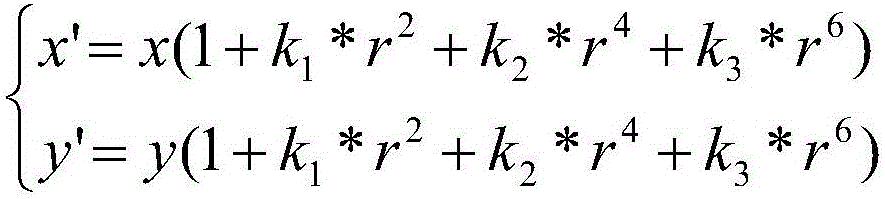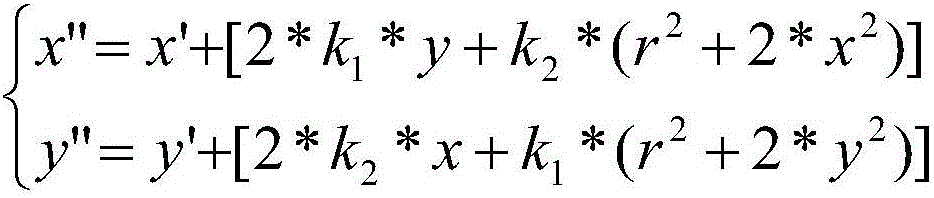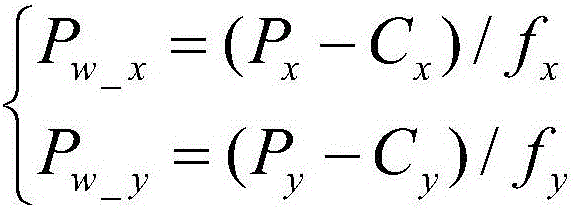Patents
Literature
51results about How to "Improve initialization speed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
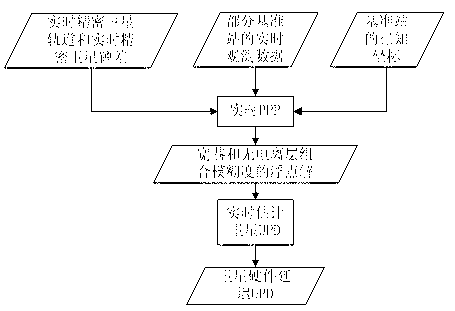
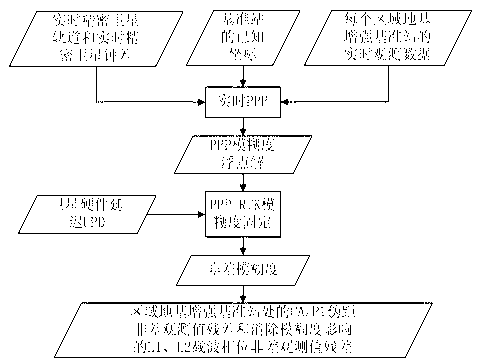
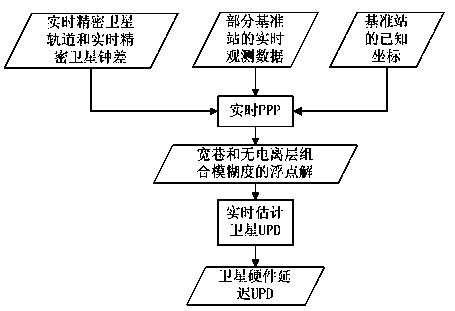
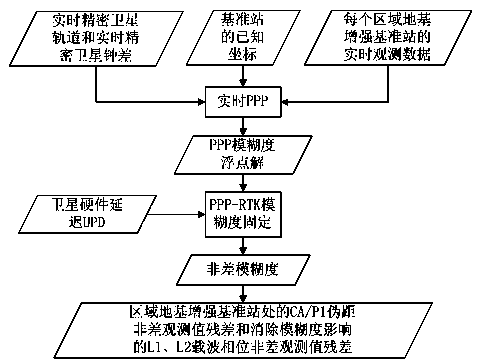
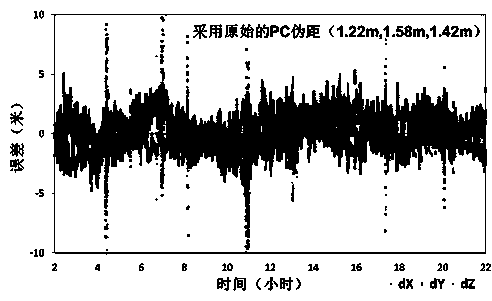
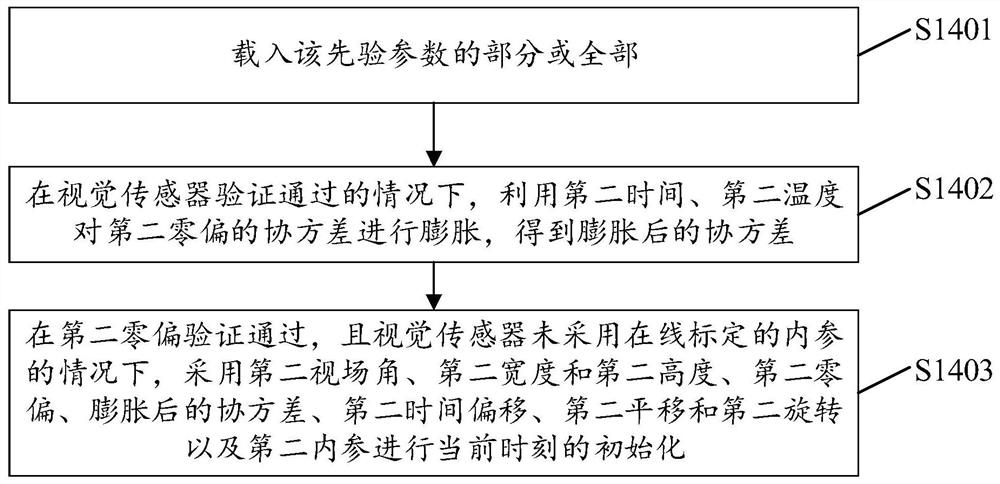
Single-epoch fixing method for enhancing PPP-RTK ambiguity of regional foundation
InactiveCN103176188AReduce ambiguity convergence timeImprove initialization speedSatellite radio beaconingAmbiguityIonization
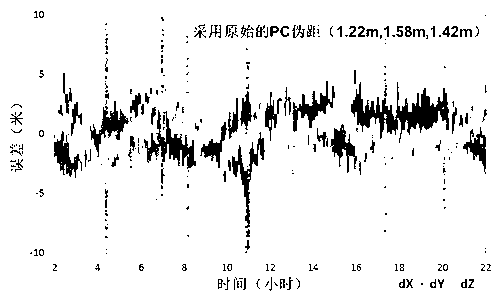
The invention provides a single-epoch fixing method for enhancing PPP-RTK ambiguity of regional foundation. The single-epoch fixing method comprises the following steps of: improving the ambiguity convergence time of a PPP-RTK method by carrying out optimizing ordering on the fixing feasibility of single-difference ambiguity between alternative satellites, respectively modeling for an observed value residual error of a CA / P1 pseudo-range and observed value residual errors of L1 and L2 phase positions by adopting a single-reference station processing mode based on a PPP-RTK technique, and realizing the single-epoch fixing of combined ambiguity of an ionization-free layer through step-by-step solving of the ambiguity in consideration of a linear constraint relationship between the high precision of a pseudo-range observed value, long wavelength of a wide-lane observed value, wide-lane ambiguity and L1 ambiguity after a user refines the models, thus the determination time of the PPP ambiguity is minimized, and the working efficiency of precisely locating the user is improved to the maximum degree.
Owner:WUHAN UNIV
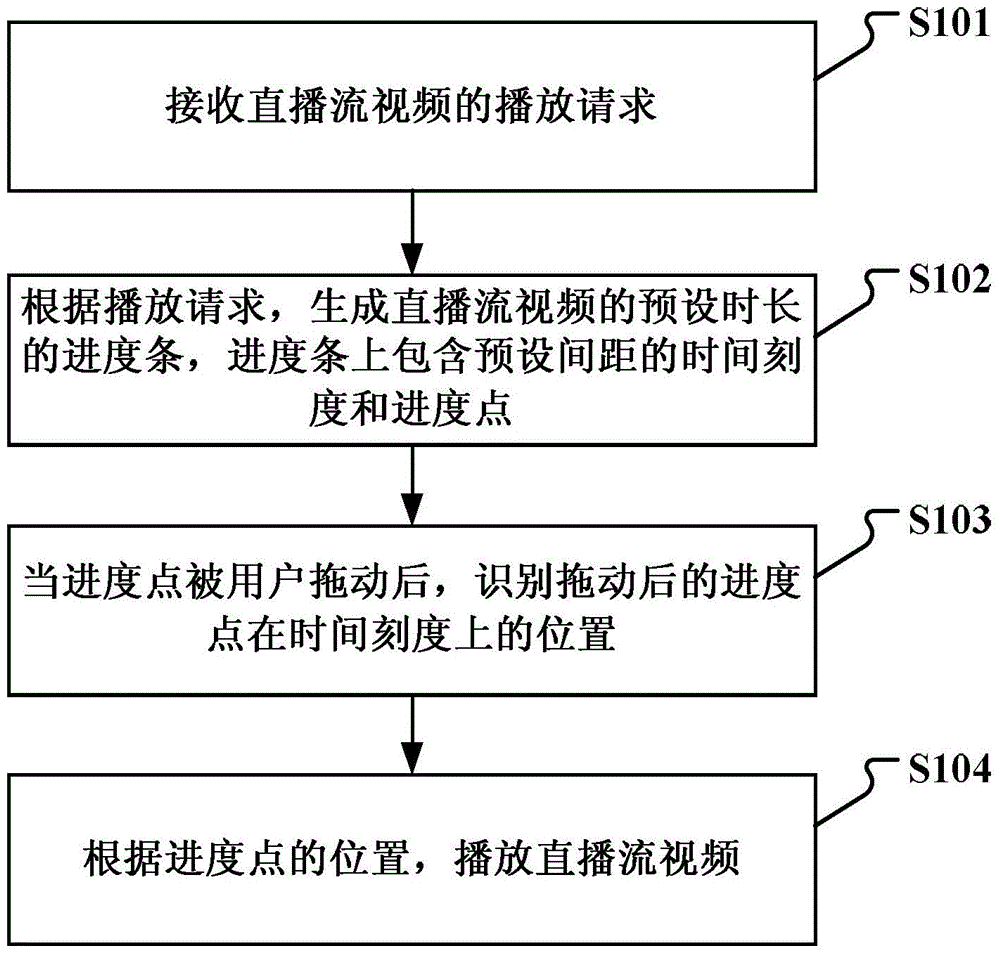
Method and device for processing live broadcast stream
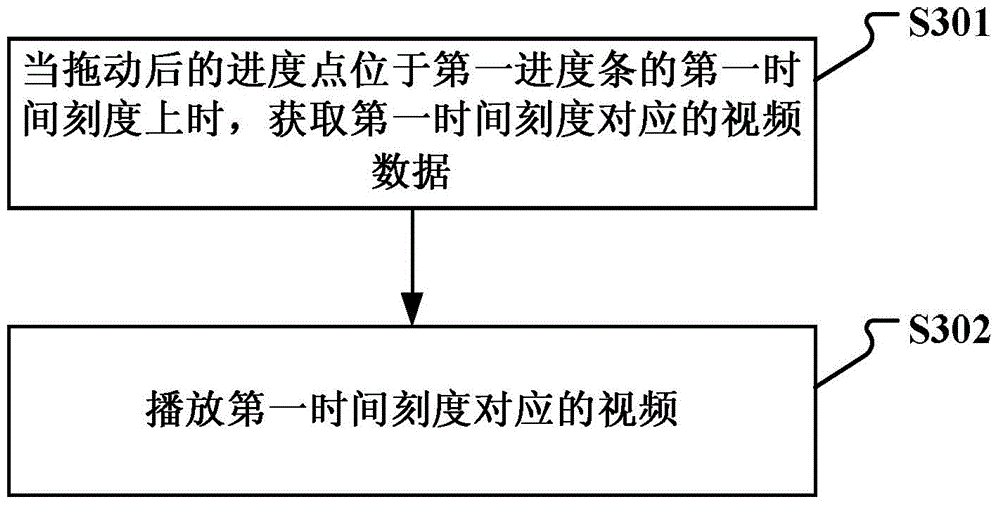
InactiveCN104105004AEasy playback controlsImprove initialization speedSelective content distributionProgress barOn demand
The invention discloses a method and a device for processing a live broadcast stream, which are used for the on-demand watching of a user for a live broadcast stream video. The method comprises the following steps of: receiving the play request of the live broadcast stream video; generating a progress bar with a preset time length, of the live broadcast stream video, time scales with a preset distance, and a progress point being contained on the progress bar; after the progress point is dragged by the user, identifying the position of the dragged progress point on the time scales; playing the live broadcast stream video according to the position. The progress bar is generated on the live broadcast stream video, and the user selects the play time of the live broadcast stream video by clicking the progress bar, thus improving the experience degree of the user, and facilitating to control the play of the live broadcast stream video; meanwhile, the video is loaded according to the dragging action of the user on the progress point, and the video at one time point can only be loaded once, thus the loading speed is increased, and moreover, the initialization speed of the video is correspondingly increased.
Owner:上海天脉聚源文化传媒有限公司
Feature based monocular SLAM (Simultaneous Localization and Mapping) quick initialization method
ActiveCN106570913ASmall amount of calculationImprove initialization speed2D-image generationMonocular slamDepth of field
The invention relates to a feature based monocular SLAM (Simultaneous Localization and Mapping) quick initialization method, which comprises the steps of 1) starting SLAM, acquiring a first frame picture and extracting ORB feature points P(x, y) for the picture; 2) performing image distortion removing on the ORB feature points P(x, y); 3) performing normalization on image coordinates of the distortion removed feature points in the step 2); 4) building a random depth for each feature point in the step 3); 5) combining results of the step 3) and the step 4) so as to build map points corresponding to the feature points, and acquiring an initial map; and 6) performing optimization on a matching result of subsequent adjacent frames and an existing map, and executing the normal feature SLAM process for each next newly increased frame so as to continuously adjust and expand the map and realize continuous tracking for SLAM. The feature based monocular SLAM quick initialization method provided by the invention is high in speed, small in calculation amount and not restricted by the depth of field.
