Patents
Literature
164 results about "Stream analytics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Streaming analytics work by allowing organizations to set up real-time analytics computations on data streaming from applications, social media, sensors, devices, websites and more. Streaming analytics provide quick and appropriate time-sensitive processing along with language integration for intuitive specifications.
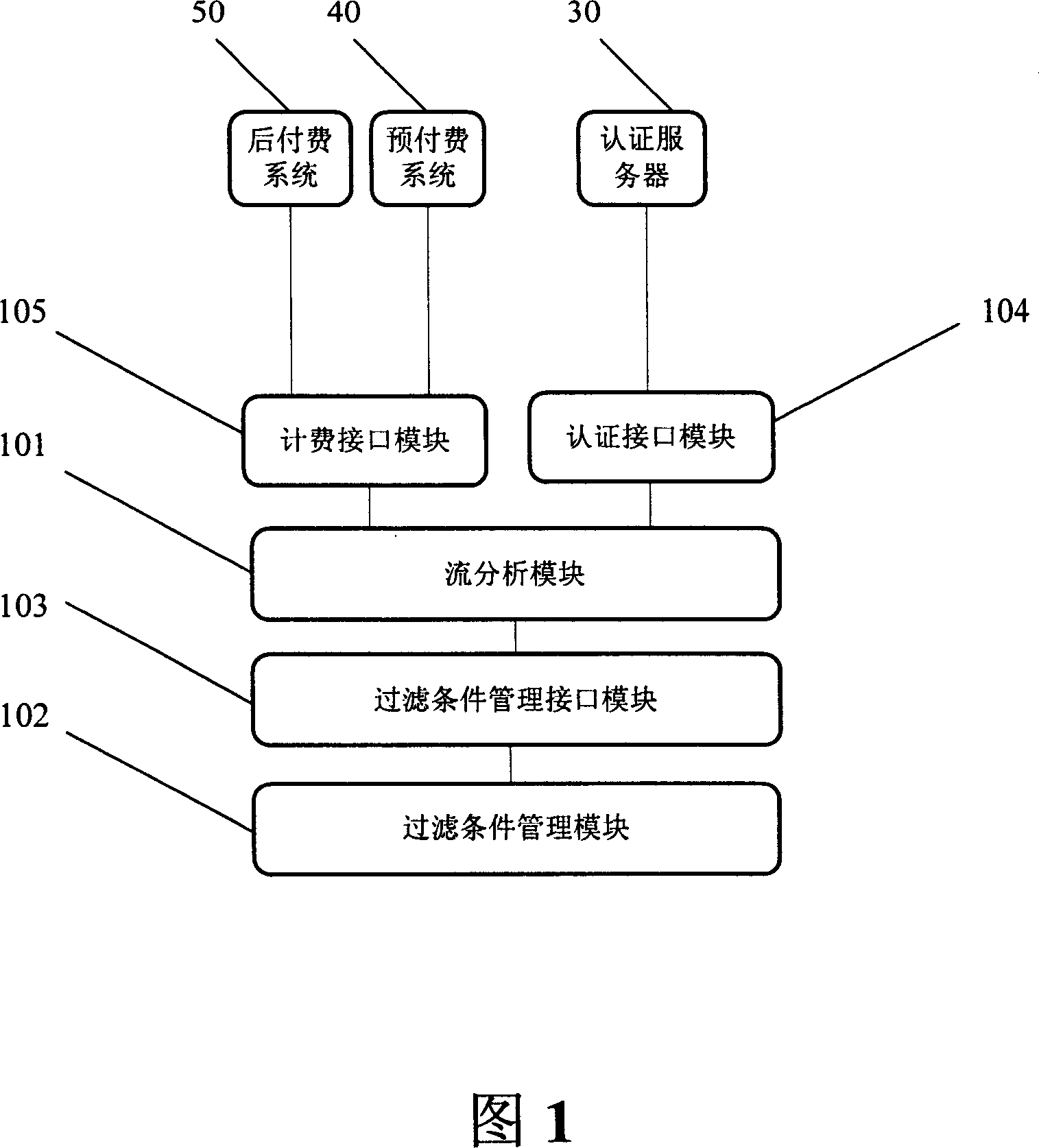
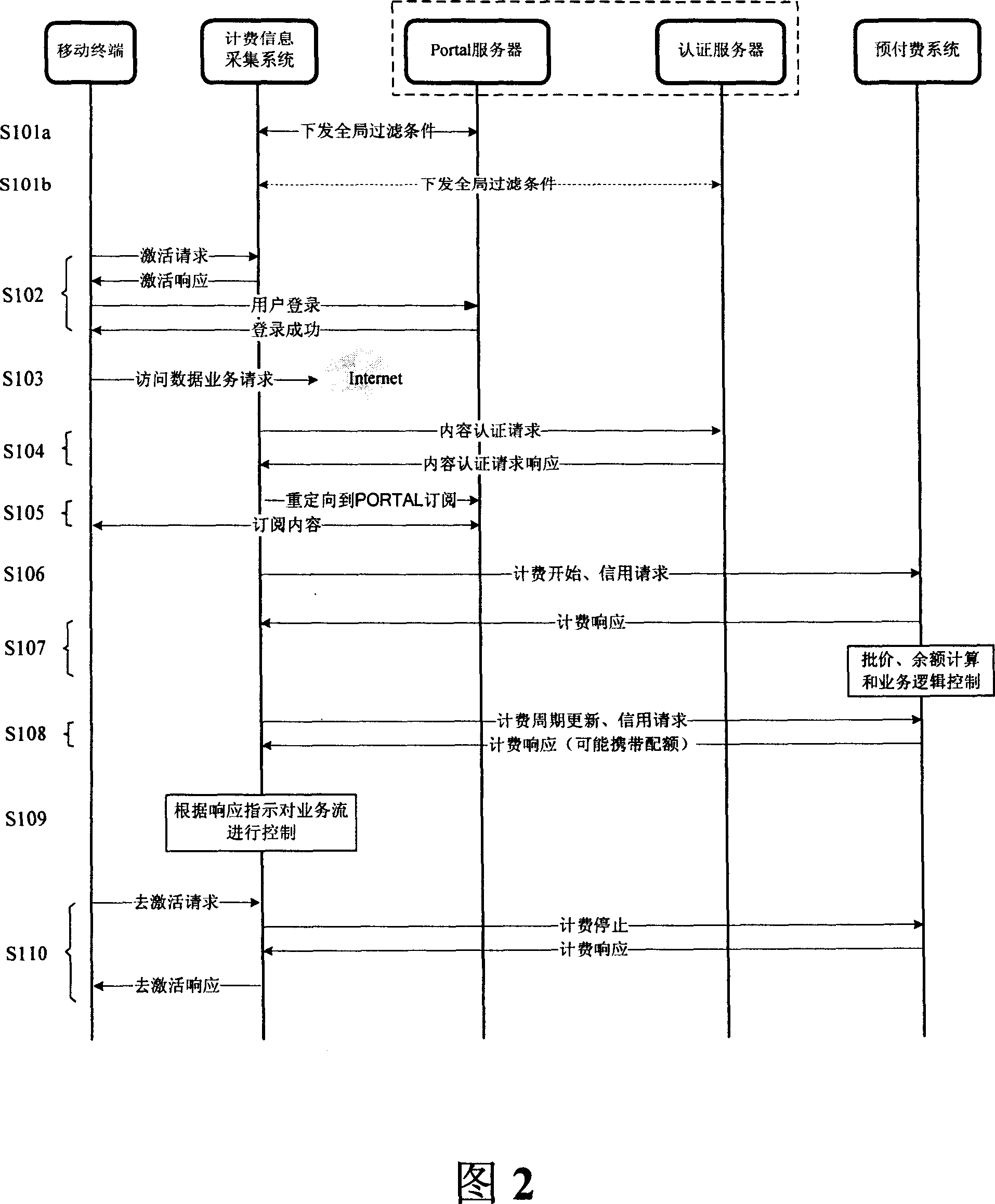
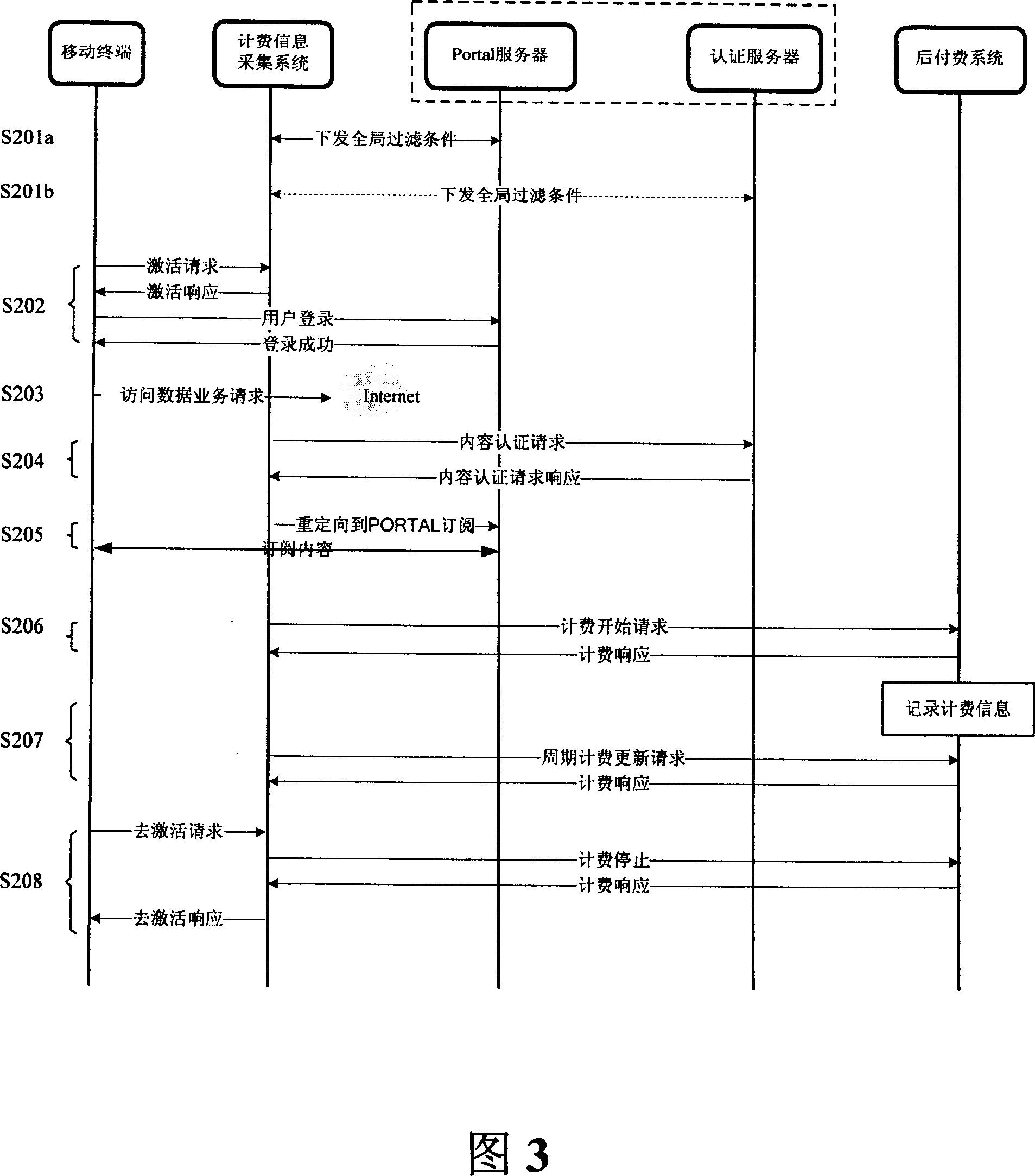
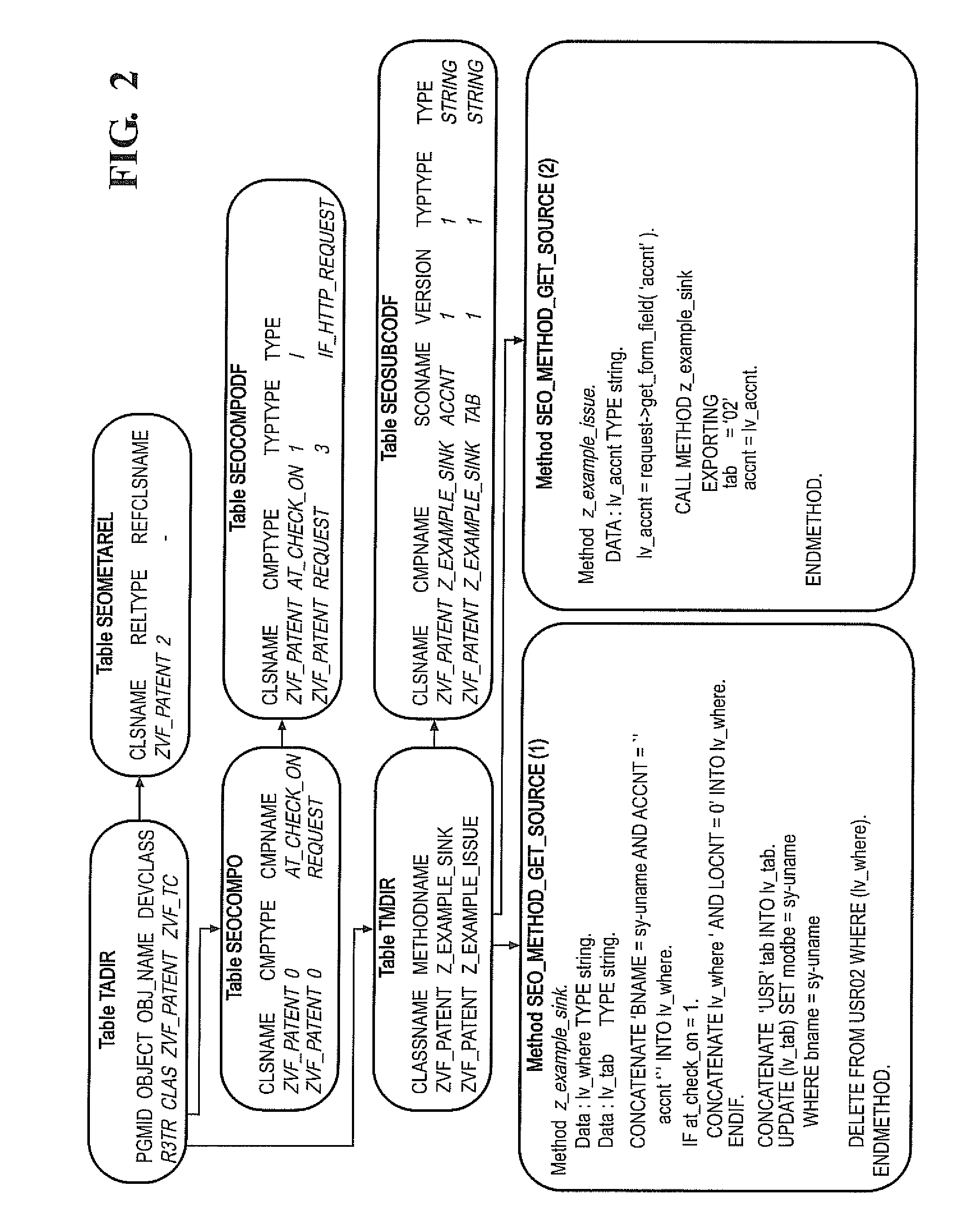
Charged information acquisition system and method, and charge realizing system and method
InactiveCN1937511AExtended business featuresMetering/charging/biilling arrangementsSoftware engineeringFiltering rules
The fare charging info collect system includes a filter condition management module (FCM) for setting and storing the filter condition being useful for flow analyze and control, a flow analyze module (FA), according to the filter condition, analyzes the business flow that mobile terminals access the data business, draws the data business content character code, business beacon and the business type info, a filter condition management interface module (FCMI) connecting FCM and FA, a authentication interface module (AI) sending the business content character code to the authentication server to authenticate. A fare charge interface module (FCI) sends the business beacon and the business type to the fare charging sub-system to charge. Via supporting user to set and modify dynamically the filter rule, this scheme extends user business features, e.g. QOS and safety features.
Owner:ZTE CORP
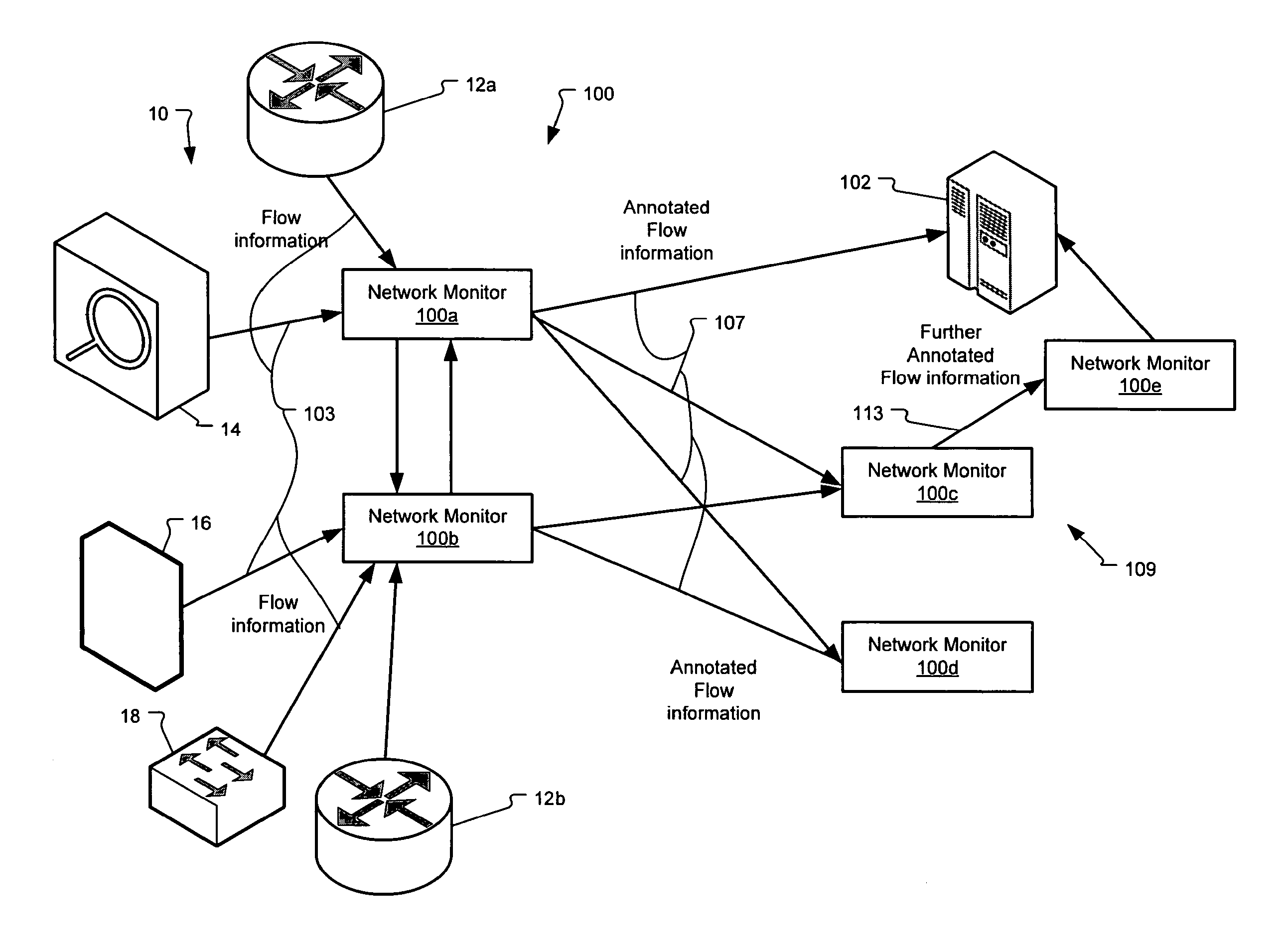
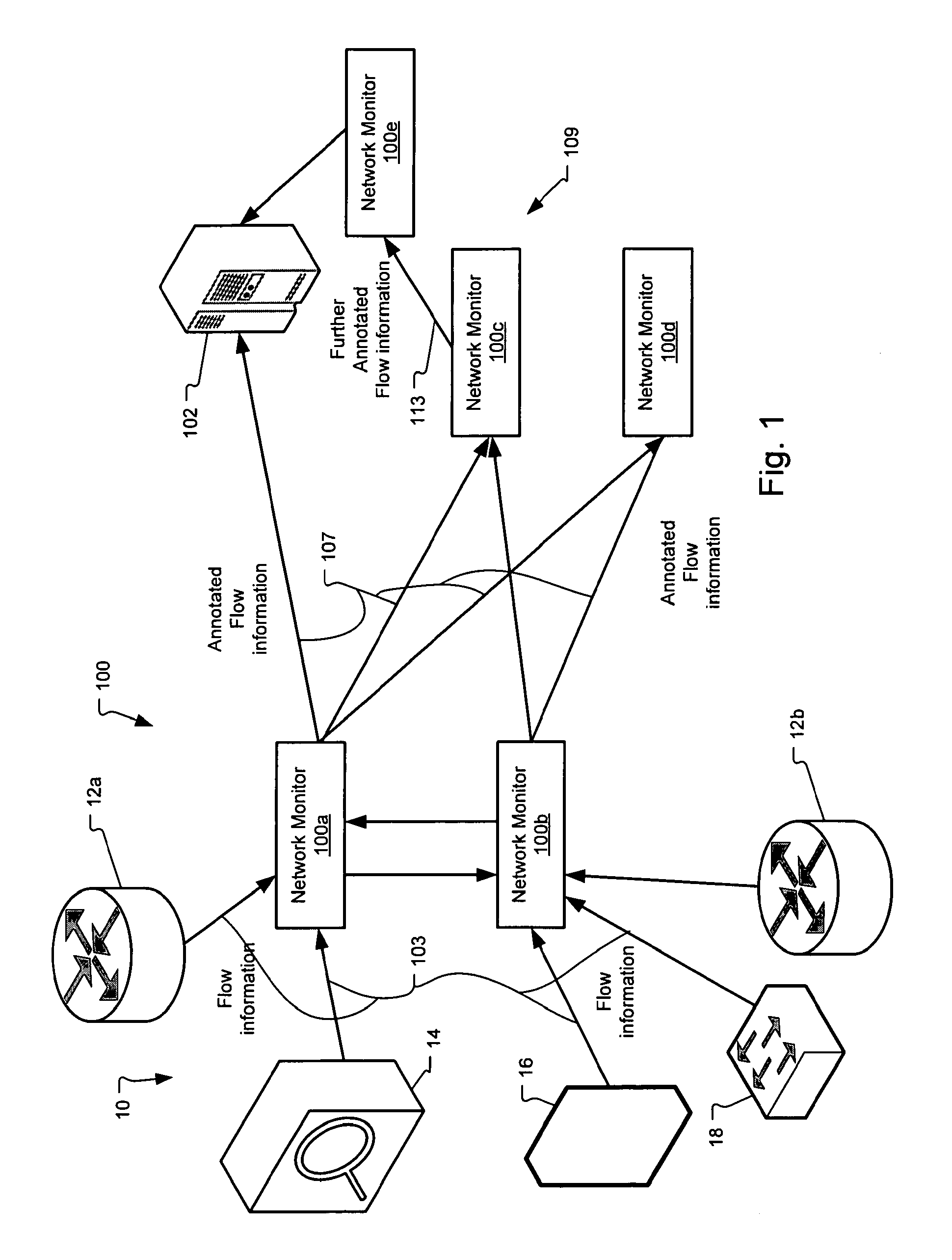
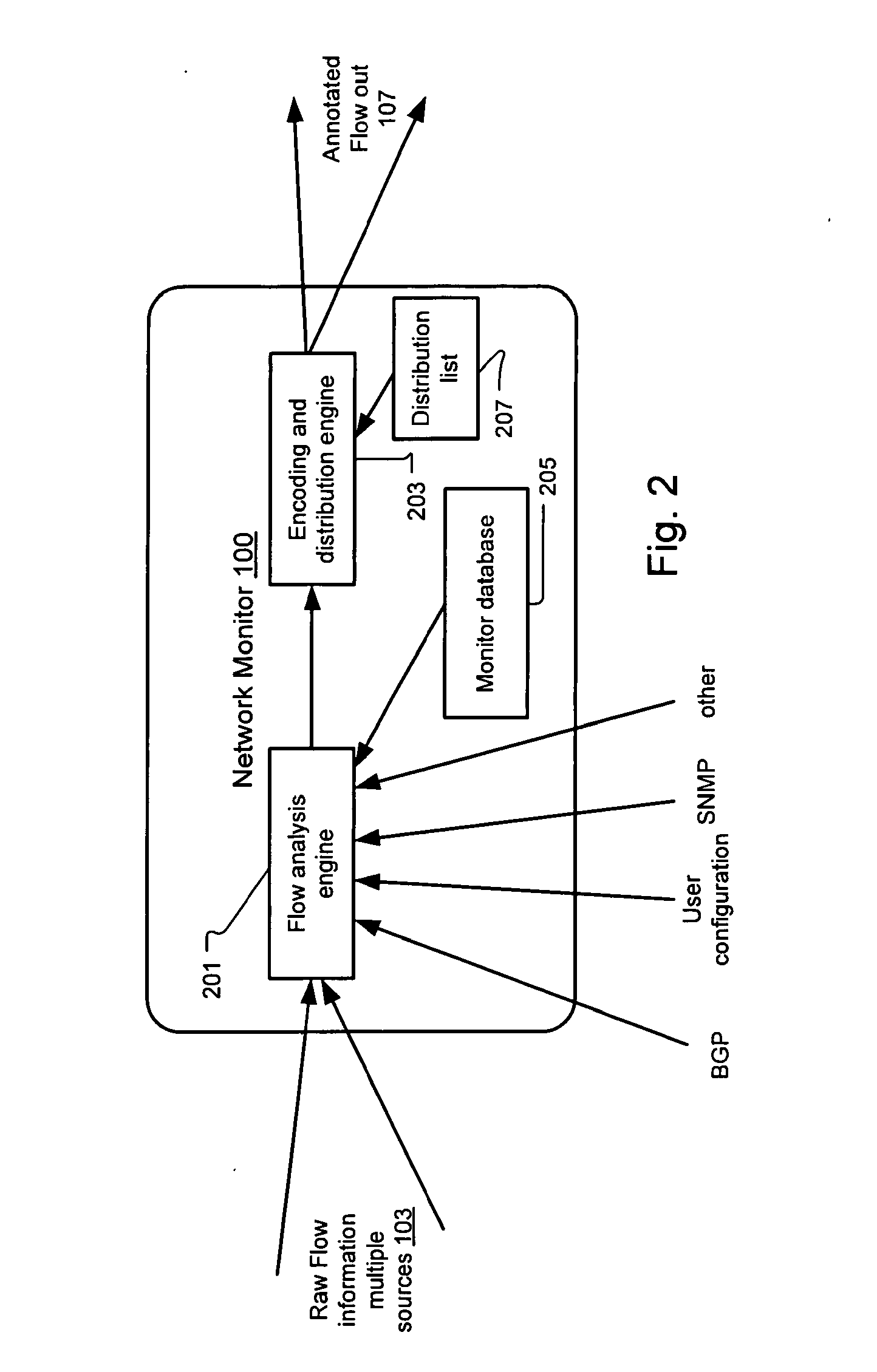
Method and system for annotating network flow information
ActiveUS20130290521A1Easy to createReduce overheadDigital computer detailsData switching networksBorder Gateway ProtocolStructure of Management Information
A scalable flow monitoring solution takes in standard flow records exported from network devices such as routers, switches, firewalls, hubs, etc., and annotates the flow with additional information. This information is derived from a number of sources, including Border Gateway Protocol (BGP), Simple Network Management Protocol (SNMP), user configuration, and other, intelligent flow analysis. These annotations add information to the flow data, and can be used to perform value-added flow analysis. The annotated flow is then resent to a configurable set of destinations using standard flow formatting, e.g., Cisco System Inc.'s NetFlow, in one implementation. This allows the annotated flow to be processed and the enhanced information to be used by other flow analysis tools and existing flow analysis infrastructure.
