Patents
Literature
45results about How to "Avoid direct communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
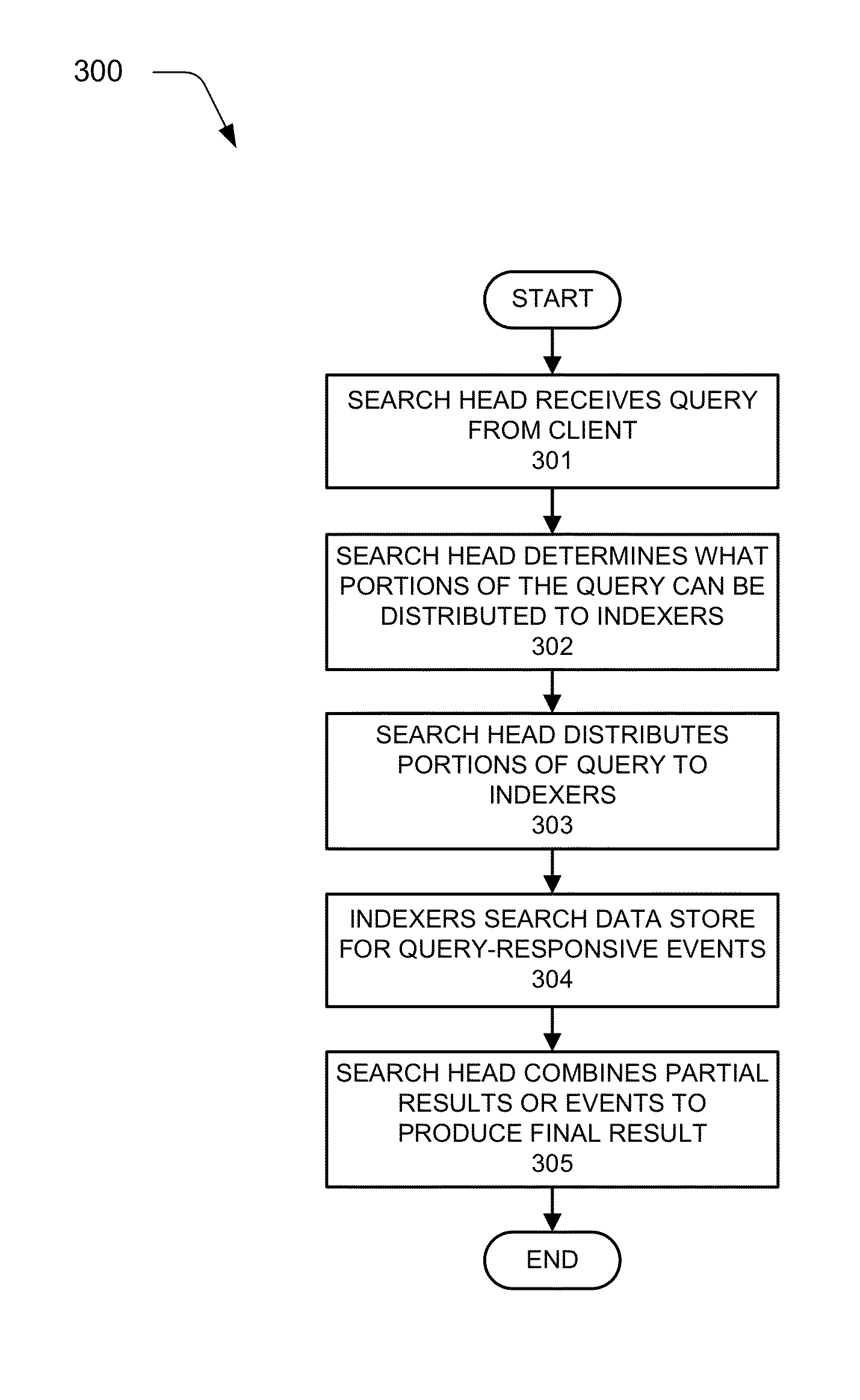
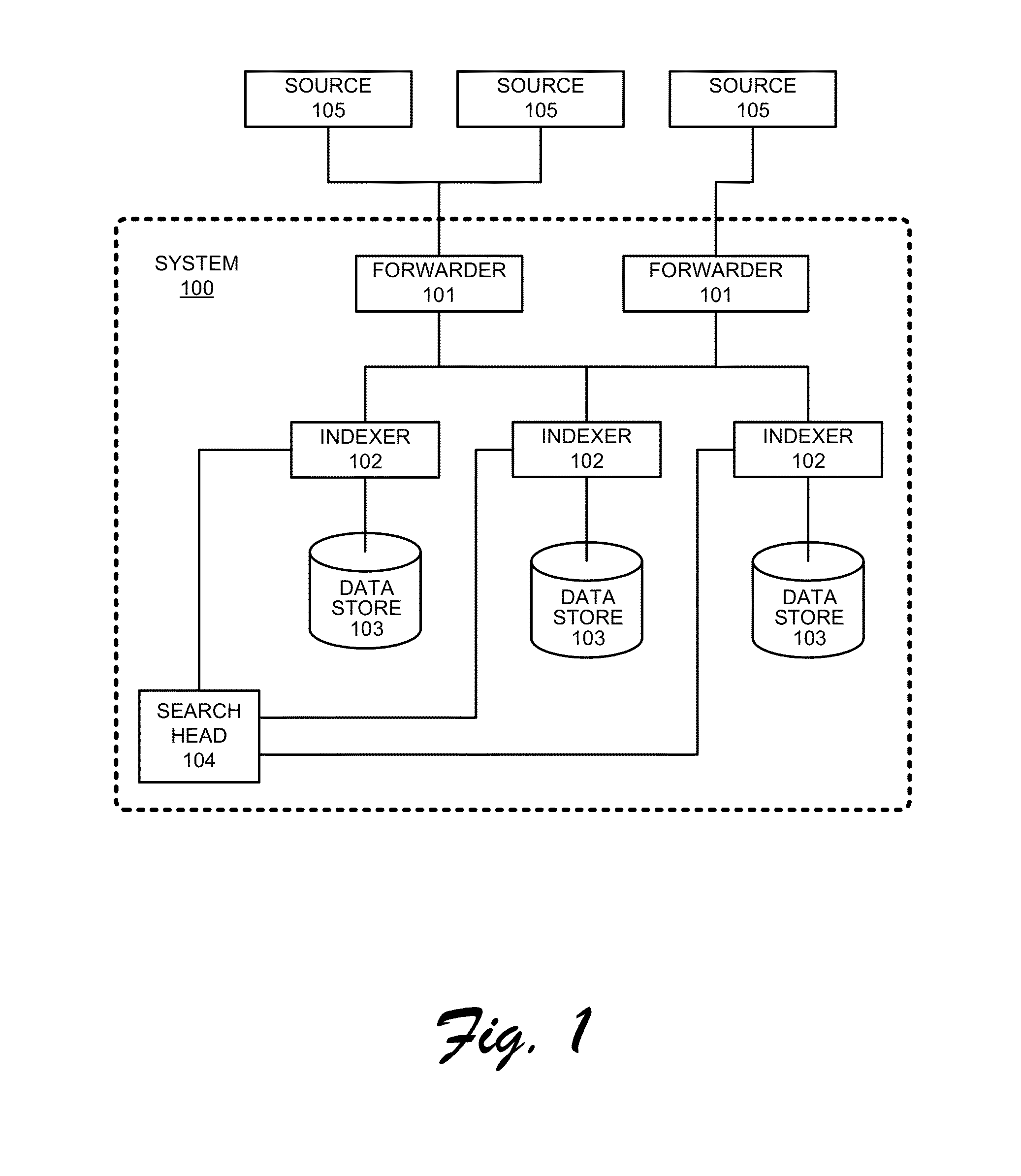
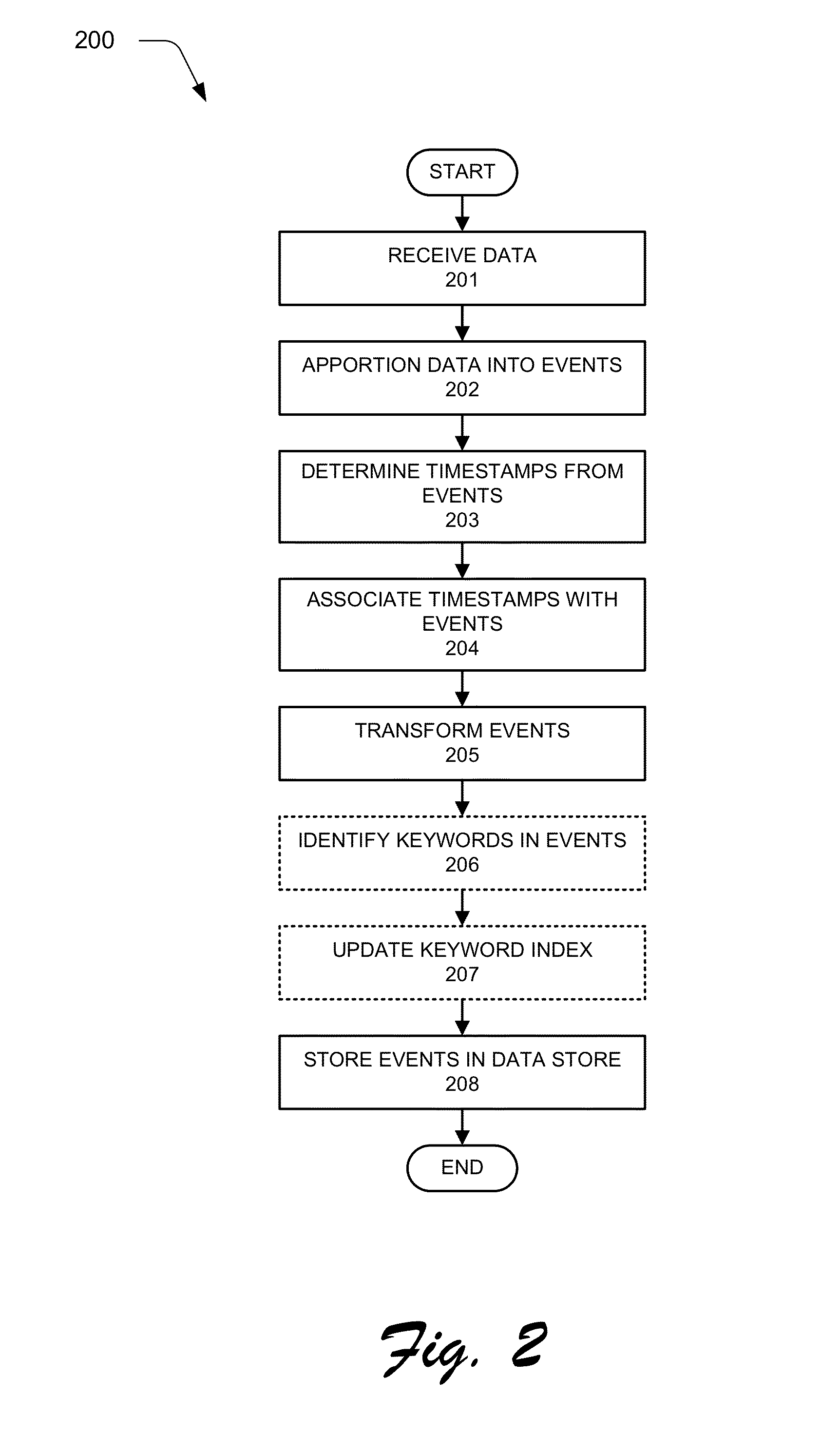
Sharing Configuration Information for Searches in Data Intake and Query Systems
ActiveUS20160092570A1Improve scalabilityEfficient leveragingWeb data indexingDigital data processing detailsMulti siteData acquisition
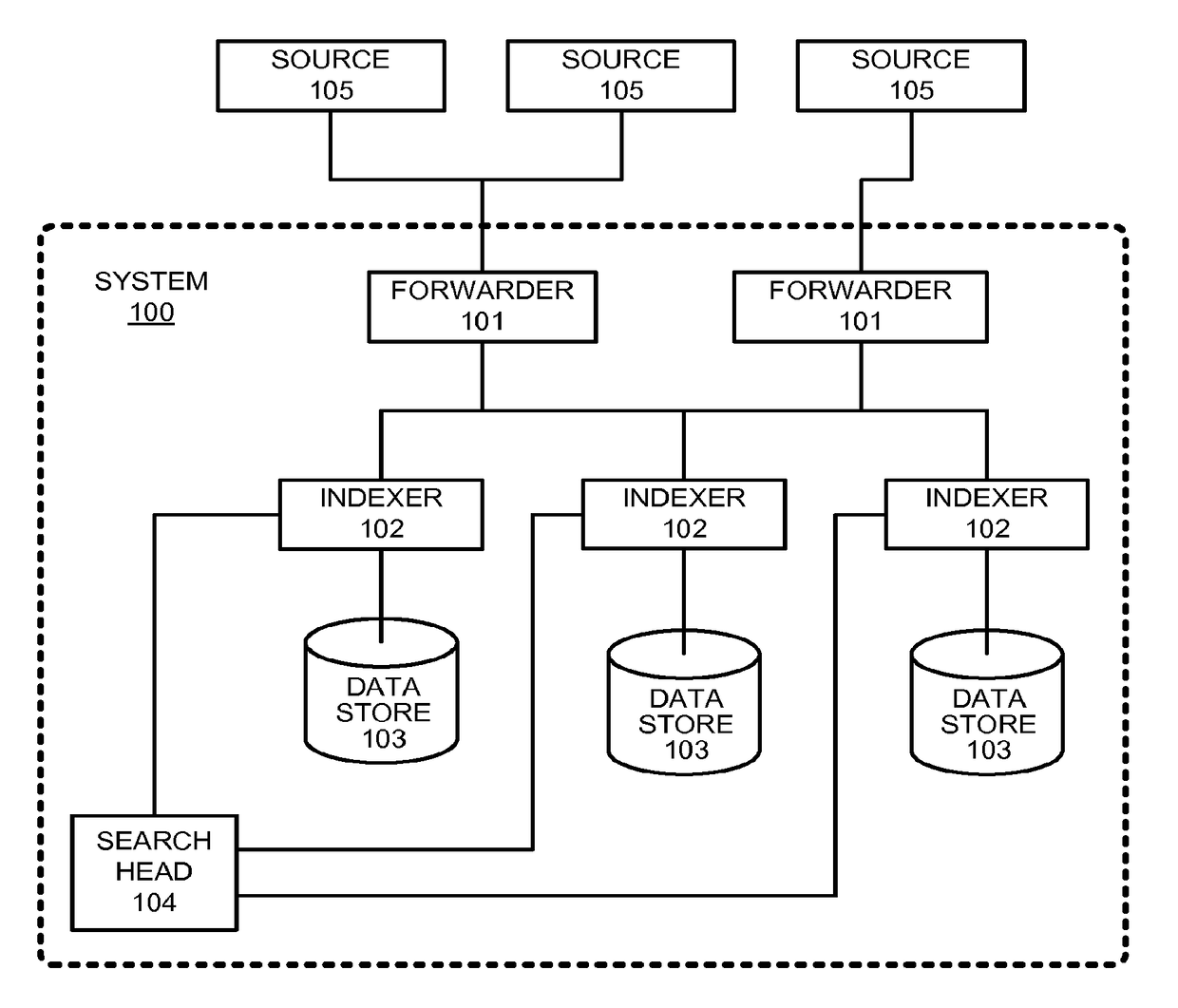
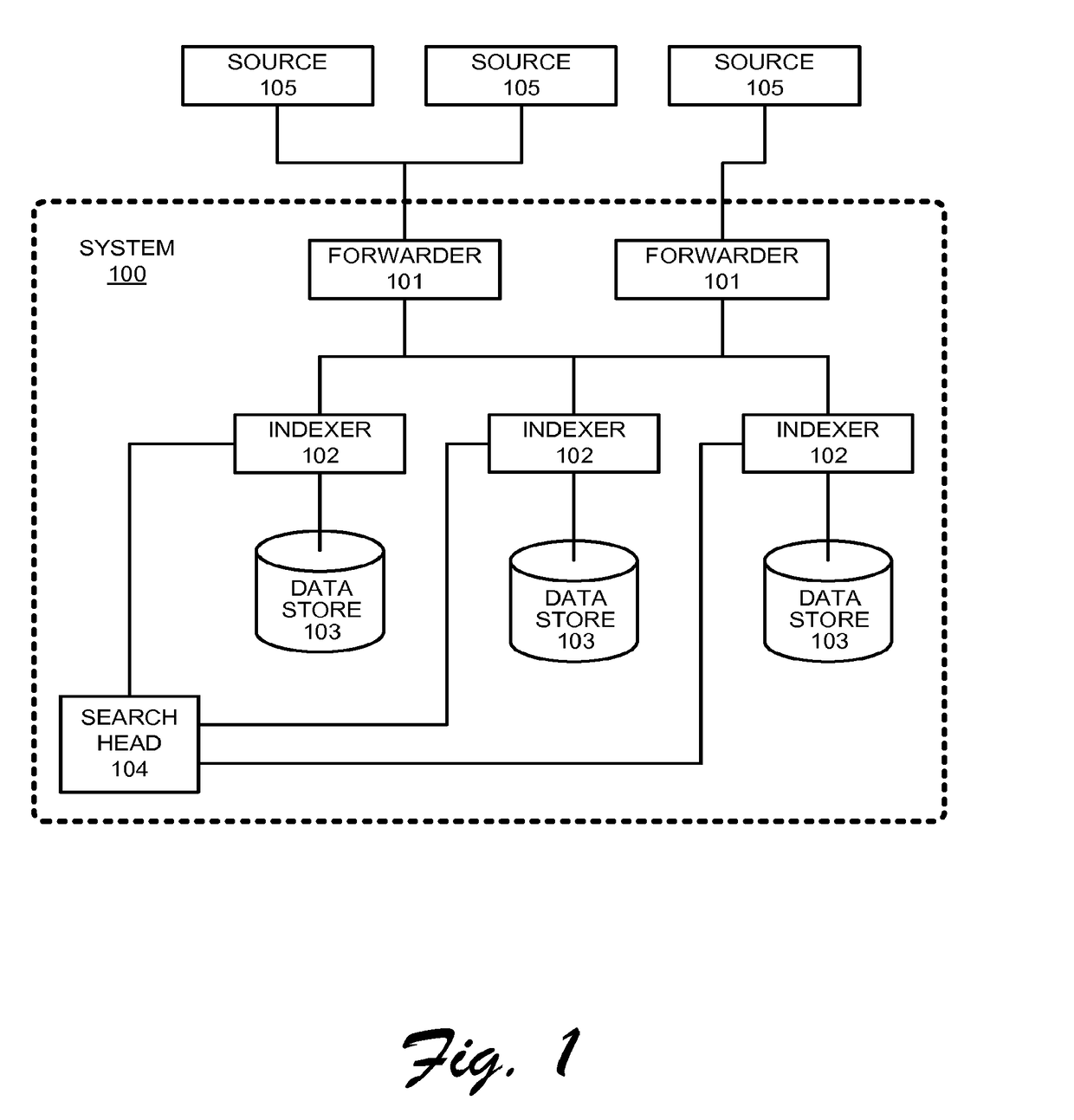
Various embodiments describe multi-site cluster-based data intake and query systems, including cloud-based data intake and query systems. Using a hybrid search system that includes cloud-based data intake and query systems working in concert with so-called “on-premises” data intake and query systems can promote the scalability of search functionality. In addition, the hybrid search system can enable data isolation in a manner in which sensitive data is maintained “on premises” and information or data that is not sensitive can be moved to the cloud-based system. Further, the cloud-based system can enable efficient leveraging of data that may already exist in the cloud.
Owner:SPLUNK INC
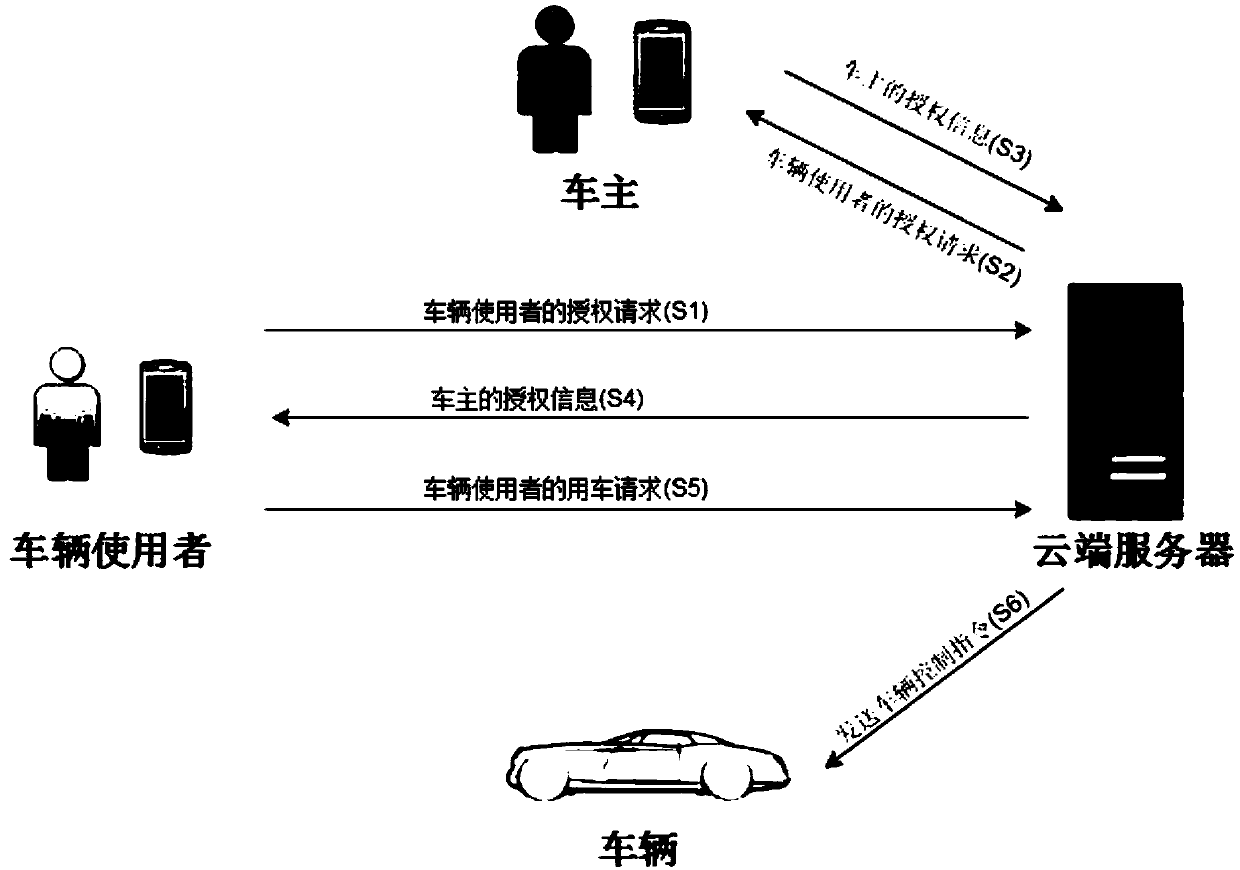
Vehicle sharing method and system
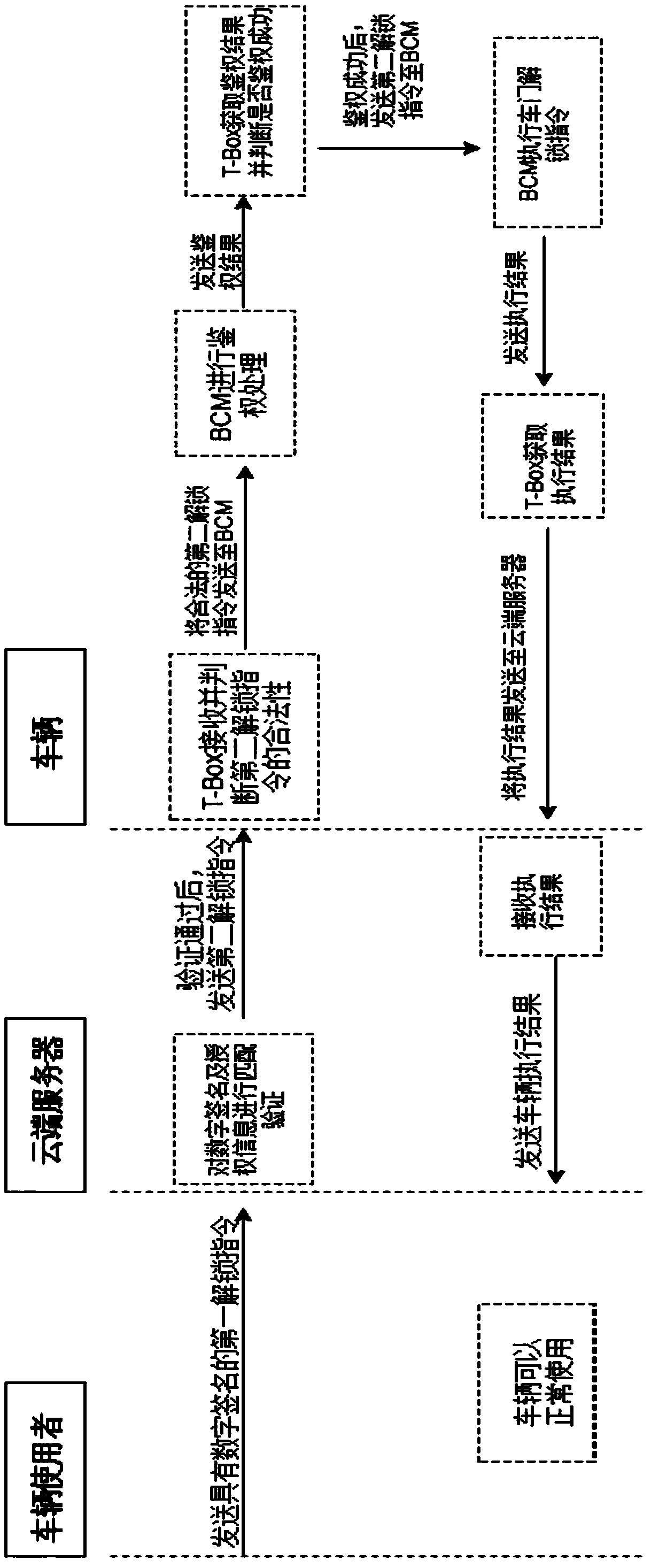
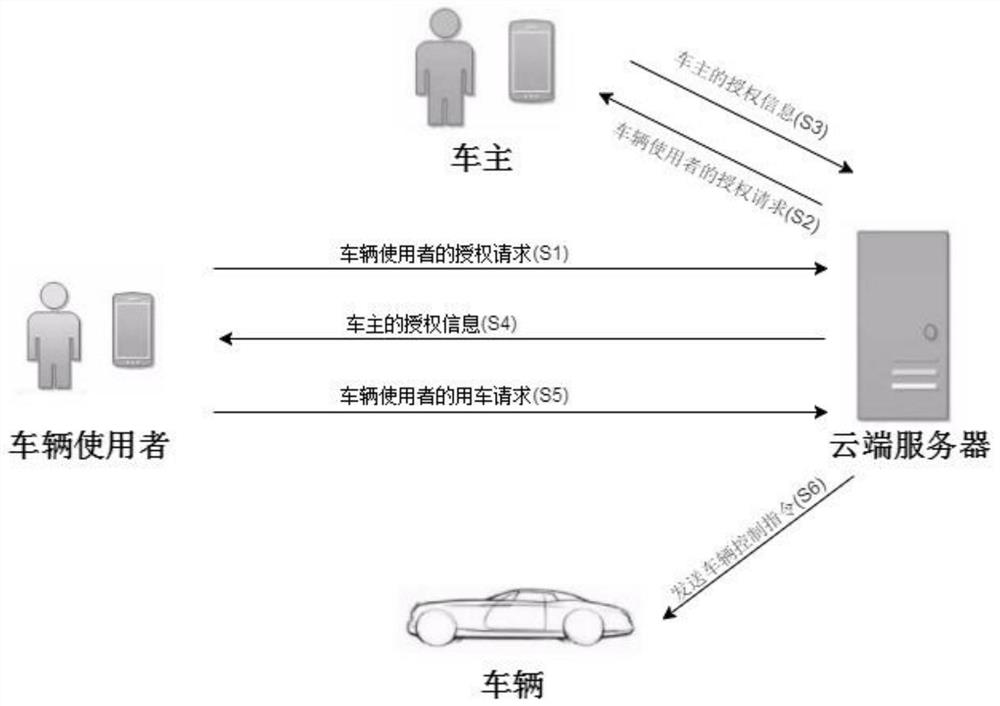
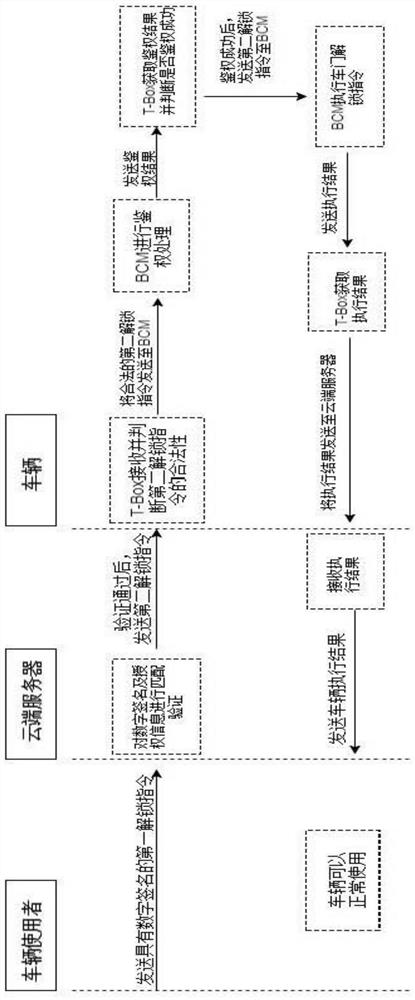
ActiveCN107650863AAvoid direct communicationImprove securityAnti-theft devicesIndividual entry/exit registersAuthorizationComputer science
The invention relates to a vehicle sharing method and system, and discloses a vehicle sharing method. The vehicle sharing method includes the steps of a permission request, specifically, the permission request includes a vehicle using authorization request and authorization information, wherein the vehicle using authorization request responds to and is sent by a vehicle user terminal, and a cloudserver transfers the authorization request to an owner terminal and receives the authorization information sent by the owner terminal; and a vehicle using request, specifically, the vehicle using request includes a first vehicle control instruction, wherein the first vehicle control instruction responds to and is sent by the vehicle user terminal, the cloud server is combined with the authorization information to carry out matching verifying on the identity of a vehicle user and the first vehicle control instruction, and after verification is passed, a second vehicle control instruction corresponding to the first vehicle control instruction is sent to a corresponding vehicle to enable the vehicle to carry out the second vehicle control instruction. By means of the vehicle sharing method and the system, the vehicle can be controlled without carrying a key, meanwhile, the risk that a transmission signal is intercepted at the close distance is avoided, and the vehicle using safety and user experience are improved.
