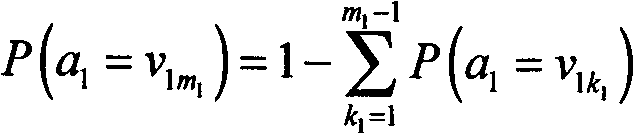Patents
Literature
117 results about "Pruning algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
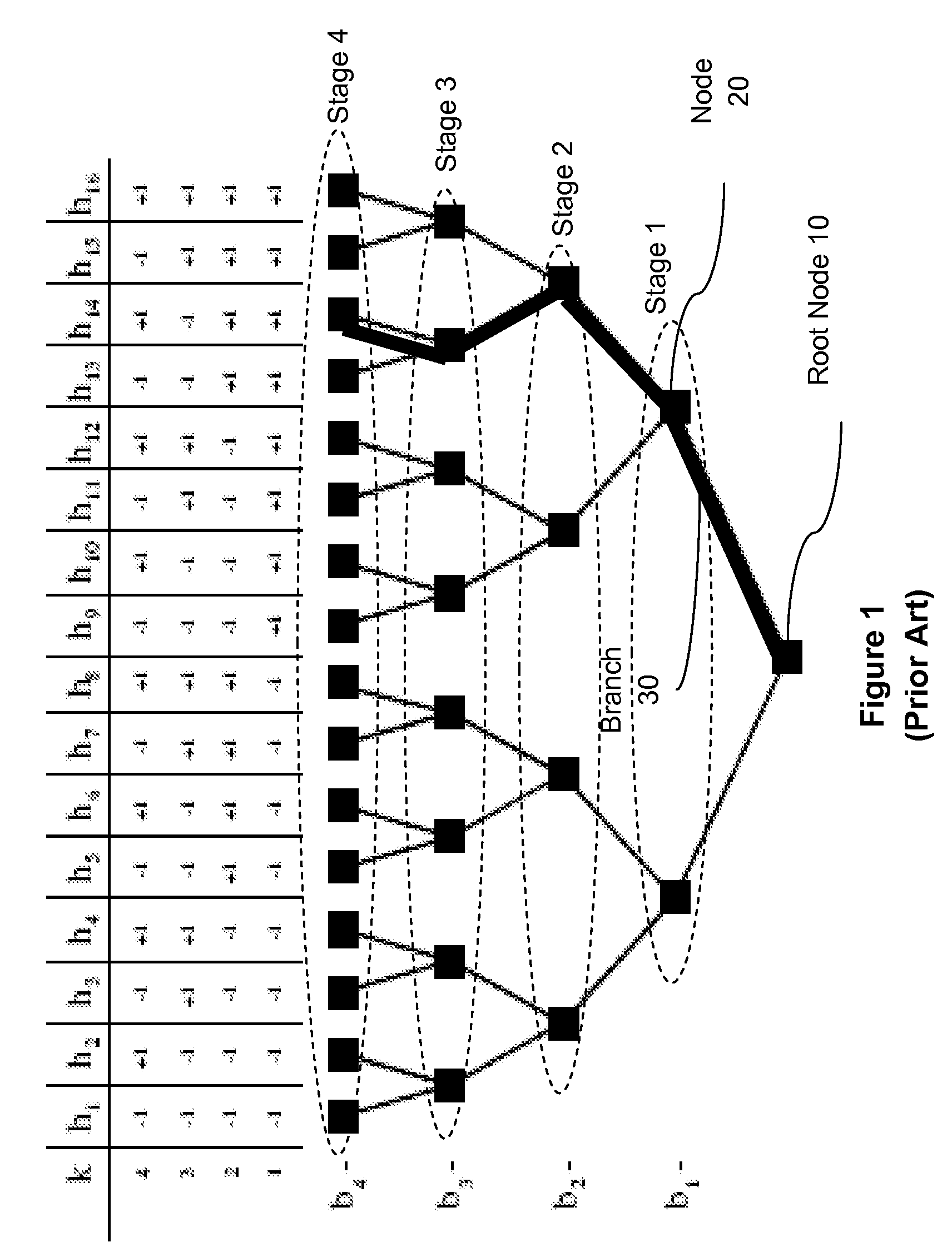
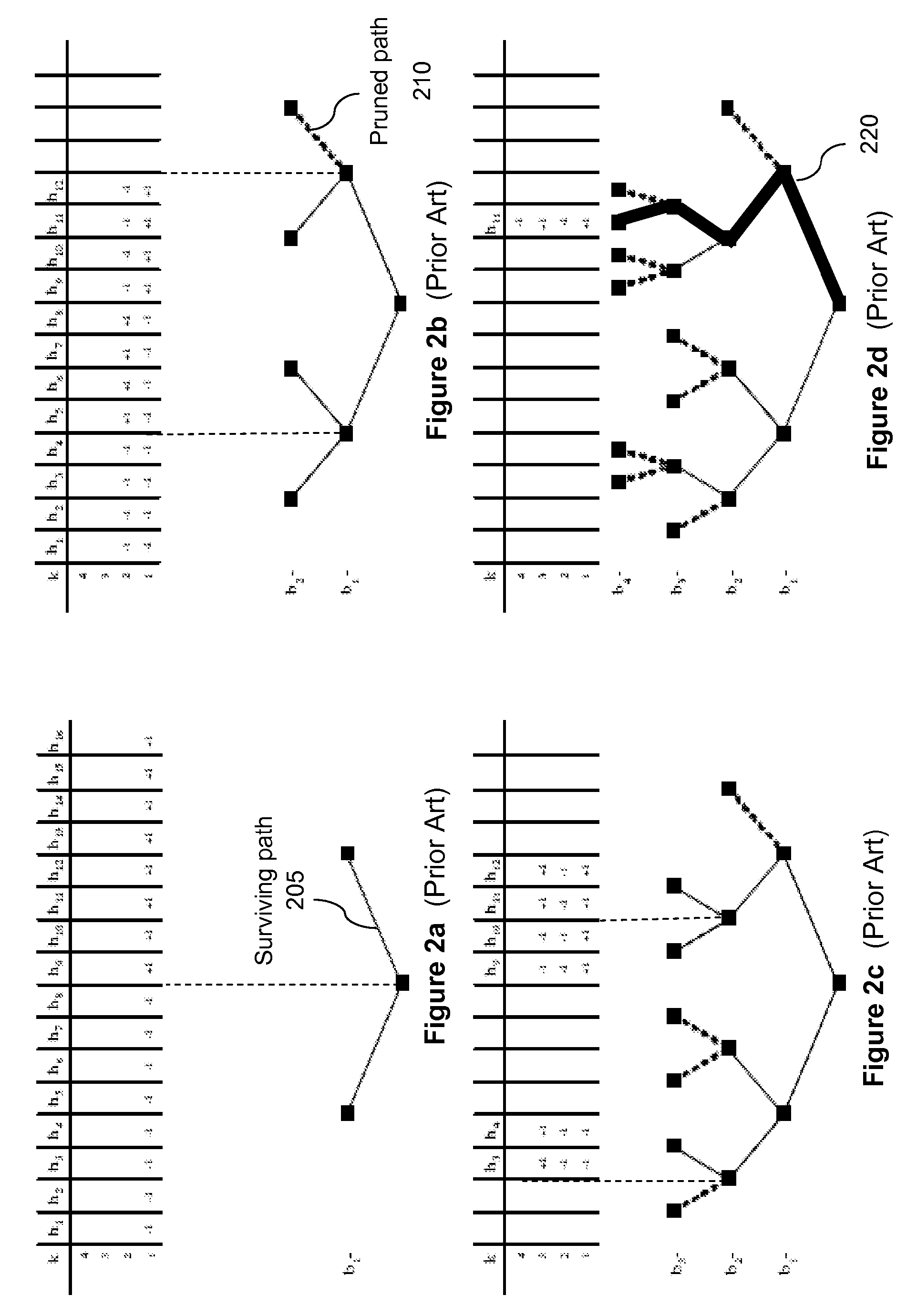
Pruning (algorithm) Pruning is a technique in machine learning that reduces the size of decision trees by removing sections of the tree that provide little power to classify instances. Pruning reduces the complexity of the final classifier, and hence improves predictive accuracy by the reduction of overfitting.
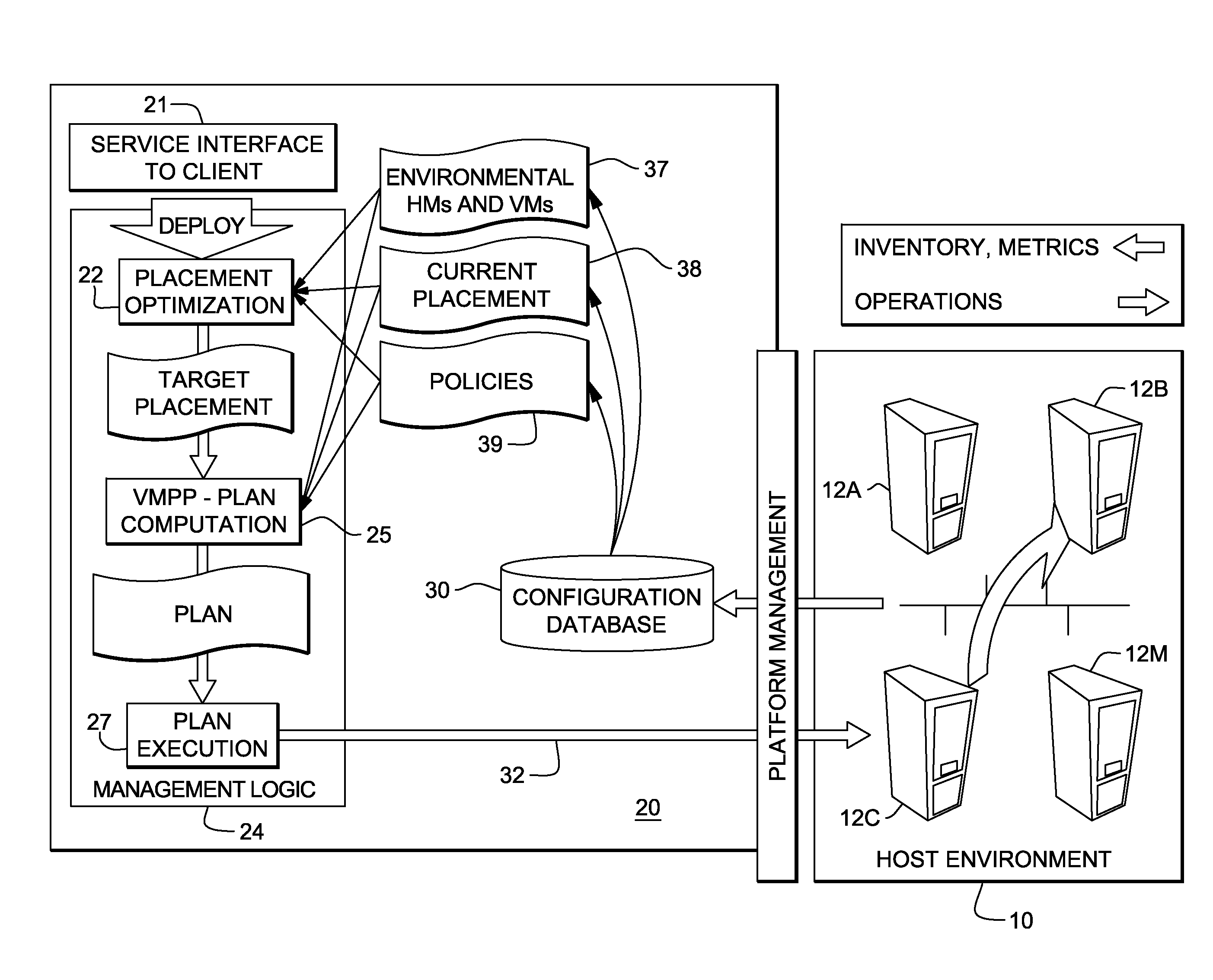
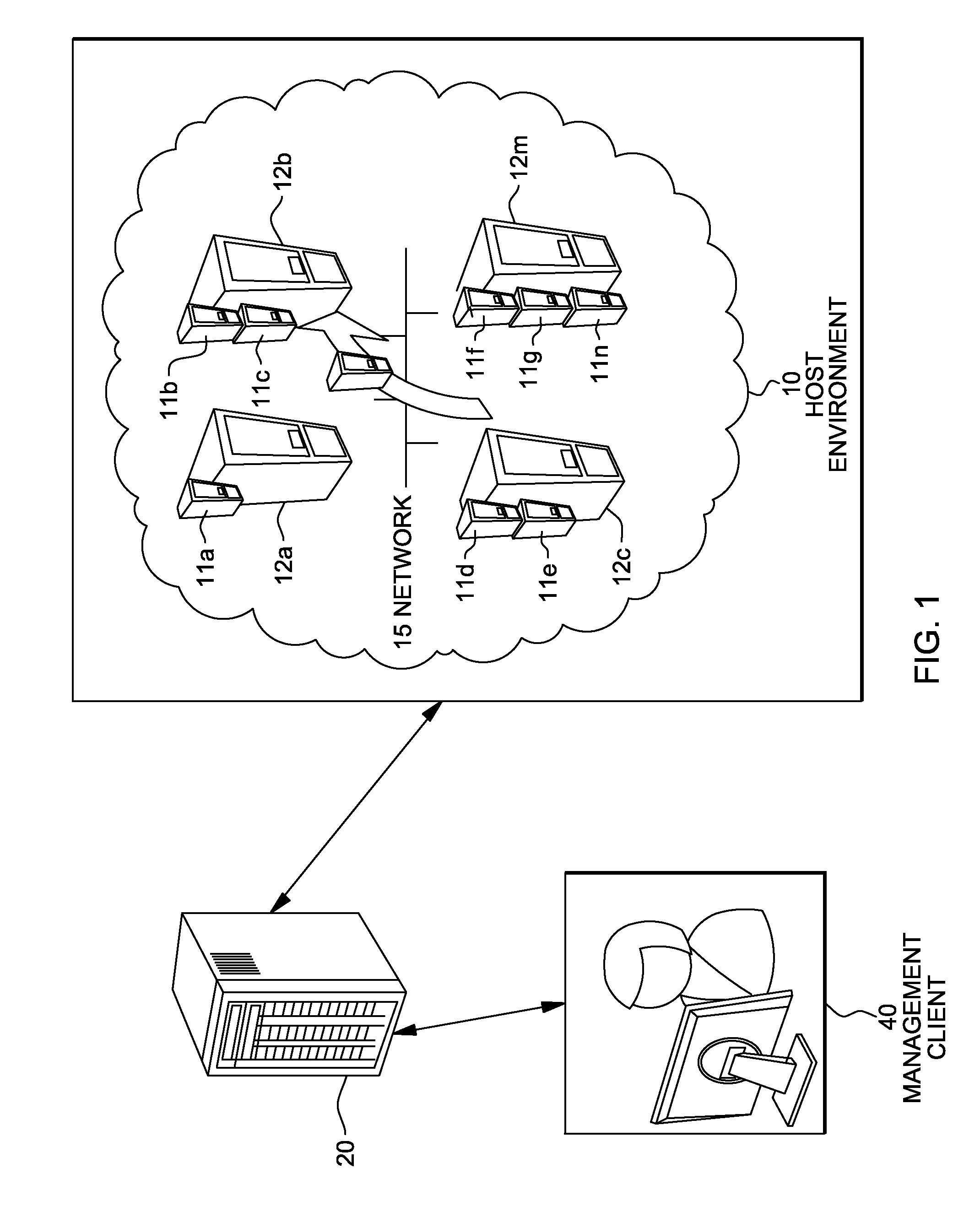
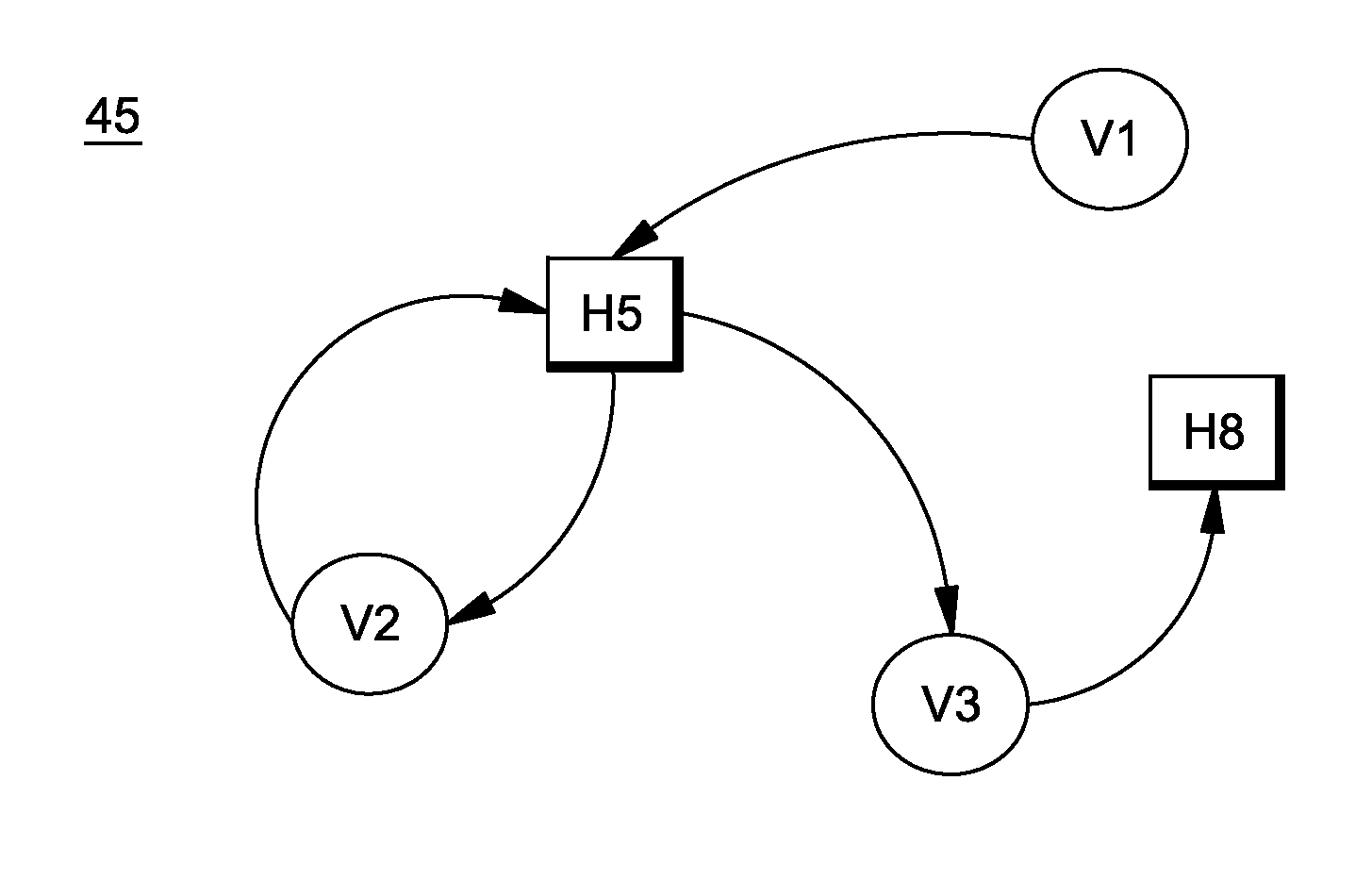
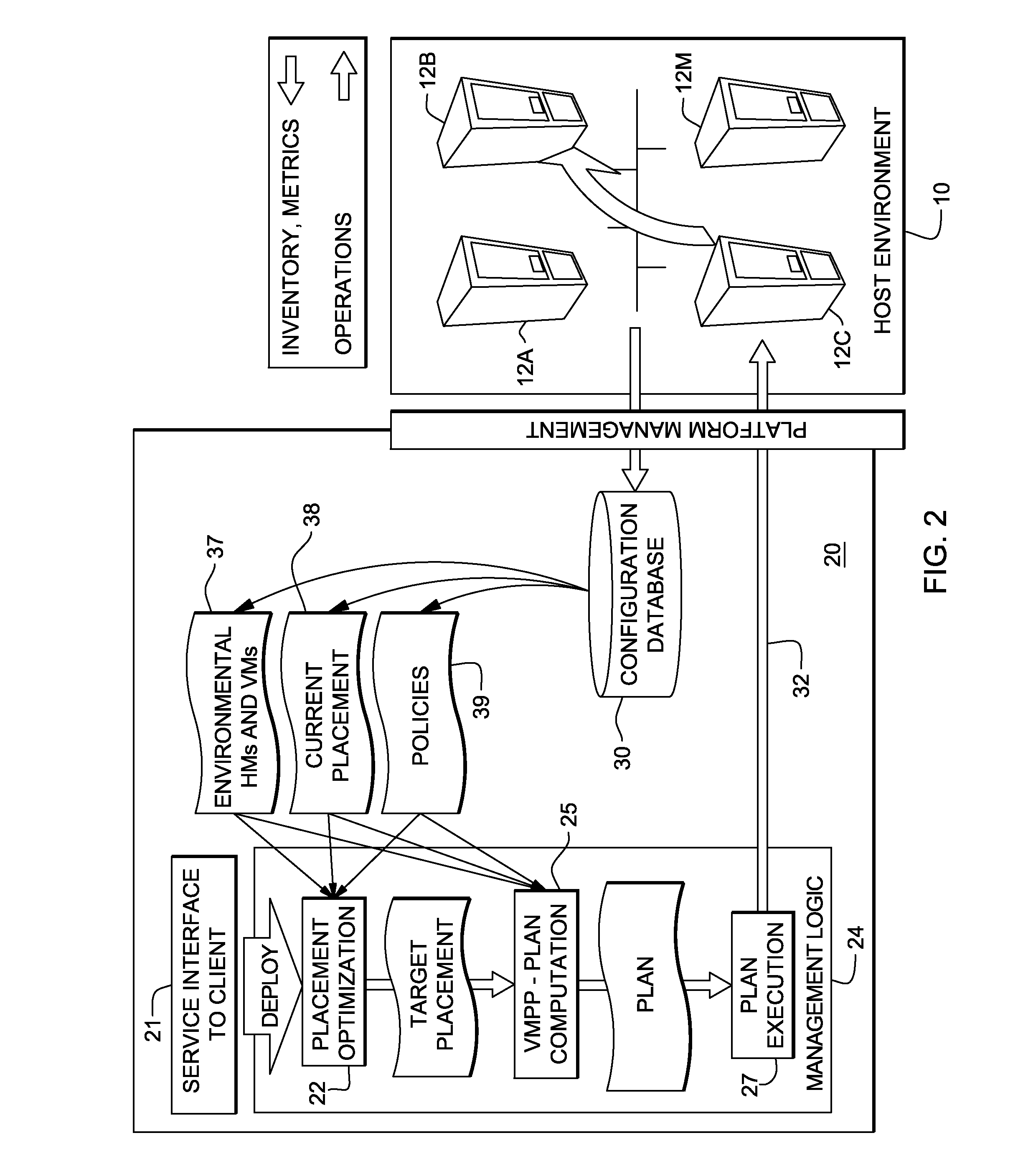
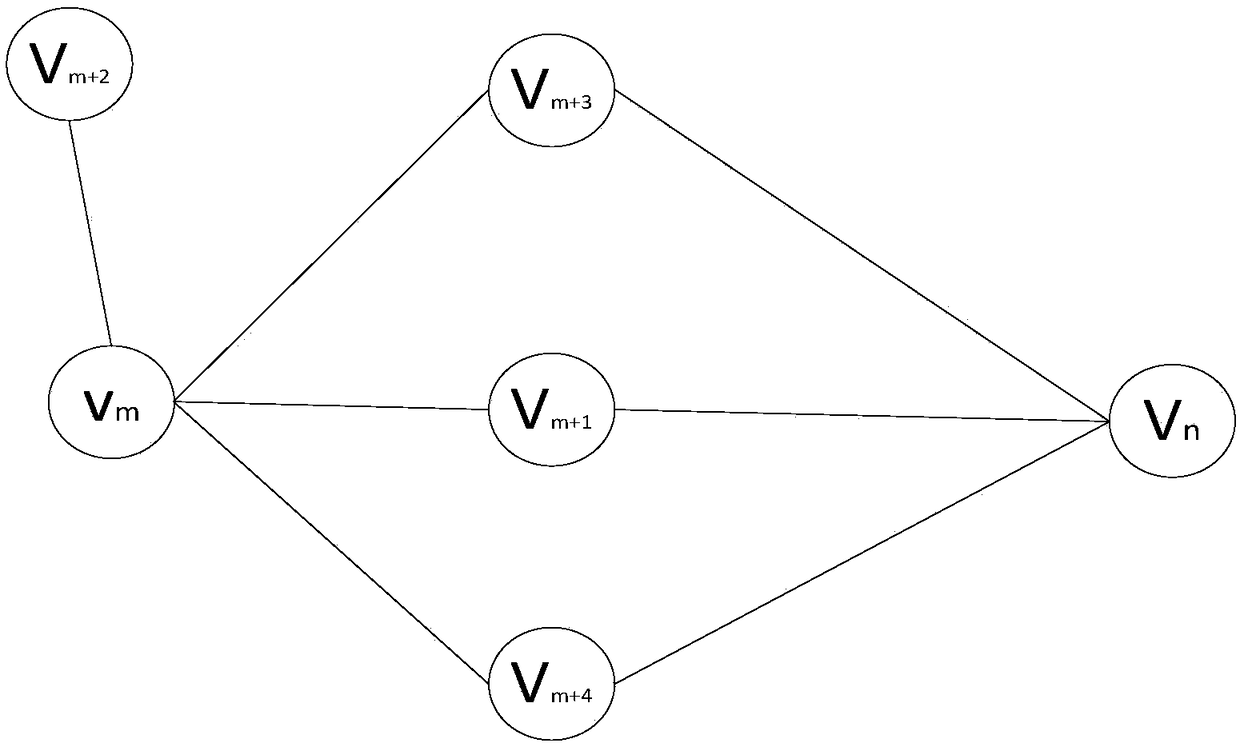
System and method for deploying virtual machines in a computing environment
InactiveUS20100250744A1Cycle brokenEffect is temporaryDigital data processing detailsAnalogue computers for electric apparatusGraphicsDirected graph
A system and method for planning placement of virtual machines VMs in a computing environment comprising a set of hosting machines HM. The method includes constructing a bipartite directed graph-based model that represents both a current and a target placement states, both including virtual machine nodes v in VM and nodes h in HM. Using a technique of graph pruning, the method iteratively generates a plan for achieving a desired target placement starting from the current placement without temporarily violating any policy or resource constraint. The application of the pruning algorithm to VM deployment automation necessarily defines a new model. The methodology employed safely manages concurrent changes in a datacenter, so that the environment can adjust faster to changing constraints. Furthermore, the present invention allows detection of migration cycles, caused by deadlocked combinations of capacity and policy constraints, and resolving them.
