Patents
Literature
30results about How to "Avoid read and write operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
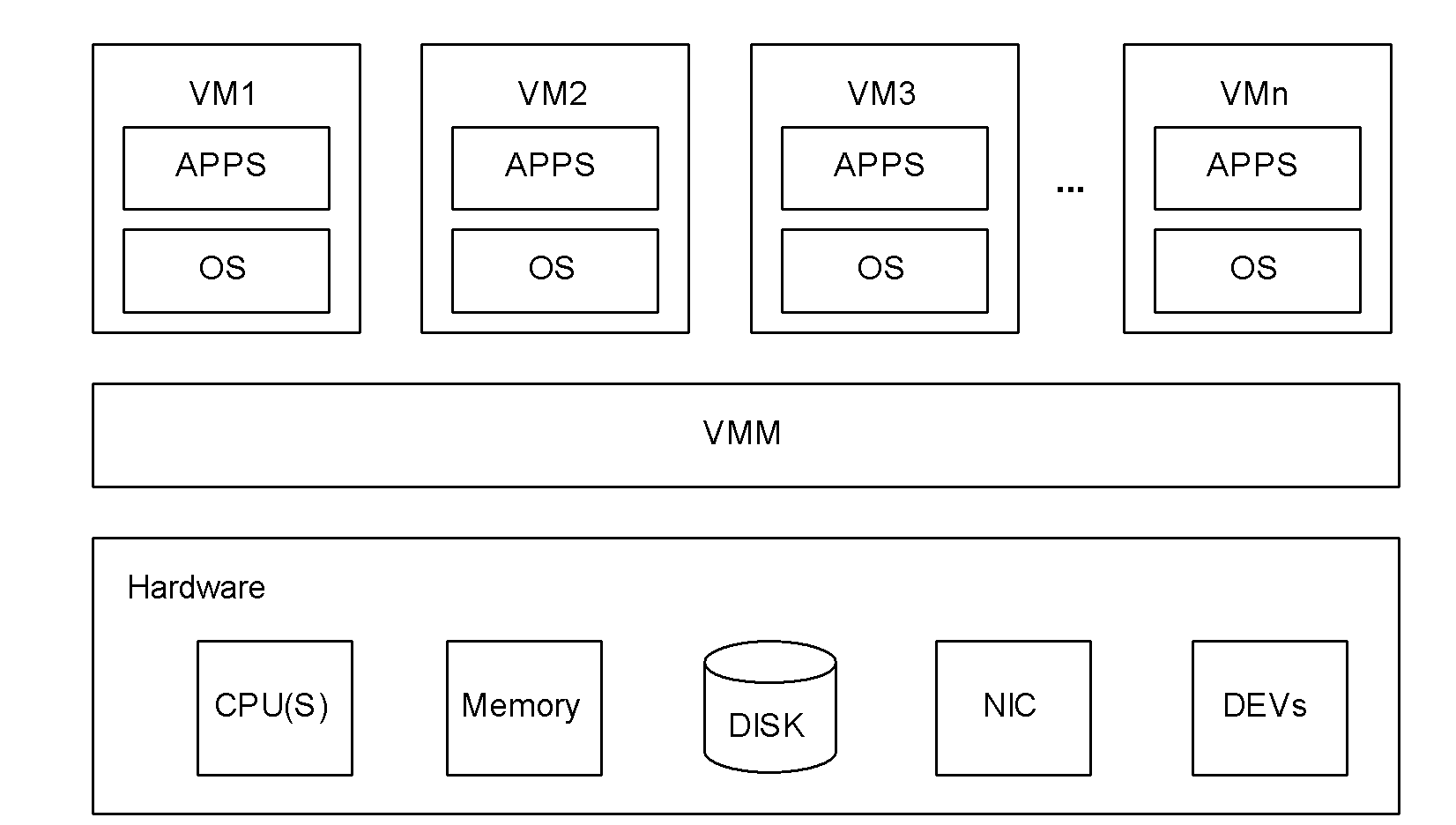
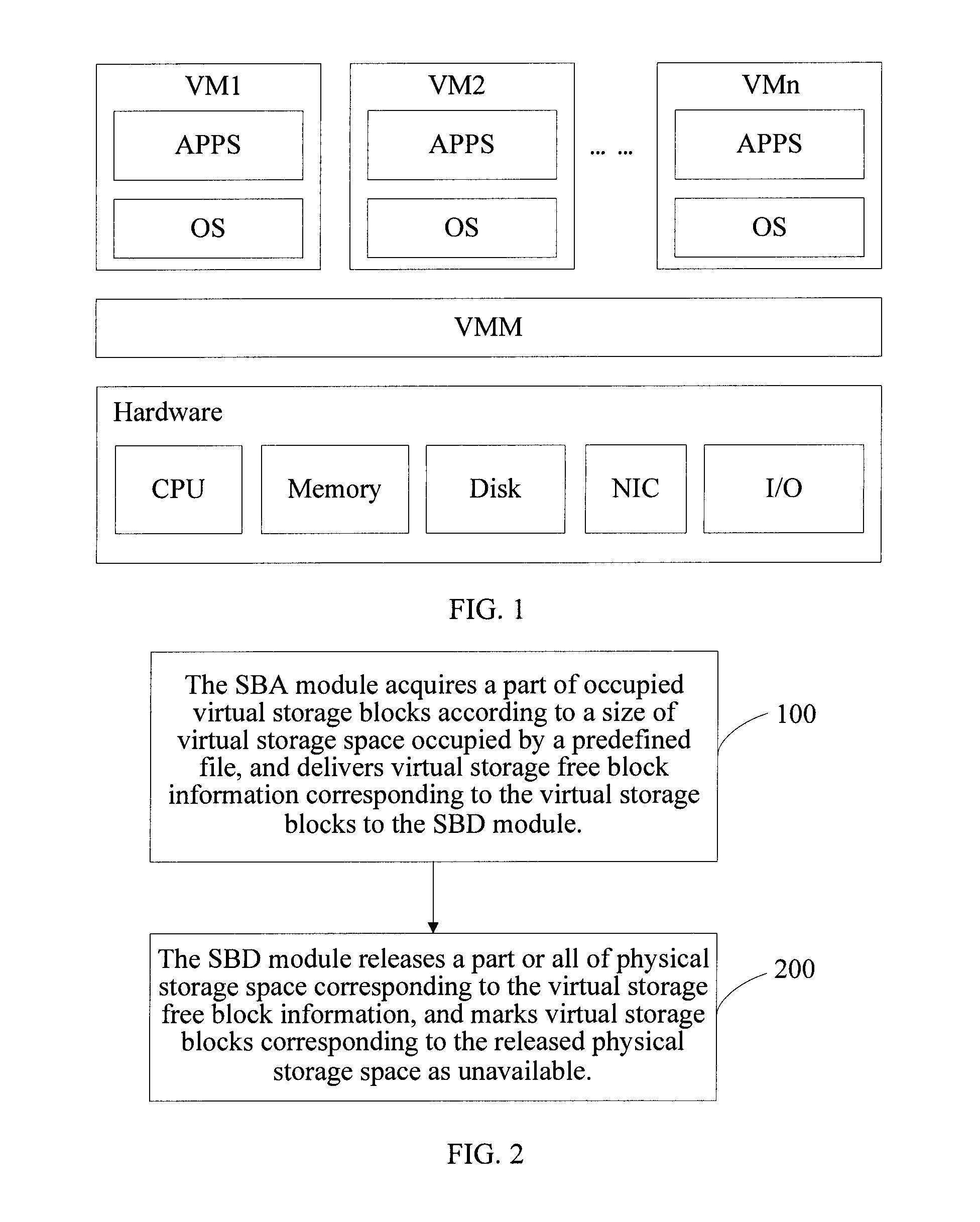
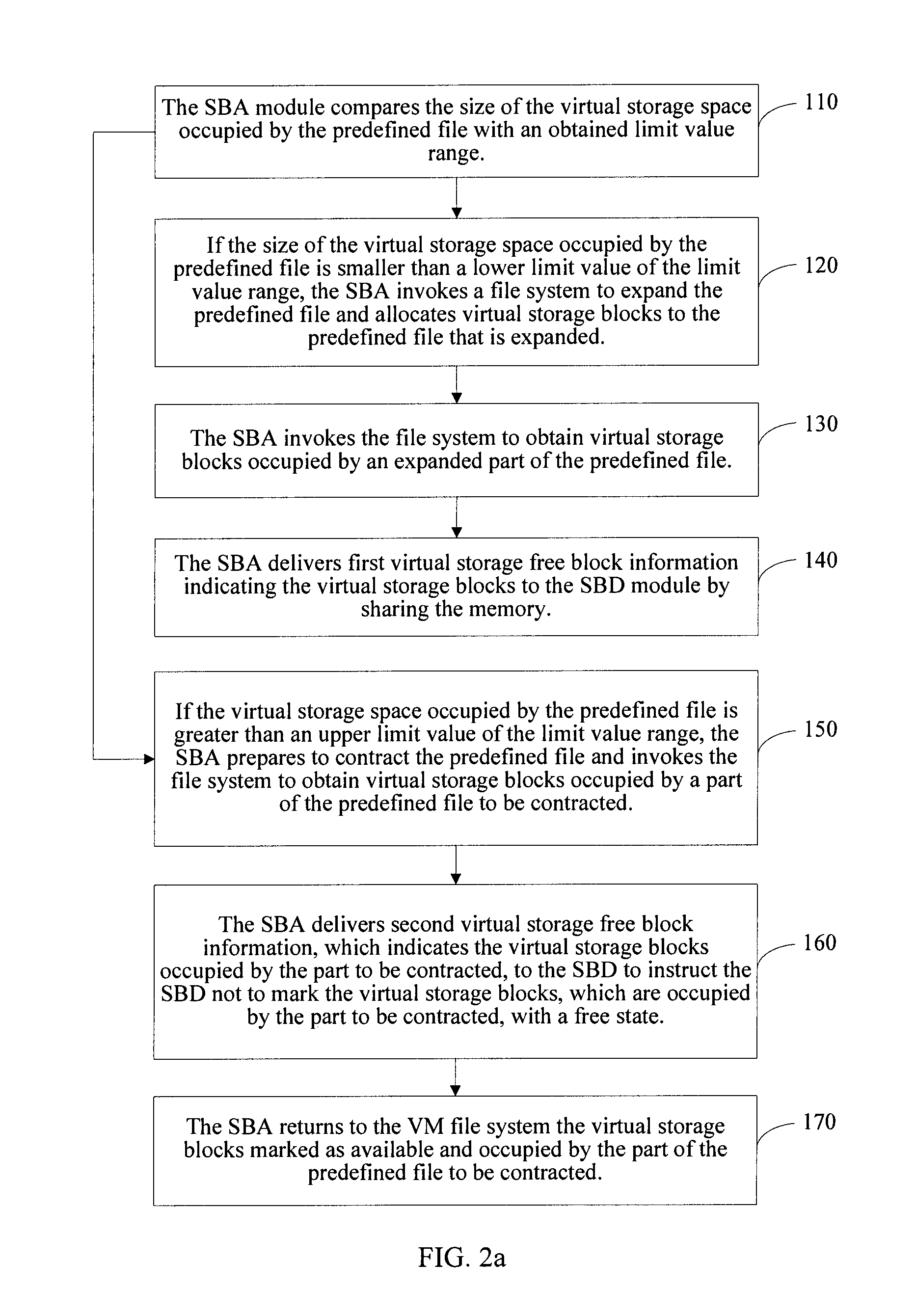
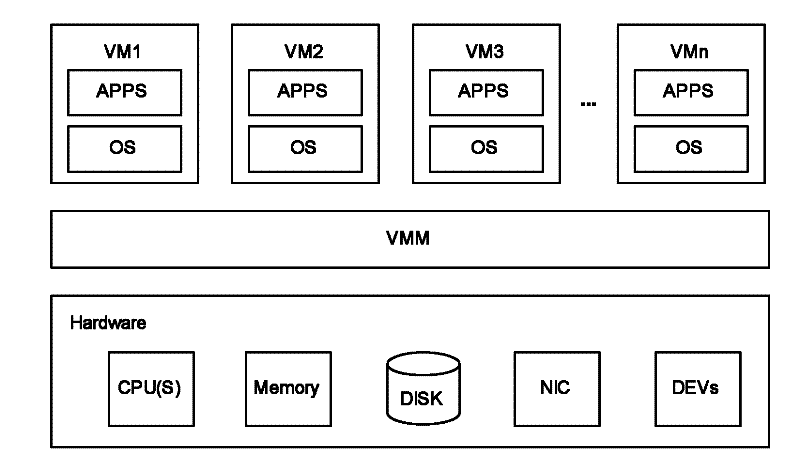
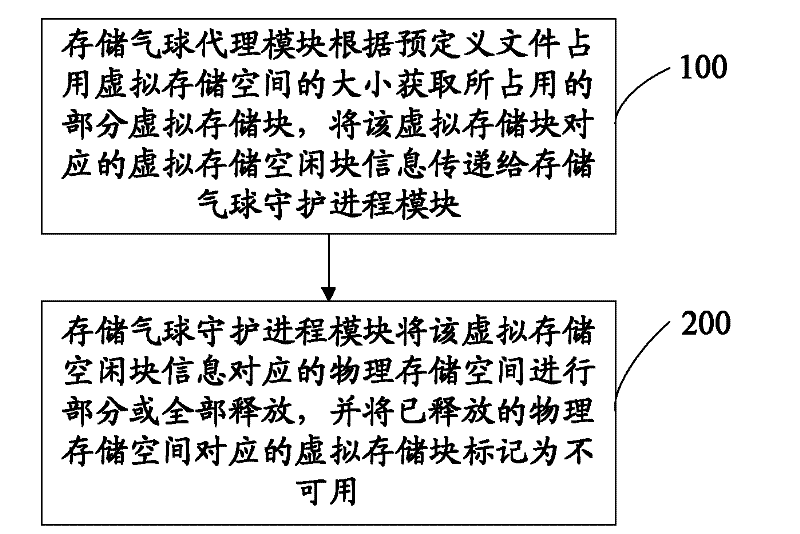
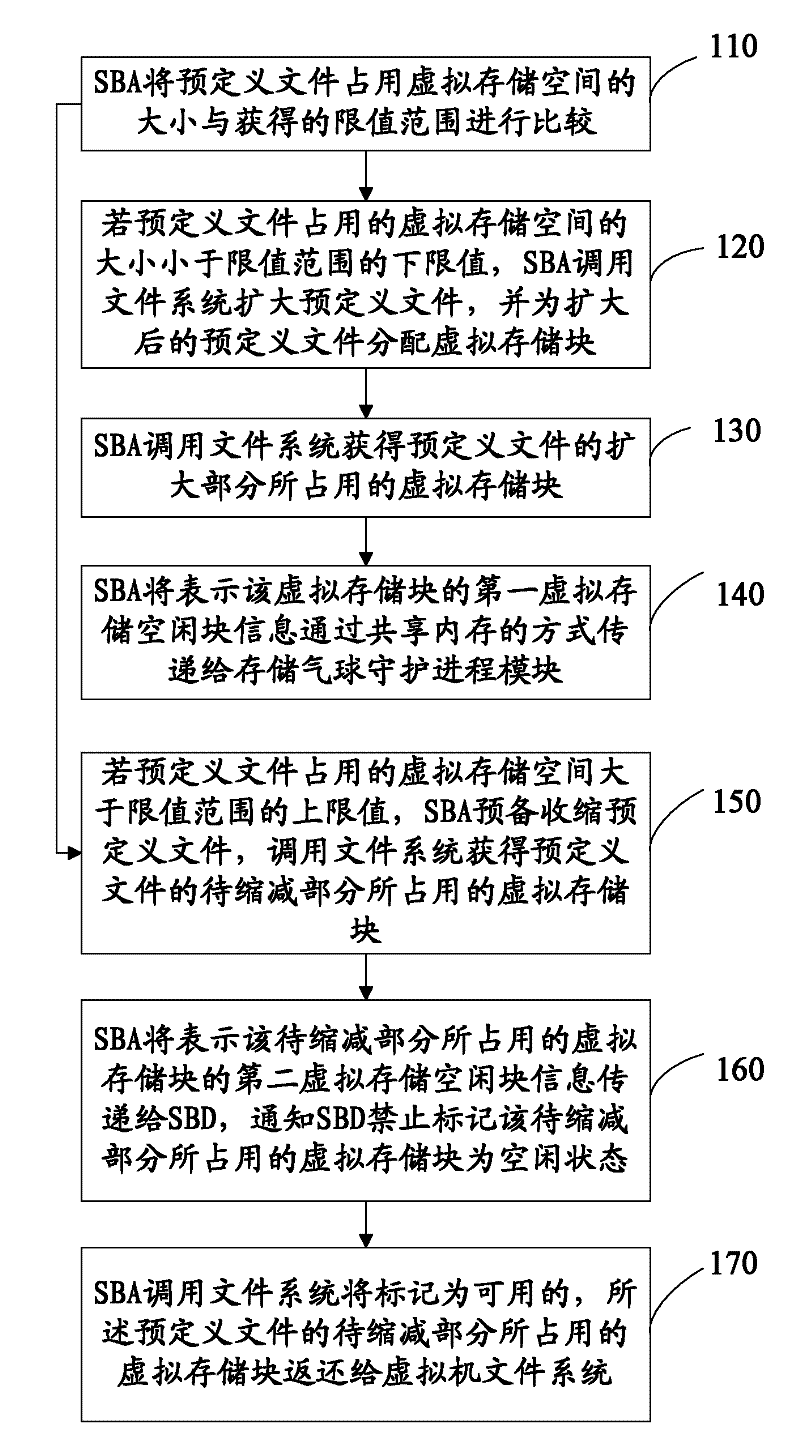
Virtual machine storage space management method, system and physical host
ActiveCN101986285AAvoid read and write operationsImprove real-time performanceMemory adressing/allocation/relocationTransmissionProcess moduleHybrid storage system
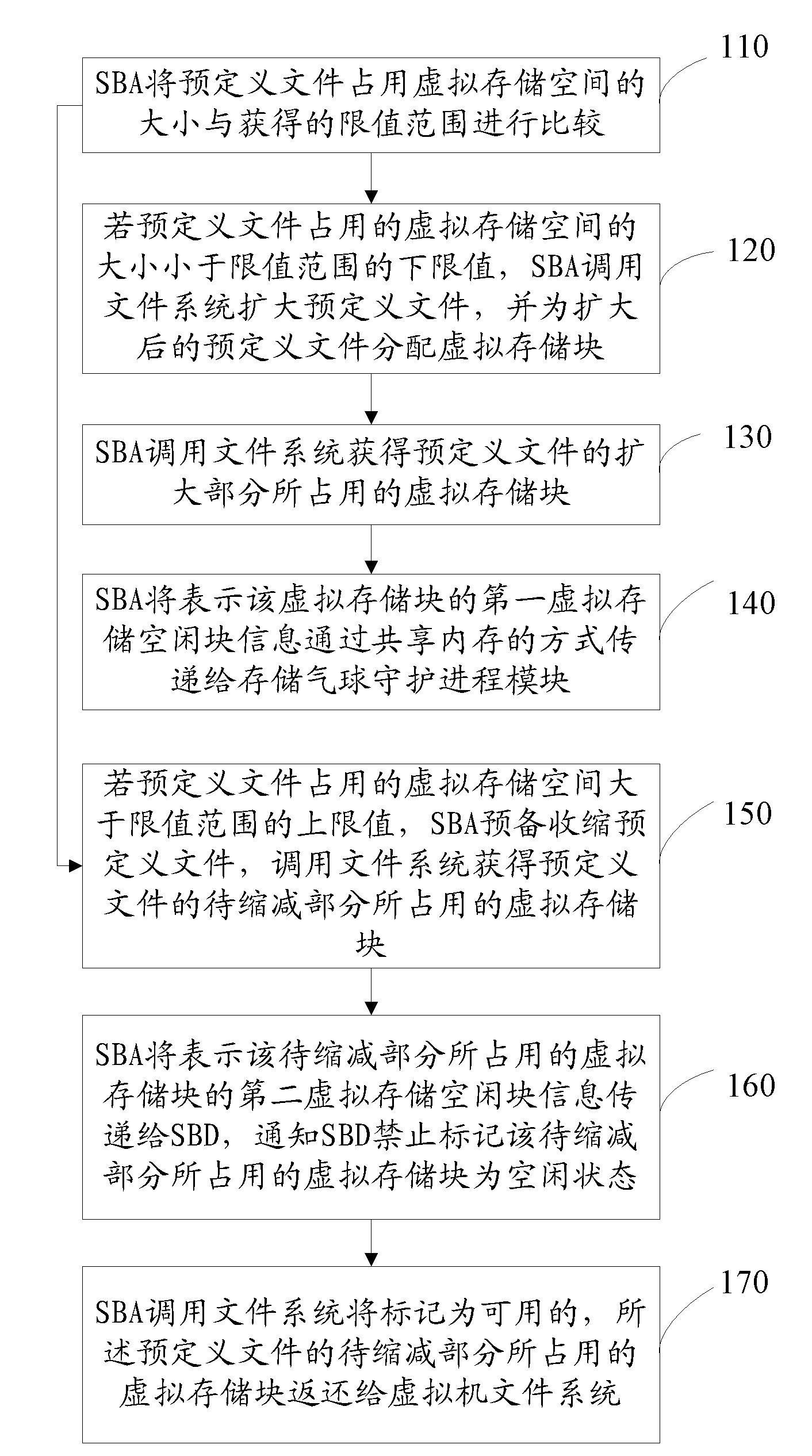
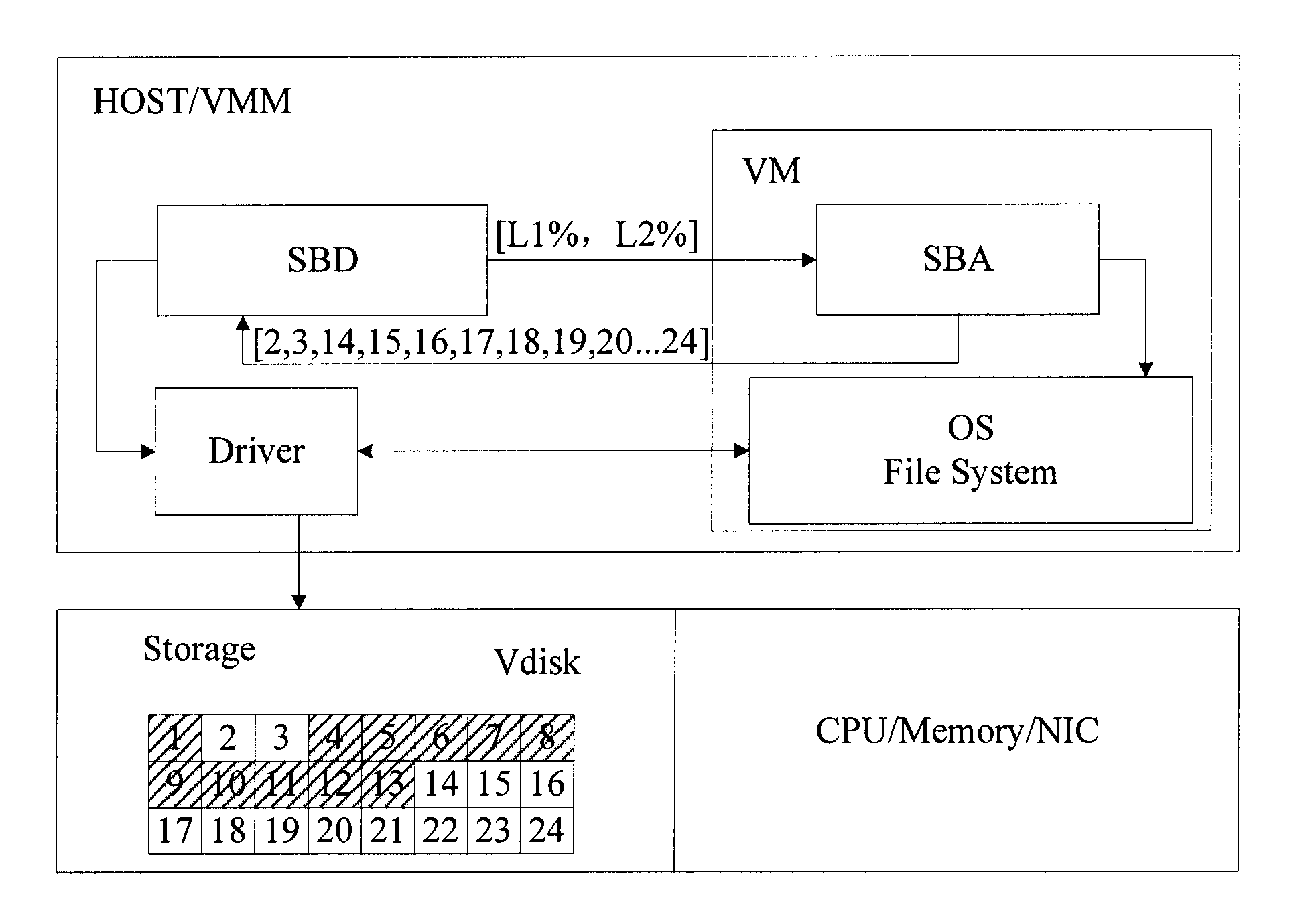
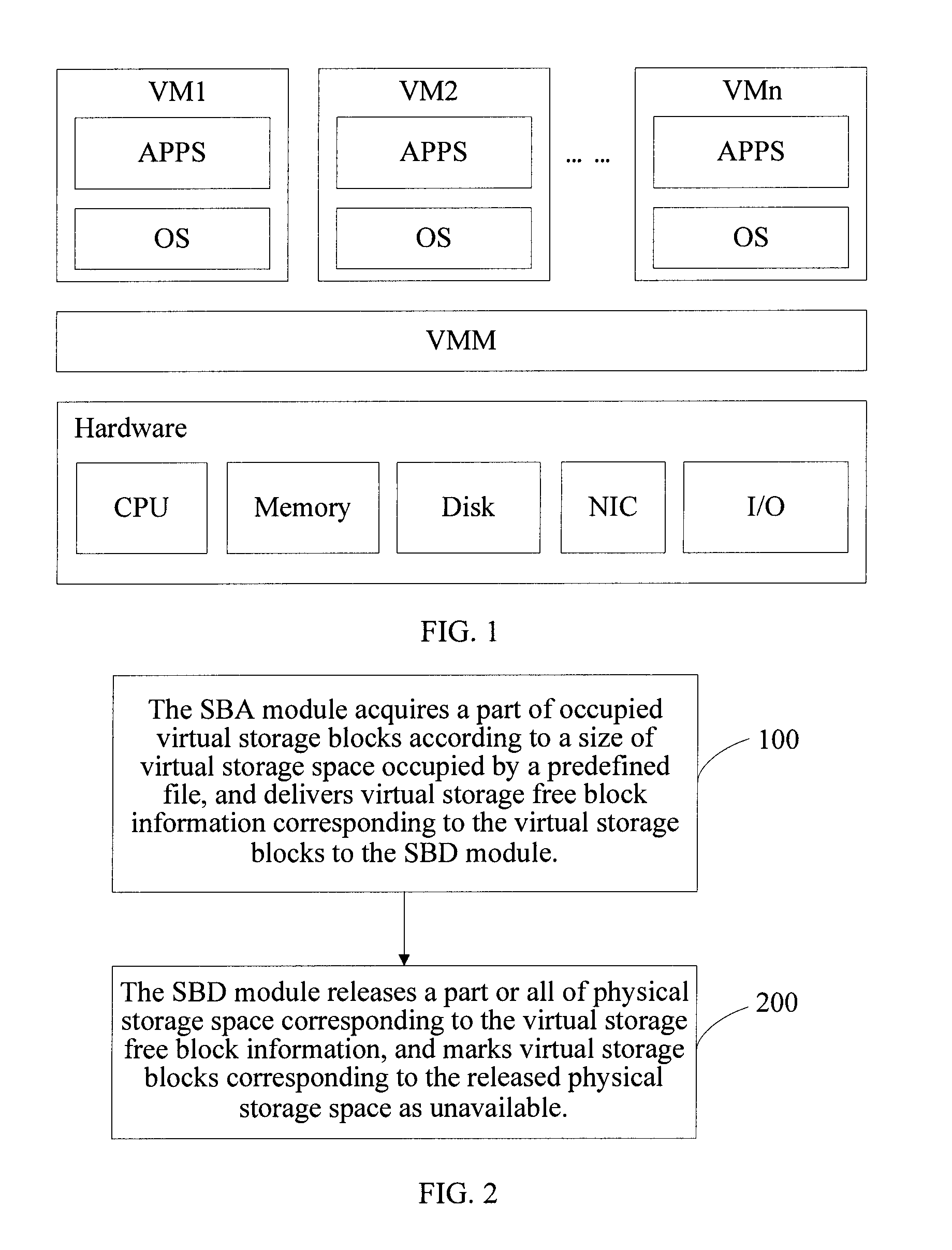
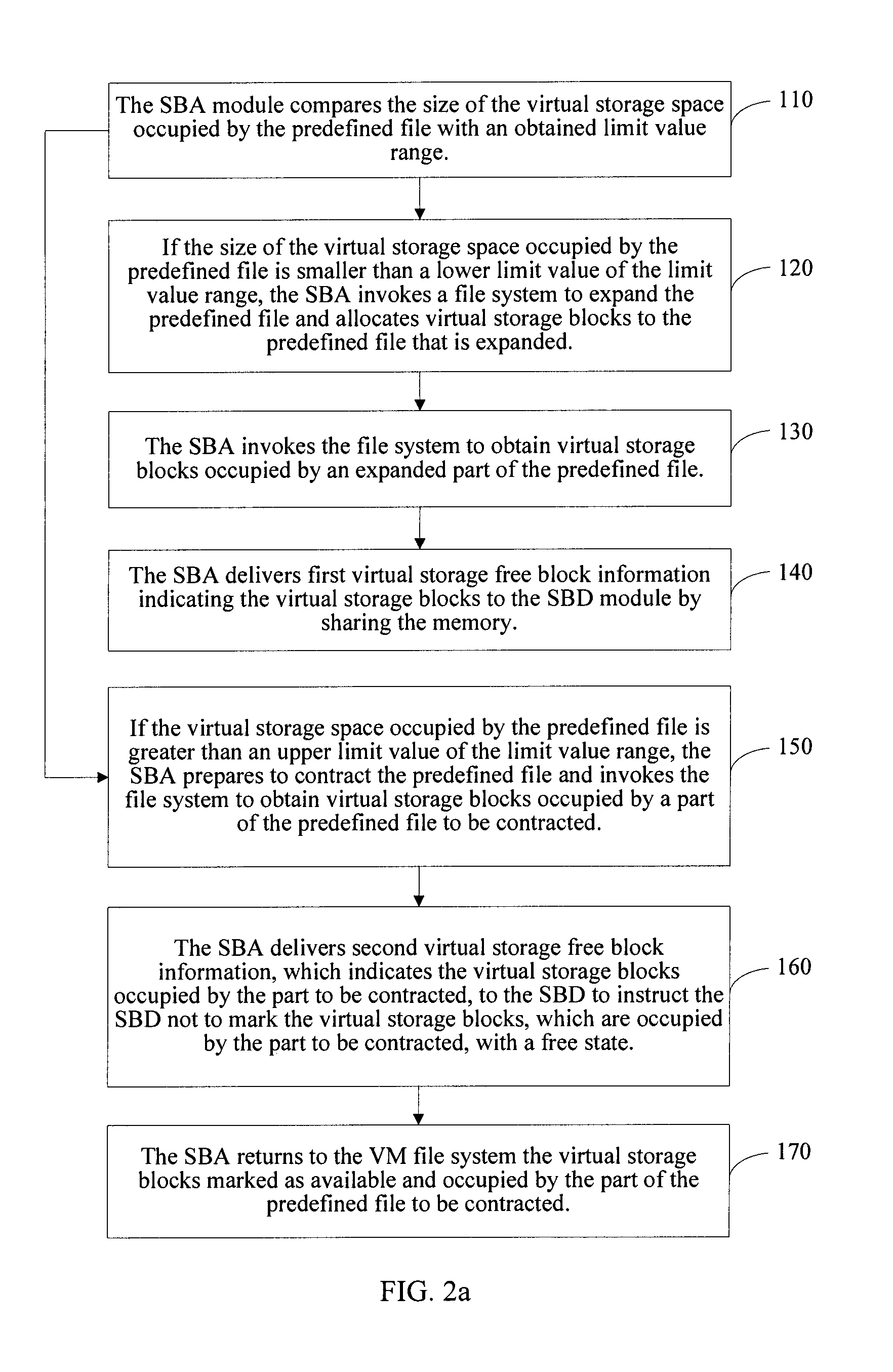
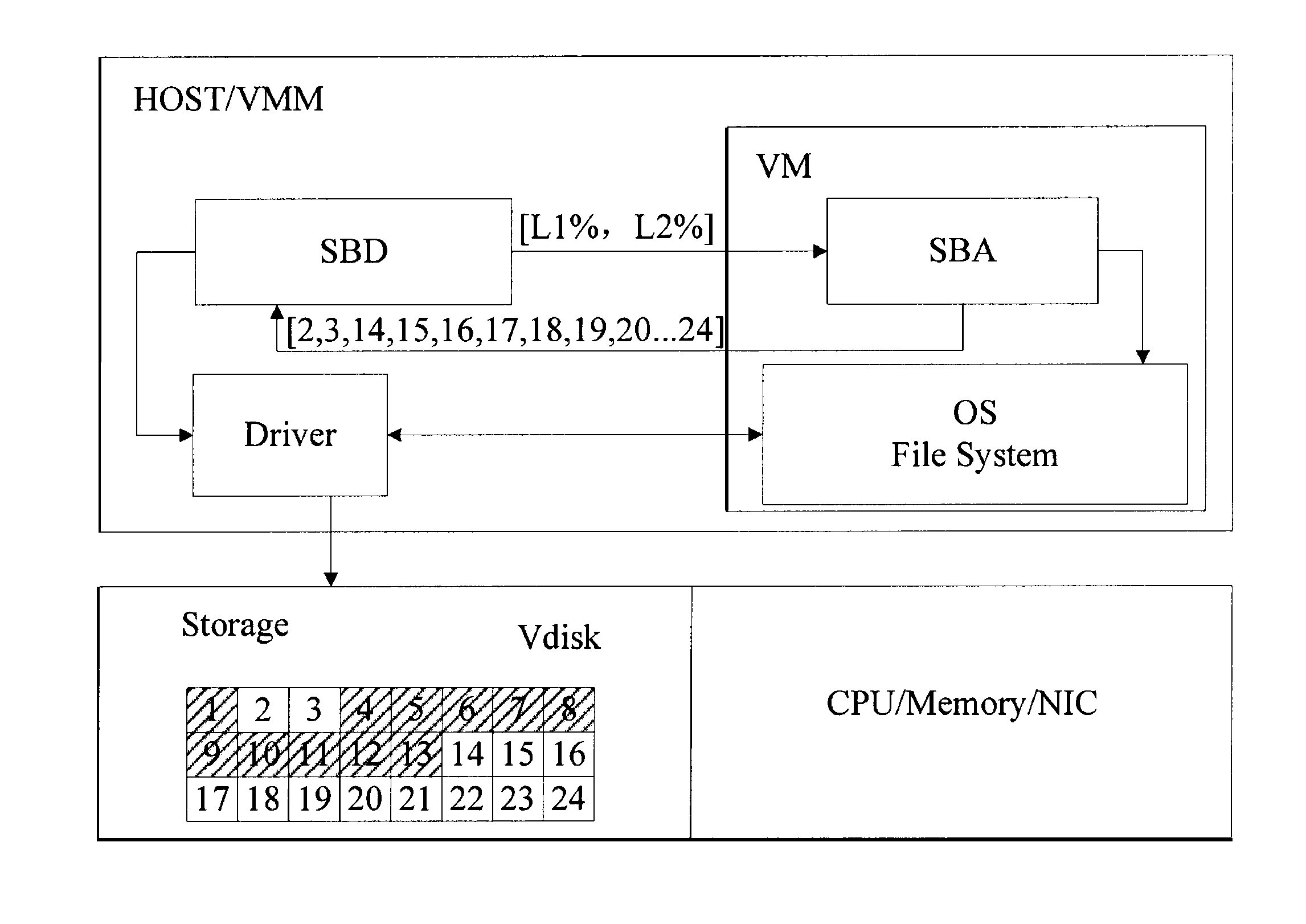
The invention discloses a virtual machine storage space management method. In the method, virtual storage free block information is directly acquired by a storage balloon agent module which is deployed in a virtual machine, and the acquired virtual storage free block information is transmitted to a storage balloon daemon process module which is deployed in a virtual machine monitoring unit layer; and the storage balloon daemon process module partially or totally releases a physical storage space corresponding to the virtual storage free block information and labels virtual storage blocks corresponding to the released physical storage space to be unavailable. The invention also discloses a corresponding system and physical host. Due to the method, the service condition of the virtual storage space can be acquired in real time, the massive reading / writing operation of a storage system can be avoided, and the method is suitable for virtual storage systems in a dynamic allocation format and a pre-allocation format.
