Patents
Literature
209 results about "Concurrent user" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
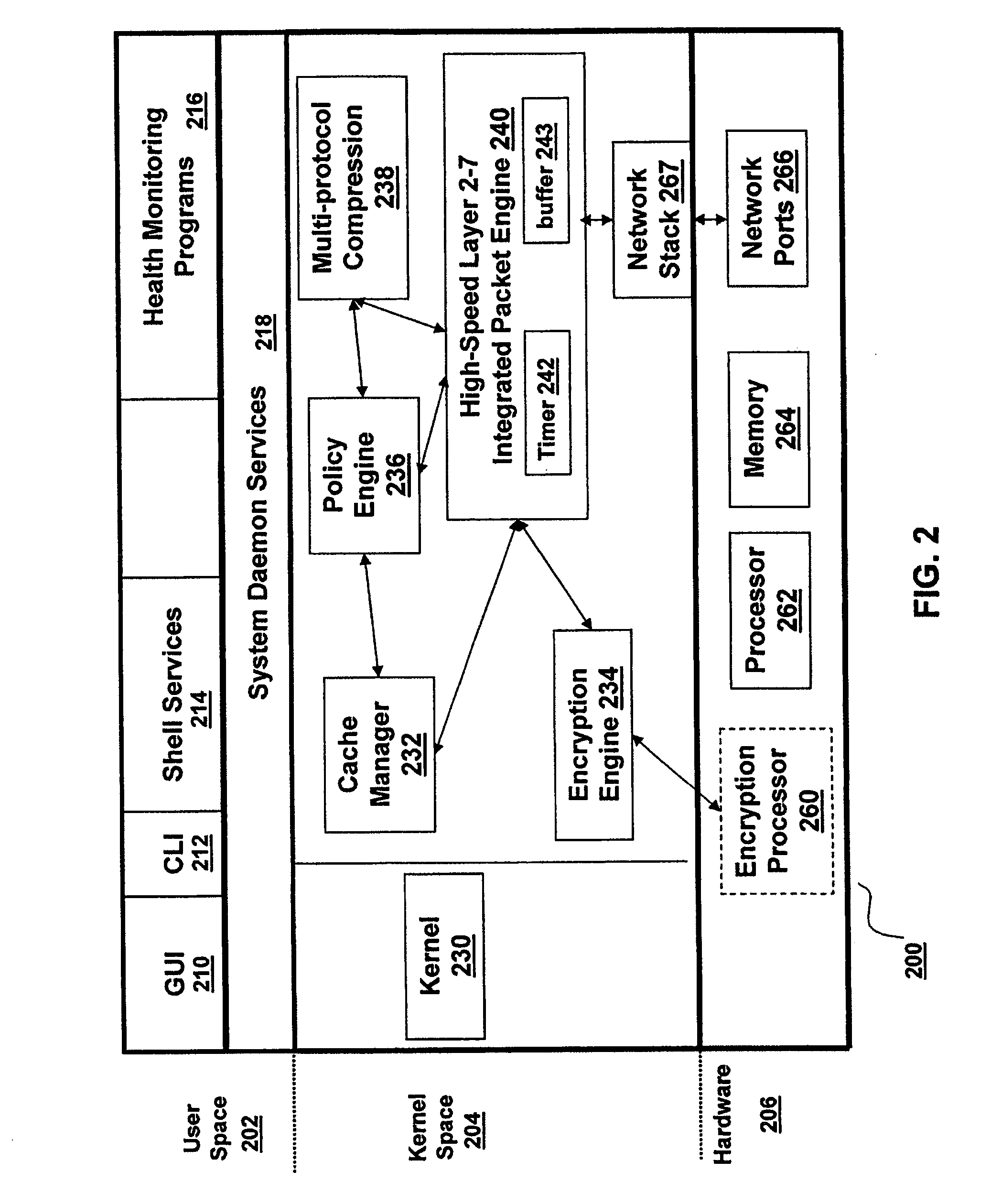
In computer science, the number of concurrent users for a resource in a location, with the location being a computing network or a single computer, refers to the total number of people simultaneously accessing or using the resource. The resource can, for example, be a computer program, a file, or the computer as a whole.
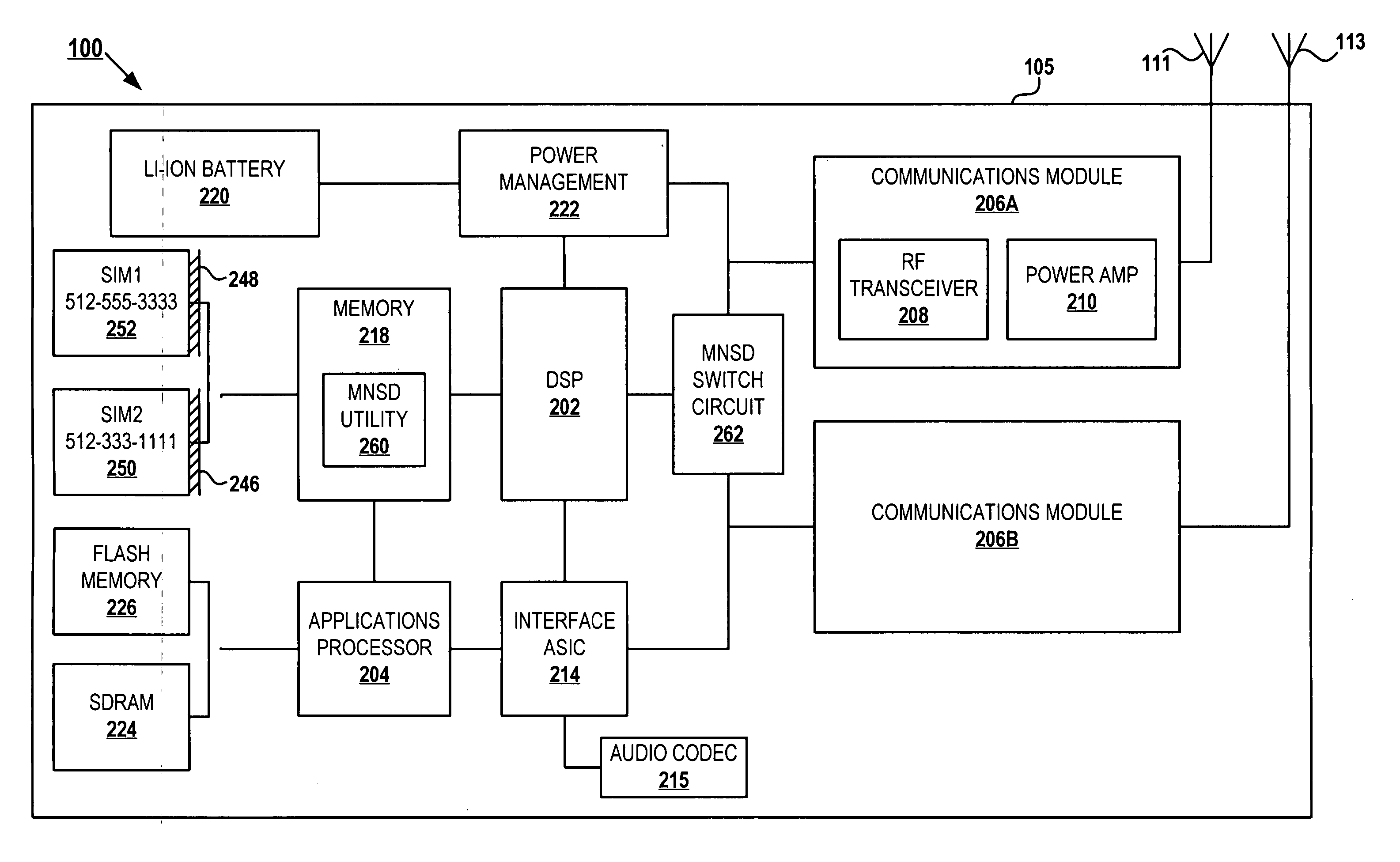
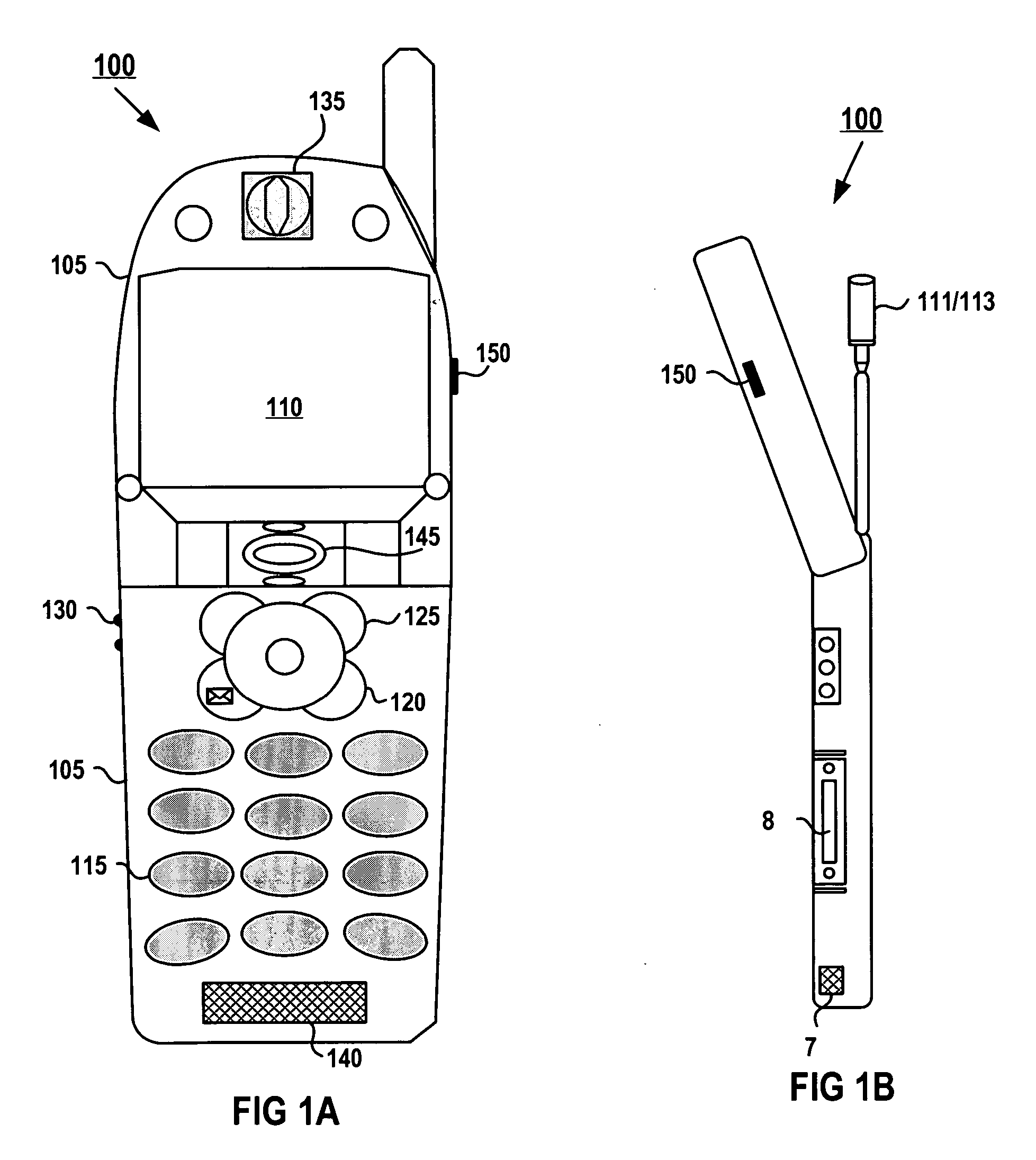
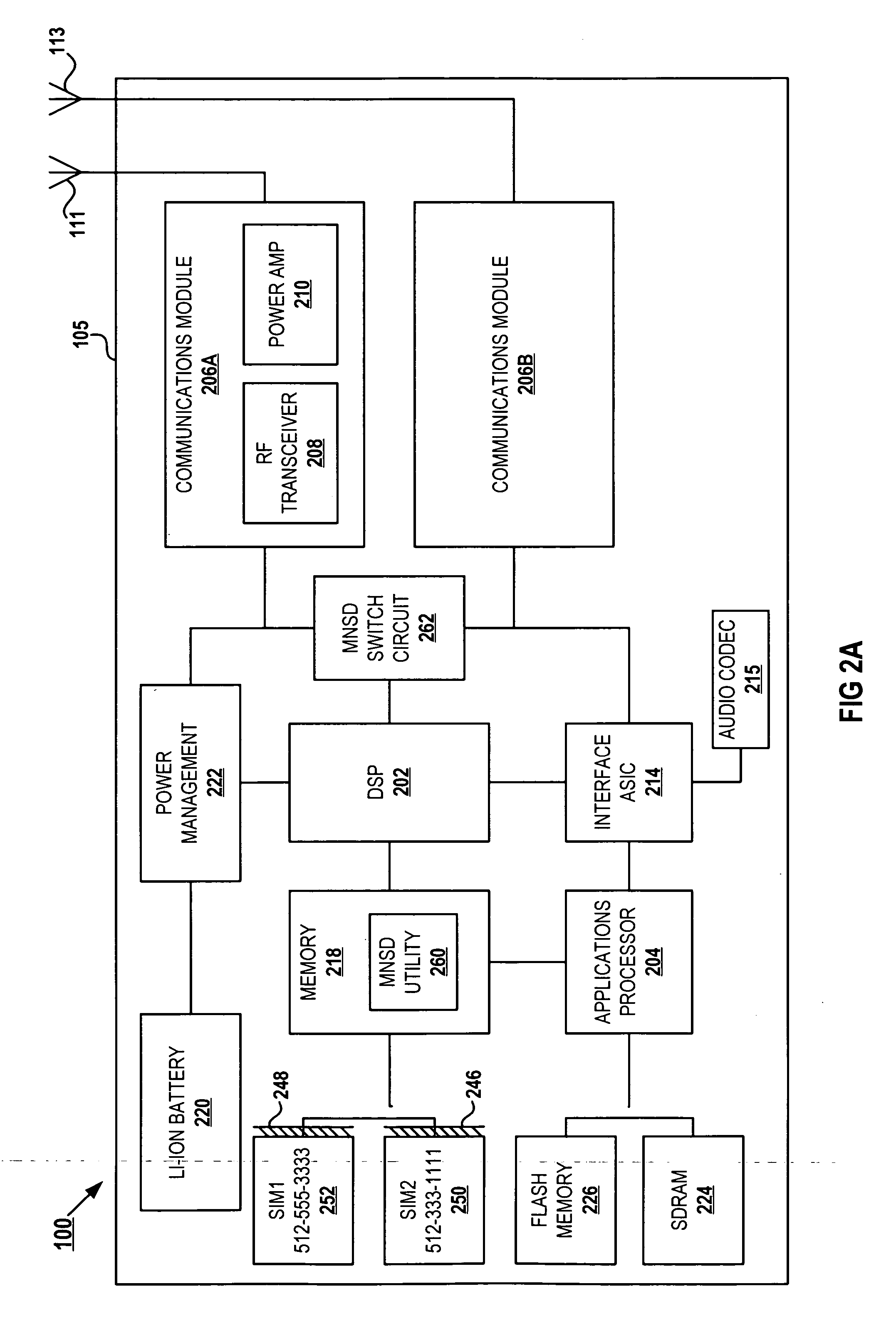
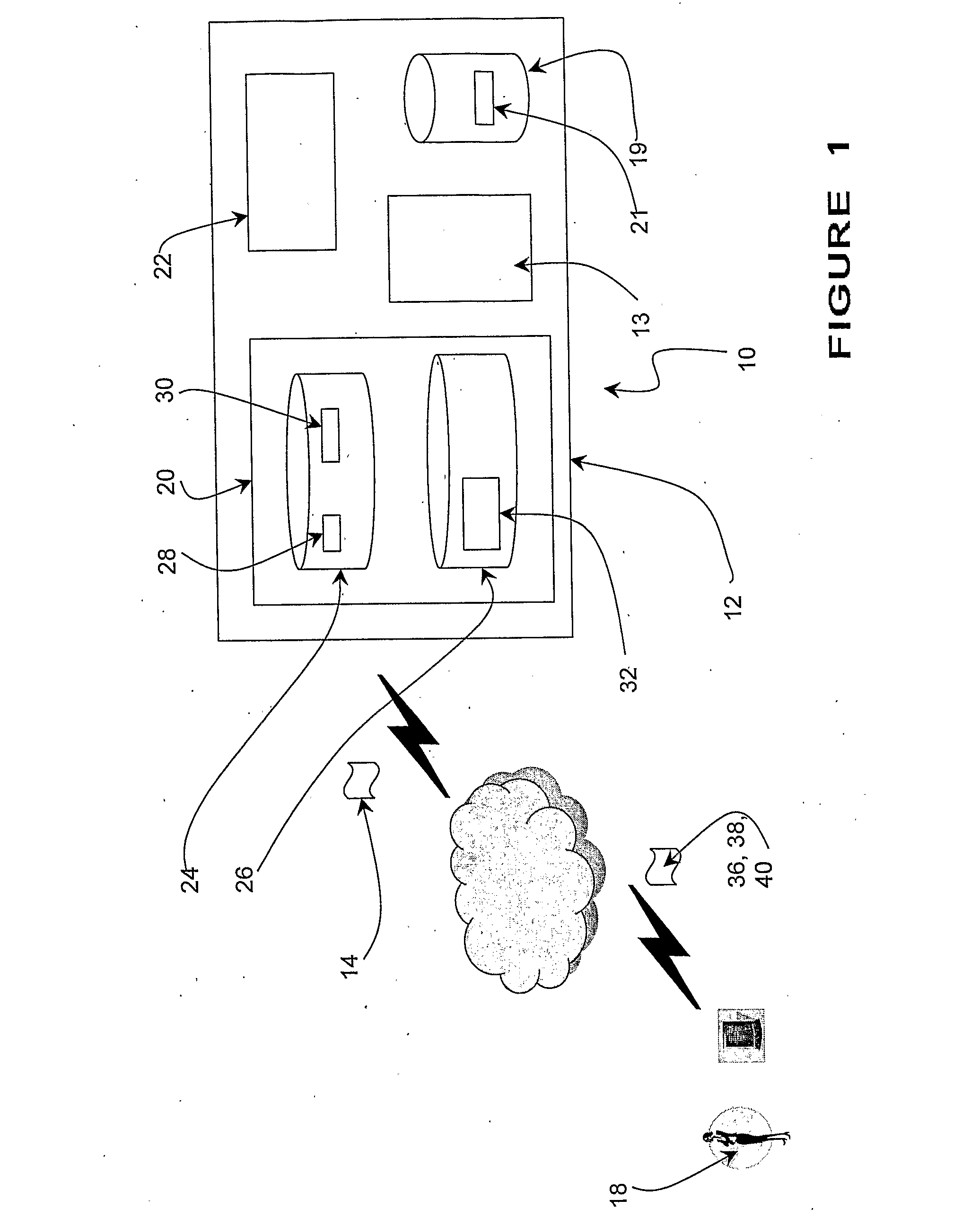
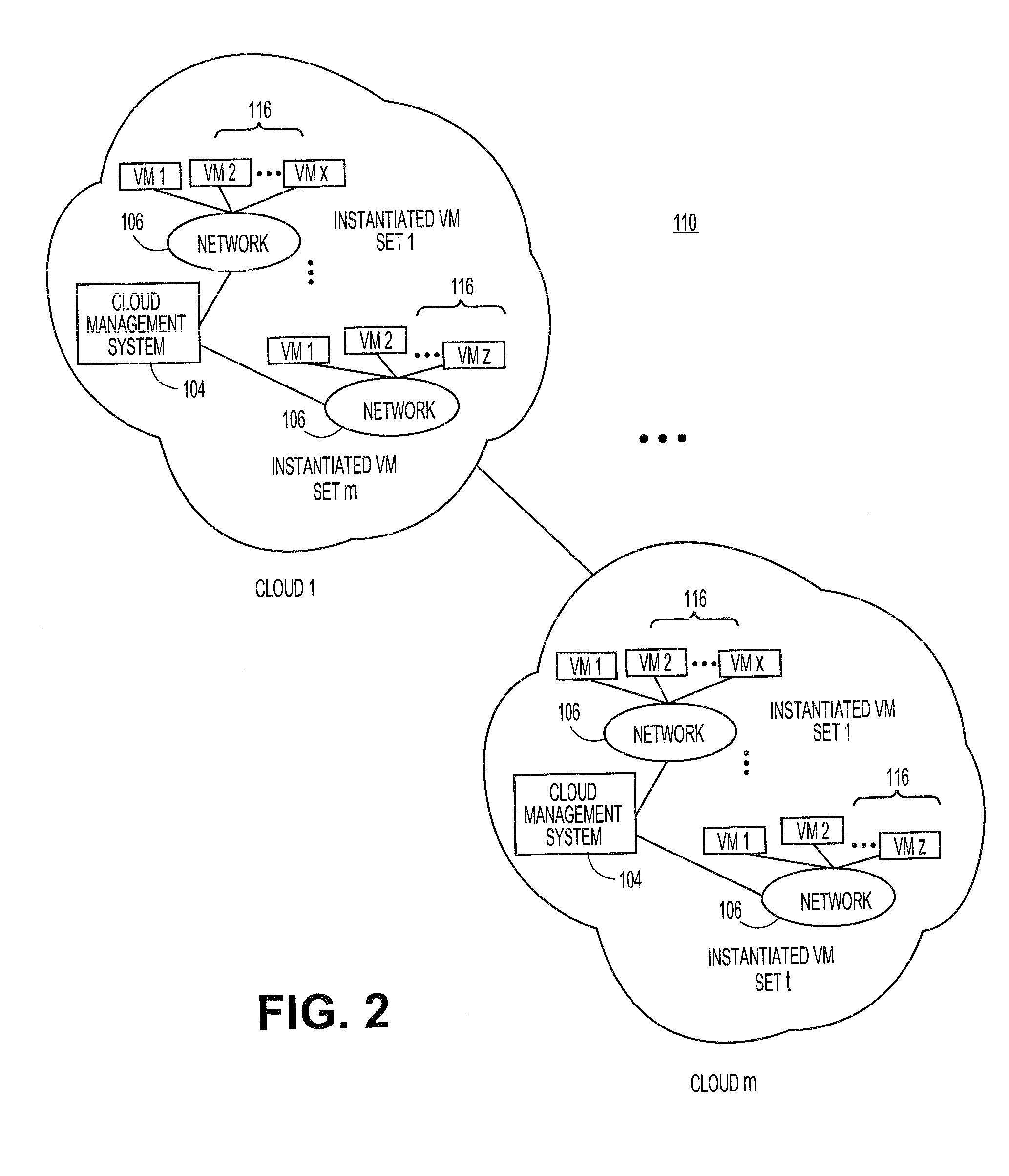
Single wireless communication device with multiple, concurrent subscriber number capability
InactiveUS20060234693A1Special service for subscribersCommmunication supplementary servicesTelecommunicationsCommunication device
A wireless communication device, a method, and a computer program product that enable multiple subscriber numbers to be concurrently assigned to and supported within a single communication device, such as a wireless / cellular phone. The communication device is designed with circuit components and logic that allows two or more subscriber numbers to be concurrently programmed into the device. Each subscriber number is individually supported, with the logic also providing some overlapping functionality. A user selectively utilizes one of the subscriber numbers to originate a new call out and / or accept an incoming call to that subscriber number and may toggle between subscriber numbers to communicate on.
Owner:E PRINCE
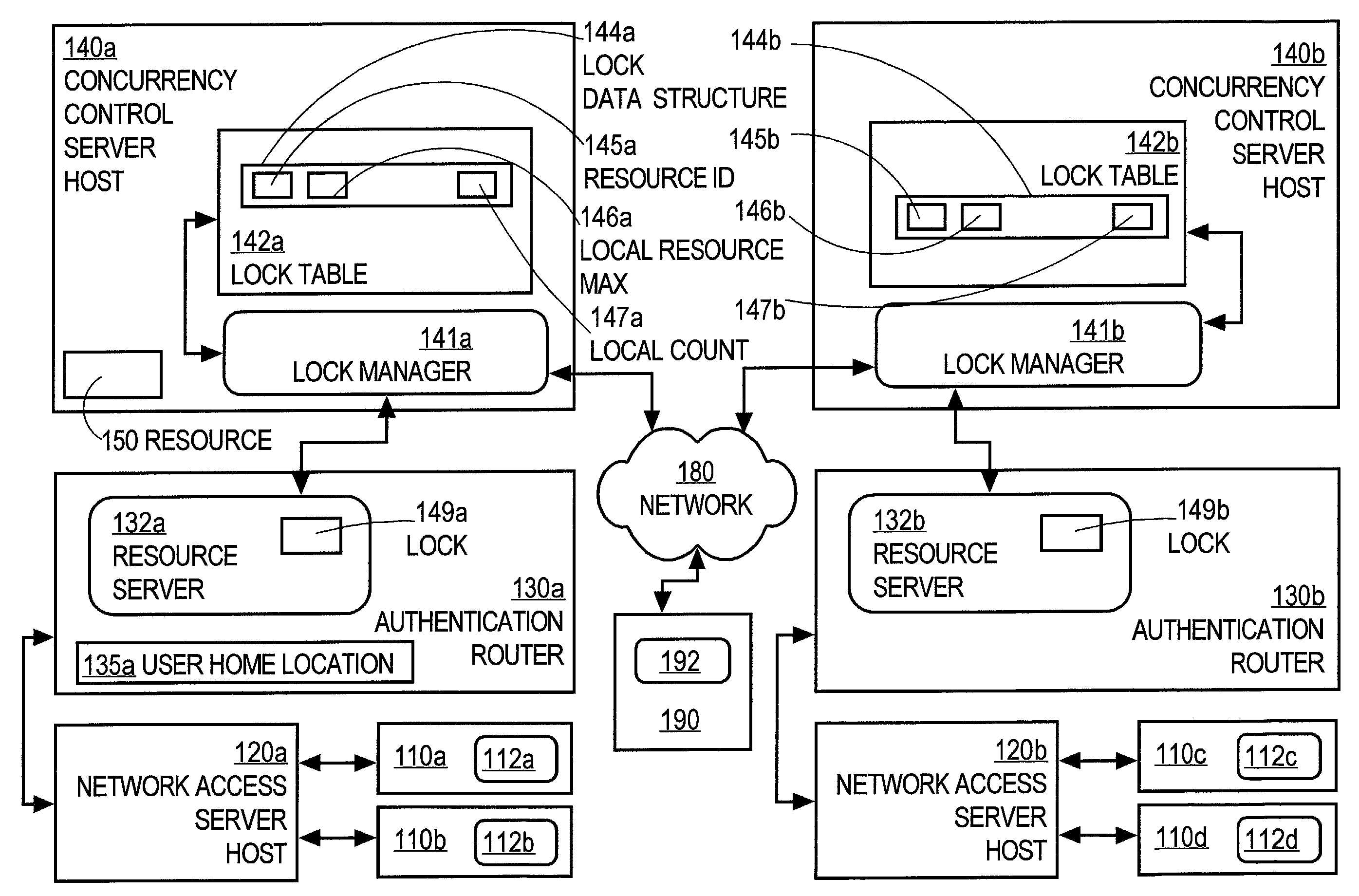
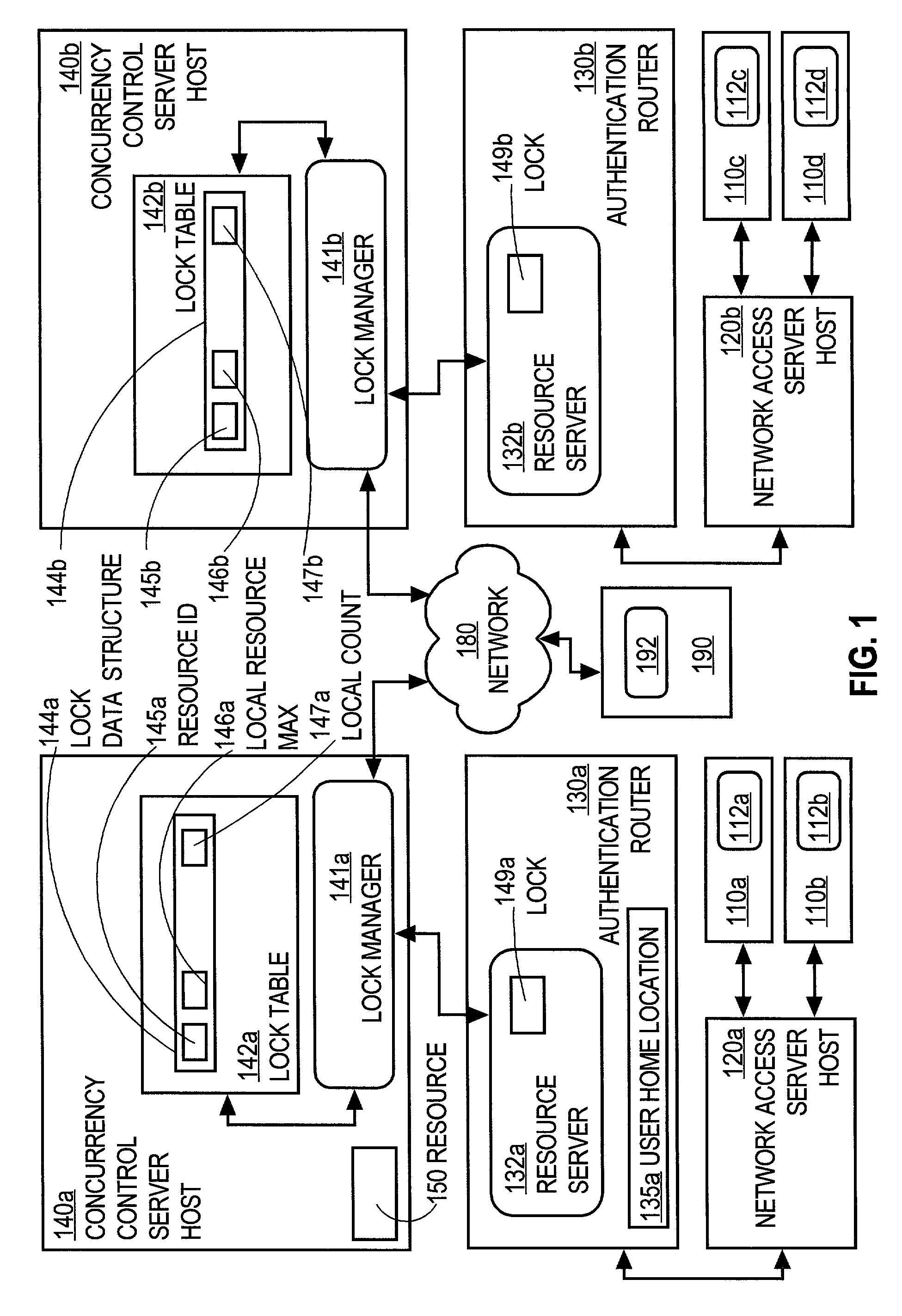
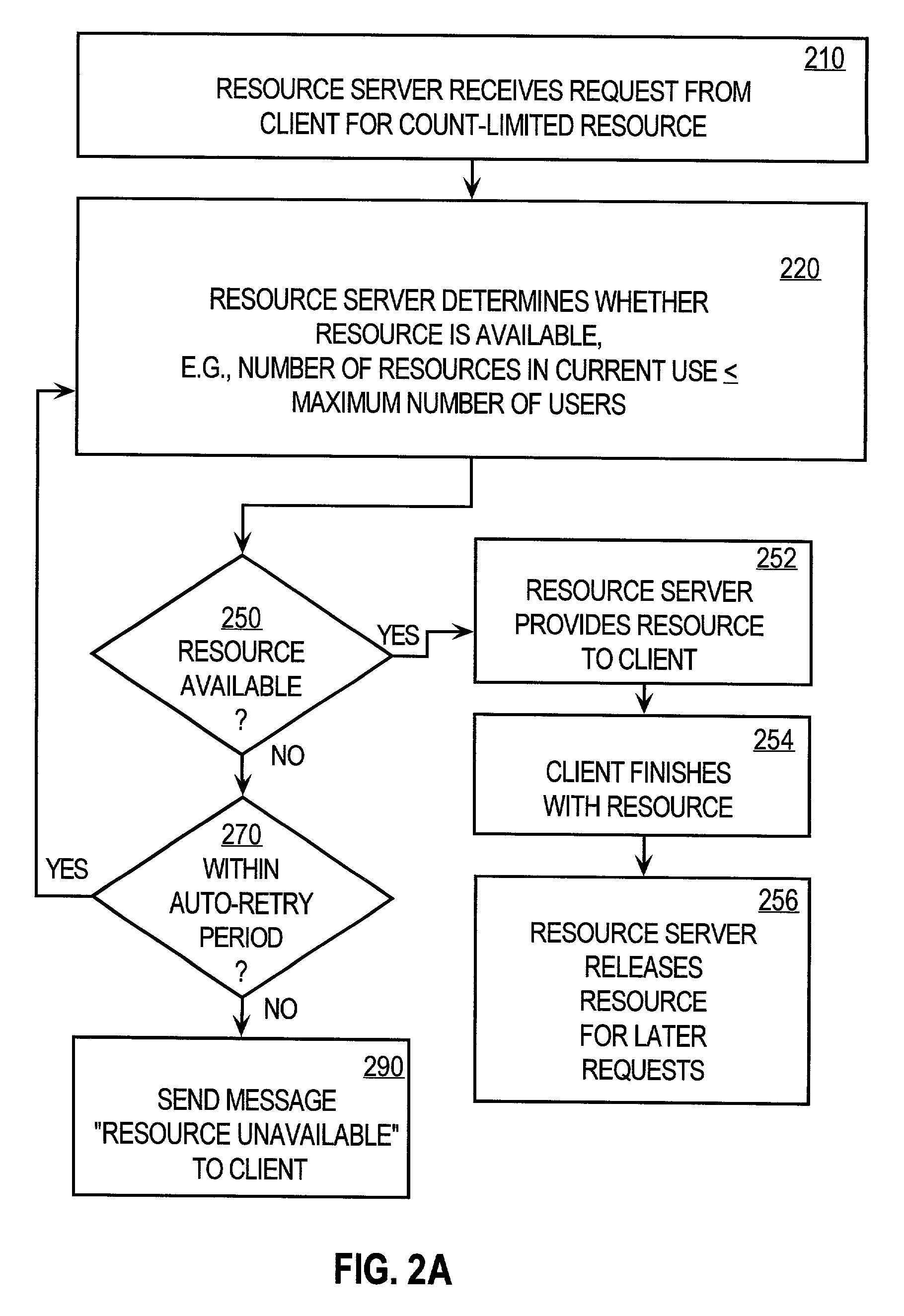
Controlling access of concurrent users of computer resources in a distributed system using an improved semaphore counting approach
ActiveUS7328263B1Data processing applicationsUnauthorized memory use protectionLimited resourcesComputer resources
A method of controlling concurrent users of a distributed resource on a network is disclosed. In one aspect, there are one or more local lock managers executing on corresponding hosts and cooperating as a distributed lock manager. The resource is limited to a maximum number of concurrent users. A user identification for each user is associated with one host. In response to a request associated with a particular user associated with a first host, a lock is requested from a first local lock manager process executing on the first host. A related method of handling a request for a count-limited resource includes receiving a request from a client process for the computer resource. If it is determined that the request exceeds a maximum count for the resource, then it is determined whether a current time is within a retry time period of the client's first request. If it is determined the current time is within the retry time period, then it is automatically determined again whether the request exceeds the maximum count for the resource. If it is determined that the request does not exceed the maximum count, then the resource is provided to the client process.
