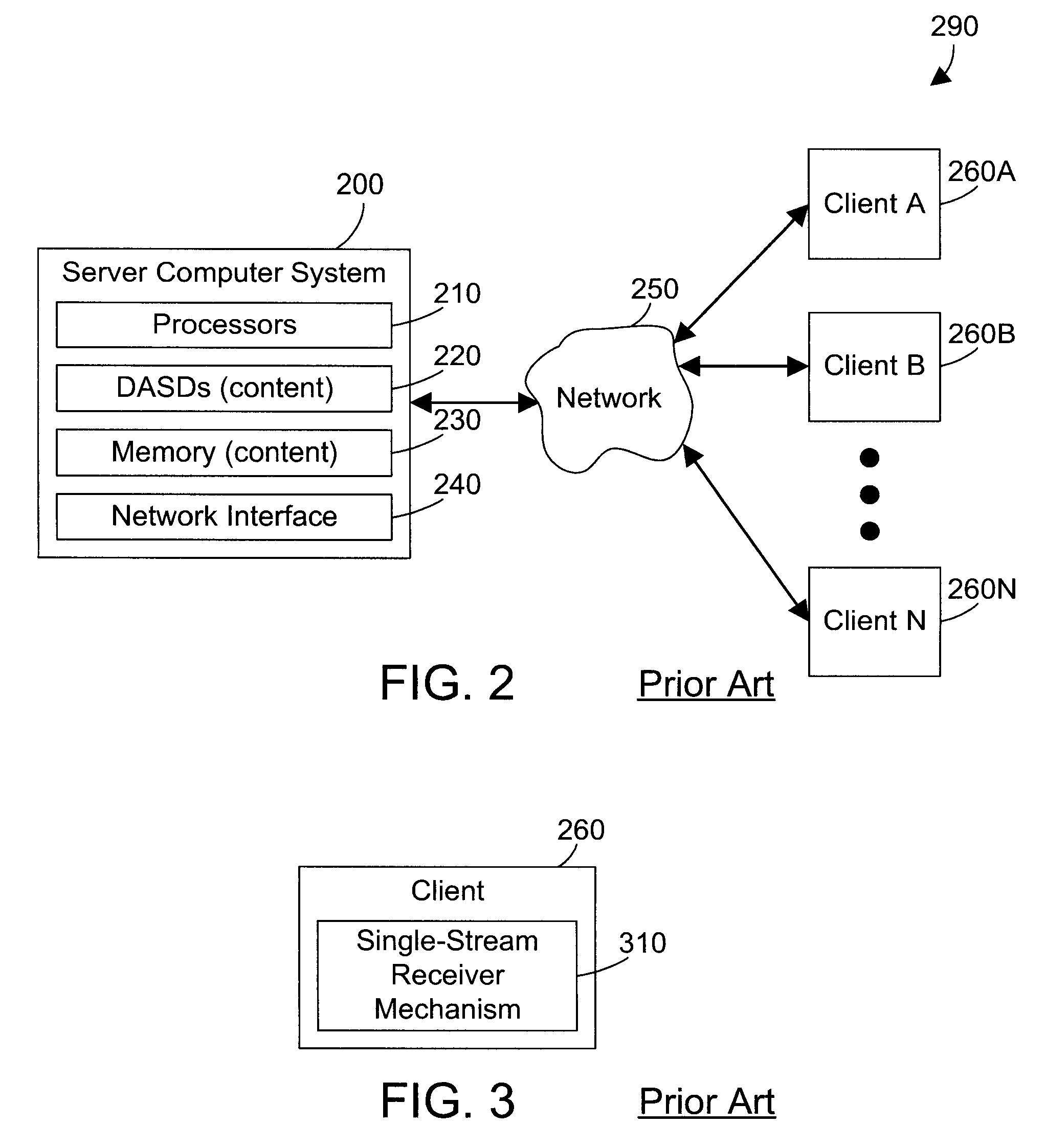
Apparatus and Method for Serving Digital Content Across Multiple Network Elements
InactiveUS20070260546A1Easy to scaleImprove abilitiesData processing applicationsComputer security arrangementsDigital contentClient-side
An apparatus and method use a scale out paradigm to spread digital content across multiple servers, which then deliver the content in parallel to a client. Spreading content over multiple servers allows easily expanding memory and I / O capabilities at a reasonable cost. The client includes a mechanism for receiving the content on multiple channels from multiple server computer systems, and for assembling the content into a single stream. The result is a system that may be easily scaled to provide digital content to an increasing number of users at a reasonable cost.
