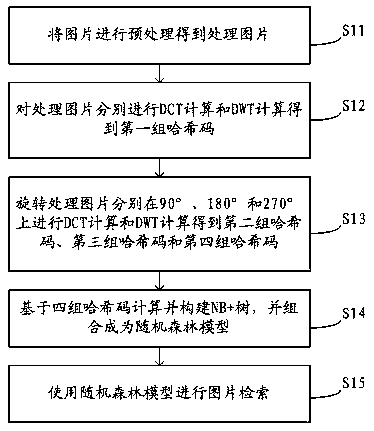
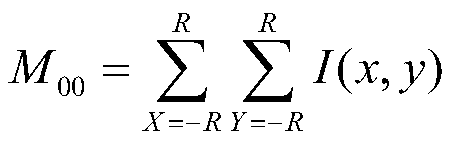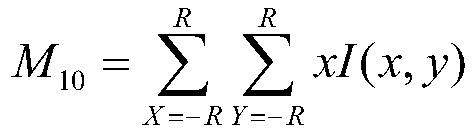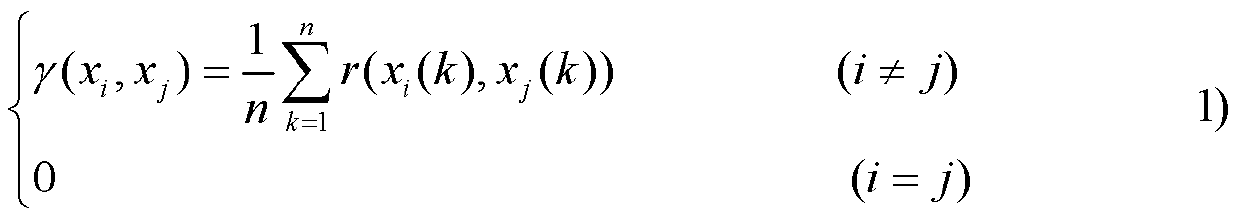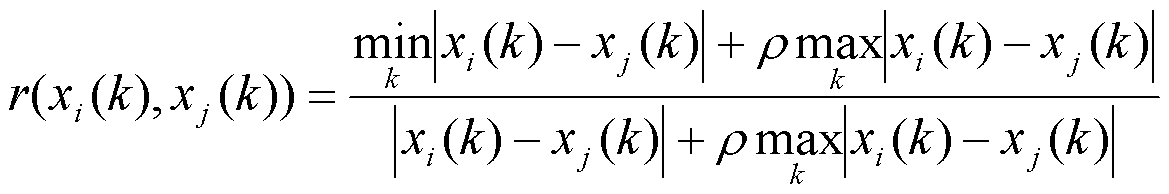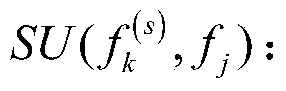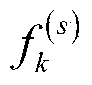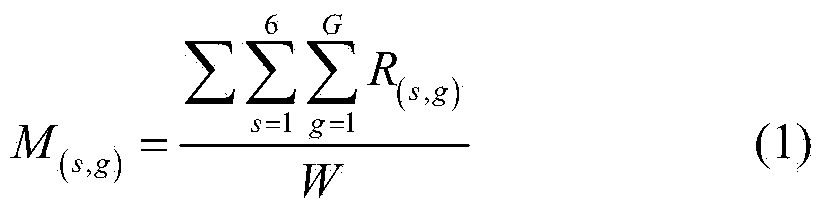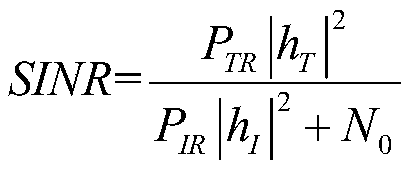Patents
Literature
45results about How to "Optimize Time Complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
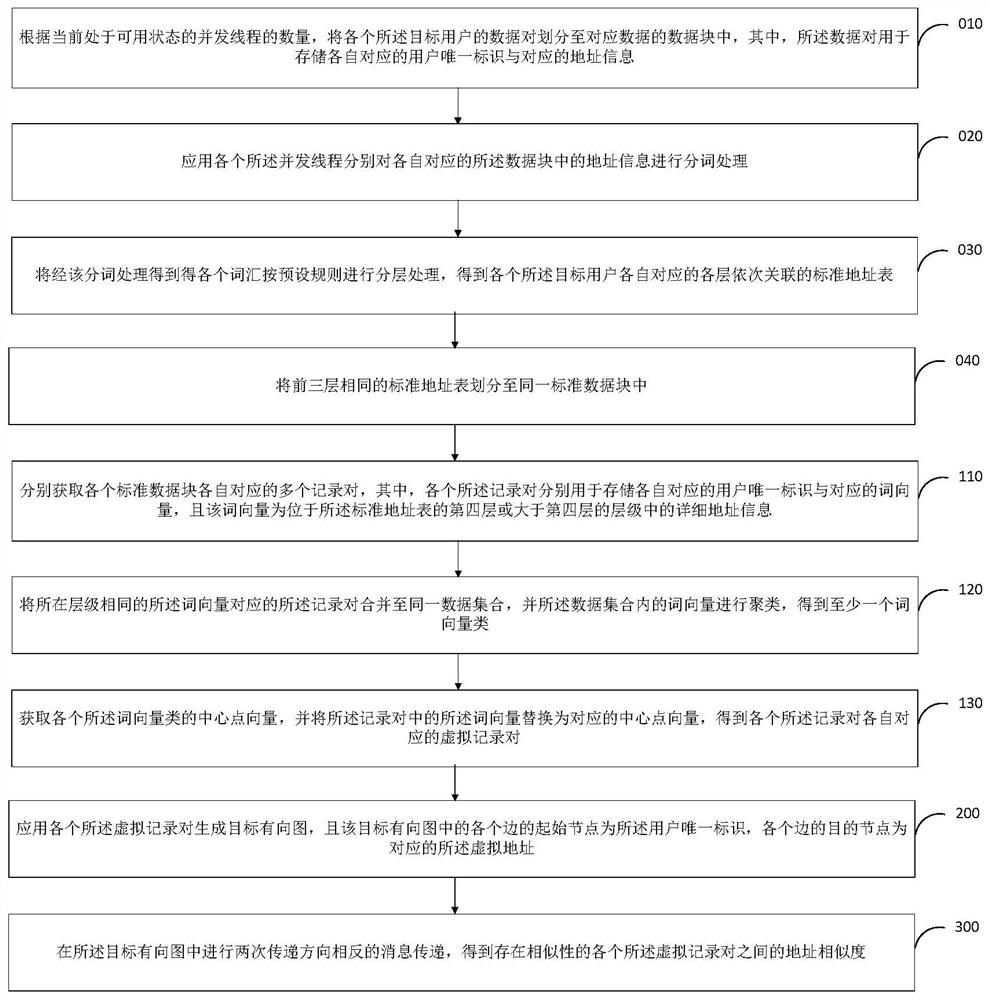
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
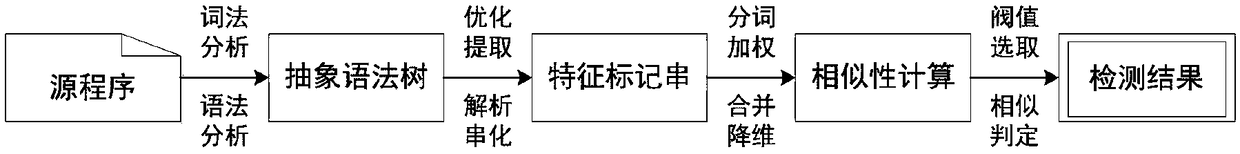
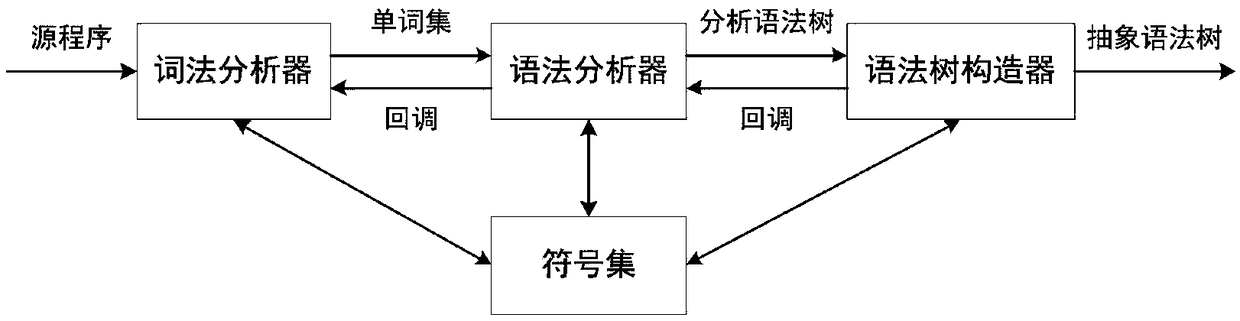
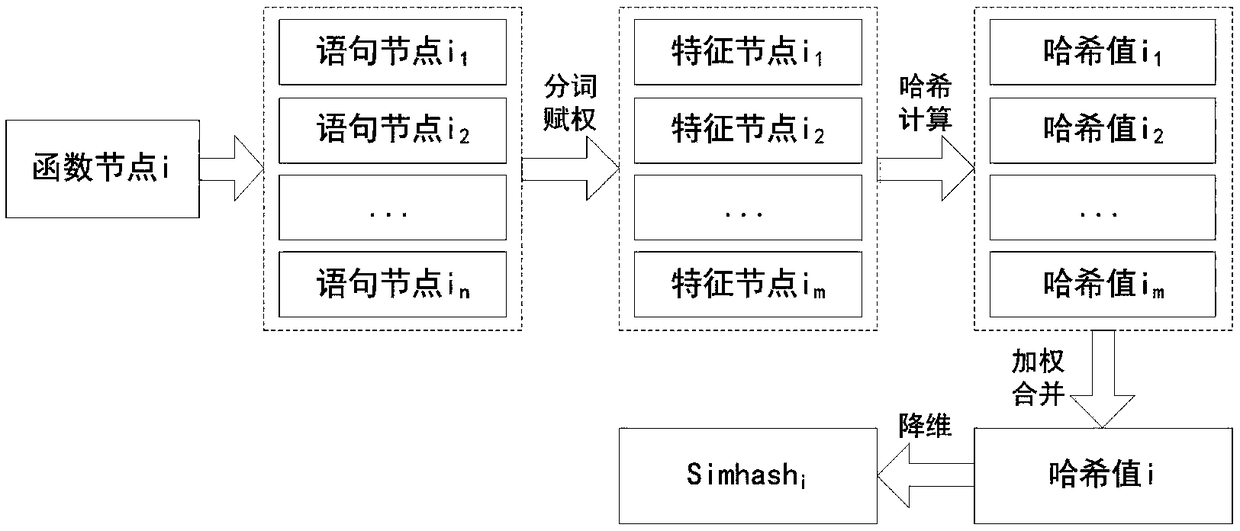
A program code similarity quick comparison method based on an abstract syntax tree,
ActiveCN109445834AImprove accuracyImprove recallSoftware maintainance/managementAbstract syntax treeHamming distance
The invention relates to a program code similarity quick comparison method based on an abstract syntax tree, which relates to the technical field of code reuse. The program code similarity quick comparison method based on the abstract syntax tree is characterized by constructing a program abstract syntax tree, extracting program code features based on the abstract syntax tree, hashing code features, and finally judging code similarity by calculating Hamming distance of code feature hash values. This method takes the abstract syntax tree of program code as the comparison object, and combines Simhash and inverted index technology to transform the similarity comparison of program code into the comparison of hash values of code features. Under the premise of ensuring high accuracy and recall rate, this method can not only realize the fast similarity comparison of program code, but also meet the needs of fast similarity comparison for massive code. This method has better time and space complexity, and can be used to compare the similarity of massive codes in application scenarios, thus providing support for software code reuse and traceability.
Owner:BEIJING INST OF COMP TECH & APPL
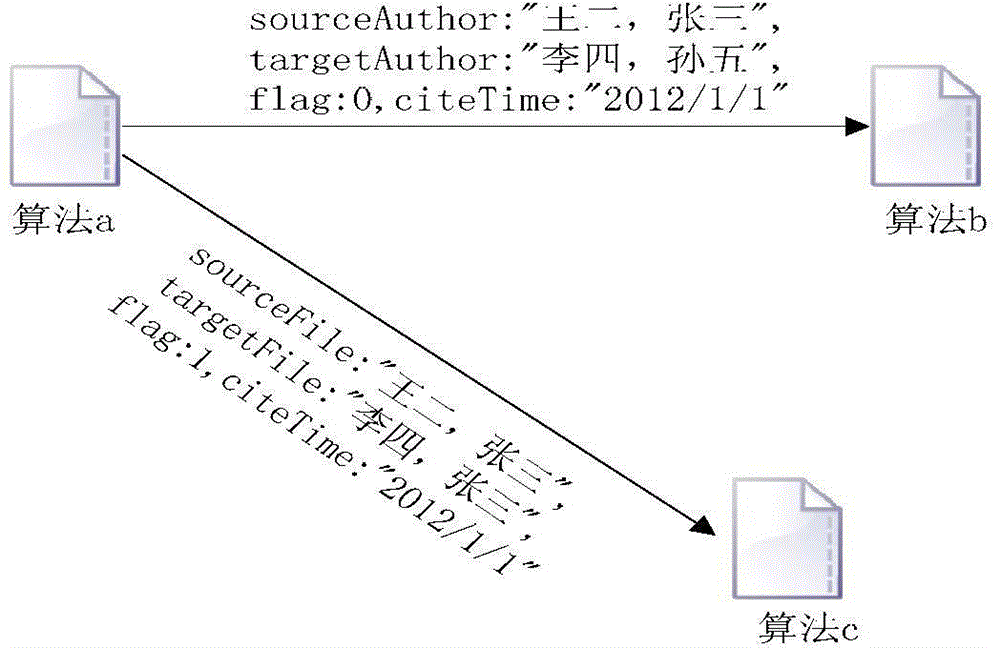
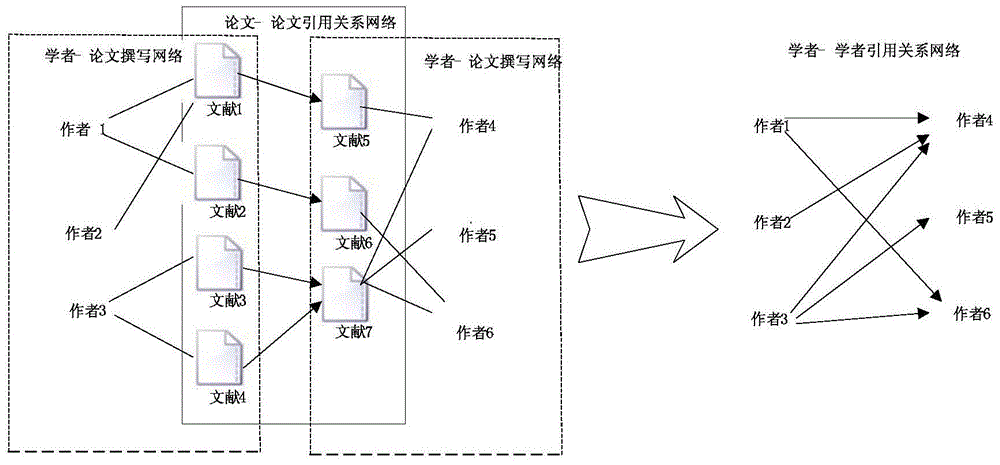
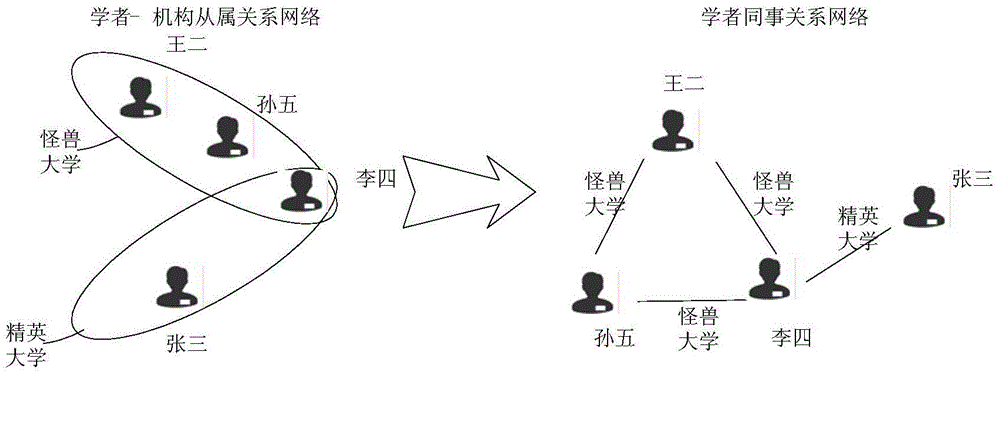
Method for calculating author influence based on citation propagation network
ActiveCN104657488ALack of timelinessIncrease time complexityWeb data indexingSpecial data processing applicationsCalculation methodsCitation
The invention discloses a method for calculating the author influence based on a citation propagation network. The method comprises the following steps of step 1, establishing a citation relationship network and a colleague relationship network: establishing an author citation relationship network and the colleague relationship network based on an essay public information database; step 2, establishing the citation propagation network, wherein the citation propagation network is an integration network of the author citation relationship network and the colleague relationship network; step 3, calculating the author influence based on the citation propagation network, wherein the calculation formula is as shown in the figure. The method for calculating the author influence based on the citation propagation network can obtain more reasonable author influence indexes, and is easy to be implemented and simple and convenient for calculation.
Owner:CENT SOUTH UNIV
Linear deviation degree method-based intelligent path planning method
ActiveCN110231824AComputational time complexity is lowShort planning timePosition/course control in two dimensionsPlanning approachTime complexity
The invention discloses a linear deviation degree method-based agent path planning method, relates to an agent path planning method, belongs to the field of artificial intelligent researches, and aimsat solving the problems that the existing graph search type algorithms are high in calculation time complexity under complicated environments and the global path planning of the mobile robots is lowin working efficiency and instantaneity in known environments. According to the method, a model which is scaled down at a same proportion is established according to a practical environment and a coordinate system is correspondingly established; and intelligent nodes are added, paths unrelated to the added nodes are deleted, modeling is carried out on the basis of a linear deviation degree, screening is carried out according to a deviation angle, and finally a path node is searched to determine a finally found optimal path. The method is mainly used for the path planning of agents.