Owner:IBM CORP
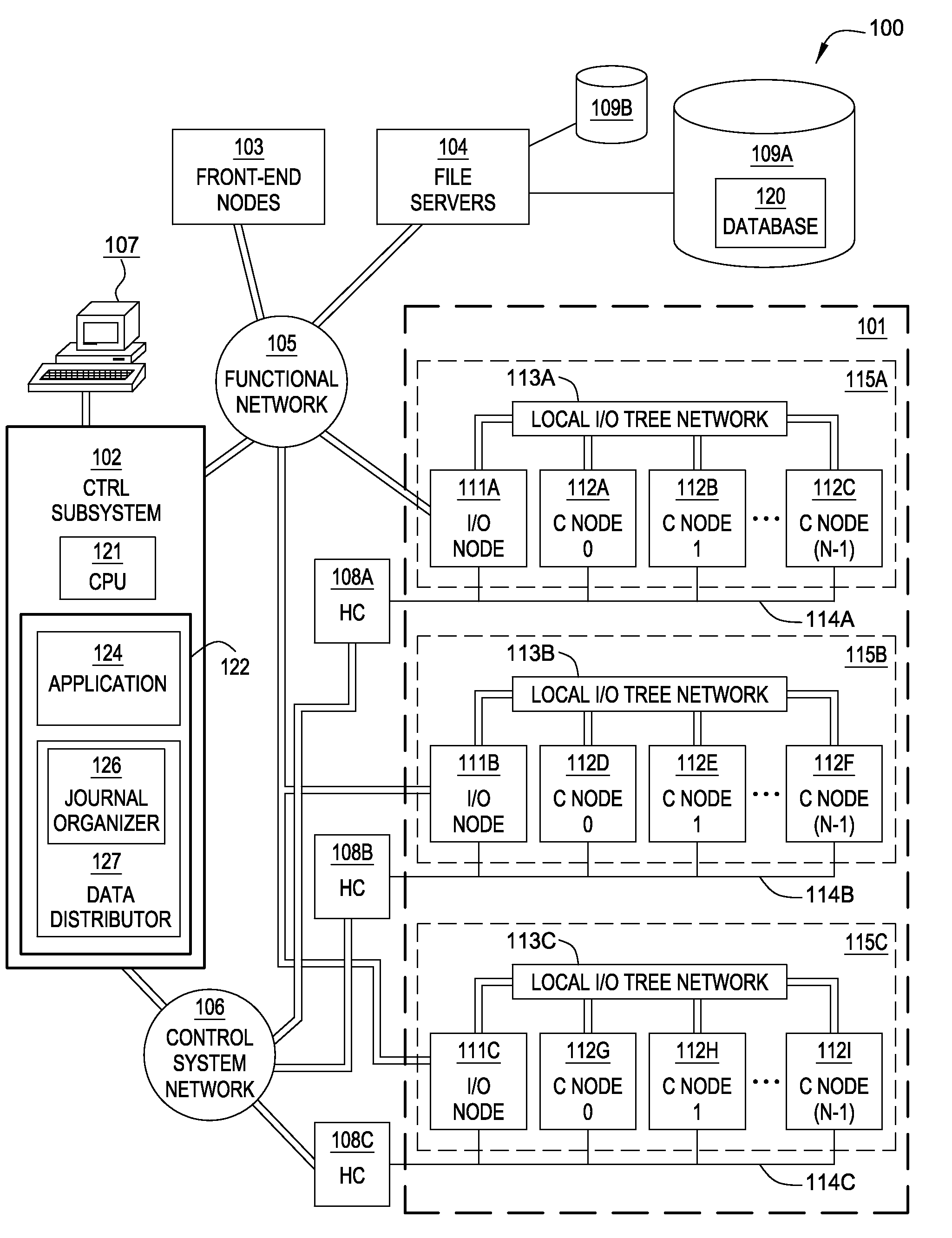
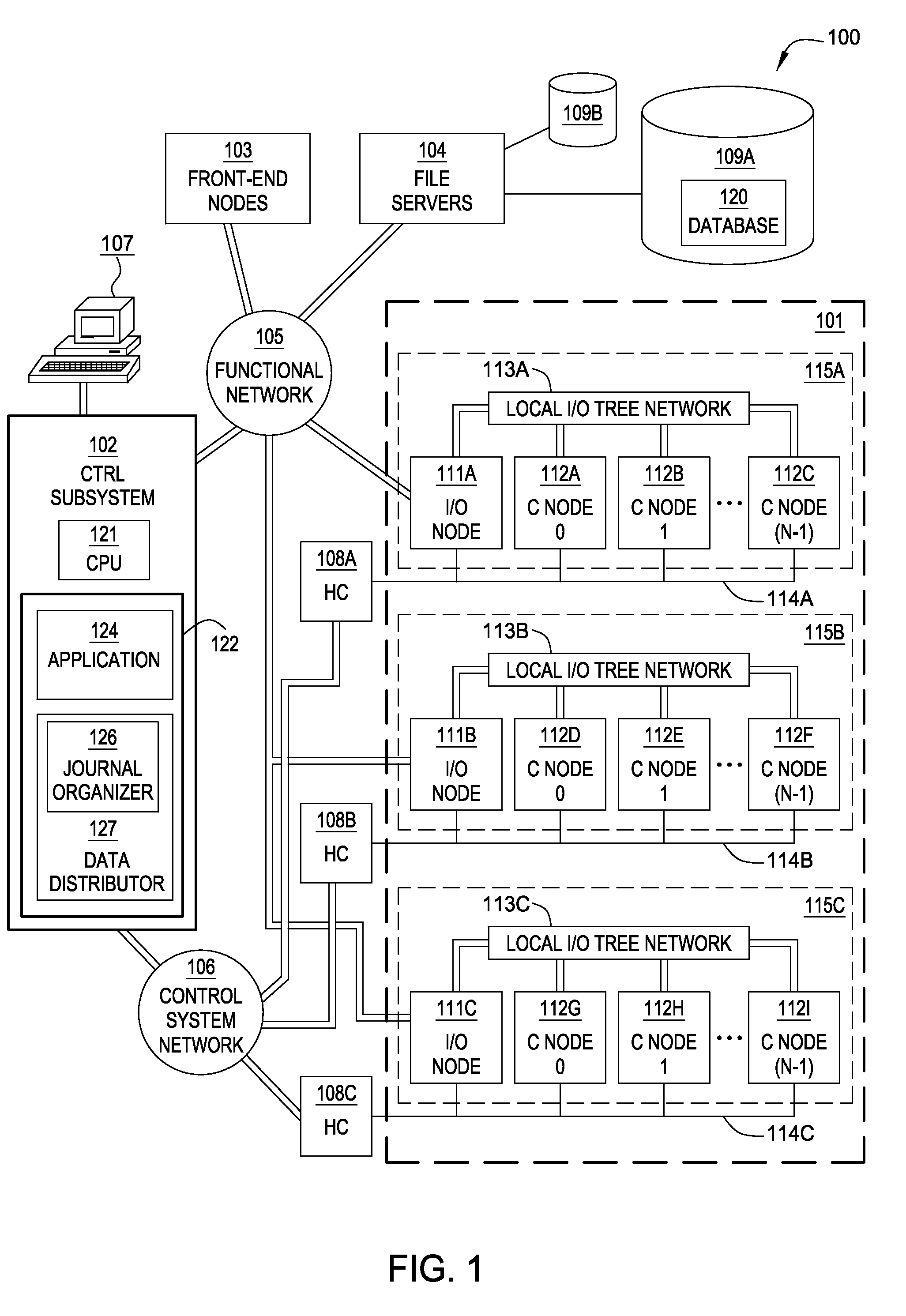
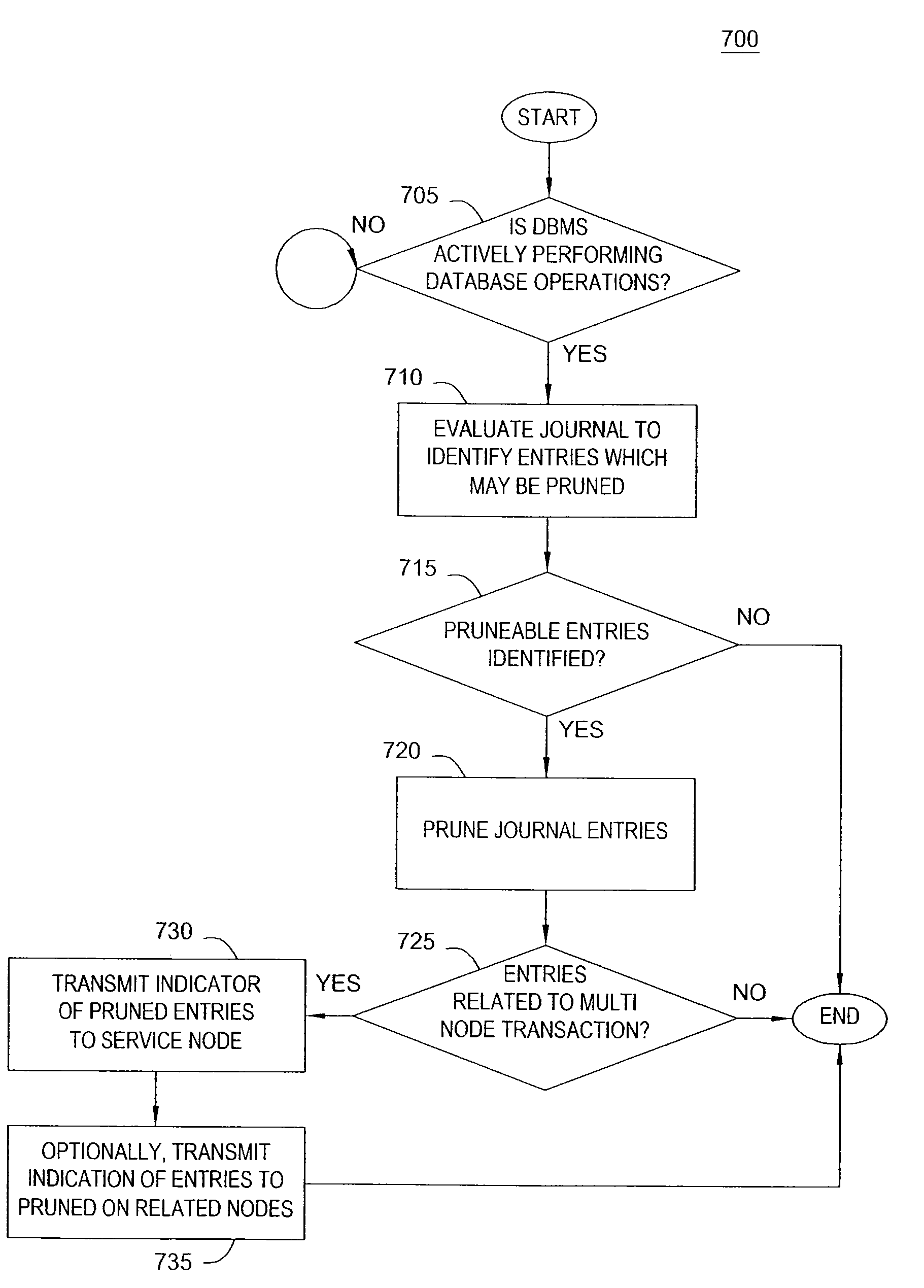
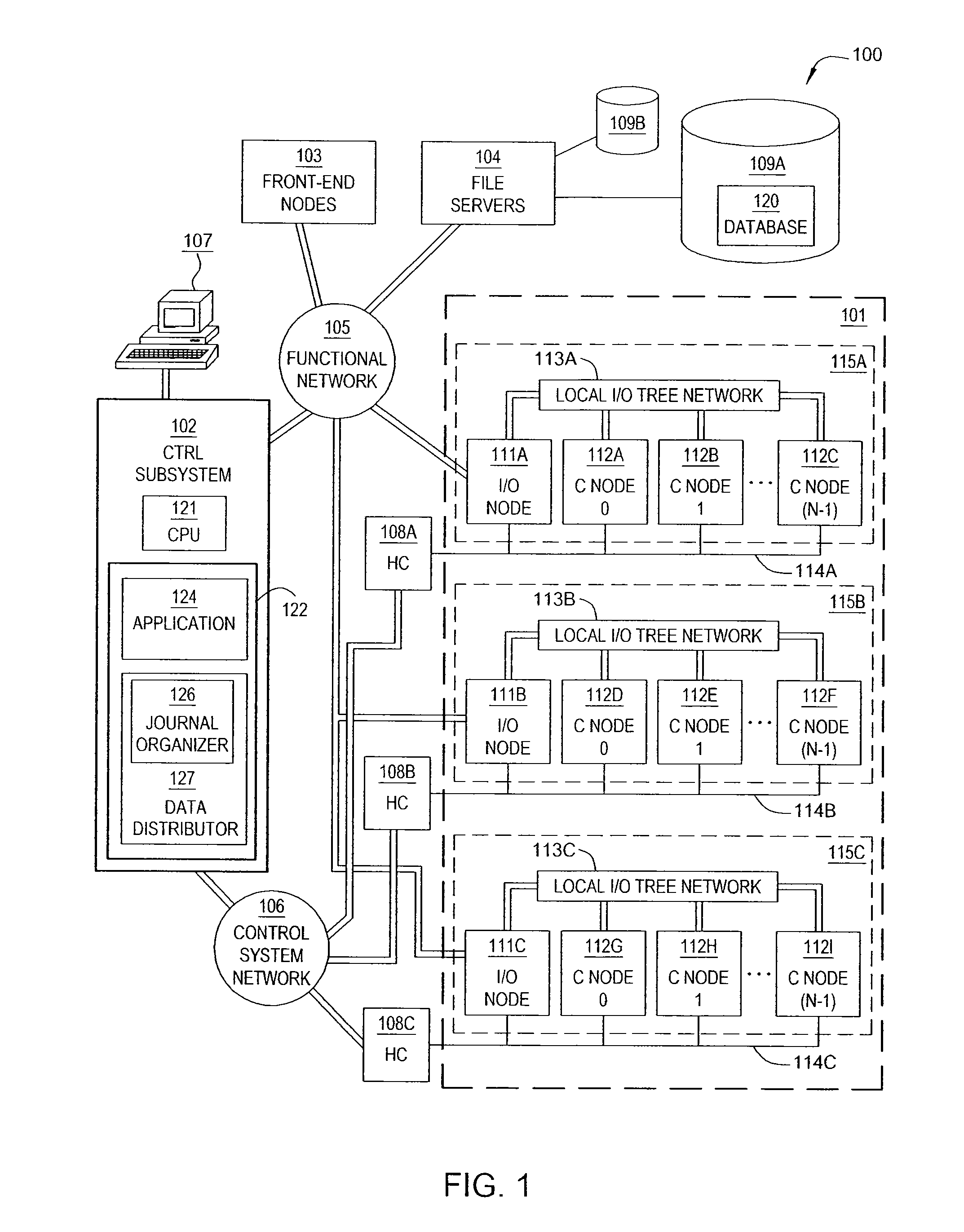
Database Journaling in a Multi-Node Environment
InactiveUS20090307290A1Digital data processing detailsDatabase distribution/replicationFinancial transactionMaximum size
A database spread over multiple nodes allows each node to store a journal recording changes made to the database and also allows a journaling component to manage the memory space available for journaling. Two threshold size values may be specified for the journal. The first threshold value specifies a journal size at which to being pruning the journal on a given node. A journal pruning algorithm may be used to identify journal entries that may be removed. For example, once a given transaction completes (i.e., commits) the journal entries related to that transaction may be pruned from the journal. The second threshold value specifies the maximum size of the journal. After reaching this size, journal entries may be written to disk instead of the in-memory journal.
Owner:IBM CORP
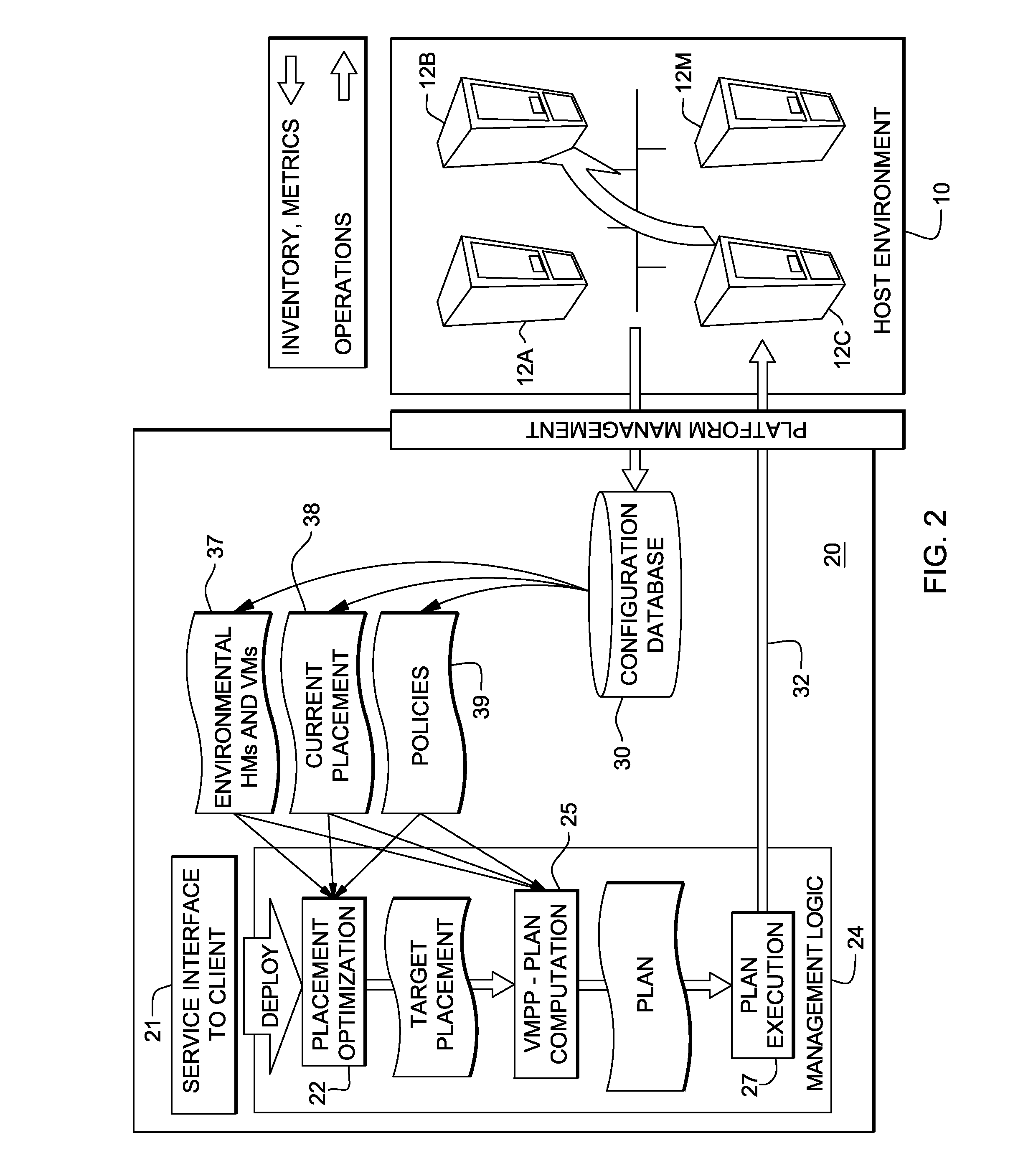
System and method for deploying virtual machines in a computing environment
InactiveUS7904540B2Digital data processing detailsAnalogue computers for electric apparatusGraphicsDirected graph
A system and method for planning placement of virtual machines VMs in a computing environment comprising a set of hosting machines HM. The method includes constructing a bipartite directed graph-based model that represents both a current and a target placement states, both including virtual machine nodes v in VM and nodes h in HM. Using a technique of graph pruning, the method iteratively generates a plan for achieving a desired target placement starting from the current placement without temporarily violating any policy or resource constraint. The application of the pruning algorithm to VM deployment automation necessarily defines a new model. The methodology employed safely manages concurrent changes in a datacenter, so that the environment can adjust faster to changing constraints. Furthermore, the present invention allows detection of migration cycles, caused by deadlocked combinations of capacity and policy constraints, and resolving them.
Owner:IBM CORP
Mobile phone screen MURA defect detection method based on convolution neural network pruning algorithm
ActiveCN106875373AGuaranteed accuracyDealing with Moiré InterferenceImage enhancementImage analysisPattern recognitionAlgorithm
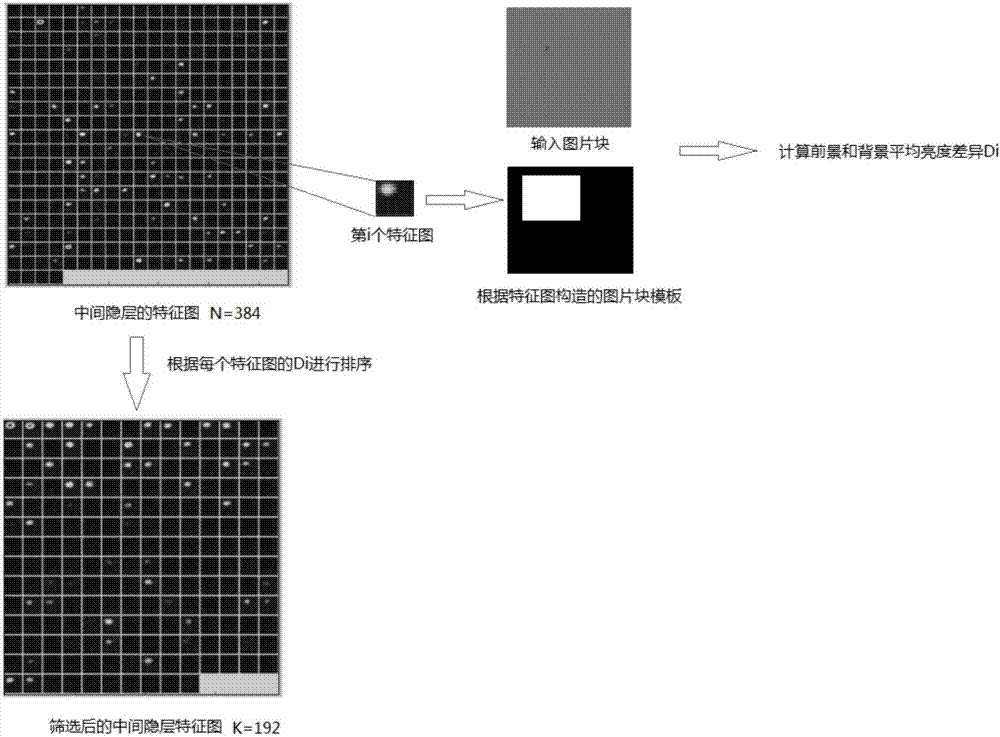
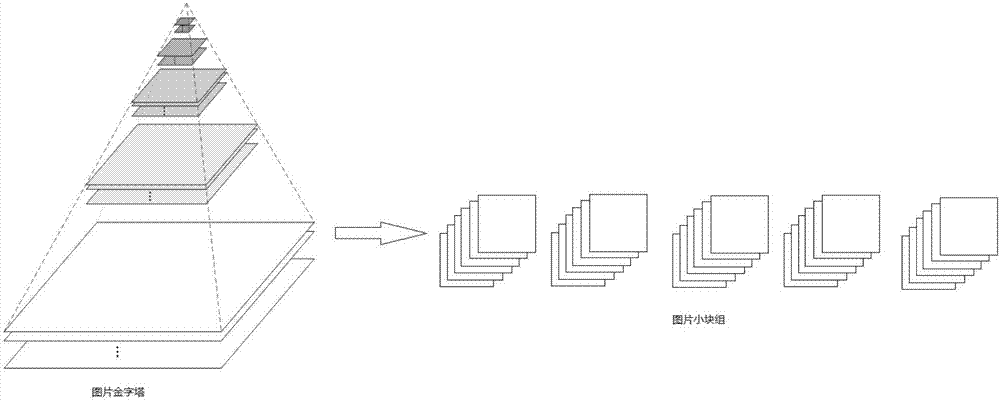
The invention relates to a mobile phone screen MURA defect detection method based on a convolution neural network pruning algorithm. The mobile phone screen MURA defect detection method based on a convolution neural network pruning algorithm includes the steps: 1) customizing a depth convolution neural network, and utilizing the existing training data to train a neural network of detecting a mobile phone screen MURA defect; 2) utilizing an adaptive template coupling method to perform pruning operation on the convolution neural network, reducing the network scale, and reducing the algorithm running time; 3) zooming the mobile phone screen images shot by a high resolution camera, forming an image pyramid, for the image of each scale, utilizing a sliding window method to segment the images into small blocks, and taking all the small blocks of images as one group and sending the group to the convolution neural network; and 4) selecting all the characteristic images of the intermediate layer as the response images for the defect, and utilizing a threshold segmentation method to finally obtain the area position of the mobile phone screen MURA defect.
Owner:HUIZHOU XUXIN PRECISION ELECTRONICS EQUIP
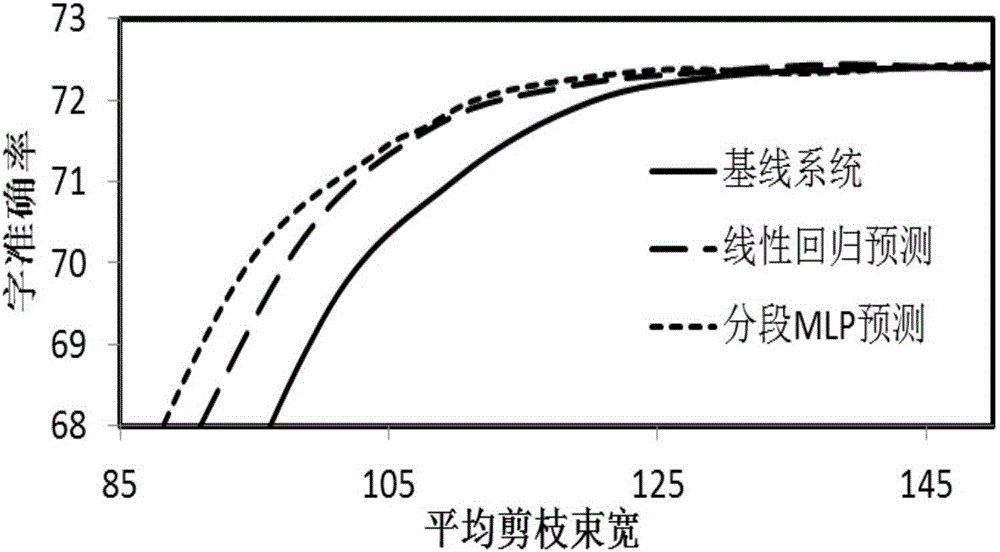
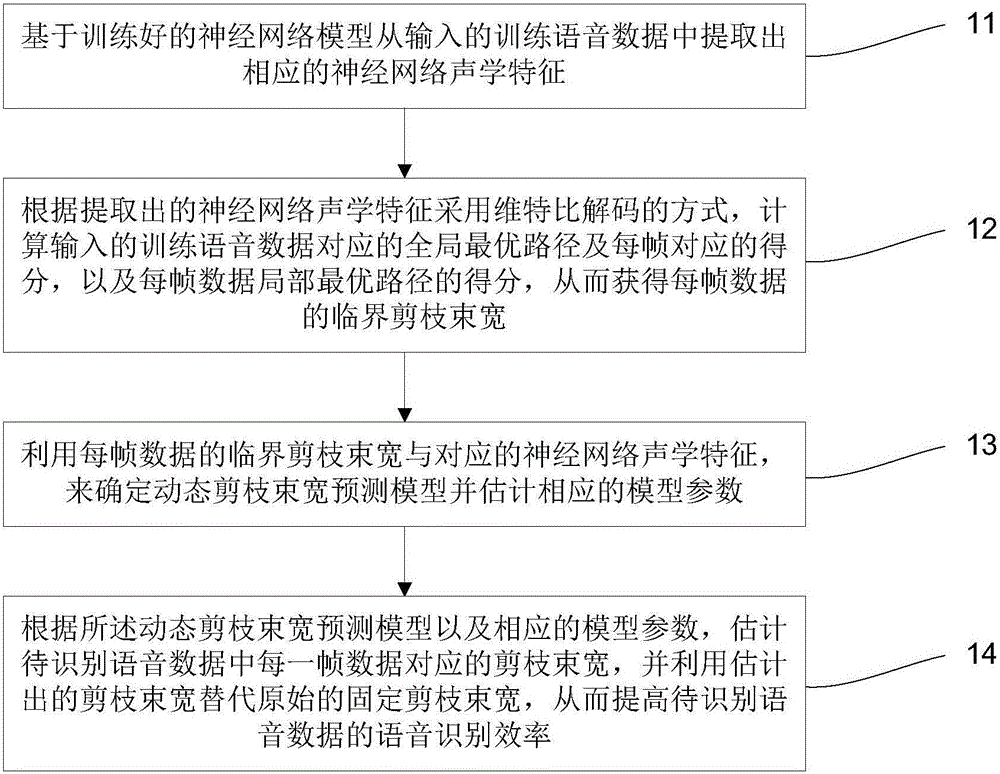
Voice identification efficiency optimization method based on dynamic pruning beam prediction
ActiveCN105845128AImprove speech recognition decoding efficiencySpeech recognitionImproved algorithmComputer science
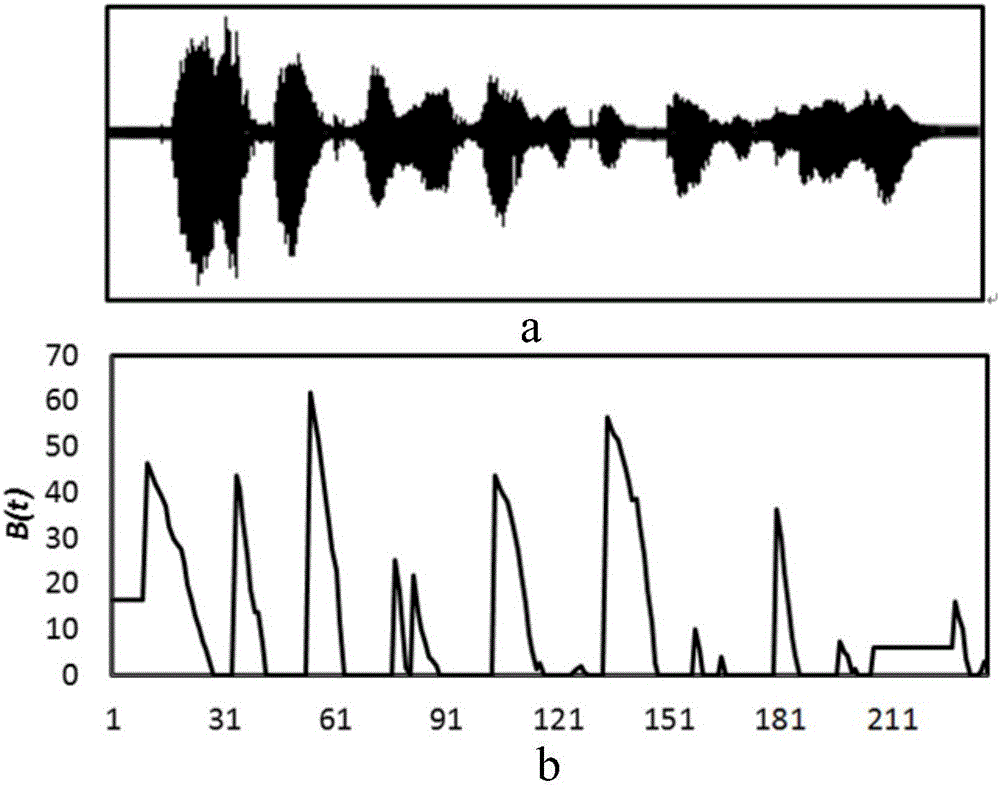
The invention discloses a voice identification efficiency optimization method based on dynamic pruning beam prediction. For problems of relatively many redundancy paths existing in a traditional voice decoding pruning algorithm and insufficient pruning validity existing in an improved algorithm in the prior art, dynamic pruning beam prediction ideas based on acoustics characteristics are proposed, and two specific modeling modes and a corresponding parameter estimation training method are proposed, and thereby voice identification decoding efficiency is improved.