Owner:ARBOR NETWORKS
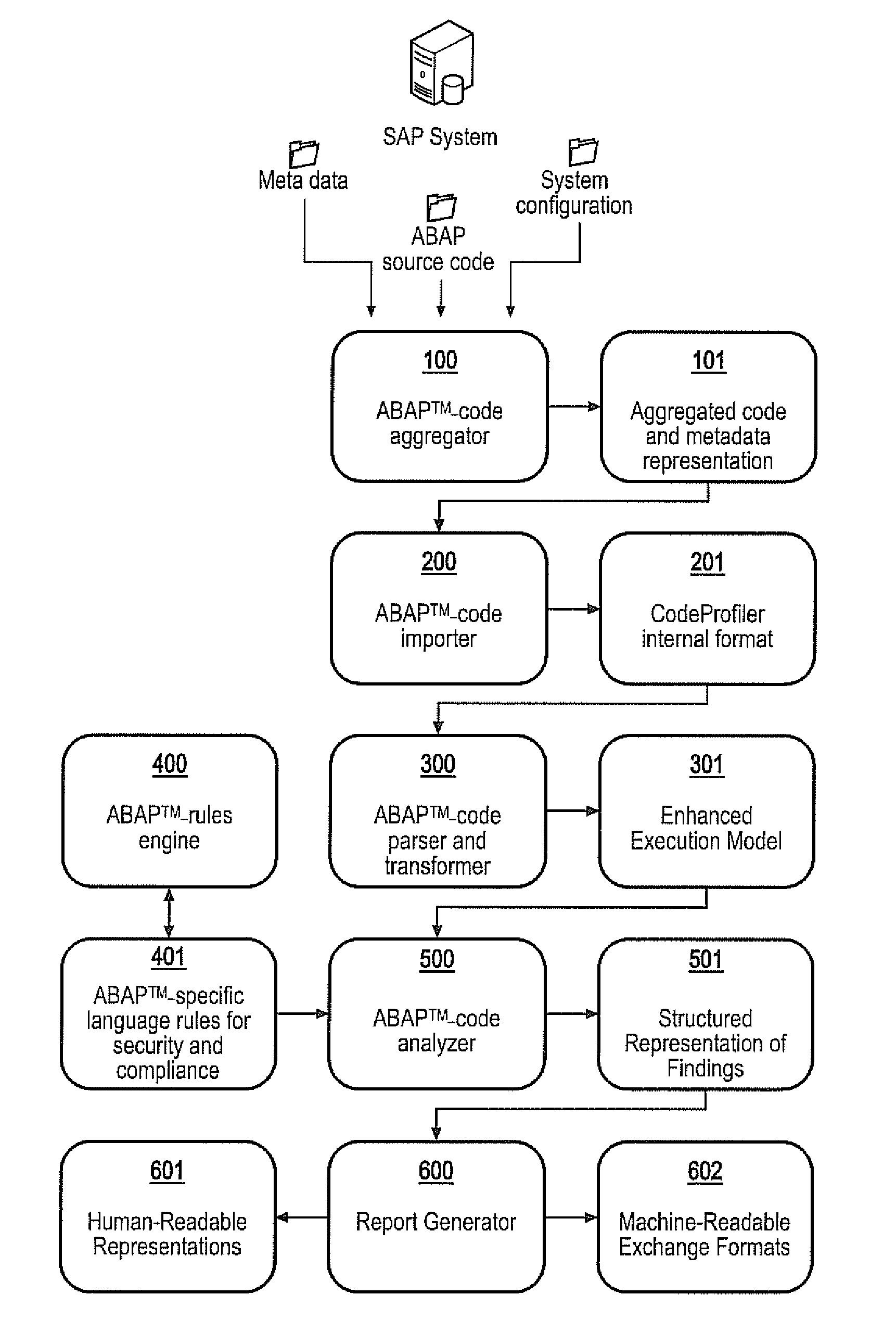
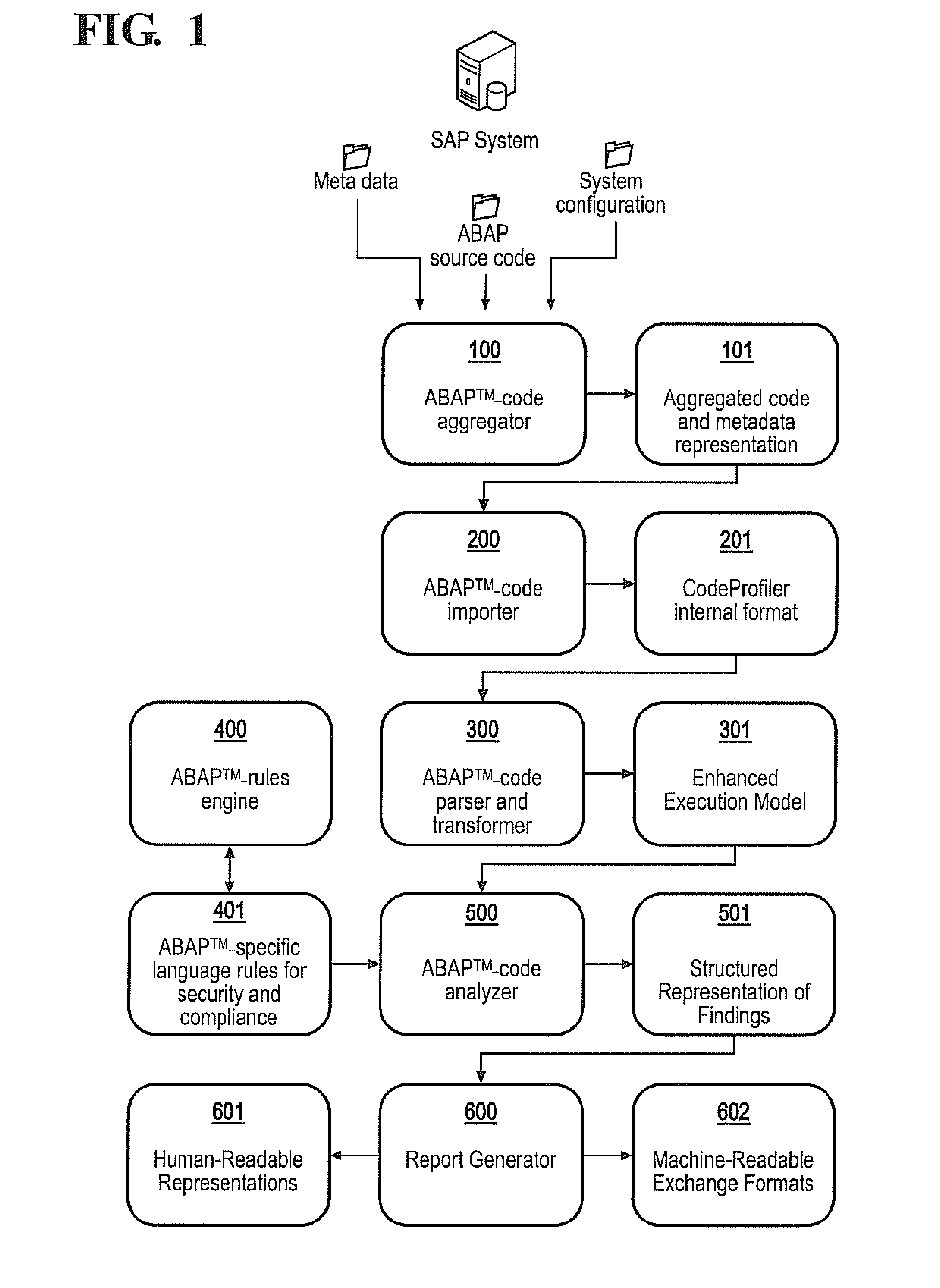
APPARATUS AND METHOD FOR DETECTING, PRIORITIZING AND FIXING SECURITY DEFECTS AND COMPLIANCE VIOLATIONS IN SAP® ABAPtm CODE
A static code analysis (SCA) tool, apparatus and method detects, prioritizes and fixes security defects and compliance violations in SAP® ABAP™ code. The code, meta information and computer system configuration settings are transformed into an interchangeable format, and parsed into an execution model. A rules engine is applied to the execution model to identify security and compliance violations. The rules engine may include information about critical database tables and critical SAP standard functions, and the step of applying the rules engine to the execution model may include the calculation of specific business risks or whether a technical defect has a business-relevant impact. In particular, an asset flow analysis may be used to determine whether critical business data is no longer protected by the computer system. Such critical business data may include credit or debit card numbers, financial data or personal data.
Owner:VIRTUAL FORGE
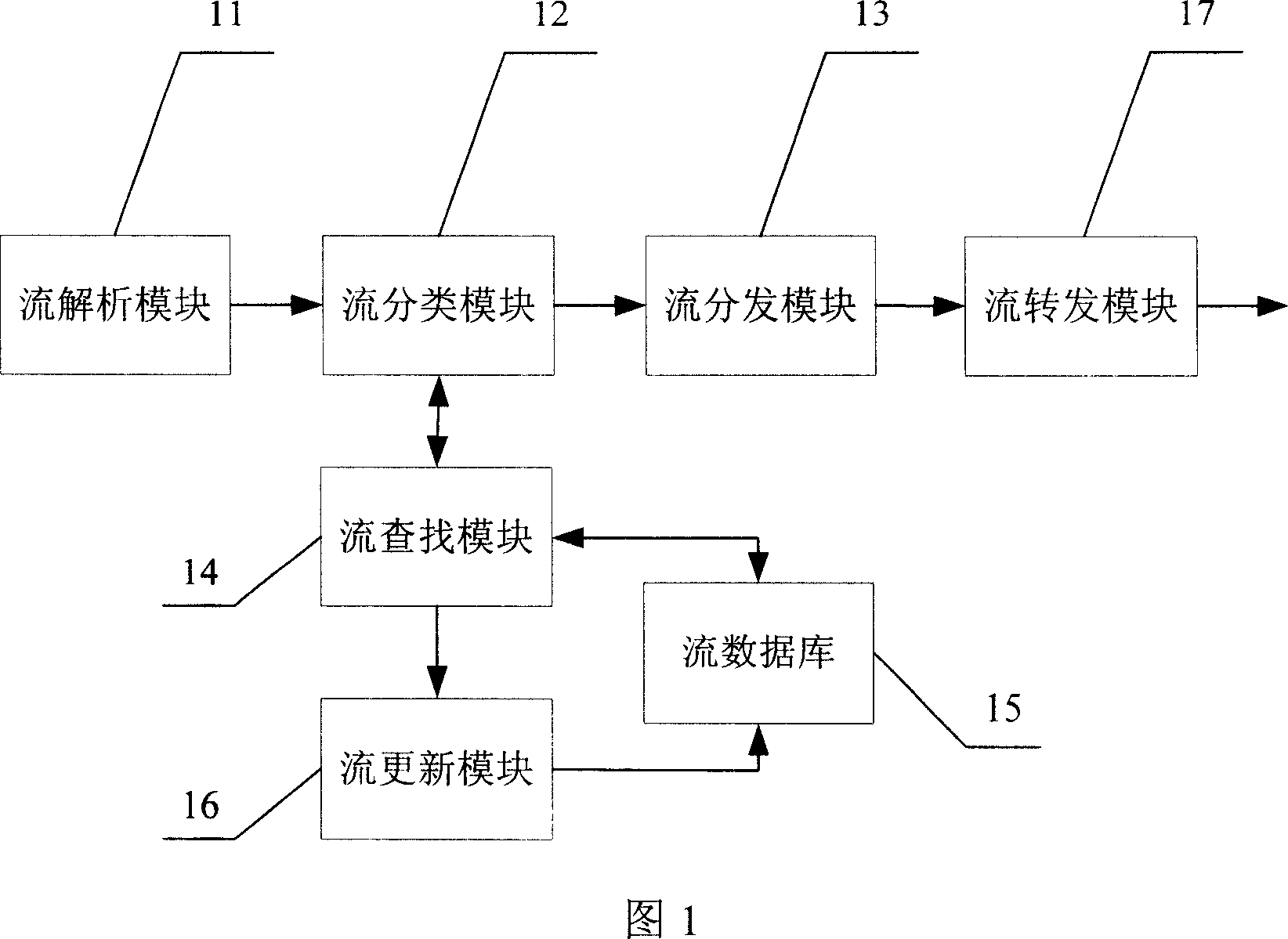
A method for implementing stream-based policy routing on network processor
InactiveCN101127691AImplement Differentiated ServicesGood loadData switching networksKey assignmentNetwork processor
The utility model discloses a stream-based strategic routing method on a network processor, comprising following procedures: after receiving the message, the processing is carried out by a stream analytic module, and the heading key assignment is extracted and supplied to a stream sorting module to process the key assignment; a stream distribution module decides to send the message to the specific threading of the stream sorting module. The searching and handling are carried out by a stream searching module in the stream database to see whether the same stream mark as that of the message already exists; if the search succeeds, the message is handed to the stream distribution module for disposal; and then the message is transferred to a stream forwarding module for further processing through the stream distribution module. If the search fails, the message is transferred to a renewal module for disposal. The stream renewal module establishes relevant stream list entries and then stores them in the stream database, and then, begins a new search. The utility model can adopt different routing strategy according to various application types, so that the availability of the network is promoted.
Owner:王玉鹏
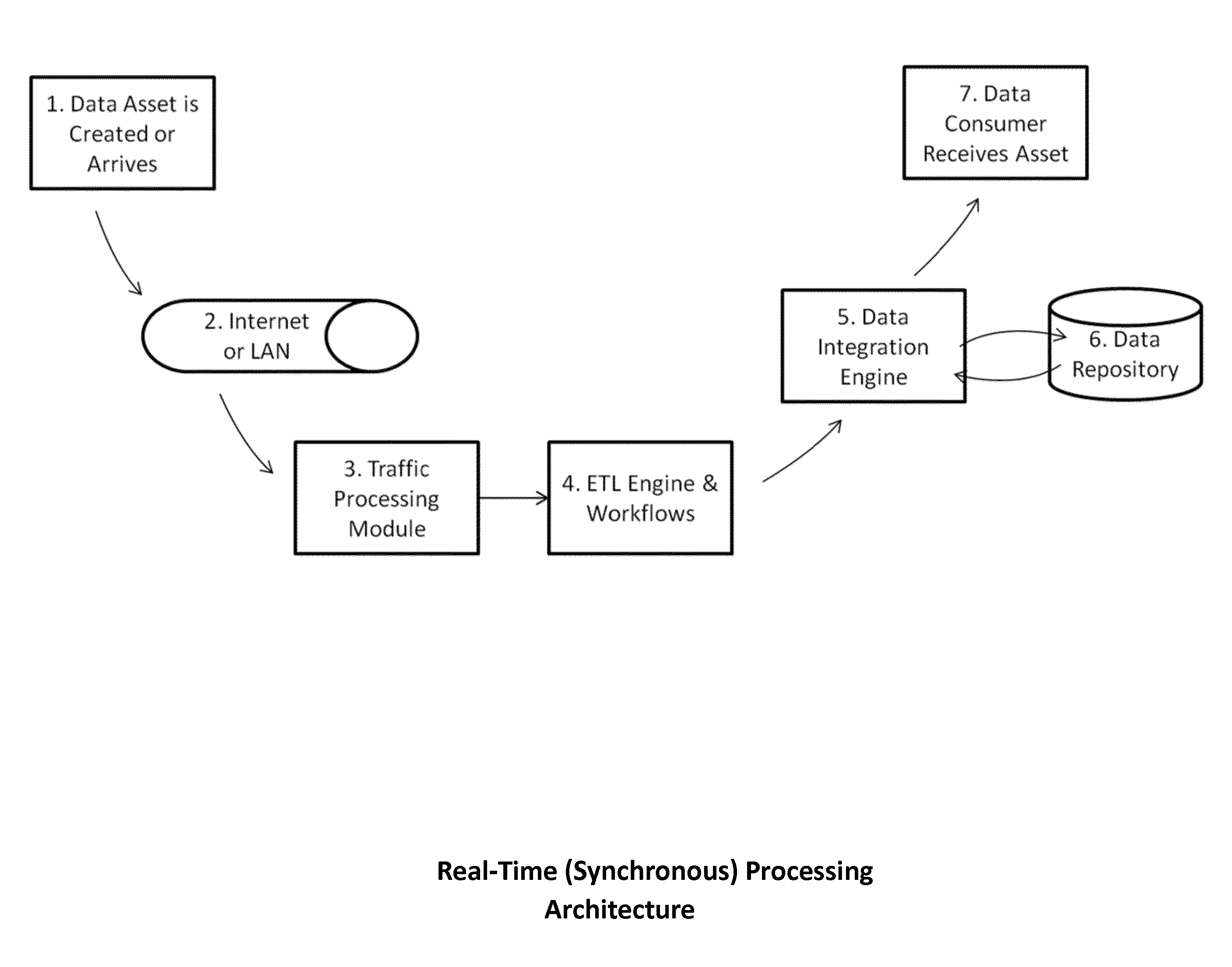
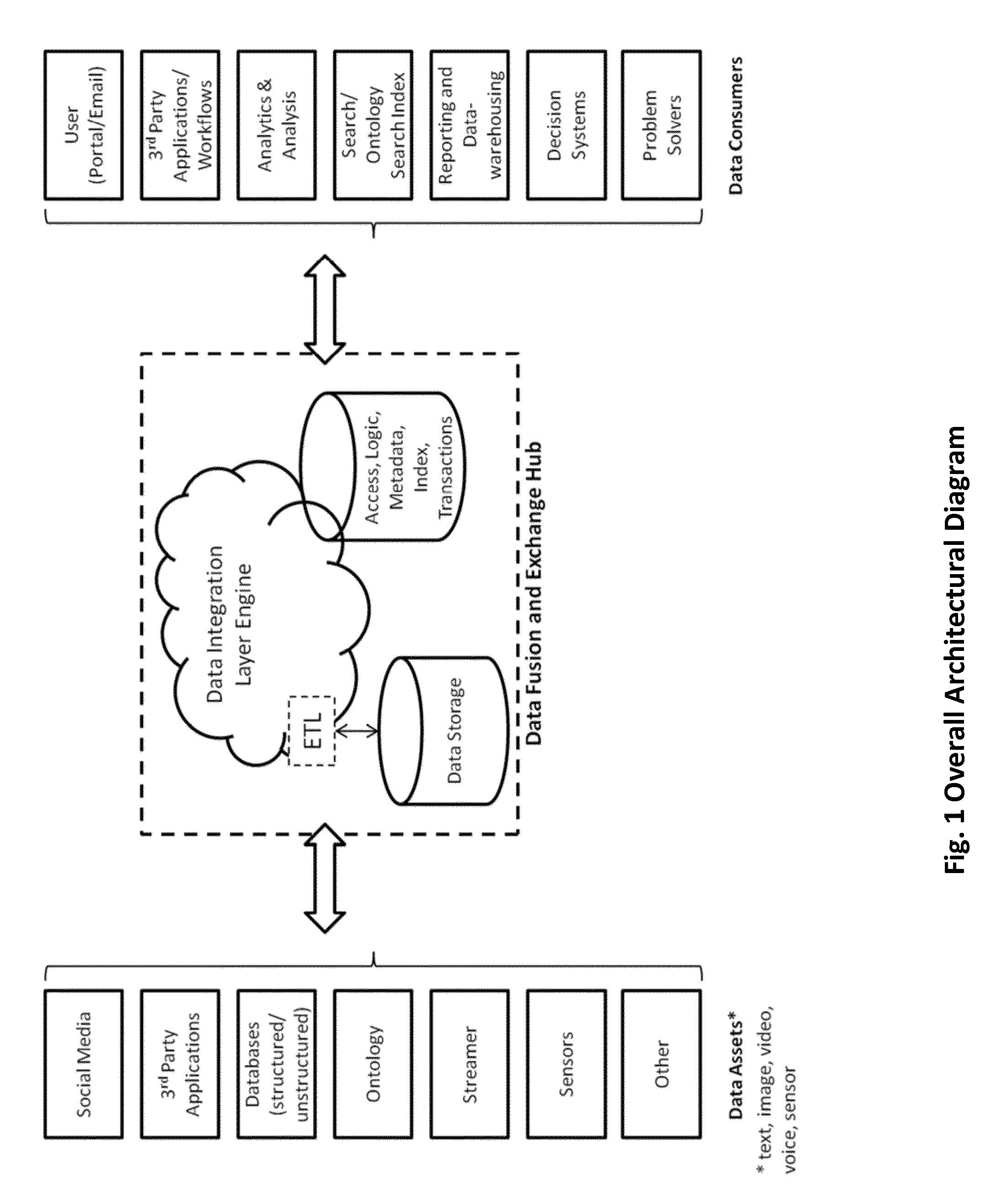
Data fusion and exchange hub - architecture, system and method
InactiveUS20160021181A1Reduce the valueFlexible processPayment architectureOffice automationApplication softwareWearable computer
A computerized method for facilitate and orchestrate the exchange and integration of data assets and data consumers, with or without computer appliances, automated framework comprised of technical devices for enabling integration of one or more of data assets including data streamer, structured data repository, unstructured data repository, 3rd party application, ontology, sensor, service provider, text, image, video, voice, and data consumers including human user, web portal, email, repository of data, reporting warehouse, 3rd party application, workflow, analytics process, model, ontology index, problem solver, decision system, mobile device, sensor, wearable computer. The automated framework can be one of asynchronous messaging-based, asynchronous near real-time, synchronous real-time; computer memory is used for storing applications for distribution to data consumers. The framework provides encryption, authentication, rights and roles controlling data assets, or data consumers. A user can interact with the framework to perform monitoring, management or analysis functions.