Owner:NORTHEAST FORESTRY UNIVERSITY
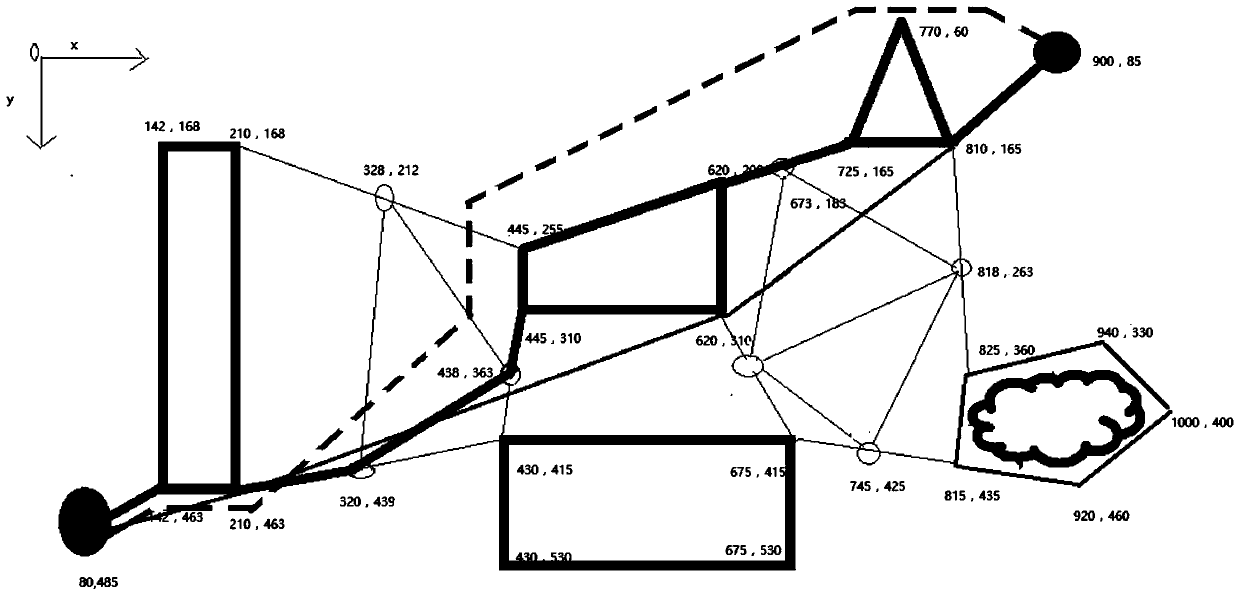
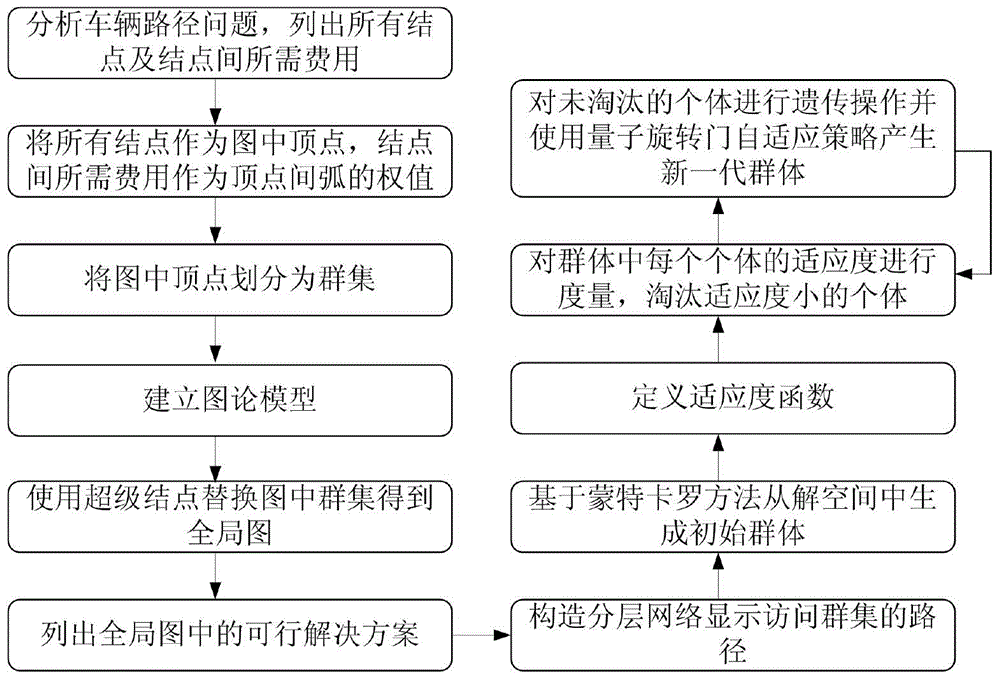
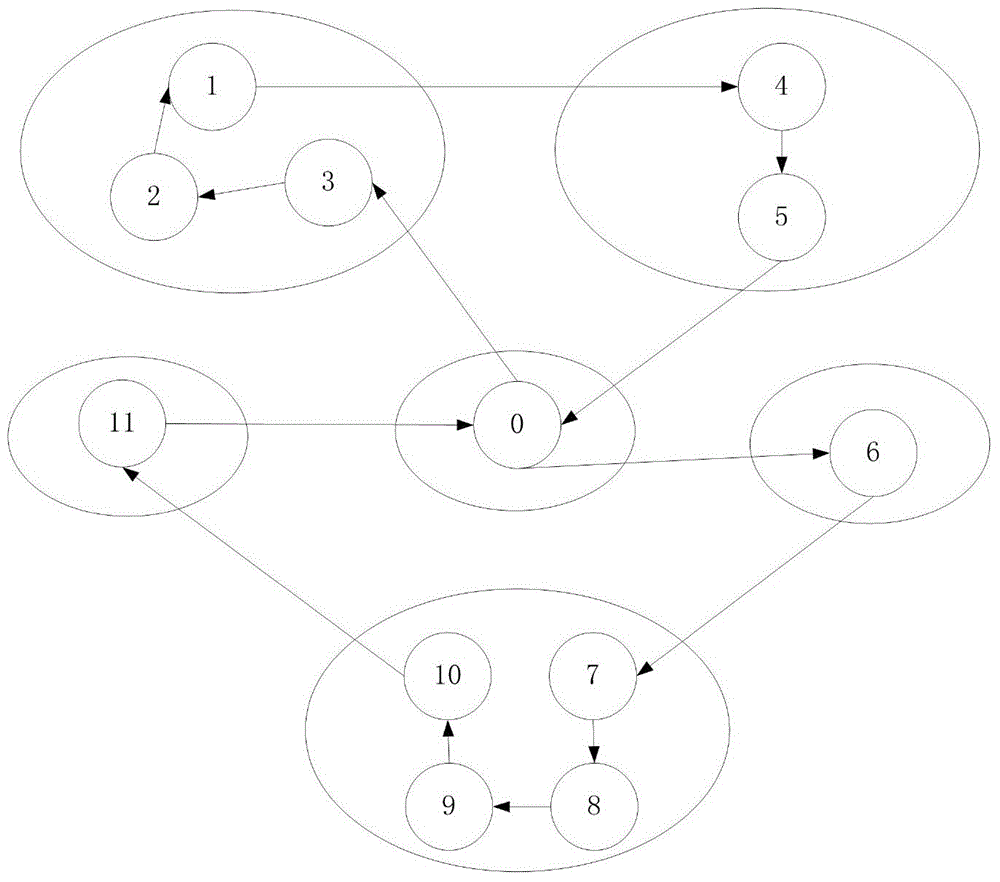
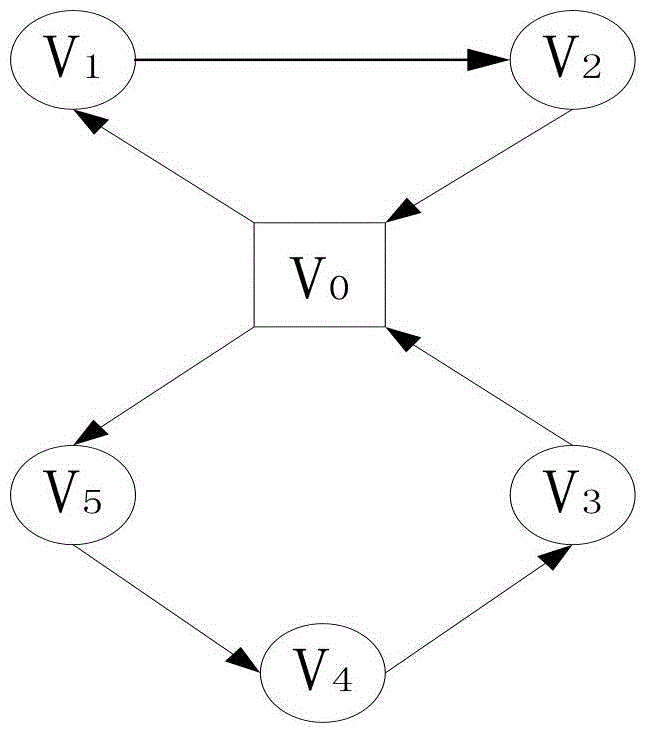
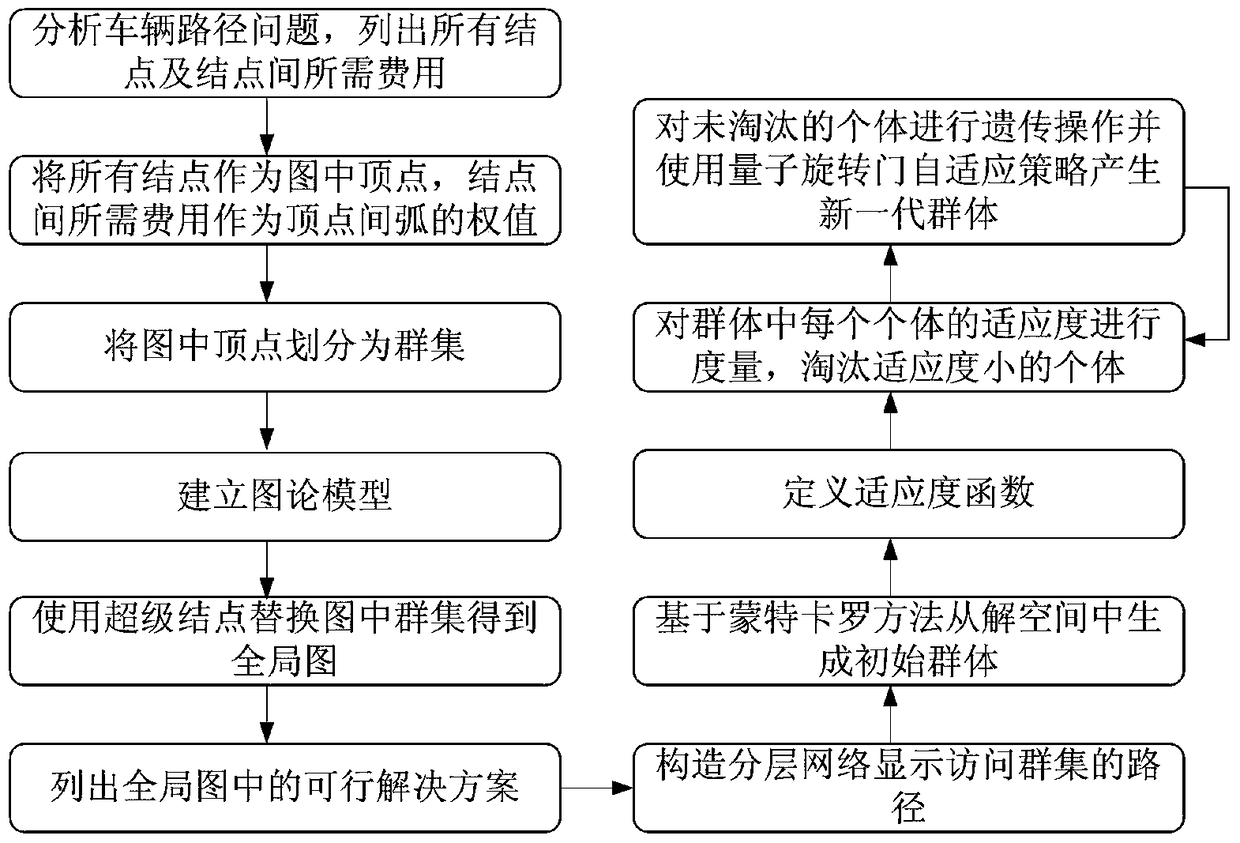
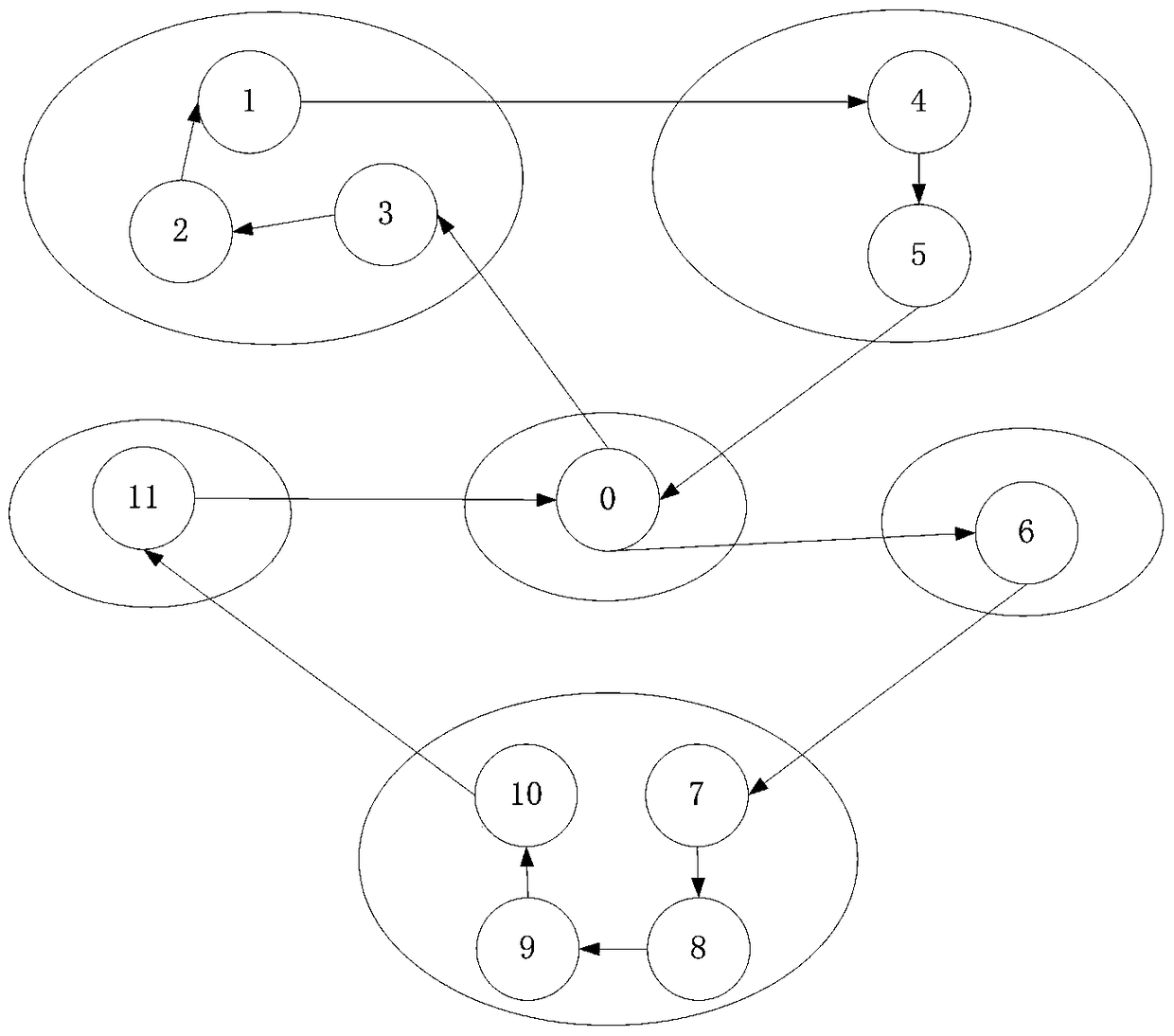
Vehicle route optimization method
ActiveCN104700160ASolving the Vehicle Routing ProblemOptimize Time ComplexityForecastingGenetic algorithmsGraph modelSelf adaptive
The invention discloses a vehicle route optimization method. The vehicle route optimization method includes that defining a vehicle route problem into a graph model, solving an inter-cluster cost route from a global view to acquire a feasible solution space, and optimizing the feasible solution space through a Monte Carlo method, genetic manipulation, a quantum rotating gate adaptive strategy and the like. The vehicle route optimization method is capable of solving the vehicle route problem in the global connection, optimizing the time and space complexity in the problem solving process, and avoiding premature convergence. The vehicle route problem refers to that a certain number of customers have different numbers of goods demands, a distribution center provides goods for the customers, one motorcade is responsible for distributing goods, and proper driving routes are organized to meet the demands of the customers and achieve the aims of shortest journey, lowest cost, shortest time consumption and the like under a certain constraints.
