Patents
Literature
485results about How to "Avoid stop" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Surgical stapler with sound producing mechanism to signal the completion of the stapling process
Owner:MATSUTANI SEISAKUSHO CO LTD
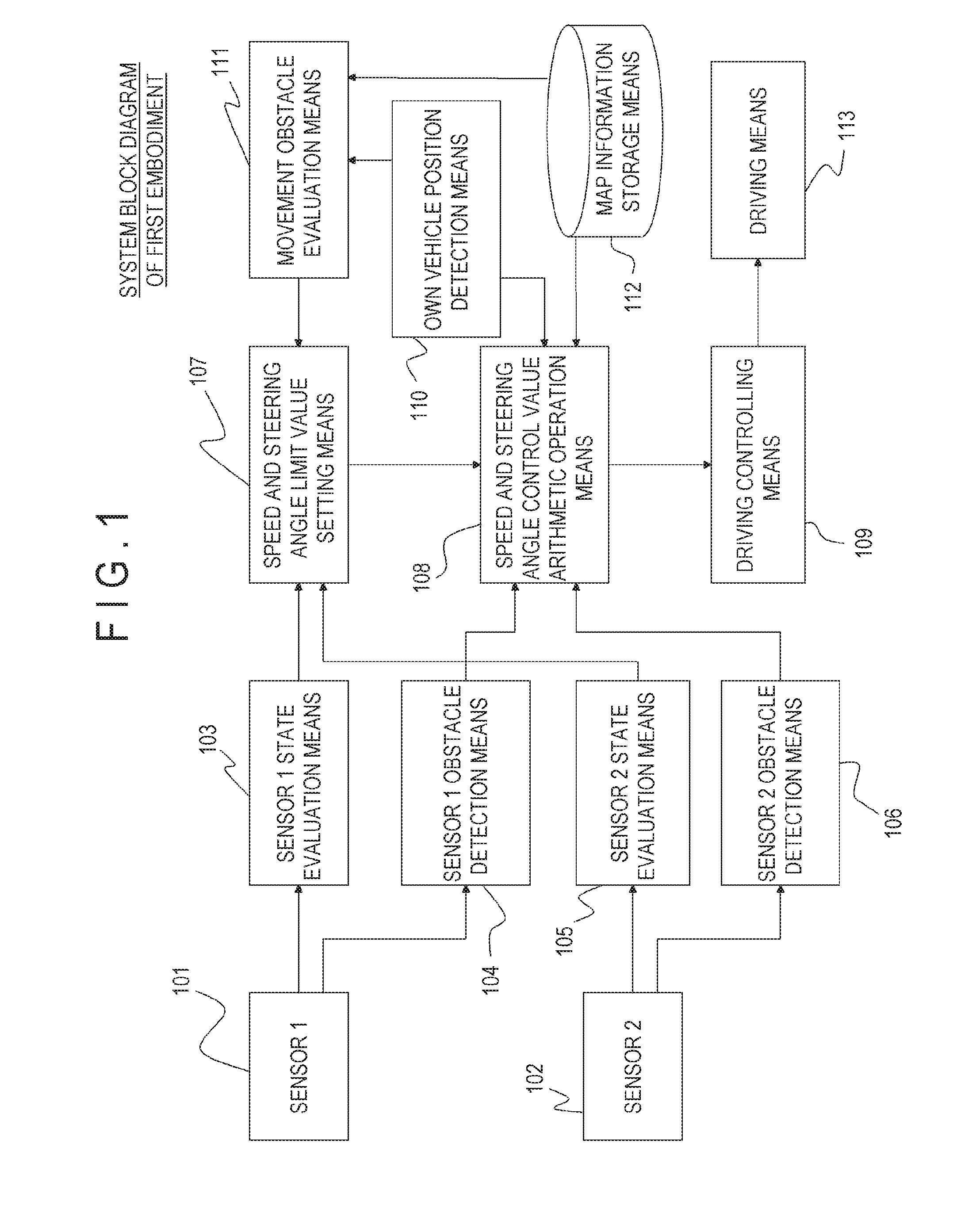
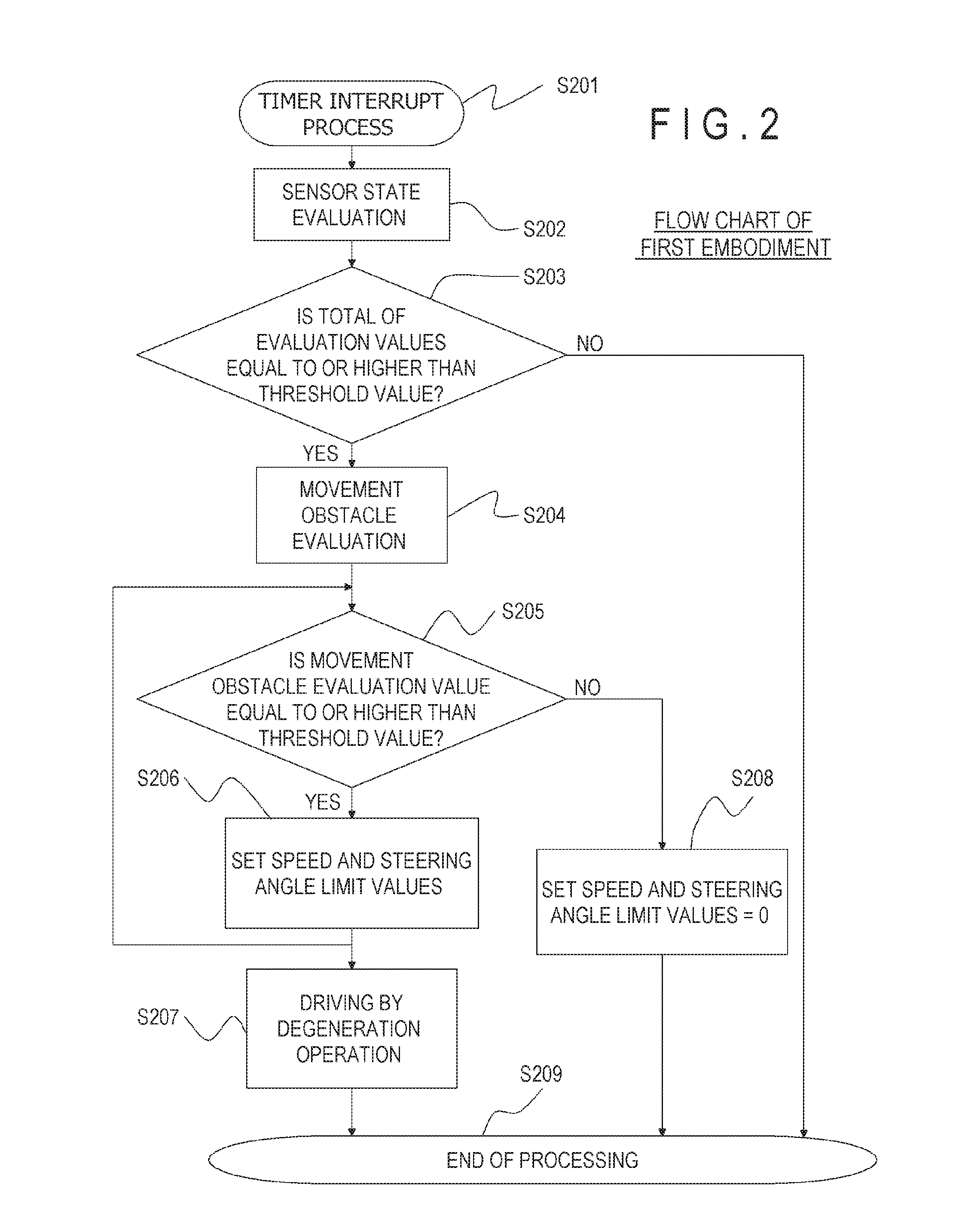
Autonomous Driving Vehicle and Autonomous Driving System
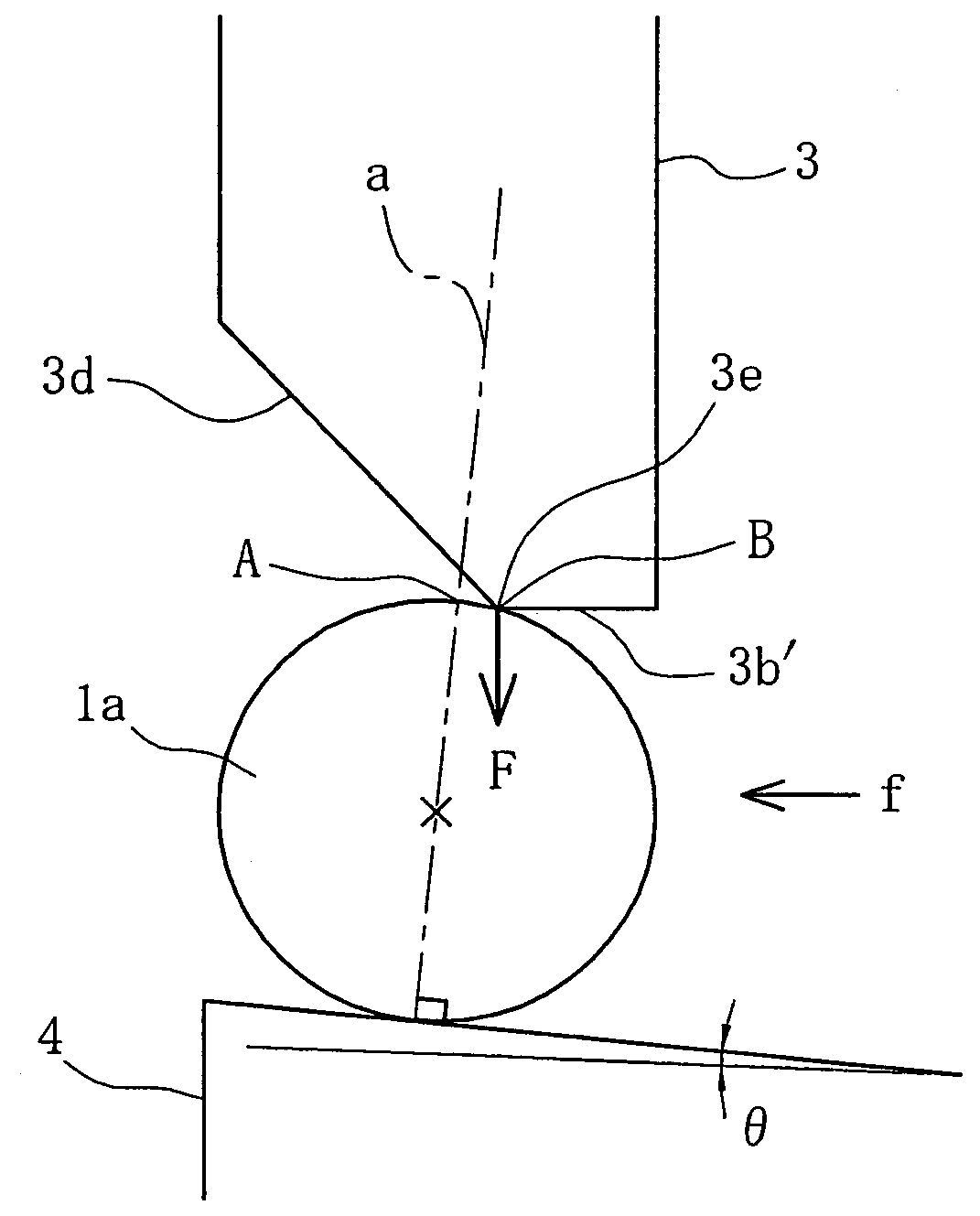
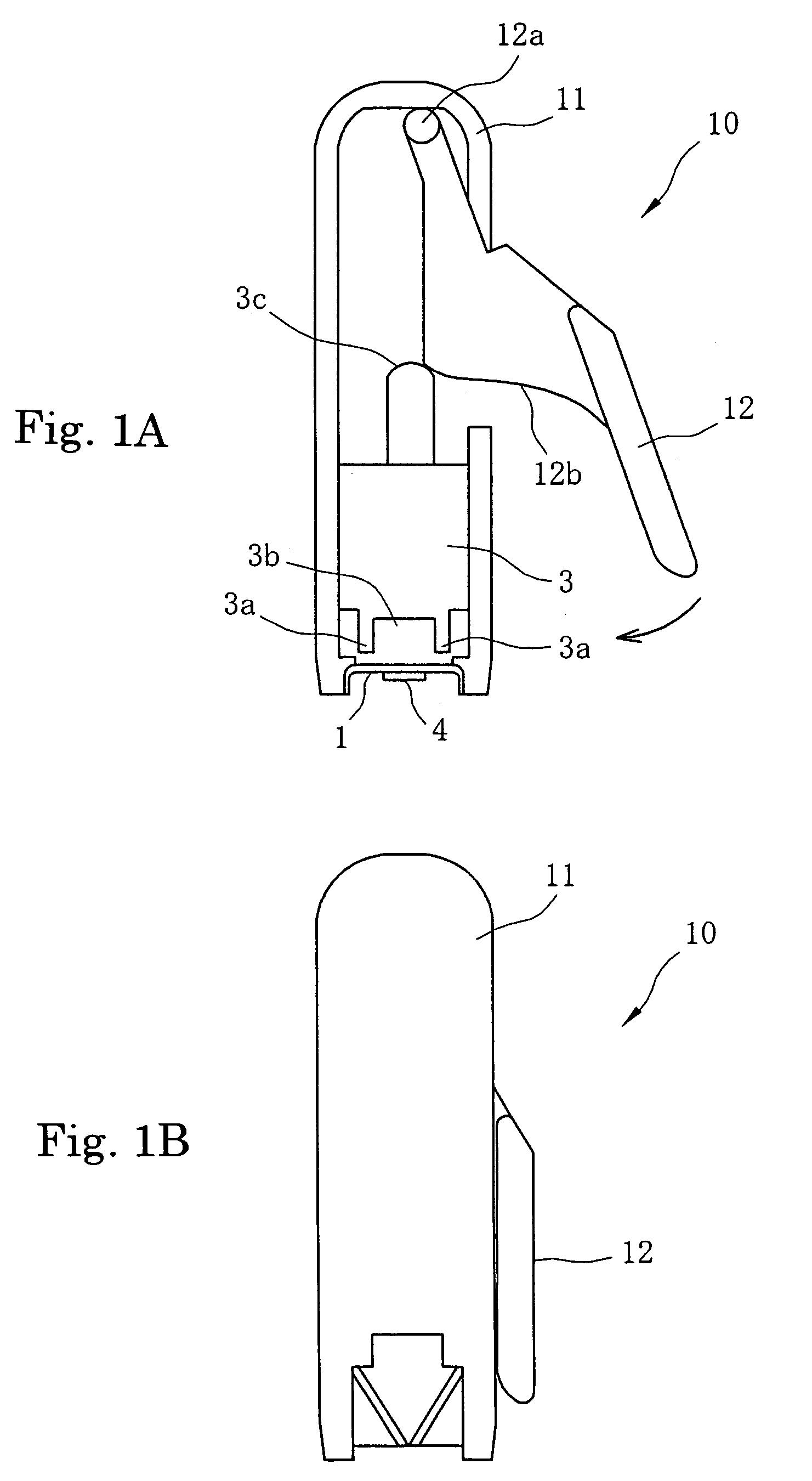
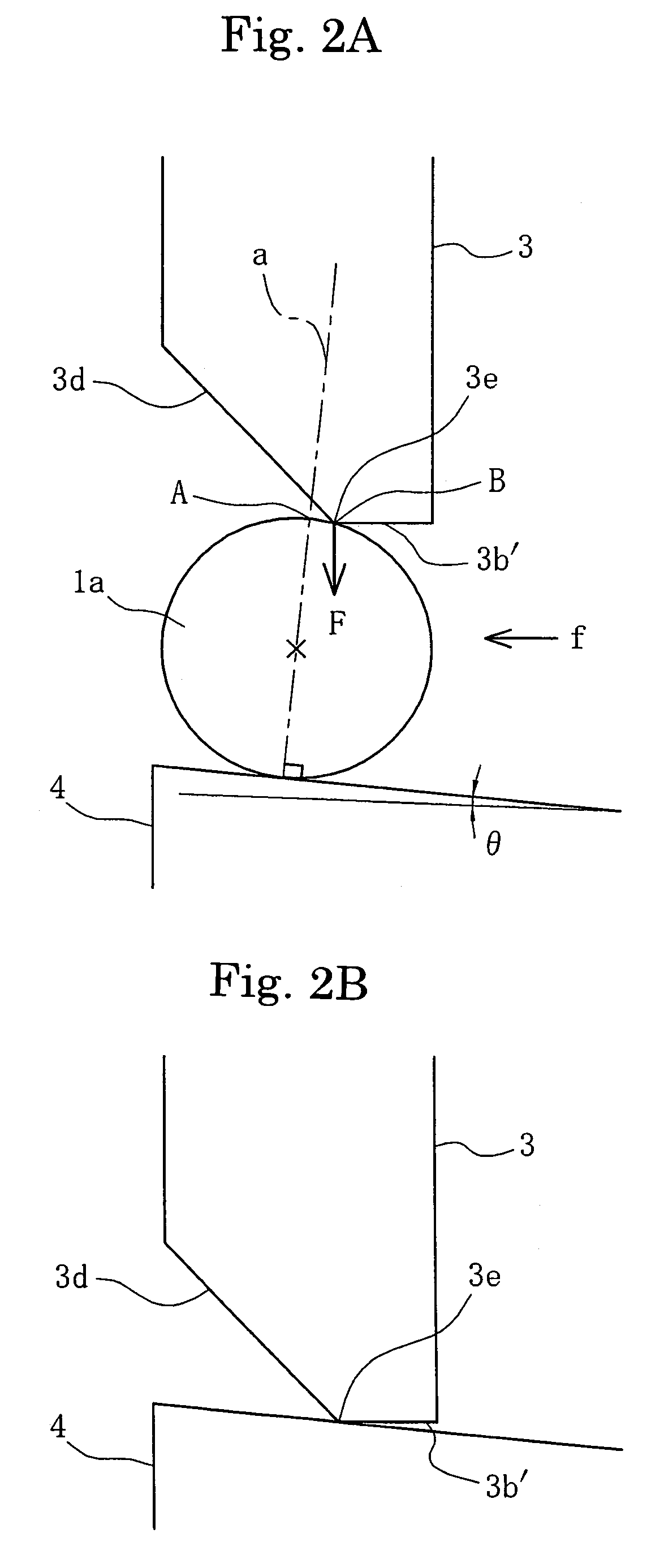
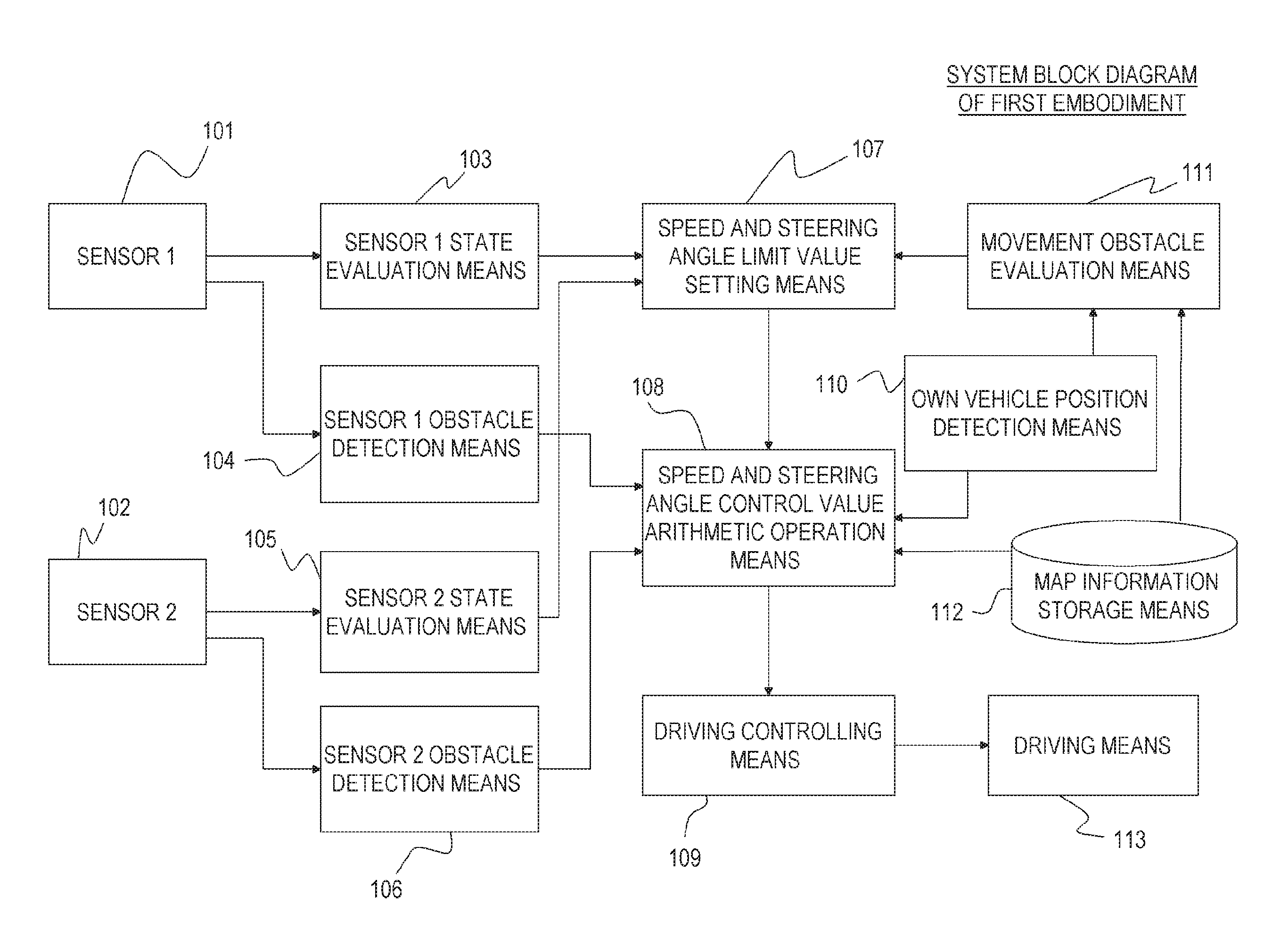
ActiveUS20160282874A1Improve securityAvoid stopAutonomous decision making processElectromagnetic wave reradiationSteering angleMotion barrier
In an autonomous driving system in which a plurality of autonomous driving vehicles drive under the control by occlusion control, such a situation is prevented that a vehicle is disabled to drive by a failure of an external world sensor for recognizing an obstacle and stops in an occlusion region thereby to obstruct advancement of overall succeeding vehicles to remarkably degrade the efficiency of the overall transportation work. In the autonomous driving system of the present invention, an autonomous driving vehicle which detects an obstacle or a driving road by a sensor and performs autonomous driving includes sensor state evaluation means configured to evaluate a state of performance degradation of the sensor, speed and steering angle control value setting means configured to provide limit values to the driving speed and the steering angle based on a state of performance degradation of the sensor, and movement obstacle evaluation means configured to evaluate an influence on movement of other vehicles when the vehicle stops at a position at present. When the sensor suffers from performance degradation, the vehicle stops after it drives within the set limit values to the speed and the steering angle to a point at which the vehicle does not obstruct movement of other vehicles.
Owner:HITACHI LTD
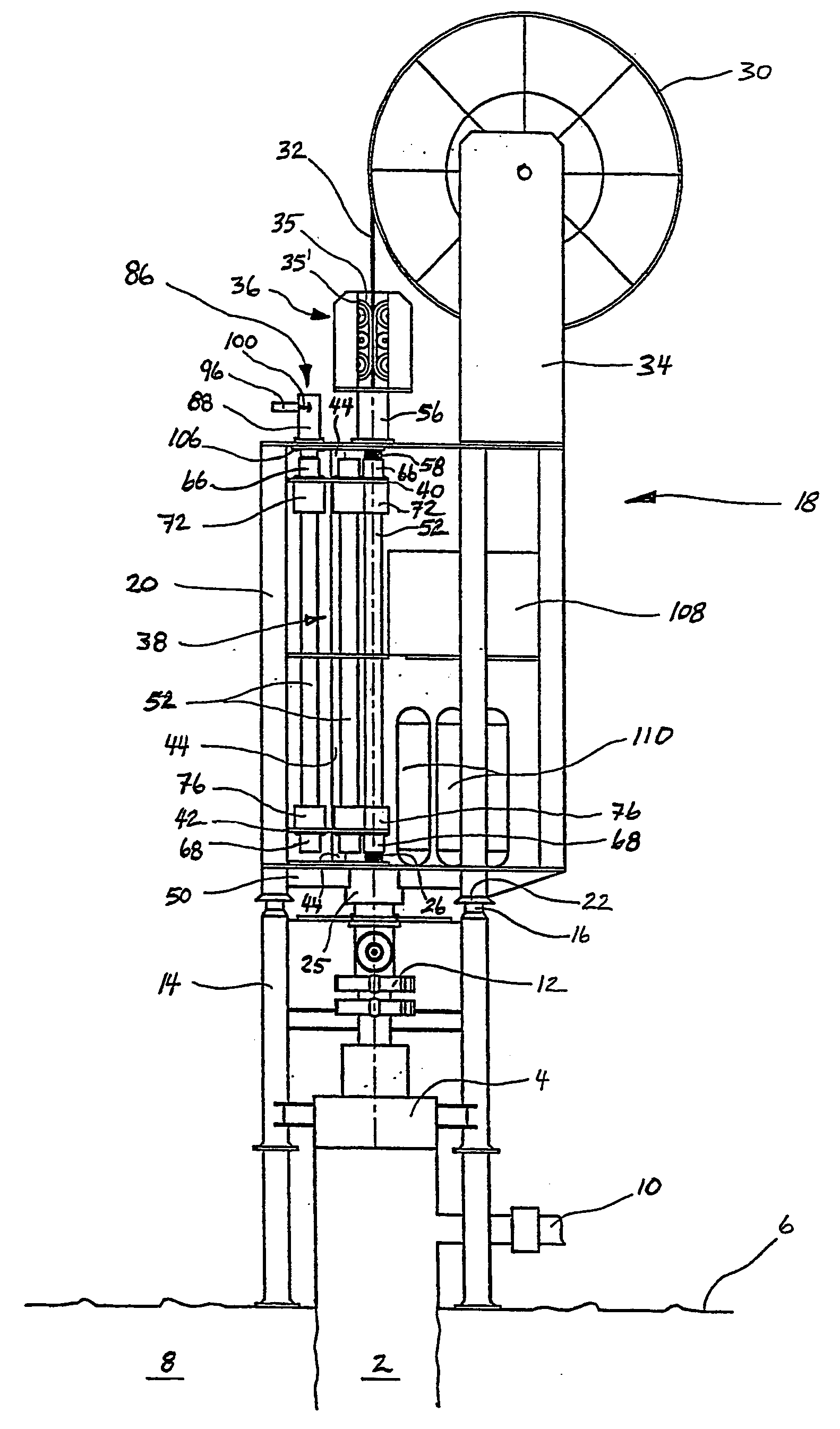
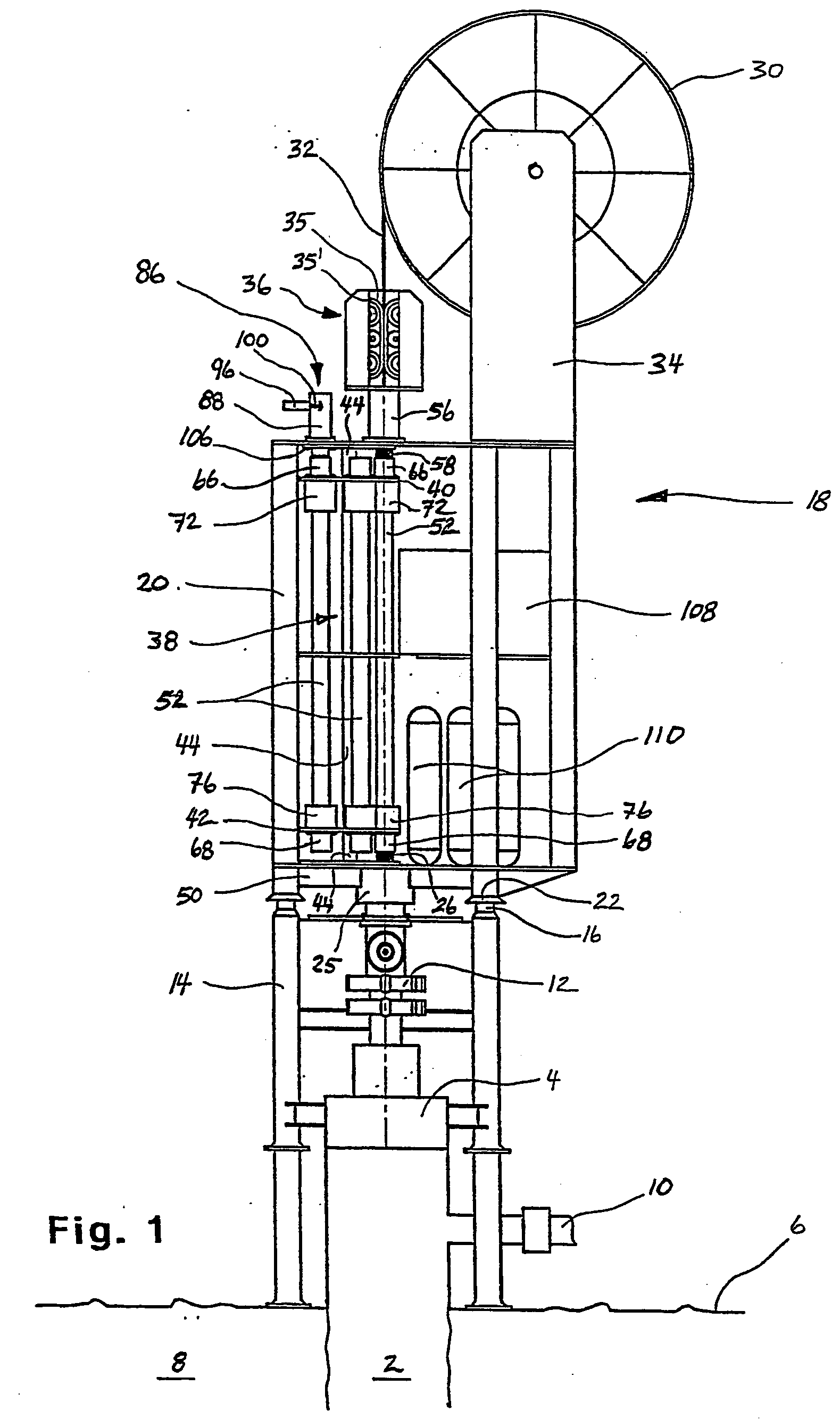
Intervention module for a well
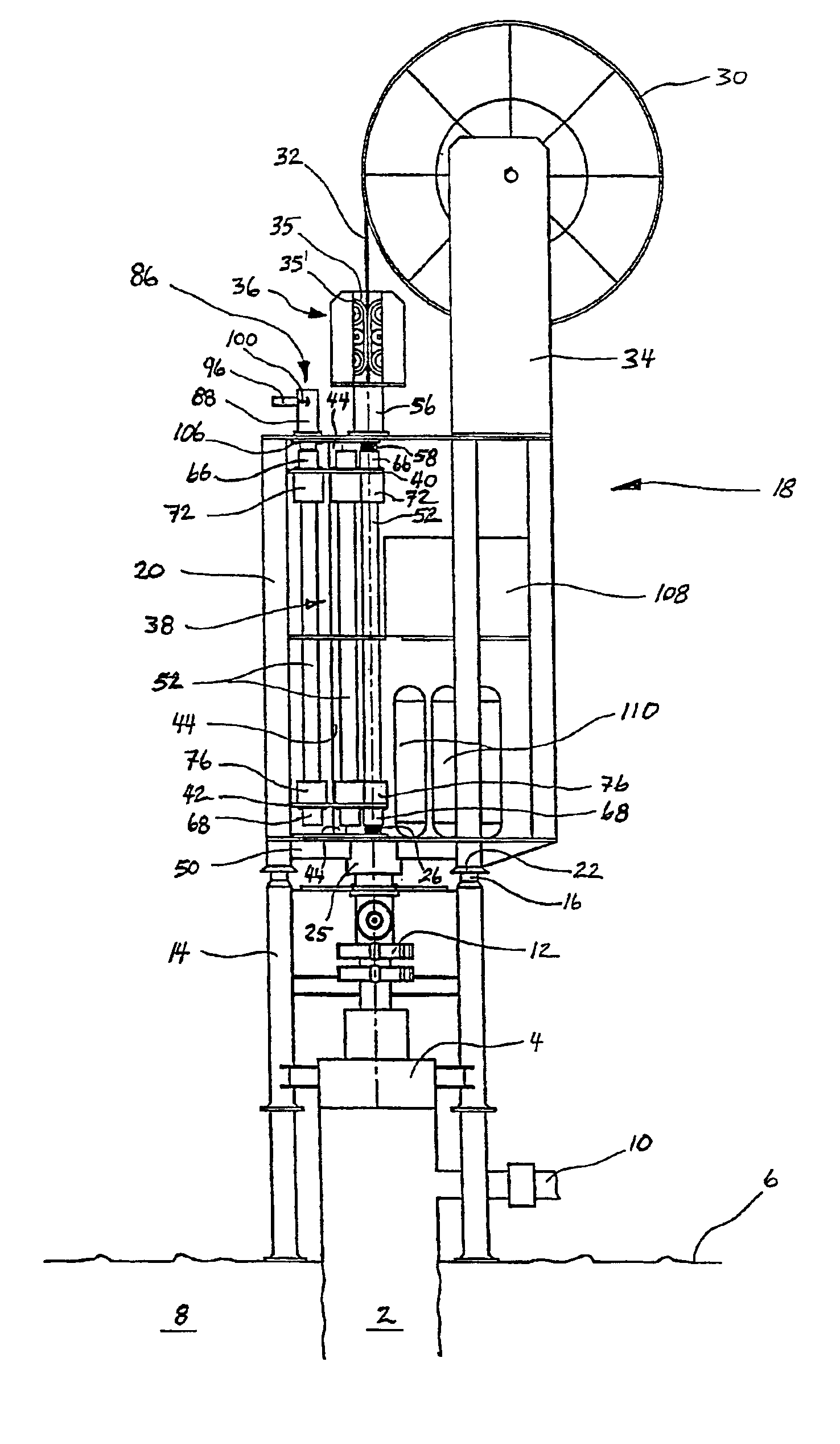
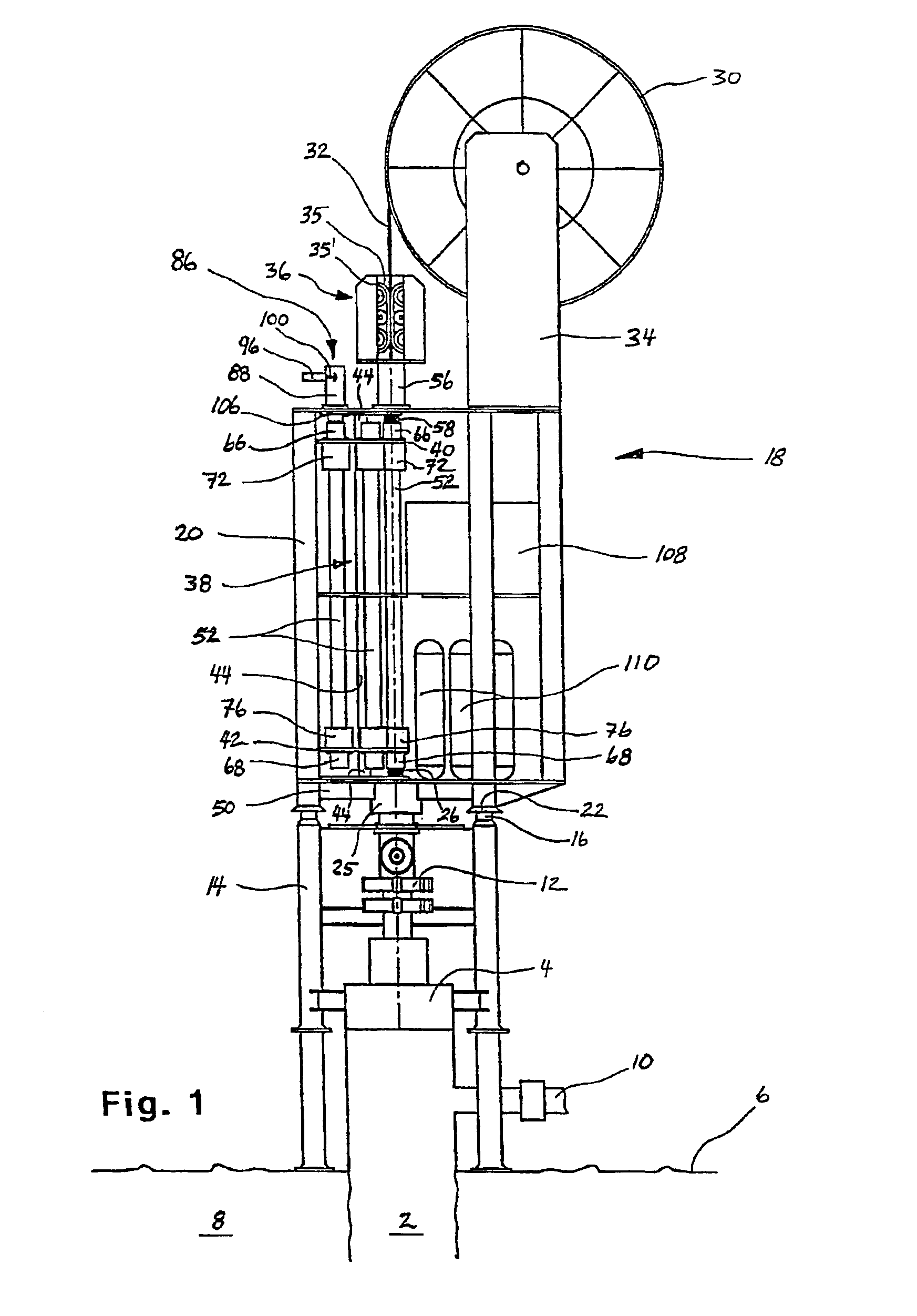
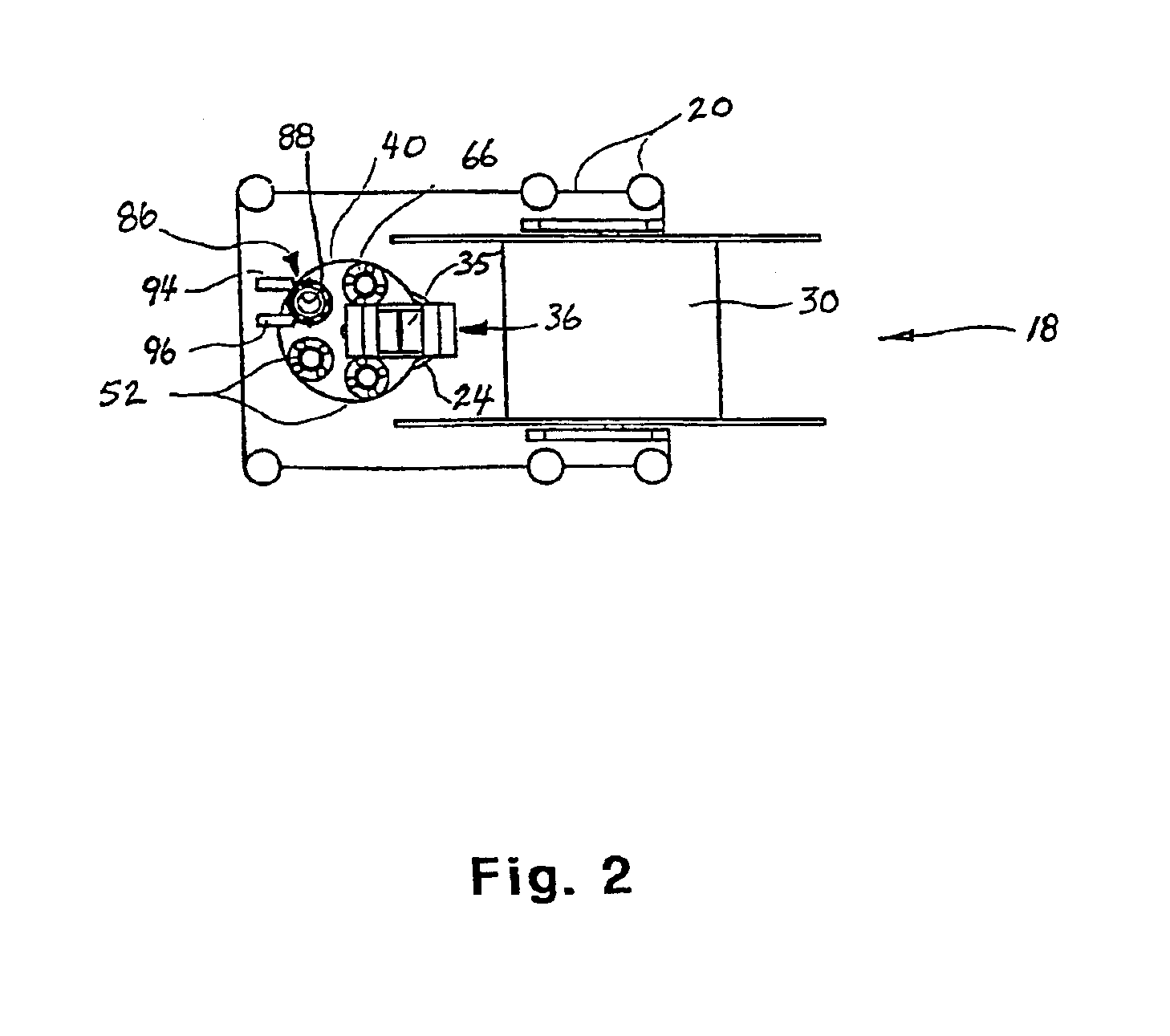
InactiveUS20040094305A1Facilitate insertion and extractionInexpensive to hire and useDrilling rodsFluid removalWellheadMarine engineering
The invention relates to an intervention module (18) for well intervention operations in preferably a pressurized subsea well (2) with a wellhead (4) disposed on a water floow. The intervention module (18) is provided with necessary equipment to replace, under water, intervention tools (54) and thereby perform several well intervention operations in one run, without the supply of equipment from a surface vessel. The module (18) is lowered from a surface vessel and placed on the wellhead (4), possibly a BOP (12), of the well (2). The intervention module (18) is connected to the surface vessel through a connecting line / hose or a wireless connection which communicates, as a minimum, necessary control and feed-back signals. The module (18) is provided with i.a. a rotatable tool magazine (38) arranged with several storage pipes (52) for intervention tools (54), the relevant storage pipe (52) being rotatable into a position immediately above the well bore (24) of the well (2), after which the intervention tool (54) is connected to a supply string (32) is passed, so that the intervention tool (54) may be inserted safely into the well (2).