Owner:CISCO TECH INC
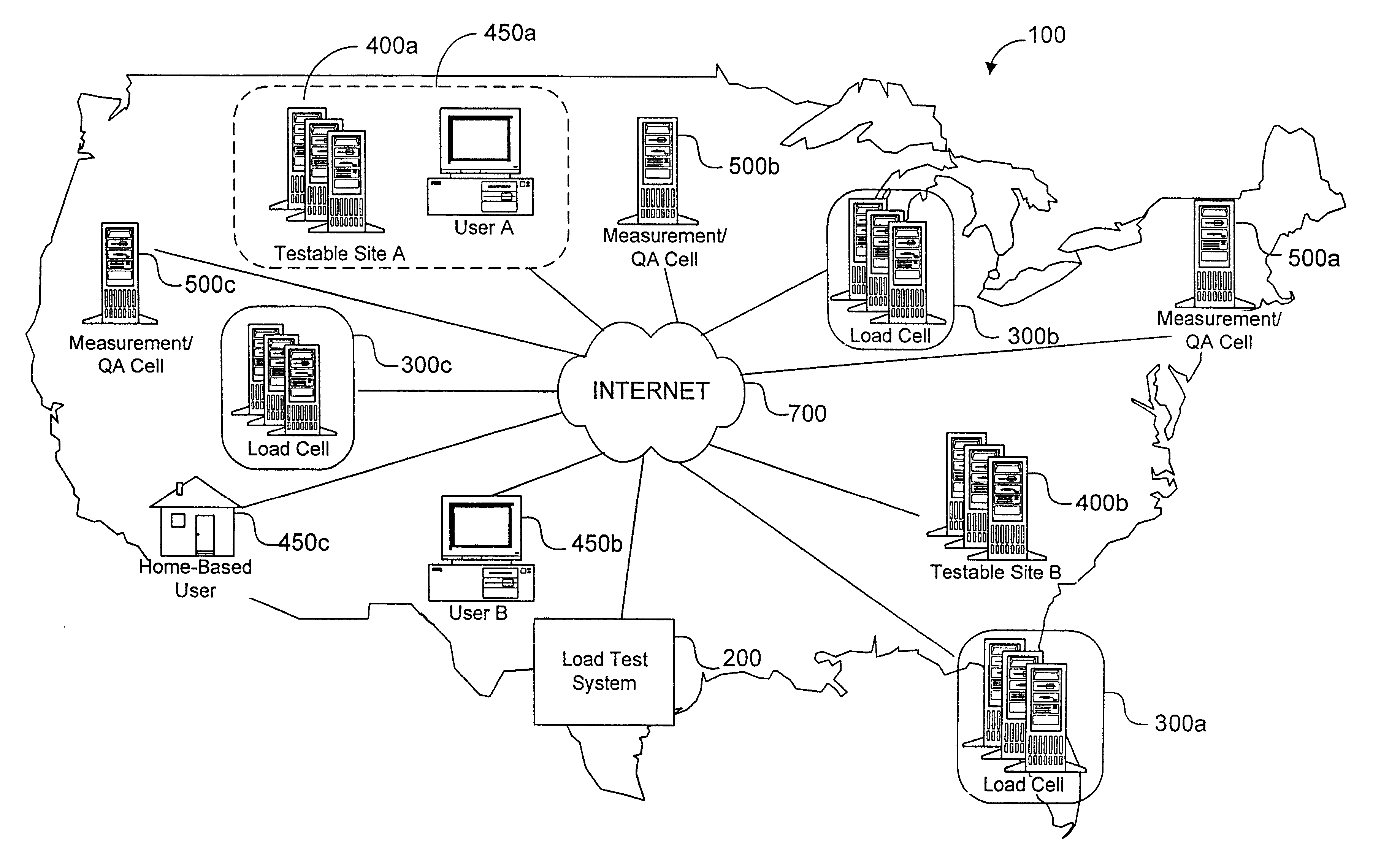
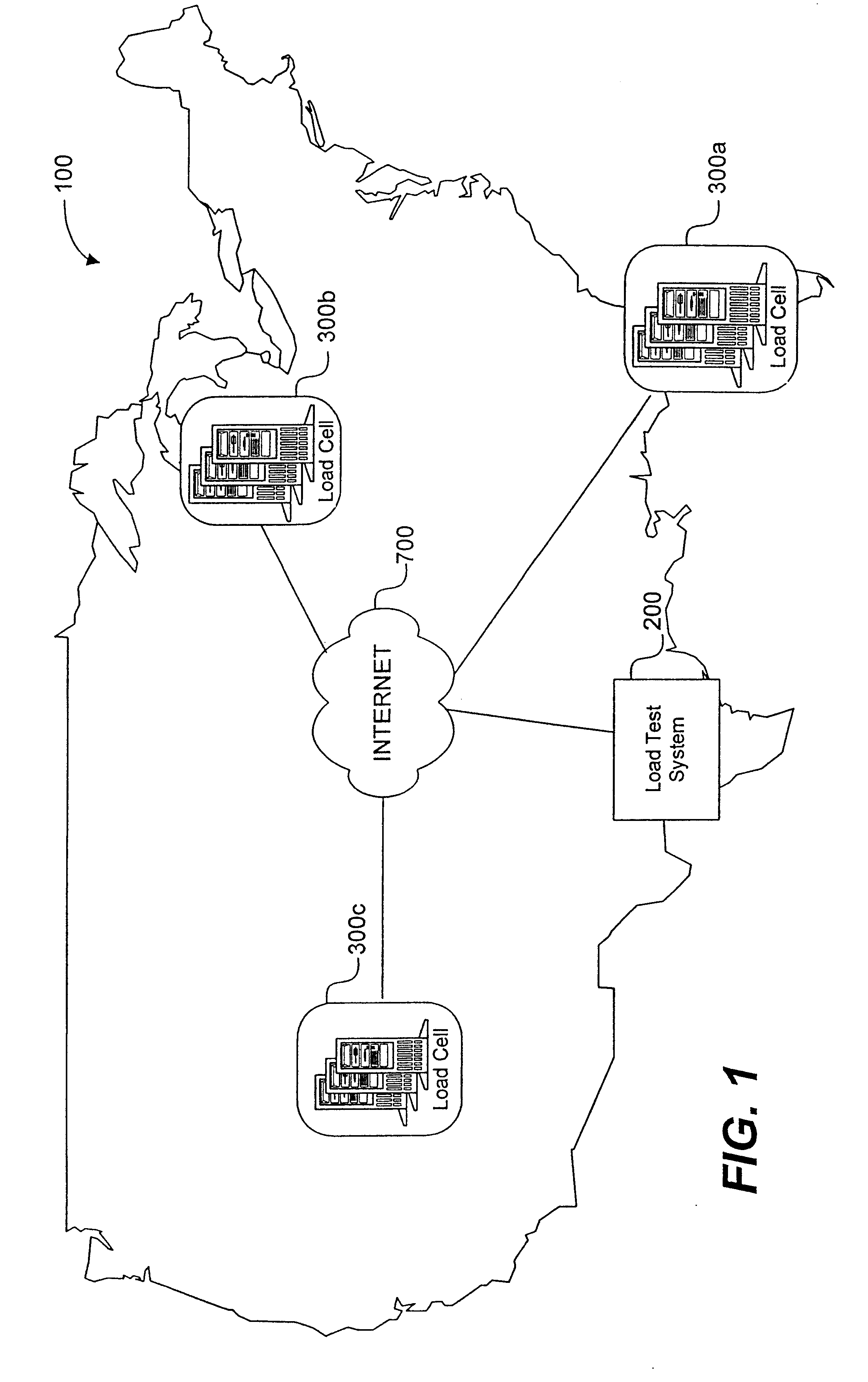
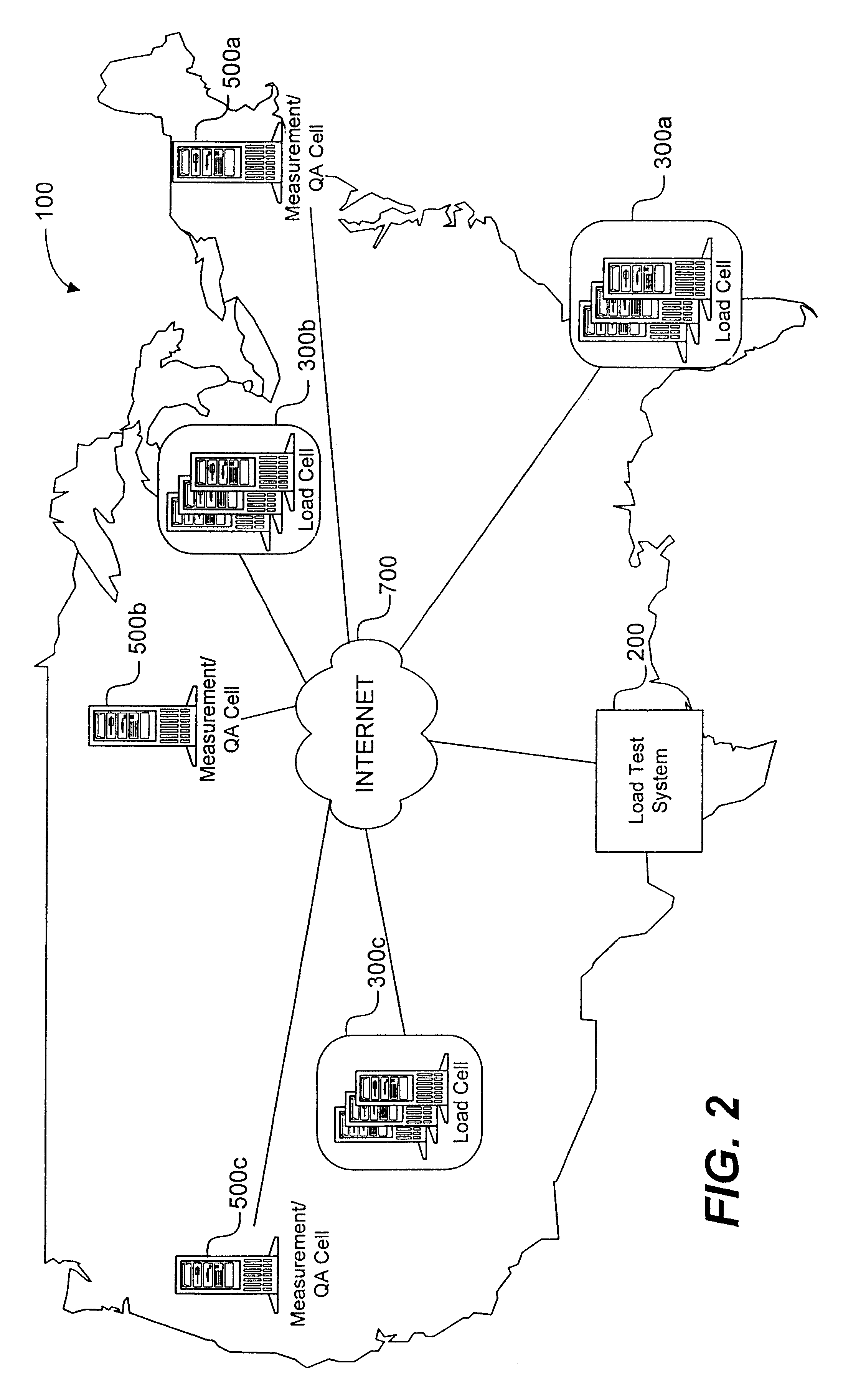
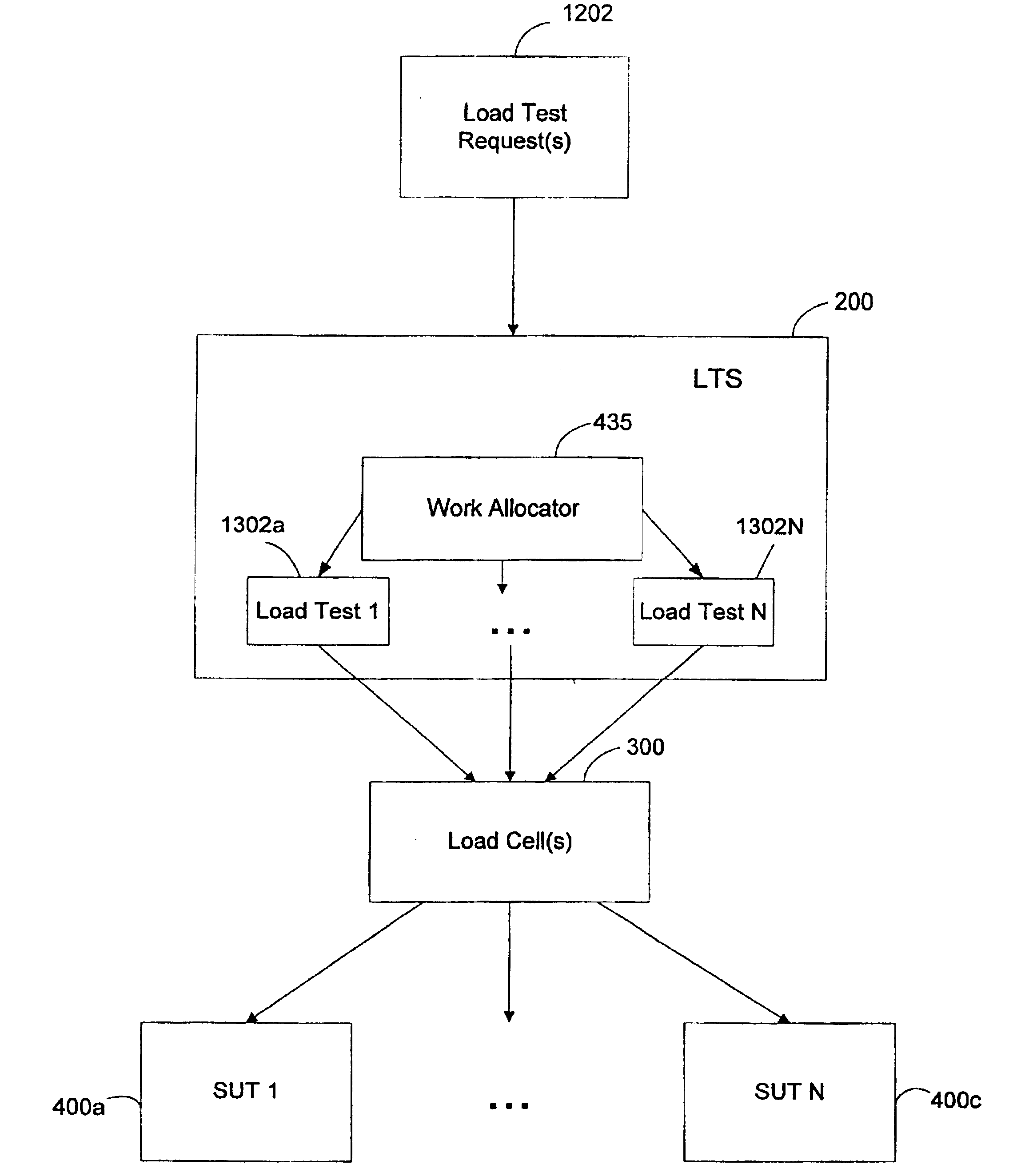
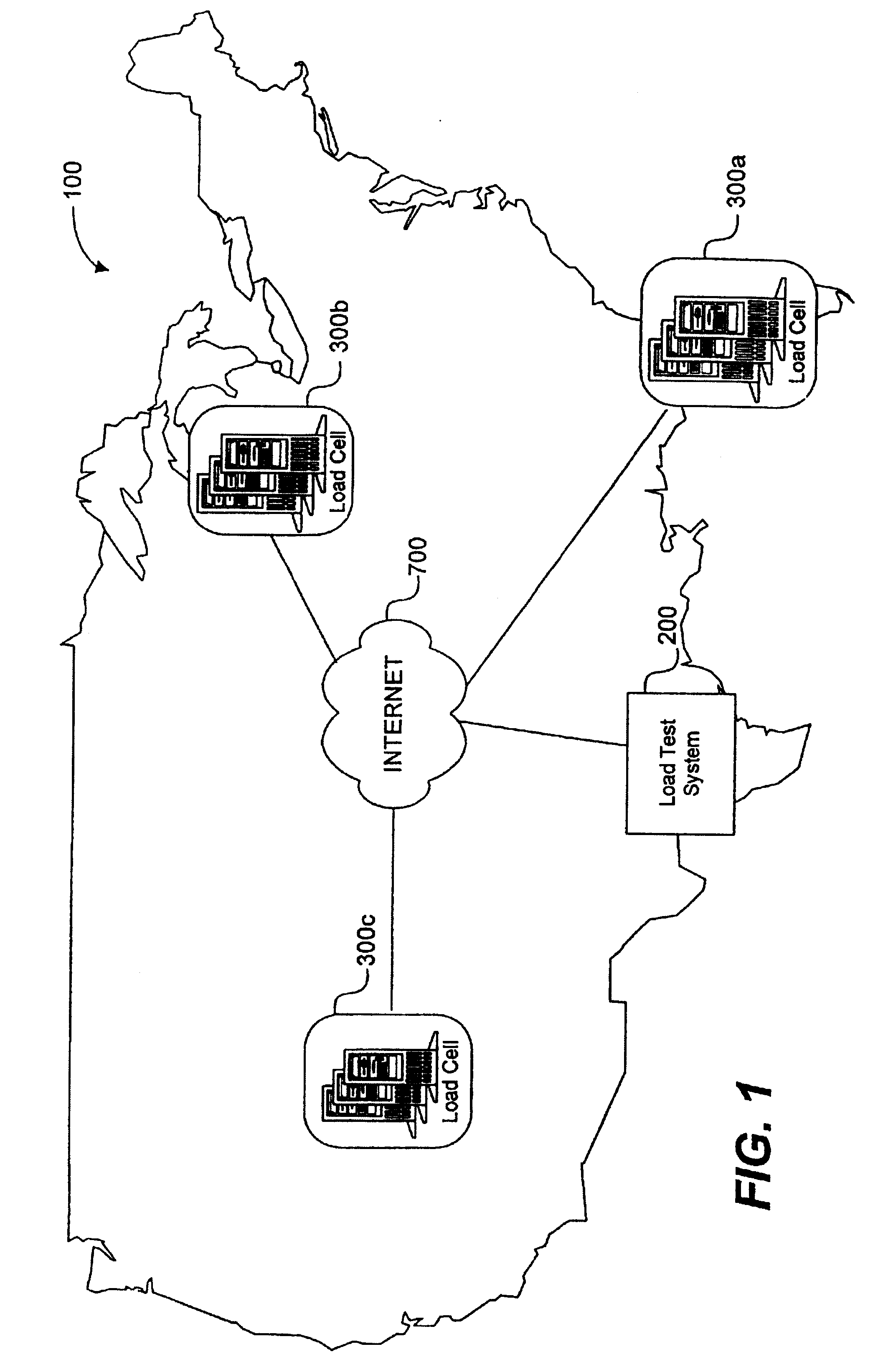
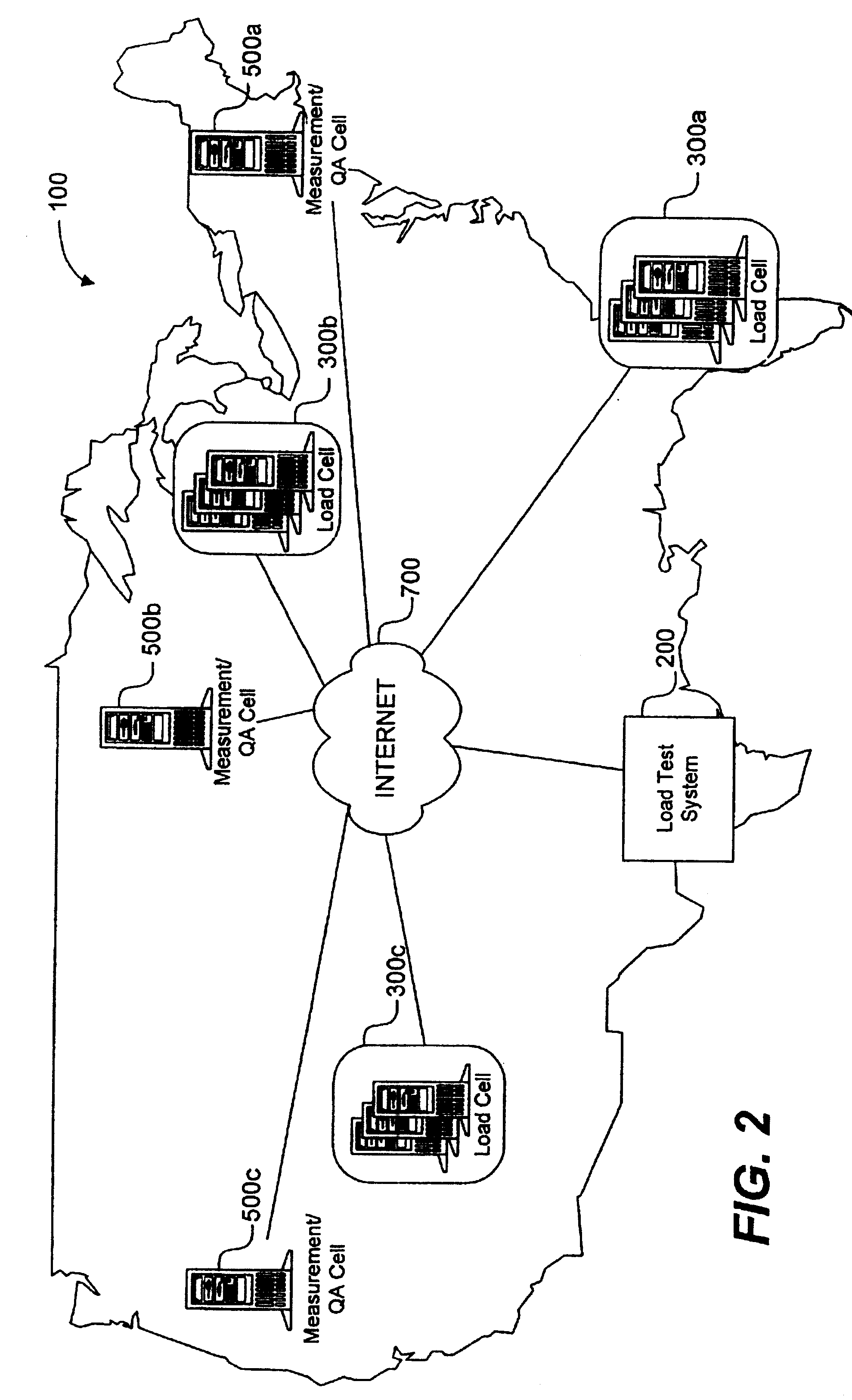
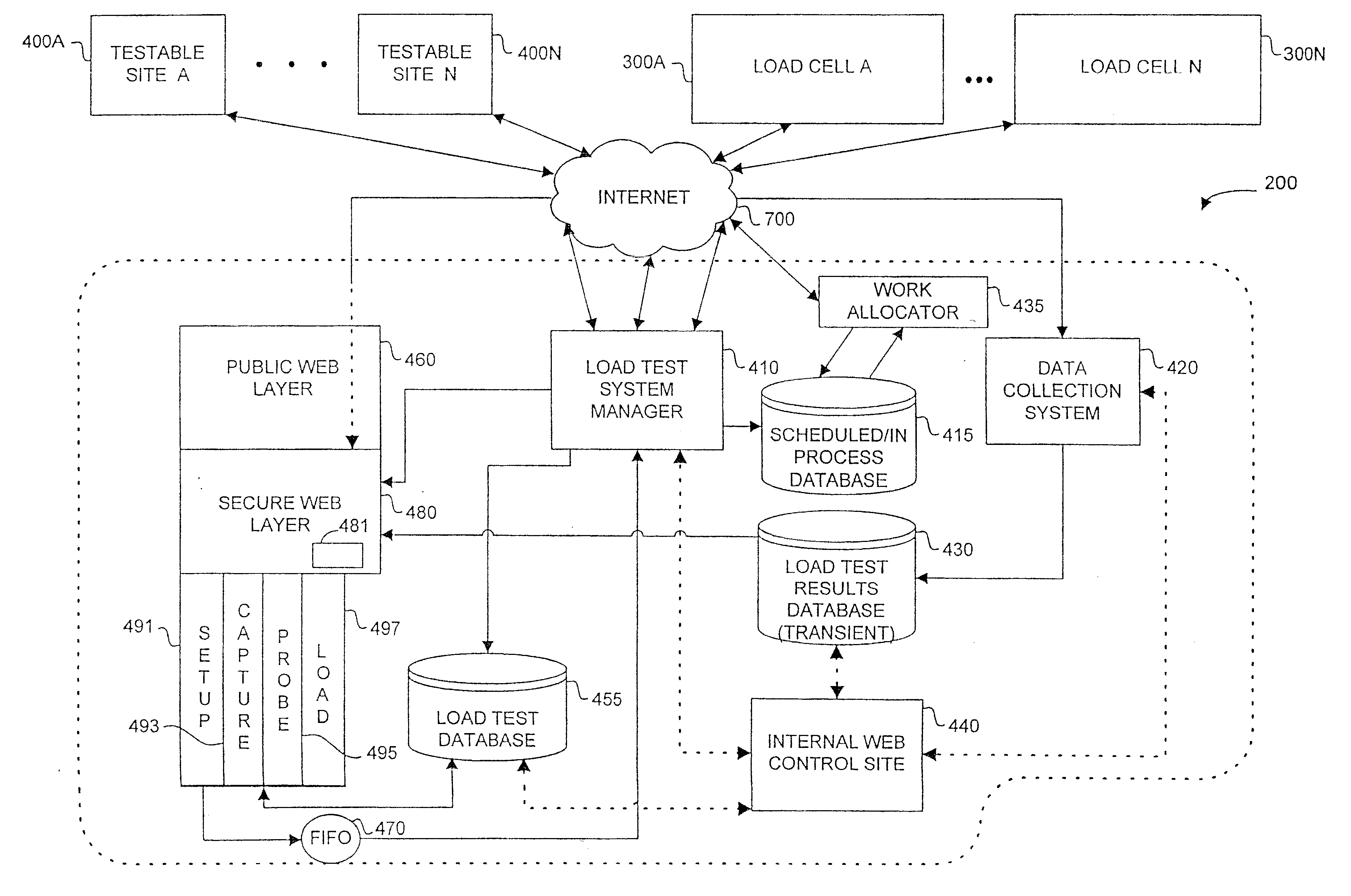
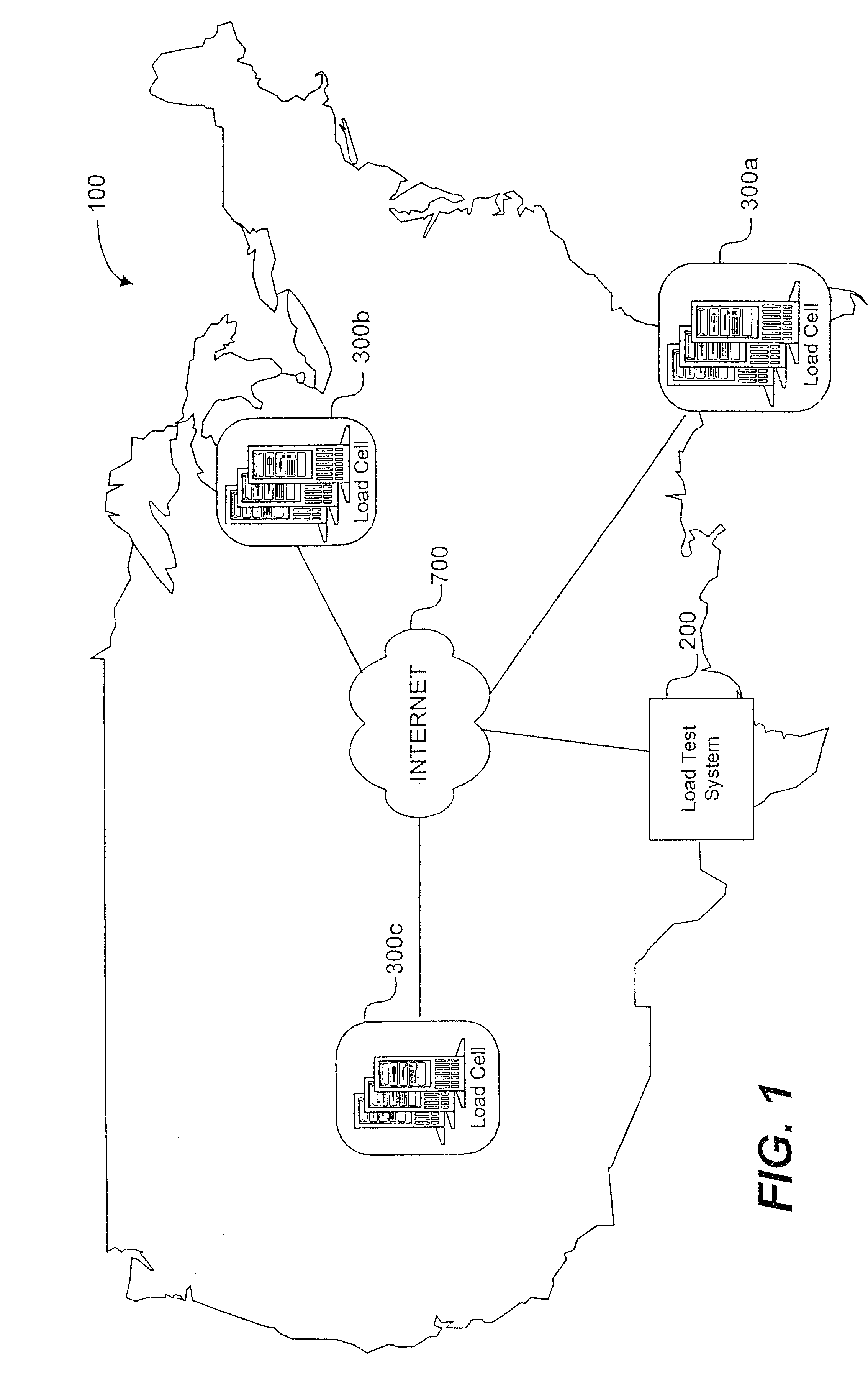
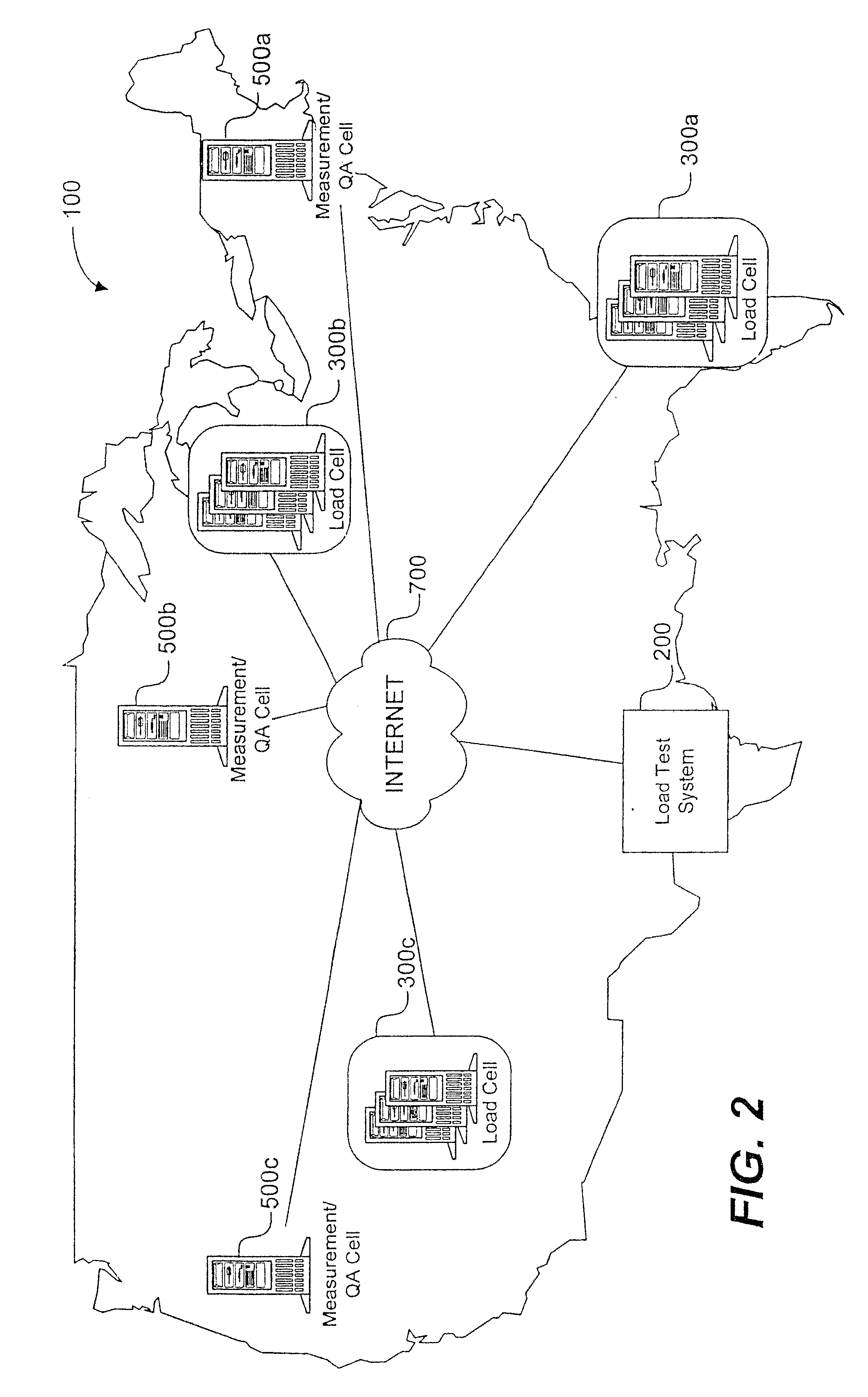
System load testing coordination over a network
A method and system using one or more load cells coordinates load testing of one or more sites under test over a network such as the Internet in accordance with one or more load test requests. In one embodiment, such method and system facilitates an economic, efficient, and accurate evaluation of the capacity of the SUTs to support concurrent users of the SUTs. A load test request is received from a User and provides information concerning a load test to be performed on a site under test (SUT). A load test is generated, and the load test is allocated to one or more load cells. The load cells perform the load test by sending load test data to the SUT and receiving responses from the SUT. Portions of a load test may be allocated to different load cells, which may be geographically remote from the SUT and / or geographically diverse. Multiple concurrent pending load tests may be processed for the same SUT. A load cell may concurrently perform all or a portion of multiple different load tests for multiple different SUT's simultaneously. A reporting function generates a report based on the responses received from the SUT. The reporting function may in addition or alternatively allow the User to view real-time results during load test execution.