Owner:NANJING UNIV OF POSTS & TELECOMM
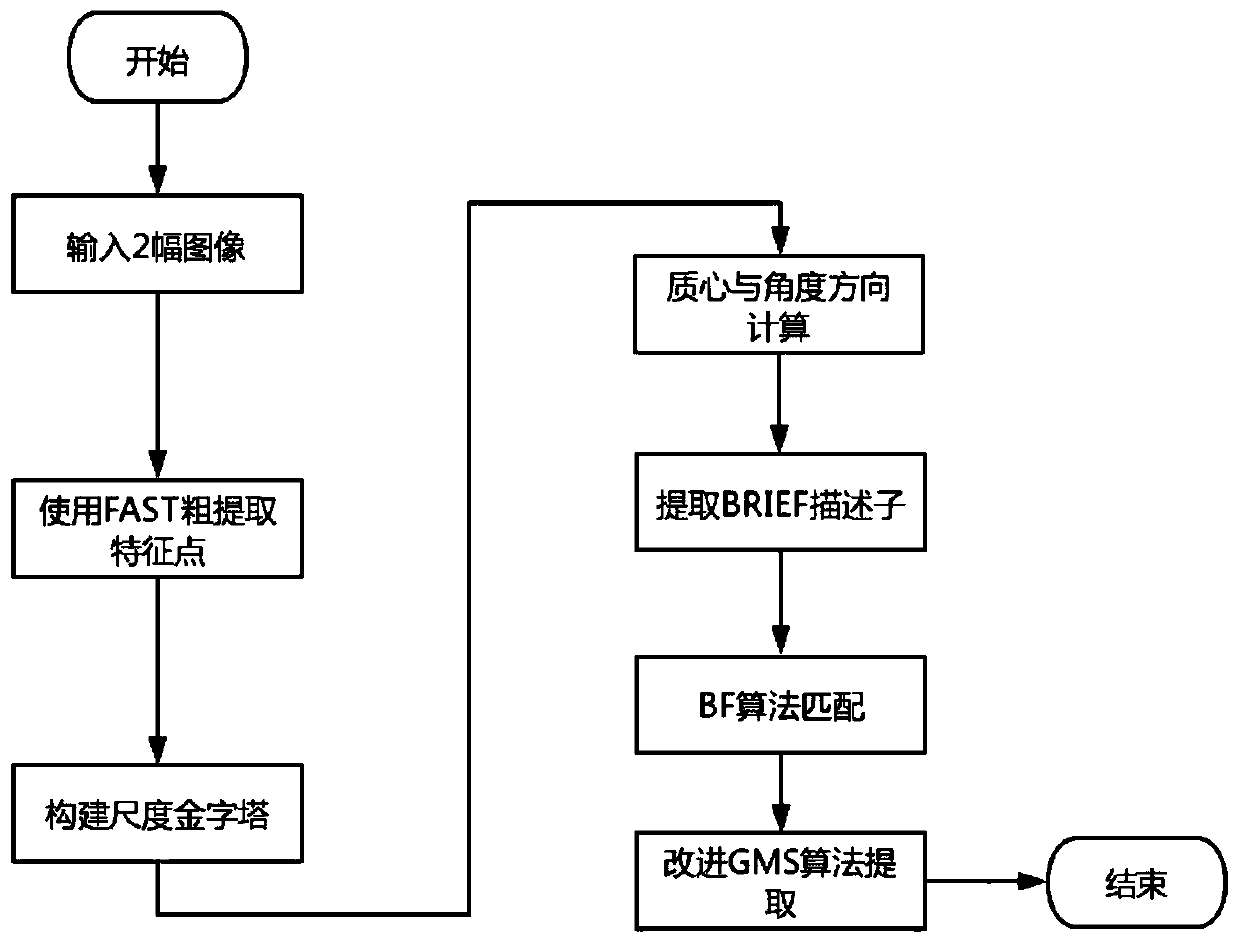
Image matching method based on improved GMS-ORB feature and storage medium
ActiveCN110675437AReduced instances of ghostingReduce matching timeImage enhancementImage analysisImage matchingLearning methods
The invention requests to protect an image matching method based on improved GMS-ORB features, and the method comprises the following steps: S1, carrying out the rough extraction of the feature pointsof an original image and a to-be-registered image through employing a Fast method, and obtaining a large number of feature points; S2, using a machine learning method to screen out optimal Fast feature points; S3, constructing a Gaussian pyramid to realize scale invariance of the feature points; S4, realizing rotation invariance of the feature points by using a gray centroid method; S5, describing the feature points extracted from the Fast corner points by using a BRIEF algorithm, and performing feature point rough matching by using a violent matching algorithm based on Hamming distance; andS6, purifying the rough matching by using an improved GMS algorithm, and removing wrong matching to complete image registration. According to the method, the quadtree and the GMS algorithm are combined, the quadtree is used for controlling the number of the grids generated by the GMS, the matching time is shortened, the grids are divided in a targeted mode, and the registration precision is improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
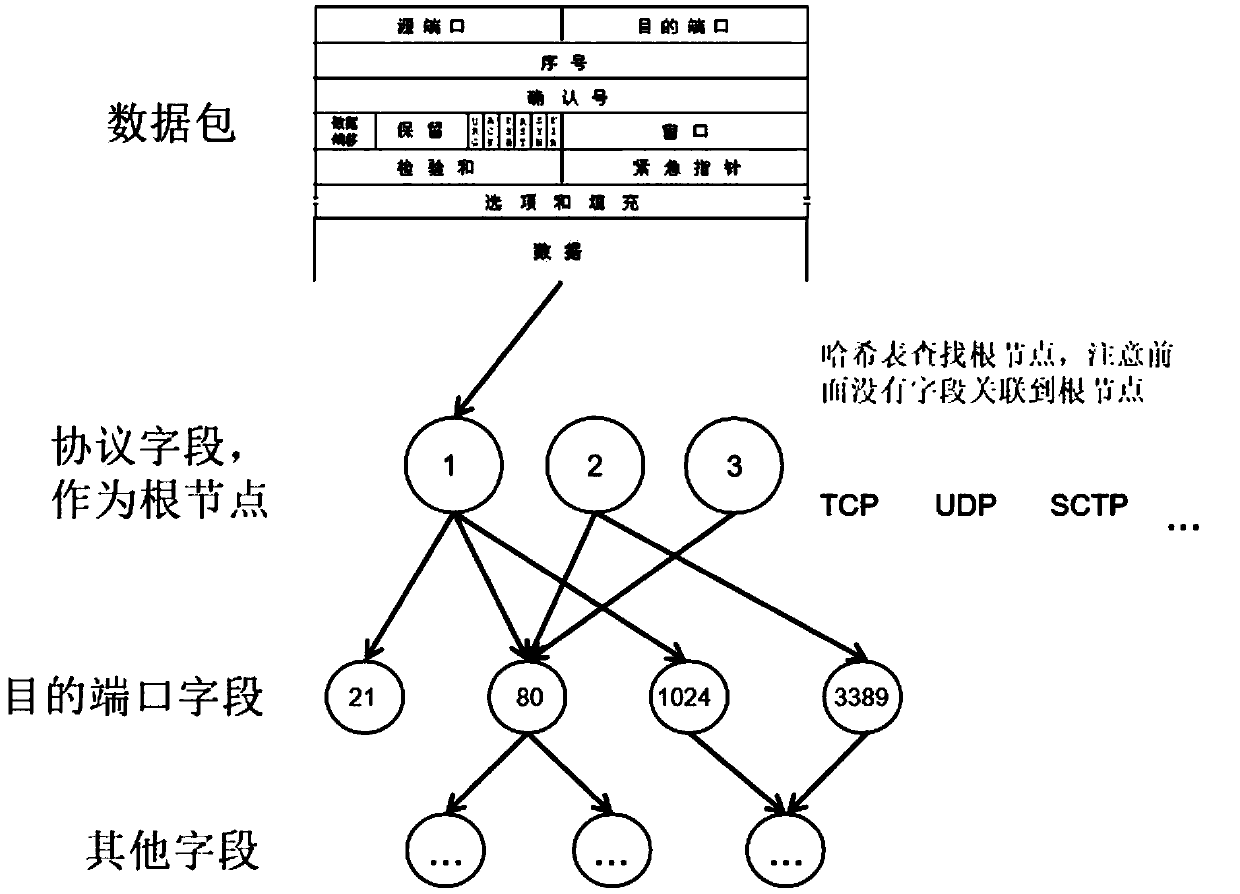
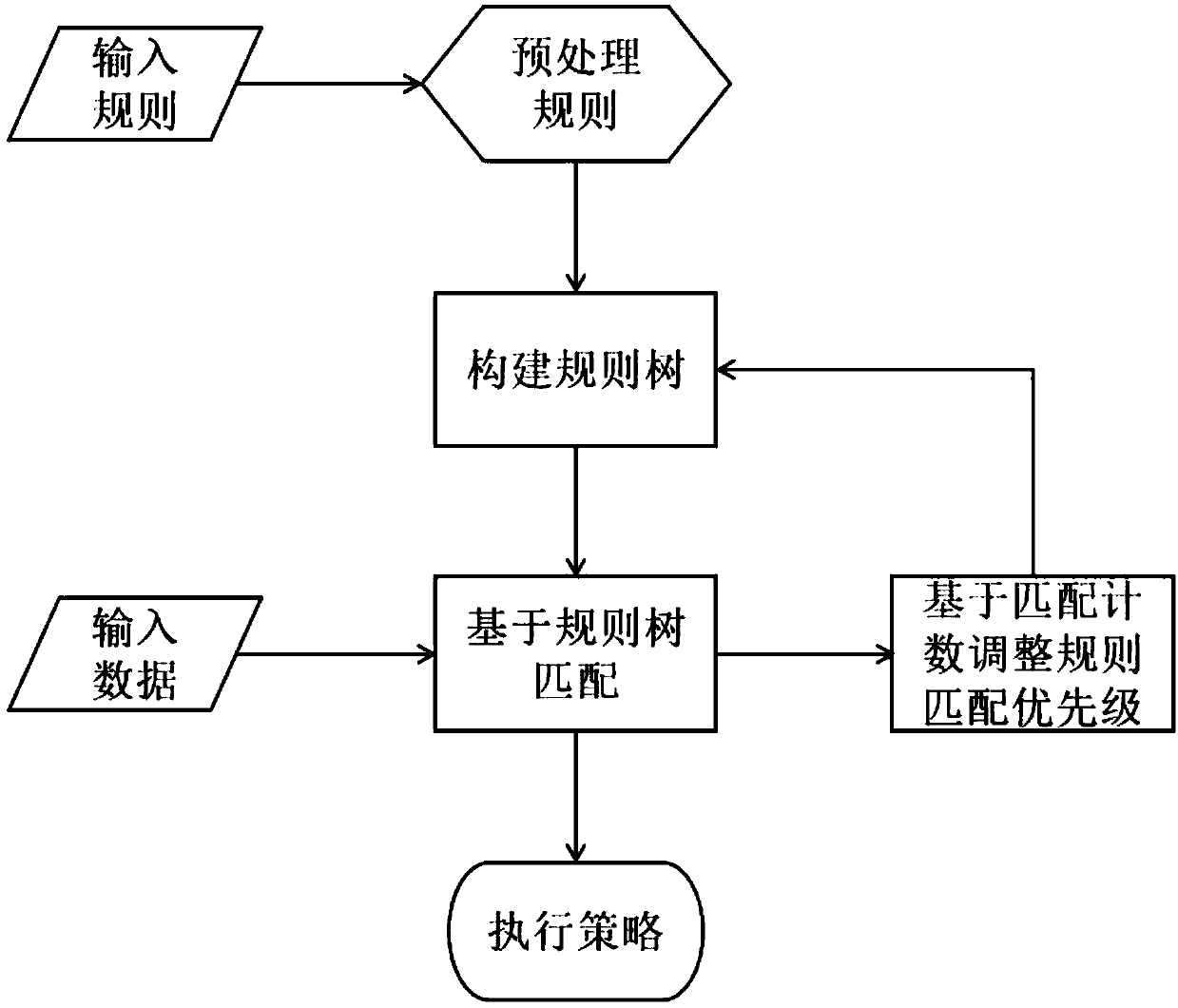
Firewall data packet matching algorithm based on rule tree retrieval
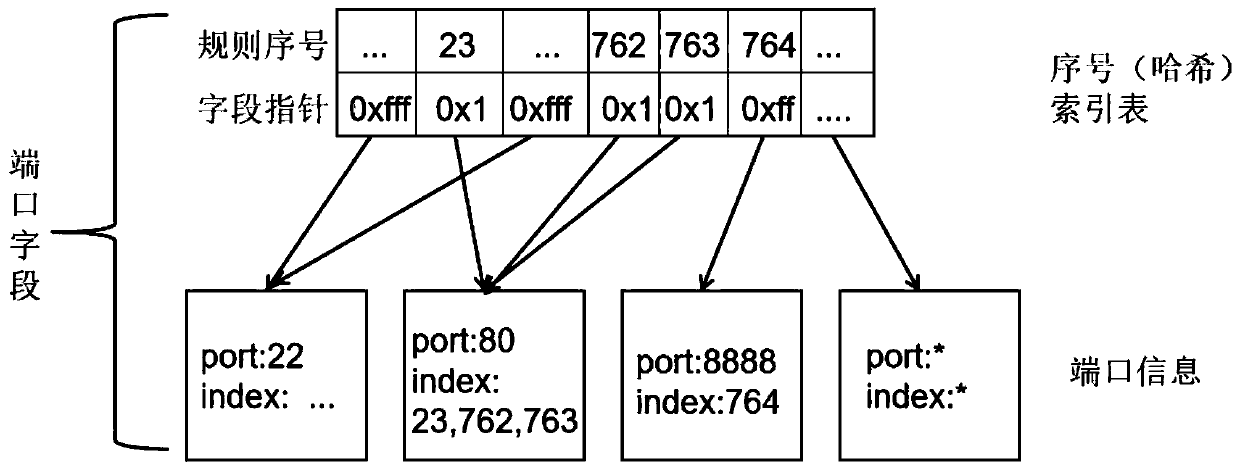
The invention relates to a firewall data packet matching algorithm based on rule tree retrieval. The method provided by the invention comprises the step of a preprocessing rules, constructing a rule tree and matching a data packet; the step of processing the rules is to perform formalization and standardization processing on the rules to generate a rule set with a complete and uniform structure; the step of constructing the rule tree is to process all rules to generate a tree data structure that is organized, stores all rule information and is easy to be retrieved quickly; and the step of matching the data packet comprises: 1. parsing the data packet to be matched to obtain data packet features; 2. performing retrieval matching on each feature of the data packet one by one according to theconstructed rule tree to finally match a certain rule; recording a matching count and a backtracking count; and 3. executing a policy set by the matched rule, or, executing a default policy if the rule is not matched. The invention provides a firewall data packet matching algorithm having excellent performance and controllable space complexity and friendly supporting the increase and decrease ofthe rules.
Owner:G CLOUD TECH
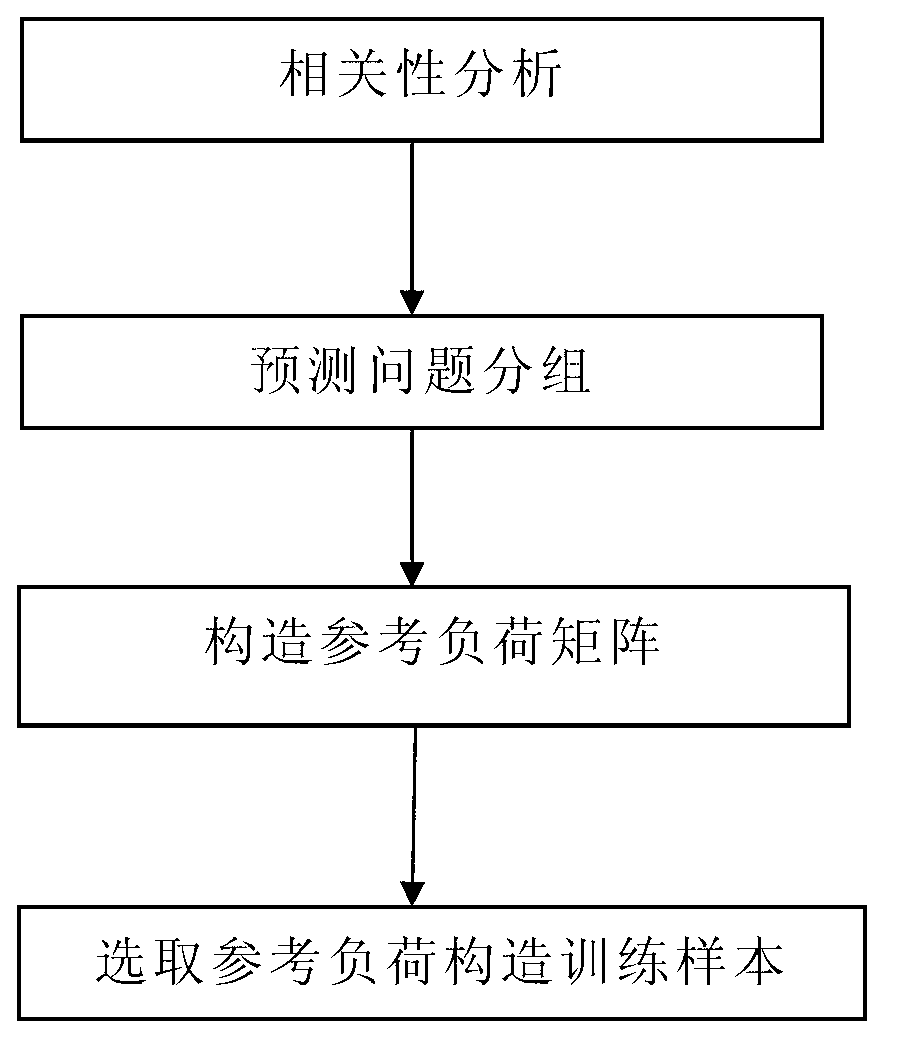
Training sample grouping construction method used for support vector regression (SVR) short-term load forecasting
InactiveCN103106329AImprove Load Forecasting AccuracyAvoid high time complexitySpecial data processing applicationsLeast squaresGrey correlation
The invention discloses a training sample grouping construction method used for support vector regression (SVR) short-term load forecasting, and belongs to the field of intelligent computing and machine study. The training sample grouping construction method comprises a step of analyzing correlation, wherein the correlation degree of the load of each time interval and the loads of other time intervals is analyzed through the Tangs correlation degree of the grey correlation degree to form a correlation degree matrix; a step of grouping prediction problems, wherein the time intervals with high load correlation degree are divided into one group according to the correlation degree matrix; a step of constructing a reference load matrix; a step of selecting a reference load to construct a training sample, wherein linear function fitting is carried out on each row of the loads in a load variation rate matrix in a least square fit mode, and fitting variance is calculated; and a step of selecting the load of the time interval with small fitting variance to serve as the forecasting reference load of the group. The training sample grouping construction method used for the SVR short-term load forecasting is capable of improving the load forecasting accuracy, and avoids the problem of high time complexity. The experiment result shows that a short-term load forecasting model trained by the training sample constructed through the method has good performance in forecasting accuracy and time complexity.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Detection method for Lamination lithium ion battery
ActiveCN104091322AOptimize Time ComplexityImproved Time AccuracyImage analysisAngular pointEngineering
The invention discloses a detection method for a lamination lithium ion battery. The method includes the following steps: carrying out statistics of a variance of each line of a lamination battery gray level image in the horizontal direction and carrying out threshold processing on a statistical result so as to determine a calculated characteristic area; carrying out angular point detection on an image of the determined characteristic area and calculating the similarity of each point of the image and calculating a direction change intensity and according to the direction change intensity, setting a threshold to filter image angular point positions, that is the angular point detection; through statistics of a maximum occurrence probability of the angular points in the horizontal direction, classifying the angular points; and after a position of a maximum occurrence probability of anode and cathode angular points is determined, using the maximum position as a reference point to screen anode and cathode piece angular points and then carrying out three-cubic fitting after the screening and carrying out compensation processing on a position at which opening is larger during the fitting. The detection efficiency and precision of the lamination lithium ion battery are improved.
Owner:WUXI UNICOMP TECH
Markov carpet embedded type feature selection method based on packaging
ActiveCN105205349AQuick identificationAvoid slow recognitionSpecial data processing applicationsEngineeringData mining
The invention discloses a Markov carpet embedded type feature selection method based on packaging. The Markov carpet embedded type feature selection method is characterized by being carried out according to the following steps: 1, acquiring an optimal feature by using a five-fold cross validation method; 2, judging whether the optimal feature is a null set not; if so, finishing feature selection; otherwise, updating a feature subset; 3, deleting redundancy features by using a Markov carpet method so as to update a feature vector; and 4, judging whether the feature vector is a null set not; if so, finishing the feature selection; otherwise, repeating the step 2. By virtue of adopting the Markov carpet embedded type feature selection method, the high-quality feature subset can be obtained; and meanwhile, the time complexity of the feature selection method based on the packaging is reduced so that relatively good classification performance and time performance can be obtained.