Owner:IANAKIEV GEORGE +1
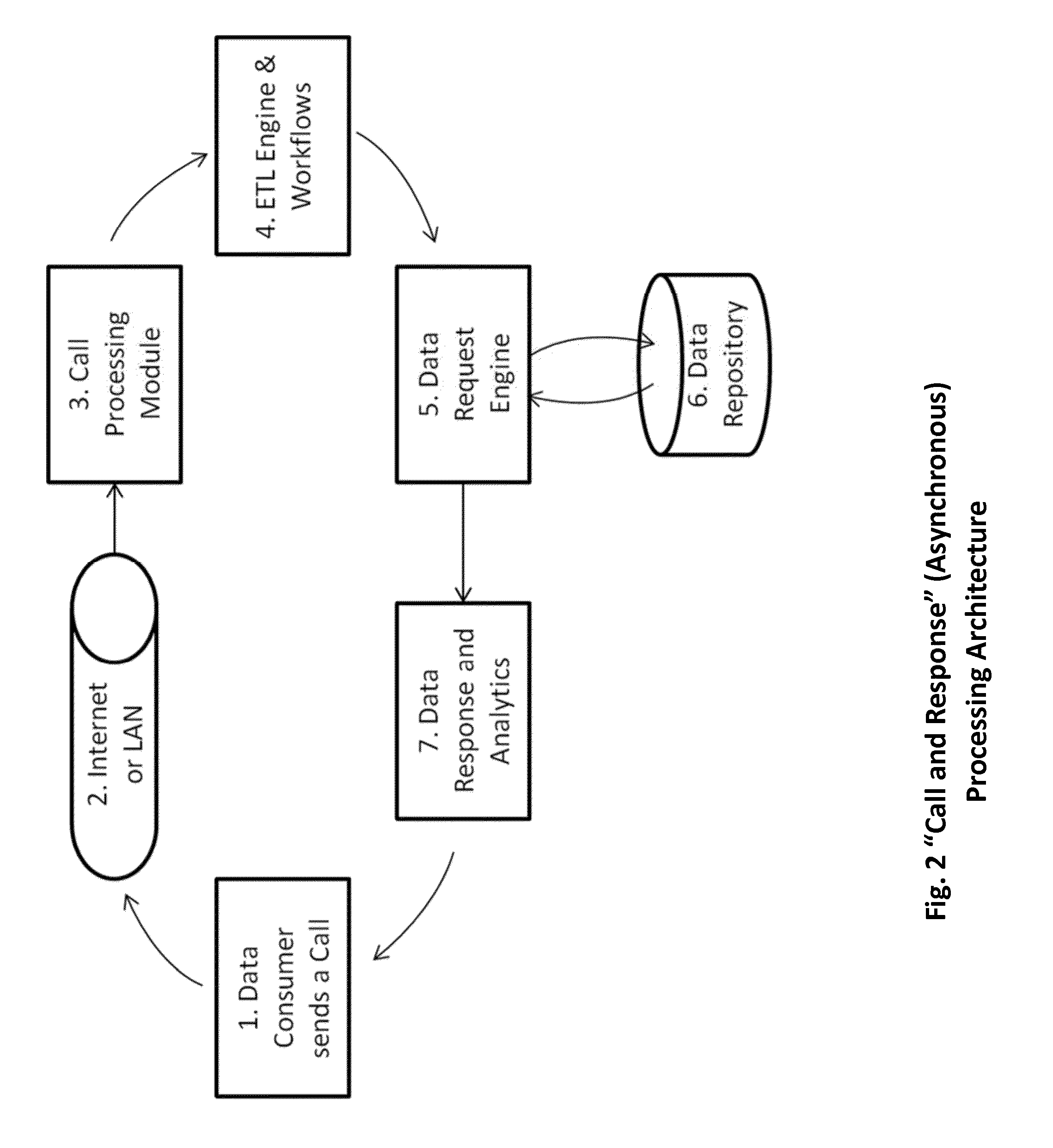
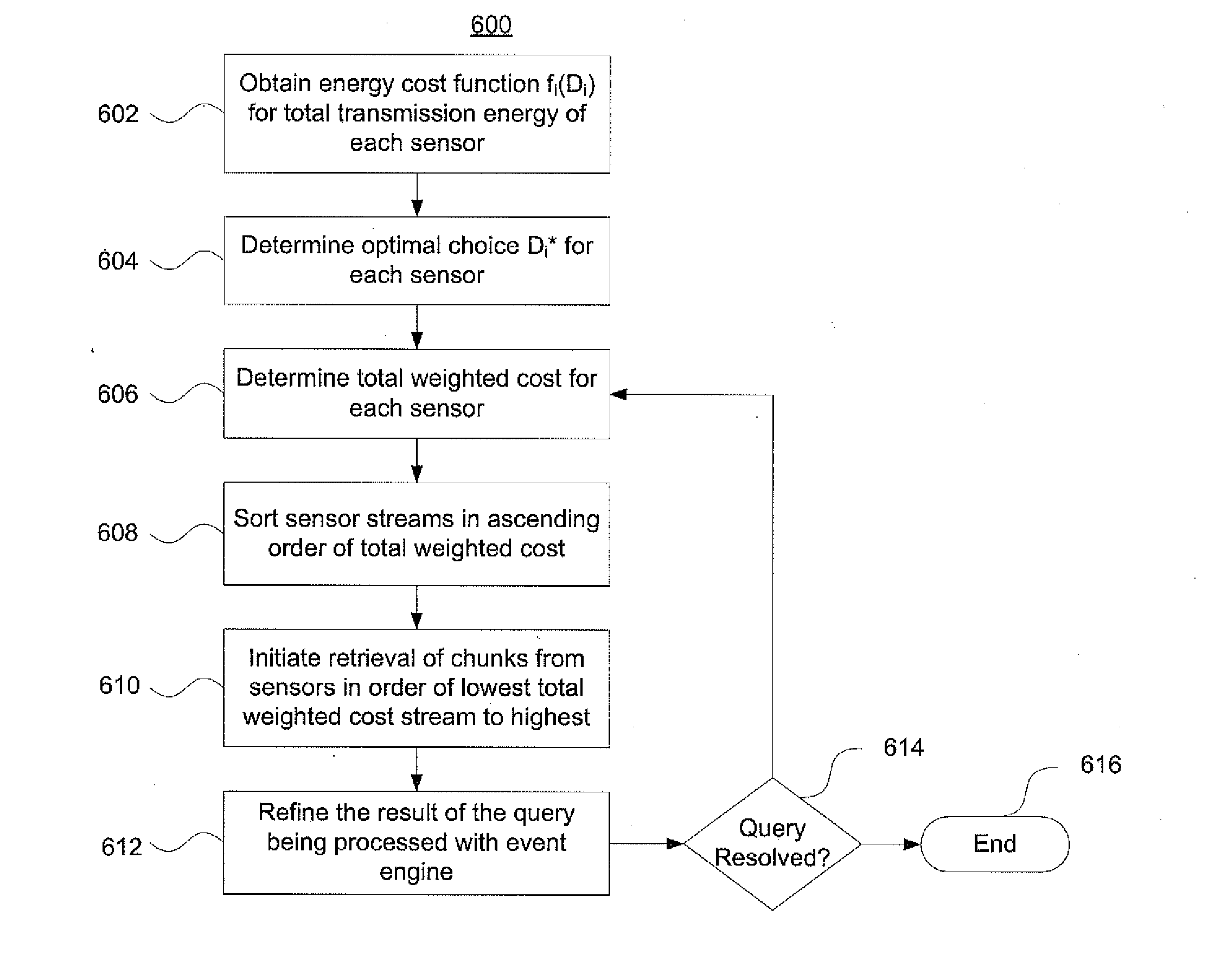
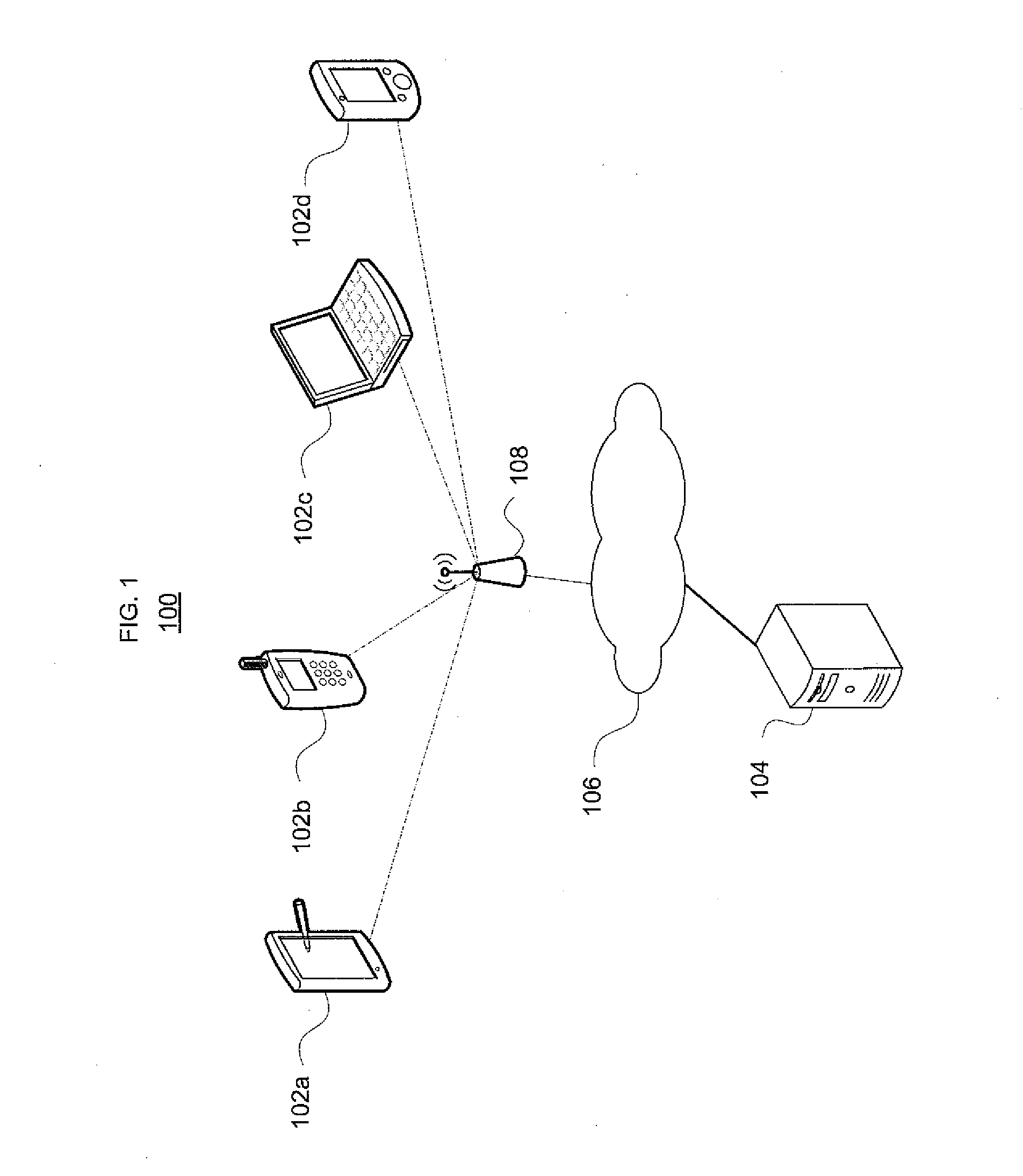
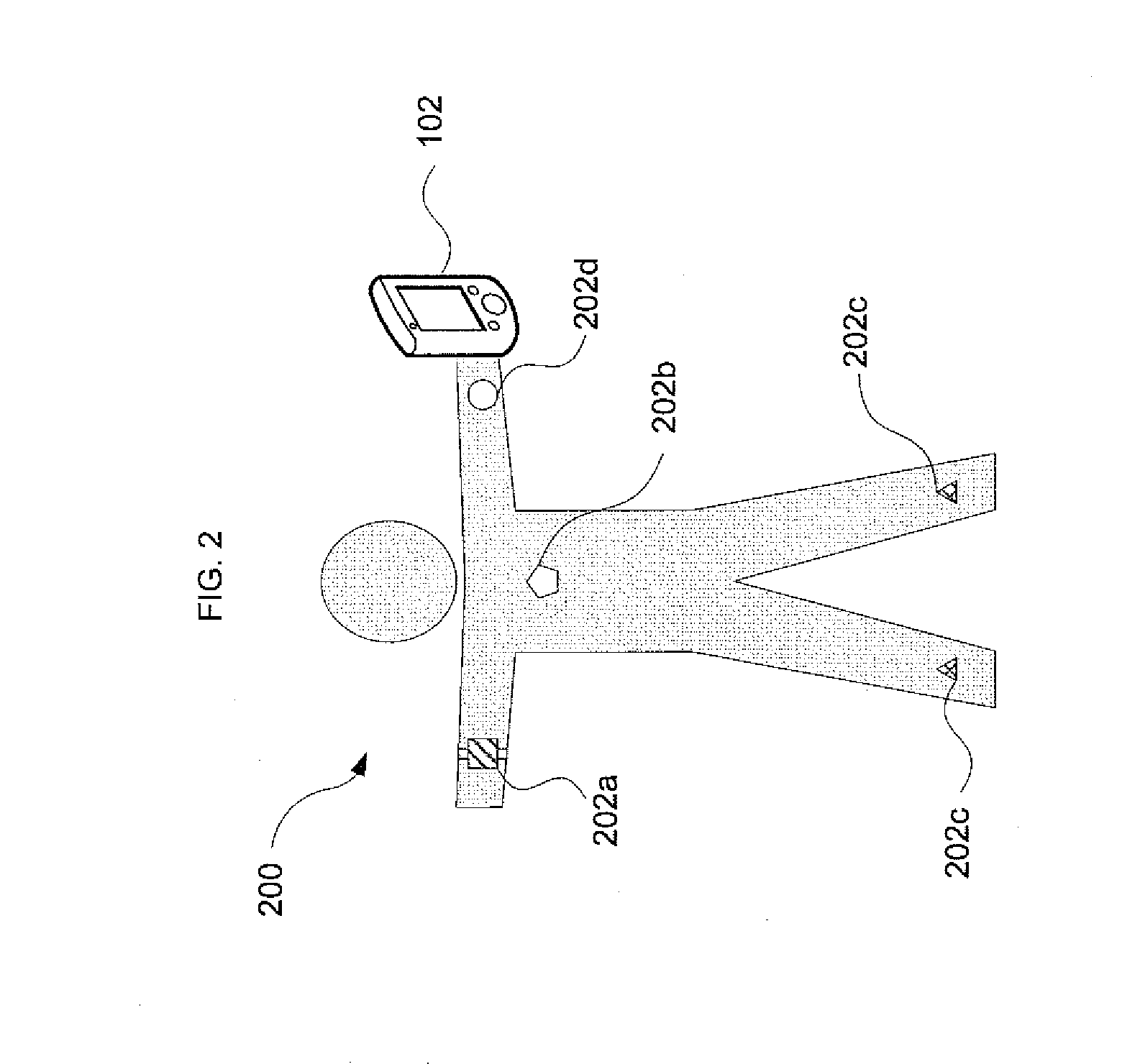
Optimizing evaluation patterns and data acquisition for stream analytics in resource-constrained wireless environments
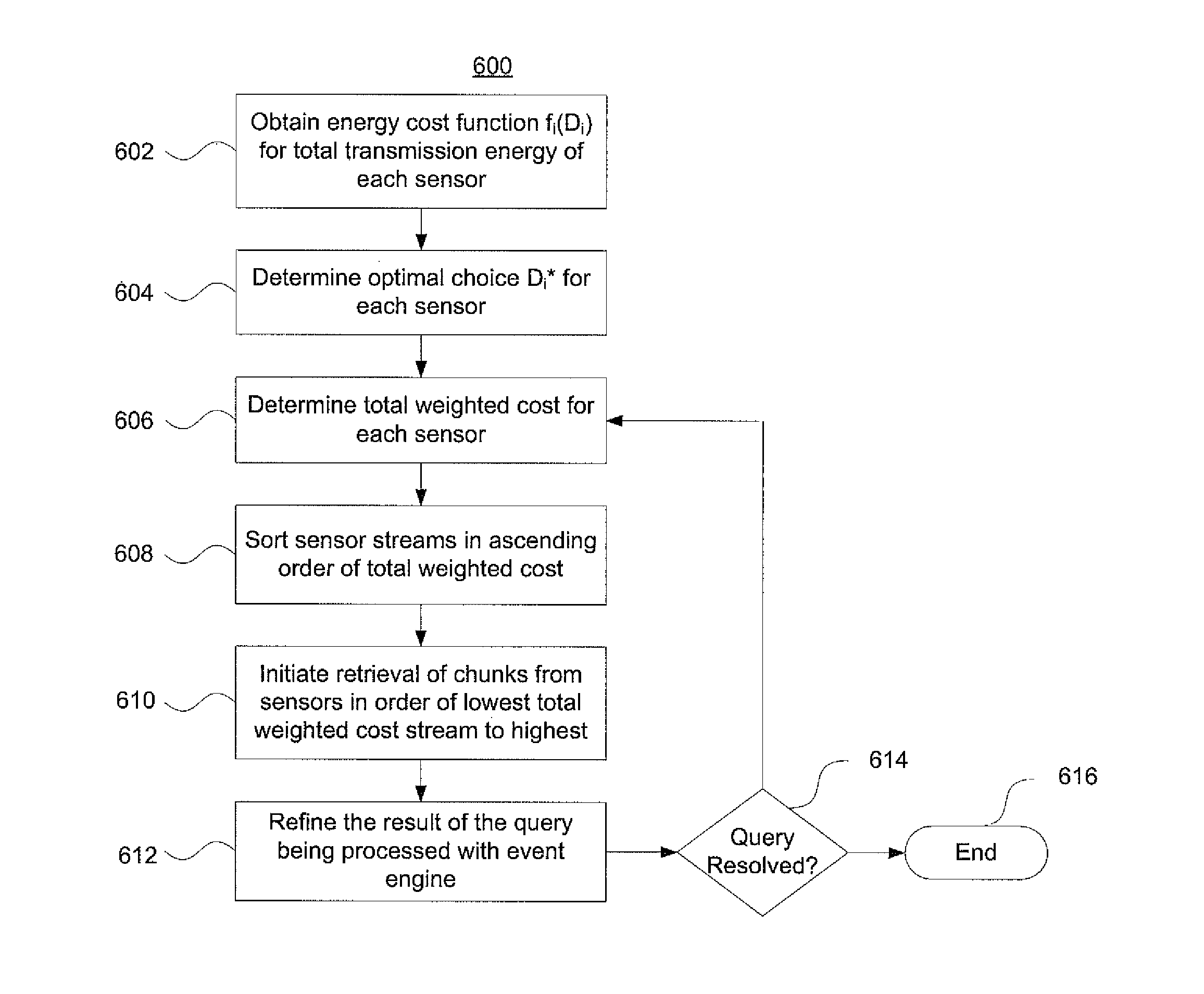
Mobile wireless devices may receive data streams from multiple remote sensors. The sensors may have limited power supplies and memory capacity. Aspects of the invention use statistical characteristics of the sensor data streams and the cost of acquiring a single element of each stream to determine what sequence the sensors should send their data streams in. The cost of acquiring the data may be, modified dynamically, depending on parameters such as block size. Additional factors, such as a sensor's buffer capacity, may limit the amount of stream elements that may be cached and affect the sensors' stream transmit sequence. The evaluation order may be dynamically modified using an event processing engine, to reflect both changing statistics of underlying sensor stream tuples and time-varying acquisition costs associated with individual streams. This helps to increase in the operational lifetime of the sensors and associated monitoring applications.
Owner:TELCORDIA TECHNOLOGIES INC
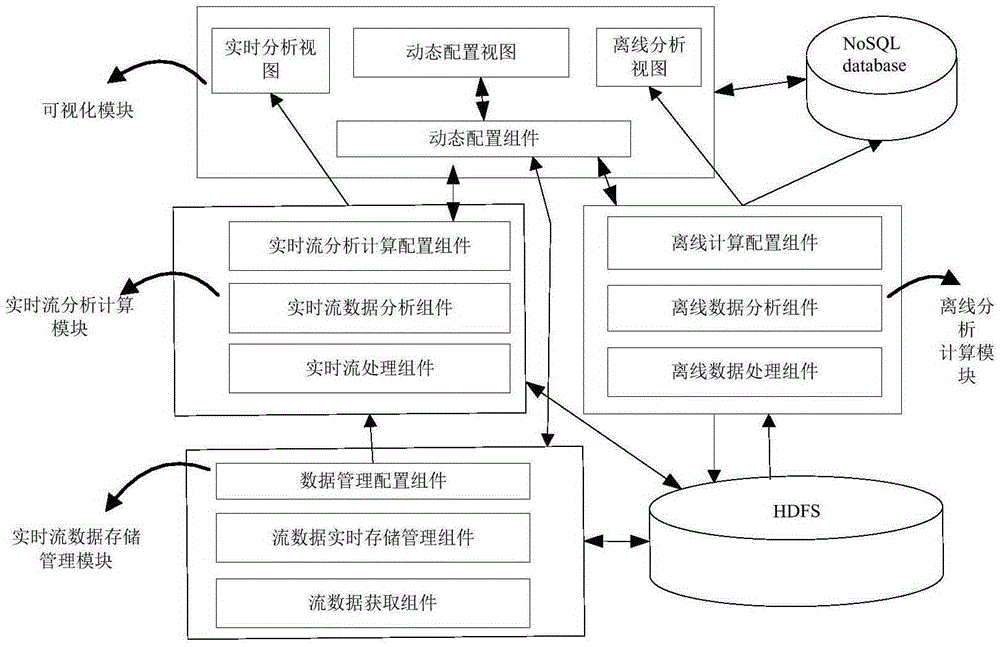
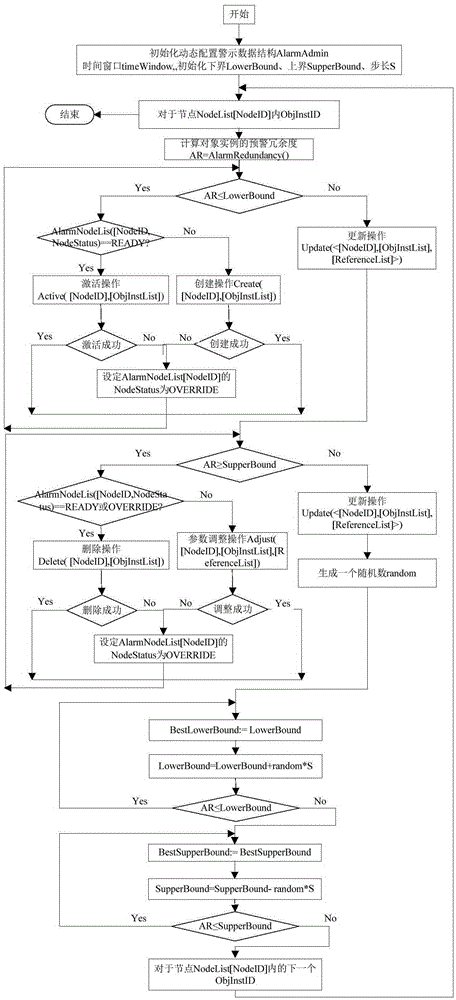
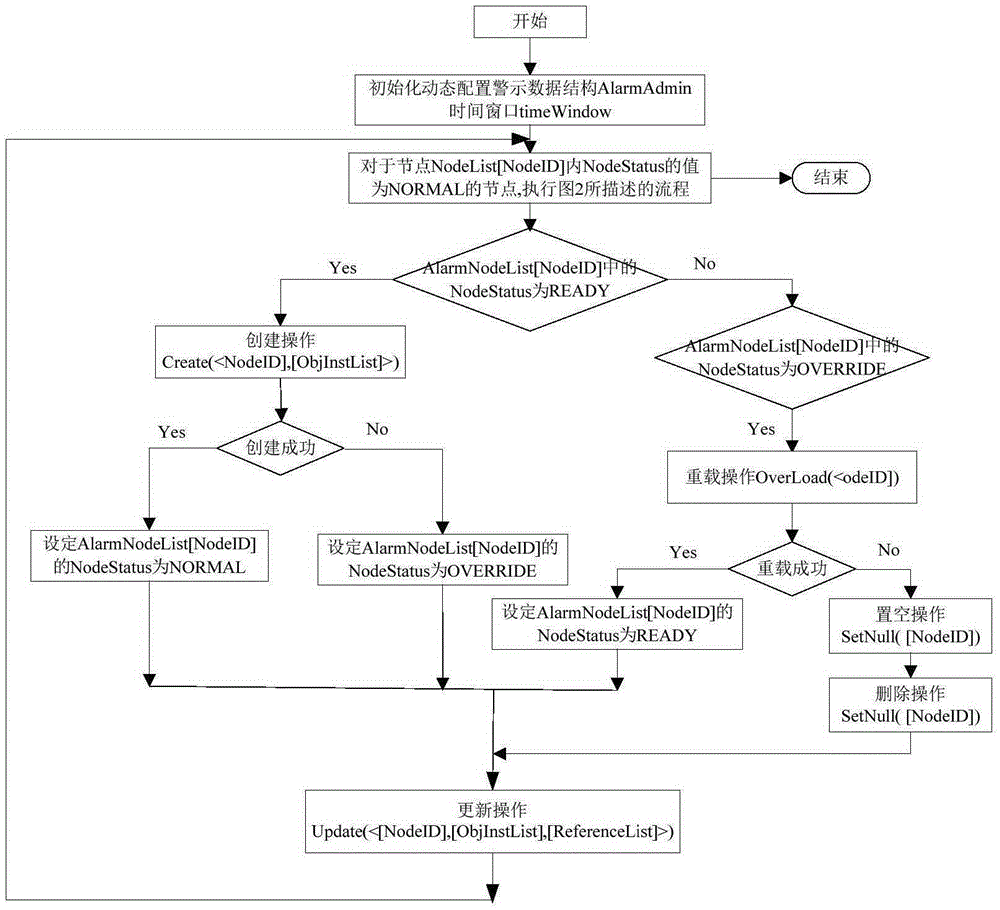
Dynamically configured big data analysis system and method
ActiveCN105279603ARealize configuration optimizationImprove reliabilityResourcesSpecial data processing applicationsData analysis systemTime data
The invention discloses a dynamically configured big data analysis system and method. The system includes a real-time data storage management module, a real-time flow analysis and calculating module, an off-line analysis module, and a visualization module. At least one assembly capable of performing dynamical configuration management is arranged in each module, for example, a data management configuration assembly, a real-time flow analysis and calculating configuration assembly, an off-line analysis and calculating configuration assembly, and a dynamic configuration assembly. The invention further provides a dynamical configuration method of the big data analysis system. A data structure and an information structure of each module are designed, and a calculating method of warning redundancy and a dynamic configuration method are provided through the dynamic configuration of a state information driving system of a warning data structure in a dynamic configuration manager. According to the invention, the system can run at an efficient big data analysis and calculating level, and the optimization process of big data analysis platform management is effectively solved.
Owner:FUJIAN NORMAL UNIV
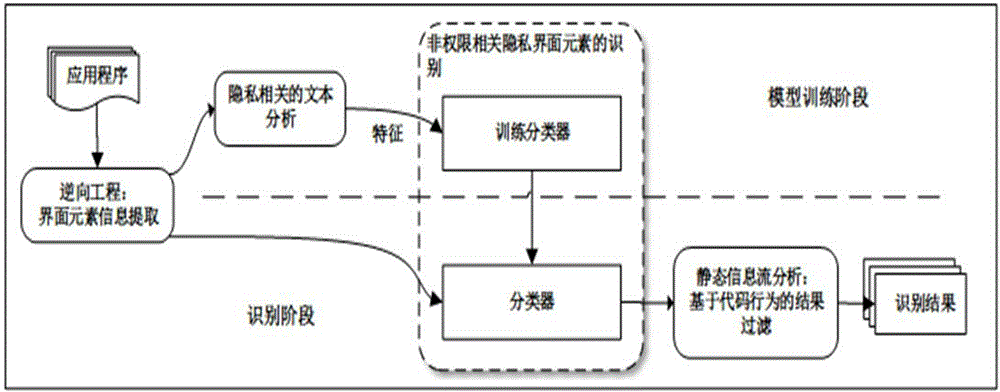
Method for identifying permission-irrelevant private data in Android application program
ActiveCN104966031AImprove securityDigital data protectionNatural language data processingData sourceUser privacy
The invention belongs to the technical field of program information security detection and particularly relates to a method for identifying permission-irrelevant private data in an Android application program. The method comprises four stages of data preprocessing, privacy related text analysis, non-permission privacy related interface element identification and static code information stream analysis based filtration; and mainly aiming at the permission-irrelevant private data in the Android application program outside the protection range of a permission model of an Android system, a machine learning technology and a conventional static information stream analysis technology are combined for identification. The private data can be marked as a sensitive data source by identifying the private data, and a basis is provided for monitoring and protection of the private data by further combination of a conventional static information stream analysis and detection technology or a dynamic stain information tracking and detection technology, so that the leakage risk of the private data of a user is lowered.
Owner:FUDAN UNIV
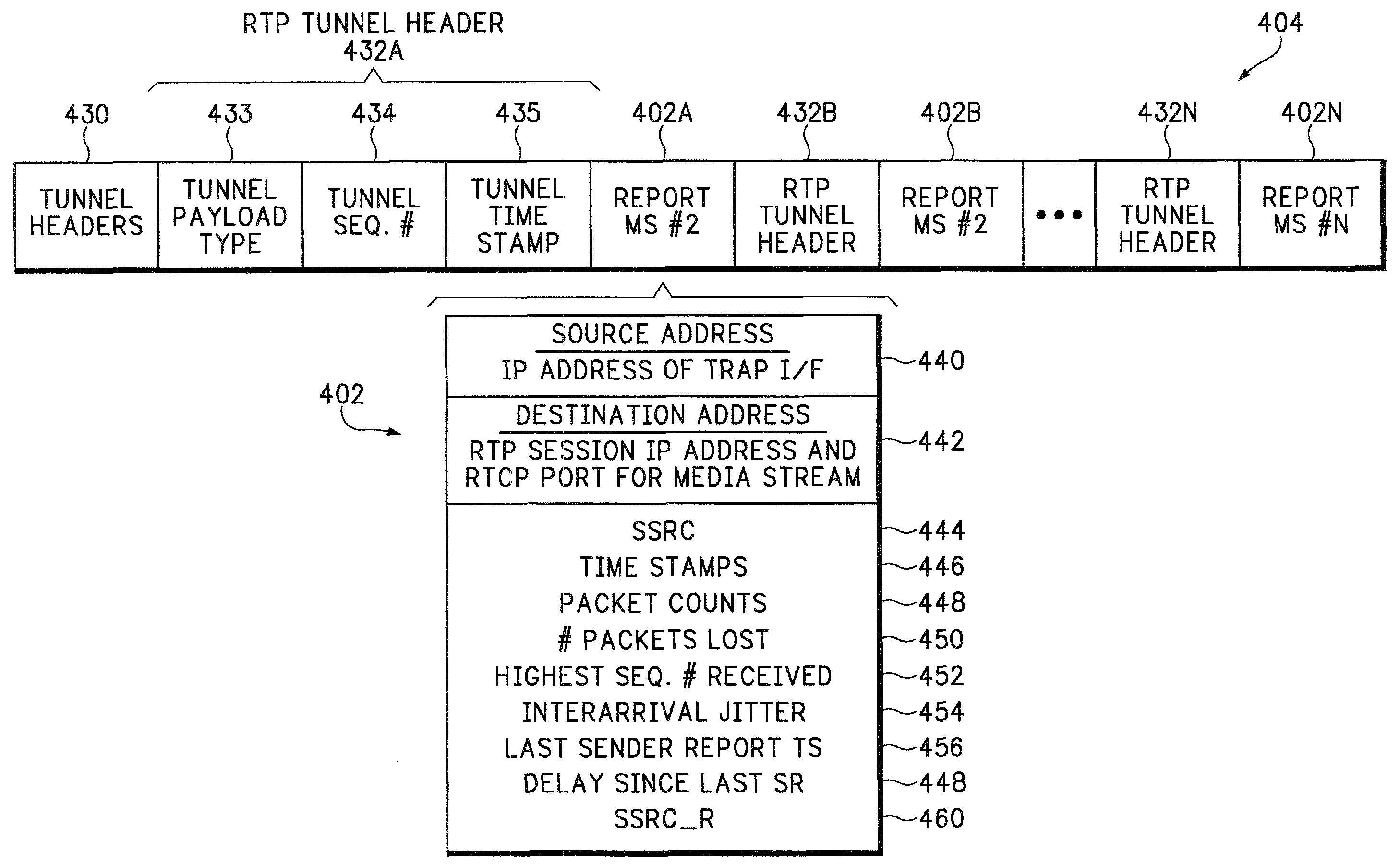
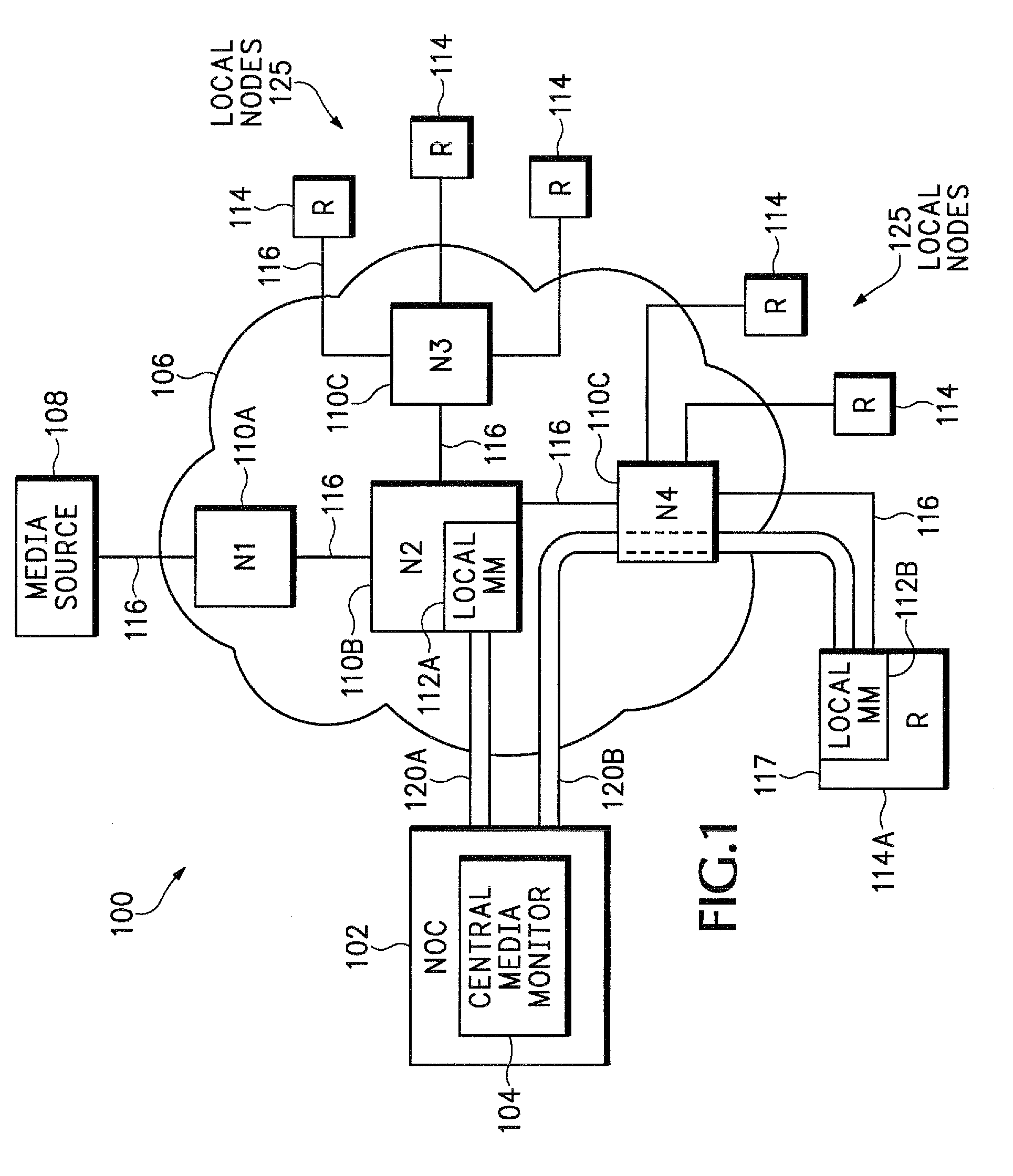
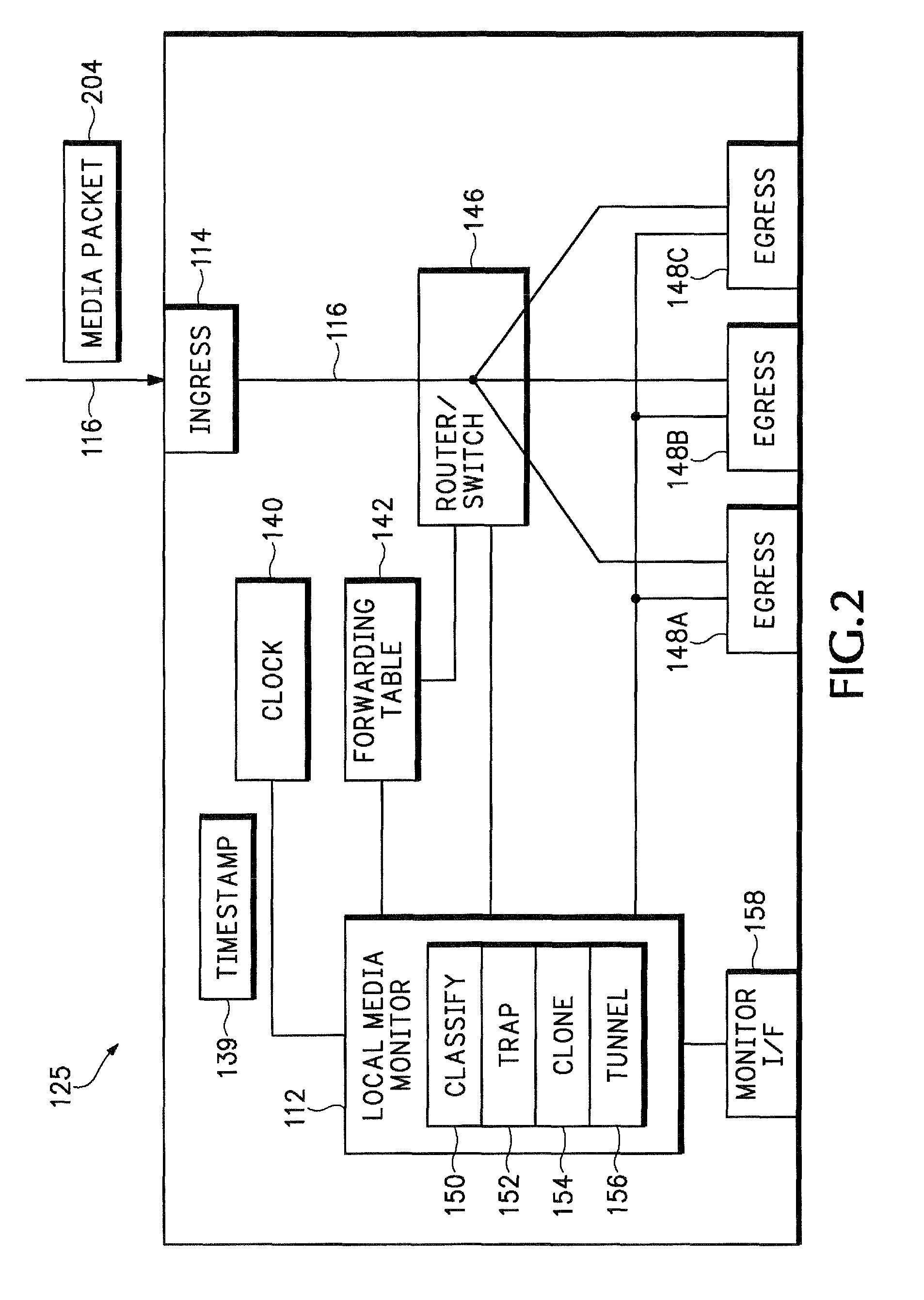
Tunneling reports for real-time internet protocol media streams
A router, switch, or other network node generates reports that contain packet level statistics and other information for a monitored media stream. The media stream reports reduce the amount of bandwidth typically required for sending monitored media stream information back to a central analysis device. However the computation of other media stream analytics, such as long term statistical averaging or quality metric computation, is performed by the central analysis device to remove some of the processing burden from the individual network nodes.