Owner:OFFSHORE & MARINE
Hybrid construction machine
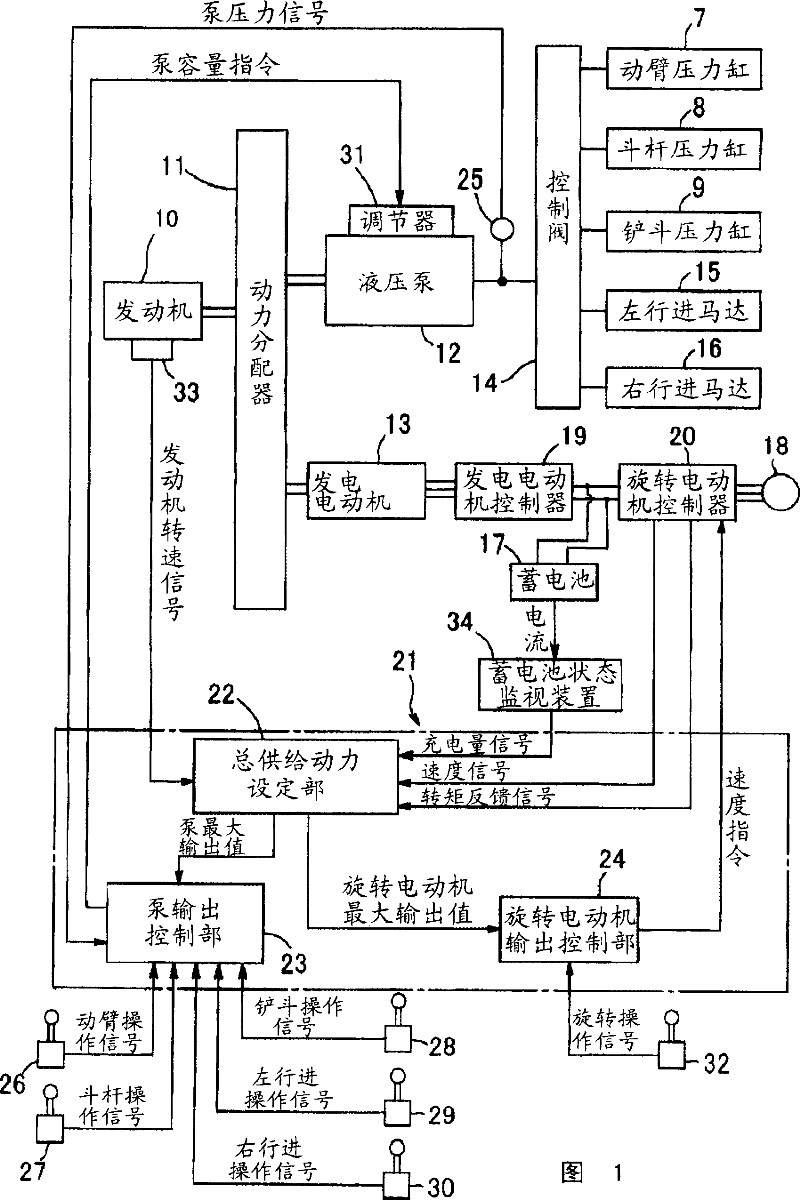
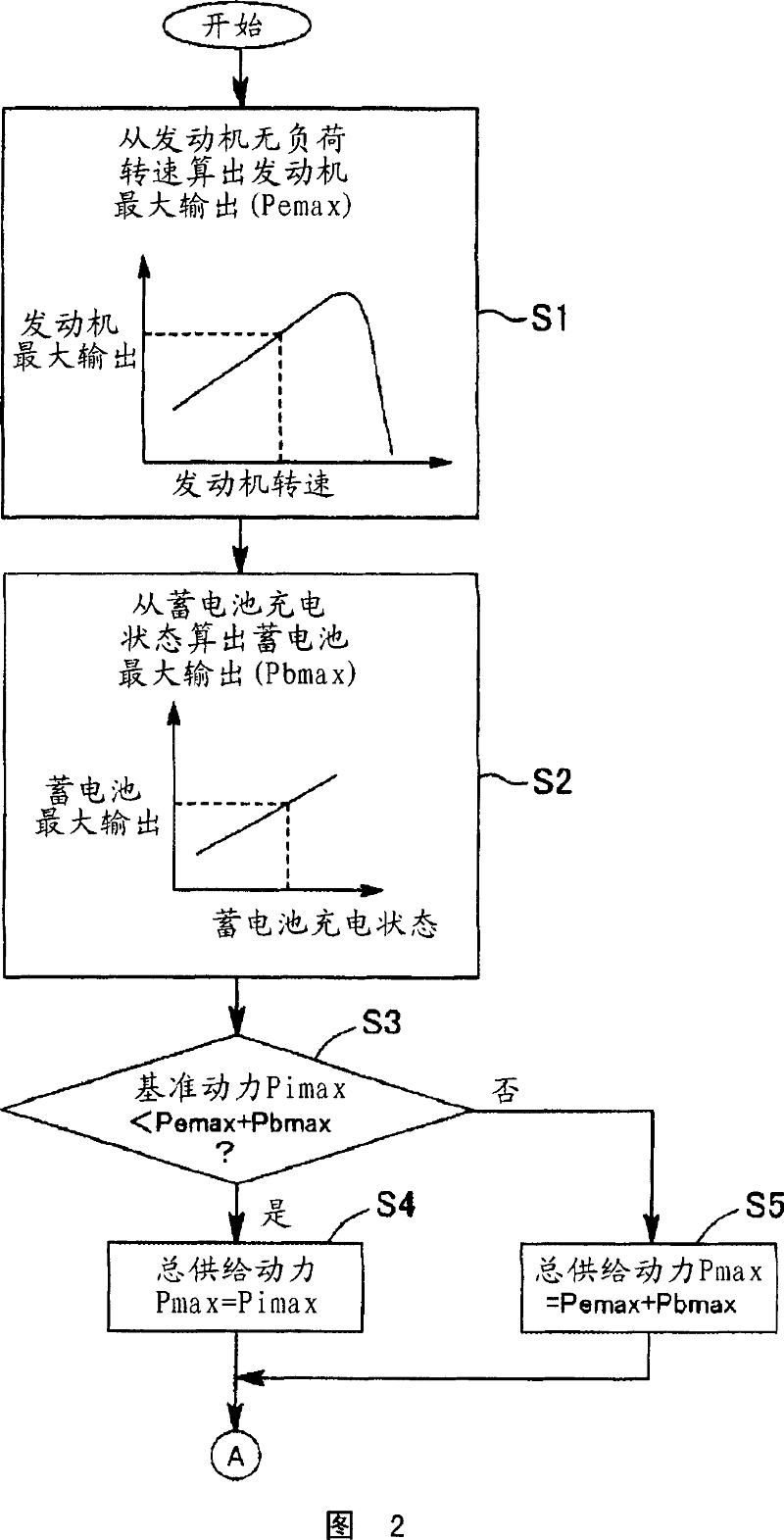
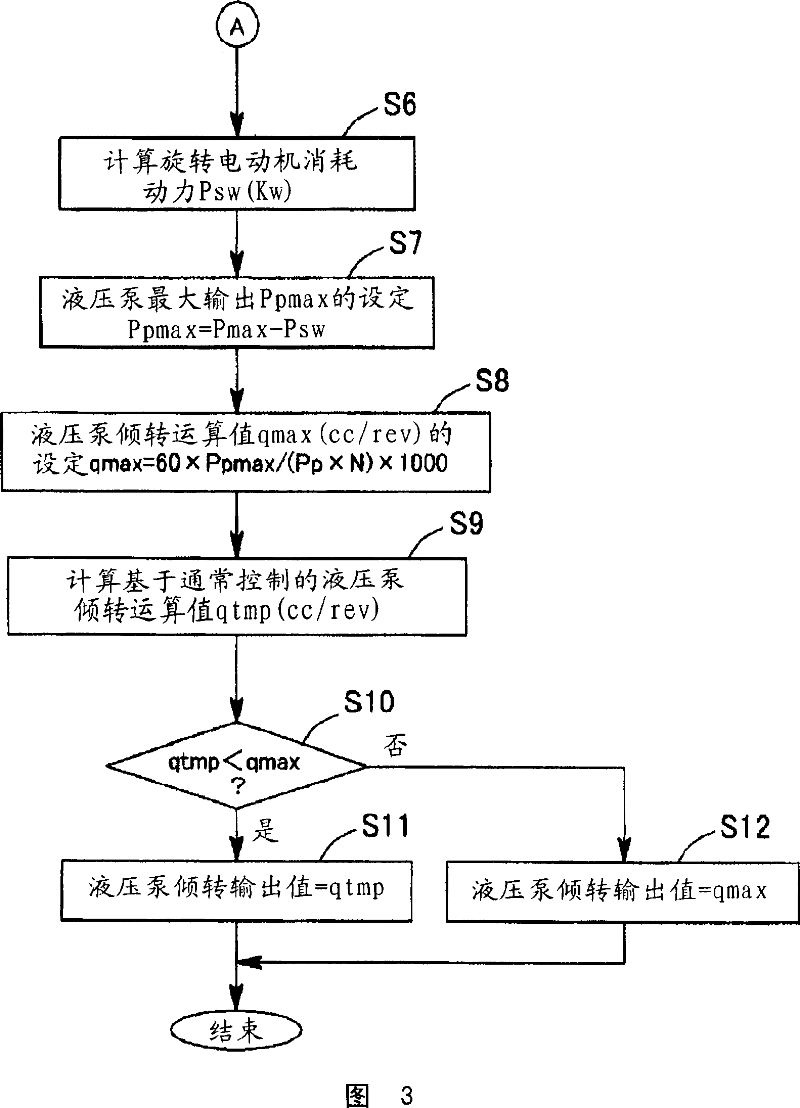
ActiveCN101037869AEnsure operabilitySolve the problem of poor operabilityElectric machinesSoil-shifting machines/dredgersHydraulic pumpMotor function
In a hybrid excavator of the invention, a hydraulic pump and a generator motor are connected in parallel to an output shaft of an engine and a rotation motor is driven by a battery. The generator motor assists the engine by performing a motor function. Power consumption of each of the hydraulic pump and the rotation motor is detected. The output of the hydraulic pump and the rotation motor is controlled such that the sum of the detected power consumption does not exceed maximum supply power set as the sum of power that can be supplied to the hydraulic pump and the rotation motor. Therefore, the equal performance and operation with the hydraulic excavator can be ensured, and the electric power storage arrangement can be protected.
Owner:KOBELCO CONSTR MASCH CO LTD
Intervention module for a well
The invention relates to an intervention module (18) for well intervention operations in preferably a pressurized subsea well (2) with a wellhead (4) disposed on a water floor. The intervention module (18) is provided with necessary equipment to replace, under water, intervention tools (54) and thereby perform several well intervention operations in one run, without the supply of equipment from a surface vessel. The module (18) is lowered from a surface vessel and placed on the wellhead (4), possibly a BOP (12), of the well (2). The intervention module (18) is connected to the surface vessel through a connecting line / hose or a wireless connection which communicates, as a minimum, necessary control and feed-back signals. The module (18) is provided with i.e. a rotatable tool magazine (38) arranged with several storage pipes (52) for intervention tools (54), the relevant storage pipe (52) being rotatable into a position immediately above the well bore (24) of the well (2), after which the intervention tool (54) is connected to a supply string (32), whereas the storage pipe (52) is connected in a pressure-sealing manner to the well bore (24) below and a pressure safety device above, through which the supply string (32) is passed, so that the intervention tool (54) may be inserted safely into the well (2).
Owner:OFFSHORE & MARINE
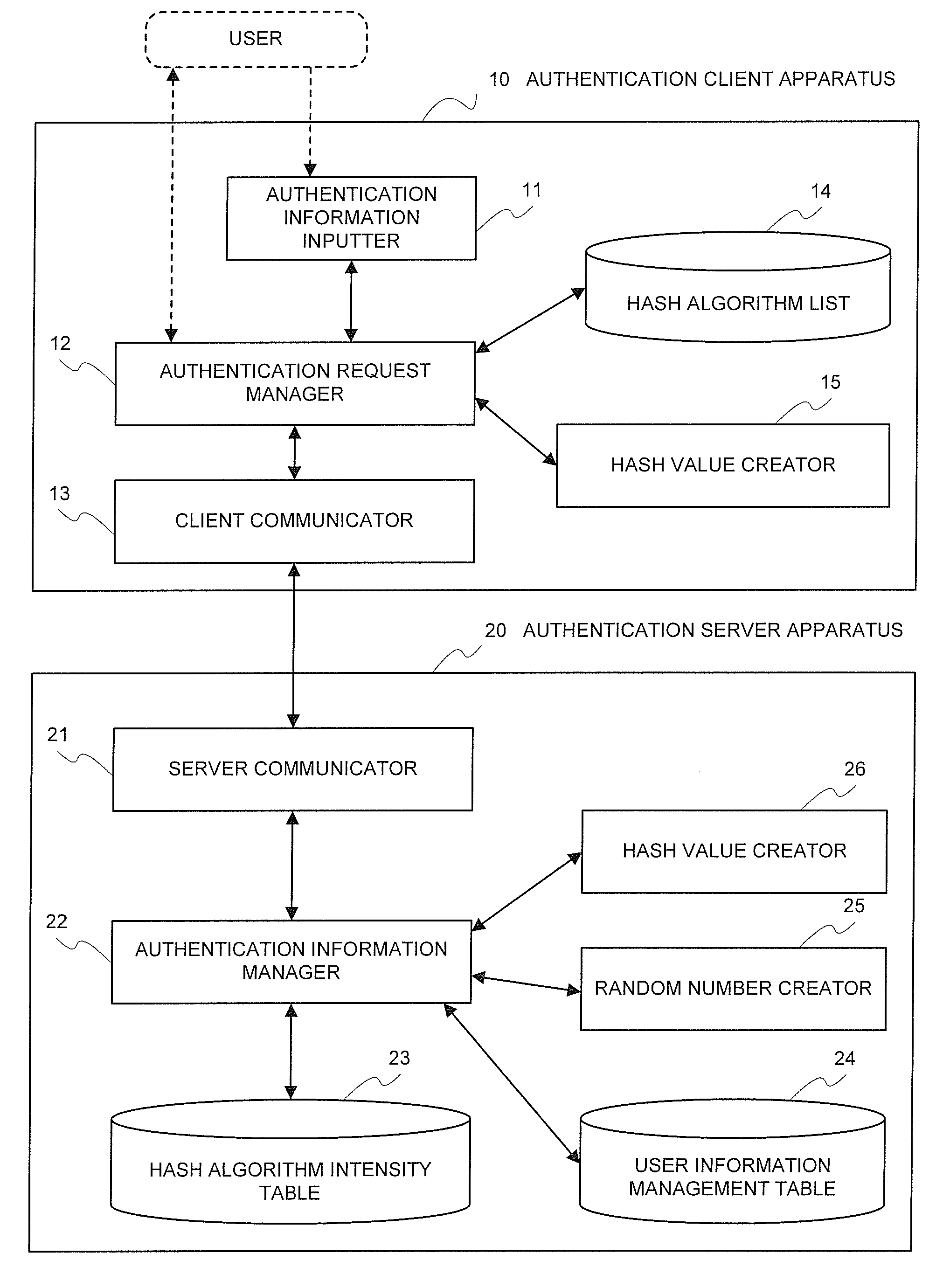
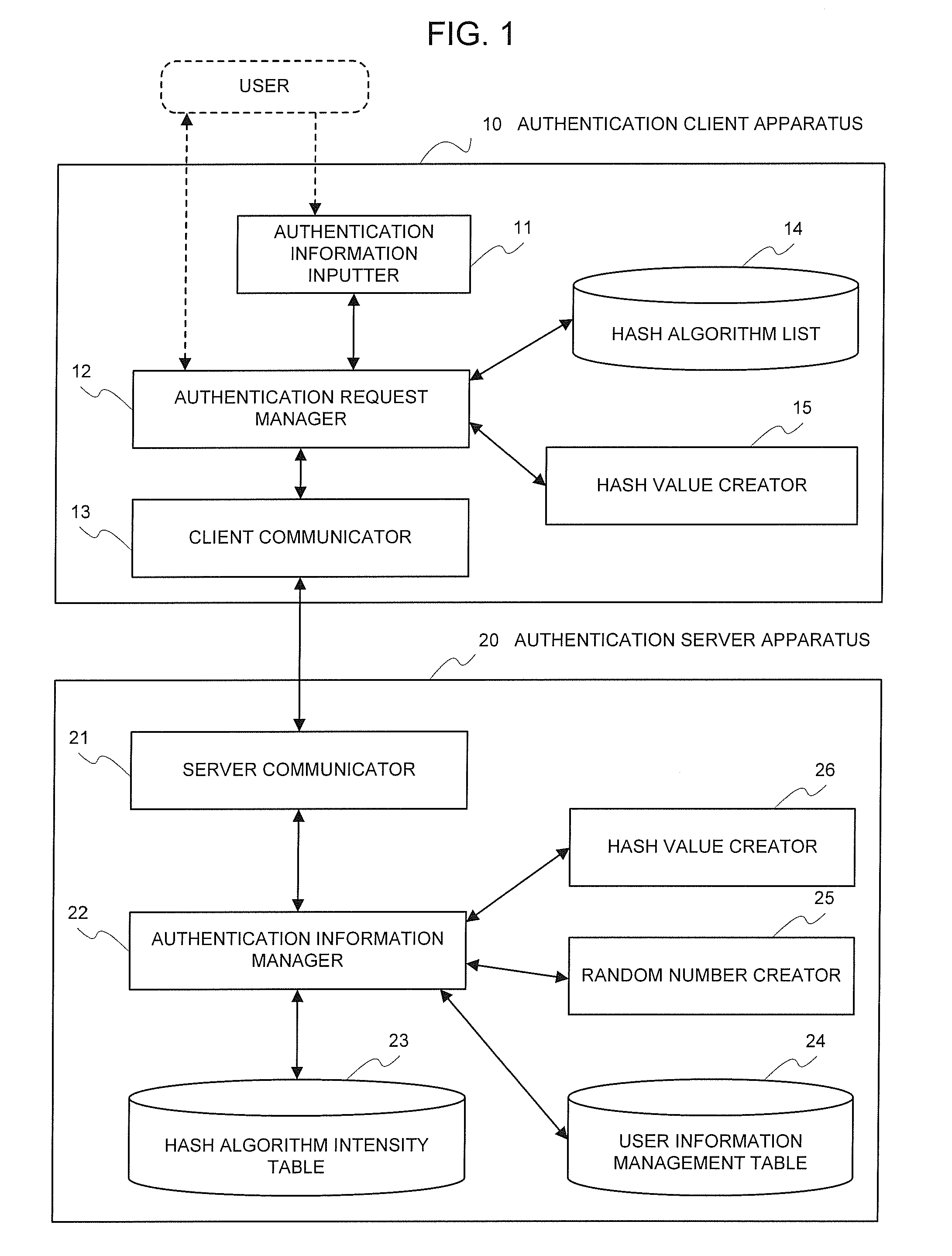
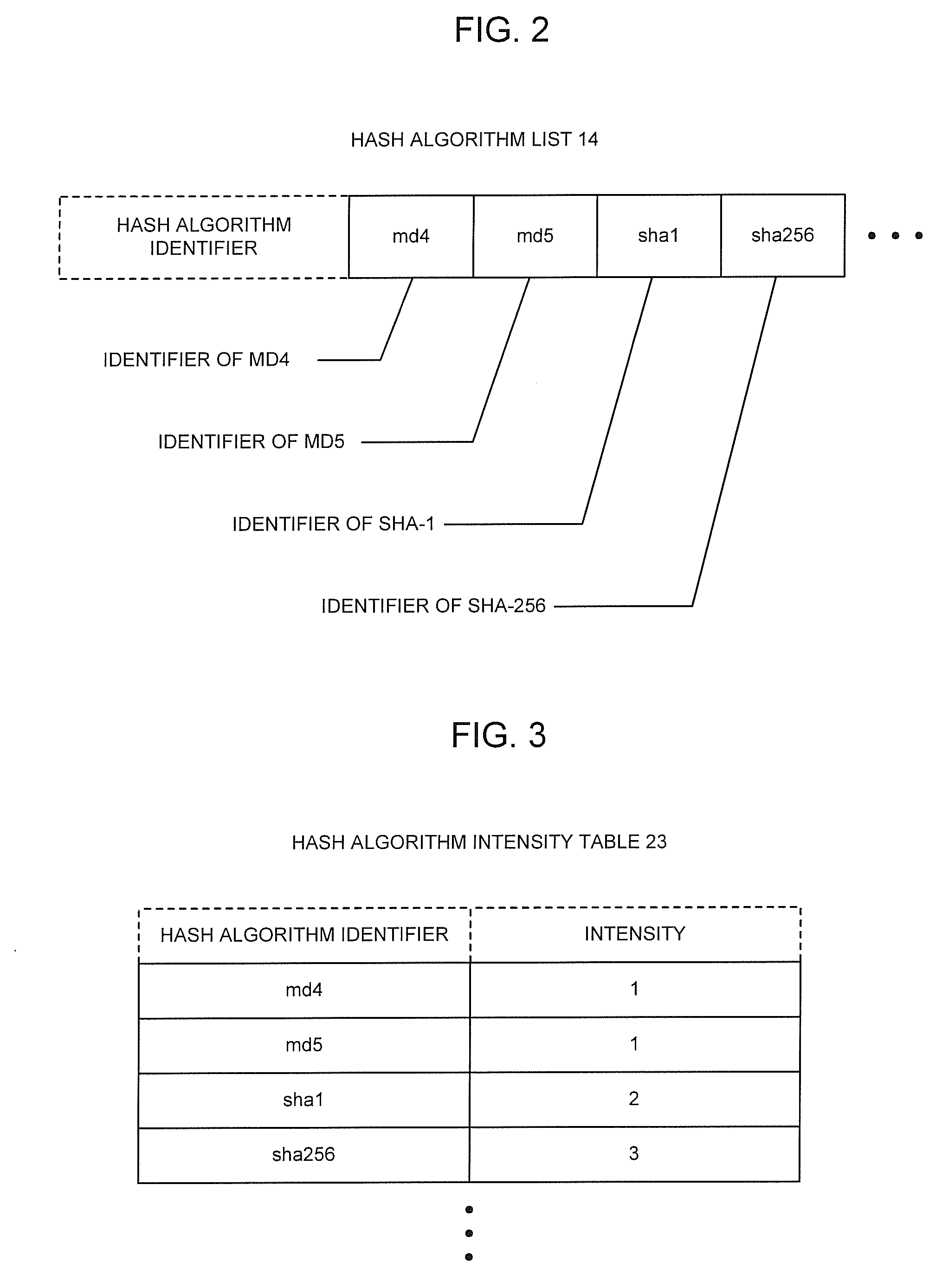
Authenticating system, authenticating method, and authenticating program
InactiveUS20080181403A1High strengthAvoid stopRandom number generatorsUser identity/authority verificationPasswordValidation methods
The present invention is an authenticating system including: a client (hereinafter, referred to as C) including a creator for, by employing a first hash algorithm (hereinafter, referred to as 1A), creating a first hash value (hereinafter, referred to as 1V) from authentication information including an ID and a password, and creating 2V from the 1V and a random number, and a receiver for receiving the random number and an 1A identifier from a server (hereinafter, referred to as S), transmitting the ID and the 2V to the S, and receiving an authentication result from the S; and the S including a storage for storing 3V created from the authentication information by employing an 2A identifier and the 2A ID by ID, and a device for transmitting the random number and the 1A identifier to a PC, receiving the ID and the 2V from the PC, determining whether the 2A identifier, which corresponds to the ID, coincides with the 1A identifier, creating 4V from the 3V and the random number by employing the 1A in a case where it coincides, determining whether the 2V coincides with the 4V, transmitting the effect that the authentication is successful to the PC in a case where it coincides, and transmitting the effect that the authentication is unsuccessful to the PC in a case where it does not coincide. Even in a case where a hash algorithm (hereinafter, referred to as A) that is used in the authentication system is changed, employing such a configuration enables the system to be successively utilized.
