Patents
Literature
61 results about "Sub types" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
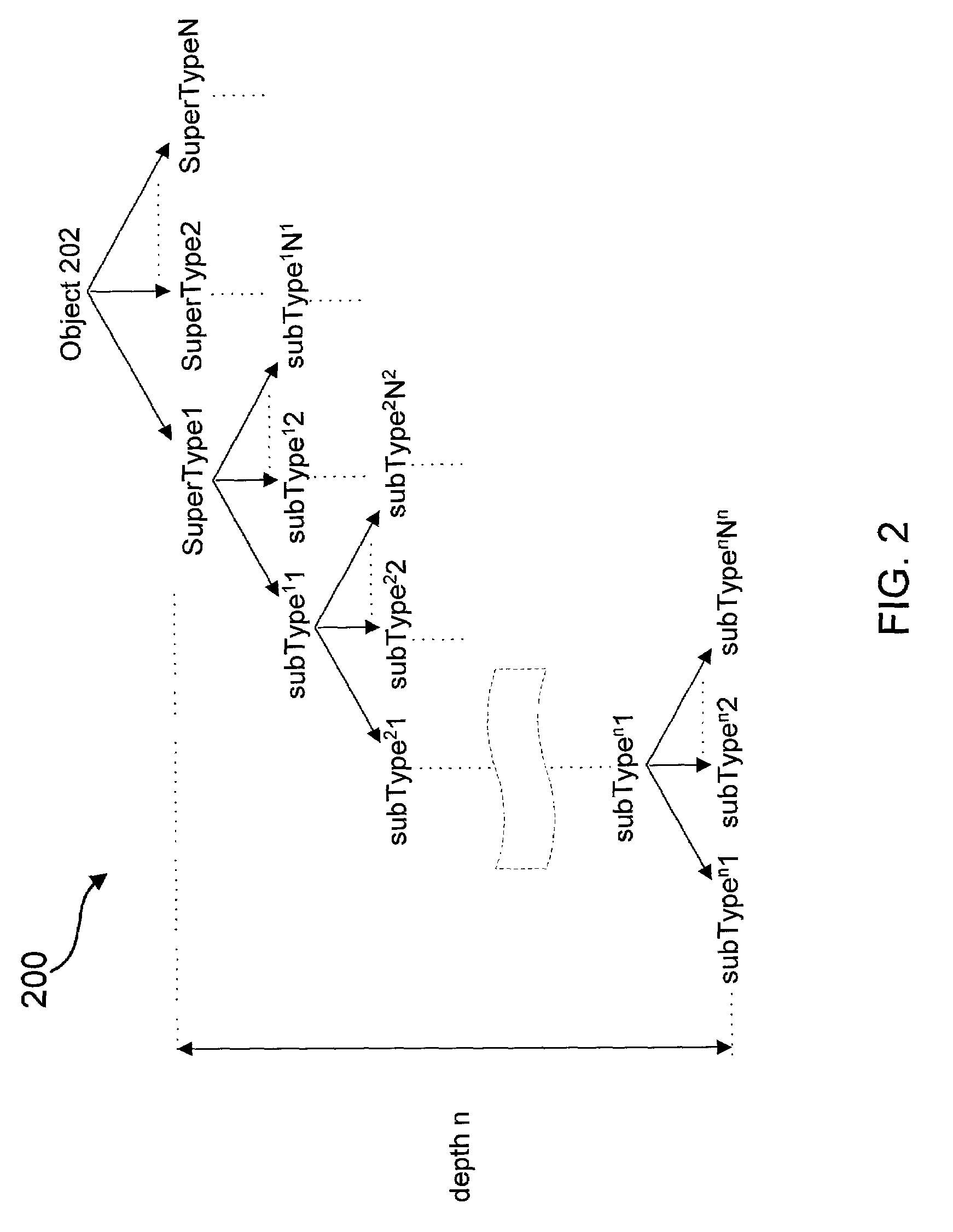
In this topic. Subtypes are a subset of features in a feature class, or objects in a table, that share the same attributes. They are used as a method to categorize your data. For example, the streets in a city streets feature class could be categorized into three subtypes: local streets, collector streets, and arterial streets.
Information recommendation method and system
PendingCN102411596AEasy to useAccurate and Valid RecommendationsSpecial data processing applicationsData scienceCurrent user
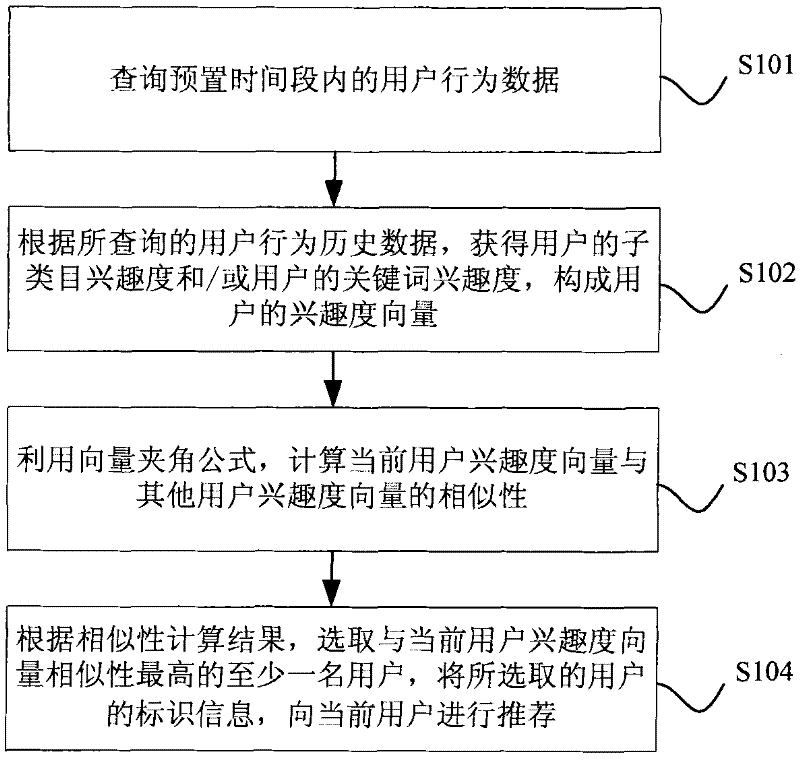
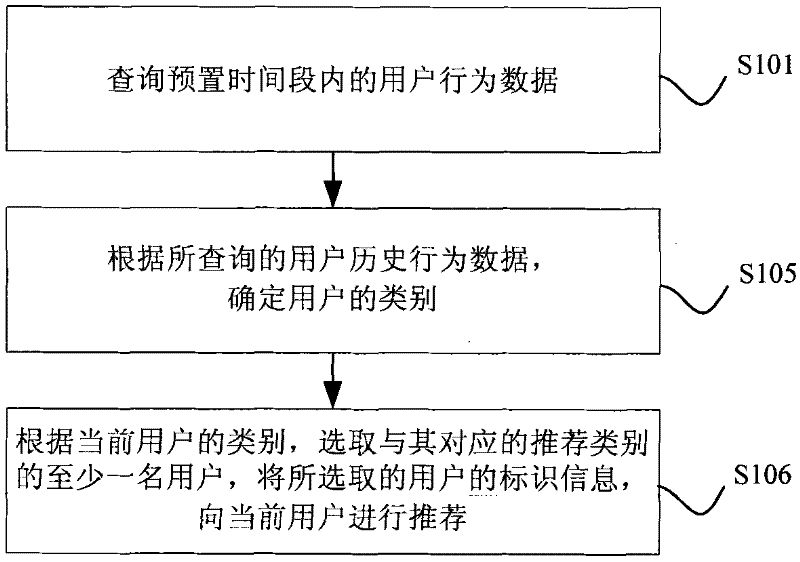
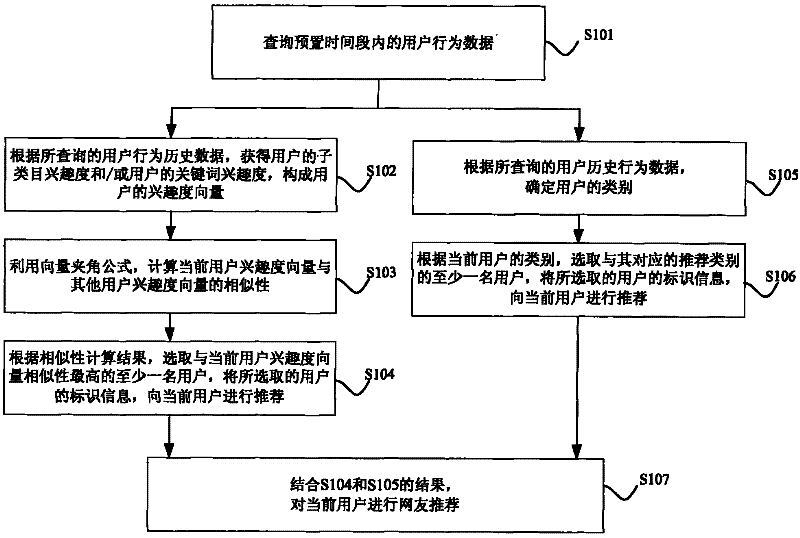
The invention discloses an information recommendation method and a system. The information recommendation method comprises the following steps of: inquiring user behavior data in a preset time period; obtaining the user sub type interesting degree and / or user keyword interesting degree according to the inquired user behavior data, and using the obtained sub type interesting degree and / or the user keyword interesting degree for forming a user interesting degree vector; using a vector included angle formula for calculating the similarity of the current user interesting vector and other user interesting degree vector; and selecting at least one user with the highest similarity to the current user interesting degree according to the similarity calculation results, and recommending information to the current users according to the selected user mark information. Through the scheme, more accurate and effective information recommendation can be realized, so the use feeling of the users is improved, the unnecessary information interaction among the users can be reduced, the load of a system server is reduced, and the network bandwidth resource occupation is saved.
Owner:ALIBABA GRP HLDG LTD
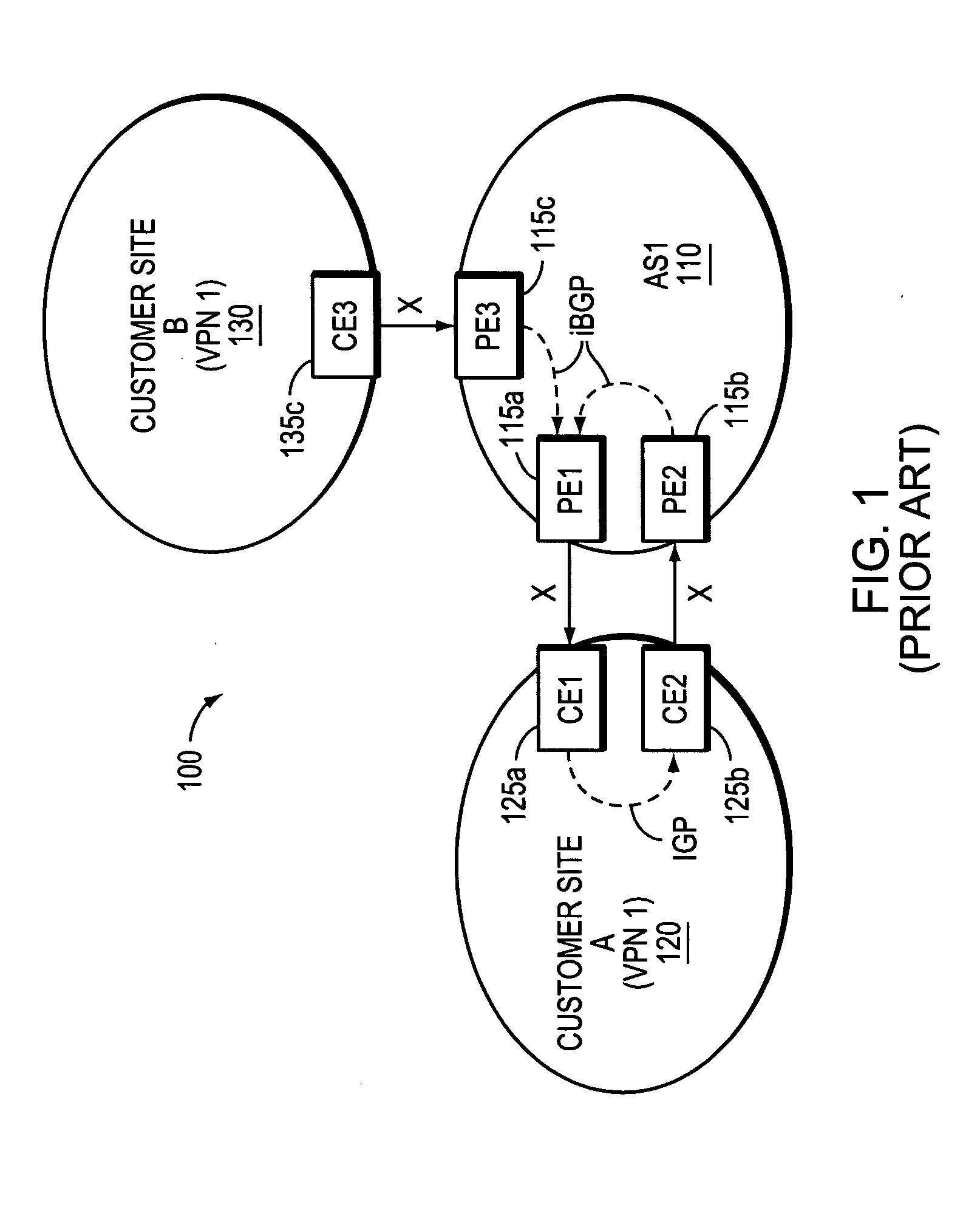
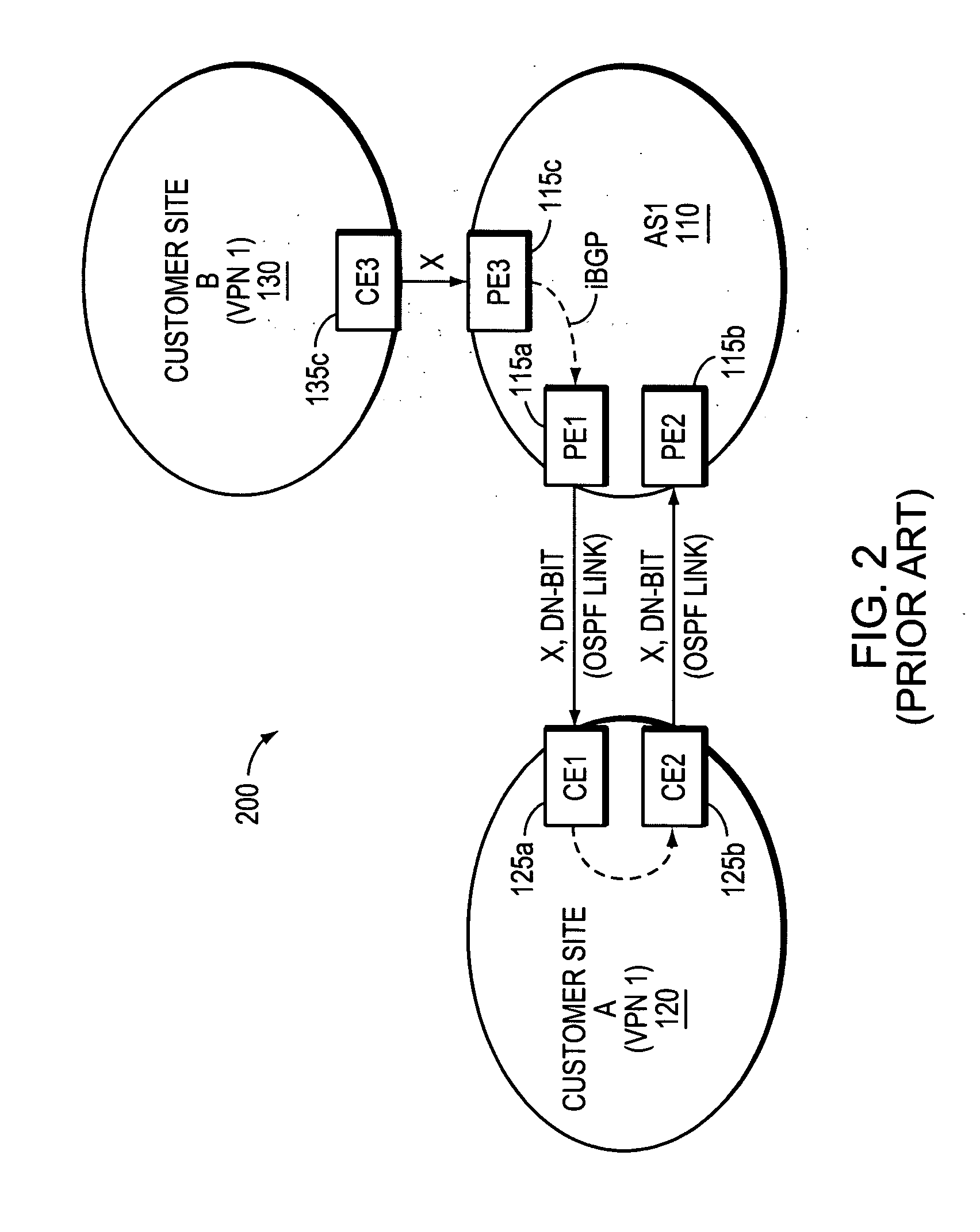
Technique for preventing routing loops by disseminating BGP attribute information in an OSPF-configured network
ActiveUS20070214275A1Overcome disadvantagesAvoid developmentMultiple digital computer combinationsTransmissionBorder Gateway ProtocolType-length-value
A novel technique is provided for preventing routing loops by disseminating Border Gateway Protocol (BGP) attribute information in an Open Shortest Path First (OSPF) configured network. Specifically, a new OSPF sub-type-length-value (TLV) is introduced for transporting a conventional BGP autonomous system (AS) path attribute through the OSPF-configured network. Like the BGP AS-path attribute, the new OSPF AS-path sub-TLV is configured to store a set of AS numbers corresponding to the AS path of one or more advertised routes. Thus, when a network device receives an OSPF link-state advertisement (LSA) containing the novel AS-path sub-TLV, the network device determines whether it resides in an autonomous system whose AS number is stored in the sub-TLV. If so, the network device does not install the LSA's advertised routes in its link-state database since the routes, if installed, could result in routing loops.
Owner:CISCO TECH INC
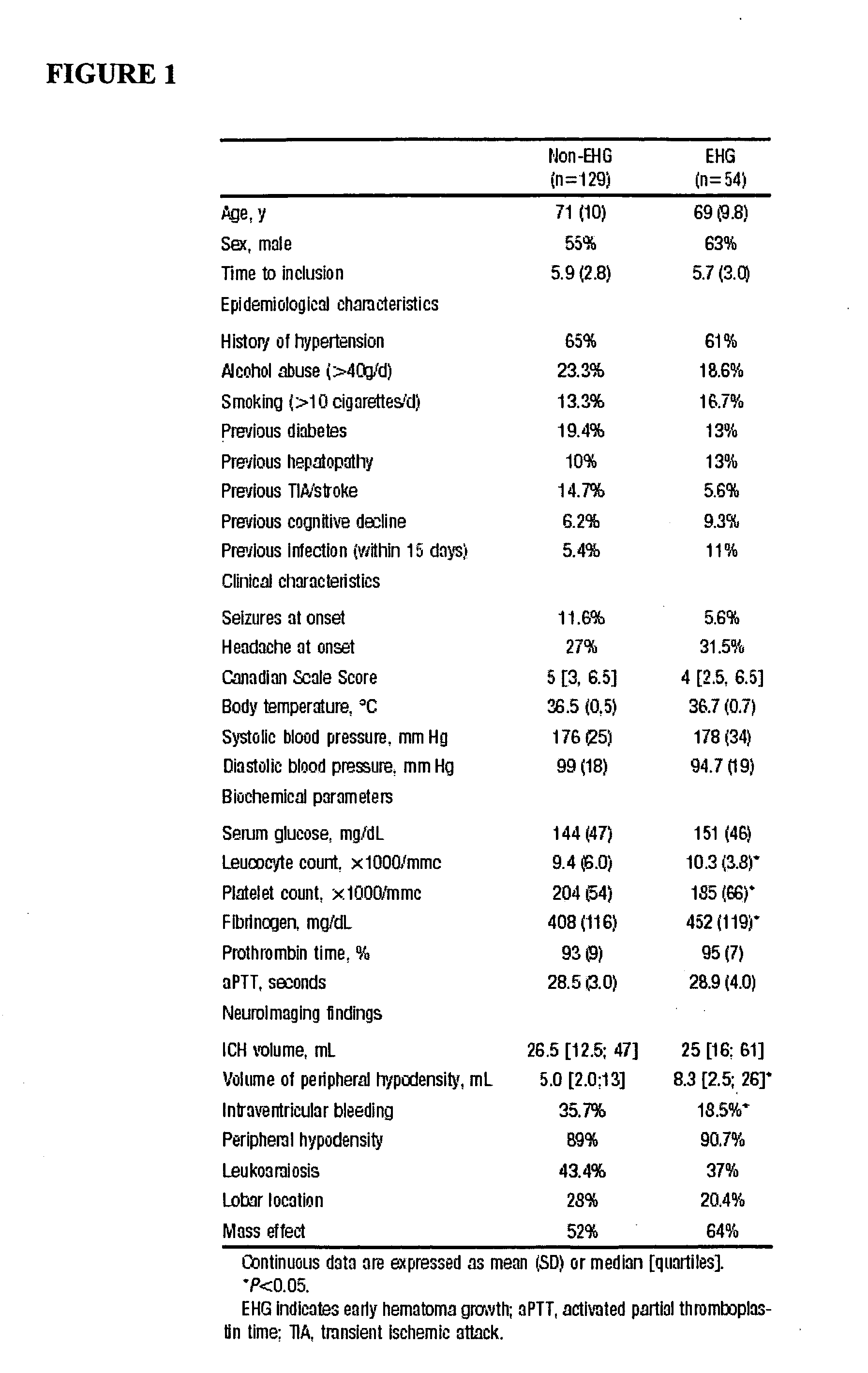
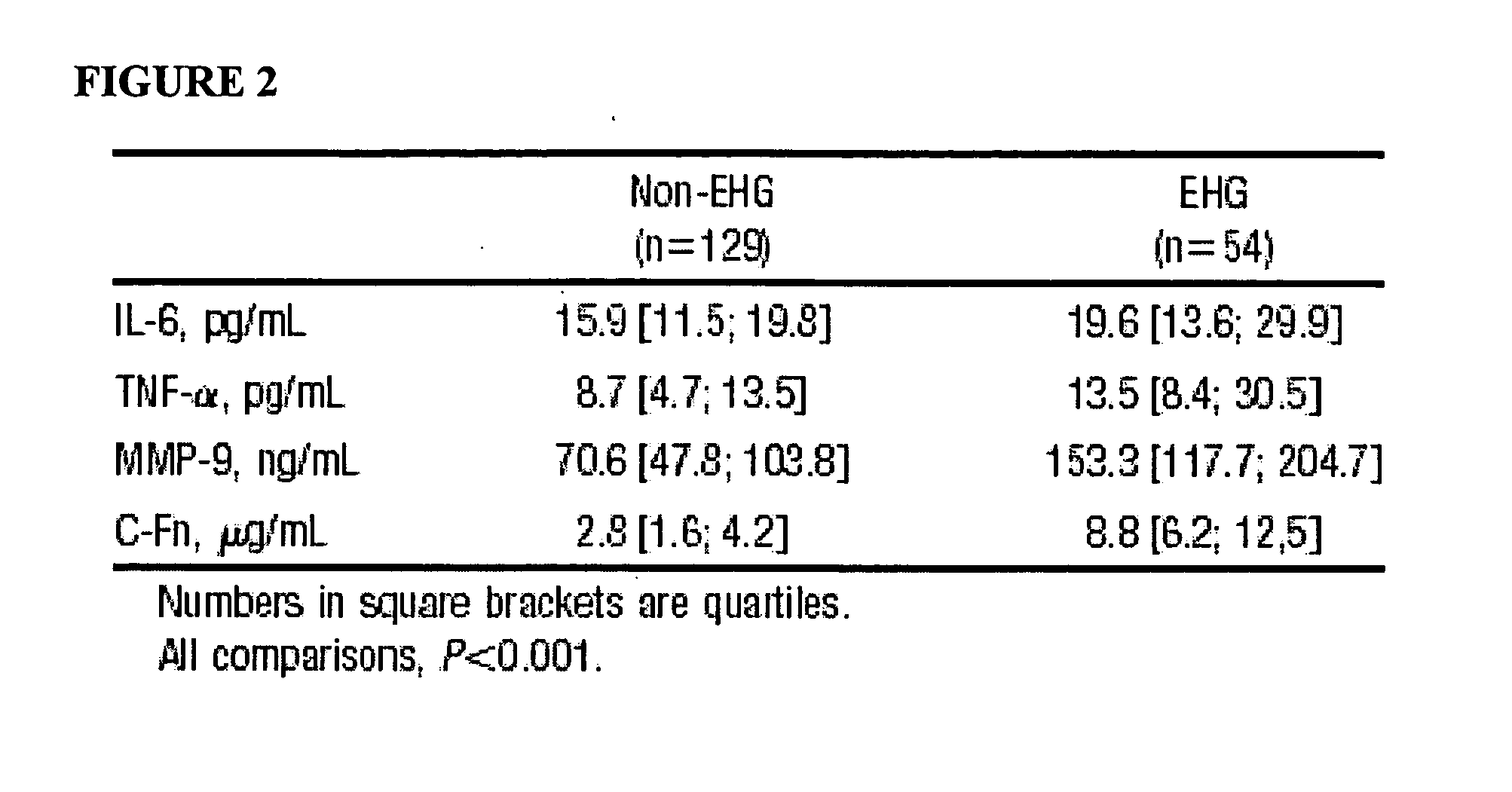
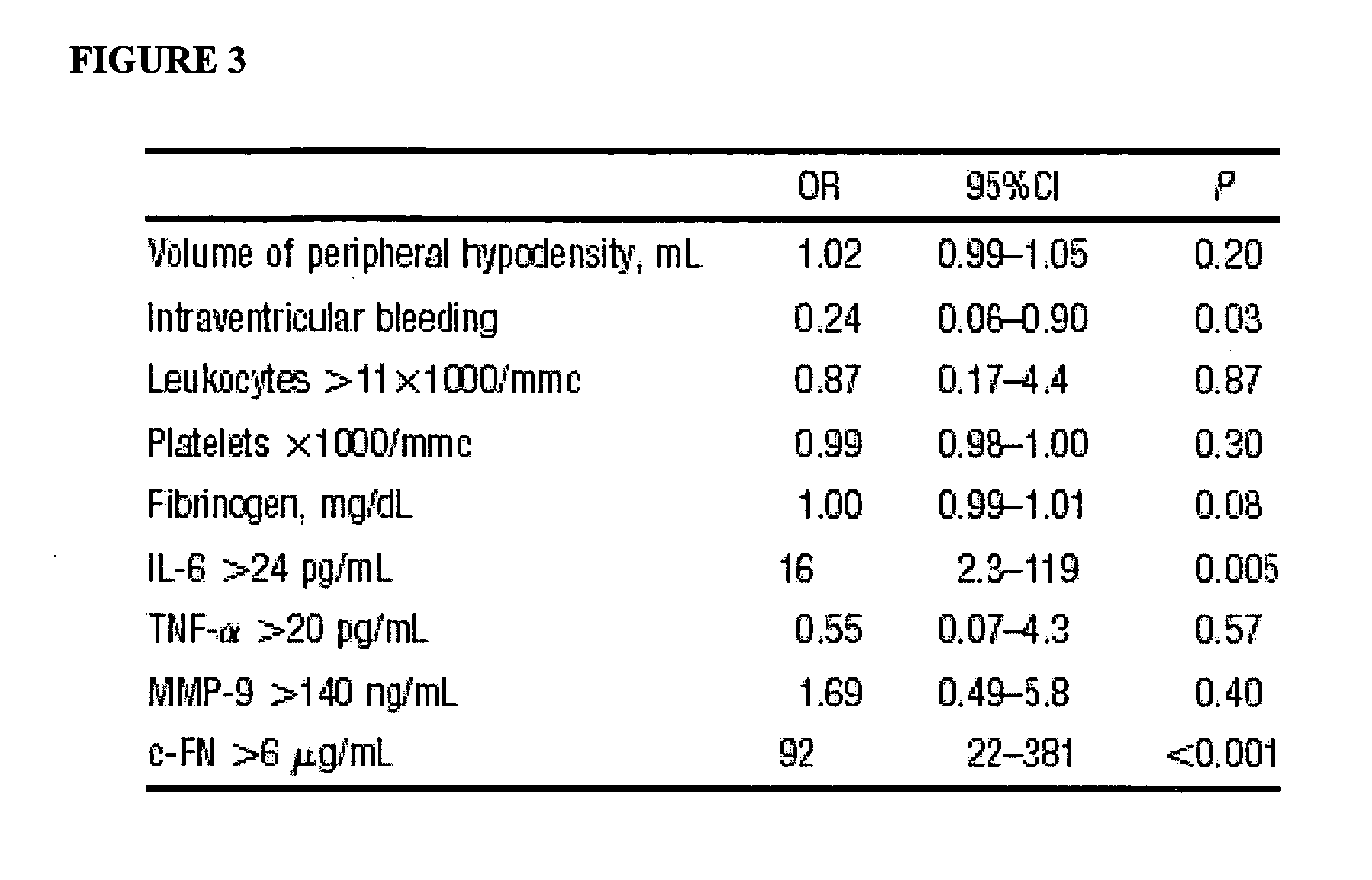
Cellular fibronectin as a diagnostic marker in stroke and methods of use thereof
InactiveUS20070005261A1Rapidly and accurately determinedMaximal sensitivityMedical data miningDisease diagnosisStroke subtypeBiomarker (petroleum)
Methods for the diagnosis and evaluation of stroke and stroke sub-type employ a variety of bio-markers including cellular fibronectin (c-Fn) assembled as a panel for stoke diagnosis and evaluation. Methods are disclosed for selecting markers and correlating their combined levels with a clinical outcome of interest. In various aspects the methods permit early detection and differentiation of stroke subtypes, determination of the prognosis of a patient presenting stroke symptoms, and identification of a patient at risk for early hematoma growth and / or malignant massive cerebral artery infarction. The disclosed methods provide rapid, sensitive and specific assays to greatly increase the number of patients that can receive beneficial stroke treatment and therapy, and to reduce the human and economic costs associated with incorrect stroke diagnosis.