Owner:HUAWEI TECH CO LTD
Method and system for managing virtual machine storage space and physical host
ActiveUS20120110293A1Efficient managementIncrease profitMemory adressing/allocation/relocationProgram loading/initiatingComputer moduleVirtual storage
A method for managing Virtual Machine (VM) storage space is provided. In the method, a Storage Balloon Agent (SBA) module deployed in a VM is adopted to directly acquire virtual storage free block information and deliver the acquired virtual storage free block information to a Storage Balloon Daemon (SBD) module deployed in a Virtual Machine Monitor (VMM) layer; and the SBD module releases a part or all of physical storage space corresponding to the virtual storage free block information, and marks virtual storage blocks corresponding to the released physical storage space as unavailable. A corresponding system and a physical host are further provided in the present invention. Through the method of an embodiment of the present invention, use condition of virtual storage space can be acquired in real time, and a large number of read and write operations of a storage system can be avoided.
Owner:HUAWEI TECH CO LTD
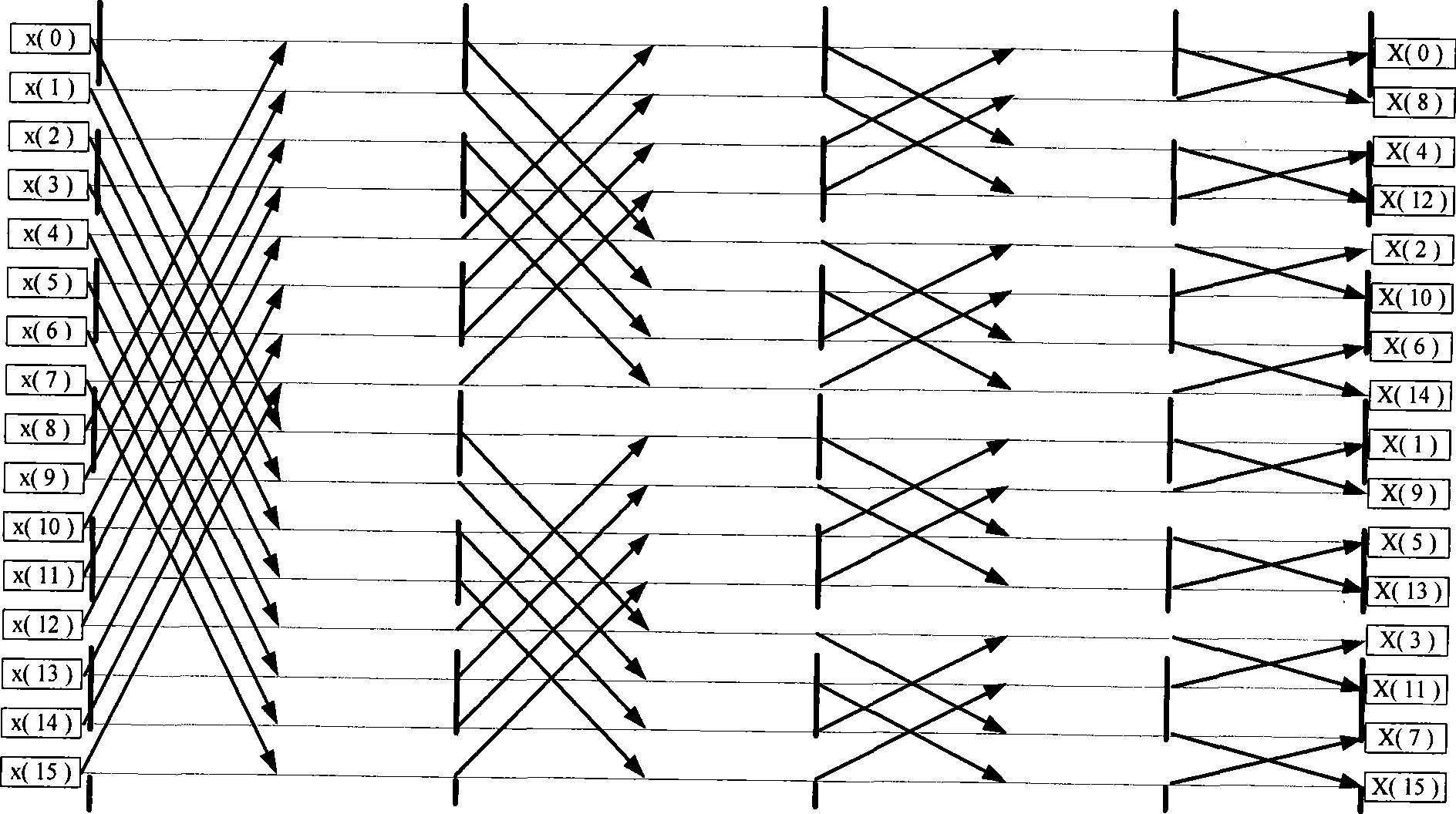
Data transposition method of sar imaging signal processing based on fpga
InactiveCN102279386AGuaranteed uptimeReduce power consumptionRadio wave reradiation/reflectionDouble data rateAzimuth direction
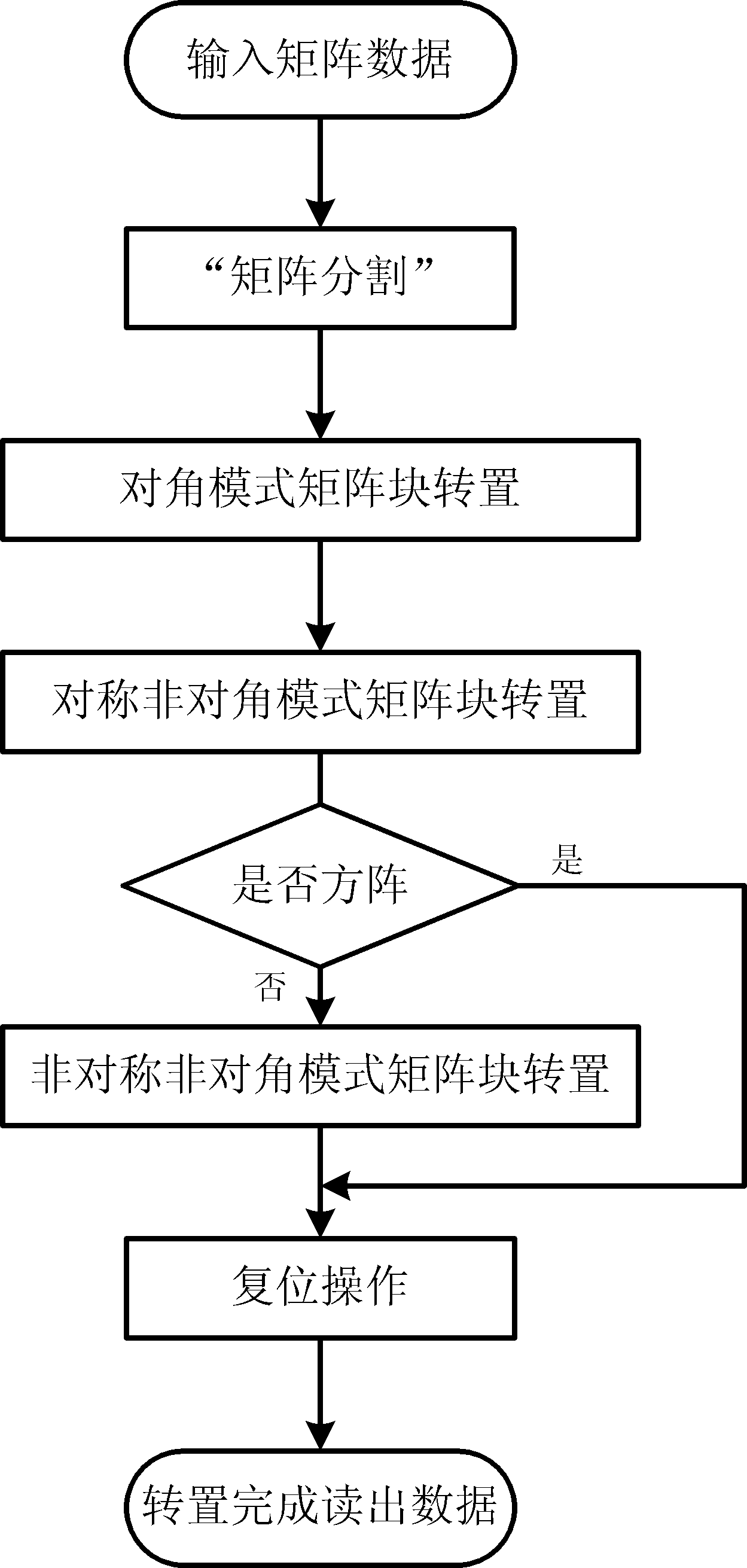
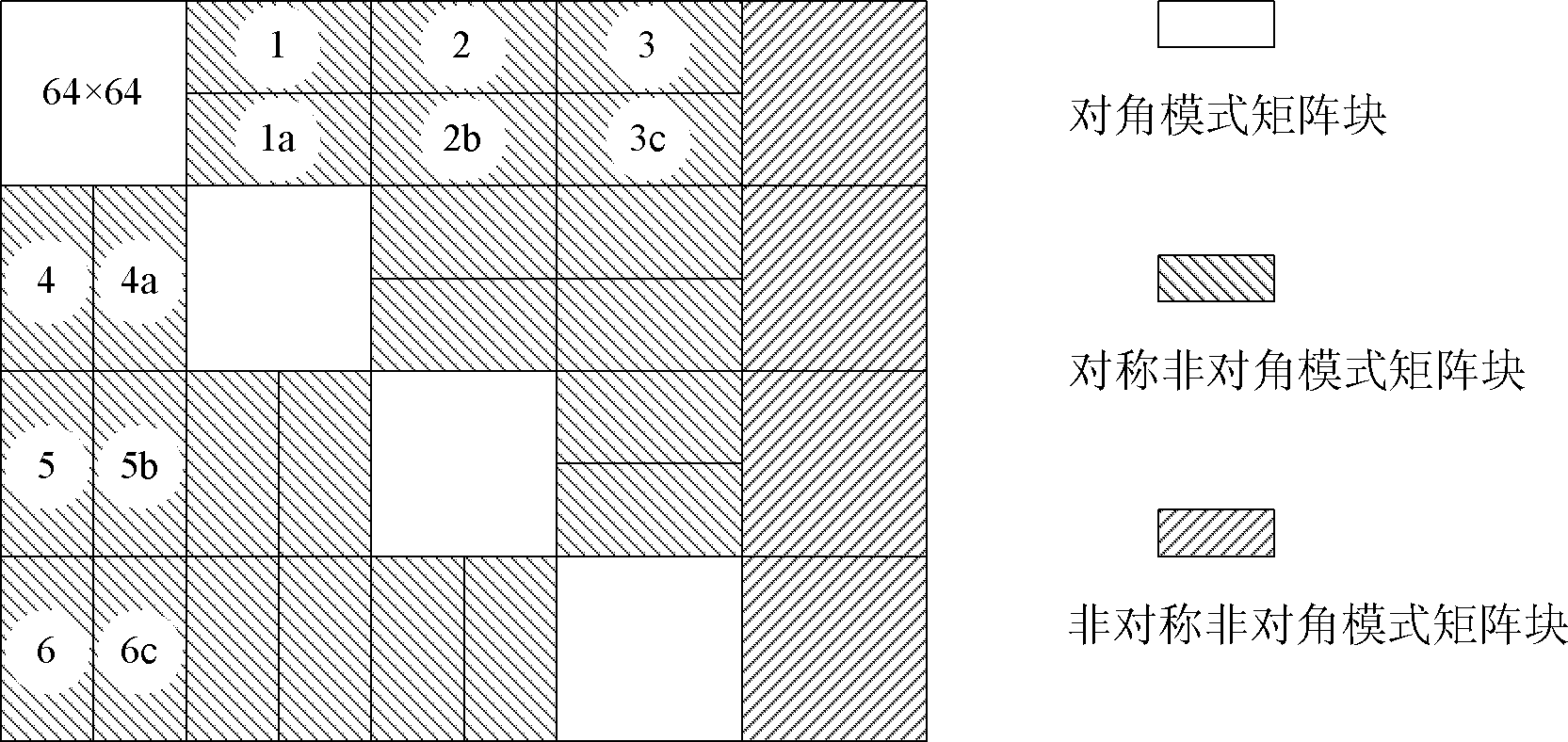
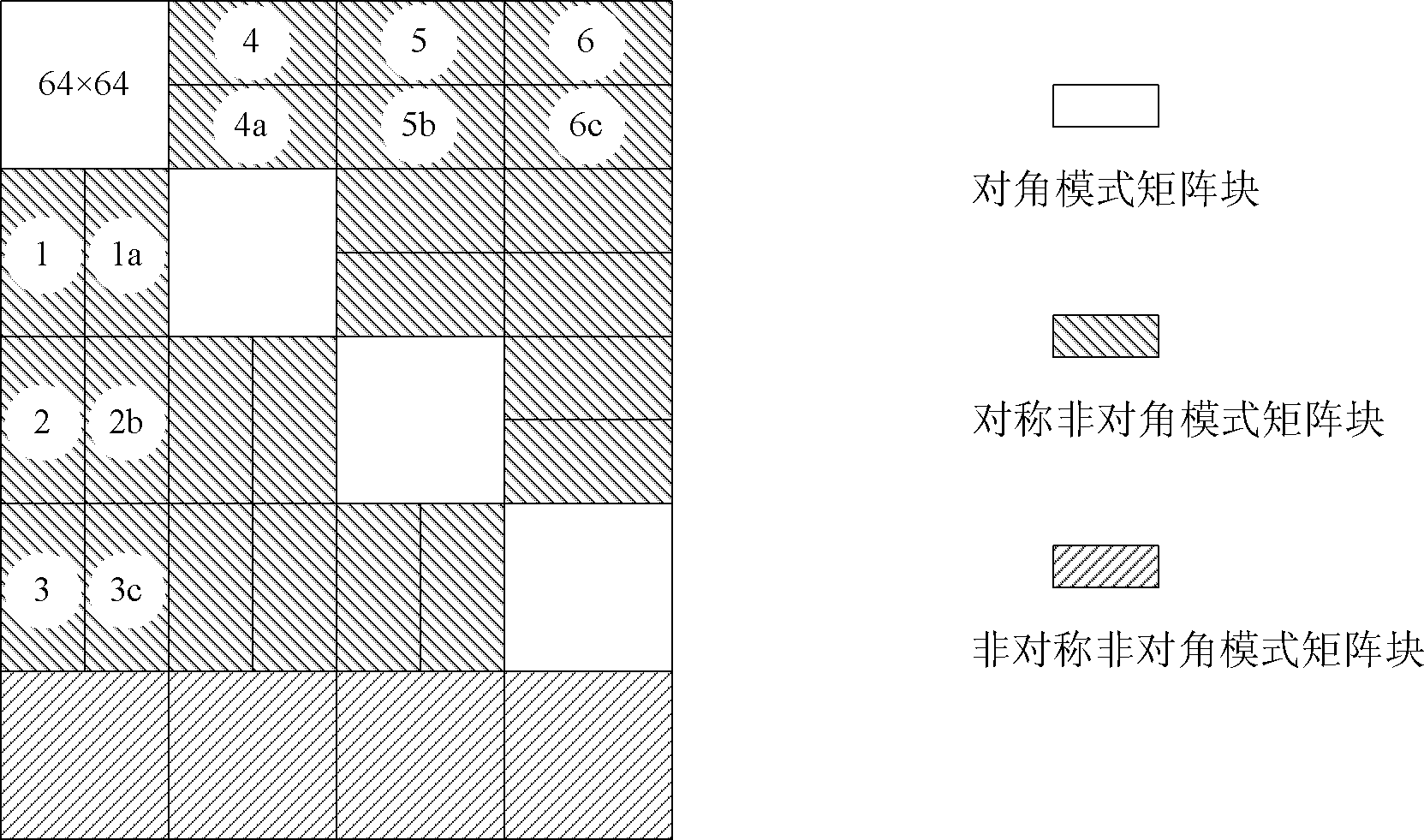
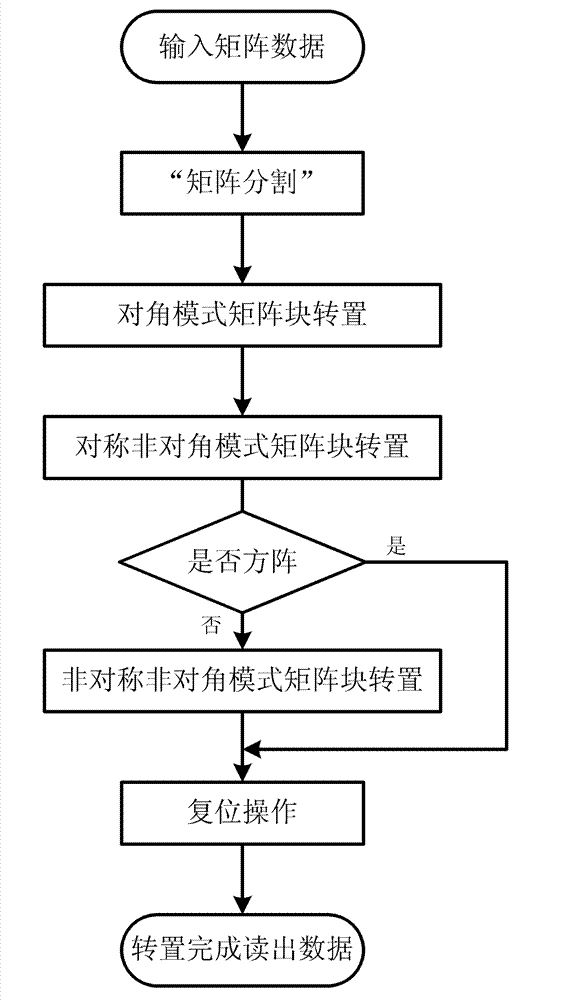
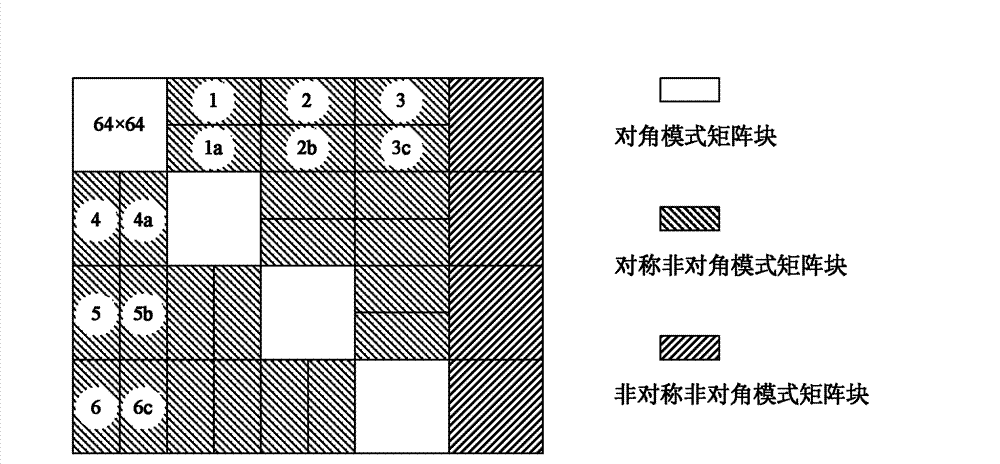
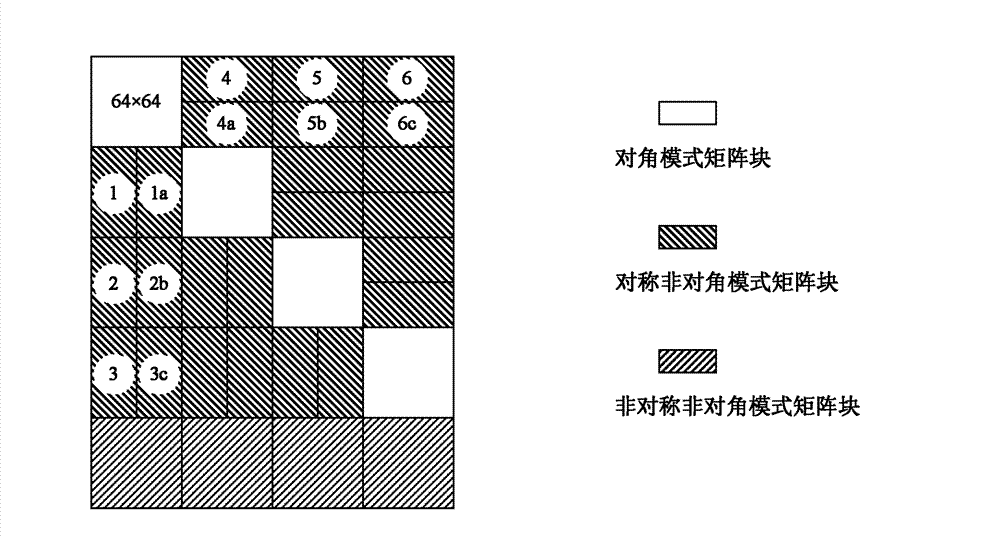
The invention discloses an SAR (Synthetic Aperture Radar) imaging signal processing data transposing method based on an FPGA (Field Programmable Gata Array), which is mainly used for solving the problems of high power consumption, low speed, low efficiency and no radiation resistance existing in a real-time imaging processing CTM (Communication Terminal Module) based on a DSP (Digital Signal Processor). The method comprises the following implementation steps of: storing signal processing data in a DDRII SDRAM (Double Data Rate II Synchronous Dynamic Random Access Memory) through the FPGA; performing matrix partitioning on matrix data in the DDRII SDRAM; transposing a diagonal mode matrix block and a symmetrical non-diagonal mode matrix block in sequence; when the quantity of distance direction sampling points is unequal to that of azimuth direction sampling points, transposing the an asymmetrical non-diagonal mode matrix block; resetting after transposition; and reading out the transposed data in the DDRII SDRAM as required by using the FPGA. Due to the adoption of the transposing method, the working efficiency of the DDRII SDRAM is improved greatly, and a transposition memory CTMsystem runs more stably, has lower power consumption, higher speed and higher efficiency and is resistant to radiation; and the transposing method can be applied to the design of an SAR imaging system.