Owner:NEC CORP
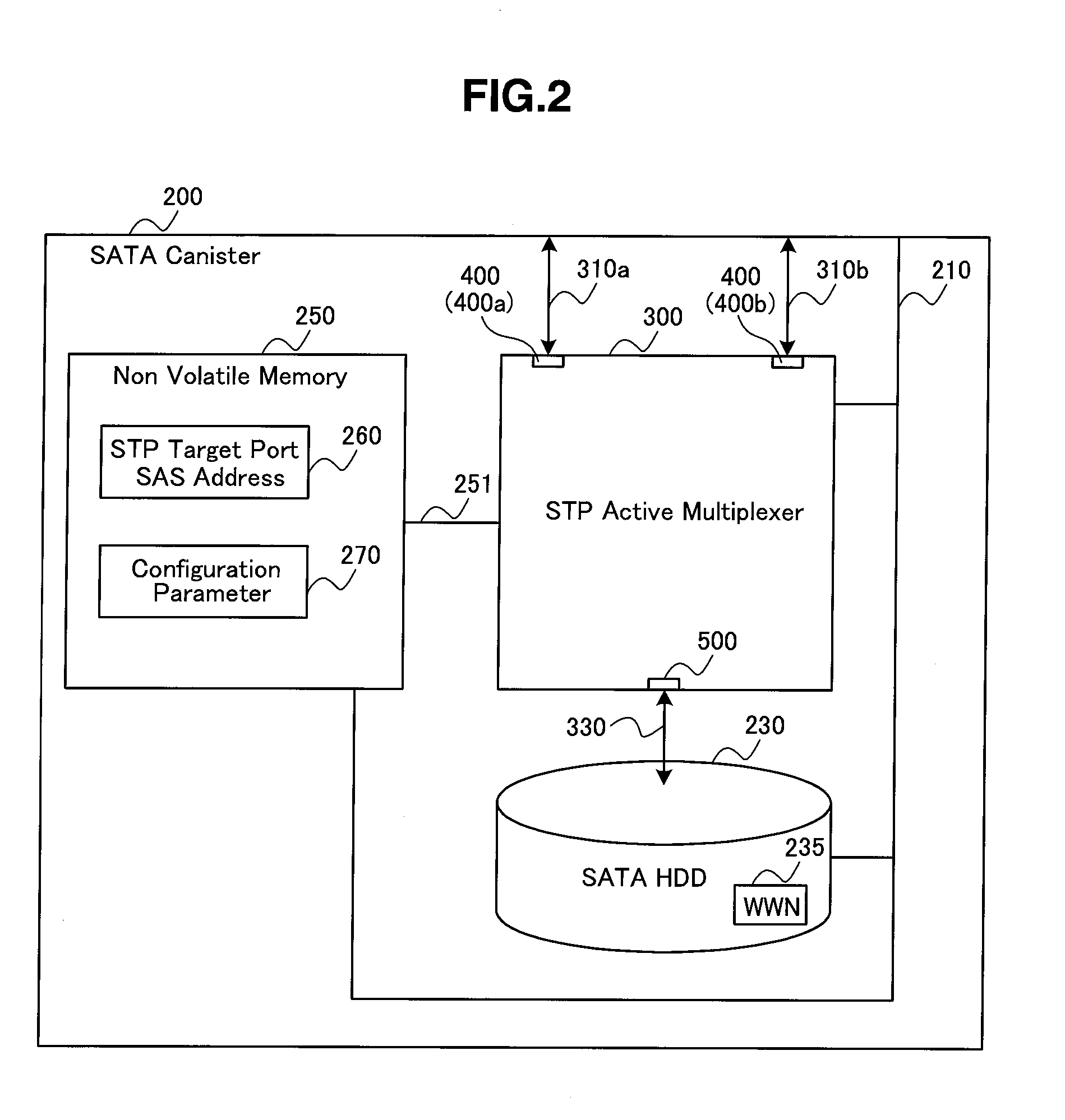
Storage apparatus and method for controlling the same
InactiveUS20110320706A1Improve reliabilityEasy to identifyNon-redundant fault processingMemory systemsMultiplexerMaster controller
A storage apparatus capable of improving the reliability of a large-scale storage system, and a method for controlling such a storage apparatus are suggested. A storage apparatus including a storage device for storing data, and a multiplexer for multiplexing a port for the storage device, the multiplexer being connected to one or more host controllers, and a method for controlling such a storage apparatus, wherein the multiplexer judges whether a command sent from the host controller to the storage device is proper or not; and if the command is improper, the multiplexer discards the command without transferring it to the storage device, and sends an error response to the host controller.
Owner:HITACHI LTD
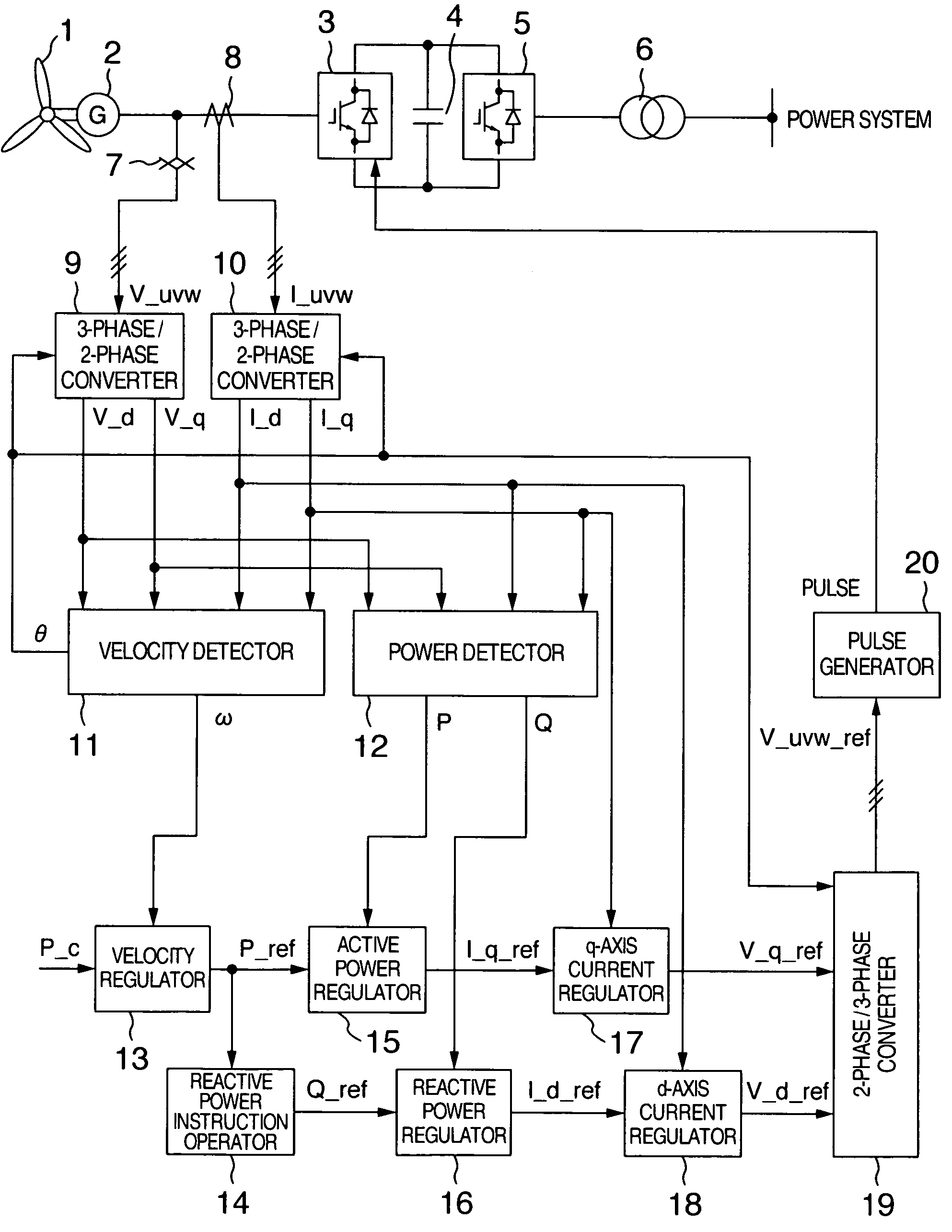
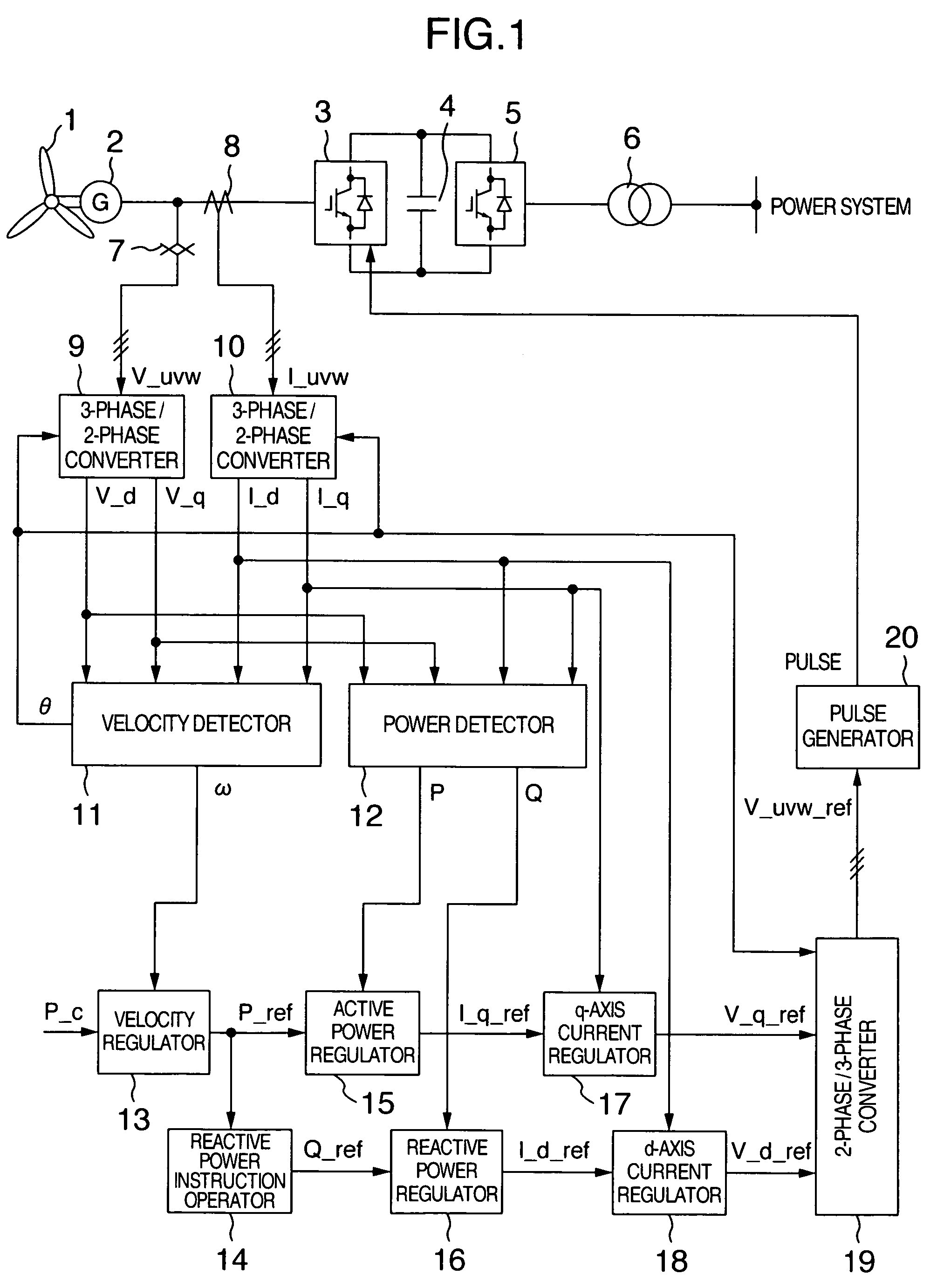
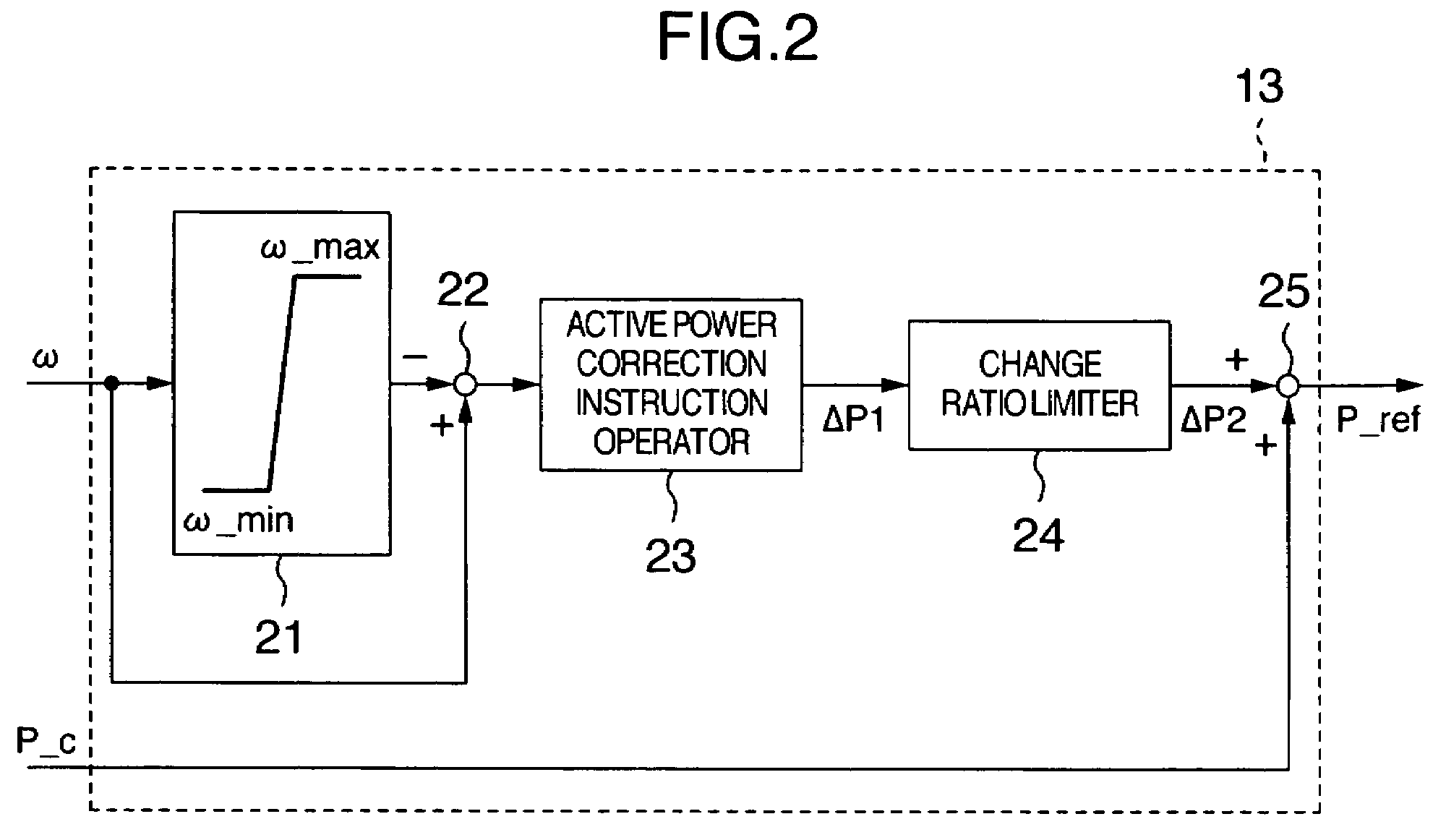
Wind turbine generator system
ActiveUS7268443B2Increase usageContinuous operationWind motor controlStatic indicating devicesRotation velocityTurbine
A wind turbine generator system can regulate the rotational velocity of the wind turbine within an operation range even when the wind velocity suddenly changes and can perform continuous operation of the wind turbine. The wind turbine generator system includes a generator connected to the shaft of the wind turbine and a converter connected to the generator. When the rotational velocity of the wind turbine is within a predetermined range, power outputted from the generator is controlled so as to follow the instruction concerning the generator output given from the wind turbine to the converter. When the rotational velocity of the wind turbine is out of the predetermined range, the power outputted from the generator is controlled without following the instruction concerning generator output given from the wind turbine to the converter.
Owner:HITACHI IND PROD LTD
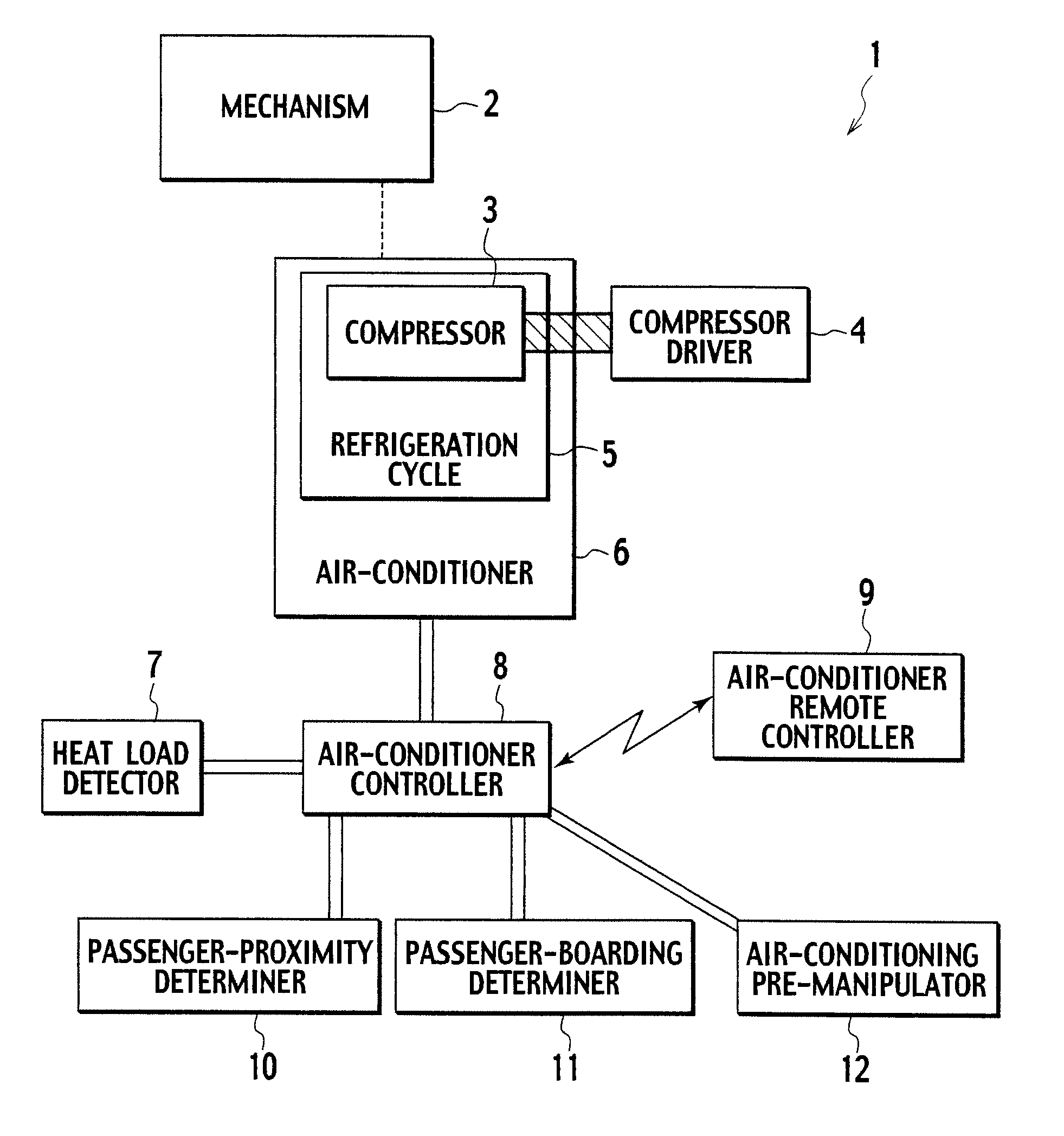
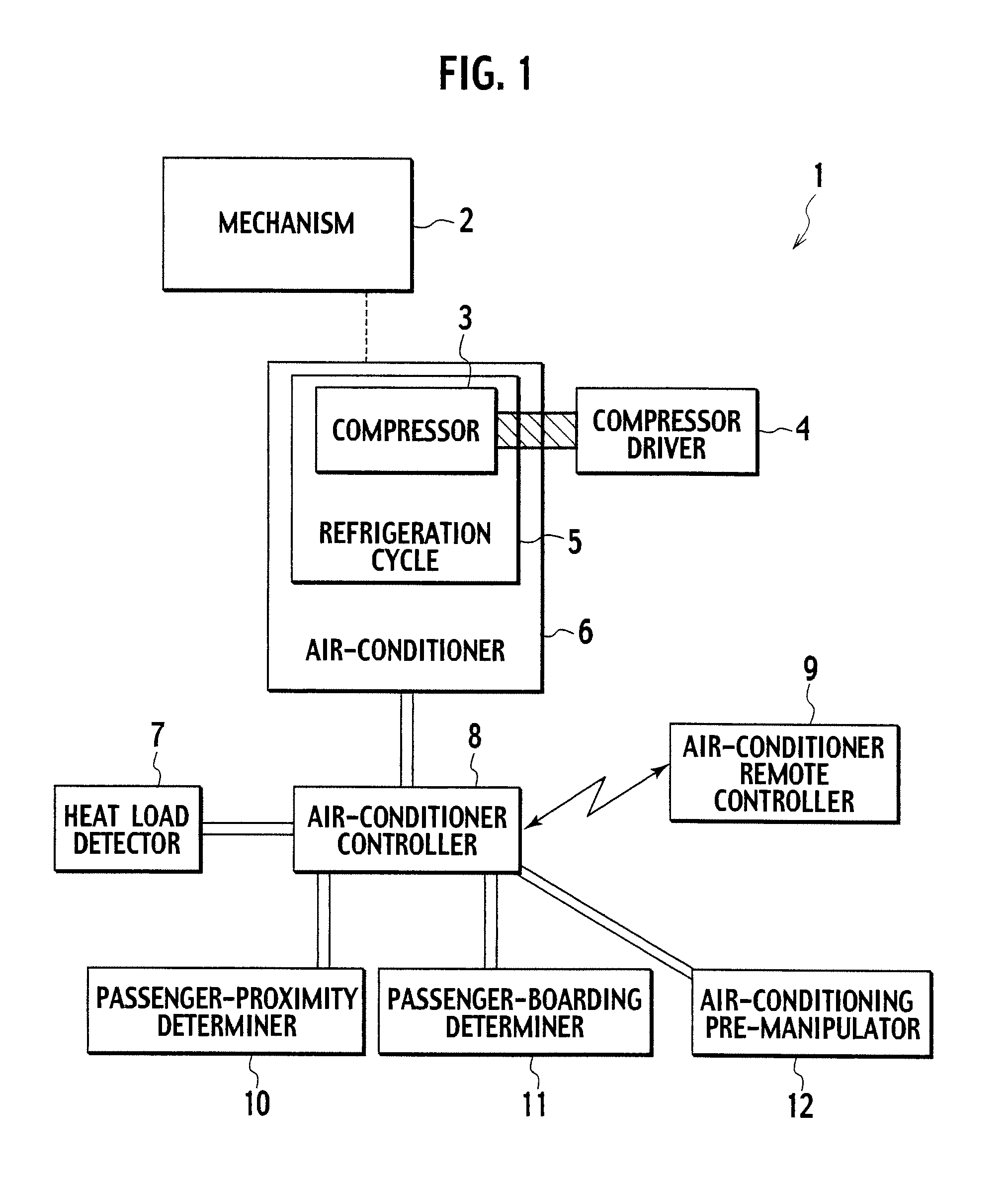
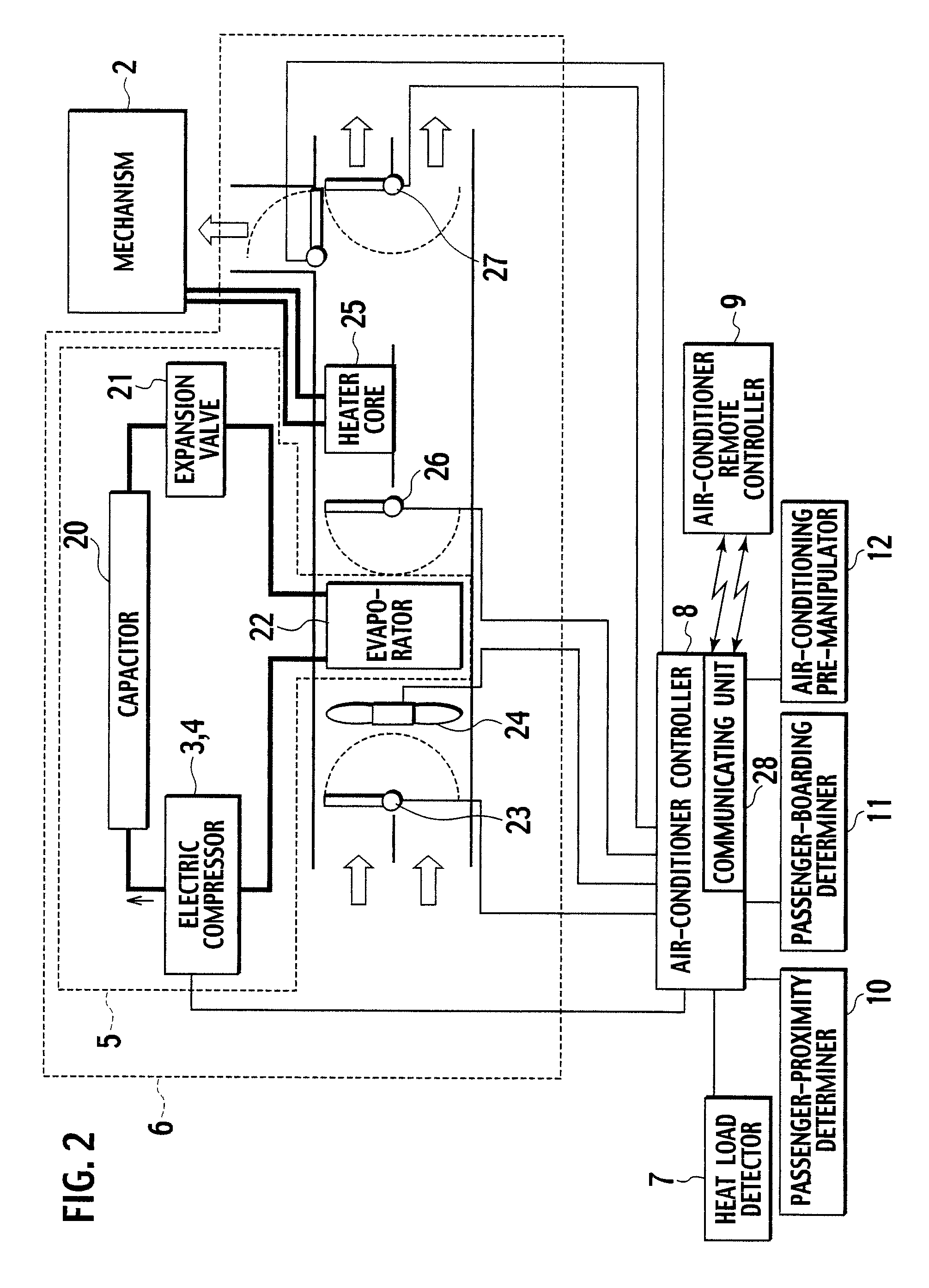
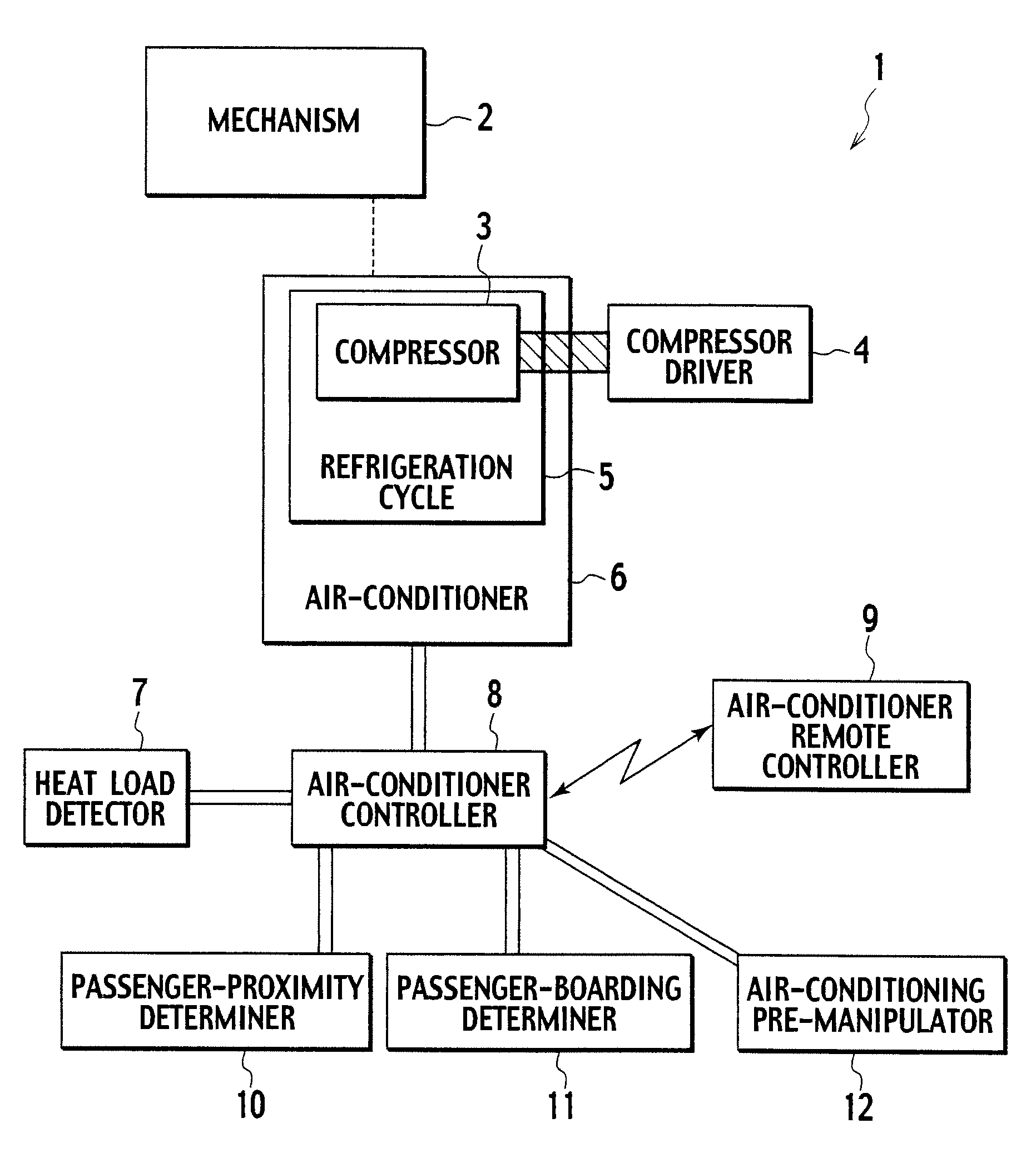
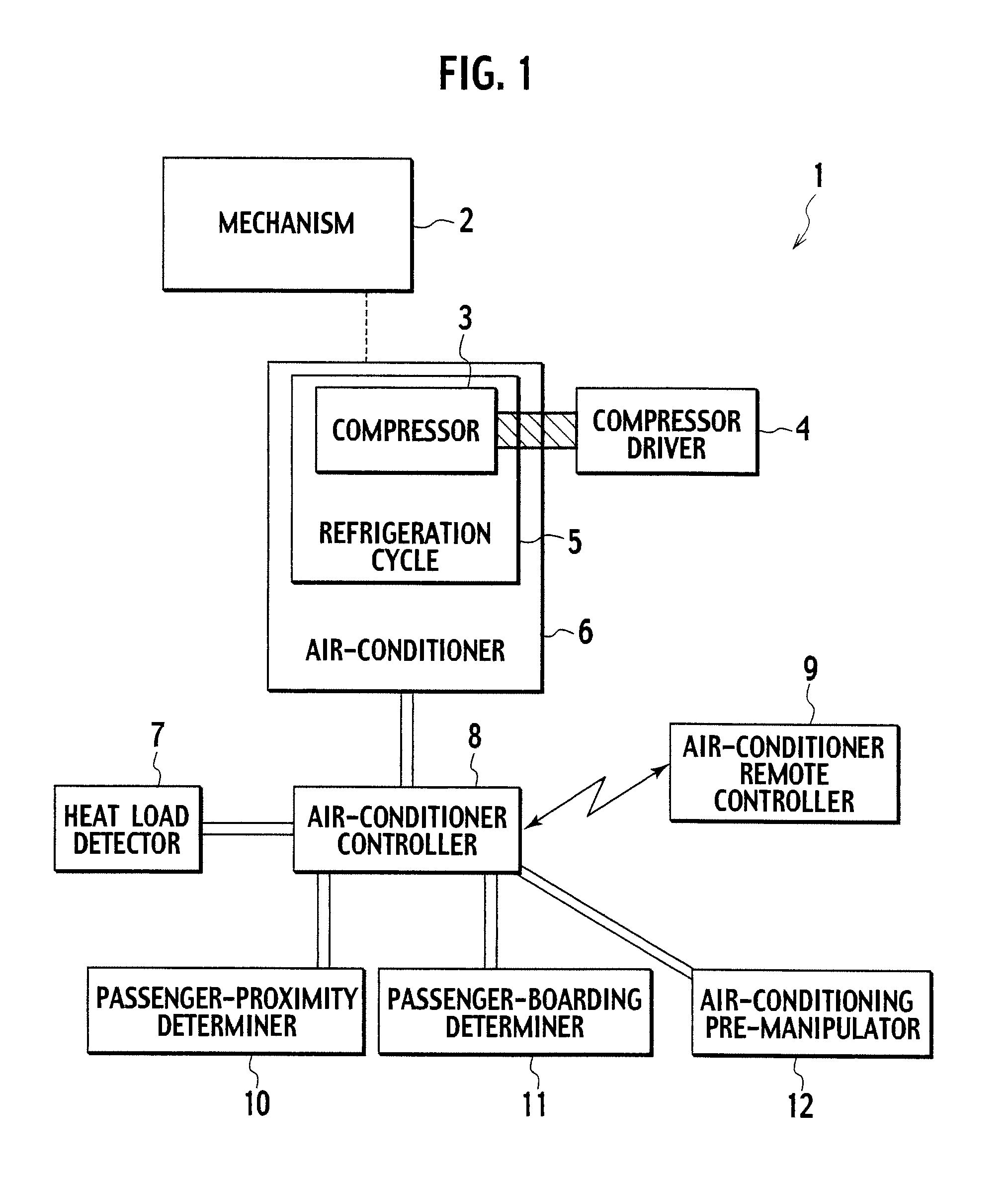
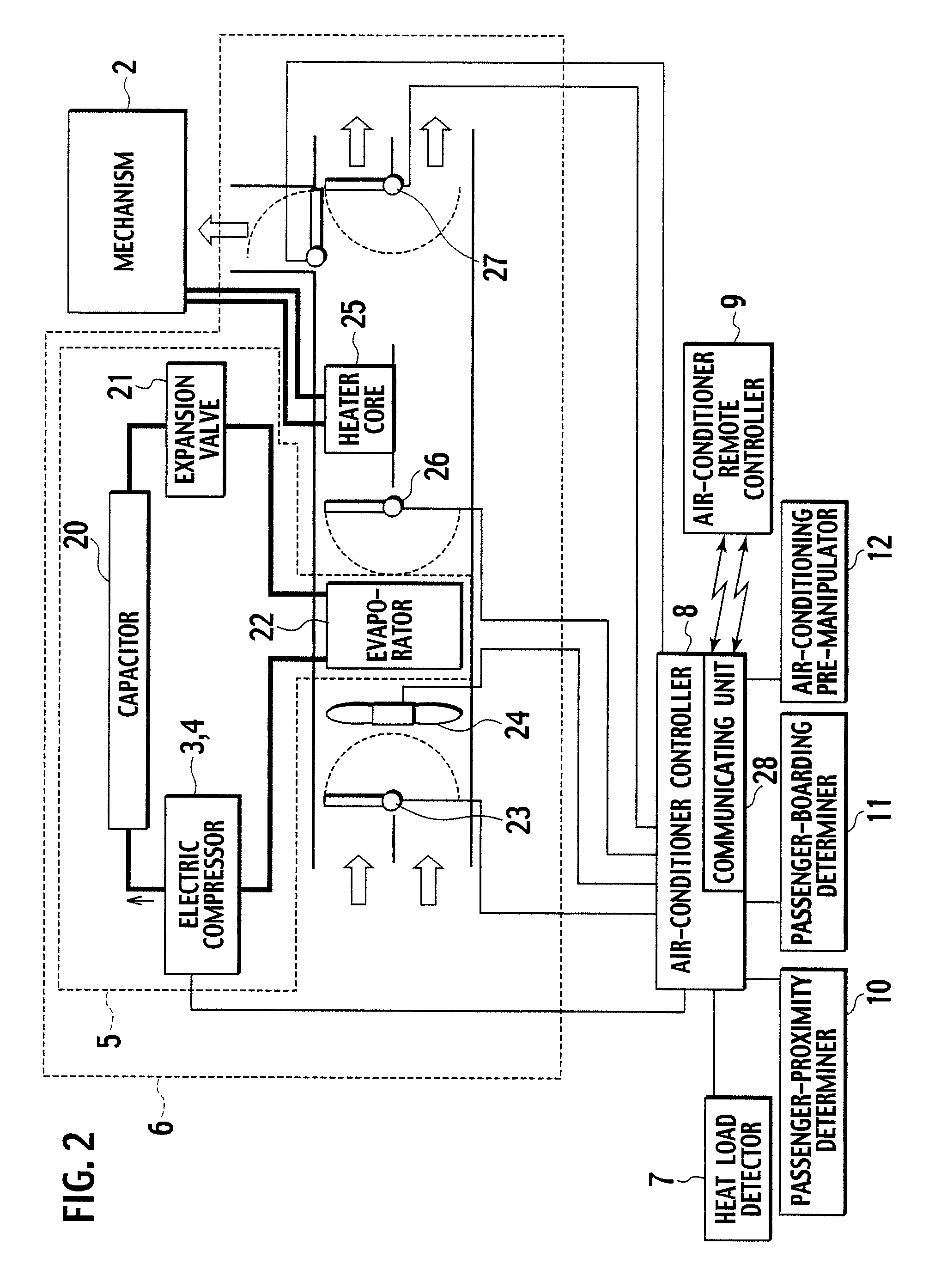
Vehicle air-conditioner control system
InactiveUS7775453B2Reduce disagreeablenessSufficient air conditioningAir-treating devicesRailway heating/coolingControl systemAir conditioning
A vehicle air-conditioner control system according to the present invention activates an air conditioner in response to a command from an air-conditioner remote controller before a passenger is onboard, controls the air conditioner based on a heat load detected by a heat load detector, controls the air conditioner to be set in a silent mode so as not to make the passenger feel uncomfortable due to an air-conditioning wind when a passenger-proximity determiner determines that the passenger is proximate to the vehicle.