Owner:CISCO TECH INC
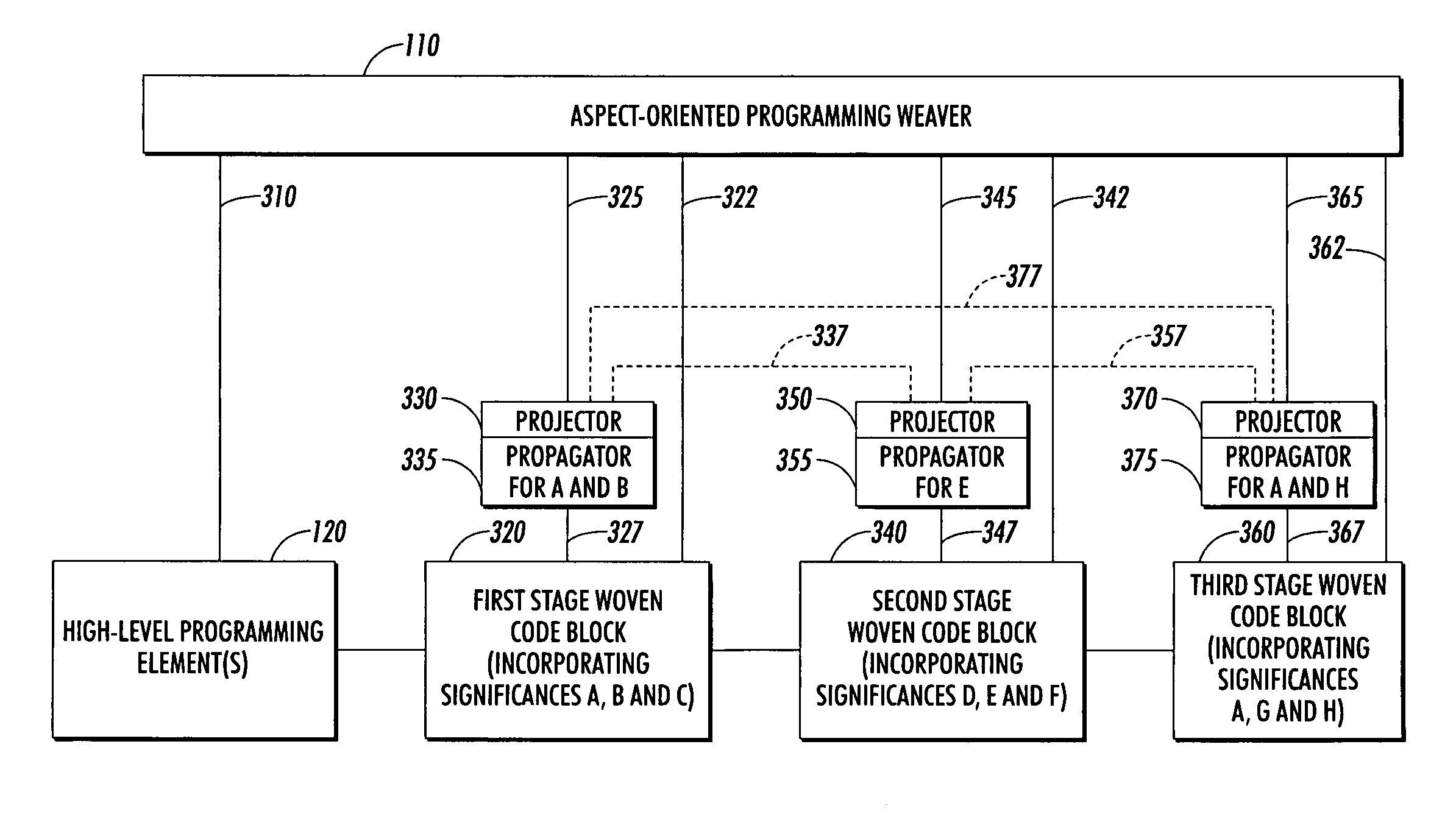
Aspect-oriented programming with multiple semantic levels
InactiveUS7140007B2Decrease in circularity“macro” style programming can be reduced or avoidedSoftware engineeringSpecific program execution arrangementsNon localTheoretical computer science
Techniques that allow the operations of a program to be intercepted and intervened with are known. These techniques are restricted by the same limited view of the program's data that is currently available at a base level of an object or method. Some aspects need access to more information about the program's data of one or more objects than is available at the base level. An aspect of aspect-oriented programming systems, methods and environments examines the results of a computation at one stage. That aspect affects only subsequent stages of the computation, so that no circularity exists. Custom flow analyses, whether local or global, can also be performed at each stage to propagate non-local information. “Macro” style programming can be reduced or avoided, as programming can be facilitated in terms of manipulating the results of various computational stages instead of in terms of manipulating blocks of code.
Owner:XEROX CORP
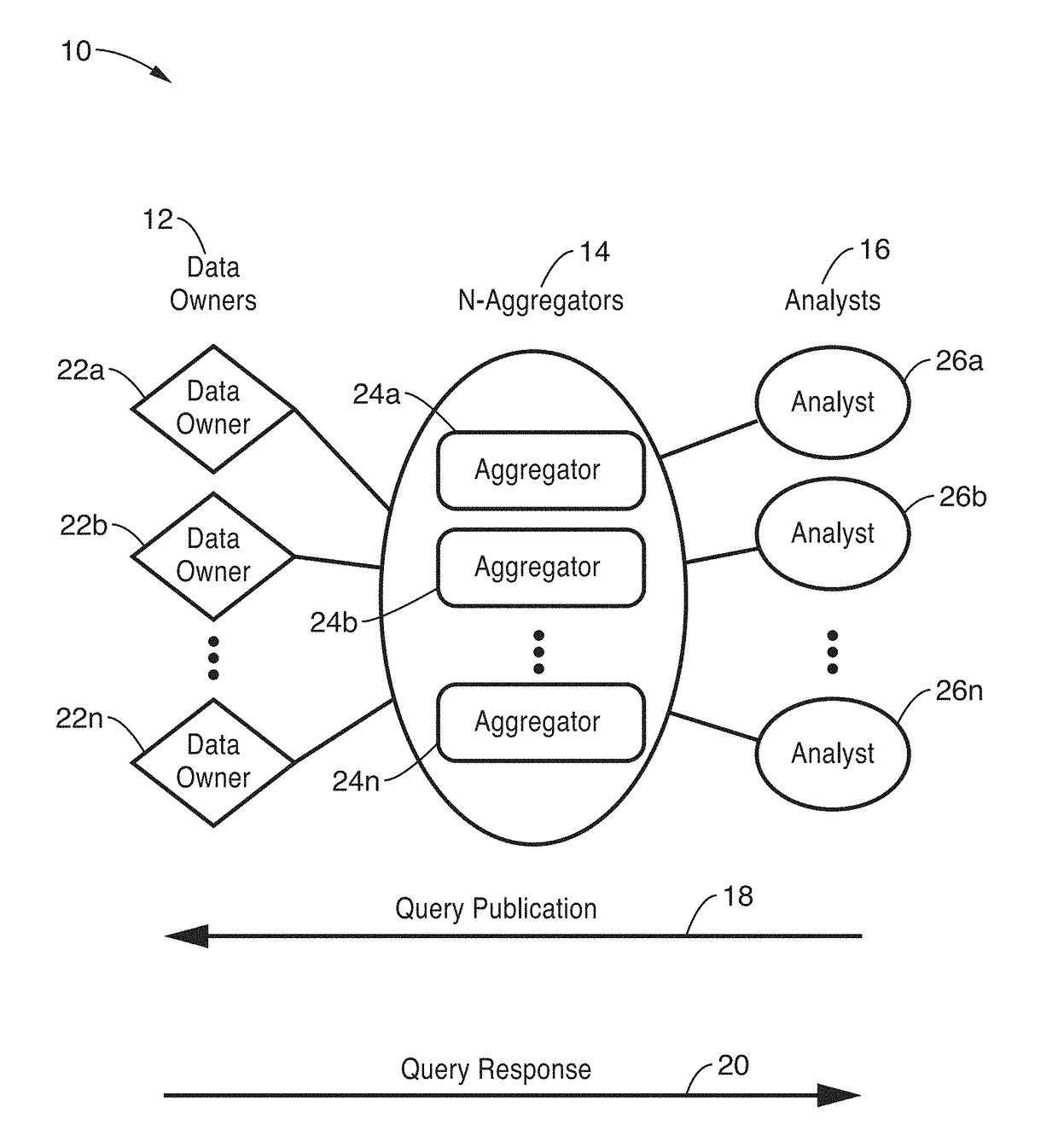
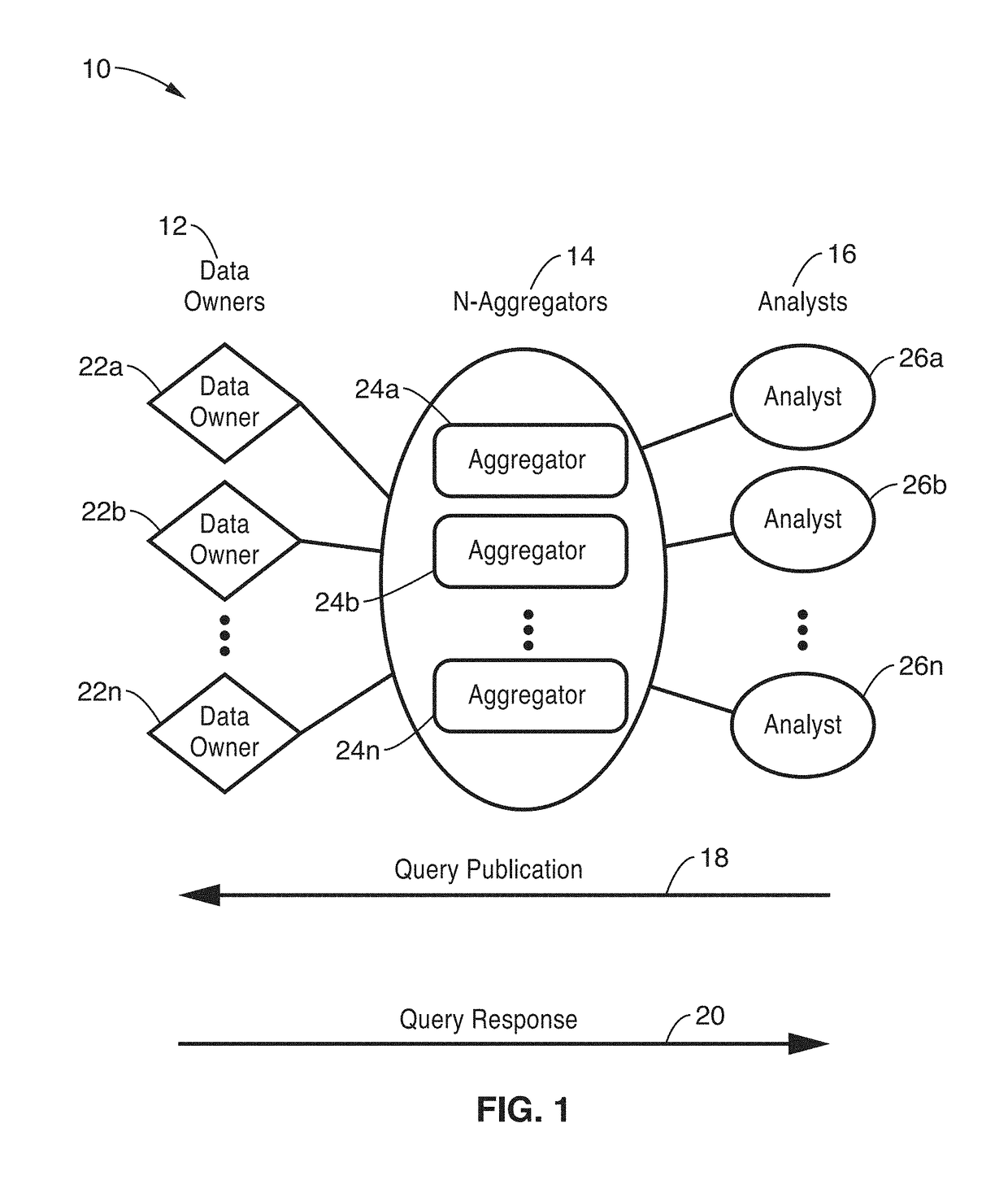
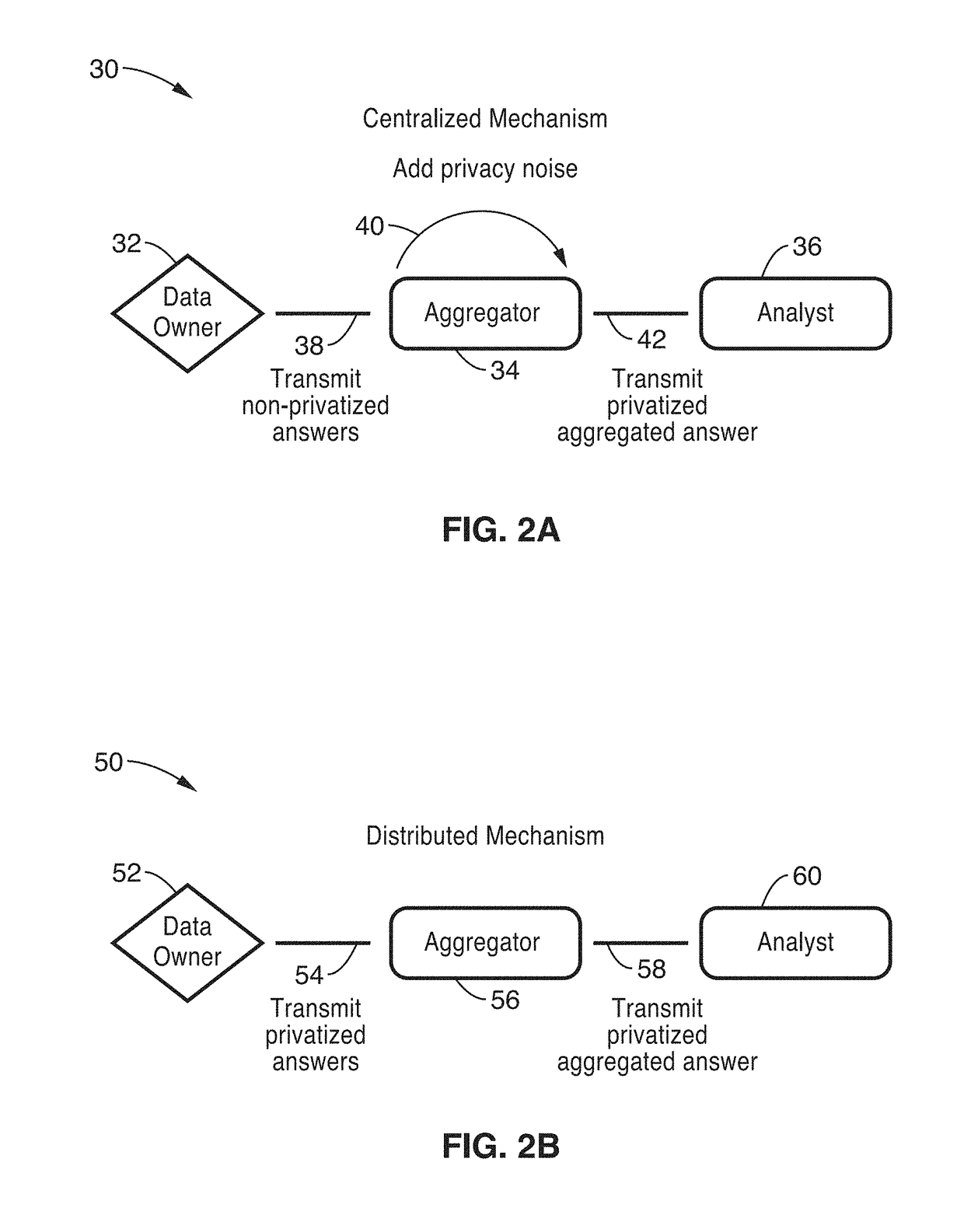
Privacy-preserving stream analytics
ActiveUS20170353855A1Shorten the timeIncrease profitDigital data protectionTransmissionInternet privacyThe Internet
Privacy-preserving stream analytics (personal data collection method, apparatus, and / or system) from an electronic (e.g., mobile) device providing communications, such as to a network (e.g., Internet). Data queries from a data analyst are received but not directly answered with a truthful query response. Truthful responses are privatized and anonymized based on a randomized response mechanism which releases privatized data and not the original answer. Anonymously transmitting randomized responses from the data owner to data aggregator using shares, each share of which is individually transmitted to an independent aggregator, which is configured for independently and asynchronously process each share, and sharing results with one another to arrive at a query response over an aggregate number of data owners.
Owner:RGT UNIV OF CALIFORNIA
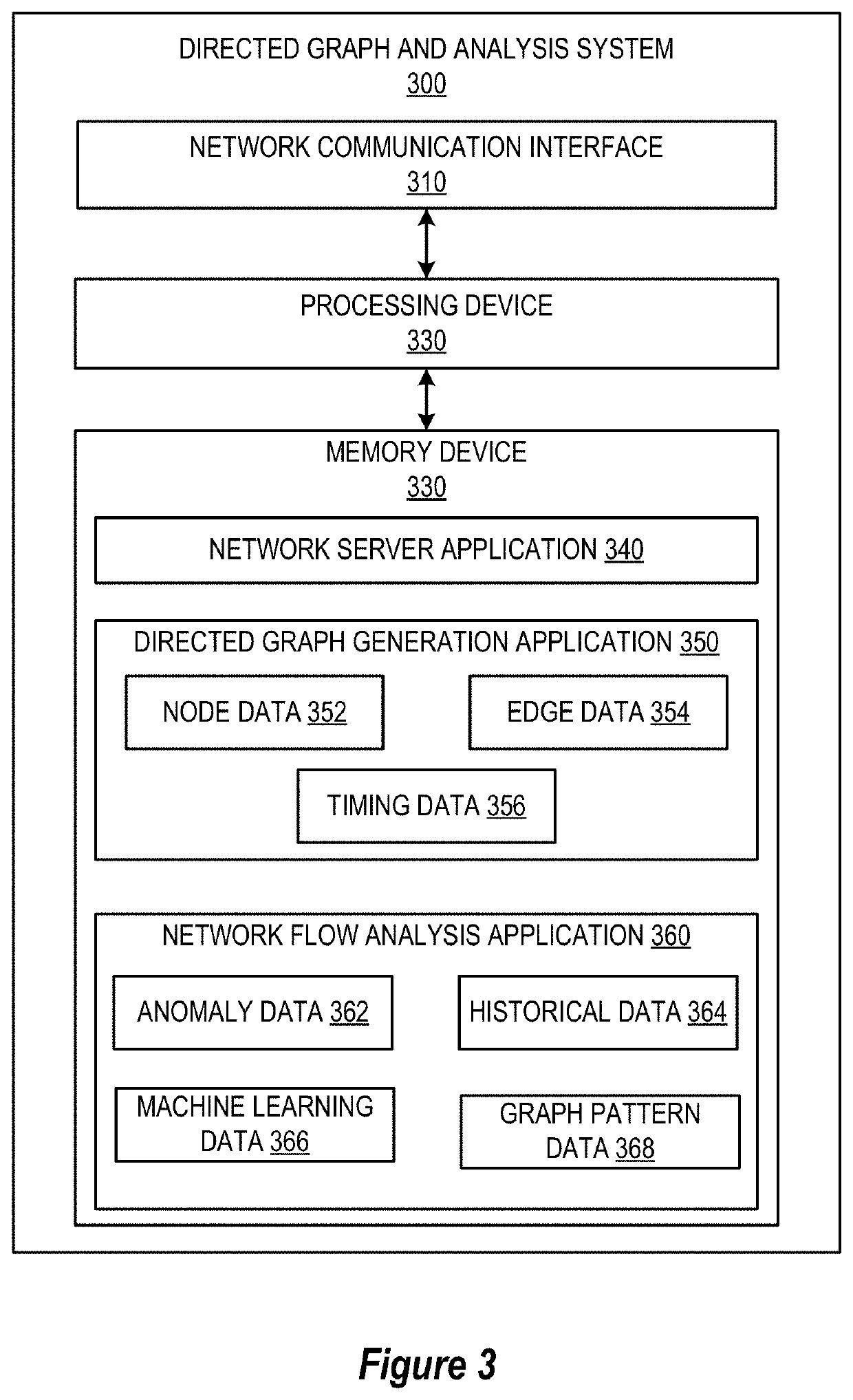
System for anomaly detection and remediation based on dynamic directed graph network flow analysis
Embodiments of the present invention provide a system for dynamic graph network flow analysis and real time remediation execution. Information for multiple accounts is extracted to generate a plurality of dynamic directed and undirected graphs made up of multiple nodes and edges. The nodes represent at least one of the multiple accounts, and each edge represents at least an association or transfer between two nodes. A custom entropy and divergence value is determined for each pair of nodes linked by an edge, as compared to similar or related nodes and edges. A nodal set of the graphs is identified as having aggregate custom entropy and divergence value that is associated with anomalous directional flow from a first node, across intermediary nodes, to a second node. A remediation action is executed with respect to one or more accounts associated with the nodal set in response to identifying the anomalous directional flow.
Owner:BANK OF AMERICA CORP
Automatic method for analyzing constitution and diversity of bacterial community of 16SrRNA gene
ActiveCN106815492AVarious methods of data mining analysisIn-depth analysis of data mining methodsSequence analysisSpecial data processing applicationsTechnical standardModularity
The invention discloses an automatic method for analyzing constitution and diversity of a bacterial community of a 16SrRNA gene. The automatic method comprises the following steps: in 16SrRNA sequencing data analysis process, by taking original sequencing sequence data as input, calling a standard analysis tool (such as Mothur and QIIME) of the industry, and performing visualization on data finally, thereby obtaining analysis results which are easy to analyze. The automatic method includes popular main analysis items at present, meanwhile analysis contents can be modularized, relatively rich and deep data mining analysis methods can be available, different analysis module contents can be combined according to different demands, and process procedures can be relatively reasonably arranged; and in addition, analysis errors caused by different sequencing depths can be eliminated, and the analysis results can be relatively comprehensive, accurate and reliable.
Owner:SHANGHAI PASSION BIOTECHNOLOGY CO LTD
Intelligent public transport cloud-brain system based on big data
InactiveCN110705747AQuick showHigh degree of intelligenceForecastingResourcesOperation schedulingReal time analysis
The invention relates to an intelligent public transport cloud-brain system based on big data. The system comprises an acquisition layer, a processing layer, an application layer and a user layer; bysetting an operation analysis module, a network planning module and a passenger flow analysis module as sub-levels, operation indexes of buses of all lines can be analyzed in real time, a network optimization scheme is formulated, and passenger flow analysis is carried out through multiple passenger flow analysis modes; therefore, four hierarchies of the intelligent public transport cloud brain system based on big data and big data cloud platform application are set; functions of operation scheduling, passenger flow analysis, network planning and the like can be realized, rapid display and real-time monitoring of data of operation scheduling, passenger flow analysis, network planning and the like by a user layer are further realized, the intelligent degree is high, and the real-time performance and the accuracy of information display are relatively good.