Owner:UNIV OF SCI & TECH OF CHINA
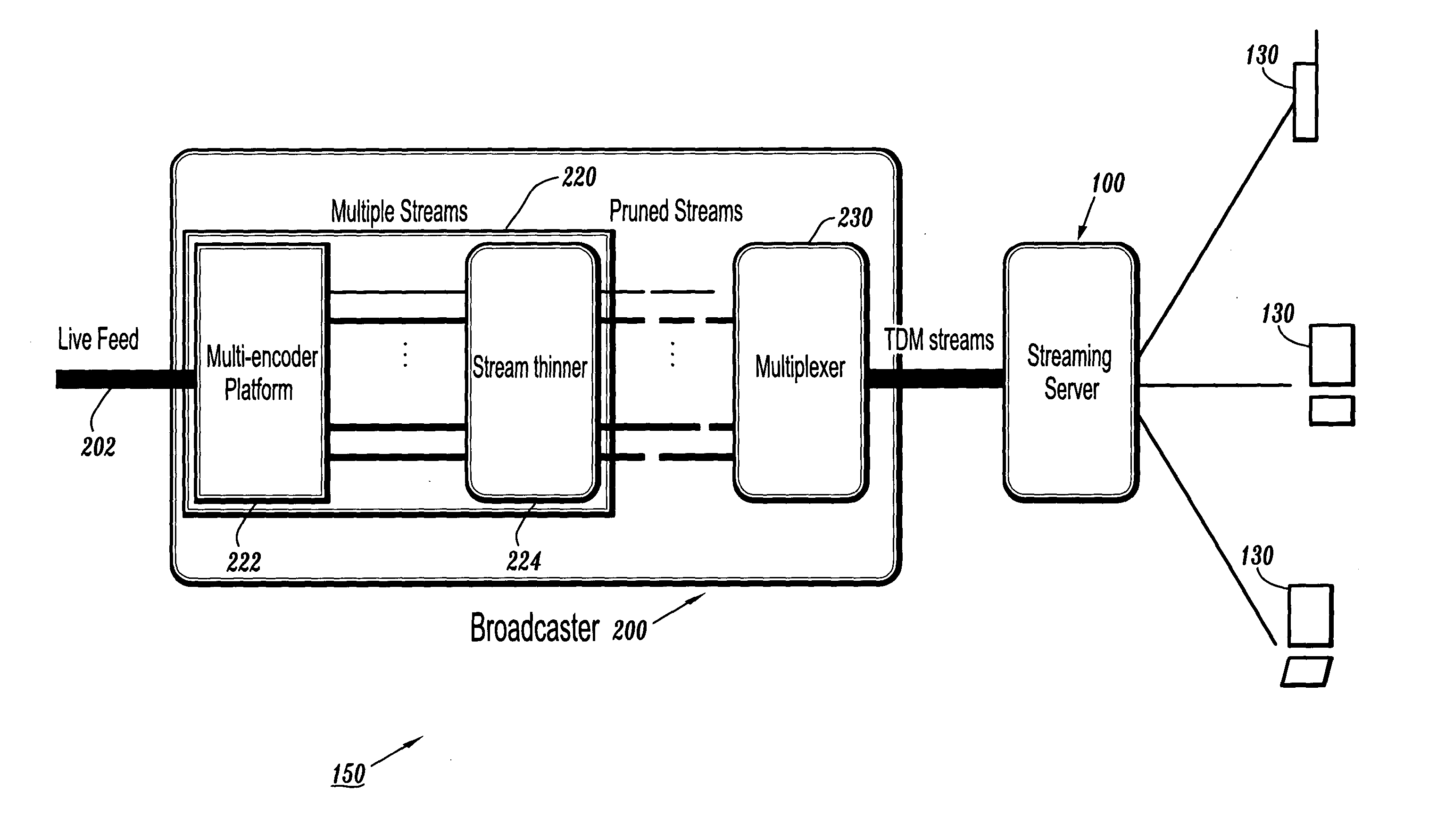
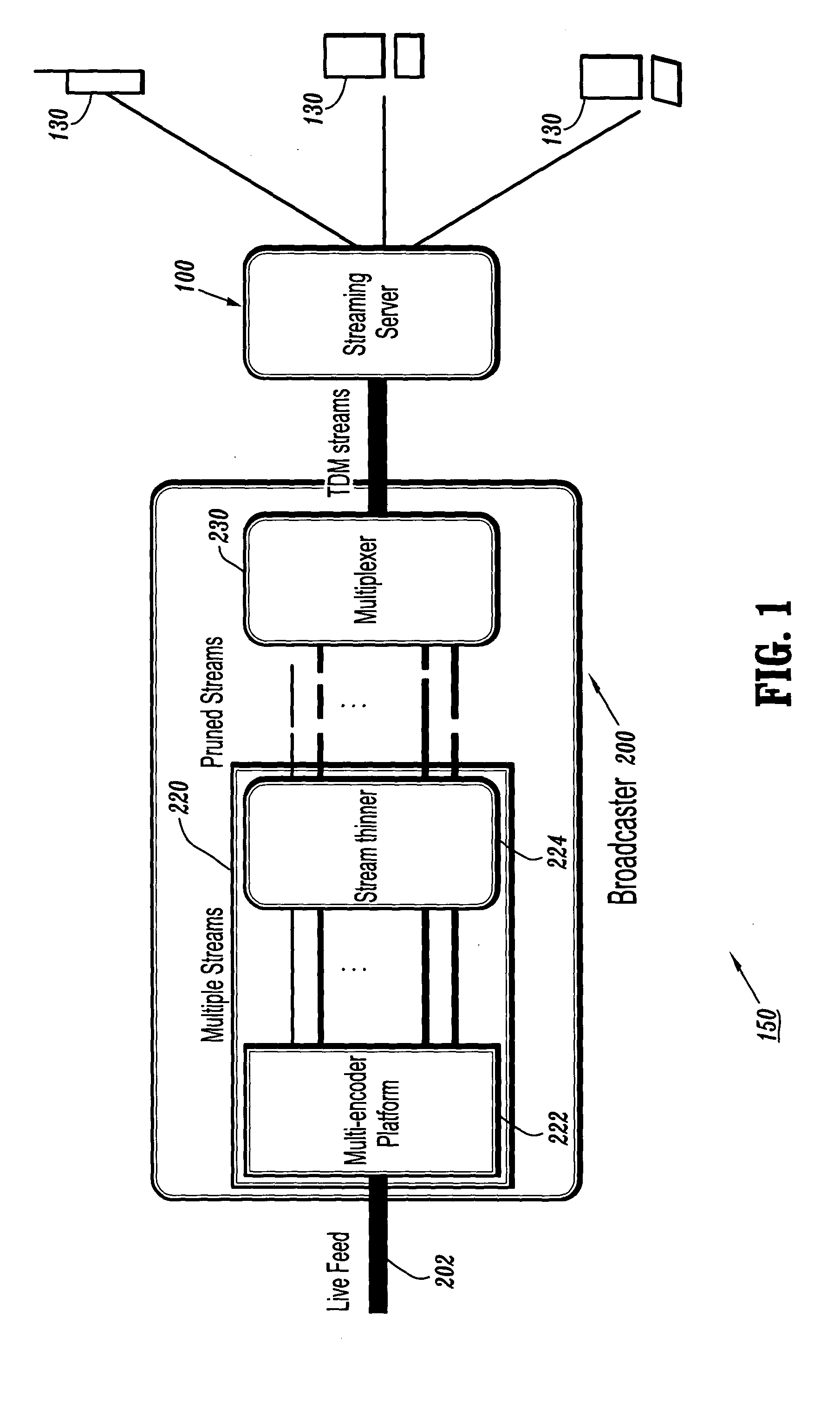
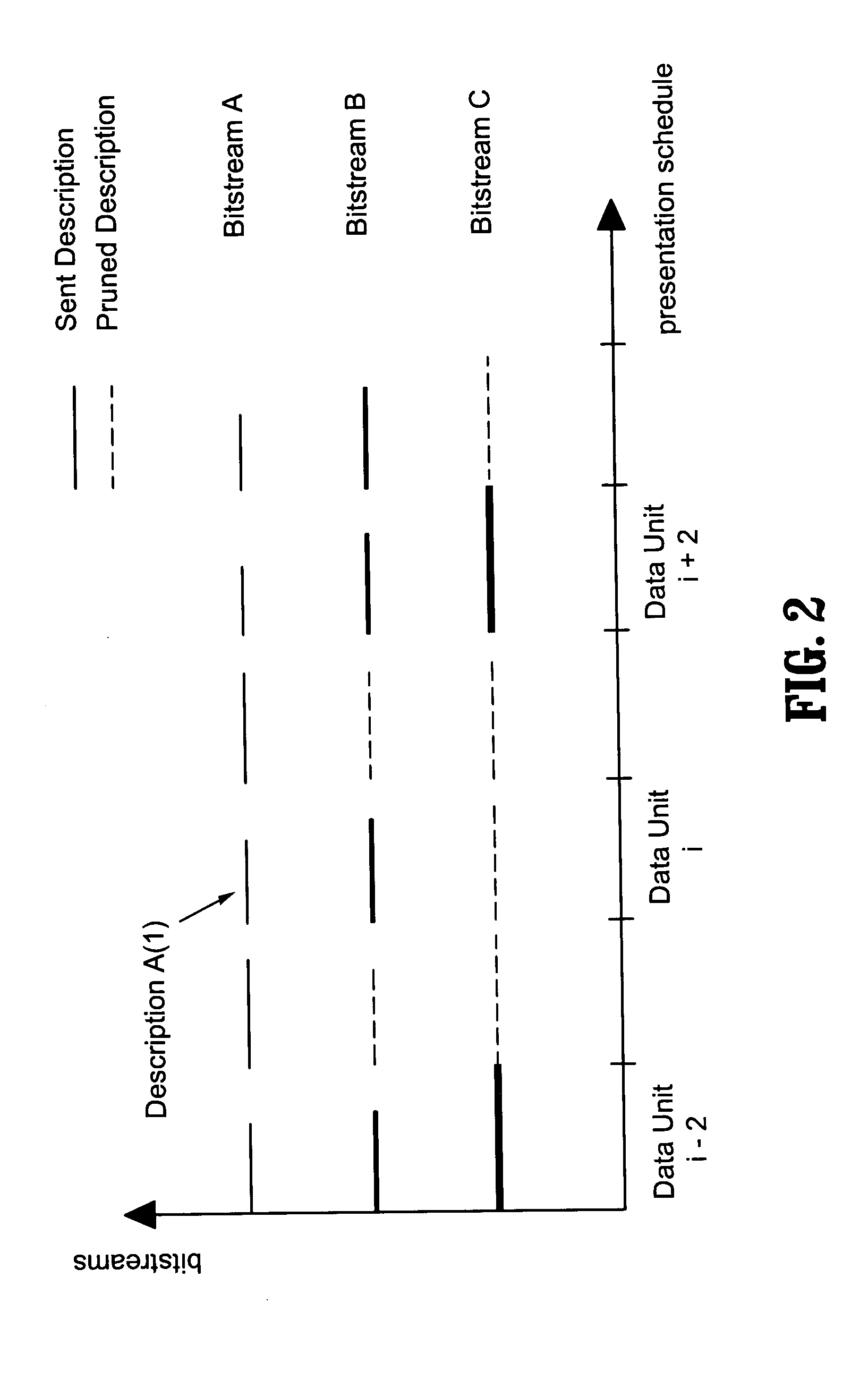
System and method for resource-efficient live media streaming to heterogeneous clients
InactiveUS20040215802A1Multiple digital computer combinationsSecuring communicationQuality of serviceTransmission channel
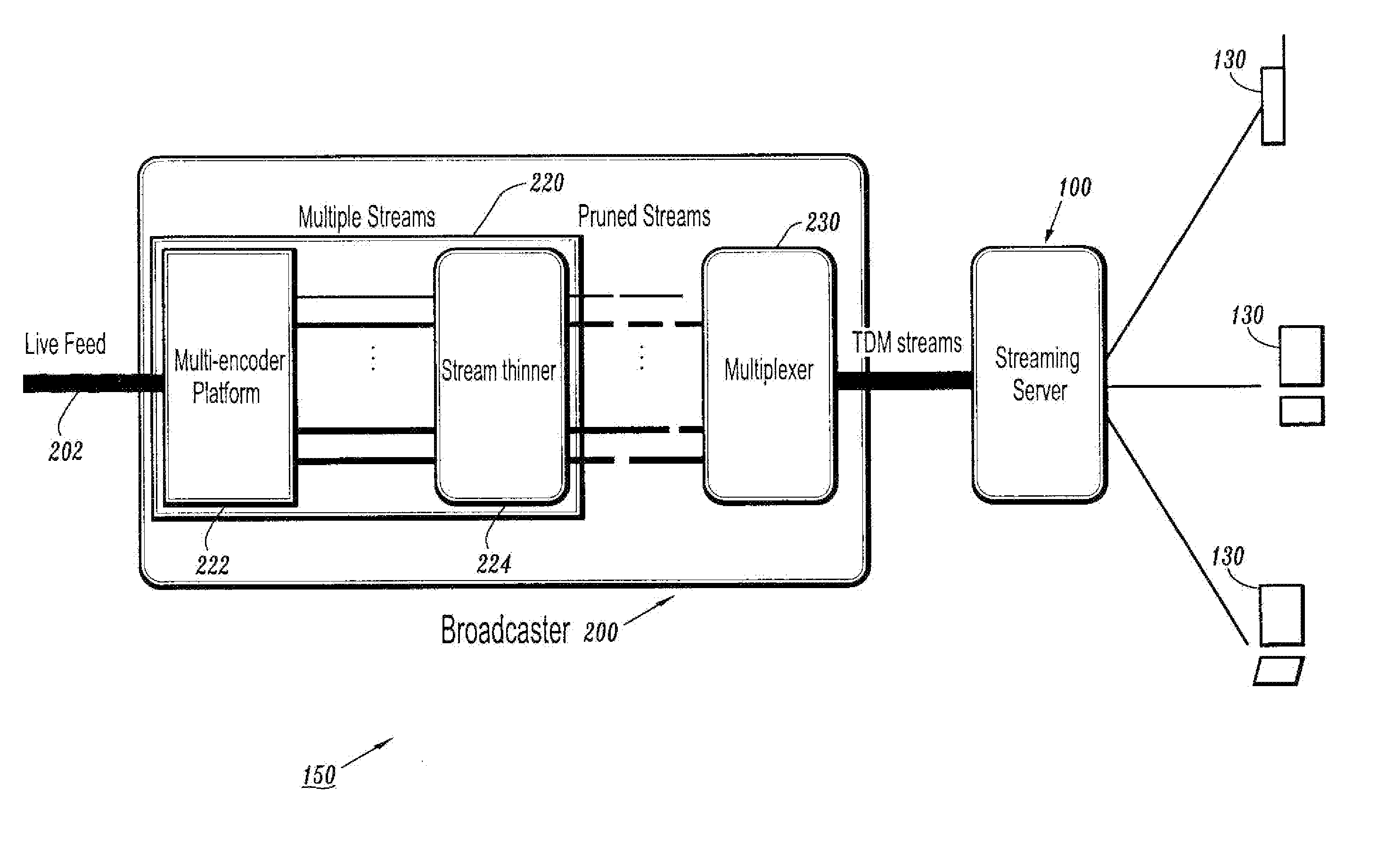
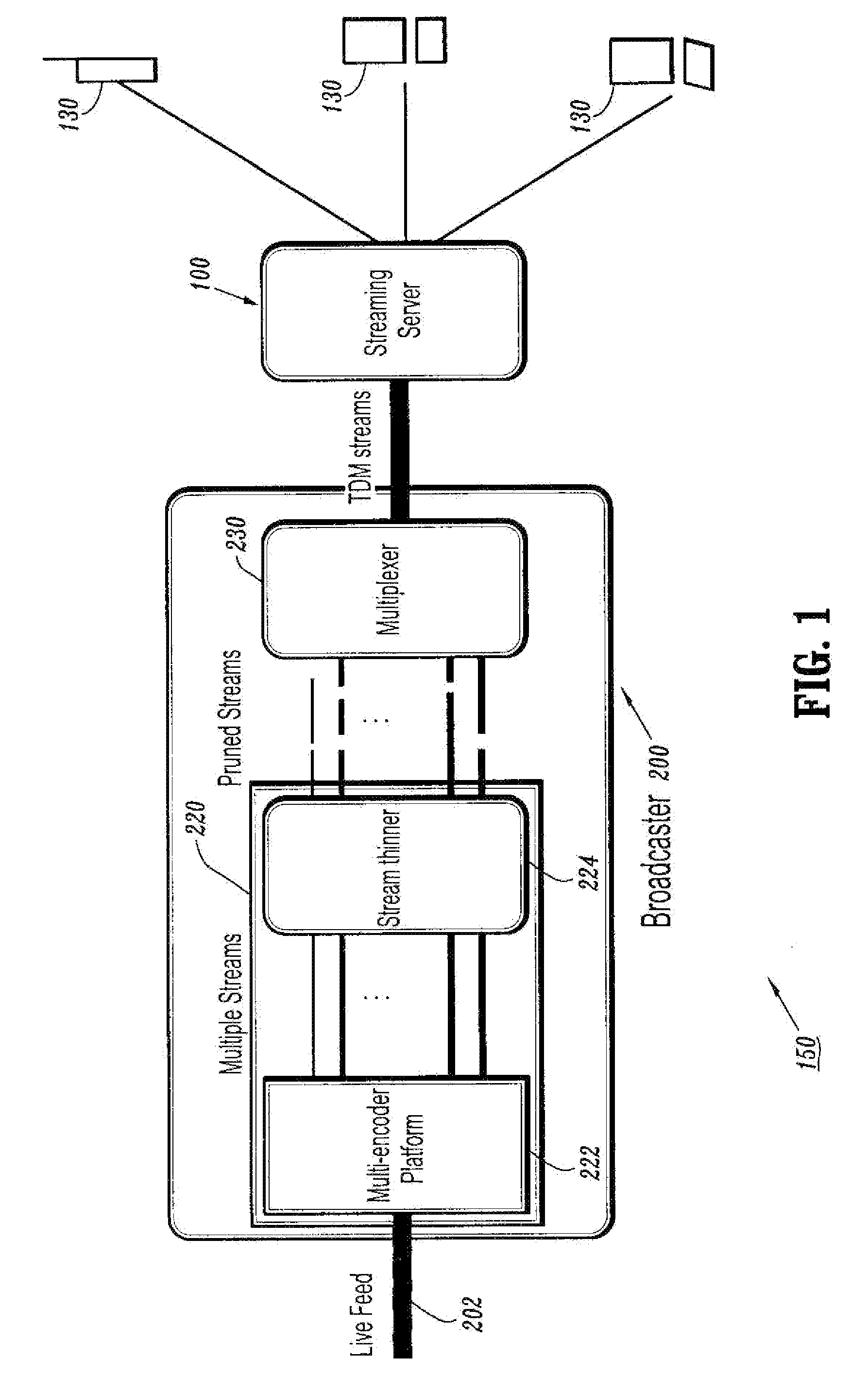
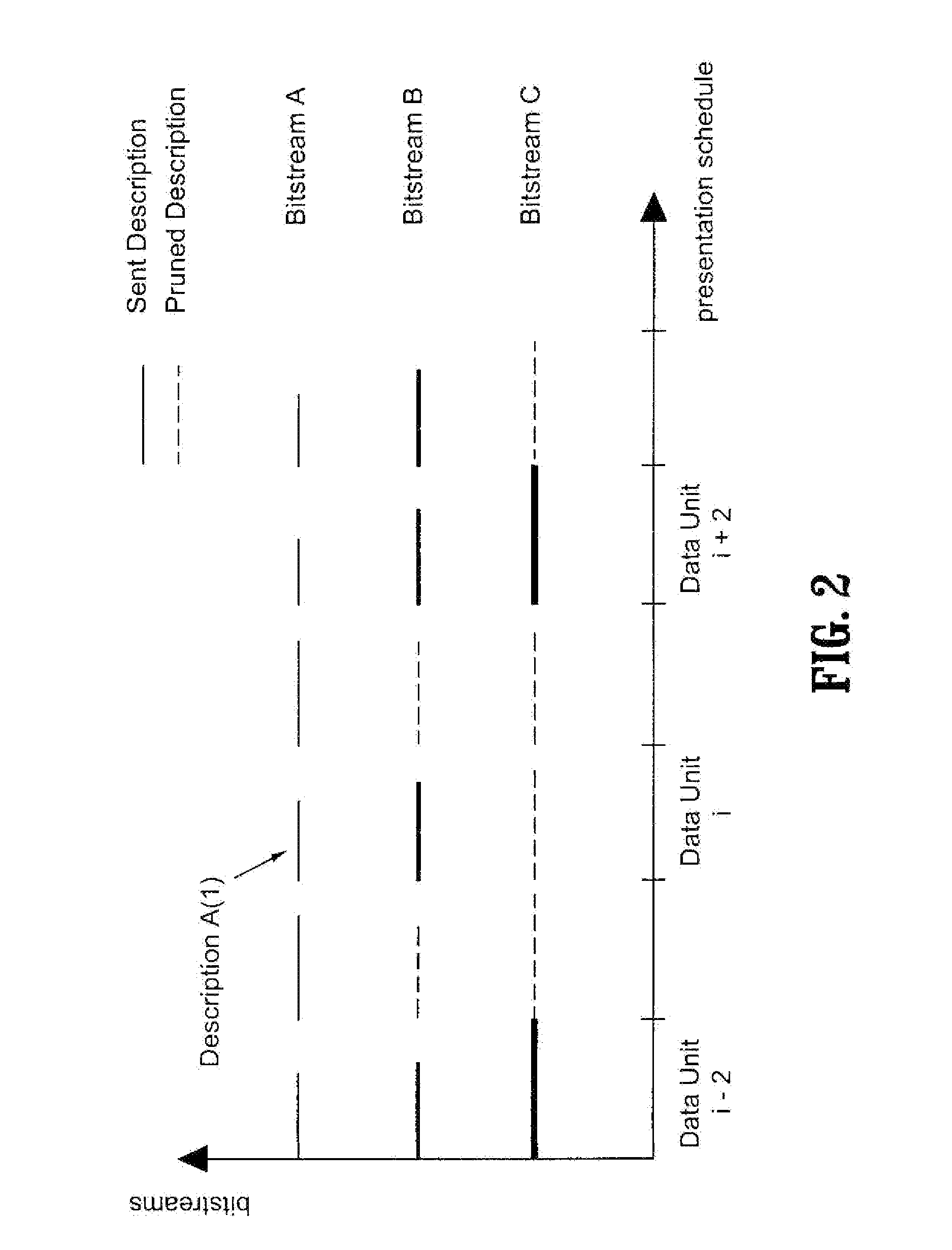
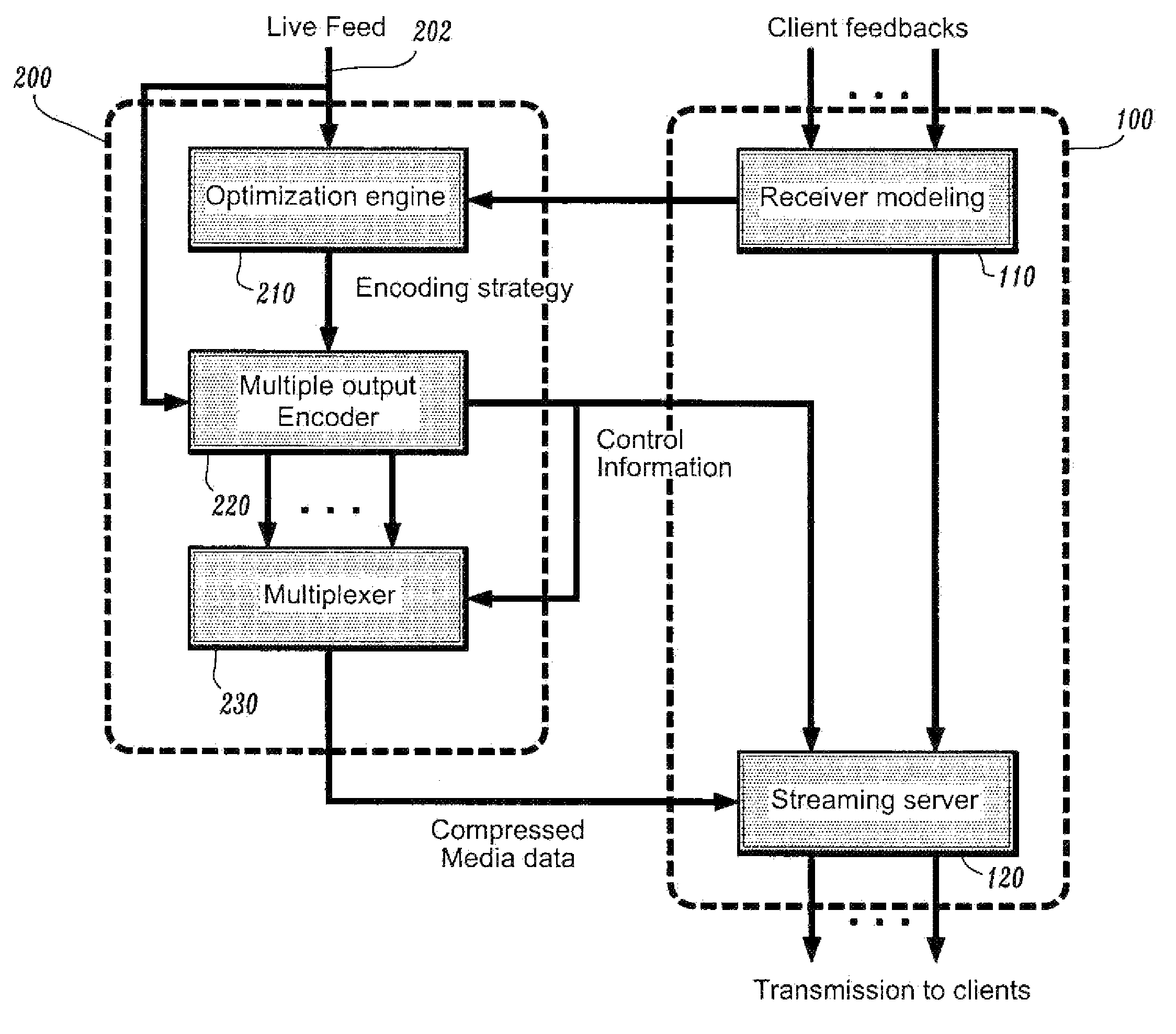
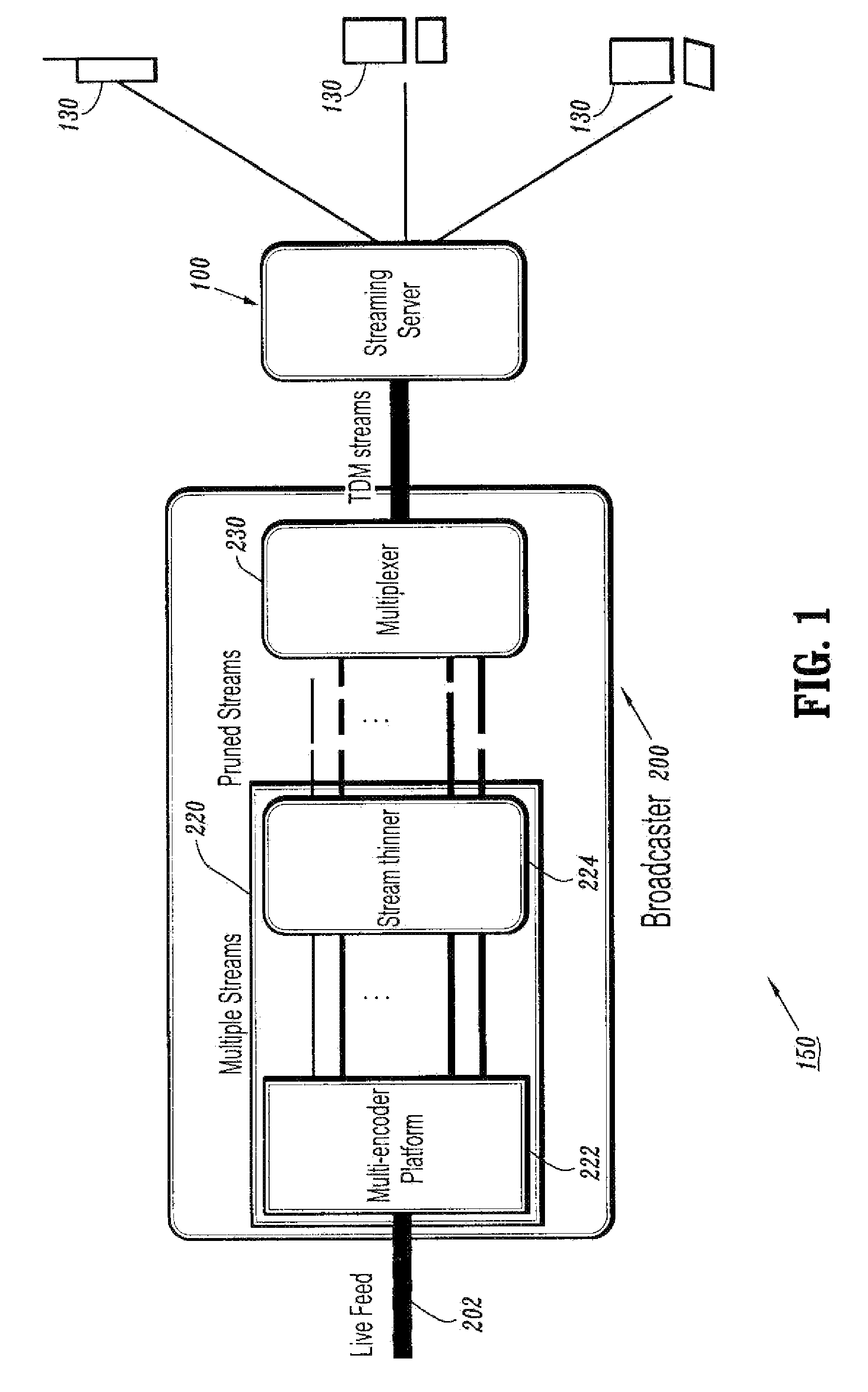
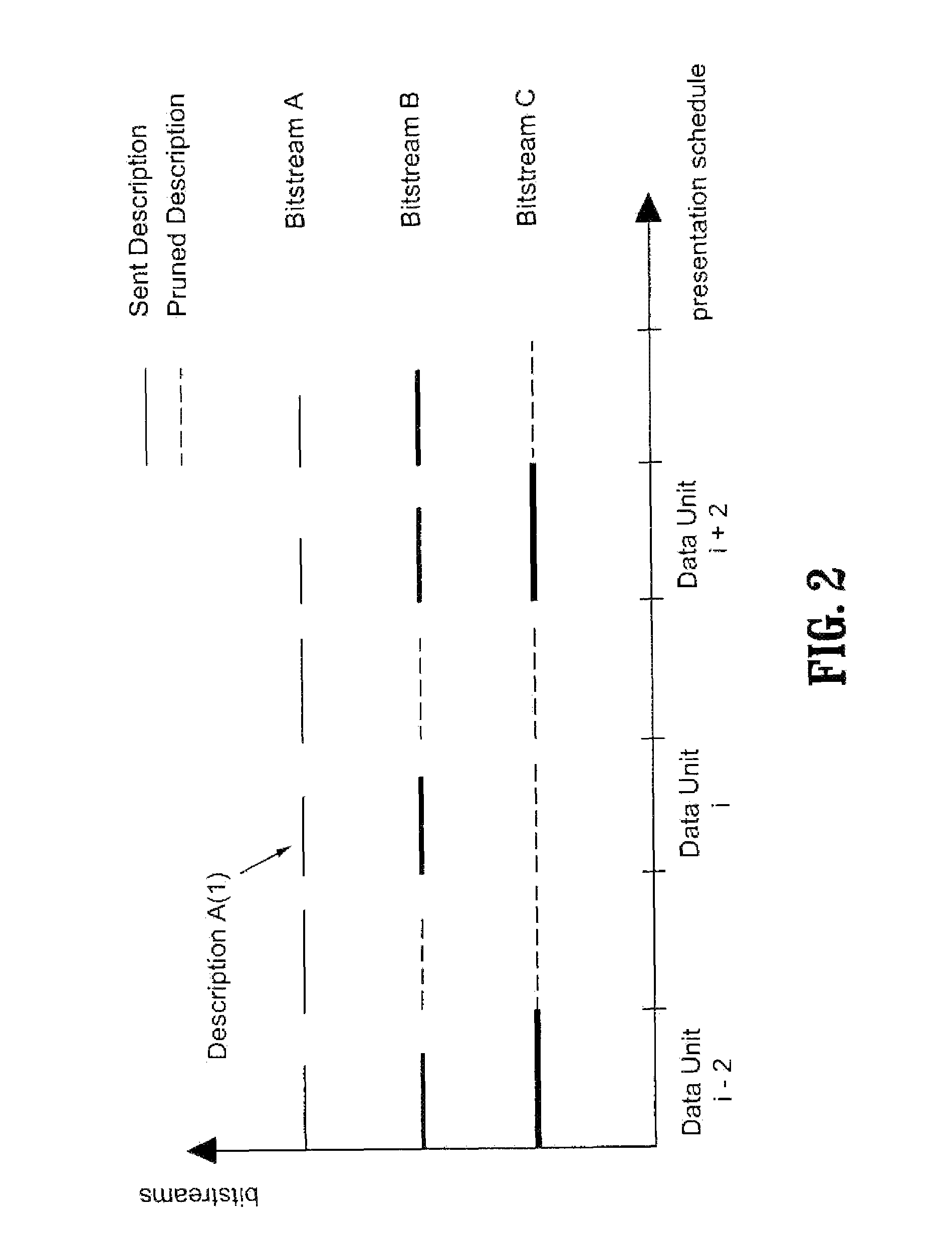
A resource-efficient live streaming system includes a broadcaster and a streaming server. The broadcaster receives a live feed and broadcasts a media stream to the streaming server containing several descriptions of the live feed along with control information. The broadcaster includes a stream thinner that implements a pruning algorithm. If descriptions from different streams are similar enough, one or more of them may be discarded without penalizing the quality of service perceived by the receivers. The streaming server assembles compressed data units into streams according to the control information from the broadcaster. The streaming server may also gather client feedback in order to estimate the status of the transmission channels and forwards the information to the broadcaster. The streaming server builds and streams media information to clients according to user preferences and receiver capabilities.