Owner:CALSONIC KANSEI CORP
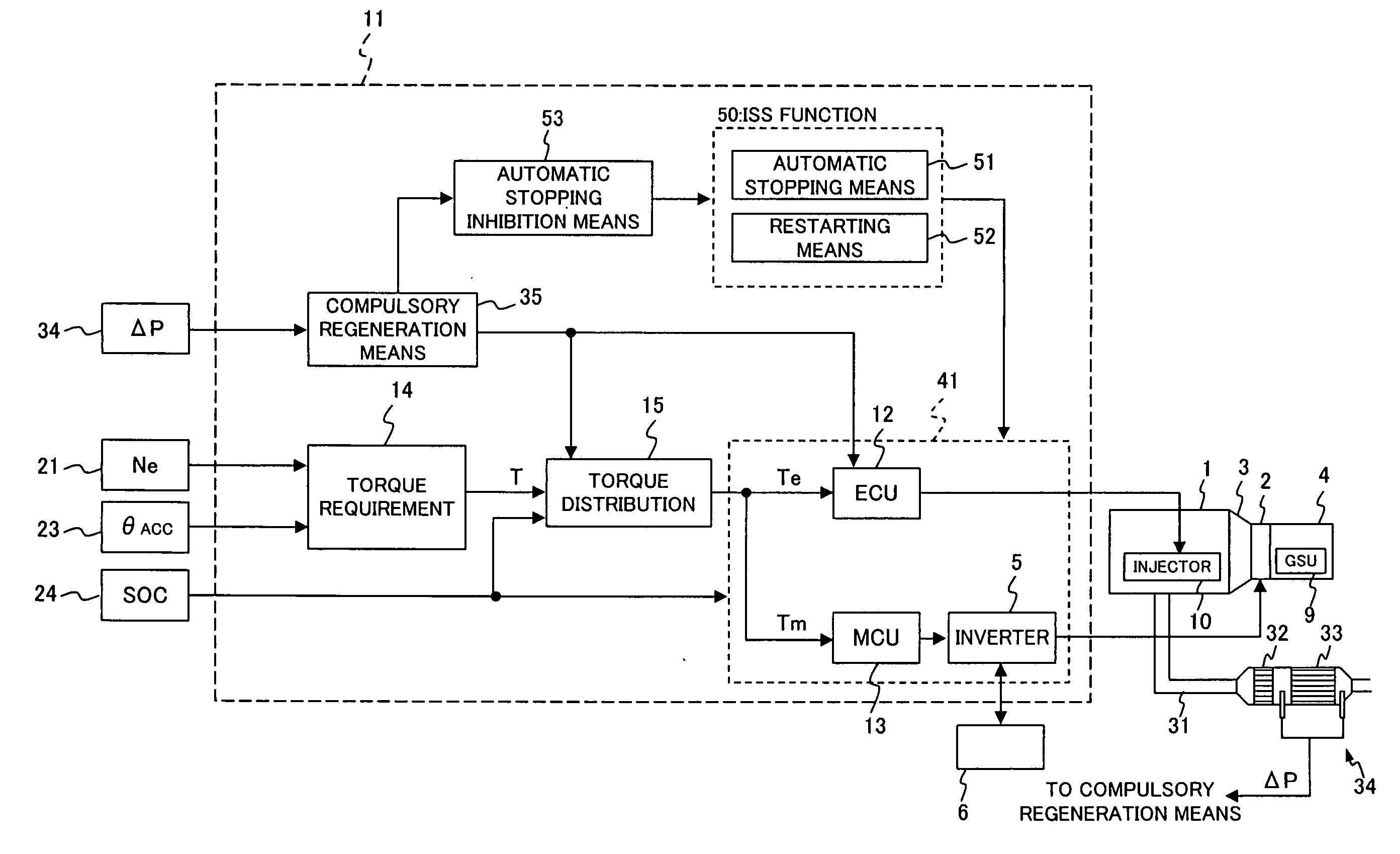
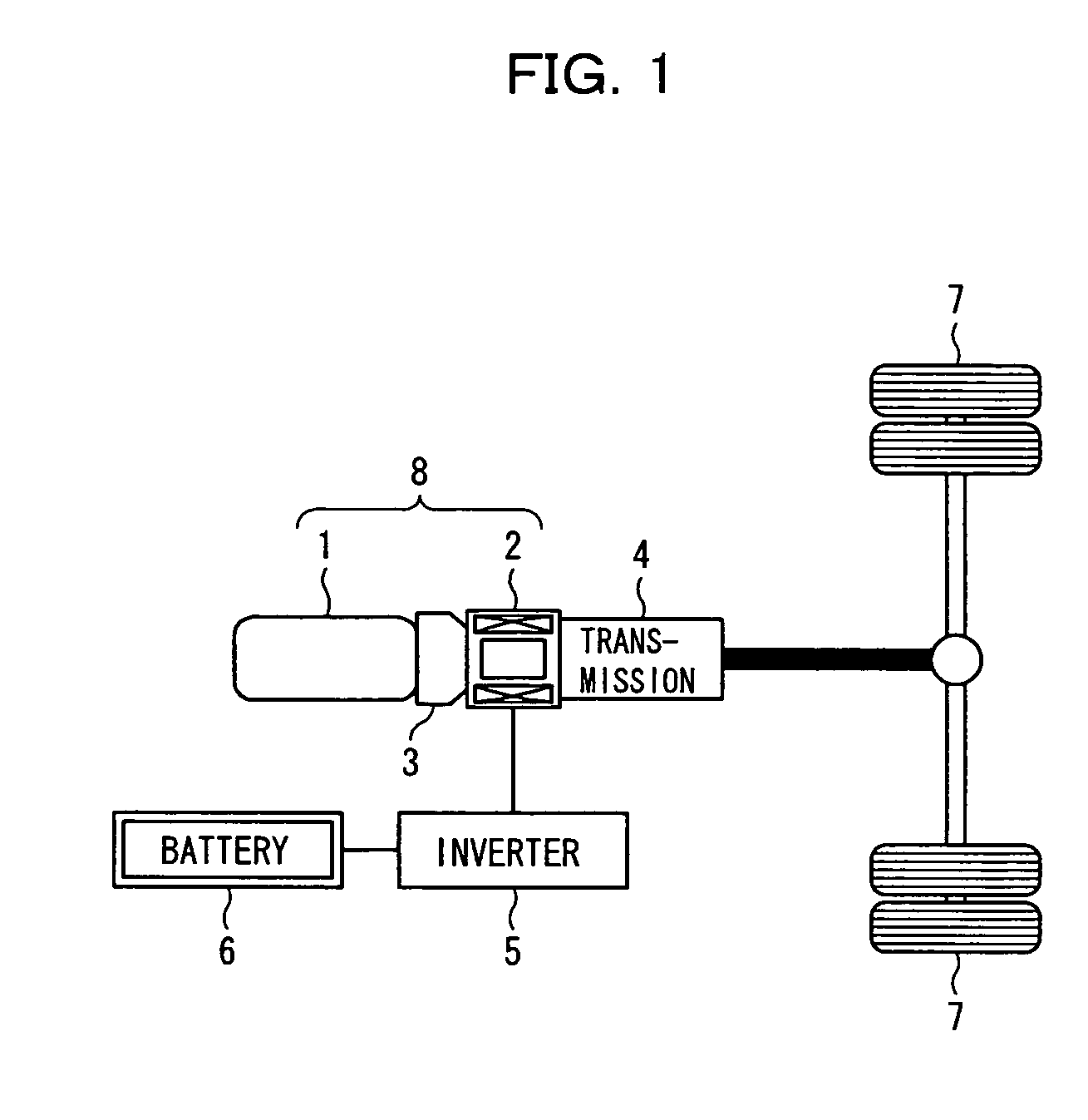
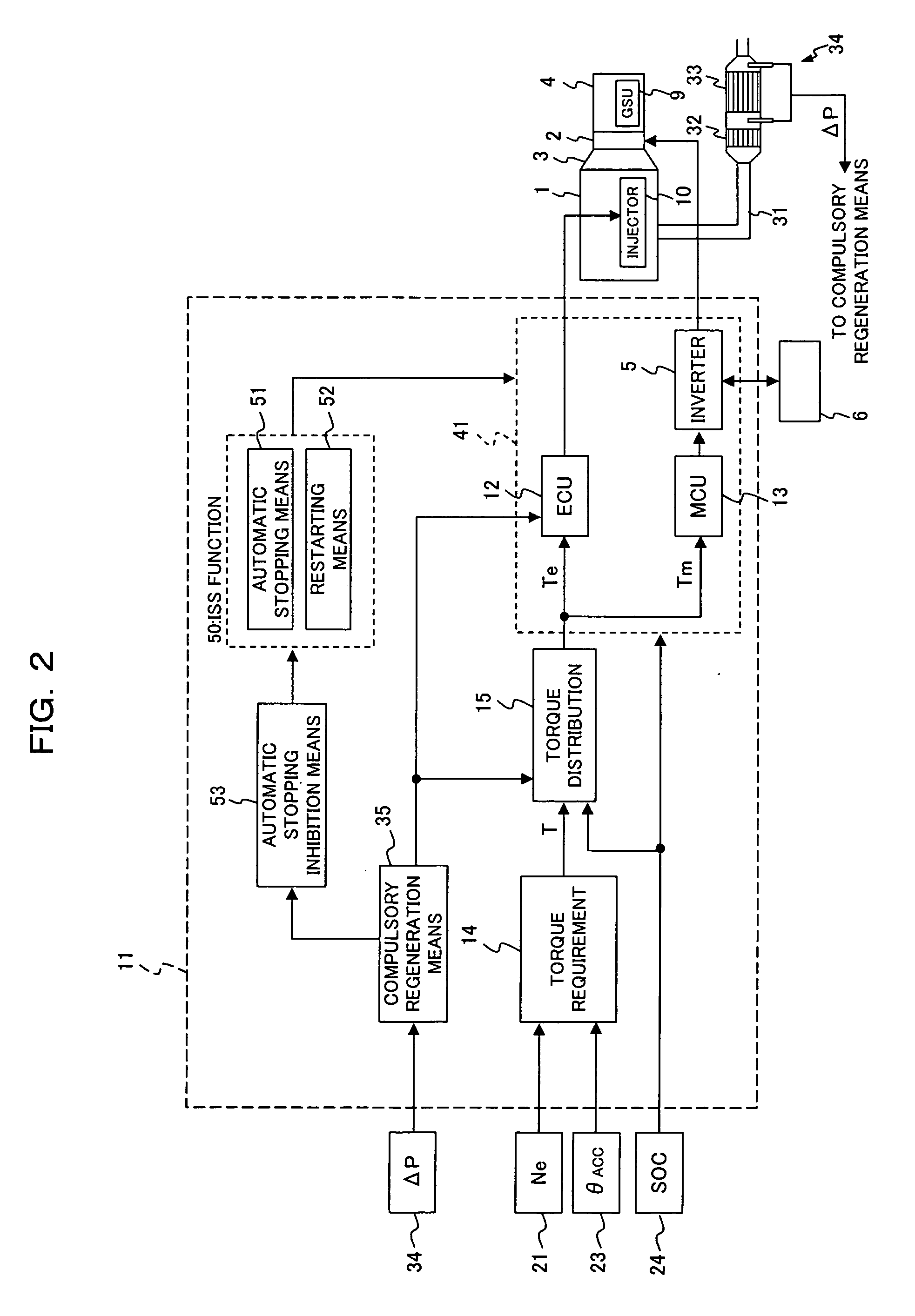
Motor control apparatus for a hybrid vehicle
InactiveUS20060218903A1Increased fuel costShorten the time periodElectrical controlInternal combustion piston enginesParticulatesElectrical battery
A motor control apparatus for a hybrid vehicle in which a diesel engine is used is disclosed by which the compulsory regeneration time period of the hybrid vehicle is reduced to achieve enhancement of the fuel cost. The motor control apparatus for a hybrid vehicle includes a filter for collecting particulate matter in exhaust gas of the diesel engine, compulsory regeneration means for compulsorily regenerating the filter, and battery charging means for converting the output power of the diesel engine into electric power based on a charged state of the battery and charging the battery with the electric power. When the compulsory regeneration is executed, the supply of electric power to the battery by the engine is inhibited.
Owner:MITSUBISHI FUSO TRUCK AND BUS CORPORATION
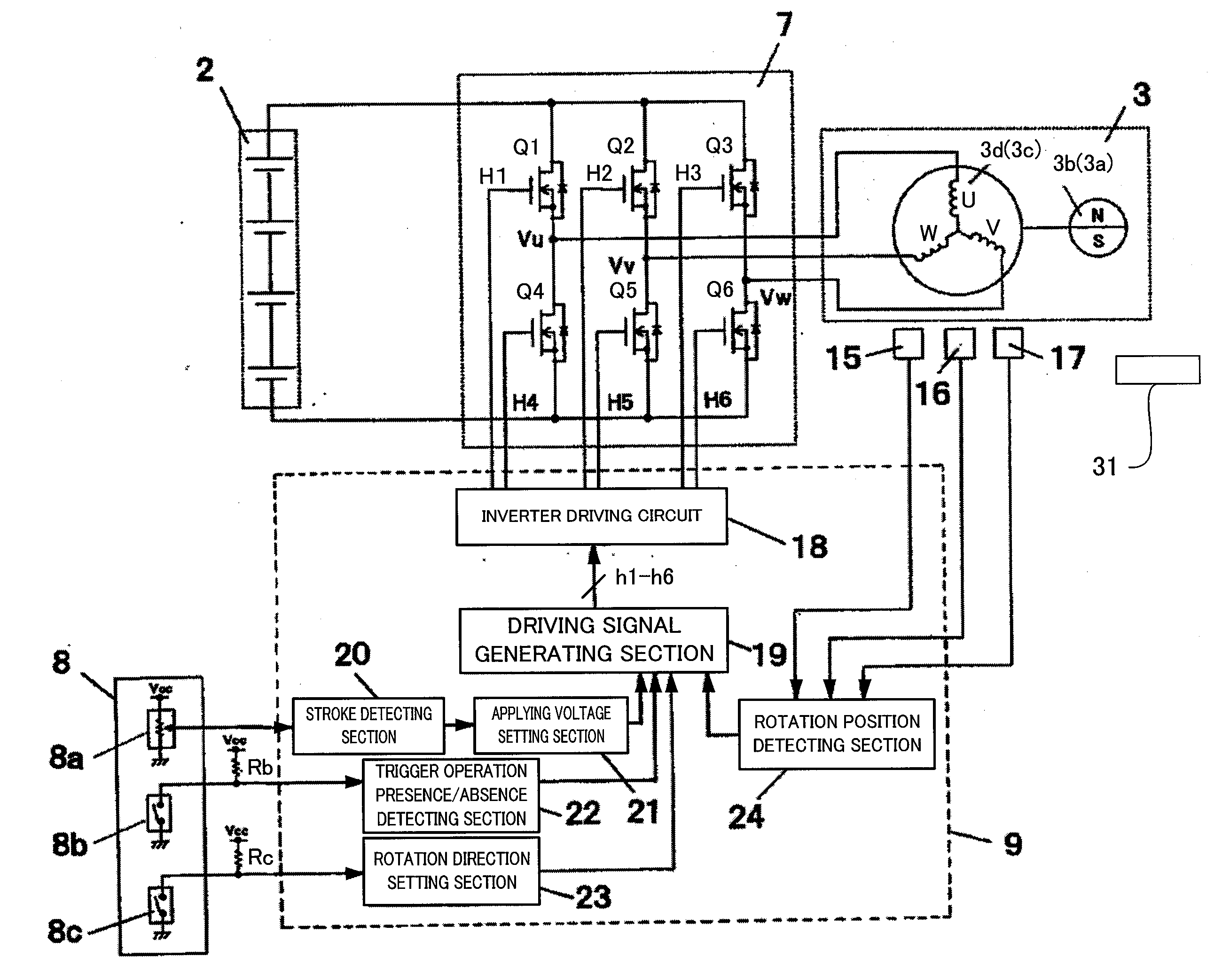
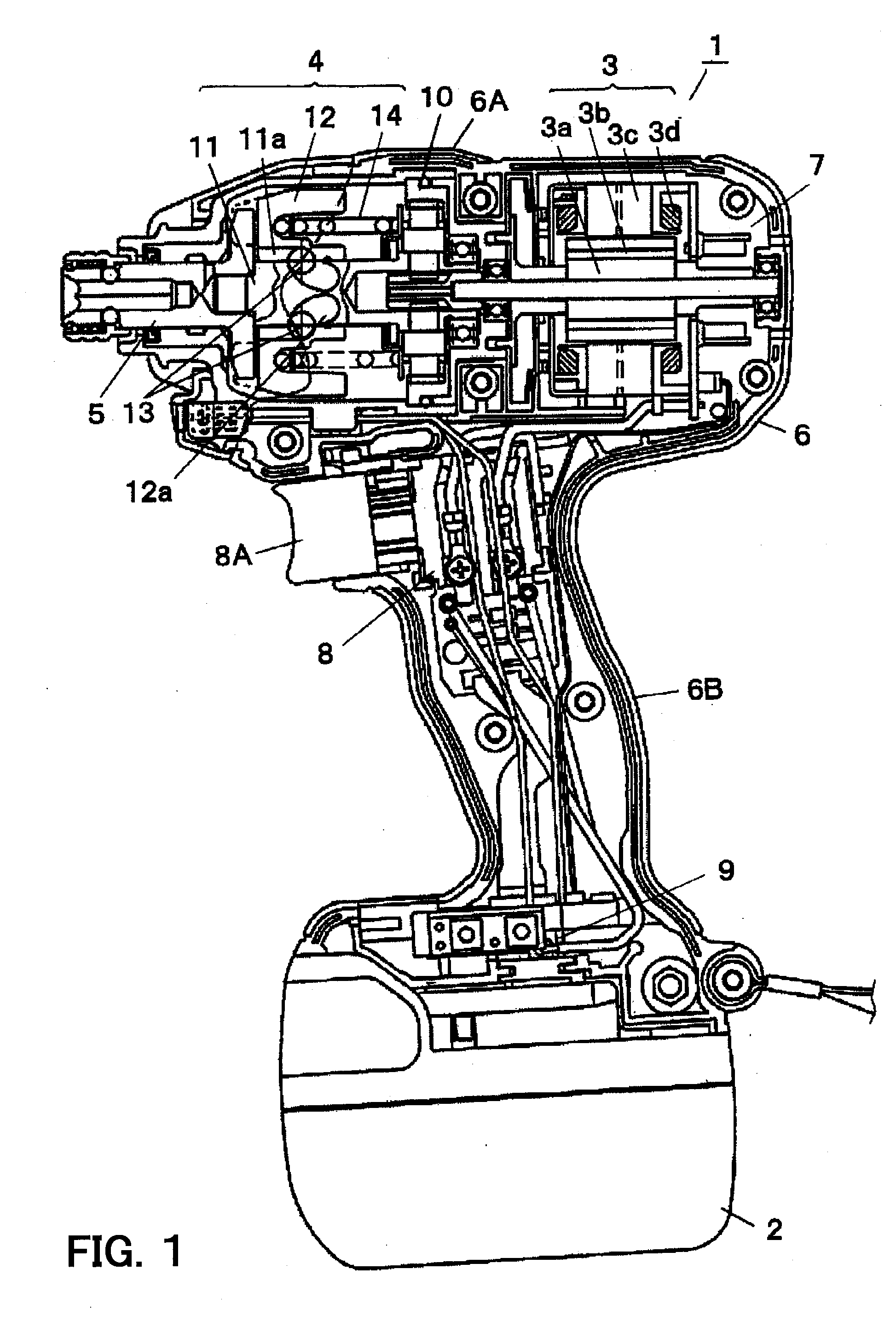
Power tool
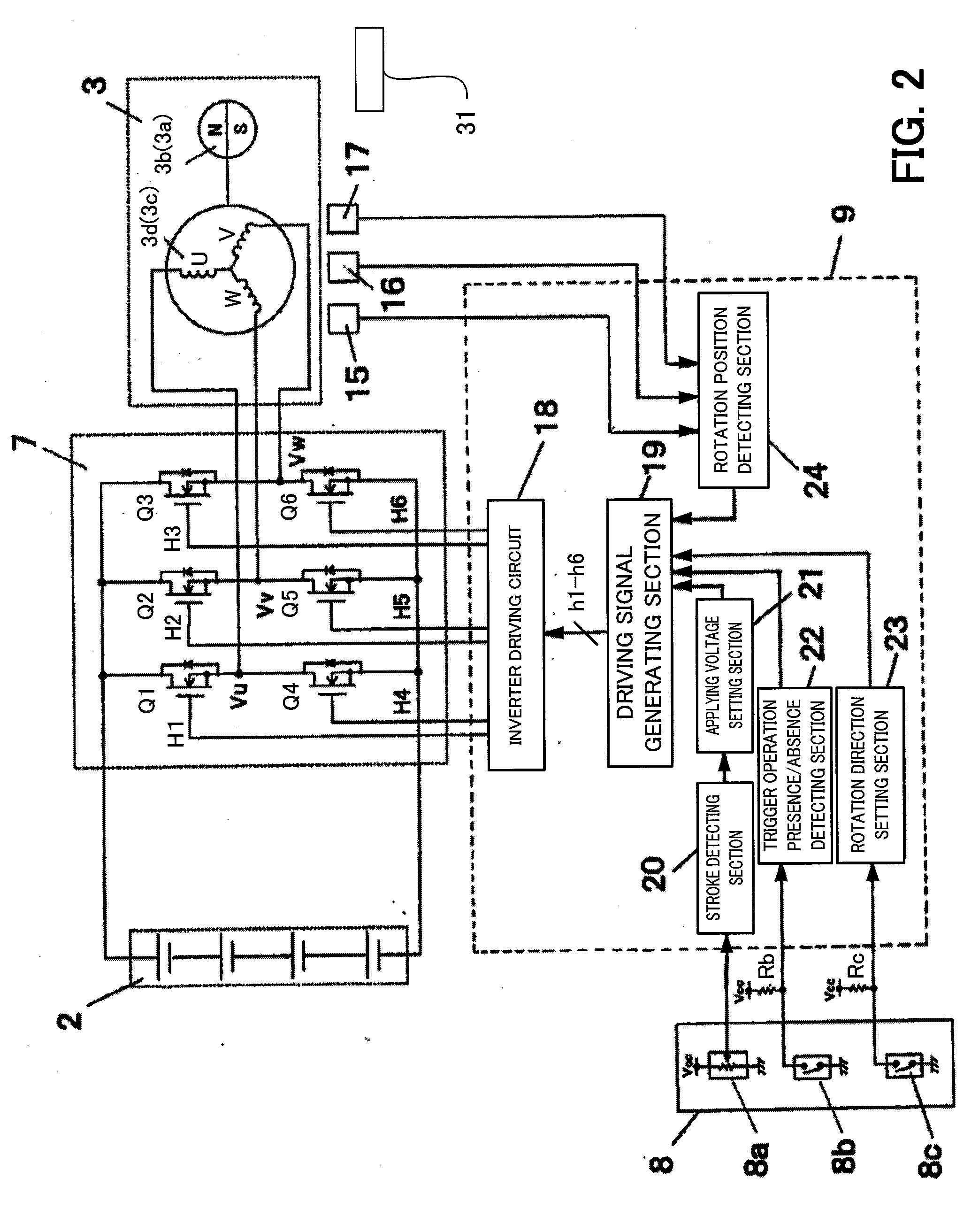
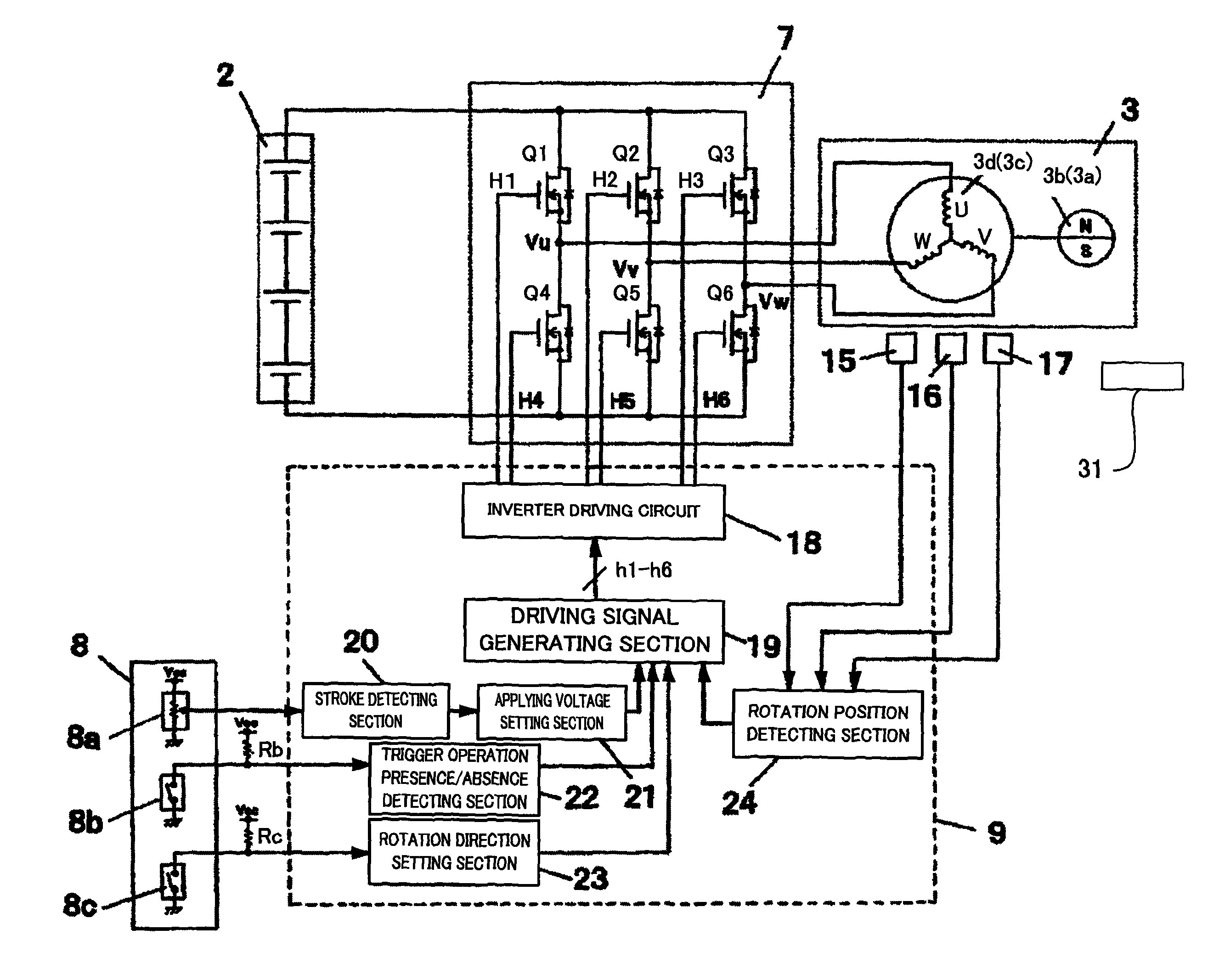
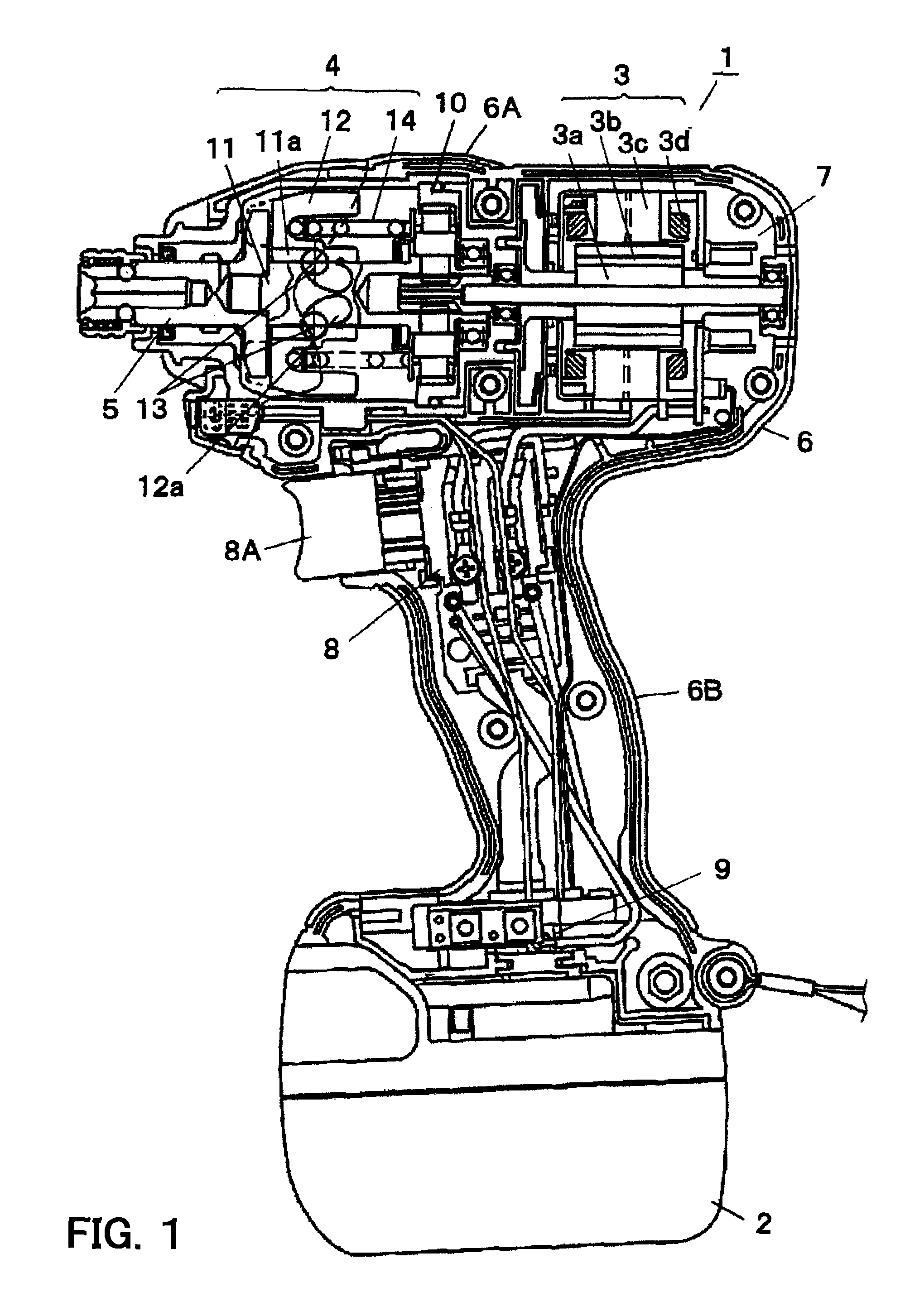
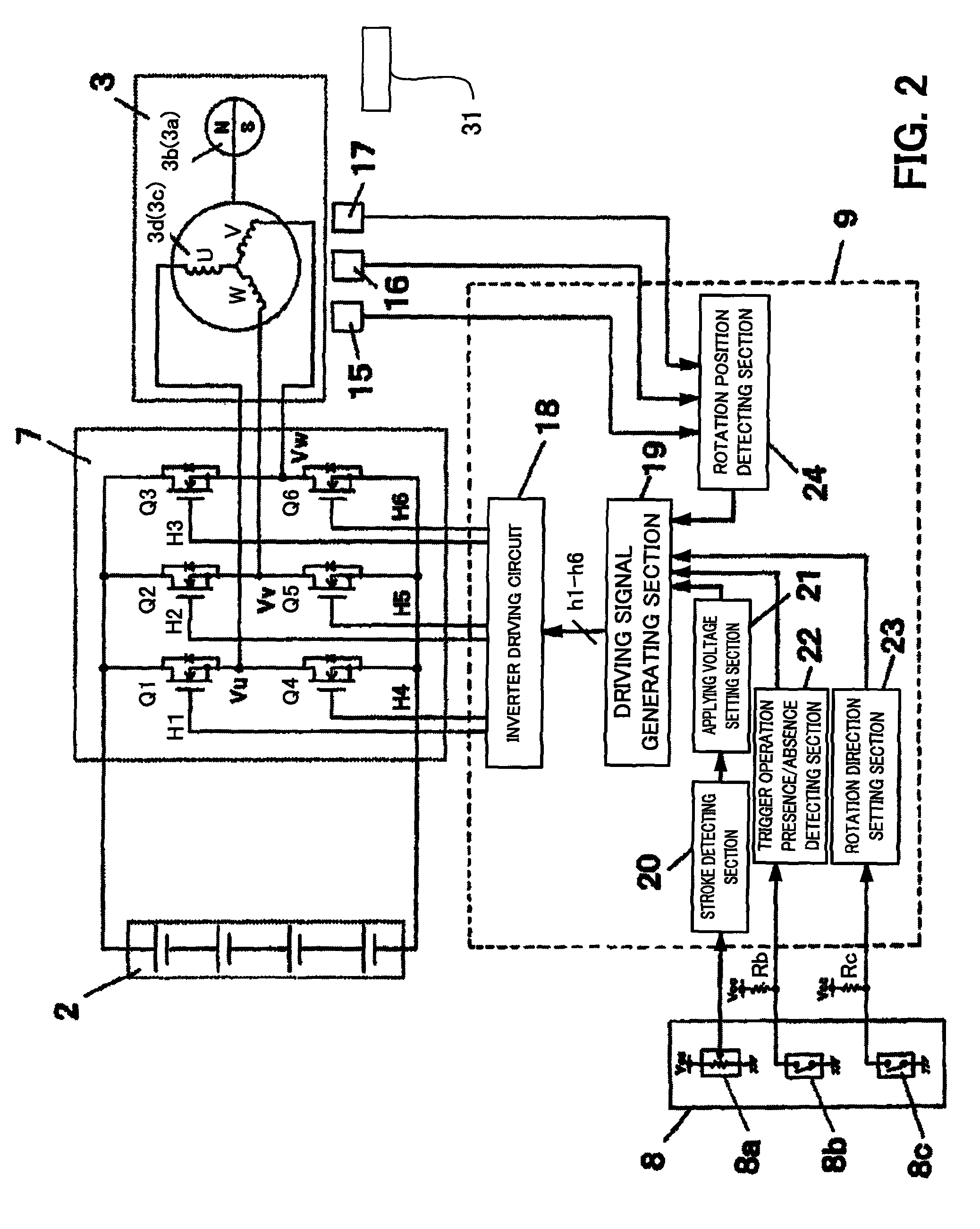
ActiveUS20090096401A1Avoid stopAvoid failureDC motor speed/torque controlAC motor controlPower toolVIT signals
The controller determines the presence or absence of operation of the trigger switch according to an ON / OFF state of the main contact of the trigger switch and designating the rotation speed of the motor based on a signal outputted from the speed contact. The controller stops the rotation of the motor, after the trigger switch is activated and the main contact is turned ON and the motor is driven according to a signal outputted from the speed contact, when an OFF state of the main contact is detected, only in the case where a signal value outputted from the speed contact is a predetermined value or less.