Owner:广州交信投科技股份有限公司
Precise thread-modular summarization of concurrent programs
ActiveUS20110078511A1Redundant data error correctionSpecific program execution arrangementsTheoretical computer scienceData-flow analysis
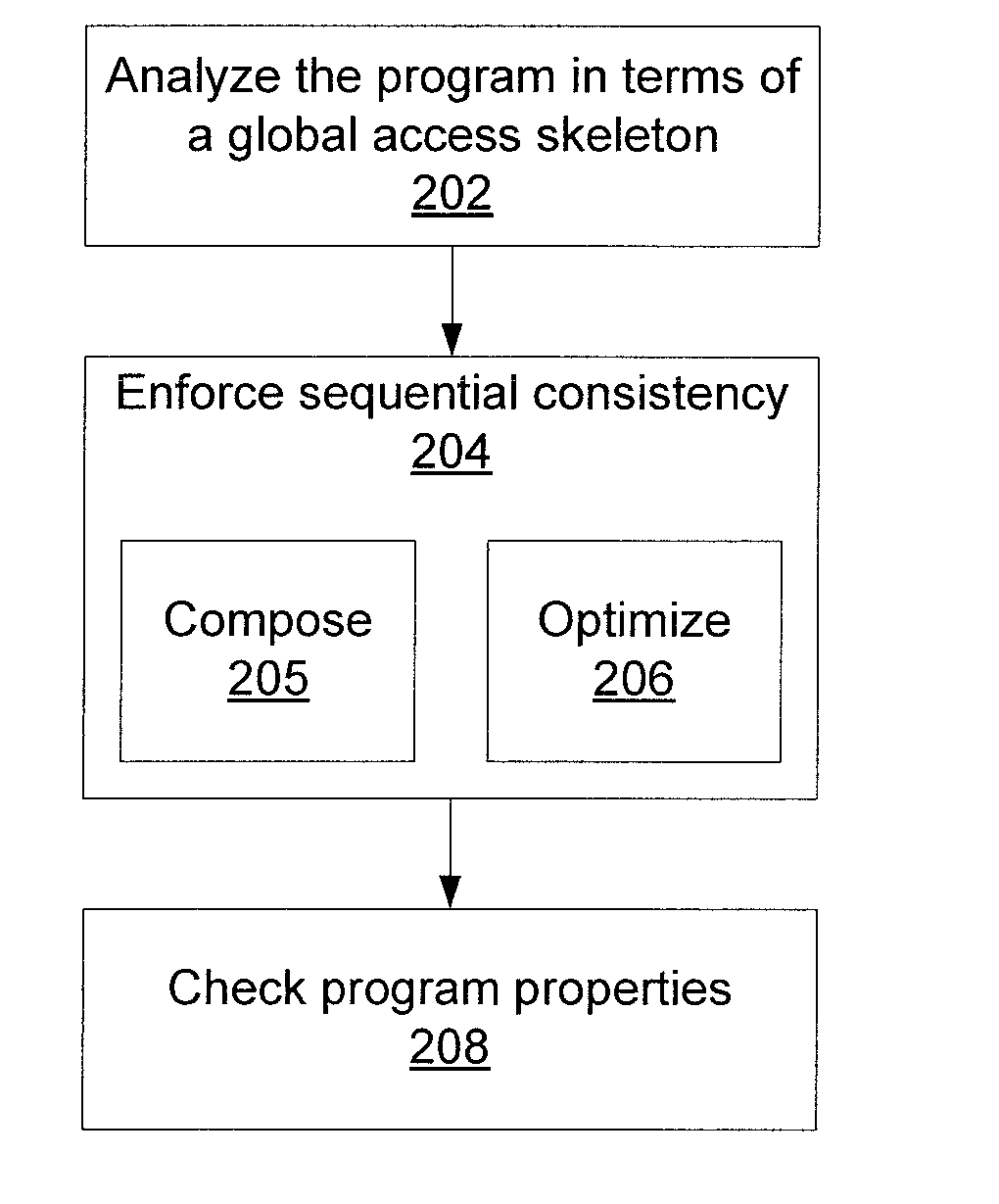
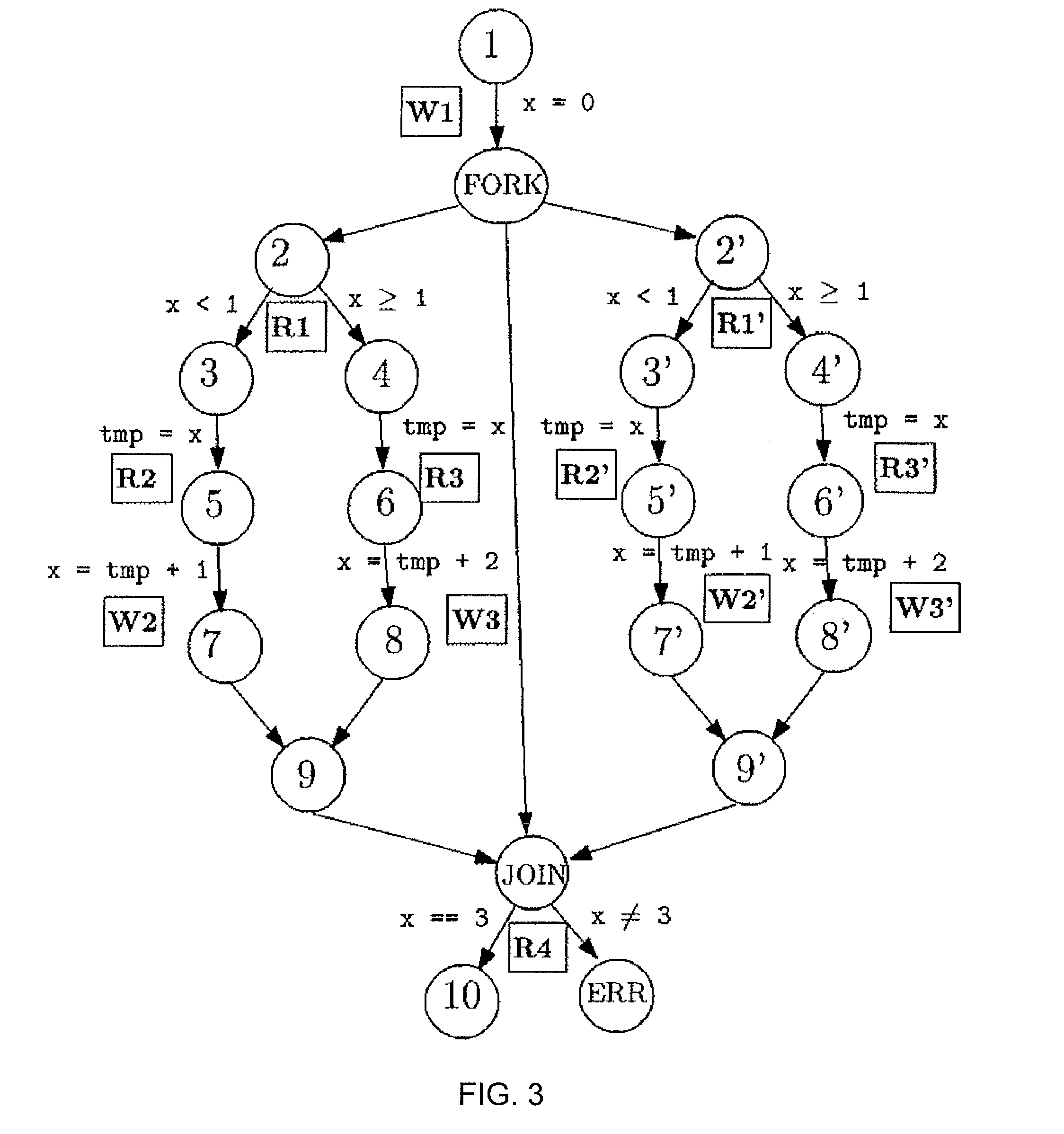
Methods and systems for concurrent program verification. A concurrent program is summarized into a symbolic interference skeleton (IS) using data flow analysis. Sequential consistency constraints are enforced on read and write events in the IS. Error conditions are checked together with the IS using a processor.
Owner:NEC CORP
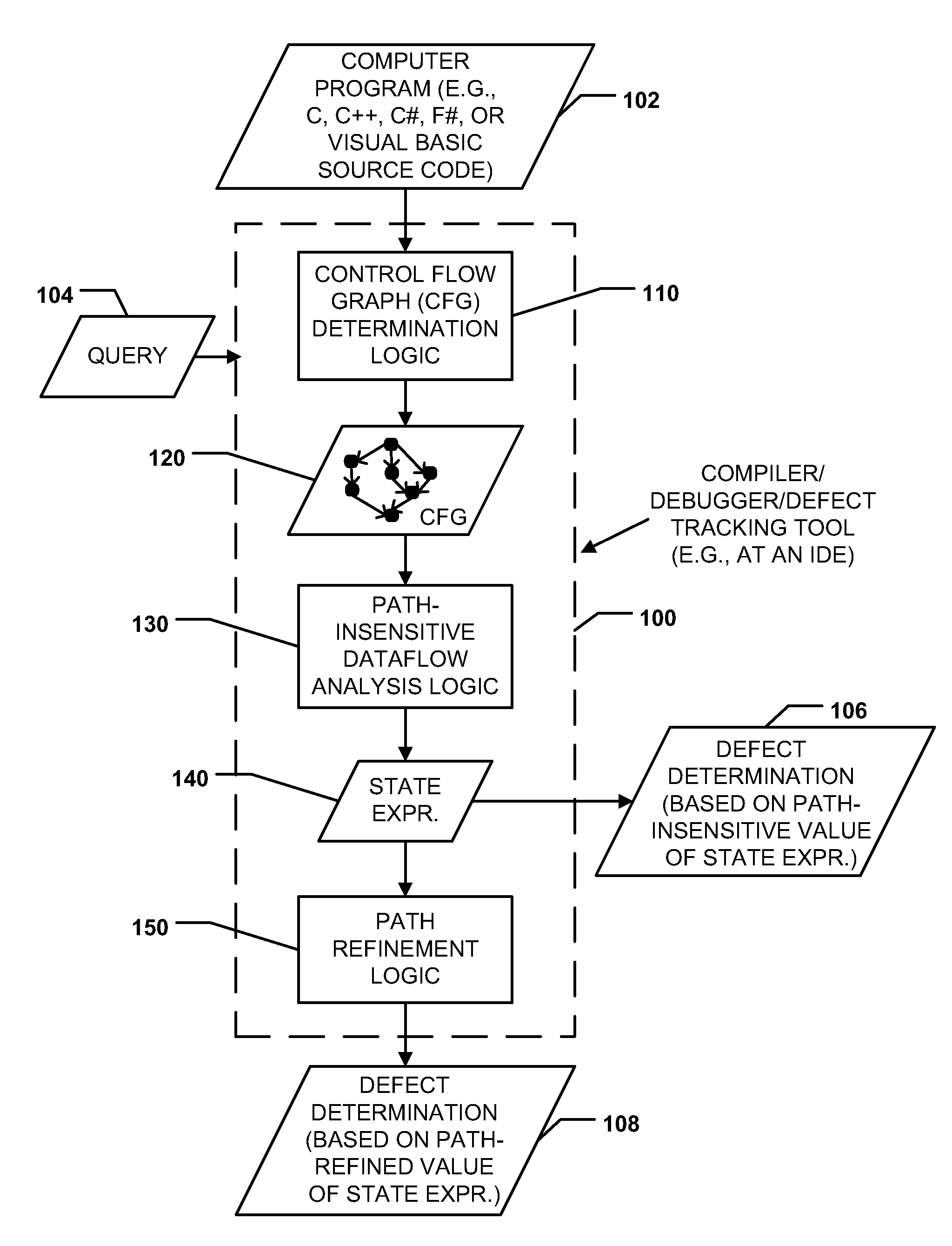
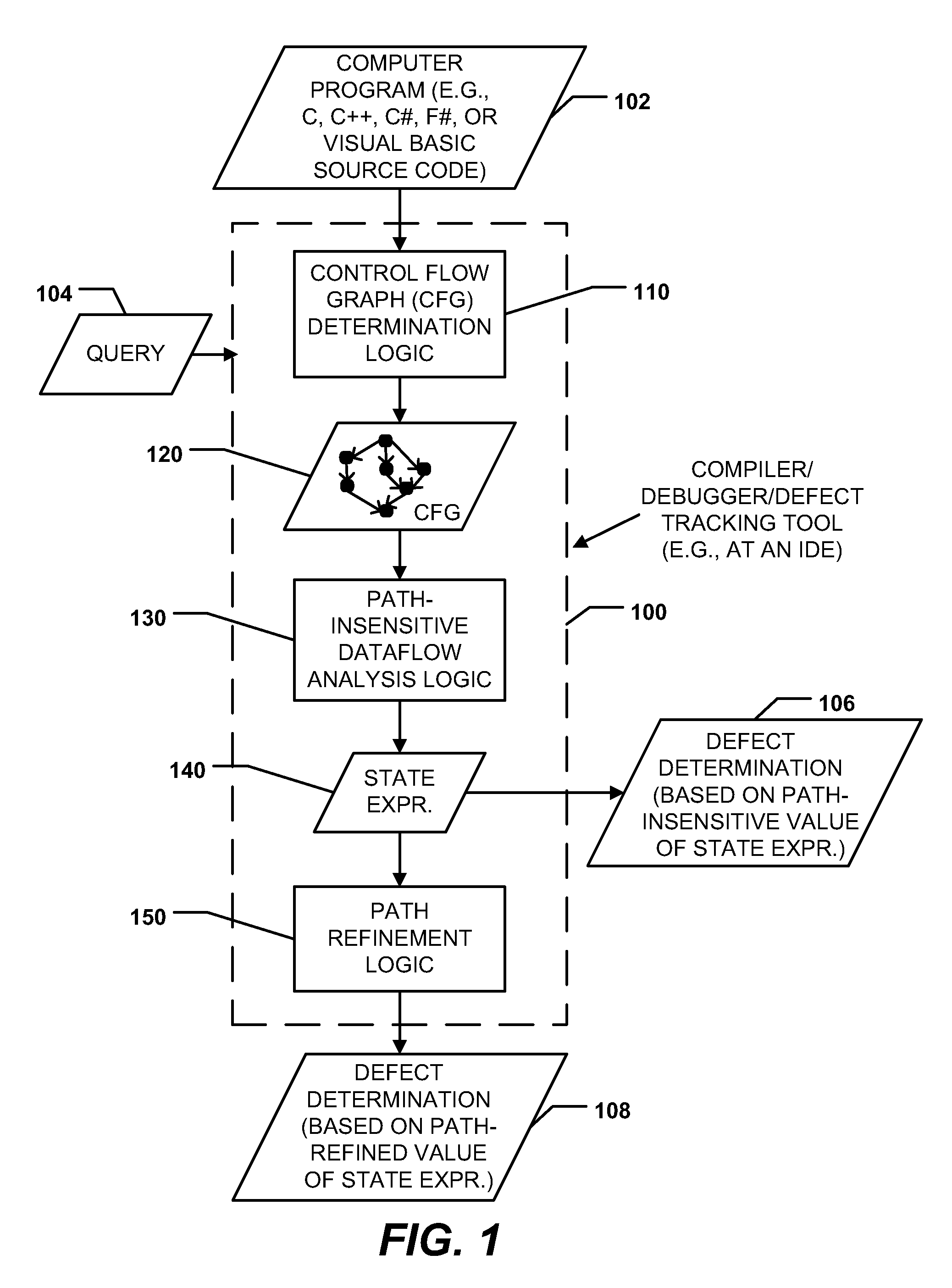
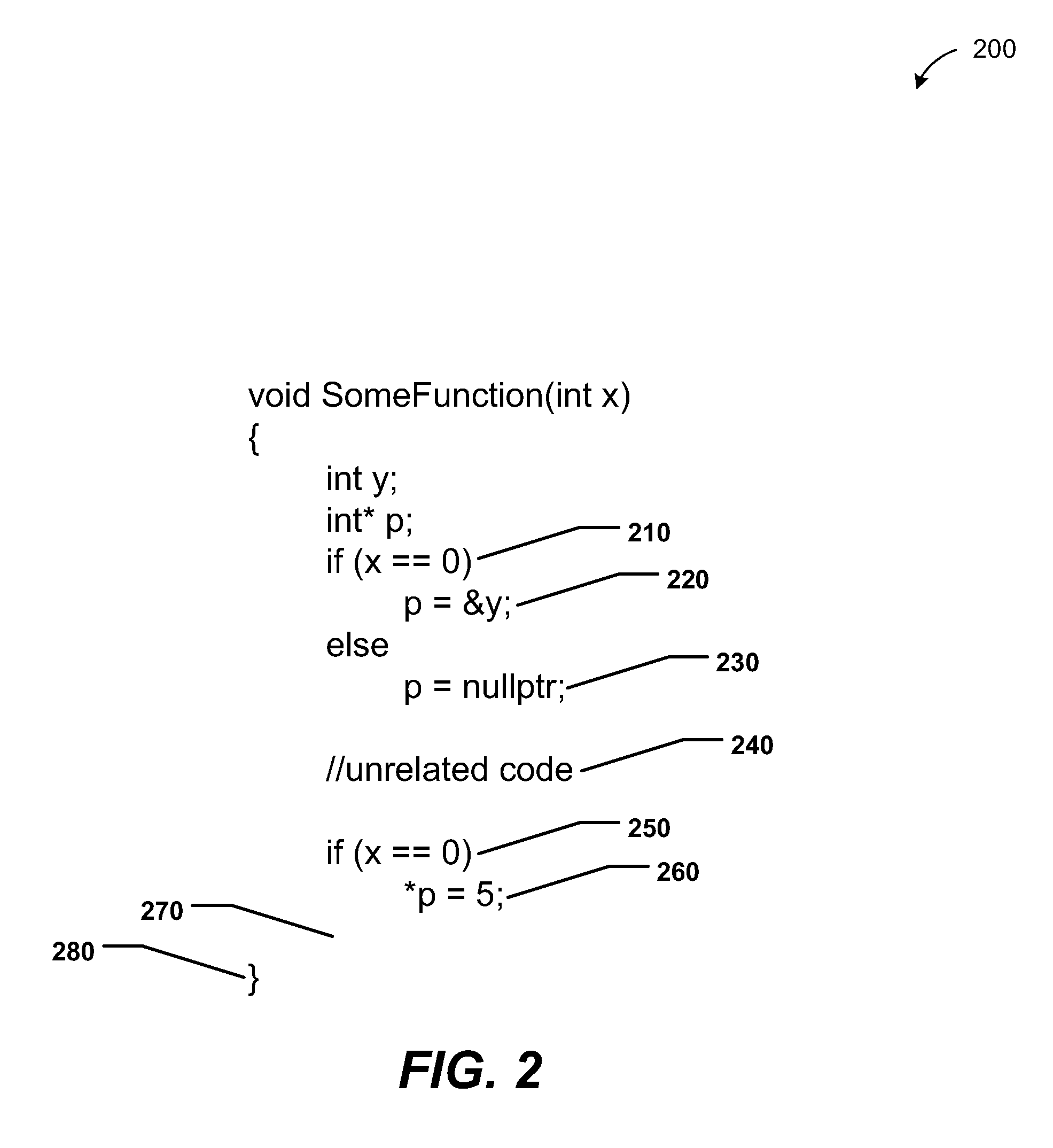
Path-sensitive dataflow analysis including path refinement
InactiveUS20110145799A1More accuracySolve excessive resource consumptionError detection/correctionSpecific program execution arrangementsComputer programDataflow
Methods, systems, and computer-readable media are disclosed to perform path-sensitive dataflow analysis including path refinement. A path-insensitive dataflow analysis may be performed on a control flow graph (CFG) of a computer program to detect a set of potential defects in the computer program. A path-sensitive dataflow analysis may be performed to identify one or more infeasible paths of the CFG without modifying the CFG. Potential defects associated with the one or more infeasible paths may be removed from the set of potential defects to produce a resulting reduced set of potential defects. The resulting reduced set of potential defects may be output.
Owner:MICROSOFT CORP
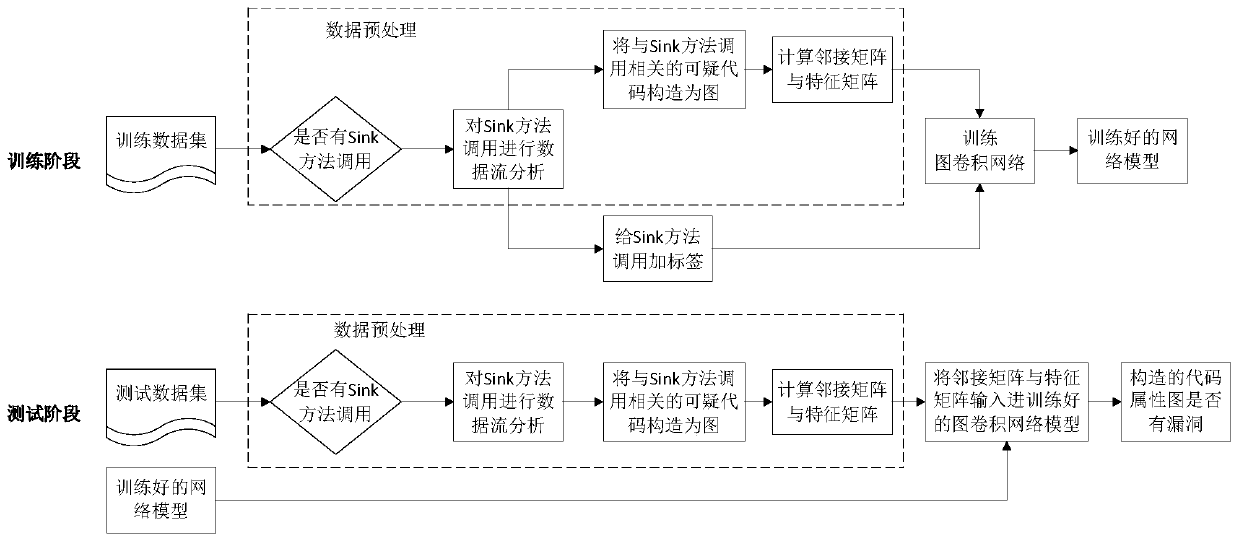
Source code vulnerability detection method based on graph convolution network
ActiveCN111460450ANarrow the scope of the auditShorten the timePlatform integrity maintainanceMachine learningData streamAlgorithm
The invention relates to a source code vulnerability automatic detection method based on a graph convolution network. In the training phase, carrying out data acquisition and data preprocessing; judging whether the source code is called by a sink method or not; calling a sink method to perform data flow analysis, constructing a code attribute graph, calculating an adjacent matrix and a feature matrix of the code attribute graph, labeling the code attribute graph, taking the adjacent matrix and the feature matrix in the code attribute graph as input of a graph convolution network, and trainingthe graph convolution network to obtain a trained network model; in the test stage, carrying out data acquisition and data preprocessing; judging whether the source code is called by a sink method ornot; and performing data flow analysis, constructing a code attribute graph, calculating an adjacent matrix and a feature matrix of the code attribute graph, inputting the trained graph convolutionalnetwork model, outputting a classification result of the code attribute graph, and representing whether the code attribute graph has vulnerabilities or not, i.e., whether the corresponding sink methodcall contains the vulnerabilities or not.
Owner:NORTHWEST UNIV
Multi-zone remote video monitoring system and method for network intelligent set top box
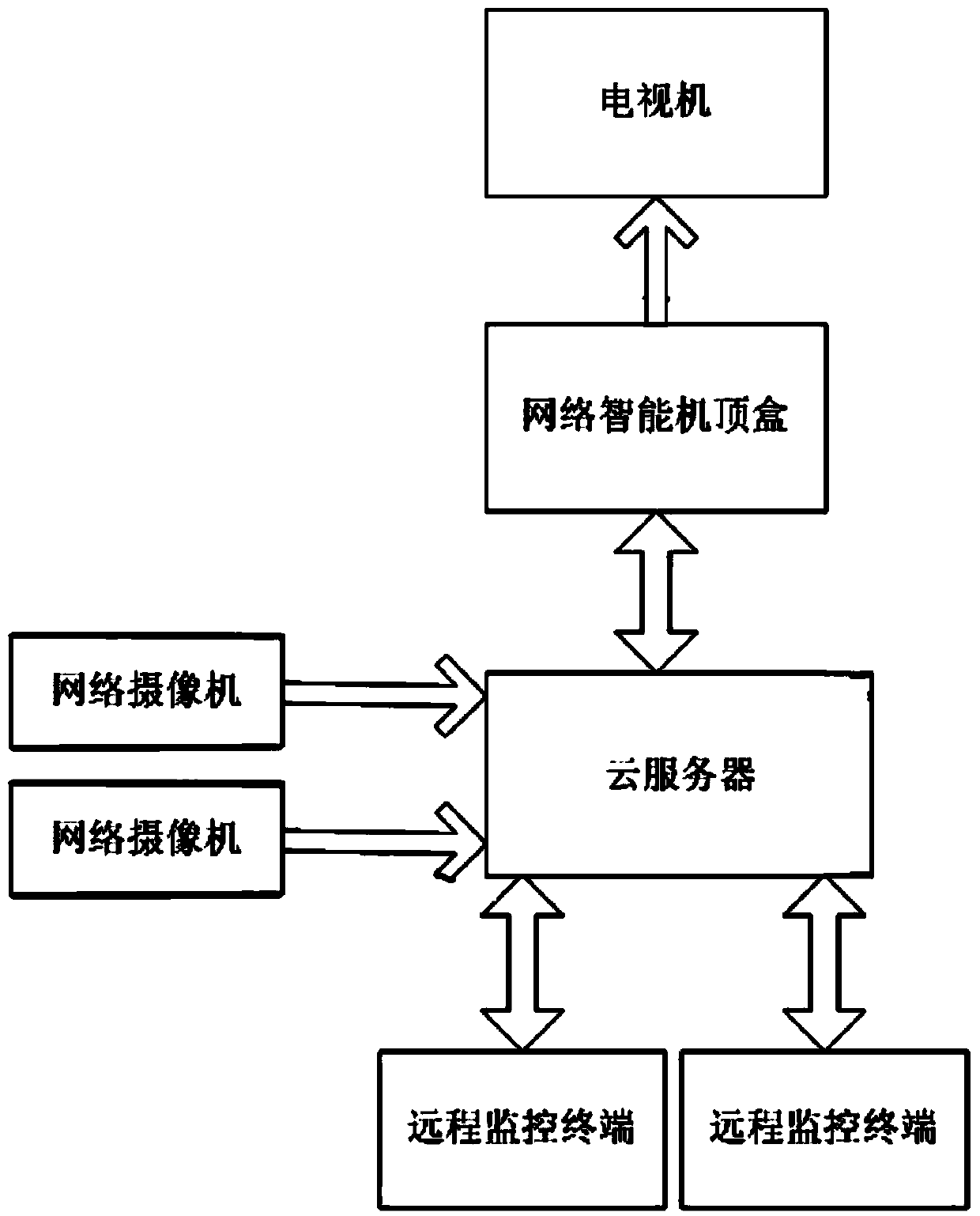
InactiveCN103747204AHas real-time monitoringHave smart careClosed circuit television systemsSelective content distributionVideo monitoringStream data
The invention relates to a multi-zone remote video monitoring system and method for a network intelligent set top box. The system comprises the network intelligent set top box, a network camera, a television, a remote monitoring terminal and a cloud server, wherein the network intelligent set top box obtains audio and video data through the network camera connected with the cloud server and displaying the audio and video data through the television and / or the remote monitoring terminal; the network intelligent set top box is connected with the front camera of the network camera through the cloud server to obtain an H264 code stream with a private header in real time, H264 data generates raw H264 data through bottom layer code stream analysis of the network intelligent set top box, and the data performs data decoding through a hard decoding core carried by the network intelligent set top box itself to generate YUV data; and the remote monitoring terminal, after receiving the YUV data, performs drawing displaying on video data. The system provided by the invention is integrated with household multimedia entertainment and safety monitoring to provide a safety guarantee for entertainment and leisure life, and is provided with such functions as real-time monitoring, intelligent care, monitoring playback, antitheft alarm and the like.
Owner:HANGZHOU JUFENG TECH
Optimizing Evaluation Patterns and Data Acquisition for Stream Analytics in Resource-Constrained Wireless Environments
Mobile wireless devices may receive data streams from multiple remote sensors. The sensors may have limited power supplies and memory capacity. Aspects of the invention use statistical characteristics of the sensor data streams and the cost of acquiring a single element of each stream to determine what sequence the sensors should send their data streams in. The cost of acquiring the data may be modified dynamically, depending on parameters such as block size. Additional factors, such as a sensor's buffer capacity, may limit the amount of stream elements that may be cached and affect the sensors' stream transmit sequence. The evaluation order may be dynamically modified using an event processing engine, to reflect both changing statistics of underlying sensor stream tuples and time-varying acquisition costs associated with individual streams. This helps to increase in the operational lifetime of the sensors and associated monitoring applications.