Owner:PREDICTION SCI
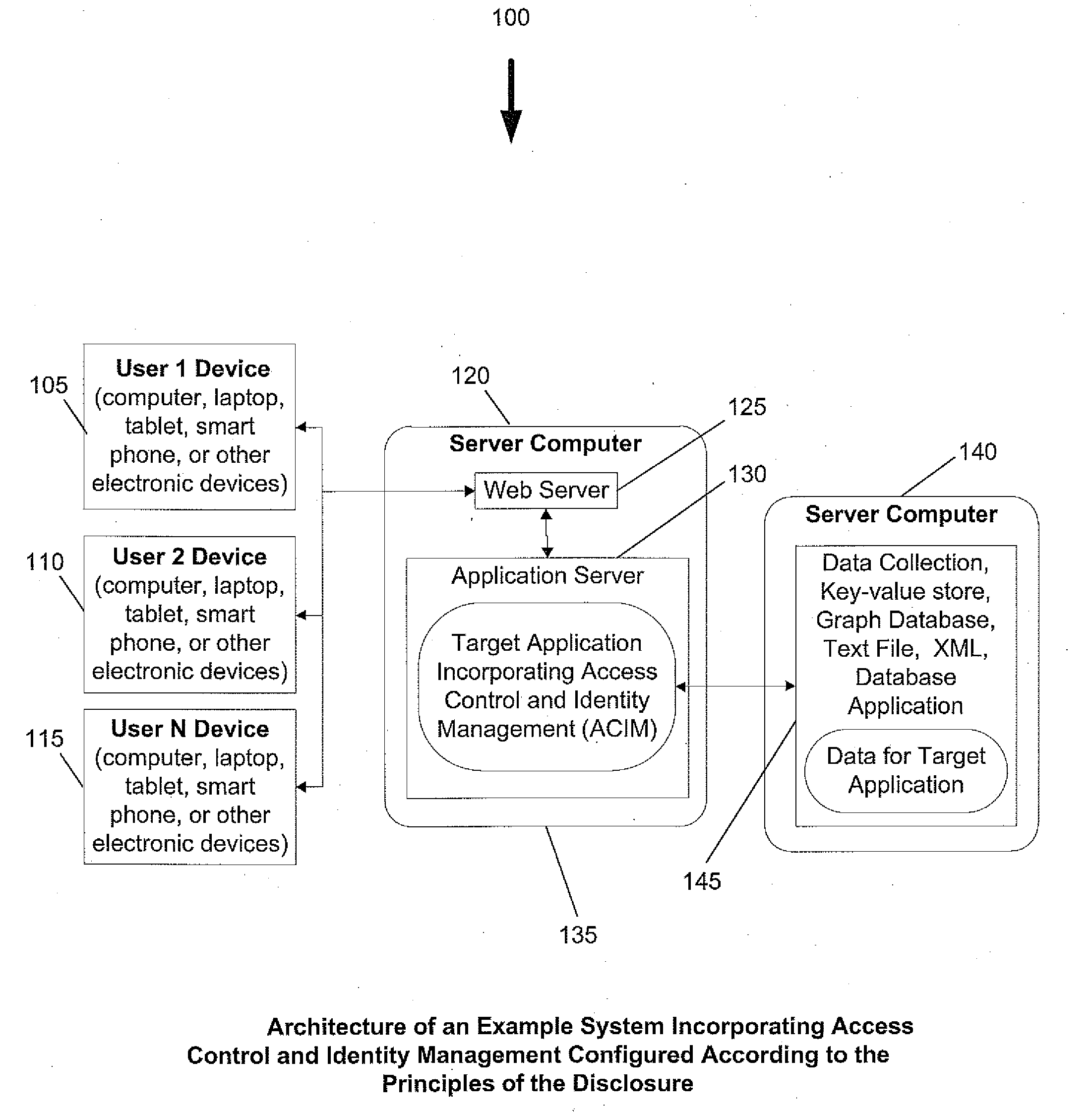
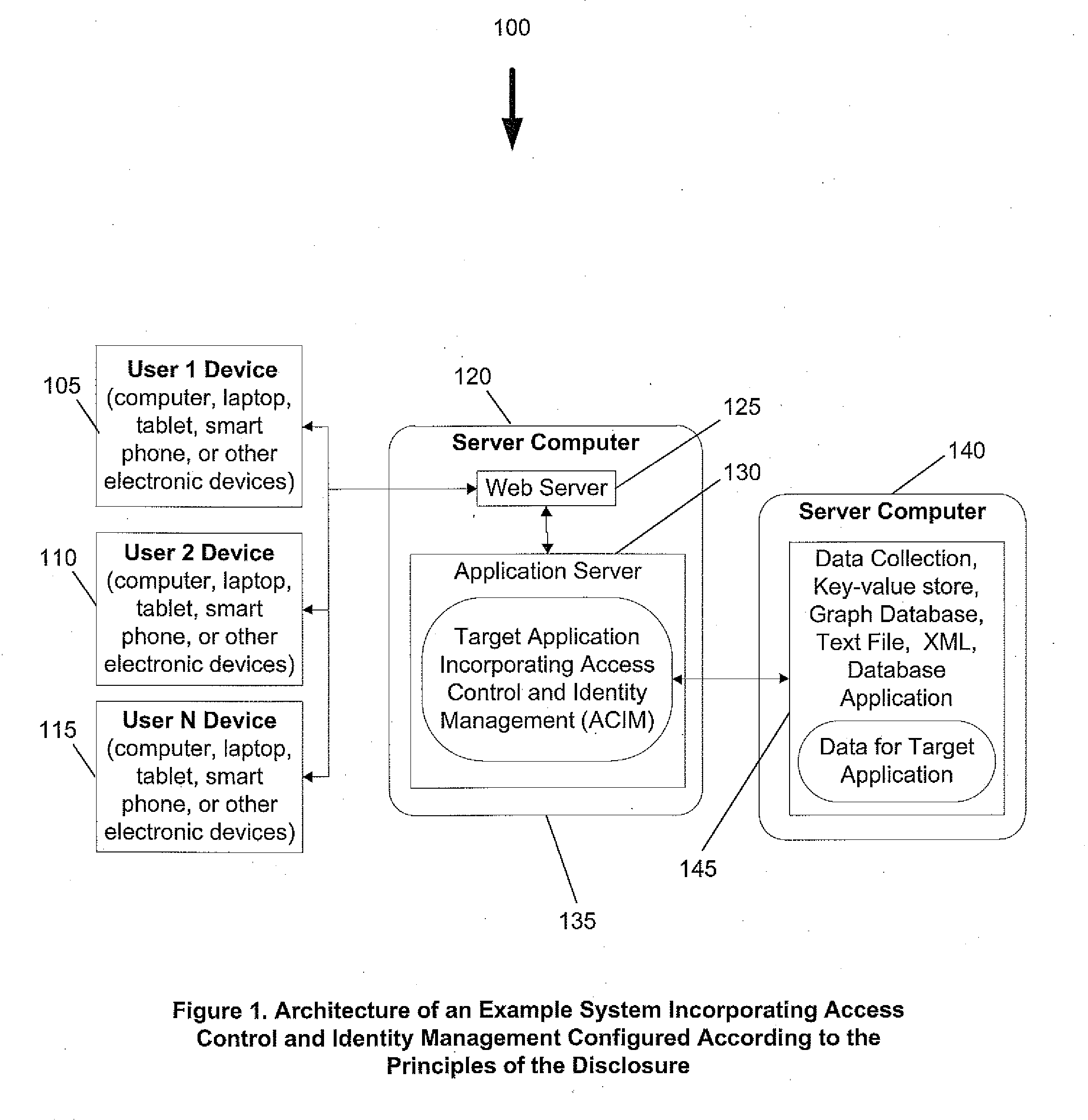
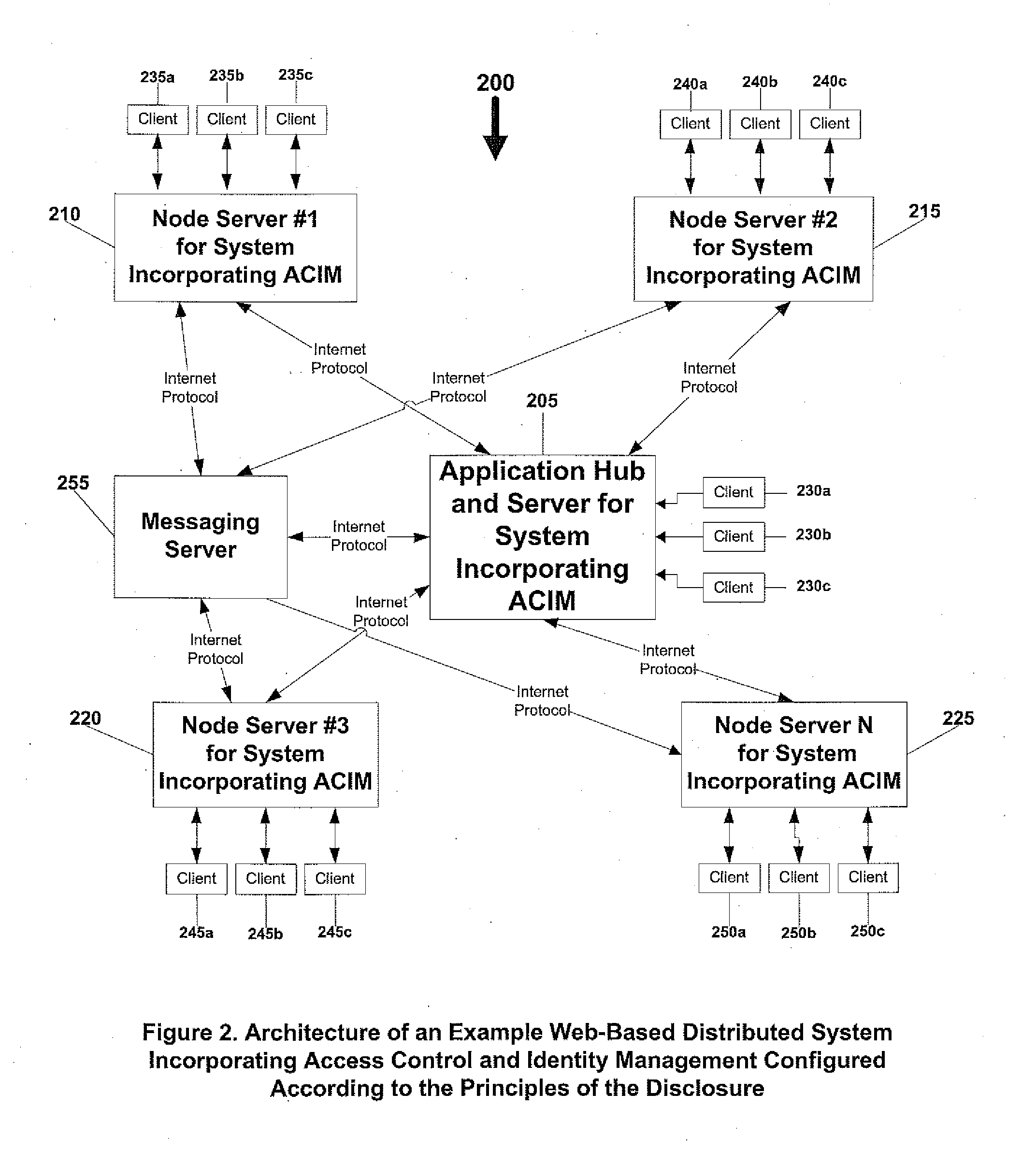
System and method for access control and identity management
InactiveUS20120137360A1Evolution be increasedSpeed up the flowDigital data processing detailsUser identity/authority verificationPoint objectIdentity management
A mechanism for the flow of access by derivation is provided. An access point may be any object, such as files or functions, to which the access recipient is granted access rights by the access provider. Access is typically represented by a relationship object referencing the access provider function, the access recipient function, and the access point object, and a set of access rights. This membership access relationship object is typically represented as a subtype of the access relationship. When a membership access relationship is created, typically a new associated persona function is generated, representing the new identity created for the access recipient function while serving as a member of the access point function. When a persona function is invited to be a member in another function, that in turn generates a membership and a second persona that is derived from the first persona, resulting in identity derivation.
Owner:SKAI
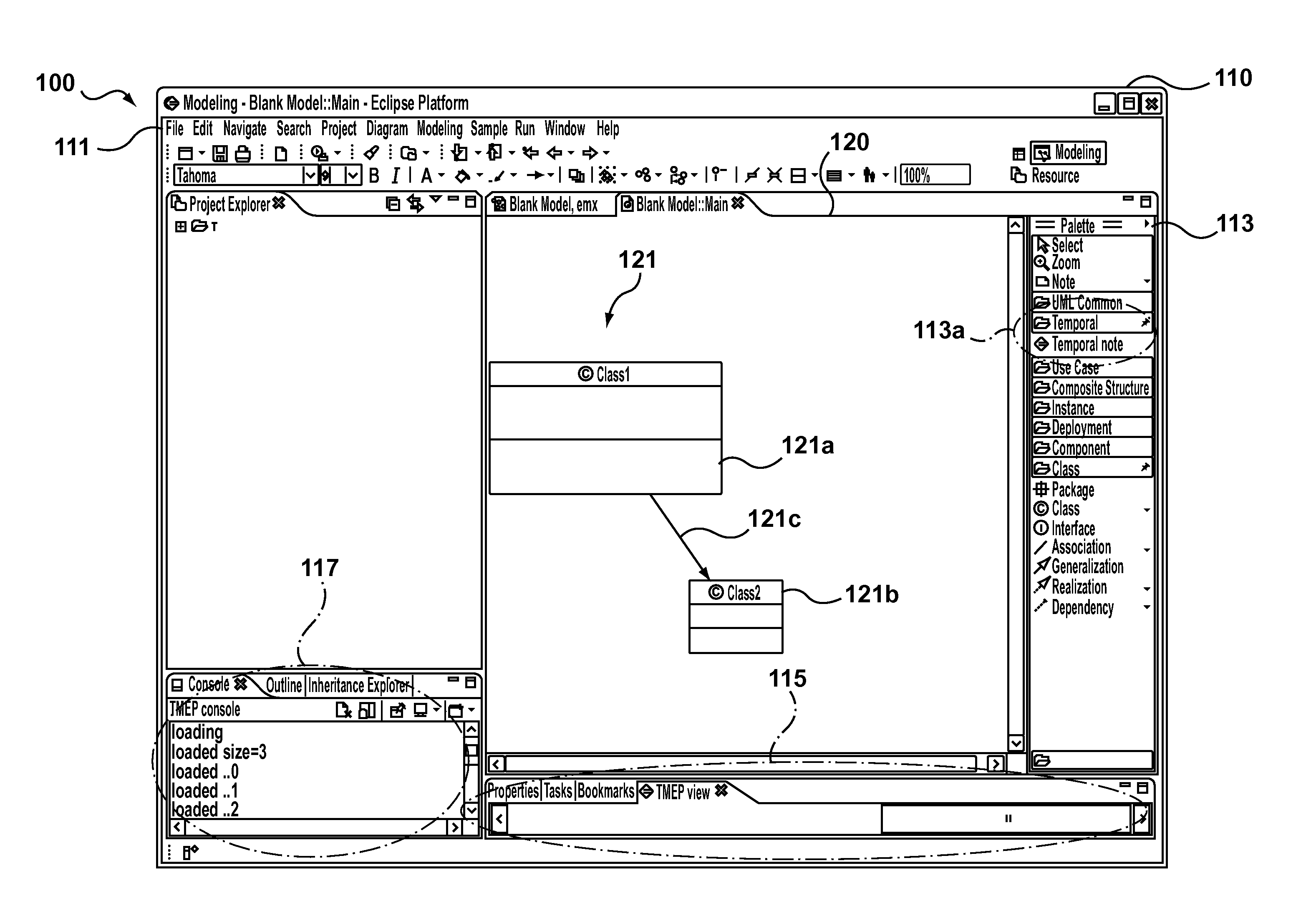
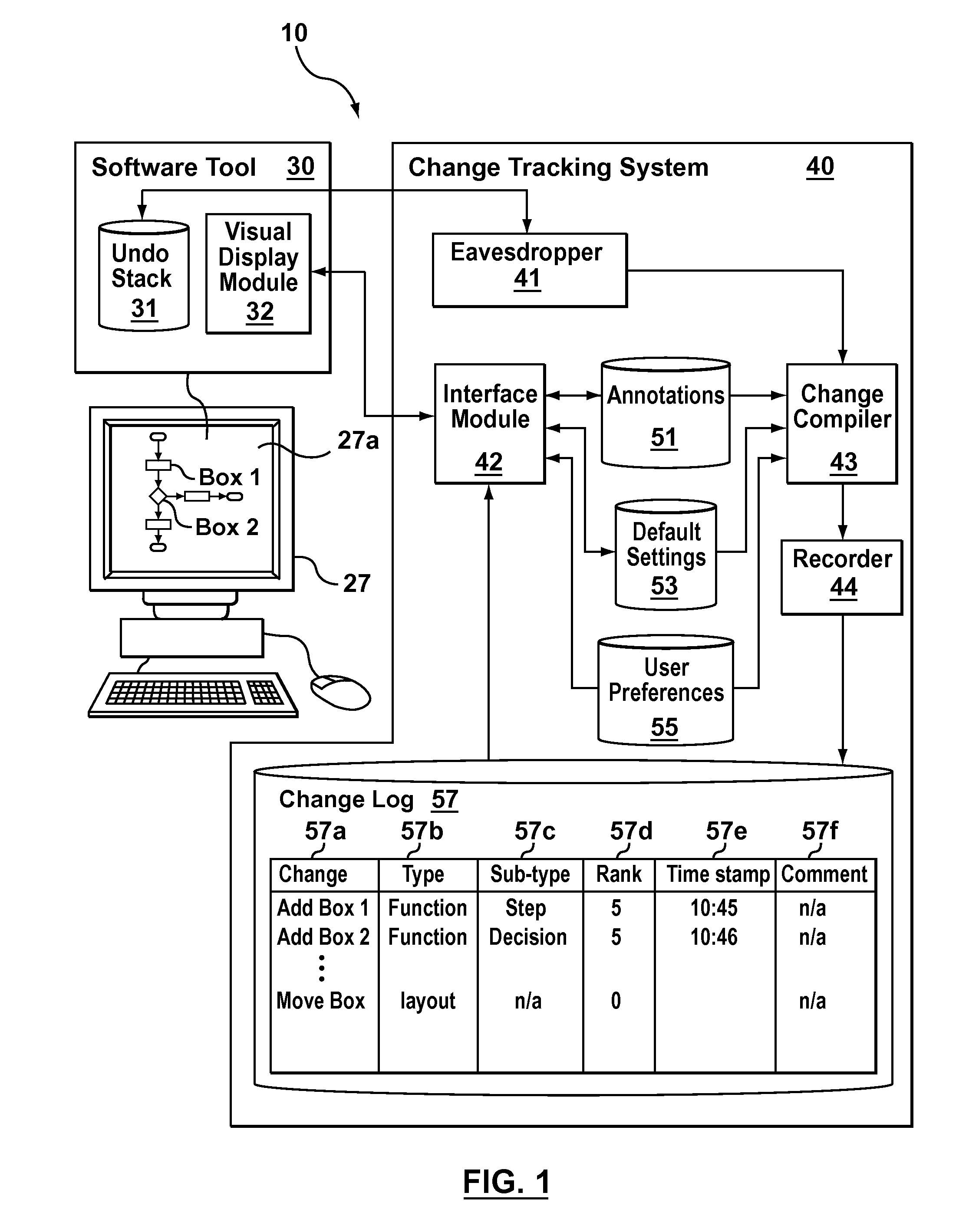
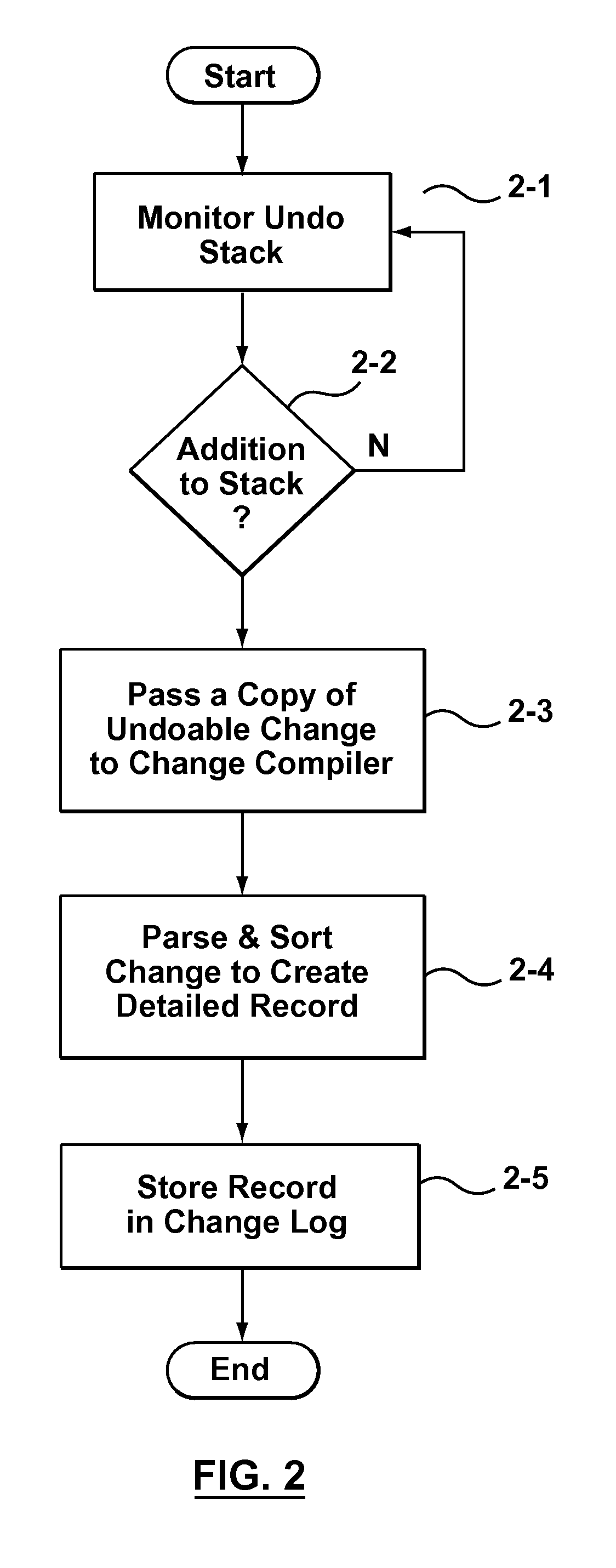
Systems, method and computer program products for tracking and viewing changes to information stored in a data structure
Previous attempts to provide systems or processes for enabling the review of the development of information stored in an electronic file are difficult to use effectively and require a user to take active steps to ensure that versions and annotations are created at regular intervals. By contrast, provided by aspects of the present invention there are systems, methods and computer program products for tracking and viewing changes to information stored in a data structure. In some embodiments the systems, methods and computer program products can be combined or integrated with software providing a visual editing environment so that changes are detected, sorted and monitored in a manner that is transparent to the user. In more specific embodiments the changes are grouped according to type, and optionally sub-type, so that a user can use the types to filter which changes in the development history of the information to review according to a particular current desire to locate specific information. In other specific embodiments, the changes are grouped in time providing temporal groups that provide “snapshots” of the development history of the information stored in a data structure at various respective points in the past.