Owner:CONTINENTAL HOLDING CHINA CO LTD
Cross-chain communication method and device, main chain node and storage medium
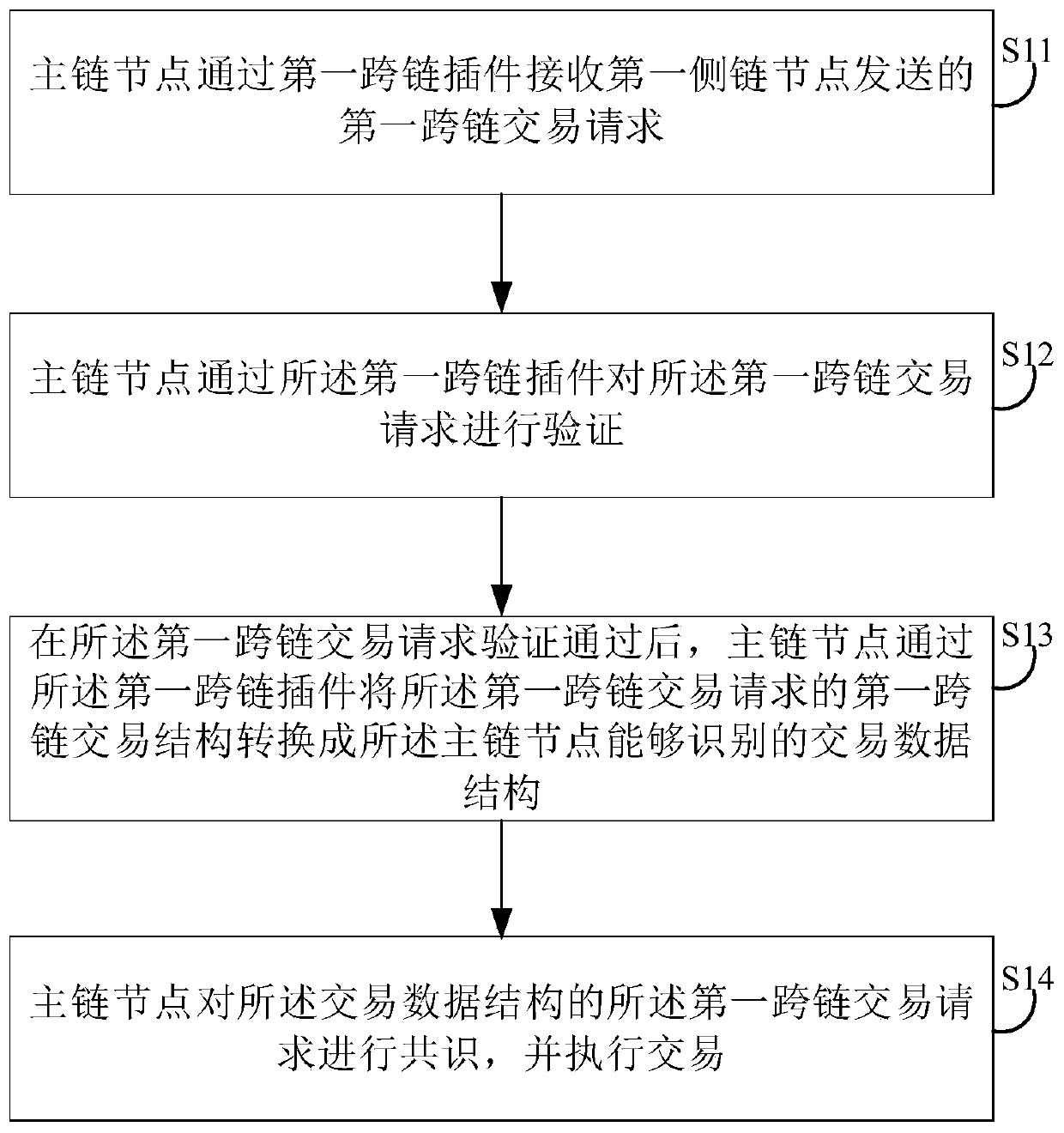
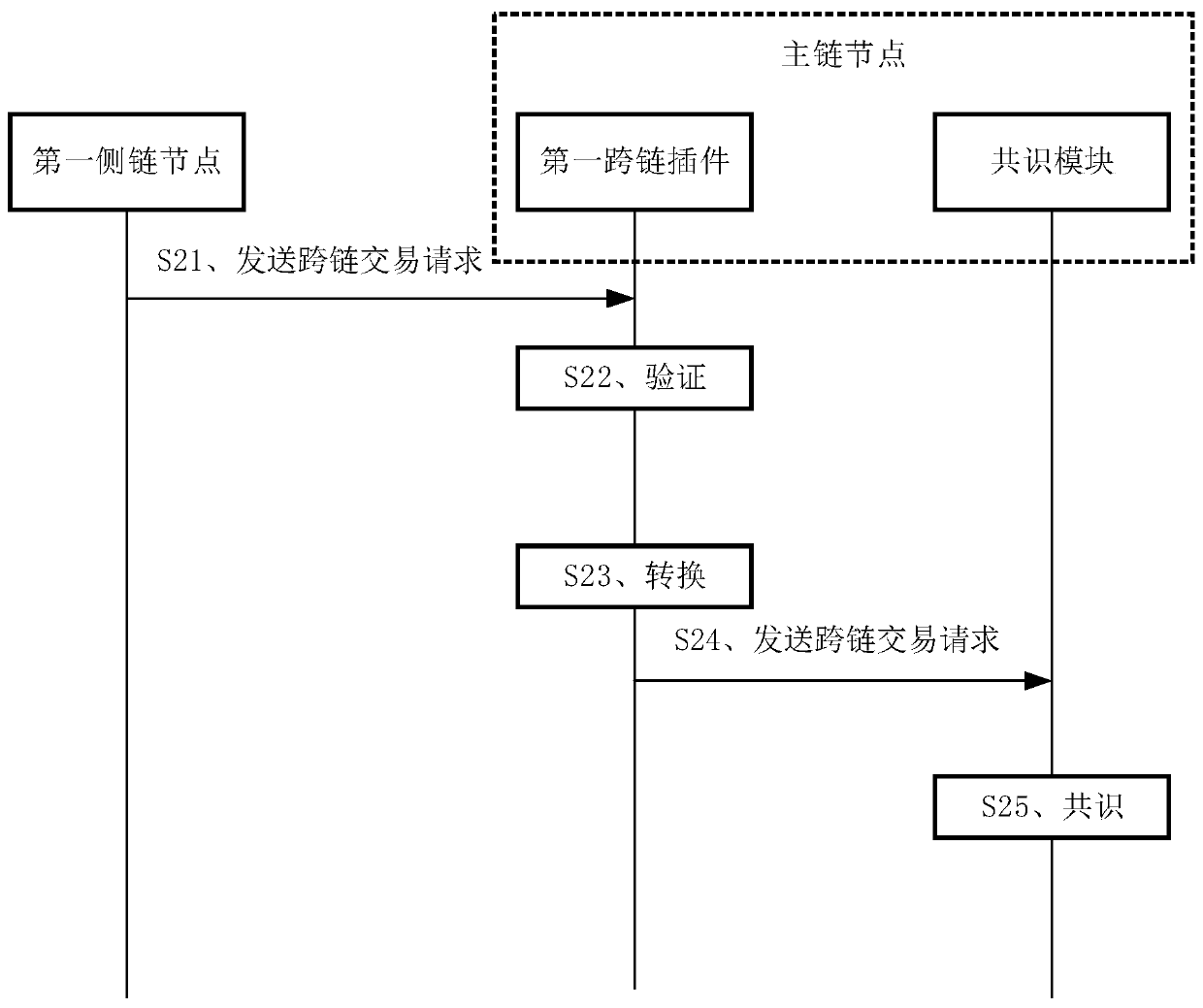
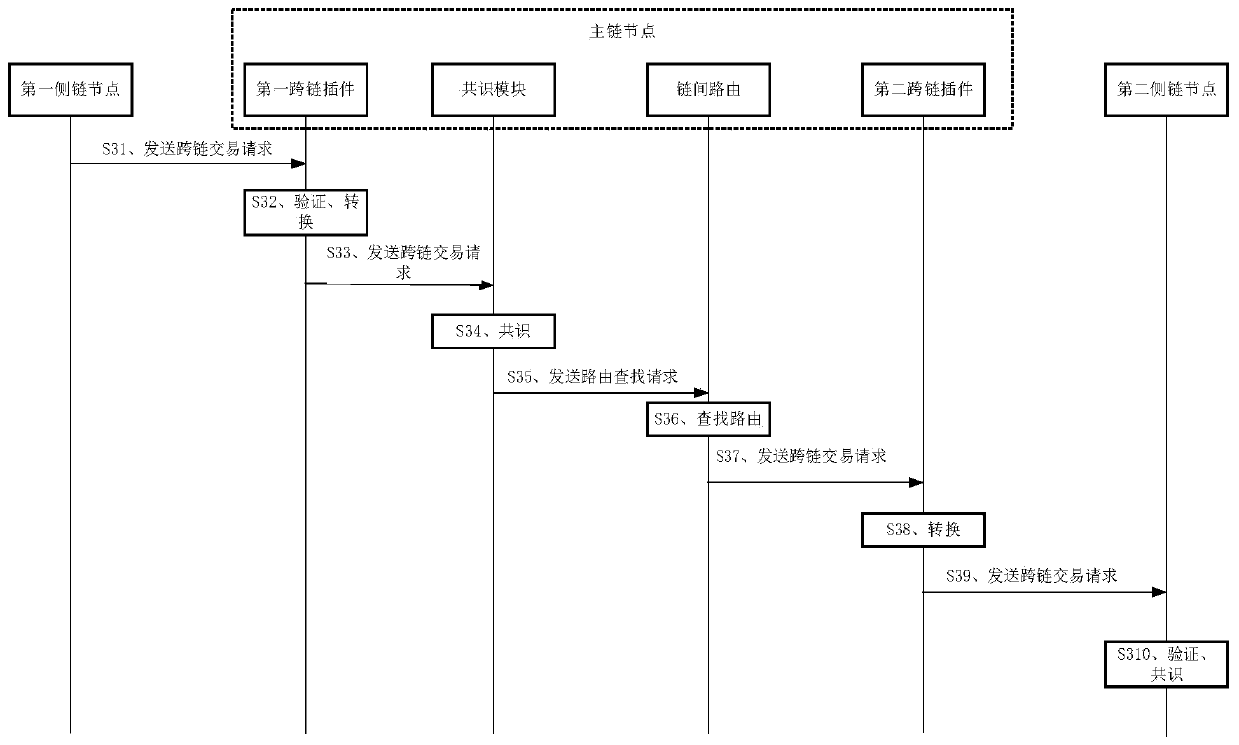
A cross-chain communication method which is applied to a main chain node, at least one cross-chain plug-in is deployed on the main chain node, each cross-chain plug-in corresponds to one side chain node, and the method comprises the steps of receiving a first cross-chain transaction request sent by a first side chain node is received through the first cross-chain plug-in; verifying the first cross-chain transaction request through the first cross-chain plug-in; after the first cross-chain transaction request passes the verification, converting a first cross-chain transaction structure of the first cross-chain transaction request into a transaction data structure which can be identified by the main chain node through the first cross-chain plug-in; and performing consensus on the first cross-chain transaction request of the transaction data structure, and executing a transaction. The invention also provides a cross-chain communication device, a main chain node and a storage medium. According to the invention, cross-chain communication between two heterogeneous block chains can be realized, meanwhile, the implementation cost is saved, and the cross-chain communication performance is improved.
Owner:SHENZHEN THUNDER NETWORK TECH +1
System and method for managing network communications
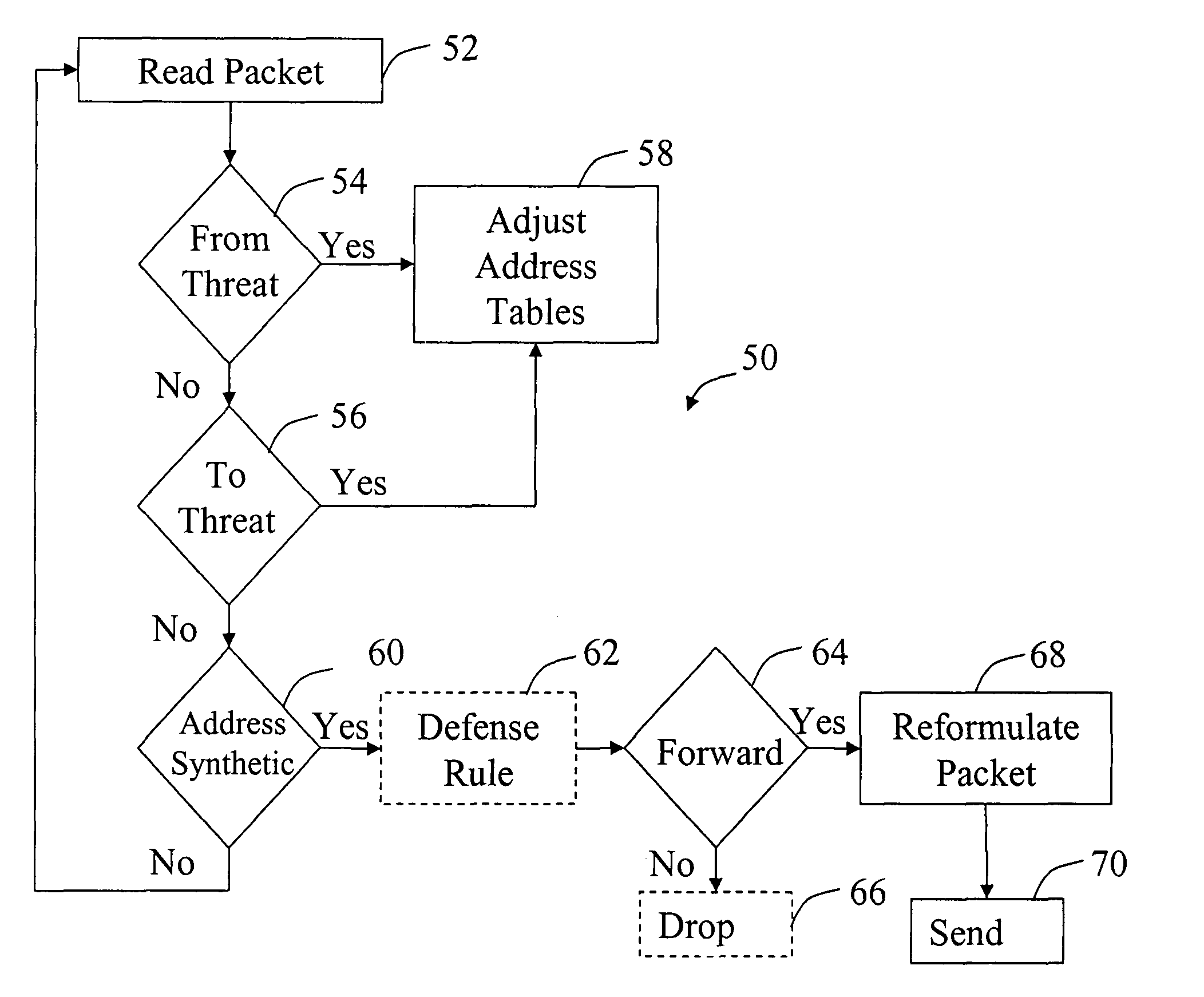
ActiveUS8819285B1Avoid direct communicationEffectively existenceMemory loss protectionError detection/correctionAddress resolutionControl manner
The invention relates to managing network communications packets on a local segment of a network. If an attack on the network segment is detected, the system creates one or more synthetic hardware addresses for substitution with existing hardware address. If this substitution is maintained in address resolution tables, packets sent to or from an attacker may be monitored, managed, dropped, or responded to in a controlled manner while preventing communication with sensitive devices on the local network segment. If a permissible packet is sent to the synthetic hardware address, the packet may be reformulated by a server, workstation, smart router, or security device, among others and sent with the appropriate hardware address. The synthetic hardware address may be a hardware address not associated with a device on the local network segment. For example, the synthetic hardware address may be synthetic MAC address.
Owner:SYSXNET
Restoration mechanism for network topologies
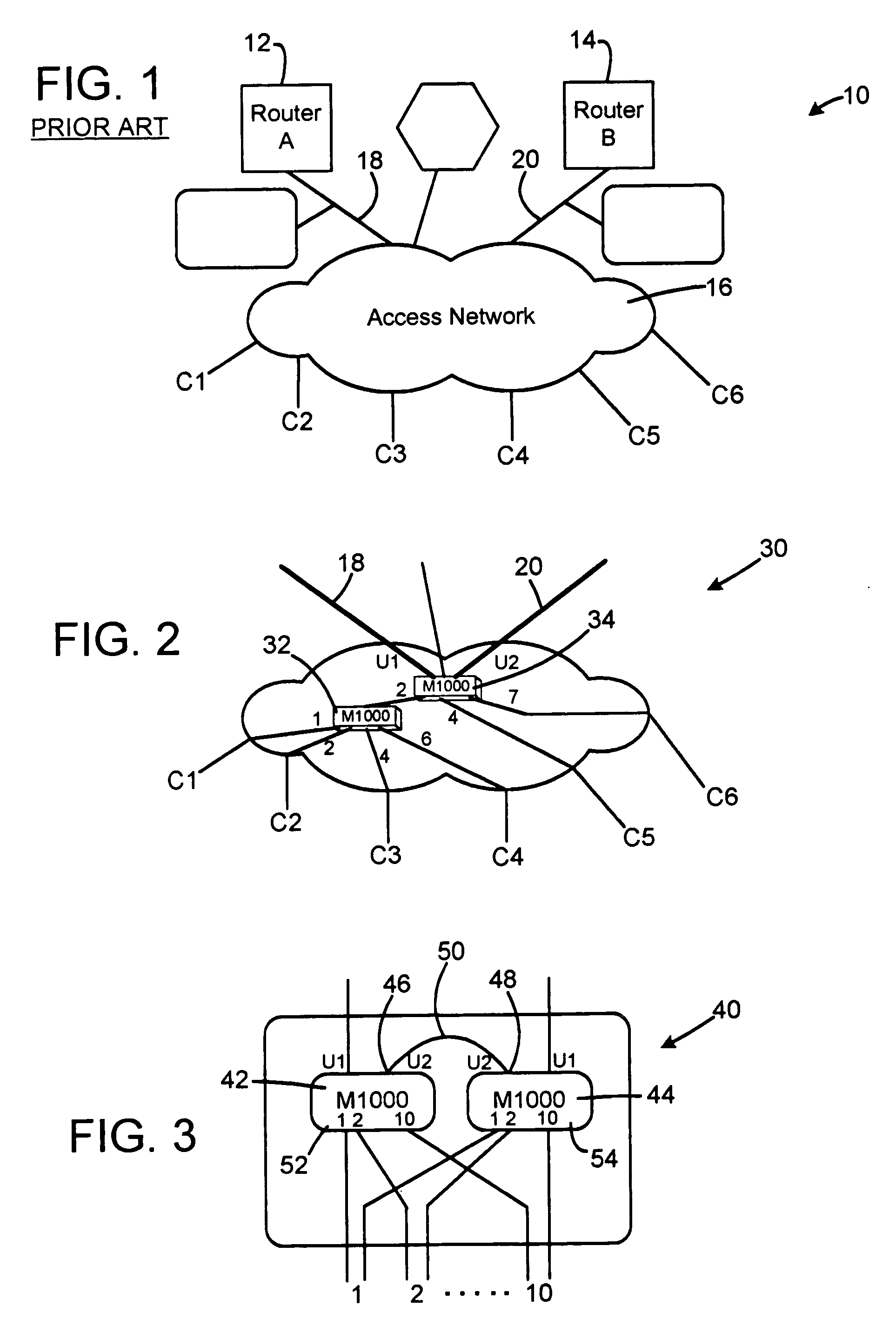
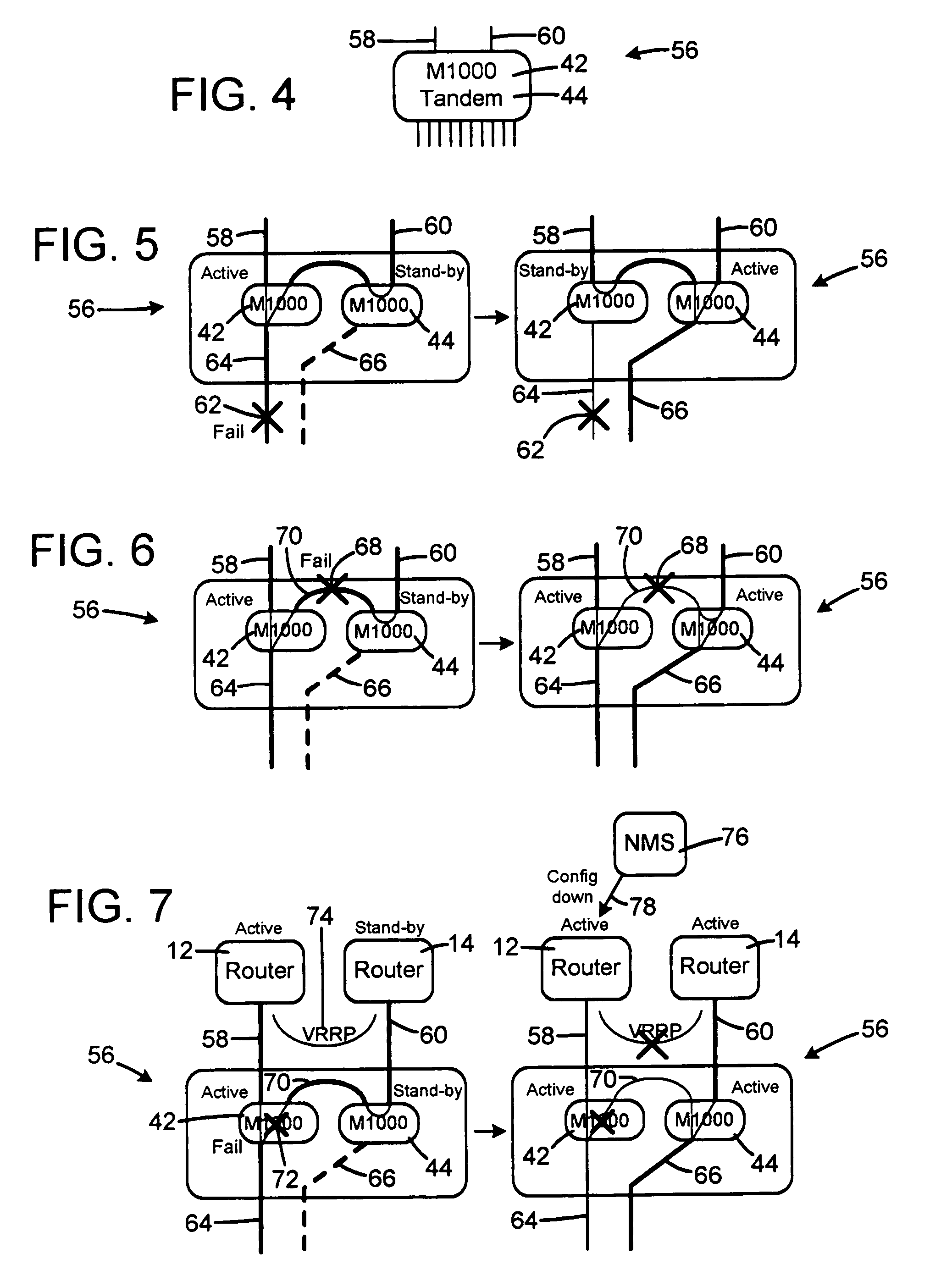
InactiveUS20050240797A1Avoid direct communicationMultiple digital computer combinationsTransmissionNetwork linkActive state
A method of restoring a failure in a network topology. A first node is provided that has a first access link connected to a first port group of a first customer and a first network link connected to a first active router. A second node has a first access link connected to the first port group of the first customer and a first network link connected to a second stand-by router. The first node has a second network link connected to the second node via a second network link of the second node. If the first access link of the first node or the first node itself fails, the second node switches to the active state. If the second network link of the first node fails, the second node switches to the active state. In this way the traffic will be forward to the first router and / or the second router.