Owner:TELCORDIA TECHNOLOGIES INC
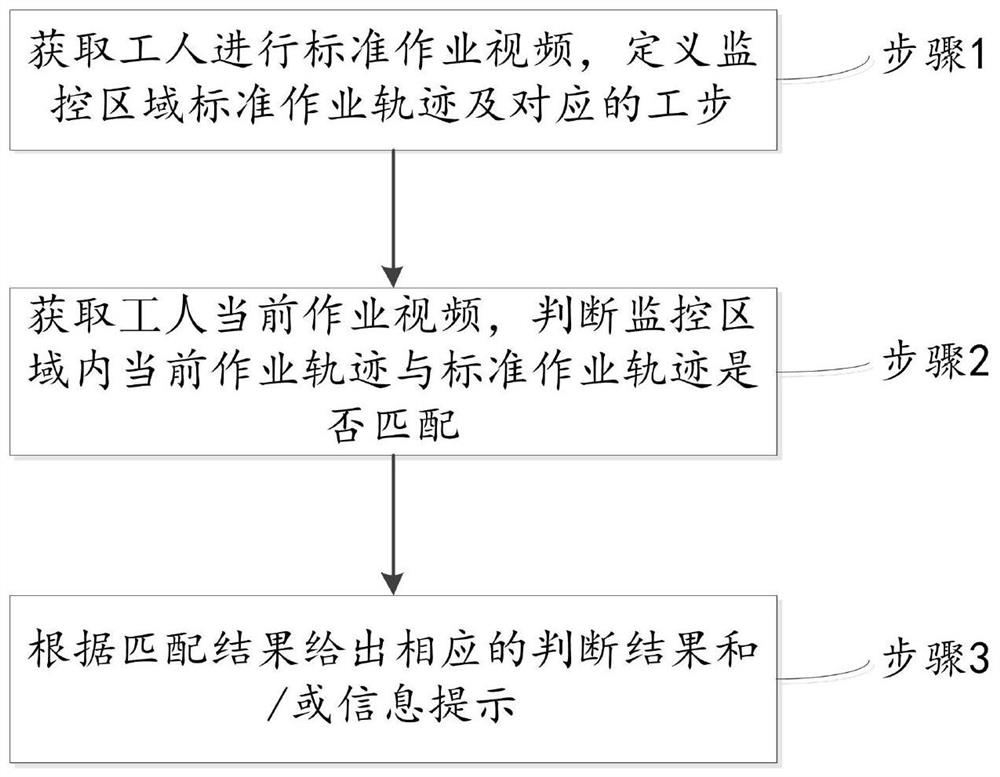
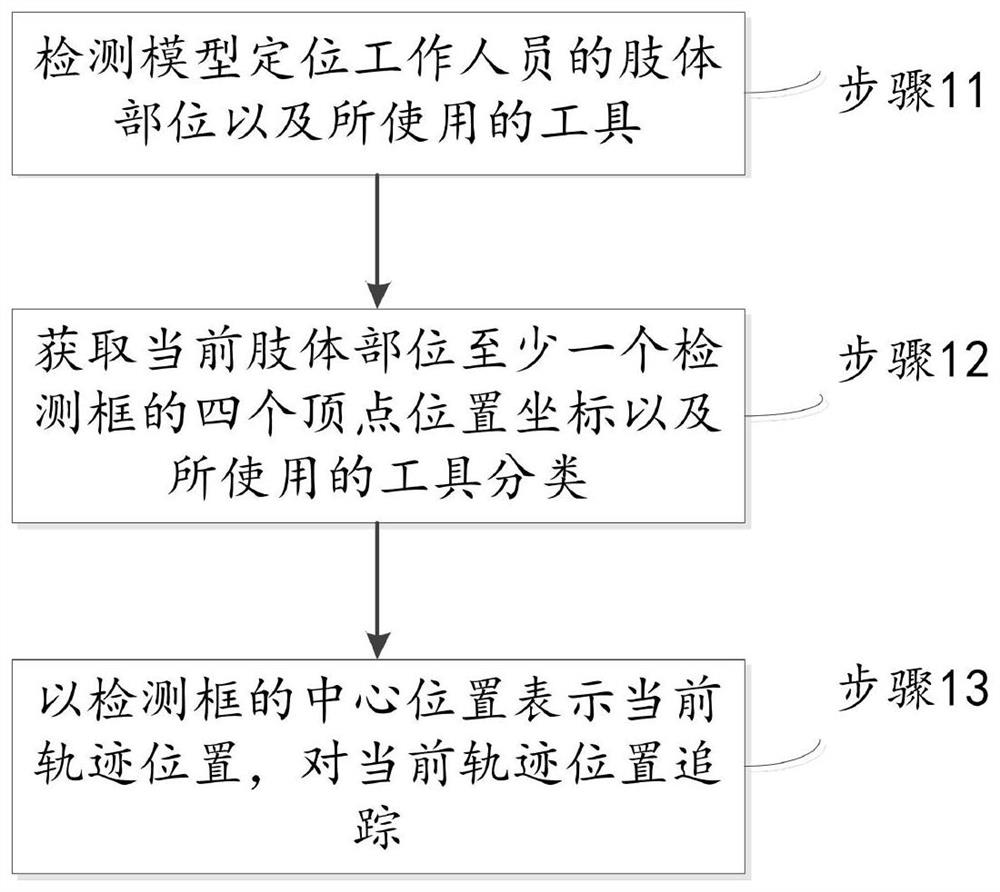
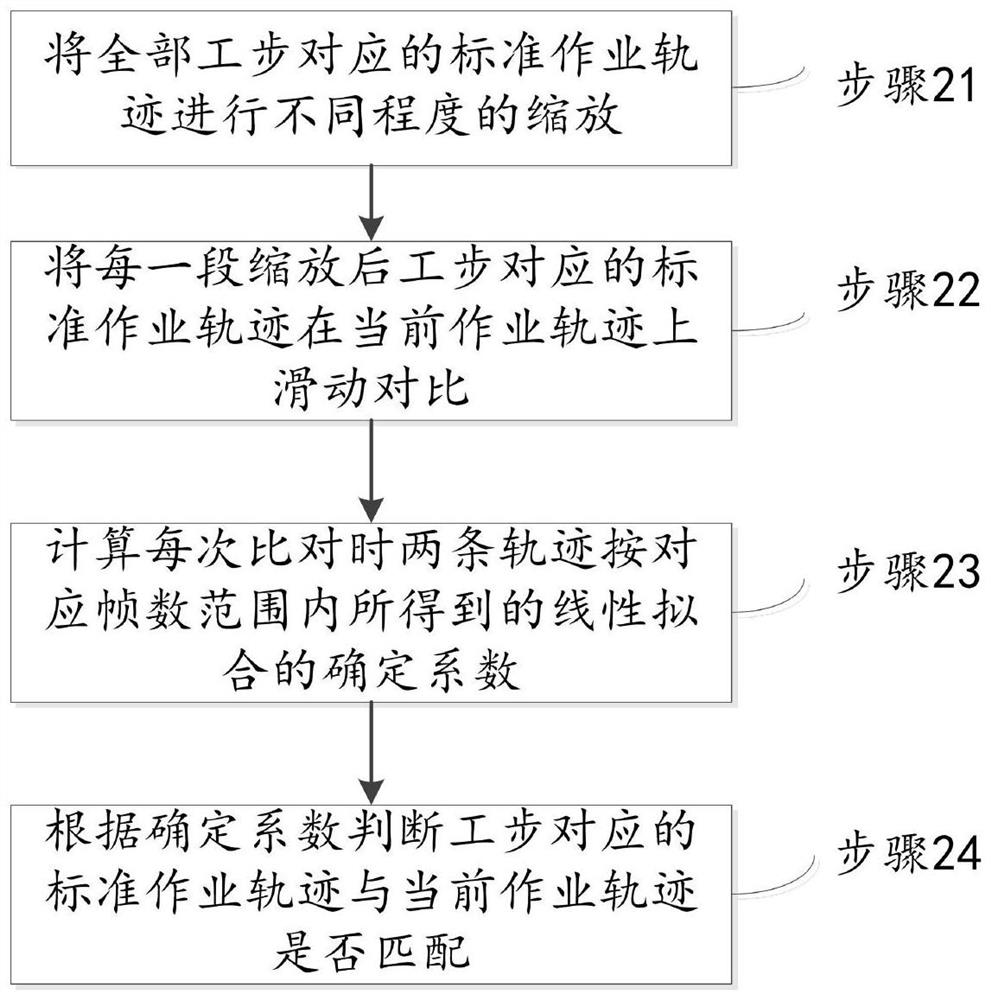
Deep learning-based work step specification visual recognition and judgment method and system
PendingCN112016409AAvoid errorsImprove yield rateCharacter and pattern recognitionVisual recognitionVisual perception
The invention discloses a step specification visual recognition judgment method and system based on deep learning. The method comprises the steps: obtaining a standard operation video of a worker, extracting a standard operation track in a corresponding monitoring region according to a target detection model, and segmenting the standard operation track into a plurality of steps according to an operation specification; obtaining a current worker operation video, and judging whether the current operation track of the worker in the monitoring area is matched with the standard operation track or not; giving a corresponding judgment result and / or information prompt according to the matching result; the system comprises a video stream receiving module, a client configurator module, a video stream analysis module, a step guide client and a main control computer, according to the embodiment of the invention, the system executes the method, compares the current operation track of the worker with the standard operation track, gives the corresponding judgment result and / or information prompt to guide the operation process of the worker and judge and standardize the operation omission and errors, effectively prevents the operation error problem, and improves the yield.
Owner:EPIC HUST TECH WUHAN
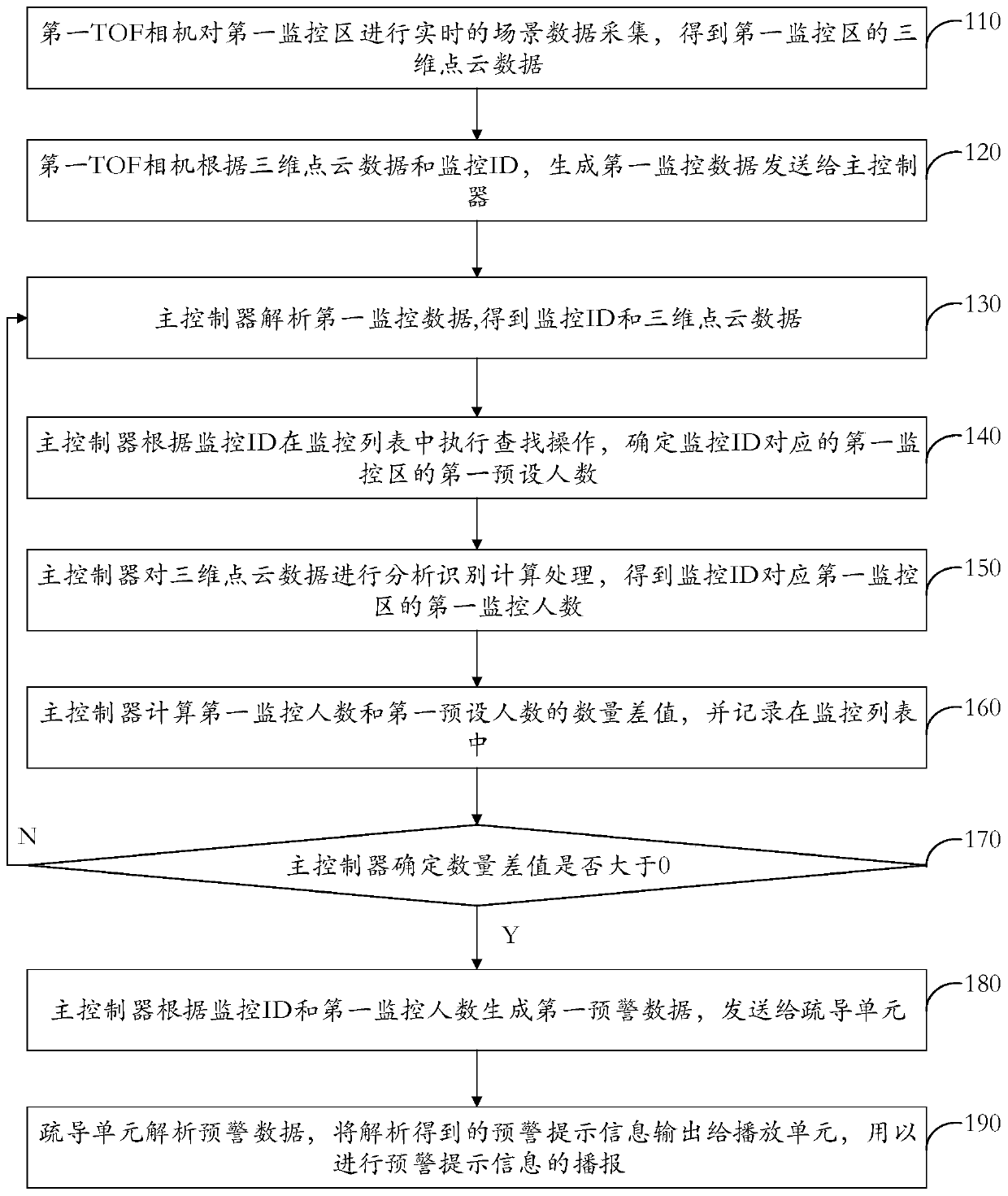
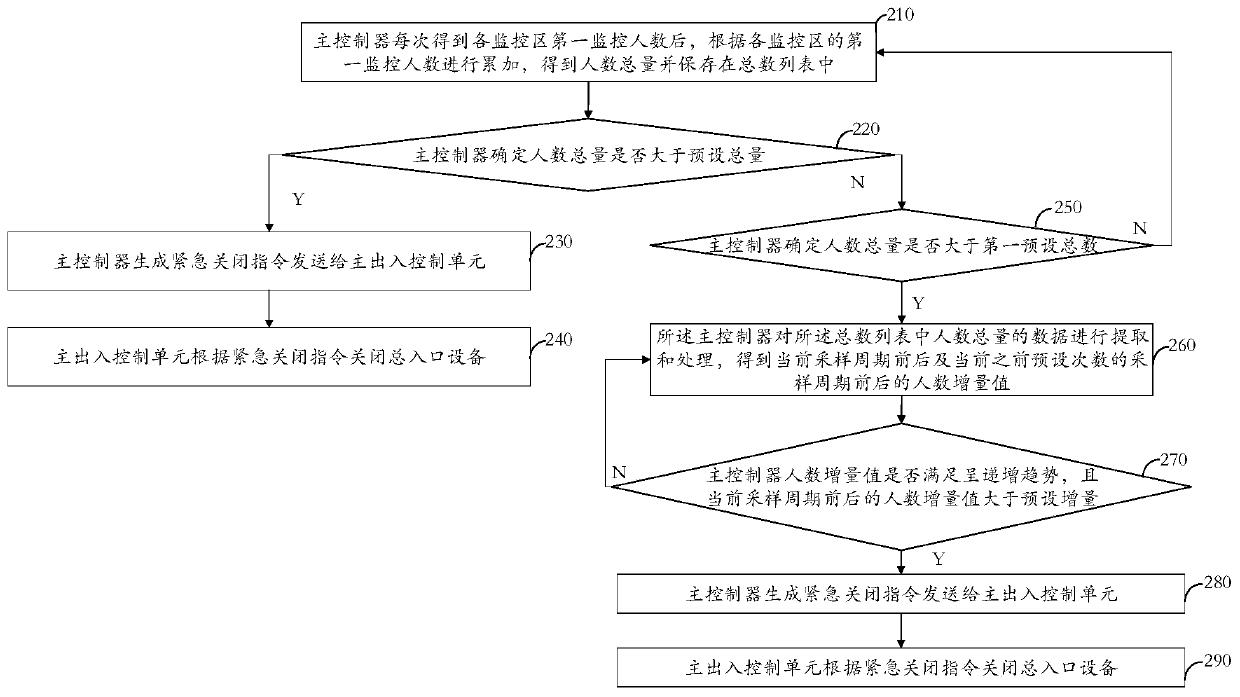
People stream analysis, early warning and dispersion method and system
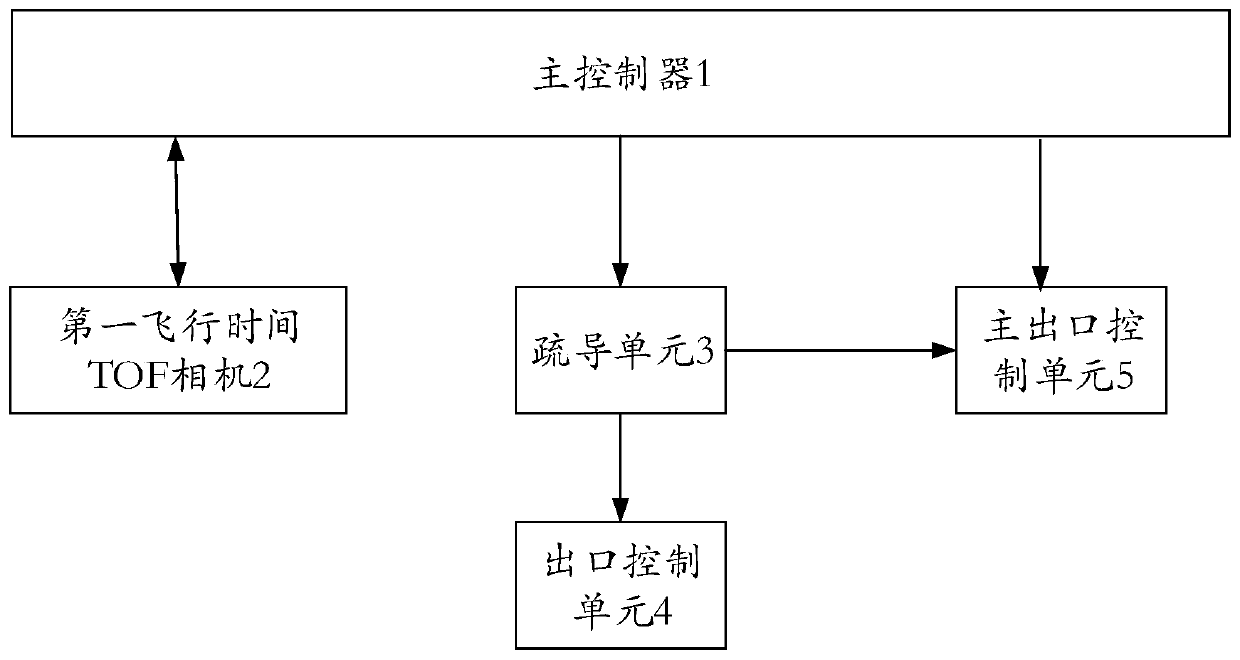
ActiveCN110708518AOperational securityFully automated monitoring and managementClosed circuit television systemsIndividual entry/exit registersPoint cloudTime-of-flight camera
The invention provides a people stream analysis, early warning and dispersion method and system, and the method comprises the steps that a first flight time TOF camera carries out the scene data collection of a first monitoring region according to a set sampling frequency, obtains the three-dimensional point cloud data of the first monitoring region, generates first monitoring data, and transmitsthe first monitoring data to a main controller; the main controller performs analysis, identification and calculation processing on the three-dimensional point cloud data to obtain a first monitoringperson number of the first monitoring region corresponding to the monitoring ID; the main controller calculates a quantity difference value between the first monitoring number of people and a first preset number of people, and records the quantity difference value in a monitoring list; the main controller determines whether the number difference value is greater than 0; when the number differencevalue is greater than or equal to 0, the main controller generates first early warning data according to the monitoring ID and the first monitoring number of people and sends the first early warning data to the dispersion unit; wherein the first early warning data comprises early warning prompt information; and the dispersion unit analyzes the early warning data and outputs early warning prompt information obtained by analysis to the playing unit for broadcasting the early warning prompt information.
Owner:北京连屏科技有限公司
Multi-dimensional power flow evaluation index method based on statistic analysis of historical information of power grid
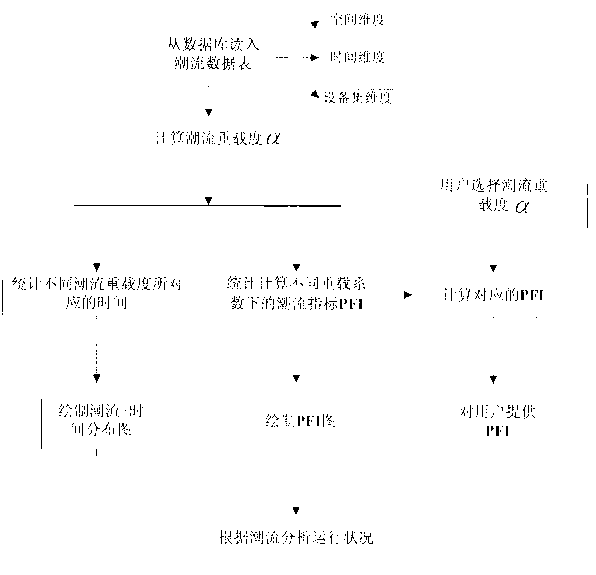
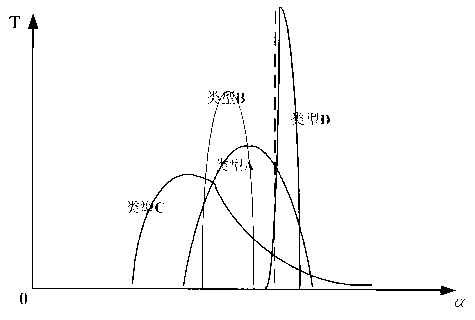
ActiveCN103077484AEasy to analyzeAchieve transformationData processing applicationsPower gridTidal current
The invention relates to a multi-dimensional power flow evaluation index method based on the statistic analysis of the historical information of a power grid. The method comprises the following steps of: preprocessing power flow information: acquiring the power flow information in a selected time interval from a database, calculating a power flow overload coefficient alpha representing the power flow overload degree of single equipment or a power transmission cross section, and comparing the acquired historical power flow data with the limit value of the equipment or the cross section; carrying out statistic calculation on power flow time features: counting time corresponding to different power flow overload degrees through the utilization of the power flow overload coefficients and the corresponding time periods, and summing the time periods to obtain the relationship between the power flow overload degrees and the running time; and carrying out statistic calculation on the multi-dimensional power flow evaluation indexes (PFI). According to the multi-dimensional power flow evaluation index method, a power flow distribution curve is drawn on the basis of the historical data of the power grid according to the power flow evaluation indexes (PFI), an auxiliary means is provided for the power flow analysis and the power flow prediction of the power transmission cross section of the power grid and the medium and long term statistic analysis of the power grid, and the key power flow control indexes of the power grid are converted to the multi-dimensional statistic indexes.
Owner:EAST CHINA GRID +1
Optimizing evaluation patterns and data acquisition for stream analytics in resource-constrained wireless environments
Owner:TELCORDIA TECHNOLOGIES INC
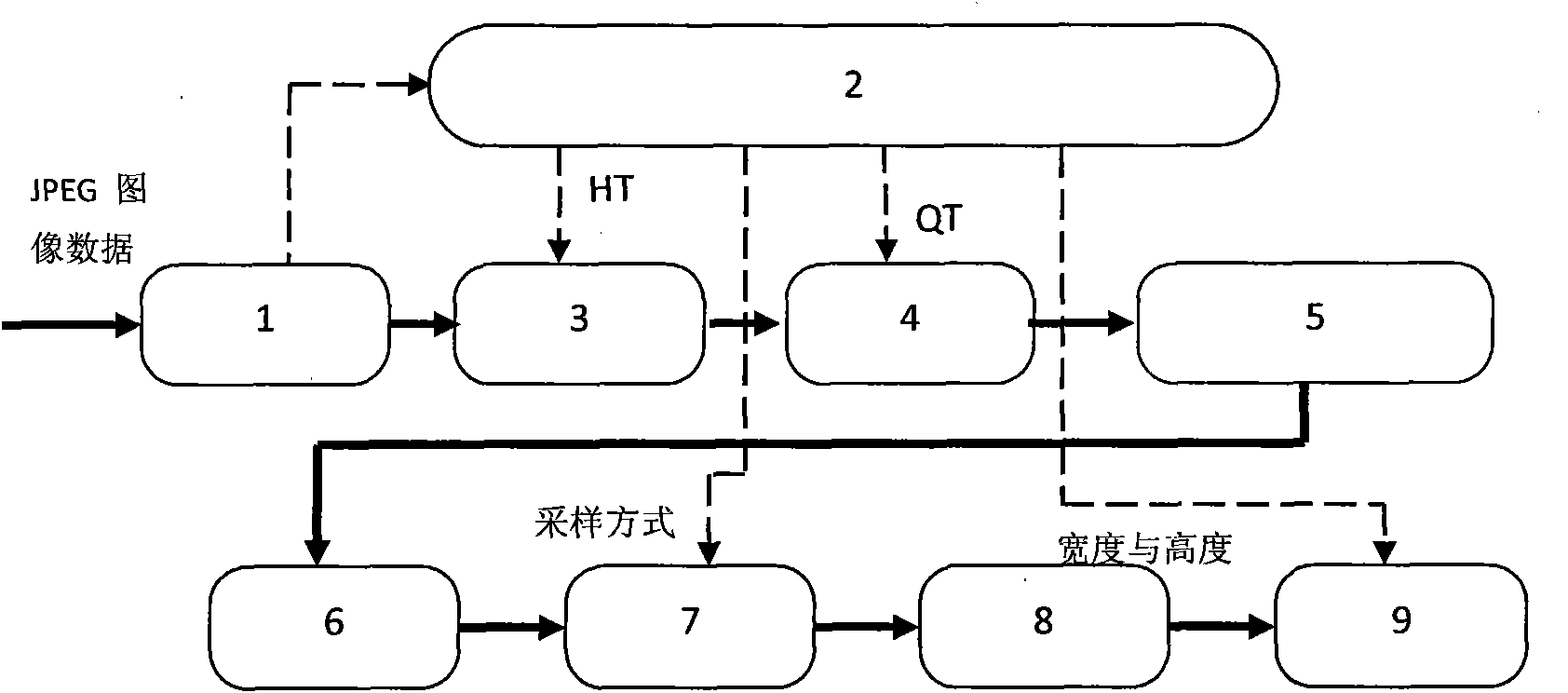
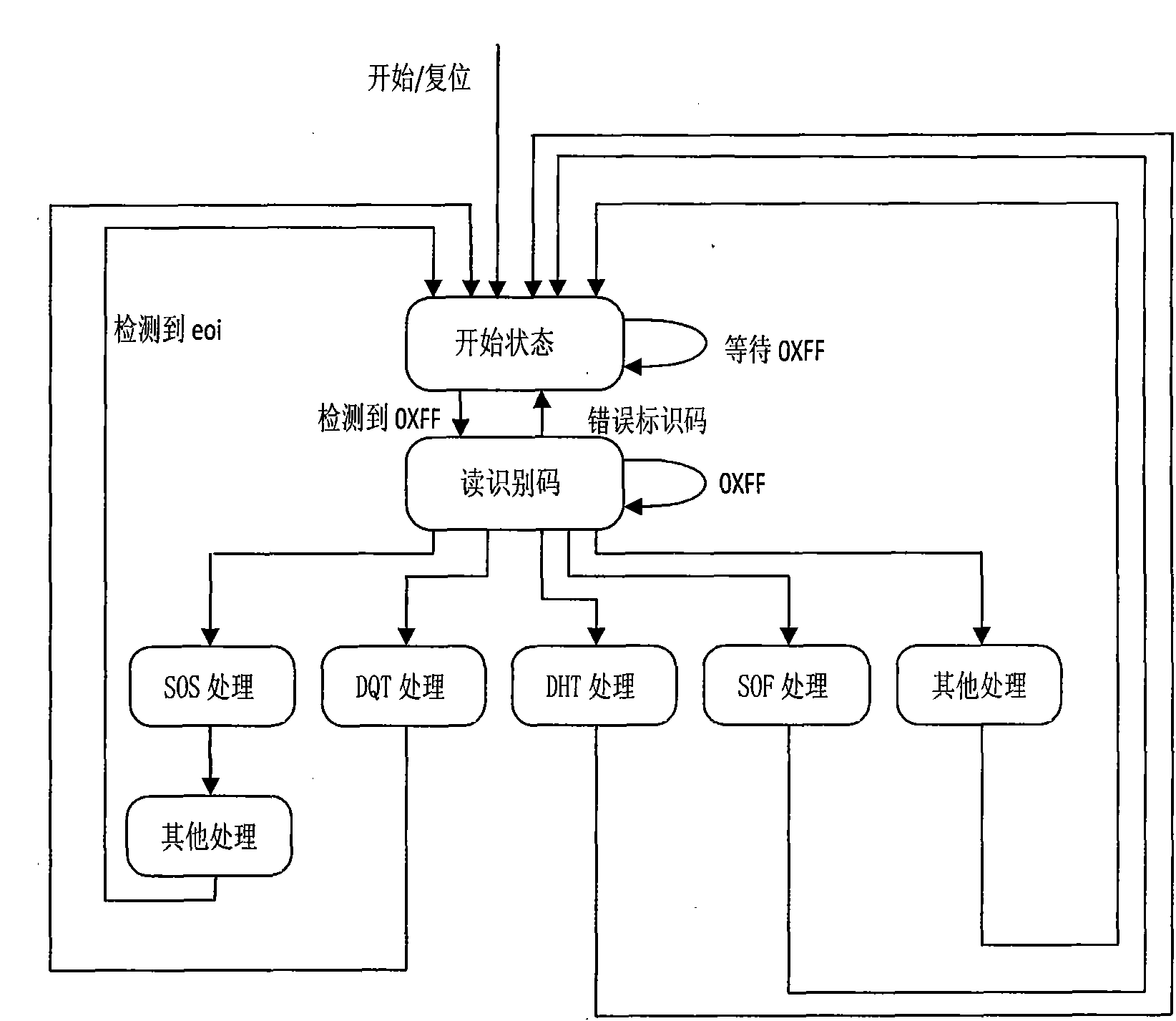
VLSI system structure of JPEG image decoder and realization method thereof
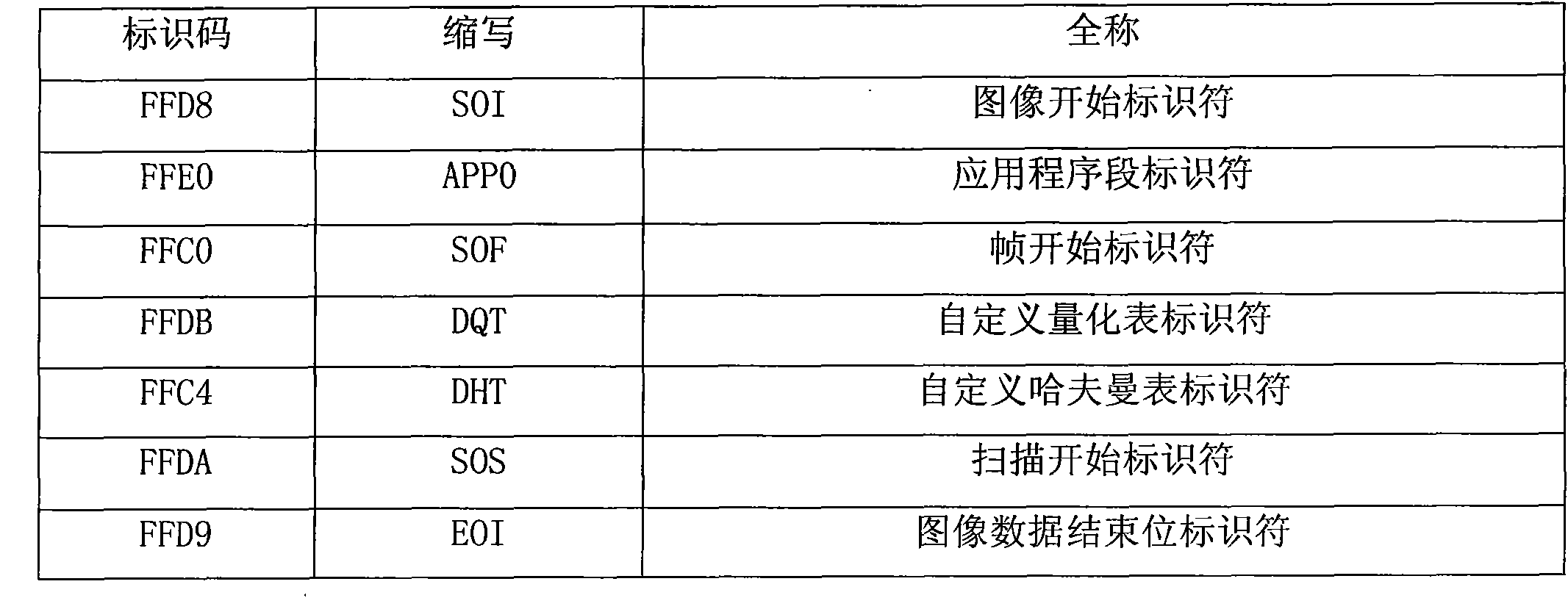
InactiveCN101790094AProcessing speedReduce areaTelevision systemsDigital video signal modificationComputer architectureHuffman decoding
The invention discloses a VLSI system structure of a JPEG image decoder and a realization method thereof. The VLSI system structure mainly comprises an input FIFO module, a header code stream analytic module, an entropy decoding module, a dequaztization module, an anti-zigzag conversion module, a inverse discrete cosine transform module, a de-sampling module, a color gamut conversion module and a display module. The entire design of the VLSI system structure adopts the assembly line design which can process multiple images simultaneously and continuously; the huffman decoding in the entropy decoding module adopts the modes of multibyte buffer and decoding word length feedback, thus increasing the operational speed of a huffman decoding module; to-be-decoded coefficient for counting and indicating is added in the inverse discrete cosine transform module which combines module data end mark method so that only nonzero coefficient data can be inputted, the data input cycle of single decoding module is greatly reduced, the decoding velocity is effectively increased, and the whole decoding speed is well improved. Simulation tests show that by using the VLSI system structure of the invention, 60fps of decoding effect can be realized under 800*600 resolution and 100MHz clock frequency.