Owner:上海玄彩美科网络科技有限公司
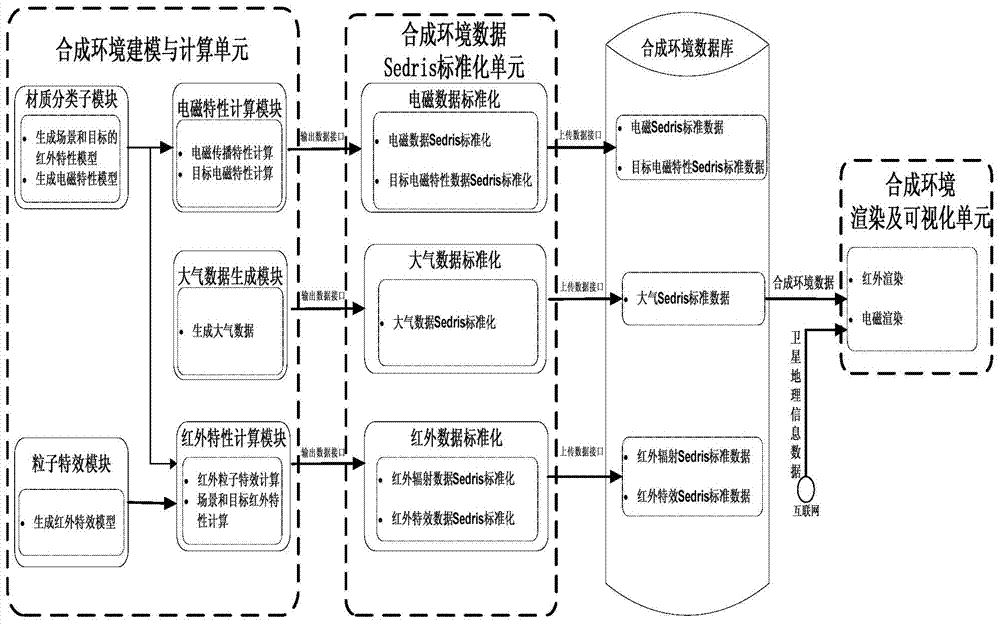
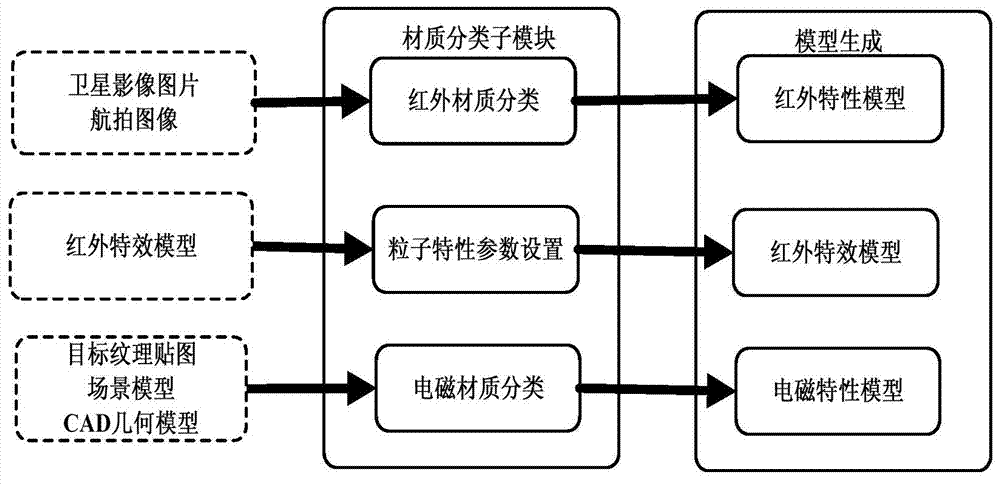
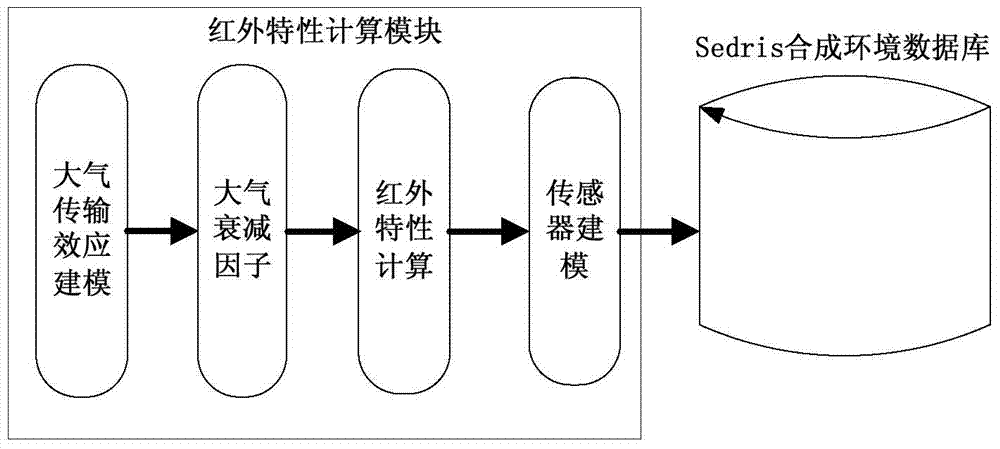
Multi-spectral-coverage synthetic environment simulation system
ActiveCN103593514AAchieve standardizationRealize the use effectSpecial data processing applicationsOperational effectivenessWeapon system
A multi-spectral-coverage synthetic environment simulation system comprises a synthetic environment modeling and calculating unit, a synthetic environment data Sedris standardization unit and a synthetic environment rendering and visualization unit. The defects in the prior art are overcome, and the problems that in a simulation test, the complex and true environment is difficult to simulate, and meanwhile accurate and effective environment support data are insufficient, so that influences on the test by environmental factors are not sufficiently embodied are solved. modeling, SEDRIS standardization and visualization of the synthetic environment of atmosphere, infrared, electromagnetism and others are achieved, standardized synthetic environment data are provided for simulation application, and support is provided for operational effectiveness evaluation of a weapon system.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
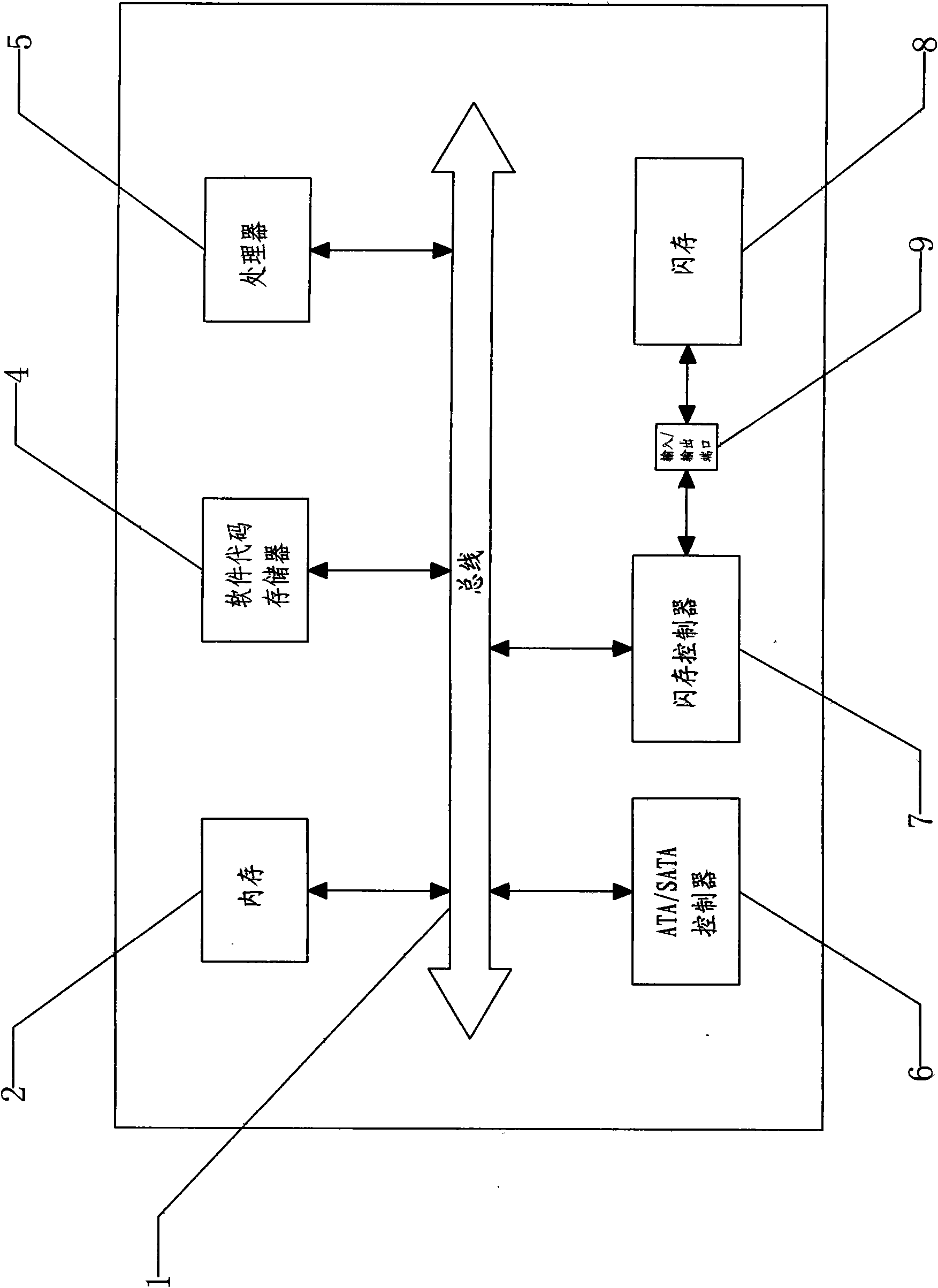
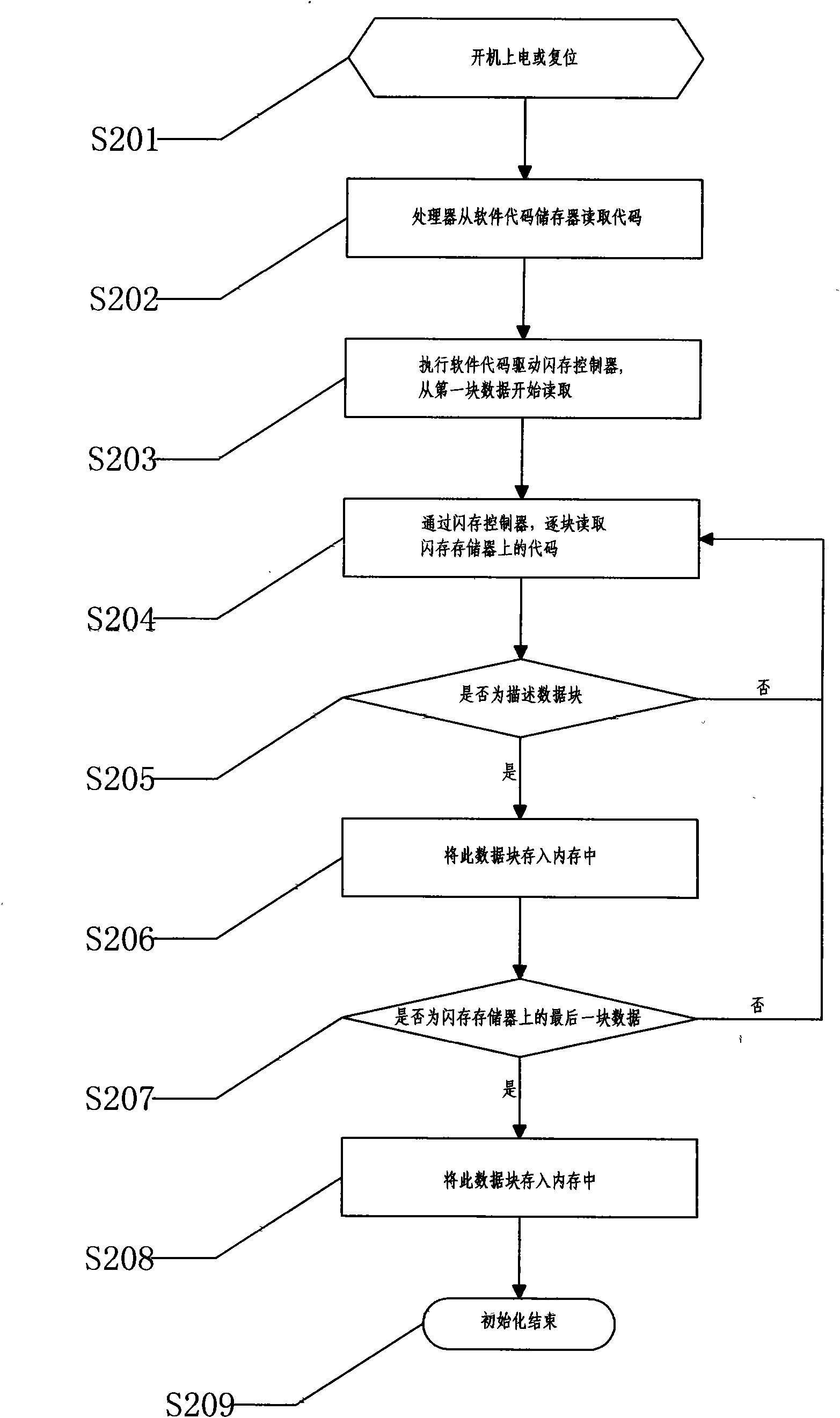
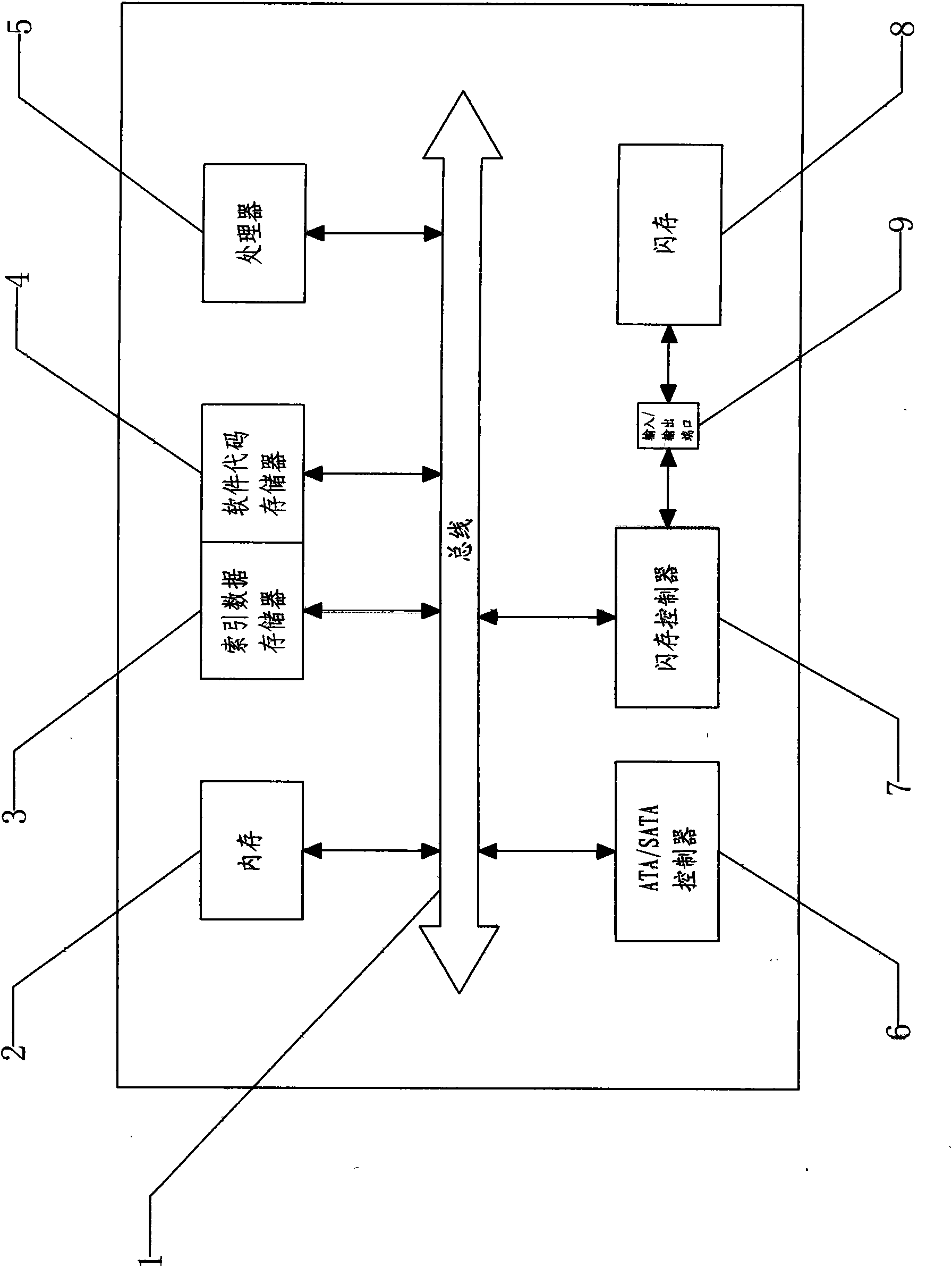
Structure of solid state disk and method for accelerating initialization thereof
InactiveCN101676872AImprove initialization speedExtended service lifeInput/output to record carriersDigital storageMemory addressAccelerated aging
The invention relates to a structure of a solid state disk, which comprises a bus, a memory, a software code memory, a processor, an ATA / SATA controller and a flash controller, wherein the memory, thesoftware code memory, the processor, the ATA / SATA controller and the flash controller are in parallel reversible connection on the bus; and the bus is in reversible connection with an index data memory. The method for accelerating initialization of the solid state disk comprises the following steps: by the index data memory on the solid state disk, enabling the processor to directly acquire the memory address of each description data block in a flash memory; and directly storing the data blocks on the flash memory into the memory through the flash controller, thereby finishing the initialization acceleration of the solid state disk. The invention has the advantages of greatly increasing the initialization speed of the solid state disk, reducing the waiting time of users and releasing moreprocessor resources, thereby increasing the writing efficiency, inhibiting the accelerated ageing of address blocks to a great extent, avoiding the failure of the address blocks, prolonging the service life of the solid state disk, meeting people's use requirements and being favorable for wide application of products.
Owner:刘杰
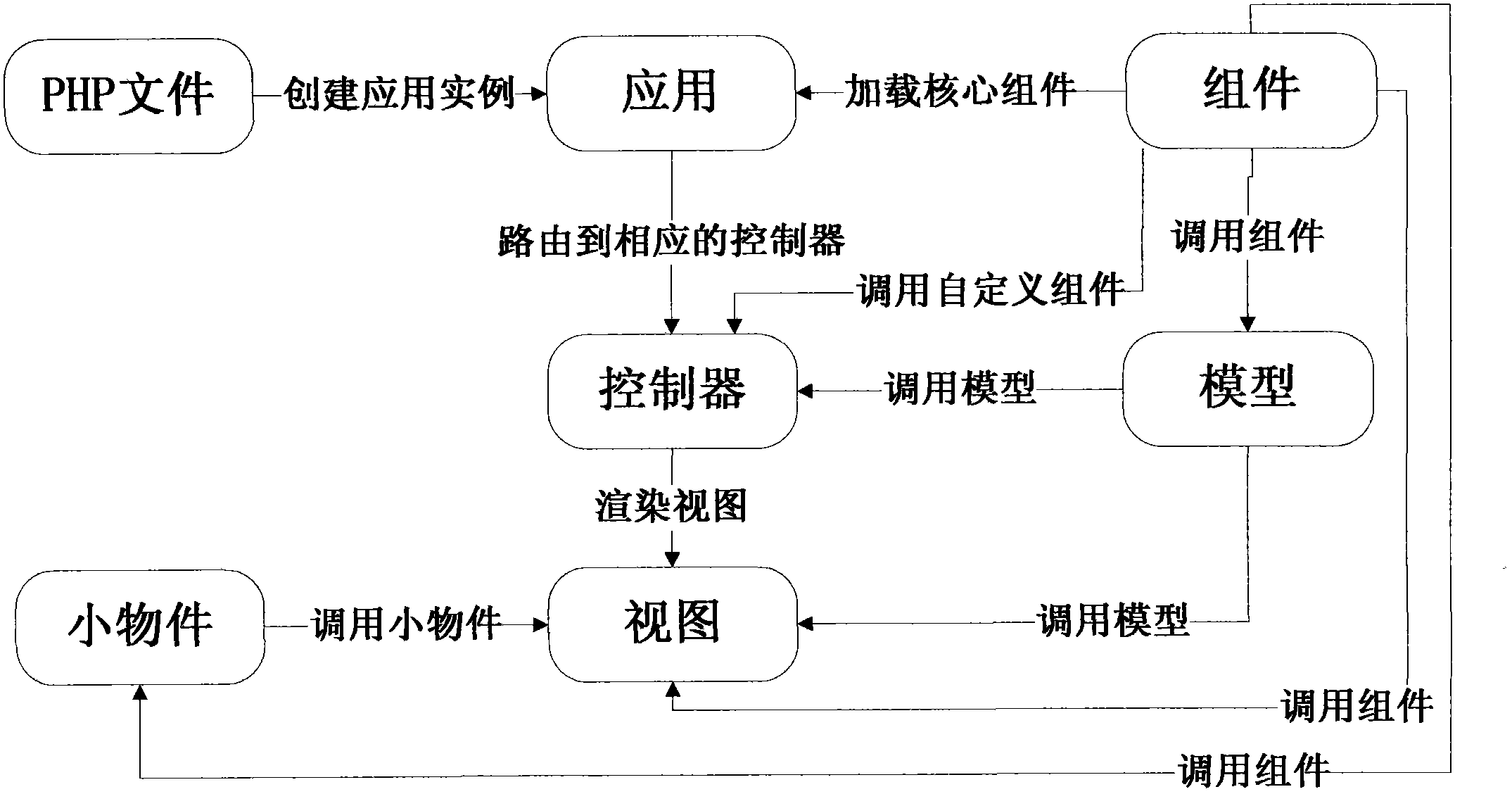
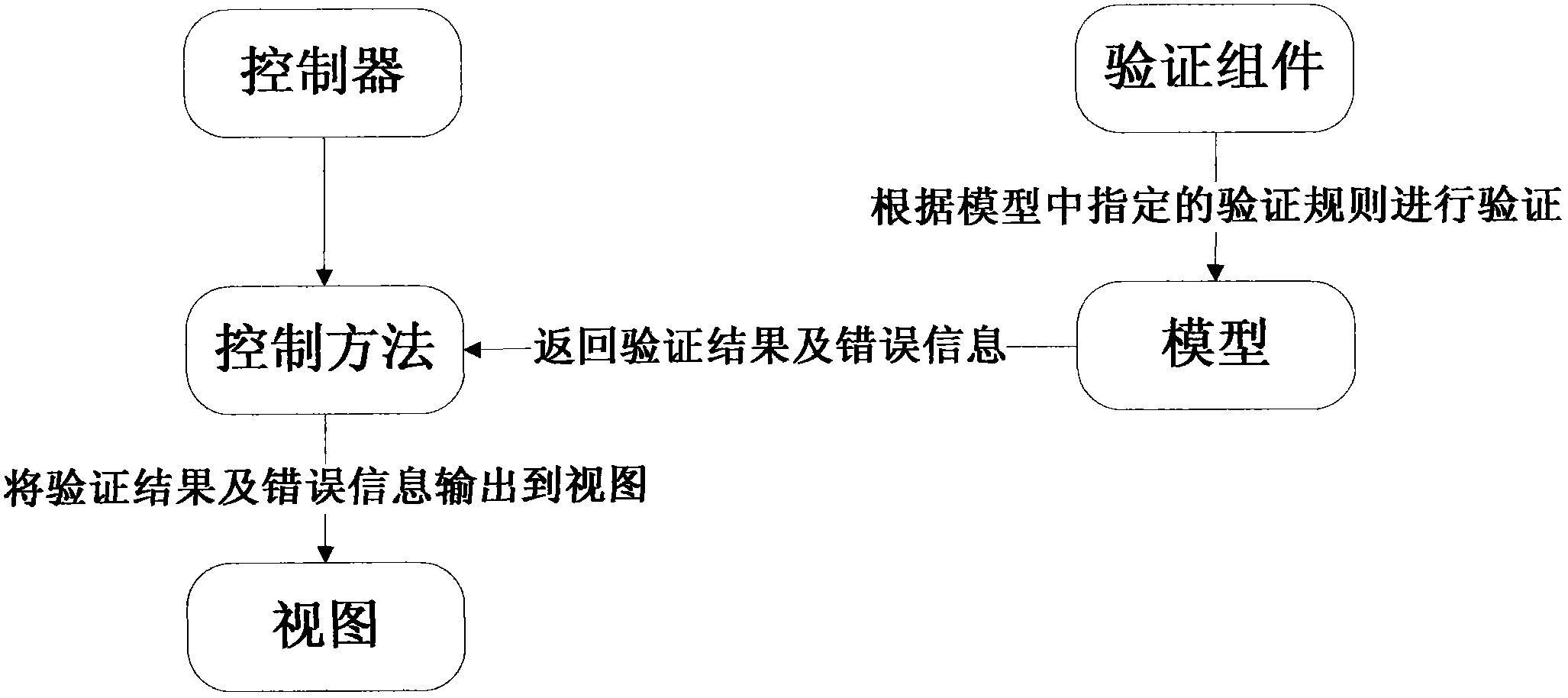
PHP developing framework based on assemblies
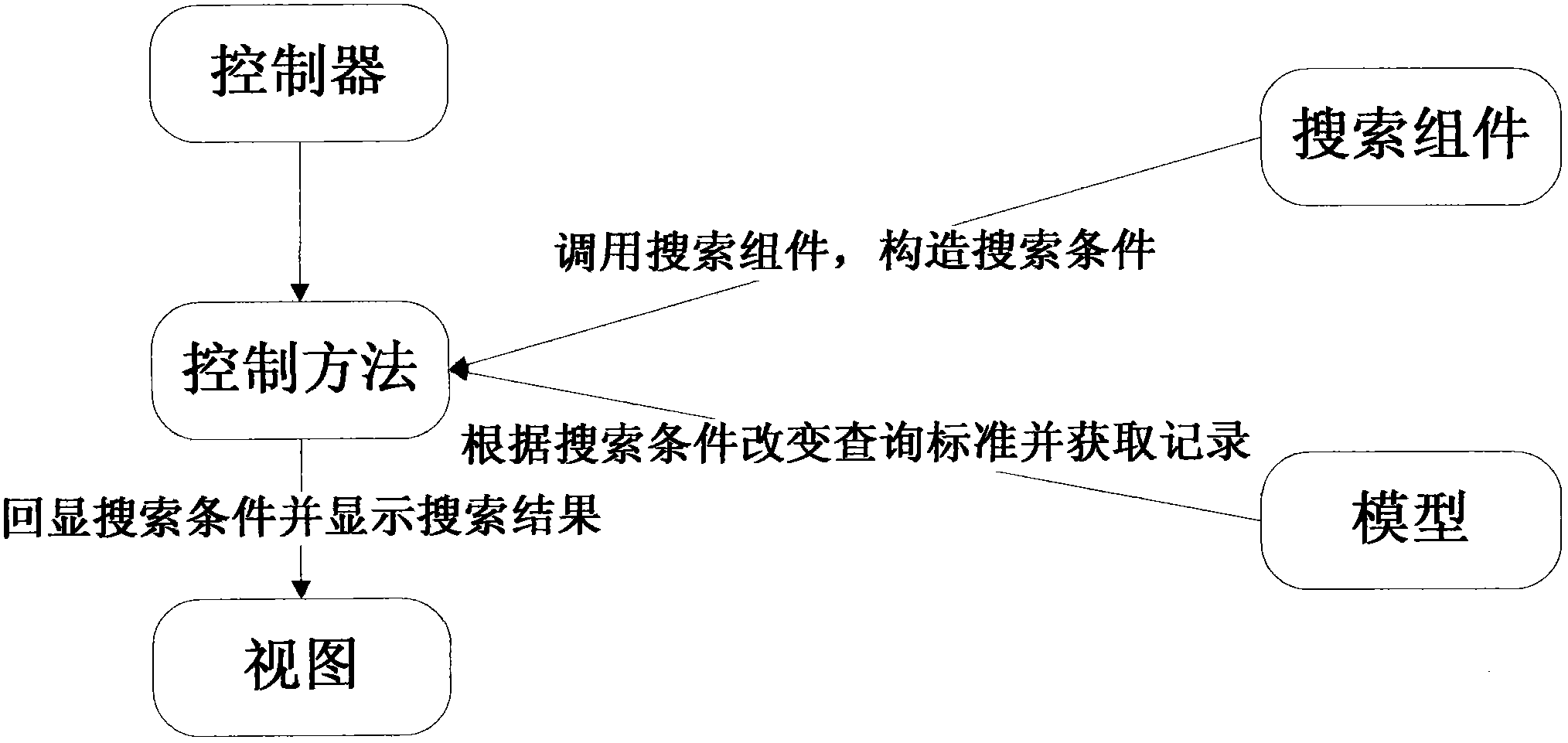
InactiveCN103513966AImprove operational efficiencyPowerfulSpecific program execution arrangementsComputer scienceBusiness logic
The invention discloses a PHP developing framework based on assemblies. An MVC mode is adopted for the framework. The framework comprises a controller, a model and a view, wherein the model is responsible for acquiring data, the view is responsible for data presentation, and the controller is responsible for service logic. By calling the model and processing the data, the data are sent into the view to undergo rendering. The framework is characterized by further comprising the assemblies which are used for developing extended functions, and the assemblies are respectively connected with the controller, the model and the view and used for performing loading when the functions are called. The developing mode based on the assemblies is adopted for the framework, the assemblies are loaded according to requirements, and operation efficiency is high; besides, all the extension can be packaged in a mode of the assemblies, and the framework is convenient to extend and flexible in use.