Owner:XIDIAN UNIV
Multi-database data access method and system and proxy server
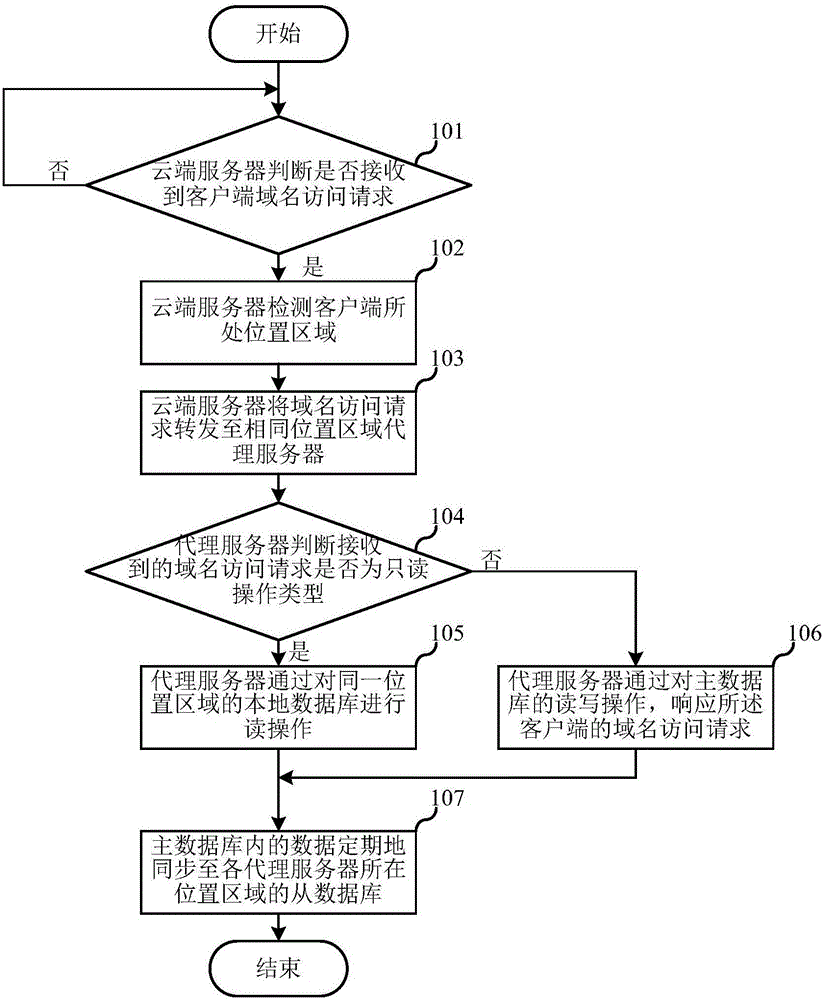
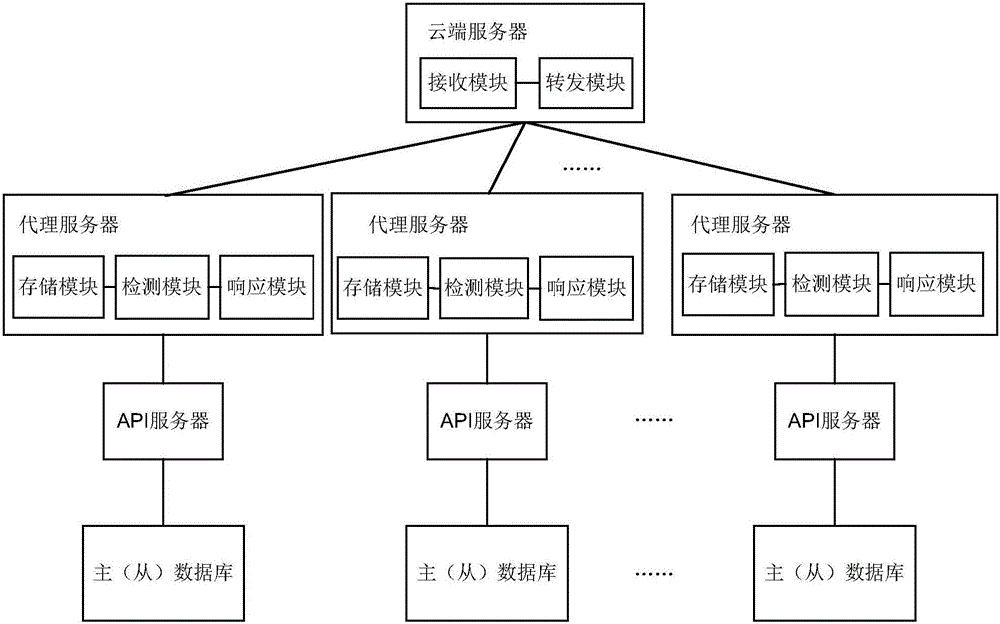
The invention relates to the field of information technologies and communication, and discloses a multi-database data access method and system and a proxy server. The multi-database data access method disclosed by the invention comprises the following steps that: access requests to various domain names are divided into a read operation type and a write operation type in advance; the proxy server, which is in the same position area with a client side initiating a domain name access request, detects the operation type of the domain name access request according to the domain name access request of the client side; if the operation type of the domain name access request is the read operation type, the proxy server responds to the domain name access request of the client side through read operation of a local database in the same position area; if the operation type of the domain name access request is the write operation type, the proxy server responds to the domain name access request of the client side through read and write operation of a master database; and data in the master database is regularly synchronized to a slave database in the position area, where various proxy servers are. Compared with the prior art, the read-only operation response speed of the databases is ensured; and furthermore, the database synchronization robustness is ensured.
Owner:LETV HLDG BEIJING CO LTD +1
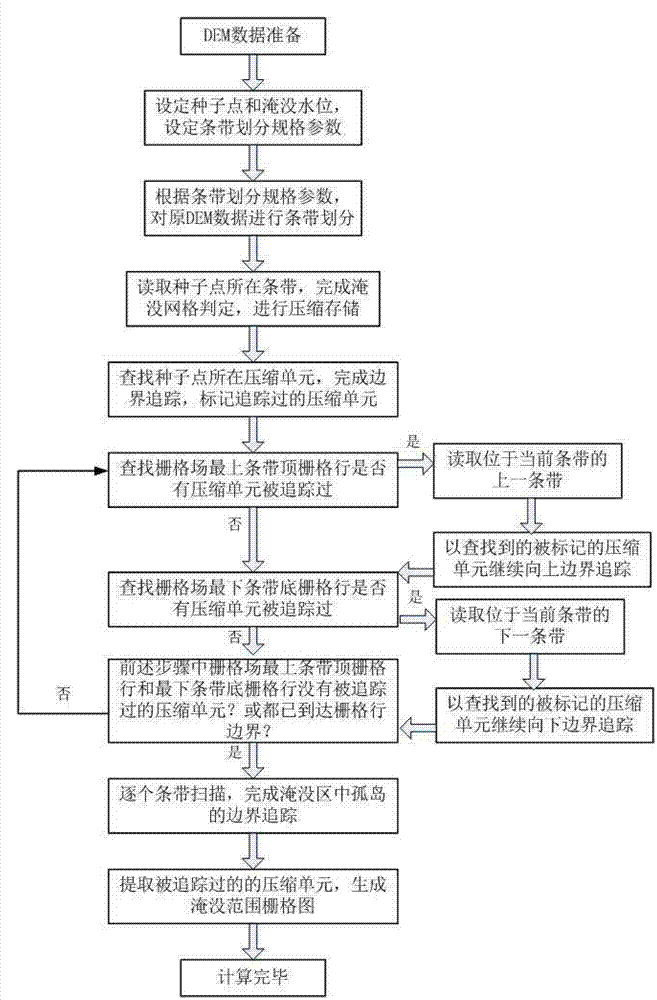
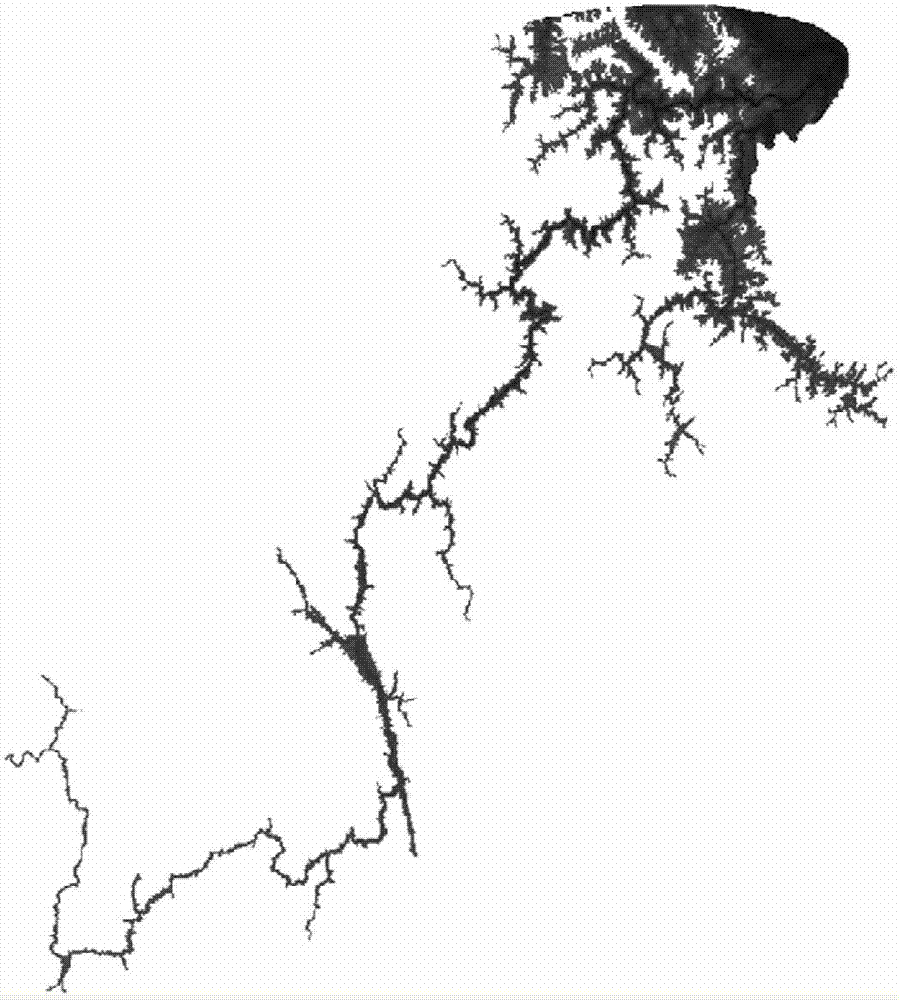
High-precision riverway flood inundated area generation method for mass DEM (Digital Elevation Model) data
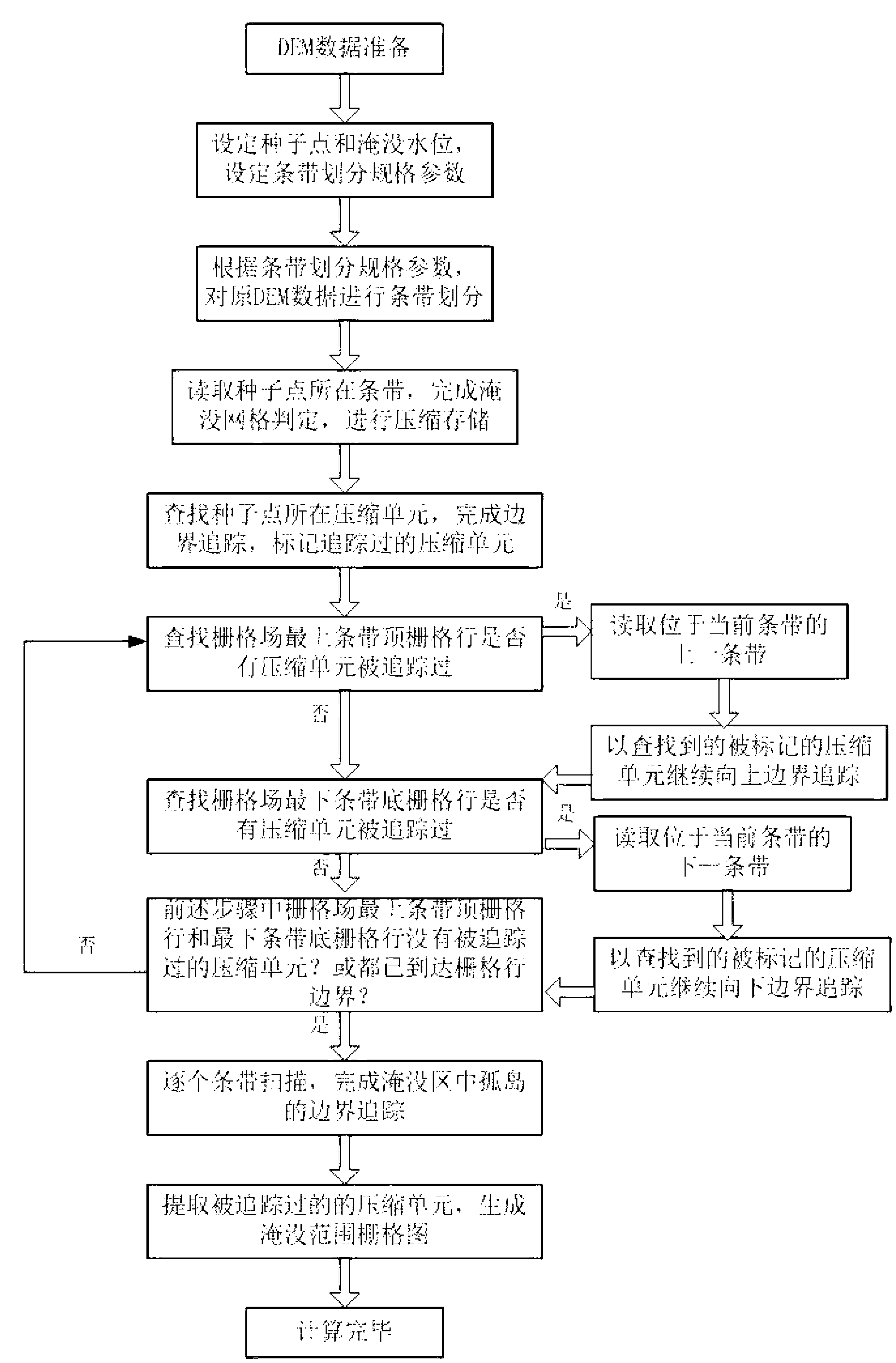
ActiveCN102842104AAvoid recursive judgmentReduce data volumeData processing applicationsClimate change adaptationData compressionDomain analysis
The invention relates to a high-precision riverway flood inundated area generation method for mass DEM (Digital Elevation Model) data. The method comprises the following steps of: performing stripe division on the mass DEM data; performing run length compression storage on a plurality of continuous inundation units on grid lines in stripes to reduce a data size; and finally extracting inundation ranges by virtue of a compression unit boundary tracing method, thereby generating an inundated area under complex terrain conditions. The method changes the conventional inundation source seed point filling method into grid compression storage and grid boundary tracing calculation, so that a large grid data size is processed with small memory configuration; and at the same time, a large amount of recursion judgment in the seed point filling method is avoided, and thus the computing speed is improved. The method fully utilizes digital terrain analysis and data compression storage technologies, avoids the problems generated by mass DEM data inundation analysis in the seed filling method, can be used for well performing connected domain analysis on complex terrain environments with rivers and lakes, and generates the wide-range and high-precision river and lake flood inundated area.
Owner:CHANGJIANG RIVER SCI RES INST CHANGJIANG WATER RESOURCES COMMISSION
Antivirus USB fast-flashing memory
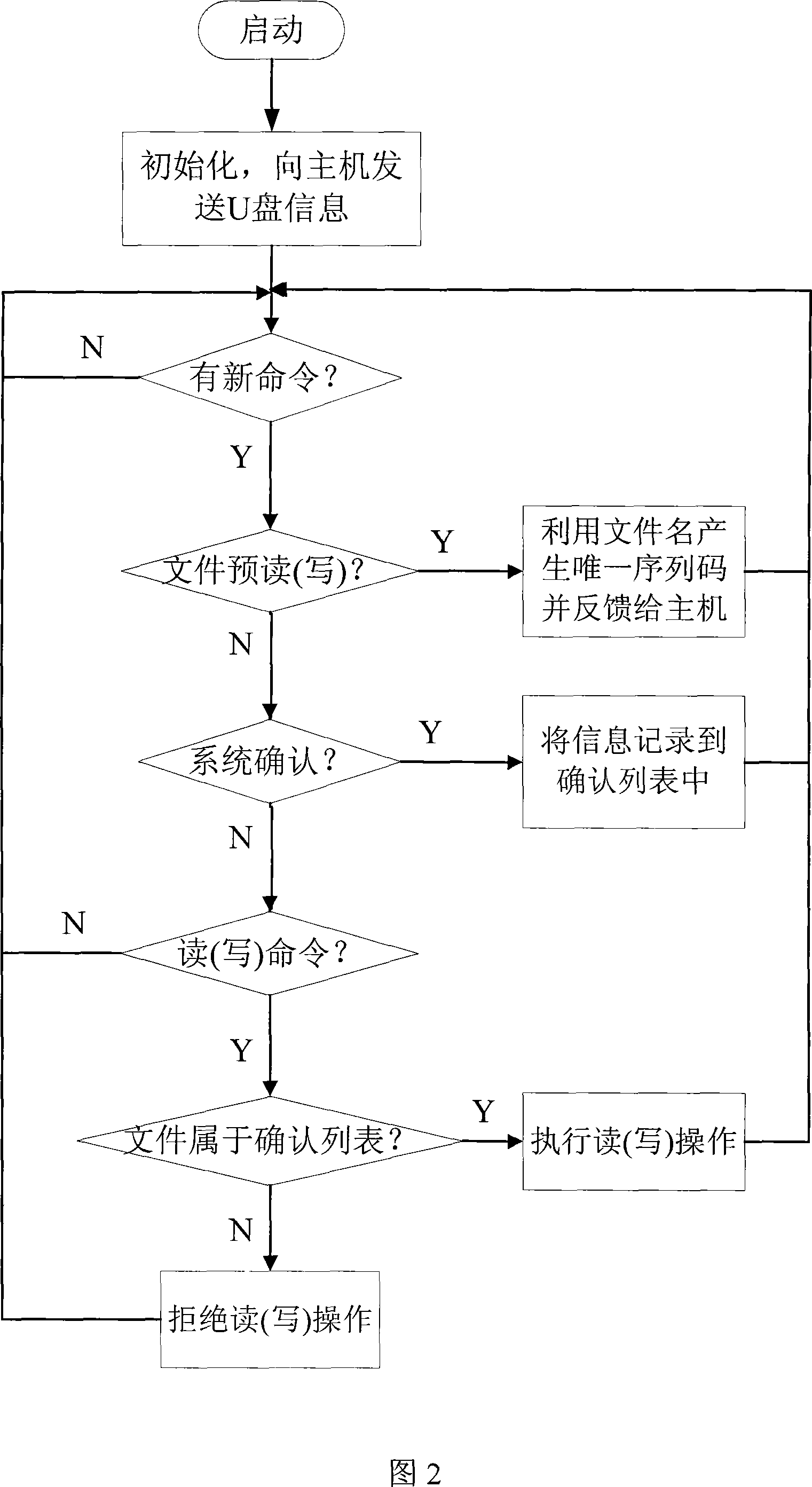
InactiveCN101075280AAvoid read and write operationsAvoid transmissionUnauthorized memory use protectionInternal/peripheral component protectionFile transmissionRemovable media
A USB flash storage of antivirus type consists of USB interface, control chip and flash storage chip. It is featured as spring out conversation frame with file name list by driving program when file-transmission requirement is submitted by system at each time, confirming whether file is to be transmitted or not by user and sending confirmed listing to U disc control chip, afterwards only receiving file-transmission command in said listing by said U disc for preventing unknown file from being written into said U disc.
Owner:NANJING UNIV
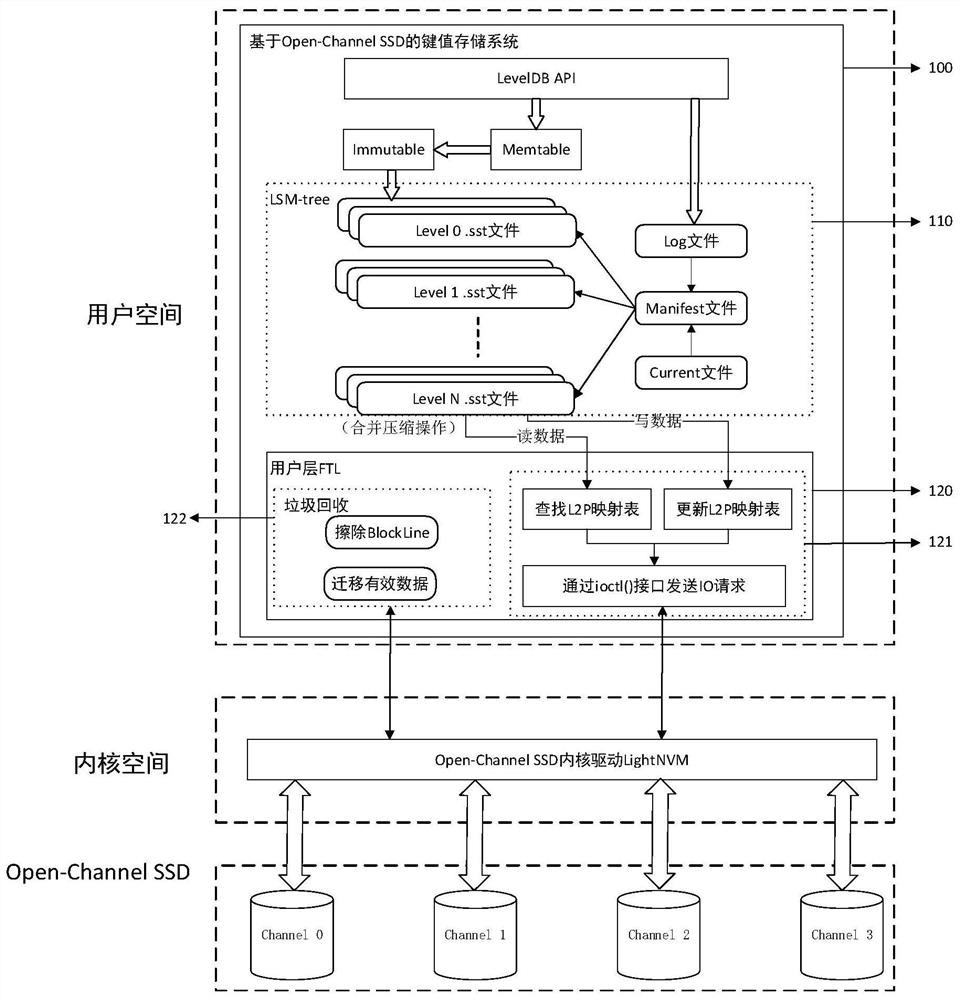
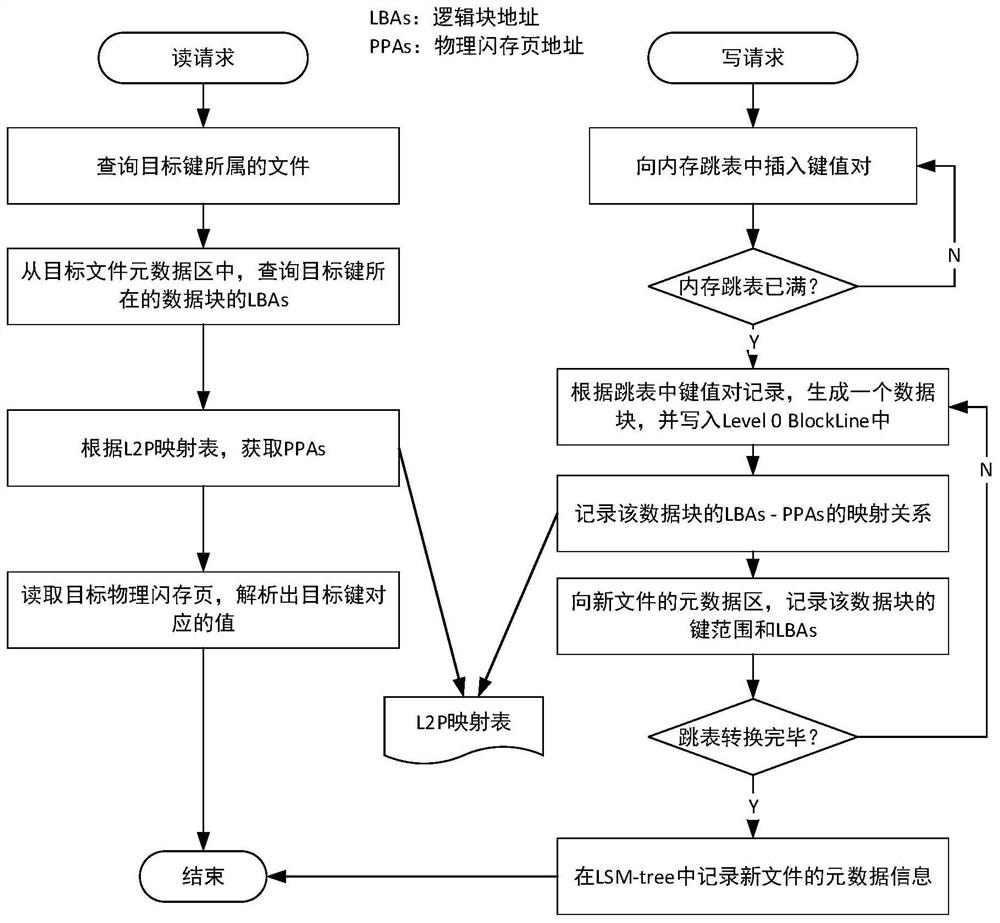
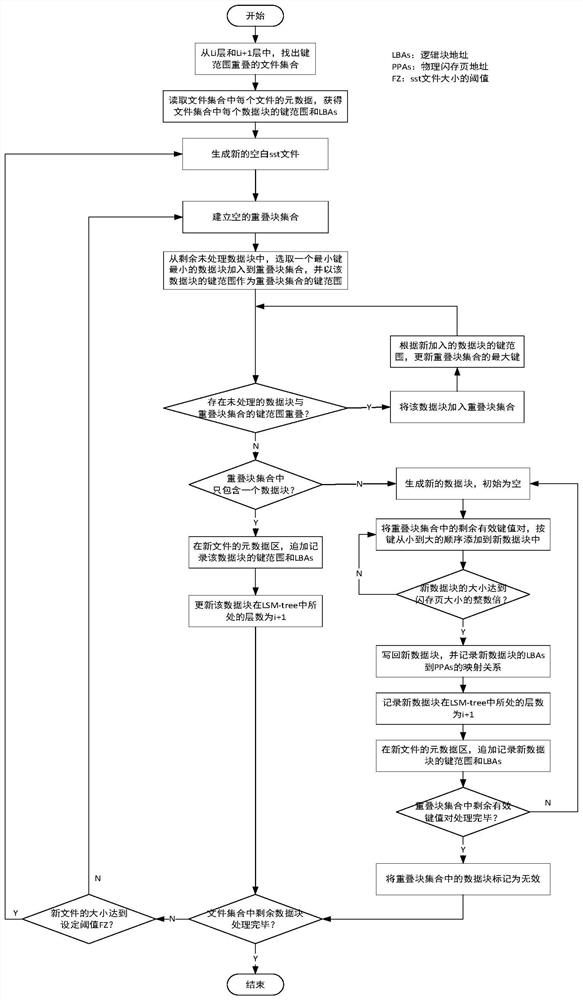
Writing and block granularity compressing and combining method and system of key value storage system based on OCSSD
ActiveCN112346666AReduce the proportionReduce the numberInput/output to record carriersWrite amplificationPERQ
The invention discloses a writing and block granularity compressing and combining method and system of a key value storage system based on an OCSSD, and belongs to the field of computer storage. Through selective compression and combination of data block granularity, read-in and write-back of non-overlapping data blocks are avoided, and the problem of read-write amplification in the LSM-tree compression and combination process can be reduced; the data blocks of the same file are uniformly distributed in all channels of the OCSSD, so that the multi-channel parallel characteristic of the OCSSD can be explicitly utilized, and the throughput of a key value storage system is improved; by directly managing a bottom storage medium at a user layer and bypassing intermediate software layers such asa file system, consumption of host resources is reduced, and semantic features of application software are conveniently transmitted. Generally speaking, the problem of read-write amplification of thekey value storage system based on the LSM-tree can be effectively reduced, semantic isolation between upper-layer application software and bottom-layer storage equipment is eliminated, and the throughput of the whole key value of the system to operation is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Data processing apparatus and method for saving memory space
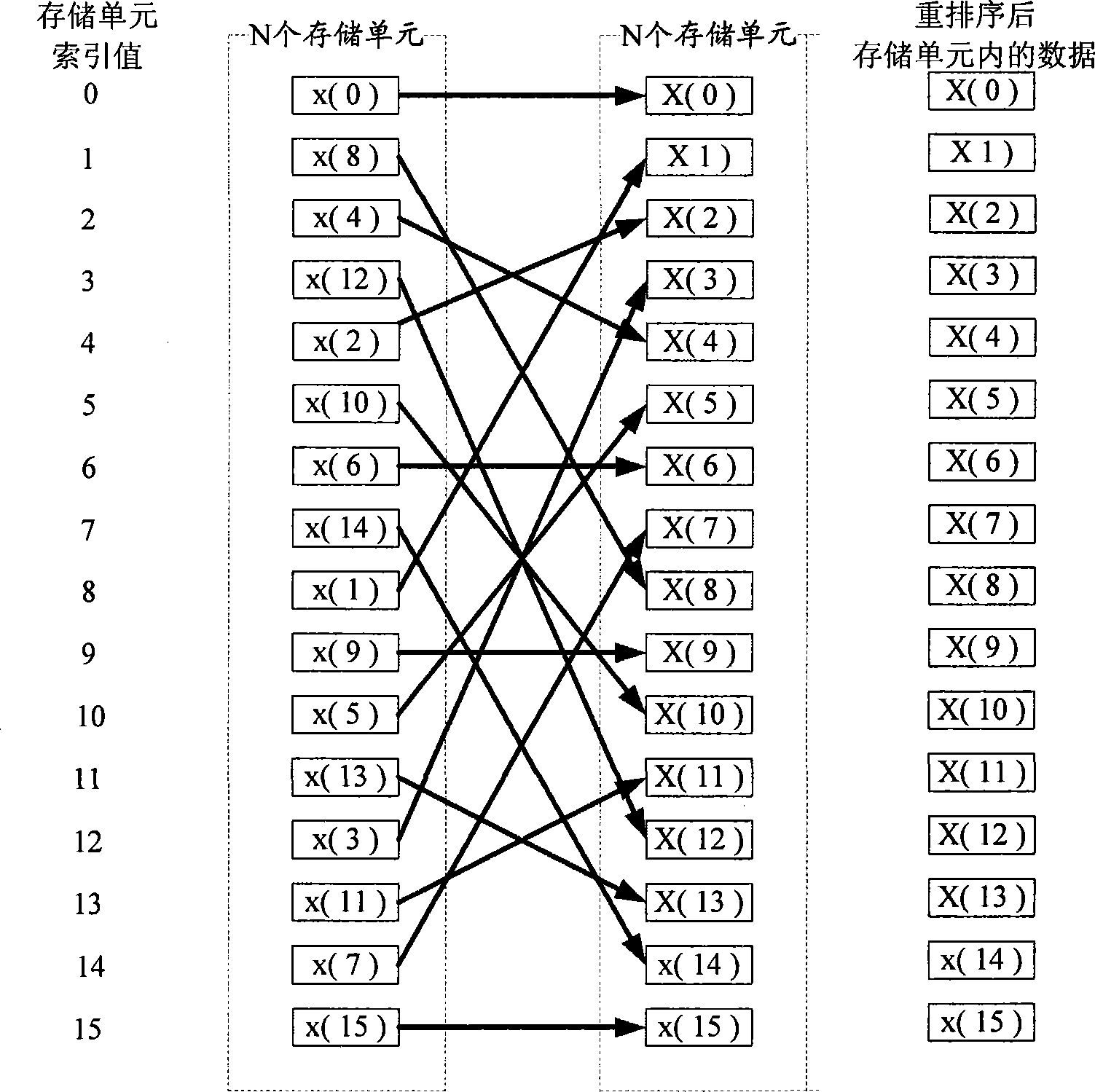
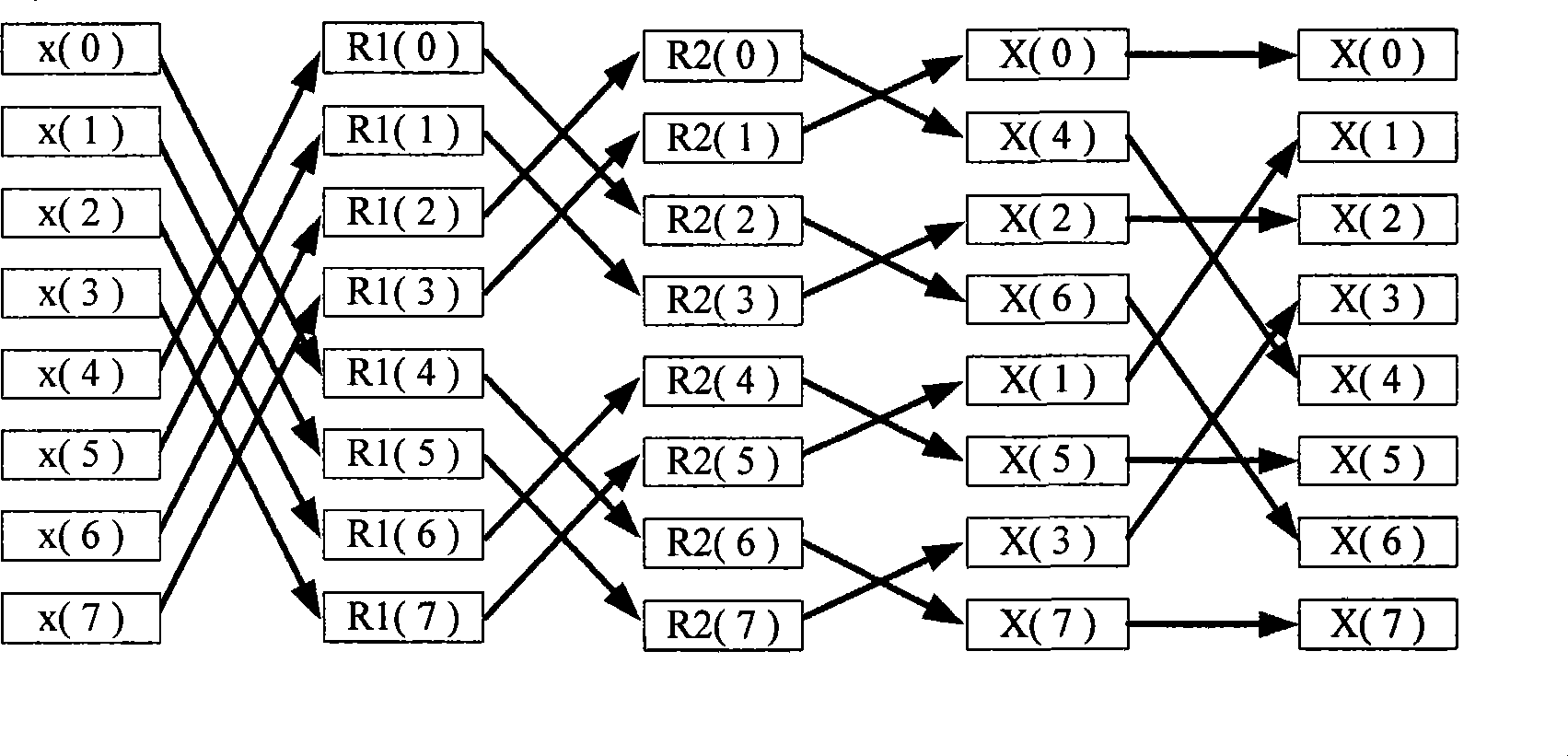
InactiveCN101364215AWon't readImprove processing efficiencyComplex mathematical operationsComputer scienceMemory module
The invention discloses a data processing device used for saving storage space, which comprises a memory module, a bit-reverse module, a comparison module and a regulation module, wherein the memory module is used for saving each data required to be reordered and each reordered data; the bit-reverse module is used for obtaining an index value of each data required to be reordered, and can carrying out bit-reverse operation to each reordered data, so as to obtain a corresponding new index value; the comparison module is used for comparing the index value of each data with the corresponding new index value, so as to obtain a comparative result; and the regulation module is used for exchanging respective corresponding data of the index value and the corresponding new index value which are compared in the memory module only when the comparative result is determined to accord with a predetermined condition, and keeping the corresponding data of the index value in the memory module invariant when the comparative result is determined not to accord with the predetermined condition. By adopting the device, the storage space can be saved during the operation, and the processing efficiency of the operation is improved. Meanwhile, the invention discloses a data processing method for saving the storage space.