Owner:SHANDONG UNIV
Method and apparatus for tone detection
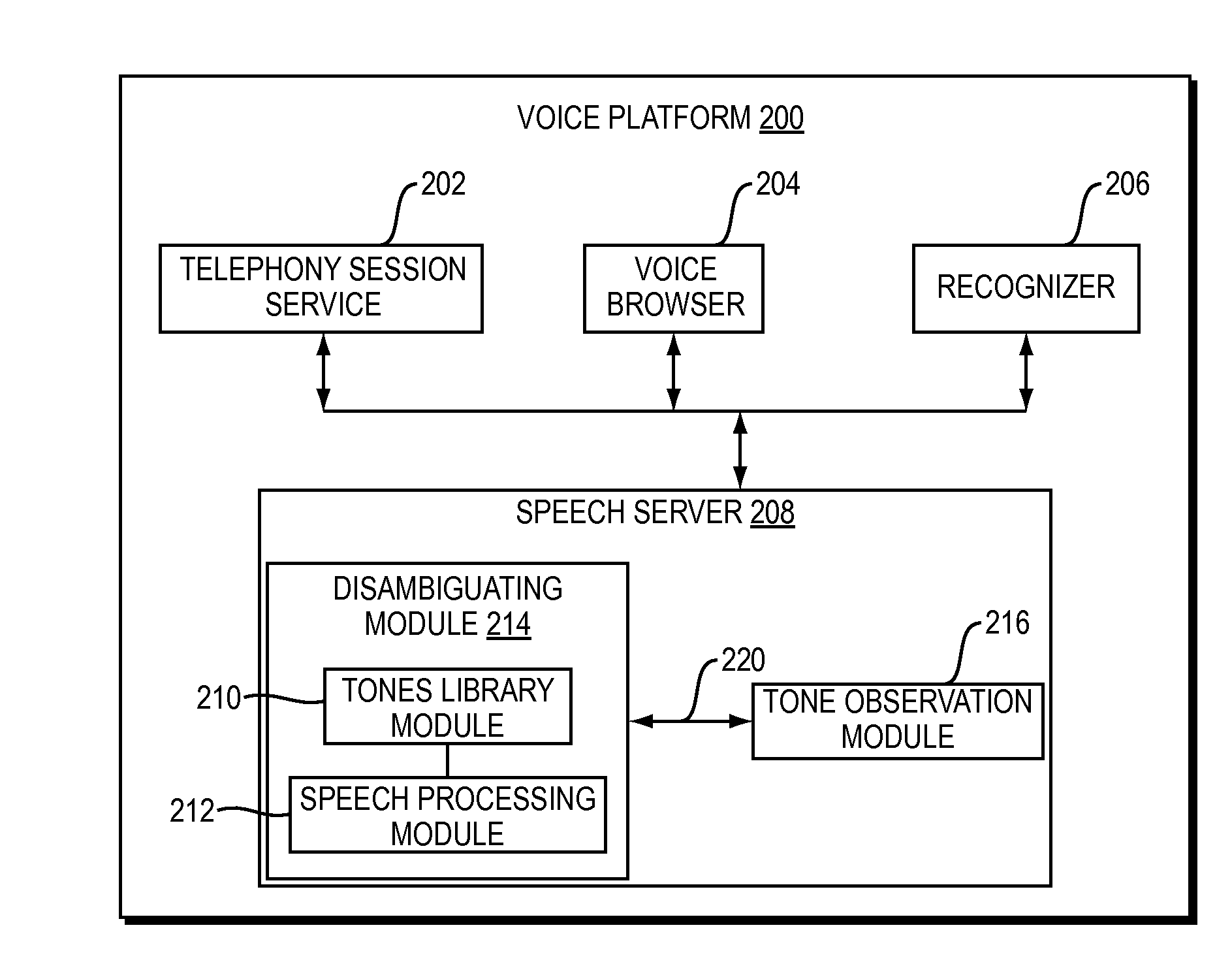
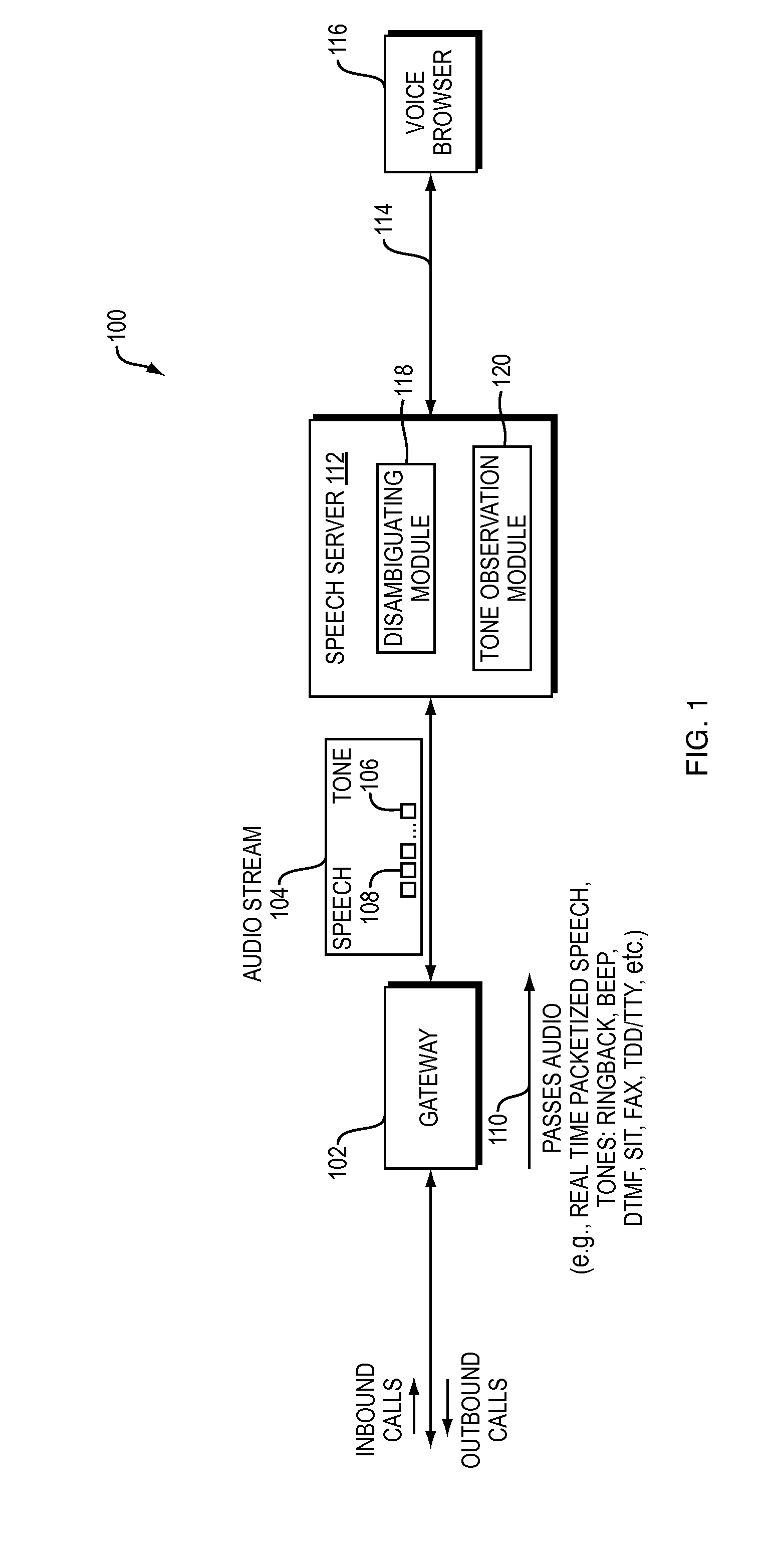
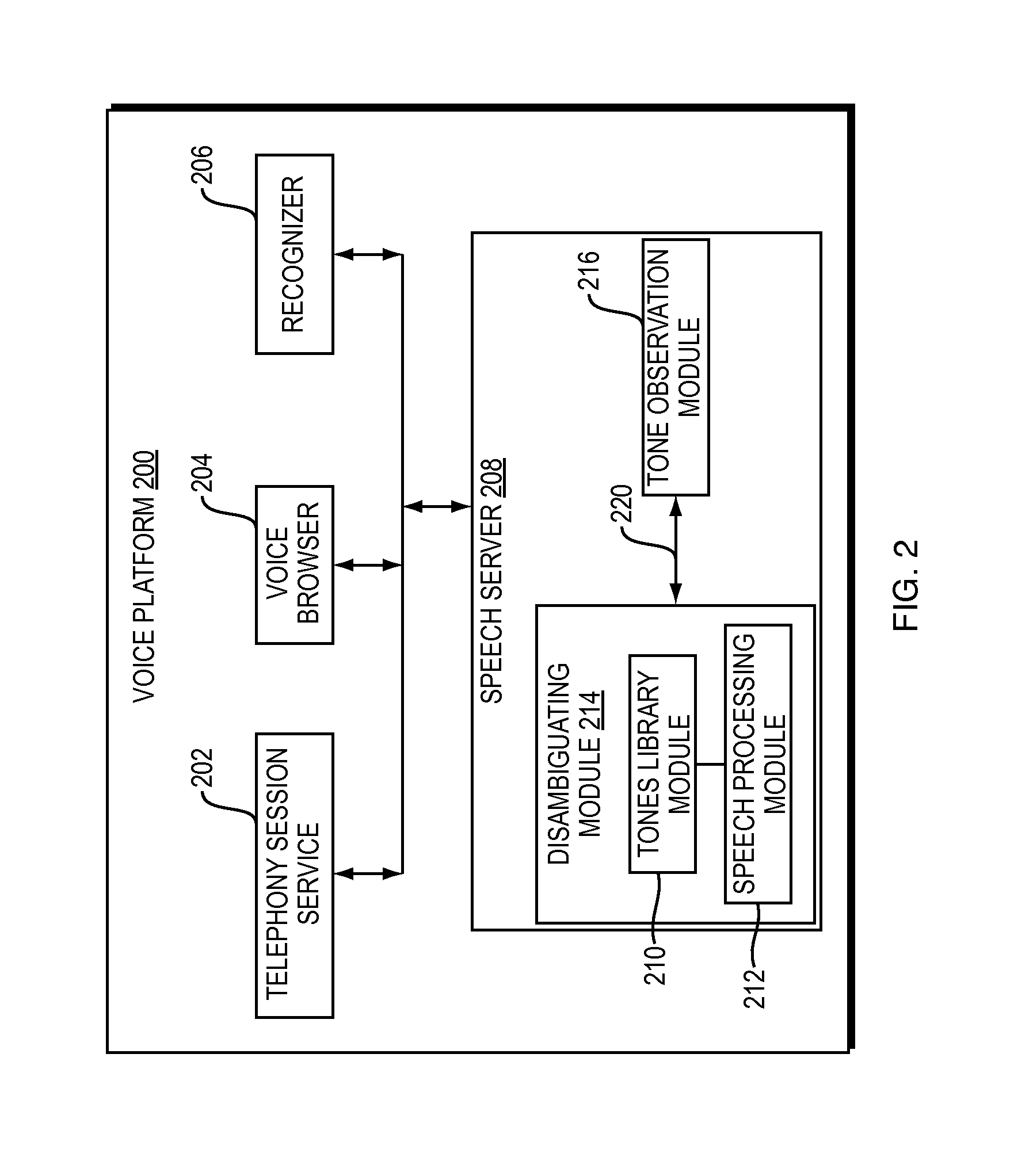
ActiveUS20140029733A1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesDigital signal processingGeolocation
A speech server and methods provide audio stream analysis for tone detection in addition to speech recognition to implement an accurate and efficient answering machine detection strategy. By performing both tone detection and speech recognition in a single component, such as the speech server, the number of components for digital signal processing may be reduced. The speech server communicates tone events detected at the telephony level and enables voice applications to detect tone events consistently and provide consistent support and accuracy of both inbound and outbound voice applications independent of the hardware or geographical location of the telephony network. In addition, an improved opportunity for signaling of an appropriate moment for an application to leave a message is provided, thereby supporting automation.
Owner:NUANCE COMM INC
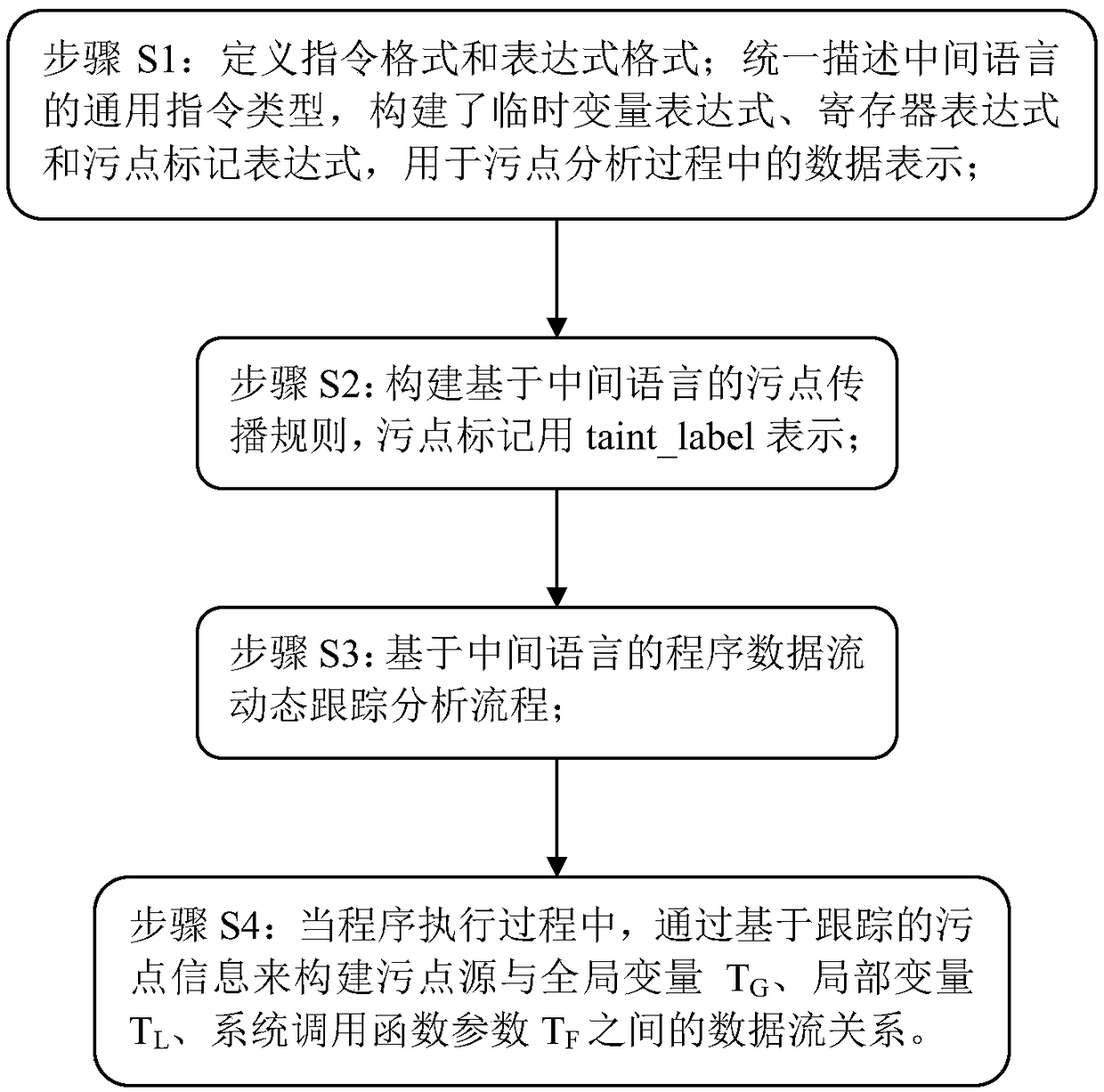
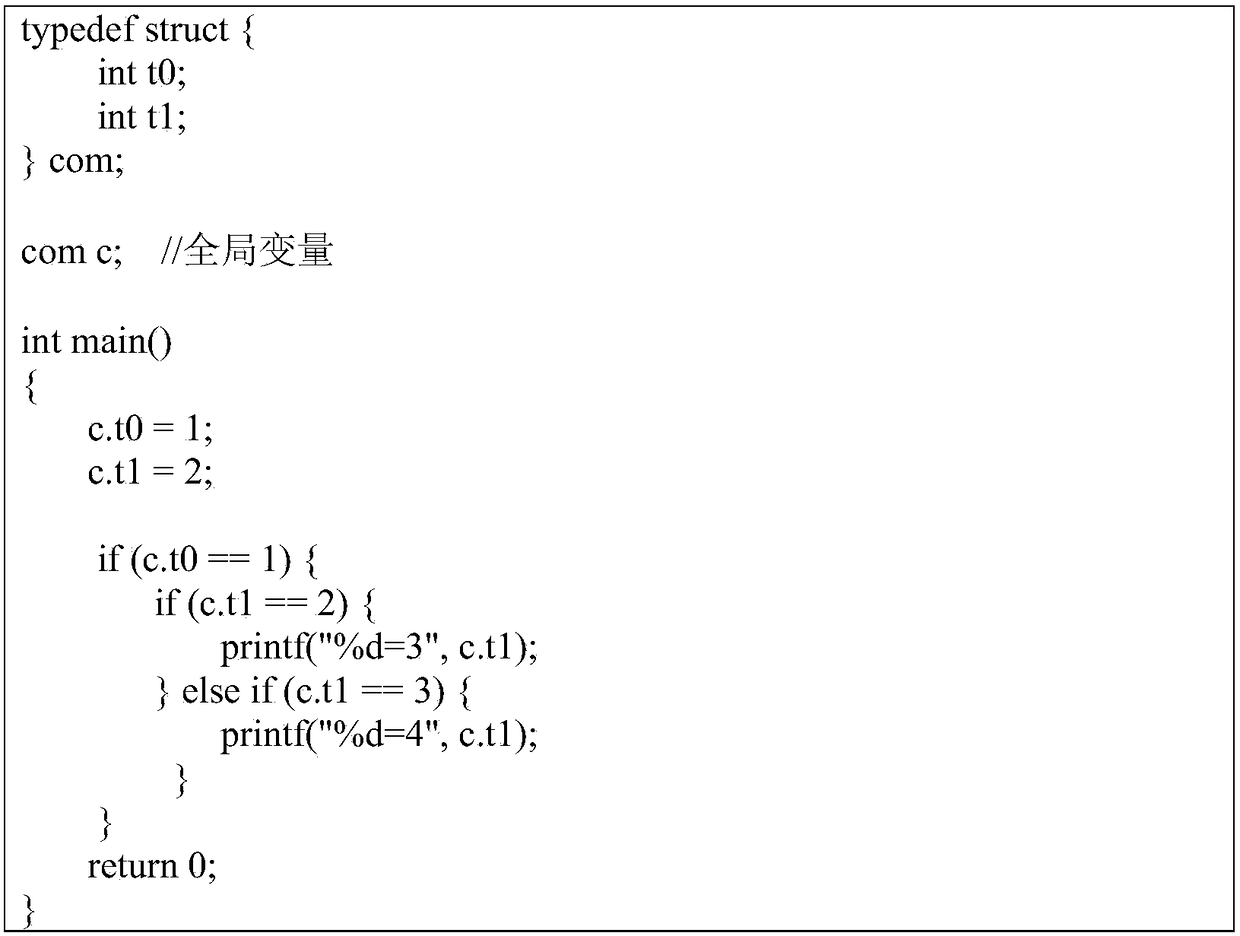
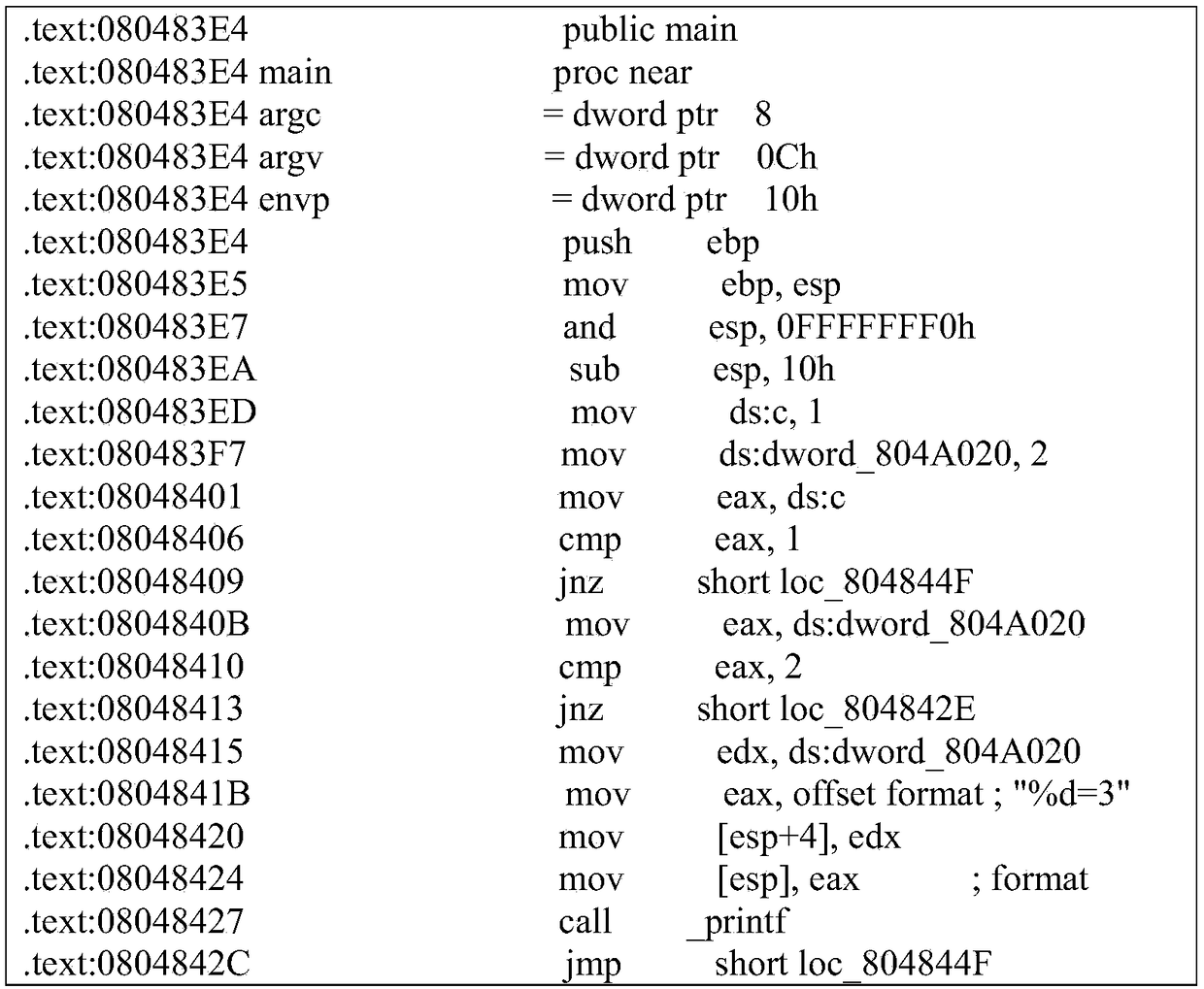
A software data stream analysis method based on intermediate language and stain analysis
ActiveCN109324971AEasy to captureRich expressive abilitySoftware testing/debuggingPlatform integrity maintainanceTemporary variableLocal variable
The invention discloses a software data flow analysis method based on intermediate language and stain analysis. The method comprises the following steps of S1 defining instruction format and expression format; uniformly describing the general instruction types of the intermediate languages, and construting the temporary variable expressions, register expressions and stain marker expressions for the data representation in stain analysis process; S2 constructing a stain propagation rule based on an intermediate language, wherein the stain mark is represented by a taint_label; S3 dynamic tracking an analysis flow based on a program data flow of the intermediate language; S4 when the program is executed, constructing the data flow relationship between the stain source and the global variableTG, the local variable TL, and the system call function parameter TF based on the tracked stain information. The method of the invention has the advantages of better accuracy, stronger comprehensiveness and richer information.