Owner:METRO PACKET SYST
Authentication of remote host via closed ports
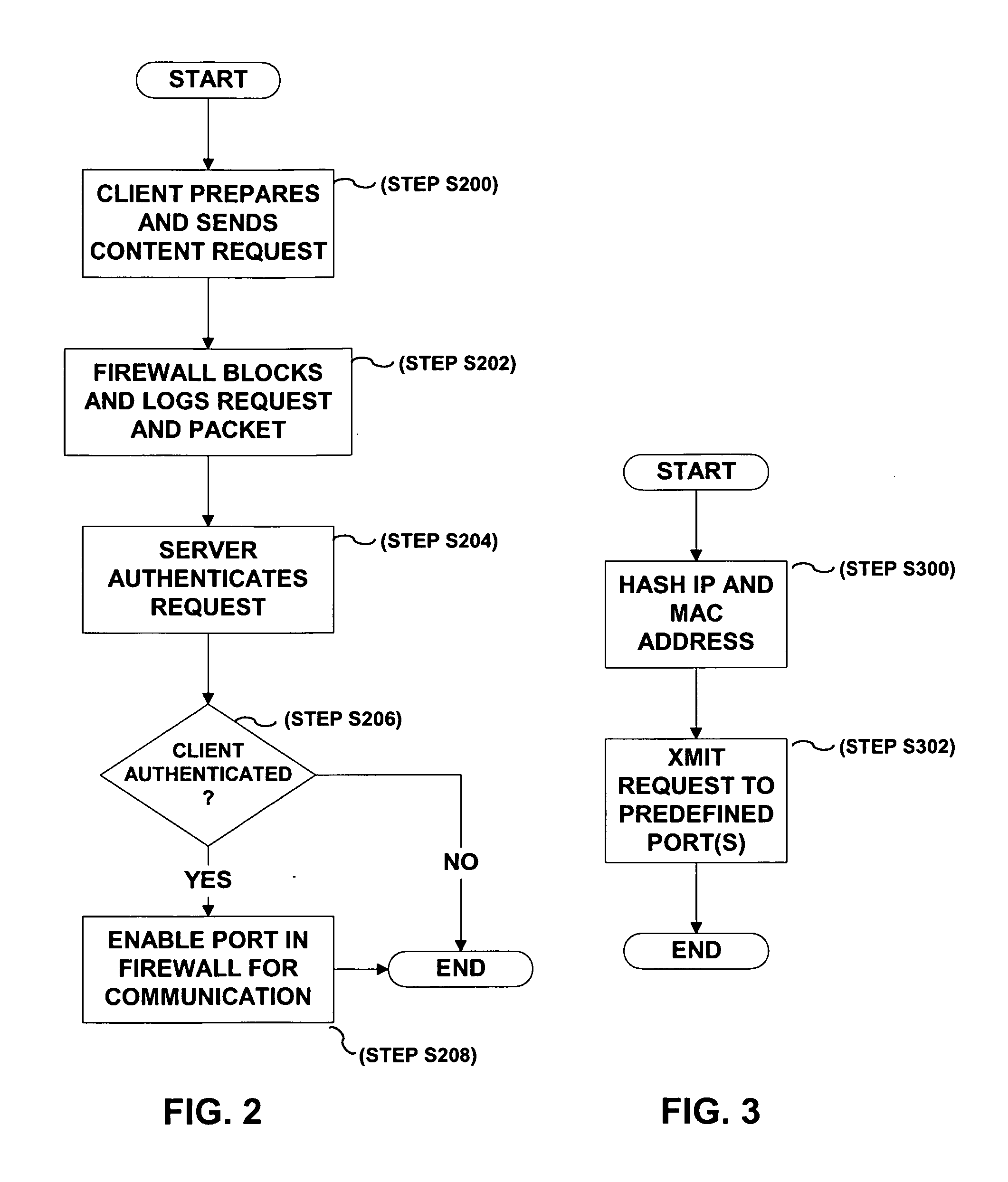
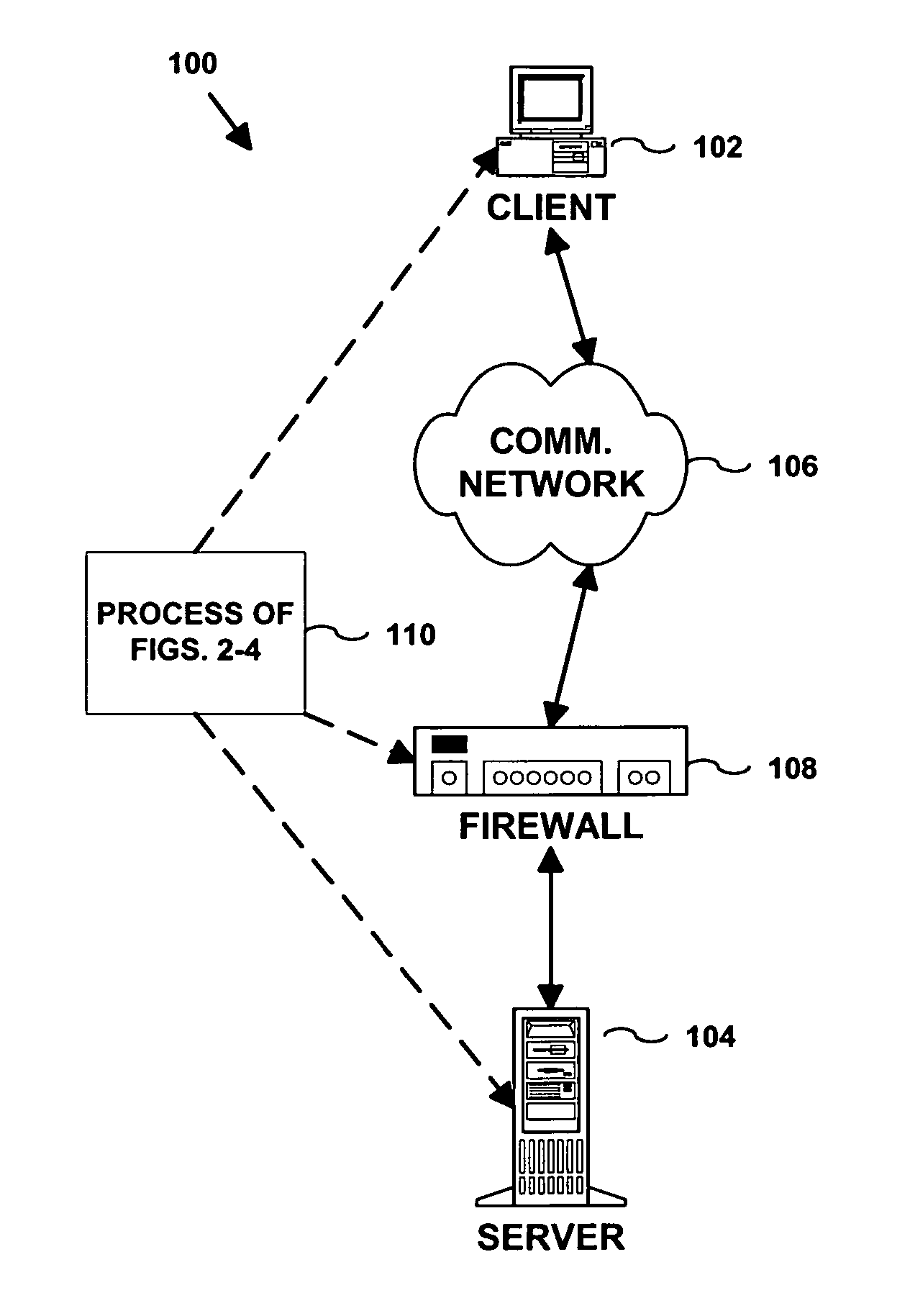
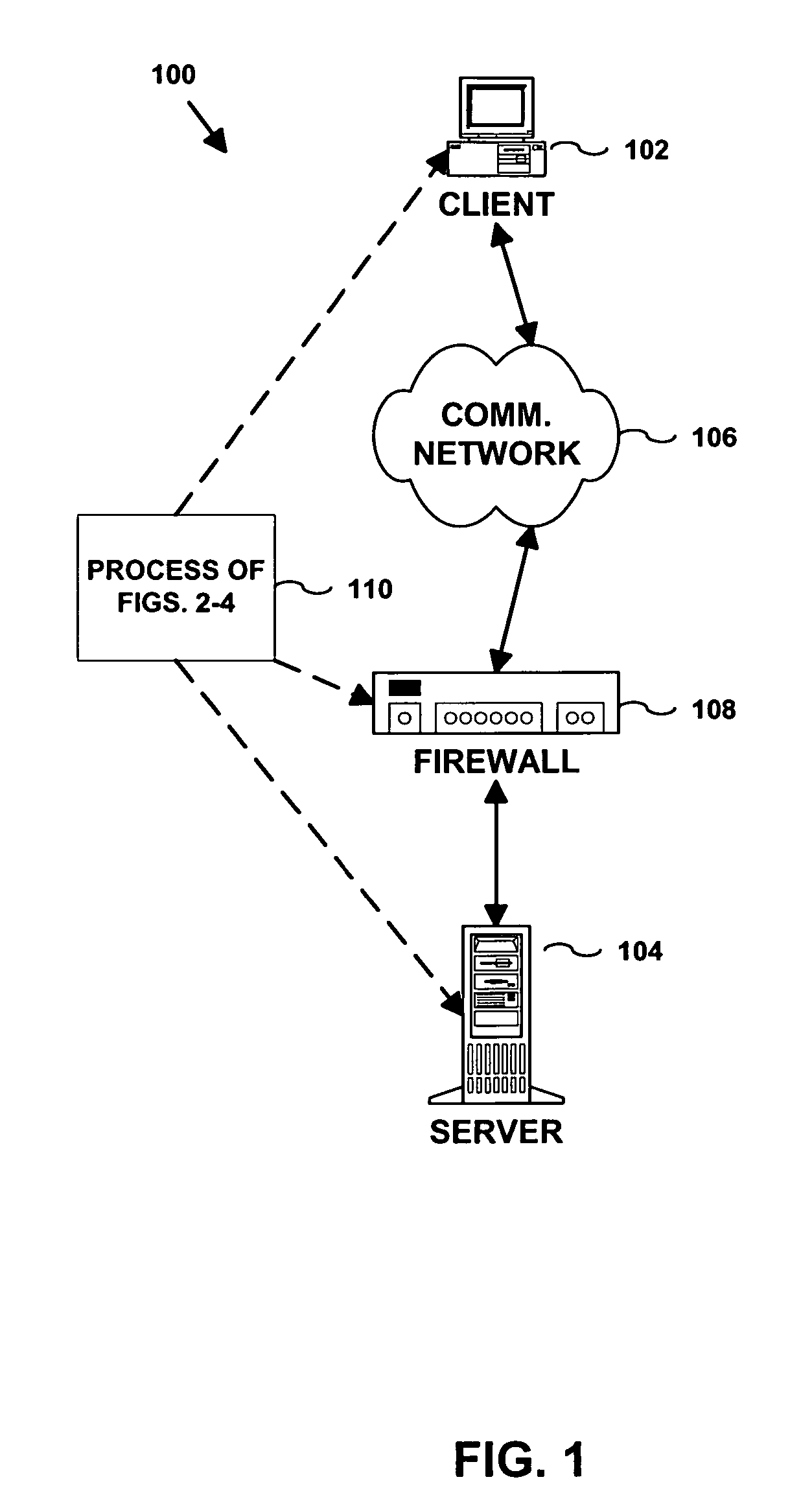
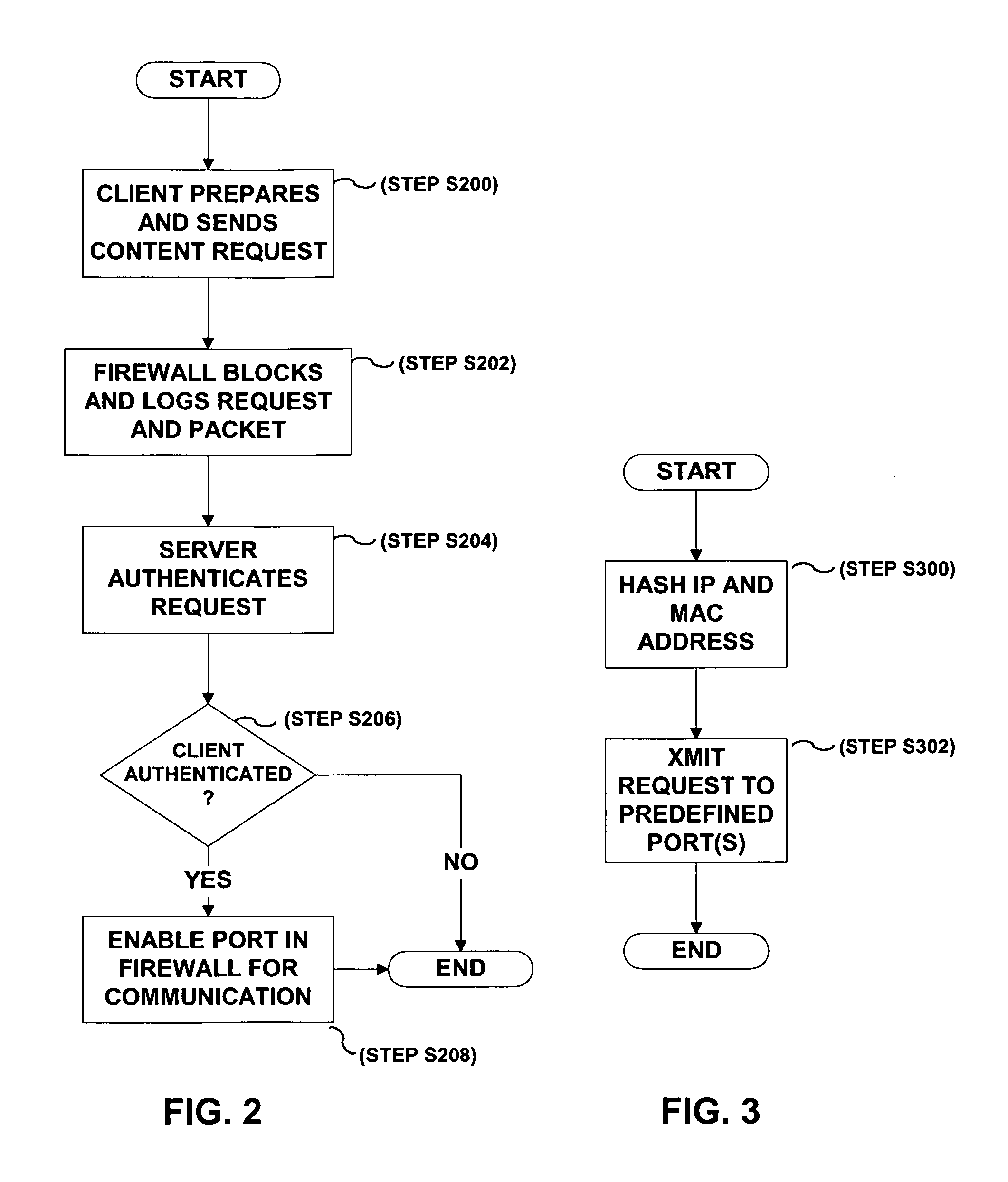
InactiveUS20060168654A1Avoid direct communicationKey distribution for secure communicationUser identity/authority verificationClient-sideAuthentication
A method, system and apparatus for authenticating a communication request sent from a client computing device. The communication request is initially blocked by a firewall preventing delivery to a server. A first logging event corresponding to the communication request is created. The communication request and the logging event are stored in a firewall. The server is notified of the first logging event. The communication request corresponding to the first logging event is authenticated. A port in the firewall is enabled if the communication request is authenticated.
Owner:LENOVO GLOBAL TECH INT LTD
Multi-device batch firmware upgrading method for mesh network device
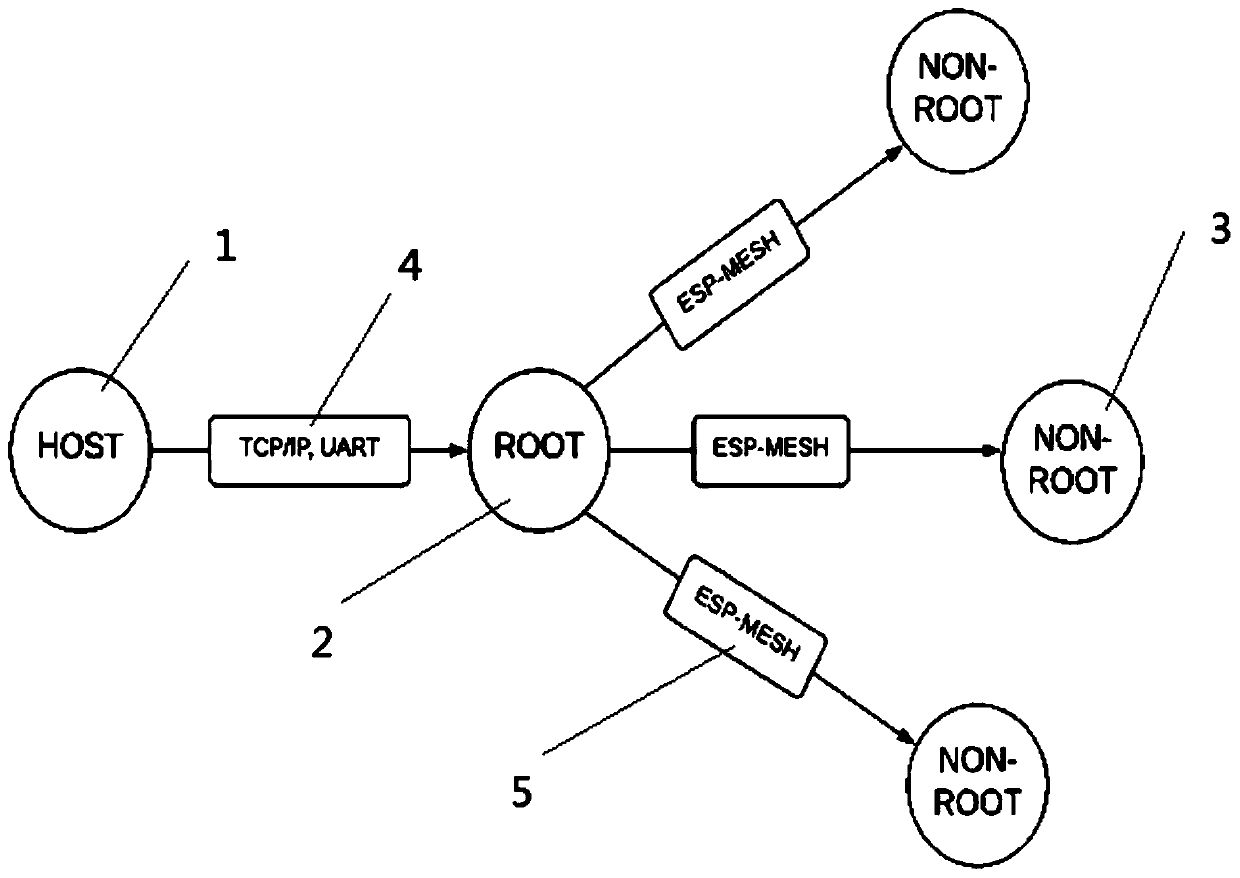
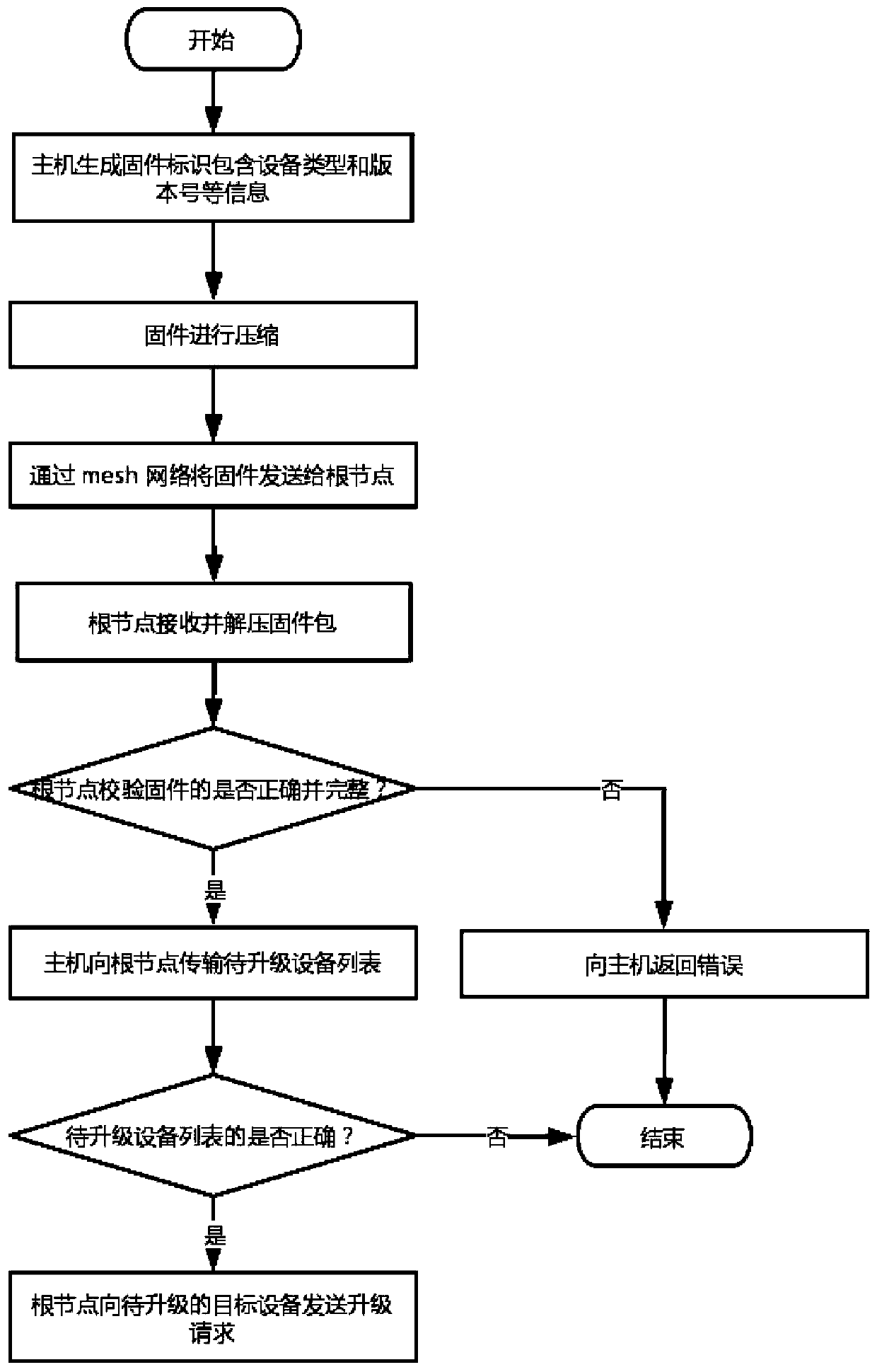
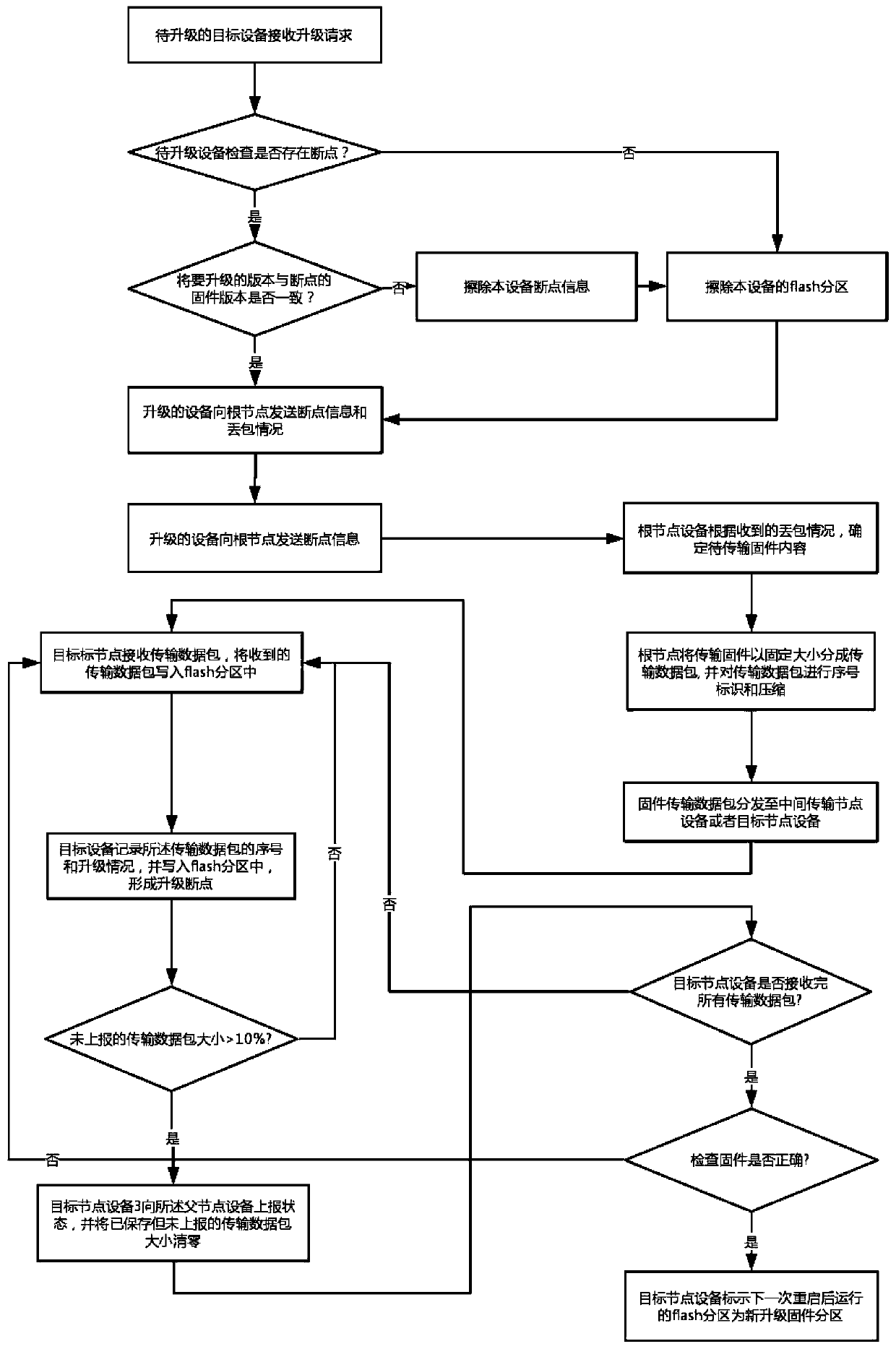
InactiveCN110730104AReduce consumptionAvoid direct communicationSoftware engineeringData switching networksComputer engineeringHost (network)
The invention provides a multi-equipment batch firmware upgrading method for a mesh network device, which comprises the following steps that: a host generates a firmware compression packet with an identifier and sends the firmware compression packet to root node device of a mesh network; the root node device decompresses the firmware package, verifies the correctness of firmware, repackages and compresses the firmware, and pushes the firmware to the target node device in a multicast mode; the upgrade firmware supports breakpoint resume in the transmission process of the mesh network; and the target node device decompresses the firmware, performs CRC on the firmware identifier, and upgrades and restarts the firmware after passing the CRC. If the target node device is restarted abnormally, returning to the old version for starting. The target node device reports the version to the host after being started, and the host confirms whether upgrading succeeds or not. Through compression and breakpoint resuming, consumption of network and storage resources in the firmware transmission process is reduced, and the batch upgrading speed is increased; through firmware type inspection and a version fallback mechanism, device upgrading exception caused by mismatching of firmware and the to-be-upgraded device is prevented.