Owner:HEFEI UNIV OF TECH
Model-independent genome structure variation detection system and method
ActiveCN111583996ALow detection sensitivityReduce error rateBiostatisticsProteomicsData miningStructural variant
The invention provides a model-independent genome structure variation detection system and method, wherein a model-independent structure variation detection theory is used as a core, and structure variation detection without depending on any variation model is achieved through a variation signal extraction module, a frequent maximum subgraph mining module and a classification module. According tothe system, a frequent variation pattern mining module is used for capturing the characteristics of structural variation left on a genome, and judging a potential structural variation region only by mining abnormal points in a large amount of normal data; and according to different genome disturbance modes of different variation types, different arrangement sequences of variation signals are further caused, and the different variation types are classified on the basis of the different arrangement sequences in combination with a deep learning model with a memory function. According to the invention, the system does not depend on any variation model, so that the variation detection sensitivity and error rate are greatly reduced; and the system is suitable for detection of complex variation types, and an additional structural variation model does not need to be established.
Owner:XI AN JIAOTONG UNIV
Two-dimensional-graphics acceleration method based on GCN (Graphics Core Next)-architecture display card
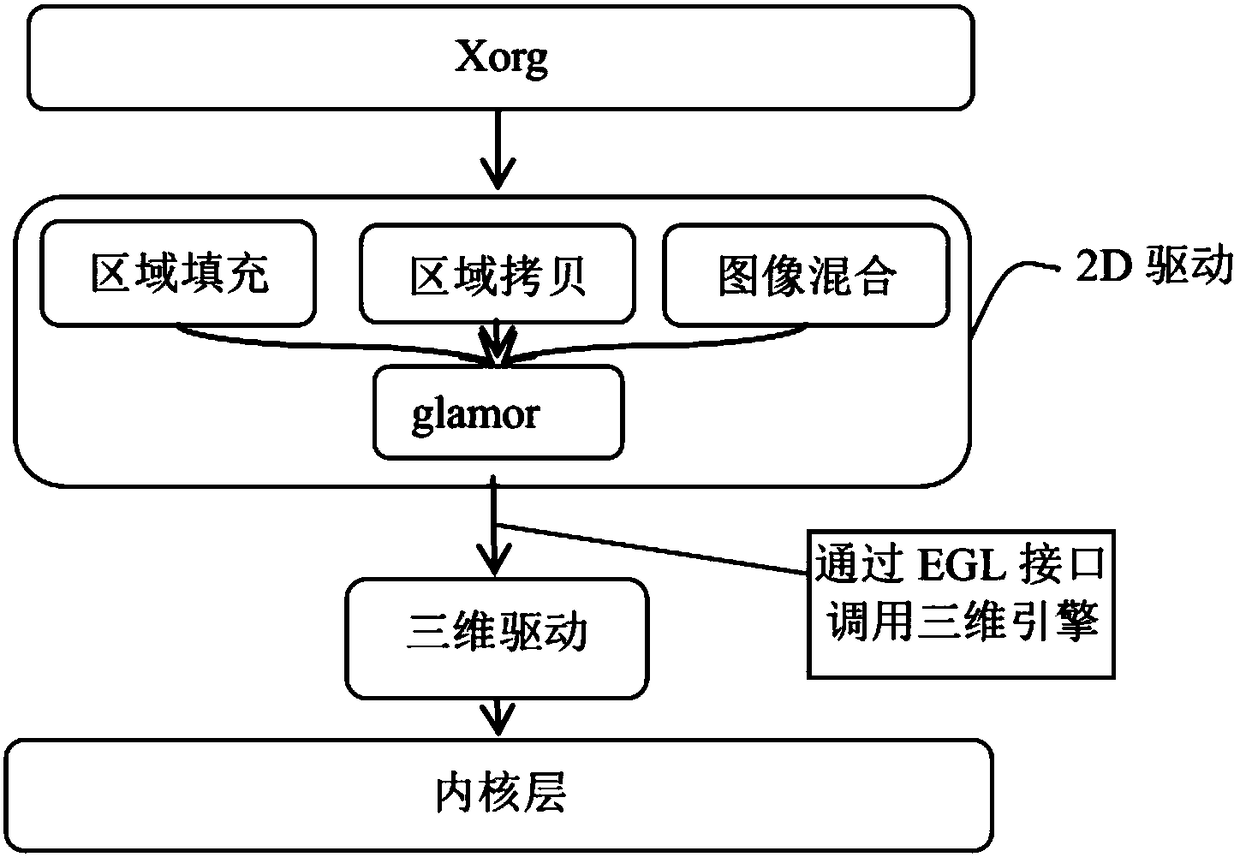
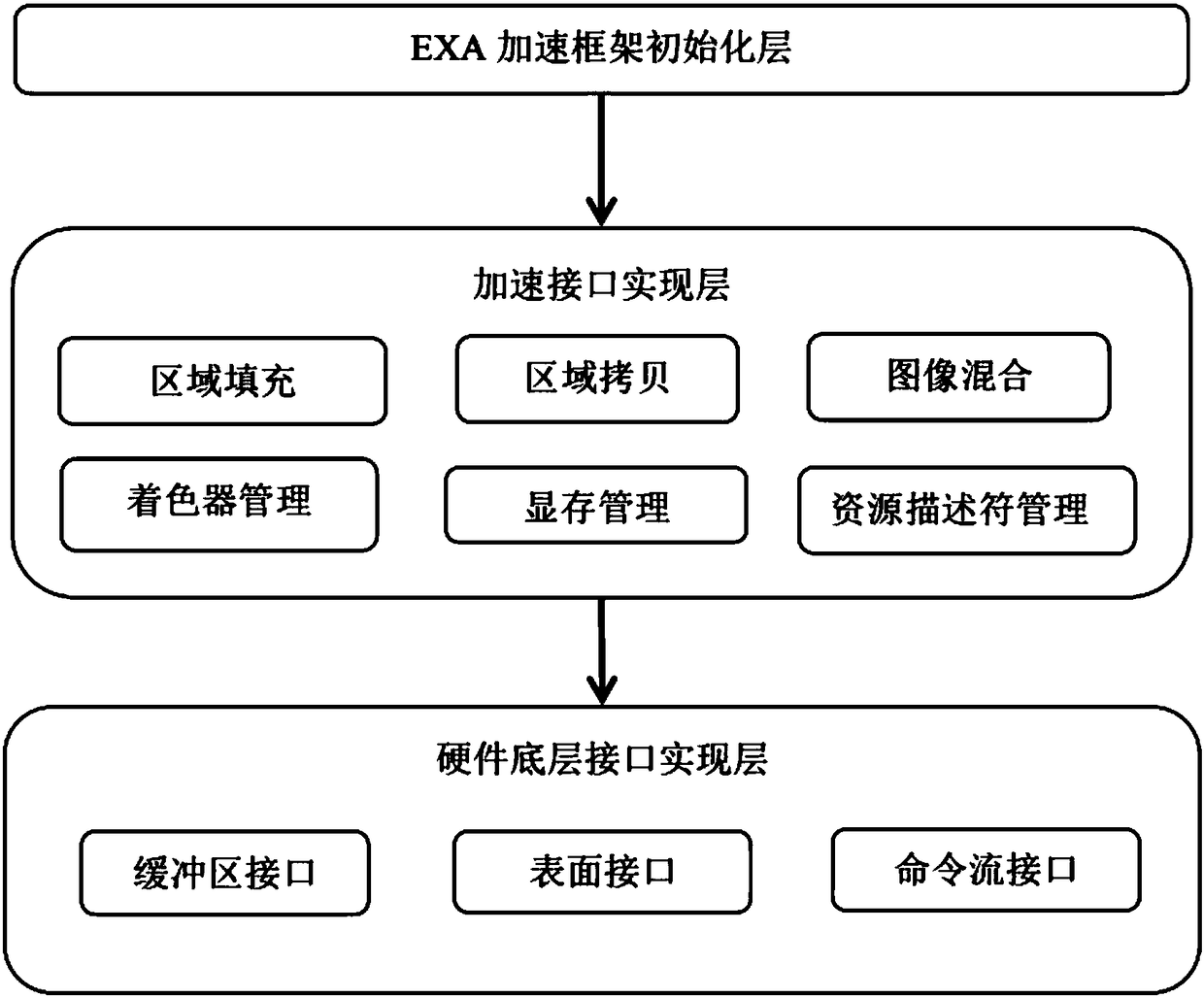
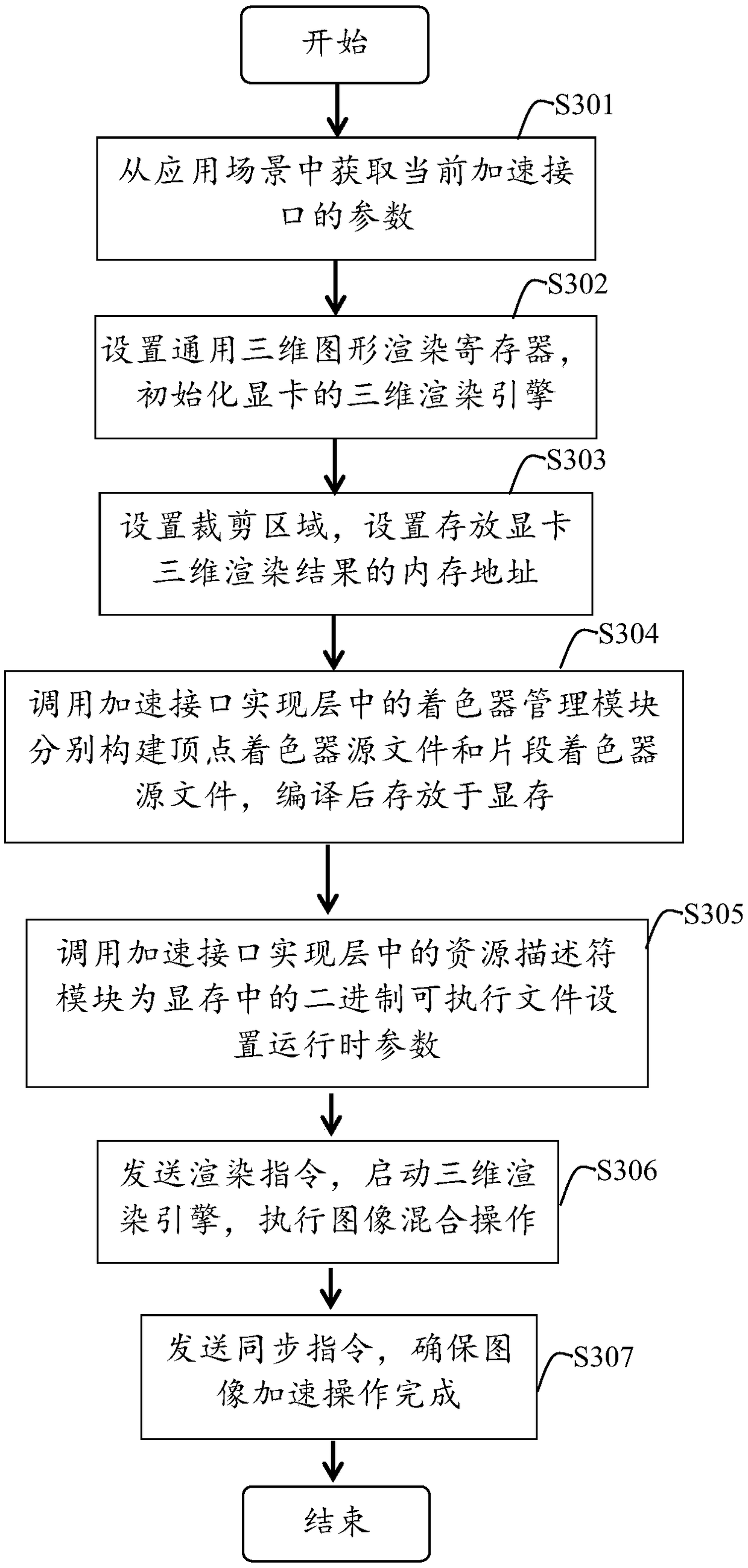
PendingCN108171644AAvoid the downsides of a cumbersome processImprove acceleration performanceImage data processing details3D-image renderingTime complexityThree dimensional graphics
The invention discloses a two-dimensional-graphics acceleration method based on a GCN (Graphics Core Next)-architecture display card. On the basis of the characteristics of a general graphics acceleration framework EXA under an X window system and the GCN-architecture display card, the two-dimensional-graphics acceleration method of the GCN-architecture display card is realized through realizing main acceleration operations under the EXA acceleration framework. The method has the advantages of: quickly establishing a rendering link, carrying out state programming and shader programming on theGCN-architecture display card, utilizing vertex resources, texture resources and constant resources, and thus completing the two-dimensional acceleration method under the EXA acceleration framework; avoiding the disadvantages that an acceleration method in a Glamor acceleration manner requires tedious processes of firstly calling EGL to initialize a graphics rendering environment, and then callingan API interface in OpenGL to switch a context process into three-dimensional-graphics rendering, realization of an entire acceleration interface is also greatly improved on aspects of time complexity, stability and memory consumption, and two-dimensional-graphics acceleration performance is greatly improved.
Owner:KYLIN CORP
Multi-target vehicle tracking method based on MDP
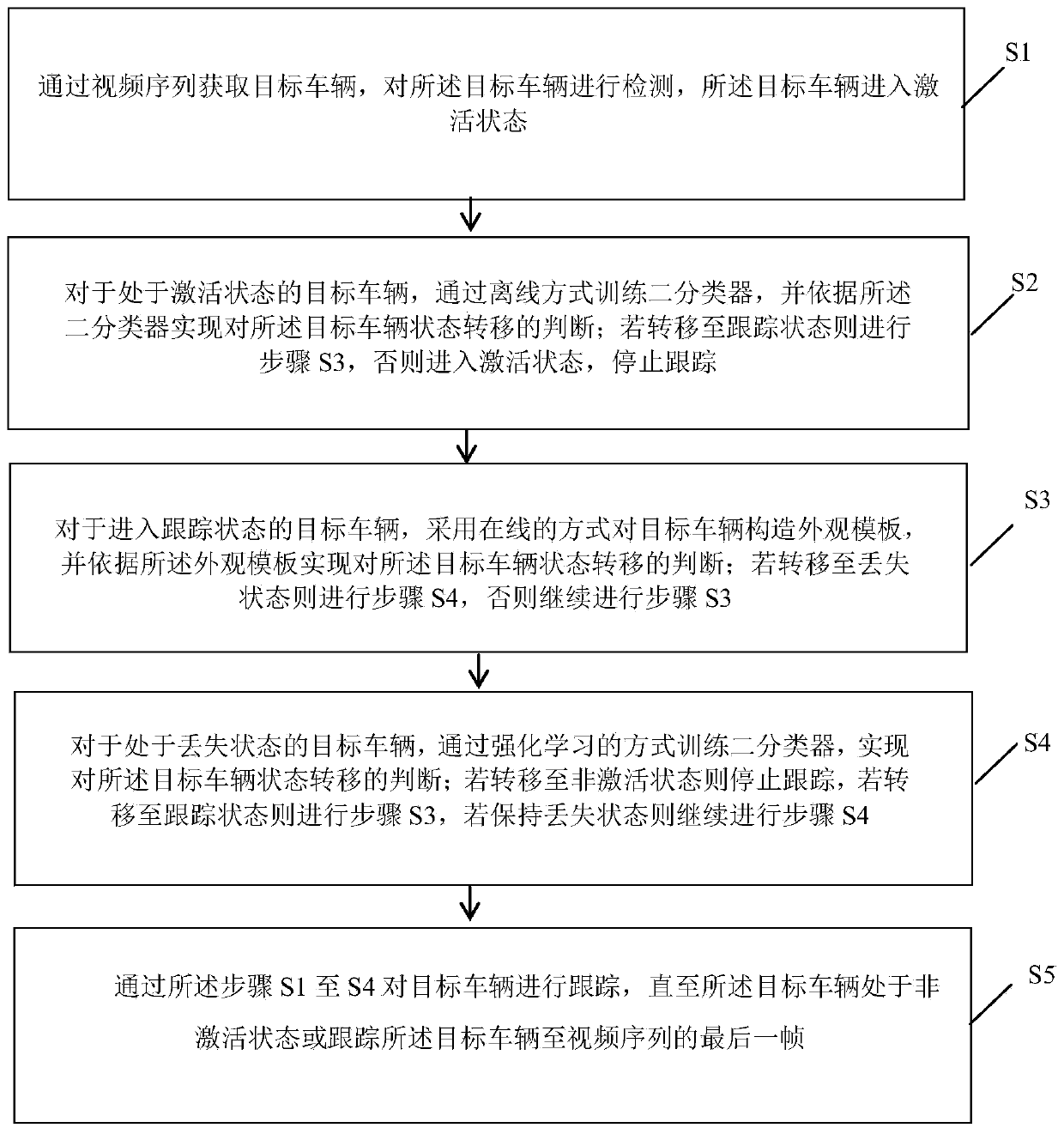
PendingCN111368938AOptimize Time ComplexityGood tracking effectCharacter and pattern recognitionSimulationVideo sequence
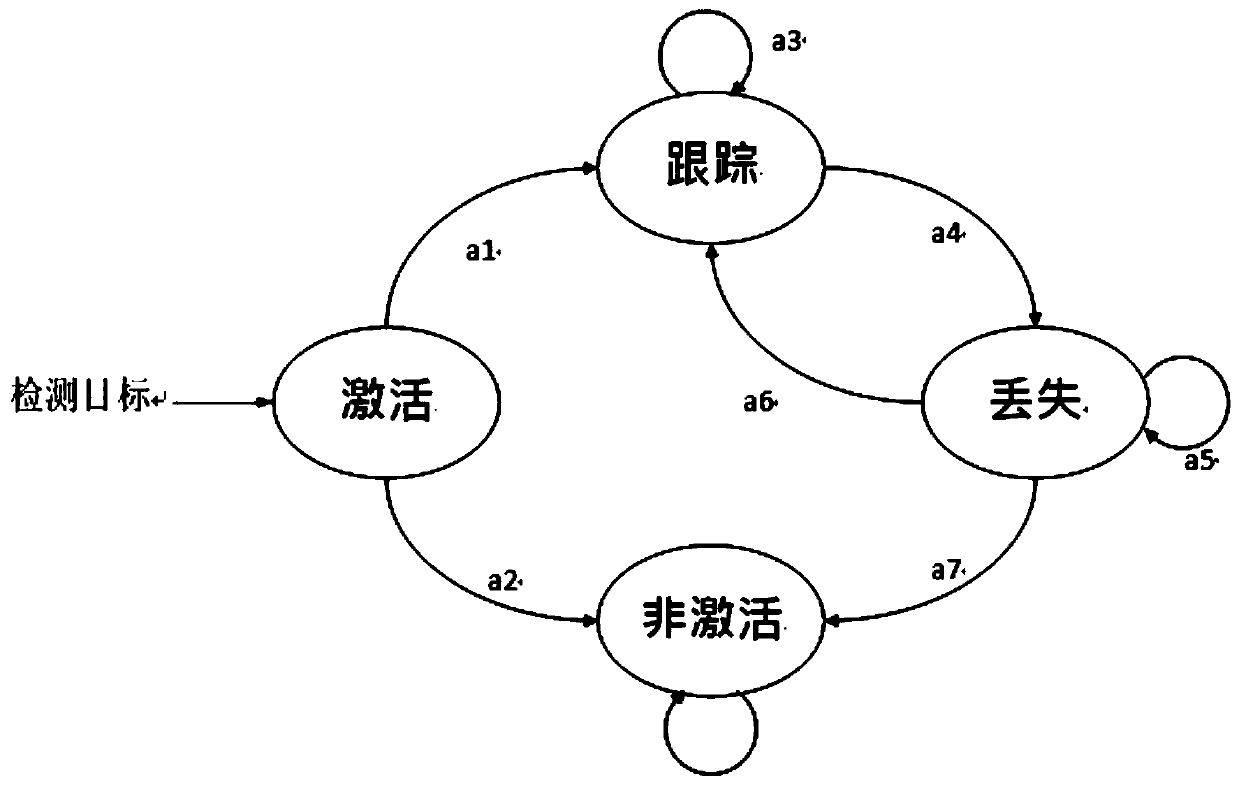
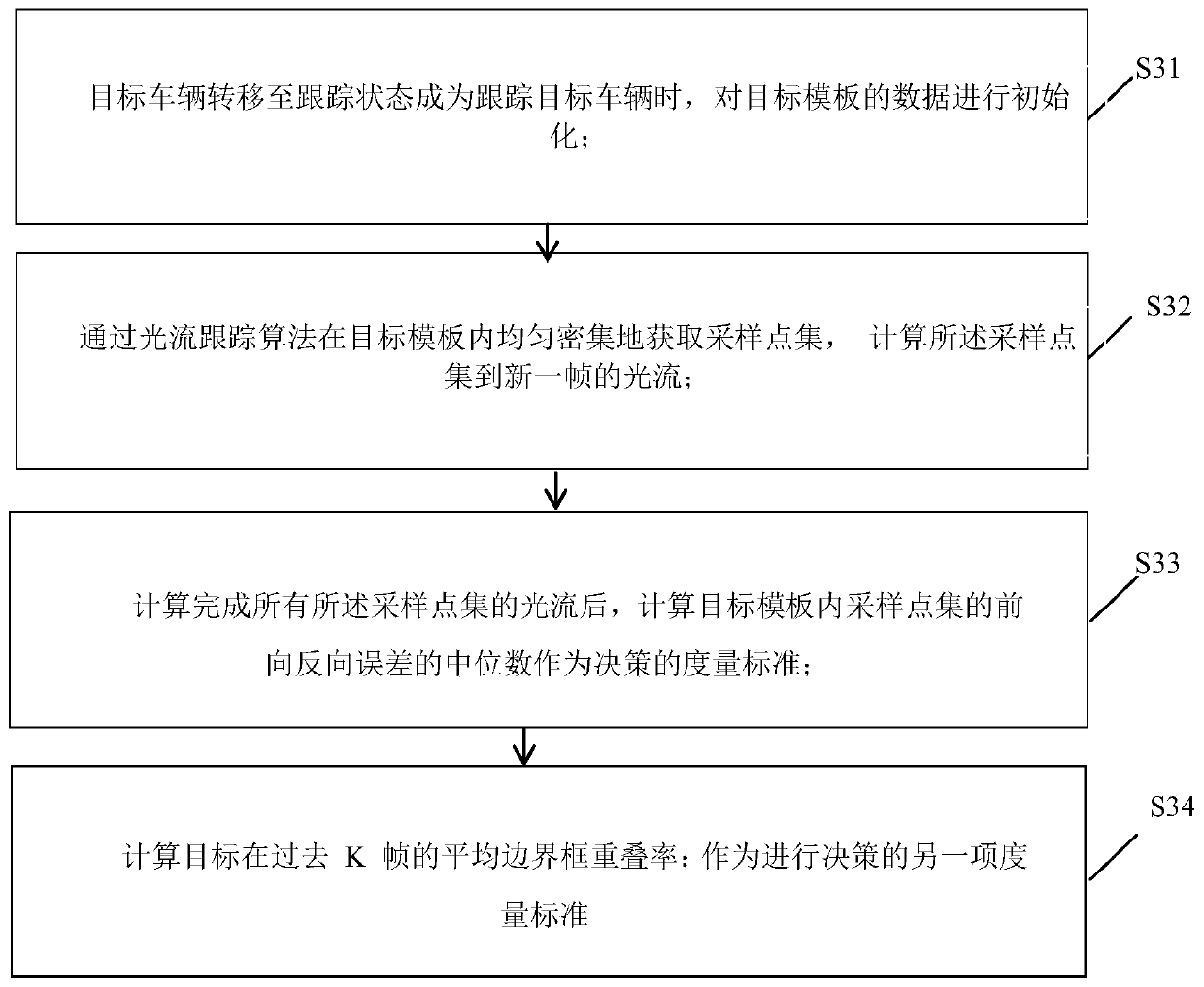
The invention discloses a multi-target vehicle tracking method based on a Markov decision process (MDP), and the method comprises the steps: obtaining a target vehicle through a video sequence, detecting the target vehicle, and enabling the target vehicle to enter an activated state; wherein the state of the target vehicle comprises an activated state, a tracking state, a non-activated state and alost state; for the target vehicle in the activated state, training a binary classifier in an offline mode, and judging the state transition of the target vehicle according to the binary classifier;for the target vehicle entering the tracking state, an appearance template is constructed for the target vehicle in an online mode, and state transition of the target vehicle is judged according to the appearance template; for a target vehicle in a lost state, judgment of state transition of the target vehicle is realized through data association binary classifier reinforcement learning; the method can overcome the main technical difficulties faced by the vehicle tracking technology, reduce the tracking error probability and improve the tracking effect.