Owner:KOKI HLDG CO LTD
Communication system and method for controlling the same
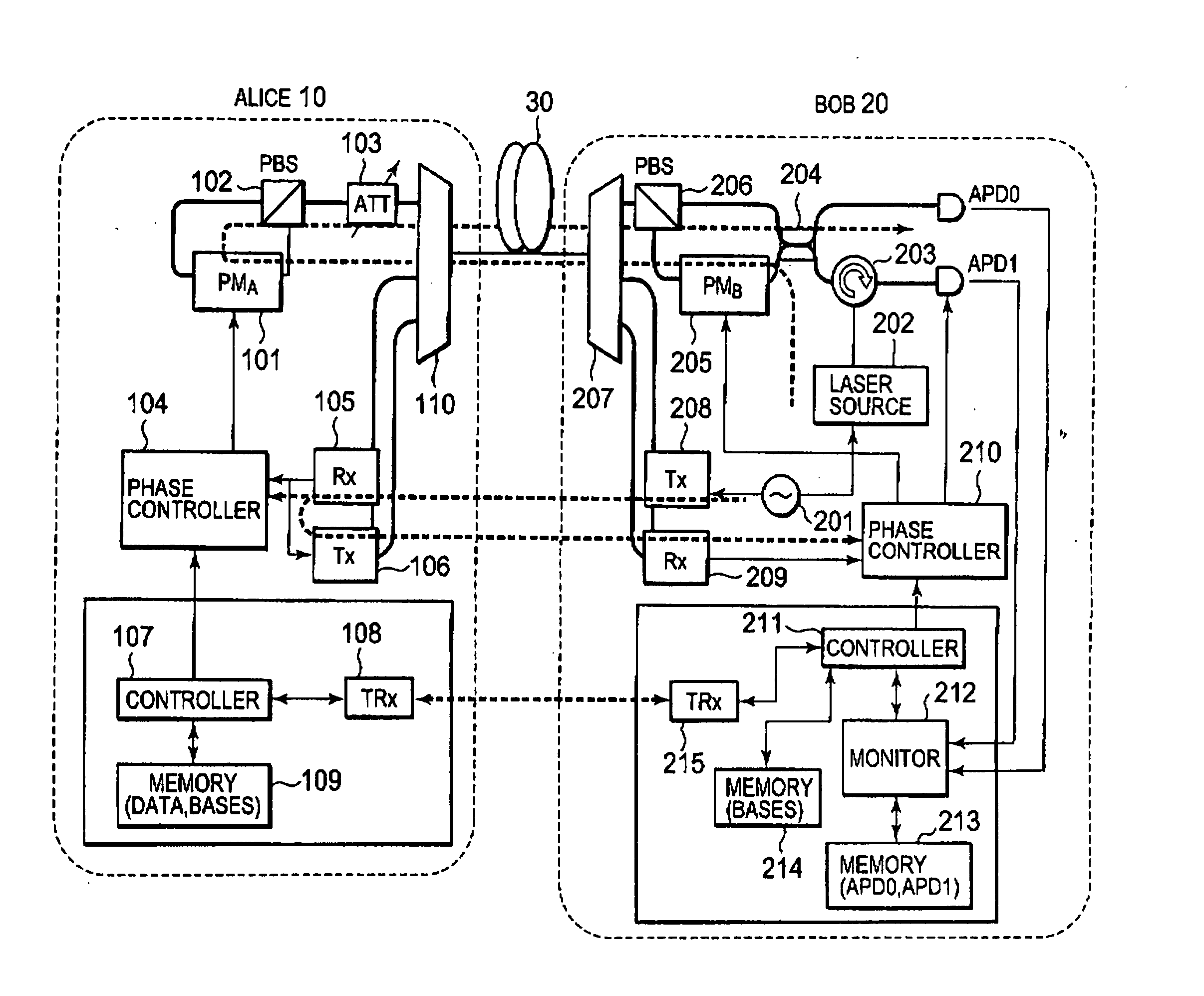
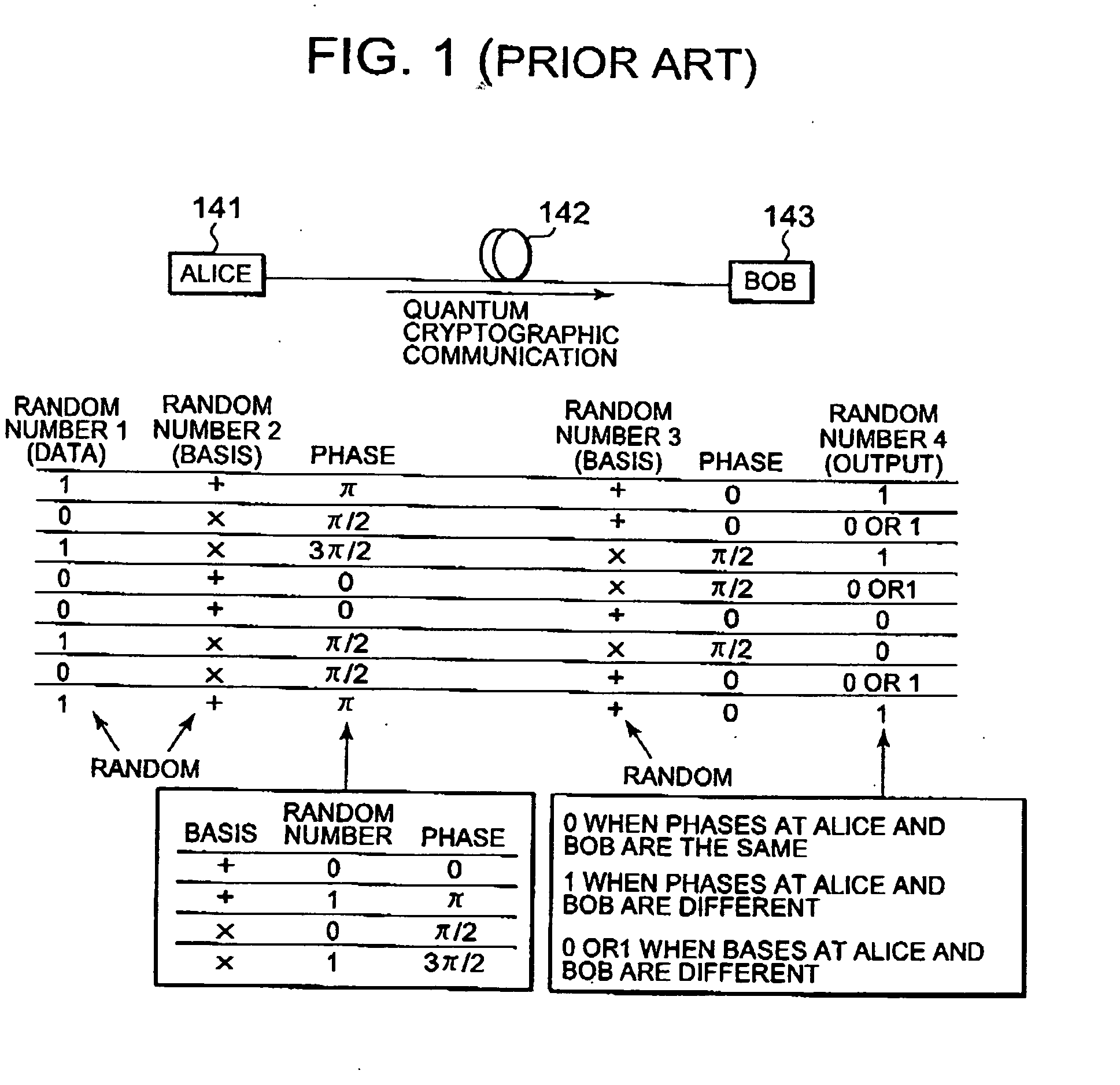
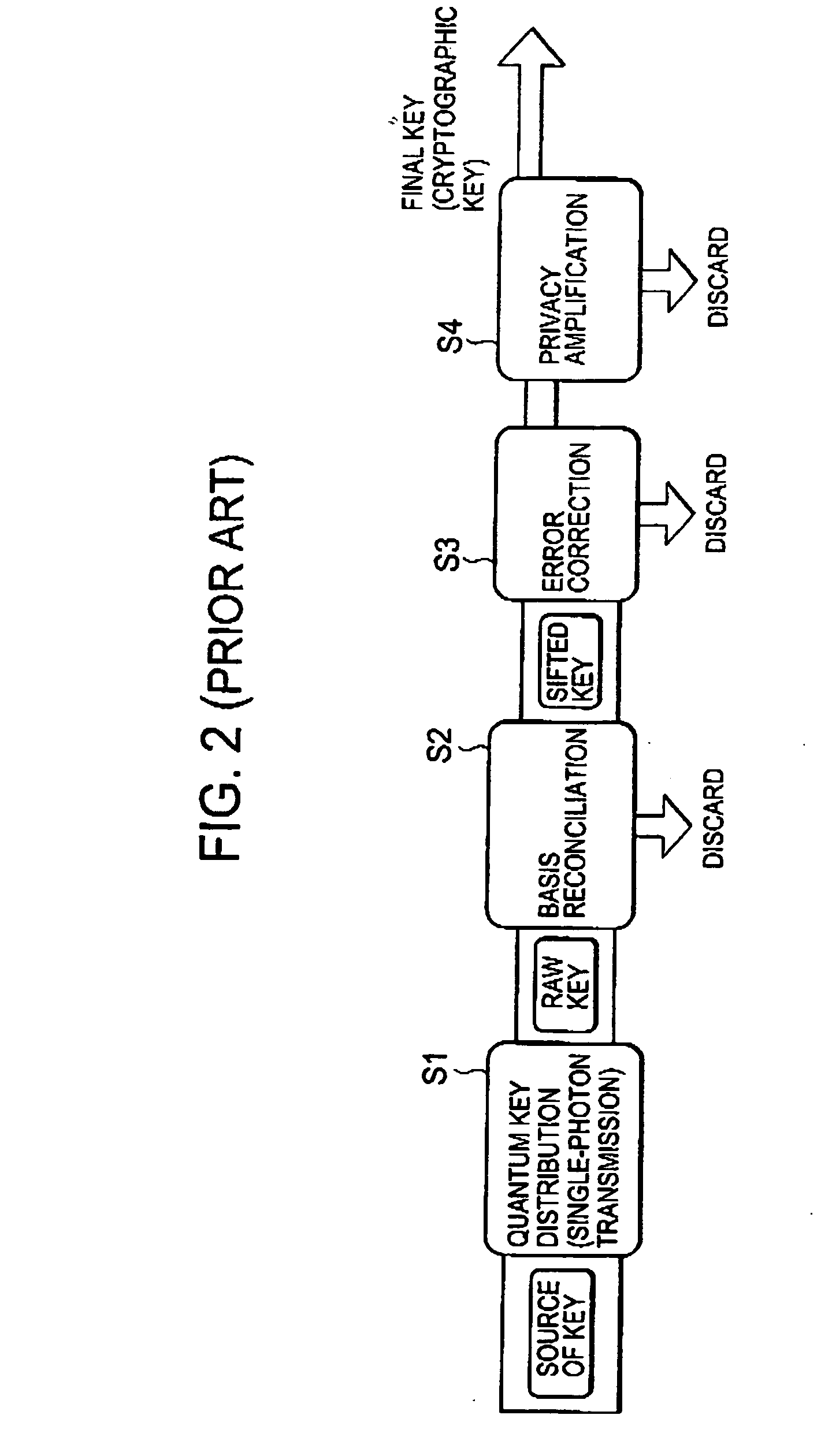
InactiveUS20070009098A1Minimize error rateEfficient processingSynchronising transmission/receiving encryption devicesError preventionPhase correctionCommunications system
For an error rate QBER, threshold values are preset, including a threshold value Qbit for frame synchronization processing, a threshold value Qphase for phase correction processing, and a threshold value QEve for eavesdropping detection. Upon the distribution of a quantum key from a sender to a receiver, when the measurement value of QBER is deteriorated more than Qbit, frame synchronization processing is performed. When the measurement value of QBER is deteriorated more than Qphase, phase correction processing and frame synchronization processing are performed. When QBER does not become better than QEve even after these recovery-processing steps are repeated N times, it is determined that there is a possibility of eavesdropping, and the processing is stopped.
Owner:NEC CORP
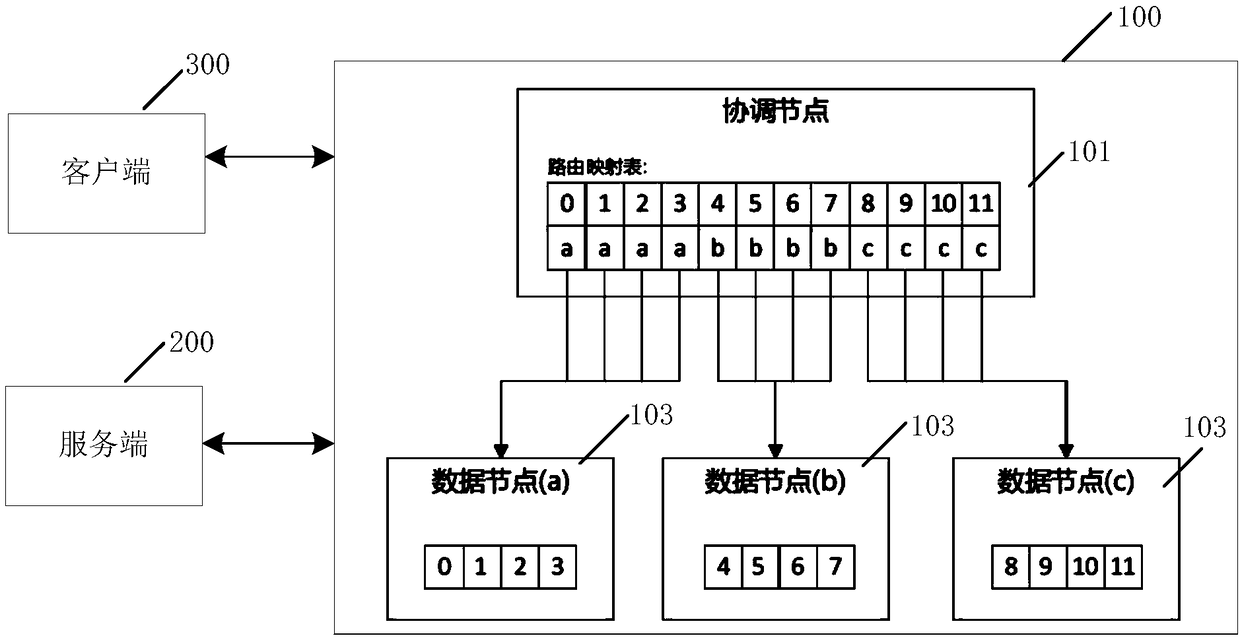
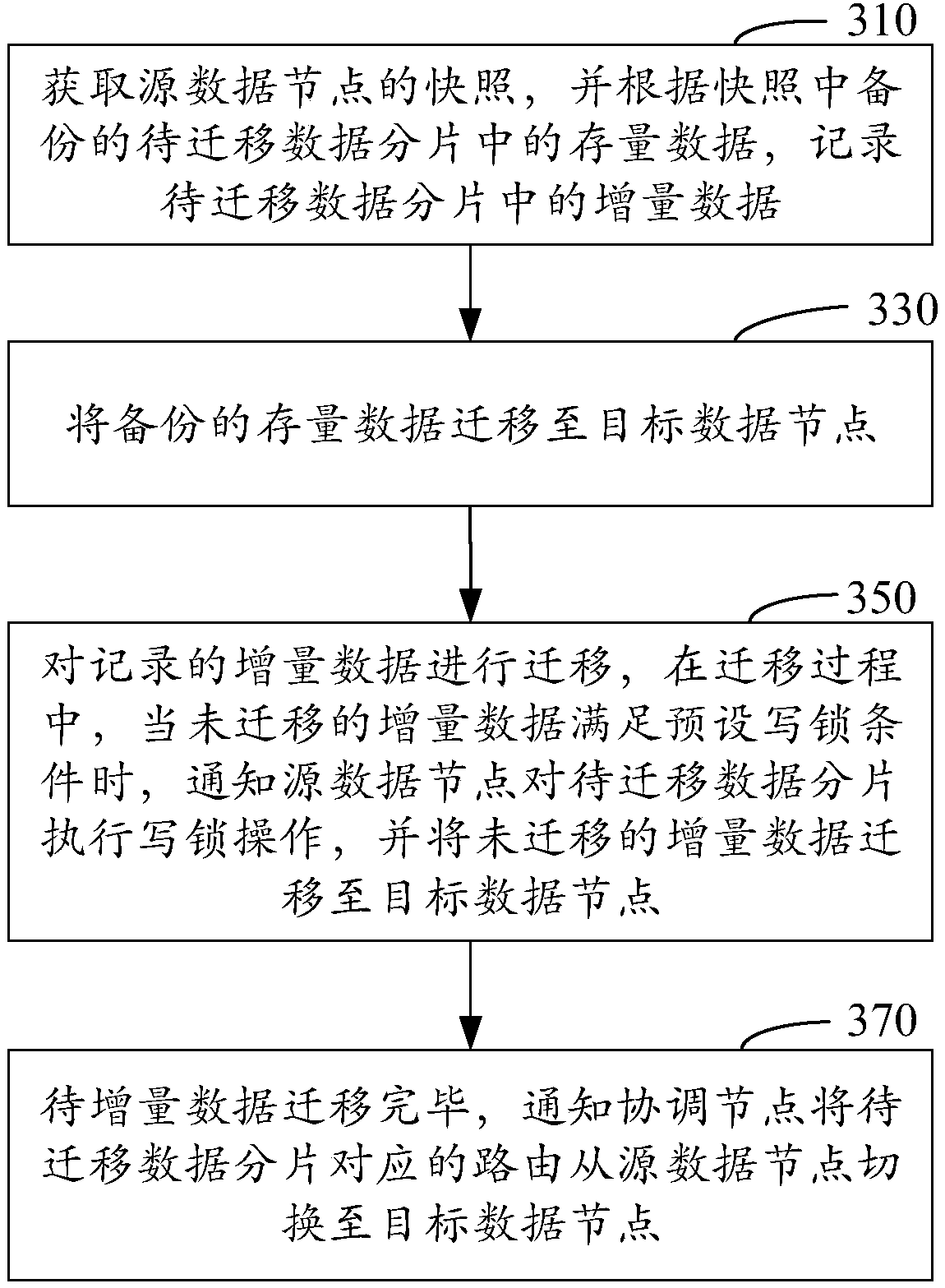
Method and device for data migration in database cluster
ActiveCN108132949AAvoid stopImprove access efficiencyError detection/correctionSpecial data processing applicationsData nodeDatabase services
The invention discloses a method and device for data migration in a database cluster. The method comprises the following steps of acquiring a snapshot of a source data node; recording incremental datain data fragments to be migrated according to stock data in the data fragments to be migrated backed up in the snapshot; migrating the backup stock data into a target data node; performing migrationon the recorded incremental data; in the migration process, when the incremental data which is not migrated meets the preset write lock conditions, notifying the source data node to execute write lockoperation on the data fragments to be migrated; migrating the incremental data which is not migrated to the target data node; after the migration of the incremental data is completed, notifying a coordination node to switch a route corresponding to the data fragments to be migrated from the source data node to the target data node. By using the method and device for data migration in the databasecluster provided by the invention, the database service interruption can be avoided in the data migration process.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and control module for controlling the drive mode of a hybrid drive to prevent jerky movements
InactiveUS20110112708A1Efficiency of drive is not substantially impairedAvoid changeInternal combustion piston enginesDigital data processing detailsComputer moduleJerky movements
The drive mode of a hybrid drive is controlled by: detecting a drive mode change signal characterizing a planned drive mode change, and determining a torque shortfall, which would occur due to the drive mode change. Furthermore, the method provides for comparing the torque shortfall with a threshold value, and blocking a drive mode change, if the comparison step reveals that the torque shortfall is above the threshold value. Otherwise, the method provides for: automatically performing a drive mode change according to the drive mode change signal, if the comparison step reveals that the torque shortfall is not above the threshold value.
Owner:ROBERT BOSCH GMBH
Single phase brushless motor and power tool utilizing same
InactiveUS10199886B2Large peak valueIncreases startup torqueMagnetic circuit rotating partsMagnetic circuit stationary partsBrushless motorsPeak value
A single phase brushless motor and a power tool are provided. The single phase brushless motor includes a stator and a rotor. The stator includes a stator core and windings wound around the stator core. The stator core includes a yoke and at least two teeth. The tooth includes a tooth body and a tooth tip. The tooth tip includes first and second pole shoes. The two pole shoes of each tooth are symmetrical about a center line of the tooth body. Each tooth defines a positioning groove facing the rotor between the two pole shoes. Pole shoes of adjacent two of the at least two teeth are spaced apart by a slot opening. A width of the positioning groove is greater than a width of the slot opening. The peak value of the cogging torque of the motor is increased, and the motor has a large startup torque.
Owner:JOHNSON ELECTRIC SA
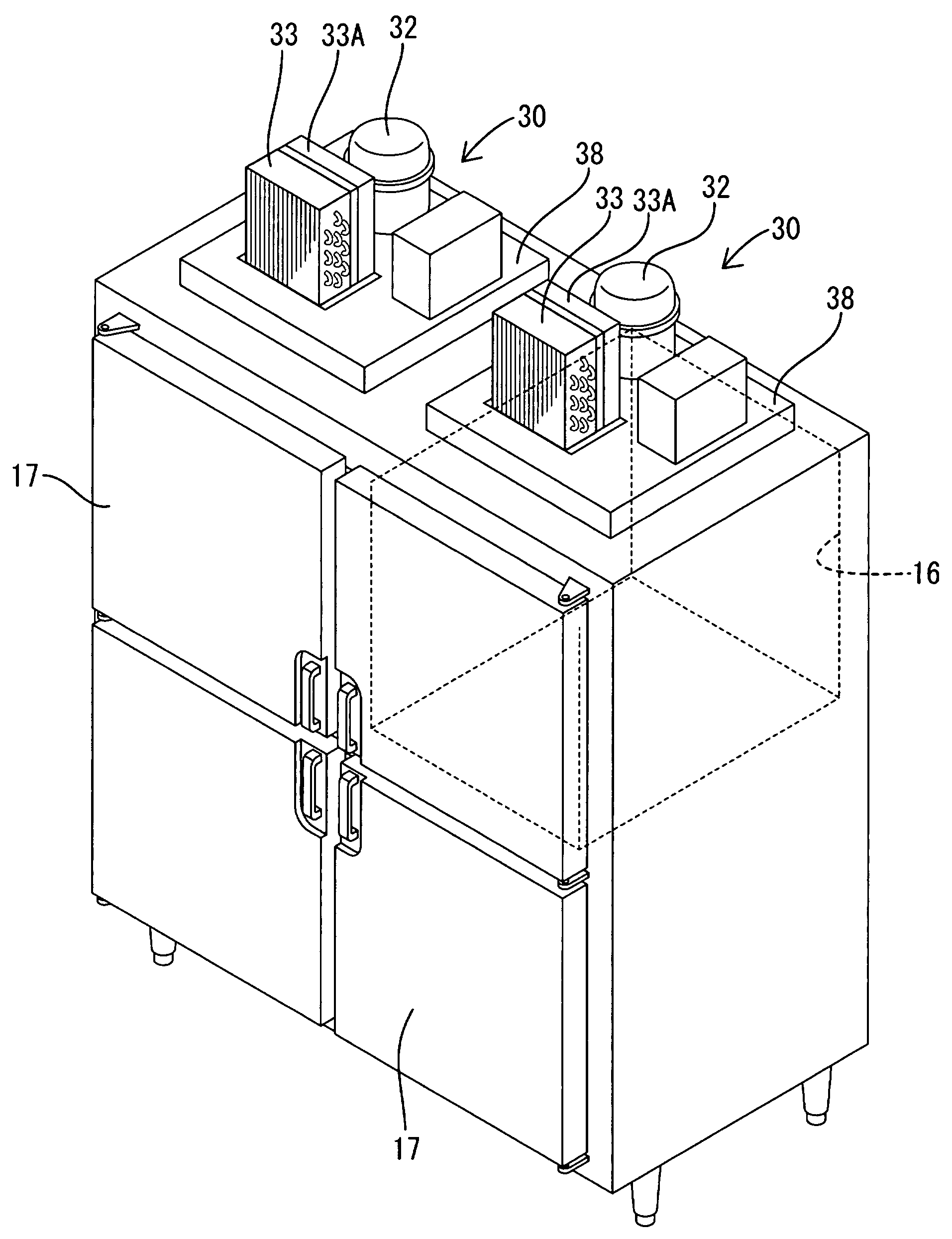
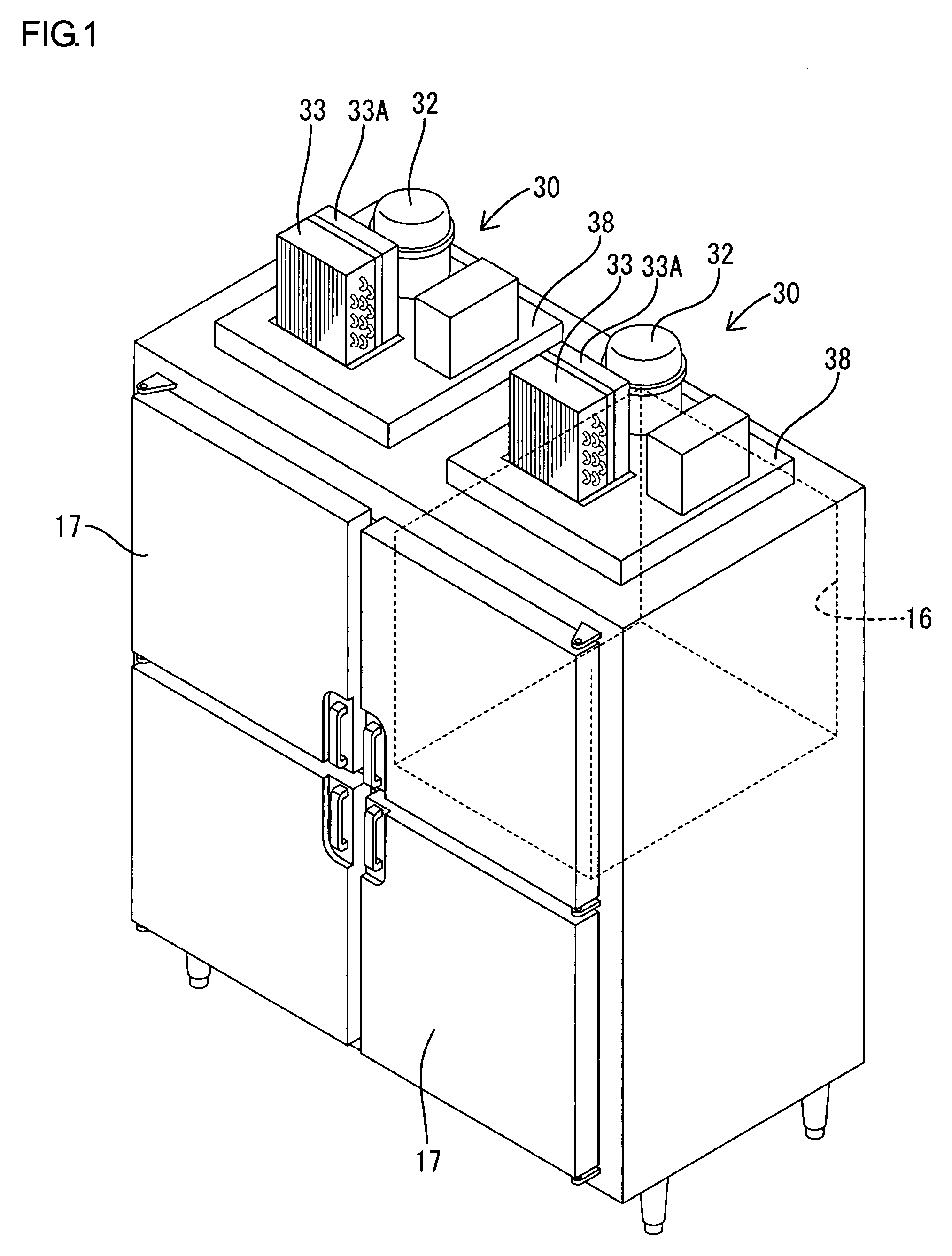
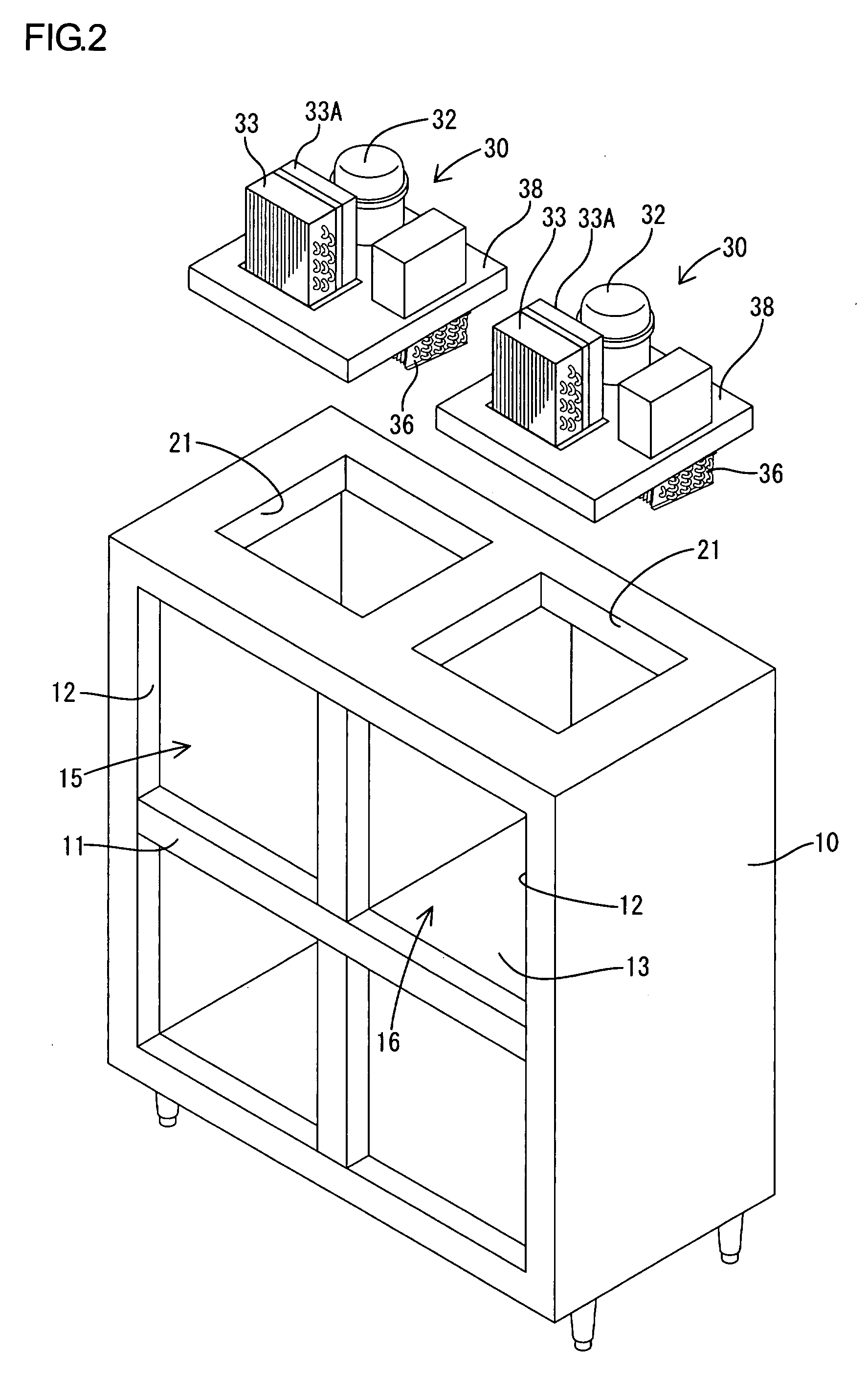
Refrigeration unit
InactiveUS20090001866A1Performance of compressor is loweredAvoid temperature riseCompression machines with non-reversible cycleFurniture partsHigh pressureRefrigerant
In a refrigeration unit including a variable performance compressor driven by an inverter motor, a sensor is configured to detect a physical amount corresponding to a refrigerant pressure on the high-pressure side of a refrigerant circuit. A measured value of the physical amount is compared with a first reference value corresponding to a first predetermined pressure of the refrigerant and a second reference value corresponding to a second predetermined pressure lower than the first predetermined pressure. A protective operation can start if the comparison result indicates that an actual refrigerant pressure is higher than the first predetermined pressure. The performance of the compressor can be gradually lowered if the comparison result indicates that an actual refrigerant pressure is between the first predetermined pressure and the second predetermined pressure.