Owner:IBM CORP
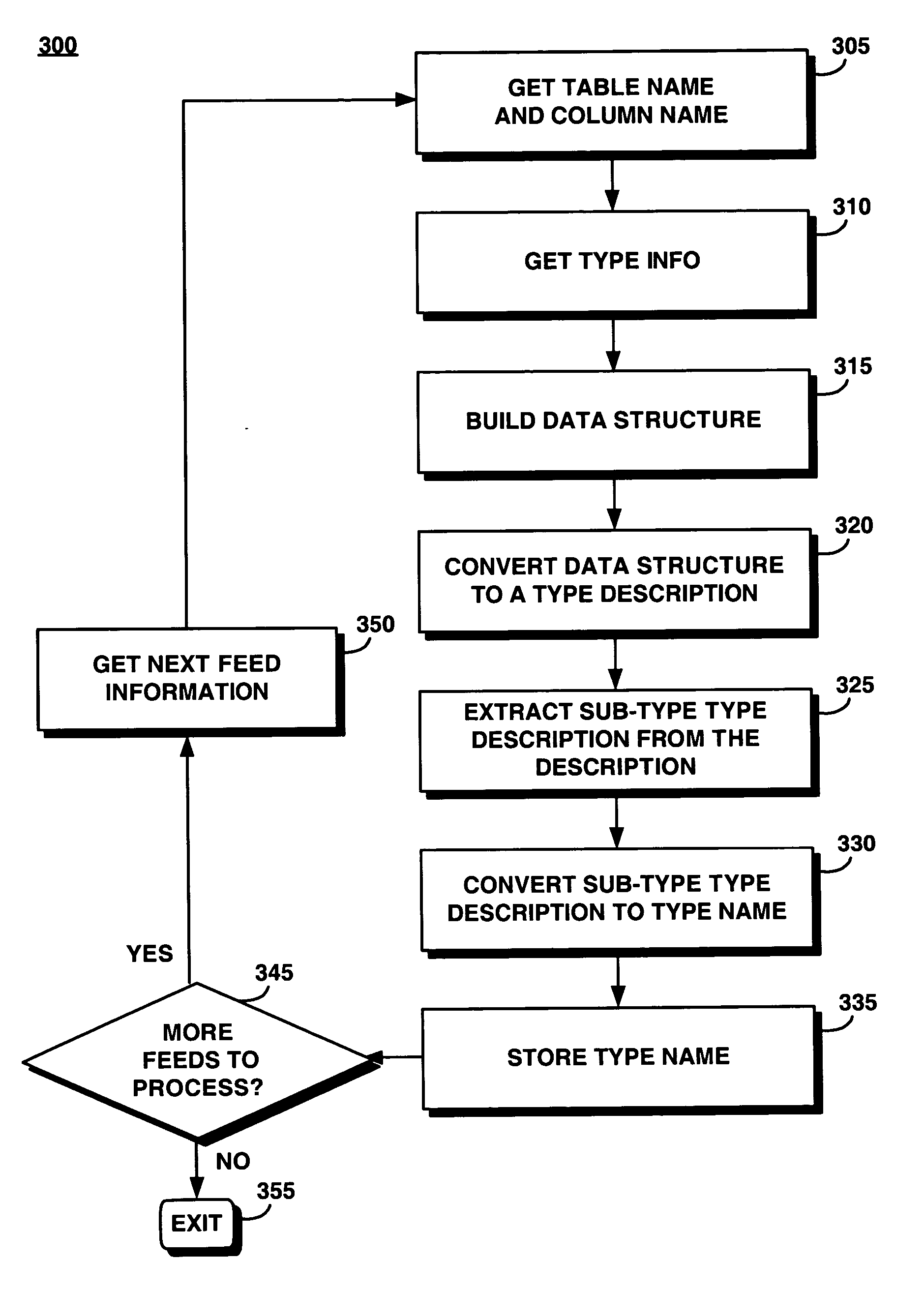
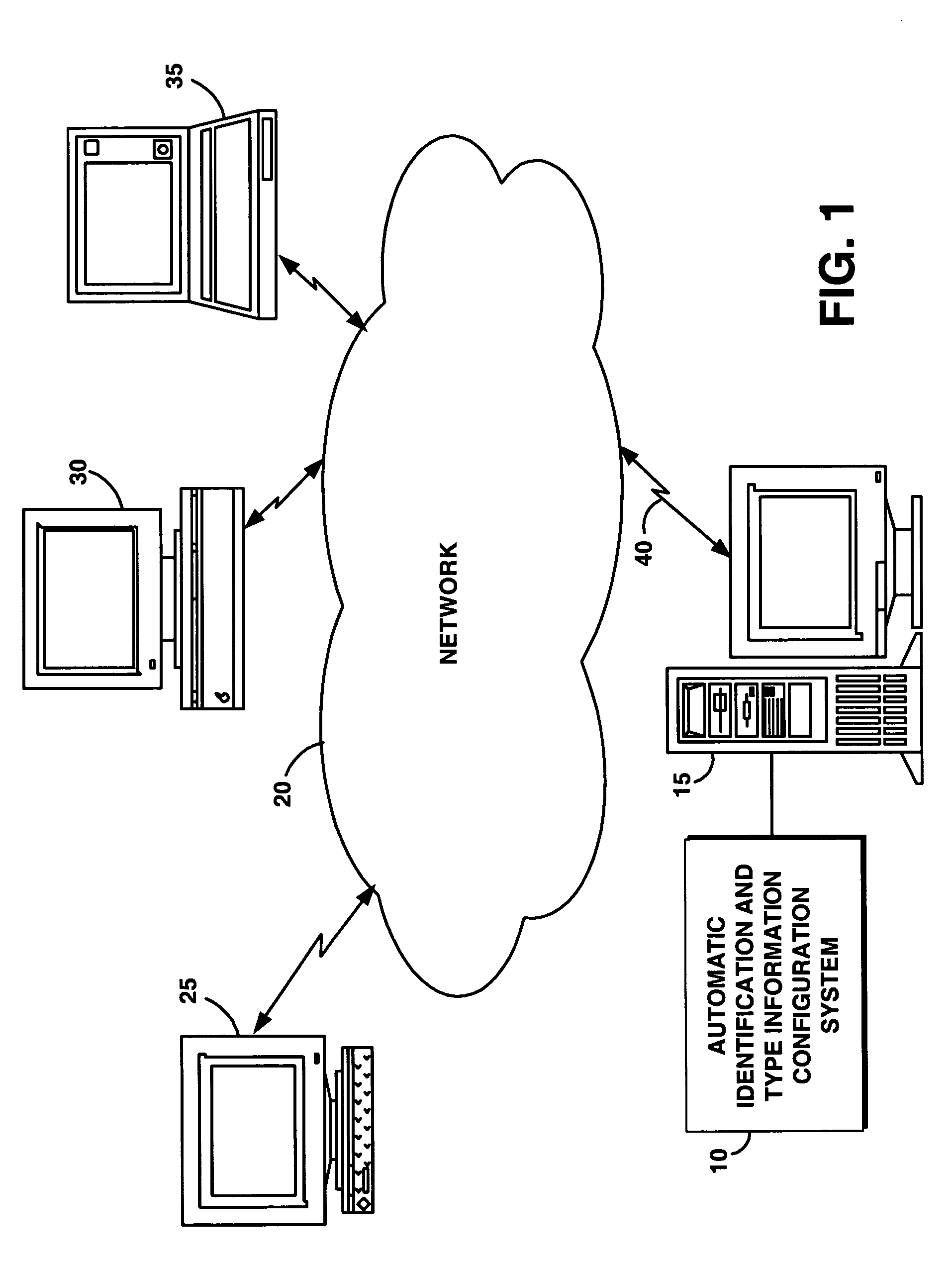
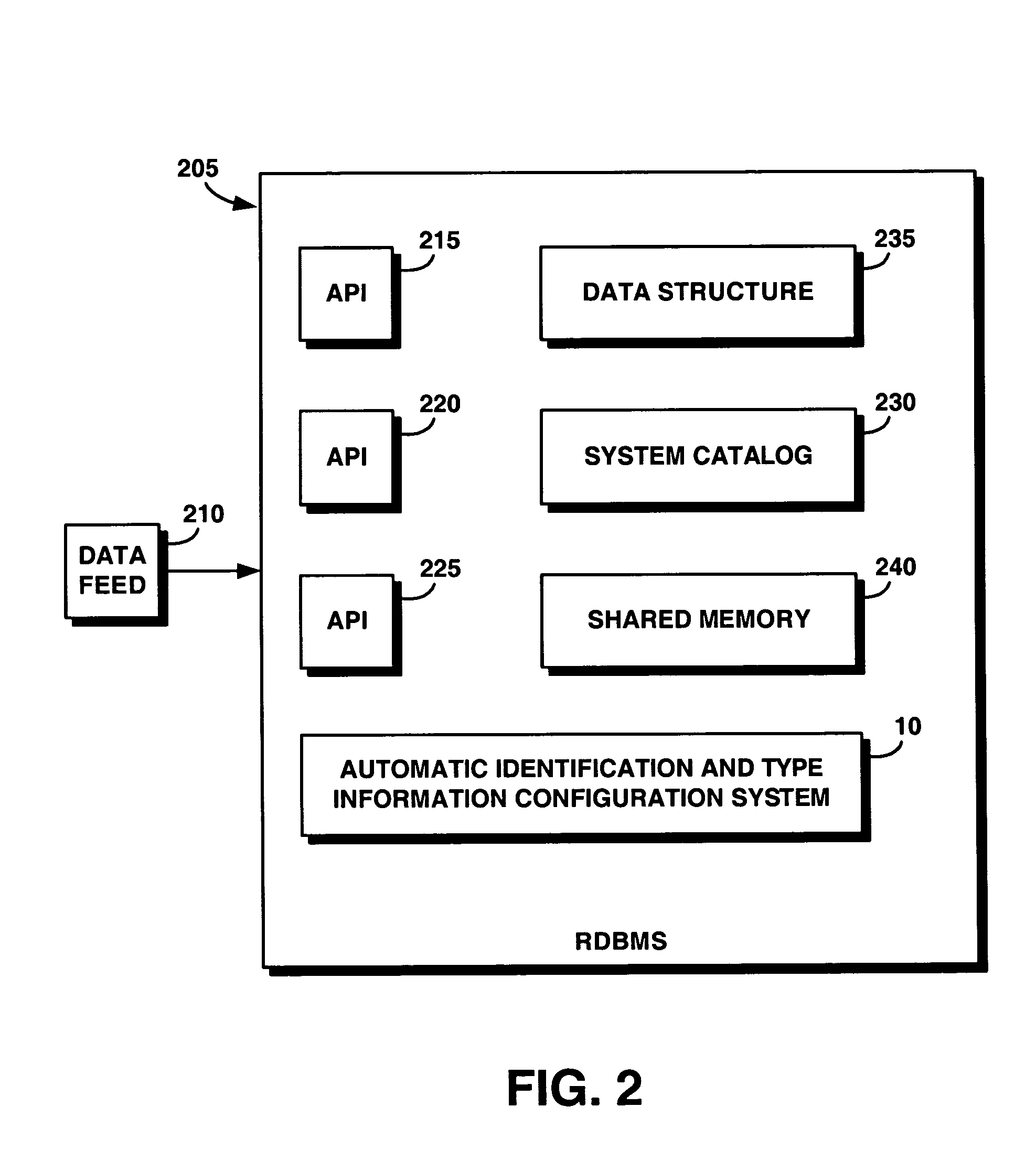
System and method for automating an identification mechanism and type information configuration process for a real-time data feed to a database
InactiveUS20050010595A1Reduce complexityImprove reliabilityDigital data information retrievalSpecial data processing applicationsData feedReal-time data
A type information configuration process automatically determines type information for all real-time data feeds being loaded into a relational database system (RDBMS). The automatic type information configuration system reduces the complexity of configuration while improving reliability and maintainability of the RDBMS. This system also removes the need for an additional database table and the resources associated with that additional database. The configuration of the real-time feed loader details the table and column of the data stream to be loaded by each data feed. The data stream is created based on the type it is expected to hold. The sub-type of the data stream is held in an encoded form in the systems catalogs of the database server. The present system accesses and decodes this subtype information based on the column and table in the configuration file to automatically find the type being loaded by the data feed.
Owner:IBM CORP
Multifunctional control channel for pseudowire emulation
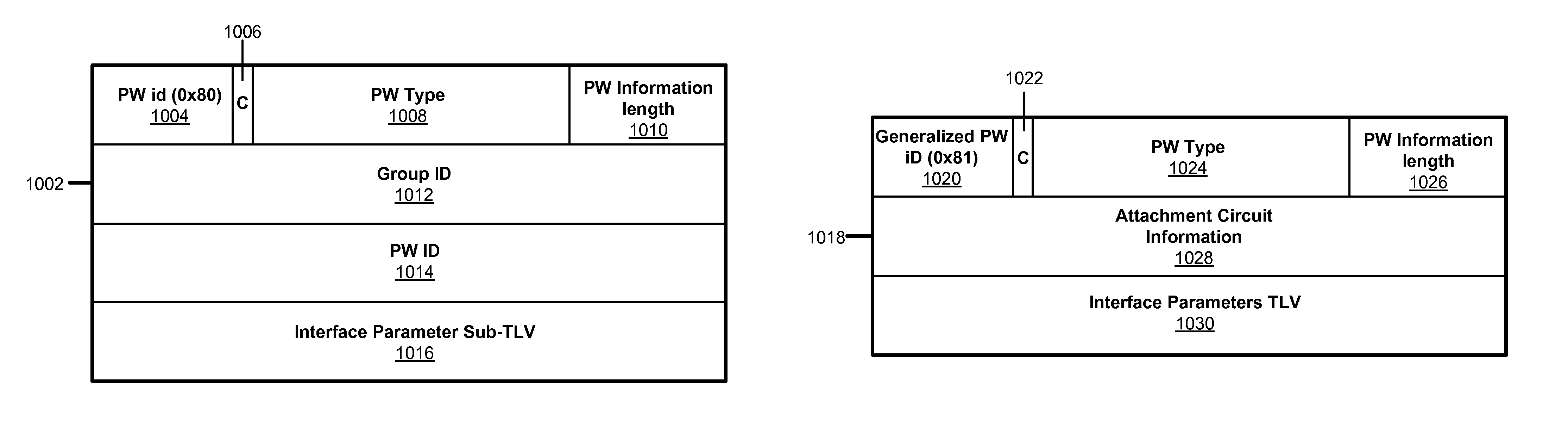
ActiveUS20080151895A1Error preventionFrequency-division multiplex detailsInformation repositoryType-length-value
A system advertises a multifunctional control channel (MFCC) in an interface parameter sub-type-length-value (TLV) of an advertisement label mapping message that is dispatched to a network device. The system also processes a reply label mapping message that is transmitted from the network device in response to the advertisement label mapping message and updates a label information base to establish a pseudowire and a MFCC associated with the pseudowire.
Owner:VERIZON PATENT & LICENSING INC
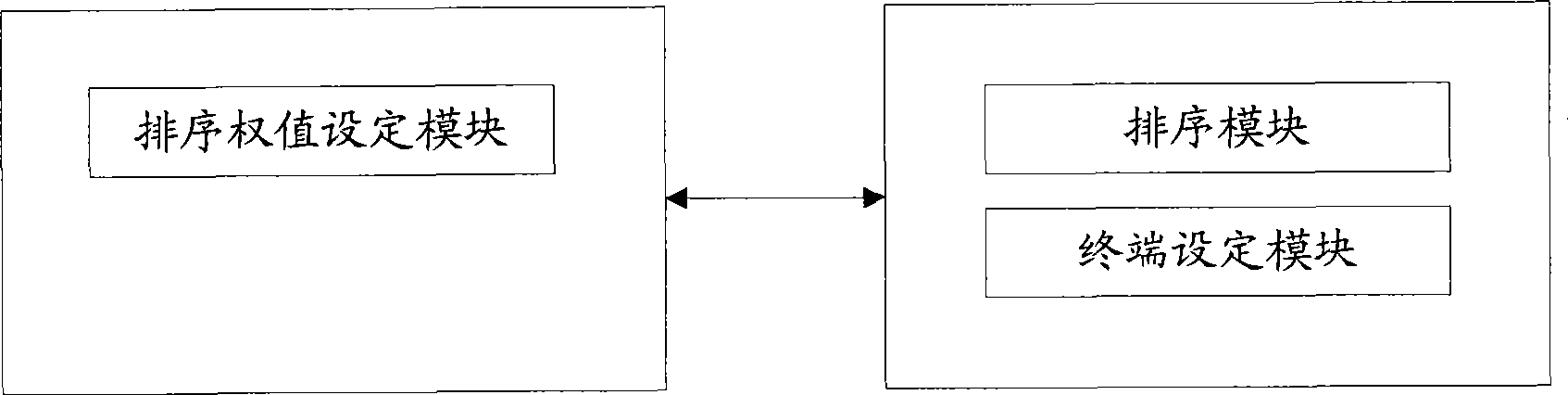
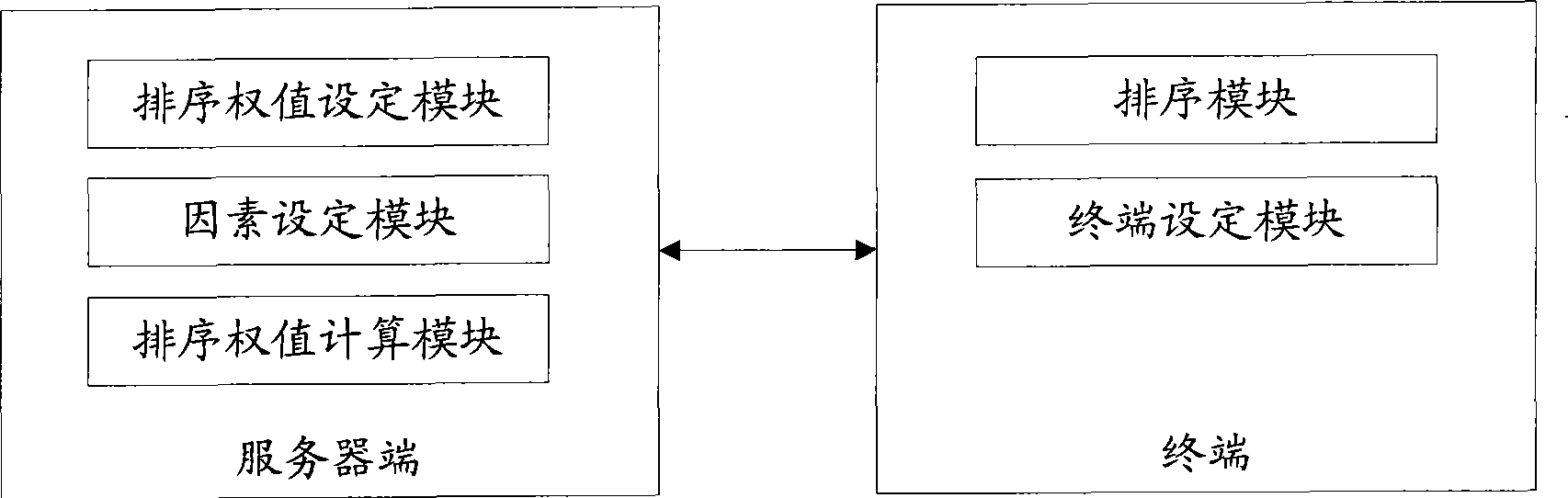
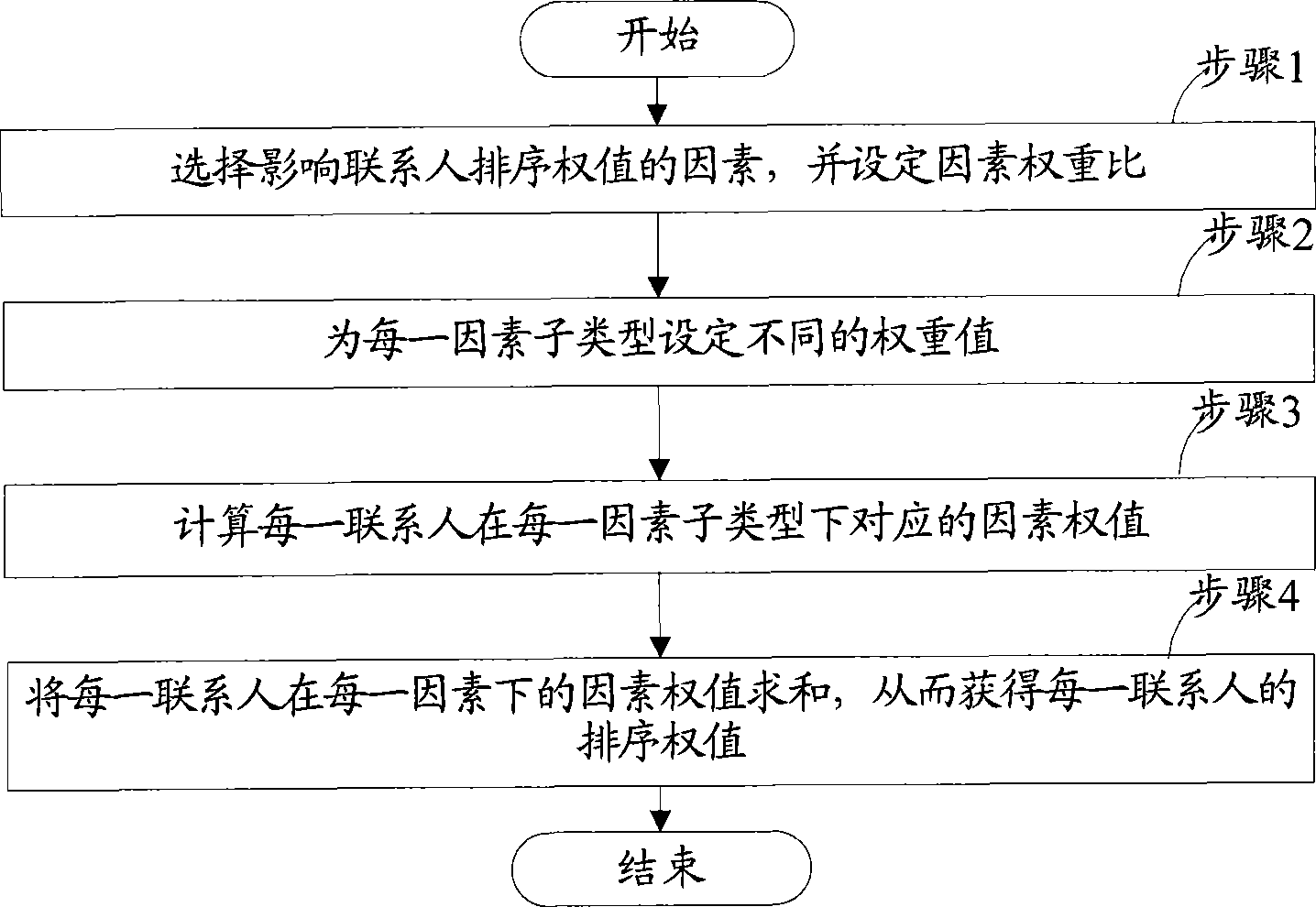
Method and system for ordering linkman
InactiveCN101465752AMeet the diverse needs of sortingVarious sorting methodsSpecial service provision for substationCommunications systemComputer science
The invention relates to sorting technology and discloses a contact list sorting method and a system, aiming at solving the technical problems that contacts cannot be displayed in a sorted way according to special requirements including ranks and positions of contacts in constant messaging system. The invention sets sorting weights for contacts on server, and a terminal displays the contacts in a sorted way according to the sorting weights. As for a plurality of factors which affect the sorting sequence of contacts, the invention proposes a method of polynomial summation of the product of factor weight ratio and factor sub-type weight value to compute contact sorting weights. Besides, the contact sorting method based on sorting weight is combined with a sorting method based on state priority to provide various and flexible contact sorting modes for enterprise users, so the special requirements of enterprise users are satisfied, and the user satisfaction degree is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Terminal configuration method and device
InactiveCN104346177AImprove experienceImplement custom configurationProgram loading/initiatingRedundant data error correctionTerminal equipmentOperating system
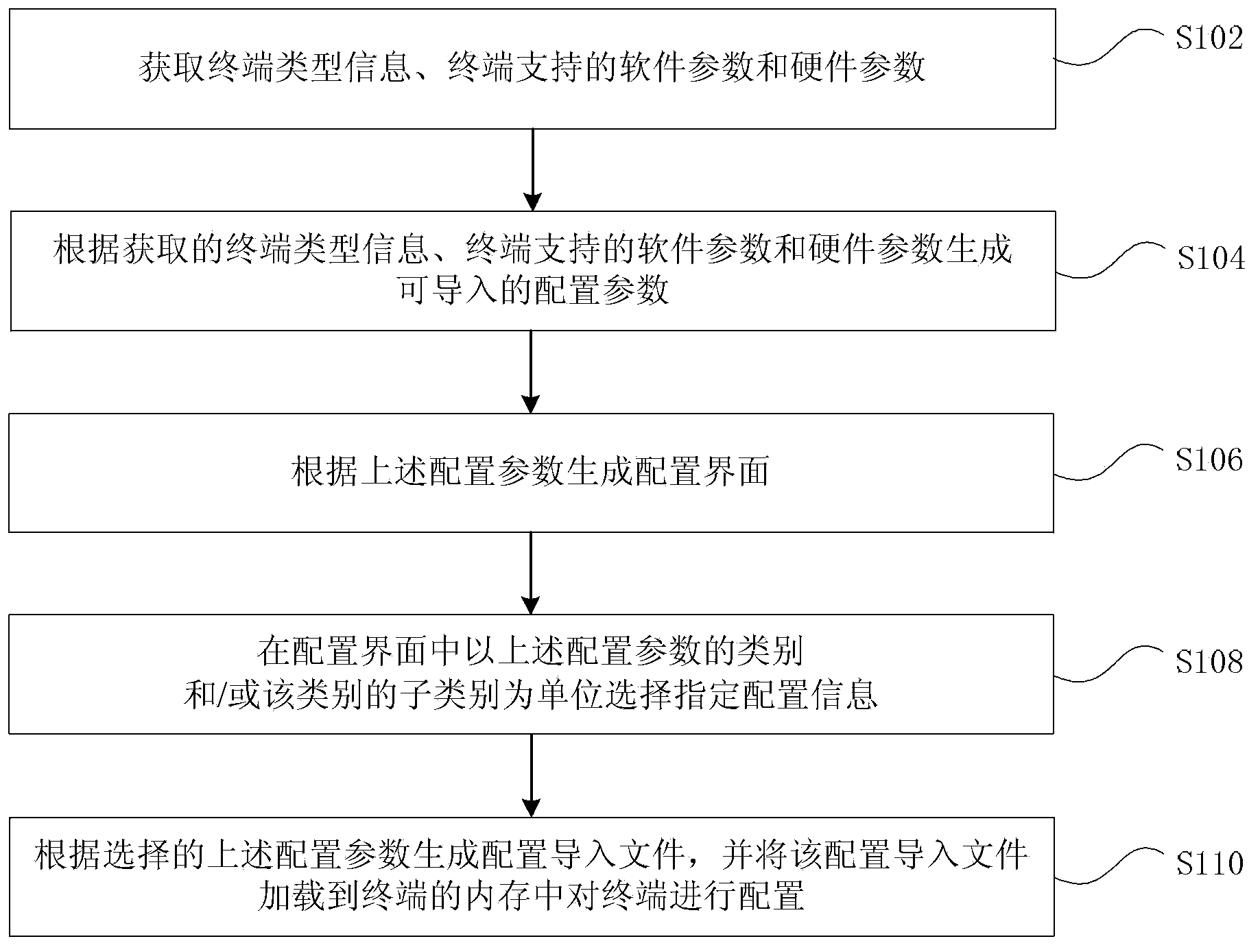
The invention provides a terminal configuration method and device. The terminal configuration method comprises the steps of obtaining terminal type information and terminal-supporting software parameters and hardware parameters; generating importable configuration parameters according to the obtained terminal type information and the terminal-supporting software parameters and hardware parameters; generating a configuration interface according to the configuration parameters; selecting the configuration parameters with the type of the configuration parameters and / or the sub-type of the types as unit in the configuration interface; generating a configuration import file according to the selected configuration parameters and loading the configuration import file to a memory of the terminal to configure the terminal. By means of the above technical scheme, the technical problem that user experience is affected due to complete cover of original configuration during a configuration process of a terminal device in related technologies can be solved. Therefore, configuration can be performed only on an item needing configuration, user customized configuration can be achieved and user experience is improved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