Owner:ESPRESSIF SYST SHANGHAI
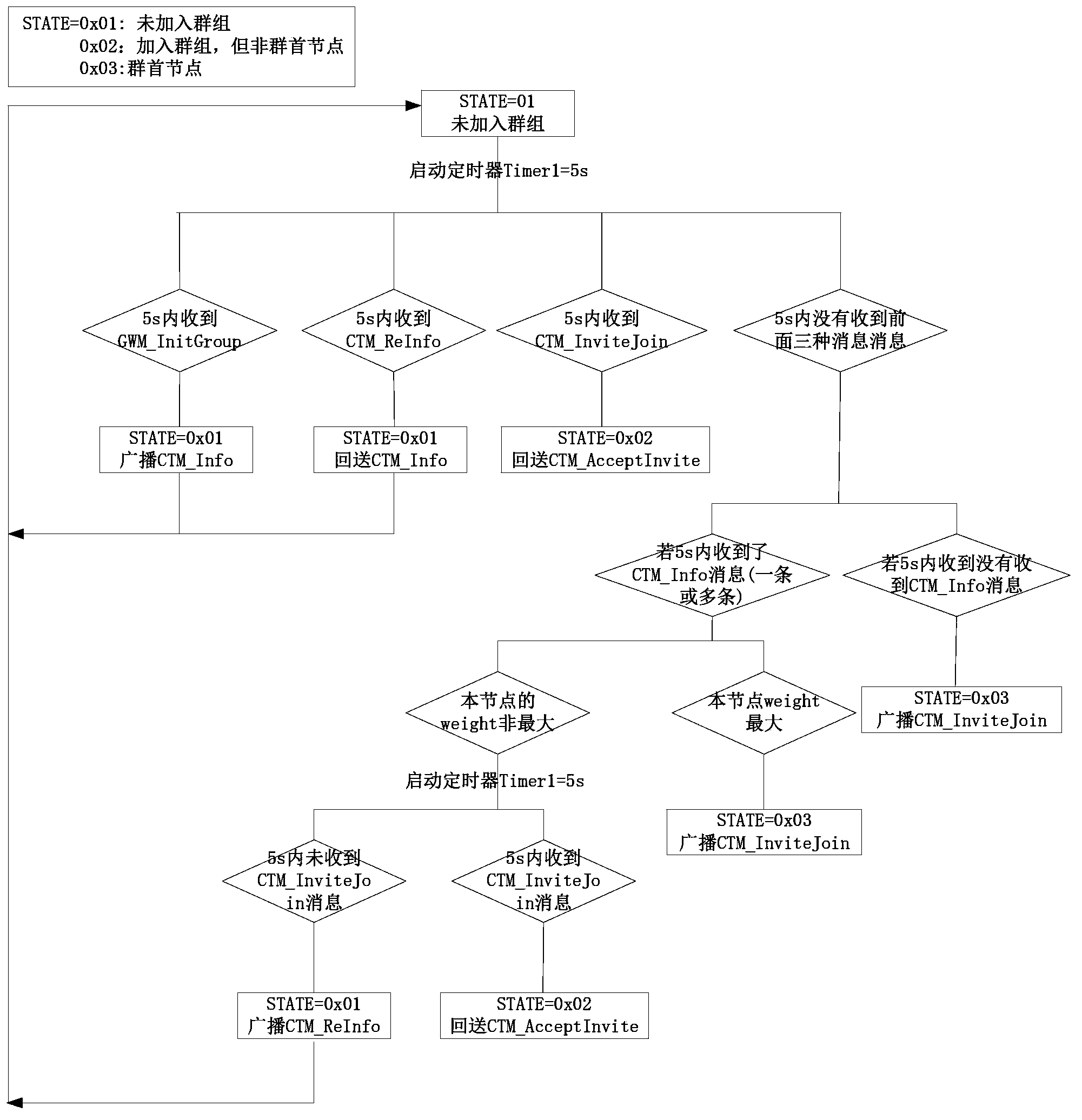
Group generation and maintenance method in wireless self-organizing network environment
InactiveCN103369578AAvoid direct communicationReduce loadNetwork topologiesMathematical modelSelf-organizing network
The invention discloses a method for generating a mobile node group in a wireless self-organizing network environment. The method is characterized in that each mobile node in a wireless self-organizing network configures a state of a node per se according to a finite-state mathematical model, and the method comprises the following steps that: (1) the mobile node broadcasts state information to a gateway at fixed time after being started until a reply message of a certain gateway in the wireless self-organizing network is received, the self-state is converted into a non-joined group state, and a message of the self-weight information is broadcast; (2) the mobile node positioned in the non-joined group state detects a joining invitation message of a peripheral cluster head node to join a mobile node group of the cluster head node, and the self-state is converted into a join group and is not a non-cluster head node state; (3) the mobile node positioned in the non-joined group state detects that a joinable mobile node group does not exist at the periphery, the mobile node converts the self-state into the cluster head node, a novel mobile node group is constructed, and the joining invitation message is broadcast. According to the method, the node can join the group or become a group in a short time after being started, the communication load of the gateway is greatly reduced, and the method has wide application prospects in a large-scale wireless self-organizing network environment.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
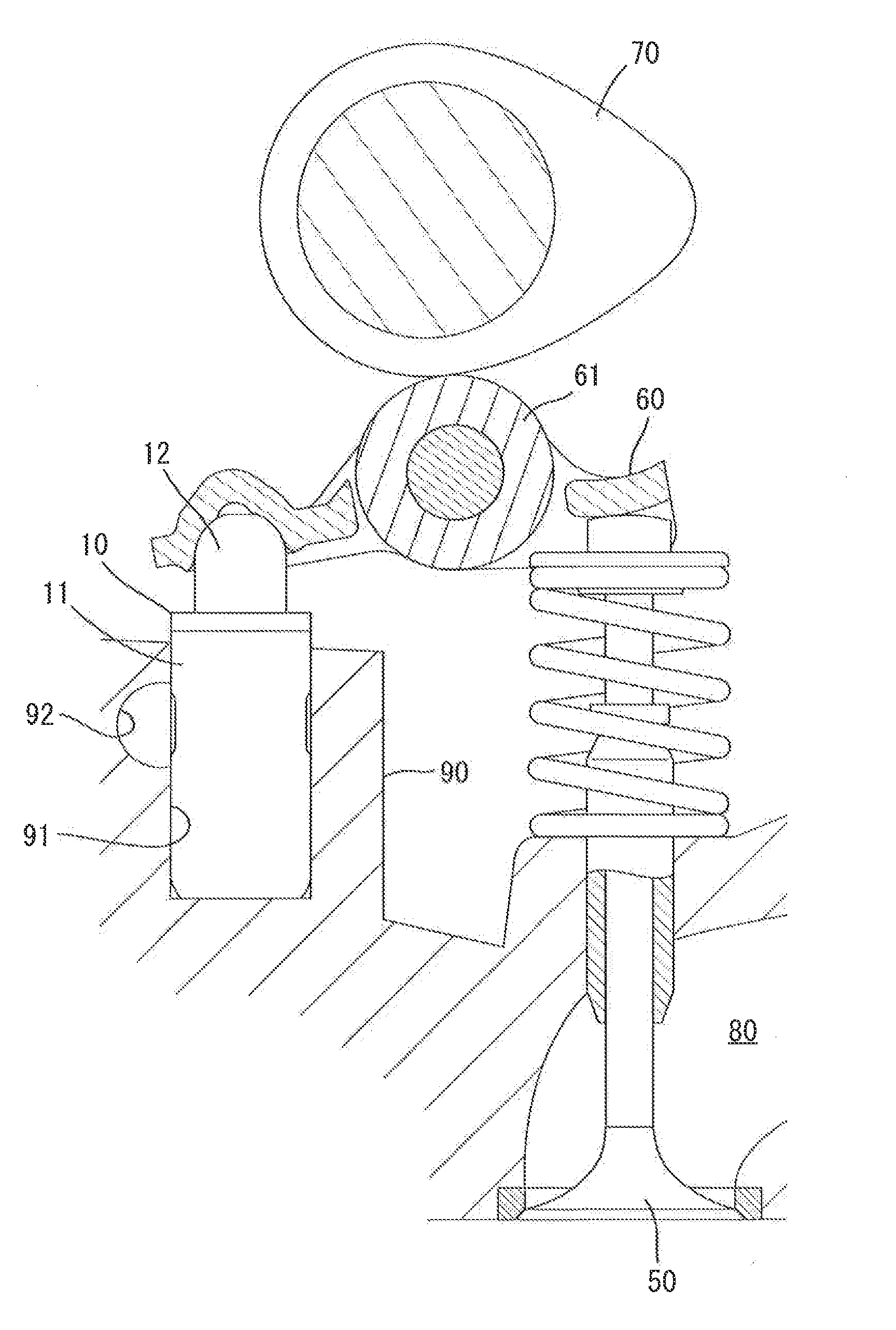
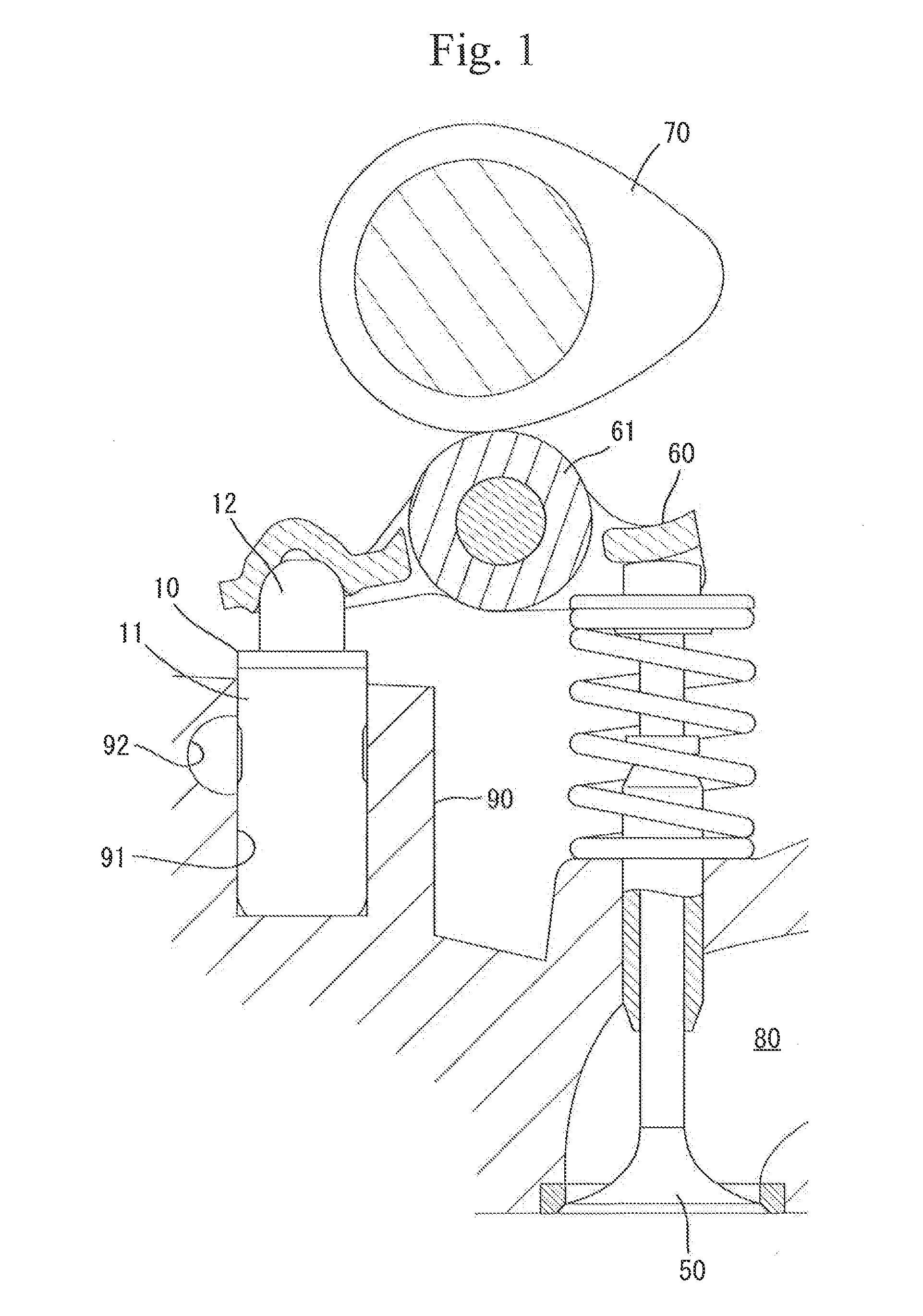
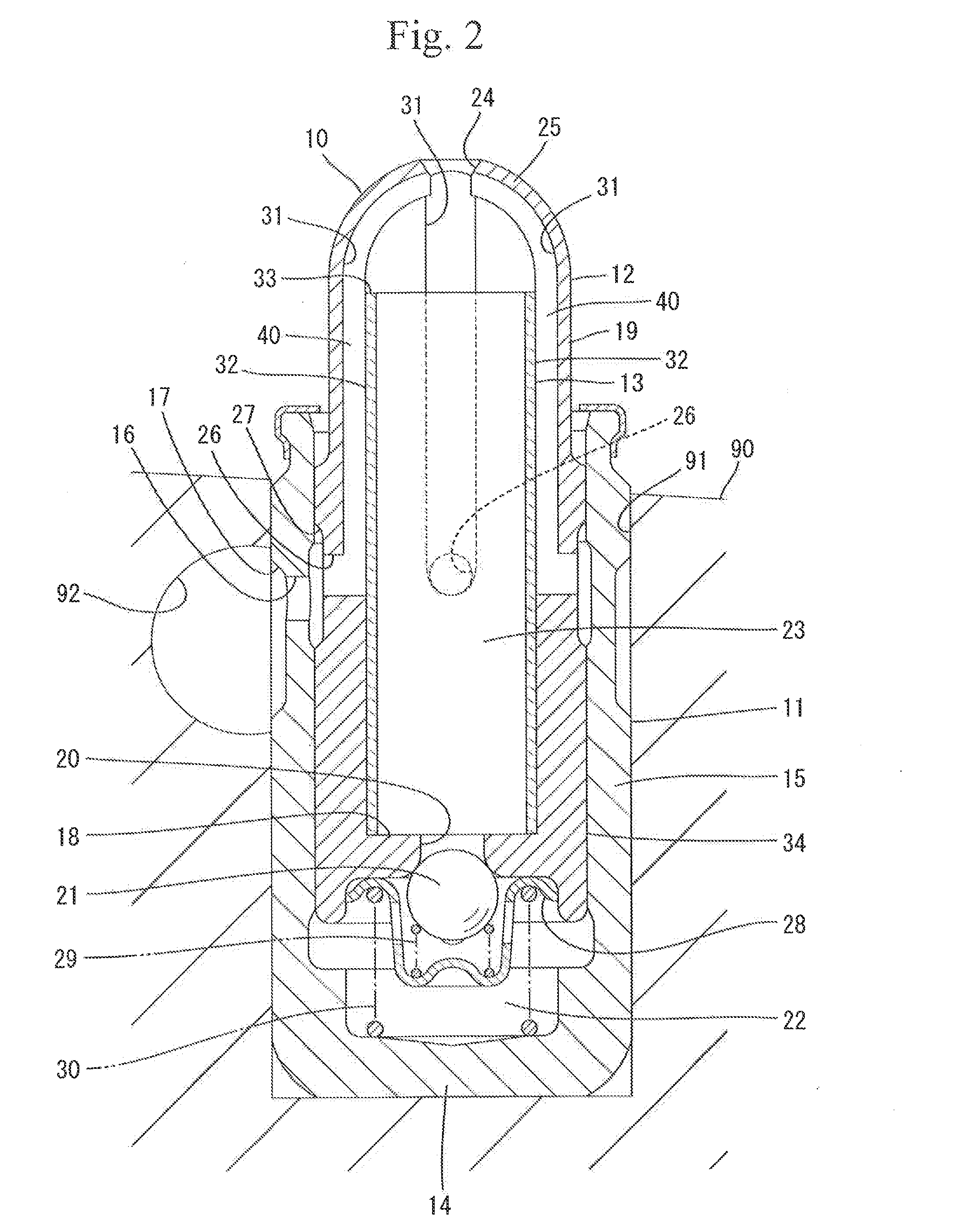
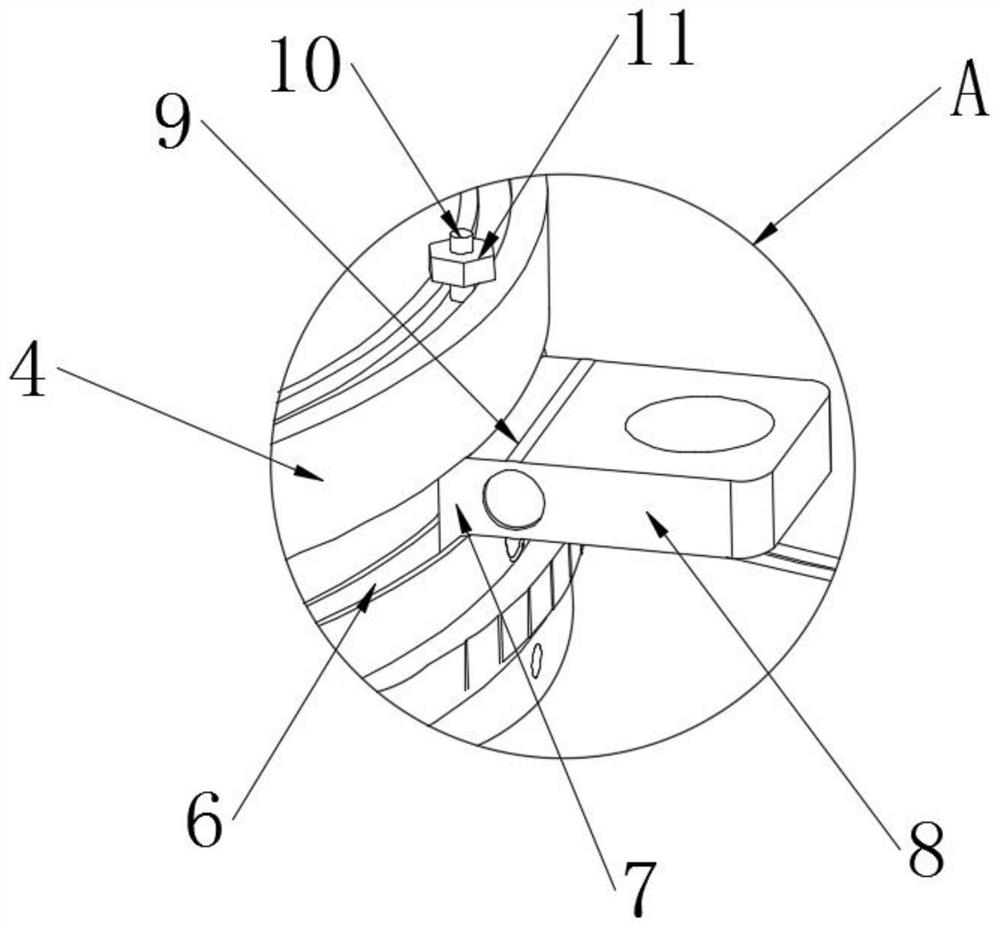
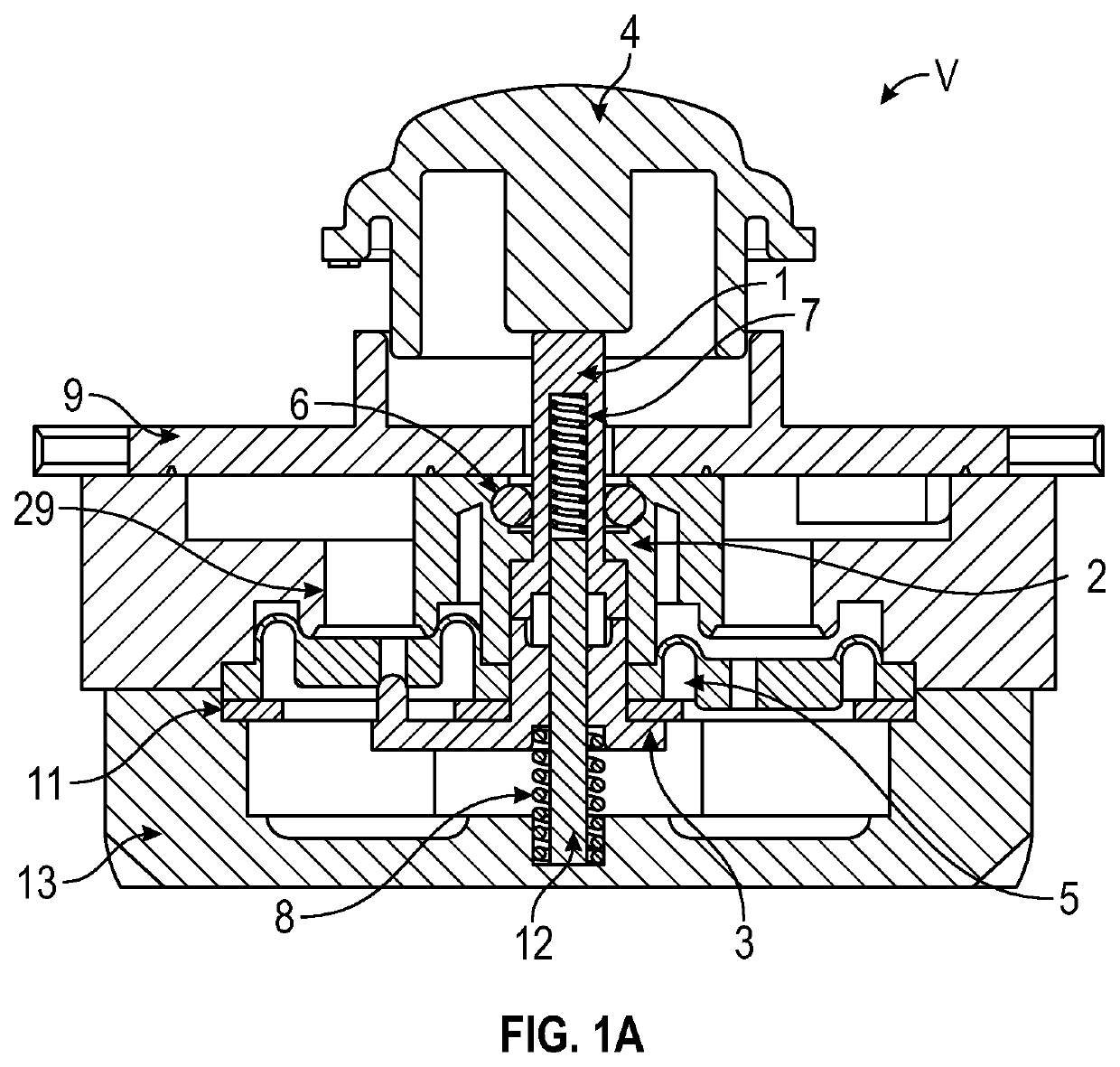
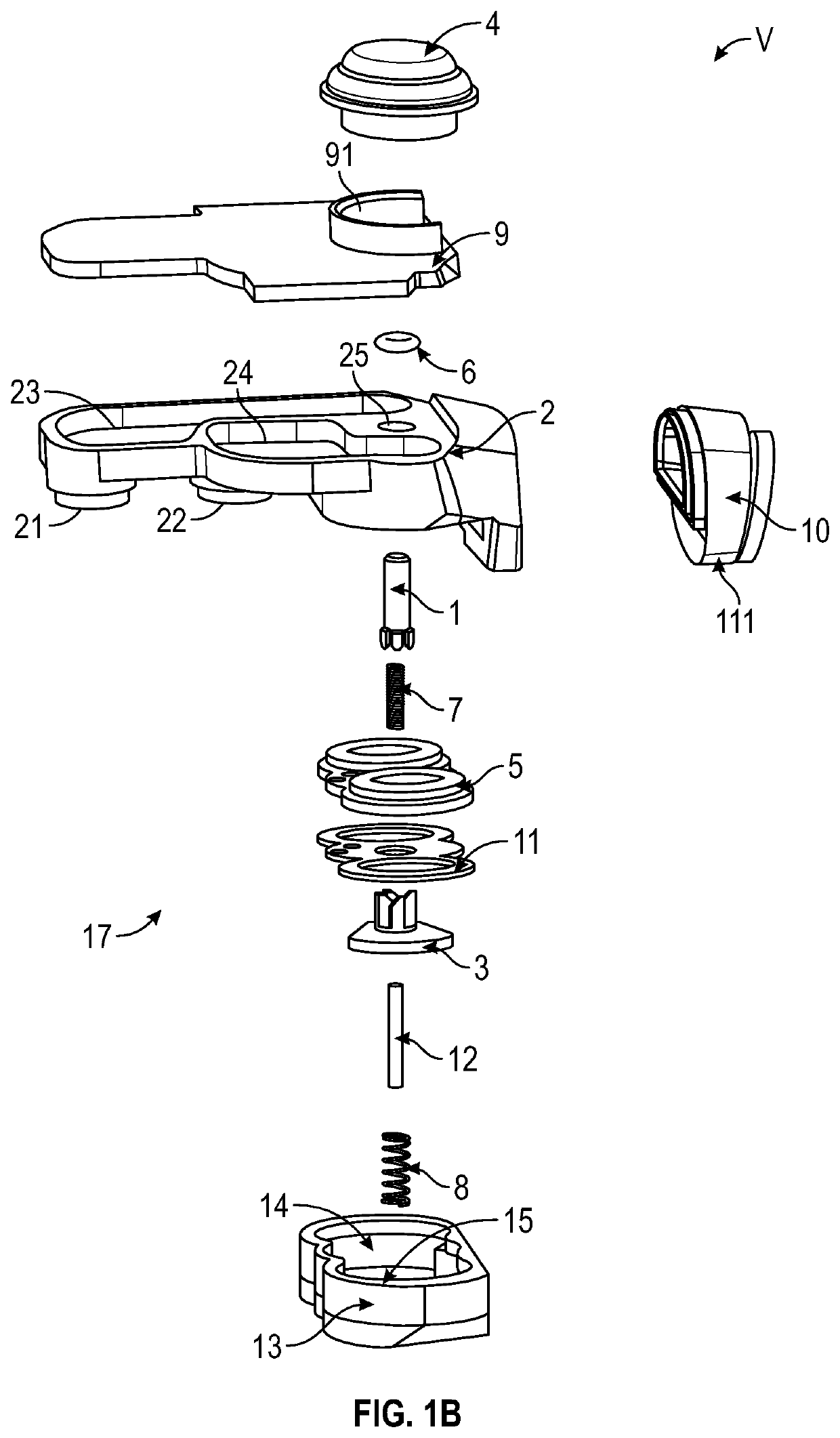
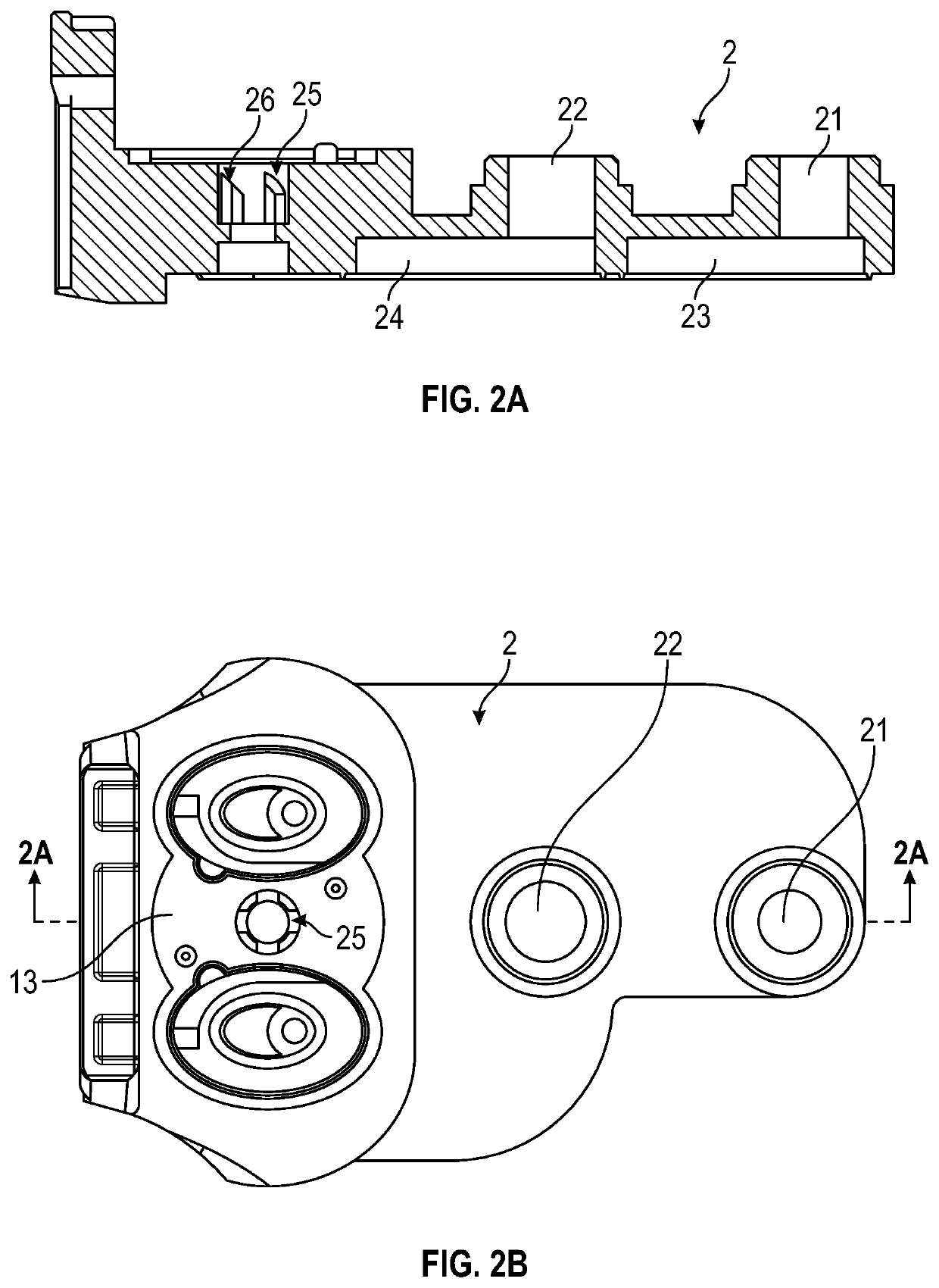
Lash adjuster
ActiveUS20140224202A1Repair firmEasy to fixValve arrangementsMachines/enginesHigh pressureHigh pressure chamber
A lash adjuster includes a body, a plunger which is inserted into the body and has a bottom wall with a valve hole and a peripheral wall having an oil passage hole and an inner periphery formed with a recessed groove, the plunger defining a high-pressure chamber between the bottom wall and the body, and a partitioning member inserted into the plunger. The partitioning member has an oil passage end located above the oil passage hole. The partitioning member has an oil-passage defining portion located opposite the recessed groove and defining an oil passage between itself and a groove face of the recessed groove. The partitioning member defines a low-pressure chamber inside. The low-pressure chamber reserves a hydraulic fluid flowing through the oil passage hole, the oil passage and the oil passage end. The low-pressure chamber causes the reserved hydraulic fluid to flow through the valve hole into the high-pressure chamber.