Owner:IBM CORP
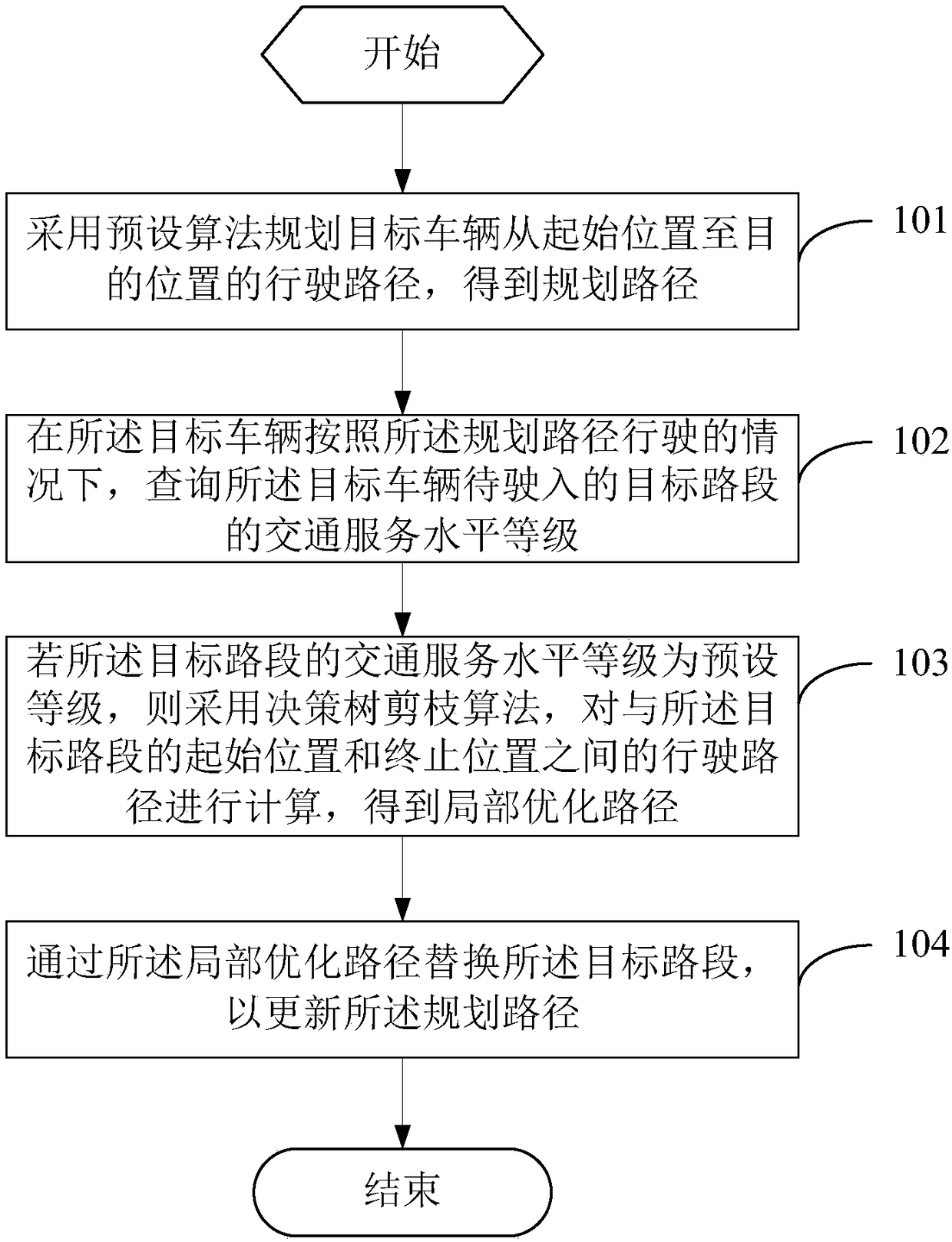
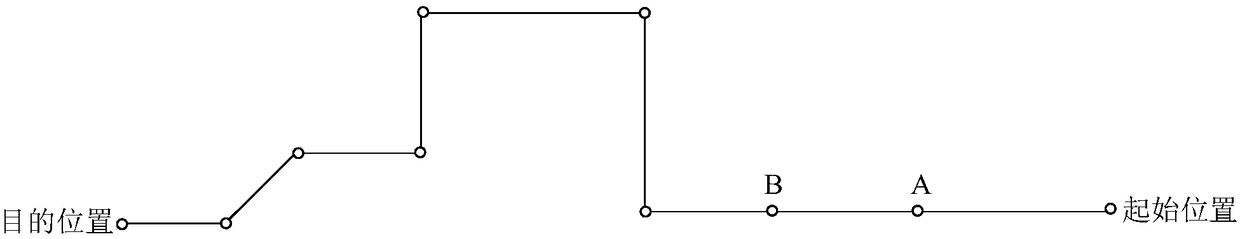
Method and device for planning driving route
InactiveCN108562301AImprove accuracyInstruments for road network navigationPlanning approachEngineering
The invention provides a method and device for planning a driving route. The method includes the steps of planning a driving route of a target vehicle from a starting position to a destination position by using a preset algorithm to obtain a planned route, wherein the planned route includes a plurality of road segments; querying the traffic service level of a target road segment to which the target vehicle enters in the case that the target vehicle runs according to the planned route; if the traffic service level of the target road segment is a preset level, adopting a decision tree pruning algorithm to calculate the driving route between the starting position and the destination position of the target road segment to obtain a local optimized route; replacing the target road segment by thelocal optimized route to update the planned route. In this way, when the target vehicle runs according to the planned route, the planned route can be updated according to the traffic service level ofthe target road segment to be entered, and the accuracy of the planned route is improved.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
Interframe mode fast selecting method and system of video compressed coding
ActiveCN106454342AReduce calculationReduce computational complexityDigital video signal modificationSpatial correlationComputation complexity
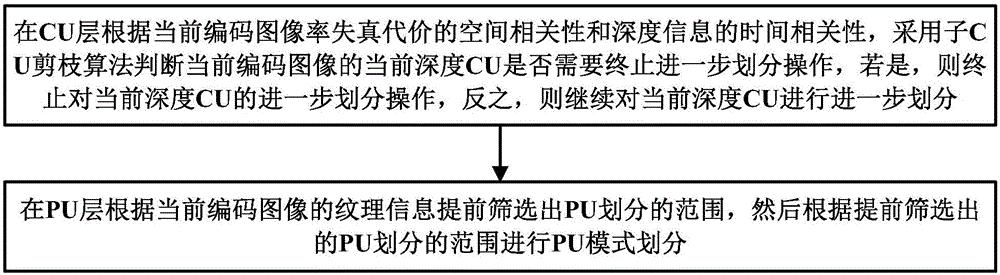
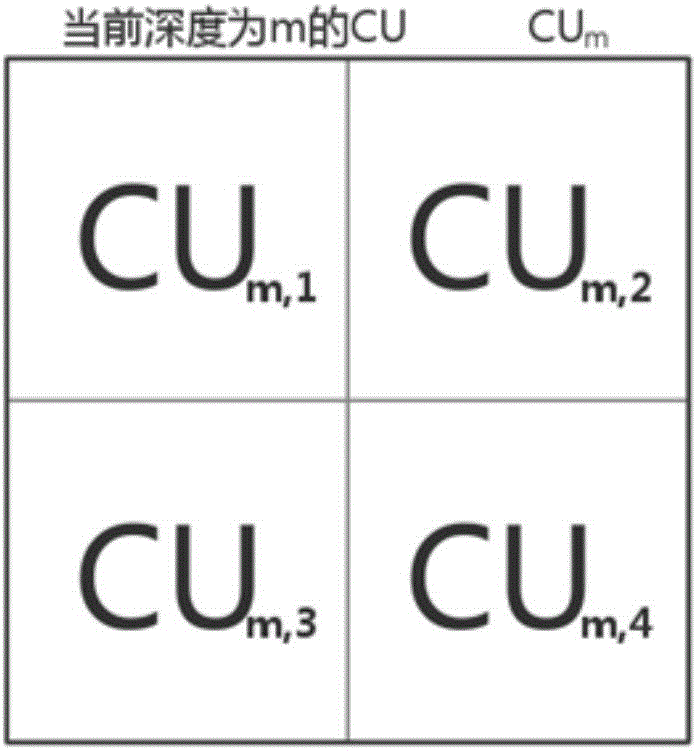
The invention discloses an interframe mode fast selecting method and system of video compressed coding. The interframe mode fast selecting method and system of video compressed coding comprises the steps of judging whether one current-depth CU of a current coding image needs to terminate a further division operation by adopting a sub-CU pruning algorithm in one CU layer based on spatial correlation of the rate-distortion cost of a current coding image and time correlation of depth information, if so, terminating the further division operation for the current-depth CU, otherwise, carrying on further division for the current-depth CU; and sieving a range of PU division in advance in a PU layer based on texture information of the current coding image, and then performing PU mode division based on the range of PU division sieved in advance. The interframe mode fast selecting method and system of video compressed coding has the advantages of low calculation complexity and fast speed, and can be widely applied to the field of video coding.
Owner:SUN YAT SEN UNIV
M-algorithm multiuser detector with correlation based pruning
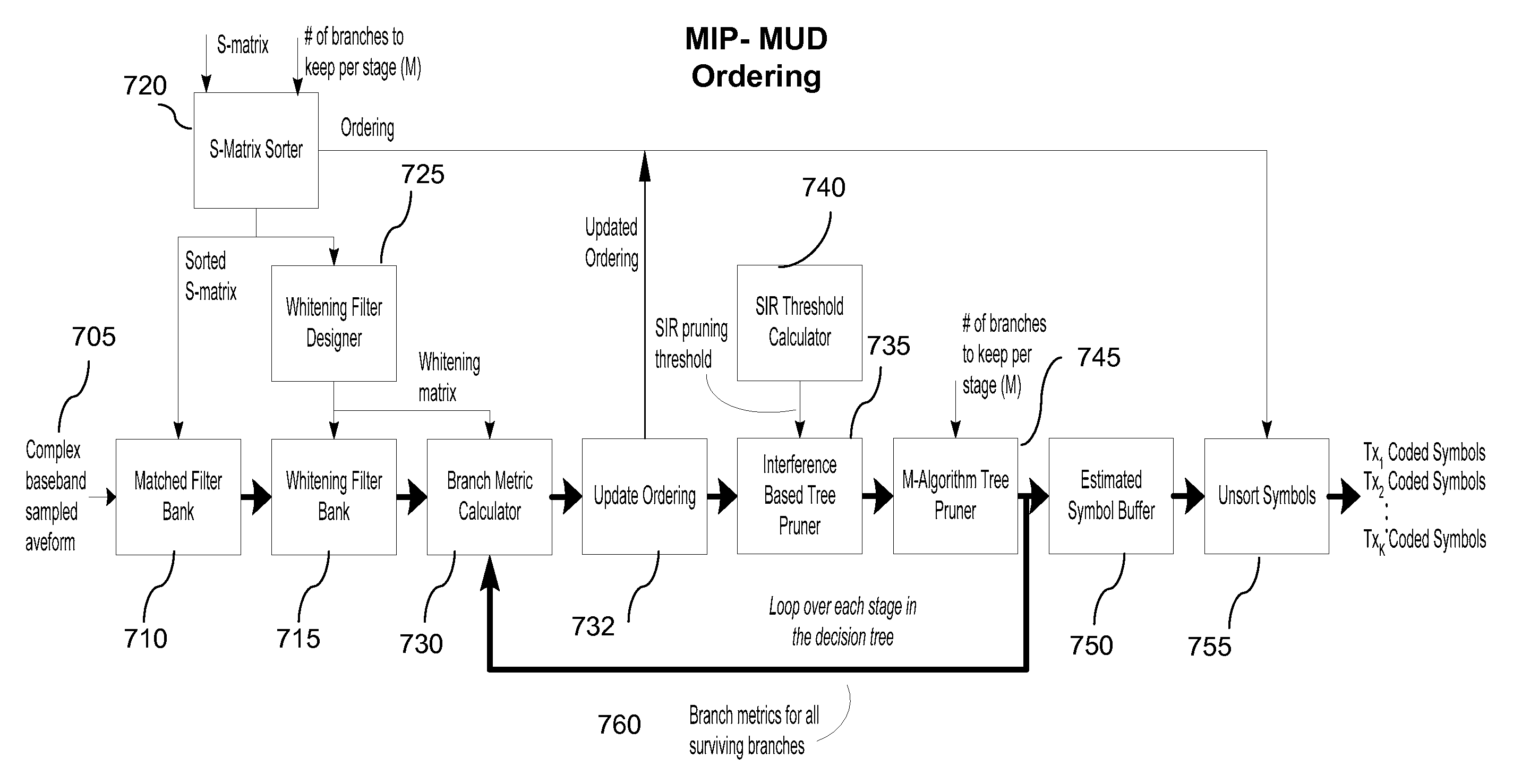
ActiveUS20070036250A1Line-faulsts/interference reductionAmplitude-modulated carrier systemsRound complexityHypothesis
A multiuser detector system with correlation based pruning including a parameter estimation module adapted to receive complex signals, and to produce estimated signature waveforms for each of K co-channel interfering signals. Pre-processing the estimated signature waveforms using an S-matrix module and producing a more valid set of hypotheses, wherein the S-matrix module uses apriori knowledge of an unnormalized cross correlation matrix, and processing the more valid set of hypotheses for pruning with an M-algorithm a multiuser detector module. An improvement to the M-algorithm in which the interference structure based on the signal correlation matrix used during the optimization process aids in selecting a better subset of hypotheses to test. This approach has the benefit of reducing computational complexity and improving performance over the existing M-algorithm
Owner:COLLISION COMM
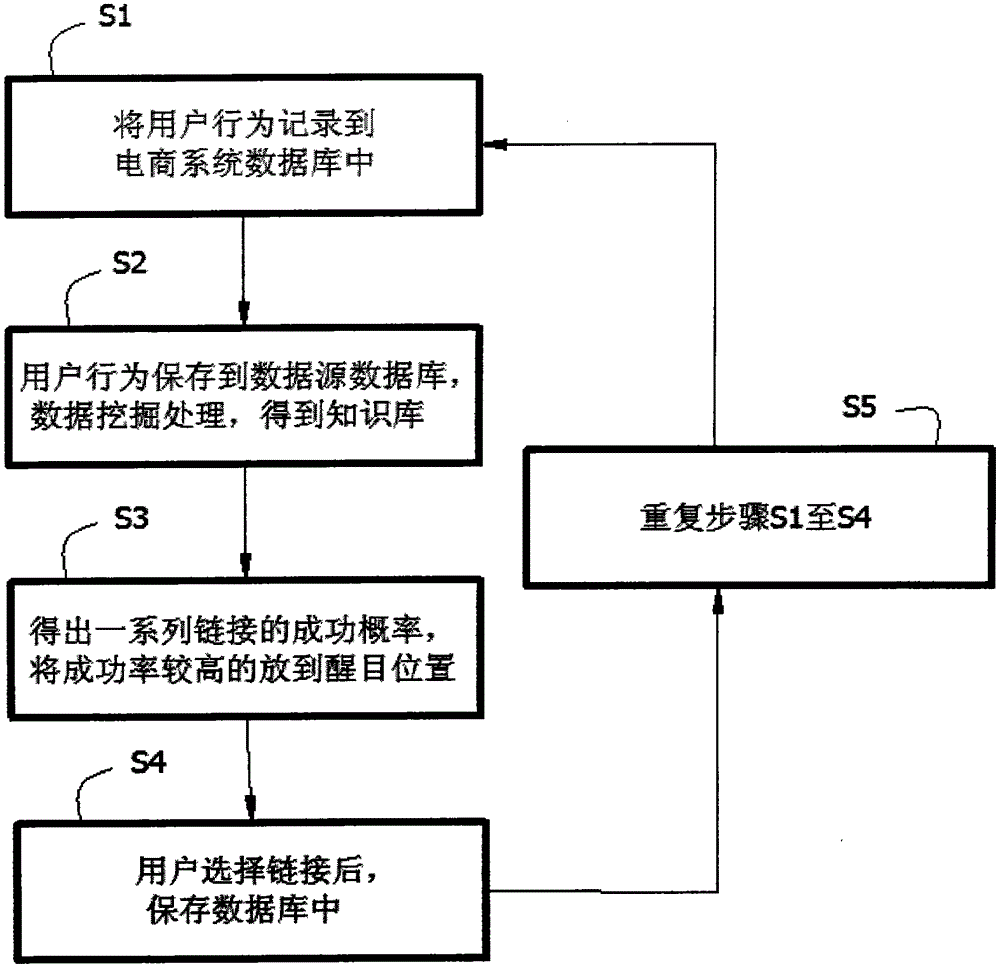
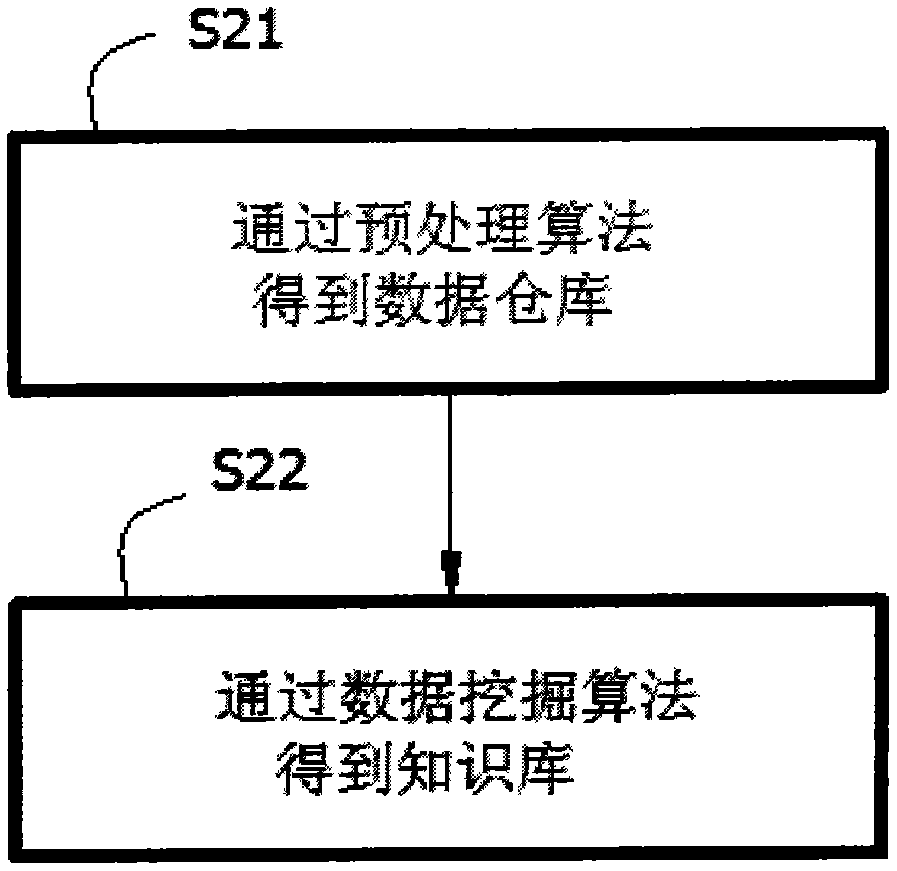
Predicting method for user behavior in e-commerce
InactiveCN104063429AEffective guidanceCommerceSpecial data processing applicationsPredictive methodsData source
The invention discloses a predicting method for user behavior in e-commerce, and belongs to the technical fields of e-commerce and data processing. The predicting method comprises the following steps of S1, recording all behaviors of a user in an e-commerce system to a database of the e-commerce system; S2, carrying out data mining processing on primary data in the database so as to obtain a knowledge base; S3, building an MVC framework according to the knowledge base, according to the pruning algorithm, obtaining a success rate sequence from high to low of a next link by a Controller, removing the links with lower success rates, putting the links with higher success rates at the most marked position of a page, and outputting a corresponding View; S4, after a user click a link, selecting a corresponding score in a game tree by the Controller according to the selection of the user, and storing the score in a data source database and the database of the e-commerce system. Next possible selection of the user can be predicted through the pruning algorithm based on MVC probability, and further, e-commerce purchasing instructions can be provided for the e-commerce and the user.
Owner:深圳德锟保税电子商务有限公司
Reverse donut model
ActiveUS20090241081A1Preserve essential performance characteristicEasy to implementComputer aided designSoftware simulation/interpretation/emulationParallel computingSingle level
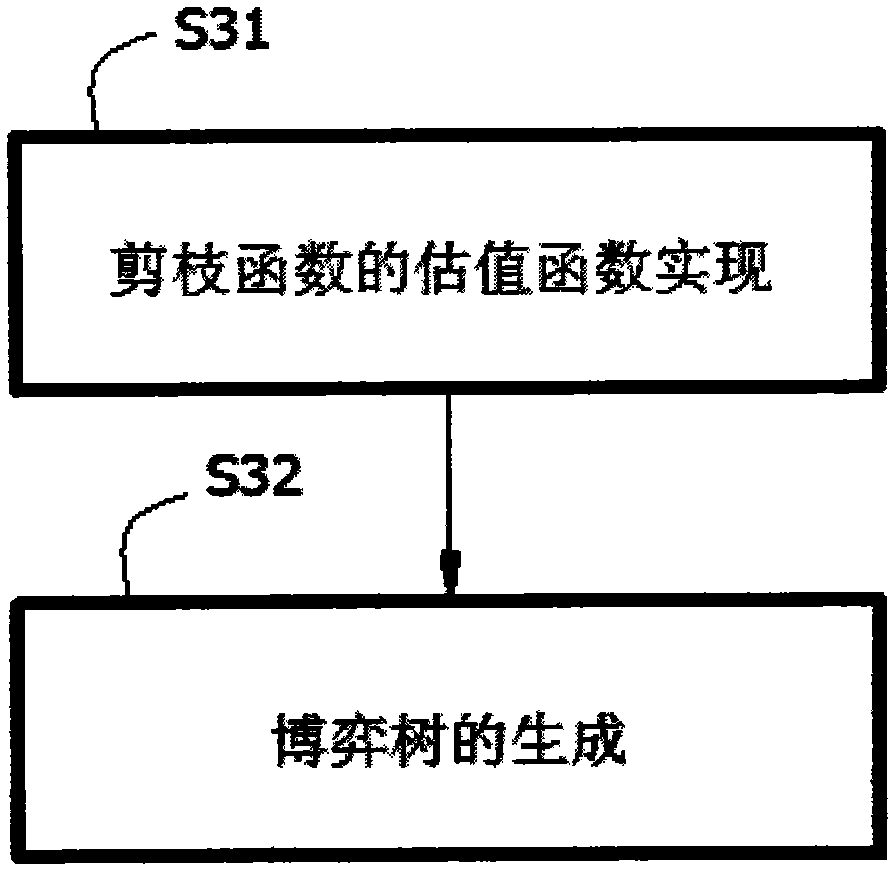
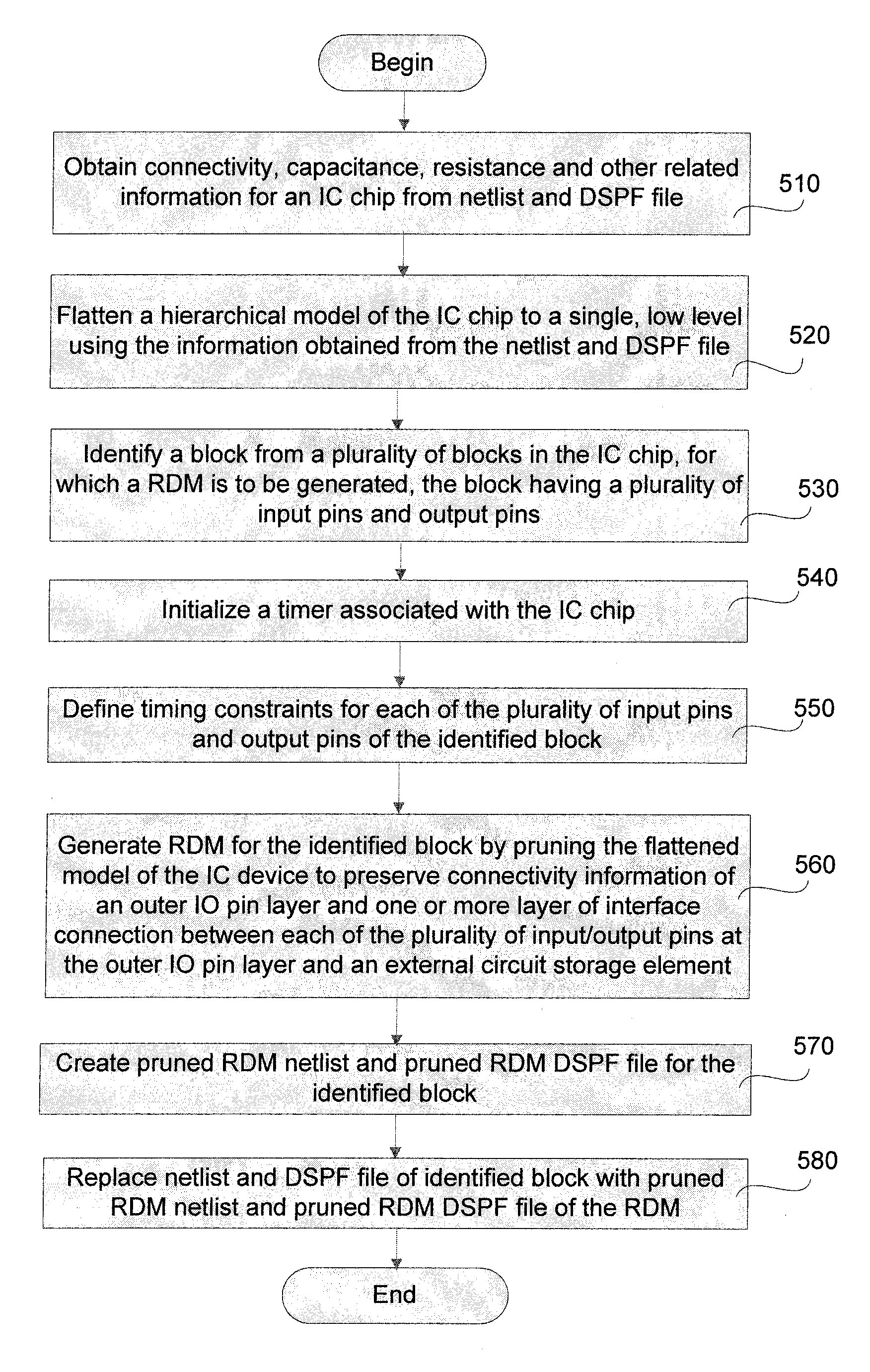
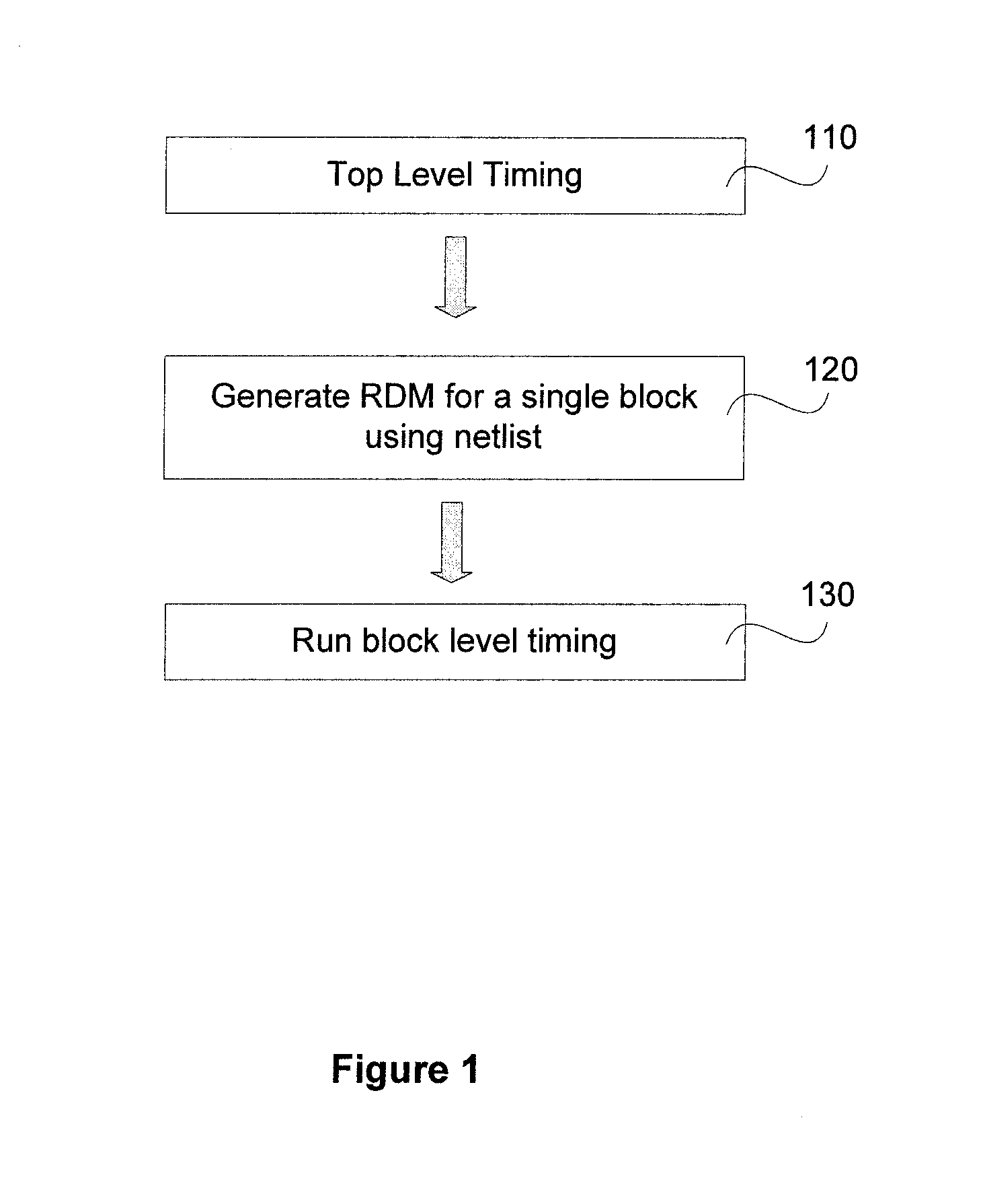
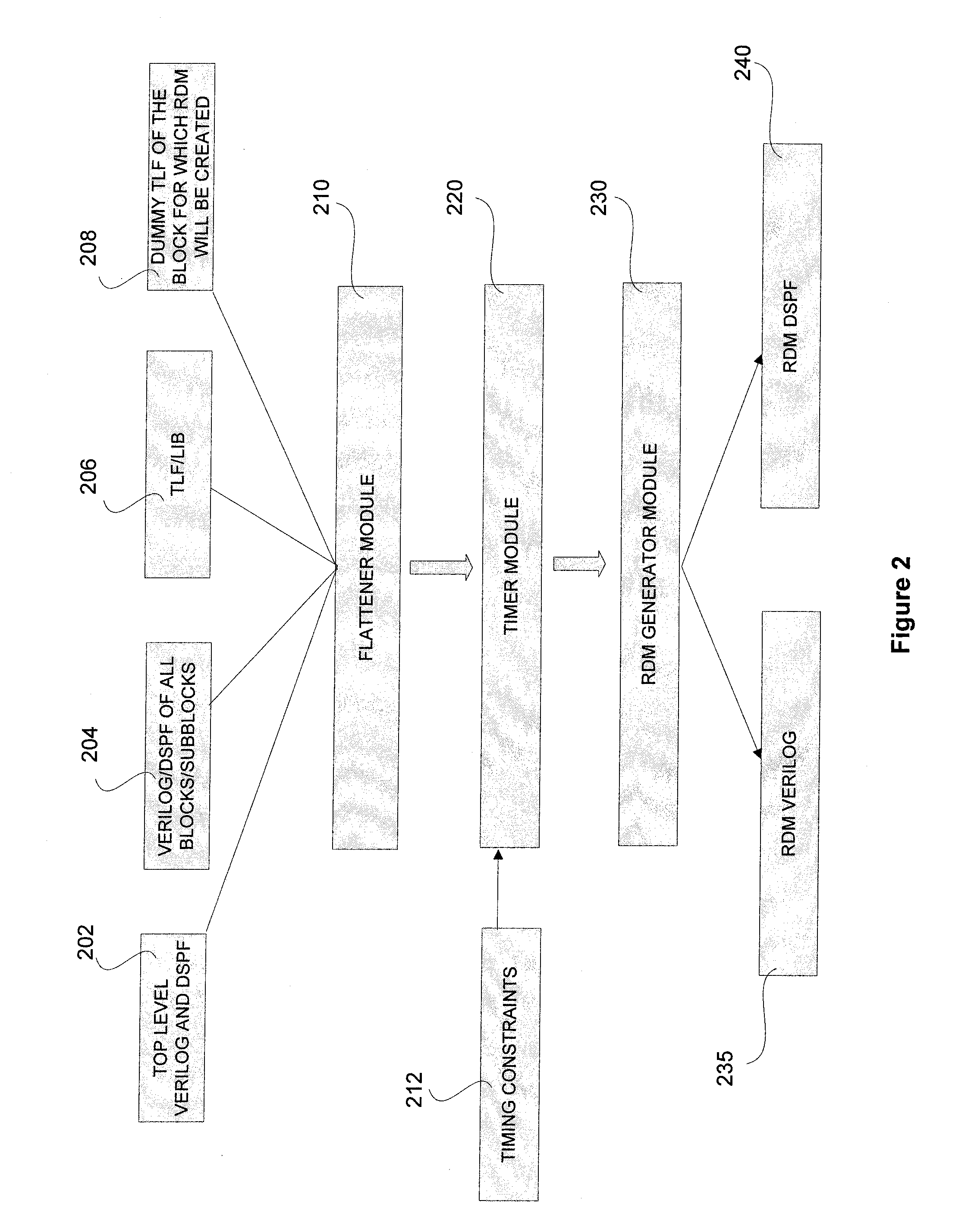
A pruning algorithm for generating a reverse donut model (RDM) for running timing analysis for a block in an IC includes logic to reduce a hierarchical model of the IC to a single level flat model. A block from a plurality of blocks that make up the IC is identified from the single level flat model of the IC. The pruning algorithm is further used to initialize a timer and to define timing constraints associated with each of a plurality of input and output pins associated with the identified block. A RDM for the identified block is generated by identifying and including connectivity information associated with a plurality of input and output pins in an outer boundary of the identified block and at least one layer of interface connection between each of the plurality of input and output pins in the outer layer of the identified block and one or more circuit elements external to the identified block in the IC interfacing with each of the plurality of input and output pins in the identified block. The generated RDM acts as a blackbox for the identified block and is used in place of the identified block for running the timing analysis.