Owner:ACTIONS ZHUHAI TECH CO
Intelligent road passing RFID (radio frequency identification device) card reader-writer
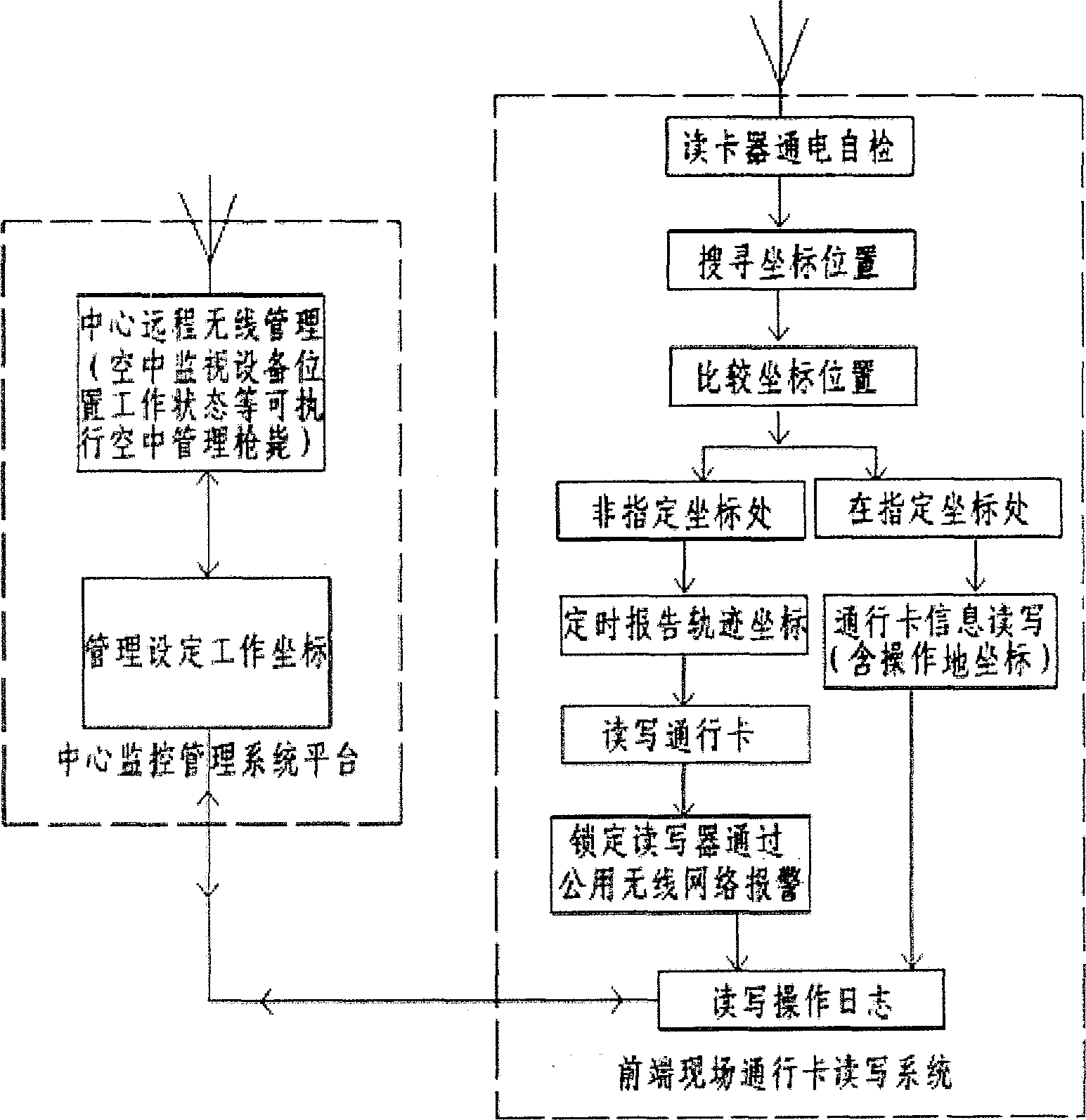
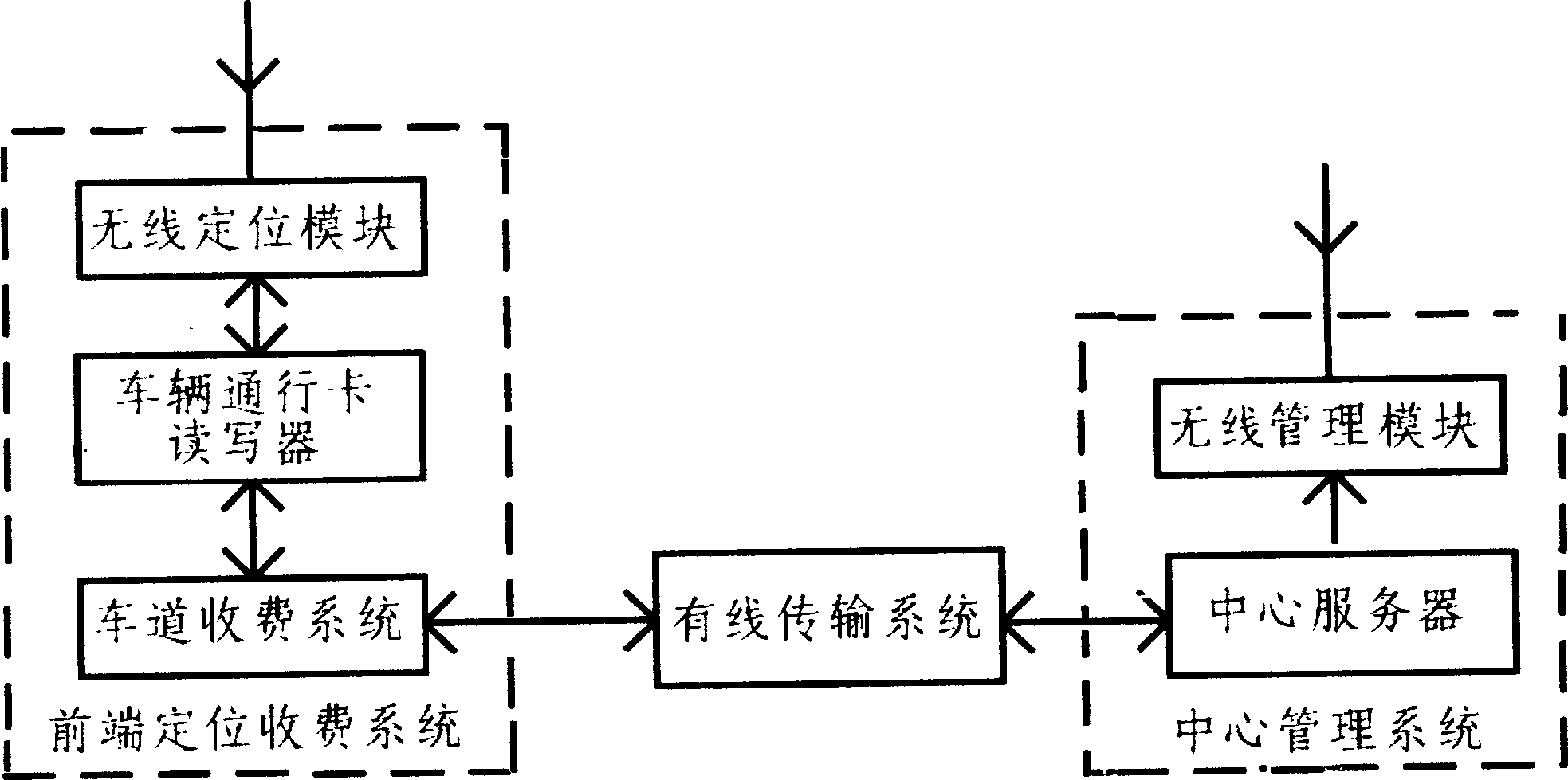
InactiveCN103236090AImprove fee management functionsReduce read and write operationsTicket-issuing apparatusPoint of entryReader writer
The invention discloses an intelligent road passing RFID (radio frequency identification device) card reader-writer. The card reader-writer comprises a wireless positioning module, a vehicle passing card reader-writer and a lane charging system. The vehicle passing card reader-writer is provided with a microprocessor, a built-in power module, a toll station information read-write module, a path identification module, a positioning and managing module and a communication module inside. Compared with the existing highway passing card reader-writer, the card reader-writer is provided with the vehicle passing card reader-writer and the lane charging system, the reader-writer can only be used in specific positions by locking read-write of the reader-writer, specific position coordinates are automatically overlapped during each read-write, updating of the existing reader-writer for management is achieved, by the intelligent card reader-writer, charging can be performed to specific coordinates at an entrance and an exit, a charging managing function is improved, passing card read-write outside a toll station can be reduced or prevented, and toll avoidance can be reduced.
Owner:CHENGDU YINLIANAN SCI & TECH
Method for testing hard disk with expandable firmware interface
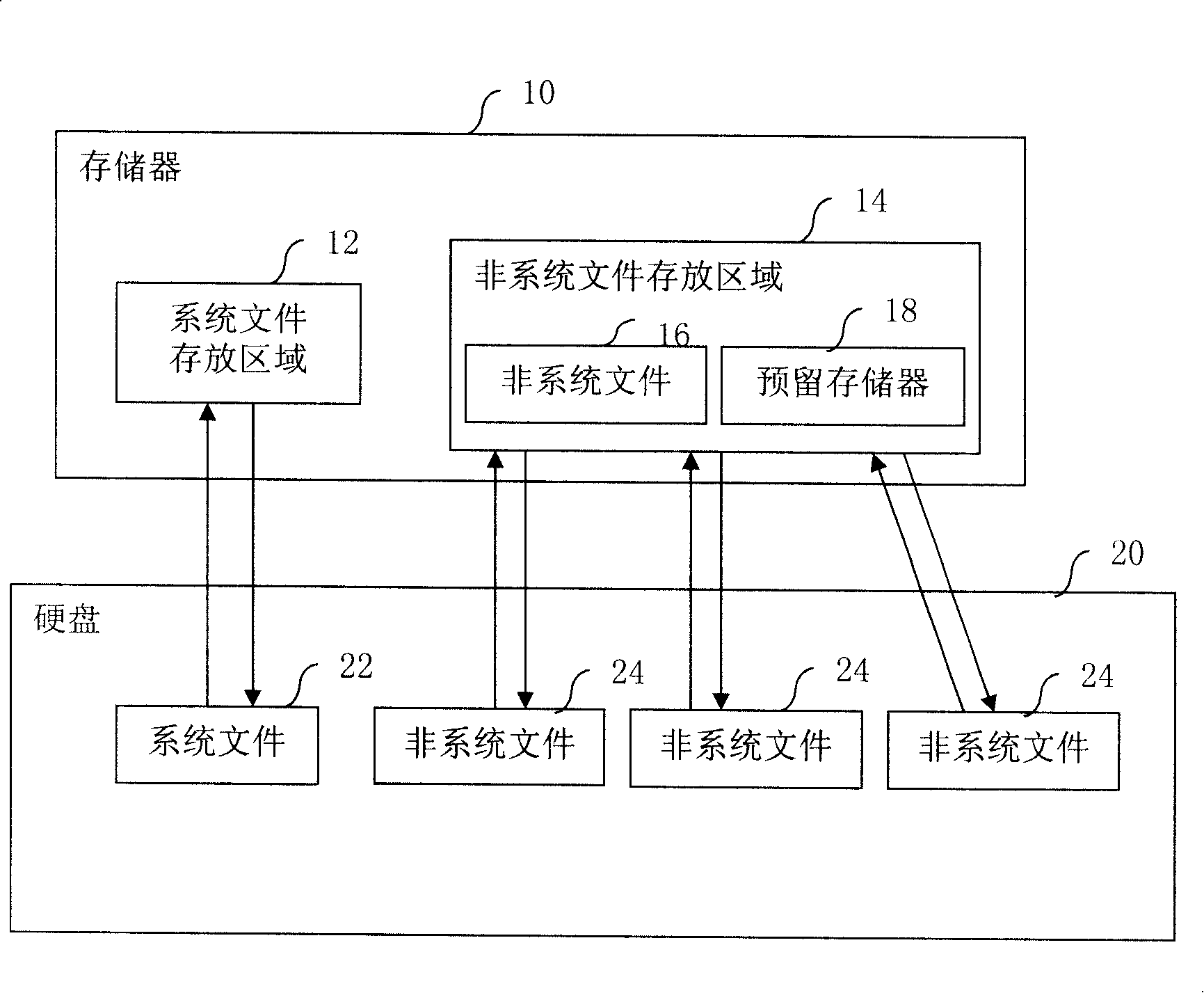
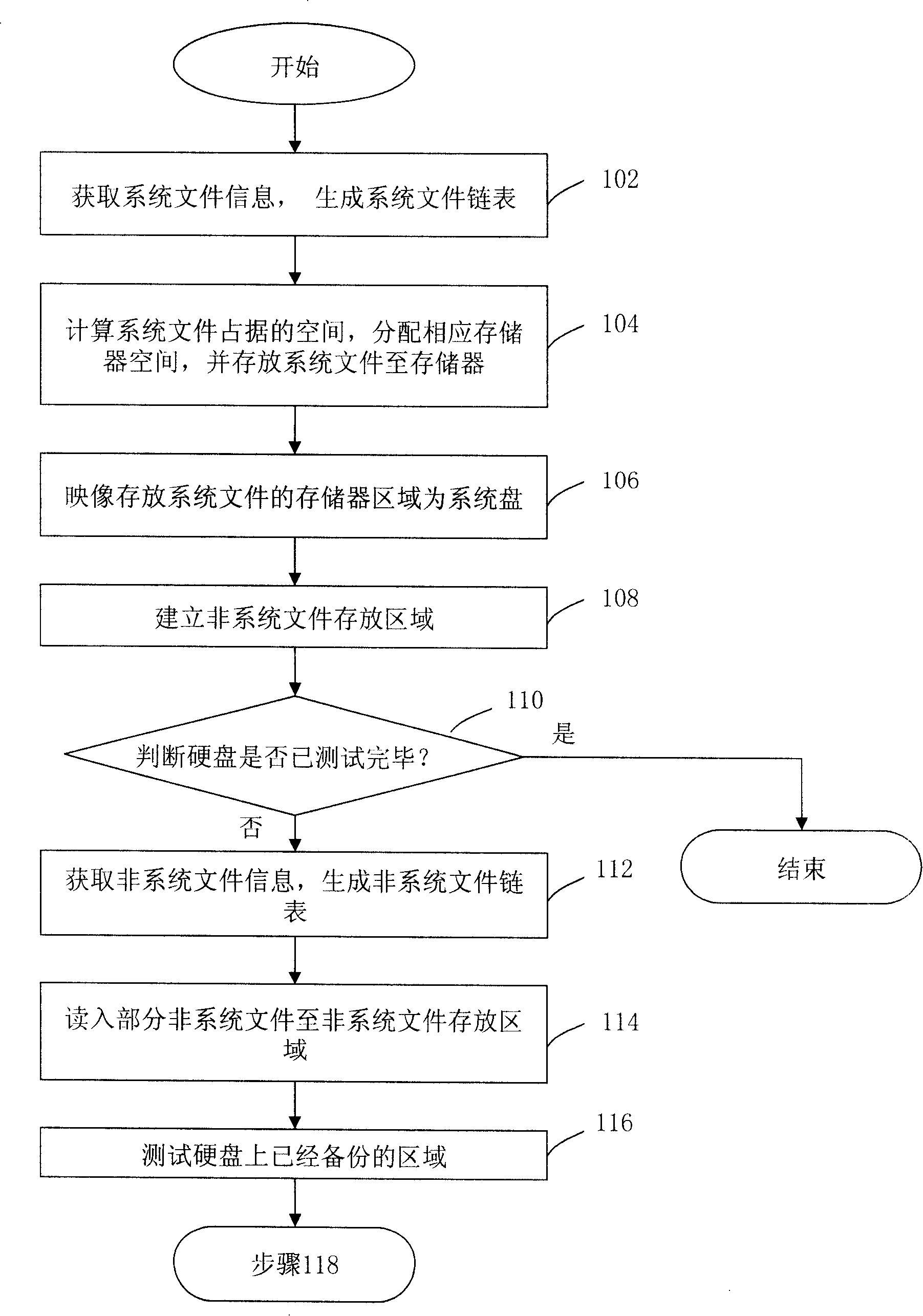
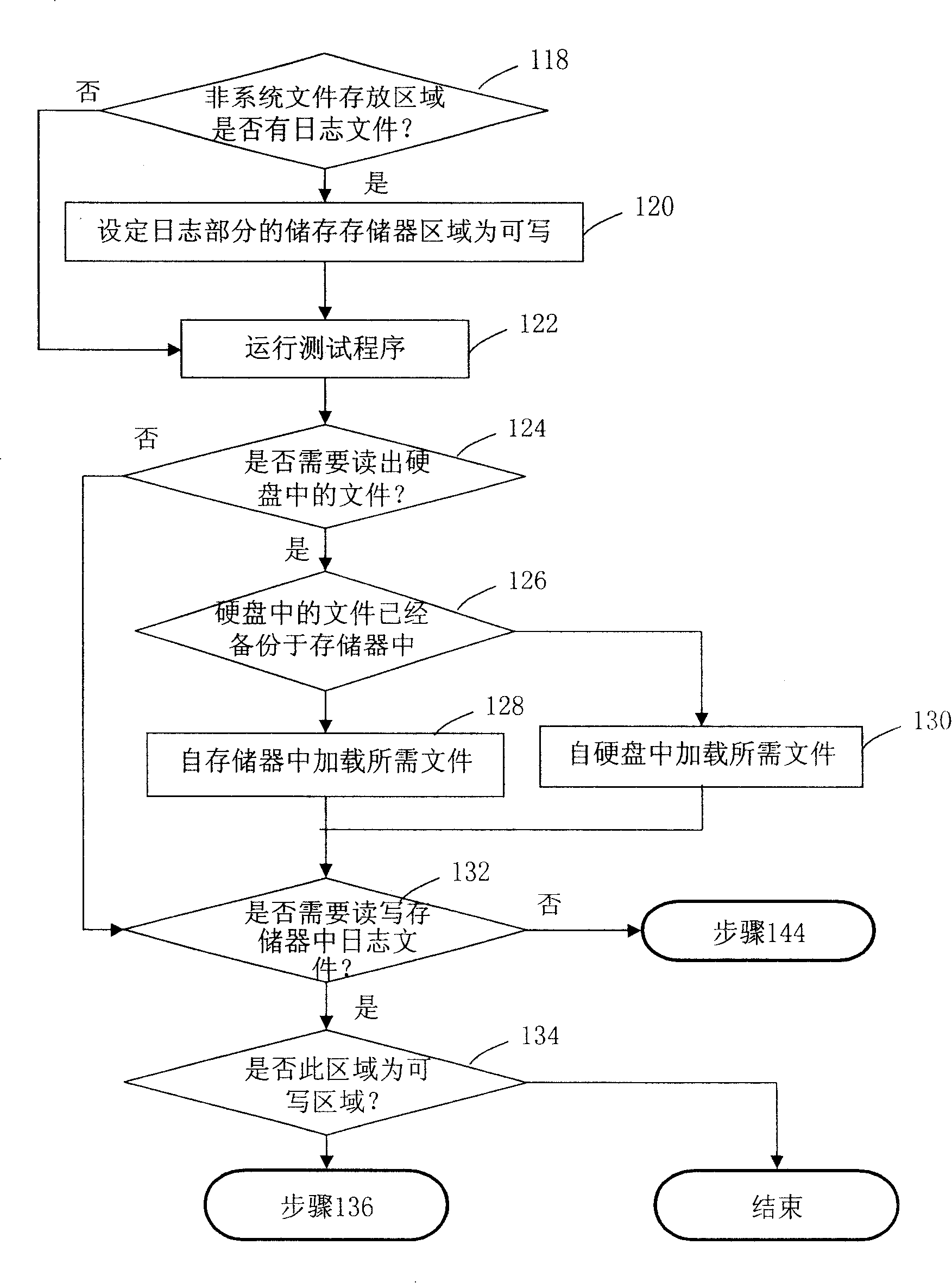
InactiveCN101201778AAvoid read and write operationsImplement testDetecting faulty computer hardwareProtection systemLinked list
A hard disk test method under an extensible firmware interface (EFI) includes the following steps: the system files of the EFI of the hard disk are backuped to the storage area in a memory; the backup area of the system files is imaged to be a real hard disk; the storage area of a non-system file is set up in the memory, which is used for storing the non-system file in file area of hard disk test; the information of the system files and the non-system file of hard disk test are obtained, and a system file list and a non-system file list are generated sequentially; the tested non-system files of hard disk test are backuped to the storage area of the non-system file when the hard disk test is executed; the system file list and / or the non-system file list are / is accessed to load the system files and / or the non-system files of hard disk test directly from the storage area in the memory. The invention can not only accelerate the seed of the test, but also can protect the system from destruction, which can realize the comprehensive test on hard disk.