Owner:BEIJING LIMEI TECH
Multi-CPU (Central Processing Unit)system starting method and module based on PCI/PCIe (Peripheral Component Interconnect/Peripheral Component Interconnect Express) bus
ActiveCN101876911AImprove initialization speedFast startupProgram initiation/switchingProgram loading/initiatingMemory mapAutomatic control
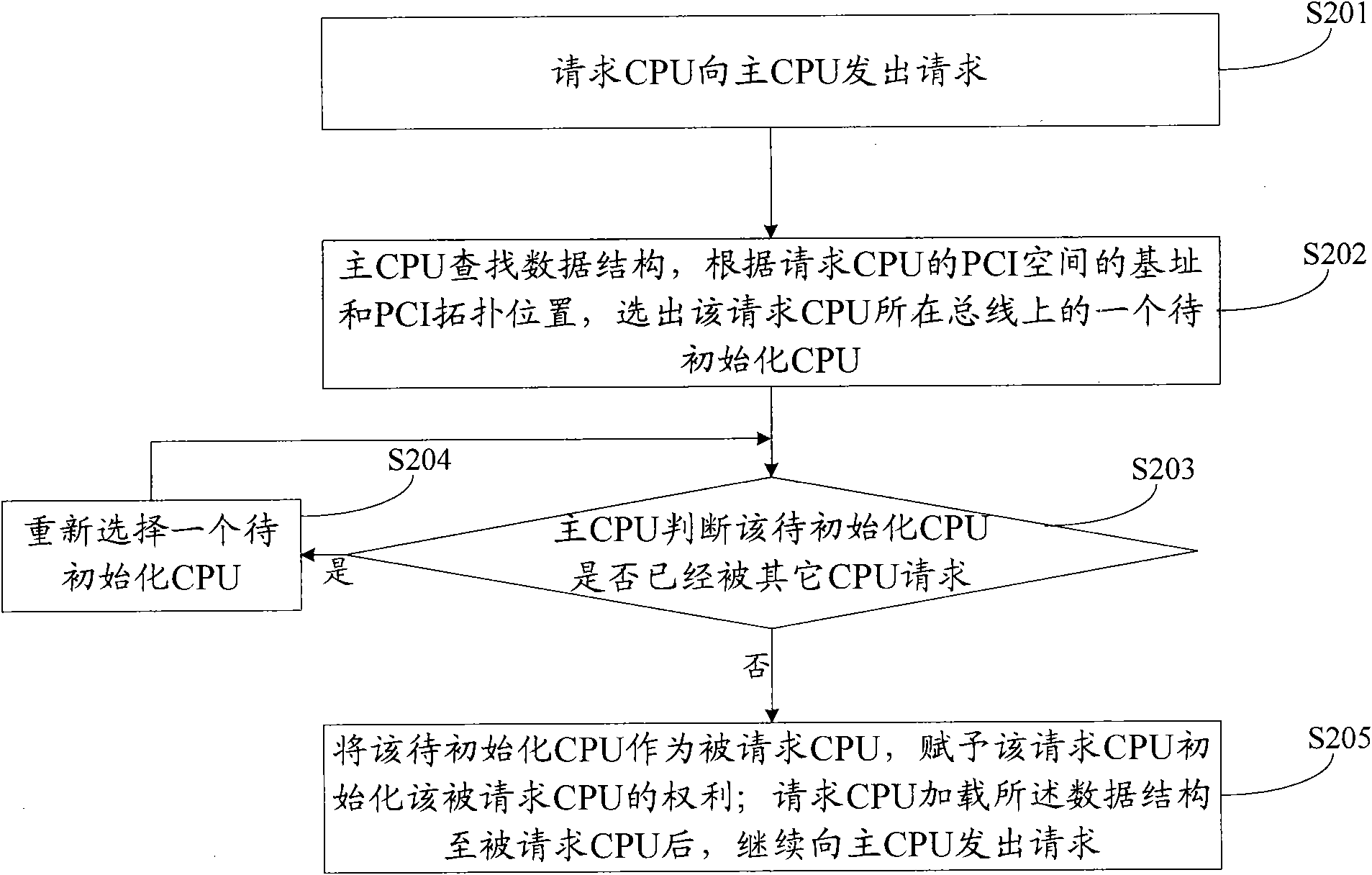
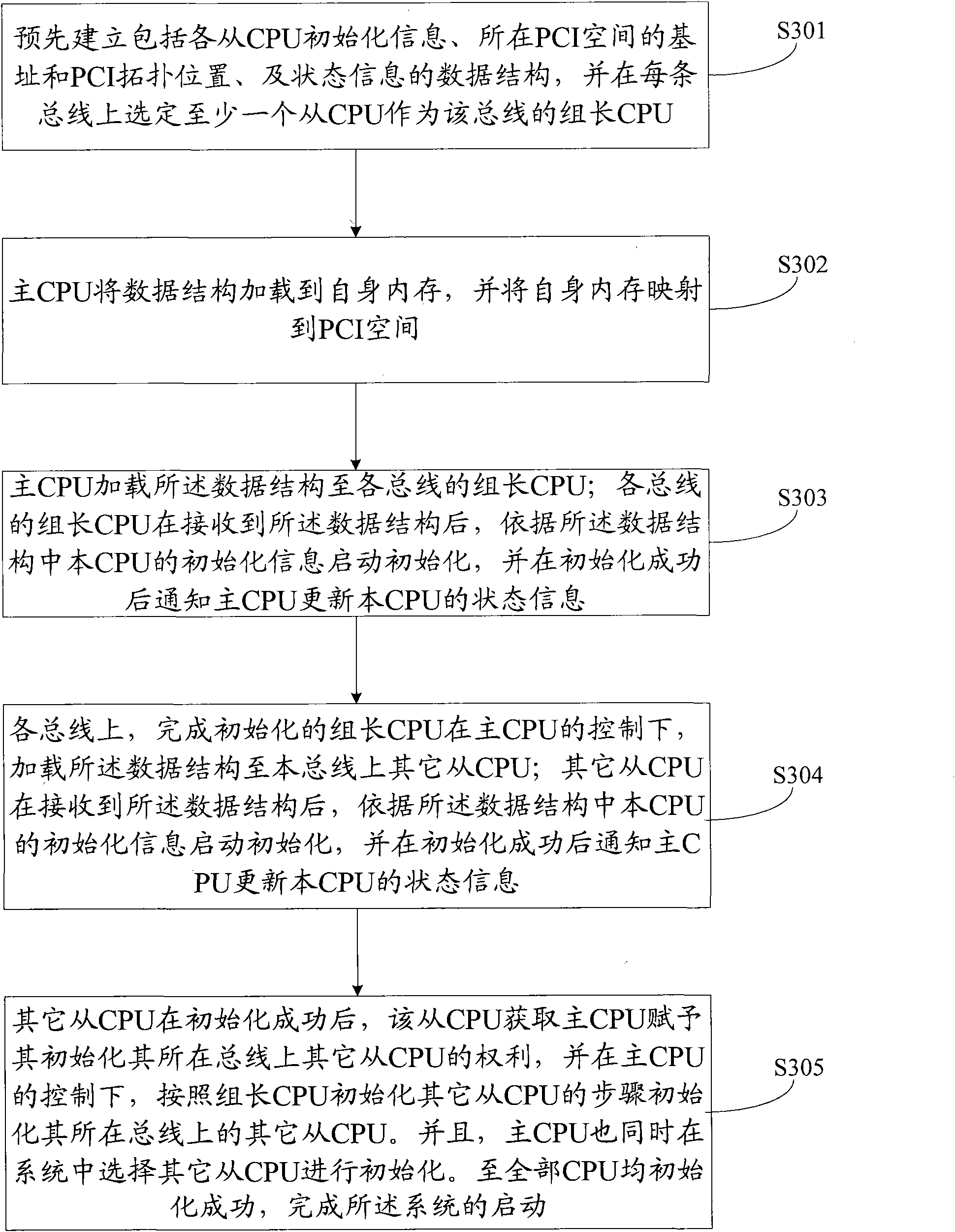
The invention discloses multi-CPU (Central Processing Unit)system starting method and module based on a PCI / PCIe (Peripheral Component Interconnect / Peripheral Component Interconnect Express) bus, which relate to the field of automatic control. The method comprises the following steps of: preestablishing a data structure and selecting a group leader CPU of each bus, loading a data structure into aself memory and mapping the self memory into a PCI space by a main CPU; loading the data structure to the group leader CPU of each bus by the main CPU; starting initialization by the group leader CPUof each bus according to the initialing information of the CPU in the data structure after receiving the data structure and informing the main CPU to update the state information of the CPU after theinitialization is successful; loading the data structure to other subordinate CPUs on the bus by the group leader CPU finishing the initialization under the control of the main CPU on each bus; and finishing the start of the system till all the CPUs are successfully initialized. The invention greatly improves the start speed of the system and saves the cost without adding new hardware.
Owner:HANGZHOU HIKVISION DIGITAL TECH
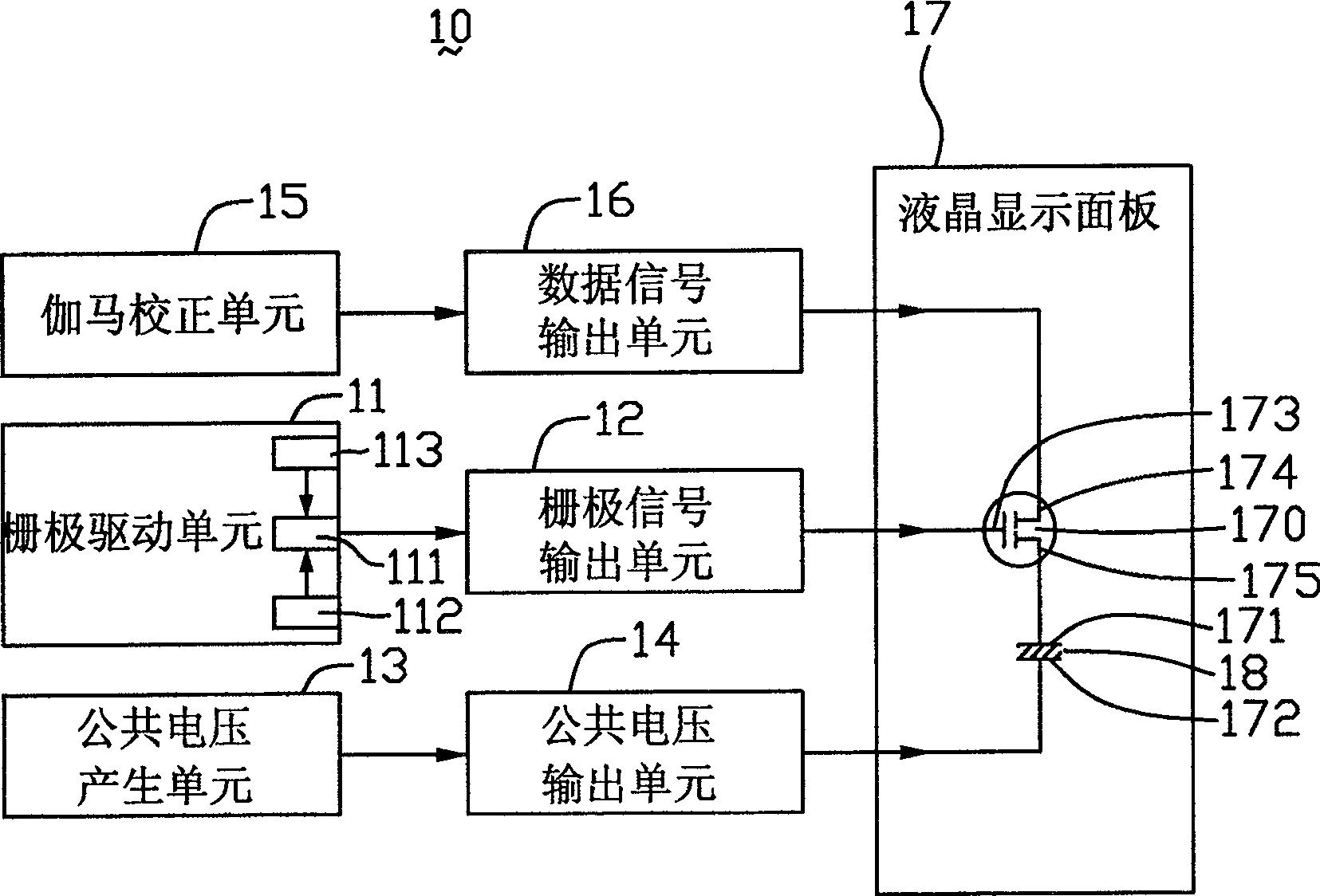
Optical compensation flexure type LCD
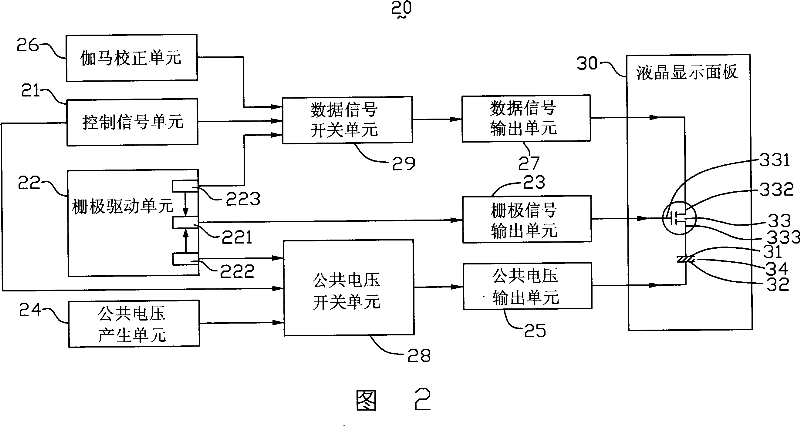
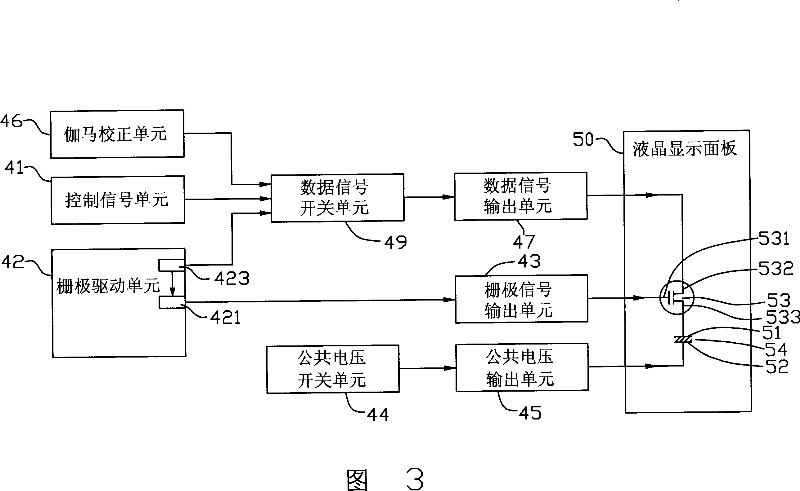
InactiveCN101042478AImprove initialization speedHigh voltageStatic indicating devicesNon-linear opticsGratingLiquid-crystal display
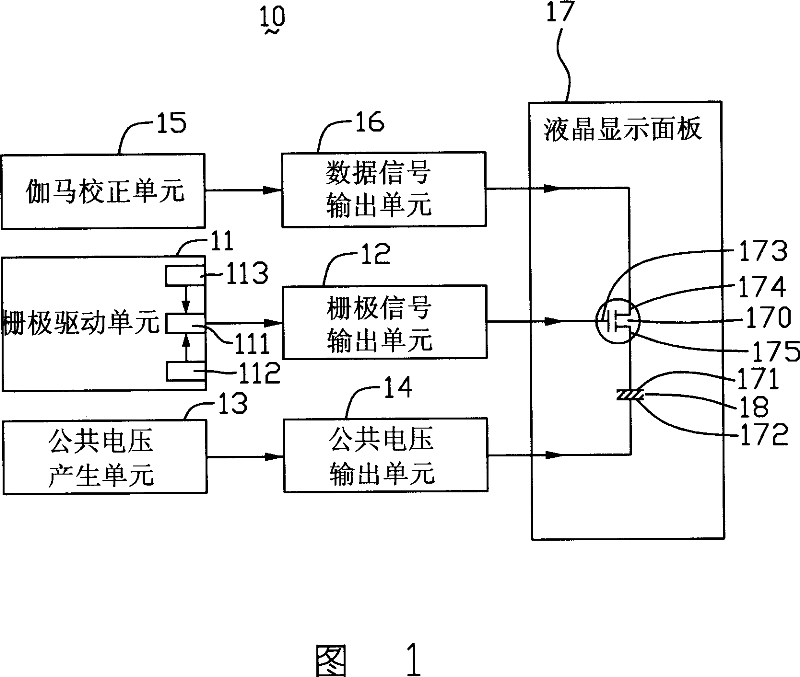
This invention relates to one optical compensation curve LCD device, which comprises one LCD panel, one Gamma correction unit, one public voltage generation unit, one grating drive unit and one data signal switch unit, wherein, the grating drive unit comprises one high voltage generation circuit with higher voltage than the correction unit; the LCD panel comprises one pixel electrode and one public electrode; the data signal switch unit is connected to the high voltage generation circuit, correction unit and panel to provide the voltage signals of the Gamma correction unit to the pixel electrode.
Owner:INNOCOM TECH SHENZHEN +1
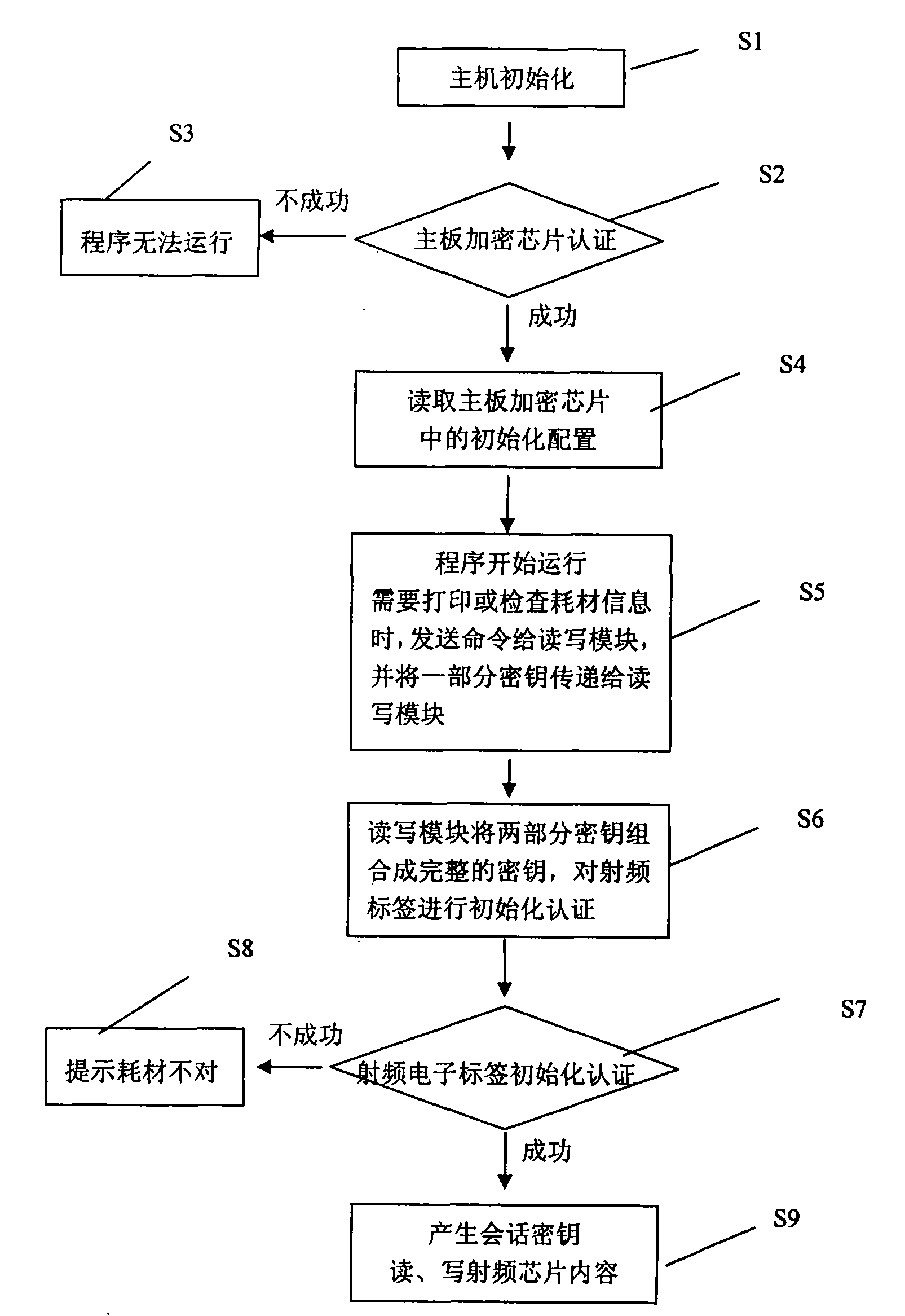
Method for encrypting consumable items through radio frequency identification electronic tag
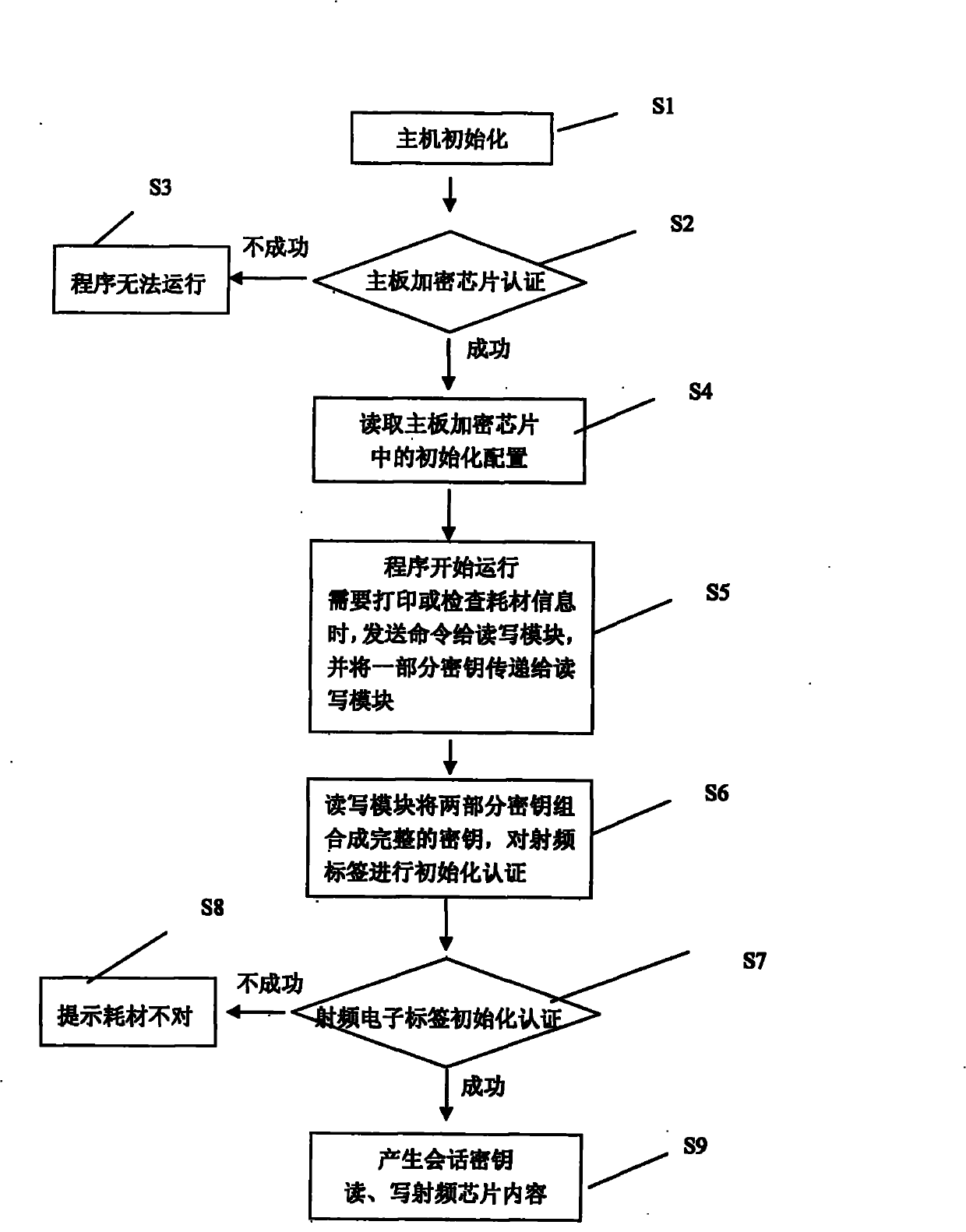
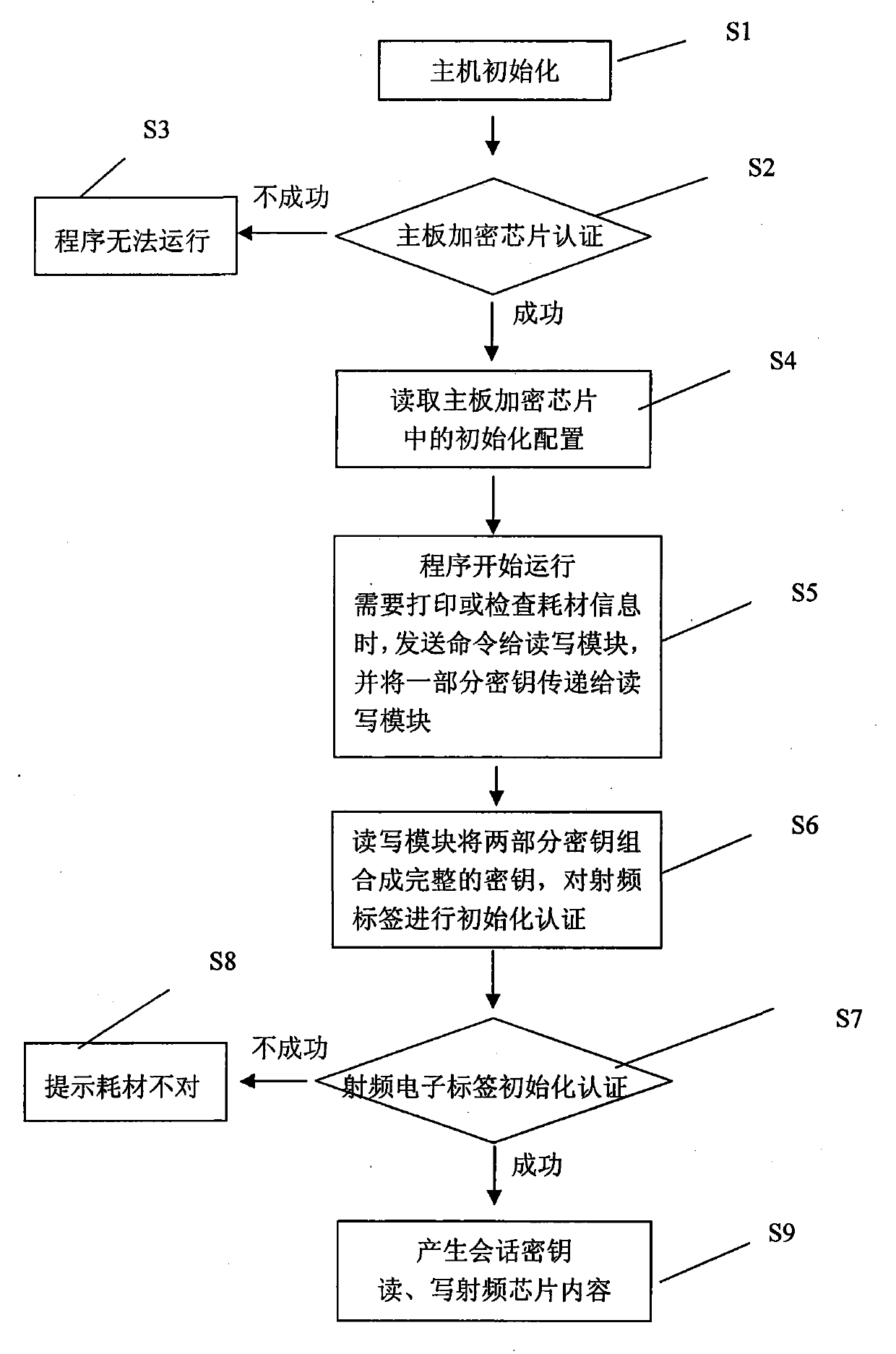
ActiveCN102087684AImprove reliabilityEasy to compileDigital data authenticationSensing record carriersPasswordInformation security
The invention provides a method for encrypting consumable items through a radio frequency identification electronic tag. By using a method of additionally arranging the radio frequency identification electronic tag on the consumable items of various devices and using the devices and the radio frequency identification electronic tag to communicate by a method for communicating through encryption information, the consumable items are encrypted and protected. The consumable items are encrypted by adopting the non-contact radio frequency identification electronic tag, so that the consumable itemsare not easy to rust and damage and the reliability is improved; the radio frequency identification electronic tag is initialized after the consumable items are assembled, thus the speed of initialization is greatly improved; the method is convenient to comply a plurality of groups of passwords and produce and manage and provides the possibility for complying different passwords according to different requirements; a module is packaged by using a physical method, so that all keys cannot be obtained by using a method of breaking a host program, and the stability for encryption is greatly improved; and by setting an automatic protecting function at the radio frequency identification electronic tag, the information security is ensured.