System and methods for transaction processing
InactiveCN1947144AData processing applicationsSpecial data processing applicationsCredit cardThird party
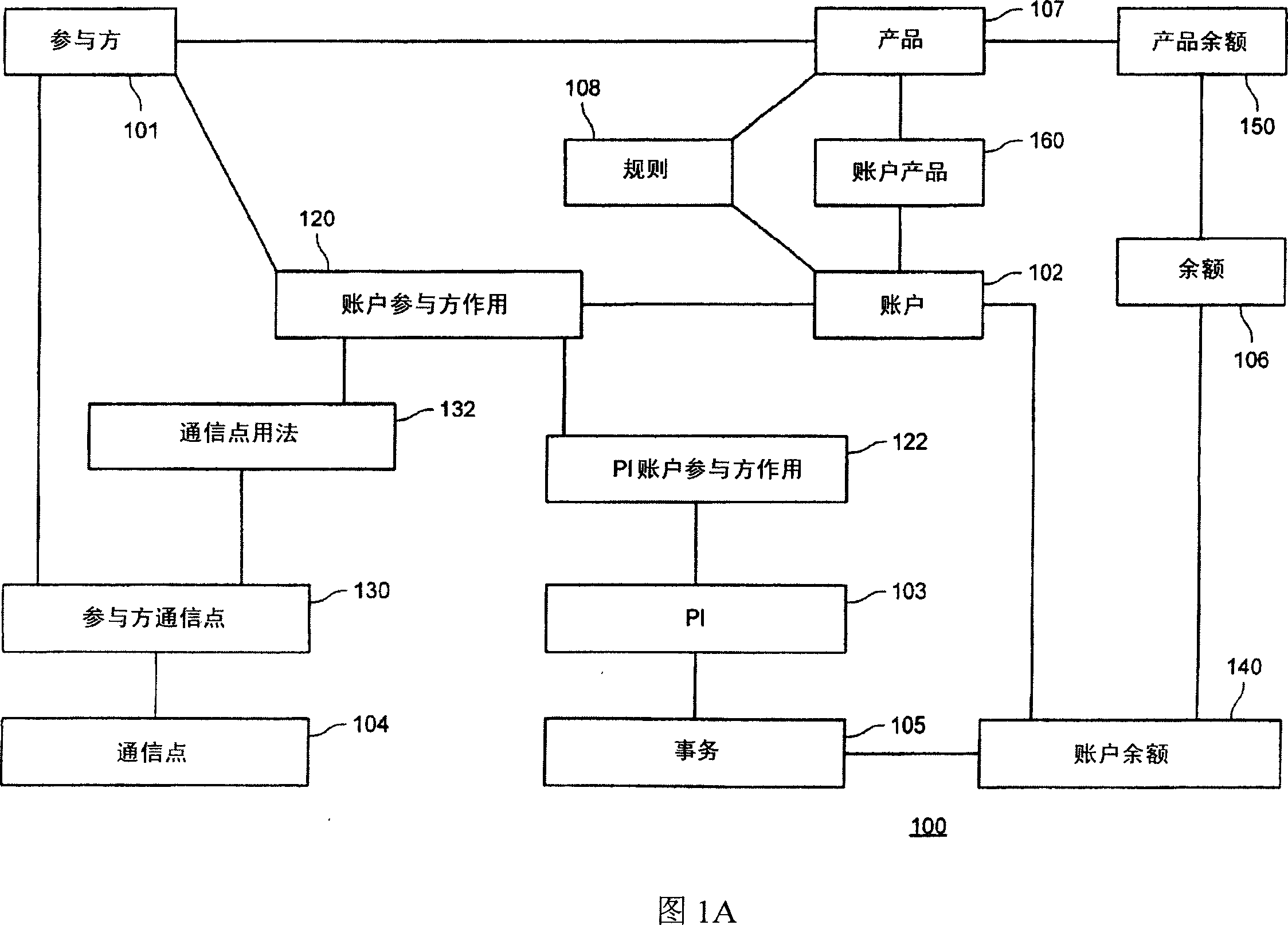
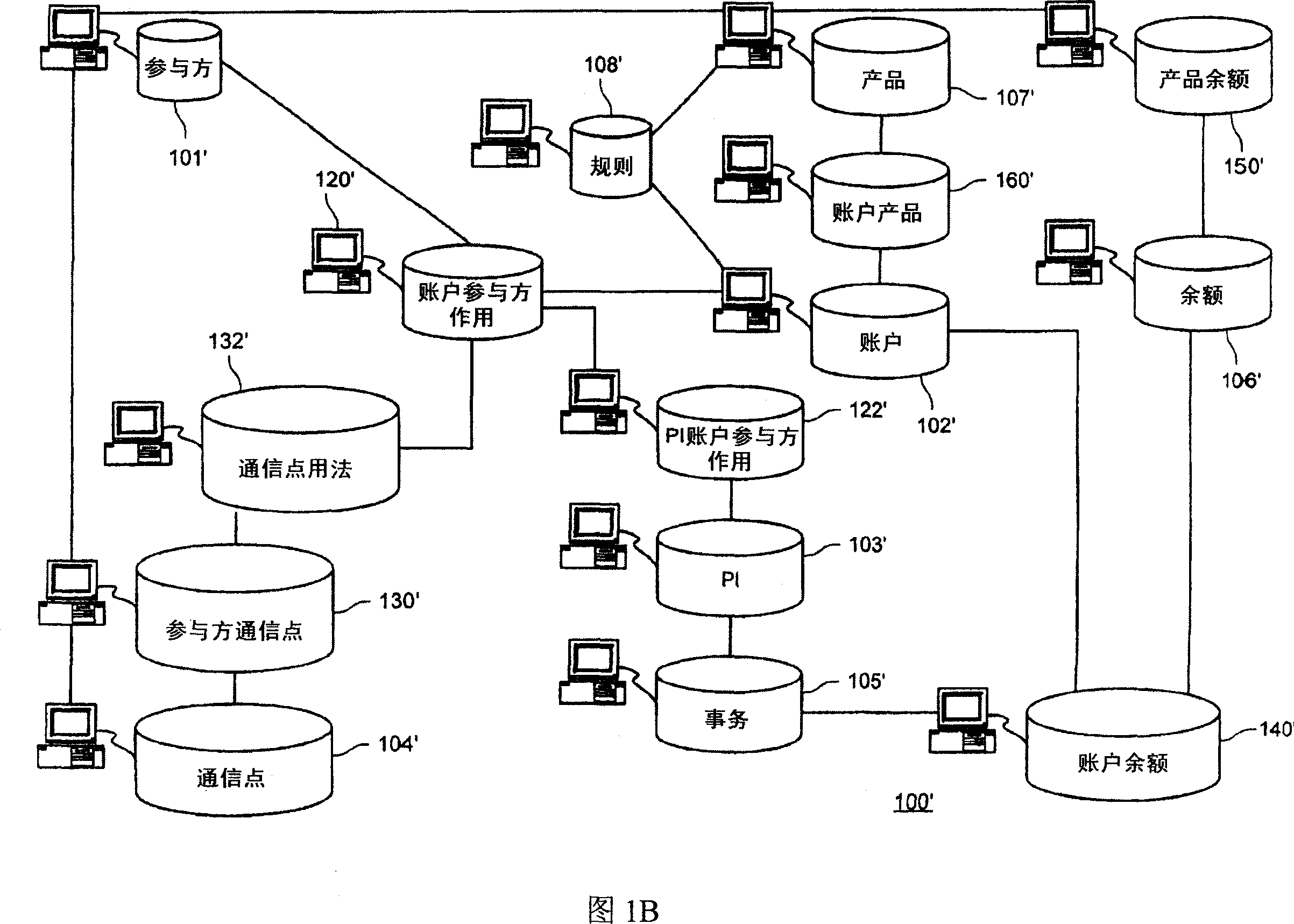
According to one embodiment of the invention, an architecture is provided for a data processing system that processes data for a service provider itself or a client of a service provider as in the case of a third party processor. The elements of the architecture can be managed separately. For example, the architecture can be organized around eight subject areas, such as account, party, communication point, presentation instrument, rules, balances, transactions, and product. Relationships between each of the subject areas as well as between sub-types of each subject area can be established to provide flexibility in the management of the data.
Owner:FIRST DATA
Method and system for analyzing biological specimens by spectral imaging
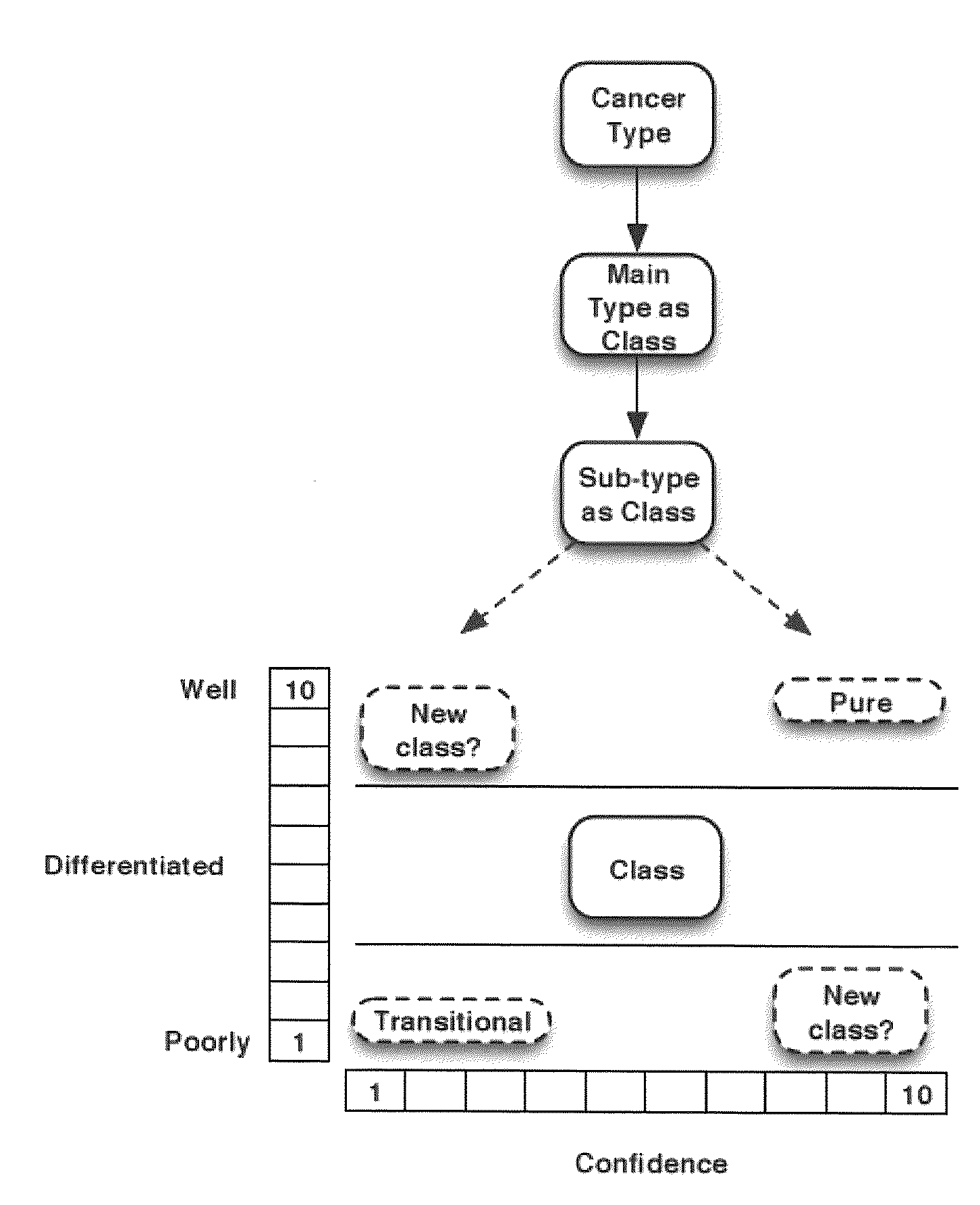
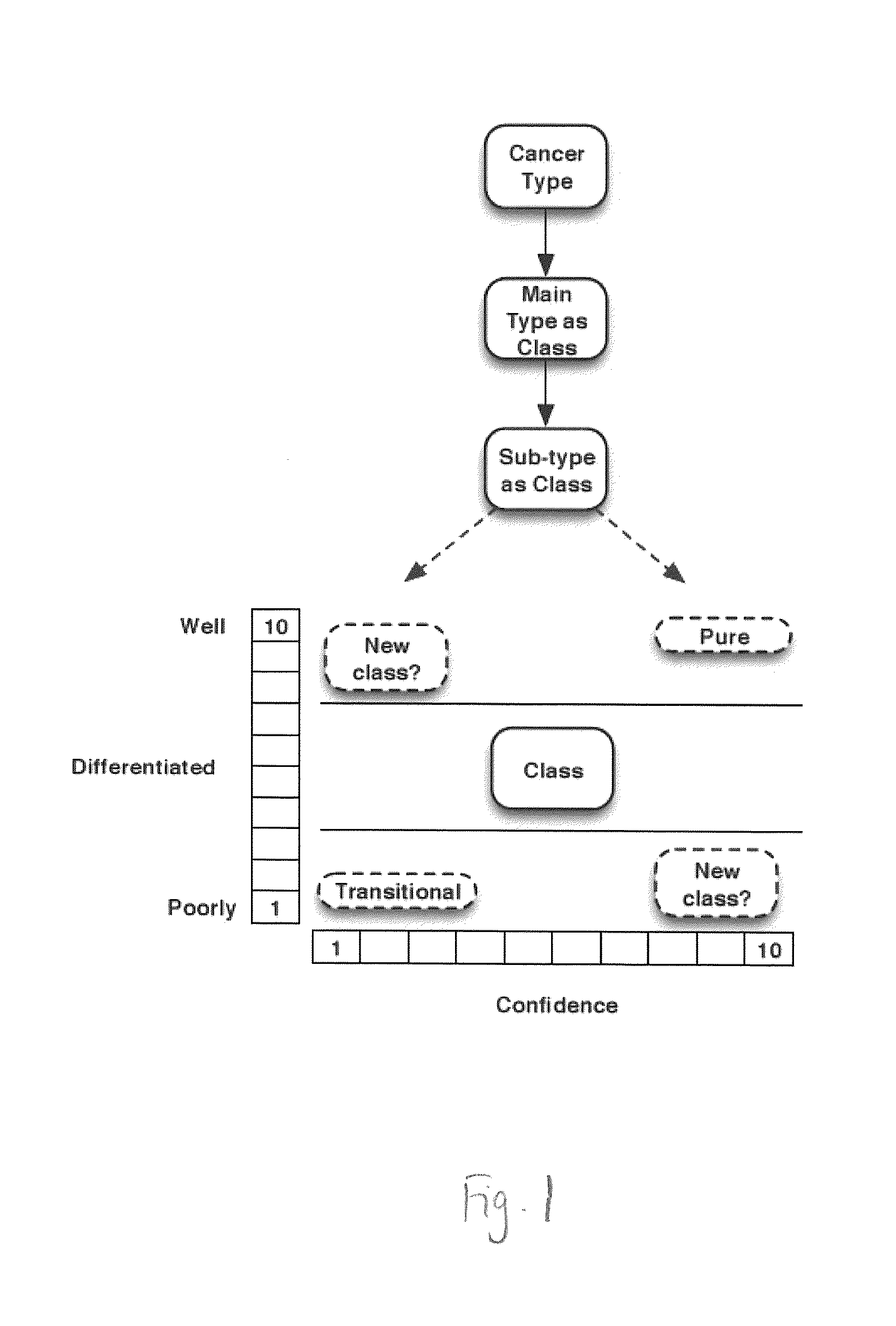
The methods, devices, and systems may allow a practitioner to obtain information regarding a biological sample, including analytical data, a medical diagnosis, and / or a prognosis or predictive analysis. The method, devices, and systems may provide a grade or level of development for identified diseases. In addition, the methods, devices and systems may generate a confidence value for the predictive classifications generated, which may, for example be generated in a format to show such confidence value or other feature in a graphical representation (e.g., a color code). Further, the methods, devices and system may aid in the identification and discovery of new classes and tissue sub-types.
Owner:CIRECA THERANOSTICS LLC
Data processing method and device and equipment
ActiveCN108648093AAccurately determineImprove accuracyData processing applicationsCharacter and pattern recognitionPositive sampleGroup type
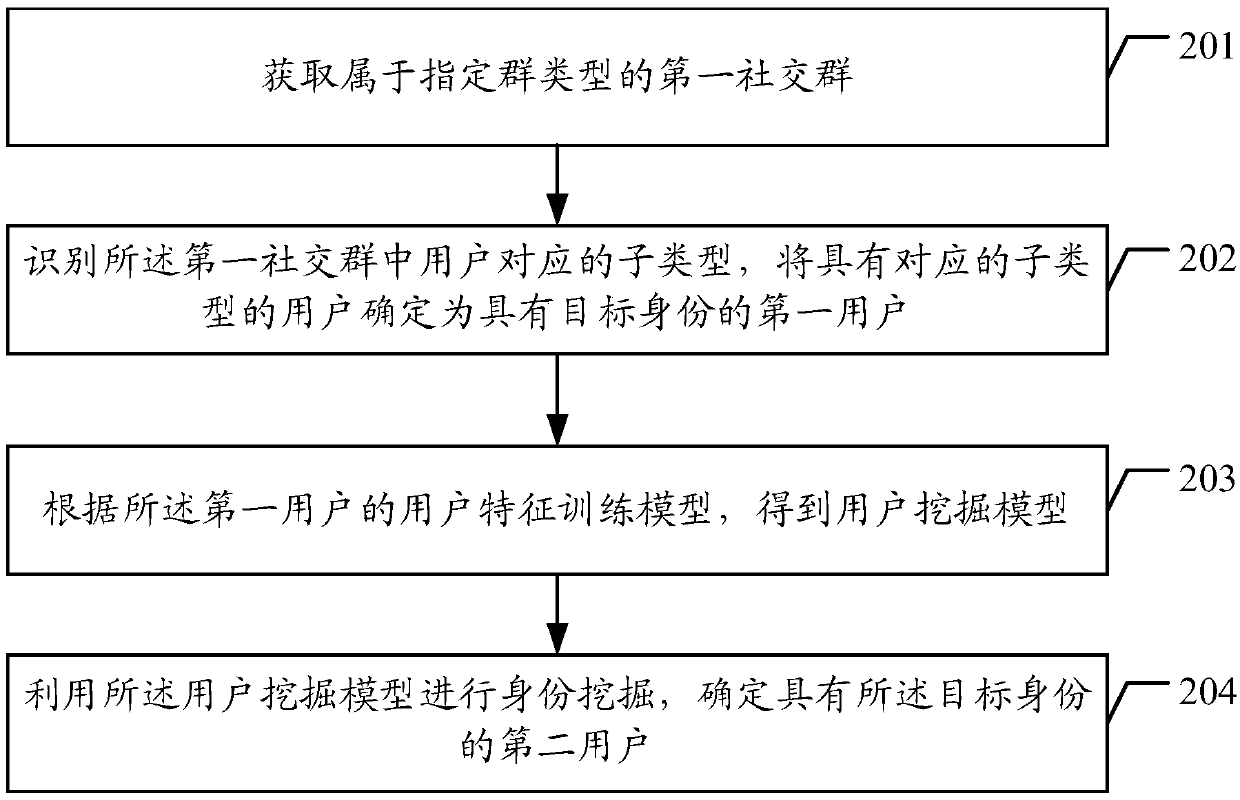
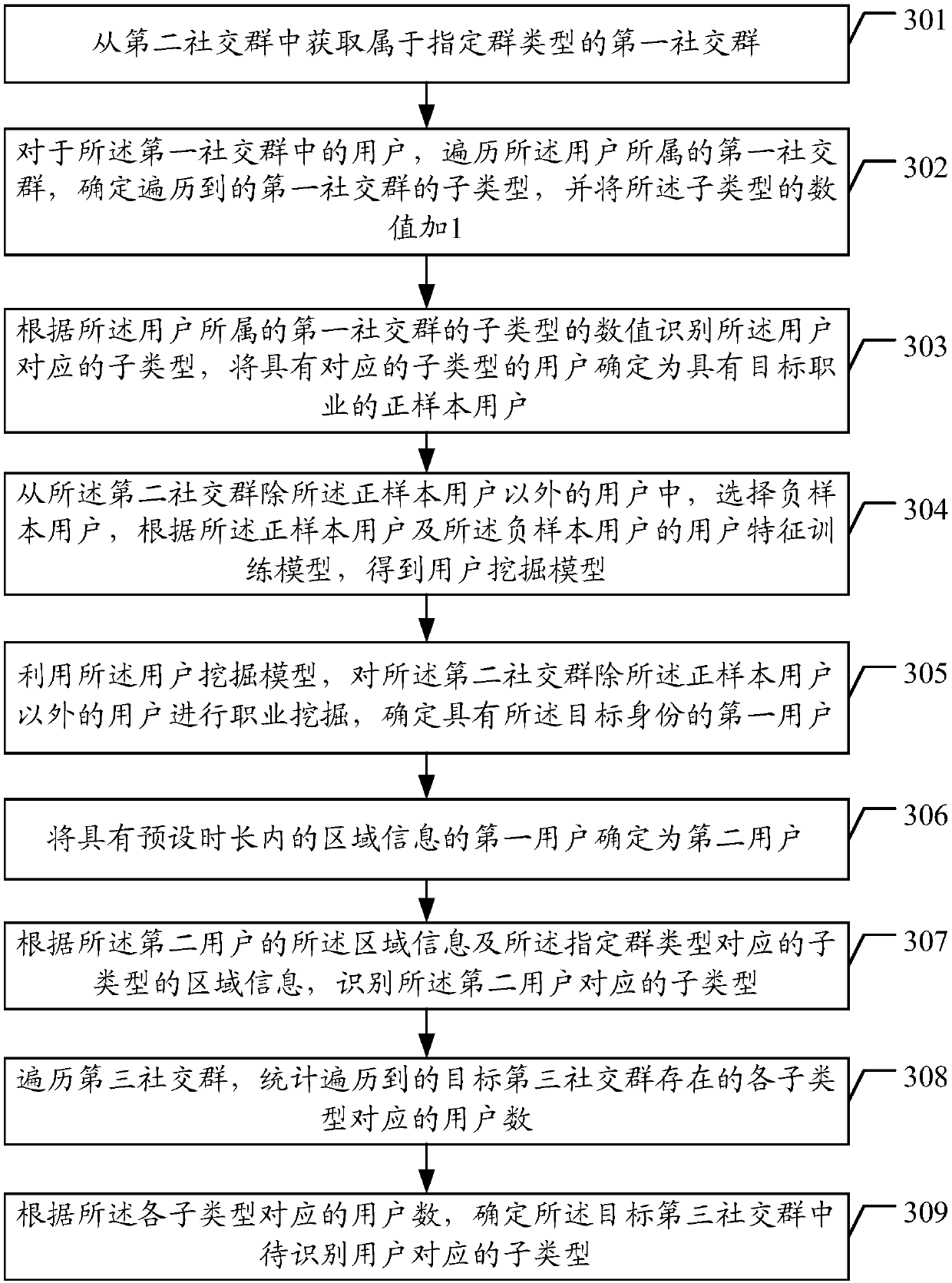
The invention discloses a data processing method and device and equipment. The method comprises the steps that a first social group belong to the specific group type is acquired from a second social group; the subtypes corresponding to users in the first social group are recognized, and the users with the corresponding subtypes are determined as positive sample users with target careers; and negative sample users are selected from users in the second social group except the positive sample users, and a model is trained according to the user characteristics of the positive sample users and thenegative sample users to obtain a user mining model. By recognizing the subtypes corresponding to the users in the first social group belong to the specific group type, the positive sample users withthe target careers corresponding to the specific group type can be precisely determined; and by taking the user characteristics of the positive sample users as training samples to train the model, theuser mining model capable of precisely recognizing the target careers can be obtained, so that the accuracy is effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Toxic sequential, its preparation and use
InactiveCN1982457AReduce inactivationExtended opening hoursNervous disorderBacteriaCDNA libraryCell membrane
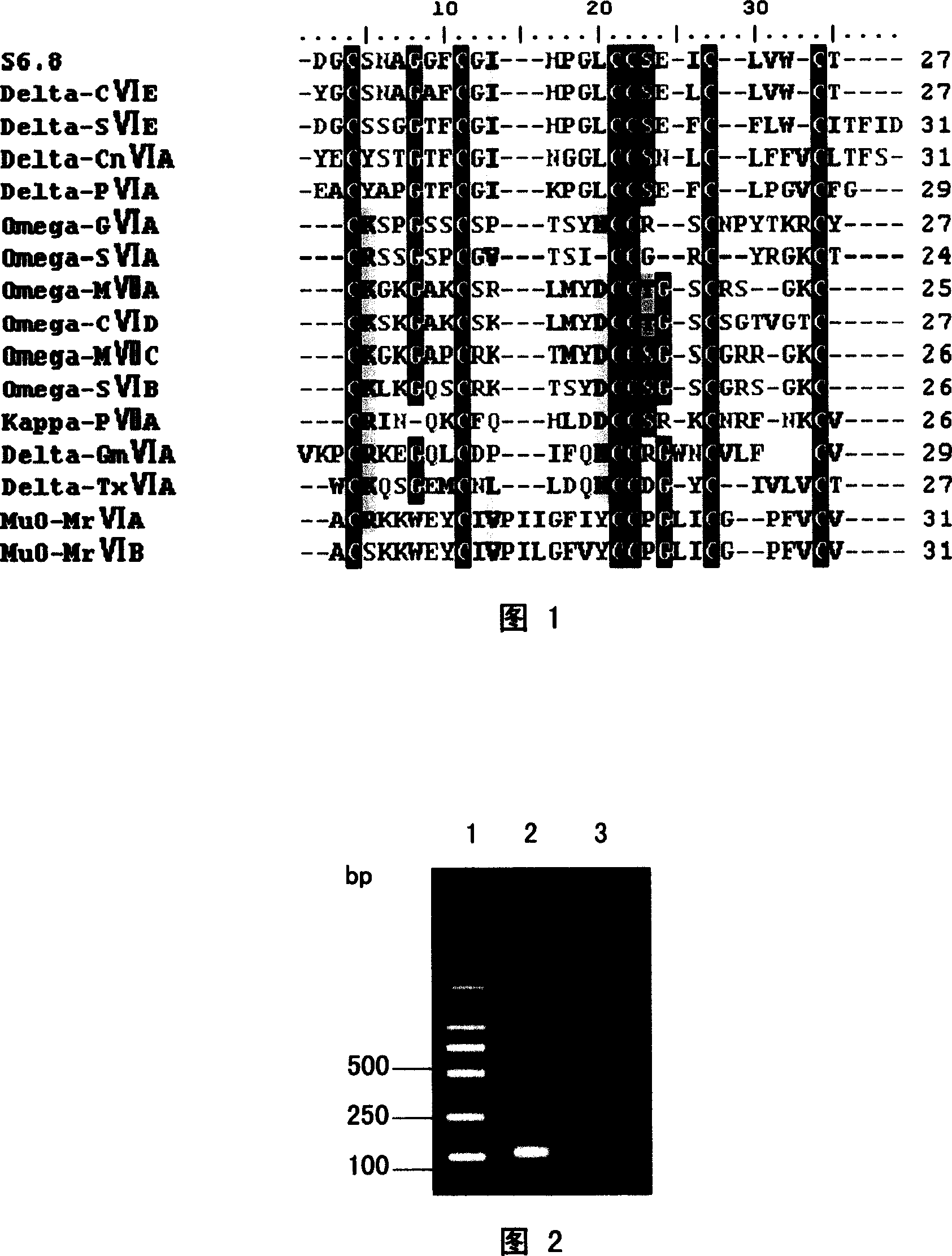
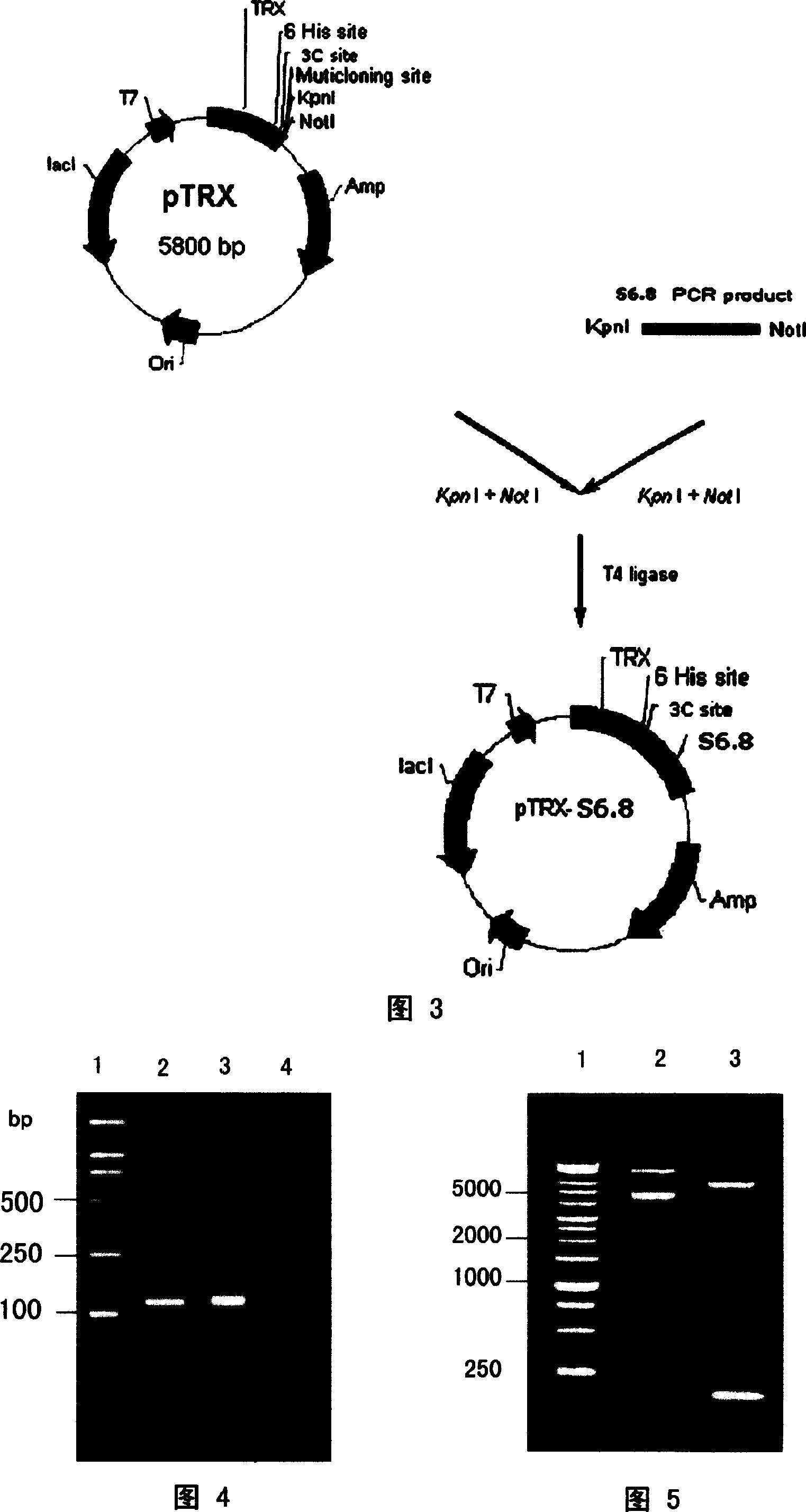
Linear conotoxin sequence and its encoded polypeptide sequence S6.8, its production and use are disclosed. The process is carried out by constructing cDNA library and cloning O-super-family conotoxin. It can delay vertebrate cerebral neuron cell membrane sodium-ion channel inactivation and sodium-ion channel opening time. It can be used as probe for ion-channel type and sub-type discrimination or as pilot compound to make research of medicine.