Owner:ORACLE INT CORP
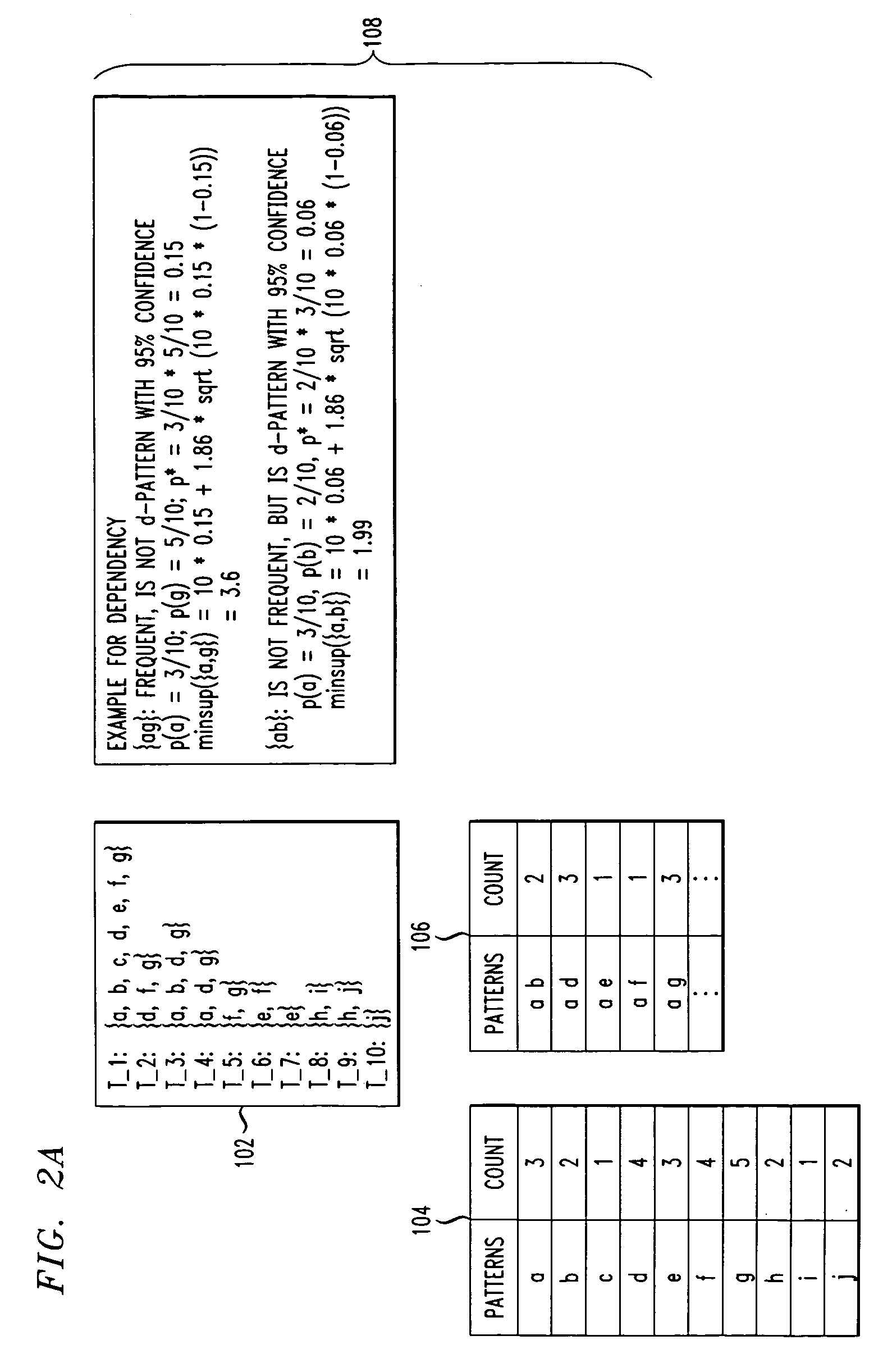
Systems and methods for discovering fully dependent patterns
InactiveUS6990486B2Efficient and effectiveData processing applicationsDigital data information retrievalEfficient algorithmLinear algorithm
A new form of pattern referred to as a fully dependent pattern or d-pattern is provided. The d-pattern captures dependence among a set of items based on a dependency test. An efficient algorithm is provided for discovering all d-patterns in data. Specifically, a linear algorithm is provided for testing whether a pattern is an d-pattern. Further, a pruning algorithm is provided that prunes the search space effectively. Still further, a level-wise algorithm for mining d-patterns is provided.
Owner:IBM CORP
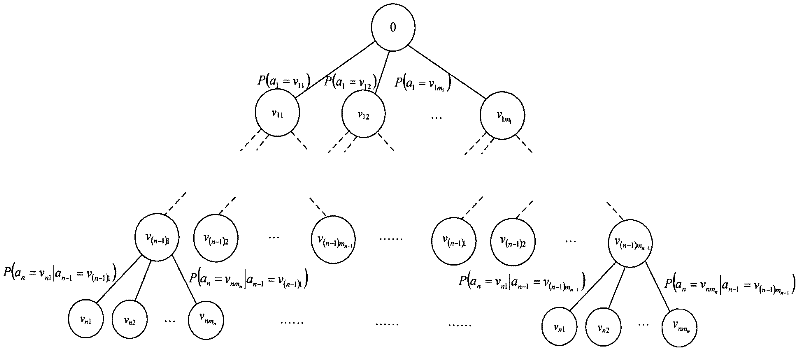
Automatic entity basic information generation system and method based on Markov model
ActiveCN102646137AGuaranteed reasonablenessThe data result is reasonableSpecial data processing applicationsAlgorithmDecision taking
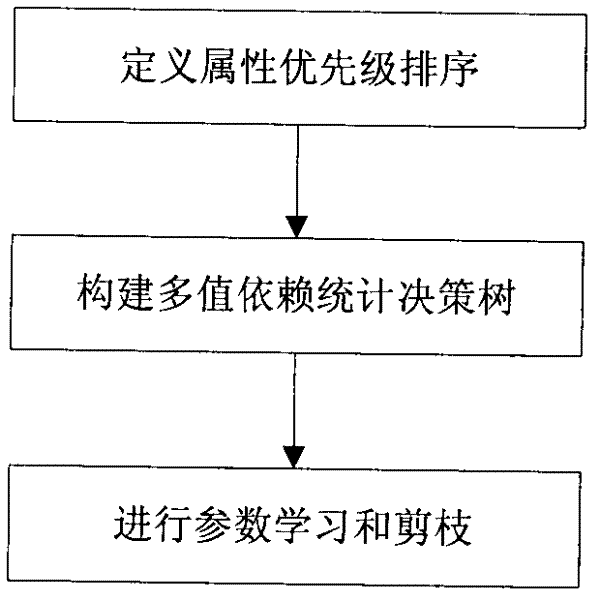
The invention provides an automatic entity basic information generation system and method based on a Markov model, which are suitable for generating basic data of a test and trial scene of an information system. Entity attribute data relating to the system and the method has an enumeration type characteristic. The method comprises a step of defining an attribute priority sequence, a step of constructing a multiple-valued depended statistical decision tree and a step of carrying out parameter study and pruning algorithm. The system comprises a device for defining attribute priority sequence, a device for constructing the multiple-valued depended statistical decision tree and a device for carrying out the parameter study and the pruning algorithm.
Owner:NO 63 RES INST HEADQUARTERS OF THE GENERAL STAFF PLA
Foundation surveillance radar multi-target tracking method based on radial velocity information
ActiveCN108303684AAchieve inhibitionImprove object tracking performanceRadio wave reradiation/reflectionNODALHypothesis
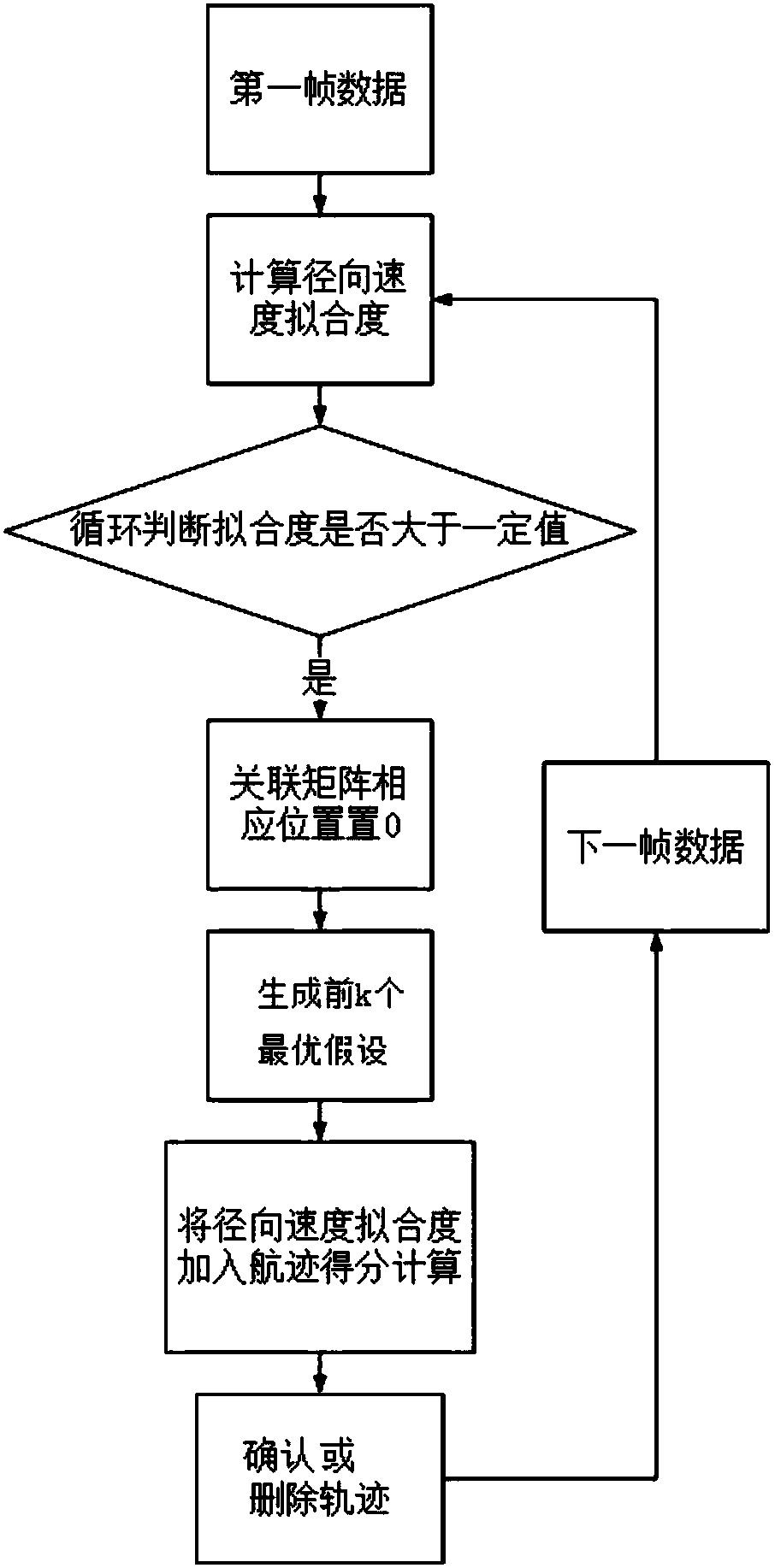
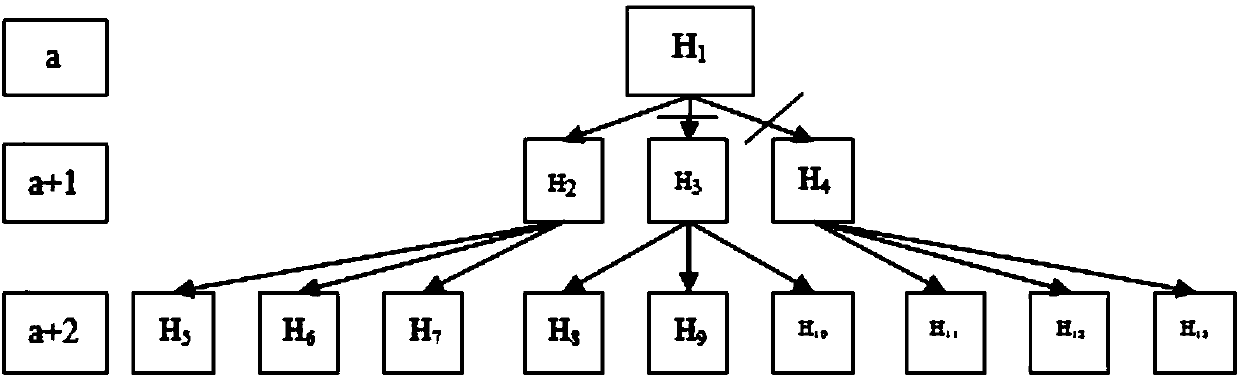
The invention discloses a foundation surveillance radar multi-target tracking method based on radial velocity information. The foundation surveillance radar multi-target tracking method based on radial velocity information includes the following steps: S1, calculating the track fitting degree by means of radial velocity; S2, generating hypothesis by means of the radial velocity fitting degree andthe positional information; S3, modifying the track scores of the first k optimal hypothesis by means of the radial velocity fitting degree, and obtaining the hypothesis probability pj of each hypothesis in the first k optimal hypothesis; S4, establishing a hypothesis tree according to the first k optimal hypothesis, based on the principle of selecting the root node in which the hypothesis probability pj is, performing pruning on the hypothesis tree by means of an N pruning algorithm, and leaving the optimal hypothesis to be determined; and S5, according to a preset determination threshold T1and a preset delete threshold T2, comparing the track scores of the optimal hypothesis to be determined in the step S4 with the determination threshold T1 and the delete threshold T2, so as to determine the track or delete the track. The foundation surveillance radar multi-target tracking method based on radial velocity information can realize inhibition of false tracks and false alarm in a strongclutter and high false alarm environment, and can greatly improve the radar multi-target tracking effect.
Owner:长沙深之瞳信息科技有限公司
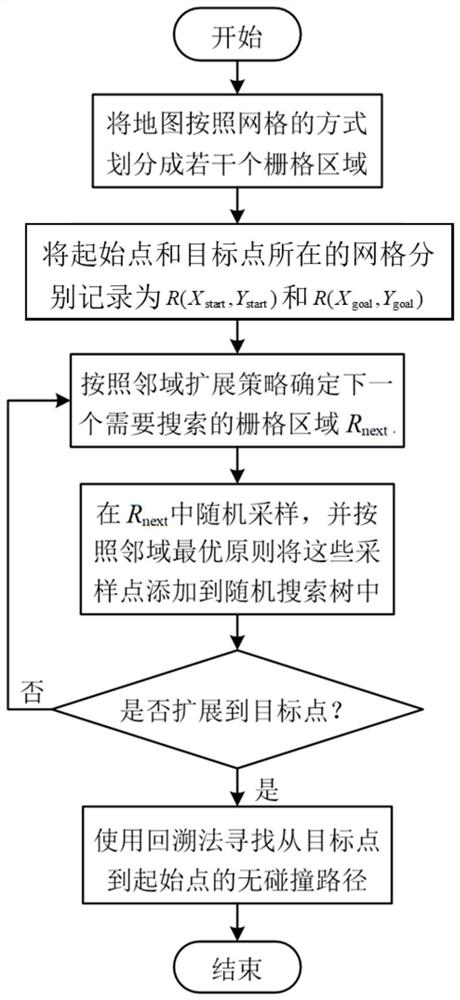
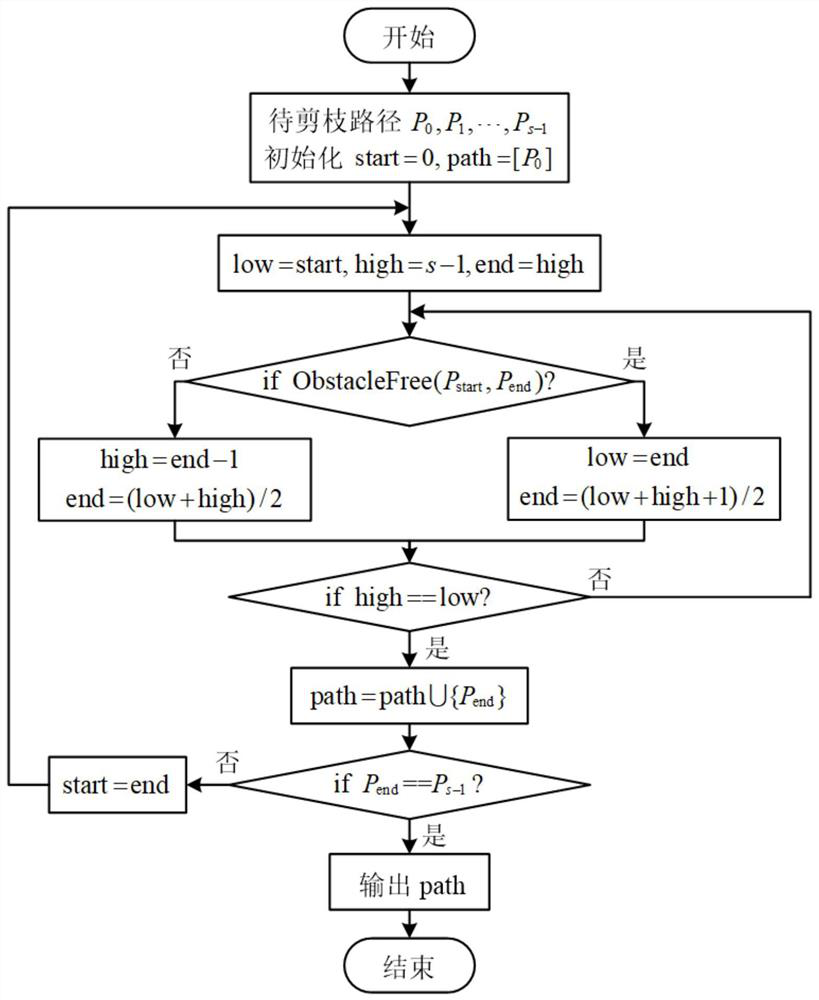
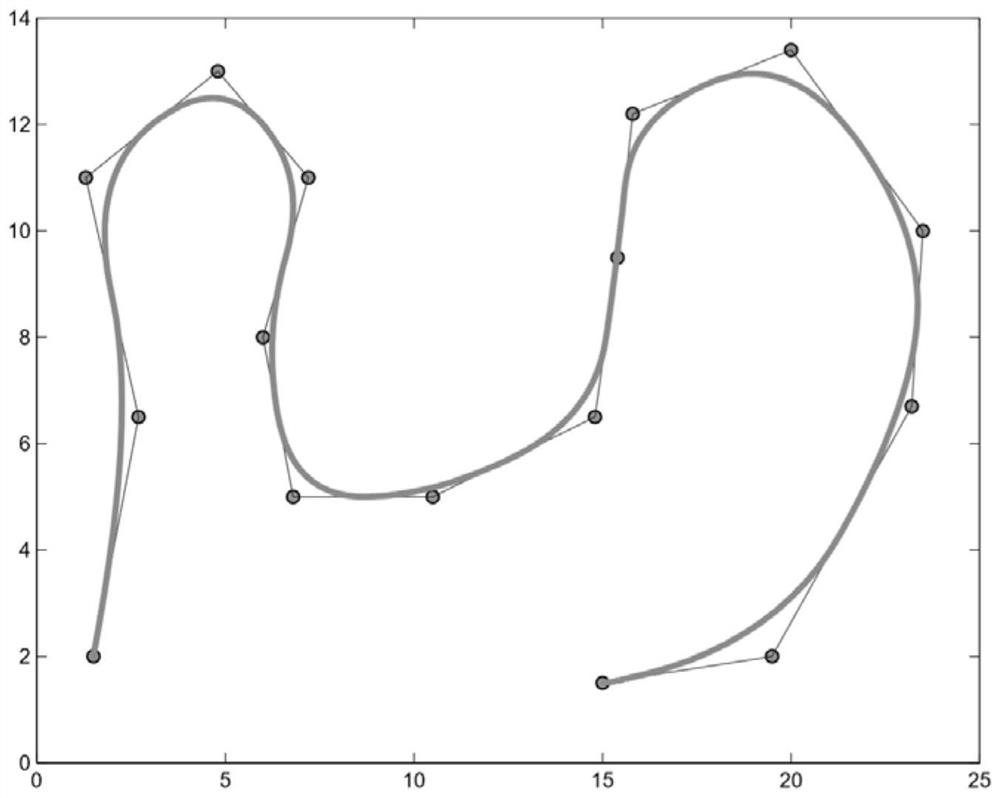
Mobile robot path planning method based on improved RRT algorithm
ActiveCN111610786AImprove sampling efficiencyAvoid Excessive Search ProblemsInternal combustion piston enginesPosition/course control in two dimensionsSimulationMobile robots path planning
The invention provides a mobile robot path planning method based on an improved RRT algorithm in an indoor environment. A high-precision grid map of a robot working environment is established; map segmentation is carried out, and then a next grid needing to be searched is determined by adopting a neighborhood extension strategy; the type of a search grid and the number of effective sampling pointsare determined through a random sampling experiment, then the effective sampling points are added into a random tree according to a neighborhood optimal principle, state updating is conducted on thegrid based on a memory strategy, and finally smoothing processing is conducted on an obtained planning path through a pruning algorithm and a Bezier curve. Due to introduction of map segmentation andobstacle edge detection ideas, the sampling efficiency of an RRT algorithm in complex maps such as narrow channels is improved; due to introduction of a memory mechanism and a neighborhood extension strategy, the planning success rate of the algorithm in a complex environment is increased; a father node is selected according to the neighborhood optimal mode, and problems that the algorithm randomness is high, and the path is not optimal are solved.