Owner:EUREKA SOFTWARE SOLUTIONS
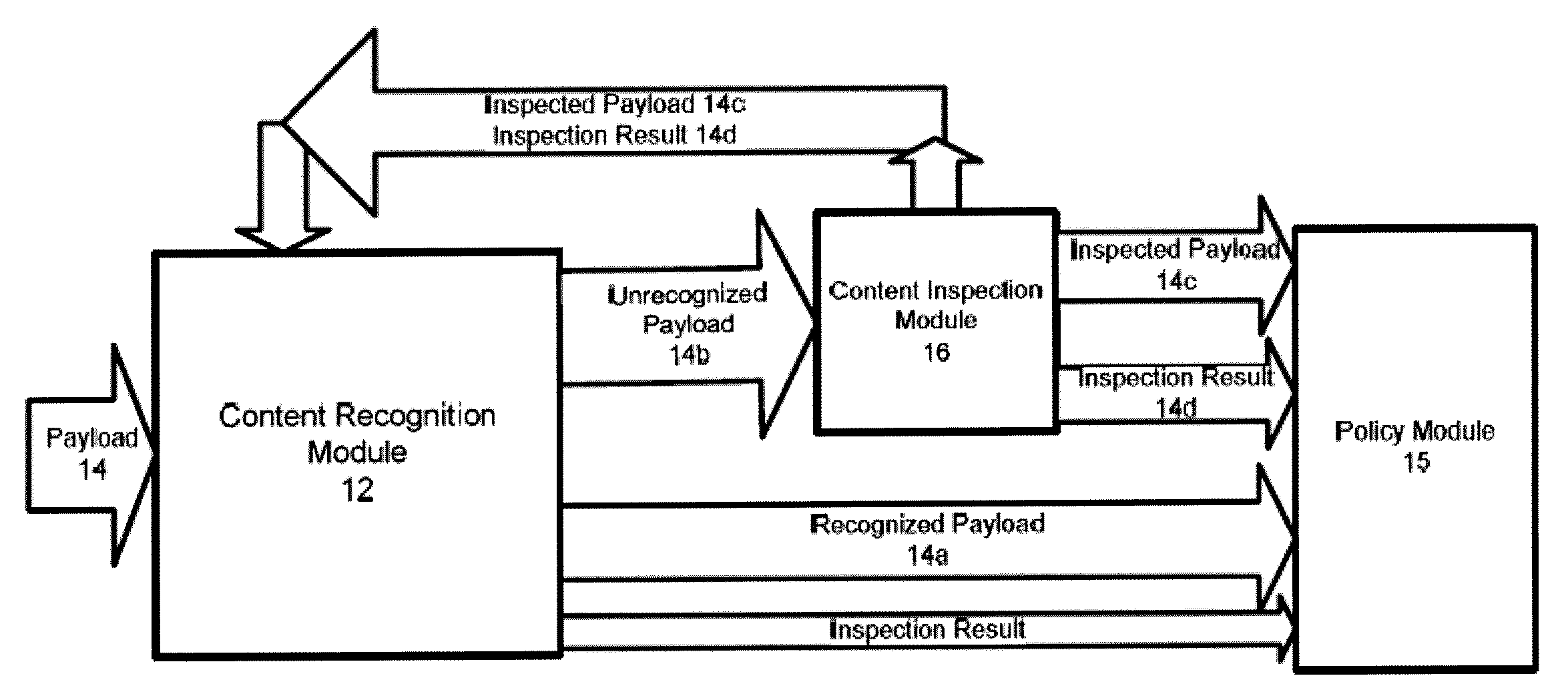
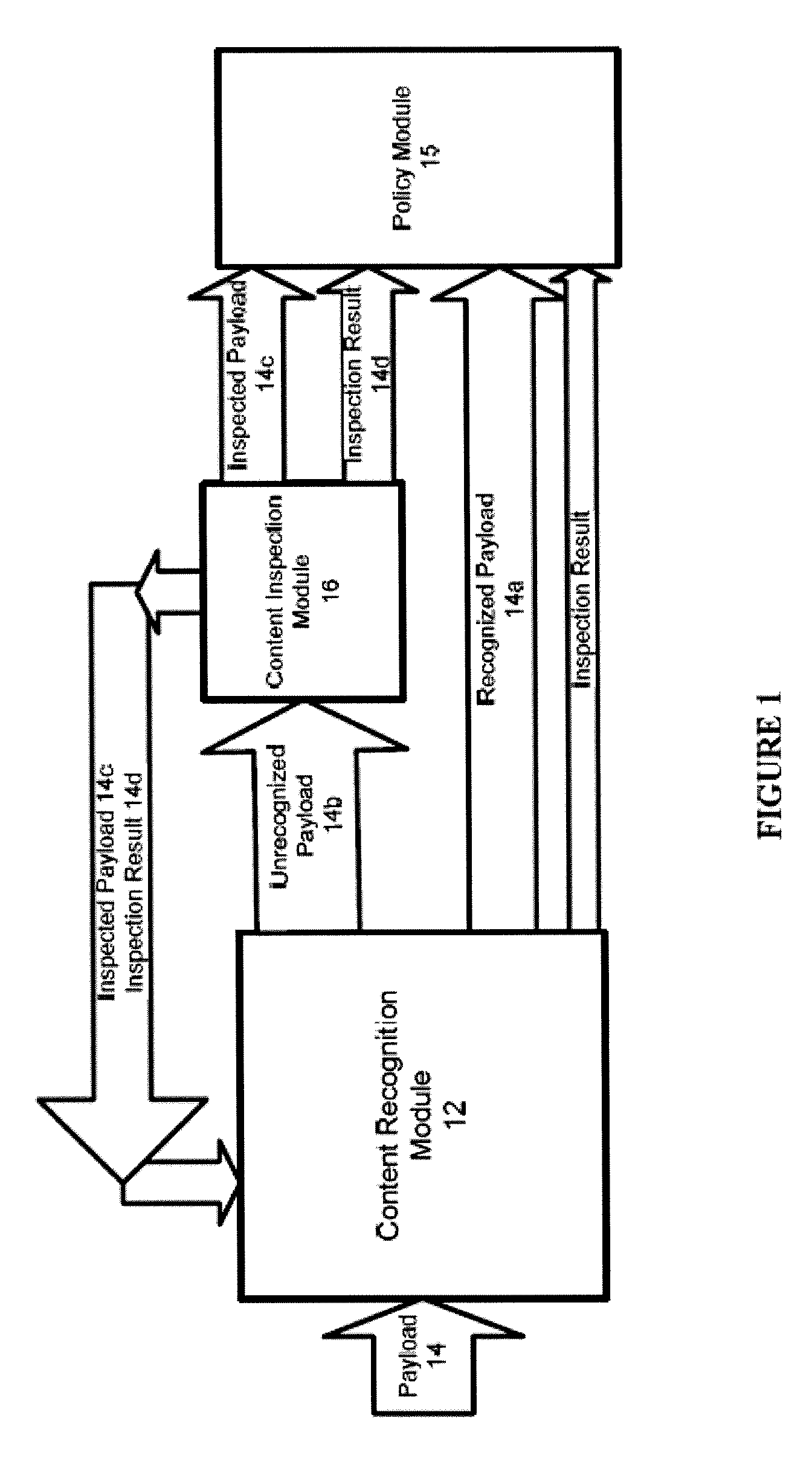
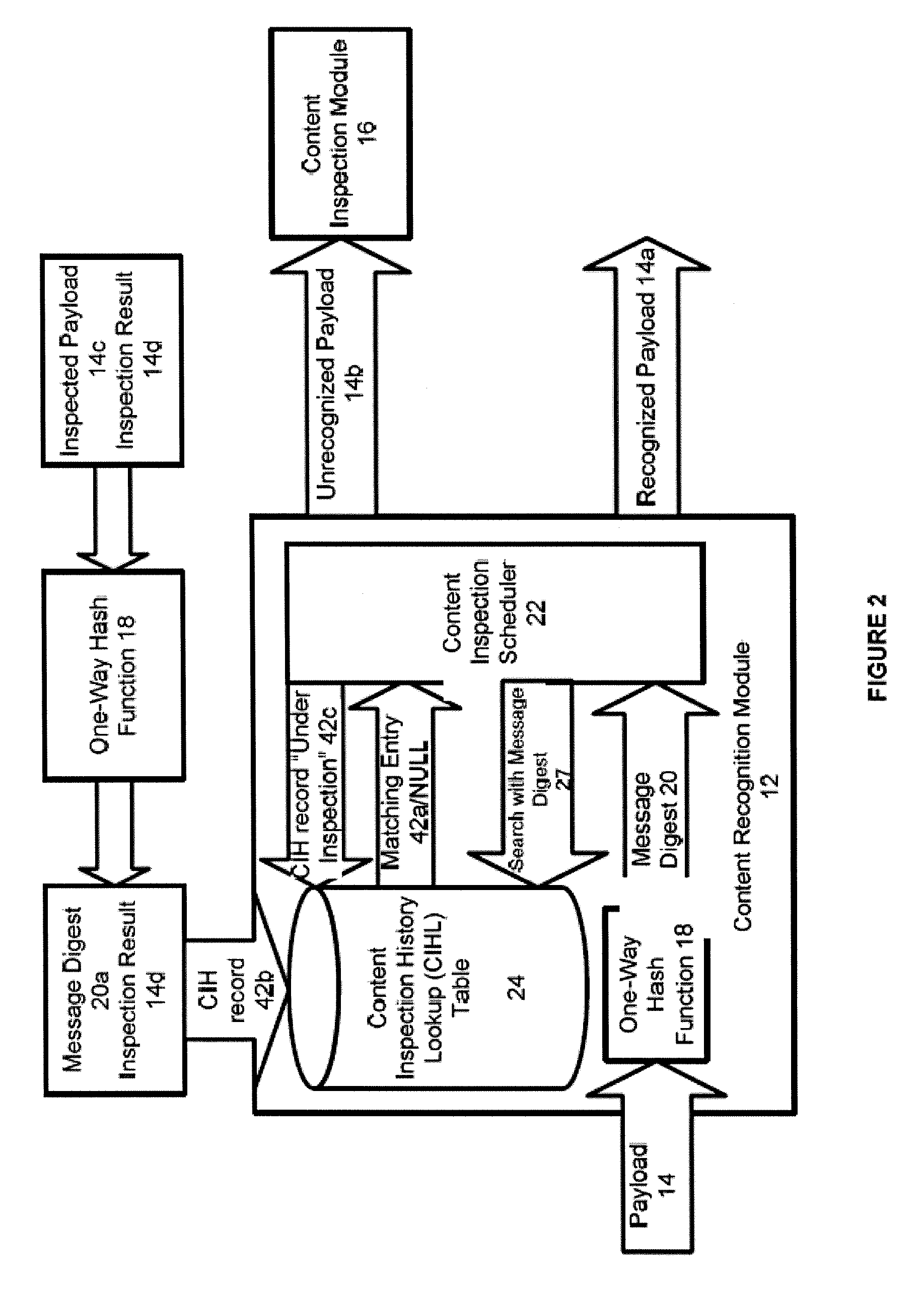
Systems And Methods For Improved Network Based Content Inspection
ActiveUS20070160062A1Efficient and effective inspectionRisk minimizationData switching by path configurationPlatform integrity maintainanceNetworking protocolKnowledge gain
The invention relates to network based content inspection (NBCI). More specifically, the invention provides systems and methods for improved NBCI in complex networks that are typical for enterprises and service providers. These networks are shared by large numbers of concurrent users who send and retrieve application content of various sizes via a variety of communication protocols. This invention improves the efficiency of the NBCI of an individual communication session by learning from the processing results of other communication sessions which may be carried via different network protocols. In addition, the invention provides methods that do not weaken the overall security for the network and that improve the stability of NBCI systems by minimizing the risk of system resource exhaustion if subjected to a burst of large payloads. The invention also improves perceived network stability by preventing the system resources from being “live-locked” by a few large content inspection tasks. Further still, the invention improves the cost-effectiveness of NBCI by allowing the optimization knowledge gained by one NBCI node be shared with other nodes.
Owner:WEDGE NETWORKS
Methods and apparatus for utilizing radio frequency spectrum simultaneously and concurrently in the presence of co-channel and/or adjacent channel television signals by adjusting transmitter power or receiver sensitivity
InactiveUS7013145B1Reduce distractionsReduce the required powerTelevision system detailsBroadcast-related systemsUltra-widebandFrequency spectrum
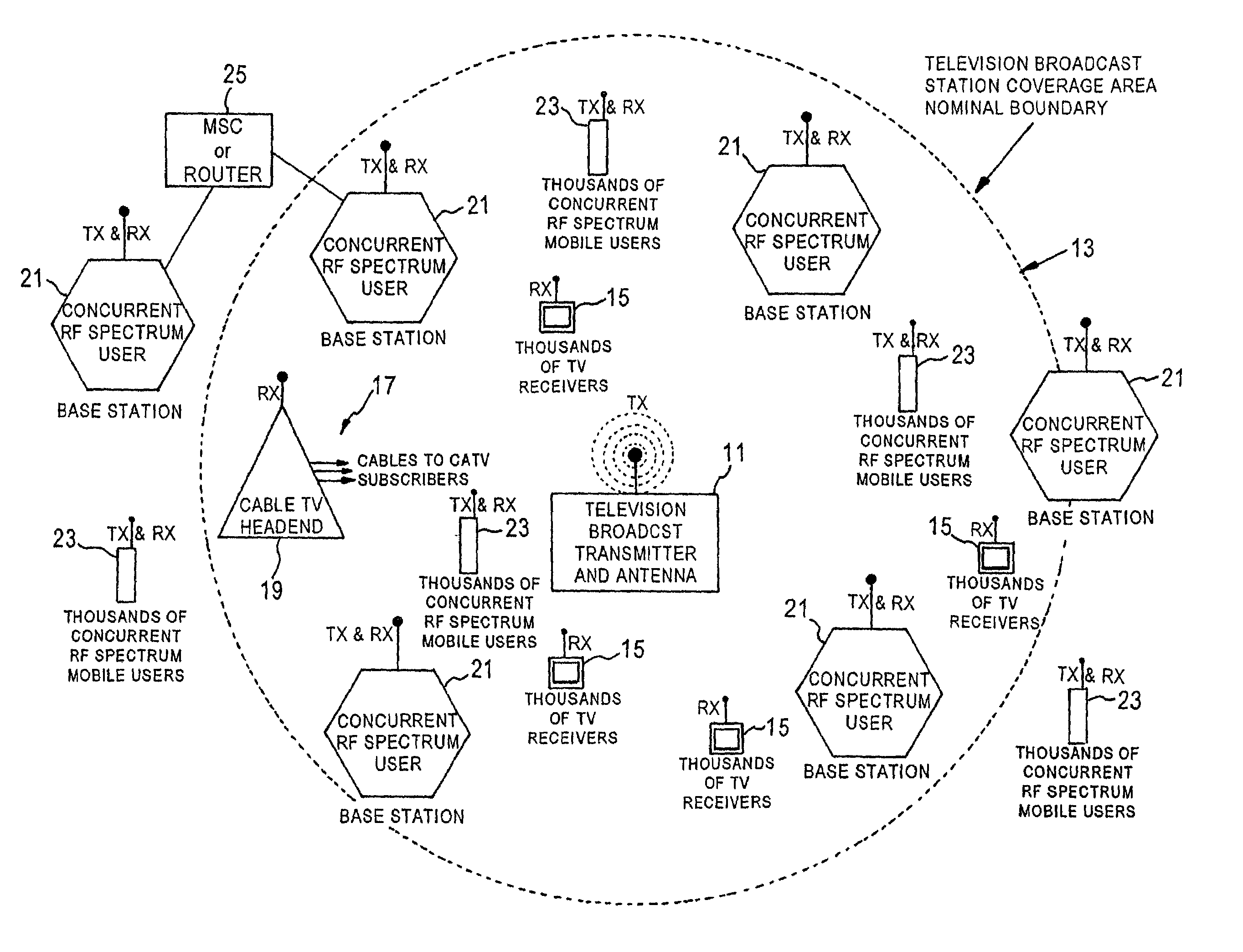
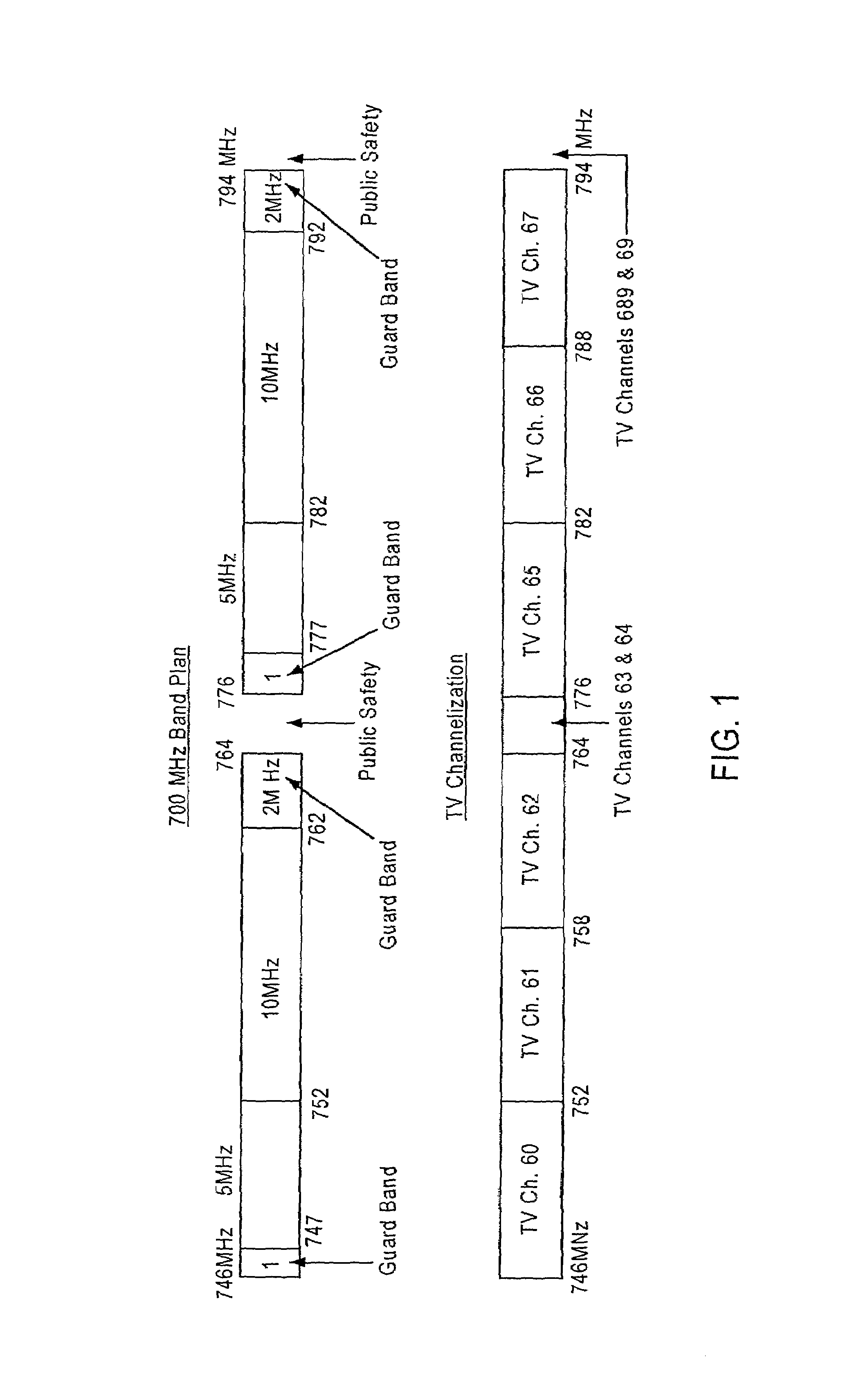
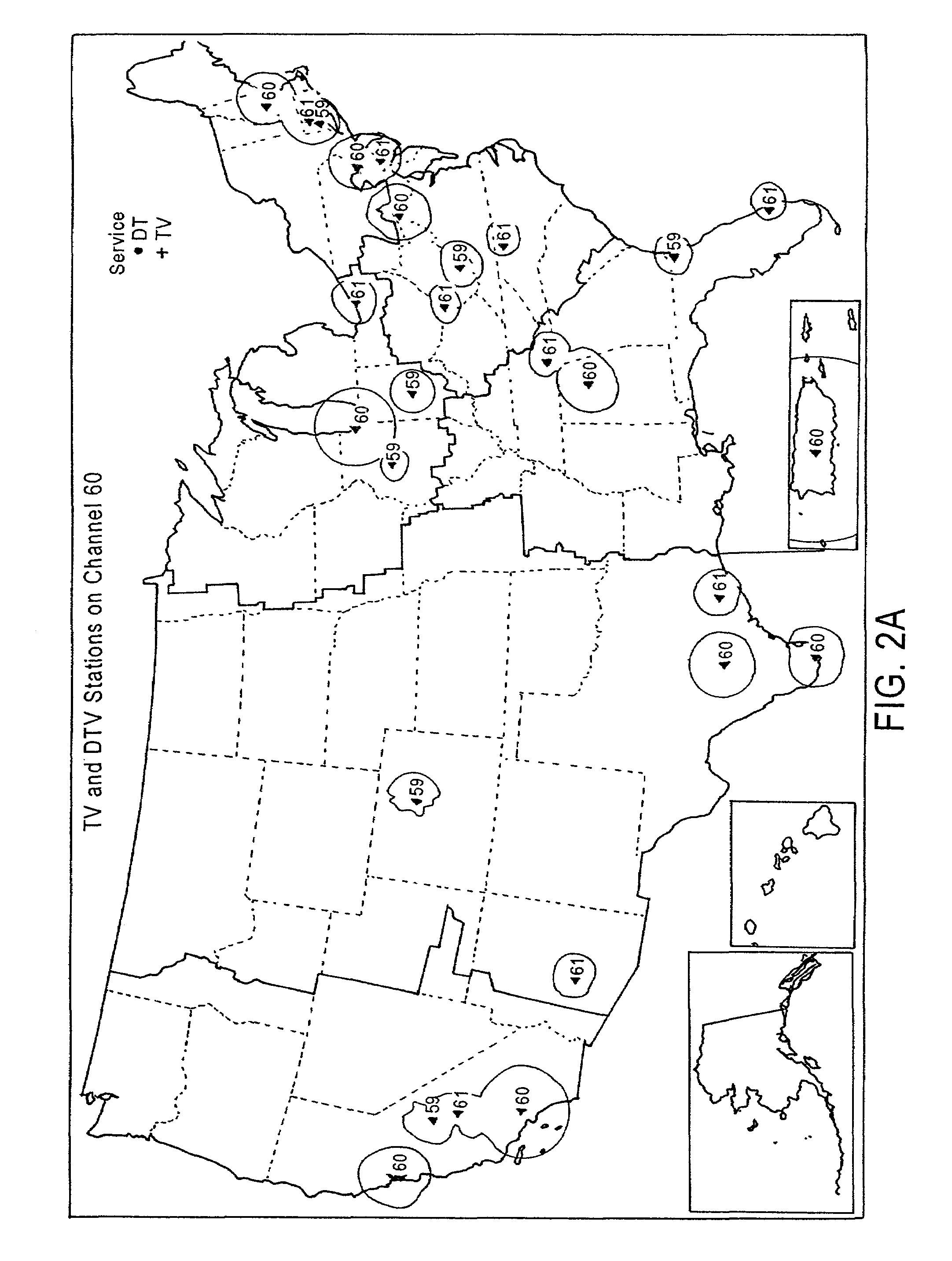
To address the scarcity of radio frequency (RF) spectrum, the disclosed systems offer unique ways to mitigate interference between television broadcasters (including their direct audience and viewers served via cable television) and other concurrent users of the RF spectrum, e.g. for one-way or two-way wireless communication. A preferred embodiment makes use of the “framing” characteristics of the “letterbox” video display format. RF emissions of the simultaneous RF spectrum user are keyed “on” only or substantially only during the time intervals when the blanking intervals and / or letterbox-border video lines are being scanned on the display, i.e. when the potentially affected (interfered with) television display is in the letterbox-frame-scanning portions of each video field. The concurrent uses may support services for voice (including telephony, music etc.), data (including Internet, intranet, etc.); image or control; fixed, portable, mobile or nomadic; narrowband, broadband or ultra-wideband; radiodetermination, diathermy, etc. Additionally, the concurrent user's emitted power and receiver sensitivity is continuously adjusted according to the broadcast television signal.
Owner:CELLCO PARTNERSHIP INC
Multiple operating system and disparate user mass storage resource separation for a computer system
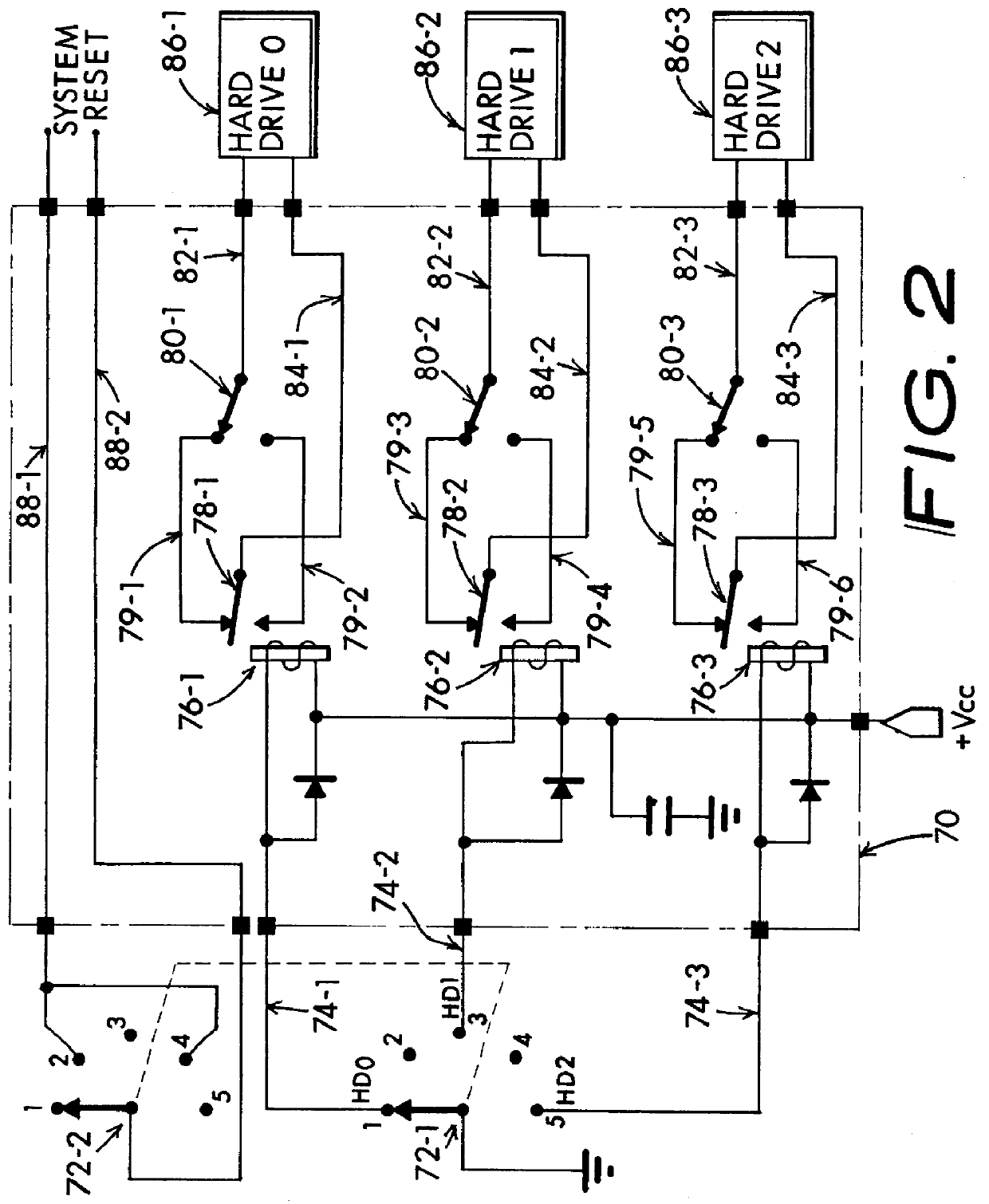
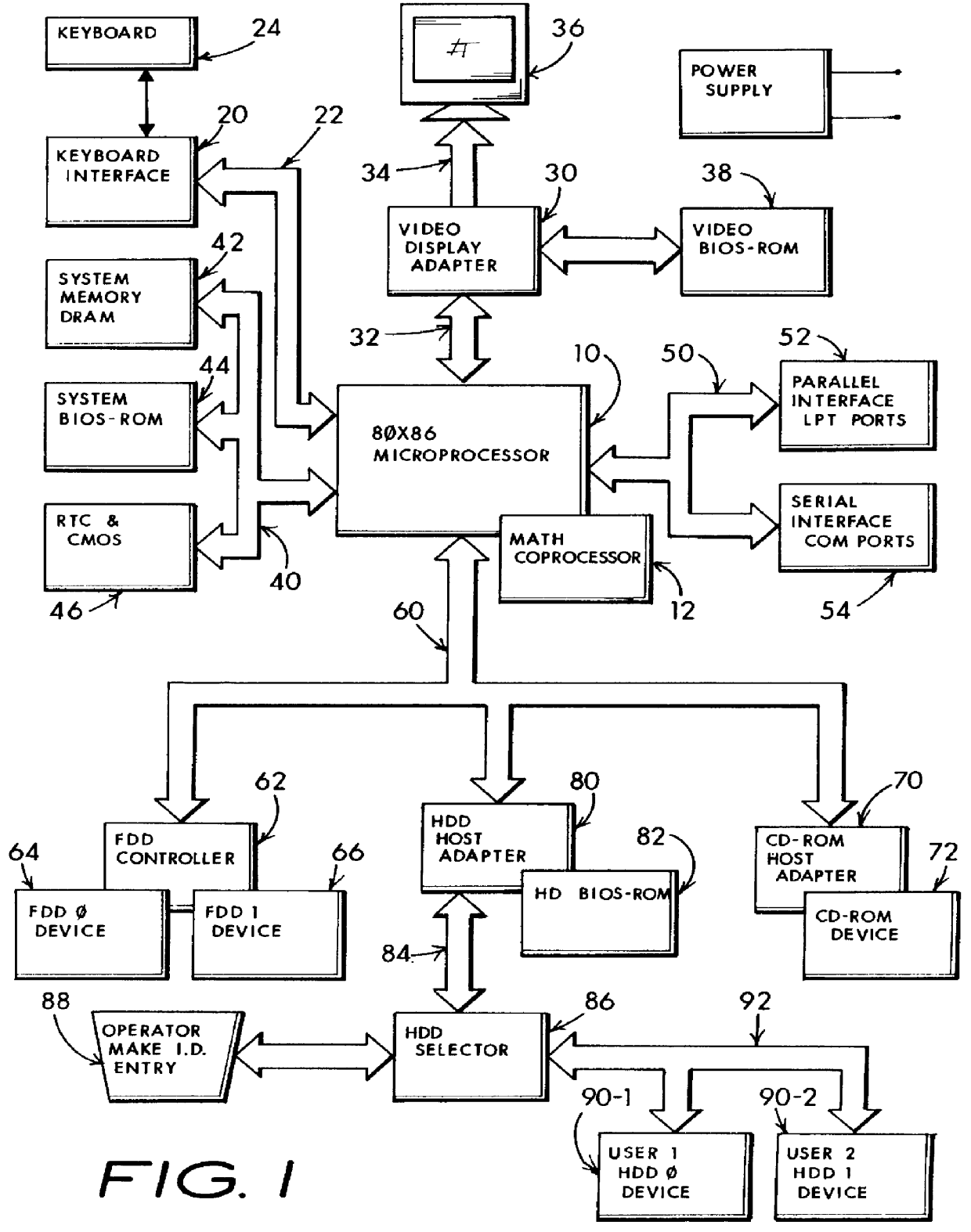
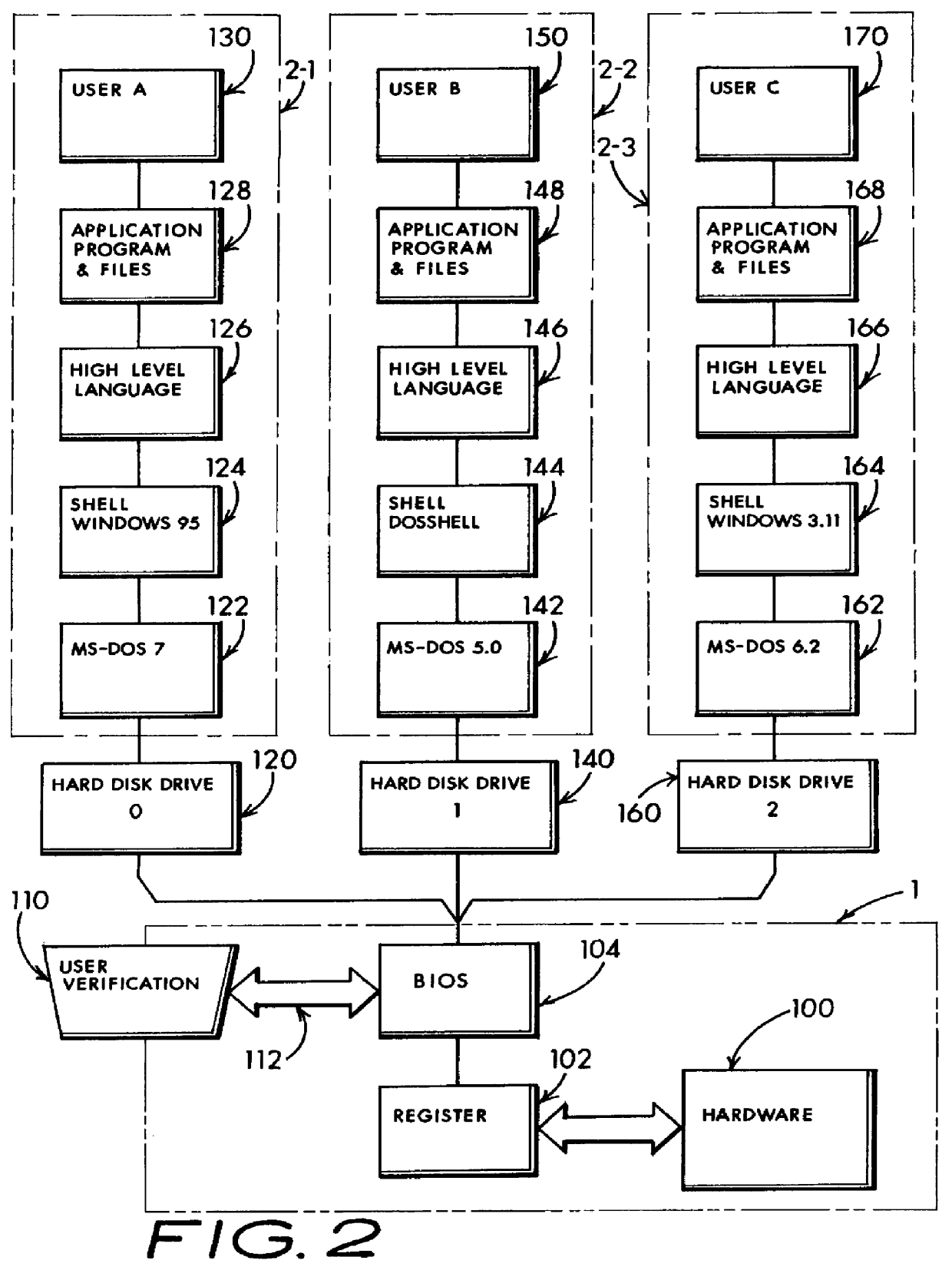
InactiveUS6067618AIsolate userAvoid possibilityDigital data processing detailsDigital computer detailsMass storageHard disc drive
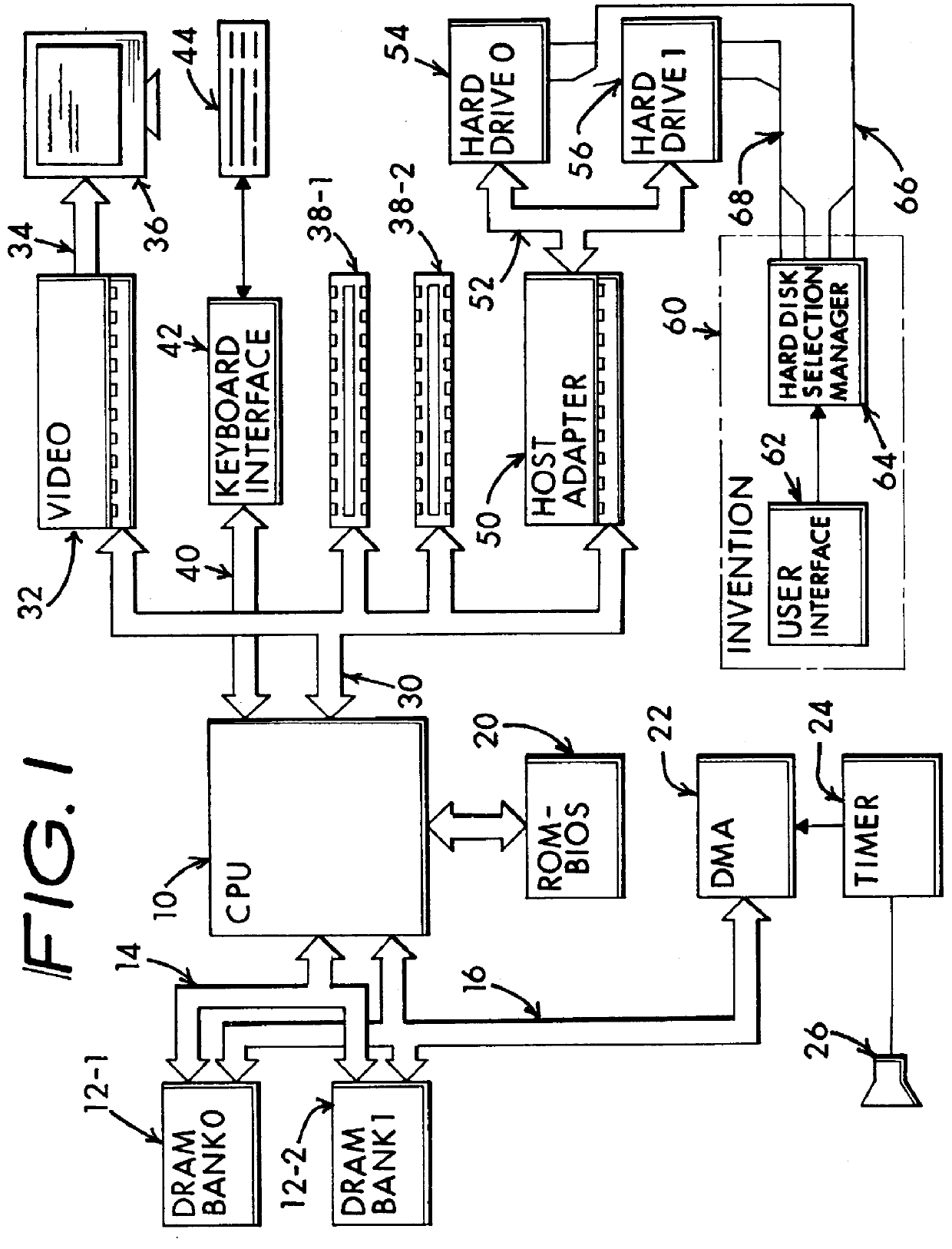
A computer system including several nonconcurrently active hard disk drives ordinarily loaded with unique software bundles. Each active hard drive introduces an especial operating system setup and applications installation which is unconditionally denied access by activities obtained under another hard disk drive's software instructions. An absolute isolation between two or more user's application programs and data files is achieved while sharing a common set of computer system hardware and peripherals. Each category of nonconcurrent user operates independently without a threat of corruption from activities of another prior or subsequent user utilizing the same computer system for another disparate activity. In an IDE / ATA interface environment, a typical arrangement includes a setting of ROM-BIOS to only recognize a MASTER drive with a subsequent user determined swapping of MASTER and SLAVE modes between at least two hard drives utilizing a manual switch-over to obtain operation under operating system and programs uniquely installed on each of the intently selected MASTER drives, while denying access to the alternant SLAVE drive. In an SCSI interface environment, several drives set with the same SCSI-ID number are selected between by manually controlling a completion of the SCSI bus SEL line to the active intended drive and interrupting the SEL line to designated inactive drives. Virus corruption of one primary drive is fire-walled against inadvertent transfer into an alternate primary drive thereby assuring system operating integrity for one user category in spite of virus contamination, command errors, or careless or malicious hacking introduced by another user category.