Owner:IBM CORP
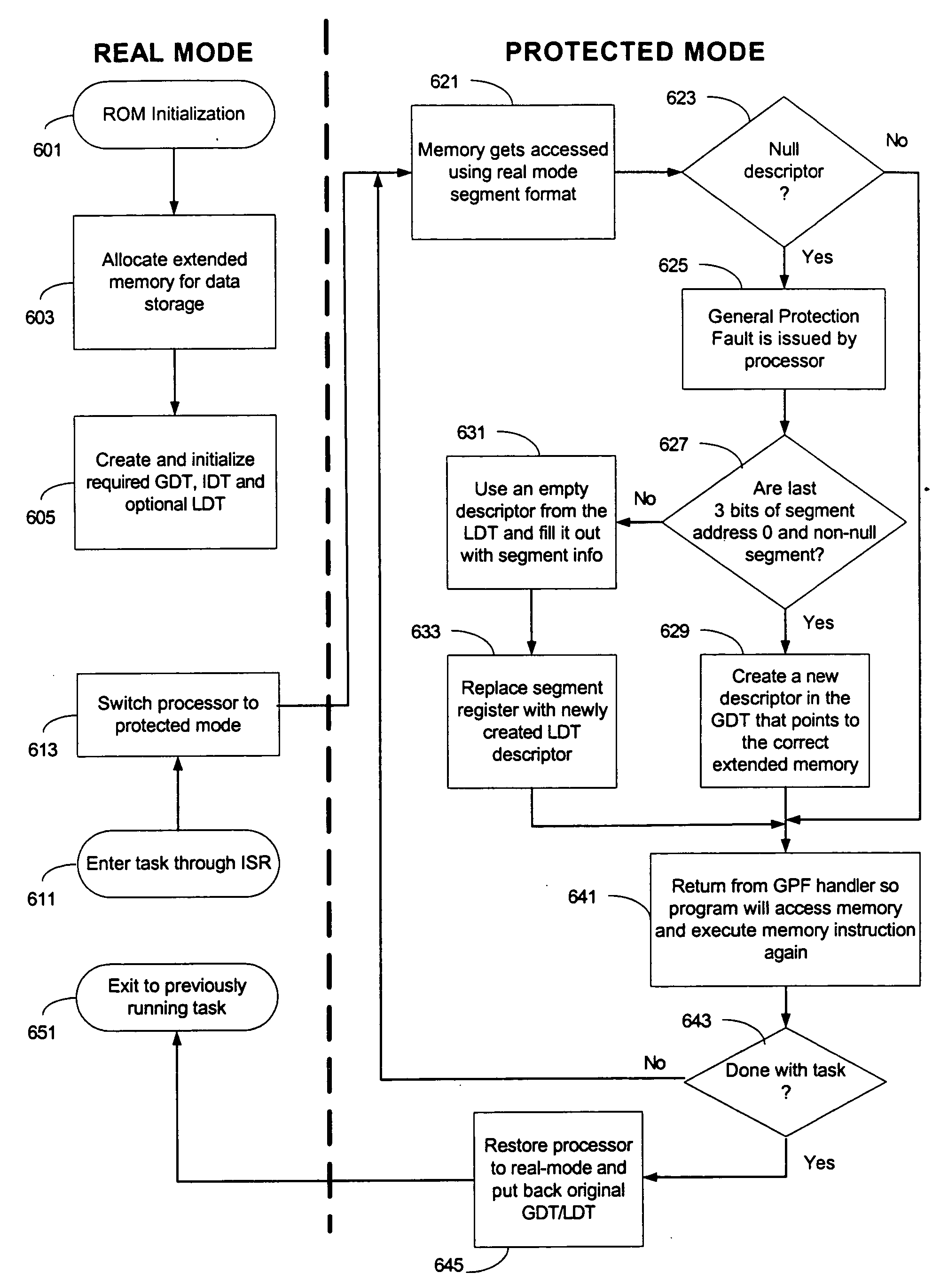
System and method for simulating real-mode memory access with access to extended memory
InactiveUS20060004982A1Memory adressing/allocation/relocationDigital computer detailsOption ROMParallel computing
In some embodiments, the invention involves a system and method relating to switching to protected mode to access extended memory while executing instruction code that is designed for real mode memory access. In at least one embodiment, the present invention is intended to enable complex option-ROM code to be executed during pre-boot without corrupting system memory used by the BIOS or other option-ROMs. Other embodiments are described and claimed.