Owner:北京力码科信息技术股份有限公司
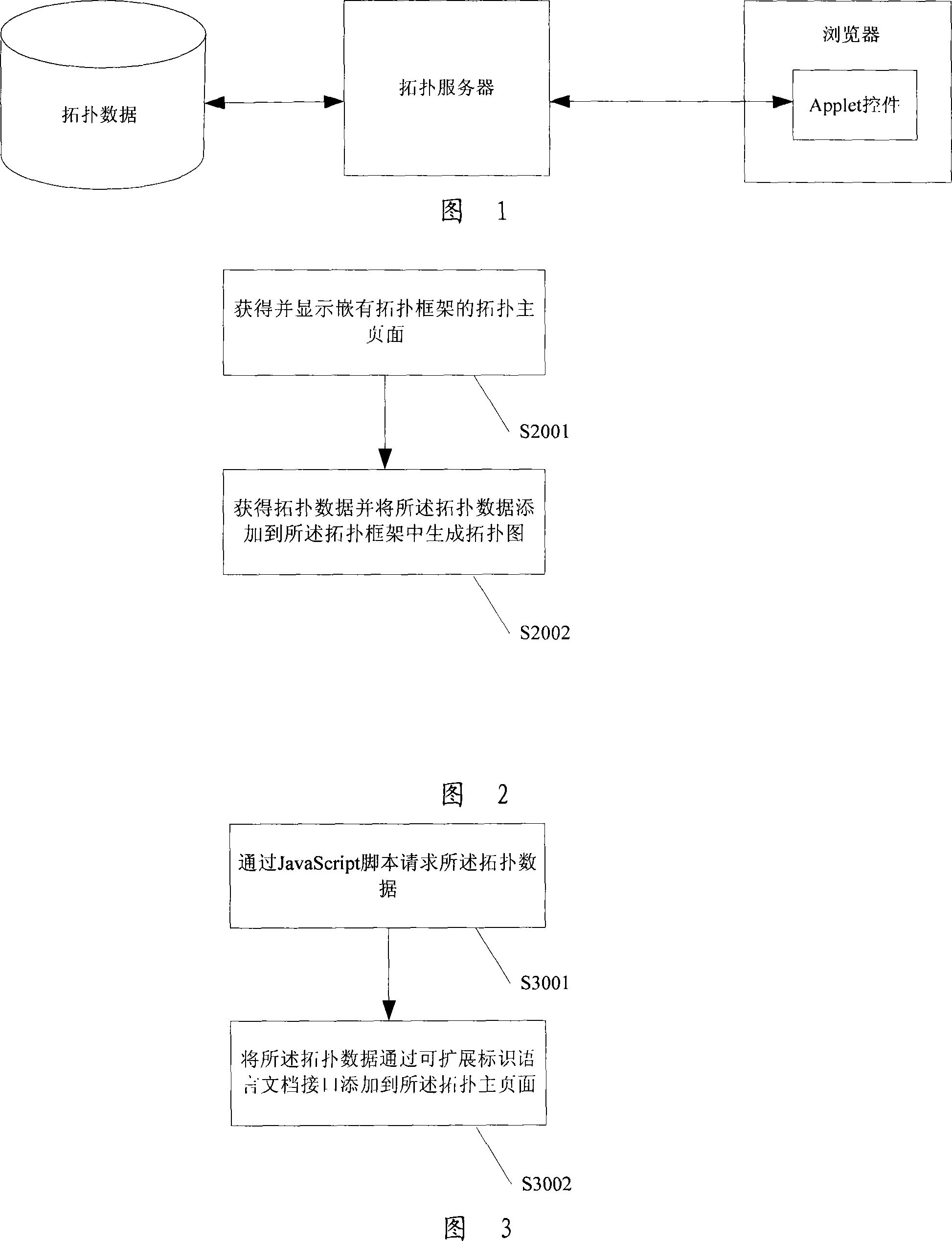
Topological diagram display process, system and device
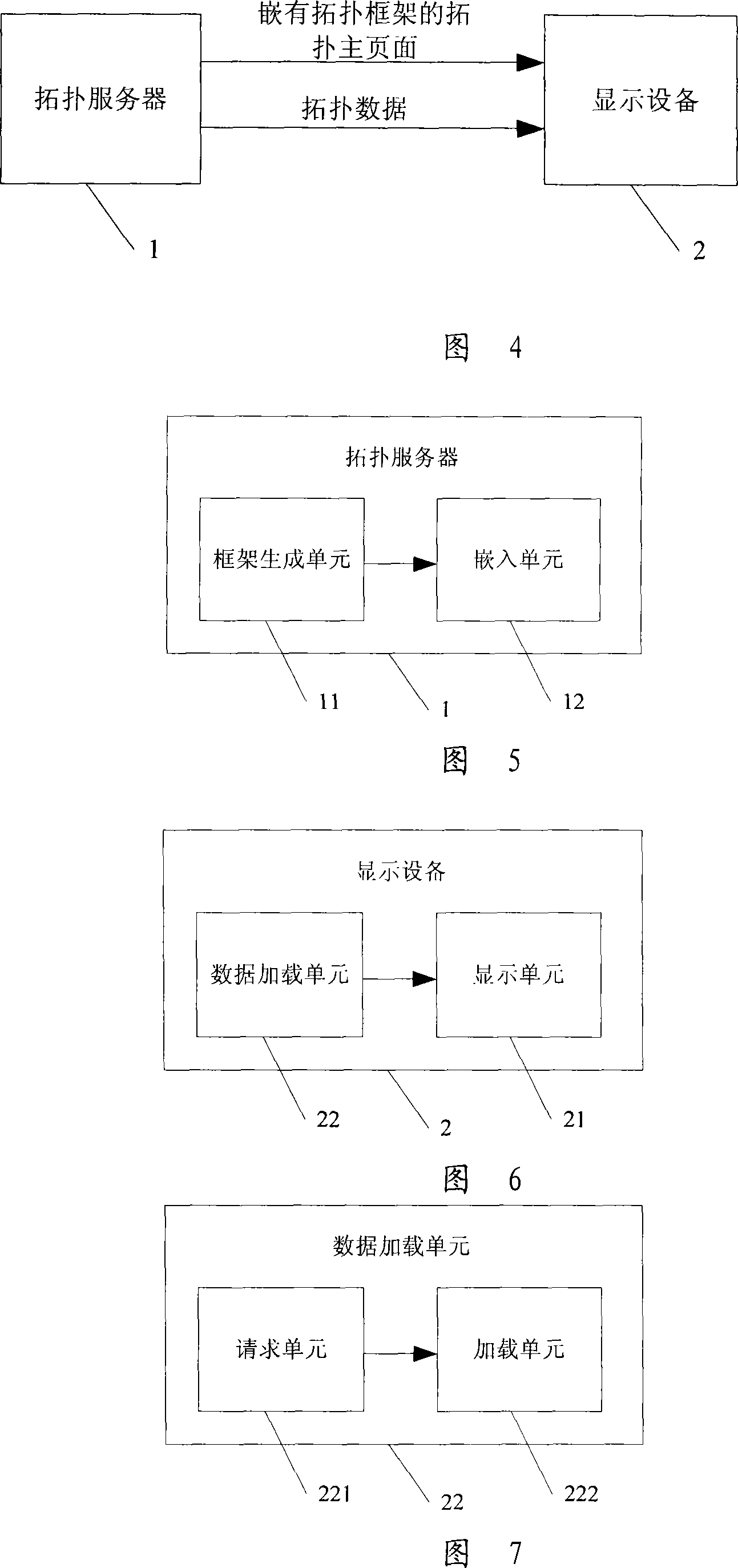
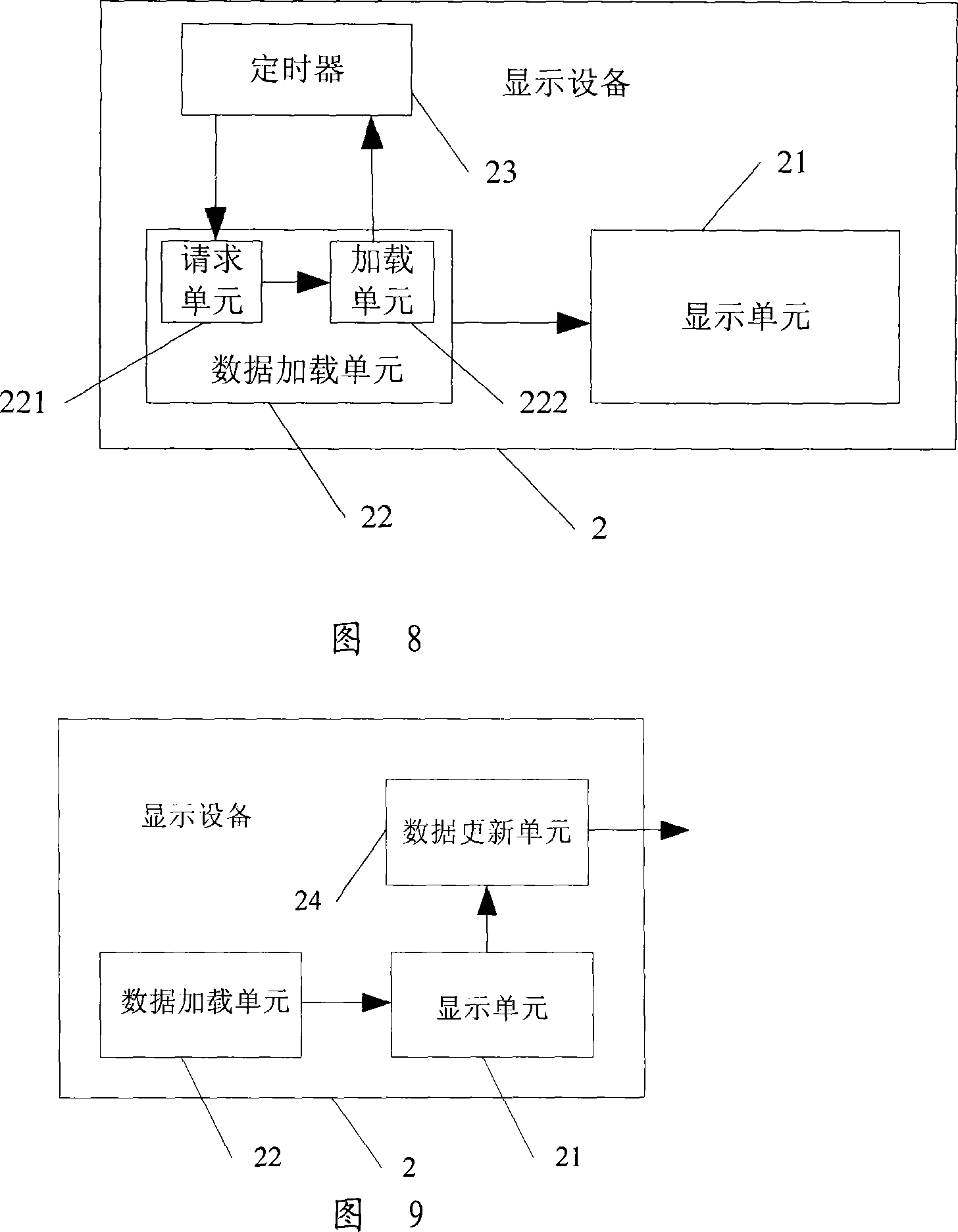
InactiveCN101114936AImprove display speedImprove initialization speedData switching networksJava virtual machineWeb page
The invention discloses a topological diagram display method; a topological frame is embedded into a topological main web page, when display equipment requests the topological main web page, the topological main web page which is embedded with the topological frame is provided for the display equipment, thus the topological main web page can be displayed quickly; then the topological data are loaded to the topological main web page to display the complete topological main web page with a topological diagram. The invention also discloses a topological diagram display system, a display equipment and a topological server. By adopting the invention, a JAVA virtual machine is not needed to be arranged in the display equipment and an Applet / ActiveX widget is not needed to be loaded in the display equipment, and thus the initializing speed of the topological diagram interface and the displaying speed of the topological diagram are improved.
Owner:HUAWEI TECH CO LTD
Rapid imaging method, device and equipment for nuclear magnetic resonance image
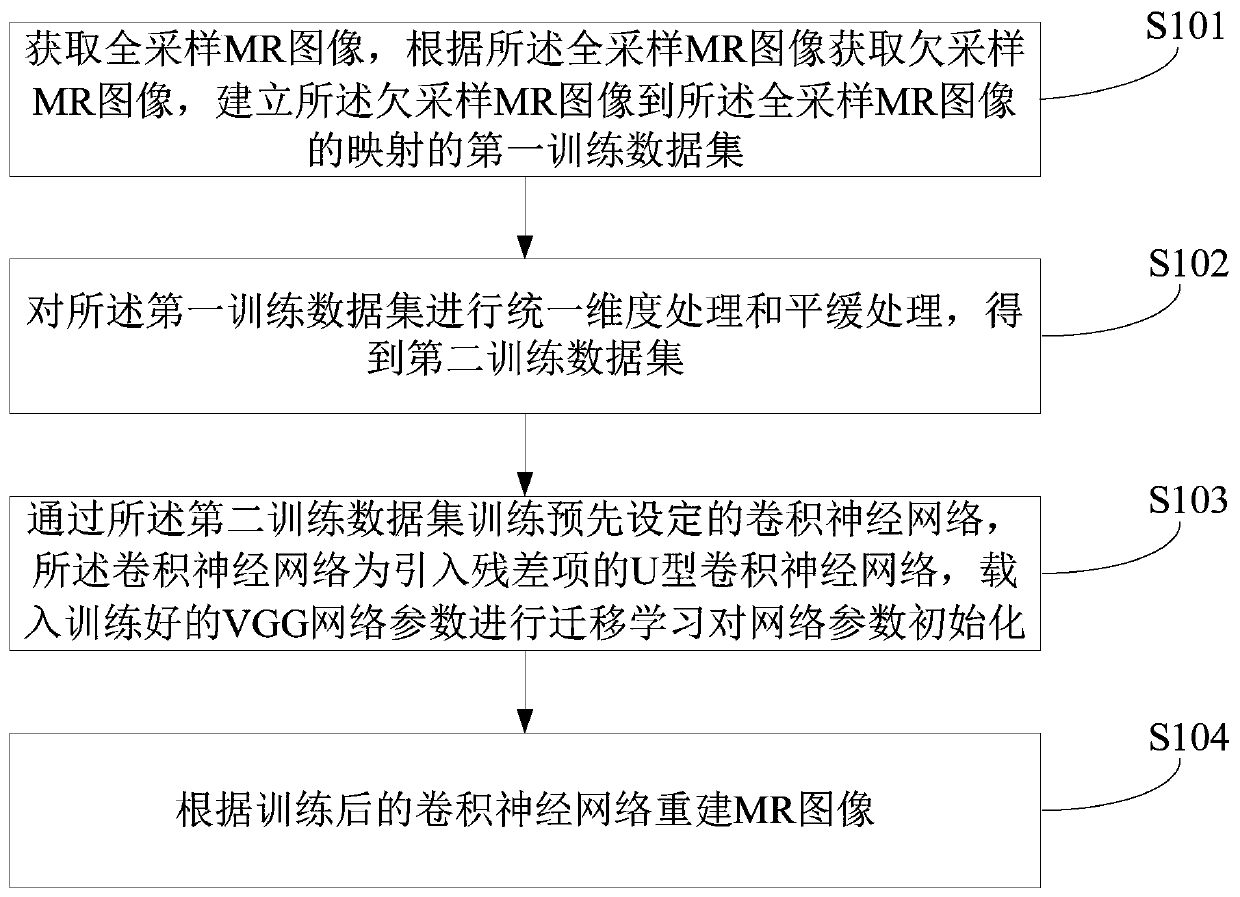
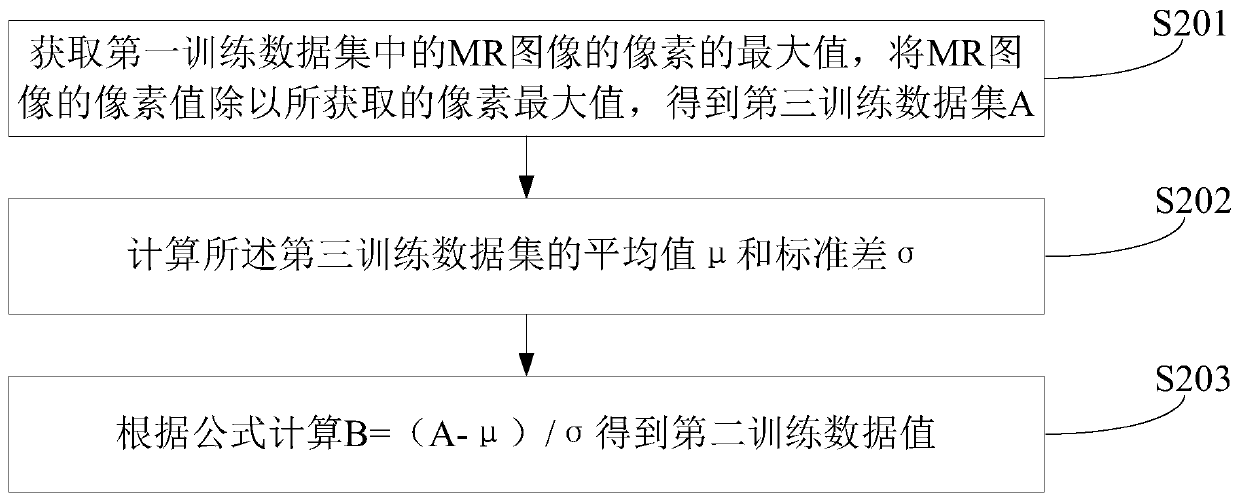
InactiveCN109801259AReduce training timeImprove accuracyImage analysisRapid imagingNMR - Nuclear magnetic resonance
A rapid imaging method of the nuclear magnetic resonance image comprises the steps of obtaining a full-sampling MR image, obtaining an under-sampling MR image according to the full-sampling MR image,and establishing a first training data set of mapping from the under-sampling MR image to the full-sampling MR image; Performing unified dimension processing and smooth processing on the first training data set to obtain a second training data set; A preset convolutional neural network is trained through the second training data set, the convolutional neural network is a U-shaped convolutional neural network with introduced residual terms, and trained VGG network parameters are loaded for transfer learning to initialize the network parameters; And reconstructing an MR image according to the trained convolutional neural network. The accuracy of network classification can be effectively improved, the initialization speed of network parameters is reduced, and the training efficiency of the network is improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
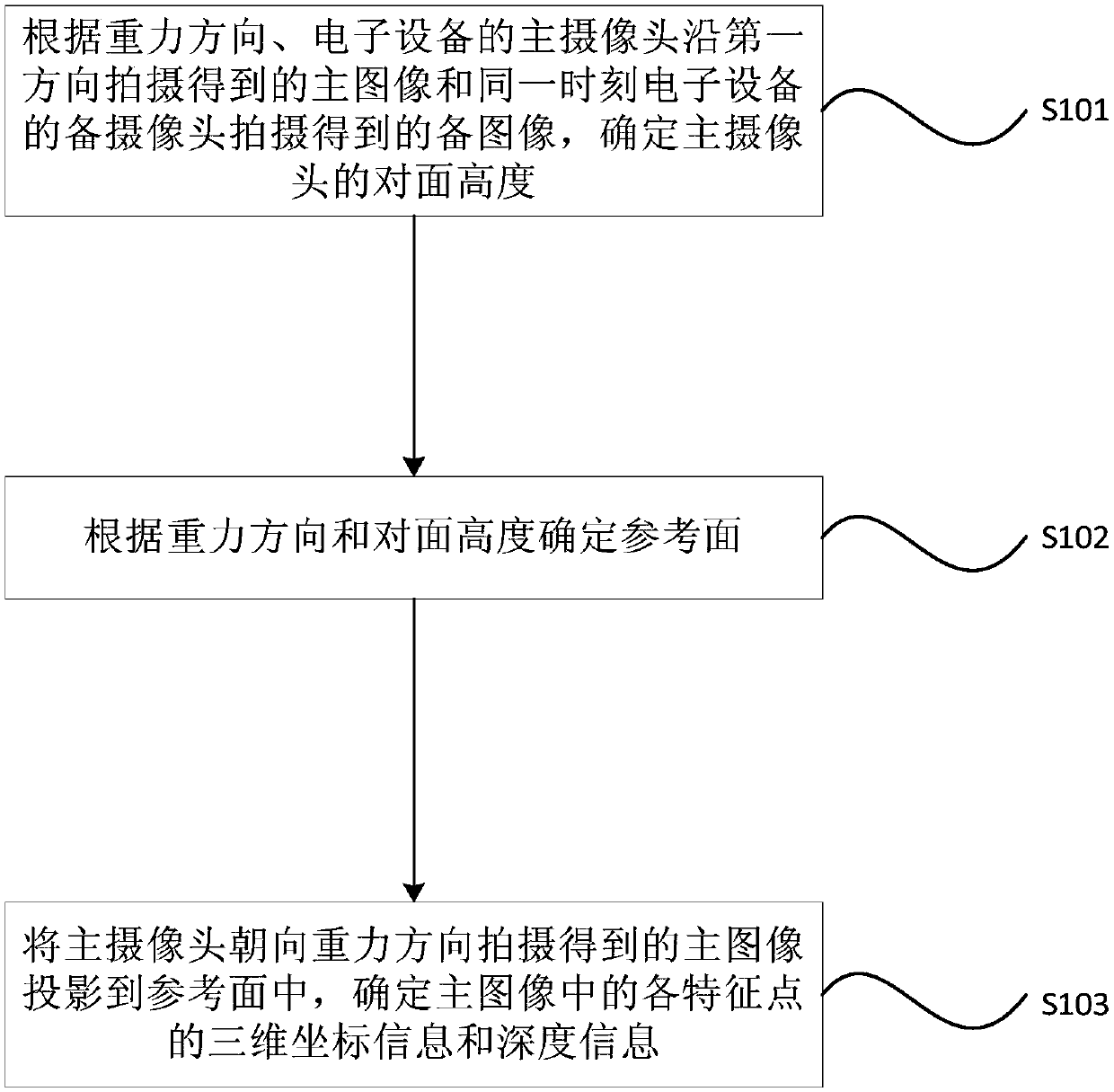
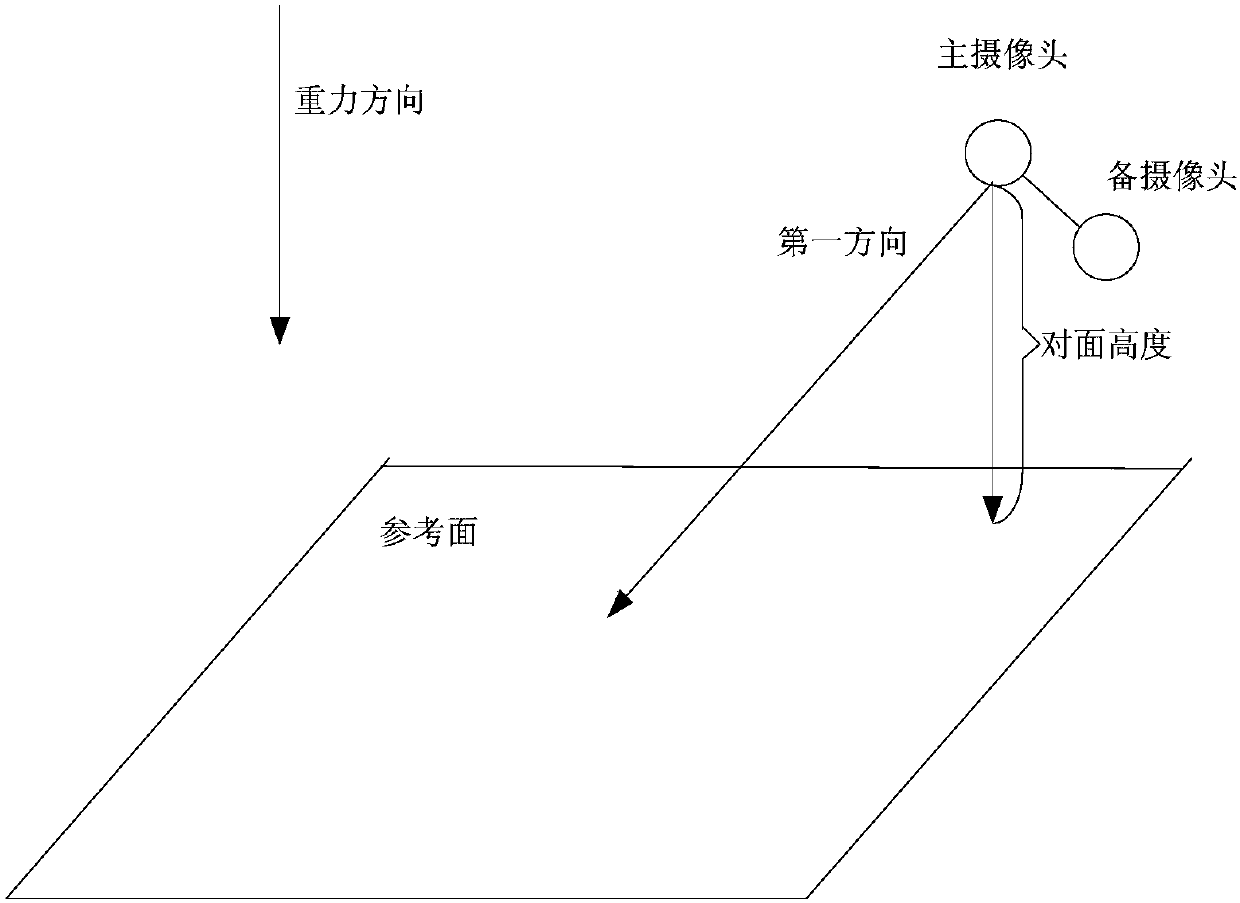
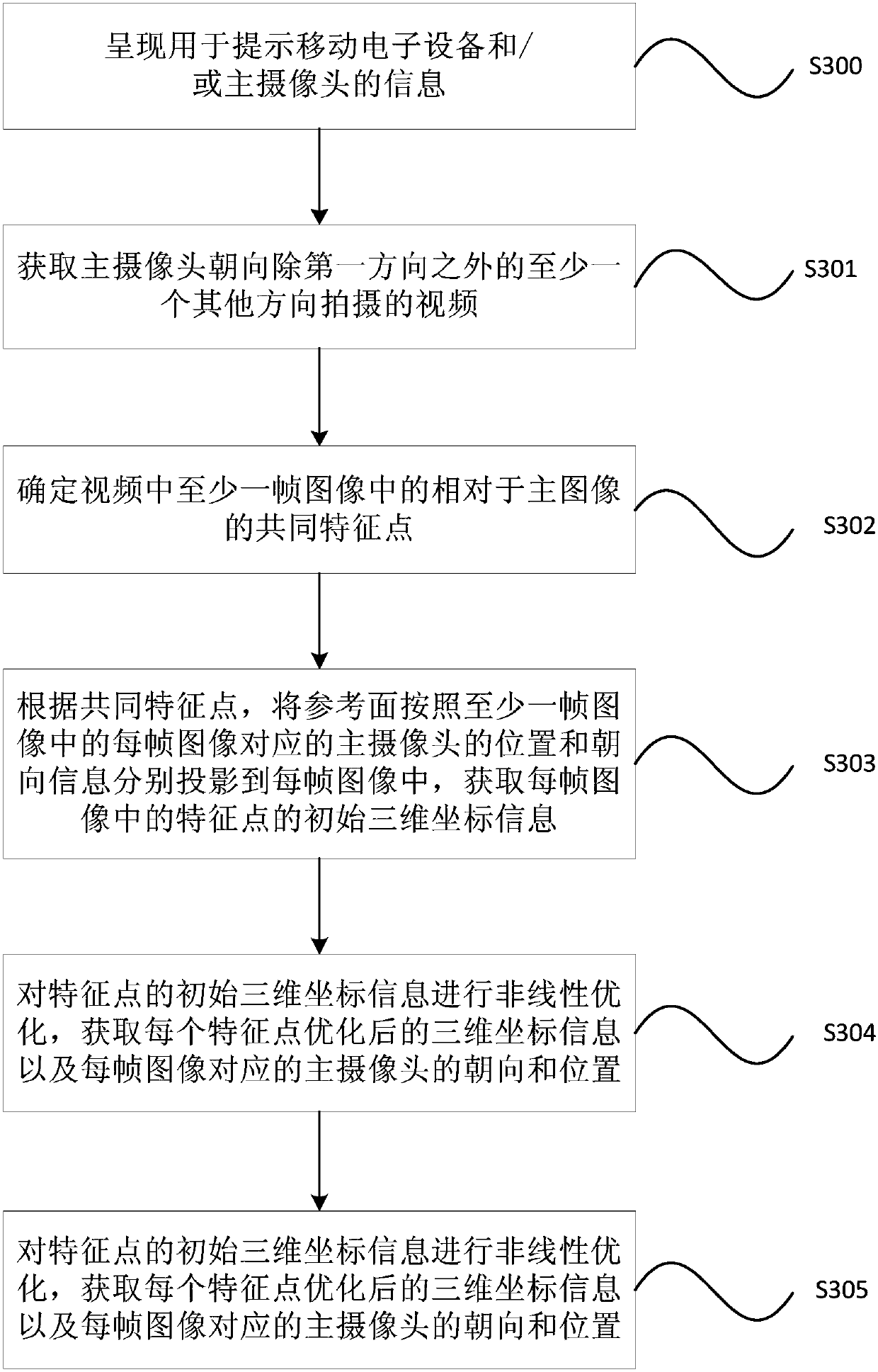
Initialization method, device and system of SLAM system, and AR control method, device and system
ActiveCN110119189AImprove initialization speedImprove accuracyInput/output for user-computer interactionGraph readingSimultaneous localization and mappingVisual perception
The invention provides an initialization method, device and system of Simultaneous Localization and Mapping (SLAM) system, and an augmented reality (AR) control method, device, and system. The methodcomprises: determining the opposite height of a main camera according to the gravity direction, a main image shot by the main camera of the electronic device in the first direction and a standby imageshot by the standby camera of the electronic device at the same moment; determining a reference surface according to the gravity direction and the opposite height; and projecting the main image intoa reference surface, and determining three-dimensional coordinate information and / or depth information of at least one feature point in the main image. According to the embodiment of the invention, the initialization speed of the SLAM is improved, and the accuracy of the opposite height and the accuracy of map construction in the visual initialization process are also improved.
Owner:ZHEJIANG SENSETIME TECH DEV CO LTD
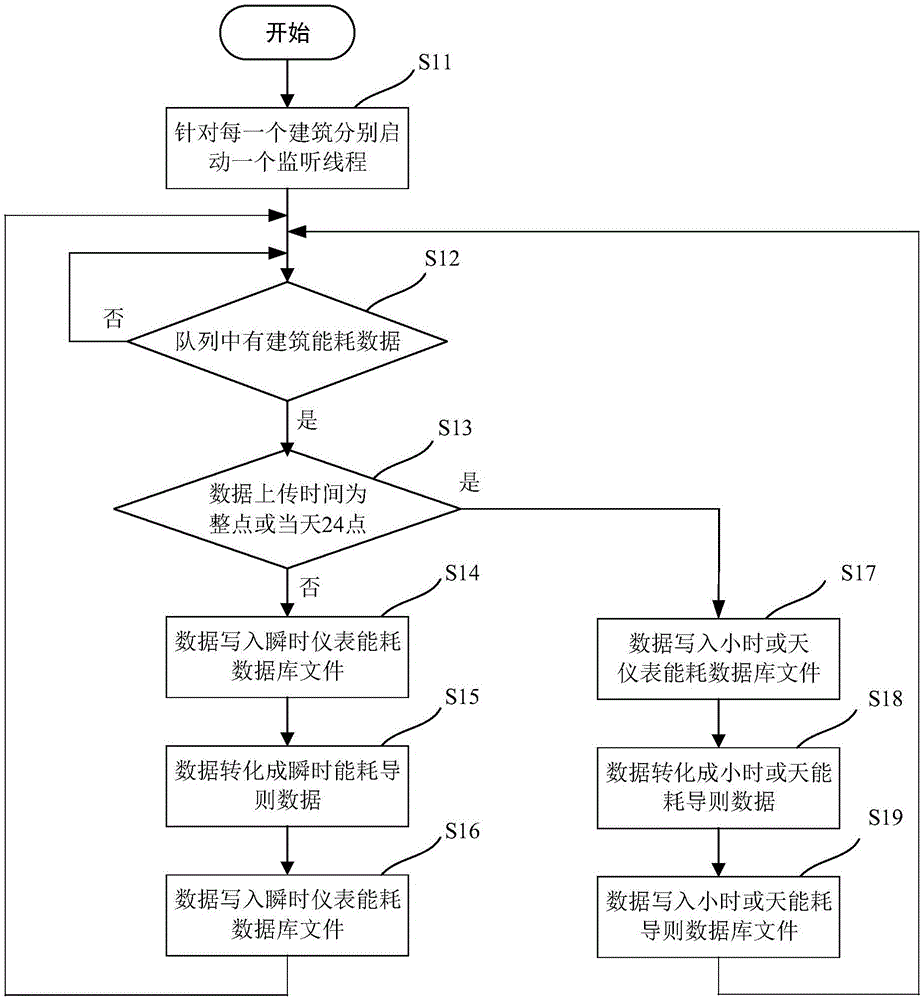
Area building energy consumption platform data storing and query method