Owner:NAT UNIV OF DEFENSE TECH
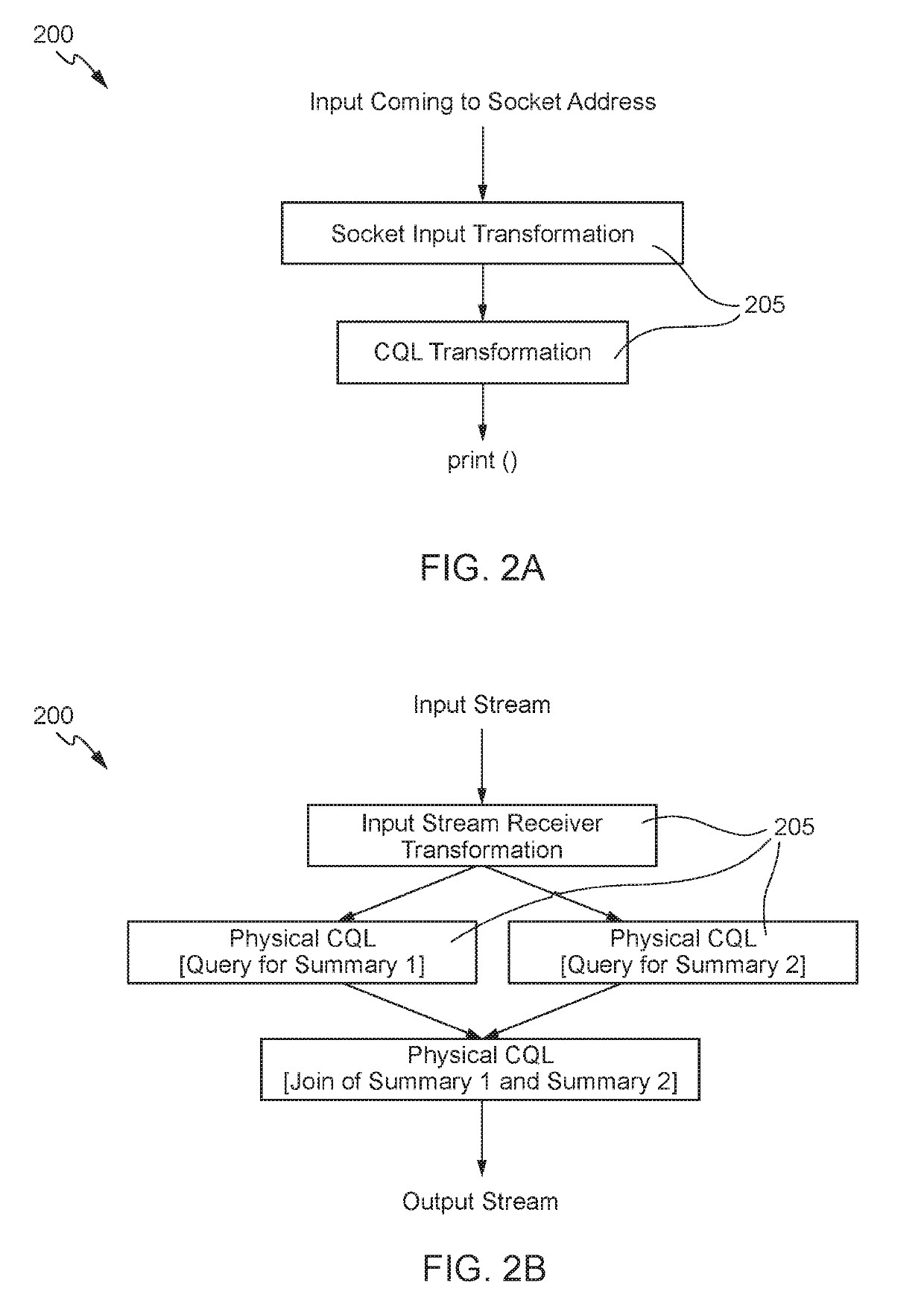
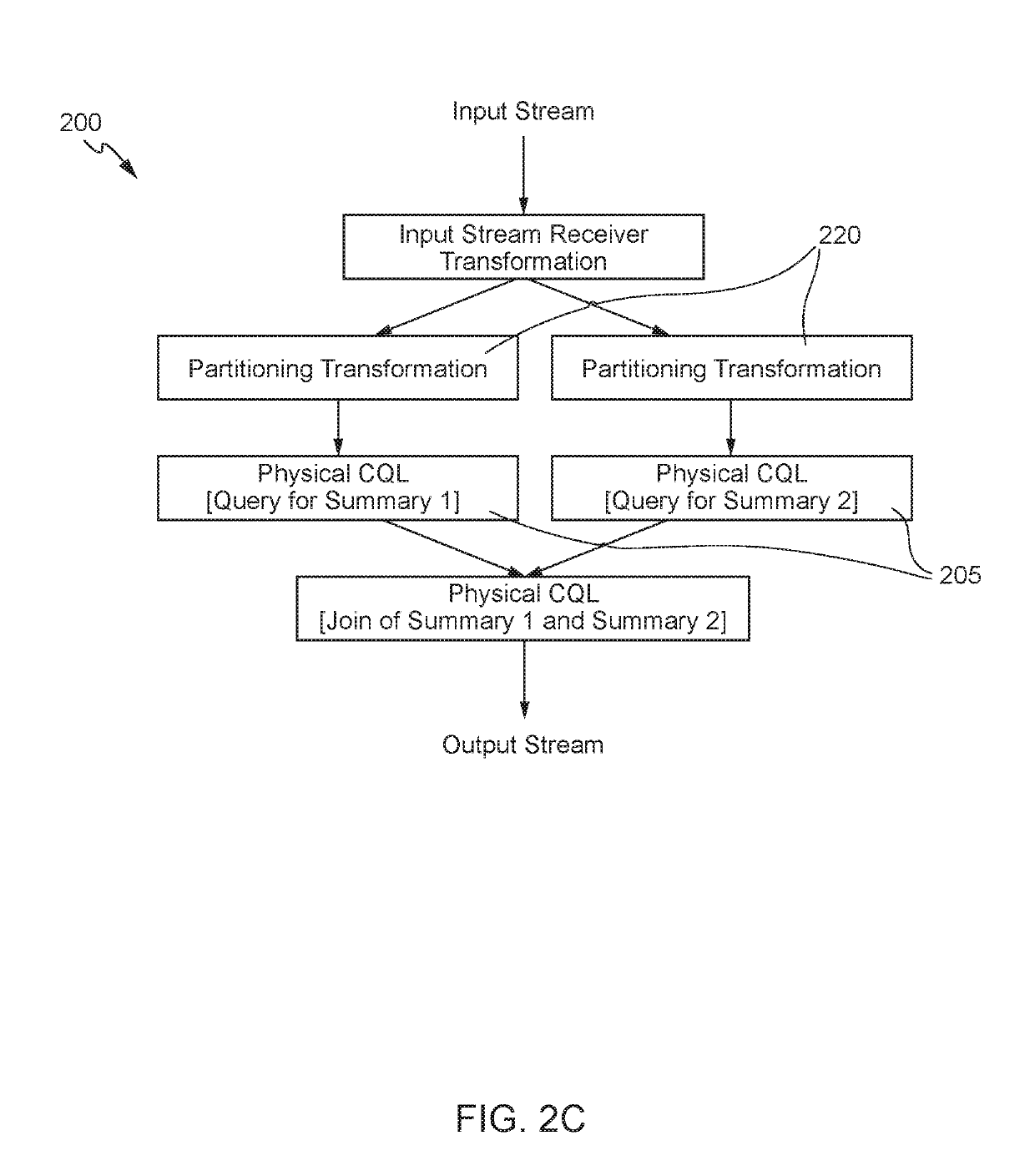
Logical queries in a distributed stream processing system
Techniques for implementing logical queries in a distributed stream processing system using automatic branching and joins. An exemplary technique includes determining a query is a logical query. The logical query includes two or more summaries based on different groups configured to execute in a single query stage of a stream analytics application. The technique further includes converting the logical query into one or more physical queries. The one or more physical queries are separated into individual query stages, and each of the query stages includes a summary from the two or more summaries that is based on an associated group. The technique further includes generating a directed acyclic graph for the one or more physical queries. The directed acyclic graph includes a physical query transformation for each of the individual query stages.
Owner:ORACLE INT CORP
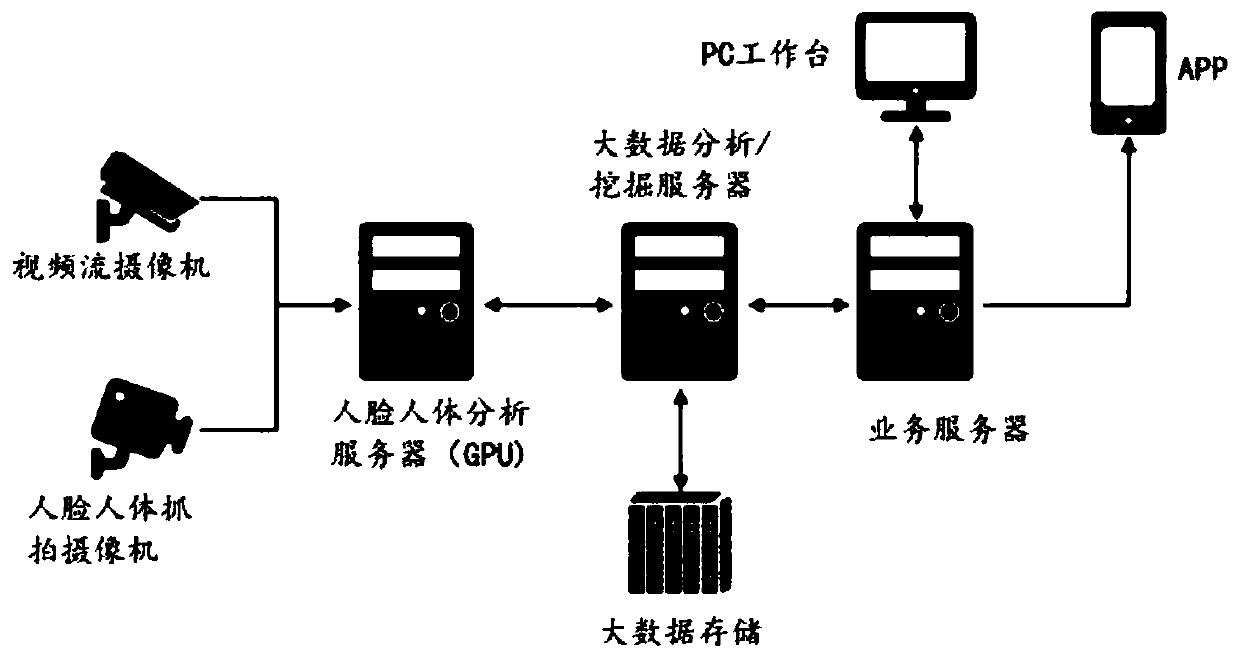
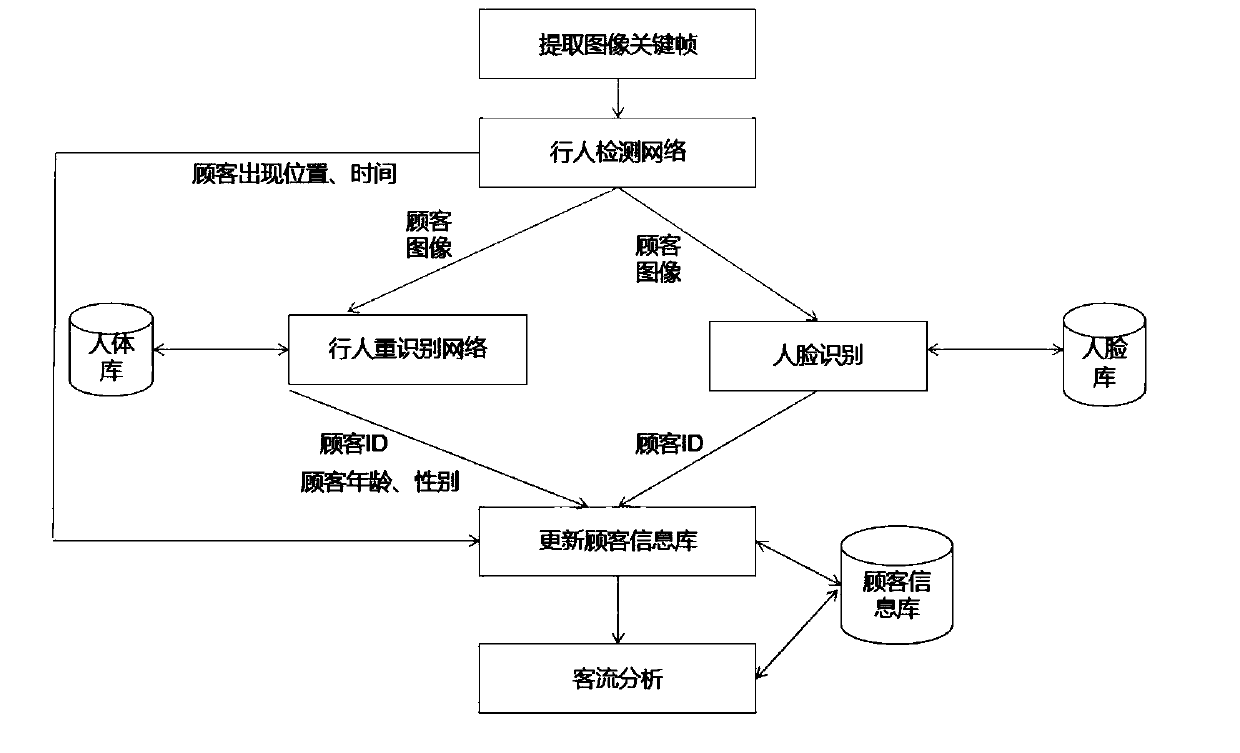
Automobile exhibition hall passenger flow detection and analysis system and method, and storage medium
PendingCN111241932ALow investment costCharacter and pattern recognitionMarket data gatheringPerson detectionComputer science
The invention discloses an automobile exhibition hall passenger flow detection and analysis system. The automobile exhibition hall passenger flow detection and analysis system comprises shooting equipment, a human face and human body analysis server and a storage module, wherein the shooting equipment shoots picture and video data in an automobile exhibition hall and sends the pictures and the video data to the human face and human body analysis server for processing and analysis; the human face and human body analysis server comprises a pedestrian detection module, a pedestrian re-identification module and an analysis module; the storage module comprises a plurality of databases; and the pedestrian detection unit and the pedestrian re-identification module carry out processing and comparison according to the picture and video data of the shooting equipment and the storage data of the databases, update the databases and provide basic analysis data for the analysis module. The automobile exhibition hall passenger flow detection and analysis system is used for realizing passenger flow detection and analysis of the automobile exhibition hall, and provides a data basis for passenger flow analysis in combination with respective advantages of face recognition and pedestrian re-recognition; and a multi-dimensional passenger flow analysis method is provided, and a basis is provided formarketing decisions from each dimension of customer portraits, visiting tracks, interested vehicle types and arrival times.
Owner:广州量视信息科技有限公司
Stream server that modifies a stream according to detected characteristics
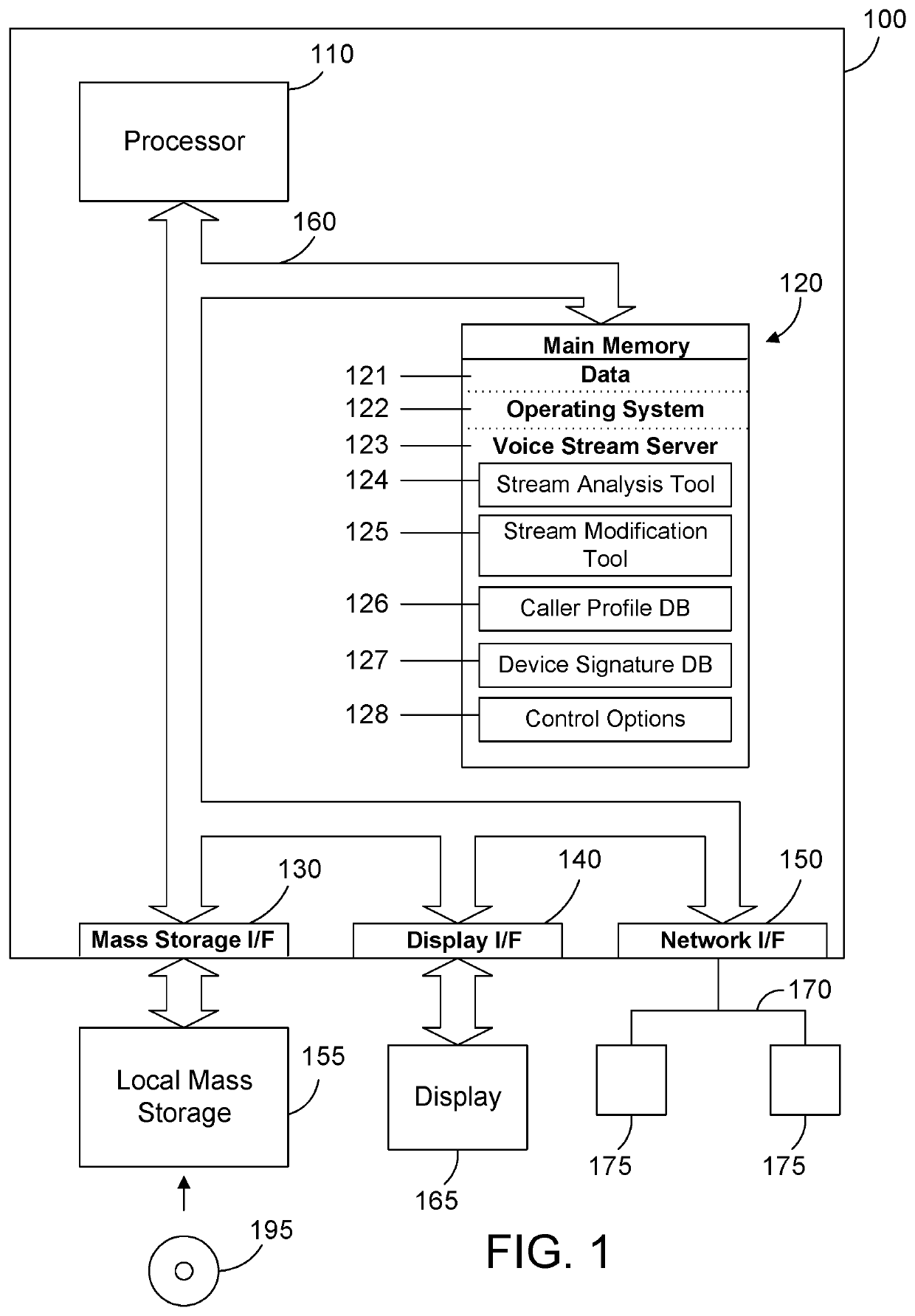
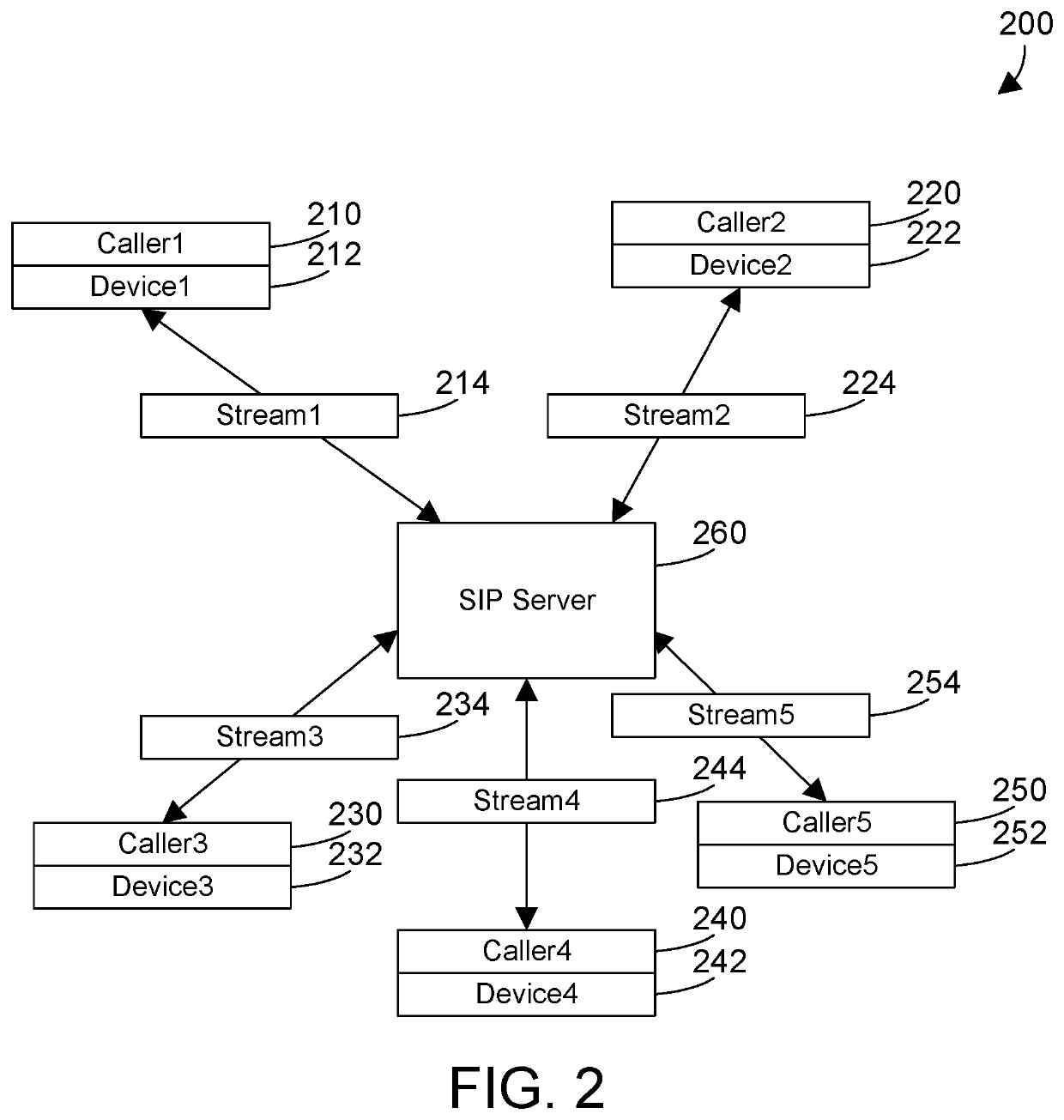
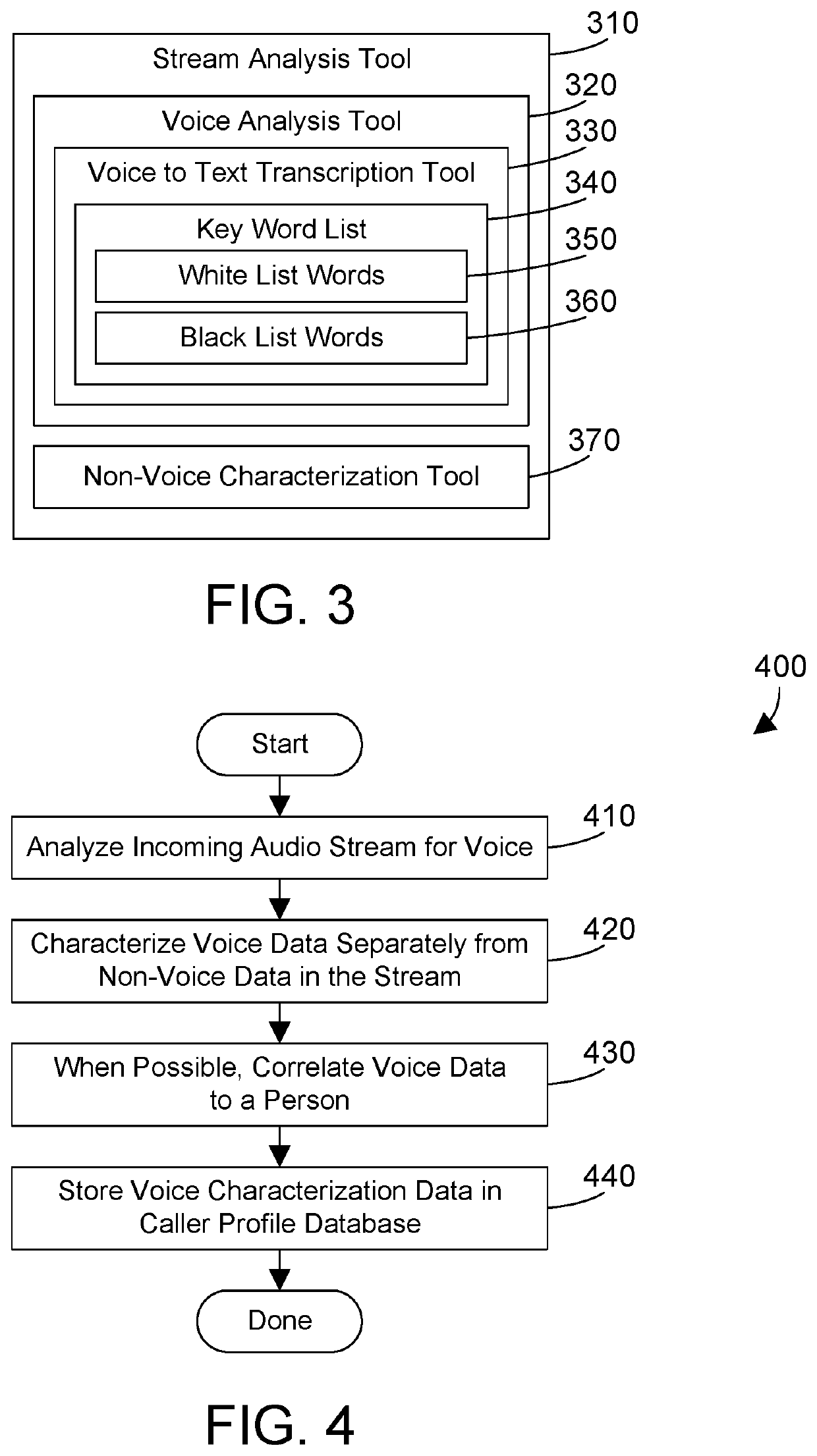
ActiveUS20200106885A1Devices with voice recognitionSpecial service for subscribersEngineeringData mining
A stream server manages connections by multiple clients. The stream server receives, sends and manages streams for each client. The stream server analyzes incoming streams and maintains a database of device signatures and a database of user profiles based on the analyzed data. The stream server receives a stream from a client, analyzes the stream to identify an applicable device signature, user profile, or both, and modifies the stream. Modification of the stream may include filtering noise, placing the user in receive-only mode, ending a session for a user, adjusting metadata, etc. In addition, modification of the stream may vary based on the role or authorization of the user, or based on commands from one or more of the users.
Owner:IBM CORP
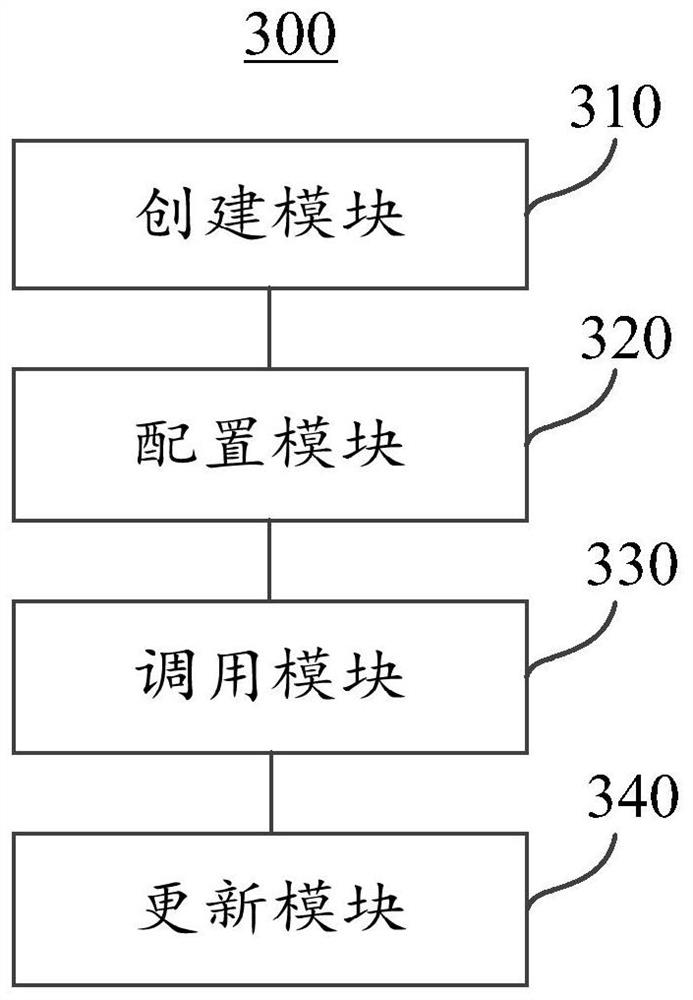
Information flow analysis method based on blockchain and mobile Internet, and cloud computing platform
ActiveCN111695903APrecise Protection Analysis Rule MechanismImprove payment securityProgram loading/initiatingProtocol authorisationPaymentAnalysis data
The embodiment of the invention provides an information flow analysis method based on a blockchain and a mobile Internet, and a cloud computing platform. The method comprises the steps of according tothe protection label of each protection consensus verification project, creating a record dynamic link library file used for recording different protection analysis rule information of respective execution protection, analyzing rule information according to protection on the basis; configuring corresponding dynamic metric tables and payment verification metric rules for the protection consensus verification items, configuring the dynamic metric tables and the payment verification metric rules to the corresponding protection consensus verification items, executing protection data flow analysis, and further performing rule updating on the record dynamic link library file according to the obtained protection information flow analysis data. Thus, in the payment verification process, protection can be carried out based on the payment verification measurement rules of multiple different protection consensus verification items, rule updating is continuously carried out according to the protection information flow analysis data, a more accurate protection analysis rule mechanism can be realized, and the payment security can be improved.
Owner:上海百源嘉合信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com