Owner:HOSHIZAKI ELECTRIC CO LTD
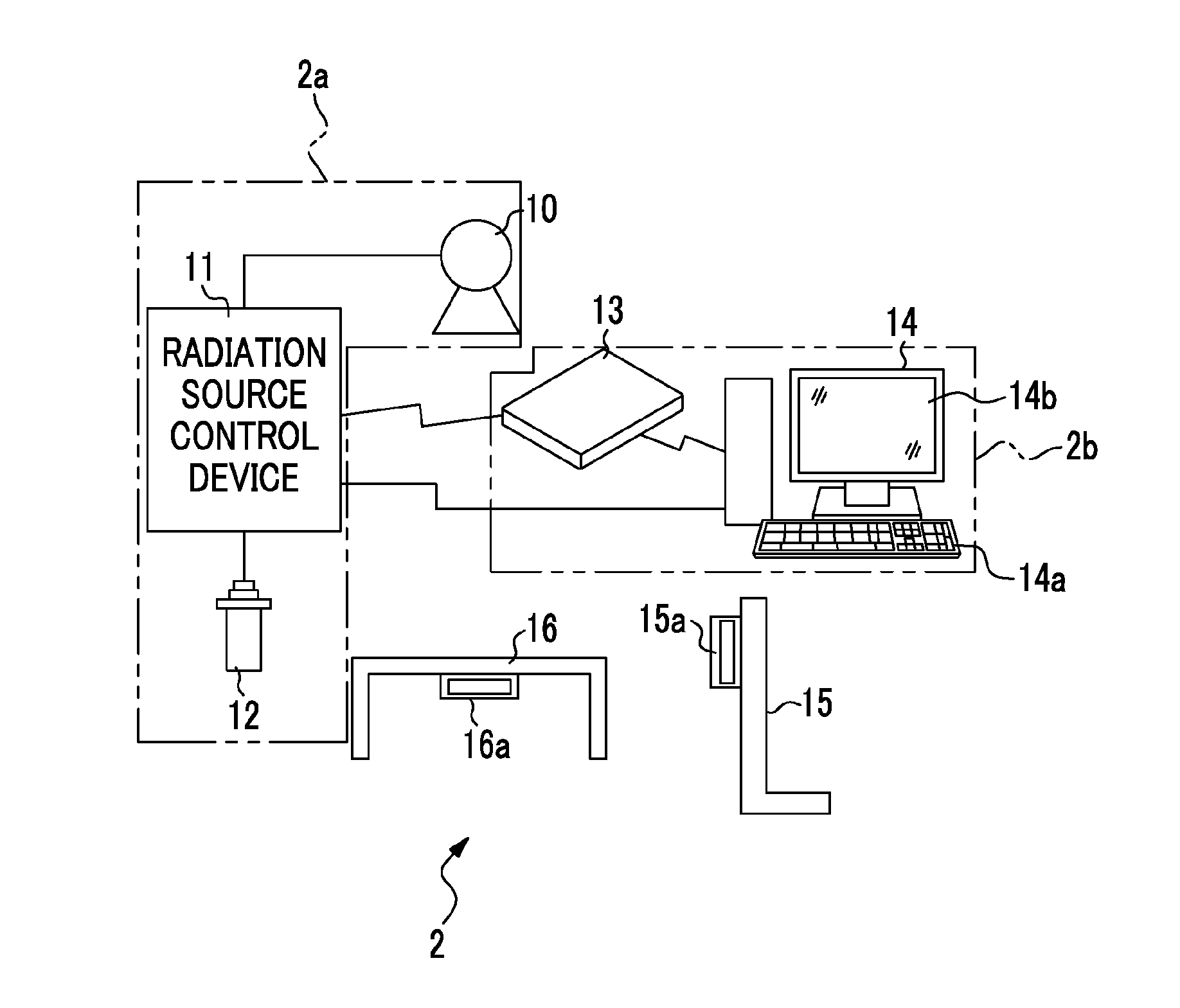
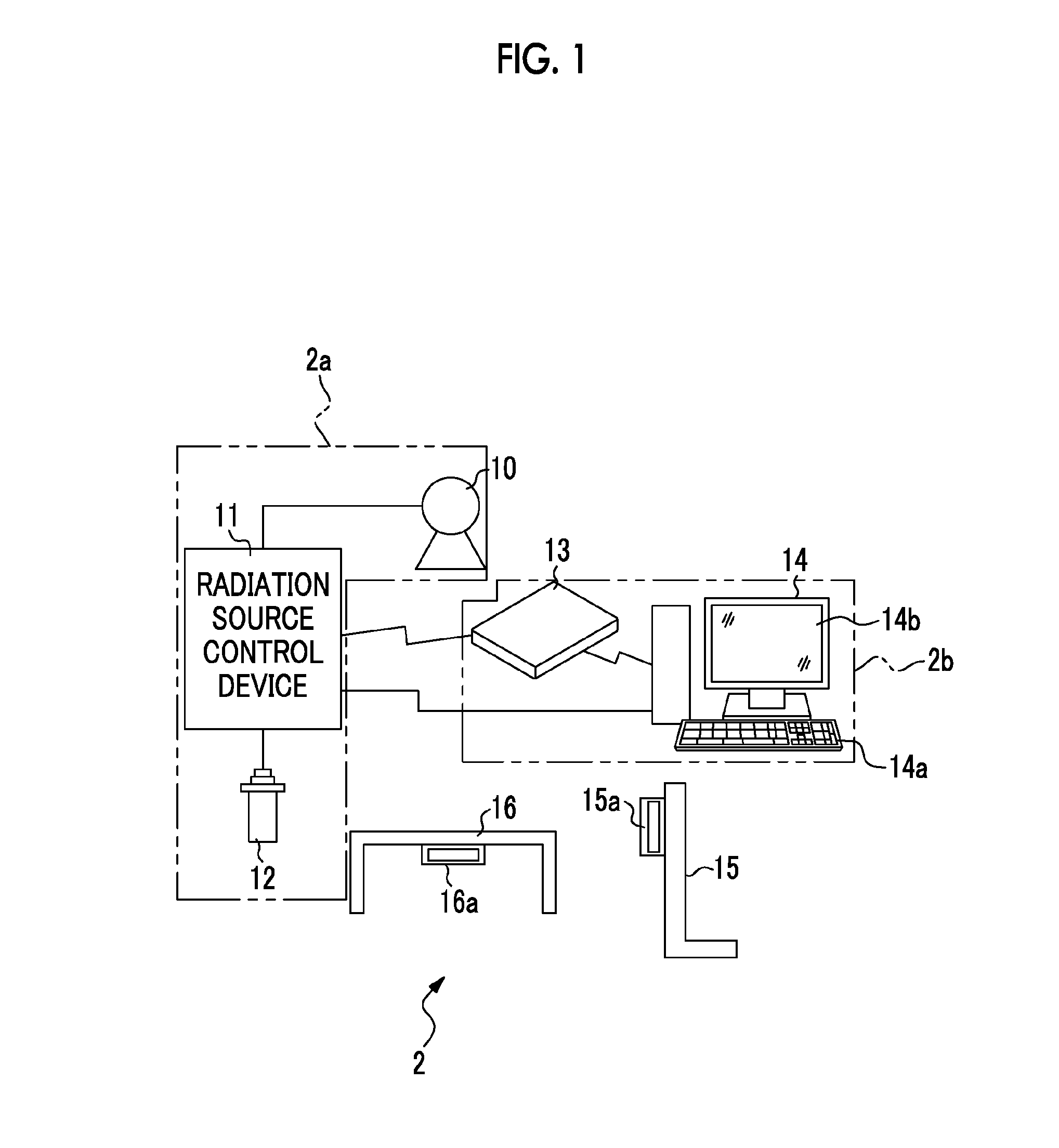
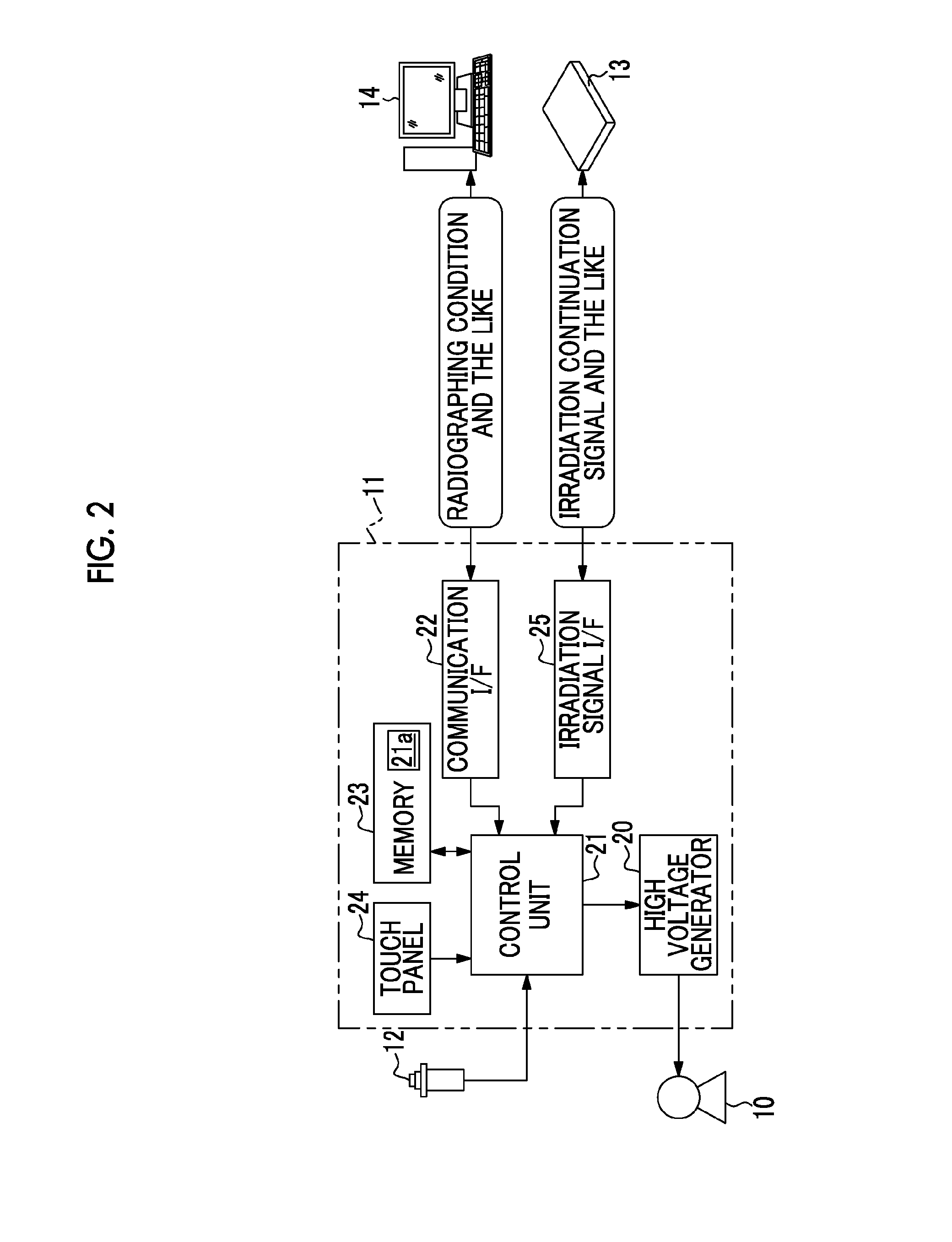
Radiographic system, drive control method for radiographic system, recording medium for drive control program and radiological image detection device
ActiveUS20130223592A1Avoid problemsReliably avoidedX-ray apparatusMaterial analysis by transmitting radiationContinuationX-ray
It is possible to reliably avoid a problem that radiation irradiation does not stop even when an accumulated radiation dose reaches a target radiation dose. An AEC unit starts monitoring an integrated value of a radiation dose detection signal from a detection pixel and an output of an irradiation continuation signal at the same time, and continuously transmits the irradiation continuation signal in a predetermined period while the integrated value does not reach a threshold value. When the integrated value reaches the threshold value, the output of the irradiation continuation signal is stopped. The irradiation continuation signal is transmitted to an irradiation signal I / F of a radiation source control device through an irradiation signal I / F by wireless. The radiation source control device stops X-ray irradiation by an X-ray source when the irradiation signal I / F does not receive the irradiation continuation signal.
Owner:FUJIFILM CORP
Steering assist system
ActiveUS20180345978A1High velocityImprove convenienceAutonomous decision making processAnti-collision systemsElectronic control unitEngineering
A steering assist system includes: a first sensor; a second sensor; and an electronic control unit. The electronic control unit is configured to start a lane change assist control when another vehicle obstructing a lane change is detected; detect a progress status of the lane change; stop the lane change assist control, when the first sensor detects an approaching vehicle; execute a center return assist control when the lane change assist control is stopped in a former part of the lane change; and execute a collision avoidance assist control when the lane change assist control is stopped in a latter part of the lane change.
Owner:TOYOTA JIDOSHA KK
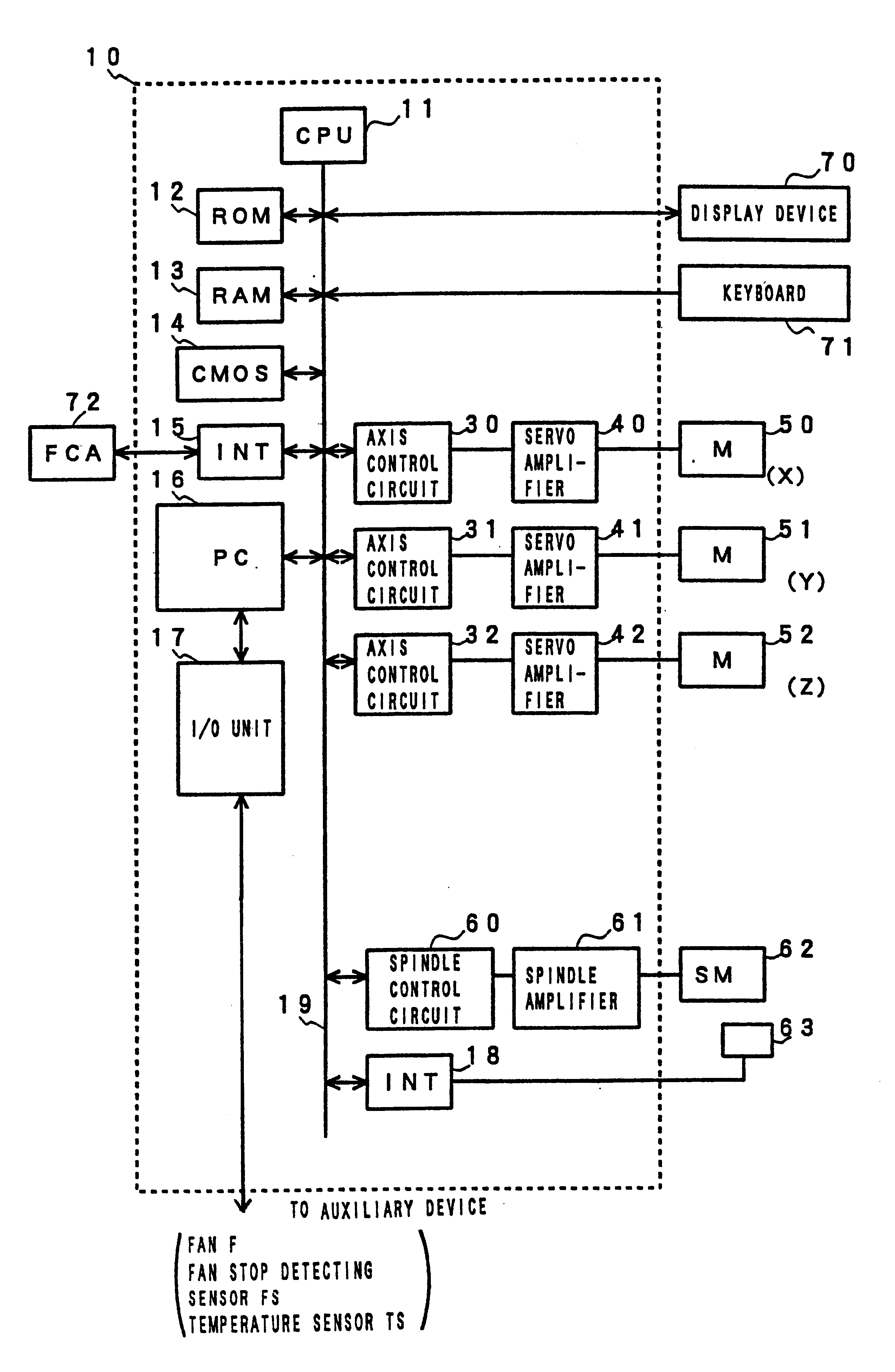
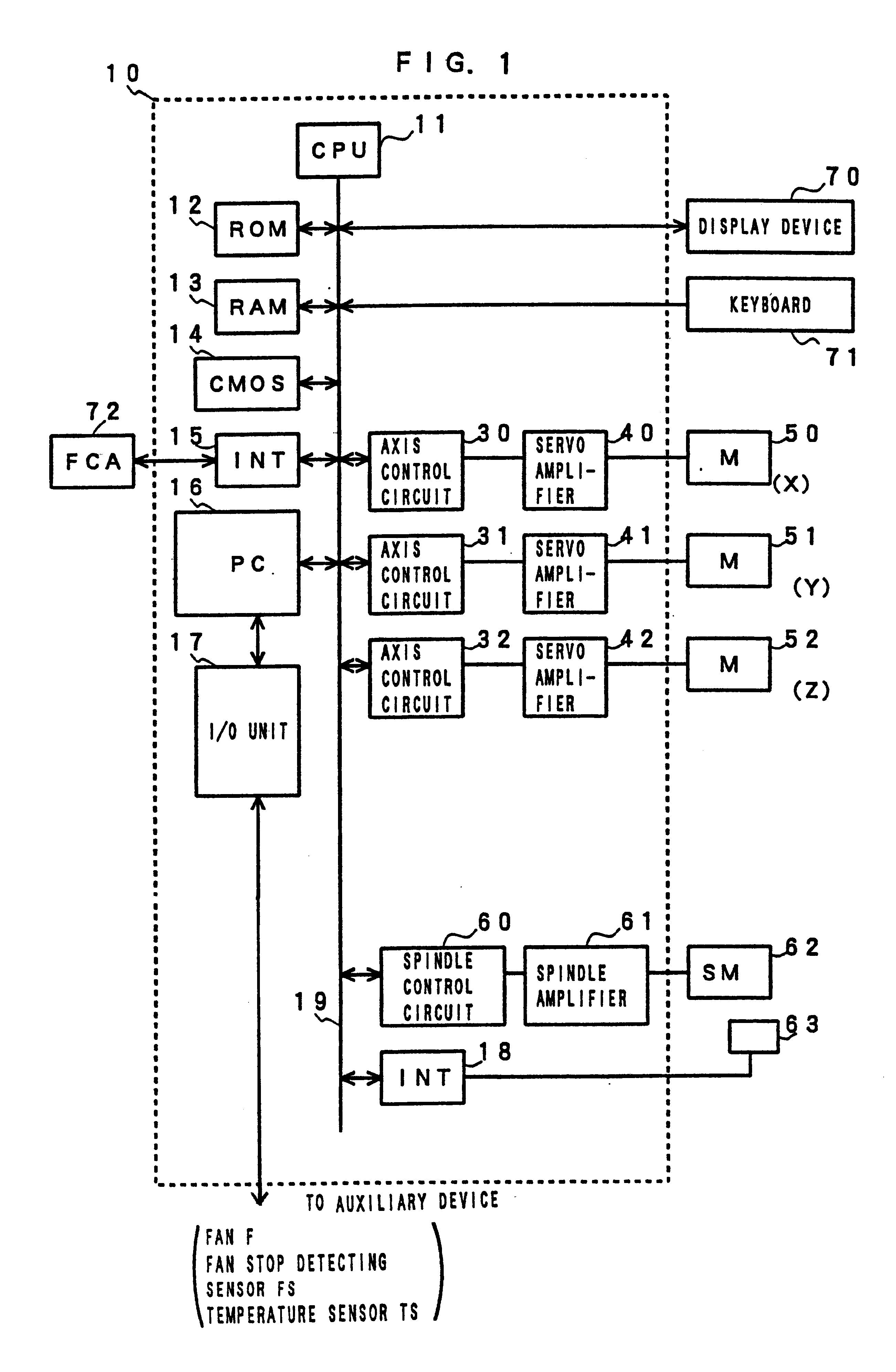
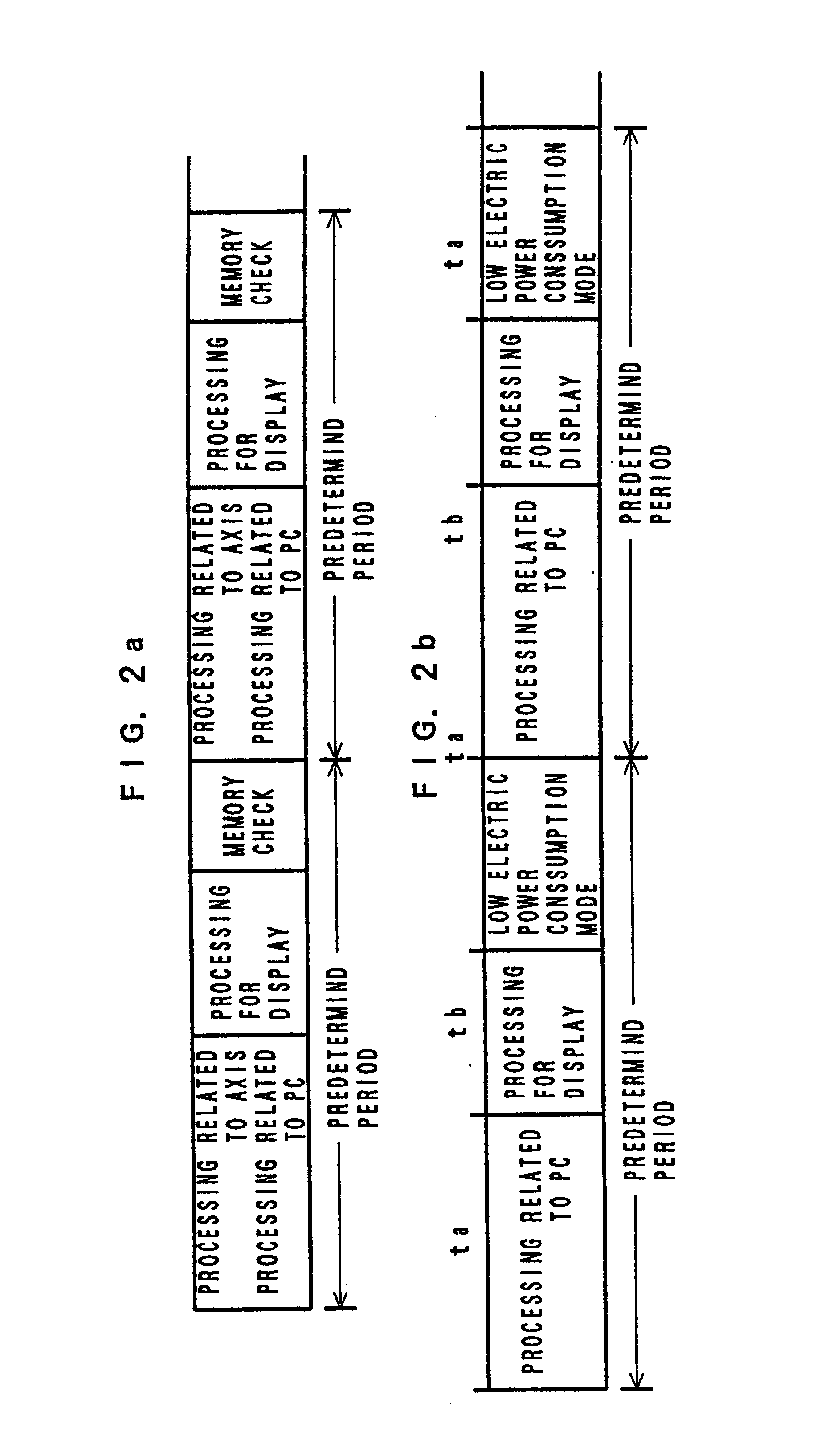
Method of operation controller having processor for controlling industrial machine
InactiveUS6704875B1Increase temperatureLimit its operationThermometer detailsTemperatue controlHuman–machine interfaceMachine control
A method of operating a controller of an industrial machine capable of reducing a rise in temperature of a processor, easily restoring and resuming the operation even if the operation is stopped by the rise in temperature, and further possibly preventing the stop of the operation of the controller by the rise in temperature. When temperature in the controller is lower than a set value, the processor performs a plurality of processings in each predetermined period to do normal operation. When the temperature rises to a set value or higher, processing related to the controlling axes is stopped, a motor is stopped, and the processor performs only minimum or limited required processing, i.e., processing related to a man / machine interface such as processing related to a programmable controller and processing for display and operates in a low-electric-power consumption mode except the period when the processor performs the minimum or limited required processing. In addition, as the temperature rises, the operating speed of a machine controlled by the controller is reduced to reduce heat generation and the rise in temperature of the processor.
Owner:FANUC LTD
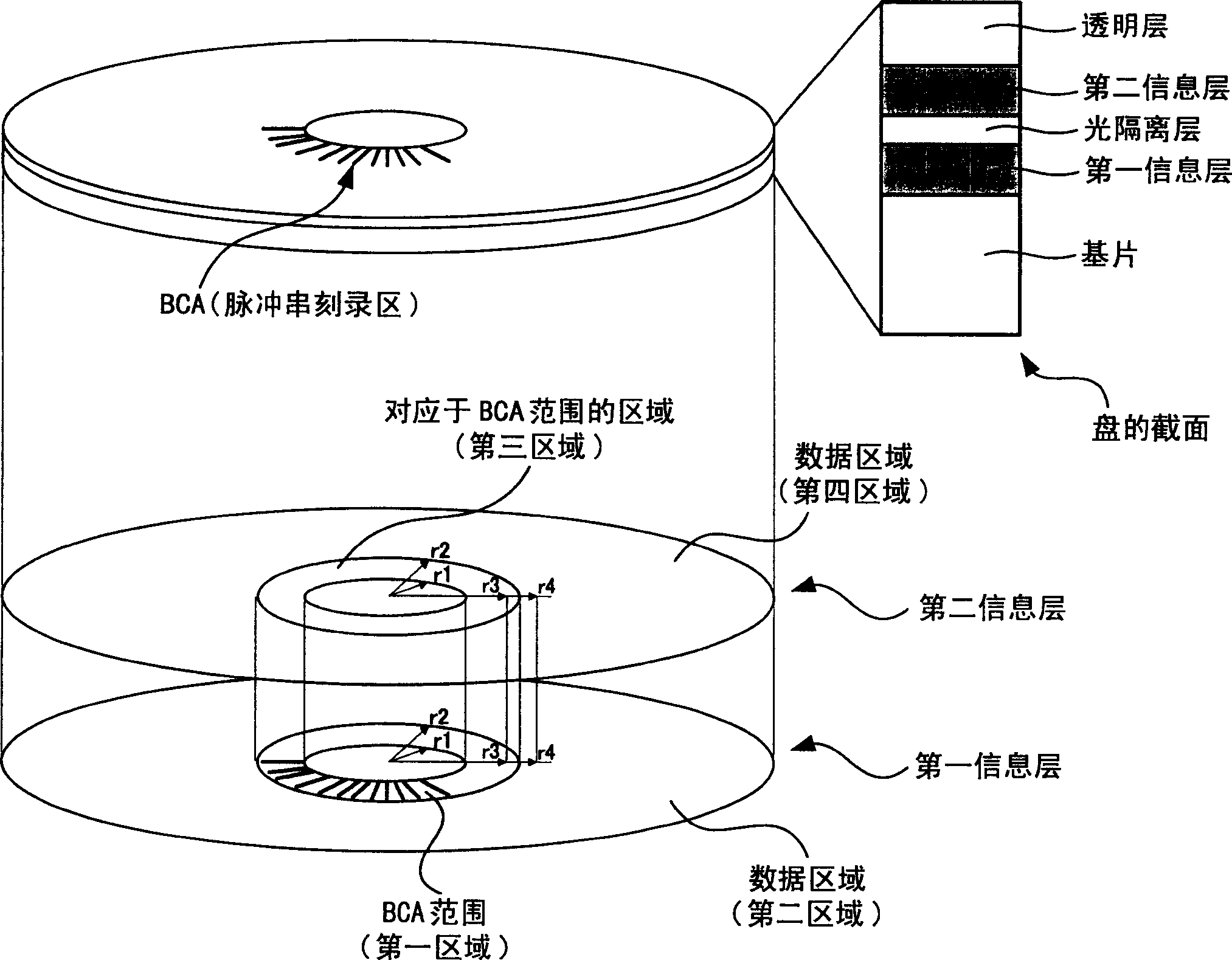
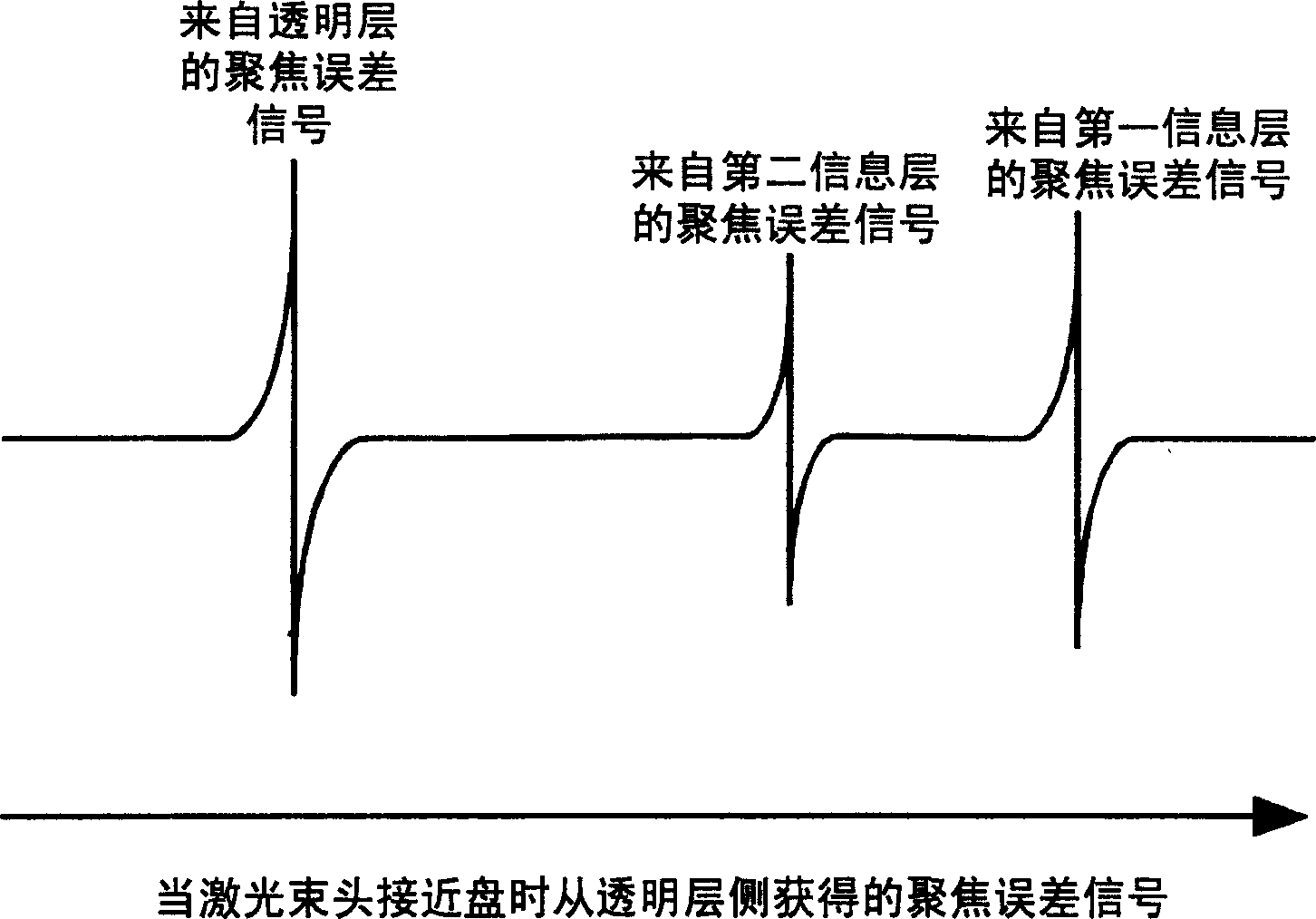
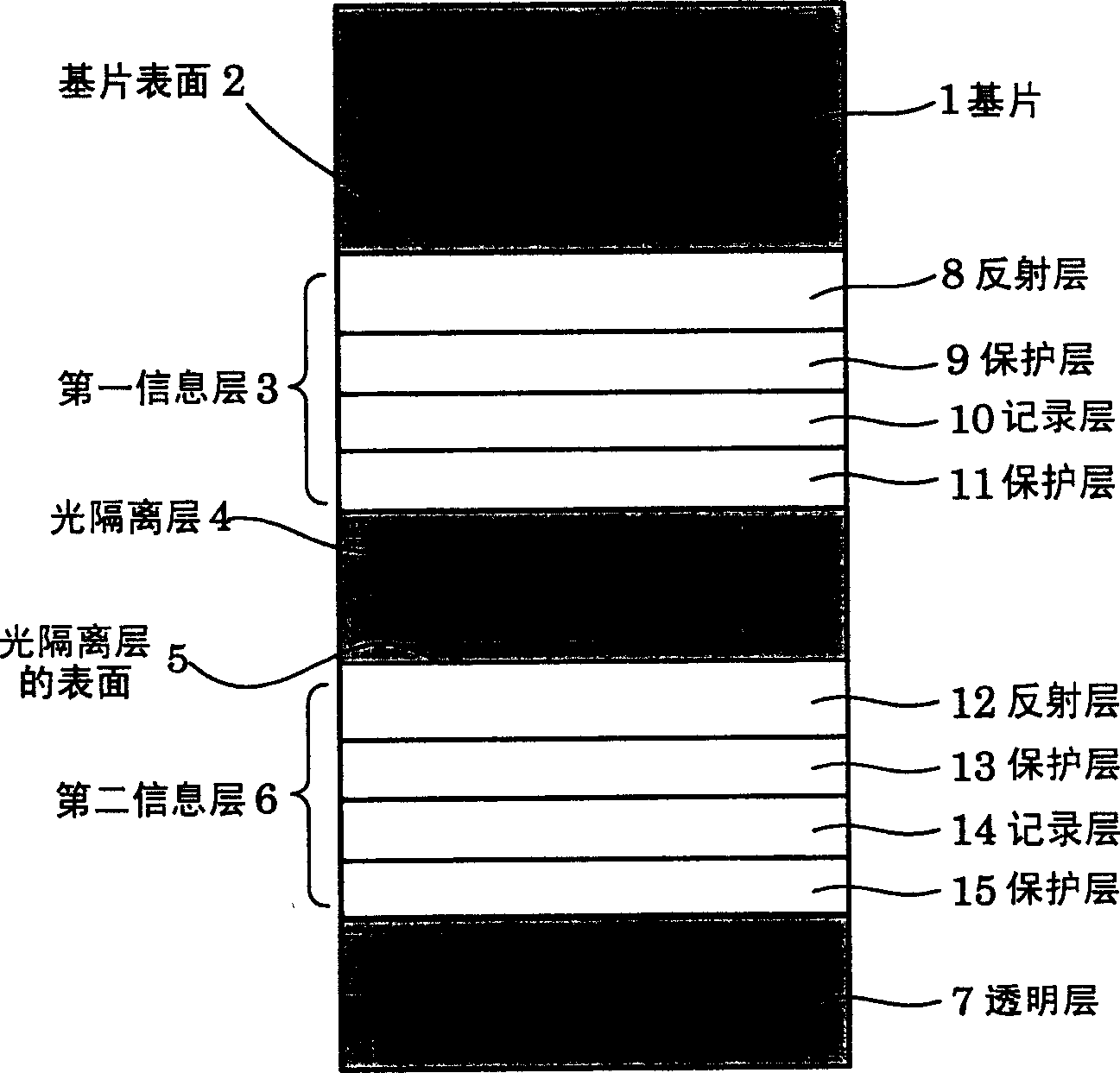
Optical information recording medium and method for manufacturing the medium
InactiveCN1627401AIncrease productionAvoid stopRecording by magnetic meansRecord information storageInformation layerComputer science
The present invention provides a method of properly performing initialization of an optical information recording medium in which the stop of the initialization process is avoided, thereby improving the yield of manufacturing the optical information recording medium. In initializing the information layer with a burst recording area (hereinafter referred to as "BCA"), the laser power, linear velocity and laser light used for the information layer are changed between the BCA range and the data area of the area for recording and reproducing information. At least one initialization condition in the focus of the bundle. In initializing the information layer without BCA, at least one initialization condition including laser power, linear velocity, and laser beam focus and feeding pitch for the information layer is changed between an area corresponding to the BCA and an area corresponding to the data area.