Owner:SUN YAT SEN UNIV
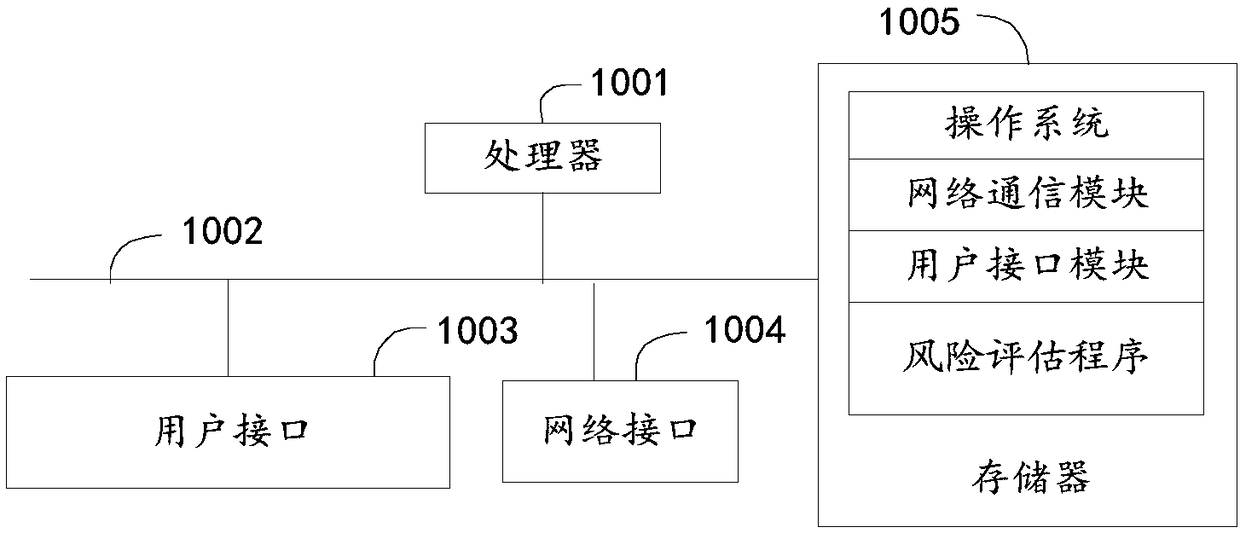
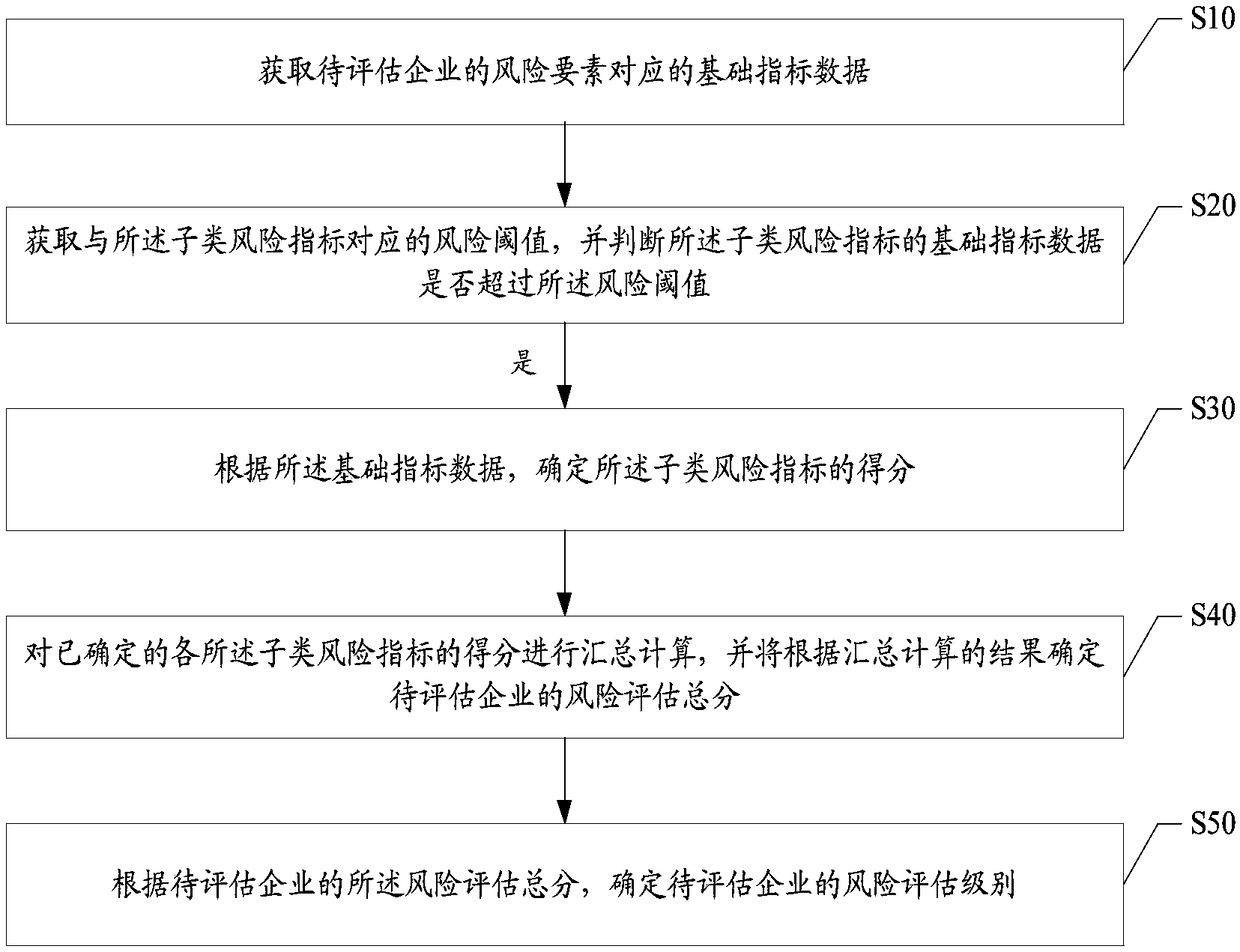
Risk assessment method, apparatus, and computer-readable storage medium
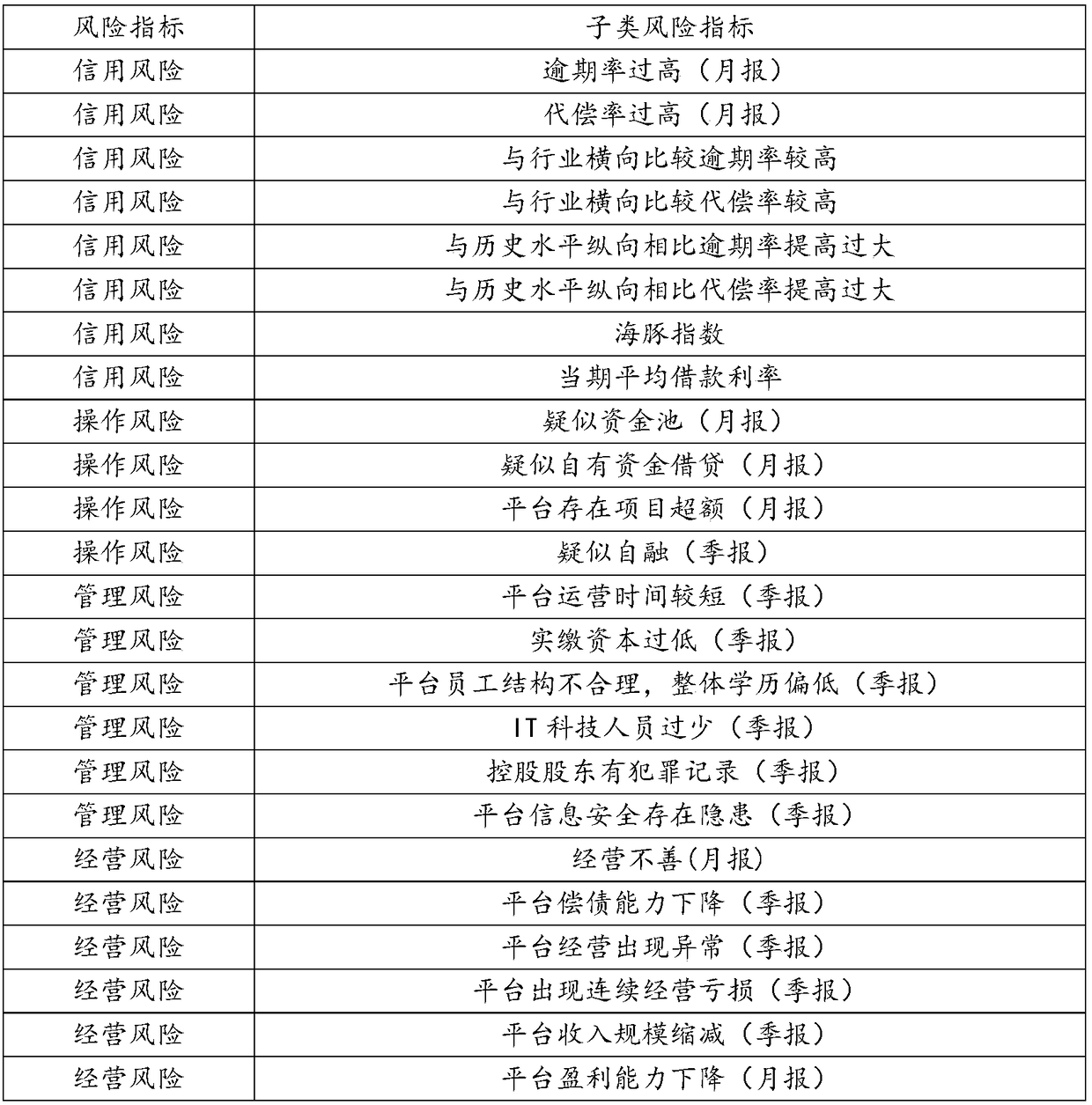
The invention provides a risk assessment method. The method comprises the following steps: acquiring basic index data corresponding to risk elements of an enterprise to be assessed; Wherein, the riskelement comprises a plurality of risk indicators, and each single risk indicator comprises a plurality of sub-type risk indicators, acquiring a risk threshold value corresponding to the sub-category risk index, and judging whether the basic index data of the sub-category risk index exceeds the risk threshold value; if exceeding, determining the score of the sub-category risk index according to thebasic index data; summarizing and calculating the scores of the determined sub-category risk indicators to determine the total score of the risk assessment of the enterprise to be evaluated; according to the total risk assessment score, the risk assessment level of the enterprise to be evaluated being determined. The invention also provides a risk assessment device and a computer-readable storagemedium. The invention solves the technical problem that the existing enterprise risk assessment method is difficult to objectively and comprehensively assess the risk status of the enterprise.
Owner:深圳市人民政府金融发展服务办公室
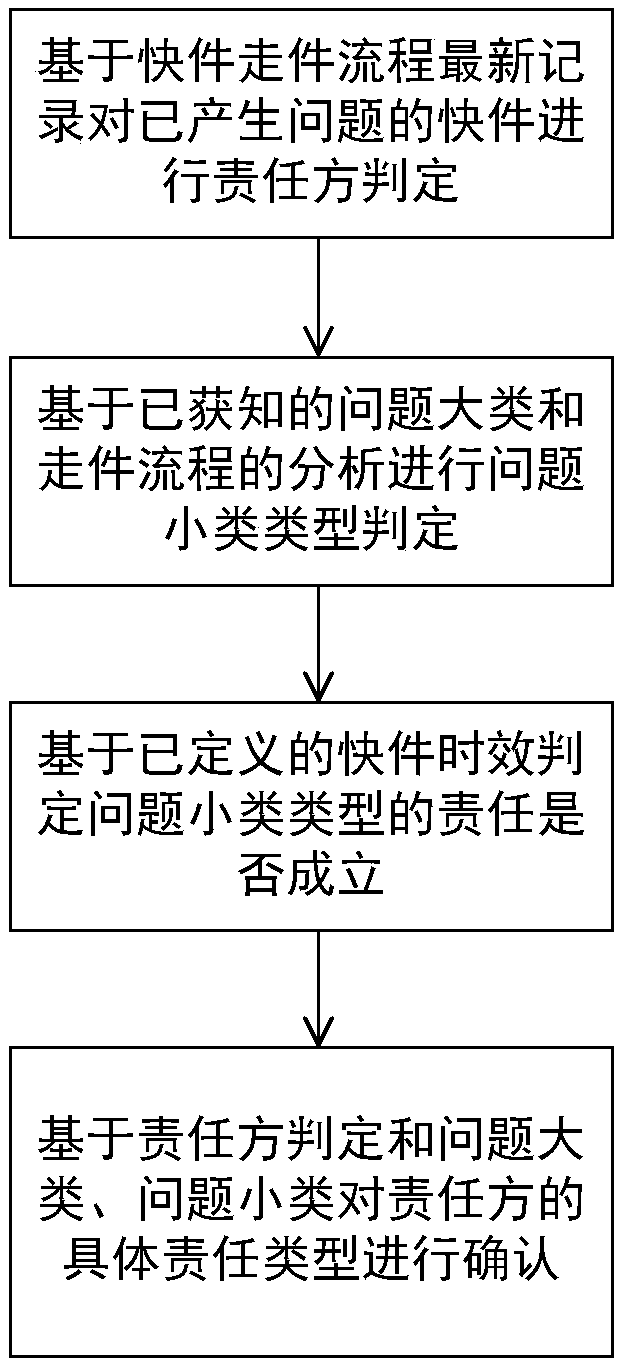
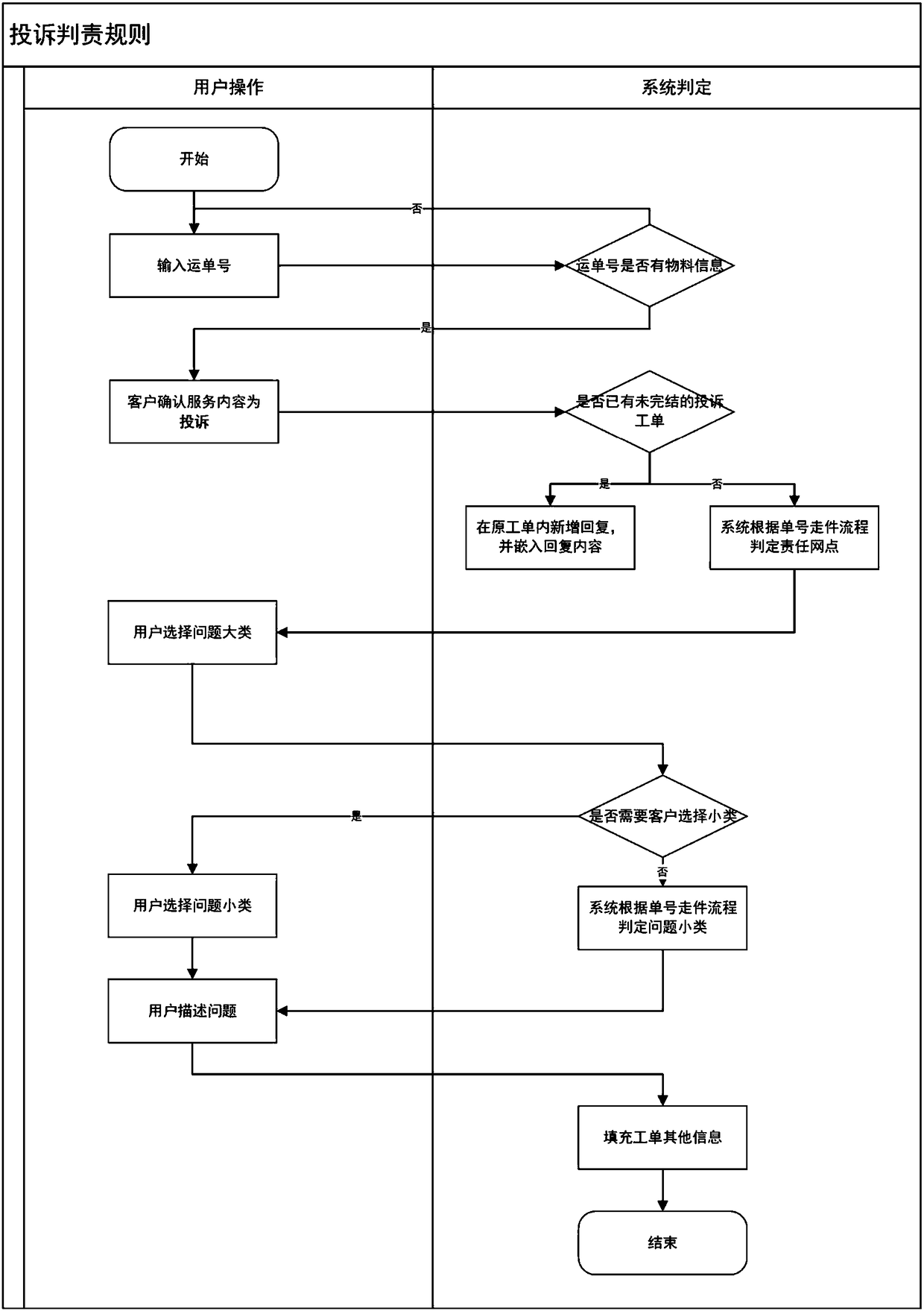
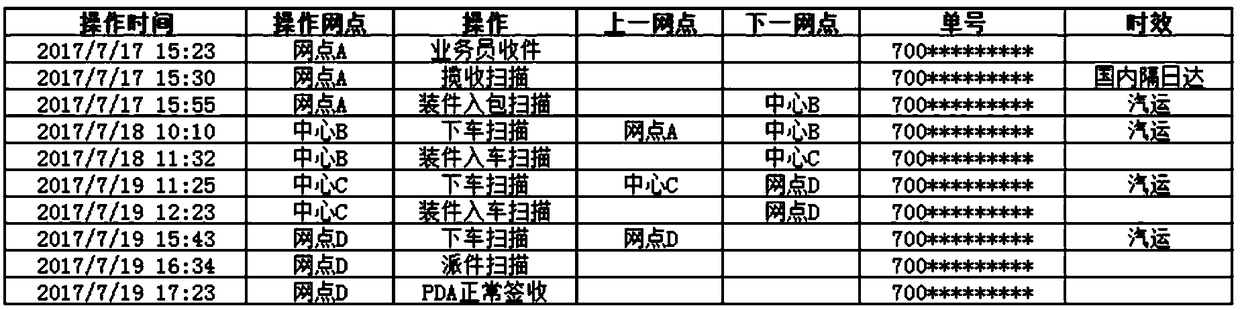
Method and system for liability judgment according to express mail transfer nodes and problem types, and medium
InactiveCN108399547AQuick identificationAccurate identificationLogisticsCommerceComputer networkSynthetic data
The present invention discloses a method and a system for liability judgment according to express mail transfer nodes and problem types, and a medium, in order to improve the liability division of theabnormal express mail and the accuracy of the liability definition, to improve the work processing efficiency, and to reduce the workload of the manual liability judgment. The technical scheme is that: according to the method for liability judgment according to express mail transfer nodes and problem types, the liable party of the express mail in the current state will be quickly and accurately identified, and the work problem that the liable party is analyzed by manually checking the express mail transfer process can be solved; and sub-types of problems of the main type of the express mail problem can be quickly and accurately identified, and the problem of the cumbersome work of manually reading various comprehensive data of the express mail to obtain sub-types of problems is solved.