Owner:INVENTEC CORP
Method and system for user action collection based on cache memory and asynchronous processing technology
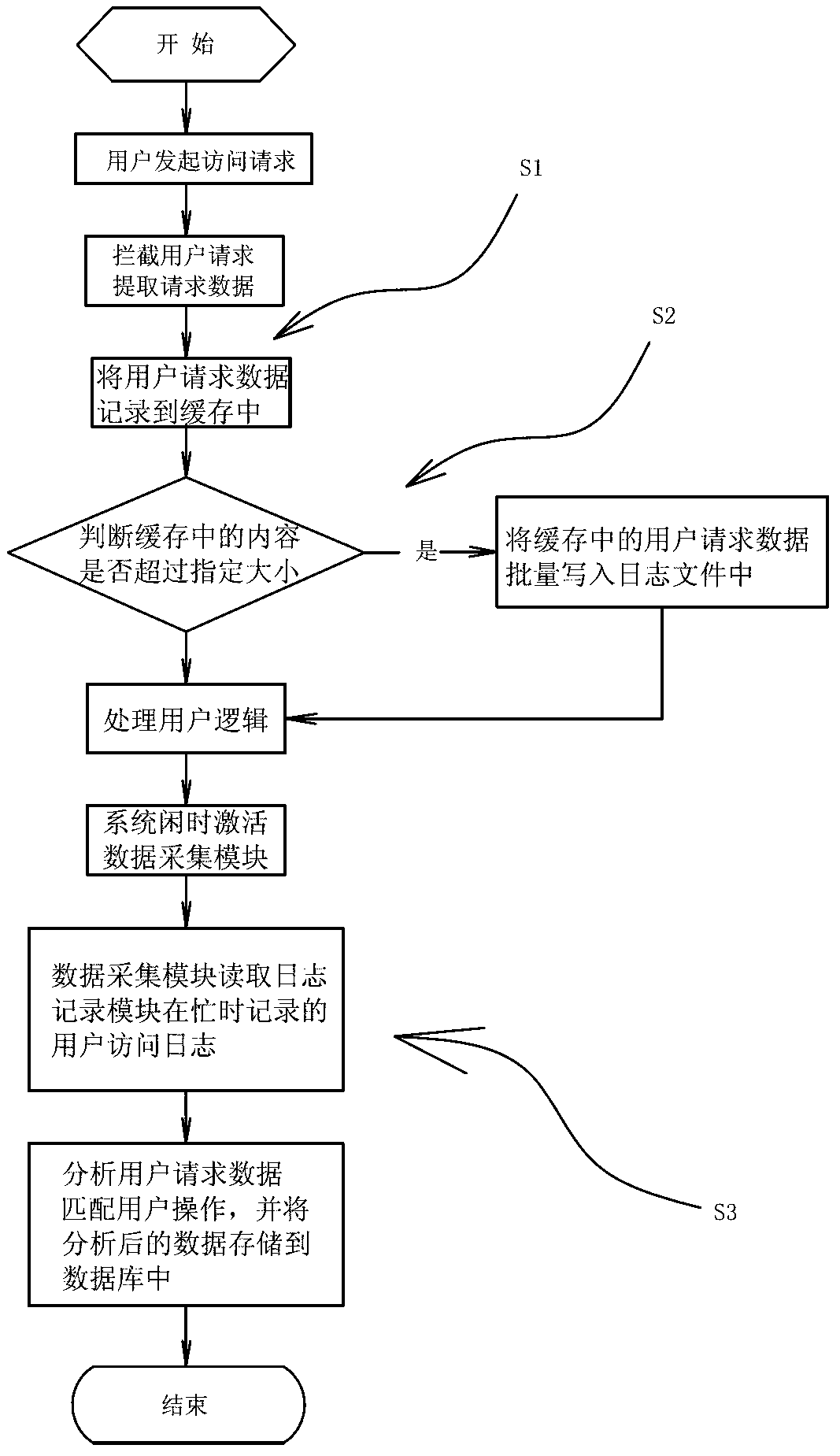
InactiveCN103236938ATake advantage ofReduce Data Acquisition StressData switching networksInternal memoryBusy hour
The invention discloses a method and a system for user action collection based on cache memory and asynchronous processing technology. The method includes S1, recording user request data into a cache memory, S2, judging whether contents in the cache memory excess a specified size or not, writing the user request data into log files in batches if so, and carrying on recording the user request data into the cache memory if not, S3, activating a data collecting module when the system is idle, reading user visiting logs recorded by a log recording module in busy hours, analyzing user request data, matching user operation, and storing analyzed data into a database. The system comprises the log recording module and the data collecting module. The log recording module is used for recording the user request data in batches; and the user request data are cached in an internal memory and excess the specified size. The data collecting module is used for analyzing user request data in logs when the system is idle, matching the user operation, and then storing the analyzed user request data into the database.
Owner:QTONE EDUCATION GROUP (GUANGDONG) CO LTD
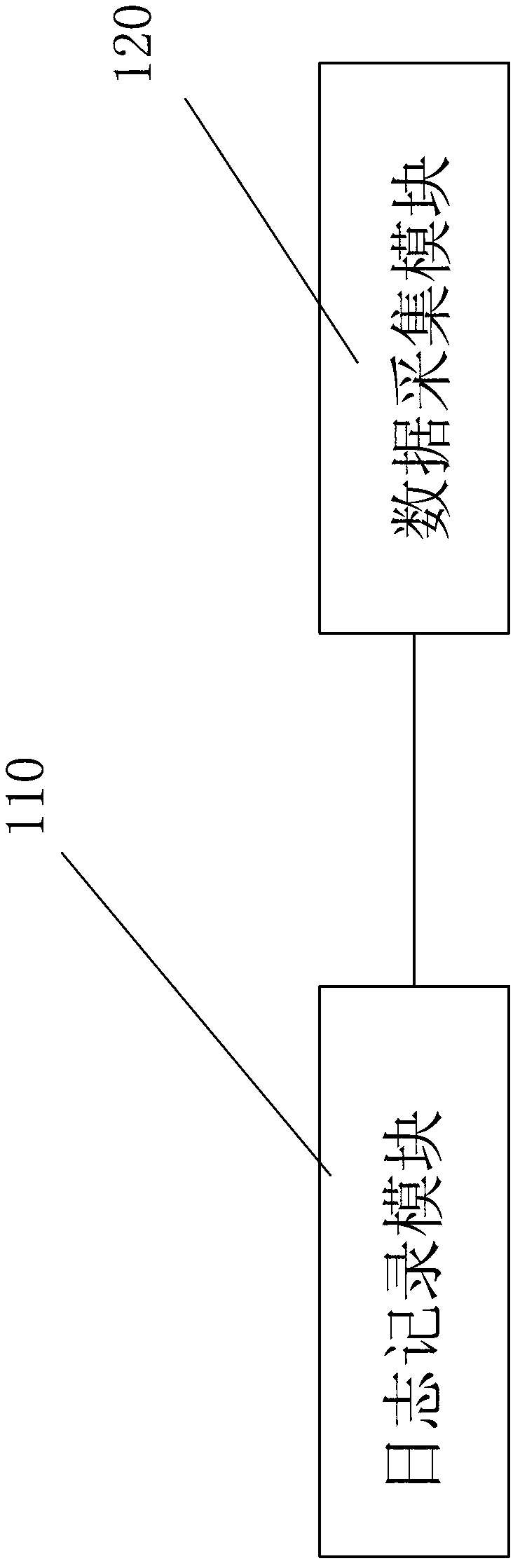
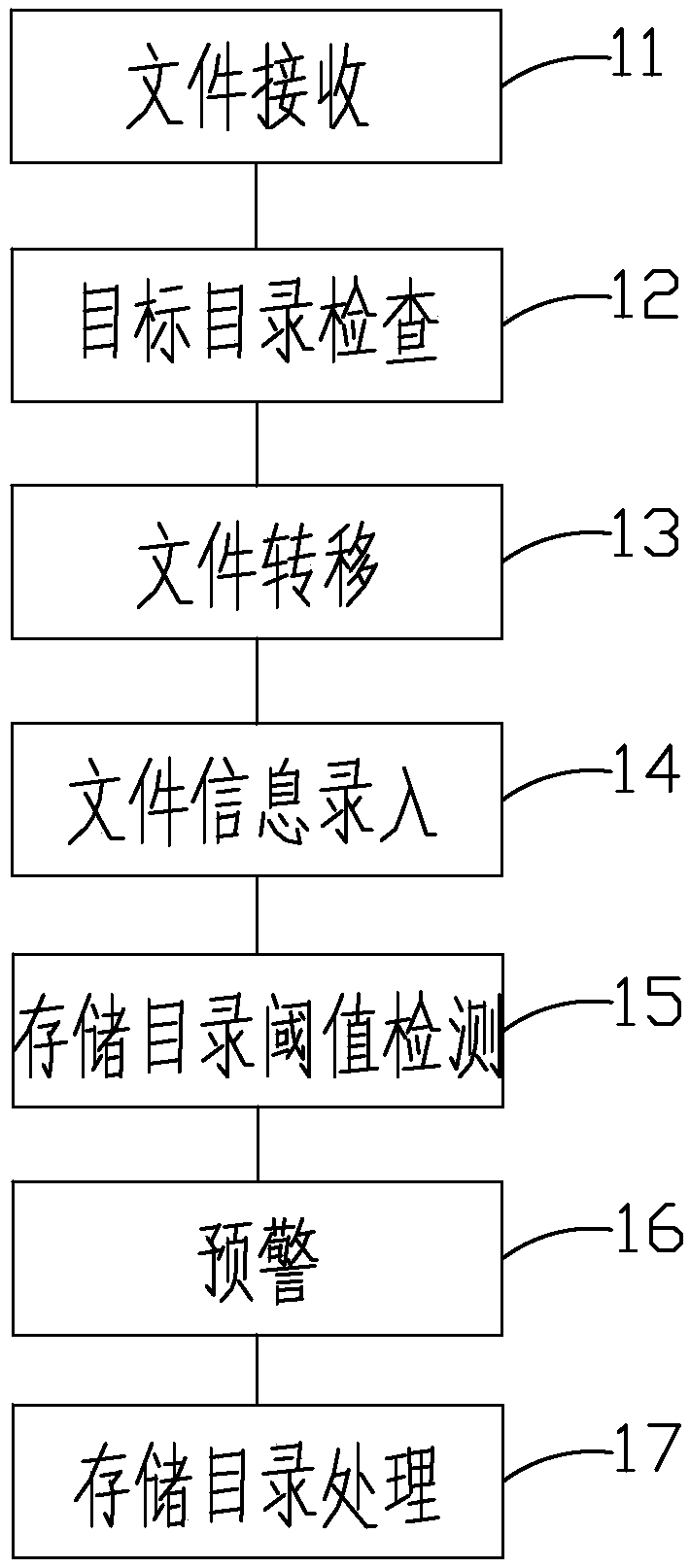
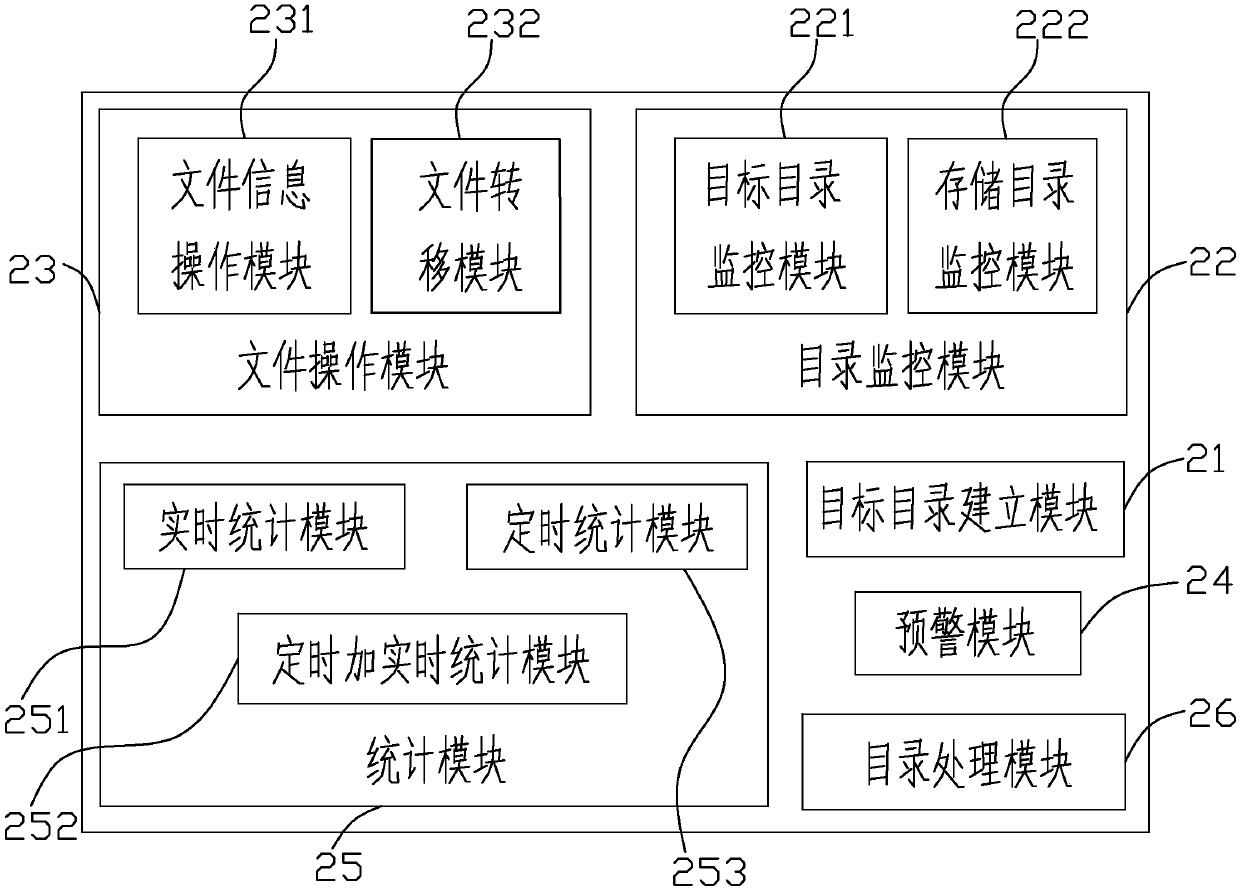
File reception and management method and device, terminal equipment and storage medium
ActiveCN107908710ARealize unified managementSolve the problem of inconvenient file searchSpecial data processing applicationsWorking pressureTerminal equipment
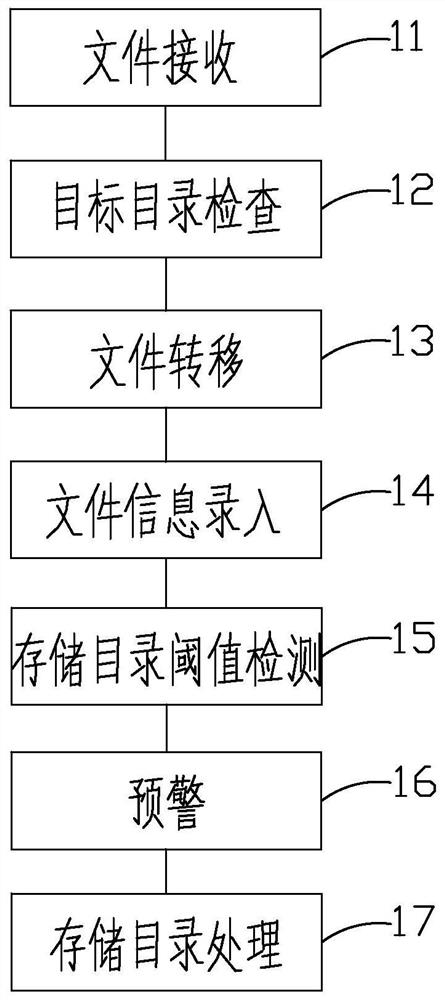
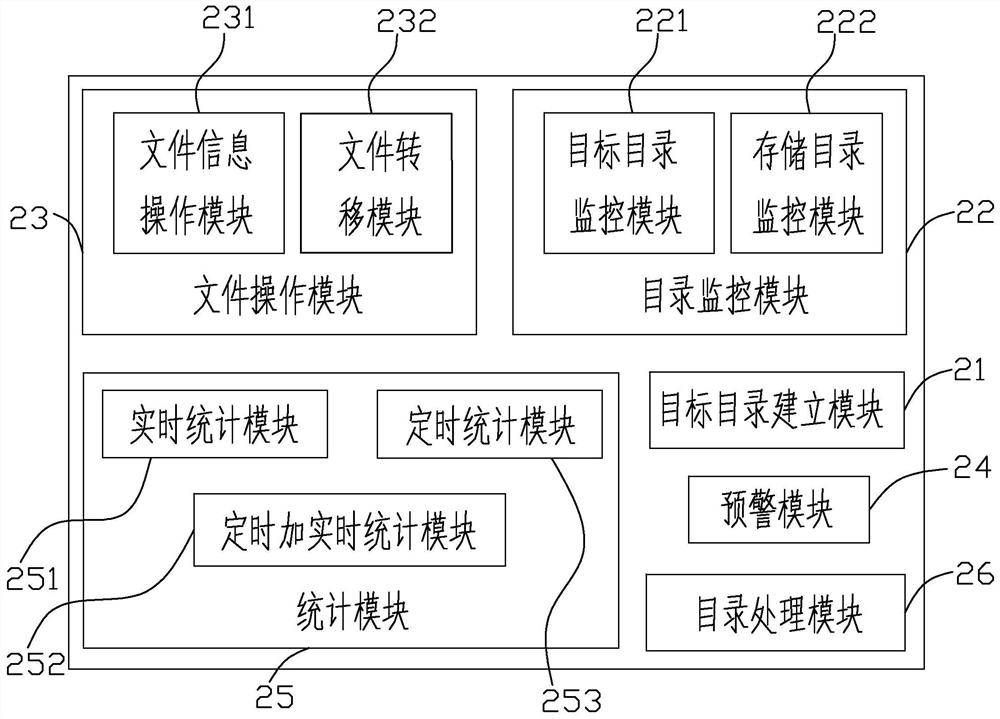
The invention discloses a file reception and management method and device, terminal equipment and a storage medium. The method comprises the following steps of: file reception: storing a file providedby a file producer in a target directory through one or more file reception manners; target directory check: periodically checking whether the file exists in the target directory or not; file transfer: if the file exists in the target directory, transferring the file in the target directory into a storage directory; file information input: after the file in the target directory is transferred tothe storage directory, storing a path of the storage directory and basic information of the file into a database; storage directory threshold value detection: detecting whether the file stored in thestorage directory achieves a threshold value or not; and pre-warning: when the file stored in the storage directory achieves the threshold value, triggering pre-warning and sending pre-warning information. According to the method, files of multiple channels are automatically received and managed, so that the work pressure of personnel can be decreased and the work efficiency can be improved.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
Method and system for managing virtual machine storage space and physical host
ActiveUS8850156B2Efficient managementIncrease profitMemory adressing/allocation/relocationProgram loading/initiatingComputer moduleVirtual storage
A method for managing Virtual Machine (VM) storage space is provided. In the method, a Storage Balloon Agent (SBA) module deployed in a VM is adopted to directly acquire virtual storage free block information and deliver the acquired virtual storage free block information to a Storage Balloon Daemon (SBD) module deployed in a Virtual Machine Monitor (VMM) layer; and the SBD module releases a part or all of physical storage space corresponding to the virtual storage free block information, and marks virtual storage blocks corresponding to the released physical storage space as unavailable. A corresponding system and a physical host are further provided in the present invention. Through the method of an embodiment of the present invention, use condition of virtual storage space can be acquired in real time, and a large number of read and write operations of a storage system can be avoided.
Owner:HUAWEI TECH CO LTD
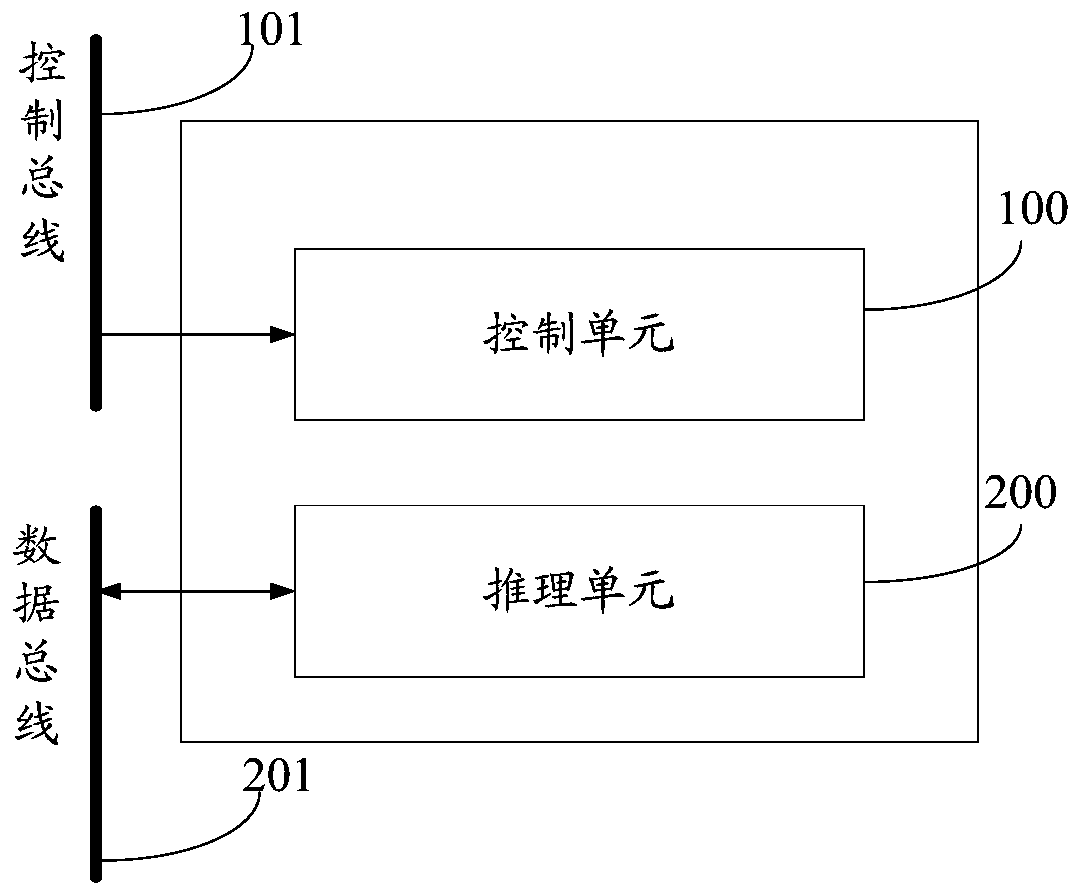
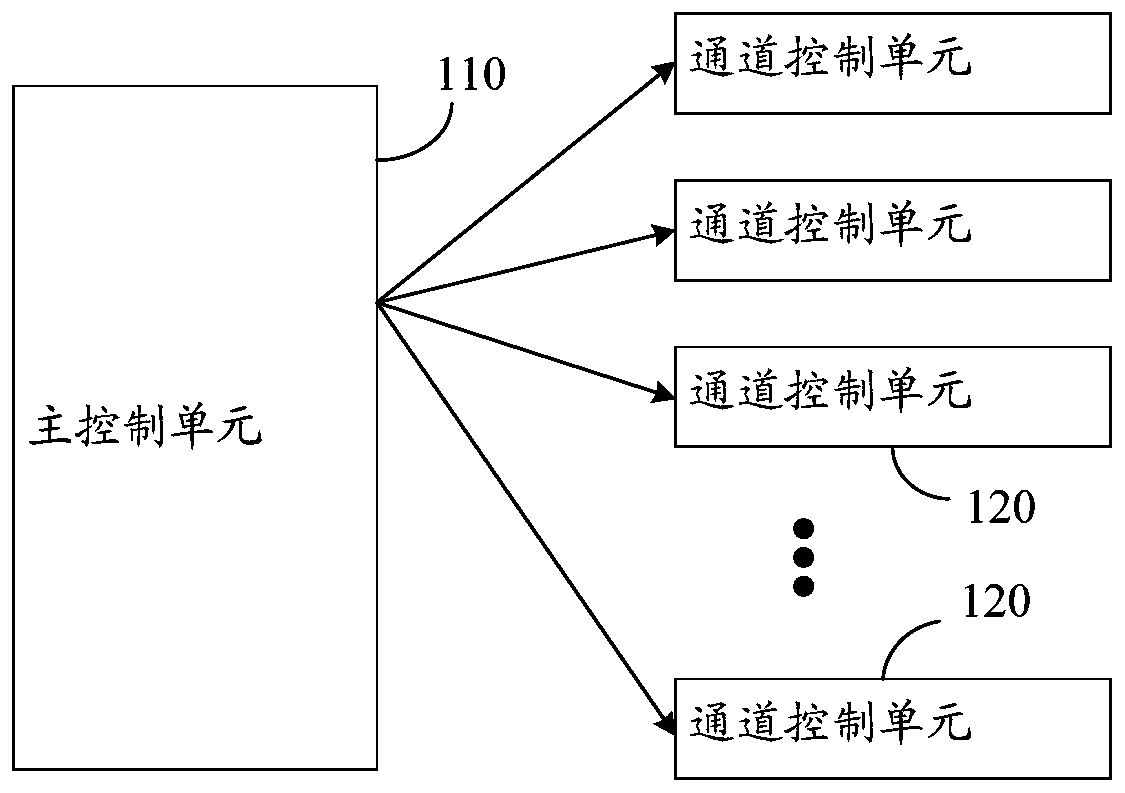
A machine learning reasoning coprocessor
ActiveCN109814927AIncrease the number ofFlexible customized designConcurrent instruction executionNeural architecturesCoprocessorTheoretical computer science
The embodiment of the invention provides a machine learning reasoning coprocessor. The machine learning reasoning coprocessor comprises a reasoning unit and a control unit. The reasoning unit is usedfor reading and calculating a task instruction, data and parameters so as to realize reasoning operation corresponding to the task instruction; and the control unit comprises a main control unit and aplurality of channel control units. Wherein the main control unit is used for realizing global control on the machine learning reasoning coprocessor; and each channel control unit in the plurality ofchannel control units is used for respectively controlling a channel corresponding to the reasoning unit in the reasoning unit to realize response to a single task or a user according to the task instruction. According to the embodiment of the invention, multiple users and multiple tasks can be supported, and flexible customized design can be realized.