Owner:PANASONIC CORP
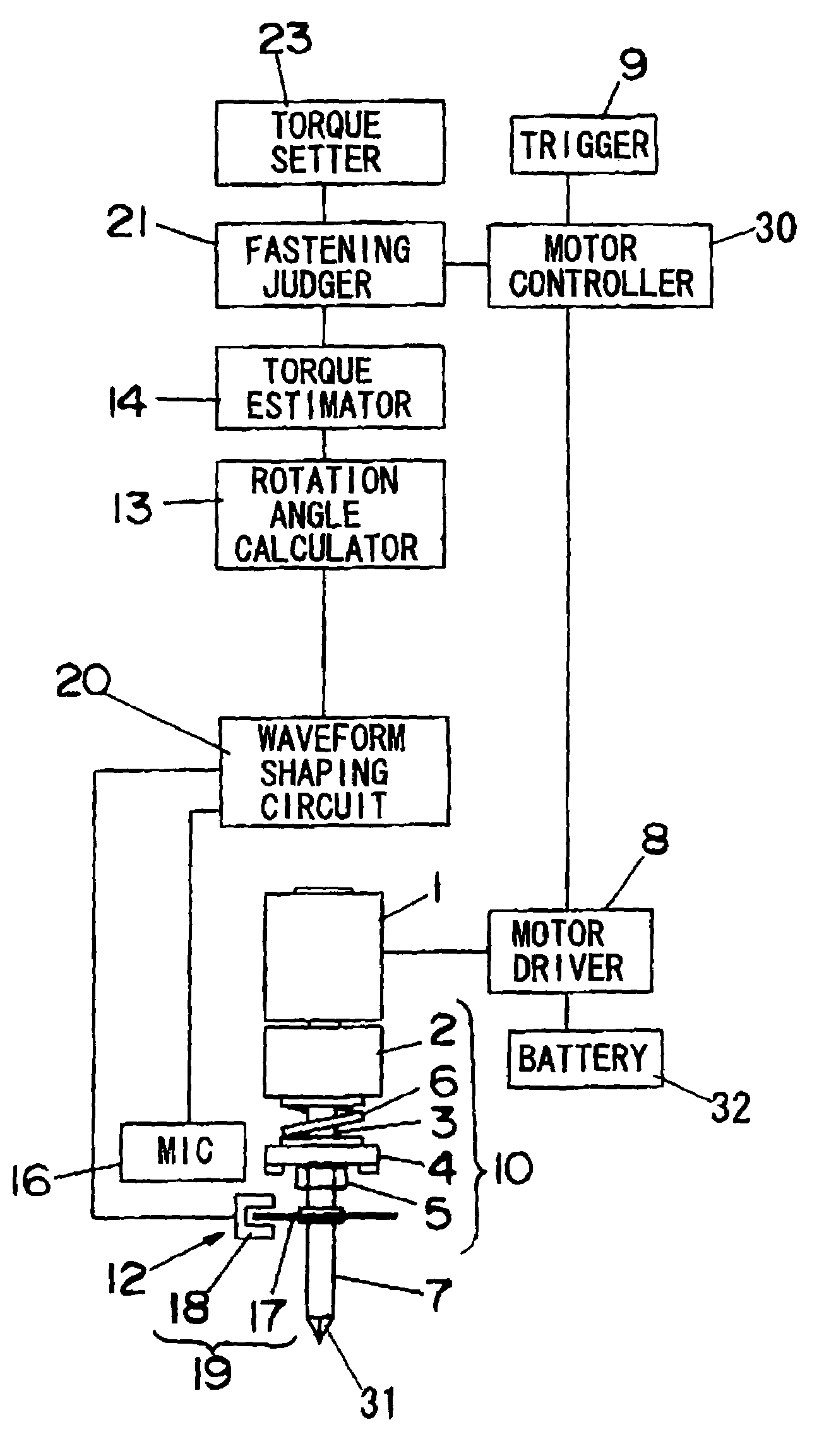
Power fastening tool
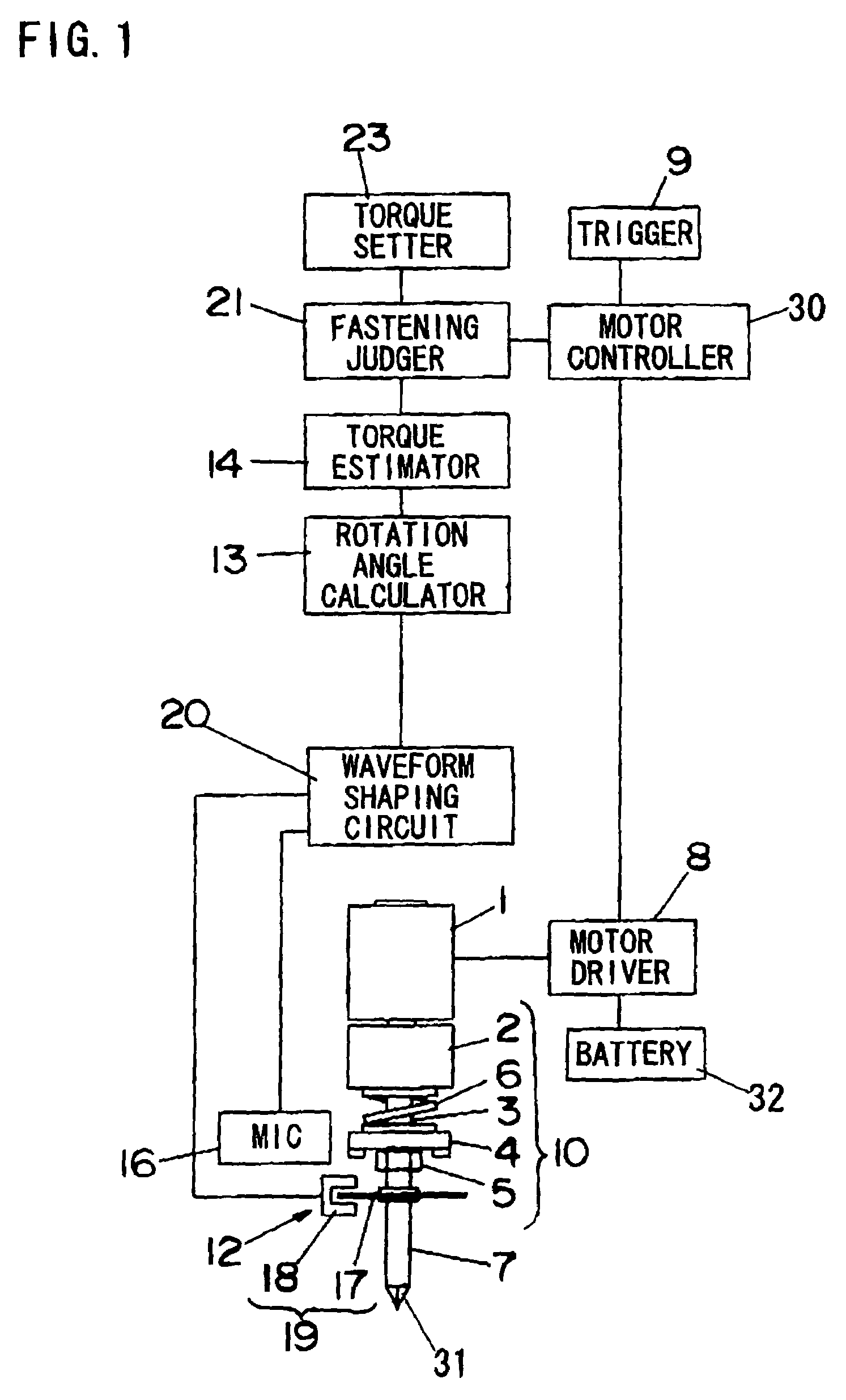
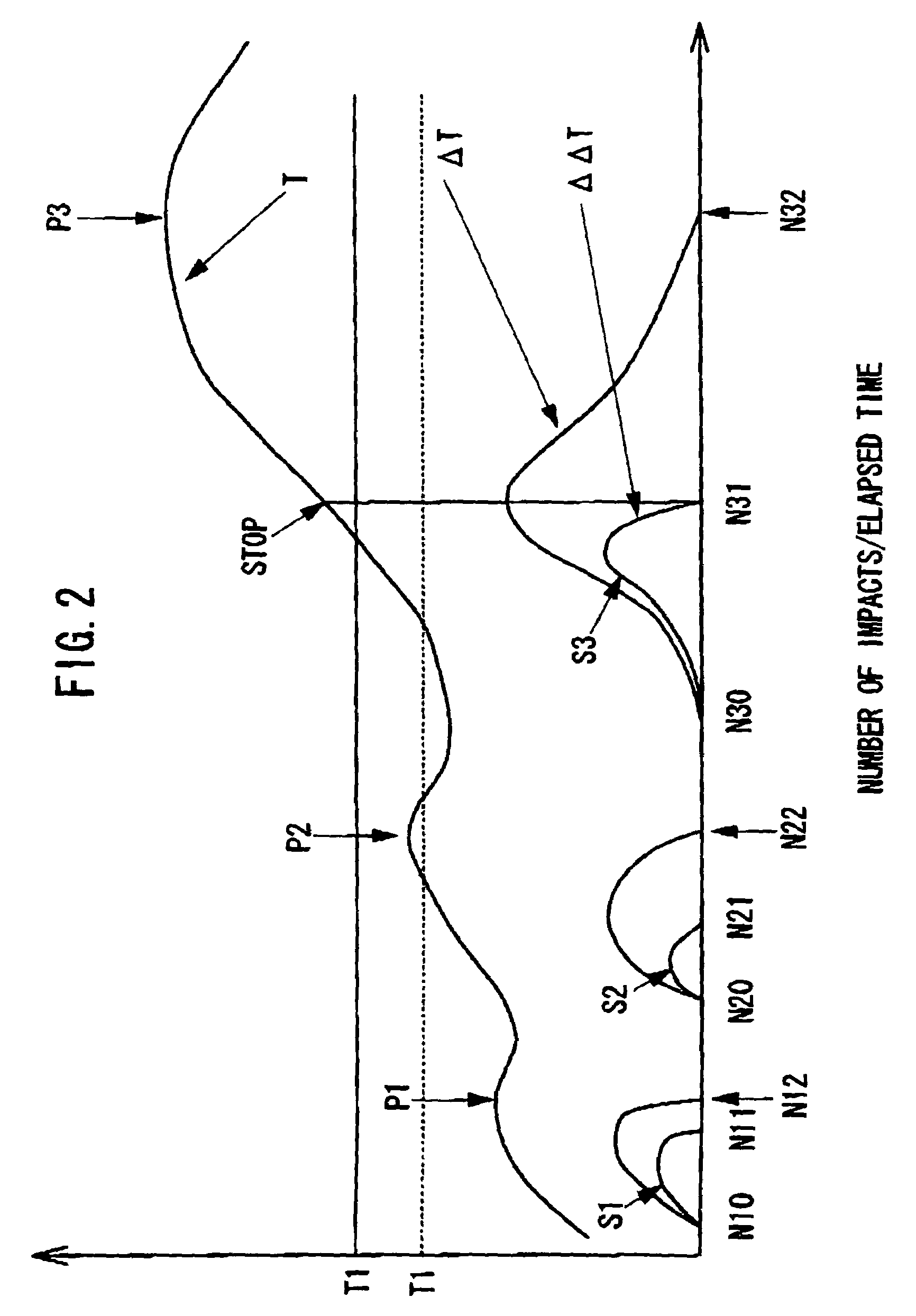
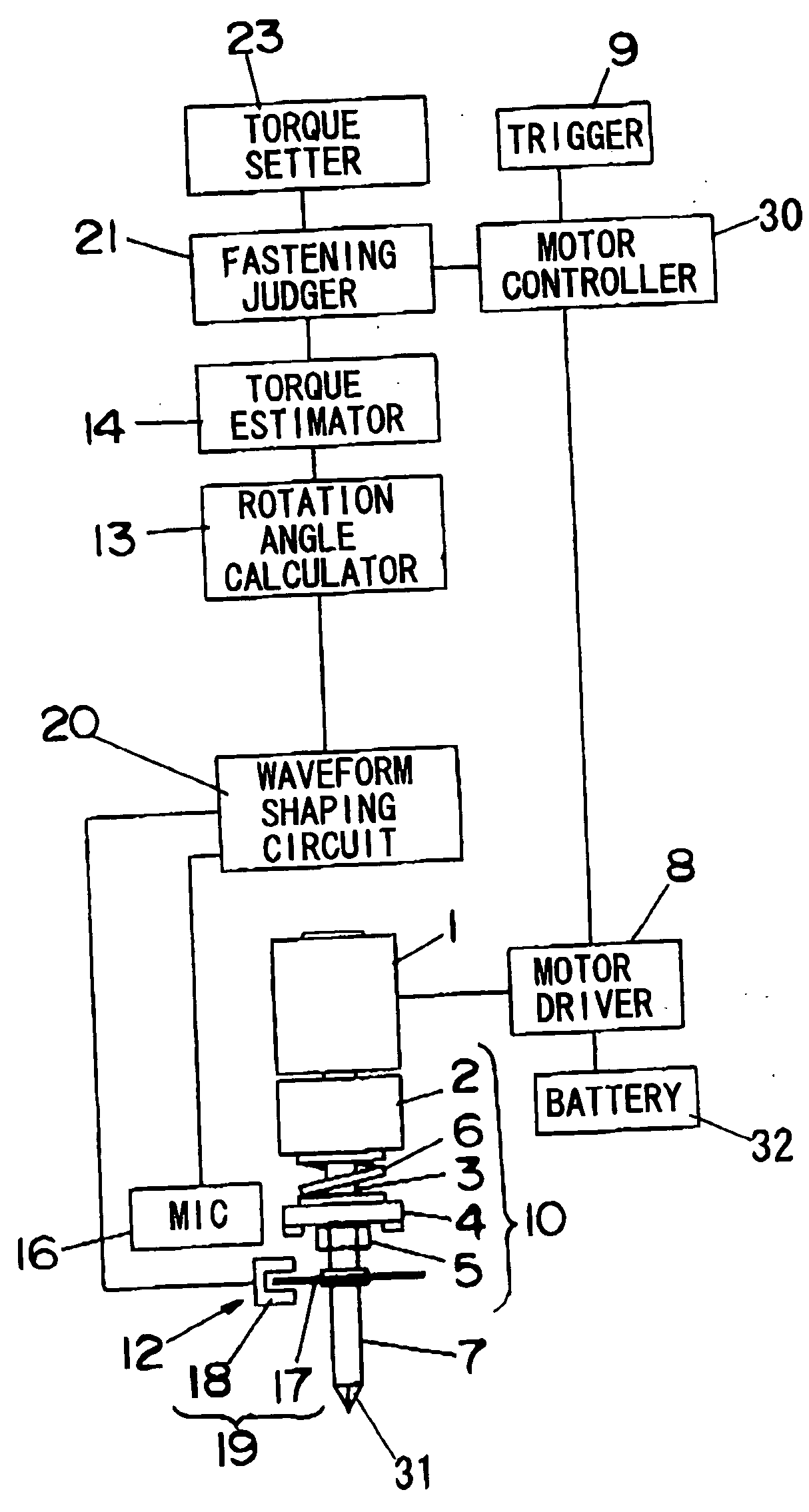
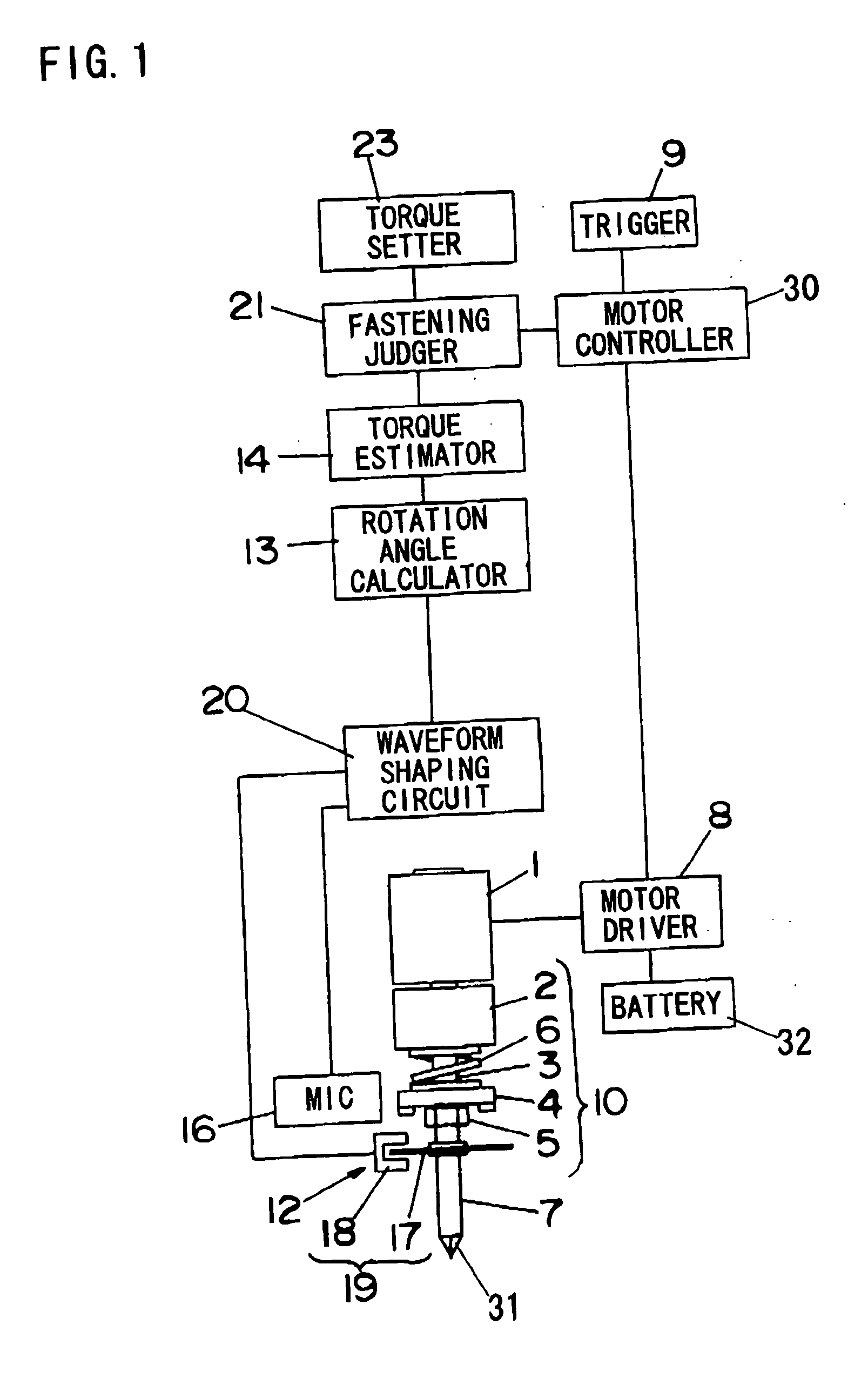
ActiveUS7155986B2Avoid stopAvoid difficult choicesMechanical power/torque controlMeasurement of torque/twisting force while tighteningLower limitControl theory
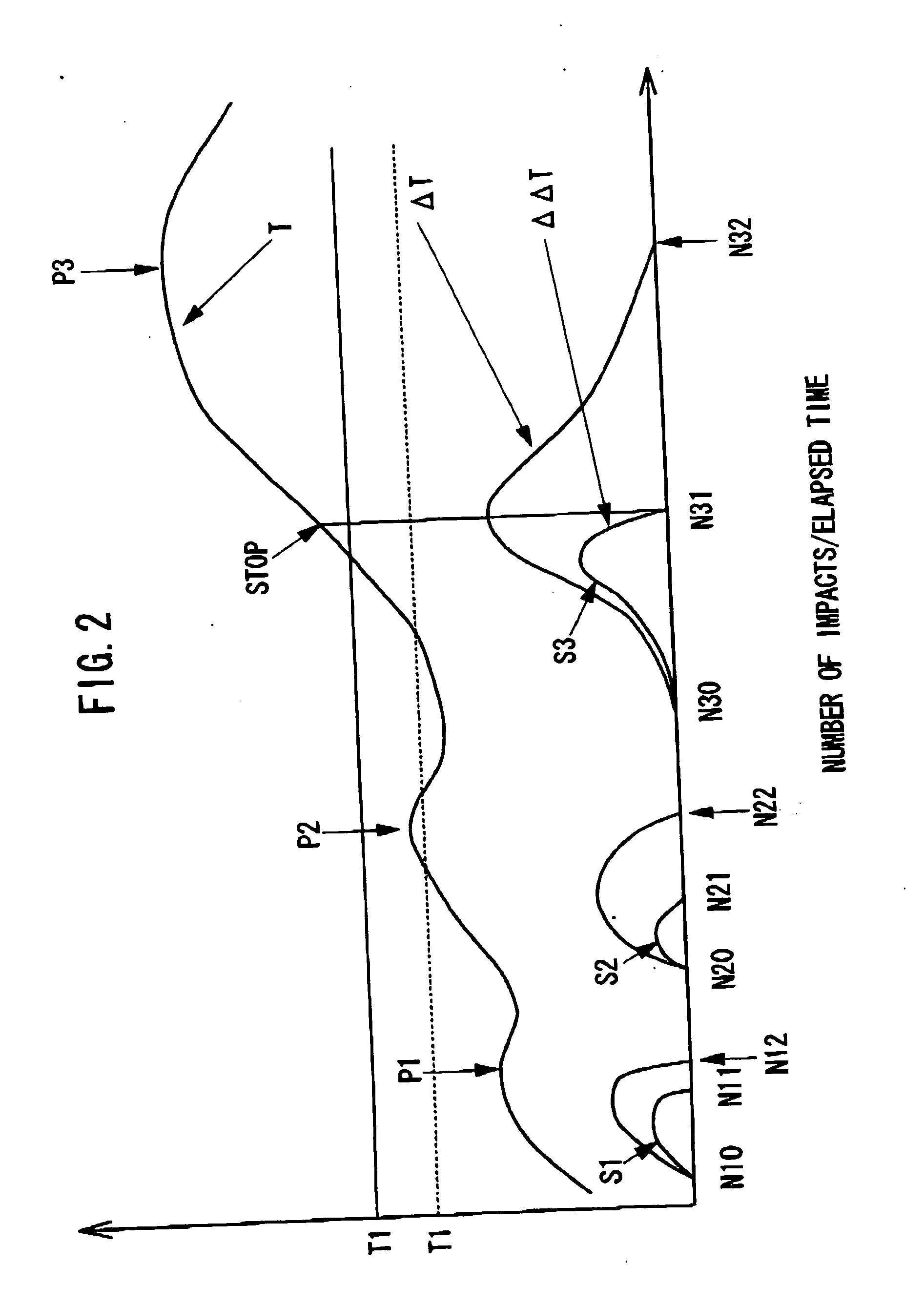
In a power fastening tool for fastening a fastening member such as a screw or a fastening member, malfunction that driving of a motor is stopped before the fastening member is fastened completely can be prevented. A fastening judger judges that the fastening operation is completed when a value of an estimated torque T for fastening the fastening member becomes larger than a predetermined lower limit value T1 previously set by a user and a value of a torque variation ratio ΔΔT varies from positive to negative. Thus, it is possible to prevent malfunction for stopping driving of a motor even when the value of the torque variation ratio ΔΔT varies from positive to negative due to trouble before the vale of the estimated torque T becomes larger than the lower limit value T1.
Owner:MATSUSHITA ELECTRIC WORKS LTD
Acceleration control apparatus for automobile dual-clutch transmission
ActiveCN101978188ASmooth accelerationIncrease connection volumeClutchesGearing controlGear trainControl theory
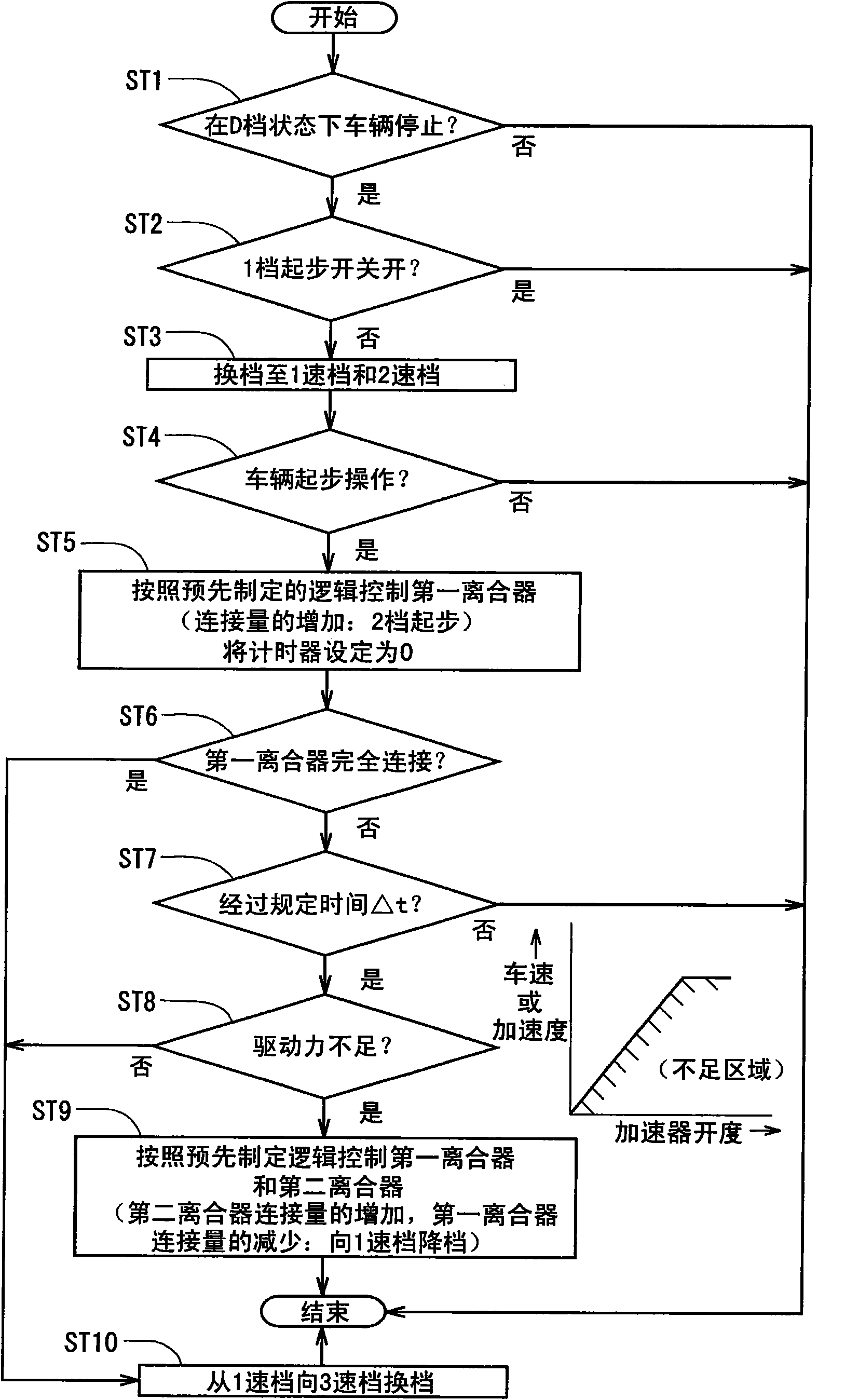
The present invention provides an acceleration control apparatus, at the start of a freight vehicle mounting a dual clutch type transmission in an ordinary condition, a smooth start is accomplished with the second speed, but the transmission is quickly shifted to the first speed when the vehicle is to start moving on the way of uphill road. At the start of the freight vehicle, first, the two input shafts of the dual clutch type transmission are set to a state of being shifted to the first speed and to the second speed and in this state, the amount of connection of the friction clutch coupled to the gear train of the second speed is increased to execute the second-speed start. After the passage of a predetermined period of time, the accelerator opening degree and the vehicle speed are detected to judge the excess or insufficiency of the driving force. If the driving force is not insufficient, the start with the second speed is continued to quickly accelerate the vehicle. If the driving force is judged to be insufficient, the friction clutch coupled to the gear train of the first speed is readily connected. The transmission has been shifted already to the gear train of the first speed. Therefore, the transmission is shifted down in a short period of time avoiding unexpected occurrence such as moving back of the vehicle even on an uphill road vehicle.