InactiveCN105912621AIncrease write speedImprove reading speedEnergy efficient computingSpecial data processing applicationsMessage queueResource utilization
The invention relates to an area building energy consumption platform data storing and query method which are used for uniformly storing and querying energy consumption data of a plurality of buildings. The method includes a data storage process and a data query process. The data storage process includes: starting up a monitoring thread for each building respectively; reading building energy consumption data in a data message queue through the monitoring threads, wherein the building energy consumption data includes building ownership and data uploading time, the monitoring threads write the building energy consumption data in a database file corresponding to a duration of the building ownership and data uploading time. The data query process includes: accessing and reading the corresponding database file according to the building ownership and the data uploading time in a query request, and then acquiring desired energy consumption data. Compared with the prior art, the method is high in utilization of hardware resources, is fast in initialization speed, is high in platform operation efficiency, and facilitates expansion of a building energy consumption platform.
Owner:SHANGHAI SIIC LONGCHUANG SMARTER ENERGY TECH CO LTD
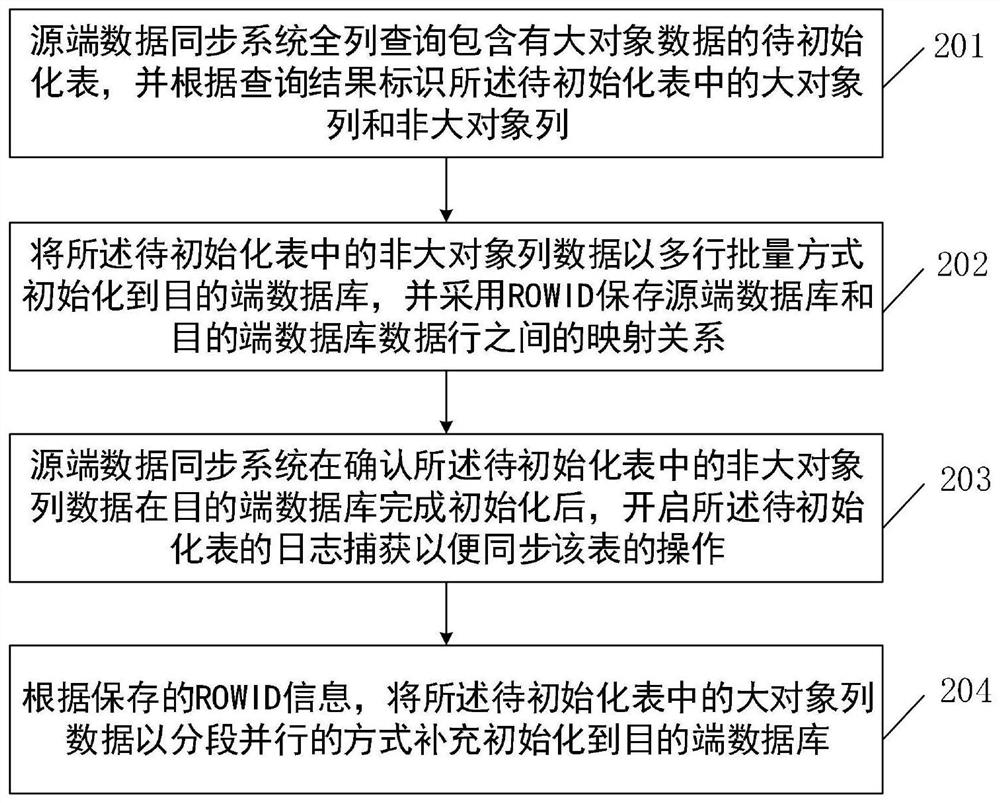
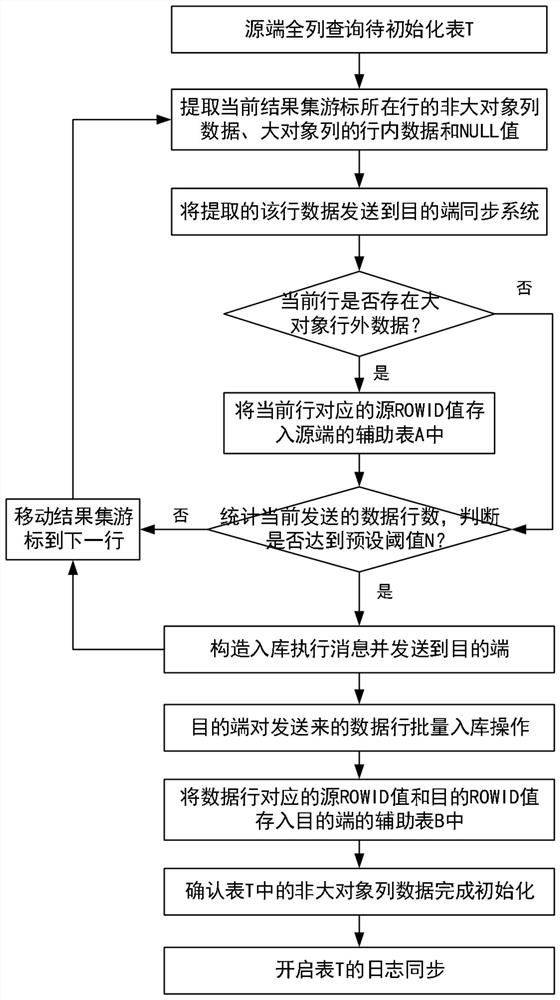
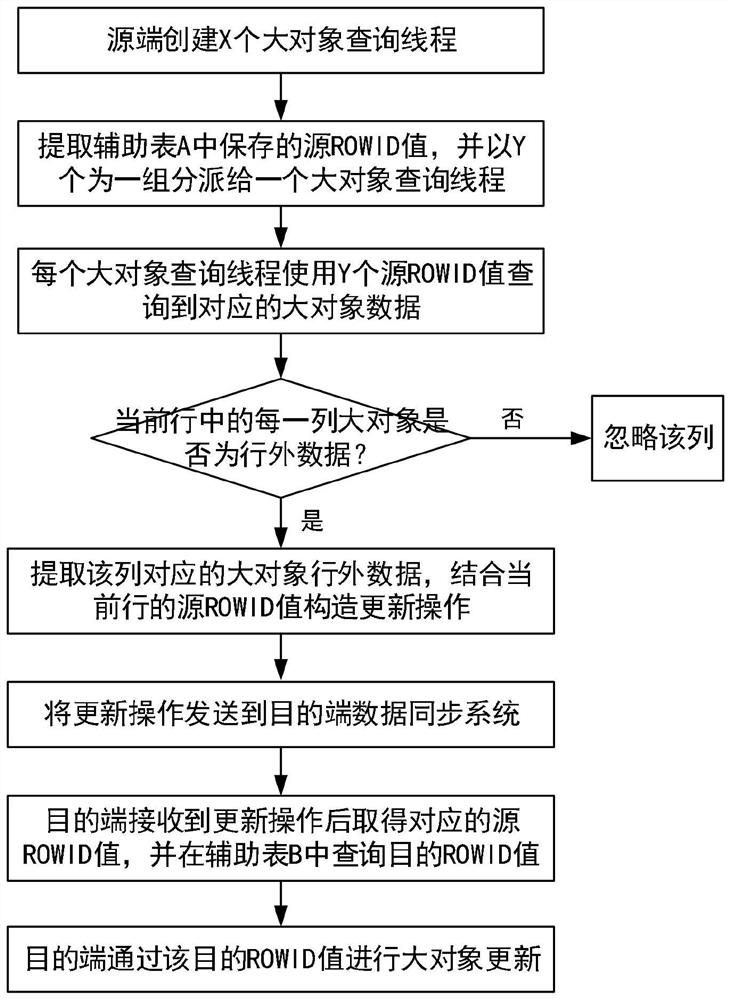
Large object initialization method and device based on log analysis synchronization
ActiveCN112559629APrevent archive log accumulationShort timeDatabase distribution/replicationSpecial data processing applicationsData synchronizationData mining
The invention relates to the technical field of computers, in particular to a large-object initialization method and device based on log analysis synchronization, and the method comprises the steps ofquerying a to-be-initialized table containing large-object data in a full-column manner through a source-end data synchronization system, and identifying a large-object column and a non-large-objectcolumn; initializing the non-large object column data to a destination end database in a multi-row batch manner, and storing a mapping relationship between data rows of the source end database and thedestination end database by adopting ROWID; after the source end data synchronization system confirms that the non-large object column data in the table is initialized in the destination end database, starting log synchronization of the table; and according to the stored ROWID information, supplementing and initializing the large object column data in the table to a destination end database in asegmented parallel mode. According to the scheme, the initialization speed of the data containing the large object table can be effectively increased, the establishment of a data synchronization environment is quickly completed, and the probability that a source end database report'snapshots too much 'is reduced.
Owner:WUHAN DAMENG DATABASE
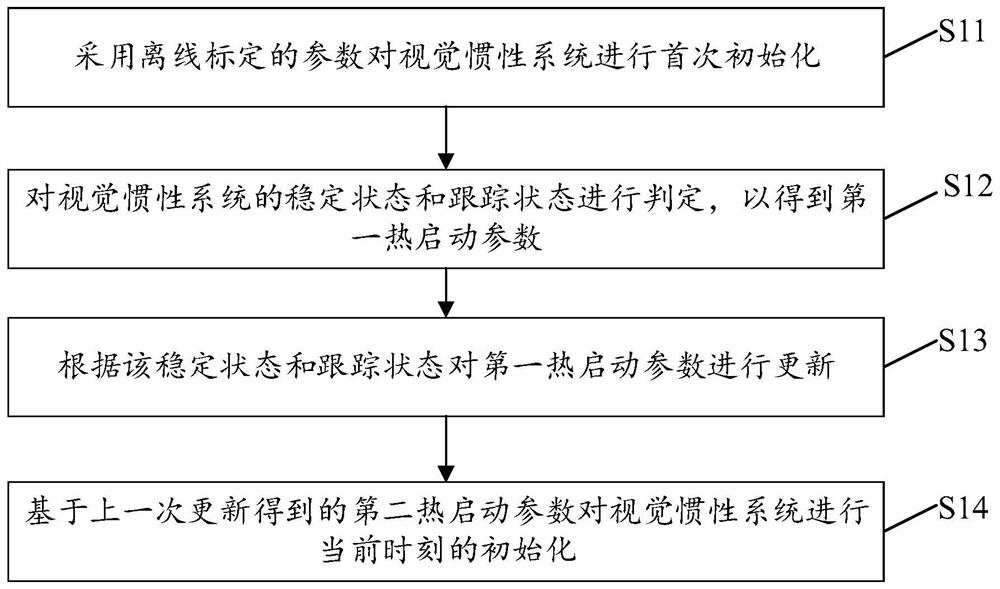
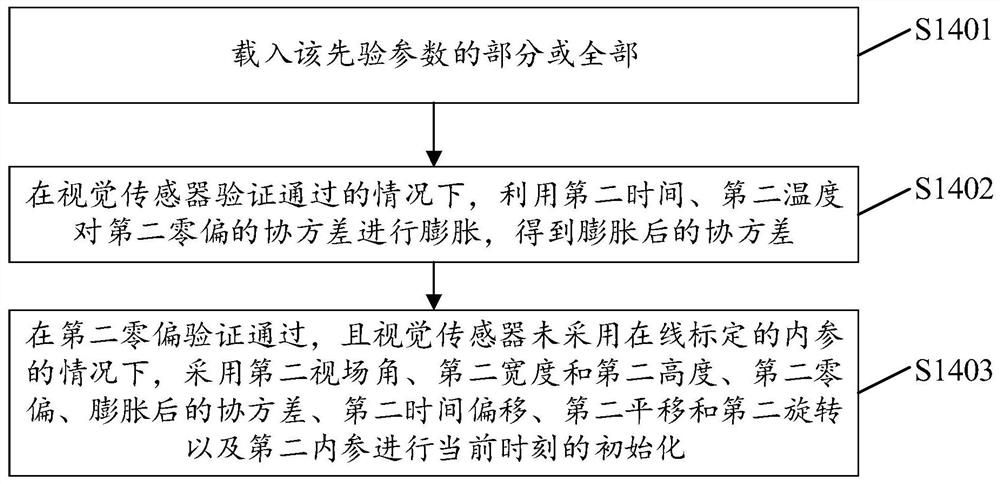
Initialization method and device for visual inertial system, electronic equipment and storage medium
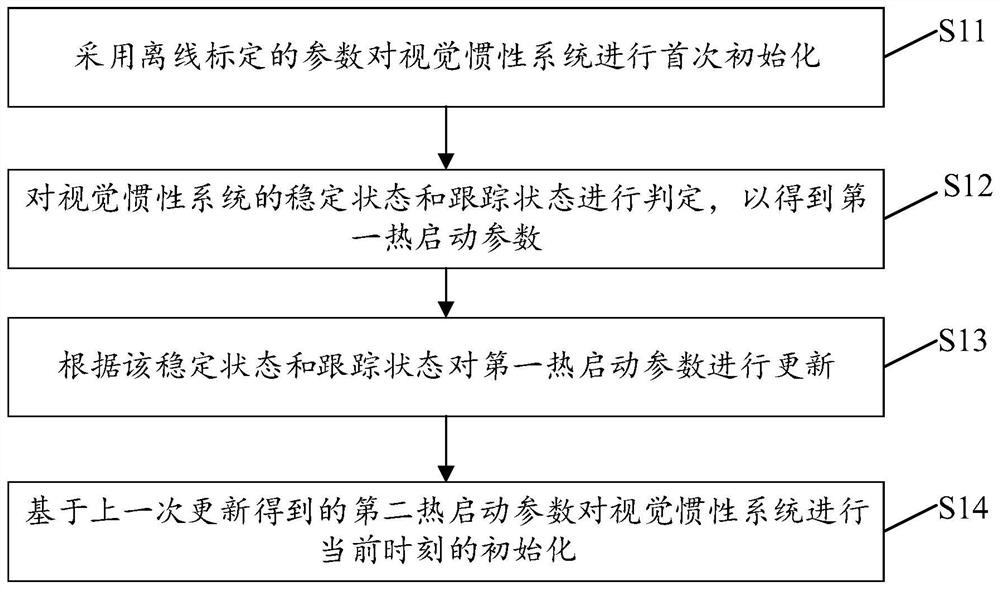
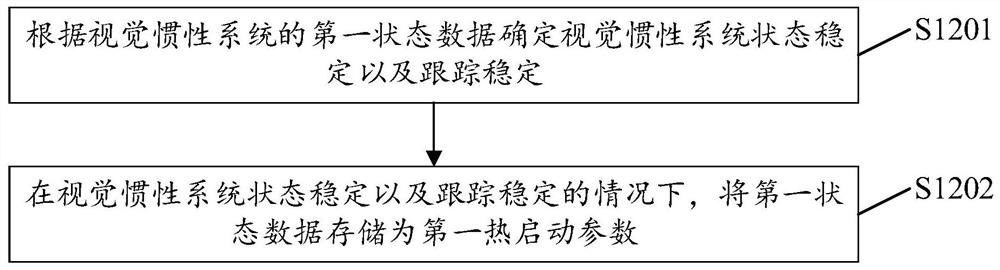
ActiveCN113029134AImprove stabilityAccelerateNavigation by speed/acceleration measurementsUsing reradiationInertial systemsReal-time computing
The invention provides an initialization method and device for a visual inertial system, electronic equipment and a storage medium. The method comprises the steps of: carrying out the first initialization of a visual inertial system through employing an offline calibrated parameter; judging a stable state and a tracking state of the visual inertial system to obtain a first hot start parameter; updating the first hot start parameter according to the stable state and the tracking state; and initializing the visual inertial system at the current moment based on the second hot start parameter obtained by the last update. The embodiment of the invention is beneficial to improving the initialization speed of the visual inertial system.