Owner:YTO EXPRESS CO LTD
Information pushing method and device
ActiveCN108549660AShorten the timeSave energySpecial data processing applicationsTime efficientWorld Wide Web
Owner:VIVO MOBILE COMM CO LTD
VPLS (Virtual Private LAN Service) implementation method and device based on DOCSIS
The invention provides a VPLS (Virtual Private LAN Service) implementation method based on a wired DOCSIS (Data Over Cable System Interface Specification), and a communication device. Through obtaining a cable modem configuration file which comprises VPLS signal parameter coding information for building a two-layer private network, the method can define the VPLS signal parameter coding information for identification through one TLV (type length value) packaged through an NSI (network system interface). The TLV can further comprises a plurality of SubTLVs (sub-type length values) which are respectively used for identifying specific VPLS signal parameter items, such as an AGI (access circuit identification), an opposite end IP address list of a net pseudo-wire, a pseudo-wire type, and a control character. Therefore, a service provider edge router PE can build and maintain the PW (pseudo-wire) along with other PEs in the network according to the VPLS signal parameter coding information.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Network data excavation method
InactiveCN104281710AOptimization logicImprove retrieval efficiencyWeb data indexingSpecial data processing applicationsText categorizationWeb data mining
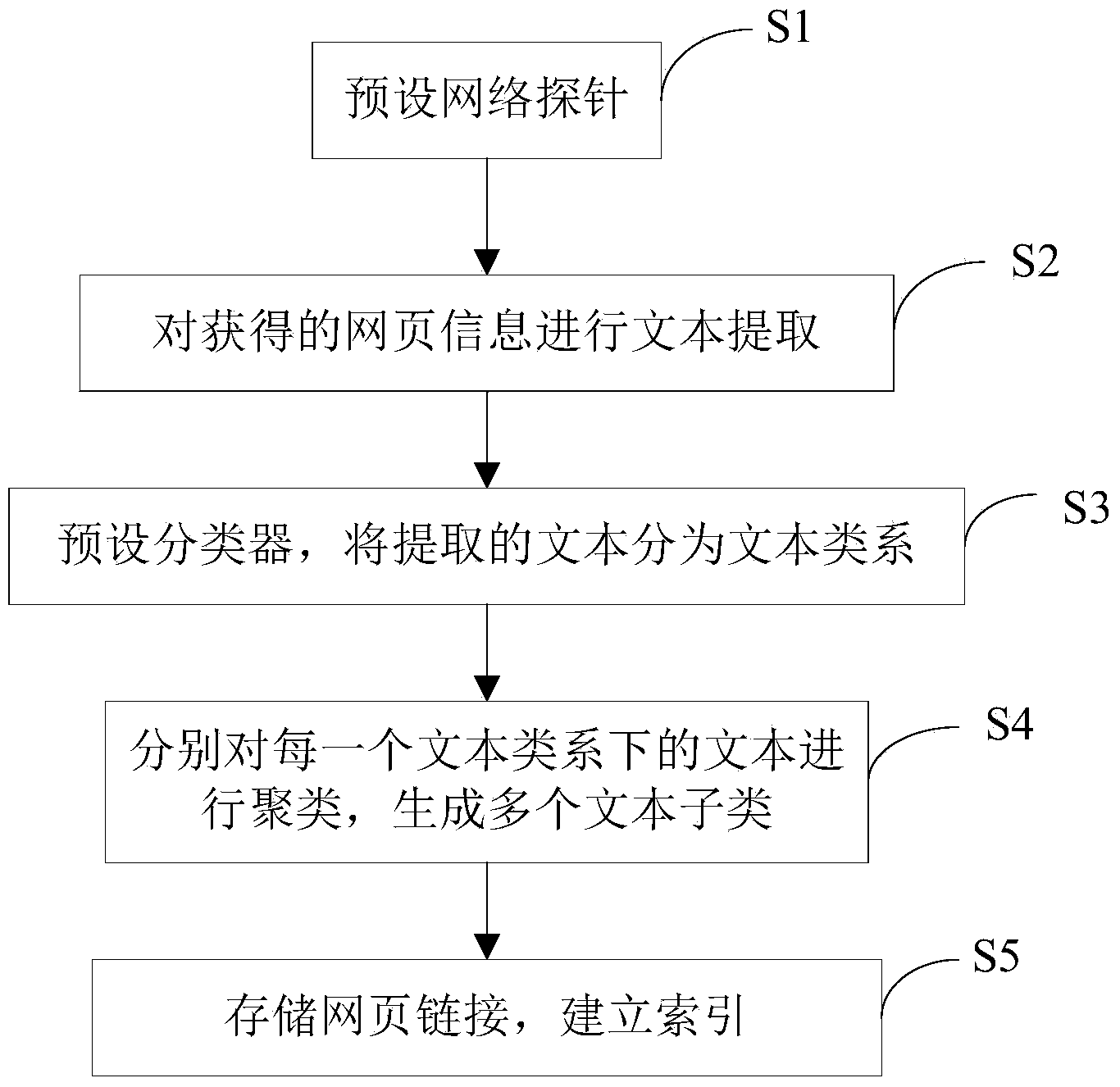
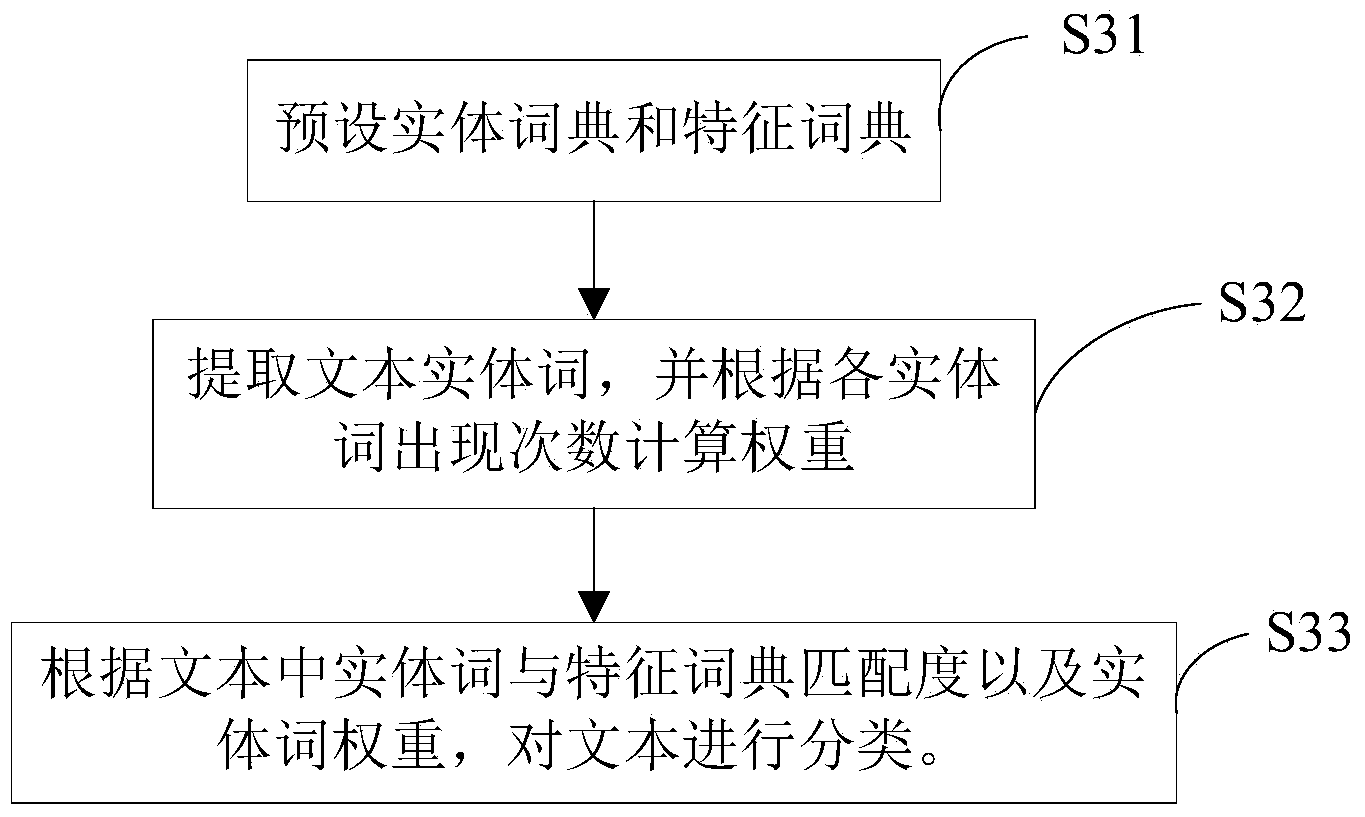
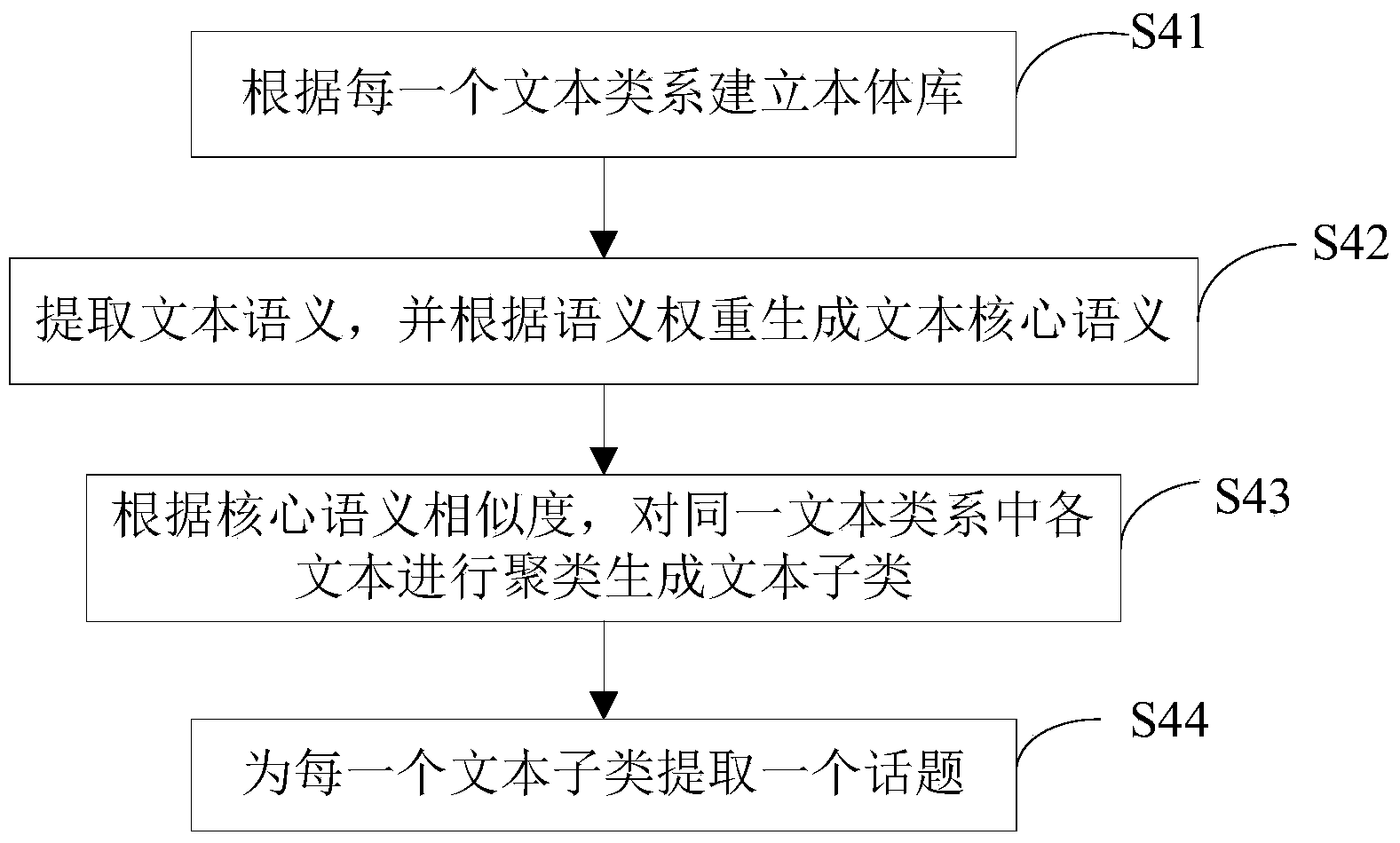
The invention provides a network data excavation method, which is used for performing text classification and text clustering on acquired webpage information so as to extract topics. The network data excavation method specifically comprises the following steps of S1, catching the webpage information by a preset network probe according to an industrial body; S2, performing text extraction on the acquired network information; S3, performing text classification on extracted texts by a preset classifier to generate a plurality of text type systems; S4, clustering texts under each text type system to generate a plurality of text sub types, wherein each text sub type corresponds to each topic; S5, storing webpage links, and constructing an index according to the text type systems and the text sub types. The network data excavation method provided by the invention can combine repeated information.
Owner:BEIJING ZHITOUJIA INTPROP OPERATION CO LTD
Method for implementing multi-characteristic optimizing storage
InactiveCN101136913AImprove storage efficiencyAdd supportTransmissionAccess networkCommunications system
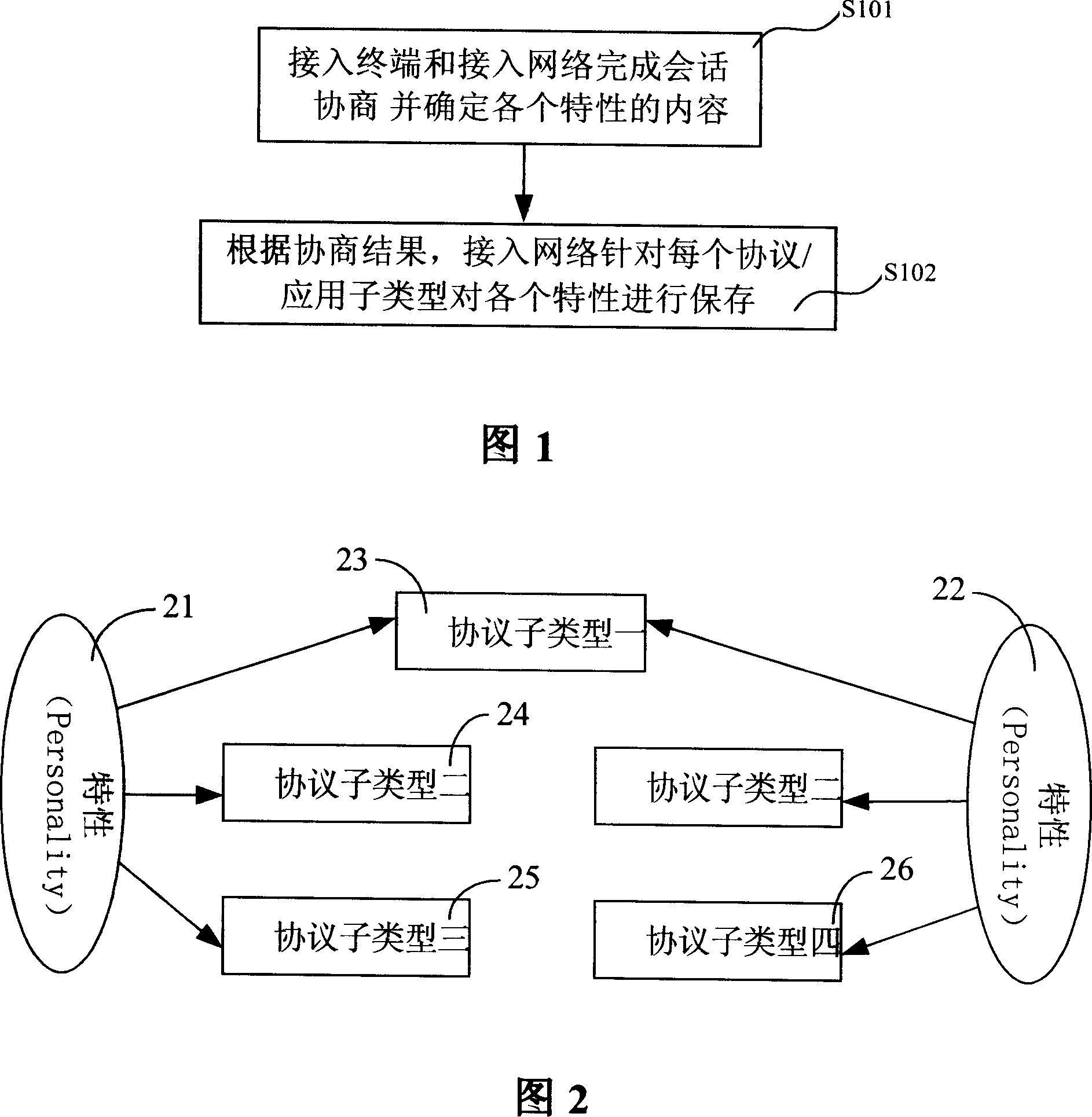
Implementing multiple characteristic optimized storages, the method is in use for CDMA2000 EVDO mobile communication system including access terminal and access network. The method includes steps: (1) using access terminal and access network accomplishes dialog negotiation at a time to determine content of each characteristic. The said characteristics include integrated sub types of protocol, sub type of application, attribute values, and set of common data; (2) the said access network saves the characteristics accordingly based on result of the dialog negotiation. The invention can raise efficiency for multiple characteristic storages effectively and better supports implementation of sub types of hard connection protocol without losing extensiveness.
Owner:ZTE CORP
Combined type pathological specimen container and use method thereof
InactiveCN102344006AAchieve the effect of "one person, one cover"Easy to manageDead animal preservationRigid containersEngineeringContainer tops
The invention relates to a combined type pathological specimen container and a use method thereof. The combined type pathological specimen container comprises a container top cover, a container opening, a container body and a container bottom cover which is connected with the container body and has a sealing property. The pathological specimen containers are classified into different types according to the diameter and relevance of the pathological specimen containers, and pathological specimen containers are classified into primary, secondary and sub types according the height and relevance of the pathological specimen containers. The containers of the same type are combined through the container bottom cover or secondary type of the pathological specimen containers and the containers of different types are combined through the secondary pathological specimen containers. Regardless of the size and quantity of specimens, all the pathological specimens of a same patient can be collected by a combined container. One combined container only needs one container top cover, thereby being called as 'one patient, one cover'. The combined type pathological specimen container has an excellent effect of solving the problems of volatilization and overflow of stationary liquid such as formaldehyde, confusion and loss of the specimens and ensuring specimen storage and fixing effect. The combined type pathological specimen container has the advantages of uniform appearance, beautiful and elegant appearance, repeatability in use, economical performance, environmentally friendliness, and the like. A condition is provided for information management of the pathological specimens.
Owner:杭州康本信息科技有限公司
Multifunctional control channel for pseudowire emulation
Owner:VERIZON PATENT & LICENSING INC
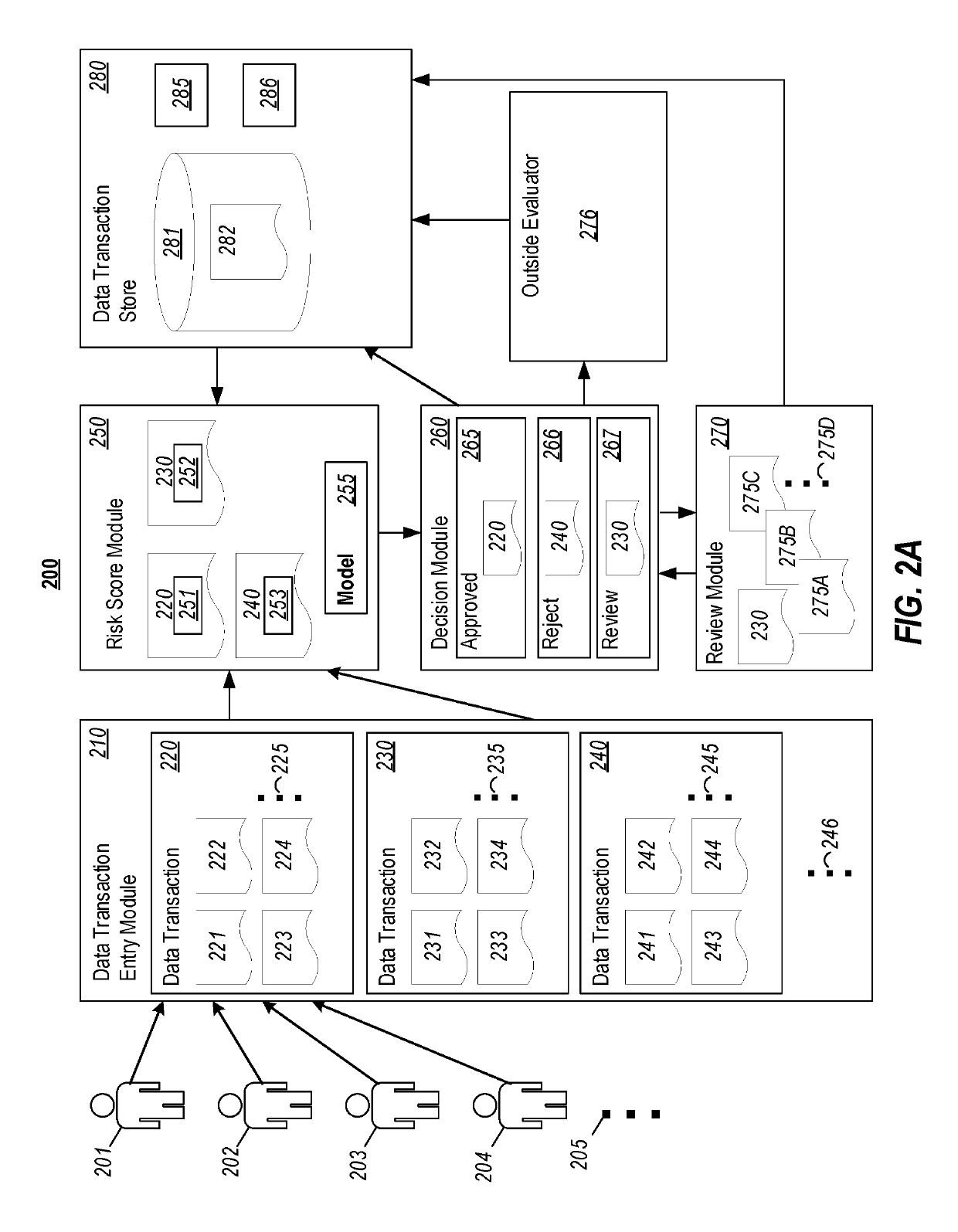
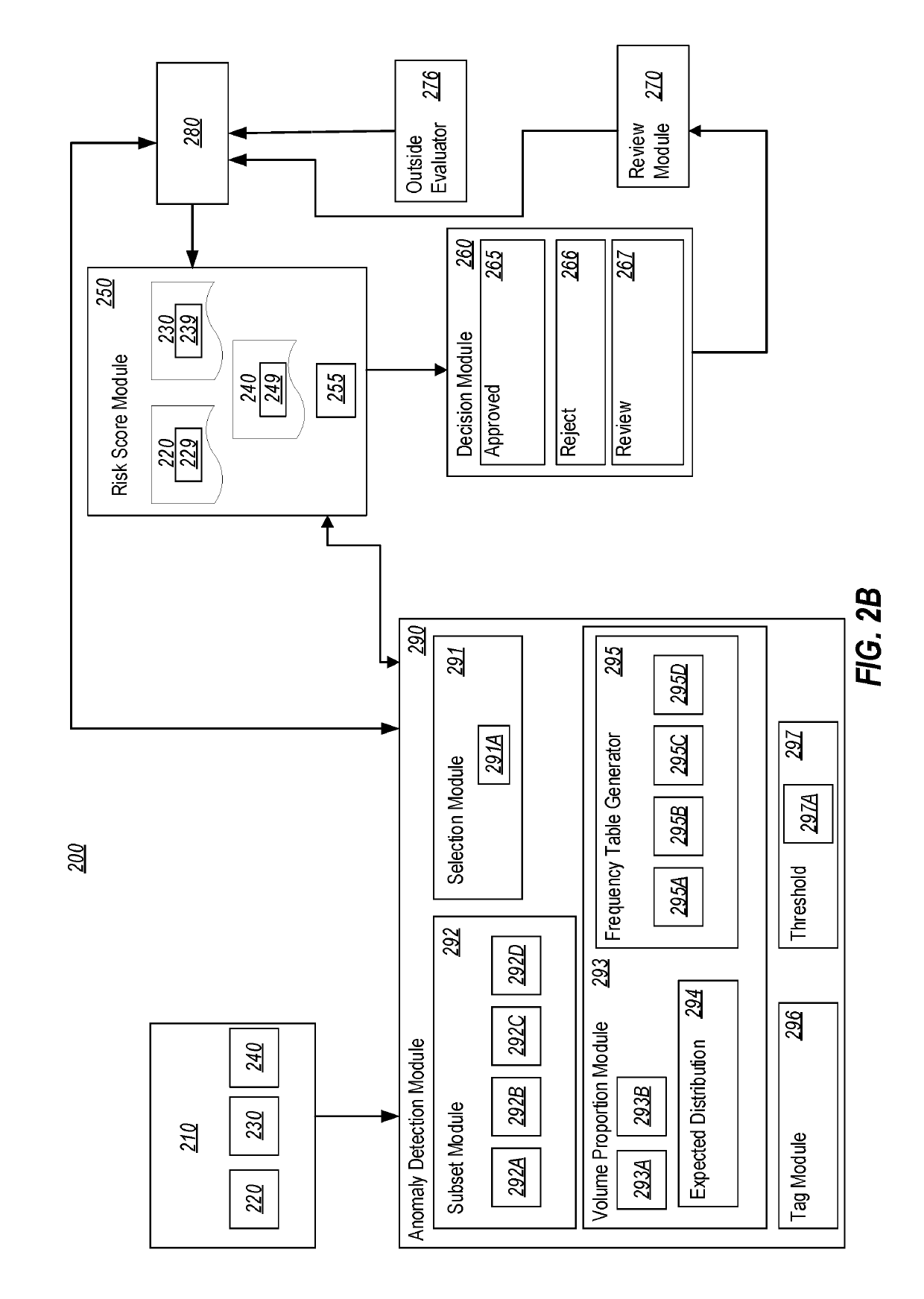
Anomaly detection in data transactions
InactiveUS20190114639A1Well formedRelational databasesSpecial data processing applicationsAnomaly detectionComputing systems
Embodiments disclosed herein are related to computing systems and methods for detecting anomalies in a distribution of one or more attributes associated with data transactions. In the embodiments, data transactions are accessed that each include various attributes. The data transactions are grouped into a first subset associated with a first sub-type of a first attribute and a second subset including any remaining sub-types of the first attribute. Second attributes in the first and second subsets are compared to determine differences in the proportion of the second attributes between the first and second subsets, where the differences are indicative of an anomaly in an expected distribution of the second attributes. Based at least on a determination that there are differences in the proportion, subsequently accessed data transactions that are associated with attributes similar to the data transactions of the first subset are rejected or subjected to a further review process.