Owner:INTEL CORP
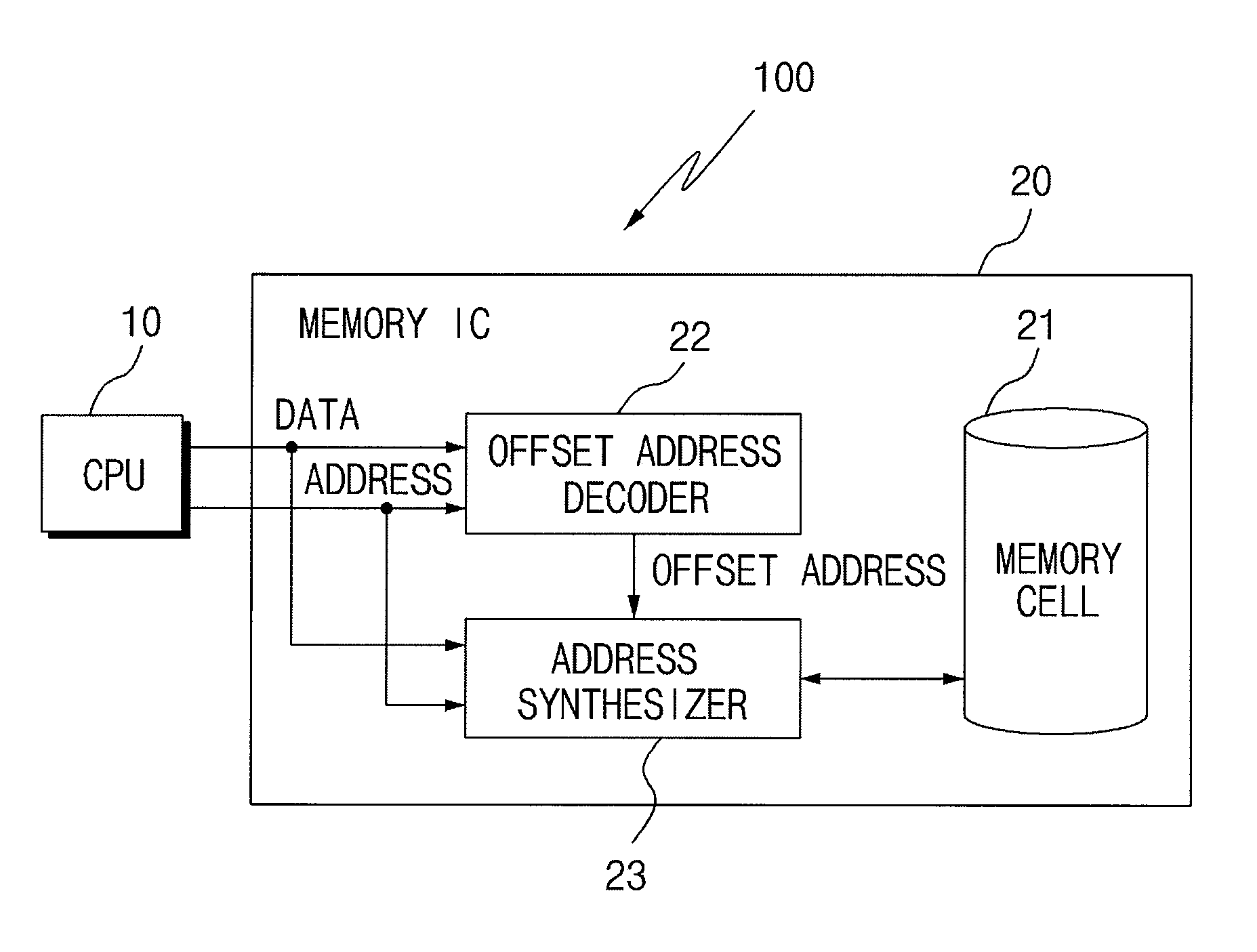
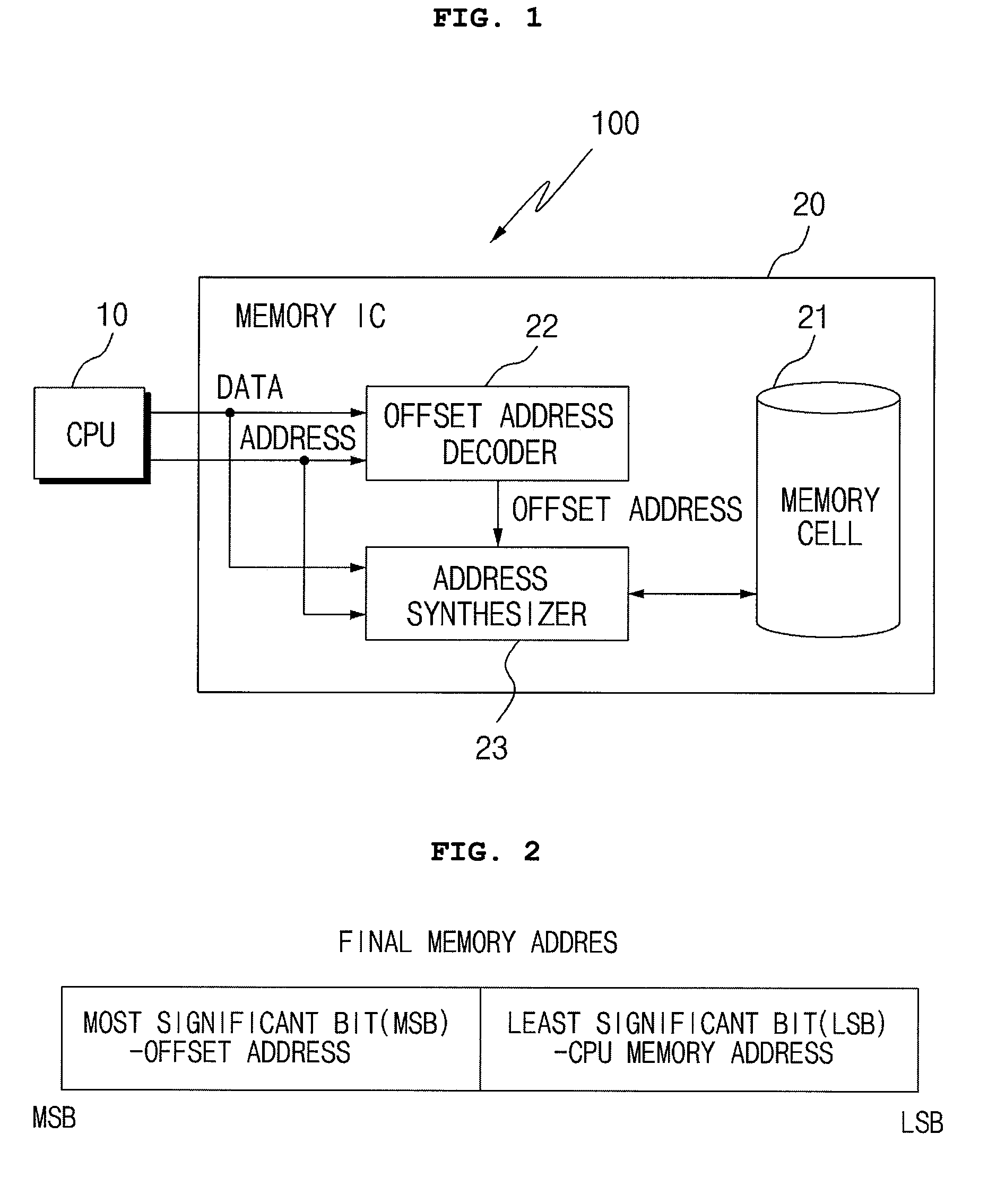
CPU and memory connection assembly to extend memory address space
InactiveUS20090327644A1Shorten the design cycleReduce design costMemory architecture accessing/allocationMemory systemsAddress decoderMemory address
Disclosed is a CPU and memory connection assembly to extend memory address space without extending address pins. The CPU and memory connection assembly extends entire accessible memory address of a CPU using a small number of address pins by synthesizing