Owner:OTICS CORP
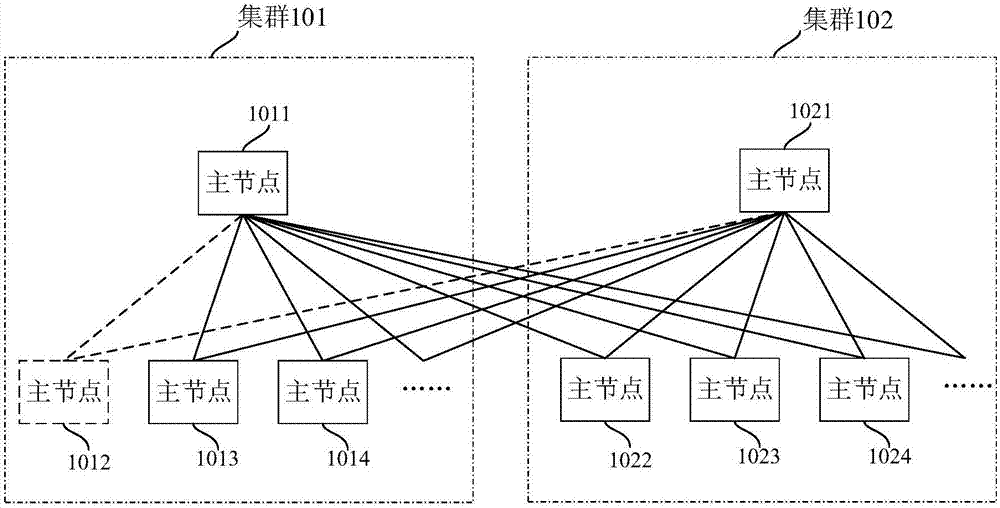
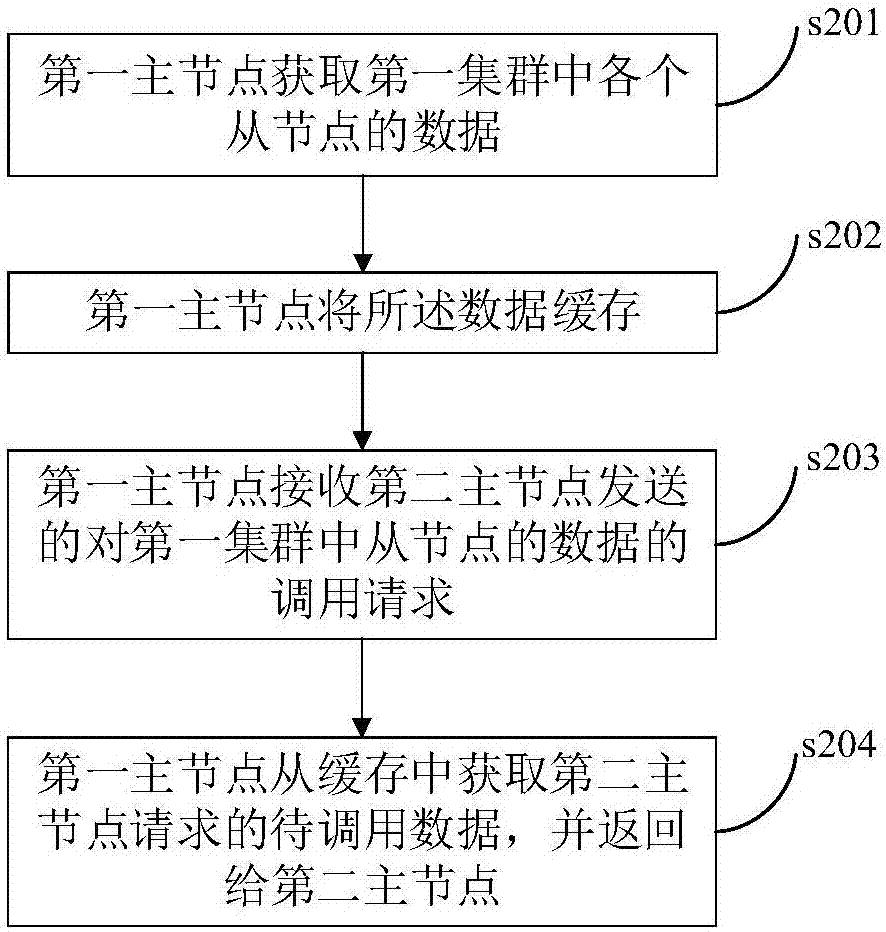
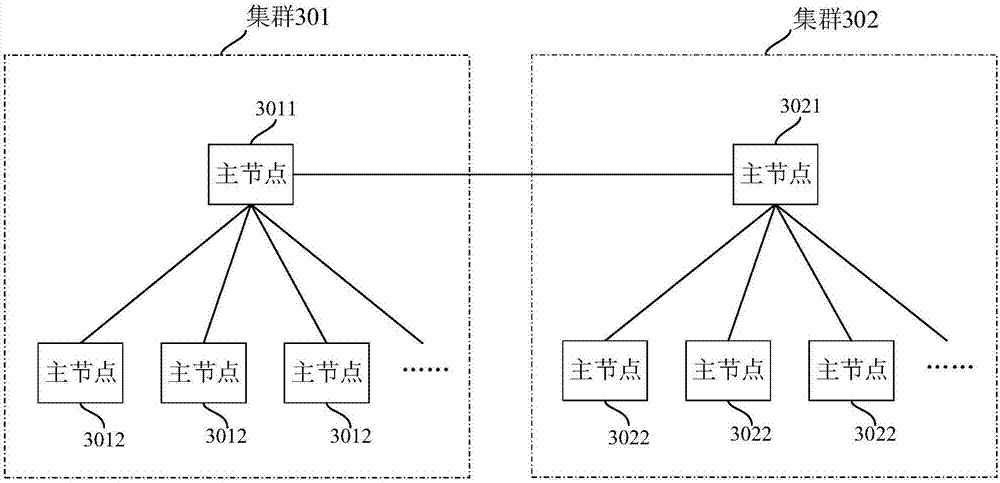
Cluster node communication method and system
ActiveCN107124469AImprove access efficiencyAvoid request response slowdownData switching networksCommunications systemDirect communication
The invention discloses a cluster node communication method. The cluster node communication method comprises the following steps: a first master node obtains data of slave nodes in a first cluster and caches the data; the first master node is located in the first cluster; the first master node receives a call request of data of the slave nodes in the first cluster sent by a second master node, wherein the second master node is located in a second cluster; and the first master node caches to-be-called data requested by the second master node obtained from the cache and returns the to-be-called data to the second master node. According to the cluster node communication method, the master node caches the data of the slave nodes in the cluster, therefore the master nodes in other clusters can access the master node to obtain the data of the slave nodes in the cluster, therefore the direct communication between the slave nodes and the master nodes in other clusters can be avoided, and thus the reduction of system request response speed caused by the fault of the slave nodes can be avoided. The invention further discloses a cluster node communication system, which has the same beneficial effects.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
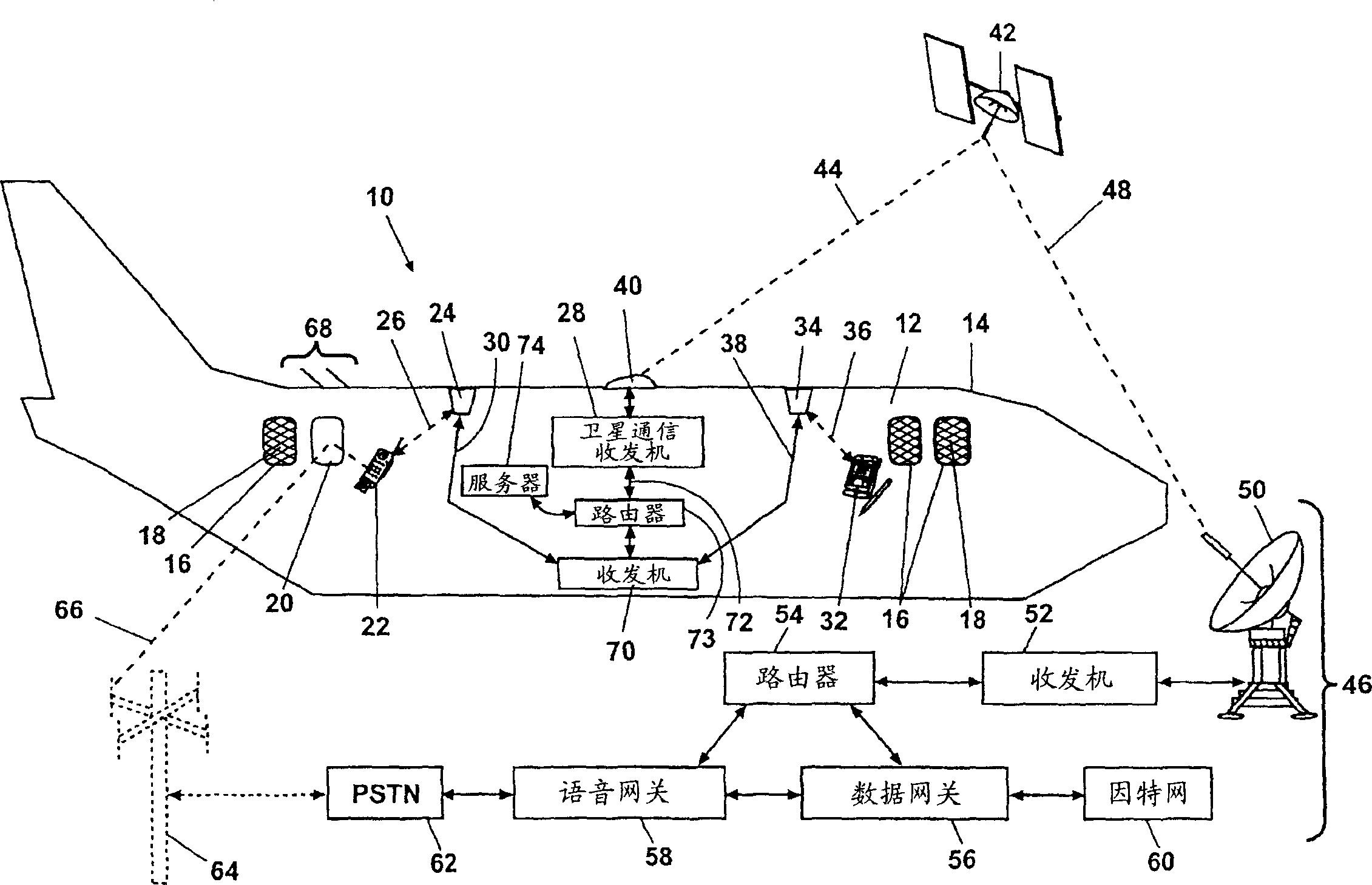
Wireless communication inside shielded envelope
InactiveCN1551245AReduce adverse effectsAvoid direct communicationAircraft accessoriesMagnetic/electric field screeningTransceiverElectricity
A system and method limit transmission of wireless electromagnetic device radiation through the windows of a mobile platform outer envelope. A shielding layer is applied to the window and electrically grounded to the outer envelope. At least one transceiver hub is located within the mobile platform receiving and / or transmitting the electromagnetic device radiation. An off-board communication device wirelessly communicates with the transceiver hub. The shielding layer attenuates a portion of the radiation contacting the window. Only a communication path between the transceiver hub and the off-board communication device is therefore operable.
Owner:THE BOEING CO
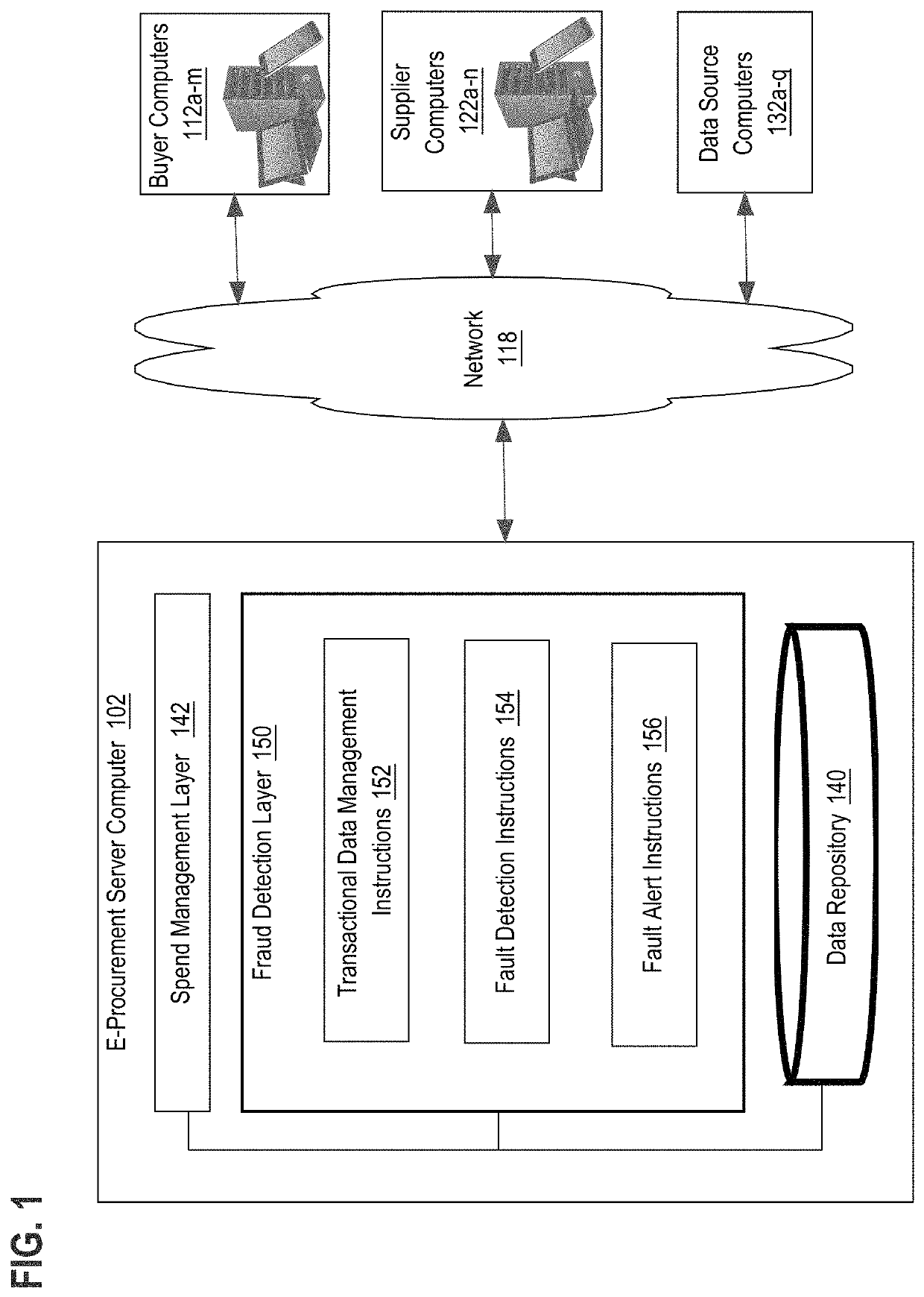
Detecting supplier fraud from digital transactional data
UndeterminedUS10896430B1Rapid responseAvoid direct communicationFinanceBuying/selling/leasing transactionsInvoiceTransaction data
A fraud detection system for detecting fraudulent acts related to payment discounts from digital transactional data is disclosed. In some embodiments, the fraud detection system is programmed or configured with data structures and / or database records that are arranged to detect an occurrence of a triggering event, such as receiving an early payment discount by a buyer account from a supplier account. The fraud detection system is programmed to analyze how a first amount charged for certain items by the supplier account to the buyer account before the triggering event has changed to a second amount after the triggering event from digital documents related to procurement transactions. The certain items may include items for sale or for other miscellaneous items. The digital documents may include catalogs, purchase requisitions, purchase orders, or invoices. The fraud detection system is programmed to further detect any potential fraud committed by the supplier account based on the analysis result and assist the buyer account with handling any potential fraud.
Owner:COUPA SOFTWARE
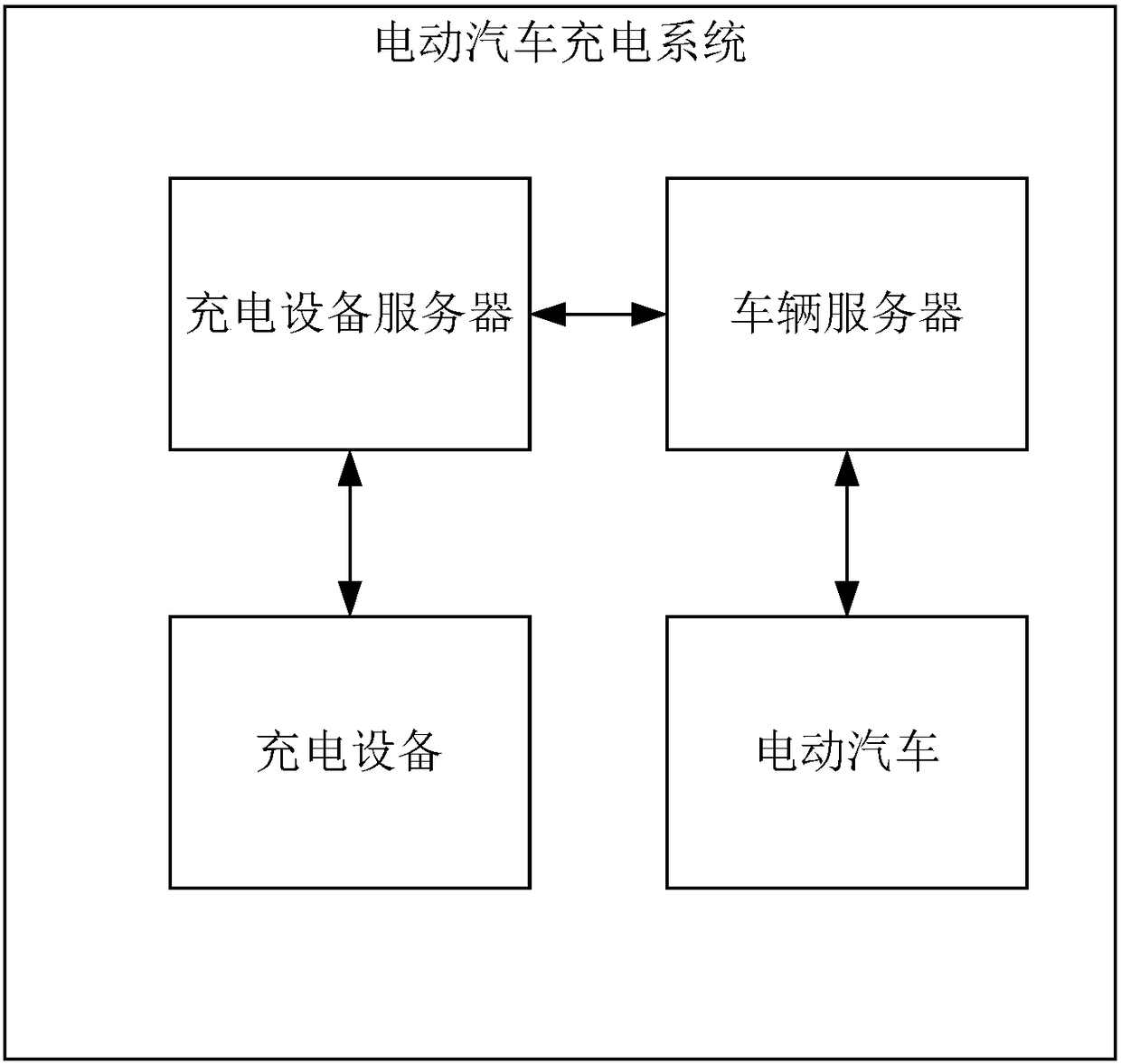
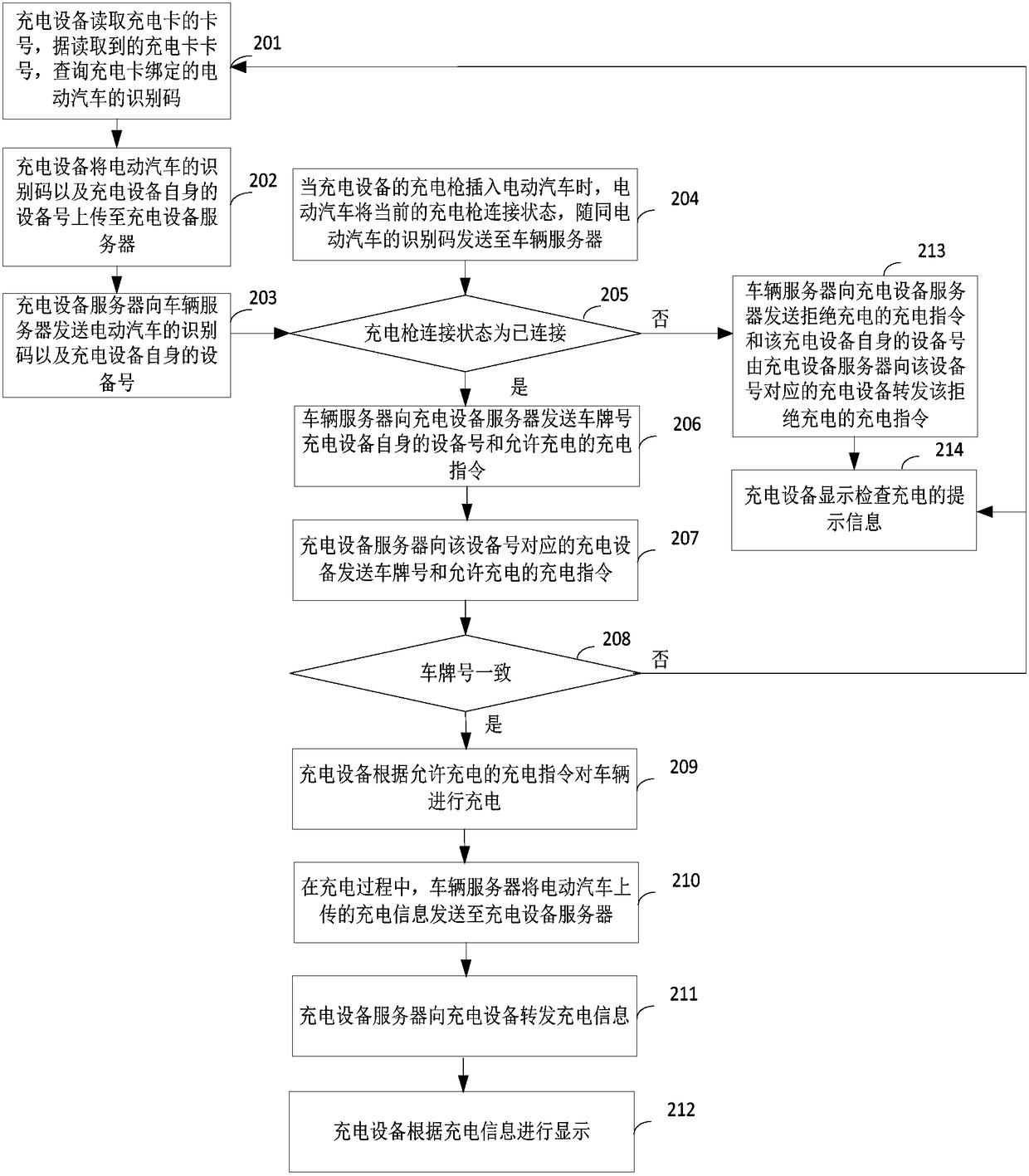
Charging method, system and charging device for electric vehicle
ActiveCN108656974AAvoid direct communicationCharging stationsElectric vehicle charging technologyAutomotive engineeringElectric vehicle
The invention provides a charging method, system and charging device for an electric vehicle. The charging method comprises the following steps that the to-be-charged electric vehicle is identified bythe charging device; and when the electric vehicle is charged, the charging device obtains charging information of the electric vehicle from a vehicle server of the electric vehicle through a charging device server, so that direct communication between the electric vehicle and the charging device is avoided, and meanwhile, the charging information of the electric vehicle is obtained by the charging device.