Owner:SHENYANG LIGONG UNIV
Multi-dimensional electric energy meter on-site state test method based on decision-making tree mass
InactiveCN108733966AAchieve depthImplement miningSpecial data processing applicationsOptimal decisionCollection system
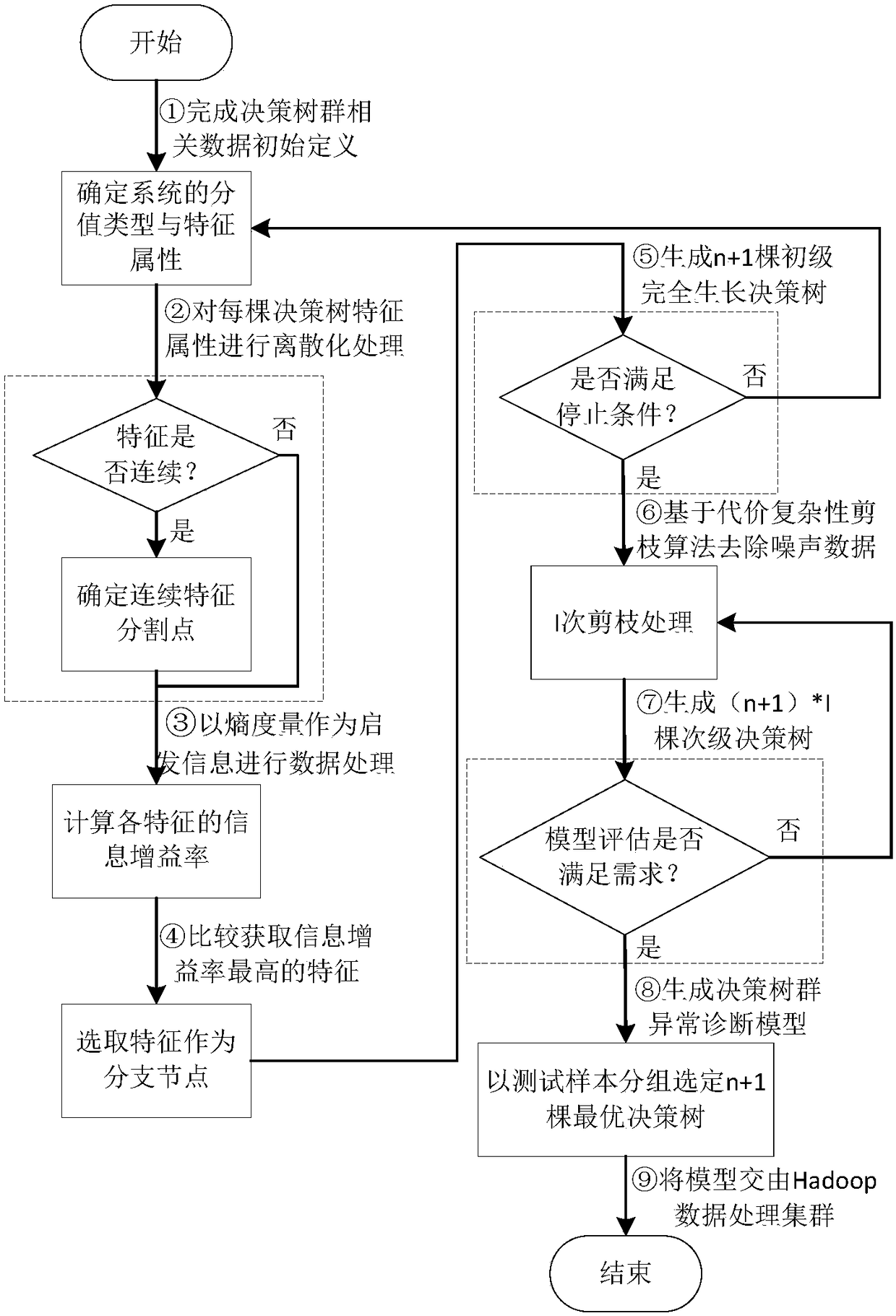
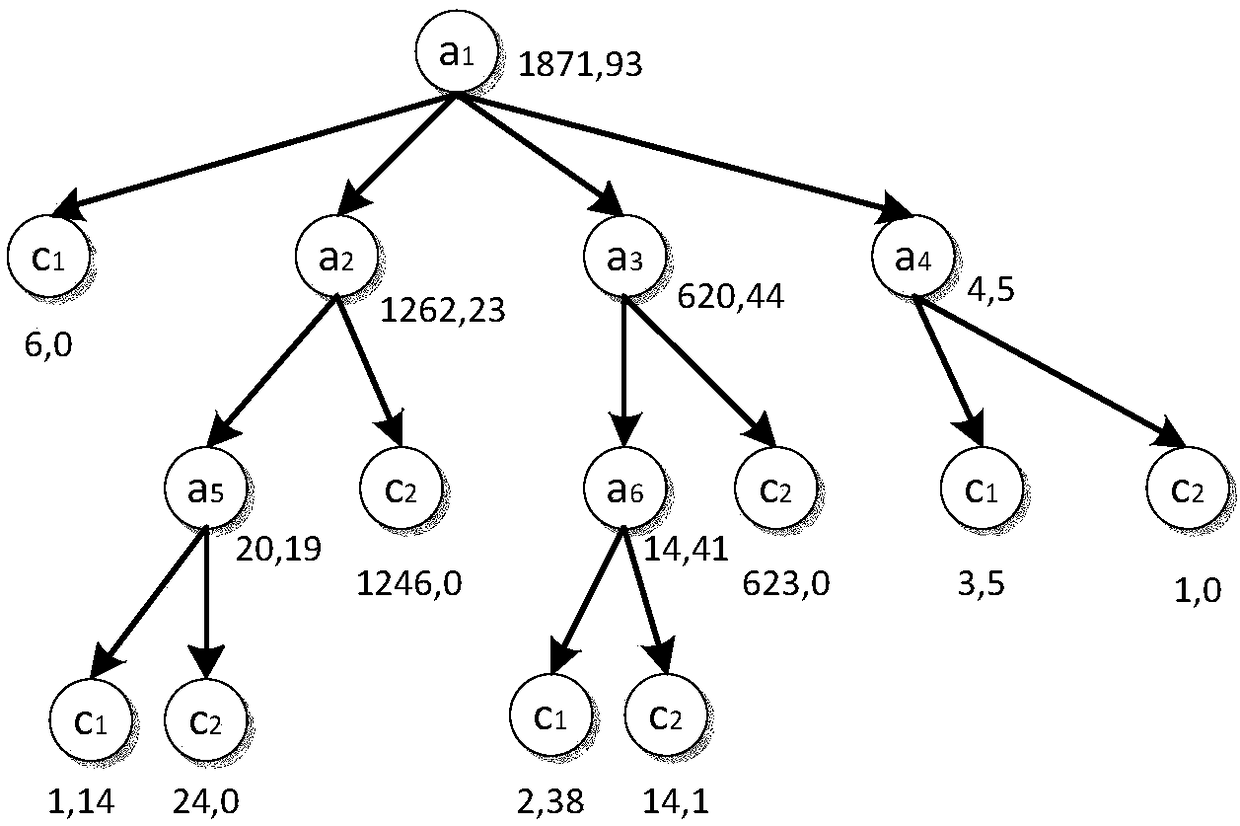
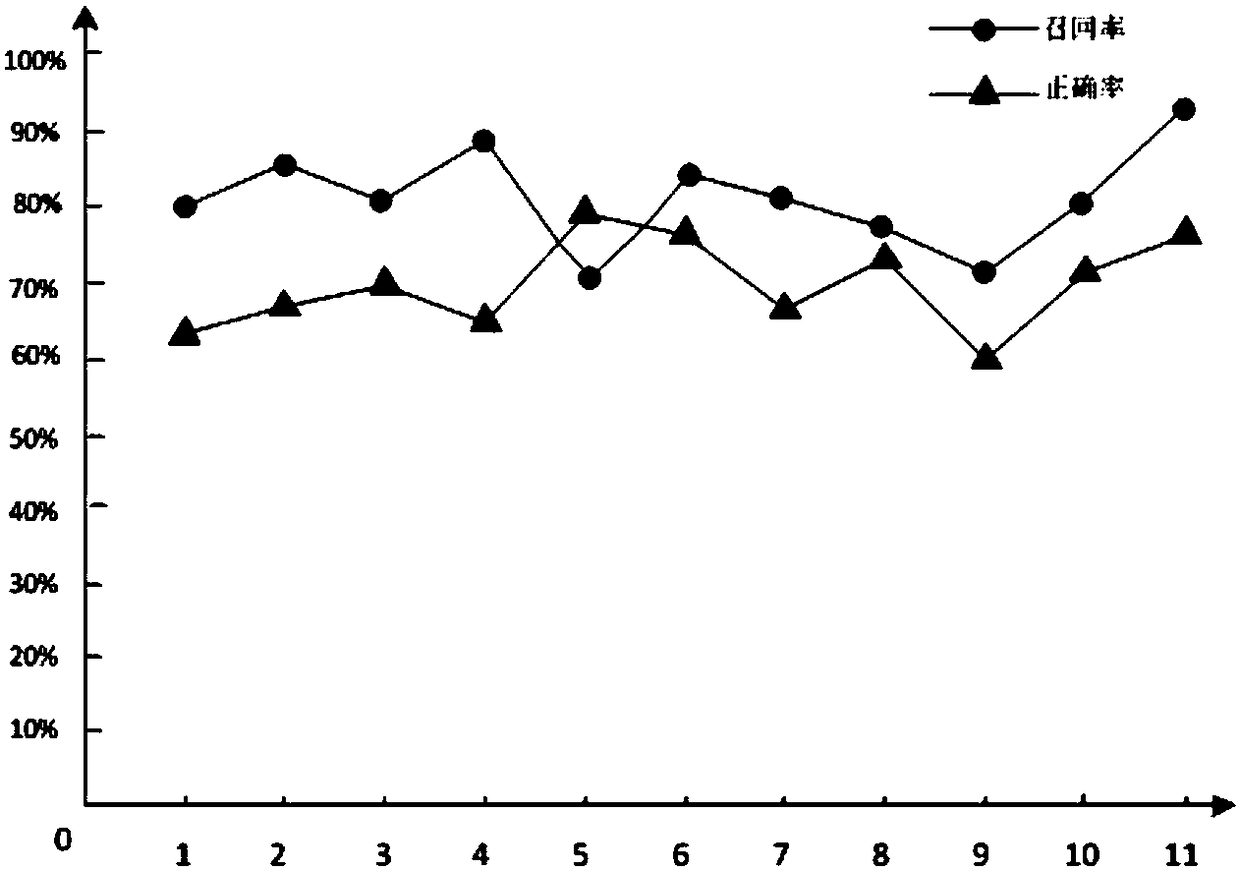
The invention discloses a multi-dimensional electric energy meter on-site state test method based on a decision-making tree mass. The method comprises the following steps of building a decision-makingtree by using collected data related to an electric energy meter and provided by an electricity information collection system; forming next-level branches through classifying each decision-making tree; generating the completely grown primary decision-making tree; pruning and optimizing on the primary decision-making tree based on a cost complexity pruning algorithm; using an independent test setto assess the accuracy of the primary decision-making tree after pruning and optimizing; selecting the optimal decision-making tree from each set of secondary decision-making trees, and forming a decision-making tree abnormity diagnostic model by all the optimal decision-making trees, wherein a judgment result wins in a voting manner; and transmitting an operational rule of the decision-making tree abnormity diagnostic model to an electricity information collection system Hadoop big data processing cluster, thus implementing abnormity detection on the abnormal running state of the running electric energy meter.
Owner:STATE GRID CHONGQING ELECTRIC POWER +2
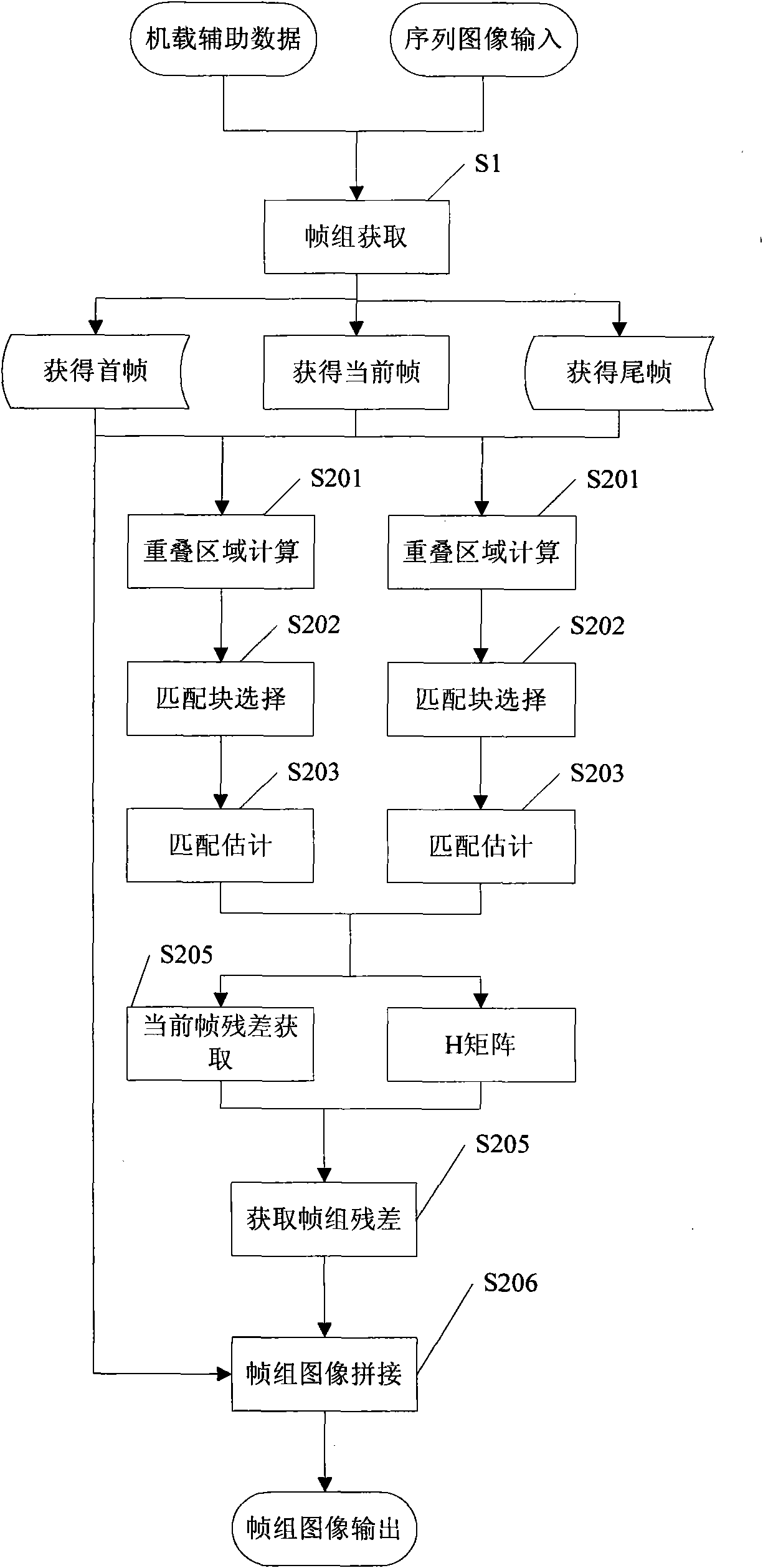
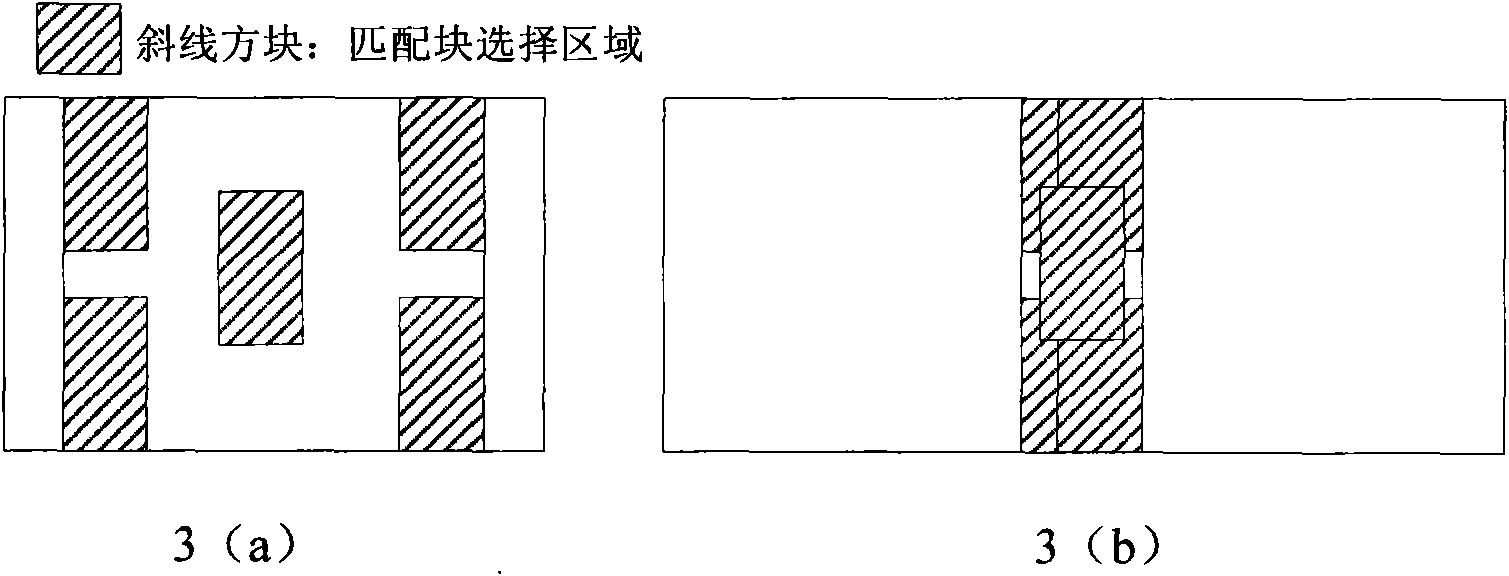
Method suitable for compressing sequence images of unmanned aerial vehicle
InactiveCN101594533AHigh precisionImprove coding efficiencyTelevision system detailsColor television detailsGlobal optimizationAncillary data
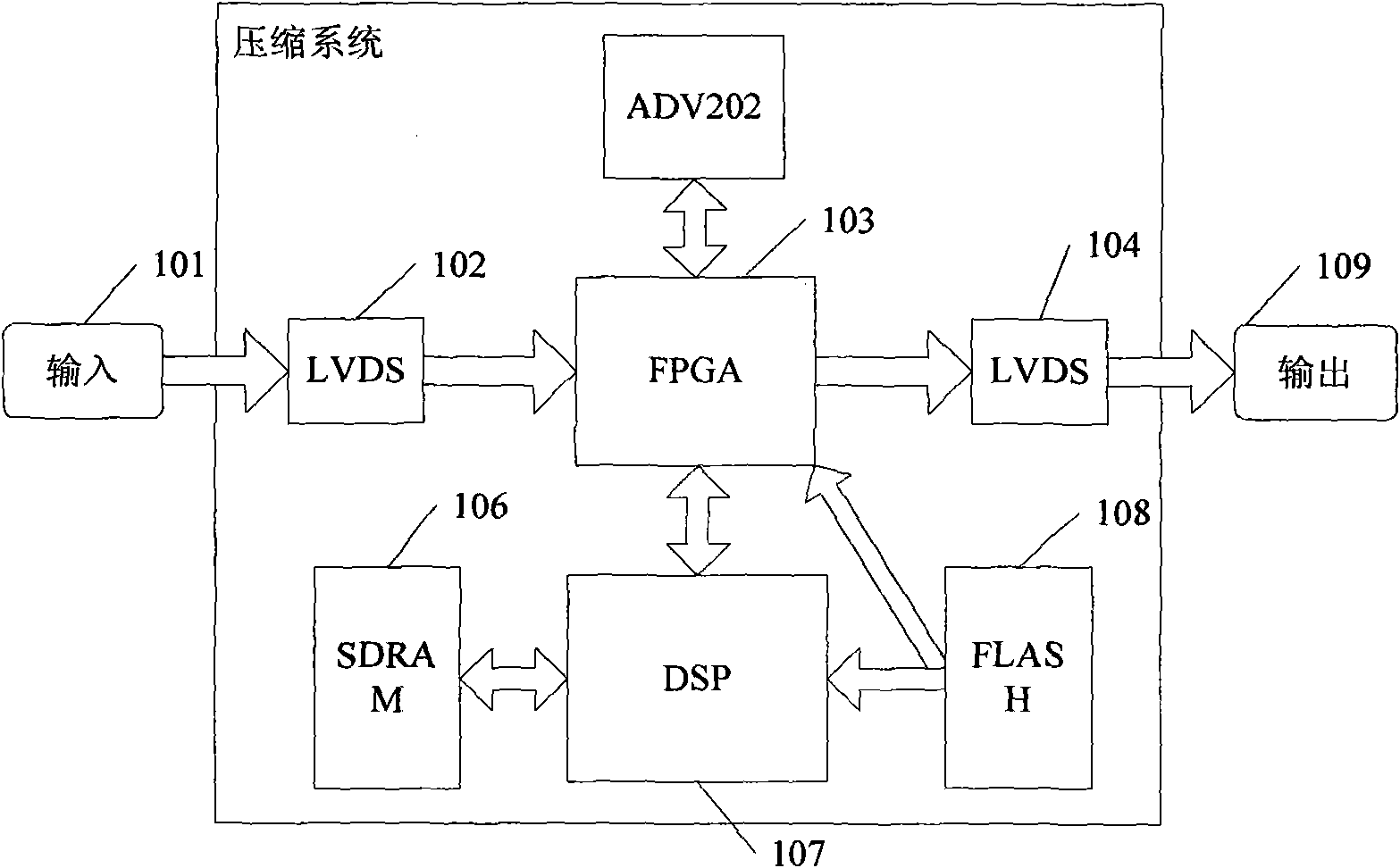
The invention discloses a method suitable for compressing sequence images of an unmanned aerial vehicle. The method comprises the following steps: according to airborne auxiliary data, carrying out intelligent dynamic coding frame group division of the sequence images of the unmanned aerial vehicle; within a frame group, carrying out high-precision quick motion estimation of the first frame and the last frame to the current frame, thereby acquiring a number pair matching point; according to corresponding matching relation, obtaining projection transformation matrixes of the first frame and the last frame to the current frame so as to acquire a forecast image and residual error; combining residual error images of the first frame and the other frames of the same frame group into a singe image; and compressing the singe image by JPEG2000 to acquire a high-performance compression result by a global optimization pruning algorithm. The method takes into account the characteristics of the sequence images of the unmanned aerial vehicle and makes full use of the characteristics of airborne auxiliary information and the JPEG2000 compression algorithm; therefore, the method has the characteristics of low algorithm complexity, good compression performance, strictly controlled compression code rate, easily realized hardware, and the like.
Owner:HUAZHONG UNIV OF SCI & TECH
Database journaling in a multi-node environment
InactiveUS7979399B2Digital data processing detailsDatabase distribution/replicationFinancial transactionData mining
Owner:INT BUSINESS MASCH CORP
Protocol keyword identification method based on lexicographic tree pruning search
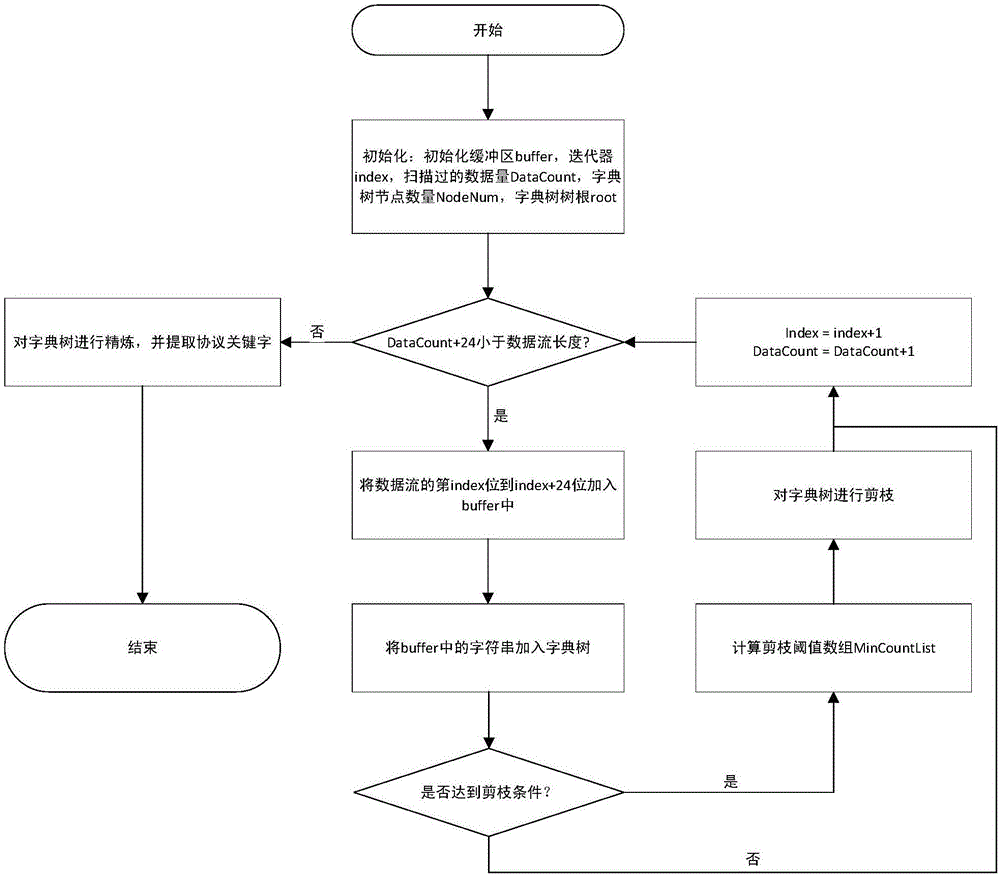
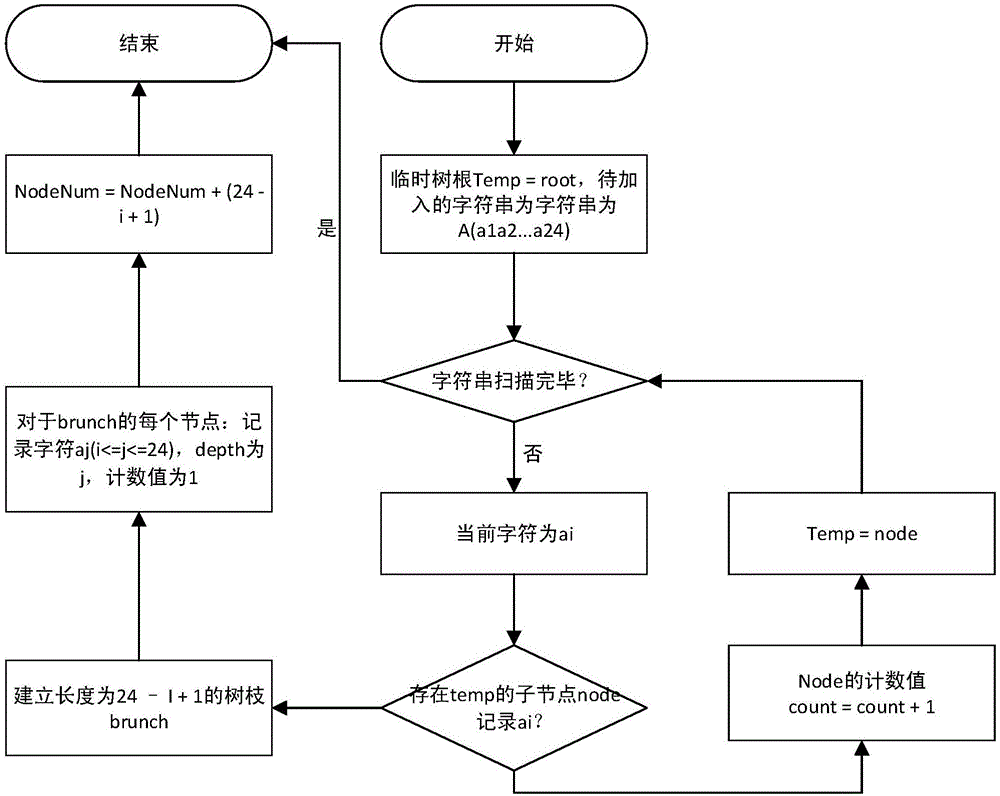
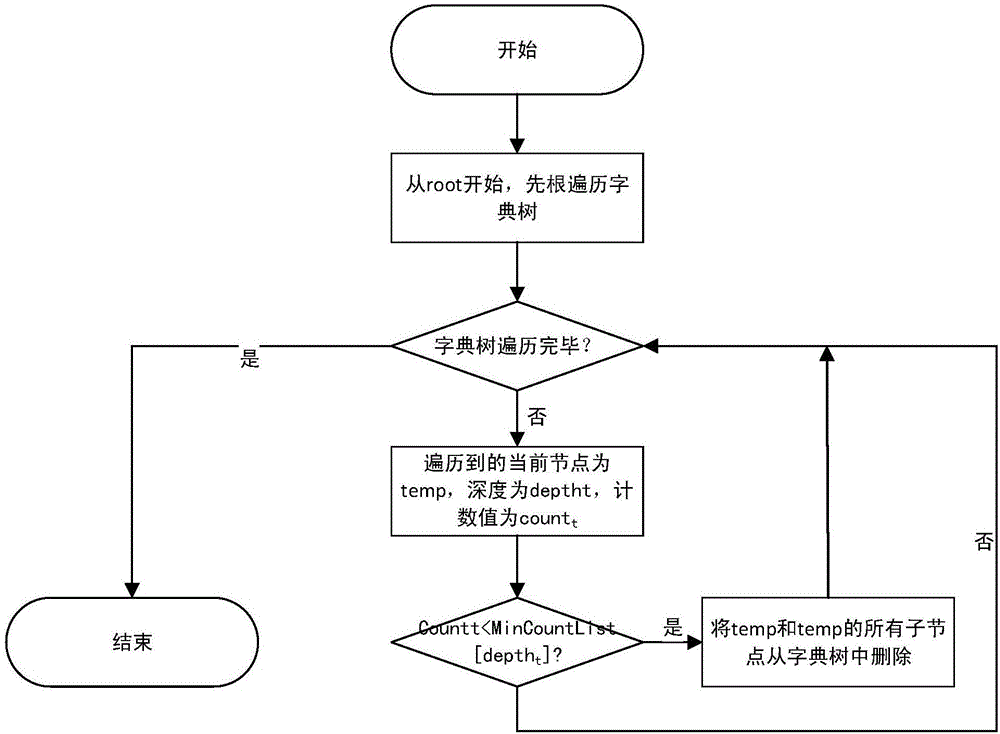
ActiveCN106713273AImprove space utilization efficiencySolve the defect of excessive storage spaceTransmissionSpecial data processing applicationsGeneration processData stream
The invention discloses a protocol keyword identification method based on lexicographic tree pruning search. The method comprises: firstly acquiring a to-be-identified data flow, saving data of the data flow into a circular queue buffer, screening character strings in the buffer, and generating branches of a lexicographic tree; in each lexicographic tree branch generation process, computing a pruning threshold of each node when pruning conditions are met, pruning the lexicographic tree, and finally acquiring a purify rate; and according to the purify rate, obtaining keywords, thereby completing keyword identification. According to the protocol keyword identification method based on the lexicographic tree pruning search, by importing a lexicographic tree pruning algorithm, a defect that the used storage space is oversize when protocol keyword identification is performed by using the traditional lexicographic tree algorithm is solved, and an advantage of improving the space utilization efficiency is achieved; and the use value is better.
Owner:CHINA ACADEMY OF SPACE TECHNOLOGY
Resource-efficient media streaming to heterogeneous clients
InactiveUS20070130359A1Multiple digital computer combinationsSecuring communicationQuality of serviceTransmission channel
A resource-efficient live streaming system includes a broadcaster and a streaming server. The broadcaster receives a live feed and broadcasts a media stream to the streaming server containing several descriptions of the live feed along with control information. The broadcaster includes a stream thinner that implements a pruning algorithm. If descriptions from different streams are similar enough, one or more of them may be discarded without penalizing the quality of service perceived by the receivers. The streaming server assembles compressed data units into streams according to the control information from the broadcaster. The streaming server may also gather client feedback in order to estimate the status of the transmission channels and forwards the information to the broadcaster. The streaming server builds and streams media information to clients according to user preferences and receiver capabilities.