a final memory address by receiving an offset address setting command inputted from a CPU through an offset address decoder to generate an offset address and by receiving CPU max address bit setting command directly inputted from the CPU through an address synthesizer to combine the CPU max address bit setting command with the address directly inputted from the CPU.
Owner:SDCMICRO
Fully-mechanized circular knitting machine control system
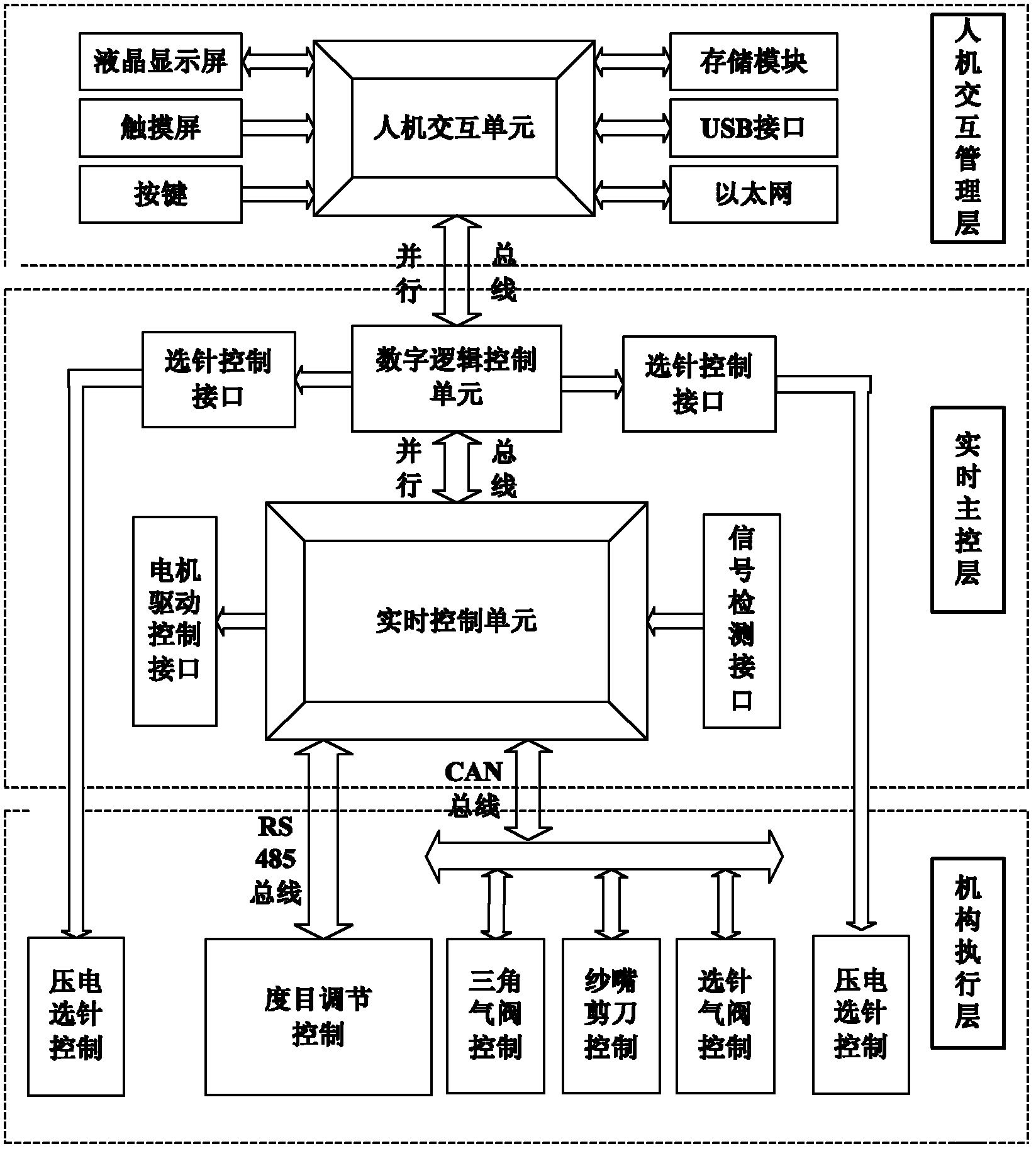
ActiveCN102634924AIncrease productivityImprove reliabilityWeft knittingEngineeringVolumetric Mass Density