Owner:MICROSOFT TECH LICENSING LLC
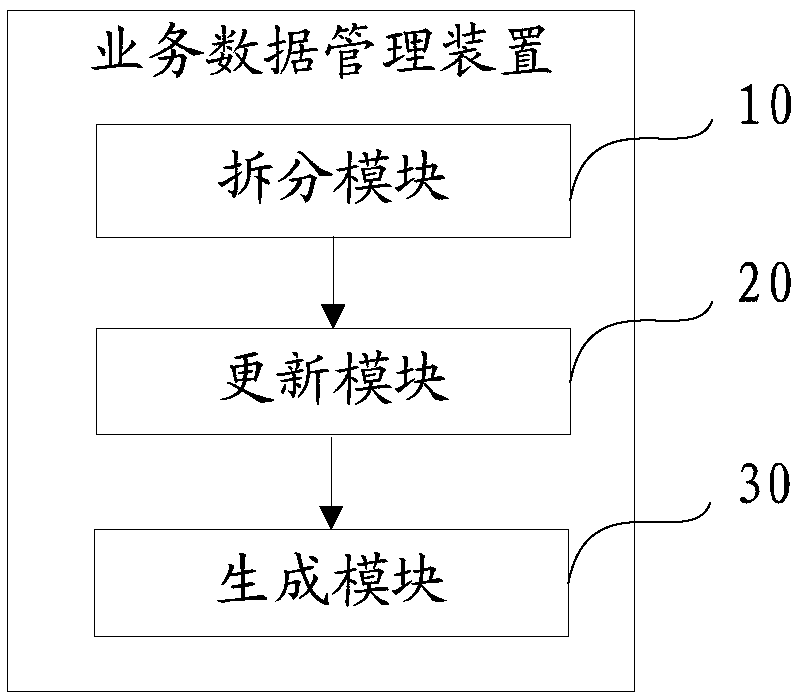
Service data management method, device and equipment and computer readable storage medium
PendingCN109634950AEnsure safetyImprove automation managementDatabase updatingFinanceBusiness dataData management
The invention discloses a business data management method, device and equipment and a computer readable storage medium. The method comprises: scanning each piece of business data when the business data is received, splitting each piece of business data based on a preset data type after the scanning is completed, and generating an associated business data table; when an updating instruction is detected, reading an updating identifier carried in the updating instruction, determining to-be-updated service sub-data in each associated service data table according to the updating identifier, and updating the to-be-updated service sub-data; and when the detection time reaches the preset time, counting the repayment amount and the debt amount in each associated business data table based on a preset data sub-type, and transmitting each type of the repayment amount and the debt amount to a preset template to generate a data report. The scheme manages the service data, ensures the security of theservice data, and improves the automatic management degree of the service data.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
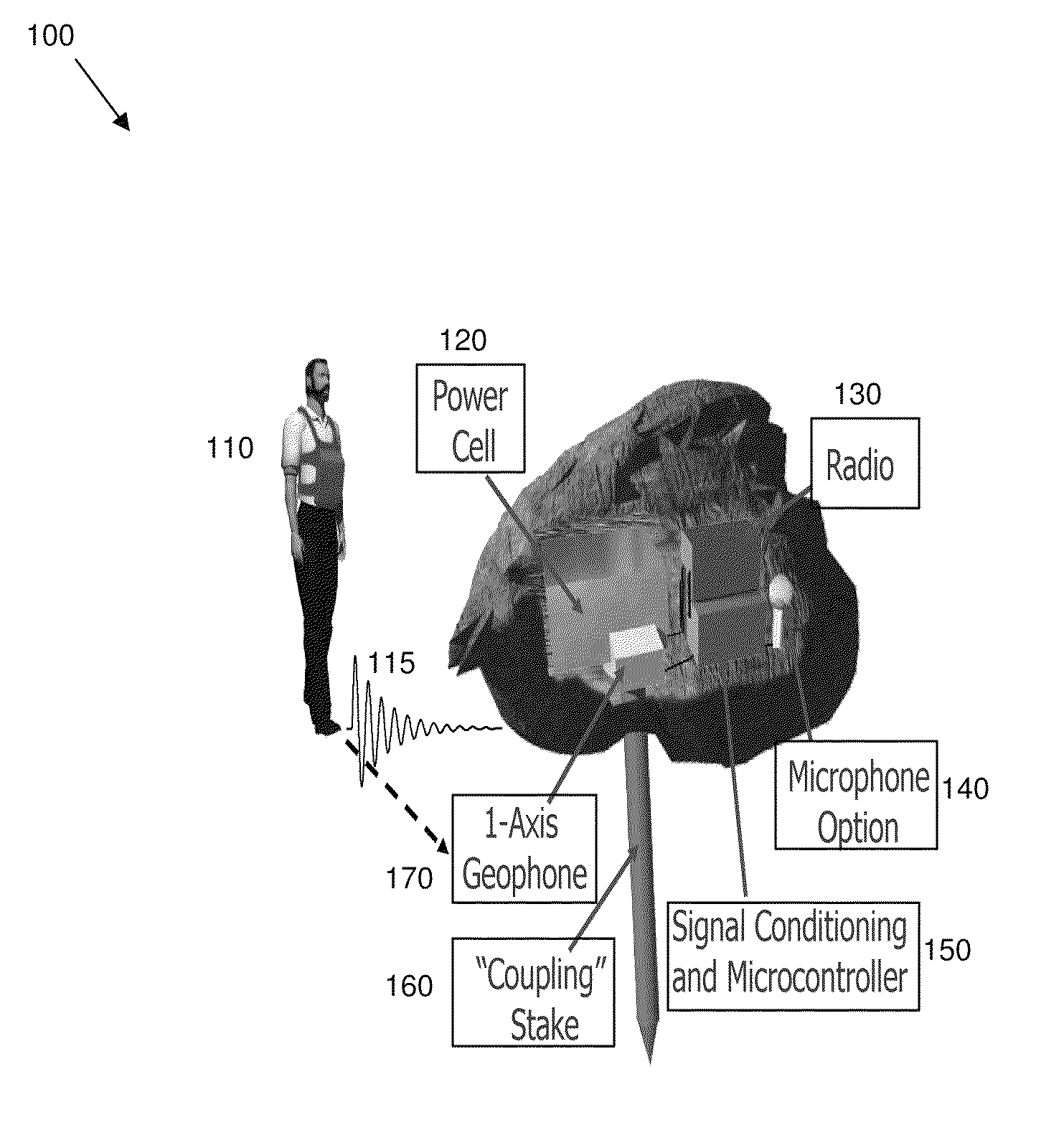
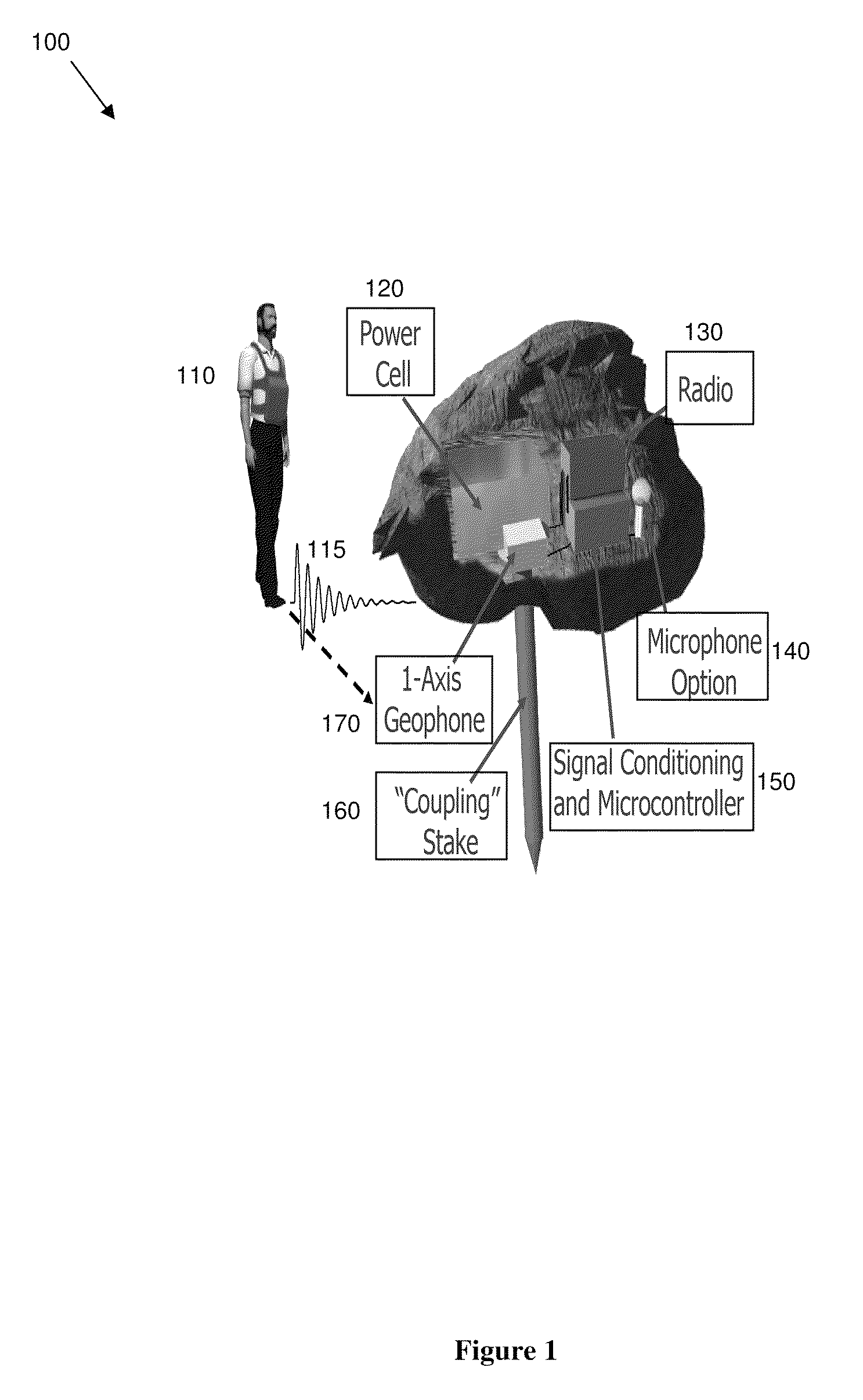
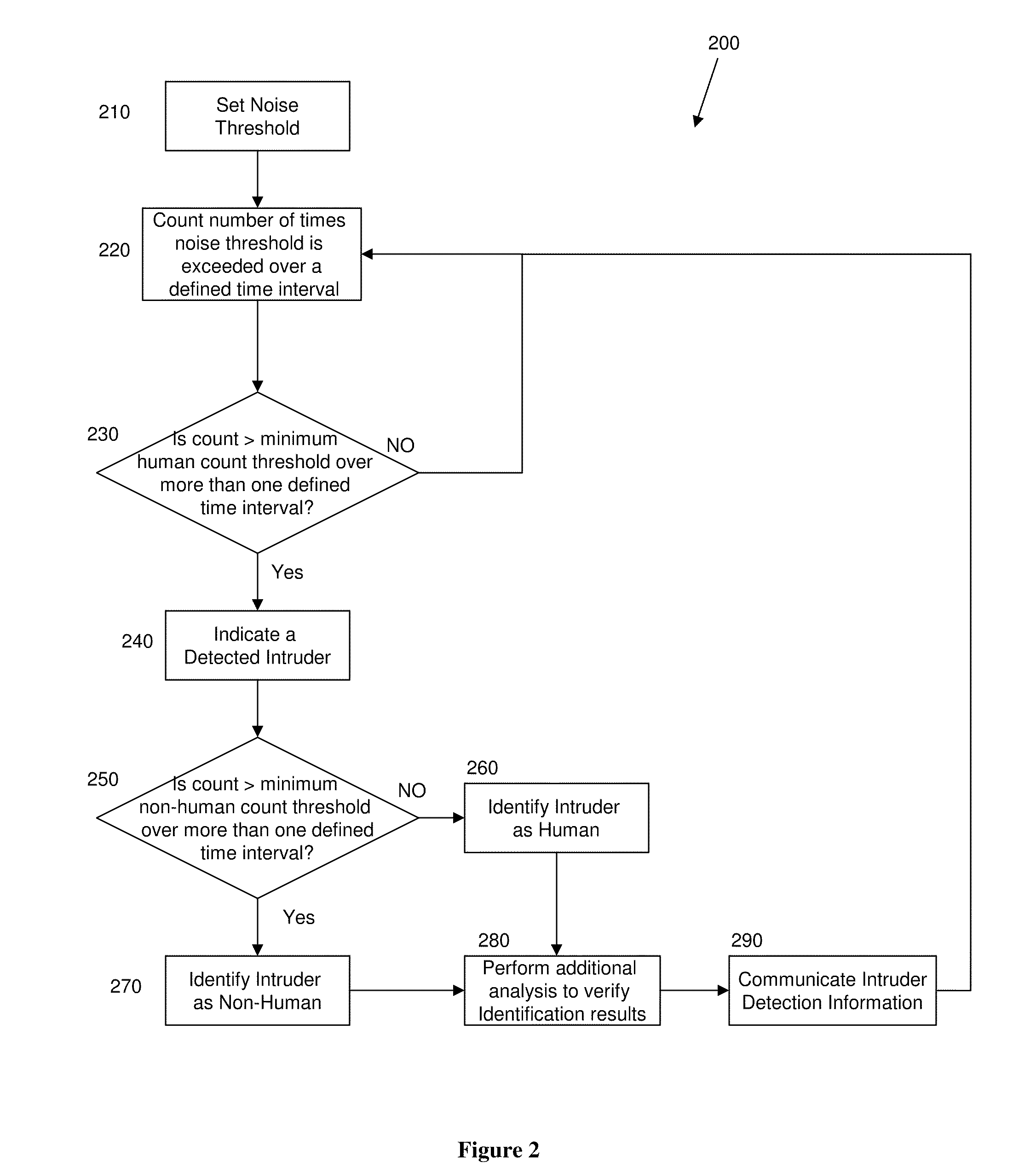
Intruder detector and classifier
InactiveUS8354929B2Direction finders using ultrasonic/sonic/infrasonic wavesBurglar alarm electric actuationMicrocontrollerComputer science
A method and system for detecting and classifying intruders is provided. A noise threshold can be determined and set based on background noise. A seismic sensor can be configured to receive a plurality of seismic data signals. A microcontroller can be configured to count the number of times the noise threshold is exceeded over a defined time interval by the plurality of seismic data signals, and then detect and classify the presence of an intruder based on the count. Additionally, an amplitude evaluation module can be configured to determine a signal amplitude for the seismic data signals associated with the detected intruder and compare the detected intruder signal amplitude to known signal amplitudes in order to determine a sub-type of the intruder. Finally, a transmission source can be configured to transmit intruder detection and classification information to a remote location.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Information processing device and method
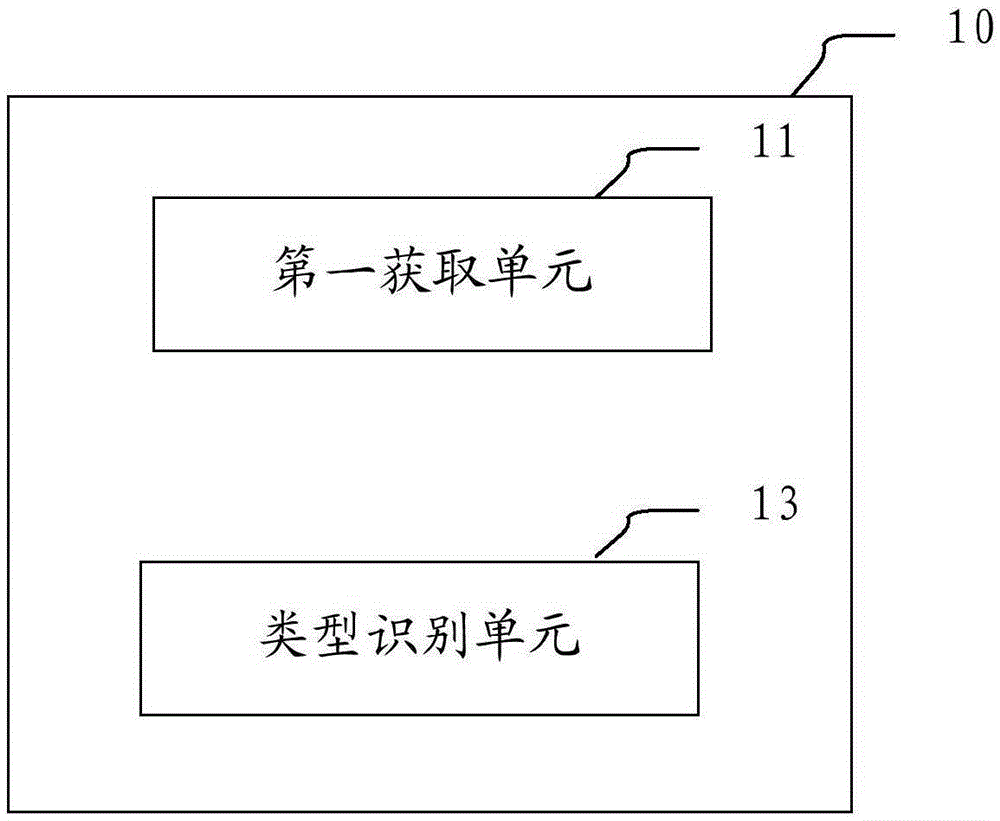
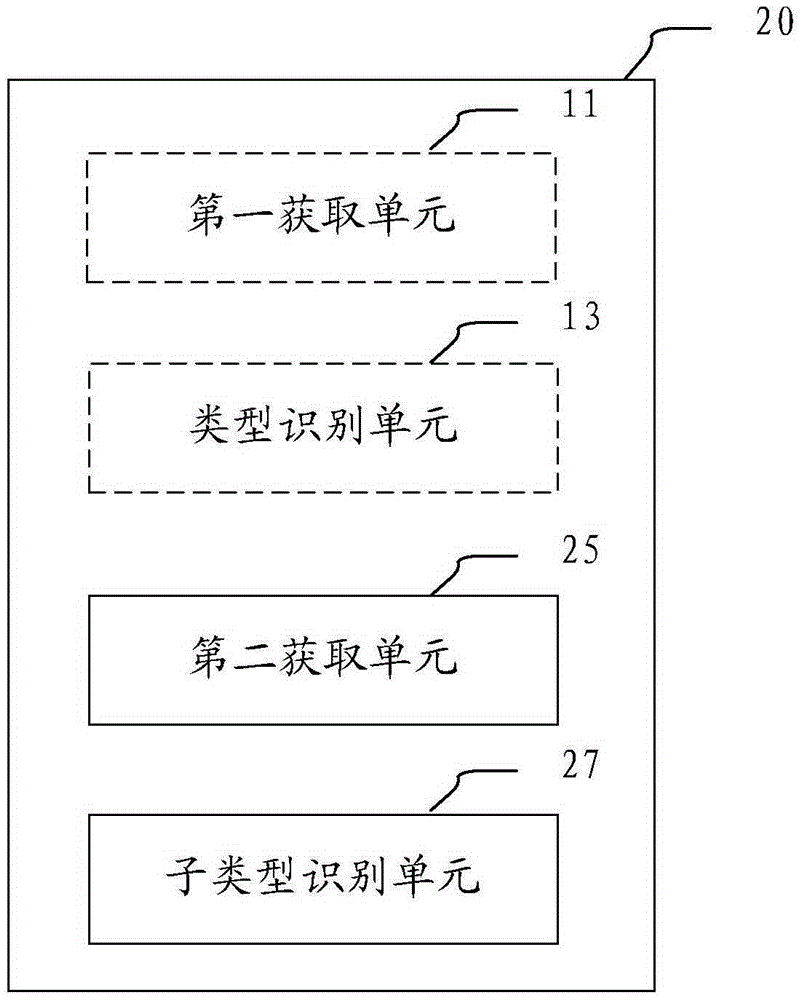
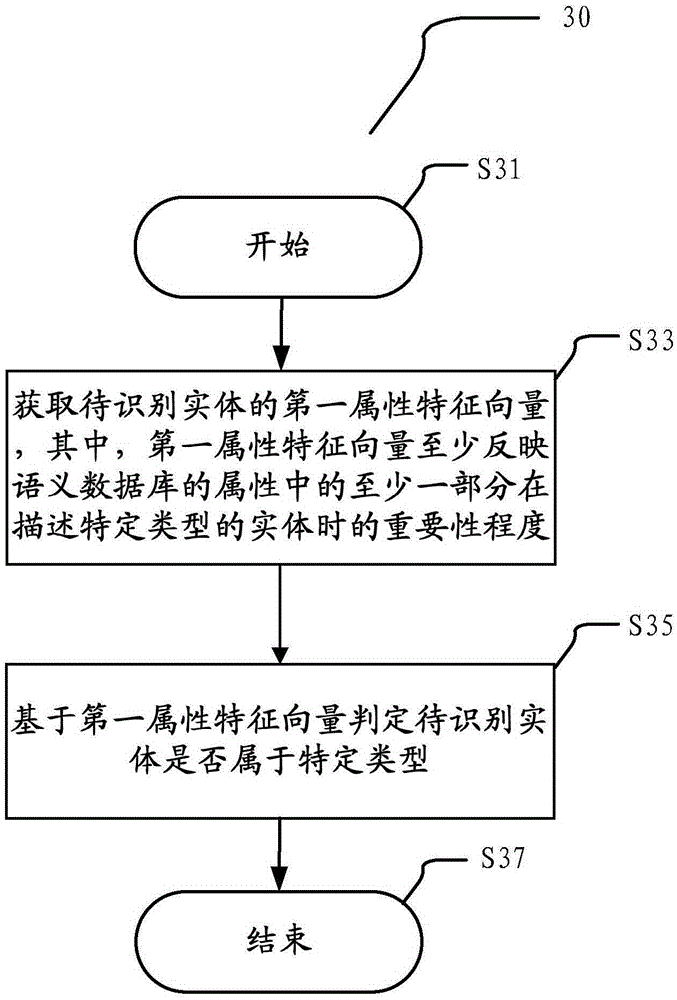
InactiveCN106557528AAutomatic judgmentAccurate judgmentSpecial data processing applicationsFeature vectorInformation processing
The invention provides an information processing device and method, wherein the information processing device comprises a first obtaining unit and a type identification unit; the first obtaining unit is configured to obtain a first property feature vector of an entity to be identified, wherein the first property feature vector at least reflects the importance degree when at least one part of properties of a semantic database describes a specific type of entity included in the semantic database; and the type identification unit is configured to judge whether the entity to be identified belongs to the specific type or not according to the first property feature vector. According to the method and the device in the embodiment of the invention, whether the entity to be identified belongs to the specific type / sub-type or not can be judged automatically and accurately; and thus, in an information processing process, the calculation amount is greatly reduced and the accuracy rate of an inquiry result is increased.
Owner:FUJITSU LTD
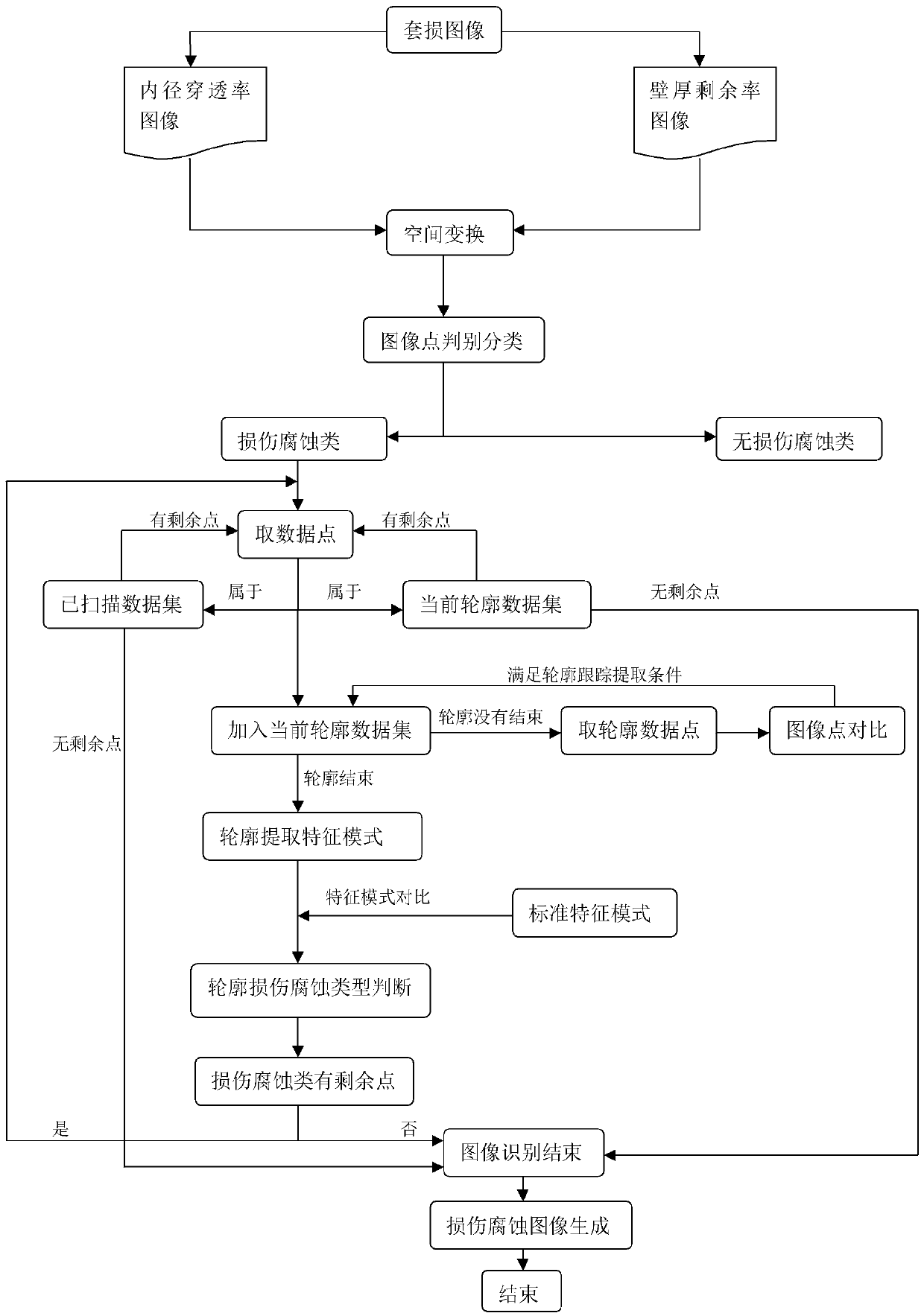
Oil casing shaft casing damage image feature pattern recognition method
ActiveCN108805147AAccurate judgmentAccurately judge and identifyImage analysisGeometric image transformationData setVirtual space
The invention discloses an oil casing shaft casing damage image feature pattern recognition method, comprising the following steps: (1) inputting a casing damage image; (2) converting the casing damage image from the two-dimensional space to the three-dimensional space, and dividing data points in the three-dimensional space into data points with damage and corrosion and data points without damageand corrosion according to the data threshold value of data points in the three-dimensional space; and (3) judging the type of damage corrosion according to the set of data points with damage corrosion. In the invention, a two-dimensional image corresponding to the casing damage image is converted into an image in a three-dimensional virtual space, the image is formed into corresponding data setsin the three-dimensional space; and by constraint of the distance threshold between points and the numerical value threshold of points in the image, in combination with the limitation of the maximumperpendicular distance allowed by image search, the data sets are divided into sub-type data sets representing different corrosion pattern features, and different corrosion pattern features correspondto different corrosion shapes, so that the corrosion types of the sub-type data sets can be accurately evaluated and recognized.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
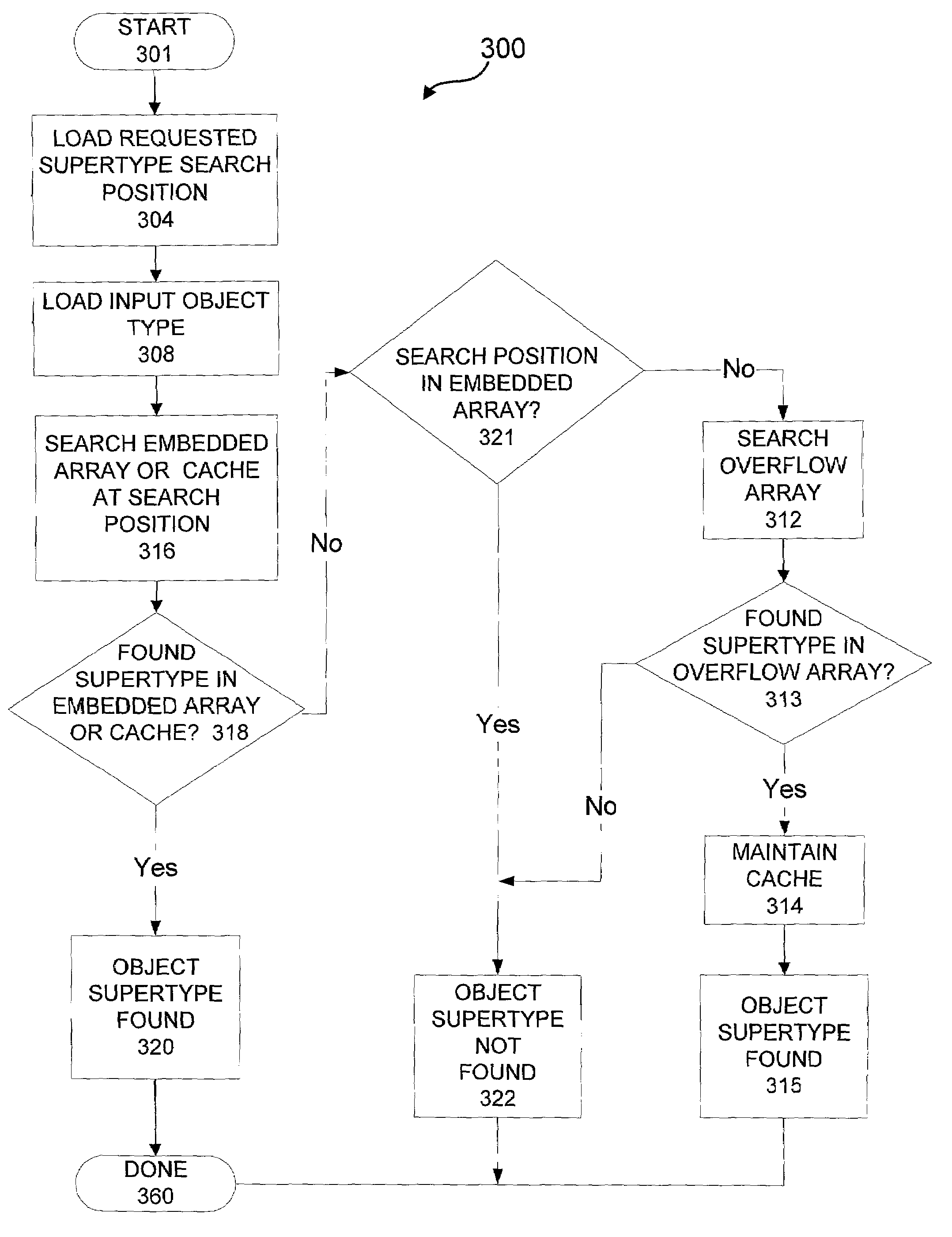
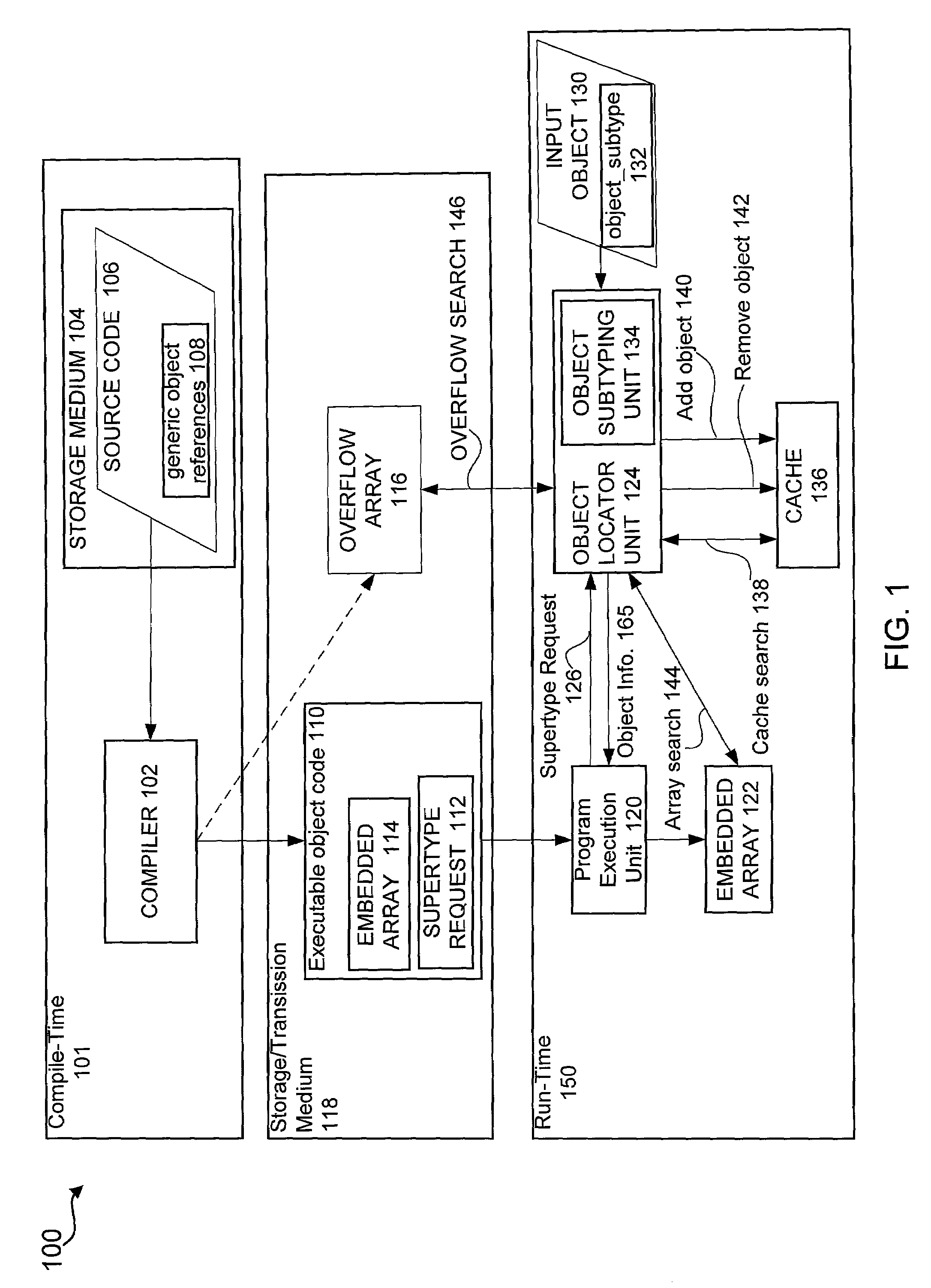
Method and apparatus for efficient object sub-typing
ActiveUS6996825B2Efficient methodEasy to operateSpecific program execution arrangementsSub typingData structure
An efficient method of sub-typing an object in an object oriented computing environment is provided. In one embodiment, the sub-typing method loads an input object having an object type, whereby an embedded array and a cache are searched for an object sub-typing data structure corresponding to the requested supertype. Any found object sub-typing data structures are associated with the input object. In some embodiments, if the object sub-typing data structure is not initially found, an overflow array is searched and the cache is updated with the object sub-typing data structure when the object sub-typing data structure is included in the overflow array. A system and software product is further provided in other embodiments whereby information associated with a particular object sub-type is obtained.