Owner:TWITTER INC
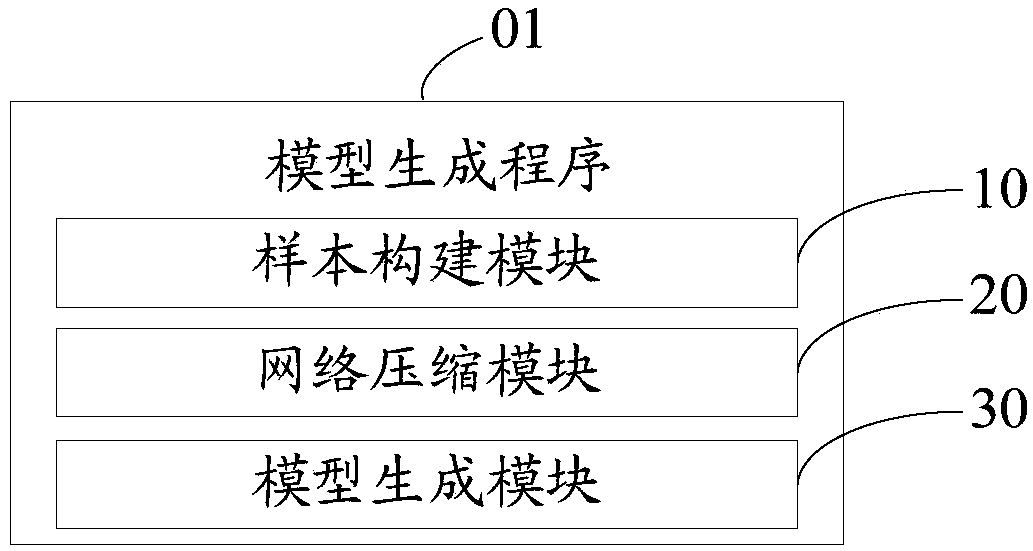
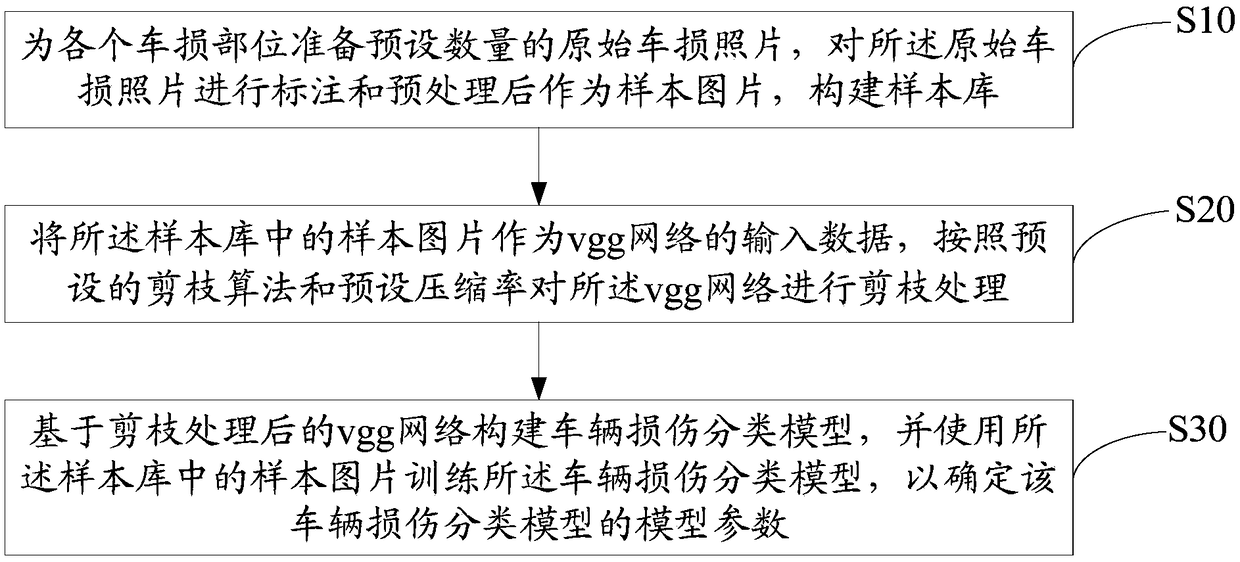
Device and method for generating vehicle damage classification model, and computer readable storage medium
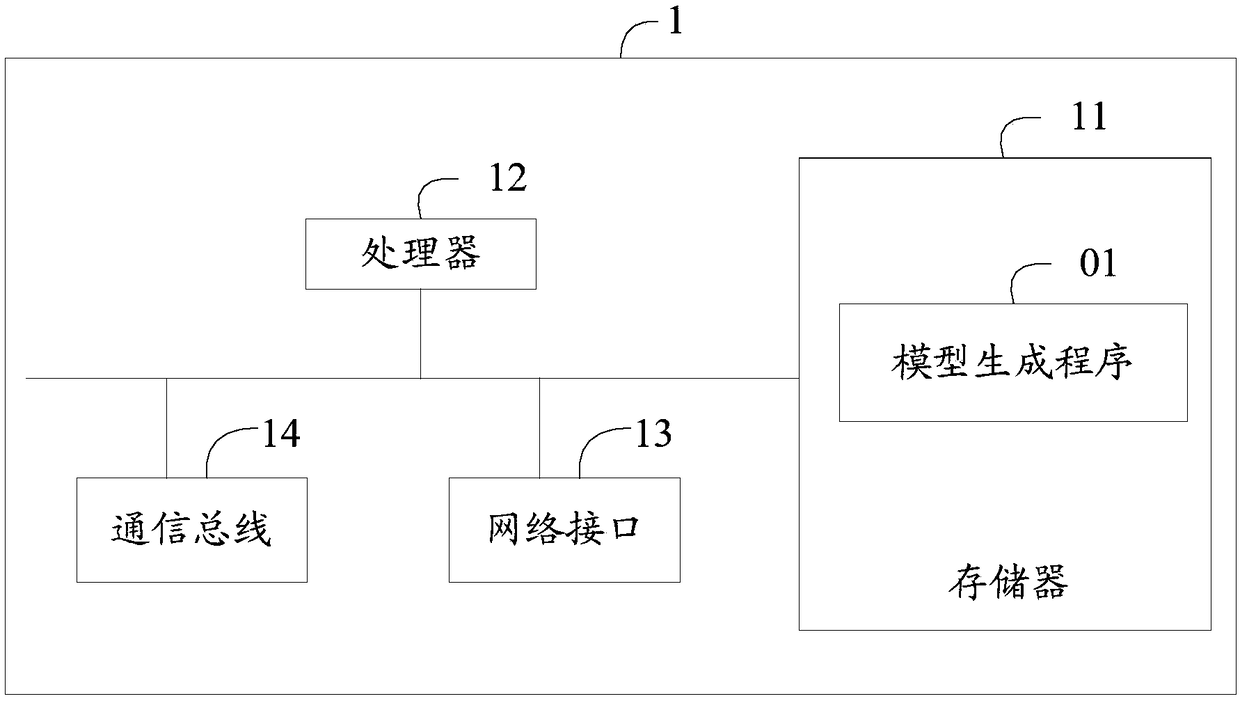
InactiveCN108764046ASmall footprintFinanceCharacter and pattern recognitionAlgorithmModel parameters
The invention discloses a device for generating a vehicle damage classification model. The device comprises a memory and a processor; the memory stores a model generating program which can run in theprocessor. When being executed by the processor, the program implements the following steps of preparing an original vehicle damage photo for each vehicle damage part, and constructing a sample library after labeling and preprocessing are carried out; by taking sample pictures in the sample library as input data of a vgg network, performing pruning processing on the vgg network according to a preset pruning algorithm and a preset compression rate; and building the vehicle damage classification model based on the pruned vgg network, and training the vehicle damage classification model by usingthe sample pictures in the sample library to determine model parameters of the model. The invention furthermore provides a method for generating the vehicle damage classification model and a computerreadable storage medium. The technical problem that vehicle damage assessment cannot be carried out in a mobile device through a convolutional neural network model in the prior art is solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Oil production data frequent pattern mining method based on weak wildcard
InactiveCN106095930ARich meaningFully portrayedData miningOther databases retrievalFiltrationTime complexity
The invention discloses an oil production data frequent pattern mining method based on weak wildcard, and relates to the field of data mining. The oil production data frequent pattern mining method based on the weak wildcard comprises the steps that 1, oil field daily fluid production time series data is converted into a coding sequence; 2, the coding sequence is mined to obtain different types of frequent sequence patterns, and an oil well is comprehensively depicted from various angles. The method has the advantages that the mining problem of three frequent sequence patterns is defined, the different types of frequent patterns can be mined from actual oil well production data, and the oil well is comprehensively depicted from the different angles; an algorithm is simple and efficient, a pruning algorithm is achieved, the time complexity is low, and the method is conveniently achieved in real time; a pattern filter technique is proposed, the different types of frequent patterns such as the powerful pattern, the special pattern and the popular pattern can be obtained through filtration for the different requirements; the method can be widely applied to various time series data.
Owner:SOUTHWEST PETROLEUM UNIV
Coal ash fusion temperature forecasting method based on construction-pruning mixed optimizing RBF (Radial Basis Function) network
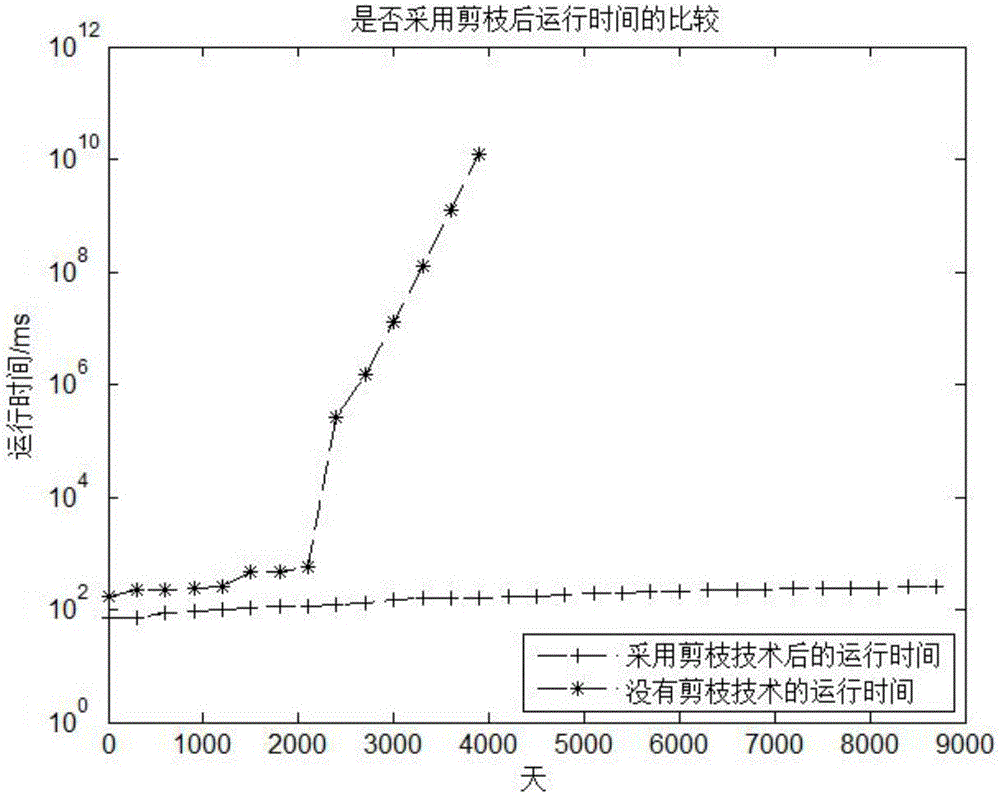
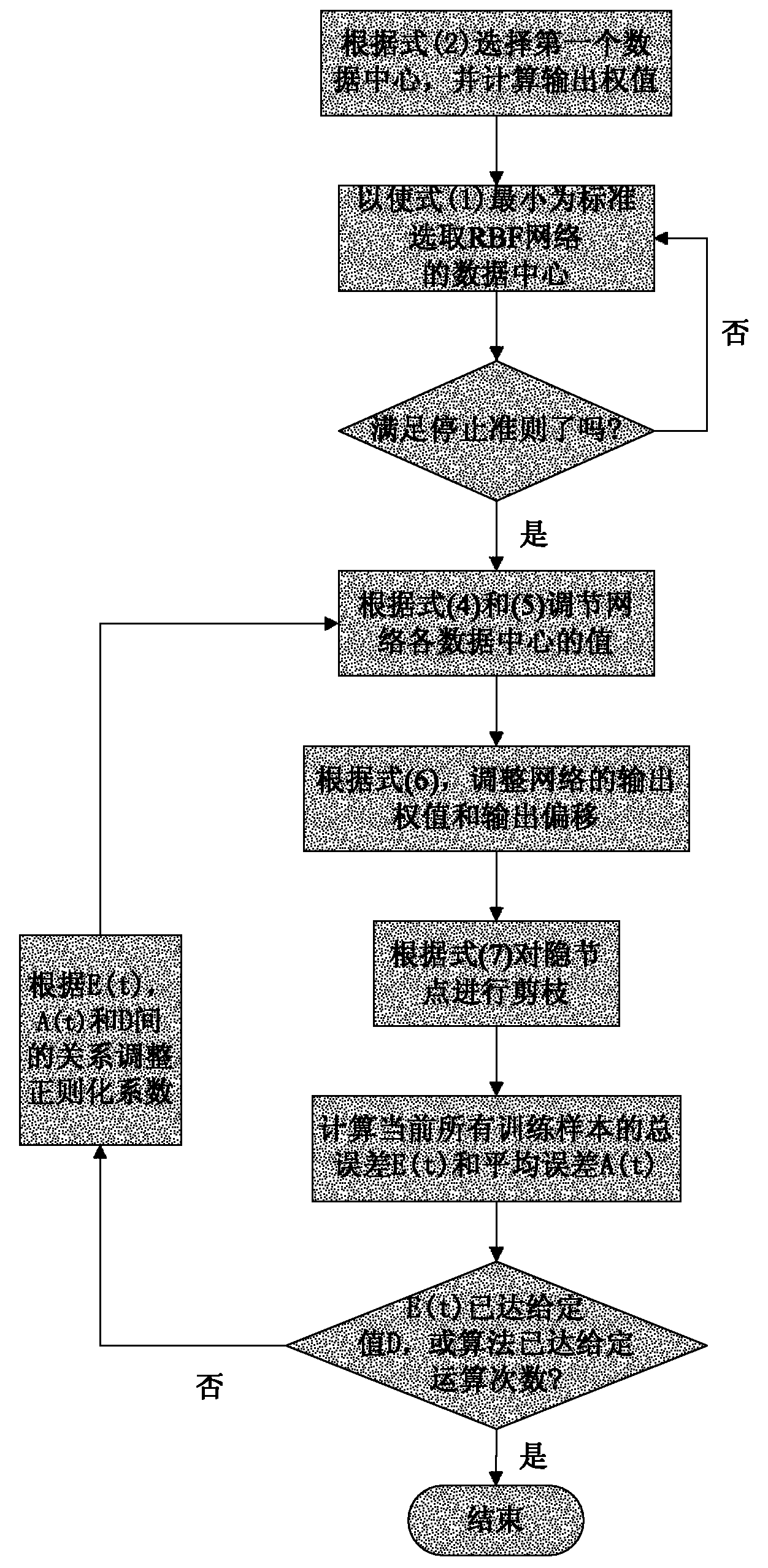
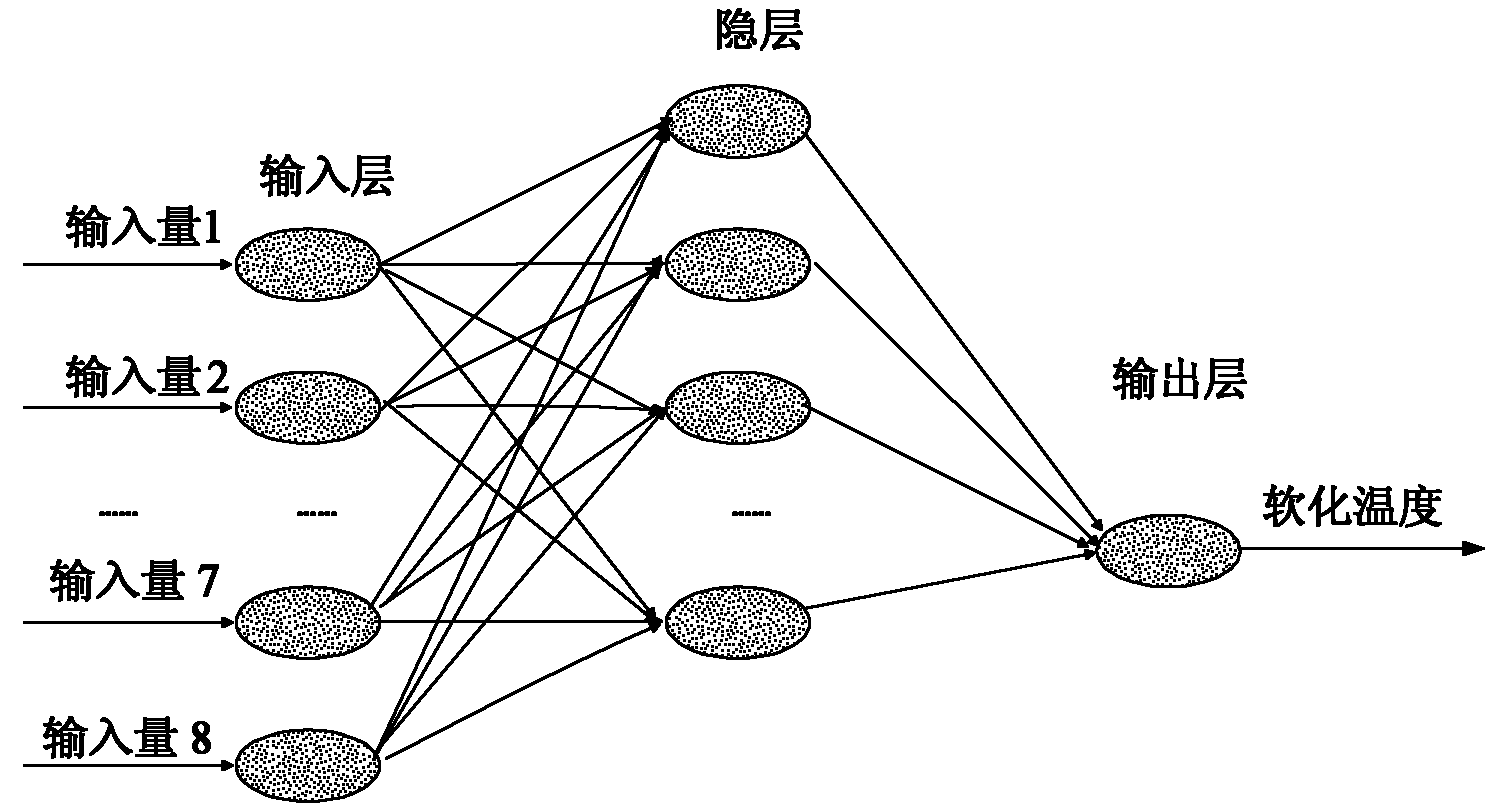
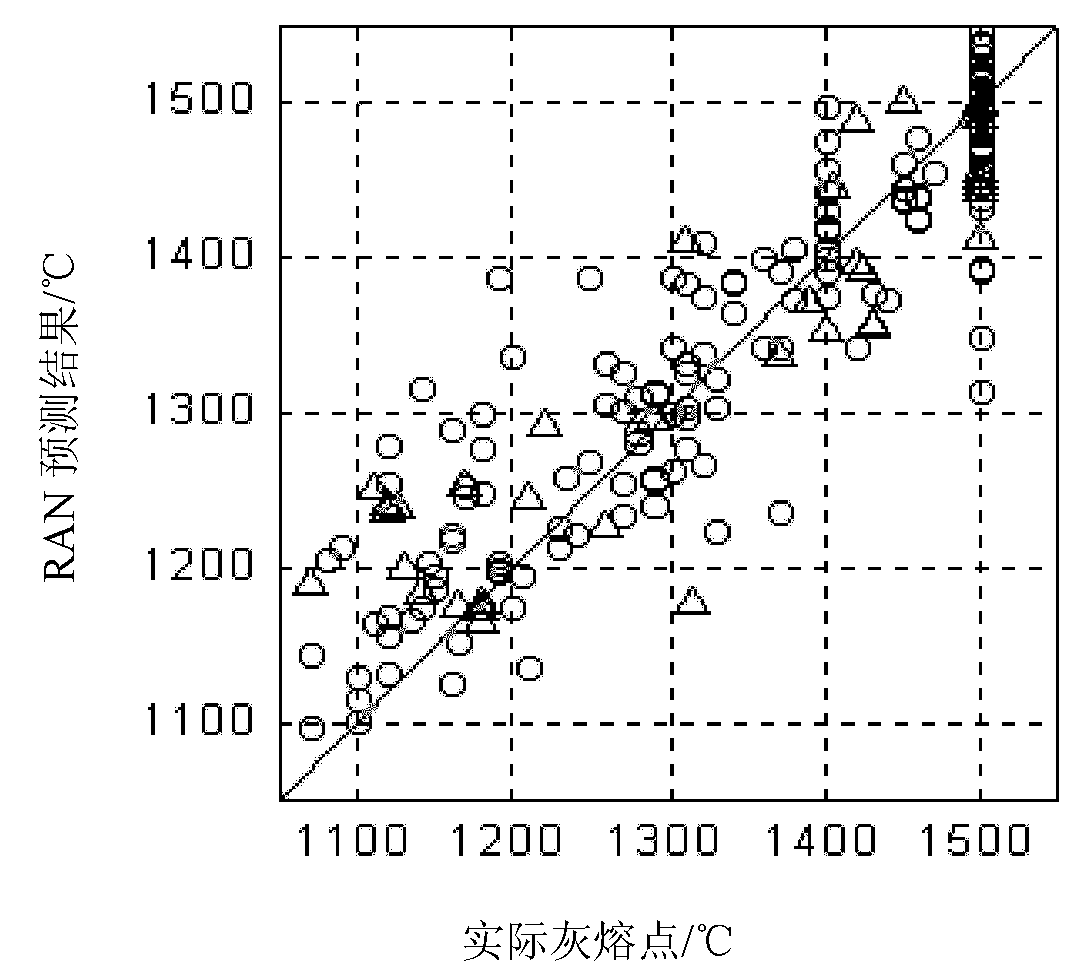
InactiveCN101968832ADynamically adjust the number of hidden nodesSmall structureSpecial data processing applicationsNeural learning methodsData centerCoal
The invention discloses a coal ash fusion temperature forecasting method based on a construction-pruning mixed optimizing RBF (Radial Basis Function) network, which is characterized by comprising the following two stages of crude regulation and fine regulation: the crude regulation stage comprises the steps of dynamically increasing the number of hidden nodes according to a principle of enabling an energy function to be minimum, selecting corresponding sample input as a data center and stopping till the number of the hidden nodes meets a stopping criterion; the fine regulation stage comprisesthe steps of further regulating the structure and the parameters of the RBF network, which are obtained through the crude regulation by using a Gaussian regularization method, establishing the corresponding construction-pruning mixed optimizing RBF network on the basis of the chemical constituents of coal ash, and forecasting coal ash fusion temperature through the construction-pruning mixed optimizing RBF network. A construction-pruning mixed optimizing algorithm (CPHM) effectively integrates the advantages of a construction algorithm and a pruning algorithm, can not only dynamically regulate the number of the hidden nodes of the RBF network, but also enable the data center of the RBF network to change in a self-adaption way; and in addition, the invention has the advantages of smaller structure, better generalization capability and higher robustness.
Owner:SOUTHEAST UNIV
Compression method and system for deep convolutional neural network
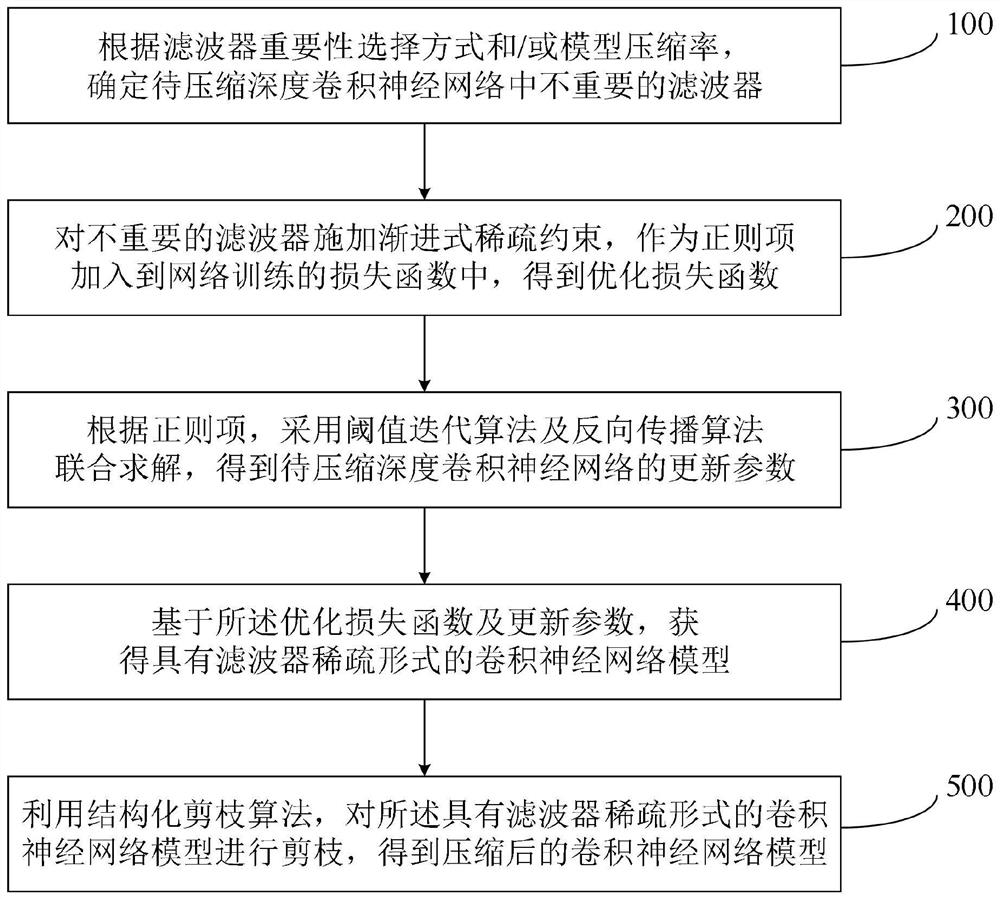
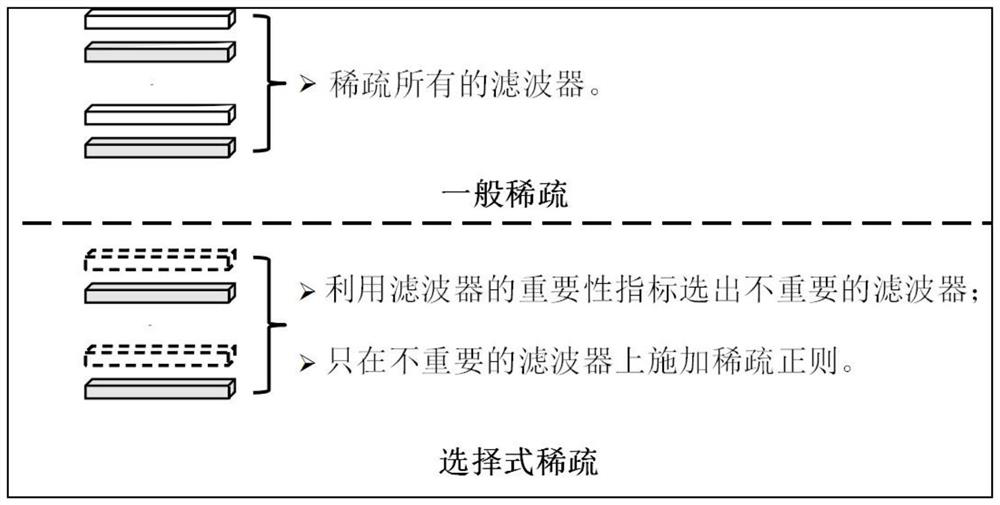
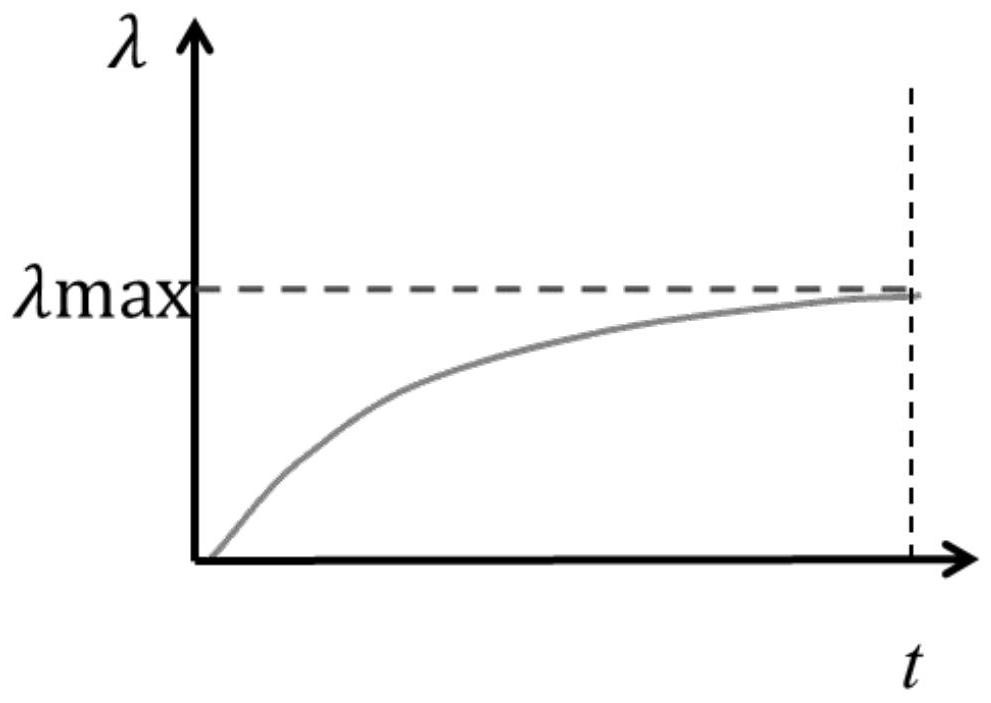
PendingCN111612143AHigh precisionImproved loss functionNeural architecturesNeural learning methodsSparse constraintAlgorithm
The invention relates to a compression method and system for a deep convolutional neural network, and the method comprises the steps: an unimportant filter in a to-be-compressed deep convolutional neural network is determined according to a filter importance selection mode and / or a model compression rate; progressive sparse constraints are applied to the unimportant filters and added into a loss function of network training as regular terms, and an optimized loss function is obtained; according to the regular term, a threshold iterative algorithm and a back propagation algorithm are adopted for combined solving, and updating parameters of the to-be-compressed deep convolutional neural network are obtained; a convolutional neural network model with a filter sparse form based is obtained onthe optimization loss function and the updating parameters; and the convolutional neural network model is pruned with the filter sparse form by using a structured pruning algorithm to obtain a compressed convolutional neural network model with relatively high network precision.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Master-slave mode snake-like robot system and position control method thereof
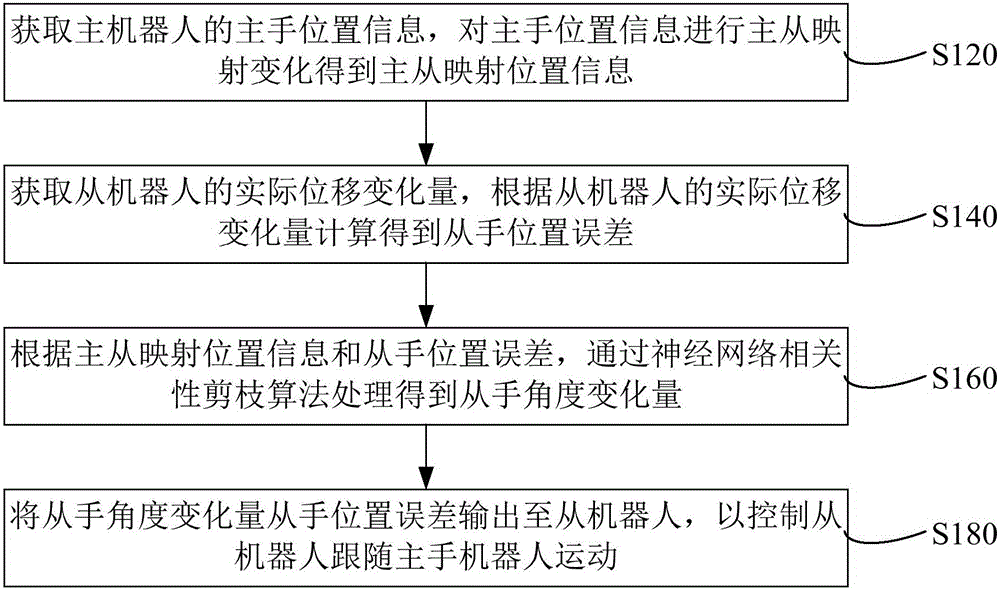
ActiveCN106041912AThere is no limit to the number of degrees of freedomAvoid ambiguityProgramme-controlled manipulatorRobotic systemsKinematics
The invention relates to a master-slave mode snake-like robot system and a position control method thereof. Master manipulator information of a master robot is obtained and subjected to master-slave mapping change to obtain master-slave mapping position information. Actual displacement variation of a slave robot is obtained, and slave manipulator position error is obtained through calculation according to the actual displacement variation of the slave robot. According to the master-slave mapping position information and the slave manipulator position error, slave manipulator angle variation is obtained by processing with a neural network correlation pruning algorithm and output to the slave robot so as to control the slave robot to move following with the master robot. Through the neural network correlation pruning algorithm, precise position control over the slave robot and the master robot is achieved, reverse kinematics does not need to be conducted on the slave robot, solution multiplicity is avoided, the number of degrees of freedom of the slave robot is not limited, and control real-time performance is improved.