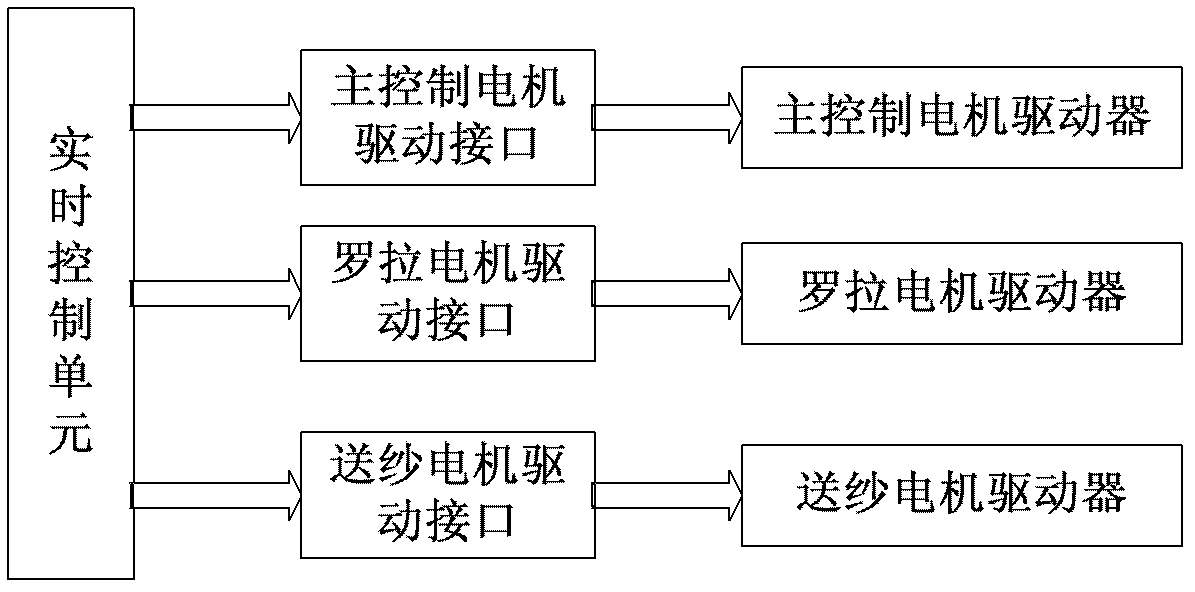
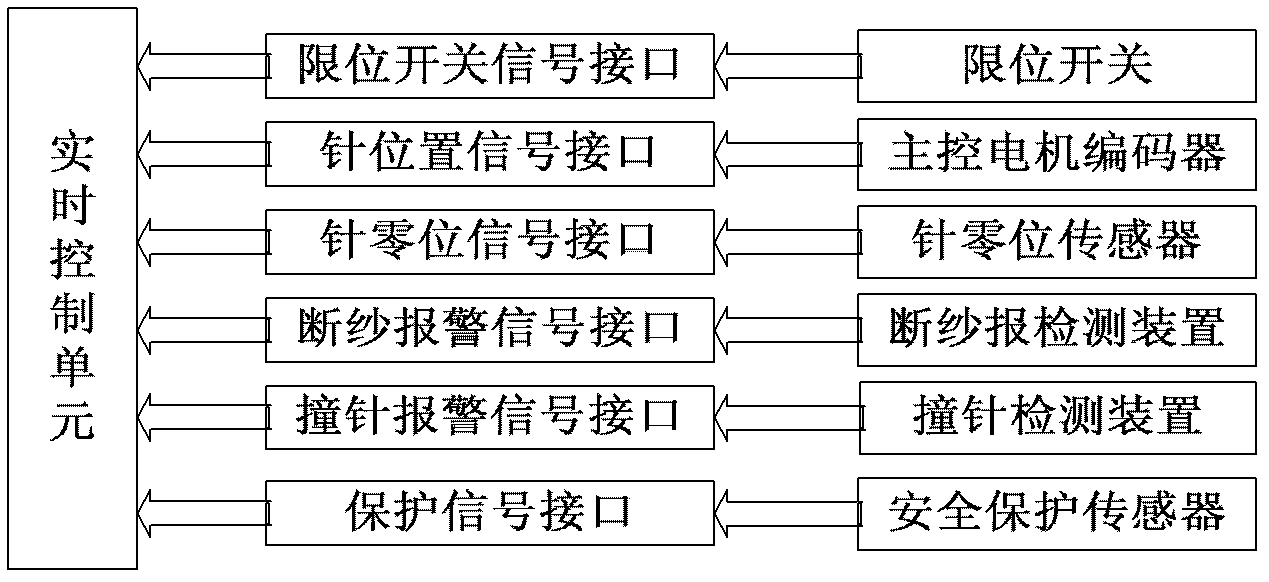
The invention discloses a fully-mechanized circular knitting machine control system which comprises a man-machine interaction unit, a real-time control unit and a mechanism executing unit, wherein the man-machine interaction unit is connected with the real-time control unit by adopting a parallel bus; the real-time control unit and the mechanism executing unit respectively realize data communication of density motor regulation control and control of various kinds of air valves by adopting a multi-path RS 485 bus and a multi-node CAN bus; the man-machine interaction unit is used for displaying state information of the fully-mechanized circular knitting machine control system, editing, storing and analyzing pattern files, editing system control parameters, and testing actions of all functional parts; the real-time control unit is used for reading process action information in a data conversion unit through the parallel bus, and storing the process action information in an external expanded memory of the real-time control unit; and the mechanism executing unit is used for controlling the action of a needle selector, density regulation action and actions of various kinds of air valves. The fully-mechanized circular knitting machine control system has the advantages of being large in pattern weaving range, being high in replacement speed, shortening the design period of products, being high in weaving speed, increasing the production efficiency and ensuring the reliability of system production.
Owner:ZHEJIANG SCI-TECH UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com