Owner:CHENGDU HAIGUANG INTEGRATED CIRCUIT DESIGN CO LTD
Data protection method, device and system
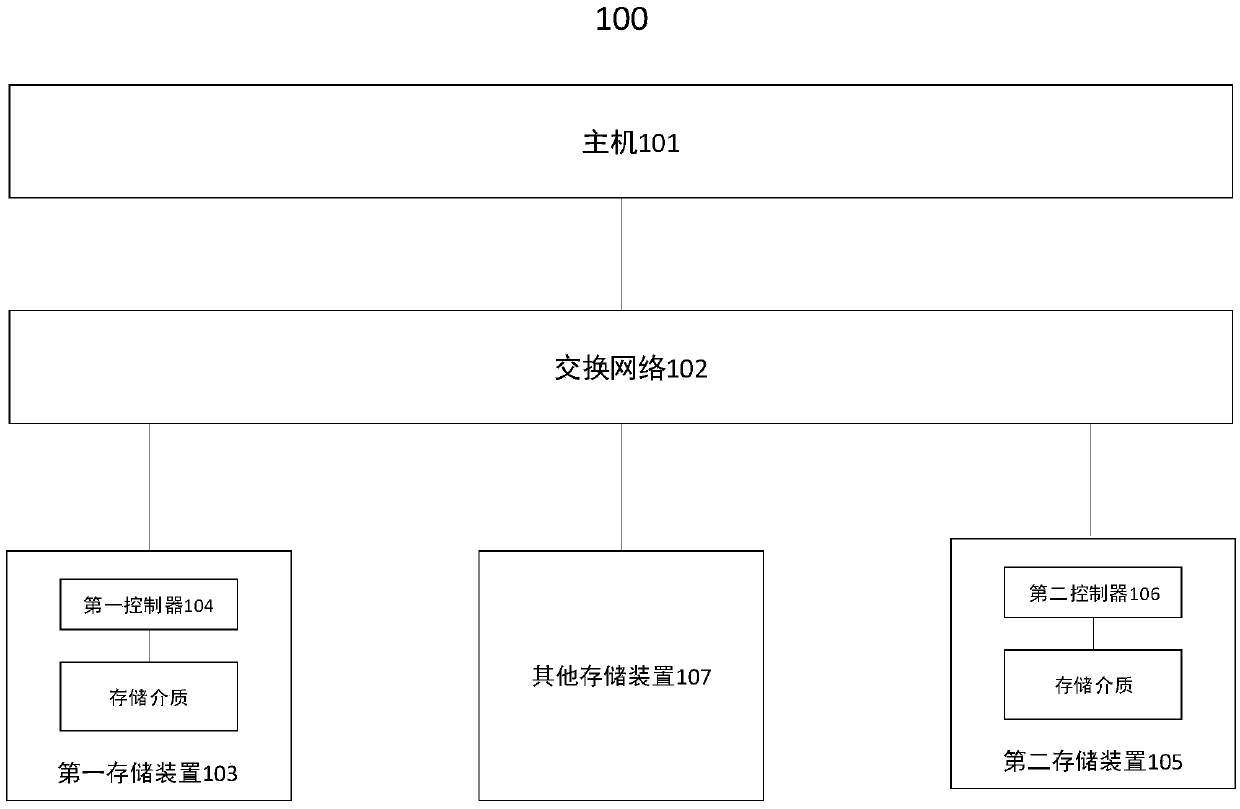
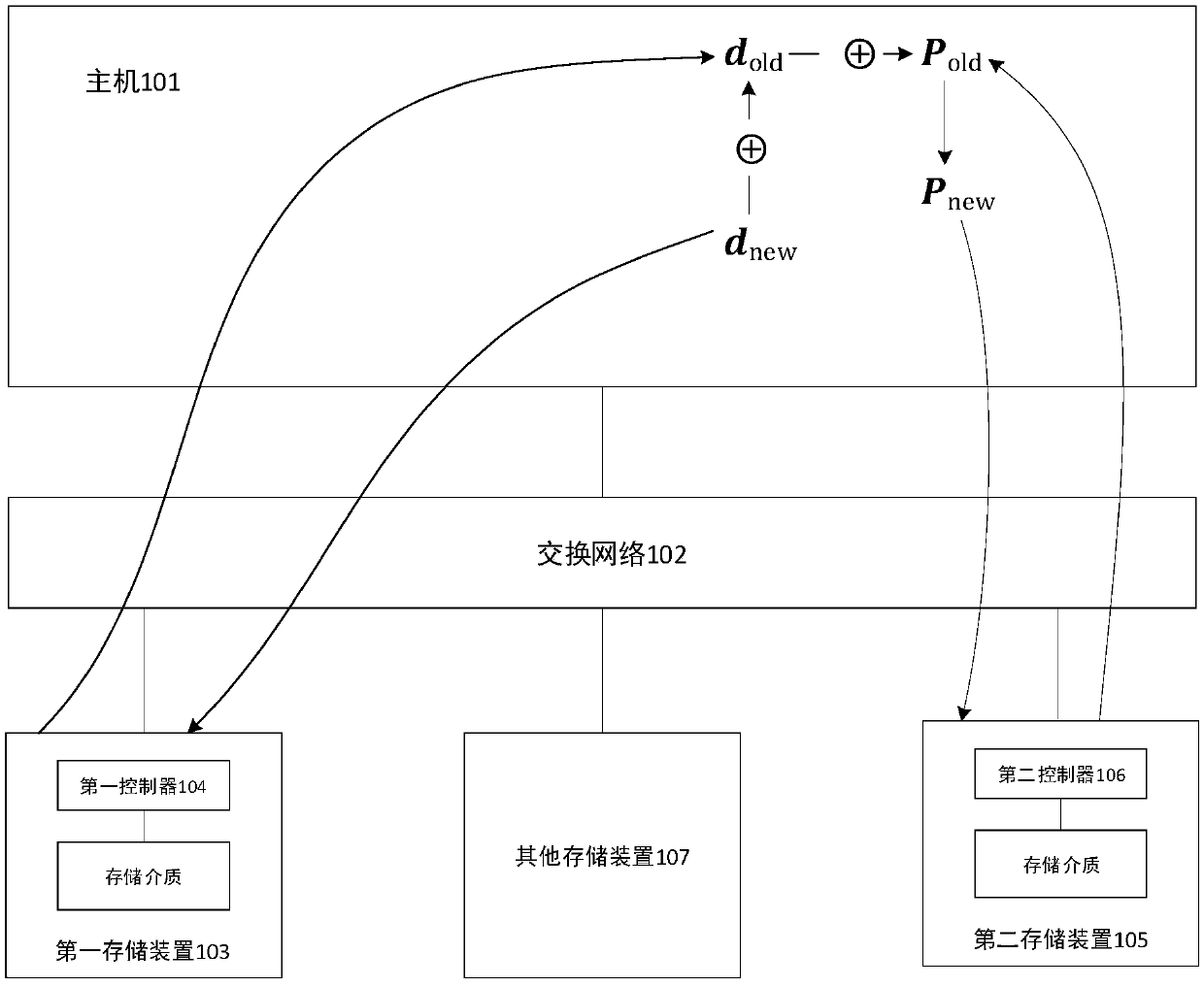
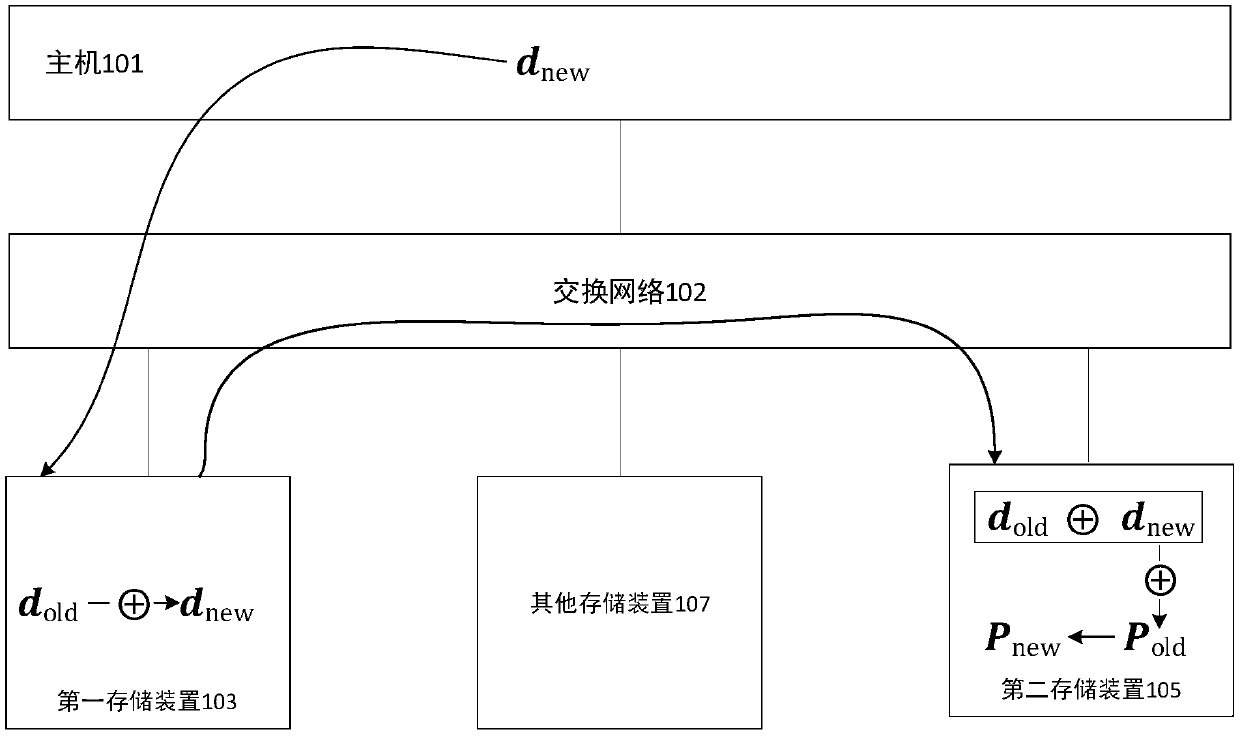
InactiveCN109634771AAvoid read and write operationsReduce data trafficInternal/peripheral component protectionRedundant data error correctionComputer hardwareExclusive or
A data protection method, apparatus and system are disclosed. The system includes a host, a first storage device, a second storage device, and at least one other storage device. Wherein the first datais stored in the first storage device and the second data is stored in the second storage device, and the second data is a parity result of the first data and at least one third data. The host is configured to trigger a first instruction and a second instruction, the first instruction carrying an association identifier for indicating the second instruction. The first storage device is used for acquiring the first instruction and the fourth data, performing exclusive OR operation on the first data and the fourth data after acquiring the first instruction to obtain the fifth data, and sending adata message to the second controller, wherein the data message comprises the fifth data and the associated identifier. The second storage device is used for acquiring the second instruction and thedata message, and performing exclusive OR operation on the fifth data and the second data according to the second instruction to obtain the sixth data.
Owner:HUAWEI TECH CO LTD
Processing system and method for reinsurance service
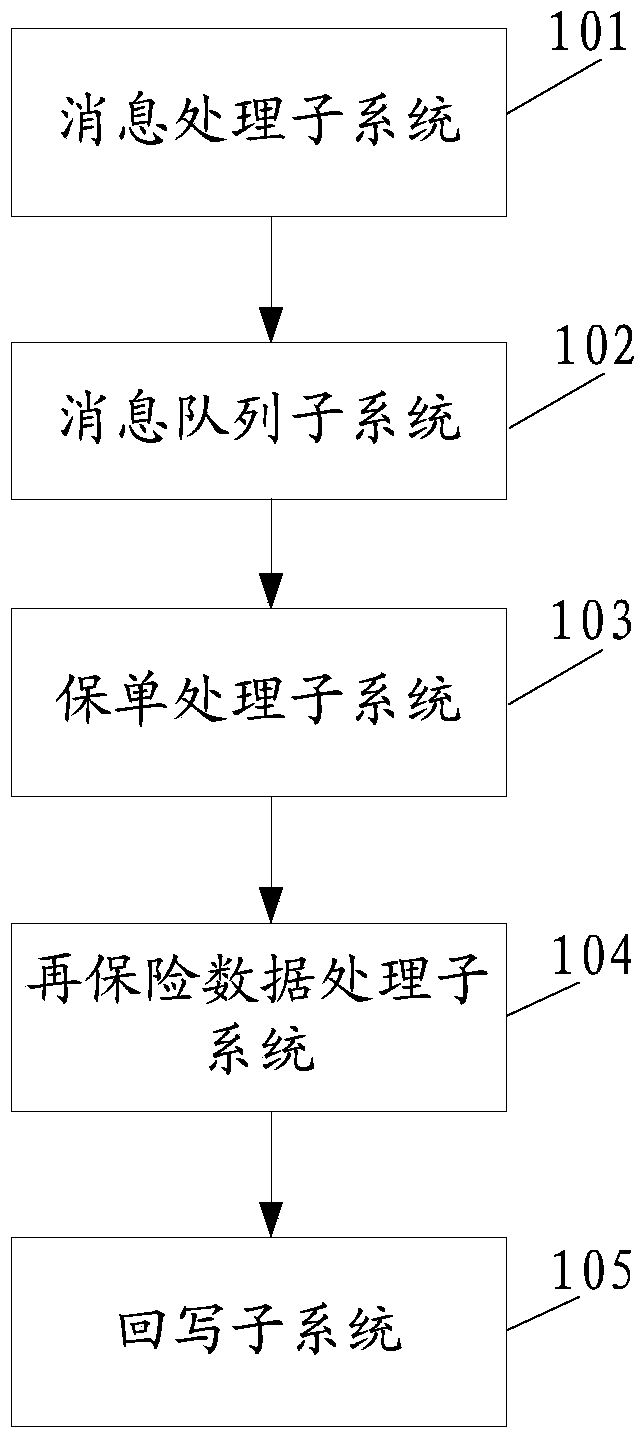
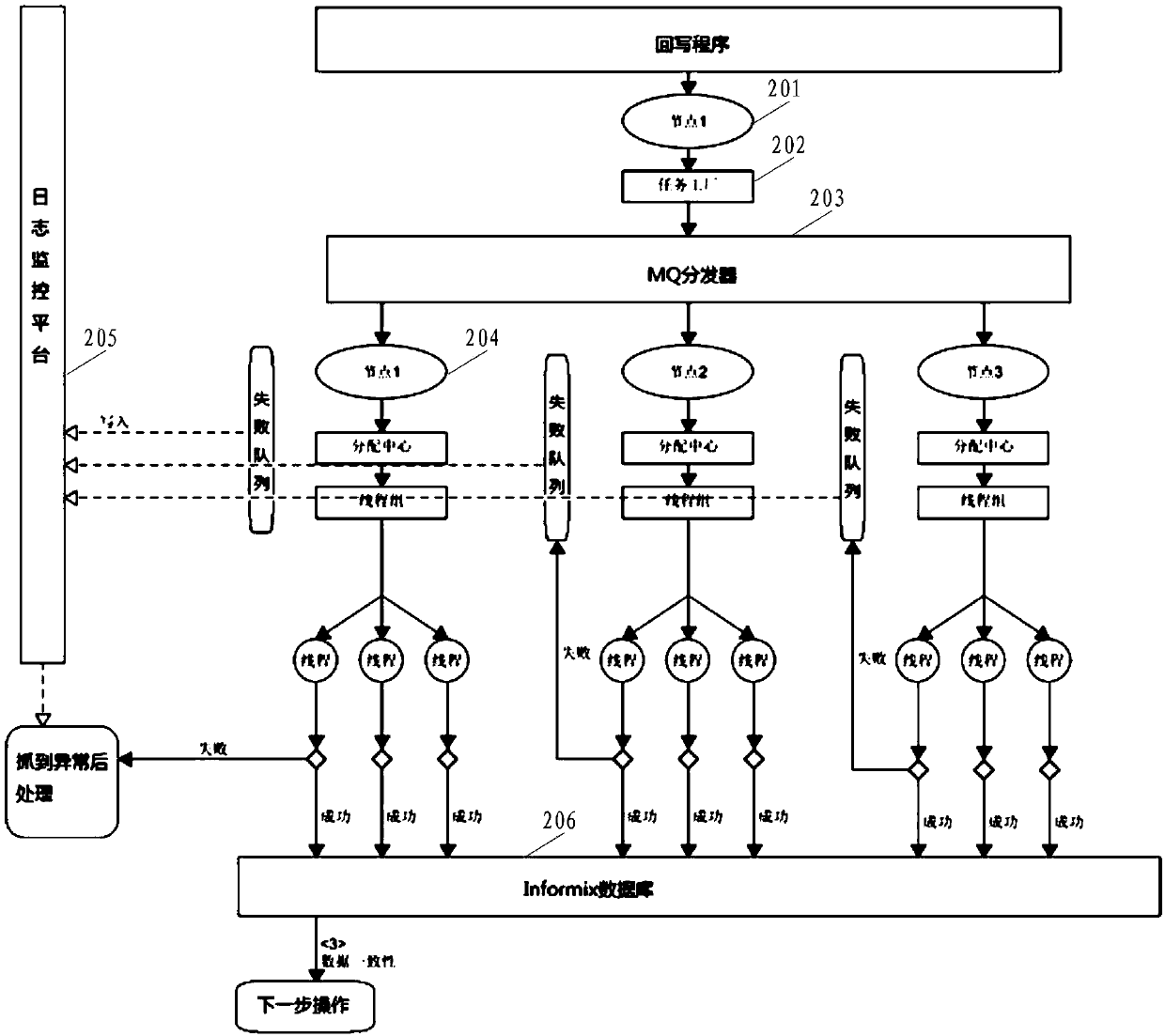
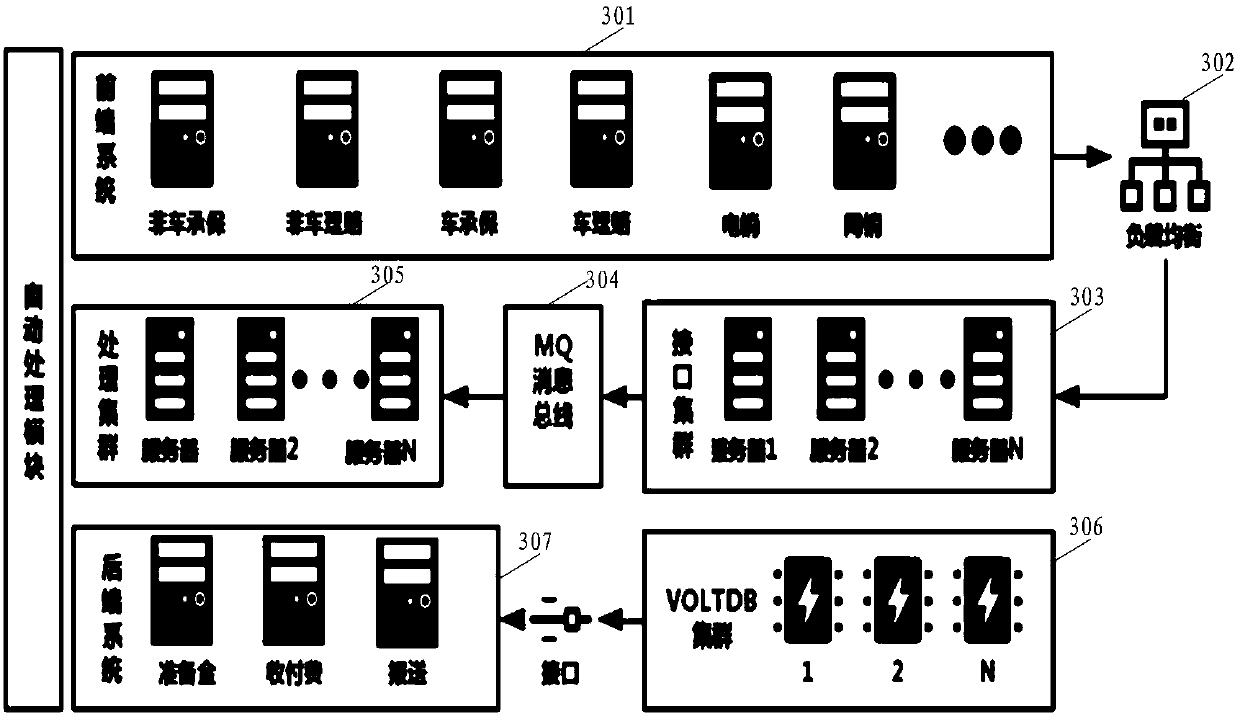
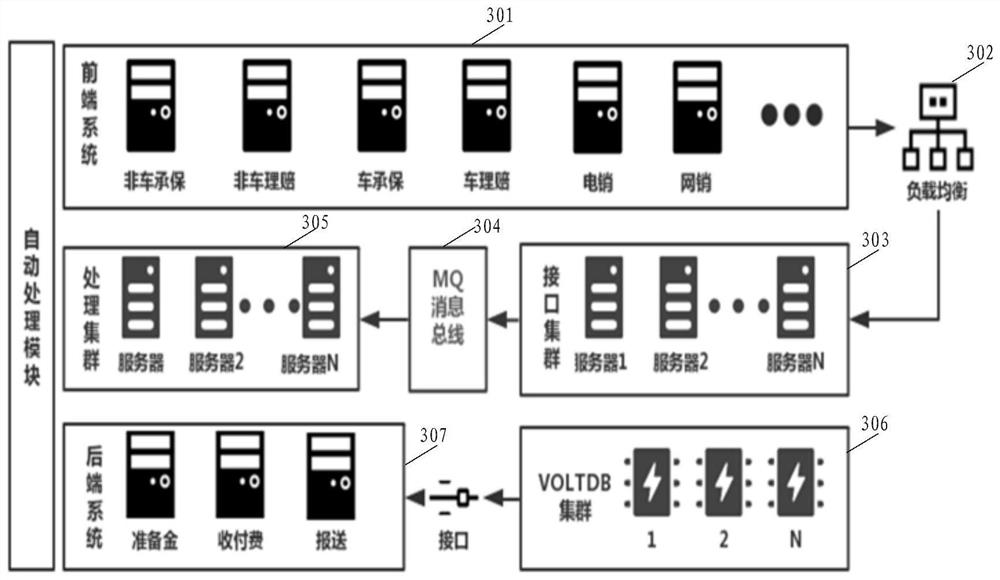
ActiveCN110349031AAvoid the risk of congestionHigh real-time requirementsFinanceMessage queueMessage processing
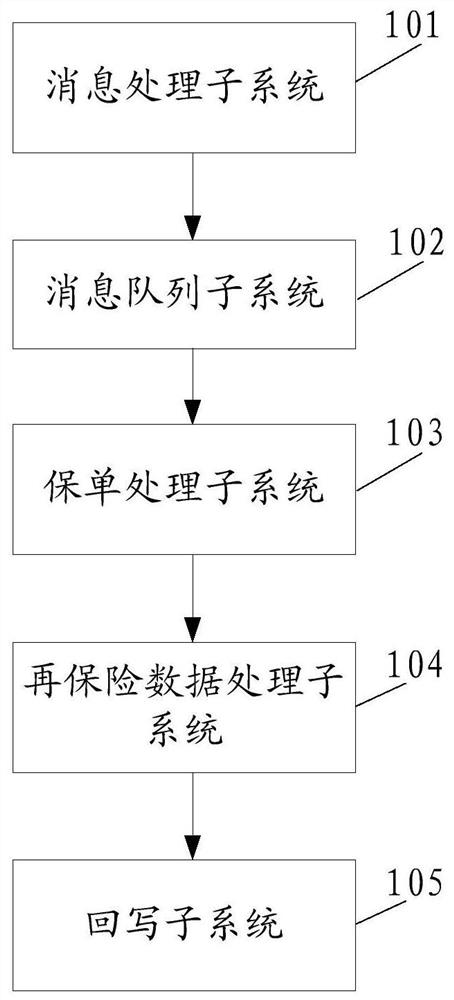
The invention discloses a processing system for a reinsurance service. The system comprises a message processing subsystem which is used for collecting and storing insurance policy data, packaging insurance policy information for indicating the insurance policy data into a reinsurance notification message, and transmitting the reinsurance notification message to a message queue subsystem; a message queue subsystem used for storing the reinsurance notification message in the form of a message queue; an insurance policy processing subsystem used for obtaining the reinsurance notification messagestored by the message queue subsystem, obtaining insurance policy data according to the insurance policy information carried by the reinsurance notification message, and matching risk target information corresponding to the insurance policy data with a reinsurance contract to obtain reinsurance contract information matched with the risk target information; and a reinsurance data processing subsystem used for obtaining the information of the risk target and the reinsurance contract information matched with the information of the risk target in batches, and establishing an association relationship between the information of the risk target and the reinsurance acceptor in batches. The invention aims to solve the problem of service congestion risk of the existing processing system for the reinsurance service.
Owner:PEOPLE'S INSURANCE COMPANY OF CHINA
Key value data storage method, device and equipment, and storage medium
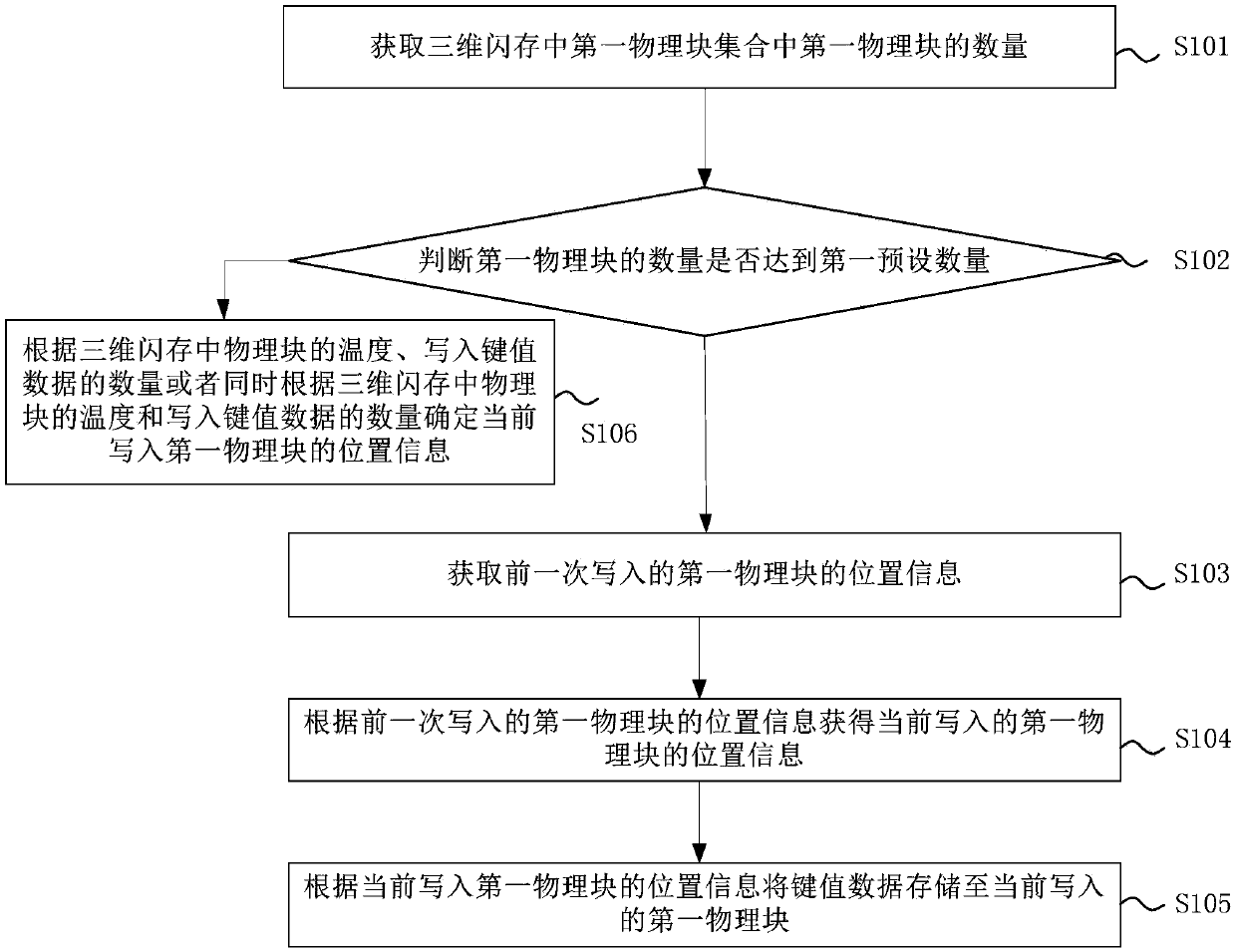
ActiveCN109634960AImprove accuracyAvoid read and write operationsInput/output to record carriersDatabase indexingFlash memory
The invention provides a key value data storage method, device and equipment, and a storage medium, and the method comprises the steps: obtaining the number of first physical blocks in a first physical block set in a three-dimensional flash memory; Judging whether the number of the first physical blocks reaches a first preset number or not; if the judgment result is no, obtaining the position information of the first physical block written in the previous time; obtaining the position information of the currently written first physical block according to the position information of the first physical block written in the previous time; wherein when the data blocks in which the key value data is not written exist inside and outside the three-dimensional flash memory at the same time, the regional information of the currently written first physical block is different from the regional information of the previously written first physical block; and storing the key value data to the currently written first physical block according to the position information of the currently written first physical block, so that the currently written first physical block is far away from the previouslywritten first physical block, and the situation that the temperature is sharply increased due to frequent operation on the physical blocks in the same region is avoided.
Owner:SHENZHEN UNIV
SAR (Synthetic Aperture Radar) imaging signal processing data transposing method based on FPGA (Field Programmable Gata Array)
InactiveCN102279386BGuaranteed uptimeReduce power consumptionRadio wave reradiation/reflectionDouble data rateLow speed
The invention discloses an SAR (Synthetic Aperture Radar) imaging signal processing data transposing method based on an FPGA (Field Programmable Gata Array), which is mainly used for solving the problems of high power consumption, low speed, low efficiency and no radiation resistance existing in a real-time imaging processing CTM (Communication Terminal Module) based on a DSP (Digital Signal Processor). The method comprises the following implementation steps of: storing signal processing data in a DDRII SDRAM (Double Data Rate II Synchronous Dynamic Random Access Memory) through the FPGA; performing matrix partitioning on matrix data in the DDRII SDRAM; transposing a diagonal mode matrix block and a symmetrical non-diagonal mode matrix block in sequence; when the quantity of distance direction sampling points is unequal to that of azimuth direction sampling points, transposing the an asymmetrical non-diagonal mode matrix block; resetting after transposition; and reading out the transposed data in the DDRII SDRAM as required by using the FPGA. Due to the adoption of the transposing method, the working efficiency of the DDRII SDRAM is improved greatly, and a transposition memory CTMsystem runs more stably, has lower power consumption, higher speed and higher efficiency and is resistant to radiation; and the transposing method can be applied to the design of an SAR imaging system.