Owner:NANJING INGO ARTIFICIAL INTELLIGENCE RES INST CO LTD
Search algorithm of all spanning trees of directed graph and undirected graph
InactiveCN103984718AReliable searchQuick searchSpecial data processing applicationsUndirected graphRound complexity
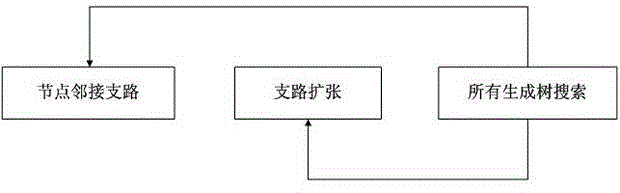
The invention discloses a search algorithm of all spanning trees of a directed graph and an undirected graph. Based on an MATLAB (matrix laboratory) platform, root nodes are found in the directed graph and the undirected graph, wherein the root nodes include all the spanning trees of given sub-trees. The search algorithm comprises the adjoining of branches by the nodes, the expansion of the branches and the seach of all the spanning trees. The search of all the spanning trees is realized by calling the adjoining of the branches by the nodes and the expansion of the branches. The search algorithm is very good in time complexity and space complexity. All the spanning trees of the directed graph and the undirected graph can be reliably and quickly searched. The search algorithm is ingenious and novel in thinking, thereby being very good in application prospect.
Owner:STATE GRID CORP OF CHINA +2
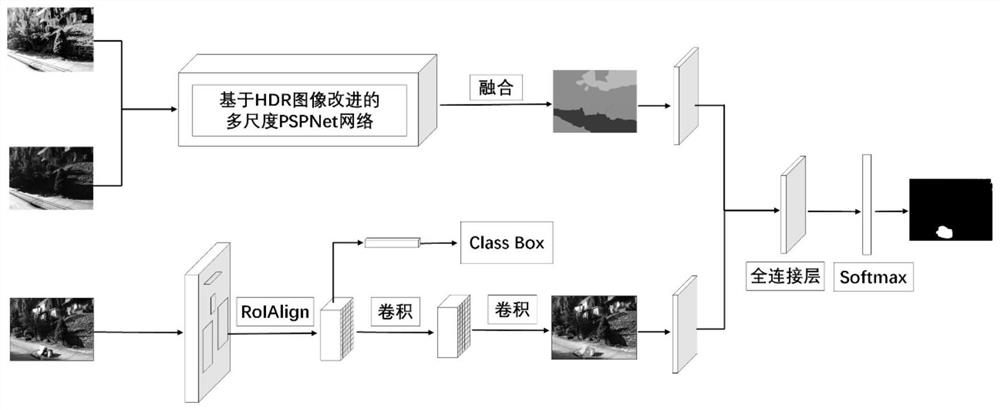
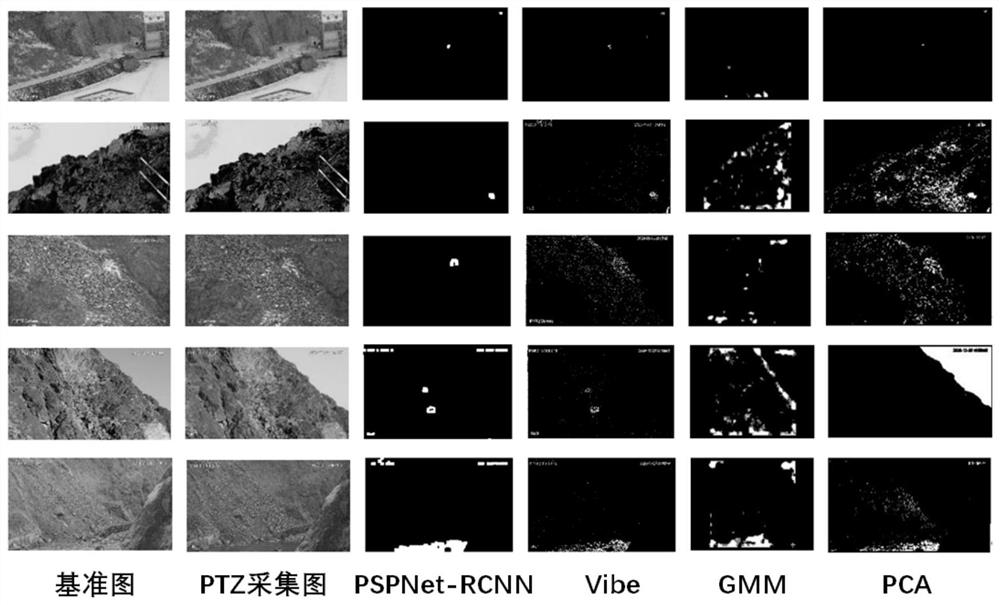
Ball machine monitoring anomaly detection method based on PSPNet-RCNN
PendingCN114298948AAccurate detectionHigh precisionImage enhancementImage analysisFeature extractionAnomaly detection
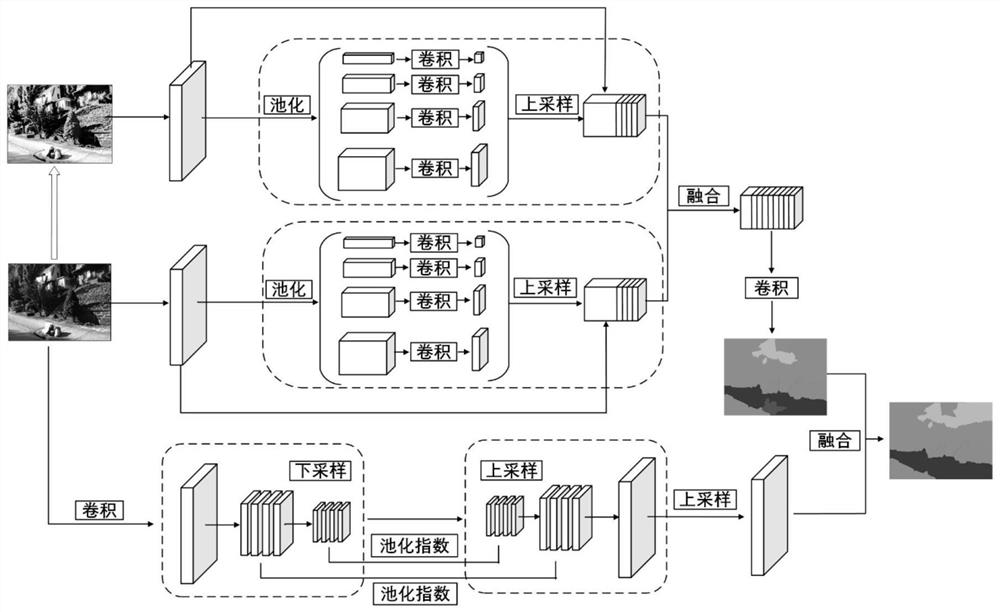
The invention discloses a PSPNet-RCNN-based dome camera monitoring anomaly detection method, and the method specifically comprises the steps: collecting multi-period exposure images at the same position, fusing the exposure images to generate an HDR image, carrying out the SIFT feature registration of the HDR image and an original position image, obtaining a registered HDR image, and carrying out the enhancement processing; the voidage of void convolution of a PSPNet network pyramid pooling module is increased, coding and decoding convolutional neural network branches are added to PSPNet, a residual convolutional network is added to an entrance of a feature extraction module for inputting double images, an improved multi-scale PSPNet network is obtained, the improved multi-scale PSPNet network is fused with a Mask R-CNN network for extracting target information in an HDR image, and the target information in the HDR image is extracted. And a PSPNet-RCNN image anomaly detection network is obtained and is used for extracting an image anomaly region. According to the invention, the universality and accuracy of the dome camera monitoring anomaly detection method are improved, and the real-time performance and robustness of the detection result are enhanced.
Owner:NANJING UNIV OF SCI & TECH
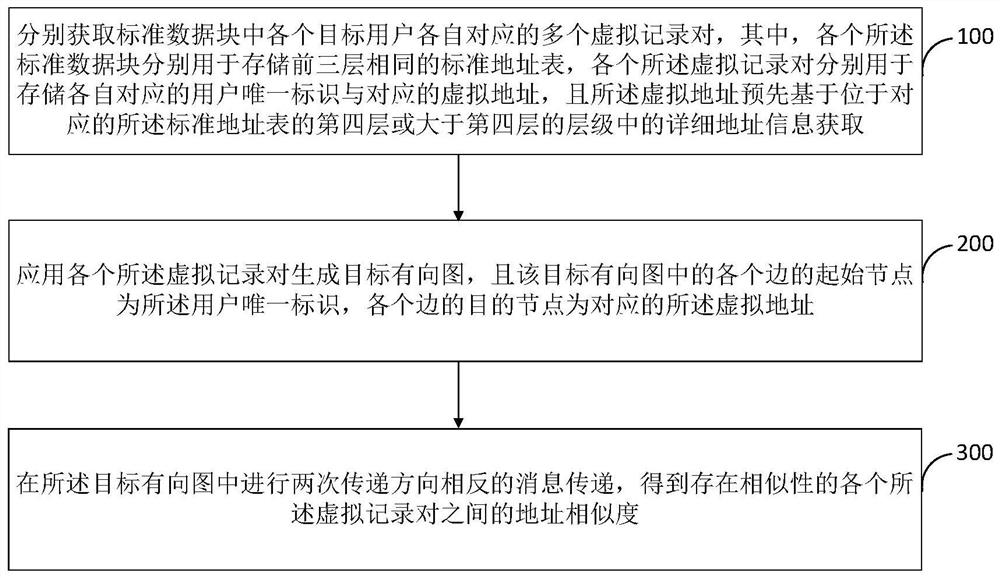
Address fuzzy matching method and device
ActiveCN111737315AImprove the efficiency of fuzzy matchingImprove efficiencyGeographical information databasesEnergy efficient computingMessage deliveryTheoretical computer science
The embodiment of the invention provides an address fuzzy matching method and device. The method comprises the following steps: respectively obtaining a plurality of virtual record pairs correspondingto each target user in the standard data block, wherein each standard data block is used for storing the same standard address tables of the first three layers respectively, each virtual record pairis used for storing a corresponding user unique identifier and a corresponding virtual address respectively, and the virtual address is acquired in advance based on detailed address information in a fourth layer of the corresponding standard address table or a layer larger than the fourth layer of the corresponding standard address table; generating a target directed graph by applying each virtualrecord pair; and carrying out message transmission in opposite transmission directions twice in the target directed graph to obtain the address similarity between the virtual record pairs with similarity. According to the method, the efficiency of user address fuzzy matching can be effectively improved, the calculation amount of user address fuzzy matching can be effectively reduced, and then theefficiency of obtaining users with high address similarity by enterprises can be effectively improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Congestion packet loss membership function construction method based on potential function
InactiveCN101753367AImprove accuracyOptimize Time ComplexityData switching networksPacket lossTime delays
The invention discloses a congestion packet loss membership function construction method based on potential function; a potential function is constructed and class partition is carried out according to the potential function, the parameters of the congestion packet loss membership function corresponding to the sample in congestion mode are determined, the parameters of the congestion packet loss membership function are adjusted in self-adaptive manner according to the changes of the sample for adapting to the change of the network environment. The congestion packet loss membership function construction method can determine the parameters of the congestion packet loss membership function based on potential function according to the bidirectional transmission time delay statistical result of the training sample when the error packet loss and congestion packet loss situations occur at the same time, so the packet loss reason is effectively differentiated. As shown in relevant experiments, the congestion packet loss membership function constructed through the method has better accuracy and time complexity.