Owner:HANGER SOLUTIONS LLC
System and method for performing flash crowd caching of dynamically generated objects in a data communication network
ActiveUS20070156852A1Digital data information retrievalMultiple digital computer combinationsFlash crowdDatabase
The present invention is directed towards a “flash crowd” technique for handling situations where the cache receives additional requests, e.g.,. nearly simultaneous requests, for the same object during the time the server is processing and returning the response object for a first requester. Once all such nearly simultaneous requests are responded to by the cache, the object is flushed from the cache, with no additional expire time or invalidation action needed. This technique of the present invention enables data to be cached and served for very small amounts of time for objects that would otherwise be considered non-cacheable. As such, this technique yields a significant improvement in applications that serve fast changing data to a large volume of concurrent users, such, for example, as real time stock quotes, or a fast evolving news story.
Owner:CITRIX SYST INC
System load testing coordination over a network
A method and system using one or more load cells coordinates load testing of one or more sites under test over a network such as the Internet in accordance with one or more load test requests. In one embodiment, such method and system facilitates an economic, efficient, and accurate evaluation of the capacity of the SUTs to support concurrent users of the SUTs. A load test request is received from a User and provides information concerning a load test to be performed on a site under test (SUT). A load test is generated, and the load test is allocated to one or more load cells. The load cells perform the load test by sending load test data to the SUT and receiving responses from the SUT. Portions of a load test may be allocated to different load cells, which may be geographically remote from the SUT and / or geographically diverse. Multiple concurrent pending load tests may be processed for the same SUT. A load cell may concurrently perform all or a portion of multiple different load tests for multiple different SUT's simultaneously. A reporting function generates a report based on the responses received from the SUT. The reporting function may in addition or alternatively allow the User to view real-time results during load test execution.
Owner:EUREKA SOFTWARE SOLUTIONS
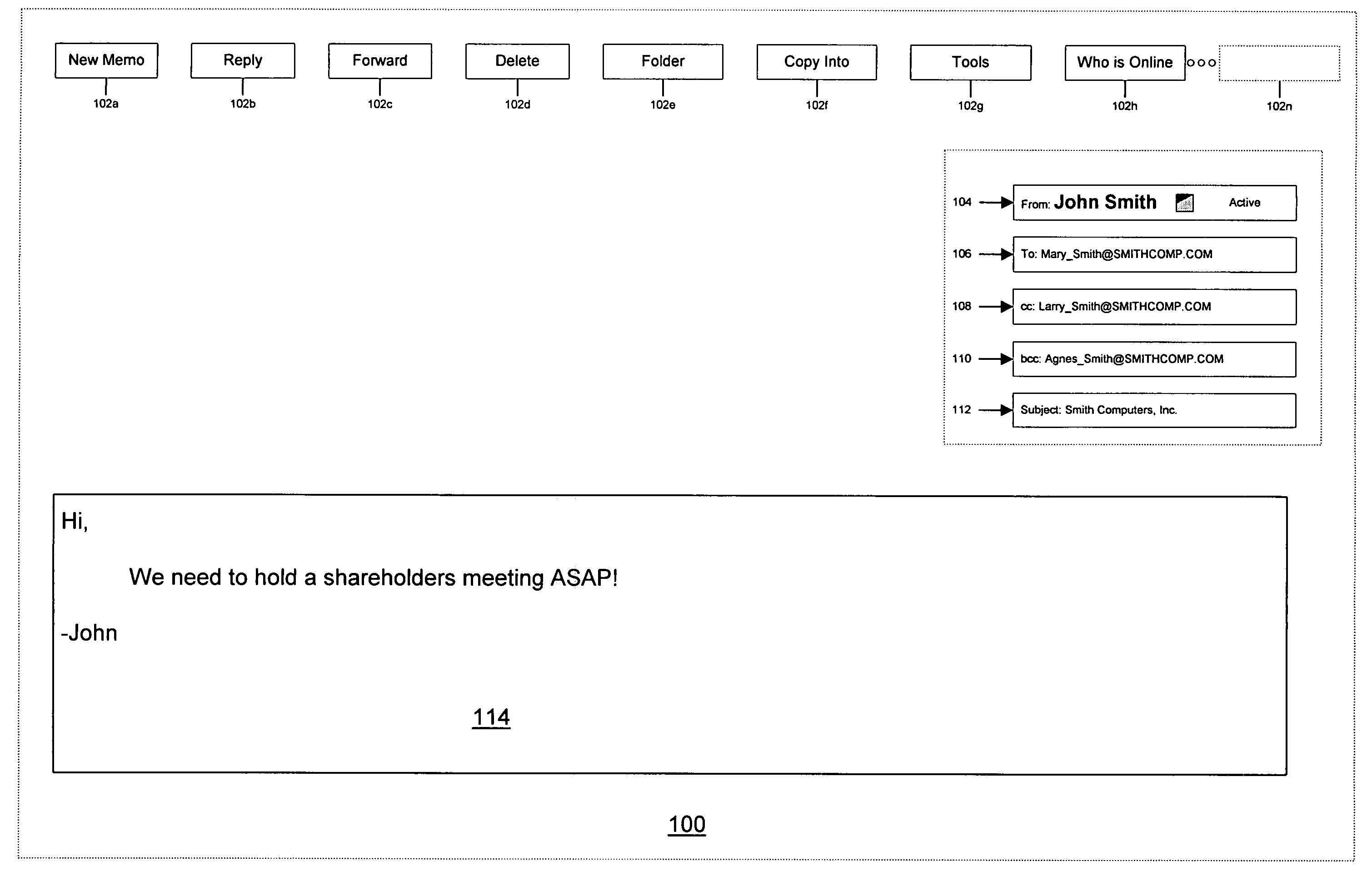
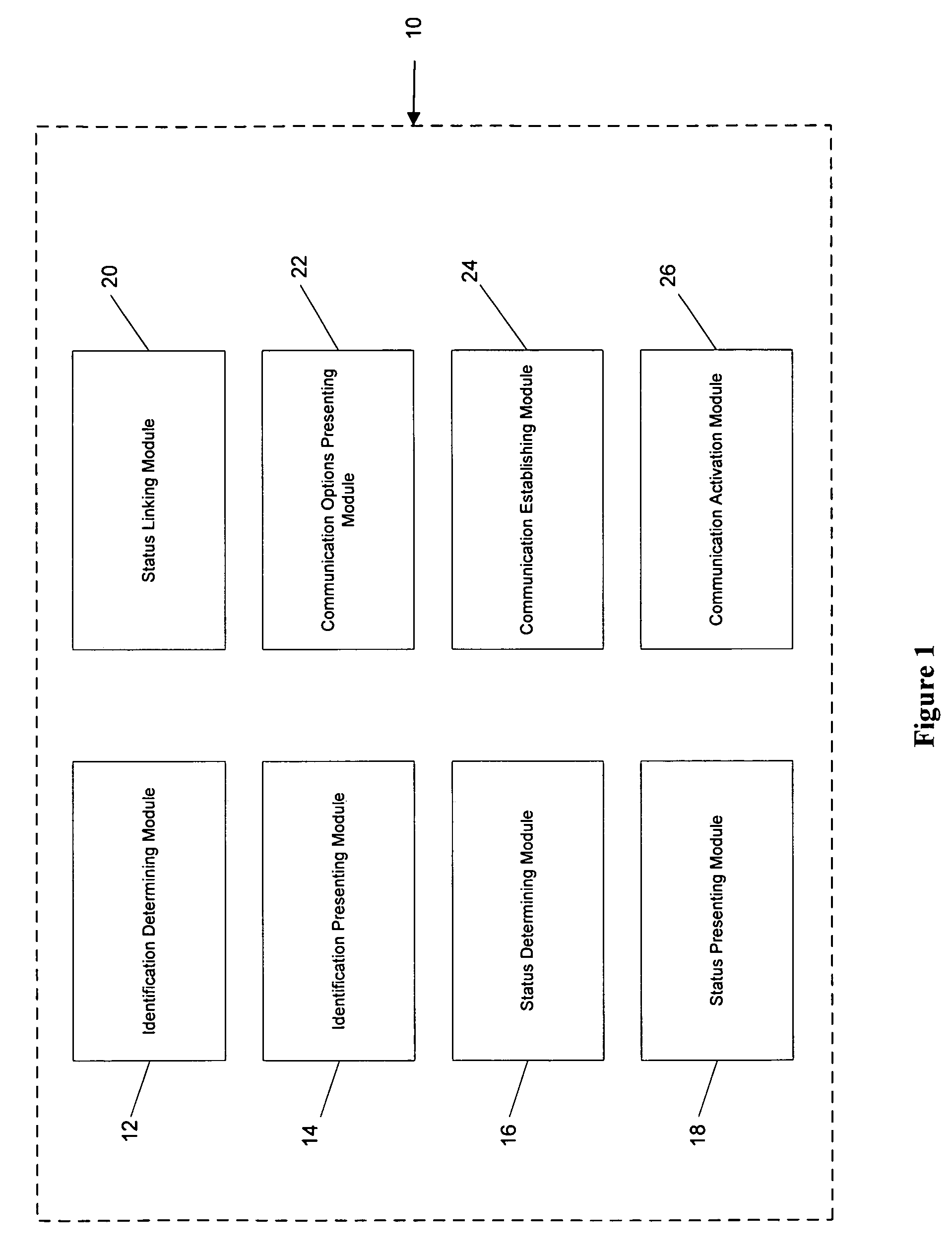
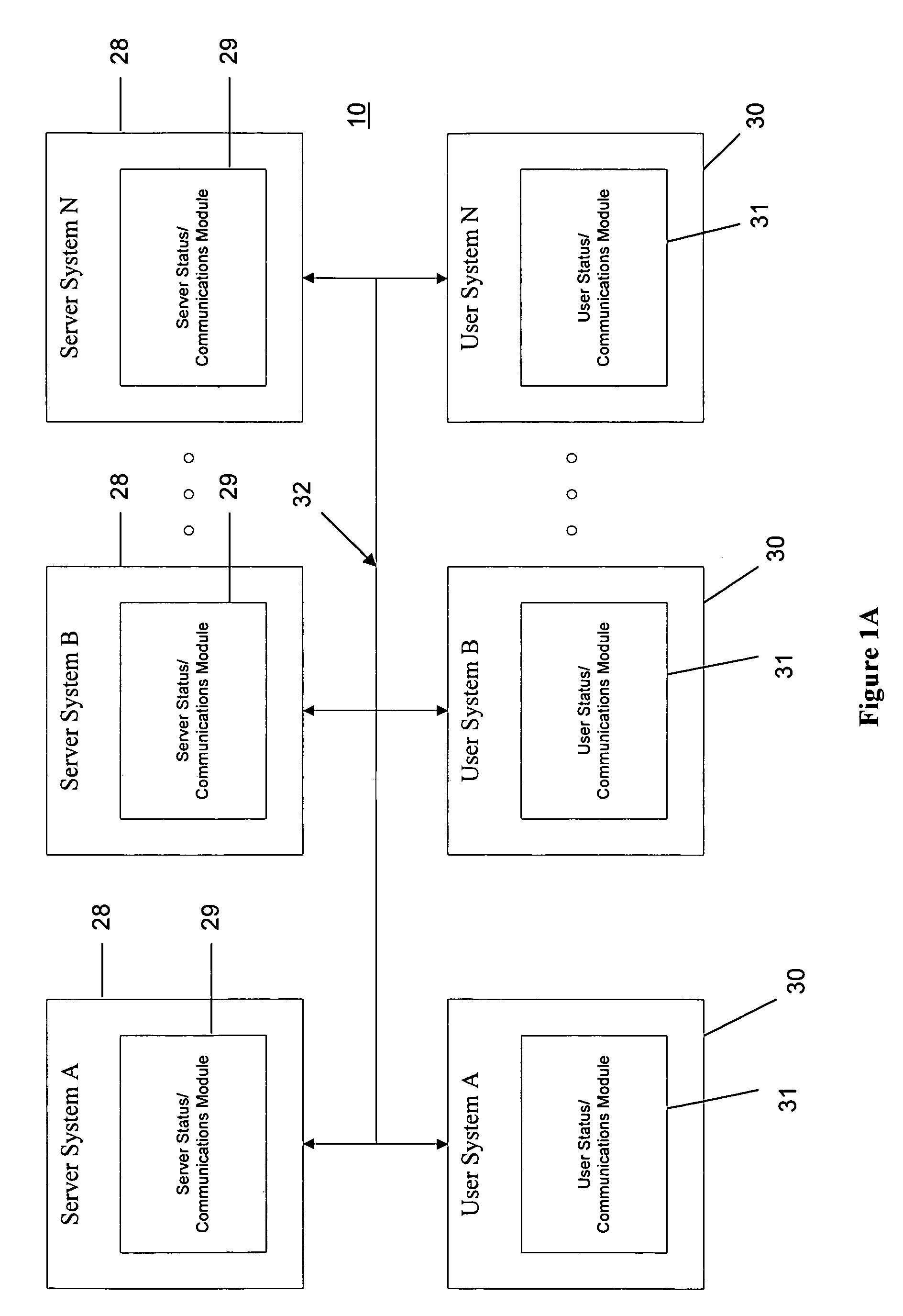
Collaborative application with indicator of concurrent users
InactiveUS7103846B1Multiple digital computer combinationsData switching networksTelecommunications linkCommunication link
A system, method, and processor readable medium containing processor readable program code embodied therein are provided that enable network users to view one or more network user's status and to establish communications with the one or more network users using a user indicator in an electronic document (e.g., electronic mail message, hypertext markup language document). The user indicator may be a network user's login identification presented as a hypertext link to one or more communication options. The system may include an identification module for identifying the one or more network users. The identification module may identify a network user's login identification (e.g., the network user's name, employee number) and provide the network user's status using the user indicator. A status module, responsive to the identification module, provides the status of the network users. The status module may provide a visual indication of a network user's status using, for example, color coding, formatting, symbols, etc. A communication module for establishing a communication link with the one or more network users using the user indicator may also be provided. The communication module may be used to establish a variety of communications with one or more of the network users. For example, a user may chat, telephone, transmit an electronic mail message, share one or more application programs, whiteboard presentations, facsimile, or page to one or more of the network users by selecting the user indicator using a conventional computer mouse or keyboard.
Owner:EBAY INC
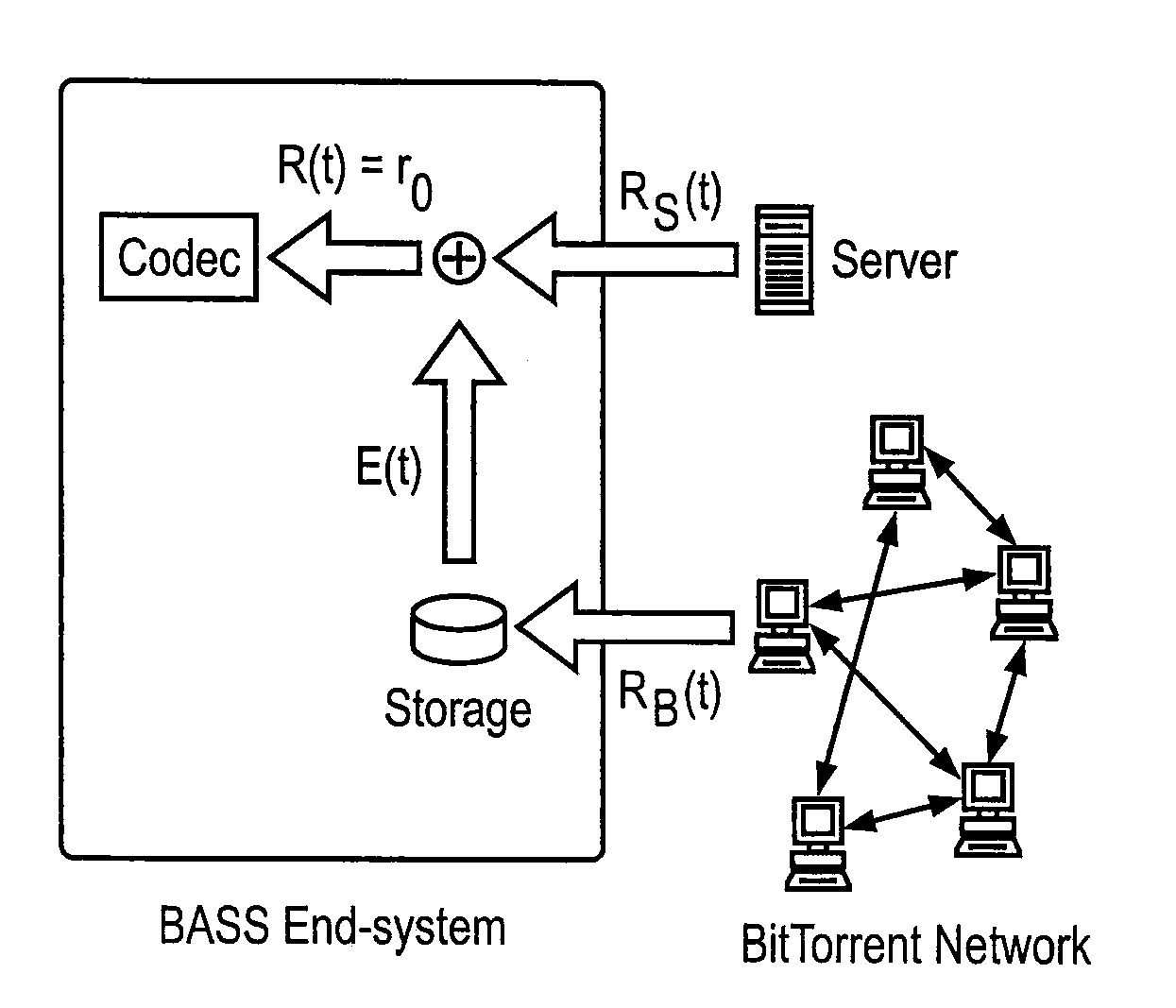
Peer-to-Peer Streaming Of Non-Live Content
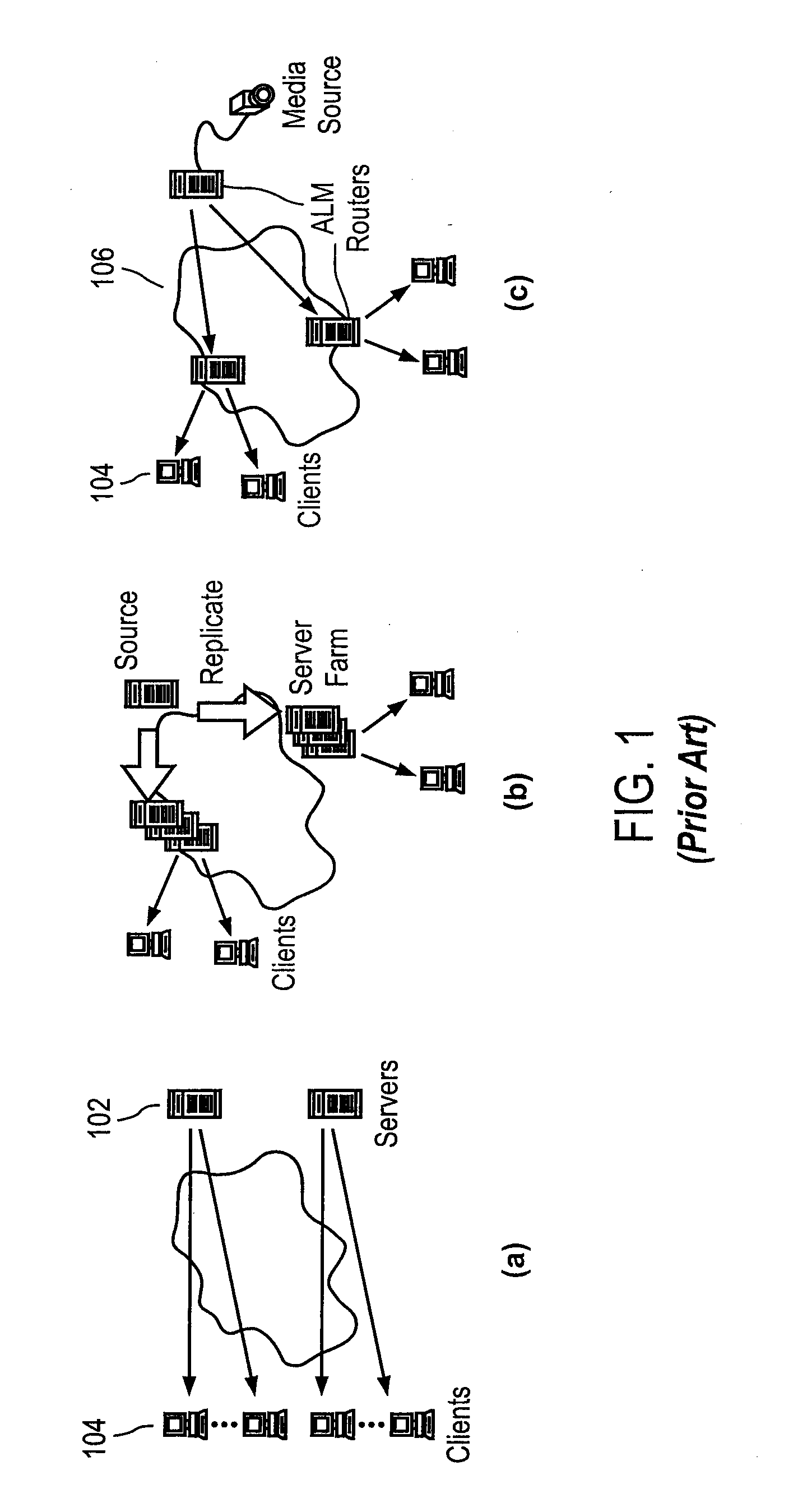
ActiveUS20080140853A1Minimal impactEasy to scaleMultiple digital computer combinationsTransmissionPoint-to-Point ProtocolEnd system
A Peer-to-Peer protocol such as BitTorrent is used to assist streaming. Peers download streaming content from the P2P network while simultaneously playing the downloaded content. As the stream plays, an end system downloads any missing pieces directly from a server or other infrastructure node. This method roughly squares server capacity and can be refined to require on average 0(1) servers regardless of the number of concurrent users. Thus BitTorrent assisted streaming scales better than traditional server-client and other infrastructure-only solutions, each of which requires a number of infrastructure nodes that scale linearly as a function of the number of users. Unlike End-System-Multicast, BitTorrent assisted streaming does not subject users to the vagaries of intermediate unreliable, potentially bandwidth-constrained end-systems; the departure of any single end-system has minimal impact on overall performance; and BitTorrent has a well-crafted incentive mechanism for encouraging users to contribute their upstream capacity.
Owner:BITTORRENT
Systems and methods for managing distributed database resources
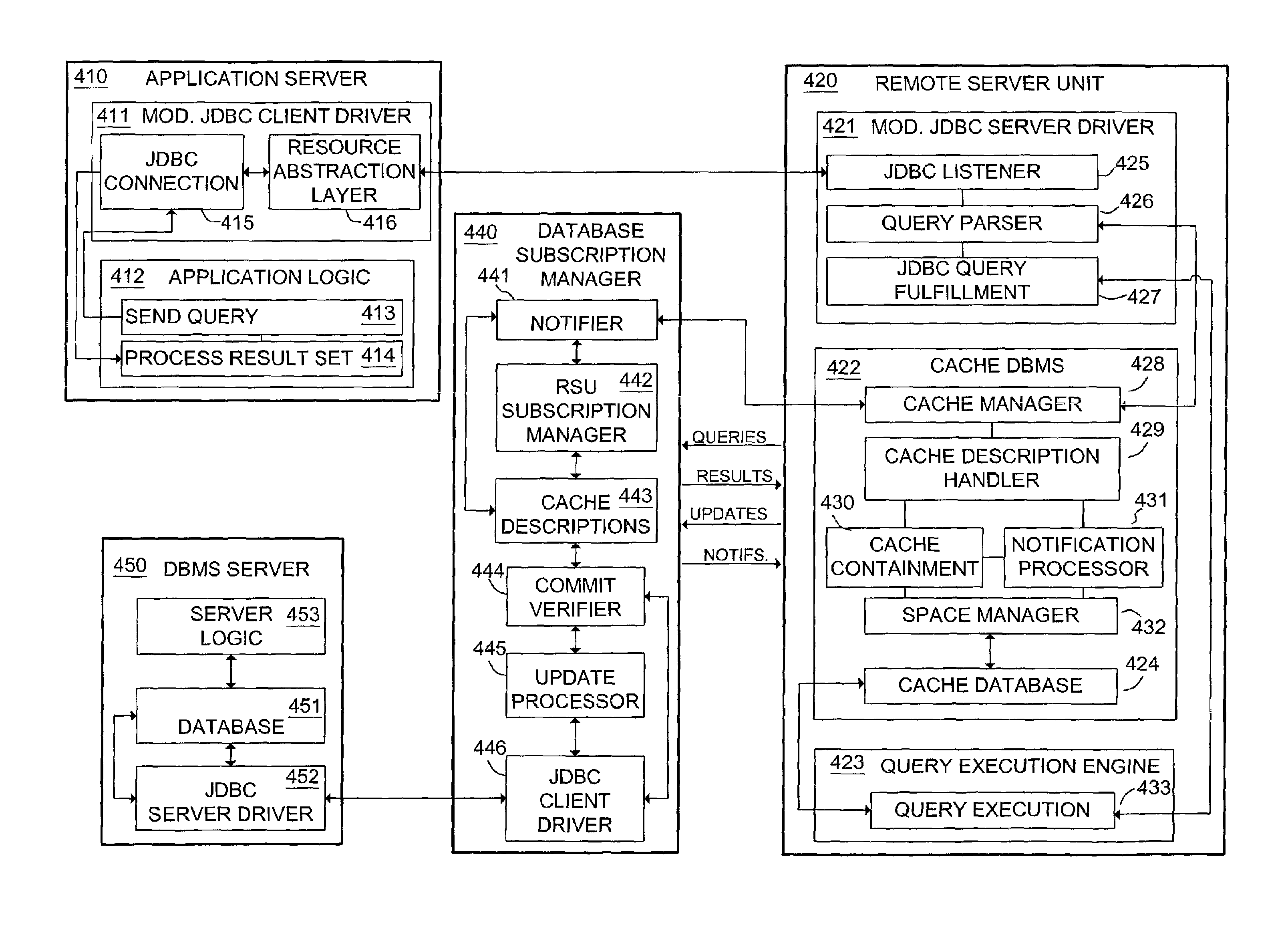
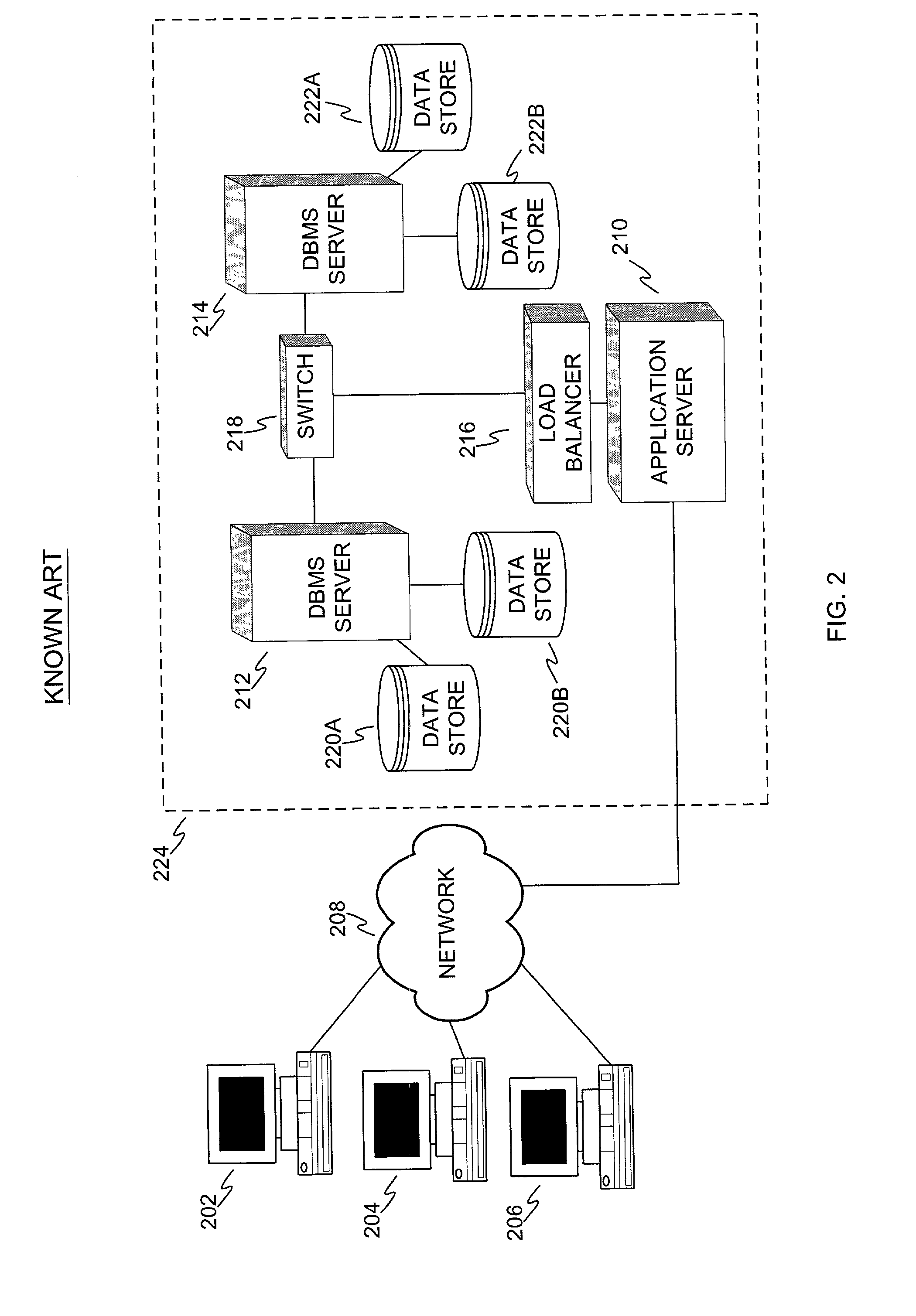
ActiveUS7162467B2Quality improvementLow costData processing applicationsDigital data processing detailsAbstraction layerCentral database
A system and method are described for implementing a distributed database caching system with the capability to support and accelerate read and update transactions to and from one or more central Database Management System (DBMS) servers for multiple concurrent users. The system and method include a resource abstraction layer in a database client driver in communication with remote server units (RSUs) having a cache database. RSUs respond to user requests using the cache database if possible. If the cache database does not have the needed data, the RSU sends the request to a database subscription manager (DSM) in communication with the DBMS server. The DSM responds to the request and sends predicate data based on queries processed by the DBMS server for use in updating the cache databases.