Owner:ORACLE INT CORP
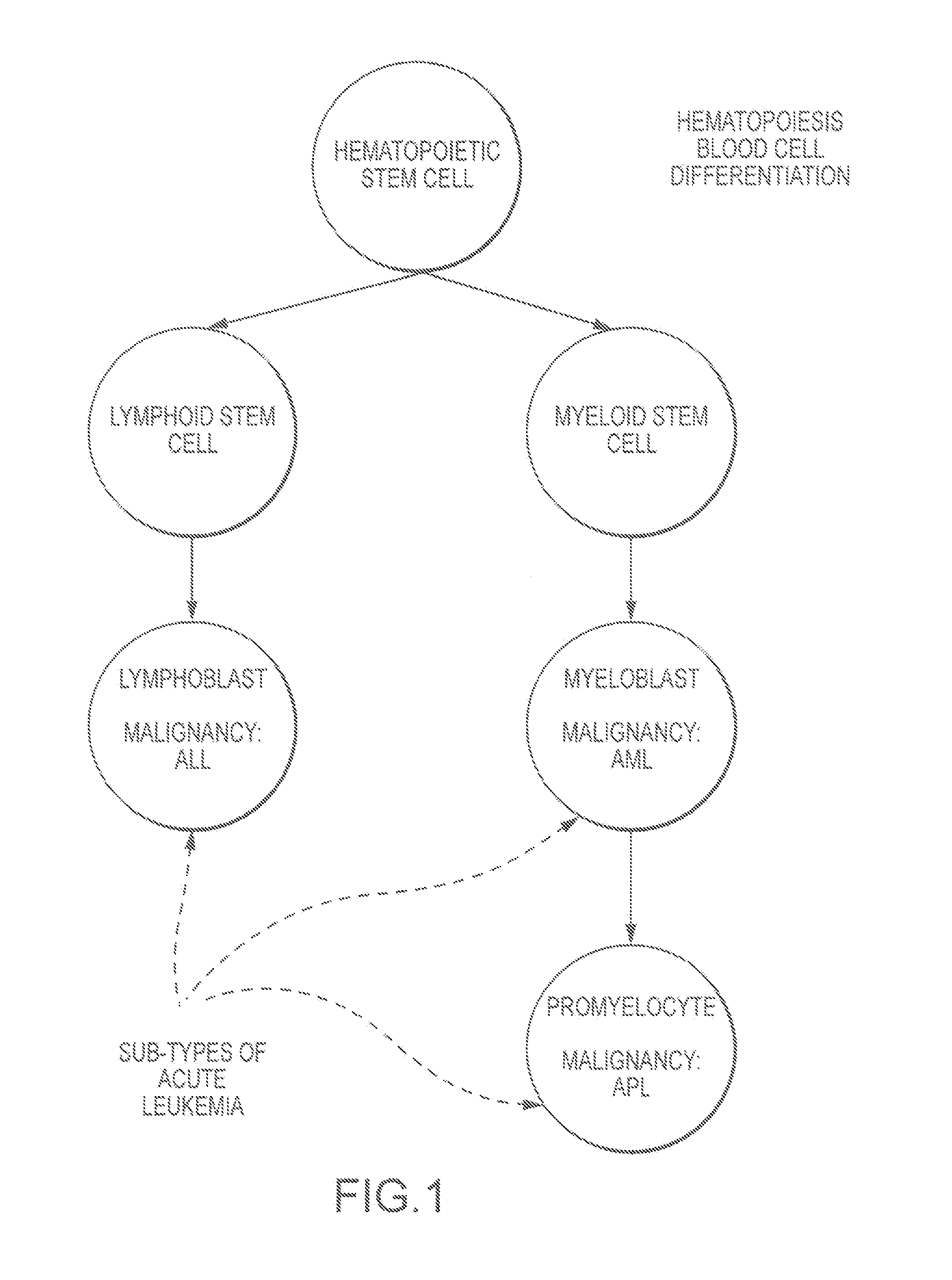
Leukemia classification using cpd data
InactiveUS20140172321A1Improved prognosisLikelihoodMedical automated diagnosisIndividual particle analysisOncologyAcute leukemia
Embodiments of the present invention encompass automated systems and methods for predicting an acute leukemia sub-type of an individual diagnosed with acute leukemia based on a biological sample obtained from blood of the individual. Exemplary techniques involve correlating aspects of direct current (DC) impedance, radiofrequency (RF) conductivity, and / or light measurement data obtained from the biological sample with an acute leukemic sub-type of the individual.
Owner:BECKMAN COULTER INC
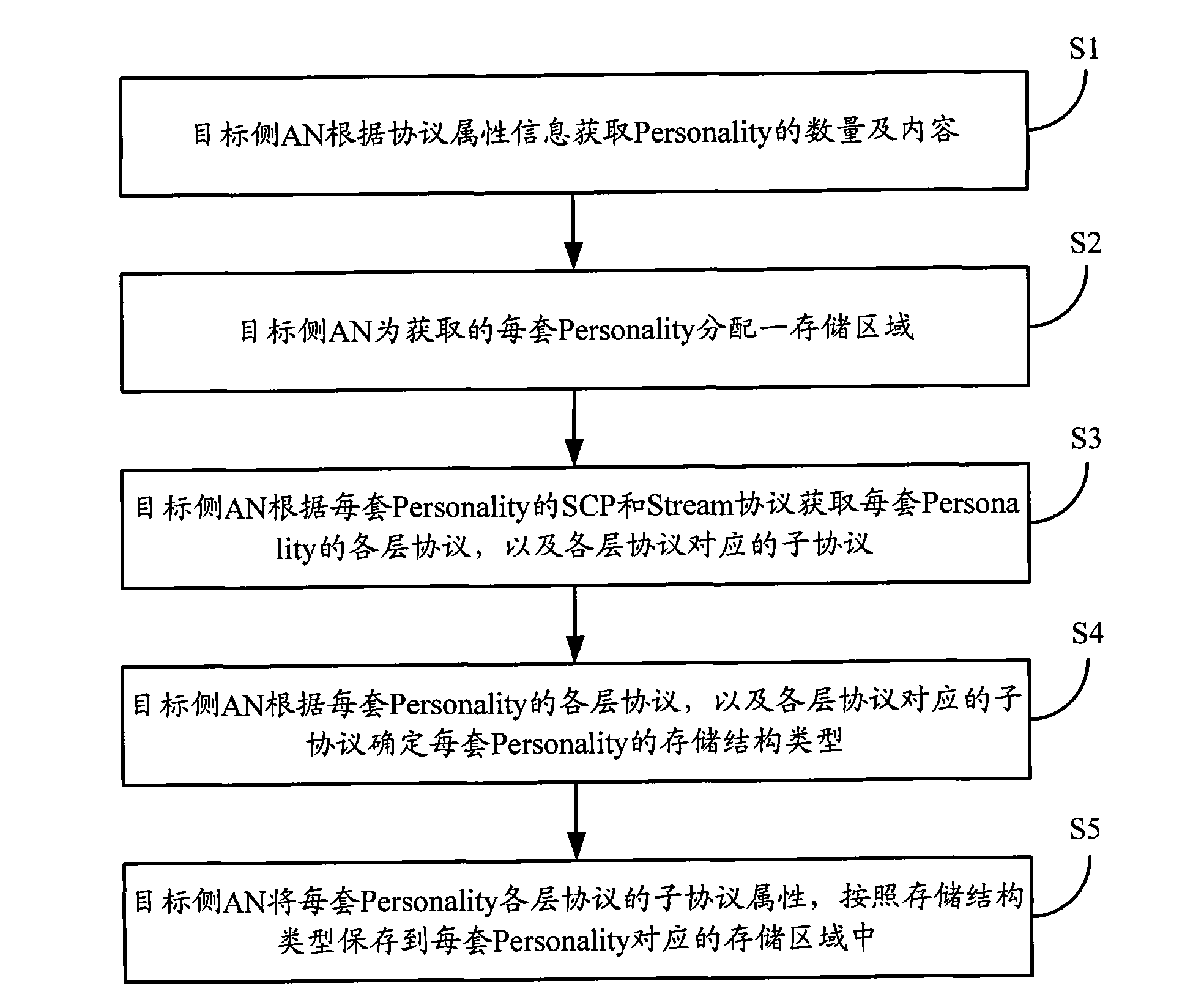
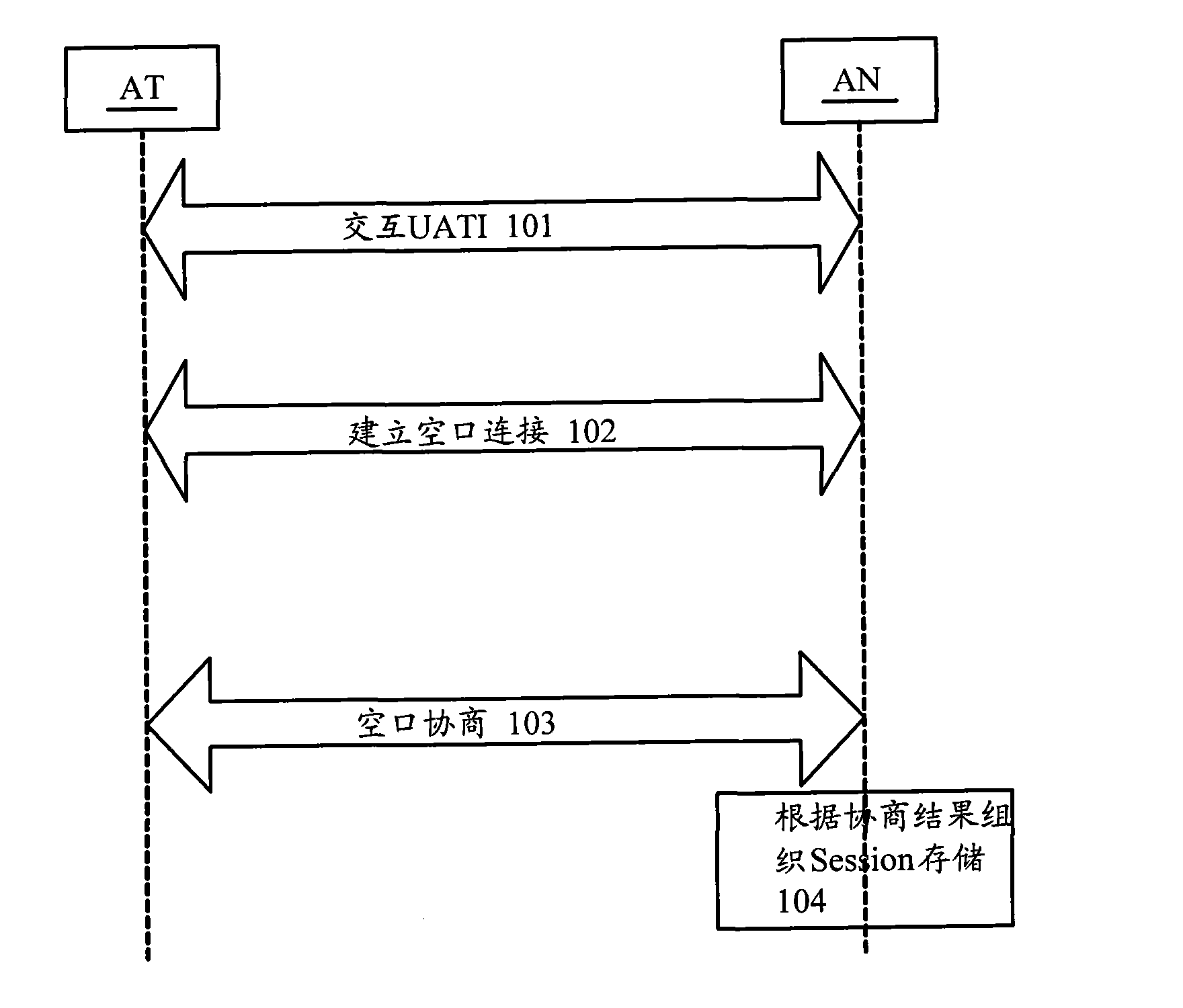
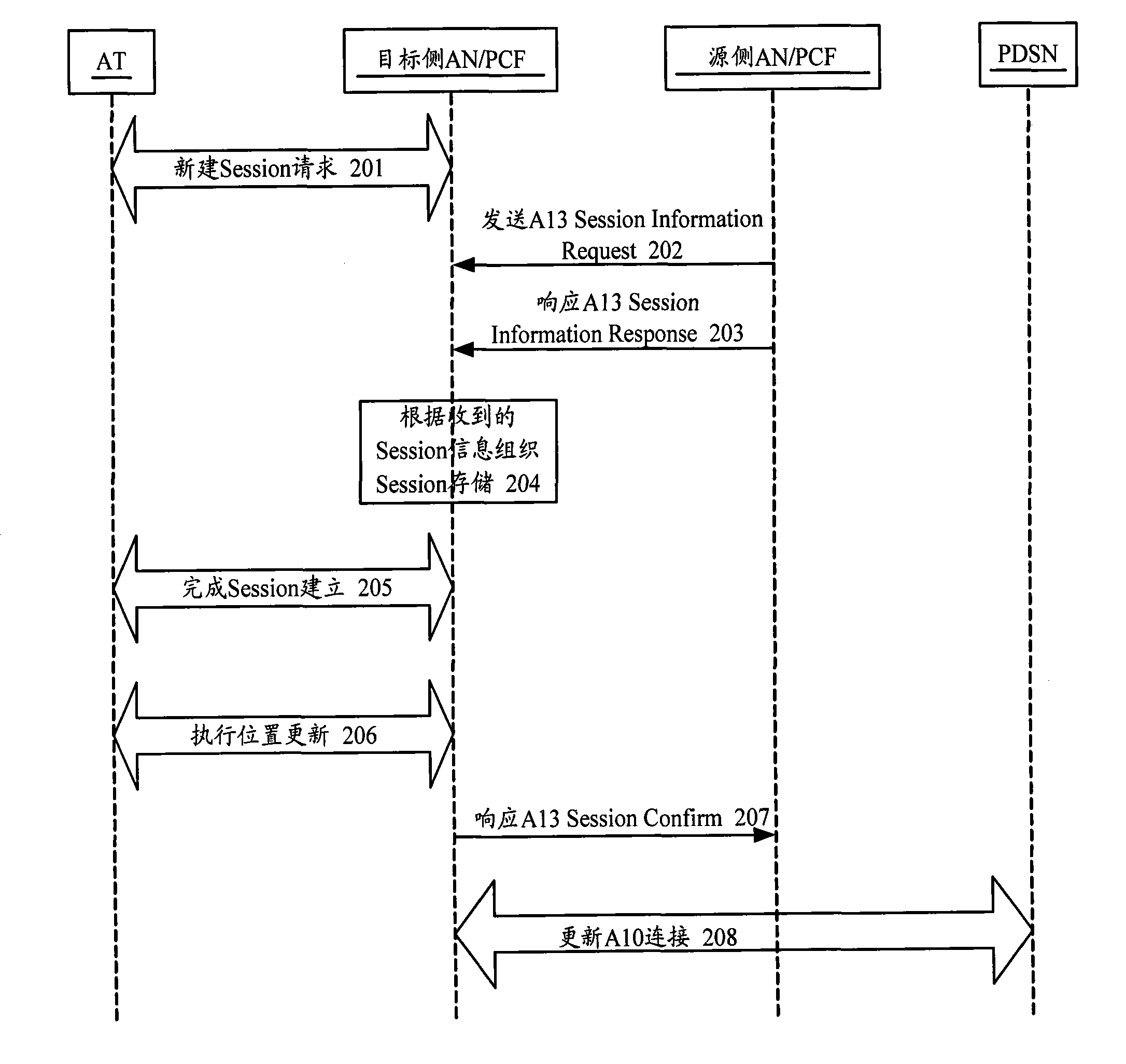
Session information storage method and access network equipment
ActiveCN101778442AMeet various requirements of constructionSupport interoperabilityConnection managementWireless network protocolsAccess networkStructure of Management Information
The invention provides a session information storage method and access network equipment, wherein the method comprises the following steps that: a target side access network obtains all personality according to protocol property information; and the target side access network distributes a storage area for each set of personality obtained, stores the properties of sub-protocols of each set of personality in the corresponding storage area, and the storage structure of each set of personality is determined according to all levels of protocols of each set of personality and the corresponding sub-protocols of each level of protocol. The invention determines the structural organization of Session information according to the mapping relationship between the protocol types and the sub-types of the personality, can be compatible with the Session information results which may be negotiated between different versions of AT and AN, can support the flexible Session negotiation in the largest scope, and can meet various requirements on network construction.
Owner:ZTE CORP
On-line access control method and system of storage region
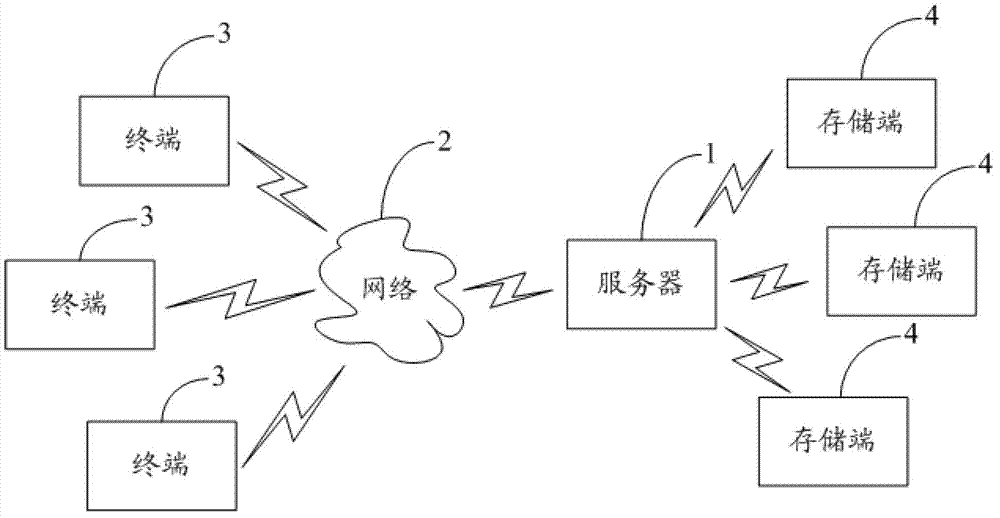
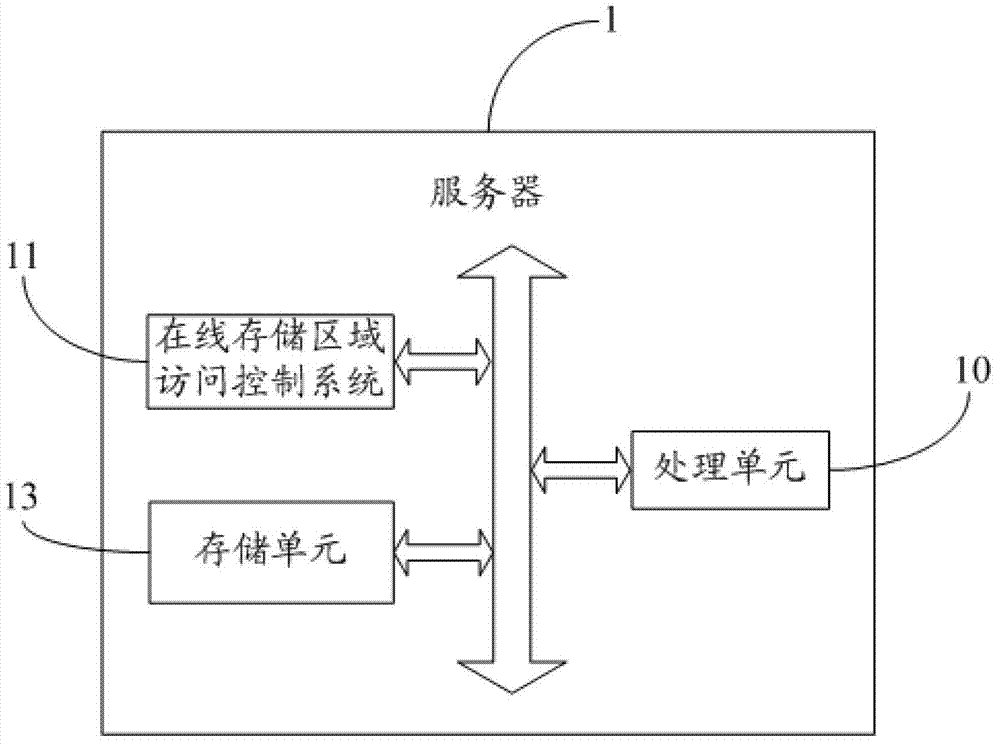
ActiveCN103248623AImprove sharing securityAvoid uncontrollableTransmissionControl systemMedia access control
The invention provides an on-line access control method of a storage region. The method comprises the steps as follows: to-be-shared data are stored in a built specific storage region, a virtual snapshot for the data in the built specific storage region is generated; an access verification code corresponding to the generated virtual snapshot is generated; and the generated access verification code is sent to a specific terminal, so that a specific user acquires the corresponding virtual snapshot through the received access verification code and processes data in the built specific storage region according to the acquired virtual snapshot, the sharing safety of the data stored on line is improved effectively, and the sharing uncontrollability caused by incapability of sharing sub-users and sub-types of the data stored on line in a specific group is avoided. The invention further provides an on-line access control system of the storage region.
Owner:GUANGDONG 115 TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com