Owner:ISUZU MOTORS LTD
Image forming apparatus
InactiveUS20120008974A1Suppress position deviationImproper transferElectrographic process apparatusLatent imageImage formation
An image forming apparatus includes a rotatable image bearing member; a cleaning blade for removing toner in contact with the image bearing member; a load adjusting device for adjusting a contact load between the cleaning blade and the image bearing member; a developing roller for developing an electrostatic latent image on the image bearing member; a developing roller moving device for moving the developing roller between a developing position in which the electrostatic latent image is to be developed and a non-developing position retracted from the developing position; and a control device for effecting control such that the developing roller is moved from the developing position to the non-developing position by the developing roller moving device during rotation of the image bearing member and after an area on the image bearing member opposed to the developing roller at the time when the developing roller is started to be moved from the developing position to the non-developing position passes through a contact area between the cleaning blade and the image bearing member, the contact load is made smaller than that during development by the load adjusting device and then the rotation of the image bearing member is stopped.
Owner:CANON KK
Power tool
ActiveUS8067913B2Avoid stopAvoid failureMotor/generator/converter stoppersAC motor controlEngineeringPower tool
The controller determines the presence or absence of operation of the trigger switch according to an ON / OFF state of the main contact of the trigger switch and designating the rotation speed of the motor based on a signal outputted from the speed contact. The controller stops the rotation of the motor, after the trigger switch is activated and the main contact is turned ON and the motor is driven according to a signal outputted from the speed contact, when an OFF state of the main contact is detected, only in the case where a signal value outputted from the speed contact is a predetermined value or less.
Owner:KOKI HLDG CO LTD
Radiation therapy treatment planning machine
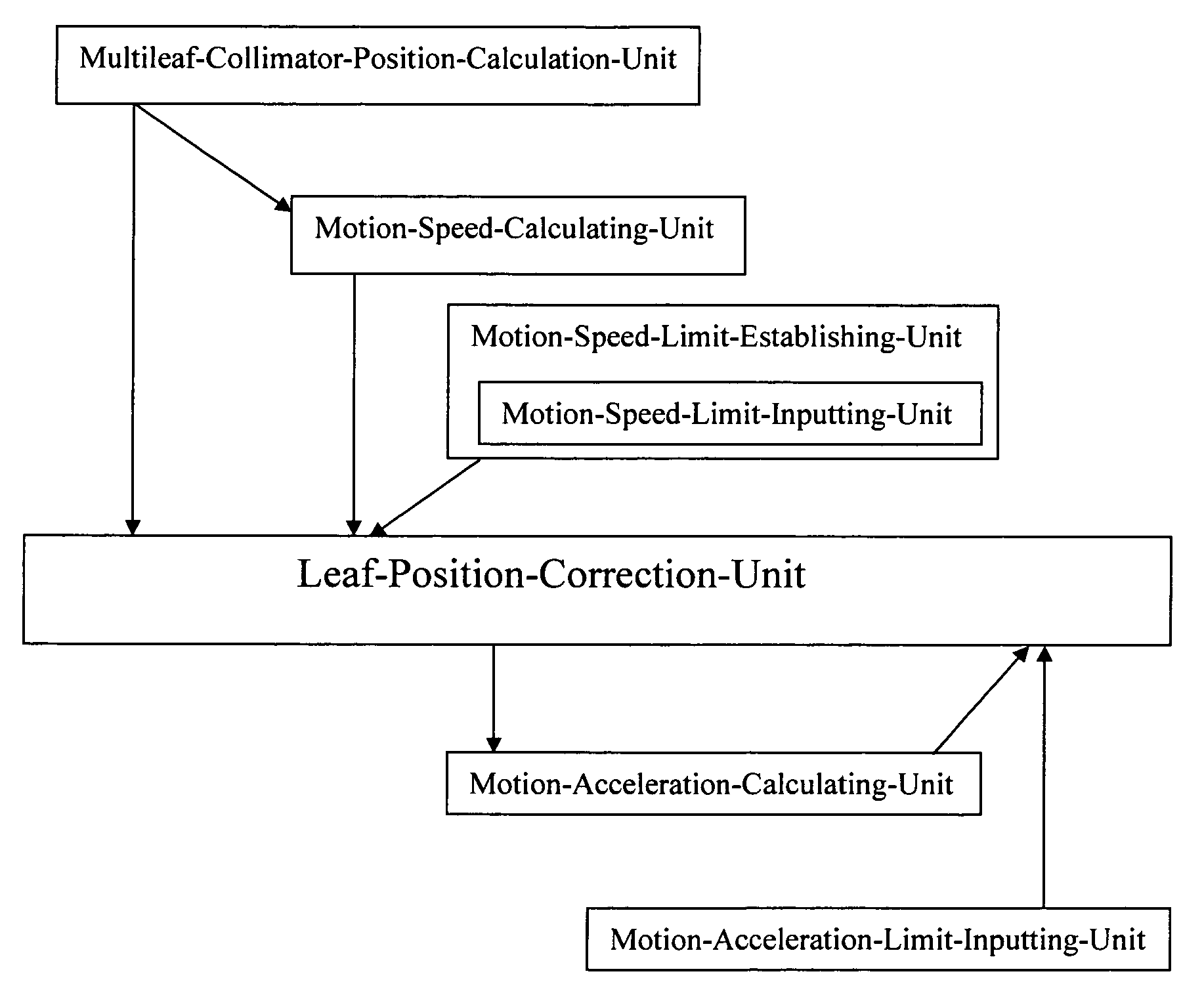
InactiveUS6999556B2Avoid stopHandling using diaphragms/collimetersComputerised tomographsEngineeringConformal Therapy
In an RTP machine, for a series of leaf positions which are generated by a Multileaf-Collimator-Position-Calculation-Unit, a speed limit is established by a Motion-Speed-Limit-Establishing-Unit. Further, a Motion-Display-Unit indicates the area where motion speed exceeds the established speed and / or a Leaf-Position-Correction-Unit controls the area in order to be equal to or less than the established speed limit. Furthermore, a Motion-Acceleration-Calculating-Unit calculates motion acceleration of the multileaf collimator, and the Motion-Display-Unit indicates the area where the calculated motion acceleration exceeds the established limit and / or the Leaf-Position-Correction-Unit controls the area in order to be equal to or less than the established acceleration limit. An interruption of irradiation due to a multileaf collimator positioning error is prevented while the treatment is being conducted by the multileaf collimator motion limit control in radiation therapy such as conformal therapy or others which the multileaf collimator moves in during irradiation.
Owner:NAKANO SYST
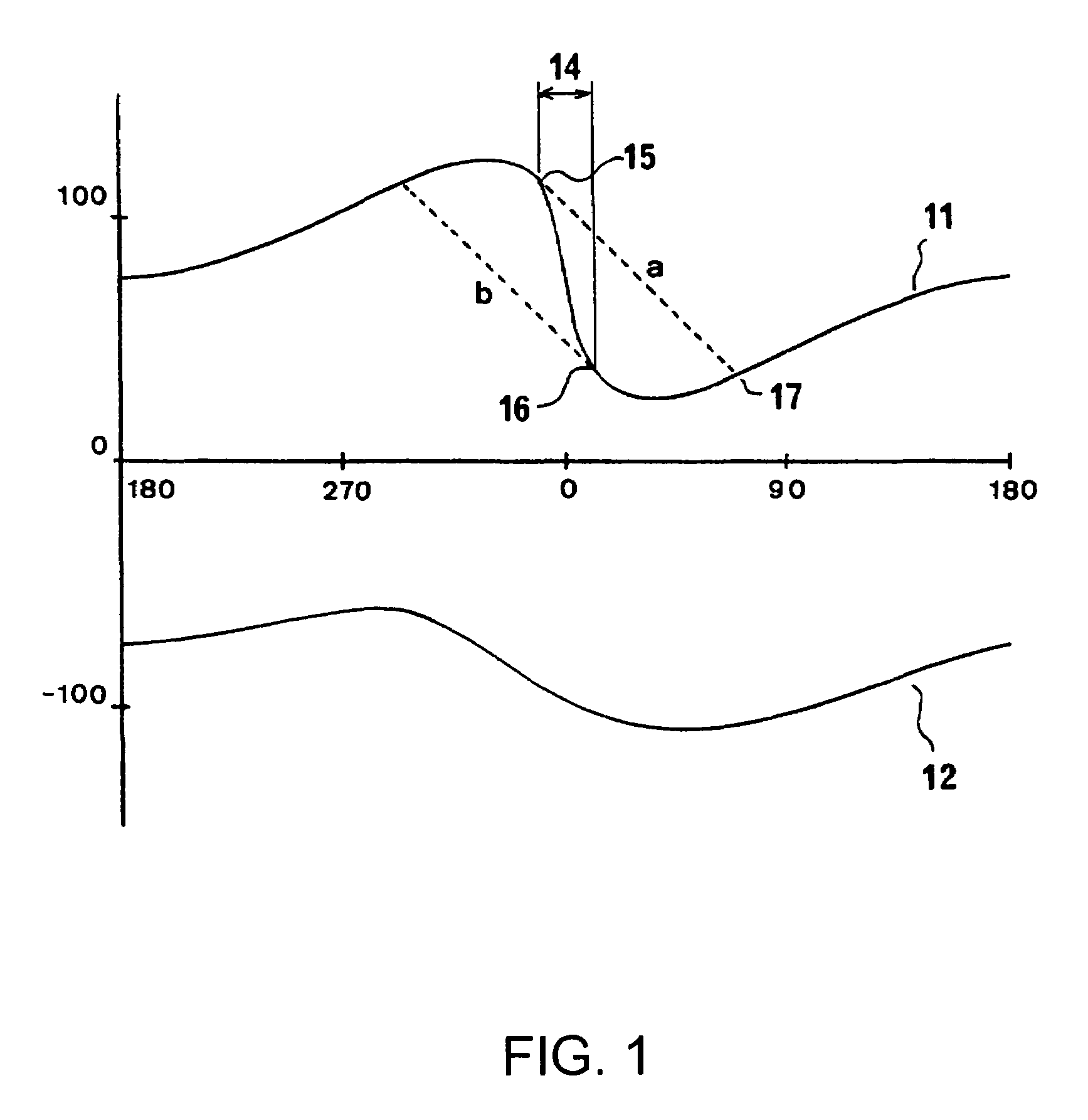
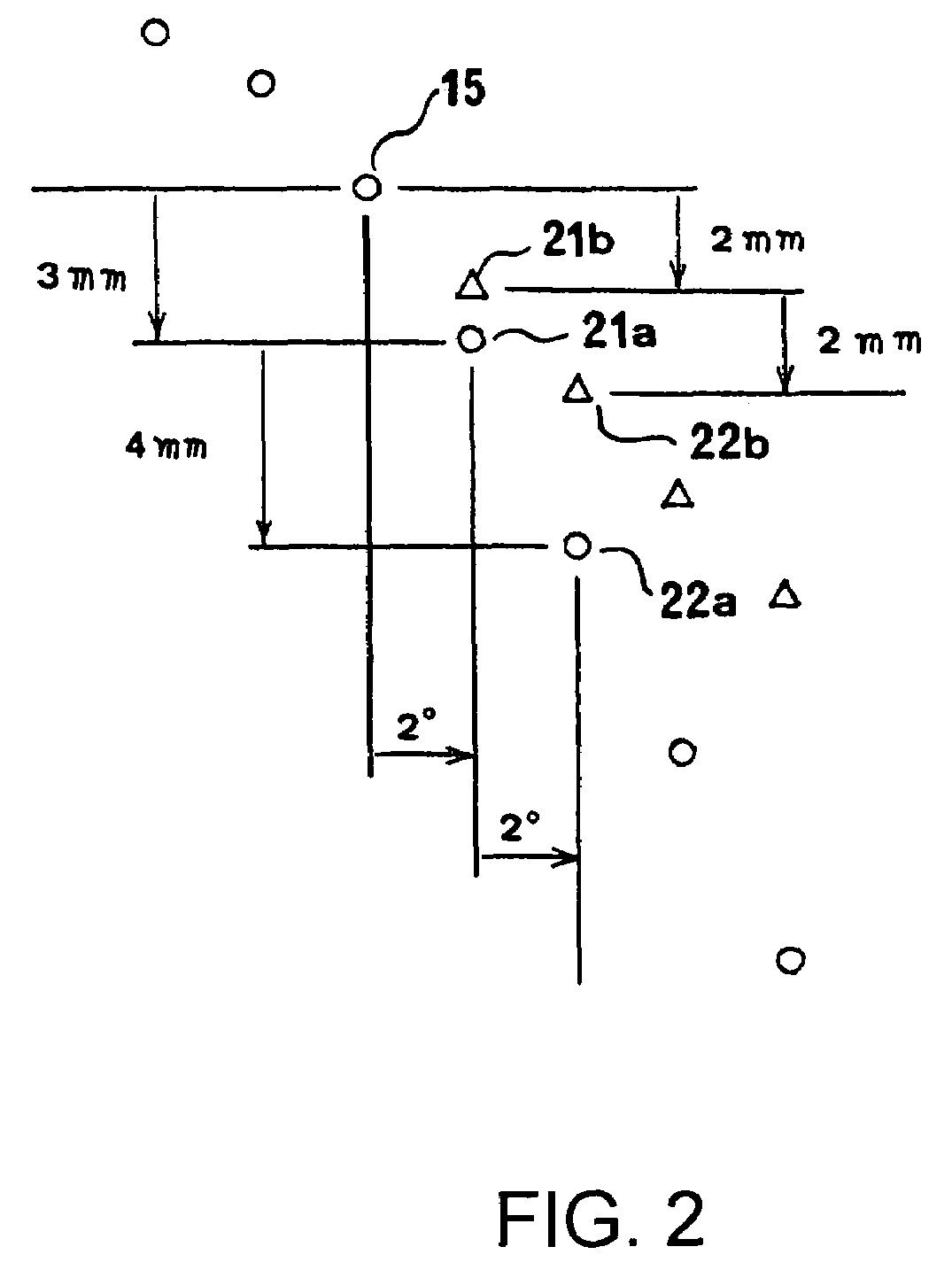
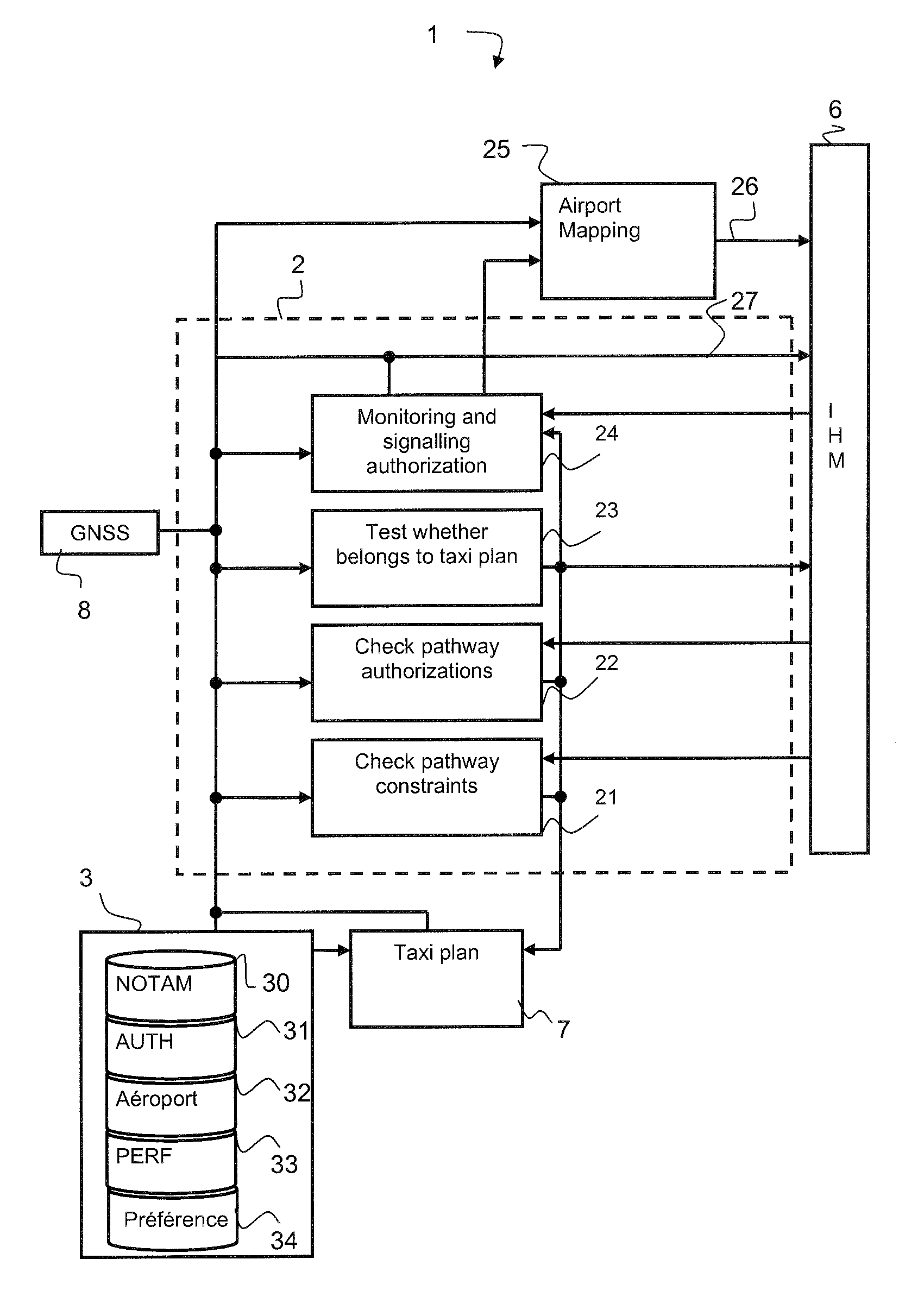
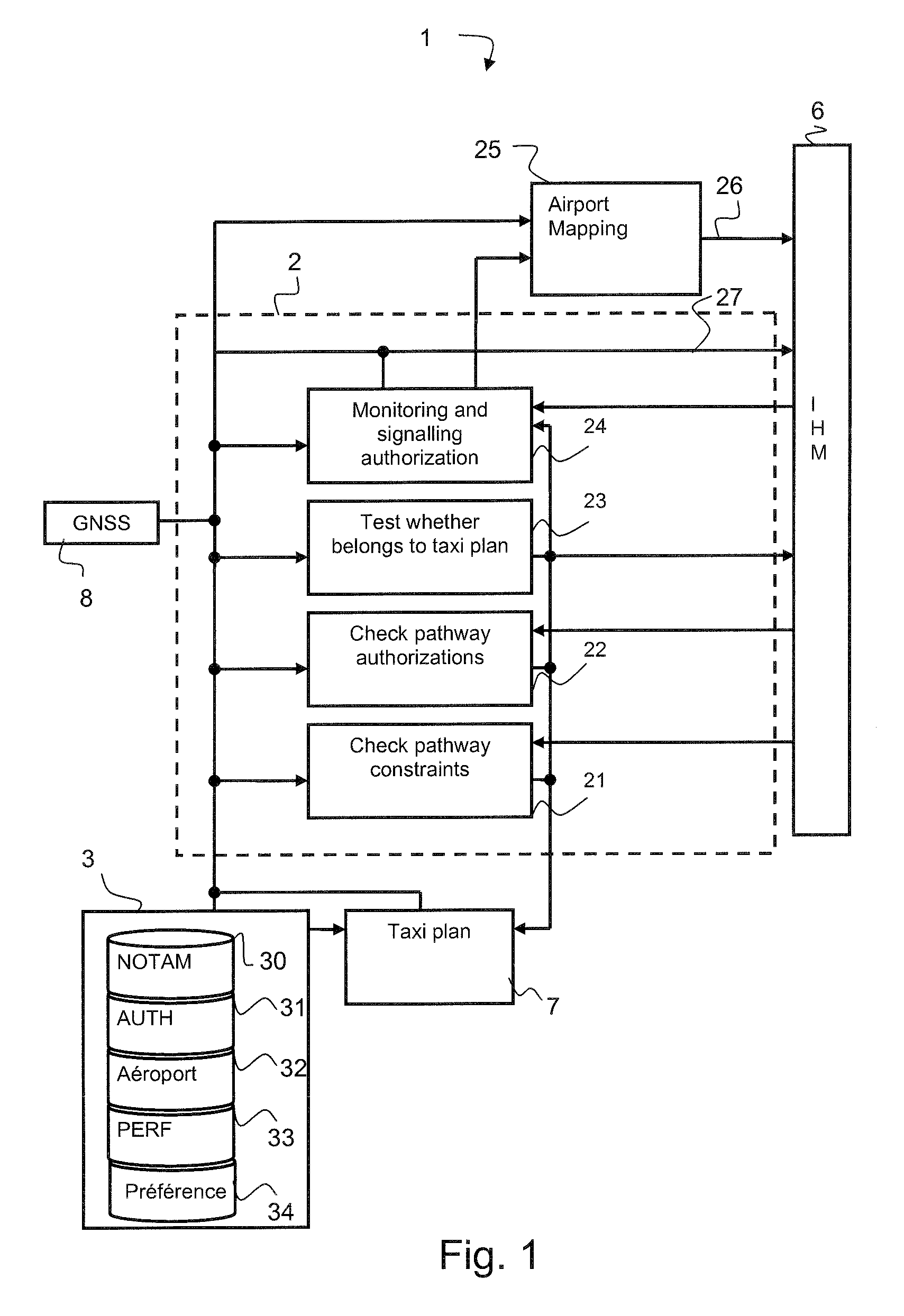
Method and System for Monitoring an Aircraft Taxiing Phase
ActiveUS20100114922A1Improve safetyImprove securityAnalogue computers for vehiclesDirection finders using radio wavesSignal onAirplane
The invention relates to the field of monitoring and aid to taxiing of an aircraft at an airport.The invention is a method of checking and monitoring the taxi plan and relates to a monitoring system comprising means for checking the pathway of the plan and means for signalling on the taxi aid the waiting time for the next clearance ahead of the aircraft along the pathway, the means for checking the pathway comprising a device for checking the pathway constraints and a device for checking the clearances, the device for checking the constraints making it possible to test and to display on the taxi plan the information descriptive of the constraints and the device for checking the clearances making it possible to check the clearances and to add the missing clearances to the taxi plan.
Owner:THALES SA
Control device for hybrid drive-type elevator
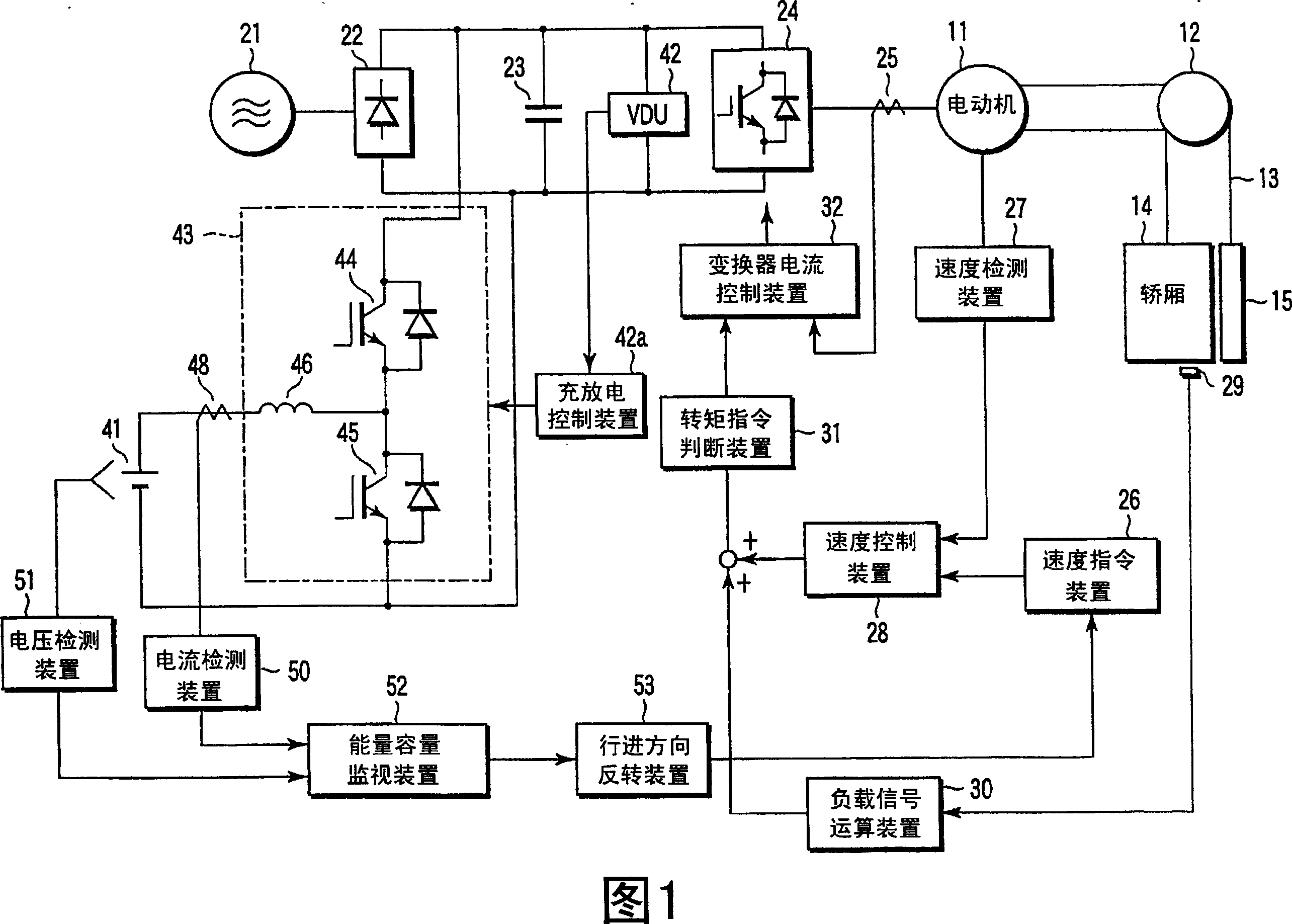
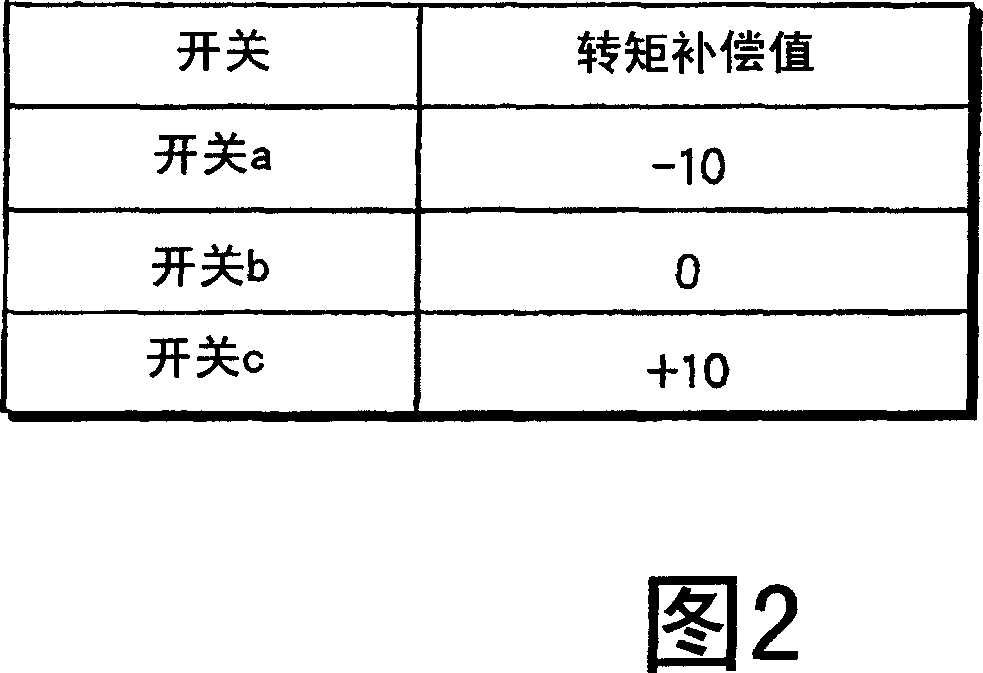
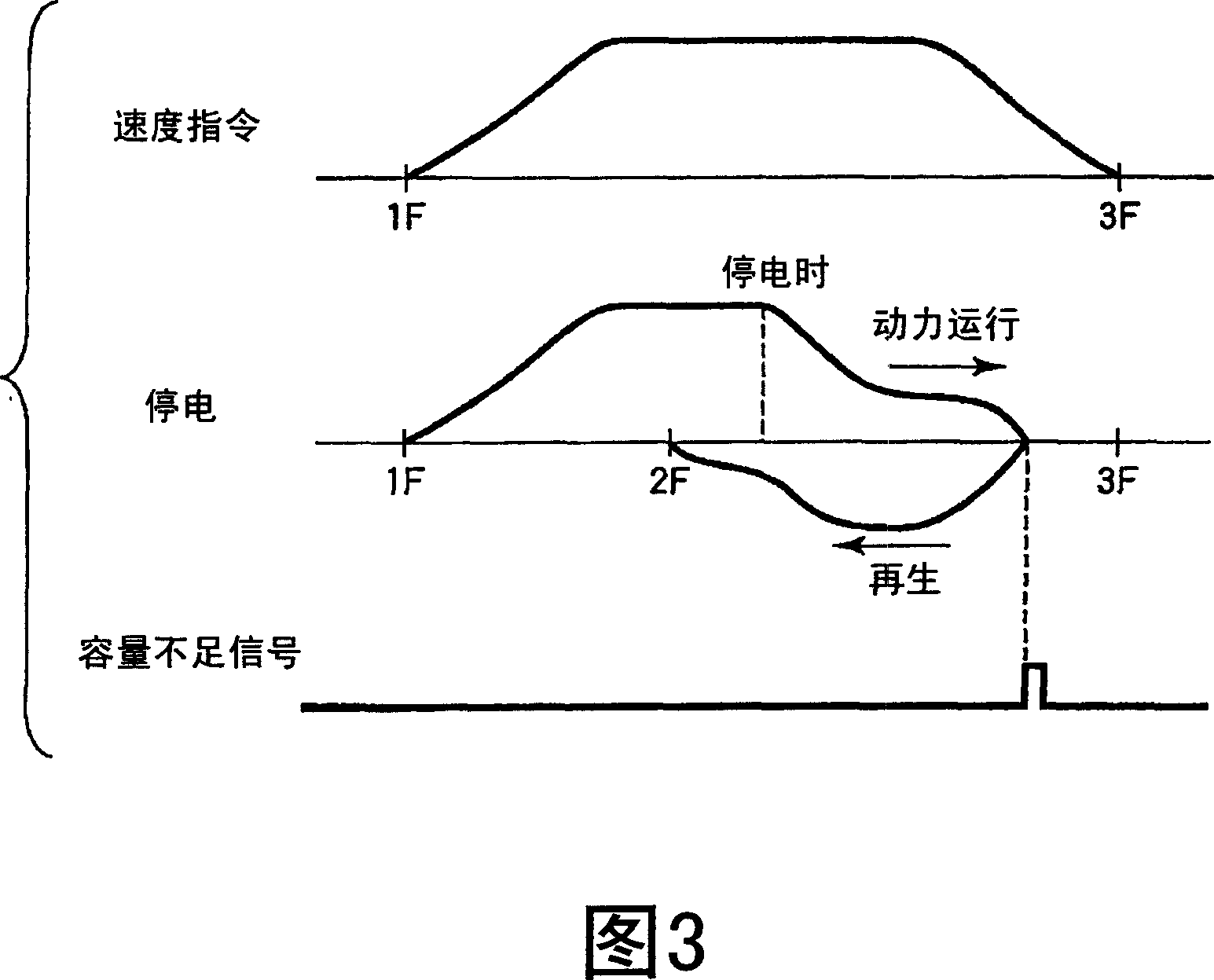
An electricity storage device (41) stores energy produced in regenerative operation of a cage (14) and supplies the stored energy to a drive system of the cage (14) in powered operation. A control device for hybrid drive-type elevator monitors energy capacity of the electricity storage device (41), and when the energy capacity is below a predetermined capacity, the control device changes the direction of travel of the cage (14) from a powered direction to a regeneration direction and stops the cage at the nearest floor. This prevents the cage (14) from stopping between floors due to the lack of energy to secure the safety of passengers.
Owner:TOSHIBA ELEVATOR KK
Vehicle air-conditioner control system
InactiveUS20090193825A1Reduce disagreeablenessSufficient air conditioningAir-treating devicesRailway heating/coolingControl systemEngineering
A vehicle air-conditioner control system according to the present invention activates an air conditioner in response to a command from an air-conditioner remote controller before a passenger is onboard, controls the air conditioner based on a heat load detected by a heat load detector, controls the air conditioner to be set in a silent mode so as not to make the passenger feel uncomfortable due to an air-conditioning wind when a passenger-proximity determiner determines that the passenger is proximate to the vehicle.
Owner:CALSONIC KANSEI CORP
Emergency braking warning system and emergency braking warning method
The invention relates to an emergency braking warning system, which is provided with a controller and an emergency braking warning lamp. The controller comprises an acquisition unit, a speed comparison unit, a time-keeping unit and a judgement unit; the acquisition unit acquires a braking signal and a speed signal, and the speed at the moment when the braking signal becomes effective is adopted as an initial speed value; the speed comparison unit acquires the initial speed value from the acquisition unit and compares the initial speed value with an emergency braking speed threshold; when the initial speed value is greater than the threshold, the time-keeping unit gives and provides emergency braking duration for the acquisition unit, and according to the emergency braking duration, the acquisition unit monitors the speed signal and adopts the speed reaching the emergency braking duration as a final speed value; the judgement unit acquires the initial speed value, the final speed valueand the emergency braking duration and determines an acceleration threshold in order to determine average acceleration and compare the average acceleration with the acceleration threshold to judge emergency braking; and the higher the initial speed value is, the shorter the emergency braking duration is and / or the lower the acceleration threshold is.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
Power fastening tool
ActiveUS20050109520A1Easily selectAvoid stopMechanical power/torque controlMeasurement of torque/twisting force while tighteningLower limitControl theory
In a power fastening tool for fastening a fastening member such as a screw or a fastening member, malfunction that driving of a motor is stopped before the fastening member is fastened completely can be prevented. A fastening judger judges that the fastening operation is completed when a value of an estimated torque T for fastening the fastening member becomes larger than a predetermined lower limit value T1 previously set by a user and a value of a torque variation ratio ΔΔT varies from positive to negative. Thus, it is possible to prevent malfunction for stopping driving of a motor even when the value of the torque variation ratio ΔΔT varies from positive to negative due to trouble before the vale of the estimated torque T becomes larger than the lower limit value T1.
Owner:MATSUSHITA ELECTRIC WORKS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com