Owner:BYD CO LTD
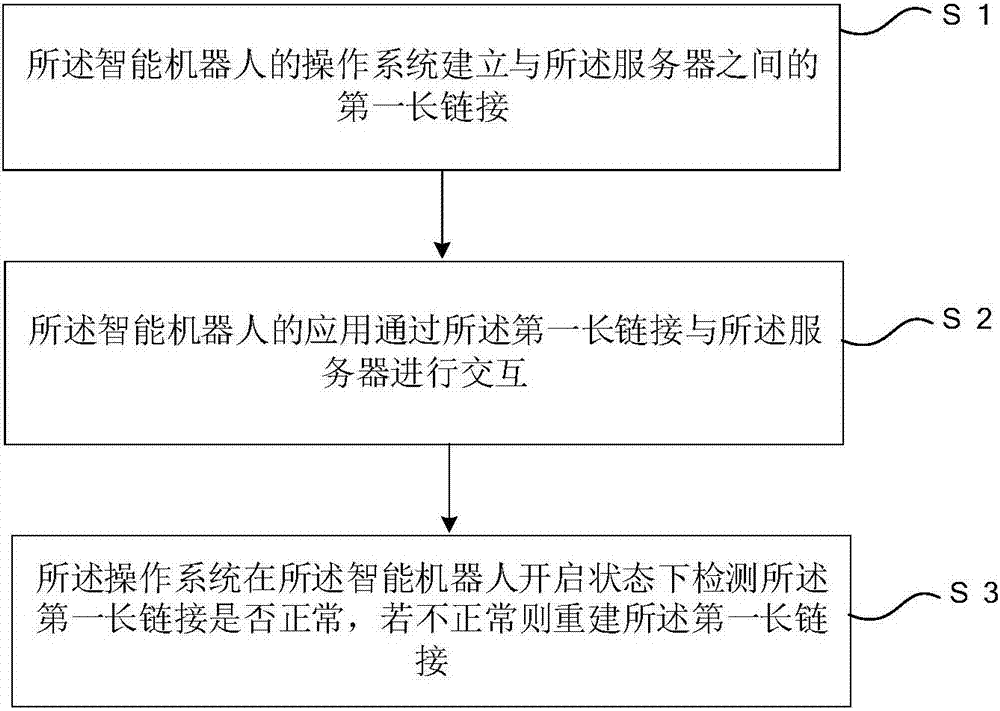
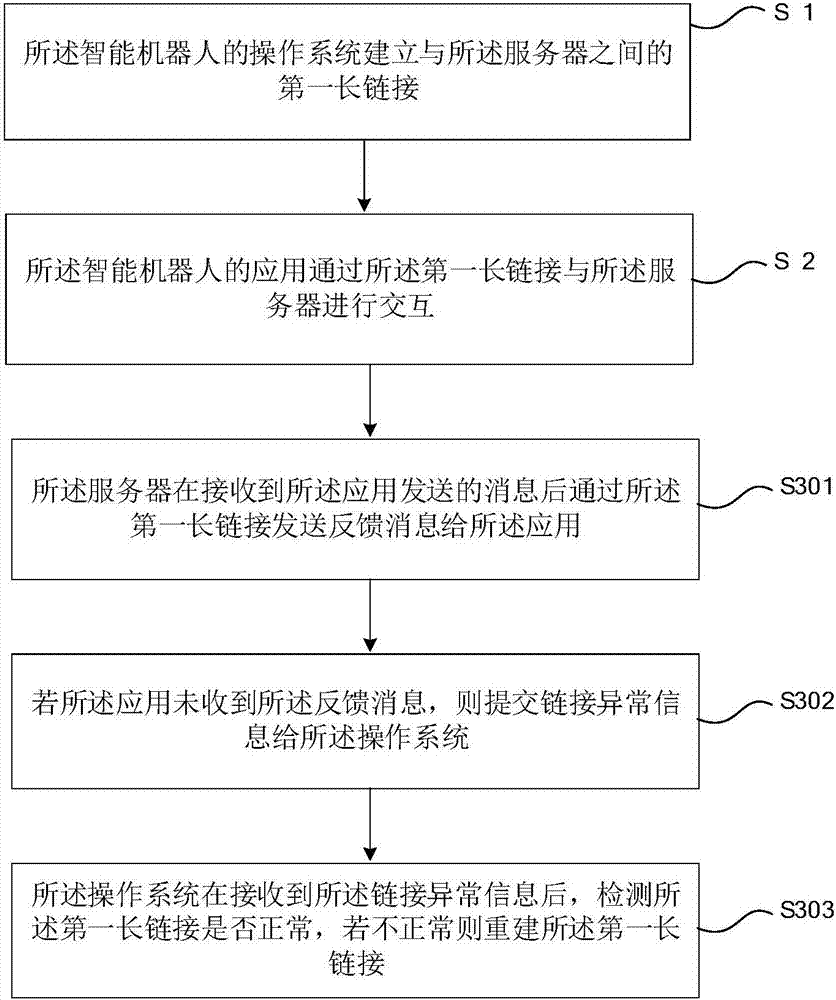
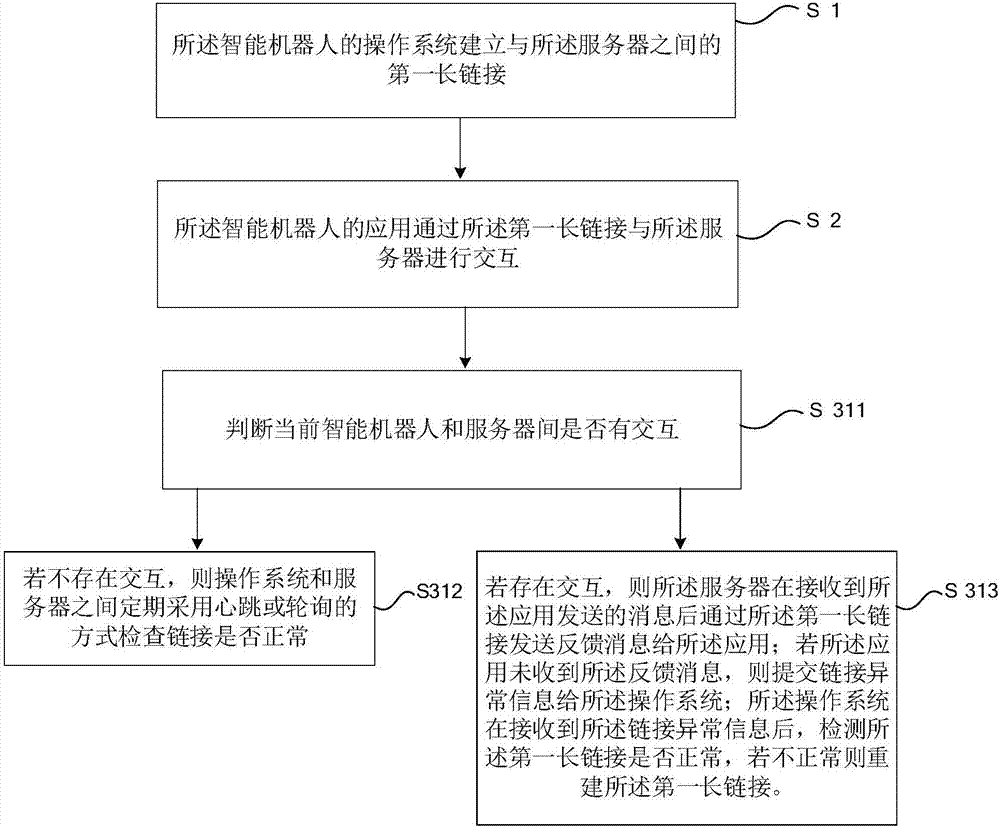
Server link management method for intelligent robot
ActiveCN107508916AReduce resource overheadSave resourcesTransmissionLink managementIntelligent robots
The invention relates to a server link management method for an intelligent robot. The method comprises the following steps: establishing a first long link with a server by an operating system of the intelligent robot; interacting with the server by an application of the intelligent robot via the first long link; and detecting whether the first long link is abnormal by the operating system when the intelligent robot is in the open state, and if not, then rebuilding the first long link. The server link management method for the intelligent robot provided by the invention saves system resources and reduces the cost of link management, so that the server link management method is applicable to the link management and maintenance of the intelligent robot.
Owner:SHENZHEN GOWILD ROBOTICS CO LTD
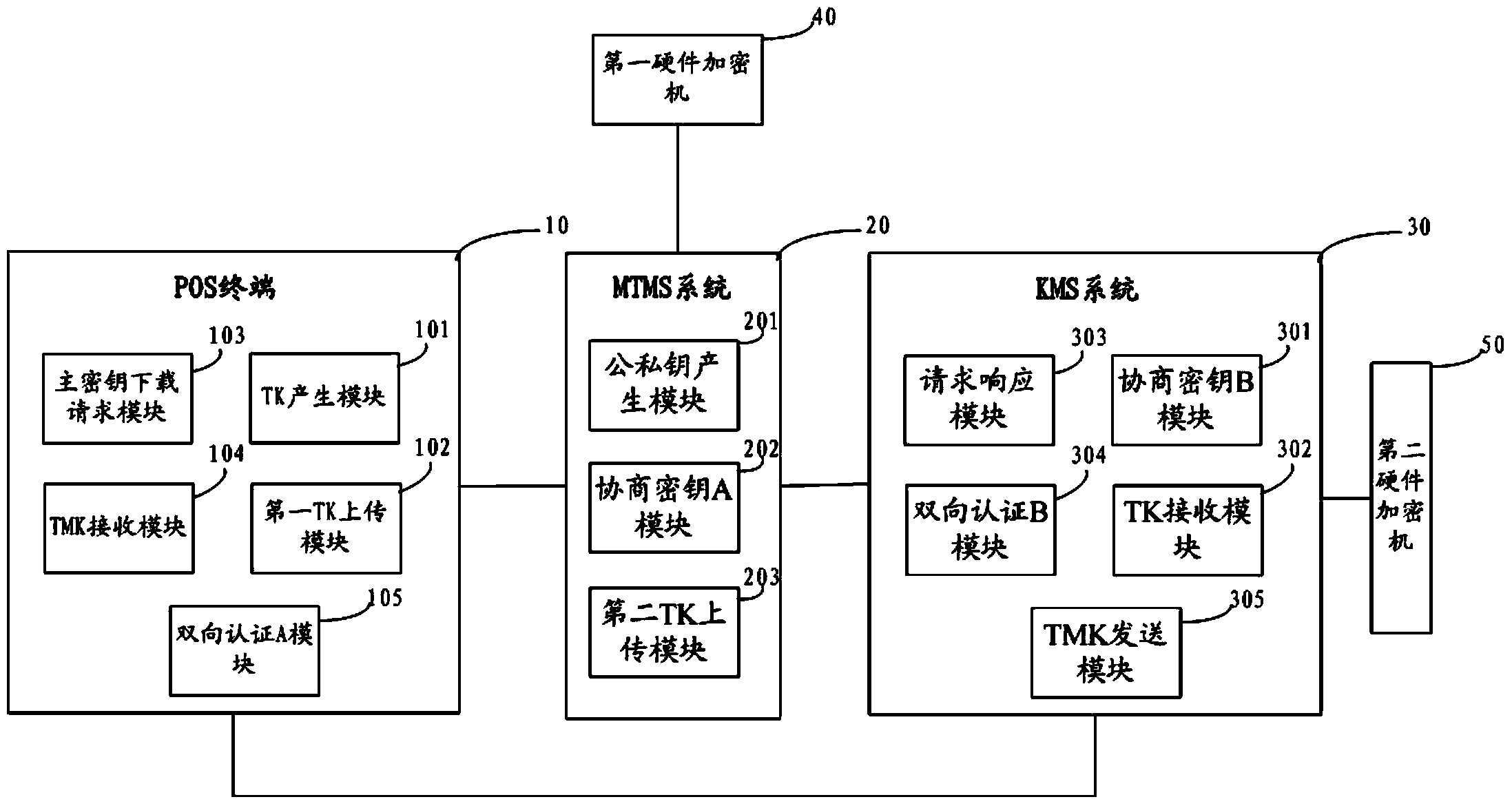
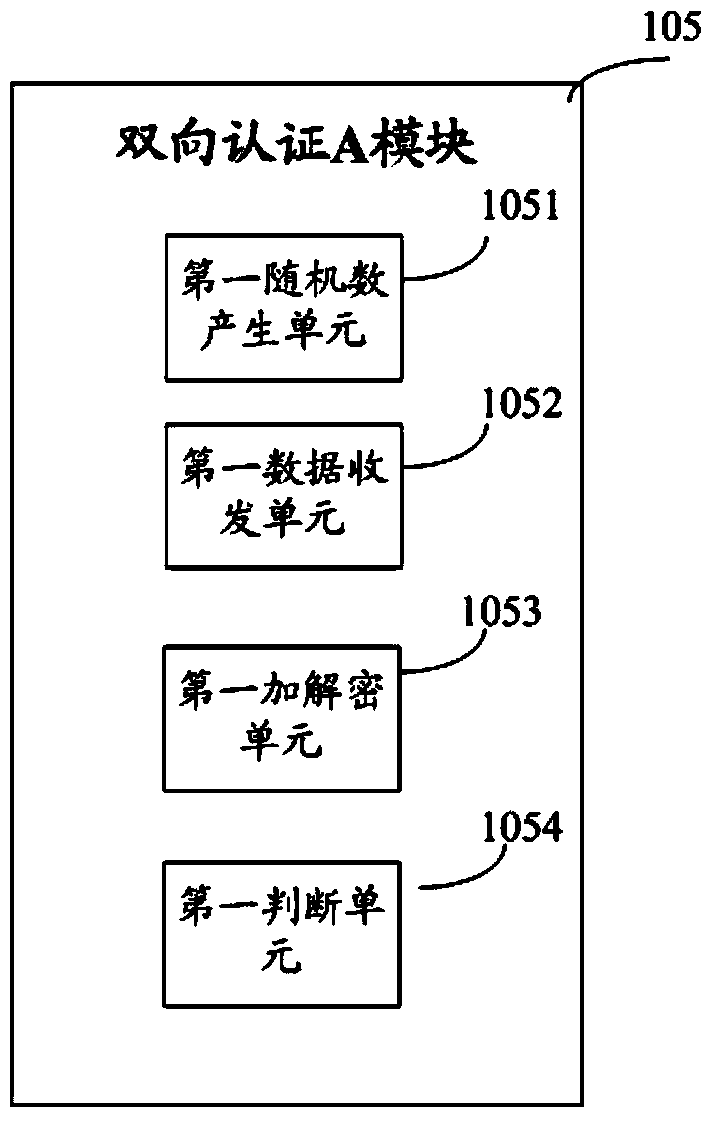
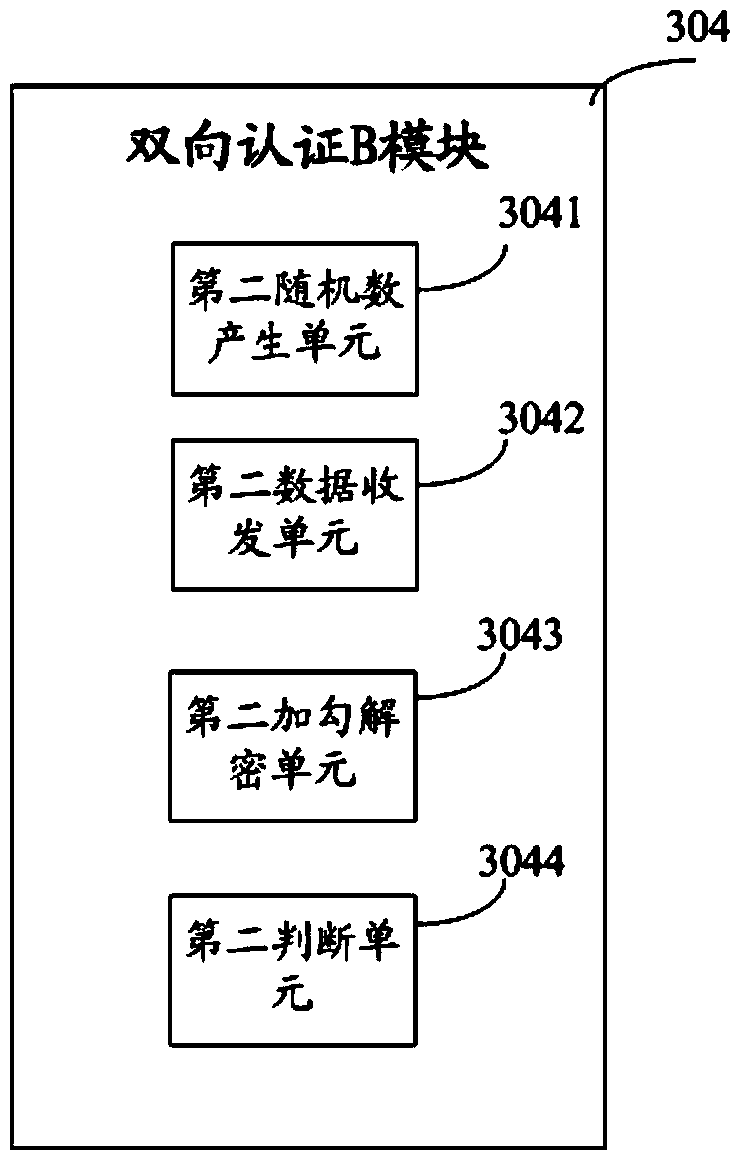
Method and system for safe downloading of TMK
ActiveCN103731260AImprove download securityEasy to collectKey distribution for secure communicationPoint-of-sale network systemsMaster keyAuthentication
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Buzzer structure convenient for installation and having combo audio
ActiveCN110400556AScientific and reasonable structureEasy to useSound producing devicesEngineeringBuzzer
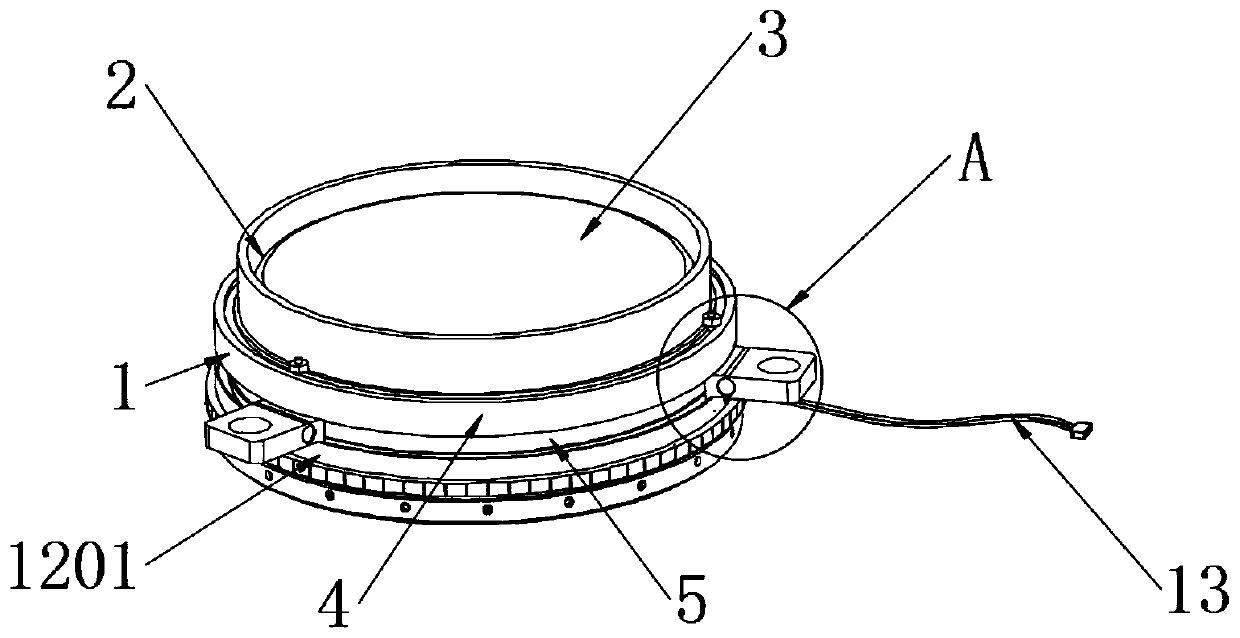
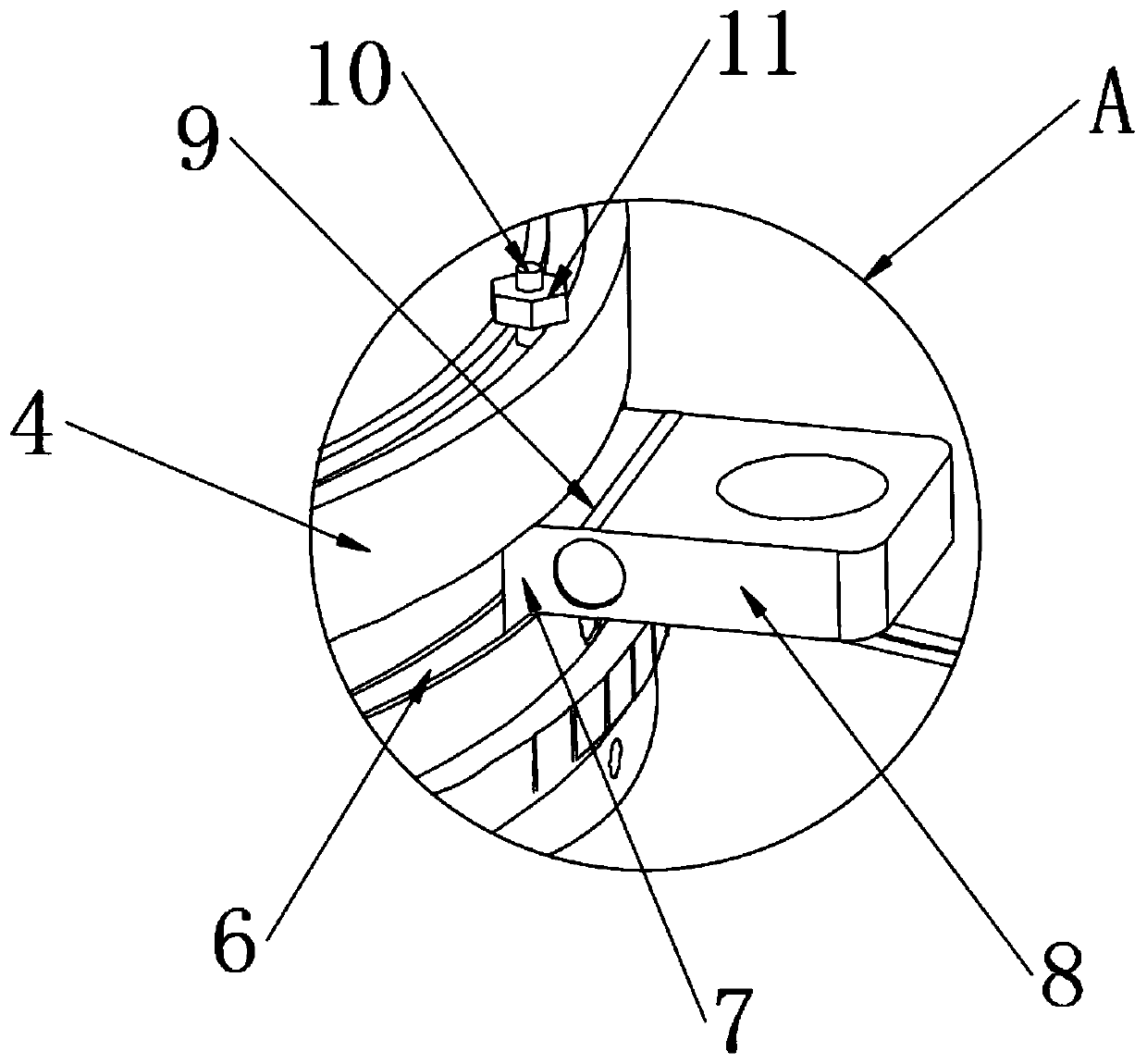
The invention discloses a buzzer structure convenient for installation and having a combo audio. The buzzer structure comprises a housing, a buzzer and a resonant chamber. A piezoelectric buzzer is installed in the housing. The resonant chamber is arranged at the top end of the piezoelectric buzzer. An outer ring is installed at the bottom of the housing. The invention is scientific and reasonablein structure, and safe and convenient in use; and an outer ring is arranged for the invention. Through the effects of a sliding slot, a groove, a sliding block and a fixing block, the sliding block slides and the position of the fixing block is adjusted according to an actual situation of the installing position. By matching the effects of a connecting screw rod and a locking nut, the position thereof is fixed, such that the buzzer is better installed and fixed. Through the effect of a movable shaft, the fixing block is folded and hidden conveniently according to an actual requirement, thereby achieving a simple operation and a convenient installation. Through the effects of a through hole, an inner ring and a bearing hole as well as an extrusion bump, the bearing hole at one side of theinner ring is made overlapped with the through hole, thereby circulating air at the bottom of the buzzer and improving heat dissipation effects of the buzzer.