Owner:BEIJING UNIV OF POSTS & TELECOMM
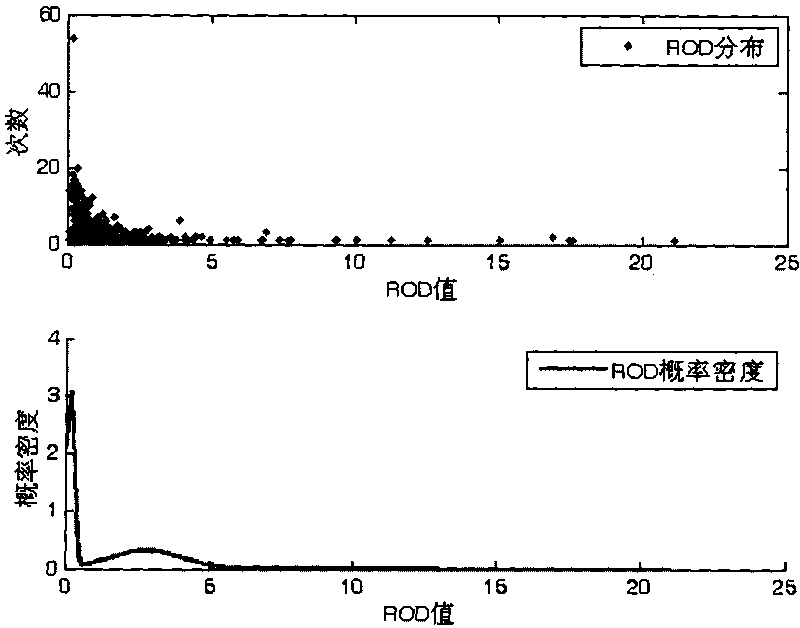
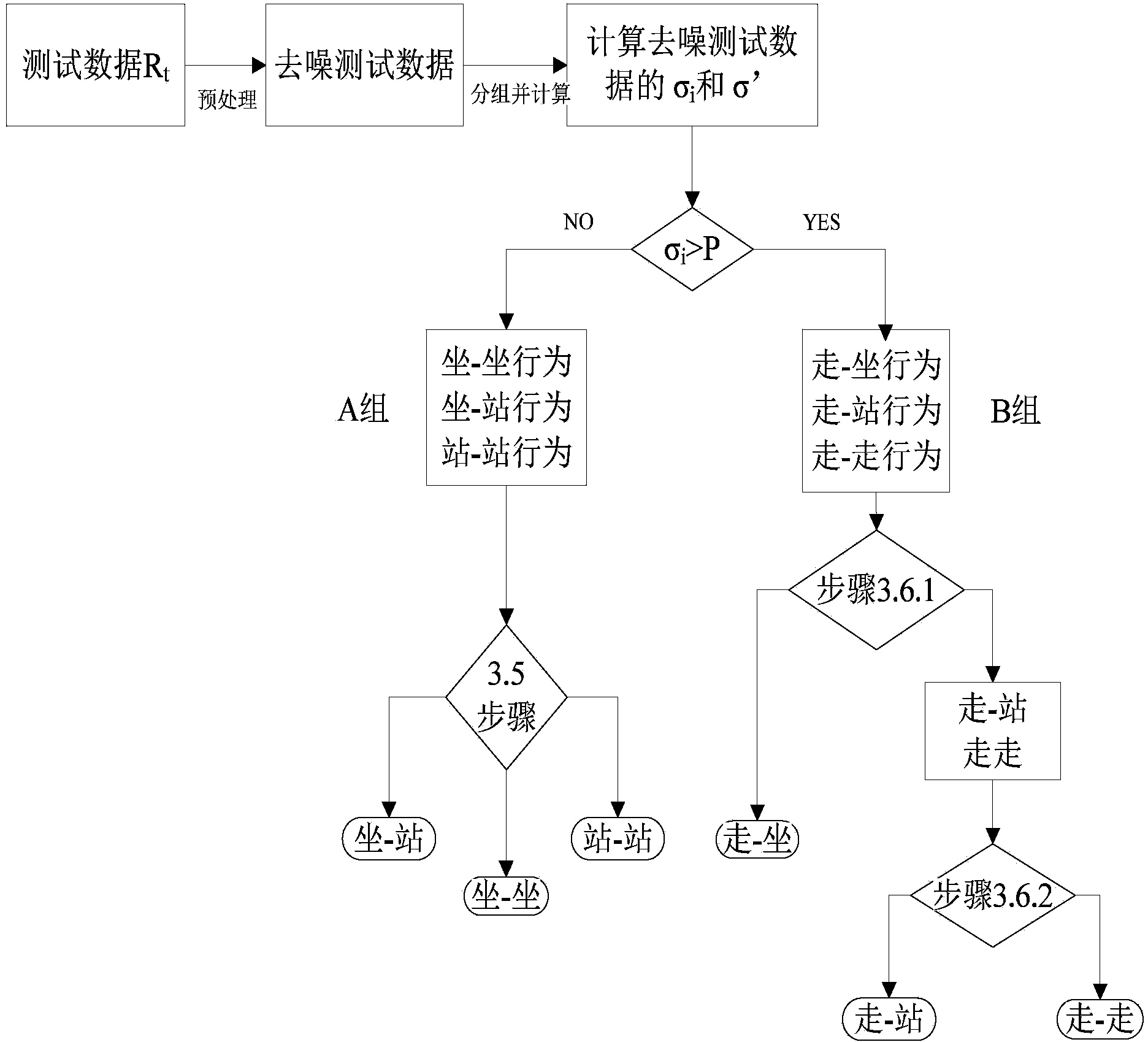
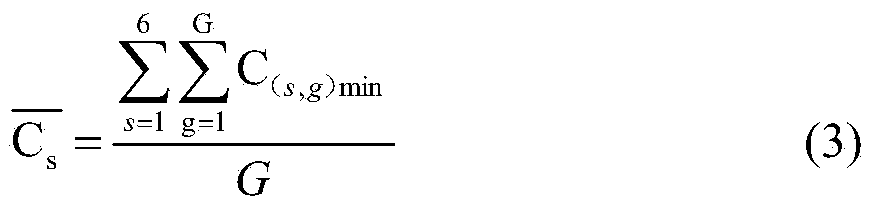
Passive type two-person behavior recognizing method based on WIFI background noise
InactiveCN104008282AEasy to identifyPracticalSpecial data processing applicationsNetwork interface controllerBackground noise
The invention discloses a passive type two-person behavior recognizing method based on WIFI background noise. The method is characterized by comprising the following steps that firstly, RSS data of combinations of six behaviors are collected through a WLAN card, secondly, wireless signal sample data are preprocessed to obtain denoised sample data, thirdly, a classification system model of the combinations of two-person behaviors is established according to the denoised sample data, and fourthly, data to be classified are recognized through the classification system model of the combinations of the two-person behaviors. According to the method, single person behavior recognition can be expanded to two-person behavior combined recognition, and a tested person can freely move indoors without carrying devices.
Owner:HEFEI UNIV OF TECH
Sensitive word detection method based on decision tree and variant recognition
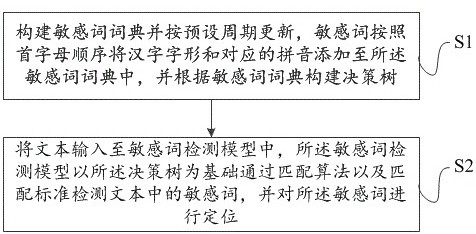
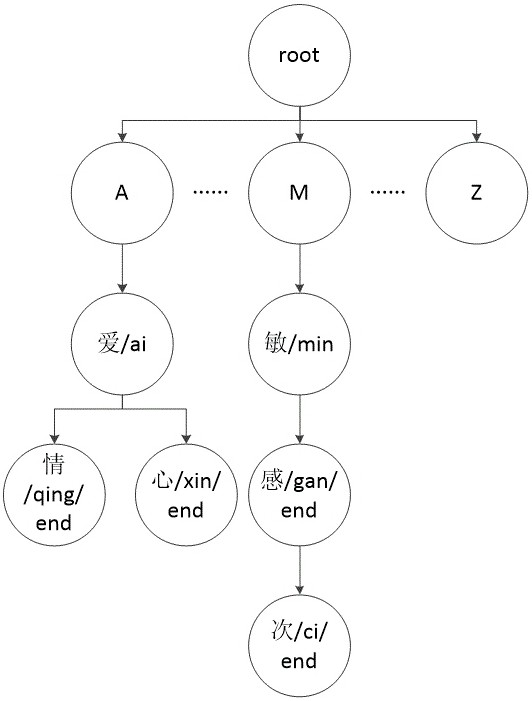
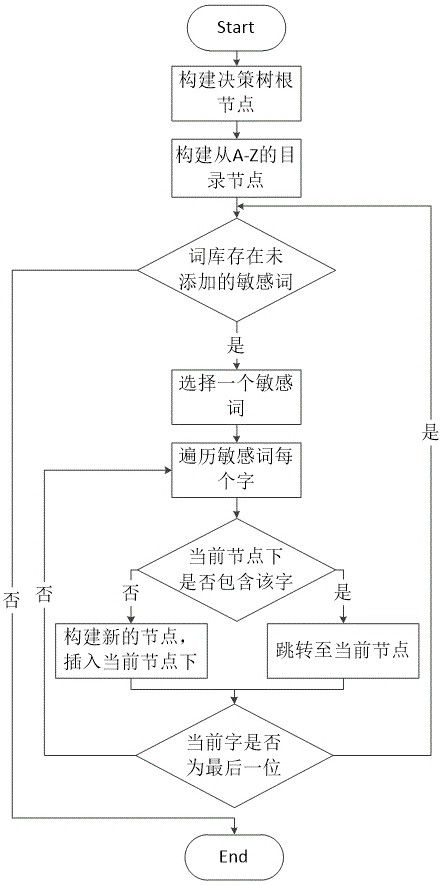
ActiveCN114091436AOptimize Time ComplexityRapid positioningNatural language data processingPattern recognitionText entry
The invention belongs to the technical field of natural language processing, and provides a sensitive word detection method based on a decision tree and variant recognition. The method comprises the following steps: S1, constructing a sensitive word dictionary and updating according to a preset period, wherein Chinese character patterns and corresponding pinyin are added into the sensitive word dictionary according to an initial sequence, and constructing a decision tree according to the sensitive word dictionary; S2, inputting a text into a sensitive word detection model, wherein the sensitive word detection model detects sensitive words in the text through a matching algorithm and a matching standard on the basis of the decision tree, and positions the sensitive words. Through direct comparison and similarity comparison of character patterns and pinyin, the problems that sensitive words are not included and detection is avoided by modifying character patterns, pinyin, or English of the sensitive words, can be effectively solved.
Owner:万商云集(成都)科技股份有限公司
Network page efficient and accurate deduplication system based on cloud computing
PendingCN112307303AExcellent time complexity and space complexityReduce overheadWebsite content managementSpecial data processing applicationsCloud computingEngineering
The invention provides a network page efficient and accurate deduplication system based on cloud computing, and aims to solve the problems that most of web pages searched by an existing search engineare static web pages, due to the existence of a large amount of transshipment and plagiarism, the main content of a large number of web pages is repeated, and for the search engine, the repeated web pages virtually increase the burden of index storage, and meanwhile, more retrieval time can be consumed; the webpage deduplication system based on the Hadoop cloud platform is designed and realized bycombining an open source framework, other modules of a search engine can be better connected by adopting a mode of detecting and judging duplicate in real time after a spider program captures a webpage; and in a massive webpage collection stage, the network page efficient and accurate deduplication system based on cloud computing can preprocess the web pages in advance, then web page similarity detection and discovery are carried out, repeated web pages or web pages with high similarity are removed, and therefore index quality is improved, retrieval results are optimized, and good search experience is provided for users.
Owner:扆亮海
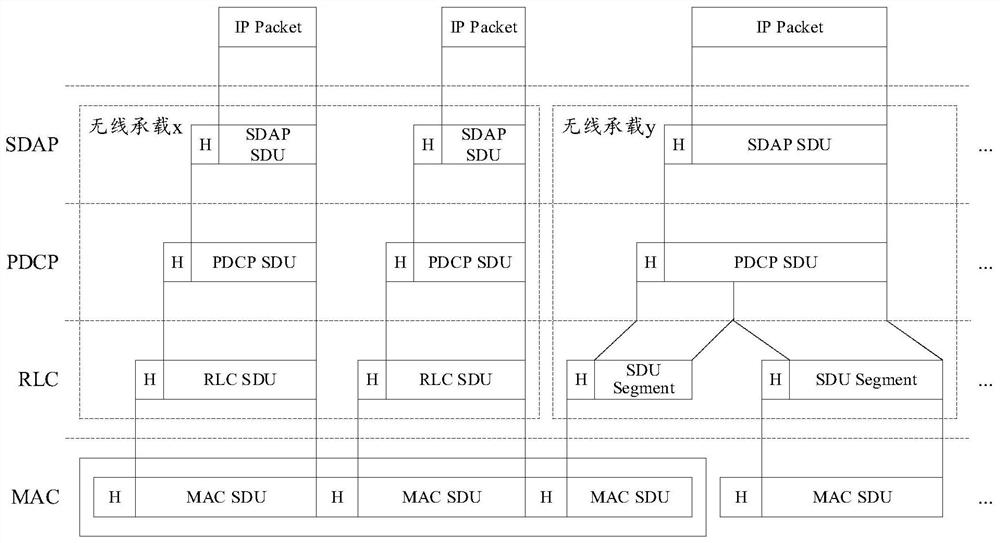
RLC SDU segmentation processing method, device and terminal
PendingCN112153696AOptimize Time ComplexityThe process is easy to realizeNetwork traffic/resource managementEngineeringReal-time computing
The embodiment of the invention provides an RLC SDU segmentation processing method and device, and a terminal, and relates to the technical field of communication. The method comprises the following steps: receiving a first radio link control RLC service data unit SDU segment; determining a hash value of a sequence number SN of the first RLC SDU segment; and according to the hash value, storing the first RLC SDU in a linked list corresponding to the hash value in a segmented manner. According to the embodiment of the invention, the SDU segment is stored in the linked list corresponding to thehash value of the SN of the SDU segment, so that the operation is simple.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
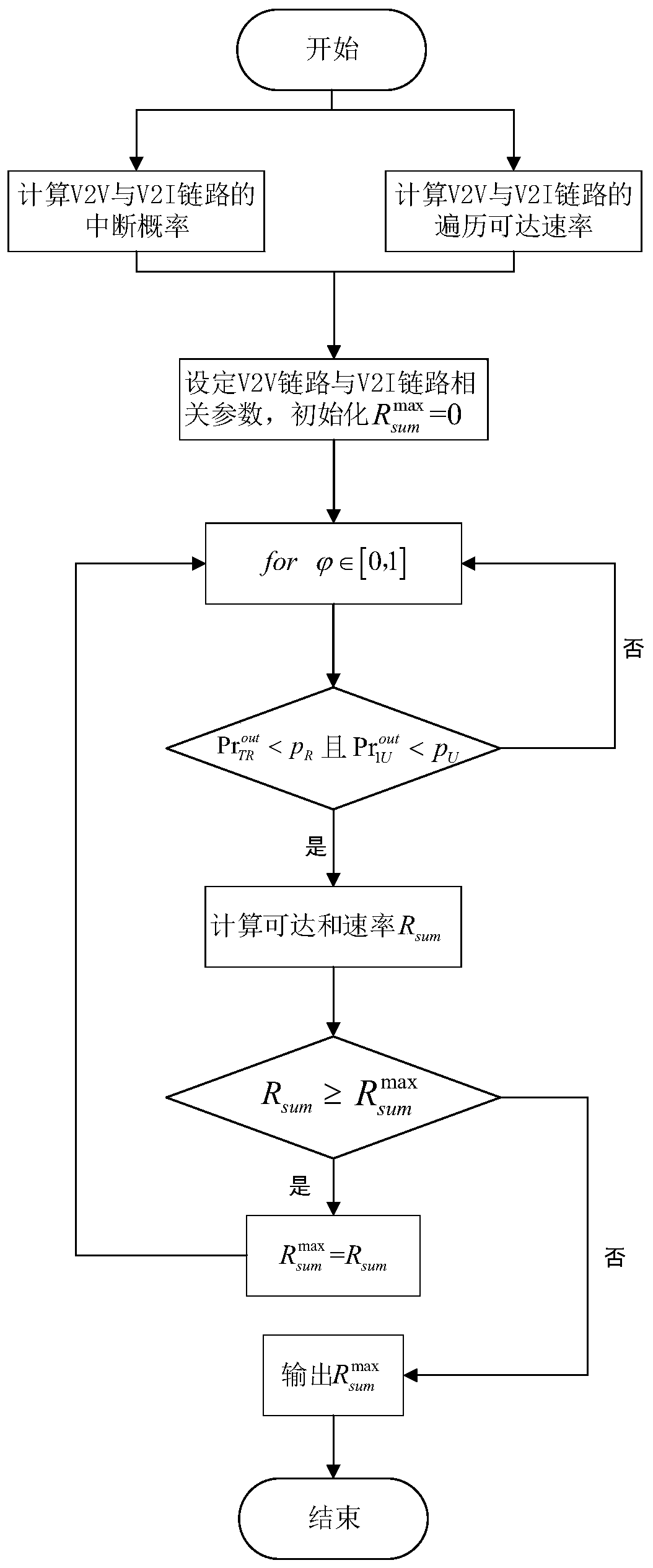
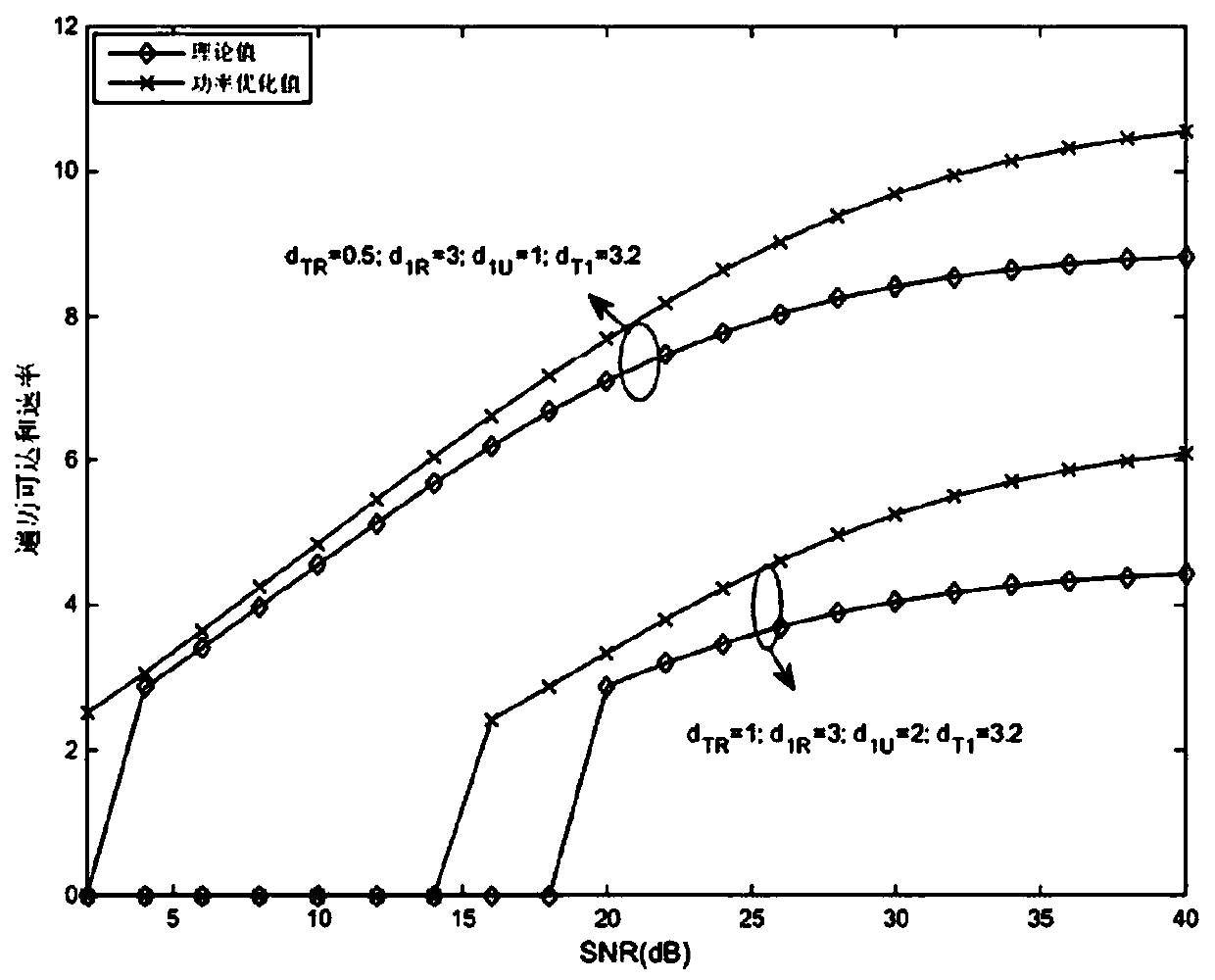
Internet of Vehicles system performance optimization method based on Nakagami-m fading
ActiveCN111556458AReduce complexityImprove performanceInternal combustion piston enginesParticular environment based servicesSimulationThe Internet
The invention discloses an Internet of Vehicles system performance optimization method based on Nakagami-m fading. The method comprises the following steps: in a time slot when a group of V2V and V2Iusers complete one-time communication, acquiring sending power and link state information of respective links, and establishing a link outage probability and traversal reachable rate compact upper bound model according to the acquired information; assuming that the total transmission power of the link is a constant value, establishing an optimization model by taking maximization of the traversal reachable rate of the V2V link and the V2I link as an objective function under the constraint of the link outage probability, and searching for a power distribution coefficient enabling the upper boundof the total reachable rate of the V2V link and the V2I link to be maximum. According to the method, the compact upper bound of the reachable rate is used for replacing complex accurate solution calculation, and the time complexity of the algorithm can be greatly improved while the error range is ensured. The total reachable rate of the system is maximized under the constraint of the outage probability of the system, and the performance of the Internet of Vehicles system is comprehensively improved.