Owner:GOPIVOTAL
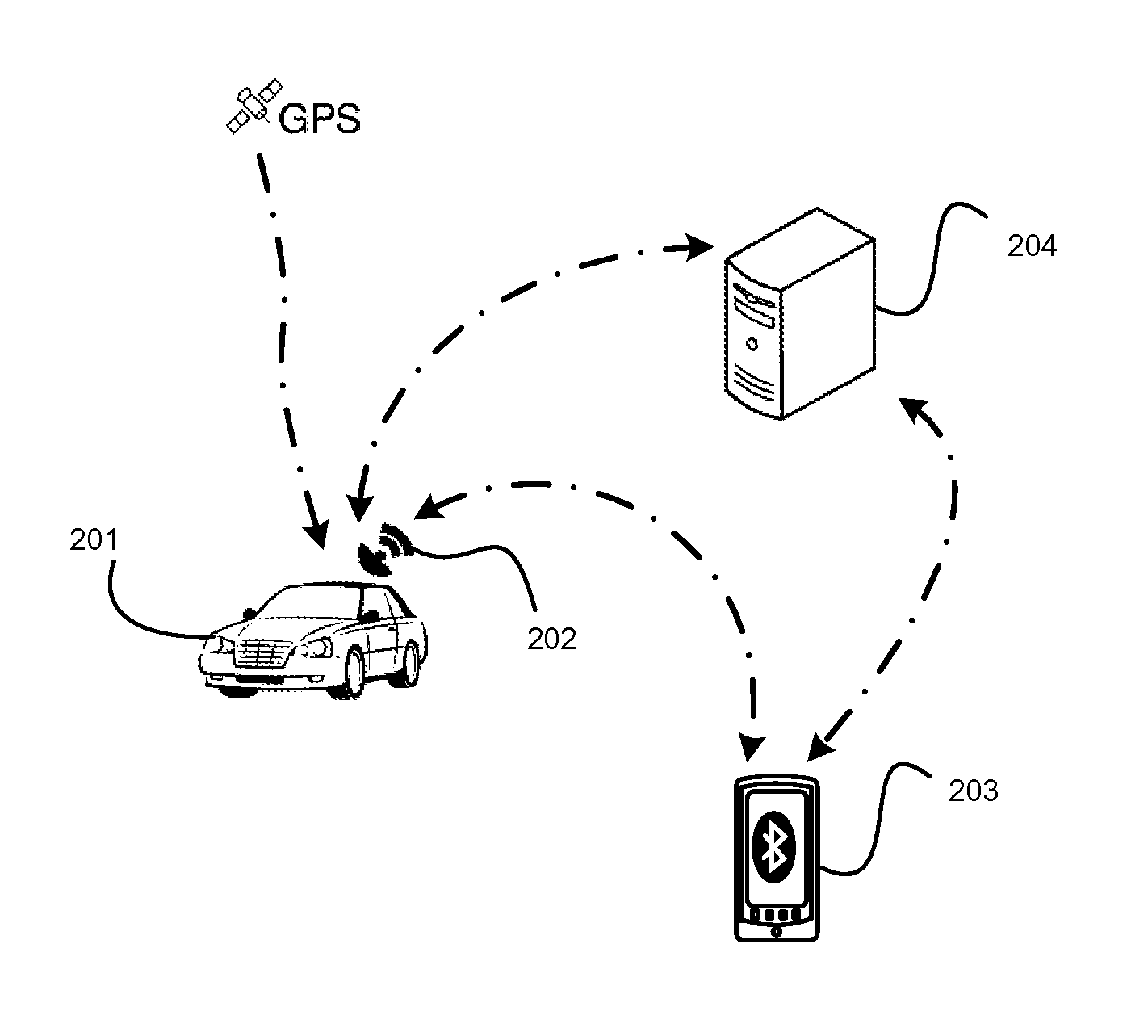
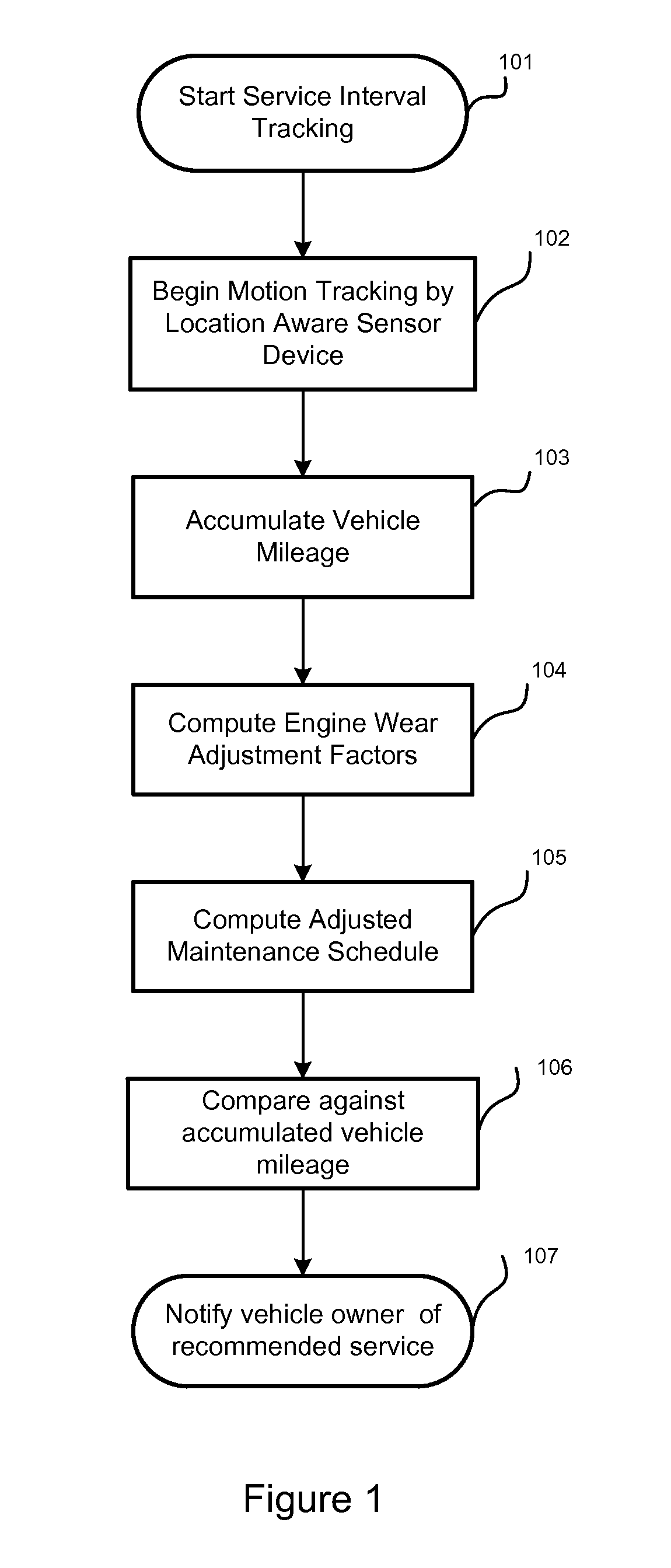
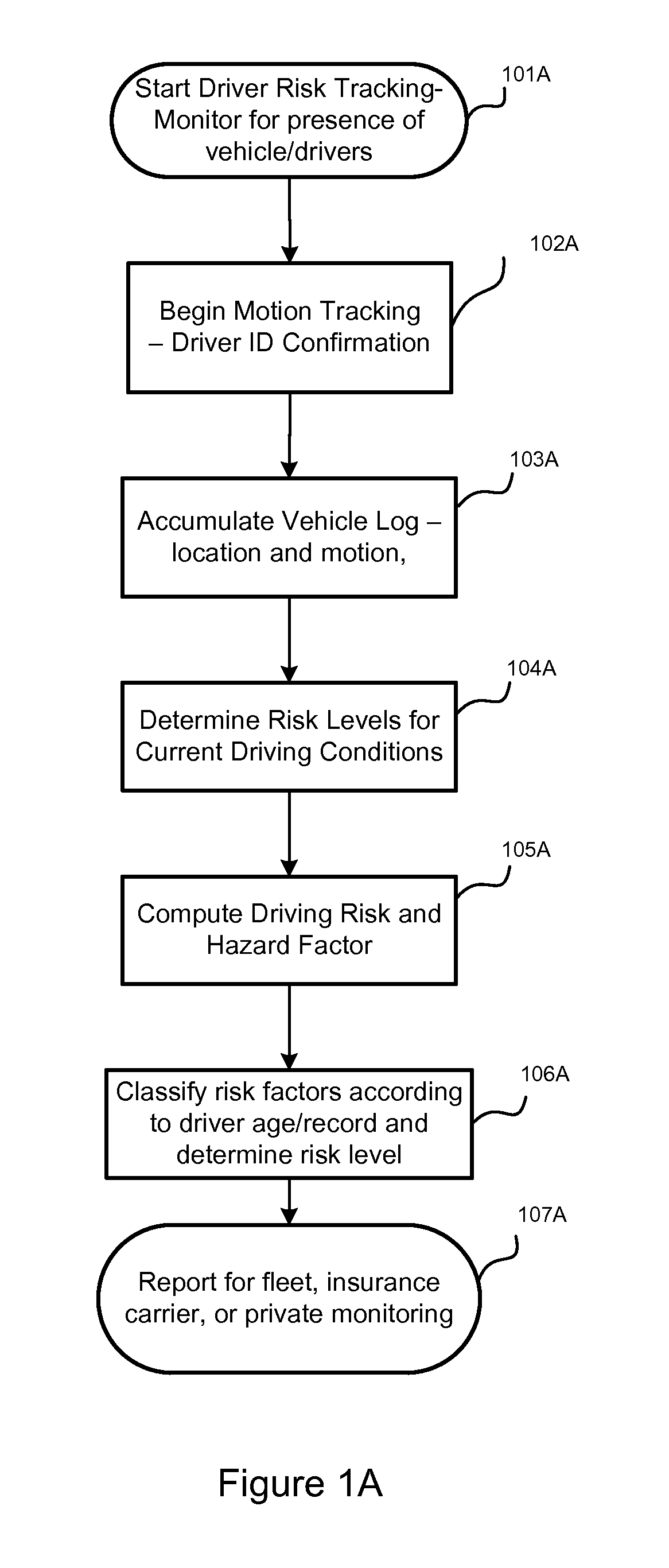
In-Car Driver Tracking Device
InactiveUS20130244210A1Accurate and reliable sensor inputAccurate and reliable inputCosmonautic condition simulationsRegistering/indicating working of vehiclesBehavioral analyticsData source
Disclosed are a device and method for providing driver tracking and behavior analysis, initiated without concurrent user input, by the presence detection of one or more drivers of the vehicle. Vehicle motion inferred from a location aware device sensor, as well as other driver smartphone sensors and application use are logged and analyzed to determine risk factors associated with identified drivers. Internet data sources are further utilized for associating road conditions and traffic regulations with the logged locations of the vehicle. Logged and analyzed data from the identified drivers is aggregated for reporting on vehicle risk.
Owner:KAARYA
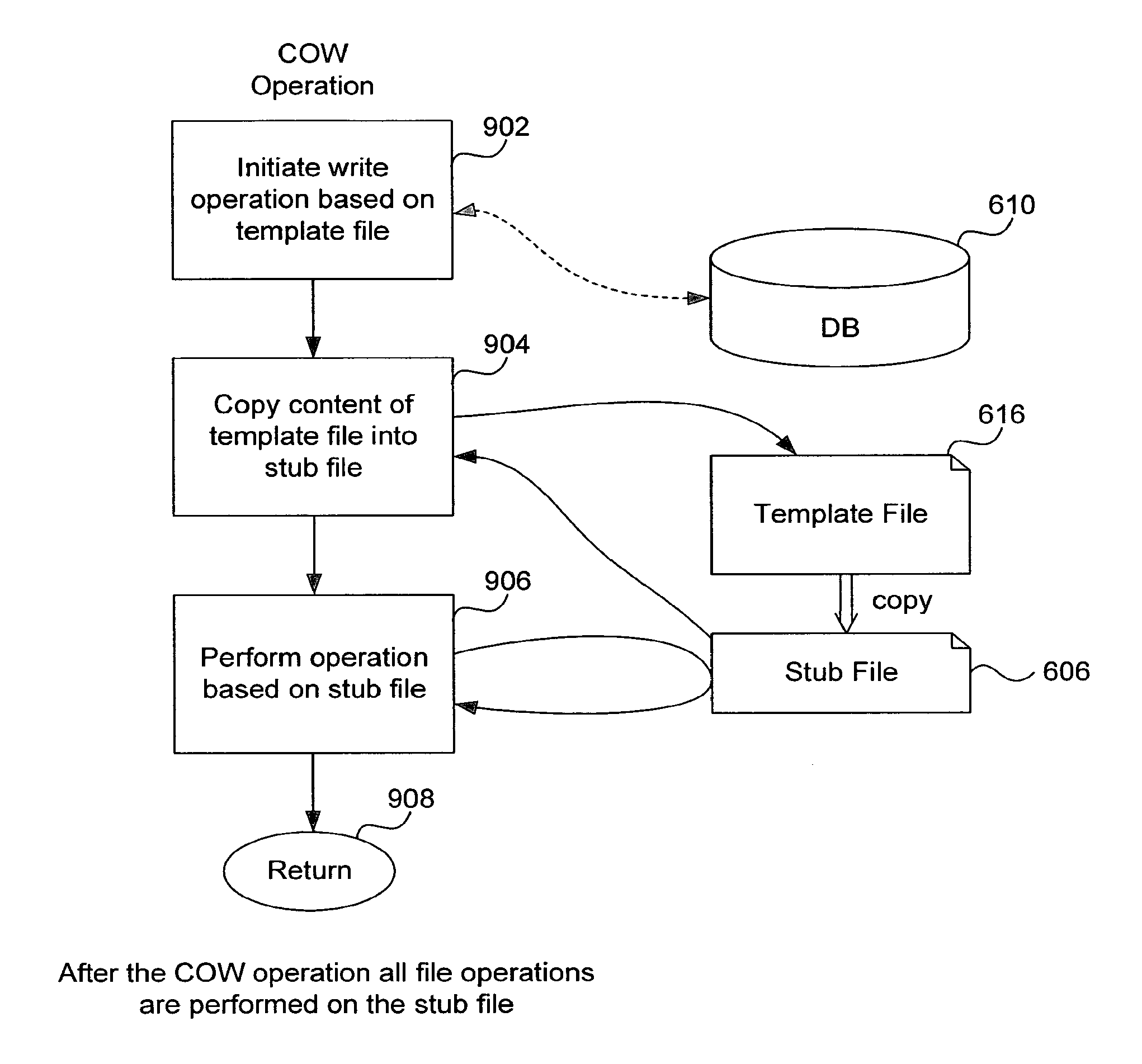
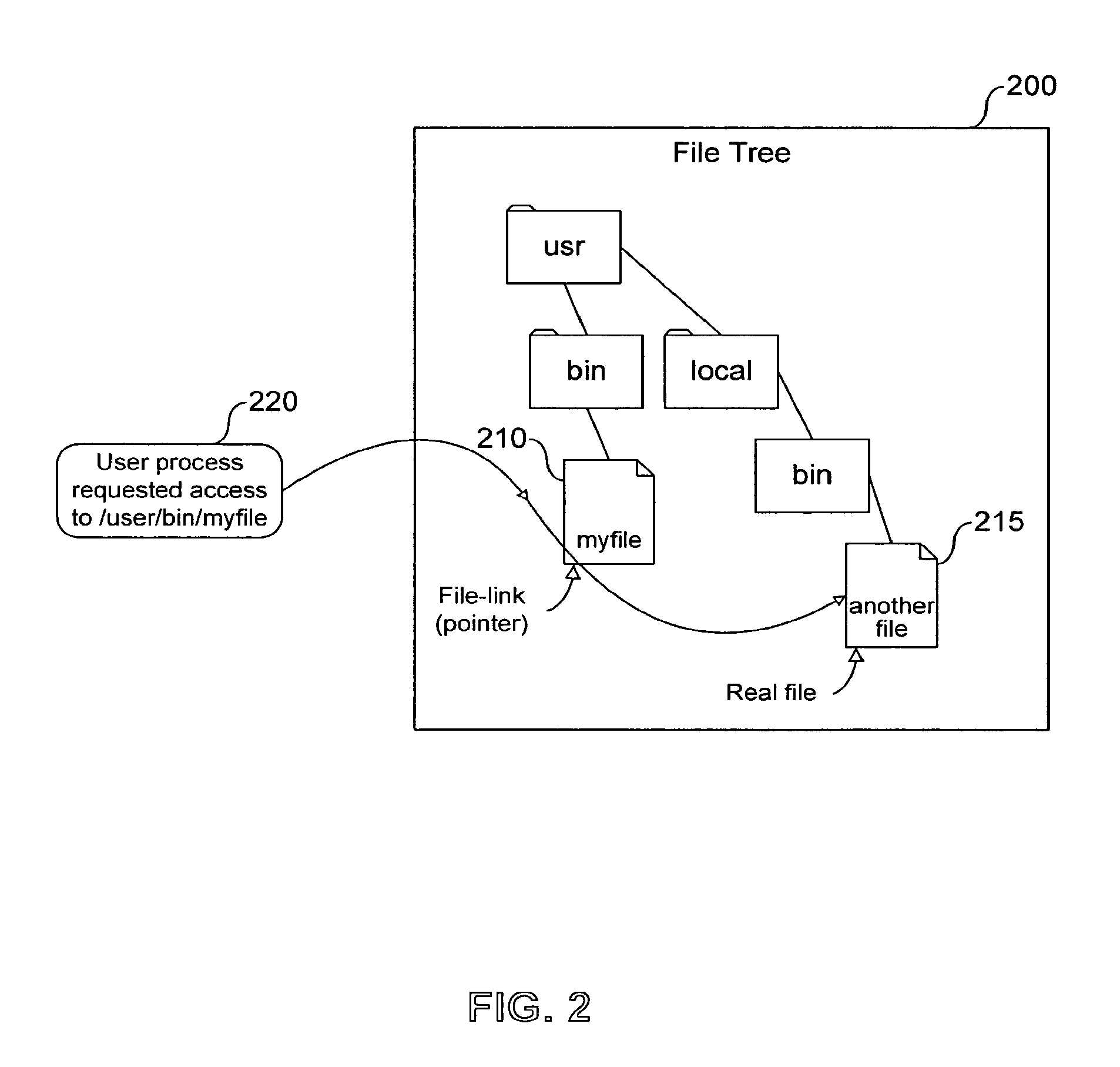
System, method and computer program product for multi-level file-sharing by concurrent users
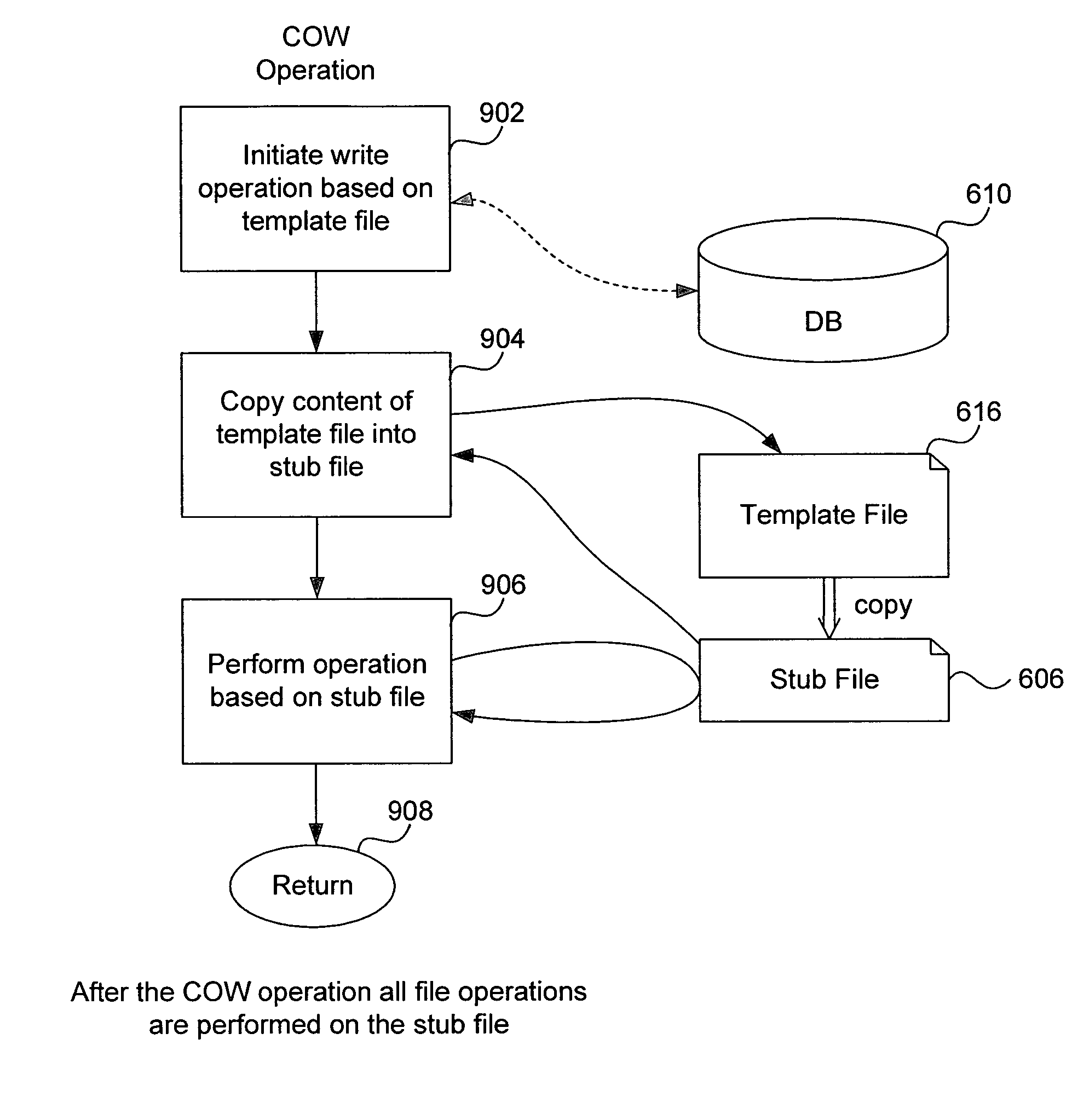
ActiveUS7328225B1Efficient multi-user accessEfficient file sharingData processing applicationsSpecial data processing applicationsOperational systemFile size
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
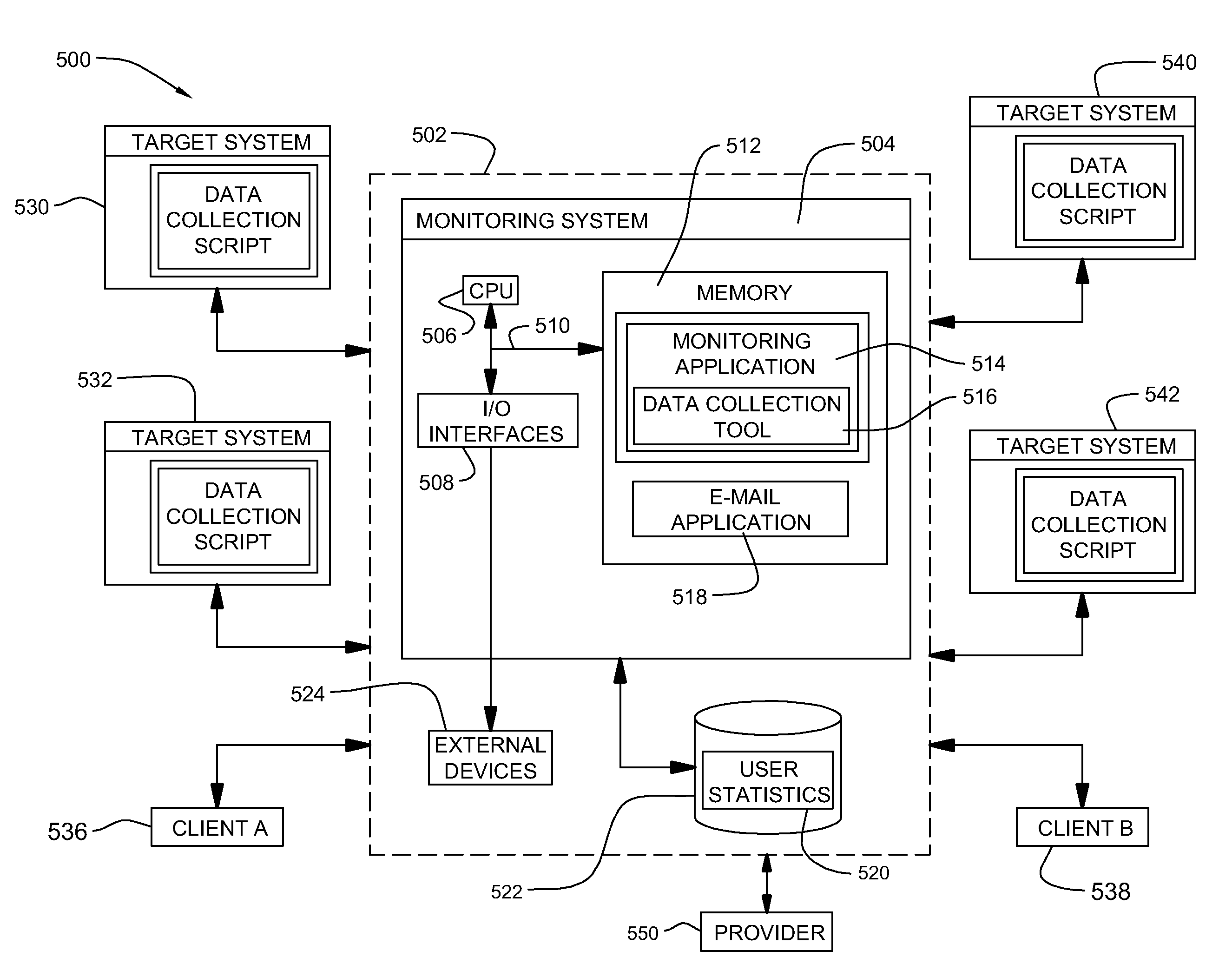
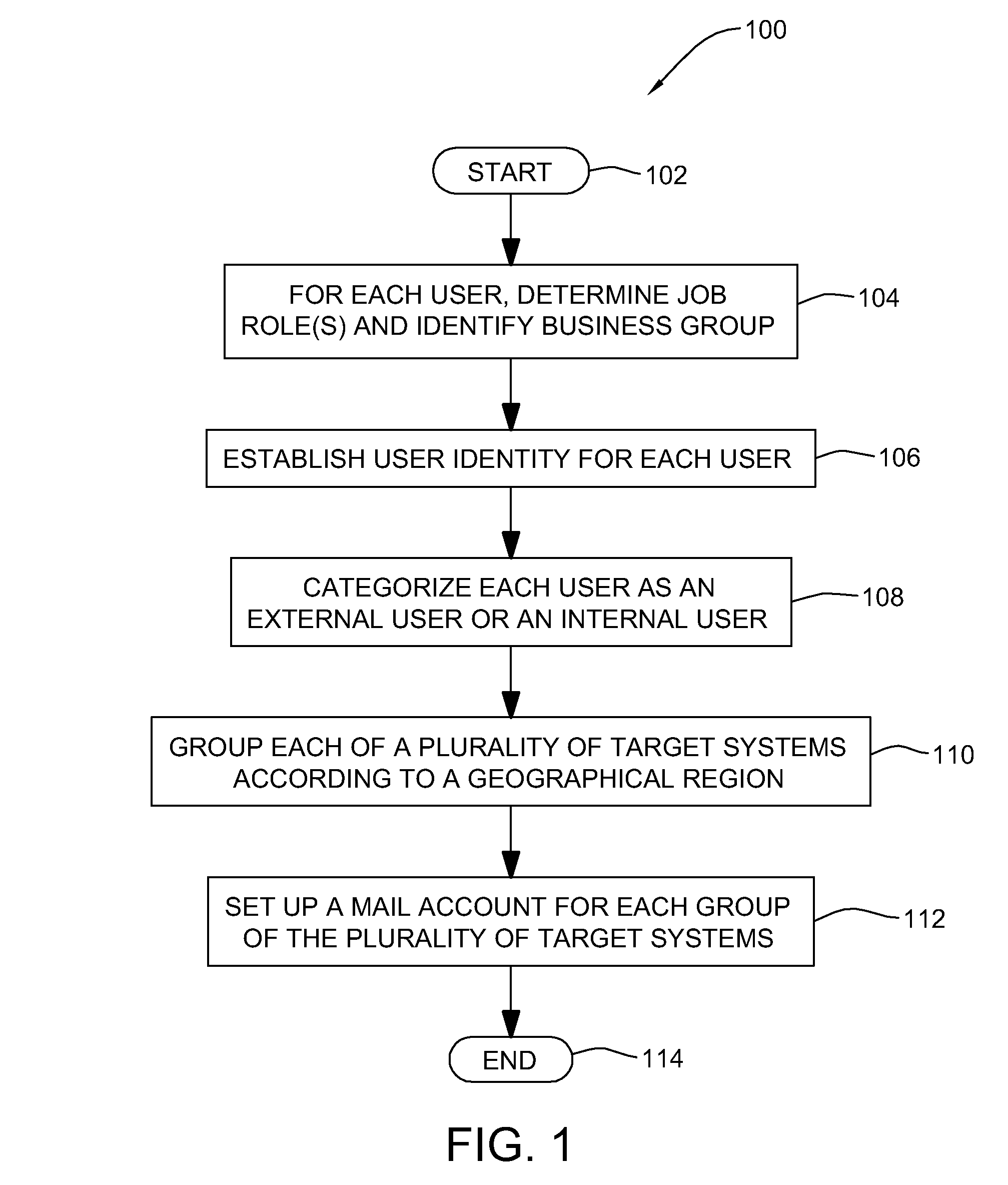
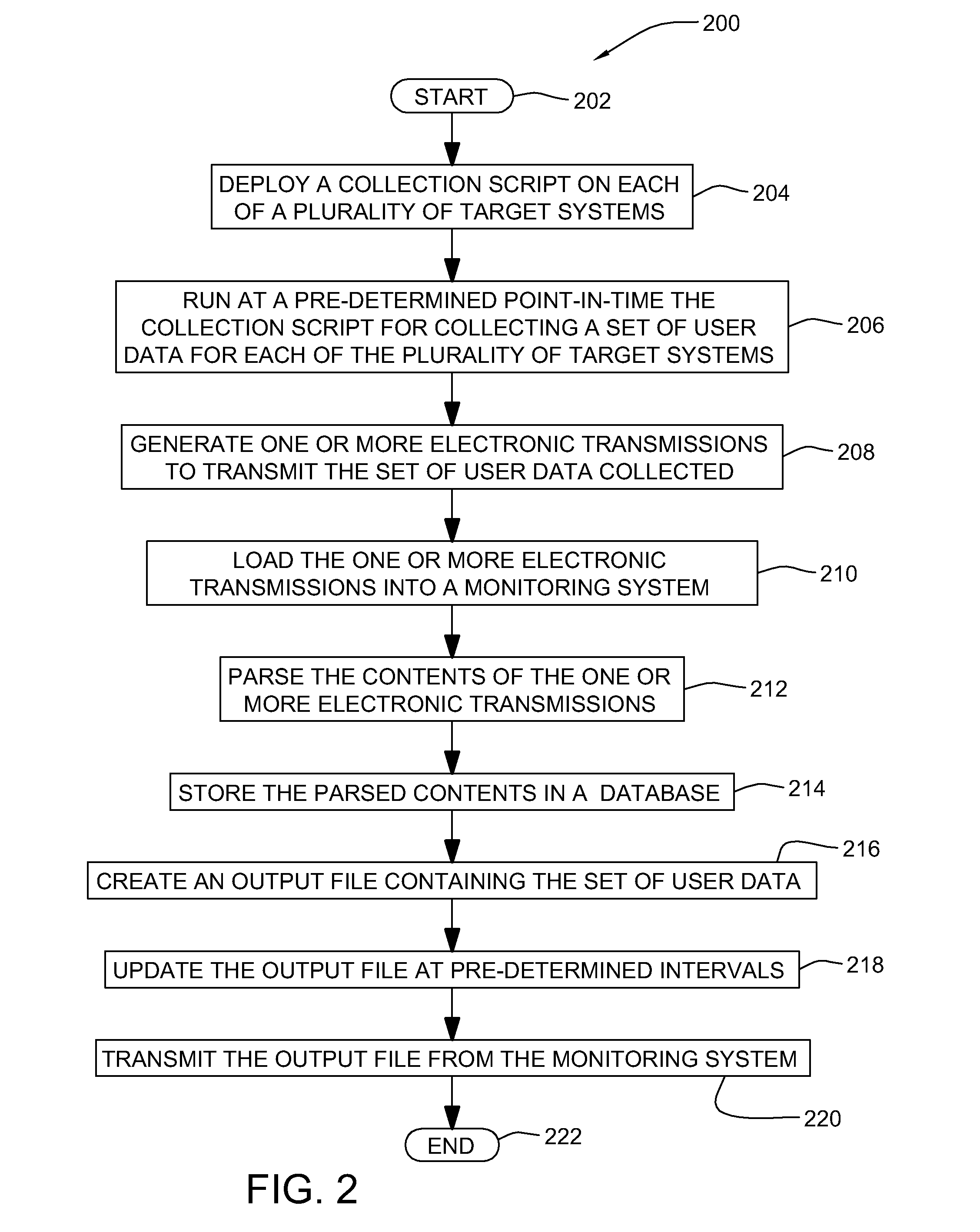
Method, system and program product for determining a number of concurrent users accessing a system
InactiveUS20080109547A1Error detection/correctionDigital computer detailsElectronic transmissionMonitoring system
A method, system and program product for determining a number of concurrent users being served by a system at a given point-in-time is provided. The method includes running, at a pre-determined point-in-time, a collection script for collecting user data from one or more target systems, the user data collected including a number of concurrent users logged into each of the target systems at the pre-determined point-in-time. The method further includes generating one or more electronic transmissions for transmitting the user data collected, loading the one or more electronic transmissions generated into a monitoring system, and creating an output file containing the user data. Further, the loading step includes parsing the user data loaded, storing the user data collected and parsed into a database and updating the stored user data. Moreover, the method includes transmitting the output file from the monitoring system to one or more monitoring system clients.
Owner:IBM CORP
System load testing coordination over a network
A method and system using one or more load cells coordinates load testing of one or more sites under test over a network such as the Internet in accordance with one or more load test requests. In one embodiment, such method and system facilitates an economic, efficient, and accurate evaluation of the capacity of the SUTs to support concurrent users of the SUTs. A load test request is received from a User and provides information concerning a load test to be performed on a site under test (SUT). A load test is generated, and the load test is allocated to one or more load cells. The load cells perform the load test by sending load test data to the SUT and receiving responses from the SUT. Portions of a load test may be allocated to different load cells, which may be geographically remote from the SUT and / or geographically diverse. Multiple concurrent pending load tests may be processed for the same SUT. A load cell may concurrently perform all or a portion of multiple different load tests for multiple different SUT's simultaneously. A reporting function generates a report based on the responses received from the SUT. The reporting function may in addition or alternatively allow the User to view real-time results during load test execution.