Owner:新沂市承翔电子有限公司
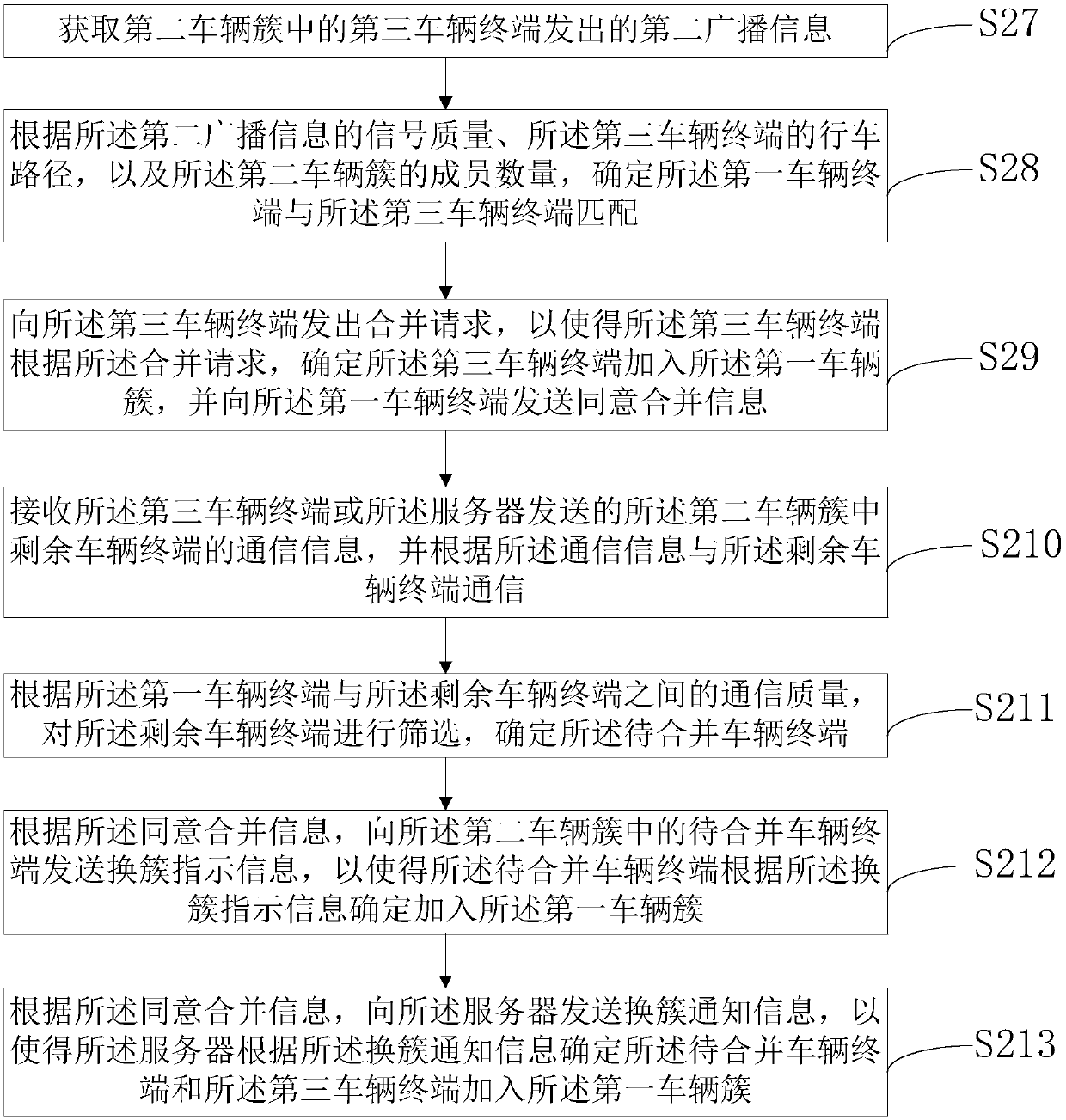
Information processing method and device for the automatic driving of vehicle
ActiveCN108684015AAvoid direct communicationRealize information interactionParticular environment based servicesBroadcast service distributionReal-time computingEnergy consumption
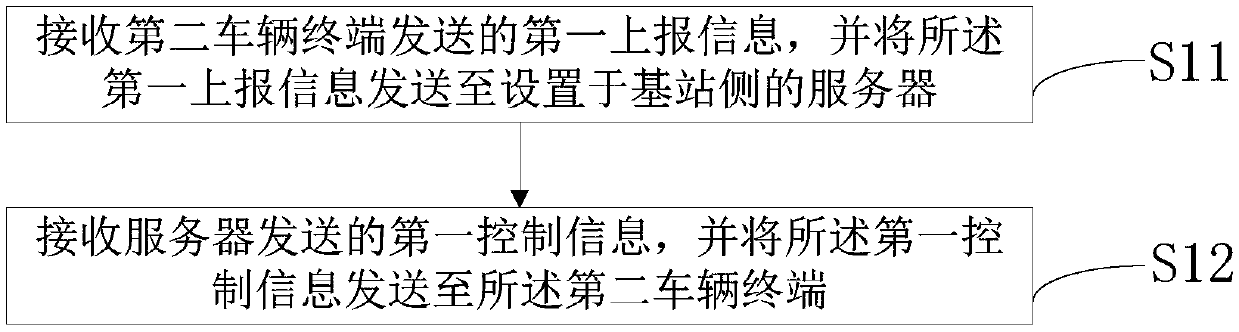
The present invention provides an information processing method and device for the automatic driving of a vehicle applied to a first vehicle terminal in a first vehicle cluster. The method comprises astep of receiving first report information sent by a second vehicle terminal and sending the first report information to a server arranged at a base station side, wherein the first report informationis information which is generated by the second vehicle terminal and needs to be reported to the server after the second vehicle terminal determines to join the first vehicle cluster; a step of receiving first control information sent by the server and transmitting the first control information to the second vehicle terminal, wherein the first control information is generated by the server and needs to be sent to the second vehicle terminal after the server determines that the second vehicle terminal joins the first vehicle cluster, and the first control information is determined by the server according to first upload information. The energy consumption of the vehicle terminal is reduced.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Multi-site cluster-based data intake and query systems
ActiveUS20180246957A1Improve scalabilityEfficient leveragingSpecial data processing applicationsText database clustering/classificationExtensibilityMulti site
The various embodiments describe multi-site cluster-based data intake and query systems, including cloud-based data intake and query systems. Using a hybrid search system that includes cloud-based data intake and query systems working in concert with so-called “on-premises” data intake and query systems can promote the scalability of search functionality. In addition, the hybrid search system can enable data isolation in a manner in which sensitive data is maintained “on premises” and information or data that is not sensitive can be moved to the cloud-based system. Further, the cloud-based system can enable efficient leveraging of data that may already exist in the cloud. In addition, various embodiments enable configuration data associated with search functionality to be shared amongst clusters in a manner that promotes cluster security. Specifically, a shared data store can be utilized to store configuration information such that when a particular cluster wishes to use the configuration information, it simply retrieves the configuration information from the shared data store, thus avoiding direct communication with other clusters. Although the invention has been described in language specific to structural features and / or methodological acts, it is to be understood that the invention defined in the appended claims is not necessarily limited to the specific features or acts described. Rather, the specific features and acts are disclosed as example forms of implementing the claimed invention.
Owner:SPLUNK INC
Automatic goods receiving system
ActiveCN112478546AImprove work efficiencyLabor reliefStorage devicesLogistics managementDelivery vehicle
The invention relates to the technical field of automatic logistics storage equipment, in particular to an automatic goods receiving system, and aims at overcoming the defects that in the prior art, in the goods warehousing process, warehousing point inspection, goods transportation classification and the like need to be achieved through manual operation, the workload of workers is large, and errors are caused easily. According to the technical scheme, the automatic goods receiving system comprises a goods feeding device used for being in butt joint with a goods delivery vehicle to receive goods, a transferring device used for receiving and transferring the goods, a conveying device used for conveying the goods and a goods storage device used for being in butt joint with a goods distribution vehicle to achieve goods distribution and storage. The automatic goods receiving system has the effects that the goods are automatically received and stored, the labor cost of manual warehousing issaved, and the efficiency of goods warehousing and information collection is improved.
Owner:昆山科望快速印务有限公司
String bumper for arrow-propelling device
A bumper for limiting a string displacement on a projectile accelerating apparatus is described for absorbing vibrations thereof, the bumper comprising an hollowed body including an opening portion at a first end of the body, an expansion portion inside the hollowed body and adjacent to the opening portion, a damper portion adjacent to the expansion portion inside the hollowed body, the damper portion including a volume of air that is compressible when the opening portion is closed, and a string-contacting portion disposed on an exterior surface of a second end of the body, the distal wall and the string-contacting portion being moveable toward the opening portion to compress the volume of air in the damper portion in consequence of a string contact on the string-contacting portion. A projectile accelerating apparatus including same and a method of using same are also presented.
Owner:PLACEMENTS GASTON HOULE
Volute of range hood with noise reducing function
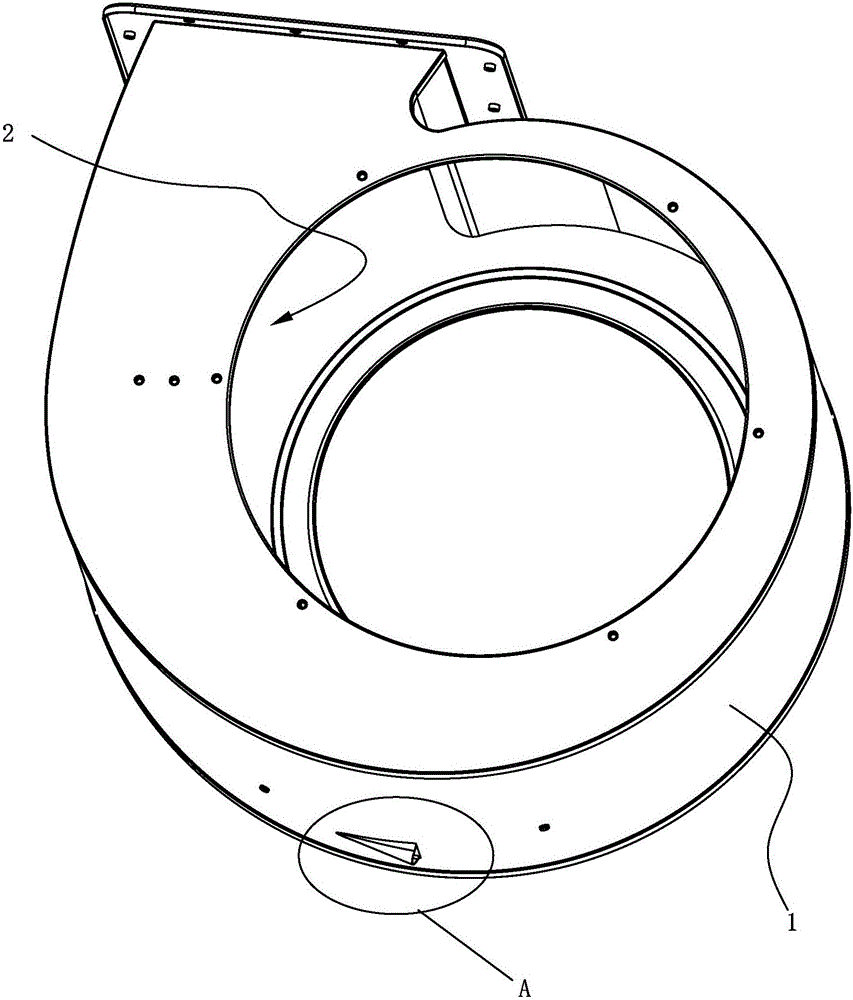
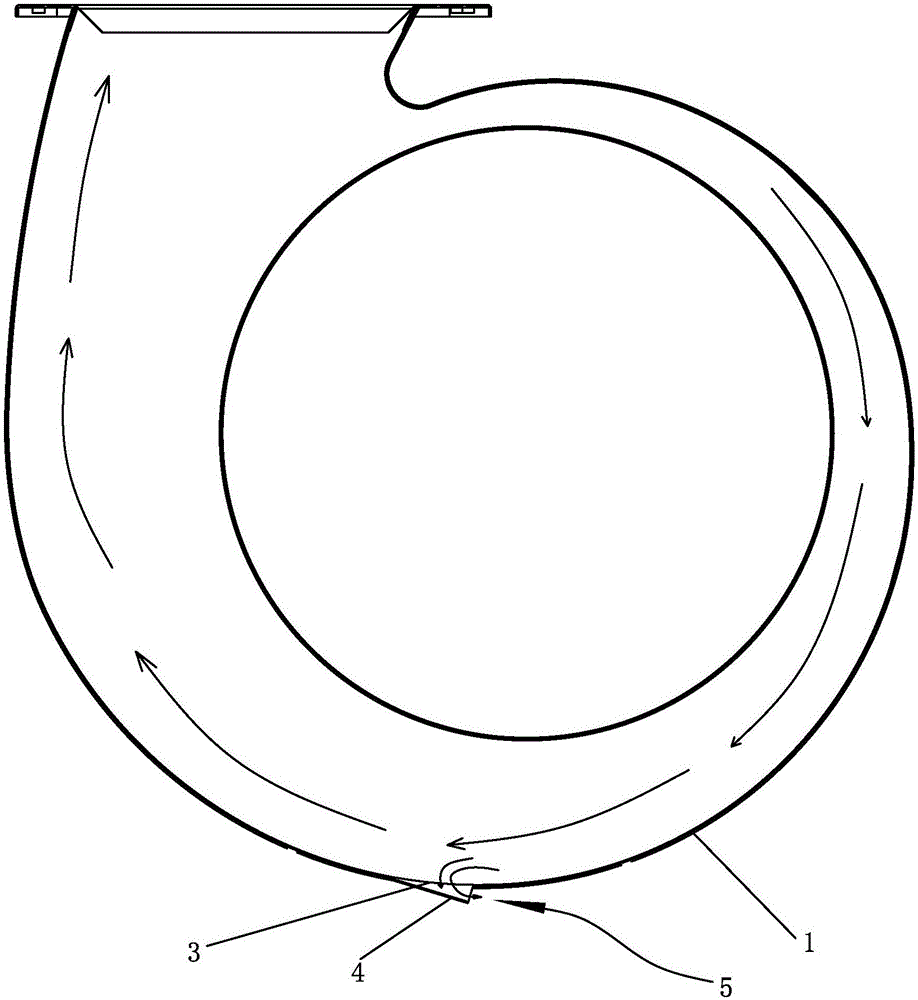
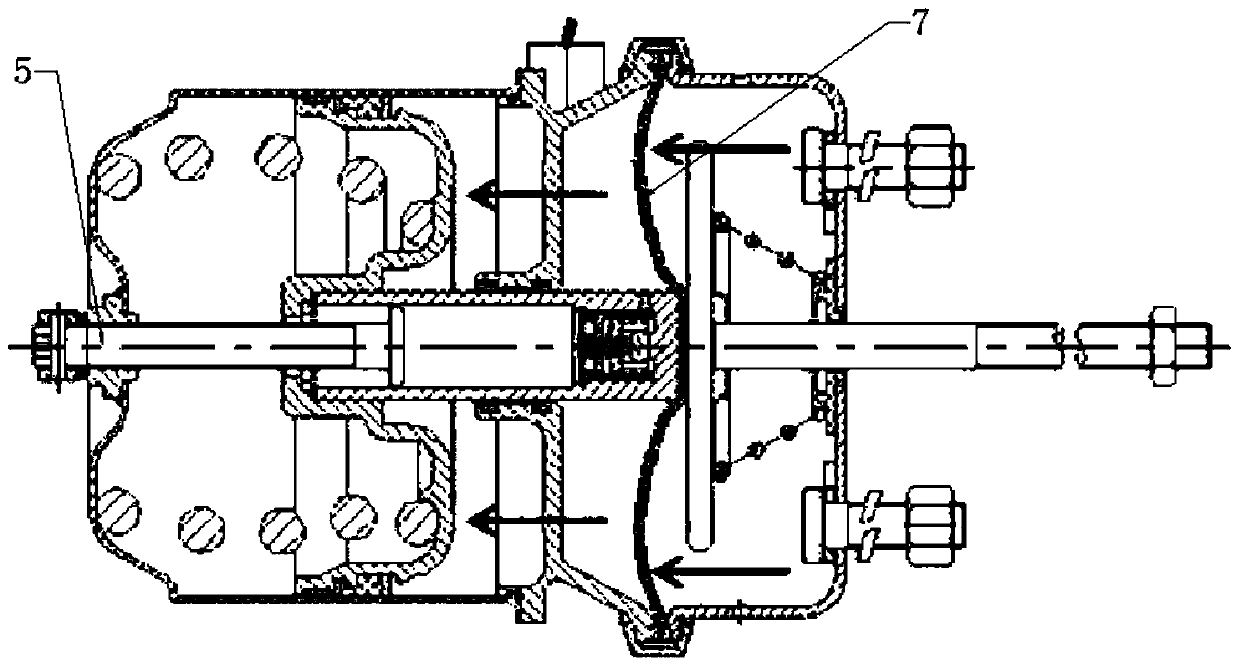
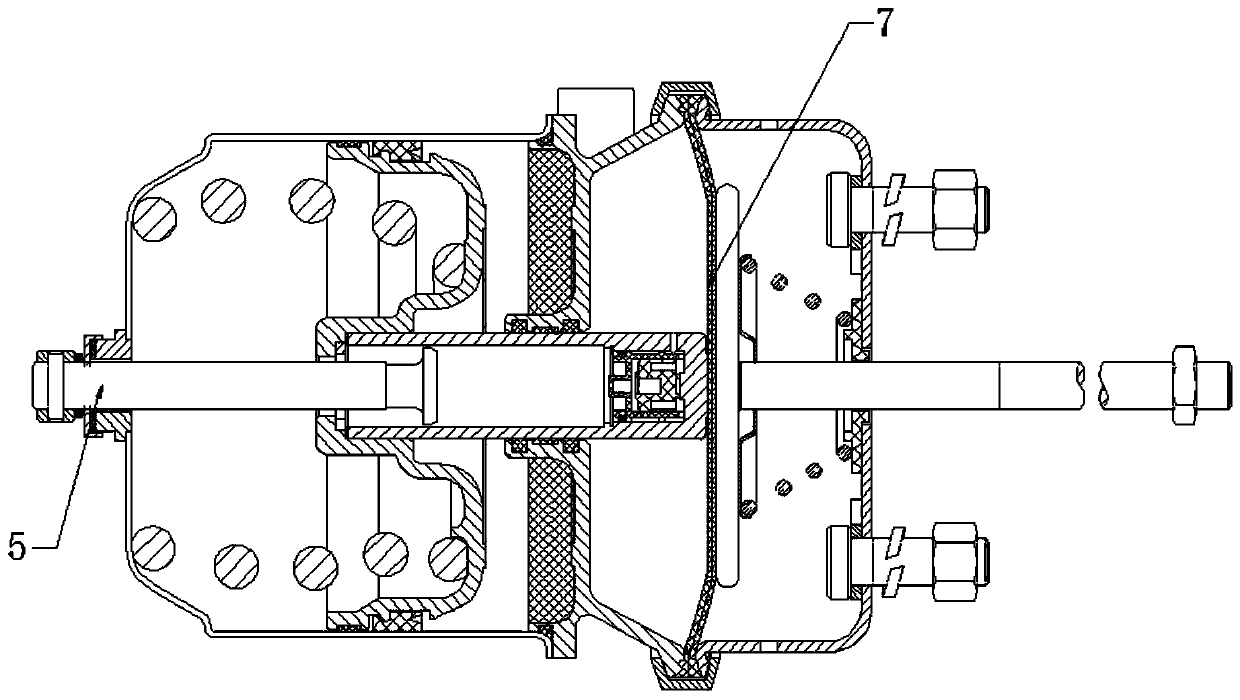
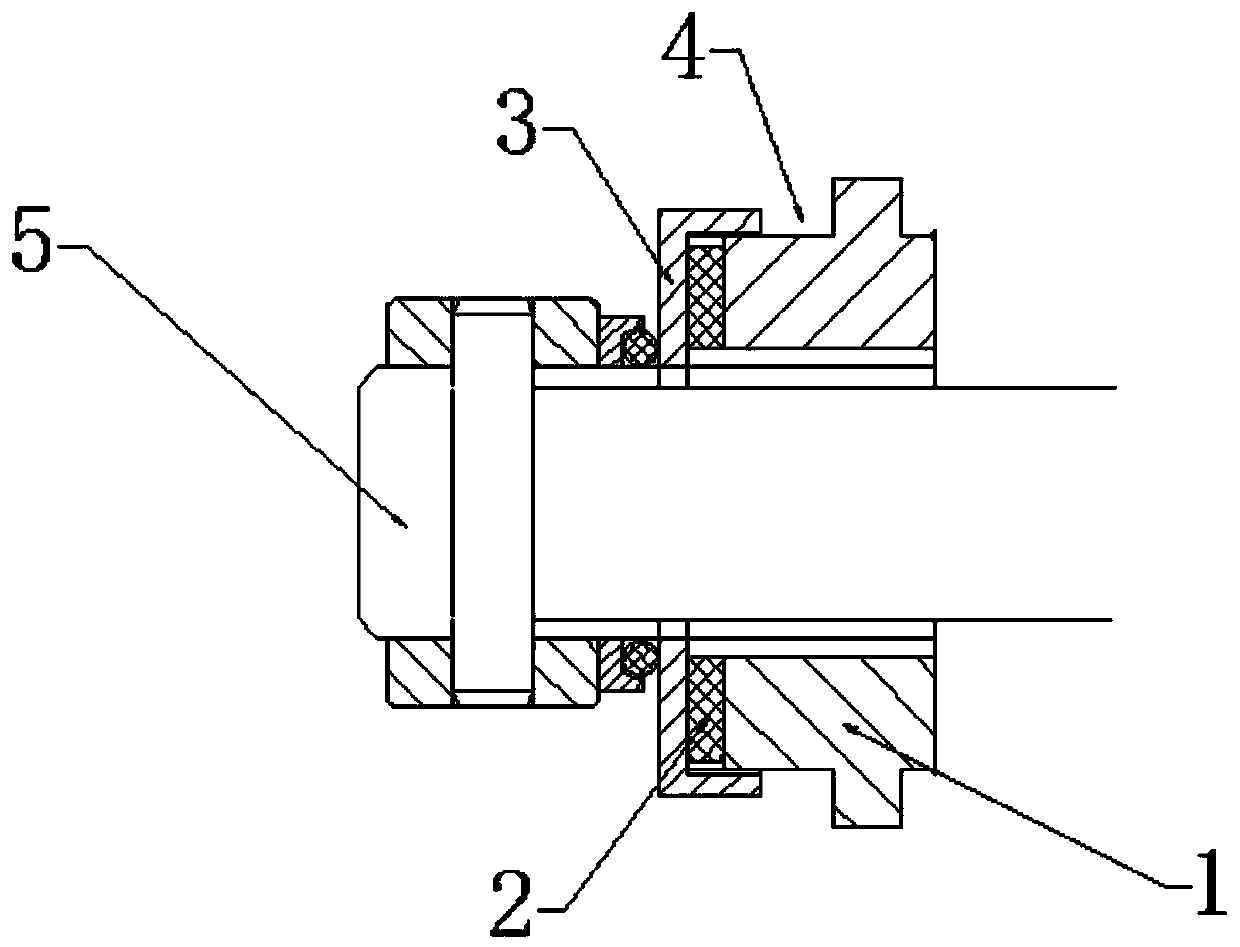
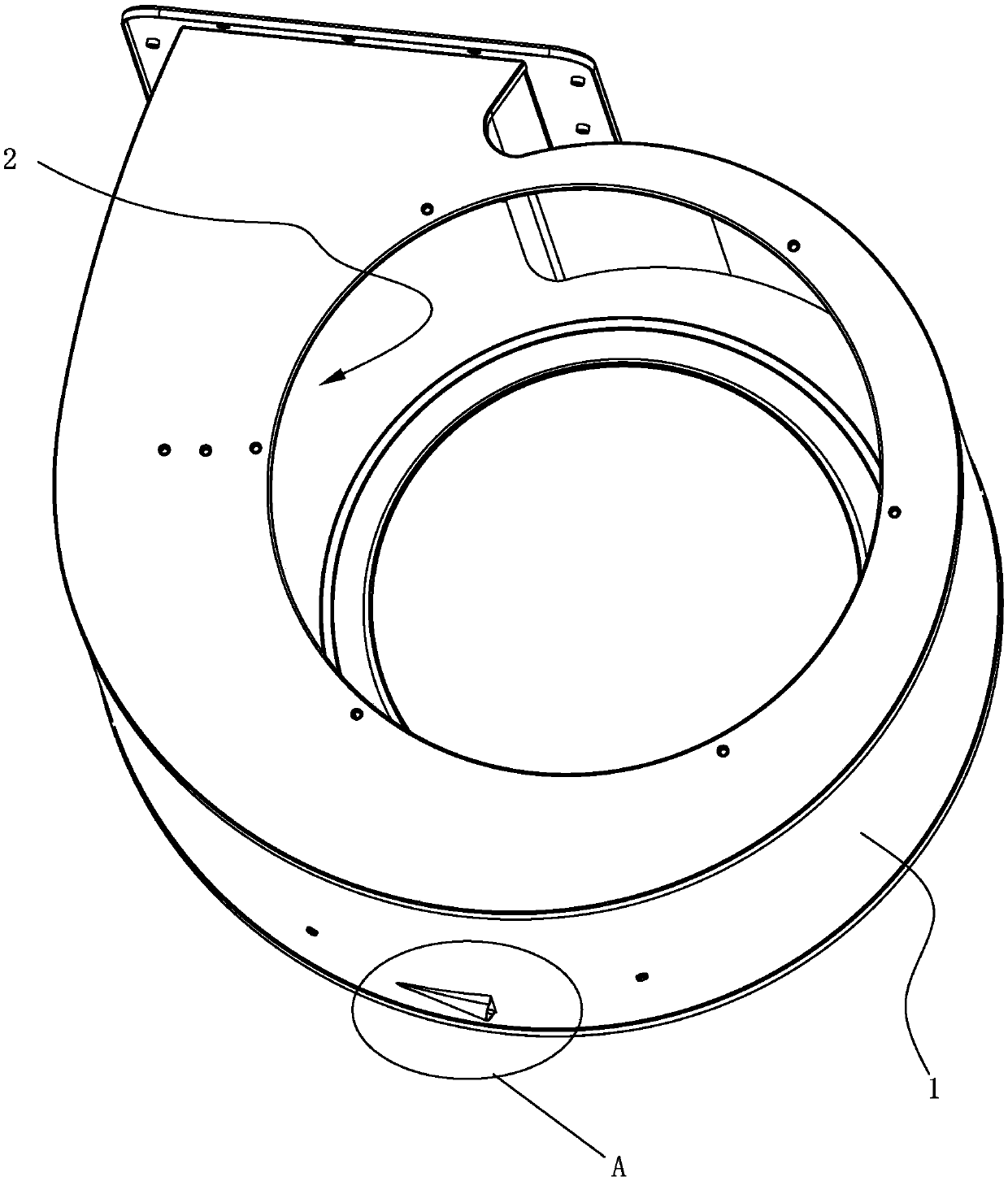
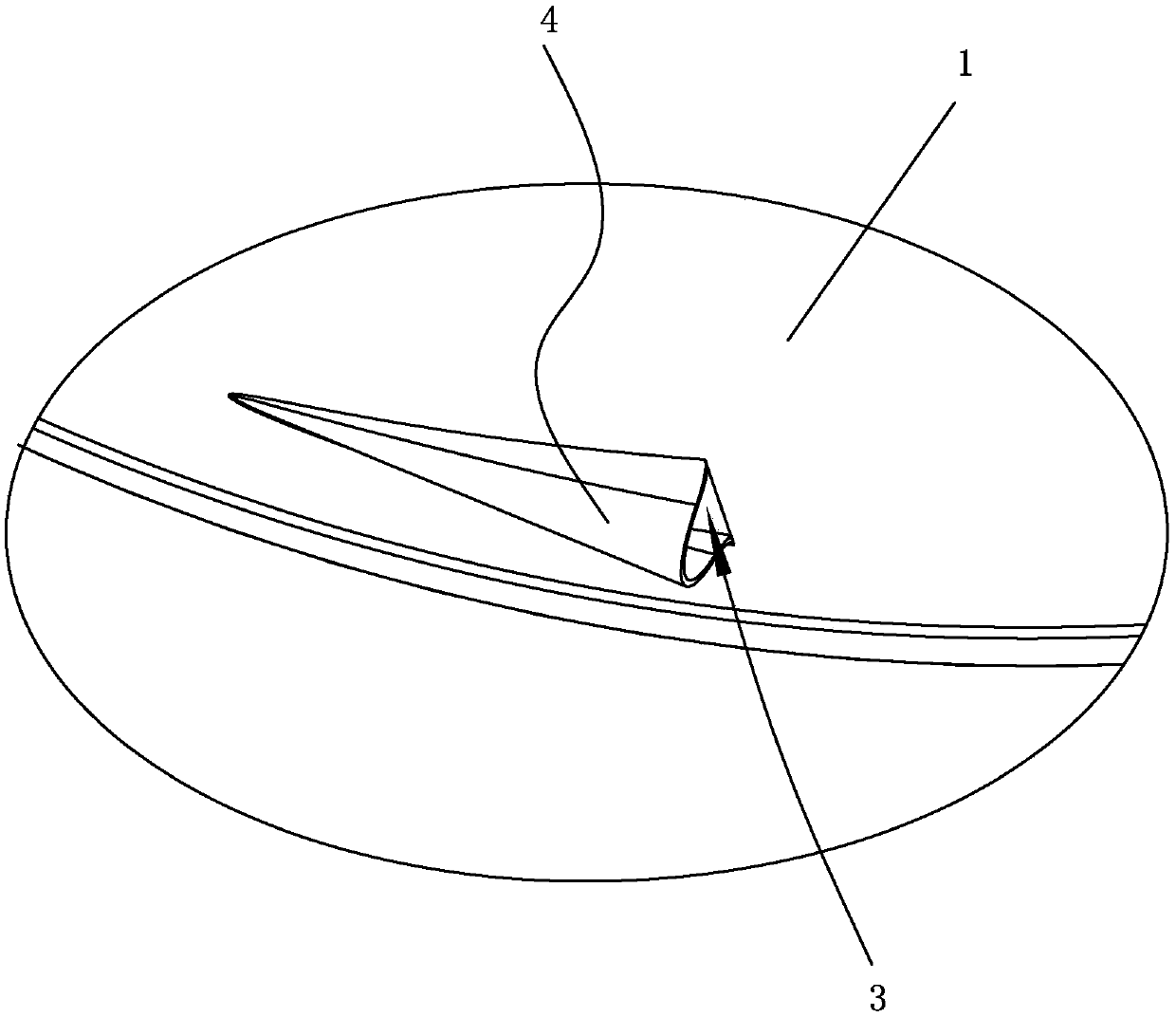
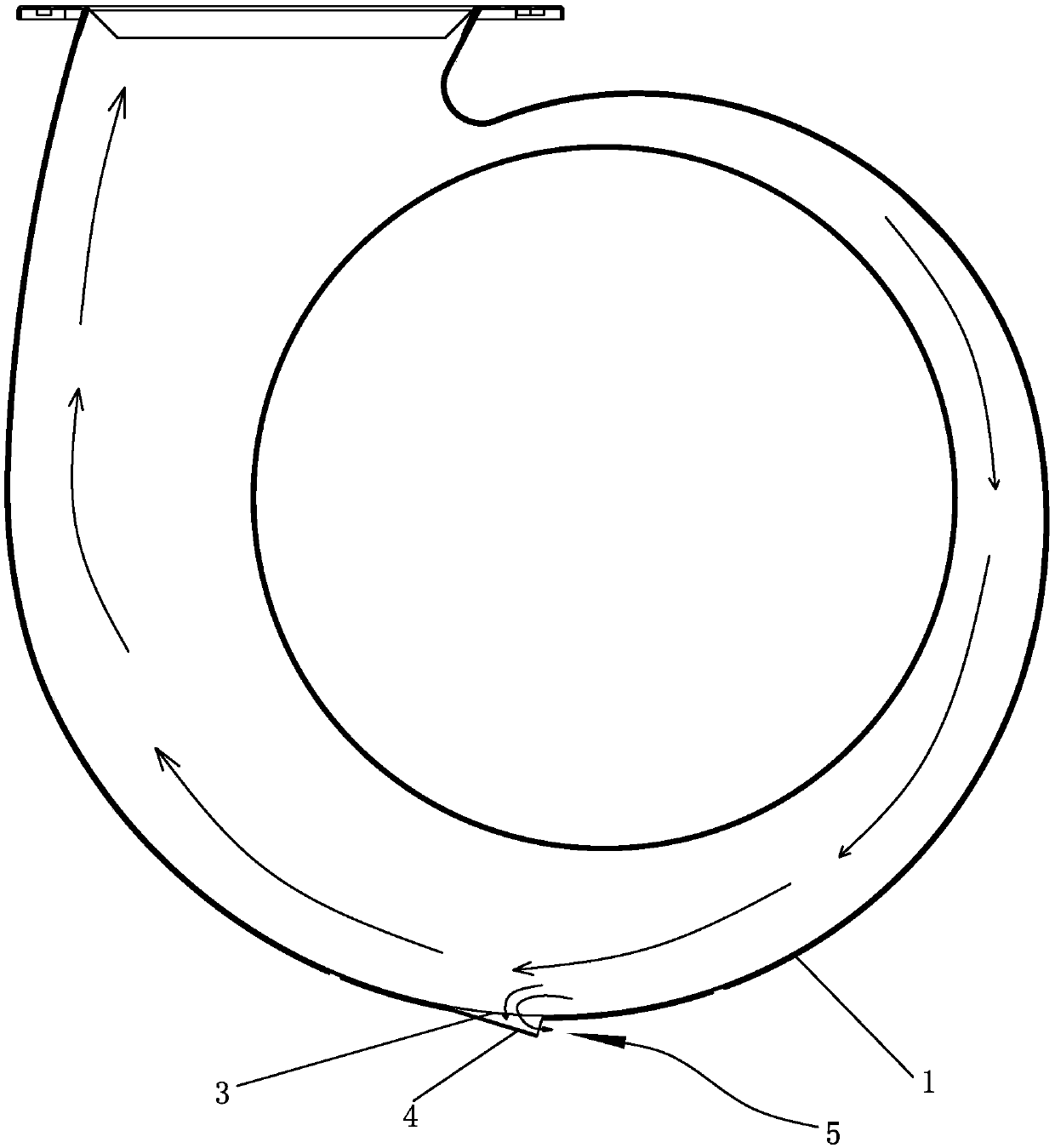
ActiveCN106402973AAvoid direct communicationReduce leakageDomestic stoves or rangesLighting and heating apparatusDischarge efficiencyFlue gas
The invention discloses a volute of a range hood with a noise reducing function. The volute of the range hood comprises a volute. An air flow channel is arranged in the volute, a leakage oil port communicating with the air flow channel is formed in the bottom of the volute, and a leakage oil nozzle is arranged in the bottom of the volute around the leakage oil port in a protruding manner. According to the volute disclosed by the invention, as the leakage oil nozzle is arranged in the bottom of the volute around the leakage oil port in the protruding manner to cover the leakage oil port, the air flow channel is prevented from directly communicating to the outer side of the volute, so that the leakage of flue gas from the leakage oil port is reduced, the noise generated at the leakage oil port is reduced, and the smoke discharge efficiency is improved.
Owner:VATTI CORP LTD
Internet of things node access authentication method, internet of things node access authentication system and internet of things master node
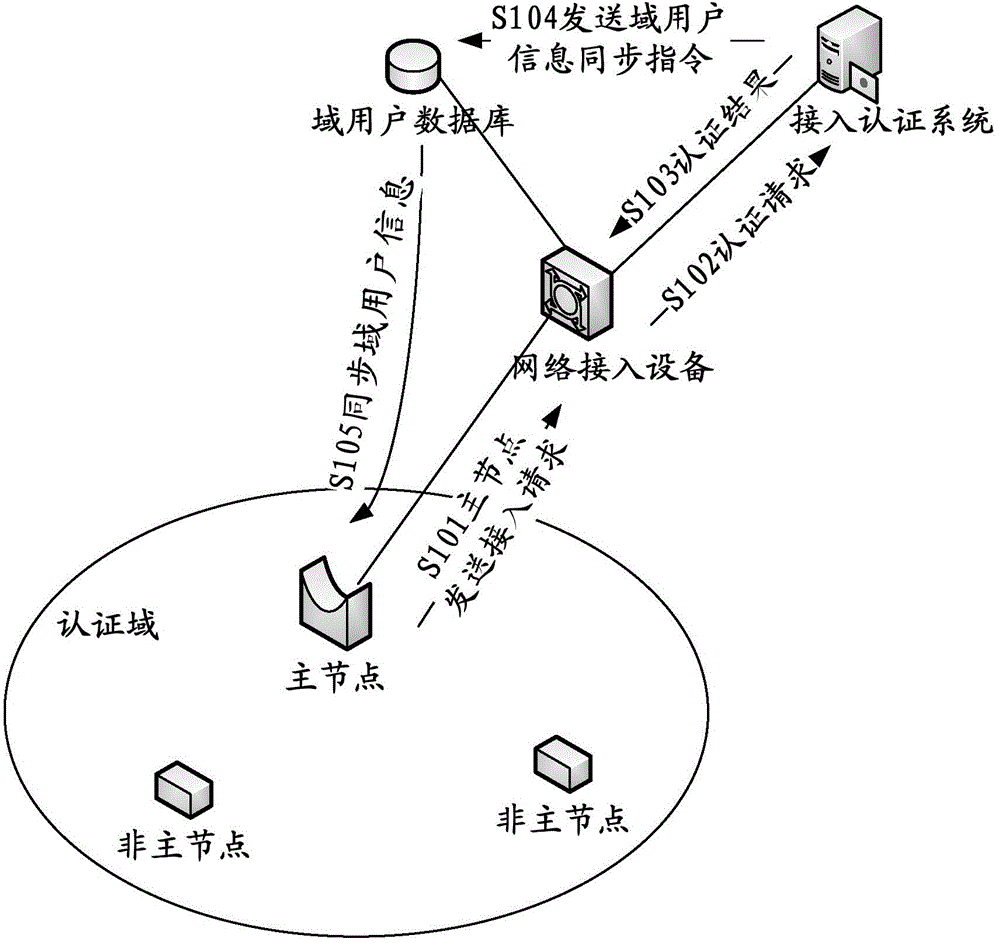
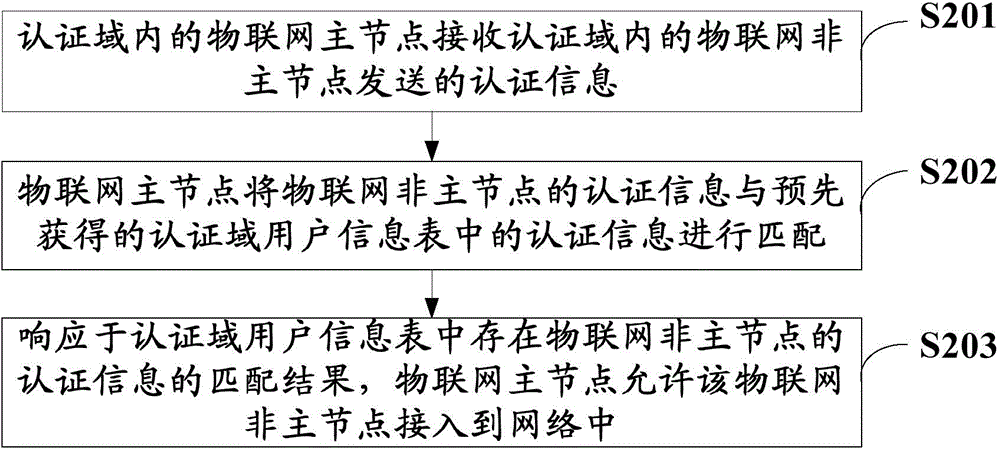
InactiveCN104811414ARelieve performance pressureAvoid the risk of network authentication stormTransmissionWeb authenticationA domain
The invention discloses an internet of things node access authentication method, an internet of things node access authentication system and an internet of things master node, and relates to the field of internet of things. According to the invention, an authentication domain is divided, a mode of domain division authentication is adopted, authentication information at a network side is synchronized to a domain master node, the domain master node carries out access authentication on other nodes in the authentication domain, the nodes are allowed to join to the network if passing the authentication, and the nodes in the domain are enabled to complete authentication in the authentication domain. On the one hand, a network authentication storm risk possibly caused by a large number of nodes can be avoided, and on the other hand, performance pressure of an access authentication system at the network side in processing authentication of the large number of nodes can be relieved.
Owner:CHINA TELECOM CORP LTD
Spring energy storage brake air chamber with function of preventing parking brake force attenuation
PendingCN110159677AIncrease parking brakeAvoid Pressure DifferencesDispersed particle filtrationBrake actuating mechanismsUltrasound attenuationRelay valve
The invention discloses a spring energy storage brake chamber with a function of preventing parking brake force attenuation. The spring energy storage brake chamber comprises a rear cylinder body anda pull rod bolt assembly which is in threaded connection with the rear cylinder body, and further comprises a ventilating and filtering device or a breathing channel with a filtering function, whereinthe ventilating and filtering device or the breathing channel with the filtering function communicates with the interior of the rear cylinder body. Therefore, the gas channel flow direction under which only gas exhausting can be performed but gas suction can not be performed through a relay valve and an adjustor during parking brake originally is changed thoroughly, so that a driving brake cavityand the rear cylinder body are effectively prevented from forming negative pressure, then the gas pressure balance of the brake chamber is realized, and the parking brake force is remarkably improved.