Owner:江苏第二师范学院
Personalized recommendation system based on user memory network and deep model with tree structure
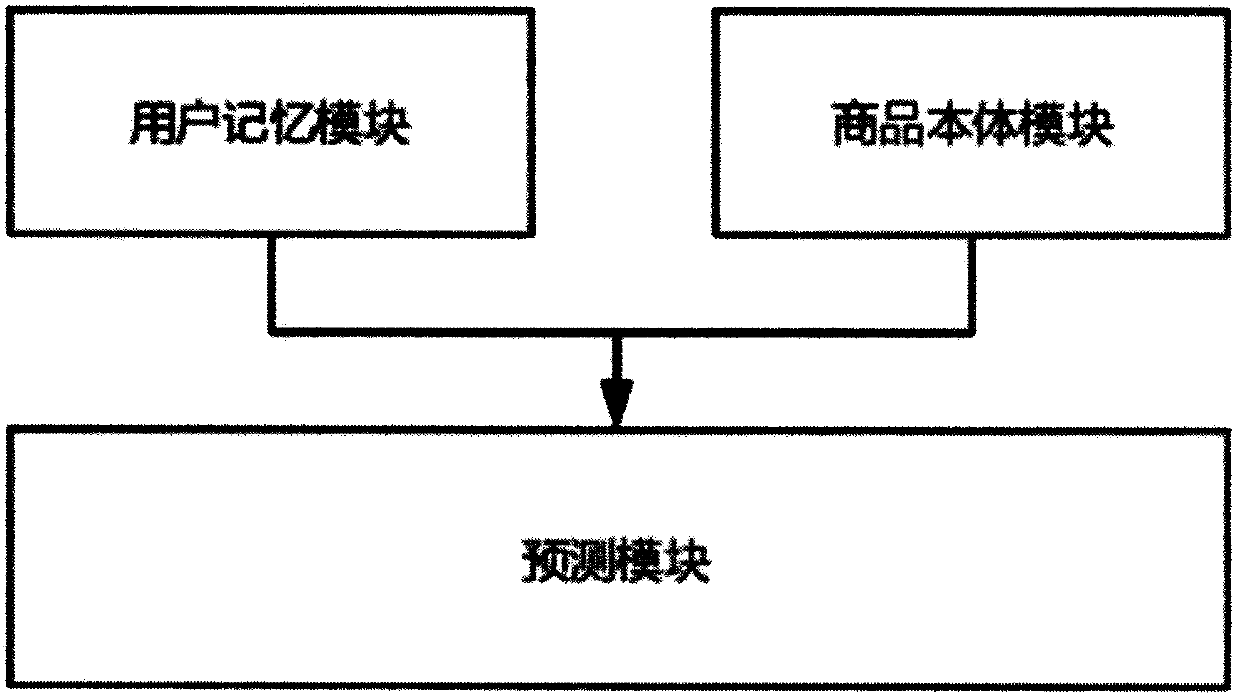
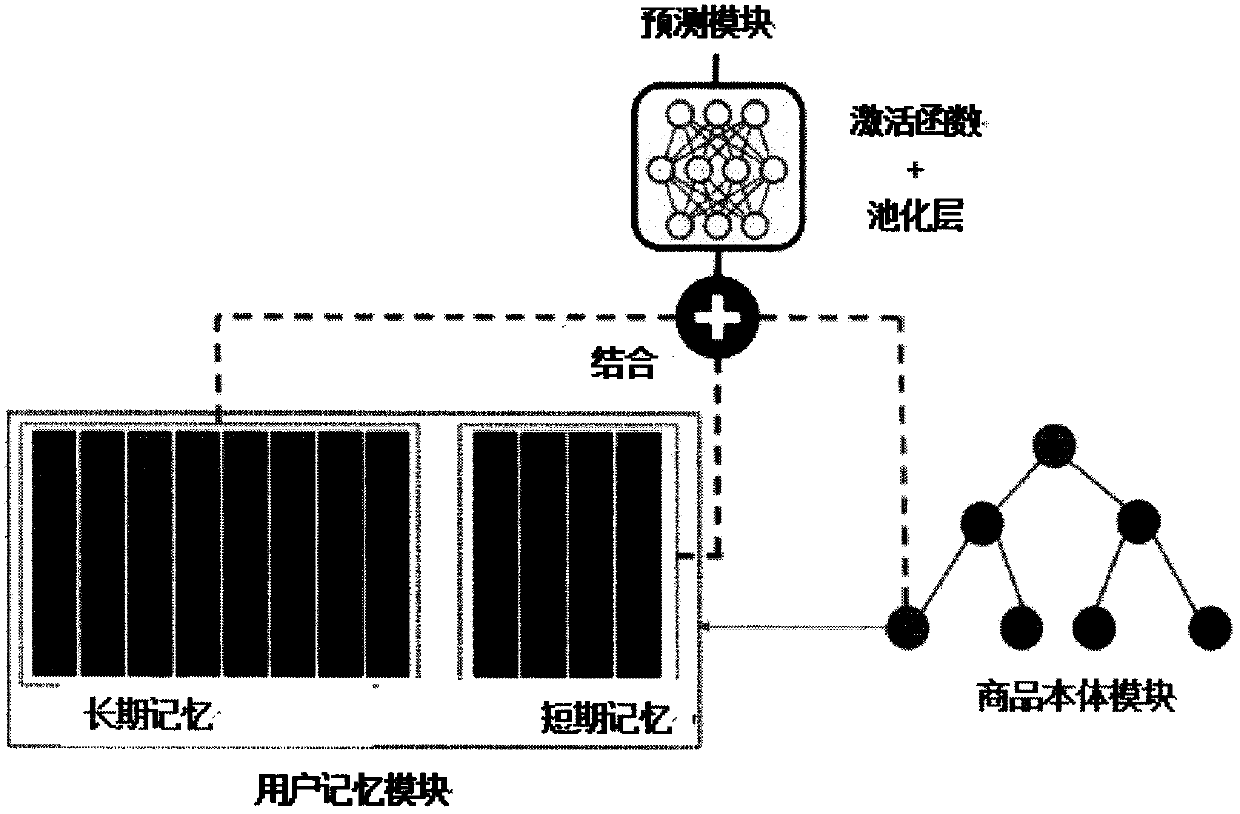
PendingCN110851694AEnhance intelligibilityIncrease diversityDigital data information retrievalBuying/selling/leasing transactionsPersonalizationEngineering
The invention discloses a personalized recommendation system based on a user memory network and a deep model with a tree structure. The personalized recommendation system is characterized by comprising a user memory module, a commodity body module and a prediction module. Wherein the user memory module is used for capturing historical data of a user; the user memory module is composed of a context-based long and short memory network framework, and captures interest dynamics of a user through short-term memory and long-term memory. The short-term memory is used for capturing records of the userfor purchasing commodities recently, and obtaining short-term memory mapping of the user through the records; the long-term memory summarizes and records the characteristics of the commodity which the user is interested in according to the long-term purchasing habit of the user and a large number of purchasing records of the user, and long-term memory mapping of the user is obtained through the records. The commodity body module obtains mapping information of the commodities through the associated information between the commodities and historical purchase records of the user; and the prediction module performs final recommendation prediction in combination with the short-term memory mapping, the long-term memory mapping and the commodity mapping output by the user memory module and the commodity body module.
Owner:王飞 +1
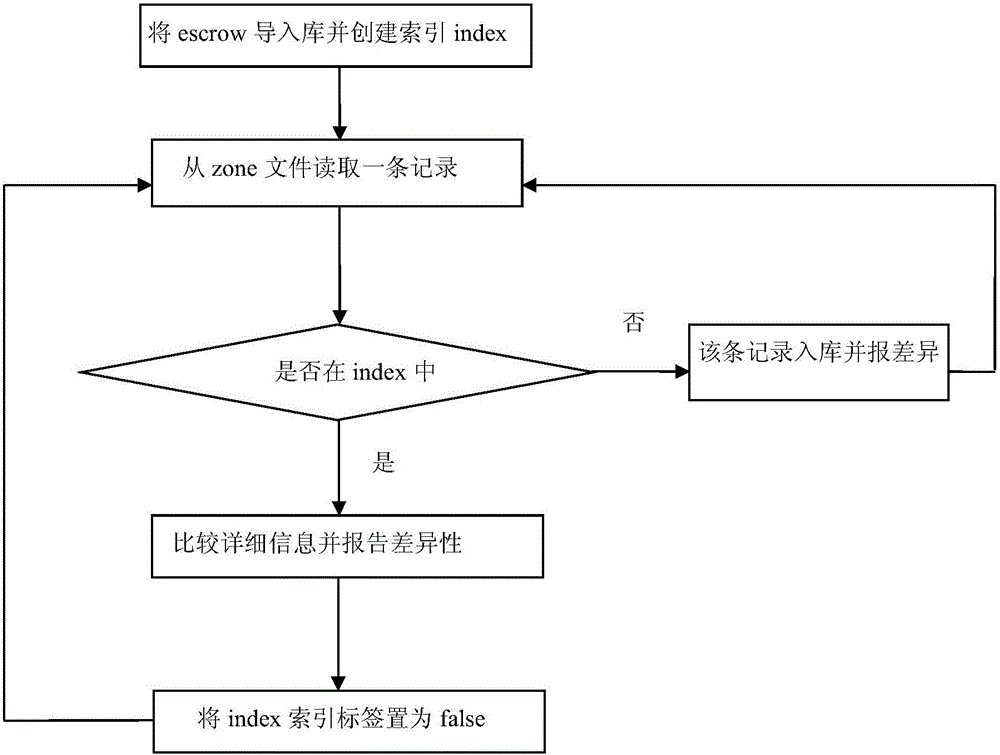
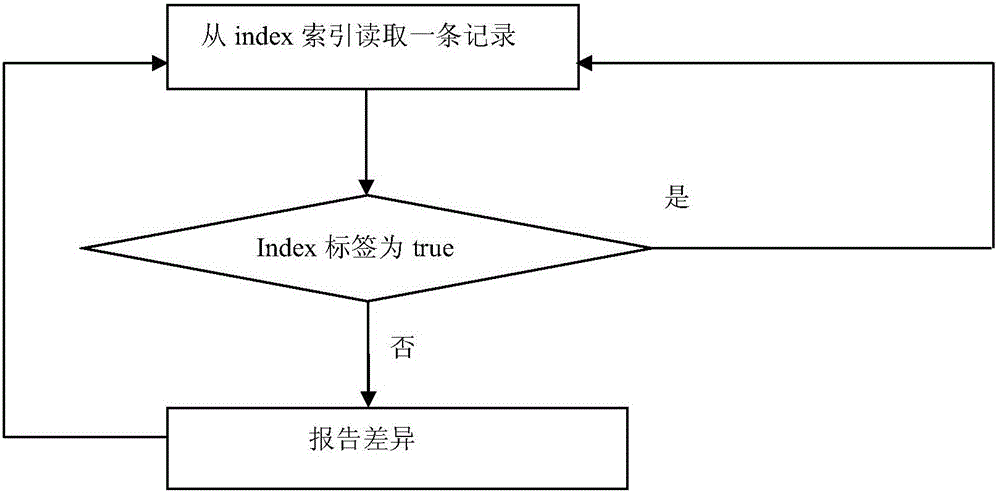
Difference analysis method for big file data in different domain name formats
ActiveCN105808783ASimplified traversal processReduce time consumptionSpecial data processing applicationsDomain nameTime complexity
The invention discloses a difference analysis method for big file data in different domain name formats.The method comprises the steps that 1, records in an escrow file are imported into a database, meanwhile, indexes generated in a memory, and a label is configured for each index; 2, each domain record in a zone is subjected to traversal, whether index information corresponding to the current record exists in the indexes or not is inquired about, if not, the record is written in a difference report A, and if yes, all field information of the record is extracted from the database and compared with corresponding domain information in a zone file, fields with differences are written in a difference report B, and meanwhile the corresponding label in the indexes is marked as true; 3, the indexes are subjected to traversal, the indexes is searched for the data with the label of false, and then corresponding escrow data is extracted and written in a difference report C.According to the method, time consumed for IO interface and database traversal is shortened, and time complexity is lowered.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
A vehicle routing optimization method
ActiveCN104700160BOptimizing Feasible Solution SpaceOptimize Time ComplexityForecastingGenetic algorithmsRound complexityPath length
The present invention provides a vehicle route optimization method, which defines the vehicle route problem as a graphical model, solves the inter-cluster cost path from a global perspective to obtain a feasible solution space, and uses the Monte Carlo method, genetic operation and quantum revolving door adaptive strategy etc. to optimize the feasible solution space. The invention can solve the problem of finding vehicle paths in global connections, optimize the problem solving process in time and space complexity, and avoid premature convergence. The vehicle routing problem to be solved by this invention refers to a certain number of customers, each of whom has a different quantity of goods requirements. The distribution center provides goods to the customers, and a fleet is responsible for distributing the goods and organizing appropriate driving paths. The goal is to make the customers The needs are met, and goals such as the shortest distance, the lowest cost, and the least time consumption can be achieved under certain constraints.
Owner:NANJING UNIV OF POSTS & TELECOMM
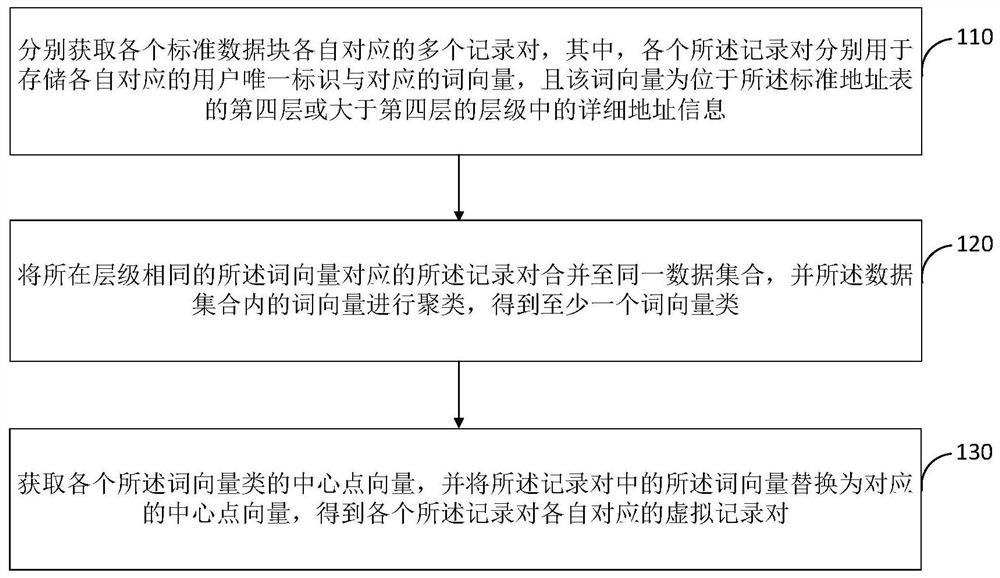
Picture retrieval method
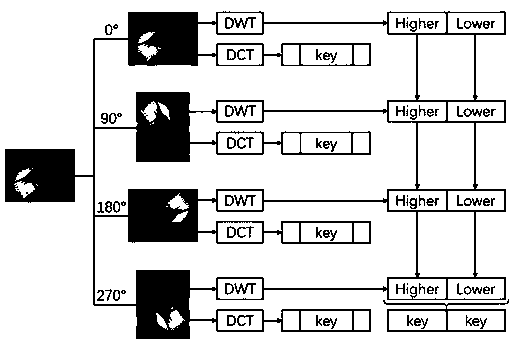
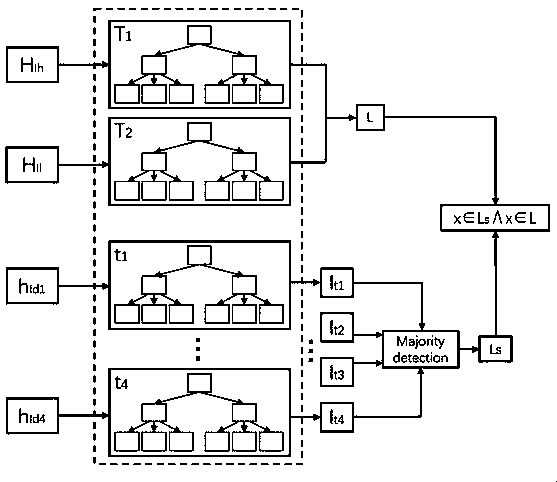
ActiveCN111191058AImprove accuracySimple structureDigital data information retrievalArtificial lifeAlgorithmRandom forest
The invention discloses a picture retrieval method. The method comprises the steps of carrying out DCT calculation and DWT calculation on a processed picture to obtain a first group of hash codes, performing DCT calculation and DWT calculation on the rotationally processed pictures at 90 degrees, 180 degrees and 270 degrees to obtain a second group of hash codes, a third group of hash codes and afourth group of hash codes, calculating and constructing an NB+tree based on the four groups of hash codes, combining the NB+tree into a random forest model, and performing picture retrieval by usingthe random forest model. A block DCT and DWT technology is used for constructing a perceptual hash code of a picture, so that the hash code construction process is accelerated; a decision tree is constructed according to the pictures with different rotation angles, so that the picture retrieval accuracy is improved; a normalized B+tree is used for reducing a high-dimensional input vector to one dimension, so that the time complexity is remarkably improved; a random forest model is used, and multiple decisions such as picture rotation, DCT and DWT hash codes are combined to improve the retrieval speed and performance.