Owner:ZHEJIANG SENSETIME TECH DEV CO LTD
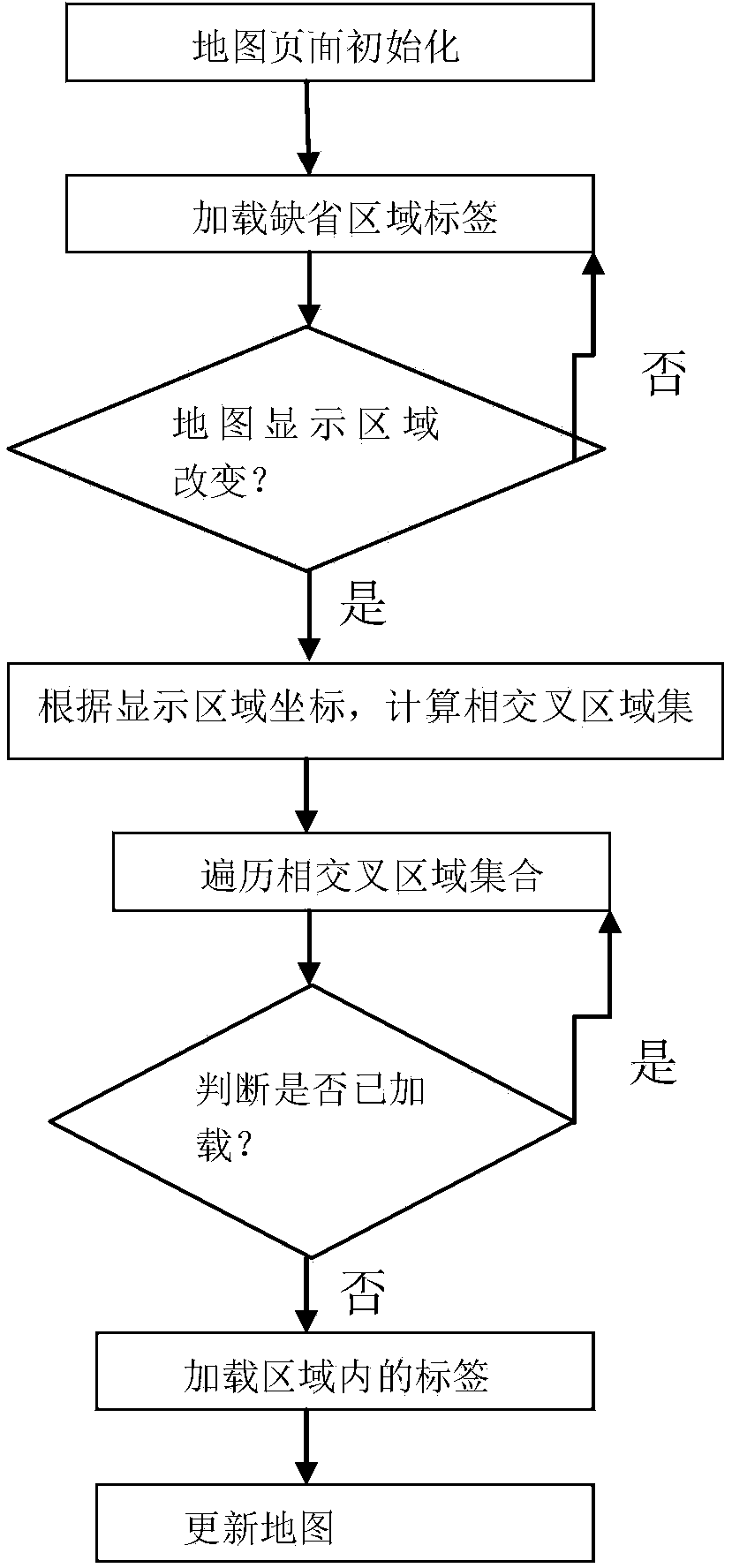
Method and device for dynamically adding map labels in zoning mode
ActiveCN103514280AFix loading delaysImprove initialization speedMaps/plans/chartsGeographical information databasesLabeled dataDynamic loading
The invention discloses a method and device for dynamically adding map labels in a zoning mode. The method includes the steps that firstly, a map page is initialized; secondly, labels of a default zone are loaded; thirdly, whether a map display zone is changed or not is judged, if yes, intersection zone sets are calculated by page logic according to coordinates of the display zone; fourthly, the intersection zone sets are traversed, and whether the labels are loaded or not is judged; fifthly, if not, the labels in the zone are loaded; sixthly, a map is updated. According to the method and device for dynamically adding the map labels in the zoning mode, the problem of page loading delay of a large number of label data can be effectively solved, the effect of dynamic loading in the zoning mode according to requirements is achieved, the initialized speed of the page is improved, and the network bandwidth of a server is saved.
Owner:BEIJING TEAMSUN TECH
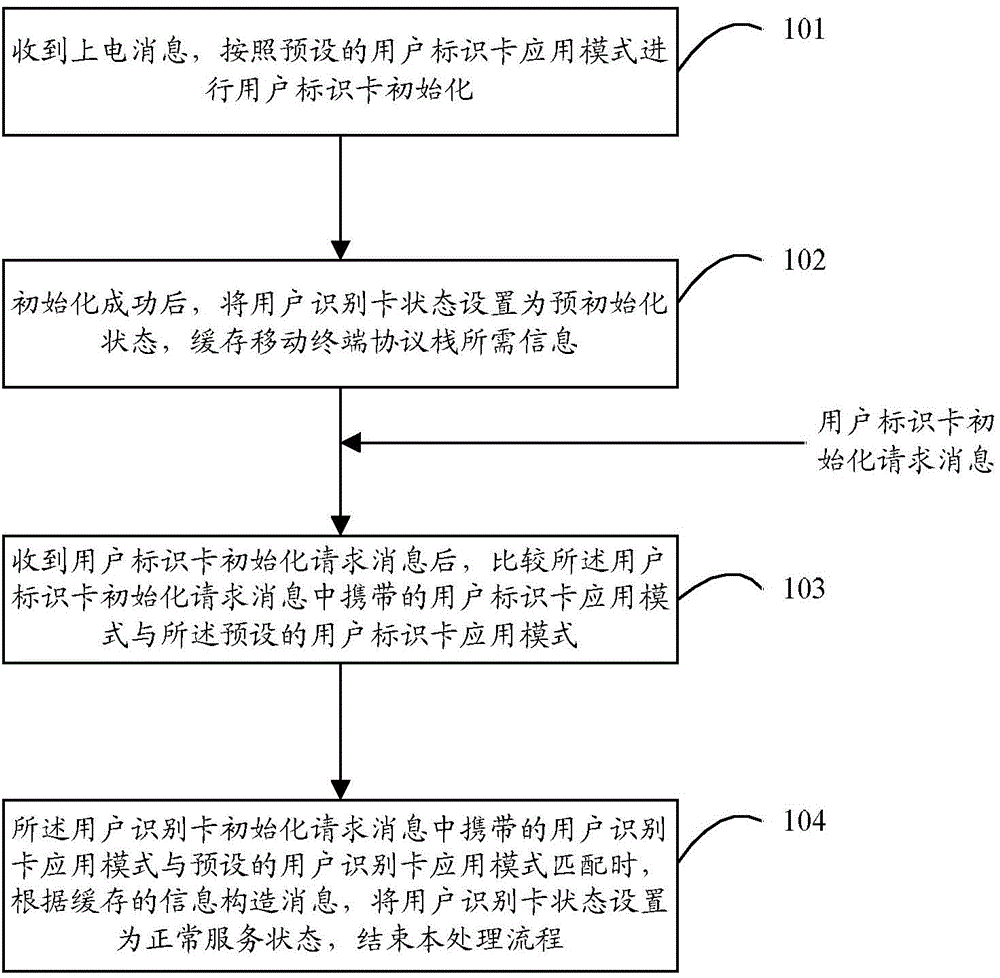
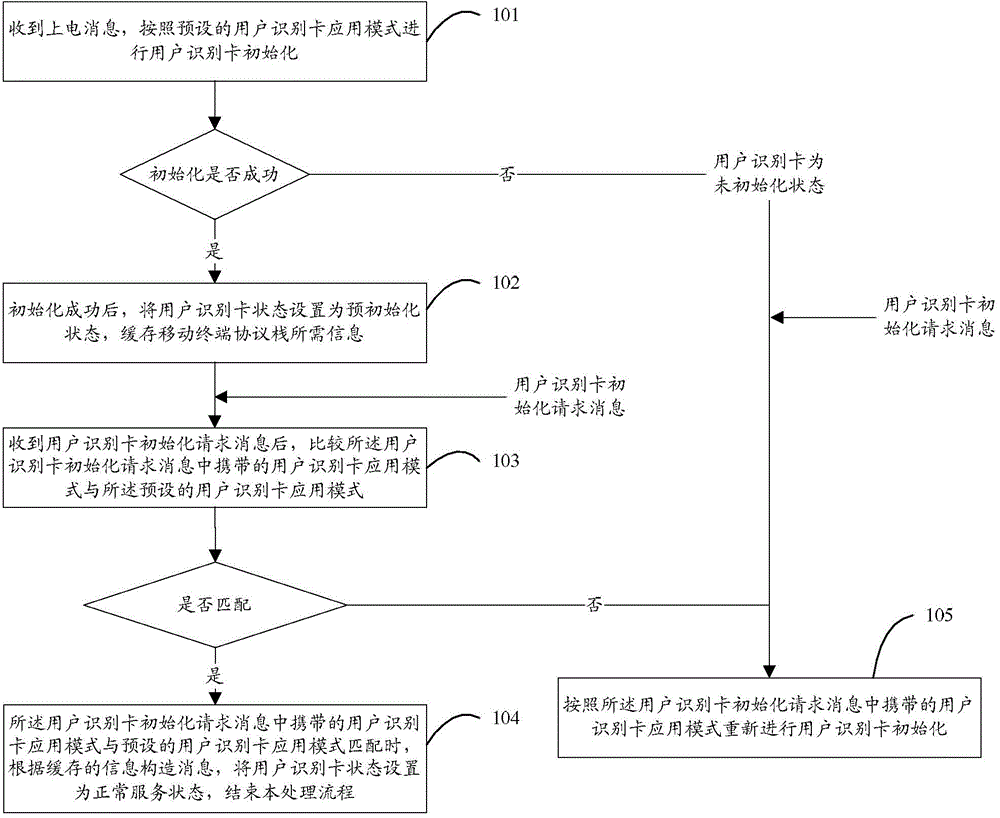
Mobile terminal, and method and device for initializing subscriber identity module card of mobile terminal
InactiveCN105323373ASpeed up the search network residency processImprove experienceSubstation equipmentNetwork data managementSubscriber identity moduleProtocol stack
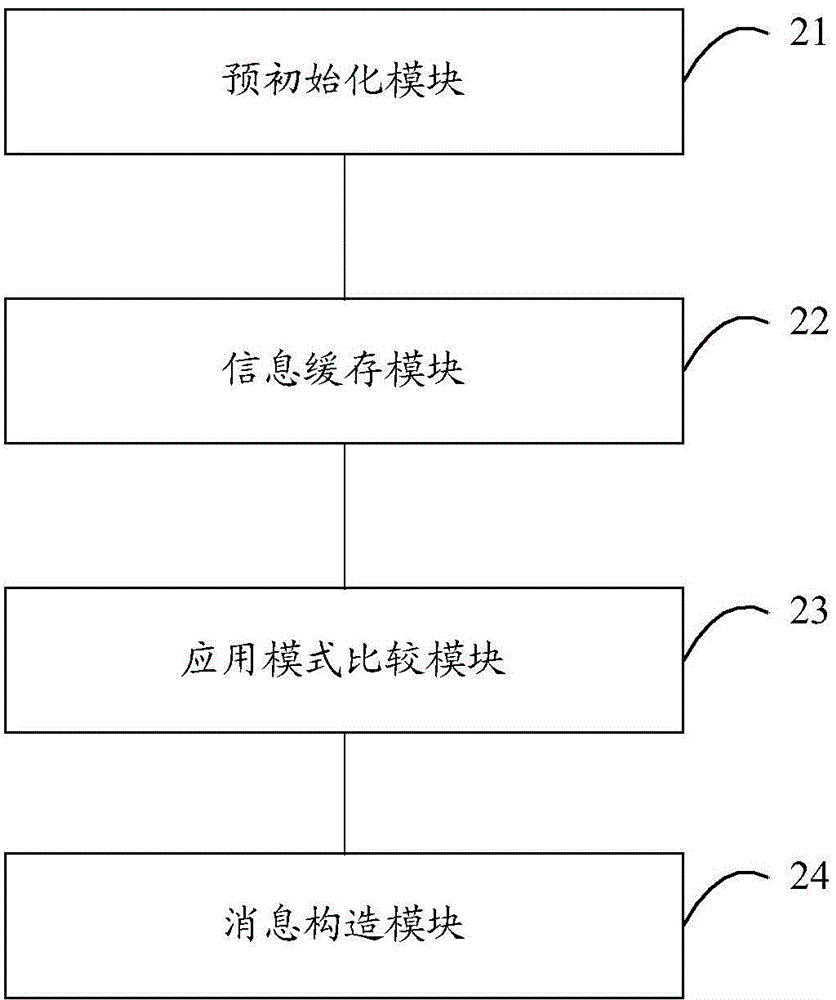
The invention discloses a method for initializing a subscriber identity module card. The method comprises the following steps: after receiving an electrifying message, initializing the subscriber identity module card according to a pre-set subscriber identity module card application mode; after successfully initializing, setting the state of the subscriber identity module card as a pre-initializing state, and caching information required by a mobile terminal protocol stack; after receiving a request message for initializing the subscriber identity module card, comparing the subscriber identity module card application mode carried in the request message for initializing the subscriber identity module card with the pre-set subscriber identity module card application mode; and, if the subscriber identity module card application mode carried in the request message for initializing the subscriber identity module card is matched with the pre-set subscriber identity module card application mode, setting the state of the subscriber identity module card as a normal service state according to the cached information construction message. The invention further discloses a mobile terminal and a device for initializing the subscriber identity module card of the mobile terminal.
Owner:SANECHIPS TECH CO LTD
Electromagnetic transient simulation initialization method
PendingCN112234598AQuick initializationImprove computing efficiencyAc networks with different sources same frequencyEffective powerTransient state
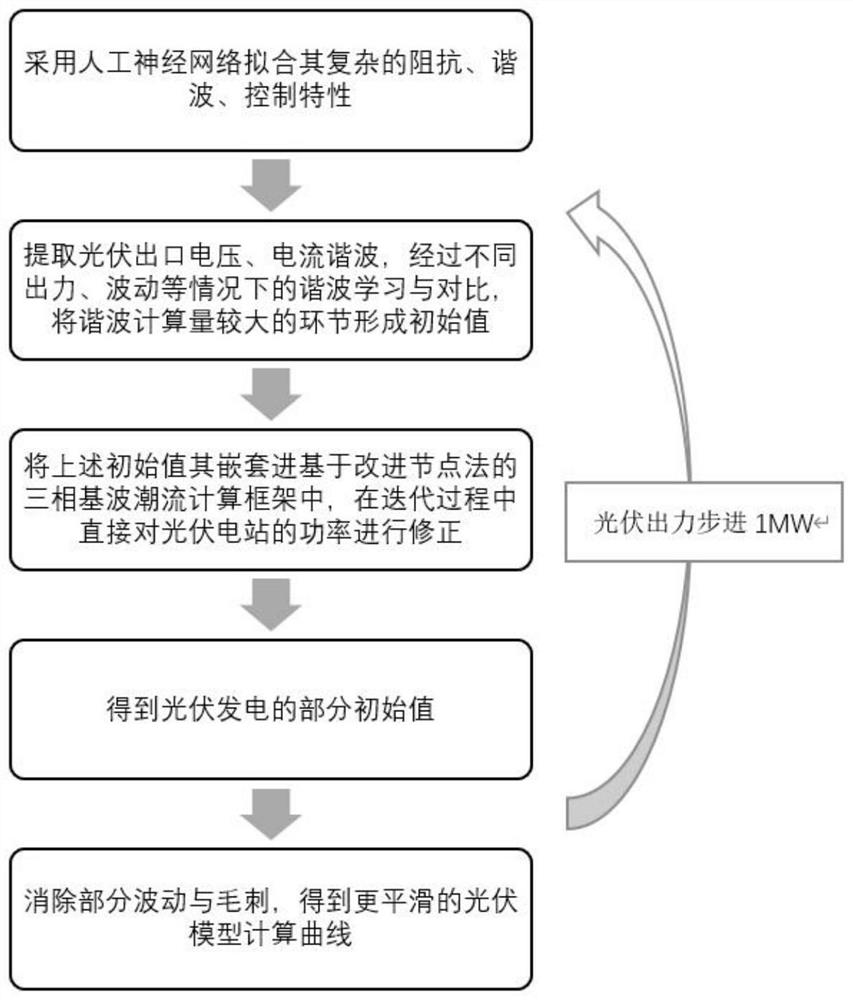
The invention relates to an electromagnetic transient simulation initialization method, which is technically characterized by comprising the following steps: constructing a node network equation of athree-phase unbalanced AC / DC hybrid power grid of a new energy station; constructing a new energy field station three-phase imbalance AC / DC hybrid power grid model based on a BP neural network according to the node network equation, and nesting load flow calculation iteration of the BP neural network; and improving the computing efficiency of the three-phase fundamental wave power flow through a multi-port equivalence-based parallel computing method. On the basis of a new energy field station sequence component model, the imbalance state of the three-phase AC / DC hybrid power grid is initialized and corrected, so that an initial point is closer to a steady-state point to improve the speed of numerical calculation; effective power flow initialization can improve the efficiency of electromagnetic transient simulation and the stability of numerical calculation, and the feasibility of power flow calculation engineering of a new energy station is improved; and according to the parallel computing method based on multi-port equivalence, the electromagnetic transient simulation initialization speed is increased, numerical convergence is fast, and interference is small.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
Single-epoch fixing method for enhancing PPP-RTK ambiguity of regional foundation
InactiveCN103176188BReduce ambiguity convergence timeImprove initialization speedSatellite radio beaconingAmbiguityIonization
The invention provides a single-epoch fixing method for enhancing PPP-RTK ambiguity of regional foundation. The single-epoch fixing method comprises the following steps of: improving the ambiguity convergence time of a PPP-RTK method by carrying out optimizing ordering on the fixing feasibility of single-difference ambiguity between alternative satellites, respectively modeling for an observed value residual error of a CA / P1 pseudo-range and observed value residual errors of L1 and L2 phase positions by adopting a single-reference station processing mode based on a PPP-RTK technique, and realizing the single-epoch fixing of combined ambiguity of an ionization-free layer through step-by-step solving of the ambiguity in consideration of a linear constraint relationship between the high precision of a pseudo-range observed value, long wavelength of a wide-lane observed value, wide-lane ambiguity and L1 ambiguity after a user refines the models, thus the determination time of the PPP ambiguity is minimized, and the working efficiency of precisely locating the user is improved to the maximum degree.
Owner:WUHAN UNIV
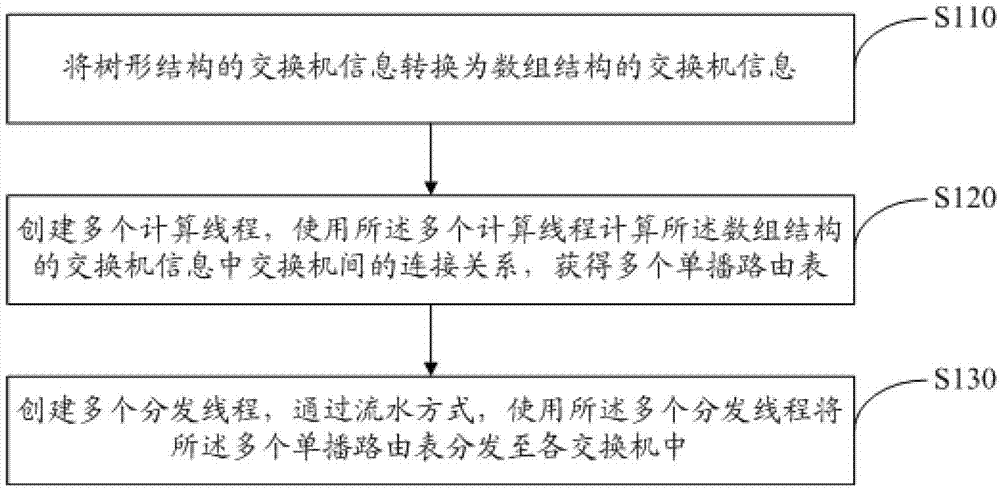
Infinite bandwidth network initializing method and system
The invention discloses an infinite bandwidth network initializing method and a system. After information of a switchboard which is in a tree structure is converted into information of a switchboard which is in an array structure, multithreading is used for calculation of the information, and a generated unicast routing list is distributed through an assembling line mode. Therefore, calculation and distribution can be achieved through the multithreading, the initialization speed of an infiniband (IB) network can be improved effectively, and at the same time, distribution is achieved through the assembling line mode, the switchboard can be used during distribution, and the initialization rate is improved further.