Owner:罗克华
A range hood volute with noise reduction function
ActiveCN106402973BAvoid direct communicationReduce leakageDomestic stoves or rangesLighting and heating apparatusDischarge efficiencyEngineering
The invention discloses a volute of a range hood with a noise reducing function. The volute of the range hood comprises a volute. An air flow channel is arranged in the volute, a leakage oil port communicating with the air flow channel is formed in the bottom of the volute, and a leakage oil nozzle is arranged in the bottom of the volute around the leakage oil port in a protruding manner. According to the volute disclosed by the invention, as the leakage oil nozzle is arranged in the bottom of the volute around the leakage oil port in the protruding manner to cover the leakage oil port, the air flow channel is prevented from directly communicating to the outer side of the volute, so that the leakage of flue gas from the leakage oil port is reduced, the noise generated at the leakage oil port is reduced, and the smoke discharge efficiency is improved.
Owner:VATTI CORP LTD
Authentication of remote host via closed ports
InactiveUS8826014B2Avoid direct communicationKey distribution for secure communicationDigital data processing detailsAuthenticationClient
A method, system and apparatus for authenticating a communication request sent from a client computing device. The communication request is initially blocked by a firewall preventing delivery to a server. A first logging event corresponding to the communication request is created. The communication request and the logging event are stored in a firewall. The server is notified of the first logging event. The communication request corresponding to the first logging event is authenticated. A port in the firewall is enabled if the communication request is authenticated.
Owner:LENOVO GLOBAL TECH INT LTD
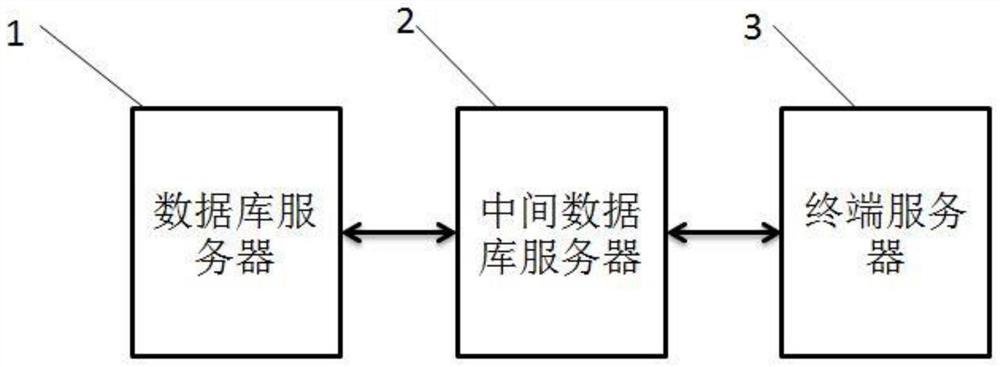
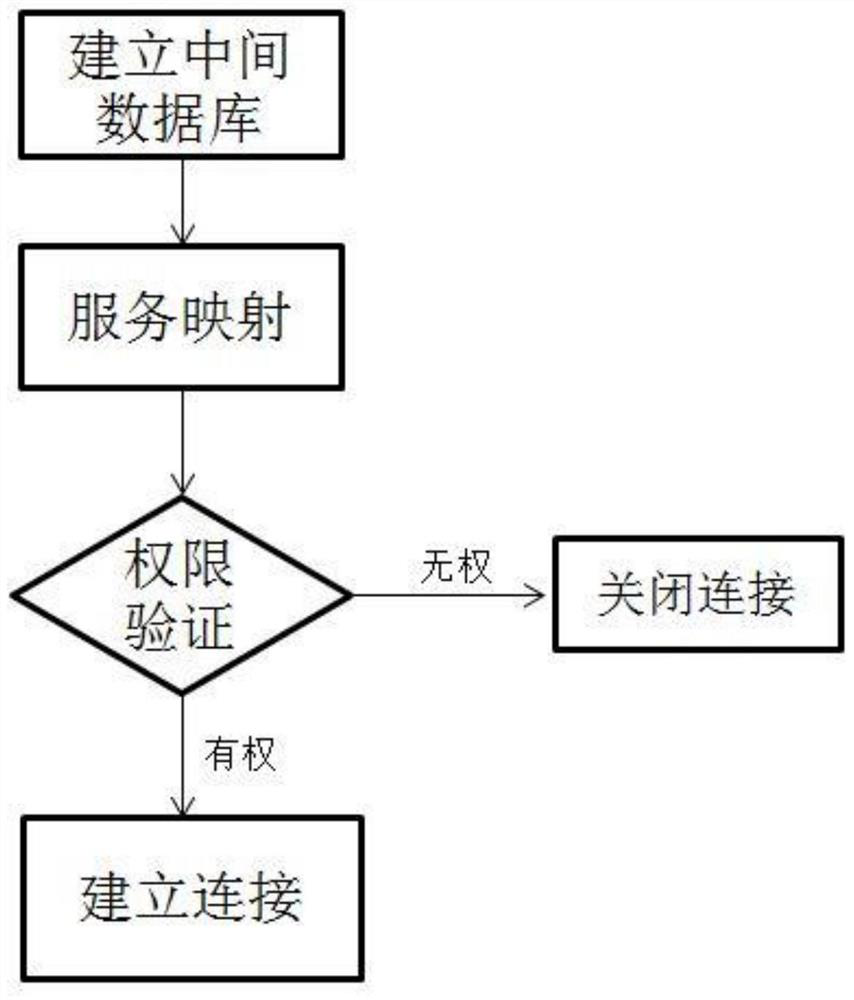
Power distribution network data protection system and method based on intermediate database
PendingCN114531266AAvoid attackAvoid direct communicationSecuring communicationInformation technology support systemTerminal serverDatabase server
The invention discloses a power distribution network data protection system based on an intermediate database and a method thereof. In order to overcome the problem of low security caused by exposure in a network during communication of a power distribution network in the prior art, an intermediate database server is adopted, a real database server is hidden, and a terminal server communicates with the real server through the intermediate database server, so that the security of the power distribution network is improved. The intermediate server performs authority verification on the communication request of the terminal server, closes an illegal communication request, and sets a double-layer key to prevent a real database server from being attacked; even if the intermediate database server is attacked, the attacker can only obtain the limited authority and cannot threaten the real database server, so that the security of the distribution network data is greatly improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD JIAXING POWER SUPPLY CO
A buzzer structure with composite audio for easy installation
ActiveCN110400556BScientific and reasonable structureEasy to useSound producing devicesMechanical engineeringAudio frequency
The invention discloses a buzzer structure with composite audio for easy installation, which includes a shell, a piezoelectric buzzer and a resonance chamber. A piezoelectric buzzer is installed inside the shell, and the top of the piezoelectric buzzer is A resonance chamber is provided, and an outer ring is installed at the bottom of the shell. The structure of the present invention is scientific and reasonable, and it is safe and convenient to use. The outer ring is provided, and through the functions of chute, groove, slider and fixed block, it is convenient to According to the situation, slide the slider, adjust the position of the fixed block, and cooperate with the function of the connecting screw and the lock nut to fix its position, so that the buzzer can be better installed and fixed. Through the function of the movable shaft, it is convenient to adjust according to the actual needs. The fixed block is folded and hidden, which is easy to operate and easy to install. Through the function of the through hole, the inner ring and the receiving hole, the receiving hole on the side of the inner ring is overlapped with the through hole by squeezing the bump, so that the air at the bottom of the buzzer Circulation, improve the heat dissipation effect of the buzzer.
Owner:新沂市承翔电子有限公司
Pipeline valve for closing and/or switching
ActiveUS20200318745A1Easy to operateAvoid direct communicationOperating means/releasing devices for valvesMultiple way valvesWater stopWater flow
The present disclosure provides an adjustable pipeline valve for changing and / or switching the discharge water flow path. The pipeline valve includes: a valve body; an inlet in communication with the valve body; and at least one outlet in communication with the valve body. The pipeline valve further includes: a water stopping member located within a chamber of the valve body and preventing direct communication between the inlet and the at least one outlet; a plugging assembly located in at least one receiving hole in a part of the valve body, the at least one receiving hole being in one-to-one correspondence with at least one water passing hole in the water stopping member; and a switching assembly 17 configured to allow the plugging assembly to block a corresponding water passing hole by a rotation of the switching assembly 17 to switch the communication between the inlet and the at least one outlet.
Owner:XIAMEN LOTA INT CO LTD
Vehicle sharing method and system
ActiveCN107650863BAvoid direct communicationImprove securityAnti-theft devicesIndividual entry/exit registersComputer scienceAuthorization
The present invention relates to a vehicle sharing method and system, and discloses a vehicle sharing method comprising: a permission request, including in response to an authorization request for using a vehicle sent by a vehicle user terminal, a cloud server forwards the authorization request to the vehicle owner terminal and receives the authorization request from the vehicle owner The authorization information sent by the terminal; and the vehicle request, including responding to the first vehicle control instruction sent by the vehicle user terminal, the cloud server combines the authorization information to verify the identity of the vehicle user and the first vehicle control instruction, and After the verification is passed, a second vehicle control instruction corresponding to the first vehicle control instruction is sent to a corresponding vehicle so that the vehicle executes the second vehicle control instruction. By adopting the method and system, the vehicle can be controlled without carrying a key, and at the same time, the risk of the transmission signal being intercepted at a short distance is avoided, and the safety of using the vehicle and user experience are improved.
Owner:CONTINENTAL HOLDING CHINA CO LTD
Method and device for preventing unfamiliar communication account in intelligent terminal
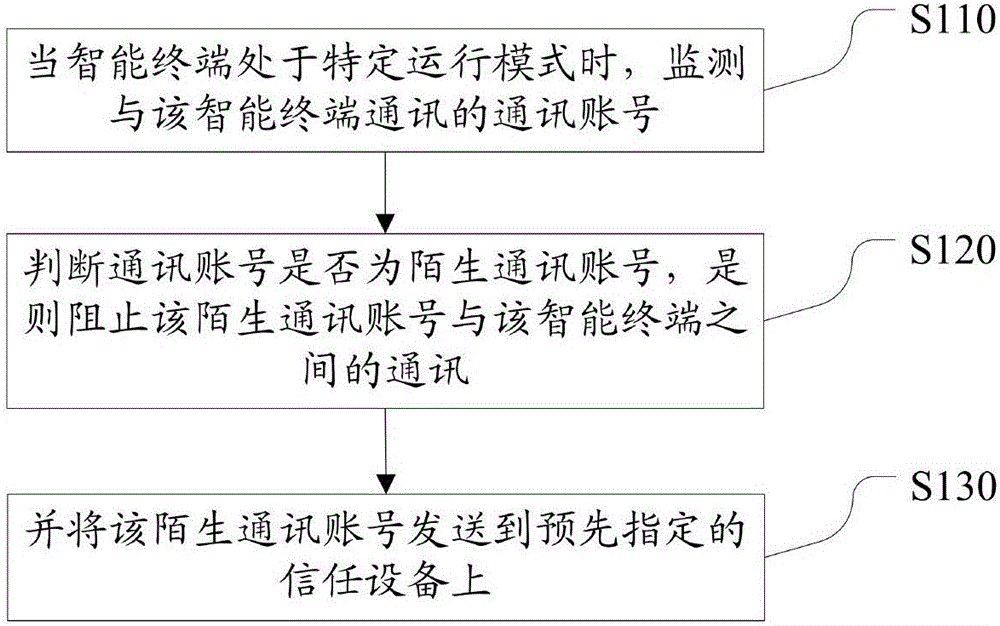
InactiveCN106656968ACommunication blockProtection securitySubstation equipmentSpeech recognitionMental healthOperation mode
The invention discloses a method and device for preventing an unfamiliar communication account in an intelligent terminal. The method comprises the following steps: when the intelligent terminal is in a specific operation mode, monitoring a communication account communicated with the intelligent terminal; judging whether the communication account is an unfamiliar communication account, and if so, preventing communication between the unfamiliar communication account and the intelligent terminal; and sending the unfamiliar communication account to a pre-specified trust device. The technical scheme prevents fraud behaviors in a mode of preventing the unfamiliar communication account, thereby protecting property safety of users, especially groups of the elderly and children and the like, who lack of self-protection awareness and social experience. The method and device can prevent direct communication between a fraud and the users, thereby preventing fraud cases, protecting property safety and protecting physical and mental health of the elderly and children.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com