Owner:XIDIAN UNIV
Local object management method and device, equipment and medium
InactiveCN111176571AAvoid read and write operationsAvoid loadInput/output to record carriersMagnetic disksData needs
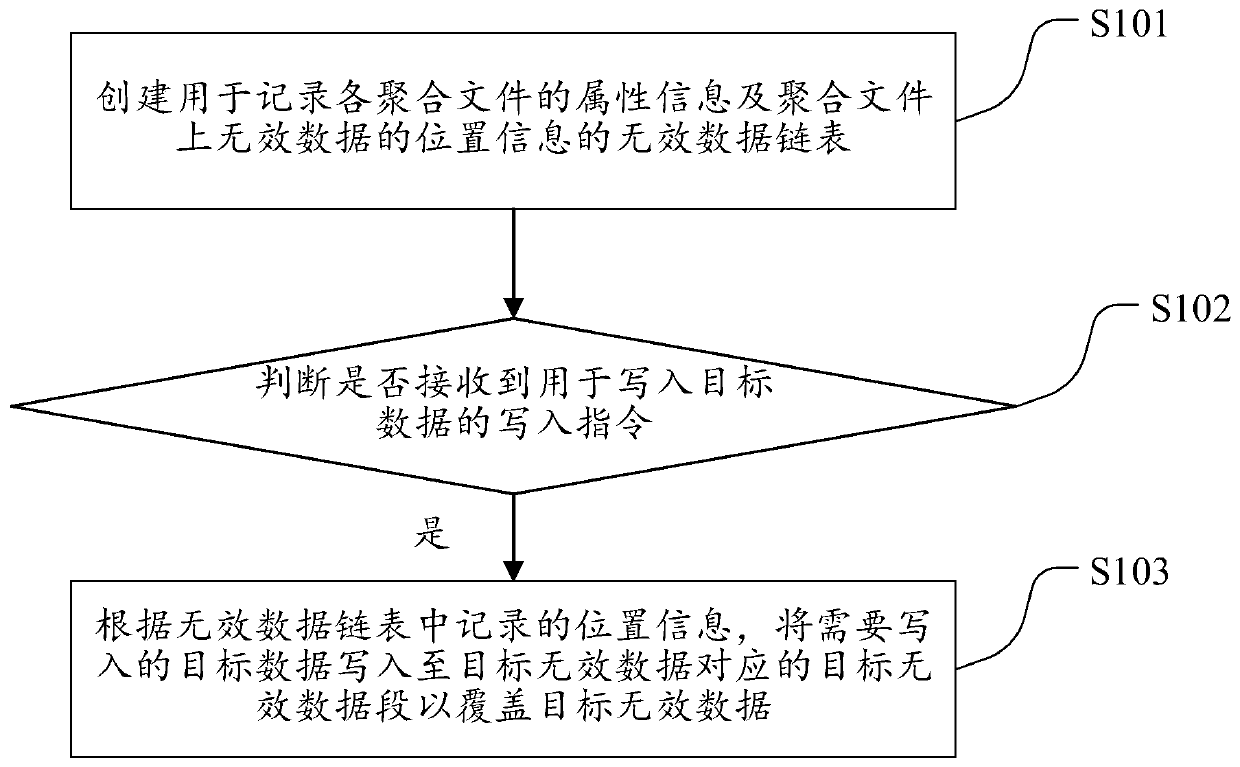
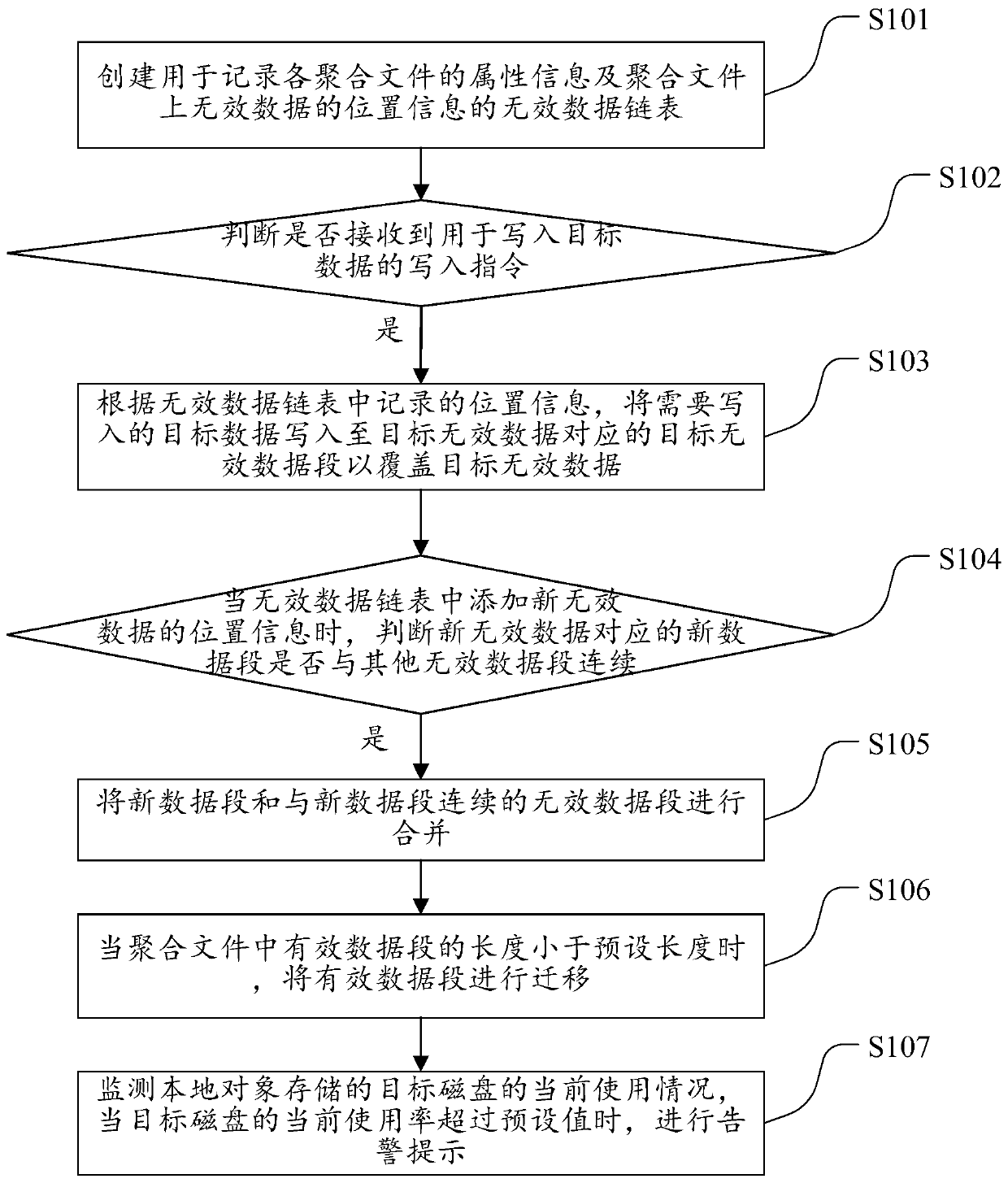
The invention discloses a local object management method. The method comprises the steps of creating an invalid data chain table used for recording attribute information of each aggregation file and position information of invalid data on the aggregation files; judging whether a writing instruction for writing the target data is received or not; and if yes, writing the target data needing to be written into the target invalid data segment corresponding to the target invalid data according to the position information recorded in the invalid data link table so as to cover the target invalid data. Therefore, the data segments of the aggregated file can be reused in time for storage, a large number of read-write operations generated by a disk in the process of transferring valid data are avoided, and the influence on the actual read-write operations of front-end services is reduced; extra load brought to the disk is avoided while quick release of the storage space is realized. In addition,the local object management device and equipment and the storage medium provided by the invention correspond to the method.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
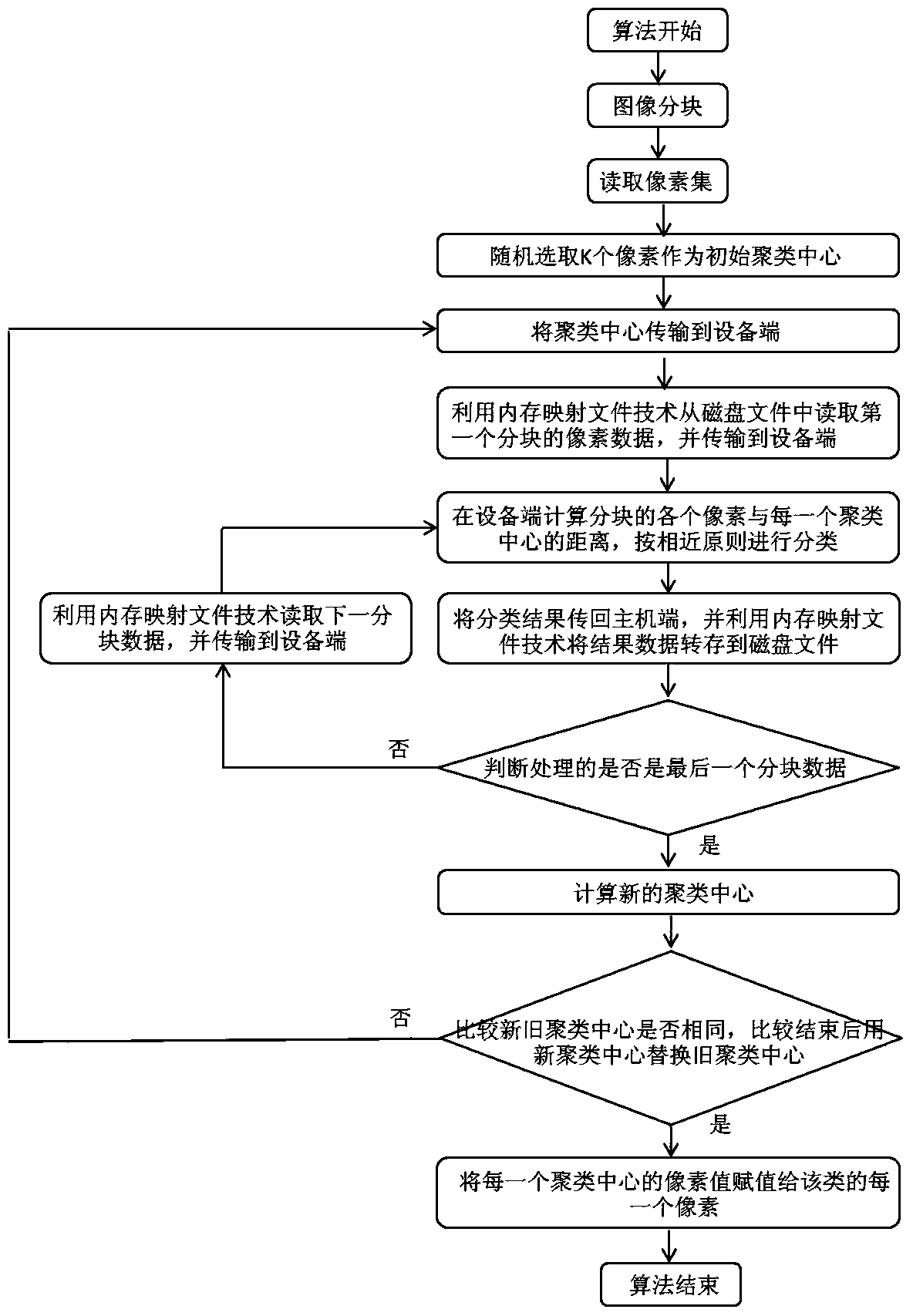
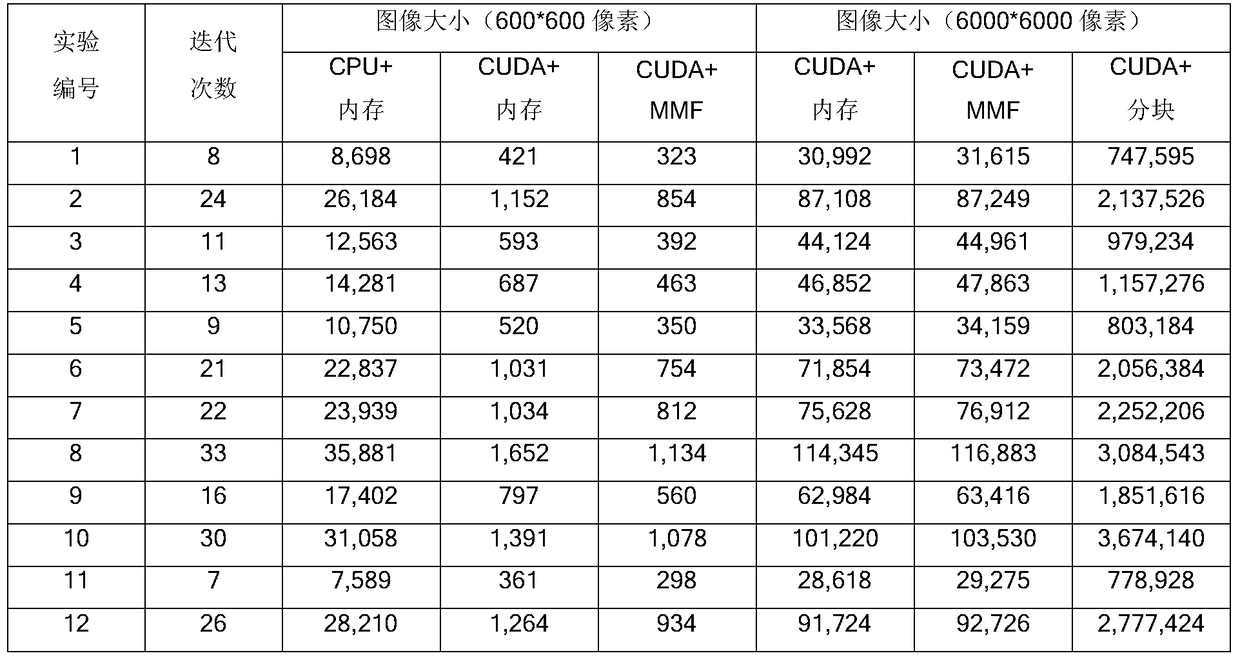
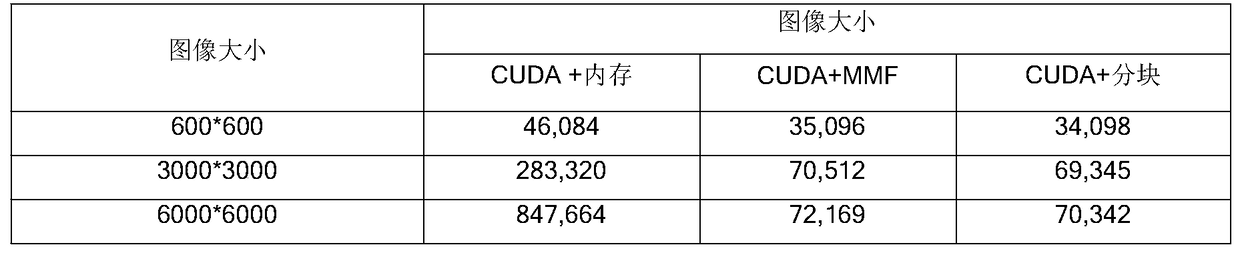
A Time-Space Efficiency Optimization Method for High-Resolution Remote Sensing Image Classification Algorithms
InactiveCN105528622BAvoid read and write operationsReduce running timeCharacter and pattern recognitionComputer imageBlock method
Owner:SHANDONG UNIV OF SCI & TECH
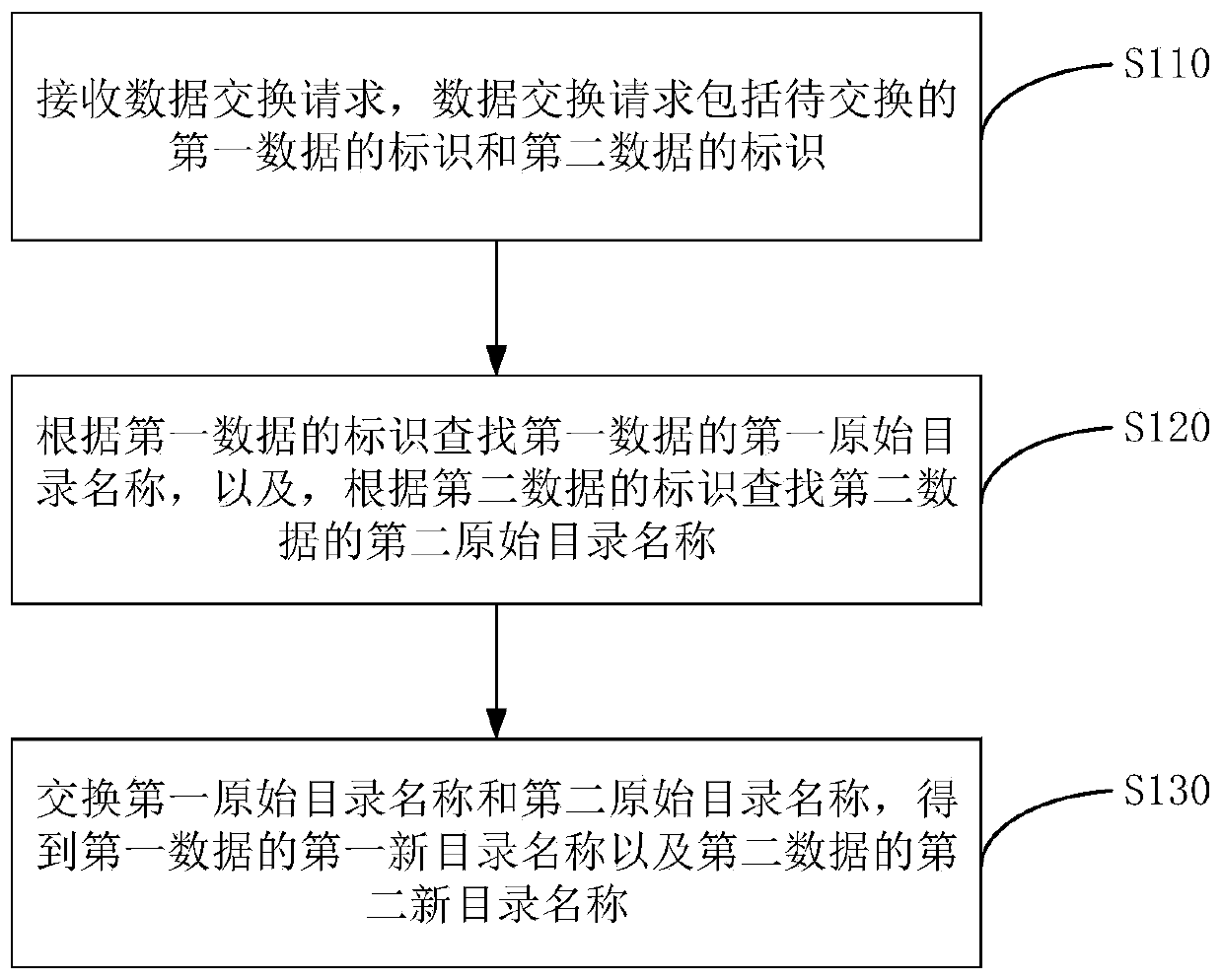
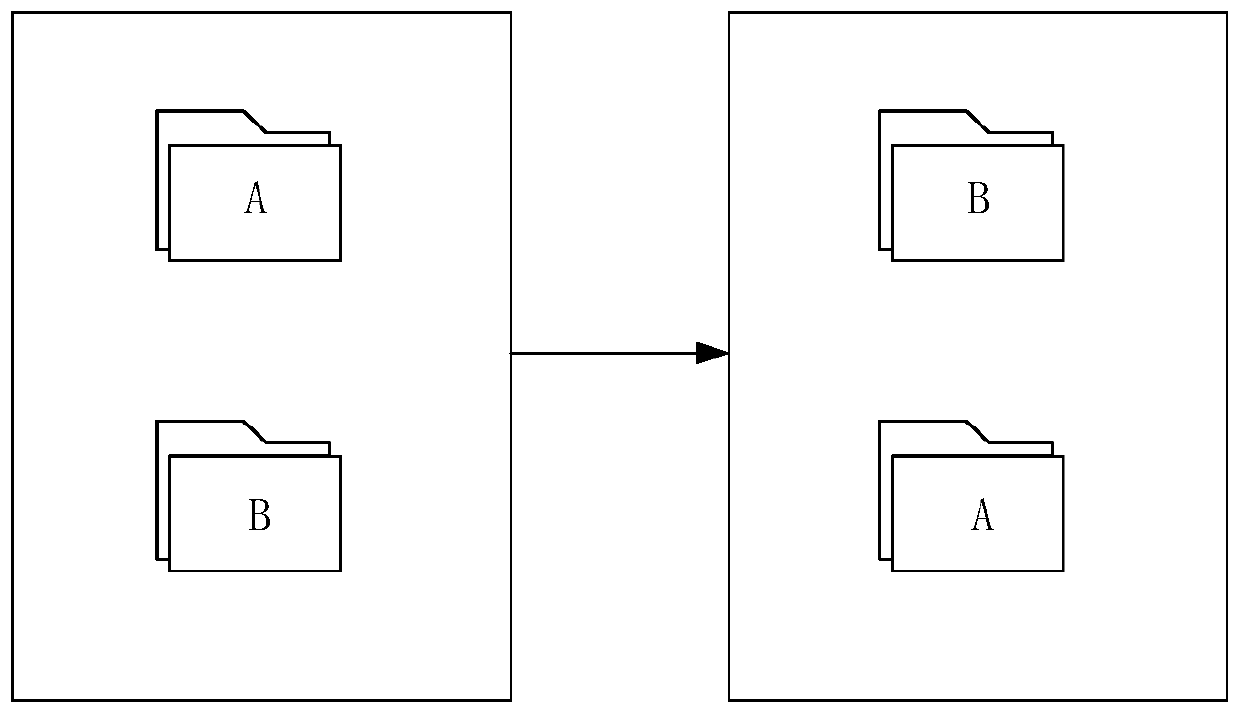
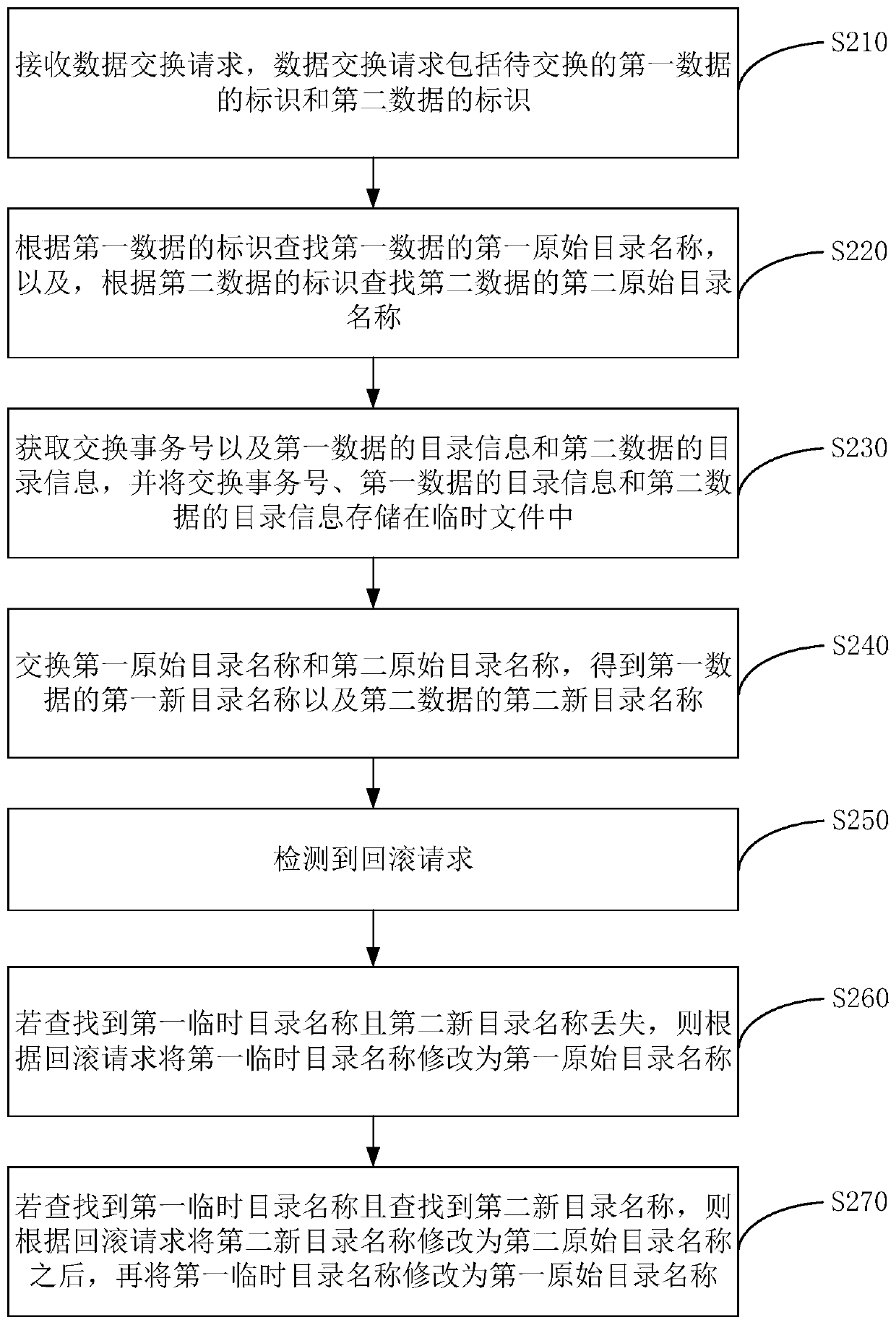
Data exchange method, device, server and storage medium
ActiveCN109740027BQuick exchangeImprove exchange efficiencyOther databases indexingData exchangeDirectory
The embodiment of the invention discloses a data exchange method and device, a server and a storage medium, and the method comprises the steps: receiving a data exchange request which comprises an identifier of to-be-exchanged first data and an identifier of to-be-exchanged second data; searching a first original directory name of the first data according to the identifier of the first data, and searching a second original directory name of the second data according to the identifier of the second data; and exchanging the first original directory name and the second original directory name toobtain a first new directory name of the first data and a second new directory name of the second data. According to the embodiment of the invention, when data exchange is carried out, the data exchange can be rapidly completed by exchanging the directory name of the to-be-exchanged data, the read-write operation of the to-be-exchanged data and the occupation of server resources are avoided, and the data exchange efficiency is improved.
Owner:SHANGHAI DAMENG DATABASE
Decoding method and decoder
ActiveCN110518918AIncrease profitImprove utilization efficiencyError correction/detection using multiple parity bitsCode conversionDecoding methodsAssembly line
The invention discloses a decoding method, which is based on a TDMP (Time Division Multiplexing Protocol) scheduling strategy, and comprises the following steps of: updating all variable nodes after updating a part of check nodes, then updating all variable nodes after updating the other part of check nodes, and repeating the process. According to the method, the operation of updating a part of check nodes is divided into a plurality of sub-operations, and the sub-operations and the operation of updating all variable nodes are organized into a two-stage assembly line, so that the utilization rate of a component decoder is improved; according to the method, control logic of an assembly line is constructed by combining parallelism degree requirements, so that all-zero pseudo blocks in a check matrix are skipped, and iteration time consumption can be reduced; particularly, the method performs row-column exchange on the check matrix to reduce the number of invalid operations, significantlyreduce the iteration time consumption and improve the throughput. The invention also discloses a decoder.
Owner:SHENZHEN XINZHILIAN TECH CO LTD
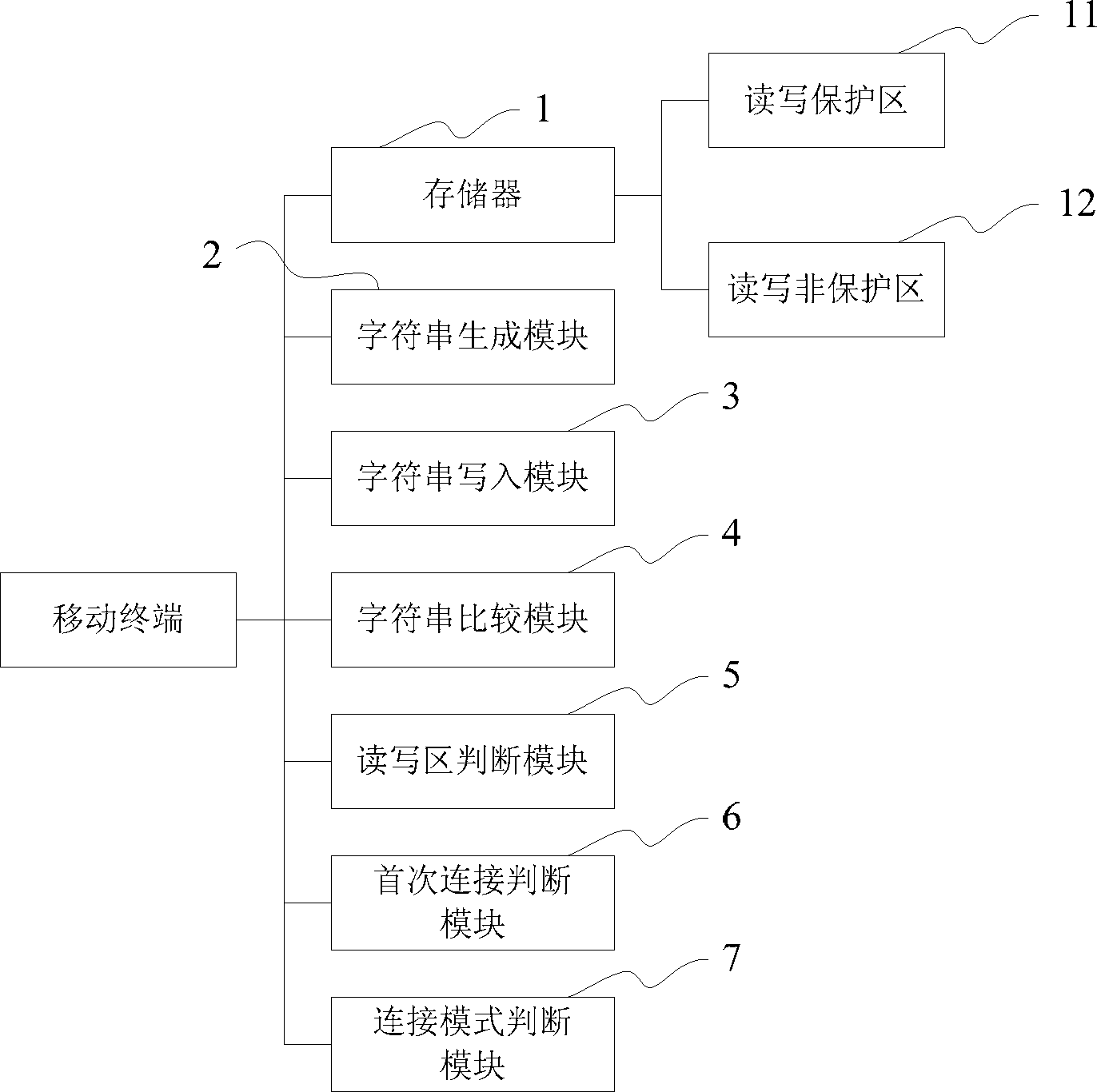
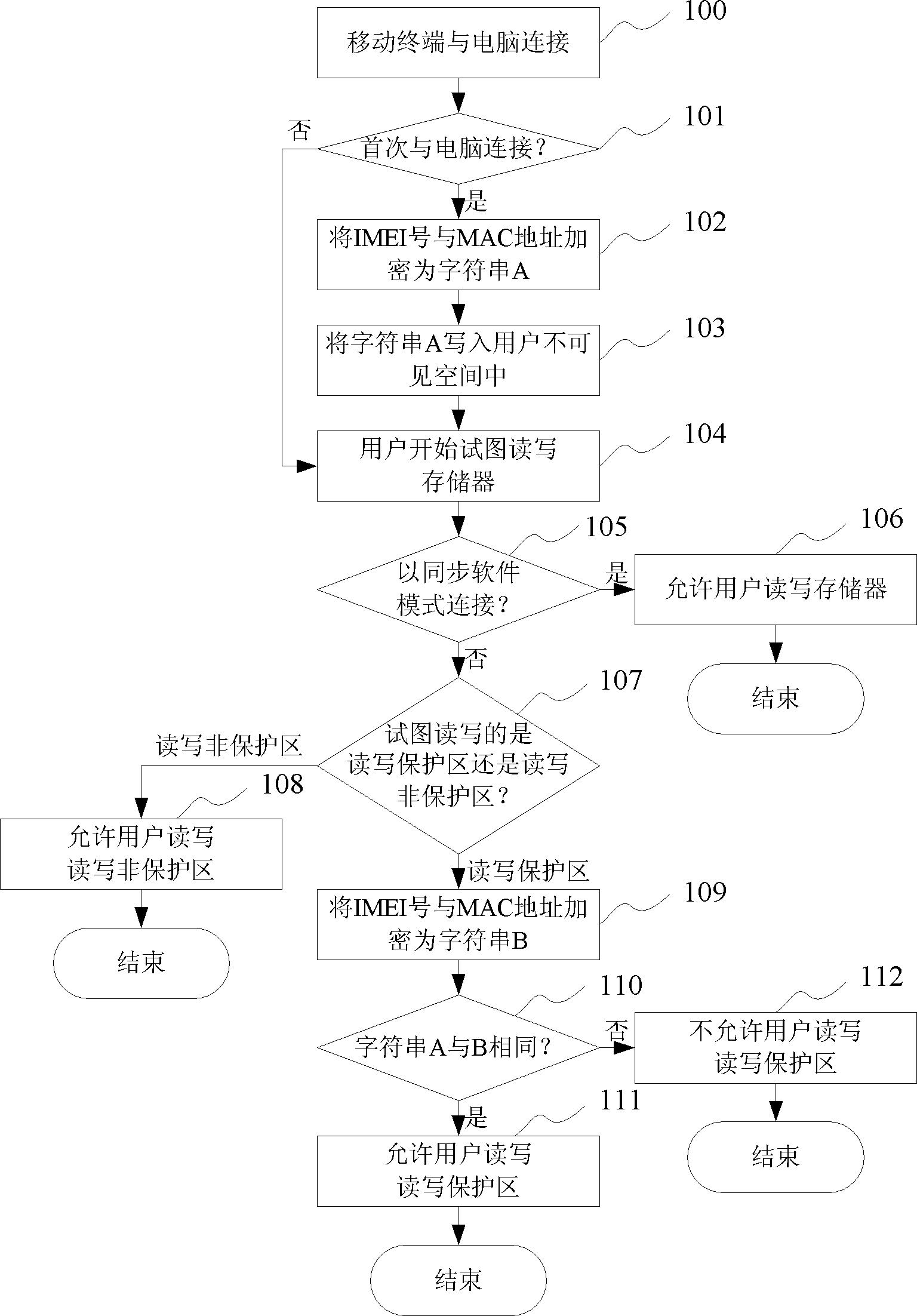
Mobile terminal and data protection method thereof
ActiveCN103139366BEffective and reliable protectionAvoid read and write operationsEncryption apparatus with shift registers/memoriesDigital data protectionWrite protectionComputer module
The invention discloses a mobile terminal and a data protection method thereof. The mobile terminal comprises a character string generation module used for generating a character string through an international mobile equipment identity (IMEI) number of the mobile terminal and a medium access control (MAC) address of a computer connected with the mobile terminal by an encryption algorithm; a character string write-in module used for writing the character string generated by the character string generation module in a space, invisible to a user, of the mobile terminal; a character string compare module used for judging whether the character string generated by the character string generation module is identical to a character string in the space, invisible to the user, of the mobile terminal; a read-write area judgment module used for judging whether the user should conduct read-write on a read-write protection zone or on a non-read-write protection zone; and a first connection judgment module used for judging whether the mobile terminal is connected with the computer for the first time when the mobile terminal is connected with the computer. According to the mobile terminal and the data protection method thereof, important data in the read-write protection zone of the mobile terminal can be protected practically and reliably.