Owner:EUREKA SOFTWARE SOLUTIONS
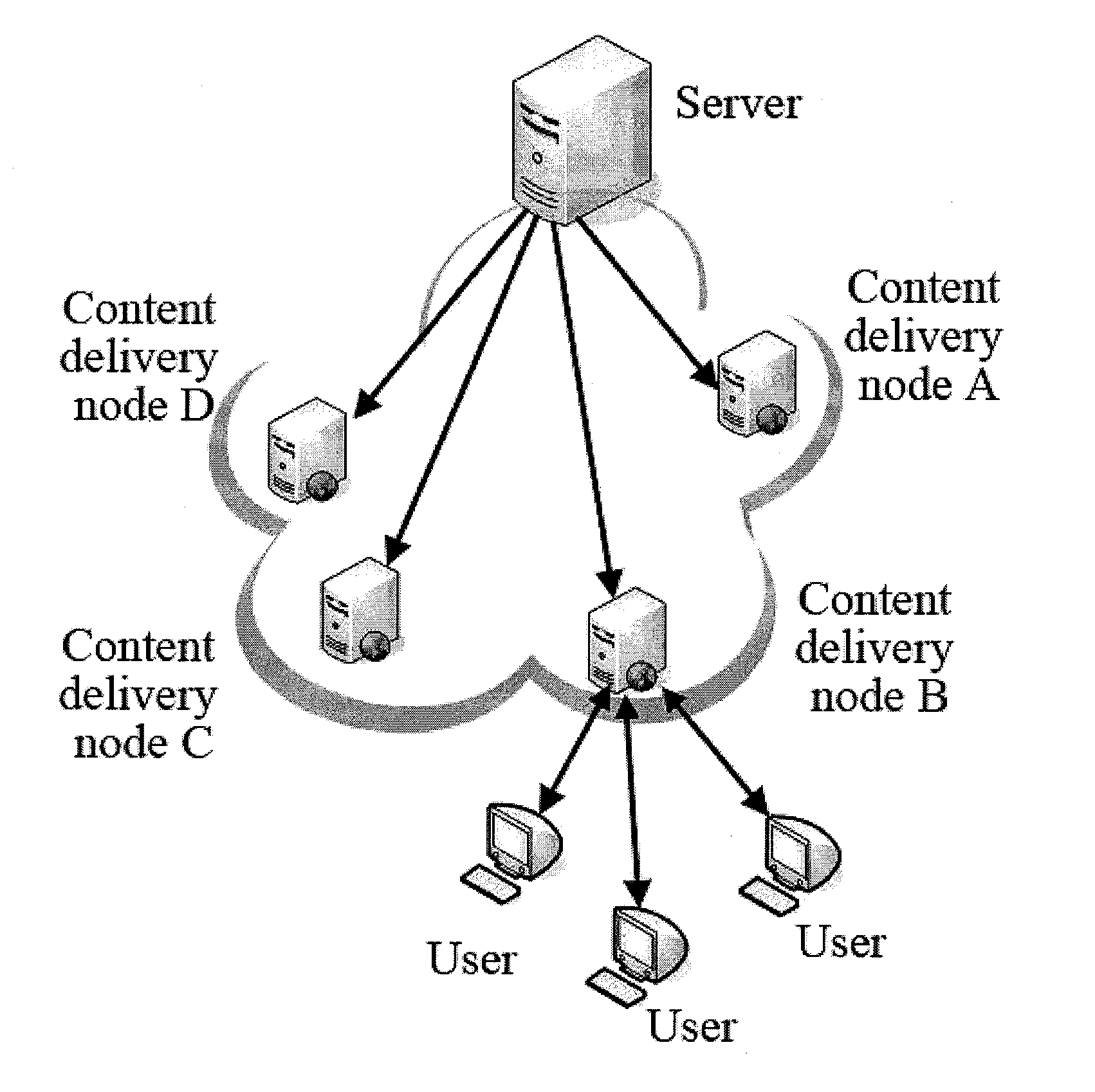
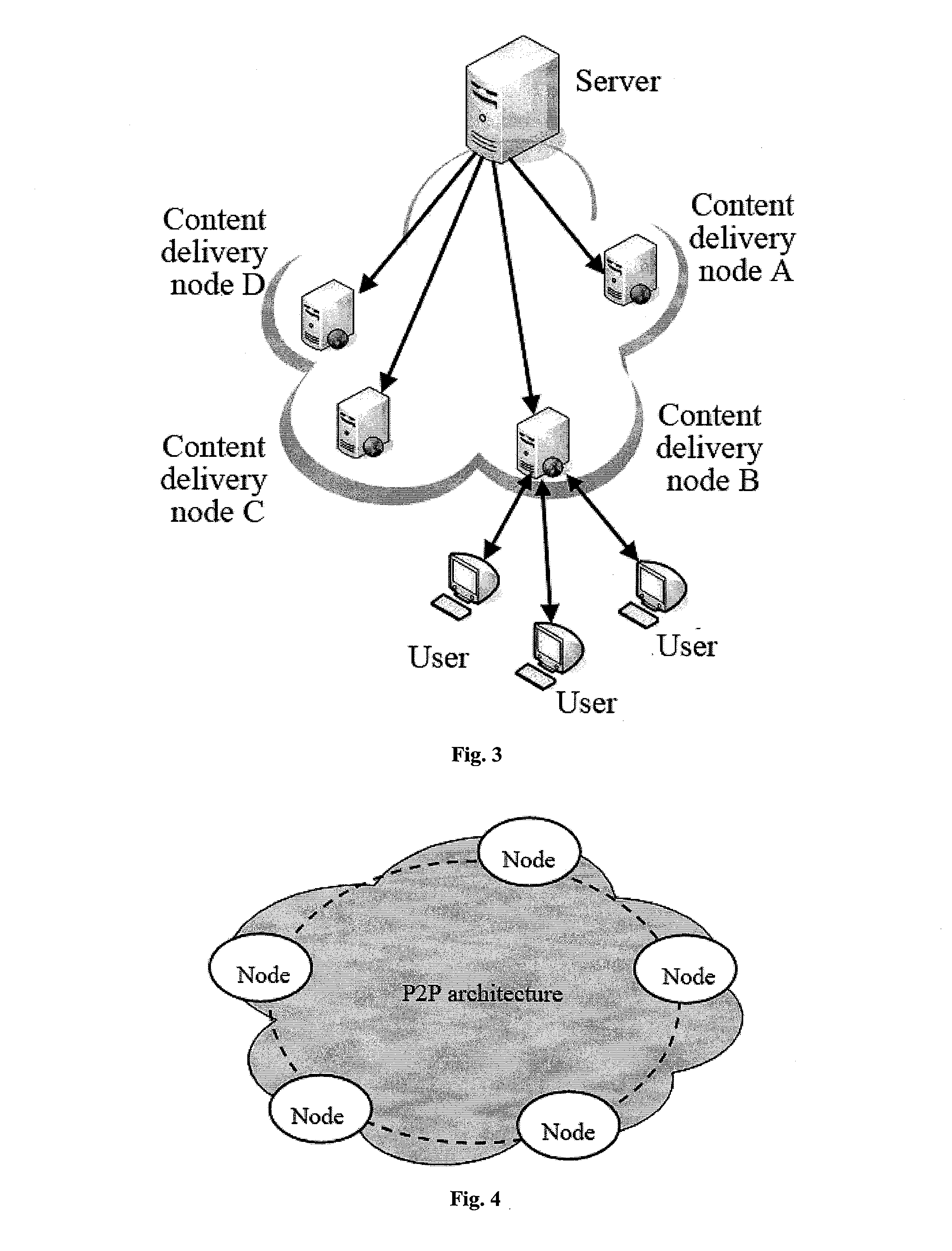
Streaming media distribution system, method and device
InactiveCN101729273ALower deployment costsSpecial service provision for substationExtensibilityDistribution system
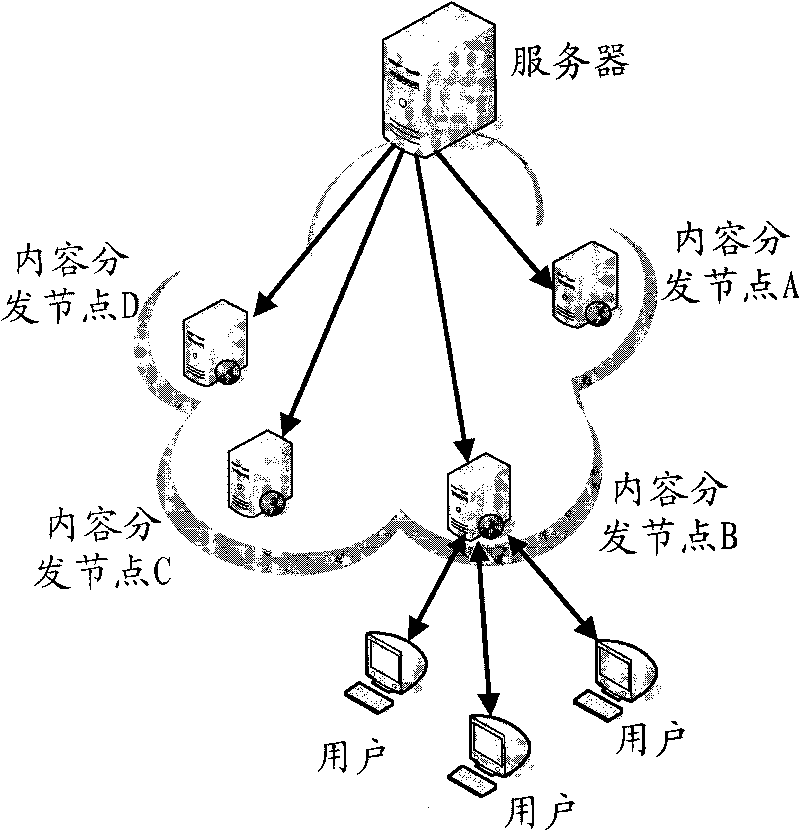
The invention discloses streaming media distribution system, method and device. The method comprises the following steps of: receiving an inquiry request sent by a terminal node by a global server, determining the domain of the terminal node according to carried address information and returning the domain server information of the domain to which the terminal node belongs; sending a streaming media data acquiring request to a domain server by the terminal node; inquiring whether the domain has the streaming media data or not by the domain server; if so, returning the streaming media data / returning other terminal node information containing the streaming media data in the domain; if not, acquiring and returning the required streaming media data from other domain servers in a core network / the global server by adopting a P2P (peer-to-peer) mode; and receiving the returned streaming media data / acquiring the streaming media data from other terminal nodes by adopting the P2P mode according to the returned information of other terminal nodes. The system combines a traditional CDN (content delivery network) and P2P streaming media technology, can meet the streaming media distribution requirements of large-scale concurrent users and has high reliability and strong expandability.
Owner:CHINA MOBILE COMM GRP CO LTD
Multiple user computer including anti-concurrent user-class based disjunctive separation of plural hard drive operation
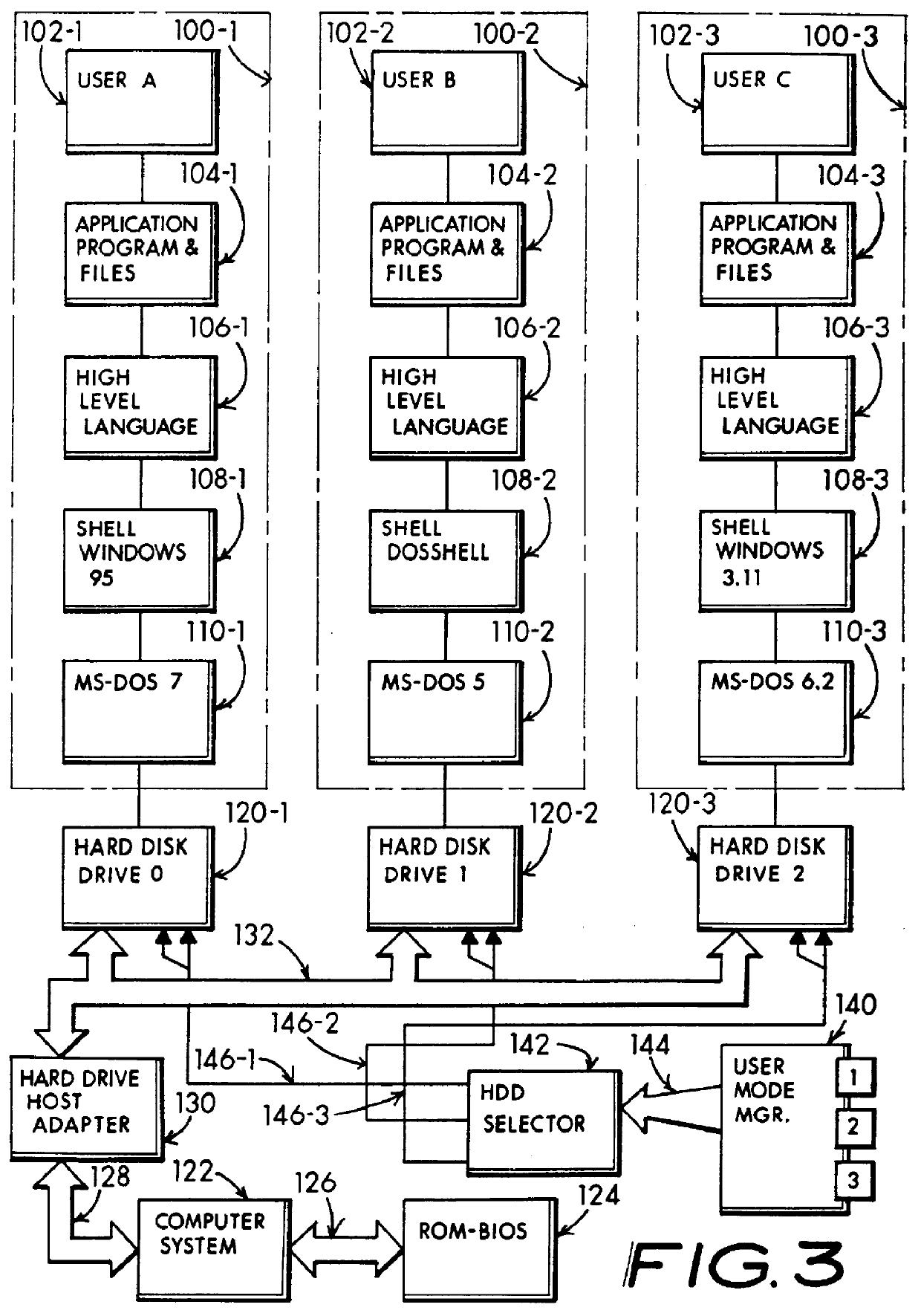
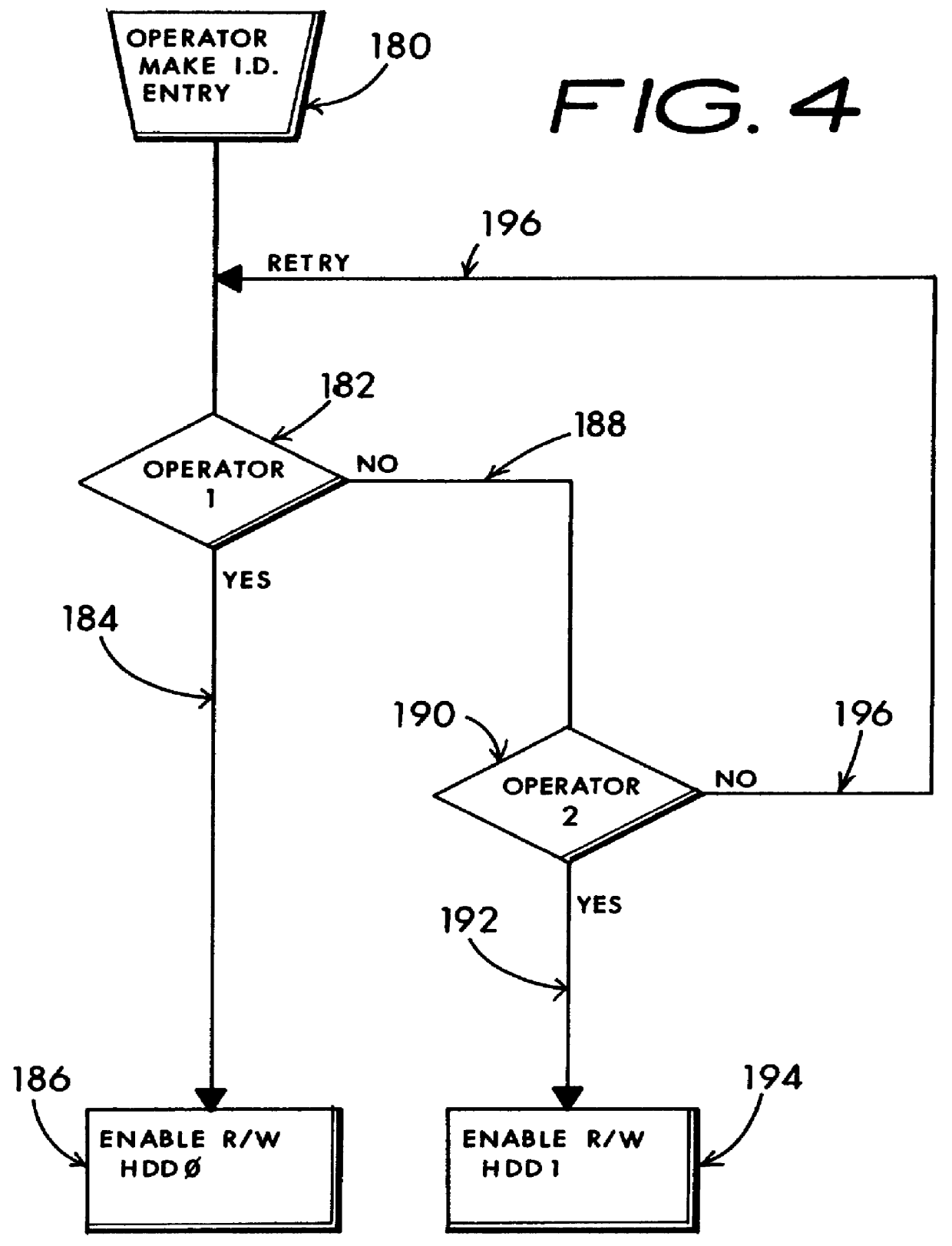
InactiveUS6052781ALow costSame level of securityMemory loss protectionError detection/correctionUnixHard disc drive
A computer sharing system which adapts a computer's hardware resources to providing virtual dual system operation for several non-concurrent system users. A separate hard disk drive including a full complement of boot, operating system, program and data file software is provided for each of the non-concurrent system users. Access by one system user to another system user's hard disk drive and attendant files is absolutely denied thereby preventing corruption of one user's hard disk dive files by another user's carelessness or malicious intent, or through unique setup adaptation of one user's program files which may otherwise interact with and impose unwanted changes on another's program file's operational performance. Each of the separate hard disk drives may be uniquely formatted to service totally different operating systems, including boot track code, in support of various operating systems including MS-DOS, Windows-NT, OS / 2, Unix and others. By definition, each separate hard disk drive may be a physically distinct hard disk drive unit, or be more economically embodied as several separately utilized media platters driven by a common hard disk drive mechanisim and having user distinctive READ and WRITE channel control for each media platter. The absolute denial of a system user's access to another system user's assigned hard disk drive may be cracked open to an limited extent whereby READ-ONLY access may be permitted. Additionally, a third hard disk drive may be enabled to be shared by one or more system users in any combination of READ-ONLY, and READ and WRITE modes. My objective is to deliver the independent performance which until now was proffered only by two completly separate computers in the economic form of one set of computer hardware offering at least two virtually separate operating systems and sets of supporting software whereby one system user is absolutely blocked from corrupting another system user's uniquely configured software and data files.
Owner:HANGER SOLUTIONS LLC
Lending System and Method
InactiveUS20070255580A1Sufficient flexibilityProgram/content distribution protectionCommerceLibrary servicesDatabase
A lending system for lending an econtent item comprises a library server having a processor and a number of databases. Borrowers can access the system using a PDA or other suitable communications device over a communications network. Each econtent item has a number of loan instances allocated to it, and the econtent item can be made available to borrowers up to a maximum number of predetermined loan instances over a set period of time. A single loan instances can be typically defined as a period of between 5 minutes and 24 hours to a single borrower, with an econtent item having an allocation of a set number of loan instances per calendar year, for example, 325 loan instances. This allows the econtent item to be made available to multiple concurrent users or single users as long as the number of loan instances has not been exceeded in any given year.
Owner:EBOOKS CORP
Method system and program product for providing enabling an interactive and social search engine
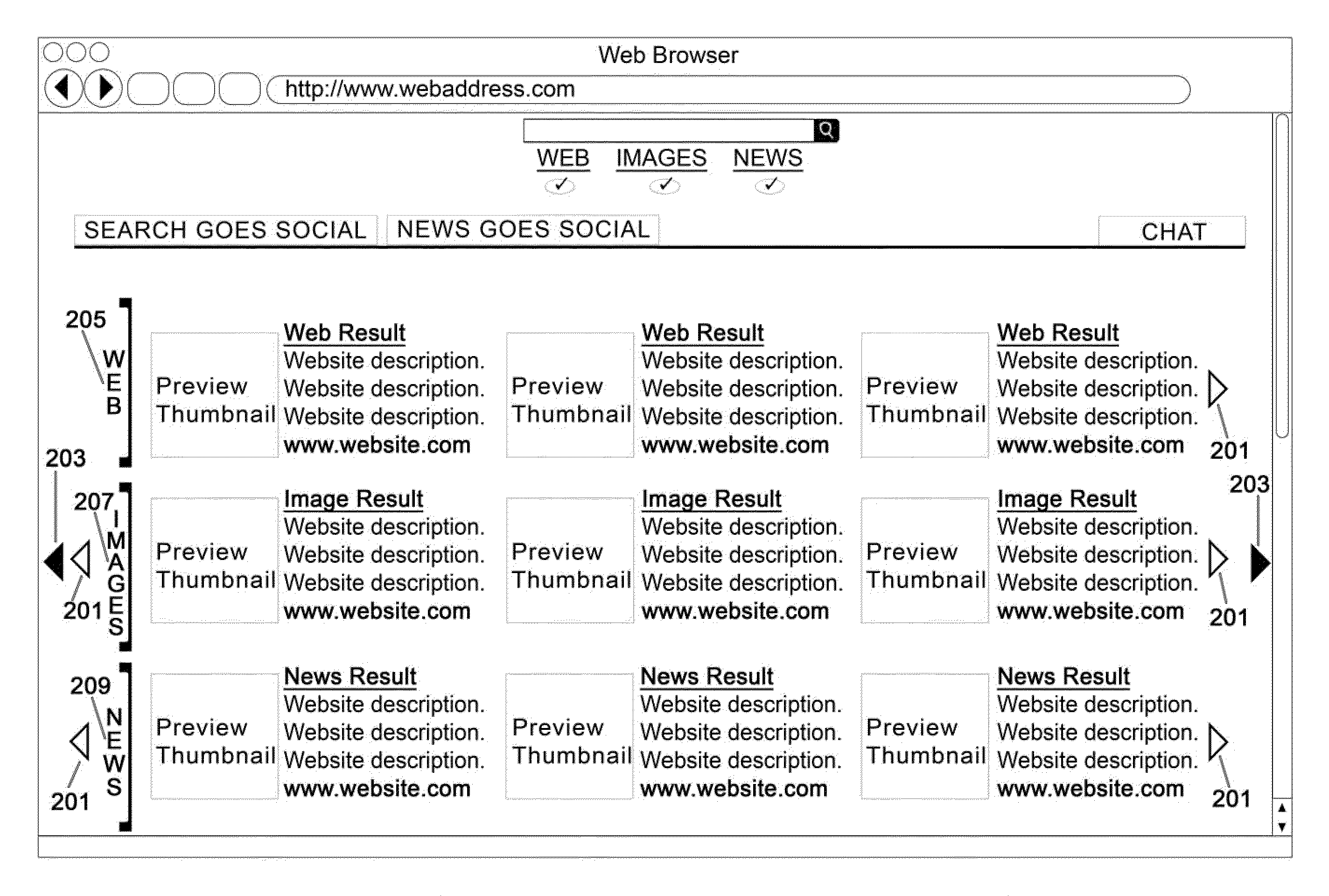
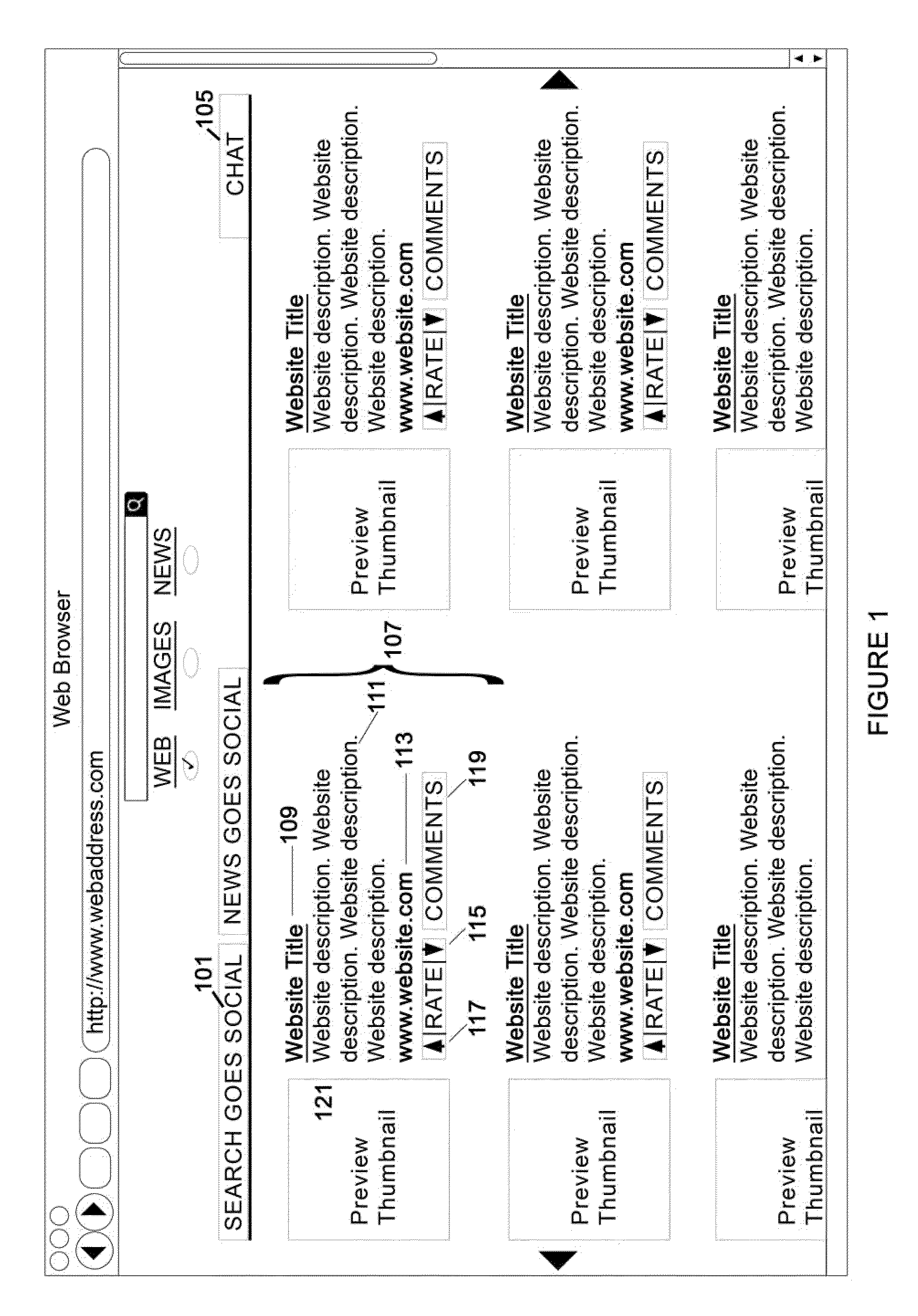
InactiveUS20100058202A1Web data indexingSpecial data processing applicationsSocial searchDisplay list
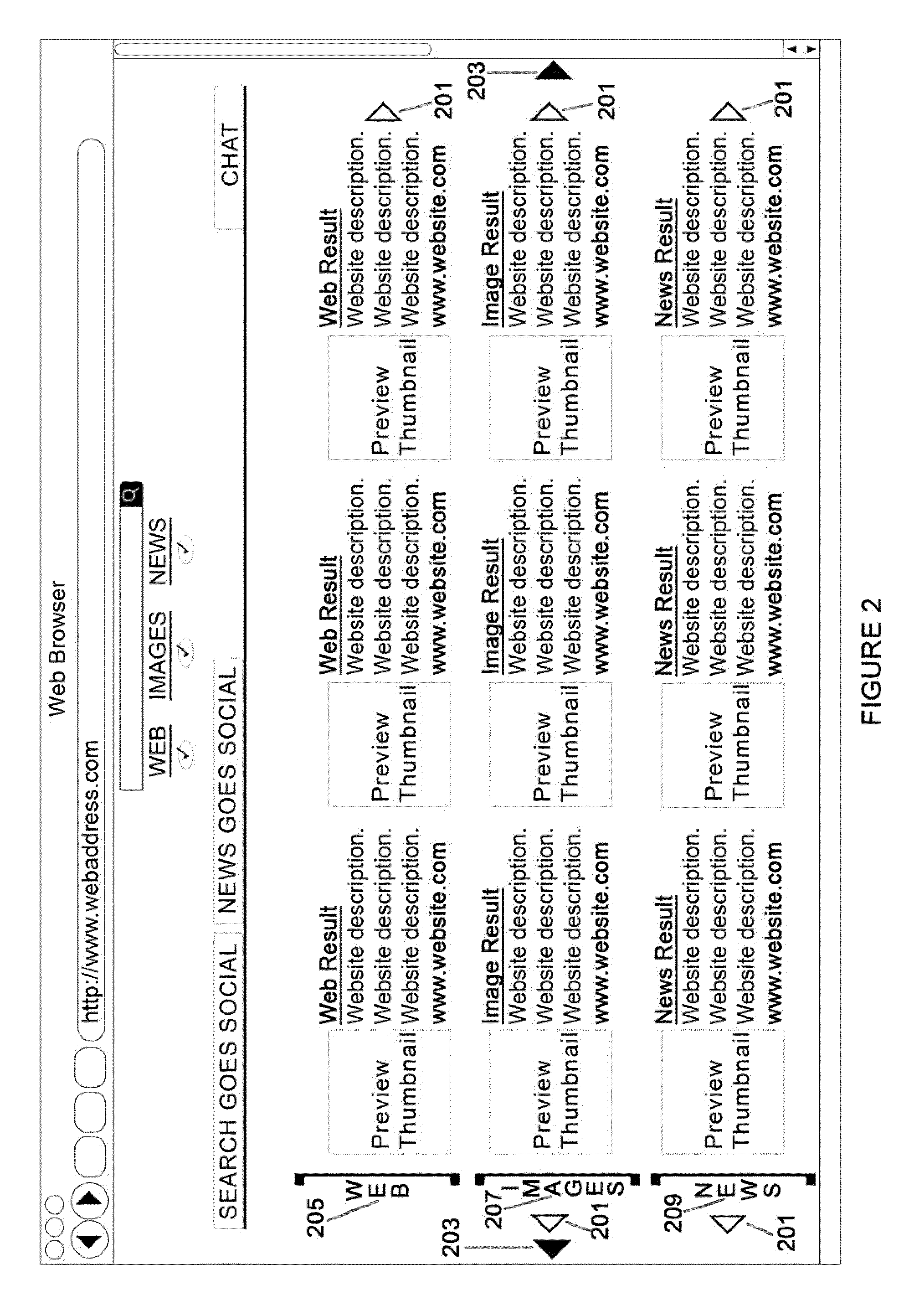
A system for an interactive and social search engine includes a search component responding to a user's search request for generating a listing of search results including site addresses. A display component displays the listing along with a rating control for each site address in the listing. A rating component accepts inputs from the rating control to affect an order of the listing where a change in a rating of a site address dynamically controls the displaying of the listing and subsequent search requests. A browsing control component scrolls through and vies content of each site address in the listing. A chat component conducts organized communication sessions between users of the system. A communication component conducts communication between users of the system in real-time. A detection component detects concurrent users of the system requesting substantially similar searches and establishes communication between the concurrent users.