Owner:SHENZHEN INST OF ADVANCED TECH
Database Journaling in a Multi-Node Environment
InactiveUS20090307287A1Digital data information retrievalDigital data processing detailsFinancial transactionMaximum size
A database spread over multiple nodes allows each node to store a journal recording changes made to the database and also allows a journaling component to manage the memory space available for journaling. Two threshold size values may be specified for the journal. The first threshold value specifies a journal size at which to being pruning the journal on a given node. A journal pruning algorithm may be used to identify journal entries that may be removed. For example, once a given transaction completes (i.e., commits) the journal entries related to that transaction may be pruned from the journal. The second threshold value specifies the maximum size of the journal. After reaching this size, journal entries may be written to disk instead of the in-memory journal.
Owner:IBM CORP
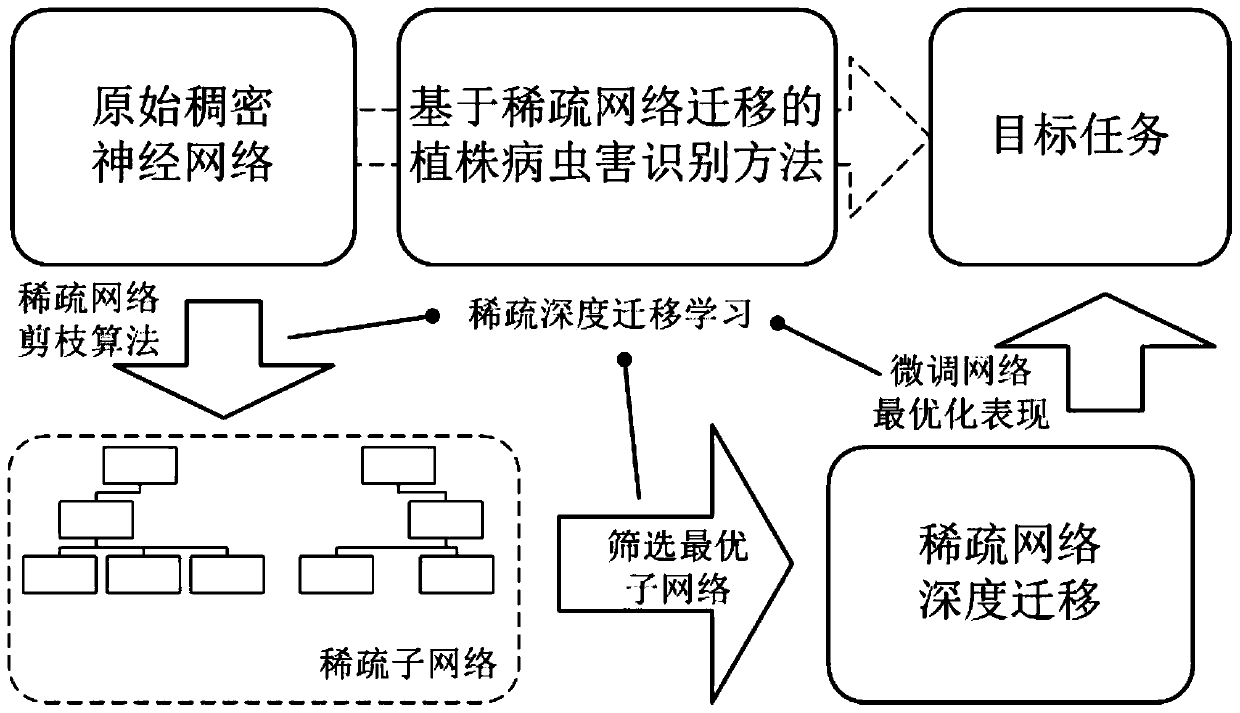
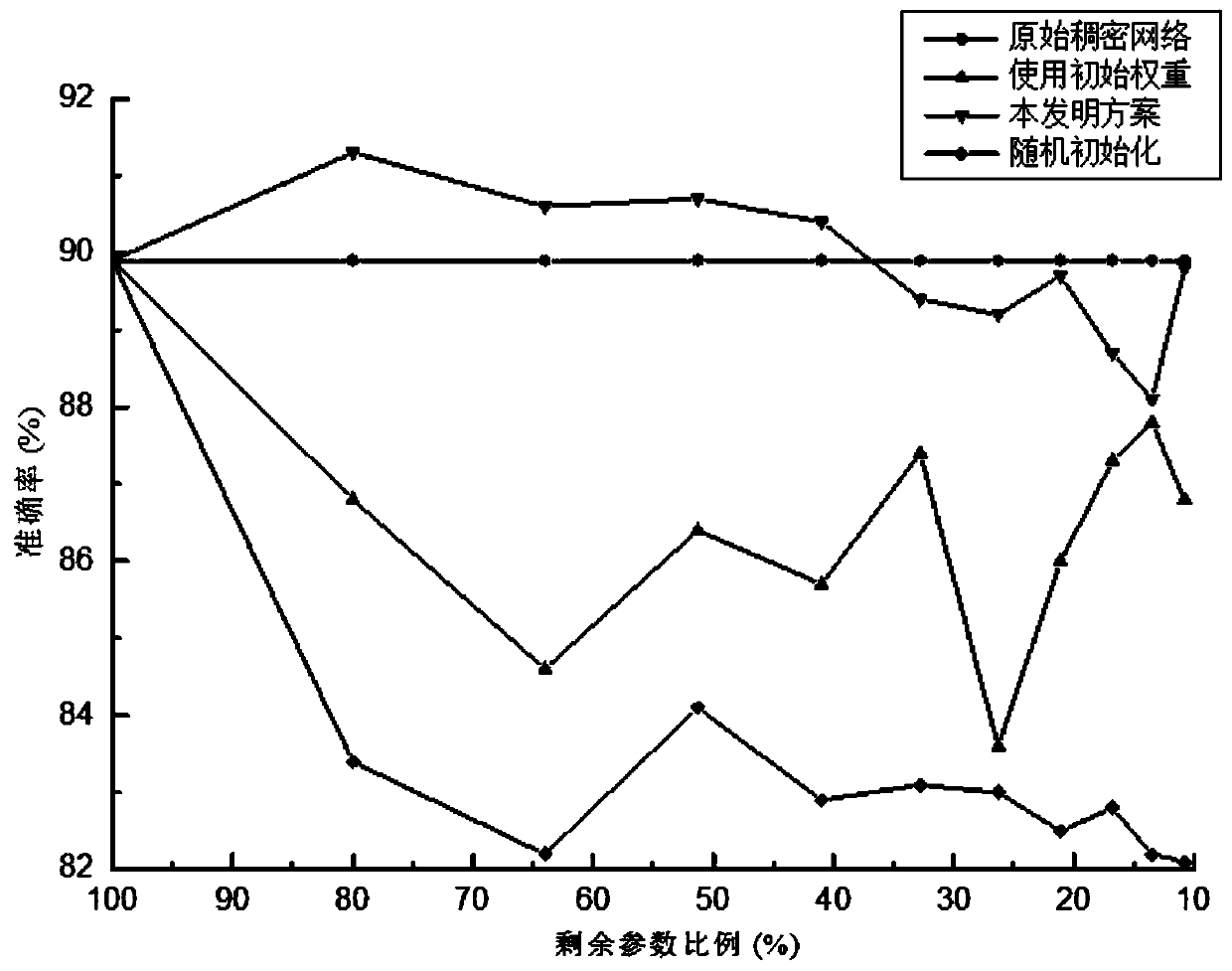
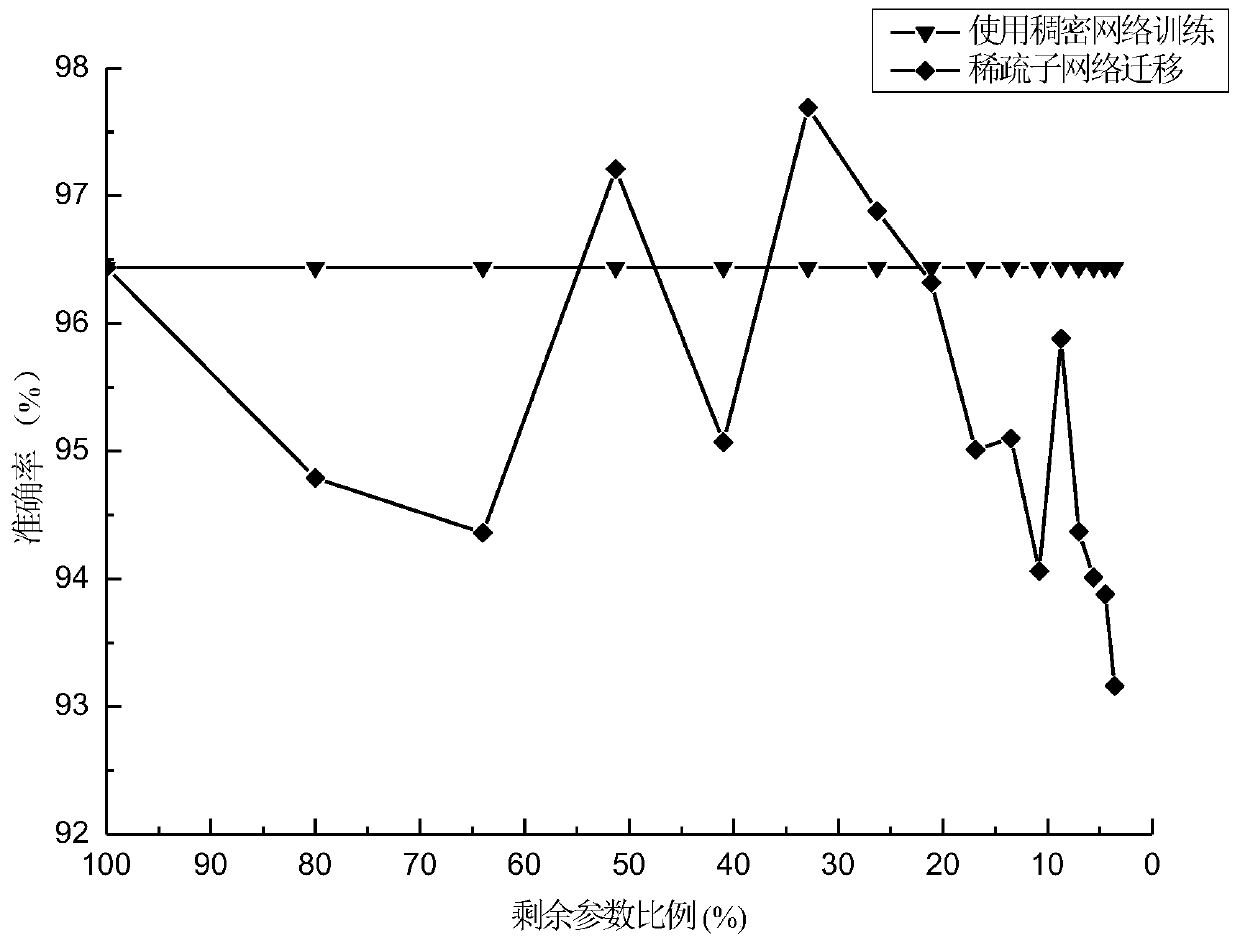
Plant disease and insect pest identification method based on sparse network migration
ActiveCN111353545AEfficient detectionImprove accuracyCharacter and pattern recognitionNeural learning methodsAlgorithmNetwork structure
The invention discloses a plant disease and insect pest identification method based on sparse network migration, and belongs to the technical field of intelligent agricultural disease and insect pestidentification. The method comprises the following steps: designing a pruning algorithm, iteratively traversing a network, freezing redundant parameters in a source domain network, and generating a retrained optimal sparse sub-network structure; employing deep migration learning, migrating the sparse network to a target domain, proposing a sparse network migration hypothesis, verifying the feasibility of the sparse network, exploring the potential association between a target task and existing knowledge, and initializing the network through the weight of a source domain, and achieving the knowledge migration and reuse on the target domain; finally, finely adjusting the sub-network by using a small number of samples of the target domain data, optimizing the network performance, and finishing the task migration, thereby solving the practical application problem. Plant diseases and insect pests can be recognized, the network detection precision is improved through sparse migration, and meanwhile, the problems that a traditional deep method needs to train a dense network, calculation expenditure is large, the requirement for hardware is high, and popularization is not facilitated are solved.
Owner:DALIAN UNIV OF TECH
Resource-efficient media streaming to heterogeneous clients
InactiveUS7657651B2Multiple digital computer combinationsElectric digital data processingQuality of serviceTransmission channel
A resource-efficient live streaming system includes a broadcaster and a streaming server. The broadcaster receives a live feed and broadcasts a media stream to the streaming server containing several descriptions of the live feed along with control information. The broadcaster includes a stream thinner that implements a pruning algorithm. If descriptions from different streams are similar enough, one or more of them may be discarded without penalizing the quality of service perceived by the receivers. The streaming server assembles compressed data units into streams according to the control information from the broadcaster. The streaming server may also gather client feedback in order to estimate the status of the transmission channels and forwards the information to the broadcaster. The streaming server builds and streams media information to clients according to user preferences and receiver capabilities.
Owner:TWITTER INC
Sparse and non-sparse data management method and system
InactiveUS7010548B2Storage requirement is minimizedEfficient methodError prevention/detection by using return channelData processing applicationsTree (data structure)Data management
A method and system for tracking data packets that utilizes a tree data structure with a recursive pruning algorithm that collapses the branches of the tree that represent contiguous ranges or regions to maintain a minimally optimum memory size. Each contiguous region is identified by a node, which includes the start and end range of packets. Each node further includes left and right pointer elements, which point to adjacent lower and higher nodes, respectively. When a packet sequence number is not contiguous with any other sequence numbers previously received, a new node is created that contains only a single value range. When a new packet is received that has a contiguous sequence number (i.e., immediately preceding or succeeding sequence number), the original node is updated so as to reflect the new contiguous range. Additionally, if this new contiguous range is contiguous with another node's range, the two nodes are “collapsed” into a new single node containing the new expanded contiguous range. Furthermore, the algorithm can quickly and efficiently determine whether there are any missing packets by simply determining if there is only a single node remaining after a designated “last packet” has been received.
Owner:AVAGO TECH INT SALES PTE LTD
3780 point discrete fourier transform processor
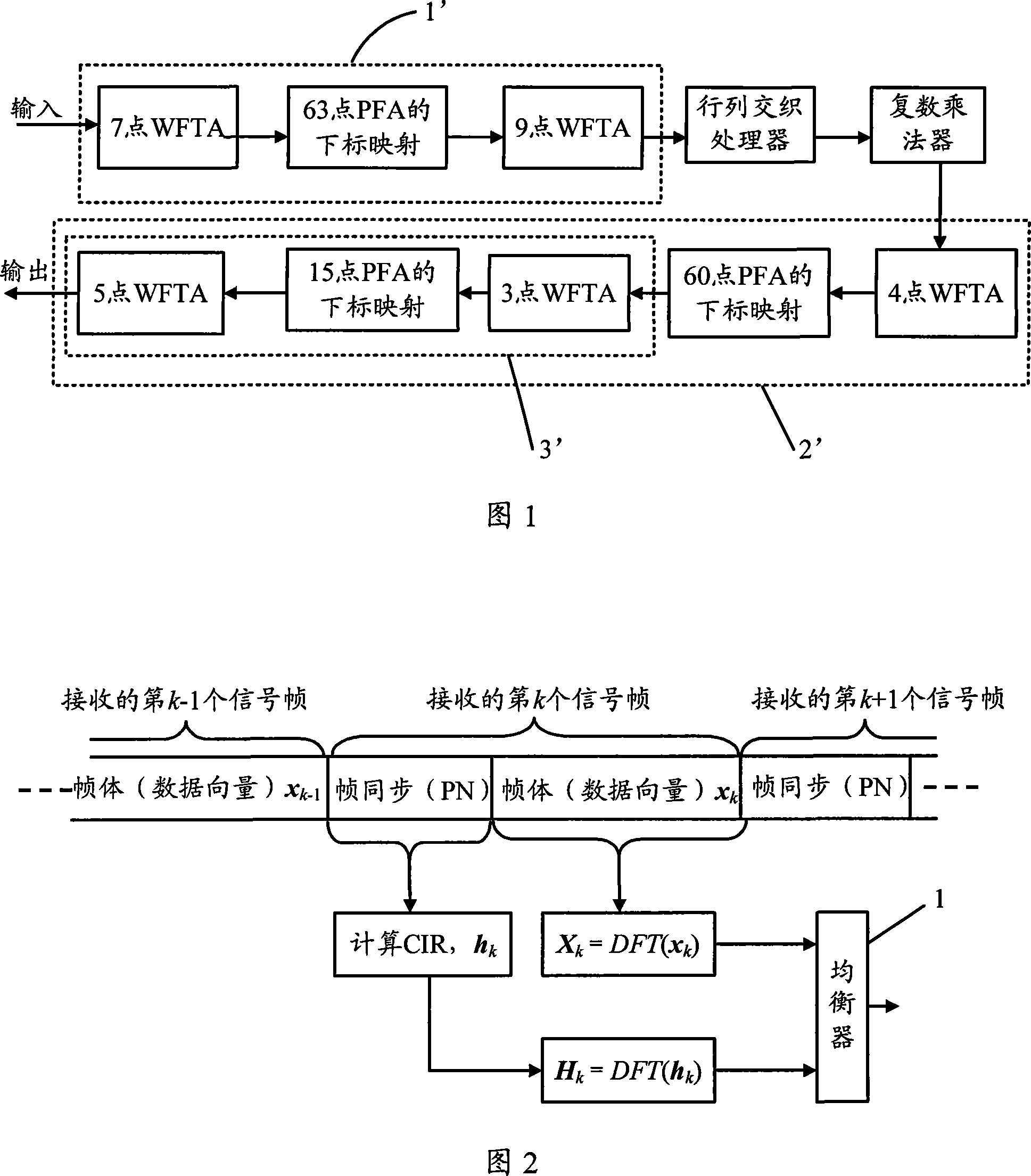
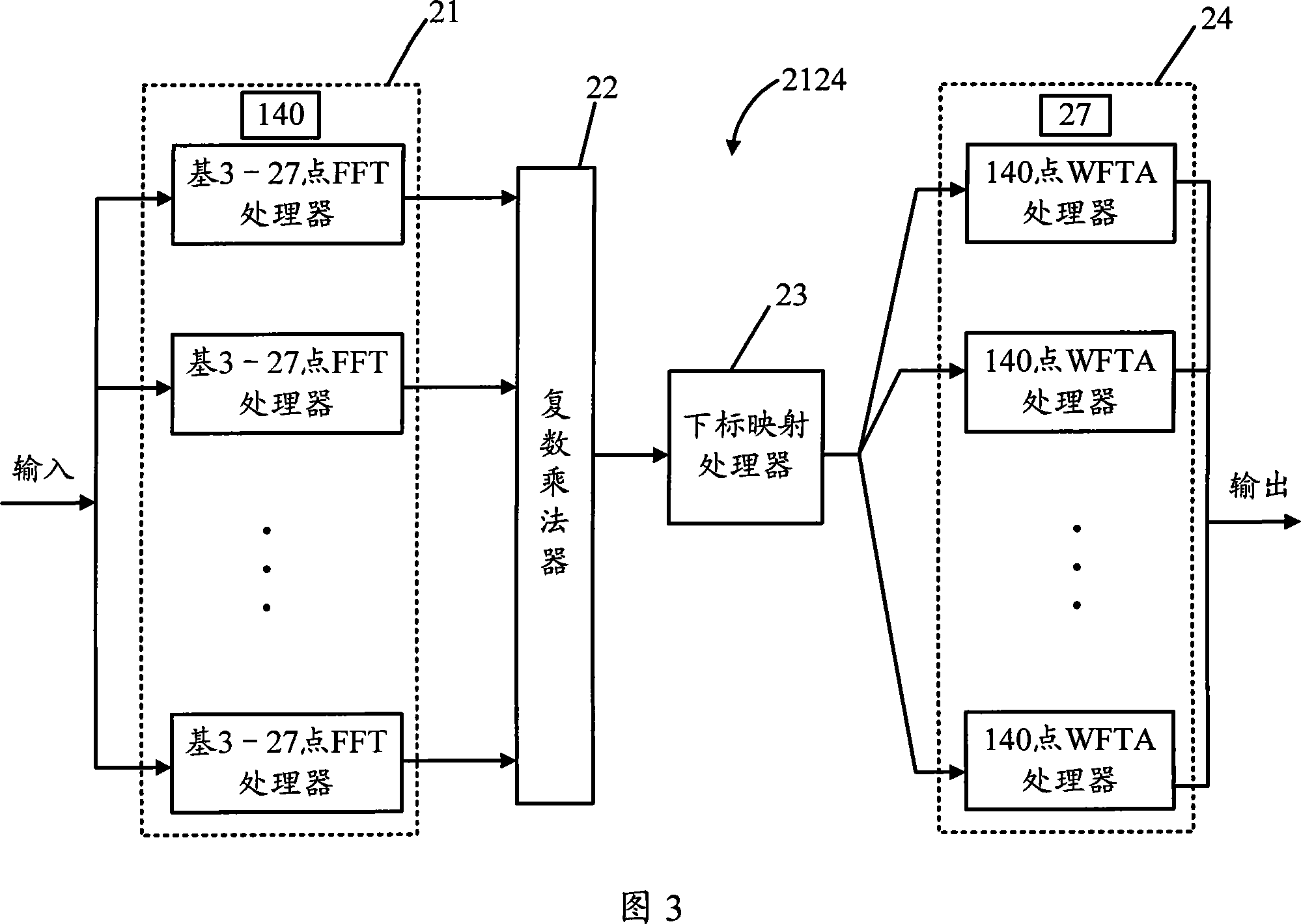
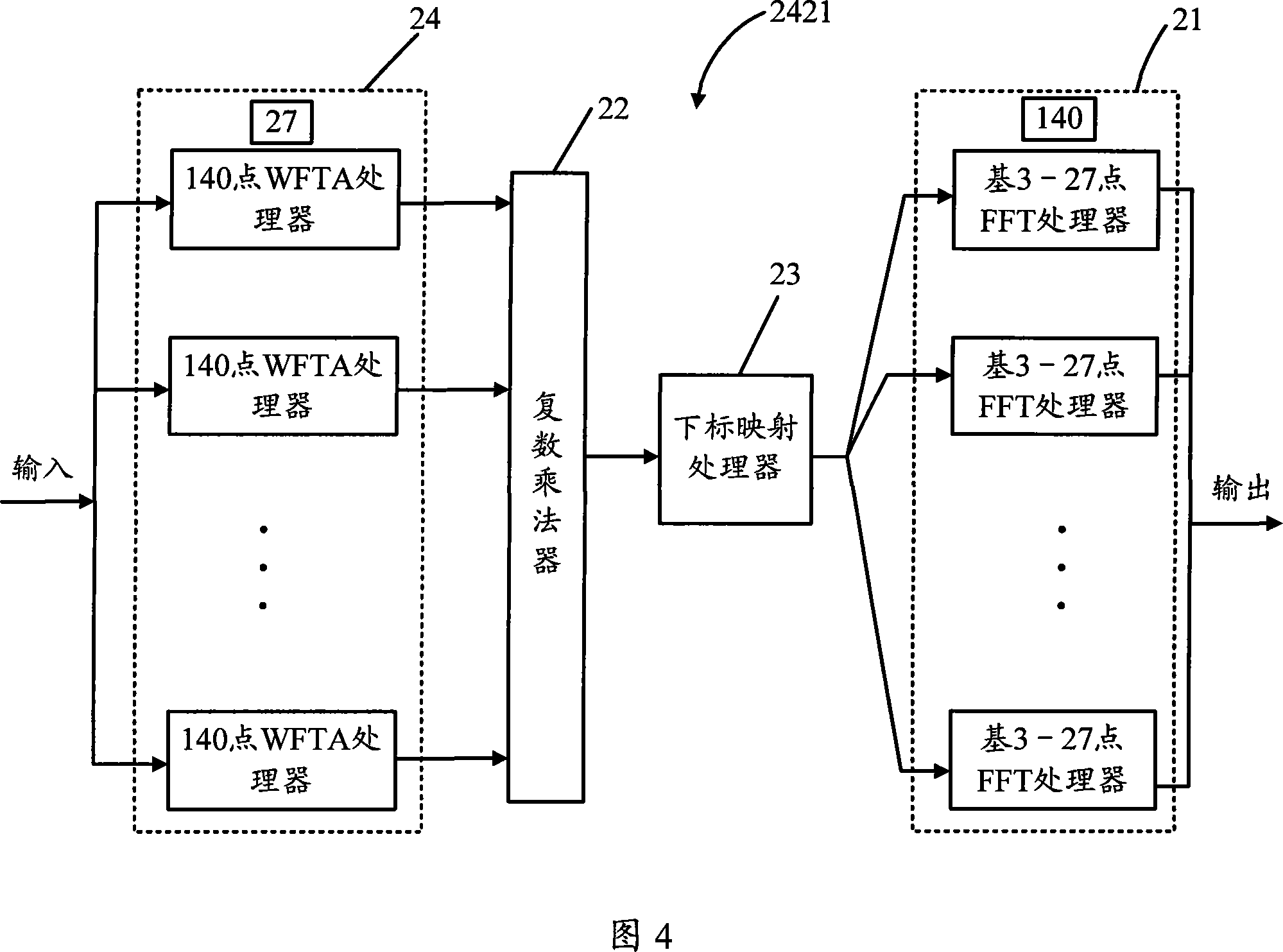
InactiveCN101196873AReduce multiplicationReduce the amount of addition operationsComplex mathematical operationsChannel impulse responseDigital television terrestrial broadcasting
The invention discloses a novel 3780 points DFT processor, which relates to a digital television terrestrial broadcasting system. The processor has one of the following two structures, of which the first structure comprises 140 27 points DFT processors, a complex multiplier, a subscript mapping processor and 27 140 points DFT processors in turn; the second structure comprises the 27 140 points DFT processors, the complex multiplier, the subscript mapping processor and the 140 27 points DFT processors. As for input information including channel impulse response (CIR) vector, the 3780 points DFT processor with the first structure also comprises pruning algorithm to remove the redundant operation in the processor related to zero element in CIR vector. Compared with the prior art, the 3780 points DFT processor provided by the invention effectively reduces the multiplication operation quantity and system power dissipation. Moreover, the invention further reduces the multiplication and addition operation quantity of the processor by pruning algorithm according to the natural characteristics of the CIR vector.
Owner:维布络网络私人有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com