Owner:LONGSUNG TECH SHANGHAI
Method for prolonging service life of flash of ONU terminal equipment and ONU terminal equipment
InactiveCN113849132AFast and reliable comparison of resultsReduce the number of erasuresInput/output to record carriersTerminal equipmentTerm memory
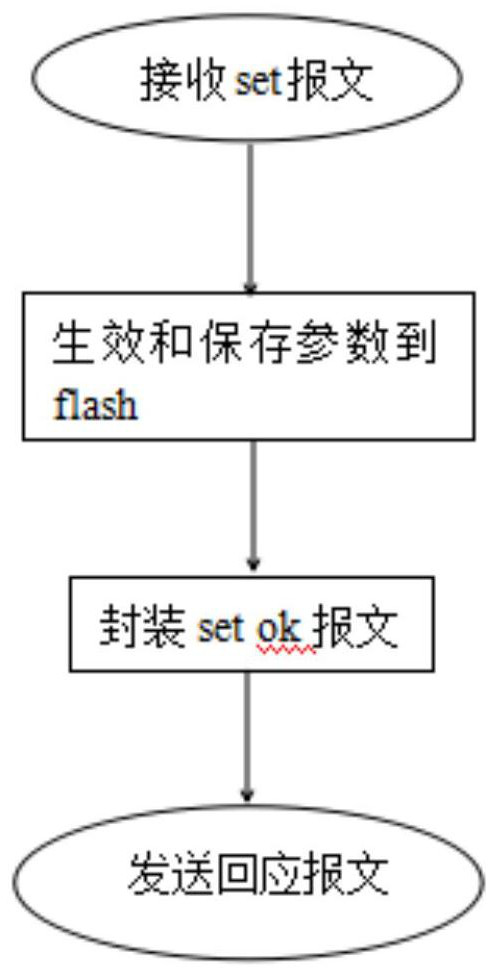
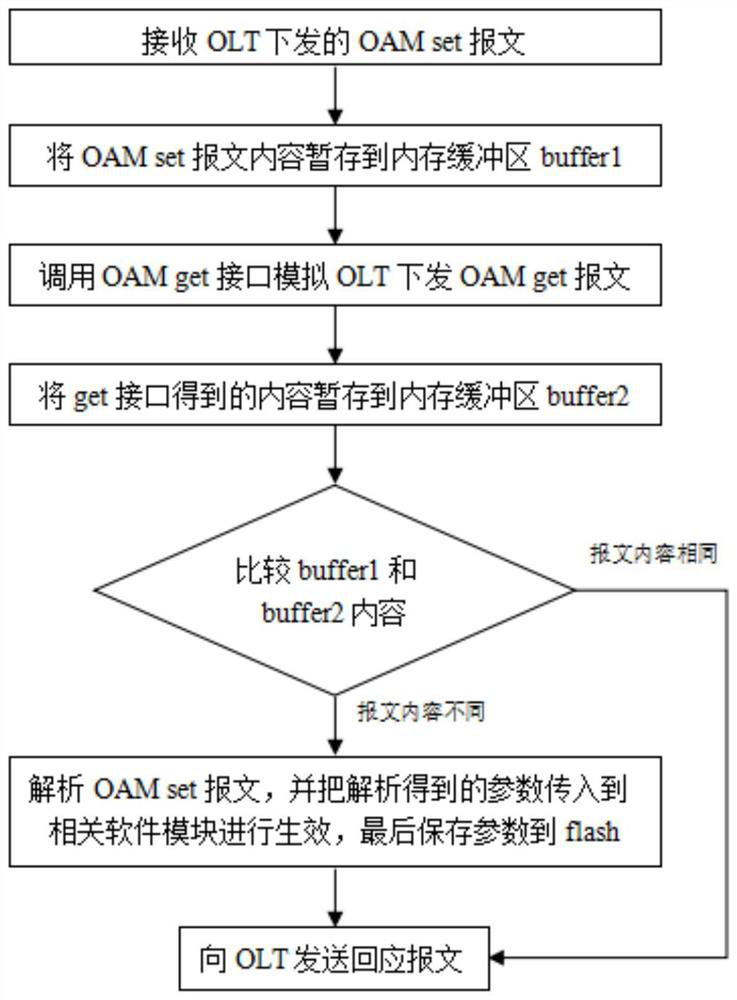
The invention discloses a method for prolonging the service life of a flash of ONU terminal equipment and the ONU terminal equipment. The method comprises the following steps: S1, receiving an OAM set message issued by an OLT; S2, temporarily storing the content of the OAM set message in a memory buffer zone (buffer 1); S3, calling a get interface, and temporarily storing the content of a get message into a buffer 2 of the memory; S4, comparing the content of the OAM set message with the content of the get message, if the message contents are different, executing the step S5, and if the message contents are the same, executing the step S6; S5, analyzing the OAM set message, transmitting parameters obtained through analysis to a related module to take effect, and finally storing the parameters in a flash; and S6, sending a response message by the ONU to the OLT. According to the invention, the reading and comparison functions of the OLT issuing configuration parameters can be realized, the comparison result of the OLT issuing parameters and the ONU terminal parameters can be quickly and reliably obtained, unnecessary parameter effectiveness and flash read-write operation are avoided, the flash erasing frequency is reduced, and thus the service life of the flash is prolonged.
Owner:广州芯德通信科技股份有限公司
A processing system and method for reinsurance business
ActiveCN110349031BAvoid the risk of congestionHigh real-time requirementsFinanceMessage queueMessage handling
This application discloses a processing system for reinsurance business, including: a message processing subsystem, which is used to collect and store policy data, encapsulate the policy information used to indicate the policy data into a reinsurance notification message, and send it to the message queue sub-system System; message queue subsystem, used to store the reinsurance notification message in the form of message queue; insurance policy processing subsystem, used to obtain the reinsurance notification message stored in the message queue subsystem, and obtain policy data according to the policy information it carries , matching the risk target information corresponding to the policy data with the reinsurance contract to obtain the reinsurance contract information matching the risk target information; the reinsurance data processing subsystem is used to obtain the risk target information in batches and the information matching the risk target information Reinsurance contract information, establish the relationship between risk target information and reinsurance recipients in batches. In order to solve the business congestion risk existing in the existing processing system for reinsurance business.
Owner:PEOPLE'S INSURANCE COMPANY OF CHINA
Water outlet control method and device and drinking equipment
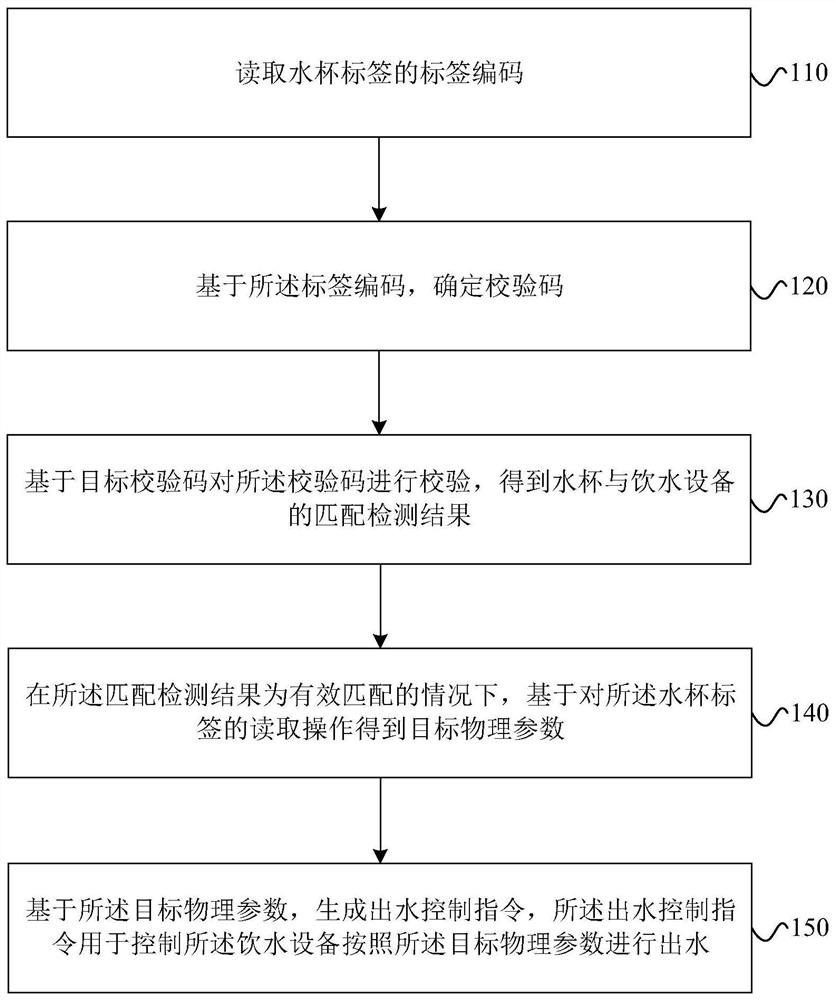
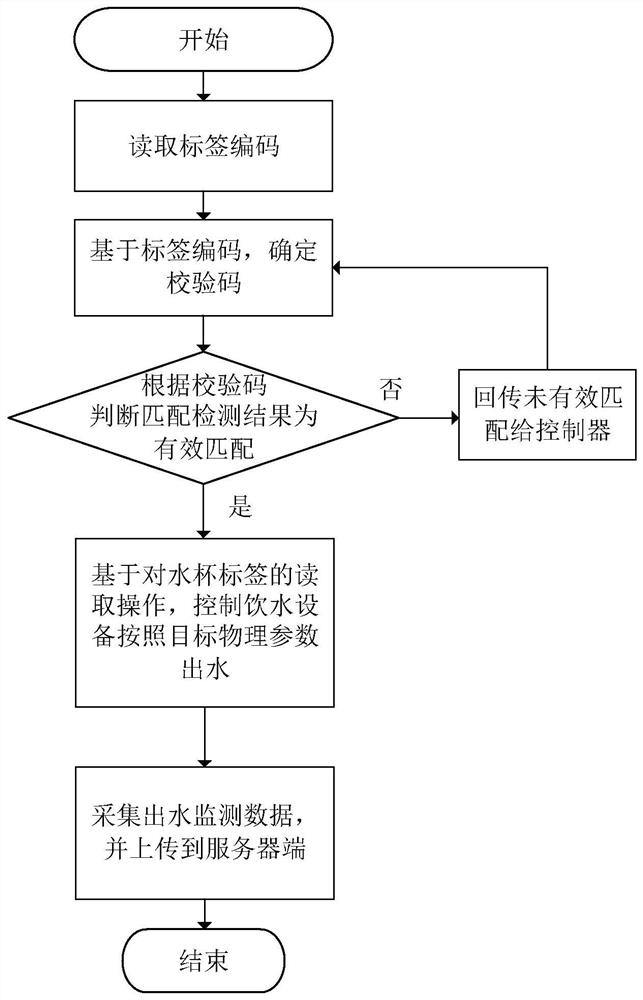
PendingCN114145632AAvoid read and write operationsReduce complexityBeverage vesselsProcess engineeringEnvironmental engineering
The invention relates to the field of household appliances, and provides a water outlet control method and device and drinking equipment. The water outlet control method comprises the steps that a label code of a water cup label is read; determining a check code based on the tag code; checking the check code based on the target check code to obtain a matching detection result of the water cup and the water drinking equipment; under the condition that the matching detection result is effective matching, target physical parameters are obtained based on reading operation on the water cup label; based on the target physical parameters, a water outlet control instruction is generated, and the water outlet control instruction is used for controlling the drinking equipment to discharge water according to the target physical parameters. According to the water outlet control method and device and the water drinking equipment, the complexity of user operation can be reduced through the reading operation on the water cup label, simple, convenient and rapid water taking is achieved, the intelligent degree is improved, the water outlet efficiency is improved, meanwhile, the water cup is verified through the verification code, read-write operation on the water cup label of an unmatched brand is avoided, and the user experience is improved. The reliability of the drinking equipment can be improved.
Owner:FOSHAN SHUNDE MIDEA WATER DISPENSER MFG +1
A high-precision channel flood submerged area generation method for massive dem data
ActiveCN102842104BSolve the problem that it is difficult to read a large amount of data DEMIncrease the compression ratioClimate change adaptationSpecial data processing applicationsData compressionDomain analysis
The invention relates to a high-precision riverway flood inundated area generation method for mass DEM (Digital Elevation Model) data. The method comprises the following steps of: performing stripe division on the mass DEM data; performing run length compression storage on a plurality of continuous inundation units on grid lines in stripes to reduce a data size; and finally extracting inundation ranges by virtue of a compression unit boundary tracing method, thereby generating an inundated area under complex terrain conditions. The method changes the conventional inundation source seed point filling method into grid compression storage and grid boundary tracing calculation, so that a large grid data size is processed with small memory configuration; and at the same time, a large amount of recursion judgment in the seed point filling method is avoided, and thus the computing speed is improved. The method fully utilizes digital terrain analysis and data compression storage technologies, avoids the problems generated by mass DEM data inundation analysis in the seed filling method, can be used for well performing connected domain analysis on complex terrain environments with rivers and lakes, and generates the wide-range and high-precision river and lake flood inundated area.
Owner:CHANGJIANG RIVER SCI RES INST CHANGJIANG WATER RESOURCES COMMISSION
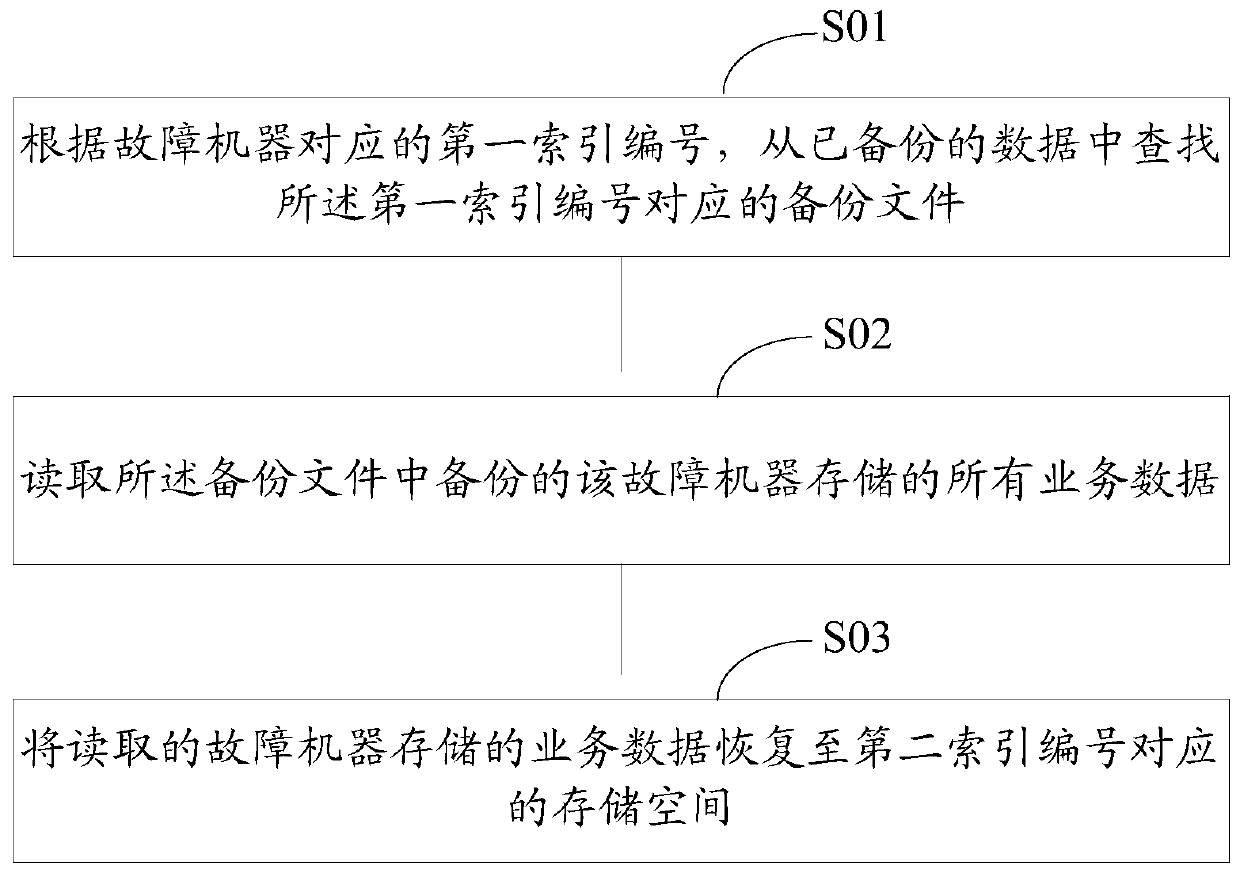
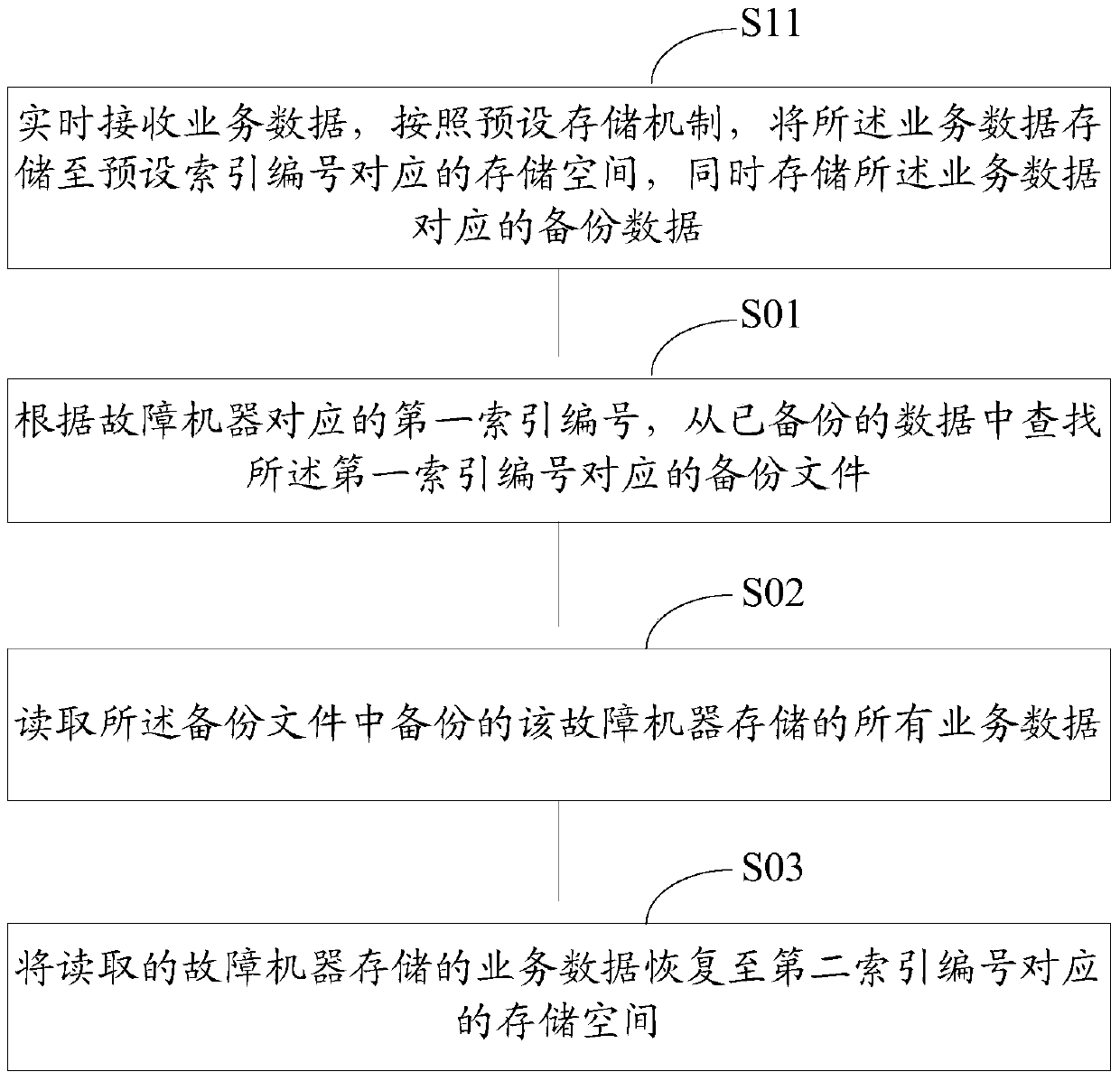
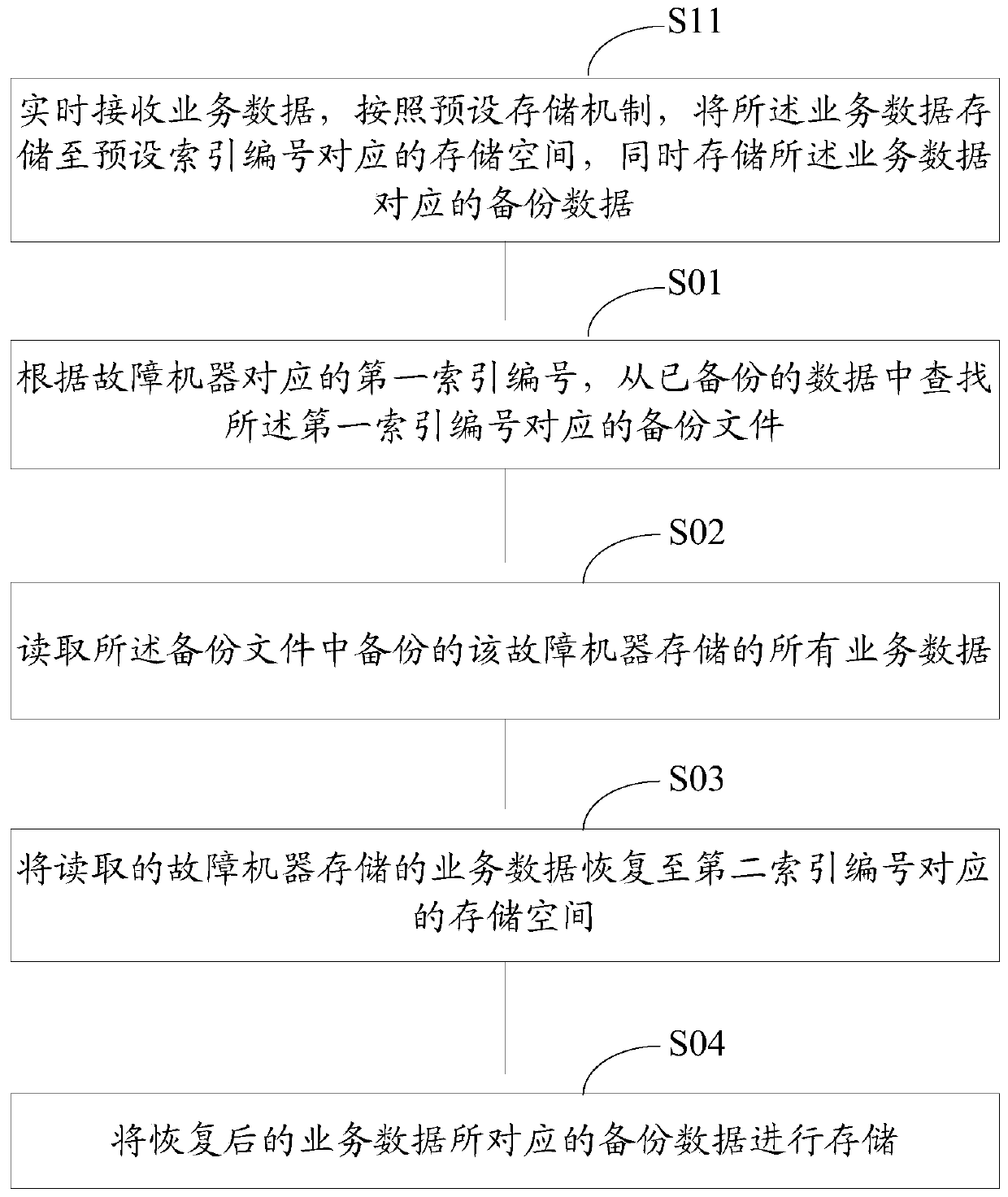
Data recovery method and device
ActiveCN104636218BSpeed up recoveryAvoid read and write operationsRedundant operation error correctionRecovery methodData storing
The invention discloses a data recovery method and device. According to a first index number corresponding to a faulty machine, backed-up data are searched for a backup file corresponding to the first index number; all service data which are stored by the faulty machine and backed up in the backup file are read; the read service data stored by the faulty machine are recovered to storage space corresponding to a second index number. Compared with a large amount of magnetic disk read-write operation produced when index data are recovered in the prior art, the data recovery method and device have the advantages that magnetic disk read-write operation produced by a machine where the storage space corresponding to the index number exists is avoided when the index data are recovered, and the data recovery speed is increased.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Virtual machine storage space management method, system and physical host
ActiveCN101986285BAvoid read and write operationsImprove real-time performanceMemory adressing/allocation/relocationTransmissionInformation transmissionProcess module
The invention discloses a virtual machine storage space management method. In the method, virtual storage free block information is directly acquired by a storage balloon agent module which is deployed in a virtual machine, and the acquired virtual storage free block information is transmitted to a storage balloon daemon process module which is deployed in a virtual machine monitoring unit layer;and the storage balloon daemon process module partially or totally releases a physical storage space corresponding to the virtual storage free block information and labels virtual storage blocks corresponding to the released physical storage space to be unavailable. The invention also discloses a corresponding system and physical host. Due to the method, the service condition of the virtual storage space can be acquired in real time, the massive reading / writing operation of a storage system can be avoided, and the method is suitable for virtual storage systems in a dynamic allocation format and a pre-allocation format.
Owner:HUAWEI TECH CO LTD
A file receiving management method, device, terminal equipment and storage medium
ActiveCN107908710BRealize unified managementSolve the problem of inconvenient file searchFile system administrationSpecial data processing applicationsPathPingTerminal equipment
The invention discloses a file receiving management method, device, terminal equipment and storage medium. The method includes the following steps: receiving the file, storing the file provided by the file producer into the target directory through one or more file receiving methods ;Target directory check, regularly check whether there are files in the target directory; file transfer, if there are files in the target directory, transfer the files in the target directory to the storage directory; file information entry, when the files in the target directory have been transferred After arriving at the storage directory, store the path of the storage directory and the basic information of the files in the database; threshold detection of the storage directory, to detect whether the files stored in the storage directory reach the threshold; early warning, when the files stored in the storage directory reach the threshold, trigger Early warning, send out early warning information. The invention can reduce the work pressure of personnel and improve the work efficiency by receiving and managing the automatic multi-channel files.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com