Owner:LAVVA
Resource self-adaptive adjusting system and method of multiple virtual machines under single physical machine
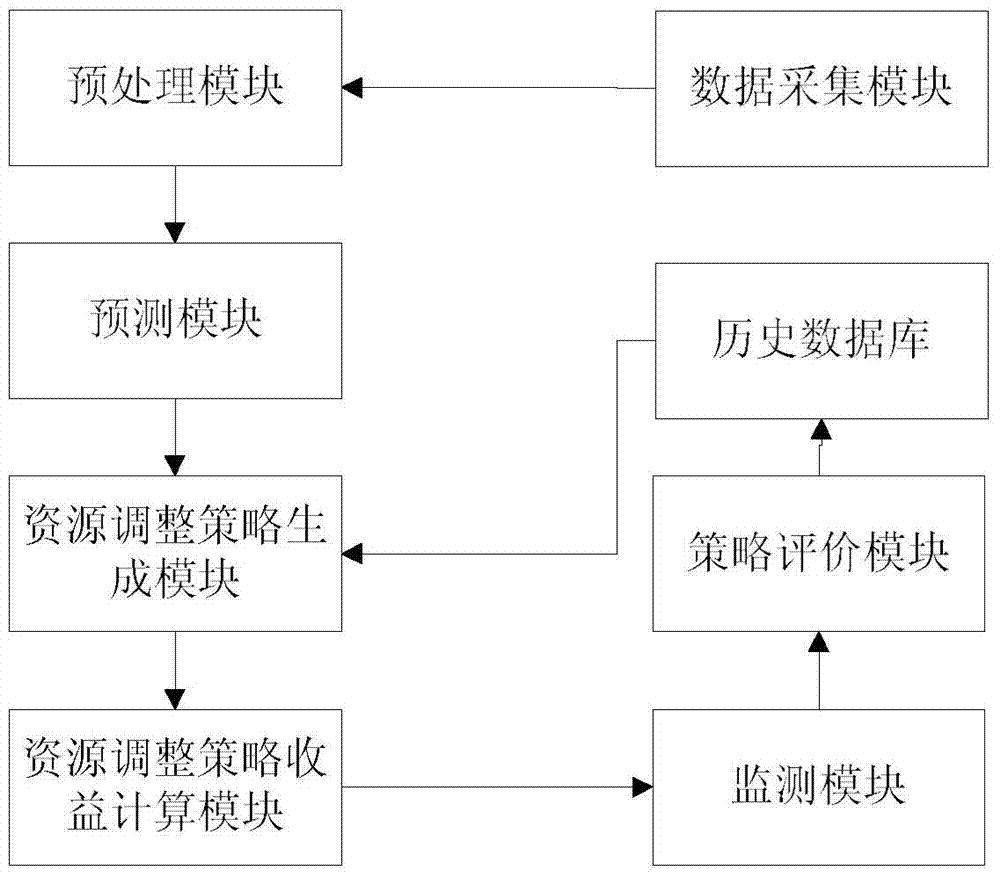
ActiveCN104283946AReduce overheadImprove regulation efficiencyProgram controlData switching networksPrediction intervalSelf adaptive
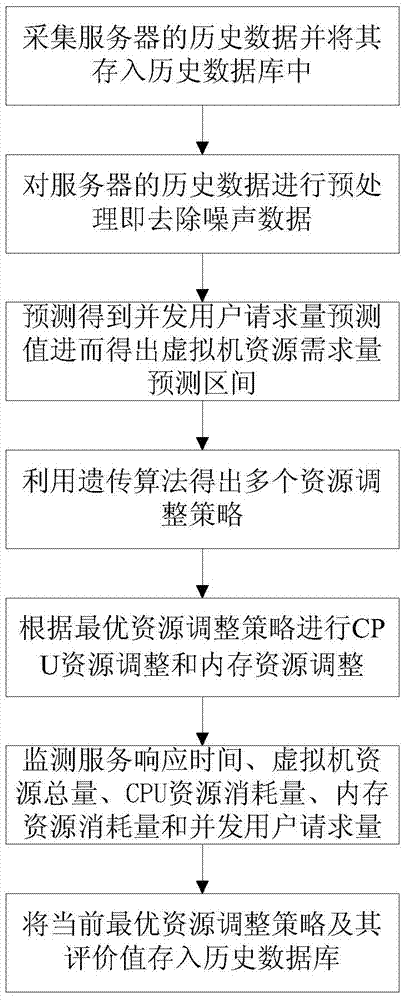
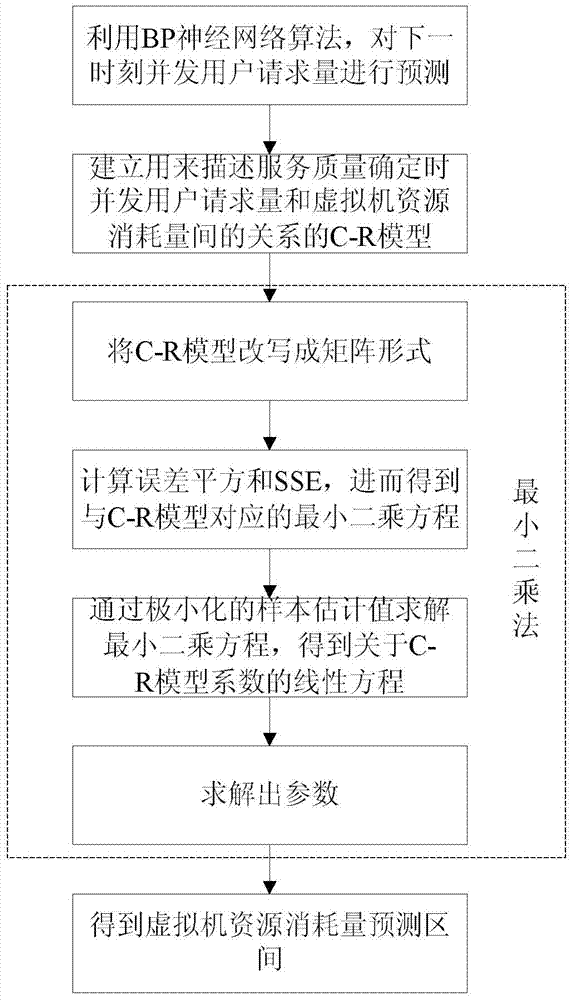
The invention provides a resource self-adaptive adjusting system and method of multiple virtual machines under a single physical machine. The system is achieved in the single physical machine and comprises a data collecting module, a preprocessing module, a prediction module, a resource adjustment strategy generating module, a resource adjustment strategy gain calculating module, a monitoring module, a strategy evaluation module and a historical database. The method comprises the steps that the historical data of a server are collected and stored in the historical database; the historical data of the server is preprocessed; the concurrent user request amount at the next moment is predicted, and then the demand amount prediction intervals of virtual machine resources is obtained by the predicted value of the concurrent user request amount; an optimal resource adjusting strategy is determined; CPU resource adjustment and internal storage resource adjustment are conducted; the optimal resource adjusting strategy is evaluated; the current optimal resource adjustment strategy and the evaluation value of the current optimal resource adjustment strategy are stored into the historical database. According to the resource self-adaptive adjusting system and method of the multiple virtual machines under the single physical machine, the resource amounts of all the virtual machines on the single physical machine can be adjusted to be adaptive to dynamically-changed resource demands, and therefore the resources of the single physical machine can obtain the biggest benefits.
Owner:北方实验室(沈阳)股份有限公司
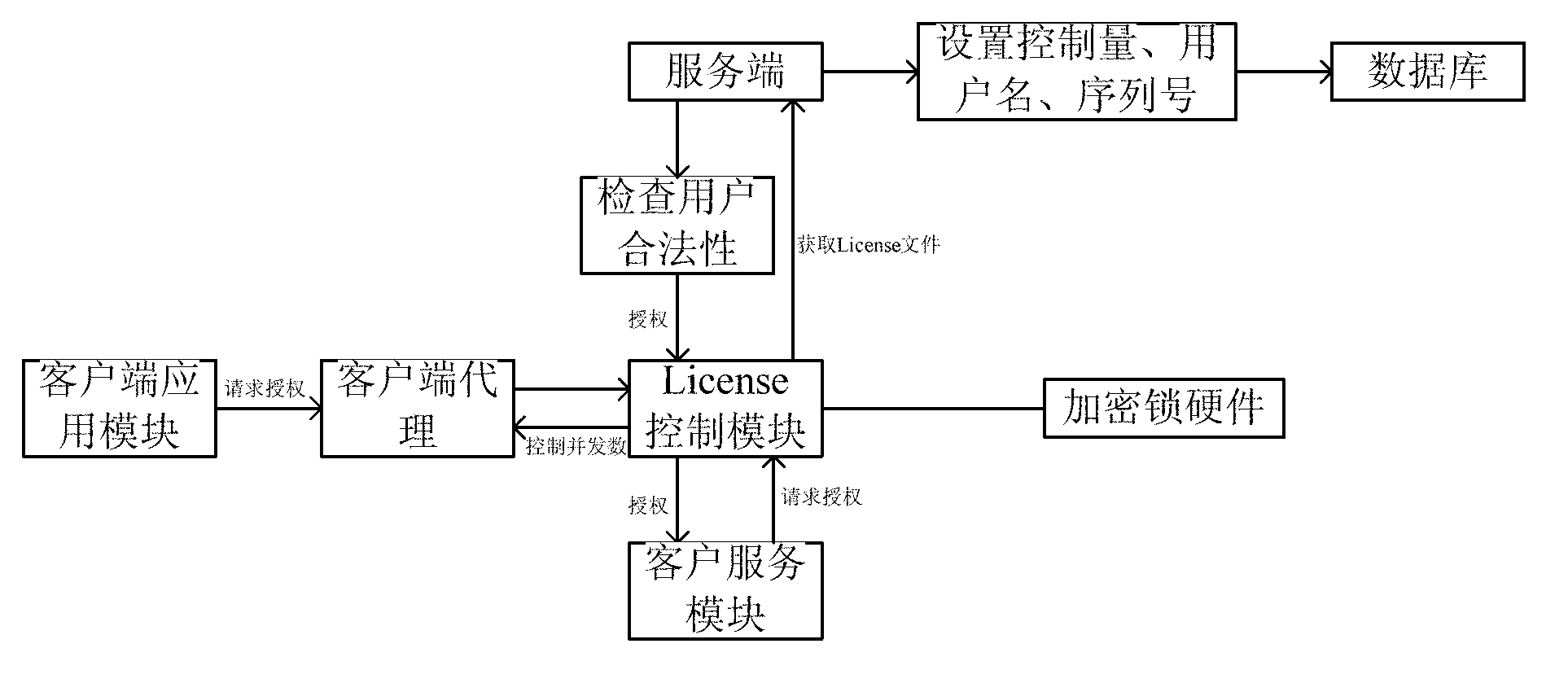
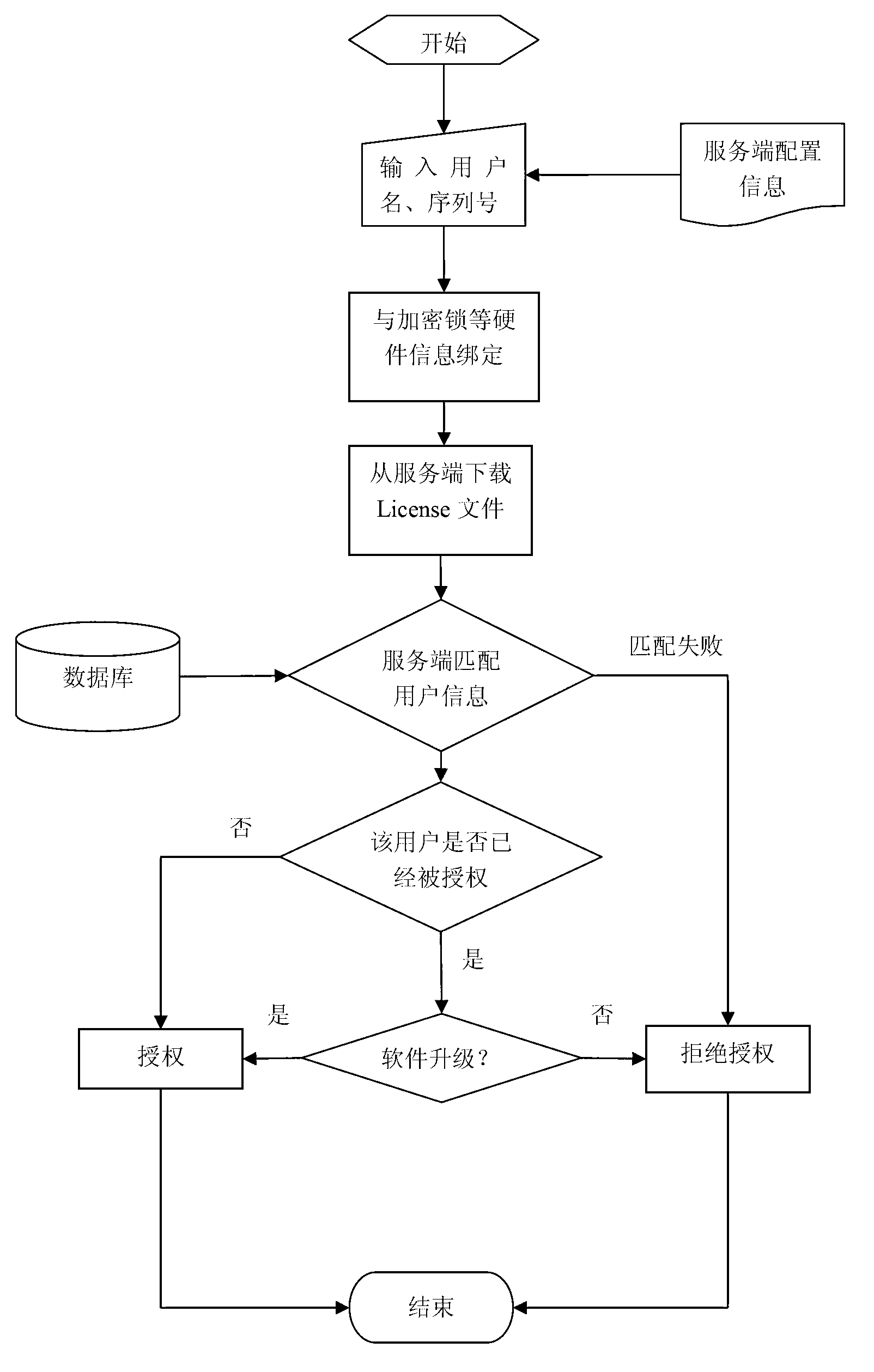
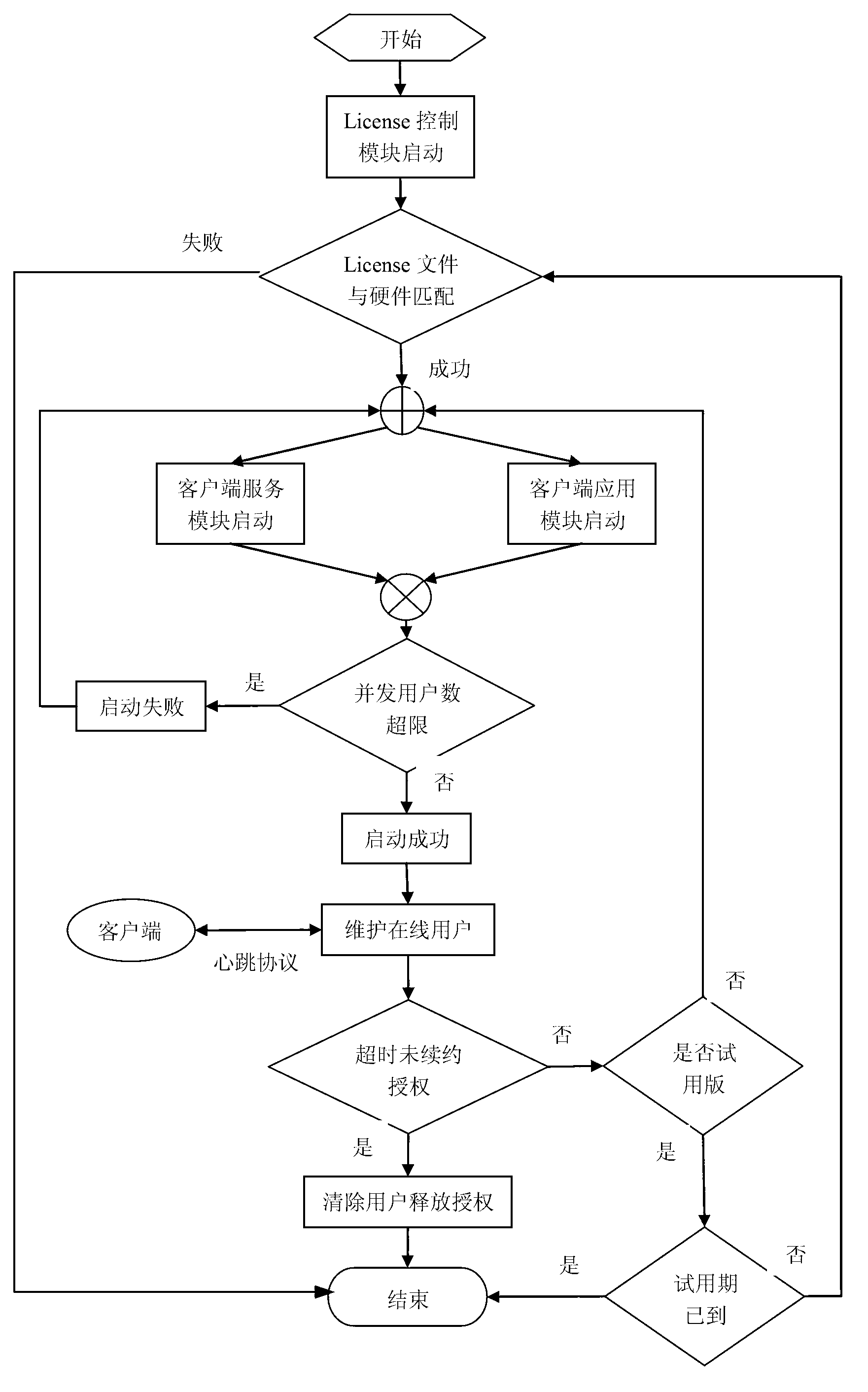
Real-time authorization software License control method
ActiveCN103258151ARealize managementEasy to controlProgram/content distribution protectionLicense controlSoftware system
The invention provides an enterprise software License control method implementing real-time authorization. The method includes the steps of using an SOA (service oriented architecture) for software, setting controlled quantities, such as the number of client application module concurrent users and the number of servers simultaneously published by a client service module, on a server, and binding the controlled quantities with user names and an automatically generate GUID (globally unique identifier) serial number; after a client binds the user names and the serial number with hardware information such as encryption lock (including computer CPU (central processing unit) serial number, network card serial number and hard disk drive serial number), allowing the client to acquire an encrypted License file from the server; and allowing a License control module to analyze the License file to allow for real-time control of authorization to the whole software system. According to the method, authorization of software can be controlled effectively as the client is communicated with the server in real time, whether the software runs in a virtual machine or not can be detected, and control of versions such as trial version and official version can be performed. The enterprise software License control method implementing real-time authorization is widely applicable to the field of authorization control for computer enterprise software.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
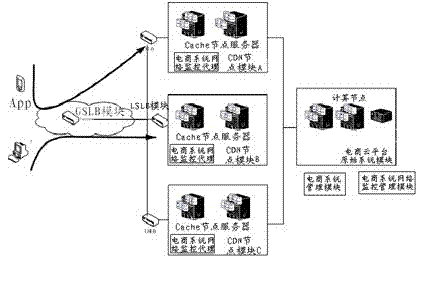
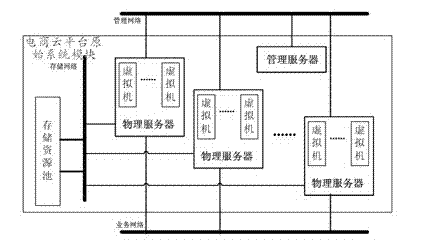
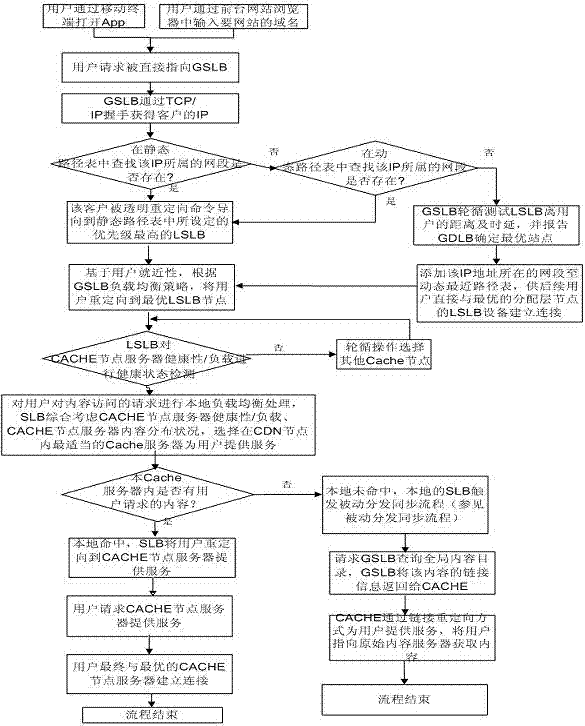
Cloud system for household electronic commerce based on CDN (Content Delivery Network) and load balancing technology as well as implementation method
InactiveCN104333568AImprove utilization efficiencyImprove response speedData switching networksData interchangeDistributed computing
The invention discloses a cloud system for household electronic commerce based on a CDN (Content Delivery Network) and a load balancing technology as well as an implementation method. The cloud system comprises a user App module, a load balancing module and a CDN node module, wherein the load balancing module comprises a GSLB (Global Server Load Balance) module and an LSLB (Local Server Load Balance) module, the CDN node module comprises a plurality of Cache node servers, the CDN node module, which is closest to the user App module, is selected through the load balancing module, and data exchange is carried out between the user App module and the closest CDN node module. The cloud system for household electronic commerce based on the CDN and the load balancing technology as well as the implementation method have the advantages of flexible system expandability and capabilities of effectively improving the utilization efficiency and the response speed of a background server and other resources, remarkably improving the efficiency for solving the IO (Input Output) bottleneck of a front network, helping to shorten the system response time during high concurrency of users and solving the network congestion problem.
Owner:江苏惠居乐信息科技有限公司
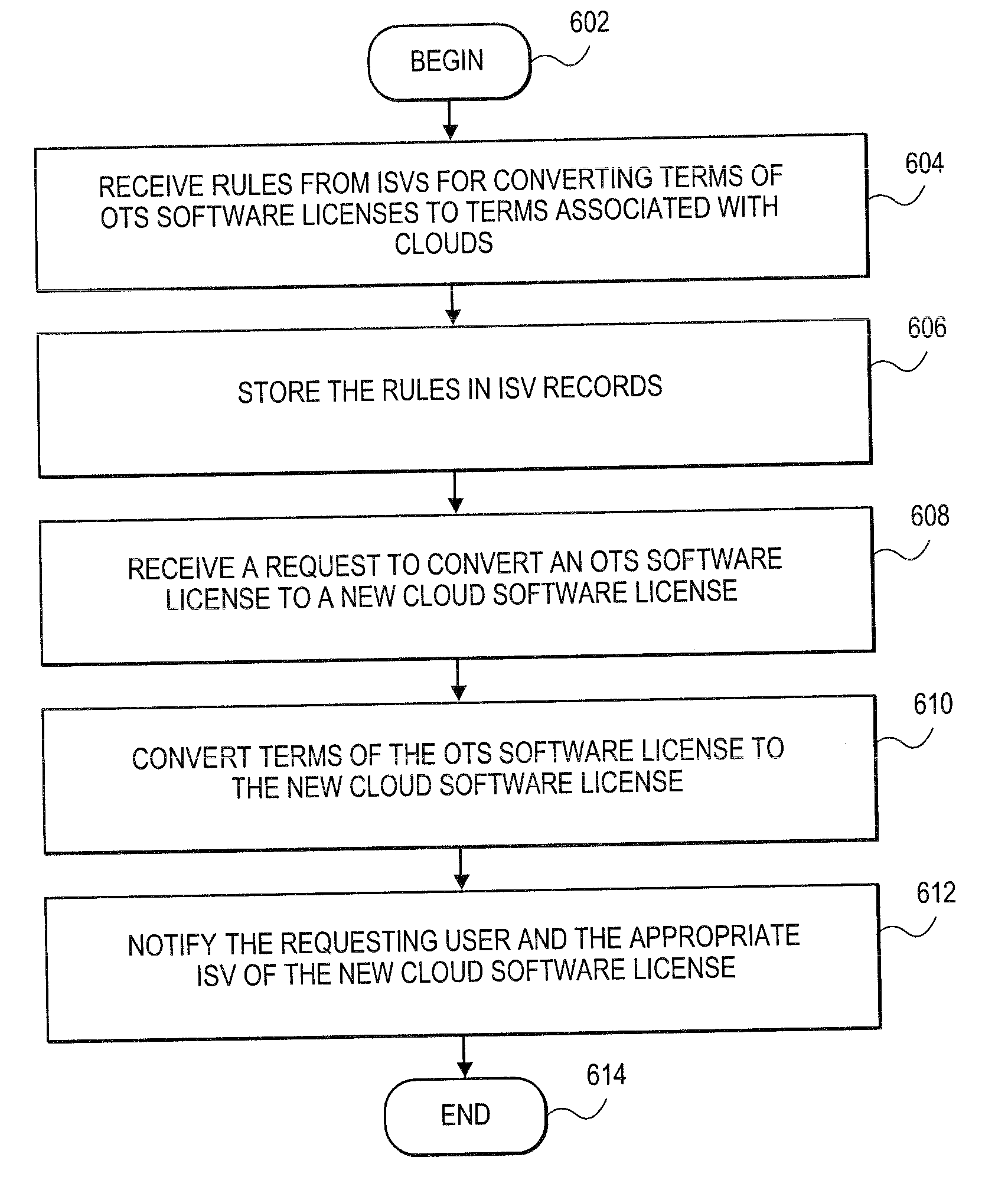
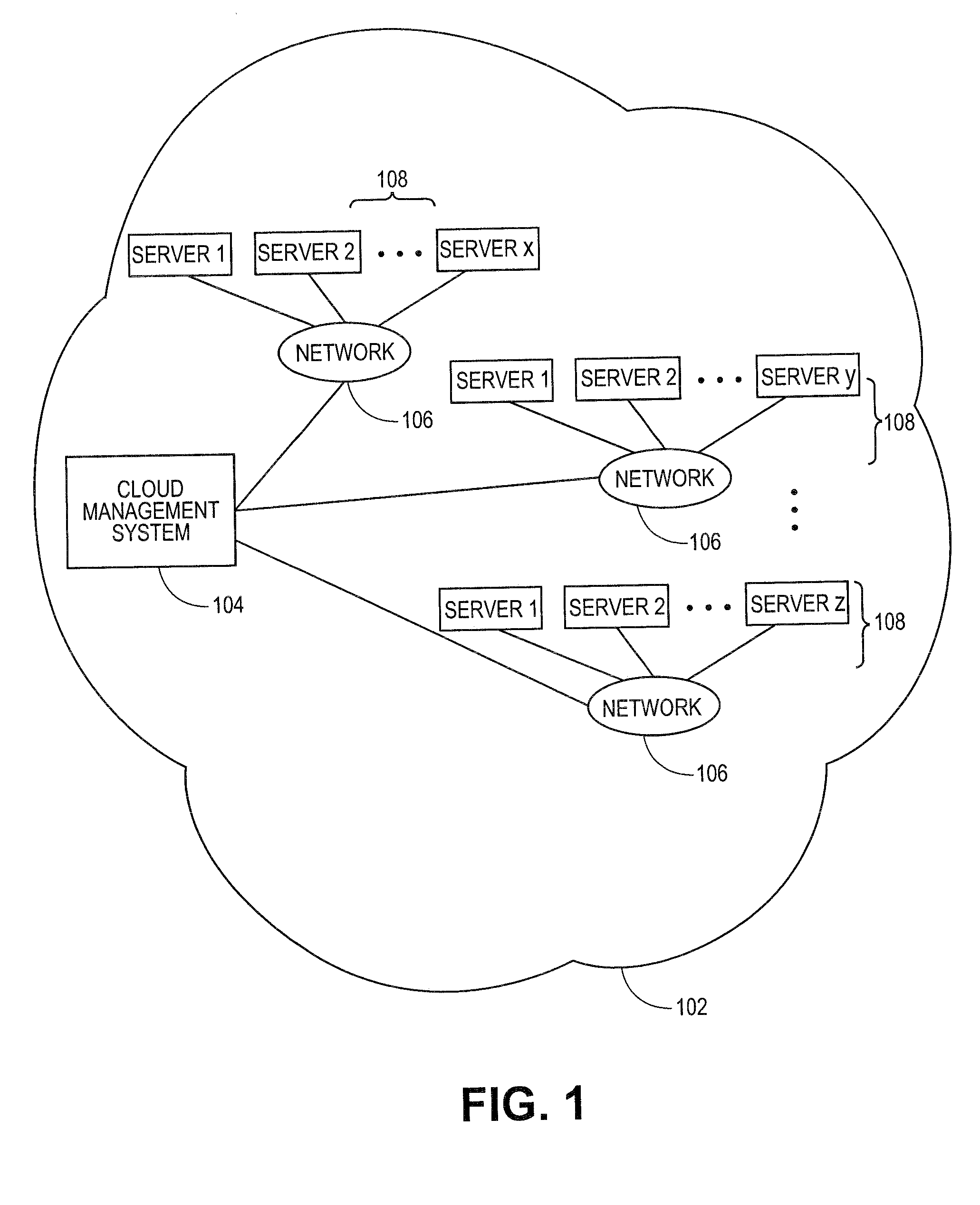
Methods and systems for converting standard software licenses for use in cloud computing environments
ActiveUS20110213719A1Computer security arrangementsPayment architectureOff the shelfSoftware license
A “Bring Your Own License” (BYOL) service can convert users' “off-the-shelf” (OTS) software licenses for use in public clouds according to rules provided by independent software vendors (ISVs). The rules provided by an ISV can convert the terms associated with the ISV's OTS software licenses (e.g. number of instances, number of users, duration, technical support provided) to terms associated with public clouds (e.g. number of concurrent users, number of virtual machines, number of different clouds, technical support). The BYOL license service can convert the OTS software licenses according to the rules provided by the ISVs.
Owner:RED HAT
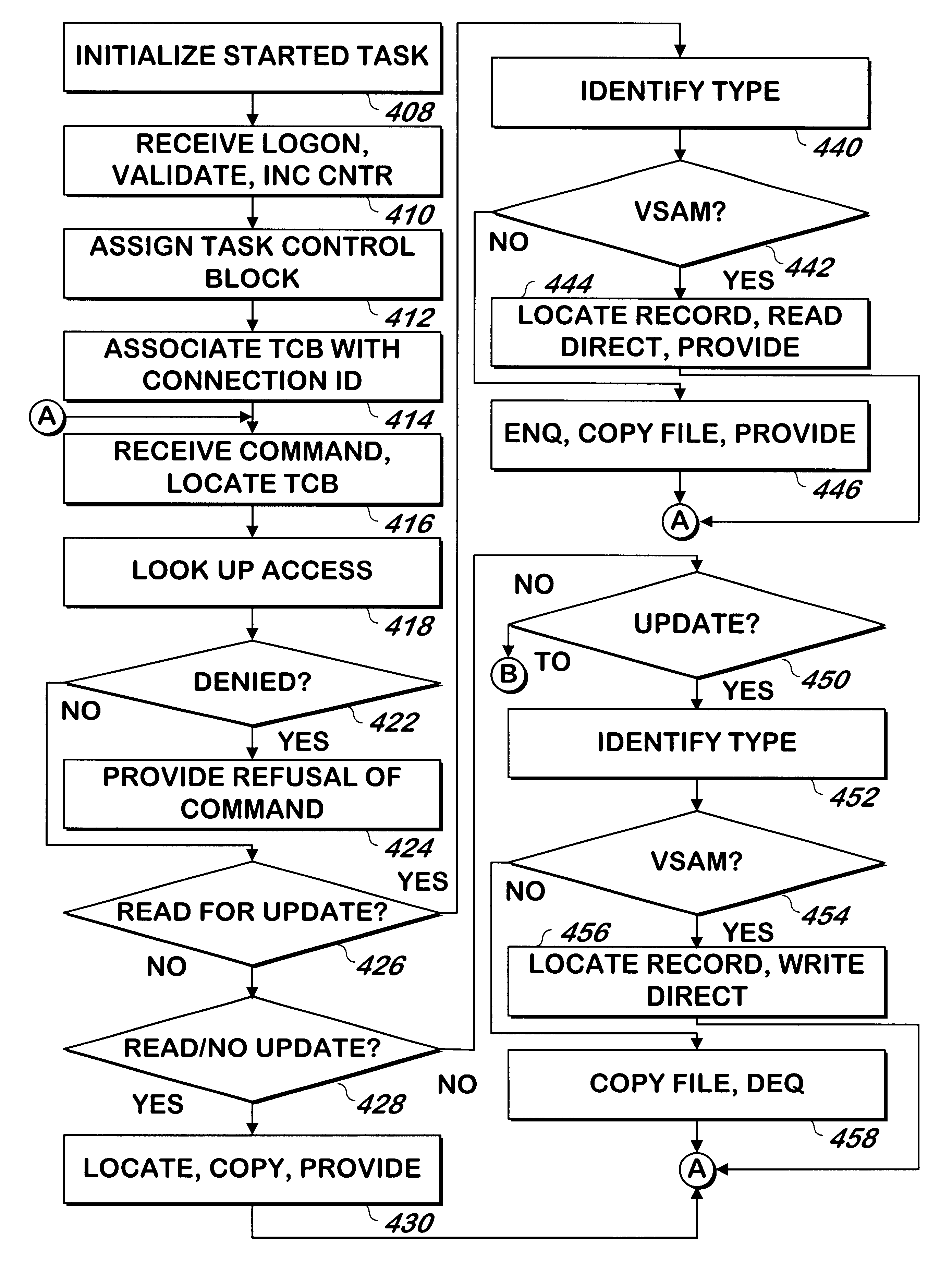
System and method for serving host computer files to one or more client computer systems
InactiveUS6253236B1Unauthorized memory use protectionComputer security arrangementsComputerized systemClient-side
A system and method allows a host computer to operate as a server in a client-server arrangement in response to requests from client computer systems. The system and computer program product performs reads, reads for update, update and deletes on some or all records in a file, depending on the type of file. Record or file locking is provided when applicable. Security is provided at the file level. Abnormal ends of communication with the client computer system are detected to allow resources and record or file locks to be freed in such event. A counter is incremented at the time a client computer system logs into the host computer system to enforce limits on the number of concurrent users, and ordinary log off as well as abnormal ends of communication decrement the counter to maintain its accuracy.