Owner:青岛海洋科技中心
ACT-Apriori algorithm based on self-encoding technology
PendingCN114791924AReduce computing timeReduce memory usageDatabase modelsSpecial data processing applicationsEngineeringTime complexity
An ACT-Apriori algorithm based on a self-encoding technology comprises the following steps: firstly, preprocessing a transactional database D, neglecting a high-frequency parameter NS of each item in the transactional database D, and replacing the high-frequency parameter NS with a self-encoding bit vector SNT to form a simplified database RBD, so that the data dimension is greatly reduced; according to the method, data records are all read into a memory after being simplified, in the process of generating candidate item sets through frequent item set connection and pruning, the process of generating the candidate item sets is improved, the candidate item sets are directly generated, the database is scanned after the candidate item sets are obtained, and the support degree is calculated; when a candidate item set is searched in each record, the search of the transaction can be stopped once a value greater than a candidate item is searched. Compared with an existing brand-new association rule algorithm, the algorithm has the advantages that the calculation time is greatly shortened, the memory occupancy is greatly reduced, and the time complexity and the space complexity are obviously optimized.
Owner:CHINA THREE GORGES UNIV
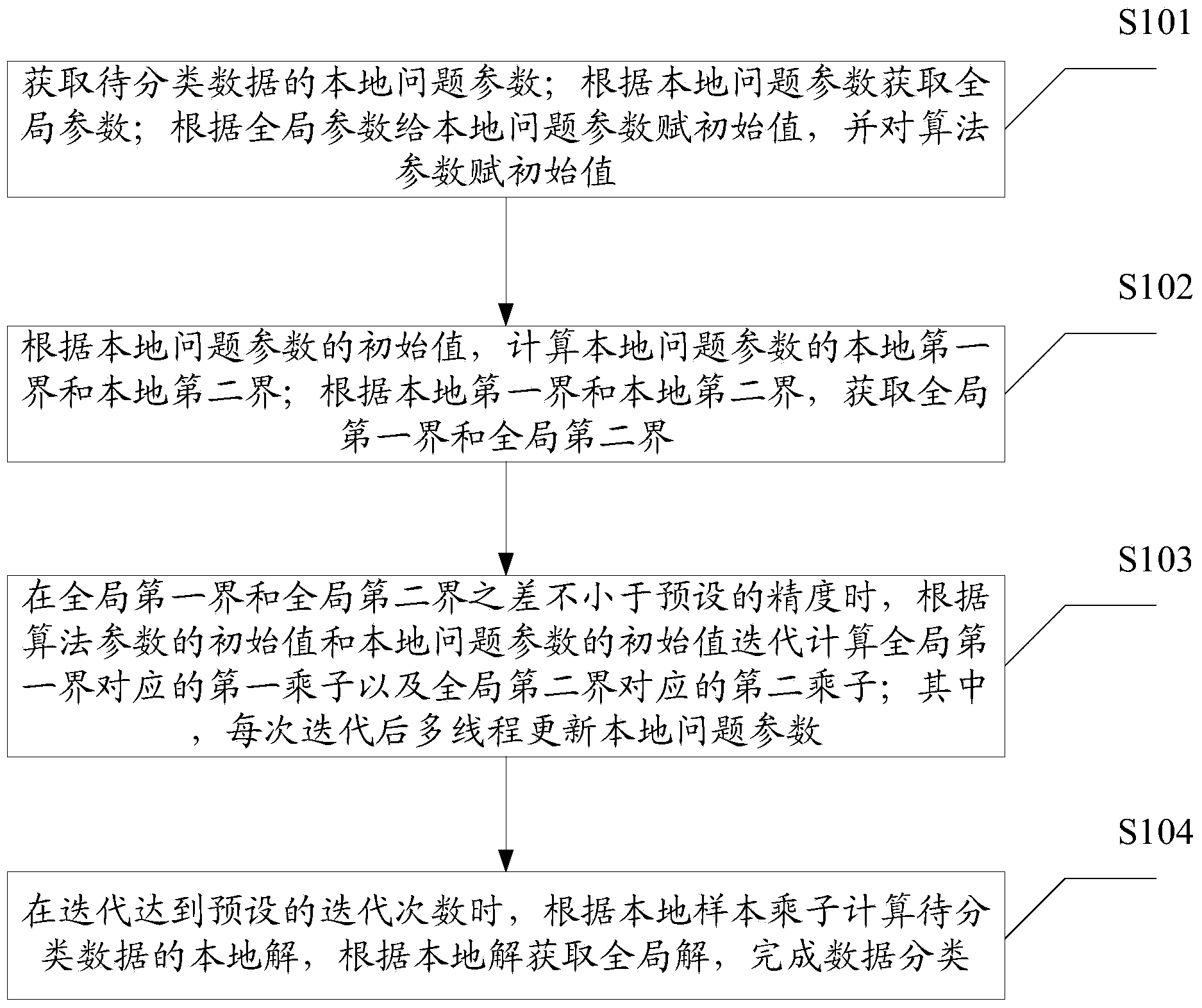
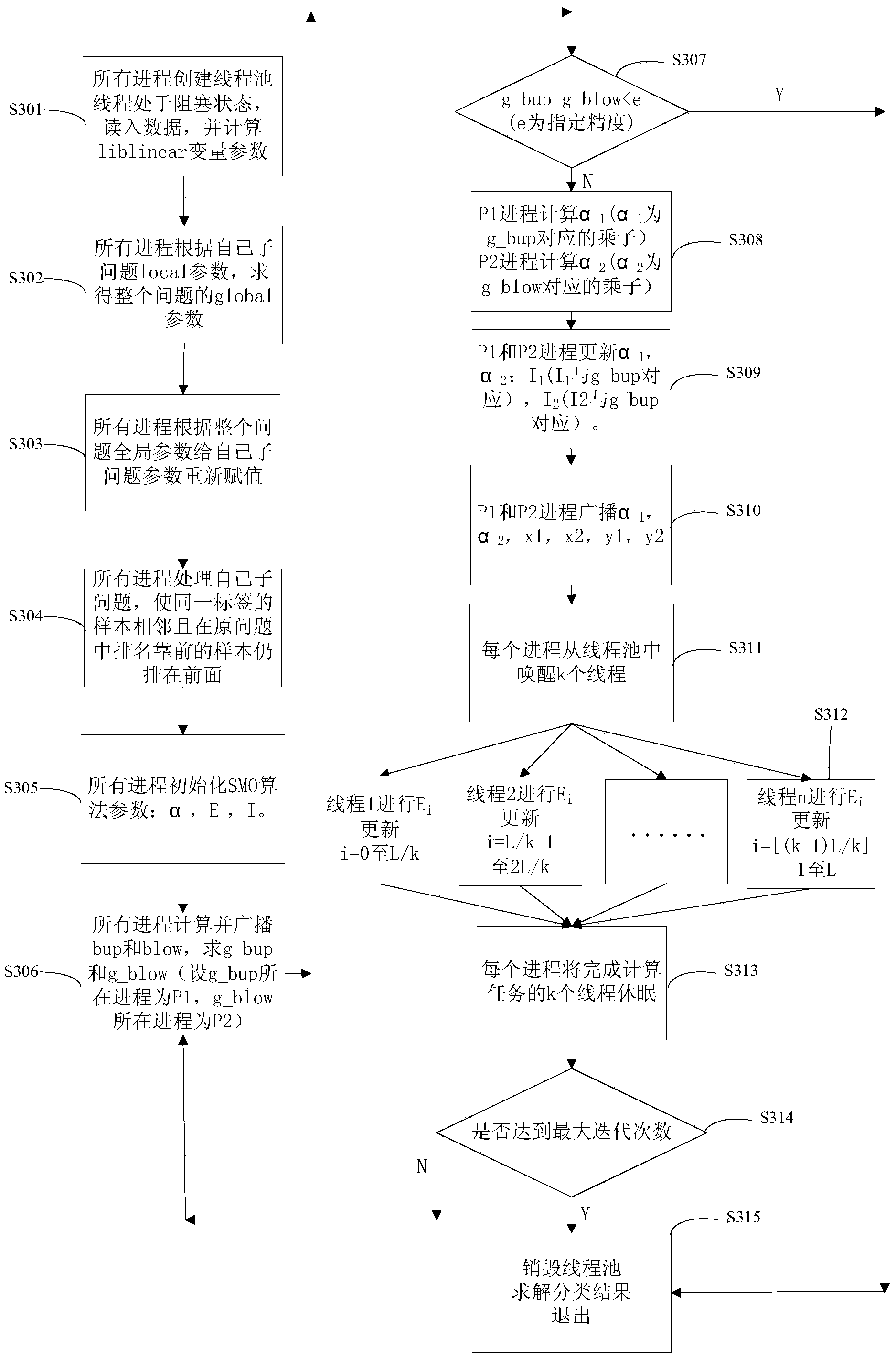
SMO parallel processing method orientated at multi-core cluster
InactiveCN103713885AOptimize Time ComplexityConcurrent instruction executionAlgorithmParallel processing
The invention relates to an SMO parallel processing method orientated at a multi-core cluster. The SMO parallel processing method orientated at the multi-core cluster comprises the steps that an initial value is assigned to a local problem parameter according to a global parameter, and an initial value is assigned to an algorithm parameter; a local first boundary and a local second boundary of the local problem parameter are calculated according to the initial value of the local problem parameter; a global first boundary and a global second boundary are obtained according to local first boundary and the local second boundary; when the difference between the global first boundary and the global second boundary is not smaller than preset accuracy, a first multiplier corresponding to the global first boundary and a second multiplier corresponding to the global second boundary are calculated in an iterative model; the local problem parameter is updated in a multithreading mode after each time of iteration; when the iteration reaches a preset iteration frequency, a local solution of data to be classified is calculated according to a local sample multiplier, a global solution is obtained according to the local solution, and data classification is finished. The SMO parallel processing method orientated at the multi-core cluster resolves the traditional problems of high data classification cost, a high error rate and low response speed.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
A Calculation Method of Author Influence Based on Citation Propagation Network
ActiveCN104657488BLack of timelinessIncrease time complexityWeb data indexingSpecial data processing applicationsCalculation methodsCitation
The invention discloses a method for calculating the author influence based on a citation propagation network. The method comprises the following steps of step 1, establishing a citation relationship network and a colleague relationship network: establishing an author citation relationship network and the colleague relationship network based on an essay public information database; step 2, establishing the citation propagation network, wherein the citation propagation network is an integration network of the author citation relationship network and the colleague relationship network; step 3, calculating the author influence based on the citation propagation network, wherein the calculation formula is as shown in the figure. The method for calculating the author influence based on the citation propagation network can obtain more reasonable author influence indexes, and is easy to be implemented and simple and convenient for calculation.
Owner:CENT SOUTH UNIV
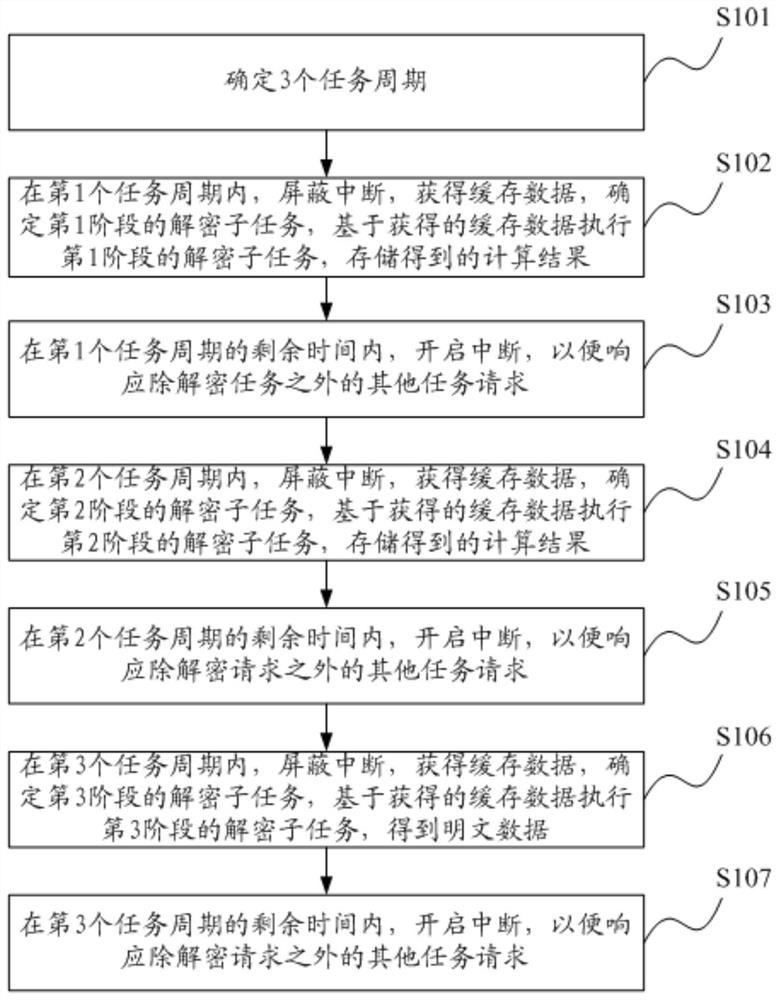
A decryption method and device
ActiveCN109949463BReduce load rateOptimize Time ComplexityIndividual entry/exit registersEngineeringComputer hardware
The present invention provides a decryption method and device. The method includes: determining N task cycles, where N is an integer greater than 1; and sequentially executing the corresponding stages of the decryption task in the N task cycles to obtain plaintext data, wherein the decryption task includes: At least two decryption subtasks executed sequentially, the decryption task can be divided into at least two stages in sequence, and one stage of the decryption task corresponds to one task period. Based on the decryption method and device disclosed in the present invention, on the premise of not changing the hardware of the RKE system, the load rate of the processor in the decryption process is reduced, and a large delay in responding to other task requests can be avoided.
Owner:天津经纬恒润科技有限公司
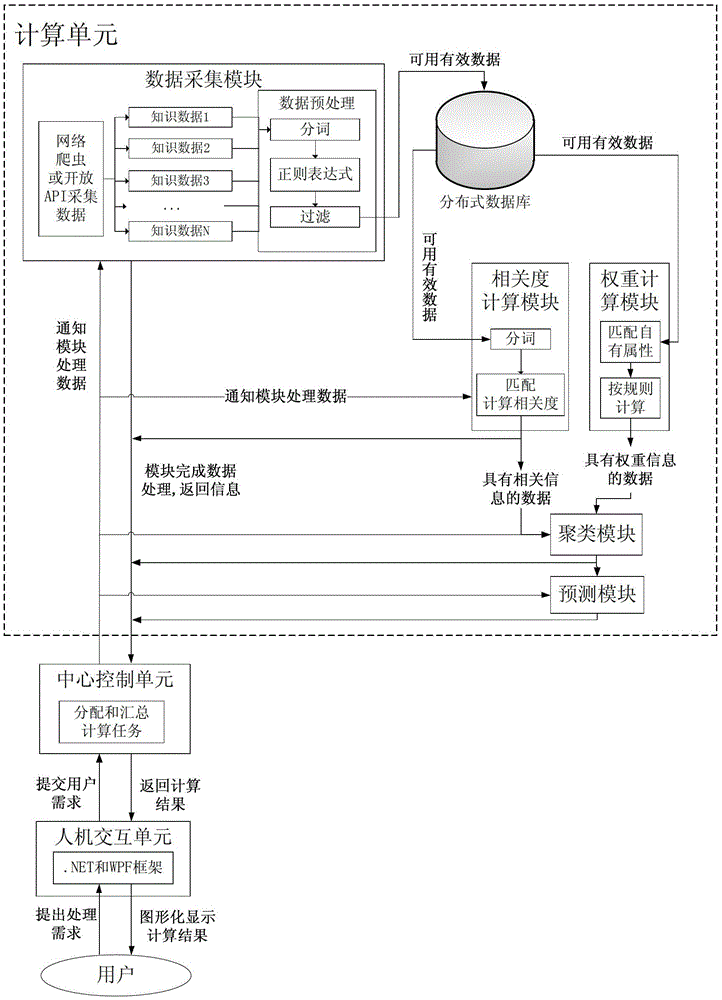
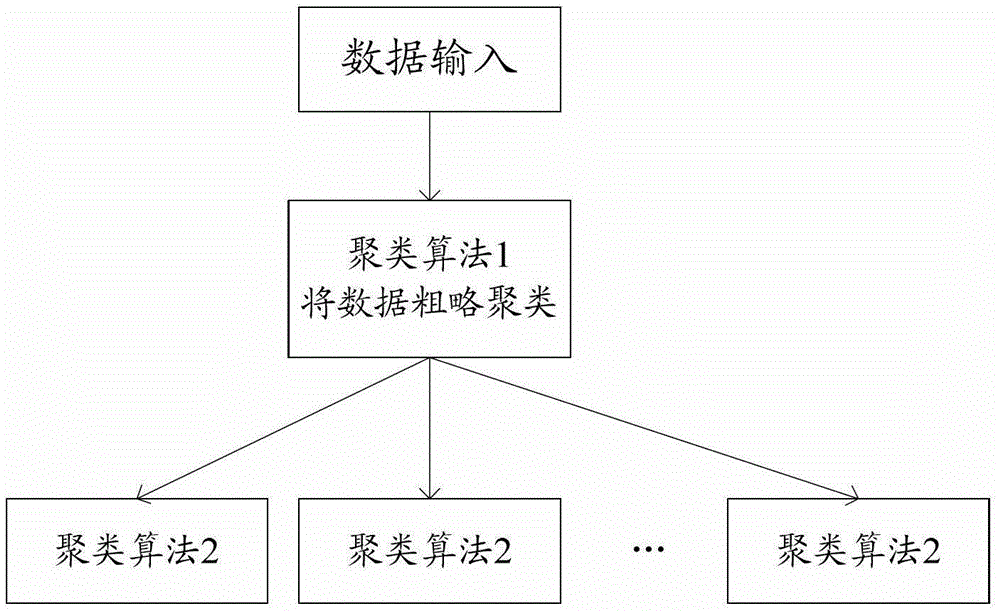
Distributed knowledge data mining device and mining method for complex network
InactiveCN103136337BReliable resultsReduce time complexitySpecial data processing applicationsComputation complexityRound complexity
The invention discloses a distributed knowledge data mining device and method used for a complex network. The distributed knowledge data mining device adopts a distributed computing platform which is composed of a control unit, a computing unit and a man-machine interaction unit, wherein the innovation key is to finish the calculated amount needed by a multifarious clustering algorithm in the data mining by different servers so as to improve the efficiency of the data mining. Aiming at different knowledge data, the degrees of relation and the weights of knowledge data also can be computed by applying different standards, so that a more credible result is obtained. A second-level clustering mode is adopted in the knowledge data mining process; the result of the first-level clustering is relatively rough, but the computing complexity is very low; and the computing complexity of the second-level clustering is relatively high, but the result is more precise. By combining the first-level clustering with the second-level clustering efficiently, the distributed knowledge data mining device improves the time complexity and clustering precision greatly in comparison with the traditional first-level clustering mode. According to the invention, as a visual and direct exhibition network structure and a dynamic evolutionary process are adopted, references are provided for the prediction in the fields of disciplinary development and hotspot research.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com