Owner:JIANGNAN INST OF COMPUTING TECH
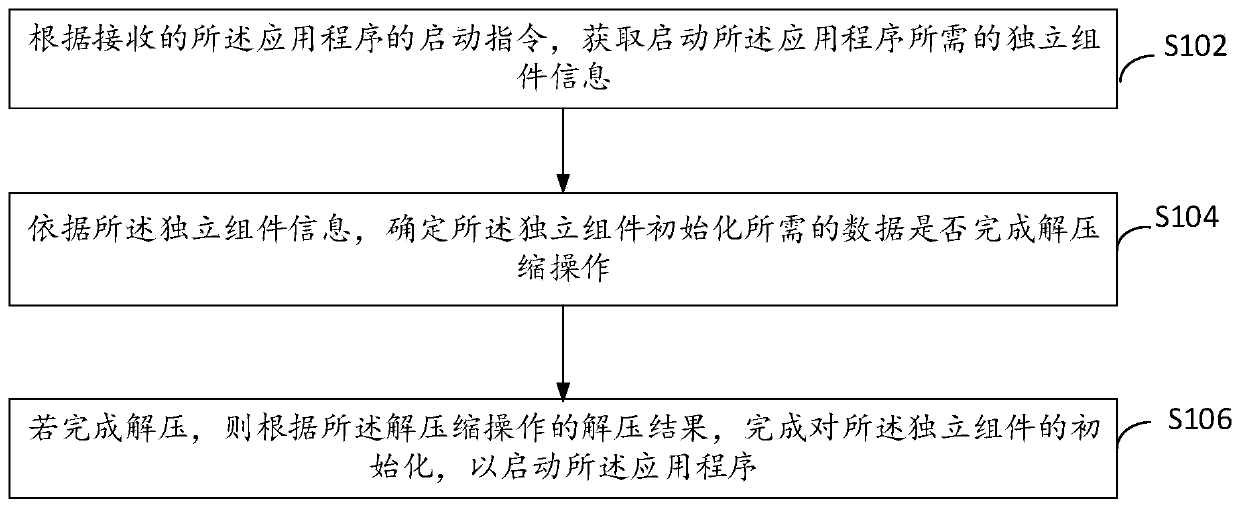
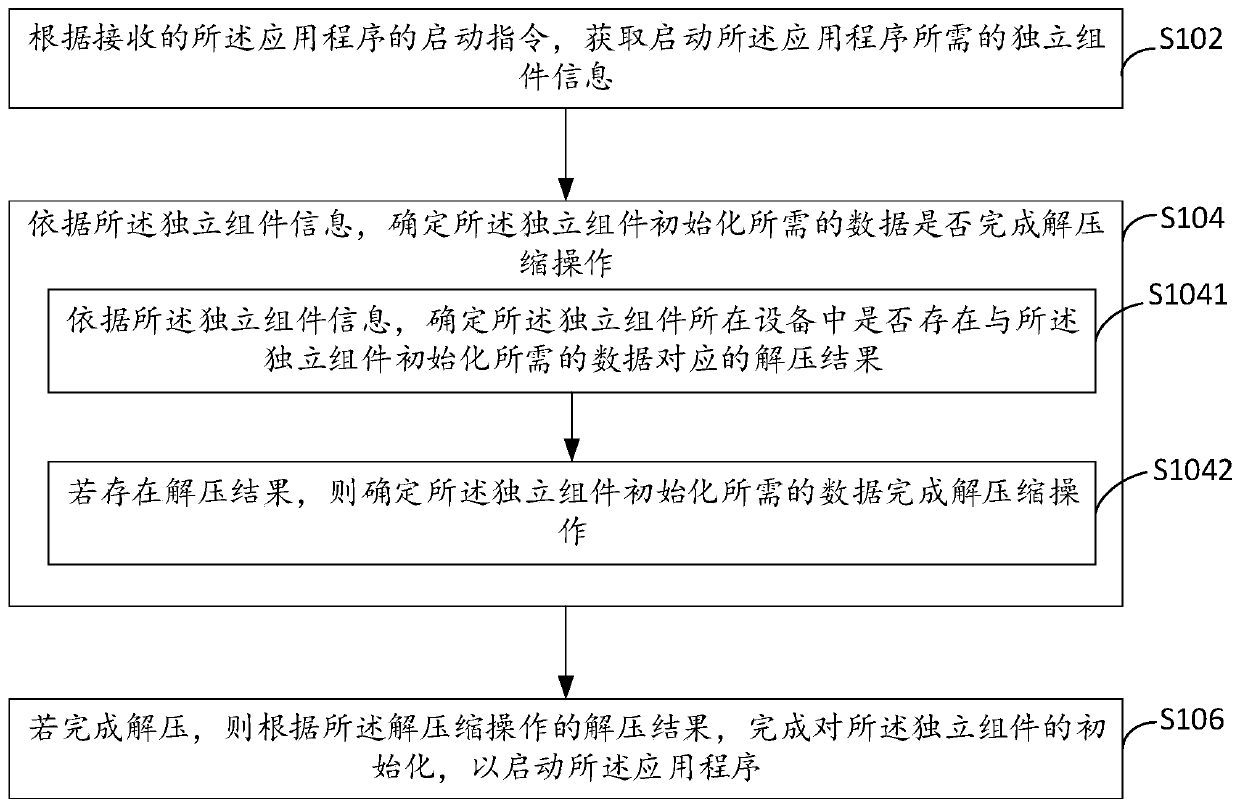
Application program starting method and device, electronic equipment and computer storage medium
ActiveCN111552517AFast startupImprove initialization speedProgram loading/initiatingEnergy efficient computingSoftware engineeringApplication procedure
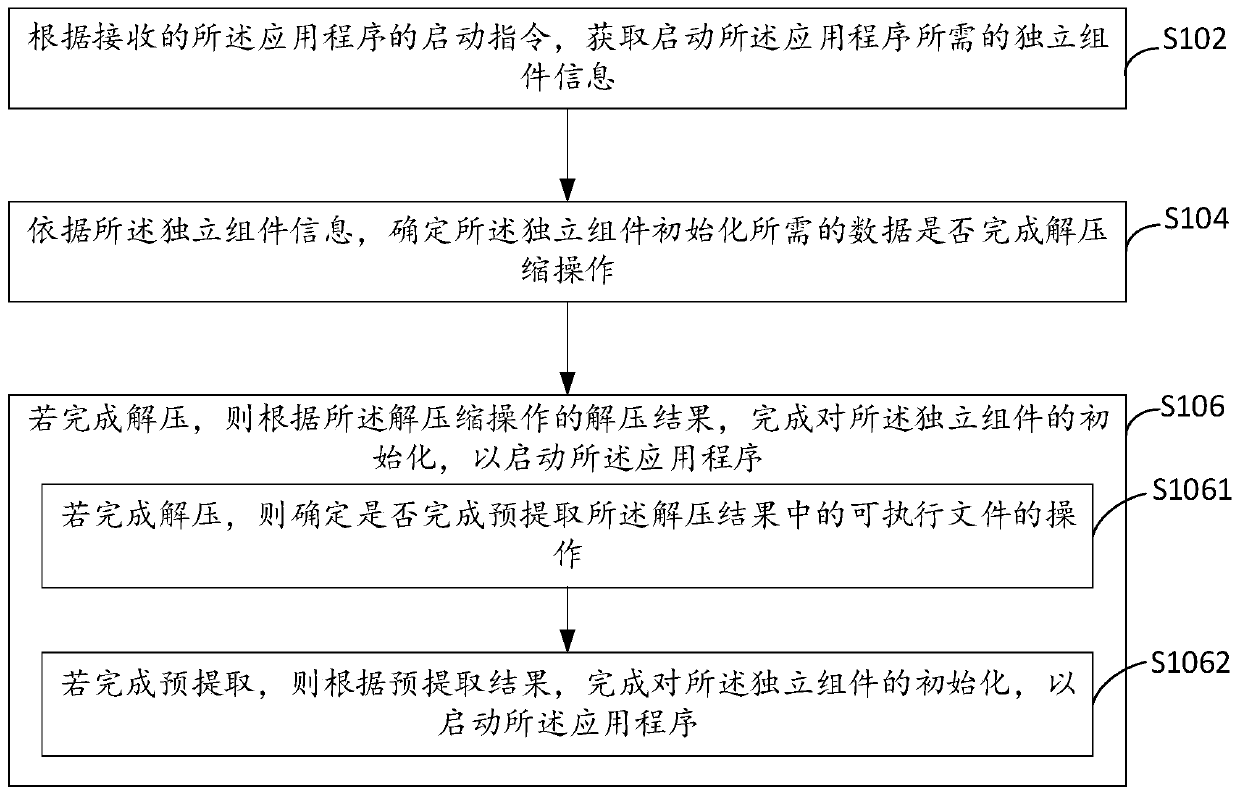
The embodiment of the invention provides an application program starting method and device, electronic equipment and a computer storage medium. The application program starting method comprises the steps of obtaining independent component information required for starting an application program according to a received starting instruction of the application program; according to the independent component information, determining whether data required by initialization of the independent component completes decompression operation or not; and if decompression is completed, completing initialization of the independent component according to a decompression result of the decompression operation so as to start the application program. Through the embodiment of the invention, the initializationspeed can be improved, and the application degree starting speed is reduced.
Owner:ALIBABA GRP HLDG LTD
Mobile terminal and startup method thereof
ActiveCN105306692AReduce boot timeImprove initialization speedSubstation equipmentElectricityComputer terminal
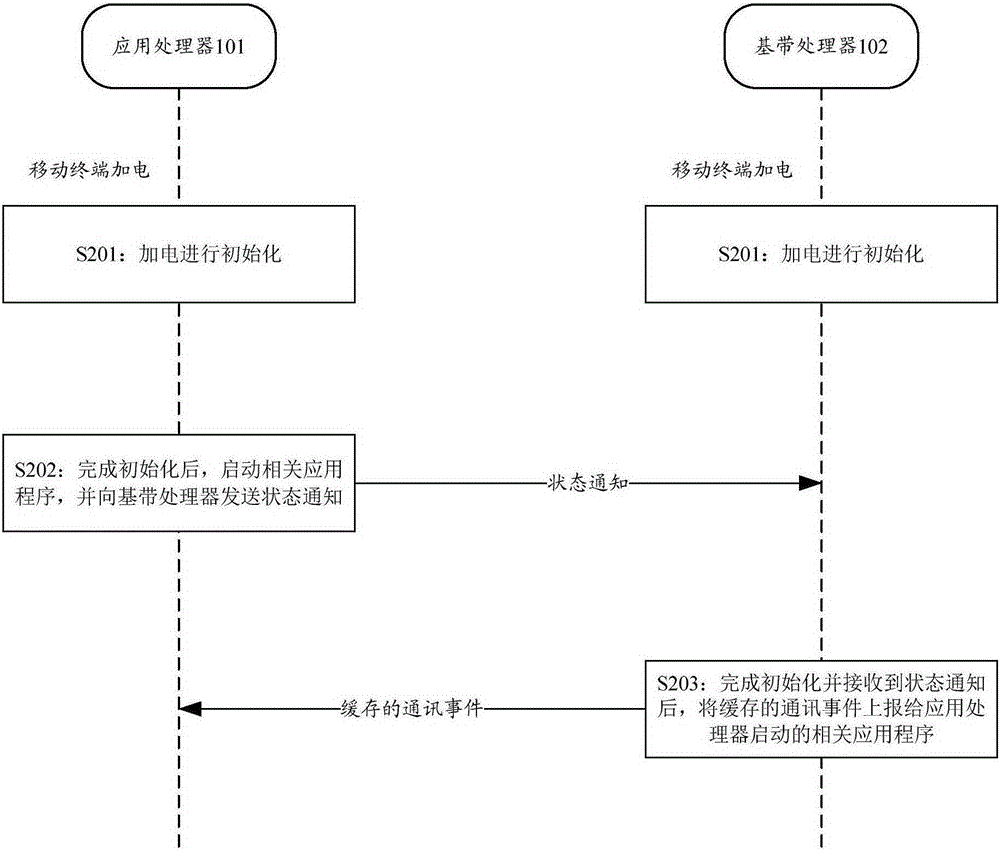
The invention provides a mobile terminal and a startup method thereof. The startup method comprises the following steps that: after an application processor finishes initialization, the application processor starts a relevant application, and sends a state notification to a baseband processor; and after the baseband processor finishes initialization and receives the state notification, the baseband processor reports a cached communication event to the relevant application started by the application processor, wherein the application processor and the baseband processor are powered up at the same time to be initialized, and the cached communication event is a communication event received after the baseband processor finishes the initialization. Through application of the mobile terminal and the startup method thereof, the initialization speed of a communication module is increased, thereby shortening the startup time of the mobile terminal.
Owner:PRANUS BEIJING TECH CO LTD
Initialization method of data processing daemon in distributed storage cluster
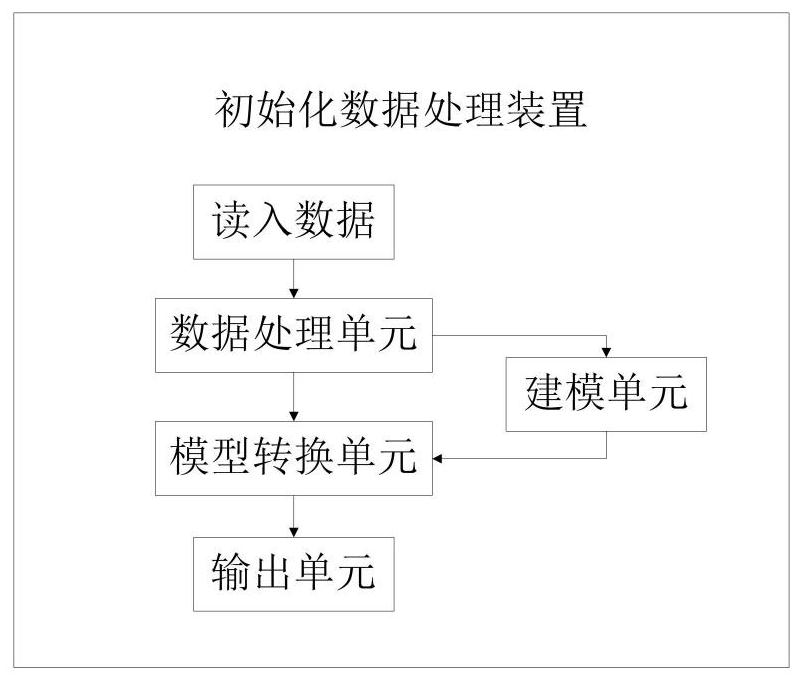
ActiveCN109375873AImprove deployment efficiencyReduce initialization timeInput/output to record carriersData processingDistributed computing
The invention discloses an initialization method of a data processing daemon process in a distributed storage cluster, apparatus, device and computer-readable storage medium, wherein, the method comprises: acquiring a plurality of process numbers at a cluster monitoring daemon process of a distributed storage cluster, and assigning the plurality of process numbers to each node included in the distributed storage cluster; obtaining a plurality of process numbers at the cluster monitoring daemon process of the distributed storage cluster; triggering each node to initialize by using the assignedprocess numbers in parallel to instruct each node to allocate the assigned process number one by one to each data processing daemon contained in the node, and triggering each data processing daemon contained in the node is triggered to initialize in parallel; obtaining a result of initialization of each data processing daemon, and returning the result to the cluster monitoring daemon. Thus, the process initialization speed is greatly improved, and the cluster deployment efficiency is further improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Changing method and device for service quality script data in communication system
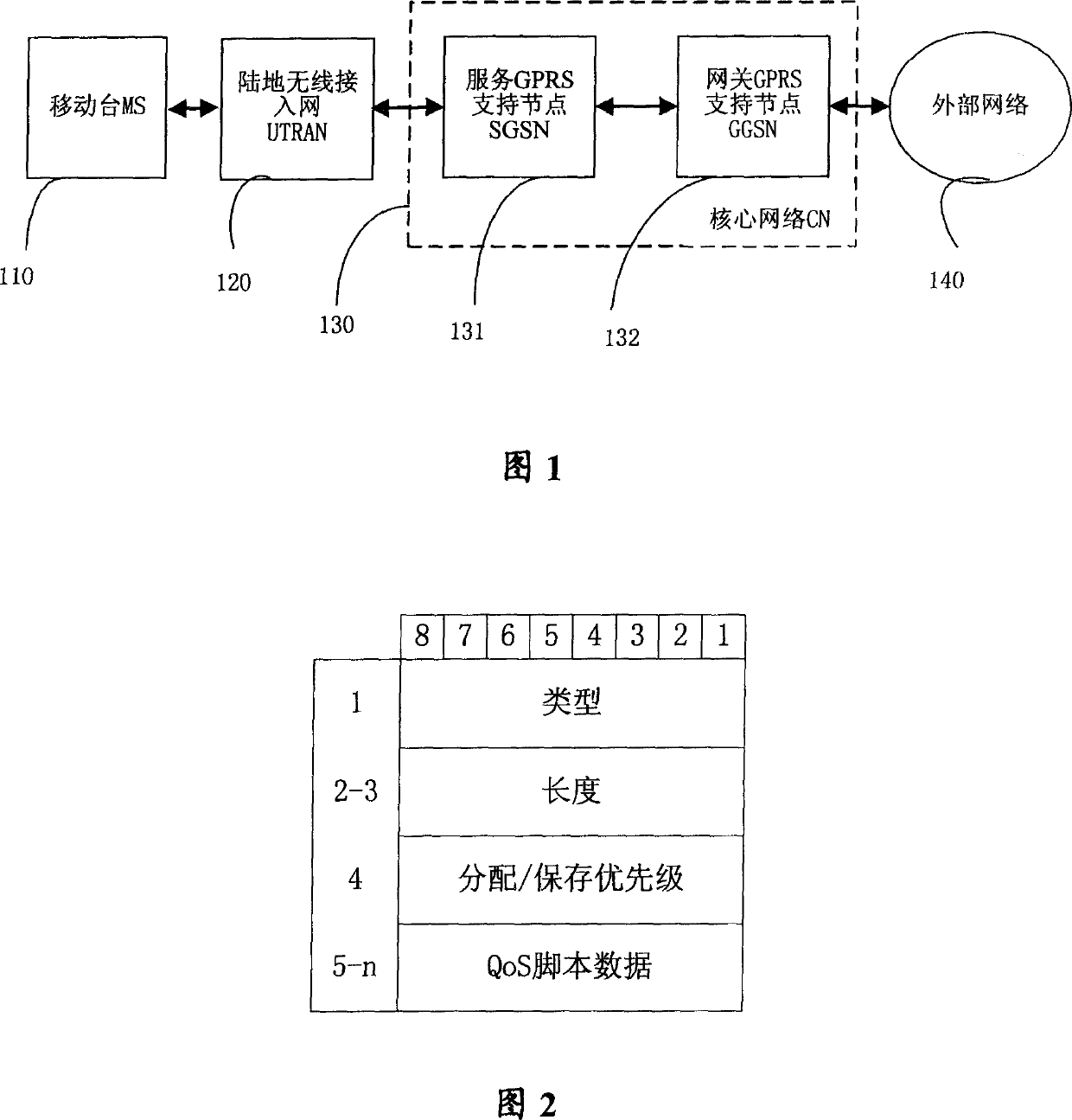
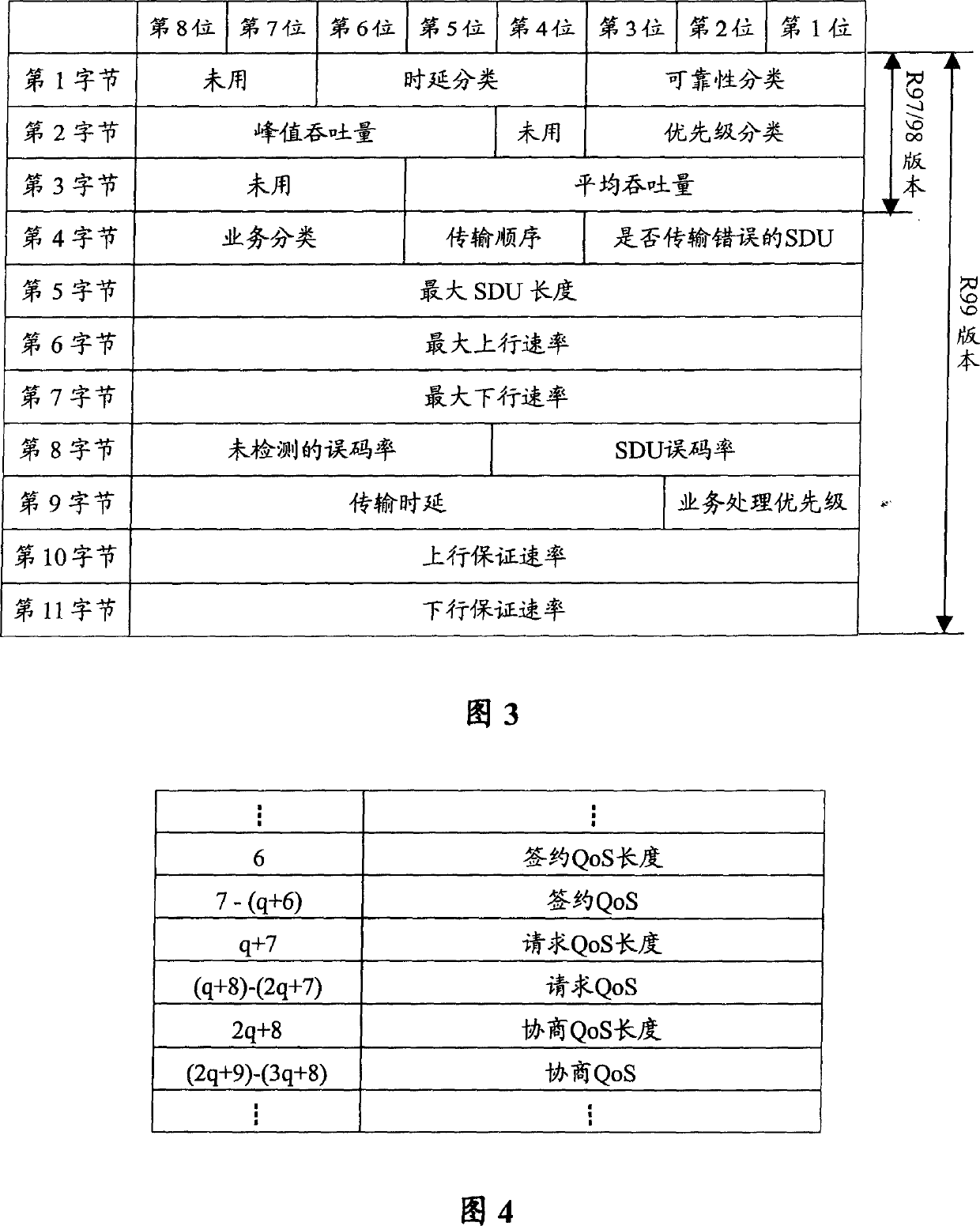
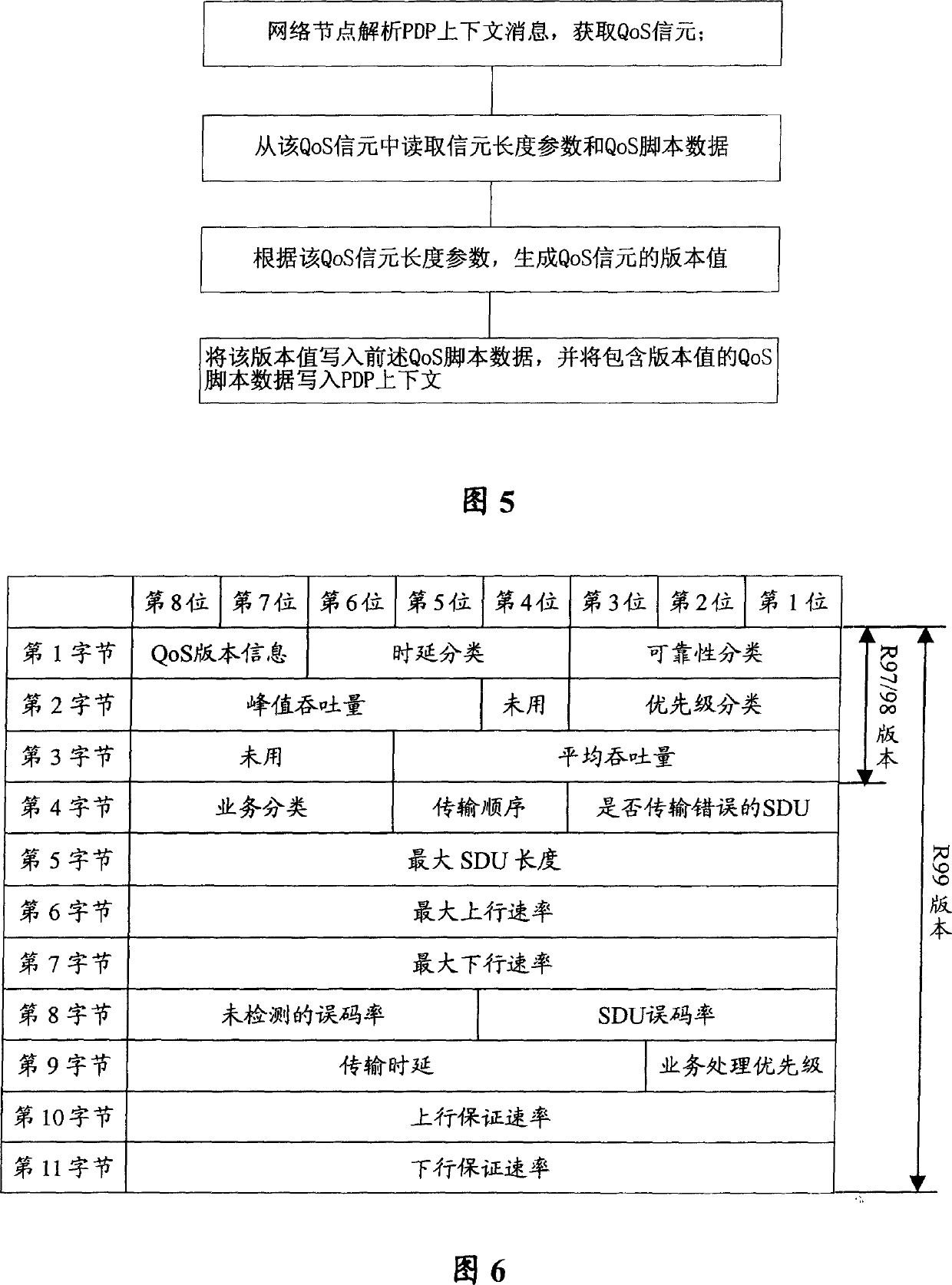
ActiveCN1750706ASimplified QoS informationSave memory spaceNetwork traffic/resource managementRadio/inductive link selection arrangementsQuality of serviceDistributed computing
This invention discloses a method for changing script data of service quality in communication system, which contains said network node of communication system analyzing content message of grouping data protocol and obtaining service quality cell, said network node accessing cell length parameter and service quality script data from said service quality cell, generating service quality cell version number according to said cell length parameter, writing the version number in above mentioned service quality script data which is then written in content of grouping data protocol. Said invention also provides a device for changing script data of service quality in communication system.