Owner:SERENA SOFTWARE
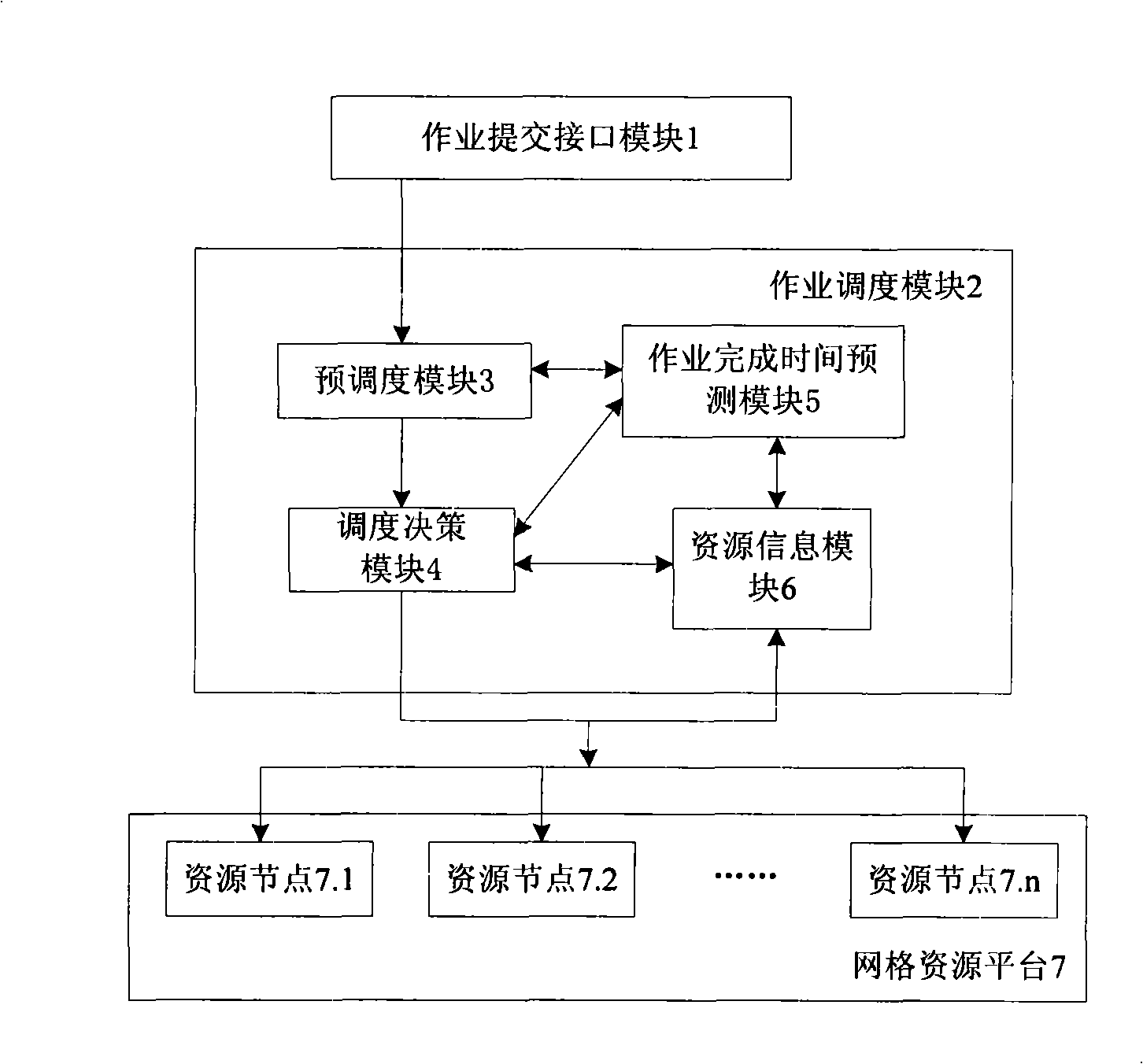
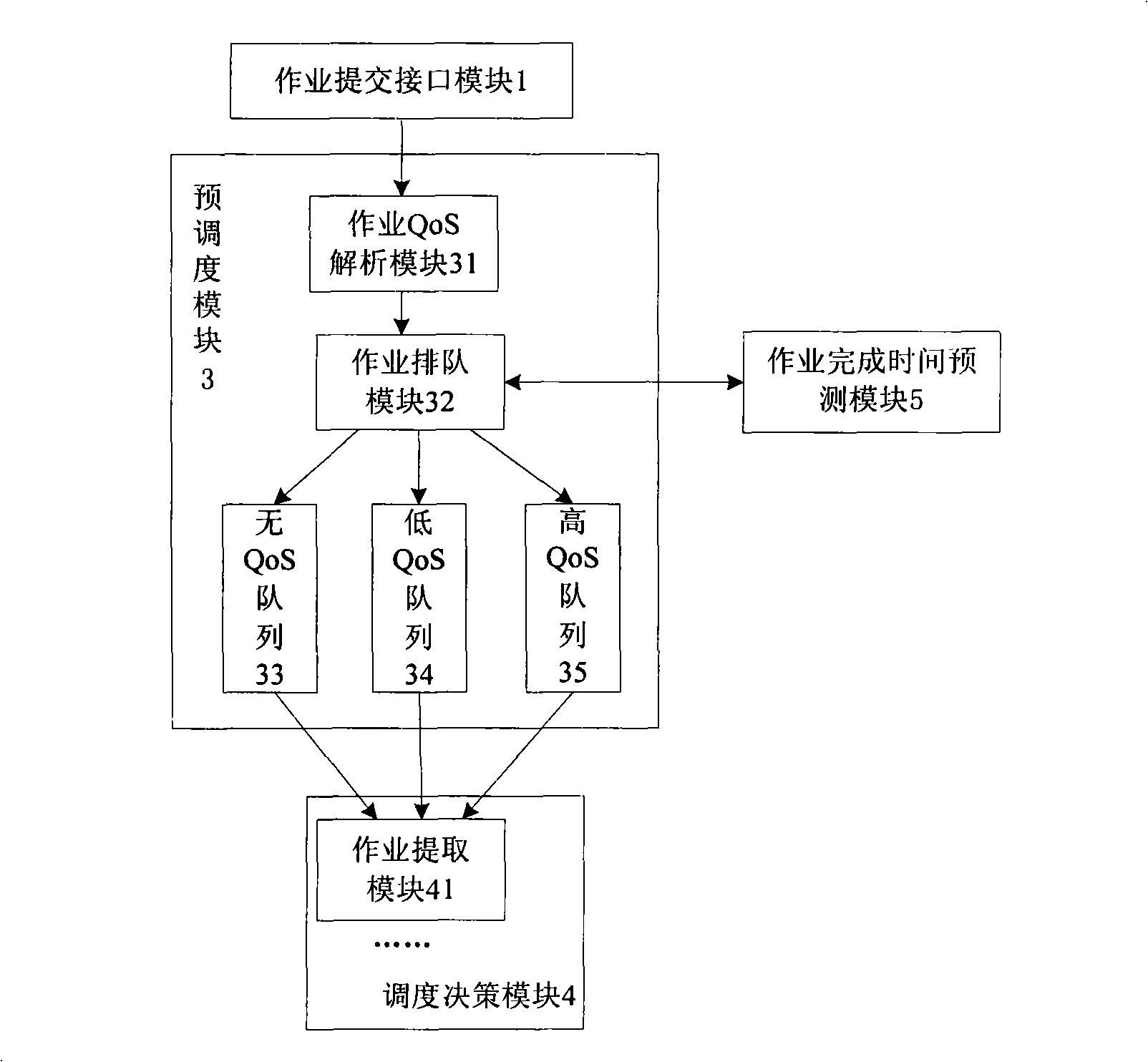
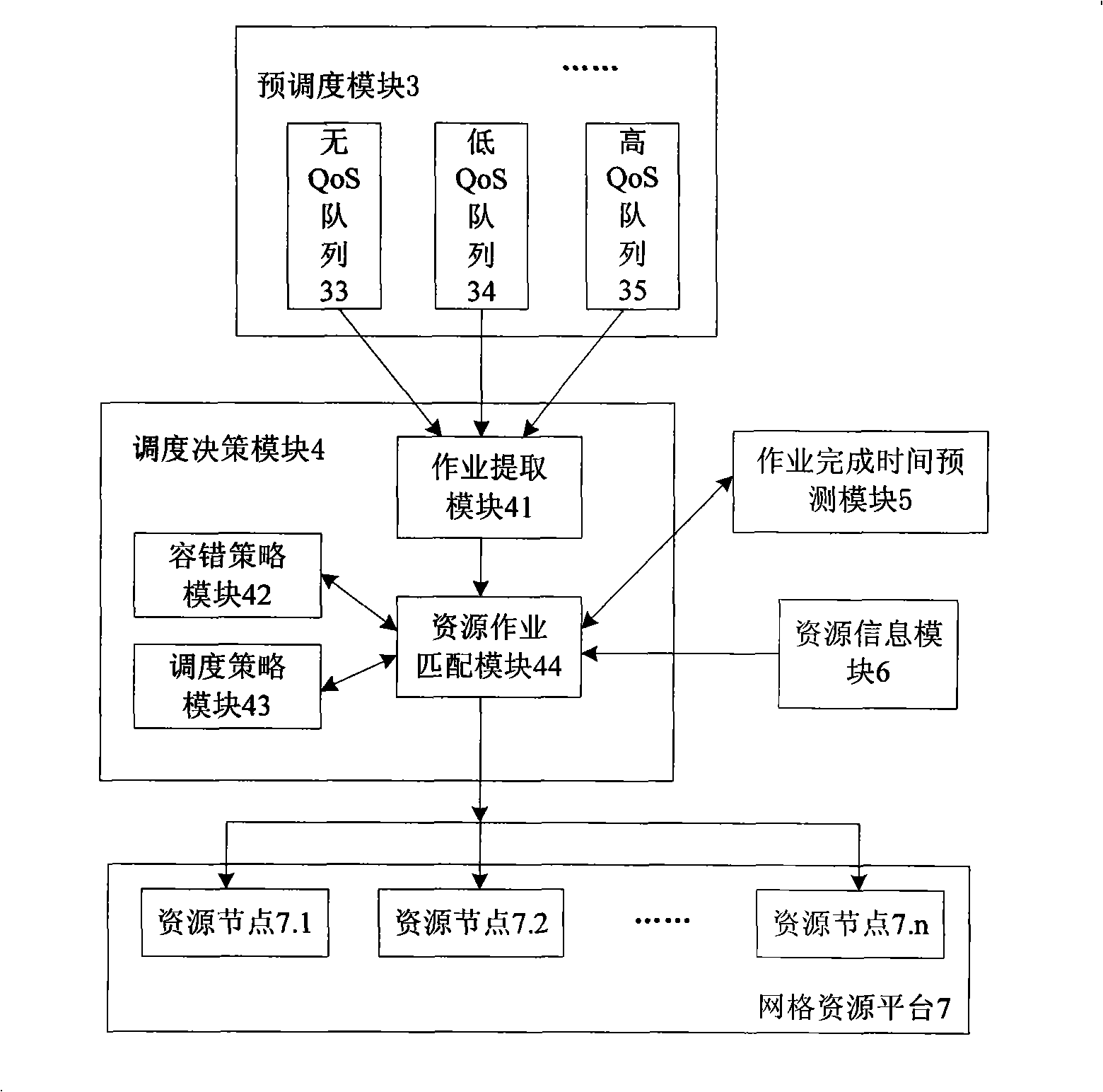
Job scheduling system suitable for grid environment and based on reliable expense
InactiveCN101309208AIncrease profitImprove accuracyError preventionData switching networksExtensibilityFault tolerance
The invention relates to an operation scheduling system which is applicable to the grid environment and based on the reliability cost; as indicated in graph 1, the whole system includes three layers: the first layer is an operation submission interface module 1; the second layer is an operation scheduling module 2 and the grid resource platform 7 as the substrate layer. From the perspective of the operational principle, the core of the invention is the operation scheduling module in the second layer, which includes a pre-scheduling module 3, a scheduling strategy module 4, an operation finish time prediction module 5 and a resource information module 6. The operation scheduling system in the invention proposes an operation running time prediction model and a resource usability prediction model; the operation running time prediction model based on the mathematical model and the resource usability prediction model based on the Markov model have high accuracy and high generality. The operation scheduling system adopts the copy fault-tolerance strategy, the primary copy asynchronous operation fault-tolerance strategy and the retry fault-tolerance respectively according to different operation service quality requirements and resource characteristics so that the operation scheduling system has high flexibility and high validity; meanwhile, the operation scheduling system supports the computation-intensive operation and the data-intensive operation to have good generality. Compared with the scheduling system in the prior art, the operation scheduling system has the advantages of supporting more concurrent users, improving the resource utilization rate, good generality, good extensibility and high system throughput.
Owner:HUAZHONG UNIV OF SCI & TECH
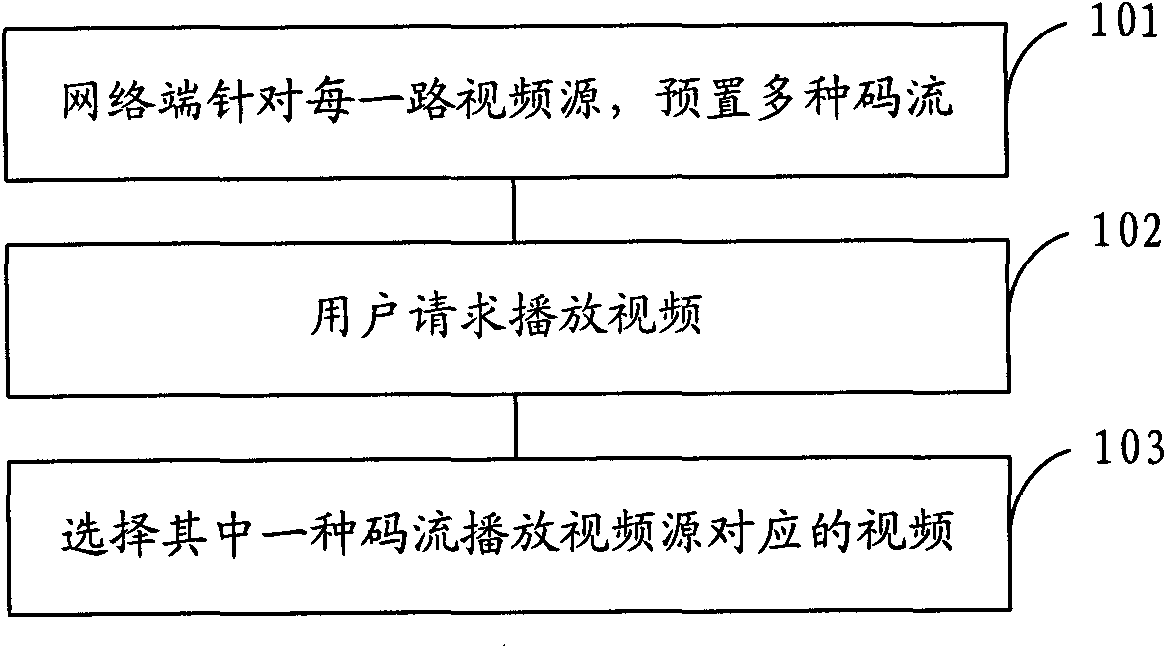
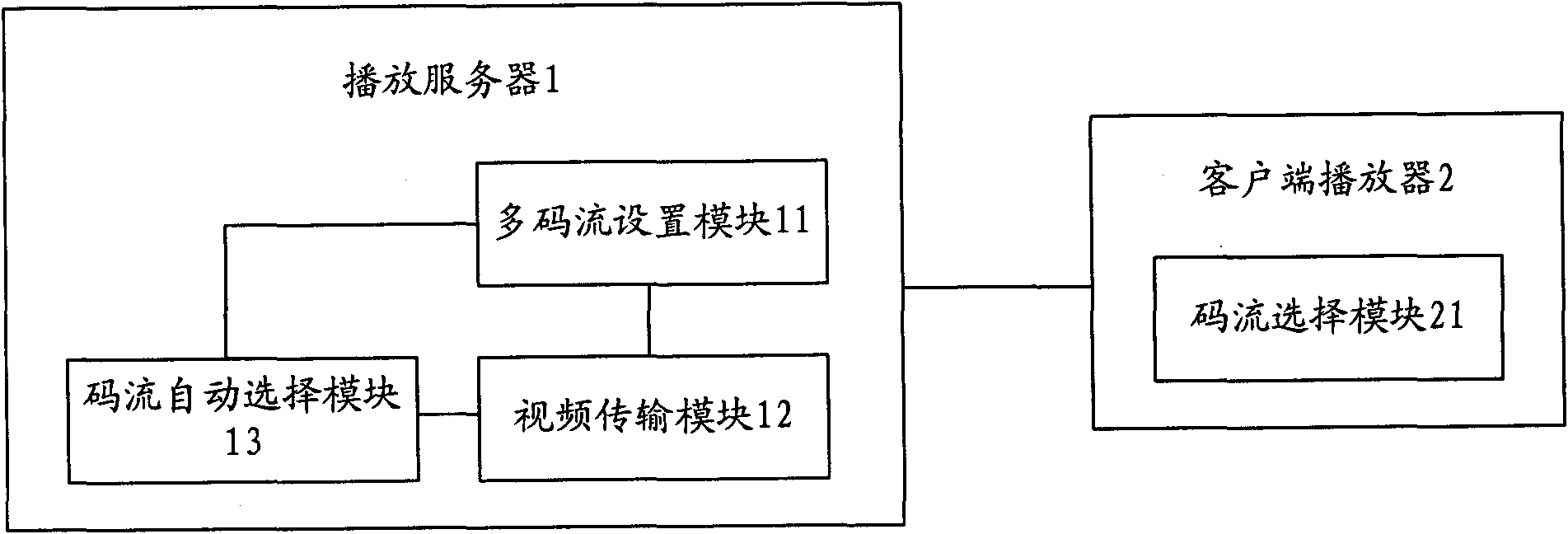
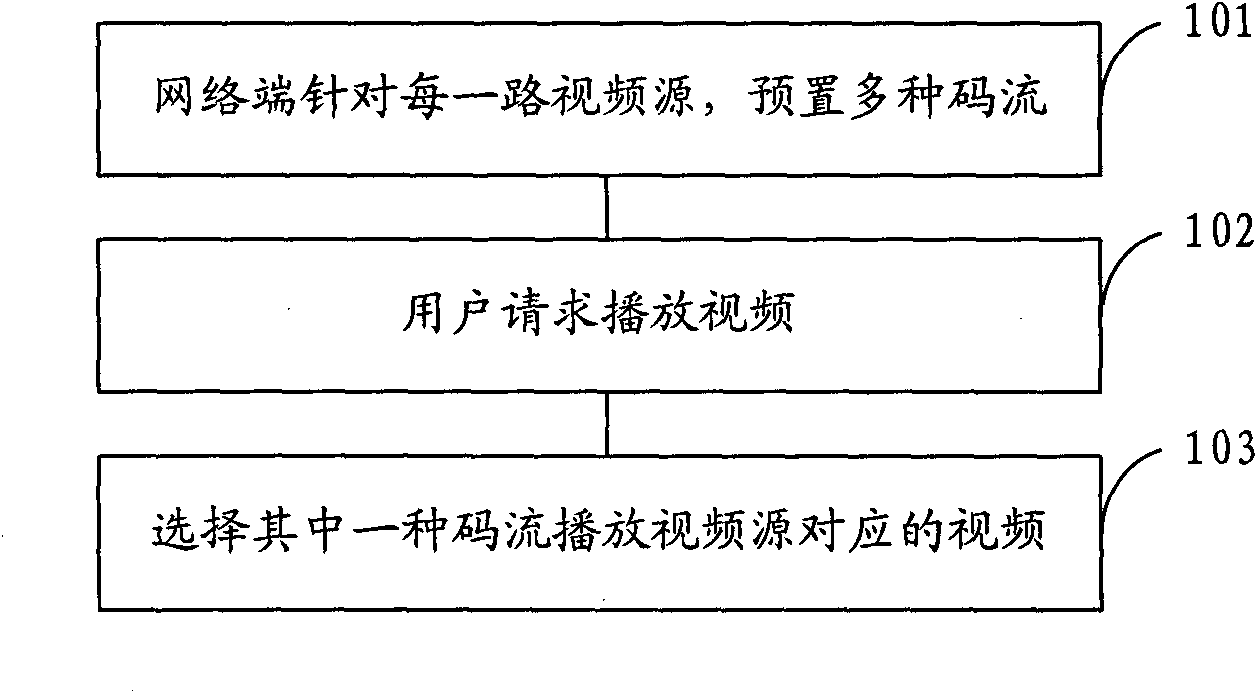
Method for playing network video and system for playing network video
InactiveCN101917391AIncrease the number of concurrent usersGuaranteed fluencyPulse modulation television signal transmissionTwo-way working systemsConcurrent user
The invention provides a method for playing network video and a system for playing the network video, which can provide video playing of various optional code streams. The method comprises the following steps of: presetting various code streams aiming at each video source; and playing the video corresponding to the video source by selecting one code stream. The method and the system can select low code streams under the condition of a few network bandwidth resources and select high code streams under the condition of abundant network bandwidth resources so as to ensure the fluency of the video playing. Moreover, the method and the system can improve the number of concurrent users of the network video playing by regulating the video code streams in the process of playing.
Owner:CHINA DIGITAL VIDEO BEIJING
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7676526B1Efficient multi-user access and file sharingSolve excessive overheadData processing applicationsSpecial data processing applicationsOperational systemFile size
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
System, method and device for delivering streaming media
InactiveUS20110246608A1Lower deployment costsImprove reliabilityMultiple digital computer combinationsTransmissionConcurrent userCore network
A system, a method and an apparatus for distributing streaming media, include that a terminal node sends the inquiry request carrying the address information of itself to a global server; the global server determines the affiliated domain of the terminal node according to the address information, and returns the domain server information of the affiliated domain; the terminal node sends streaming media data obtaining request to the domain server of the affiliated domain; the domain server of the affiliated domain inquires whether there is the streaming media data in its local domain; if yes, the streaming media data is returned and / or the information of the other terminal nodes which have the streaming media data in their local domains is returned; if not, the requested streaming media data is obtained from the other domain servers in the core network and / or the global server and sent to the terminal node by the way of P2P; the terminal node receives the returned streaming media data and / or obtains the requested streaming media data from the other terminal nodes by the way of P2P according to the returned information of the other terminal nodes. The system can satisfy the demand of streaming media distributing of the large-scale concurrent users.
Owner:CHINA MOBILE COMM GRP CO LTD
Ad hoc one-time pairing of remote devices using online audio fingerprinting
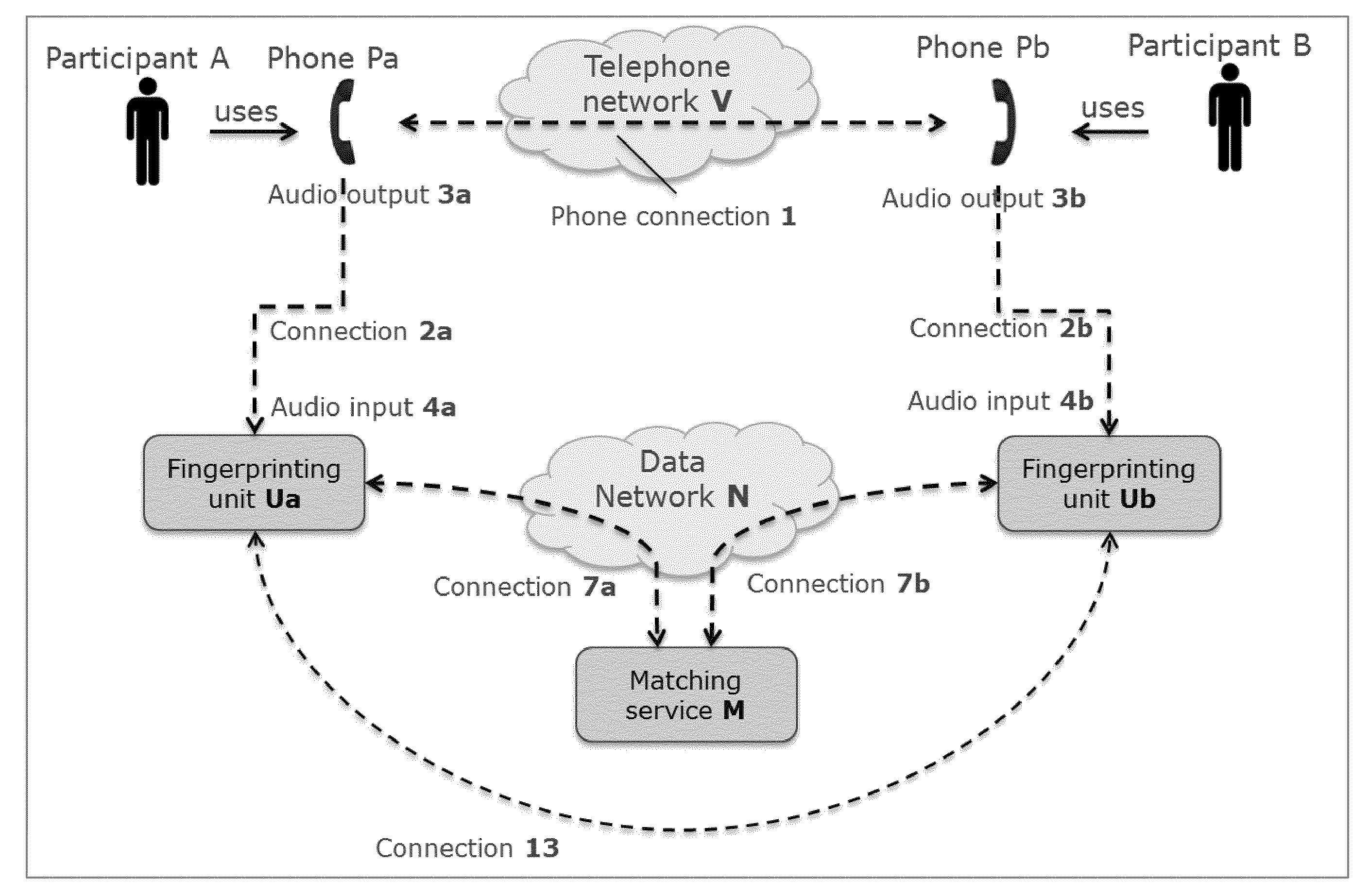
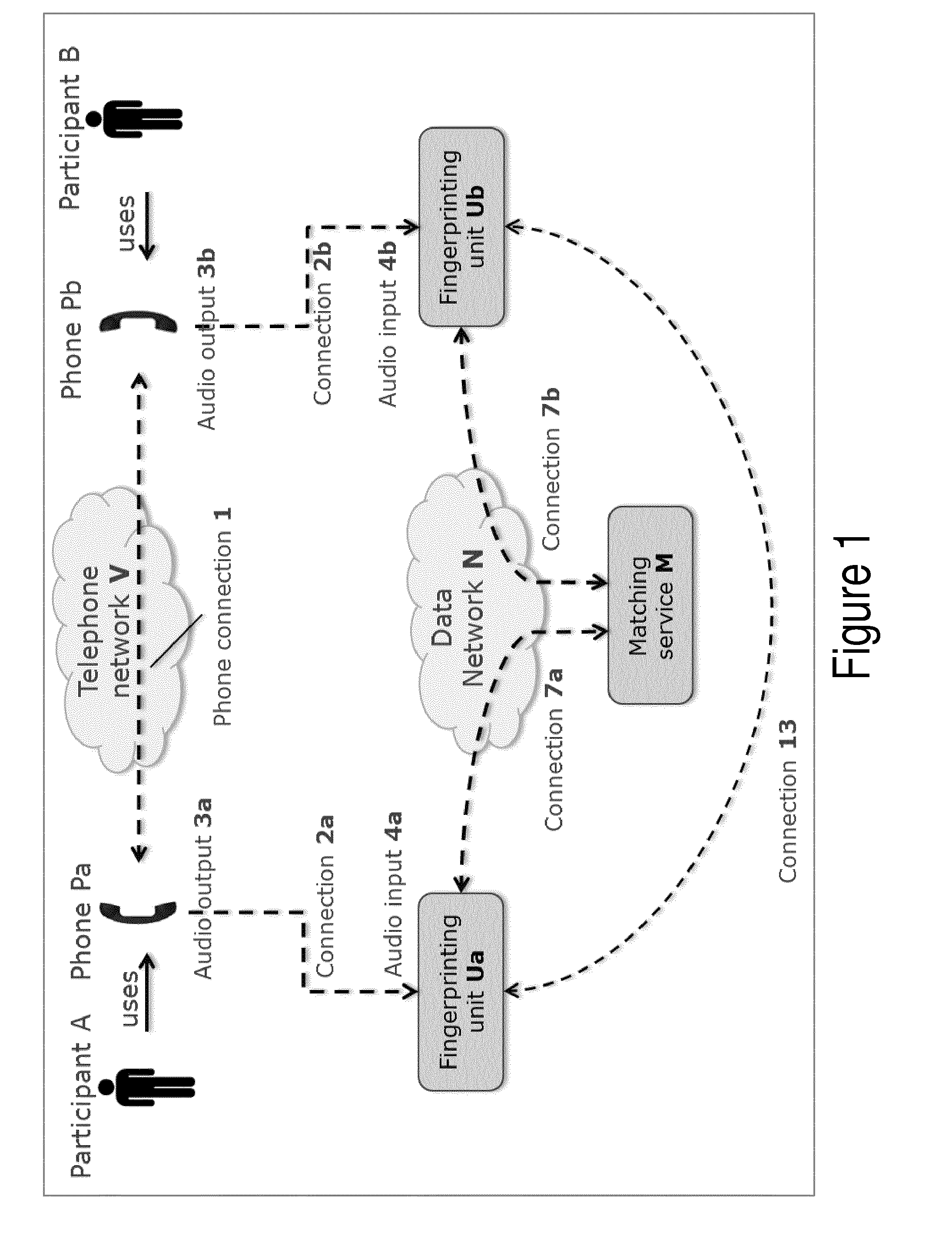
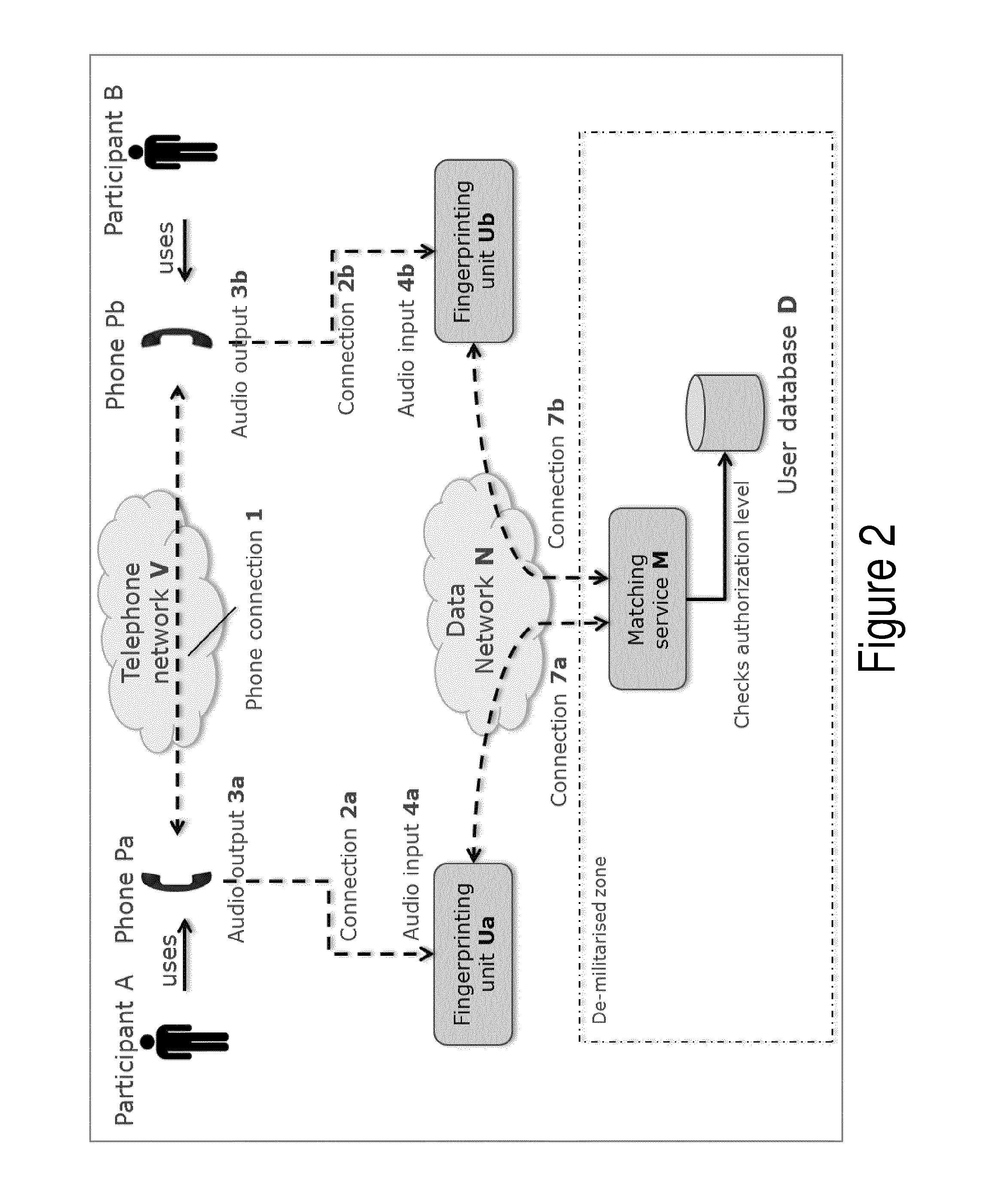
ActiveUS20170034160A1Improve protectionEasy to useSpecial service for subscribersSpeech analysisData connectionIp address
A system and method for sharing electronic data between participants of a phone conference, such as an online presentation, without a need to exchange passwords to link two devices together for data transfer nor go through a login procedure to access the data resource. To achieve this, the participants use a device or software application that samples the audio of the phone conversation and creates a stream of audio fingerprints. The streams of fingerprints are sent to a matching service on the internet. This matching service finds the fingerprints that correspond to the same conversation among the streams of simultaneous users. Once a match is found with a high enough confidence level, the matching service exchanges identifiers such as public IP addresses and sends those back to the fingerprinting units. When instructed by the user, the units can then proceed to setup a secure data connection.
Owner:BARCO NV
Arcuate multi-dispensing beverage dispenser
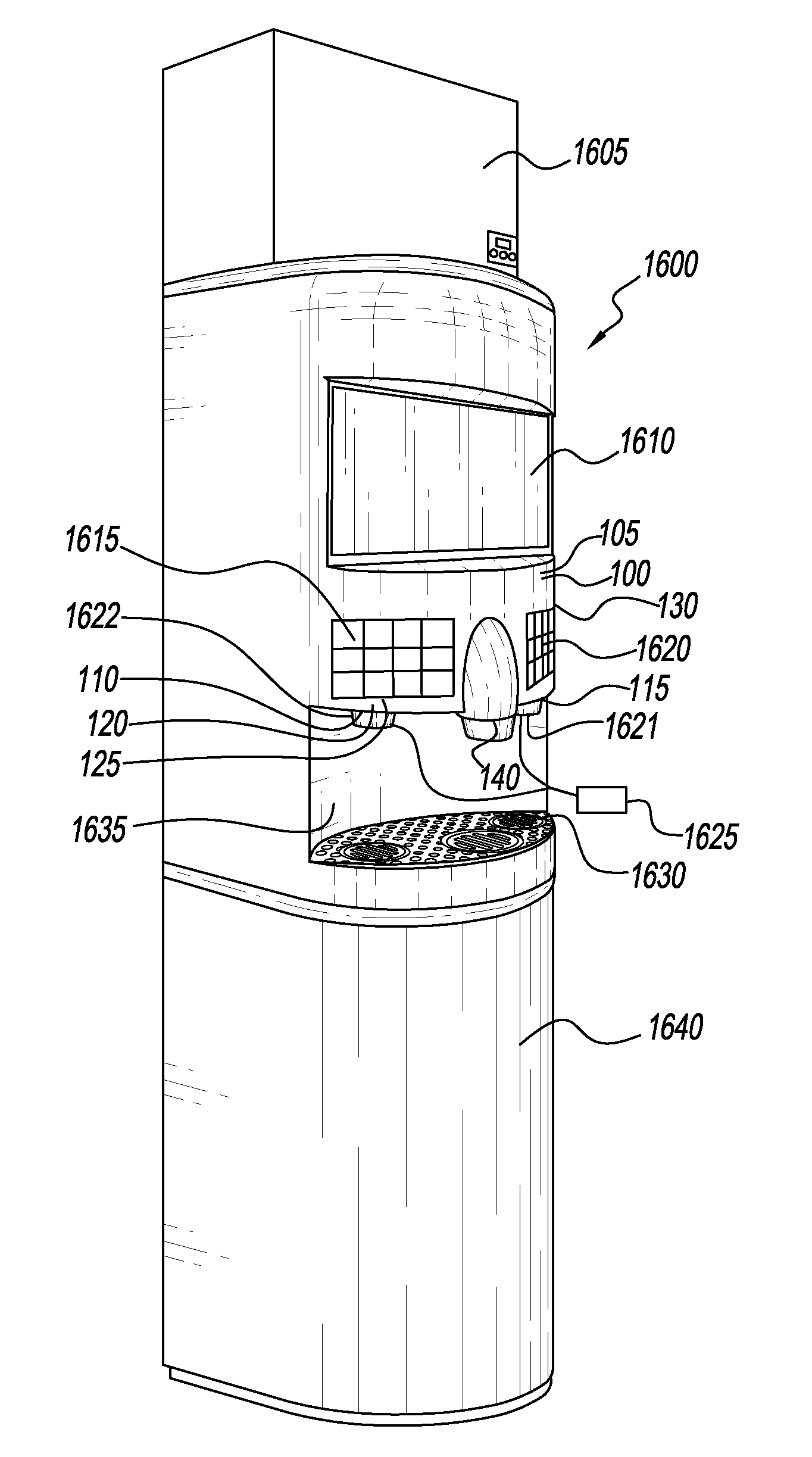
ActiveUS20140299630A1Easy to useLighting and heating apparatusLiquid flow controllersEngineeringComputer terminal
Disclosed is a beverage dispenser having a plurality of non-linear dispensing sides each having a dispensing station of a dimension suitable to comfortably accommodate a user / operator. Each dispensing station is of a dimension narrower than that of a dispensing station of a conventional dispenser. The beverage dispenser of the present disclosure allows for variations and flexibility in the shape of the unit, and a user-friendly touch screen accommodates one or more concurrent users / operators, while also allowing a choice of various beverage selections. The touch screen provides a user interface that may be configured for use by a restaurant employee and / or self-service applications. In addition, the user friendly touchscreen interface also facilitates the use of ADA compliant controls. The beverage dispenser of the present disclosure also allows for “banking” of multiple units into a “kiosk” type formation.
Owner:MANITOWOC FOODSERVICE CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com