Owner:HUAWEI TECH CO LTD
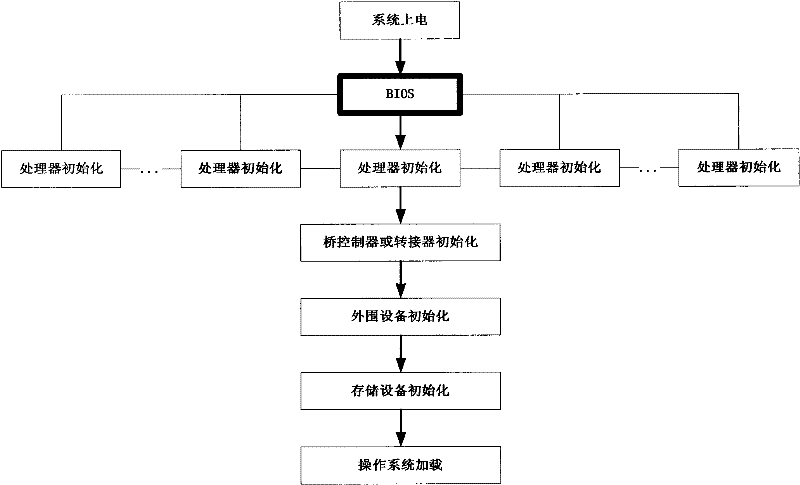
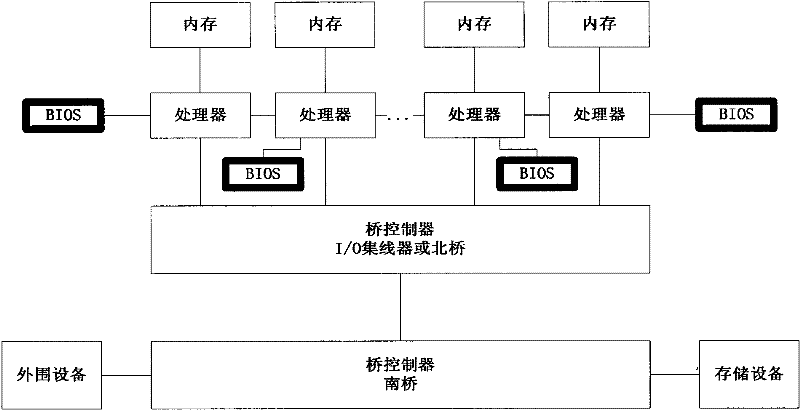
Multi-BIOS mapping parallel initialization method
ActiveCN101609406BImprove initialization speedImprove operational efficiencyProgram loading/initiatingComputer architectureComputerized system
The invention provides a multi-BIOS mapping parallel initialization method. The method is different from a traditional single-BIOS serial initialization method. The method designs a traditional computer system to an initialization computer system with that multi-BIOS is directly connected with a processor for parallelism through a method that a single-BIOS is carried on a multi-level bridge controller for initializing system in a parallel mode on the basis of creatively altering traditional computer system structure. The multi-BIOS mapping parallel initialization method realizes direct connection of the multi-BIOS with the processor, fastens the speed of system initialization, and enhances running efficiency of the system and high availability of the system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
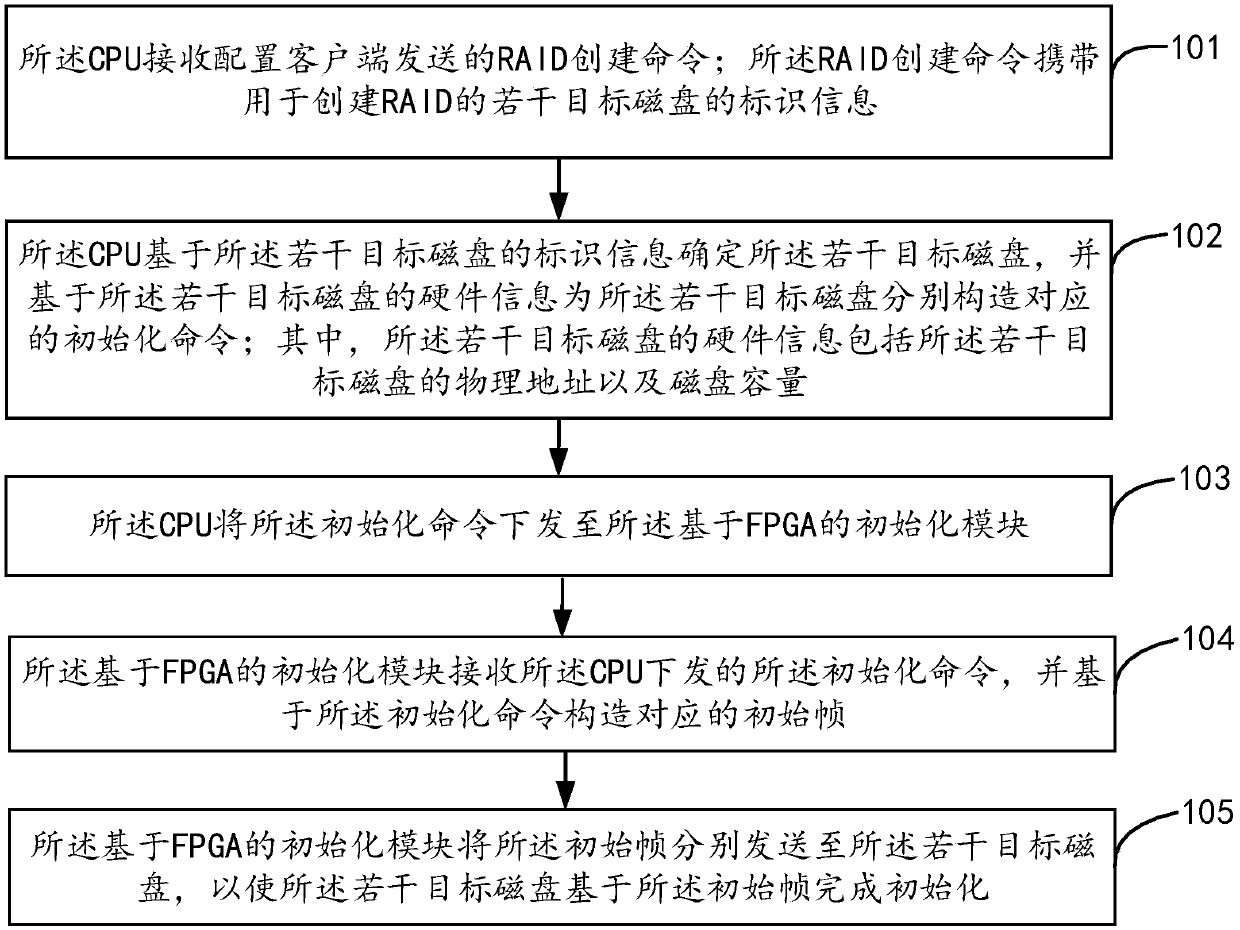
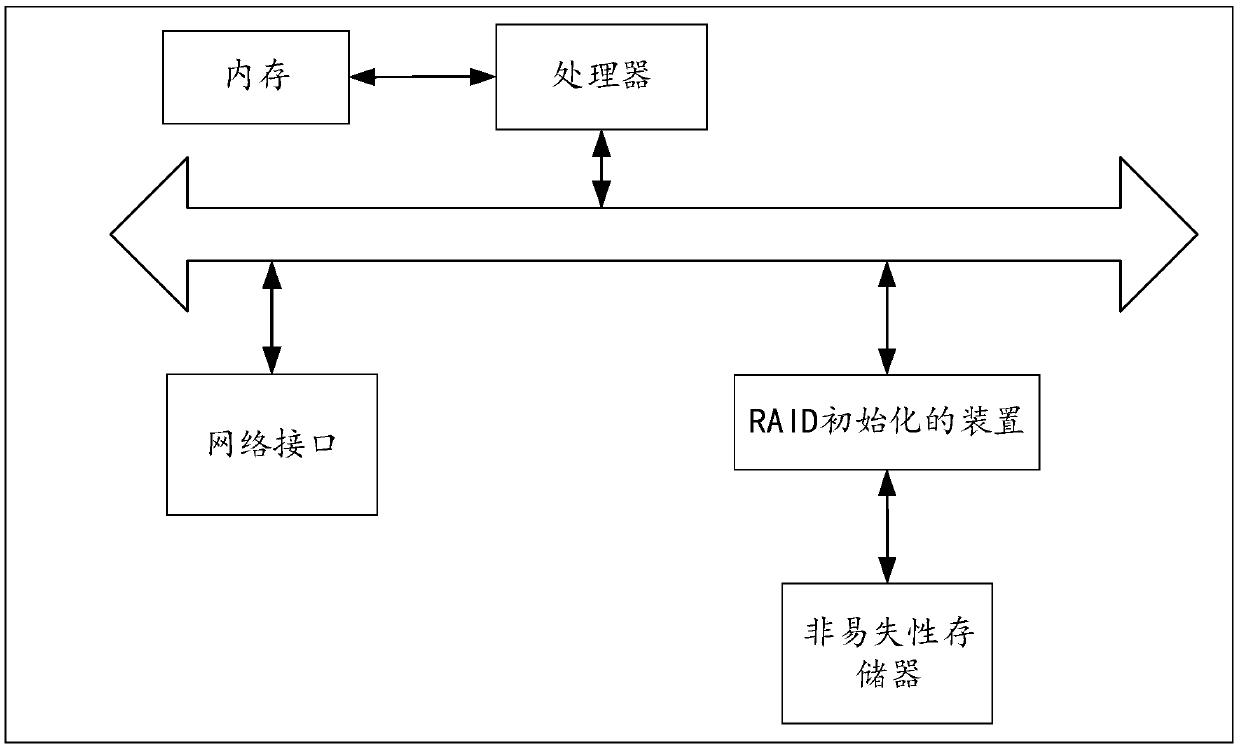
Method and device for raid initialization
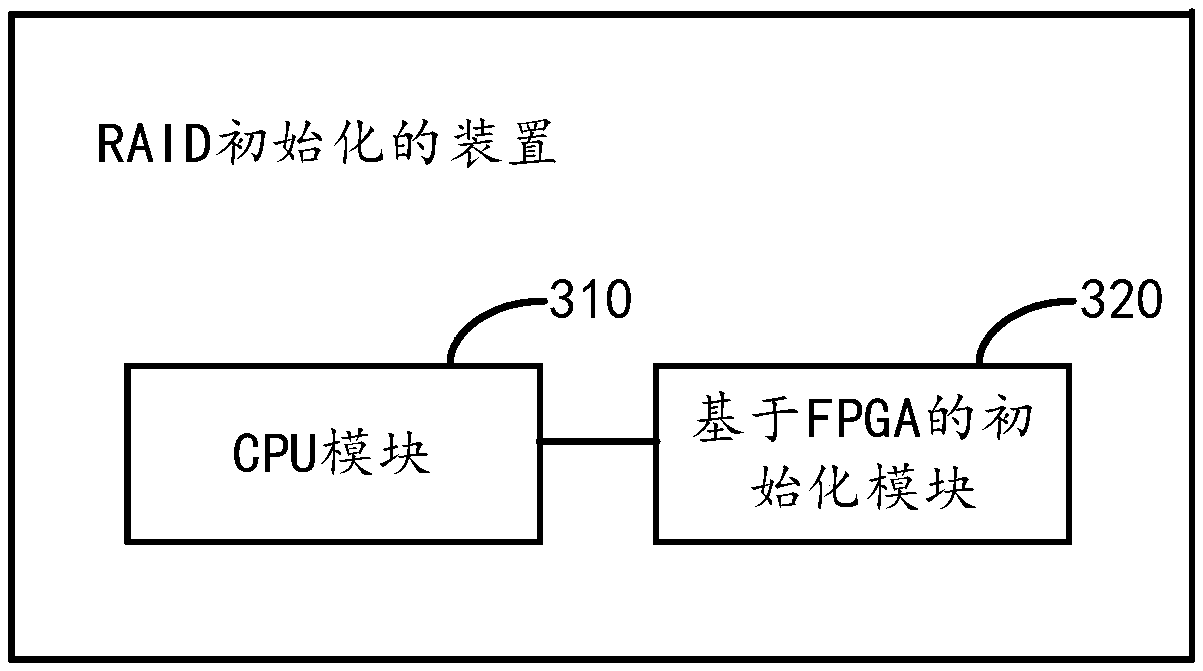
ActiveCN106354435BReduce IO operationsReduce the burden onInput/output to record carriersRAIDFrame based
The invention relates to a method and device for initializing RAID. The method comprises the steps that a CPU receives an RAID establishing command sent by a client side; the CPU determines a plurality of target disks based on identification information of the target disks in the establishing command and constructs corresponding initializing commands for the target disks respectively based on hardware information of the target disks; the CPU sends the initializing commands to an initializing module based on an FPGA; the initializing module based on the FPGA receives the initializing commands issued by the CPU and constructs corresponding initial frames based on the initializing commands; the initializing module based on the FPGA sends the initial frames to the target disks respectively, so that the target disks are initialized based on the initial frames. According to the method and device, the initializing module based on the FPGA can directly interact with the disks, therefore, IO operation in most operation systems can be reduced, and the loads of the operation systems can be relieved.
Owner:BEIJING TENGLING TECH CO LTD
Method for encrypting consumable items through radio frequency identification electronic tag
ActiveCN102087684BImprove reliabilityEasy to compileDigital data protectionDigital data authenticationPasswordRadio frequency
The invention provides a method for encrypting consumable items through a radio frequency identification electronic tag. By using a method of additionally arranging the radio frequency identification electronic tag on the consumable items of various devices and using the devices and the radio frequency identification electronic tag to communicate by a method for communicating through encryption information, the consumable items are encrypted and protected. The consumable items are encrypted by adopting the non-contact radio frequency identification electronic tag, so that the consumable itemsare not easy to rust and damage and the reliability is improved; the radio frequency identification electronic tag is initialized after the consumable items are assembled, thus the speed of initialization is greatly improved; the method is convenient to comply a plurality of groups of passwords and produce and manage and provides the possibility for complying different passwords according to different requirements; a module is packaged by using a physical method, so that all keys cannot be obtained by using a method of breaking a host program, and the stability for encryption is greatly improved; and by setting an automatic protecting function at the radio frequency identification electronic tag, the information security is ensured.
Owner:北京力码科信息技术股份有限公司
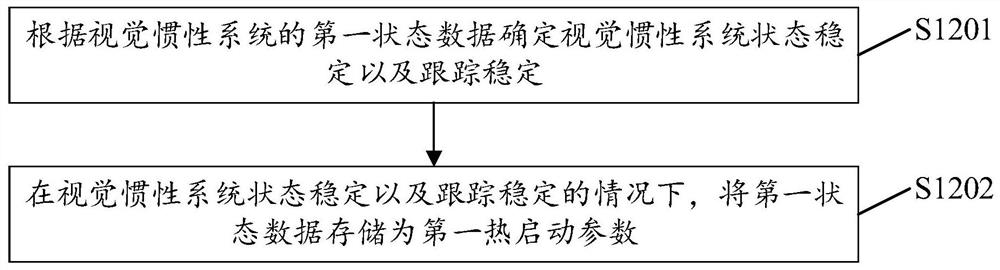
Initialization method, device, electronic equipment and storage medium of visual-inertial system
ActiveCN113029134BImprove stabilityImprove initialization speedNavigation by speed/acceleration measurementsUsing reradiationSimulationVisual perception
Owner:ZHEJIANG SENSETIME TECH DEV CO LTD
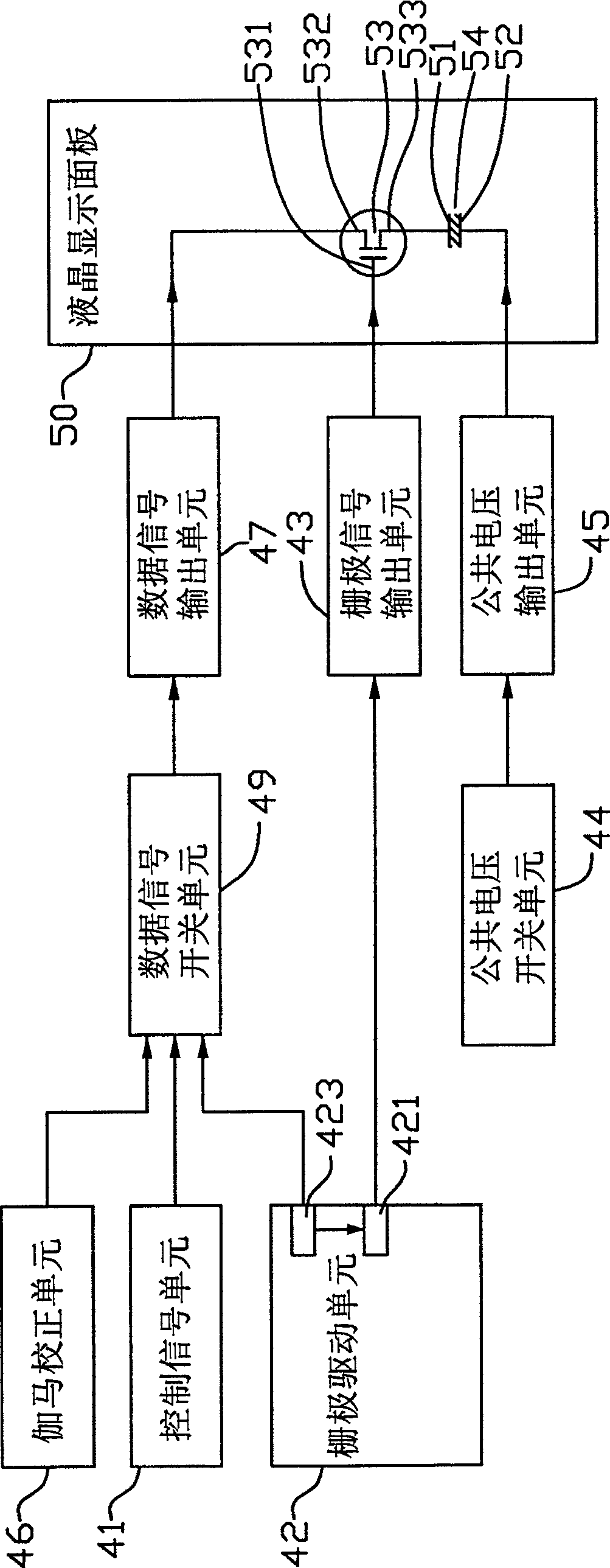
Optical compensation flexure type LCD
InactiveCN100543525CImprove initialization speedHigh voltageStatic indicating devicesNon-linear opticsLiquid-crystal displayData signal
The present invention relates to an optically compensated curved liquid crystal display, which includes a liquid crystal display panel, a gamma correction unit, a common voltage generation unit, a gate drive unit and a data signal switch unit. The gate driving unit includes a gate signal generating circuit and a high voltage generating circuit, the gate signal generating circuit is used to generate a gate driving signal, and the output voltage of the high voltage generating circuit is higher than that generated by the gamma correction unit maximum voltage. The liquid crystal display panel includes a pixel electrode and a common electrode. The data signal switching unit is respectively connected with the high voltage generating circuit, the gamma correction unit and the liquid crystal display panel, and can selectively provide the voltage signal of the high voltage generating circuit or the gamma correction unit to the pixel electrode. The optical compensation curved liquid crystal display of the invention has short initialization time and low cost.
Owner:INNOCOM TECH (SHENZHEN) CO LTD +1
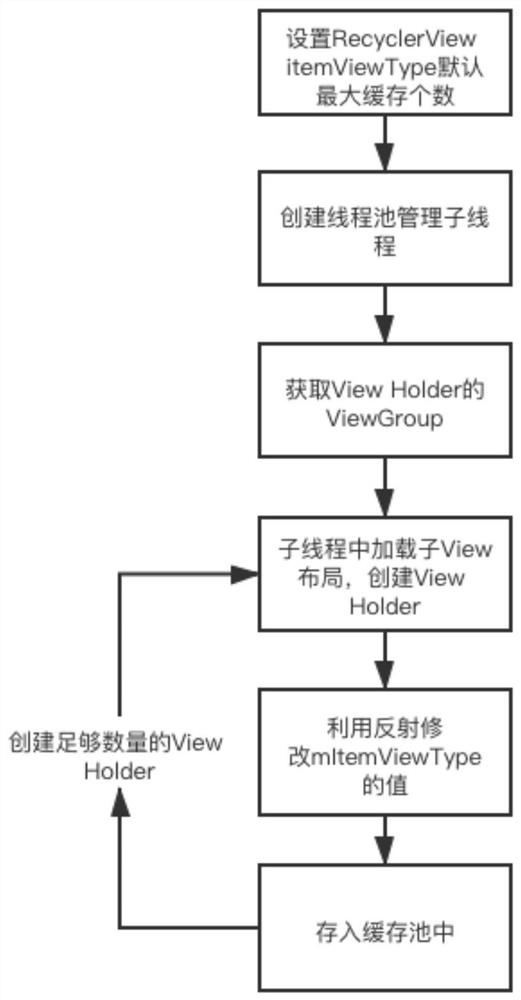
Method for optimizing use performance of RecyclerView control
InactiveCN112364276AIncrease capacityImprove initialization speedSpecial data processing applicationsWeb data browsing optimisationParallel computingPool
The invention discloses a method for optimizing the use performance of a RecyclerView control, and belongs to the technical field of software. The detection method comprises the following steps of S1,before an interface is started, creating a sub-thread, asynchronously initializing a sub-View layout in the sub-thread, and generating a ViewHolder; and S2, storing the ViewHolder into a cache pool to be used by the Recycler View. The optimized Recycler View control has the advantages that the accommodating quantity of cache pools is increased, a large quantity of ViewHolders are pre-created in sub-threads and stored in the cache pools, the value of intemViewType of the ViewHolders is modified into the type value of the target ViewHolder by utilizing a reflection mechanism, the consistency ofthe stored and searched intemViewType is kept and the effect of reuse is achieved. And enough ViewHolder is created in the sub-thread, and a main thread is not occupied to execute a task, so that thepage initialization speed is increased.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com